Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
911 results about "Electronic transaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
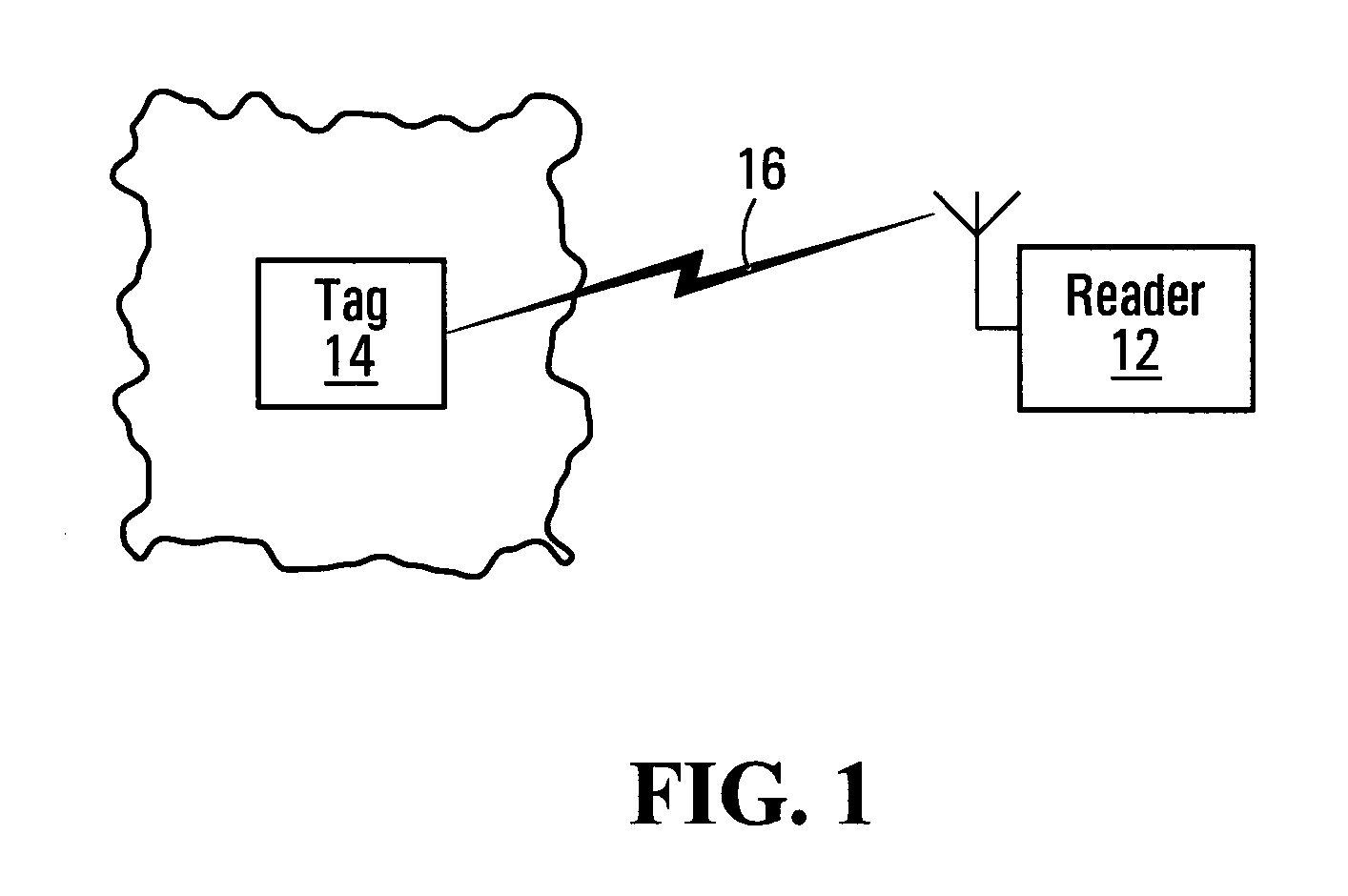
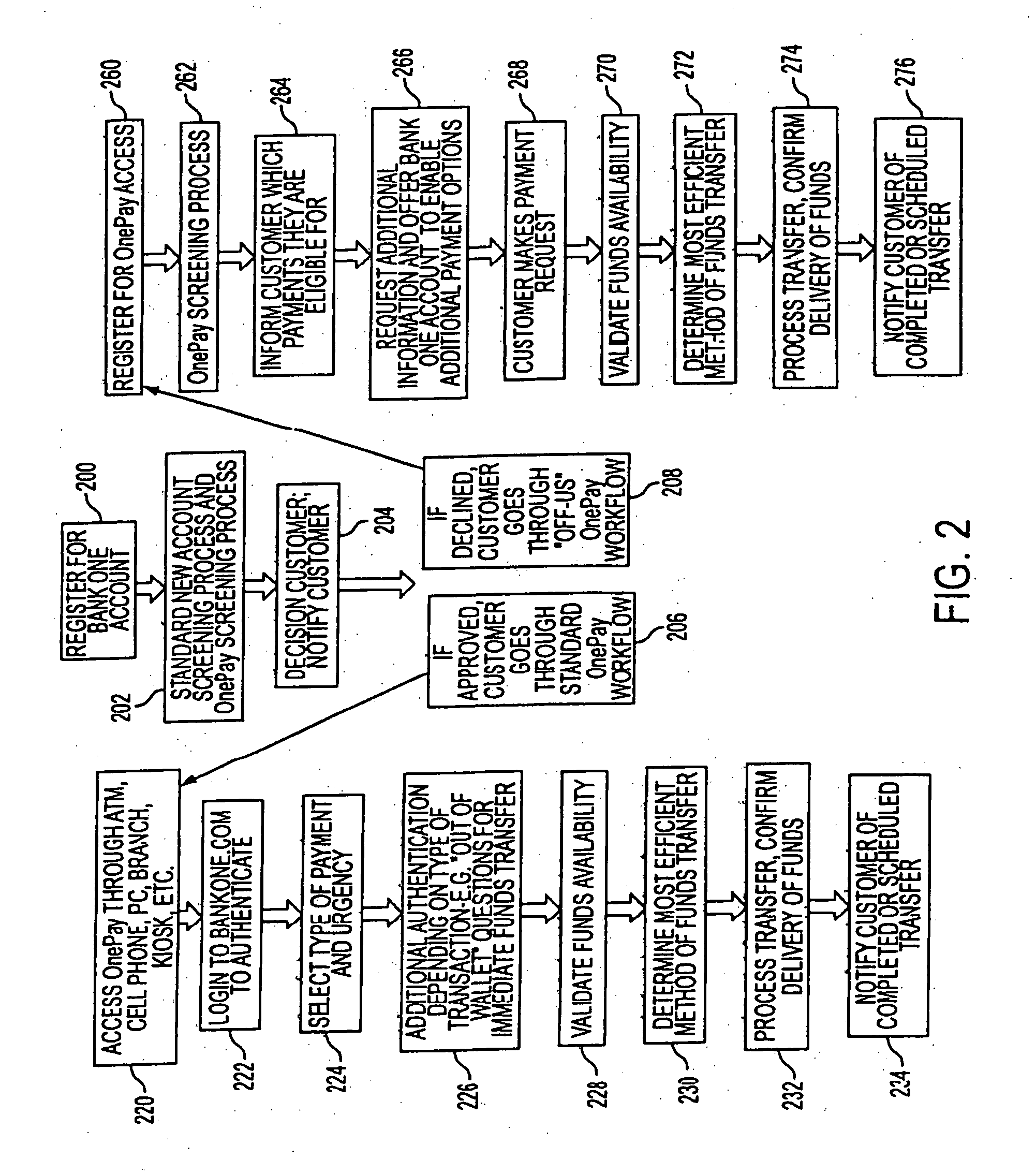
An electronic transaction is any transaction that you complete yourself, without the help of ASB staff. These include EFTPOS, ASB ATM transactions, automatic payments, bill payments, One-Off Payment, direct debits, direct credits, FastNet Classic or FastPhone transfers and Mobile Top-ups.
Transactional services
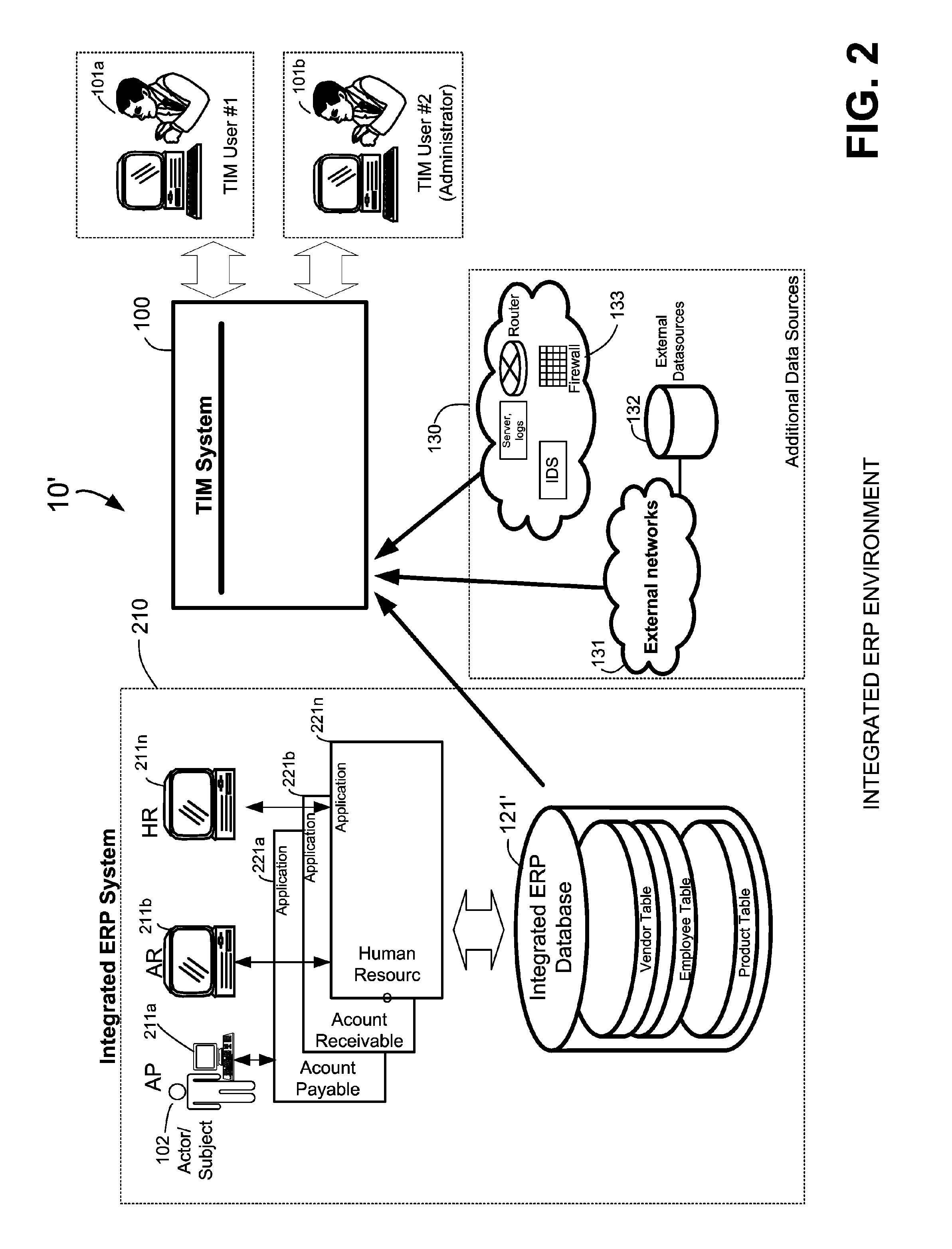
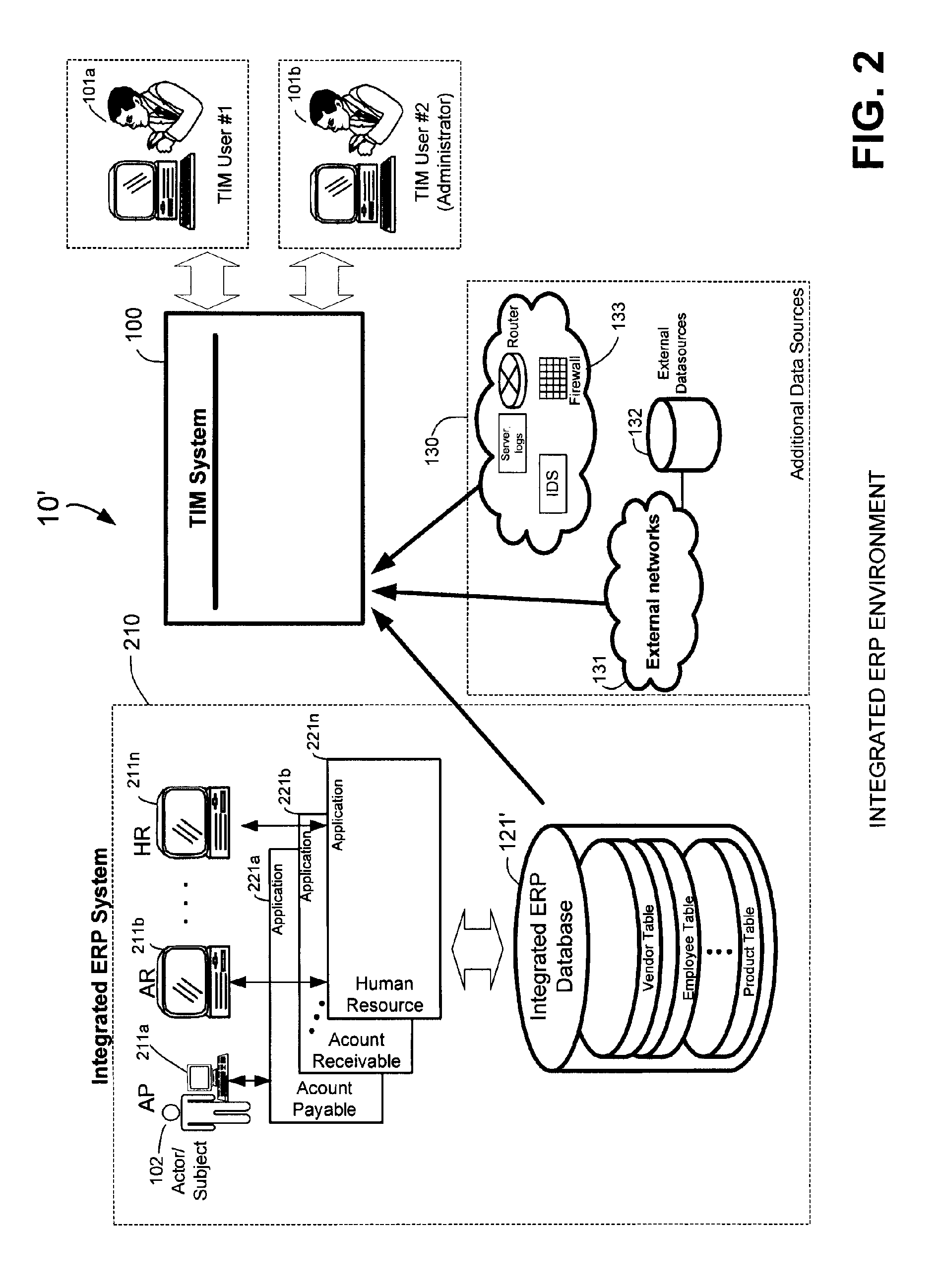
InactiveUS20070198432A1High level of throughputHigh level of efficiencyCryptography processingComputer security arrangementsTransaction serviceDatabase
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
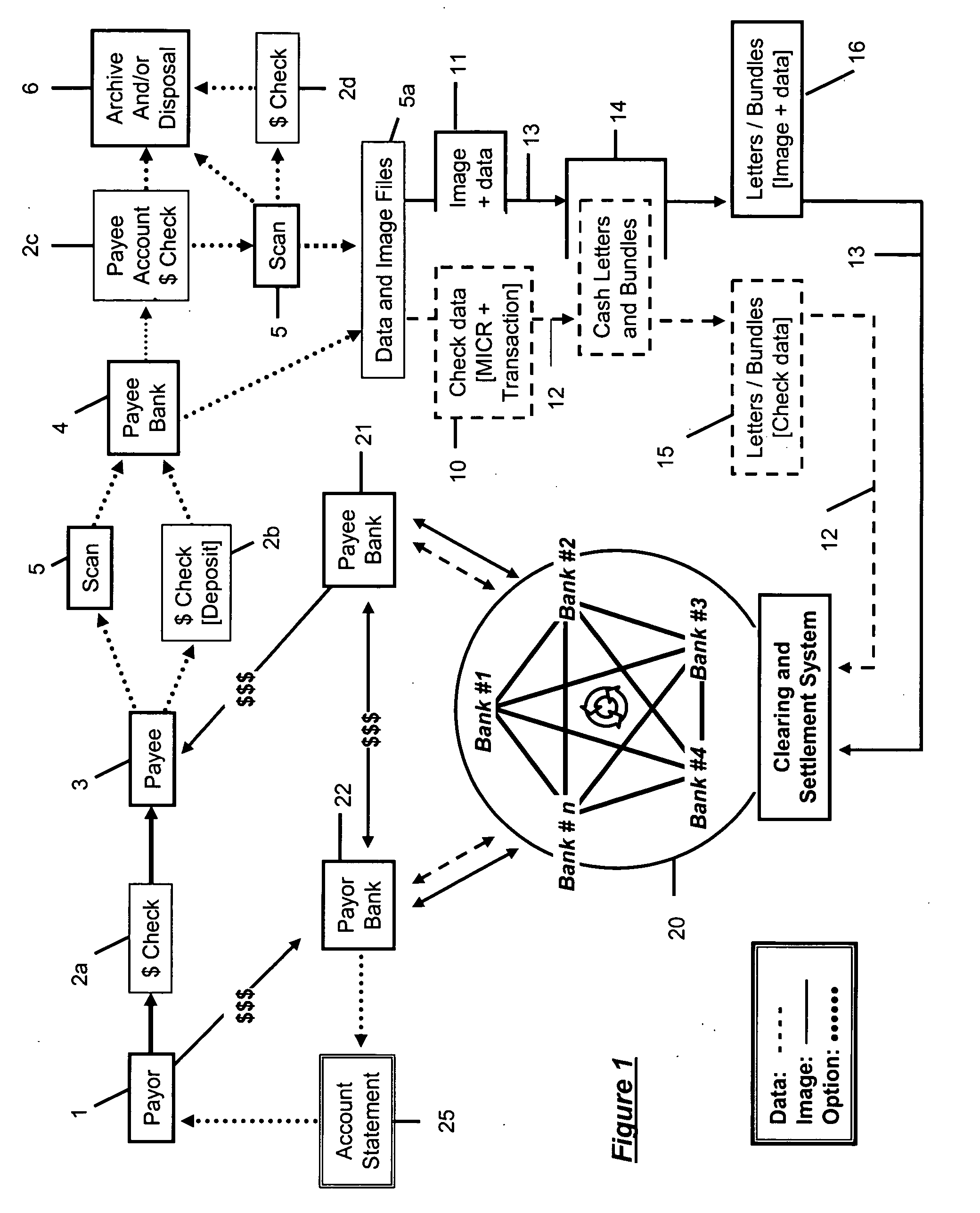
Quality assured secure and coordinated transmission of separate image and data records representing a transaction
InactiveUS20050071283A1Reduces network impactOptimize network bandwidth utilizationFinanceBilling/invoicingQuality assuranceDocument preparation
A system and method of securely processing an electronic transaction in which an image and data associated with the transaction are separately processed and 1) a legally acceptable substitute record of the transaction may be recreated at any step in processing, 2) unauthorized access to the image, data and or substitute document is detectable, 3) quality assurance of the image and data is provided, and 4) participants in a network may create additional security for the transactions.
Owner:WMR E PIN
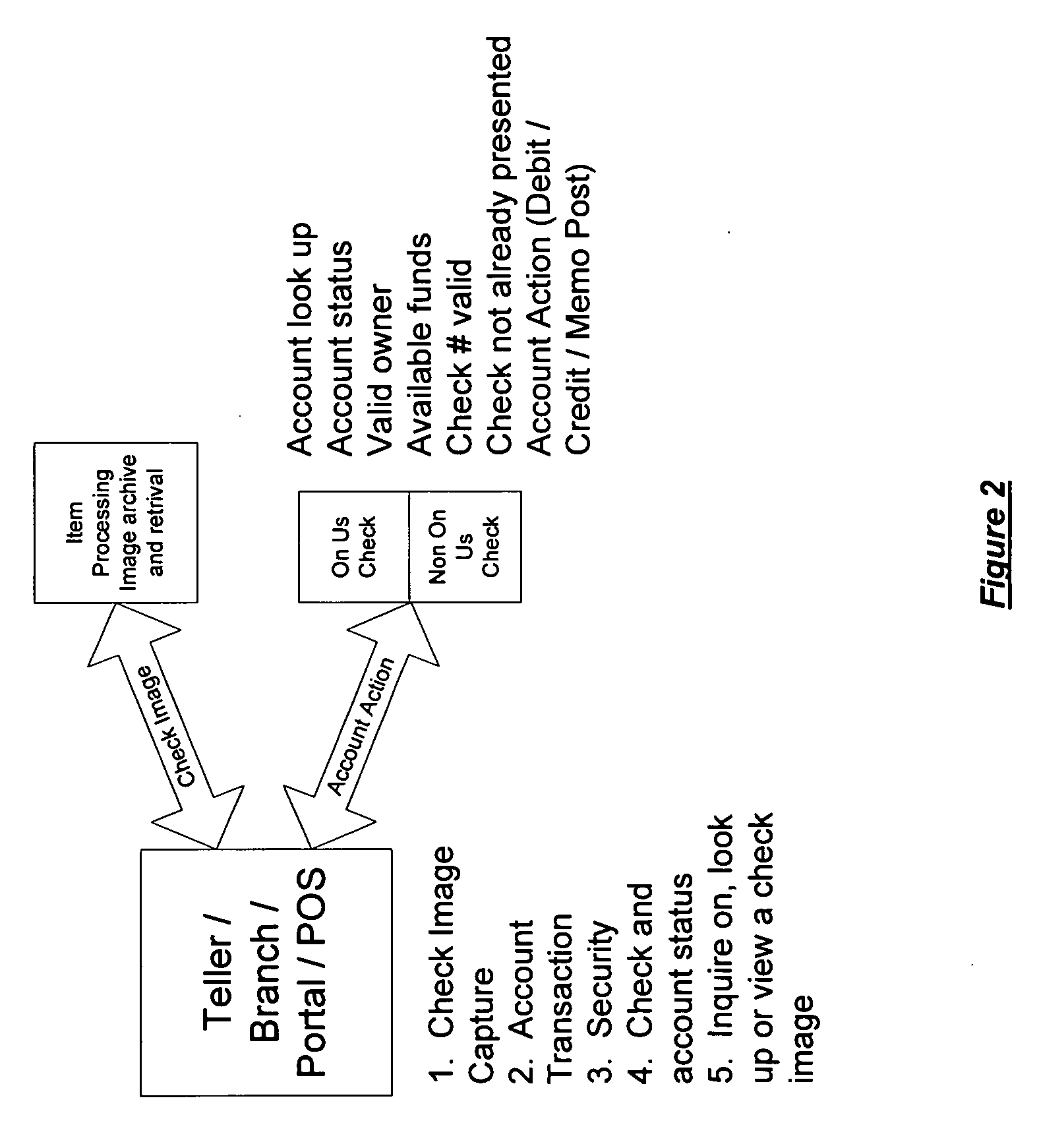
Automated banking machine system and method
InactiveUS20030217005A1Good user interfaceFunction increaseBuying/selling/leasing transactionsSpecific program execution arrangementsEmail addressCheque
A system and method of providing an electronic transaction receipt from a cash dispensing ATM. A bank host computer is operable to submit the receipt to a system address of record with the bank. The address of record corresponds to an e-mail address, phone number or other address associated with an account involved in the transaction. The receipt may include an image or images associated with the transaction. Thus, a user of an ATM is able to receive an electronic receipt corresponding to the ATM transaction. The system may also operate to image deposited checks deposited at an ATM. Copies of the imaged checks and other information can be electronically sent to a maker, payee, a clearinghouse or banks involved with the transaction. The system may also operate to provide the user with blank checks in hard copy or virtual checks for transactions.
Owner:DIEBOLD NIXDORF
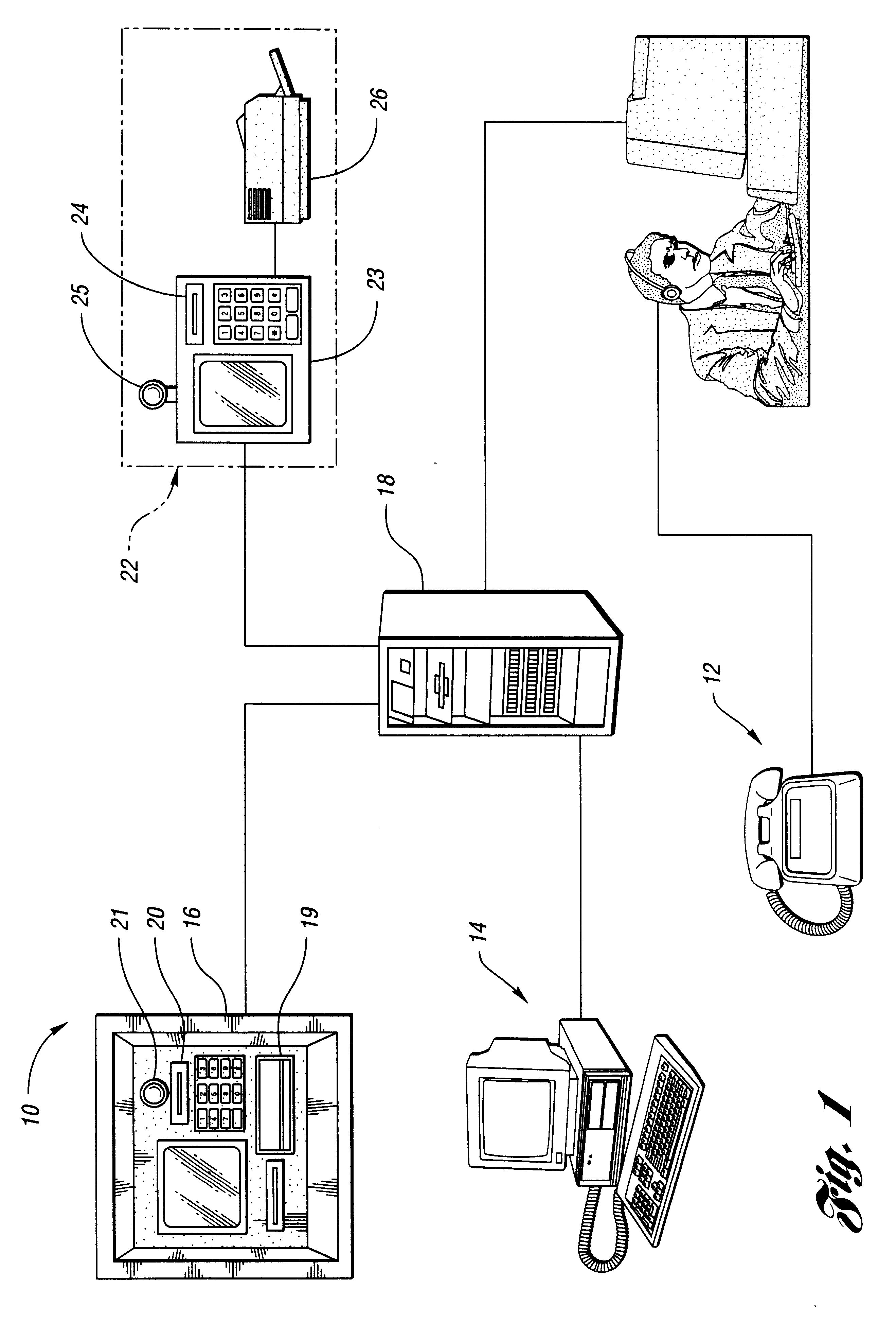
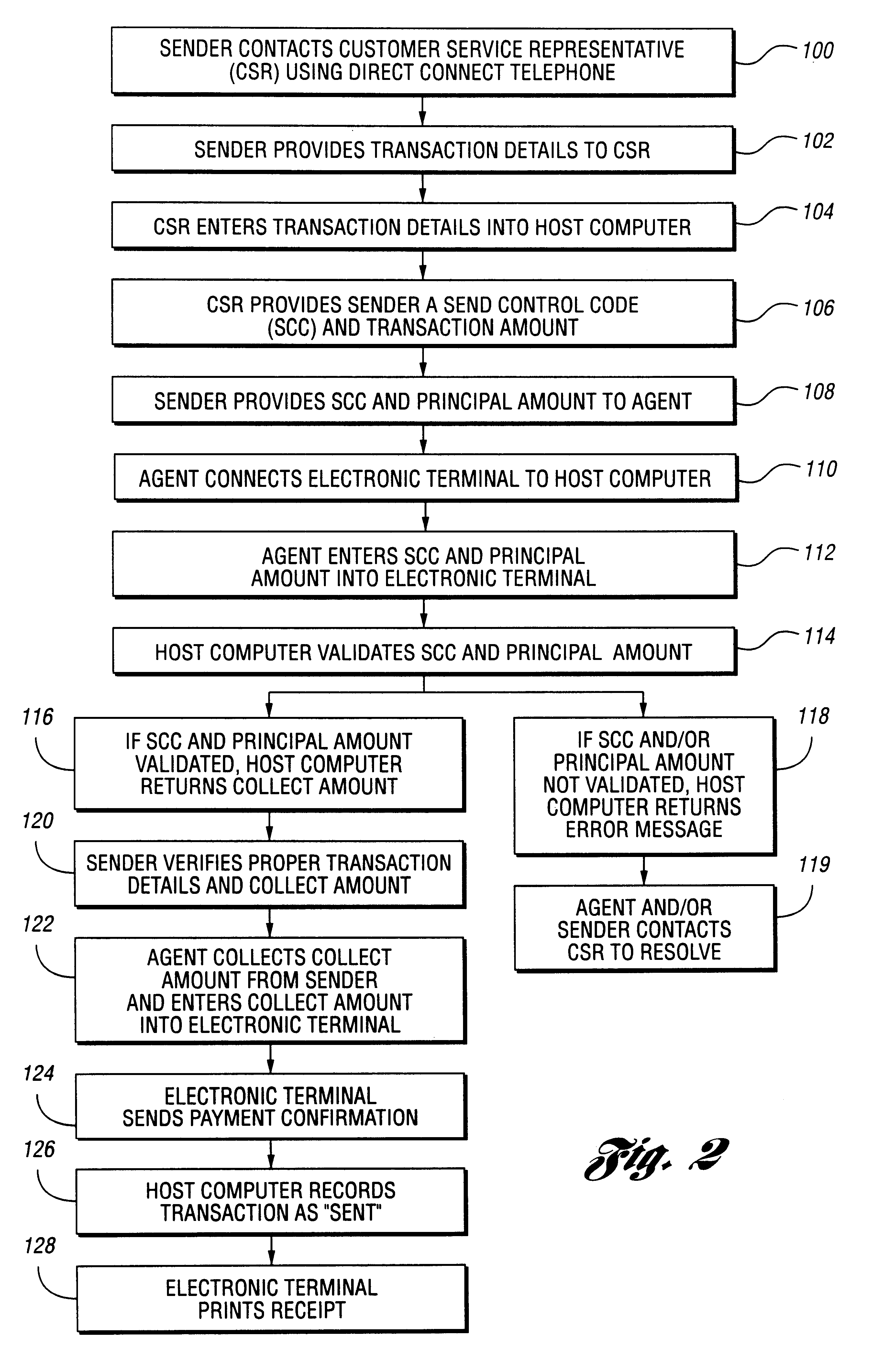
Method and system for performing money transfer transactions
InactiveUS6488203B1Shorten transaction timeImprove accuracyComplete banking machinesFinanceComputer scienceDatabase
A method of performing a send money transfer transaction through a financial services institution includes storing transaction details on a data base, wherein the transaction details include a desired amount of money to be sent; establishing a code that corresponds to the transaction details stored on the data base; entering the code into an electronic transaction fulfillment device in communication with the data base to retrieve the transaction details from the data base; and determining a collect amount based on the transaction details. A system for performing a send money transfer transaction is also disclosed.
Owner:THE WESTERN UNION CO
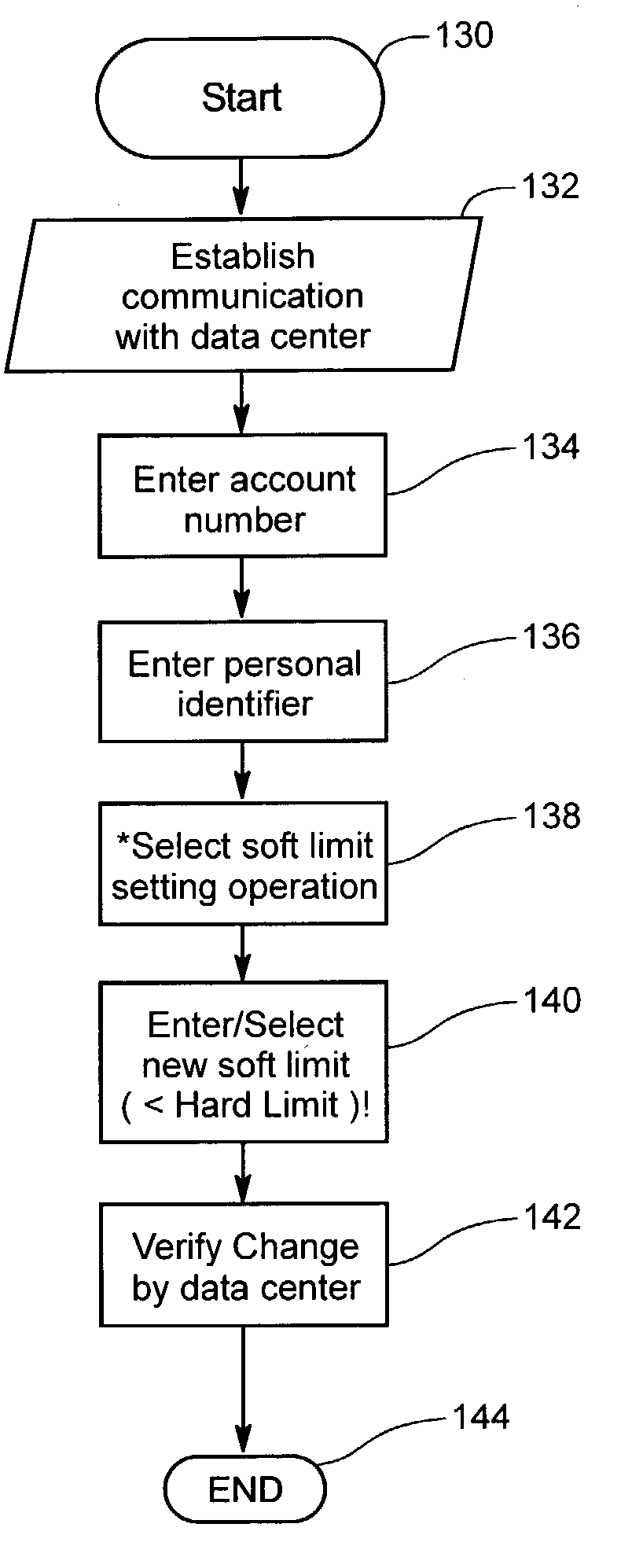
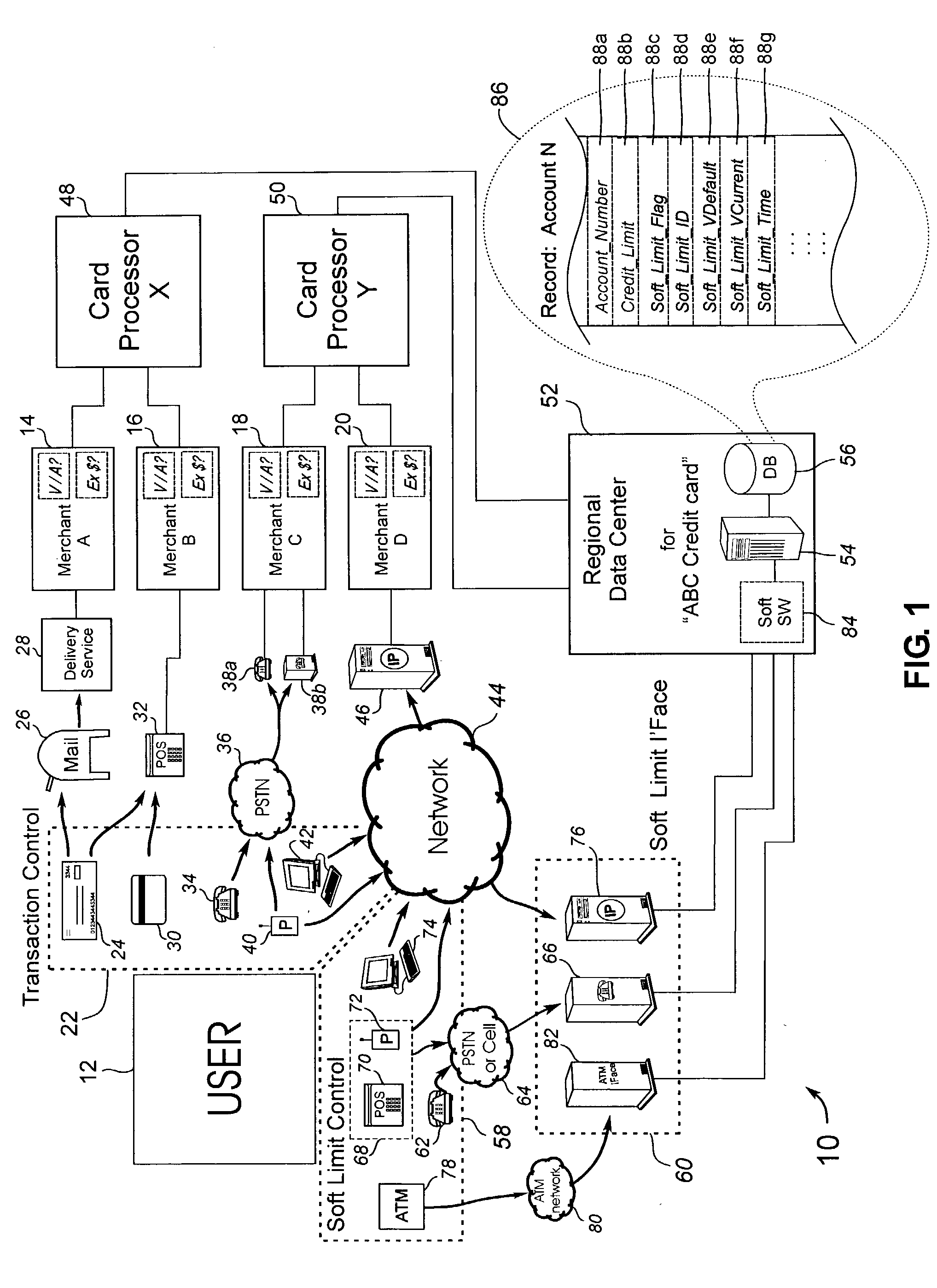
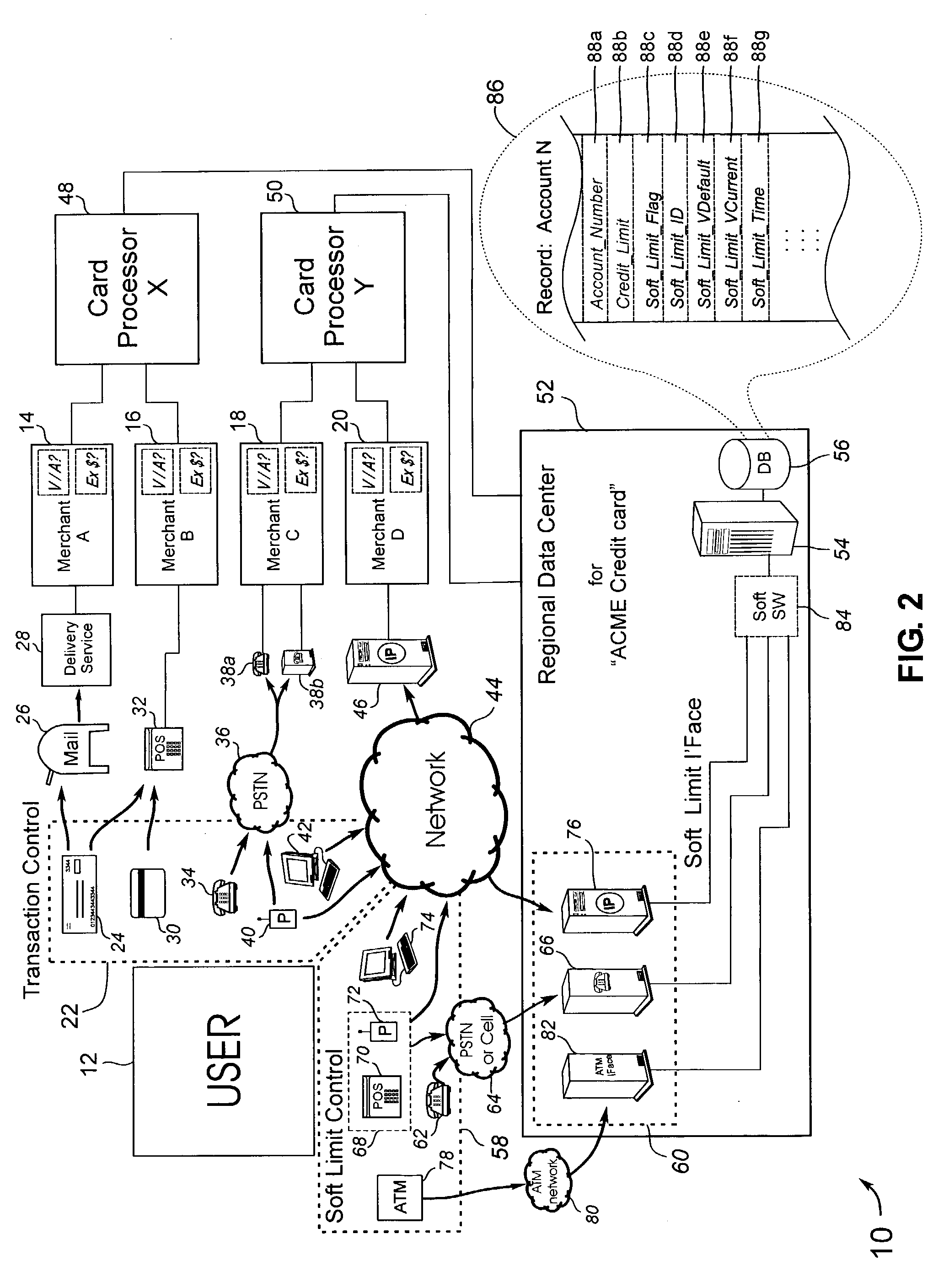
Automated soft limit control of electronic transaction accounts
InactiveUS20030208439A1Low gearLower card lossesFinancePayment circuitsComputer scienceElectronic transaction
A system and method of providing one or more user selectable transaction limits (soft limit) for an associated account, generally within the constraints of fixed transaction limits for the account. The soft limit may be adjusted by the user in response to anticipated transaction volume to reduce fraudulent charge risk. By way of example, the soft limit remains at a low default transaction limit that is generally sufficient for covering daily expenditures when utilizing the account, and may be temporarily set to a higher limit by the user contemplating making a purchases which may exceed the soft limit. After a time period has elapsed or a given number of transactions have occurred after user selection of the soft limit it drops back to the default value. The inventive system and method may be practiced within or interfaced to "card processing centers" of transactions cards or other account tokens.
Owner:RAST RODGER H
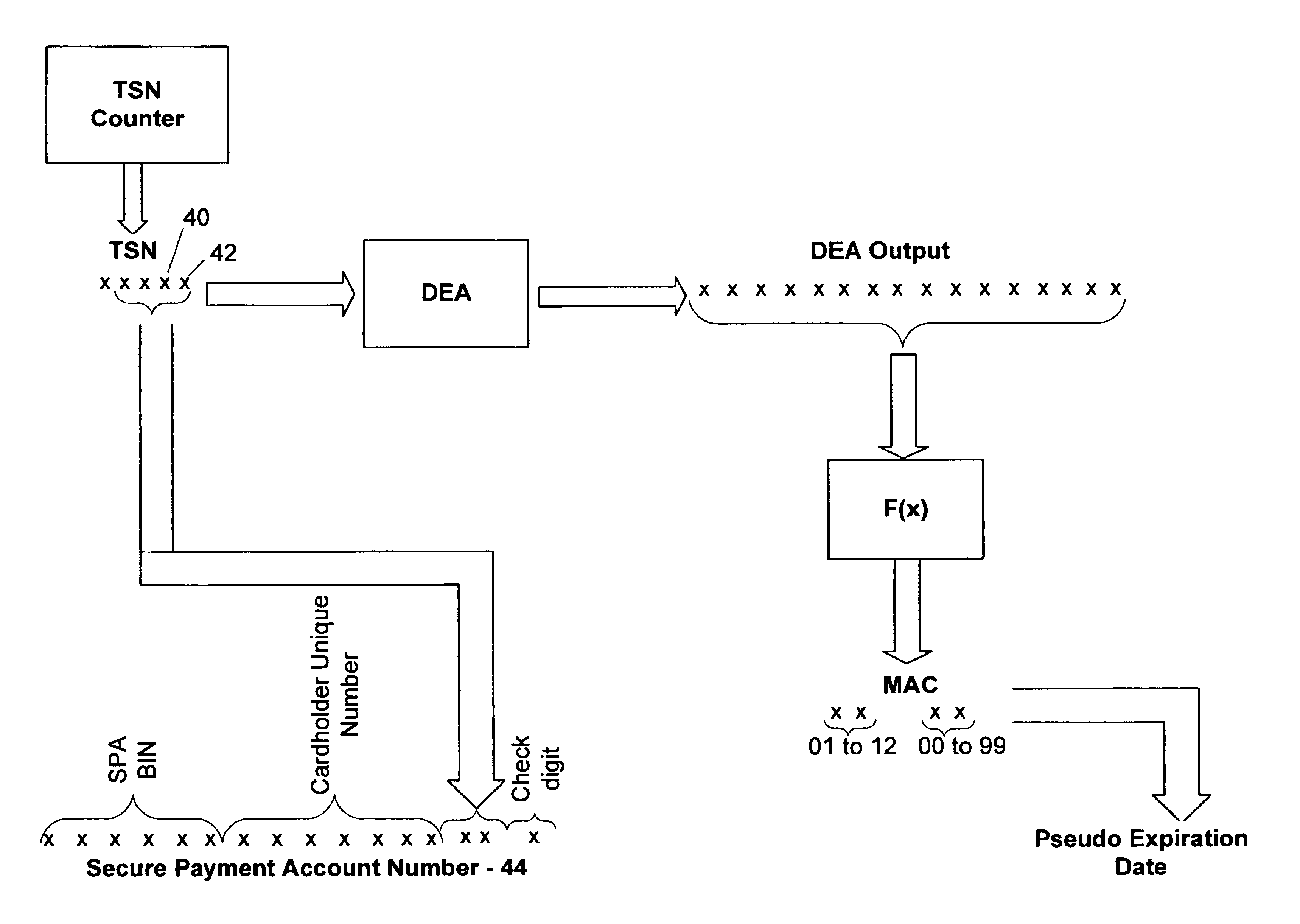
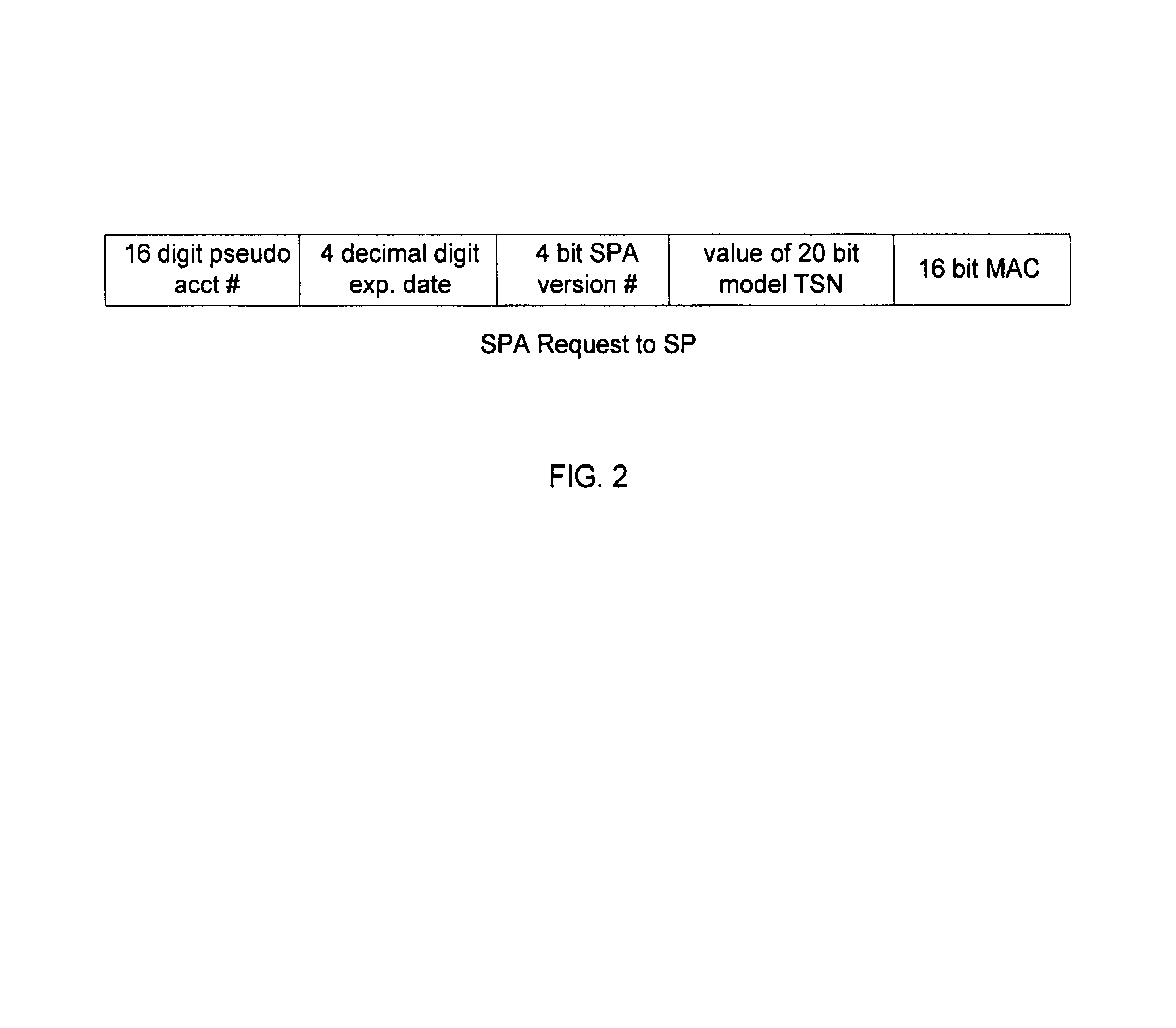
Method and system for conducting secure payments over a computer network
A secure method of conducting an electronic transaction over a public communications network is provided which utilizes a pseudo-expiration date in the expiration date field of an authorization request. One of the preferred methods comprises:generating a per-card key associated with an account number;generating a message authentication code using the per-card key;converting the message authentication code into a pseudo expiration date;generating an authorization request for the transaction, the request having an expiration date field containing the pseudo expiration date; andverifying the message authentication code based on the pseudo expiration date.Another embodiment of the invention includes a method of conducting an electronic transaction over a public communications network, with a payment account number having an associated pseudo account number, comprising:(a) providing the pseudo account number with a control field indicating one of a plurality of key-generation processes to be used to generate an authentication key;(b) generating an authentication key associated with the pseudo account number using one of the plurality of key-generation processes indicated in the control field of the pseudo account number;(c) using the authentication key to generate a message authentication code specific to the transaction;(d) generating an authorization request message including the message authentication code and the pseudo account number; and(e) verifying the message authentication code using the indicated key-generation process and the authentication key.
Owner:MASTERCARD INT INC
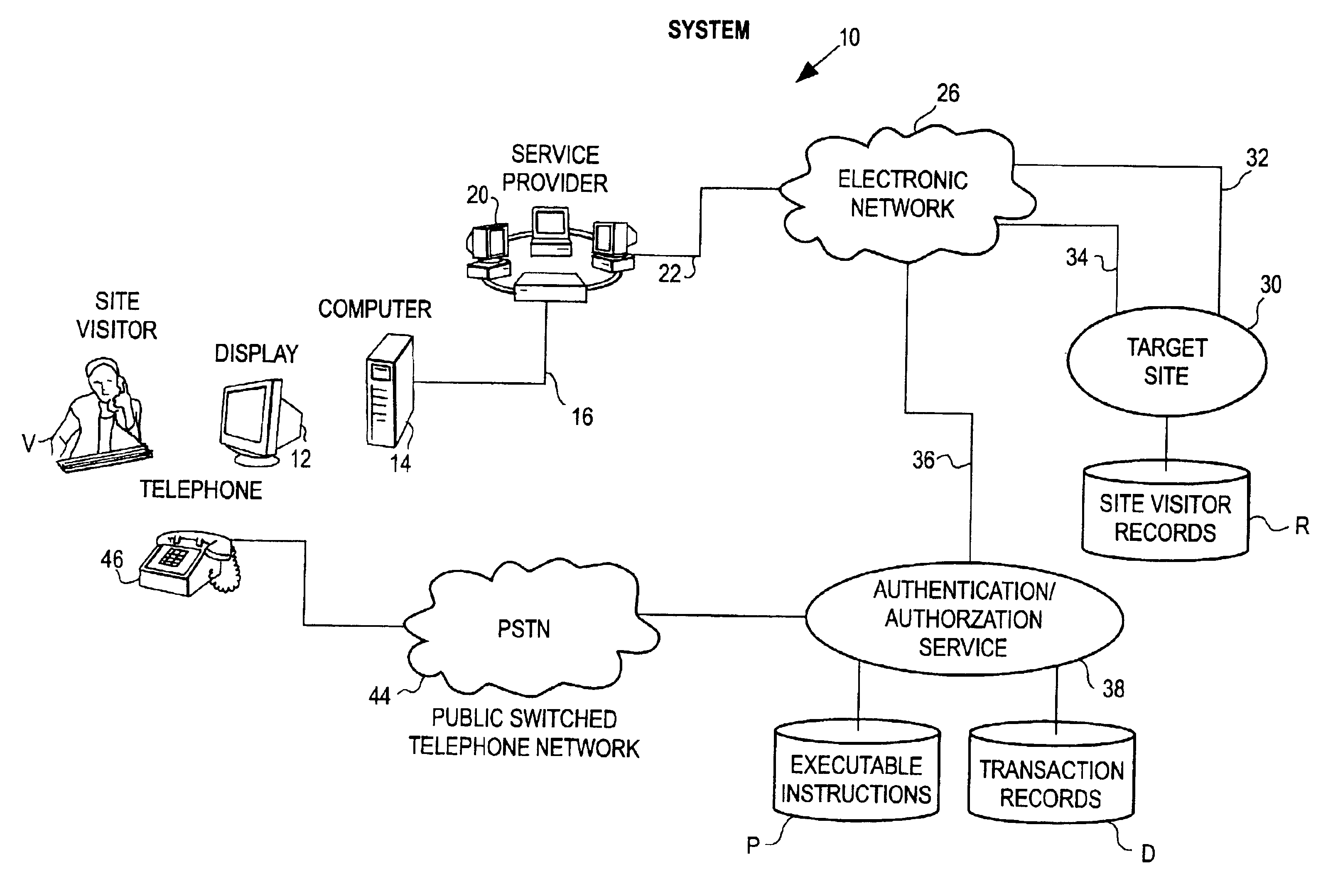
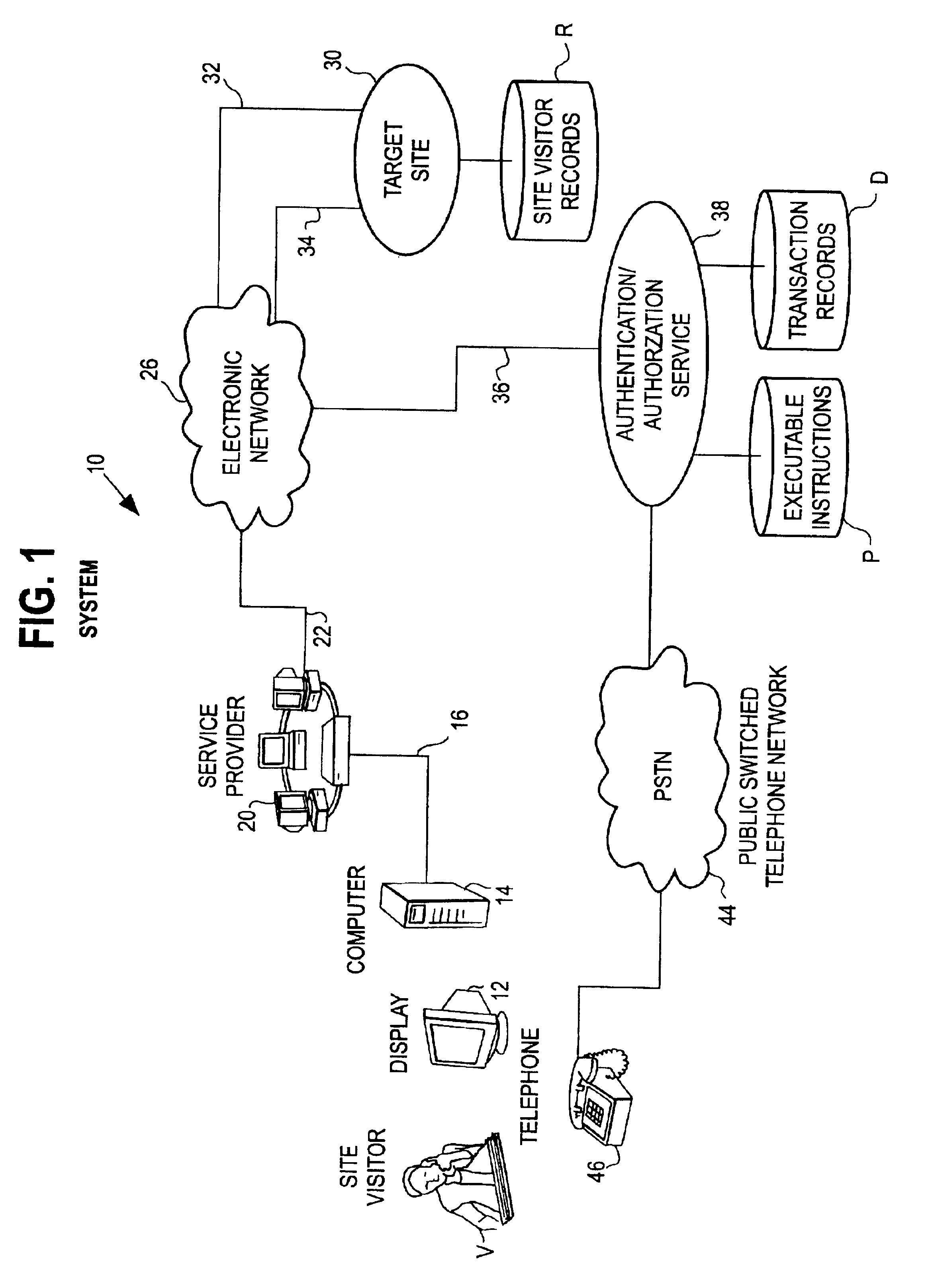
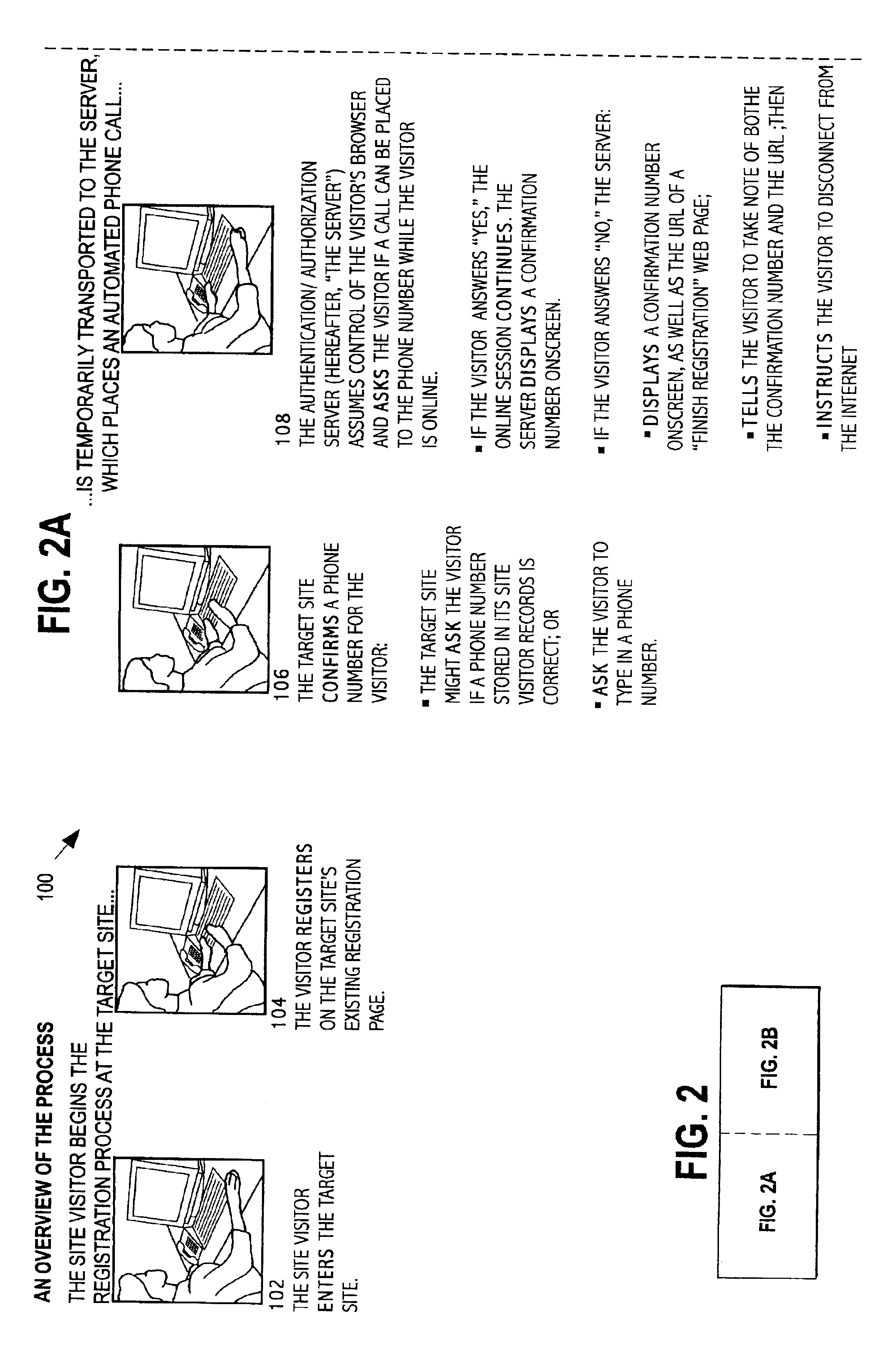
System and method of using the public switched telephone network in providing authentication or authorization for online transactions
InactiveUS6934858B2Quickly and reliably verifyingTelephone data network interconnectionsDigital data processing detailsTelecommunications linkThe Internet
An authentication or authorization system to facilitate electronic transactions uses simultaneous or substantially simultaneous communications on two different networks to verify a user's identity. When a user logs onto a site, via the internet, a telephone number, either pre-stored or obtained in real time from the visitor, where the visitor can be called essentially immediately is used to set up, via the switched telephone network another communication link. Where the user has multiple communication links available, the telephone call is automatically placed via the authentication or authorization software simultaneously while the user is on-line. In the event that the user has only a single communication link, that individual will have to log off temporarily for purposes of receiving the telephone call. Confirmatory information is provided via the internet to the user. The automatically placed telephone call requests that the user feed back this confirmatory information for verification purposes. The telephone number which is being called is adjacent to the user's internet terminal. The user's response, via the telephone network, can be compared to the originally transmitted confirmatory information to determine whether the authentication or authorization process should go forward.
Owner:PAYFONE
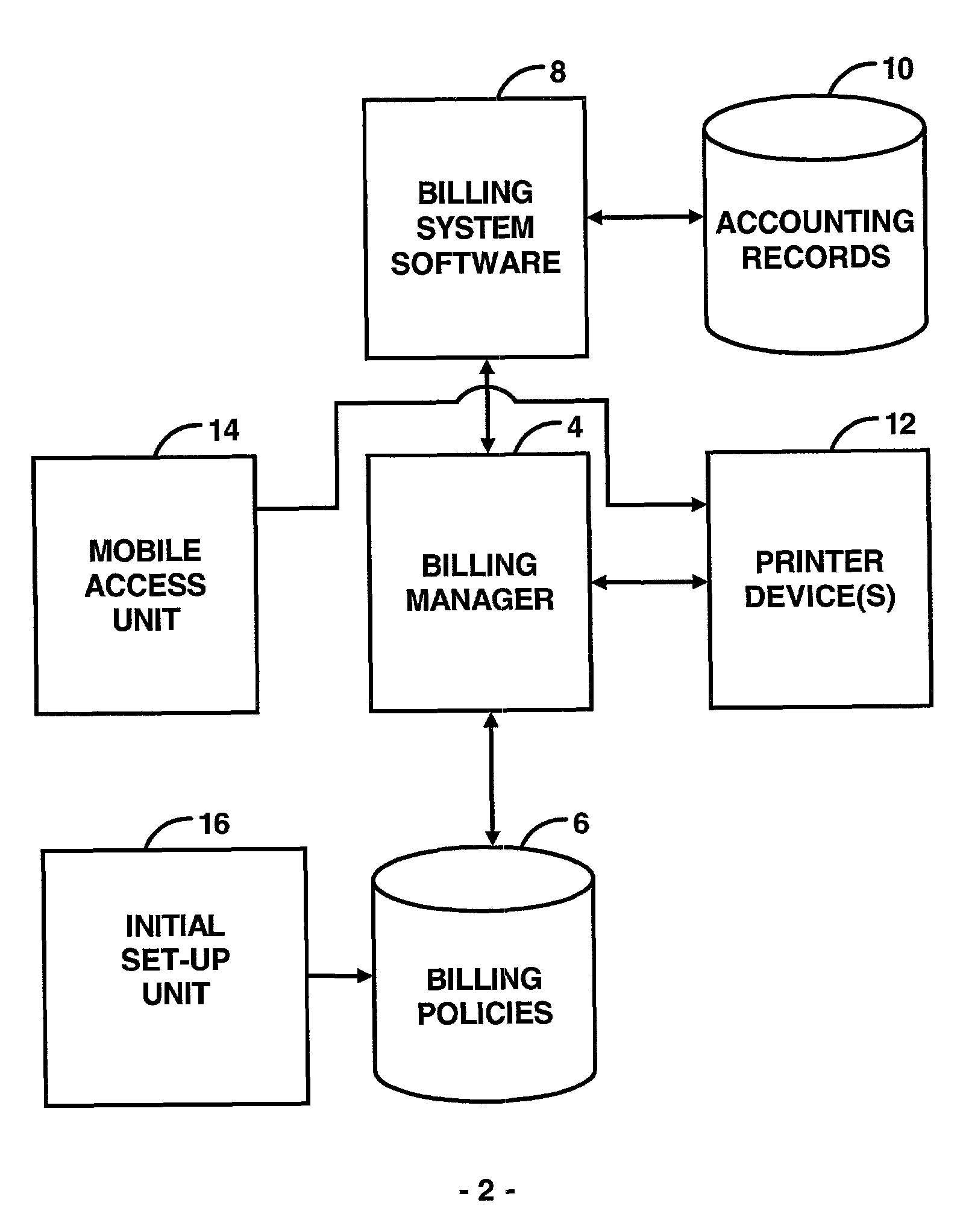
Centralized billing credit system utilizing a predetermined unit of usage
InactiveUS7882029B2Ease of configurationEase of controlFinancePayment architectureCredit systemAuthorization
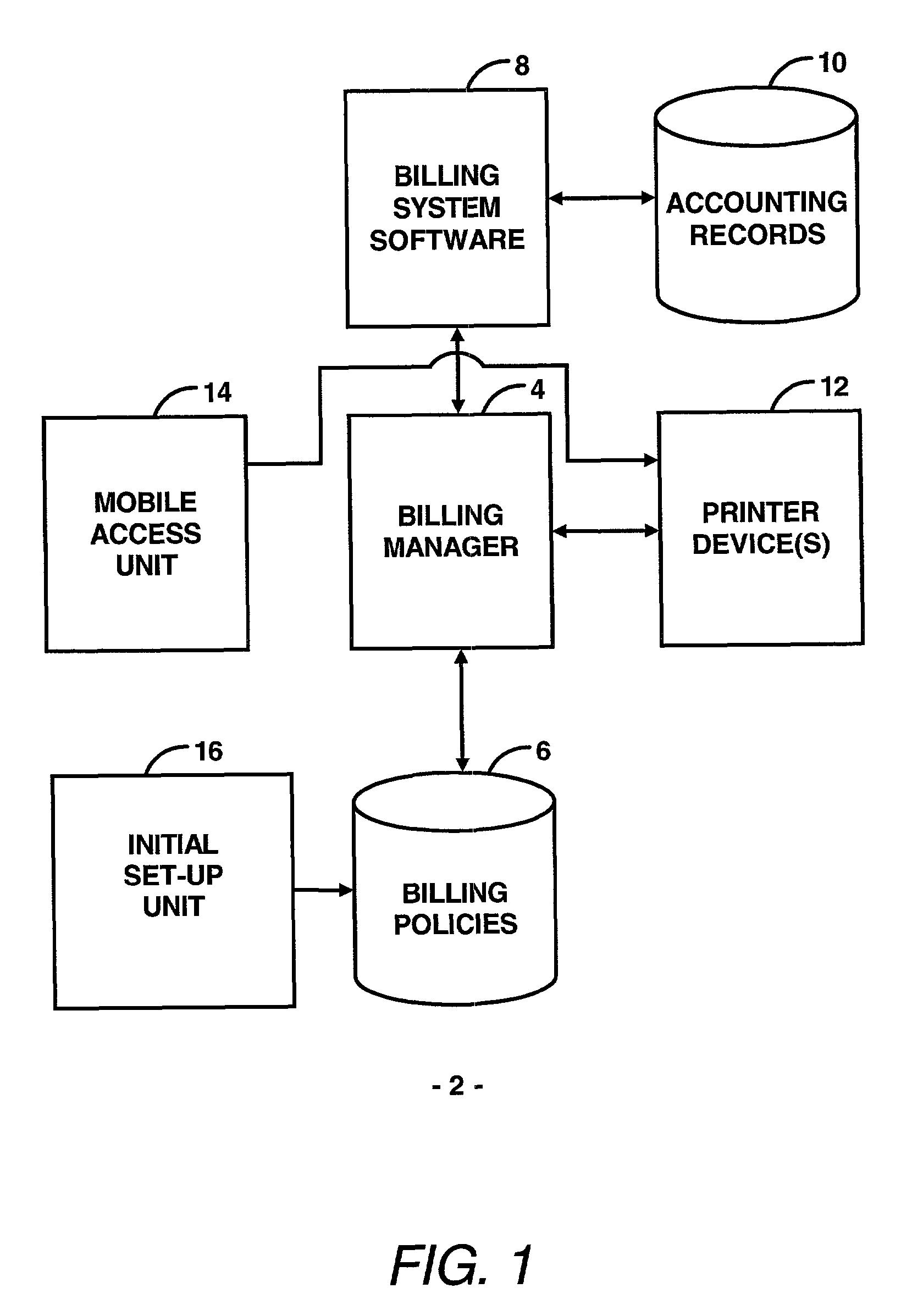
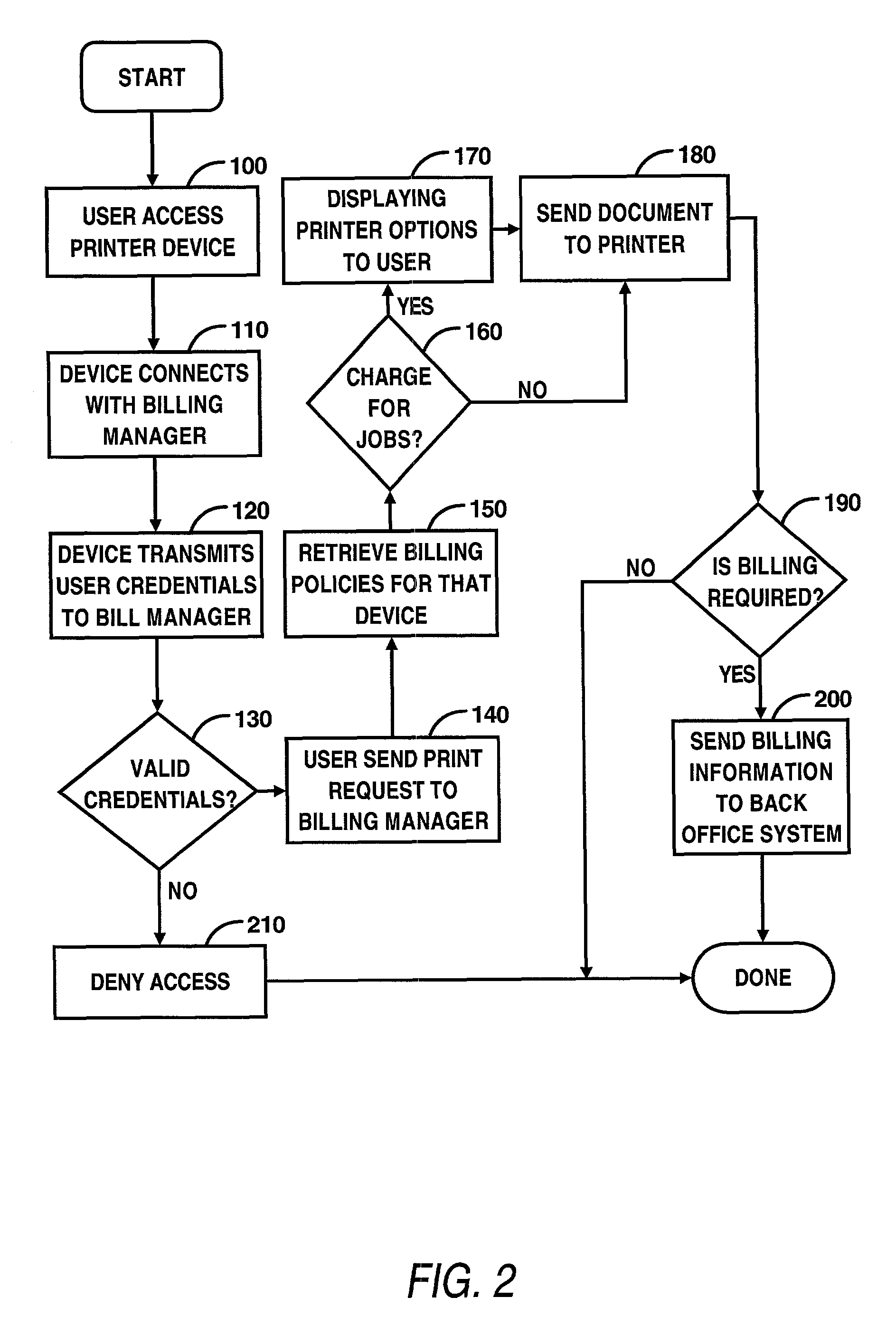
Disclosed is an electronic transaction recording system for accumulating data from printer devices comprising a mobile access unit containing content which is to be printed, a printer device which receives the content from the mobile access unit and prints the content in response to a authorization process, a billing manager coupled to the printer device and the mobile access unit for determining the amount of printer usage and associating a predetermined amount of token values with the costs of printing and generates an accounting of usage based on a predetermined measure of usage and a billing system for maintaining accounting records of user and associating user account information with the predetermined measure of usage and stores account information in an account records database.
Owner:HEWLETT PACKARD DEV CO LP
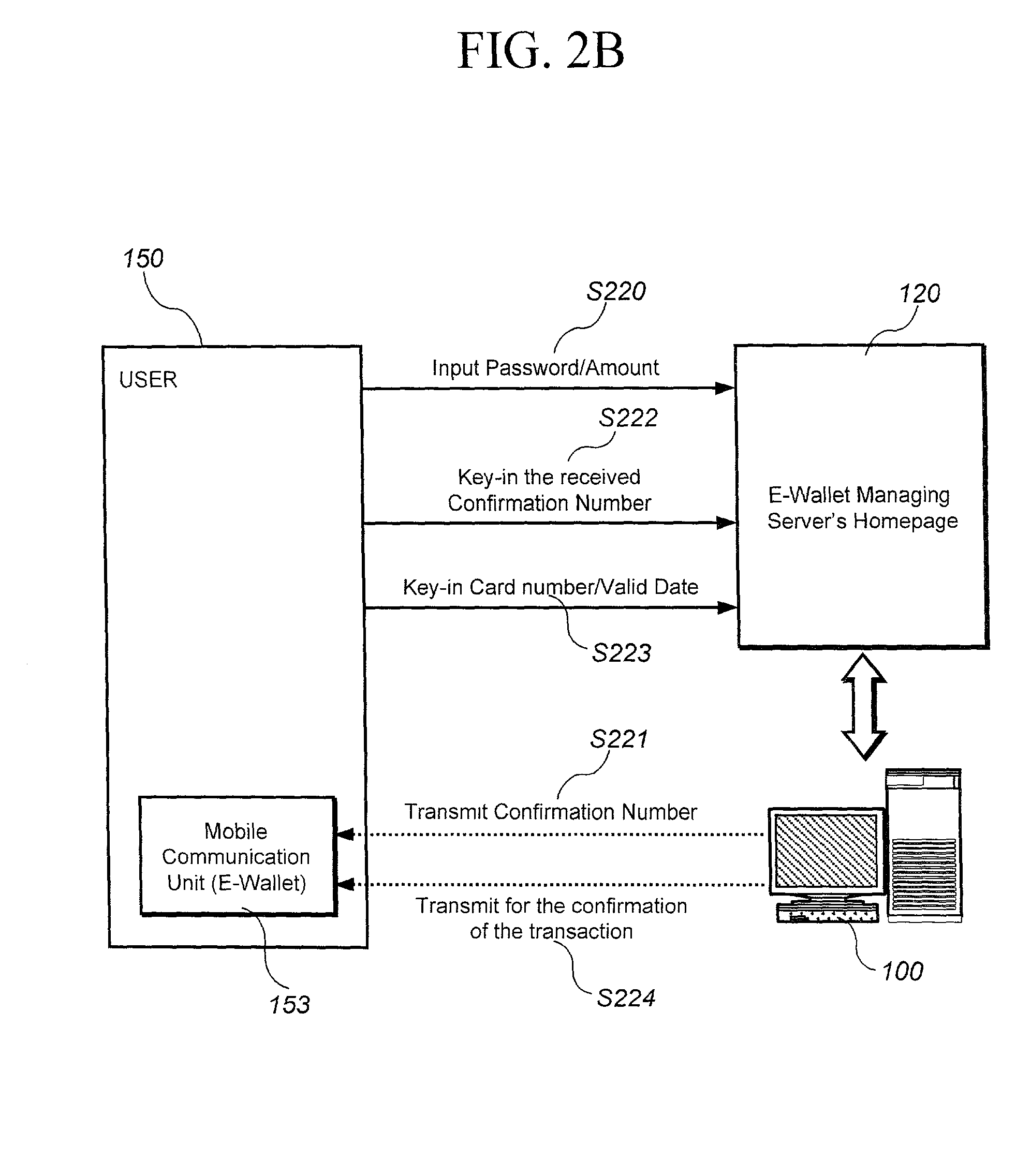
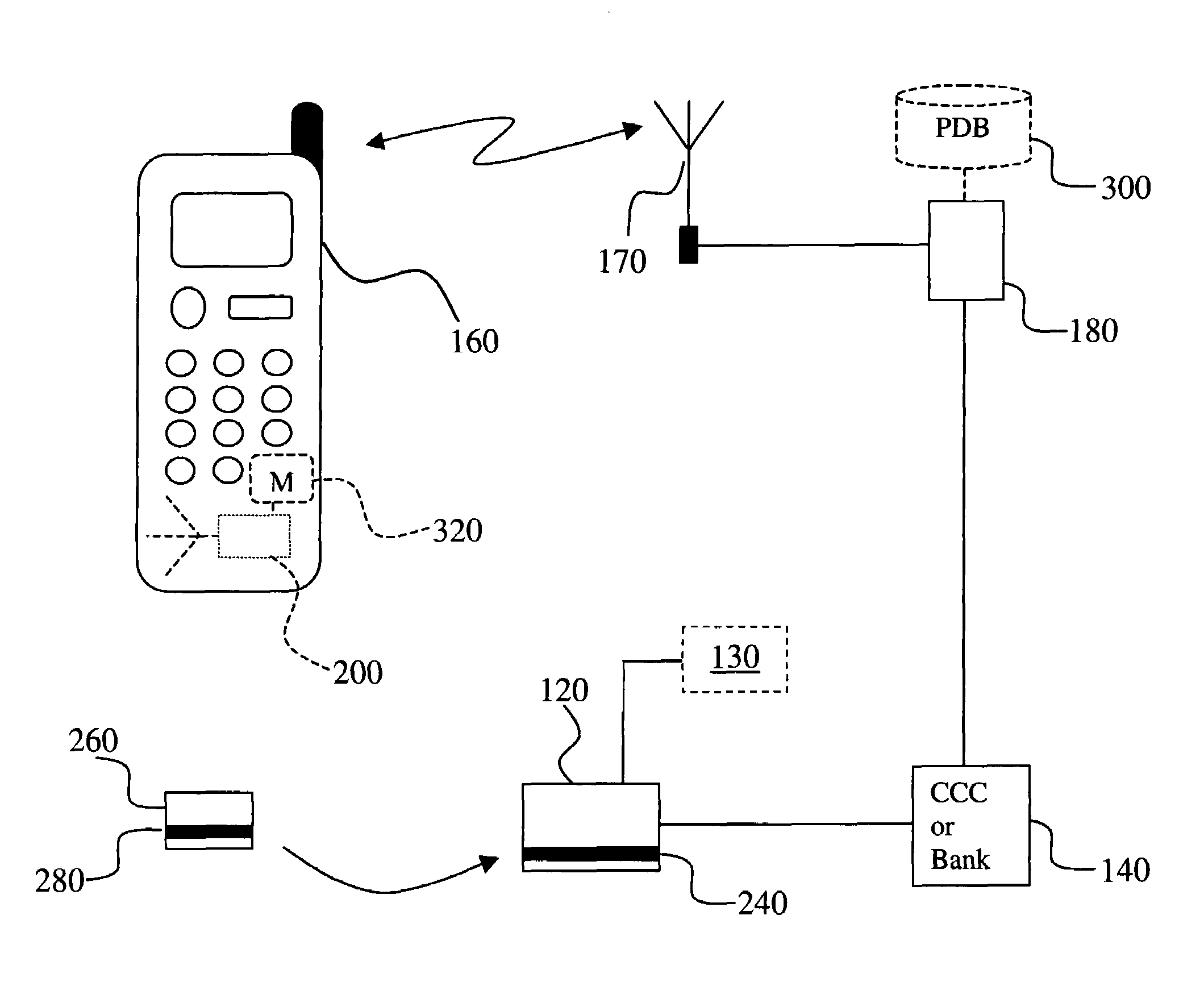
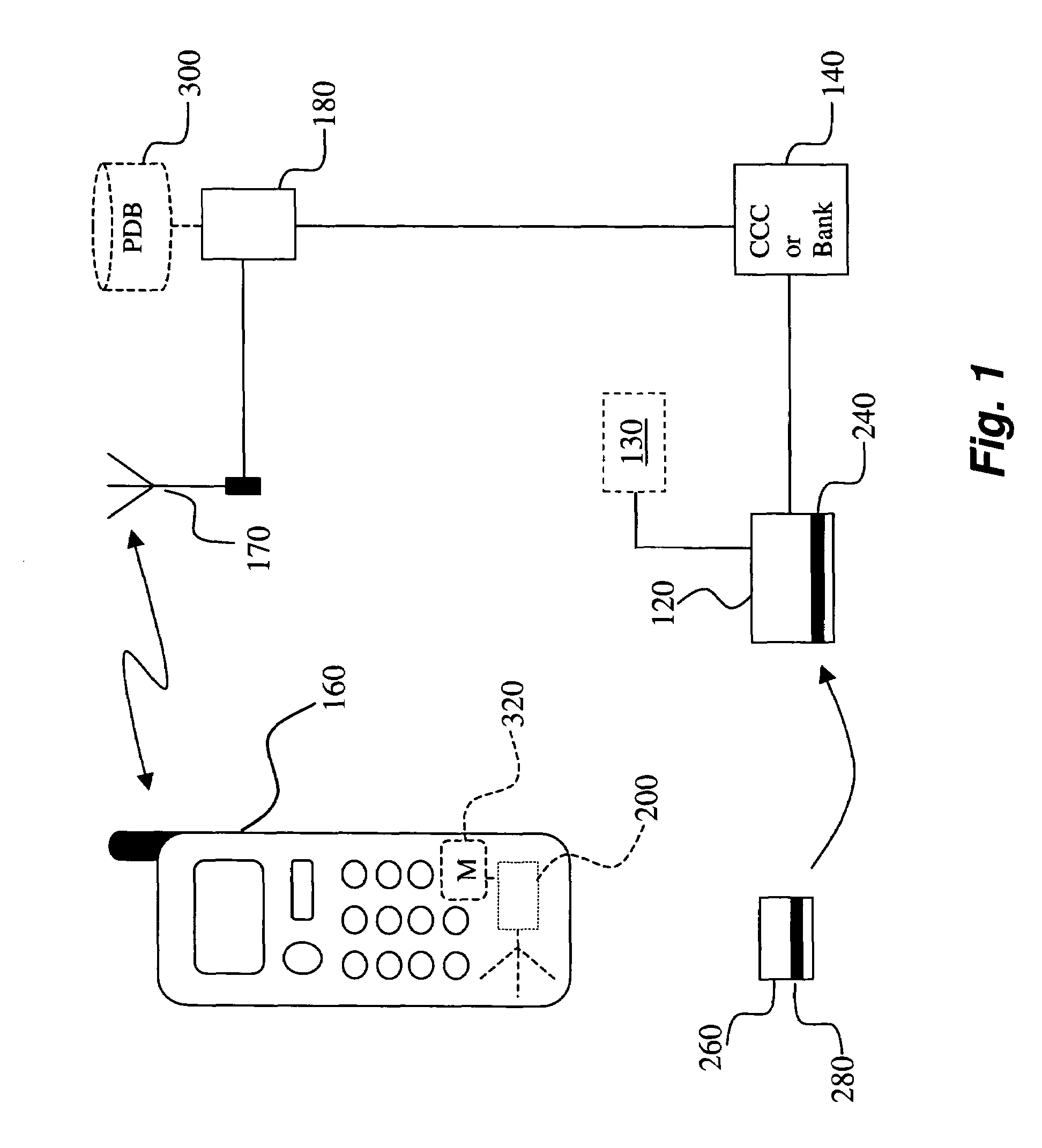
Method and system for transaction of electronic money with a mobile communication unit as an electronic wallet
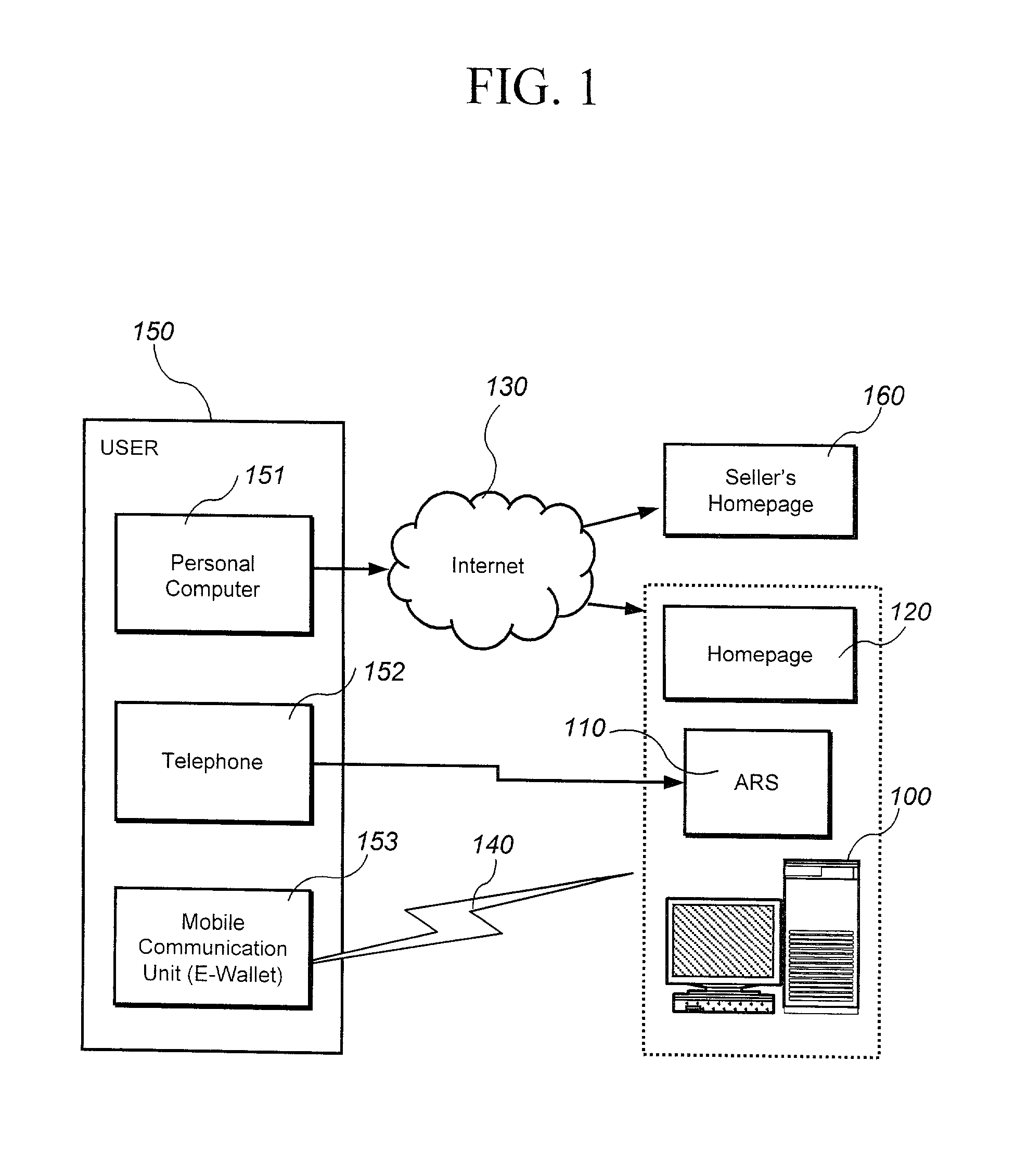
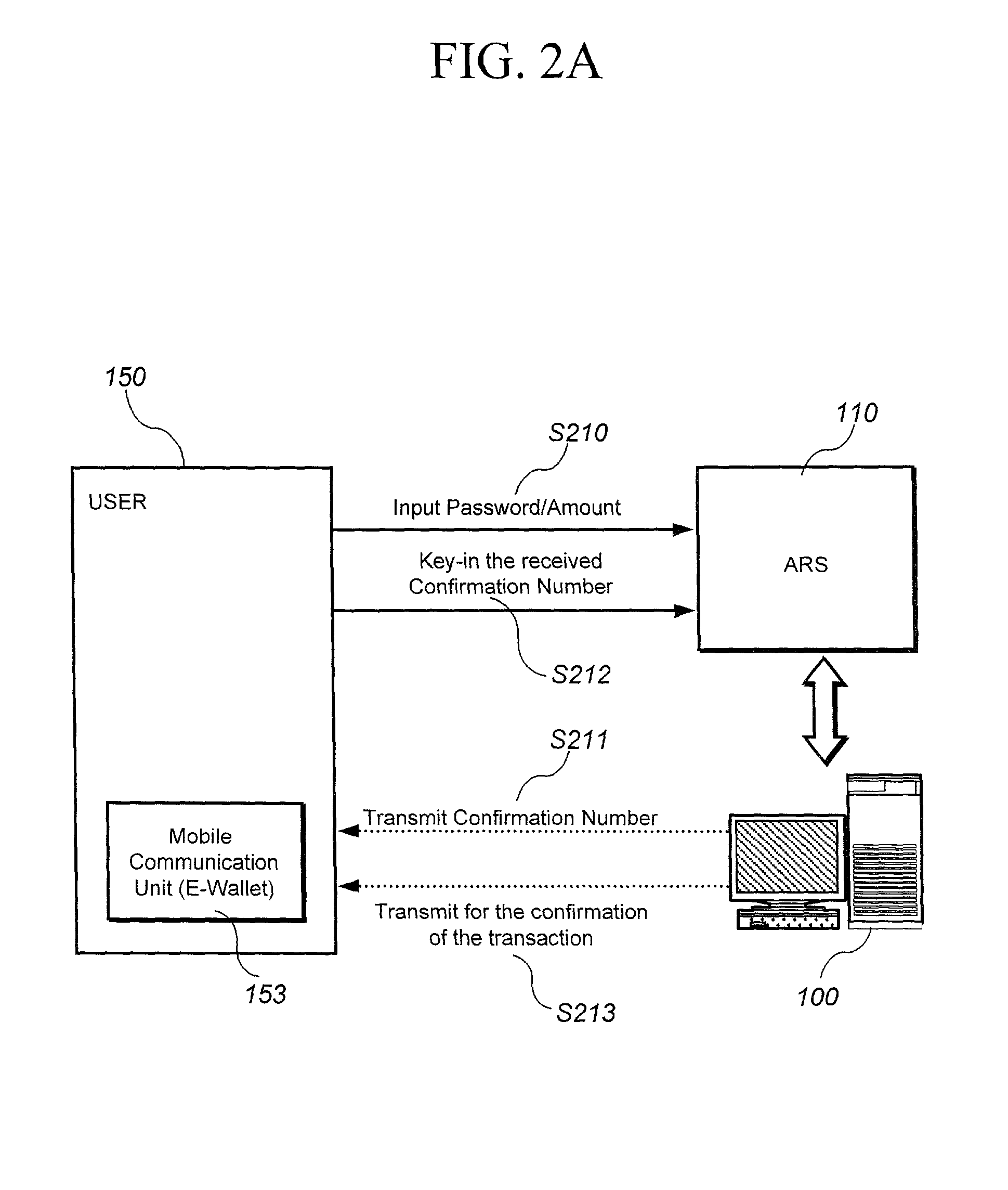
InactiveUS20010007983A1Performed conveniently and safelyFinancePayment protocolsCommunication unitComputer science
A electronic monetary system comprising a mobile communication unit as an electronic wallet for transactions including electronic payments, money transfer, and recharging the electronic account. The security of the electronic transactions is confirmed by circulating a confirmation number through a loop formed by an E-wallet managing server through the wireless network to the mobile communication unit of the user.
Owner:INFOHUB
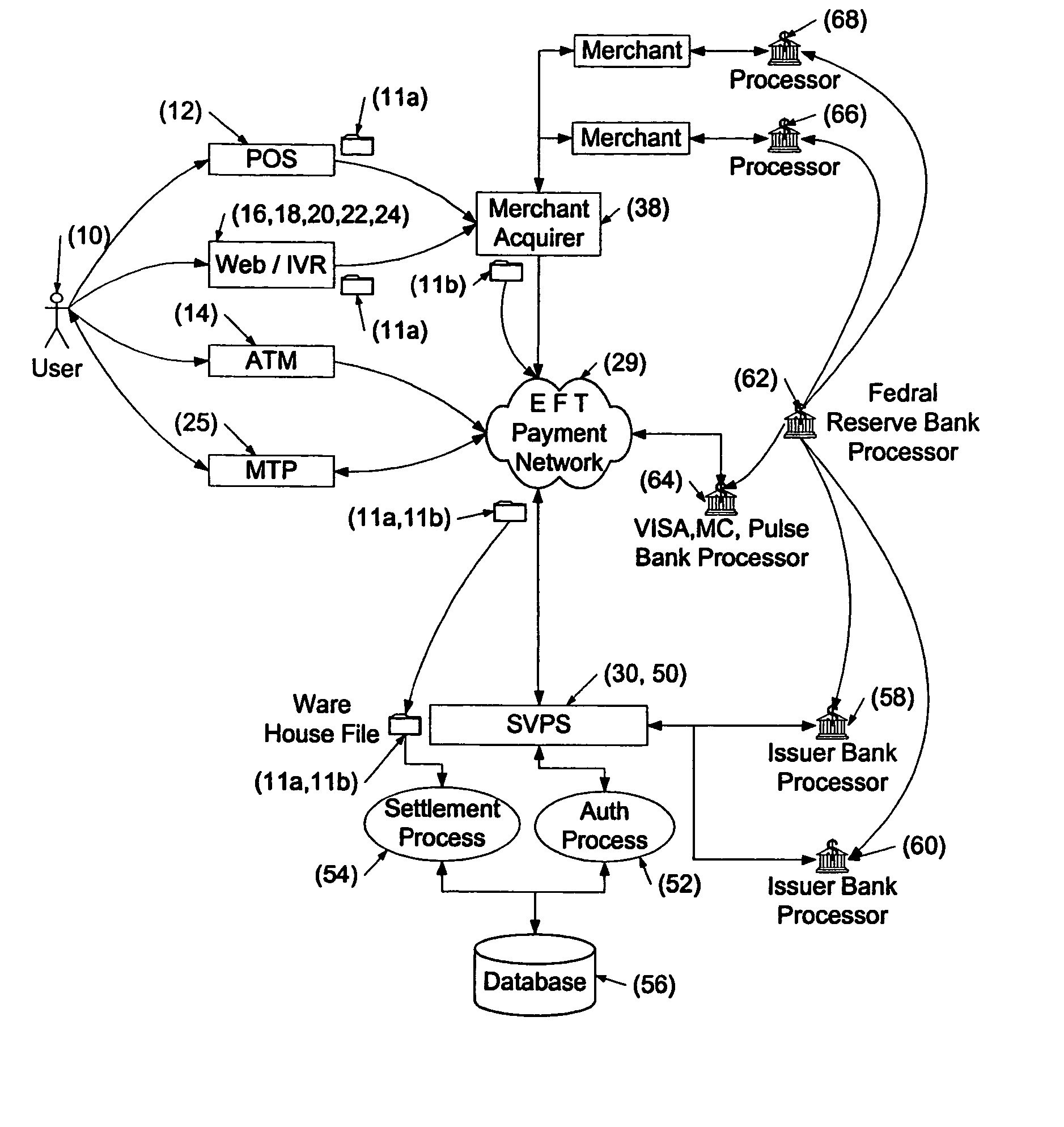
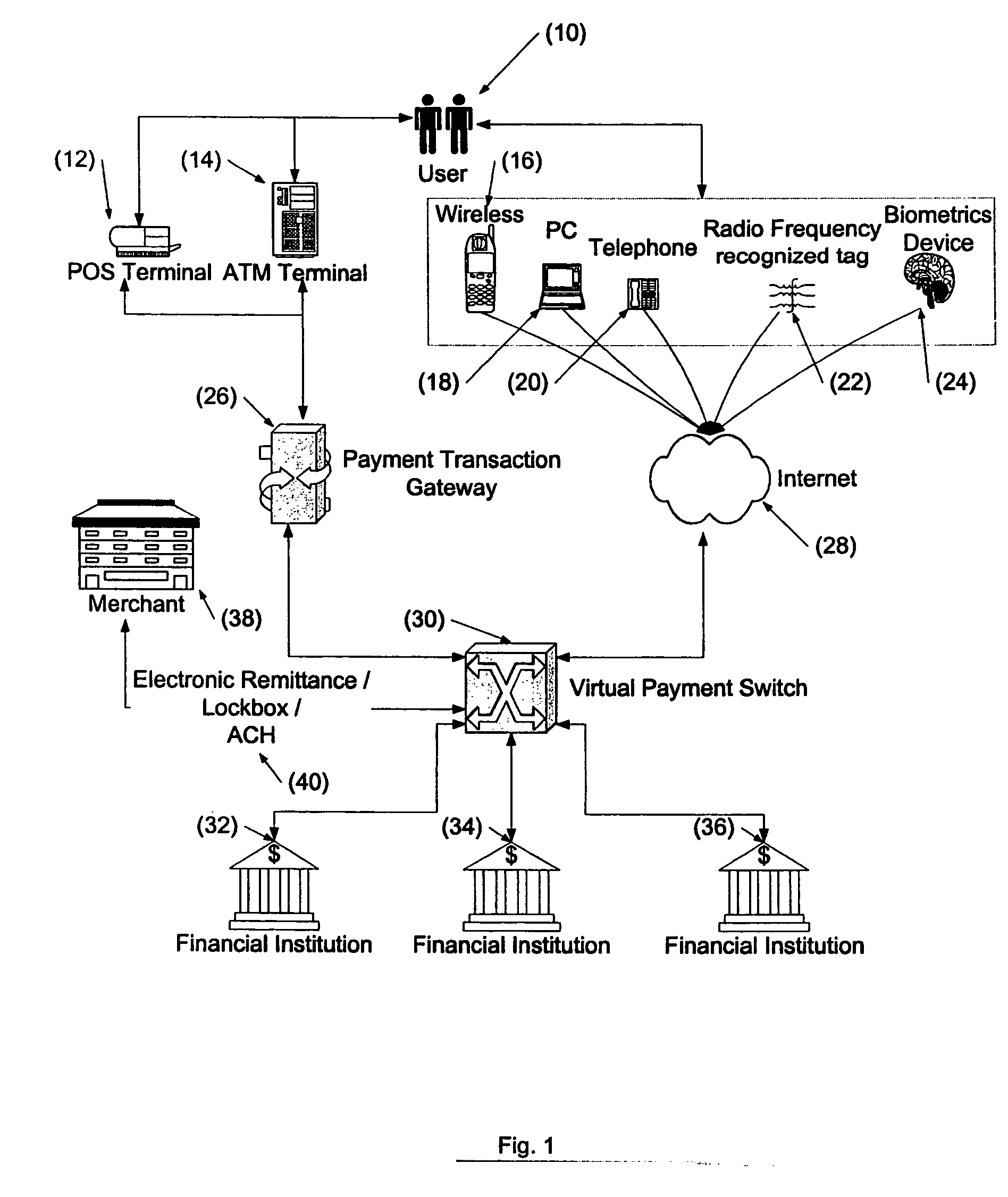
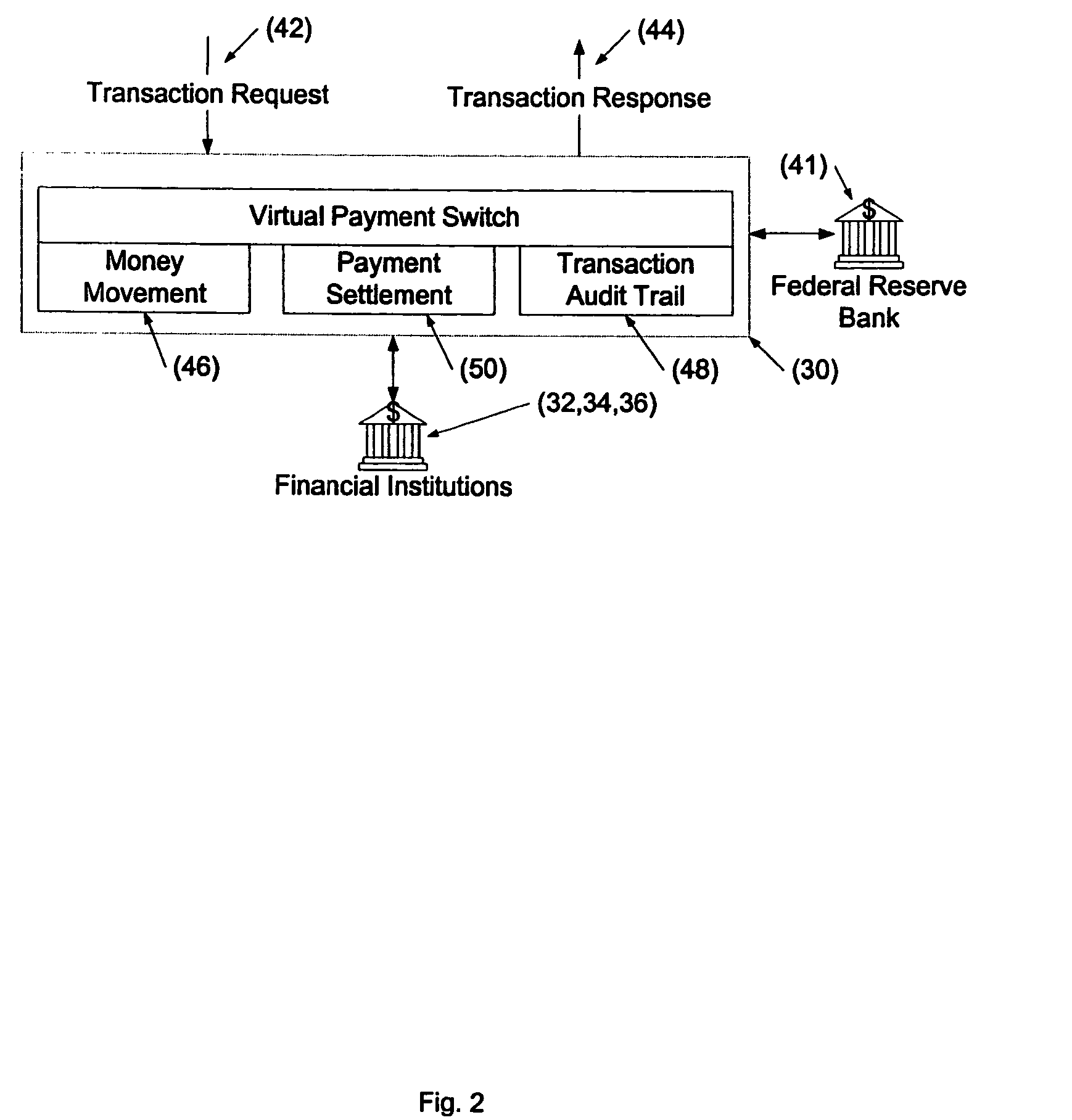
Cashless payment system
InactiveUS20050015332A1Without any loss of transaction processing flexibilityWidespread acceptanceFinanceBuying/selling/leasing transactionsComputer networkEngineering
A payment system that does not rely on credit or debit cards, does not require the merchant and purchaser to have compatible memberships to complete a transaction, and does not limit single transactions to a single account provides a wide range of flexibility permitting debit, credit, pre-paid and payroll cards to be accommodated in a seamless and invisible manner to the electronic transaction network. The transaction may be verified and approved at the point-of-sale whether or not the merchant is a member of a specific financial transaction system. Specifically, the point-of-sale transaction system permits an identified customer to use any of a variety of payment options to complete the transaction without requiring the merchant to pre-approve the type of payment selected by the customer. In one configuration, and in order to take advantage of the widespread use of the ATM / POS network, the invention uses a typical credit / debit card format to provide the identifying information in a stored value card. When a transaction is to be completed, the user enters the identifying information carried on the card at the point-of-sale. This can be a merchant or other service provider at a retail establishment, or on-line while the user is logged onto a web site, or other location. The information can be swiped by a card reader, or manually entered via a keyboard or other input device. The system supports a wide range of flexibility, permitting issuing systems such as parents and state welfare agencies to restrict the types of authorized uses, and permitting users to access accounts in a prioritized manner. Further, the accepting merchant is not required to be a member because settlement with the merchant may be made via the Federal Reserve Automatic Clearing House (ACH) system by typical and standard electronic transfer. This permits the merchant to take advantage of the lower ACH transaction fees with even greater convenience and flexibility than the current ATM / POS system. The system supports numerous types of identification methods from typical credit card structures with magnetic data strips to various biometric systems such as finger prints, facial recognition and the like. Specifically, once the user is identified, the transaction is managed by his membership data on record with the transaction processing system.
Owner:ECOMMLINK
Device, system and methods of conducting paperless transactions
InactiveUS20050247777A1Eliminate pointEliminate all paper transactions and billsCash registersPatient personal data managementCredit cardDisplay device
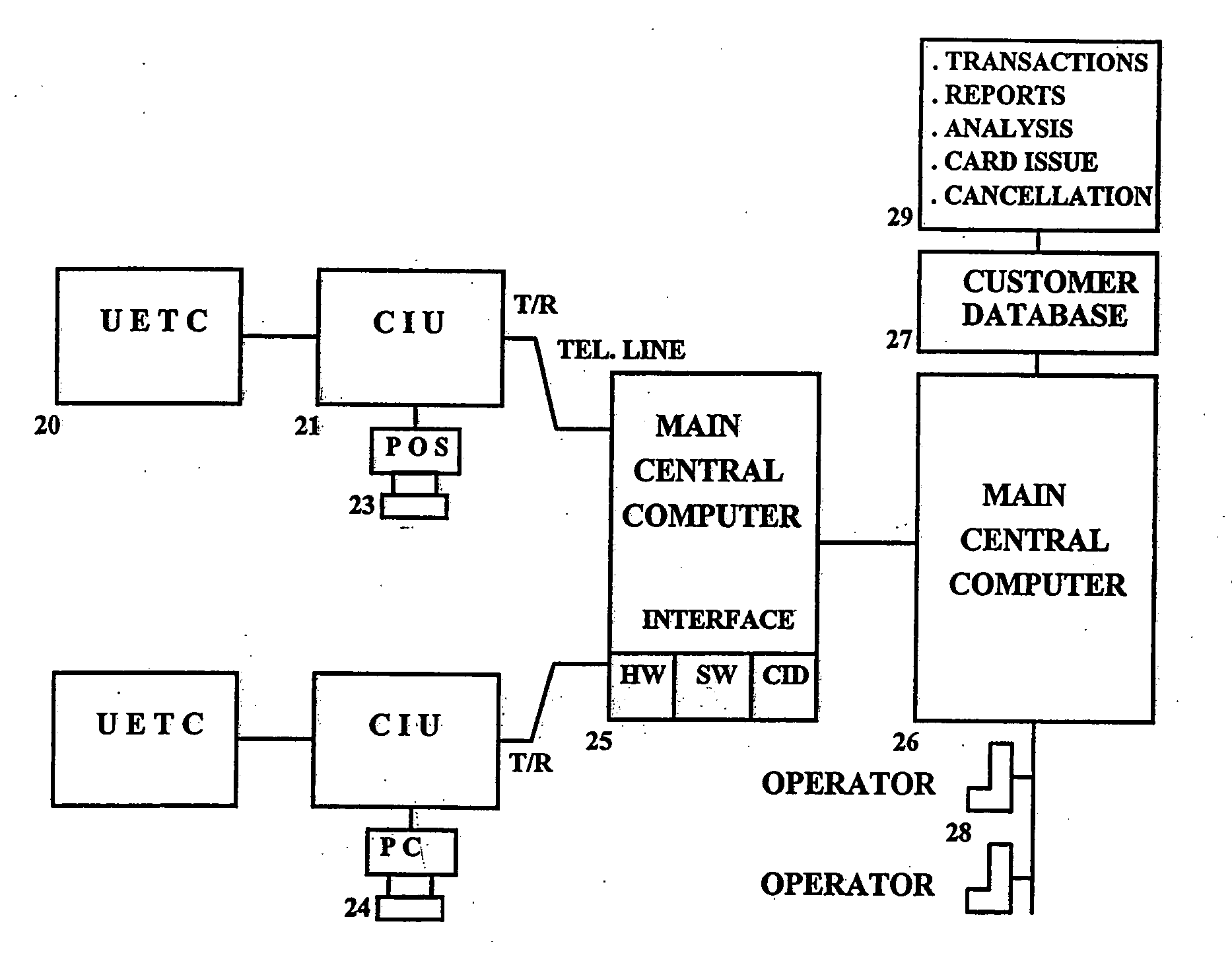
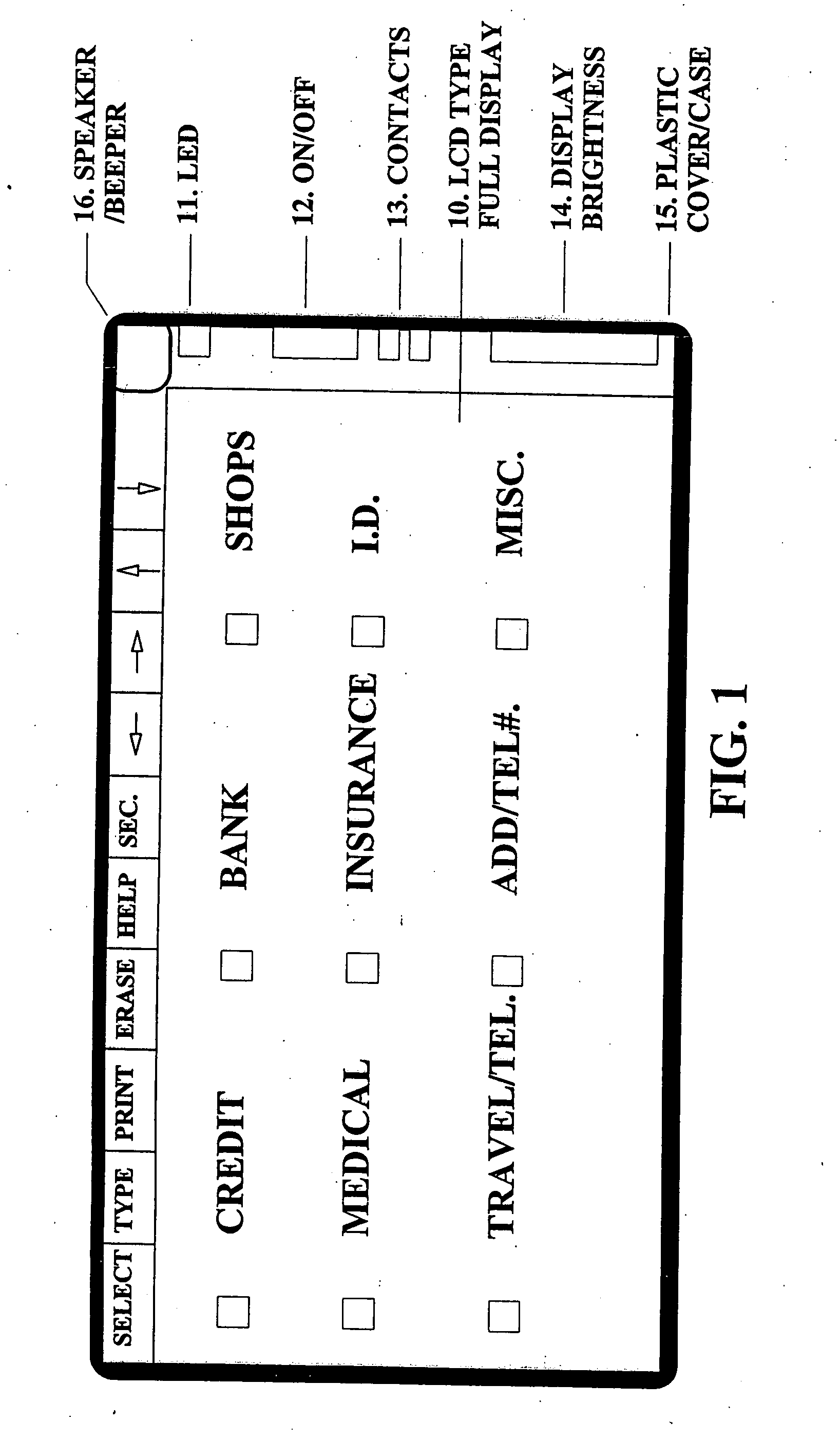
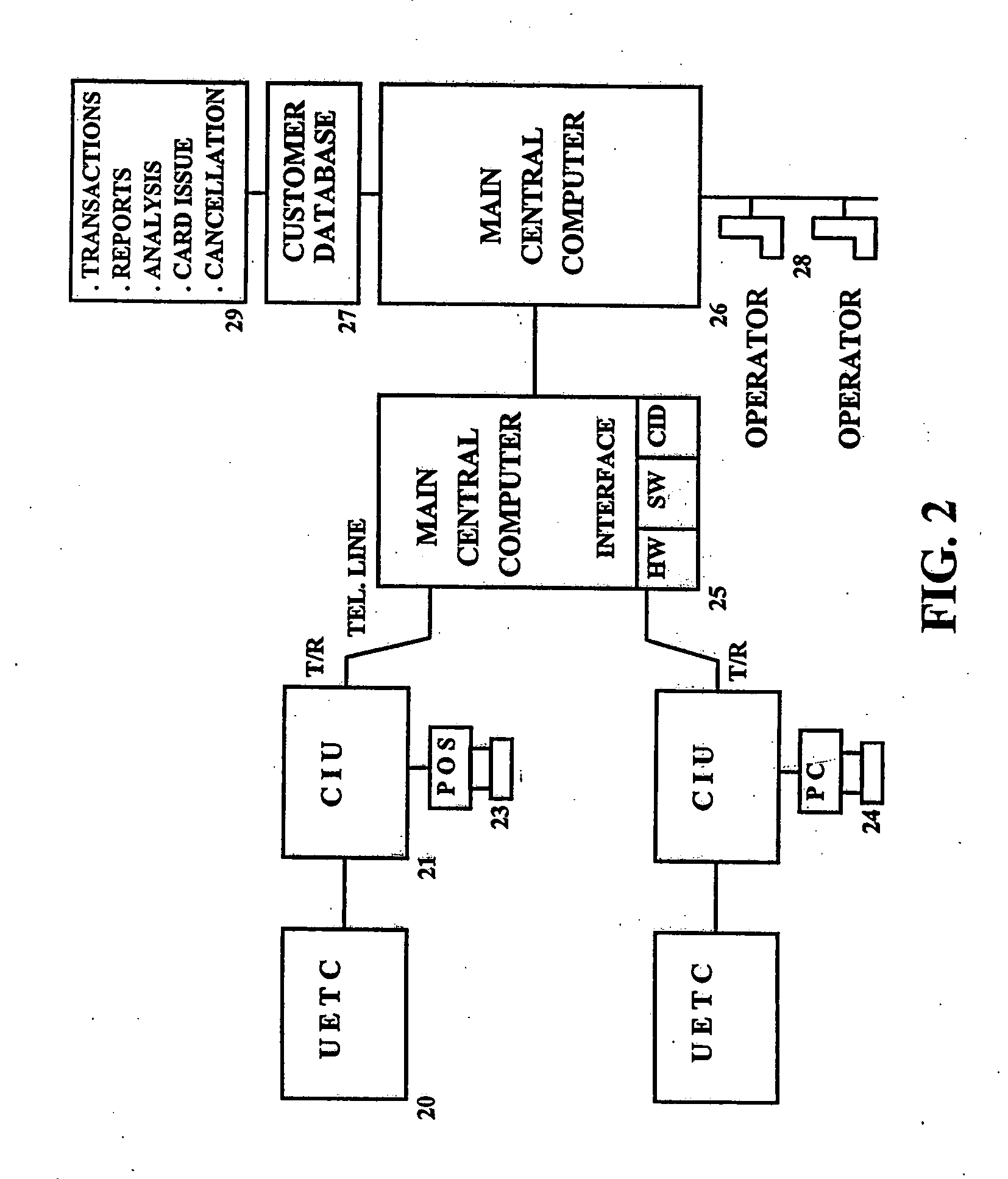
A universal electronic transaction card (“UET card”) is capable of serving as a number of different credit cards, bank cards, identification cards, employee cards, medical cards and the like. The UET card includes storage elements, an input interface, a processor, a display, and a communications interface. In a preferred embodiment, the UET card stores transactional information to eliminate paper receipts and includes security features to prevent unauthorized use. The UET card may also be used to replace conventional currency and traveler's checks, and may be configured to store and display promotional information, such as advertising and incentives. A communications interface unit (“CIU”) may be provided to interface between the UET card and a personal computer, automatic banking terminal (commonly referred to as ATM machines) and / or an institutional mainframe computer. CIU devices may include electrical contact for recharging a UET card. A system of utilizing the UET card is also provided which includes UET cards and CIU devices which enable the transmission of information between point of sales (or point of transactions) computers and the UET cards. The system further includes point of sales computers configured to communicate with the UET card and with service institution computers. The invention also includes a health care management system utilizing UET cards. In the health care management system, all medical information for a patient may be stored in the UET card so that when a patient receives services from a health care provider, that health care provider connects the patient's UET card to the health care provider's computer system and can then obtain all pertinent medical information concerning the patient, including the patient's medical history, insurance information and the like. In addition, the treatment or services provided by the health care provider are stored in the patient's UET card. The invention also includes methods of issuing an account authorization to a UET card, a method of transferring transactional and account information between a UET card and a personal computer or a mainframe computer, a method of using the UET card as a remote terminal for a mainframe computer, and a method of conducting an electronic transaction.
Owner:C SAM INC
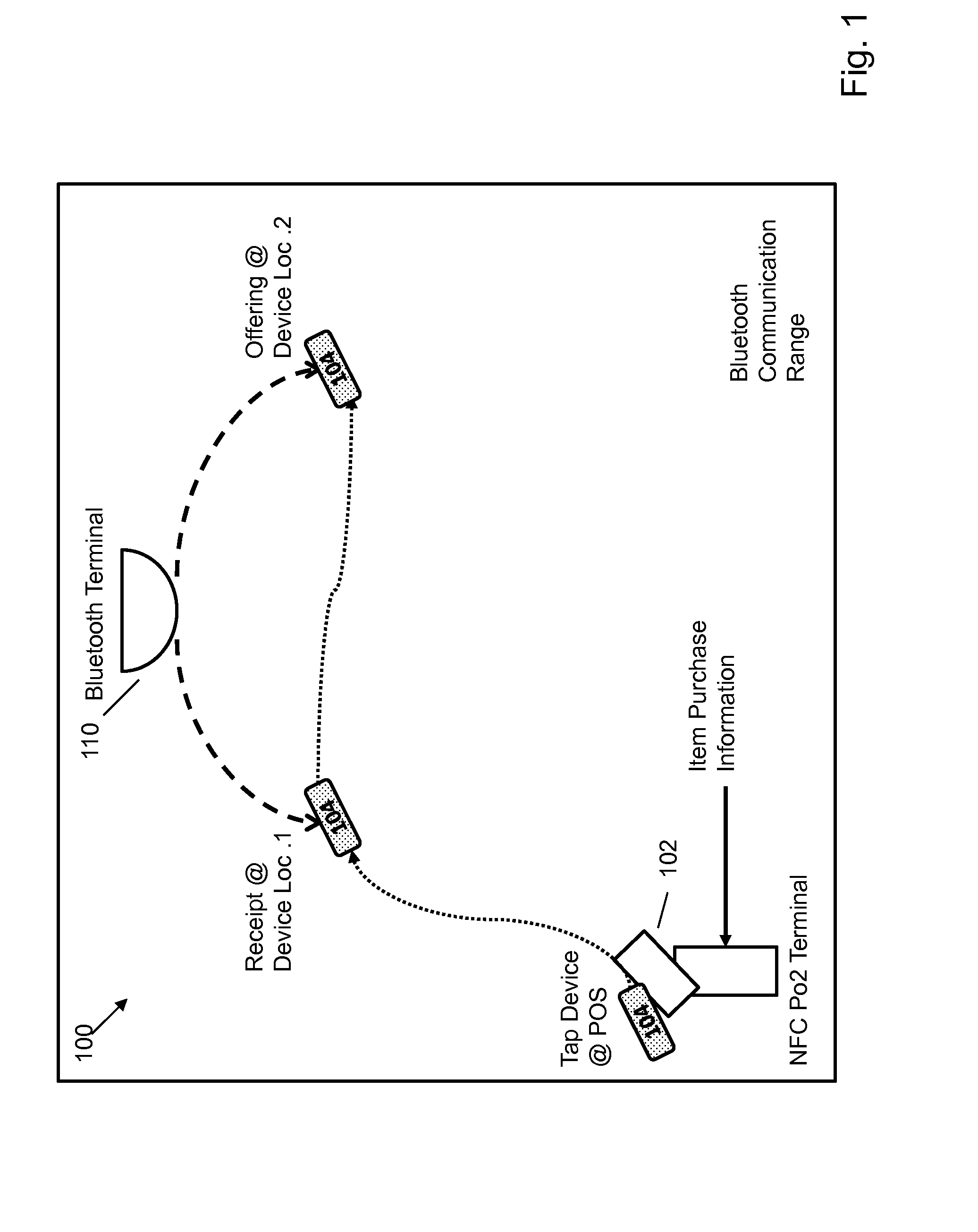
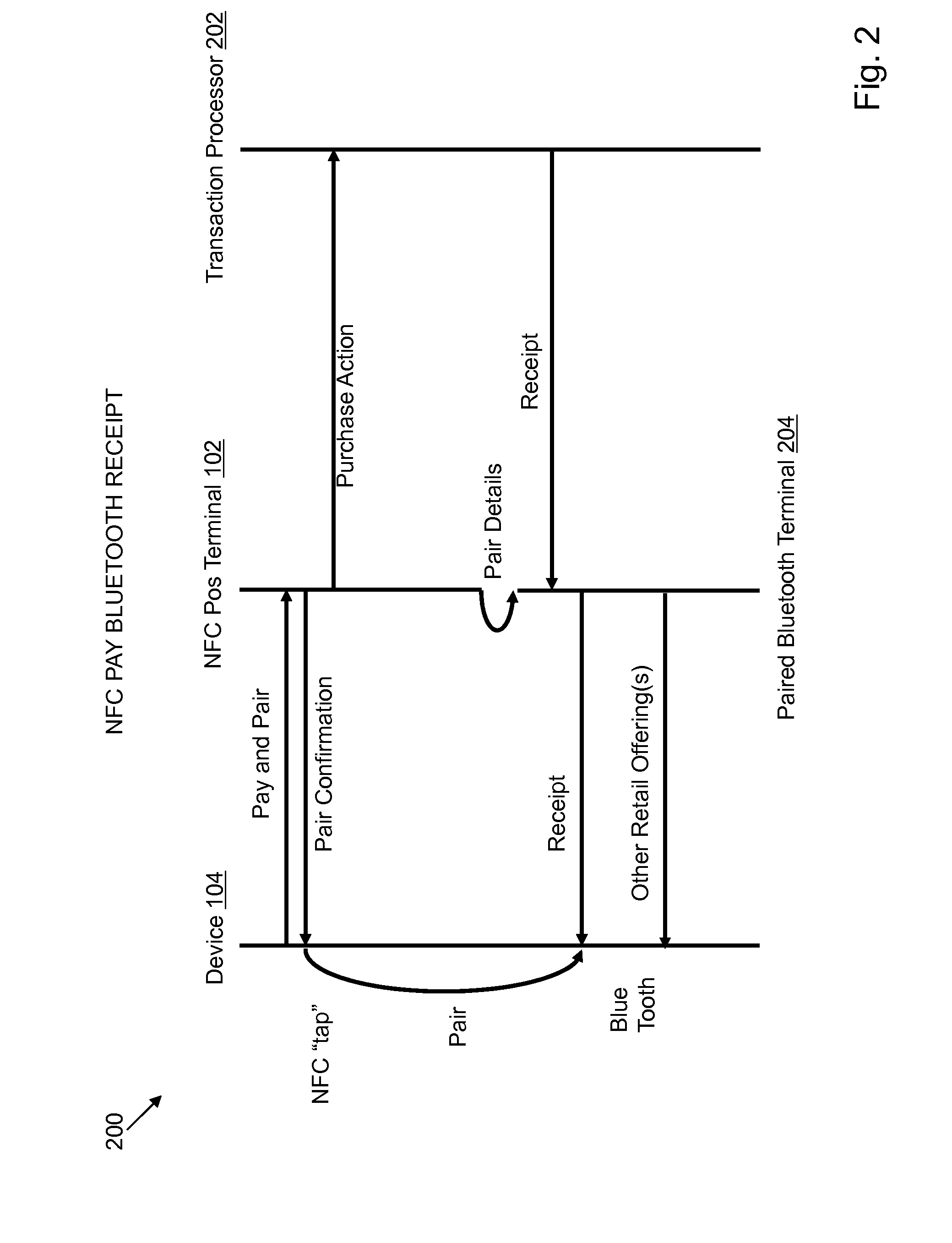
NFC paired bluetooth e-commerce
InactiveUS20140279479A1Fast transferFacilitate Bluetooth pairingFinanceBuying/selling/leasing transactionsPaymentService provision
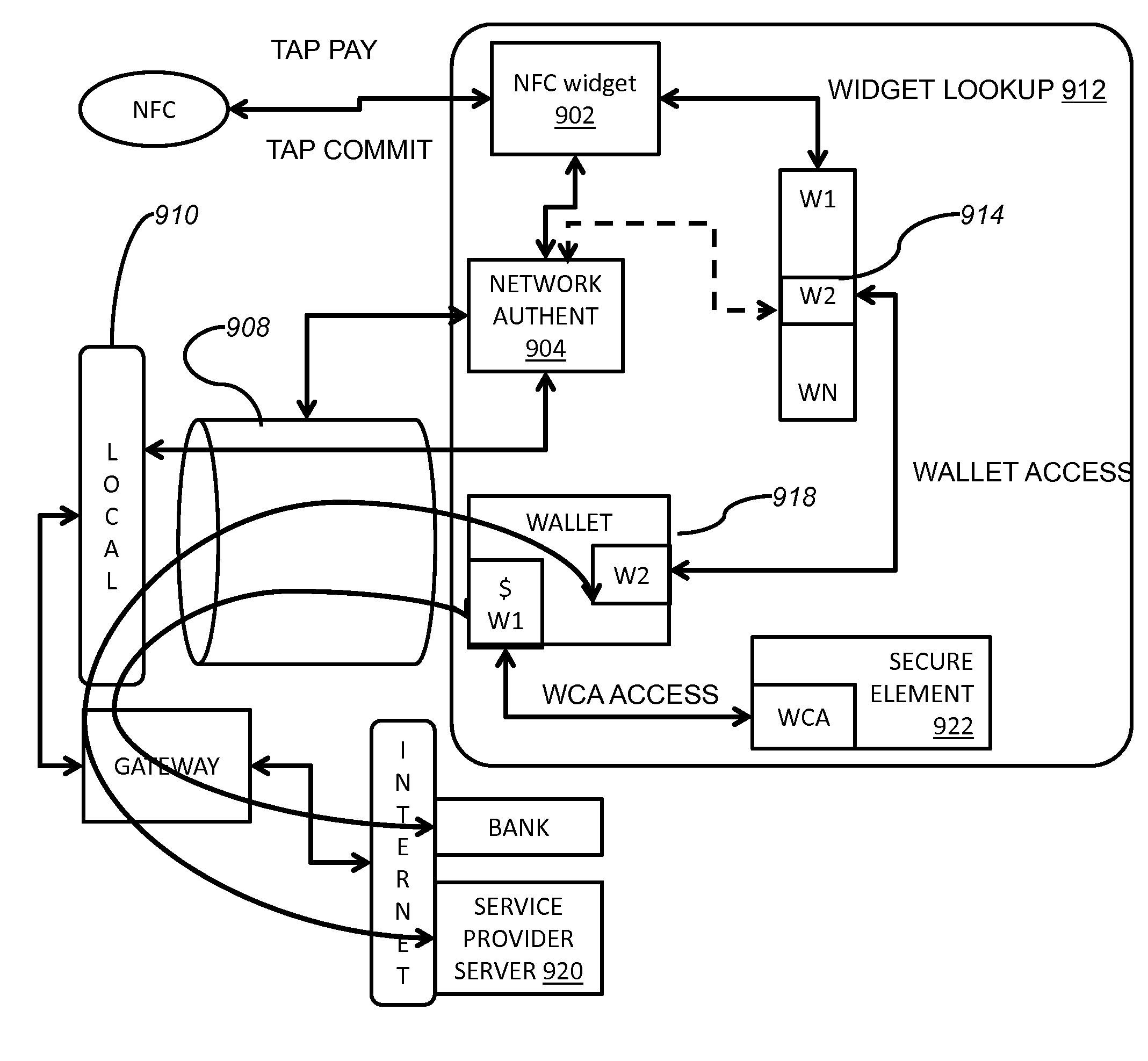
A method for performing an electronic transaction over two distinct networks with a mobile wallet comprises the steps of receiving form of payment information from a mobile wallet over a first wireless network of a retail environment with a mobile device on which the mobile wallet is deployed; sending second wireless network description information of the retail environment over the first wireless network to facilitate access to the second wireless network by the mobile device, wherein the first wireless network operates within access range of the second wireless network; sending service information from a service provider associated with the retail environment over the second wireless network to request execution of a service provider-specific widget on the mobile device; and completing the electronic transaction, that was initiated by receiving the default form of payment information, by exchanging payment confirmation information over the second network via the service provider-specific widget.
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
Method and system for monitoring electronic purchases and cash-withdrawals
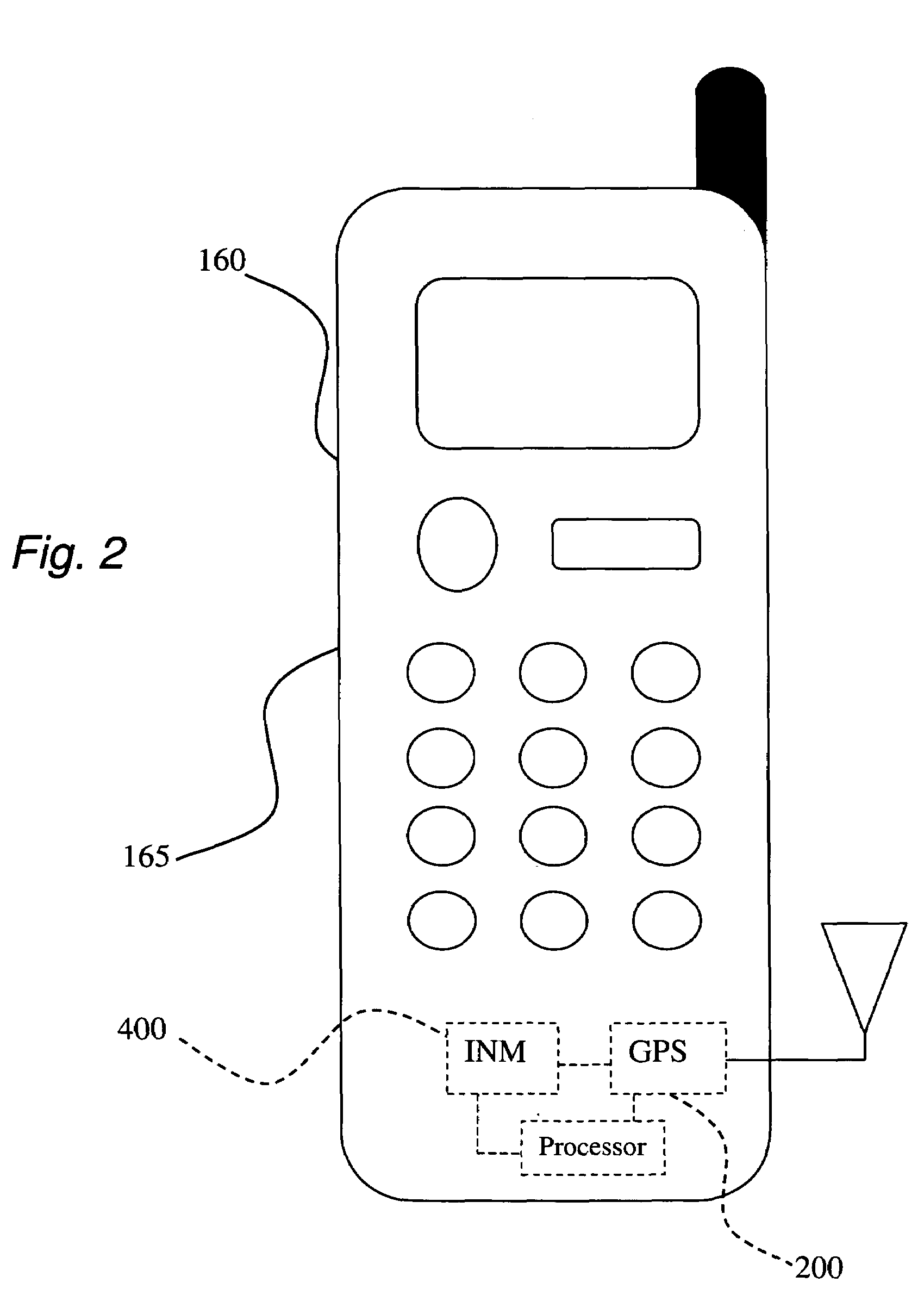
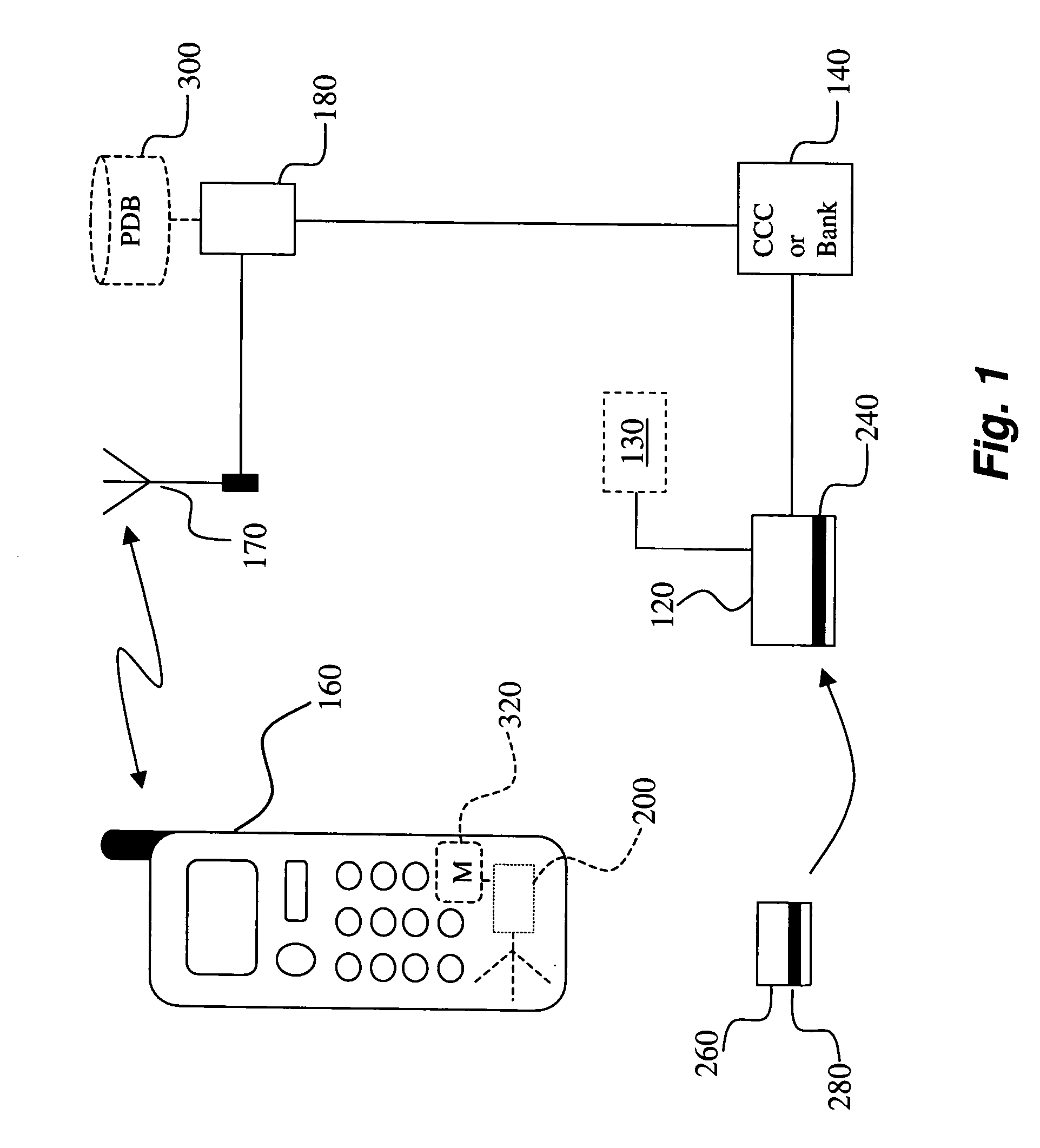
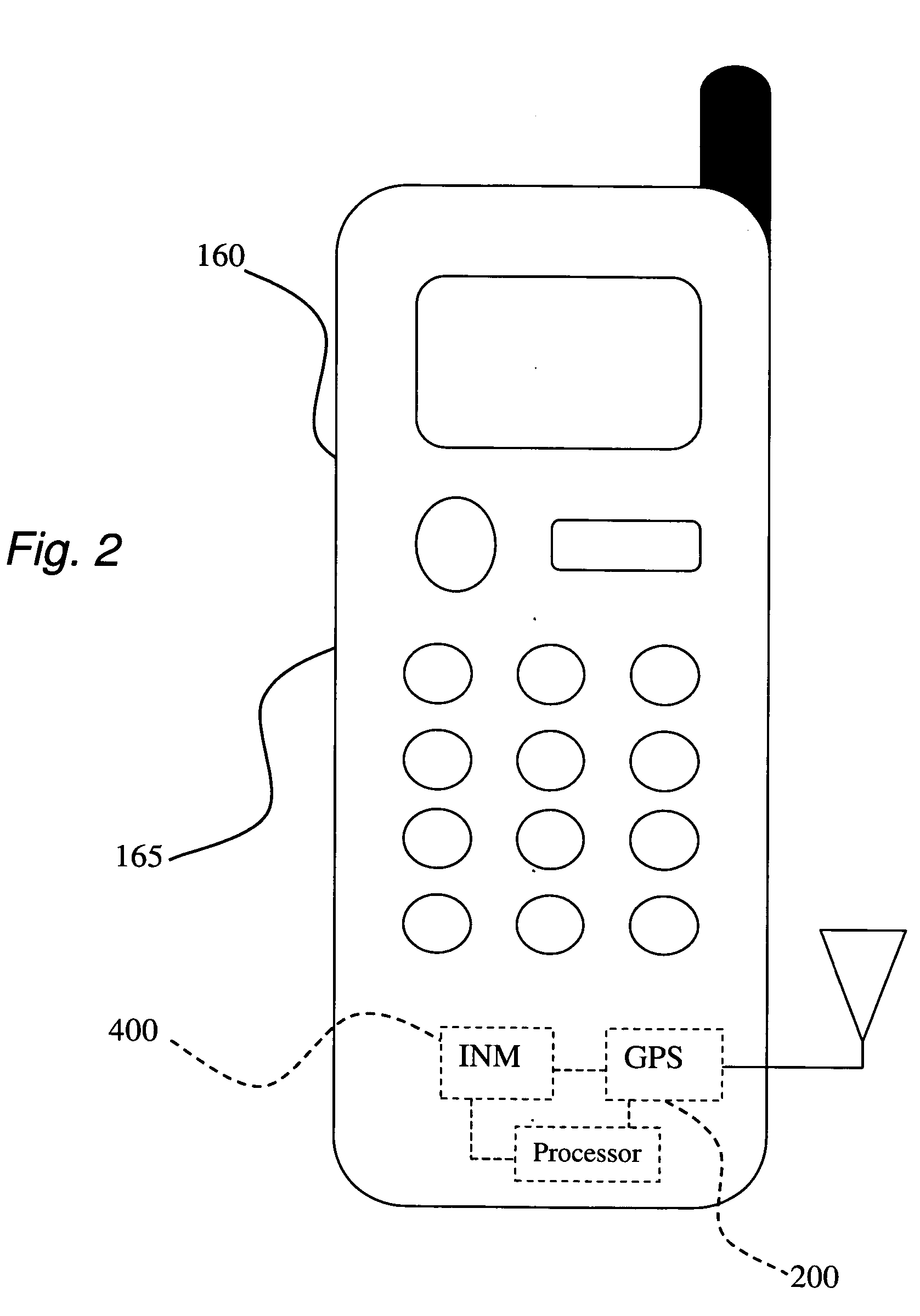
A method for facilitating the detection of misuse of an identity during an electronic transaction. The invention comprises at least five embodiments. In a first embodiment, the method comprises the step of: receiving a notification to authenticate the use of an identity at a first location, wherein the identity is associated with a first wireless terminal; determining an approximate location of the first wireless terminal based on cached position information, the approximate location of the first wireless terminal being a second location; determining whether the first and second locations match in geographical proximity; and generating an alert if the first and second locations do not match in geographical proximity. In a second embodiment, an approximate location of the first wireless terminal is determined based on cached position information stored on a GPS position database.
Owner:LOCKIP
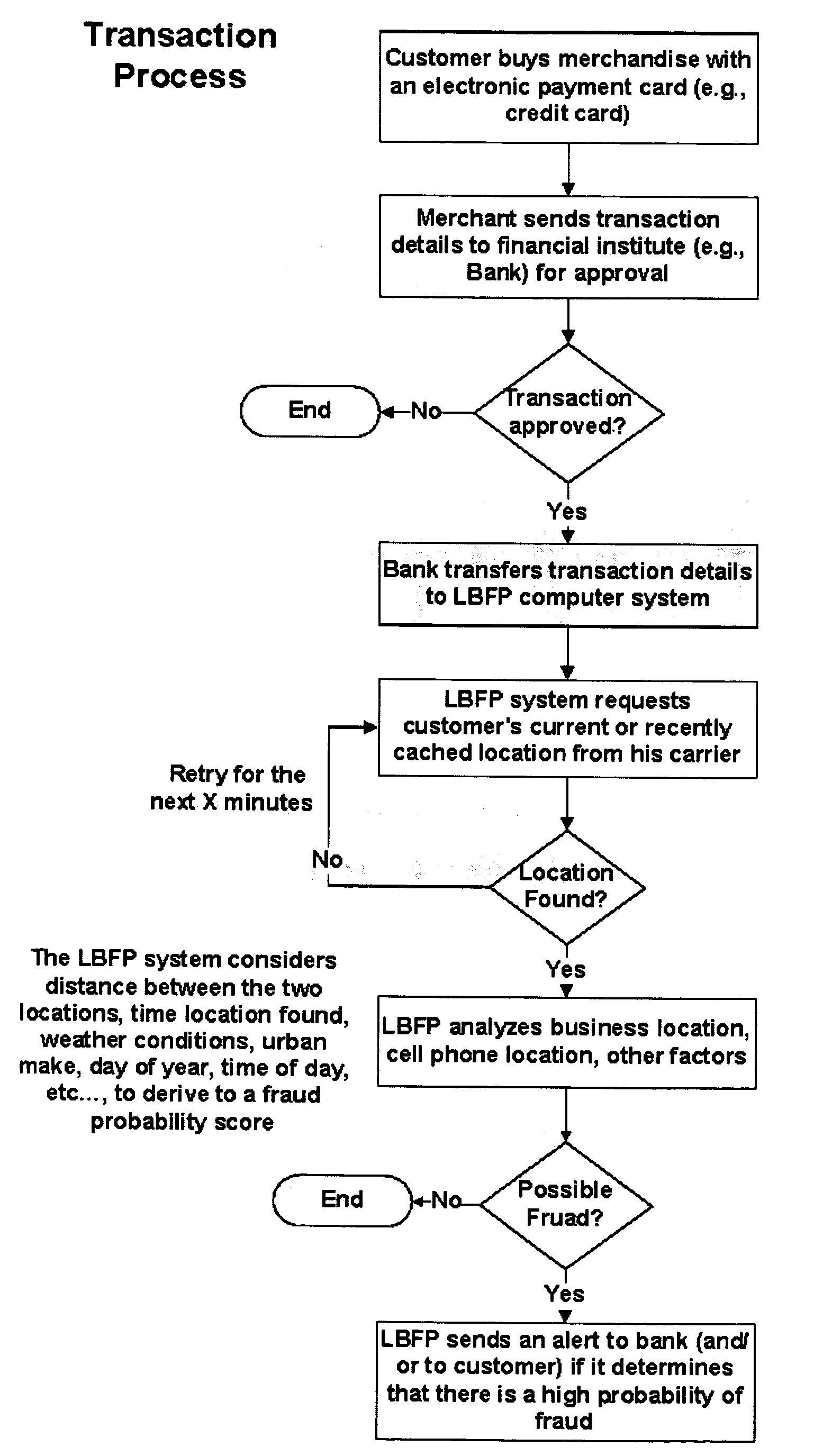
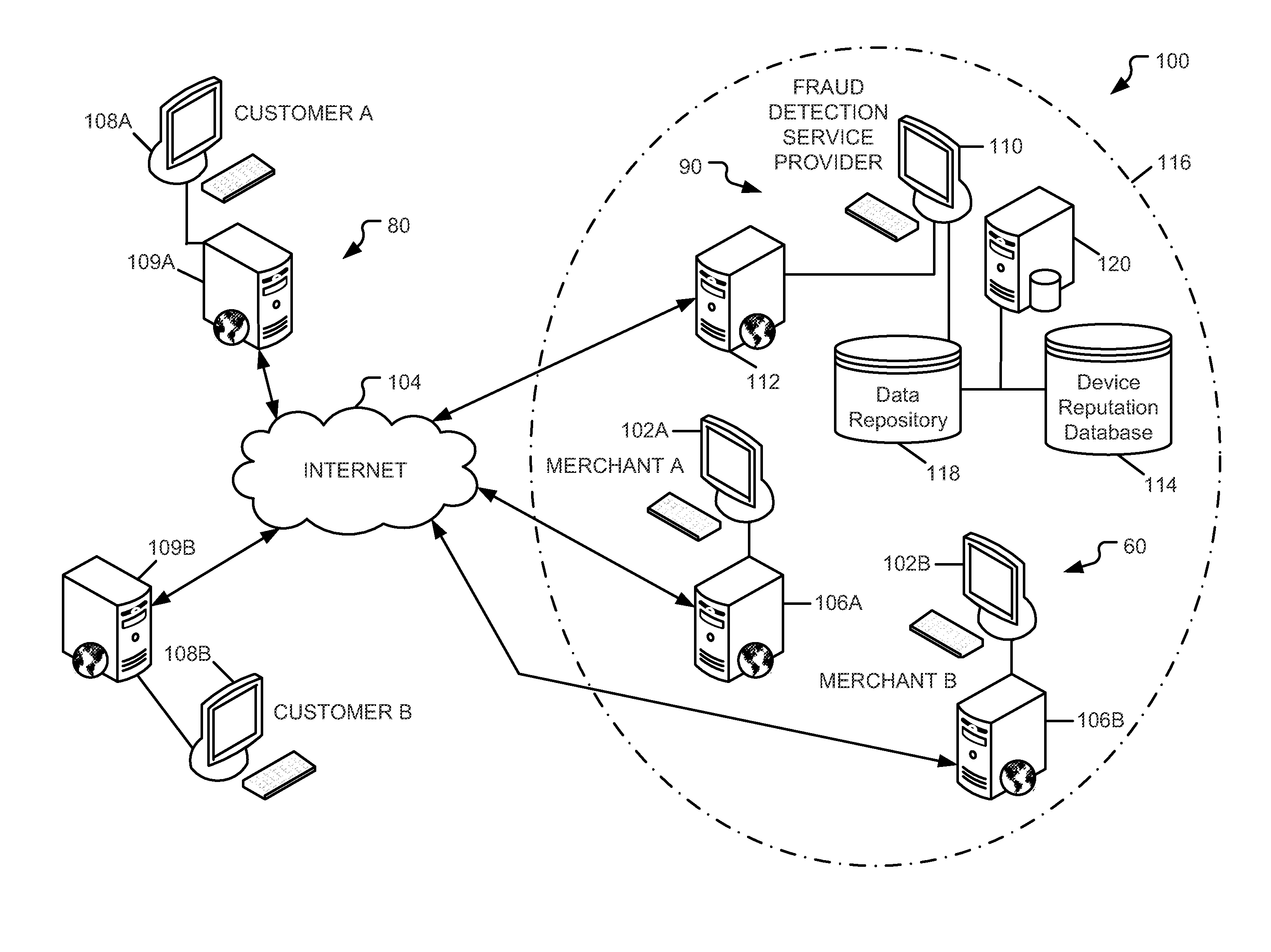
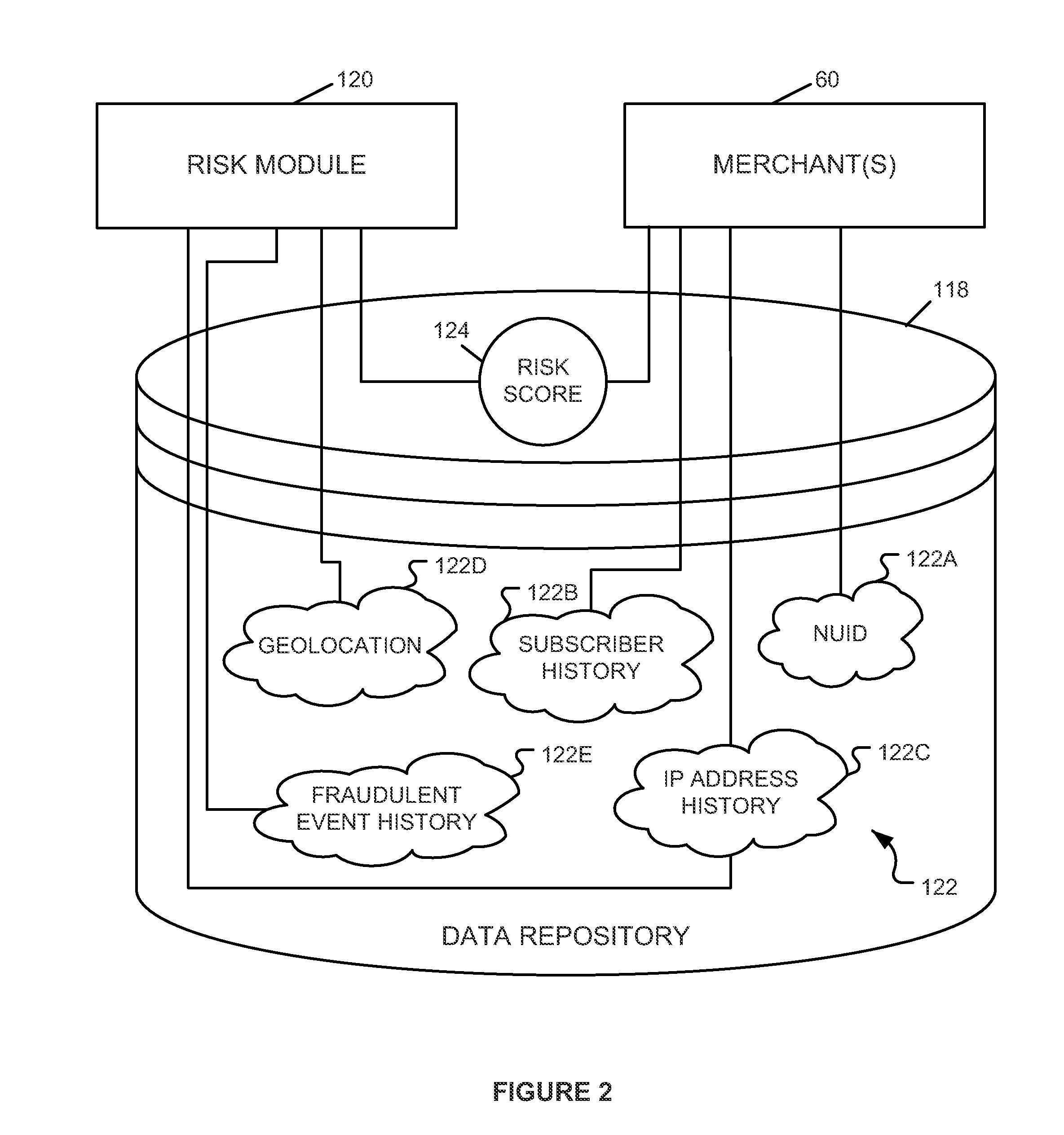
System and method for evaluating risk in fraud prevention
A method of determining a risk score indicating a risk that an electronic transaction will involve fraud and / or abuse. The method includes receiving transaction data associated with a not yet completed transaction from a merchant. The transaction data includes one or more characteristics related to the transaction. A profile is selected that identifies network devices each associated with the characteristics and having a device reputation. Next, a profile-based risk factor is determined as a function of a percentage of the network devices having a negative reputation. The risk score is determined as a function of the profile-based risk factor. In some embodiments, a transaction-based risk factor may also be determined. In such embodiments, the risk score is determined as a function of the profile-based and transaction-based risk factors. The risk score is provided to the merchant to be used thereby to determine whether to proceed with the transaction.
Owner:IOVATION
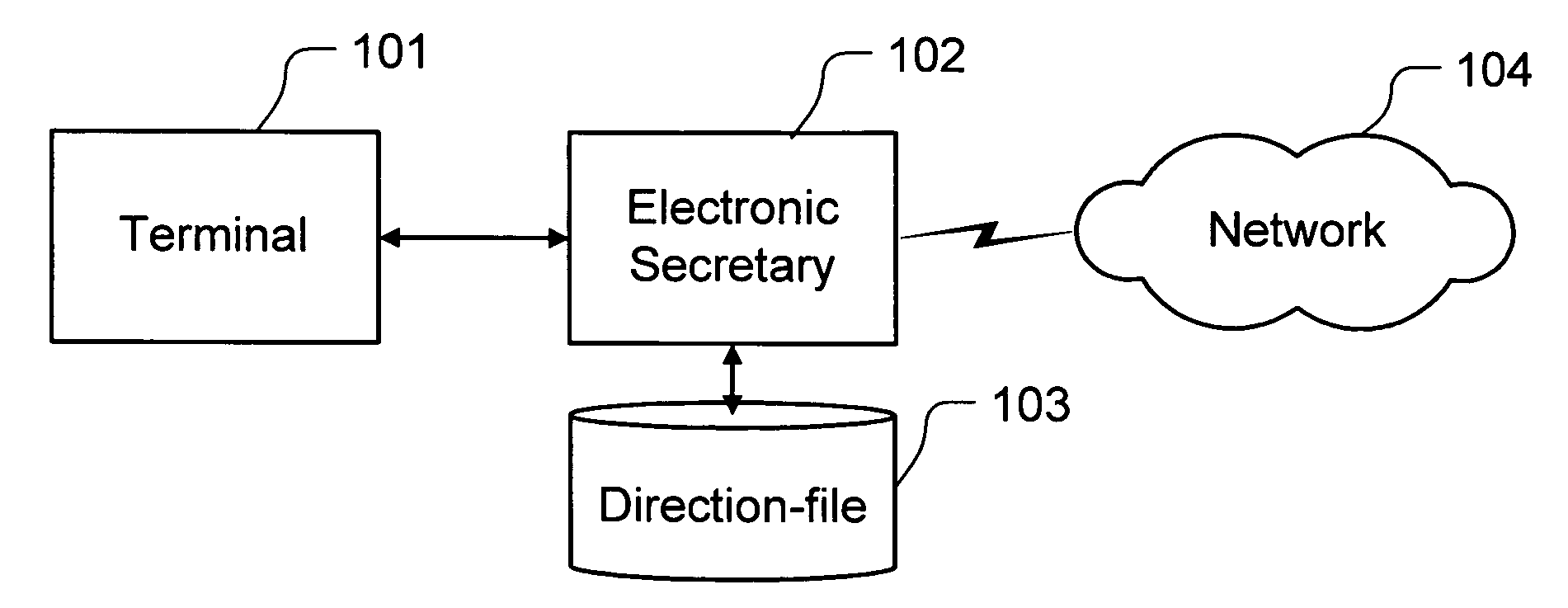
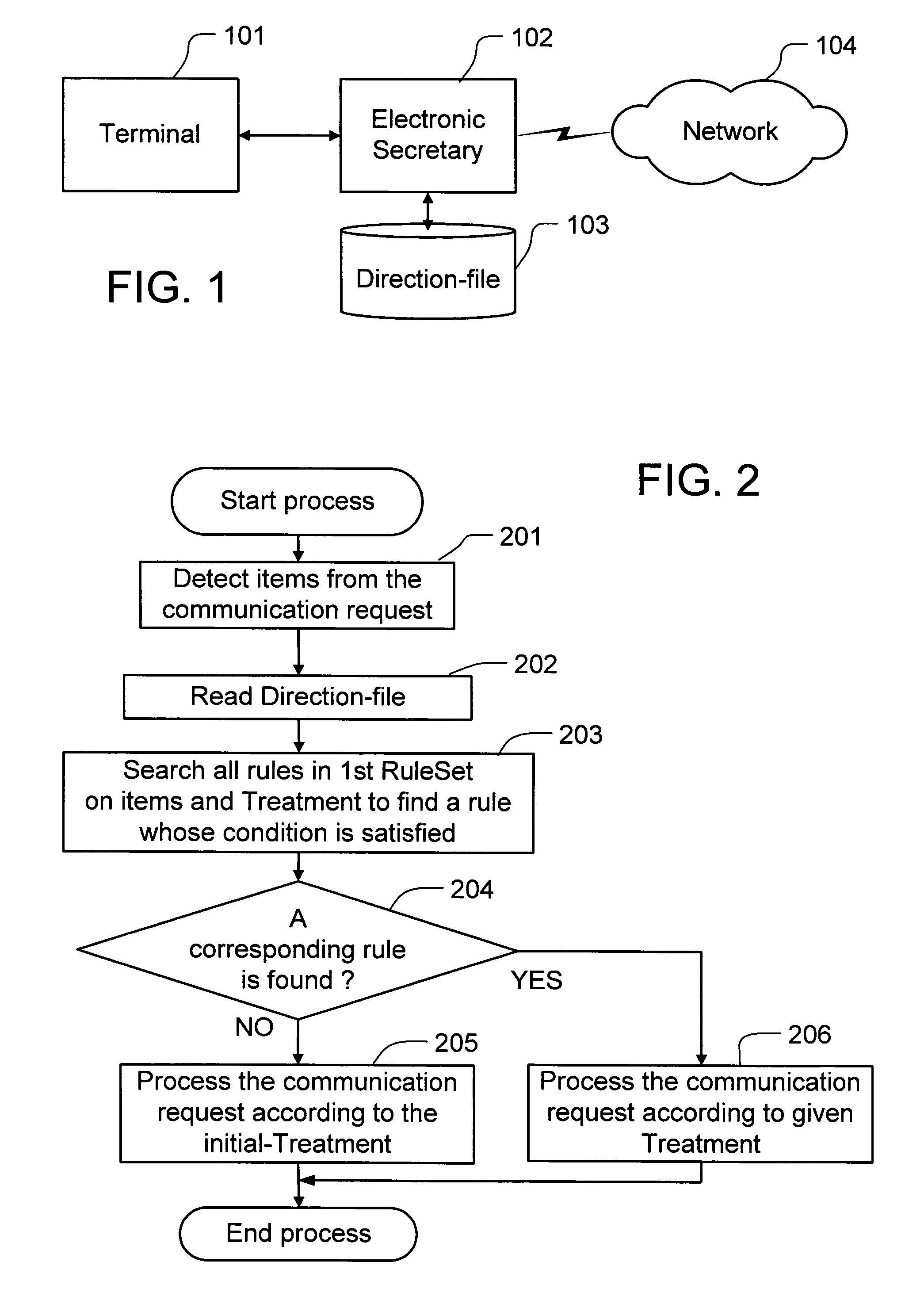
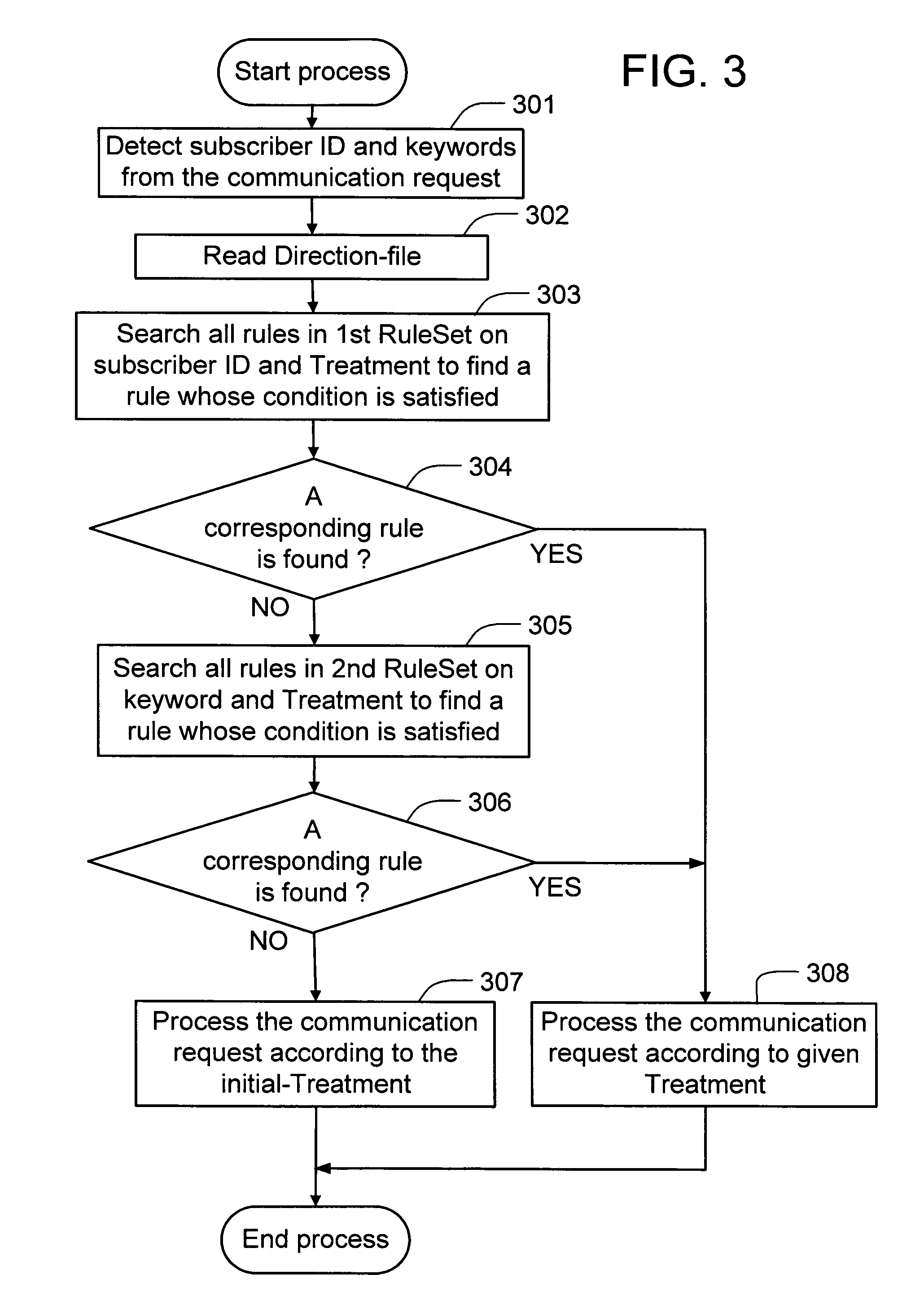
Method and apparatus for controllable communication
ActiveUS20060212561A1Reduce riskDigital computer detailsData switching networksPaymentComputer hardware
Communication and a communications apparatus are controlled with a communication intermediating apparatus. Multiple methods of processing communication requests are provided. Decided rules comprising of pairs of identification information of communication requests and methods of processing are recorded beforehand. When a communication request is received, the identification of the communication request is distinguished, an applying rule is picked from the recorded rules, and the communication request is processed. A virtual account to be set maximum payment amount beforehand is used, and electronic transactions communication is done.
Owner:FENG GUANG
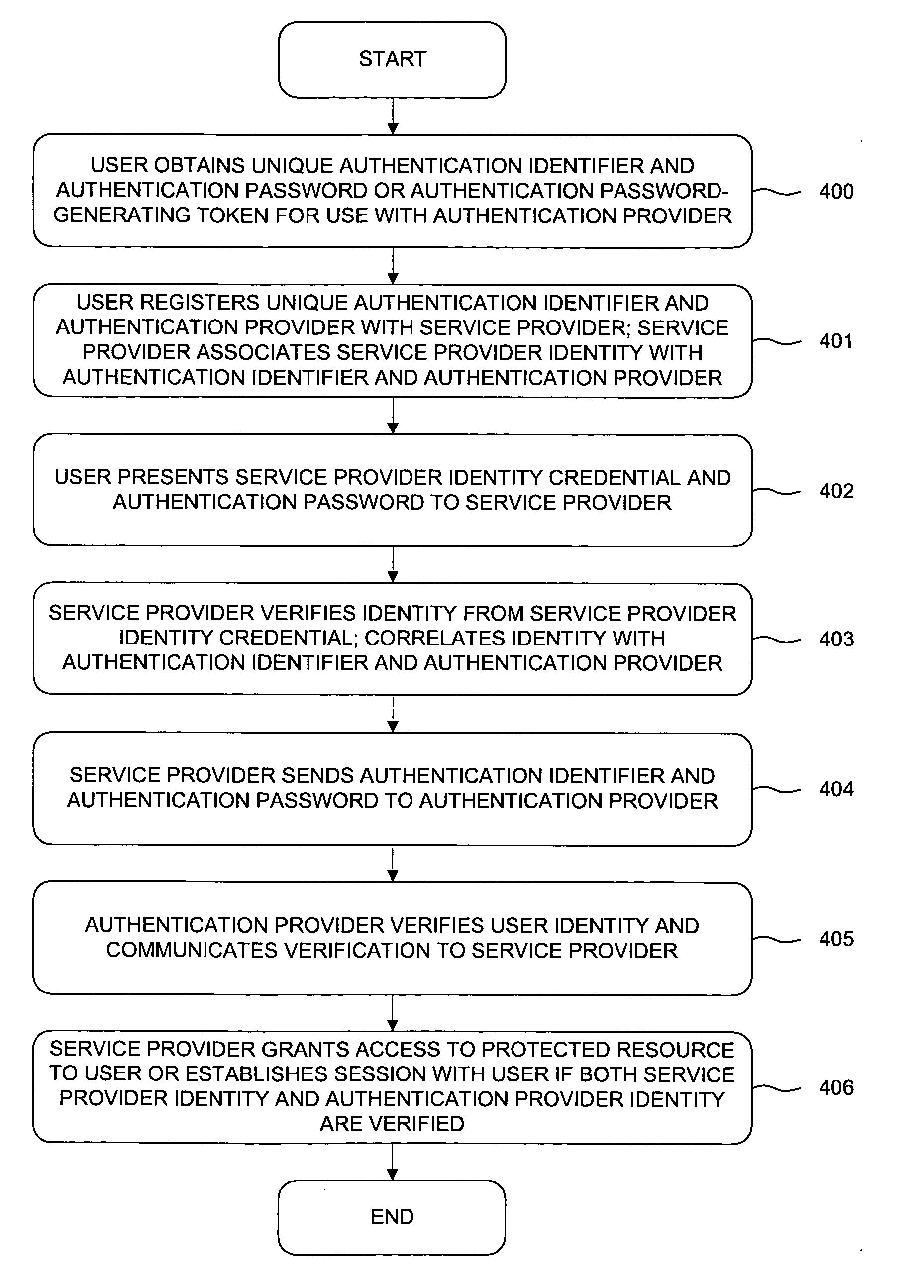
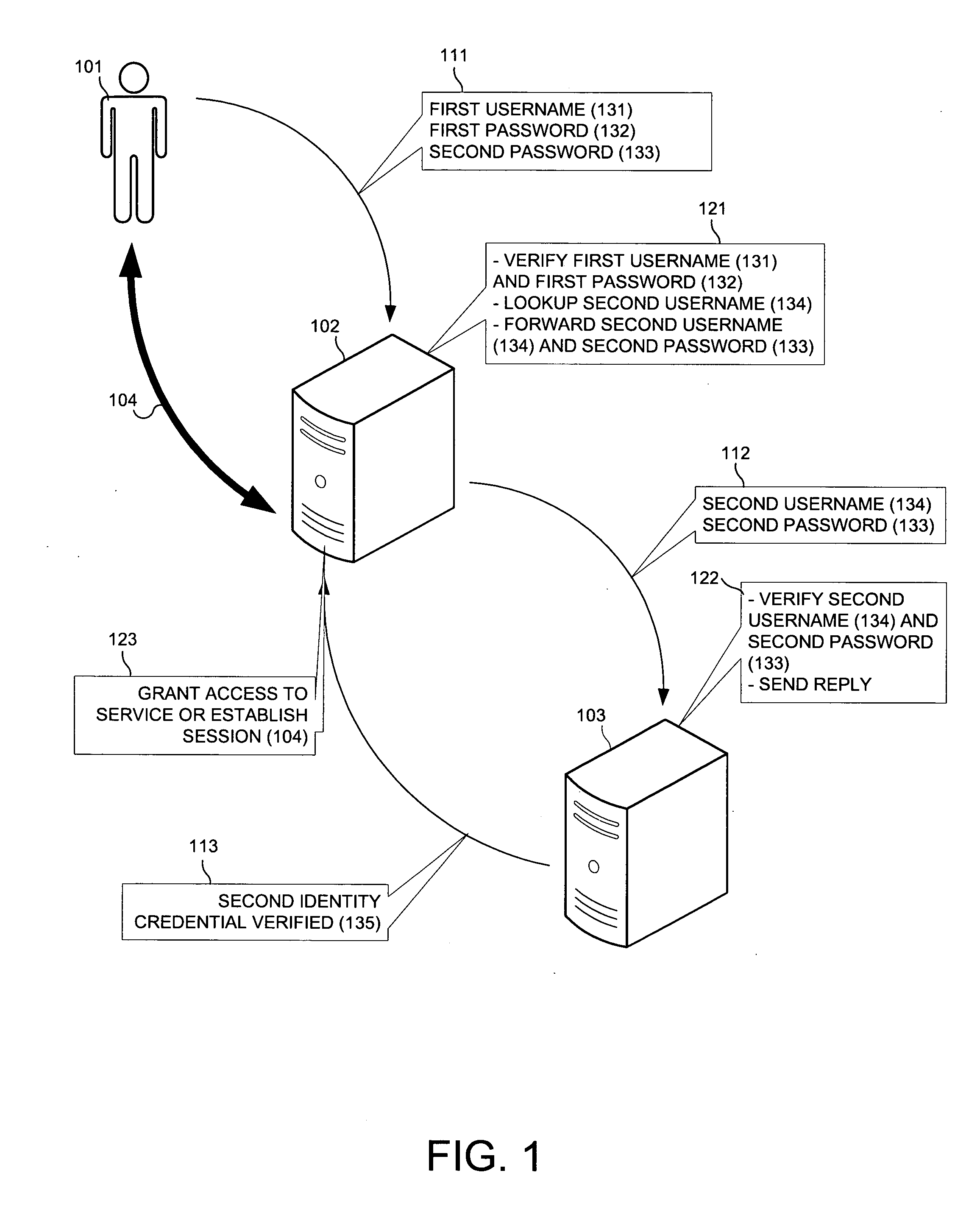
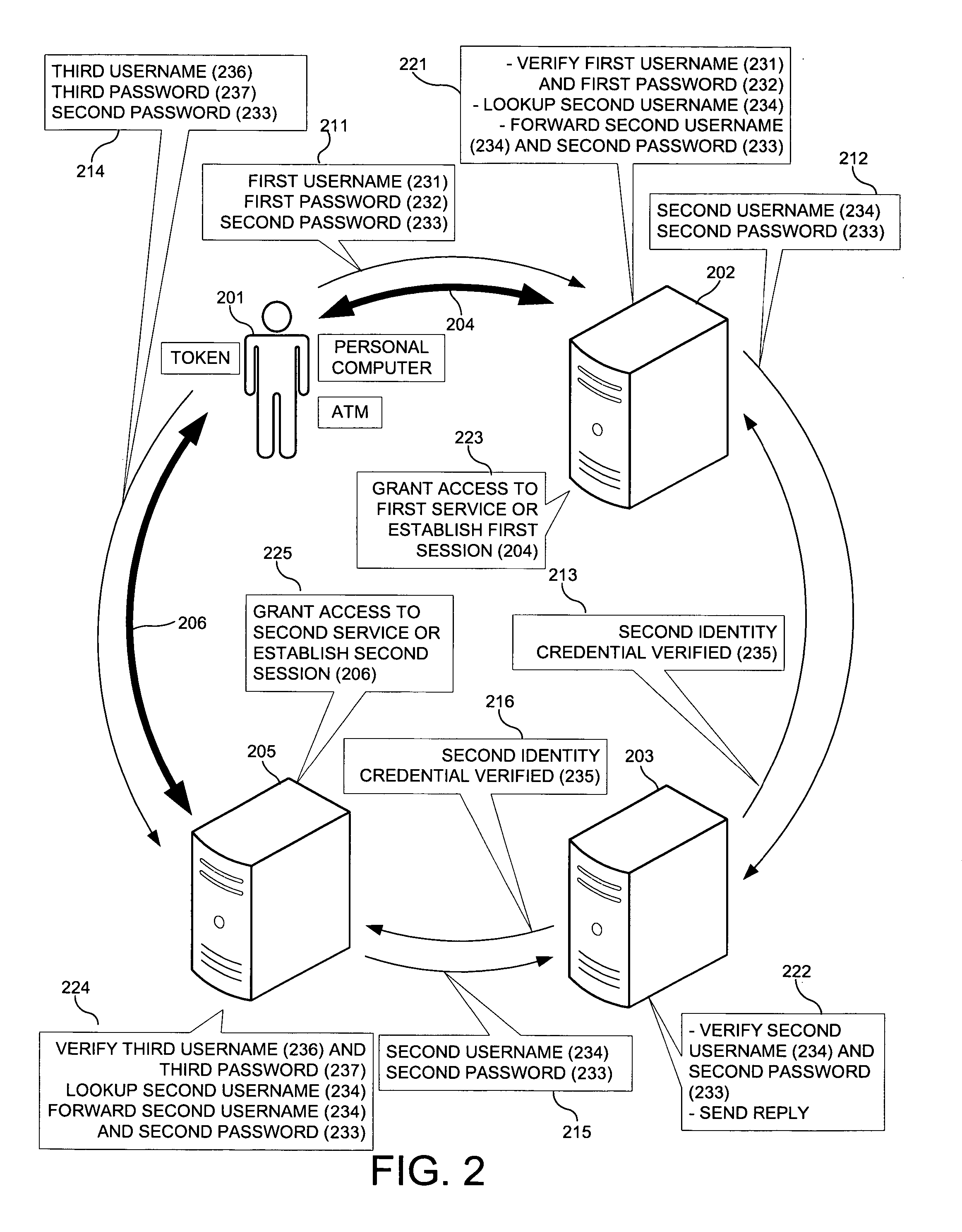
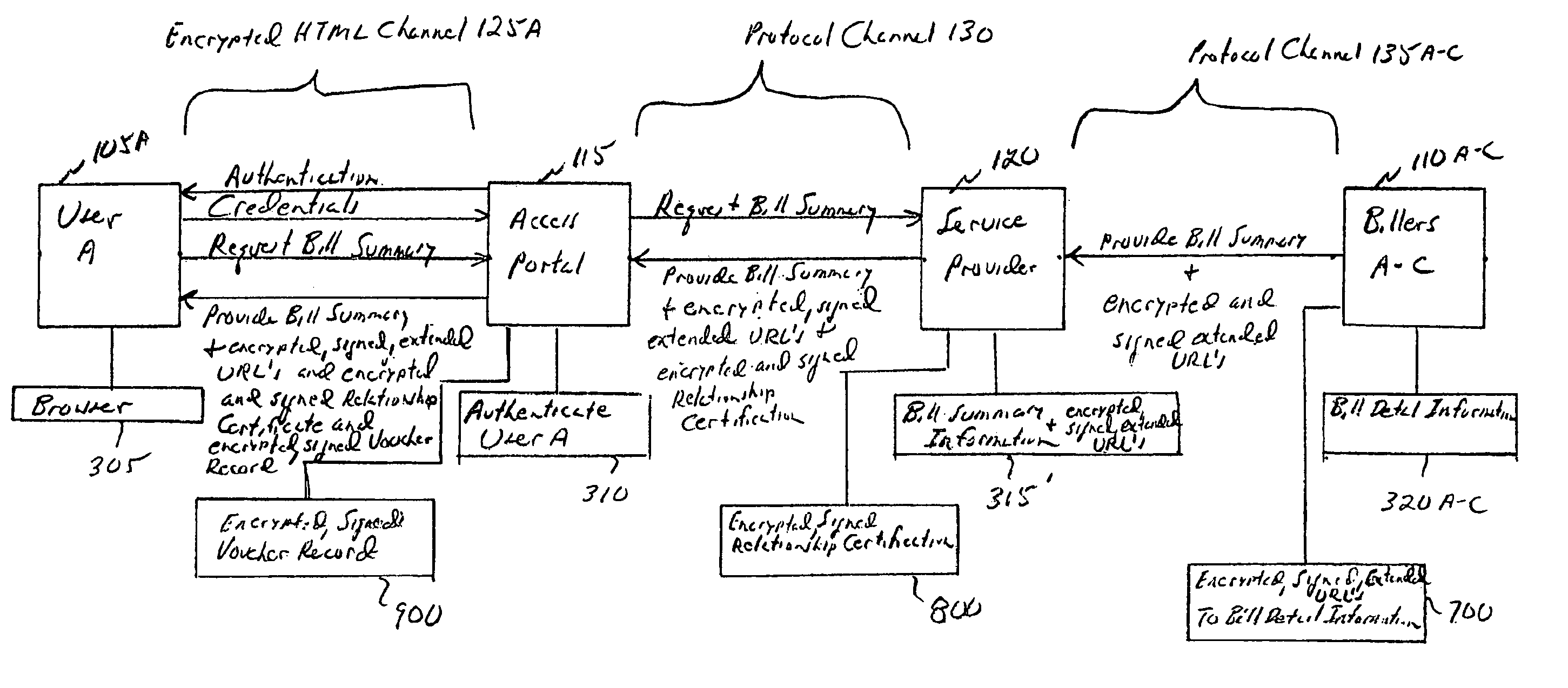
Third party authentication of an electronic transaction
A first identity credential (for example, a username and password), in conjunction with a second identity credential (for example, a token identifier and a token-generated password) verified by an authentication provider, permits access to a protected resource (for example, a bank account) maintained by a service provider (for example, a bank) where the service provider is a separate entity from the authentication provider. Such separation of the service provider from the authentication provider allows multiple service providers to use the same authentication provider such that subscribers of services from multiple service providers may register a single authentication provider, and thus use a single method to produce the second identity credential. An authentication provider provides a common validation service to a plurality of unrelated service providers. An electronic user interface and a key-chain token for carrying out the authentication process are also disclosed.
Owner:CHUA BRYAN S M
Hand-held electronics device for aggregation of and management of personal electronic data
A readable and rewriteable card blank for use with a hand-held electronics device having a card reading and writing interface for aggregation of and management of personal electronic data sets is provided including a readable and rewriteable media disposed on a credit card form factor, a first touch enabled display, internal micro-circuitry such as an embedded smart chip, a proximity sensing capability characterized in that the personal electronic data sets are read into the card form factor selectively or collectively via a personal electronics device enabled as a smart phone for use in electronic transacting or fulfillment of electronic identification queries.
Owner:EDGE MOBILE PAYMENTS LLC
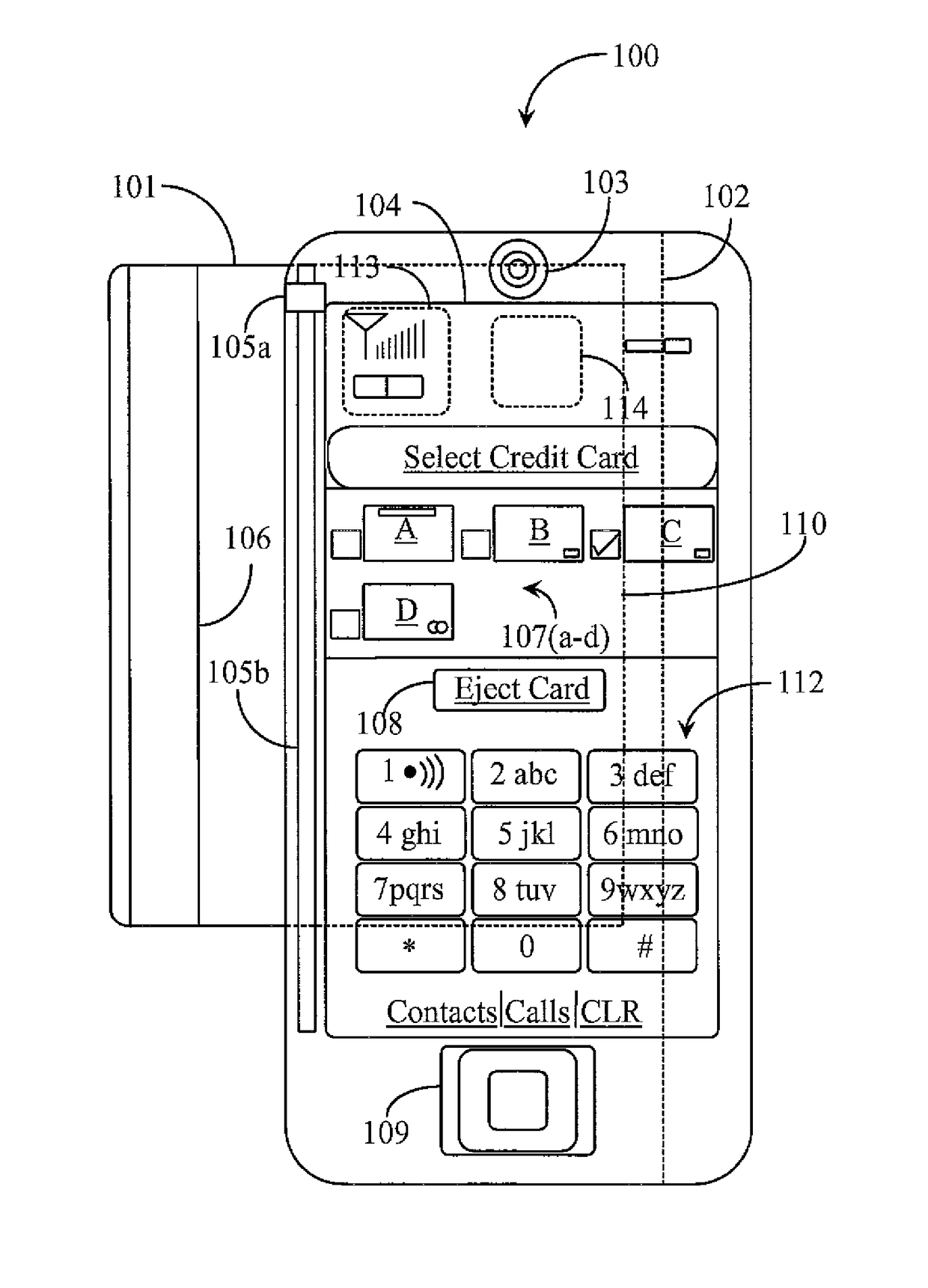
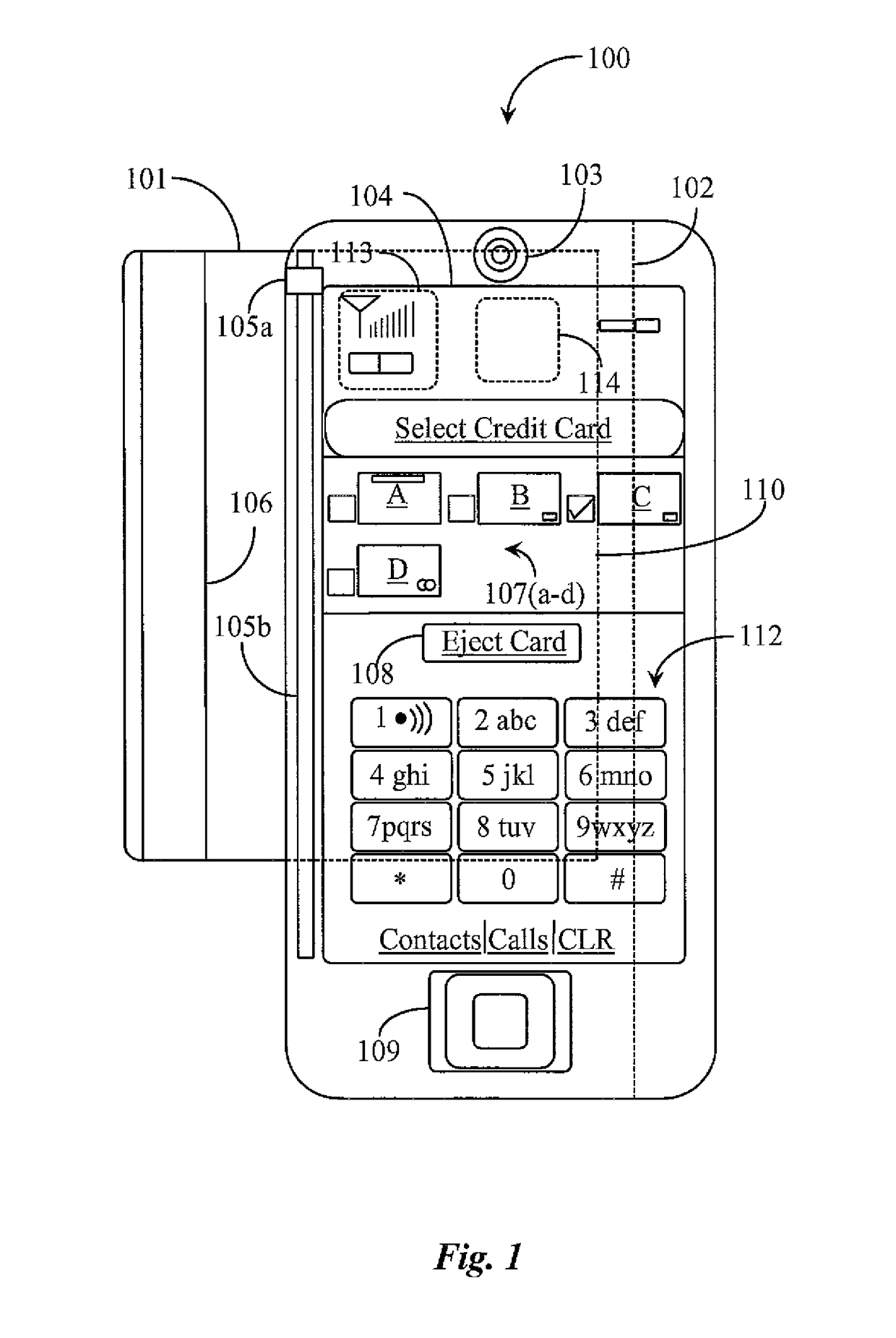
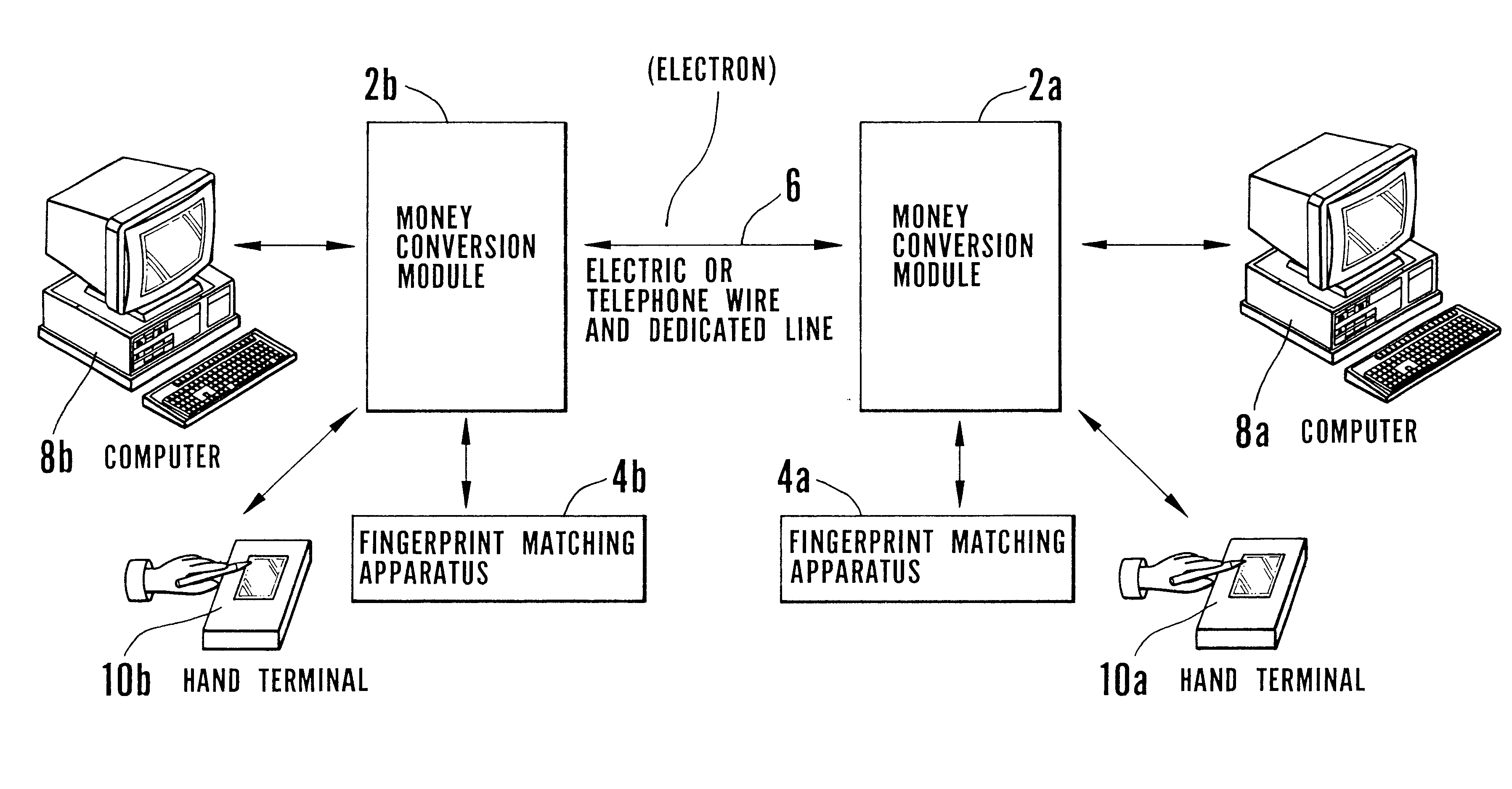
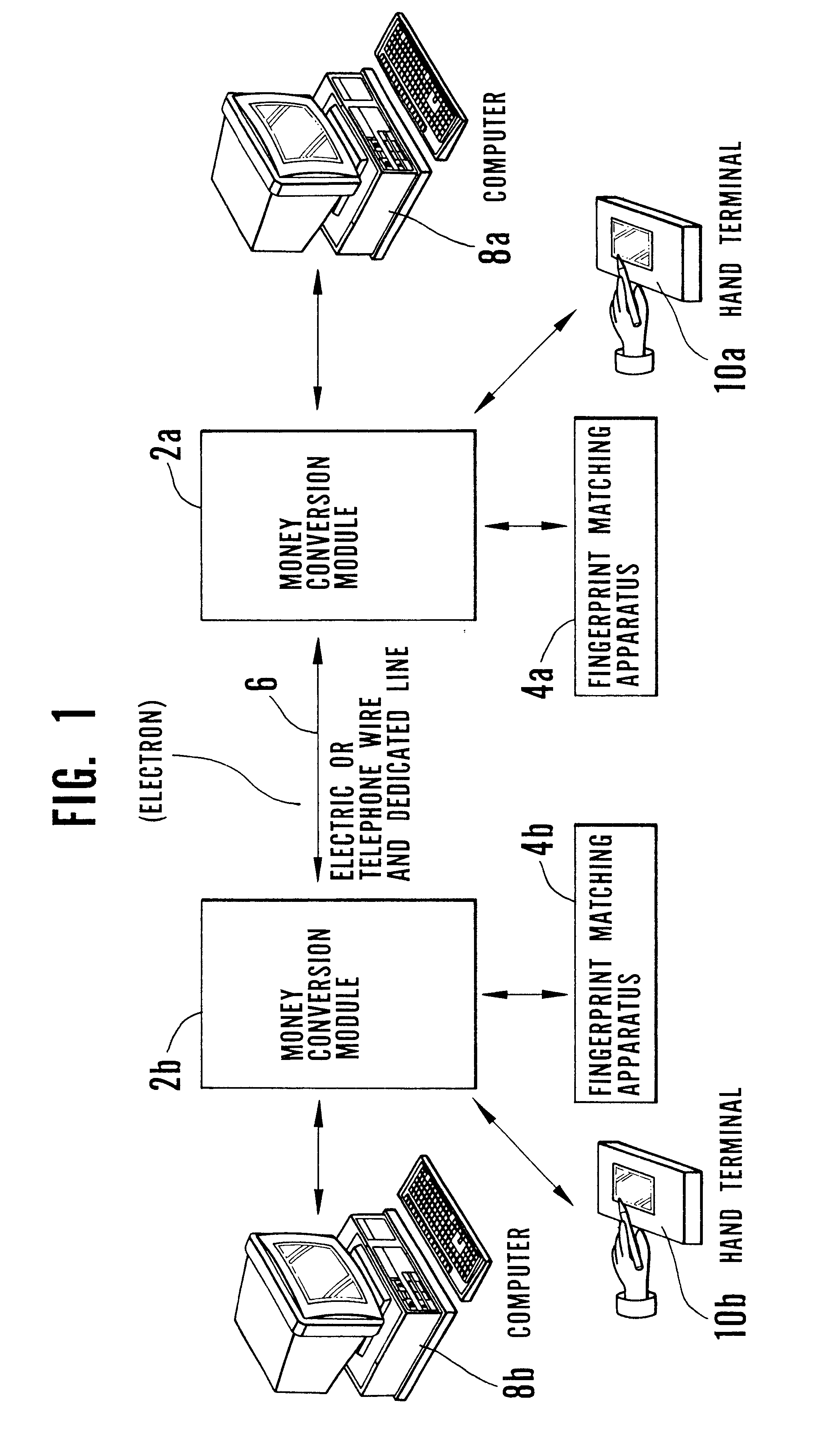
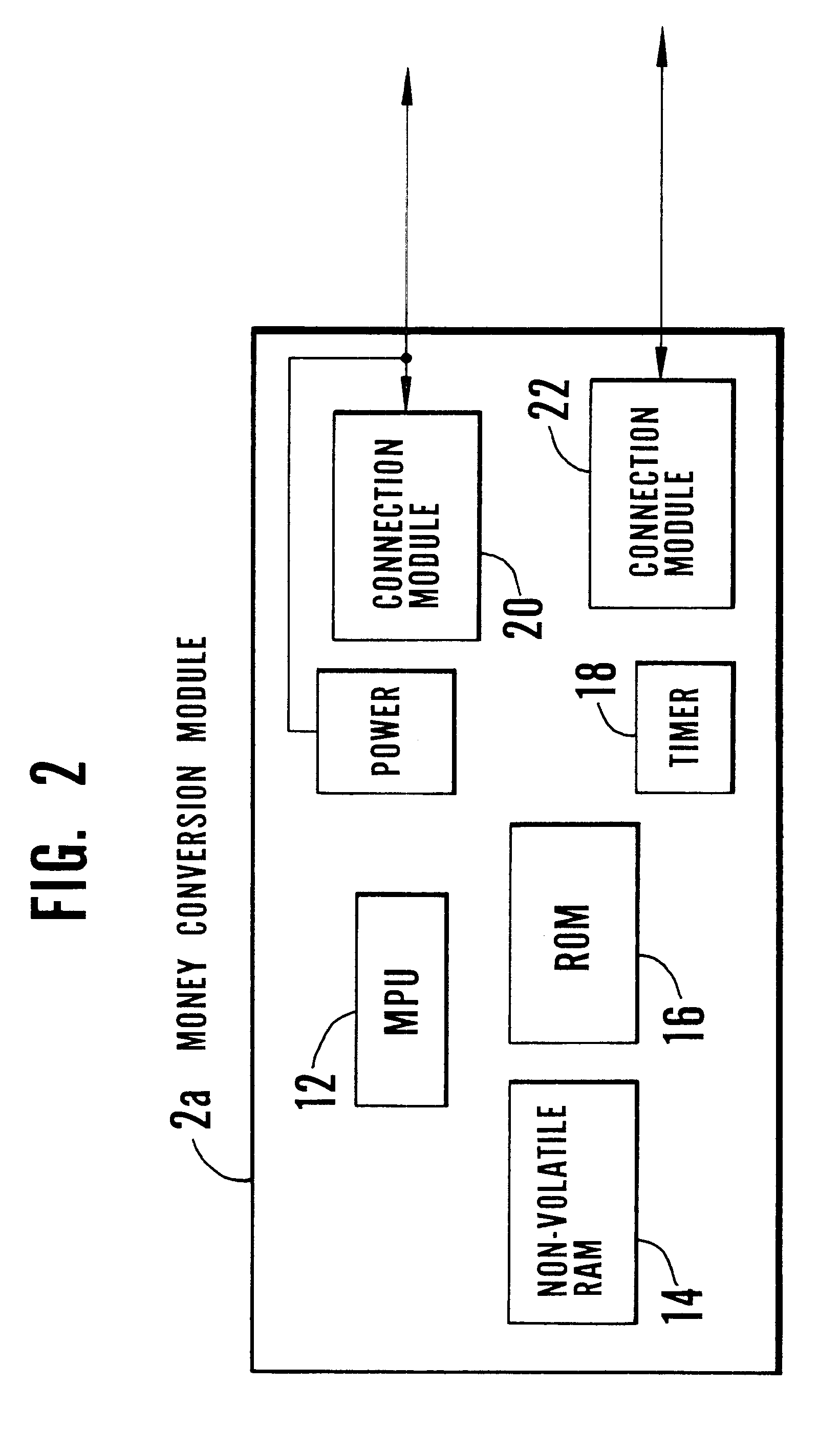
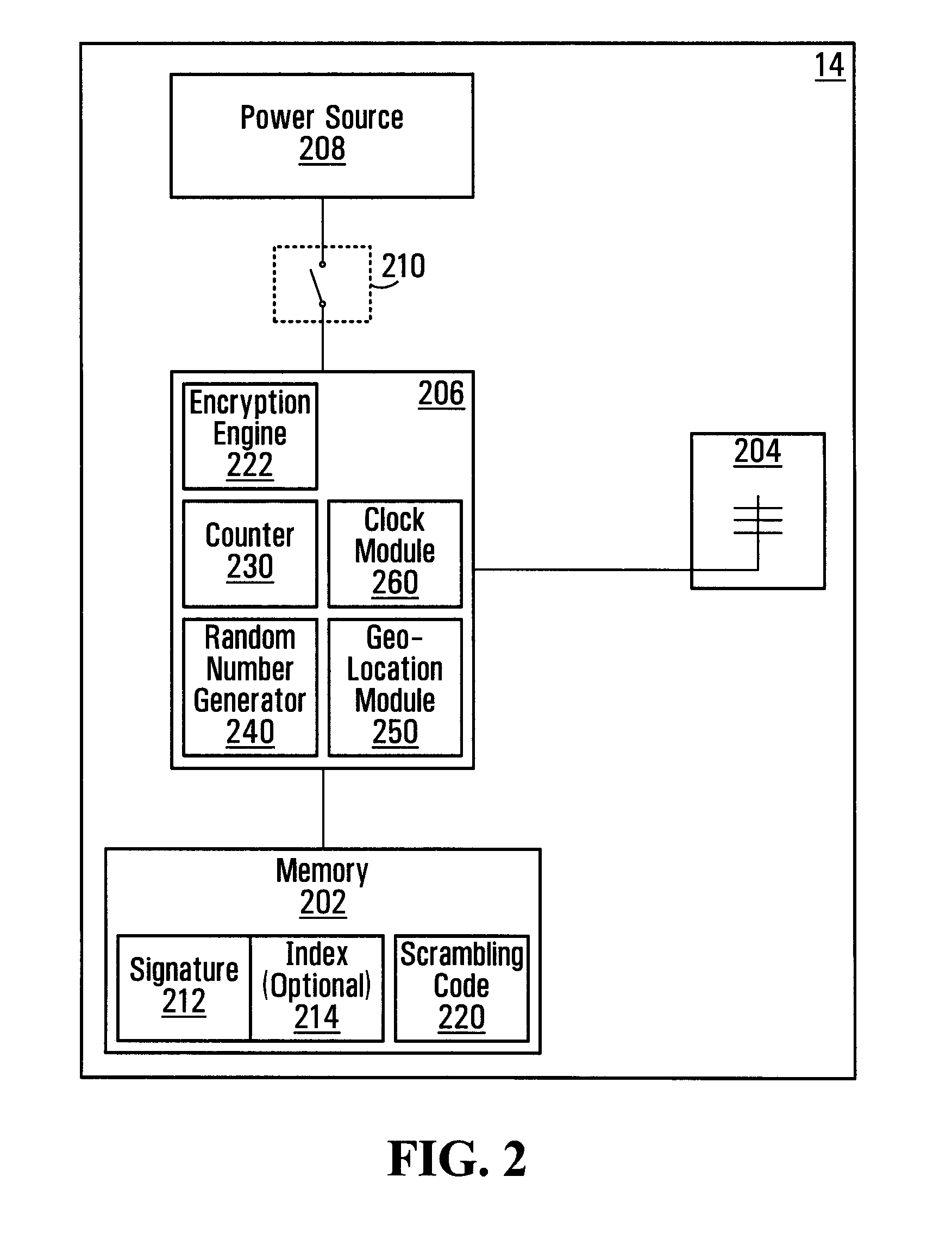
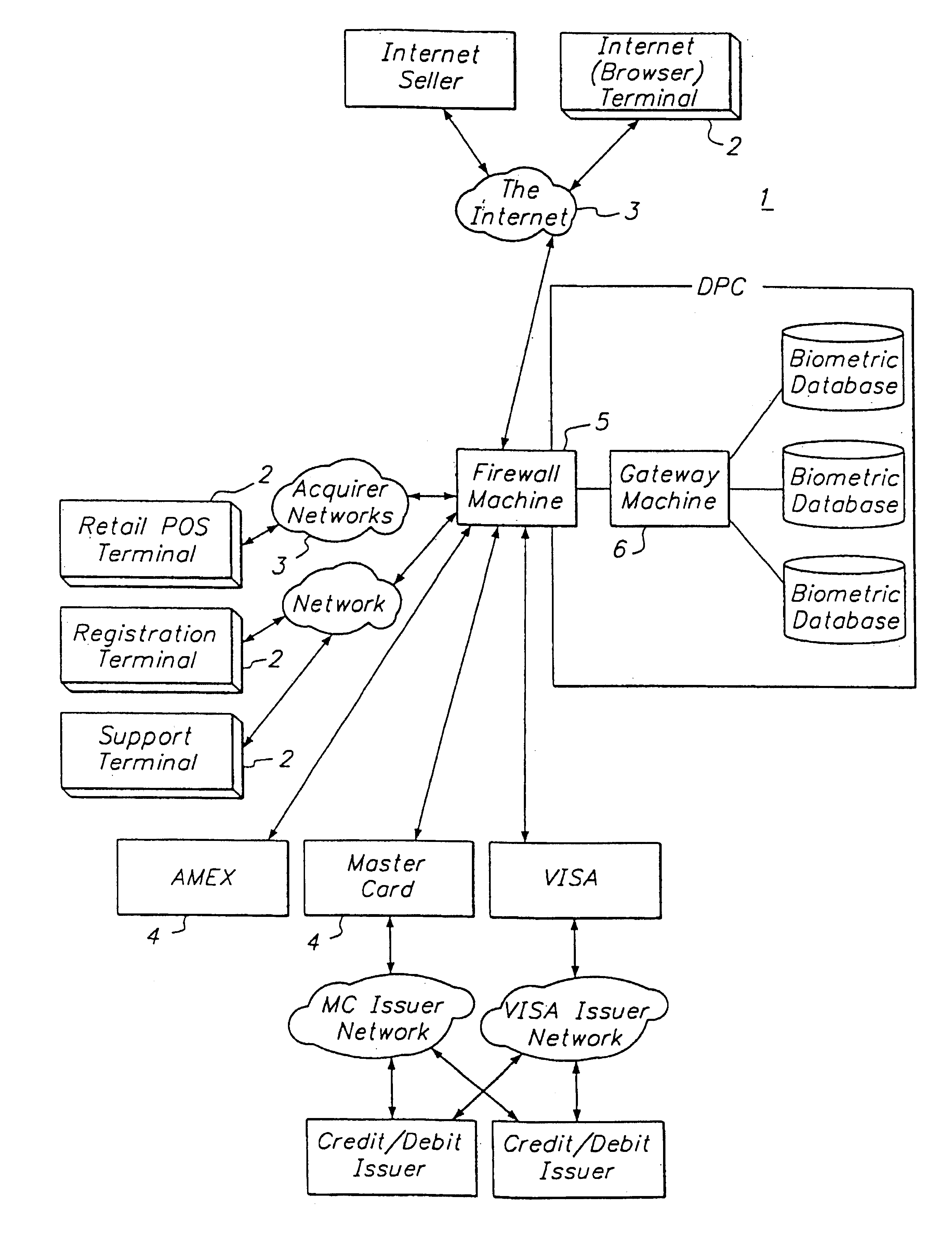
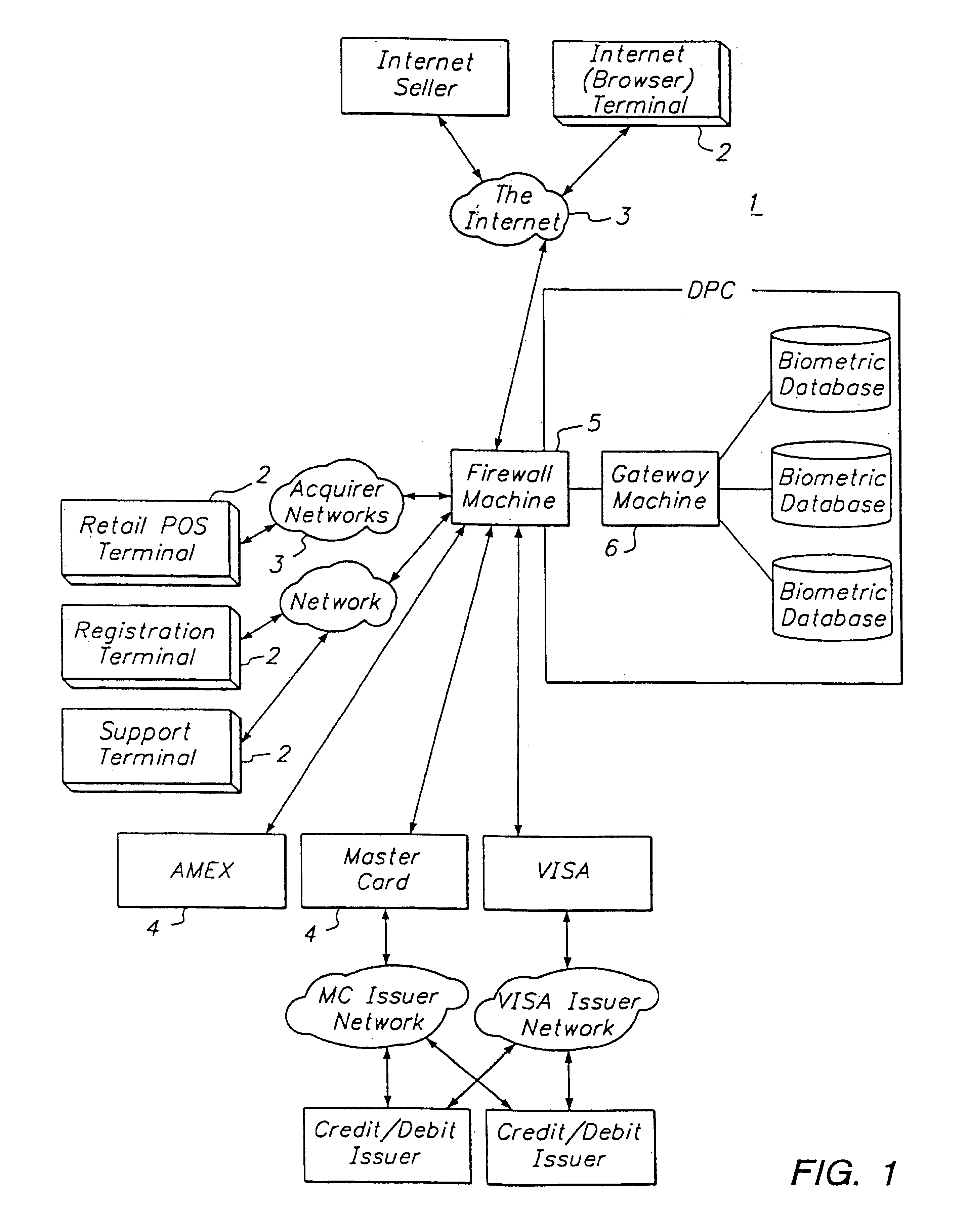
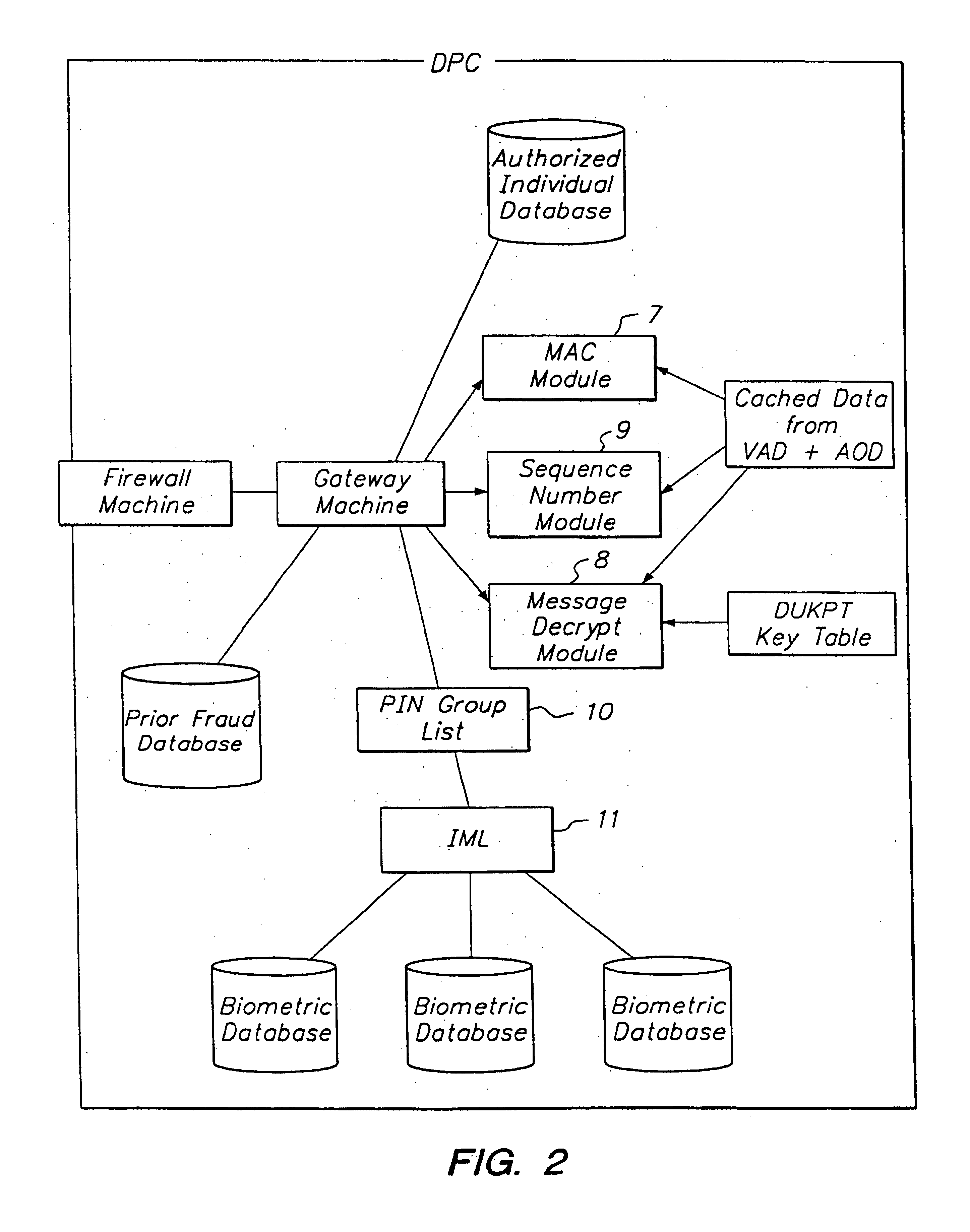
Electronic transaction system including a fingerprint identification encoding
InactiveUS6523745B1Raise security concernsEasy to useComplete banking machinesFinanceComputer moduleSoftware engineering
An apparatus and process of authorizing an electronic transaction system includes a computer located at the site of a transaction, a conversion module for enabling connection between the computer located at the site of the transaction and the conversion module to authorize the transaction, and a connection between the conversion module and the computer at the site of the transaction. The system uses fingerprint input data panel for obtaining fingerprint input data from a finger impressed on the fingerprint input data panel and converts the fingerprint input data to characteristic fingerprint points including minutiae. These characteristic fingerprint points including minutiae are used in conjunction with at least one code at the conversion module to encode messages sent across the system.
Owner:BMF CORPORATION
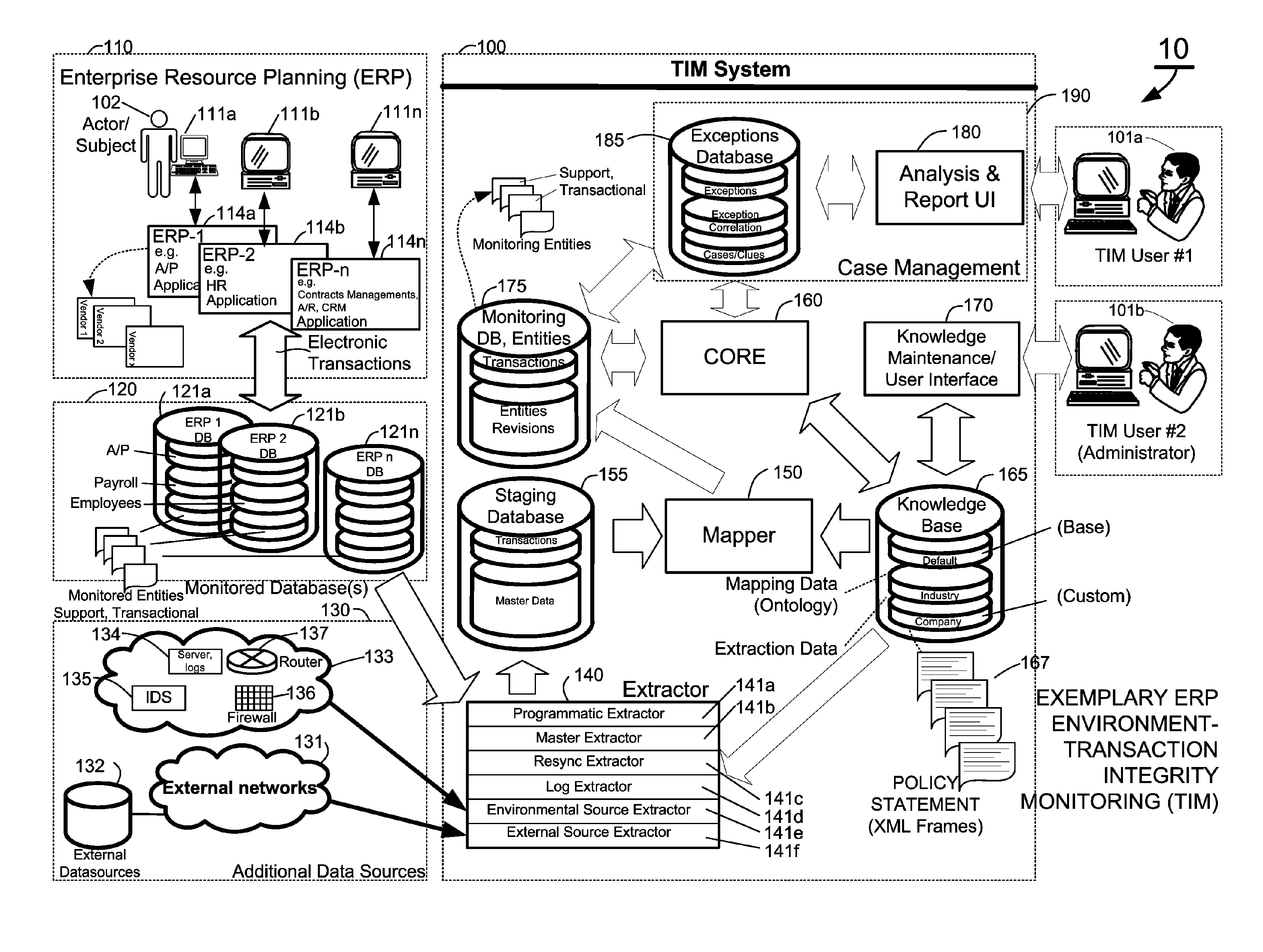
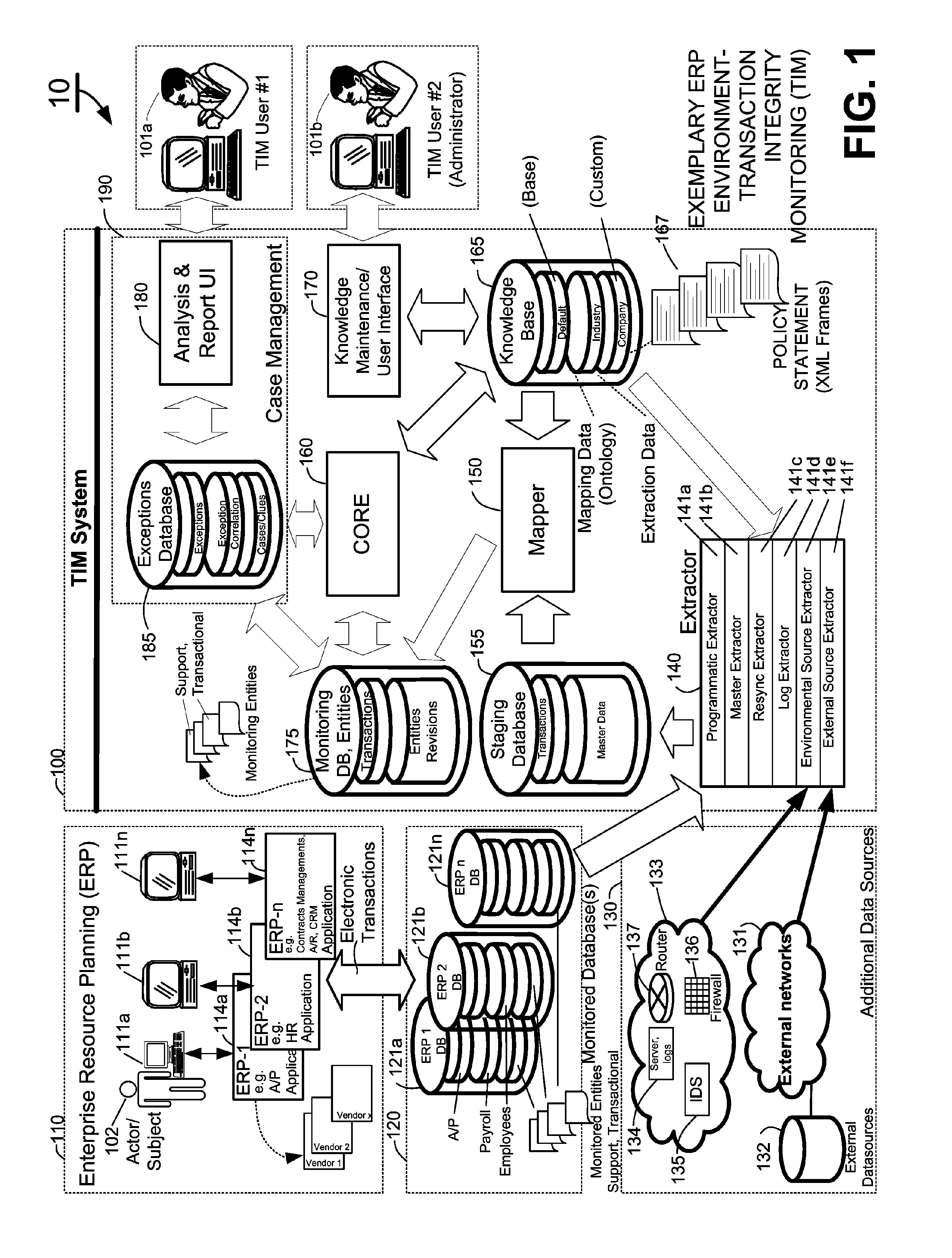
Methods and systems for mapping transaction data to common ontology for compliance monitoring
InactiveUS20080082374A1Improve performanceMinimizes financial lossDigital data information retrievalFinanceCompliance MonitoringData source
An automated transaction integrity monitoring system operative to monitor electronic transactions of an enterprise and detect exceptions indicating noncompliance with enterprise policies. The system allows establishment, codification, and maintenance of enterprise policies, monitors electronic transactions of the enterprise from various and possibly heterogeneous data sources, detects exceptions to established policies, reports such exceptions to authorized users such as managers and auditors, and / or provides a case management system for tracking such exceptions and their underlying transactions. The invention specifically relates to systems and methods for transforming or mapping information from a data source relating to a transactional entity associated with an enterprise into a form for processing by a transaction analysis engine operative upon data expressed in a predetermined ontology. The ontology expresses data items in a manner common across plural heterogeneous databases. The enterprise policies are expressed in terms of the ontology.
Owner:KENNIS PETER H +7
Methods and systems for compliance monitoring knowledge base
ActiveUS20060212486A1Reduced asset lossImprove operational efficiencyDigital data information retrievalFinanceCompliance MonitoringMonitoring system
A knowledge base and methods for use in connection with a policy compliance monitoring system operative to determine exceptions to policies expressed by computer-executable policy statements. The system allows establishment, codification, and maintenance of enterprise policies, monitors electronic transactions of the enterprise from various and possibly heterogeneous data sources, detects exceptions to established policies, reports exceptions to authorized users such as managers and auditors, and / or provides a case management system for tracking exceptions and their underlying transactions. The knowledge base comprises extractor files that are utilized for extracting information from data sources for utilization in policy compliance monitoring, a mapper for normalizing data from the data sources against a system ontology and storing normalized data in a monitoring database, and computer-executable compliance policy statements used by a transaction analysis engine. The policy statements represent predetermined policies of the enterprise that apply to data stored in the monitoring database.
Owner:OVERSIGHT SYST INC
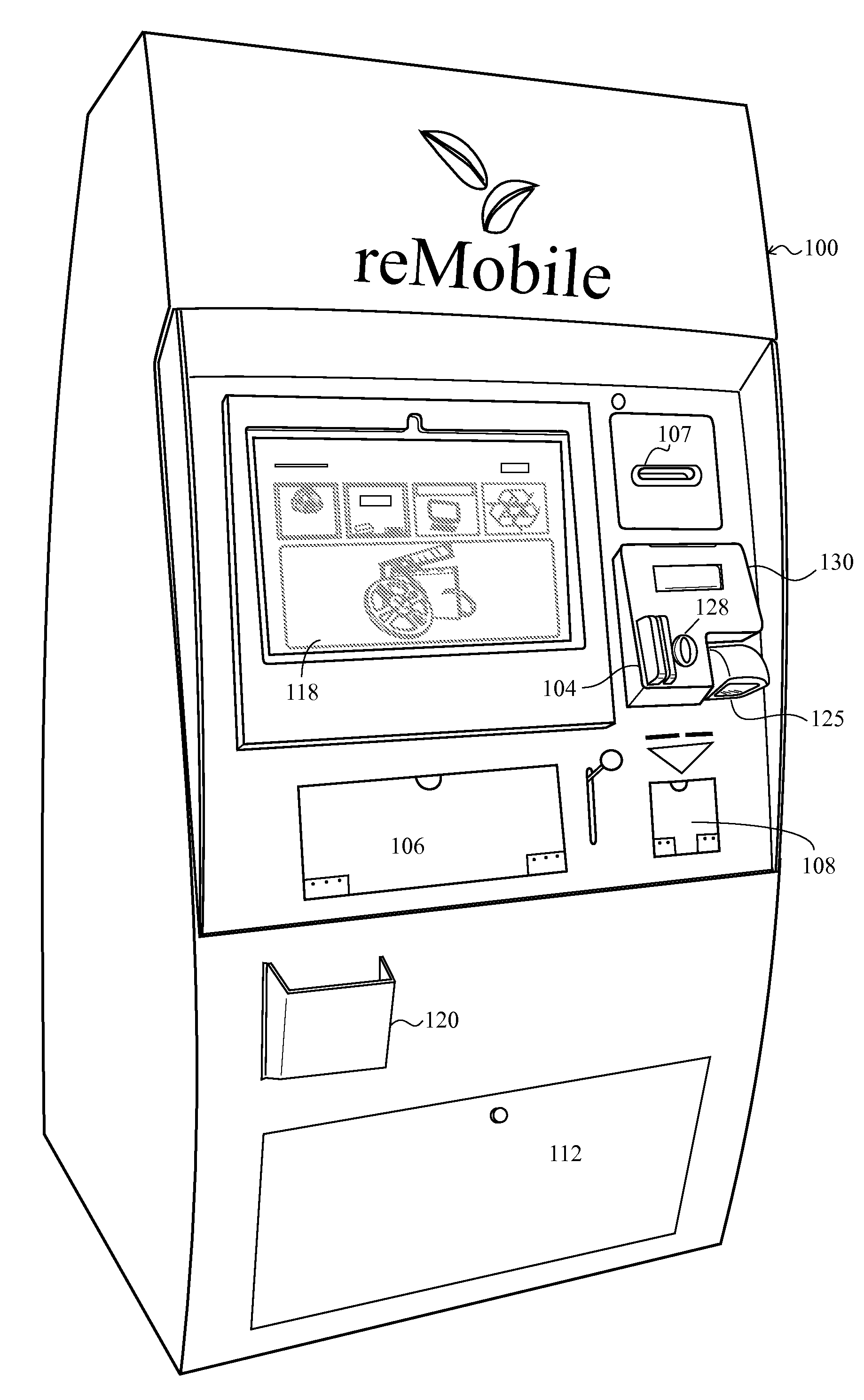
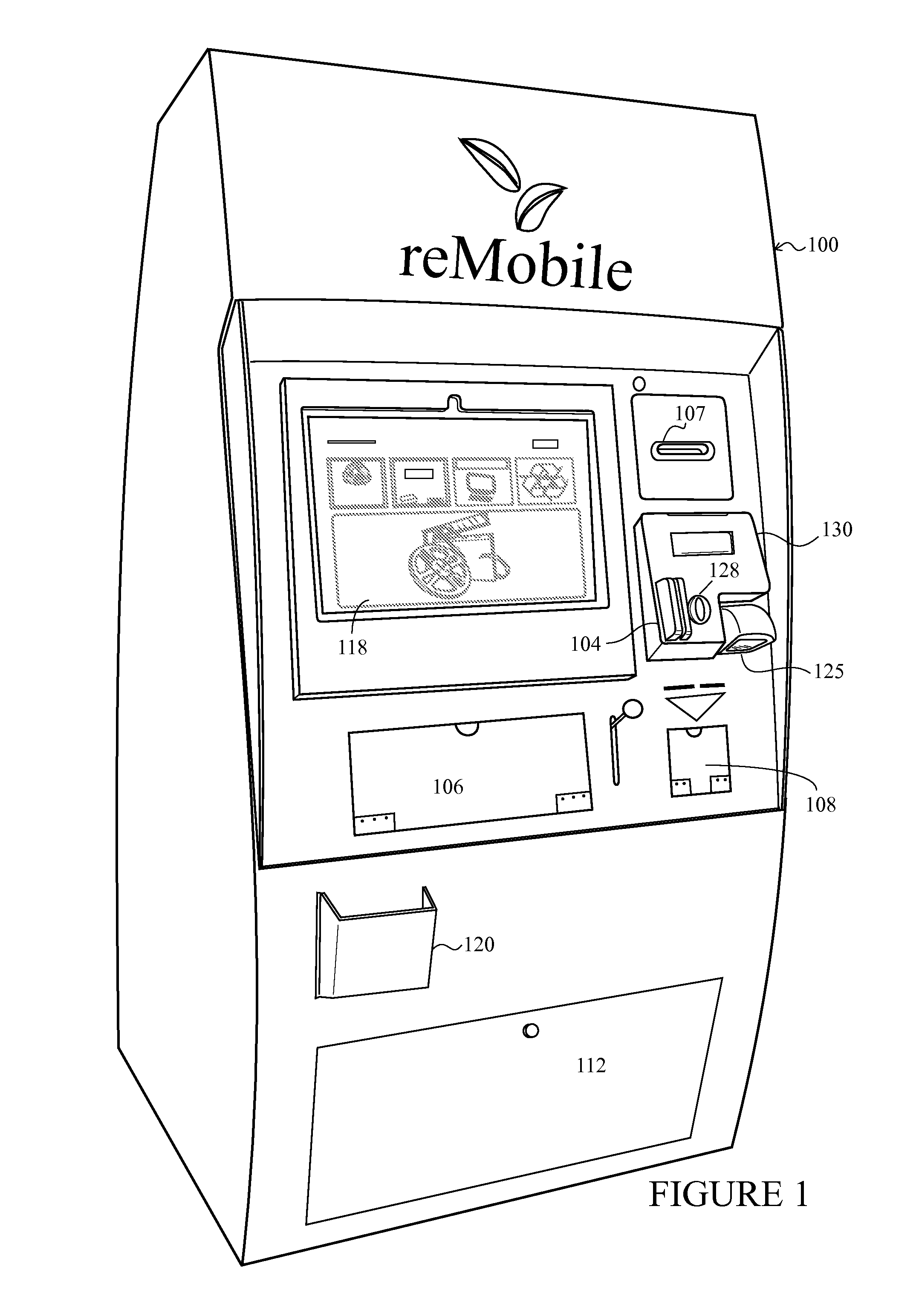
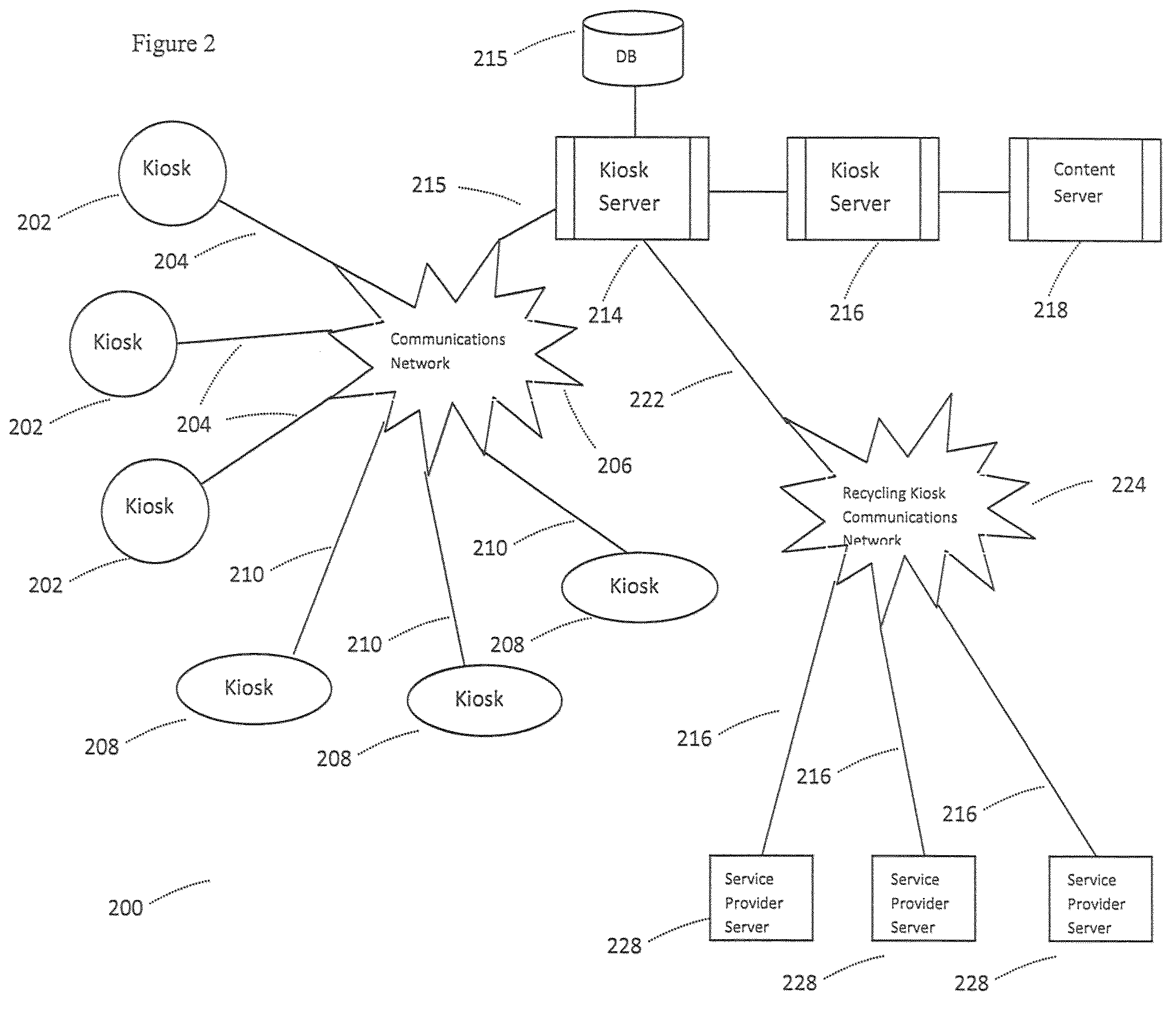
Secondary market and vending system for devices
The system enables one to securely recycle an electronic device in a publicly accessible location. In particular, the embodiment described may be used by a mobile phone owner to submit his / her mobile phone for recycling via an electronic kiosk and receive compensation in some form. The compensation might be dispersed via cash, voucher, credit or debit card, or other magnetic or electronic transaction methods.
Owner:ECOATM LLC
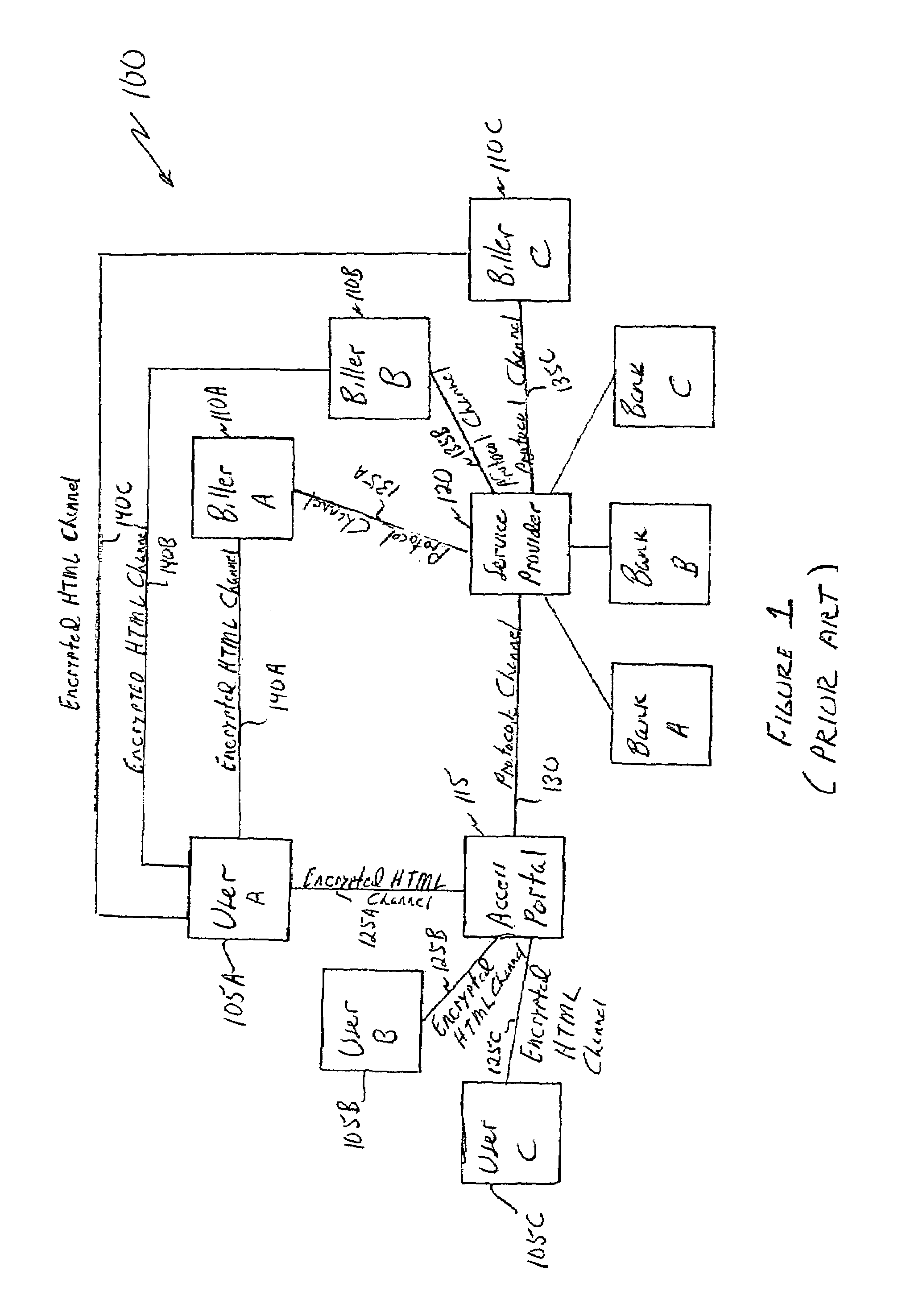
Securing electronic transactions over public networks
InactiveUS6948063B1Enhance authenticationEnhances secrecyMultiple keys/algorithms usageUser identity/authority verificationComputer securityNon symmetric
An electronic message for transmission over a network, such as the Internet, is created by encrypting a first component with a first crypto-key, which is associated with a first network entity, such that the encrypted first component can be decrypted by only the first network entity. The first crypto-key could, for example, be a symmetric crypto-key known only to the first network entity or the public non-symmetric crypto-key of a private-public non-symmetric key pair, where the private non-symmetric crypto key is known only to the first network entity. A second component, which is different than the first component, is encrypted with a second crypto-key, which is associated with a second network entity, such that the encrypted second component can also be decrypted by the first network entity. The second crypto-key could, for example, be a symmetric crypto-key known to both the first and second network entities or the private non-symmetric crypto-key of a private-public non-symmetric key pair of the second network entity, where the public non-symmetric crypto key is known to the first network entity. The encrypted first and second components are combined to create the electronic message.
Owner:CHECKFREE CORP
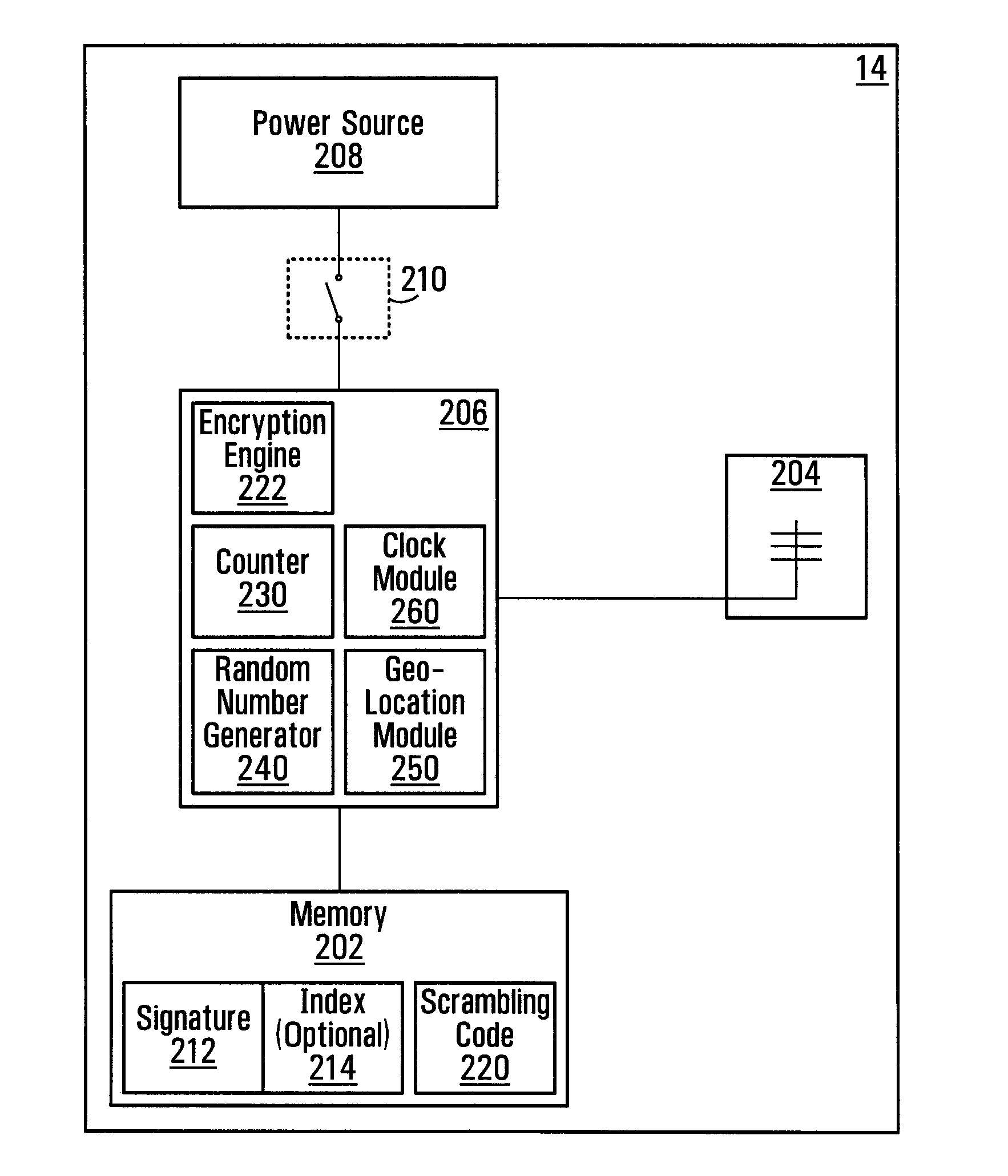
Validation method and system for use in securing nomadic electronic transactions
ActiveUS20110246780A1Improve securityKey distribution for secure communicationFinanceData setValidation methods
A method involving a communication device, which comprises sending a request to a communication device; receiving a response from the communication device over a local communication path; deriving a received data set from said response; determining at least one data set that had been previously transmitted to the communication device over a wireless portion of a second communication path different from the local communication path; and validating the response based on the received data set and the at least one previously transmitted data set.
Owner:BCE
Risk-link authentication for optimizing decisions of multi-factor authentications
A system for evaluating risk in an electronic banking transaction by estimating an aggregated risk value from a set of risk factors that are either dependent or independent of each other, comprising: user input means for enabling an end user to provide authentication information related to a desired electronic banking transaction; financial institution authentication means for authenticating that an end user is authorized to conduct the desired electronic transaction; risk computation means for imposing authentication requirements upon the end user in adaptation to a risk value of the desired banking electronic banking transaction; transaction session means for tracking an amount of time that the desired electronic banking transaction is taking; and financial institution transaction means for storing data related to the desired electronic banking transaction.
Owner:ALNAJEM ABDULLAH ABDULAZIZ I
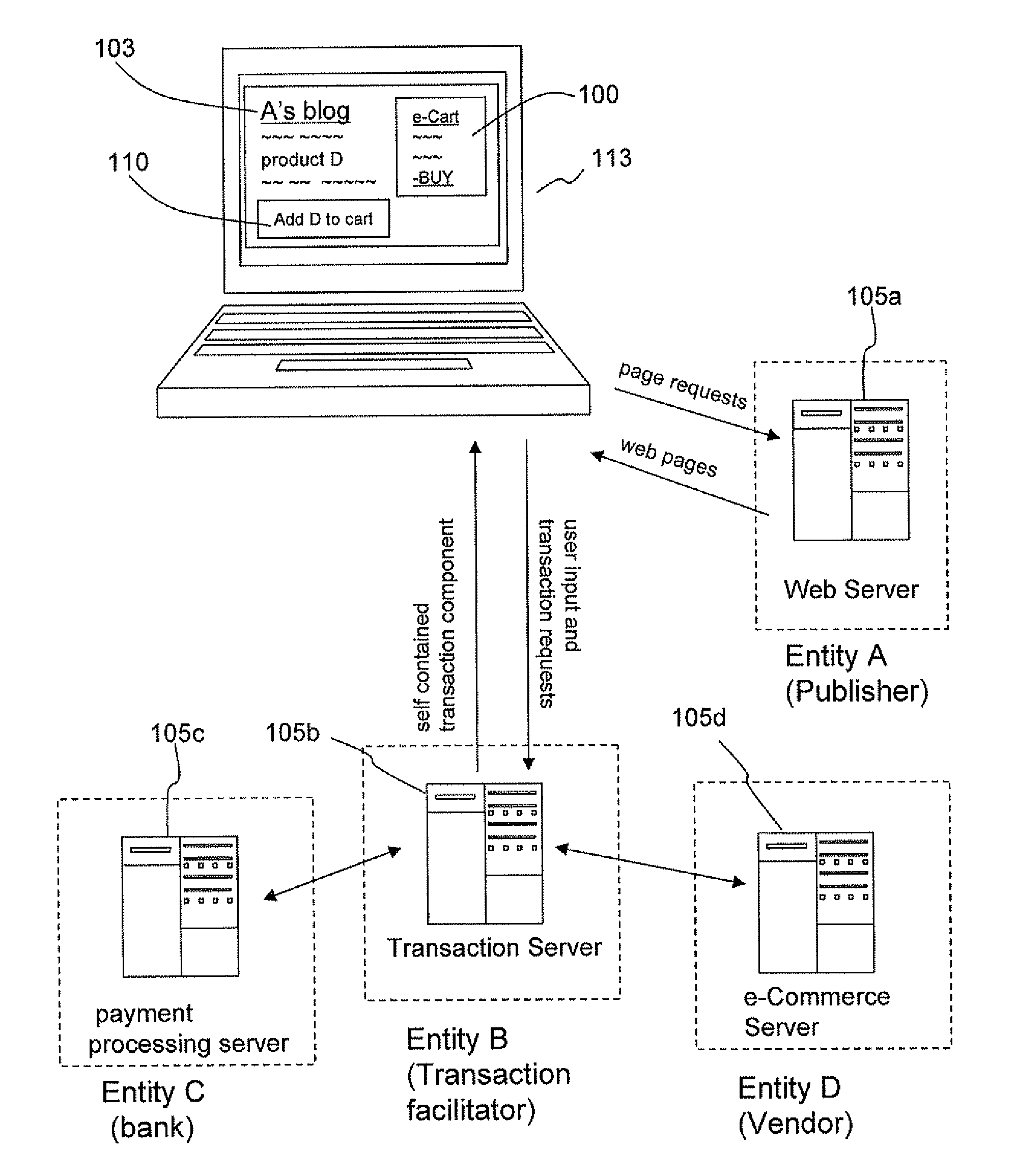
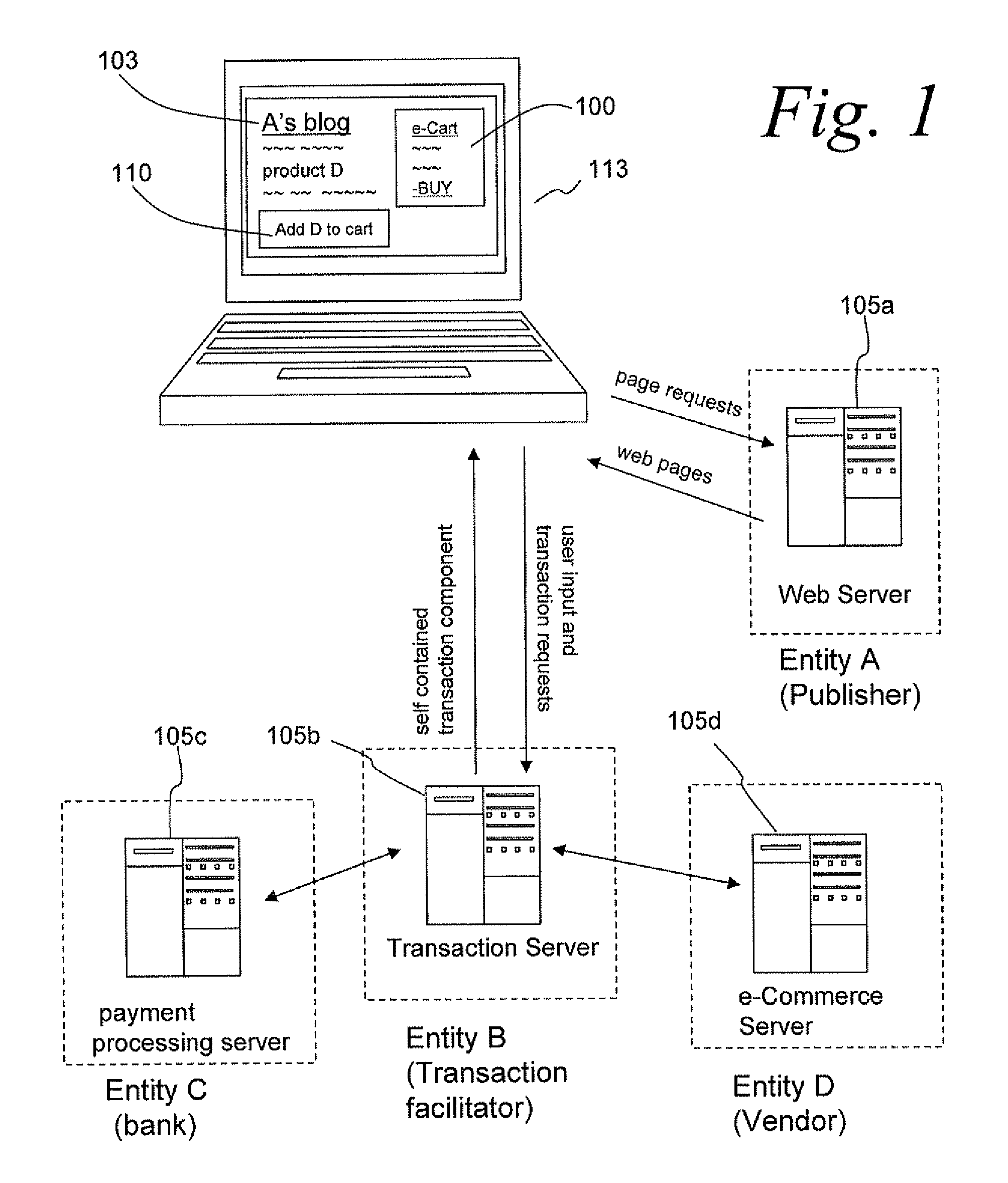
Methods and apparatus for using self-contained transaction components to facilitate online transactions
Systems and methods are described for enabling electronic transactions using self-contained transaction components displayed in a portion of a web page. A method comprises: displaying, in a portion of a web page, a self-contained transaction component; receiving, via the self-contained transaction component, input from a user; transmitting, from the self-contained transaction component to a server, information corresponding to the user and the input; and transmitting, from the self-contained transaction component to the server, an indication to complete a transaction corresponding to the user and the previous input. In one embodiment, the self-contained transaction component comprises an e-cart. Corresponding systems are also described.
Owner:RAKUTEN GRP INC
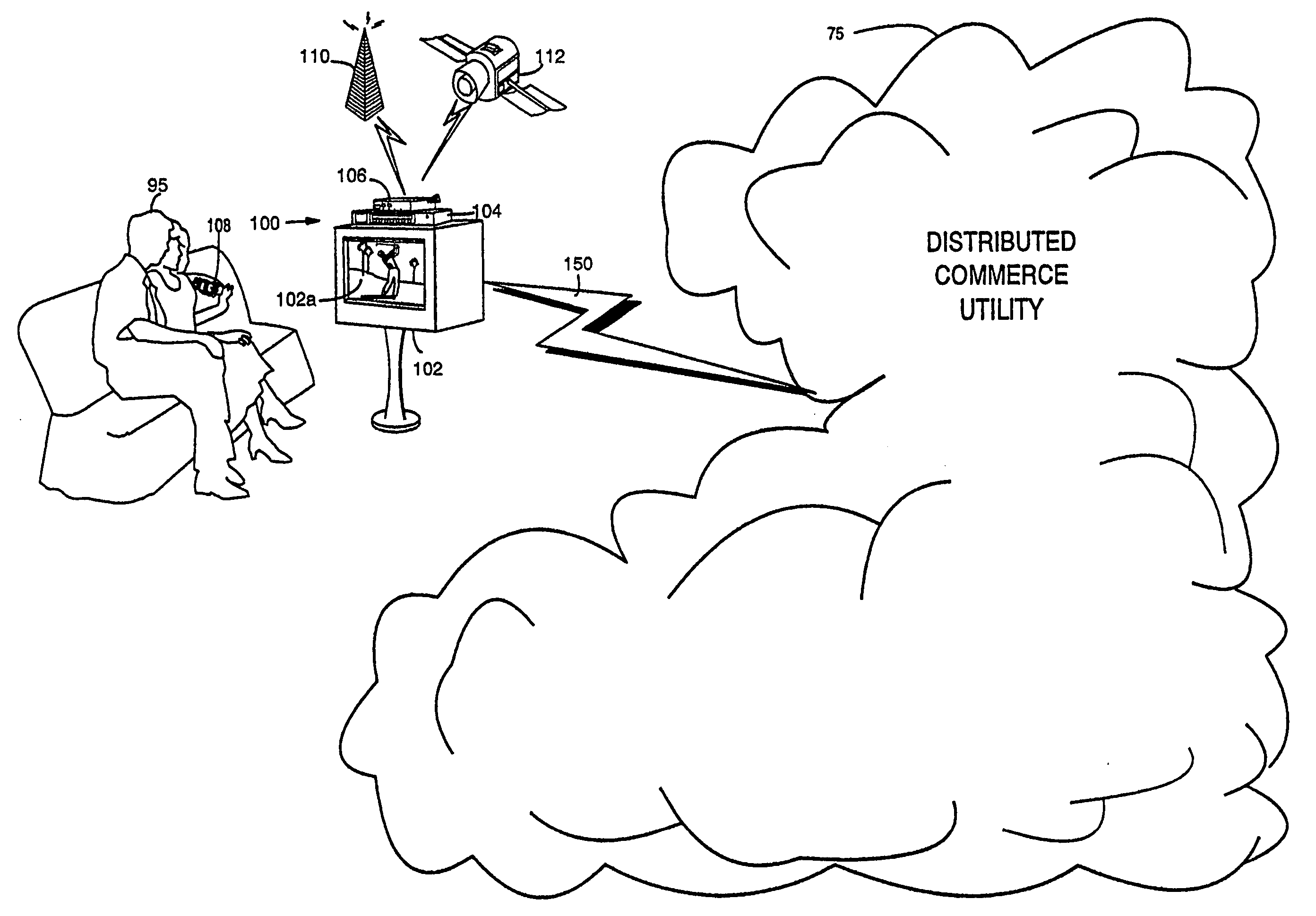
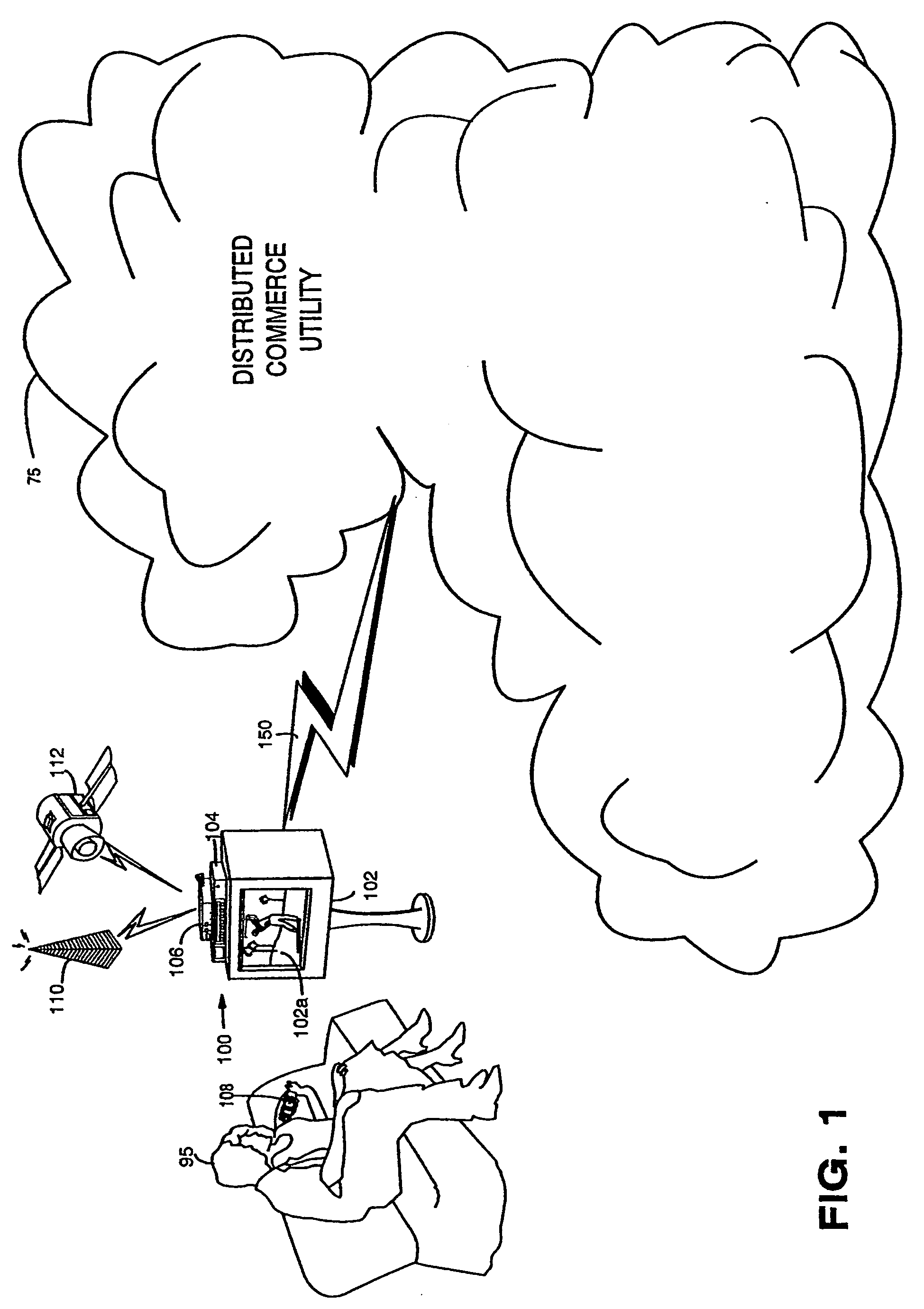
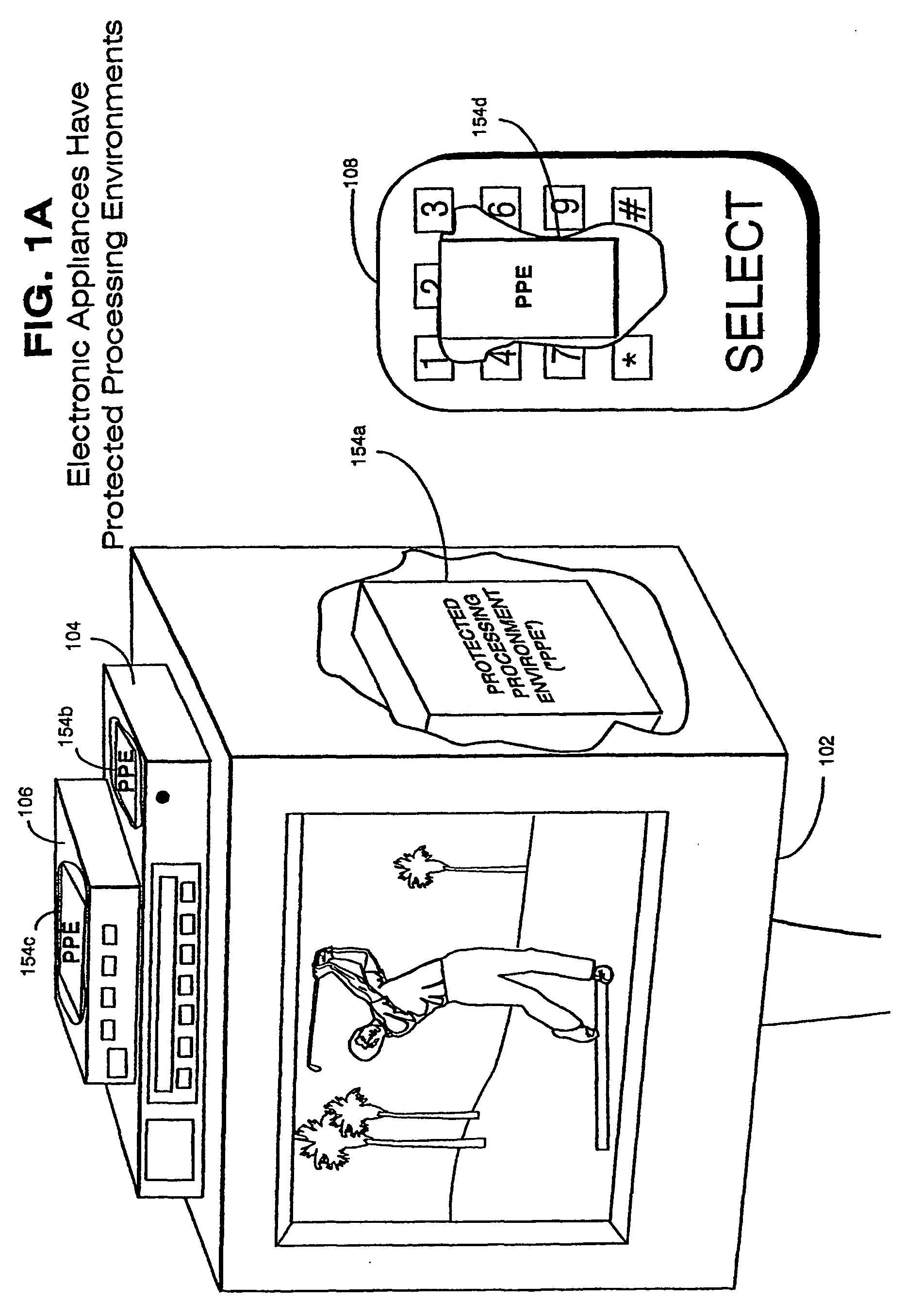
Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management
InactiveUS20060218651A1Improve powerIncrease flexibilityTelevision system detailsPulse modulation television signal transmissionTransaction managementElectronic network
The present inventions provide an integrated, modular array of administrative and support services for electronic commerce and electronic rights and transaction management. These administrative and support services supply a secure foundation for conducting financial management, rights management, certificate authority, rules clearing, usage clearing, secure directory services, and other transaction related capabilities functioning over a vast electronic network such as the Internet and / or over organization internal Intranets. These administrative and support services can be adapted to the specific needs of electronic commerce value chains. Electronic commerce participants can use these administrative and support services to support their interests, and can shape and reuse these services in response to competitive business realities. A Distributed Commerce Utility having a secure, programmable, distributed architecture provides administrative and support services. The Distributed Commerce Utility makes optimally efficient use of commerce administration resources, and can scale in a practical fashion to accommodate the demands of electronic commerce growth. The Distributed Commerce Utility may comprise a number of Commerce Utility Systems. These Commerce Utility Systems provide a web of infrastructure support available to, and reusable by, the entire electronic community and / or many or all of its participants. Different support functions can be collected together in hierarchical and / or in networked relationships to suit various business models and / or other objectives. Modular support functions can combined in different arrays to form different Commerce Utility Systems for different design implementations and purposes. These Commerce Utility Systems can be distributed across a large number of electronic appliances with varying degrees of distribution.
Owner:INTERTRUST TECH CORP
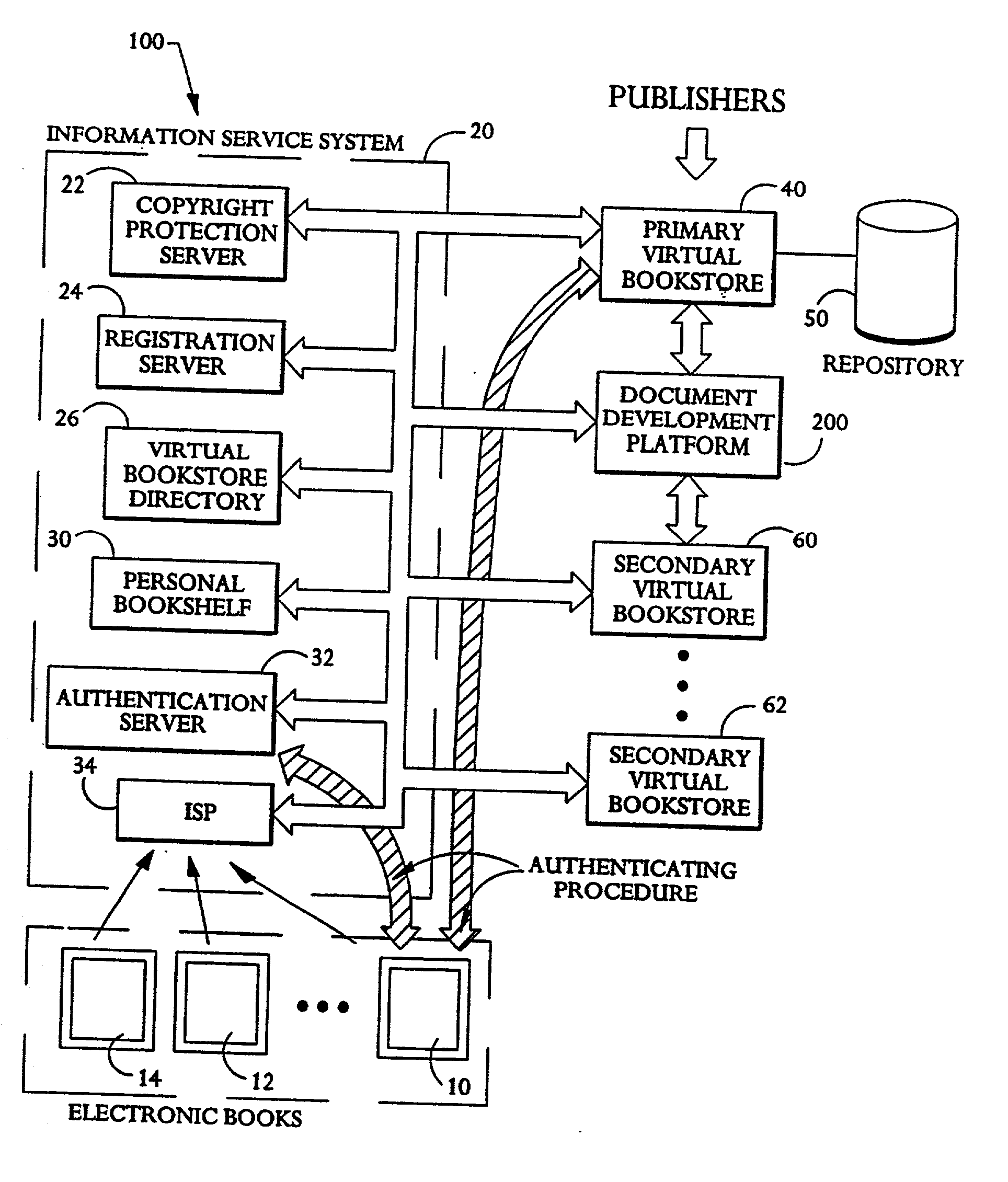
Systems and methods for electronic off-line catalog
ActiveUS20030069812A1Buying/selling/leasing transactionsSpecial data processing applicationsWorld Wide WebElectronic transaction
Owner:ROVI GUIDES INC +1
System and method for optimized funding of electronic transactions
The invention provides systems and methods for managing transactions. The system includes a data input portion that communicates first information regarding a payment request, as well as a decision reference data store for communicating second information regarding parameters for use in determining a payment option for the payment request. The system also includes a processor. The processor inputs the first information and the second information. Then, the processor selectably determines the payment option to direct a transmission of funds from at least one payment source to at least one payee account based on an optimization determination performed by the processor. The optimization determination may provide savings to the institution processing the transaction, or alternatively, may provide savings to the customer initiating the transaction, for example.
Owner:JPMORGAN CHASE BANK NA
Tokenless electronic transaction system
InactiveUS6985608B2Simple and cost-effectiveDigital data processing detailsCharacter and pattern recognitionPaymentComputerized system
The invention as described provides a method and system for tokenless authorization of commercial transactions between a buyer and a seller using a computer system. The method comprises the steps of registering a buyer, wherein the buyer registers with the computer system a PIN, at least one registration biometric sample, and at least one buyer financial account. The method also includes a seller registration step, wherein the seller registers with the computer system at least one seller financial account. In a proposal step, the seller offers a proposed commercial transaction to the buyer usually comprising price information. If the buyer accepts the seller's proposal, in an acceptance step, the buyer signals his / her acceptance by adding to the proposed commercial transaction the buyer's personal authentication information comprising a PIN and at least one bid biometric sample which is obtained from the buyer's person. In a transmission step, the bid biometric sample and PIN are forwarded to the computer system. The computer system compares the bid biometric sample with registration biometric samples for producing either a successful or failed identification of the buyer in a buyer identification step. Upon determination of sufficient resources, a financial account of the buyer is debited and a financial account of the seller is credited, in a payment step. Therefore, a commercial transaction is conducted without the buyer having to use any portable man-made memory devices such as smartcards or swipe cards.
Owner:EXCEL INNOVATIONS +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com