Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42676results about "Specific program execution arrangements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
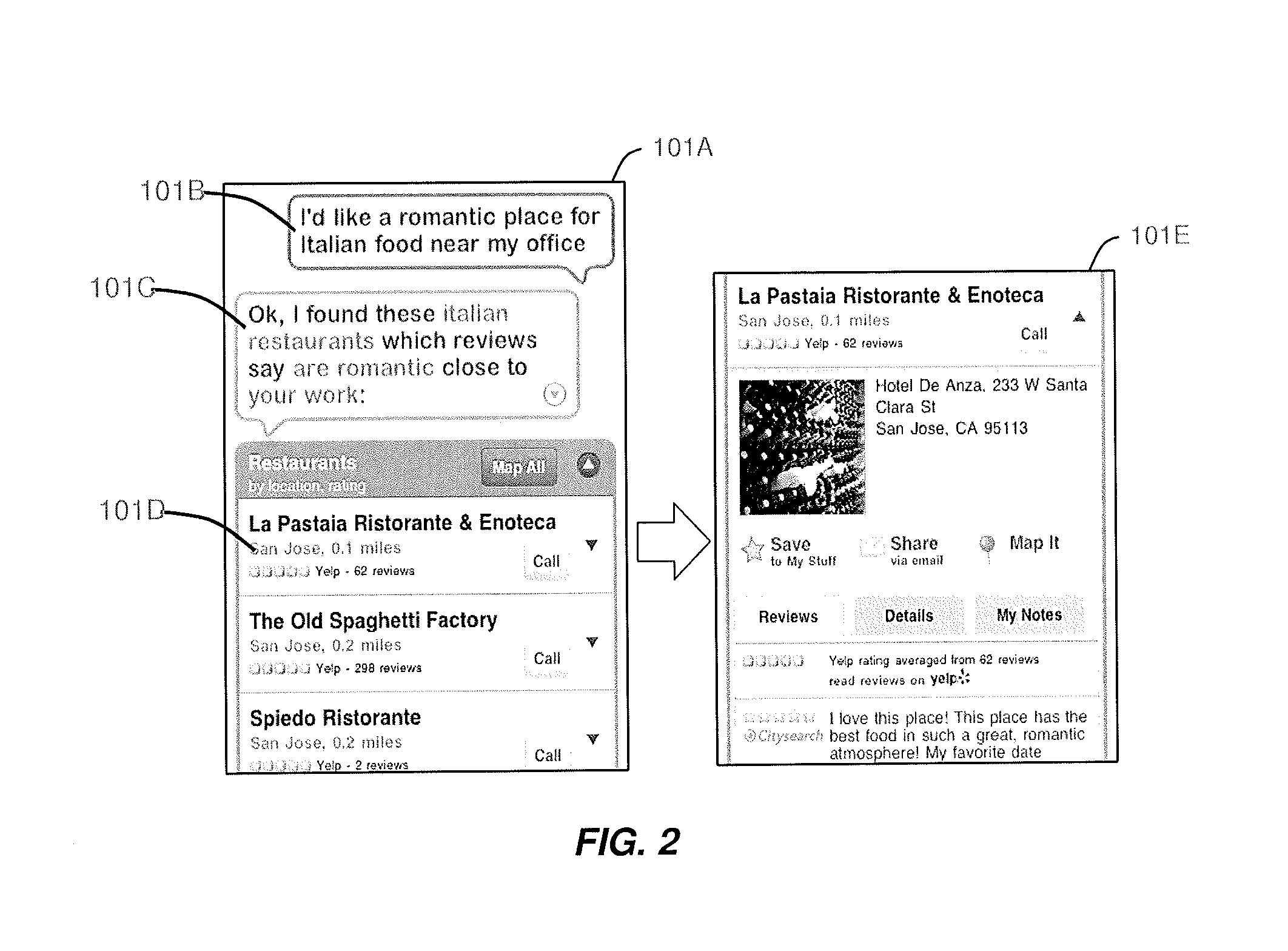
Methods and apparatus for interpreting user selections in the context of a relation distributed as a set of orthogonalized sub-relations
Owner:ORACLE INT CORP
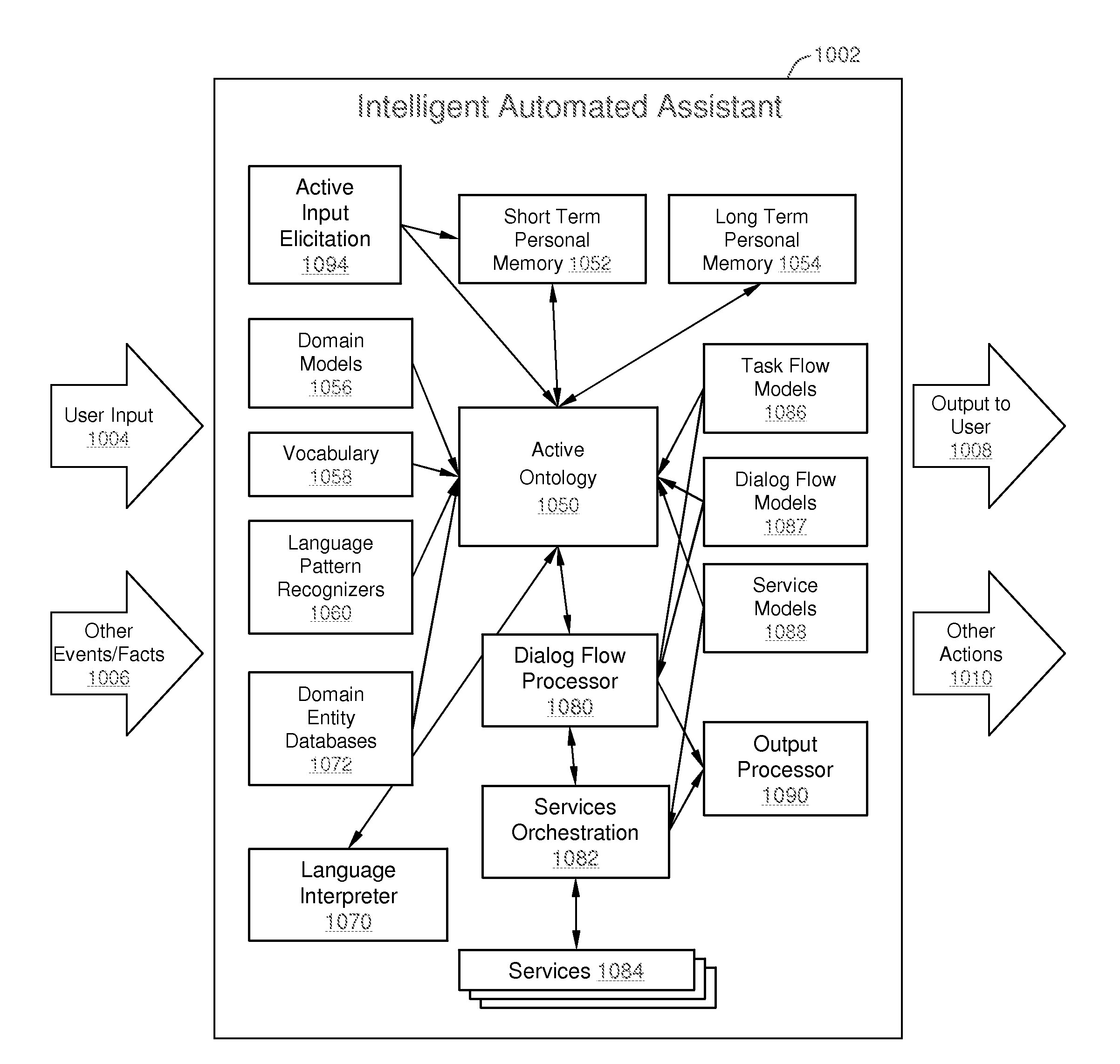
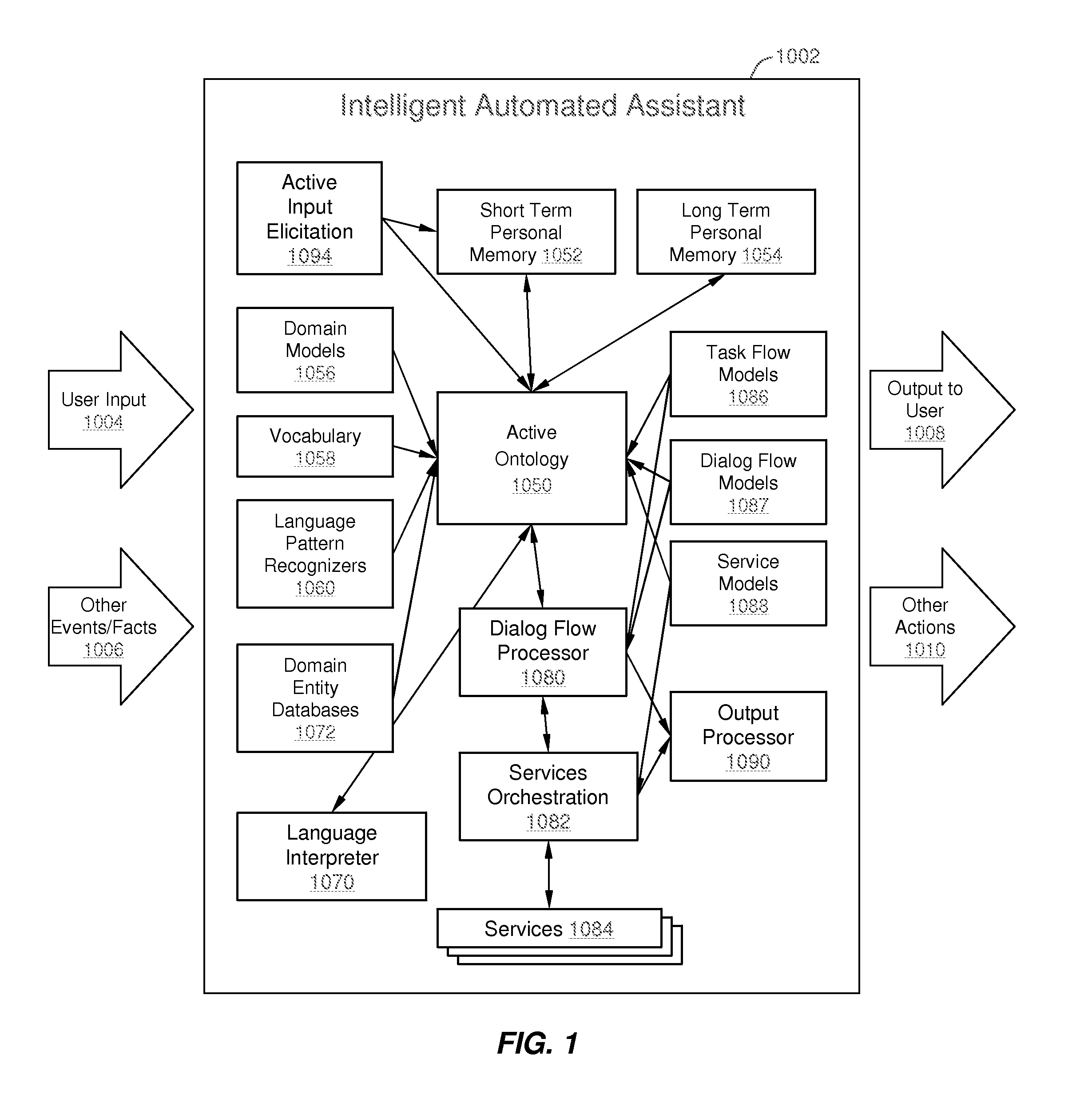
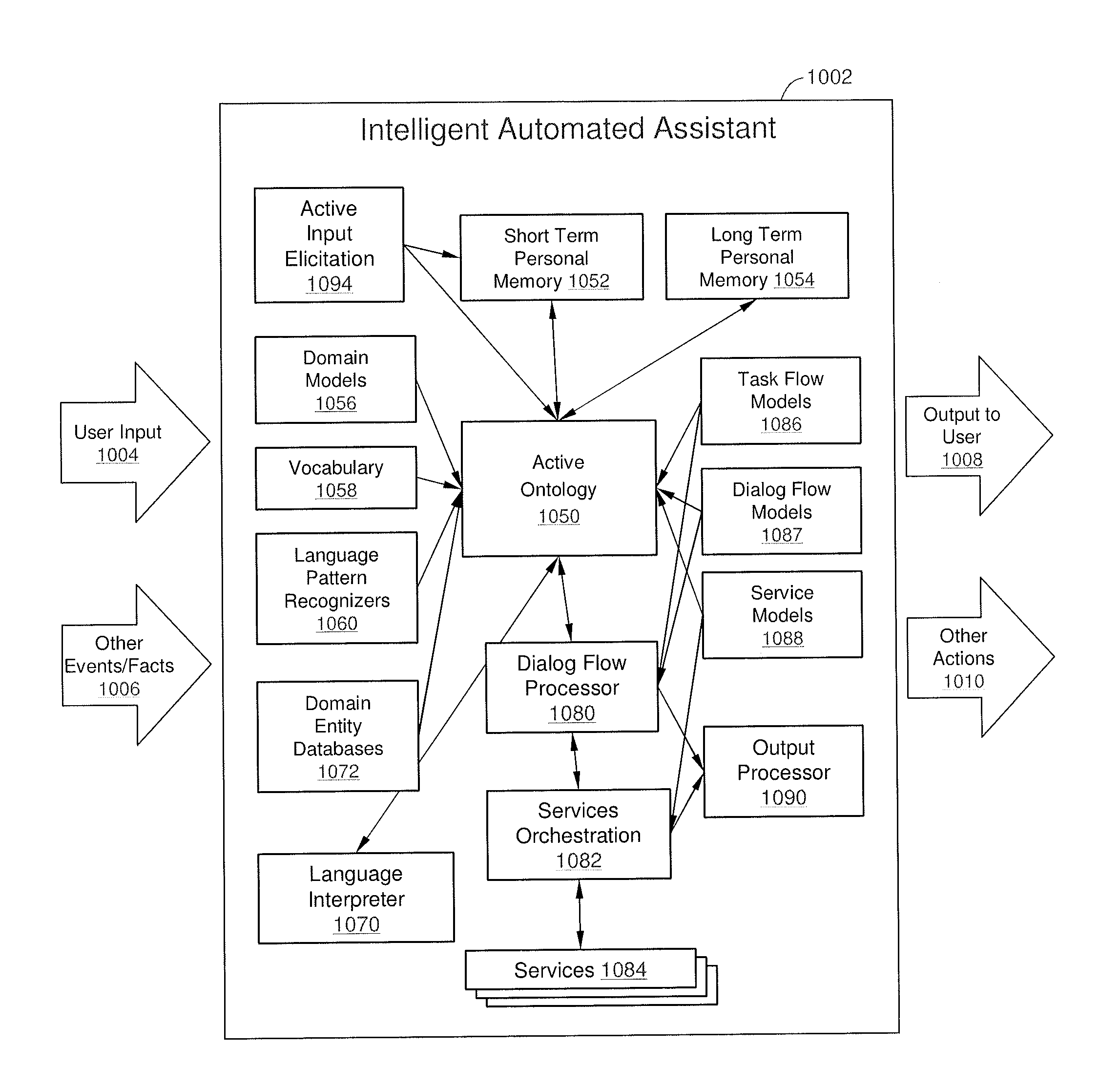
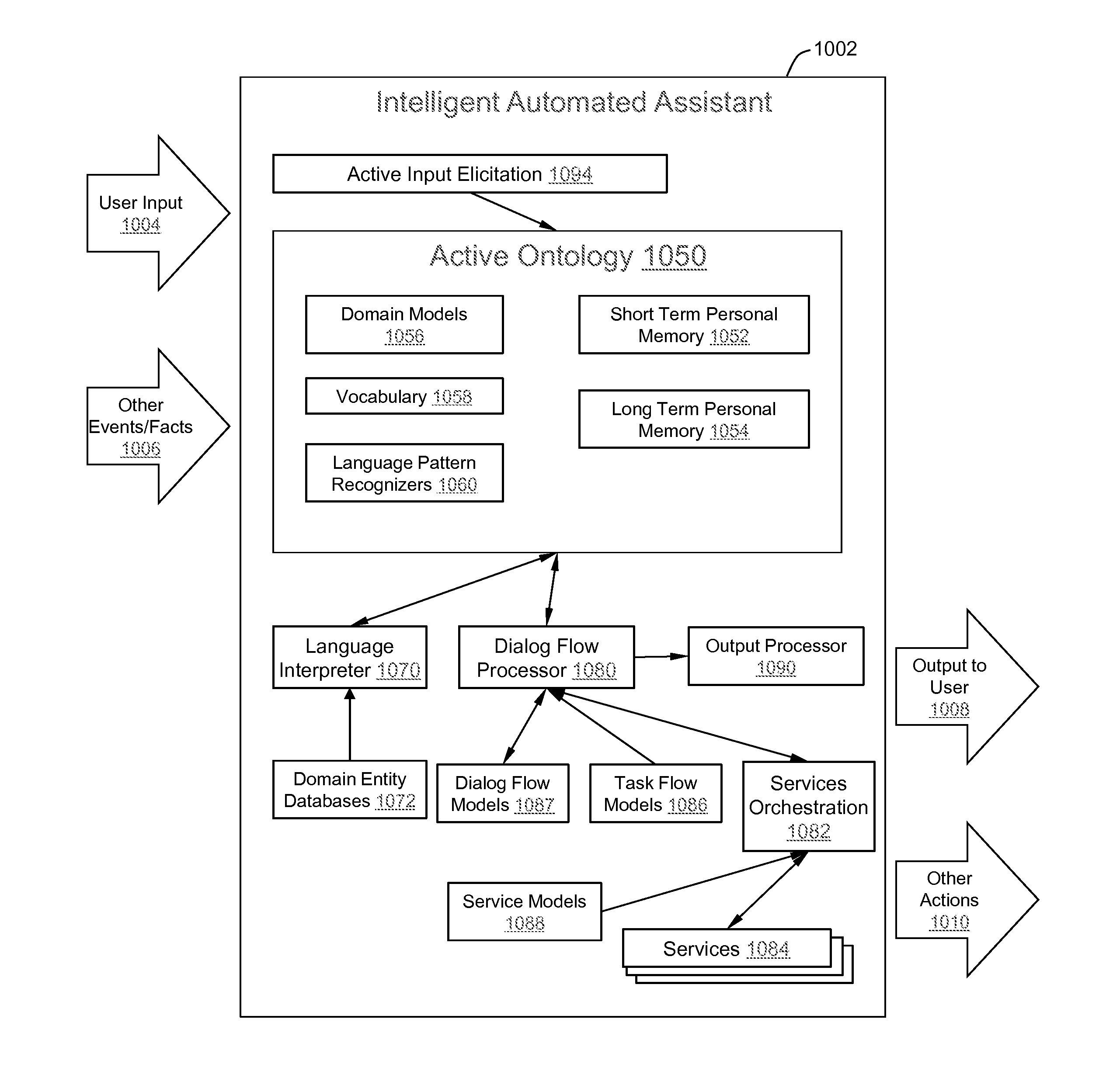
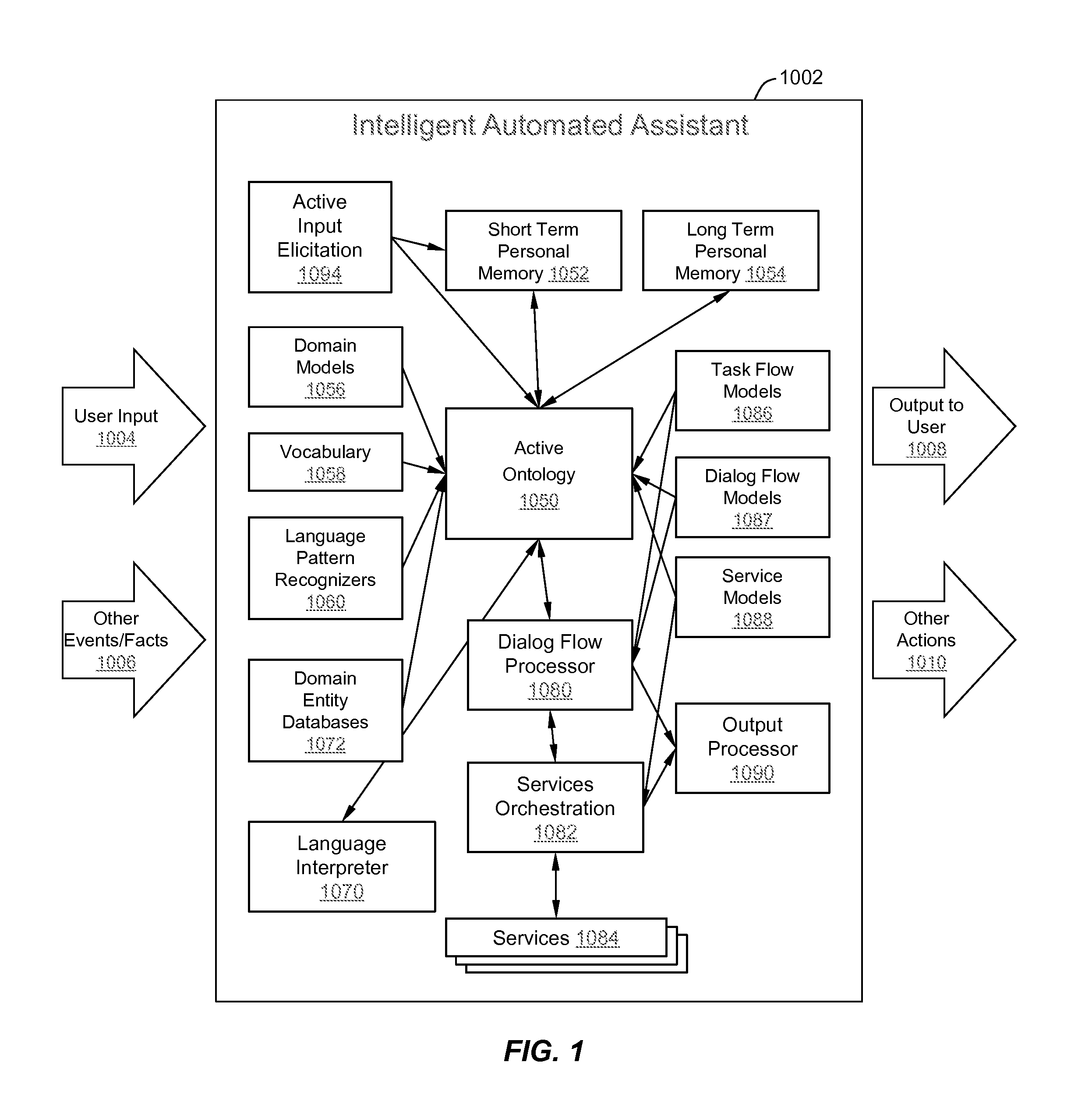
Intelligent Automated Assistant
ActiveUS20120016678A1Improve user interactionPromote effective engagementNatural language translationSemantic analysisService provisionSystem usage
An intelligent automated assistant system engages with the user in an integrated, conversational manner using natural language dialog, and invokes external services when appropriate to obtain information or perform various actions. The system can be implemented using any of a number of different platforms, such as the web, email, smartphone, and the like, or any combination thereof. In one embodiment, the system is based on sets of interrelated domains and tasks, and employs additional functionally powered by external services with which the system can interact.
Owner:APPLE INC
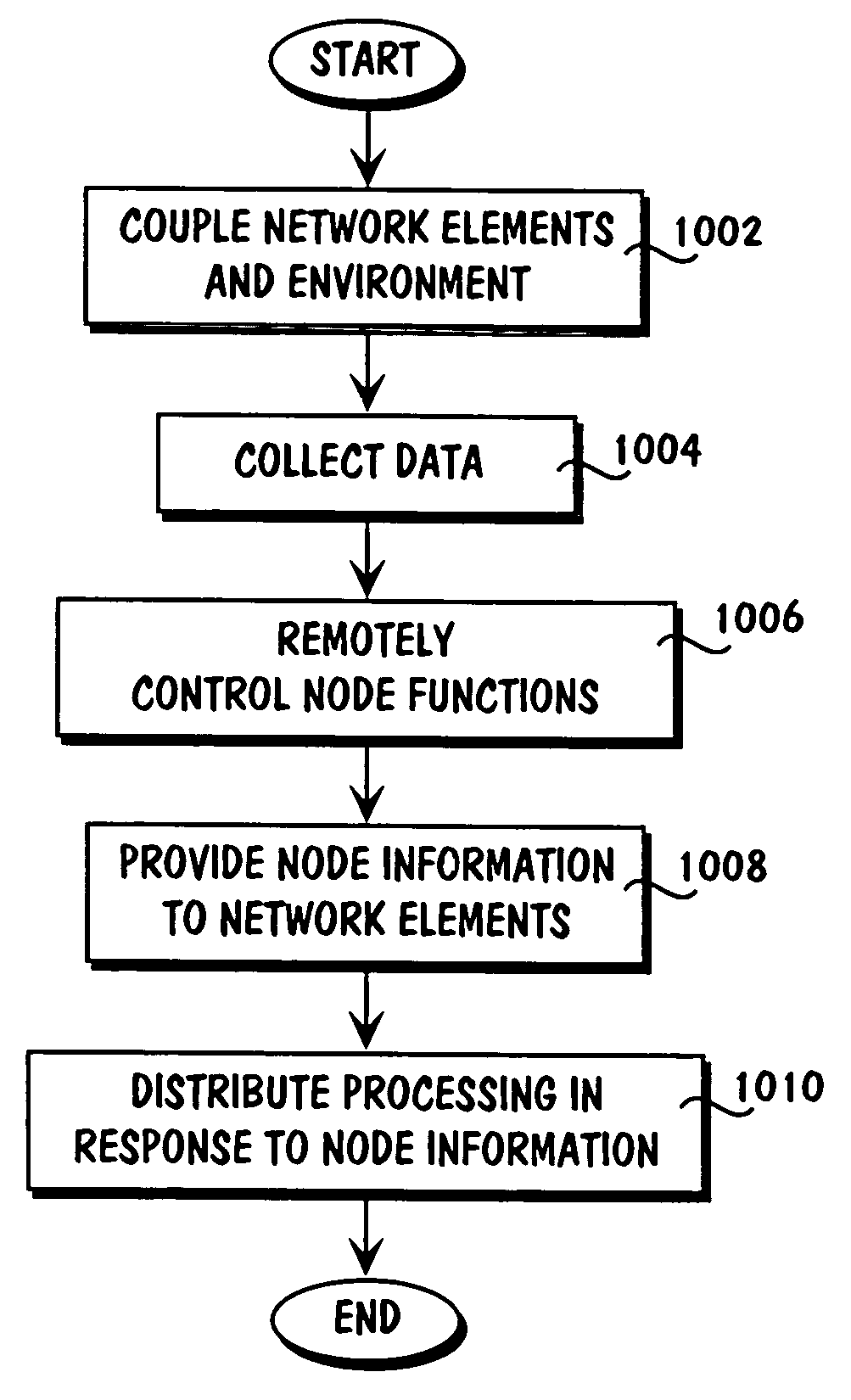
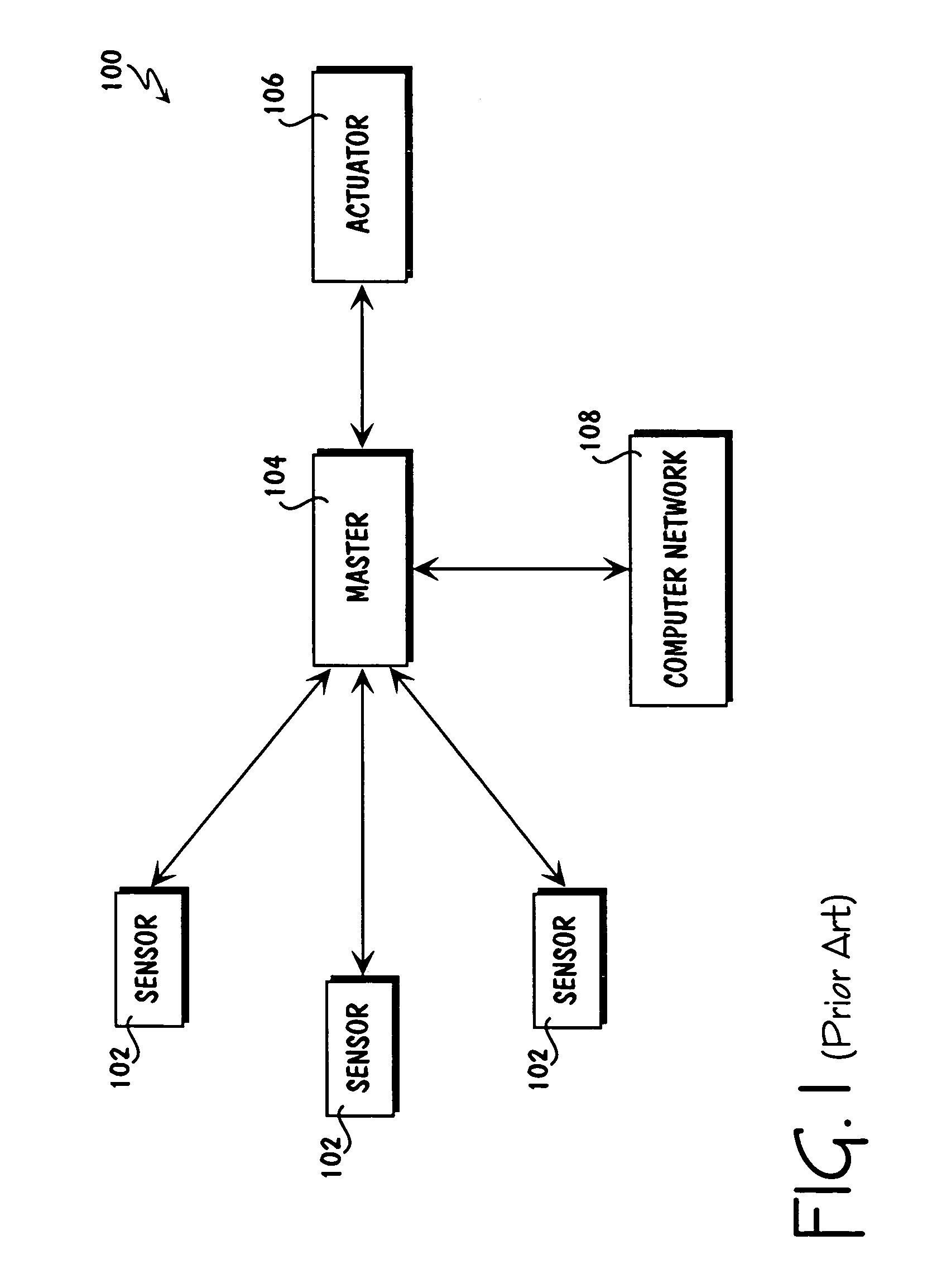
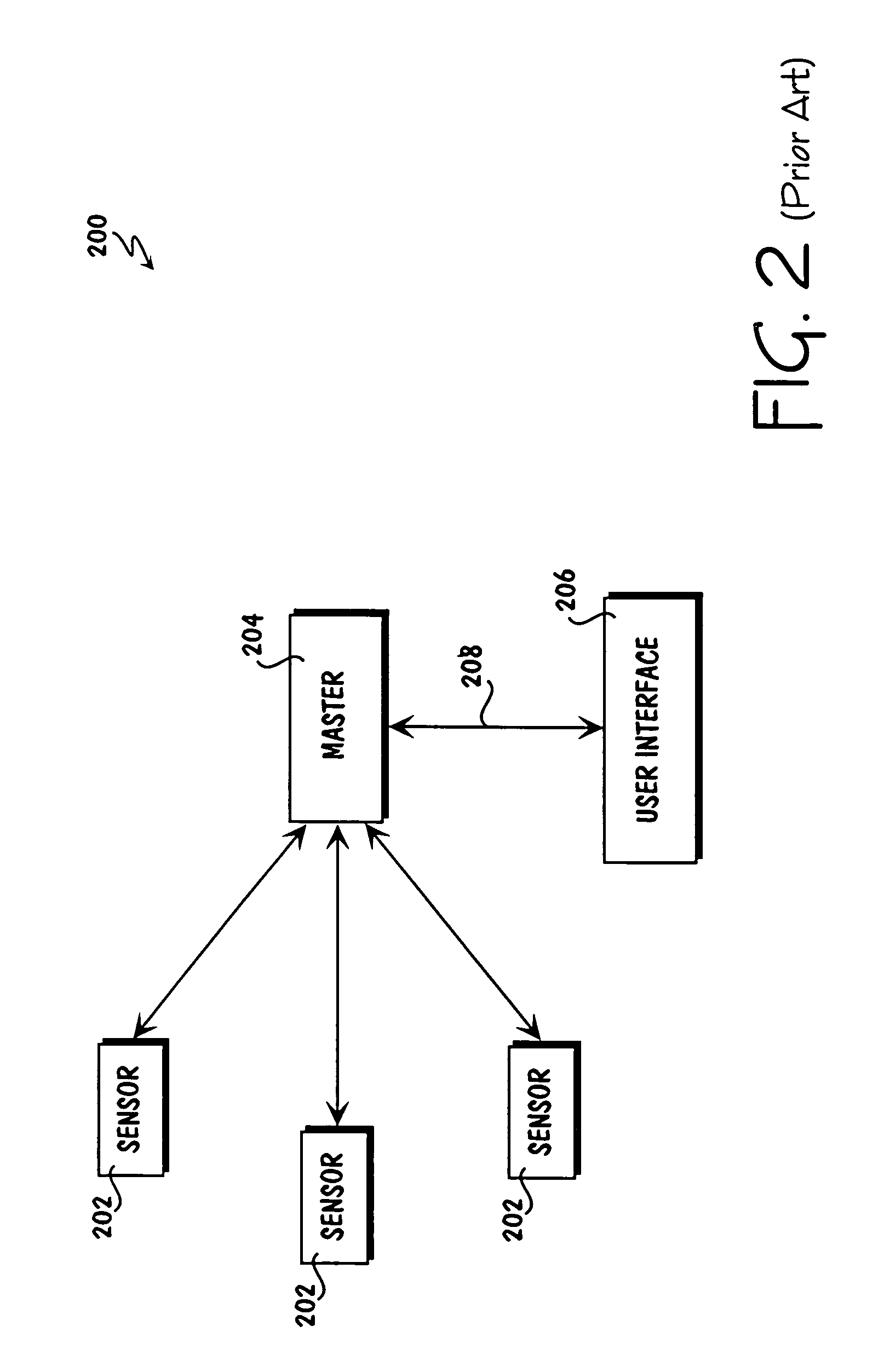
Method for collecting and processing data using internetworked wireless integrated network sensors (WINS)
InactiveUS7020701B1High reliability accessEasy to operateEnergy efficient ICTPower managementReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
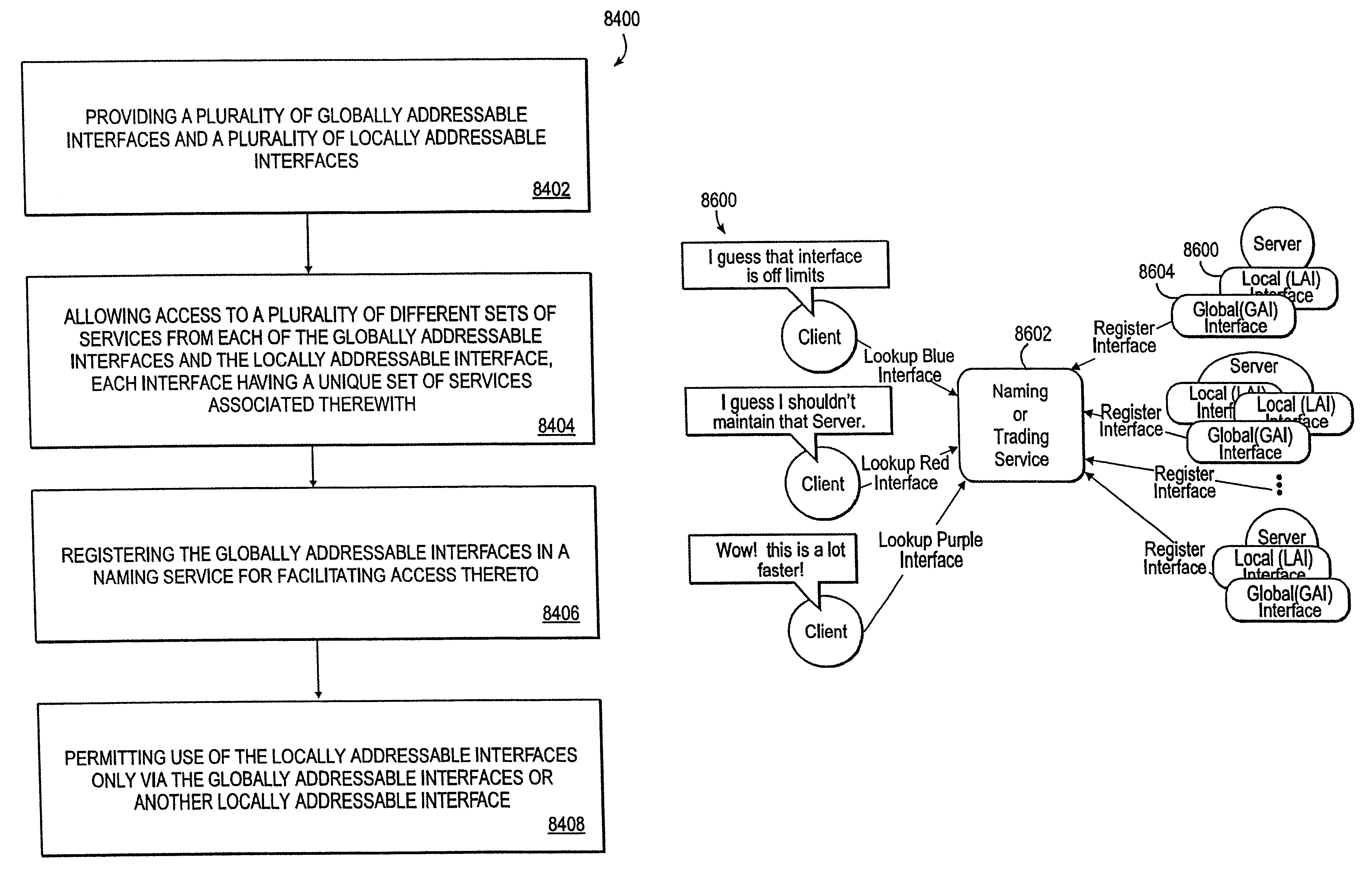
Delivering service to a client via a locally addressable interface
InactiveUS6438594B1Multiple digital computer combinationsSpecific program execution arrangementsComputer hardwareClient-side
A system, method, and article of manufacture are provided for delivering service via a locally addressable interface. A plurality of globally addressable interfaces and a plurality of locally addressable interfaces are provided. Access is allowed to a plurality of different sets of services from each of the globally addressable interfaces and the locally addressable interface. Each interface has a unique set of services associated therewith. The globally addressable interfaces are registered in a naming service for facilitating access thereto. Use of the locally addressable interfaces is permitted only via the globally addressable interfaces or another locally addressable interface.
Owner:ACCENTURE GLOBAL SERVICES LTD
Multi-object fetch component
InactiveUS6529948B1Digital data processing detailsMultiprogramming arrangementsBusiness objectSoftware engineering
A system, method, and article of manufacture are provided for retrieving multiple business objects across a network in one access operation. A business object and a plurality of remaining objects are provided on a persistent store. Upon receiving a request for the business object, it is established which of the remaining objects are related to the business object. The related objects and the business object are retrieved from the persistent store in one operation and it is determined how the retrieved related objects relate to the business object and each other. A graph of relationships of the business and related objects is instantiated in memory.
Owner:ACCENTURE GLOBAL SERVICES LTD
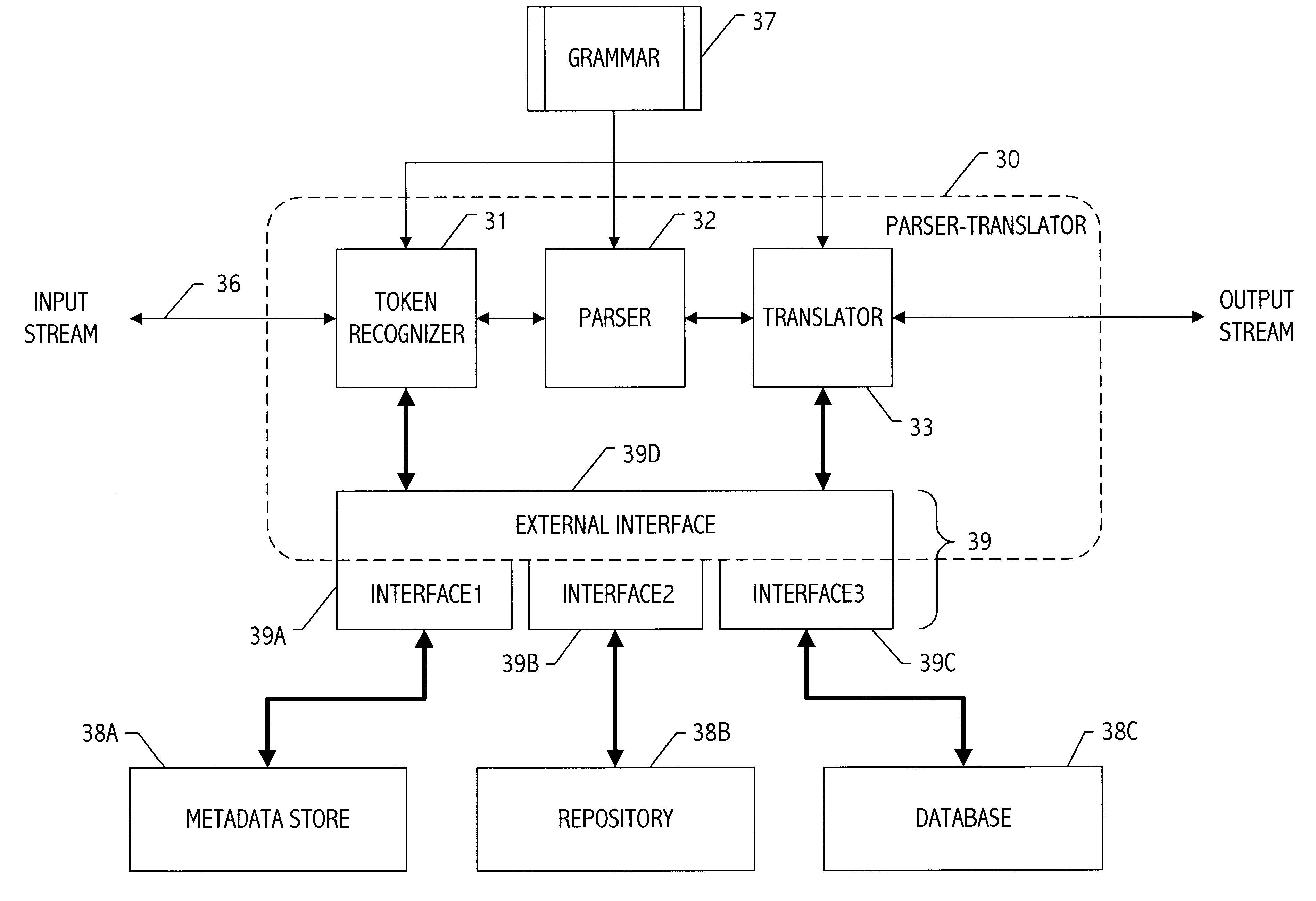
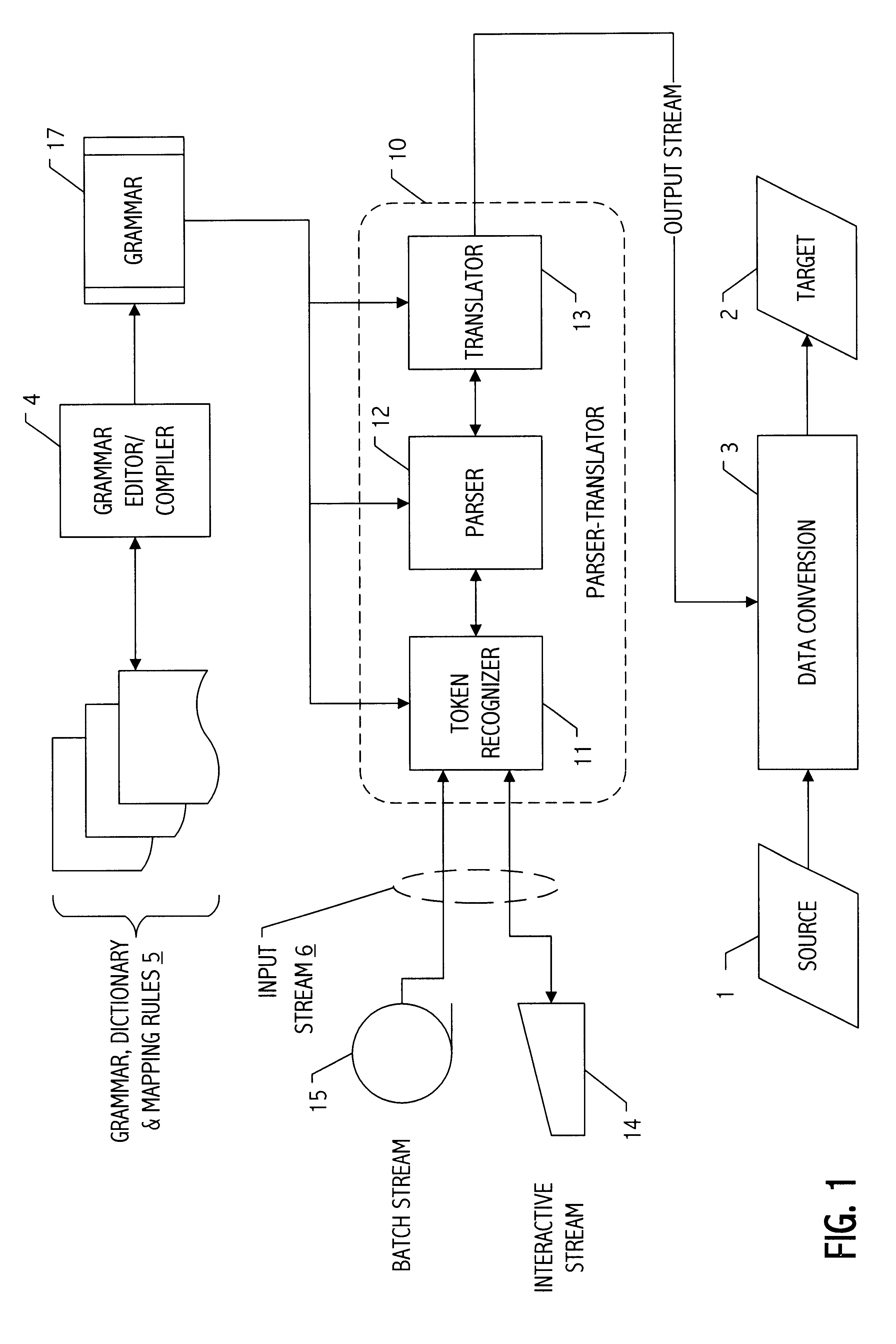
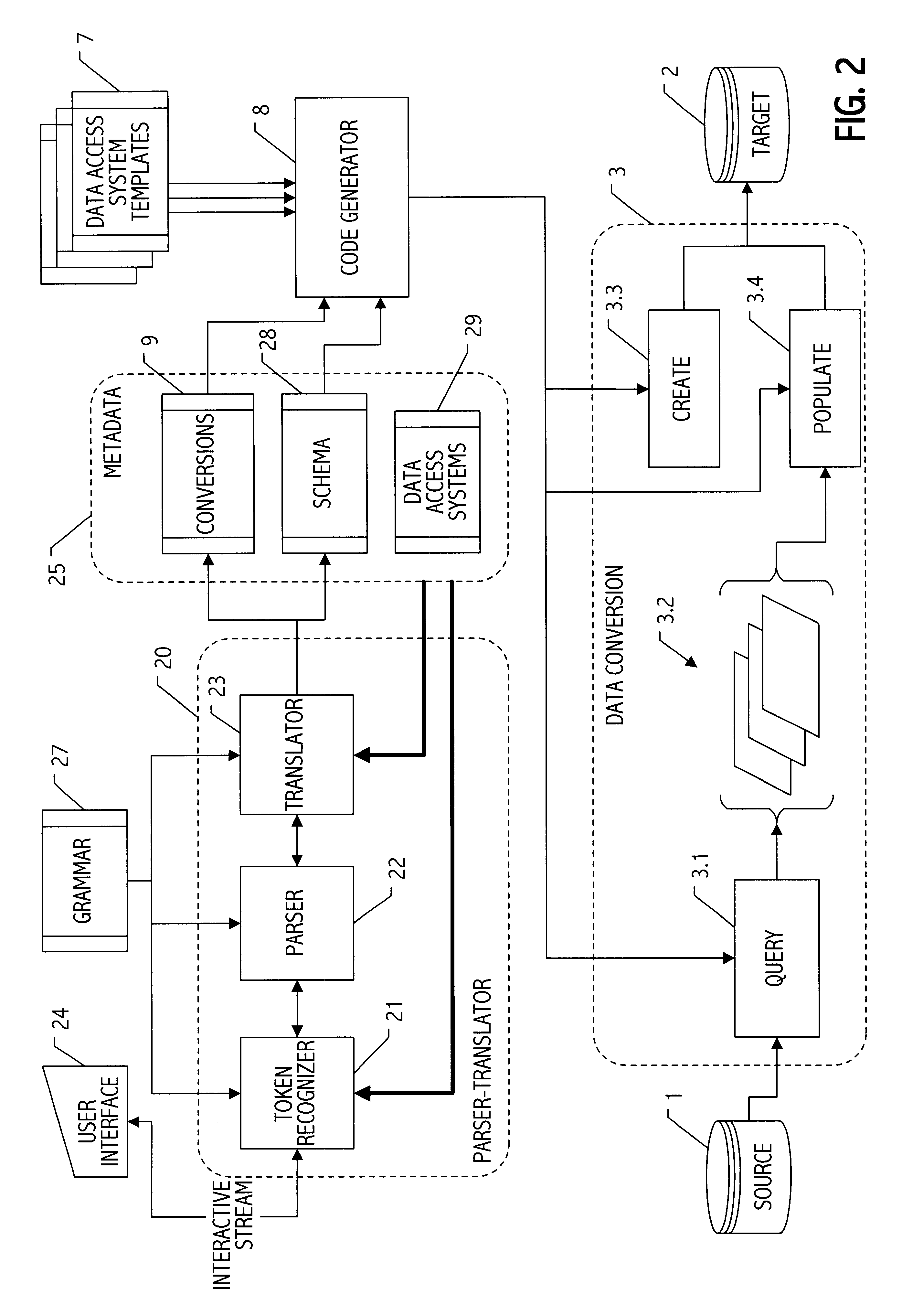
Parser translator system and method
A parser-translator technology allows a user to specify complex test and / or transformation statements in a high-level user language, to ensure that such test and / or transformation statements are well-formed in accordance with a grammar defining legal statements in the user language, and to translate statements defined by the user into logically and syntactically correct directives for performing the desired data transformations or operations. Using the parser-translator technology, a user can focus on the semantics of the desired operations and need not be concerned with the proper syntax of a language for a particular system. Instead, grammars (i.e., data) define the behavior of a parser-translator implementation by encoding the universe of statements (e.g., legal test and / or transformation statements) and by encoding translations appropriate to a particular data processing application (e.g., a data conversion program, etc.). Some parser-translator implementations described herein interface dynamically with other systems and / or repositories to query for information about objects, systems and states represented therein, and / or their respective interfaces. Some grammars described herein encode sensitivity to an external context. In this way, context-sensitive prompting and validation of correct specification of statements is provided. A combination of parser technology and dynamic querying of external system state allows users to build complex statements (e.g., using natural languages within a user interface environment) and to translate those complex statements into statements or directives appropriate to a particular data processing application.
Owner:VERSATA
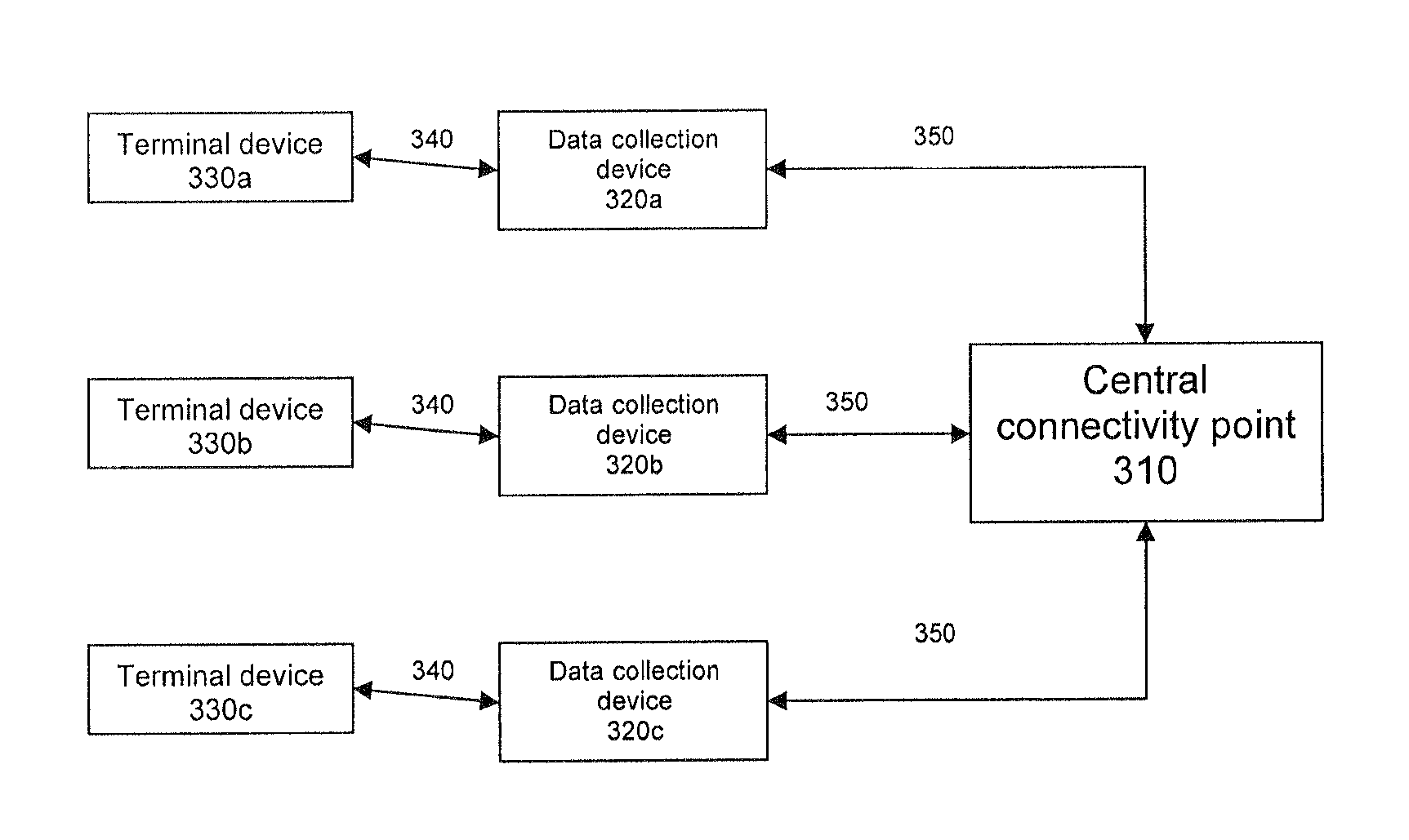
Universal connectivity for non-universal devices
A system including at least one data collection device, each connected to a corresponding data terminal via a primary communication channel; and a central connectivity point connected to each data collection device via a wireless secondary communication channel so as to communicate with the at least one data collection device without disrupting communication between the at least data collection device and the corresponding data terminal via the primary communication channel and to permit remote administration of each data collection device.
Owner:HAND HELD PRODS
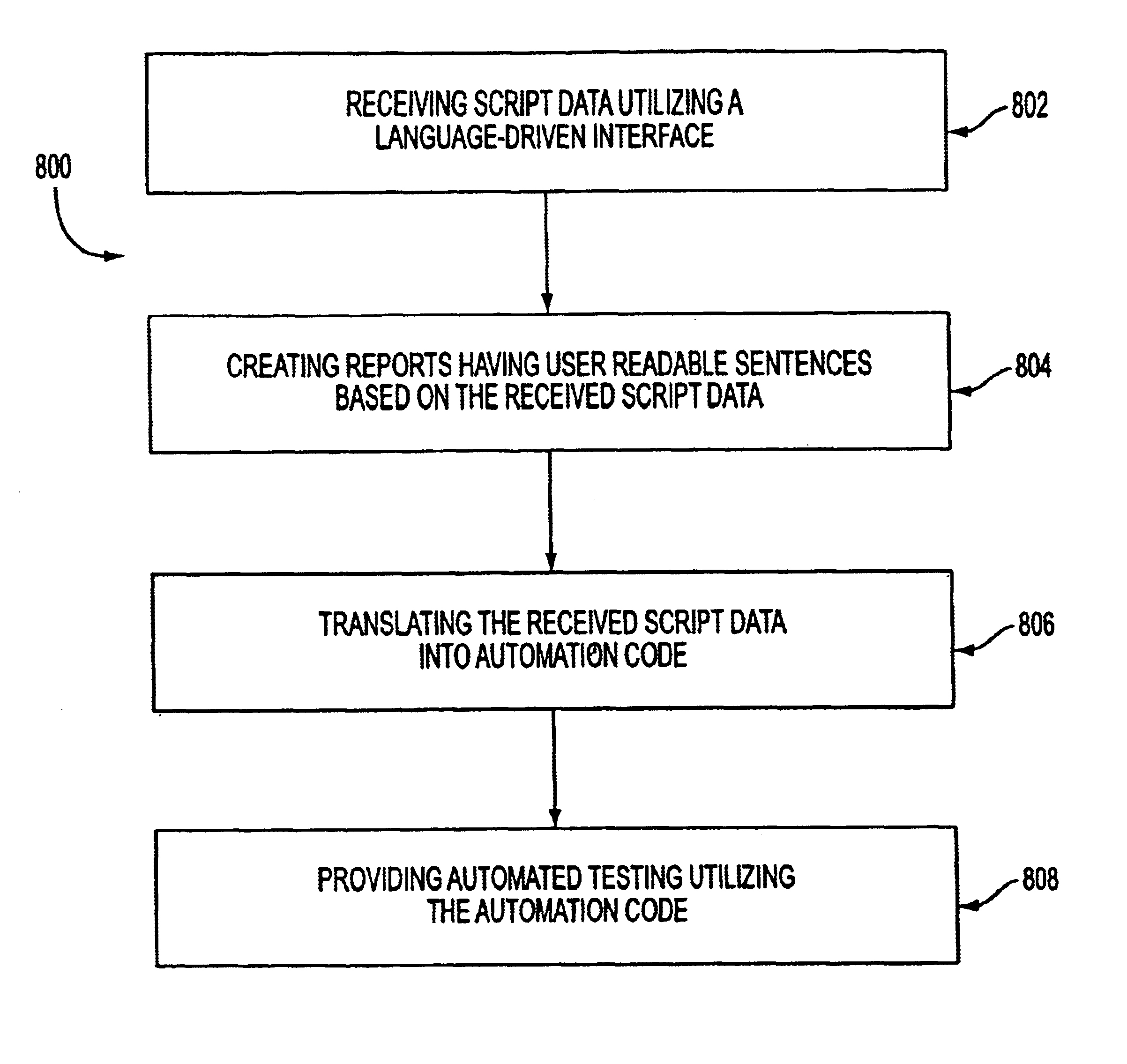
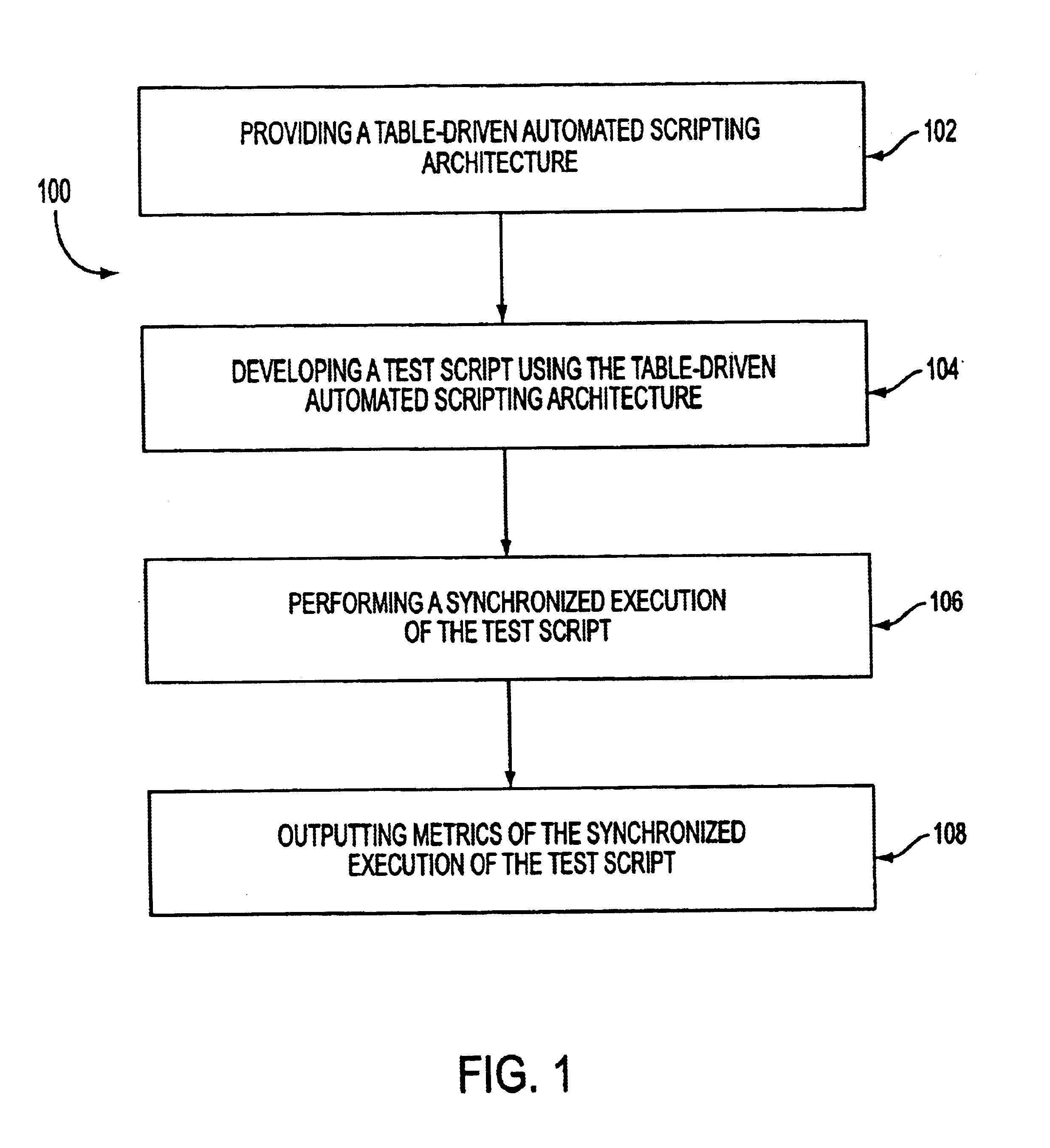
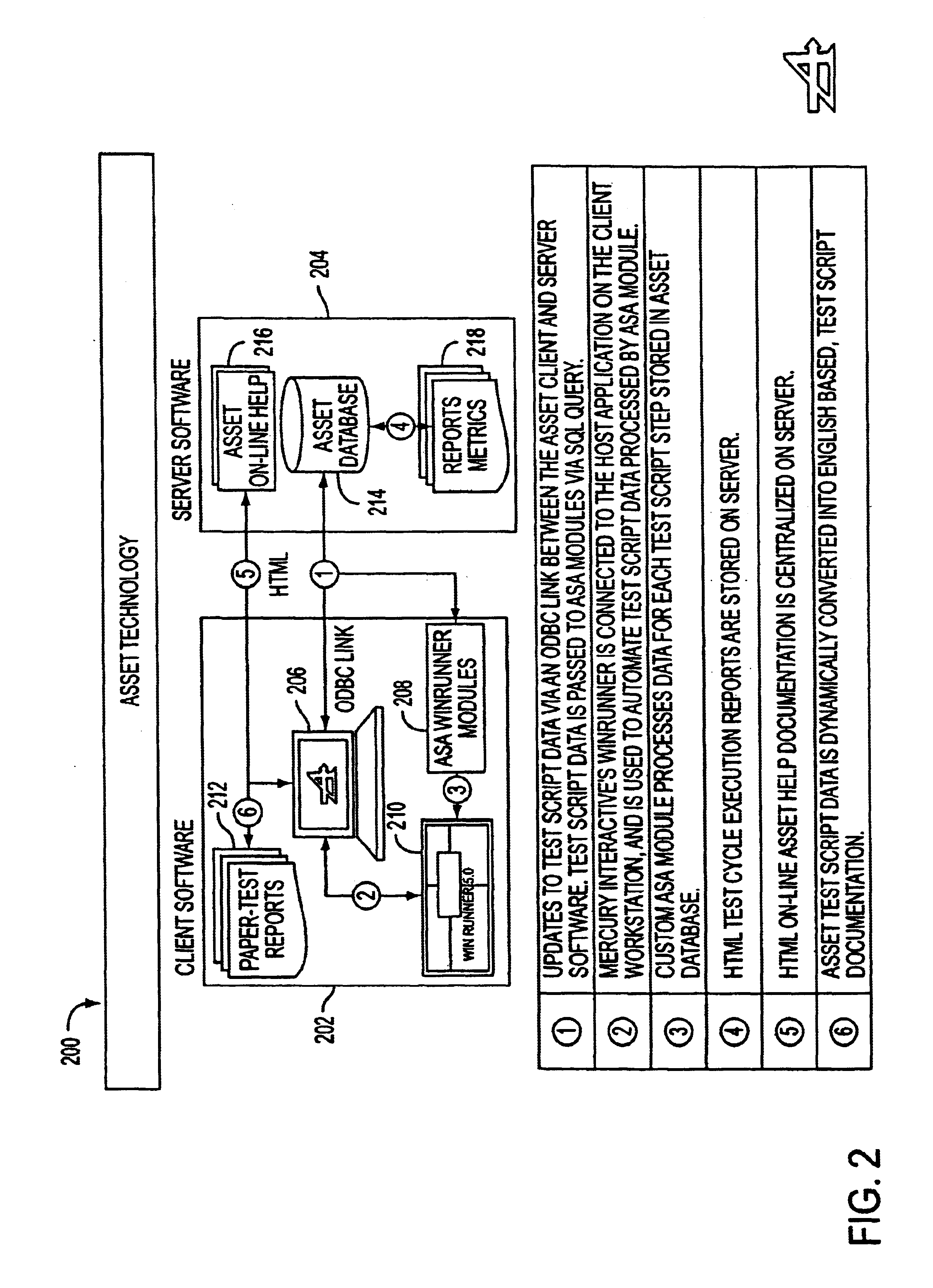
Language-driven interface for an automated testing framework
InactiveUS6907546B1Software testing/debuggingSpecific program execution arrangementsCrowdsAutomatic testing
To test the functionality of a computer system, automated testing may use an automation testing tool that emulates user interactions. A database may store words each having a colloquial meaning that is understood by a general population. For each of these words, the database may store associated computer instructions that can be executed to cause a computer to perform the function that is related to the meaning of the word. During testing, a word may be received having a colloquial meaning that is understood by a general population. The database may be queried for the received word and the set of computer instructions may be returned by the database. The automated testing tool may then perform the function returned to the colloquial meaning of the word. The words stored in the database may be in English or another language.
Owner:ACCENTURE GLOBAL SERVICES LTD
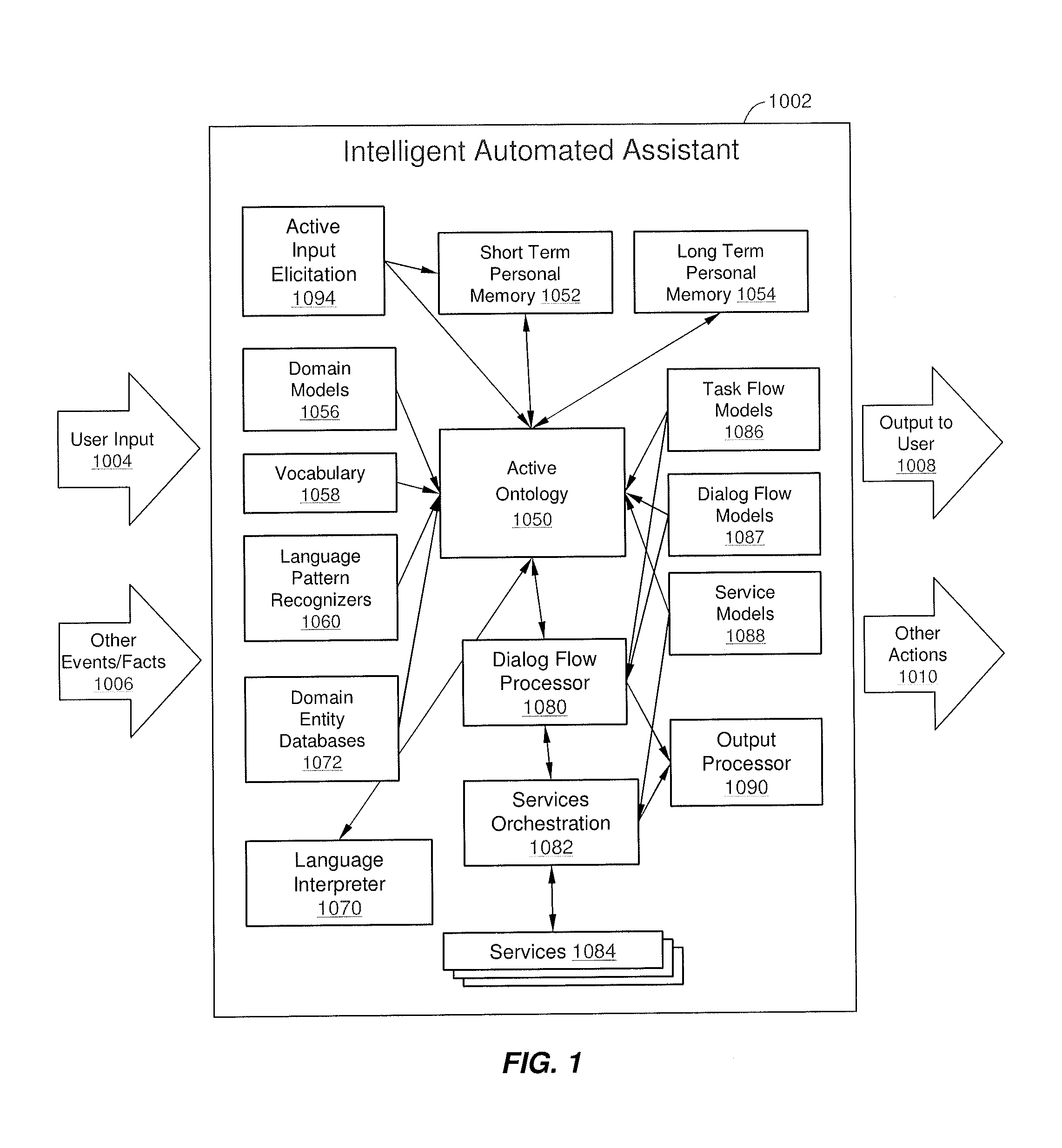
Intelligent Automated Assistant
ActiveUS20120245944A1Improve user interactionEffectively engageNatural language translationSemantic analysisService provisionComputer science
The intelligent automated assistant system engages with the user in an integrated, conversational manner using natural language dialog, and invokes external services when appropriate to obtain information or perform various actions. The system can be implemented using any of a number of different platforms, such as the web, email, smartphone, and the like, or any combination thereof. In one embodiment, the system is based on sets of interrelated domains and tasks, and employs additional functionally powered by external services with which the system can interact.
Owner:APPLE INC
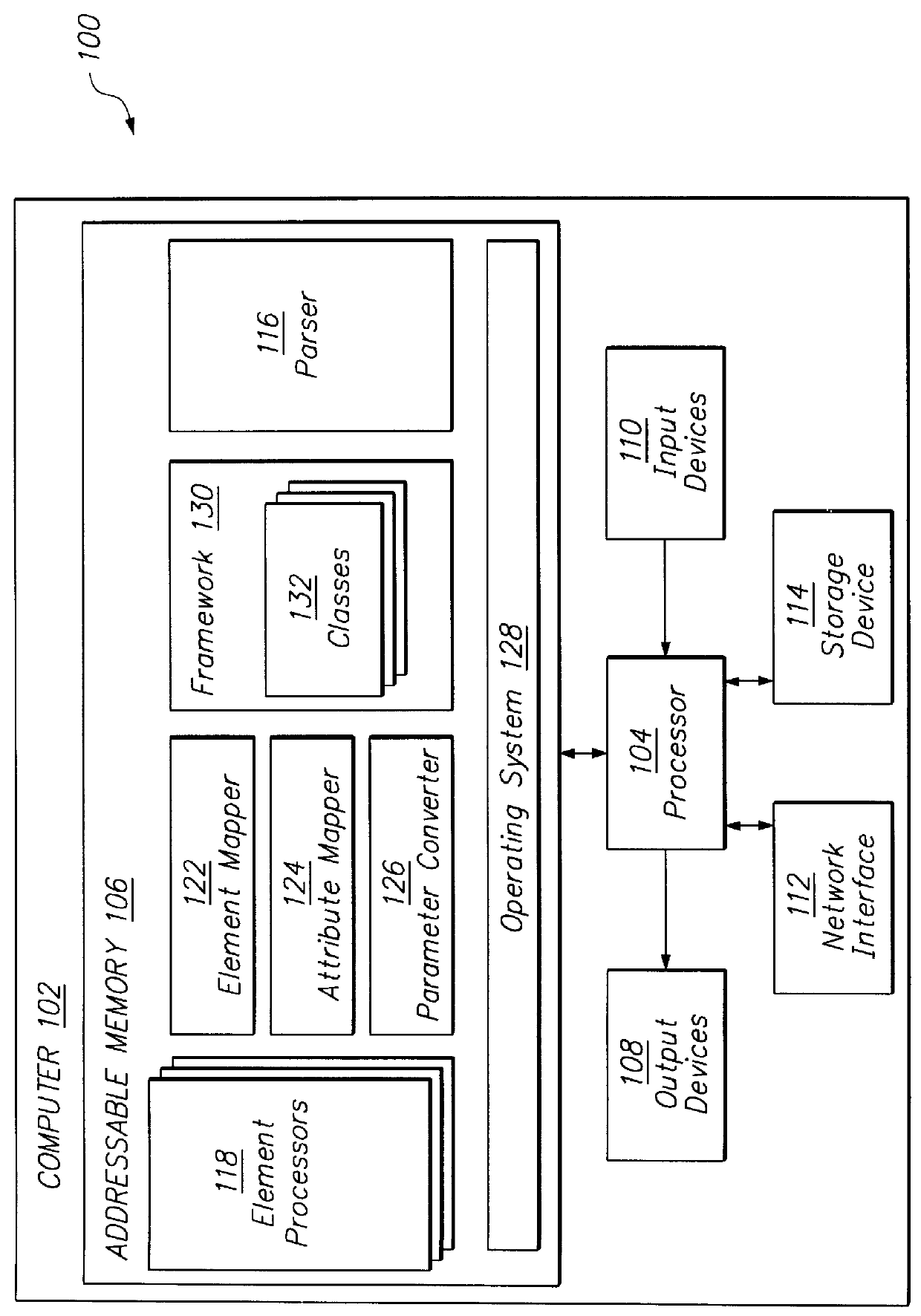
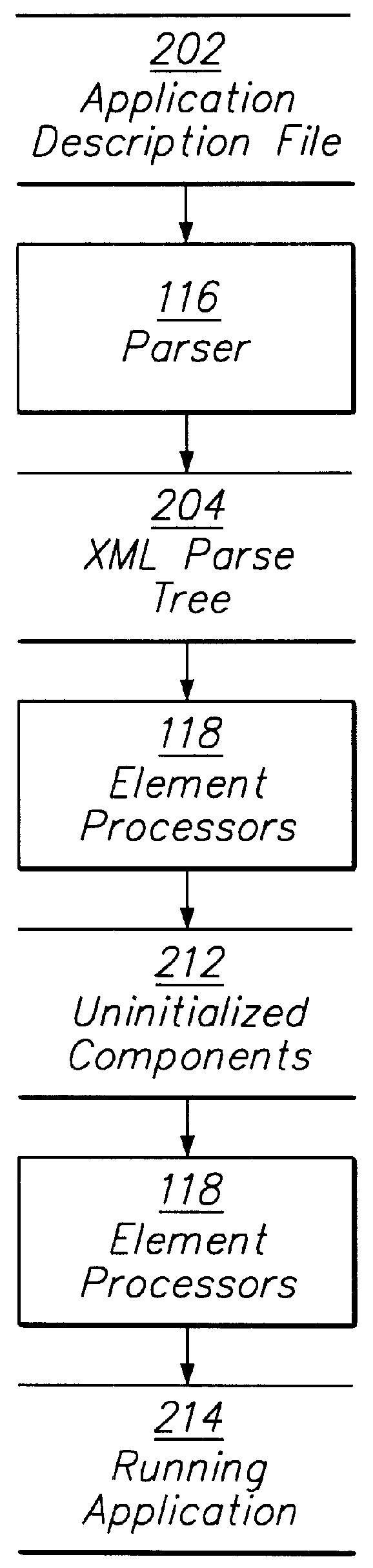
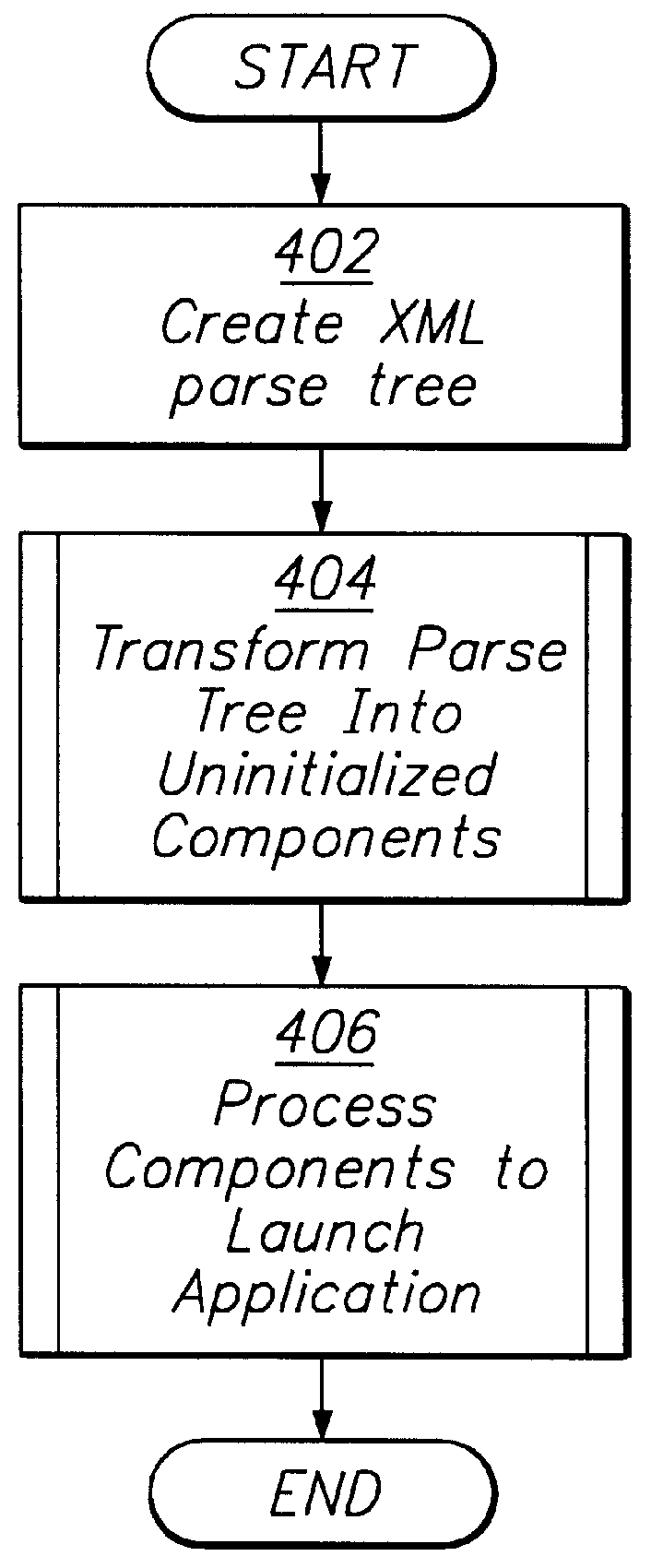
Creating and configuring component-based applications using a text-based descriptive attribute grammar
InactiveUS6083276AVersion controlSpecific program execution arrangementsProgramming languageAttribute grammar
A method for creating and configuring a component-based application through text-based descriptive attribute grammar includes creating a parse tree from an application description file, transforming the parse tree into a plurality of components corresponding to instances of classes in an application framework, and initializing and further processing the components to launch the component-based application. Additionally, a system for creating and configuring a component-based application includes a parser, a plurality of element processors, an element mapper, an attribute mapper, and a parameter converter.
Owner:COREL CORP +1
System and method for autonomously generating heterogeneous data source interoperability bridges based on semantic modeling derived from self adapting ontology
InactiveUS20030172368A1Reduce dependenceImprove data securityVersion controlKnowledge representationTime errorData source
A system, including software components, that efficiently and dynamically analyzes changes to data sources, including application programs, within an integration environment and simultaneously re-codes dynamic adapters between the data sources is disclosed. The system also monitors at least two of said data sources to detect similarities within the data structures of said data sources and generates new dynamic adapters to integrate said at least two of said data sources. The system also provides real time error validation of dynamic adapters as well as performance optimization of newly created dynamic adapters that have been generated under changing environmental conditions.
Owner:COMPASS AL INC +1
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS7093239B1Memory loss protectionDigital data processing detailsTheoretical computer scienceComputerized system
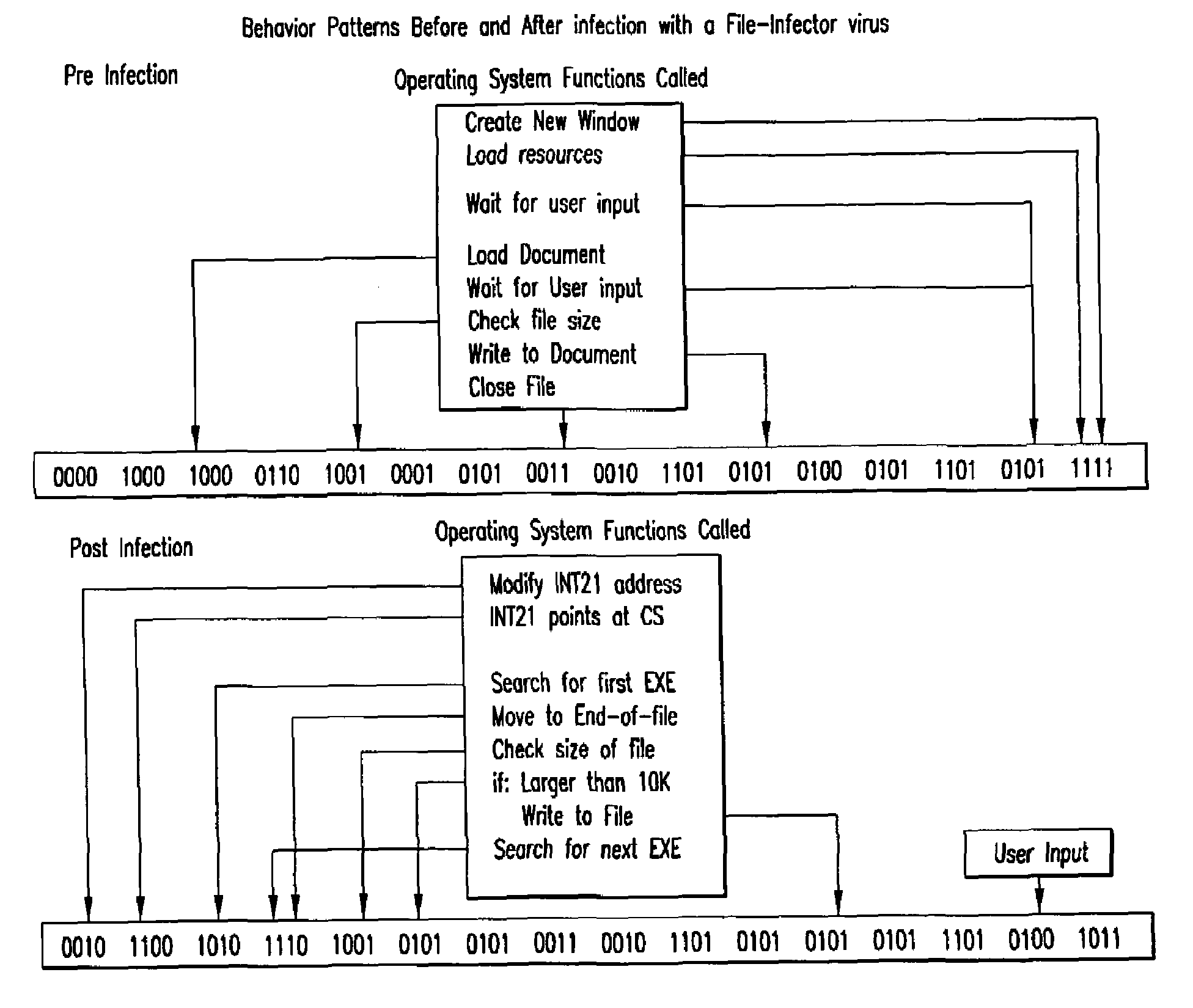
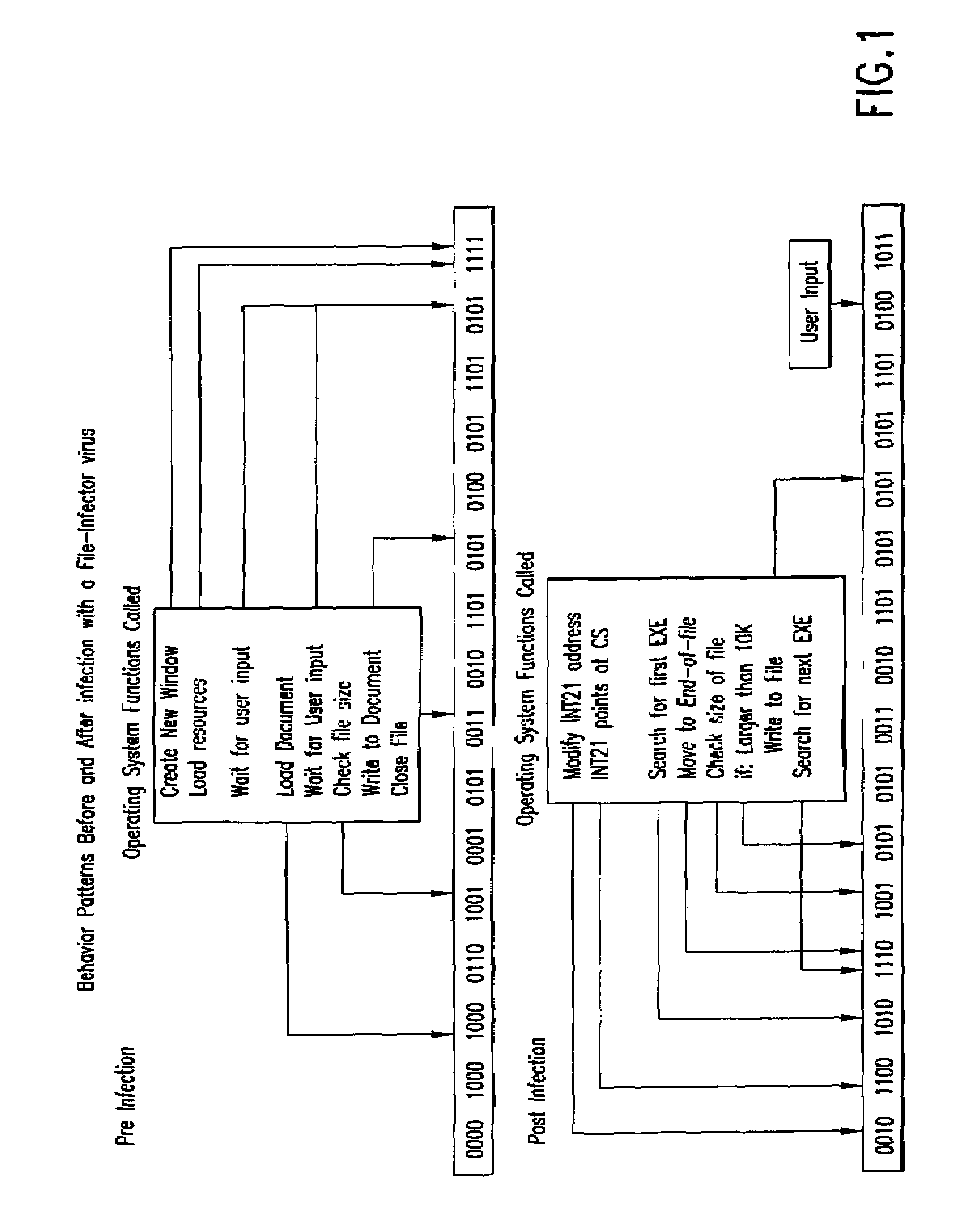
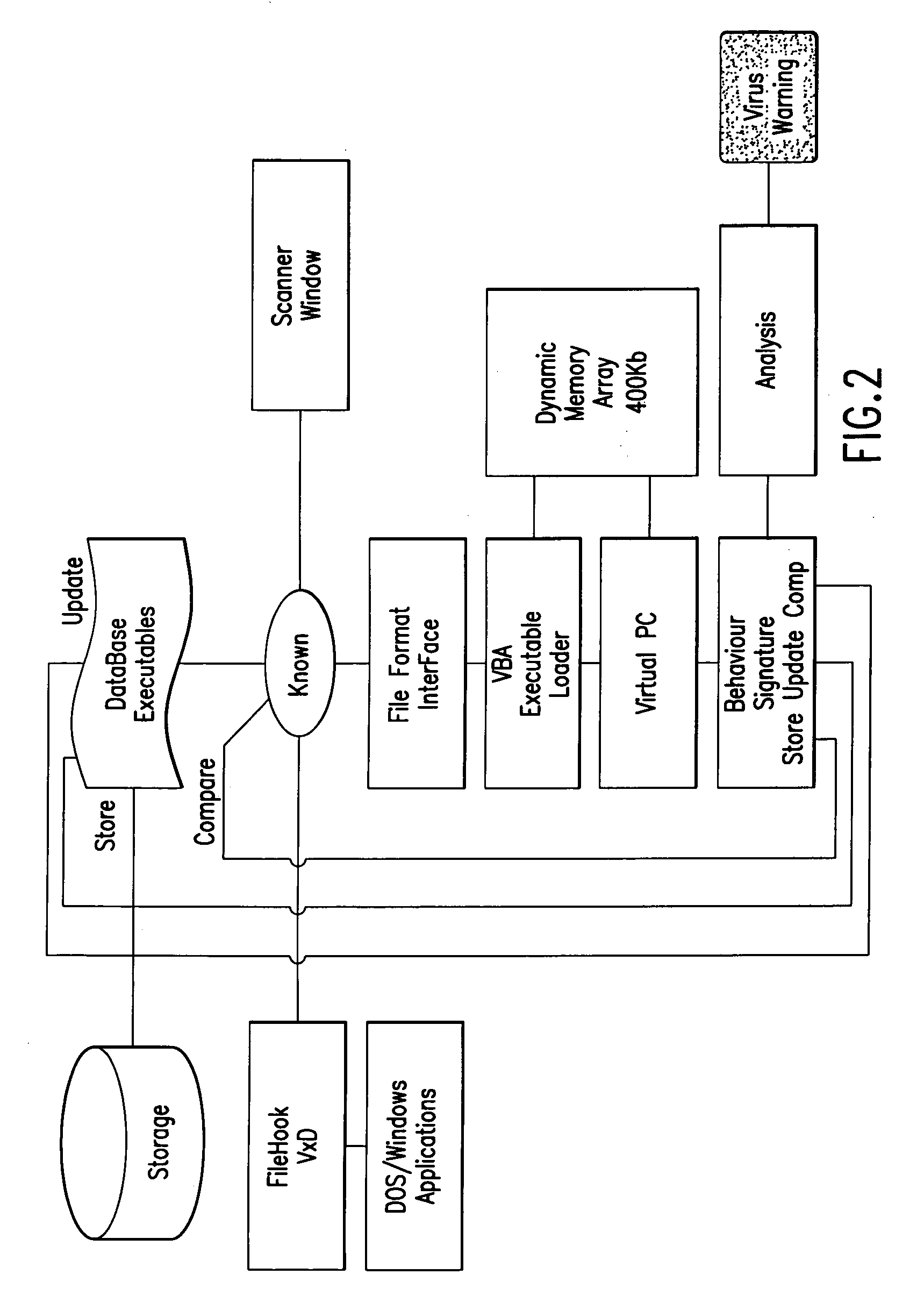
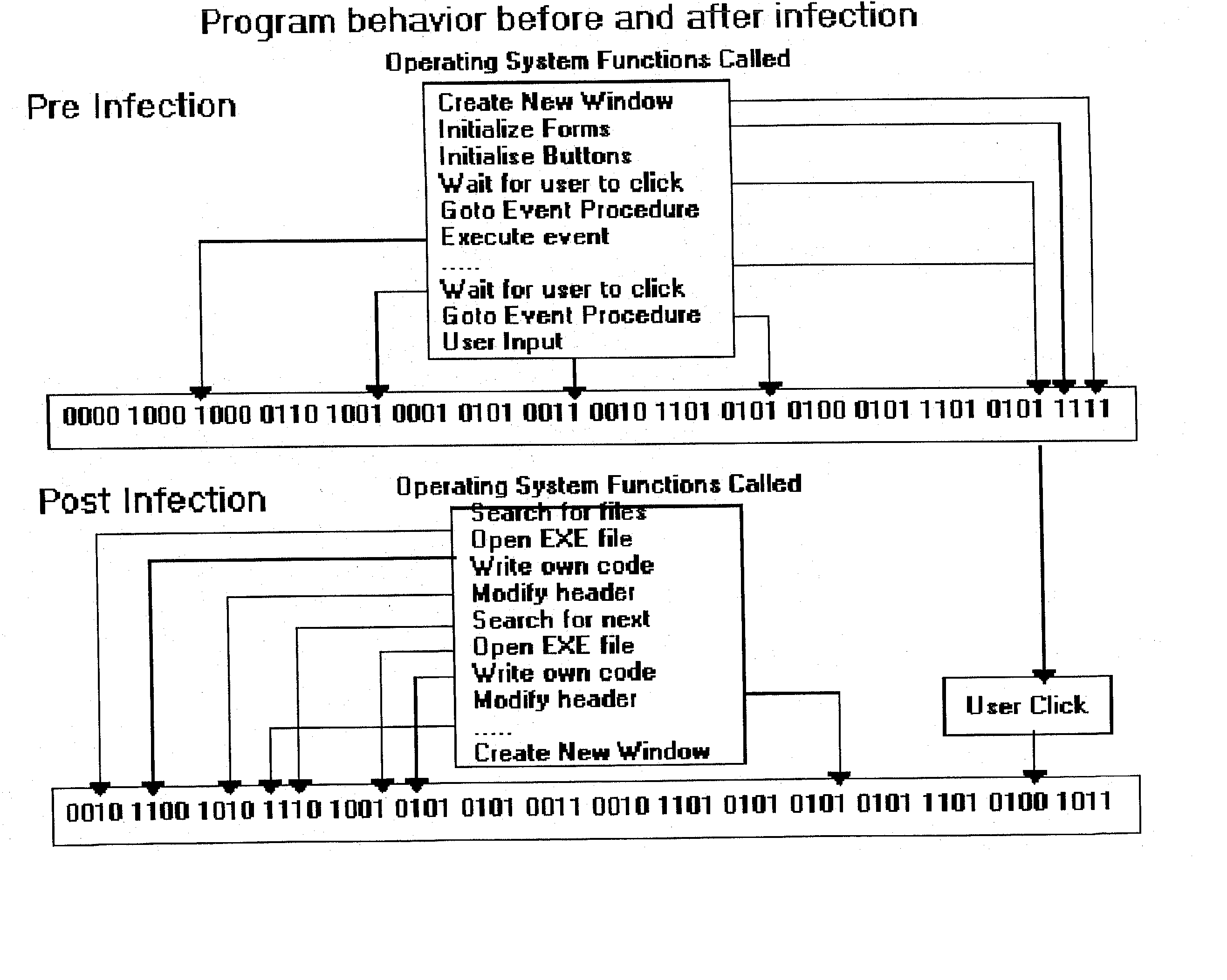
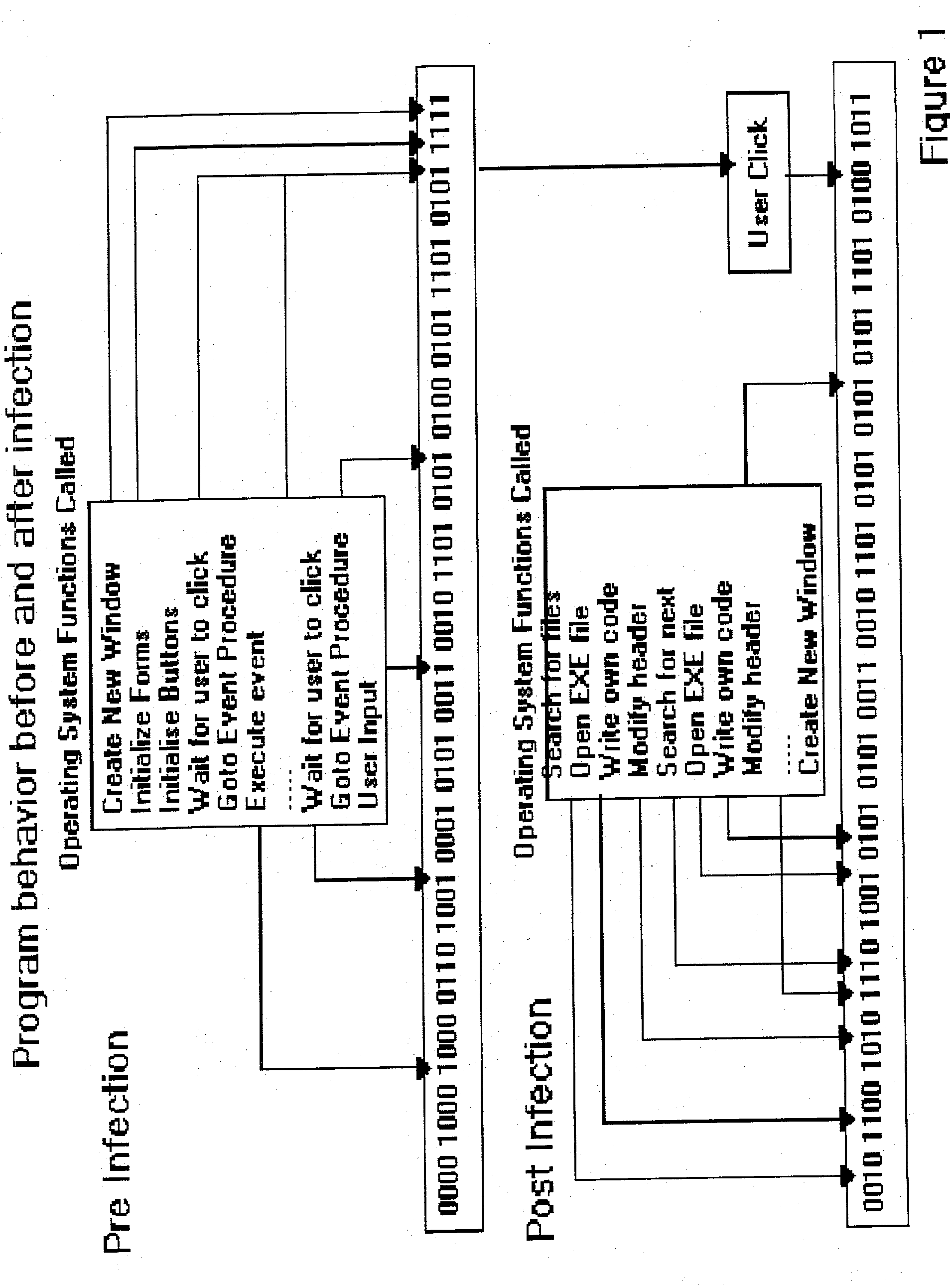
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
Computer-implemented system and method for project development
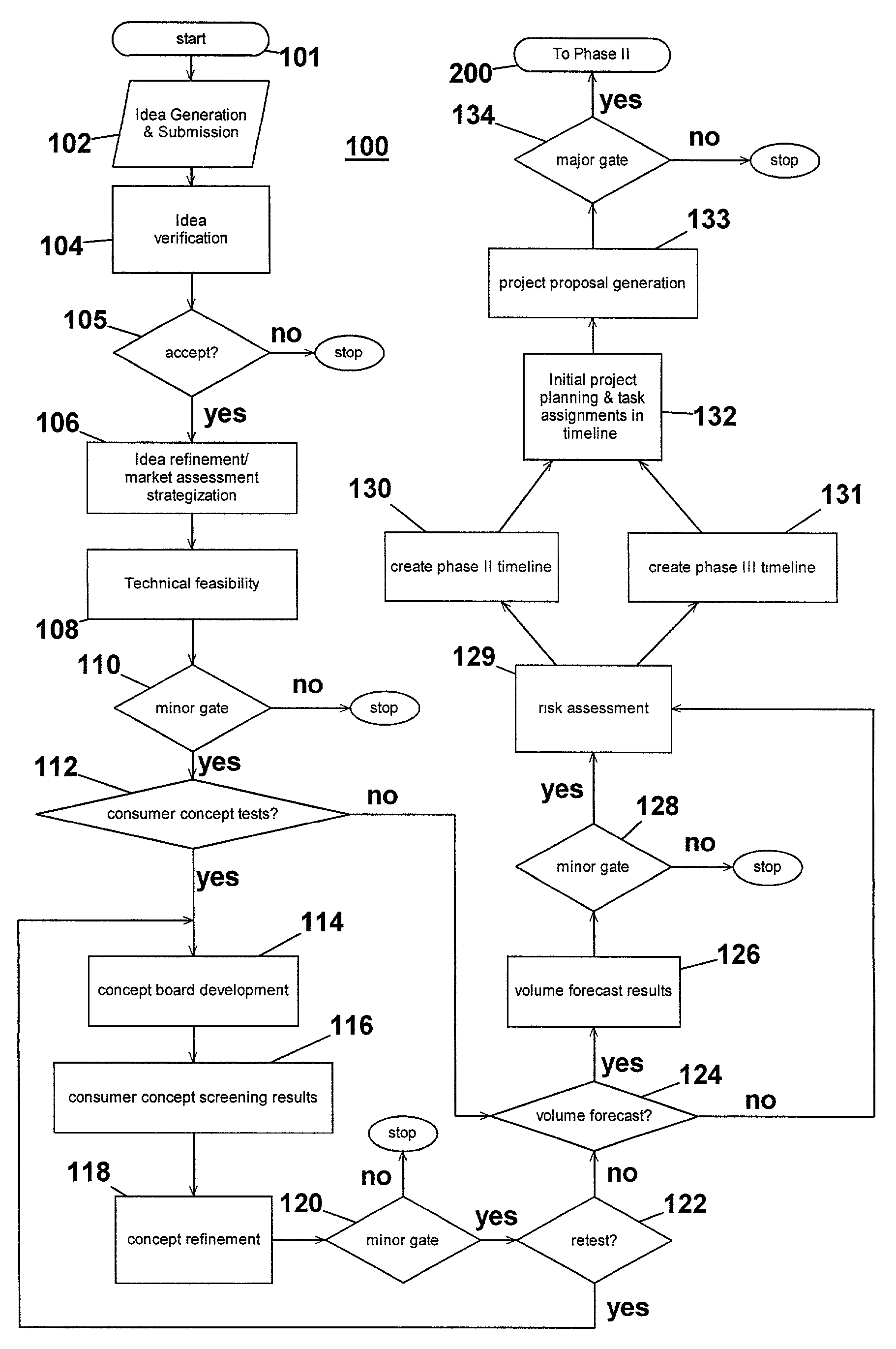
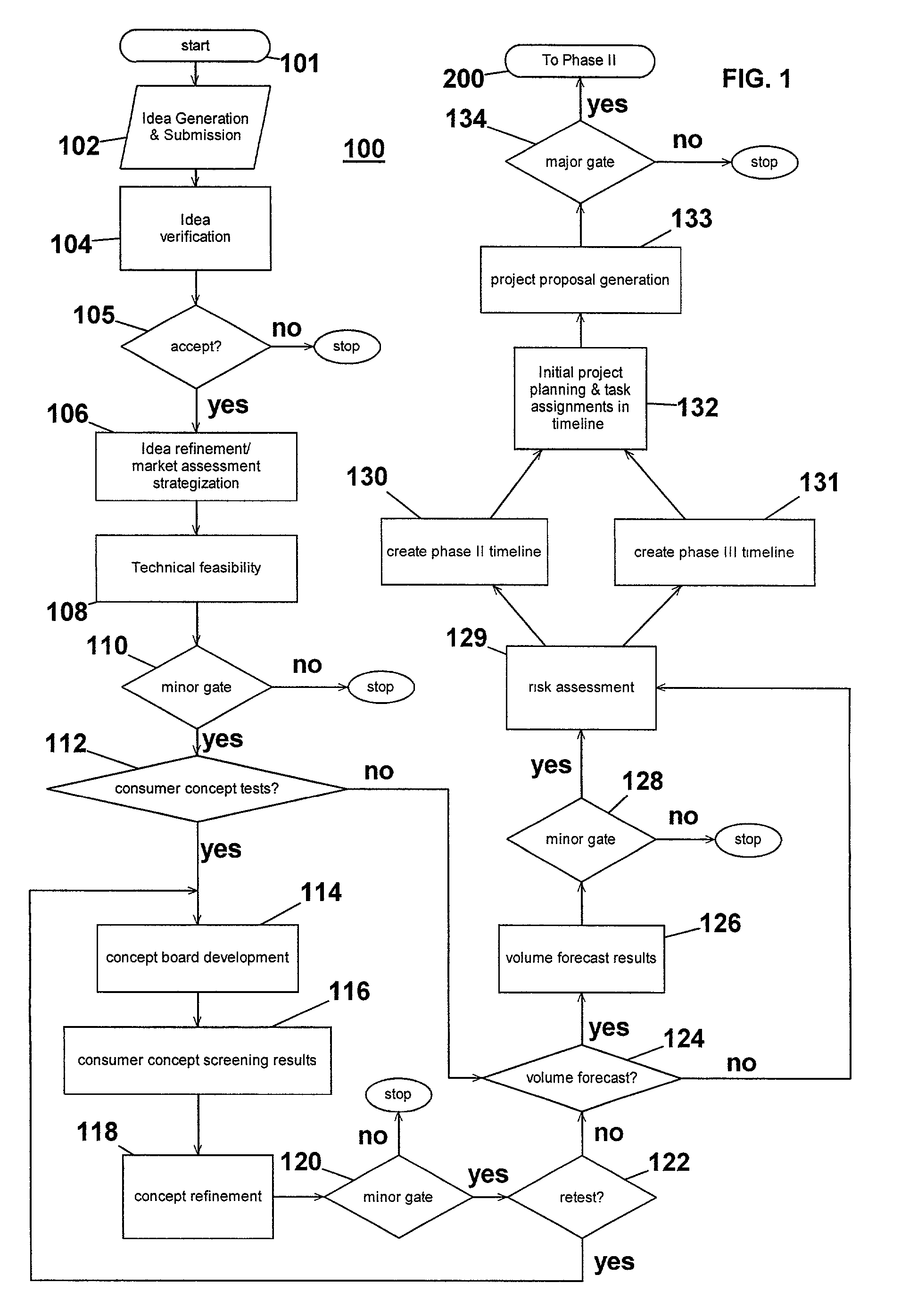
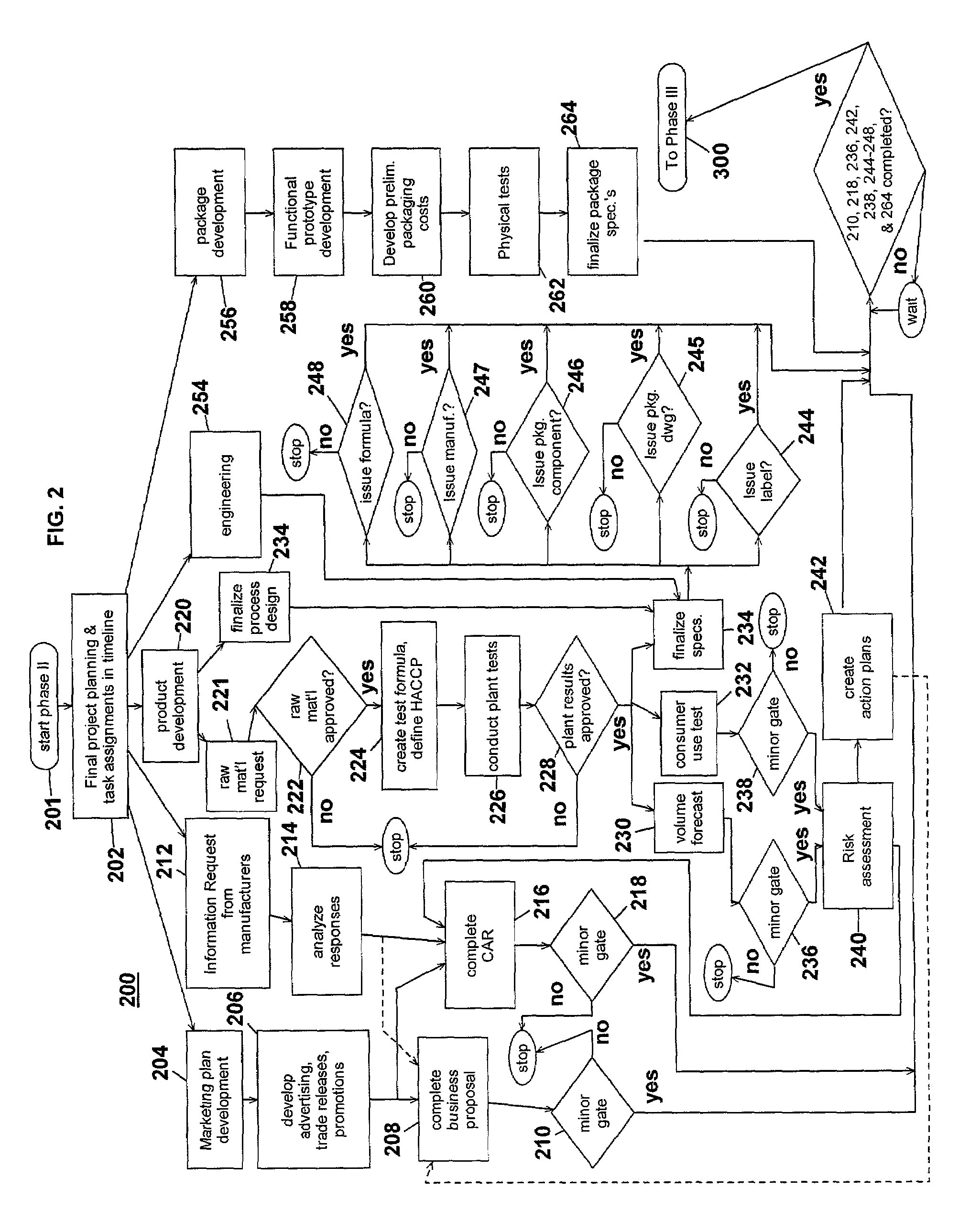
InactiveUS7051036B2Avoid repetitionPractical and convenientDigital data processing detailsResourcesProject proposalComputer science
The present invention generally relates to an inventive automated system, and method for its use, including a computer having a computer program defining three development phases including project proposal development, business proposition development, and implementation for market introduction. The project proposal development phase includes a unique idea verification feature by automated reference to an internal knowledge repository and database. The computer is coupled for intercommunication to a plurality of stations or clients from which respective authorized users each have a browser-based interface with the computer.
Owner:KRAFT FOODS GRP BRANDS LLC
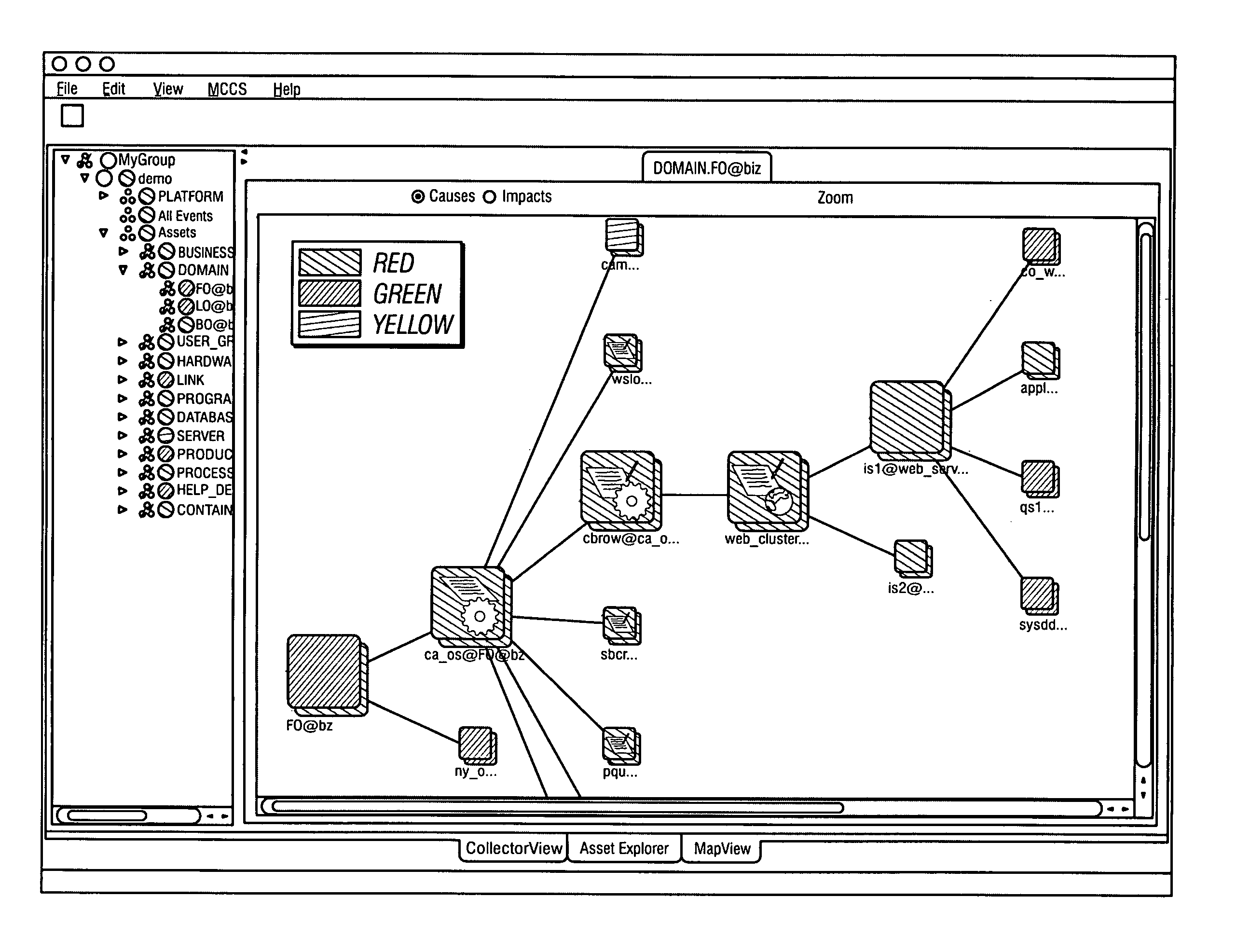
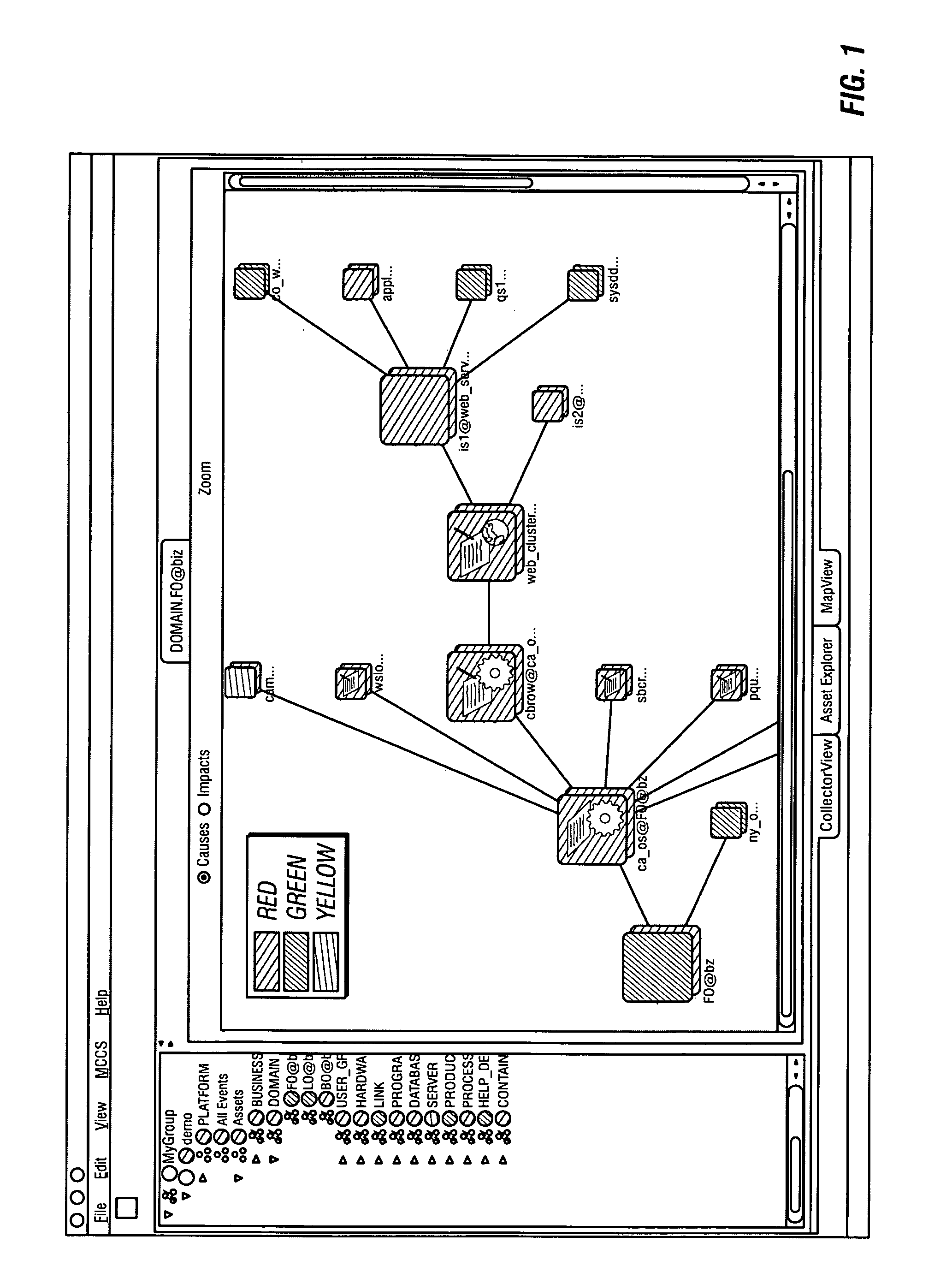
System and method for assessing and indicating the health of components
A system and method for visualization of the components of an enterprise system and the rendering of information about the health or status of the enterprise system, its components, and / or its subcomponents. The invention uses a combination of color codes or other indicators and a combination of algorithms and / or rules-based systems to control the computation of status / severities to associate to components and setup the color codes and indicators.
Owner:BMC SOFTWARE
Computer immune system and method for detecting unwanted code in a P-code or partially compiled native-code program executing within a virtual machine
InactiveUS20030212902A1Memory loss protectionDigital data processing detailsComputerized systemBehaviour pattern
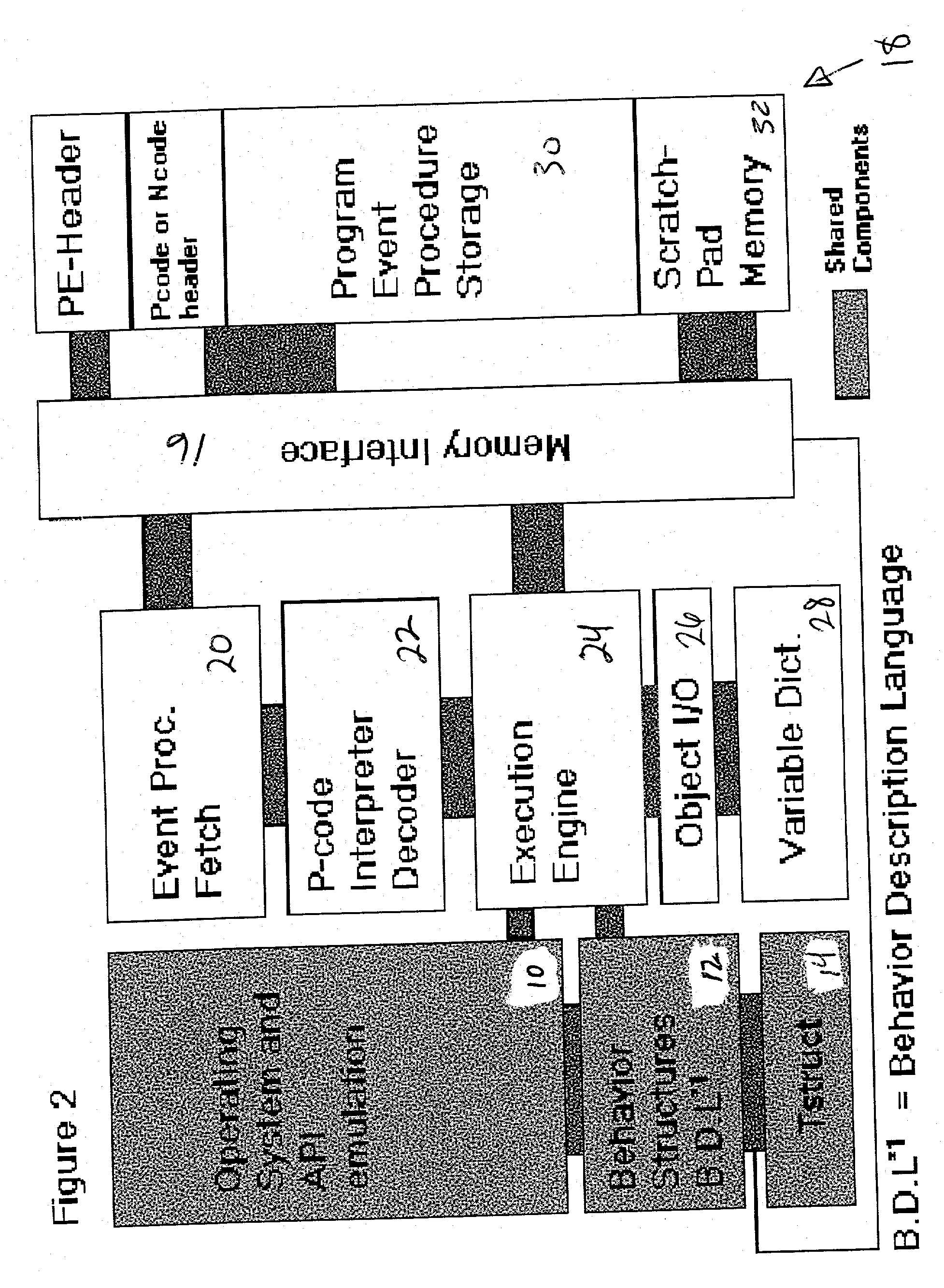
An automated analysis system identifies the presence of malicious P-code or N-code programs in a manner that limits the possibility of the malicious code infecting a target computer. The target computer system initializes an analytical virtual P-code engine (AVPE). As initialized, the AVPE comprises software simulating the functionality of a P-code or intermediate language engine as well as machine language facilities simulating the P-code library routines that allow the execution of N-code programs. The AVPE executes a target program so that the target program does not interact with the target computer. The AVPE analyzes the behavior of the target program to identify occurrence of malicious code behavior and to indicate in a behavior pattern the occurrence of malicious code behavior. The AVPE is terminated at the end of the analysis process, thereby removing from the computer system the copy of the target program that was contained within the AVPE.
Owner:PALO ALTO NETWORKS INC
Apparatus and method for analyzing and supplementing a program to provide security
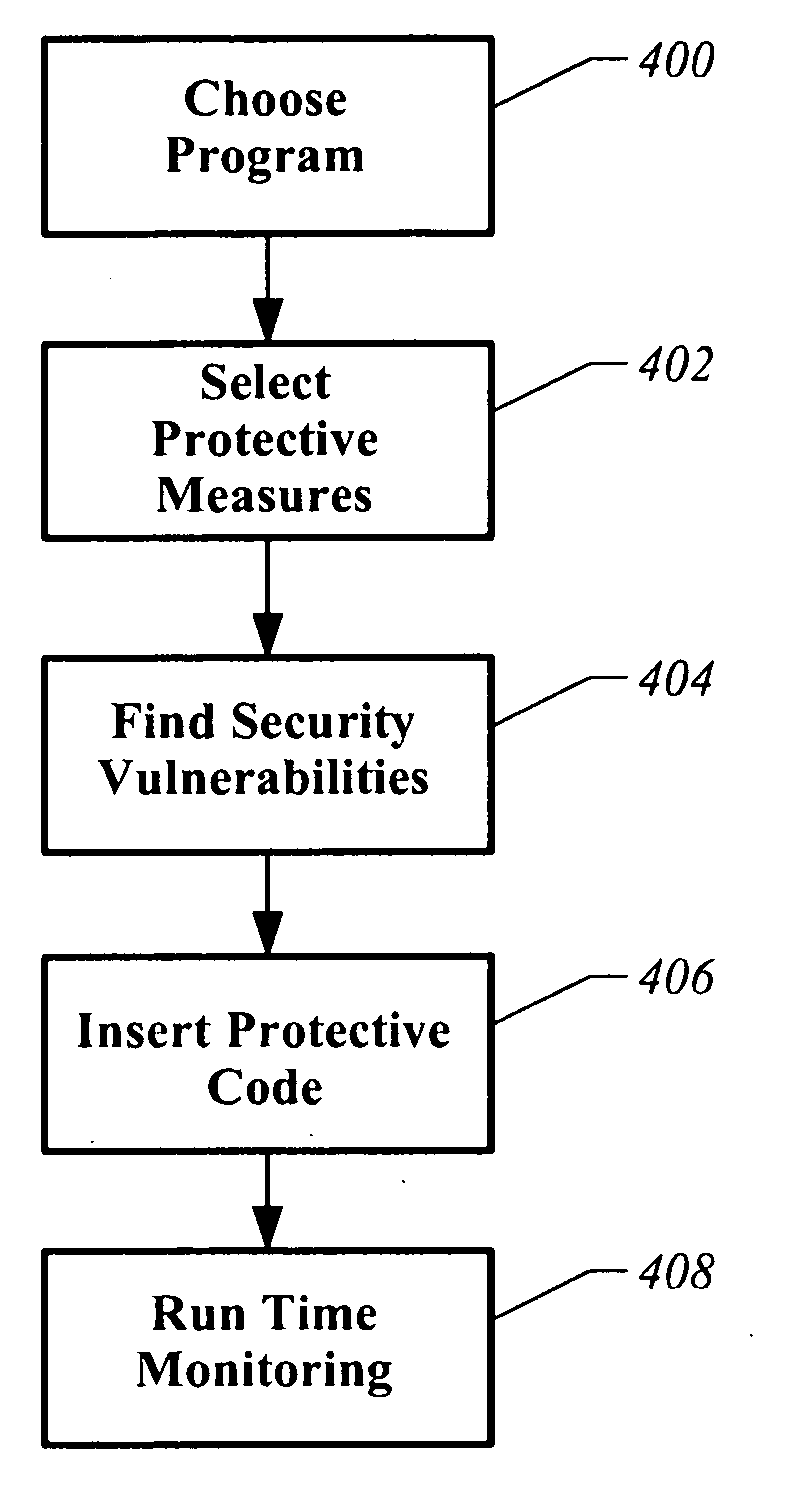
ActiveUS20070074169A1Memory loss protectionError detection/correctionProgramming languageProgram instruction
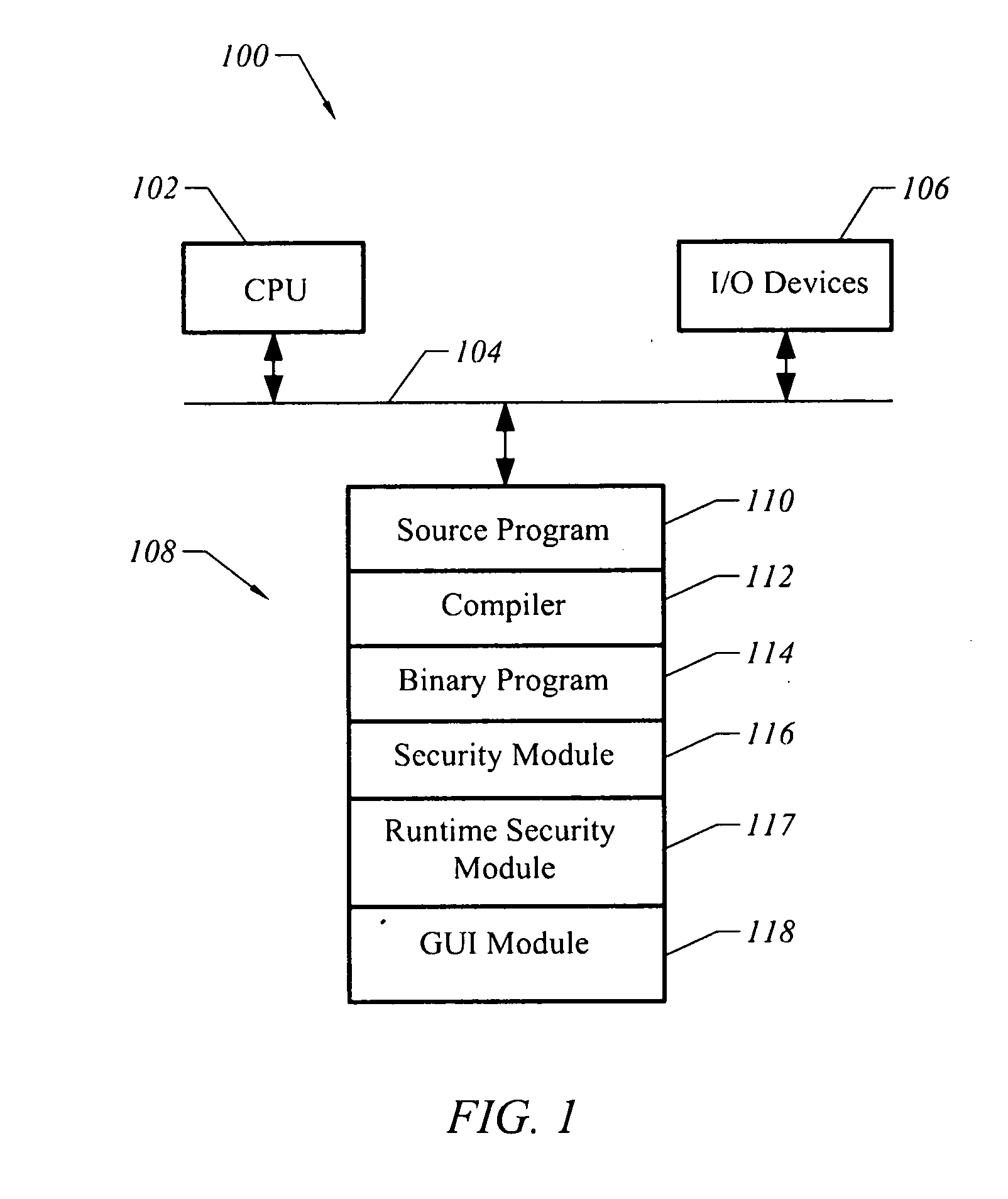
A computer readable storage medium has executable instructions to perform an automated analysis of program instructions. The automated analysis includes at least two analyses selected from an automated analysis of injection vulnerabilities, an automated analysis of potential repetitive attacks, an automated analysis of sensitive information, and an automated analysis of specific HTTP attributes. Protective instructions are inserted into the program instructions. The protective instructions are utilized to detect and respond to attacks during execution of the program instructions.
Owner:MICRO FOCUS LLC
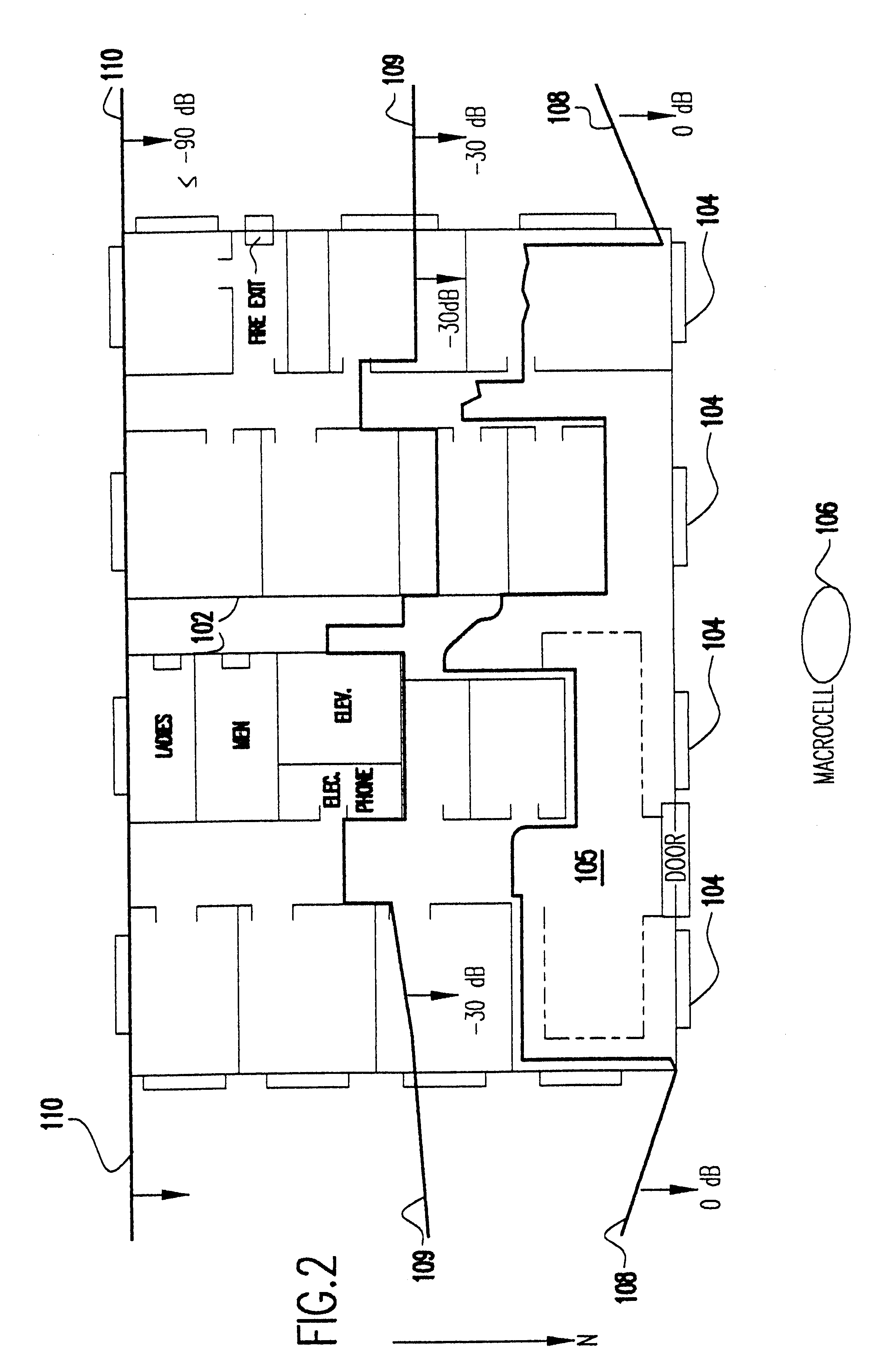
Method and system for automated optimization of antenna positioning in 3-D
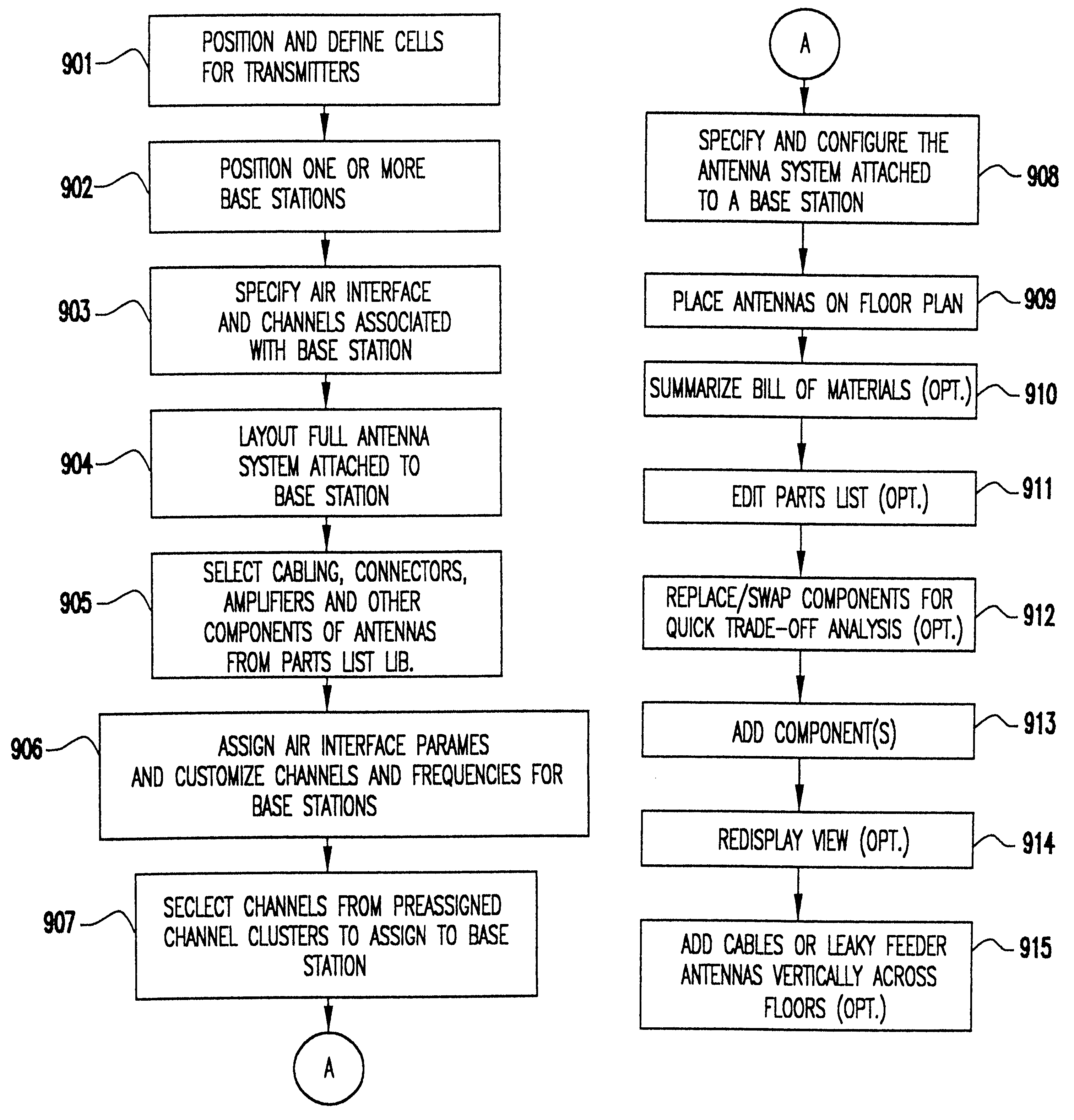
InactiveUS6317599B1Quick fixSignificant valueMachines/enginesComputation using non-denominational number representationEngineeringRadio frequency
A method for engineering management and planning for the design of a wireless communications network in three-dimensions (3-D) combines computerized organization, database fusion, and radio frequency (RF) site-specific planning models. The method enables a designer to keep track of wireless system performance throughout the process of pre-bid design, installation and maintenance of a wireless system. Using a database of information that defines the desired environment, predictions of antenna coverage, system coverage and interference, and other wireless system performance criteria, such as frame error rate and network throughput, can be made. Watch points are created to ensure, in real time, that any modifications to the design of the wireless system do not degrade the performance of the system with respect to the watch point locations.
Owner:EXTREME NETWORKS INC
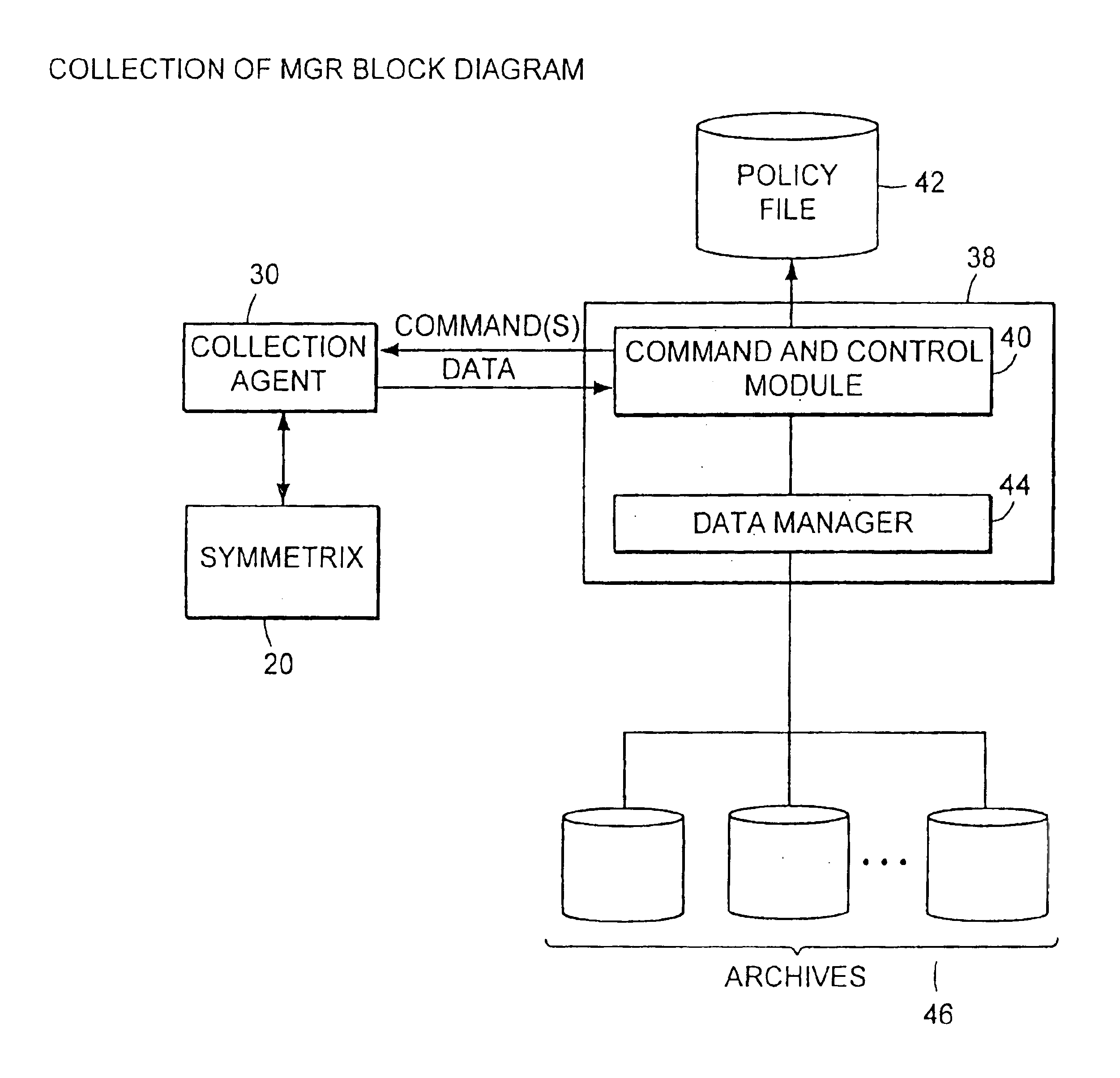
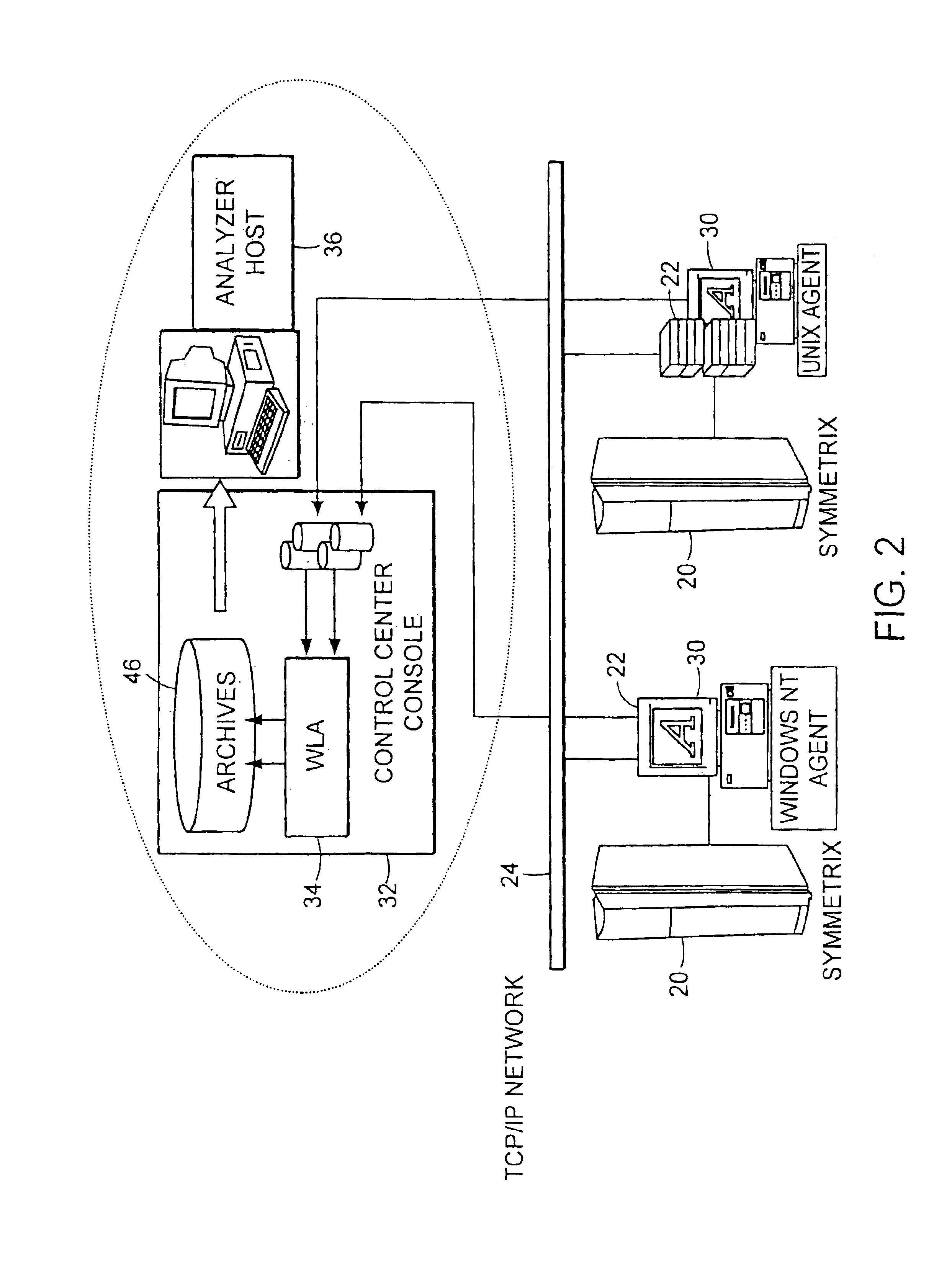
Method and apparatus for storage system metrics management and archive
InactiveUS6886020B1Promote generationEasy accessData processing applicationsDigital data information retrievalCommand and controlData management
A data management and archive method and apparatus, such as for implementation in an automated system to monitor and manage status, performance and configuration data for a plurality of networked storage components. Analysis and cross-correlation of data related to the plurality of storage components can be done individually, collectively and / or comparatively. A collection manager component of a workload analyzer is implemented to start and stop data collection in the context of a system comprising at least one storage component (or at least two networked storage components). The collection manager includes a command and control module that coordinates requests of data from at least one collection agent configured on at least one host connected to the storage component(s).
Owner:EMC IP HLDG CO LLC
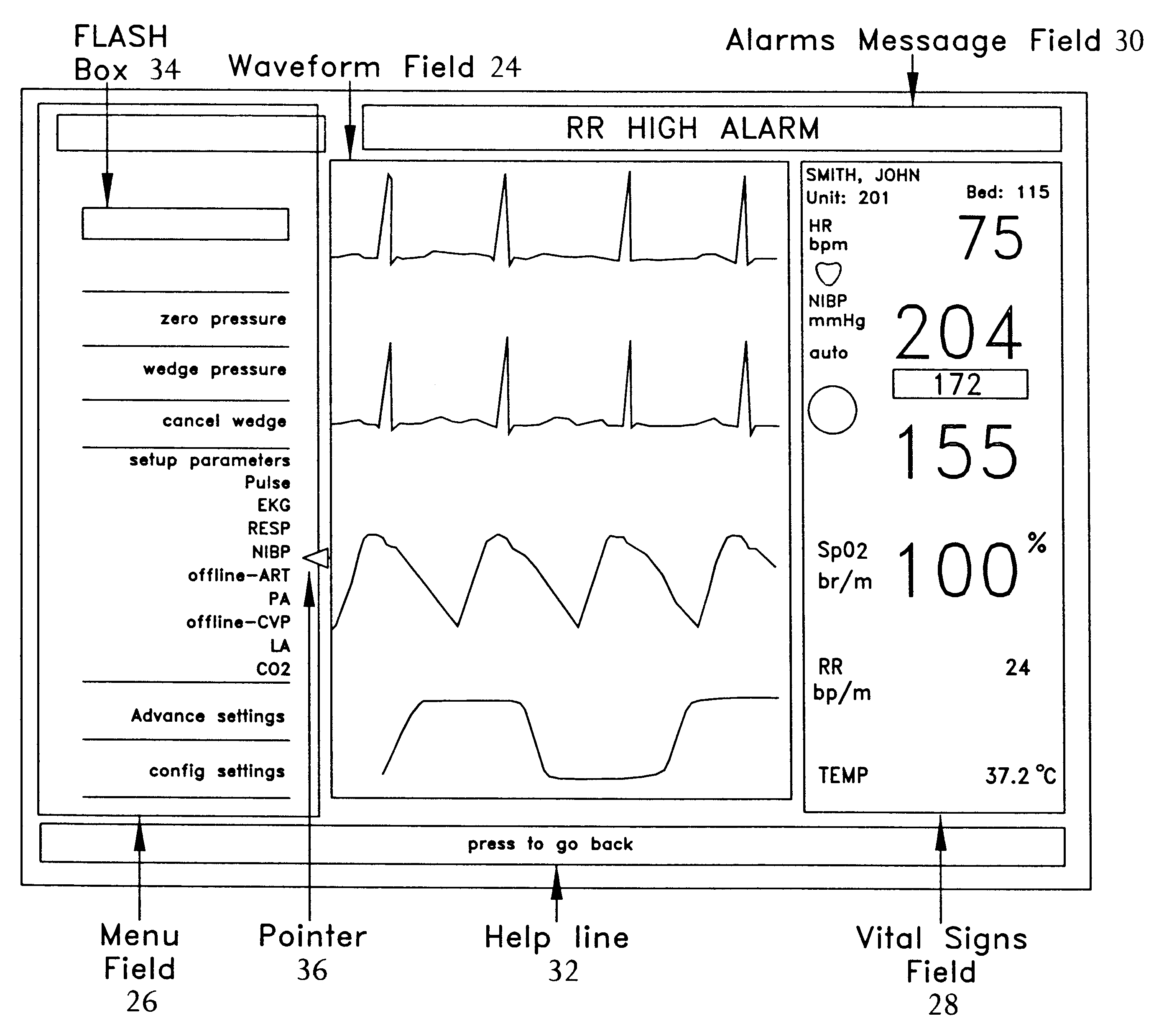
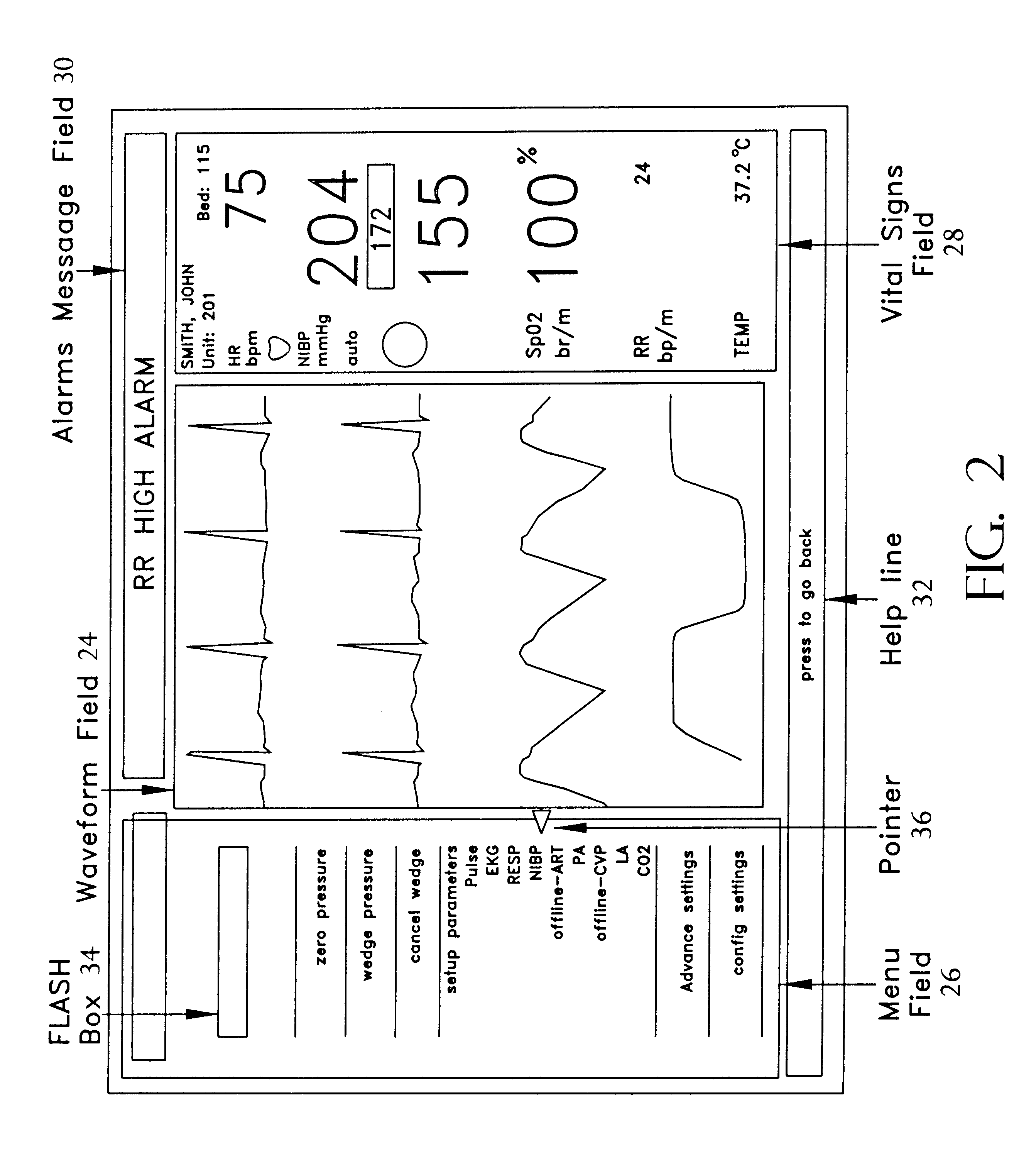
Reconfigurable user interface for modular patient monitor
InactiveUS6188407B1Maximize useMinimizing navigationData processing applicationsElectrocardiographyOperational systemModularity
A reconfigurable user interface for a modular patient monitor which selectively populates menus for operator selection based on the parameters which are available at any given time. Due to event processing, when a parameter module is added or removed from the system, the reconfigurable user interface is updated immediately to reflect the addition or subtraction of the associated parameter. A flash box in each menu provides shortcuts to the most likely menu option in response to asynchronous events such as alarms and the like. The flash box also assists the operator with the particular steps that must be followed to properly setup or operate a particular feature of the system. Since the menus are not modal, an operator may navigate the menus without making any selections or changing the state of the device.
Owner:GE MEDICAL SYST INFORMATION TECH
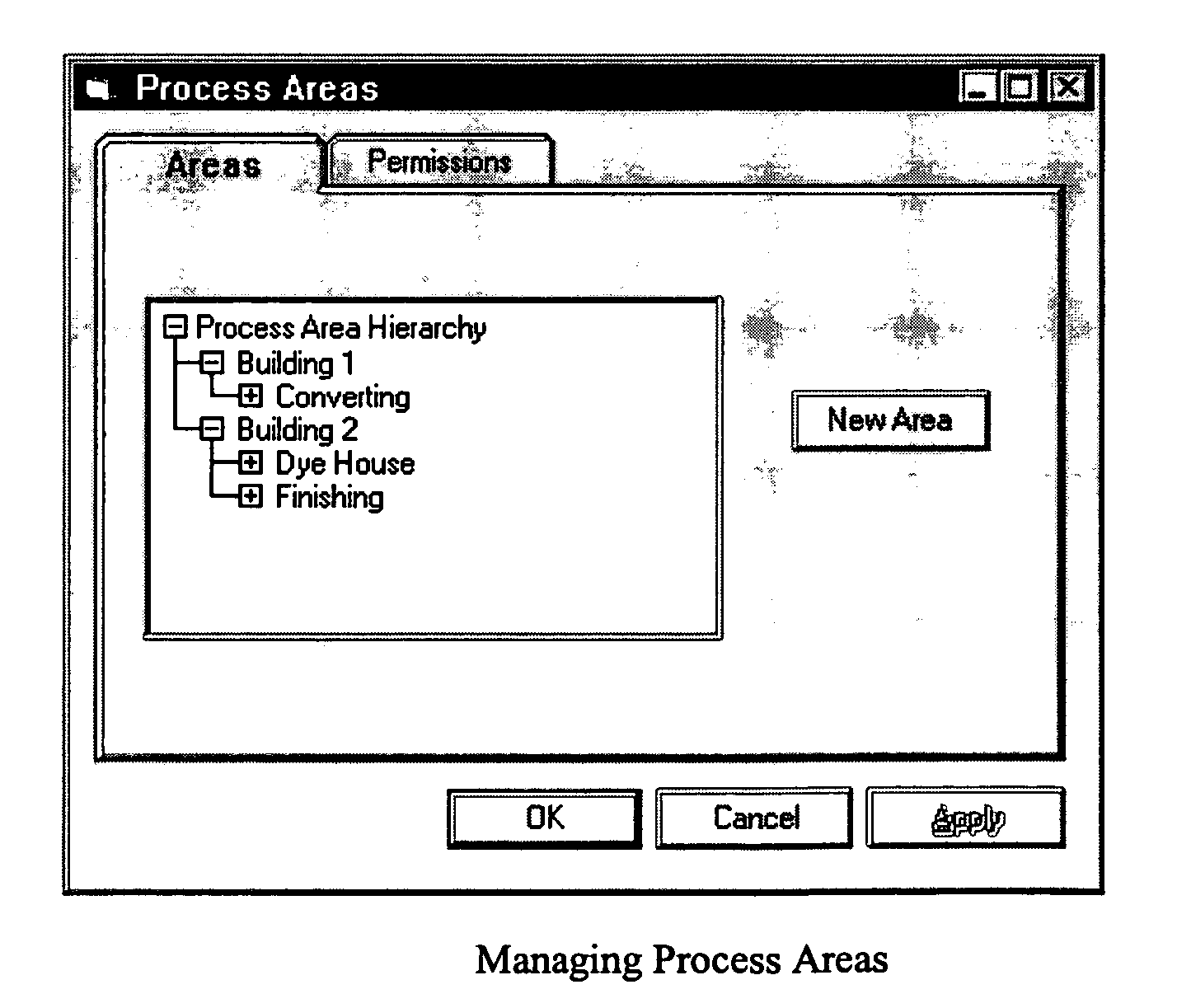
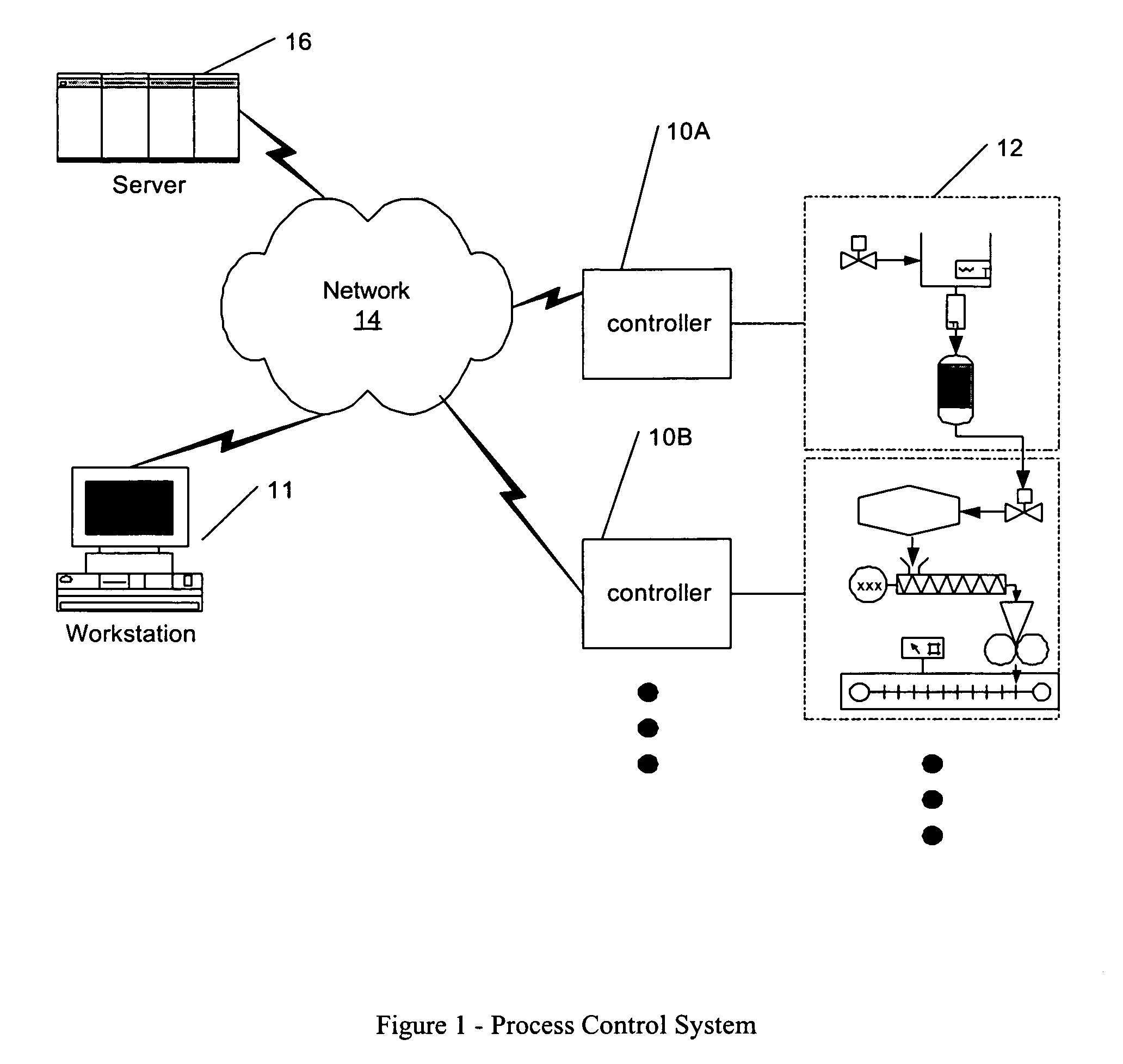
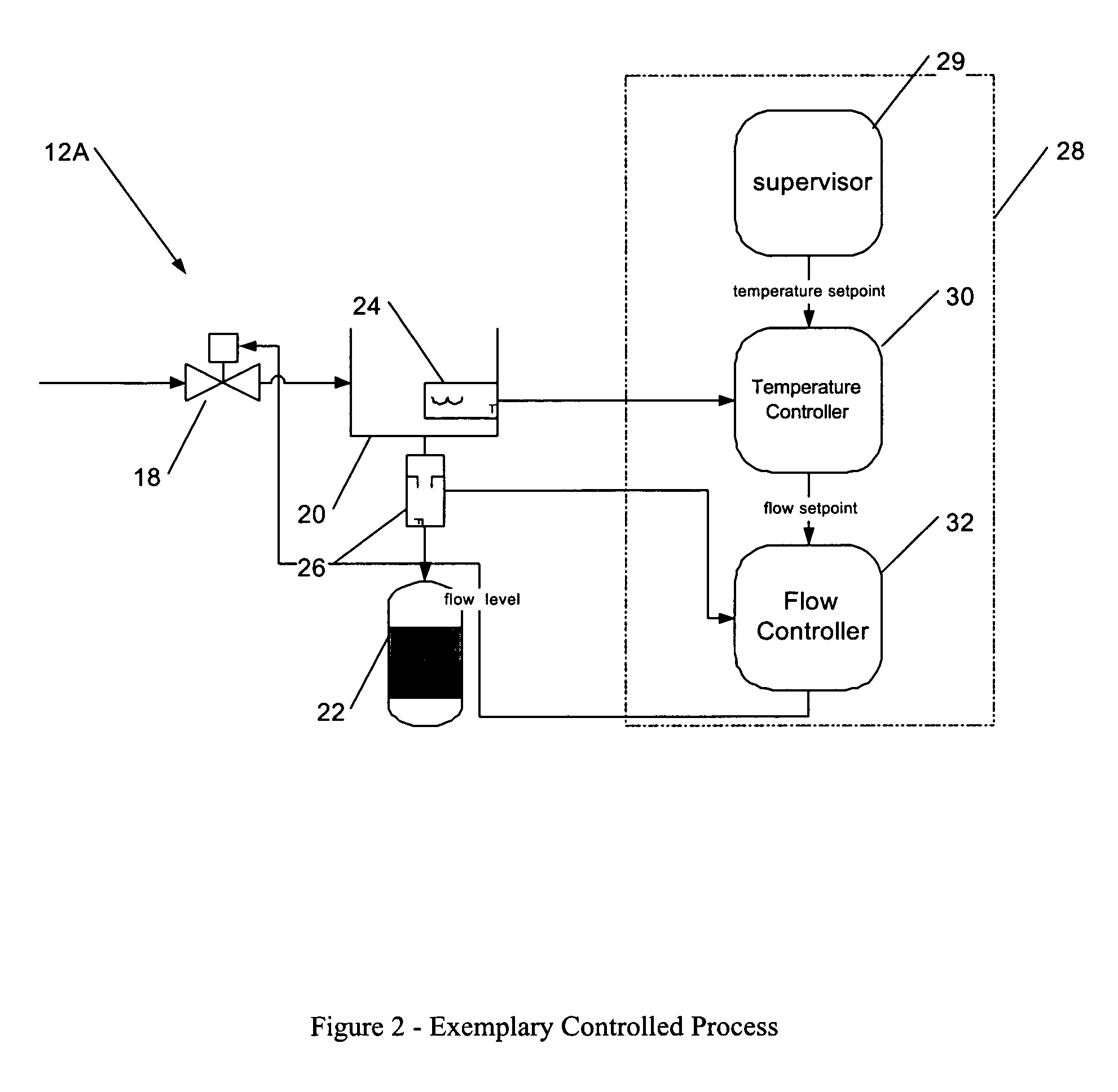
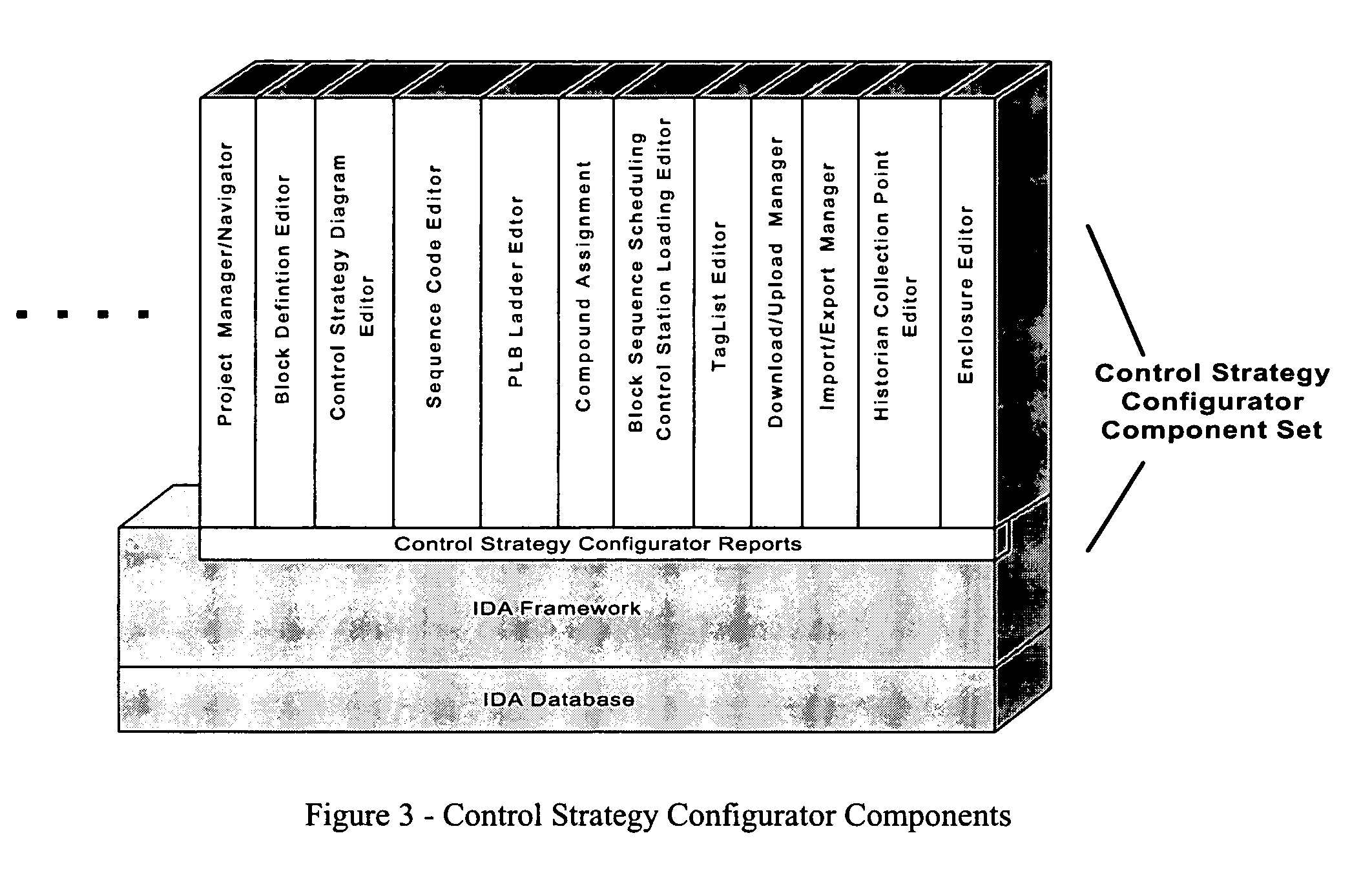
Methods and apparatus for control configuration with versioning, security, composite blocks, edit selection, object swapping, formulaic values and other aspects
InactiveUS7272815B1OptimizationOptimize system configurationData processing applicationsDigital data processing detailsGraphical user interfaceComposite object
Methods and apparatus for configuring process, environmental, industrial and other control systems generate and / or utilize models representing configurations of control systems and / or the systems controlled by them. Records of changes to the models or the configurations represented by them are maintained, thereby, for example, providing bases for determining current states, prior states and histories of changes. Objects in the model have characteristics, such as an object type characteristic and an area characteristic. Users can have corresponding permissions. A security mechanism apparatus controls access by users to the objects. Composite objects are defined by definition objects and are displayed in encapsulated or expanded formats. Objects can include an edit control type identifier that determines how they are presented for editing. Functionality responds to user commands by transferring characteristics of a first object depicted by the graphical user interface to a second object. Configuration-time formulas contained objects are evaluated to constants prior to downloading to the control system.
Owner:SCHNEIDER ELECTRIC SYST USA INC
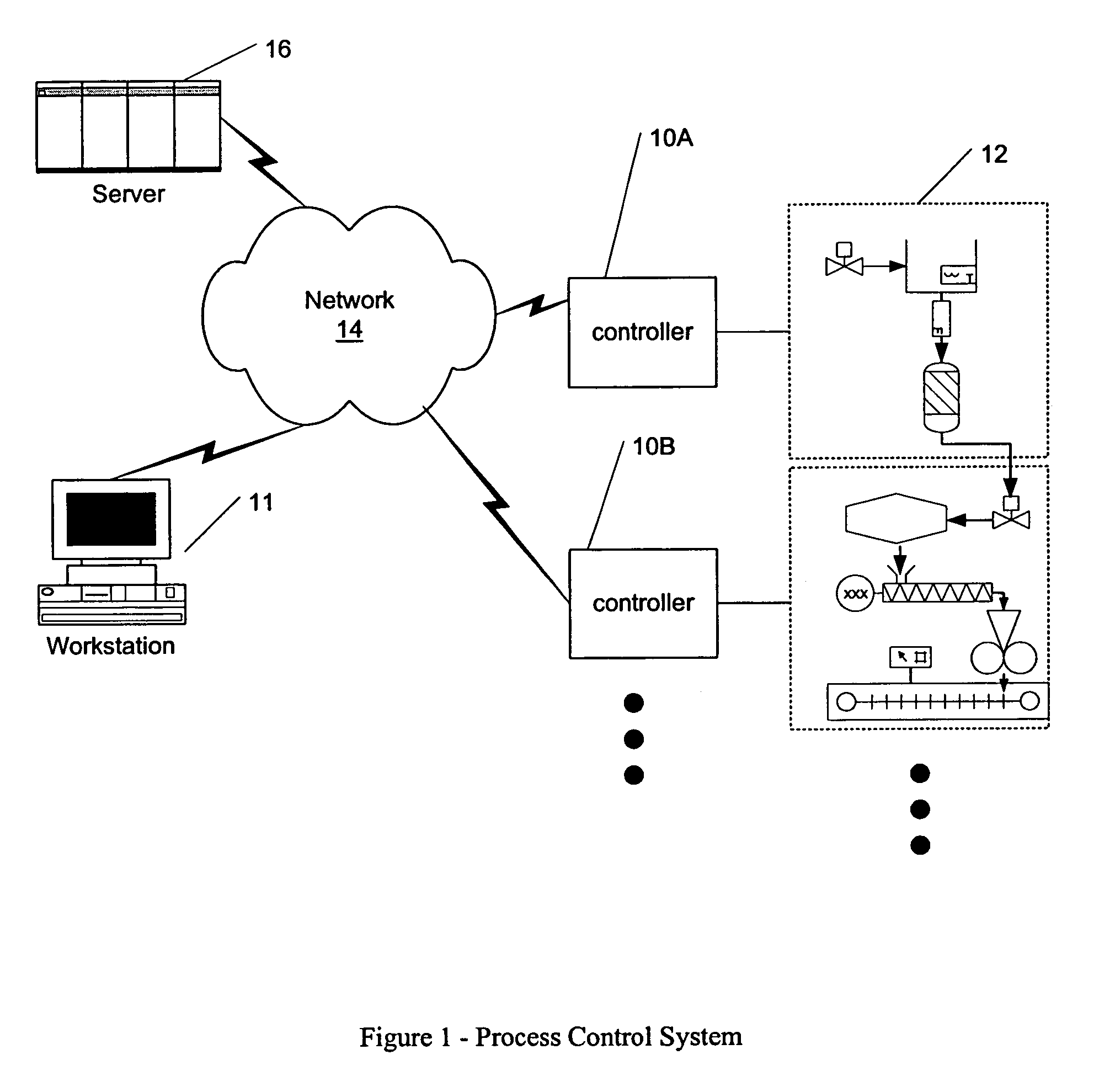
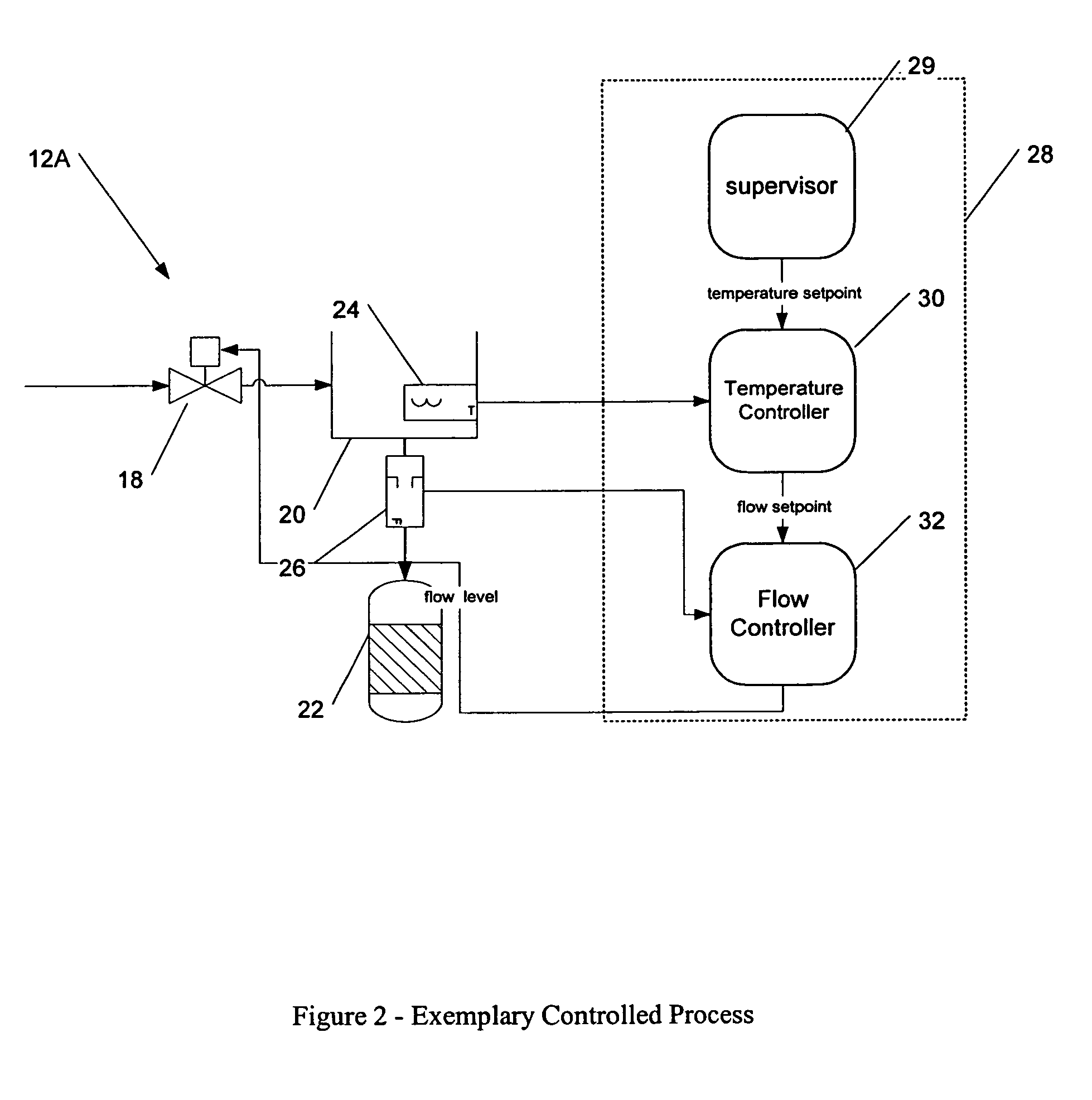
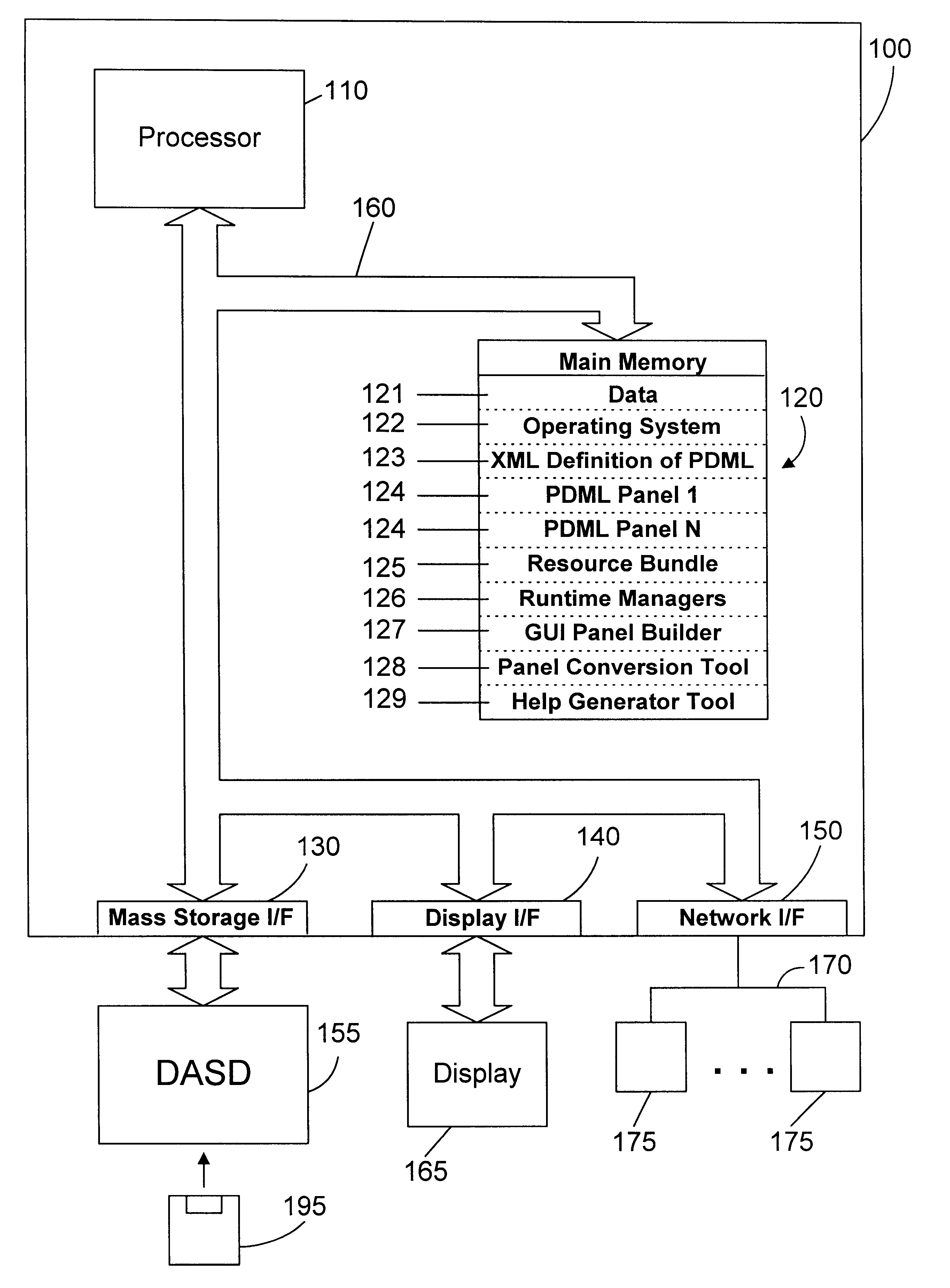
Specification language for defining user interface panels that are platform-independent
InactiveUS6342907B1Promote generationRequirement analysisSpecific program execution arrangementsGraphicsGraph editor
A specification language allows a user to define platform-independent user interface panels without detailed knowledge of complex computer programming languages. The specification language is referred to herein as a Panel Definition Markup Language (PDML), which defines tags that are used in similar fashion to those defined in Hypertext Markup Language (HTML), that allow a user to specify the exact location of components displayed in the panel. A graphical editor allows the creation and modification of platform-independent user interface panels without programming directly in the specification language. A conversion tool may be used to convert platform-specific user interface panels to corresponding platform-independent user interface panels. A help generator tool also facilitates the generation of context-sensitive help for a user interface panel.
Owner:IBM CORP
System and method for accessing object capabilities in a graphical program
A system and method for creating a graphical program, wherein the graphical program is operable to access capabilities of an object. During creation of the graphical program, the user operates to place an object node in the graphical program, wherein the object node is operable to access capabilities of the object. This preferably includes the user arranging on the screen the graphical program, including the object node and various other nodes, and connecting the various nodes to create the graphical program. The user then configures the object node to receive information on the object, preferably by the user configuring the object node with a reference to the object, e.g., a pointer, address, or other information which specifies the identity and / or location of the object. The user also selects one or more methods to be invoked on the object and / or one or more properties to get / set on the object. Once the graphical program has been created, then during execution of the graphical program, the object node accesses the capabilities of the object.
Owner:NATIONAL INSTRUMENTS
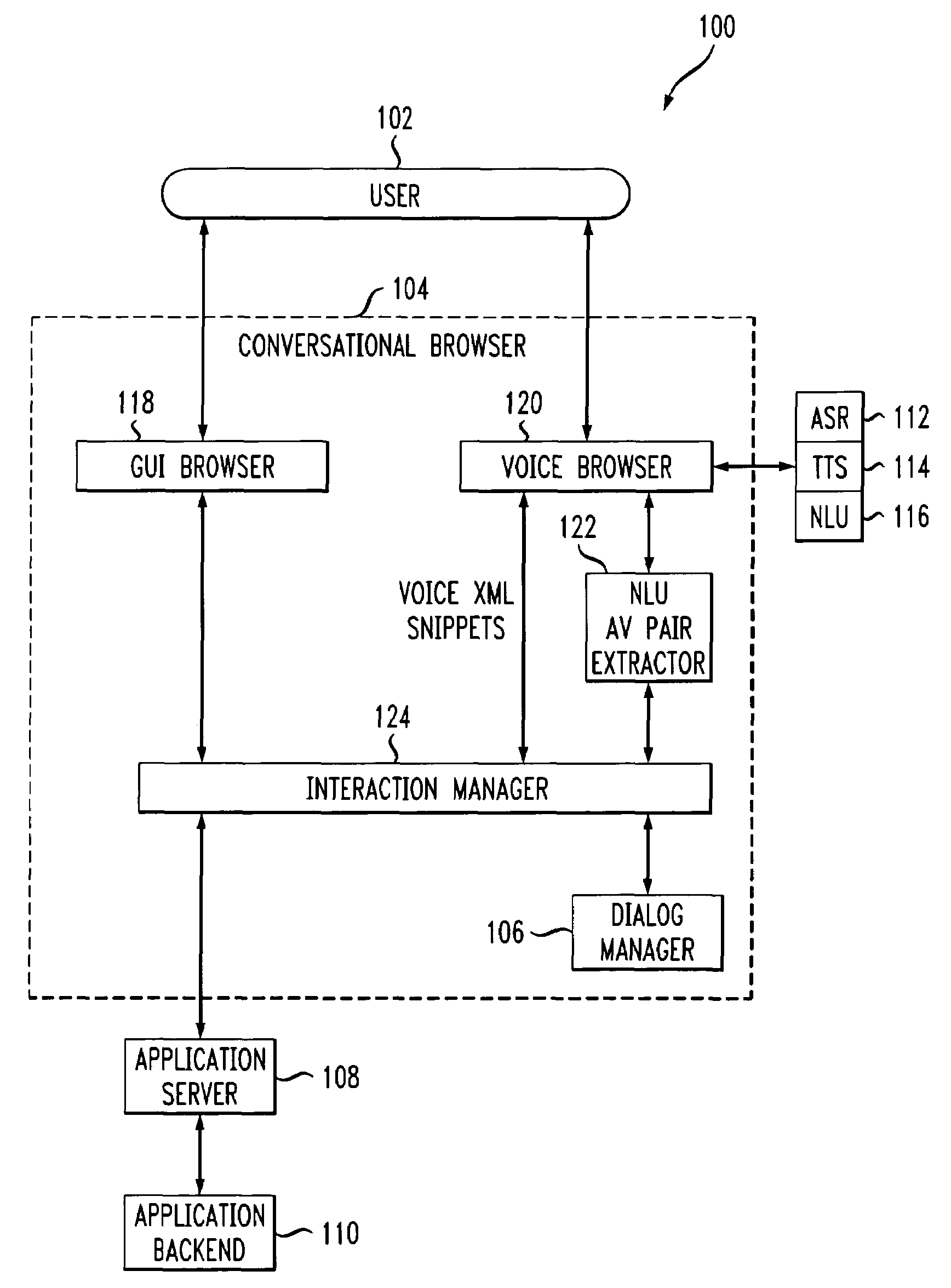
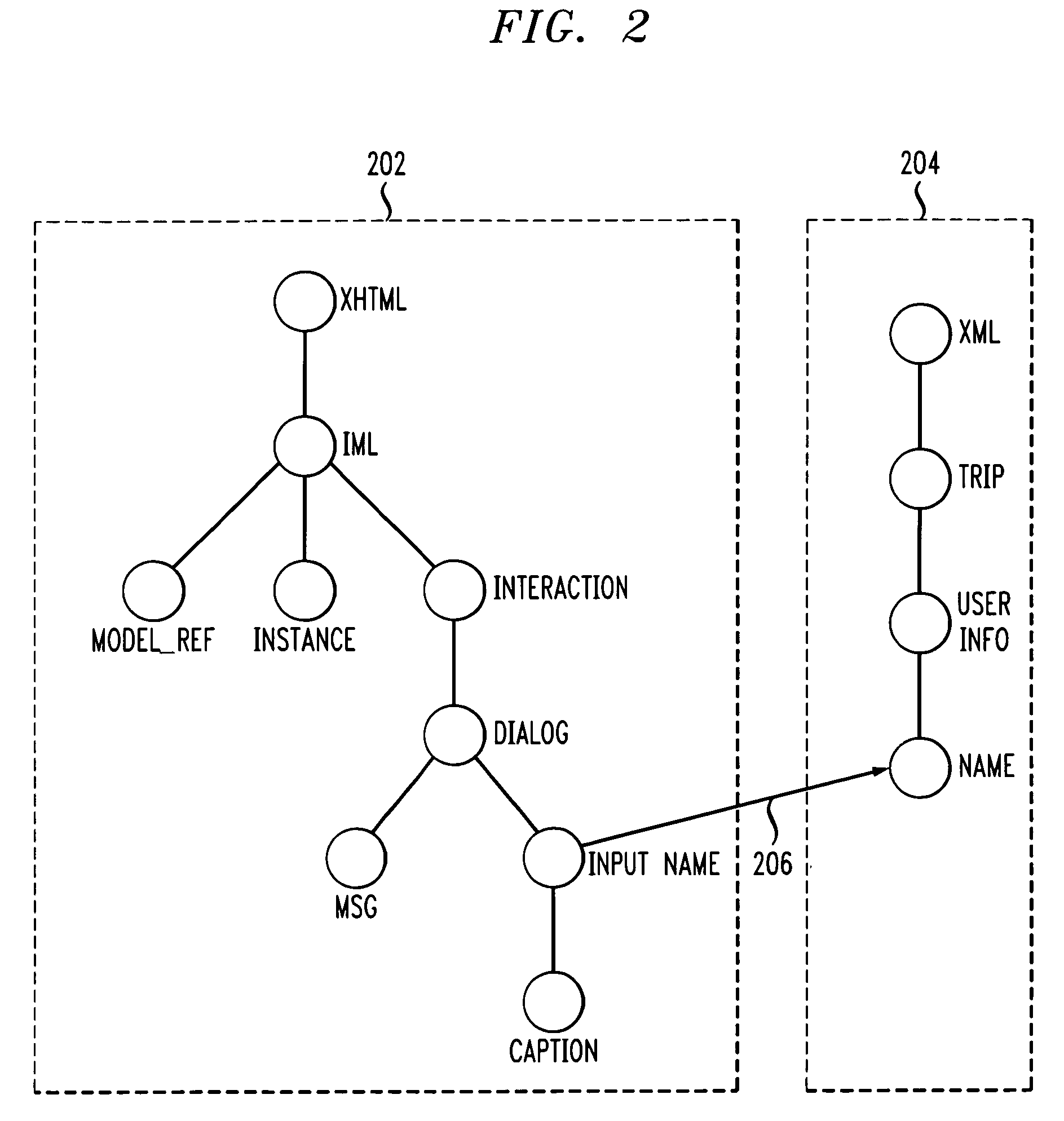
Methods and systems for authoring of mixed-initiative multi-modal interactions and related browsing mechanisms
Application authoring techniques, and information browsing mechanisms associated therewith, which employ programming in association with mixed-initiative multi-modal interactions and natural language understanding for use in dialog systems. Also, a conversational browsing architecture is provided for use with these and other authoring techniques.
Owner:INT BUSINESS MASCH CORP
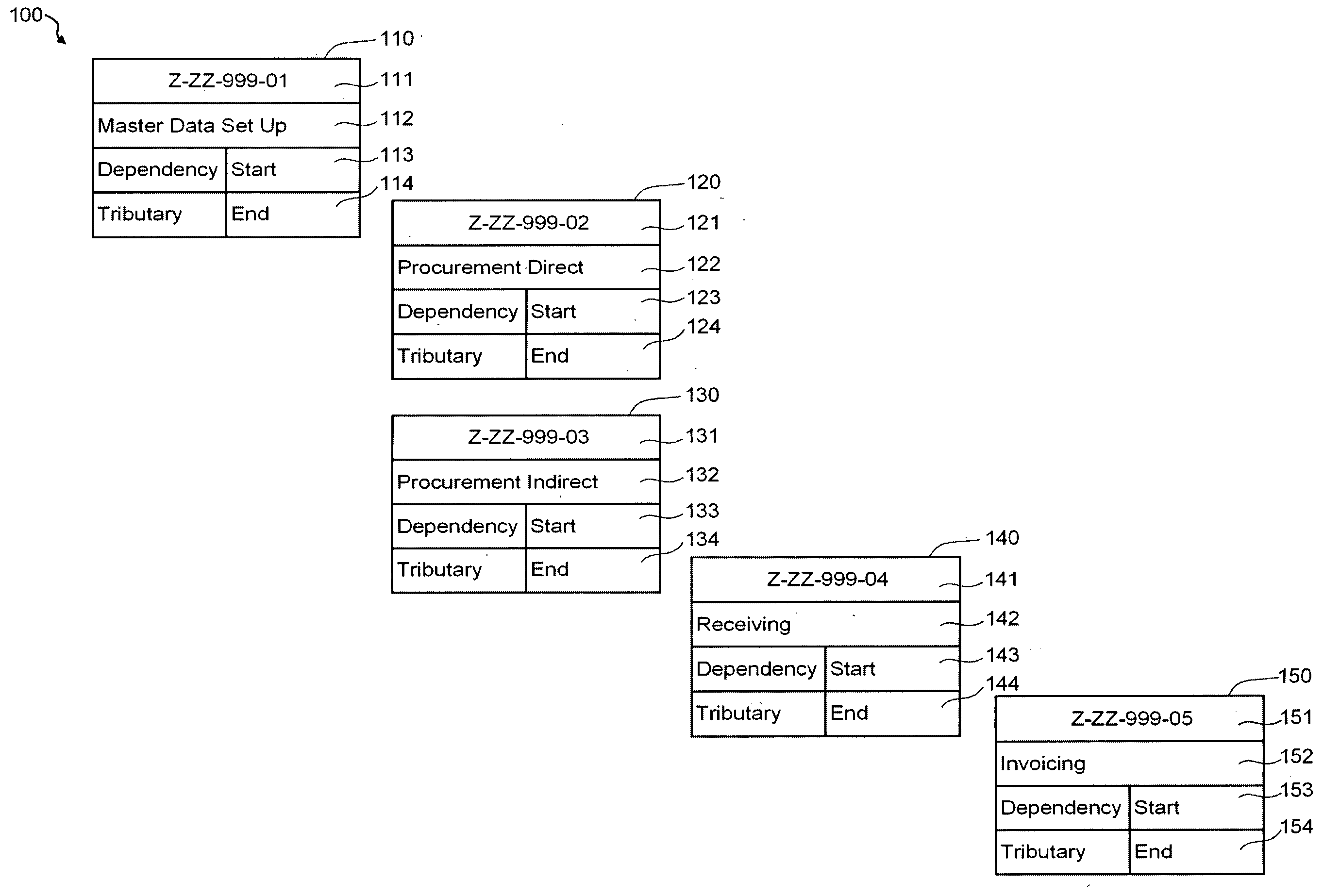
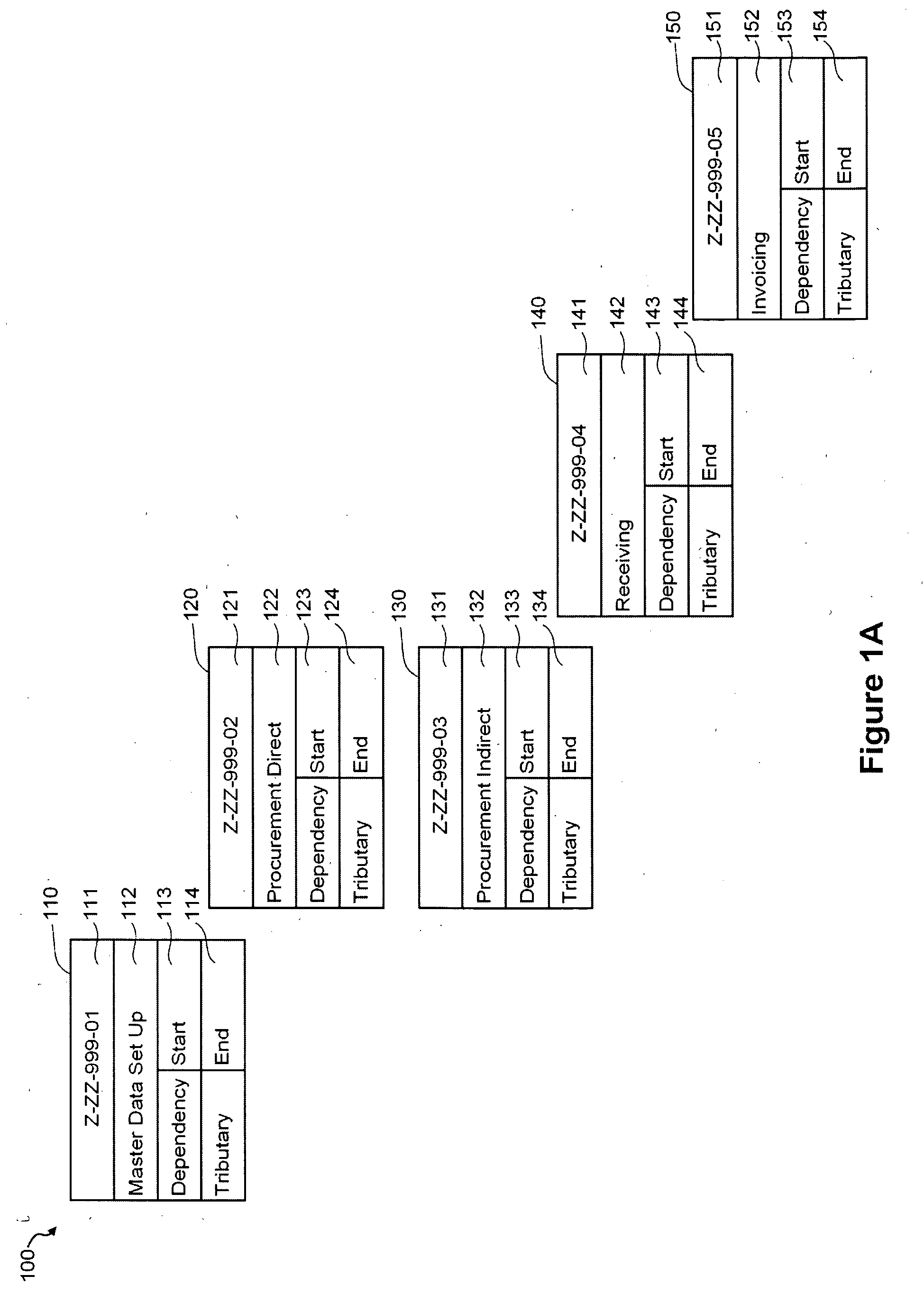
Testing tool comprising an automated multidimensional traceability matrix for implementing and validating complex software systems
InactiveUS20050166094A1Easy to createSoftware testing/debuggingSpecific program execution arrangementsSoftware systemComputer science
The present invention relates to a testing tool for testing of complex software systems having a plurality of interrelated system components and a suite of test scenarios for testing the performance of the plurality of interrelated system components. The testing tool includes an Automated Multidimensional Traceability Matrix system for determining linkages between interrelated system components, a means for identifying a change in one or more of the interrelated system components, a means for applying the Automated Multidimensional Traceability Matrix, a means for executing all of or a subset of the test scenarios associated with the interrelated system components that may be affected by the change and a means for evaluating the results of the executed test scenarios.
Owner:KIMBERLY-CLARK WORLDWIDE INC
Signatures for facilitating hot upgrades of modular software components
InactiveUS6880086B2Facilitating hot upgradeAccurately determineSynchronisation information channelsMemory loss protectionComputer hardwareTelecommunications network
The present invention provides a method and apparatus for facilitating hot upgrades of software components within a telecommunications network device through the use of “signatures” generated by a signature generating program. After installation of a new software release within the network device, only those software components whose signatures do not match the signatures of corresponding and currently executing software components are upgraded. Signatures promote hot upgrades by identifying only those software components that need to be upgraded. Since signatures are automatically generated for each software component as part of putting together a new release a quick comparison of two signatures provides an accurate assurance that either the software component has changed or has not. Thus, signatures provide a quick, easy way to accurately determine the upgrade status of each software component.
Owner:CIENA
Process control configuration system with connection validation and configuration
Connection objects or other such data structures facilitate establishing and configuring connections between objects that model components in a process control system. A first set of data structures (e.g. the object connection type structures) identify valid types for component-to-component pairings and the respective roles of each component in the pairing (e.g., parent or child, source or sink). A second set of data structures (e.g., the parameter connection type structures) supply similar information for parameter-to-parameter connections. Together, these data structures can be used, for example, to validate component-to-component connections suggested by the user and to automatically configure parameter-to-parameter connections. Actual connections, both at the component or parameter level, are reflected using parameter overrides within the parameterized object model—with which the connection objects are constructed.
Owner:SCHNEIDER ELECTRIC SYST USA INC
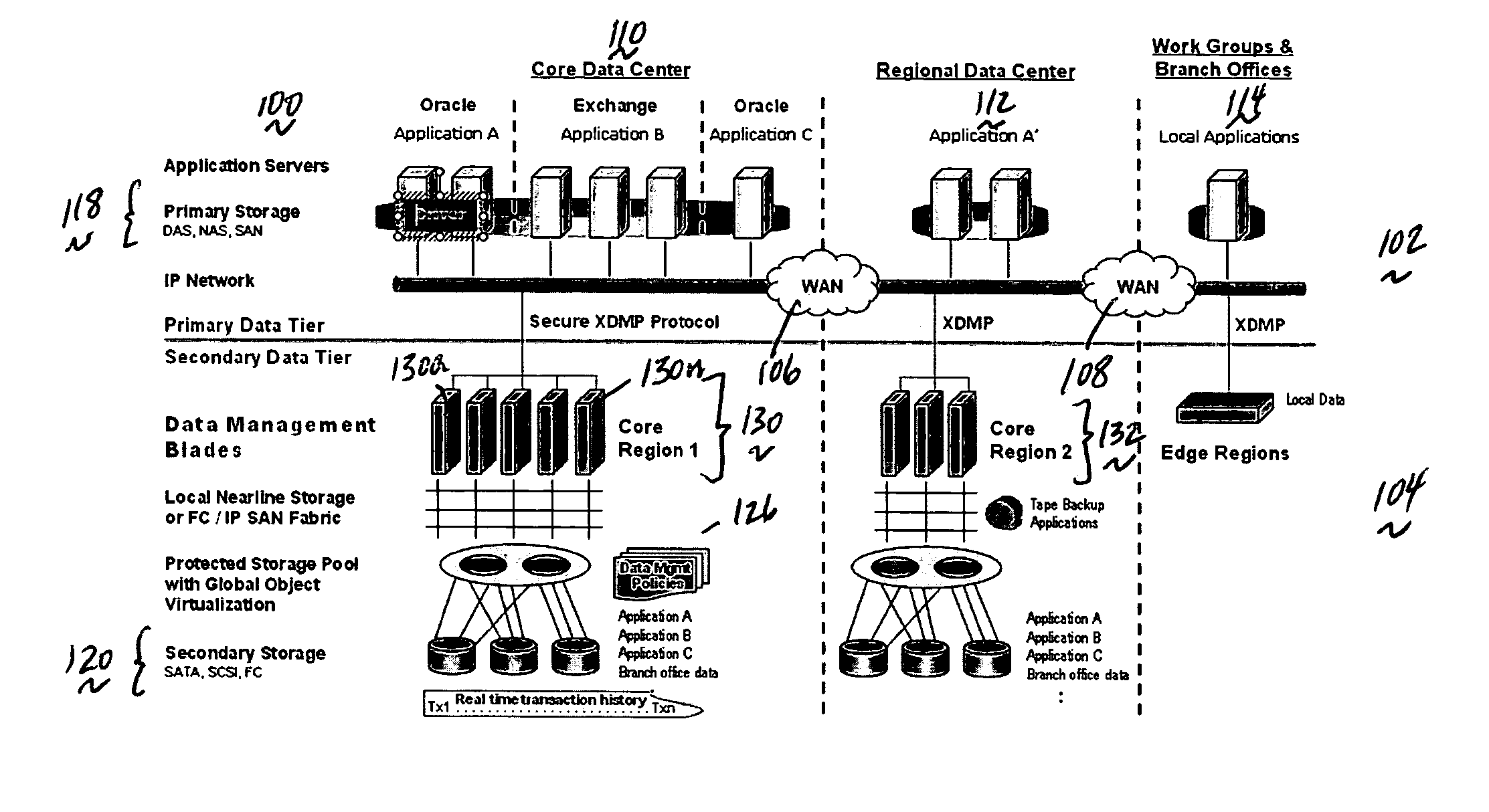
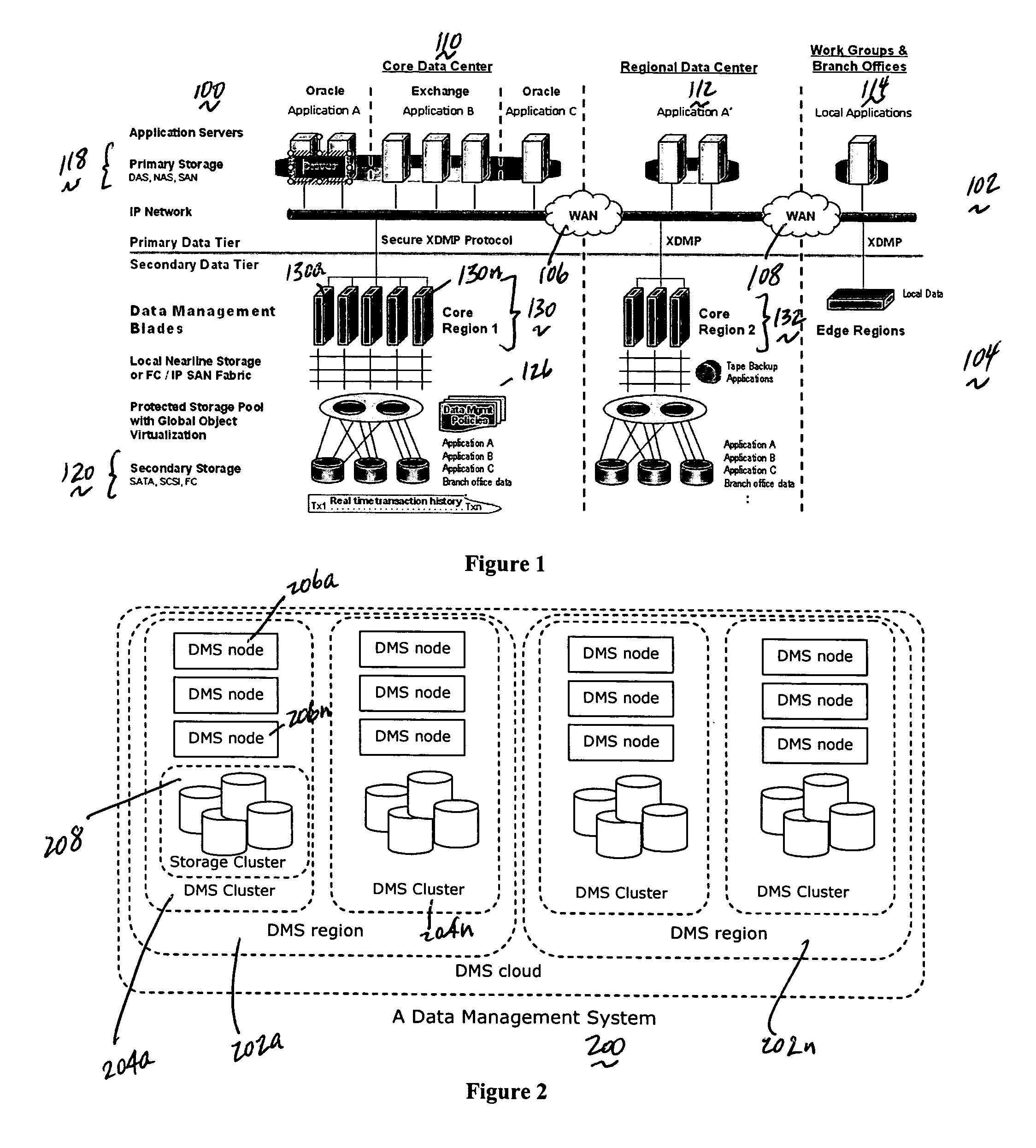
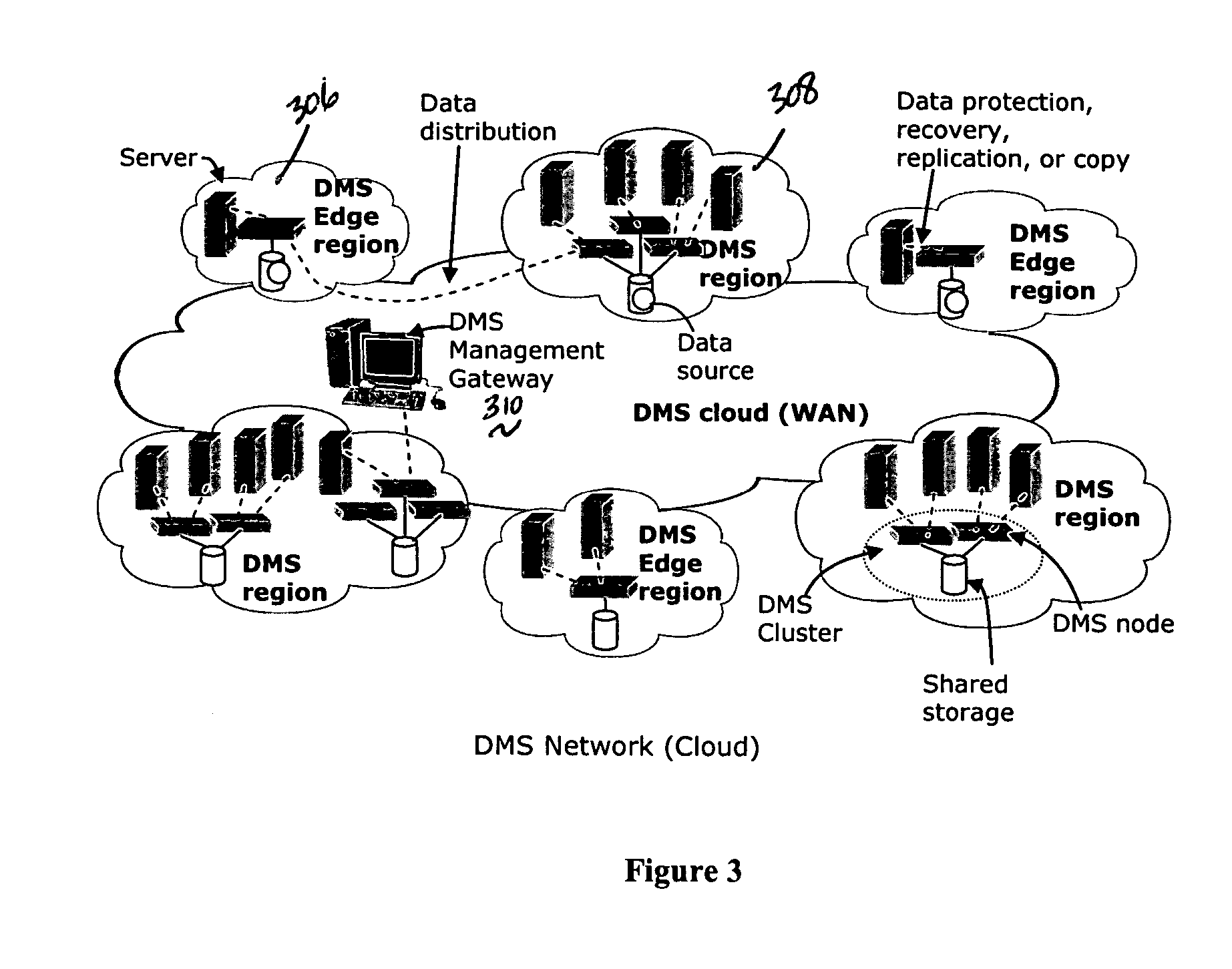
System for moving real-time data events across a plurality of devices in a network for simultaneous data protection, replication, and access services
ActiveUS20050262097A1Efficiently parallel processEfficiently route application-aware data changeDigital data information retrievalDigital data processing detailsData connectionData stream
A data management system or “DMS” provides a wide range of data services to data sources associated with a set of application host servers. The data management system typically comprises one or more regions, with each region having one or more clusters. A given cluster has one or more nodes that share storage. To facilitate the data service, a host driver embedded in an application server connects an application and its data to a cluster. The host driver provides a method and apparatus for capturing real-time data transactions in the form of an event journal that is provided to the data management system. The driver functions to translate traditional file / database / block I / O into a continuous, application-aware, output data stream. Using the streams generated in this manner, the DMS offers a wide range of data services that include, by way of example only: data protection (and recovery), disaster recovery (data distribution and data replication), data copy, and data query and access.
Owner:QUEST SOFTWARE INC
Prioritizing Selection Criteria by Automated Assistant
ActiveUS20130111348A1Improve user interactionEffectively engageNatural language translationSemantic analysisSelection criterionSpeech input
Methods, systems, and computer readable storage medium related to operating an intelligent digital assistant are disclosed. A user request is received, the user request including at least a speech input received from a user. The user request including the speech input is processed to obtain a representation of user intent for identifying items of a selection domain based on at least one selection criterion. A prompt is provided to the user, the prompt presenting two or more properties relevant to items of the selection domain and requesting the user to specify relative importance between the two or more properties. A listing of search results is provided to the user, where the listing of search results has been obtained based on the at least one selection criterion and the relative importance provided by the user.
Owner:APPLE INC
Method and system for recording and replaying the execution of distributed java programs
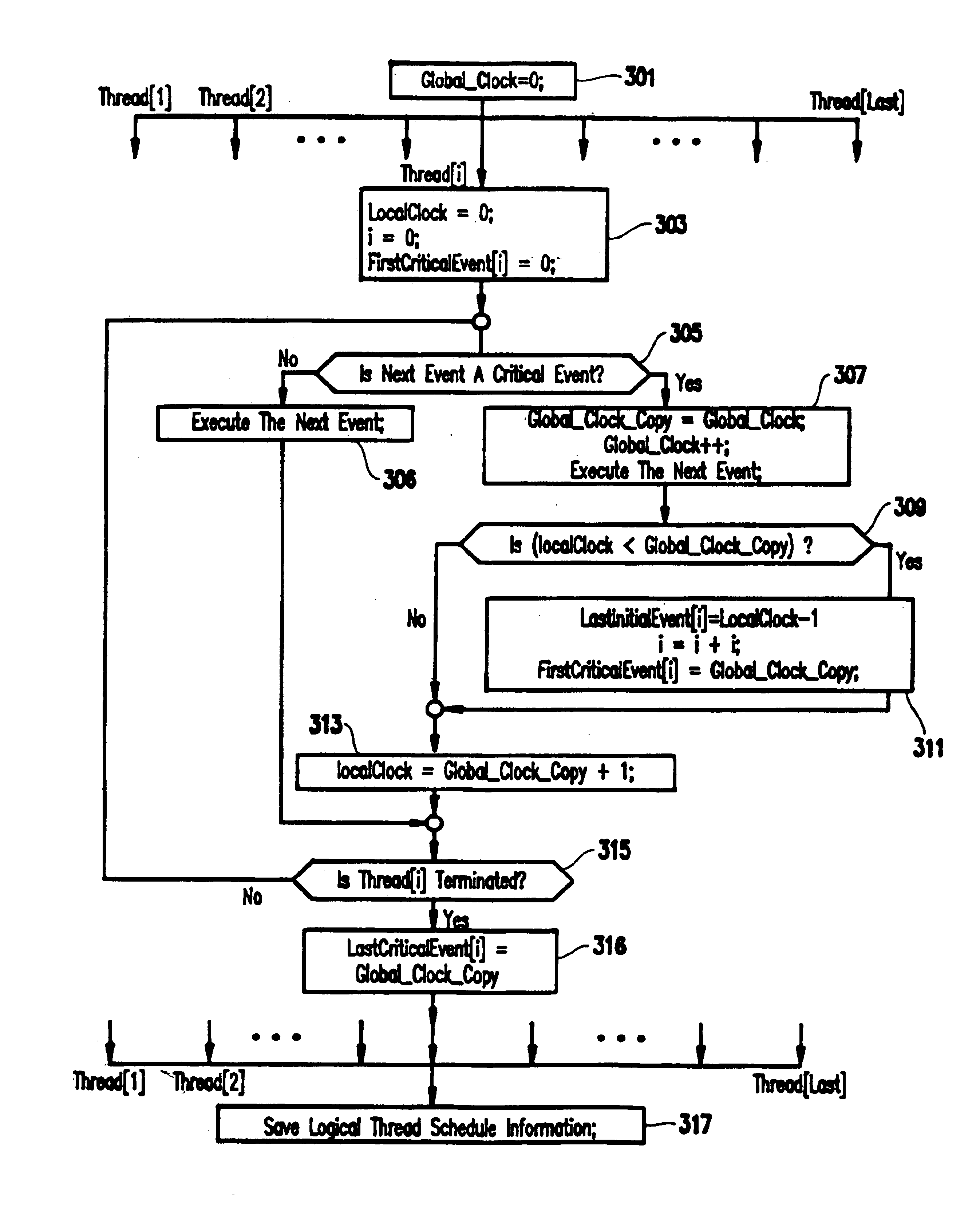
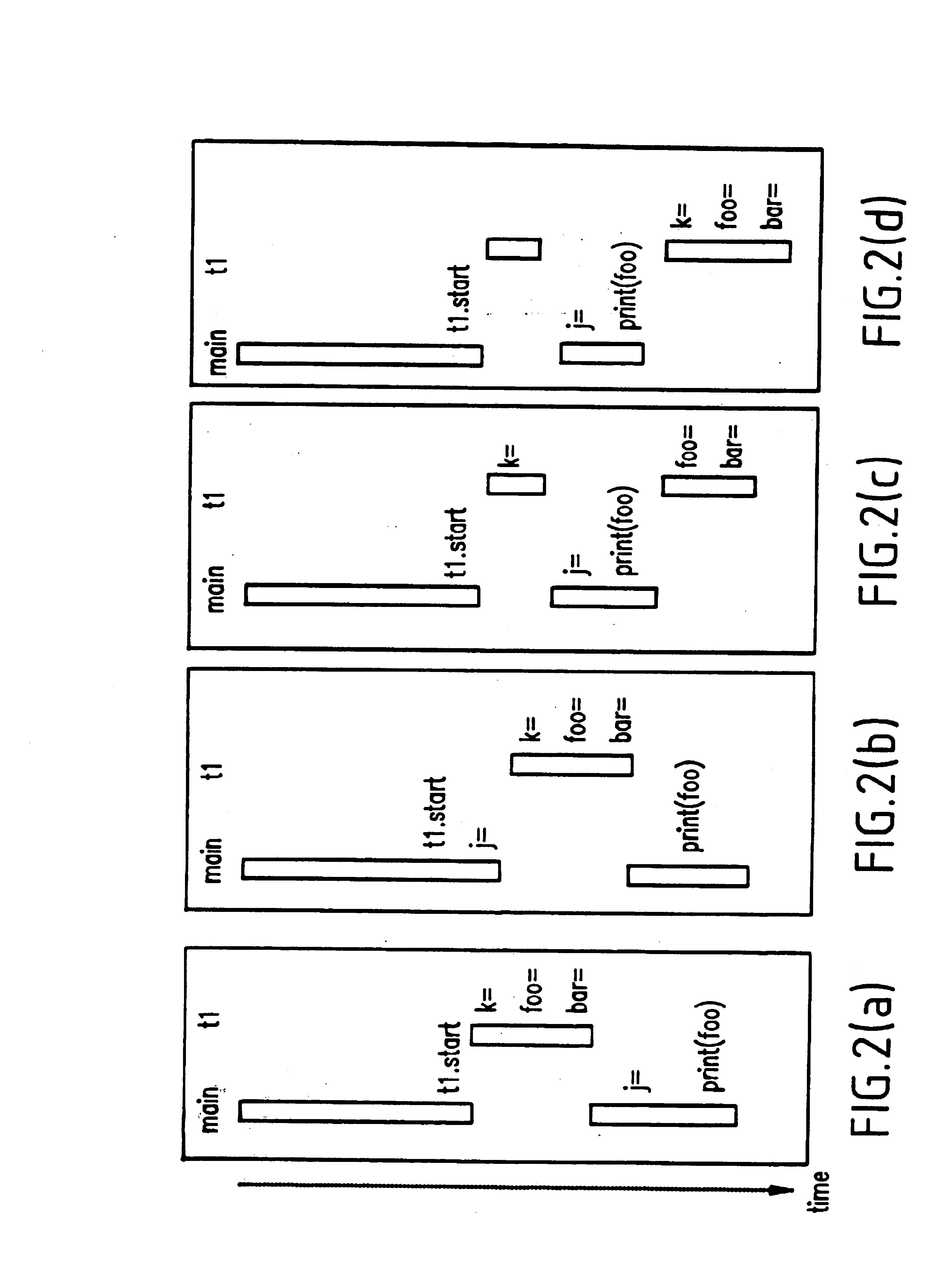
InactiveUS6832367B1Easy to copyGuaranteed orderError detection/correctionSpecific program execution arrangementsStream socketThread scheduling
A method for recording and replaying execution of distributed programs on a computer system in a distributed environment, includes identifying an execution order of critical events of a program, generating groups of critical events of the program, wherein for each group, critical events belonging to the group belong to a common execution thread, and generating for each execution thread a logical thread schedule that identifies a sequence of the groups so as to allow deterministically replaying a non-deterministic arrival of stream socket connection requests, a non-deterministic number of bytes received during message reads, and a non-deterministic binding of stream sockets to local ports.
Owner:IBM CORP
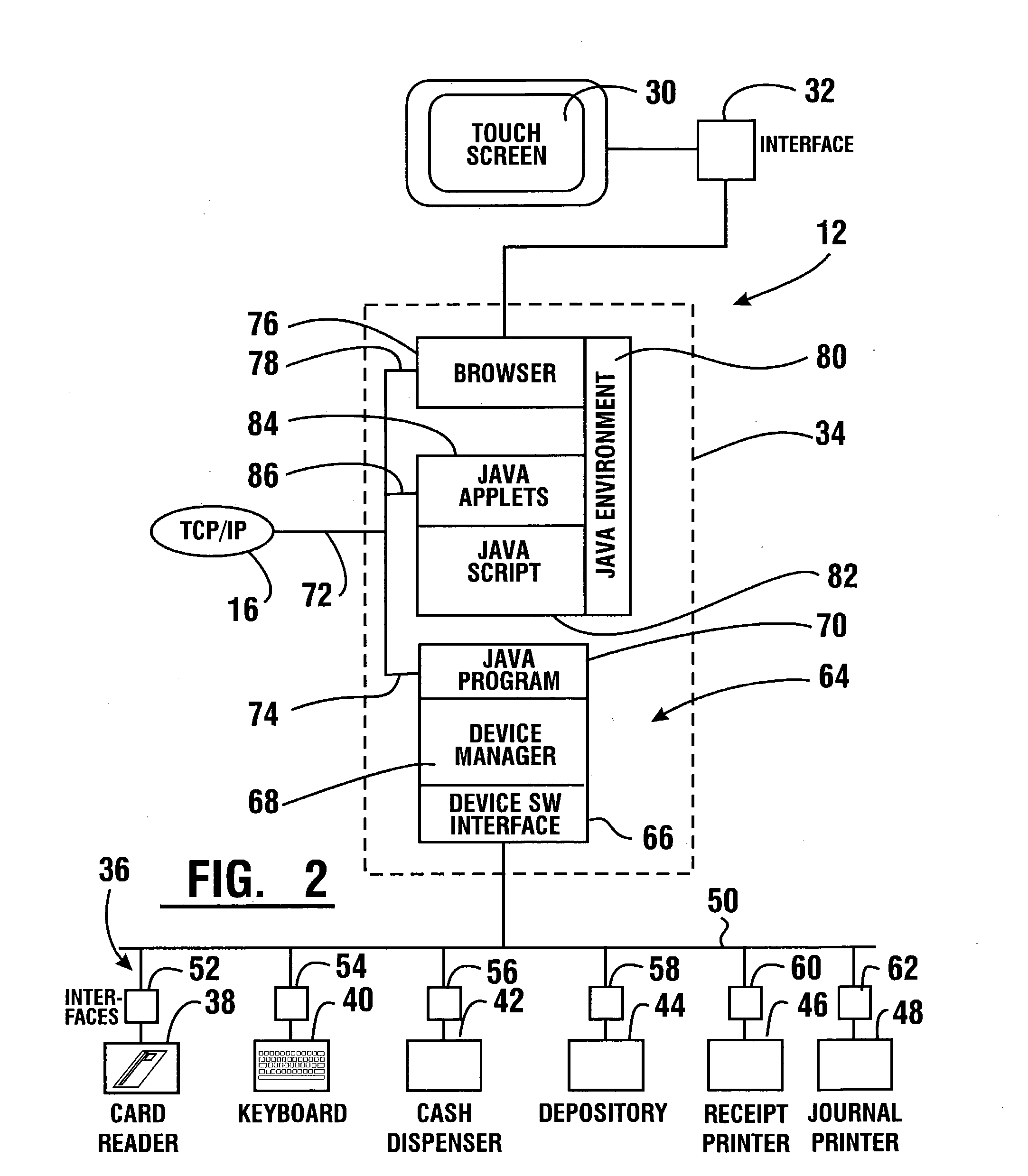
Automated banking machine system and method
InactiveUS20030217005A1Good user interfaceFunction increaseBuying/selling/leasing transactionsSpecific program execution arrangementsEmail addressCheque
A system and method of providing an electronic transaction receipt from a cash dispensing ATM. A bank host computer is operable to submit the receipt to a system address of record with the bank. The address of record corresponds to an e-mail address, phone number or other address associated with an account involved in the transaction. The receipt may include an image or images associated with the transaction. Thus, a user of an ATM is able to receive an electronic receipt corresponding to the ATM transaction. The system may also operate to image deposited checks deposited at an ATM. Copies of the imaged checks and other information can be electronically sent to a maker, payee, a clearinghouse or banks involved with the transaction. The system may also operate to provide the user with blank checks in hard copy or virtual checks for transactions.
Owner:DIEBOLD NIXDORF
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com