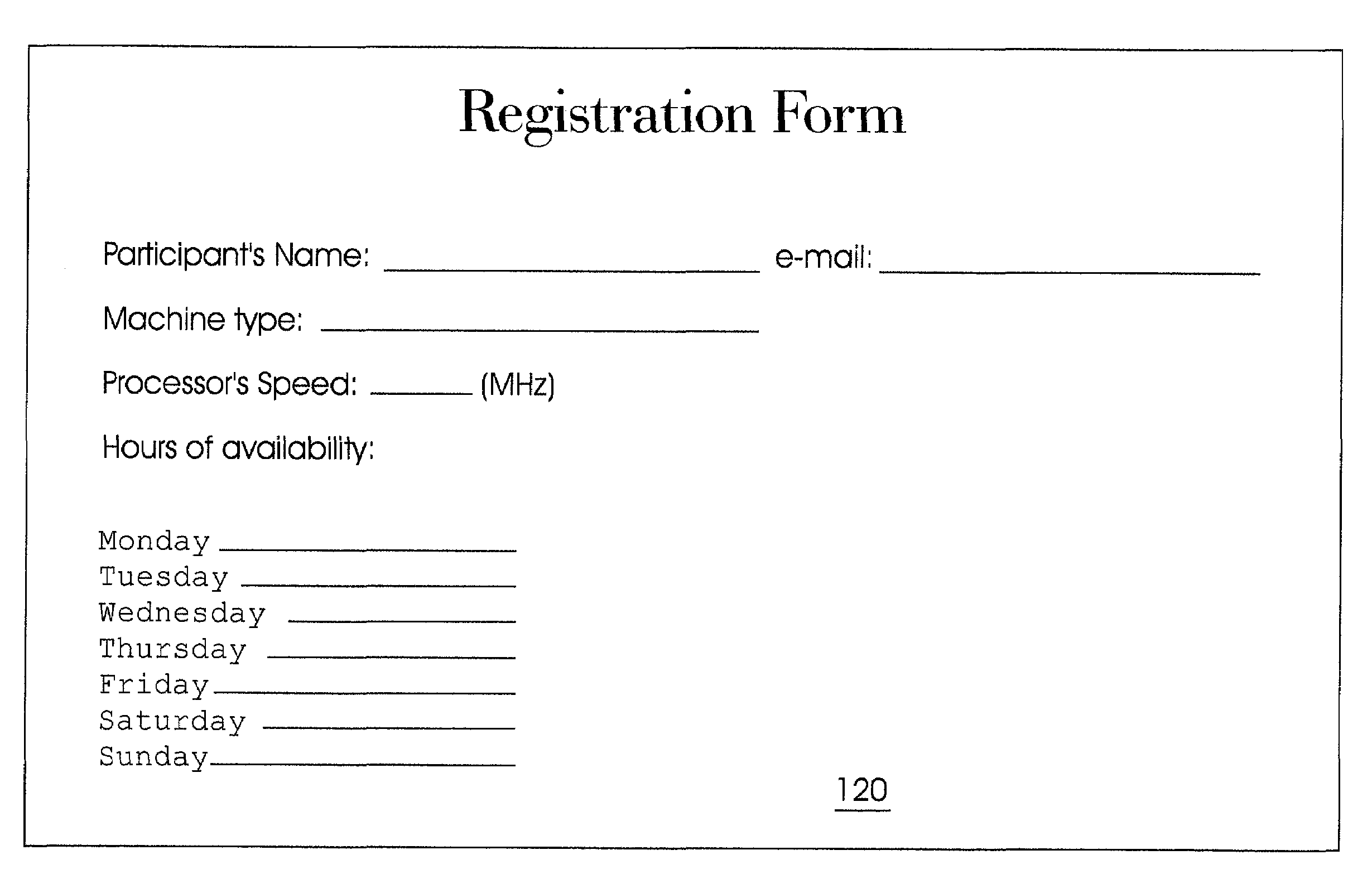
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
254 results about "Mainframe computer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Mainframe computers or mainframes (colloquially referred to as "big iron") are computers used primarily by large organizations for critical applications; bulk data processing, such as census, industry and consumer statistics, enterprise resource planning; and transaction processing. They are larger and have more processing power than some other classes of computers: minicomputers, servers, workstations, and personal computers.
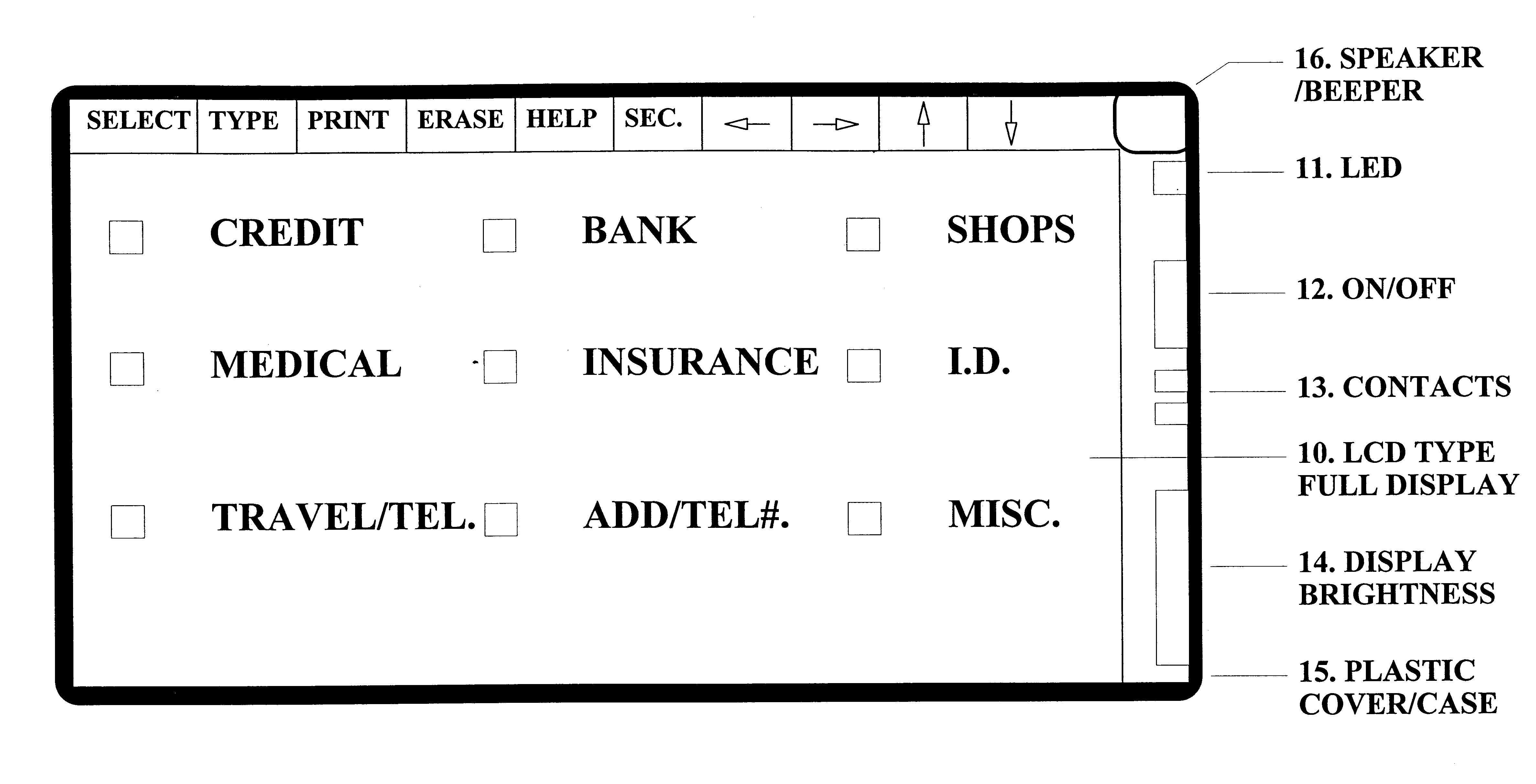
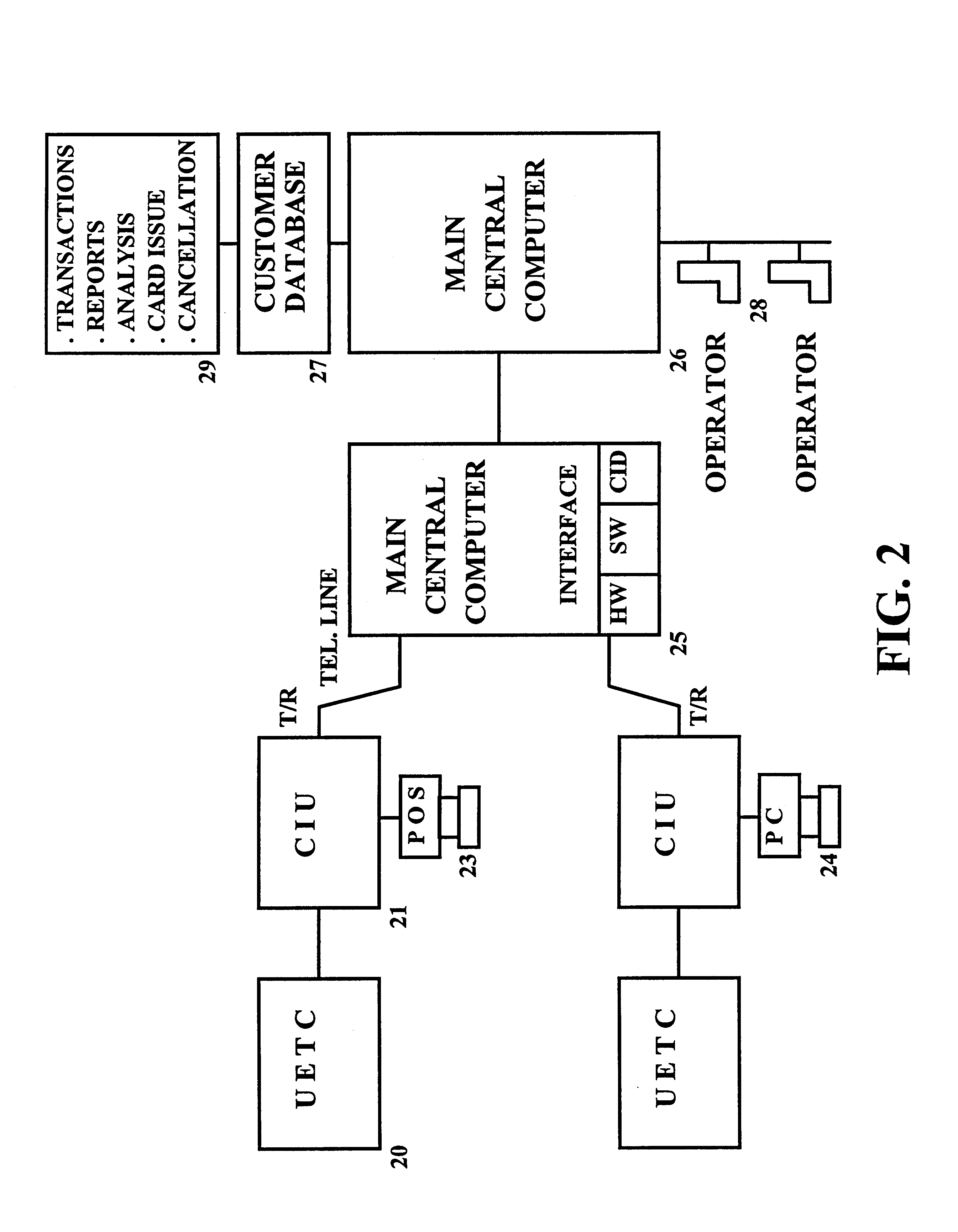
Device, system and methods of conducting paperless transactions
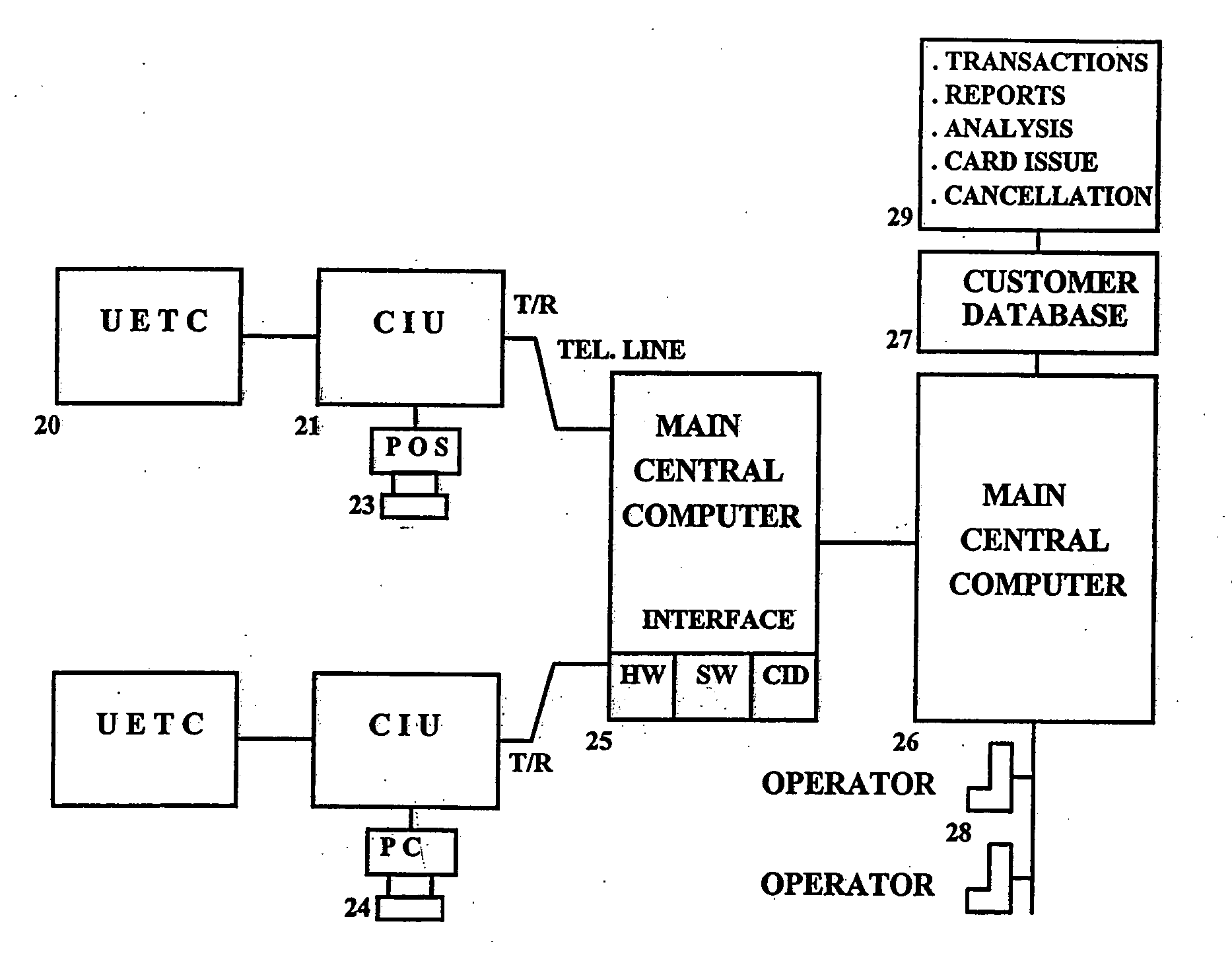
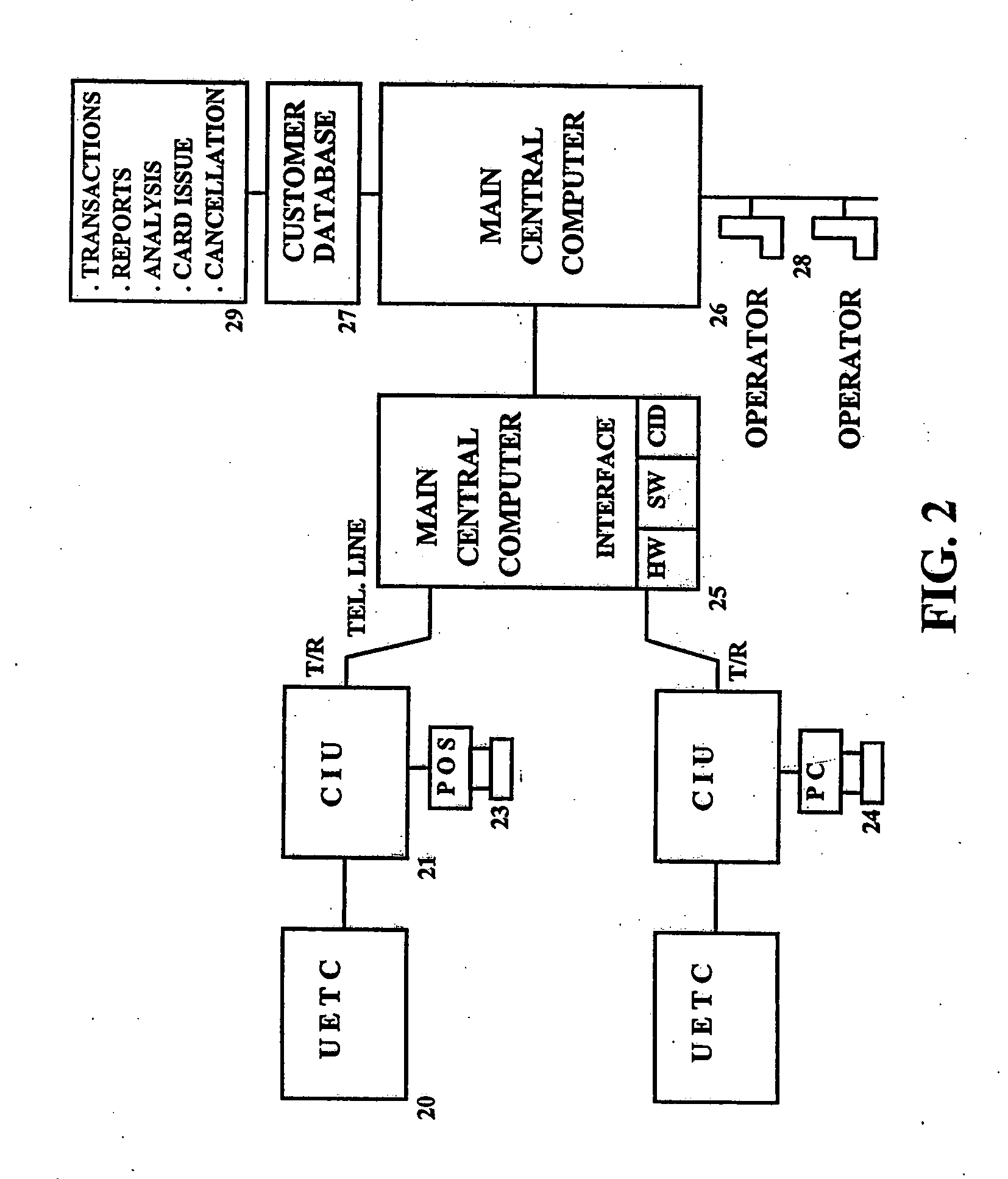
InactiveUS6925439B1Eliminate pointEliminate all paper transactions and billsFinancePayment circuitsPersonal computerComputer terminal
The invention also includes methods of issuing an account authorization to a UET card, a method of transferring transactional and account information between a UET card and a personal computer or a mainframe computer, a method of using the UET card as a remote terminal for a mainframe computer, and a method of conducting an electronic transaction.
Owner:C SAM INC
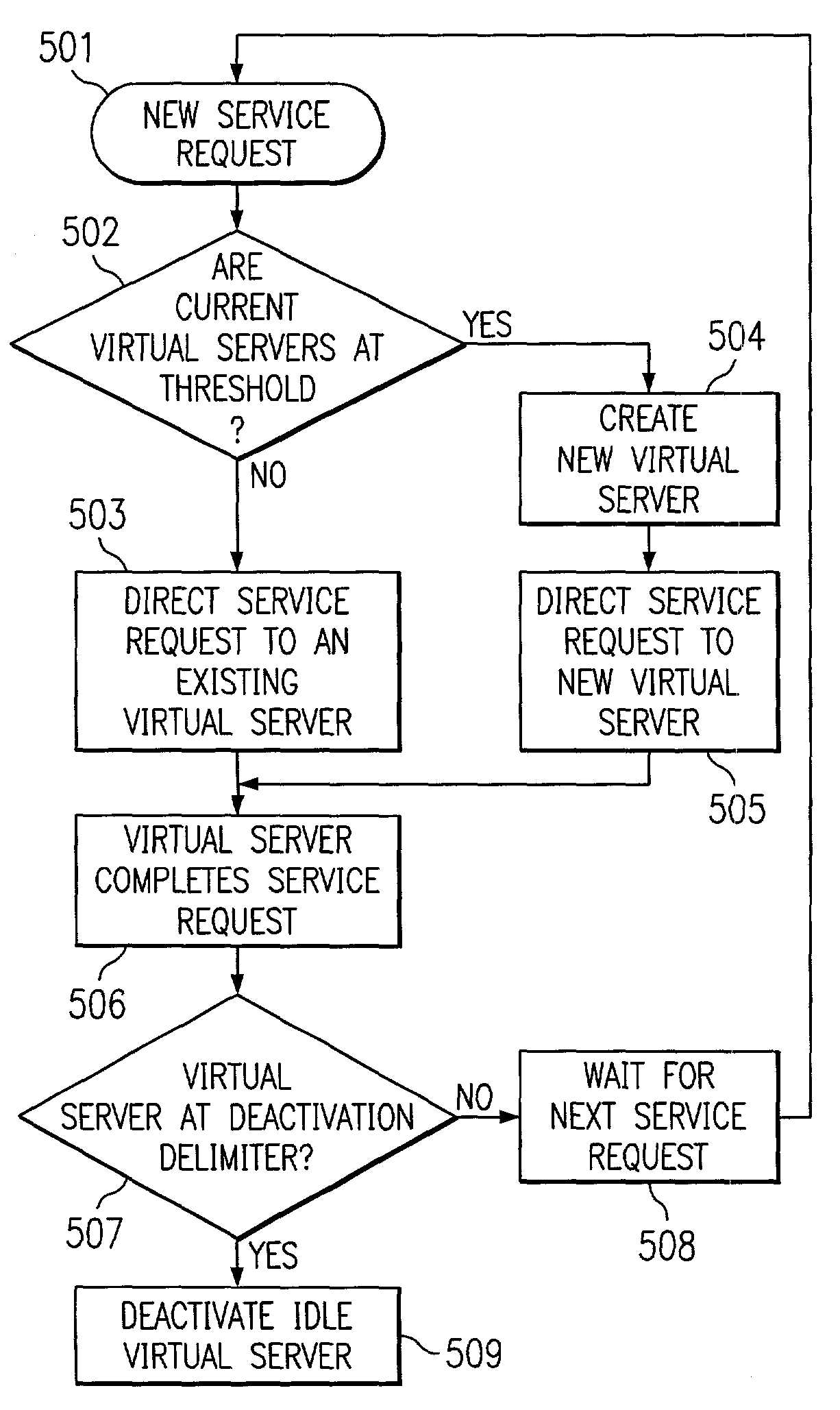
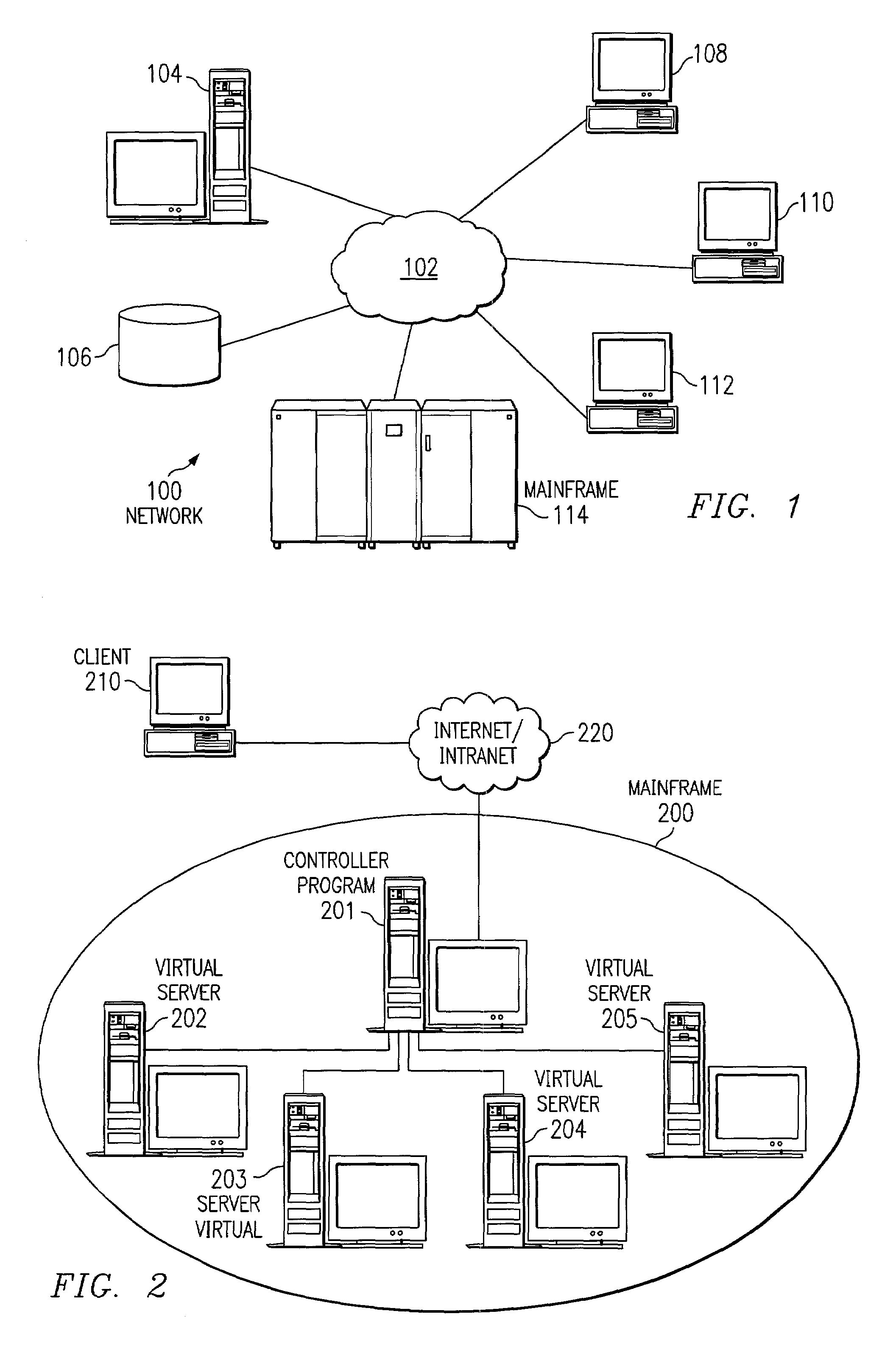
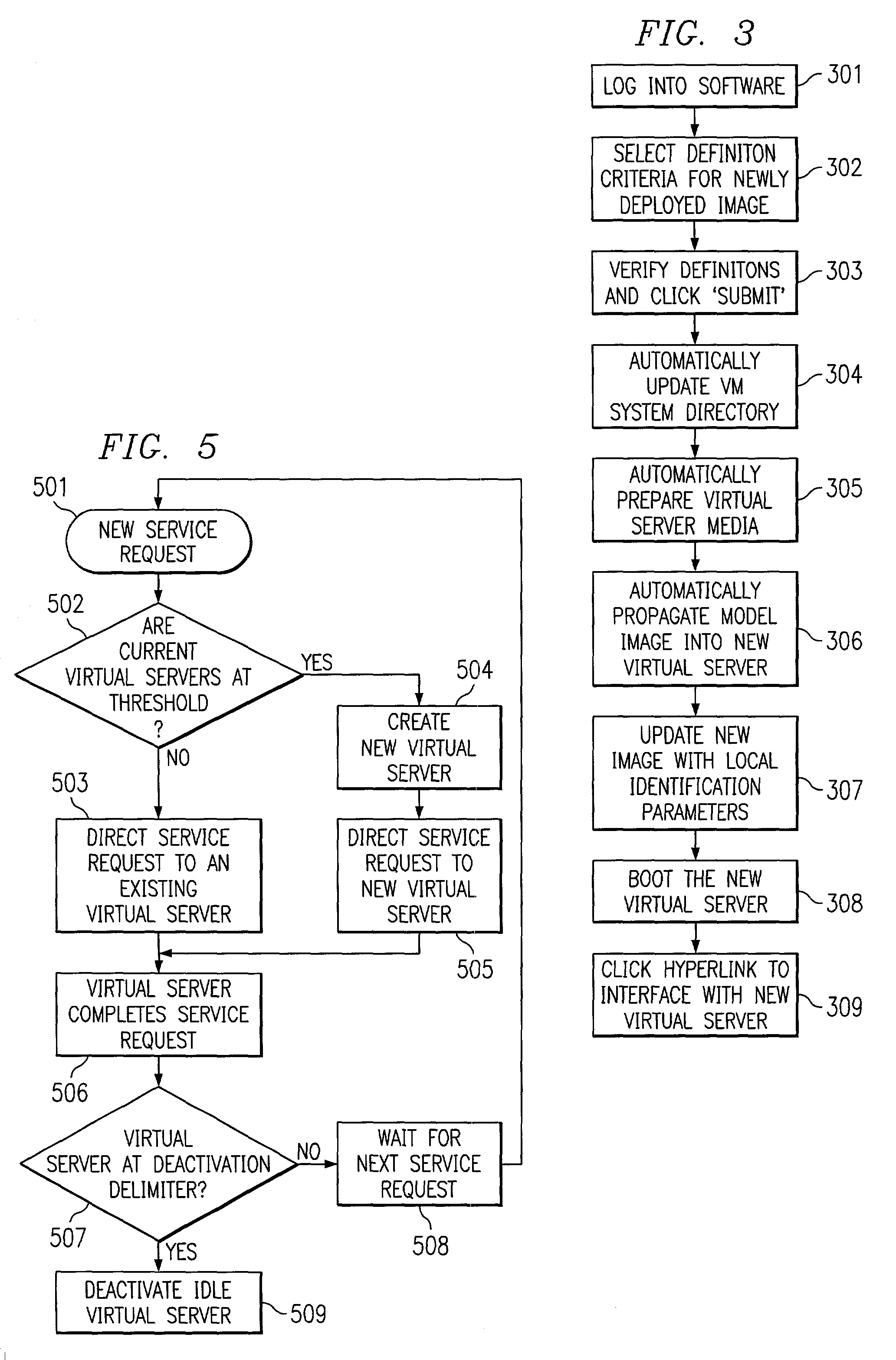
Workload balancing using dynamically allocated virtual servers
A method for scaling resources according to workload among virtual servers running on a mainframe computer is provided. The invention comprises monitoring the number of service requests received by a cluster of virtual servers and determining if the service requests exceed a specified service limit for the servers. If the number of service requests exceeds the specified service limit, a new virtual server is automatically deployed by a software solution. This additional virtual server performs identical services as the other virtual servers in the cluster. This process is repeated until there are a sufficient number of servers to handle the workload. Service requests are then allocated among the cluster of virtual servers, until the number of requests falls below a certain threshold, at which point the extra servers are automatically deactivated.
Owner:ORACLE INT CORP
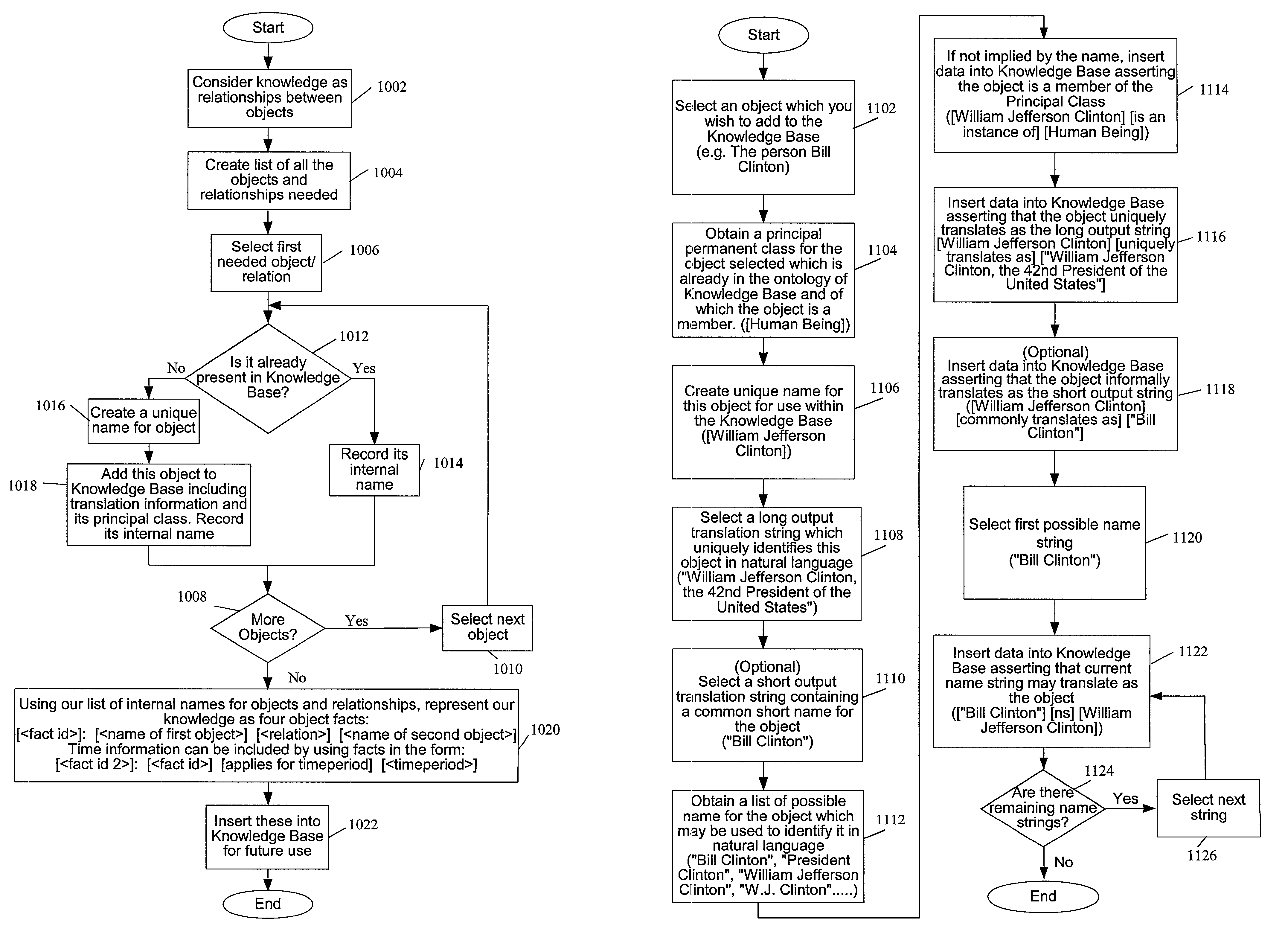
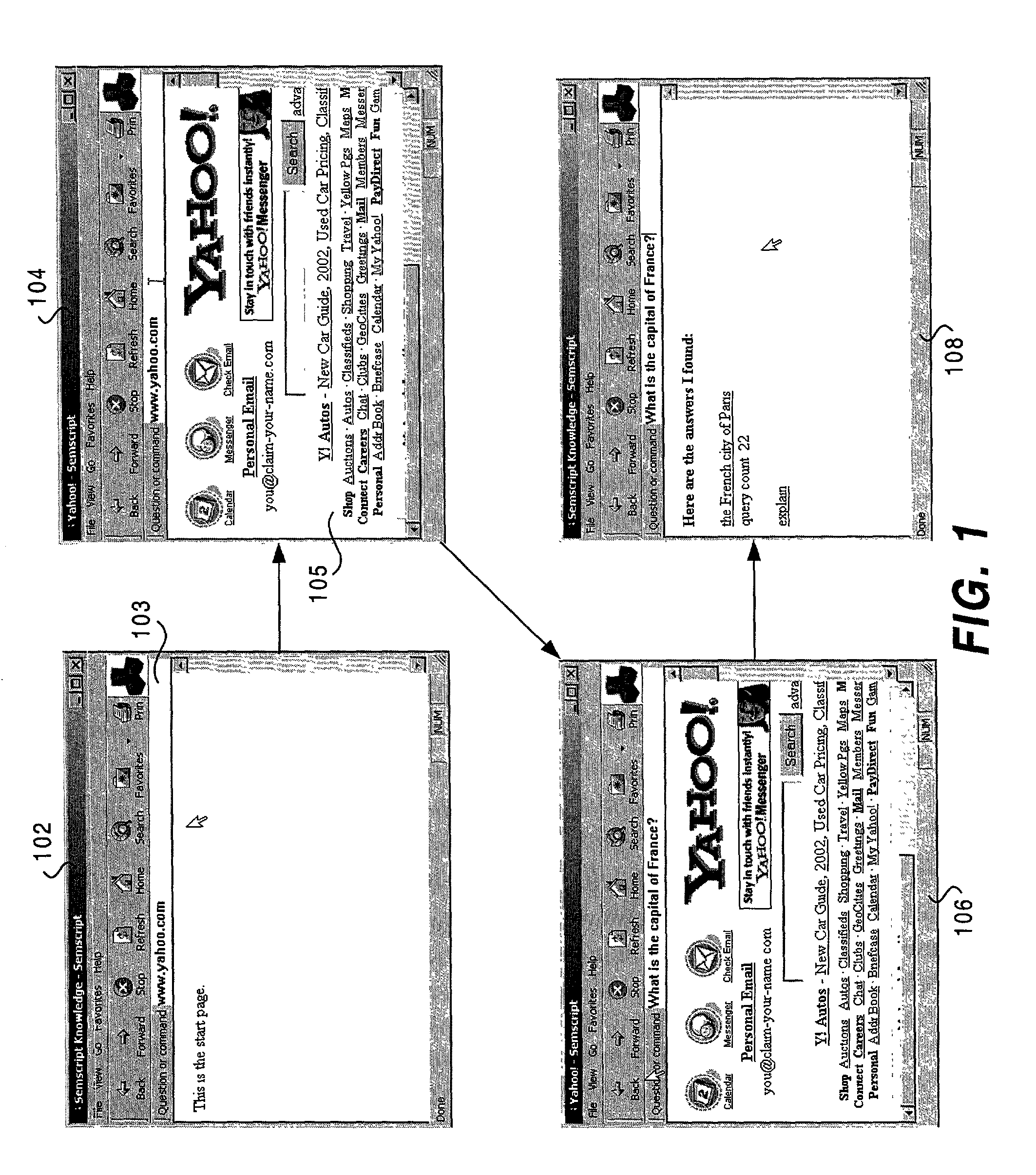
Knowledge storage and retrieval system and method
InactiveUS7013308B1Smooth interfaceSimple processDigital data information retrievalData processing applicationsProgramming languageWeb browser
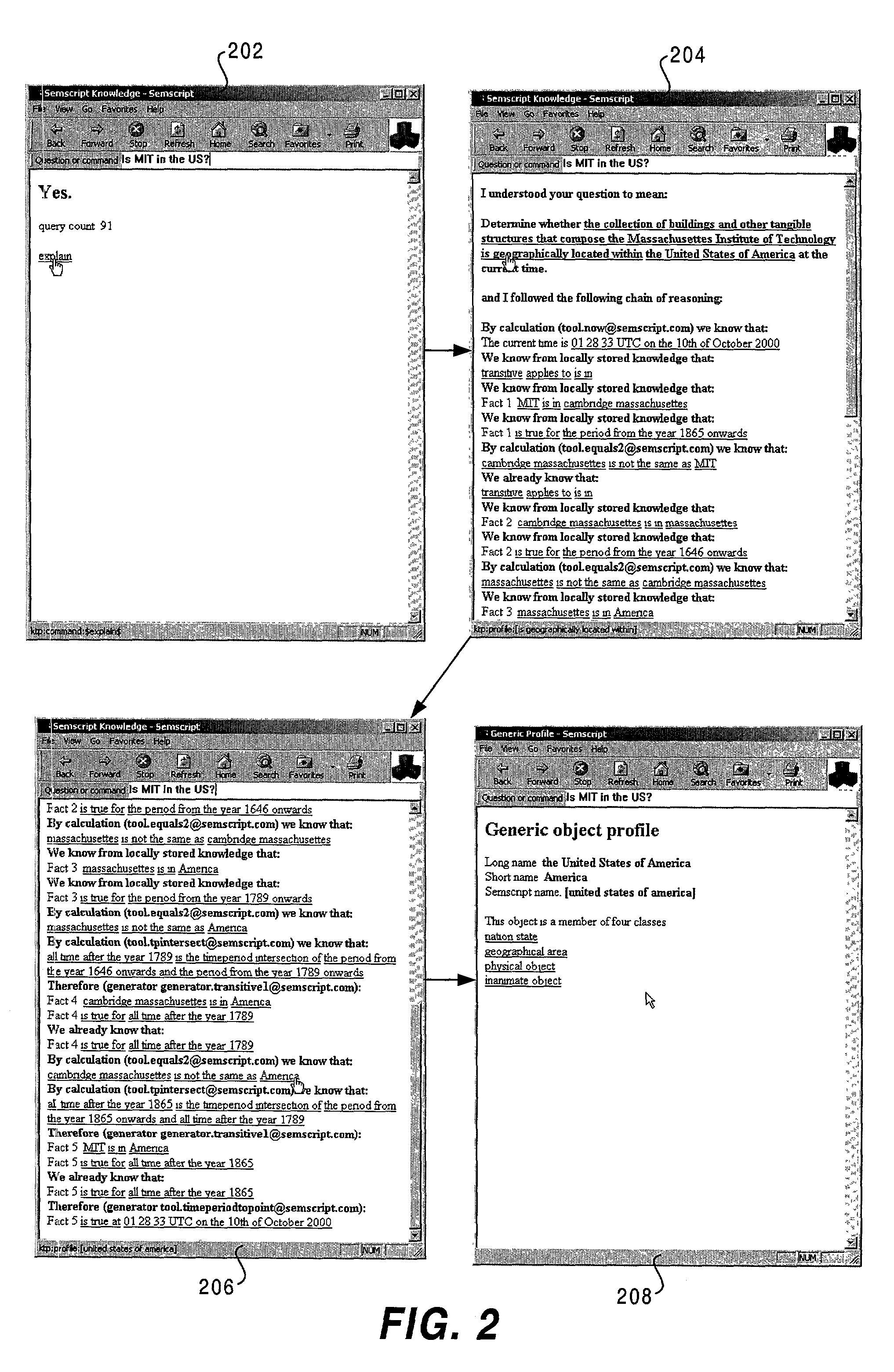
A system and method for representing, storing and retrieving real-world knowledge on a computer or network of computers is disclosed. Knowledge is broken down into permanent atomic “facts” which can be stored in a standard relational database and processed very efficiently. It also provides for the efficient querying of a knowledge base, efficient inference of new knowledge and translation into and out of natural language. Queries can also be processed with full natural language explanations of where the answers came from. The method can also be used in a distributed fashion enabling the system to be a large network of computers and the technology can be integrated into a web browser adding to the browser's functionality.
Owner:AMAZON TECH INC
Device, system and methods of conducting paperless transactions
InactiveUS20050247777A1Eliminate pointEliminate all paper transactions and billsCash registersPatient personal data managementCredit cardDisplay device
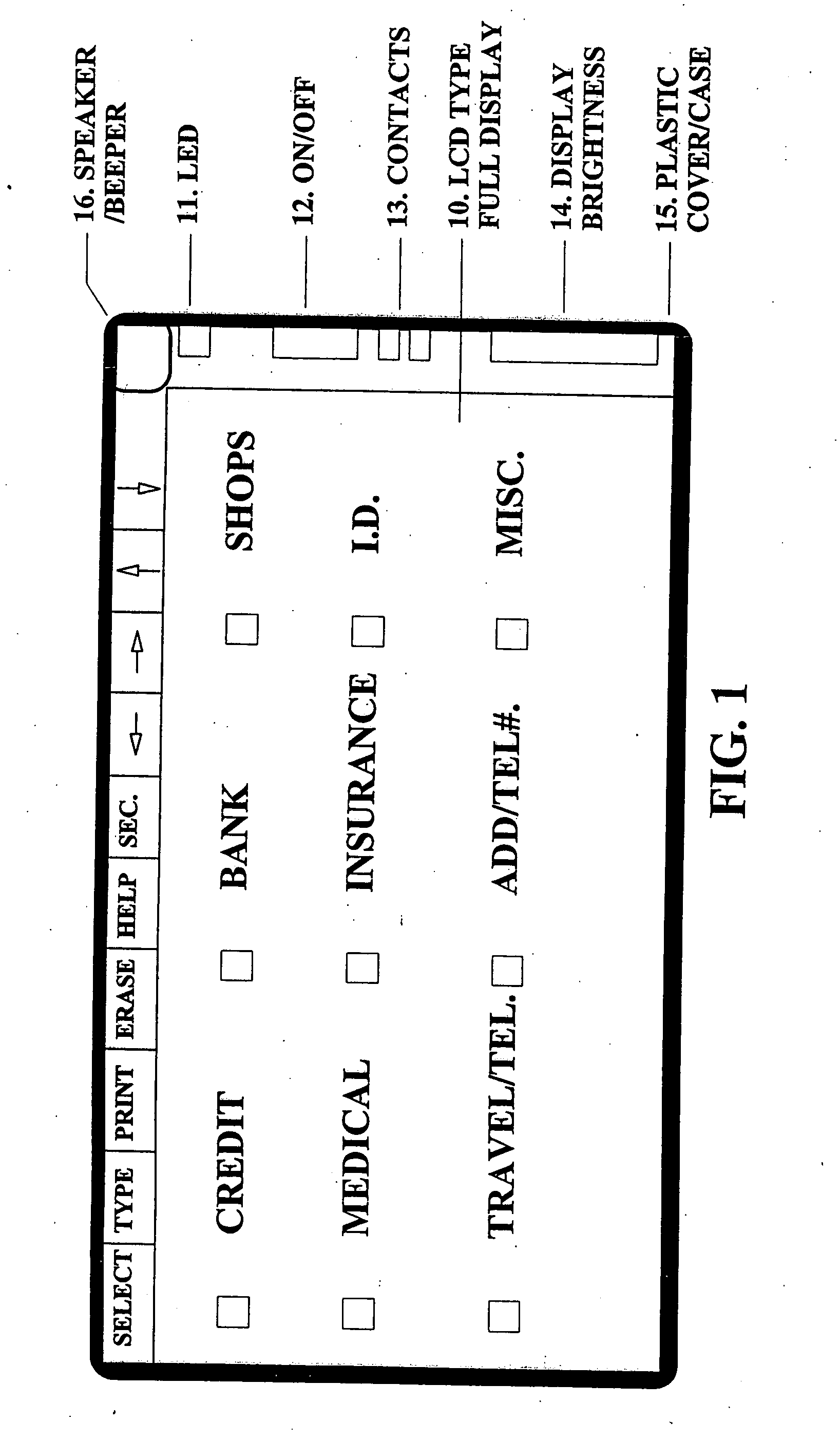
A universal electronic transaction card (“UET card”) is capable of serving as a number of different credit cards, bank cards, identification cards, employee cards, medical cards and the like. The UET card includes storage elements, an input interface, a processor, a display, and a communications interface. In a preferred embodiment, the UET card stores transactional information to eliminate paper receipts and includes security features to prevent unauthorized use. The UET card may also be used to replace conventional currency and traveler's checks, and may be configured to store and display promotional information, such as advertising and incentives. A communications interface unit (“CIU”) may be provided to interface between the UET card and a personal computer, automatic banking terminal (commonly referred to as ATM machines) and / or an institutional mainframe computer. CIU devices may include electrical contact for recharging a UET card. A system of utilizing the UET card is also provided which includes UET cards and CIU devices which enable the transmission of information between point of sales (or point of transactions) computers and the UET cards. The system further includes point of sales computers configured to communicate with the UET card and with service institution computers. The invention also includes a health care management system utilizing UET cards. In the health care management system, all medical information for a patient may be stored in the UET card so that when a patient receives services from a health care provider, that health care provider connects the patient's UET card to the health care provider's computer system and can then obtain all pertinent medical information concerning the patient, including the patient's medical history, insurance information and the like. In addition, the treatment or services provided by the health care provider are stored in the patient's UET card. The invention also includes methods of issuing an account authorization to a UET card, a method of transferring transactional and account information between a UET card and a personal computer or a mainframe computer, a method of using the UET card as a remote terminal for a mainframe computer, and a method of conducting an electronic transaction.
Owner:C SAM INC
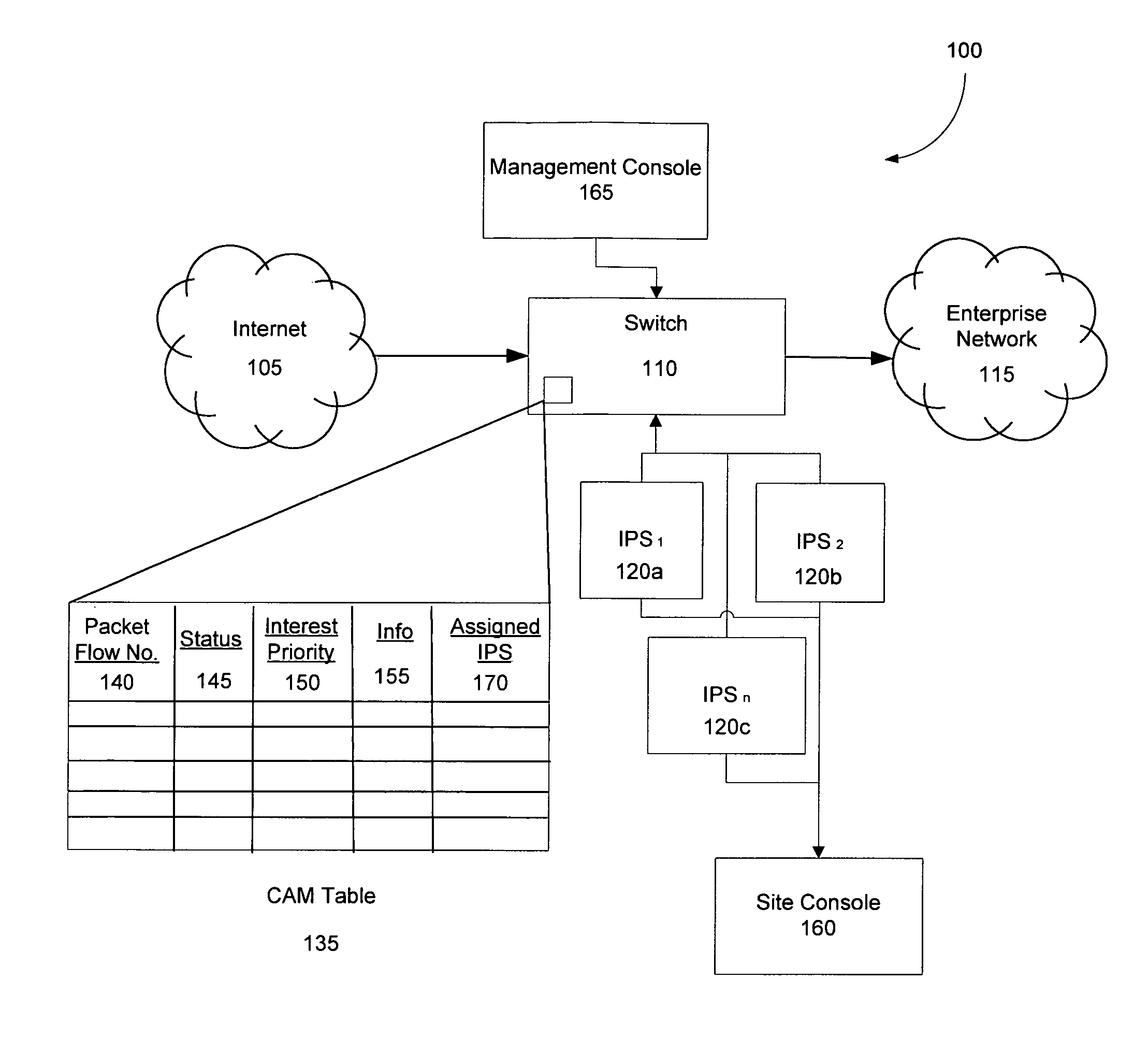
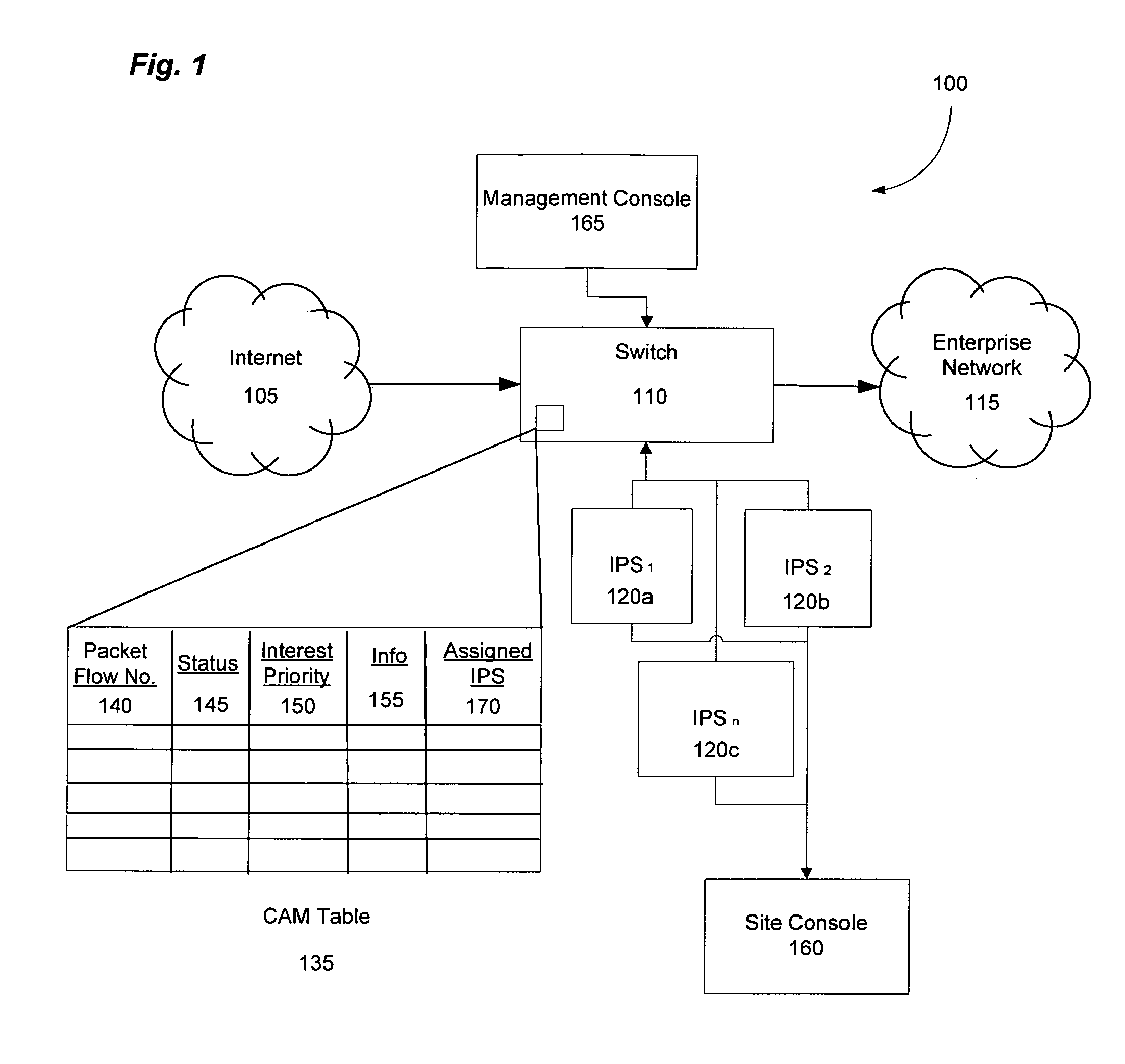
Fast network security utilizing intrusion prevention systems
InactiveUS7808897B1Avoid OverloadingIncrease the number ofError preventionFrequency-division multiplex detailsTraffic capacityNetwork data
Intrusion Prevention Systems (“IPSs”) are used to detect and / or prevent intrusion events from infiltrating a computer network. However, in large computer networks the IPSs cannot conduct their analysis on network data traffic quickly enough in the network core to meet the demand placed on them by the computer networks, thereby causing delays in the transmission of network data traffic from a source to a destination. To prevent this delay, the IPSs can be configured to intelligently communicate with a high-capacity network switch. The IPSs conduct the initial inspection of the network data traffic flows to determine if an intrusion event is present. However, after the initial inspection, the IPS can inform the switch of what actions to take for future traffic flows including determining which future traffic flows are inspected by the IPSs and which future traffic flows are allowed to be blocked or transmitted to their destination by the switch.
Owner:LINKEDIN
Systems and methods to detect copy number variation
InactiveUS20120046877A1Correction biasMicrobiological testing/measurementProteomicsData fileWorkstation
In one aspect, a system for implementing a copy number variation analysis method, is disclosed. The system can include a nucleic acid sequencer and a computing device in communications with the nucleic acid sequencer. The nucleic acid sequencer can be configured to interrogate a sample to produce a nucleic acid sequence data file containing a plurality of nucleic acid sequence reads. In various embodiments, the computing device can be a workstation, mainframe computer, personal computer, mobile device, etc.The computing device can comprise a sequencing mapping engine, a coverage normalization engine, a segmentation engine and a copy number variation identification engine. The sequence mapping engine can be configured to align the plurality of nucleic acid sequence reads to a reference sequence, wherein the aligned nucleic acid sequence reads merge to form a plurality of chromosomal regions. The coverage normalization engine can be configured to divide each chromosomal region into one or more non-overlapping window regions, determine nucleic acid sequence read coverage for each window region and normalize the nucleic acid sequence read coverage determined for each window region to correct for bias. The segmentation engine can be configured to convert the normalized nucleic acid sequence read coverage for each window region to discrete copy number states. The copy number variation identification engine can be configured to identify copy number variation in the chromosomal regions by utilizing the copy number states of each window region.
Owner:LIFE TECH CORP
Information technology process workflow for data centers
InactiveUS7900206B1Error detection/correctionDigital computer detailsData centerComputer compatibility
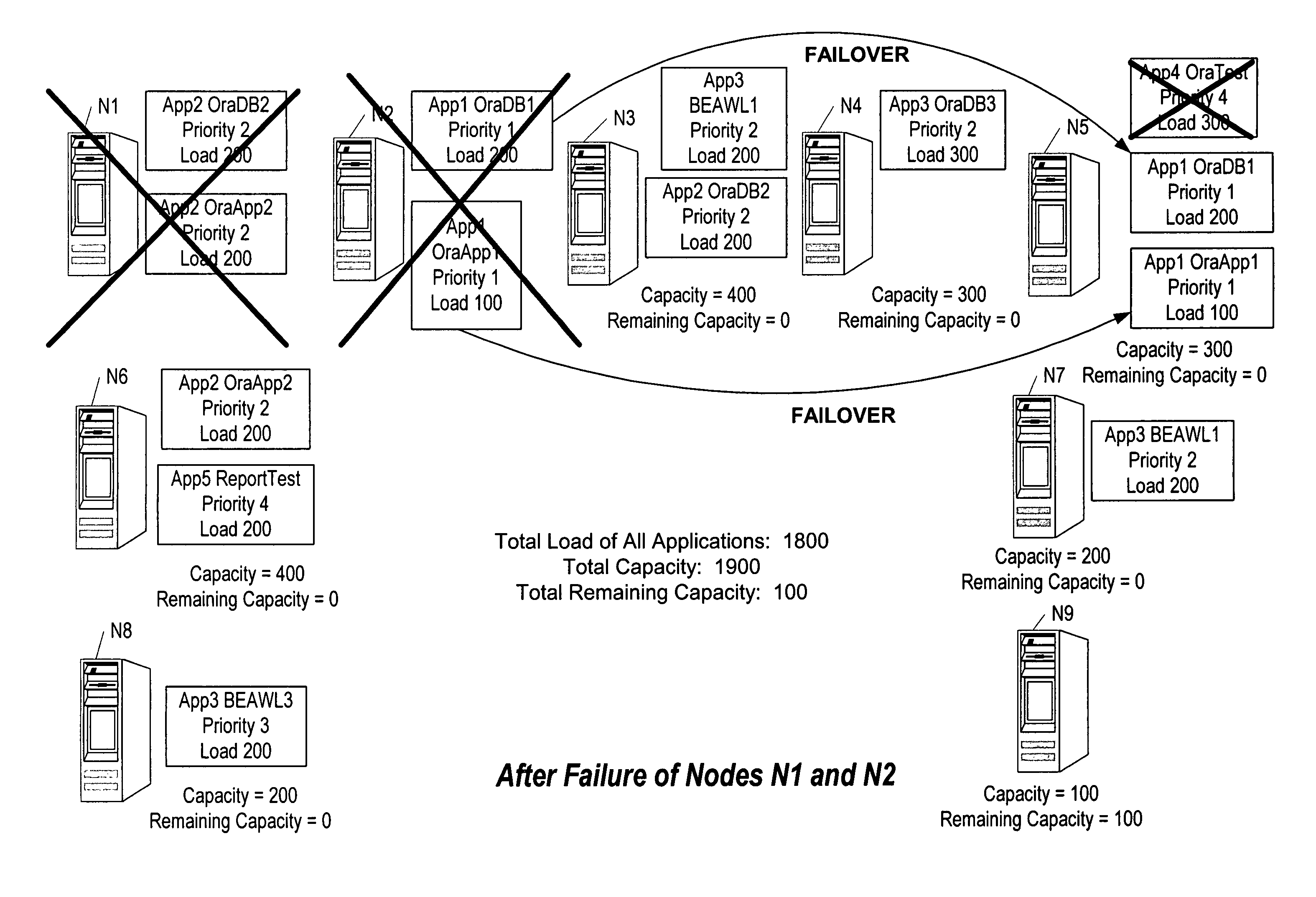
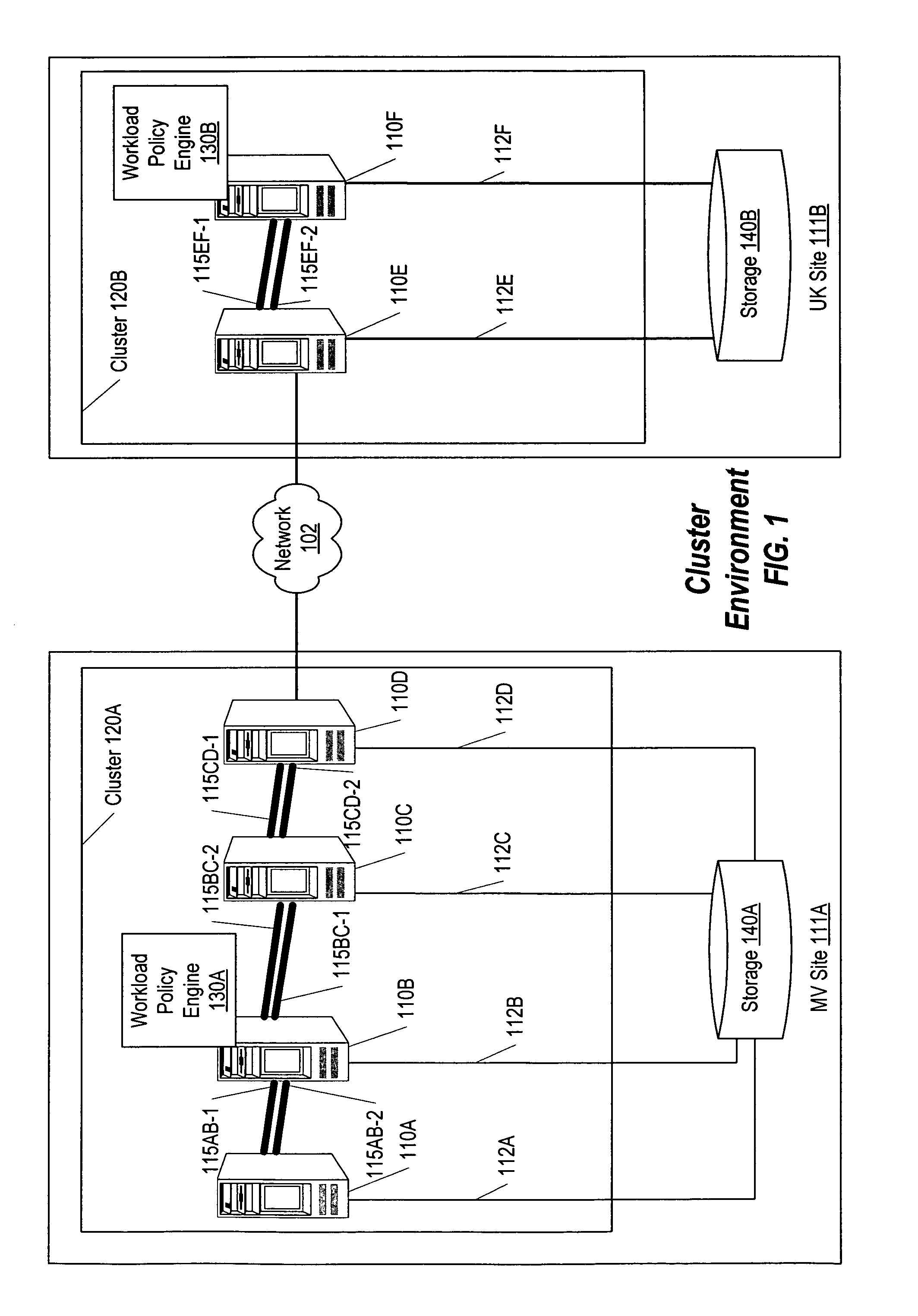
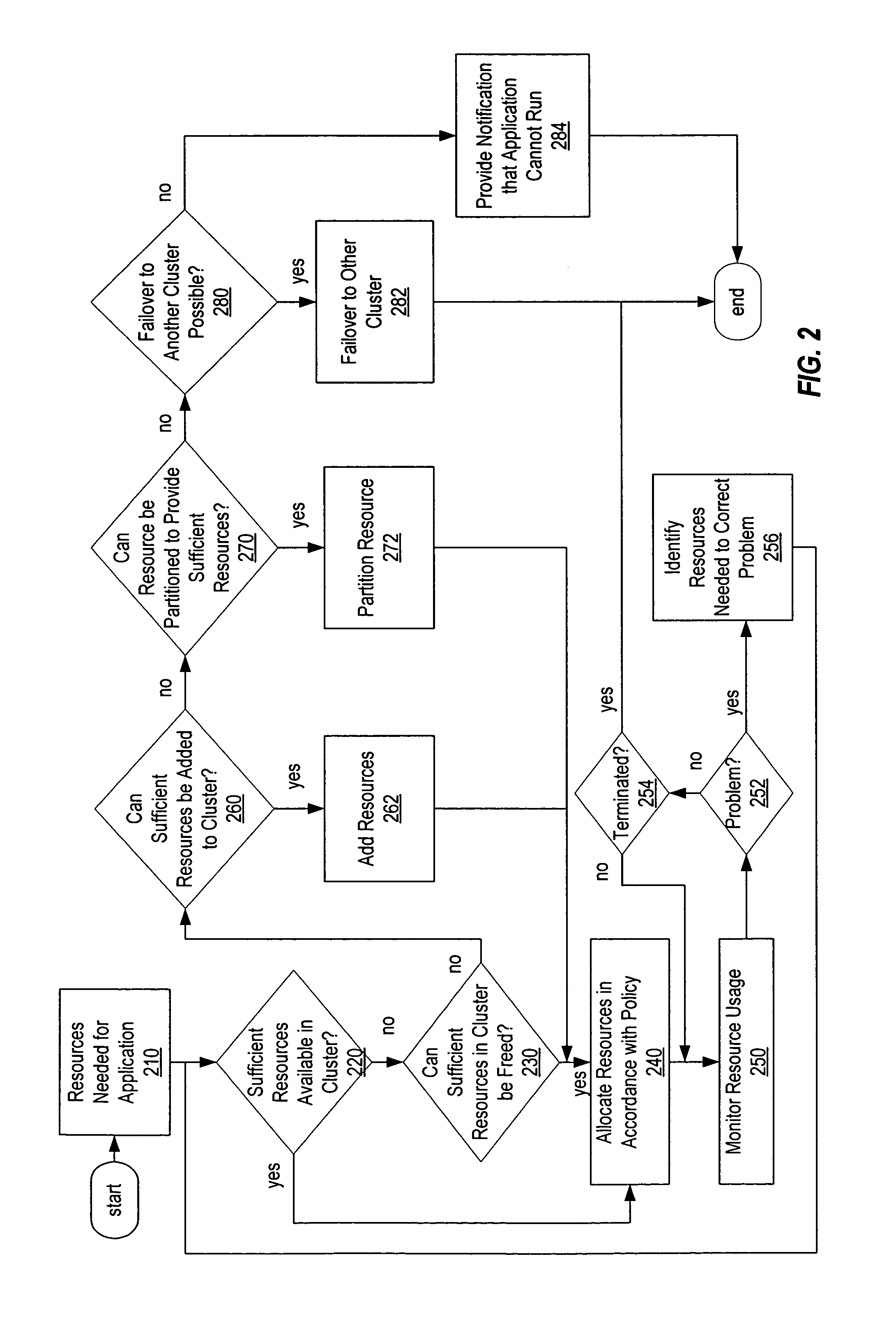
A method, system, computer system, and computer program product that use application requirements, business priorities, and compatibility and dependency among applications to allocate resources among those applications in a clustering environment. A workload policy engine is aware of the resources available within each cluster, as well as the capacities of those resources. Multiple instances of the workload policy engine can be run in different clusters. The workload policy engine can be used in conjunction with disaster recovery products as well as with provisioning software so that new machines can be provisioned in and out of a cluster dynamically, such as in a blade environment. Furthermore, the workload policy engine can be used in conjunction with dynamic repartitioning capabilities provided by different hardware platforms for large computer systems, as well as with performance monitoring software.
Owner:SYMANTEC OPERATING CORP
Method and apparatus for incremental code signing
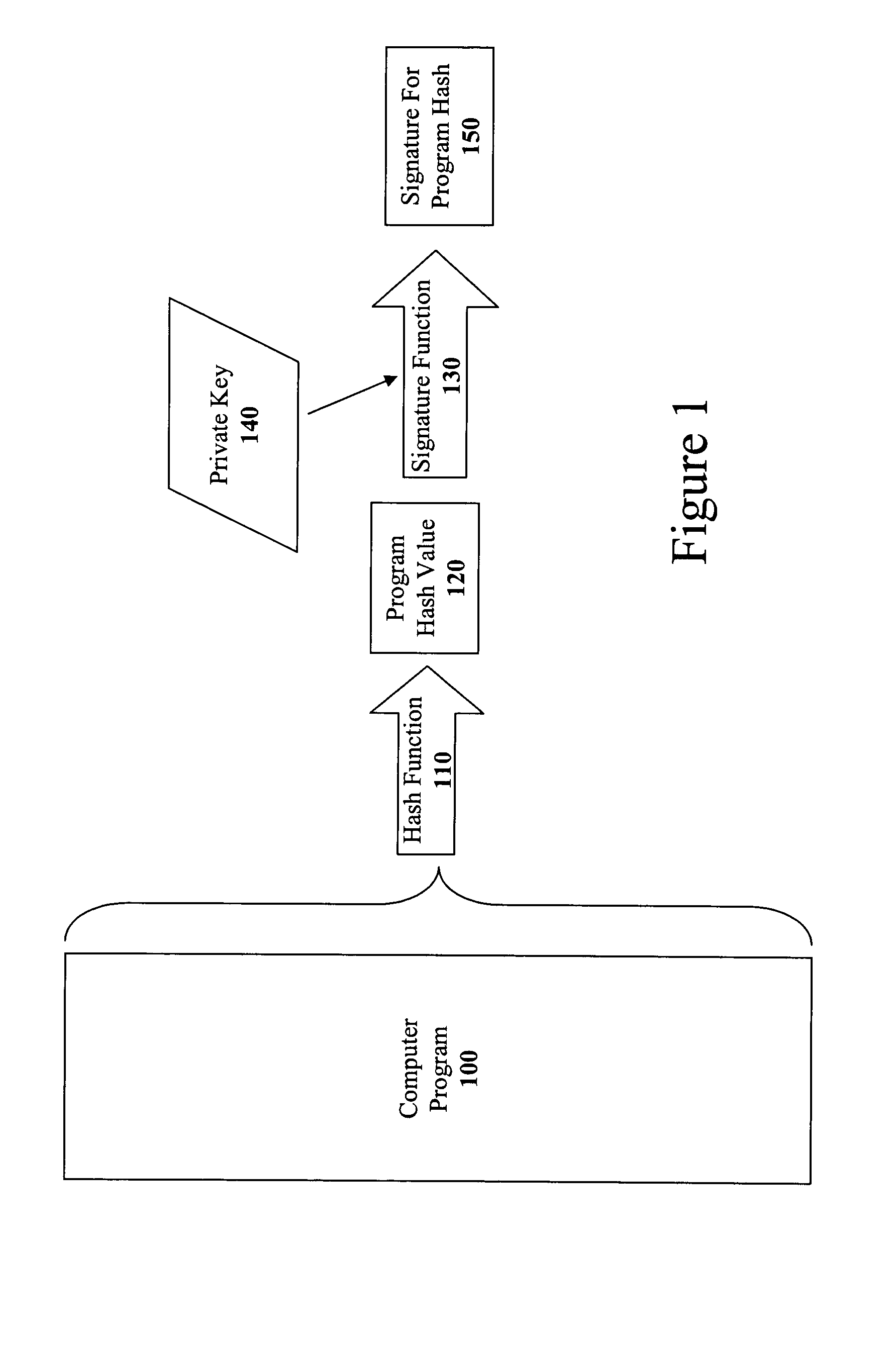
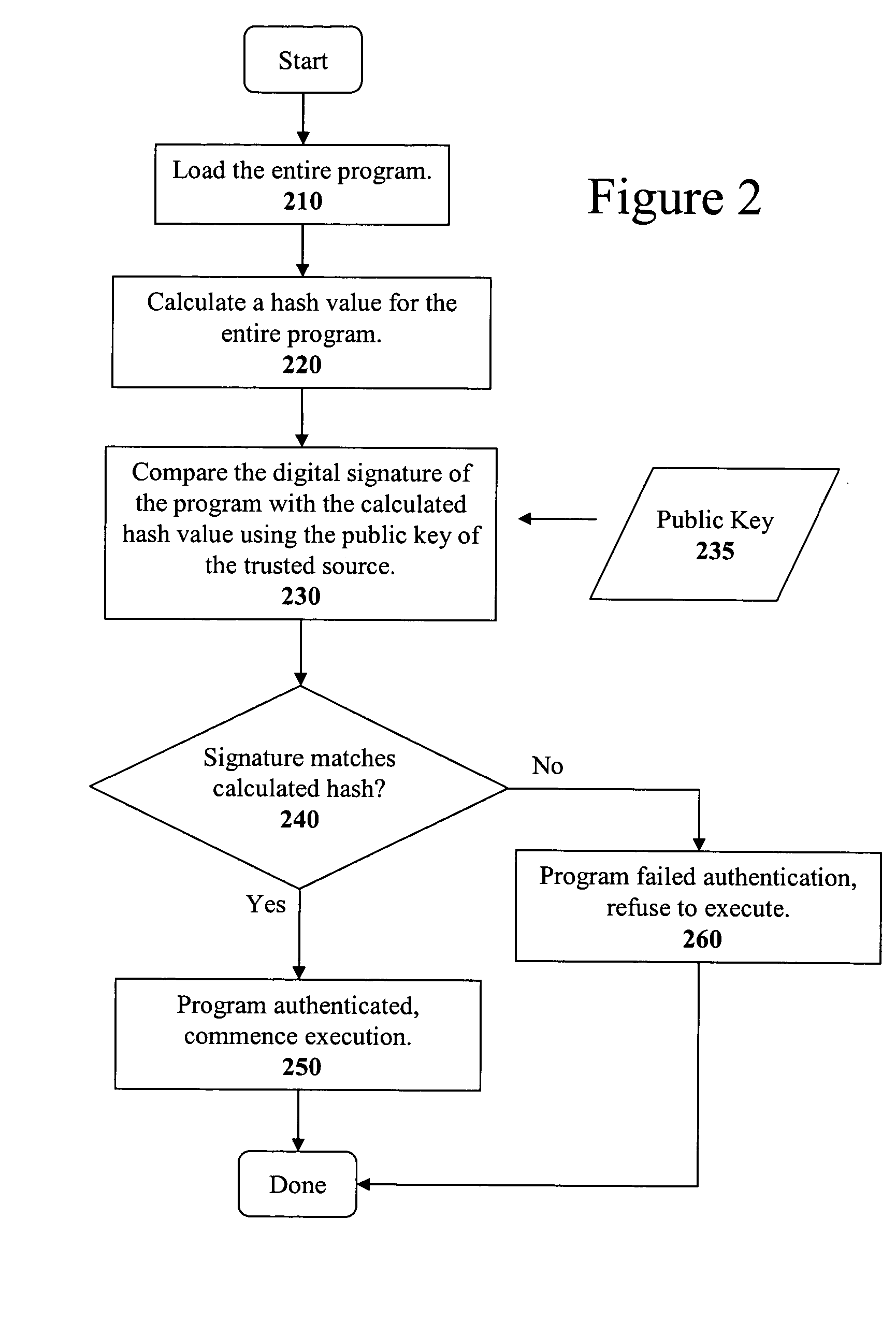
ActiveUS7103779B2Memory loss protectionUser identity/authority verificationArray data structureCode signing
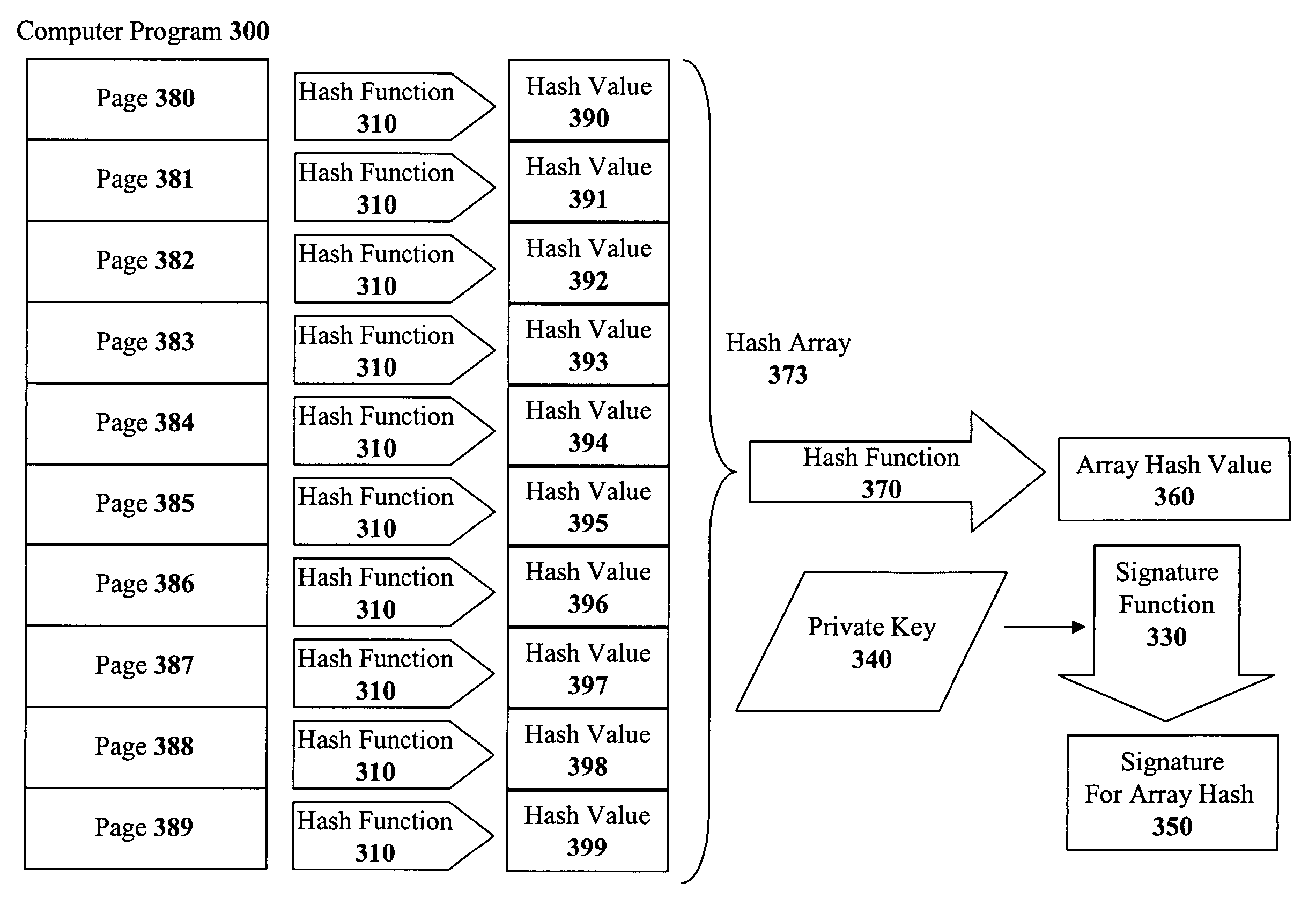
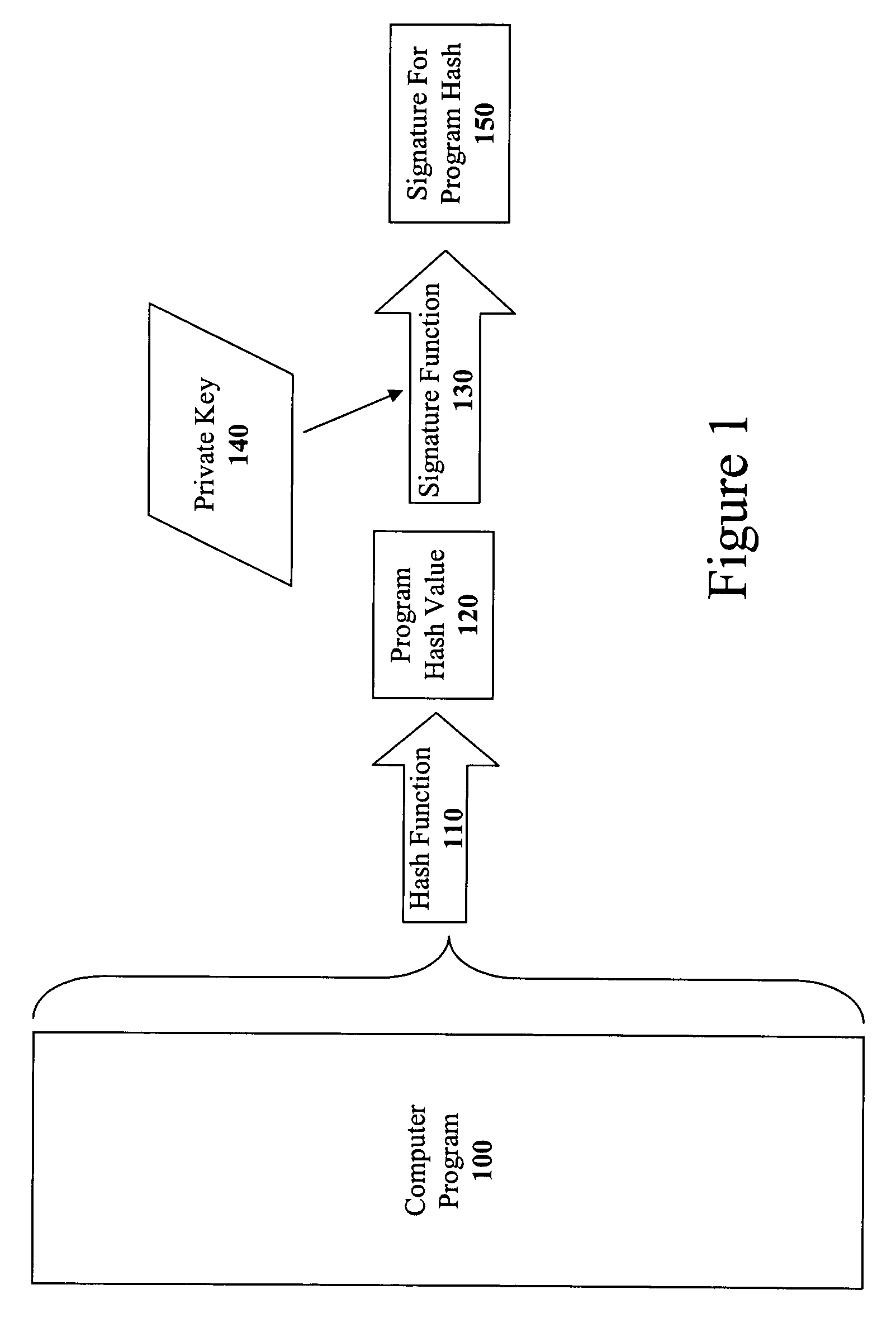
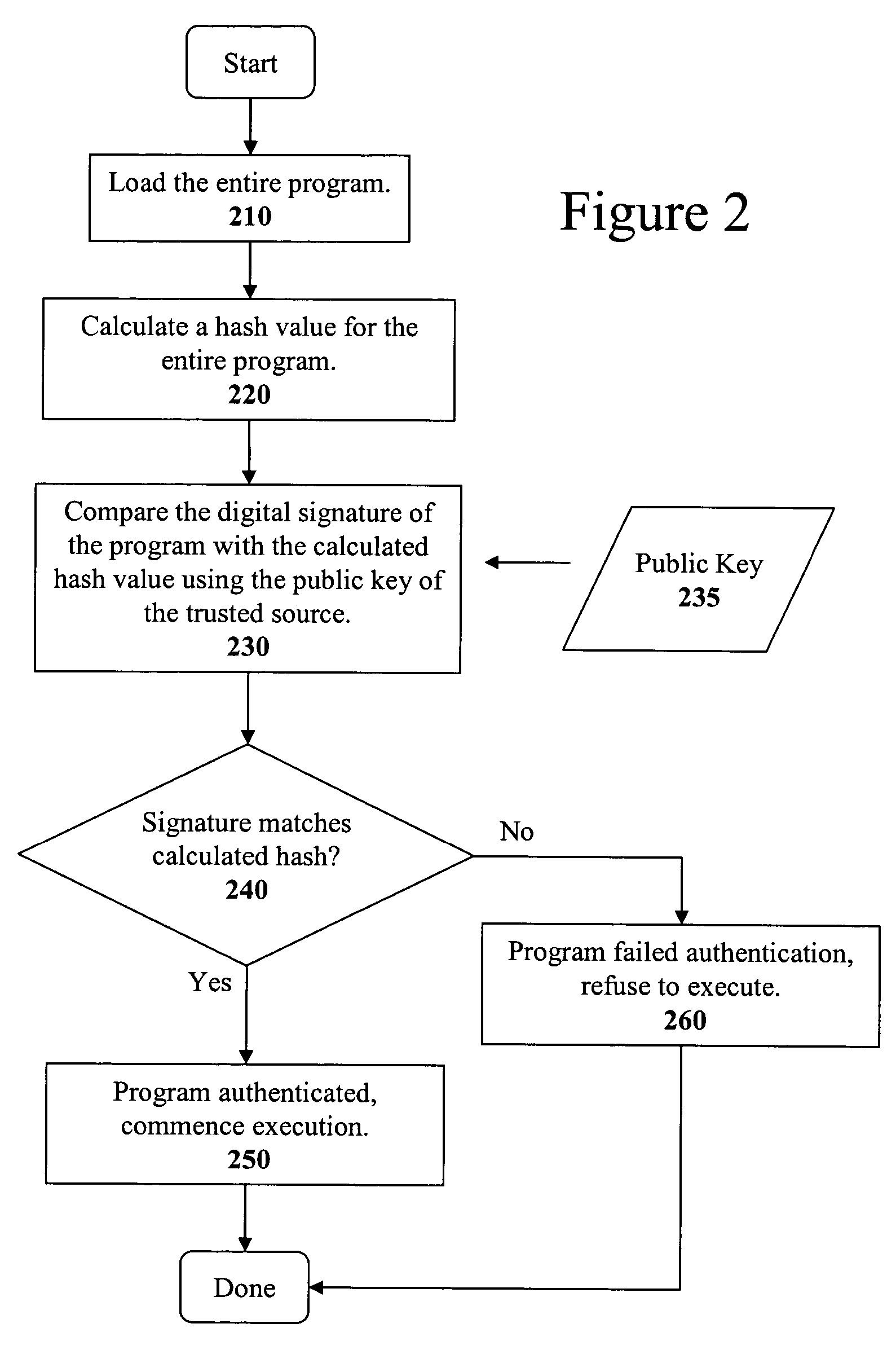
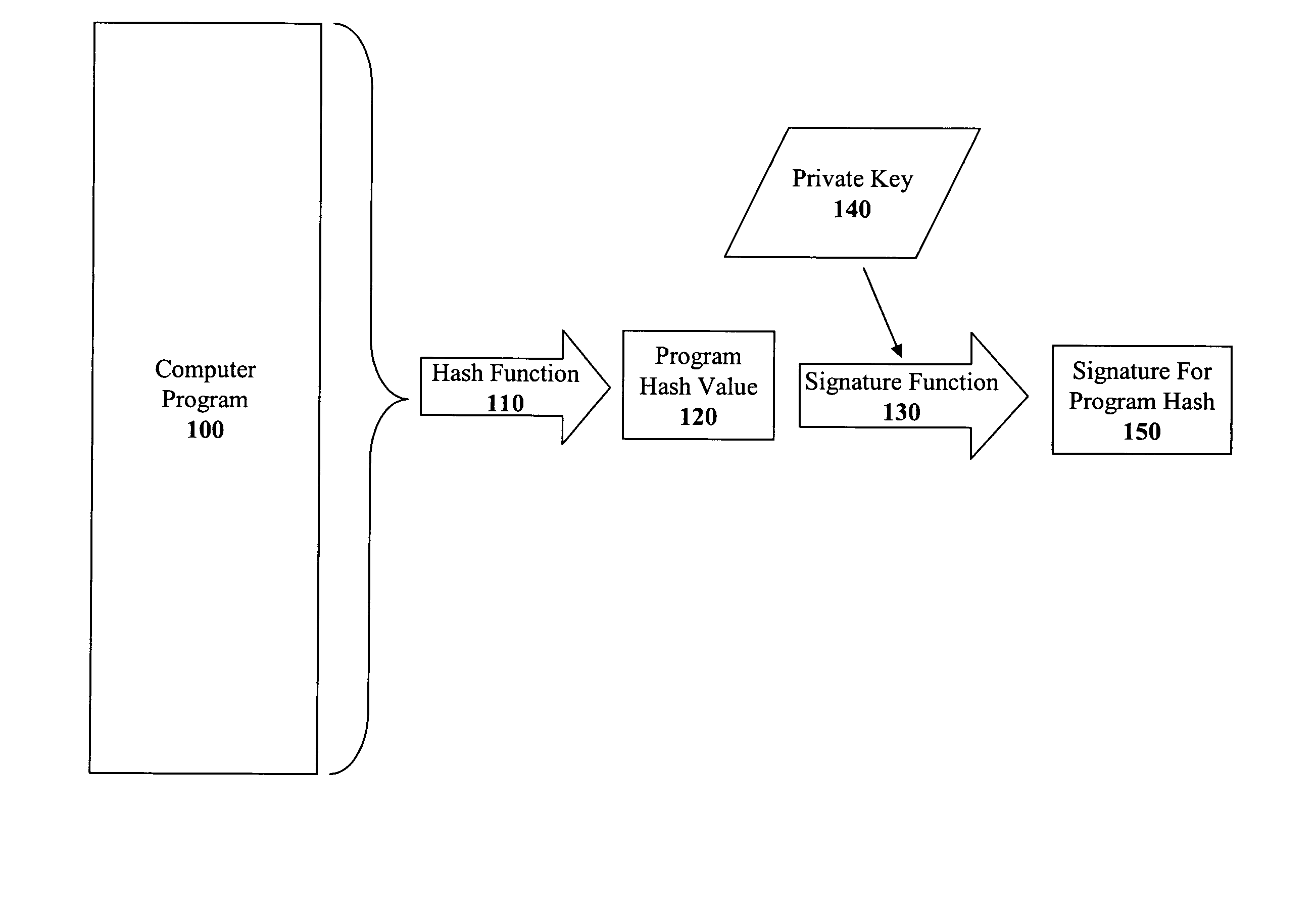
The present invention discloses a method for quickly and easily authenticating large computer program. The system operates by first sealing the computer program with digital signature in an incremental manner. Specifically, the computer program is divided into a set of pages and a hash value is calculated for each page. The set of hash values is formed into a hash value array and then the hash value array is then sealed with a digital signature. The computer program is then distributed along with the hash value array and the digital signature. To authenticate the computer program, a recipient first verifies the authenticity of the hash value array with the digital signature and a public key. Once the hash value array has been authenticated, the recipient can then verify the authenticity of each page of the computer program by calculating a hash of a page to be loaded and then comparing with an associated hash value in the authenticated hash value array. If the hash values do not match, then execution may be halted.
Owner:APPLE INC
Method and apparatus for sketch-based detection of changes in network traffic
InactiveUS20050039086A1Easy to useImprove accuracyError preventionTransmission systemsData streamInternet traffic
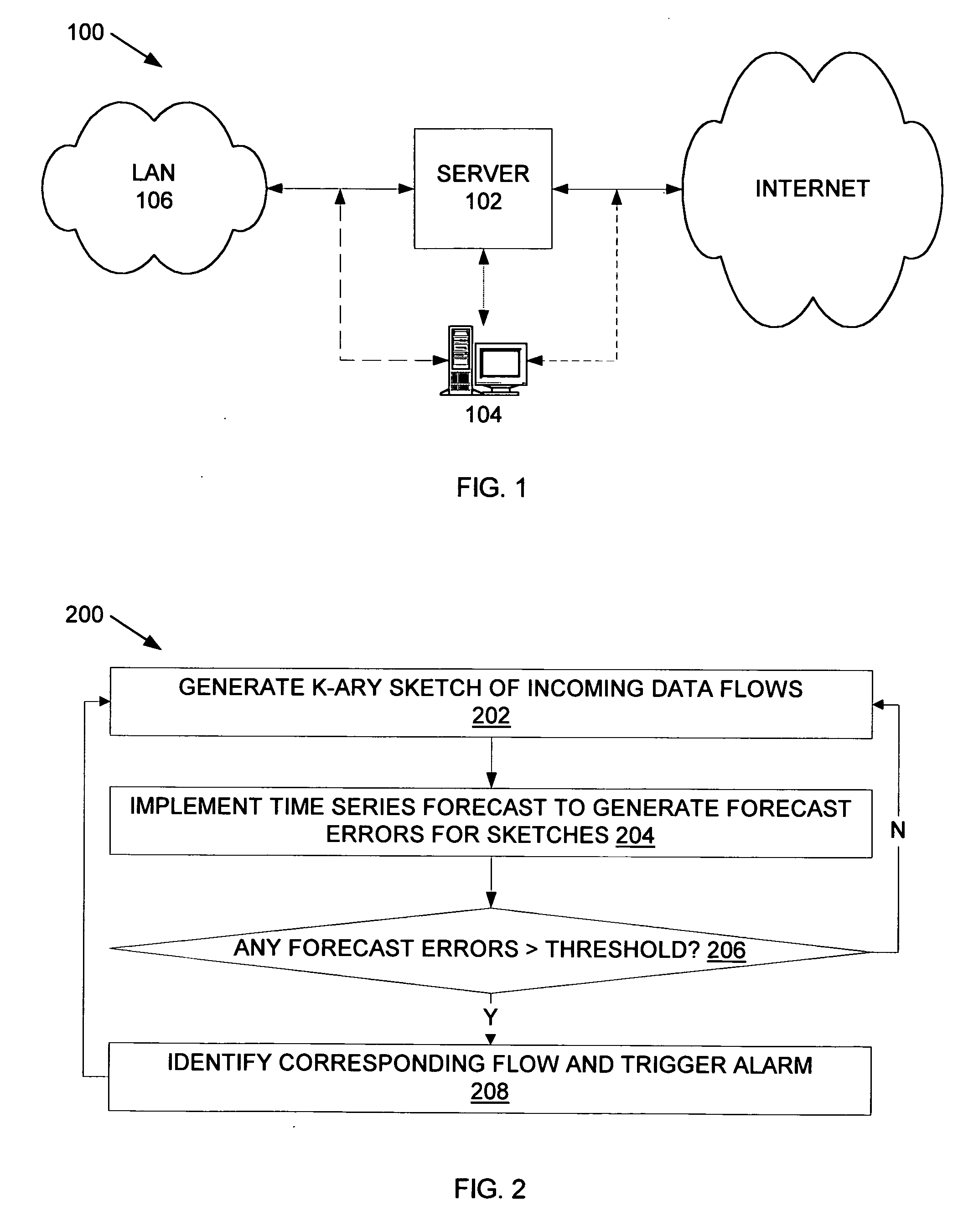
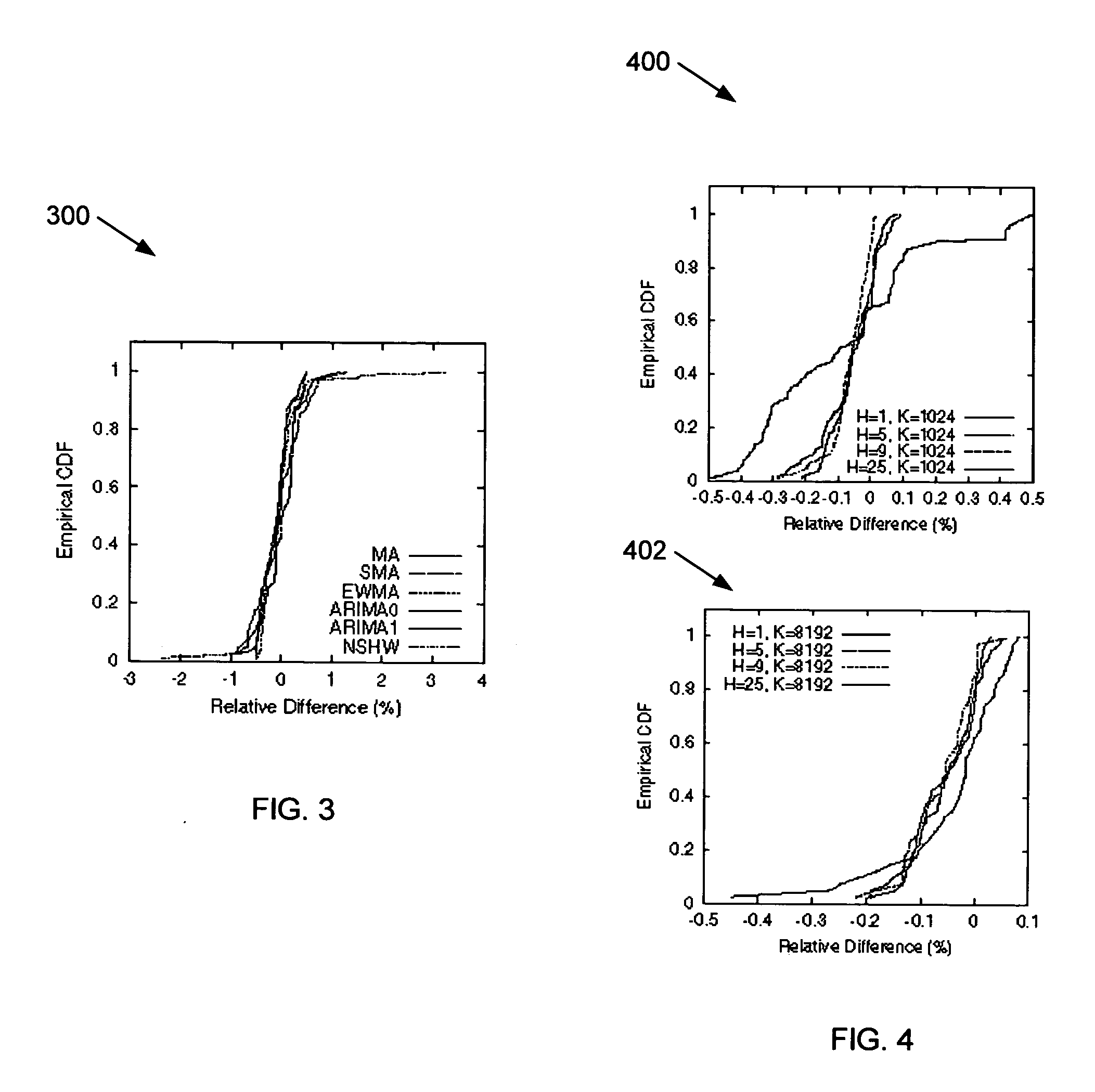
A sketch-based change detection technique is introduced for anomaly detection and other applications that can benefit from having a quick and efficient change detection mechanism. The technique is capable of detecting significant changes in massive data streams with a large number of network time series. As part of the technique, we designed a variant of the sketch data structure, called k-ary sketch, uses a constant, small amount of memory, and has constant per-record update and reconstruction cost. A variety of time series forecast models are implemented on top of such summaries and detect significant changes by looking for flows with large forecast errors. Heuristics for automatically configuring the forecast model parameters are presented. Real Internet traffic data is used to demonstrate that the sketch-based change detection method is highly accurate when compared with per-flow analysis, and can be implemented at low computation and memory costs. The results validate using the technique as a building block for network anomaly detection and traffic measurement in large computer networks.
Owner:AT&T INTPROP I L P +1
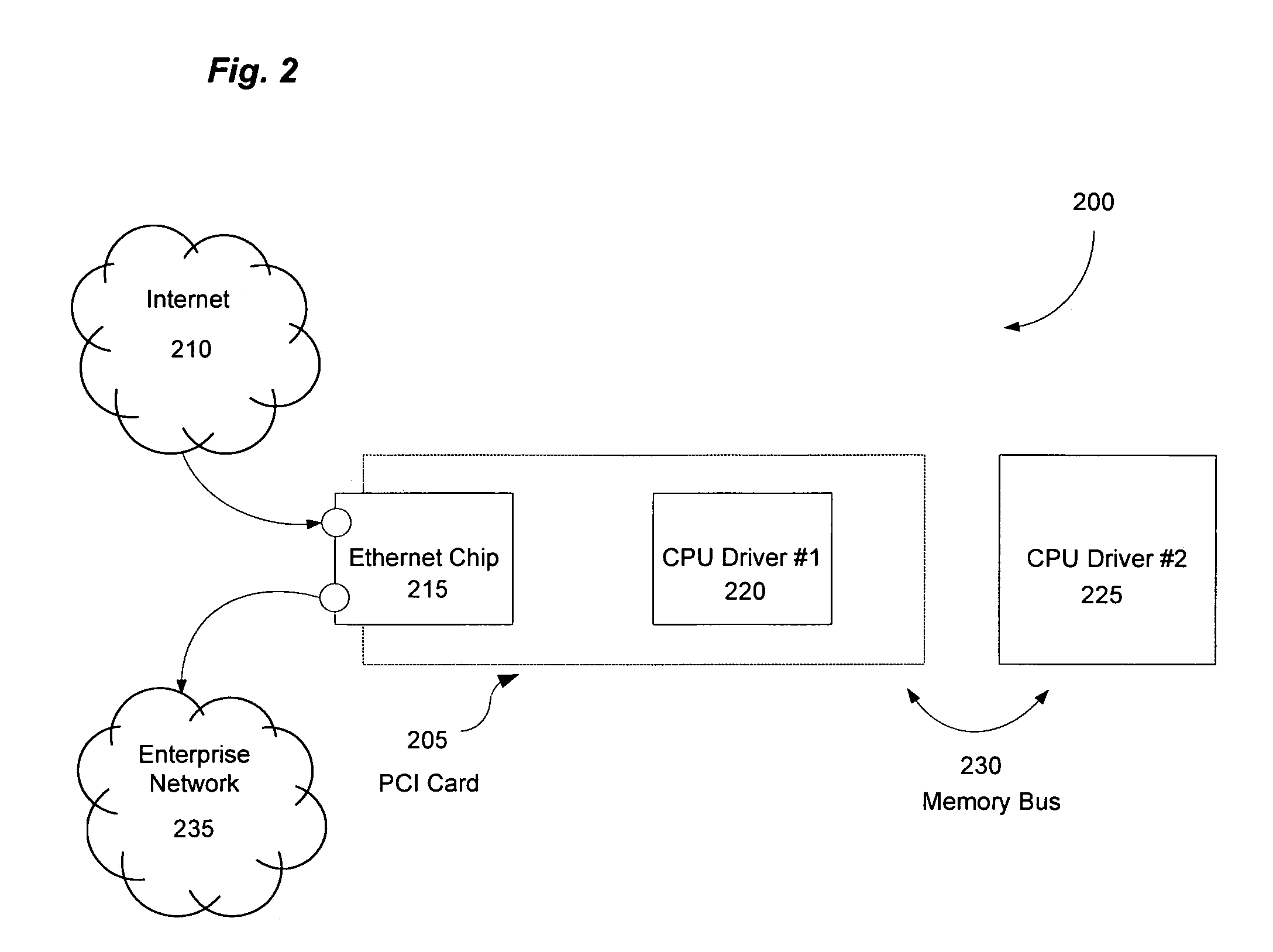
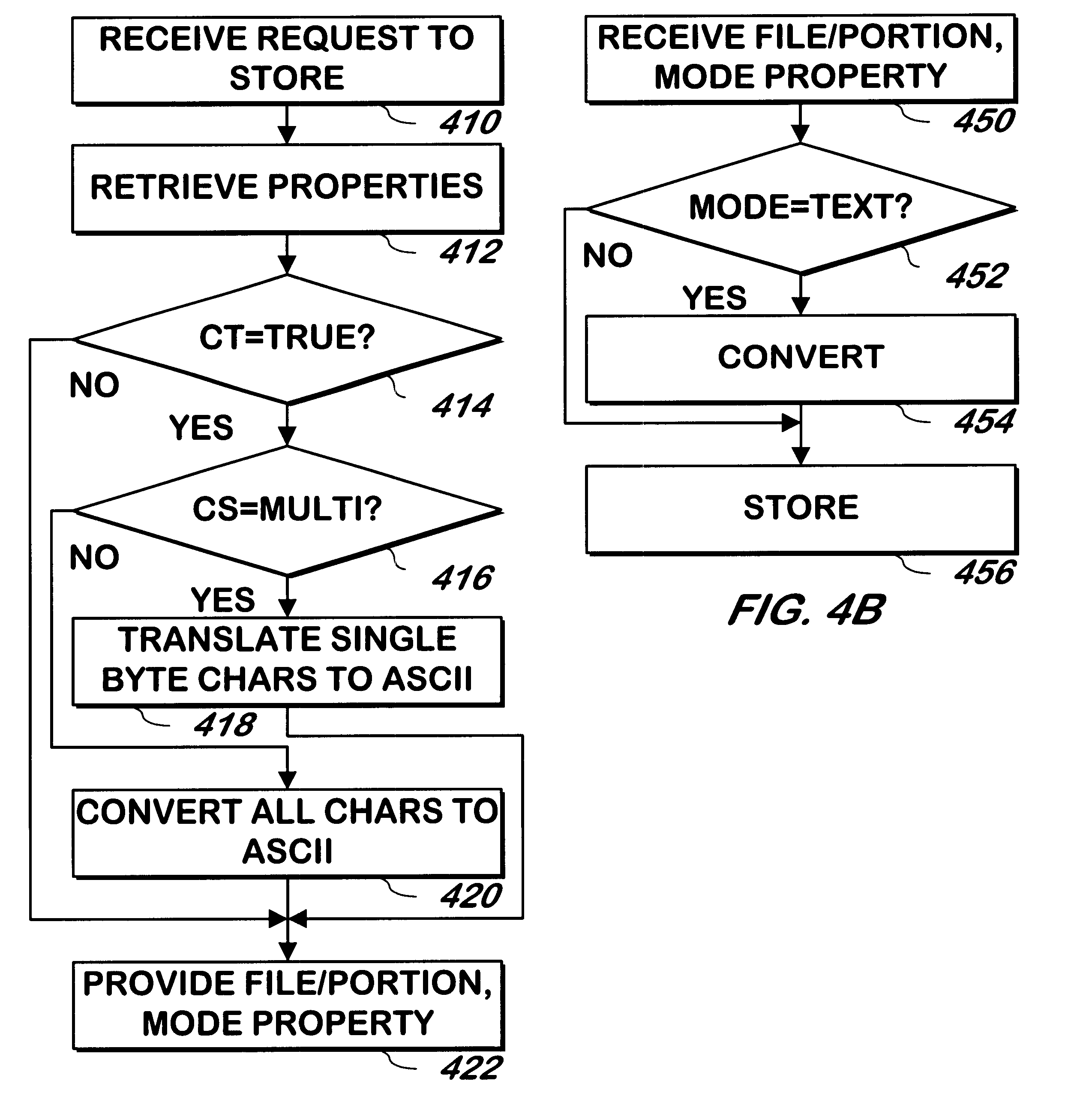
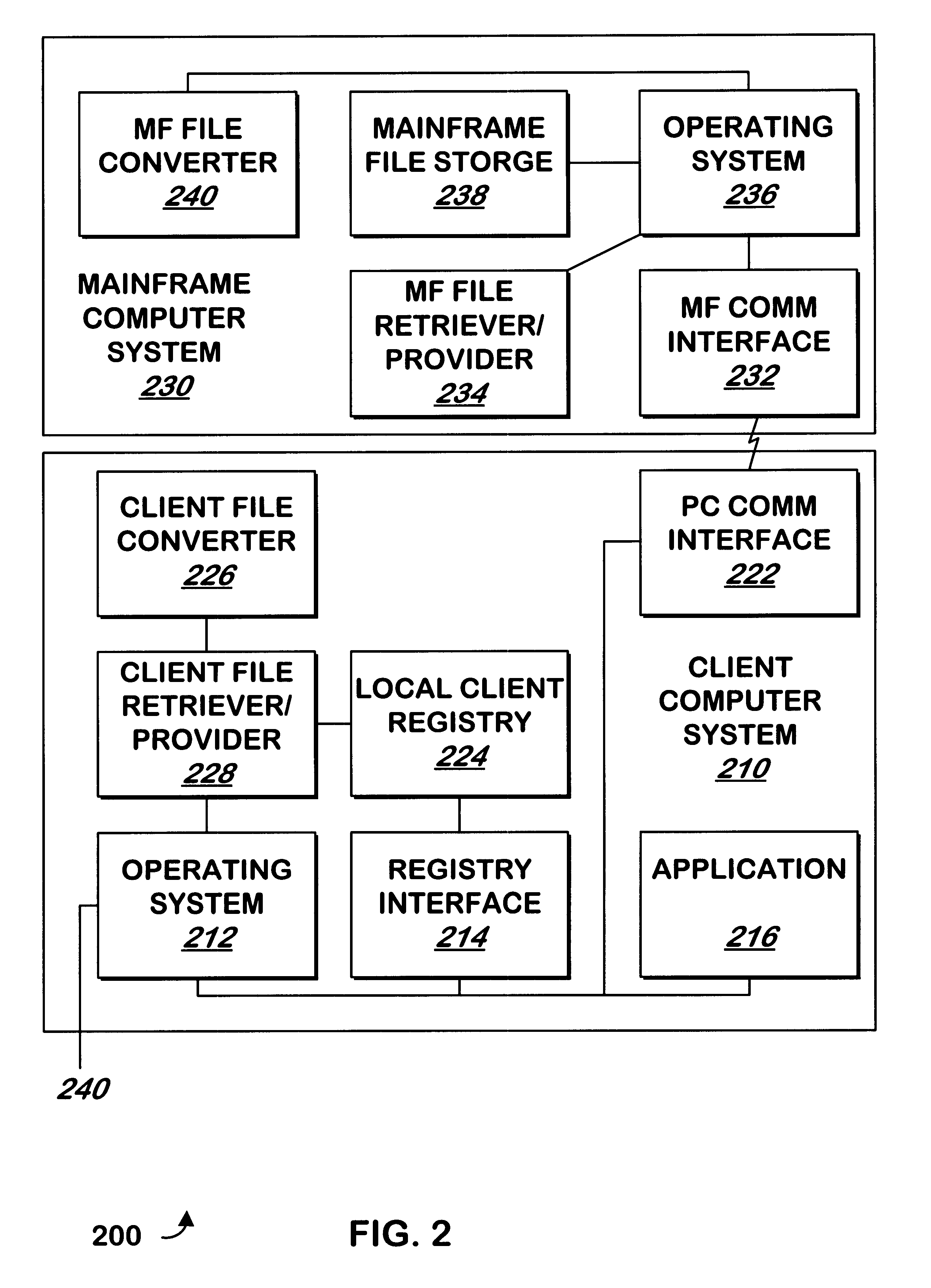
Method and apparatus for converting files stored on a mainframe computer for use by a client computer
InactiveUS6691125B1Data processing applicationsMultiple digital computer combinationsClient-sideMainframe computer
A method and apparatus allows a file to be transferred from a mainframe computer to a client computer. A folder is set up on the client computer with a list of filenames and / or filters that designates some of the files on the mainframe computer as belonging to the folder. Conversion properties are assigned to the folder. A file is requested using the folder name and filename, and the file is transferred from the mainframe to the client computer and converted according to the properties of the folder to which the file belongs.
Owner:SERENA SOFTWARE
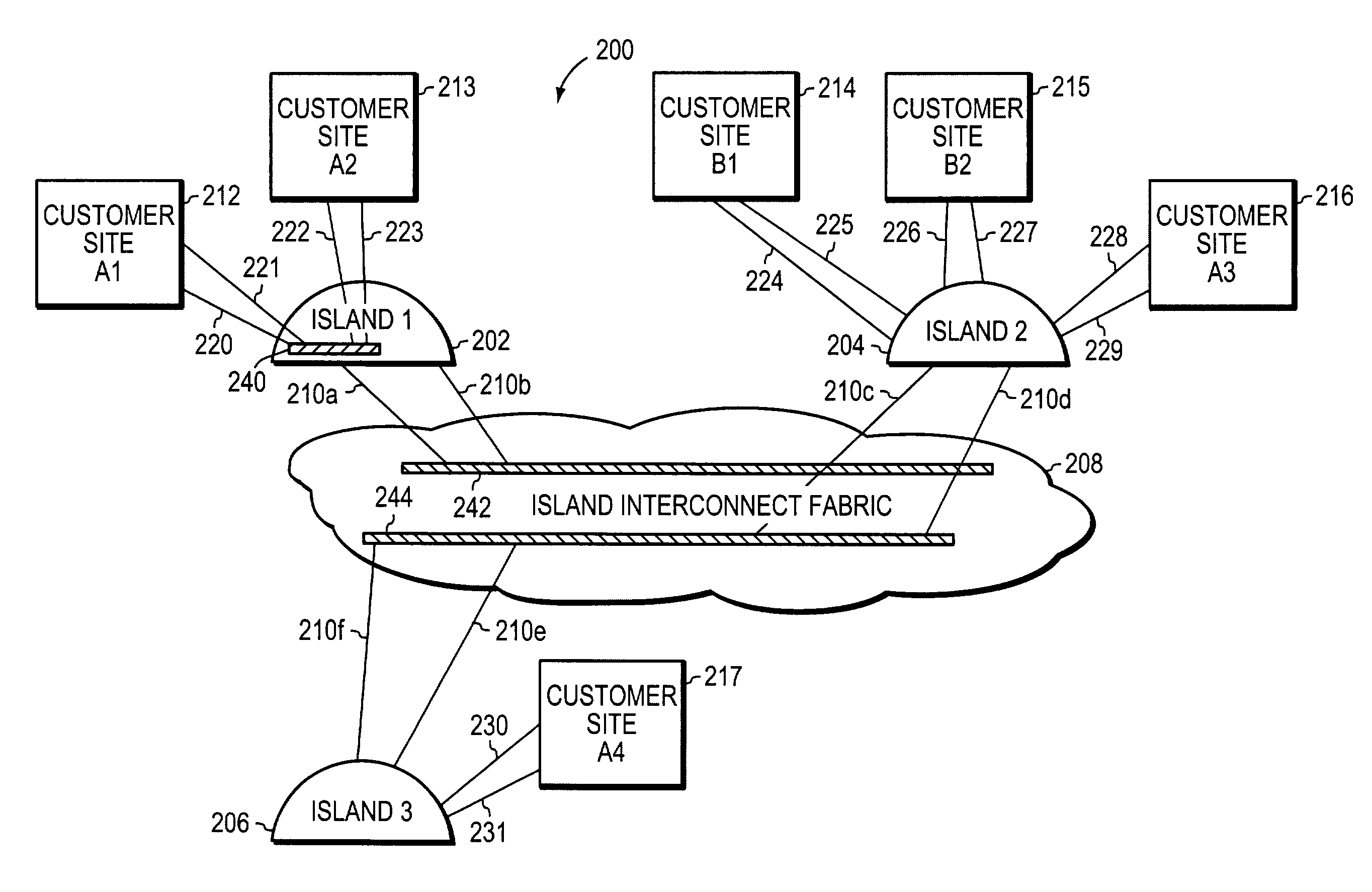
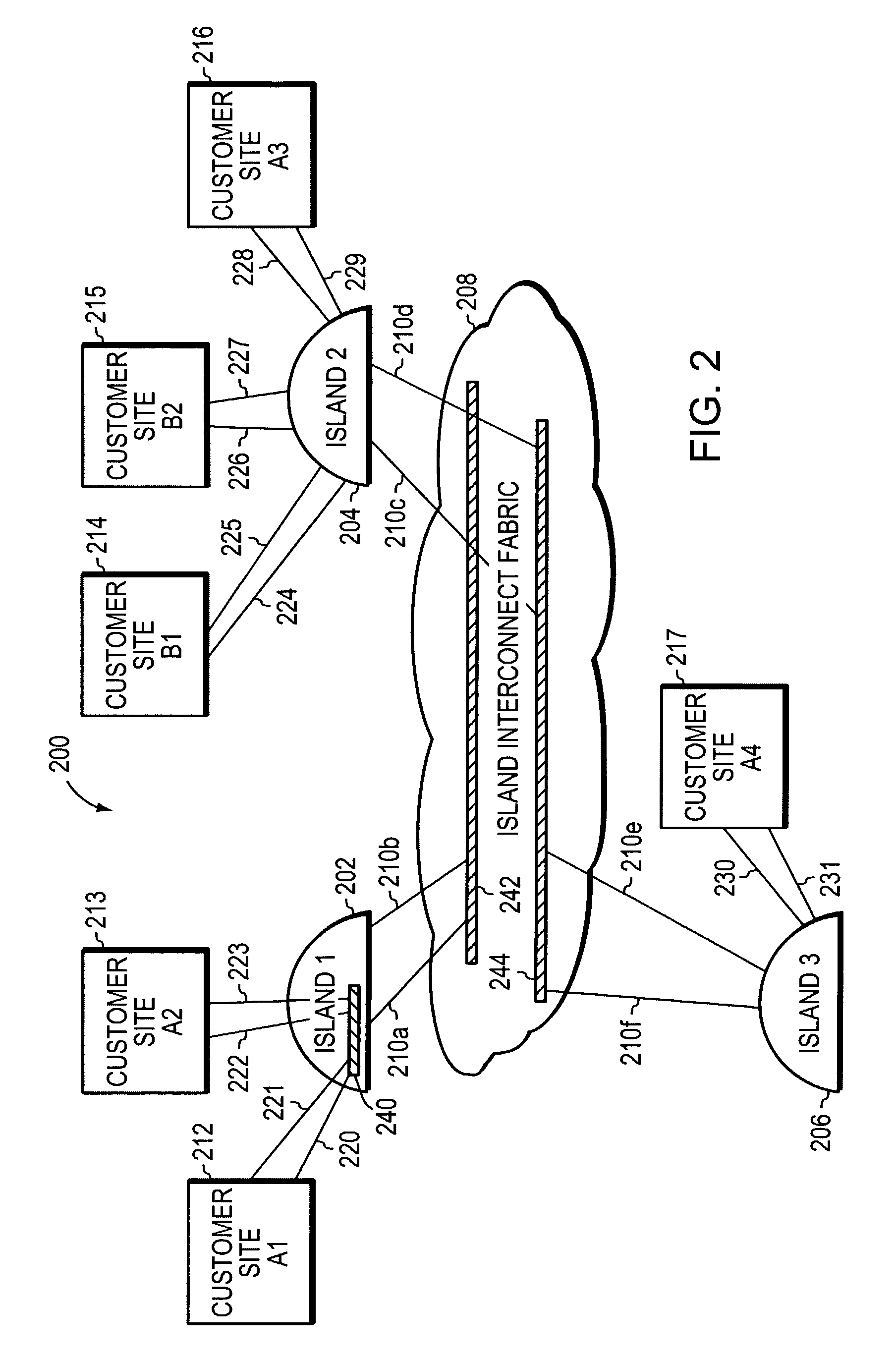
Scaling private virtual local area networks (VLANs) across large metropolitan area networks (MANs).
InactiveUS7606939B1Multiple digital computer combinationsMetropolitian area networksVirtual LANPrivate VLAN
A system and method scales private Virtual Local Area Networks (VLANs) to a large computer network, such as a very large Metropolitan Area Network (MAN), so that the VLAN designations can be re-used across the network. In the illustrative embodiment, the MAN includes different groups of Layer 2 (L2) switches that are logically organized into Islands interconnected by an interconnect fabric. Within each Island, Customer-Equipment VLAN Identifiers (CE-VLAN IDs) are mapped to MAN Provider-Equipment VLAN IDs (PE-VLAN IDs). The PE-VLAN IDs defined within the MAN support the creation of Private VLANs. Each Private VLAN includes one Primary VLAN, one Isolated VLAN and may include one or more Community VLANs. Different PE-VLAN IDs may be used as the Primary, Isolated and Community VLANs in different Islands. Nonetheless, the Primary, Isolated and Community VLANs from all of the Islands are assigned the same Virtual Circuit IDs, which are loaded into encapsulated frames traversing the interconnect fabric, thereby maintaining the message's association with the Primary, Isolated and Community VLANs.
Owner:CISCO TECH INC
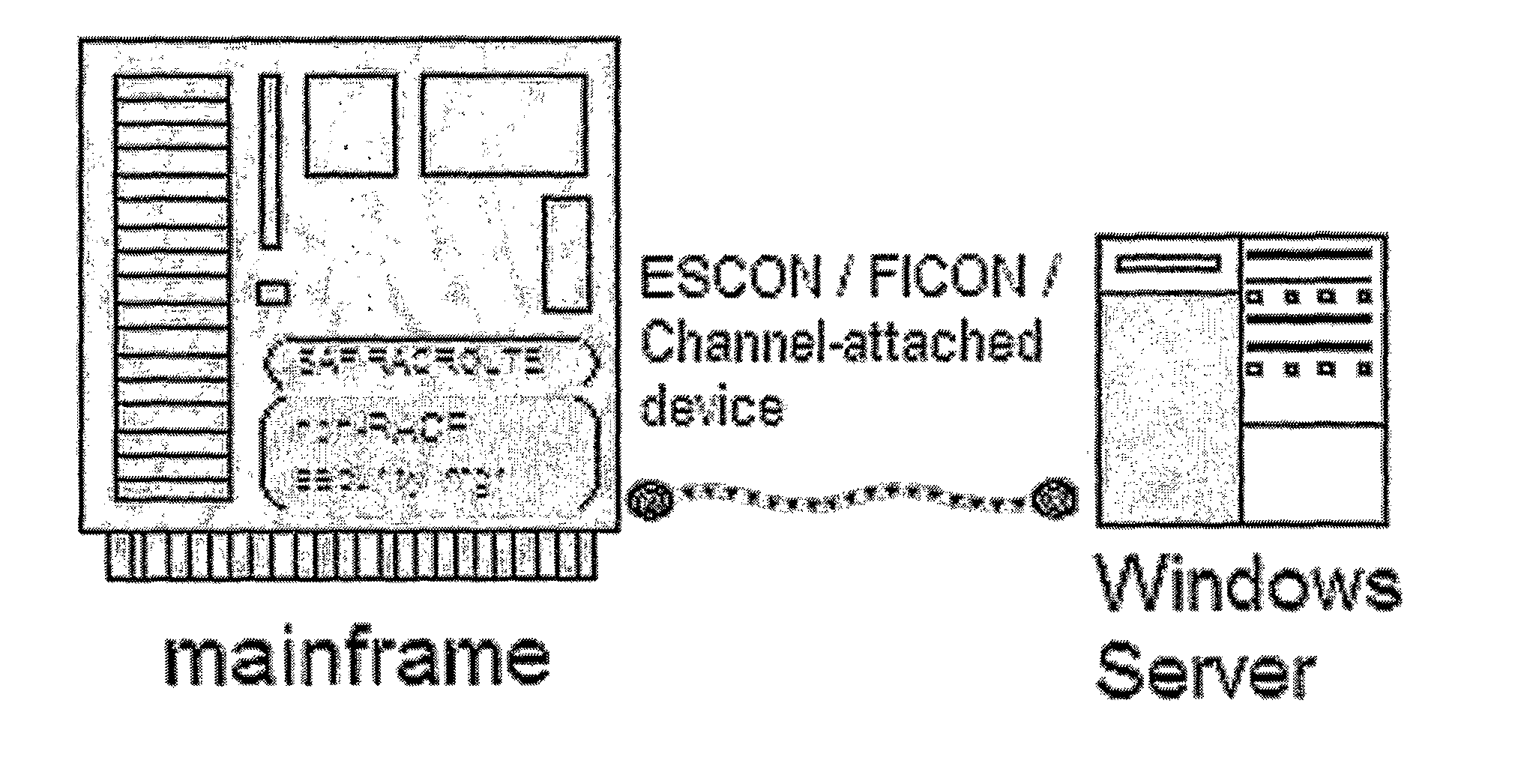
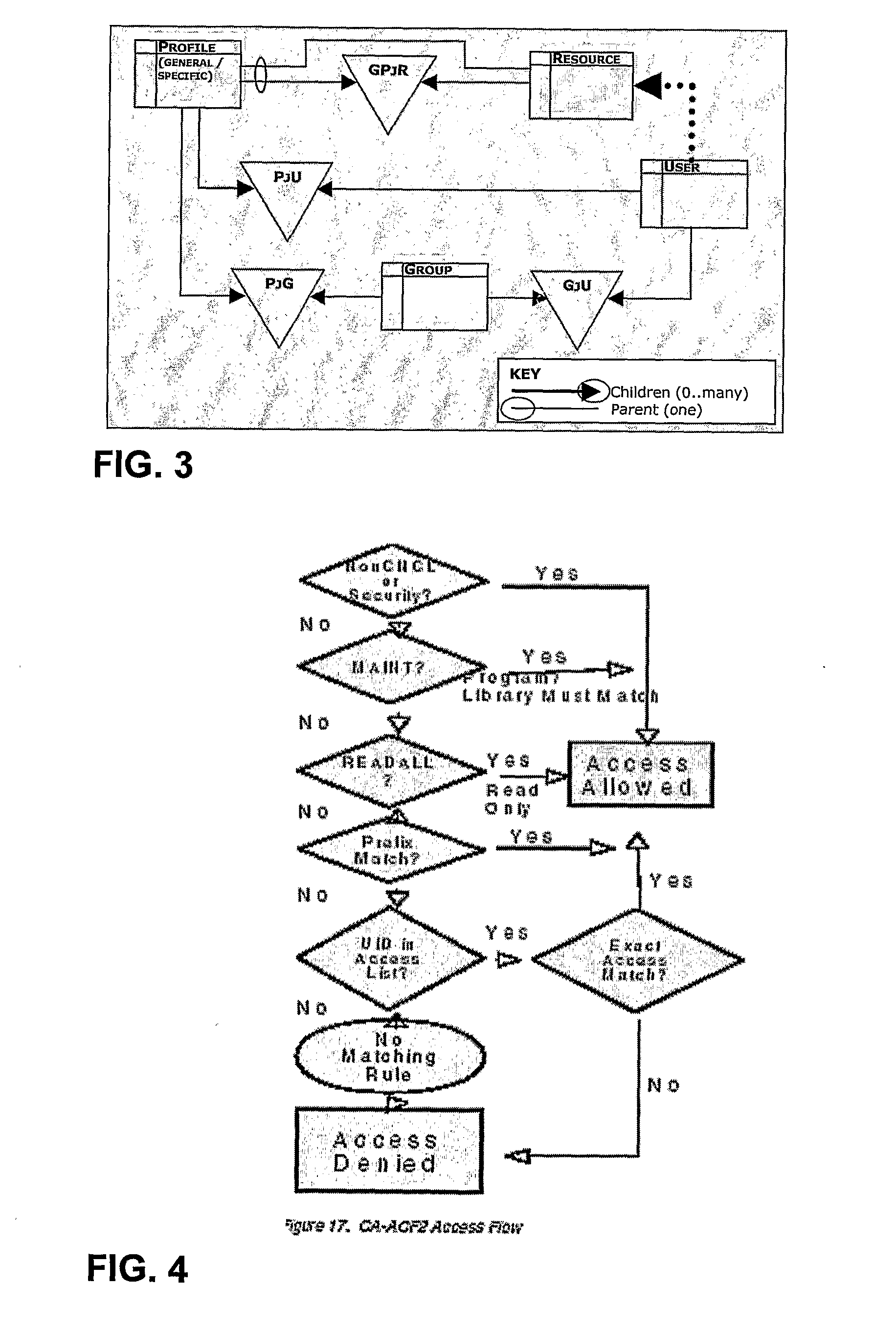
Translation Engine for Computer Authorizations Between Active Directory and Mainframe System
InactiveUS20080263640A1Extended processing timeImproved security flexibilityDigital data processing detailsComputer security arrangementsComputer accessMainframe computer
The invention provides a method and system of implementing a high performance “non-RACF external security-manager product,” which maintains and translates a merged single source of authorizations to both mainframe and Microsoft Windows Active Directory (AD) systems. In one embodiment, a method comprises generating at a server computer access information for a mainframe computer indicative of mainframe authorization for a set of users, receiving from the mainframe computer information indicative of an authorization request, the information indicative of the authorization request identifying a user trying to access the mainframe computer, and sending at least a portion of the access information from the server computer to the mainframe computer, the portion of the access information including mainframe access information for the user.
Owner:REDPHONE SECURITY INC
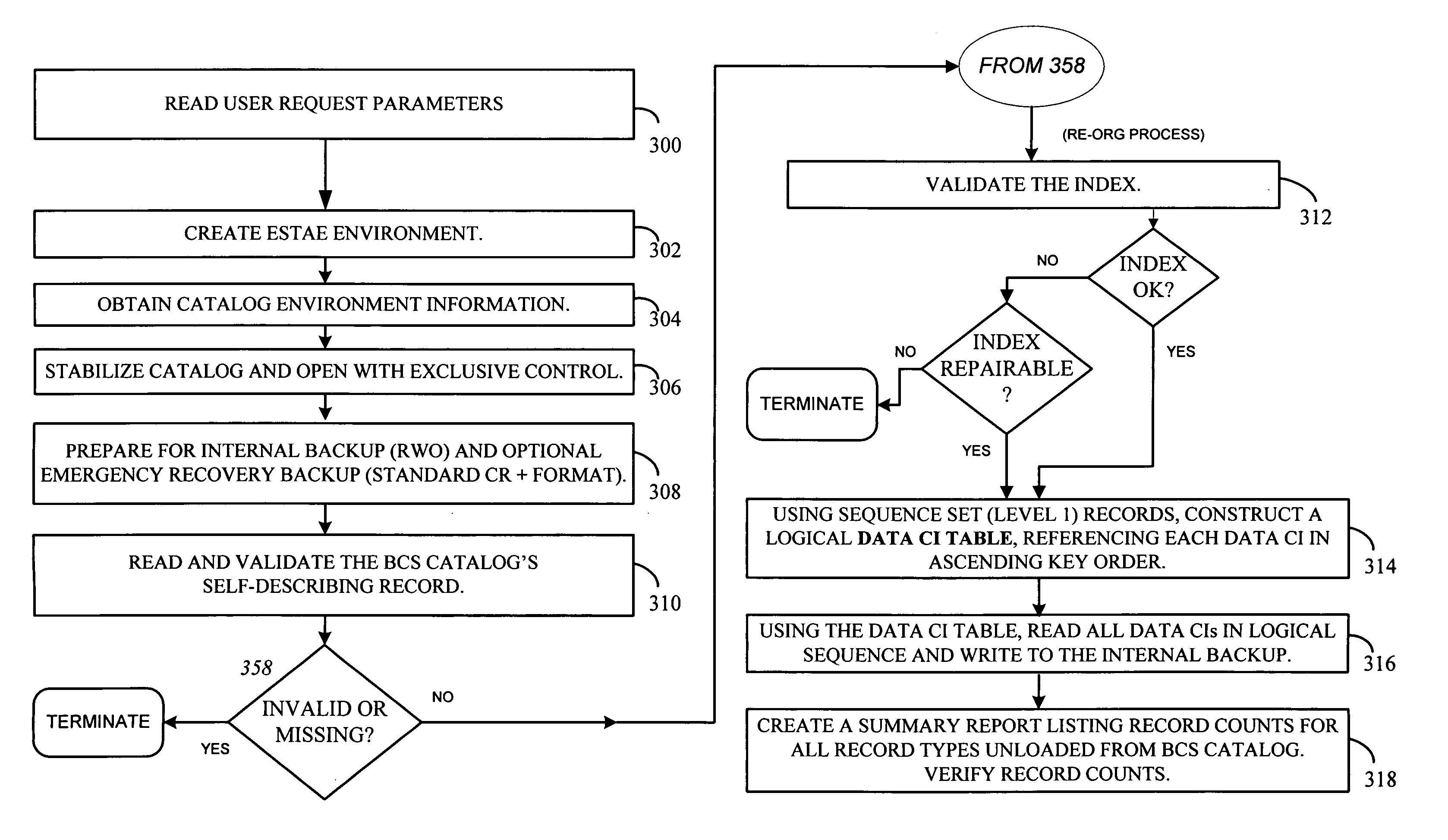
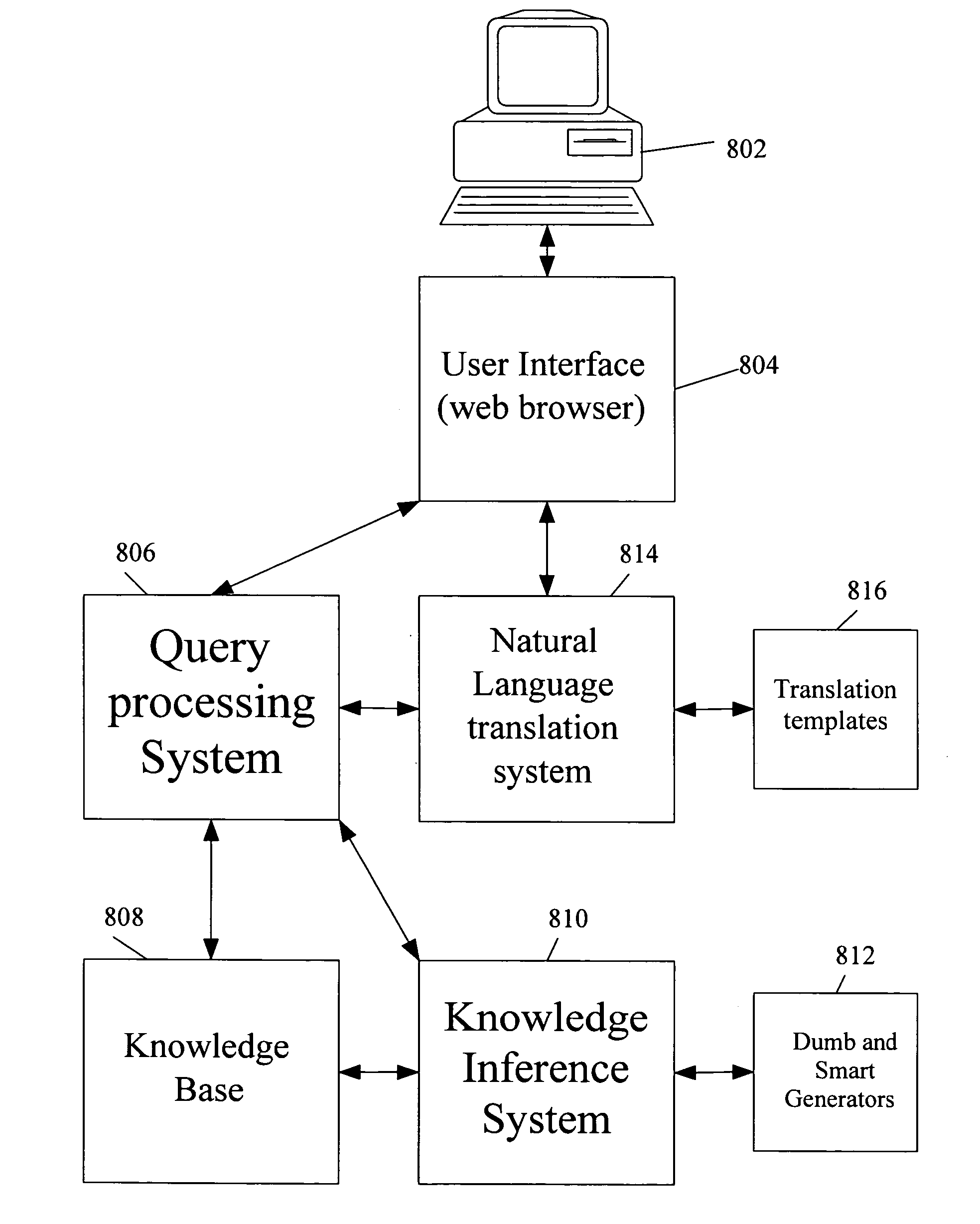
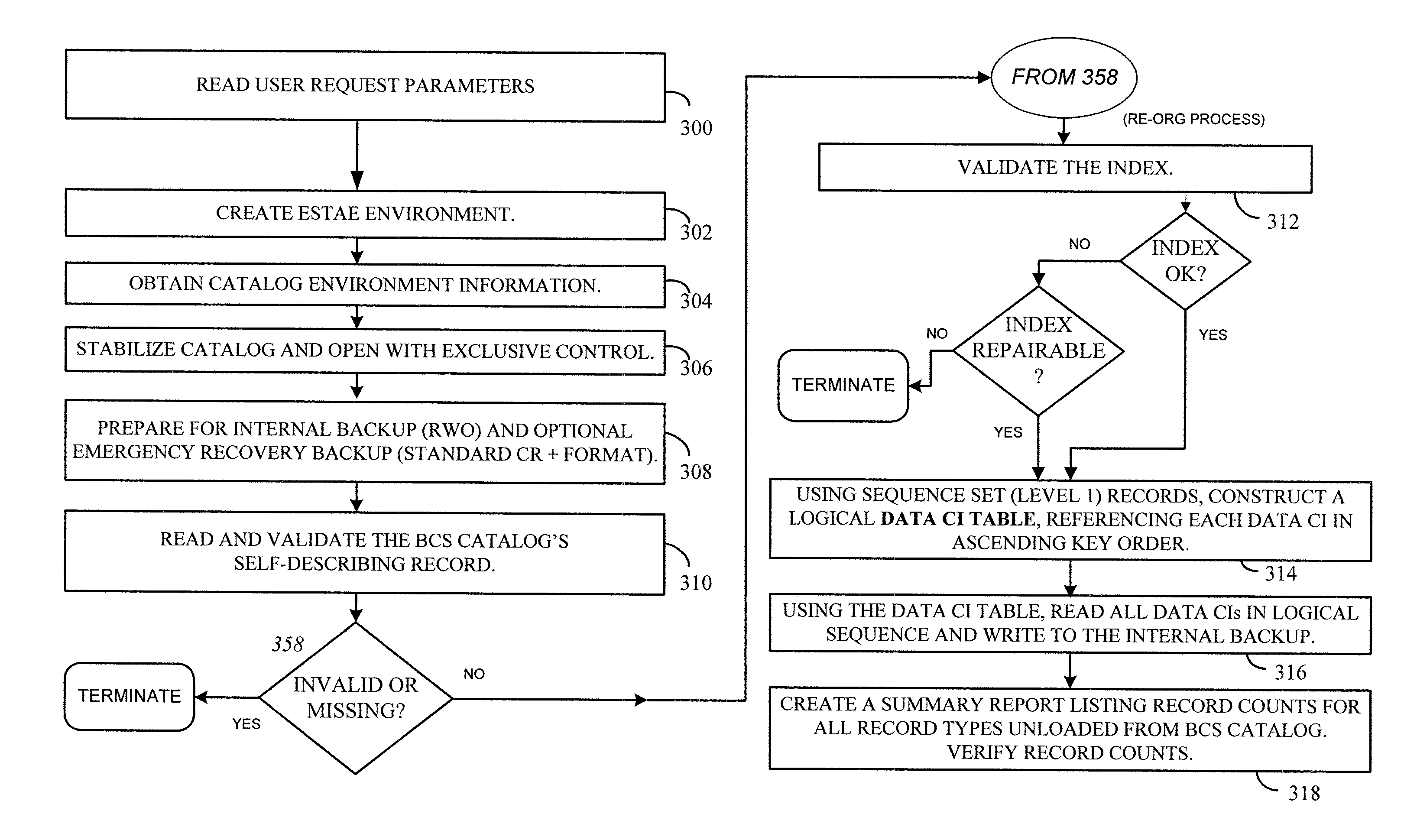
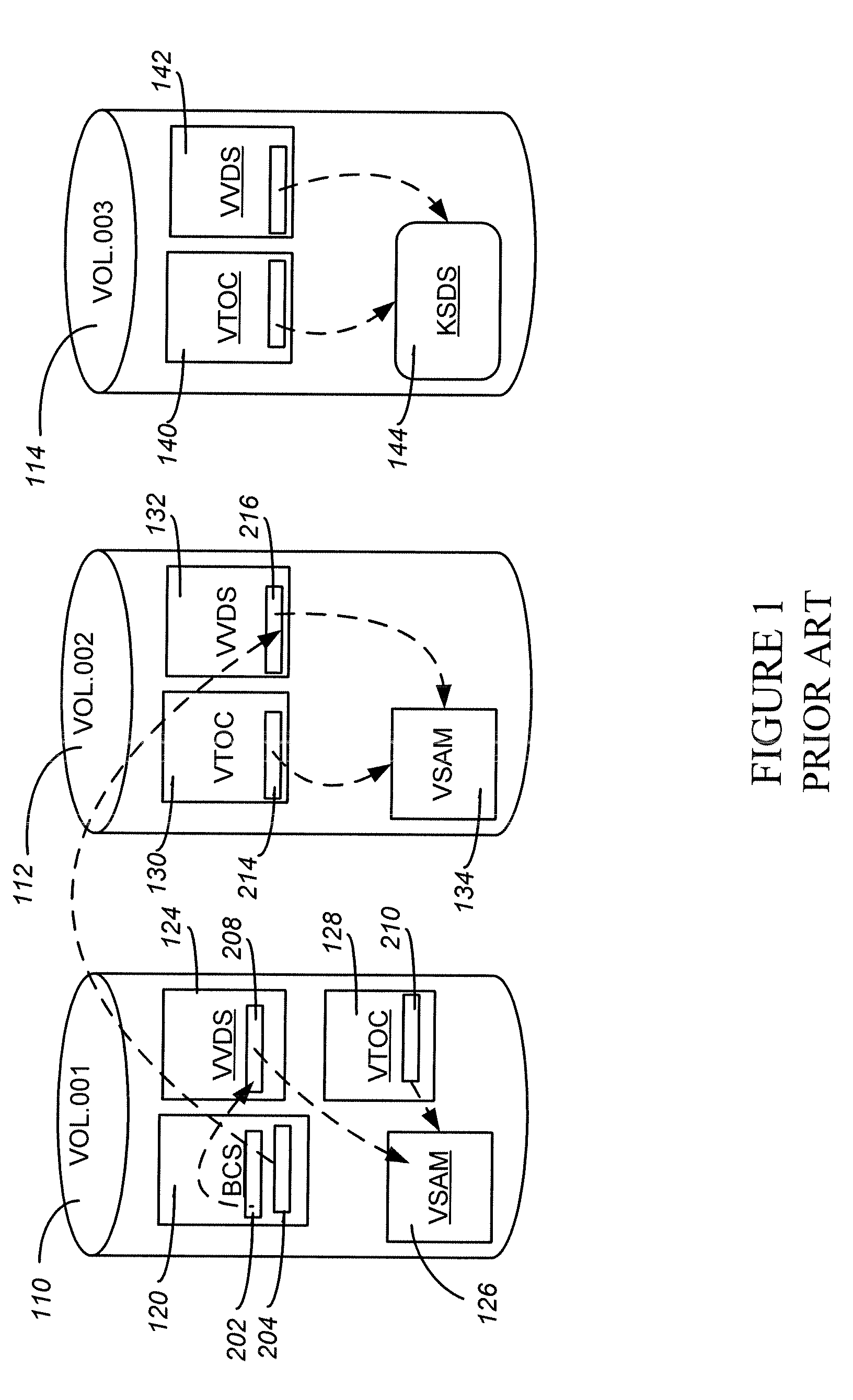
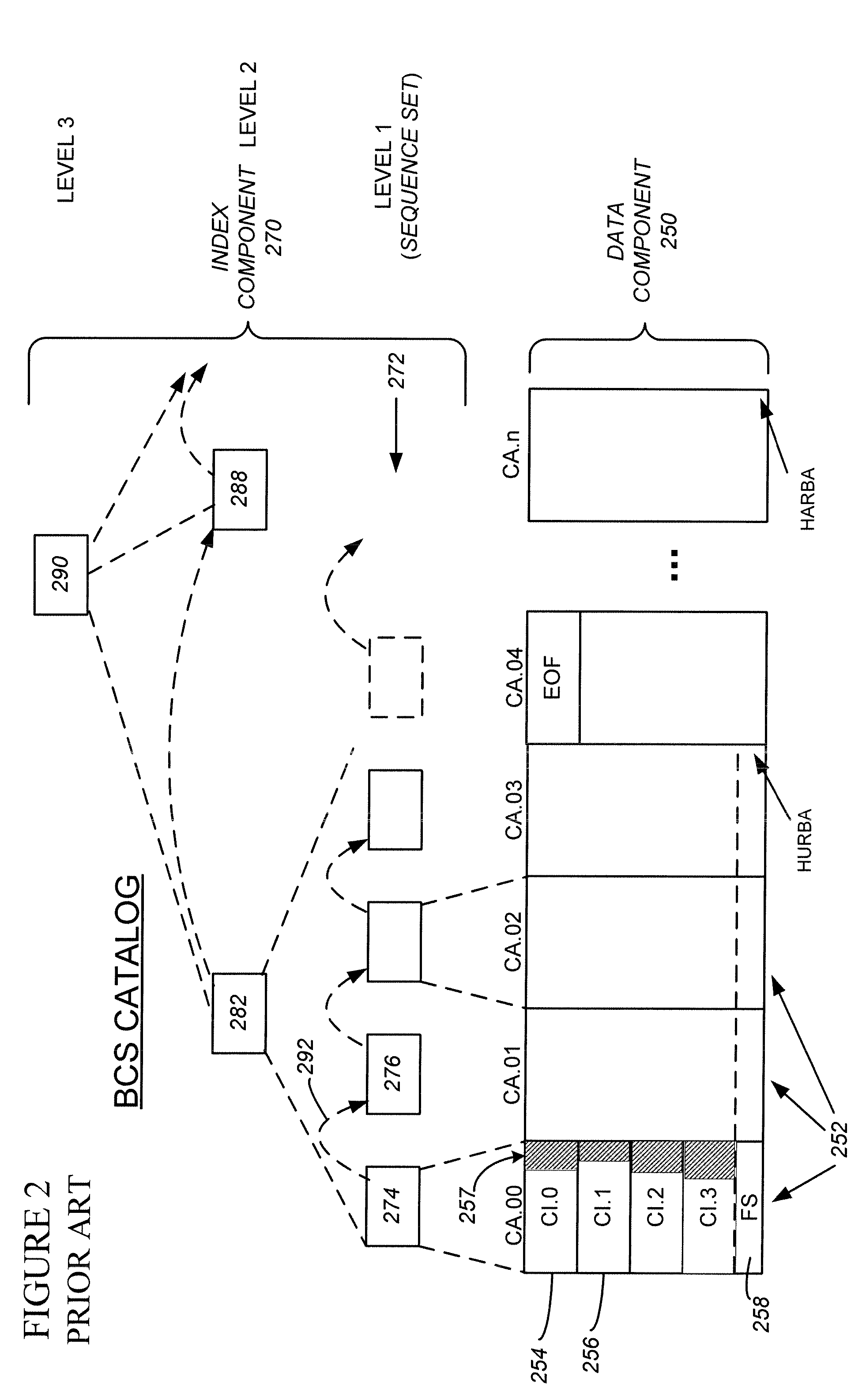
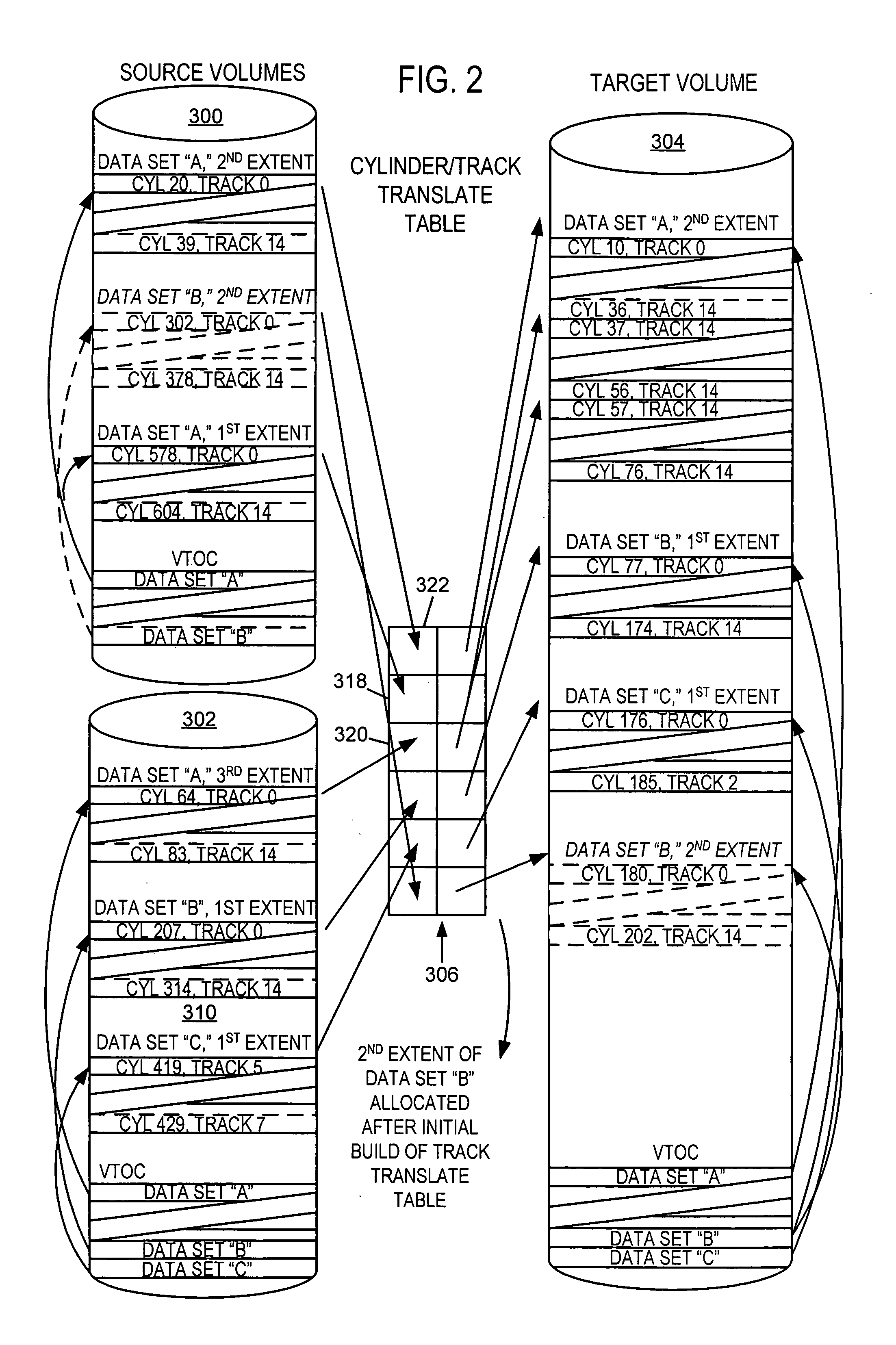
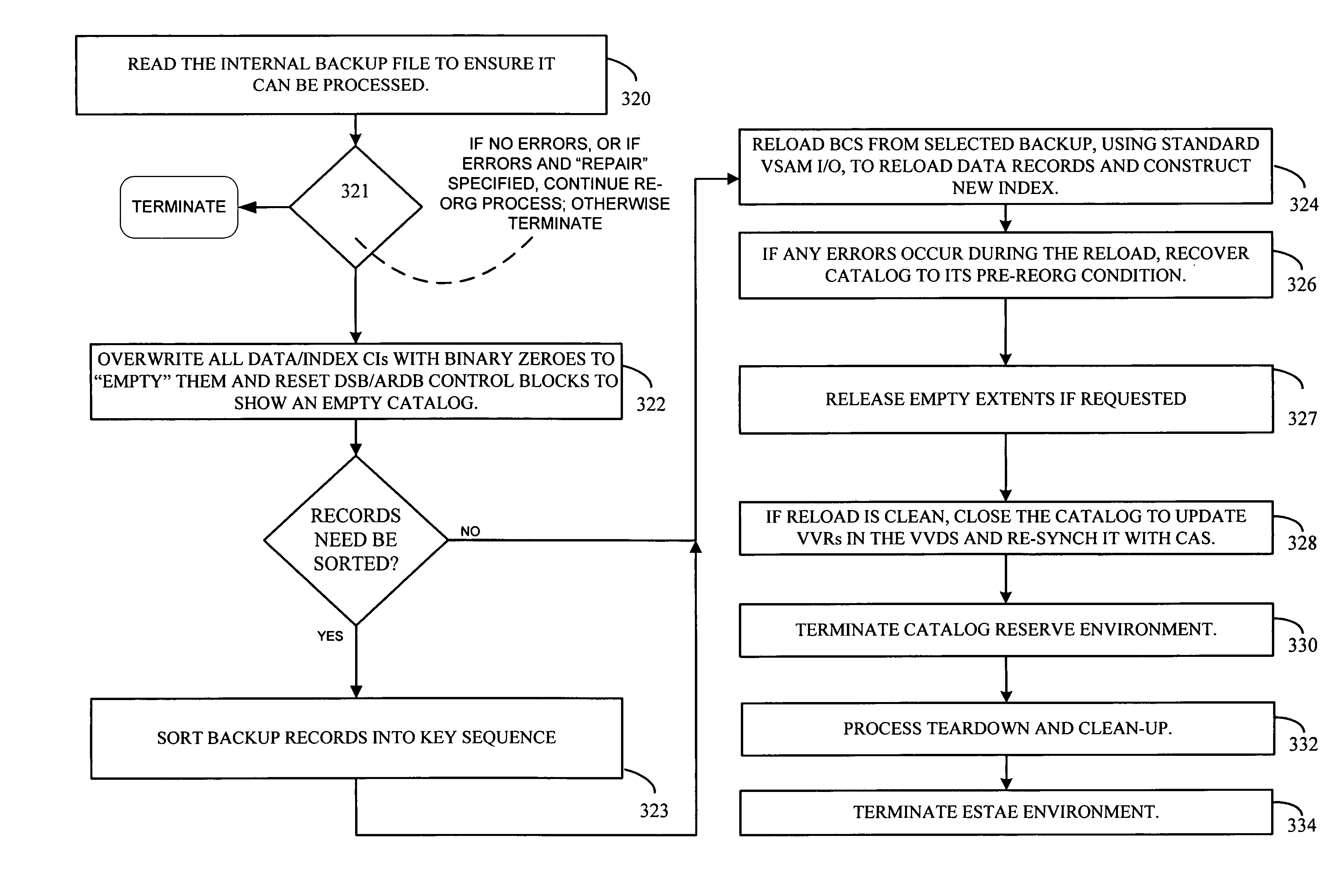
Reorganization and repair of an ICF catalog while open and in-use in a digital data storage system
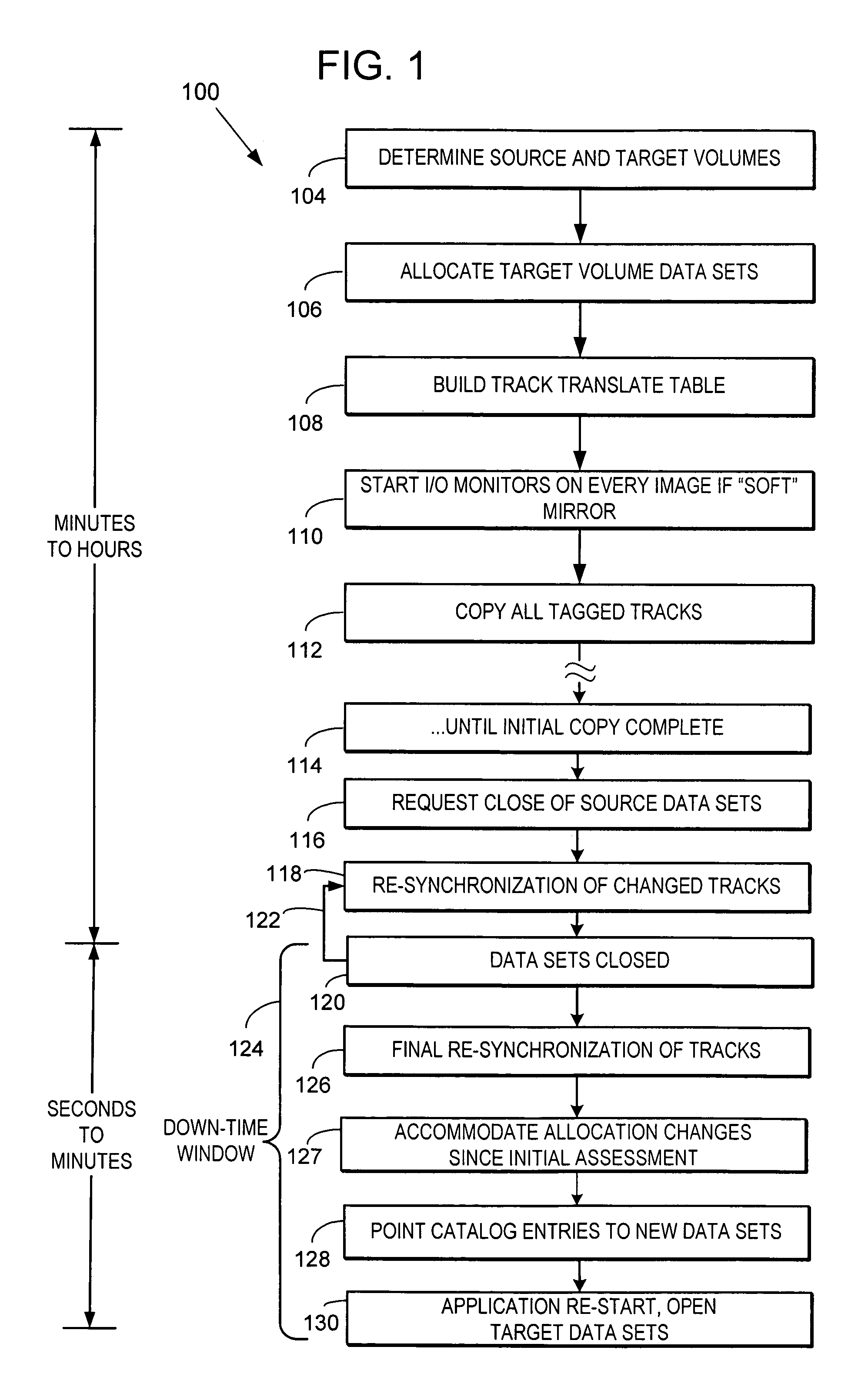
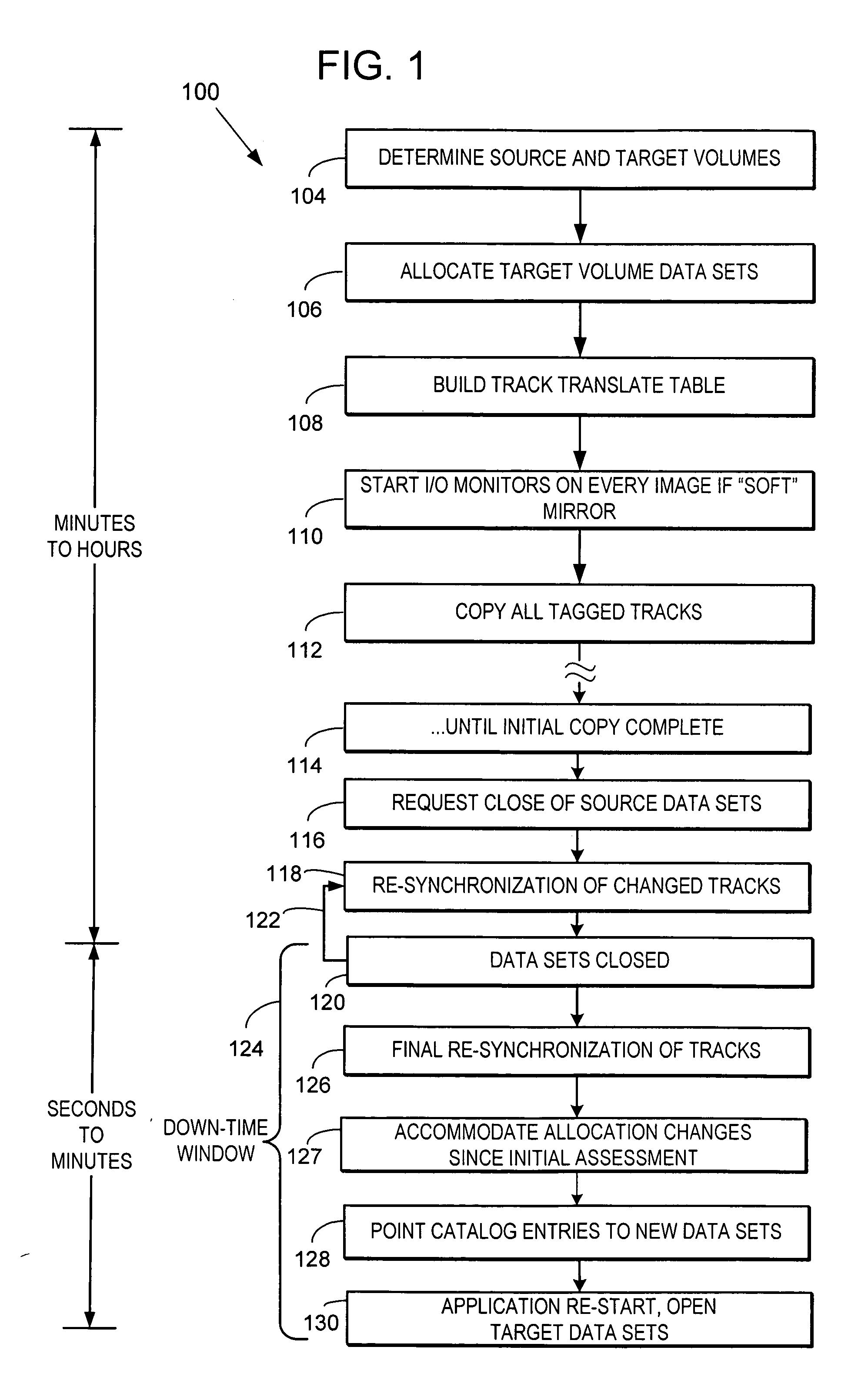
ActiveUS20050187990A1Minimal impactData processing applicationsSpecial data processing applicationsData setDowntime
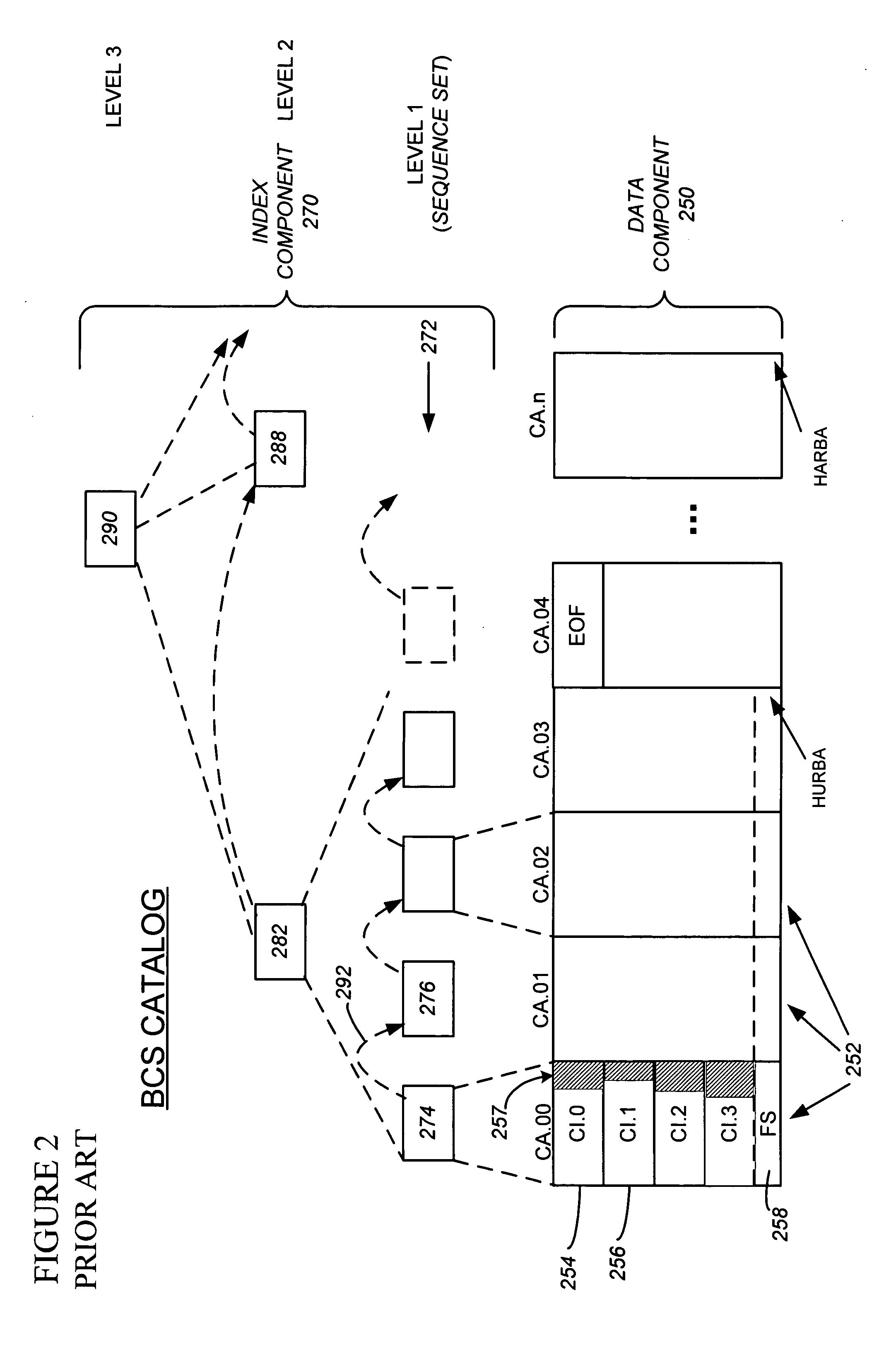
MVS mainframe computer systems employ the ICF (Integrated Catalog Facility) catalog environment to manage numerous data sets. To provide 24×7 availability of those data sets, the BCS (250,270) must be re-organized while leaving the catalog open to access by applications. To perform a re-org while open, a data CI correlation table (500) is constructed (314) and used to lay the data CIs into a backup file in logical order (316), so that they can be loaded into the new BCS (324) without sorting, thereby reducing downtime. Additionally, if the BCS is damaged during normal operation, repair of the structure must also be performed to ensure that correct access is maintained to all data that is cataloged in the BCS. Throughout the re-org process, structural integrity checks are performed on the data and index component of the BCS, and if errors are encountered, they can be repaired.
Owner:ROCKET SOFTWARE
Multi-processor reconfigurable computing system
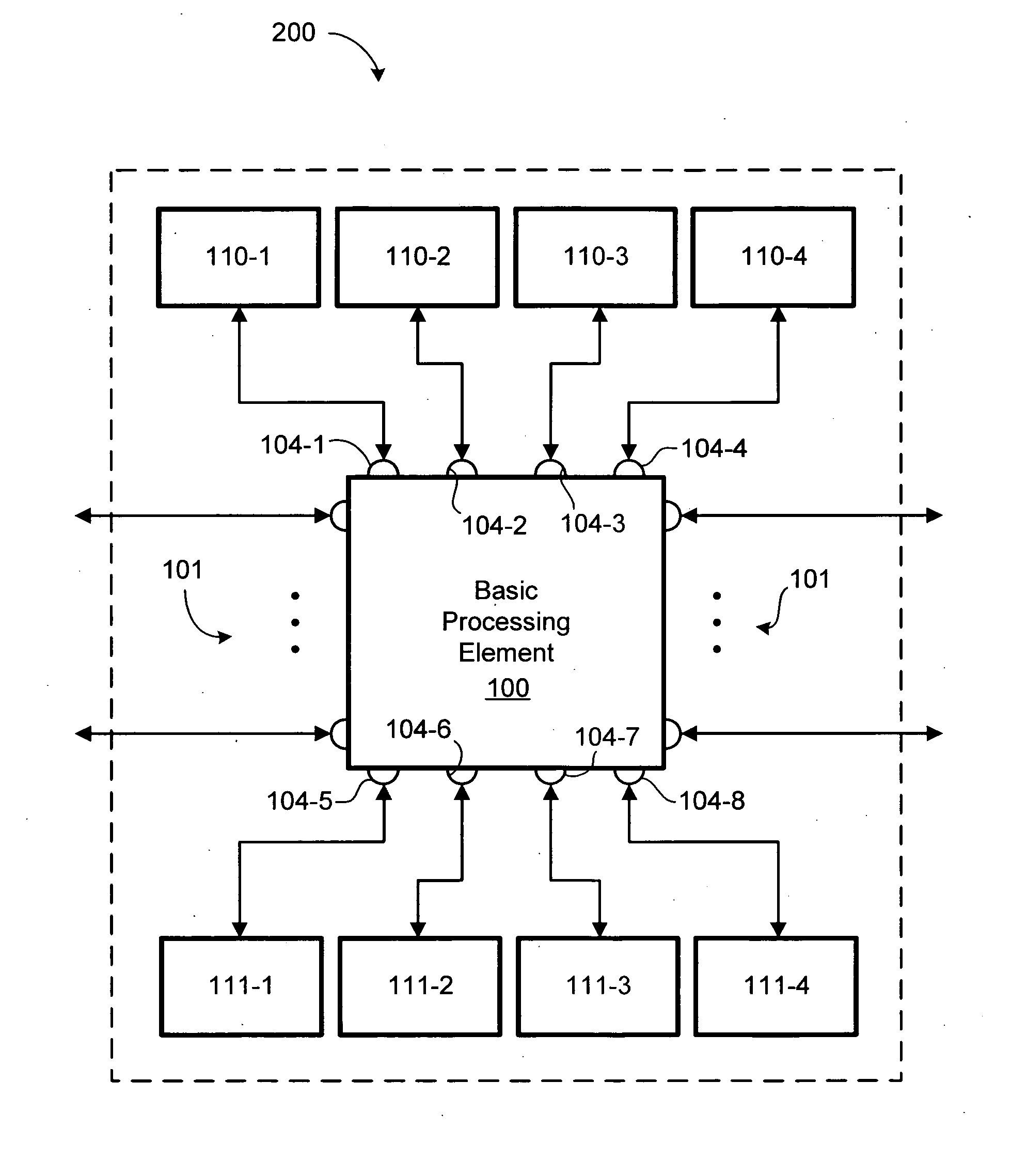
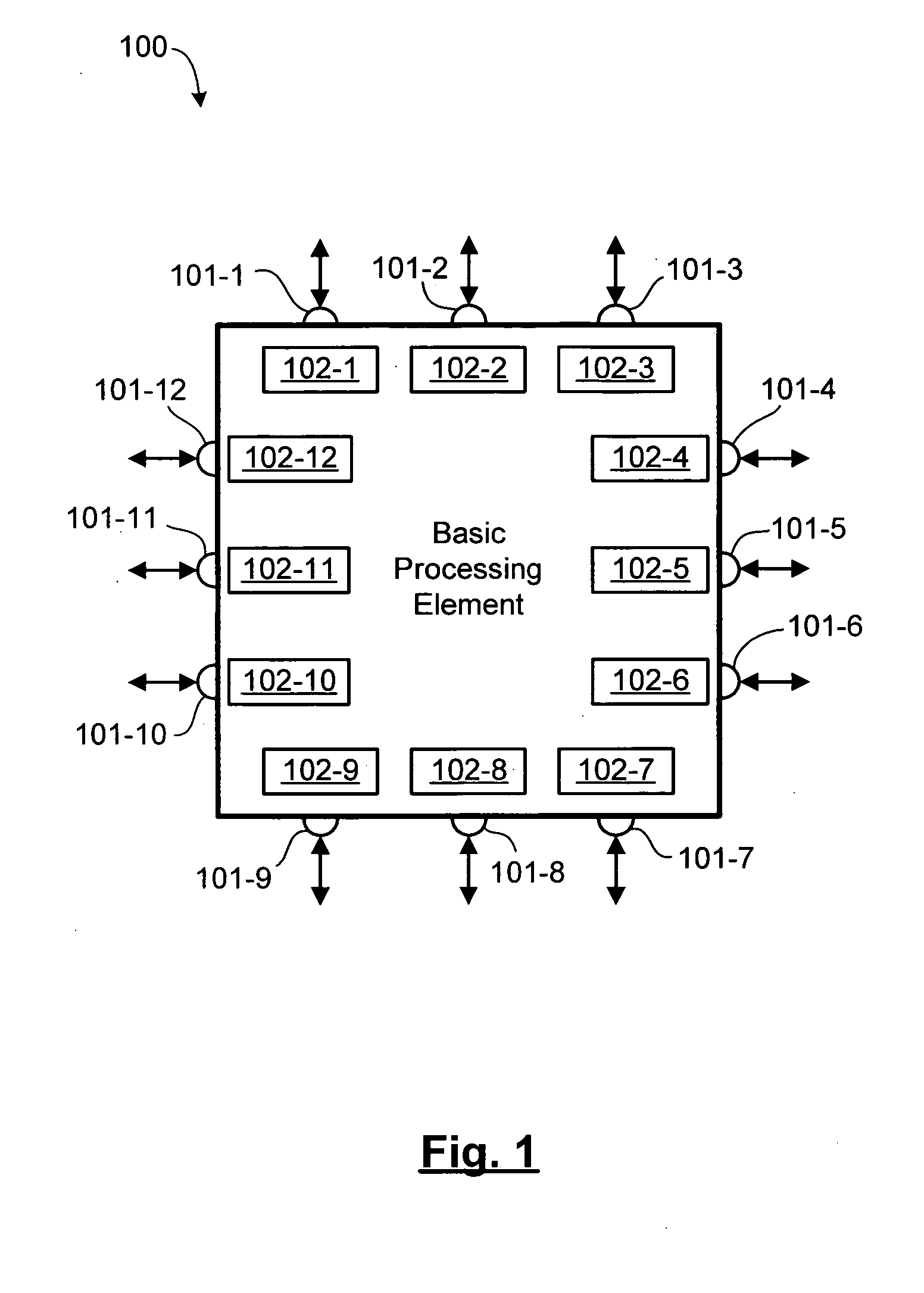
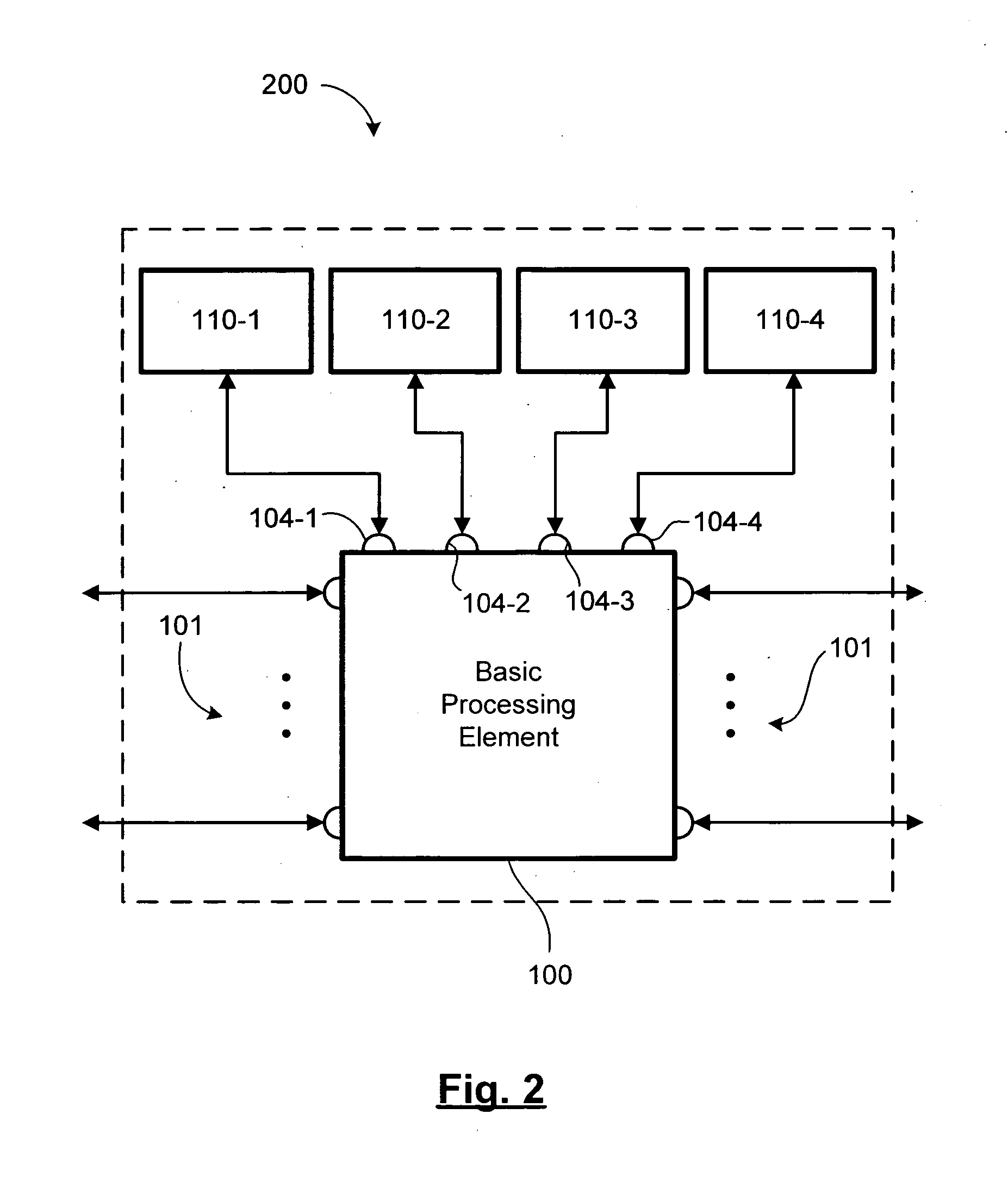
ActiveUS20060031659A1Reduce communication delayImproved bandwidth throughputGeneral purpose stored program computerInput/output processes for data processingCross connectionMulti processor
A reconfigurable multi-processor computing system including a plurality of configurable processing elements each having a plurality of integrated high-speed serial input / output ports. Interconnects link the plurality of processing elements, wherein at least one of the integrated high-speed serial input / output ports of each processing element is connected by at least one interconnect to at least one of the integrated high-speed serial input / output ports of each other processing element, thereby creating a full mesh network. The full mesh network is located on a processor card, multiples of which may be grouped in a shelf having a backplane card with a shelf controller card for providing cross-connects between processor cards. Multiple shelves may be interconnected to form a large computer system.
Owner:ARCHES COMPUTING SYST
Massively computational parallizable optimization management system and method
ActiveUS7013344B2Reduced execution timeReduce search timeResource allocationMultiple digital computer combinationsProgram planningMainframe computer
Owner:TWITTER INC
Method and apparatus for incremental code signing
ActiveUS20050066169A1Quickly and easily authenticatingMemory loss protectionUser identity/authority verificationArray data structureCode signing
The present invention discloses a method for quickly and easily authenticating large computer program. The system operates by first sealing the computer program with digital signature in an incremental manner. Specifically, the computer program is divided into a set of pages and a hash value is calculated for each page. The set of hash values is formed into a hash value array and then the hash value array is then sealed with a digital signature. The computer program is then distributed along with the hash value array and the digital signature. To authenticate the computer program, a recipient first verifies the authenticity of the hash value array with the digital signature and a public key. Once the hash value array has been authenticated, the recipient can then verify the authenticity of each page of the computer program by calculating a hash of a page to be loaded and then comparing with an associated hash value in the authenticated hash value array. If the hash values do not match, then execution may be halted.
Owner:APPLE INC
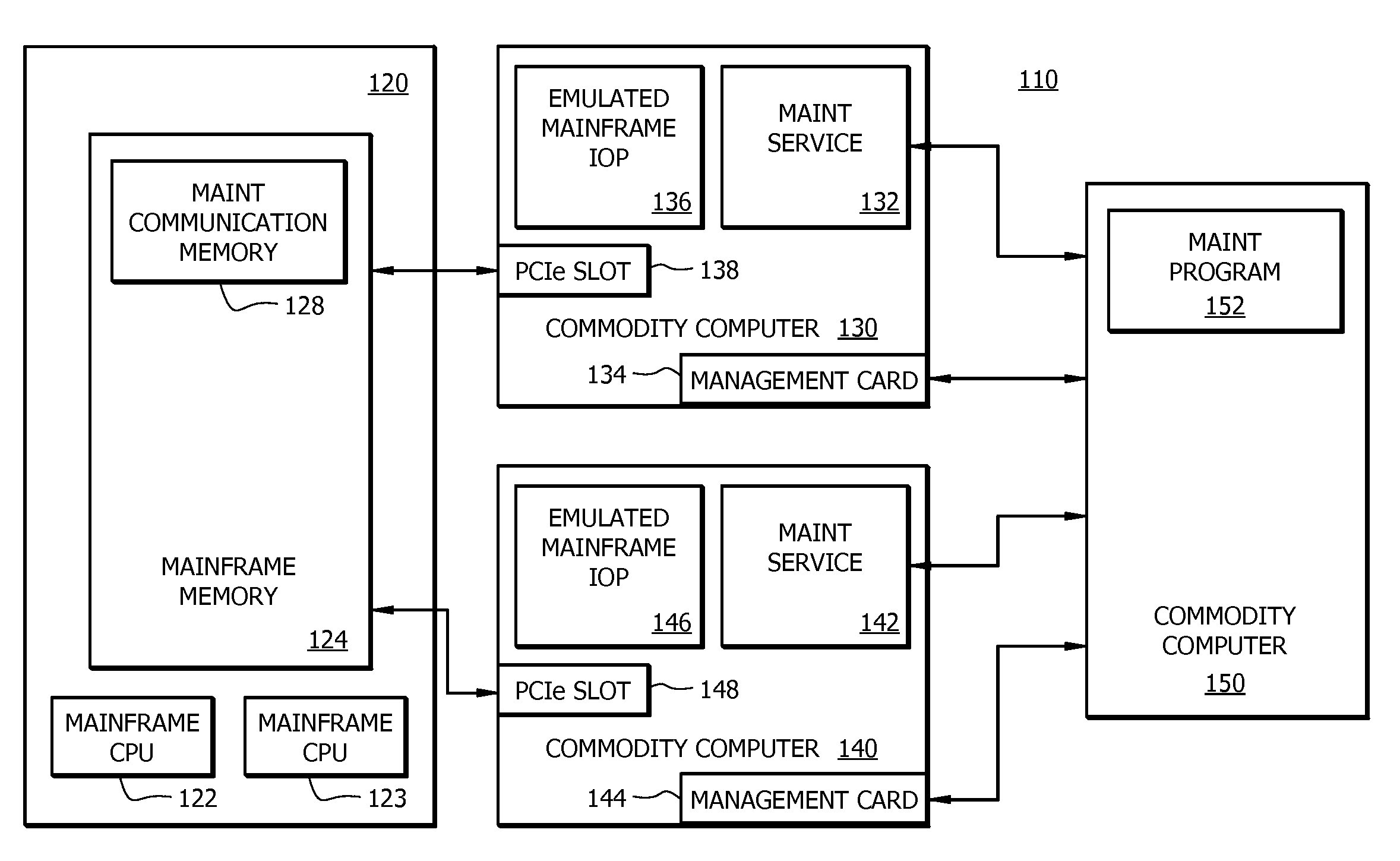
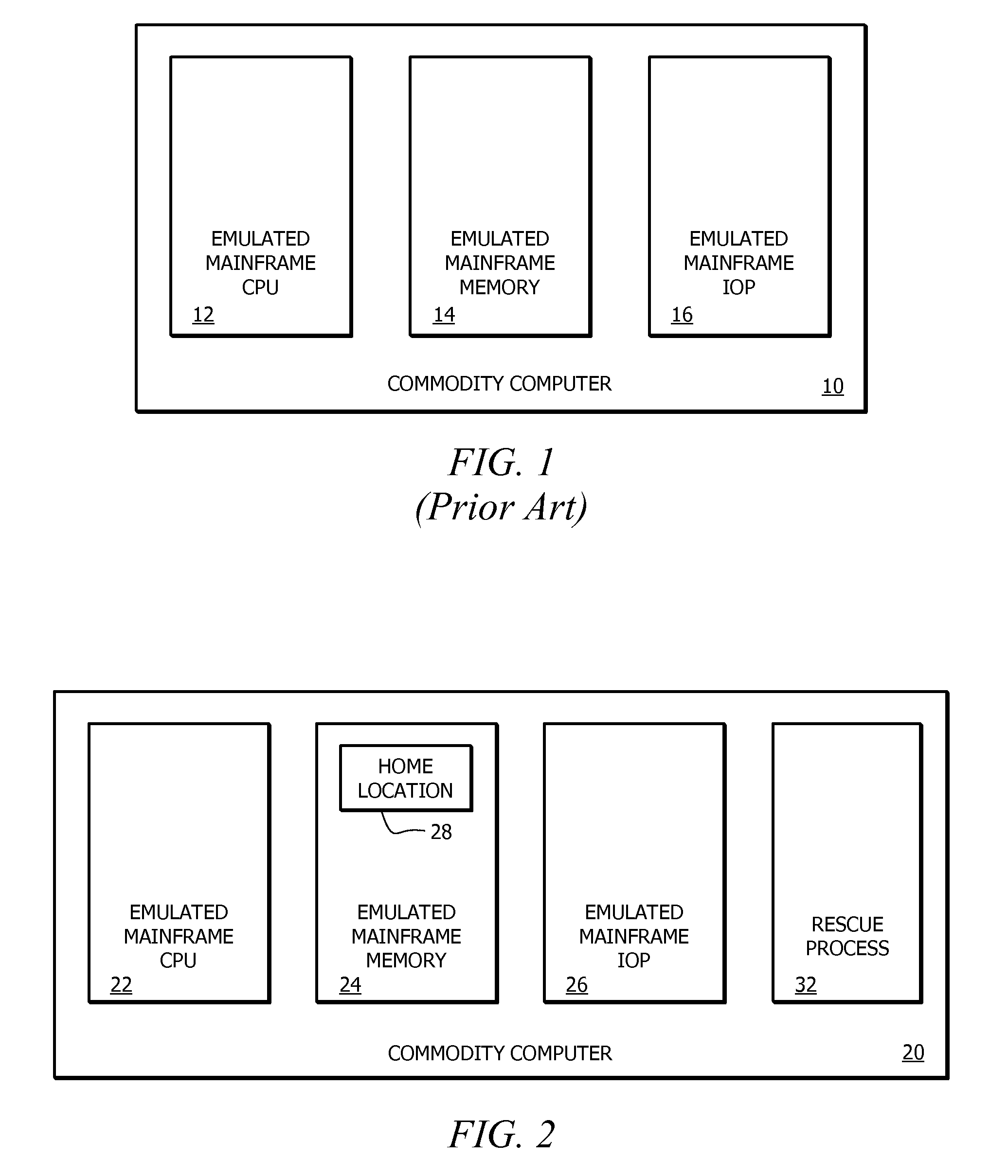
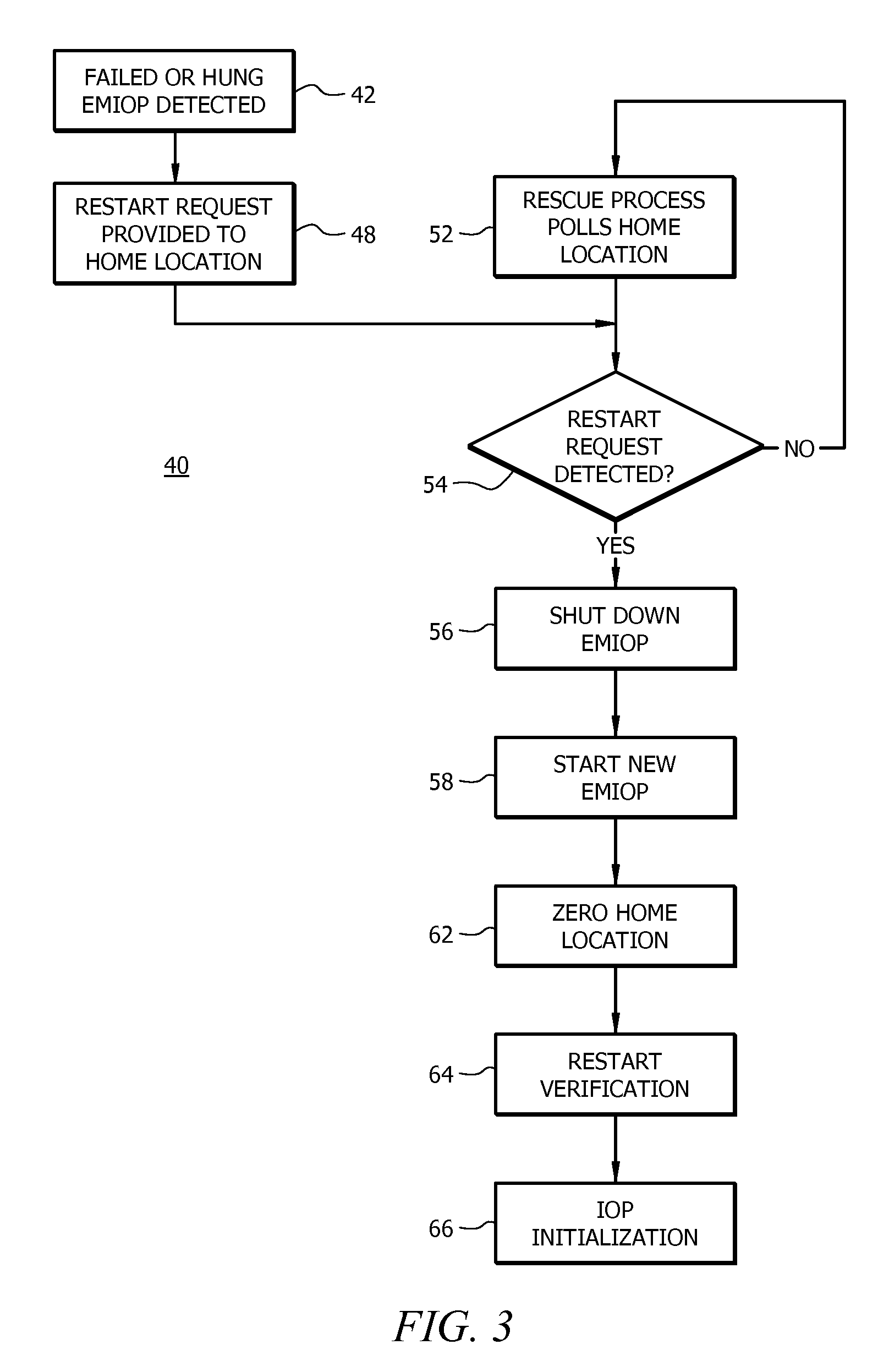
Method, apparatus and system for restarting an emulated mainframe iop
A method, apparatus and system for restarting an emulated mainframe IOP, such as a failed or hung emulated mainframe IOP within an emulated mainframe commodity computer. The method includes a rescue process that polls a home location for Restart Request information. In response to receiving Restart Request information, the rescue process is configured to shut down the existing emulated mainframe IOP, start a new emulated mainframe IOP, and reset the home location. The Restart Request information can be provided to the home location by the mainframe computer being emulated. Alternatively, the rescue mechanism can use an interface management card instructed to restart the commodity computer hosting the failed or hung IOP, e.g., from a maintenance service and / or a maintenance program residing in an active commodity computer coupled to the commodity computers hosting one of several emulated mainframe IOPs.
Owner:RUSS CRAIG F +1
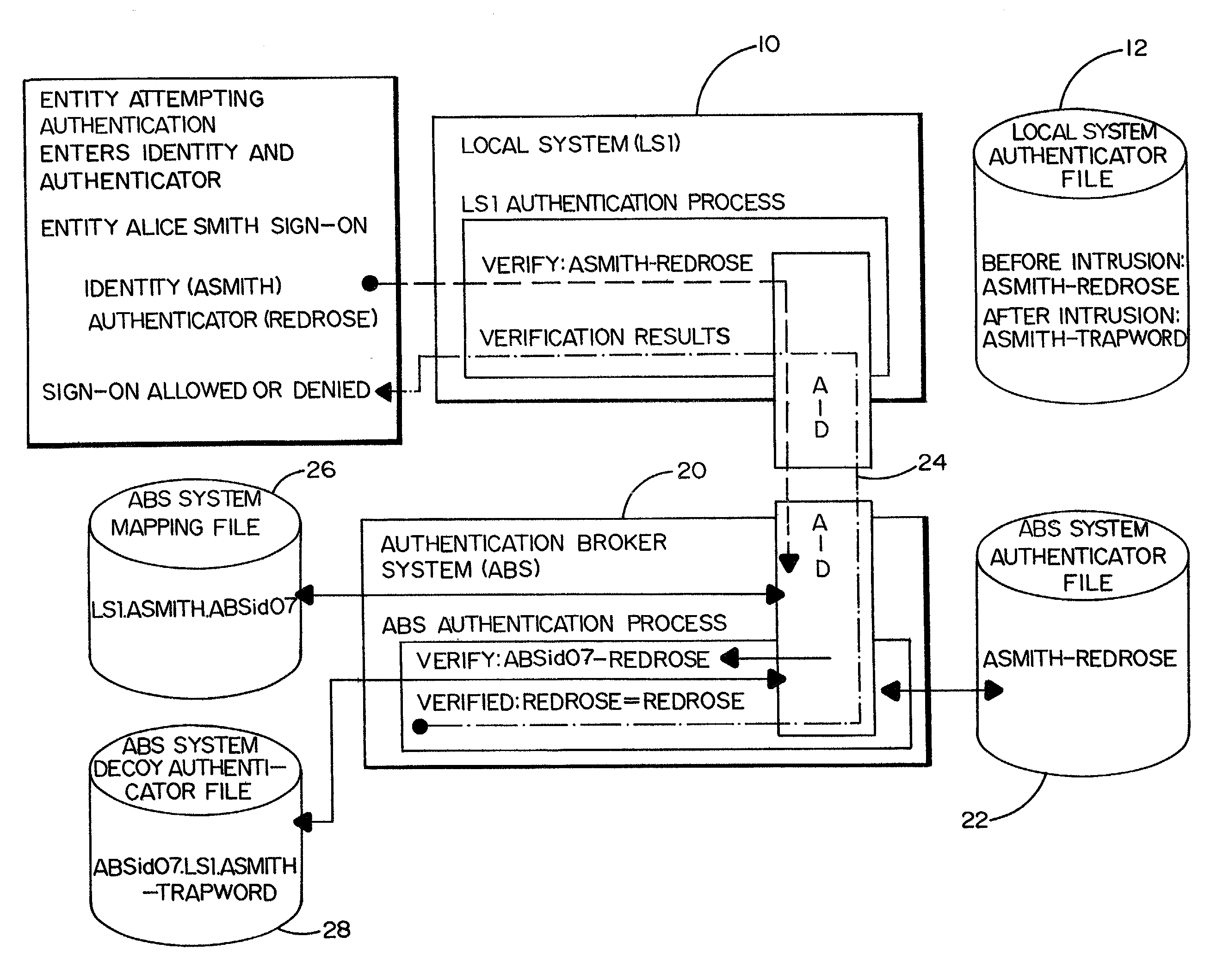
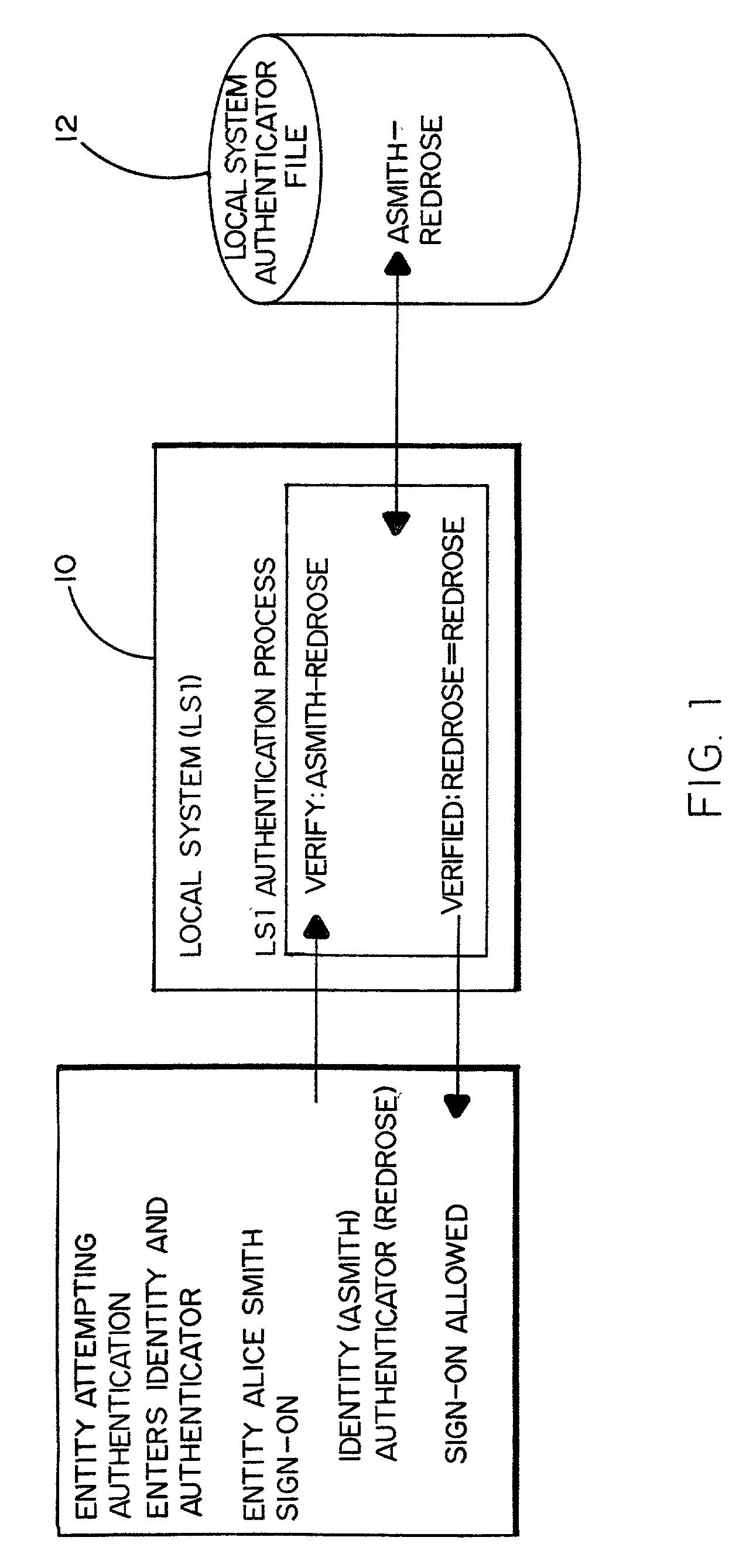
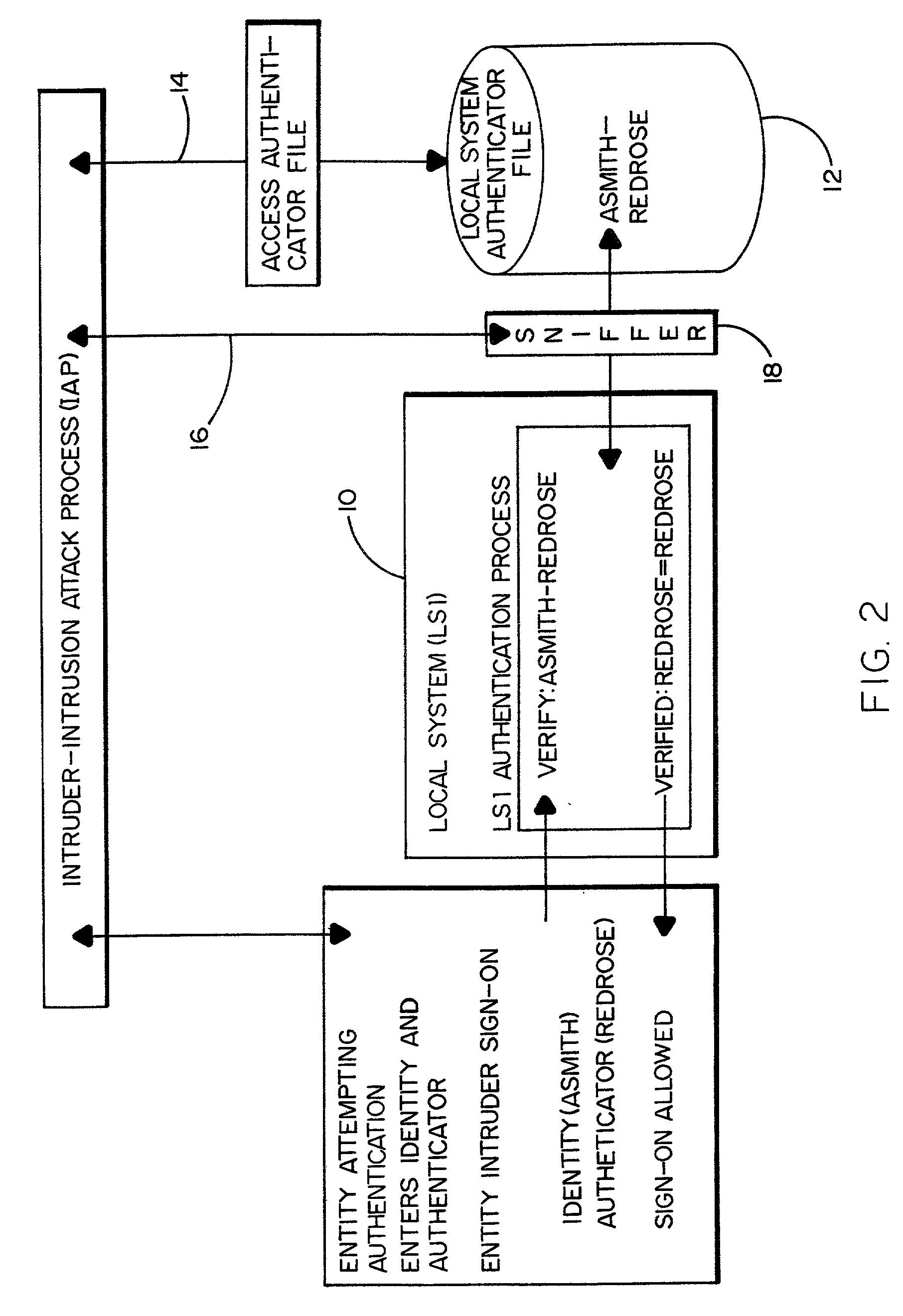
Method and system for detecting and preventing an intrusion in multiple platform computing environments
A method and a system by which to achieve authentication intrusion detection so as to effectively detect and prevent unauthorized access to and use of a local computer system, or the like, and take appropriate measures. The local system authentication process is redirected to an authenticator broker system (i.e. a secondary authentication system) that makes use of the local system authentication process paths and the local system authenticator file. The authenticator broker system includes an authenticator broker system file having stored therein secret authenticators of prospective users, a mapping file to assign a replacement identifier for the identifier entered by a particular user at the local system and redirected to the secondary system, and a decoy authenticator file to assign a decoy authenticator for the secret authenticator entered by the user and originally stored in the local system authentication file. It is the decoy authenticator that is captured and unknowingly used by the intruder to give away his or her presence. By way of example, the authenticator broker system may be a mainframe computer that is responsible for authentication and access control with respect to a local computer system.
Owner:BAILEY RONN H
Knowledge storage and retrieval system and method
ActiveUS20070043708A1Simple processProcessing timeData processing applicationsNatural language data processingProgramming languageWeb browser
A system and method for representing, storing and retrieving real-world knowledge on a computer or network of computers is disclosed. Knowledge is broken down into permanent atomic “facts” which can be stored in a standard relational database and processed very efficiently. It also provides for the efficient querying of a knowledge base, efficient inference of new knowledge and translation into and out of natural language. Queries can also be processed with full natural language explanations of where the answers came from. The method can also be used in a distributed fashion enabling the system to be a large network of computers and the technology can be integrated into a web browser adding to the browser's functionality.
Owner:AMAZON TECH INC
Reorganization and repair of an icf catalog while open and in-use in a digital data storage system
InactiveUS20070088769A1Minimal impactData processing applicationsSpecial data processing applicationsData setDowntime
MVS mainframe computer systems employ the ICF (Integrated Catalog Facility) catalog environment to manage numerous data sets. To provide nearly continuous availability of those data sets, the BCS catalog (250,270) must be re-organized while leaving the catalog open to access by applications. To perform a re-org while open, a data CI correlation table (500) can be constructed (314) and used to lay the data CIs into a backup file in logical order (316), so that they can be loaded into the new BCS catalog (324) without sorting, thereby reducing downtime.
Owner:MAINSTAR SOFTWARE CORP
Systems and methods to detect copy number variation
InactiveUS20140051154A1Bioreactor/fermenter combinationsBiological substance pretreatmentsData filePersonal computer
In one aspect, a system for implementing a copy number variation analysis method, is disclosed. The system can include a nucleic acid sequencer and a computing device in communications with the nucleic acid sequencer. The nucleic acid sequencer can be configured to interrogate a sample to produce a nucleic acid sequence data file containing a plurality of nucleic acid sequence reads. In various embodiments, the computing device can be a workstation, mainframe computer, personal computer, mobile device, etc.
Owner:LIFE TECH CORP
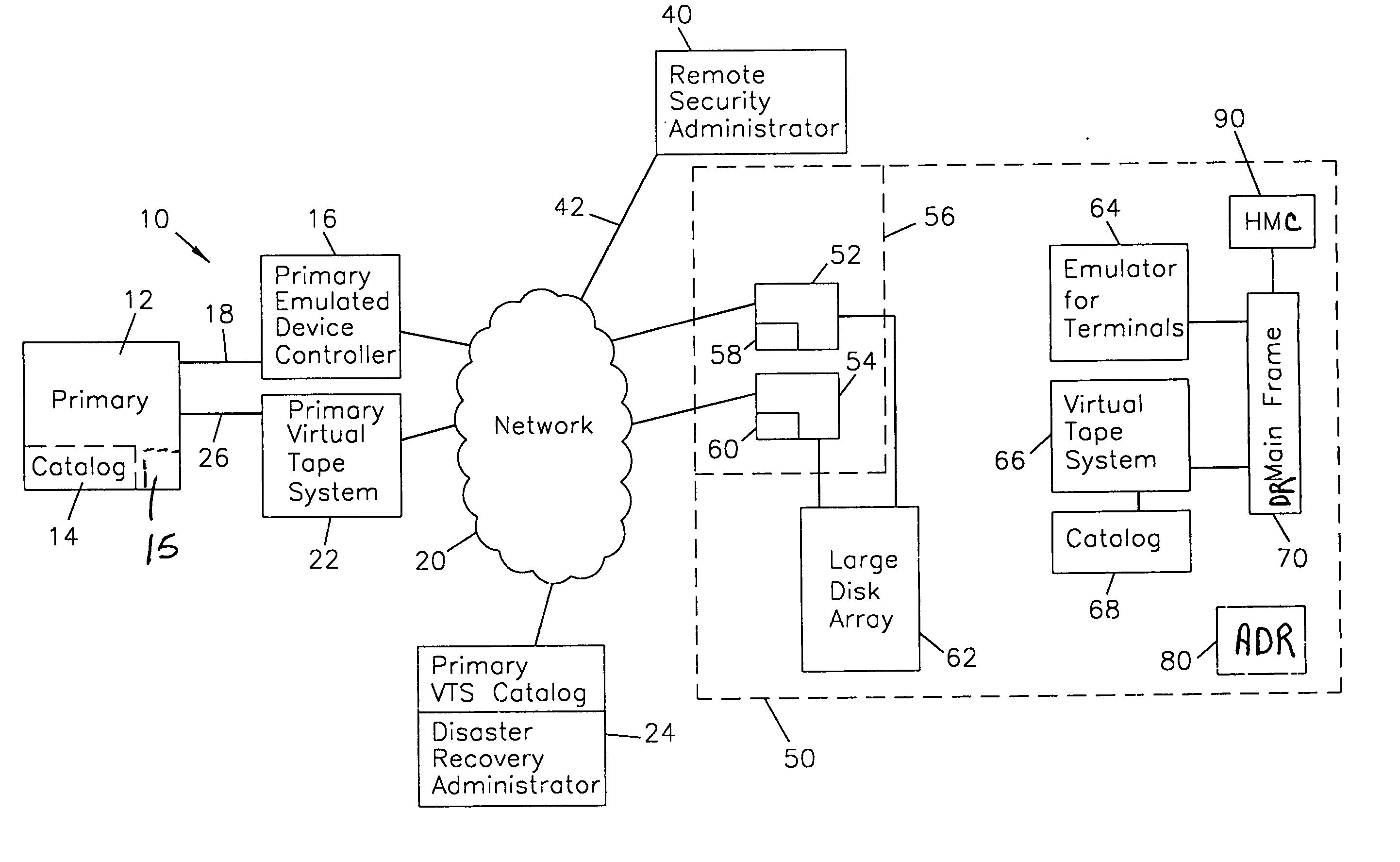
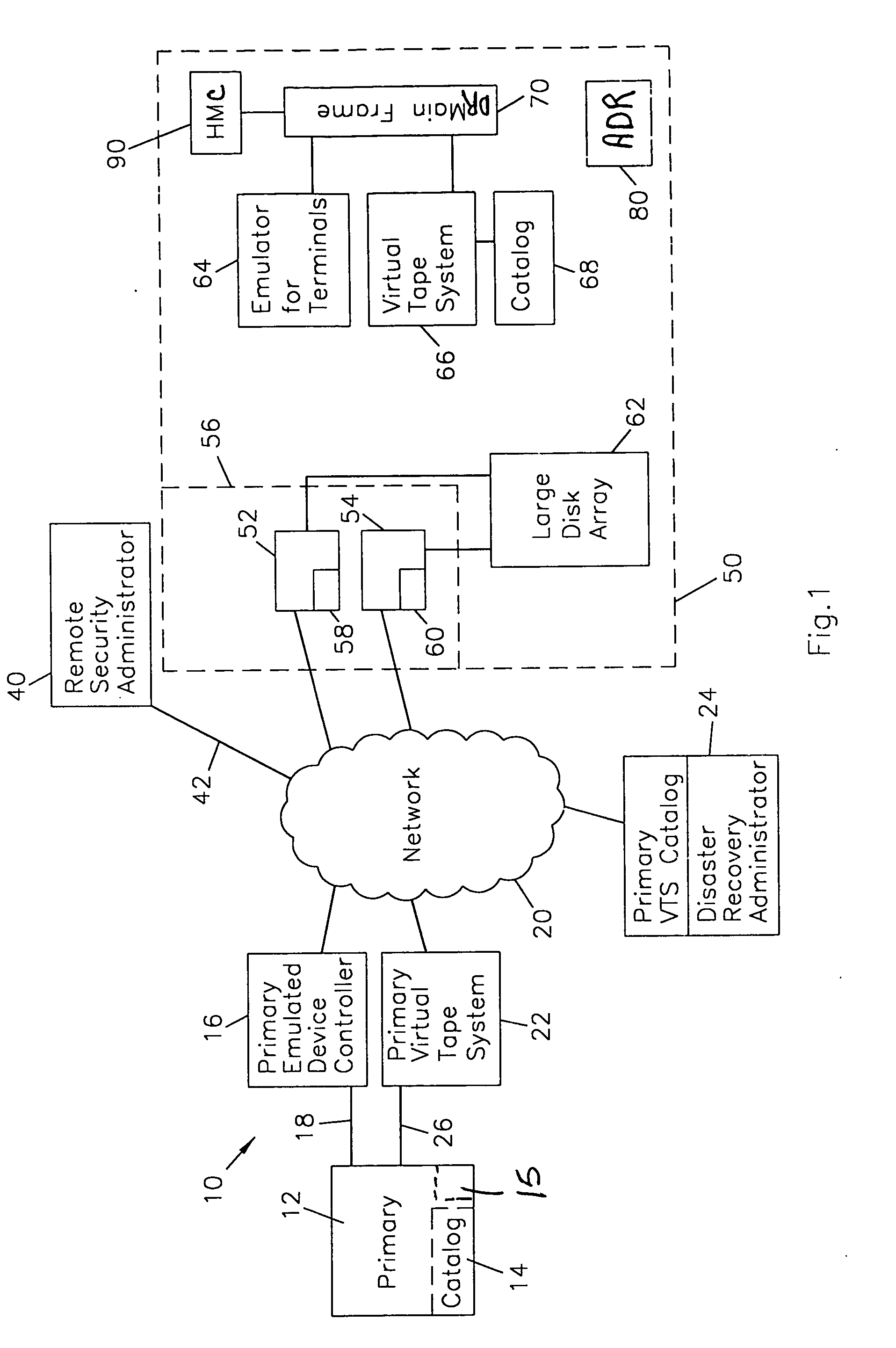
Data center virtual tape off-site disaster recovery planning and implementation system
ActiveUS20060123208A1Memory loss protectionError detection/correctionComputer hardwareProgram planning
A system for planning and verifying off-site disaster recovery plans as well as implementing alternate fall back operations in the event of a disaster. The system includes at least one primary mainframe computer having an inboard catalog component, a primary emulated device controller connected to the primary computer, and a primary virtual tape system connected to the primary computer. A primary virtual tape system catalog is connected to the primary virtual tape system. A disaster recovery administrator using remote management tools maintains user and resource profiles and controls configuration of the primary emulated device controller and the primary virtual tape system. A disaster recovery facility includes at least one customer virtual tape system including a virtual tape system catalog component, a terminal emulator in communication with a disaster recovery mainframe computer and a disaster recovery virtual tape system having a virtual tape system catalog in communication with the disaster recovery mainframe wherein customer virtual tape system images are mirrored on the disaster recovery virtual tape system and catalog information from the customer virtual tape catalog is mirrored on the disaster recovery tape system of the disaster recovery facility.
Owner:GLOBAL INTERFACE SOLUTIONS INC D B A SECUREAGENT SOFTWARE
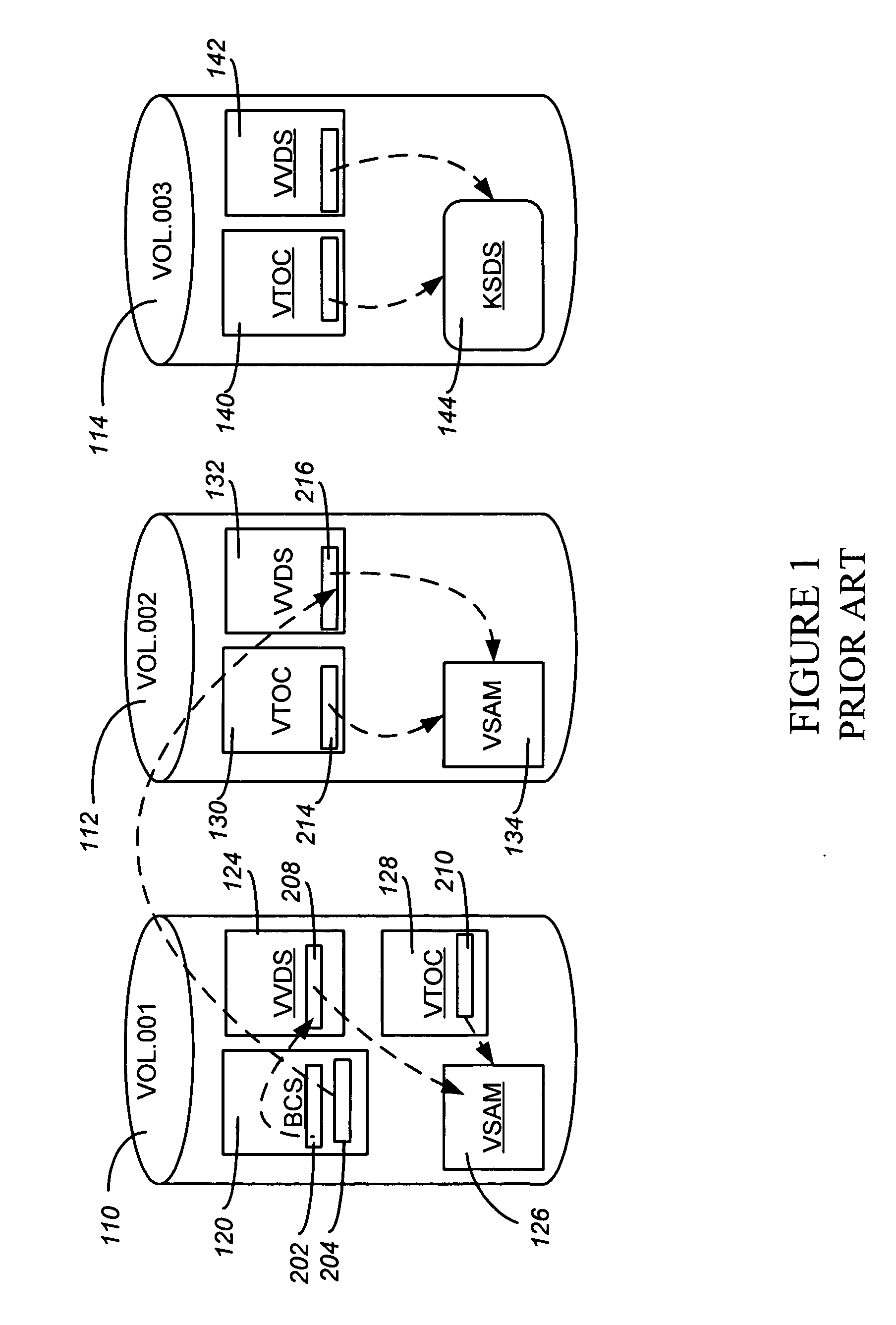
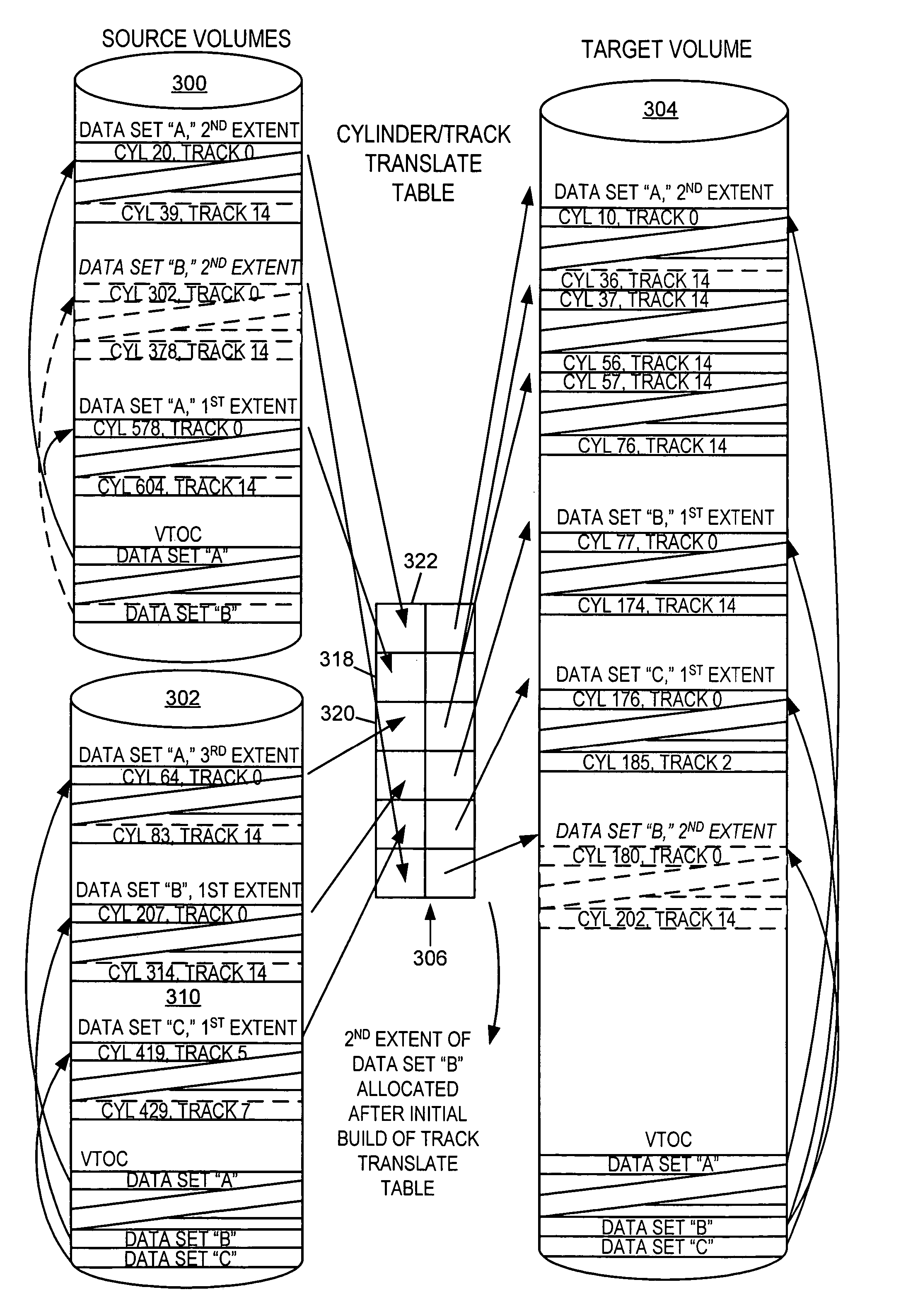
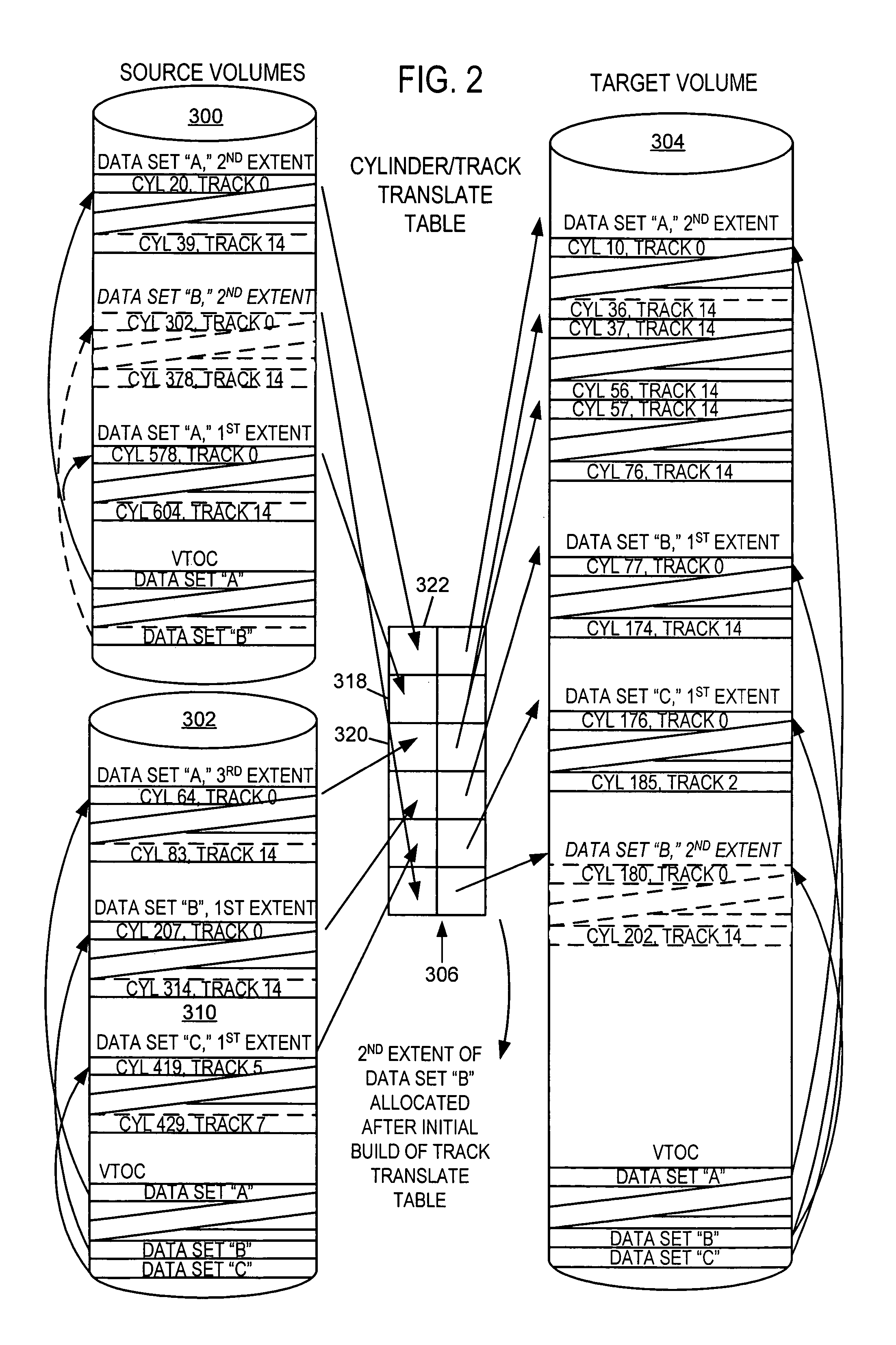
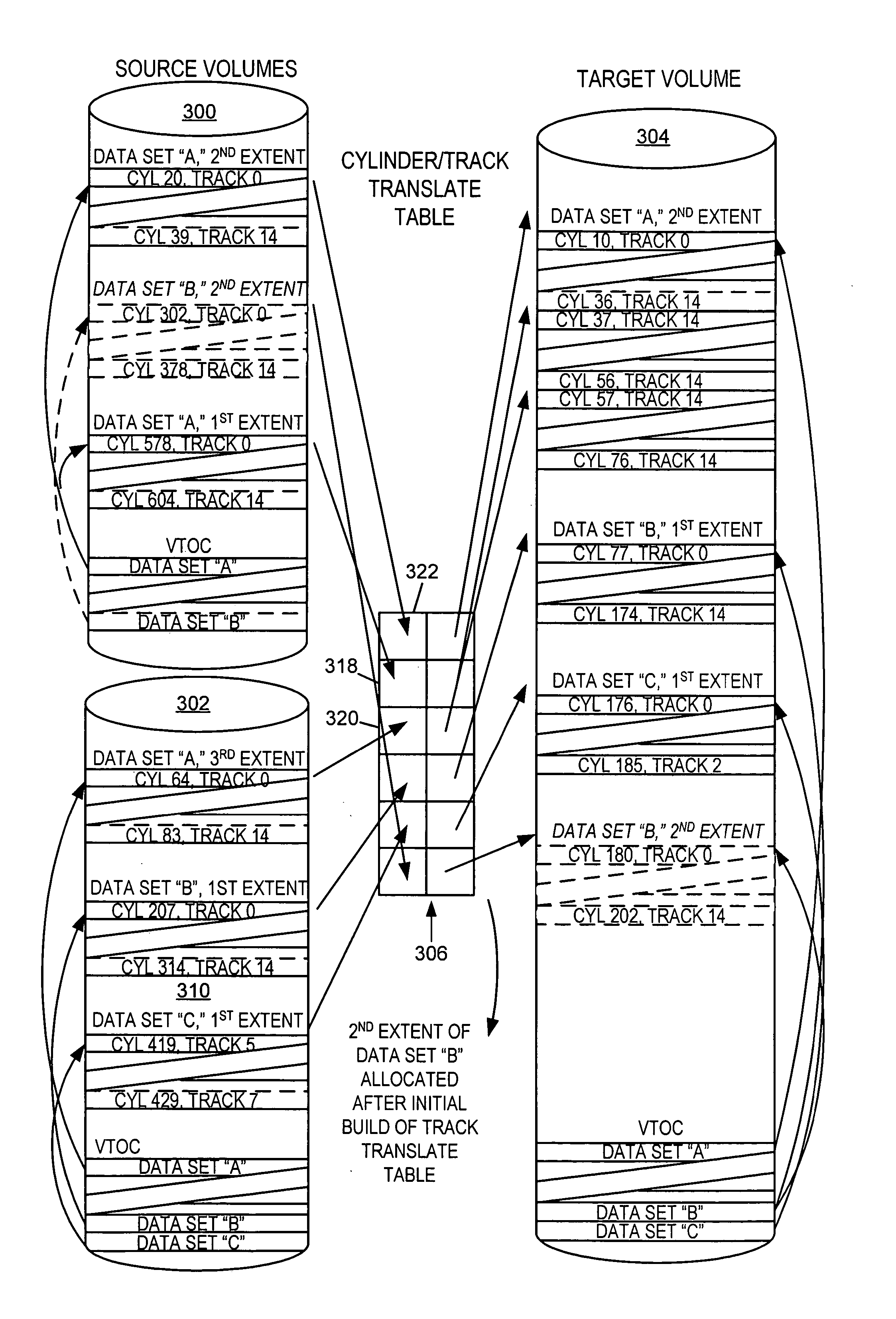
Data set level mirroring to accomplish a volume merge/migrate in a digital data storage system
ActiveUS7146475B2Data processing applicationsInput/output to record carriersData setOperational system
Owner:ROCKET SOFTWARE
Data set level mirroring to accomplish a volume merge/migrate in a digital data storage system
ActiveUS20050108485A1Data processing applicationsInput/output to record carriersData setOperational system
Users of Mainframe computers running under IBM's MVS operating systems have a need to merge migrate data from multiple smaller DASD devices (disk volumes) to larger DASD devices, and / or to migrate data in order to combine data set extents. A method is disclosed for migrating data where a volume merge is involved, and / or when combining of extents is desired, that minimizes the down time of applications using the involved data while satisfying MVS rules for volume and catalog meta-data files as well as data extent limitations. The method may be implemented such that source and target volumes need not be in like manufacturer DASD devices.
Owner:ROCKET SOFTWARE
Reorganization and repair of an ICF catalog while open and in-use in a digital data storage system
ActiveUS7158999B2Minimal impactData processing applicationsDigital data processing detailsData setDowntime
MVS mainframe computer systems employ the ICF (Integrated Catalog Facility) catalog environment to manage numerous data sets. To provide 24×7 availability of those data sets, the BCS (250,270) must be re-organized while leaving the catalog open to access by applications. To perform a re-org while open, a data CI correlation table (500) is constructed (314) and used to lay the data CIs into a backup file in logical order (316), so that they can be loaded into the new BCS (324) without sorting, thereby reducing downtime. Additionally, if the BCS is damaged during normal operation, repair of the structure must also be performed to ensure that correct access is maintained to all data that is cataloged in the BCS. Throughout the re-org process, structural integrity checks are performed on the data and index component of the BCS, and if errors are encountered, they can be repaired.
Owner:ROCKET SOFTWARE
Test apparatus to facilitate building and testing complex computer products with contract manufacturers without proprietary information
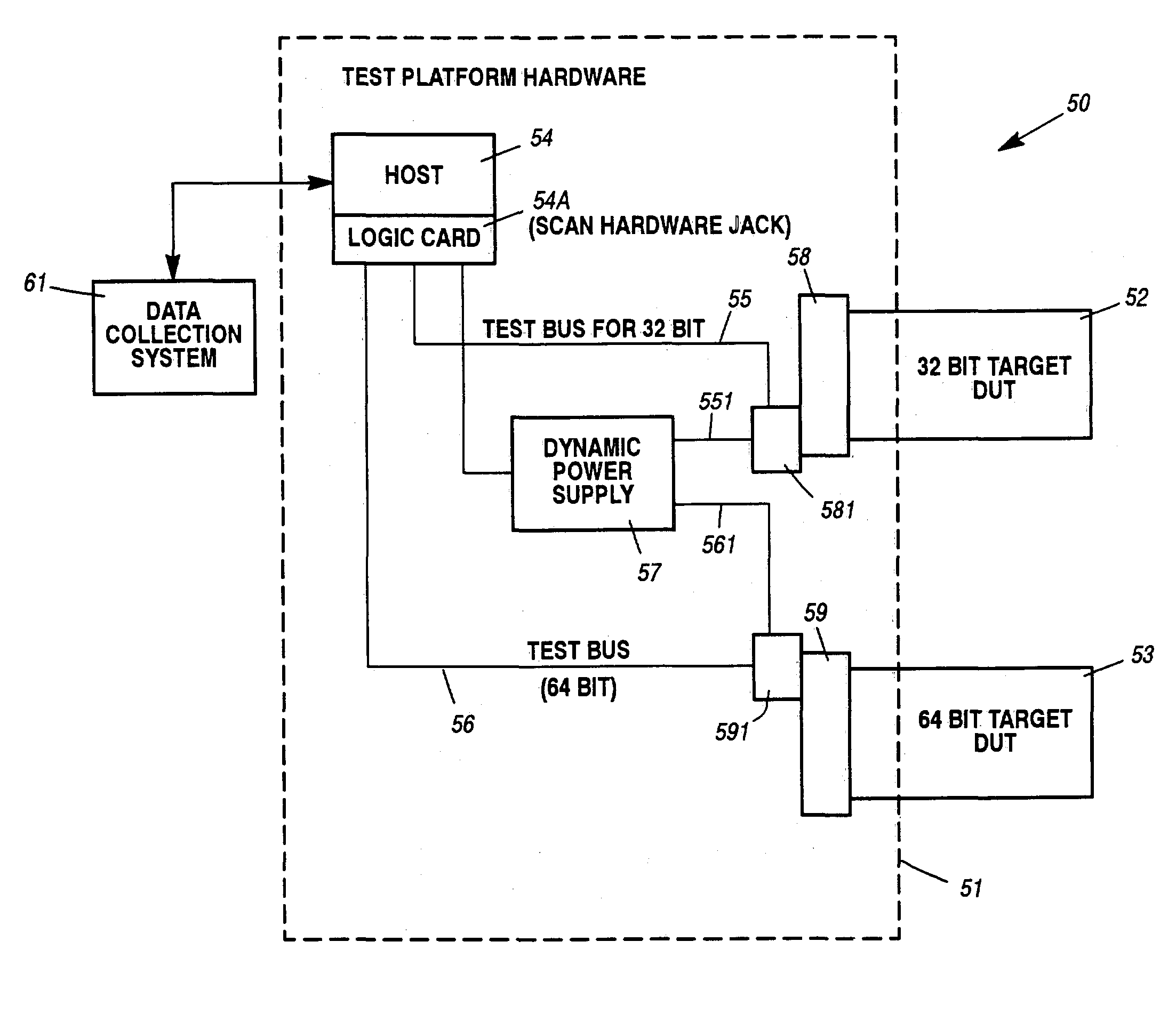
InactiveUS7139949B1Easy to useLow costResistance/reactance/impedenceElectronic circuit testingSoftware engineeringComputerized system
Building and testing complex electronic products especially large scale computer systems are handled with control remaining with the owner of the design while a contract manufacturer does the basic manufacturing processes and testing. Nearly all levels of testing are accomplished without sharing high level descriptions of the end product or its features by providing only low level files for test functions. A tester used by the contract manufacturer to exercise the testing function for multiple circuit boards and that tester has numerous features that make it more useful and efficient. The tester has a computer system in it to run the tests using the low level files, and mimics the platform into which the boards will eventually become inserted. Various features provide additional ease of use and functionality.
Owner:UNISYS CORP
Mechanized tax worksheet
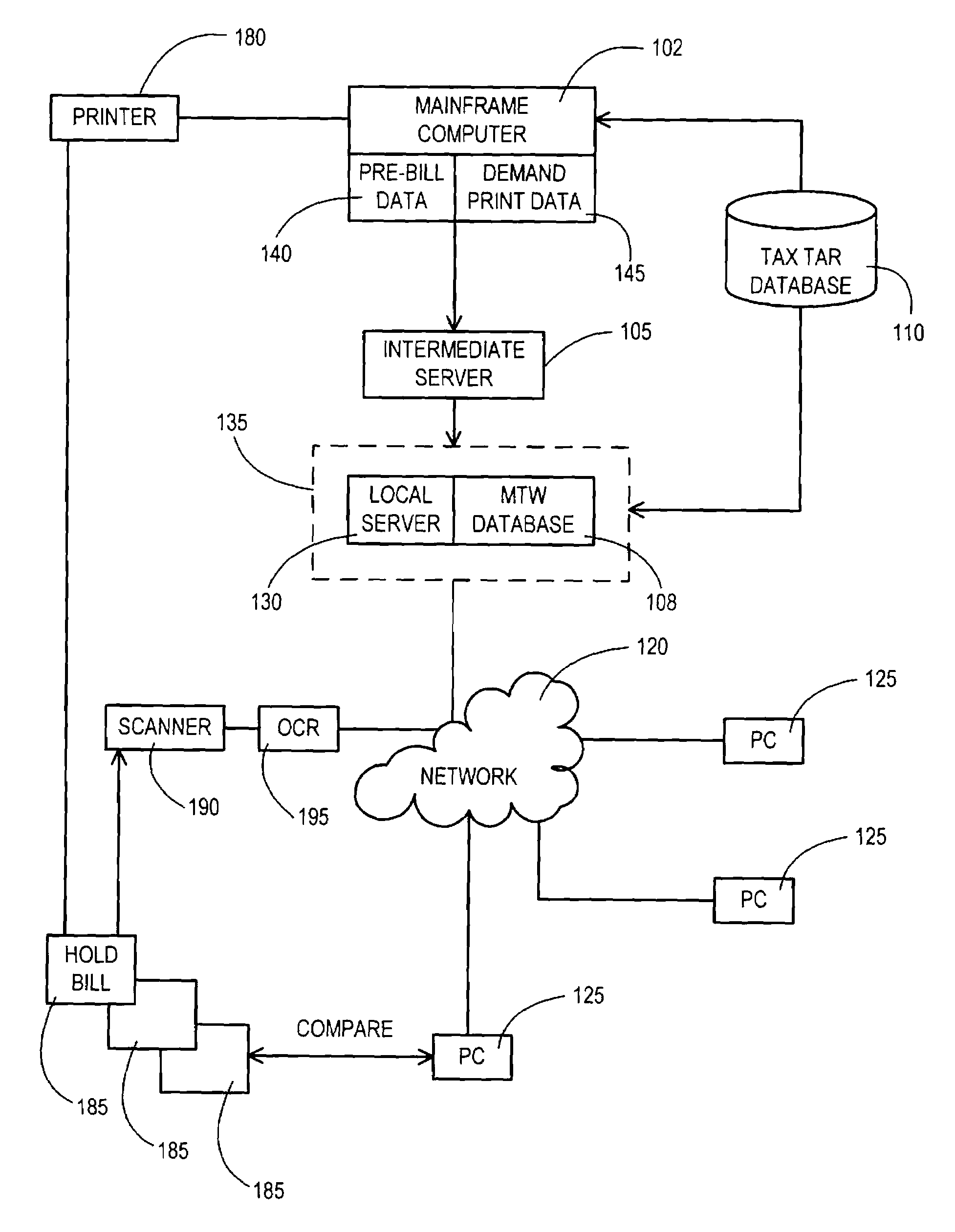
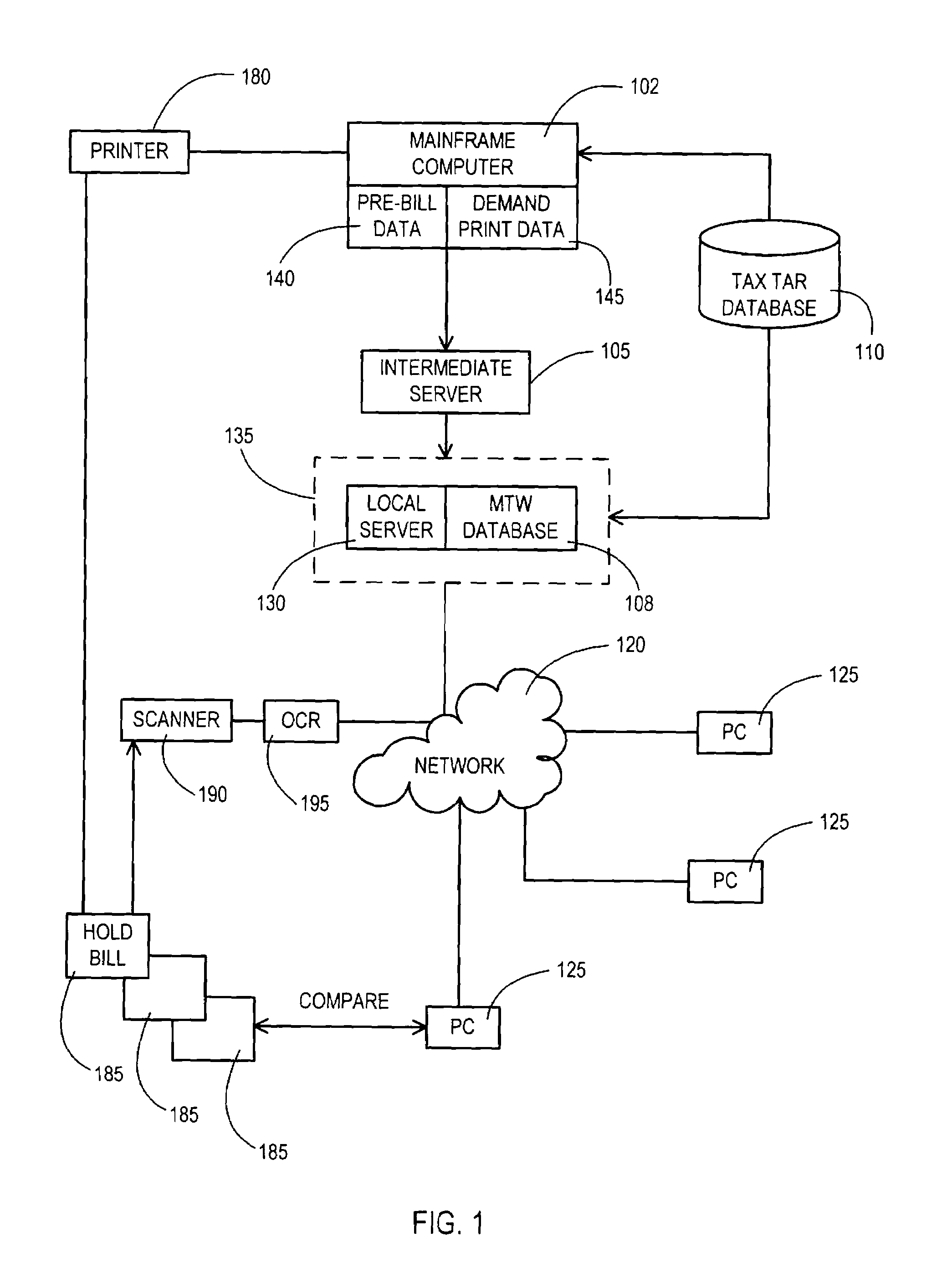
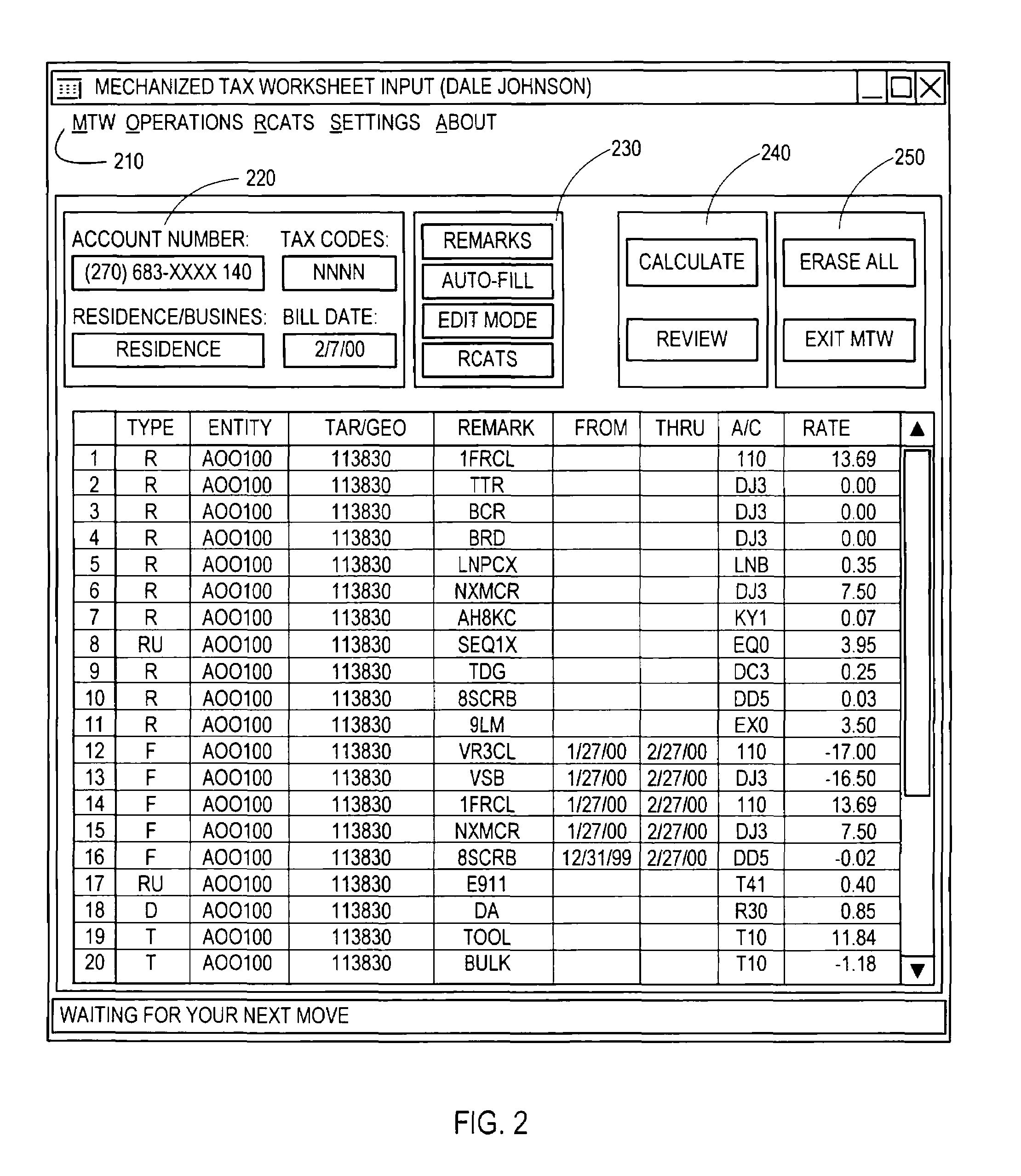
InactiveUS7155404B1Error free and efficient bill verificationAddress urgencyComplete banking machinesElectric devicesMainframe computerData bank
A system and method for verifying charges on a customer bill includes a computers for downloading, from a mainframe computer, to a local server billing data associated with a customer account, populating a database with a portion of the billing data, performing pre-calculation functions on another portion of the billing data and populating the database with results of the pre-calculation functions, displaying predetermined categories of information stored in the database, calculating the taxes for each of several charges in the billing data and storing tax results in the database, and comparing the tax results with tax information on the customer bill.
Owner:BELLSOUTH INTPROP COR
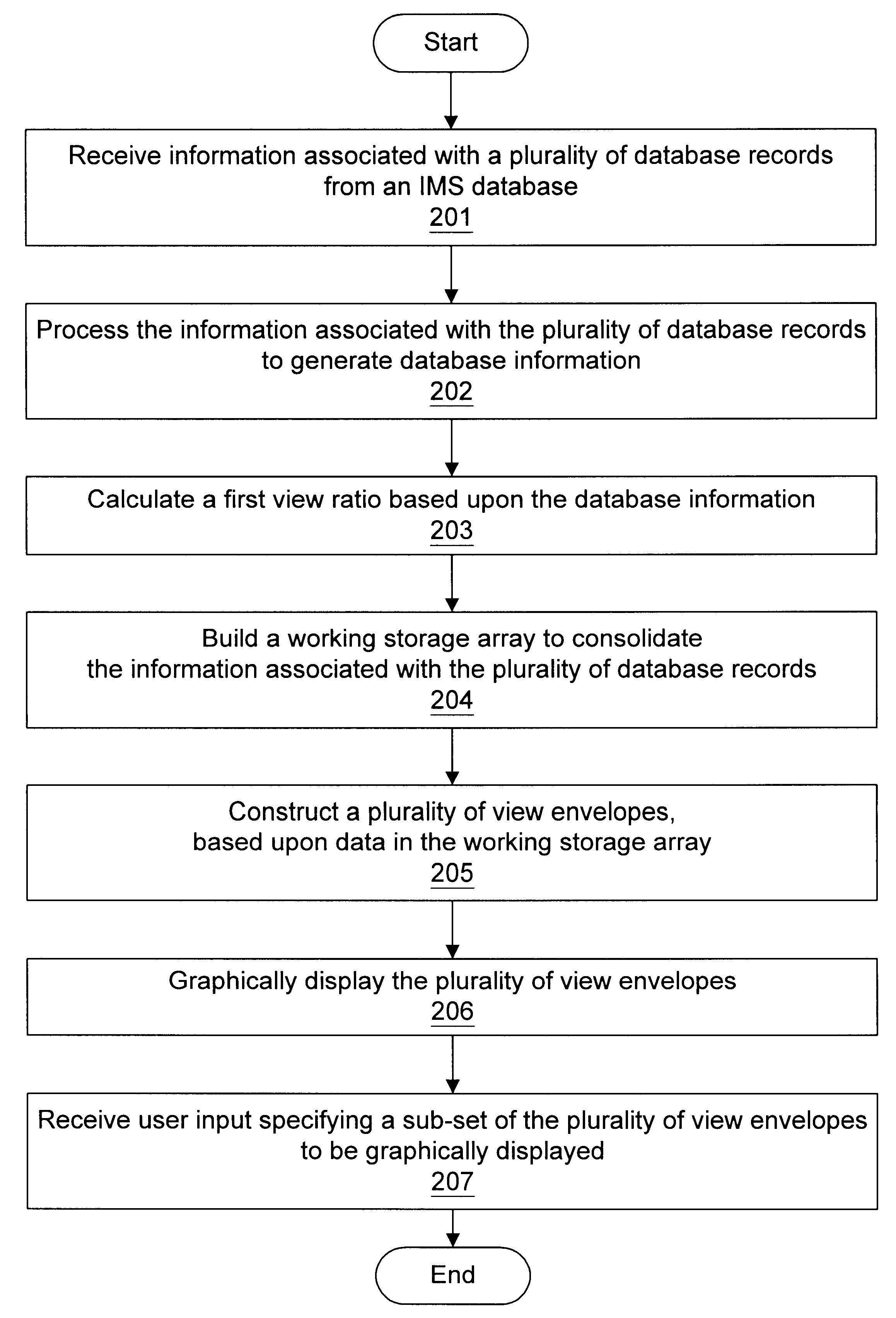
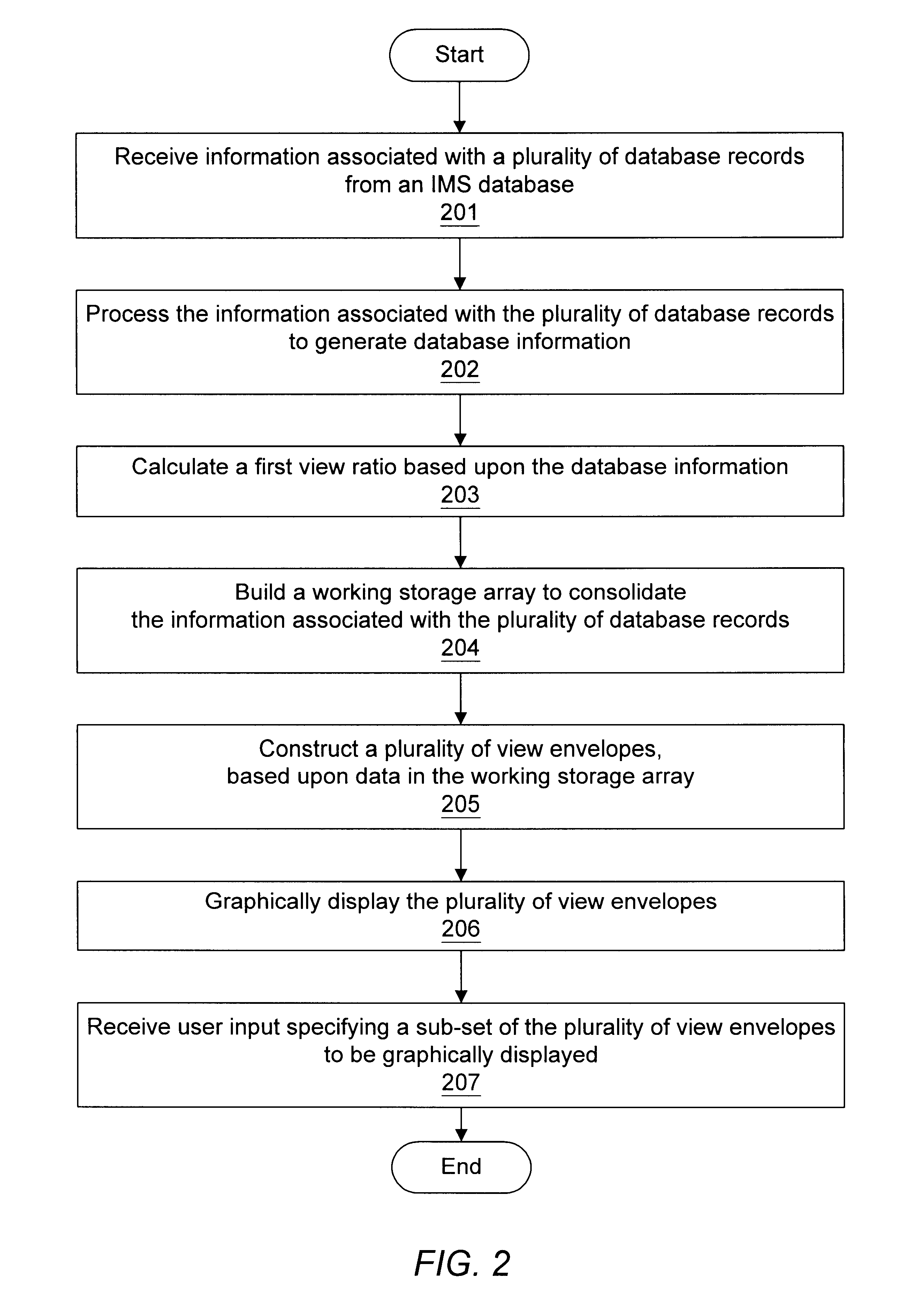
Graphical representation of disorganized database records in an IMS database
A method and system for displaying database record organization characteristics of IMS databases. In one embodiment, the method involves receiving information associated with a plurality of database records from an IMS database (e.g., information associated with ranges of database records). The database information may comprise information concerning database record organization characteristics. A working storage array may be built to consolidate the information associated with the plurality of database records. A plurality of view envelopes may be constructed. The plurality of view envelopes, along with a legend, may be graphically displayed on a display. User input may be received to request "inspection", "identification", "inspection / identification", or "detailed inspection" of a selected view envelope. Various methods may be used to "mark", "unmark", and "submit" at least one DBR to the mainframe computer system for reorganization. Display of database record organization characteristics after reorganization may also be requested by the user.
Owner:BMC SOFTWARE
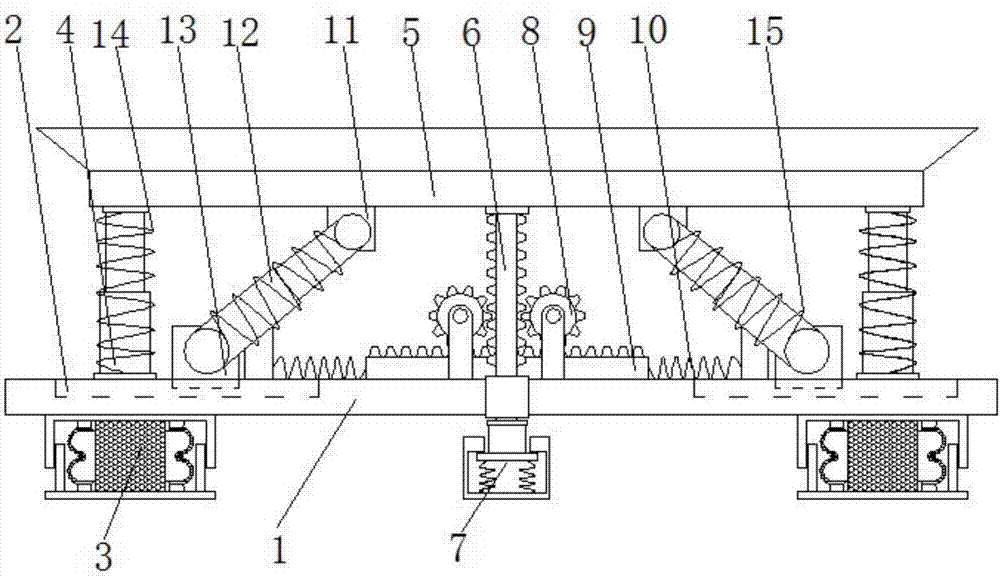
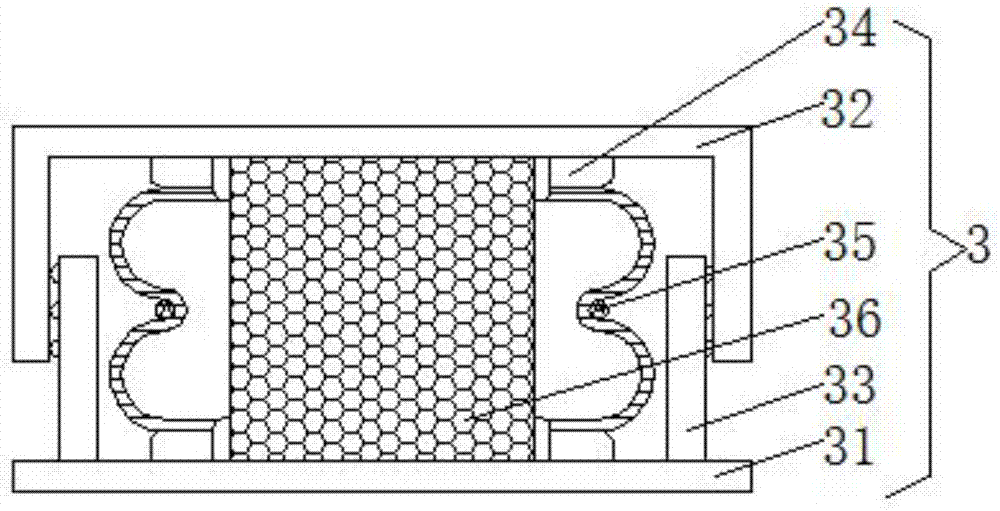
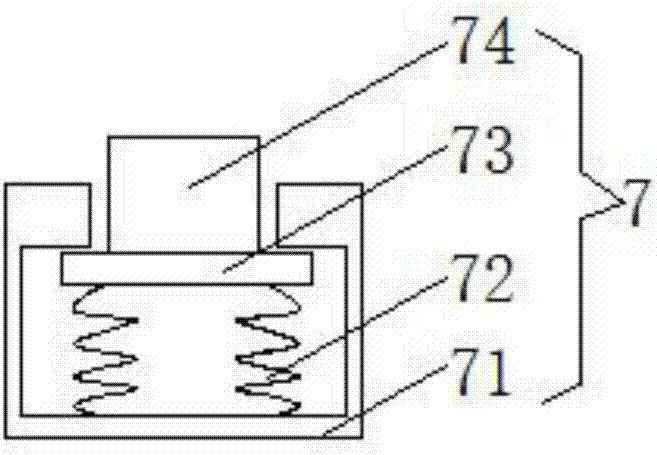
Large-scale computer fixing base with shock-absorption function
InactiveCN107299958AFix damageNot easy to damageNon-rotating vibration suppressionDigital data processing detailsMainframe computerAbsorption effect
The invention discloses a large-scale computer fixing seat with a shock absorbing function, which comprises a load bearing plate. Both sides of the top of the load bearing plate are provided with slide grooves, and both sides of the bottom of the load bearing plate are fixedly connected with shock absorbing devices. Both sides are fixedly connected with a first telescopic rod, the top of the first telescopic rod is fixedly connected with a fixed plate, and the middle of the bottom of the fixed plate is fixedly connected with a double rack, and the bottom of the double rack runs through the load-bearing plate and extends to the bottom of the load-bearing plate , The present invention relates to the field of computer technology. The large-scale computer fixing seat with shock-absorbing function solves the problem that the current large-scale computer has a poor shock-absorbing effect and is easy to cause damage to the computer during the moving process, prolongs the service life of the computer, and ensures the normal operation of the computer. operation, to avoid causing huge economic losses to people, the computer is not easy to be damaged, and the maintenance times are reduced.
Owner:合肥雷呈信息技术有限公司
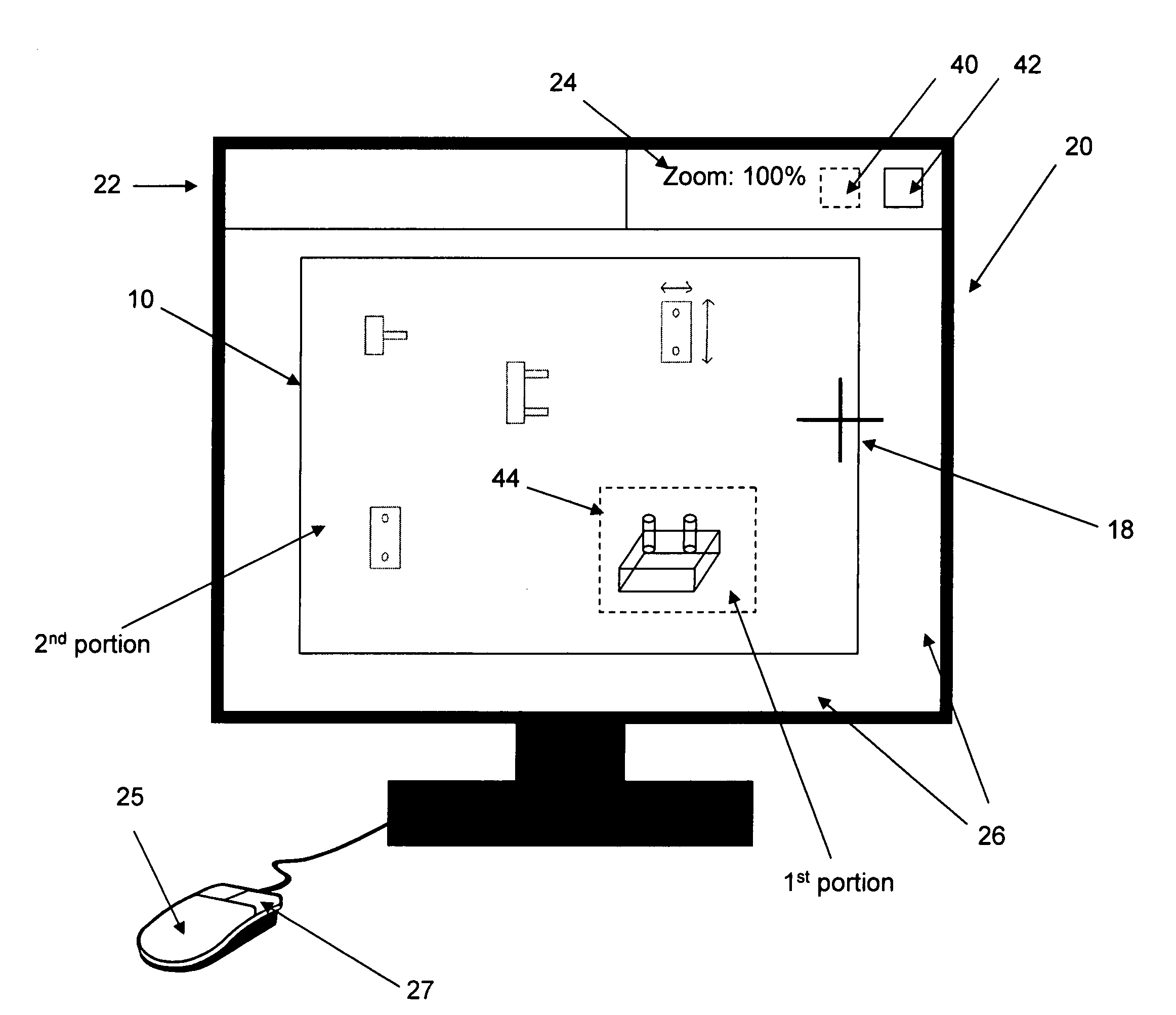
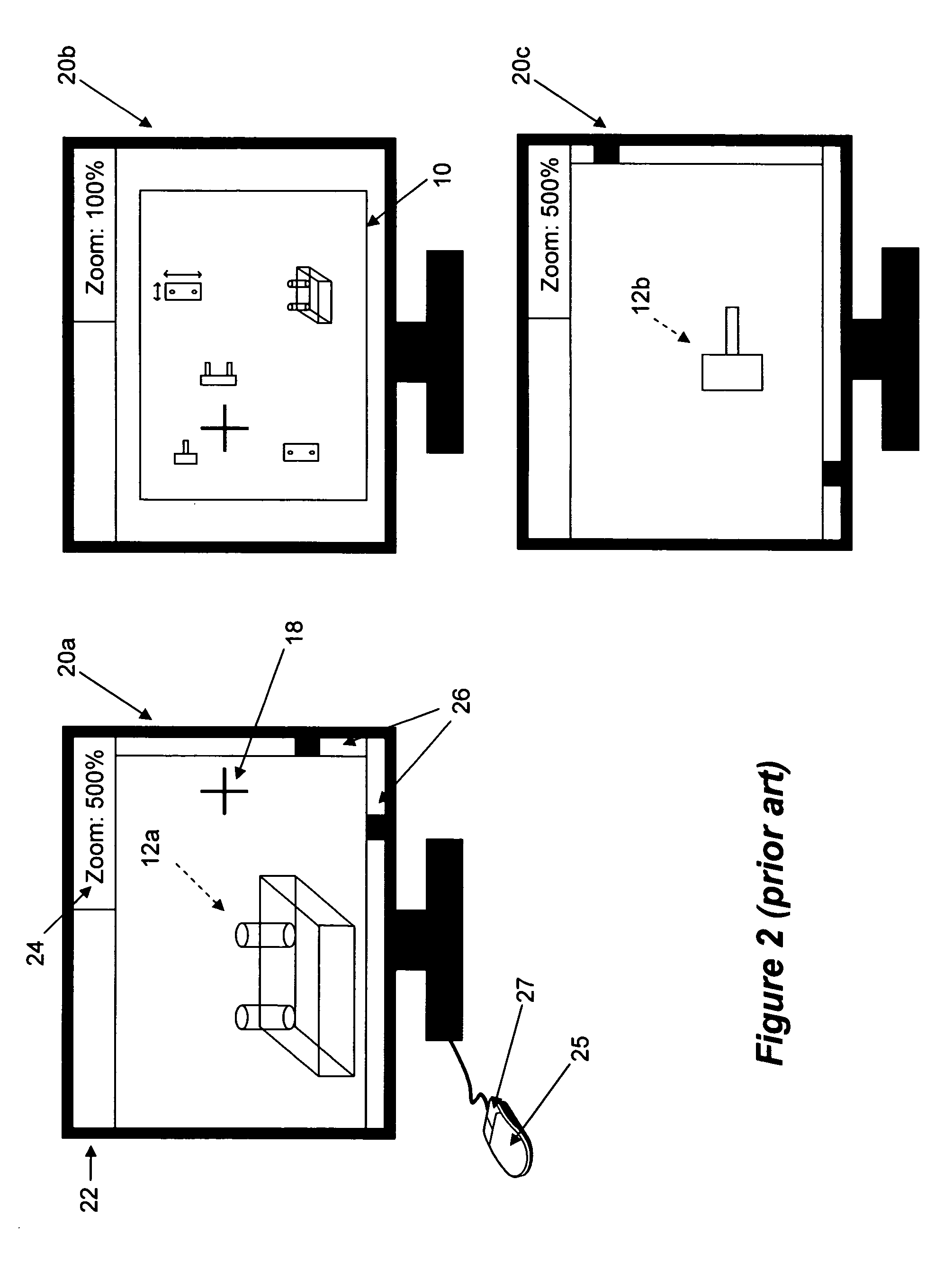
Navigation within a large computer file
InactiveUS20050179705A1Reduce magnification2D-image generationCathode-ray tube indicatorsGraphicsGraphical user interface
Disclosed herein is a method and graphical user interface (GUI) for navigating within the contents of a computer file, and specifically within a large non-paginated graphical file. A first portion of the file is displayed at a first magnification. Thereafter, an option is selected to display a second portion of the contents of the file (preferably the entire file) at a second lower magnification. An area is defined within the displayed second portion that highlights the first portion. This area is moveable, preferably by clicking and dragging the area using a mouse pointer, to a new (third location) on the file. Thereafter, the method allows the third portion to be automatically or manually magnified as was the first portion.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com