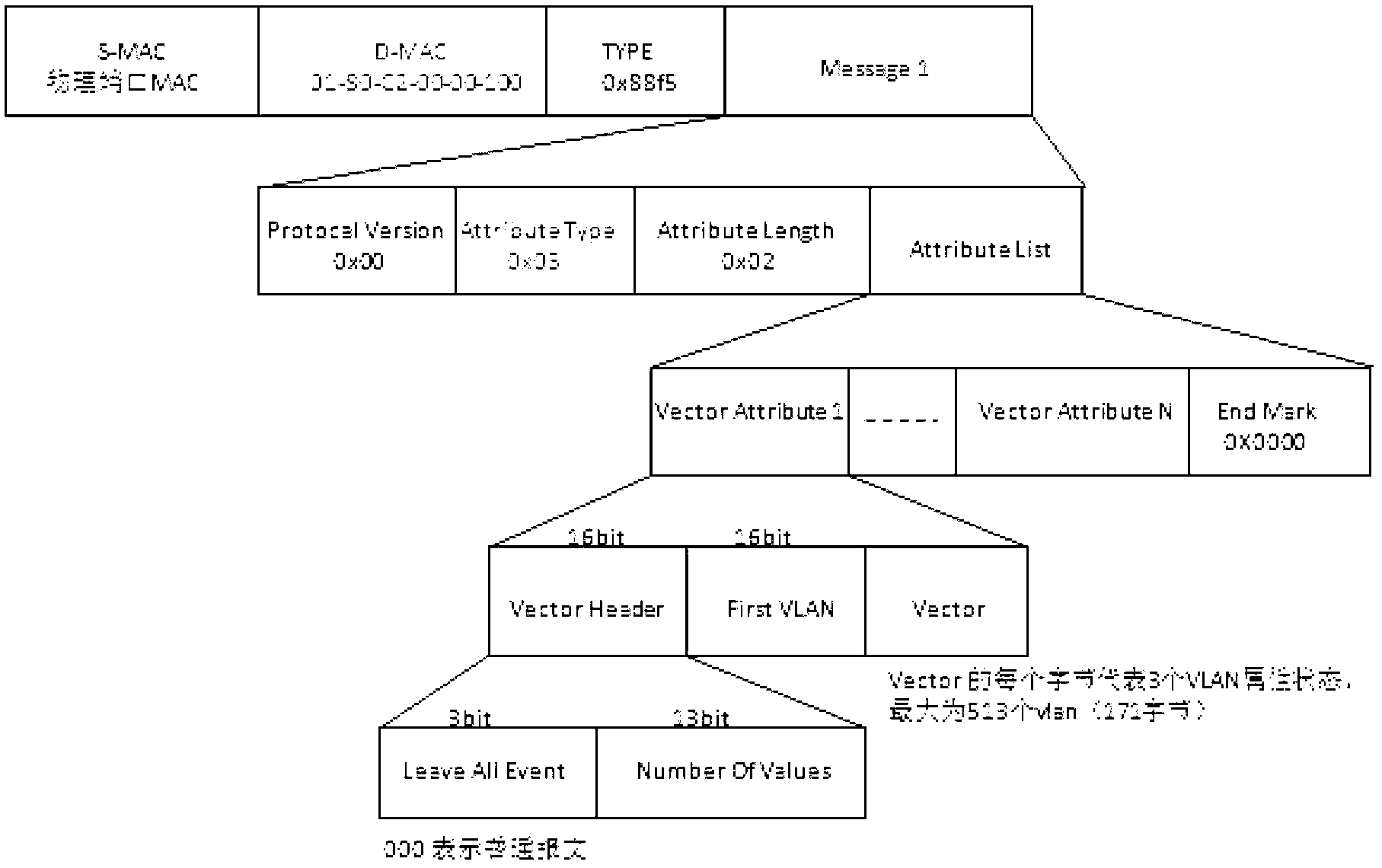
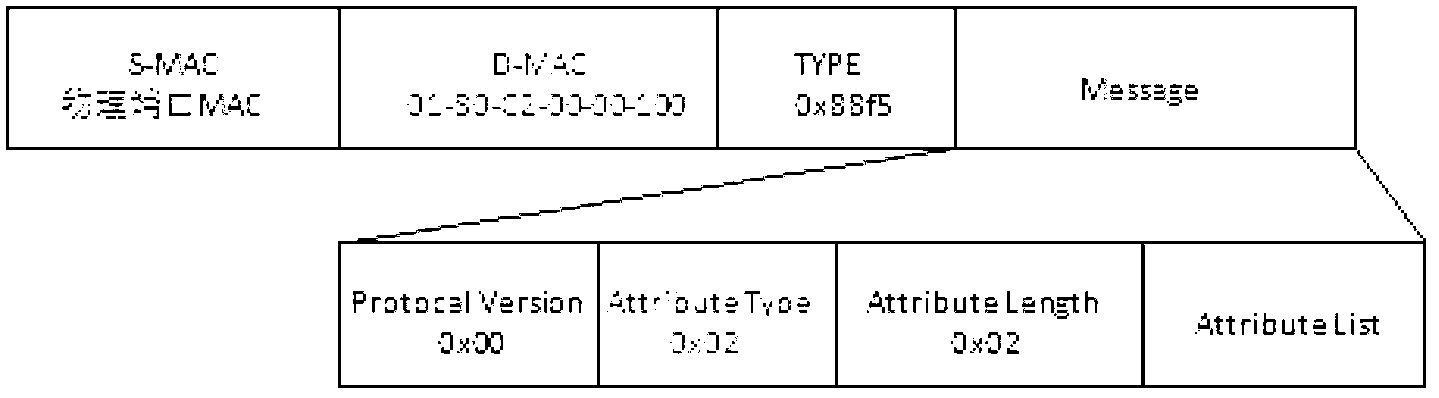
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33 results about "Private VLAN" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
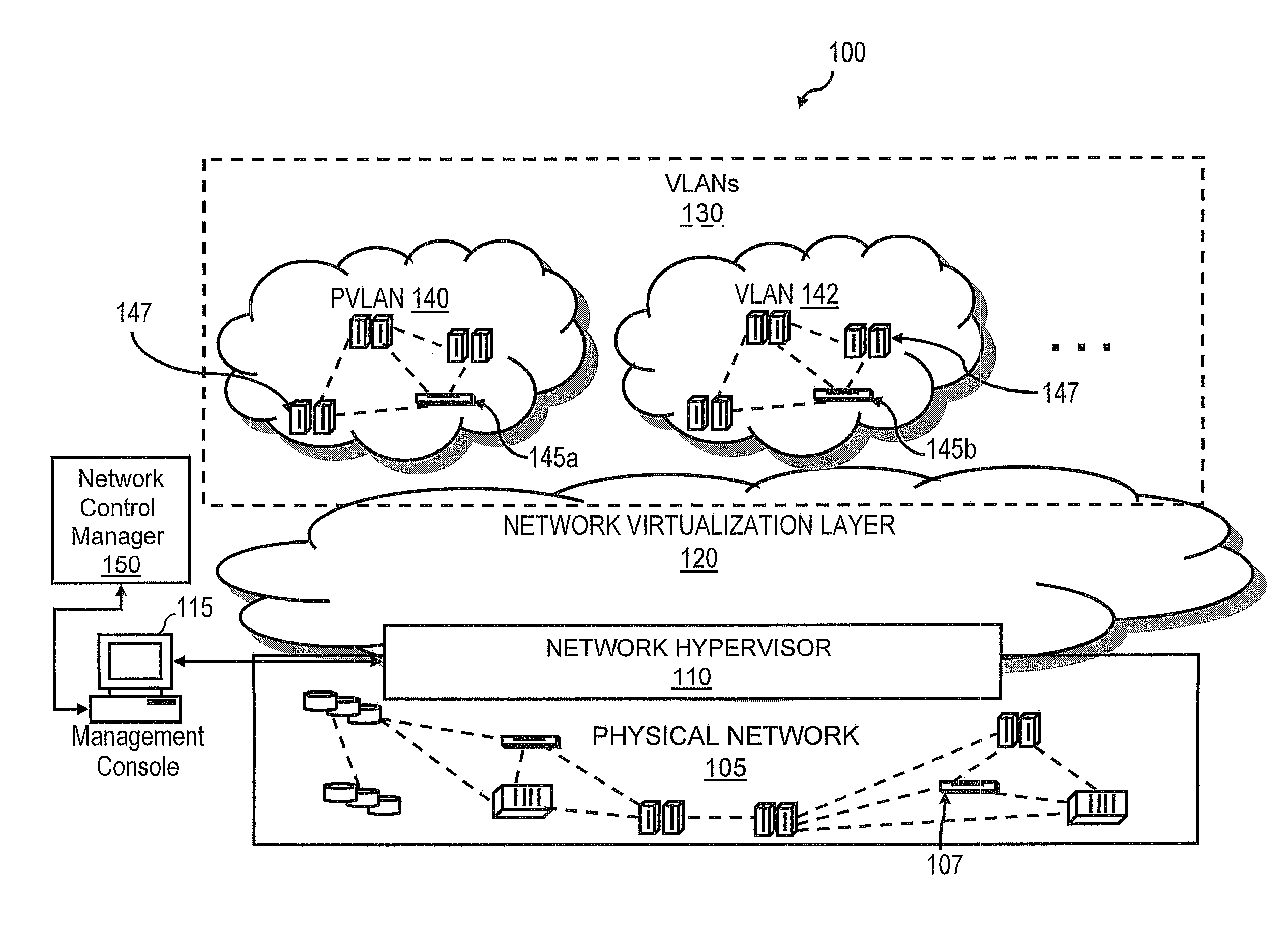
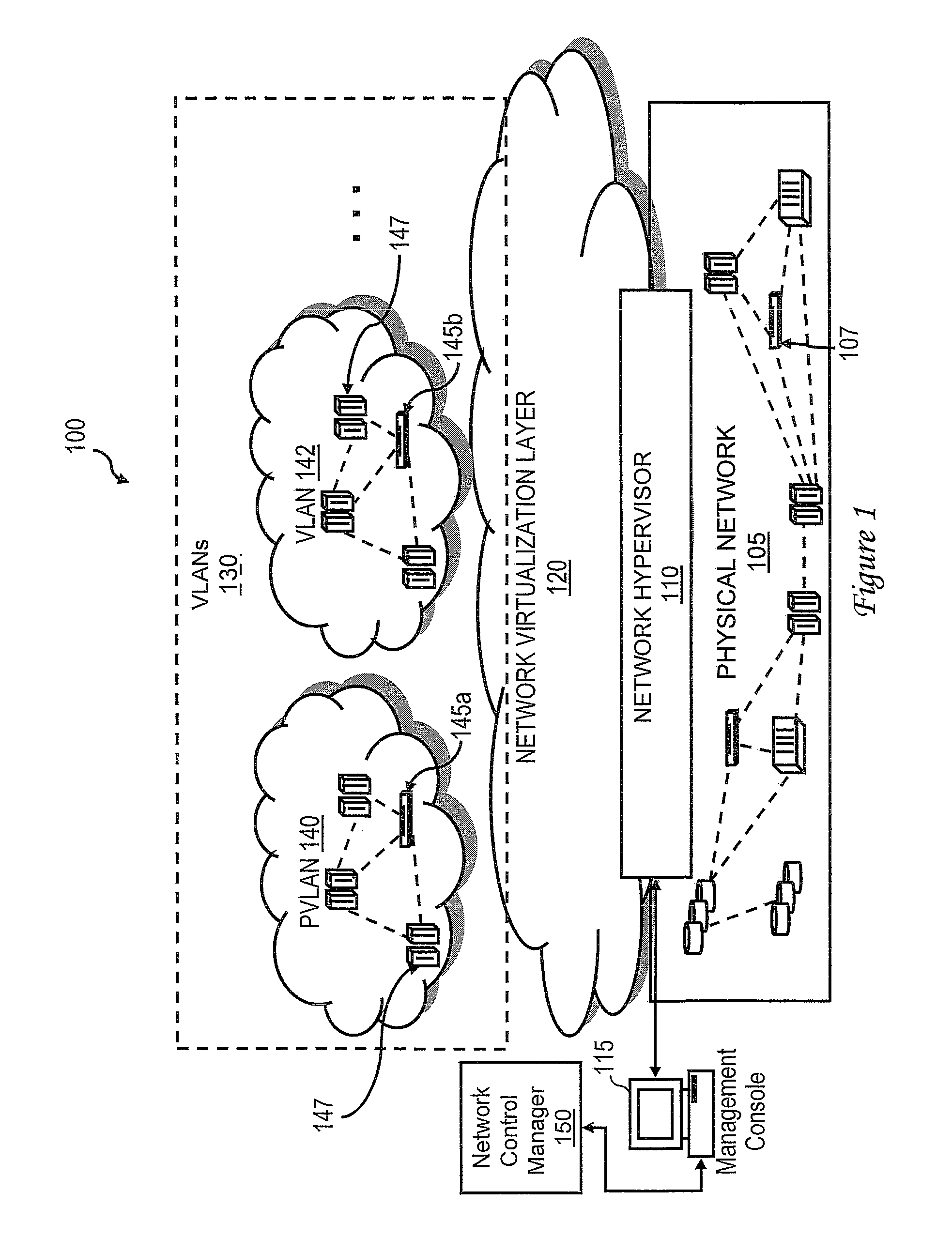
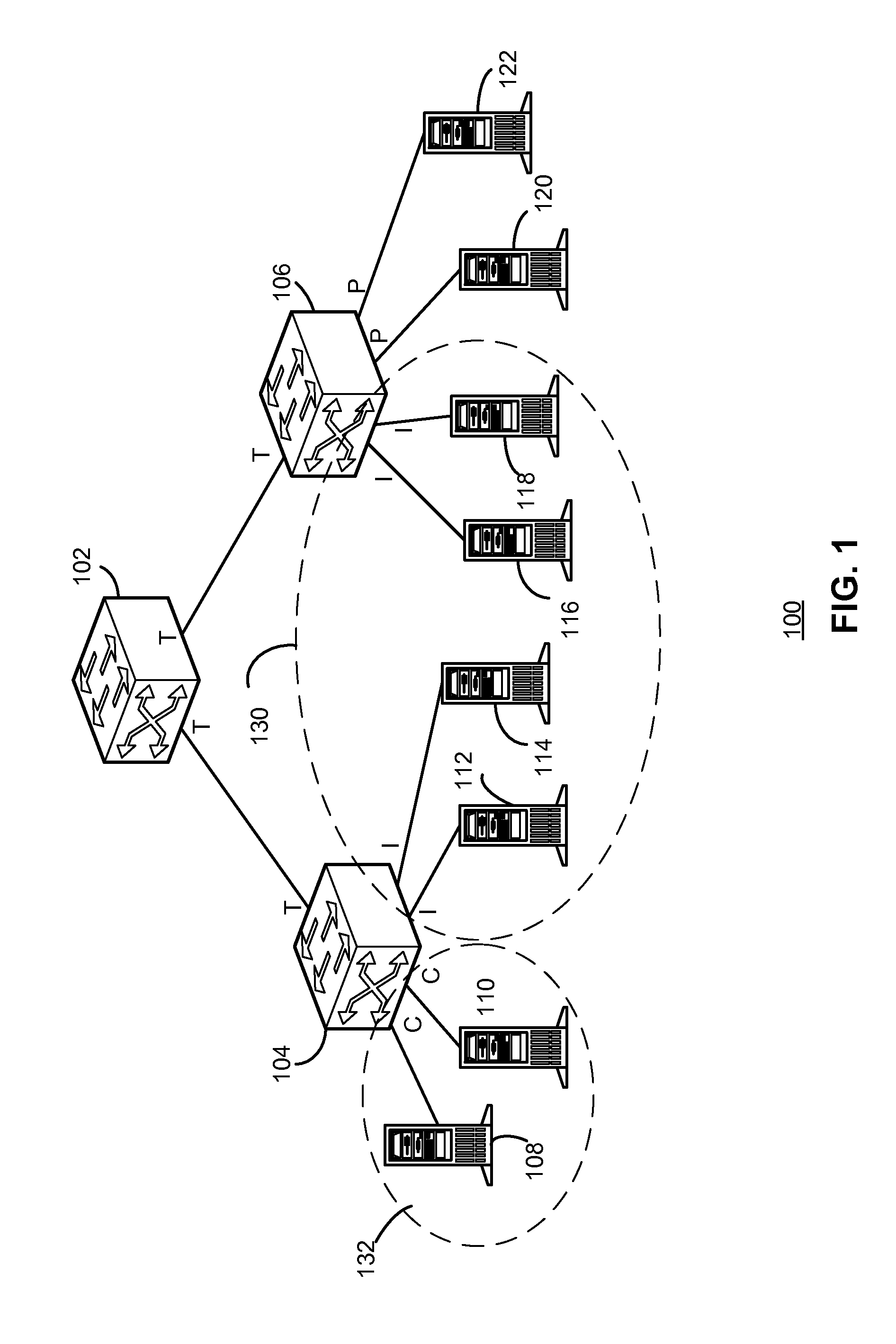
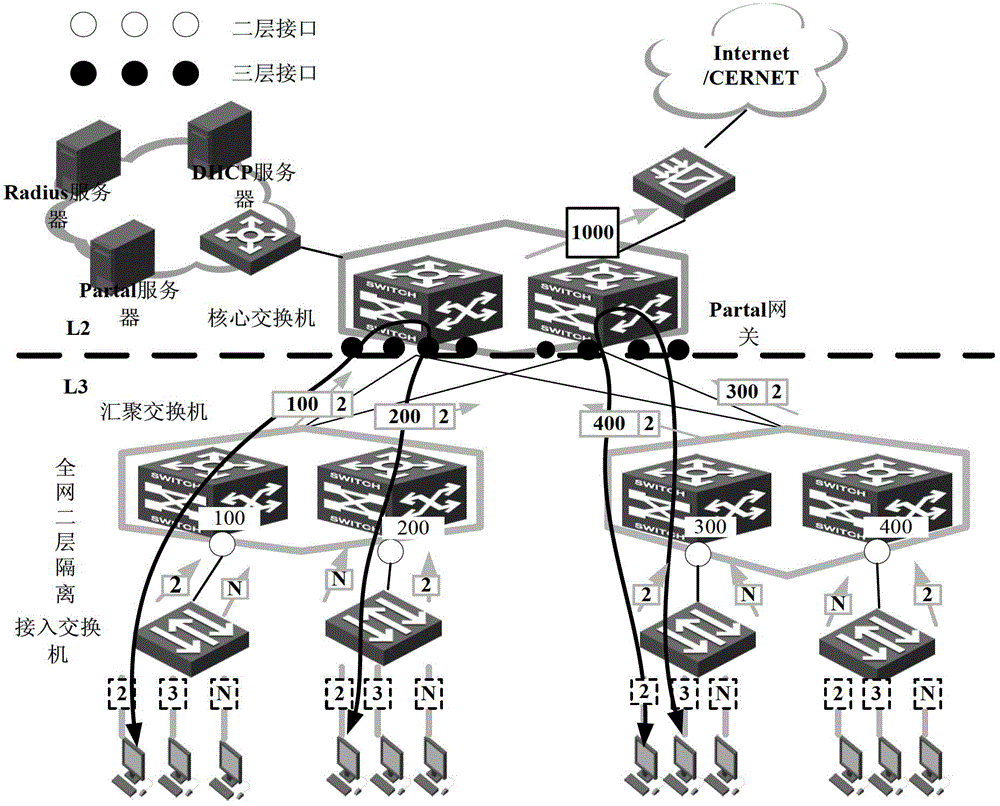
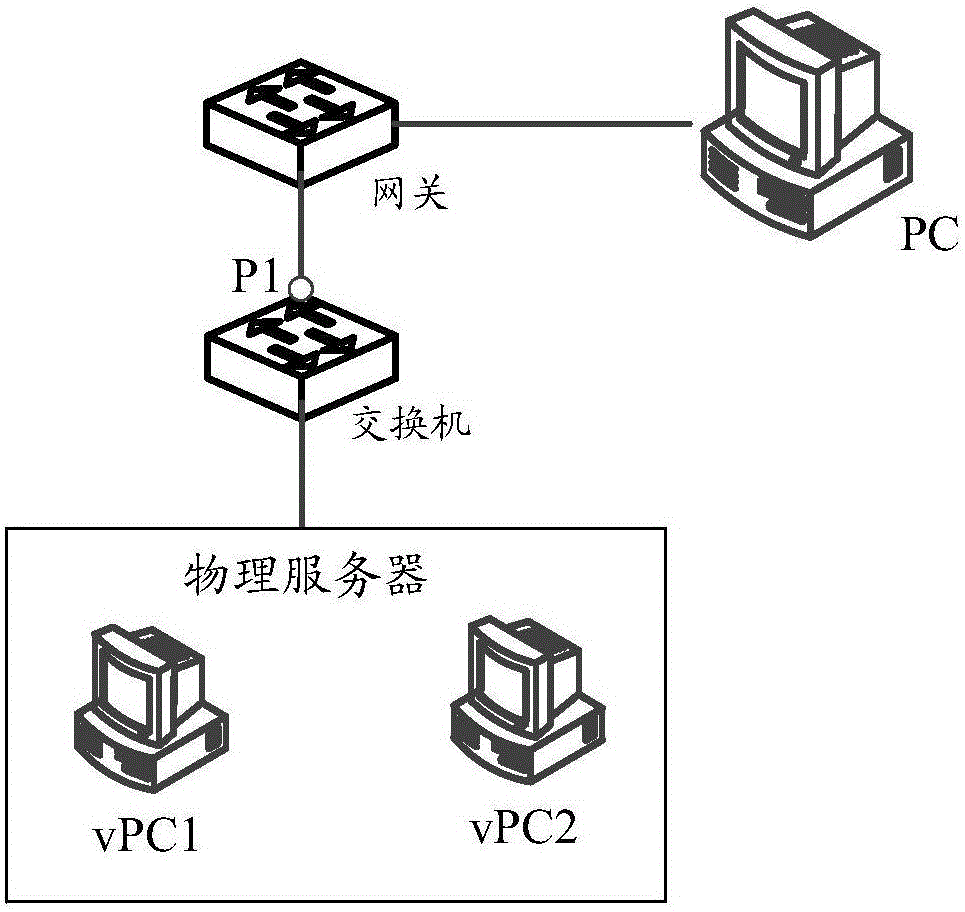
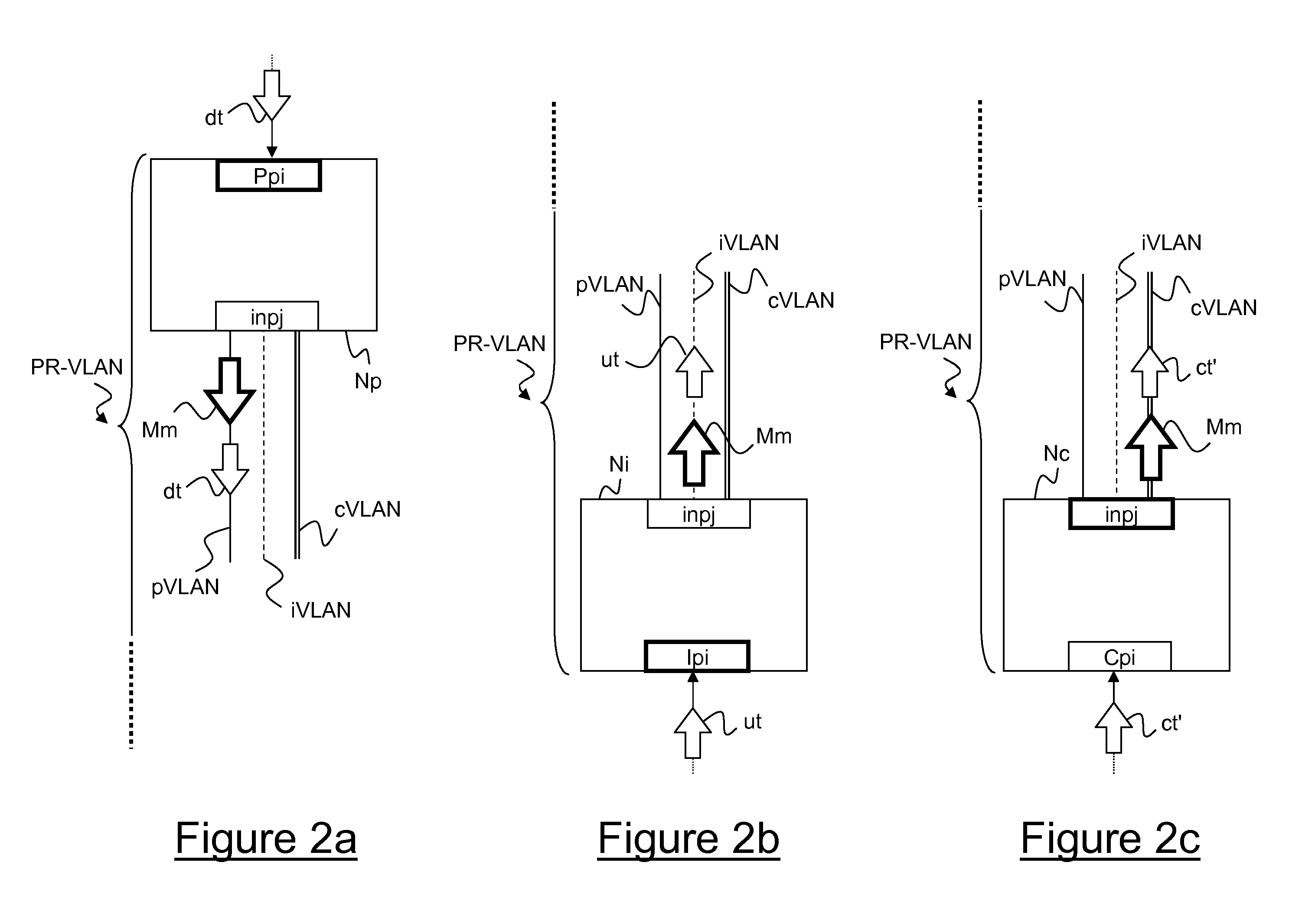
Private VLAN, also known as port isolation, is a technique in computer networking where a VLAN contains switch ports that are restricted such that they can only communicate with a given "uplink". The restricted ports are called "private ports". Each private VLAN typically contains many private ports, and a single uplink. The uplink will typically be a port (or link aggregation group) connected to a router, firewall, server, provider network, or similar central resource.
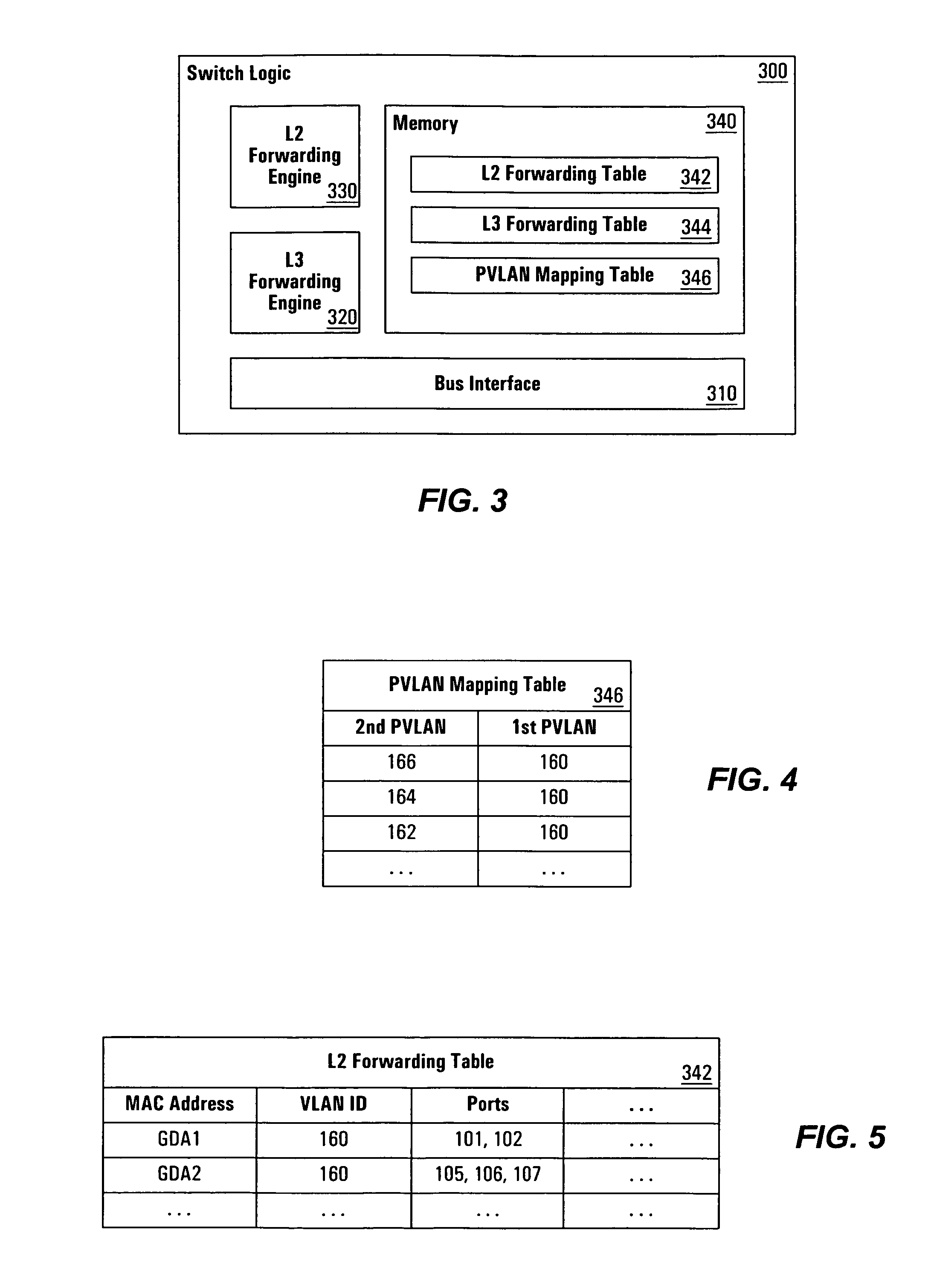
Systems and methods for multicast switching in a private VLAN
ActiveUS8625603B1Data switching by path configurationMultiple digital computer combinationsReverse path forwardingPrivate VLAN
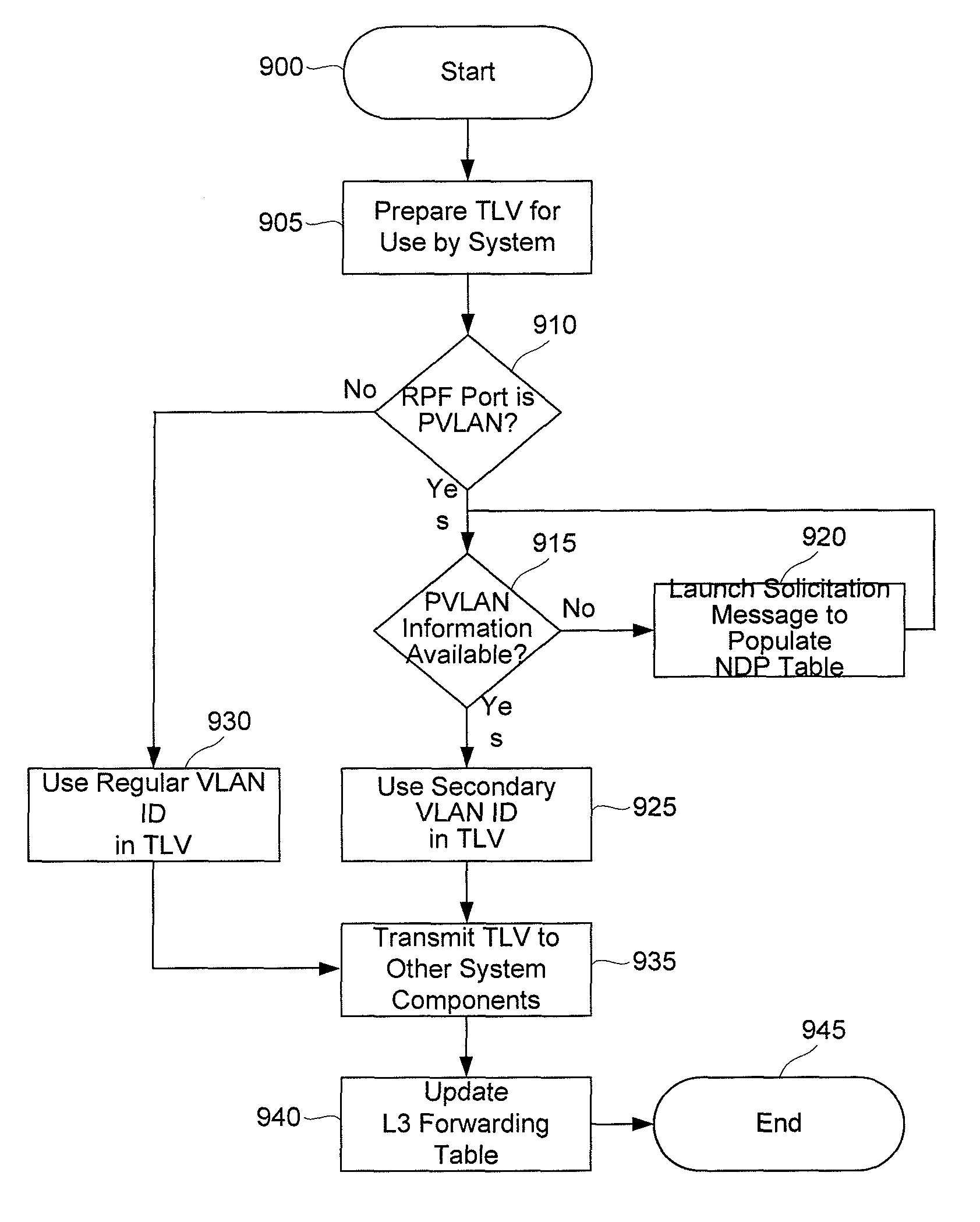
A Multicast Listener Discovery (MLD) protocol query and / or report snooping process is modified to appropriately map secondary PVLAN identifiers to corresponding primary PVLAN identifiers, thereby accommodating other system elements that are otherwise unaware of primary / secondary PVLAN distinctions. Special cases are also accommodated where reverse path forwarding (RPF) checks in support of multicast operation might otherwise fail due to primary / secondary PVLAN distinctions. Additional steps are taken to ensure that PVLAN information properly accounts for changes in configuration and / or location of various network hosts.
Owner:CISCO TECH INC
Platform independent implementation of private VLANS
ActiveUS7808992B2Multiplex system selection arrangementsData switching by path configurationNetwork packetPrivate VLAN
Owner:CISCO TECH INC
Mapping virtual machines from a private network to a multi-tenant public datacenter
ActiveUS20150172331A1Interprogram communicationTransmissionPrivate networkApplication programming interface
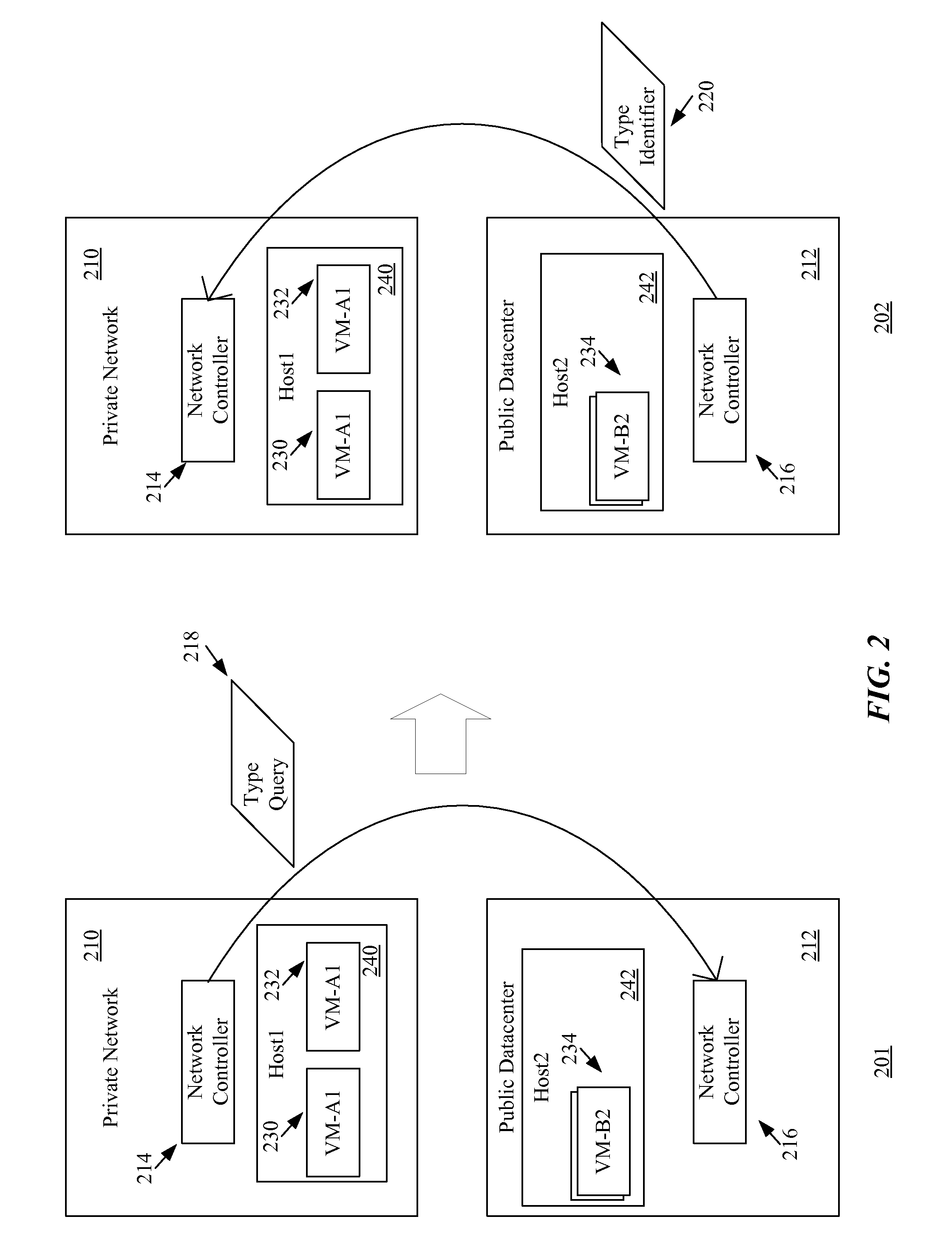
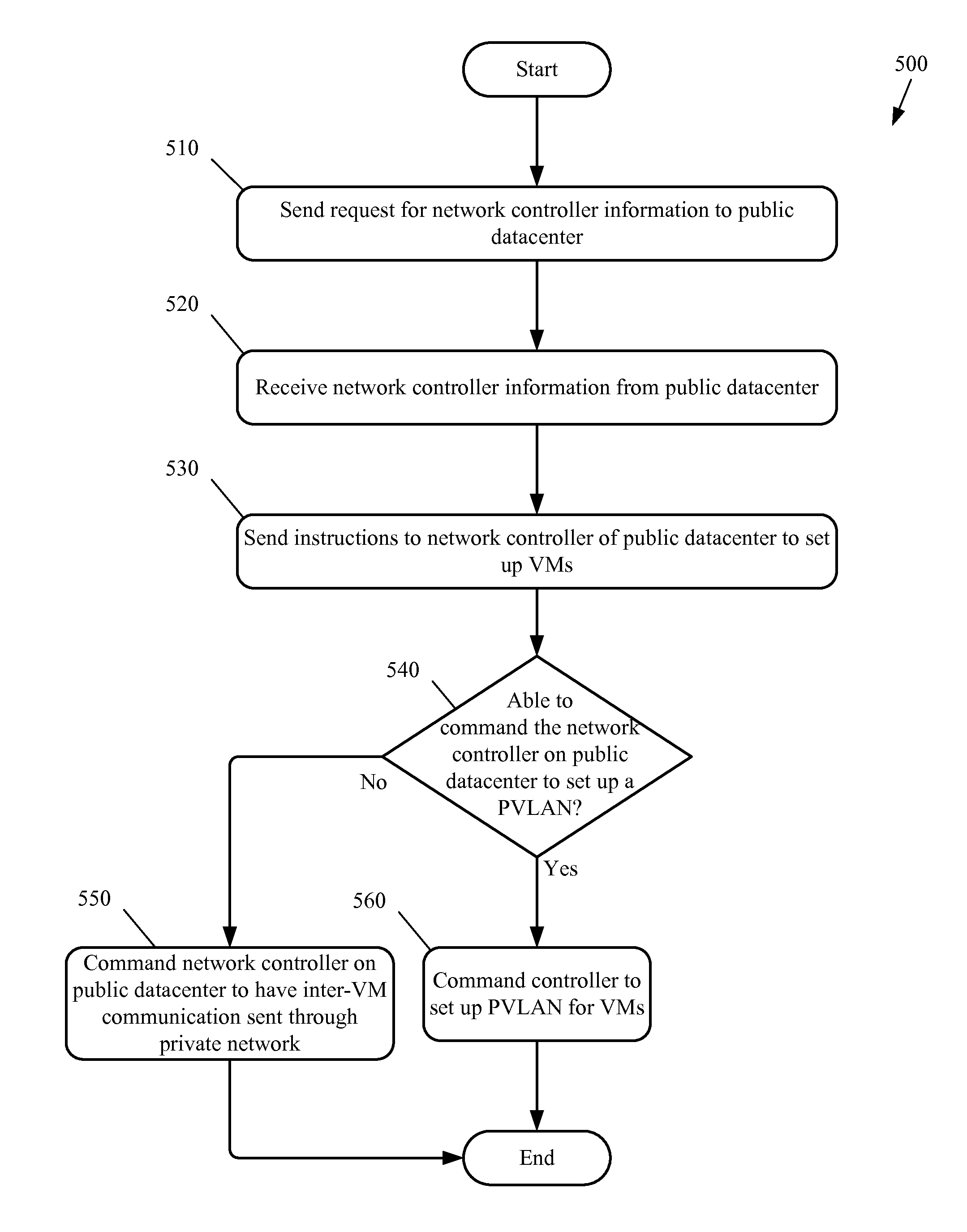
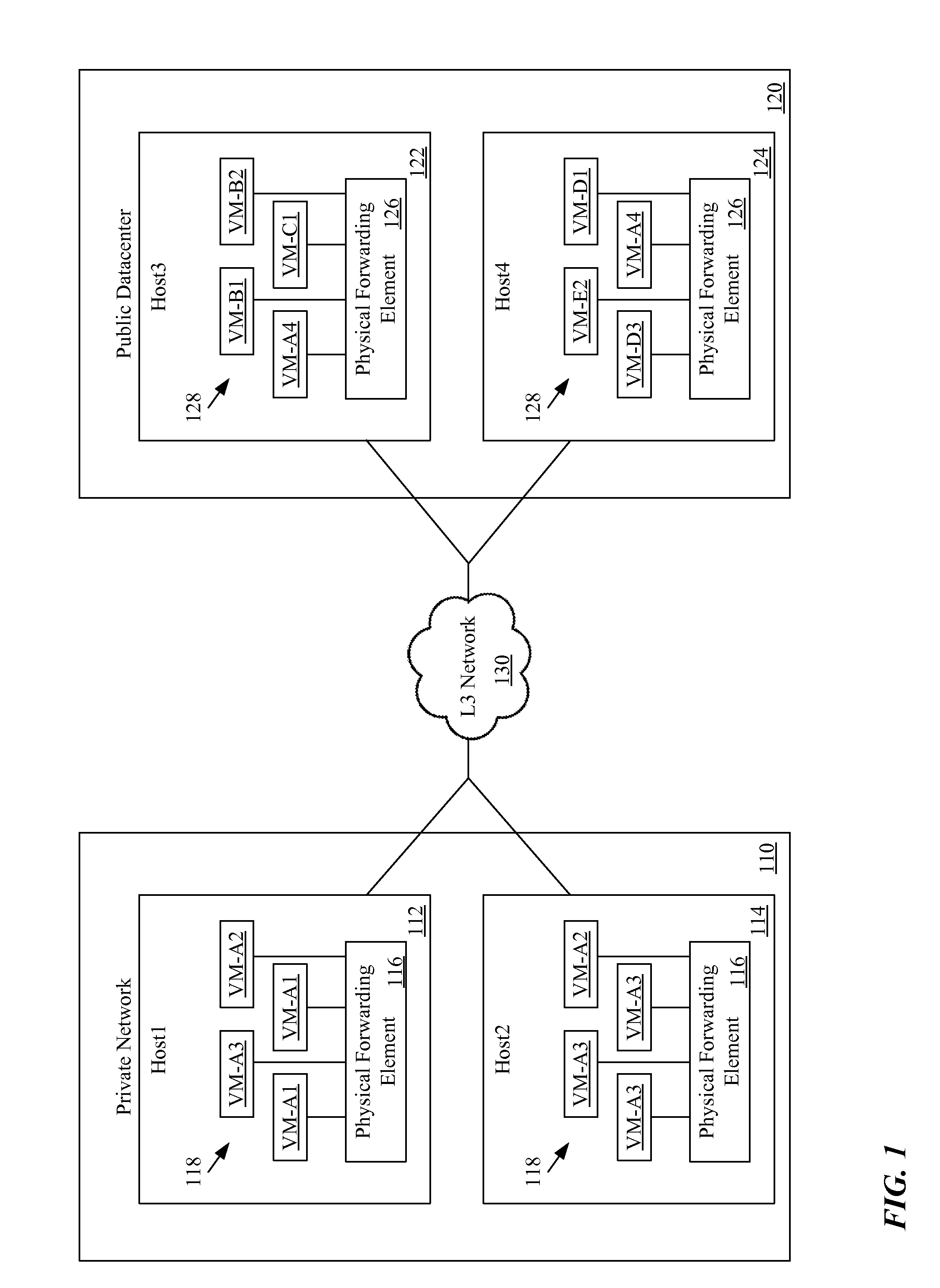
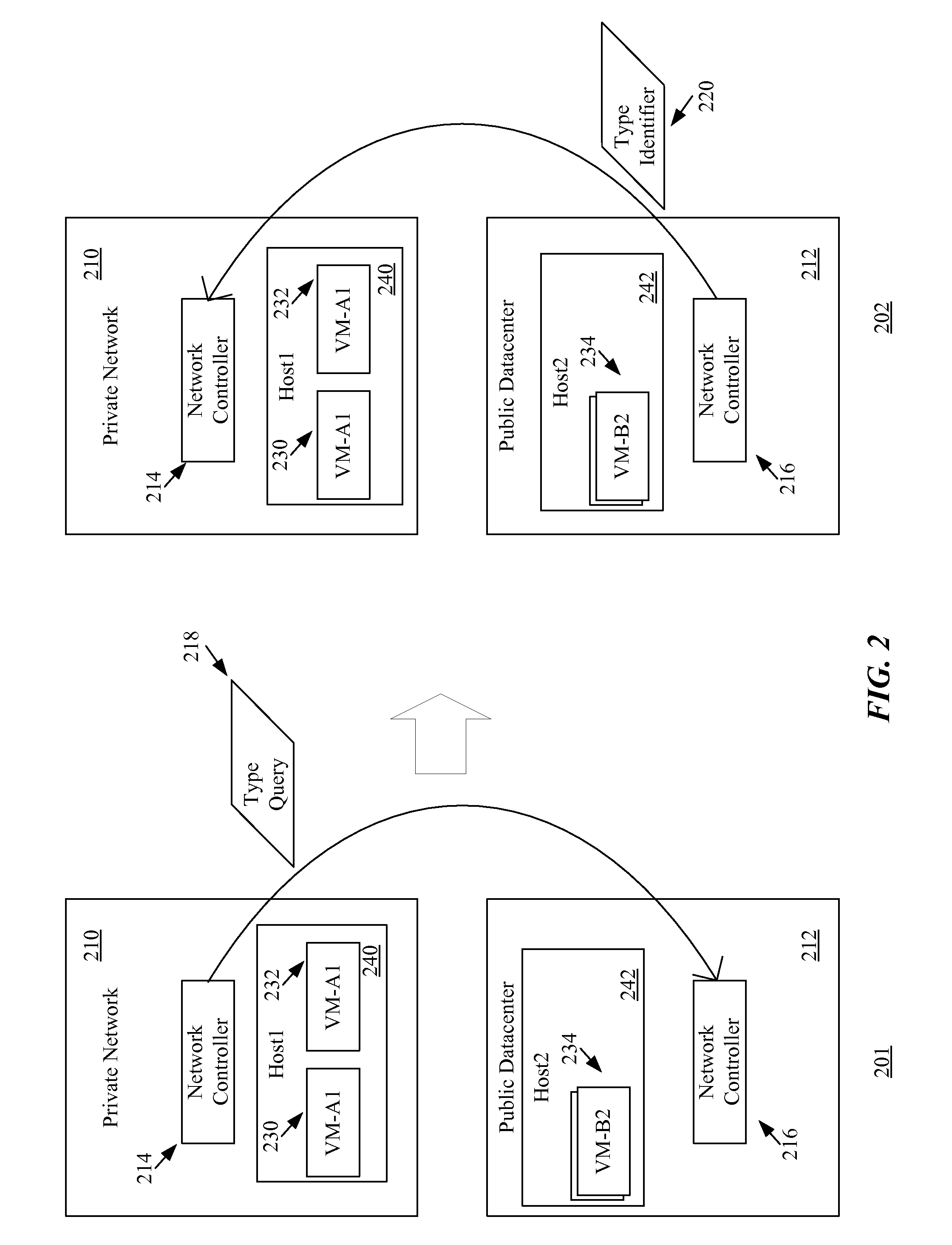
A method for creating a set of virtual machines on a public datacenter. The method, from a first network controller of a private network, commands a second network controller of the public datacenter to create the virtual machines. The method, from the first network controller of the private network, communicates with the second network controller of the public datacenter to determine a type of the second network controller. When the first network controller includes instructions for using application programming interfaces (APIs) of the type of the second network controller, the method uses the APIs to set up a VLAN for the set of virtual machines in order to allow the virtual machines of the set of virtual machines to communicate securely with each other without sending the communications through the private network. In some embodiments, the VLAN is a private VLAN (PVLAN).
Owner:NICIRA
Scaling private virtual local area networks (VLANs) across large metropolitan area networks (MANs).
InactiveUS7606939B1Multiple digital computer combinationsMetropolitian area networksVirtual LANPrivate VLAN
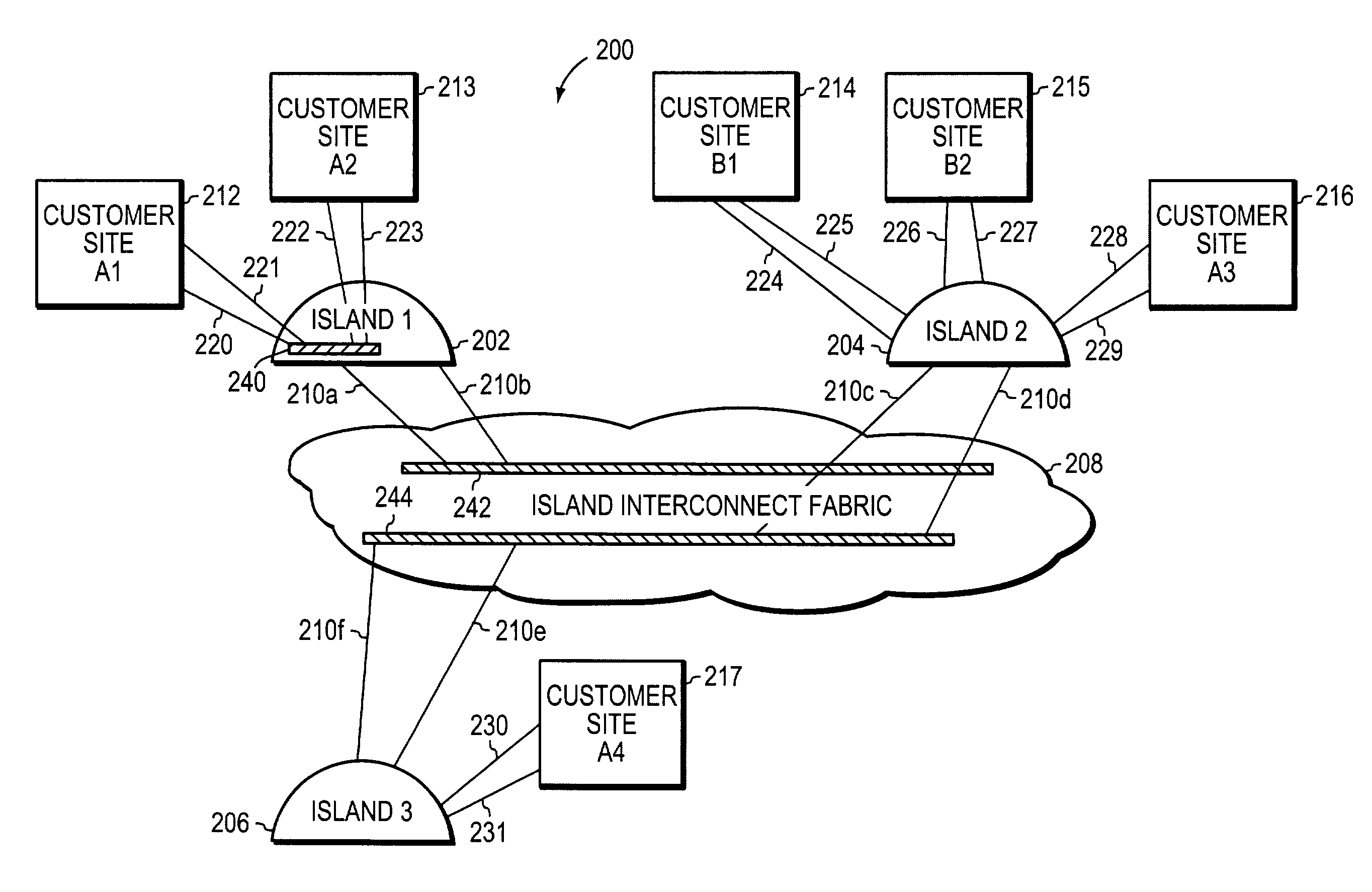
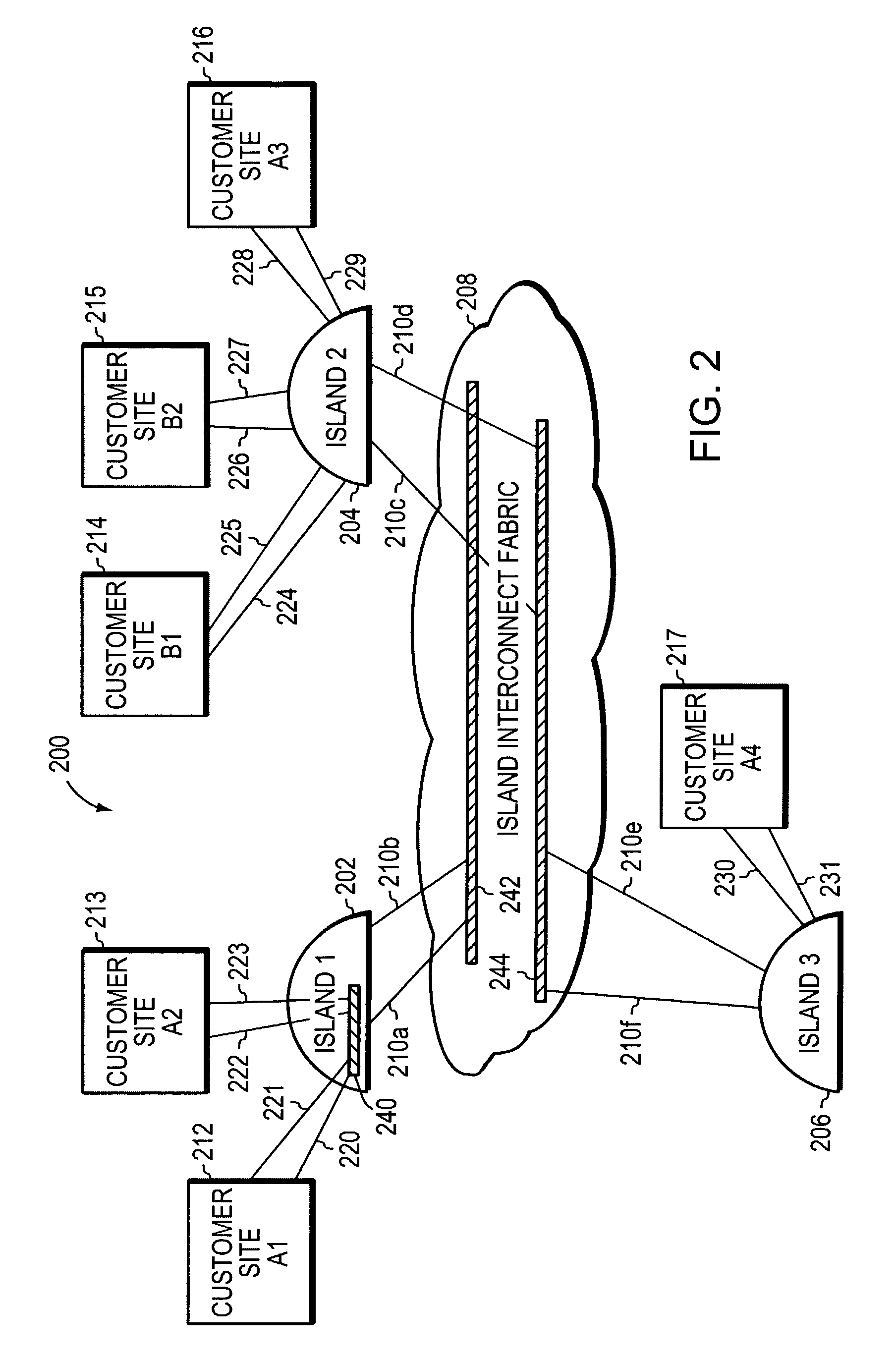
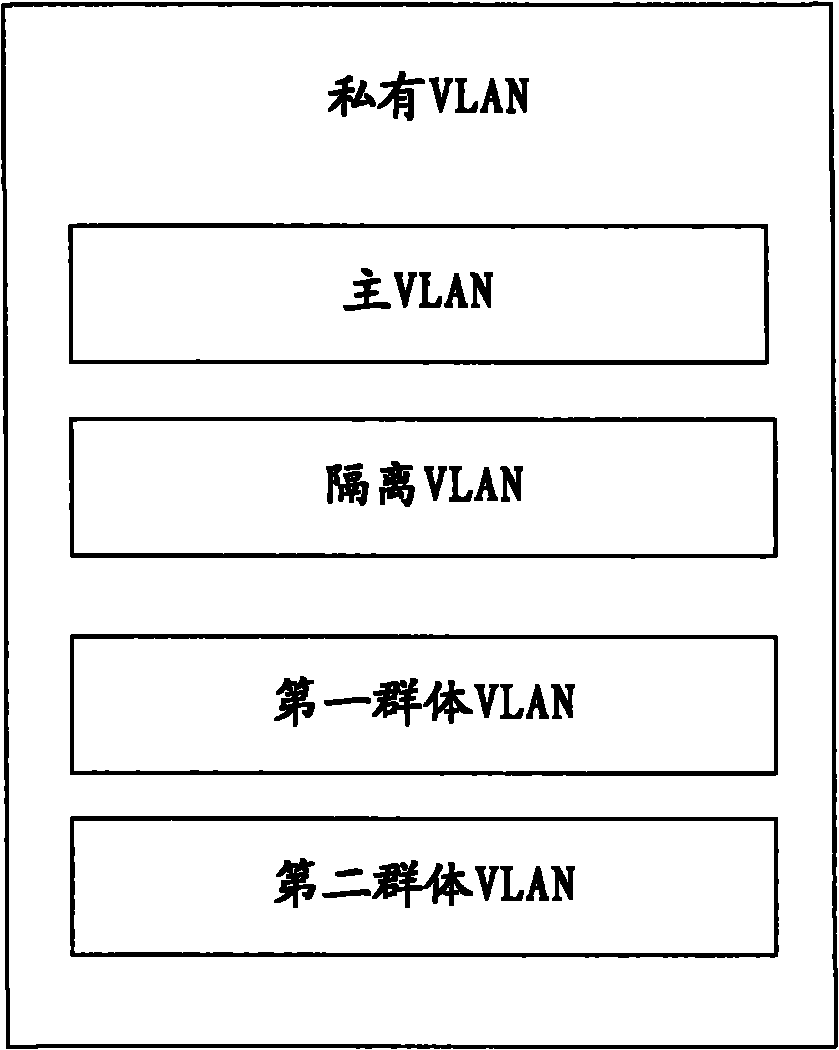
A system and method scales private Virtual Local Area Networks (VLANs) to a large computer network, such as a very large Metropolitan Area Network (MAN), so that the VLAN designations can be re-used across the network. In the illustrative embodiment, the MAN includes different groups of Layer 2 (L2) switches that are logically organized into Islands interconnected by an interconnect fabric. Within each Island, Customer-Equipment VLAN Identifiers (CE-VLAN IDs) are mapped to MAN Provider-Equipment VLAN IDs (PE-VLAN IDs). The PE-VLAN IDs defined within the MAN support the creation of Private VLANs. Each Private VLAN includes one Primary VLAN, one Isolated VLAN and may include one or more Community VLANs. Different PE-VLAN IDs may be used as the Primary, Isolated and Community VLANs in different Islands. Nonetheless, the Primary, Isolated and Community VLANs from all of the Islands are assigned the same Virtual Circuit IDs, which are loaded into encapsulated frames traversing the interconnect fabric, thereby maintaining the message's association with the Primary, Isolated and Community VLANs.
Owner:CISCO TECH INC
Systems and methods for multicast switching in a private VLAN
ActiveUS7953089B1Data switching by path configurationStore-and-forward switching systemsReverse path forwardingPrivate VLAN
A Multicast Listener Discovery (MLD) protocol query and / or report snooping process is modified to appropriately map secondary PVLAN identifiers to corresponding primary PVLAN identifiers, thereby accommodating other system elements that are otherwise unaware of primary / secondary PVLAN distinctions. Special cases are also accommodated where reverse path forwarding (RPF) checks in support of multicast operation might otherwise fail due to primary / secondary PVLAN distinctions. Additional steps are taken to ensure that PVLAN information properly accounts for changes in configuration and / or location of various network hosts.
Owner:CISCO TECH INC
Private lines traversing a packet network and re-arrangement of channels among packet network connections
InactiveUS6882652B1Easy to adaptReduce needTime-division multiplexNetworks interconnectionPacket generatorNetwork connection
Techniques for providing communication services include provisioning a packet network connection that has packet channels, each of which is independently capable of carrying narrowband signals so as to emulate a private line circuit. A narrowband private line that traverses the packet network connection using a particular one of the packet channels is established. Delays that might otherwise be introduced as a result of packetizing the narrowband signals can be reduced. Private lines that traverse the packet network connection using other packet channels can be added or removed without adversely affecting the existing lines. Additionally, a narrowband communication line that traverses a channel in a first virtual circuit connection in a packet network can be rolled over to a channel in a second virtual circuit connection in the packet network. The latter technique can improve the use of available bandwidth and can be applied to non-private line applications as well.
Owner:TELLABS OPERATIONS
Efficient software-based private VLAN solution for distributed virtual switches
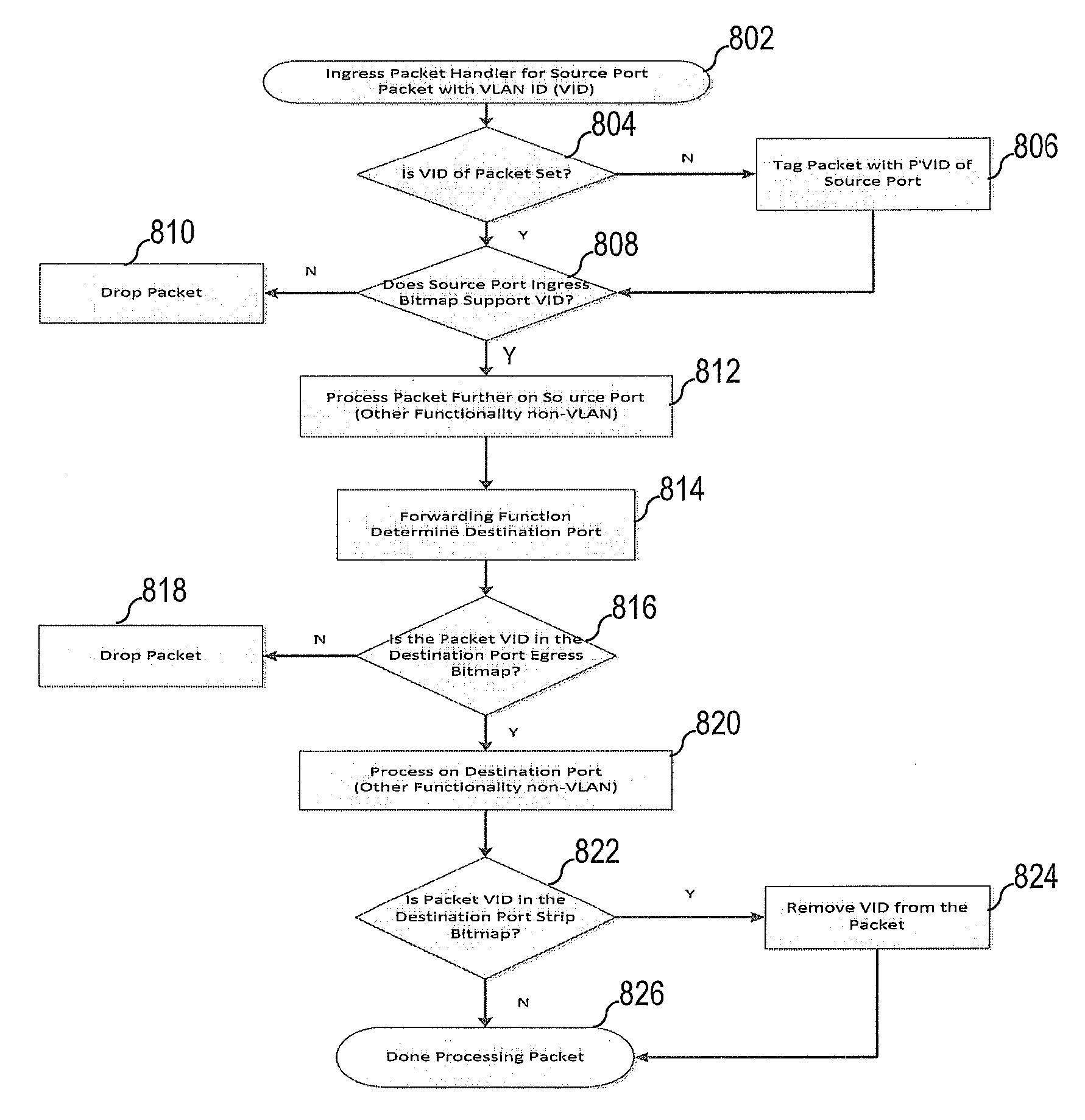
InactiveUS20120287936A1Easy to handleData switching by path configurationVirtualizationArray data structure
Packet processing logic of a host system's virtualization manager detects packets on the ingress or the egress path to / from a virtual port having three bitmap arrays for processing packets within a virtual local area network (VLAN). The logic checks the VLAN identifier (VID) of the packet to determine, based on an offset position within the corresponding bitmap array, whether the port supports the VLAN. Both the ingress array offset position and egress array offset positions correspond to the value of the VID, and are set within the specific bitmap array during configuration of the VLAN on the port. When the VLAN is supported by the port, the logic enables the packet to be processed by the port. Otherwise, the logic discards the packet. A strip bitmap array indicates when a packet's VID should be removed prior to forwarding the packet on the egress of a port (or destination port).
Owner:IBM CORP
Platform independent implementation of private VLANS
ActiveUS20060146835A1Multiplex system selection arrangementsData switching by path configurationPrivate VLANComputer science
Owner:CISCO TECH INC
Private VLANs
InactiveUS7200145B1Increase the number ofDigital computer detailsData switching by path configurationVirtual LANTelecommunications
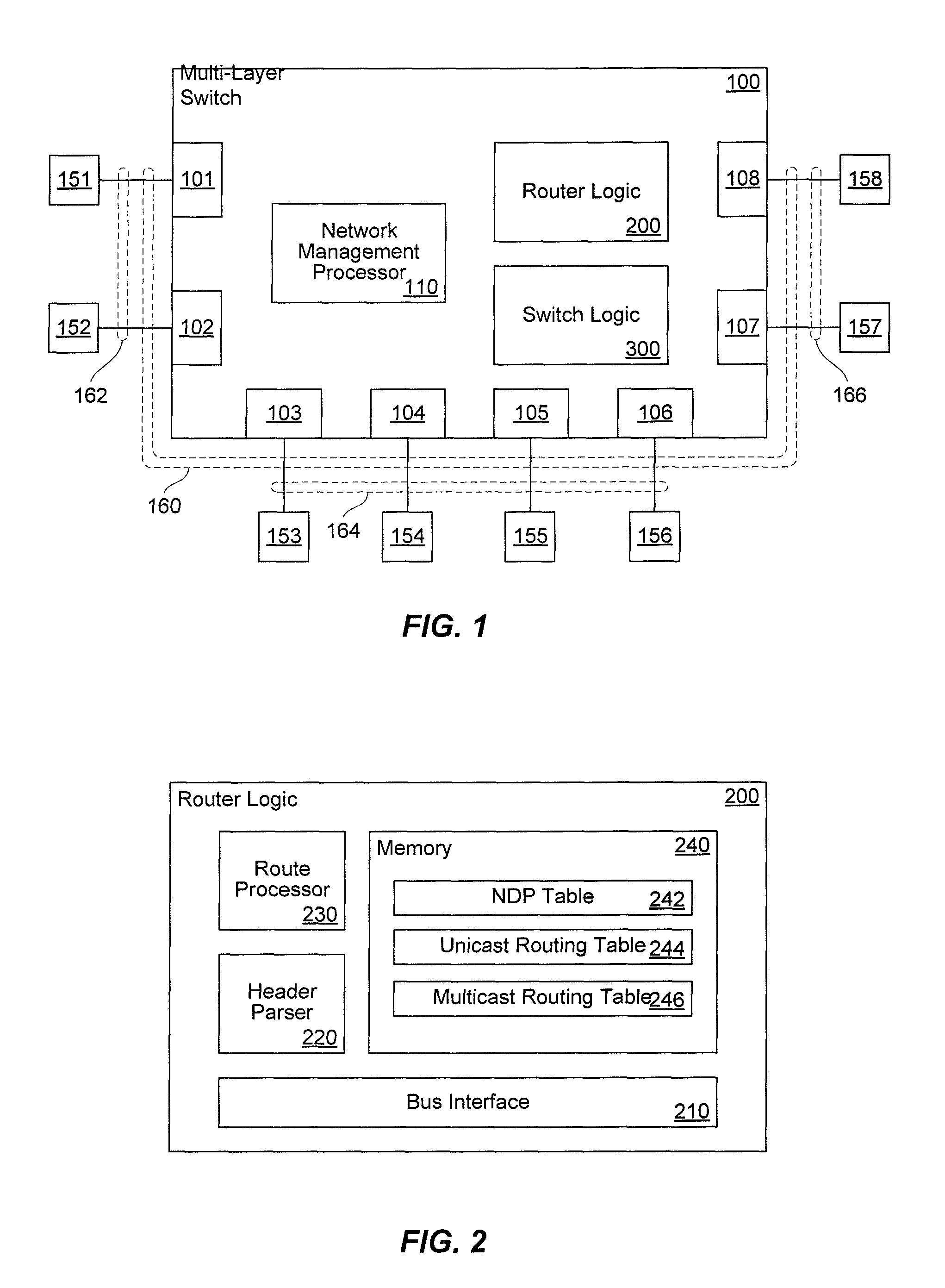
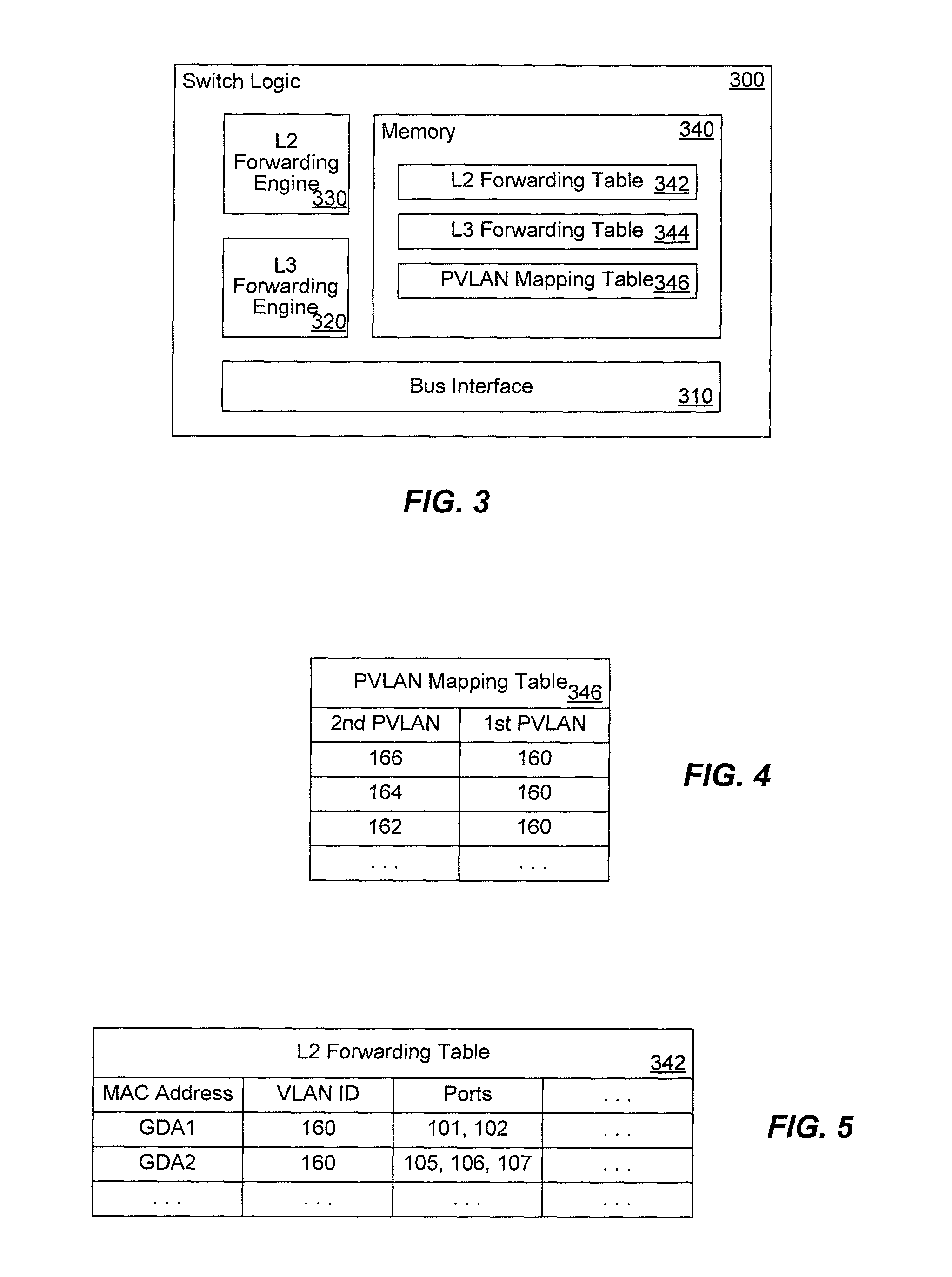
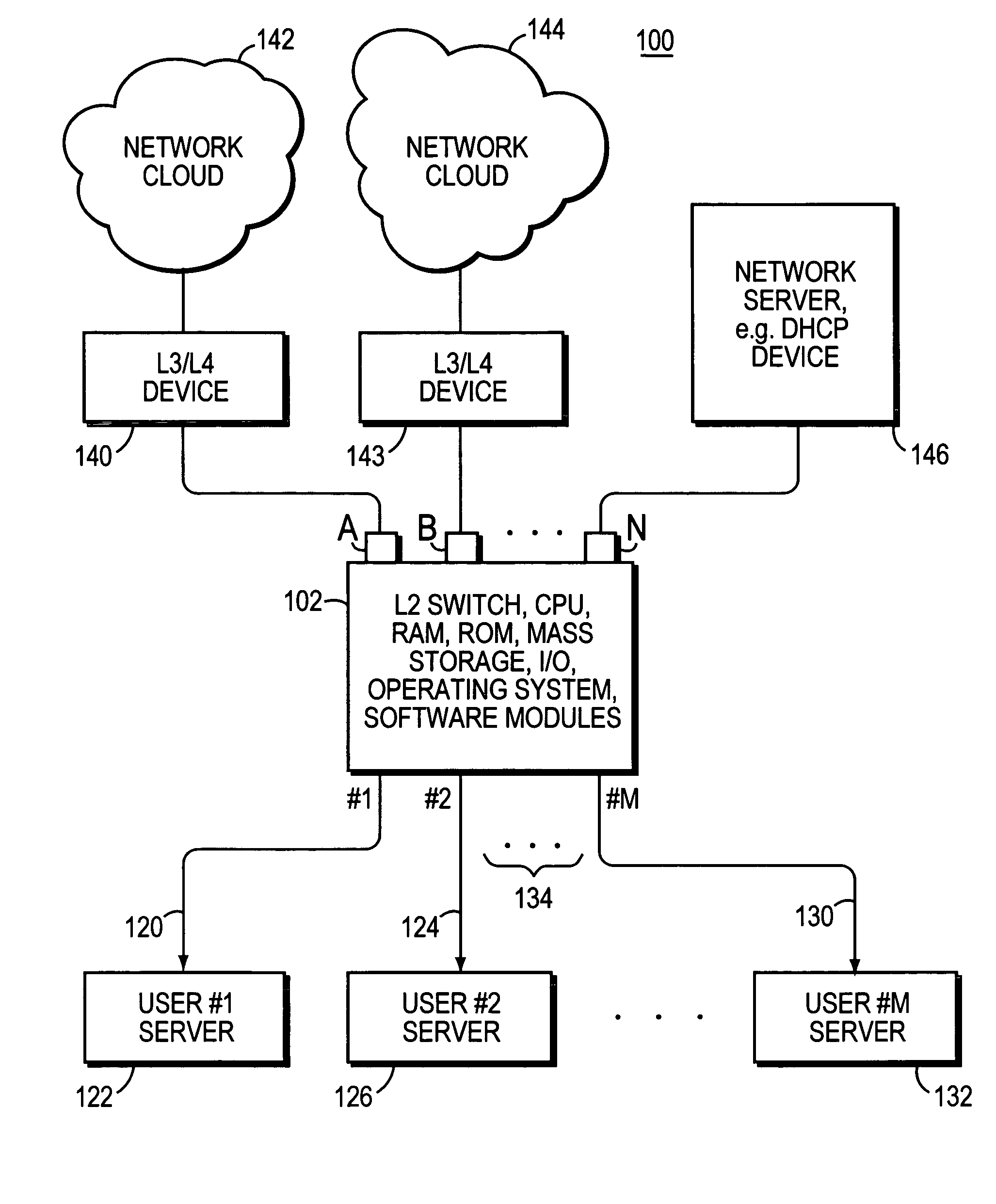
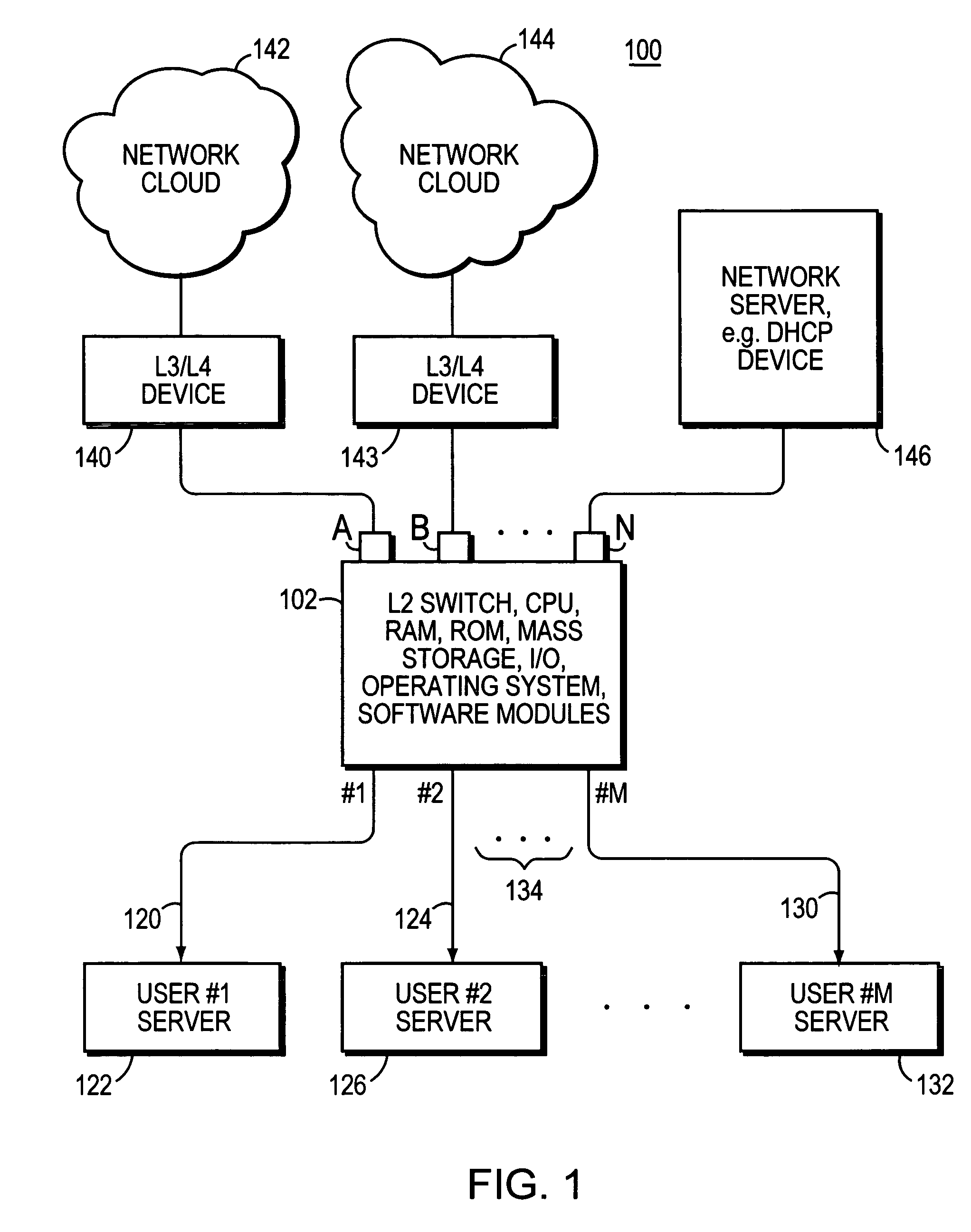
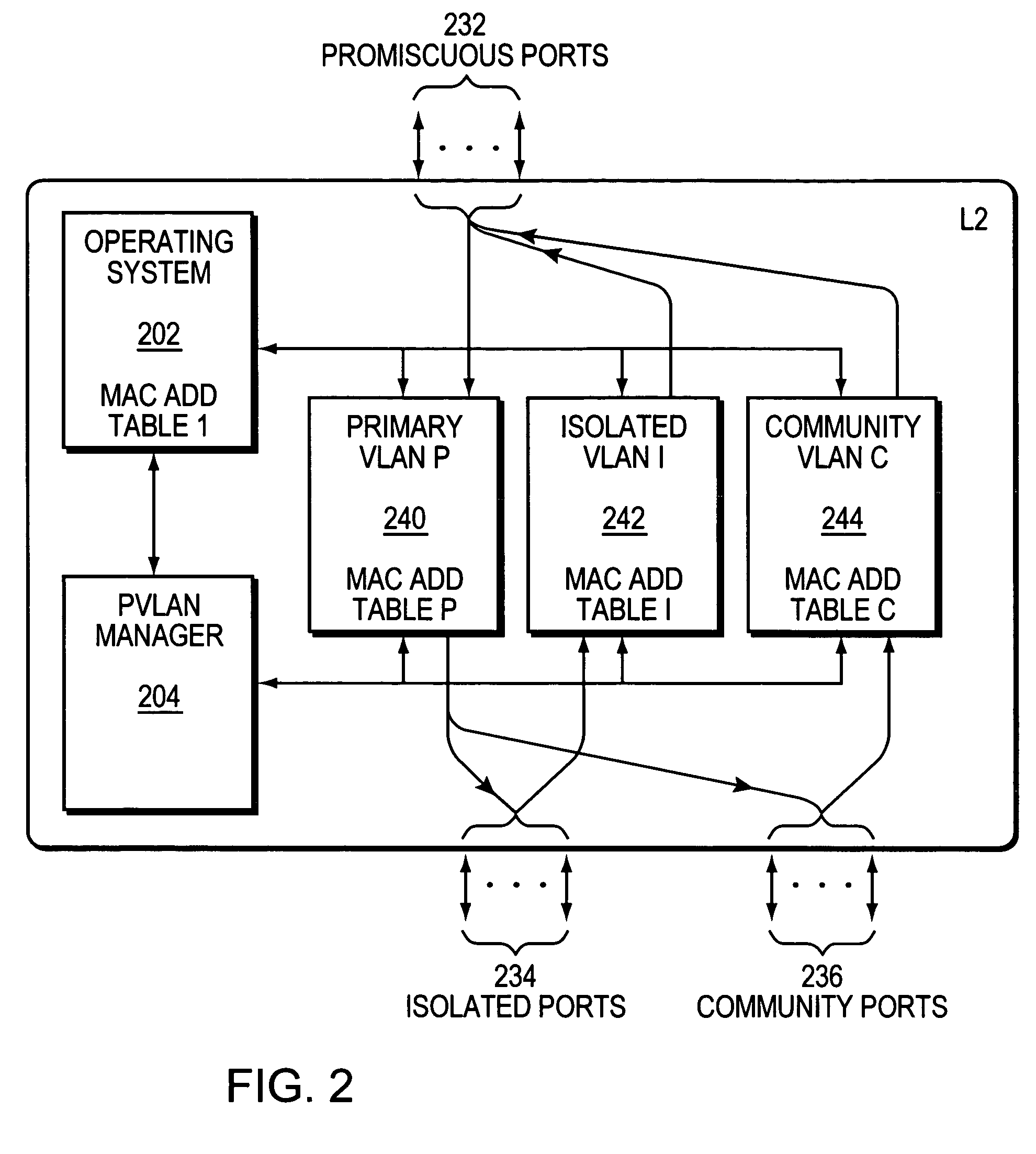
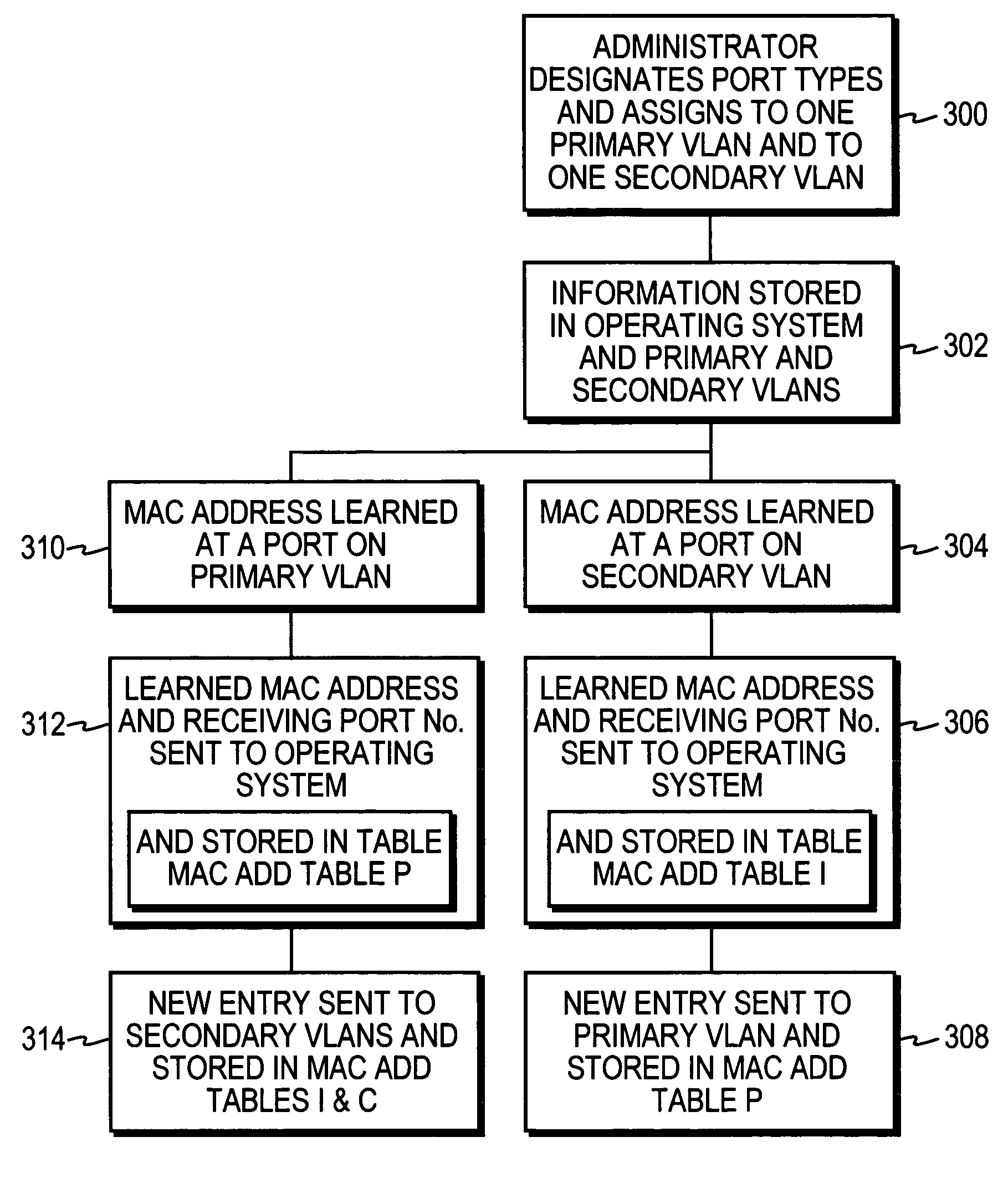
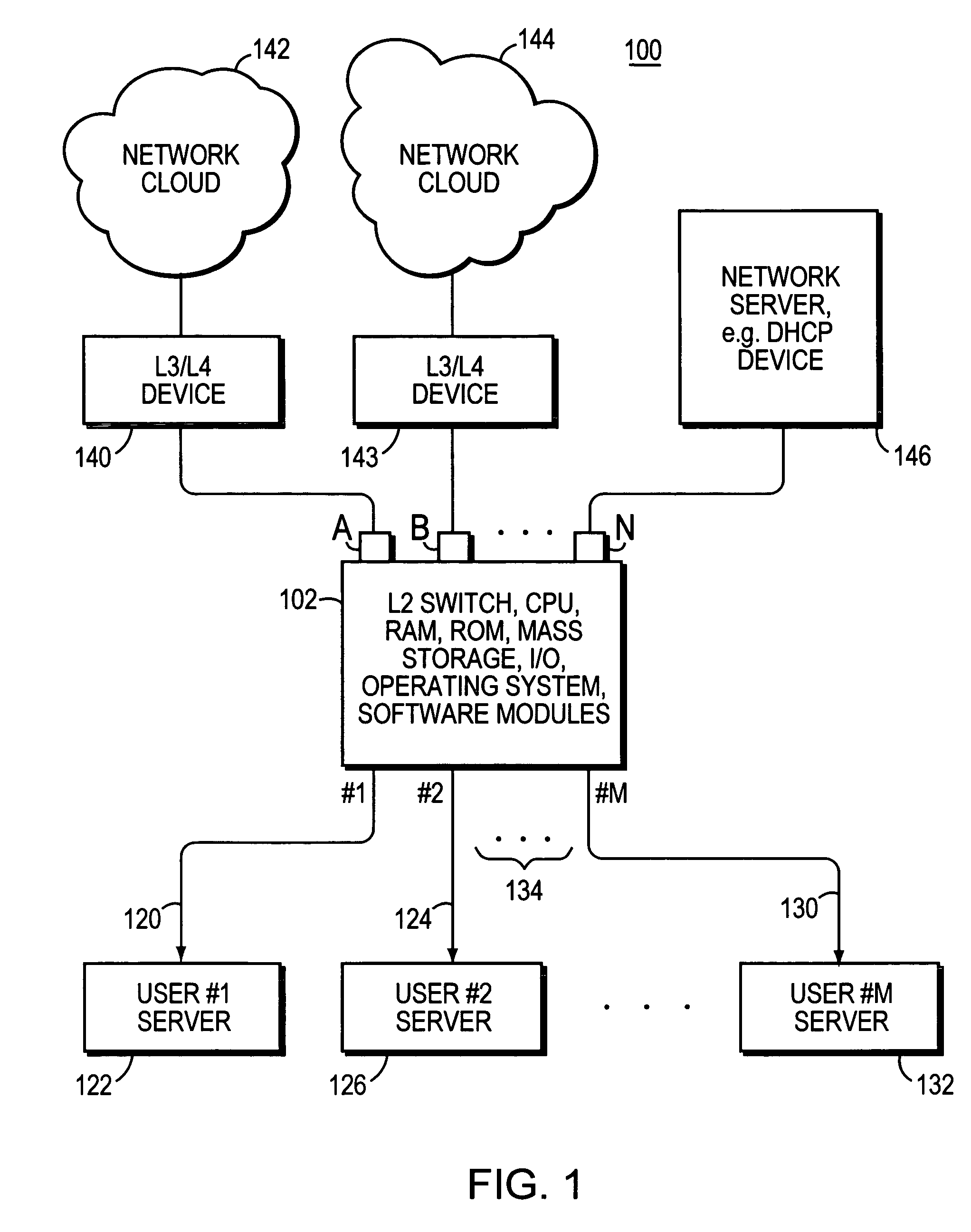
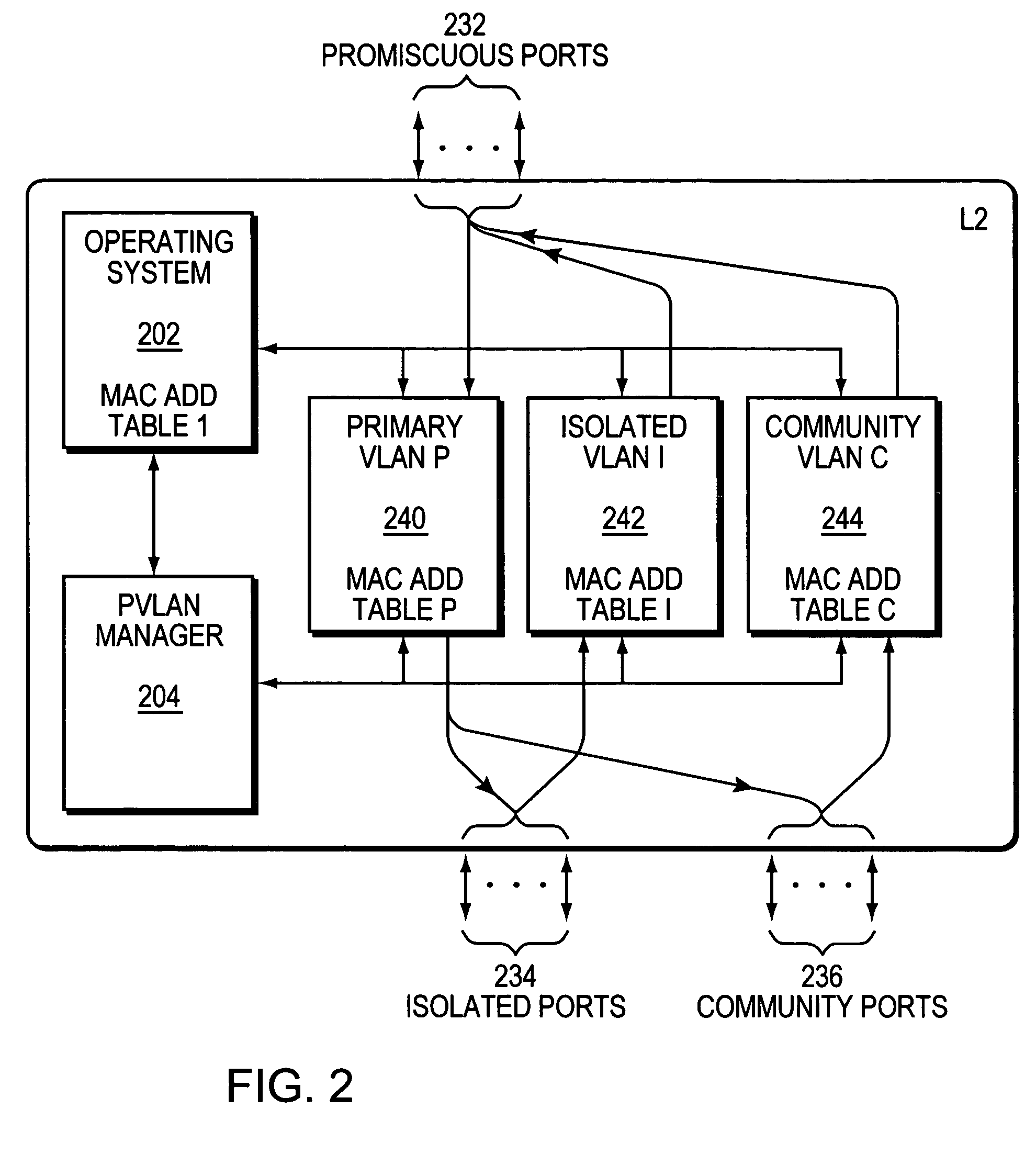
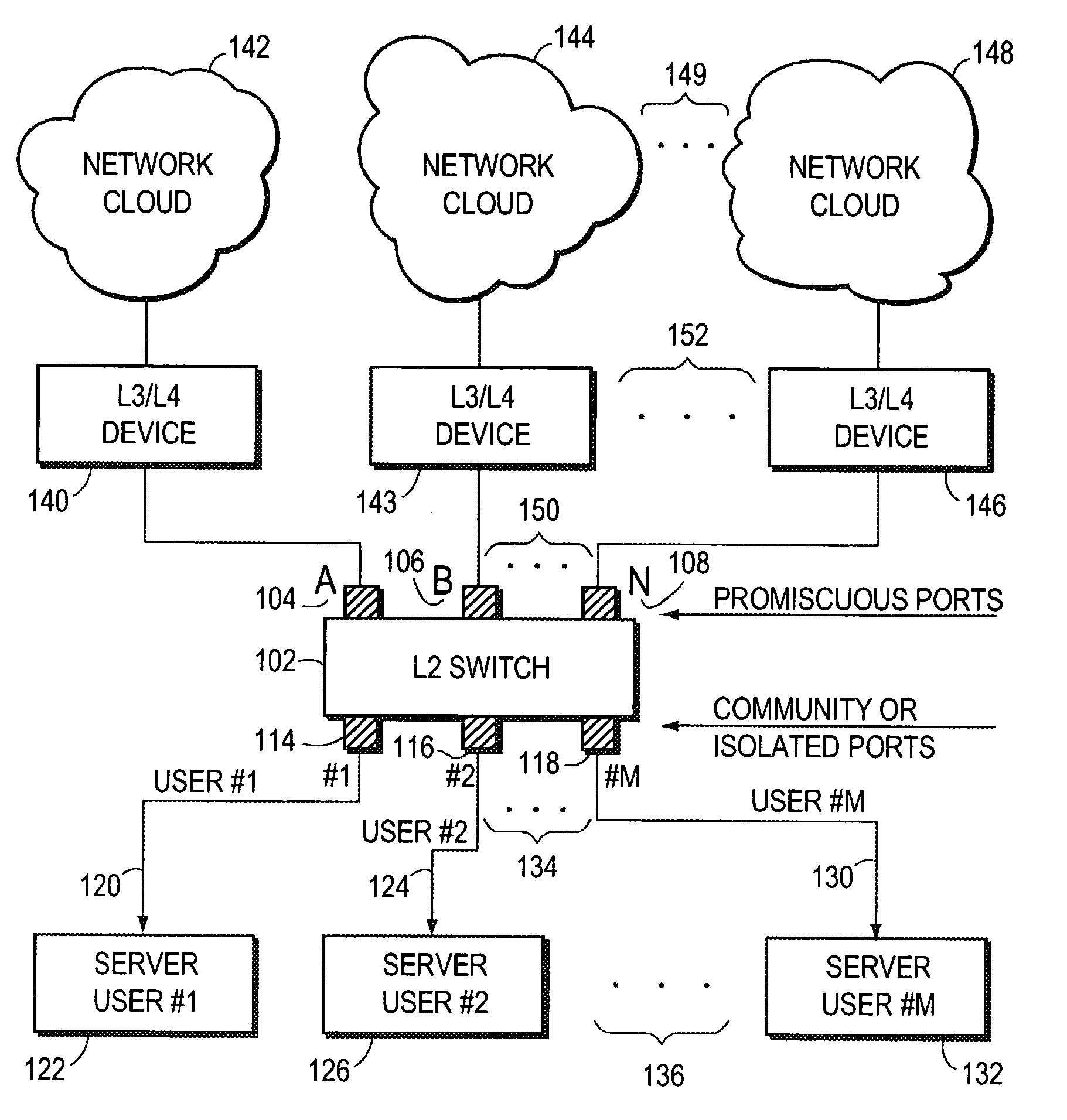
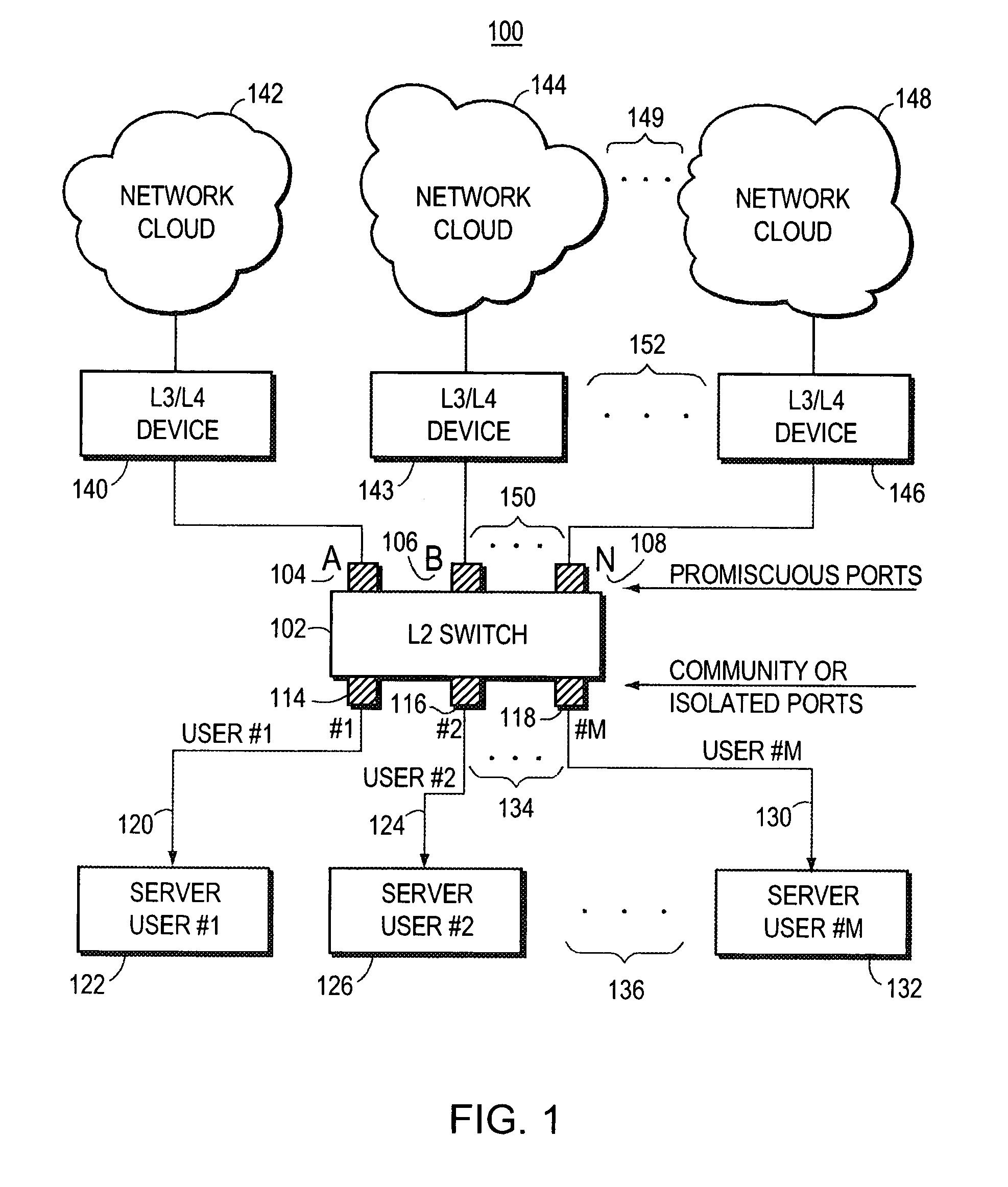
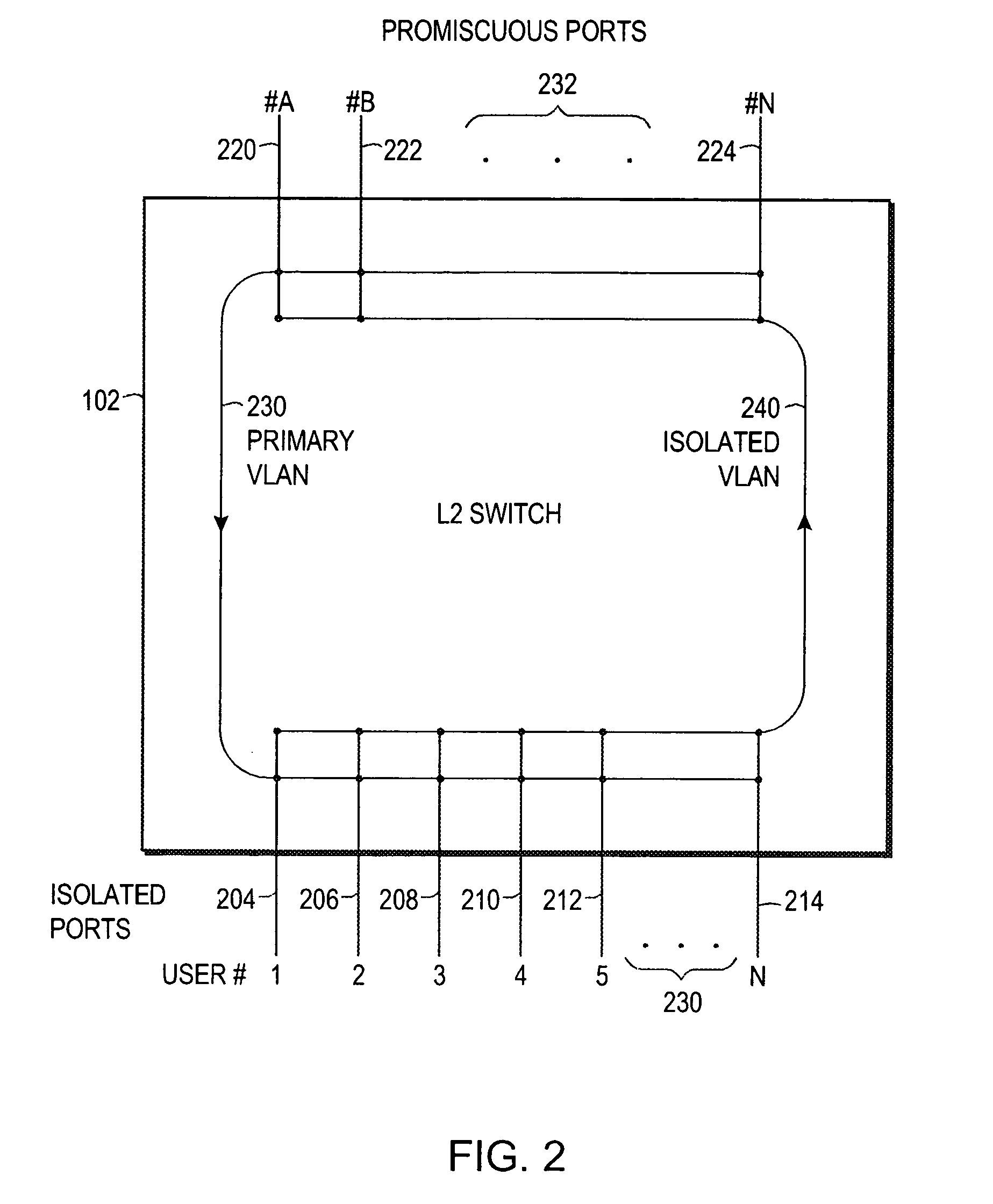
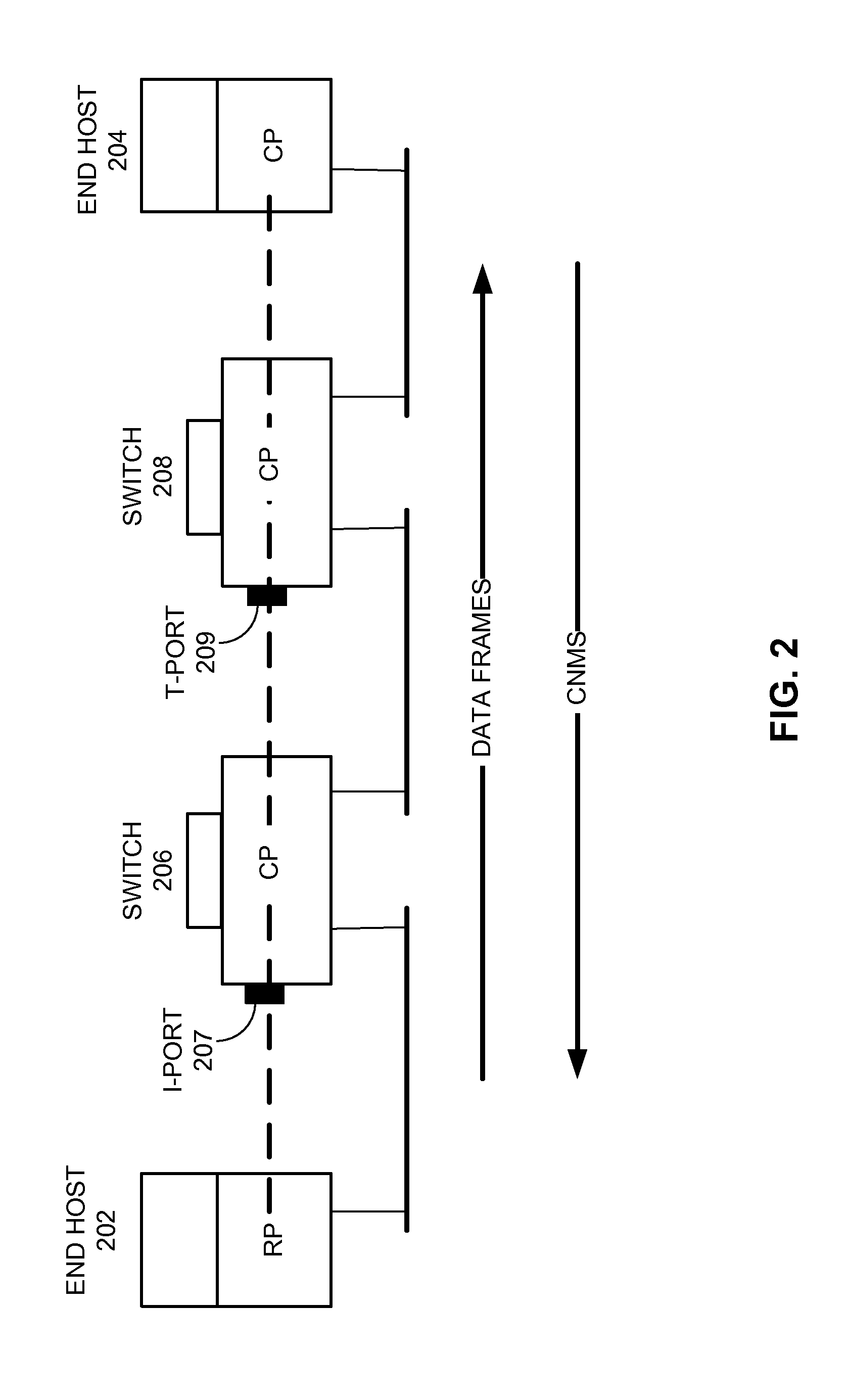
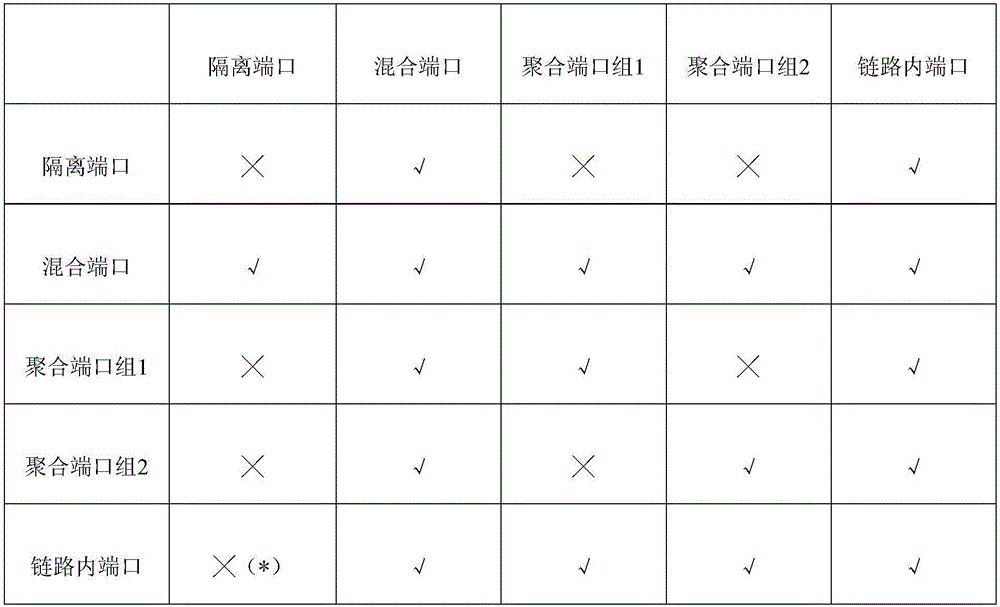
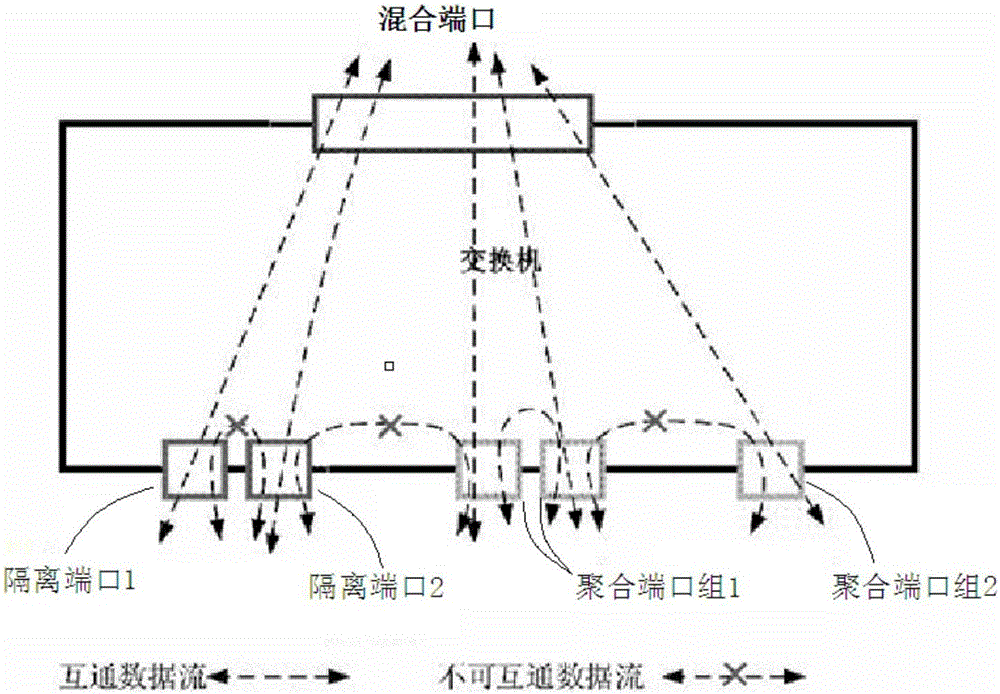
The invention uses a layer 2 switch (L2 switch), or bridge, to separate user's message traffic by use of Virtual Local Area Networks (VLANs) defined within the switch. Three new types of ports are defined, “promiscuous” ports “isolated” ports, and “community” ports. Three types of VLANs internal to the switch are defined, “primary” VLANs, “isolated” VLANs and “community” VLANs. The promiscuous ports are connected to layer 3 or layer 4 devices. Isolated ports and community ports are connected to individual user's servers, etc., and maintain traffic for each user separate from other users. The primary VLAN connects to all promiscuous ports, to all isolated ports, and to all community ports. The primary VLAN is a one way connection from promiscuous ports to isolated or community ports. An isolated VLAN connects to all promiscuous ports and to all isolated ports. The isolated VLAN is a one way connection from an isolated port to the promiscuous ports. A community VLAN is defined as connecting to a group of community ports, and also connecting to all of the promiscuous ports. The group of community ports is referred to as a “community” of community ports. A community VLAN is a one way connection from a community of ports to the promiscuous ports, but allows a packet received by one community port to be transmitted out of the switch, through the other community ports connected to that community VLAN.
Owner:CISCO SYSTEMS INC
Method for testing stability of switch
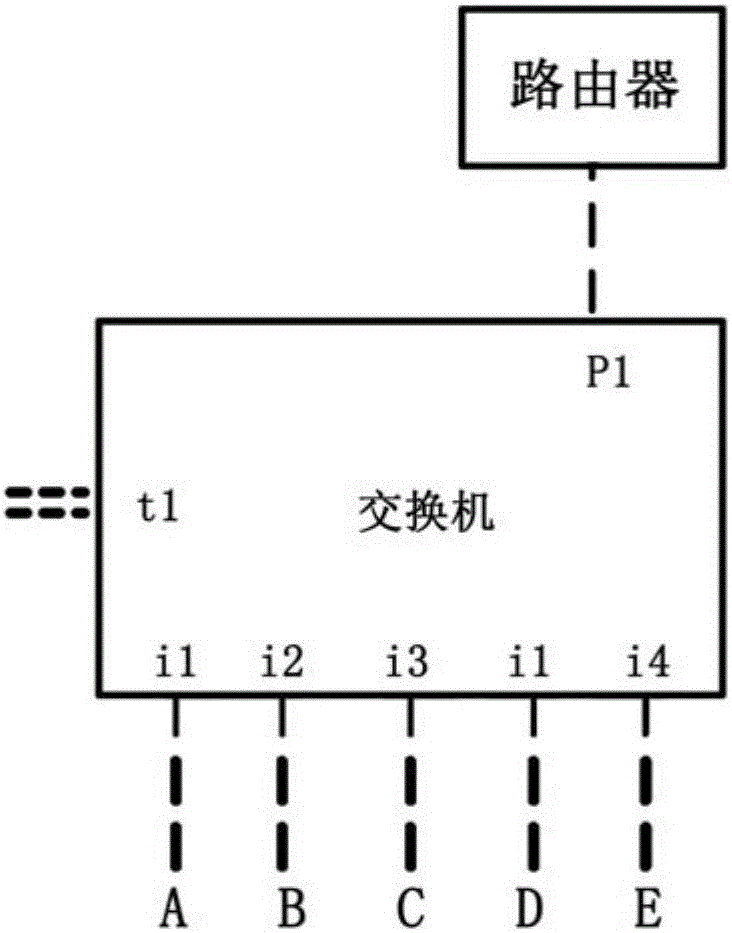
InactiveCN103078770ATo achieve the effect of full load testWith VLAN functionNetworks interconnectionSpecific testVirtual LAN
The invention provides a method for testing the stability of a switch. The method specifically comprises the following steps of: interconnecting a front port and a tail port of the switch with two communication ports of a network tester respectively, and interconnecting each port of the switch in a serpentine networking way; configuring a corresponding untagged virtual local area network (VLAN) and a port attribute Pvlan on the switch, wherein the untagged VLAN is a VLAN without tags, and the Pvlan is a private VLAN; and transmitting test traffic from one port to the other port of the network tester. Compared with the prior art, the method for testing the stability of the switch has the advantages that a piece of test traffic sequentially flows through all the ports of the switch instantly in a serpentine way to achieve a full load effect, test work is simpler and easier, and the method is easy to popularize and use.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
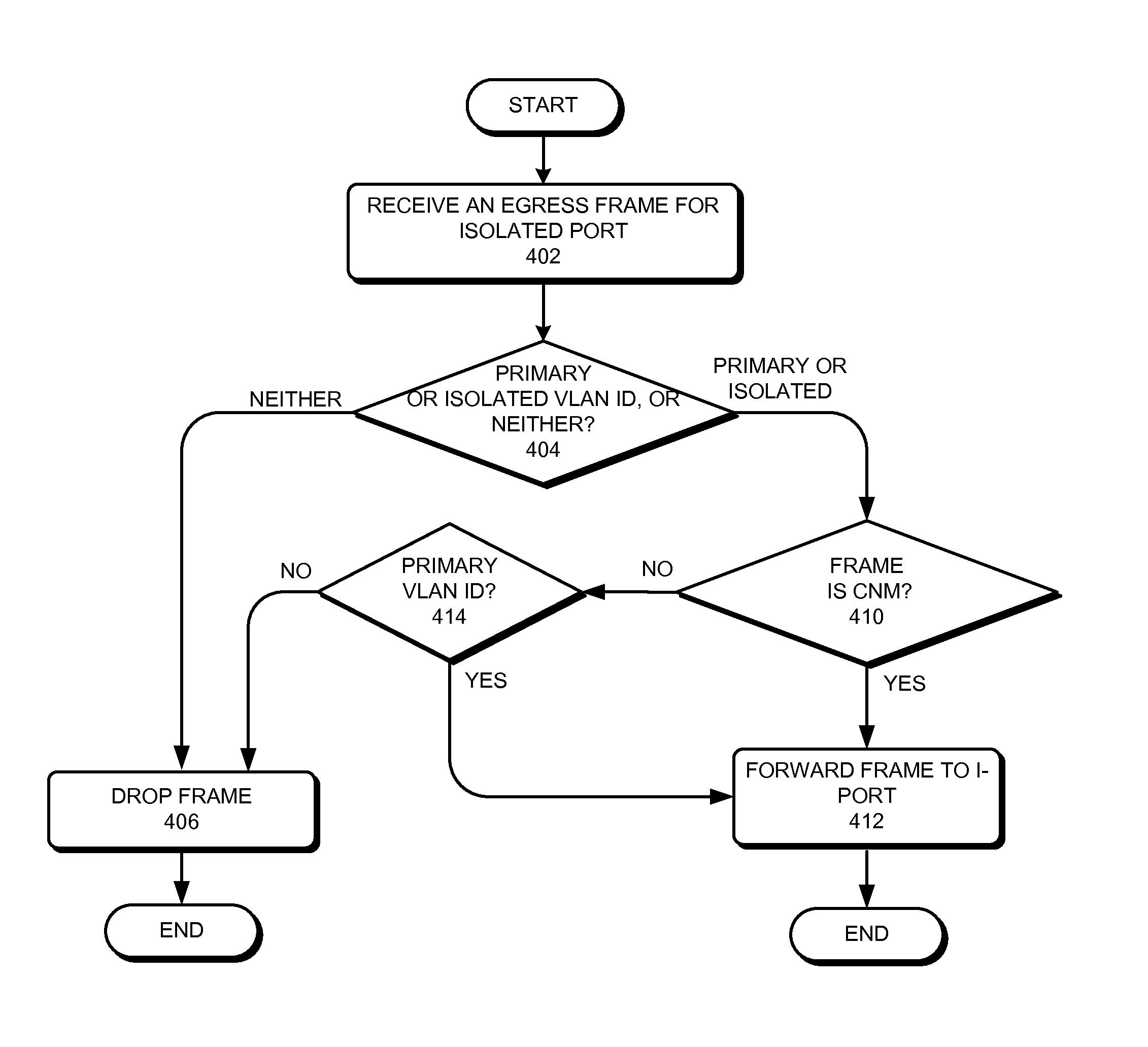
Congestion notification in private vlans
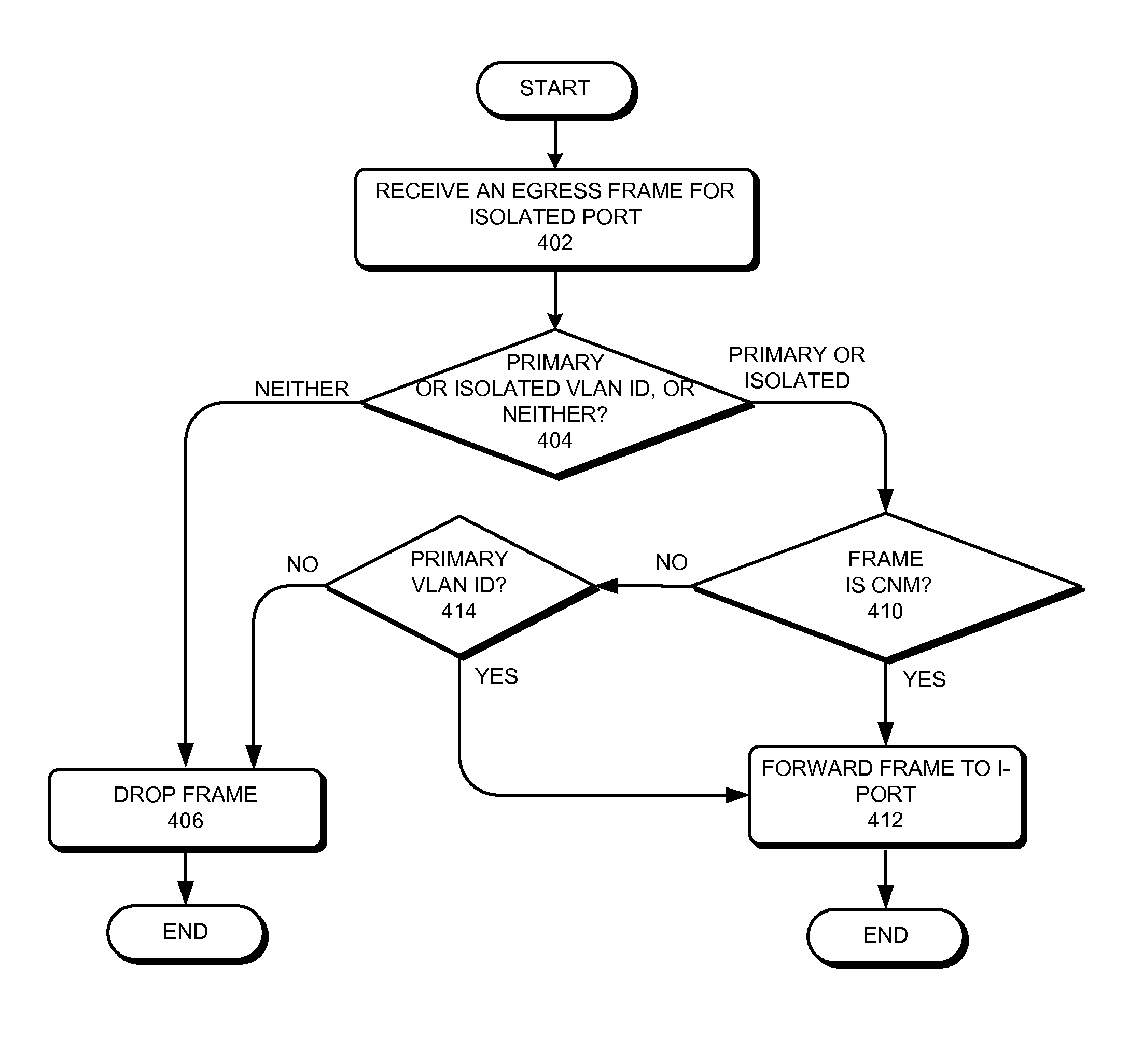
One embodiment of the present invention provides a switch. During operation, in a network with a private VLAN configuration, the switch allows a congestion notification message with an isolated virtual local area network identifier (VLAN ID) to be forwarded via an isolated VLAN port.
Owner:AVAGO TECH INT SALES PTE LTD
Method and device for private VLAN (virtual local area network) information management
ActiveCN103166864AReduce configuration operationsData switching networksPrivate VLANInformation management
The invention discloses a method and a device for private VLAN (virtual local area network) information management. The method and the device are applied to a QinQ network, and a core switching device maintains private VLAN table entries according to private VLAN information carried in exchanged messages by exchanging query messages and report messages related to the private VLAN information between an access switching device and the core switching device. Compared with the prior art, the method and the device have the advantage that VLAN configuration operations of QinQ on the core switching device are decreased.
Owner:XINHUASAN INFORMATION TECH CO LTD
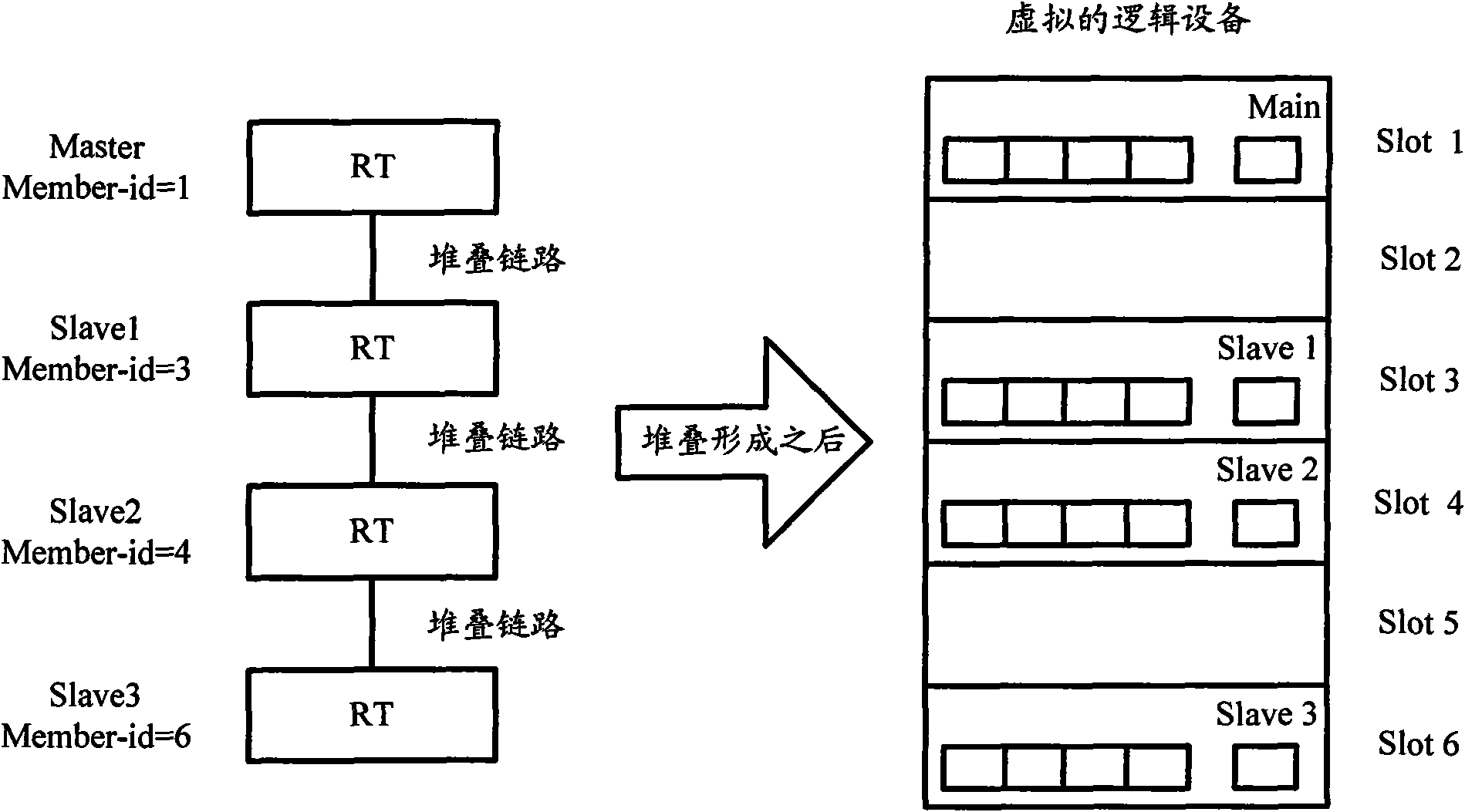
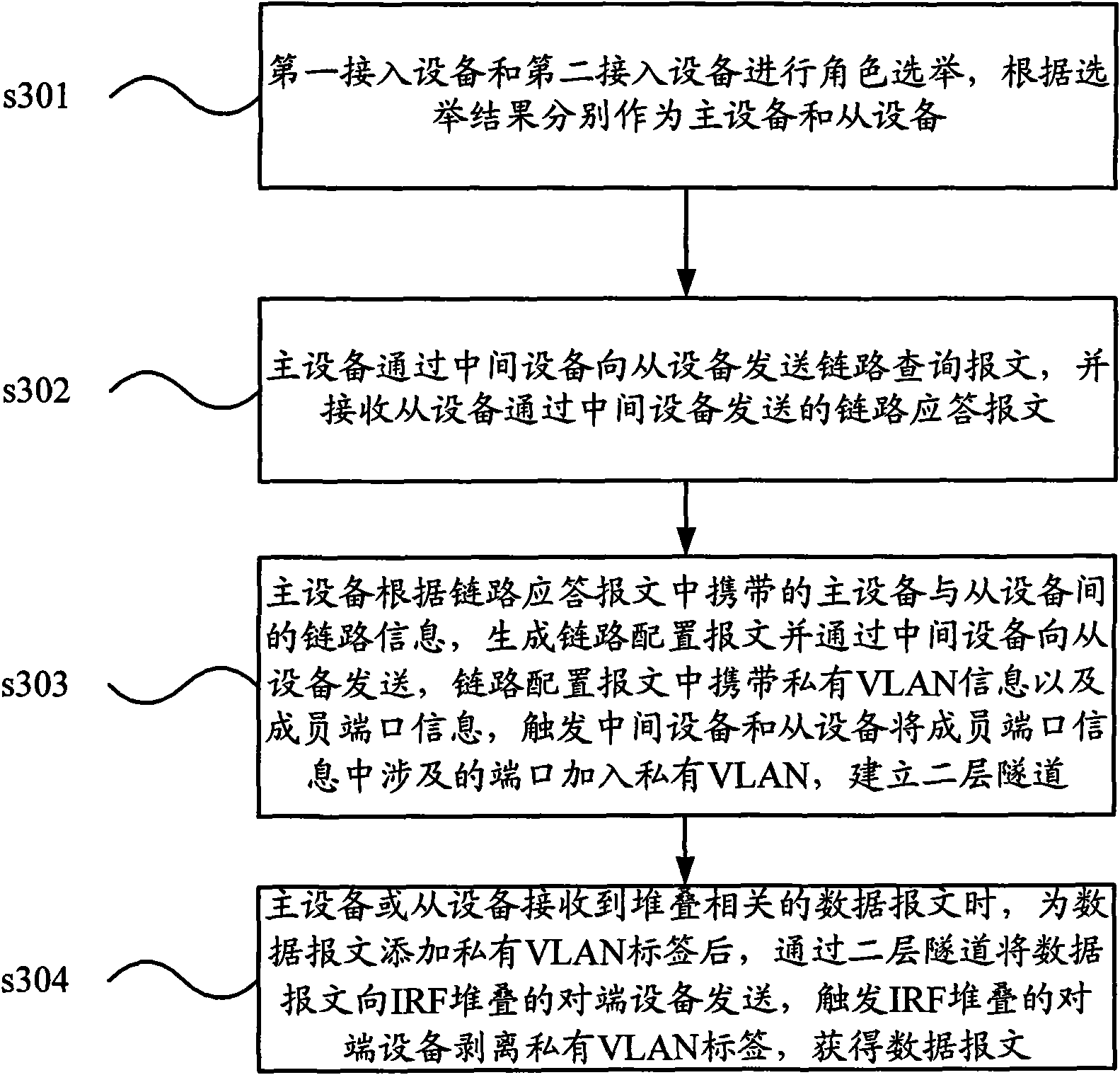
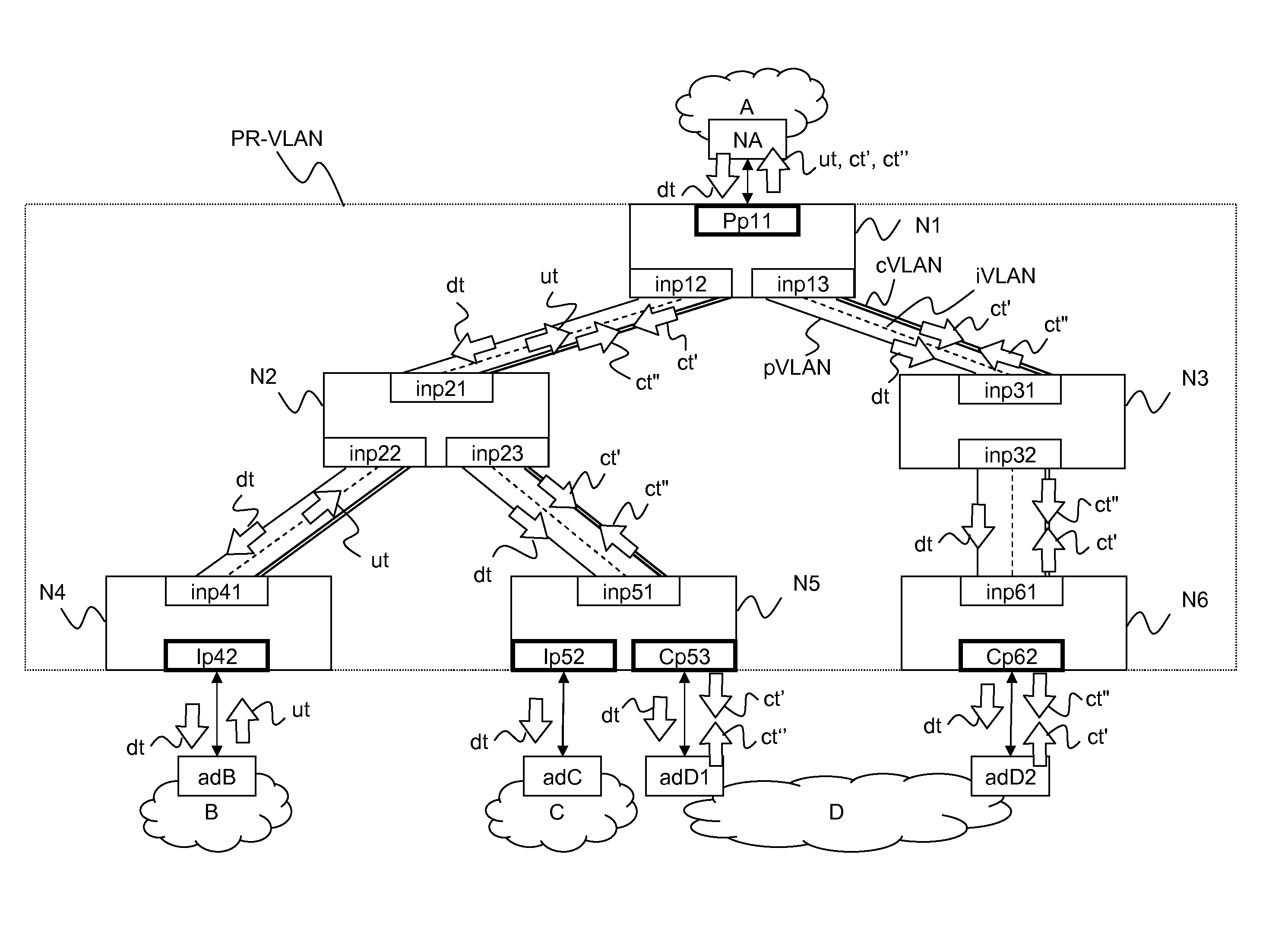
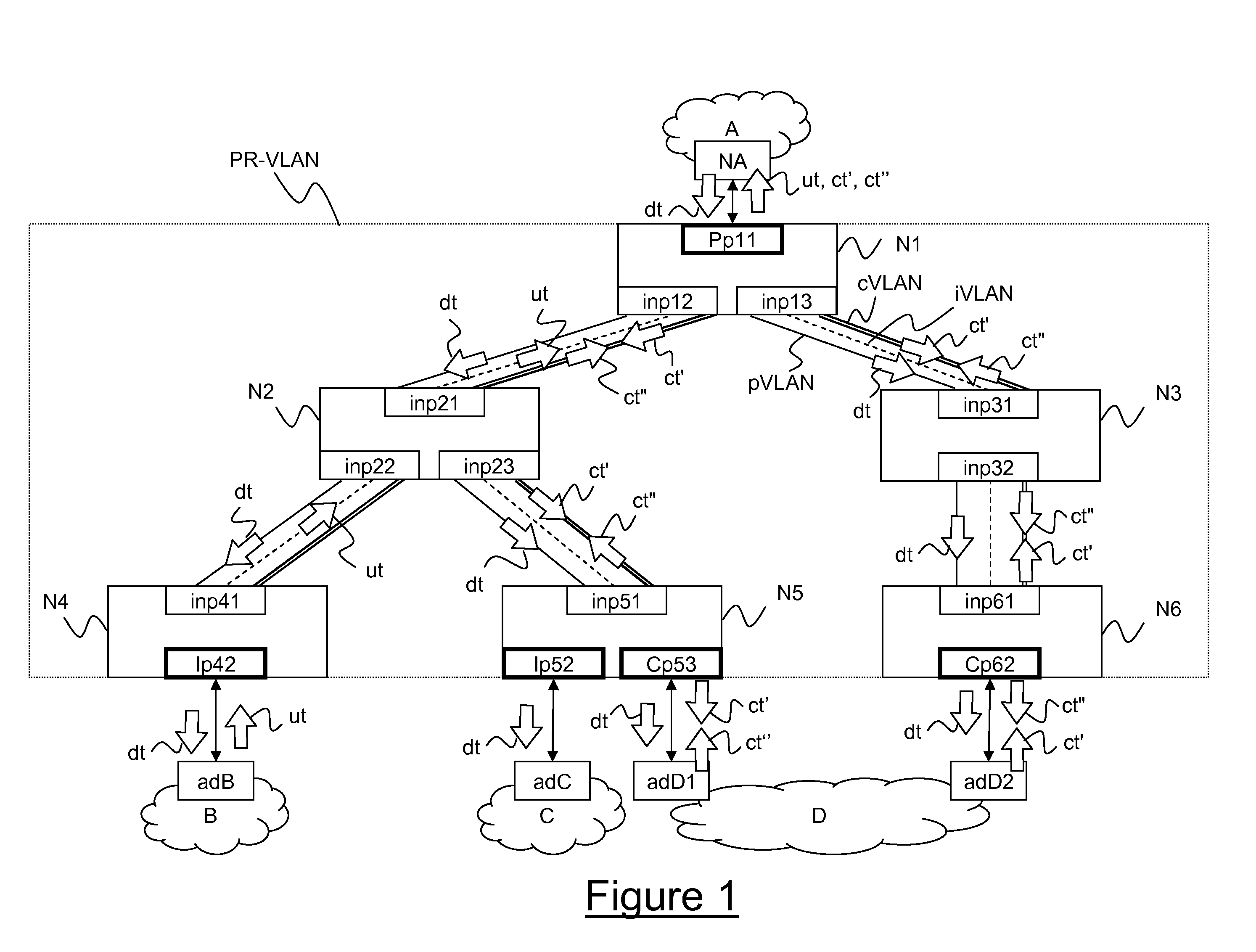
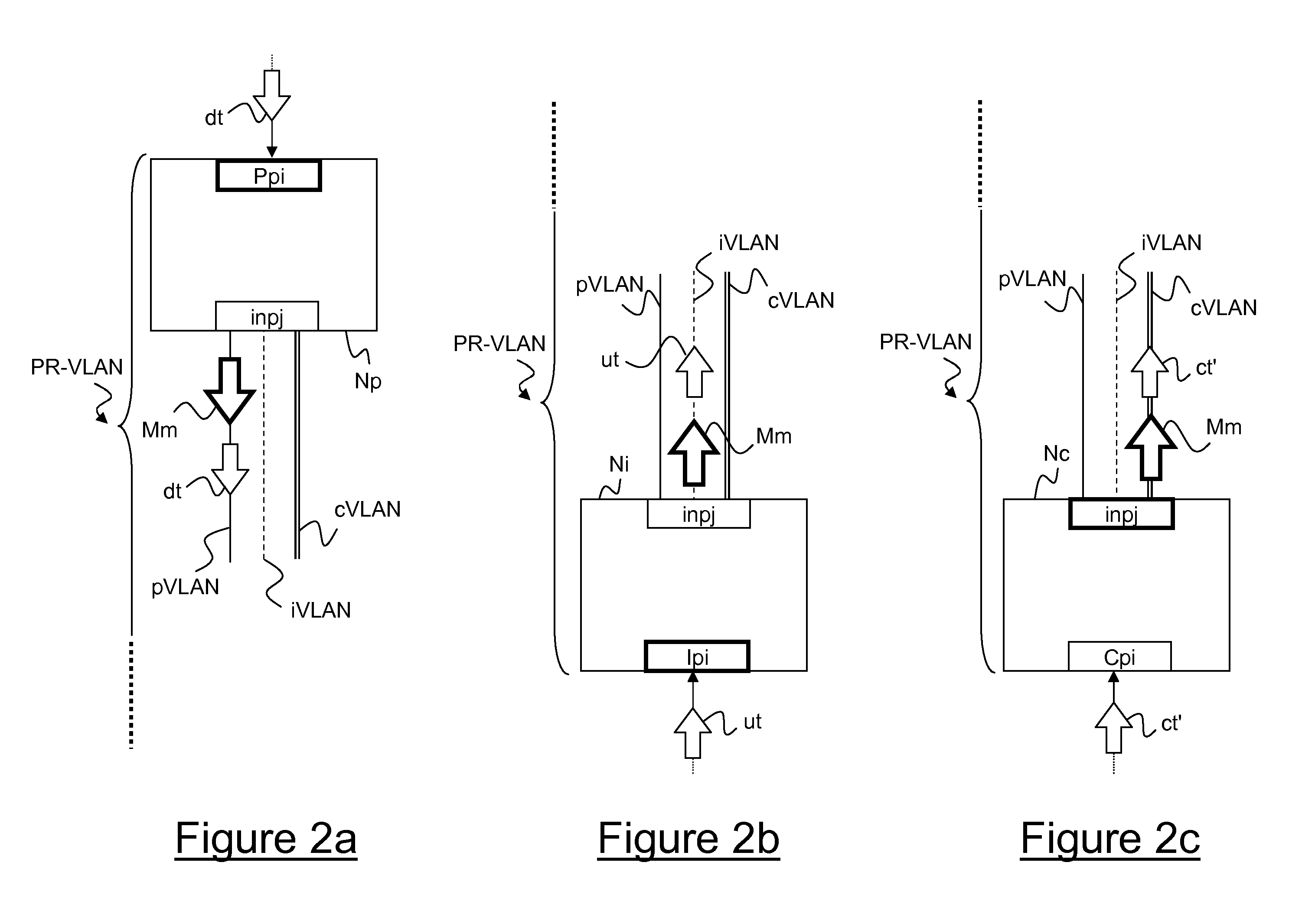
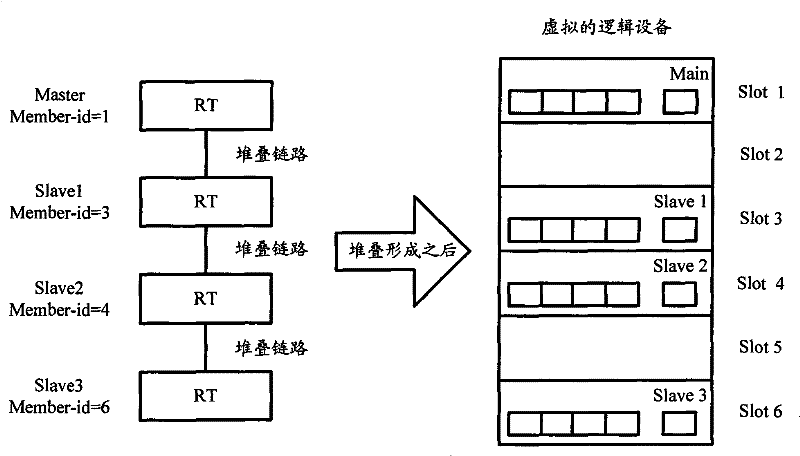
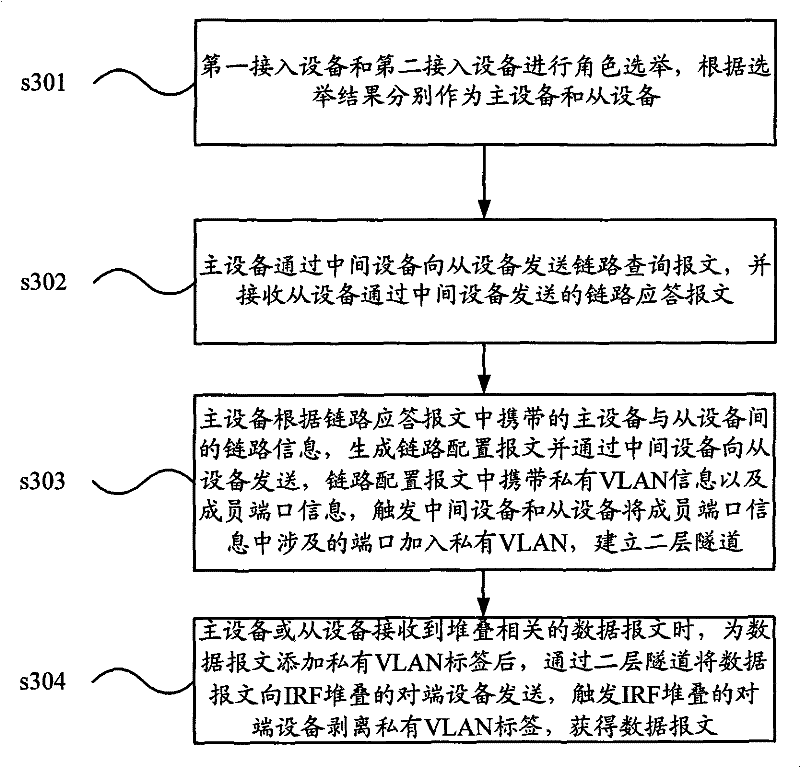
Implementation method of remote IRF stacking and equipment thereof
The invention discloses an implementation method of remote IRF stacking and stacking equipment. The method is applied to first access equipment and second access equipment which need to establish IRF stacking, and the first access equipment is connected with the second access equipment by intermediate equipment. The method comprises the following steps: performing role election among access equipment crossing networks, and transmitting link information; sending a link configuration message to the access equipment of master equipment according to the election result to trigger the intermediate equipment and slave equipment among the access equipment to add a member port to a private VLAN; and establishing a layer-two tunnel, and performing data message interaction by virtue of the layer-two tunnel to realize the IRF stacking crossing networks among the access equipment.
Owner:NEW H3C TECH CO LTD
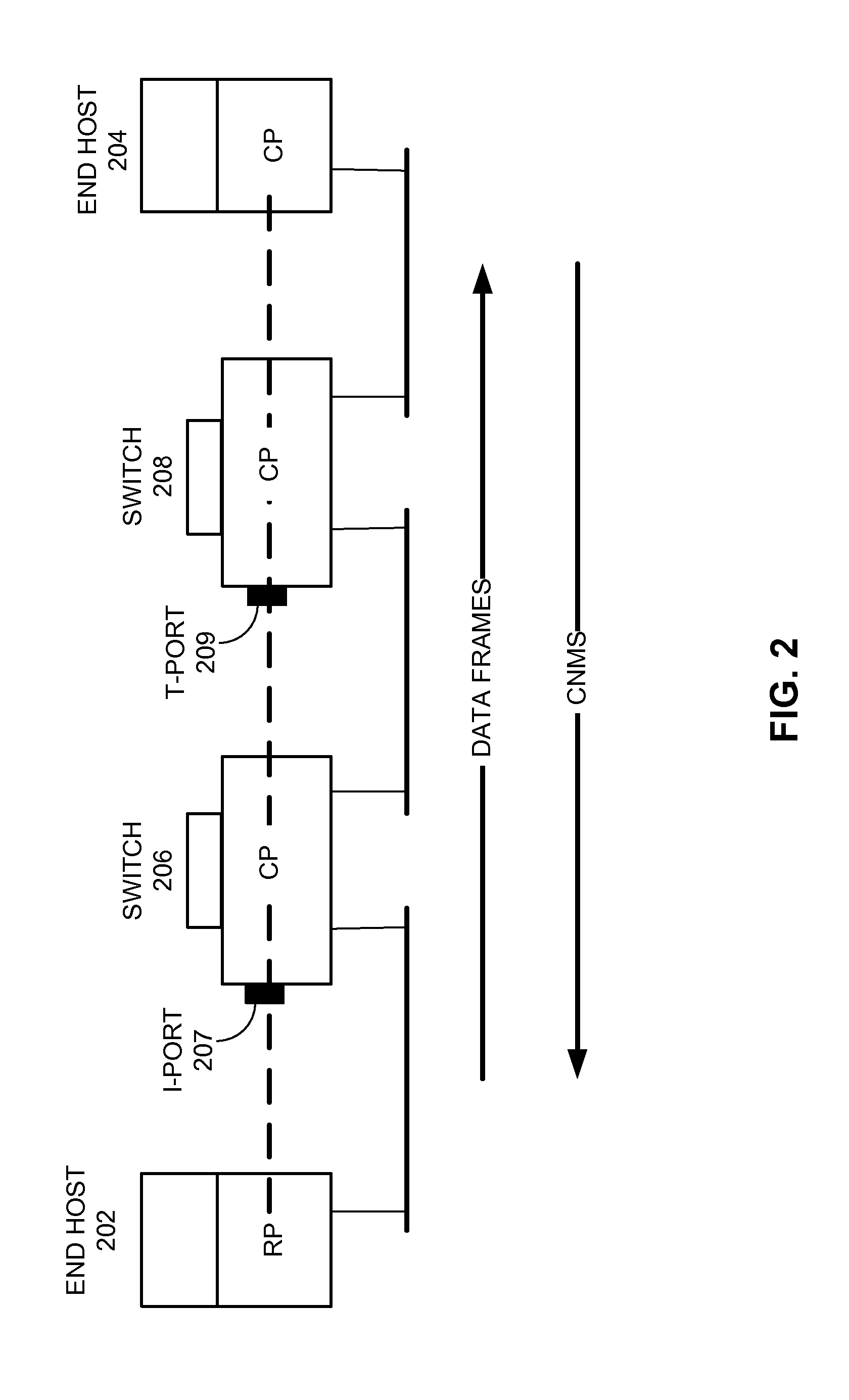
Method and network node for monitoring traffic in a private VLAN
ActiveUS20080031261A1Overcome problemsData switching by path configurationPrivate VLANReal-time computing
It is disclosed a method for monitoring traffic in a private VLAN, the traffic bidirectionally propagating across the private VLAN through a sequence of nodes sequentially connected by a primary VLAN and a secondary VLAN, the sequence of nodes comprising a first node and a second node, wherein the method comprises: transmitting a monitoring message from the first node to the second node either along the primary VLAN or the secondary VLAN, according to a first criterion based upon a type of the first node; receiving the monitoring message at the second node; and upon reception of the monitoring message at the second node, transmitting a reply message from the second node to the first node either along the primary VLAN or the secondary VLAN, according to a second criterion based upon a type of the second node and upon a VLAN different from the VLAN from which the monitoring message has been received.
Owner:WSOU INVESTMENTS LLC
Method, device and network equipment for processing messages
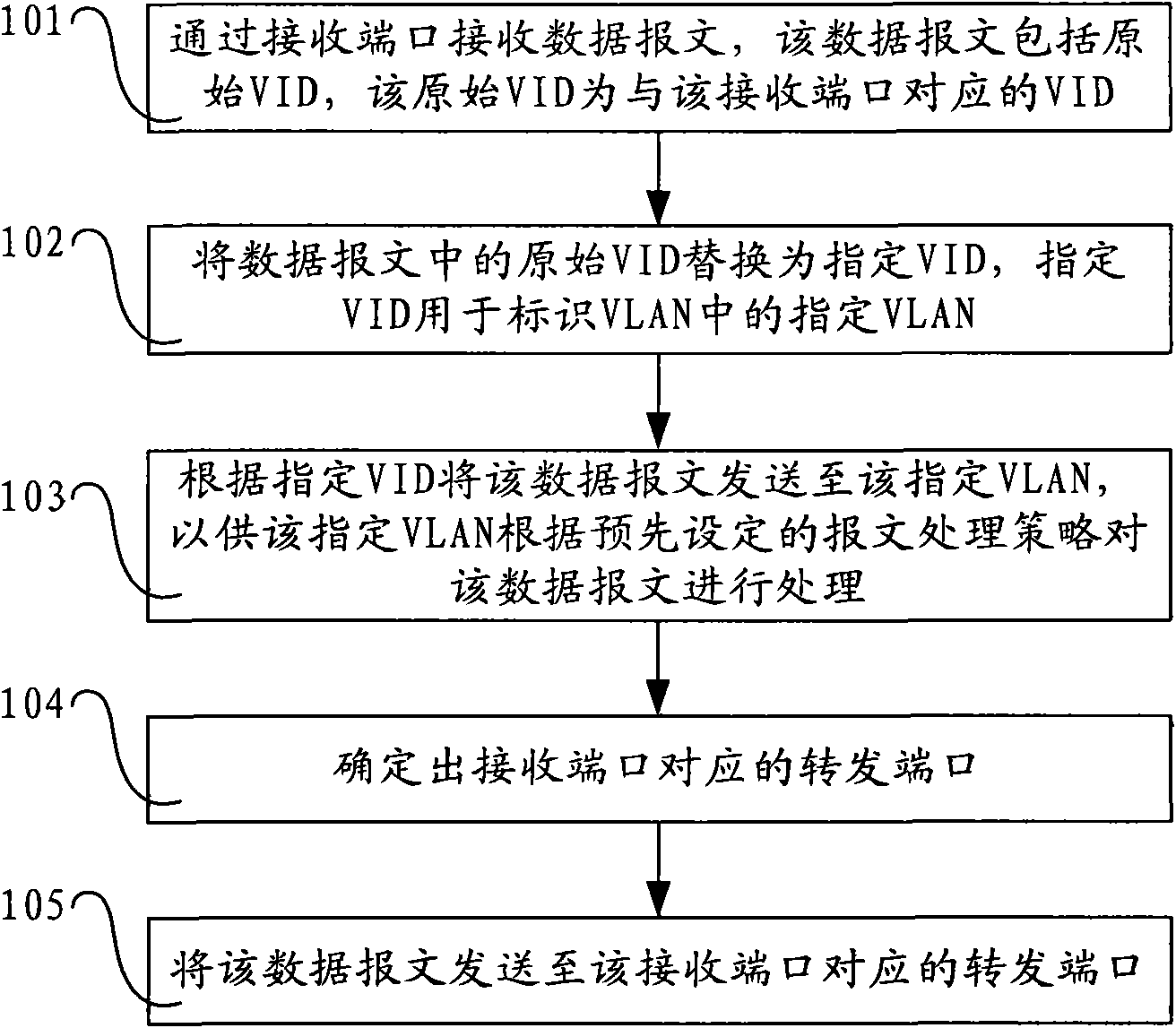
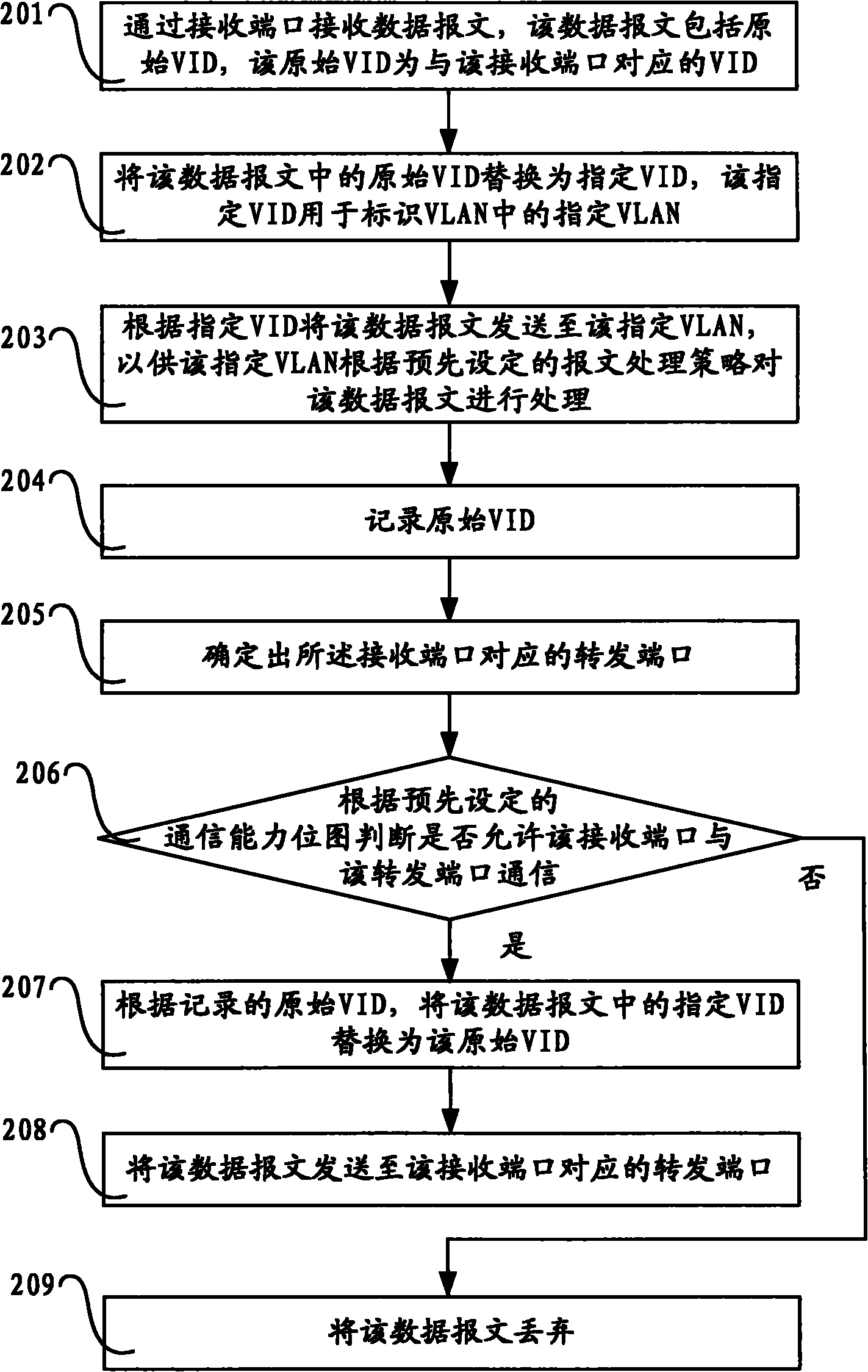
InactiveCN101924700AReduce complexityReduce resource requirementsNetworks interconnectionLocal area networkPrivate VLAN
The invention discloses a method, a device and network equipment for processing messages. The method comprises the following steps: receiving a data message through a receiving port, wherein the data message comprises original virtual local area network identification VID, and the original VID corresponds to the receiving port; replacing the original VID in the data message by the specified VID, wherein the specified VID is used for identifying the specified VLAN in the VLAN; sending the data message to the specified VLAN according to the specified VID so that the specified VLAN can process the data message according to the preset message processing policy; determining a forwarding port corresponding to the receiving port; and sending the data message to the forwarding port corresponding to the receiving port. In the embodiment of the invention, the message processing policy only needs to be set on the specified VLAN in the private VLAN, thereby reducing the system complexity and the resource consumption of the private VLAN.
Owner:RUIJIE NETWORKS CO LTD
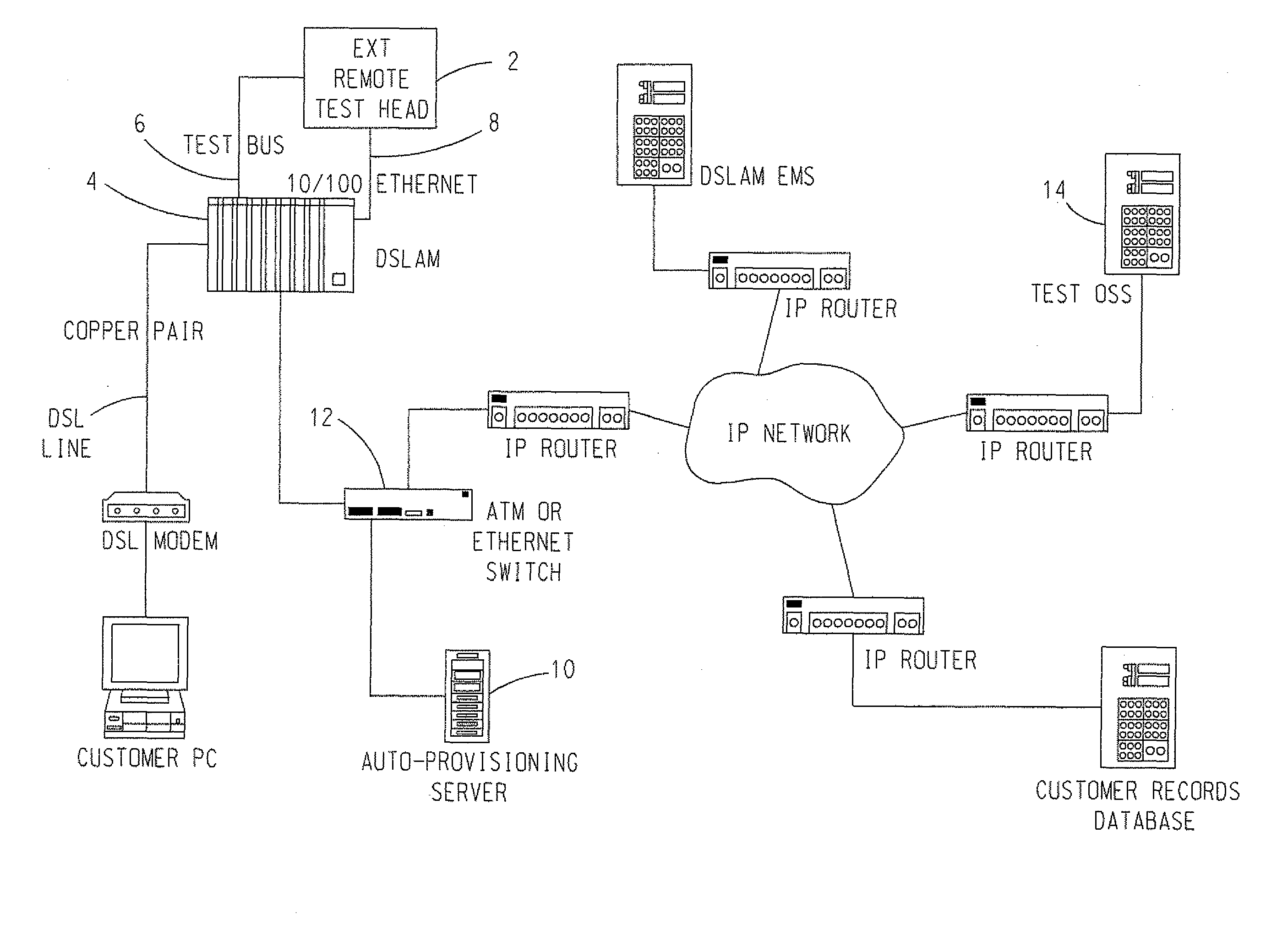
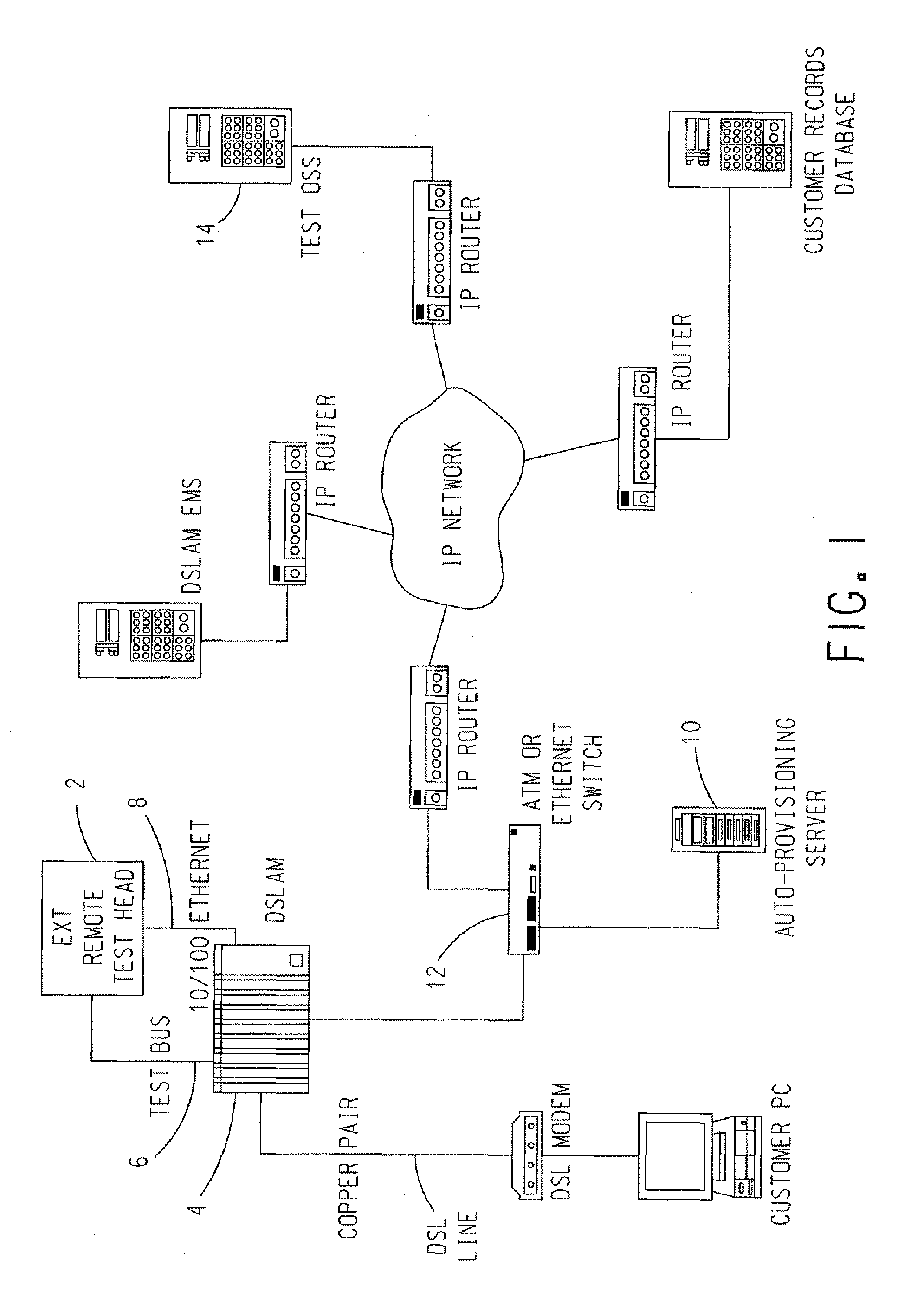
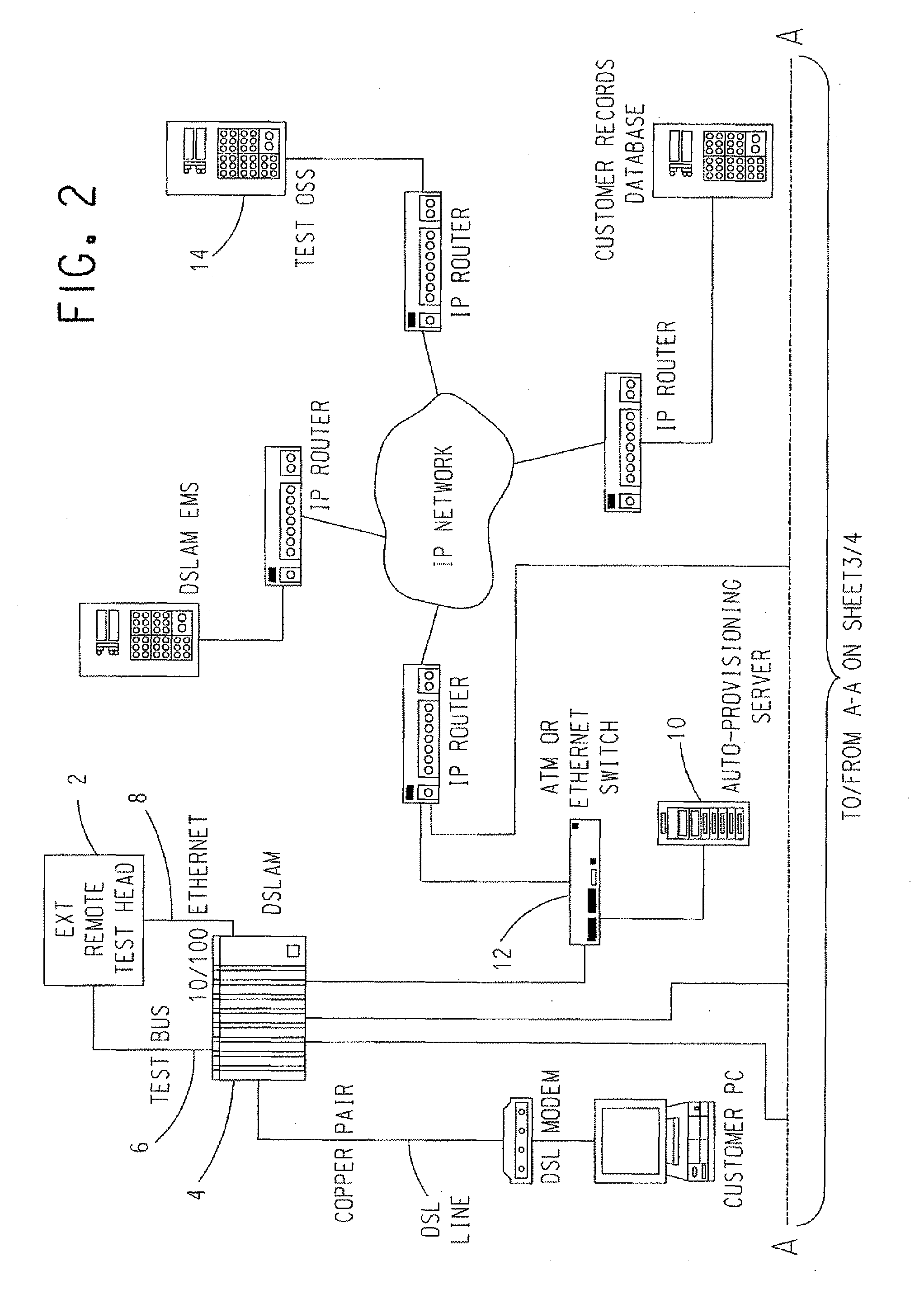
Automatic provisioning of a remote test head of a combined ip/telephony/cable network
In a telecommunications network that includes: a Digital Subscriber Line Access Multiplexer (DSLAM) (4) that has a DSLAM ID assigned thereto, a test head (2) coupled to the DSLAM (4) including a VLAN ID and a MAC address, and an auto-provisioning server (10), a public IP network is created between the auto-provisioning server (10) and a Test Operations Support System (OSS) (14) coupled to the telecommunications network. A private IP network is created between the test head (2) and the auto-provisioning server (10). The auto-provisioning server (10) acts as a gateway for the dispatch of data from the test head (2) to the Test OSS, and vice versa, across the private VLAN network and the public IP network.
Owner:TOLLGRADE COMM INC
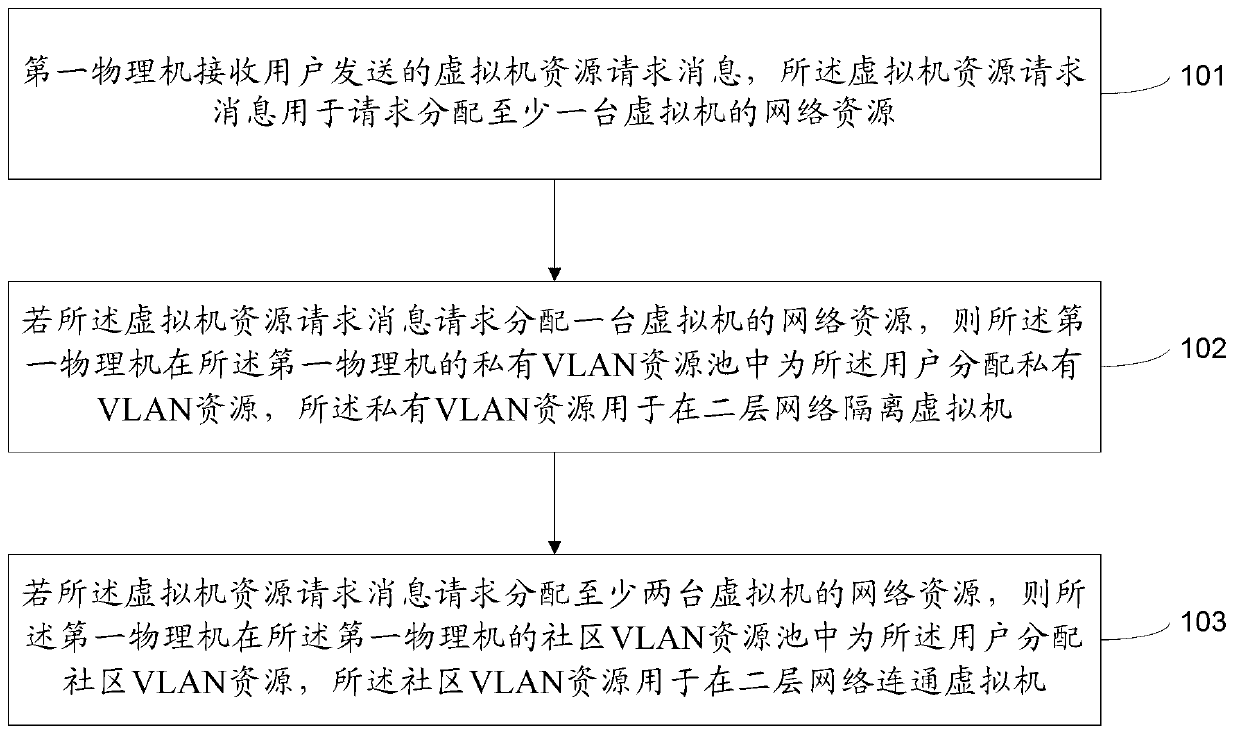
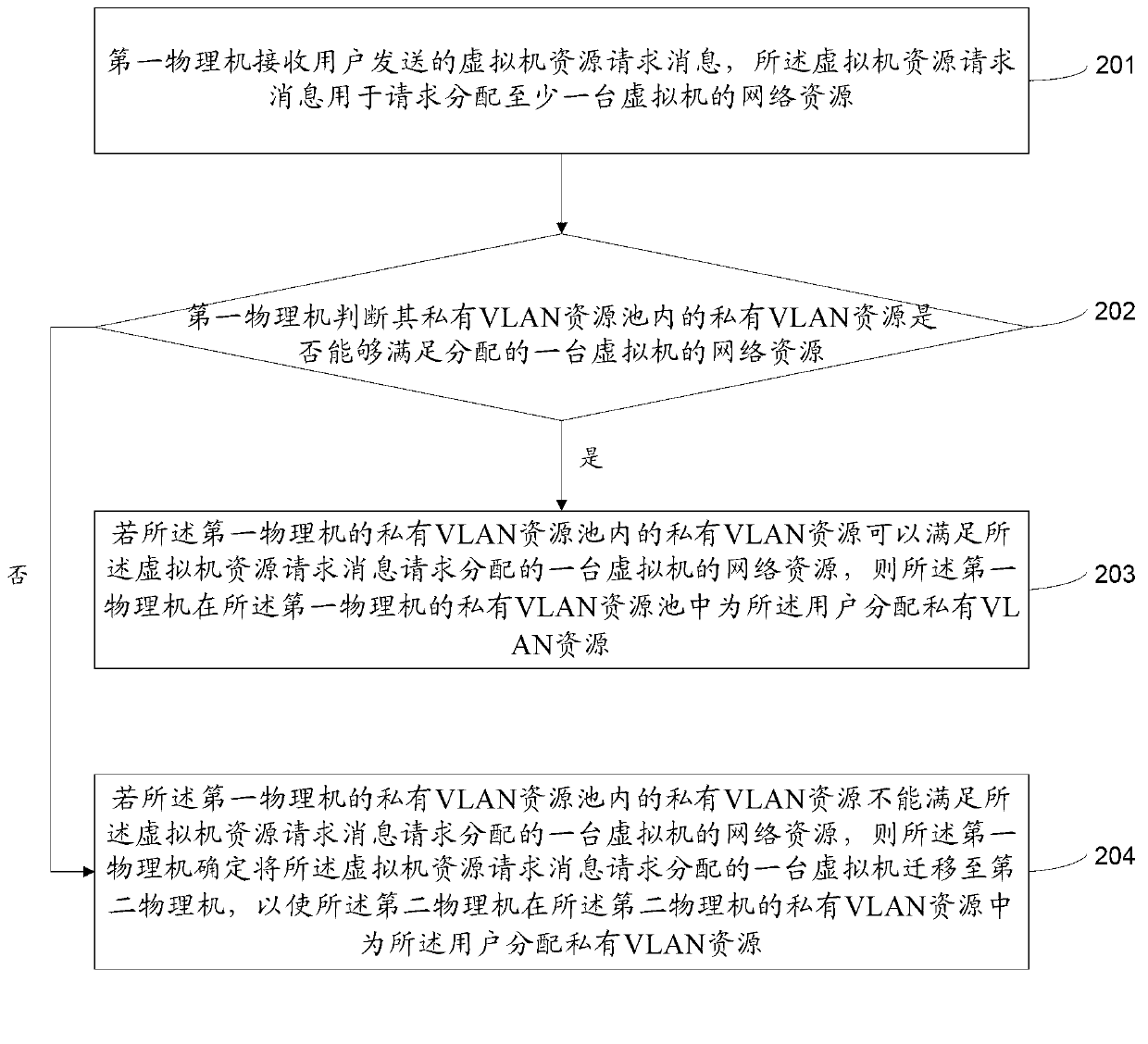
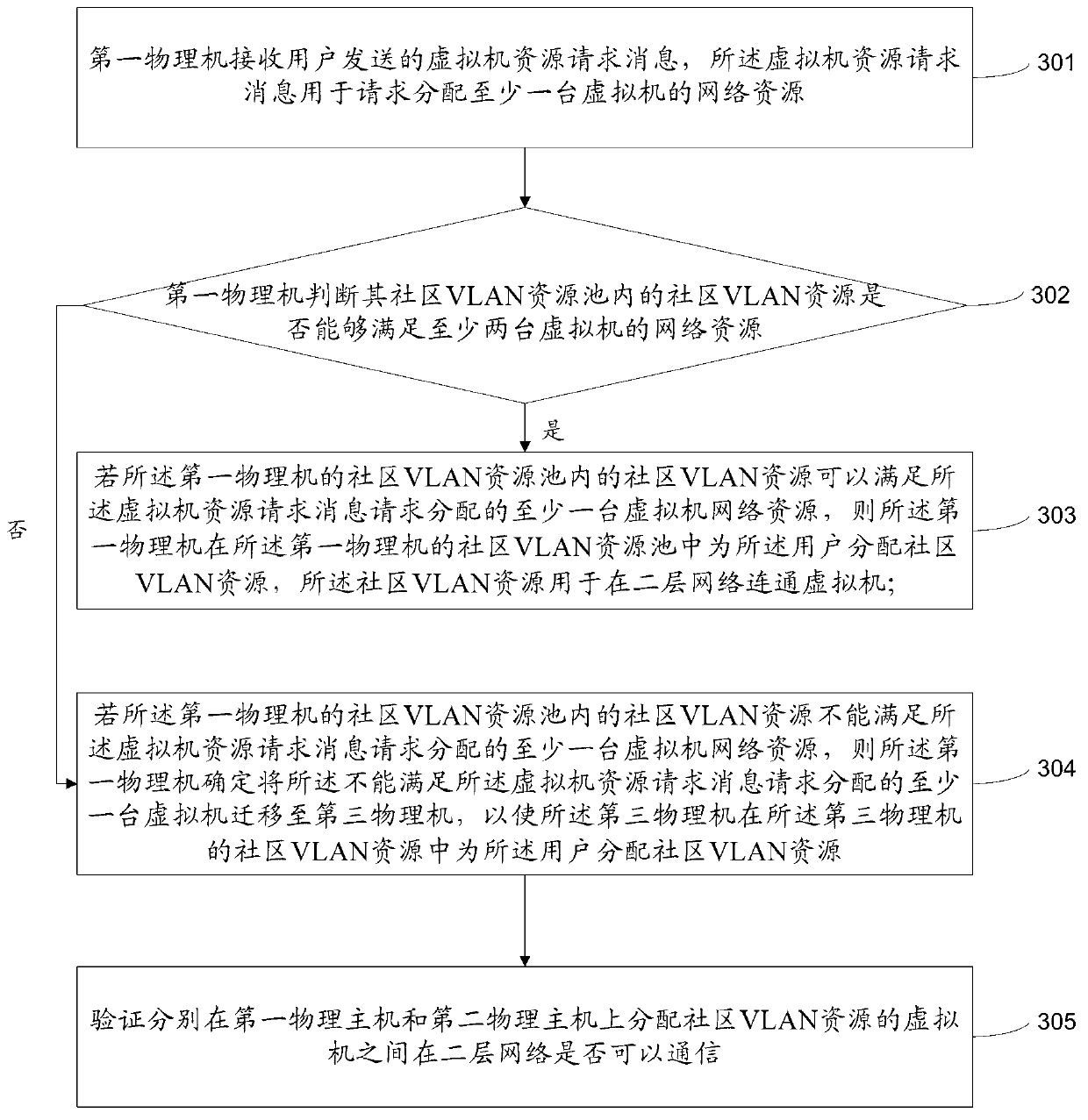
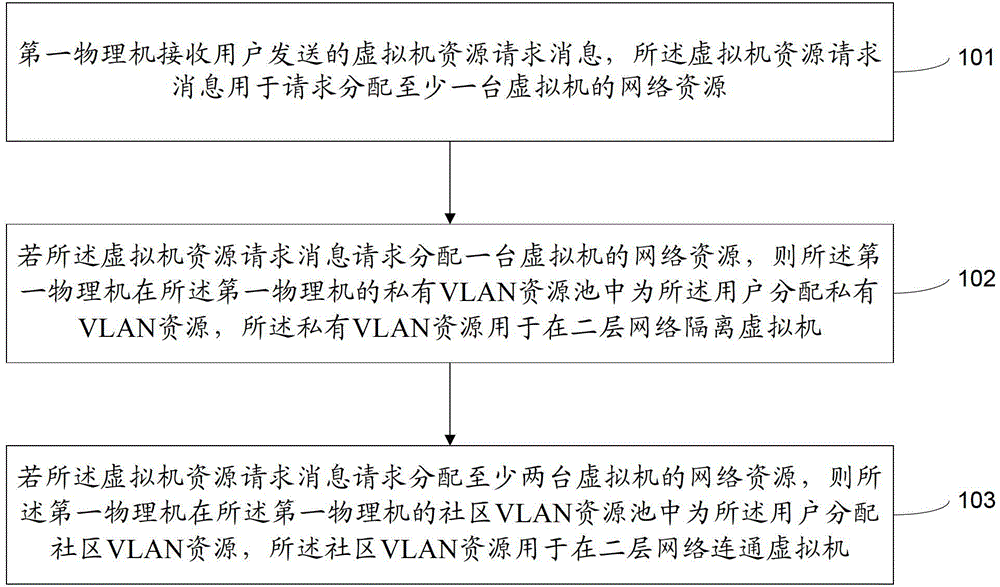
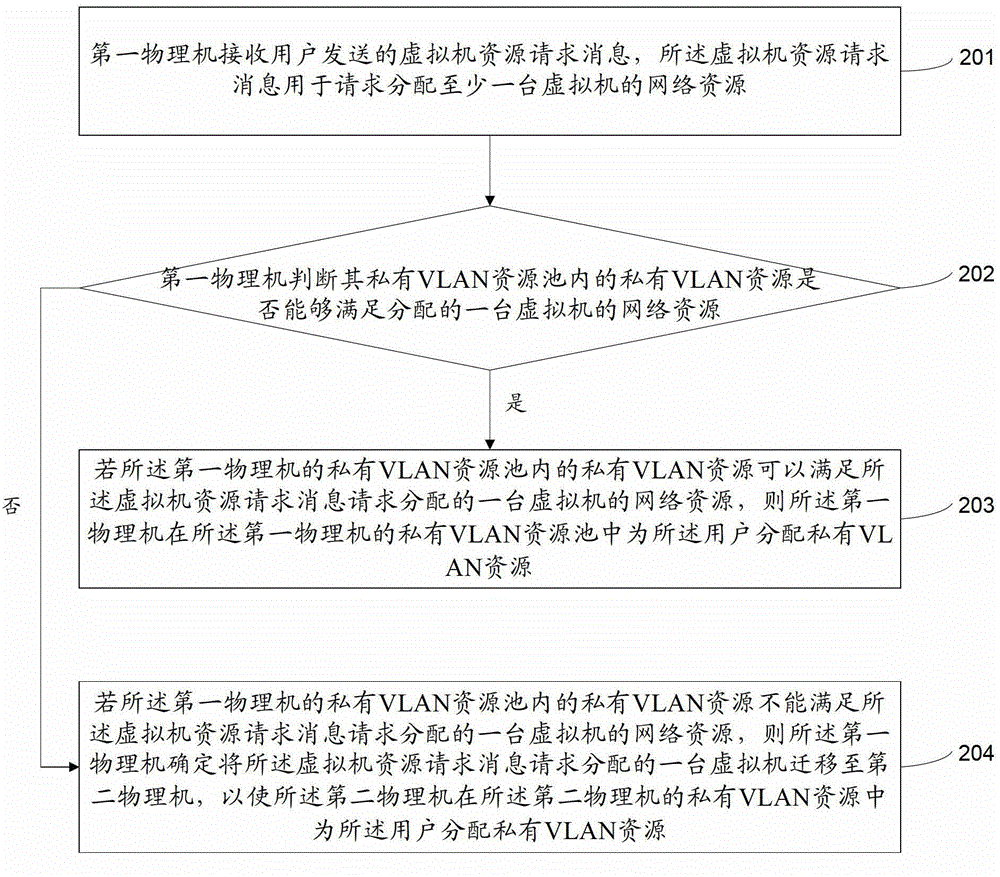
Method and device for allocating network resources of virtual machines
The invention provides a method and a device for allocating network resources of virtual machines. The method comprises that a first physical host receives virtual information resource request messages sent by a user, and the virtual machine resource request messages are used for requesting for allocating network resources of at least one virtual machine; the first physical host allocates private virtual local area network (VLAN) resources for the user in a private VLAN resource pool of the first physical host if the virtual machine resource request messages request for allocating network resources of one virtual machine, and the private VLAN resources are used for separating the virtual machine in two-layer networks; and if the virtual machine resource request messages request for allocating network resources of at least two virtual machines, the first physical host allocates community VLAN resources for the user in a community VLAN resource pool of the first physical host, and the community VLAN resources are used for being communicated with the virtual machine in the two-layer networks. A great many user demands are met through the method and the device.
Owner:BEIHANG UNIV
Efficient Software-Based Private VLAN Solution for Distributed Virtual Switches
InactiveUS20130010799A1Easy to handleData switching by path configurationVirtualizationArray data structure
Packet processing logic of a host system's virtualization manager detects packets on the ingress or the egress path to / from a virtual port having three bitmap arrays for processing packets within a virtual local area network (VLAN). The logic checks the VLAN identifier (VID) of the packet to determine, based on an offset position within the corresponding bitmap array, whether the port supports the VLAN. Both the ingress array offset position and egress array offset positions correspond to the value of the VID, and are set within the specific bitmap array during configuration of the VLAN on the port. When the VLAN is supported by the port, the logic enables the packet to be processed by the port. Otherwise, the logic discards the packet. A strip bitmap array indicates when a packet's VID should be removed prior to forwarding the packet on the egress of a port (or destination port).
Owner:IBM CORP
Mapping virtual machines from a private network to a multi-tenant public datacenter
ActiveUS9294524B2Interprogram communicationMultiple digital computer combinationsPrivate networkApplication programming interface
A method for creating a set of virtual machines on a public datacenter. The method, from a first network controller of a private network, commands a second network controller of the public datacenter to create the virtual machines. The method, from the first network controller of the private network, communicates with the second network controller of the public datacenter to determine a type of the second network controller. When the first network controller includes instructions for using application programming interfaces (APIs) of the type of the second network controller, the method uses the APIs to set up a VLAN for the set of virtual machines in order to allow the virtual machines of the set of virtual machines to communicate securely with each other without sending the communications through the private network. In some embodiments, the VLAN is a private VLAN (PVLAN).
Owner:NICIRA
Congestion notification in private VLANs
One embodiment of the present invention provides a switch. During operation, in a network with a private VLAN configuration, the switch allows a congestion notification message with an isolated virtual local area network identifier (VLAN ID) to be forwarded via an isolated VLAN port.
Owner:AVAGO TECH INT SALES PTE LTD
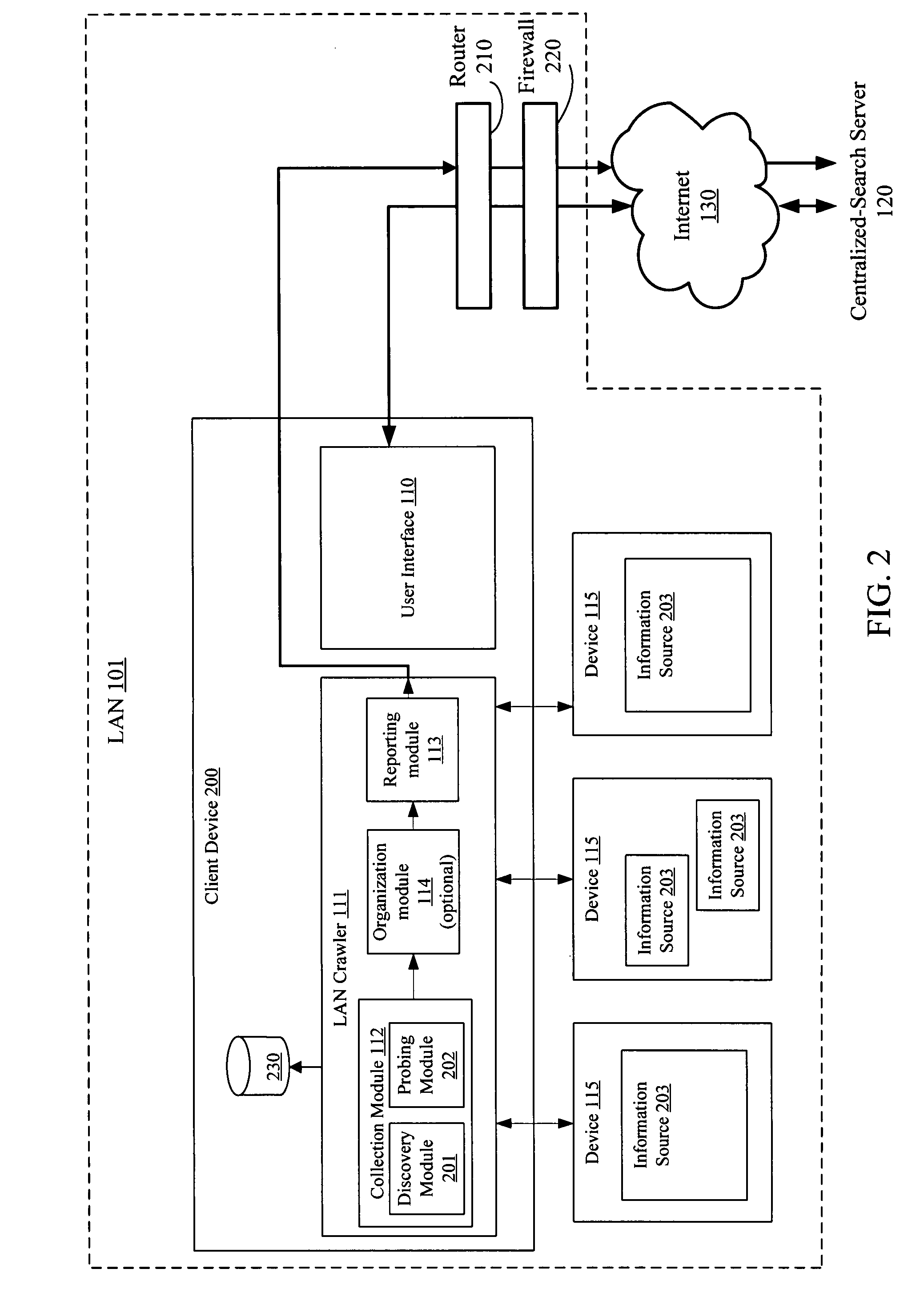
Hosted searching of private local area network information
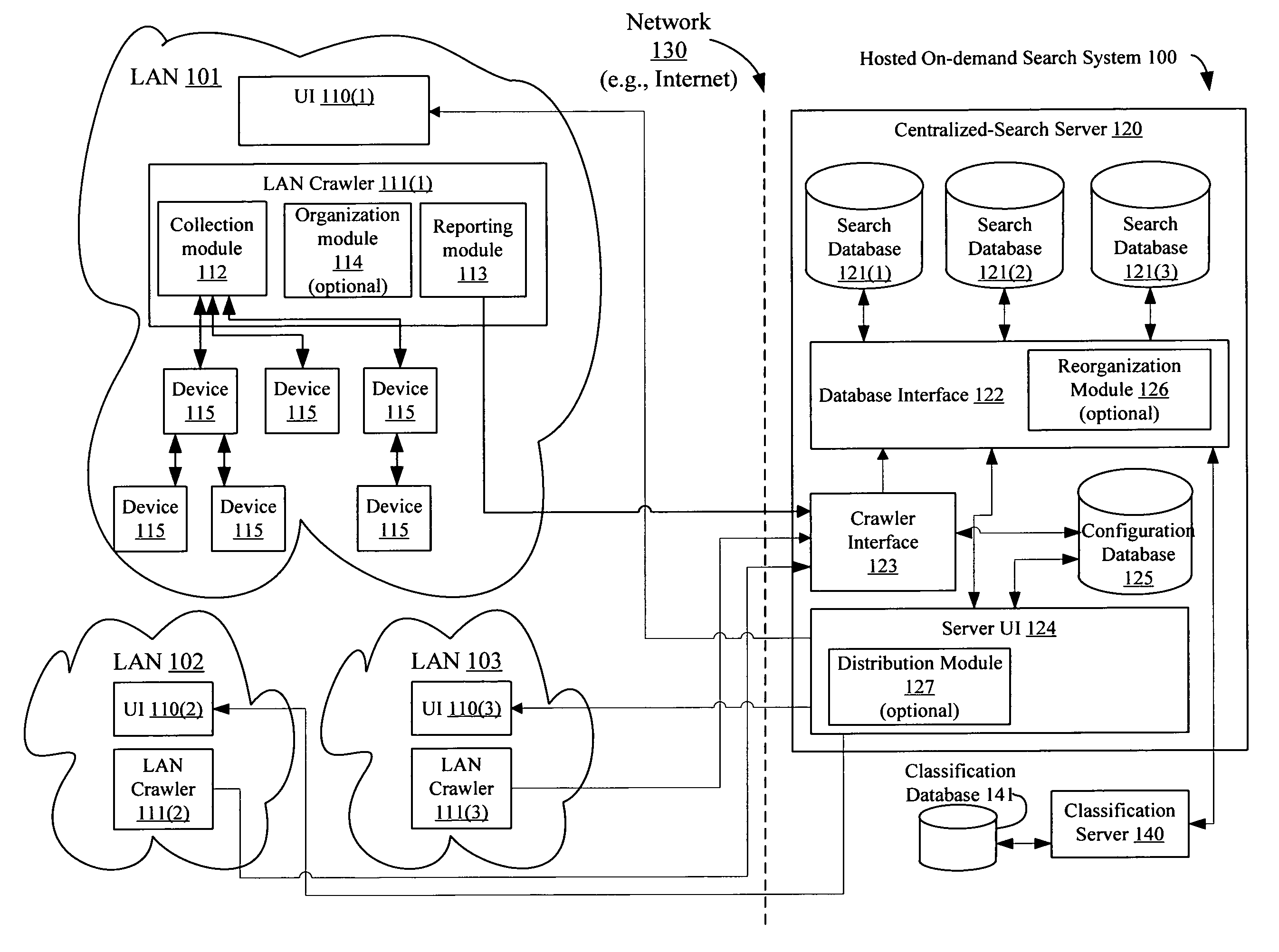
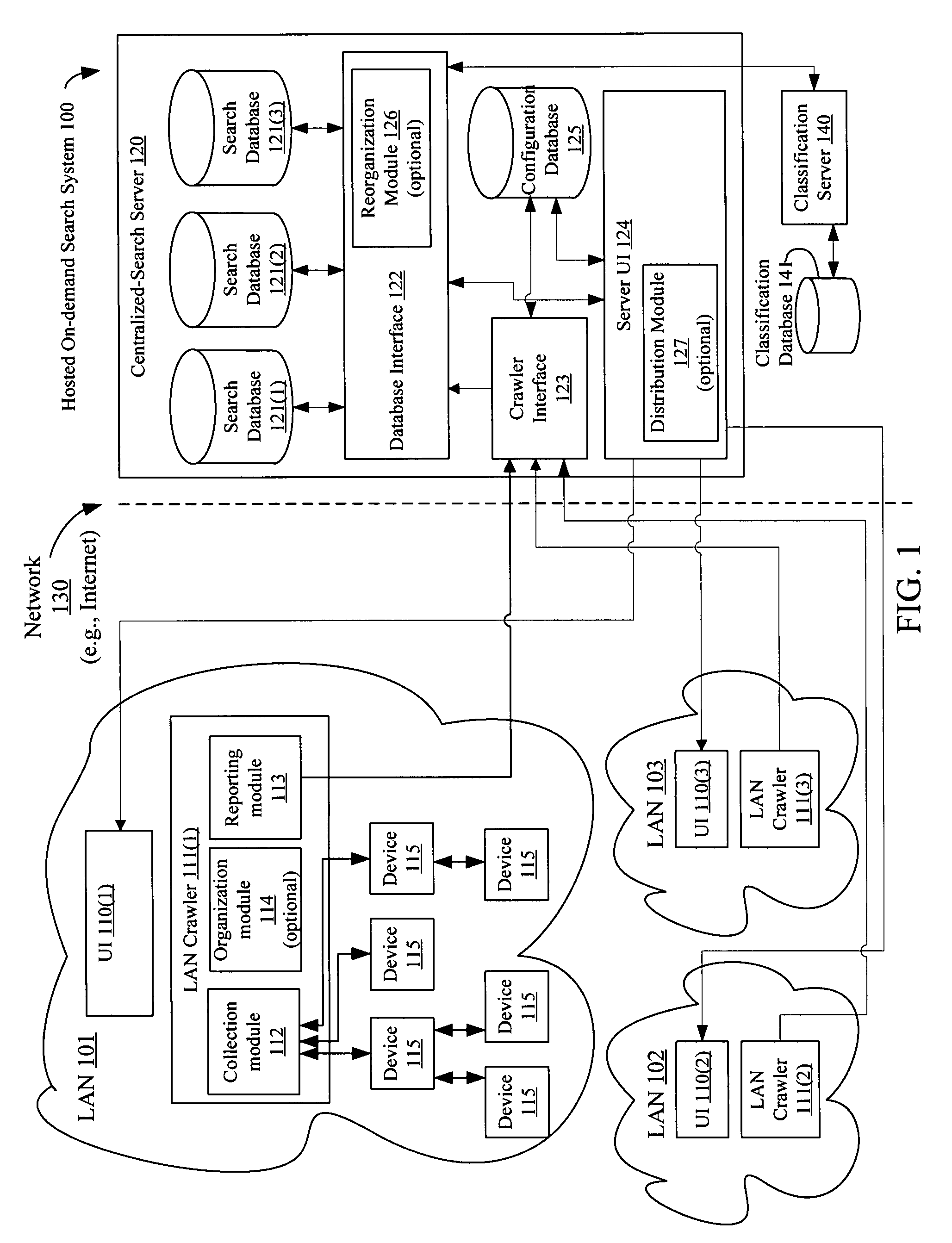
ActiveUS7877369B2Digital data information retrievalDigital data processing detailsPrivate VLANOn demand
Hosted searching of different local area network (LAN) information is described. The apparatus for hosted searching of different private LAN information includes a LAN crawler to automatically and repeatedly crawl a LAN having multiple devices, and a hosted on-demand search system including a set of one or more centralized-search servers to create and synchronize a separate private search database for each of the private LANs based on received reports from of different instances of the LAN crawler deployed on the multiple private LANs, at least some of which are operated by different entities.
Owner:CITRIX SYST INC
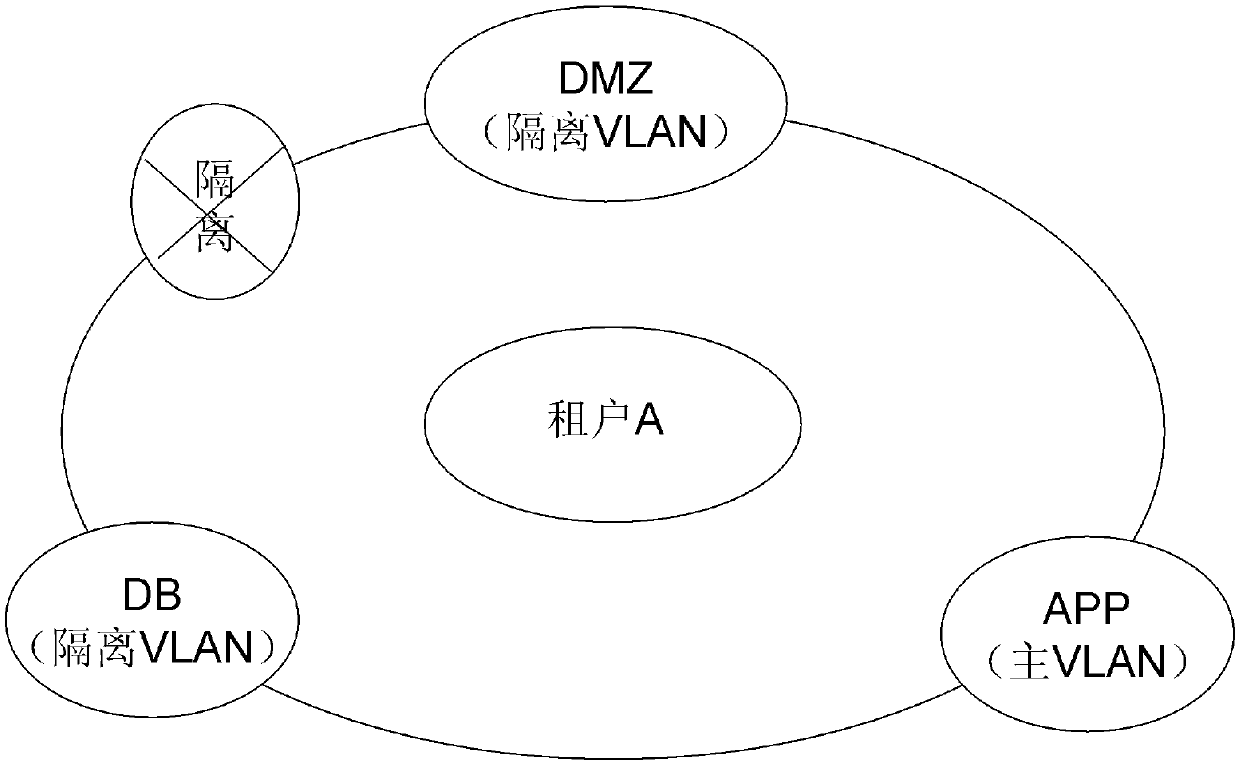
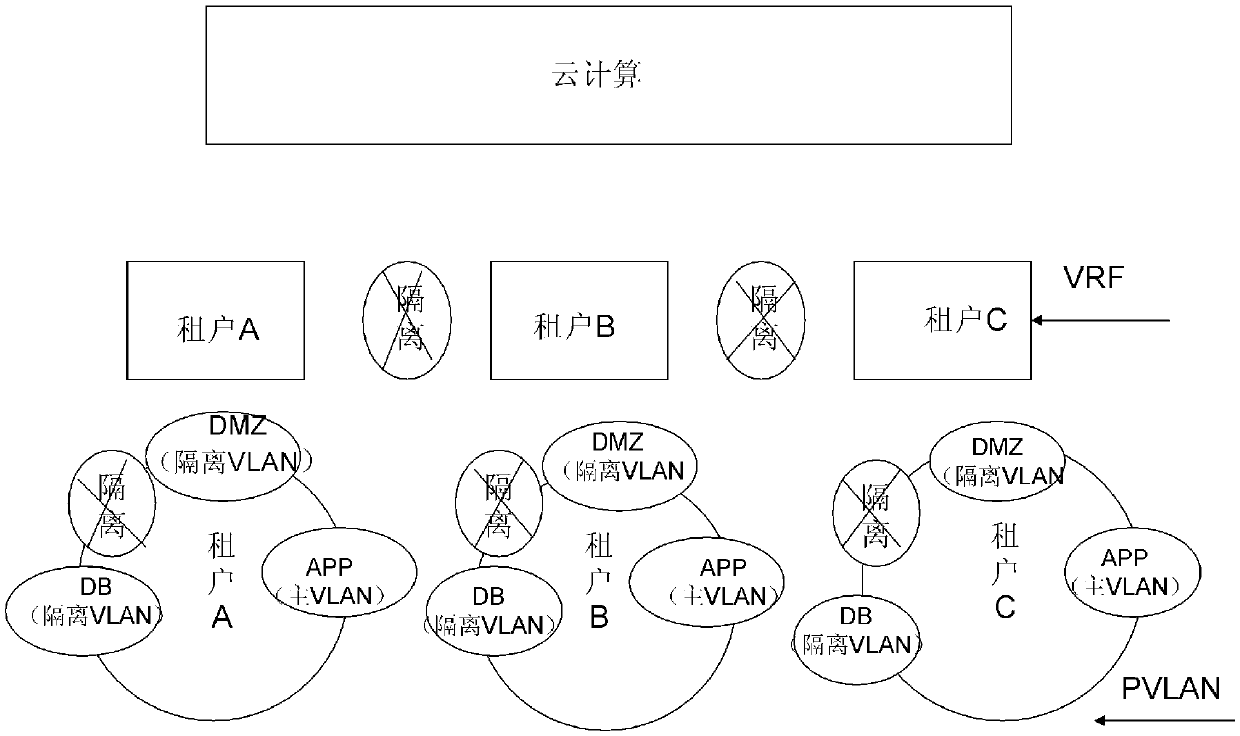
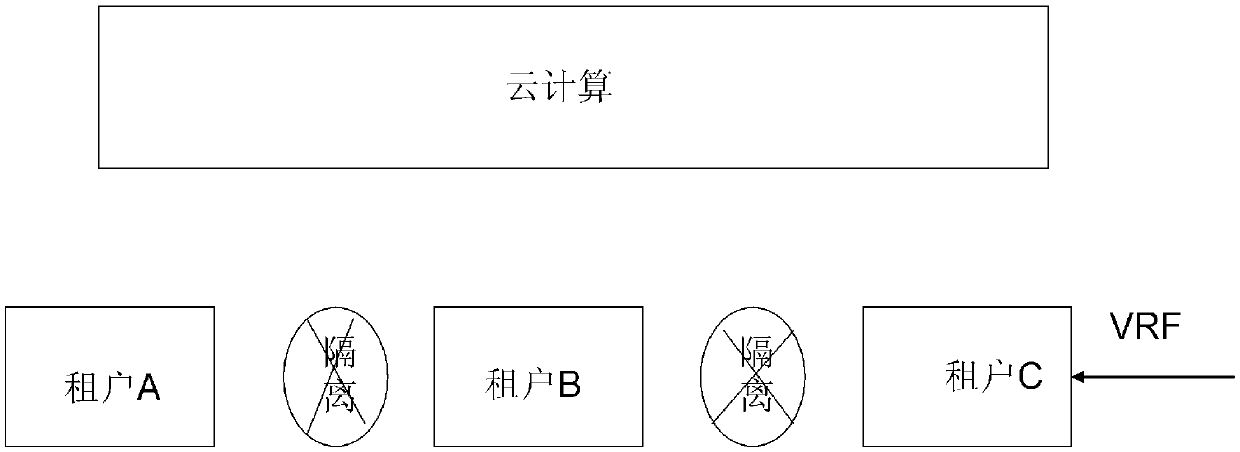
Tenant security isolation method under cloud computing
The invention relates to a tenant security isolation method under cloud computing, comprising a tenant isolation step: distinguishing different tenants based on a VRF (Virtual Routing & Forwarding Instance) so as to isolate tenants; and a tenant inner isolation step: for each tenant, utilizing the PVLAN (Private VLAN) technology to realize tenant inner security isolation. Accordingly, the tenant security isolation method under cloud computing can meanwhile realize external isolation and internal isolation, is applicable to cloud computing multi-tenant conditions, and can reasonably program and manage tenants, and improve data security.
Owner:CHINA UNIONPAY
A private network vlan information management method and device
ActiveCN103166864BReduce configuration operationsData switching networksTelecommunicationsPrivate network
The invention discloses a private network VLAN information management method and device, which is applied to QinQ network. The private network VLAN table entry is maintained according to the private network VLAN information carried in the exchanged messages, and compared with the prior art, the QinQ VLAN configuration operation on the core switching device is reduced.
Owner:XINHUASAN INFORMATION TECH CO LTD
Virtual machine isolation method and device
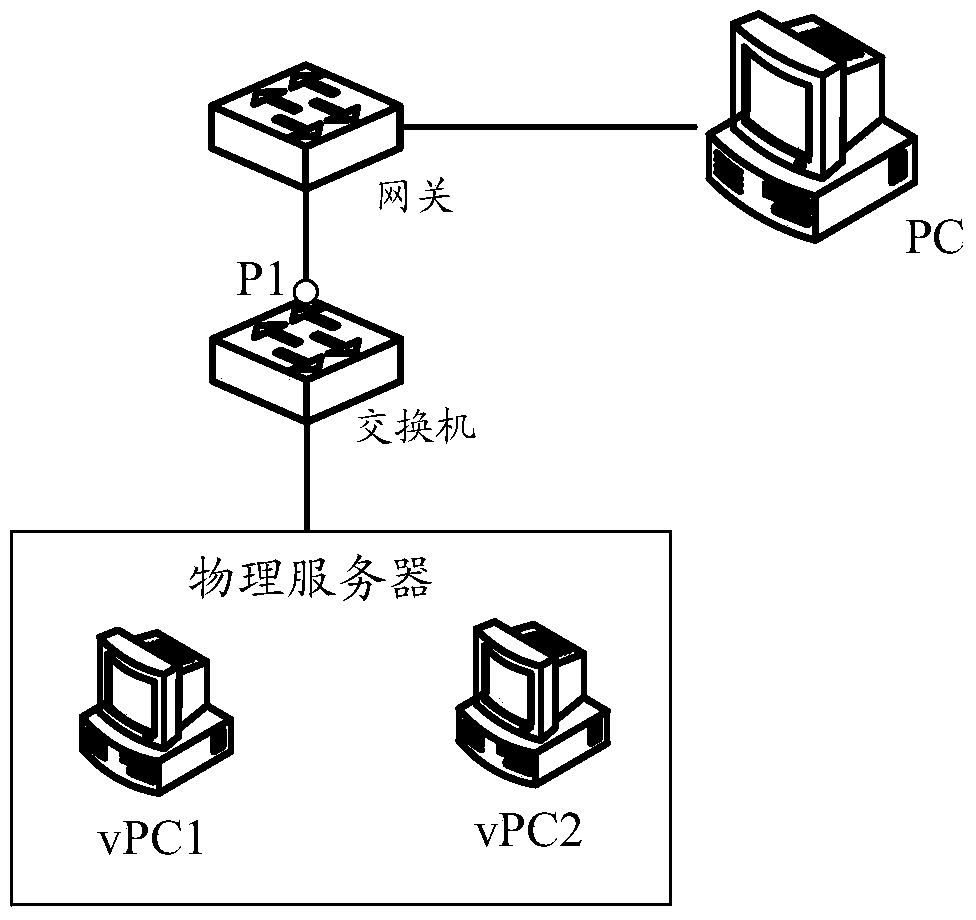
ActiveCN105939309AImprove application flexibilityImprove securityData switching networksComputer hardwareTraffic capacity
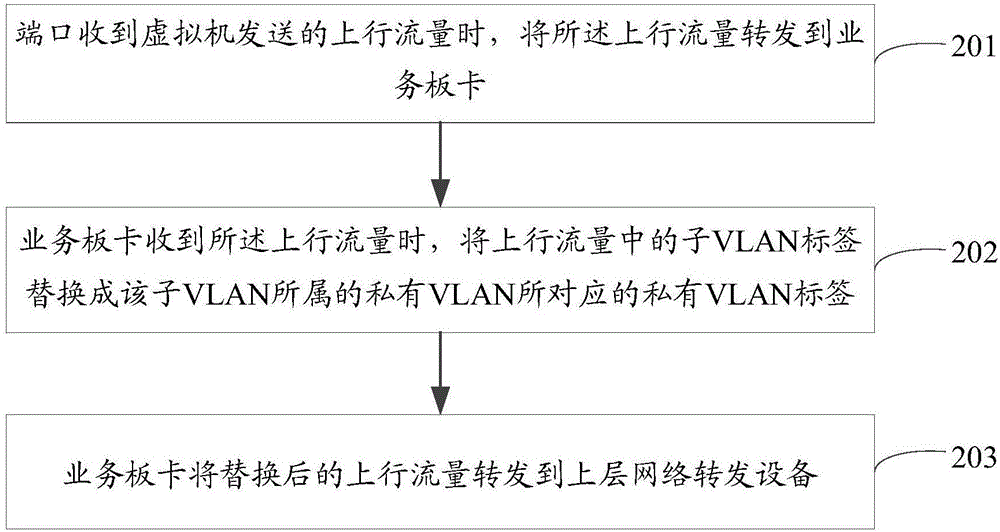
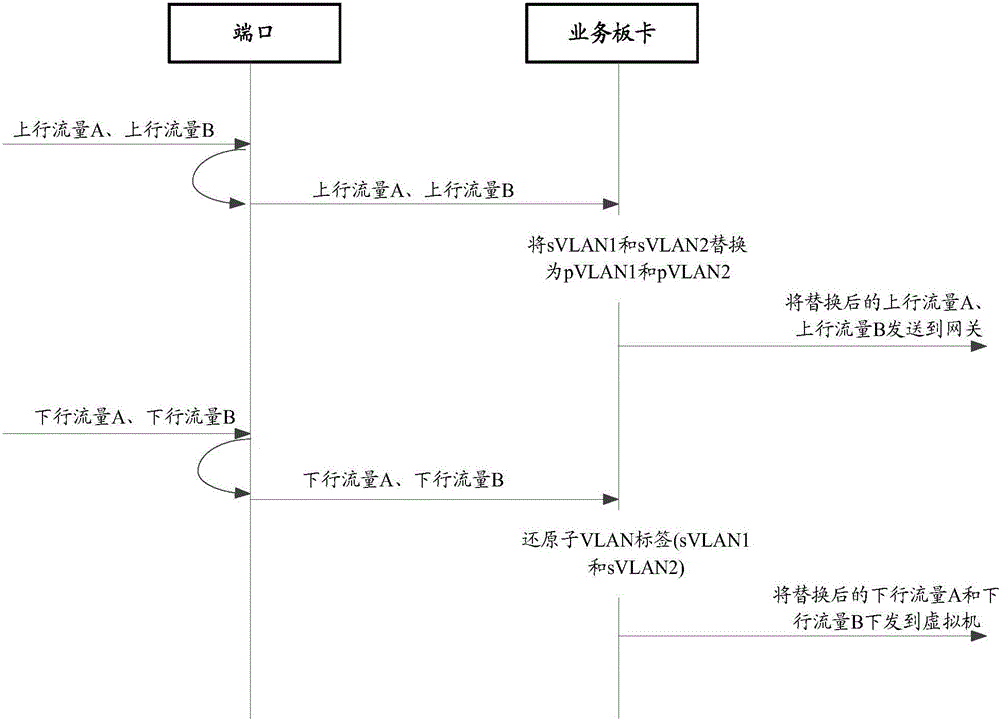
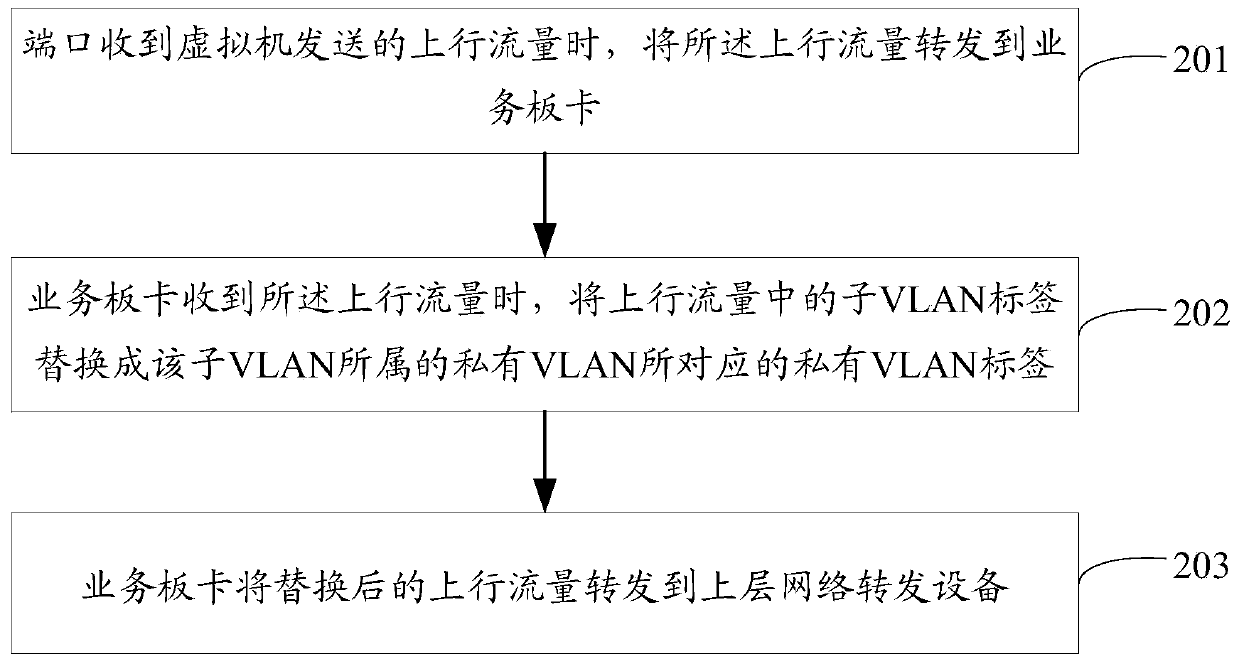
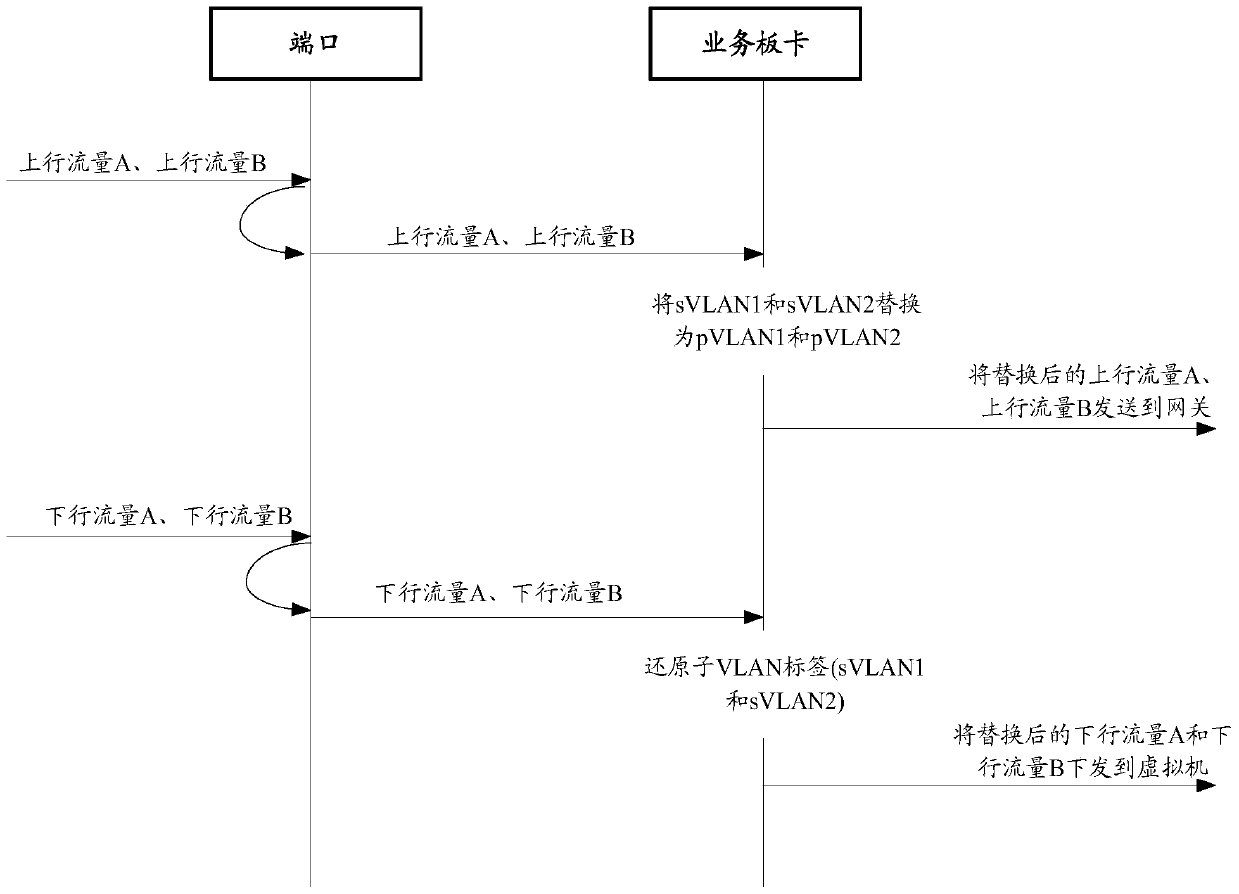
The invention provides a virtual machine isolation method and a virtual machine isolation device. The method is applied to a network forwarding device that comprises a business board card and a port, and a plurality of private VLANs are pre-configured on the business board card. The method comprises the steps that when receiving uplink data sent by a virtual machine, the port forwards the uplink data to the business board card; when receiving the uplink data, the business board card replaces a sub-VLAN label in the uplink traffic with a private VLAN label corresponding to the private VLAN to which the sub-VLAN belongs; and the business board card forwards the replaced uplink data to an upper network forwarding device. Therefore, the method can achieve that the single physical port can identify different private VLANs, and can be applied to the security isolation networking environment of the virtual machine, thus improving the application flexibility and security of the data center.
Owner:HANGZHOU DPTECH TECH
Virtual machine network resource allocation method and device
The invention provides a method and a device for allocating network resources of virtual machines. The method comprises that a first physical host receives virtual information resource request messages sent by a user, and the virtual machine resource request messages are used for requesting for allocating network resources of at least one virtual machine; the first physical host allocates private virtual local area network (VLAN) resources for the user in a private VLAN resource pool of the first physical host if the virtual machine resource request messages request for allocating network resources of one virtual machine, and the private VLAN resources are used for separating the virtual machine in two-layer networks; and if the virtual machine resource request messages request for allocating network resources of at least two virtual machines, the first physical host allocates community VLAN resources for the user in a community VLAN resource pool of the first physical host, and the community VLAN resources are used for being communicated with the virtual machine in the two-layer networks. A great many user demands are met through the method and the device.
Owner:BEIHANG UNIV
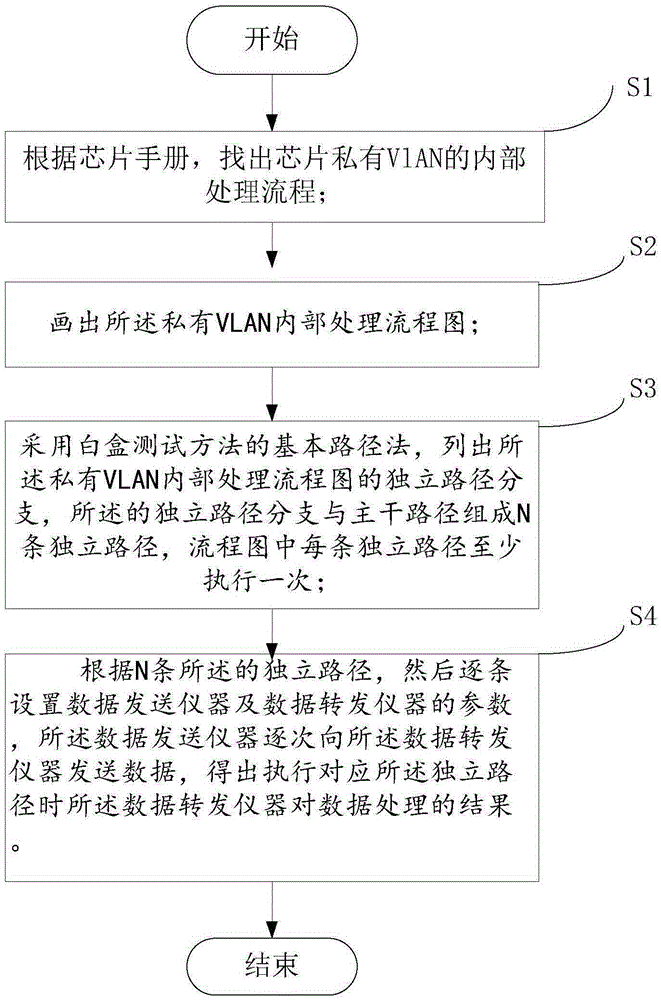
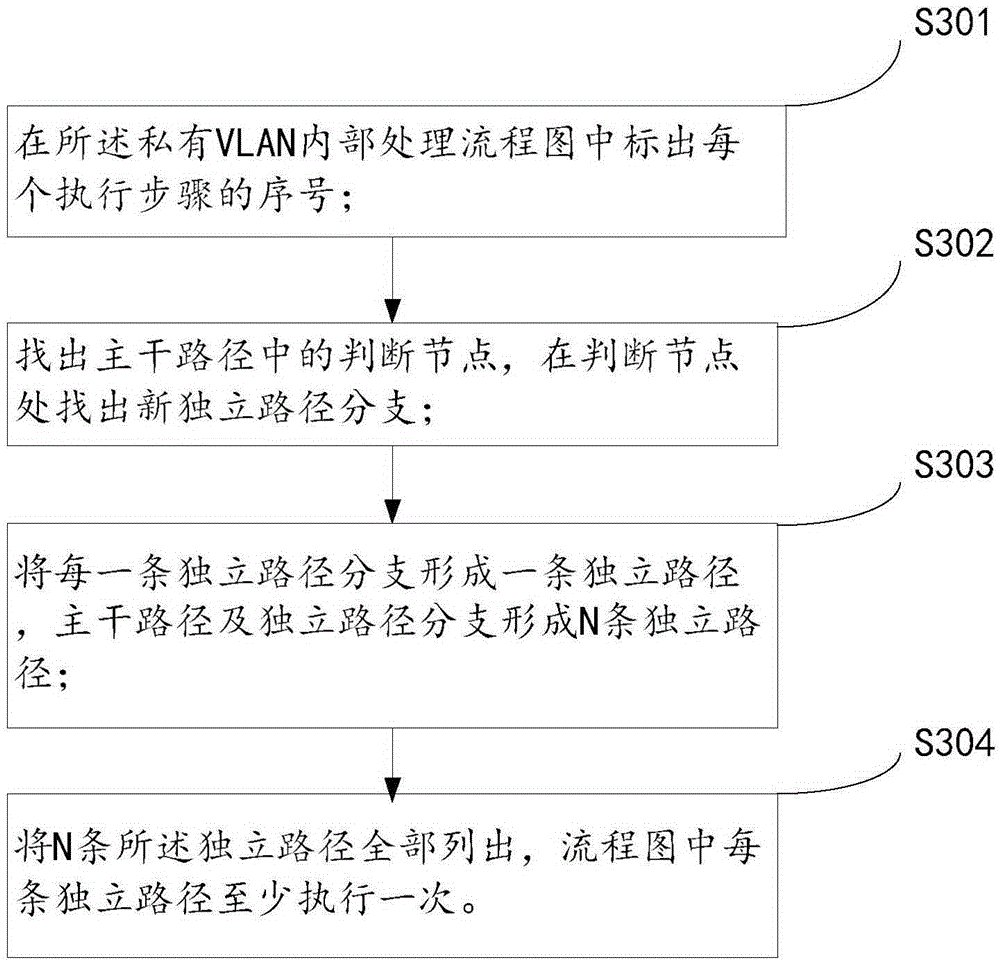
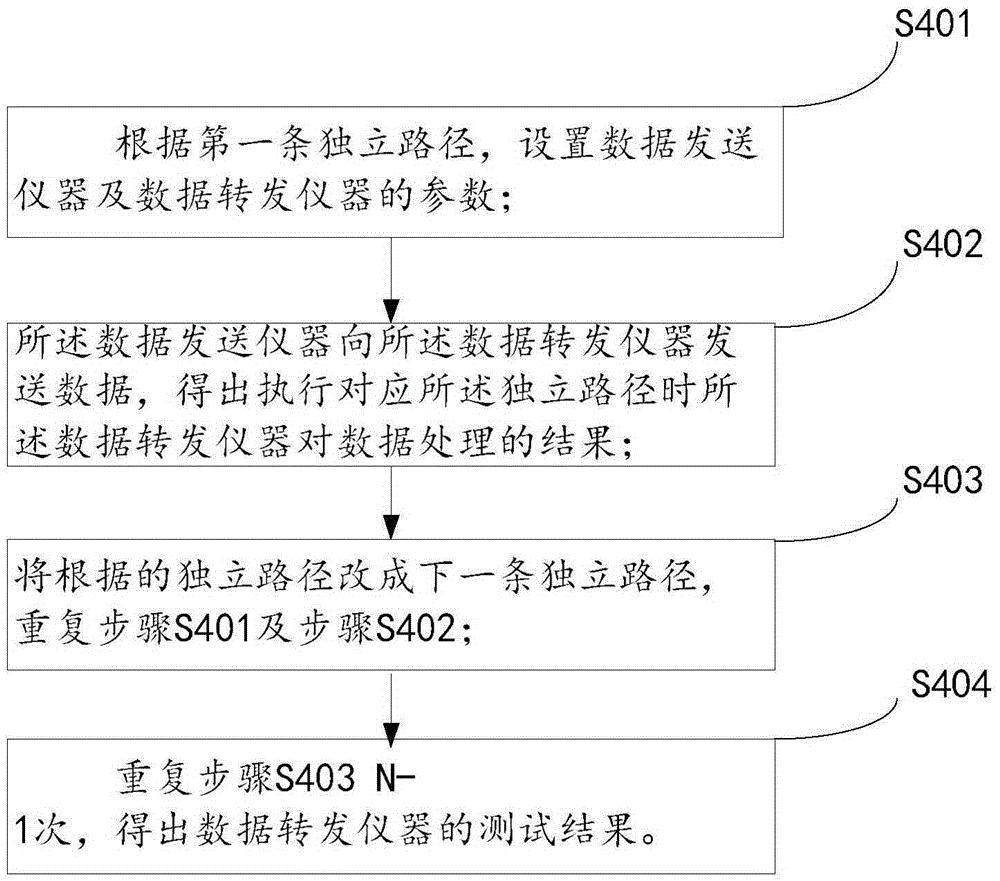
Block-box testing case design method based on combination with basic path method
The invention discloses a block-box testing case design method based on combination with a basic path method. The method comprises the following steps: S1, according to a chip manual, an internal process flow of a private VIAN of the chip is found out; S2, an internal process flow chart of the private VIAN is drawn; S3, with a basic path method of a white-box testing method, independent path branches of the internal process flow chart of the private VIAN are listed, all independent path branches and a main path form N independent paths, and each independent path in the flow chart is executed at least once; and S4, according to the N independent paths, parameters of a data sending instrument and a data forwarding instrument are set one path by one path, the data sending instrument sends data to the data forwarding instrument successively, and a result of data processing by the data forwarding instruction when the corresponding independent path is executed is obtained. According to the method, the obtained case is close to internal implementation of the product; and the minimized testing efficiency can be realized by using minimal cases.
Owner:PHICOMM (SHANGHAI) CO LTD
Implementation method of chip of PVLAN in stacked mode
ActiveCN106685789AReduce use costReduce in quantityNetworks interconnectionComputer architectureFiltering rules
The invention provides an implementation method of a chip of PVLAN (Private VLAN) in a stacked mode. The implementation method of a chip of PVLAN in a stacking mode is characterized by distributing corresponding VLANS for ports of a stacked chip; setting VLAN filtering rules for the in direction and the out direction for the ports participating PVLAN; and after the chip receives a massage, processing the message according to the VLAN filtering rules on the out port. The implementation method of a chip of PVLAN in a stacked mode greatly expands the application range of the PVLAN technology so as to enable application of PVLAN to be more flexible and efficient.
Owner:SUZHOU CENTEC COMM CO LTD
Method and network node for monitoring traffic in a private VLAN
It is disclosed a method for monitoring traffic in a private VLAN, the traffic bidirectionally propagating across the private VLAN through a sequence of nodes sequentially connected by a primary VLAN and a secondary VLAN, the sequence of nodes comprising a first node and a second node, wherein the method comprises: transmitting a monitoring message from the first node to the second node either along the primary VLAN or the secondary VLAN, according to a first criterion based upon a type of the first node; receiving the monitoring message at the second node; and upon reception of the monitoring message at the second node, transmitting a reply message from the second node to the first node either along the primary VLAN or the secondary VLAN, according to a second criterion based upon a type of the second node and upon a VLAN different from the VLAN from which the monitoring message has been received.
Owner:WSOU INVESTMENTS LLC
Implementation method of remote IRF stacking and equipment thereof
The invention discloses an implementation method of remote IRF stacking and stacking equipment. The method is applied to first access equipment and second access equipment which need to establish IRF stacking, and the first access equipment is connected with the second access equipment by intermediate equipment. The method comprises the following steps: performing role election among access equipment crossing networks, and transmitting link information; sending a link configuration message to the access equipment of master equipment according to the election result to trigger the intermediateequipment and slave equipment among the access equipment to add a member port to a private VLAN; and establishing a layer-two tunnel, and performing data message interaction by virtue of the layer-twotunnel to realize the IRF stacking crossing networks among the access equipment.
Owner:NEW H3C TECH CO LTD
A virtual machine isolation method and device
ActiveCN105939309BImprove application flexibilityImprove securityData switching networksComputer hardwareData center
The present invention provides a virtual machine isolation method and device. The method is applied to network forwarding equipment. The network forwarding equipment includes service boards and ports, and multiple private VLANs are pre-configured on the service boards. The method includes : When the port receives the upstream traffic sent by the virtual machine, it forwards the upstream traffic to the service board; when the service board receives the upstream traffic, it replaces the sub-VLAN tag in the upstream traffic with the private The private VLAN tag corresponding to the VLAN; the service board forwards the replaced upstream traffic to the upper-layer network forwarding device. Therefore, the present invention can realize the identification of different private VLANs by a single physical port, and can be applied to the security isolation networking environment of virtual machines, thereby improving the application flexibility and security of the data center.
Owner:HANGZHOU DPTECH TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com