Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
407 results about "Database application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
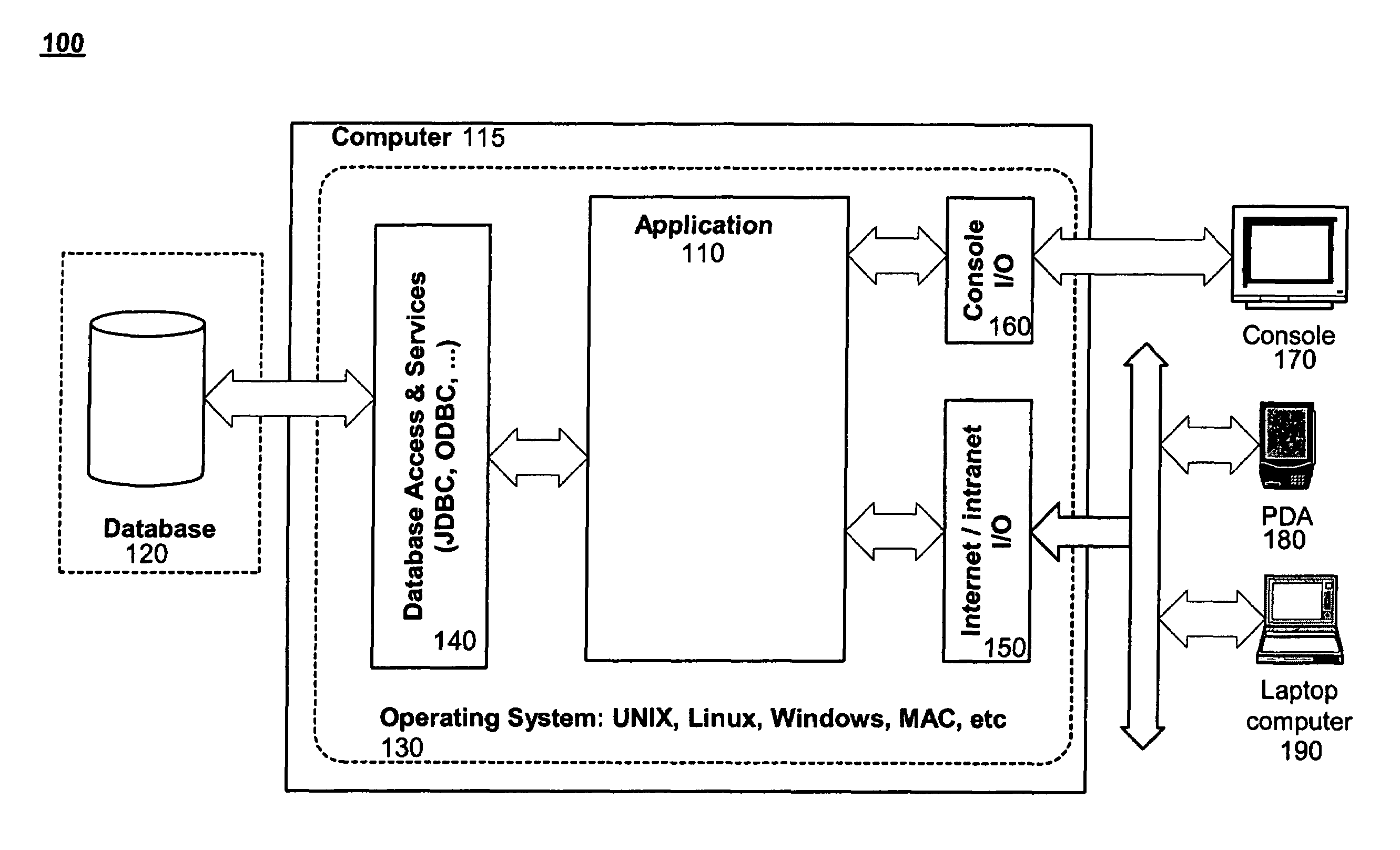
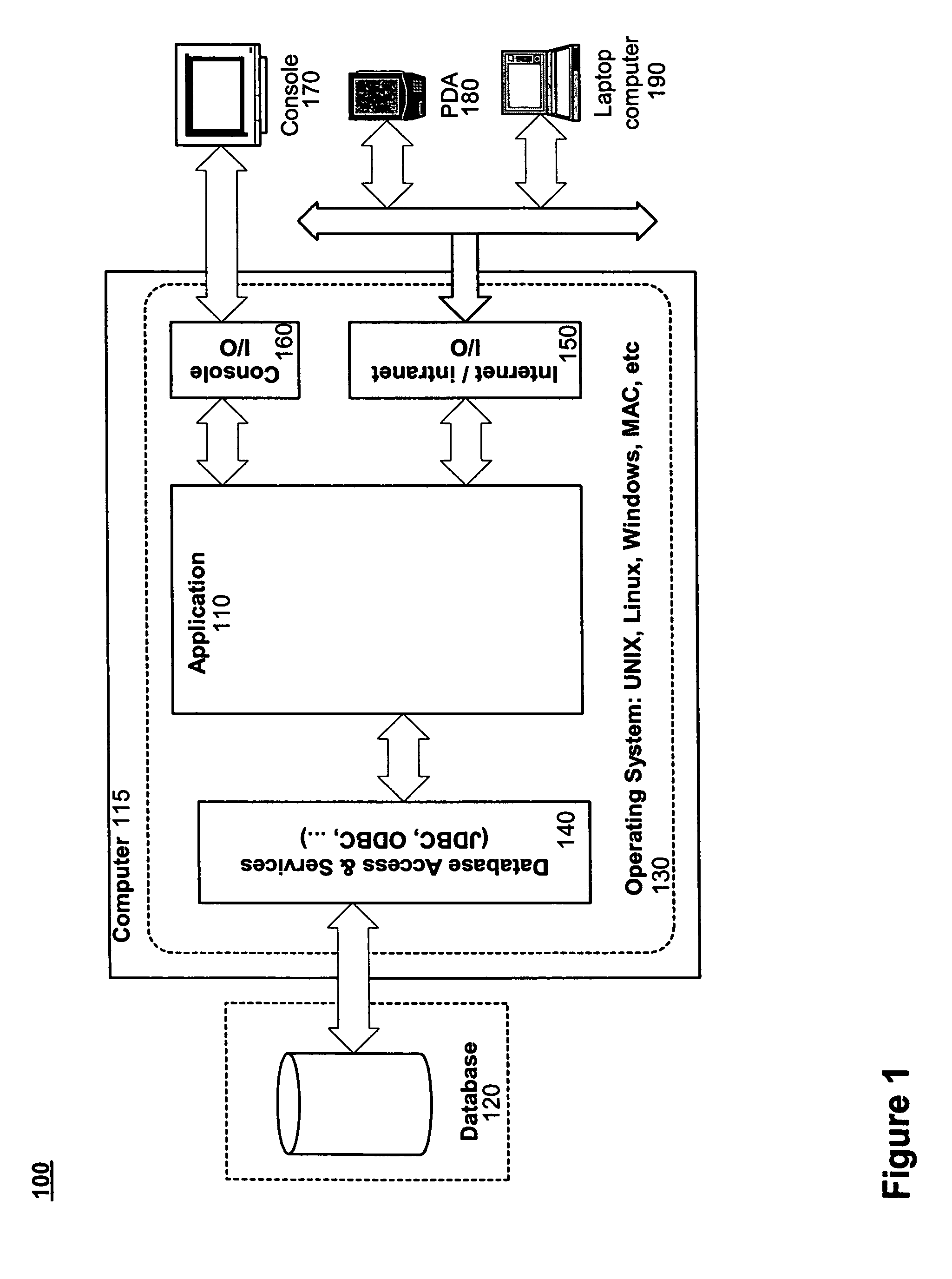
A database application is a computer program whose primary purpose is entering and retrieving information from a computerized database. Early examples of database applications were accounting systems and airline reservations systems, such as SABRE, developed starting in 1957.
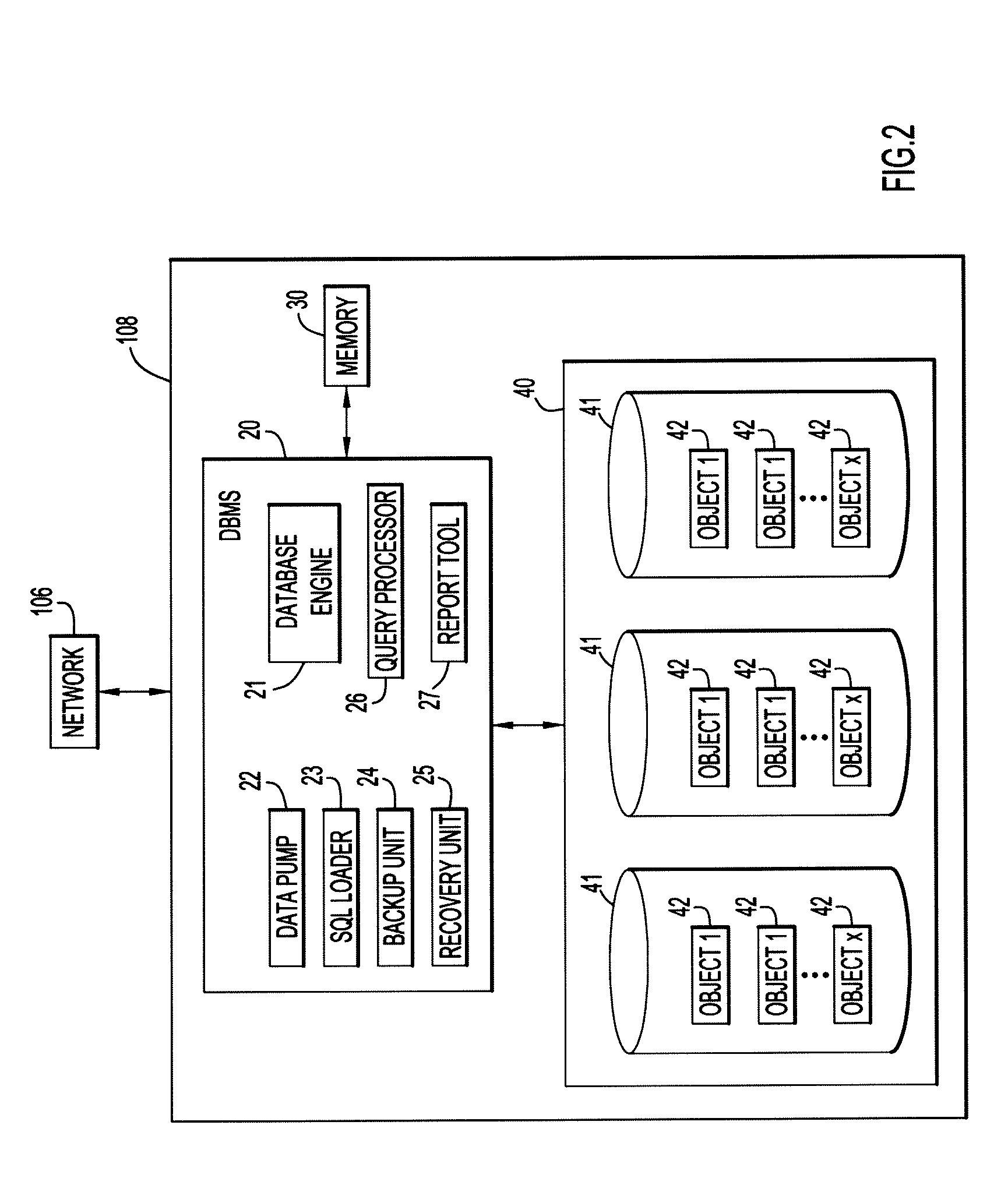
Software framework that facilitates design and implementation of database applications
InactiveUS7412455B2Facilitates efficient design and implementationData processing applicationsDigital data information retrievalSoftware engineeringDatabase application
An intelligent framework is provided that is disposed between a high-level language environment and a database system environment. According to one embodiment, the framework programmatically receives information regarding definitions of data structures of objects participating in a software application and information regarding relationships among the objects. Based upon the particular request from the high-level language environment and upon the definitions and relationships, the framework programmatically and dynamically generates appropriate statements associated with the database system environment that accomplish the request. For example, the framework may issue statements to define the structure of a database, access information from the database, and / or manipulate information within the database.
Owner:RPX CORP
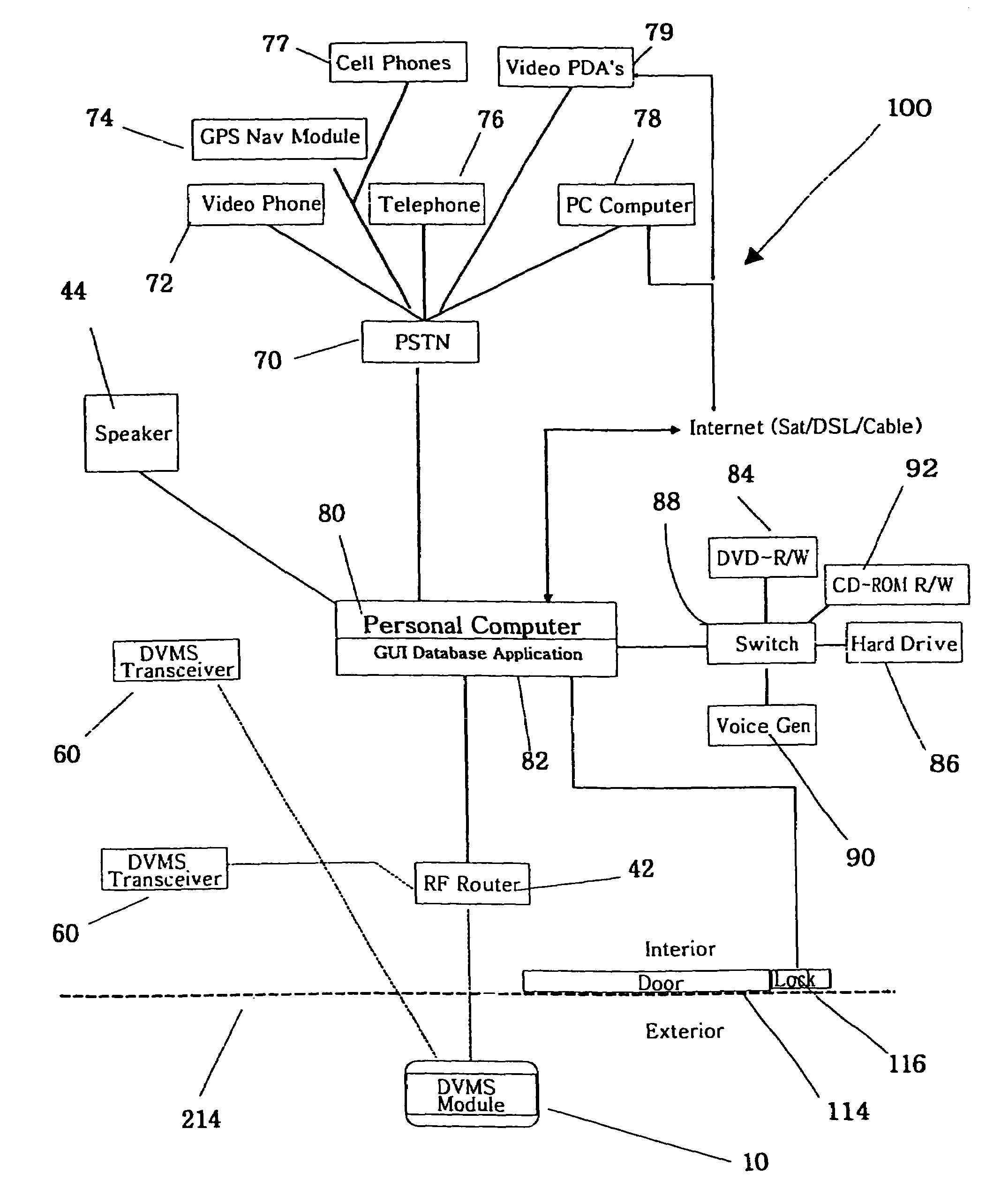
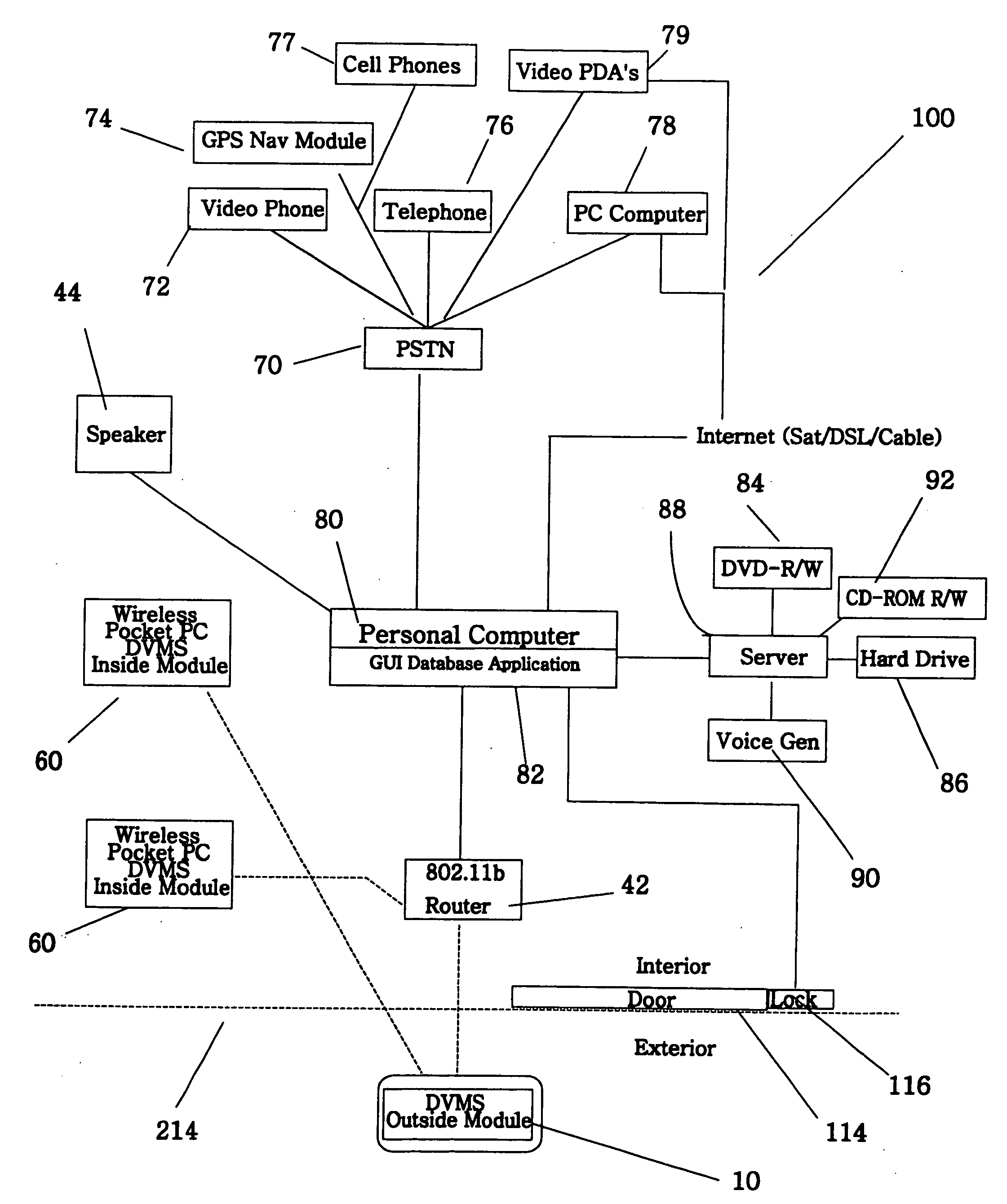
Automated audio video messaging and answering system
ActiveUS7193644B2Weaken energyReduce energy consumptionTelephonic communicationTwo-way working systemsProximity sensorDatabase application
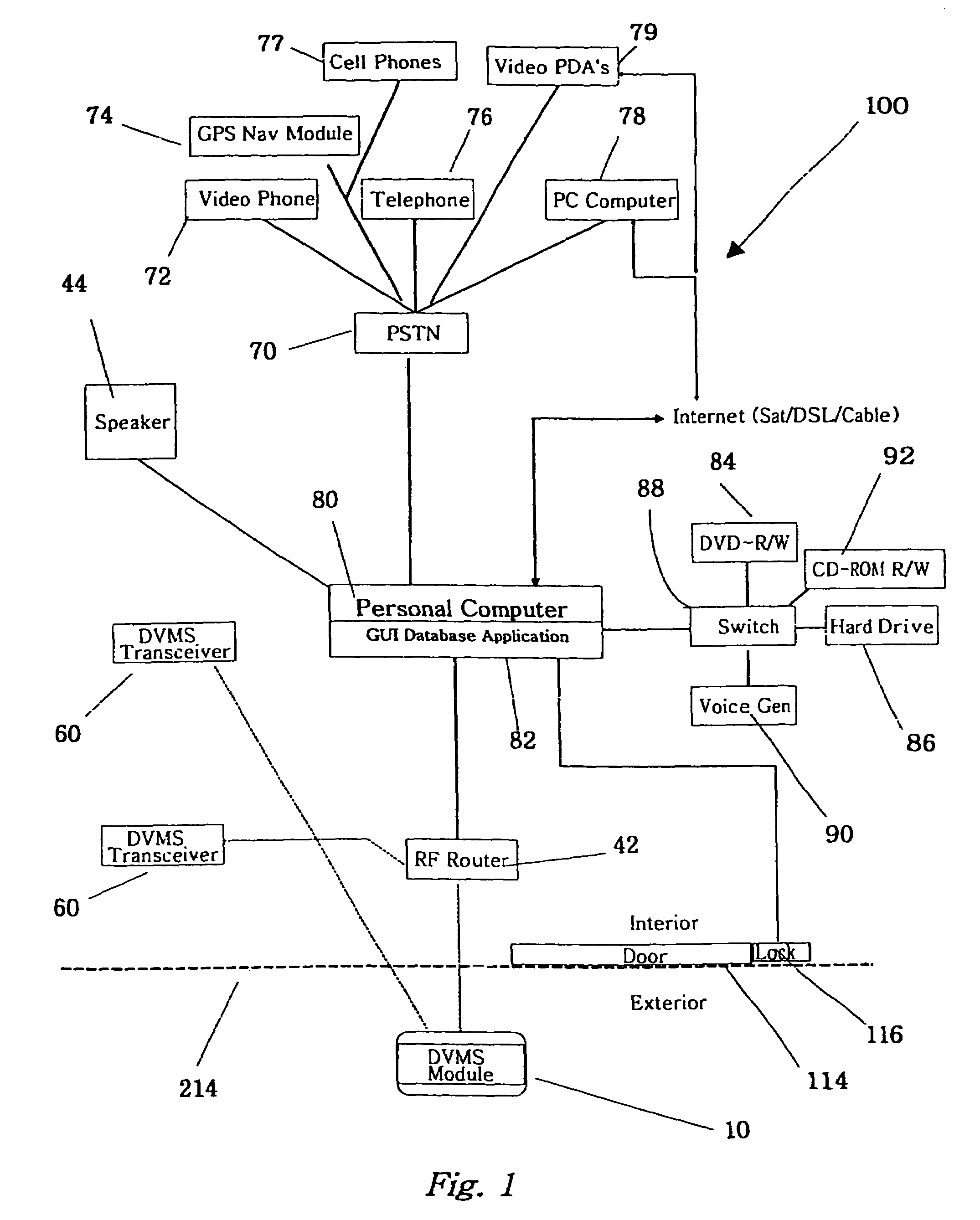
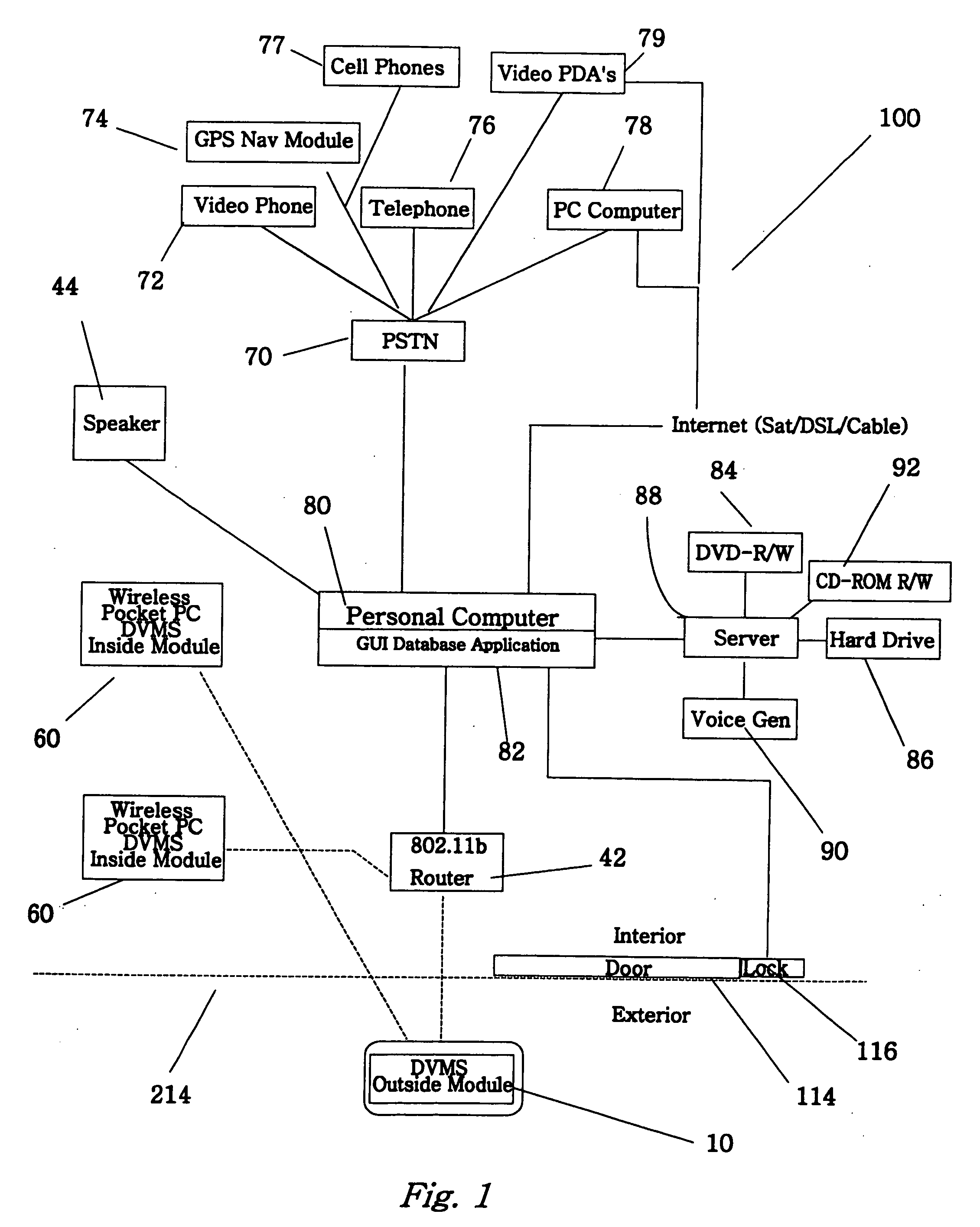
The invention is an audio-video communication and answering system that synergistically improves communication between an exterior and an interior of a business or residence and a remote location, enables messages to be stored and accessed from both locally and remotely, and enables viewing, listening, and recording from a remote location. The system's properties make it particularly suitable as a sophisticated door answering-messaging system. The system has a DVMS module on the exterior. The DVMS module has a proximity sensor, a video camera, a microphone, a speaker, an RF transmitter, and an RF receiver. The system also has a computerized controller with a graphic user interface DVMS database application. The computerized controller is in communication with a public switching telephone network, and an RF switching device. The RF switching device enables communication between the DVMS module and the computerized controller. The RF switching device can be in communication with other RF devices, such as a cell phone, PDA, or computer.
Owner:SB IP HLDG LLC
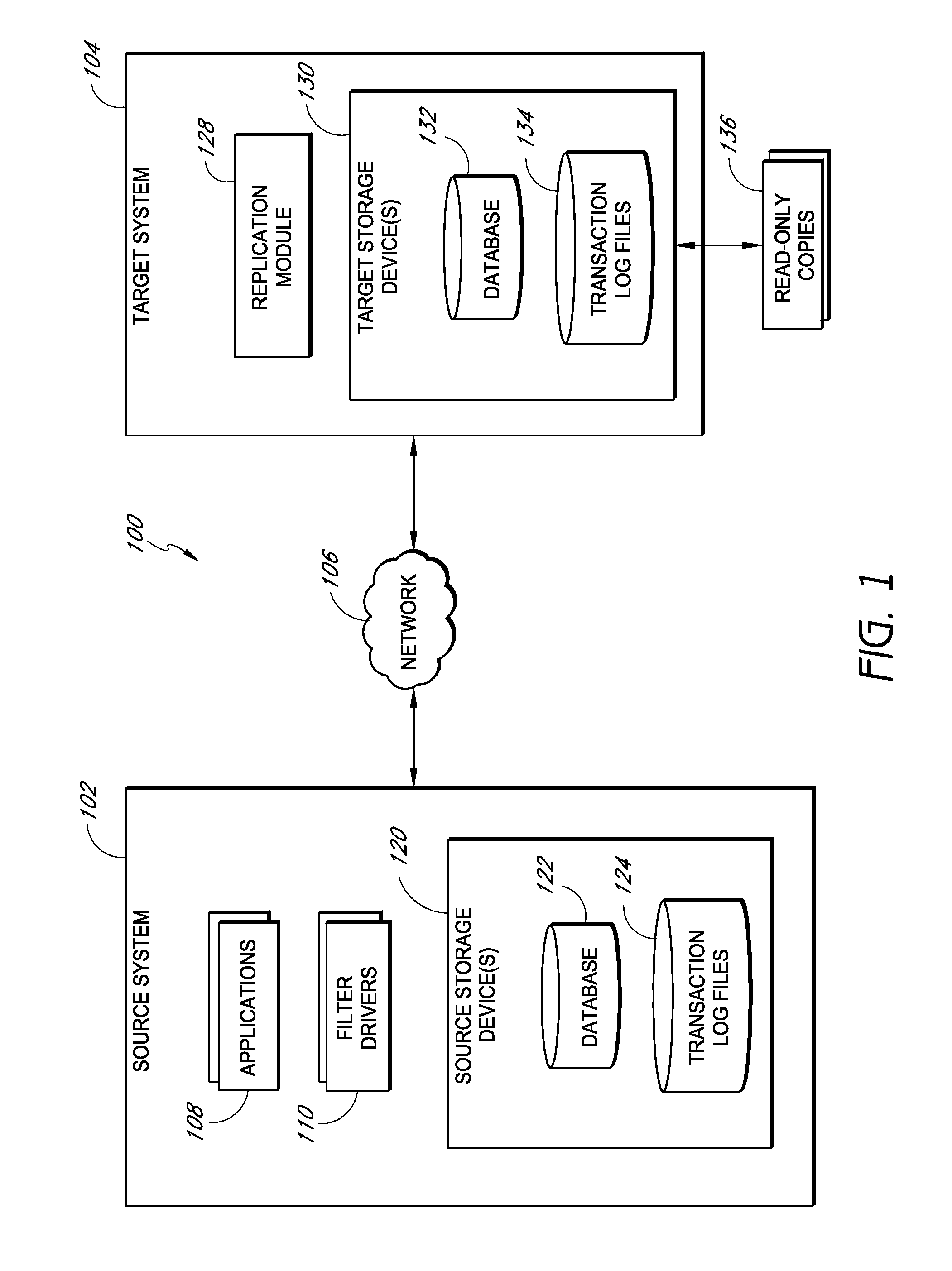
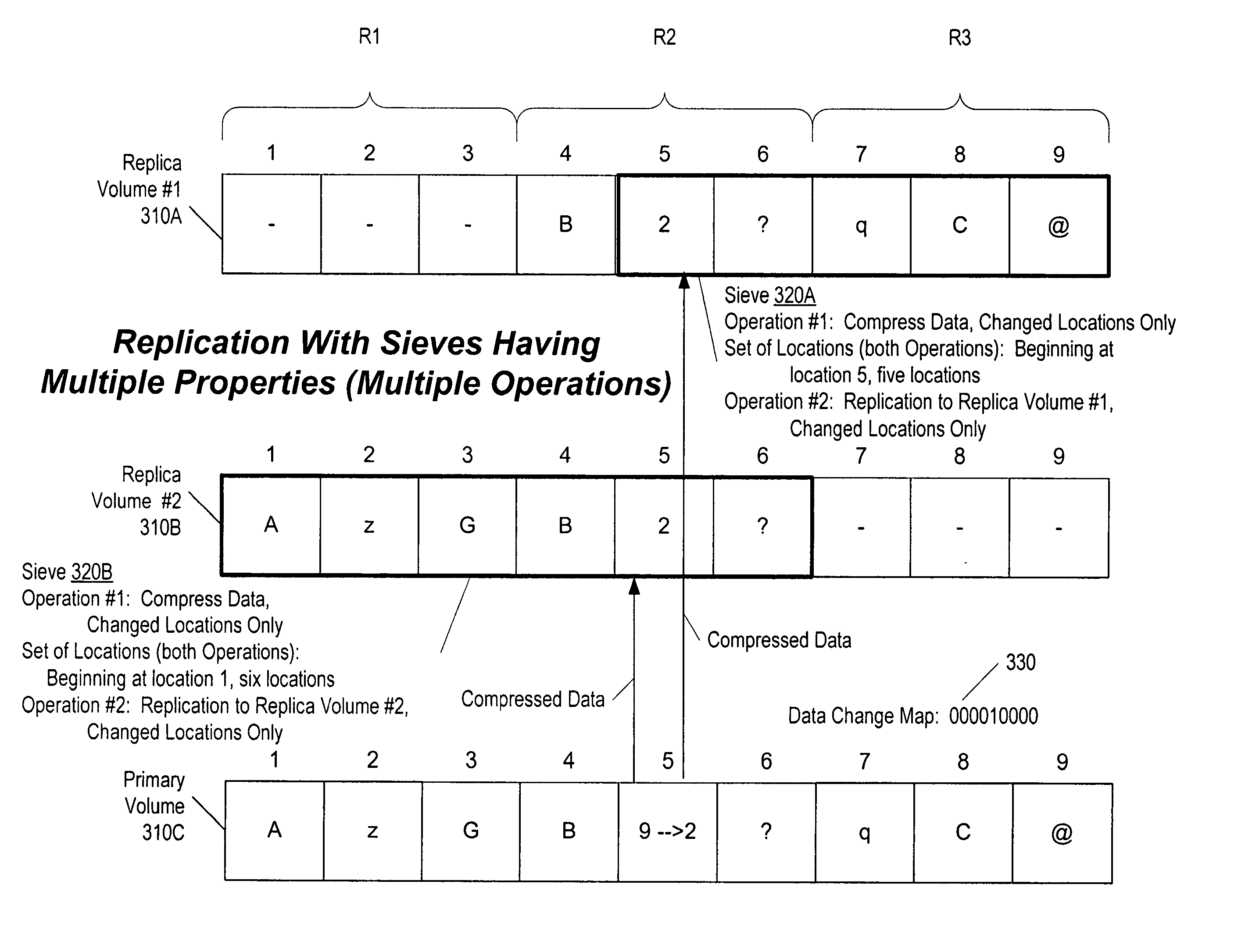
Systems and methods for managing replicated database data
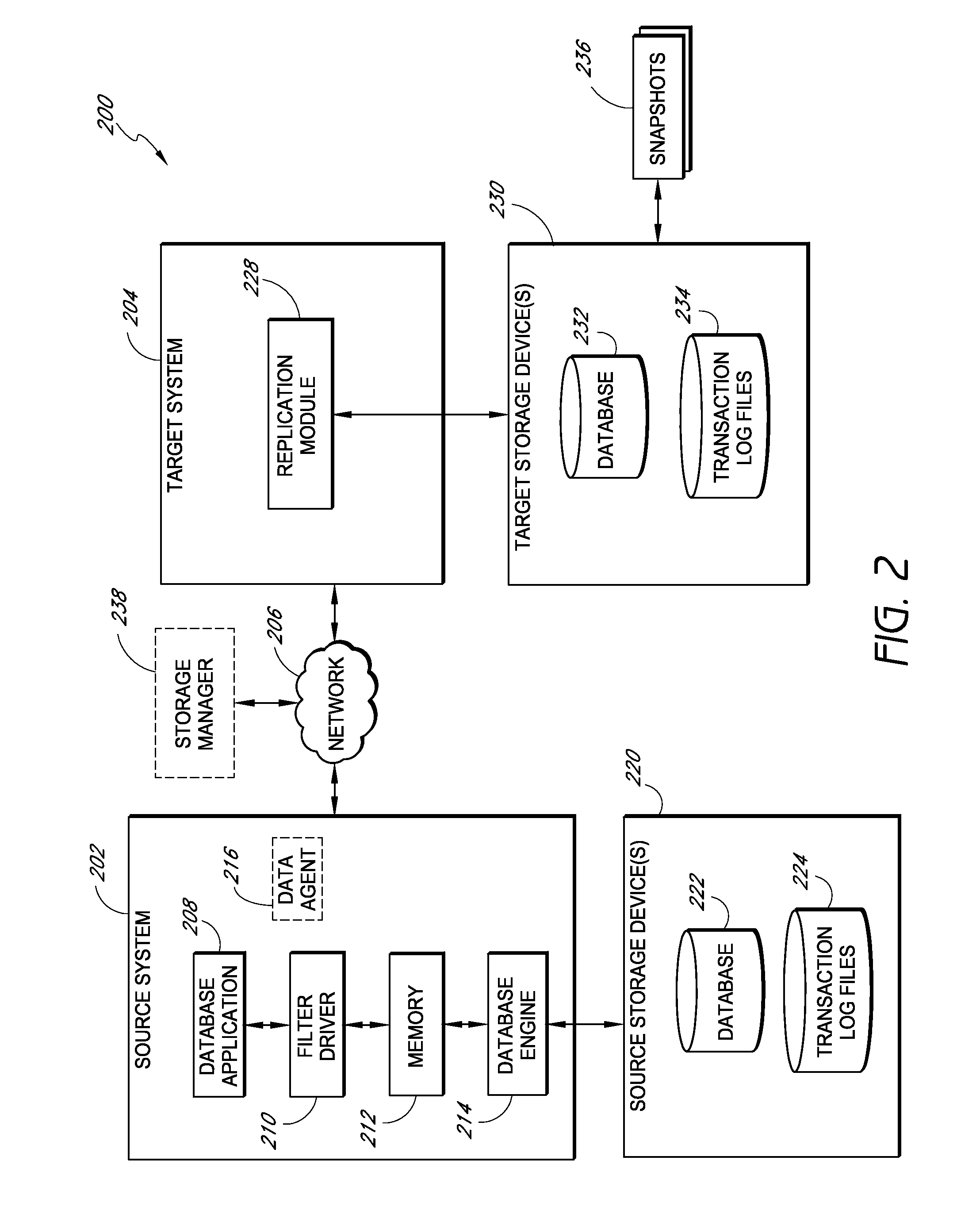
ActiveUS20100145909A1Reduce memory requirementsImprove performanceError detection/correctionDigital data processing detailsDatabase applicationApplication software
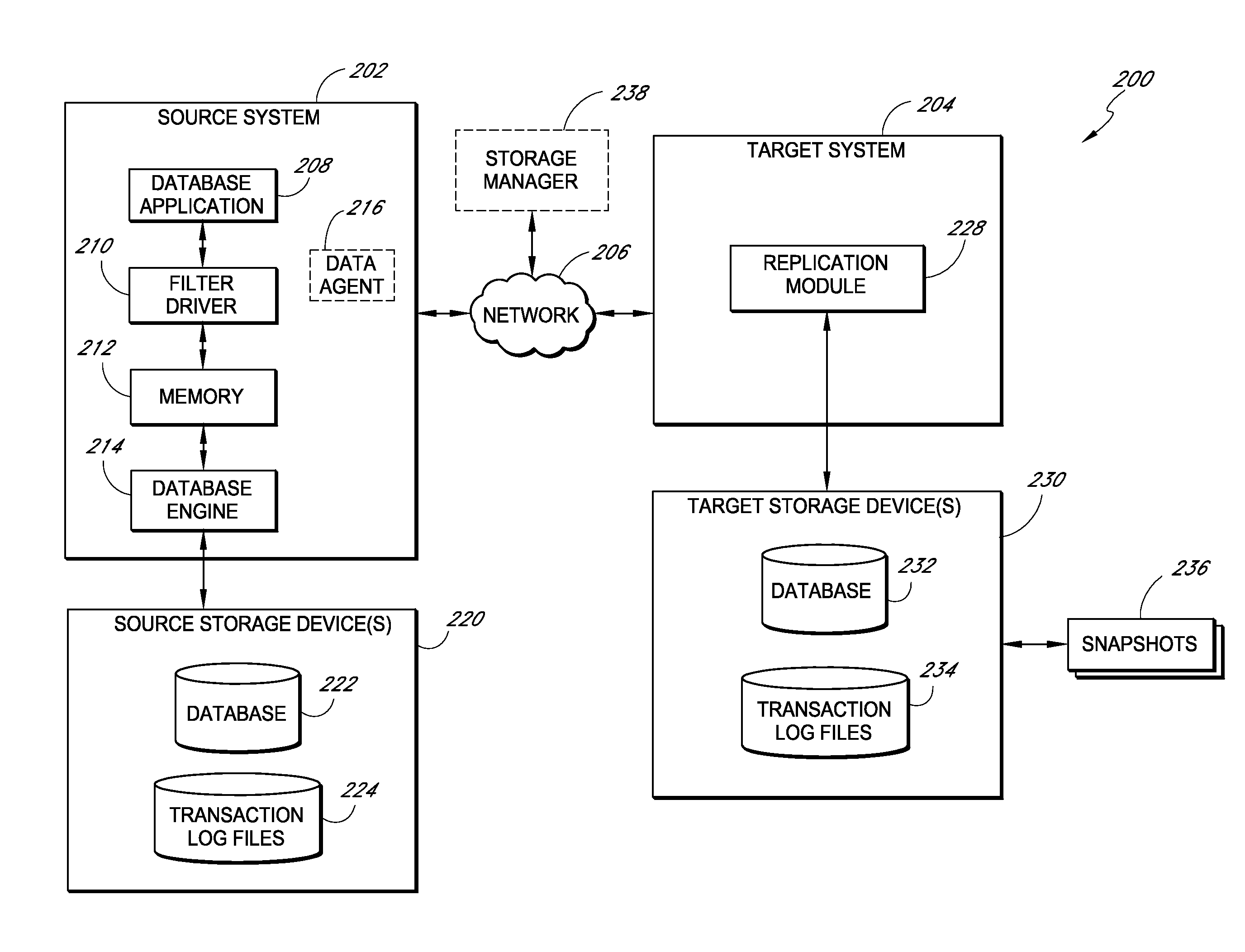
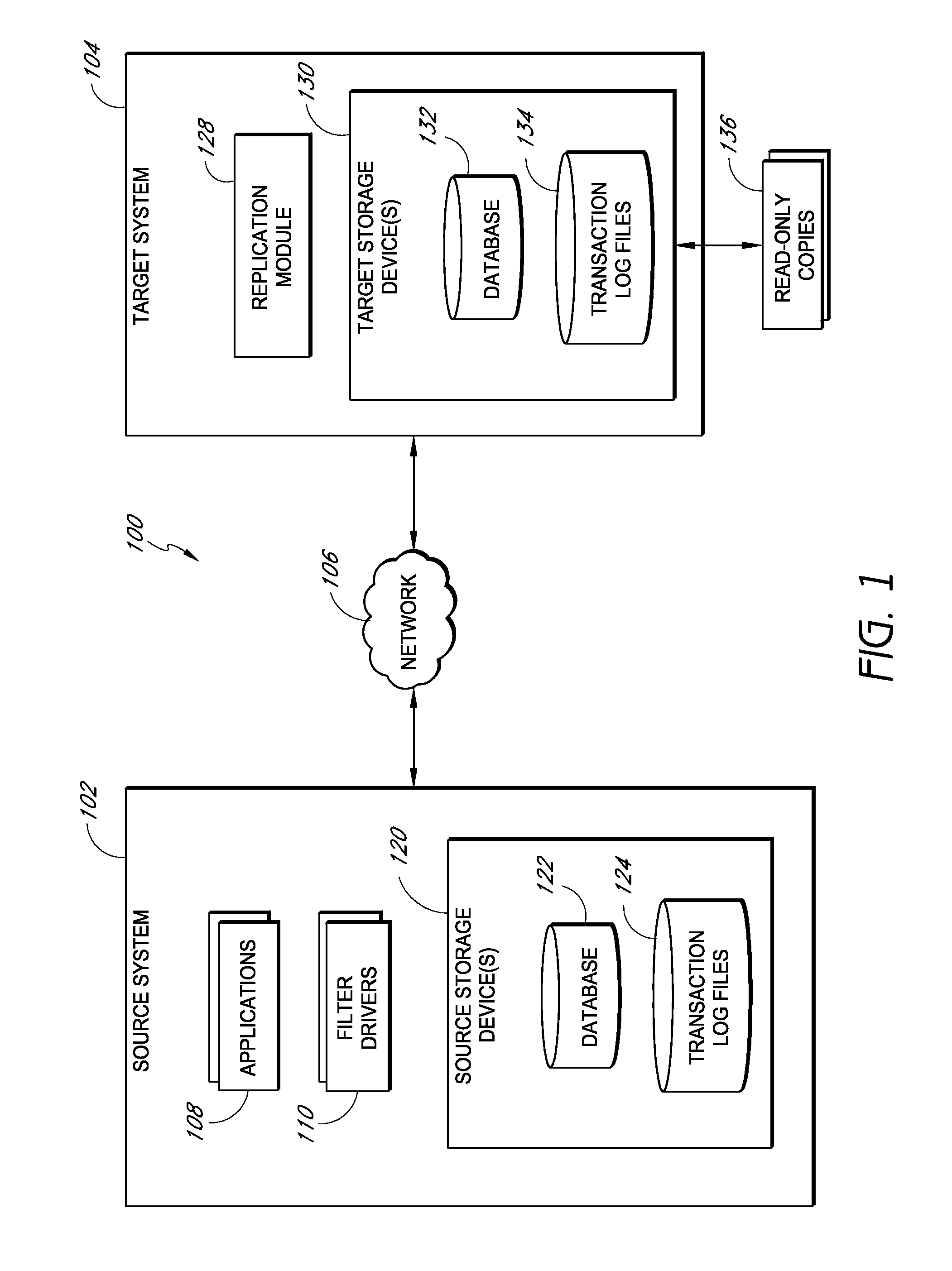
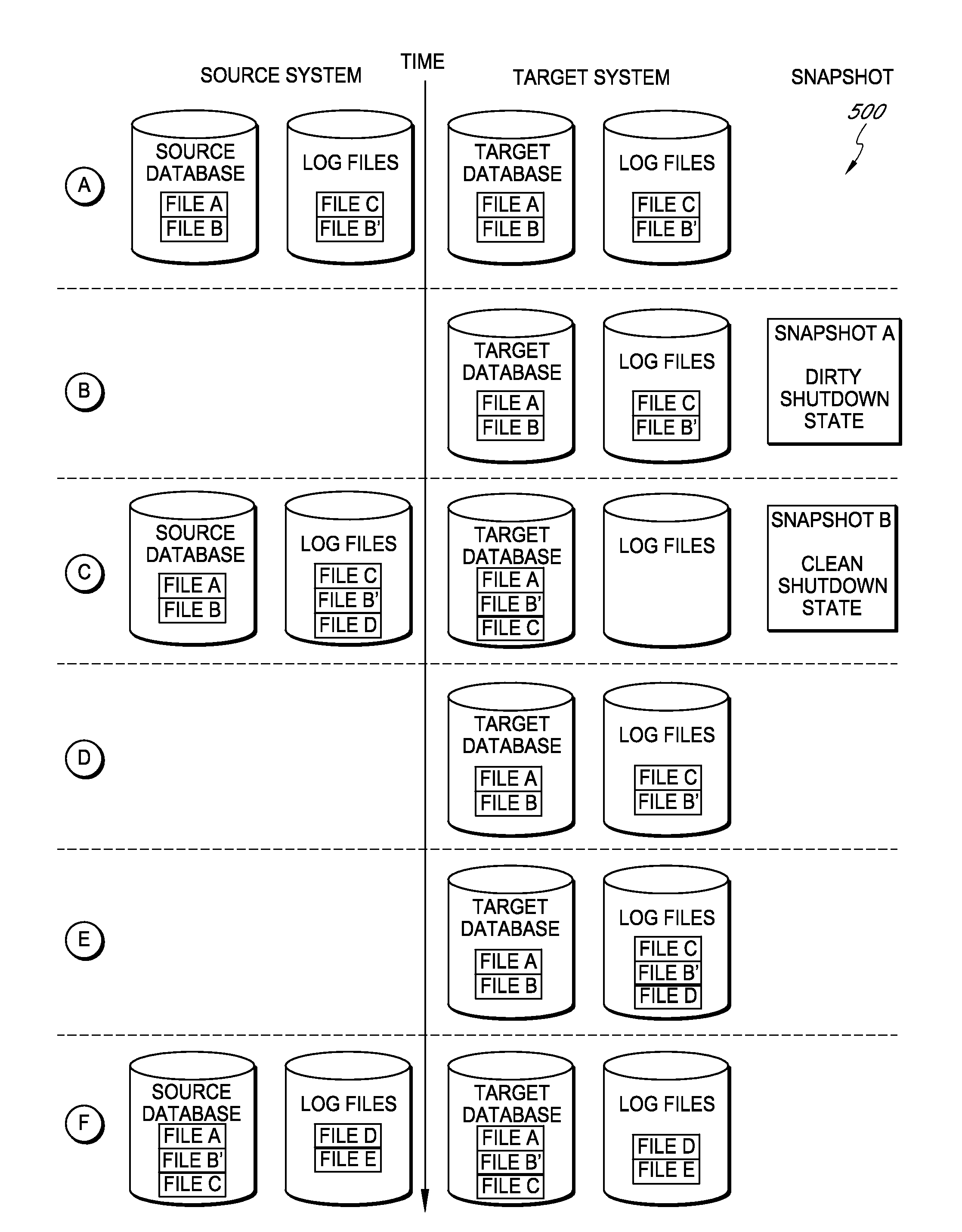
Systems and methods for replicating database data and generating read-only copies of the replicated data in a clean shutdown state. For example, systems can include a tracking module (e.g., a filter driver) that monitors transactions from a database application to a source storage device to generate log entries having at least one marker indicating a known good state of the application. The systems further include a computer coupled to a target storage device comprising a database and log files. The computer processes the transactions, based on the log entries, to replicate data to the target storage device; performs a first snapshot on data stored in the database and log files; replays into the database data stored in the log files; performs another snapshot on the database; and reverts the database back to a state in which the database existed at the time of the first snapshot.
Owner:COMMVAULT SYST INC
Method and apparatus for tracking objects and people
InactiveUS6933849B2Robust designEasy to operateMemory record carrier reading problemsCo-operative working arrangementsMonitoring systemThe Internet
An object locating, identifying, tracking, and surveillance system, denoted the Assets Locating, Tracking, and Surveillance System (ALTSS), is provided for managing physical objects and evidence in environments such as police departments, law offices, and the Courts. ALTSS employs radio frequency identification (RFID) technology, computer programming and database applications, networking technologies, and hardware elements. ALTSS may locate and track physical evidence, merchandise, information carriers like files, folders or individual pieces of paper, and people, under certain conditions, in near-real time. It may be configured as part of a local area network, a wide area network, or the Internet. ALTSS may employ exemplary components such as RFID transponders, scanners, strategically located antennas and computers to facilitate tracking of objects and people as needed. Any number of users having access privileges and connected to the network may access ALTSS directly or remotely via the Internet to locate and track evidence or objects.
Owner:AUTOMATED TRACKING SOLUTIONS
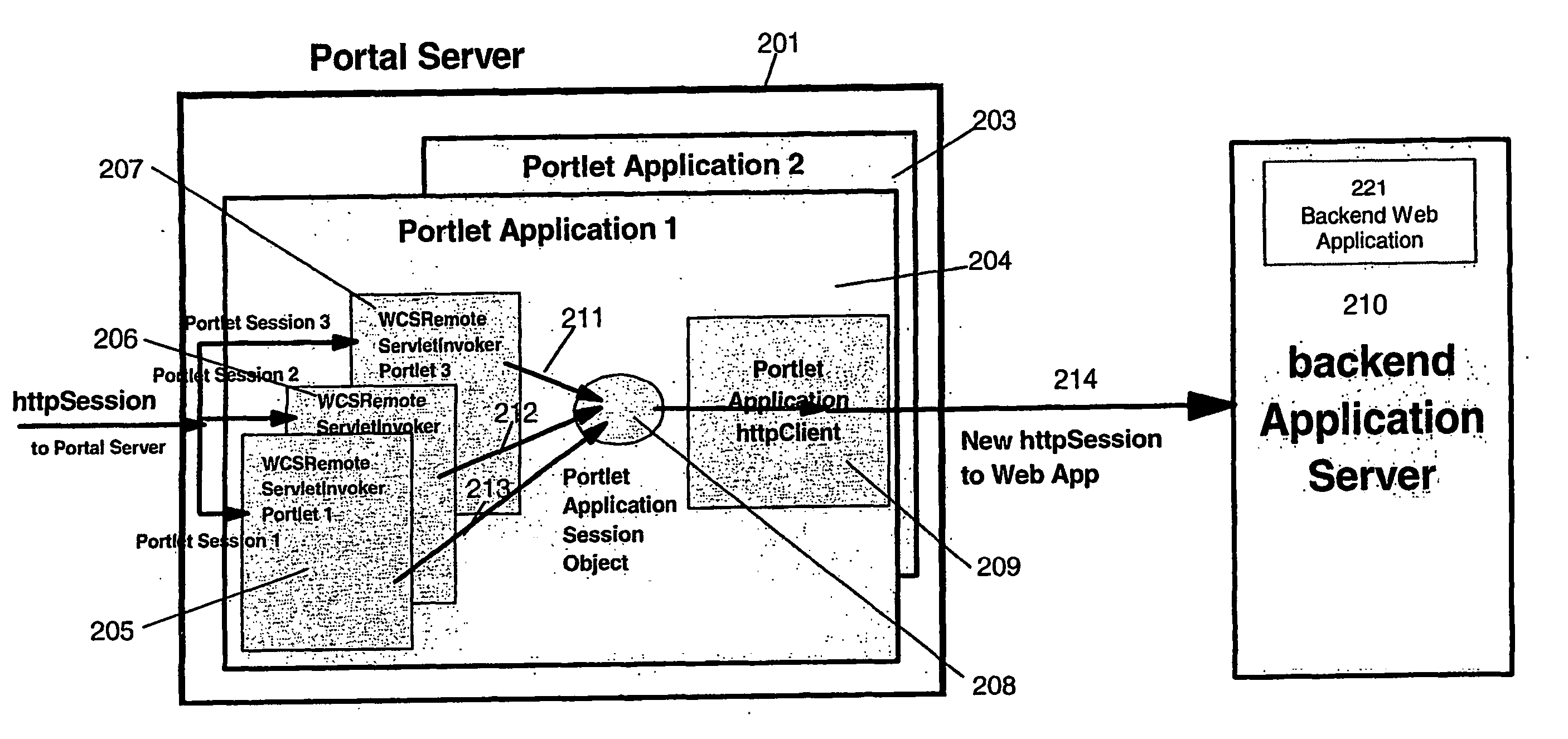
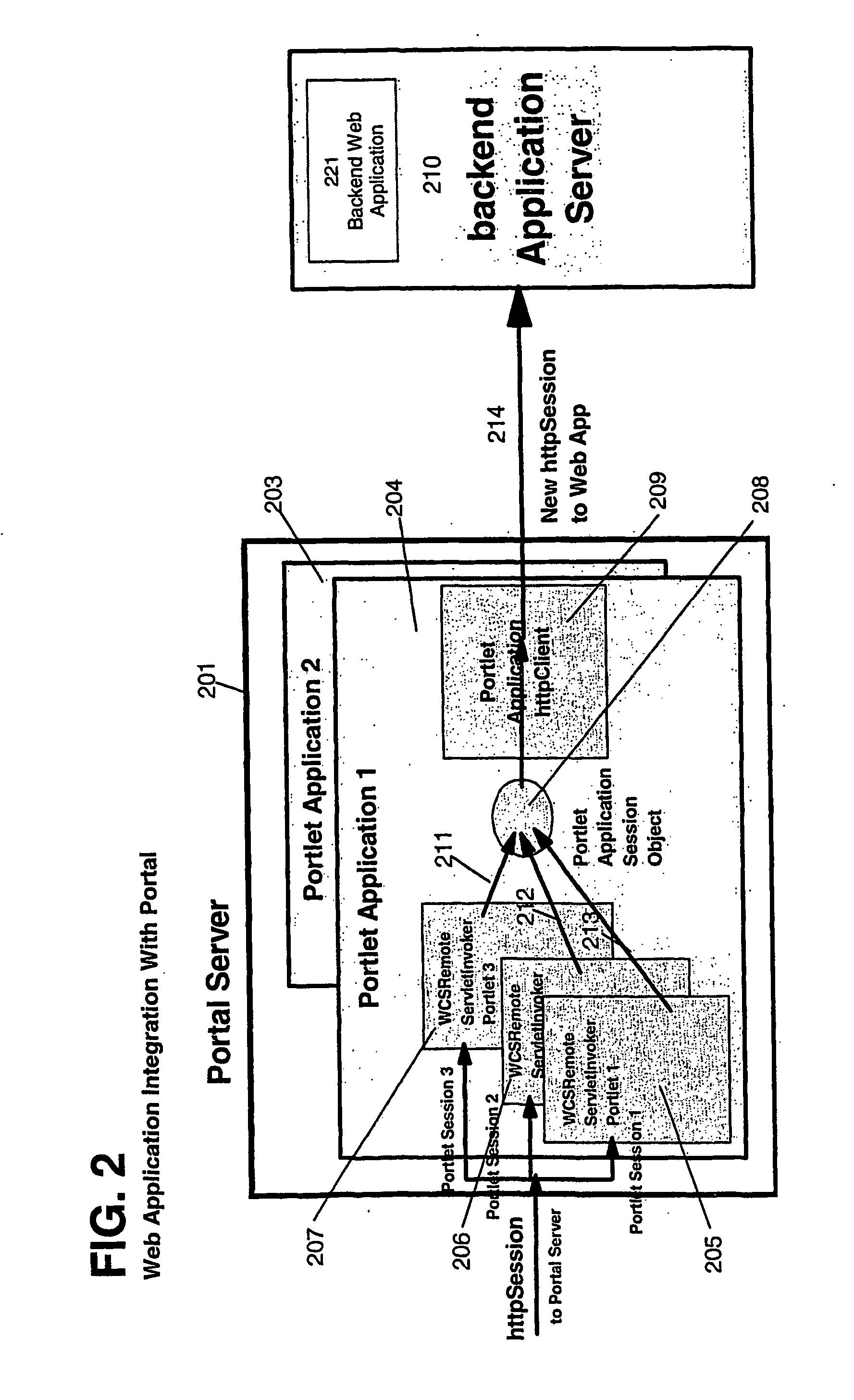
Method and apparatus for using business rules or user roles for selecting portlets in a web portal
InactiveUS20060235935A1Improve the level ofDigital data protectionMultiple digital computer combinationsPortletApplication software
An embodiment of the invention includes means to select portal resources (portlets, page and page groups) as displayed to a user based on pluggable rules engine; a rules database; and a portlet application aggregation engine which applies rules to select and display selected portlets, pages and page groups to a user.
Owner:IBM CORP
Automated audio video messaging and answering system
ActiveUS20050285934A1Facilitate communicationWide bandwidthTwo-way working systemsDigital videoAudio Media
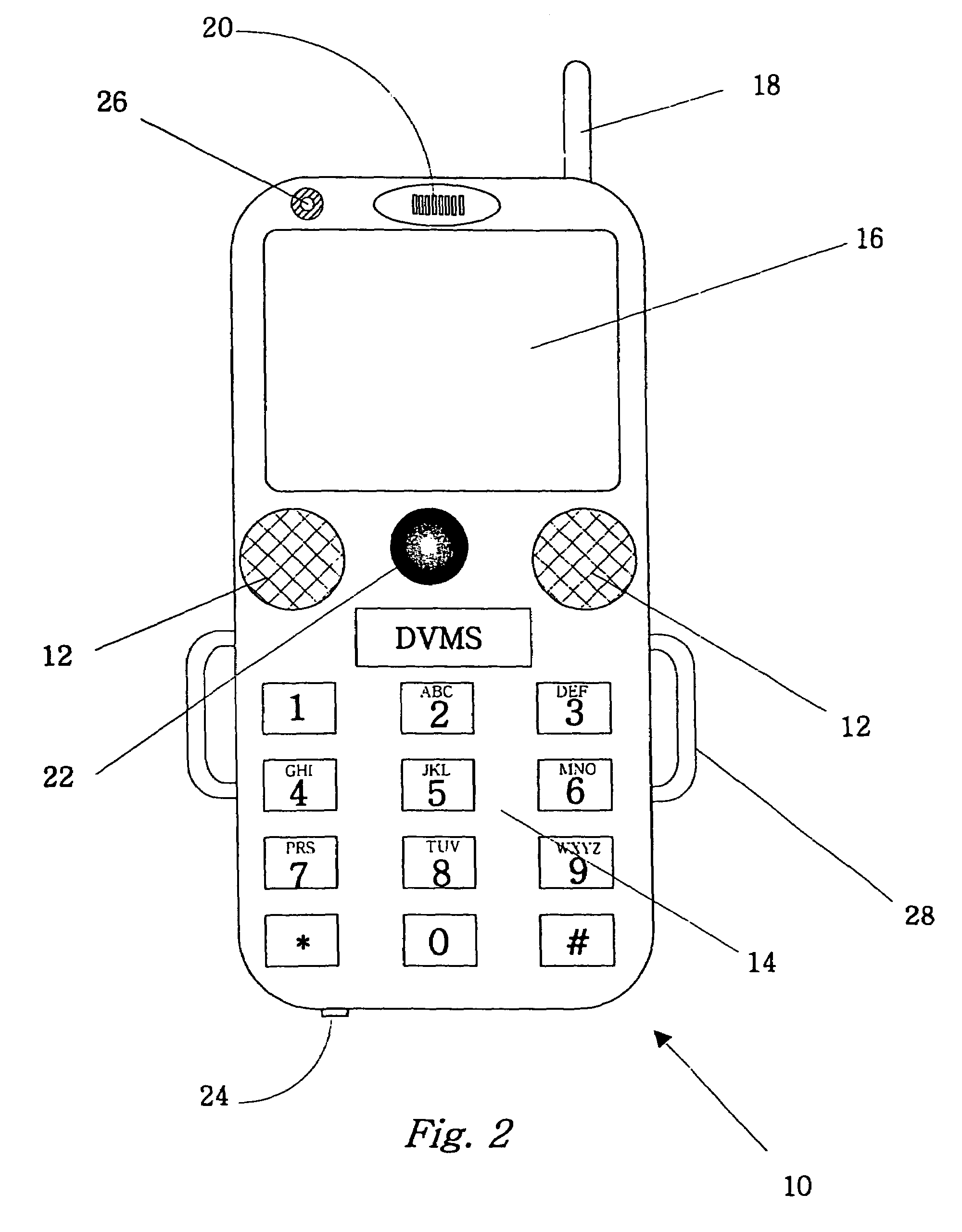
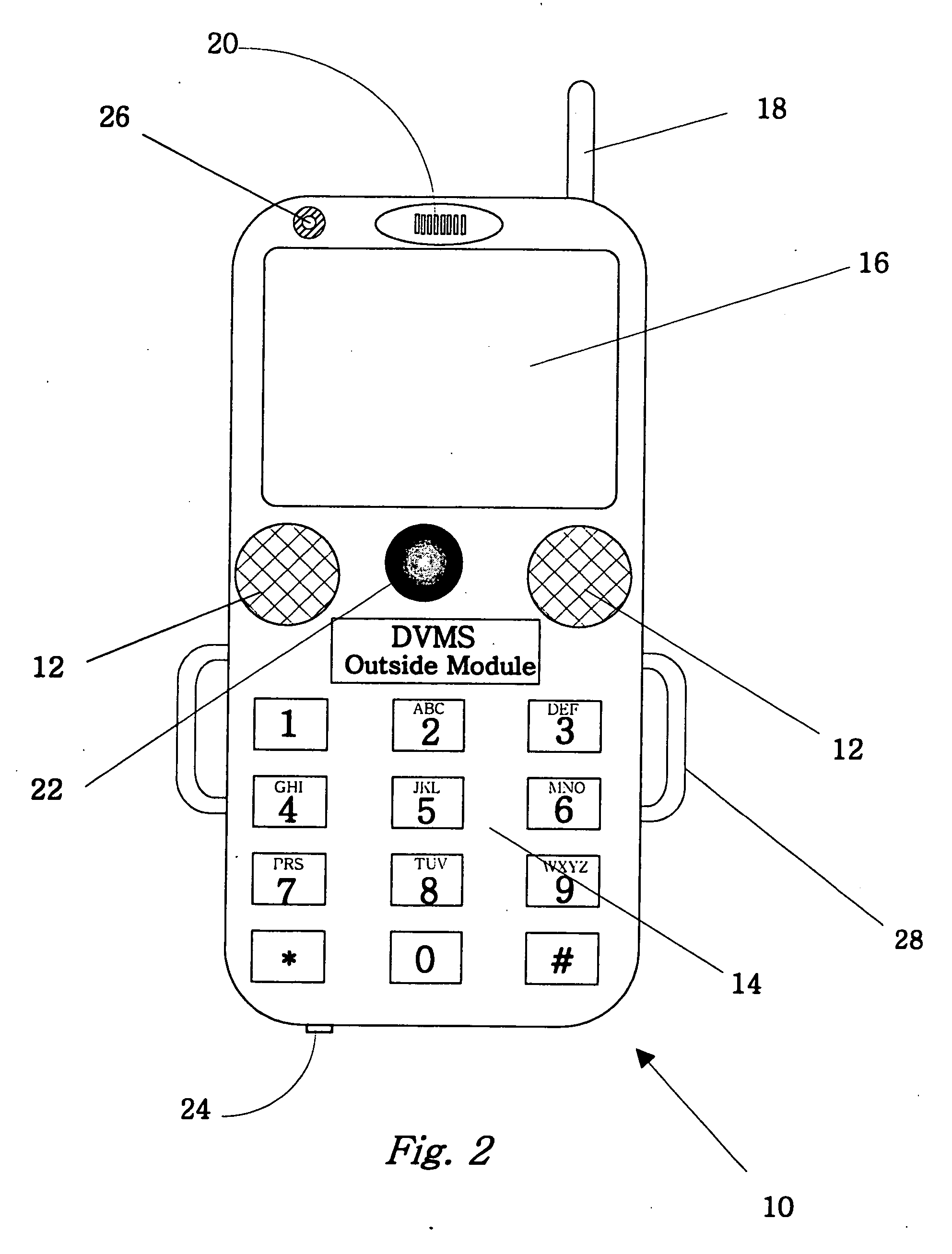
The invention is an audio-video communication and answering system, where system's properties make it particularly suitable as a Digital Video Messaging System for, amongst other things, answering the door. The elements of the system are a DVMS outside module that is a wireless pocket PC with a proximity sensing, a video camera, a microphone, a speaker, a digital transmitter, a digital receiver, and a keypad; a computerized controller that is a personal computer with components for plaving and recording video and audio media; a DVMS inside module having a screen, a microphone, a speaker, a digital transmitter, a digital receiver, and a keypad; a wireless mode; and a DVMS database application with a graphic user interface. The computerized controller is in communication with a public switching telephone network enabling communication with remote peripheral devices, such as a cell phone, PDA, or computer. The system is based on the Microsoft Windows® Mobile 802.11b to coordinate communication between elements. The database application coordinates responses to prompts and events. The proximity sensor activates the system when the sensor detects the visitor's presence. This then starts a series of prompts and interaction prescribed by the application. The system includes an electrically actuated lock that can be actuated through a code entry or remotely. The system enables a visitor to communicate with an occupant either offsite or onsite, where the visitor never knows the occupant's location, unless the occupant discloses his location.
Owner:SB IP HLDG LLC
System for protecting database applications from unauthorized activity
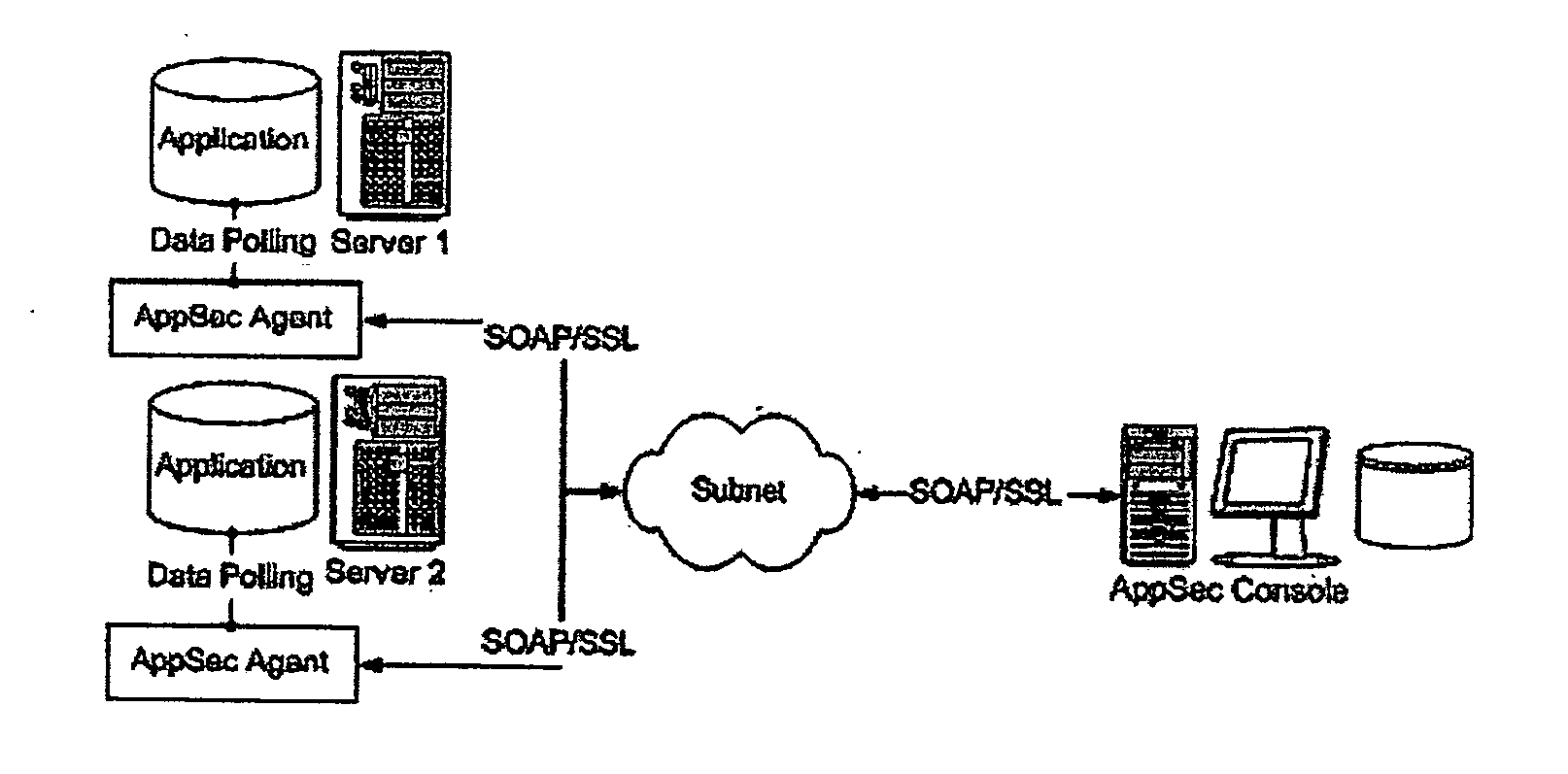
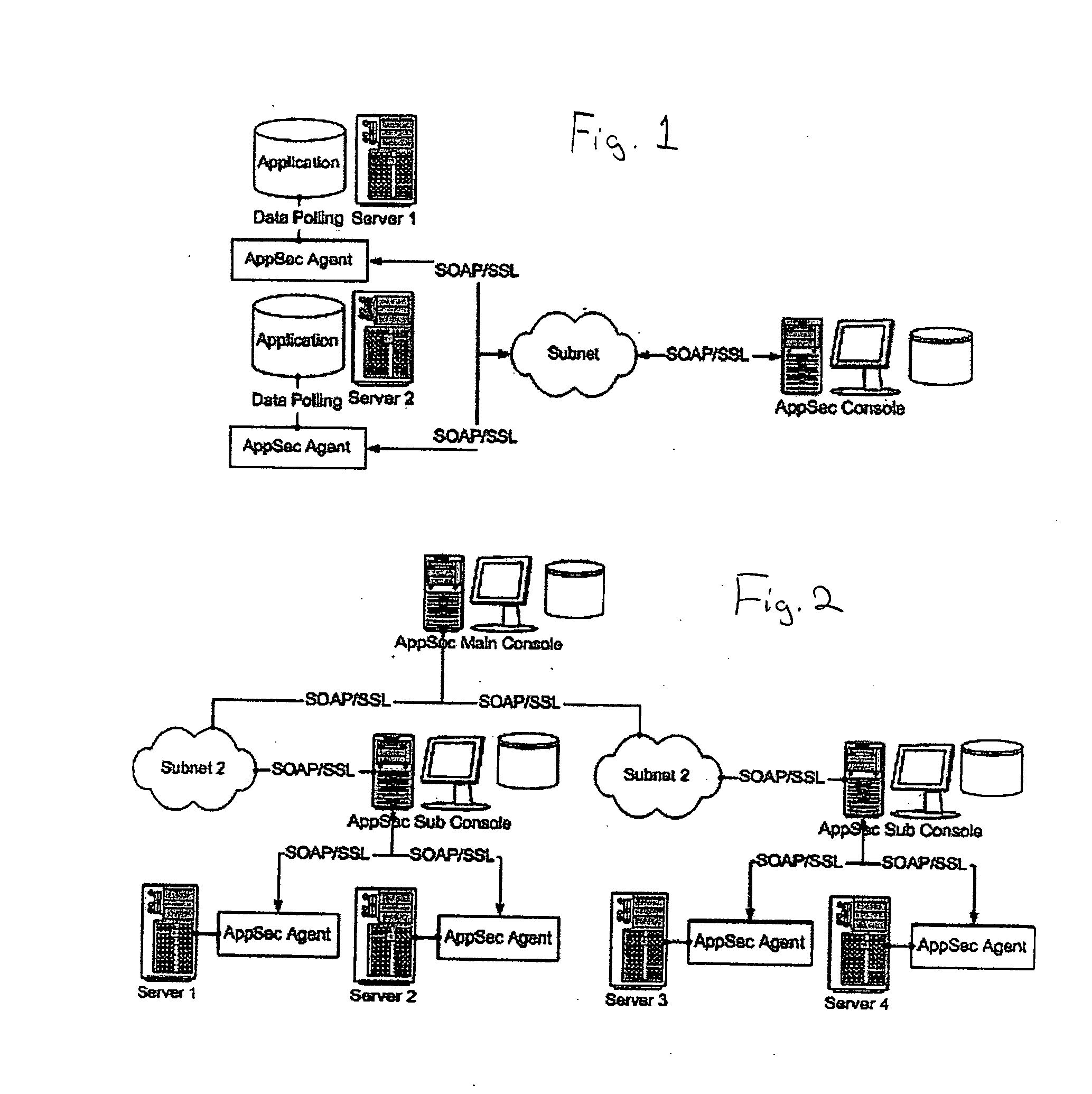
InactiveUS20050203921A1Easy to configureEasy to monitorDigital data processing detailsPlatform integrity maintainanceDatabase applicationComputer science
A method for protecting database applications including analyzing the activity on the server, analyzing the response from the server, and blocking malicious or unauthorized activity. Commands are analyzed for suspicious or malicious SQL statements or access to unauthorized data. Server responses are monitored for suspicious results likely to have occurred from a successful attack or unauthorized access to data. When malicious or unauthorized activity occurs, activity by the source is blocked or an alert is issued.
Owner:NEWMAN AARON CHARLES +1
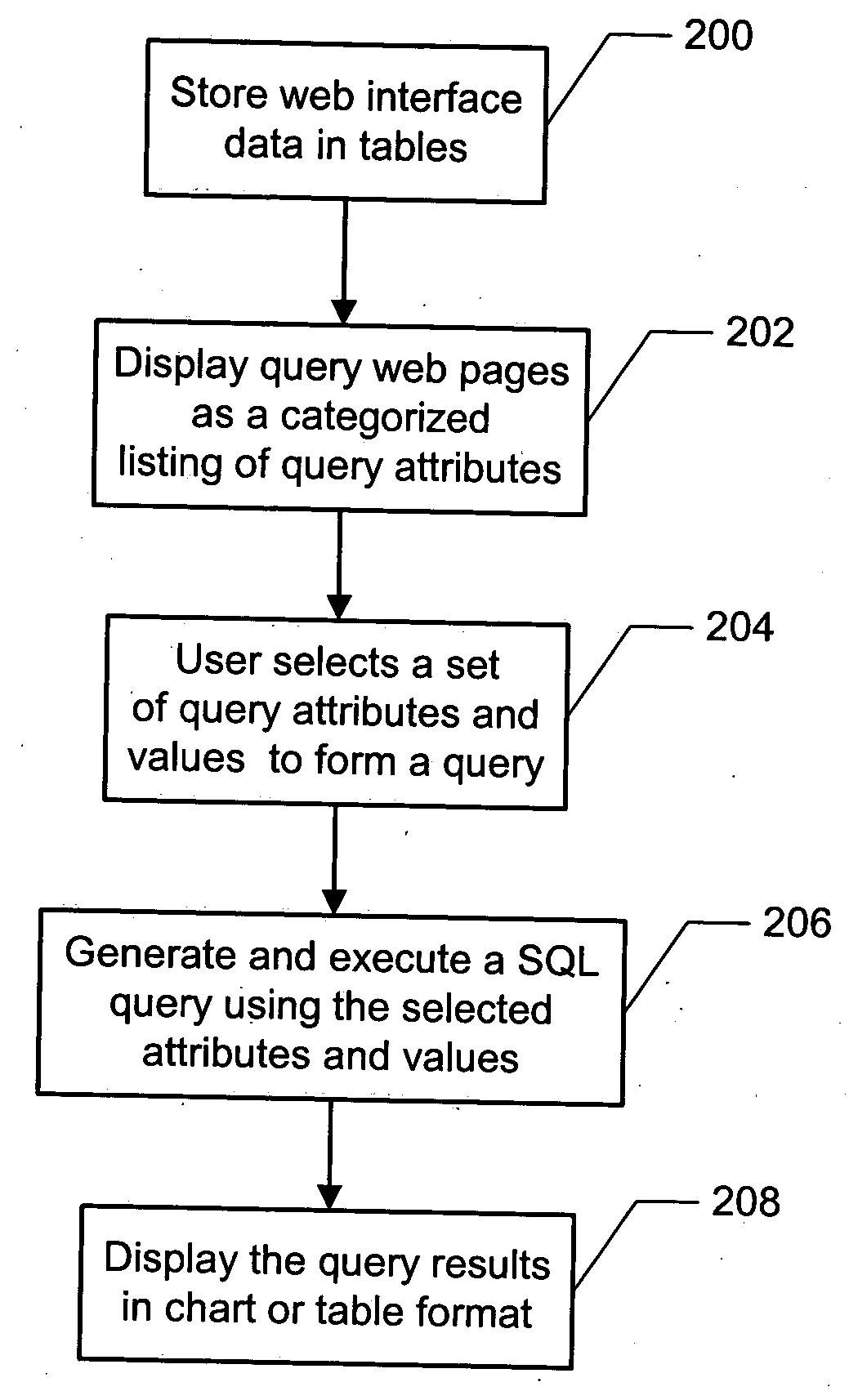
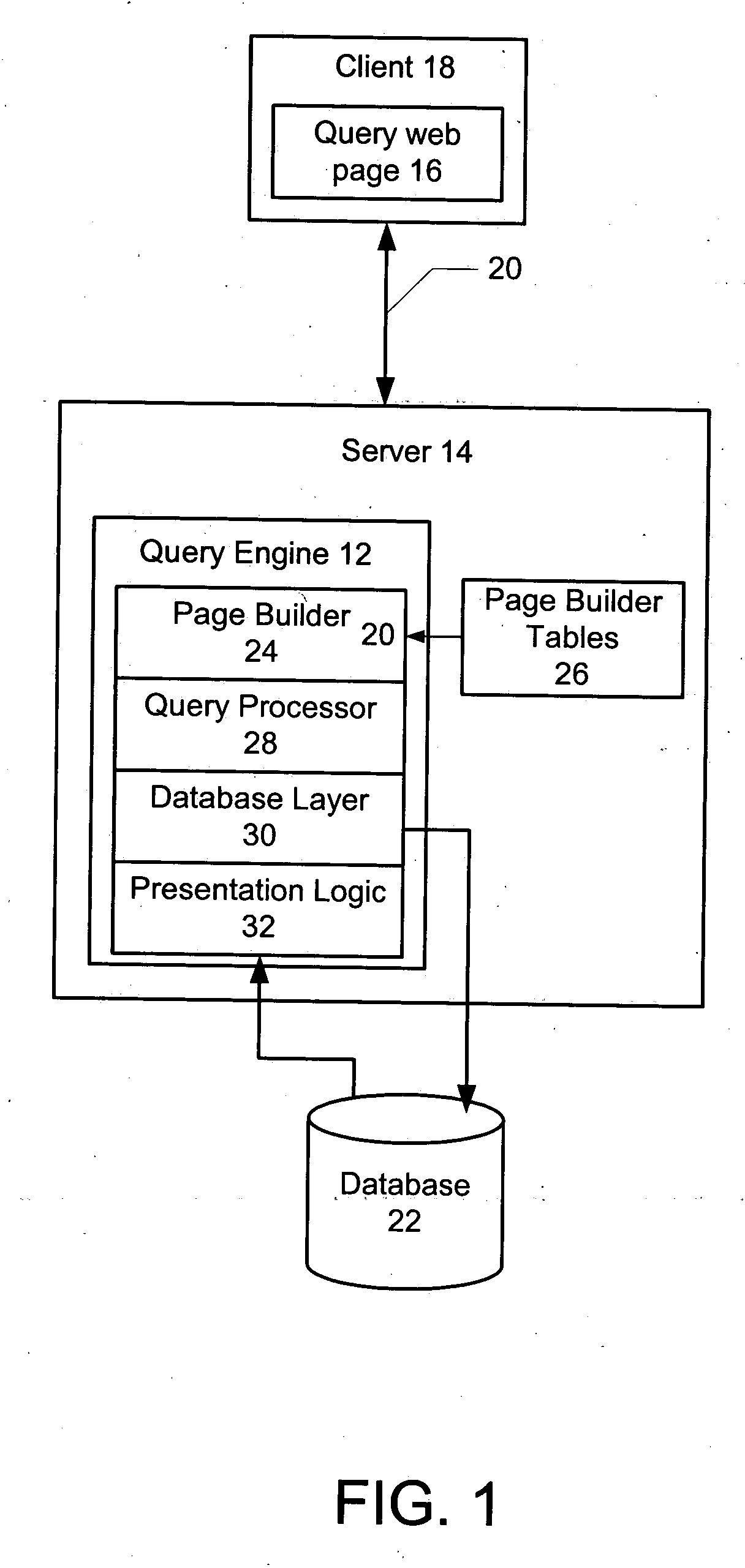
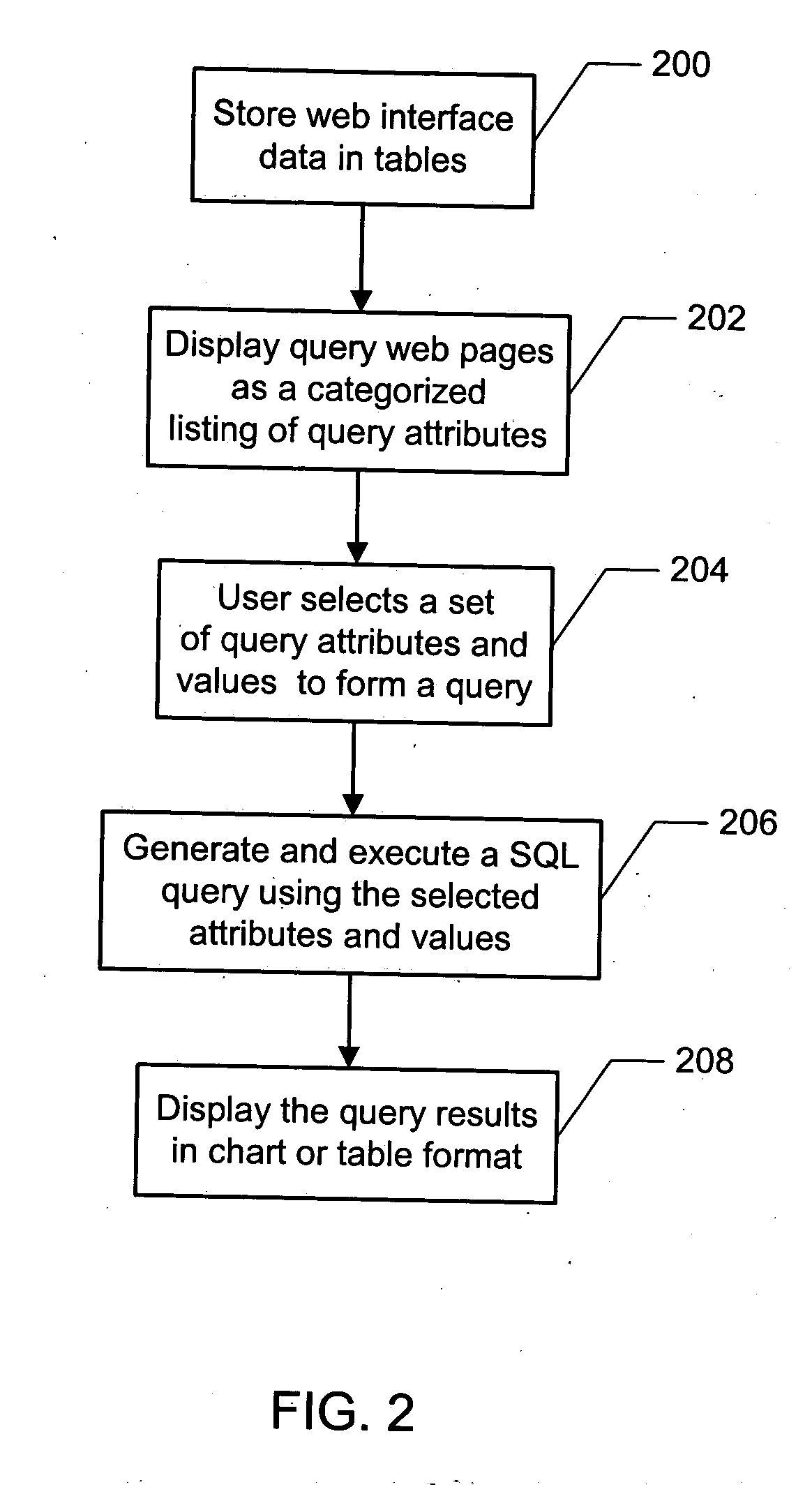
Dynamic graphical user interface and query logic SQL generator used for developing Web-based database applications
InactiveUS20050102284A1Improve scalabilityMinimal investmentDigital data information retrievalSpecial data processing applicationsGraphicsGraphical user interface
A method and system for dynamically generating database queries is disclosed. The method and system include storing web interface data, including query attributes for a database, in one more tables. The attributes are then retrieved from the tables and displayed in a graphical user interface web page for user selection. Based on the attributes selected by the user, a SQL query is dynamically generated. The method and system further include displaying results of the SQL query to the user in graphical format, thereby enabling dynamic generation of custom queries.
Owner:LSI CORPORATION
Methods and systems for runtime optimization and customization of database applications and application entities
InactiveUS6574631B1Data processing applicationsDigital data processing detailsDatabase applicationApplication software
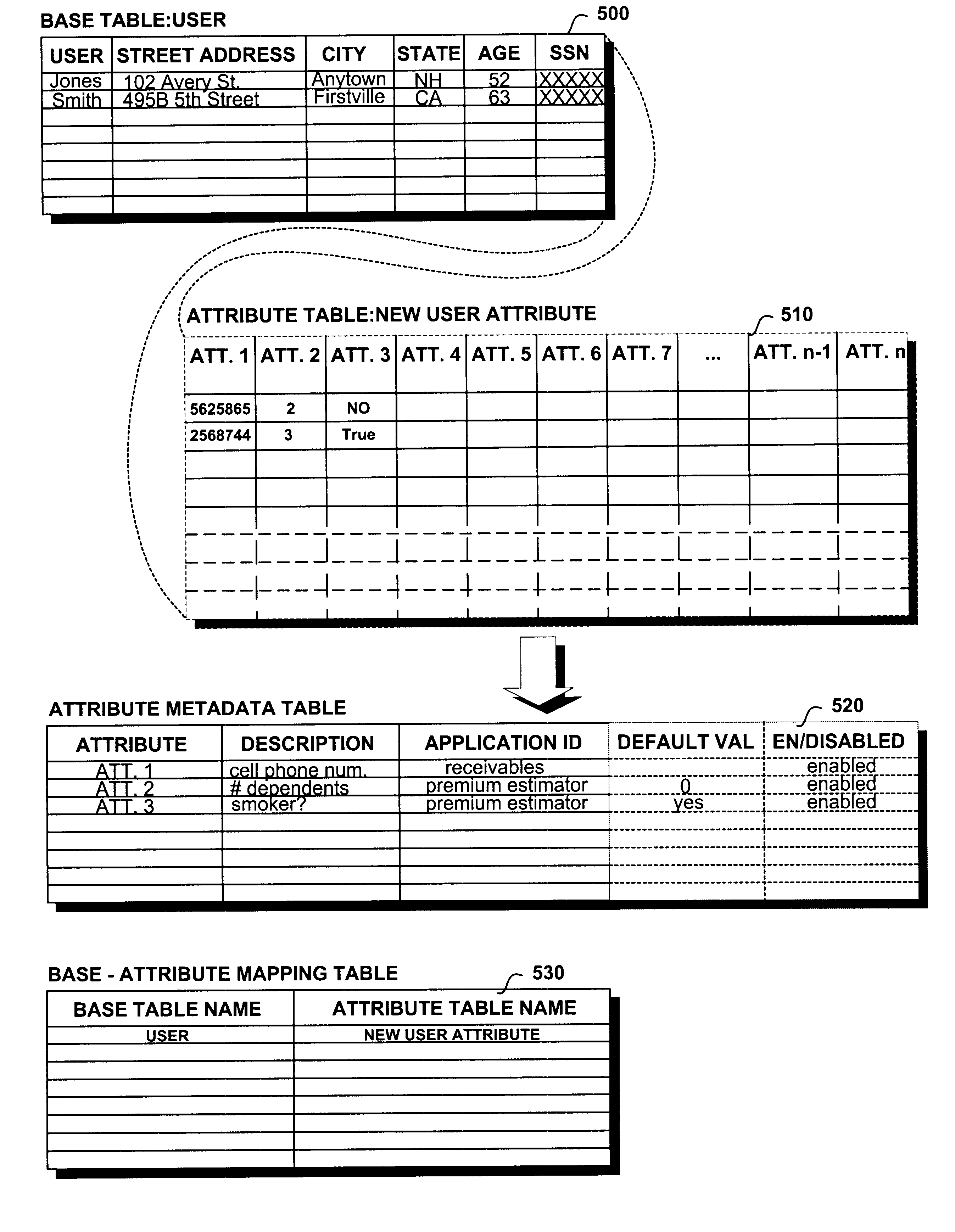
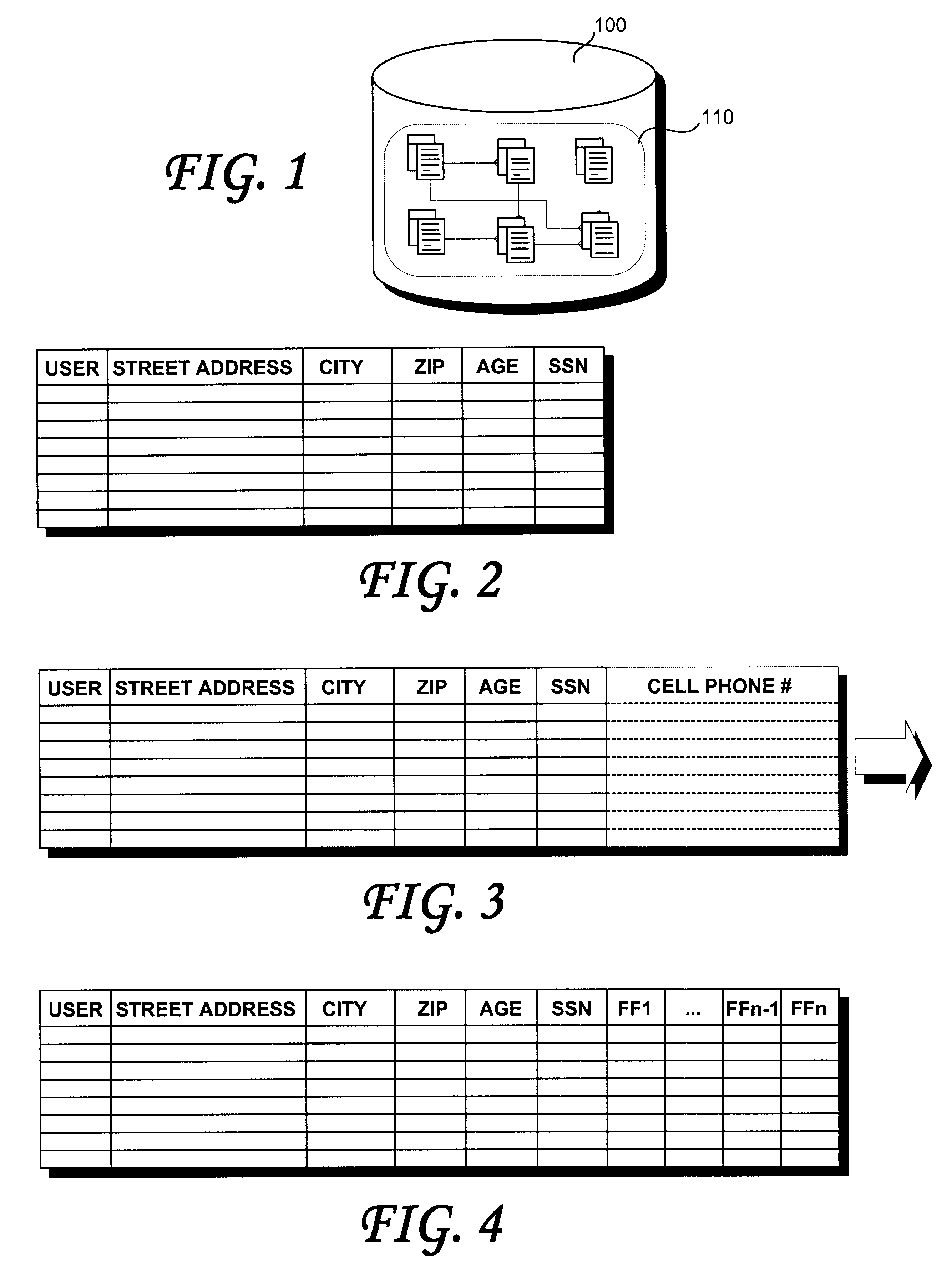
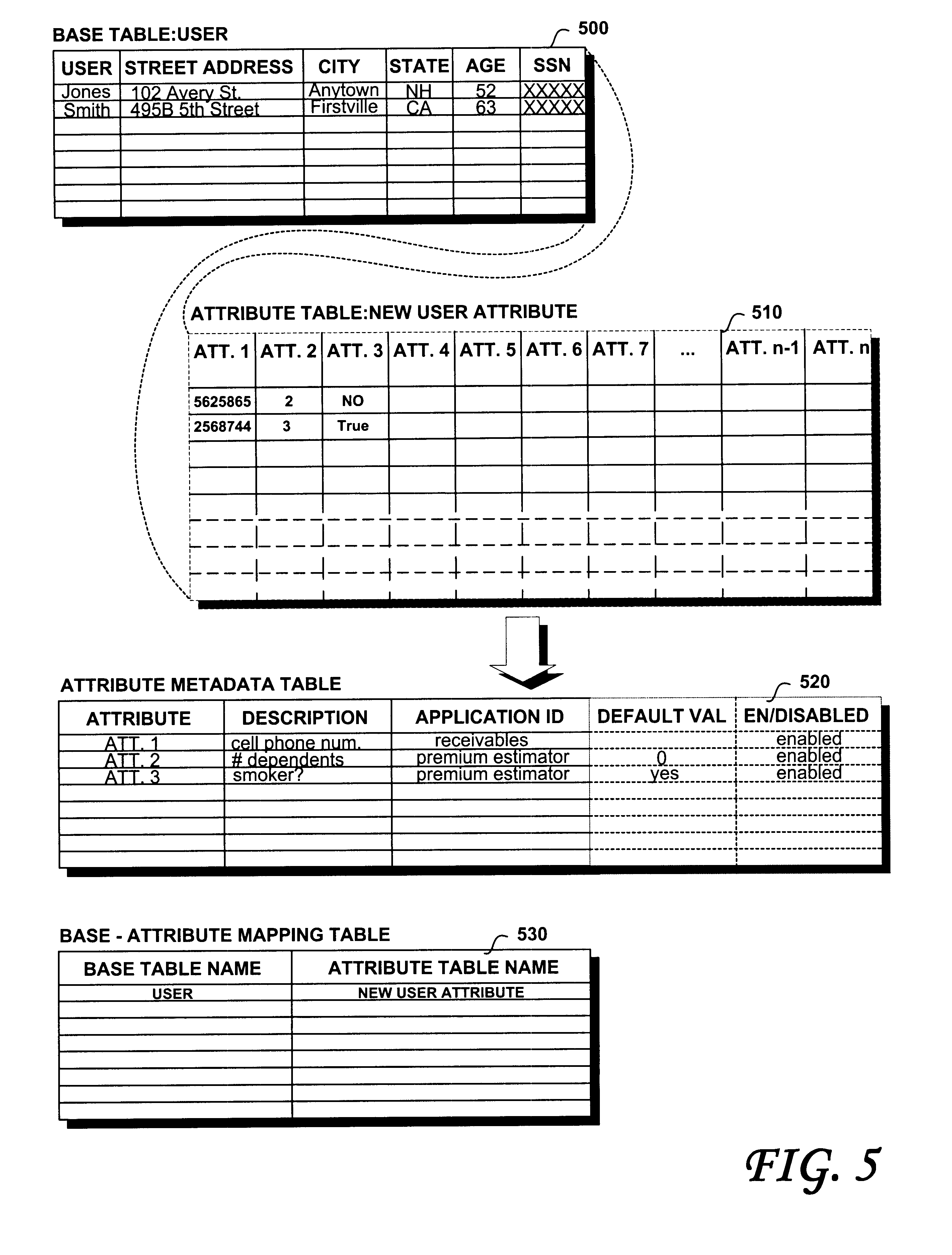
A computer-implemented method of customizing a database application at runtime includes steps of storing a value associated with a new attribute in an attribute table. The attribute table is configured as a logical extension of a base table that is configured to store values associated with a number of base attributes. The definitions of the new attributes may be stored in an attribute metadata table that is adapted to store the definition of each of the new attributes of the attribute table. A base-attribute pair may be stored in a base-attribute mapping table, the base-attribute pair mapping the name of the base table to the name of the attribute table. An extended attribute may also be stored in an extended attribute table, the extended attribute table including a name column configured to store the extended attribute and a value column configured to store an extended attribute value corresponding to the extended attribute. Rows of the extended value table may be mapped to corresponding rows in the base table. A rule may be stored in a rules table, the evaluation of the rule determining whether the extended attribute value in the extended attribute table is valid.
Owner:ORACLE INT CORP
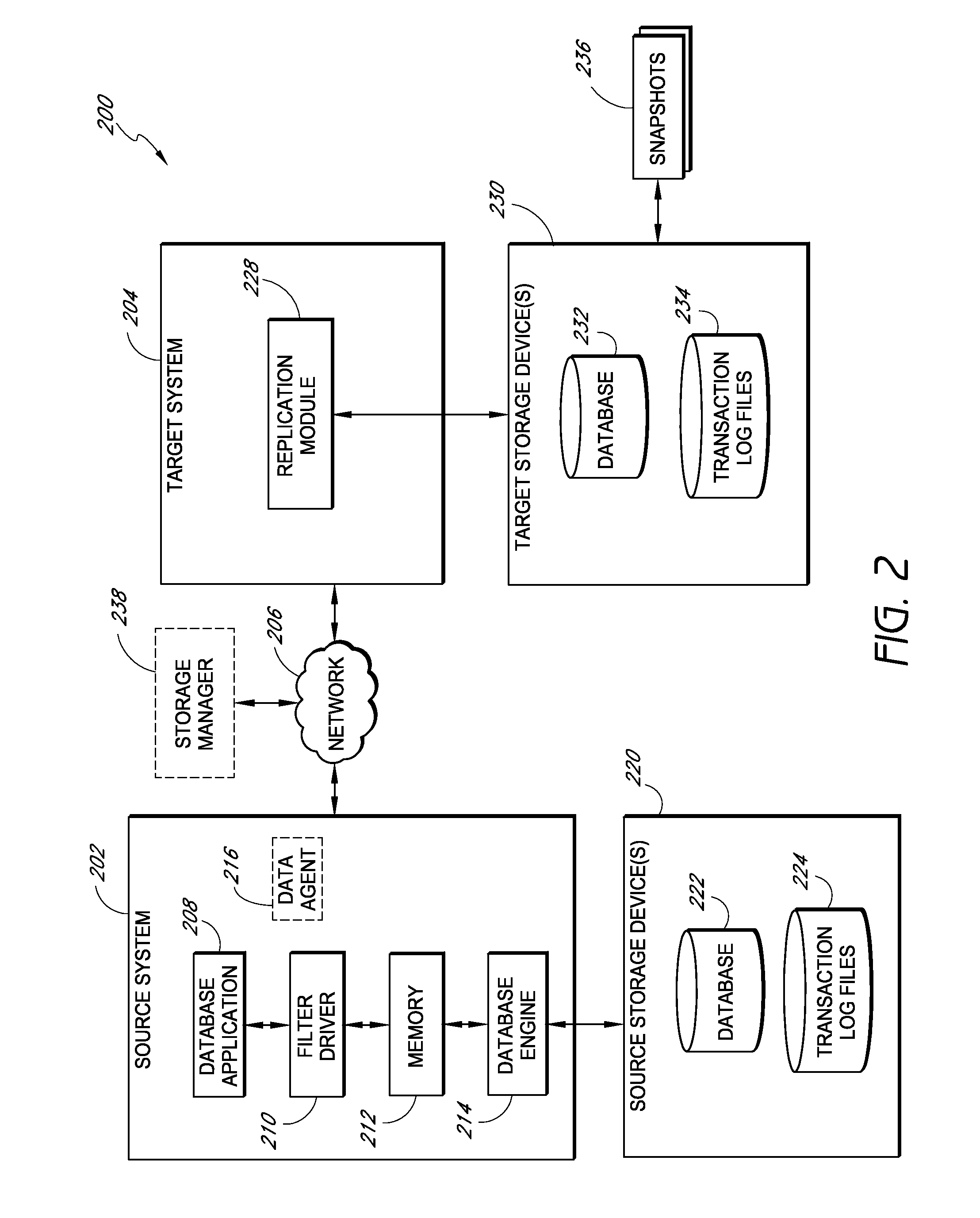
Systems and methods for managing replicated database data
ActiveUS8204859B2Reduce memory requirementsImprove performanceDigital data processing detailsError detection/correctionDatabase applicationApplication software
Systems and methods for replicating database data and generating read-only copies of the replicated data in a clean shutdown state. For example, systems can include a tracking module (e.g., a filter driver) that monitors transactions from a database application to a source storage device to generate log entries having at least one marker indicating a known good state of the application. The systems further include a computer coupled to a target storage device comprising a database and log files. The computer processes the transactions, based on the log entries, to replicate data to the target storage device; performs a first snapshot on data stored in the database and log files; replays into the database data stored in the log files; performs another snapshot on the database; and reverts the database back to a state in which the database existed at the time of the first snapshot.
Owner:COMMVAULT SYST INC
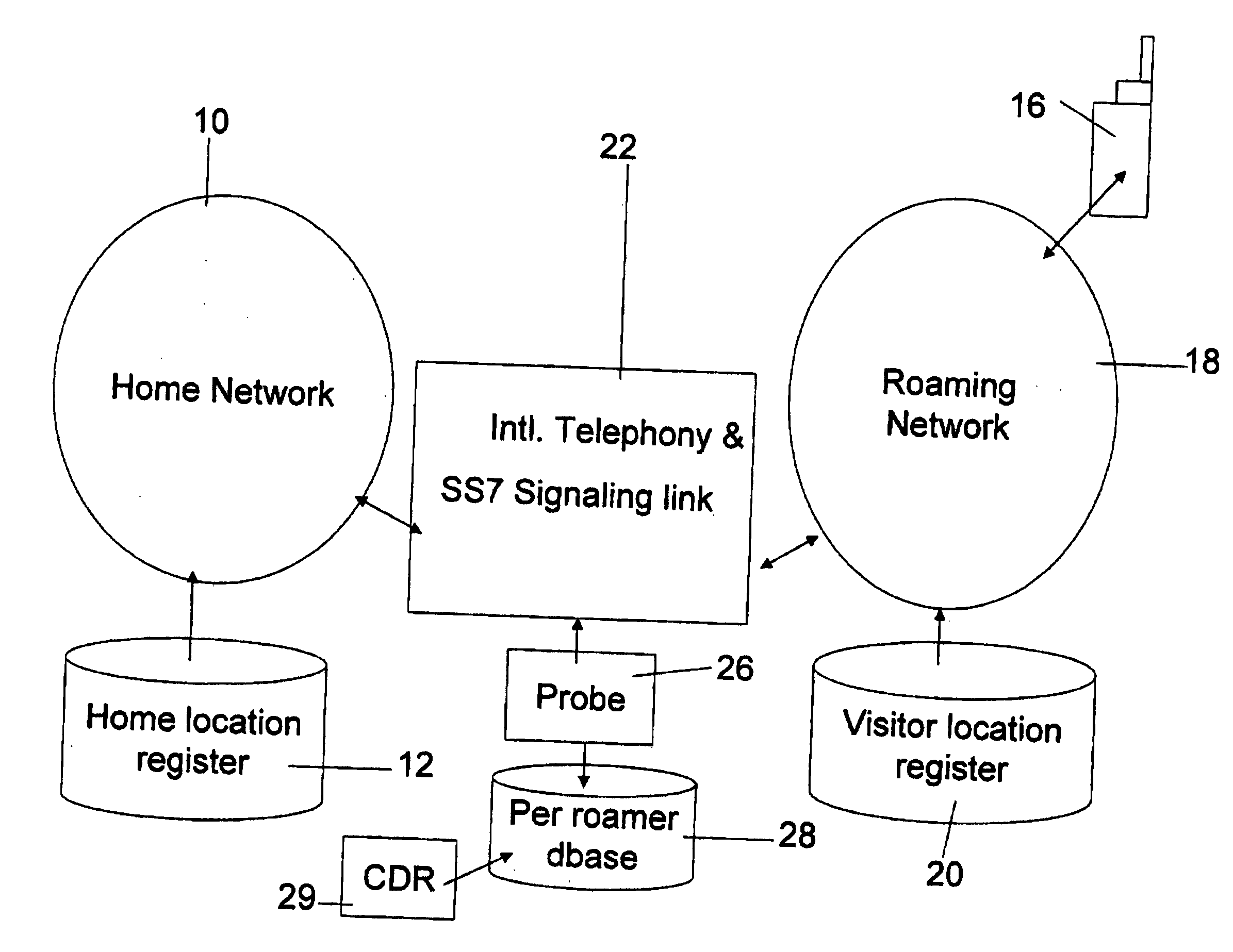
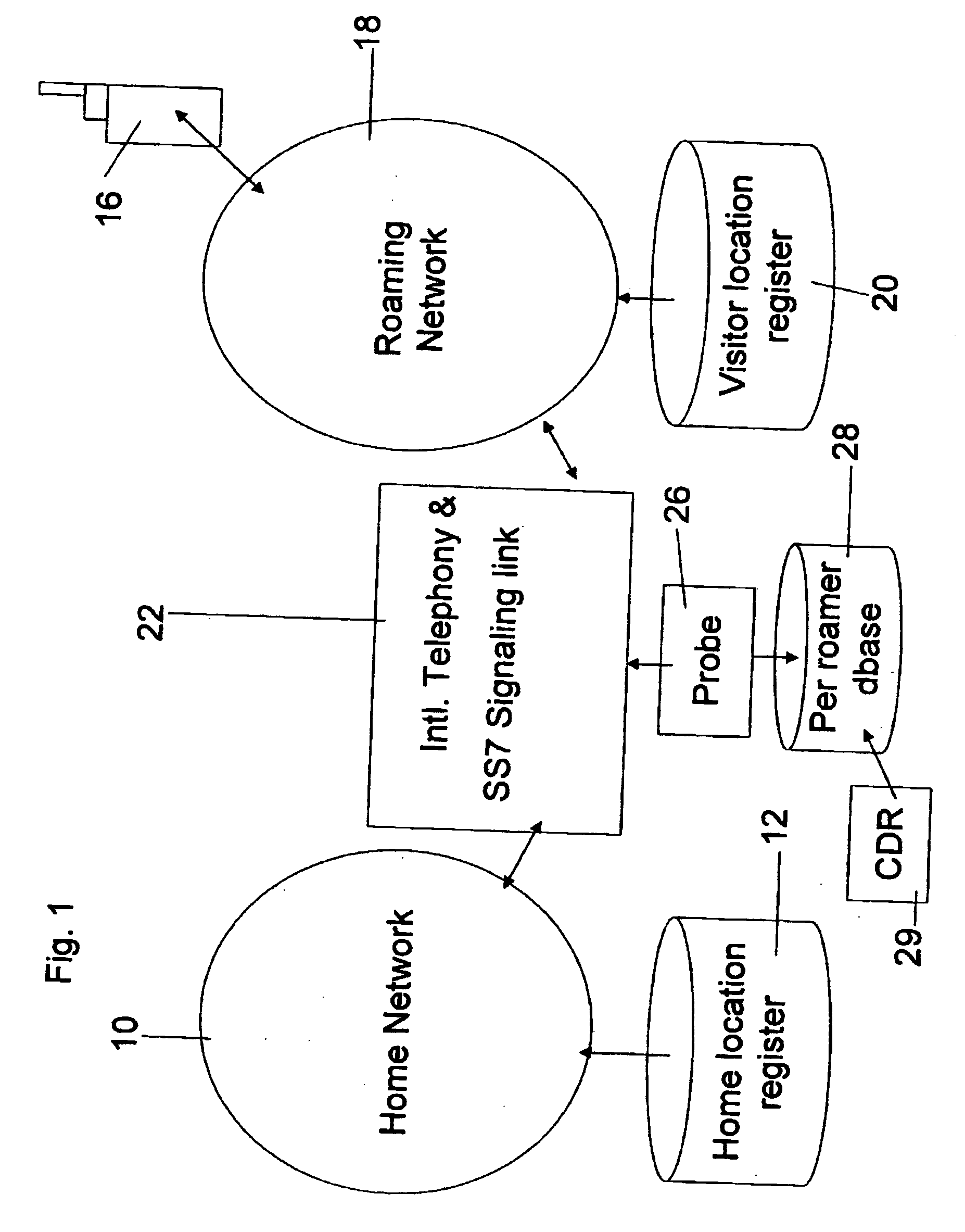
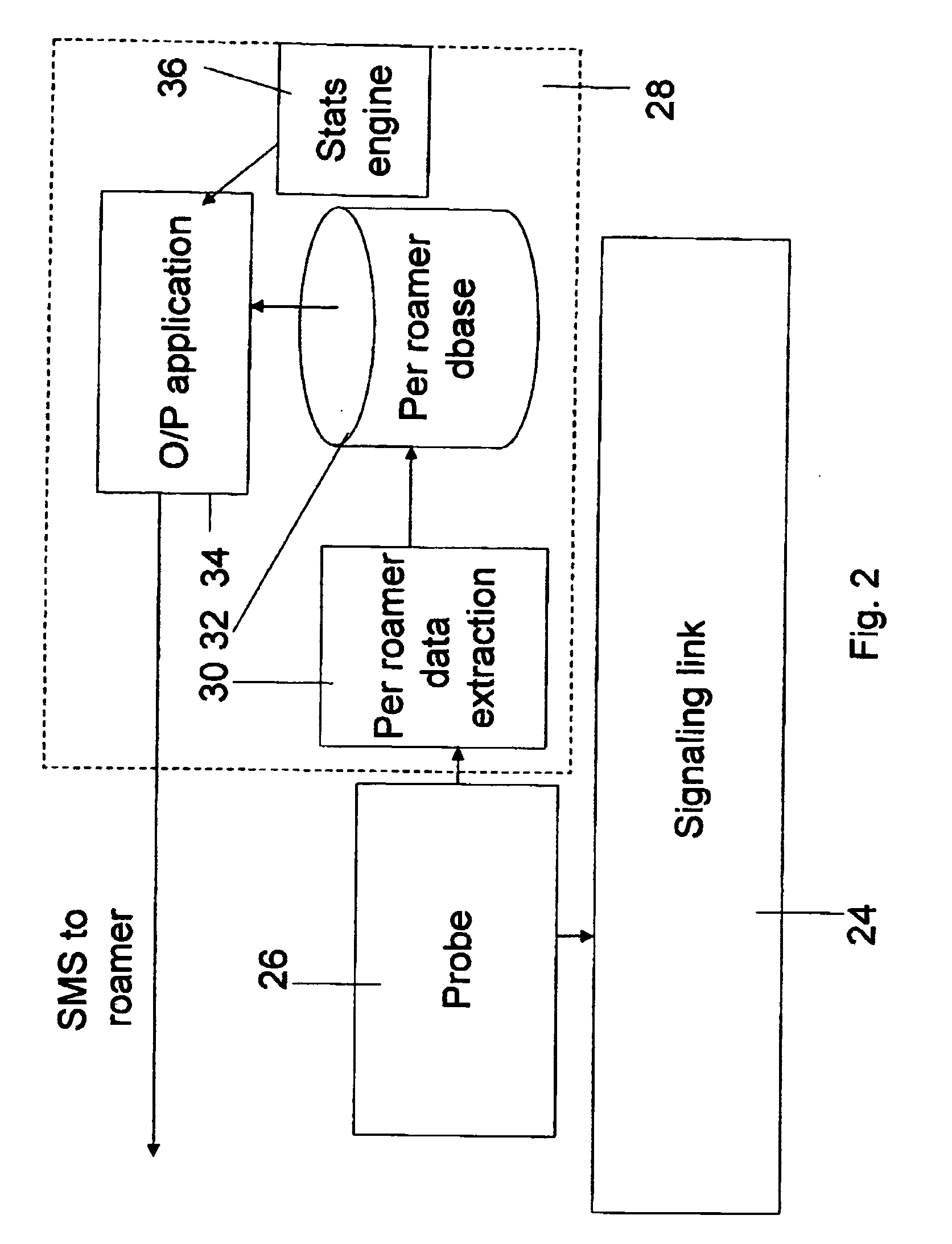
Monitoring and management of roaming users
InactiveUS20050186939A1Accounting/billing servicesAutomatic exchangesTelecommunicationsDatabase application
Roaming usage management apparatus for managing roaming mobile devices connected to roaming networks. The management apparatus includes a data gathering application for gathering roaming activity data, a database application, which aggregates the records into activity logs of calls per roaming device, and an output unit which sends outputs to or concerning respective roaming devices, in order to manage them based on activity levels or kinds of activity recorded in the logs. The embodiments thus provide management of roaming devices. The management is per roaming device, preferably real time, and may be used to leverage takeup of roaming services.
Owner:STARHOME GMBH
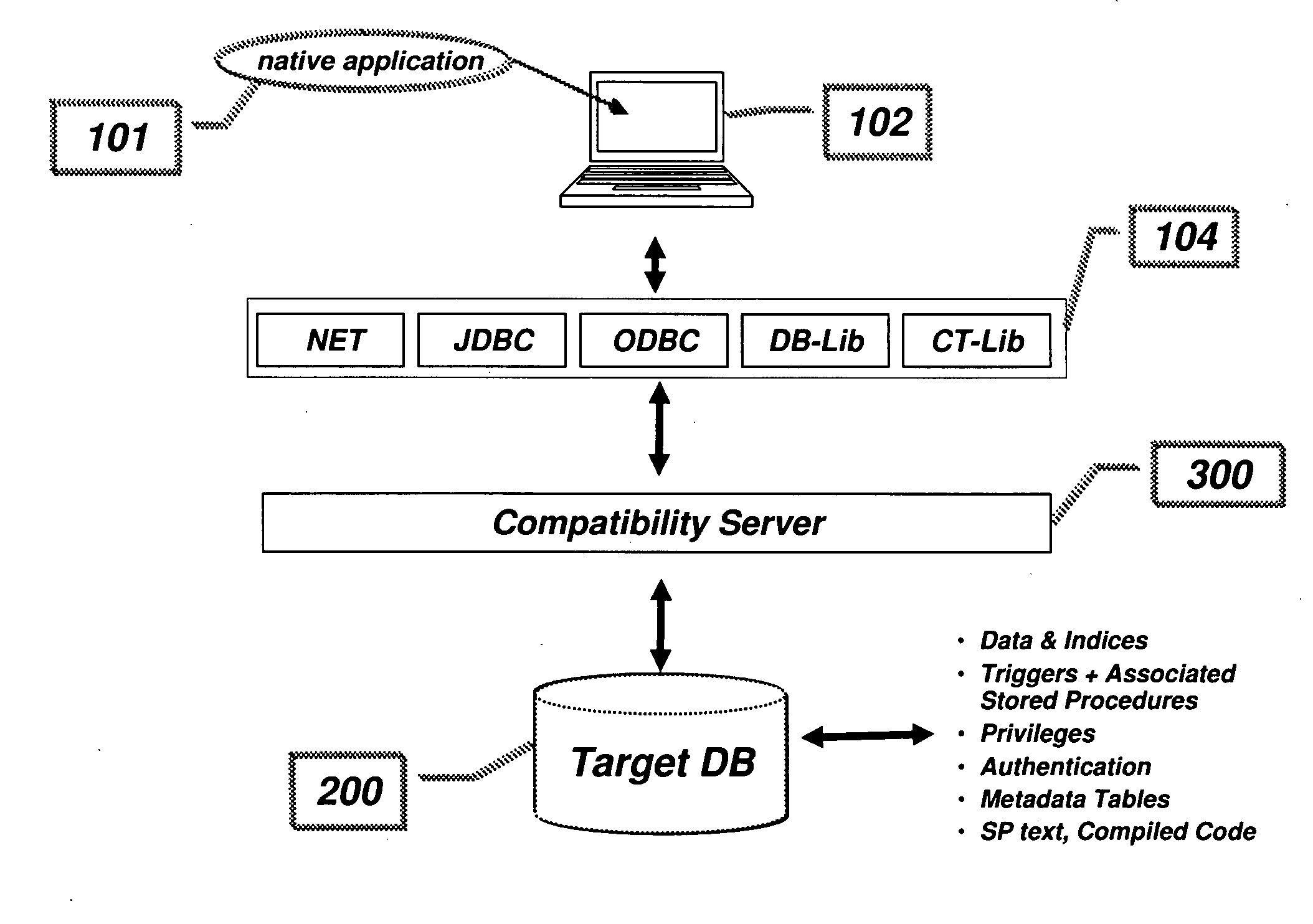
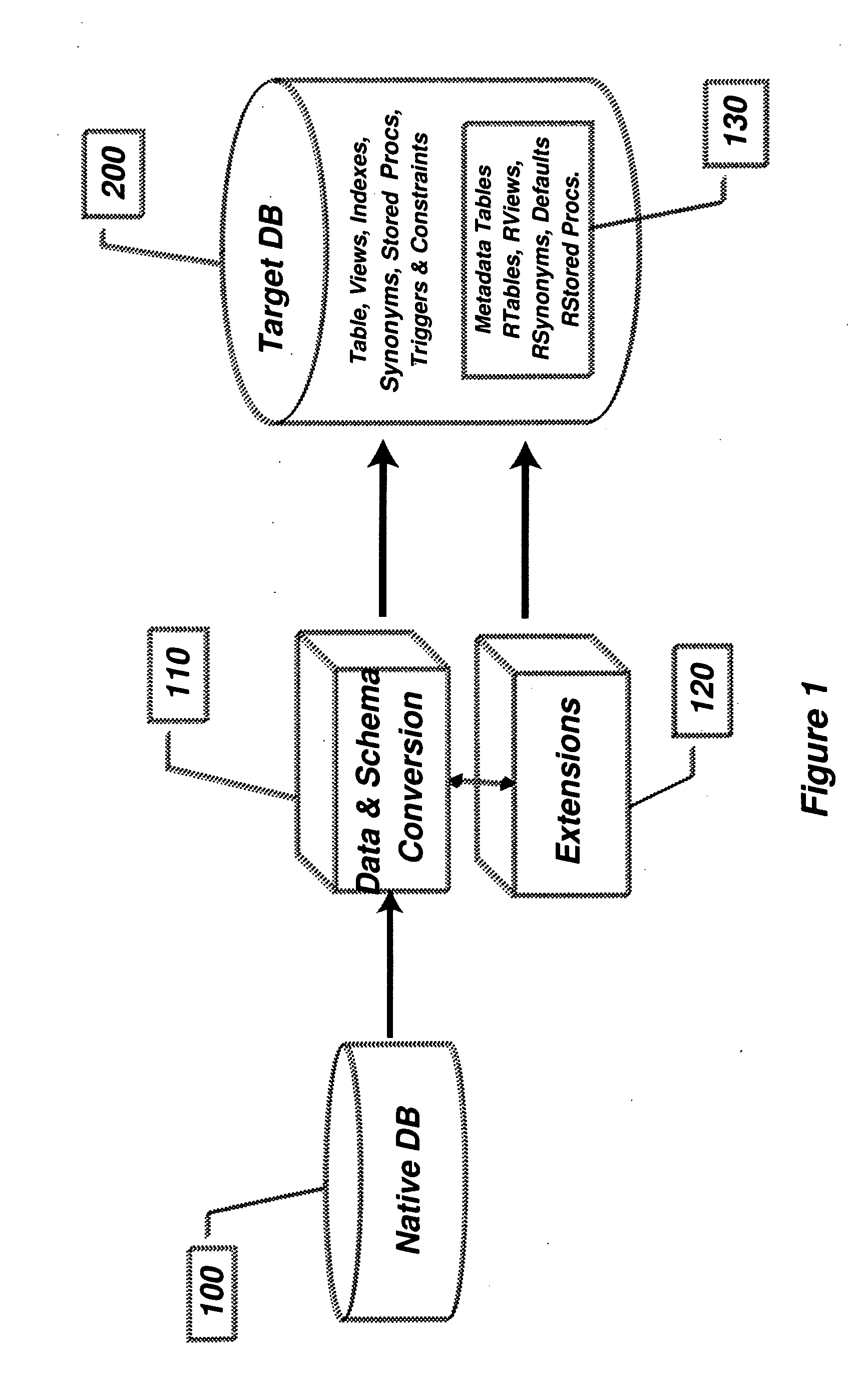
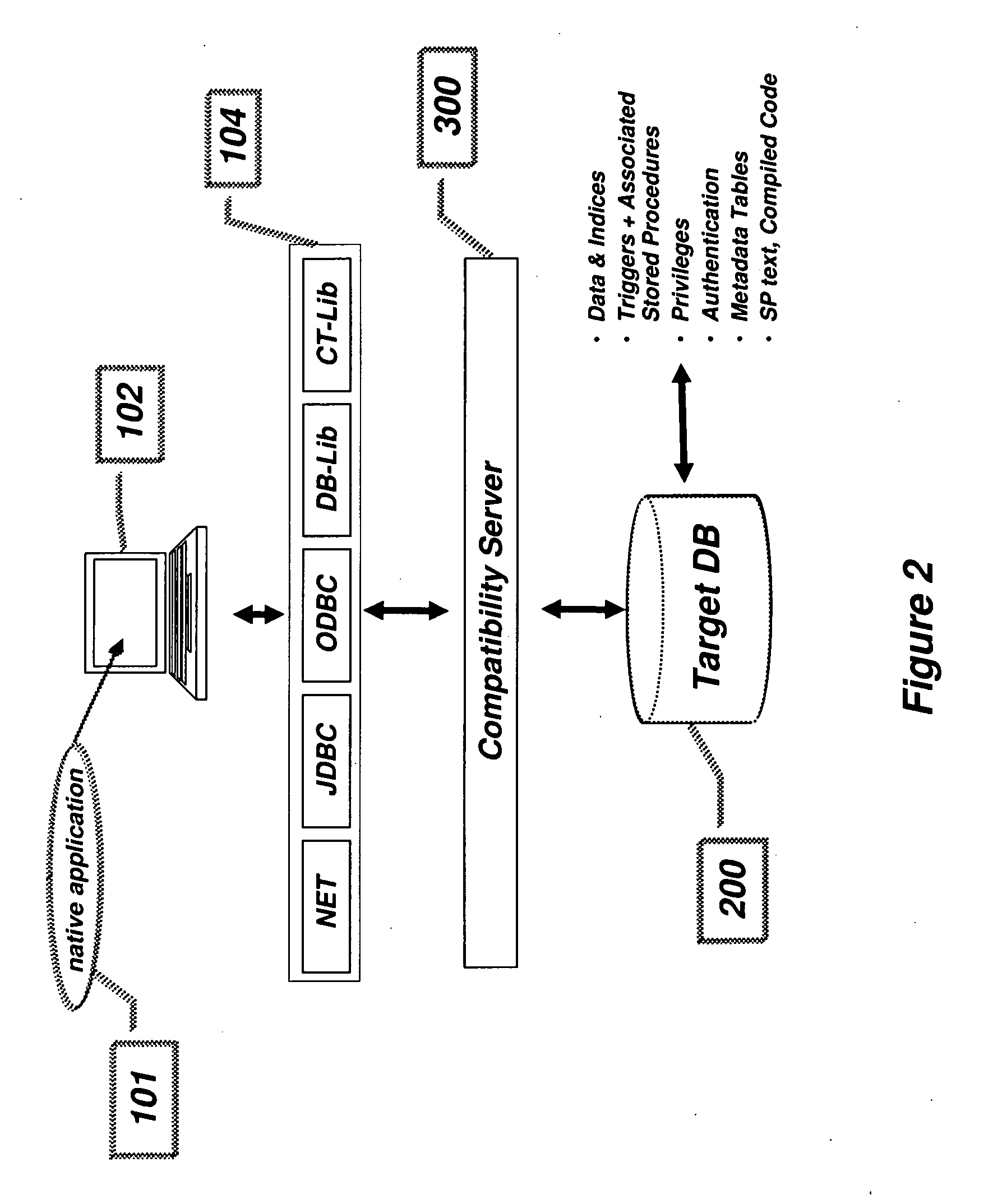
Compatibility Server for Database Rehosting
InactiveUS20100094838A1Digital data information retrievalDigital data processing detailsApplication programming interfaceDatabase application
A system and method describing a compatibility server for rehosting database applications written for a specific vendor's database on the database of a second vendor, without the need of rewriting the application to take into account differences in the application programming interfaces between the first vendor's database and the second vendor's database. Requests for access to the database are translated from one format to another at execution time. The server is also capable of translating error messages, data types and data formatting from the format used by the second database to that expected when making requests to the first database. Stored procedures defined in the first database are migrated to the second database as text blocks, and are translated at execution time into a high level programming language, compiled and executed against the second database. All information necessary for the mapping of schema, data, data types, error and status messages and data formatting, as well as information necessary to execute stored procedures, is stored in a plurality of metadata tables in the second database, which are created during a migration phase prior to executing the application.
Owner:ANTS SOFTWARE
Performance of operations on selected data in a storage area
InactiveUS20050138306A1Memory loss protectionRedundant operation error correctionFile systemDatabase application
A method, system, computer-readable medium, and computer system to perform operations on selected data in a storage area. Storage locations in the storage area can be identified by a requester for performing an operation only on the data in the identified storage locations. The requester can be an application managing the data (such as a database application, file system, or user application program) or a storage manager. The storage locations containing the data are obtained by software performing the operation, which can be a storage manager or an application operating in conjunction with a storage manager, such as a storage area replication facility. The software performing the operation operates only upon the identified locations, thereby affecting only the data stored within the identified locations. The requester can specify the operation to be performed as well as entities having permission to perform the operation on specified subsets of the storage locations.
Owner:SYMANTEC OPERATING CORP
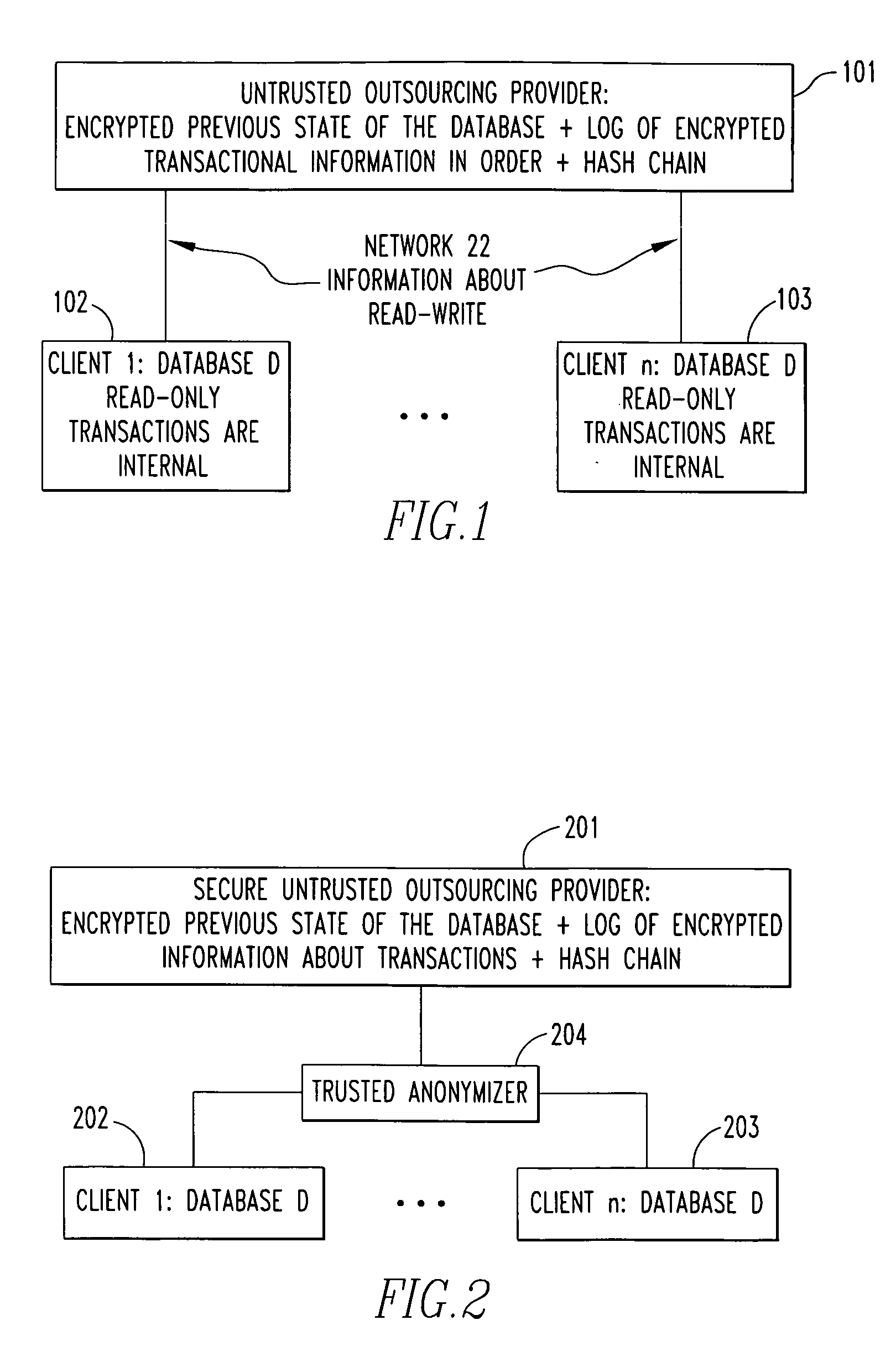
Database outsourcing with access privacy
ActiveUS20100185847A1Digital data processing detailsUnauthorized memory use protectionDatabase applicationSerialization
This invention introduces a new paradigm for outsourcing the transaction processing backend of a multi-client database application to an untrusted service provider. Specifically, the invention enables untrusted service providers to support transaction serialization, backup and recovery for clients, with full data confidentiality and correctness. Moreover, providers learn nothing about transactions (except their size and timing), thus achieving read and write access pattern privacy.
Owner:NEW YORK UNIV +1
Autonomic self-tuning of database management system in dynamic logical partitioning environment
ActiveUS20060101224A1Improve artError detection/correctionProgram controlSelf-tuningDatabase application
Database partition monitoring and dynamic logical partition reconfiguration in support of an autonomic self-tunable database management system are provided by an automated monitor that monitors one or more resource parameters in a logical partition running a database application in a logically partitioned data processing host. The monitor initiates dynamic logical partition reconfiguration in the event that the parameters vary from predetermined parameter values. In particular, the monitor can initiate removal of resources if one of the resource parameters is being underutilized and initiate addition of resources if one of the resource parameters is being overutilized. The monitor can also calculate an amount of resources to be removed or added. The monitor can interact directly with a dynamic logical partition reconfiguration function of the data processing host or it can utilize an intelligent intermediary that listens for a partition reconfiguration suggestion from the monitor. In the latter configuration, the listener can determine where available resources are located and attempt to fully or partially satisfy the resource needs suggested by the monitor.
Owner:SAP AG
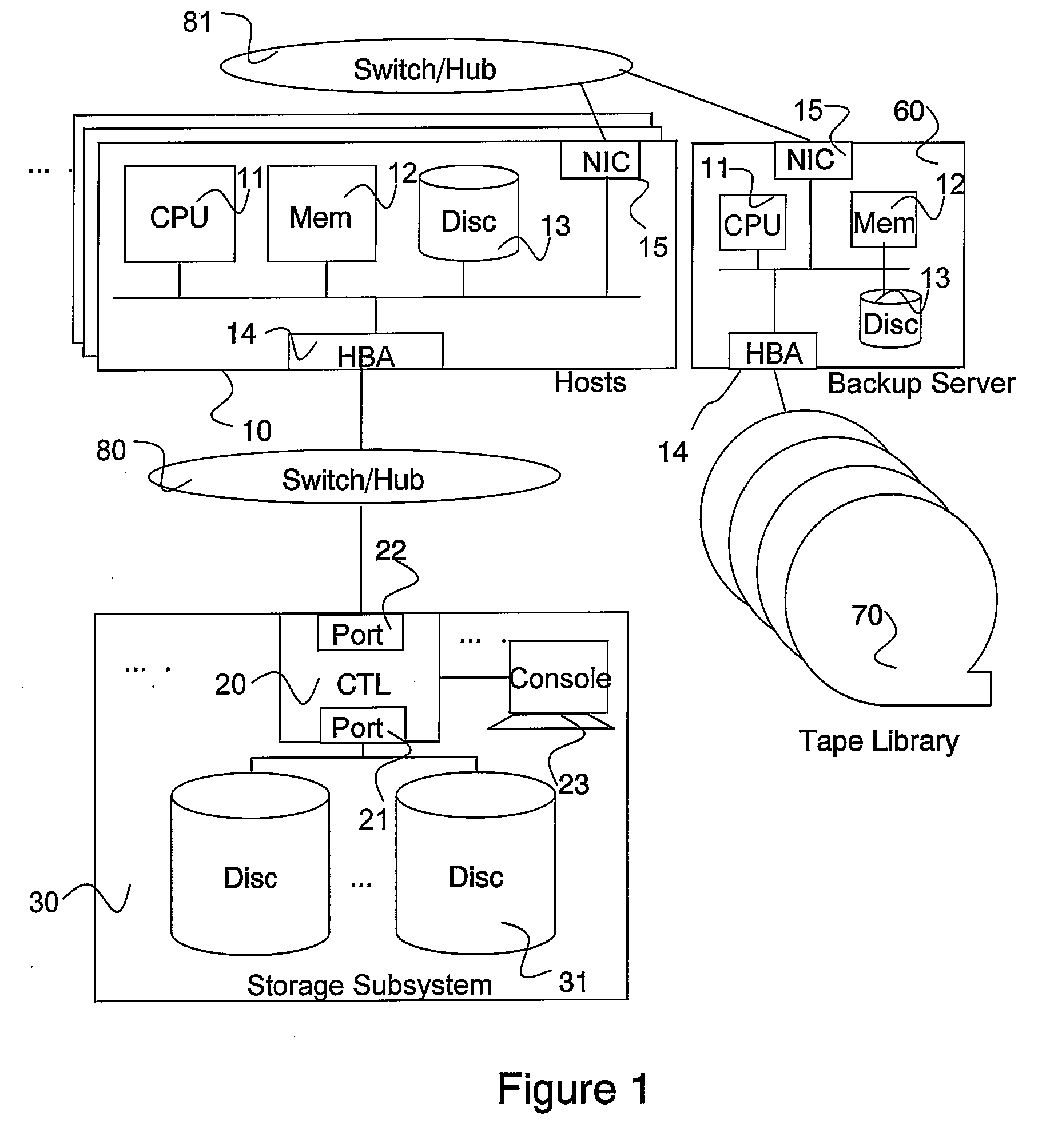
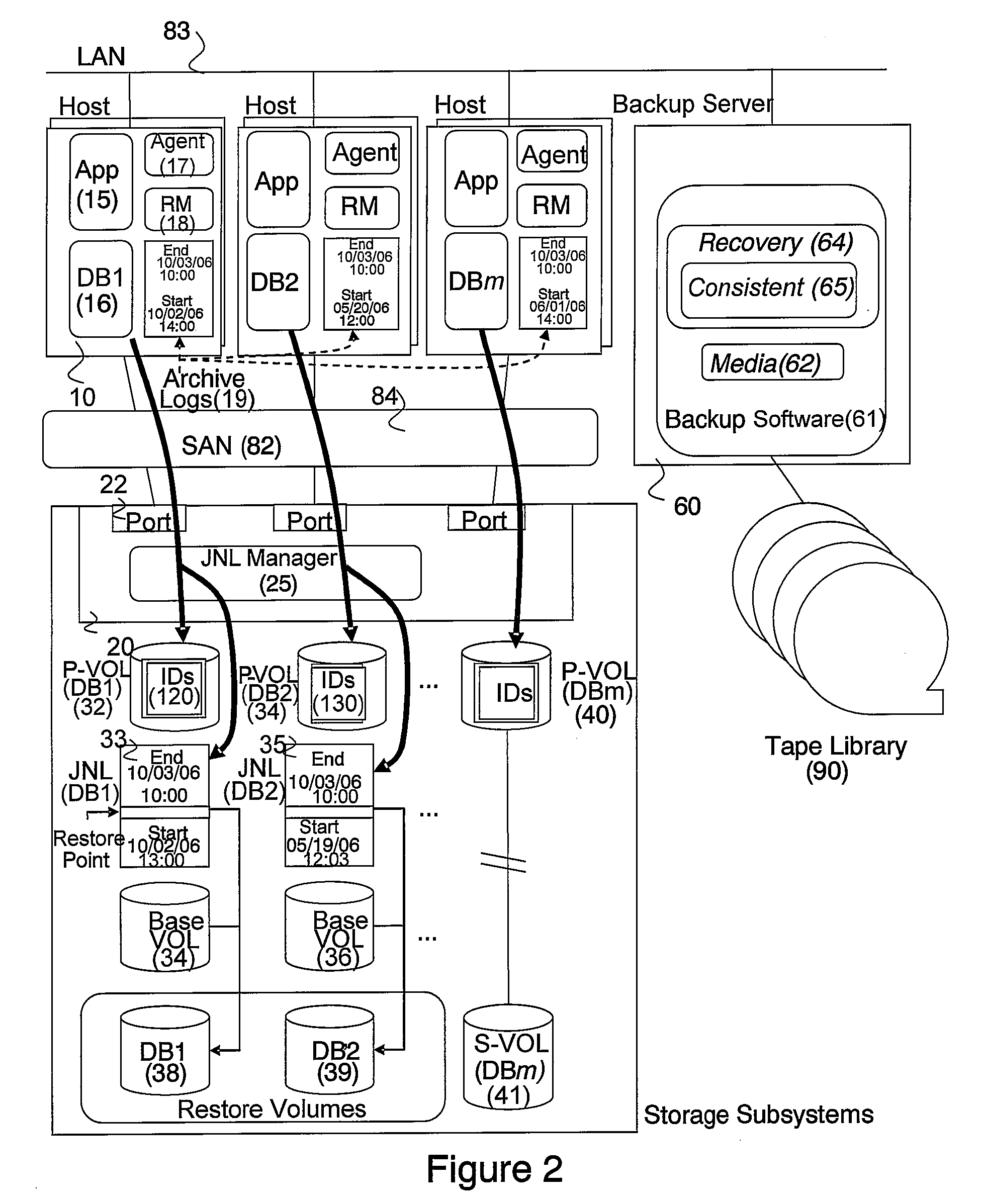
System and method for managing consistency among volumes based on application information
InactiveUS20080228833A1Eliminate the problemData processing applicationsDigital data information retrievalDatabase applicationApplication software
In accordance with new technique, a computerized data recovery system includes a storage subsystem and a backup server operatively coupled to backup storage medium, the storage subsystem including a continuous data protection system. The backup server executes a recovery manager which: collects consistency points from at least two database applications executing on at least one host; collects journal terms of the continuous data protection system for each of the at least two database applications; collects log terms associated with each of the at least two database applications; displays to a user a timeline for a protected term and consistency points for the at least two database applications; receives recovery time selection from a user; receives recovery database application selection from the user; receives baseline database application selection from the user; performs crash recovery for each database application; and performs recovery of data based on transactions associated with the at least two database applications.
Owner:HITACHI LTD
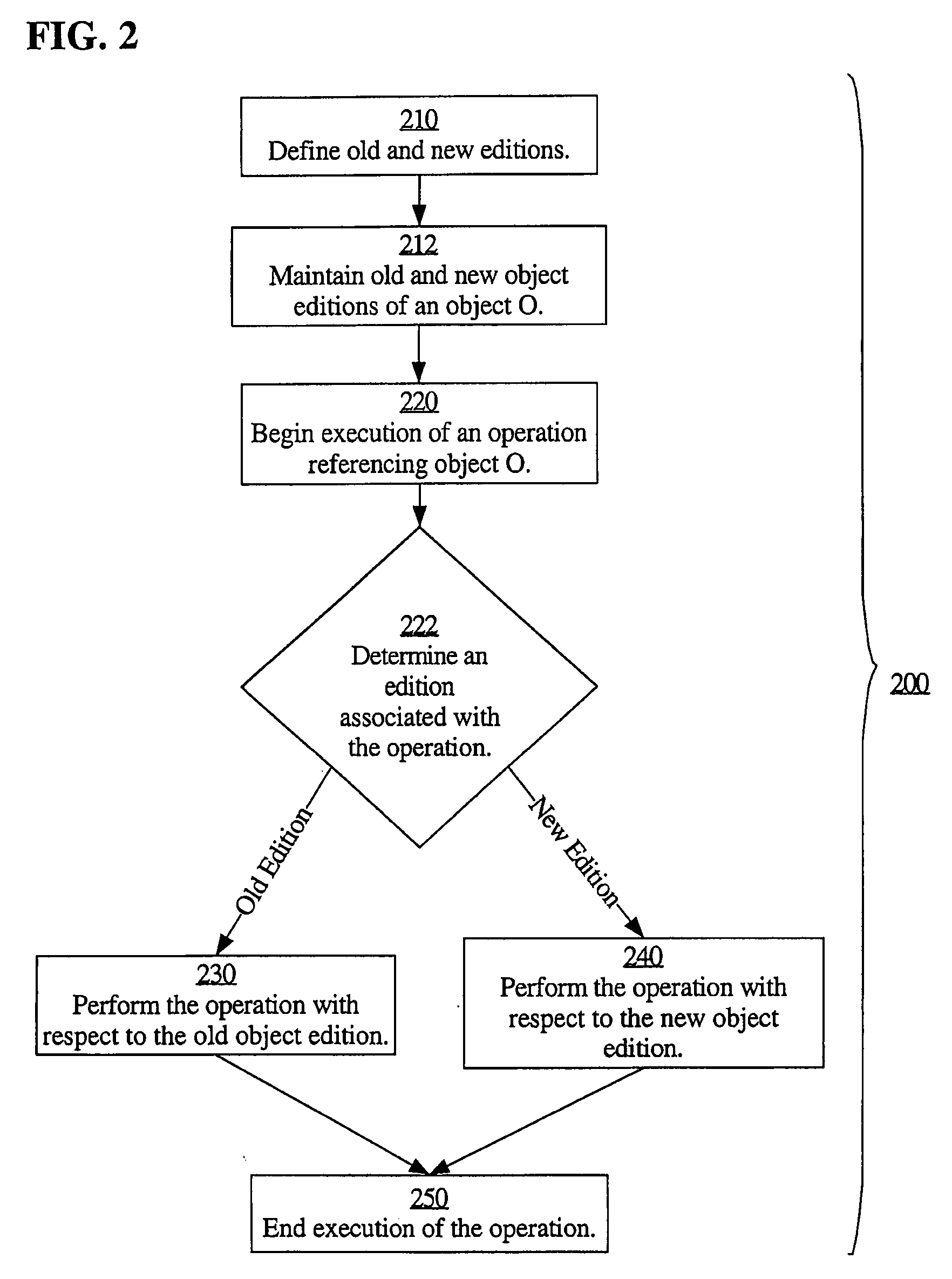
Low-downtime and zero-downtime upgrades of database-centric applications
ActiveUS20080098046A1Digital data information retrievalDigital data processing detailsDowntimeDatabase application
A database may facilitate zero-downtime upgrades by concurrently maintaining multiple editions of database objects for use by both pre-upgrade and post-upgrade clients of a database application. Operations performed within the database are associated with an edition based on, for example, an initiating client or transaction. When an operation references an object or data, the database automatically performs the operation using the object or data associated with the edition with which the operation is itself associated. The database may determine the associated edition without explicit identification of the associated edition in a query or in code. Thus, no client or stored procedure code changes are necessary to reflect a new edition added during an update. Data changes in one edition may be automatically and immediately propagated to the other edition through the use of cross-edition triggers, thereby allowing both pre-upgrade and post-upgrade clients to remain fully functional throughout an upgrade.
Owner:ORACLE INT CORP
Techniques for automatically provisioning a database over a wide area network
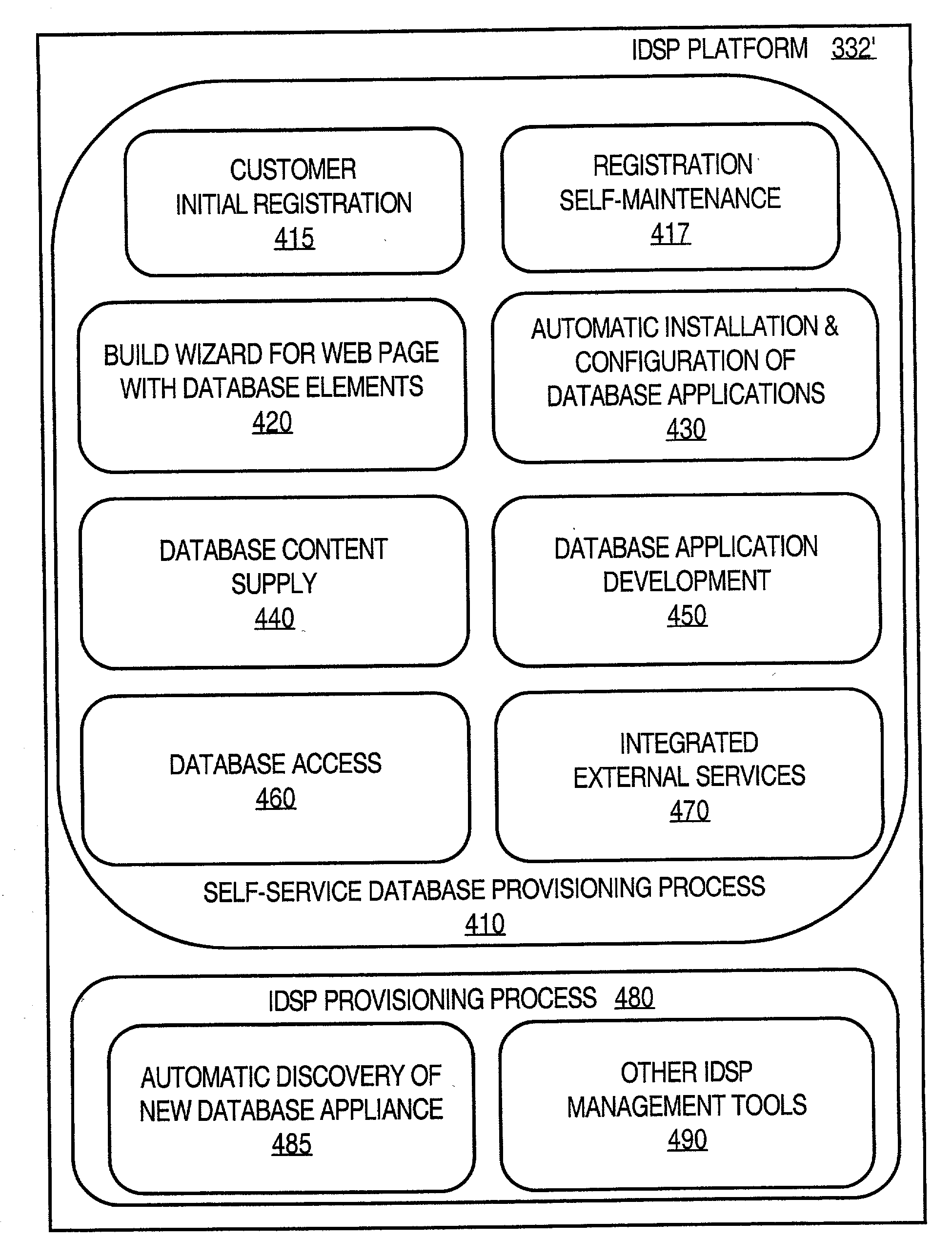
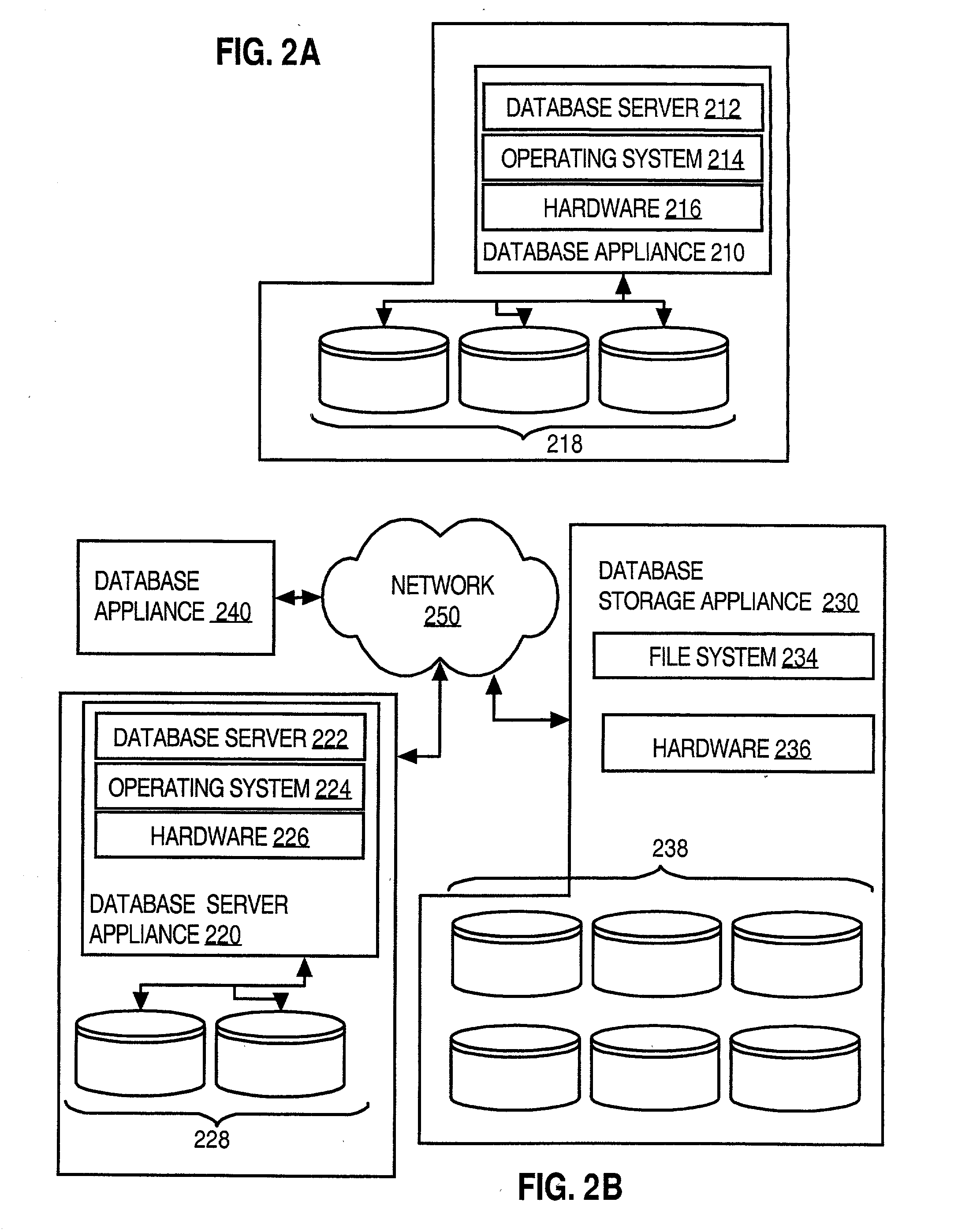
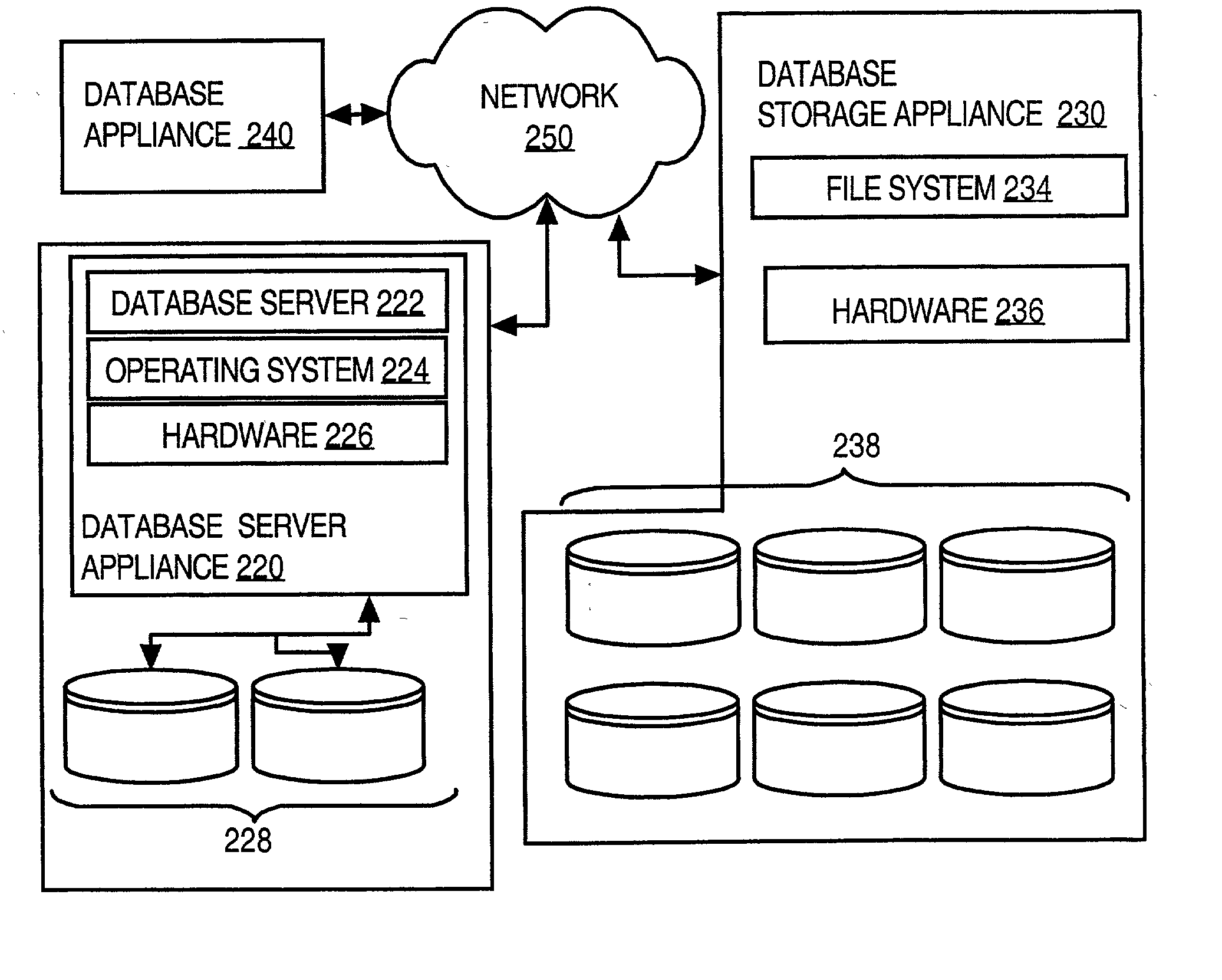
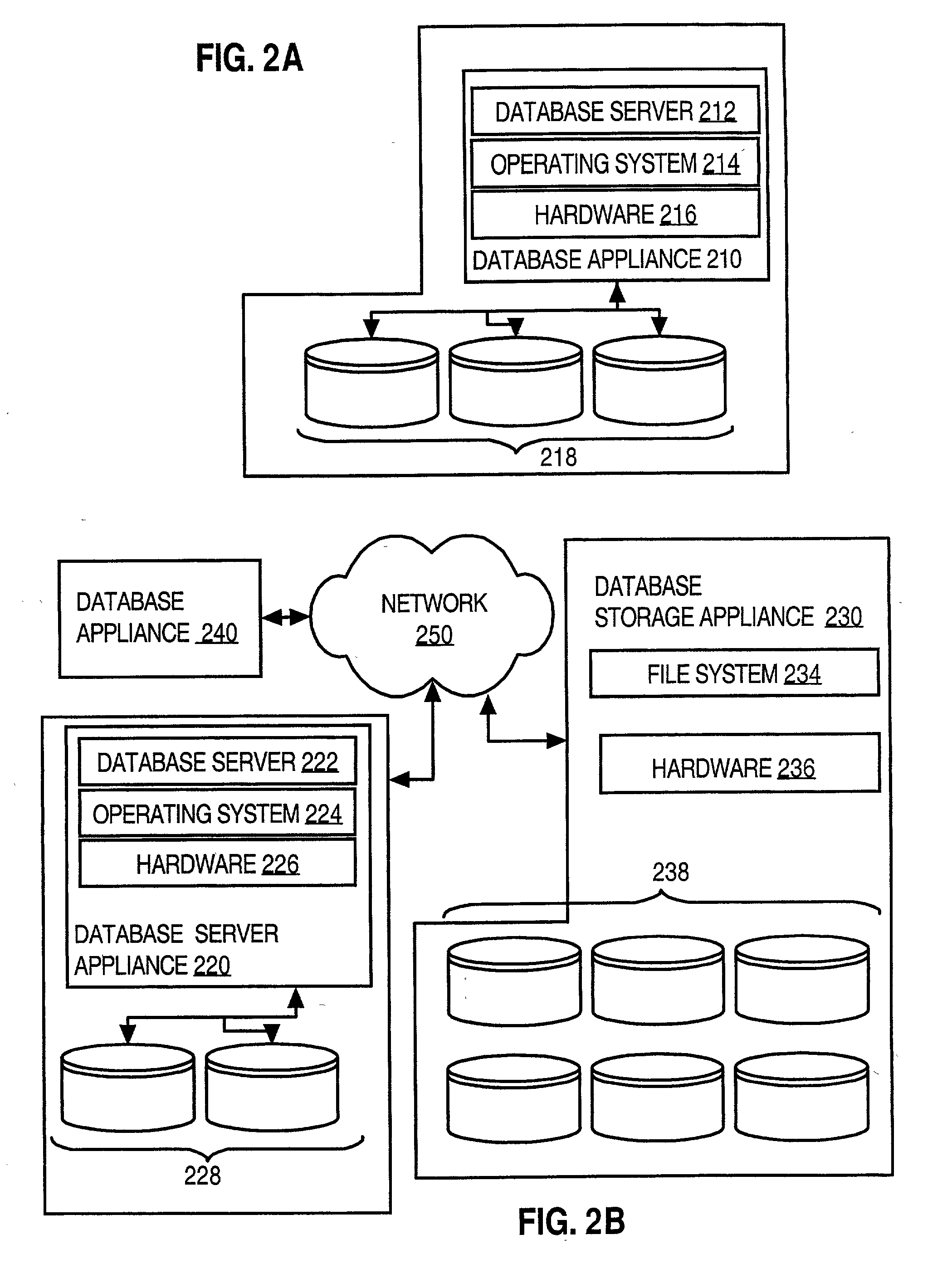
InactiveUS20080306883A1Low costService is expensiveError detection/correctionDigital data processing detailsThe InternetDatabase application
Techniques for provisioning databases for users on a wide area network include a first party managing one or more database systems. Multiple second parties subscribe to database services supported by the database systems managed by the first party. The first party provides, over a network, to database applications controlled by the second parties, access to the database services to which the second parties are subscribed.The database systems may use database appliances. A database appliance includes a database process and a non-database process that is-tailored to the needs of the database process. The wide area network may be a public network of computer networks, such as the Internet. With the present invention, a user is able to obtain needed database resources from an Internet Database Service Provider (IDSP) with a minimum of user effort and without the user incurring the full costs of one or more database administrators, or the costs of a dedicated database equipment facility, or even the costs of a dedicated database device, depending on usage. At the same time, the IDSP can readily provide for several database users with minimum staffing loads on the IDSP because of self-service tools provided. Furthermore, the IDSP start-up and maintenance efforts are reduced through several tools, such as the costing model and automatic billing features.
Owner:ORACLE INT CORP
Techniques for automatically installing and configuring database applications
InactiveUS20080295092A1Improve reliabilityImprove simplicityError detection/correctionDatabase distribution/replicationNetwork onEngineering
Techniques for automatically installing an application on a device on a network include sending, to a server, data indicating device resources on the device. The device requests a database application from the server. The device downloads from the server an initial customized value for a configuration parameter based on the device resources and the database application. The device also downloads the database application. The device installs the database application with the initial customized value for the configuration parameter.
Owner:ORACLE INT CORP
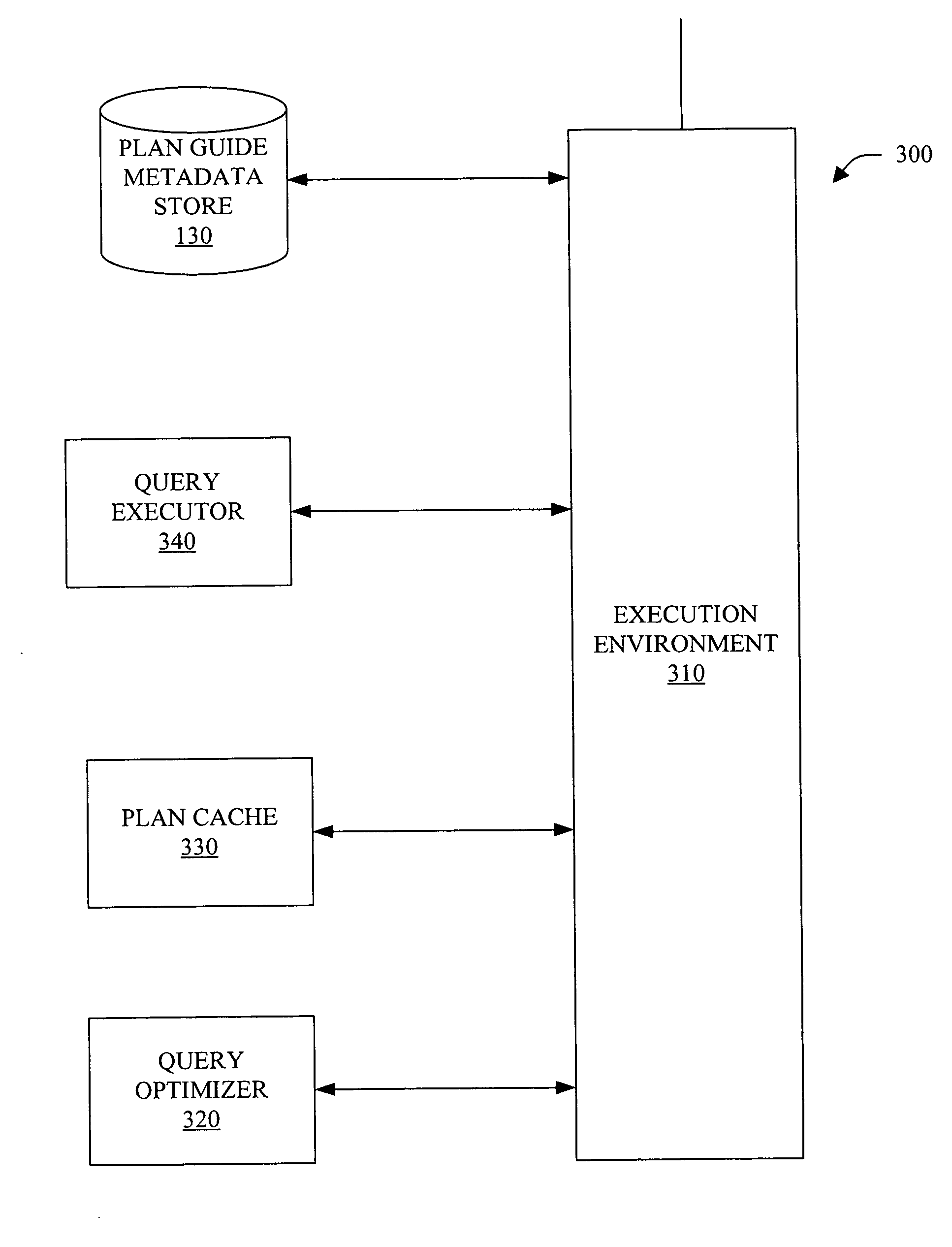
Query plan selection control using run-time association mechanism
InactiveUS20060224563A1Well formedData processing applicationsDigital data information retrievalQuery planThird party
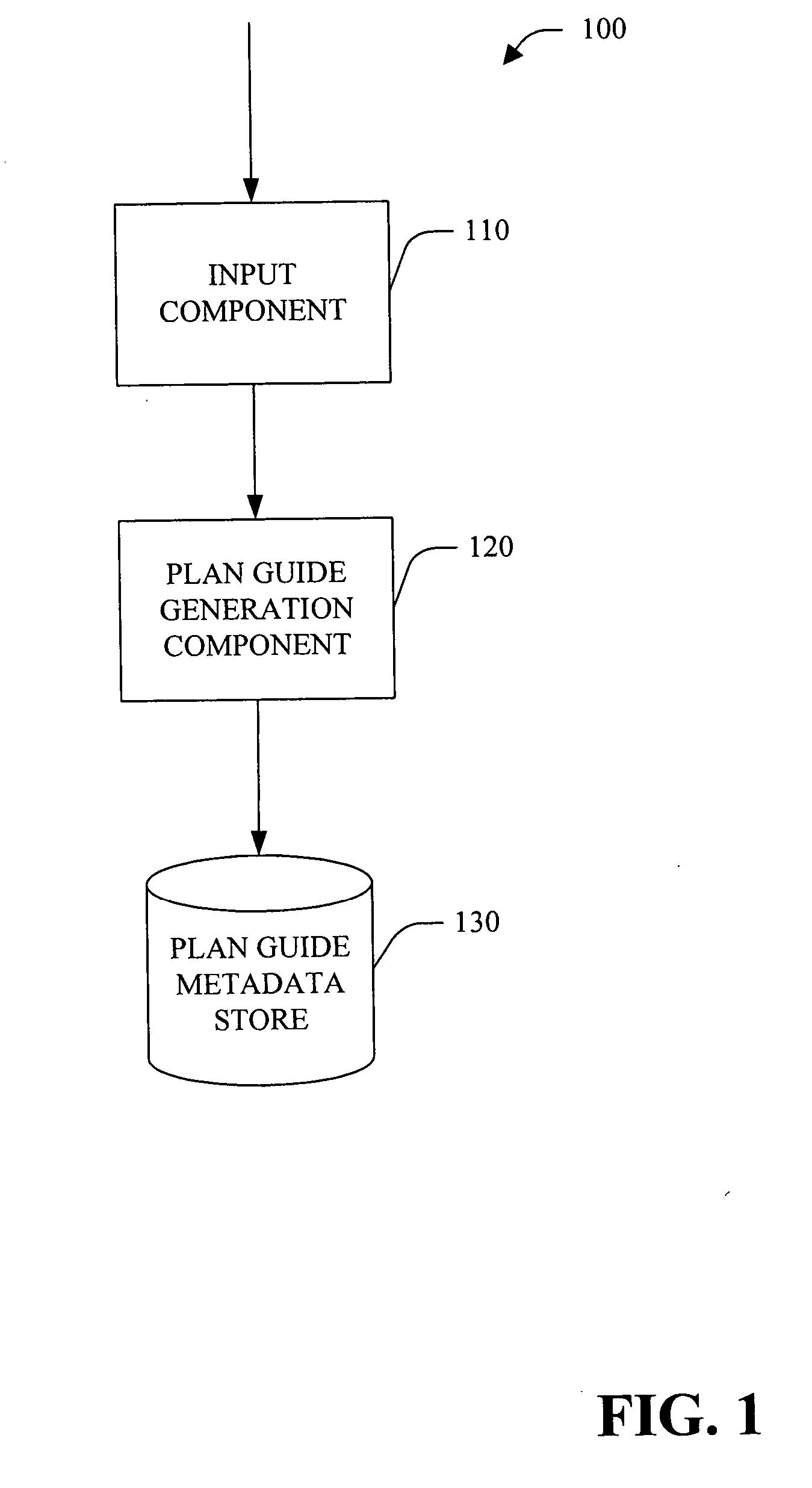
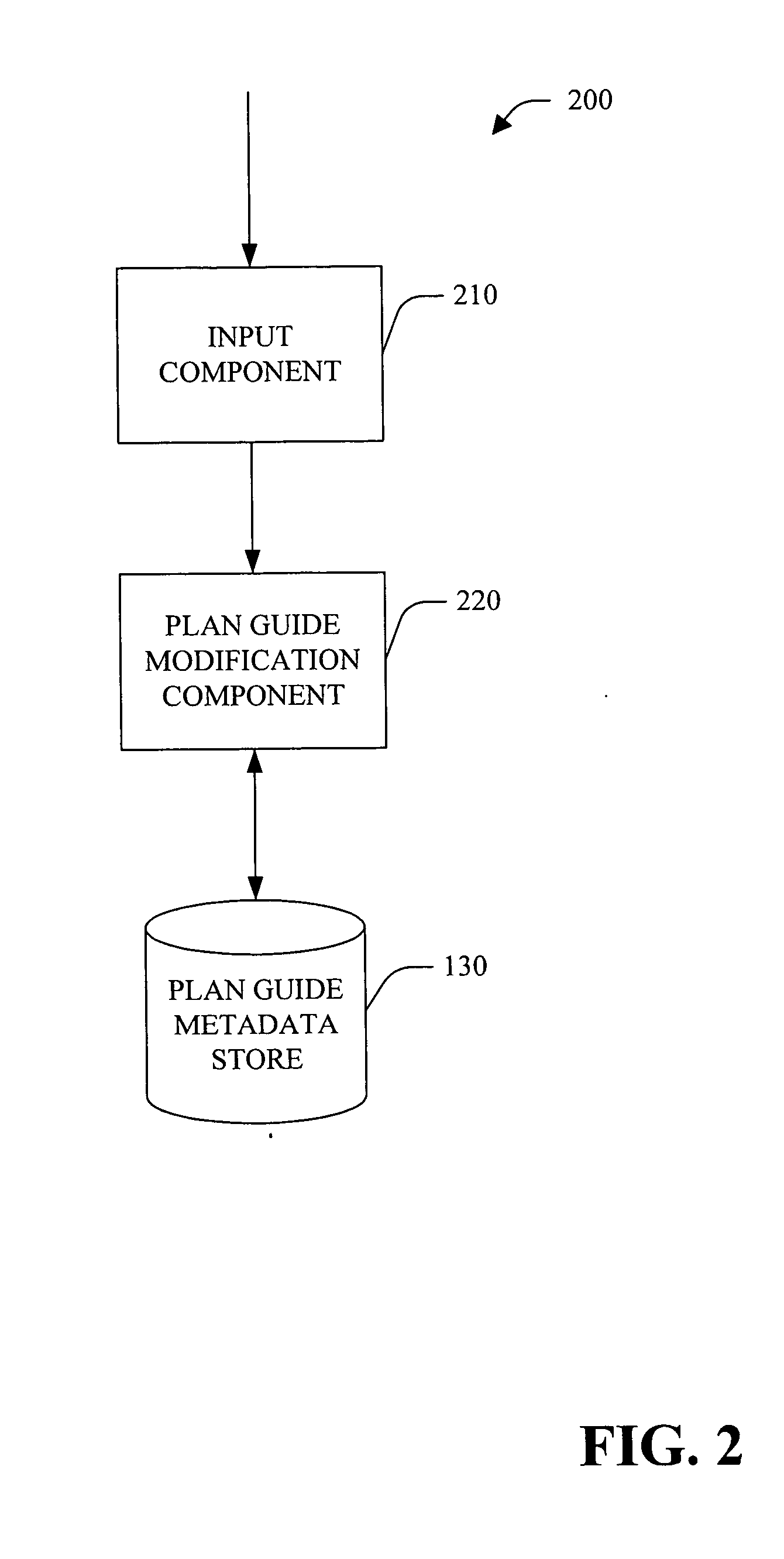
A system and method for creation, modification and / or use of plan guide(s) is provided. Plan guide(s) can be employed to optimize the performance of query(ies) when it is not possible and / or desirable to change the text of the query directly. Plan guides can be useful, for example, when a small subset of queries in a database application deployed from a third-party vendor is not performing as expected. Plan guides influence optimization of queries by attaching query hints to them. In accordance with an aspect of the subject invention, a query plan execution system is provided. The system includes an execution component, a query optimizer, and, a plan cache. Plan guides and other associated metadata are stored in a plan guide metadata store.
Owner:MICROSOFT TECH LICENSING LLC
Multi-device support for mobile applications using XML
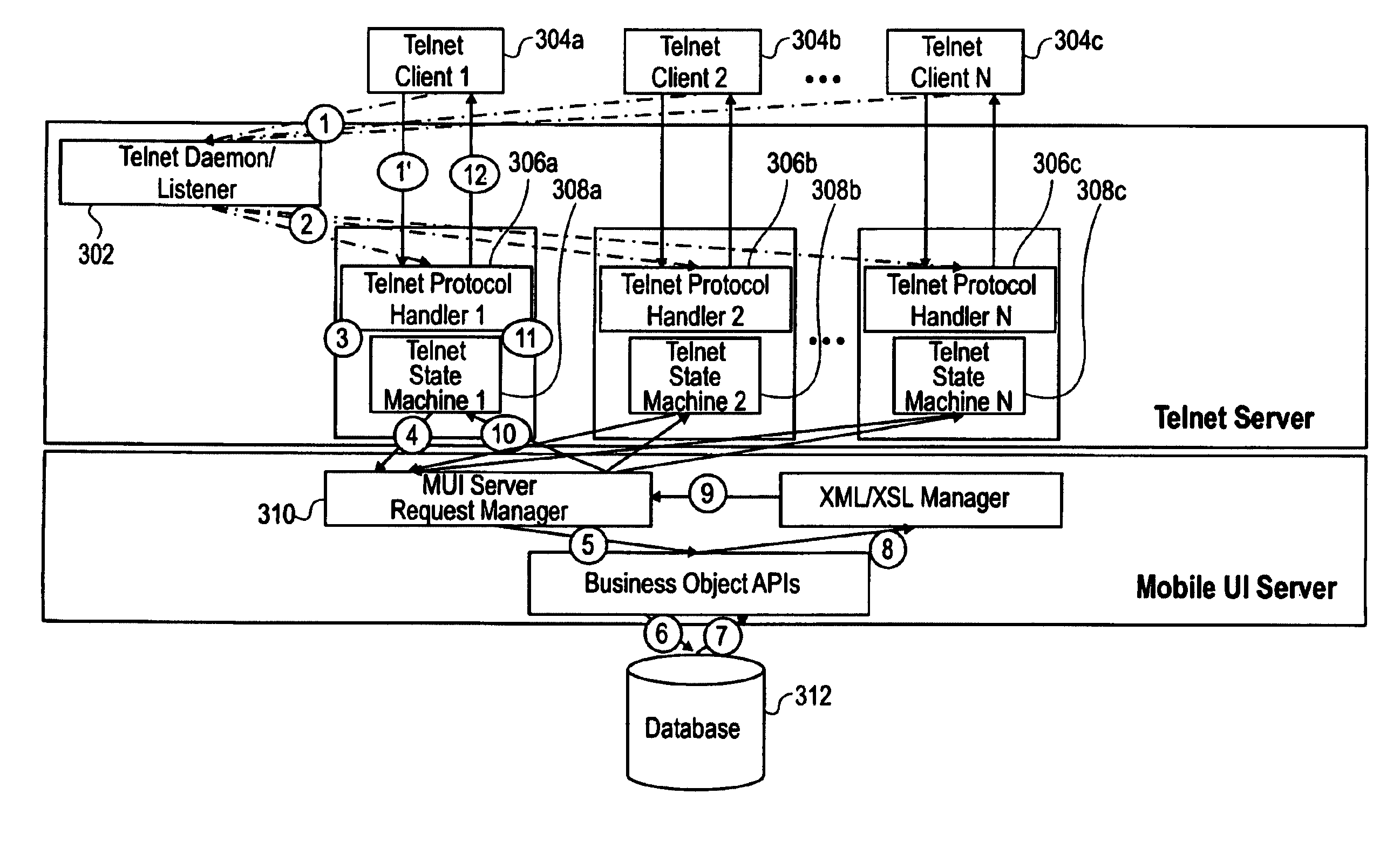
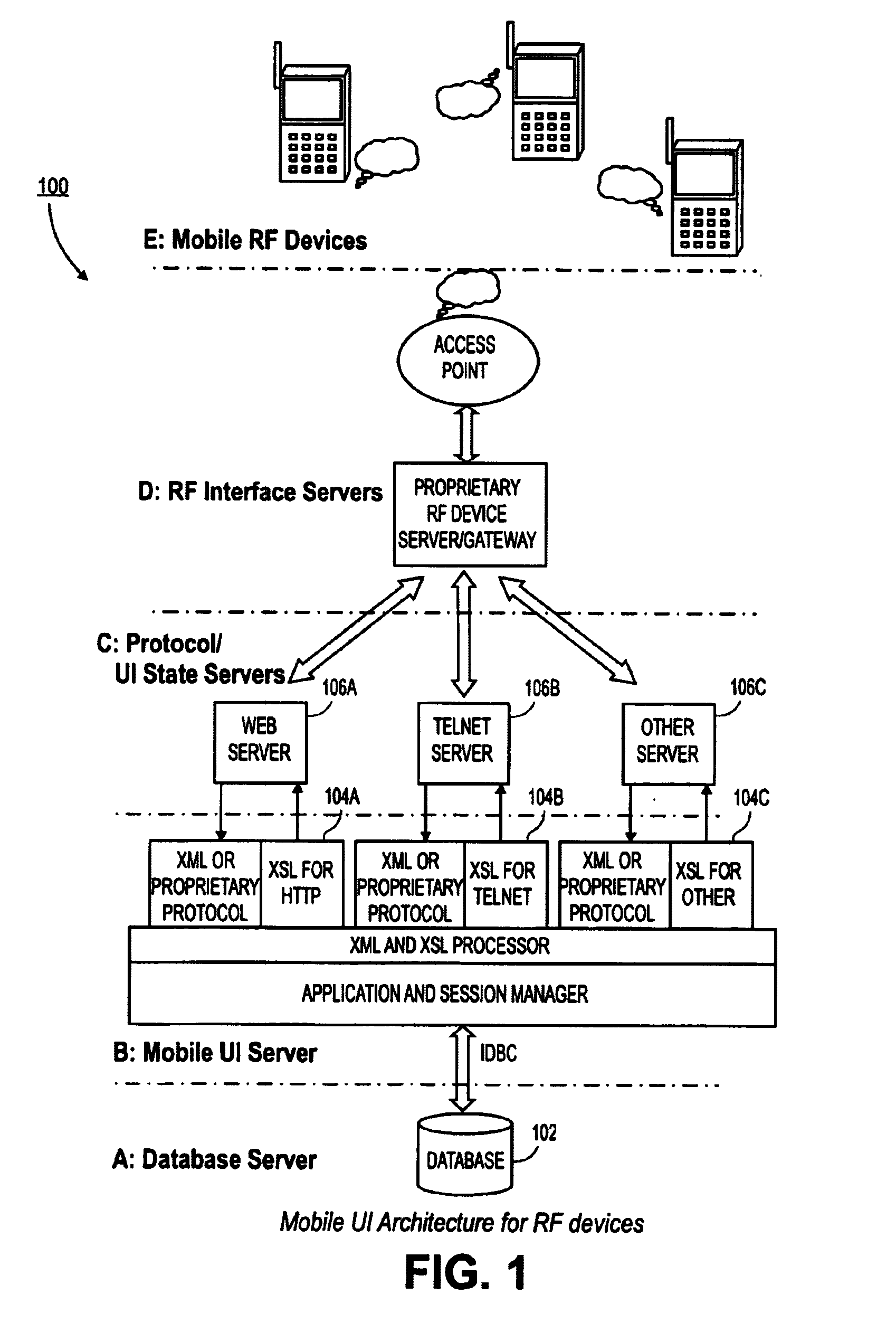
Techniques are provided that allow mobile devices to use database applications without having to specifically design the database applications to support all forms of mobile devices. In particular, techniques are provided in which the data coming out of a database application is formatted into Extended Markup Language (XML). The XML is the same regardless of which client is to receive the data. Prior to supplying the data to a client, the Extended Style Sheet (XSL) is applied to the data to format the data into the format required by the client.
Owner:ORACLE INT CORP
Systems and methods for appflow for datastream
ActiveUS20140136680A1Without impairment of administrative processDigital computer detailsTransmissionData streamDatabase application
The present disclosure is directed towards systems and methods for monitoring application level flow for database applications served by a cluster of servers. An application flow monitor may receive and distribute write requests of a client to at least one master server and read requests of the client to one or more slave servers, based on load balancing or similar policies. The application flow monitor may receive responses from the recipient server and may aggregate the requests and responses into Internet Protocol Flow Information Export (IPFIX) messages that may describe the entire communication flow for the application. Accordingly, application flow statistics may be monitored, regardless of which server was involved in any particular request / response exchange, allowing scalability without impairment of administrative processes.
Owner:CITRIX SYST INC
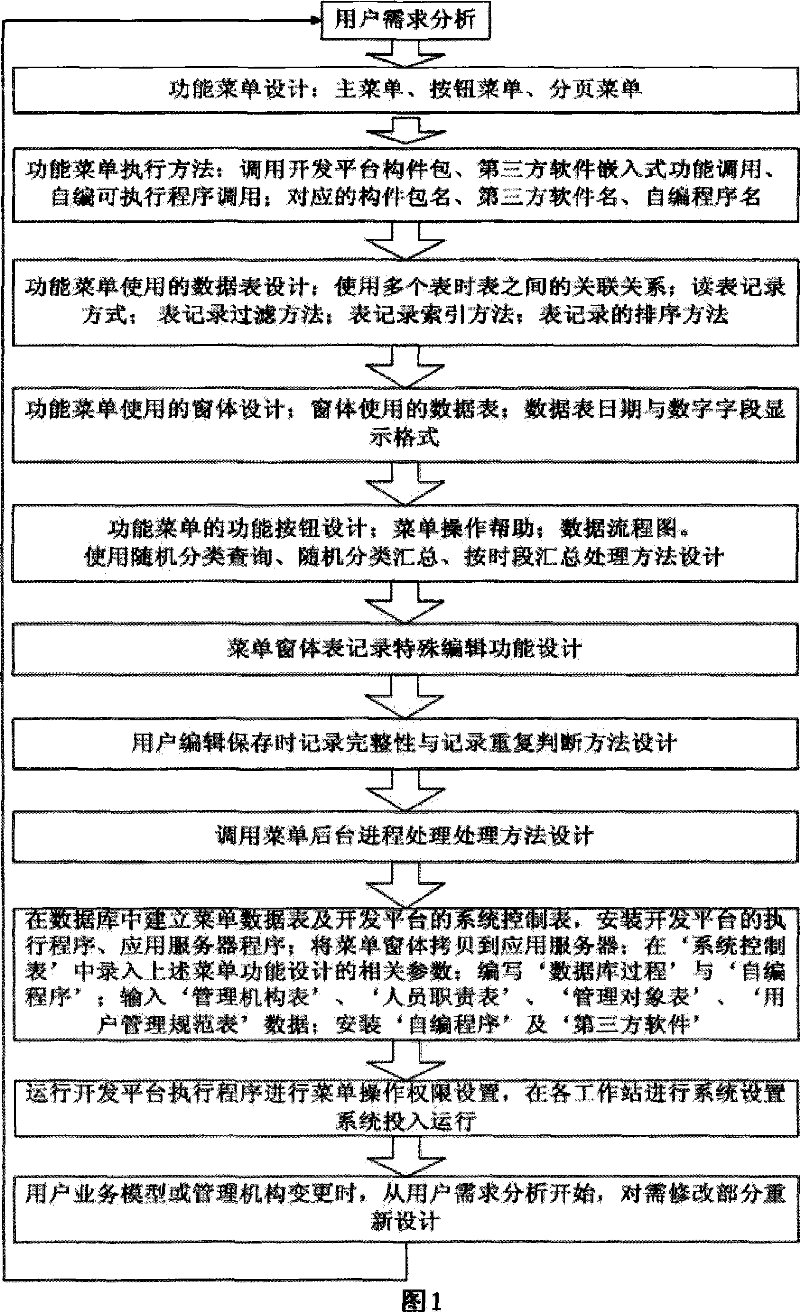
Data base application system development platform based on functional design
InactiveCN101034349ASpecial data processing applicationsSpecific program execution arrangementsRelational databaseSystem maintenance
The present invention introduces a development platforms based on the database application systems with function design, the development platform includes system control table, the menu component kits and code generator, the menu component kits is the module of reusable menu classification implementation; System control table is the carrier of description parameters both of storage application system architecture and menu functions, the carrier is the data tables of the relational database; The code generator dynamically generates code execution under storage parameters in the system control table. Development and application of the system using development platform just require system functional design, data table design, menu Form design, without the need to write code or only a very small number of special features menu prepared by the code, which can be generated applications; Application of the system's operation, reading system control table parameters and dynamic generating code execution, completion of system functions; when users change the business model, only a modification of system parameters control table, or to amend the use of the data table menu, and the menu forms can complete system maintenance.
Owner:XIAN WANNIAN TECH INDAL
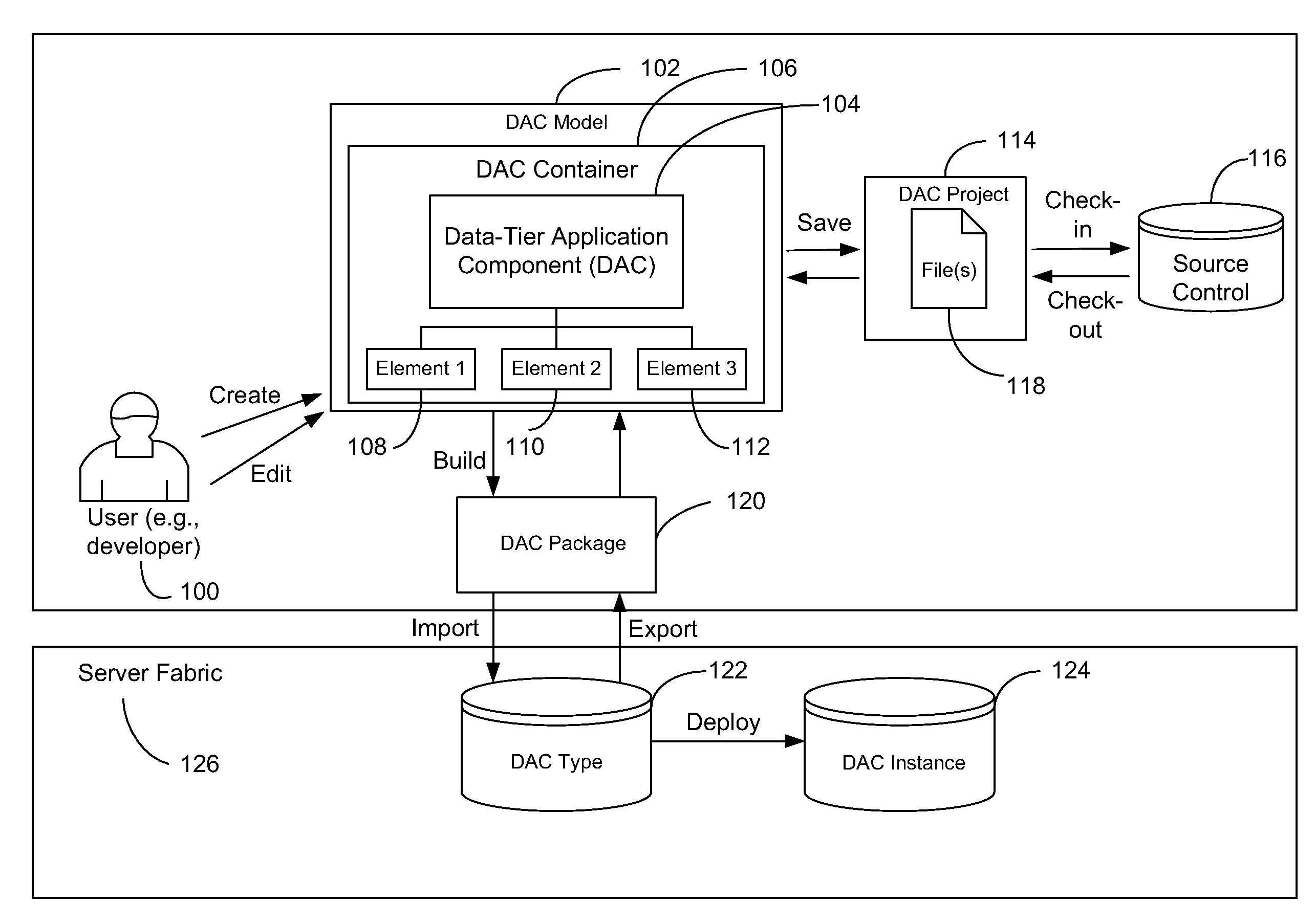
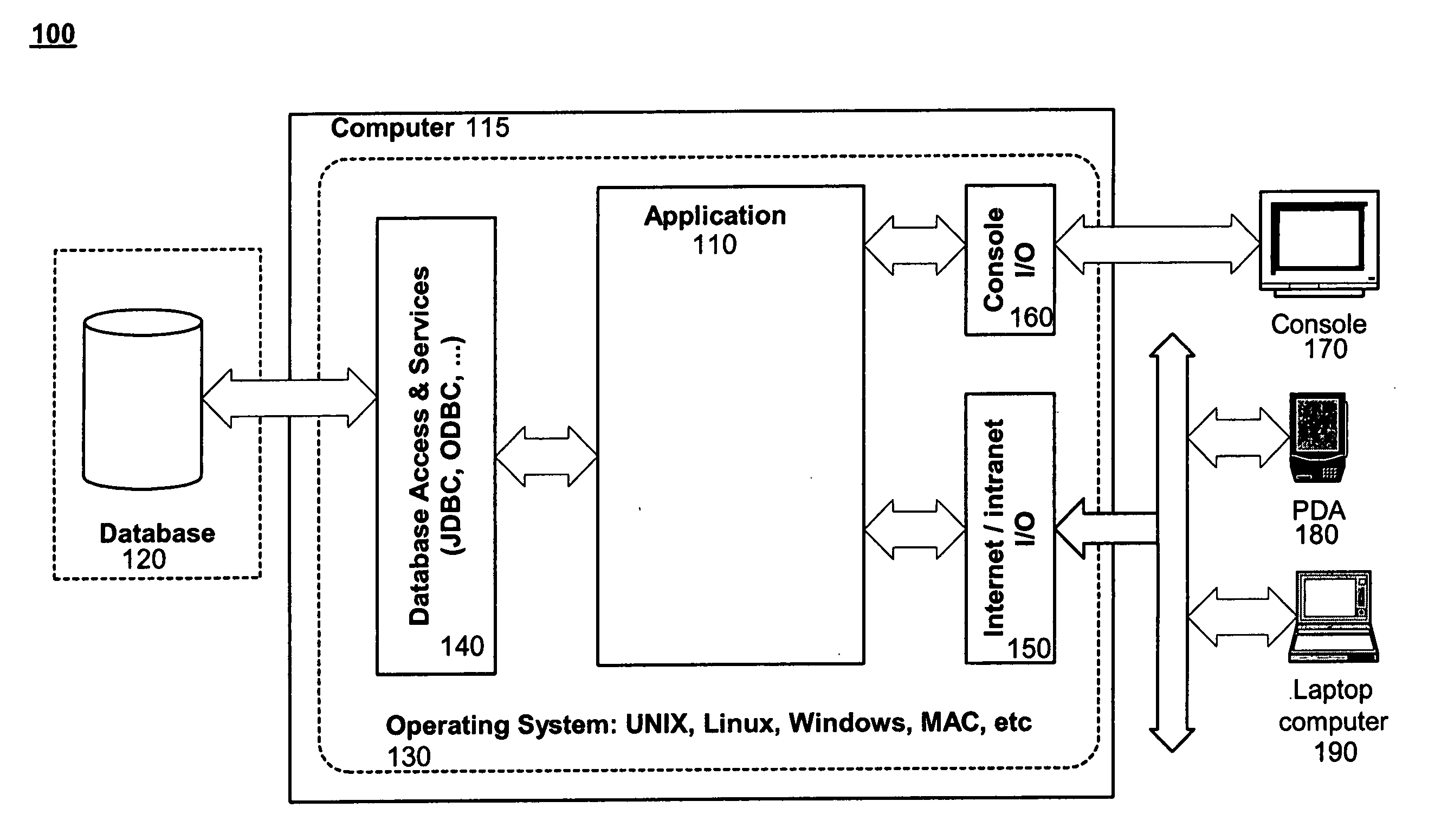
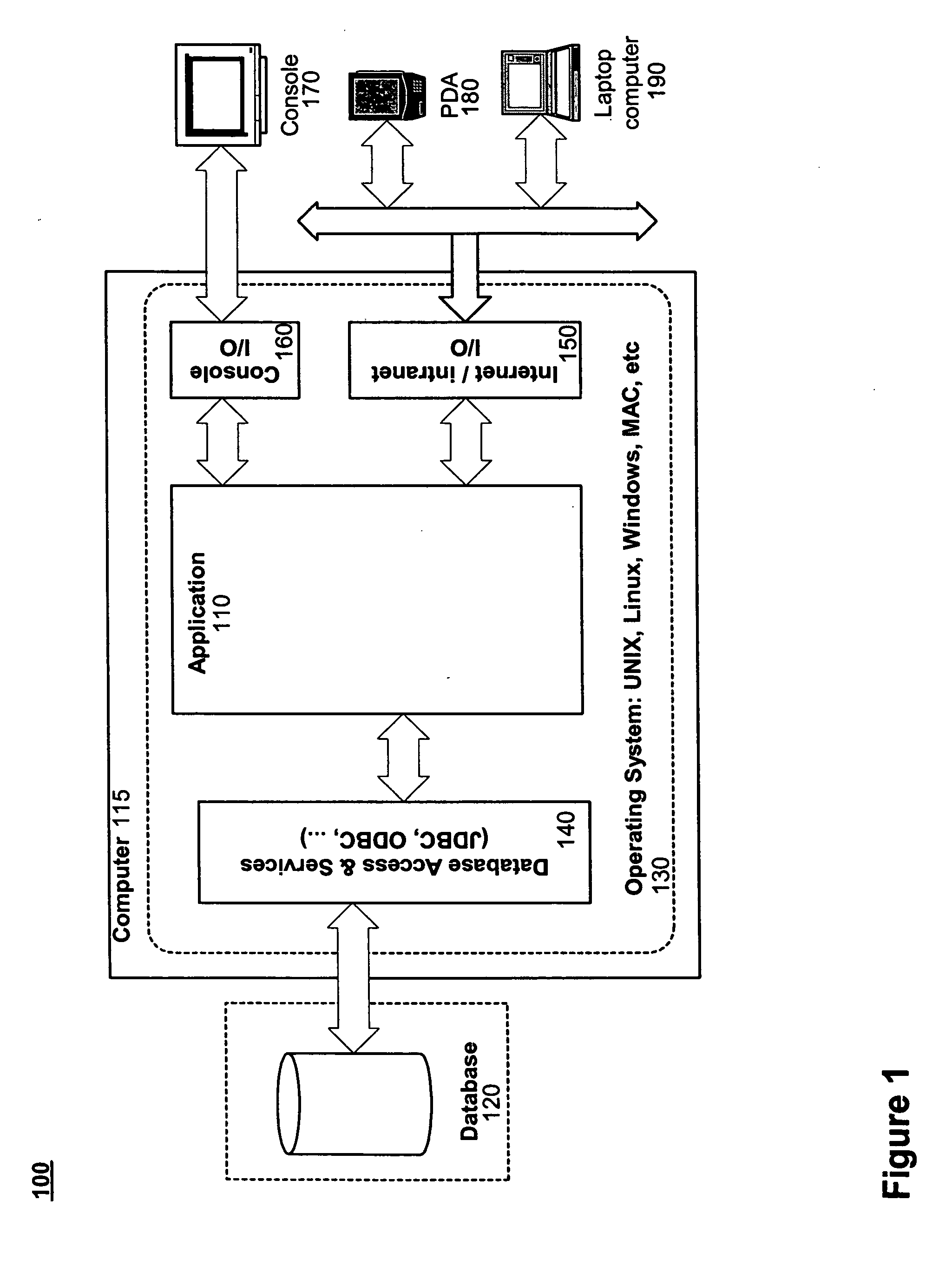
Data-tier application component
ActiveUS20100083285A1Well formedDigital data processing detailsMultiprogramming arrangementsManagement unitDatabase application
Owner:MICROSOFT TECH LICENSING LLC
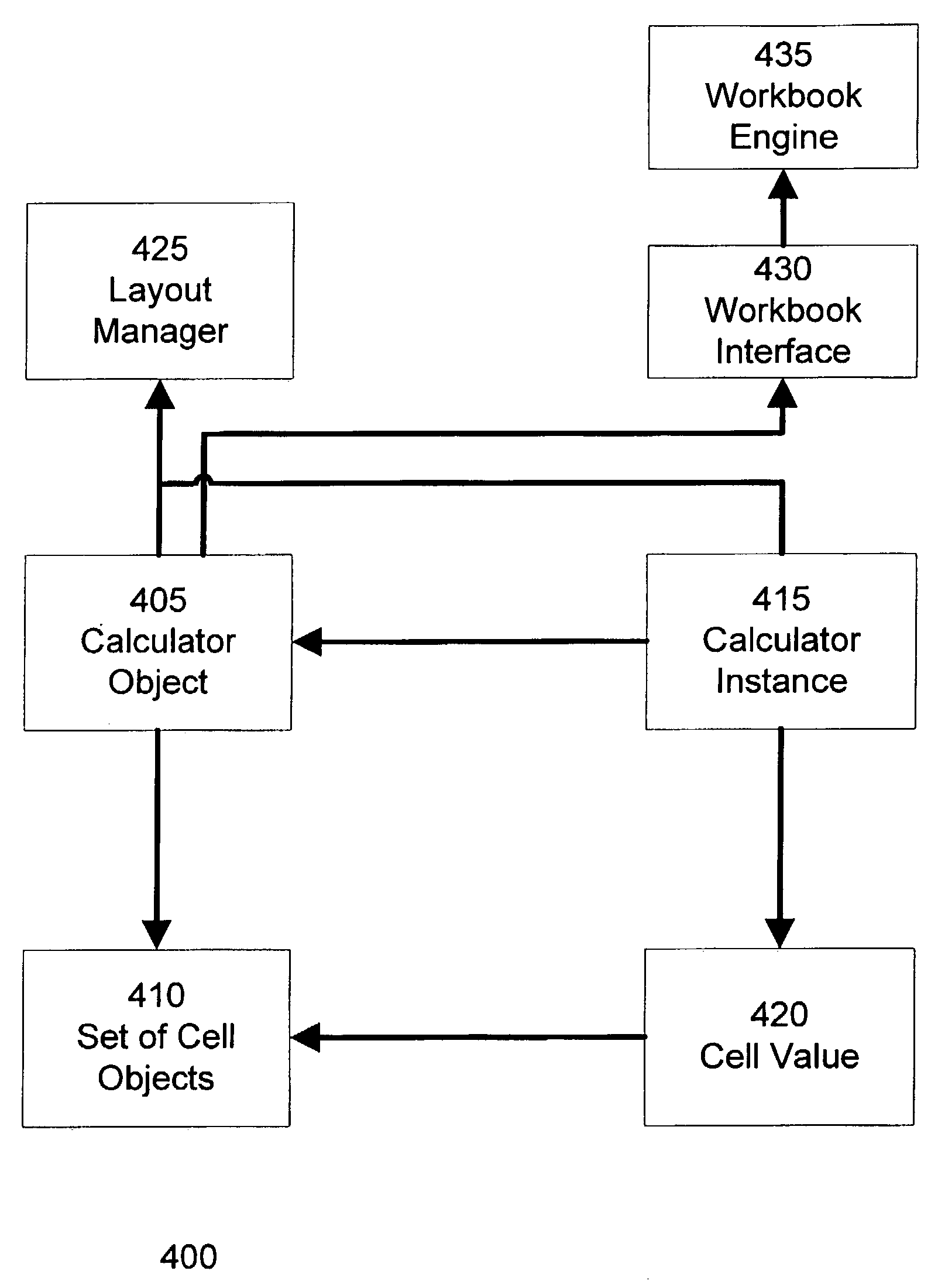
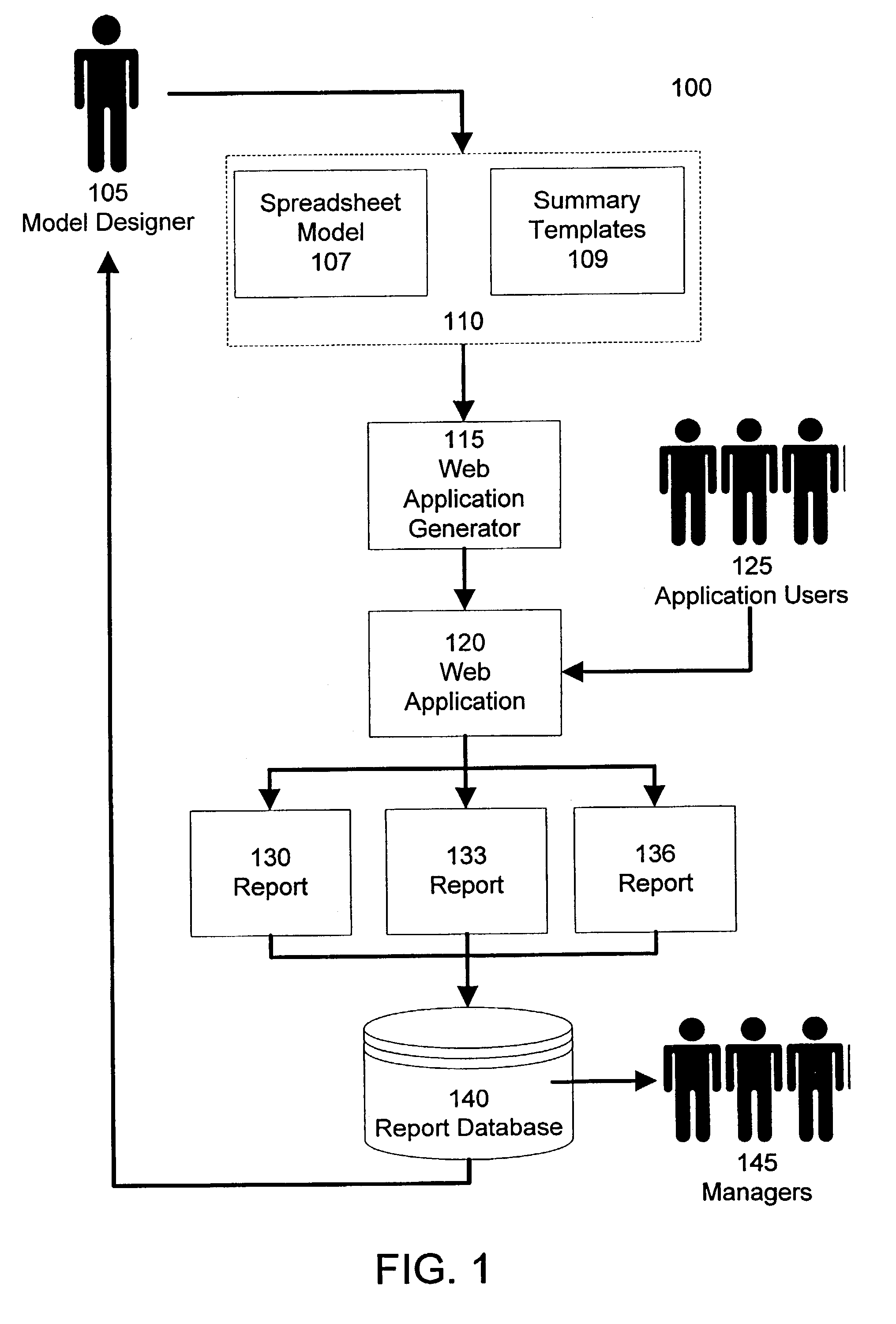
Web application generator for spreadsheet calculators
ActiveUS7523395B1Quickly and efficiently creatingRapidly and inexpensively distributedText processingWebsite content managementWeb applicationData set
A method and system automatically creates and operates a web application from a spreadsheet without the need for specialized programming. The web application includes a guided data entry process created from spreadsheet worksheets. The web application interfaces with a database application, so that model data may be retrieved for analysis. The web application implements the model as a calculator data defining the relationships between the model values. A rendering data defines the appearance of the model values in the web application. A instance data includes the model values for an instance of the web application. A calculation engine calculates model values. A layout engine creates display information from the calculator, rendering, and instance data set. The rendering data includes objects having display methods for creating display information in accordance with its object type. Object types include inputs, outputs, and user interface elements.
Owner:ORACLE INT CORP
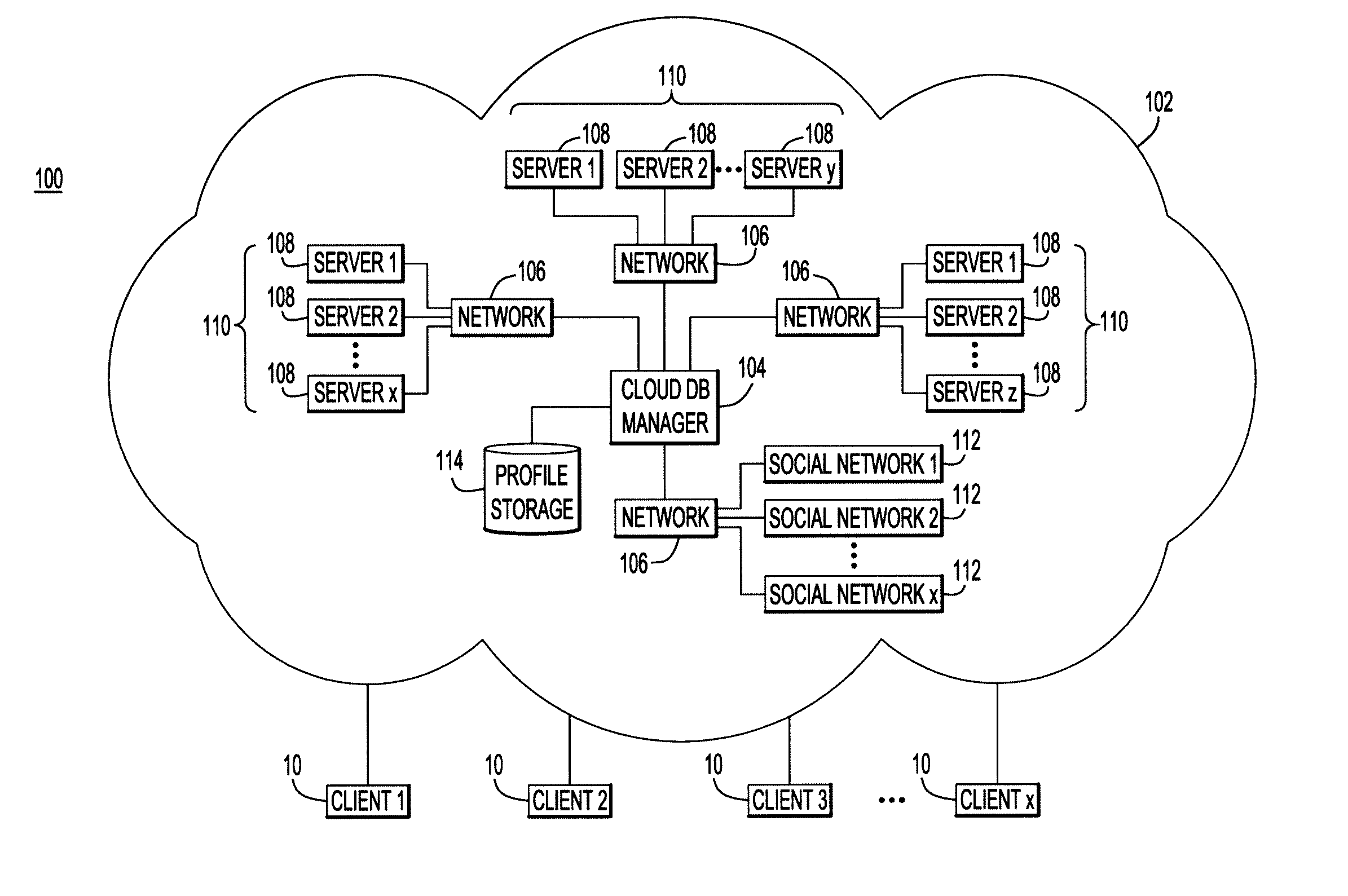
Sharing Cloud Data Resources With Social Network Associates
InactiveUS20120054280A1Multiple digital computer combinationsProgram controlDatabase applicationCloud data
A method, computer program product, and system for sharing cloud data resources among associated users. Upon receipt of a request from an associate of a primary user to share a cloud data resource, a sharing profile of the primary user is evaluated to determine if the associate is permitted to share the requested resource, and if so, the requested resource is made available to the associate. The shared cloud data resource can be a database application, data object, data storage resource, or a portion thereof.
Owner:IBM CORP +1
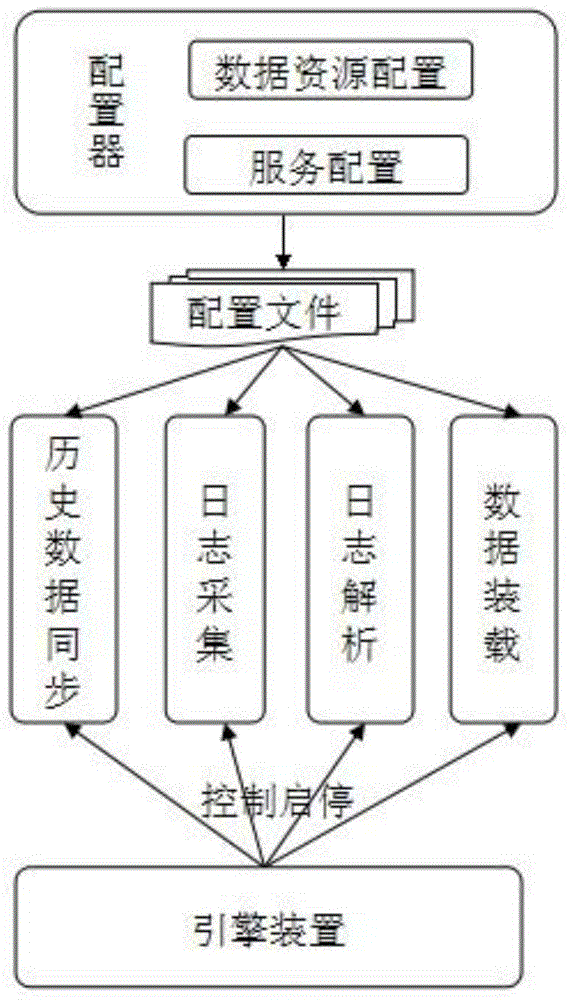
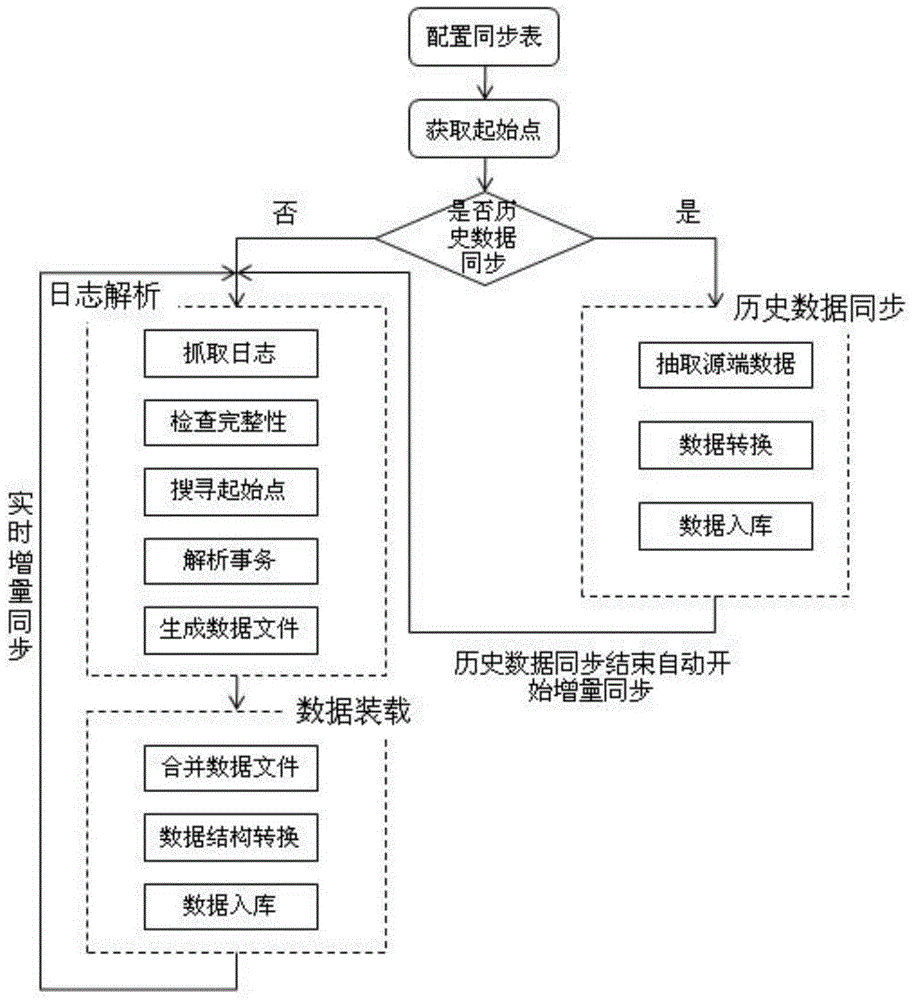
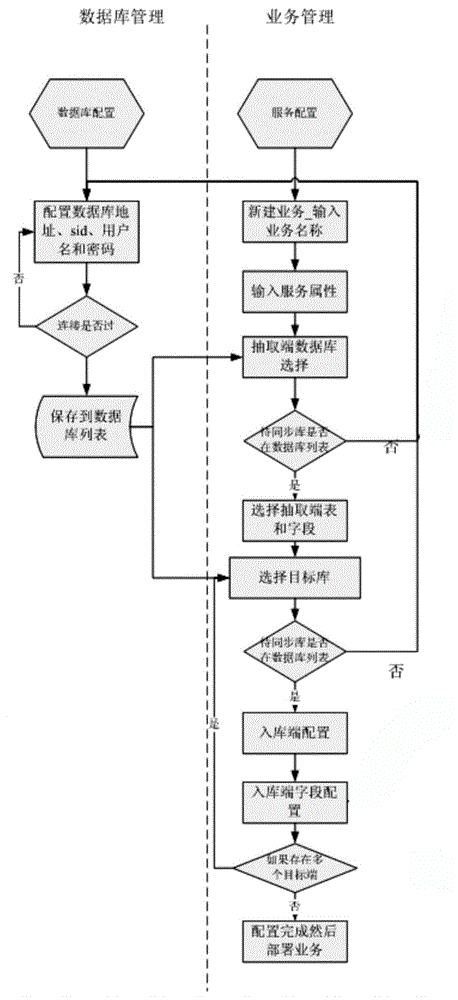
Data synchronization method and system among heterogeneous databases
InactiveCN105005618AReduce the impactReduce dependenceDatabase distribution/replicationSpecial data processing applicationsData synchronizationComplete data
The invention relates to a data synchronization method and system among heterogeneous databases, by which the two purposes of historical data synchronization and incremental data synchronization are achieved. According to the method, heterogeneous synchronization among various types of main databases is supported, other tools and scripts are not needed, the historical data synchronization and the incremental data synchronization can be easily configured and are automatically linked, and the complexity is reduced. The system is simple and easy to understand, backstage scrip writing and database command input are not needed, and a whole data synchronization service can be configured even by a person who has no experience in database application. The method and the system are applicable for a synchronization scenario of various types of data.
Owner:HANGZHOU HEZHONG DATA TECH CO LTD
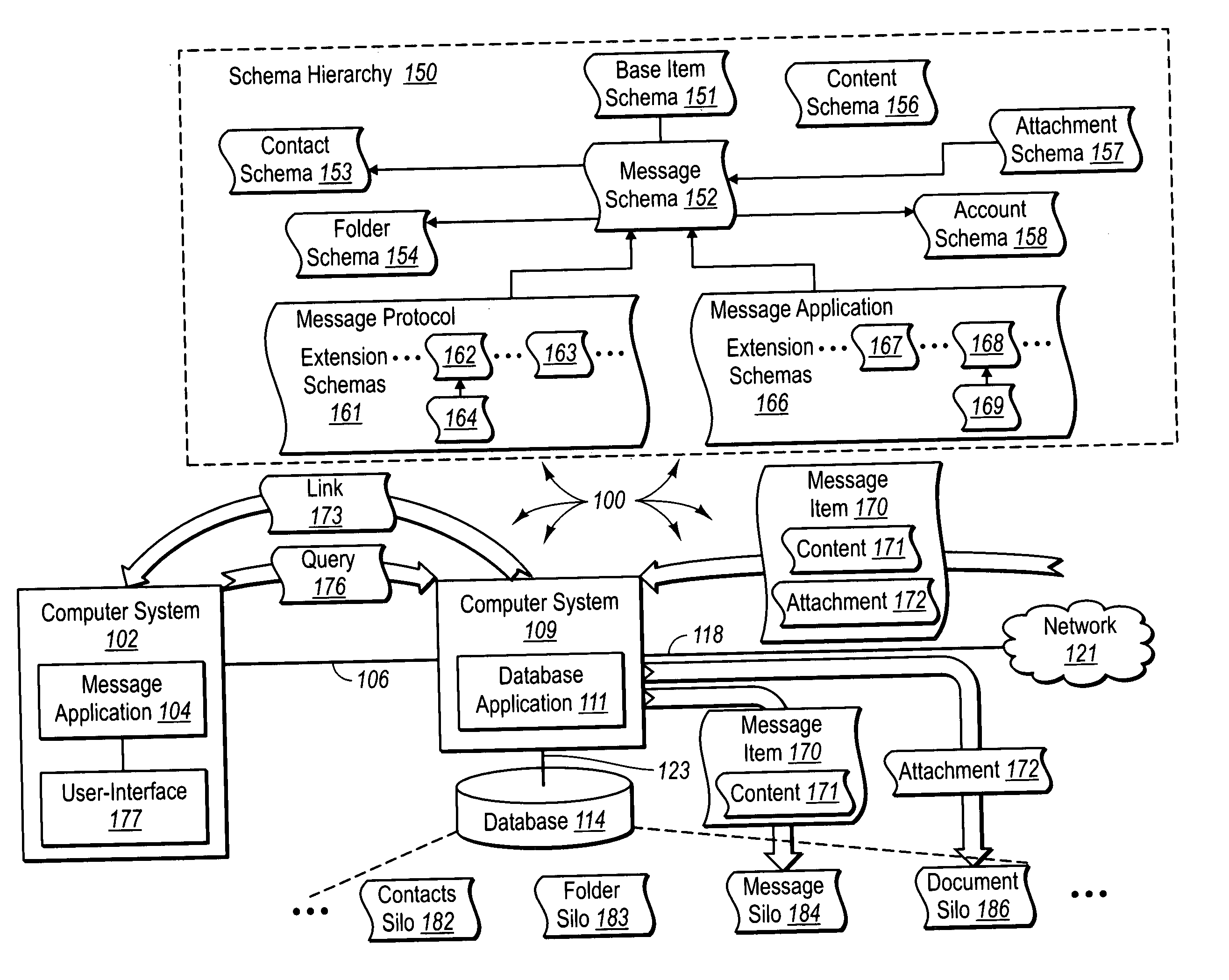
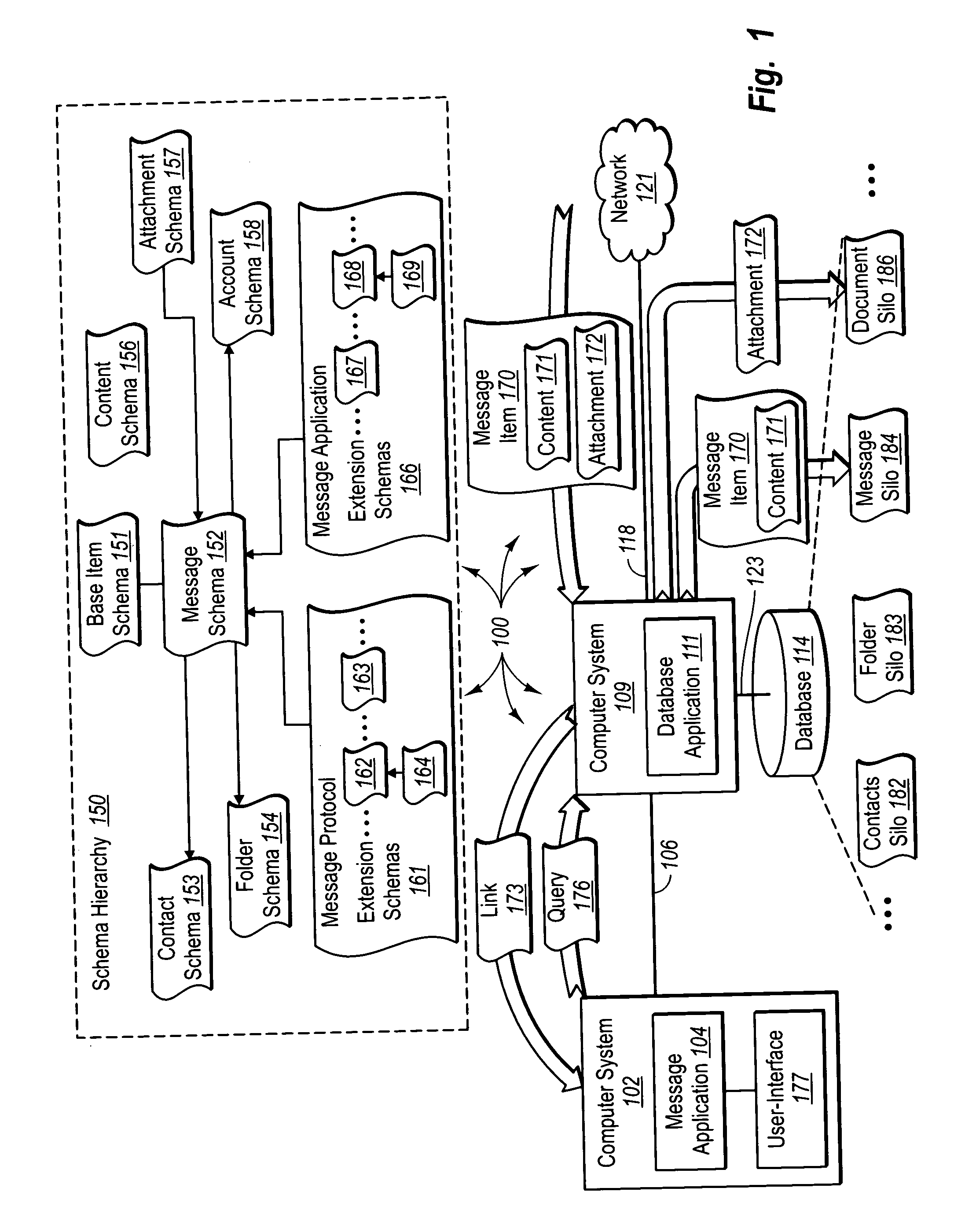
Presenting message attachments independent of electronic messages at a user-interface
The present invention extends to methods, systems, computer program products, and data structures for presenting message attachments independent of electronic messages at a user-interface. A message application submits a query for message related data that satisfies query criteria. A database application receives the query and identifies a message attachment that satisfies the query criteria. The database application returns a message attachment link to the message attachment in response to the query. The message attachment link provides access to the message attachment independent of an electronic message that included the message attachment. The message application receives the message attachment link. The message application presents the message attachment link at a user-interface independent of the electronic message such that the message attachment can be accessed without first accessing the electronic message
Owner:MICROSOFT TECH LICENSING LLC
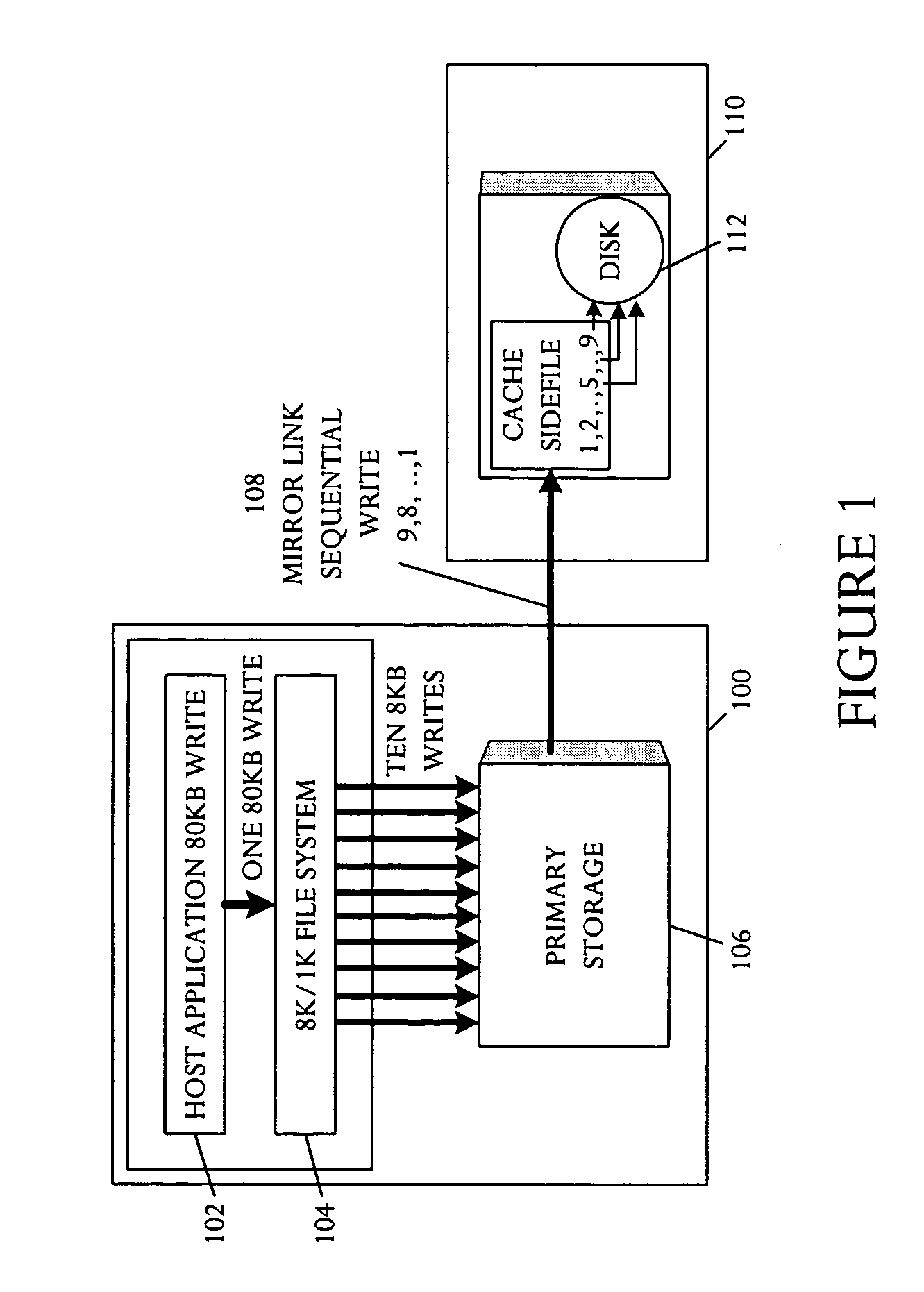
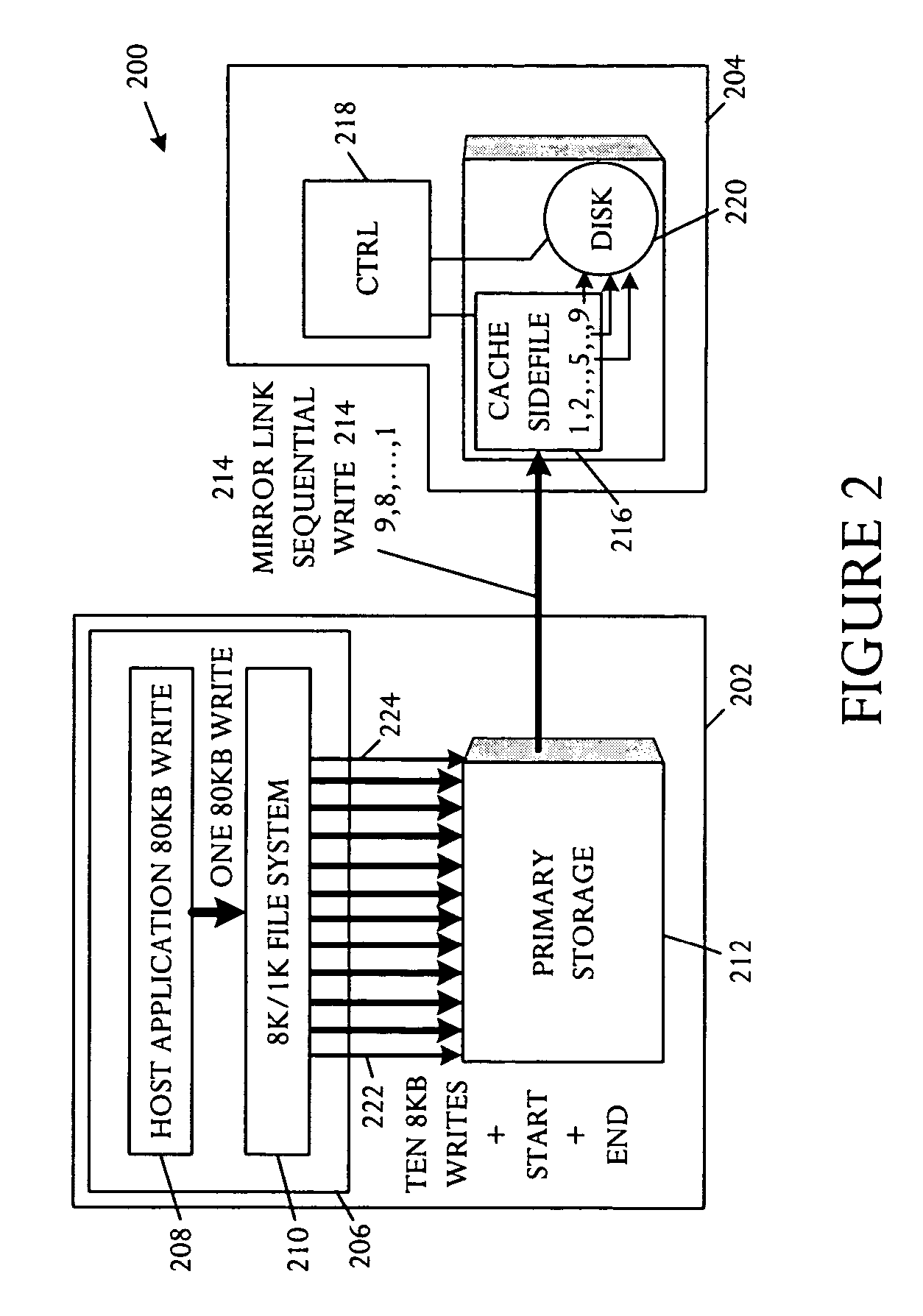
System for preserving logical object integrity within a remote mirror cache
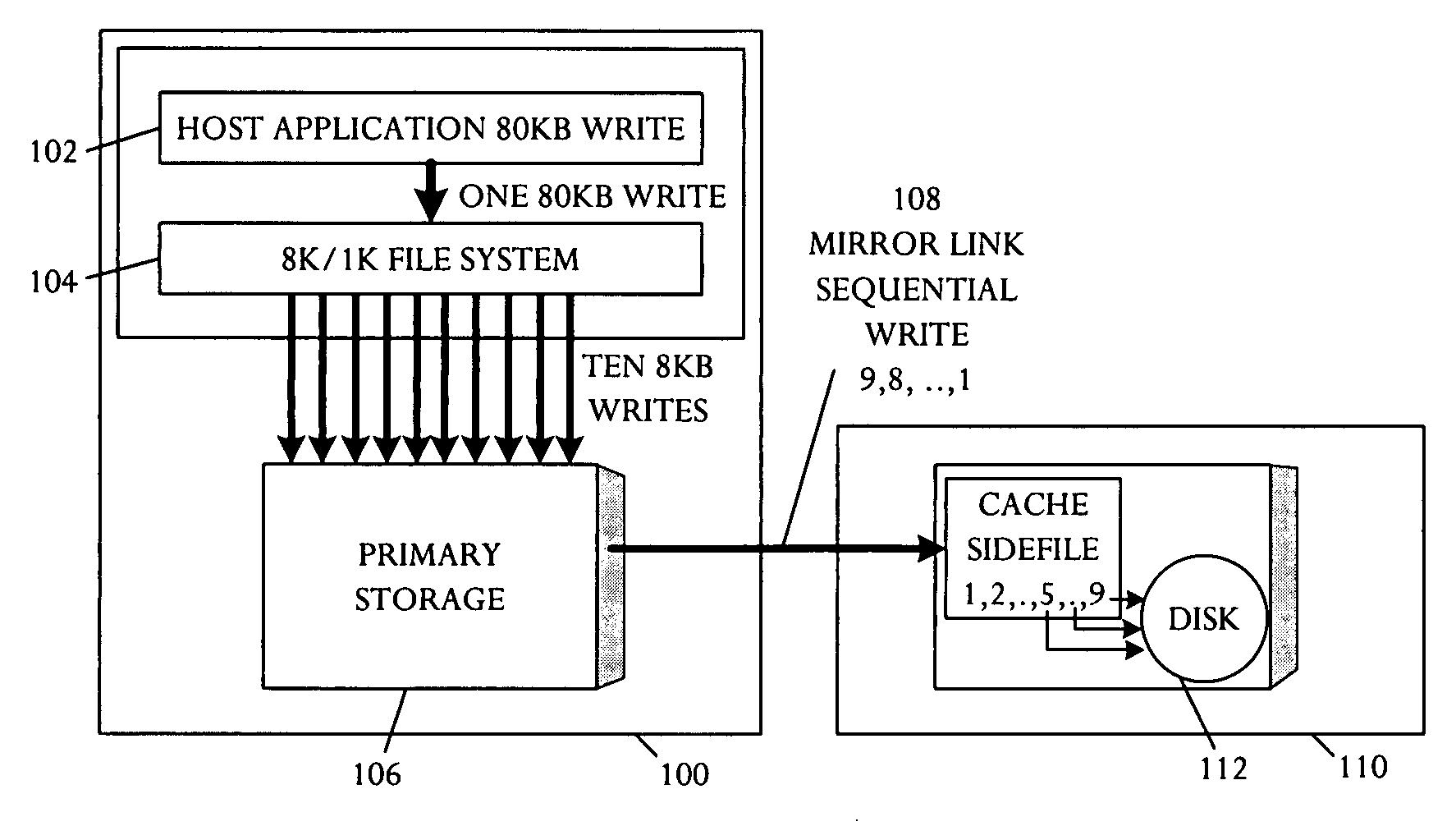
InactiveUS20050102553A1Input/output to record carriersData processing applicationsRecordsetDatabase application
A database system is capable of executing a database application that transfers a logical object in multiple fragments. The database system comprises a main storage site, a remote storage site, a main protocol executable on the main storage site, and a remote protocol executable on the remote storage site. The remote storage site is capable of linking to the main storage site and mirroring information stored in the main storage site. The remote storage site includes a storage and a cache sidefile divided into a plurality of array sidefile recordsets. The main protocol is capable of including information indicative of logical object fragment commencement and completion in the multiple fragment database application transfer. The remote protocol is capable of controlling the cache sidefile to cache the multiple fragments as received and to enable destaging of the logical object to the storage on receipt of all fragments.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
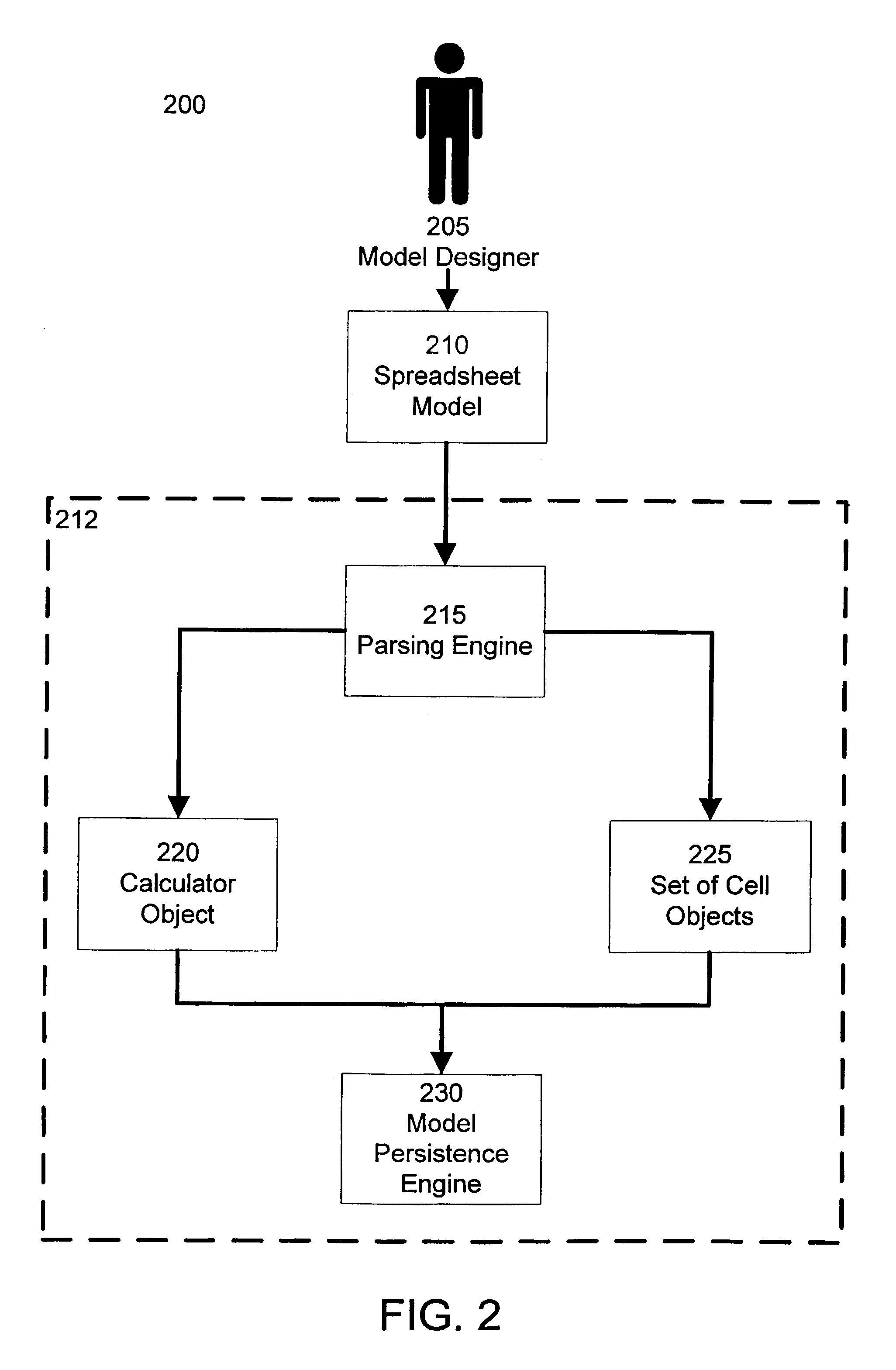
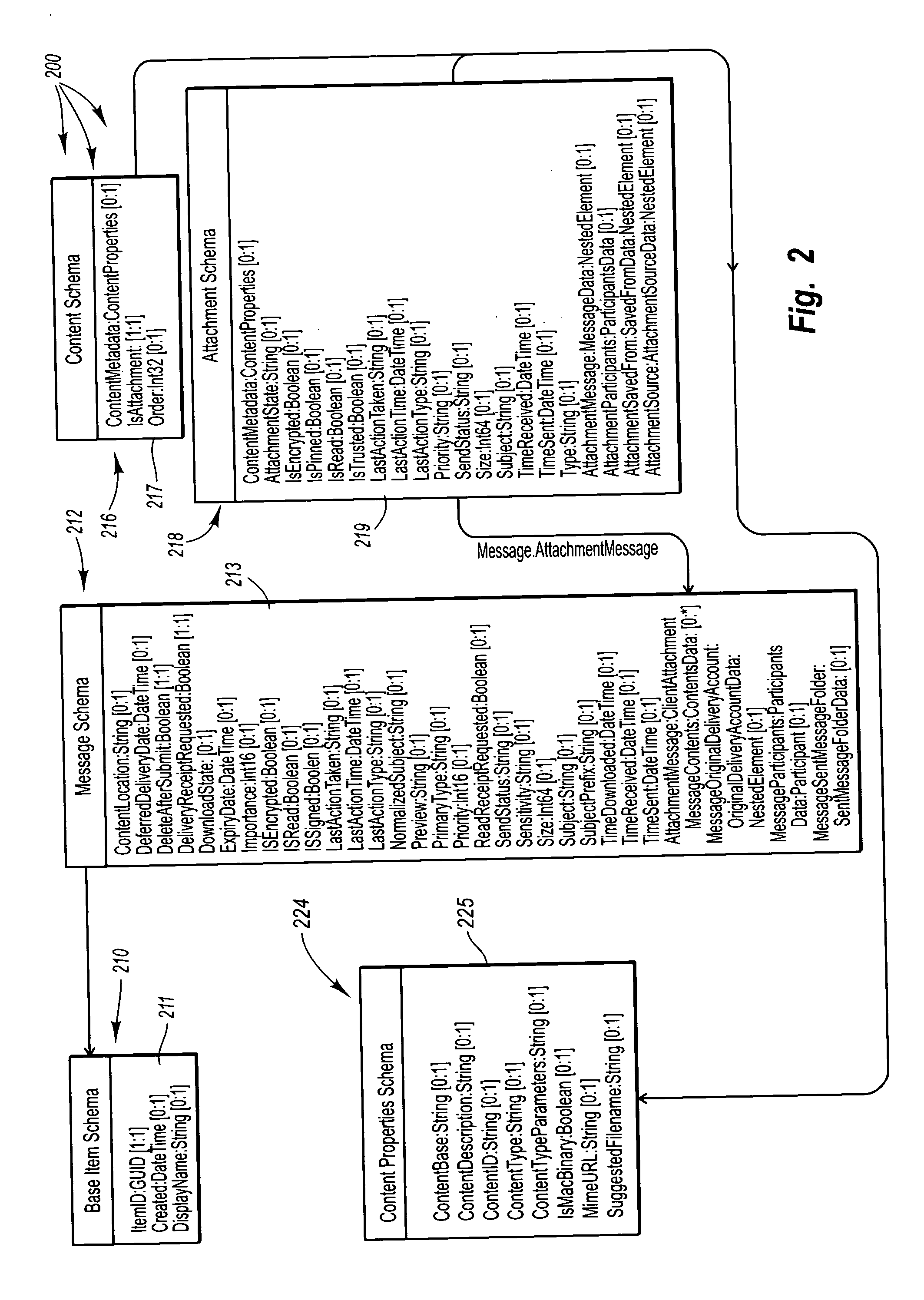
Software framework that facilitates design and implementation of database applications
InactiveUS20040220956A1Data processing applicationsDigital data information retrievalDatabase applicationHigh-level programming language
An intelligent framework is provided that is disposed between a high-level language environment and a database system environment. According to one embodiment, the framework programmatically receives information regarding definitions of data structures of objects participating in a software application and information regarding relationships among the objects. Based upon the particular request from the high-level language environment and upon the definitions and relationships, the framework programmatically and dynamically generates appropriate statements associated with the database system environment that accomplish the request. For example, the framework may issue statements to define the structure of a database, access information from the database, and / or manipulate information within the database.
Owner:RPX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com