Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1813 results about "Information resource" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
What is Information Resource. 1. An element of infrastructure that enables the transaction of certain selected significant and relevant data, prepared so as to provide content and information services that can be used directly by the user. It is necessary to establish some minimum socio-technical requirements for an element to qualify as a resource.
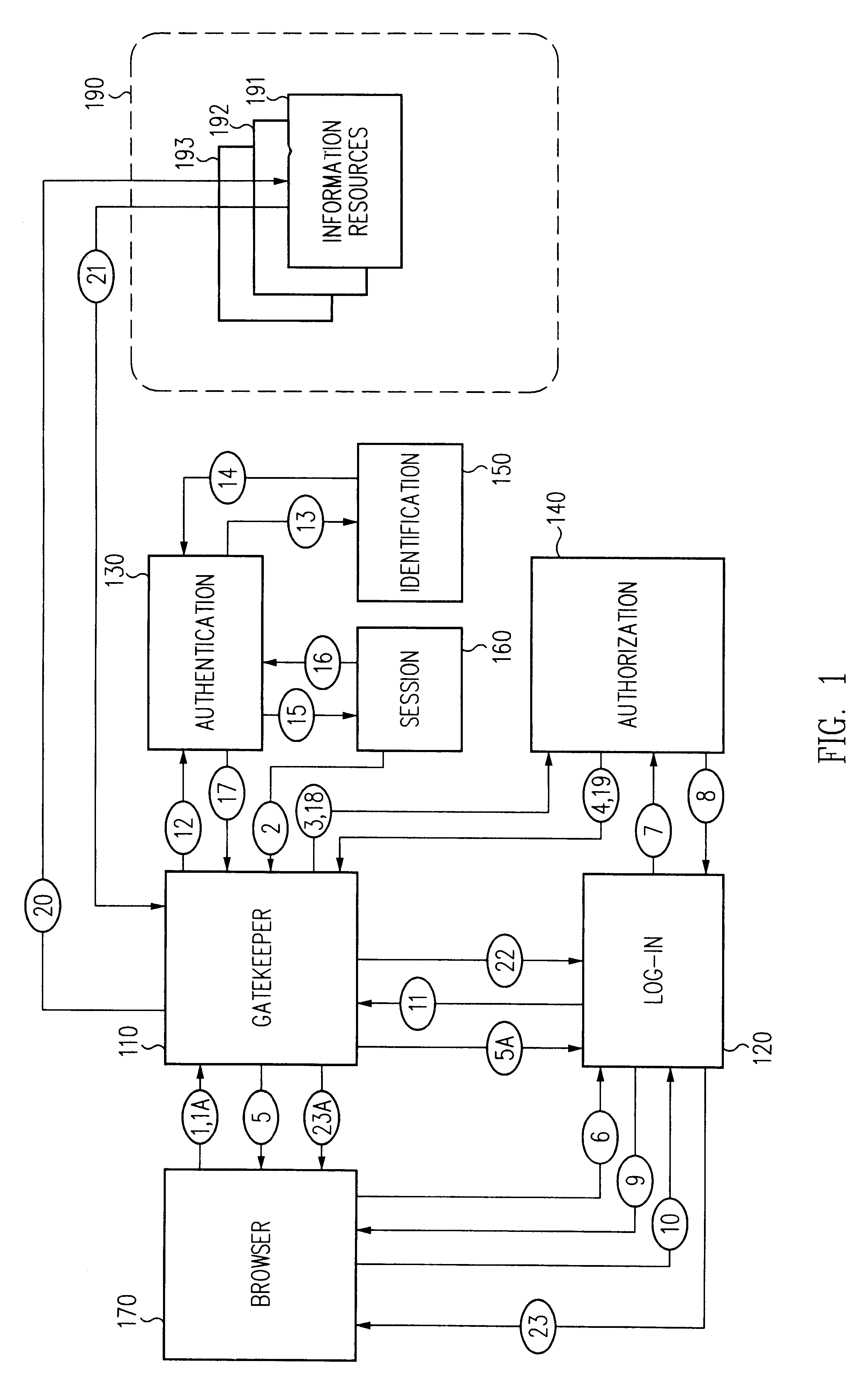
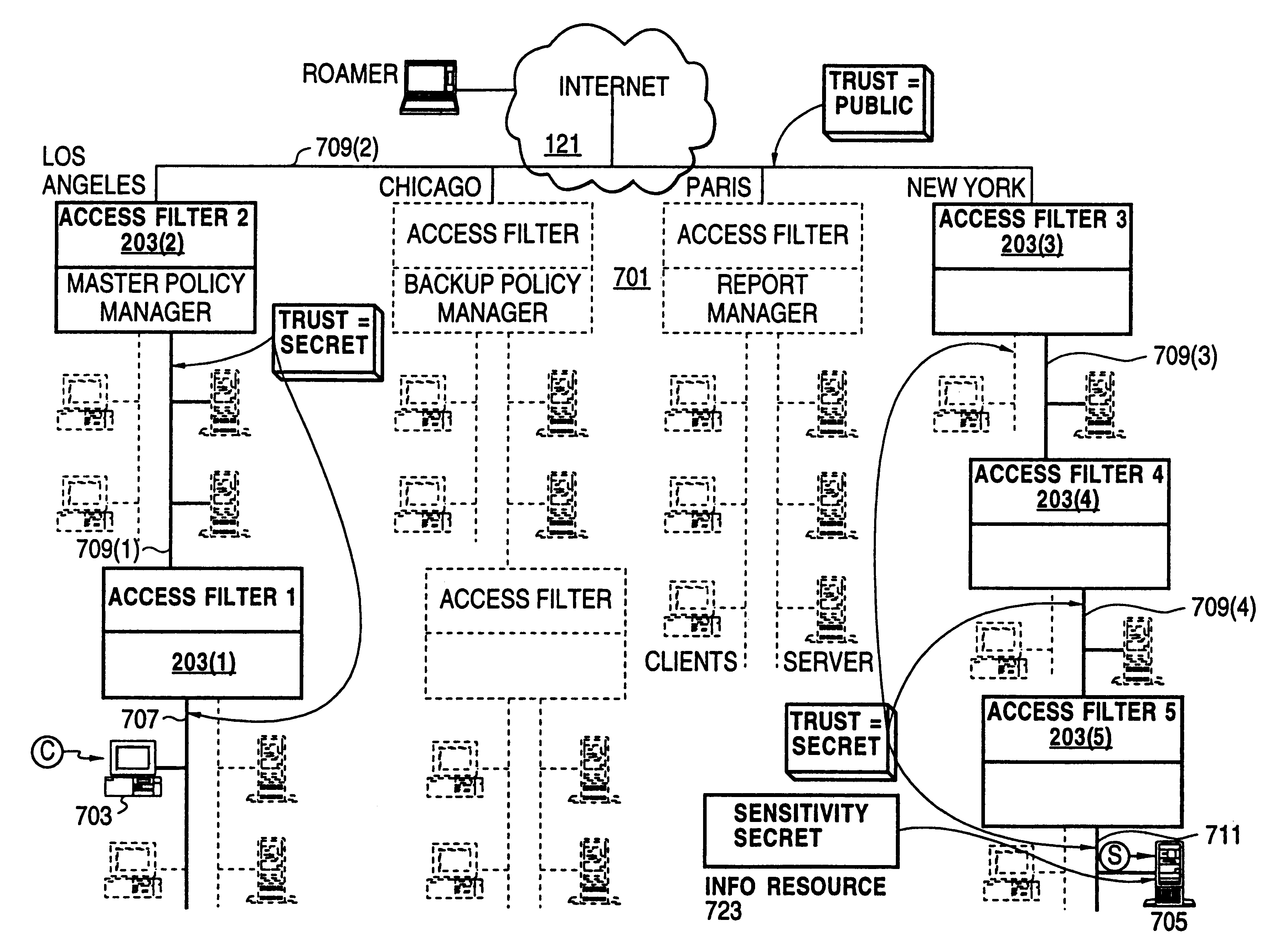
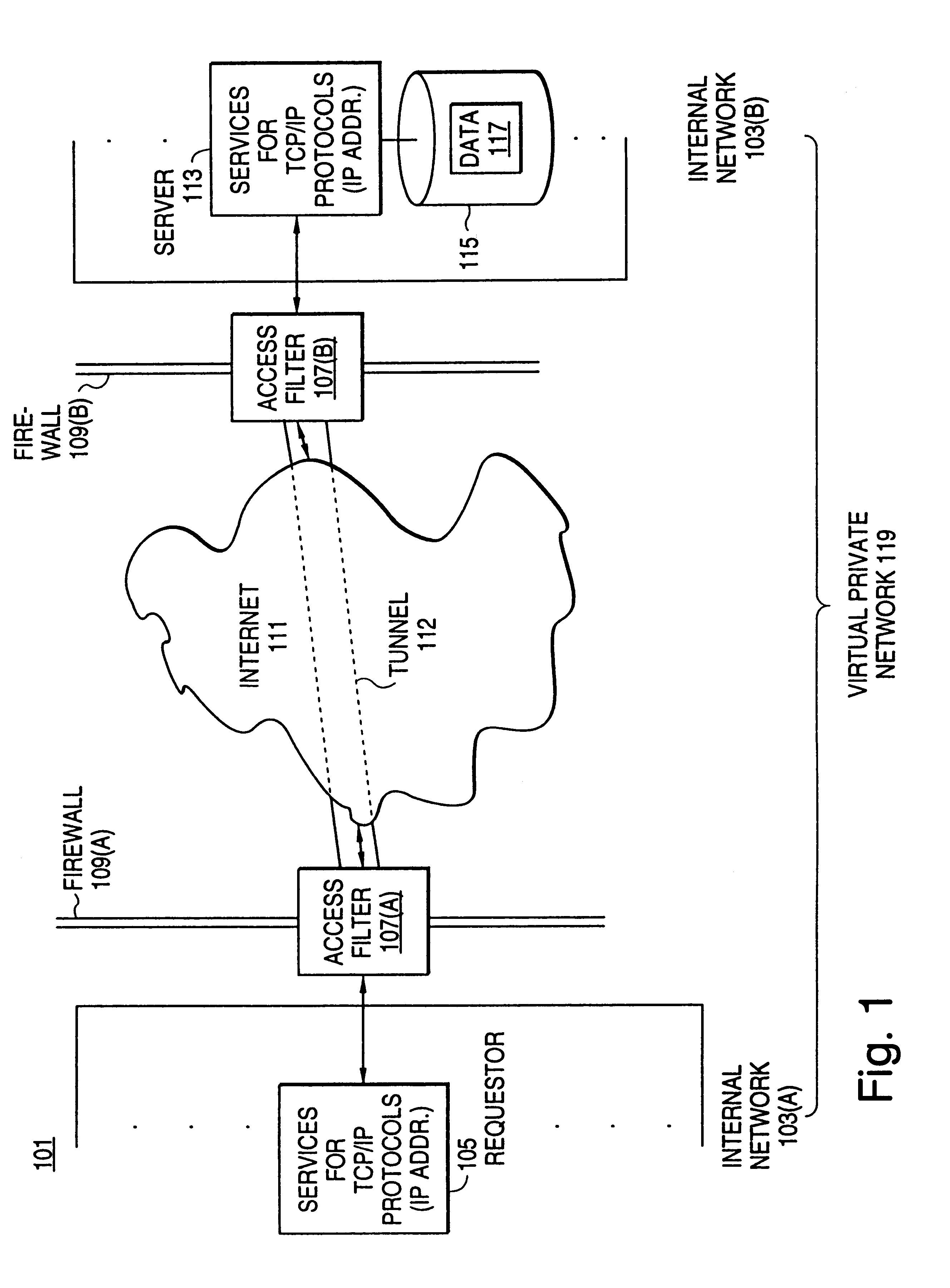
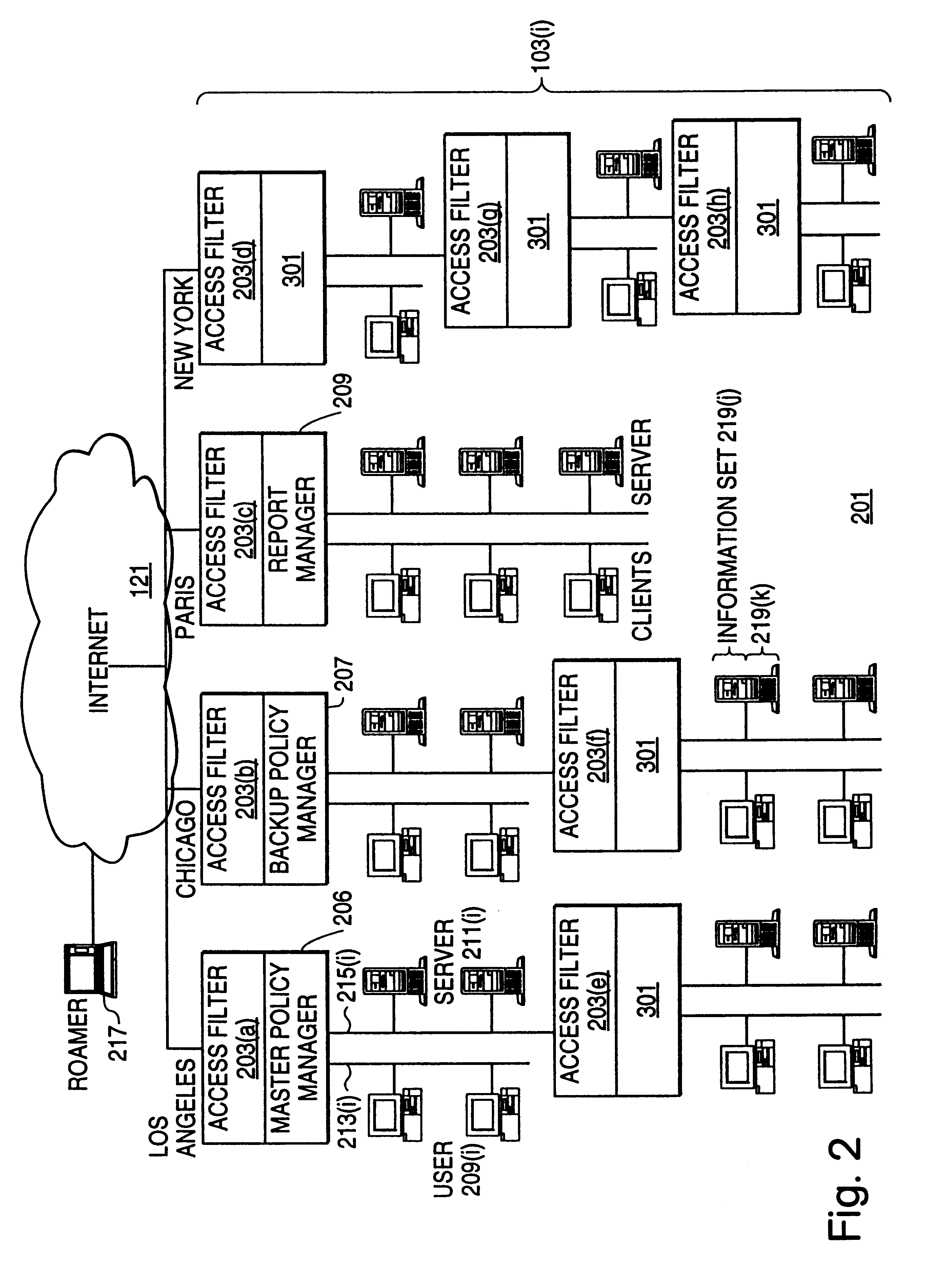
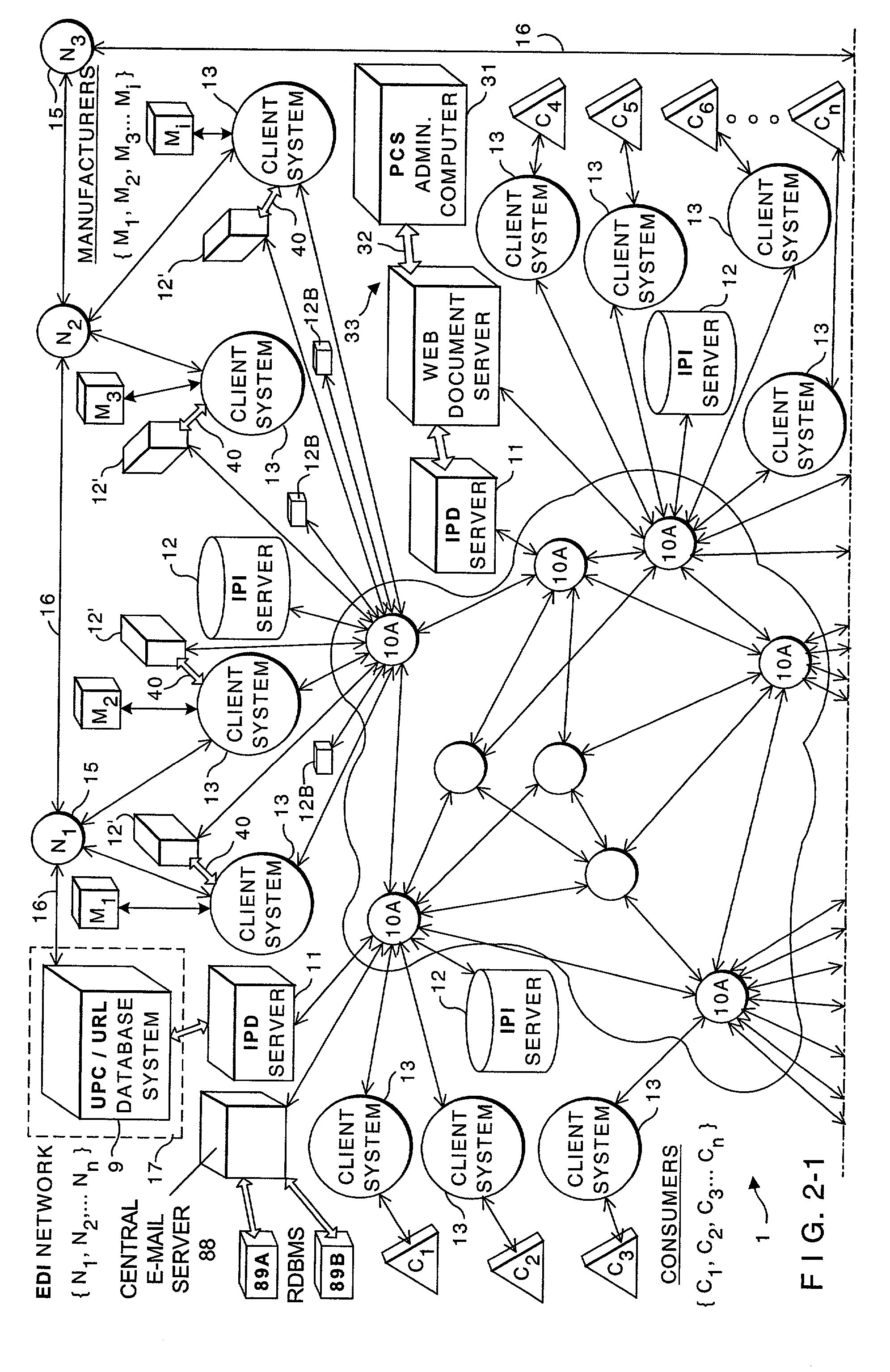
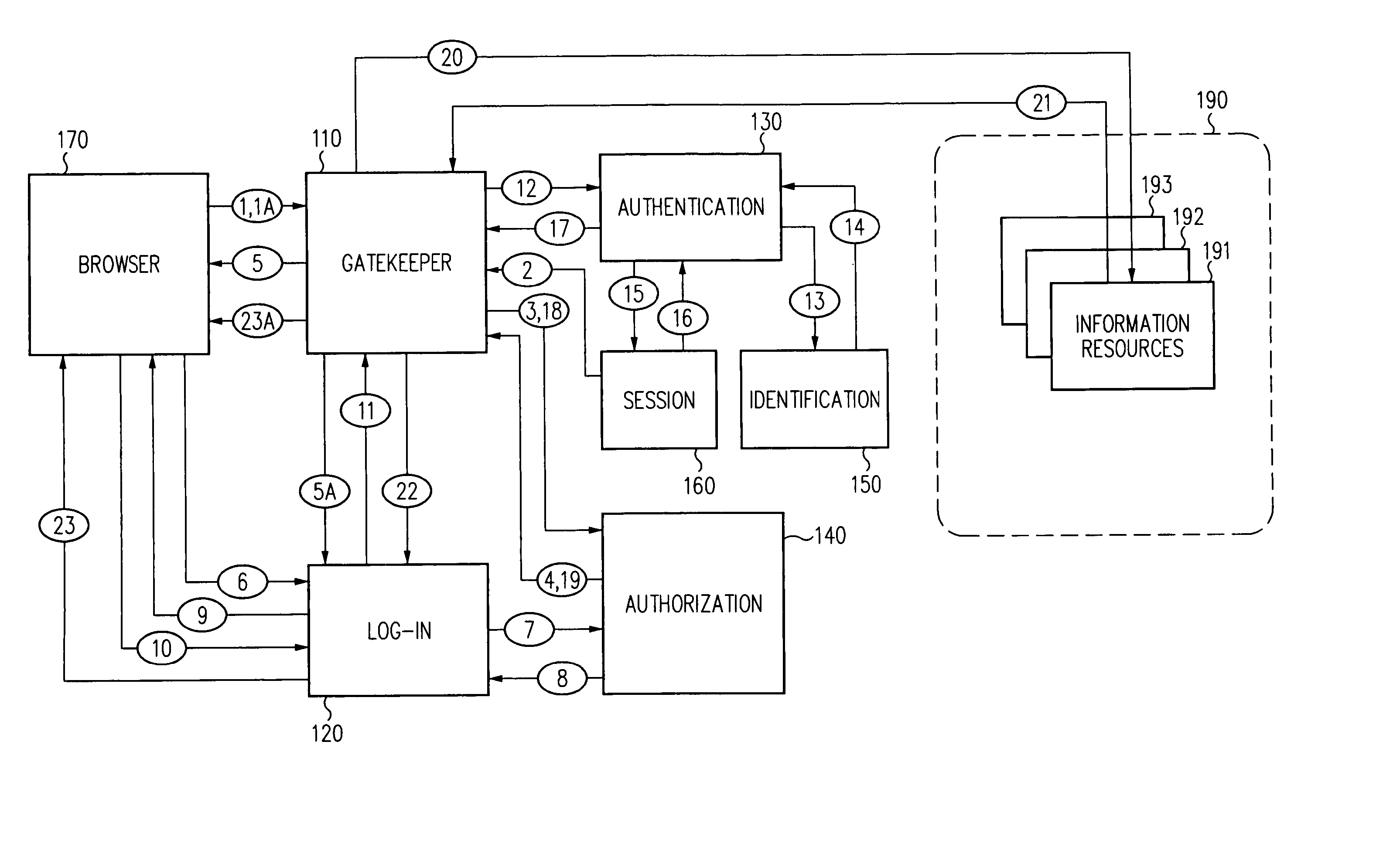
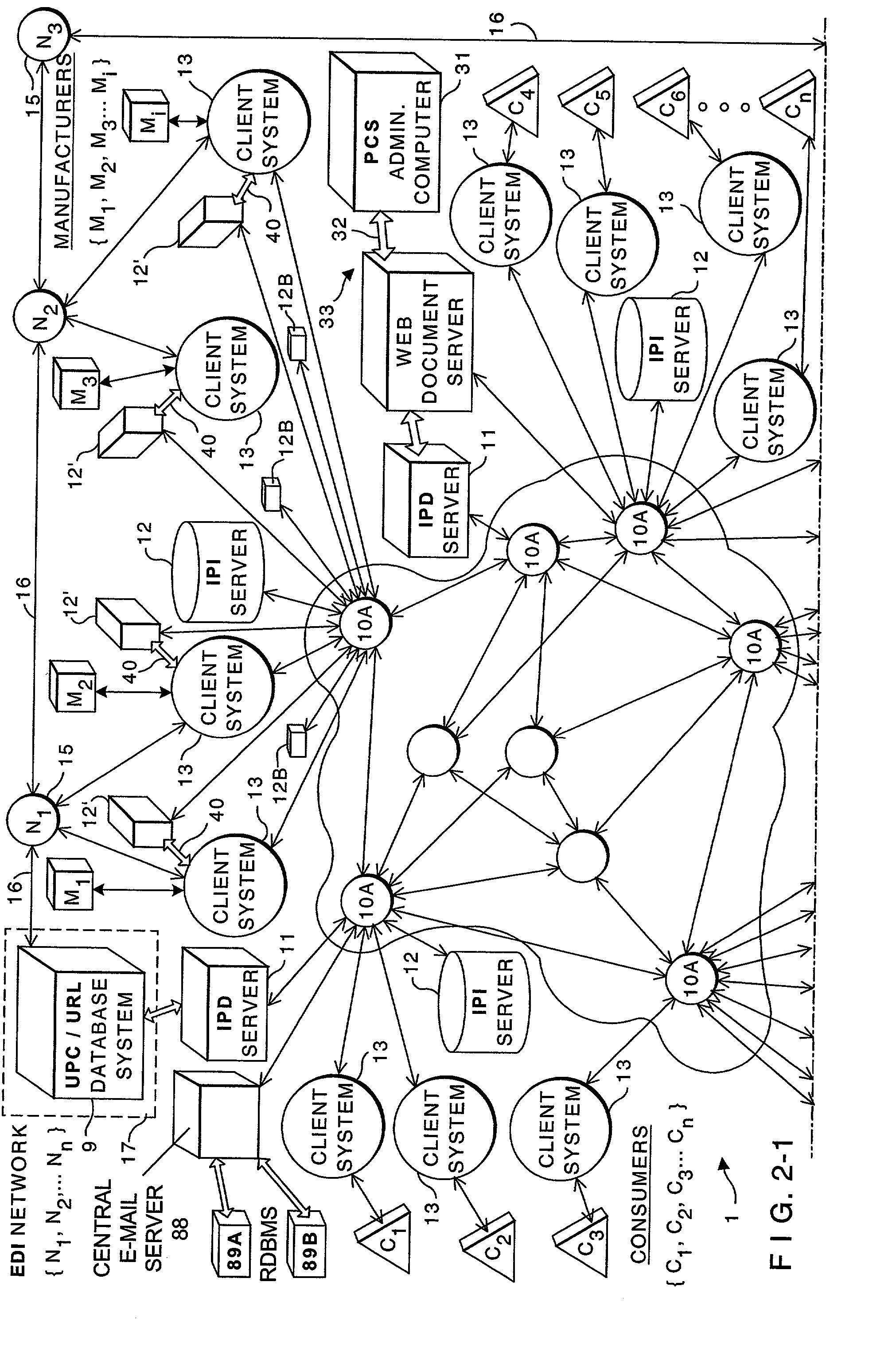
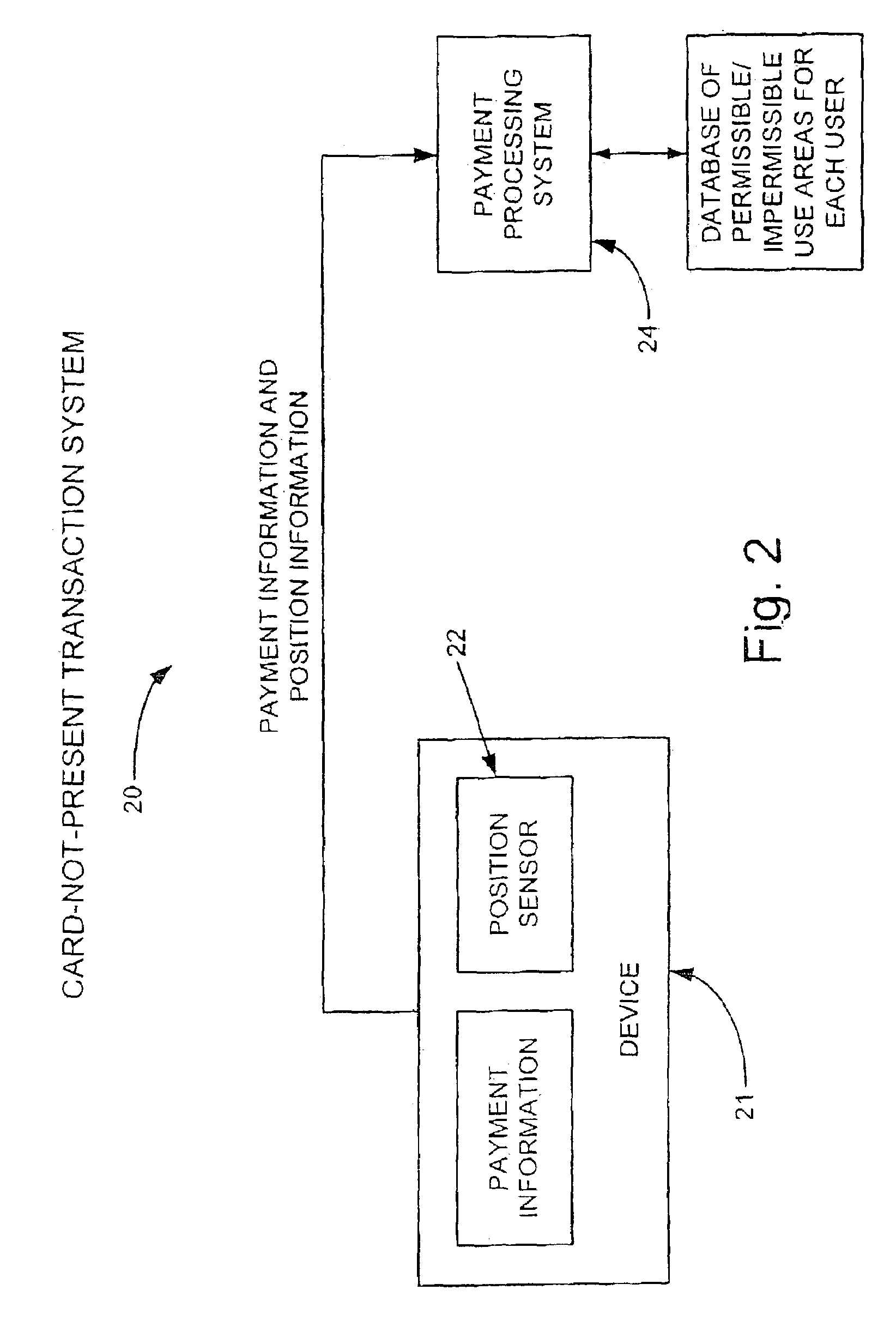
Distributed administration of access to information
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
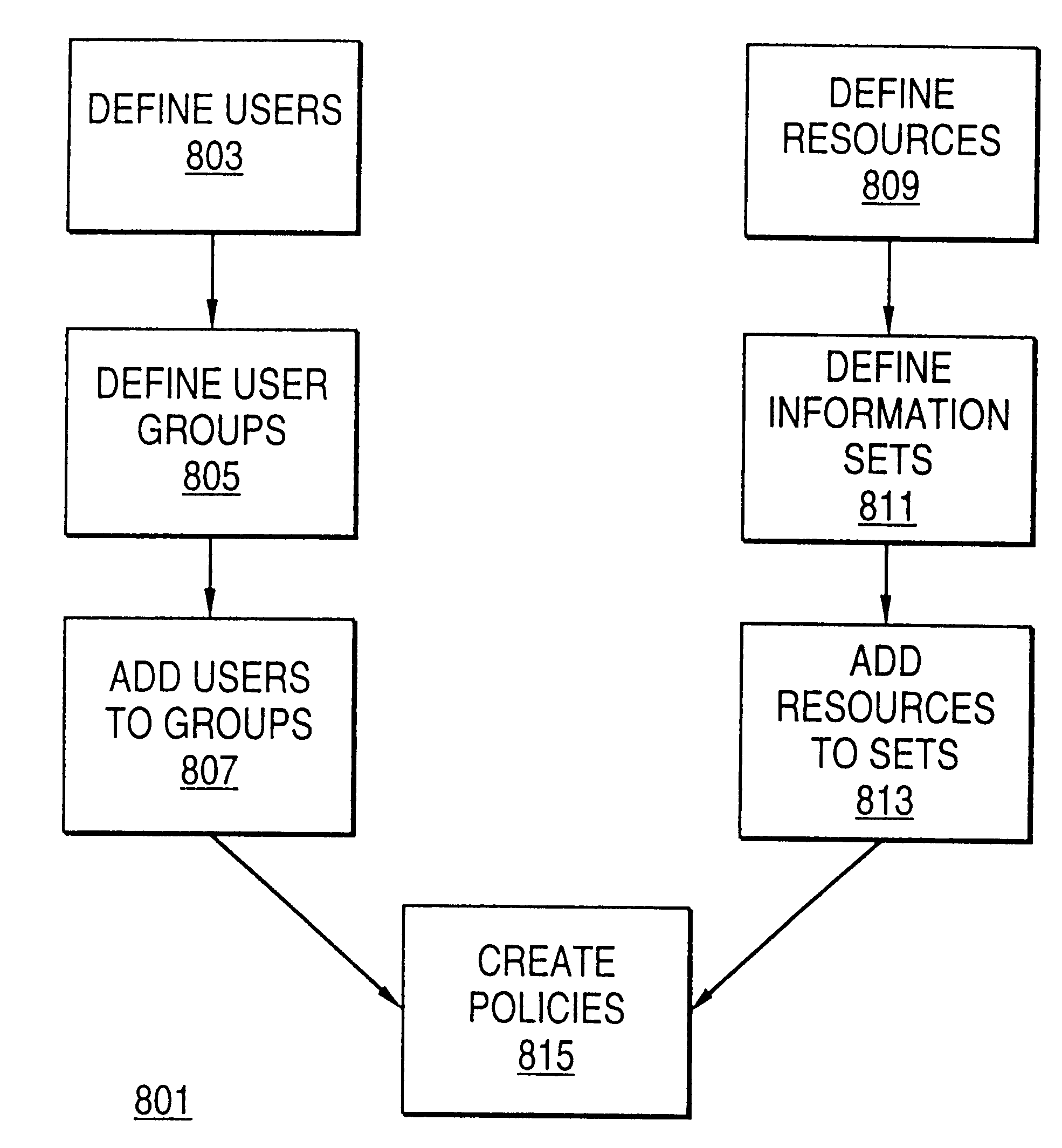
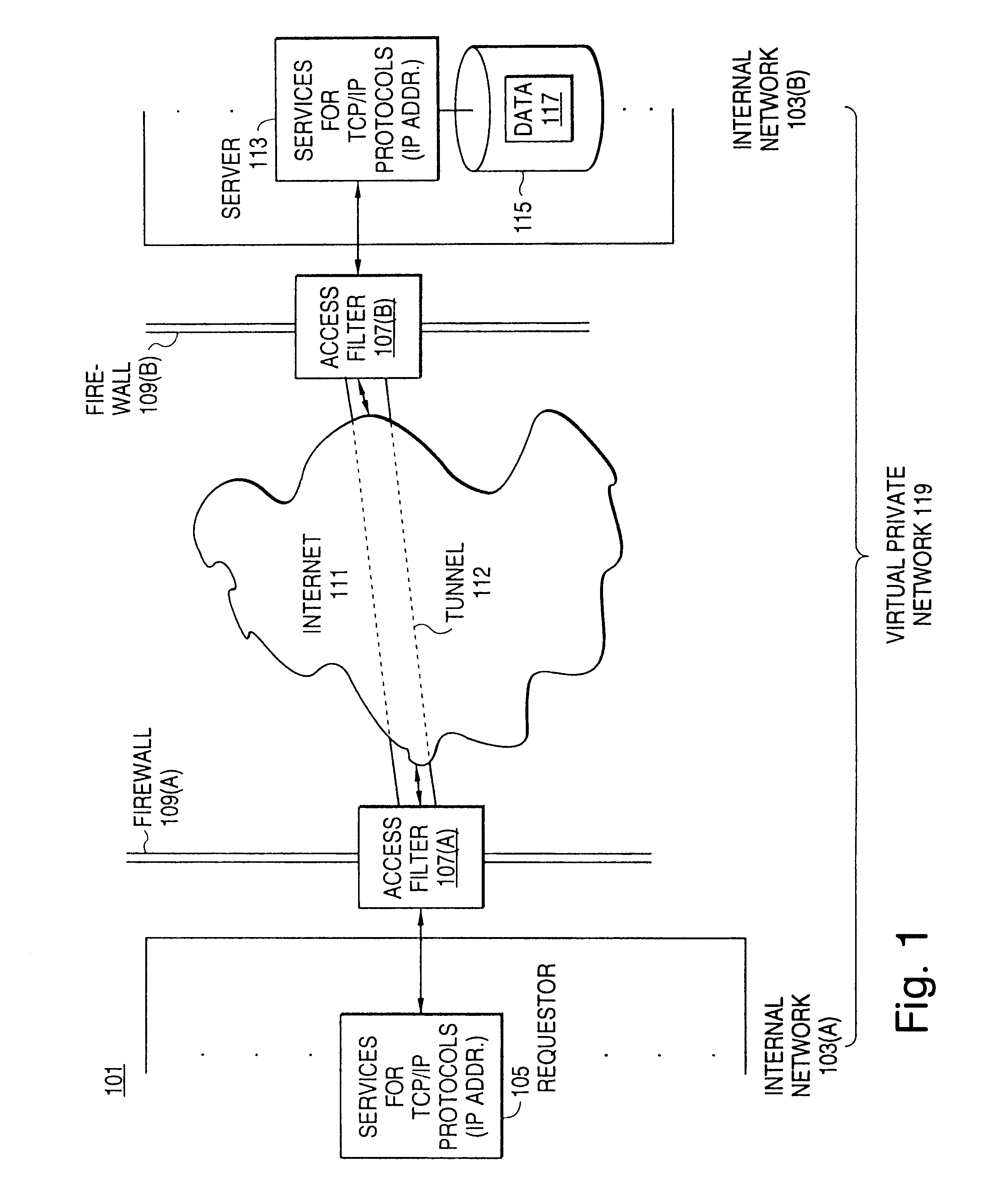
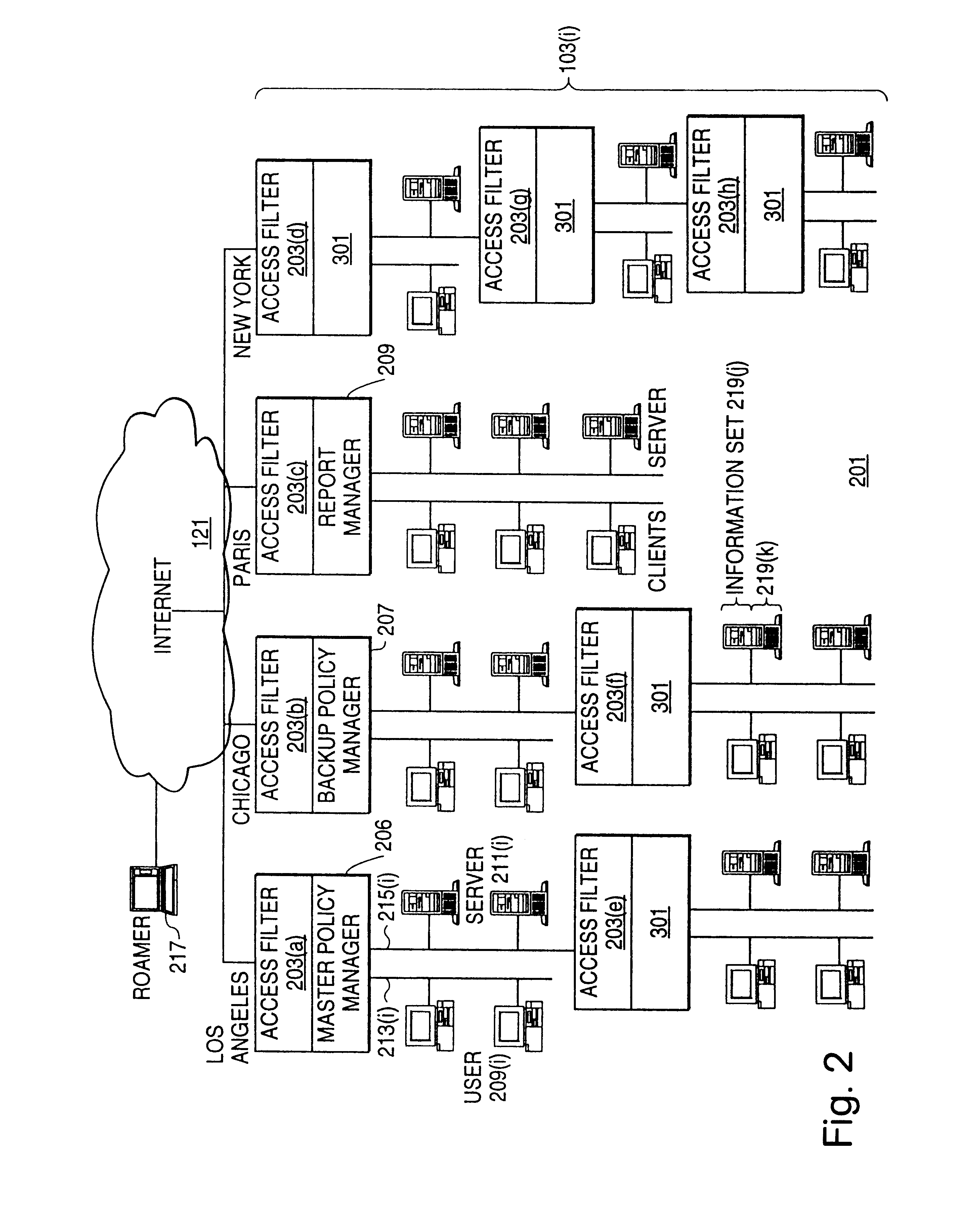
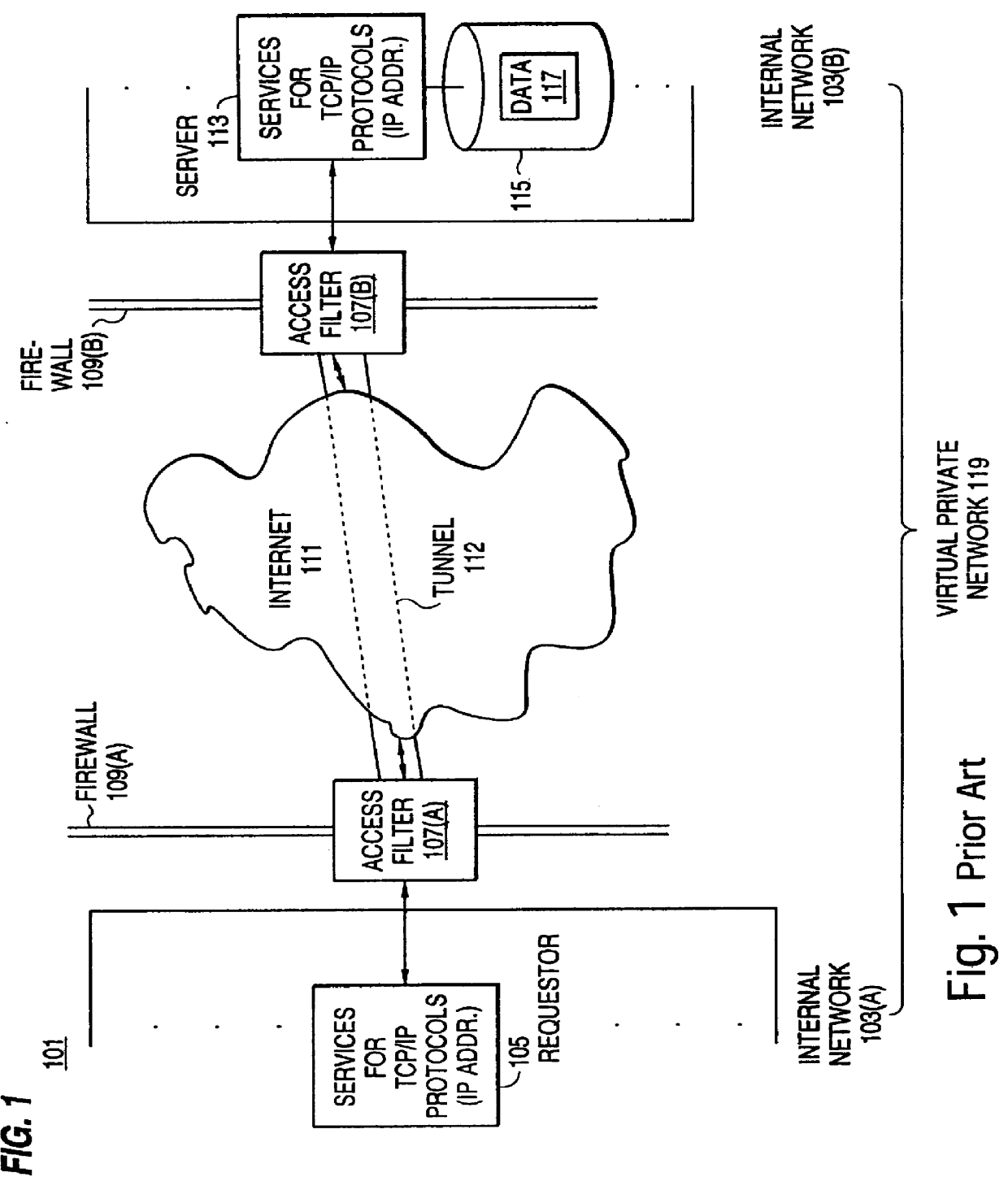
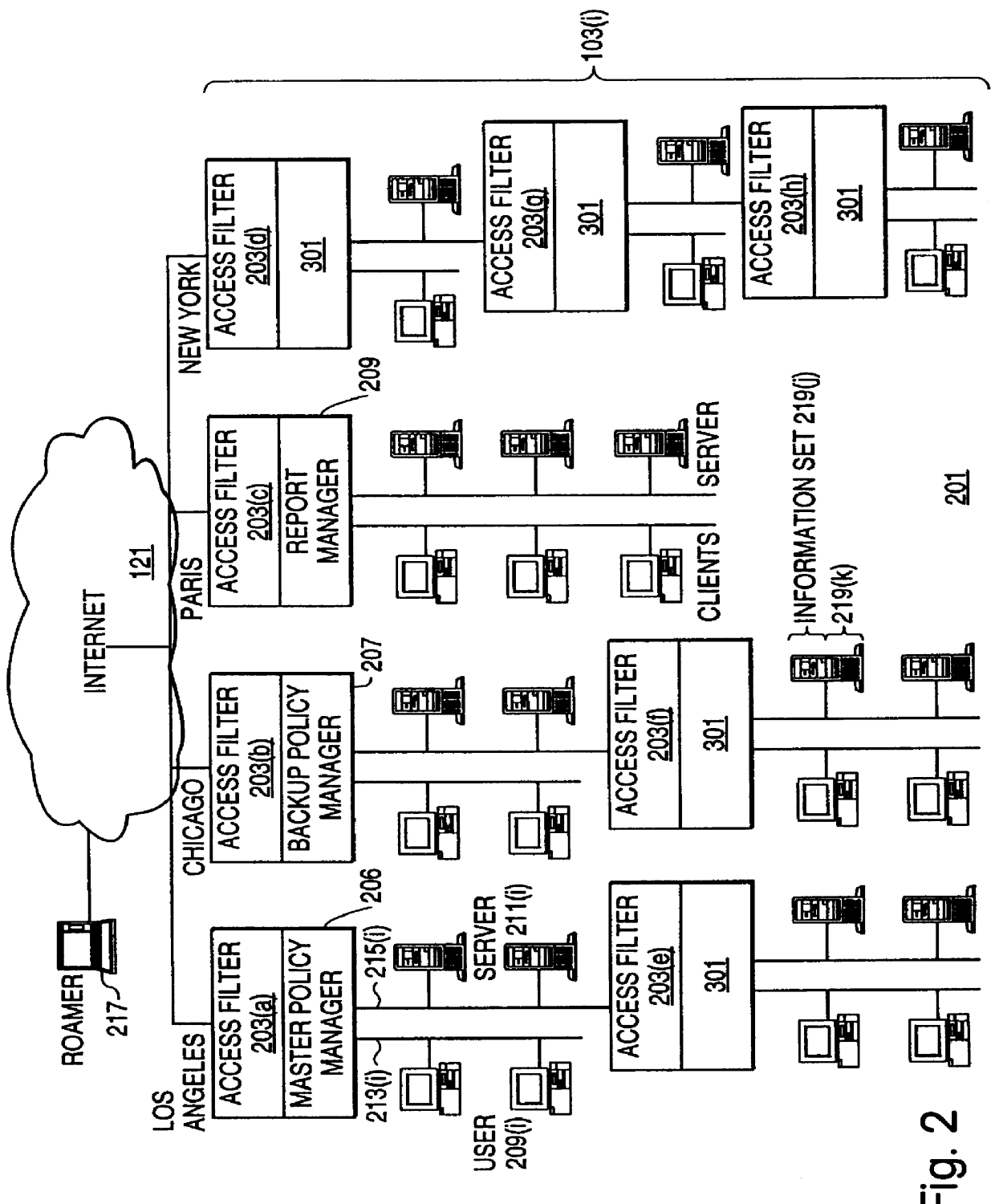
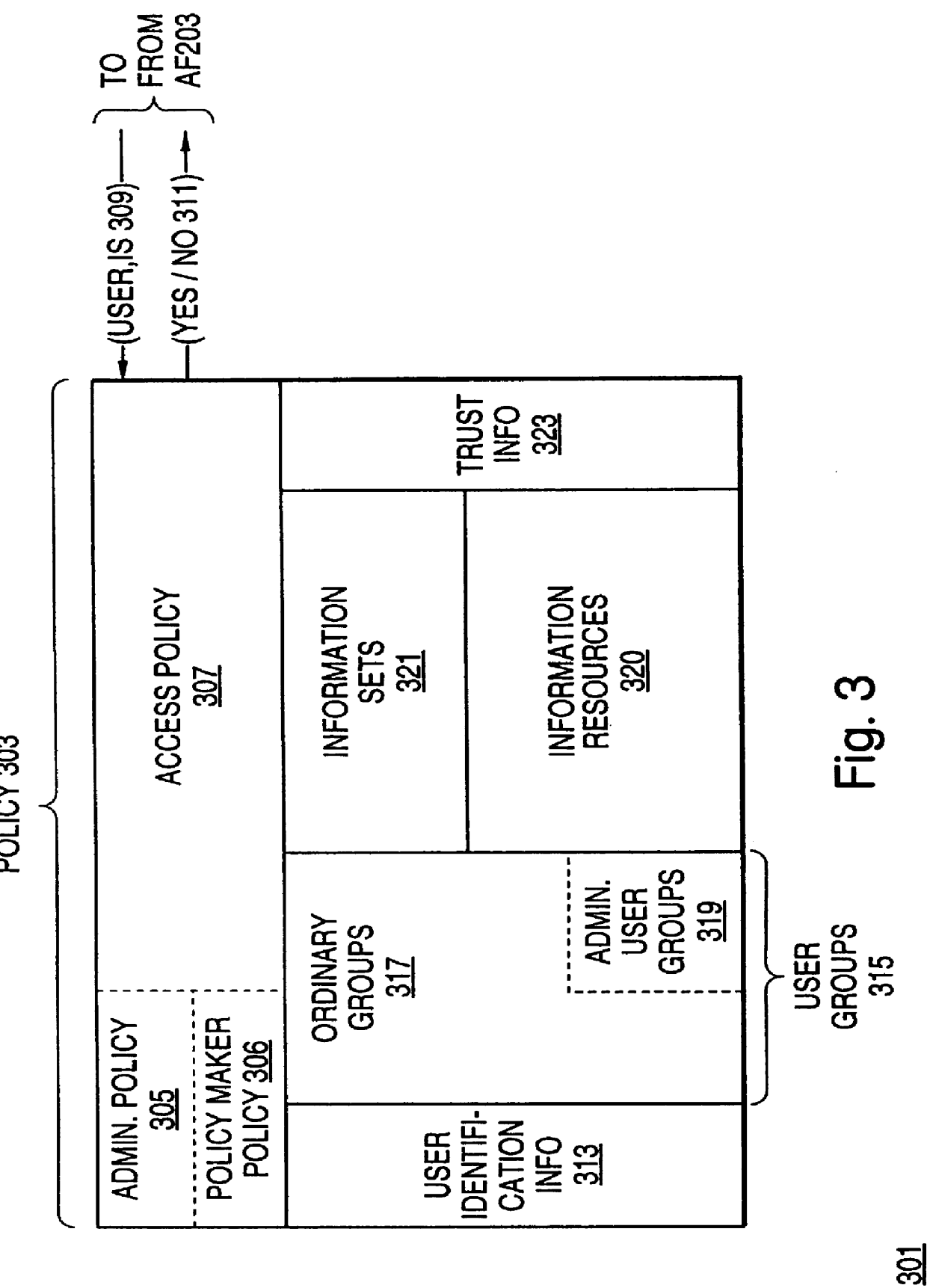
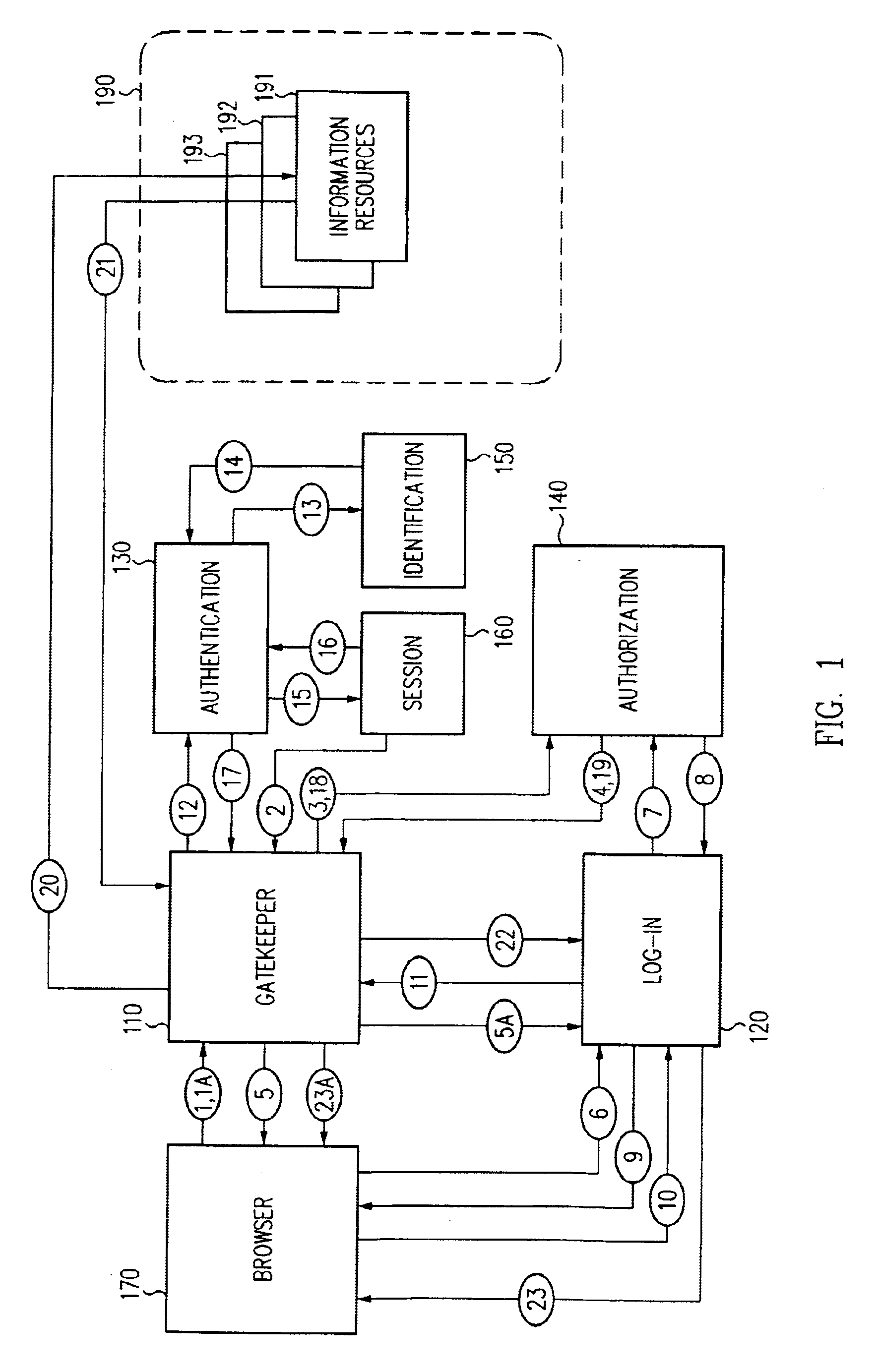
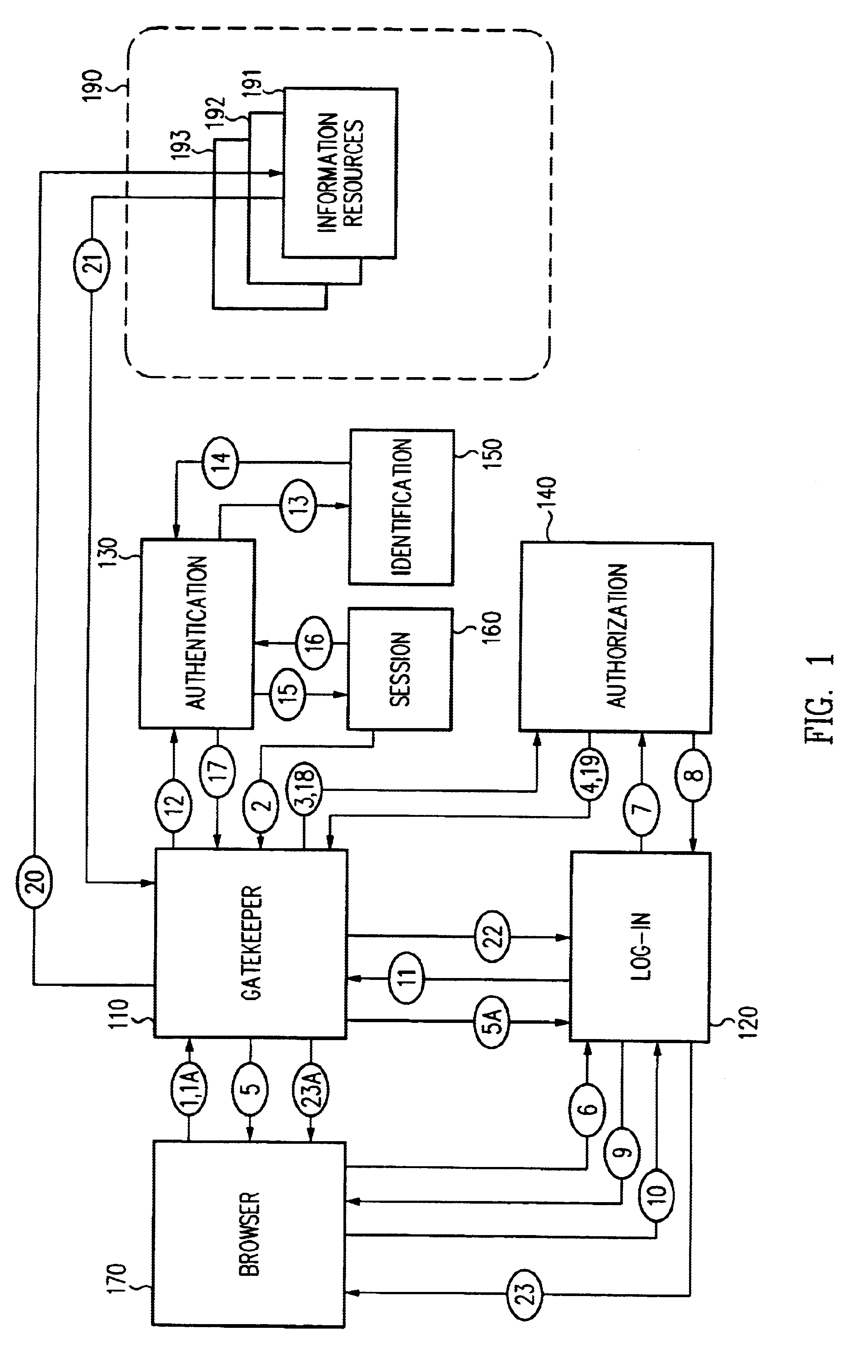
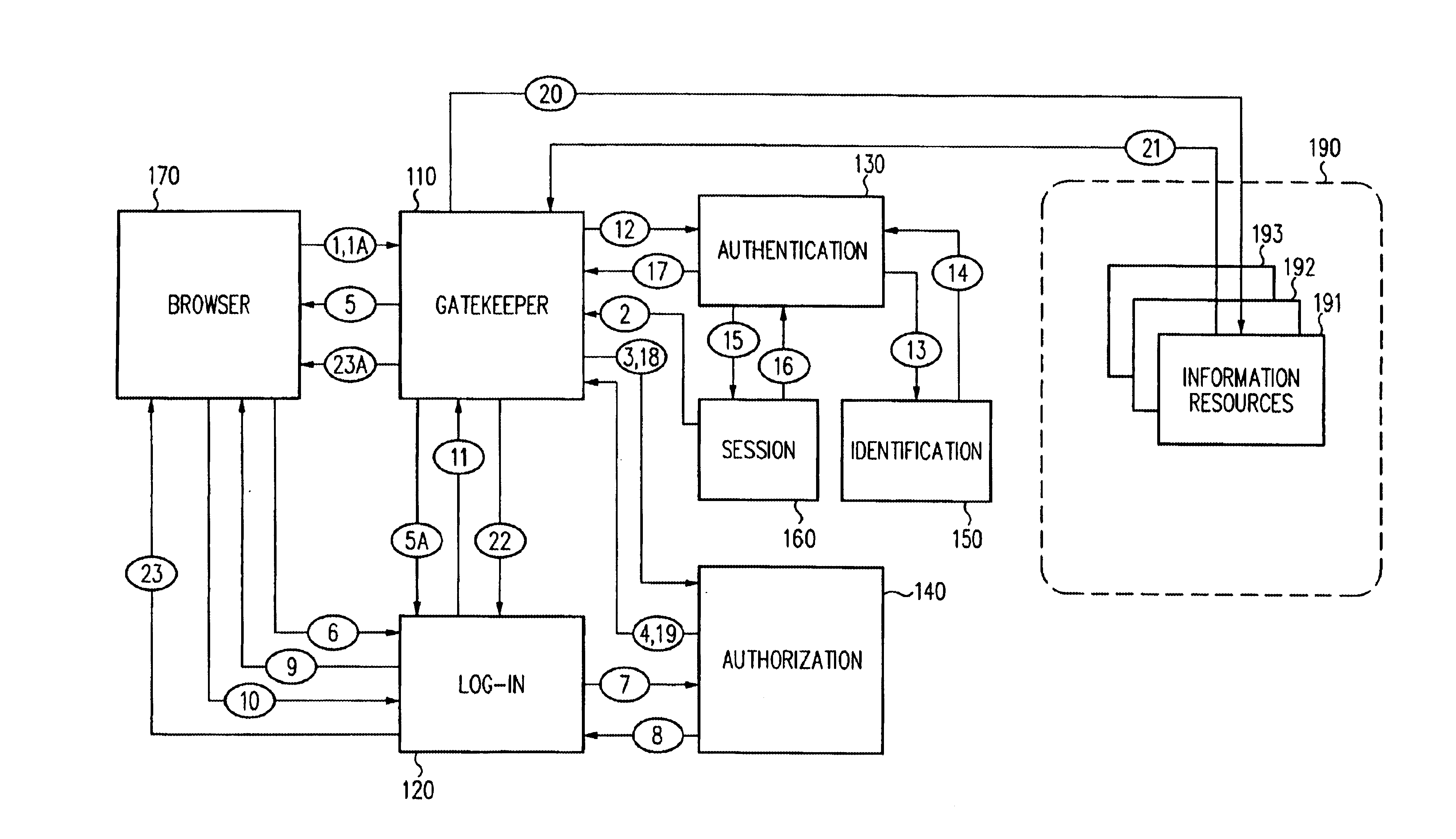
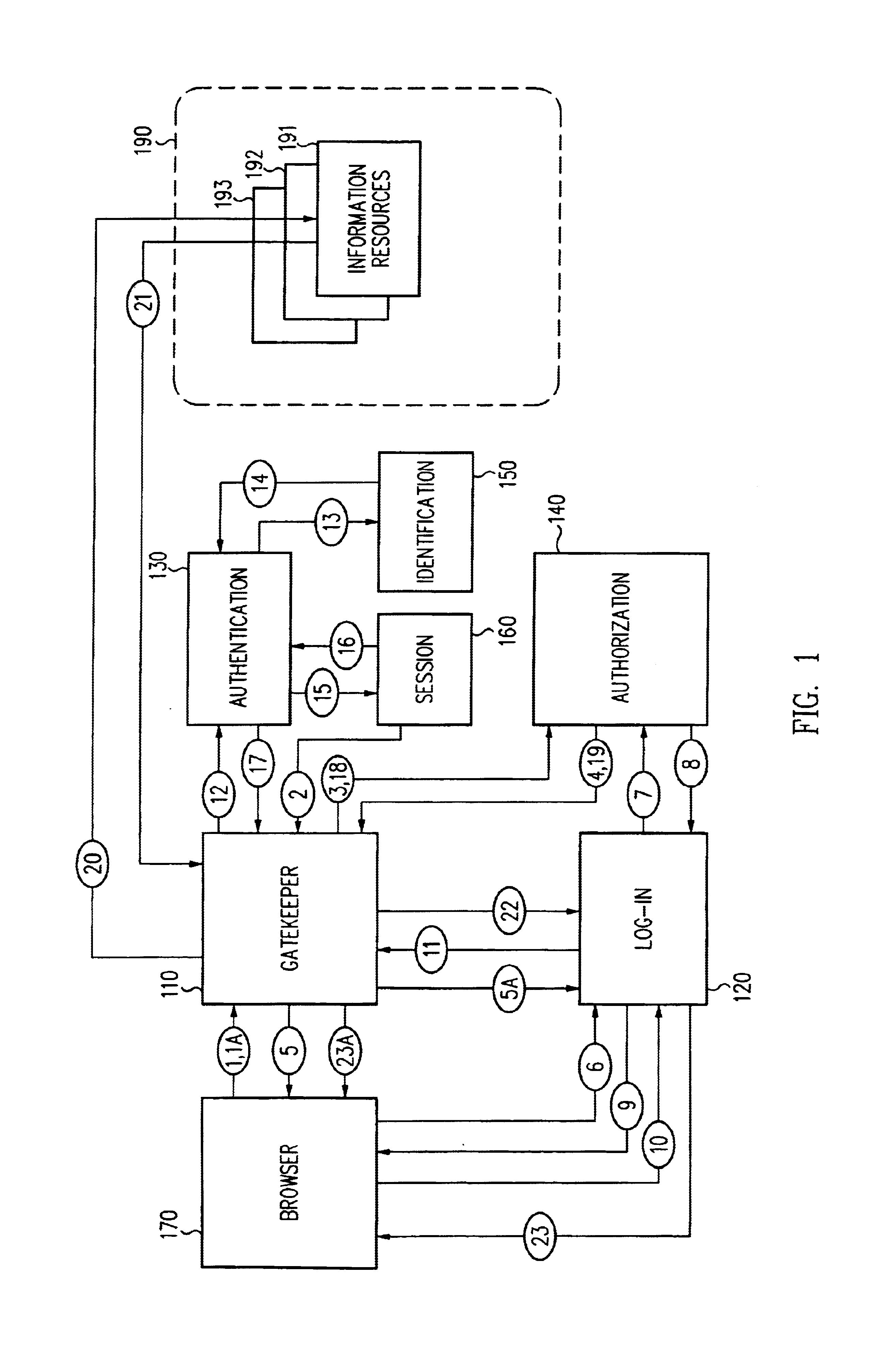
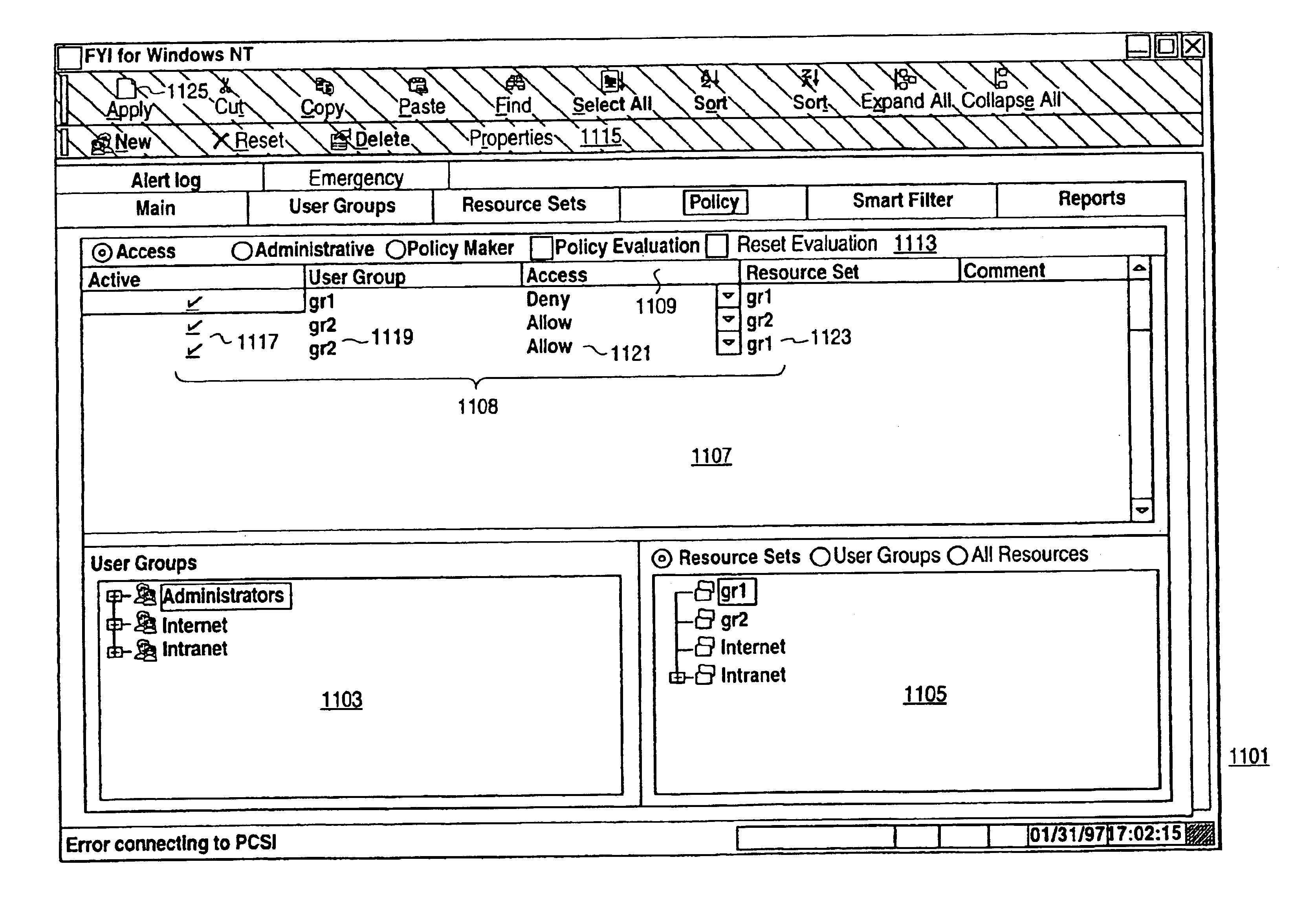
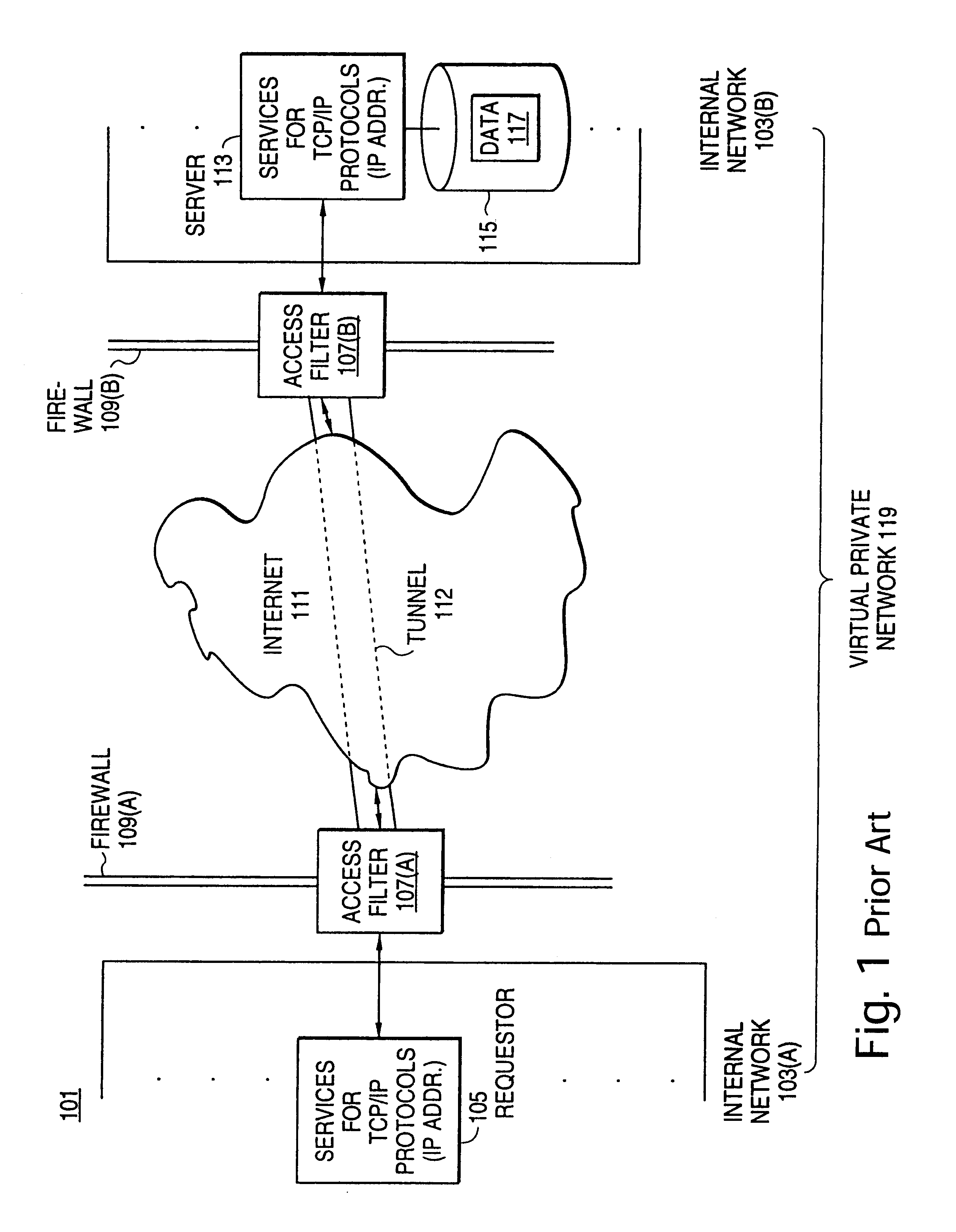
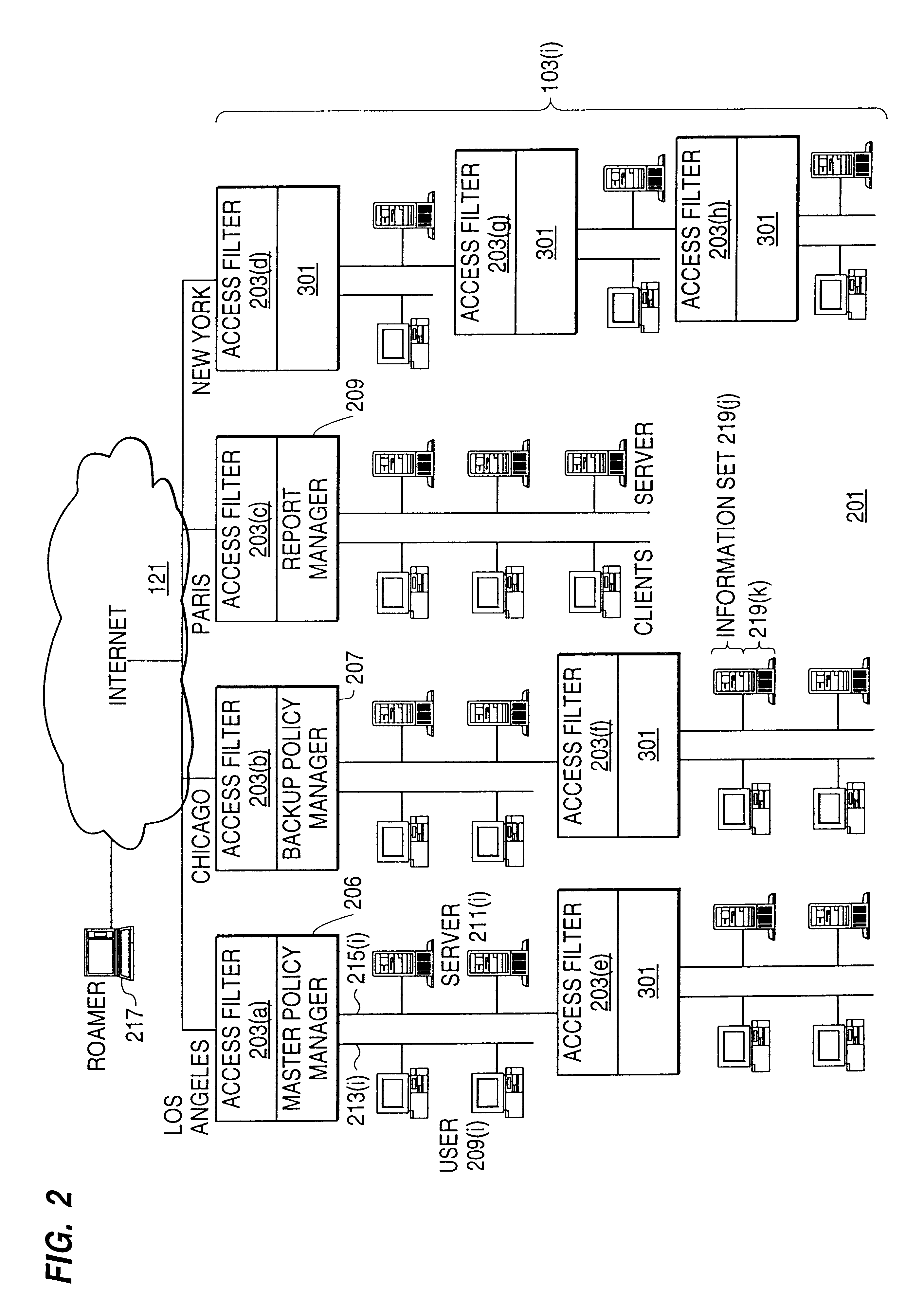
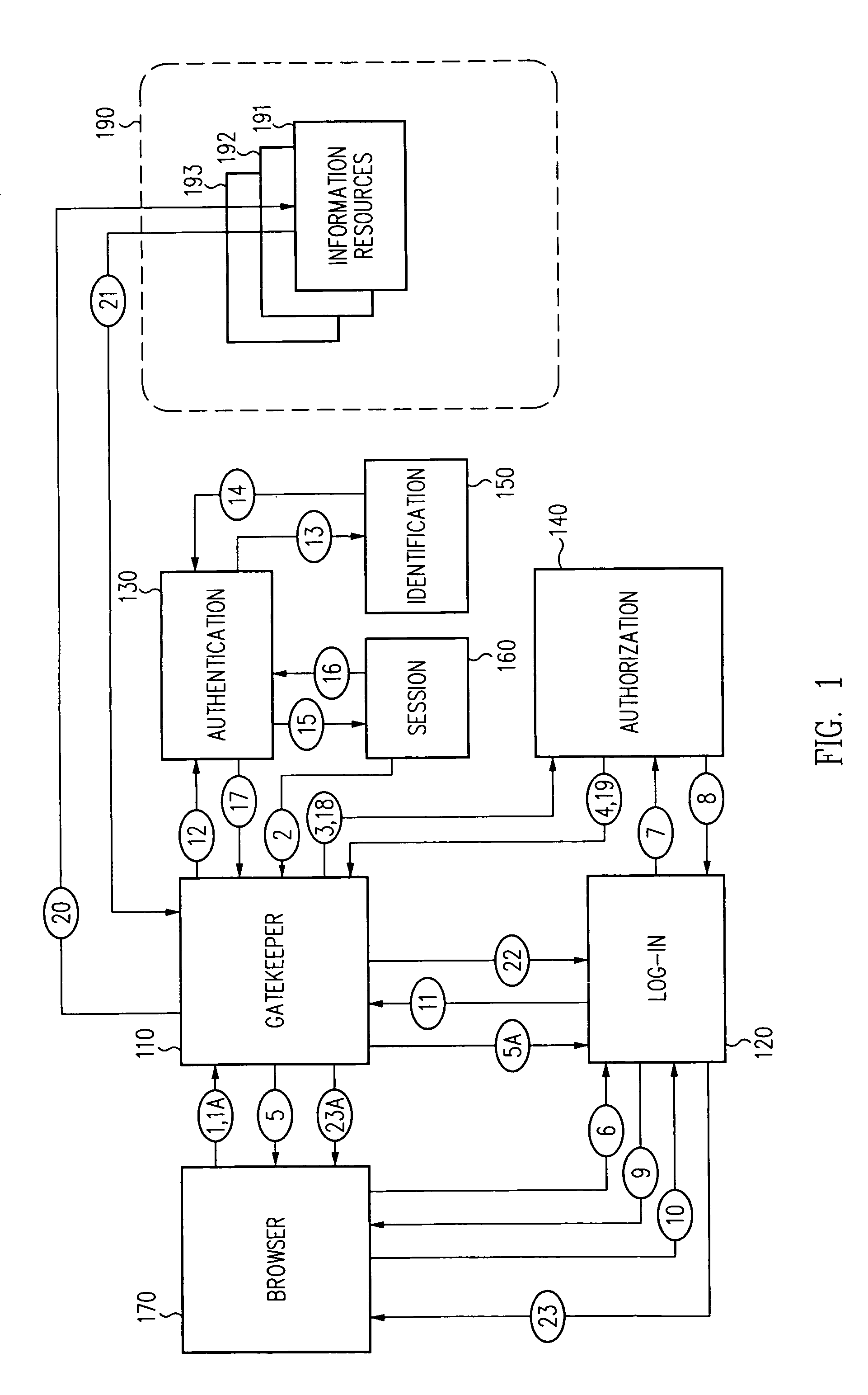
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
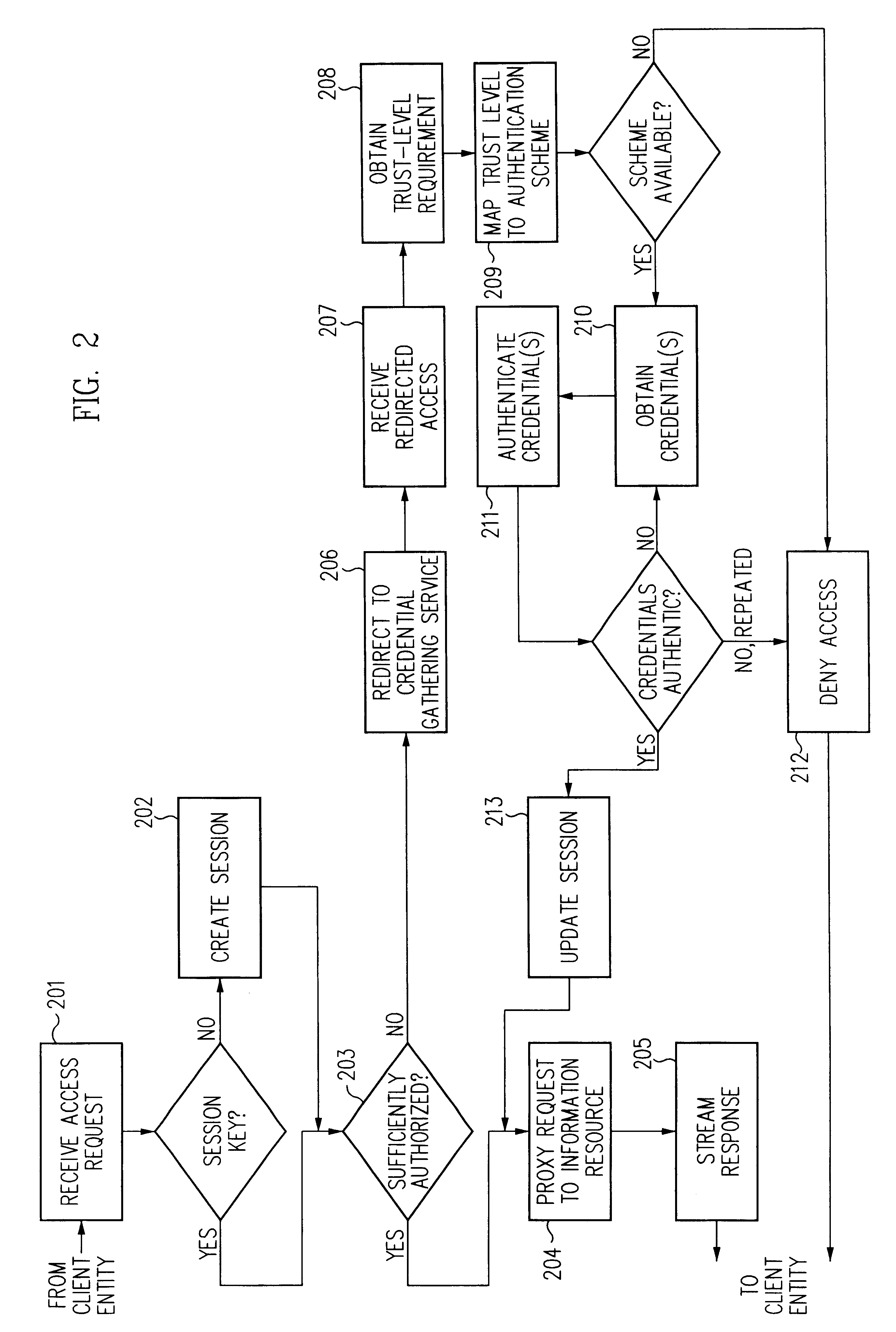
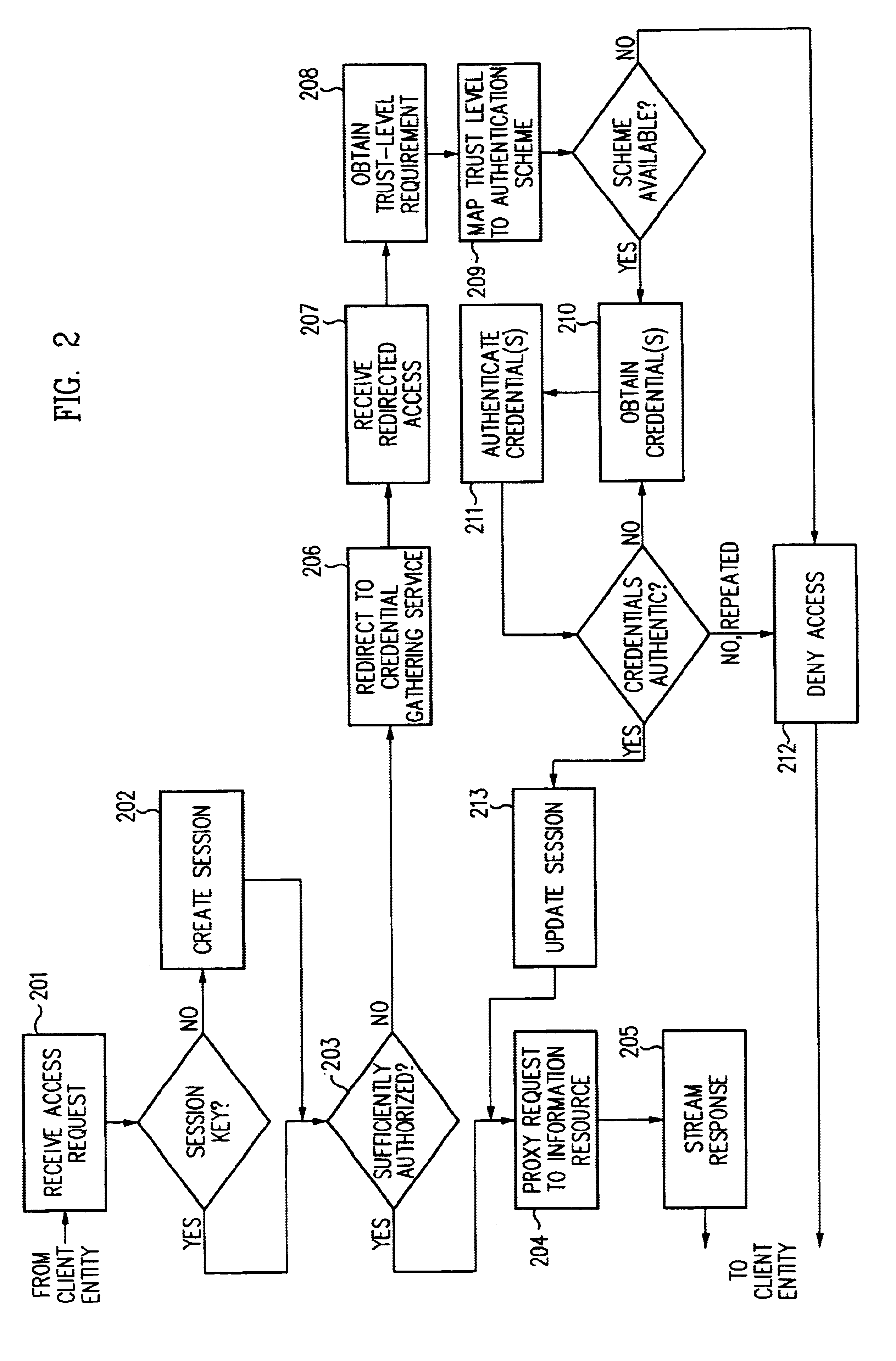
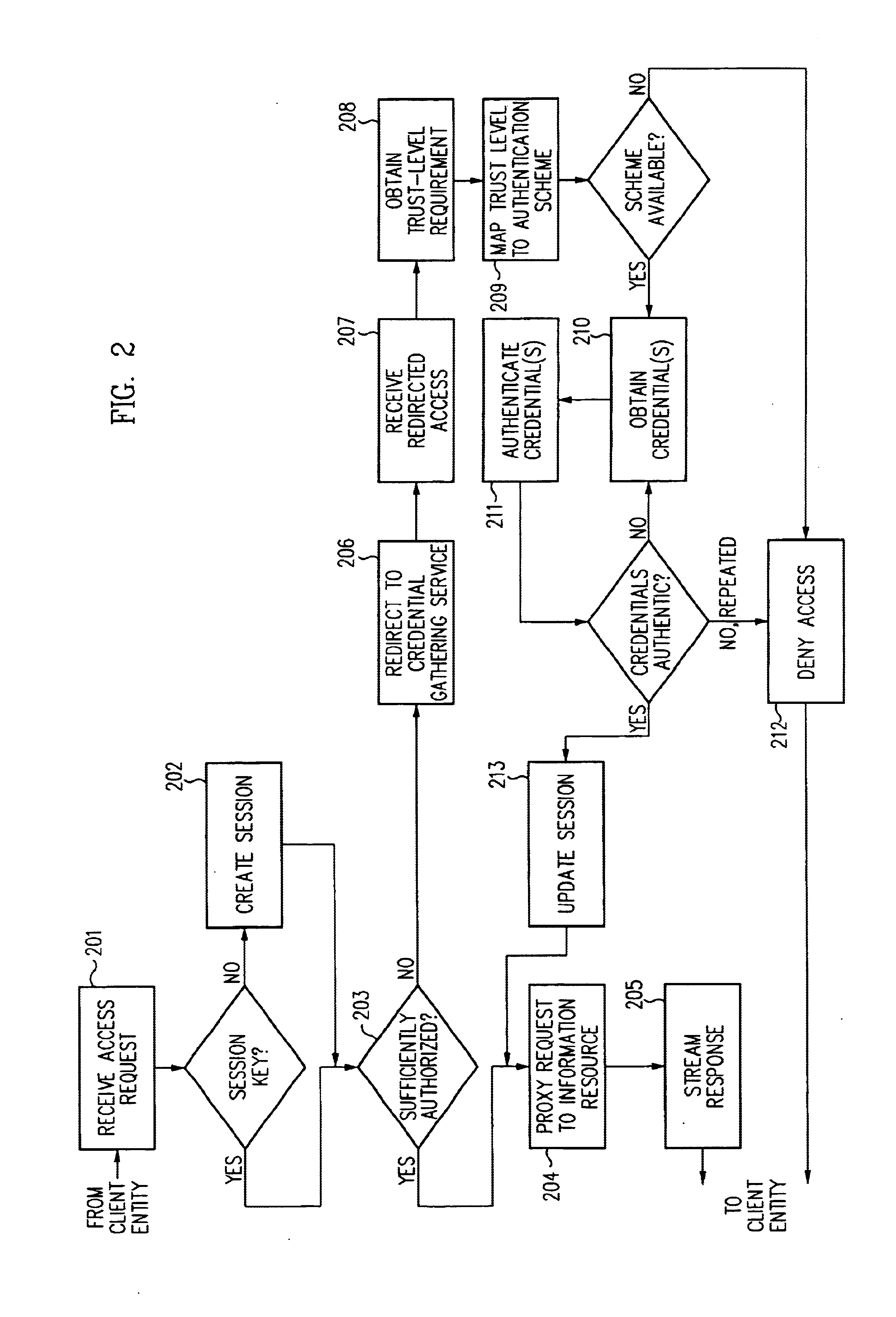
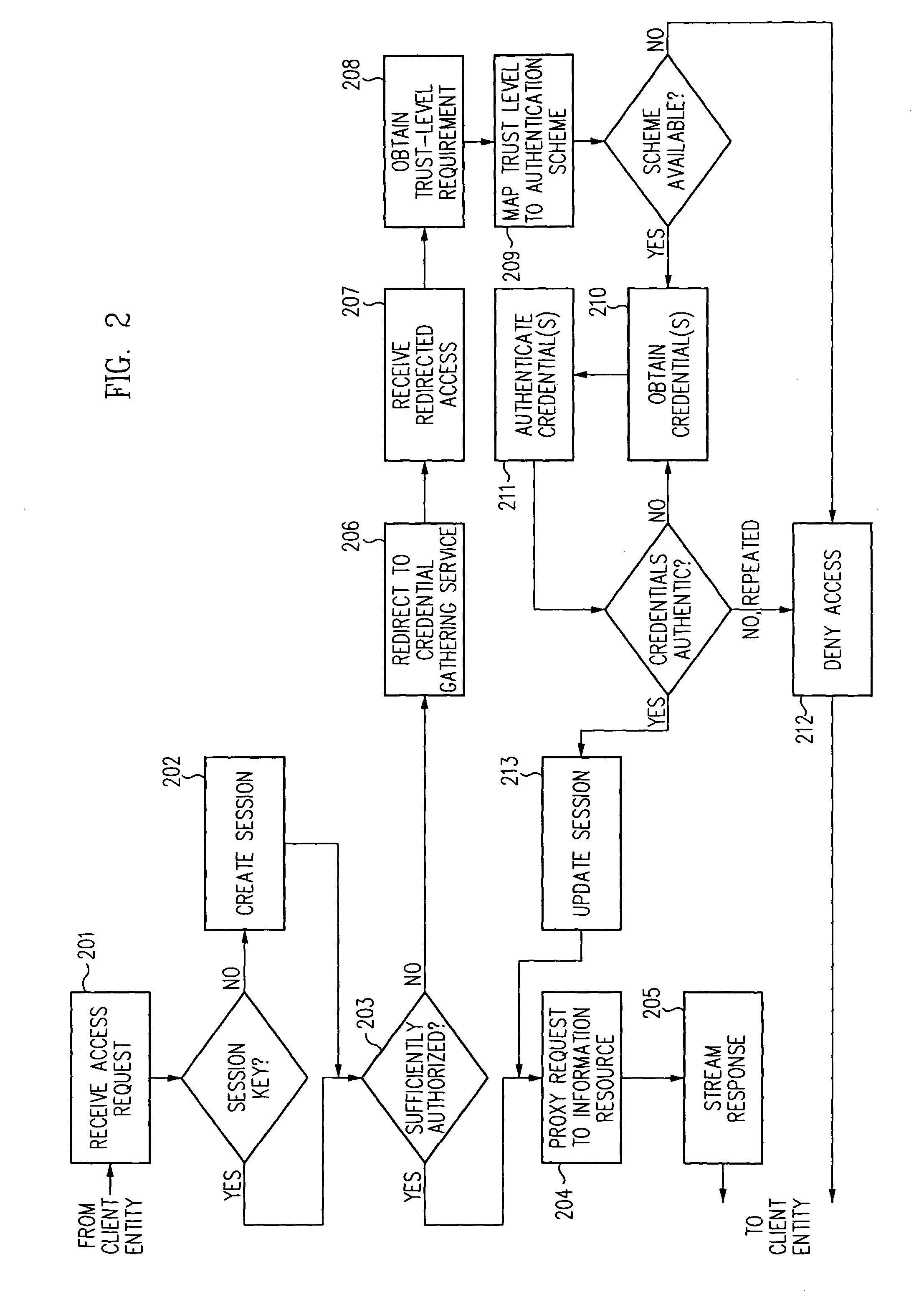
Log-on service providing credential level change without loss of session continuity
InactiveUS6609198B1Volume/mass flow measurementMultiple digital computer combinationsInformation resourceTrust level
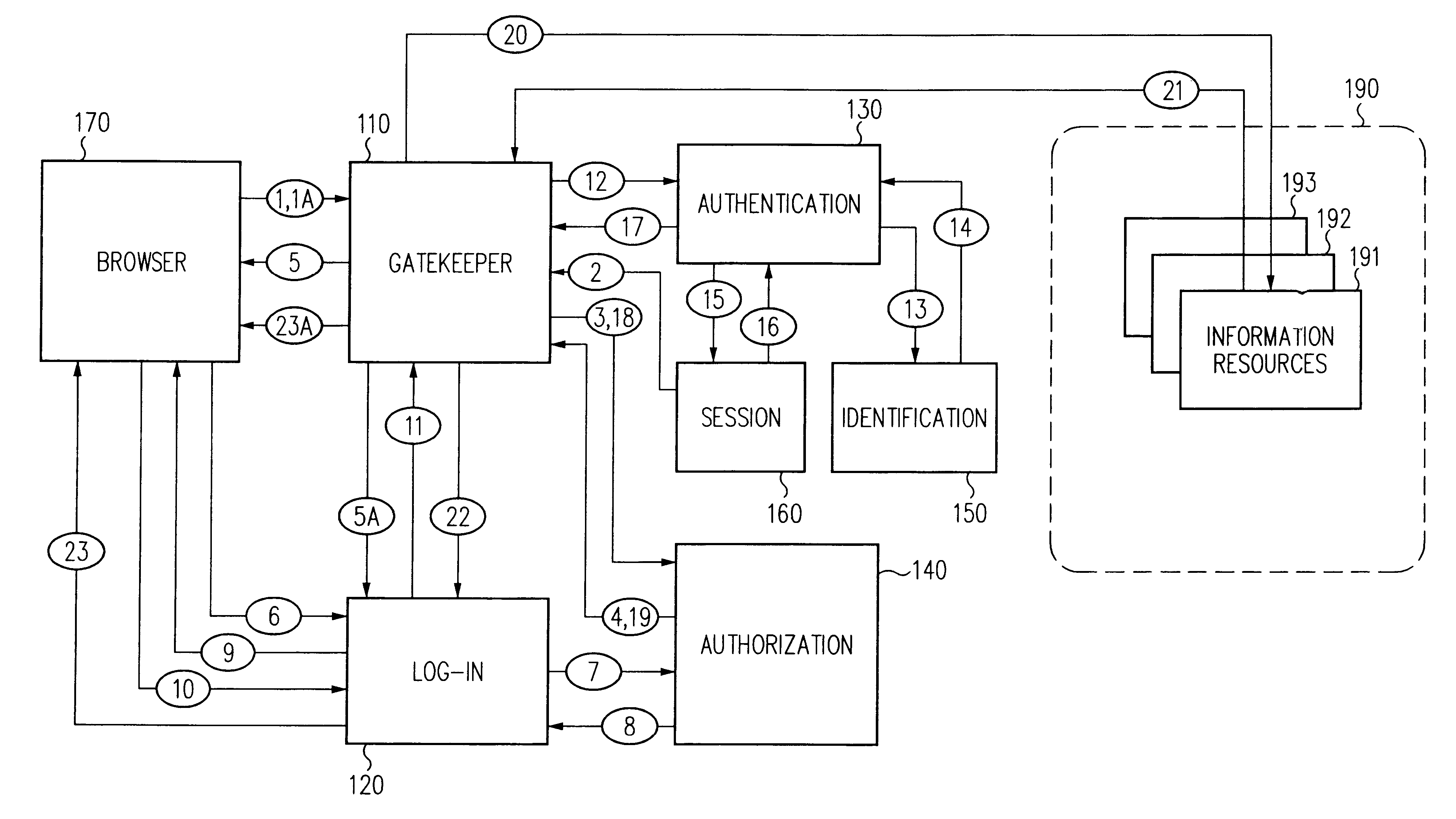
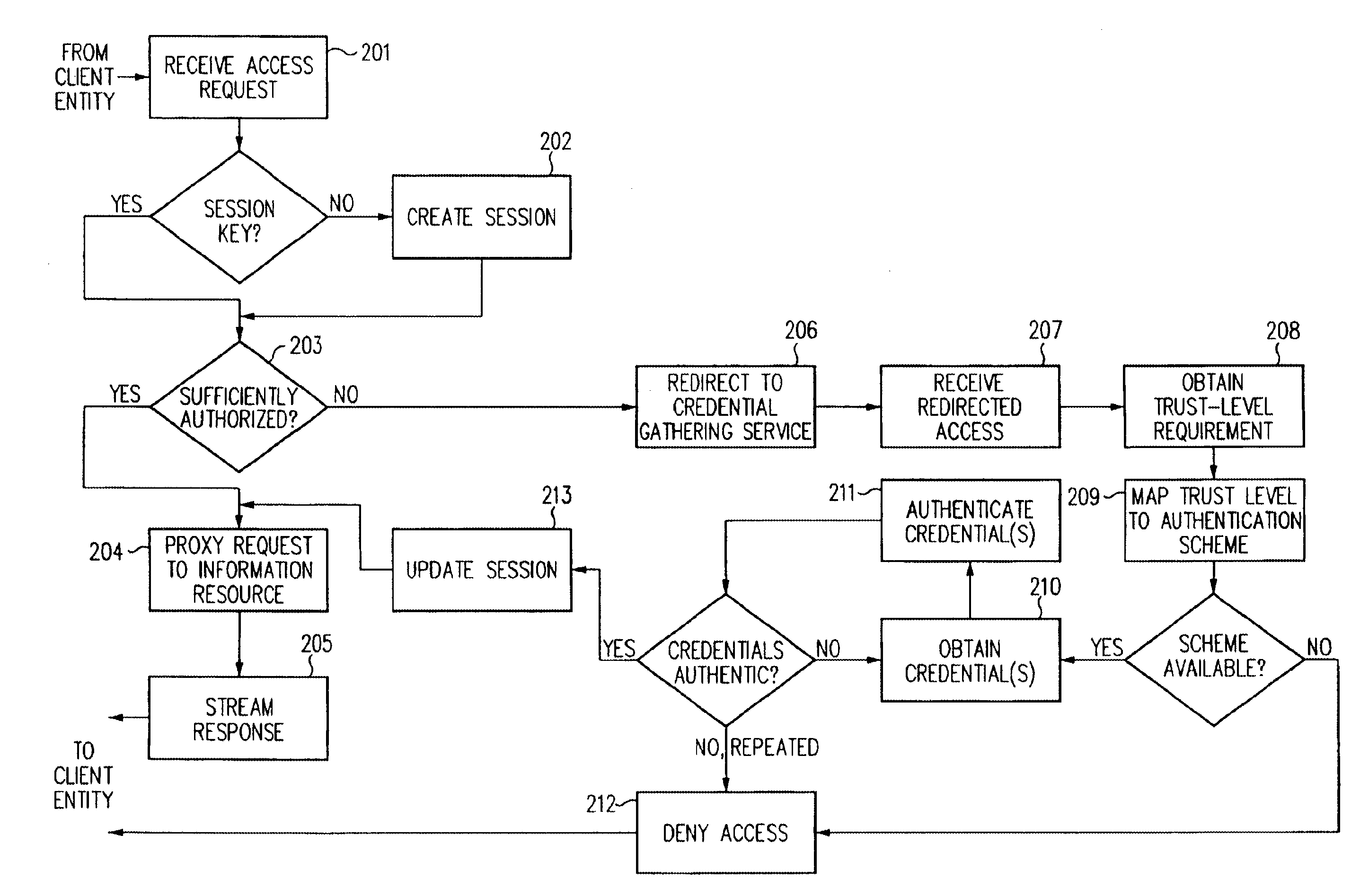
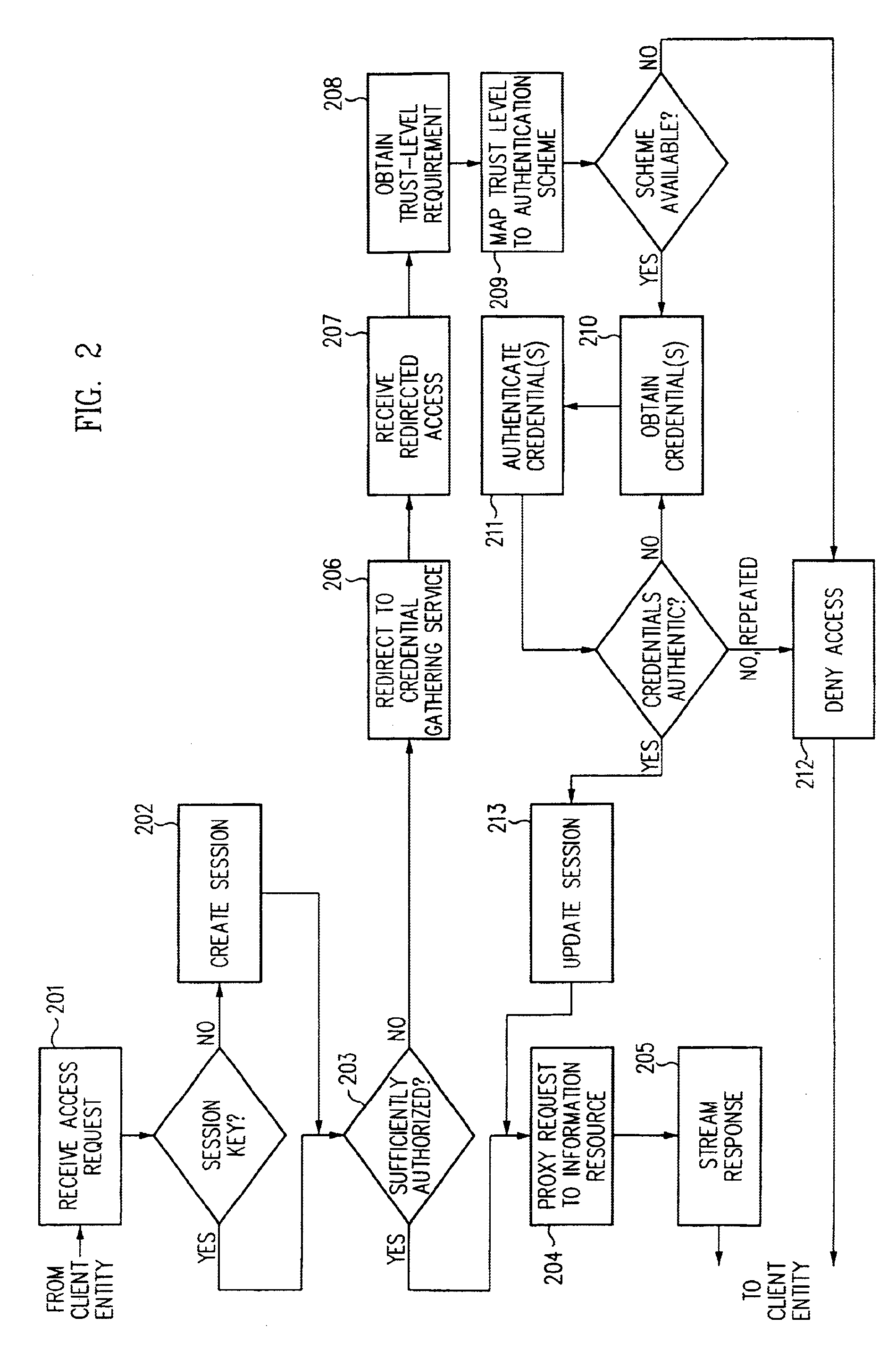
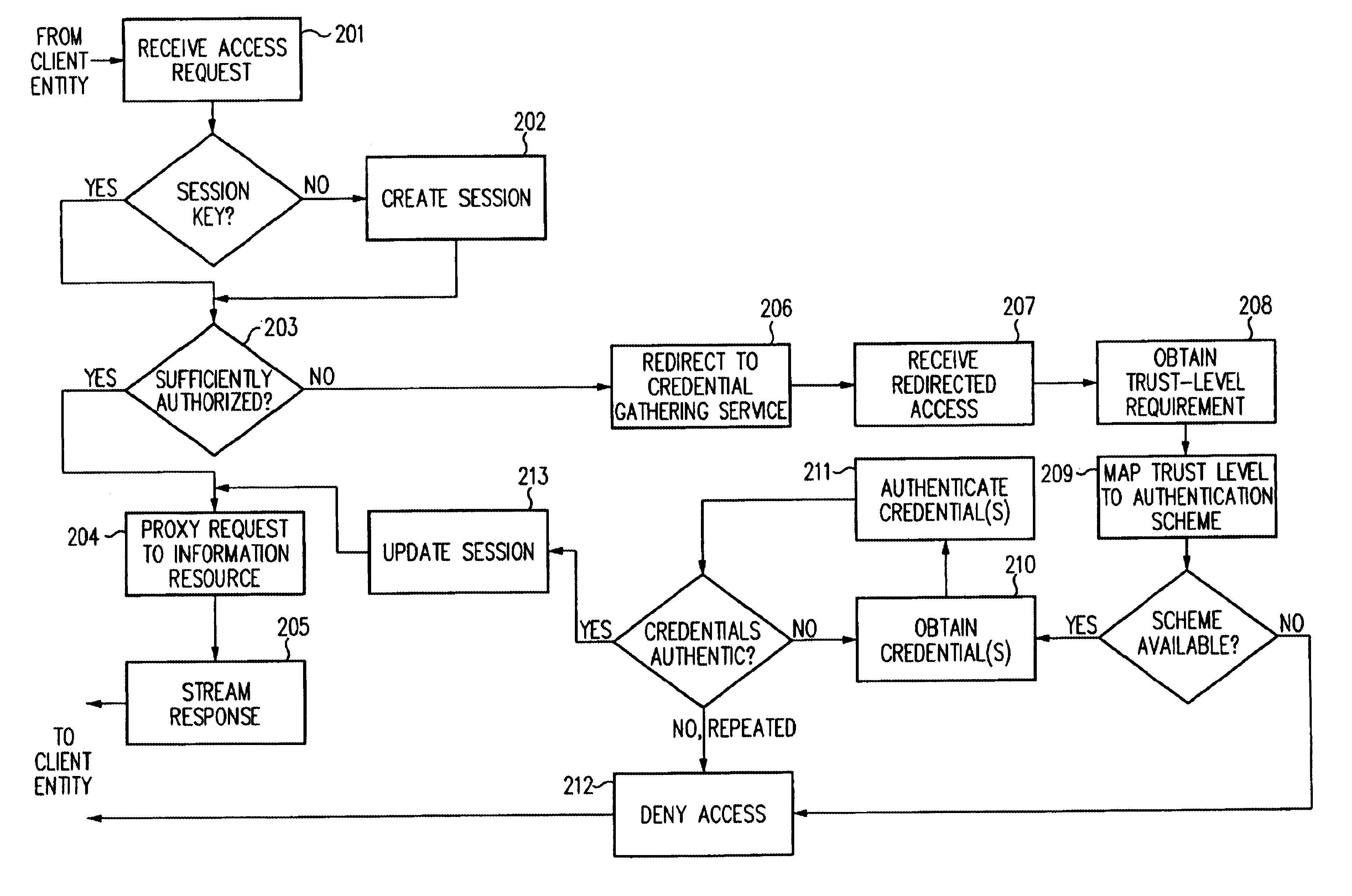
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient. The security architecture allows upgrade of credentials for a given session. This capability is particularly advantageous in the context of a single, enterprise-wide log-on. An entity (e.g., a user or an application) may initially log-on with a credential suitable for one or more resources in an initial resource set, but then require access to resource requiring authentication at higher trust level. In such case, the log-on service allows additional credentials to be provided to authenticate at the higher trust level. The log-on service allows upgrading and / or downgrading without loss of session continuity (i.e., without loss of identity mappings, authorizations, permissions, and environmental variables, etc.).
Owner:ORACLE INT CORP
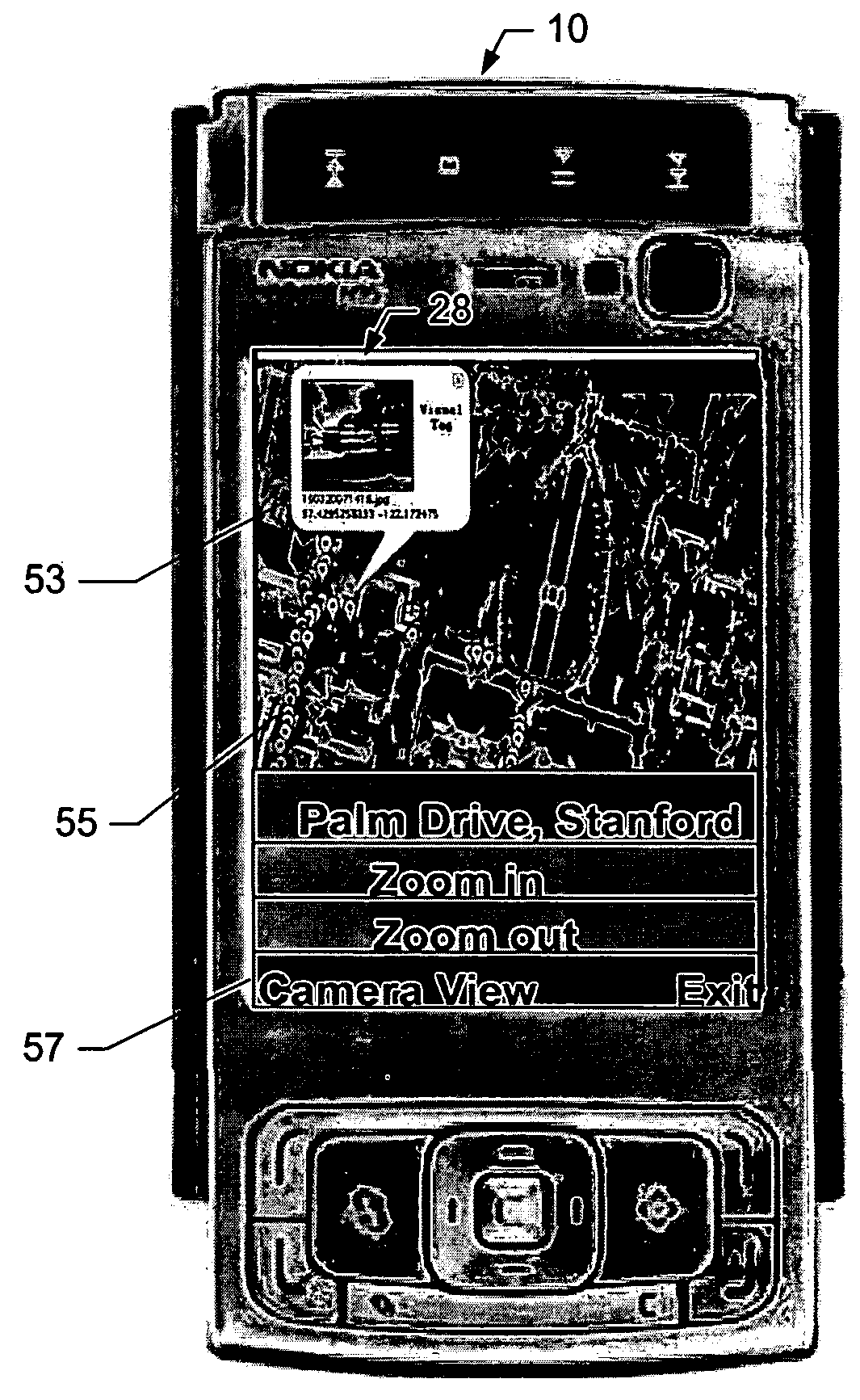
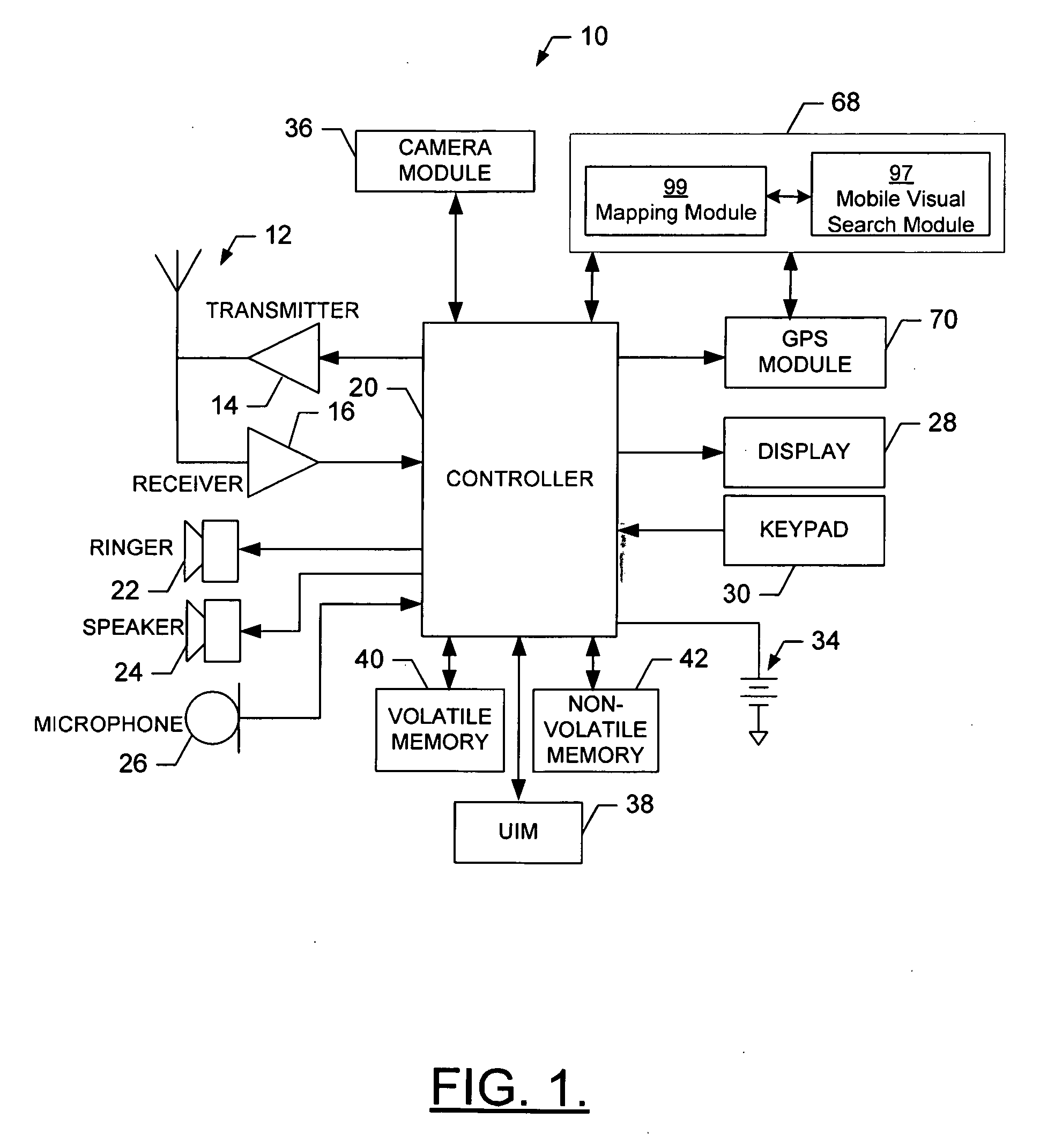
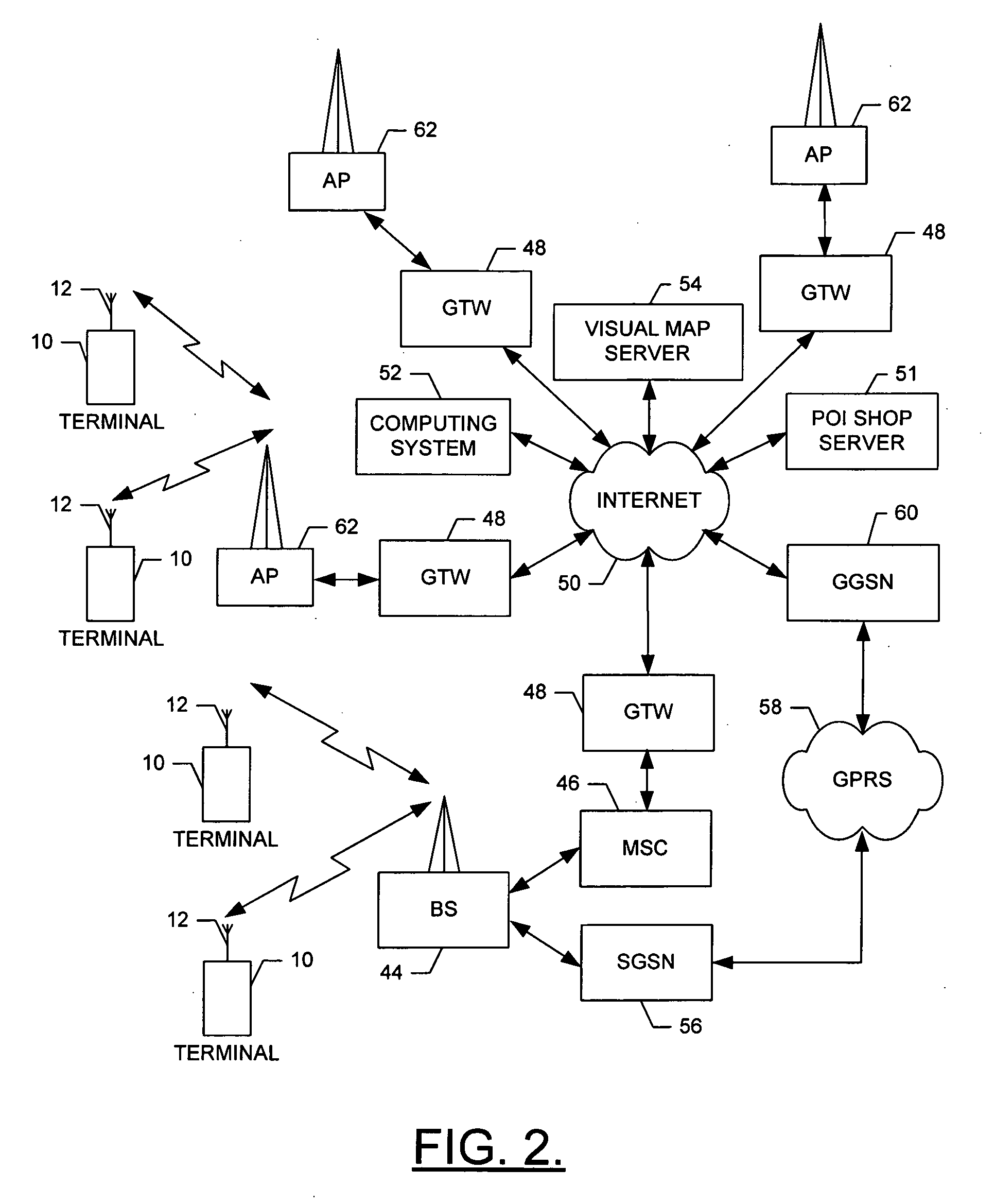
Method, Device, Mobile Terminal, and Computer Program Product for a Point of Interest Based Scheme for Improving Mobile Visual Searching Functionalities
InactiveUS20080268876A1Easy accessImprove experienceSubstation equipmentRadio/inductive link selection arrangementsInformation resourceMobile vision
Owner:NOKIA TECHNOLOGLES OY
Secure delivery of information in a network
InactiveUS6178505B1User identity/authority verificationData switching networksPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Techniques for eliminating redundant access checking by access filters
InactiveUS6105027AData processing applicationsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter uses a local copy of an access control data base to determine whether an access request is made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Single sign-on framework with trust-level mapping to authentication requirements
InactiveUS6892307B1Digital data processing detailsUser identity/authority verificationPasswordInformation resource
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels and a log-on service obtains credentials for an entity commensurate with the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:ORACLE INT CORP
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
Security architecture with environment sensitive credential sufficiency evaluation
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
Scaleable web server and method of efficiently managing multiple servers
InactiveUS6330602B1Improve performanceEfficient managementData switching by path configurationMultiple digital computer combinationsInformation resourceWeb service
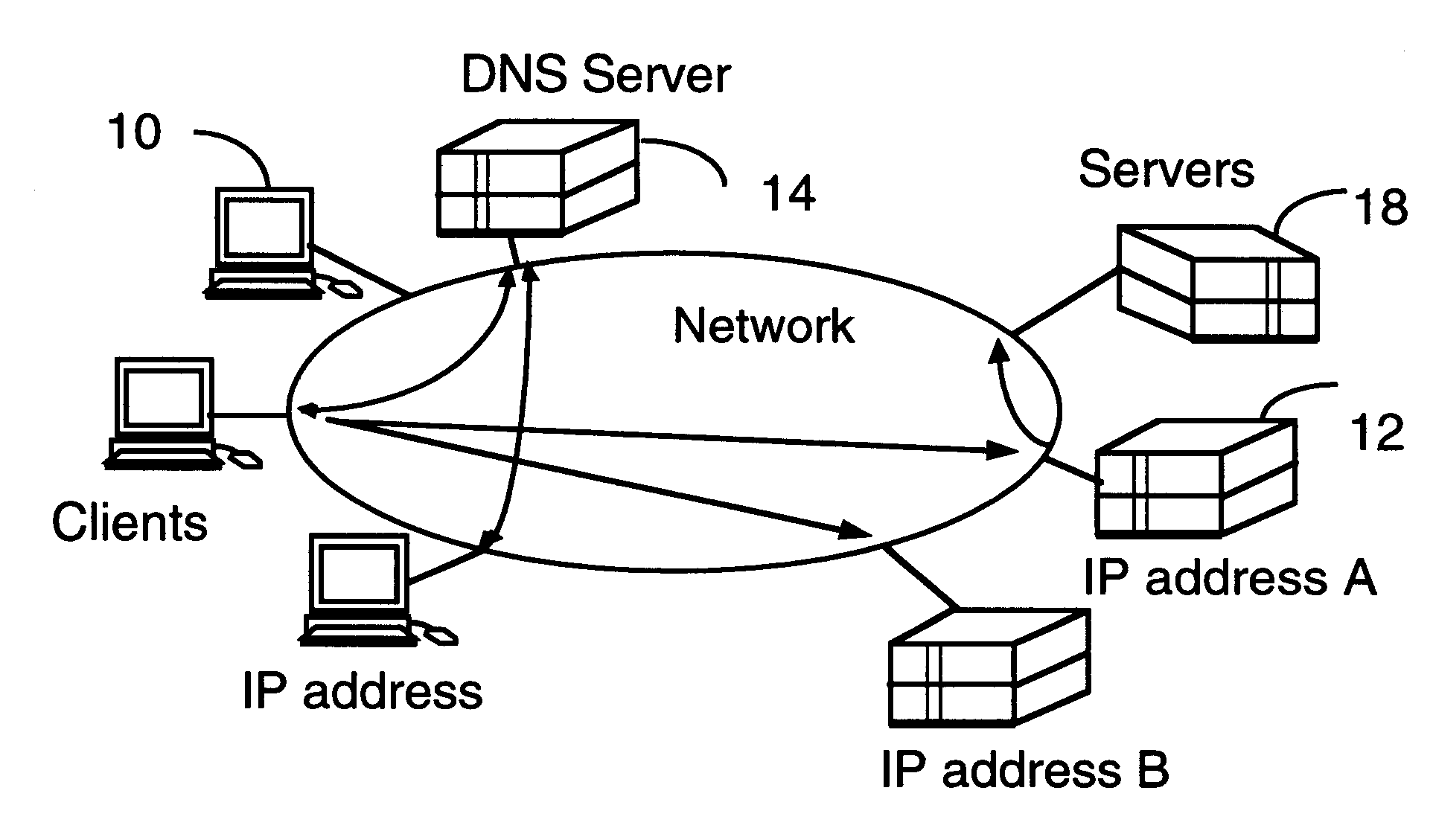
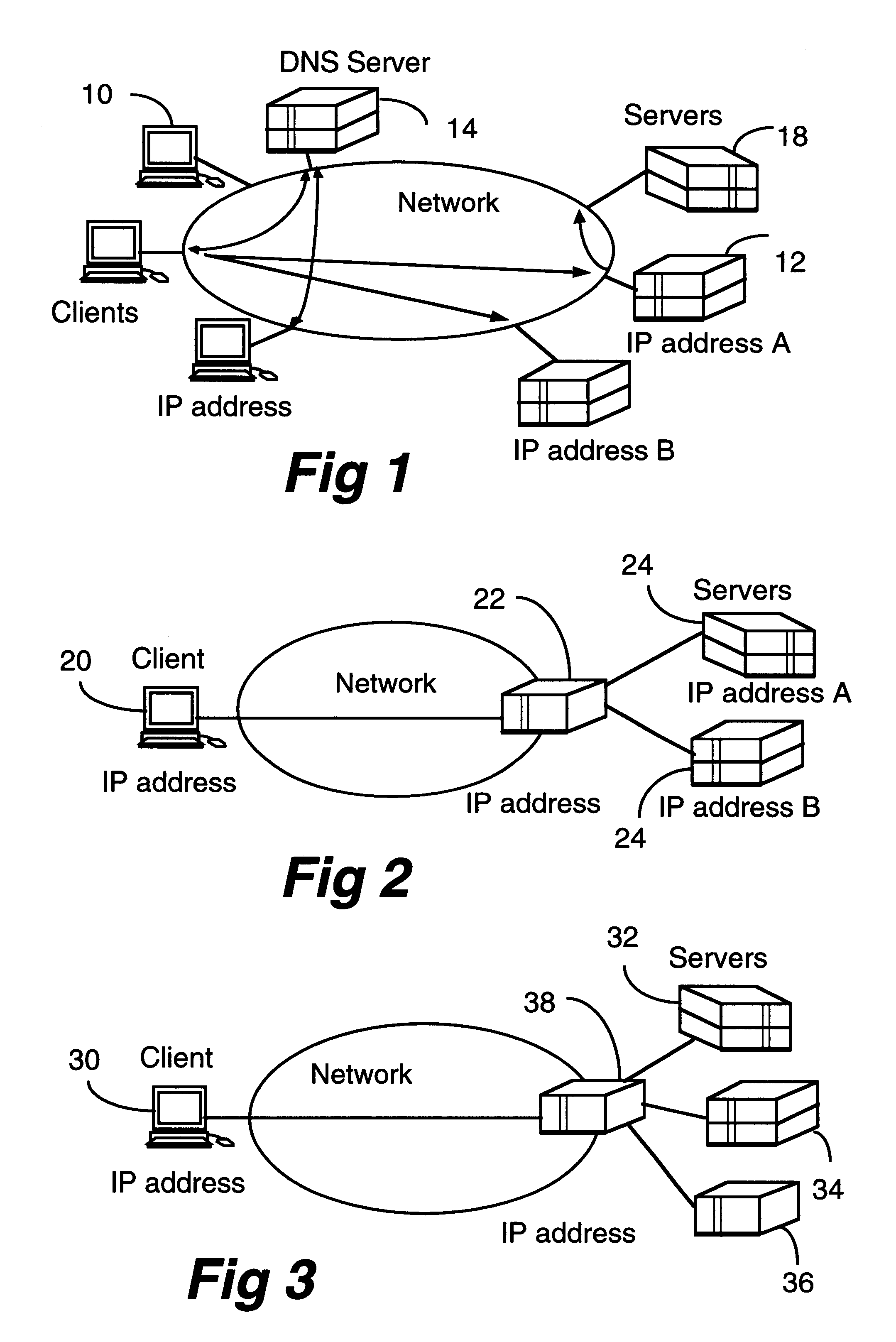
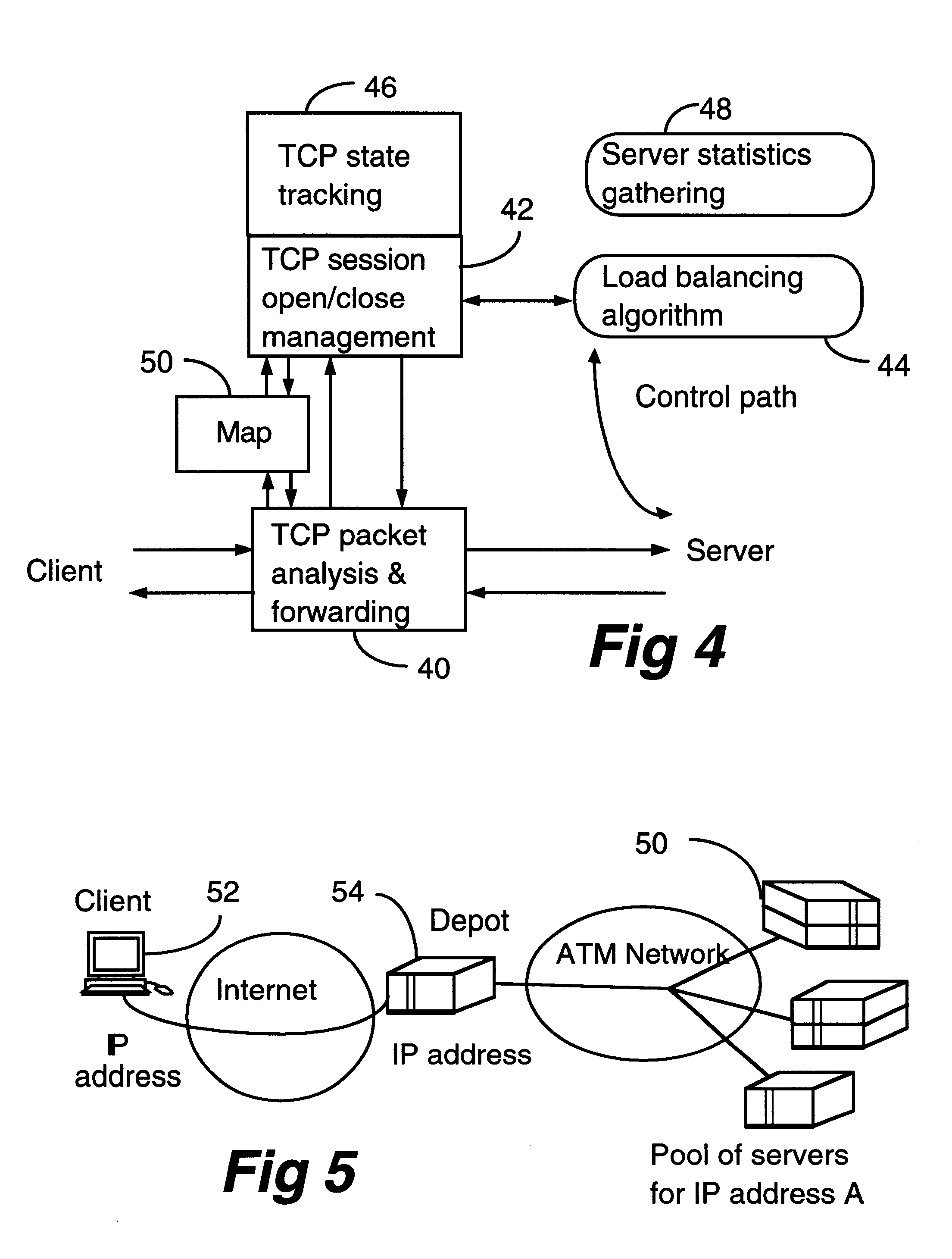
A client-server architecture includes a plurality of clients and a plurality of servers. Information resources are replicated among the servers. According to one aspect, the invention includes an intermediary device called a "depot" sitting transparently between a client and a pool of servers which have the replicated information resources. The depot dynamically distributes multiple sessions contained in a client request among the servers. This architecture realizes a good granular scaleability of servers, and improved server throughput with a good response time. Multiple depots also realize robustness.
Owner:AVAYA INC
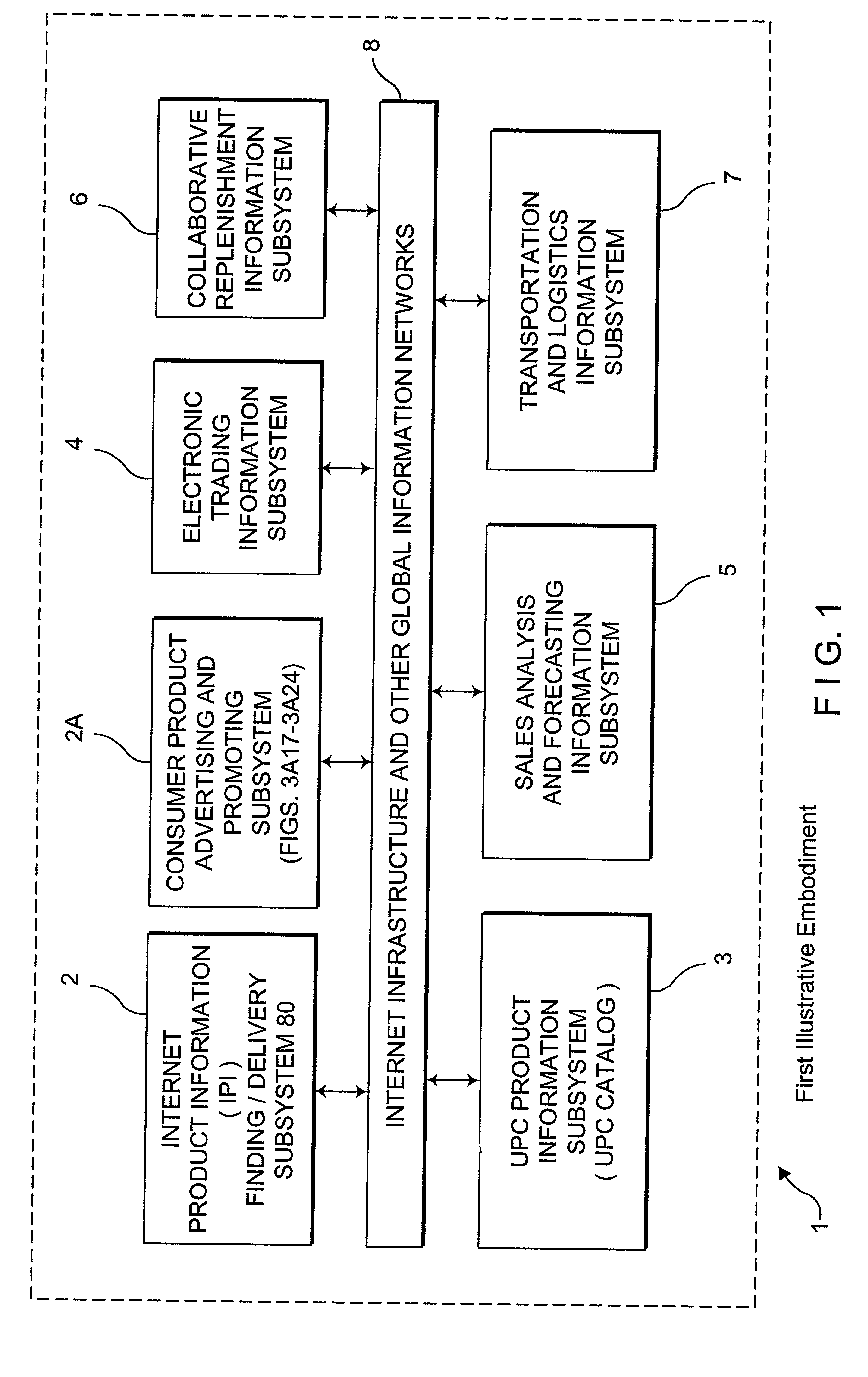
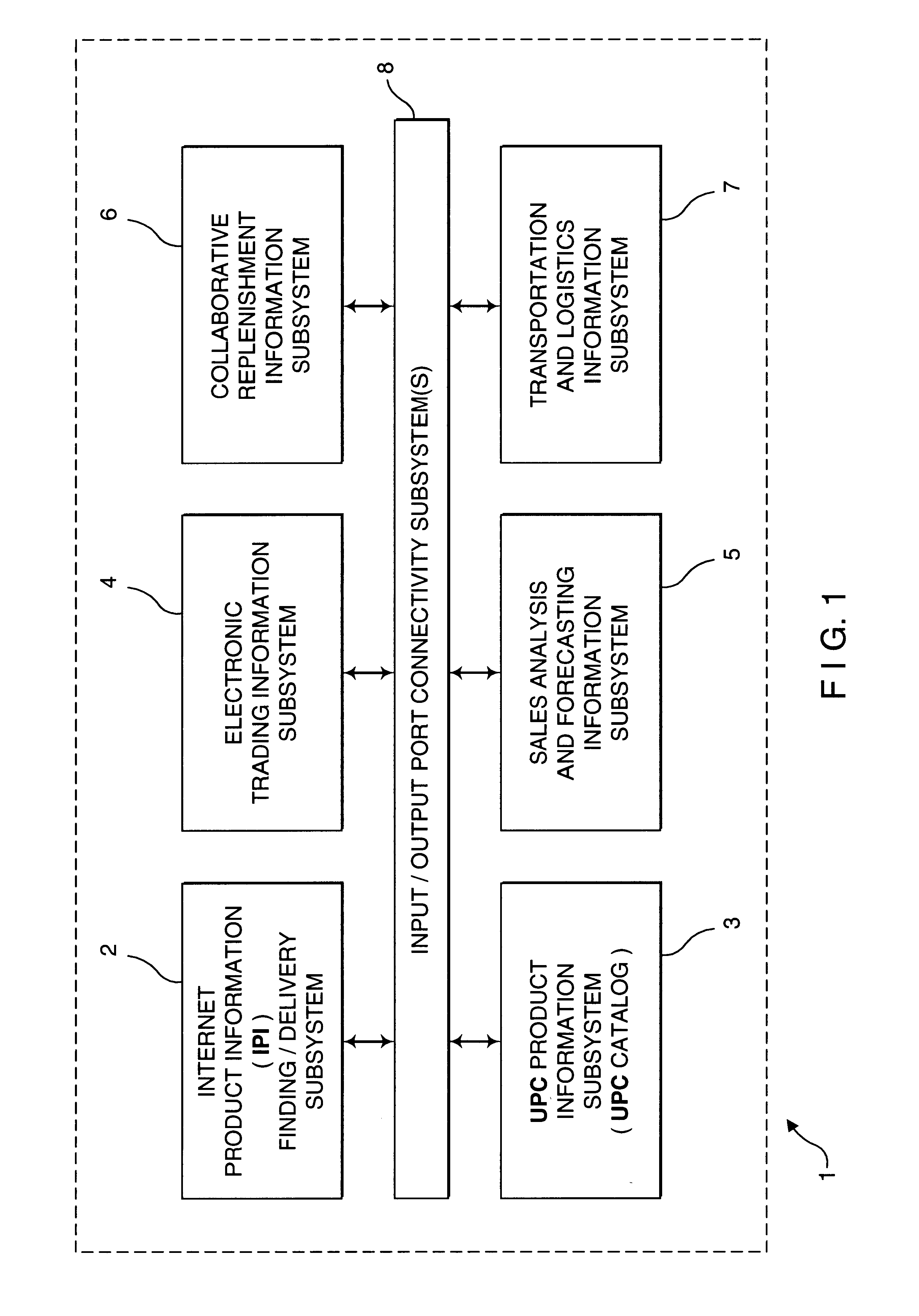
Internet-based consumer service brand marketing communication system which enables service-providers, retailers, and their respective agents and consumers to carry out service-related functions along the demand side of the retail chain in an integrated manner
InactiveUS20020194081A1Easy accessEasy alignmentDigital data information retrievalData switching by path configurationUniversal serviceCommunications system
An Internet-based consumer service marketing, merchandising and education / information system which enables service-providers, retailers and their respective agents, and consumers to carry out service-related functions along the demand side of the retail chain. A central USN / SM / SN / URL RDBMS stores a central database of USN / SM / SN / URL links, wherein the USN represents a Universal Service Number assigned to a particular service offered by a service-provider, the SM represents a Service Mark used in connection with the particular service, the SD is representative of one or more Universal Resource Locators pointing to information resources on the WWW relating to the particular service. A first subsystem enables a service-provider's marketing, brand and / or service managers to create and manage a local database of USN / SM / SN / URL links related to the consumer services of the service-provider being offered for sale in both physical and / or electronic marketplaces, and periodically transport the local database of USN / SM / SN / URL links to the central USN / SM / SN URL RDBMS by electronic data transport techniques. The local database of USN / SM / SN / URL links is managed with a local USN / SM / SN / URL RDBMS, and selected by the service-provider's marketing, brand and / or service managers so as to create a desired brand image for each consumer service of the service-provider. A second subsystem enables consumers to access one or more USN / SM / SN / URL links in the central USN / SM / SN / URL RDBMS, to request and obtain information about a service-provider's consumer service so as to make informed / educated purchases along the demand side of the retail chain. A third subsystem enables service-providers and their advertising and marketing agents to access one or more USN / SM / SN / URL links in the central USN / SM / SN / URL RDBMS, to display consumer service advertisements to consumers, at or near the point of purchase or sale within both physical and / or electronic retail shopping environments so as to project the desired brand image to consumers. A fourth subsystem enables retailers and their marketing and promotional agents to access one or more USN / SM / SN / URL links in the central USN / SM / SN / URL RDBMS, to promote consumer services to consumers, at or near the point of purchase or sale within both physical and / or electronic retail shopping environments so as to promote the sale of such services.
Owner:PERKOWSKI THOMAS J
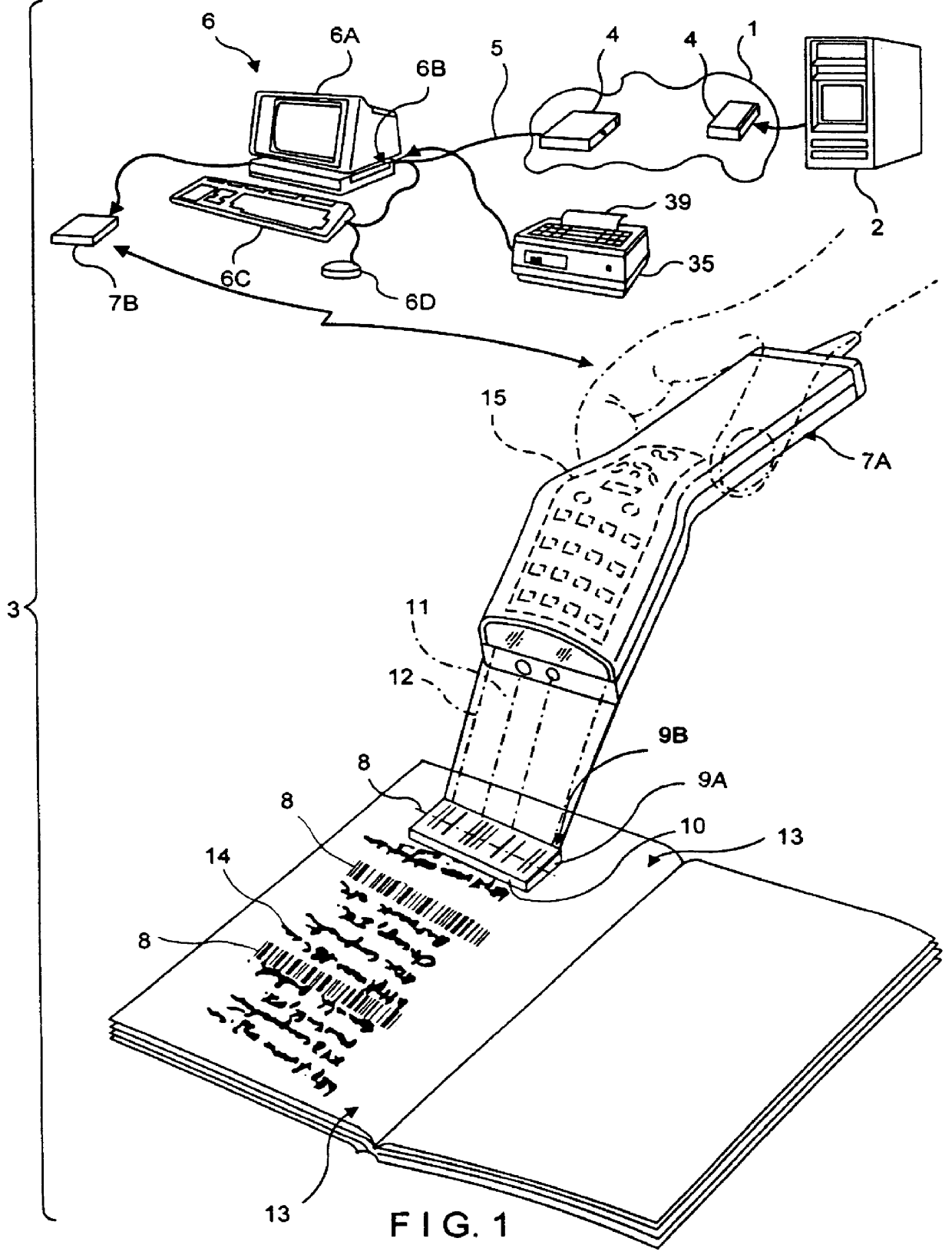
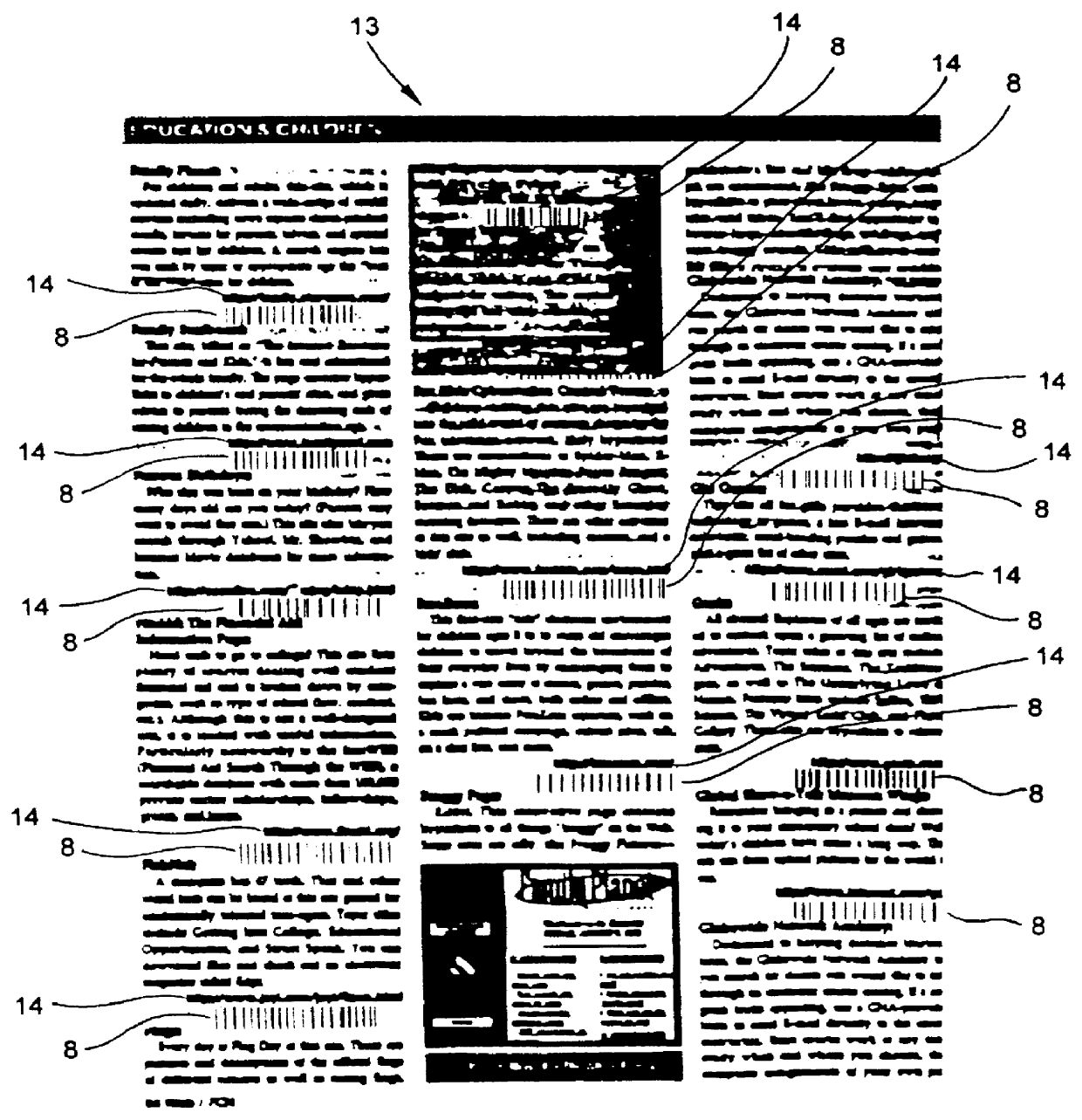
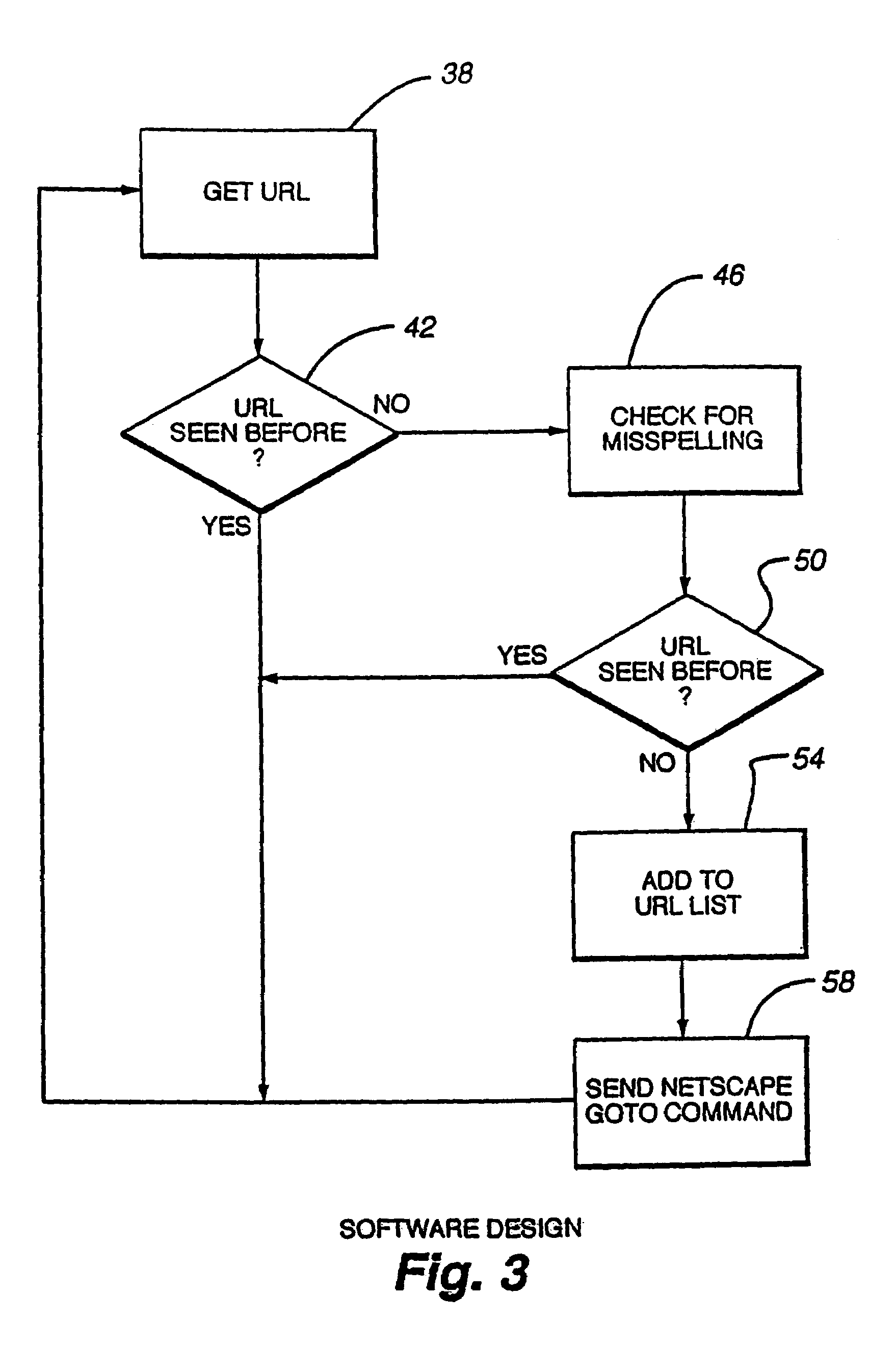
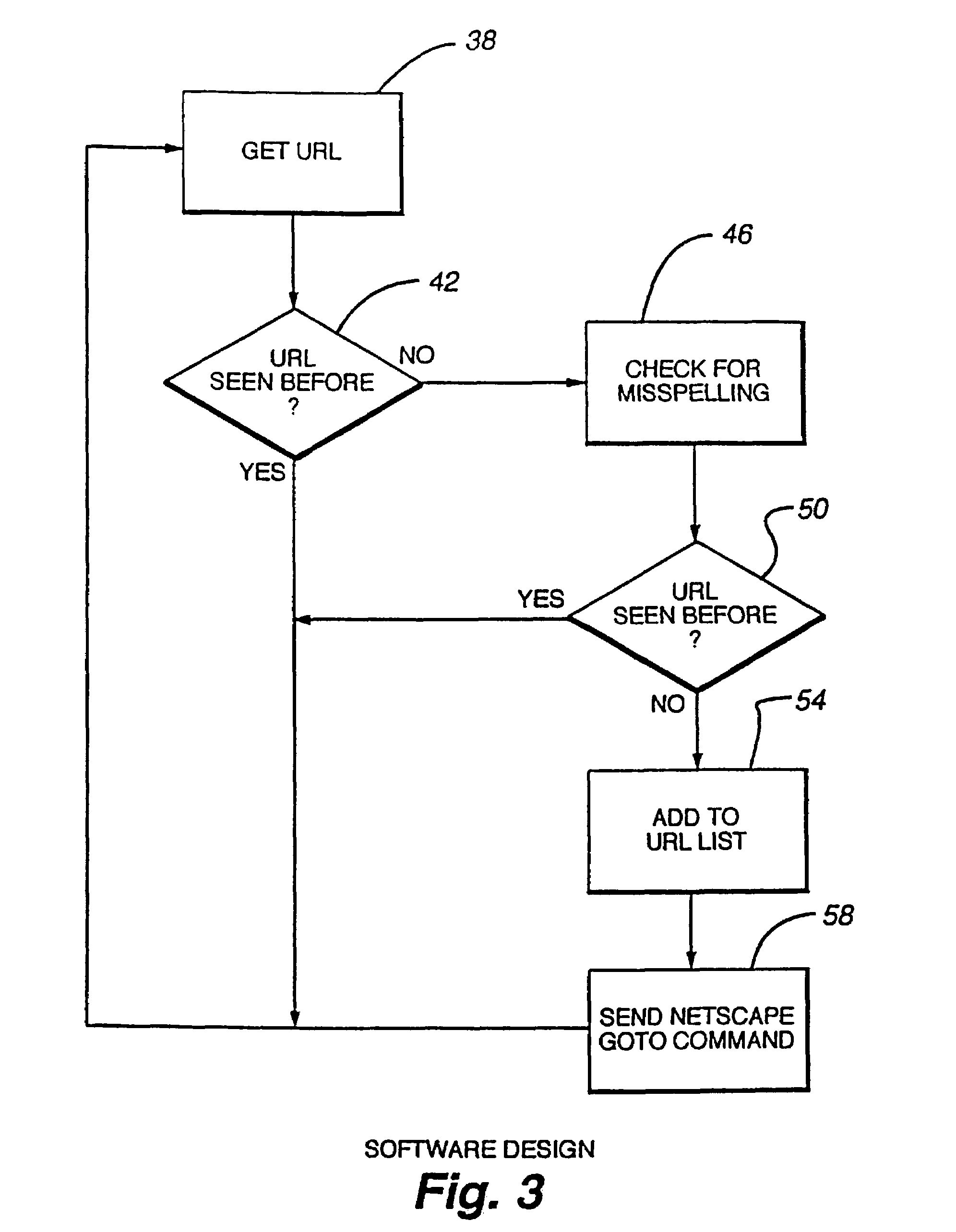
System and method for composing menus of URL-encoded bar code symbols while surfing the internet using an internet browser program
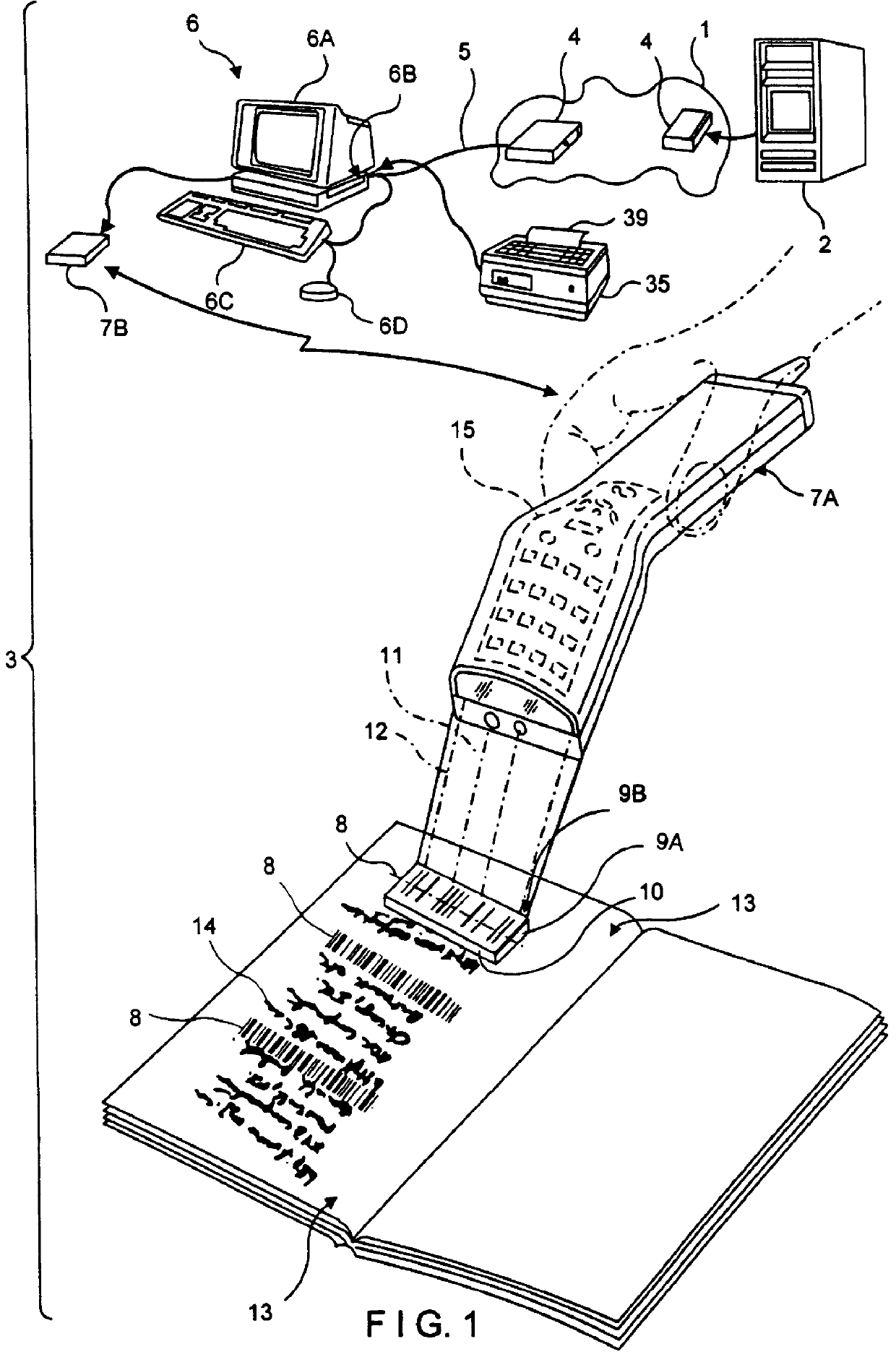
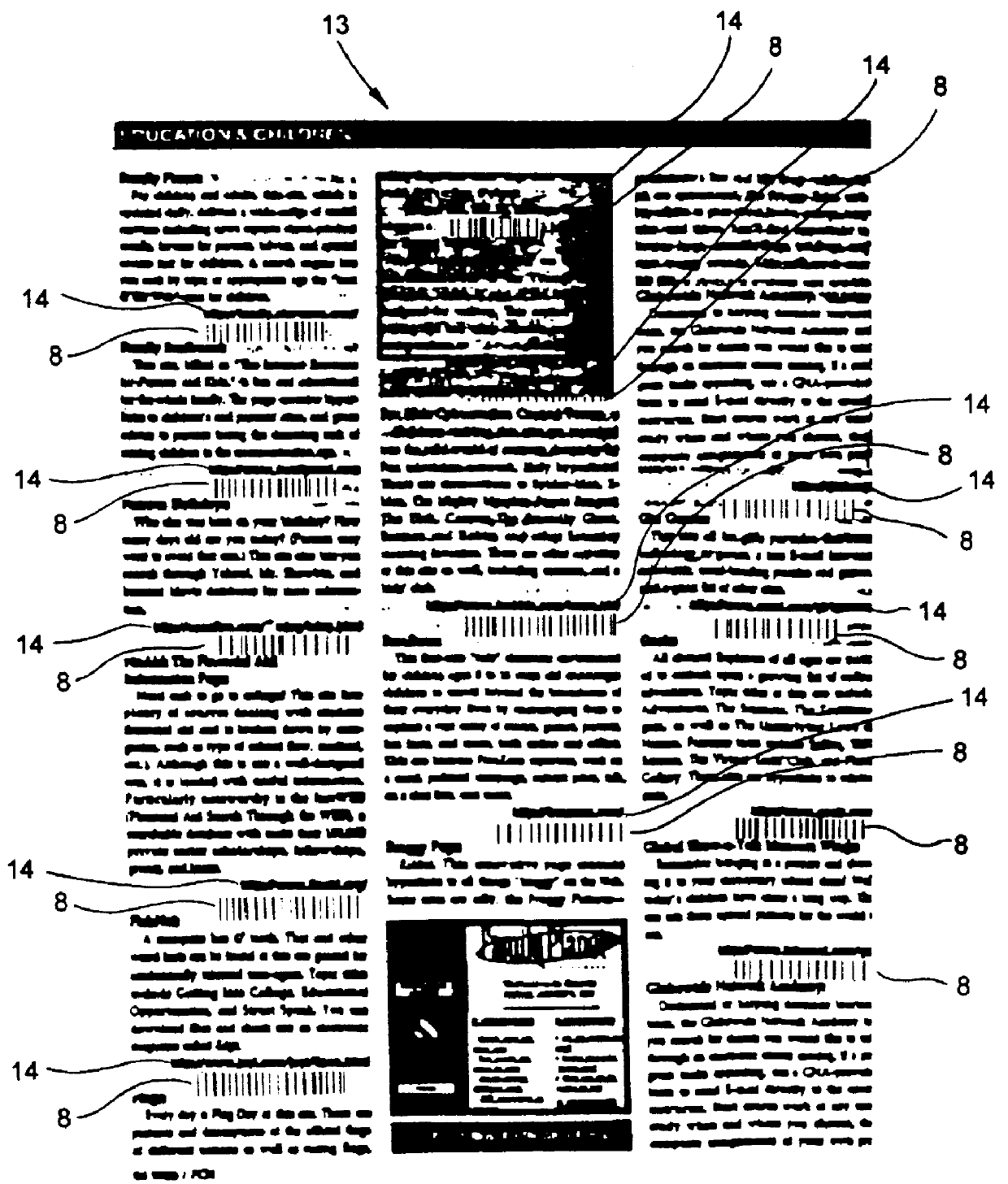
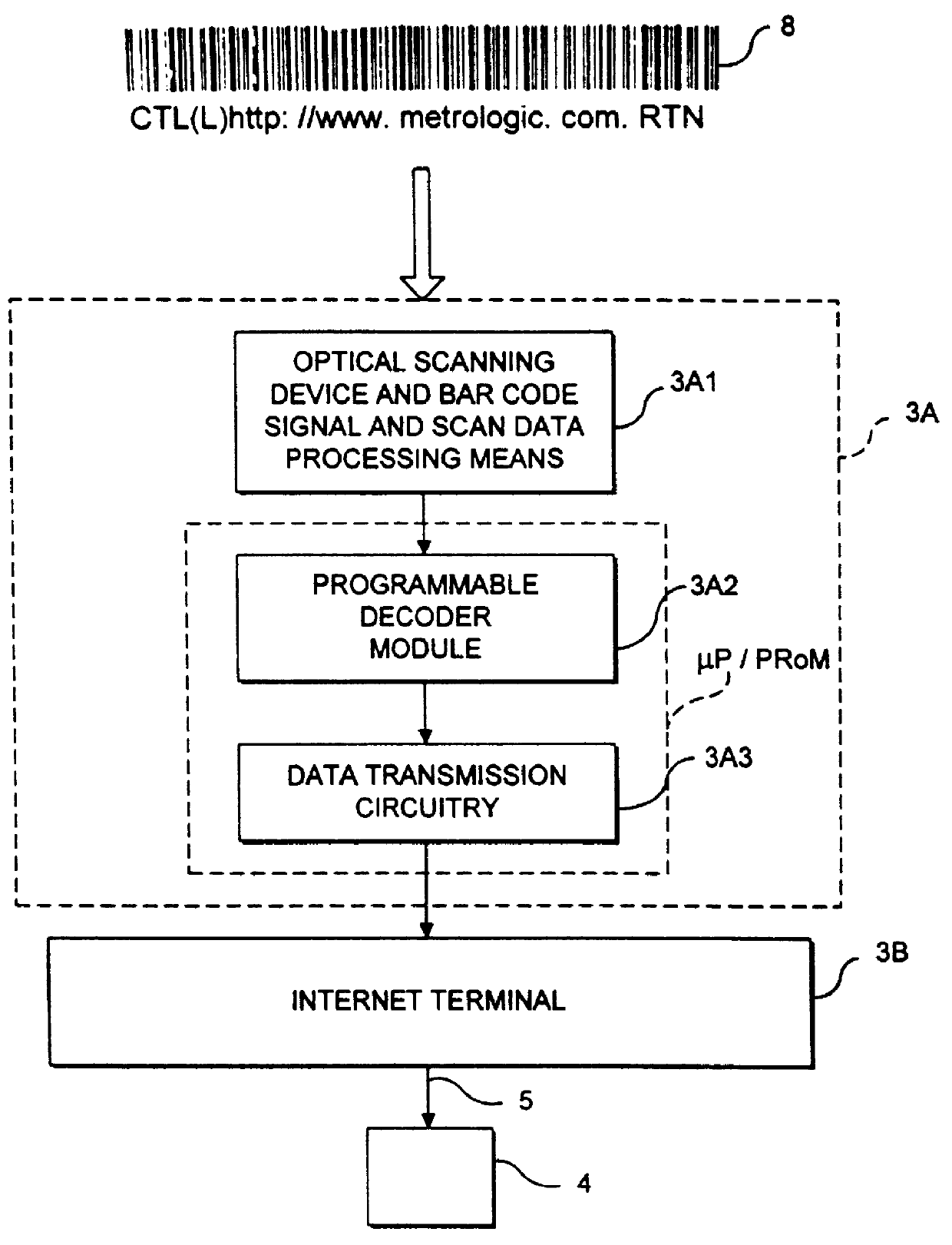
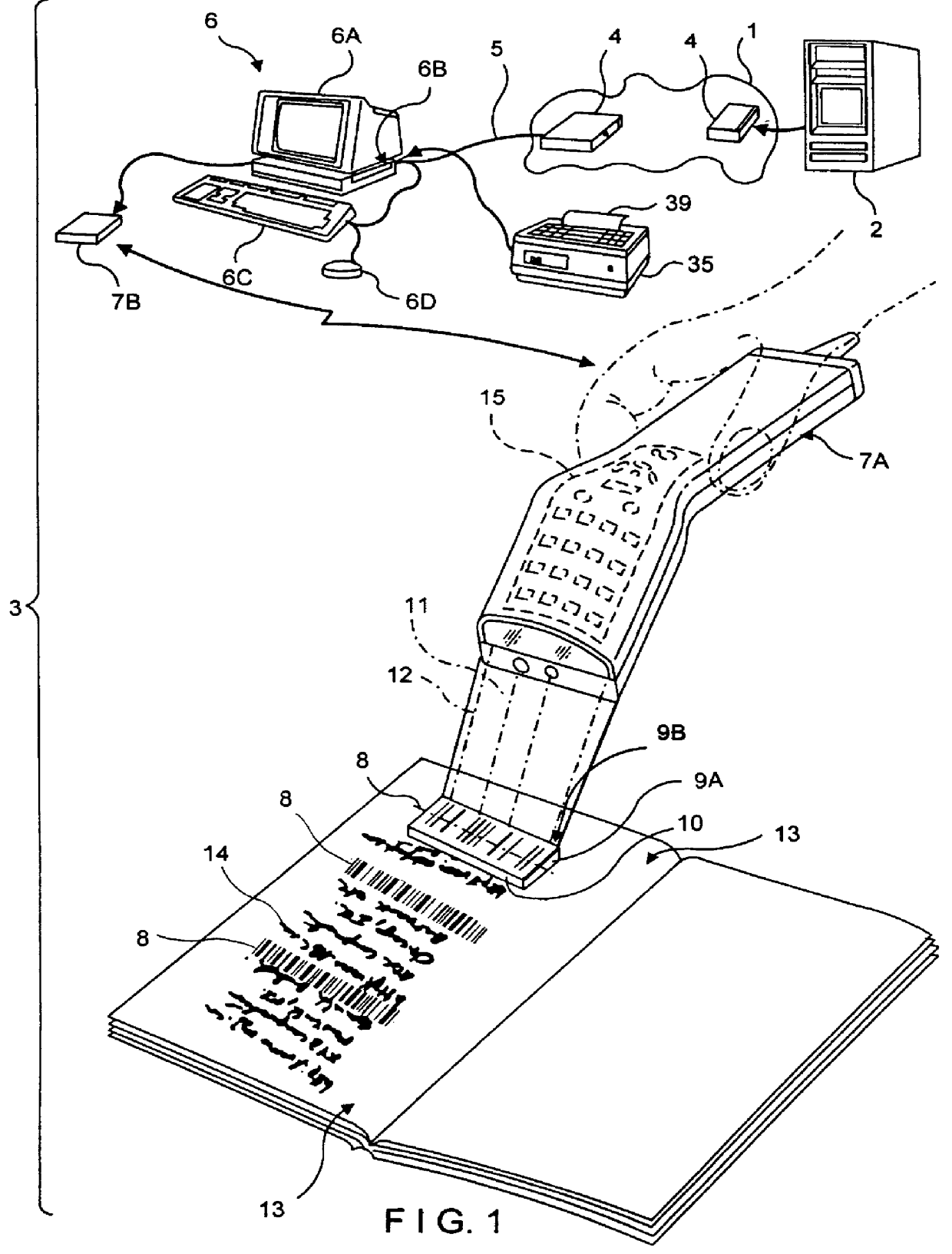
InactiveUS6045048AEasy accessDigital data information retrievalCharacter and pattern recognitionInformation resourceBarcode
A computer-based system is provided for composing menus of URL-encoded bar code symbols specifying the location of Internet-based information resources on the Internet. In the illustrative embodiment, the system comprises a computer system operably connectable to the Internet and including a visual display screen, a keyboard, and printer. The system also includes a GUI-based Internet browser program and a URL-menu composition program supported by the computer system. The function of the GUI-based Internet browser program is to enable a user to access and display Internet-based information resources stored on an Internet information server at a location specified by a Uniform Resource Locator (URL). The function of the URL-menu composition program is to enable the user to compose a menu of URL-encoded bar code symbols while surfing the Internet using the GUI-based Internet browser program. After the menu of URL-encoded bar code symbols has been composed, it may be edited and then printed on a selected print medium. By virtue of the present invention, any Internet-based information resource can be automatically accessed and displayed by reading its URL-encoded bar code symbol from the printed menu using a bar code symbol reader operably connected to an Internet-enabled computer system supporting a bar code driven Internet browser program.
Owner:METROLOGIC INSTR
Distributed administration of access to information
InactiveUS6785728B1Cathode-ray tube indicatorsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
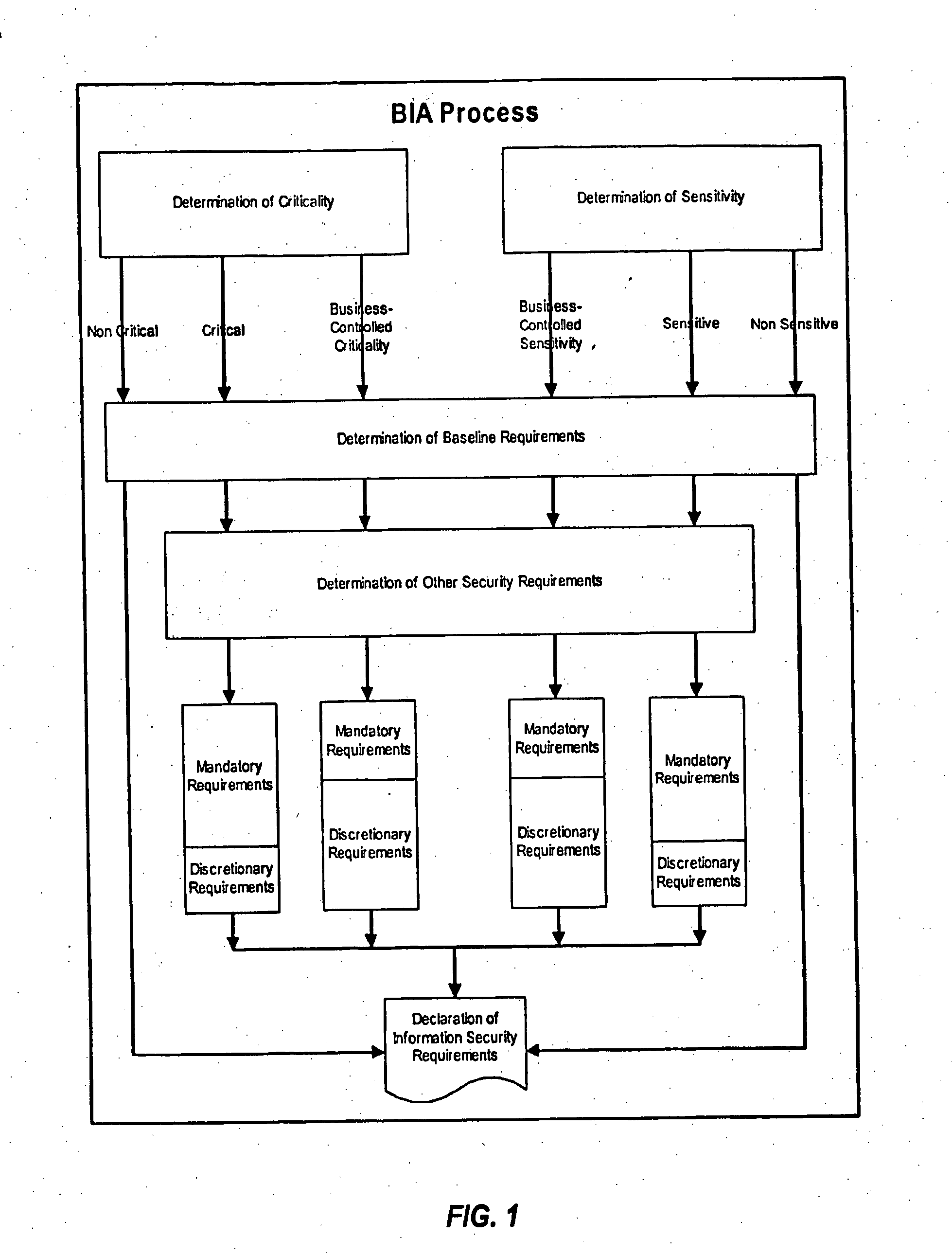
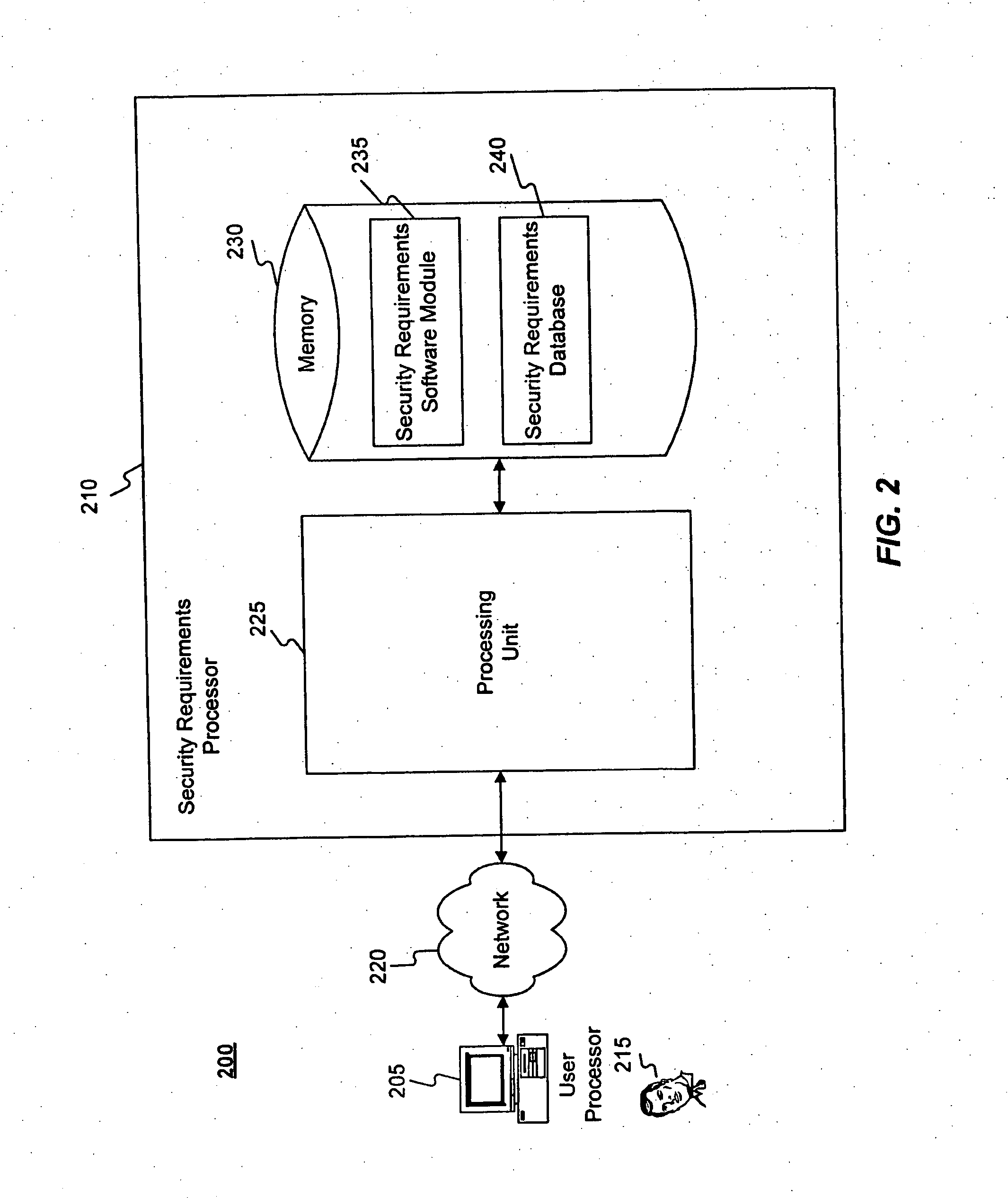
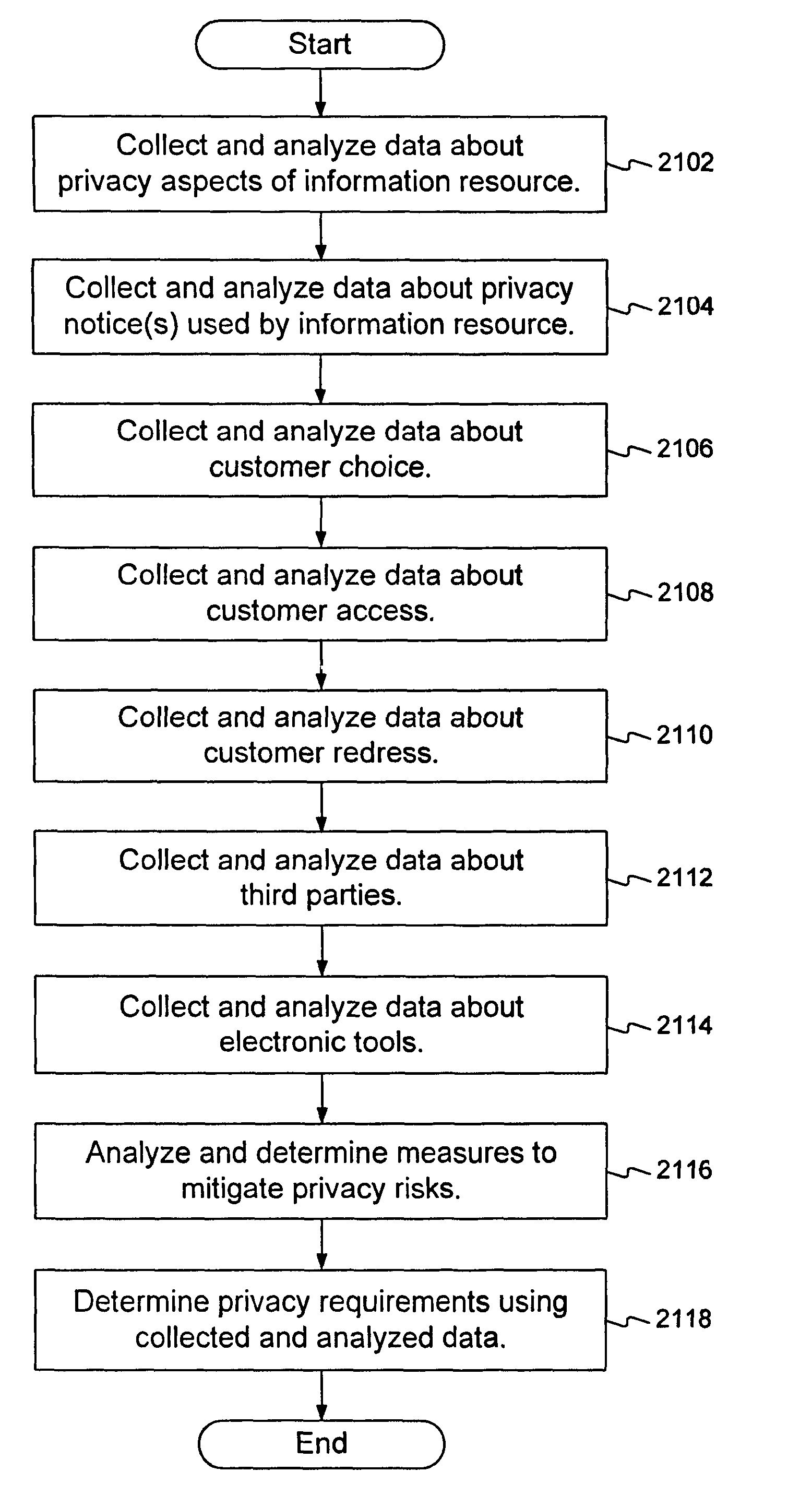
Methods and systems for determining privacy requirements for an informatin resource
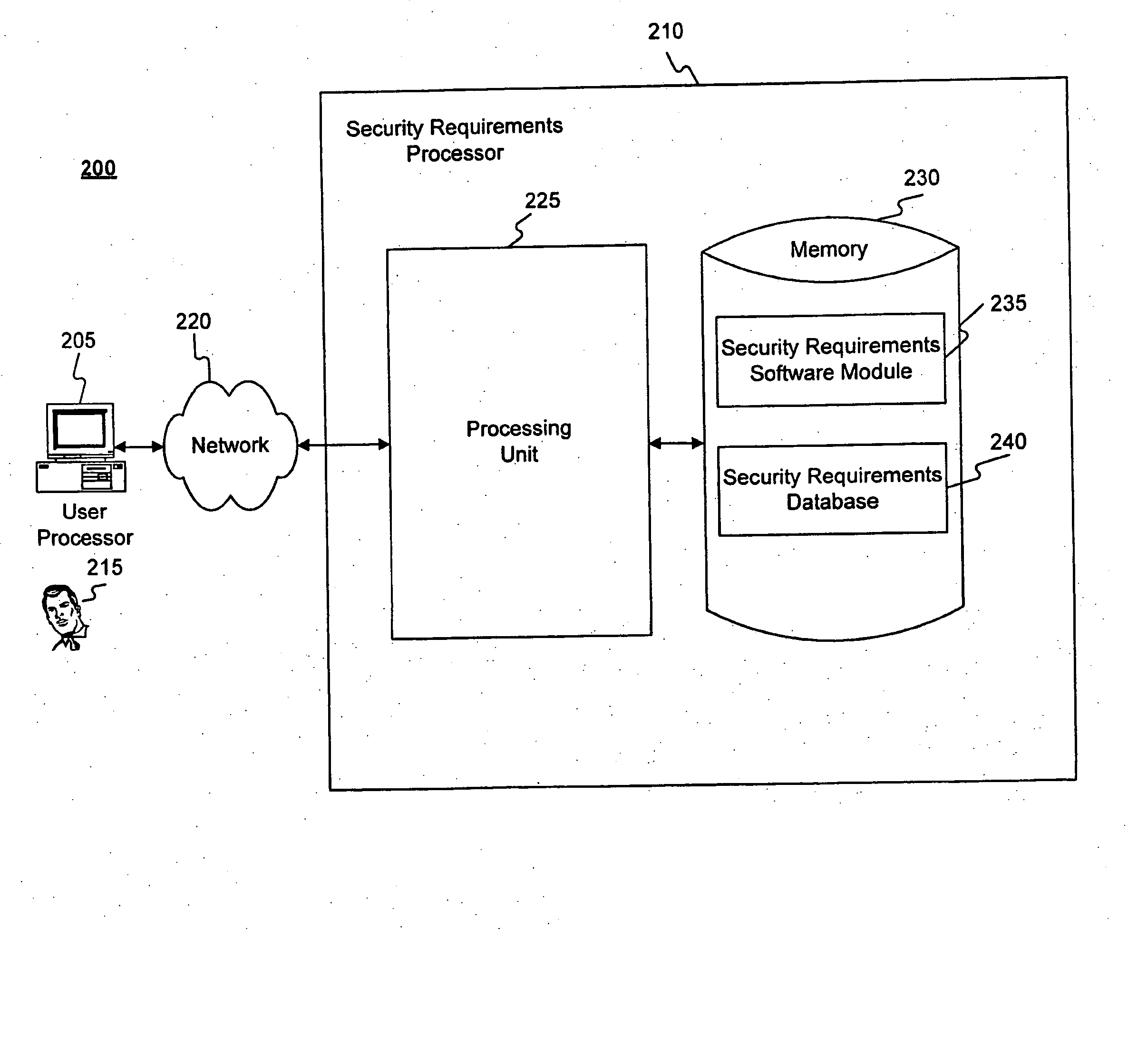
InactiveUS20080028435A1Digital data processing detailsAnalogue secracy/subscription systemsRetention periodPrivacy Impact Assessment
A privacy impact assessment is performed to determine and implement privacy requirements for any information resource that uses personal information. Data may be collected and analyzed regarding the information resource and the personal information, and applicable laws, regulations, and policies may be considered to determine privacy requirements. Such requirements may include, for example, access controls, information retention periods, systems requirements, and risk assessments.
Owner:US POSTAL SERVICE
Methods and systems for determining privacy requirements for an information resource
InactiveUS7966663B2Digital data processing detailsAnalogue secracy/subscription systemsRetention periodPrivacy Impact Assessment
A privacy impact assessment is performed to determine and implement privacy requirements for any information resource that uses personal information. Data may be collected and analyzed regarding the information resource and the personal information, and applicable laws, regulations, and policies may be considered to determine privacy requirements. Such requirements may include, for example, access controls, information retention periods, systems requirements, and risk assessments.
Owner:US POSTAL SERVICE
Log-on service providing credential level change without loss of session continuity
InactiveUS20040210771A1Digital data processing detailsUser identity/authority verificationInformation resourcePassword
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:SUN MICROSYSTEMS INC
Internet-based consumer product brand marketing communication system which enables manufacturers, retailers and their respective agents, and consumers to carryout product-related functions along the demand side of the retail chain in an integrated manner
InactiveUS20030009392A1Easy accessEasy alignmentDigital data information retrievalData switching by path configurationInformation resourceGeneric Product
An Internet-based consumer product brand marketing communication system which enables manufacturers, retailers and their respective agents, and consumers to carryout product-related functions along the demand side of the retail chain. A central RDBMS (i.e. data warehouse) stores a central database of consumer product related information resource files (IRFs) each IRF being indexed with a Universal Product Number (UPN) assigned thereto by the manufacturer of the consumer product, or its designated agent, which relates to the consumer product. A first subsystem enables a manufacturer's marketing, brand and / or product managers to create and manage a local RDBMS containing UPN-indexed IRFs related to the consumer products of the manufacturer being offered for sale in both physical and / or electronic marketplaces, and periodically transport the local RDBMS of UPN-indexed IRFs to the central RDBMS by electronic data transport techniques. The local RDBMS of UPN-indexed IRFs is selected by the manufacturer's marketing, brand and / or product managers so as to create a desired brand image for each the consumer product of the manufacturer. A second subsystem enables consumers to access one or more UPN-indexed IRFs in the central RDBMS, to request and obtain information about a manufacturer's consumer product so as to make informed / educated purchases along the demand side of the retail chain. A third subsystem enables manufacturers and their advertising and marketing agents to access one or more UPN-indexed IRFs in the central RDBMS to display consumer product advertisements to consumers, at or near the point of purchase or sale within both physical and / or electronic retail shopping environments so as to project the desired brand image to consumers. A fourth subsystem enables retailers and their marketing and promotional agents to access one or more UPN-indexed IRFs in the central RDBMS, to promote consumer products to consumers, at or near the point of purchase or sale within both physical and / or electronic retail shopping environments so as to promote the sale of such products in inventory.
Owner:PERKOWSKI THOMAS J
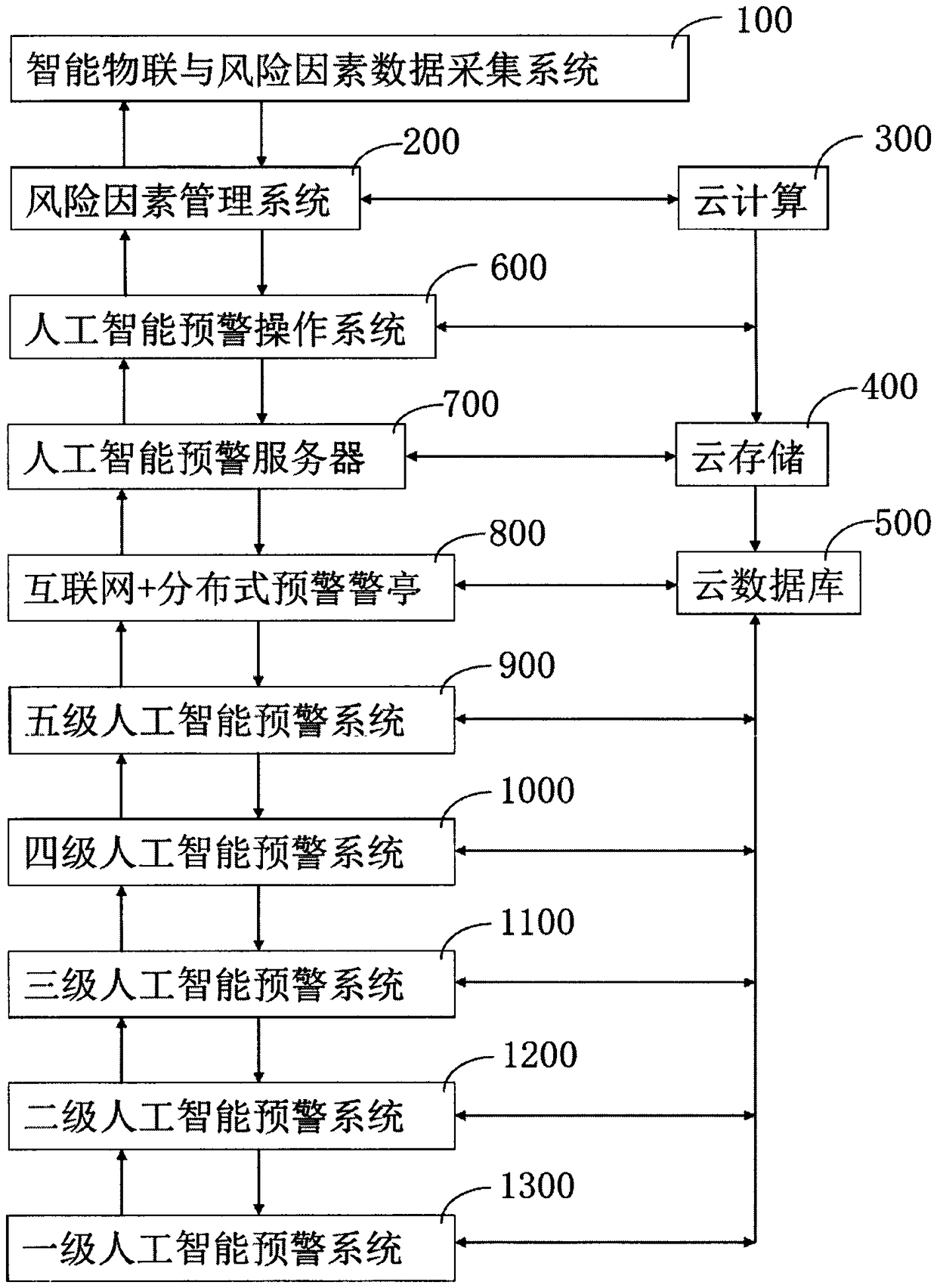
Artificial intelligence early warning system
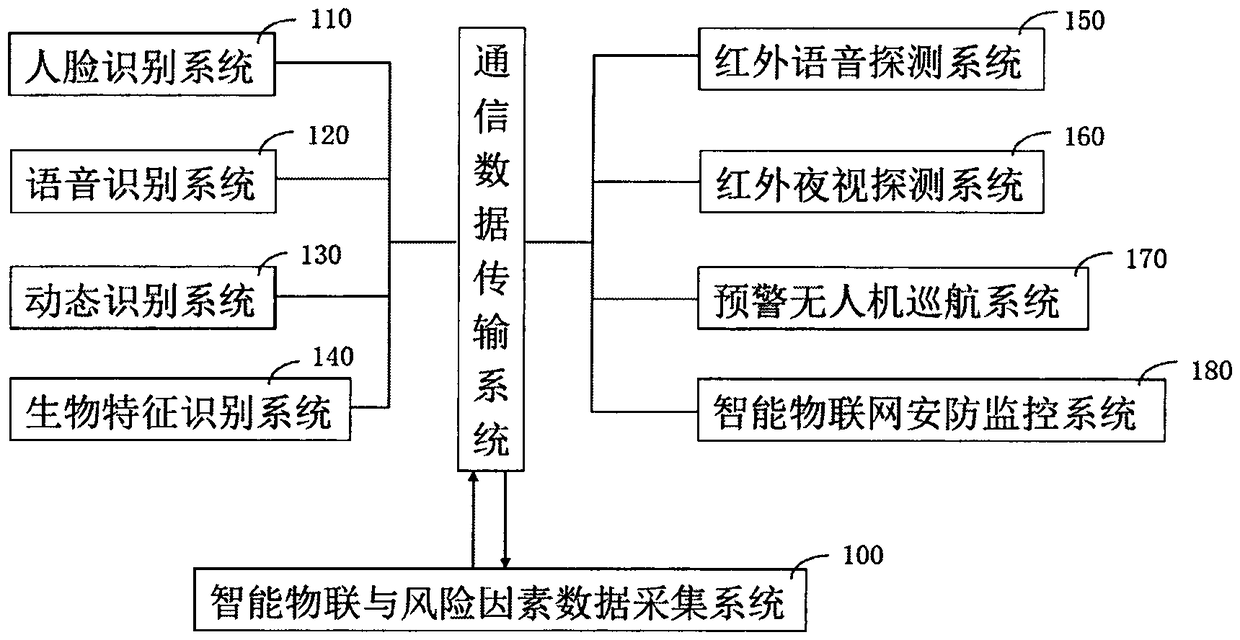
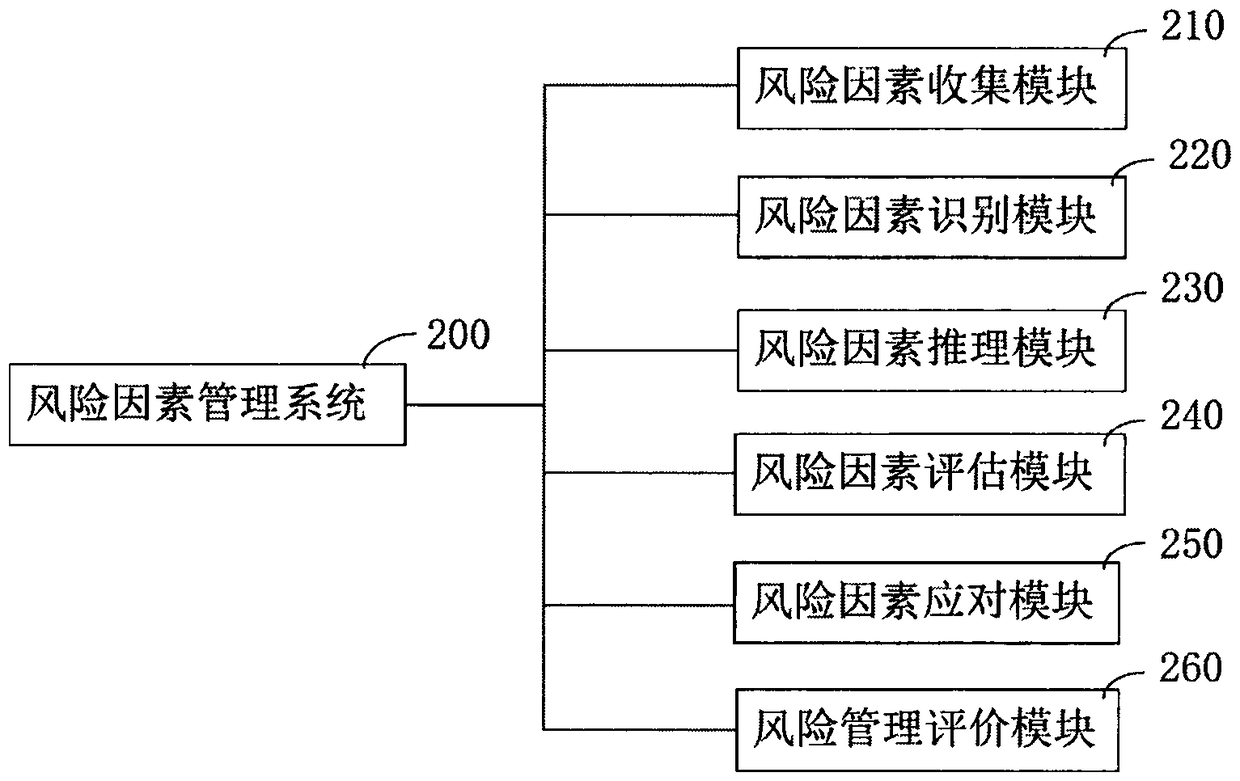
ActiveCN109447048APrevent overpassSemantic analysisOther databases indexingThree levelInformation resource
The invention relates to an artificial intelligence early warning system. The system comprises an intelligent Internet of Things and risk factor data acquisition system (100), and a risk factor management system (200), a cloud computing device (300), a cloud storage device (400), a cloud database (500), and an artificial intelligence early warning operation system (600), an artificial intelligenceearly warning server (700), an internet + distributed early warning police booth (800), a five-level artificial intelligence early warning system (900), a four-level artificial intelligence early warning system (1000), a three-level artificial intelligence early warning system (1100), a two-level artificial intelligence early warning system (1200) and a one-level artificial intelligence early warning system (1300). The artificial intelligence early warning system of the present invention collects, compares, analyzes, deduces, evaluates the risk factors, and carries out the cloud computing, cloud storage, graded alarming and prevention and control, so that all-weather 24-hour monitoring on monitoring points around the police box is achieved, a user can share information, the utilization rate of information resources is increased, and the safety guarantee is increased for maintaining the stability of the borderlands.
Owner:苏州闪驰数控系统集成有限公司
Web-based system and method for enabling a viewer to access and display HTML-encoded documents located on the world wide web (WWW) by reading URL-encoded bar code symbols printed on a web-based information resource guide
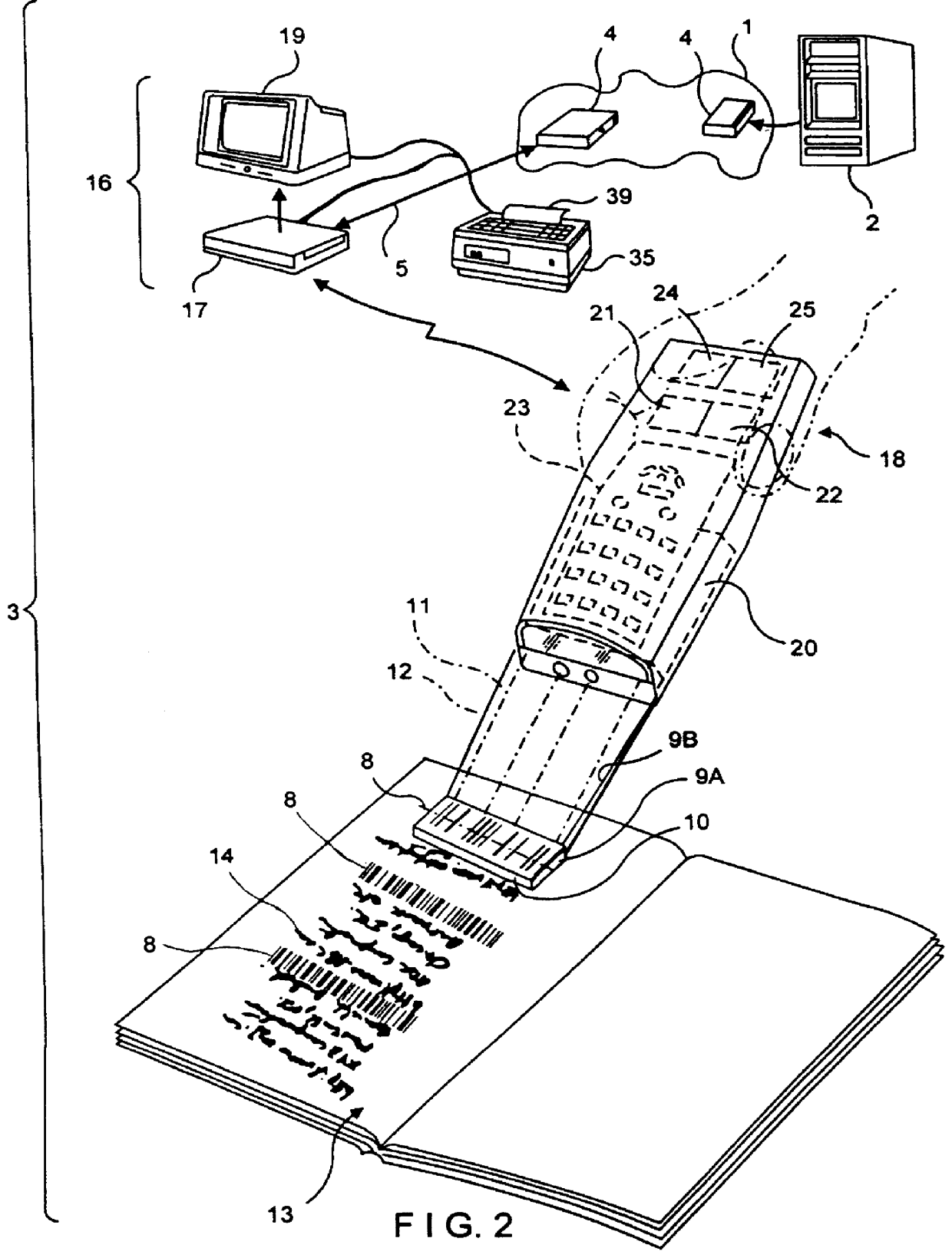
InactiveUS6076733AEasy accessDigital data information retrievalCharacter and pattern recognitionNetworking protocolInformation resource
A Web-based system and method for enabling an operator to access and display HTML-encoded documents located on the WWW. The system comprises one or more Internet information servers, an Internet access terminal, and an audio-visual monitor. The Internet information servers store a plurality of HTML-encoded documents at a plurality of storage locations specified by a plurality of Uniform Resource Locators (URLs). The Internet access terminal is operably connected to the infrastructure of the Internet and embodies a GUI-based Internet browser program, supporting the TCP / IP networking protocol. The Internet access terminal includes a bar code symbol reader for reading bar code symbols. The bar code symbol reader is programmed for reading bar code symbols encoded with URLs specifying the location of HTML-encoded documents on the WWW, and producing data representative of each encoded URL. In response to reading a URL-encoded bar code symbol on the pages of a printed WWW-site guide, the bar code symbol reader produces data representative of the URL, and the produced data is transmitted to the Internet access terminal. Thereupon, the GUI-based Internet browser program automatically accesses the HTML-encoded document specified by the URLusing the TCP / IP networking protocol, and the Internet access terminal automatically displays the accessed HTML-encoded document on the audio-visual monitor for viewing.
Owner:METROLOGIC INSTR INC
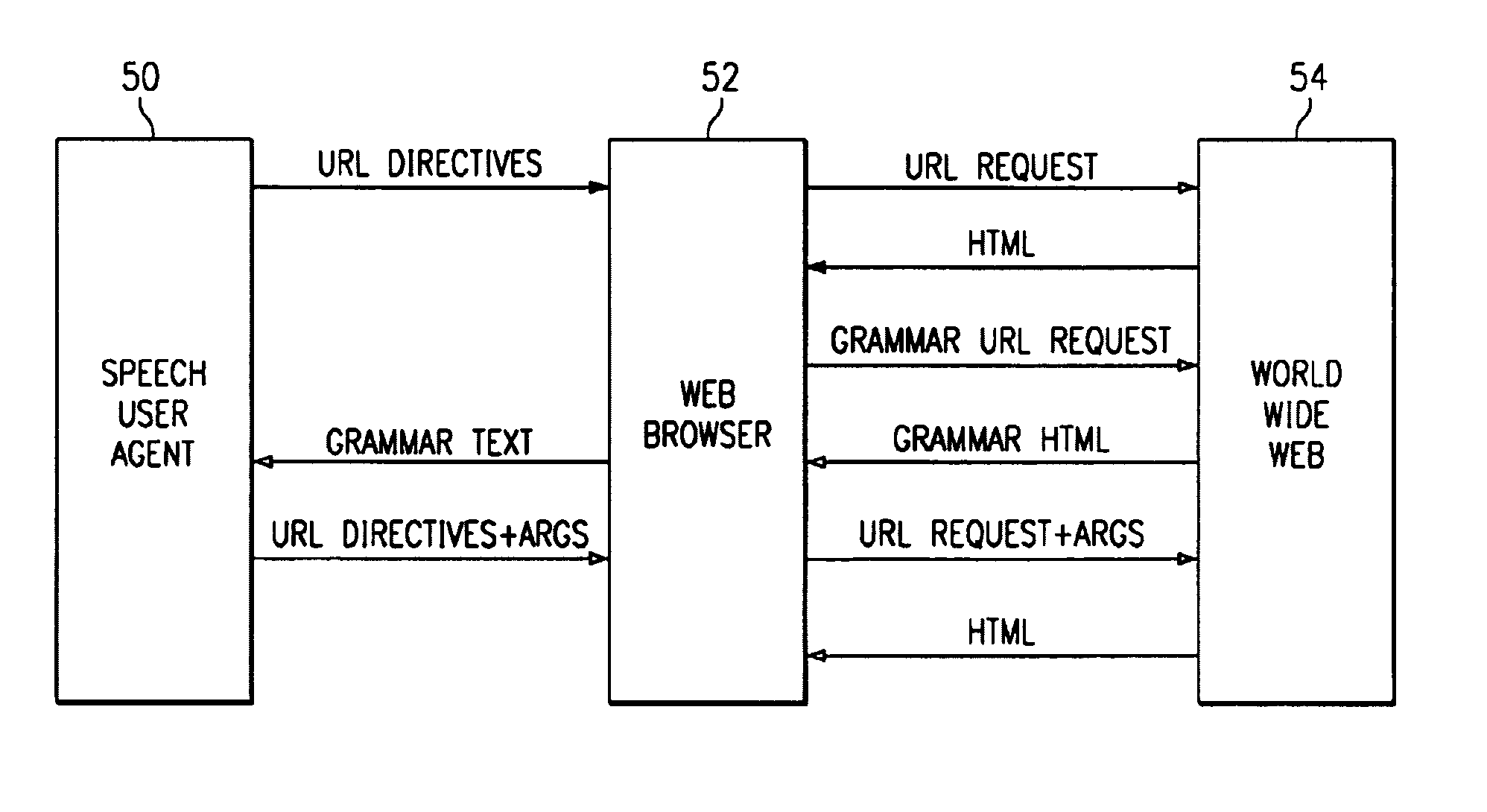
Voice activated apparatus for accessing information on the World Wide Web
InactiveUS7020609B2Easy accessAvoid overwritingAutomatic exchangesSpeech recognitionInformation resourceComputer module
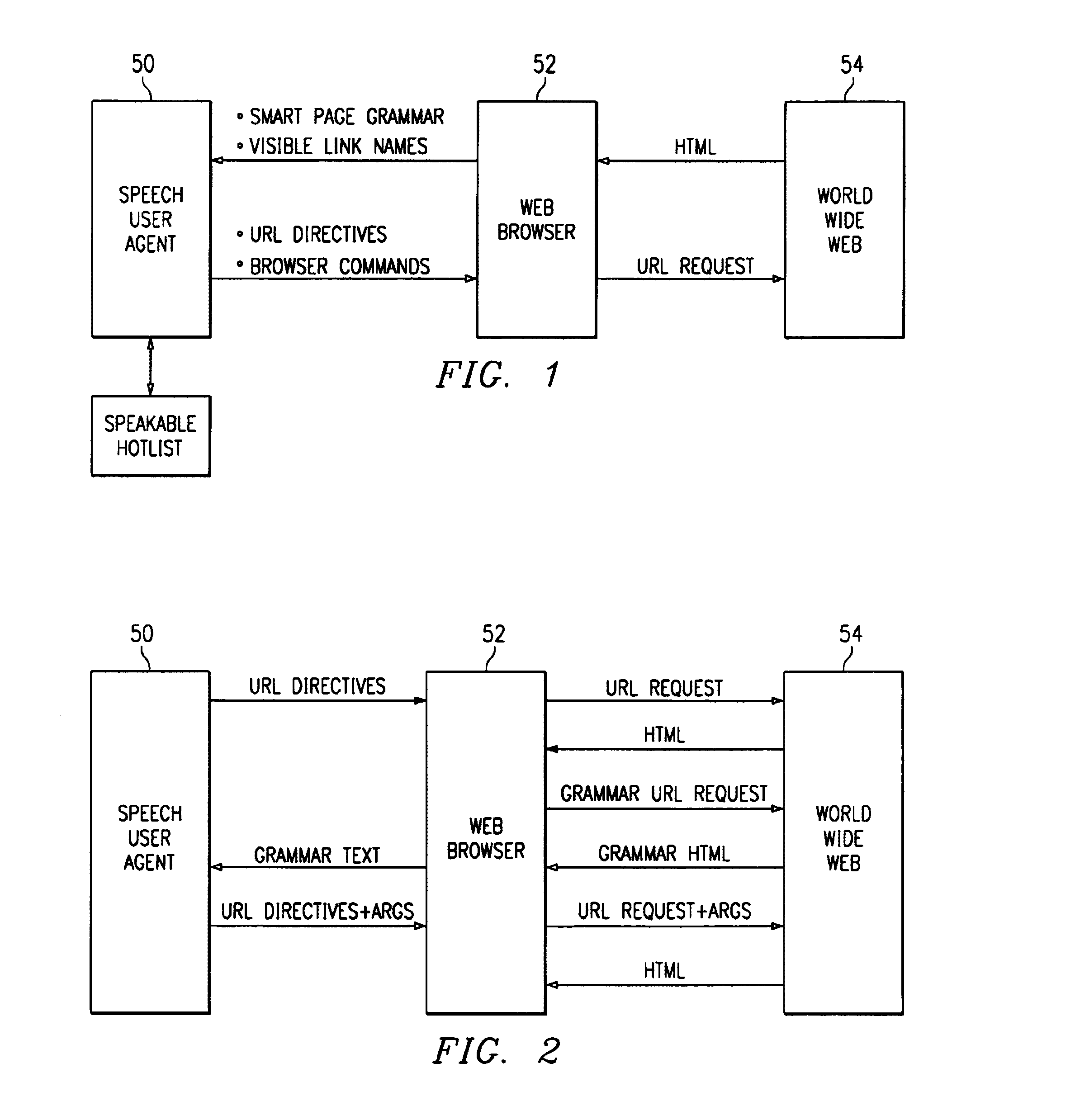
This is a voice activated Hypermedia system using grammatical metadata, the system comprising: a speech user agent; a browsing module; and an information resource. The system may include: embedded intelligence in hypermedia source; a means for processing the actions of a user based on the embedded intelligence; a means for returning a result of the actions to the user. In addition, the hypermedia source maybe a HTML page or an instructional module for communicating allowed actions by a user. The system may also include embedded intelligence as a grammar or reference to a grammar. The grammar may be dynamically added to a speech recognizer. In addition, the actions can come from a speech recognizer. Furthermore, the system may include voice activated hypermedia links and intelligent modules that process information from the information resources for allowing actions from the user. Other devices, systems and methods are also disclosed.
Owner:TEXAS INSTR INC
System and method for providing global information on risks and related hedging strategies
InactiveUS20050144114A1Increase productivityIncrease valueFinanceSpecial data processing applicationsAnalytic modelManagement tool
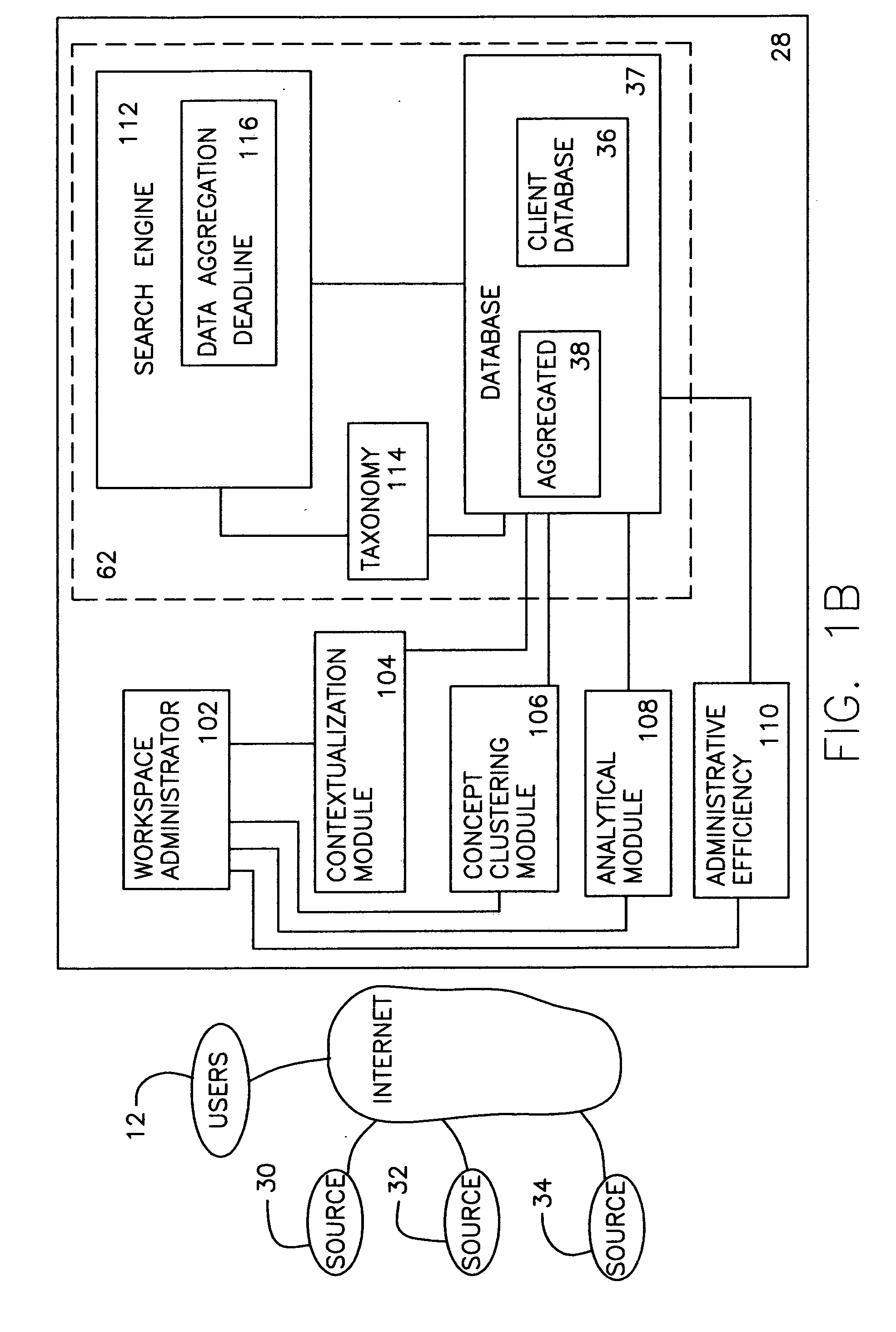
The present invention provides a system and method for information and data aggregation and analysis which provides risk managers, benefits managers, brokers, insurers and other insurance professional to have access to information resources, knowledge management tools, and powerful analytical models needed to increase their value and productivity. In accordance with one embodiment of the invention, the system and method provided is designed for information and data aggregation that allows for the compilation of data for mining and categorization by a knowledge management system, which stores all retrieved information in accordance with categories provided by a categorization engine referred to as a Taxonomy module. A contextualization module is configured to retrieve relevant information, based on various factors, including the user's profile, and the user's particular task. The system dynamically provides relevant information as the user interacts and conducts various tasks. The stored information is analyzed by a concept clustering module, so that various concepts relating to a particular topic can be uncovered and stored. In accordance with another embodiment of the invention, the system provides for various analytical tools that allow users to carry on with highly complex analysis of insurance related topics. The range of available analytical tool dynamically varies based on the user's needs and research topics. In accordance with yet another embodiment of the invention, the system provides for a unique interactive workspace that combines the features explained above in a logical manner. To this end, the system interface provides for various job templates, so as to enable the user's to carry various projects by a template driven task assignments. As the user navigates through the workspace, the range of available information to the user changes, based on the user's profile and navigation pattern.
Owner:ADVISEN
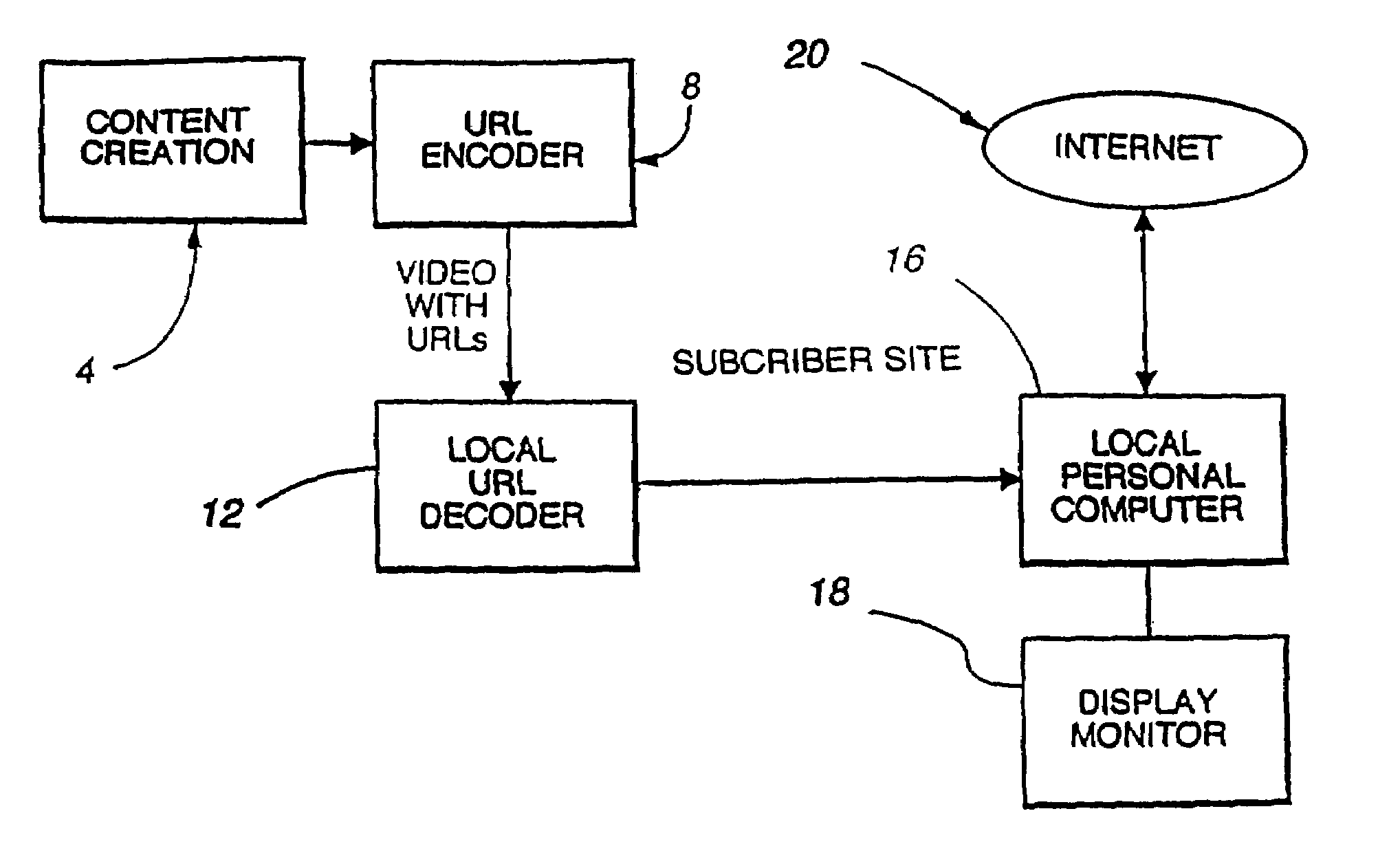
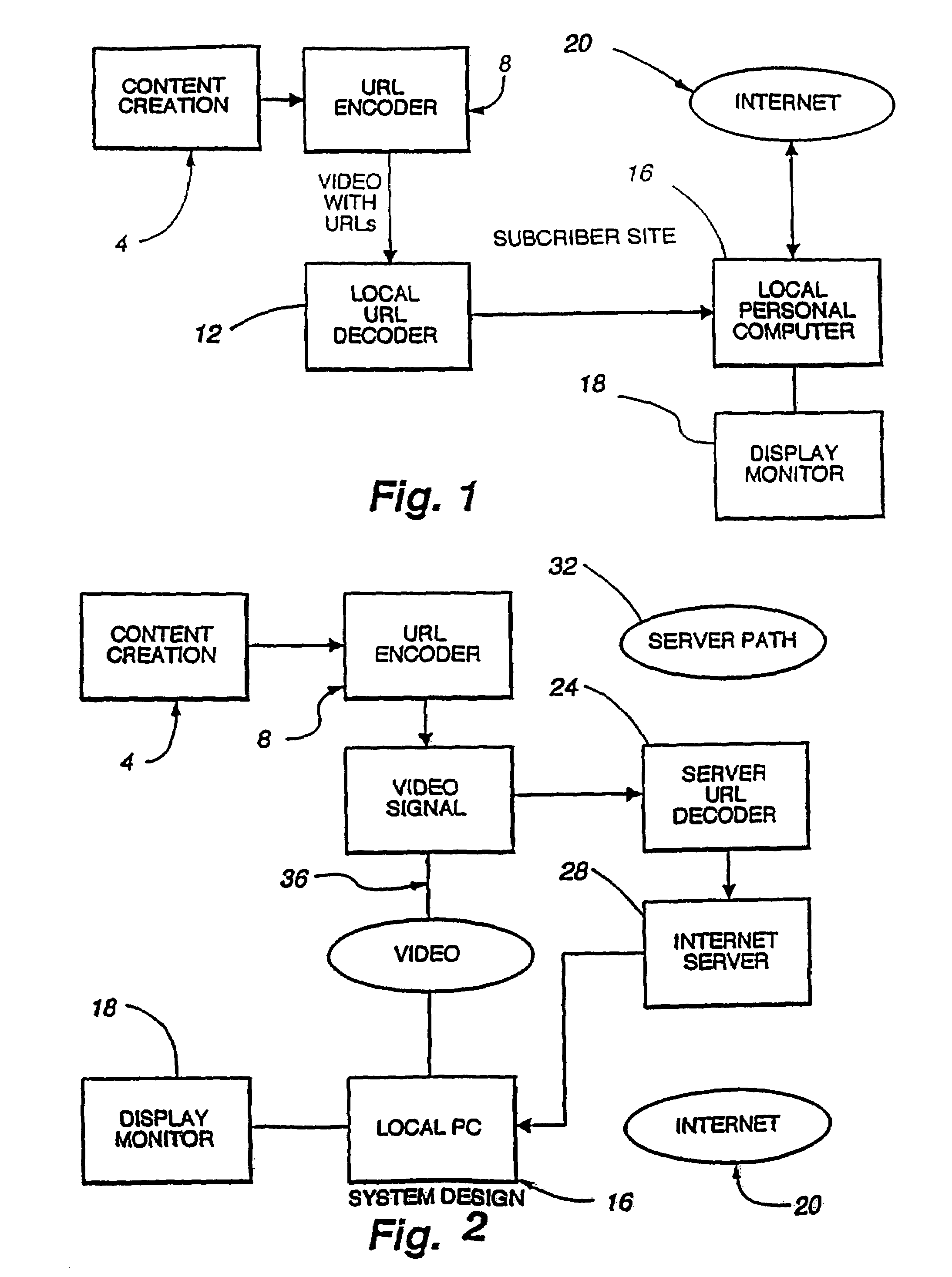
Enhanced video programming system and method for incorporating and displaying retrieved integrated Internet information segments
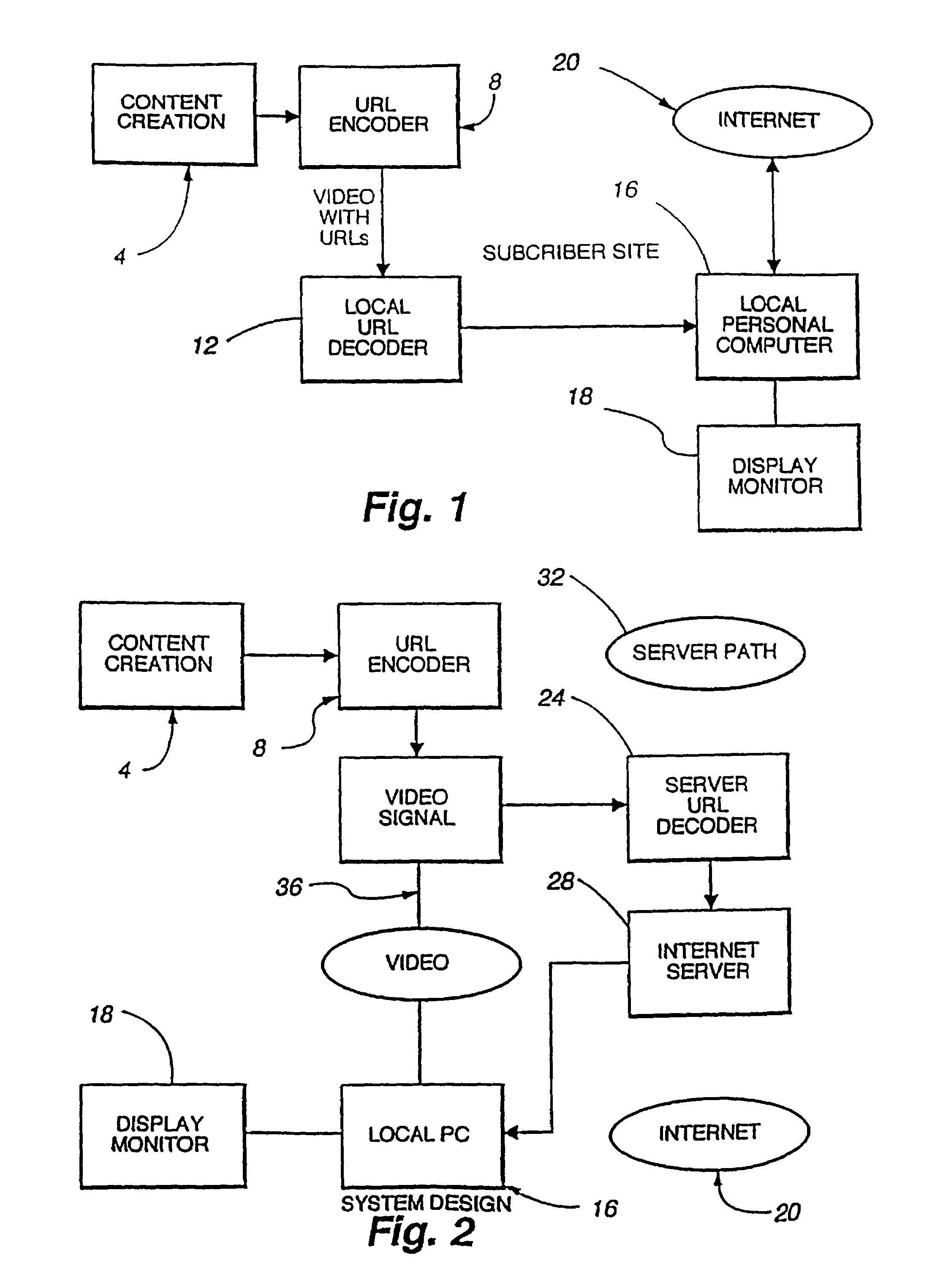
InactiveUS7243139B2Information receivedTelevision system detailsRecording carrier detailsWeb siteInformation resource
A system for integrating video programming with the vast information resources of the Internet. A computer-based system receives a video program with embedded uniform resource locators (URLs). The URLs, the effective addresses of locations or Web sites on the Internet, are interpreted by the system and direct the system to the Web site locations to retrieve related Web pages. Upon receipt of the Web pages by the system, the Web pages are synchronized to the video content for display. The video program signal can be displayed in a video window on a conventional personal computer screen. The actual retrieved Web pages are time stamped to also be displayed, on another portion of the display screen, when predetermined related video content is displayed in the video window. As an alternative, the computer-based system receives the URLs directly through an Internet connection, at times specified by TV broadcasters in advance. The system interprets the URLs and retrieves the appropriate Web pages. The Web pages are synchronized to the video content for display in conjunction with a television program being broadcast to the user at that time. This alternative system allows the URLs to be entered for live transmission to the user.
Owner:OPEN TV INC
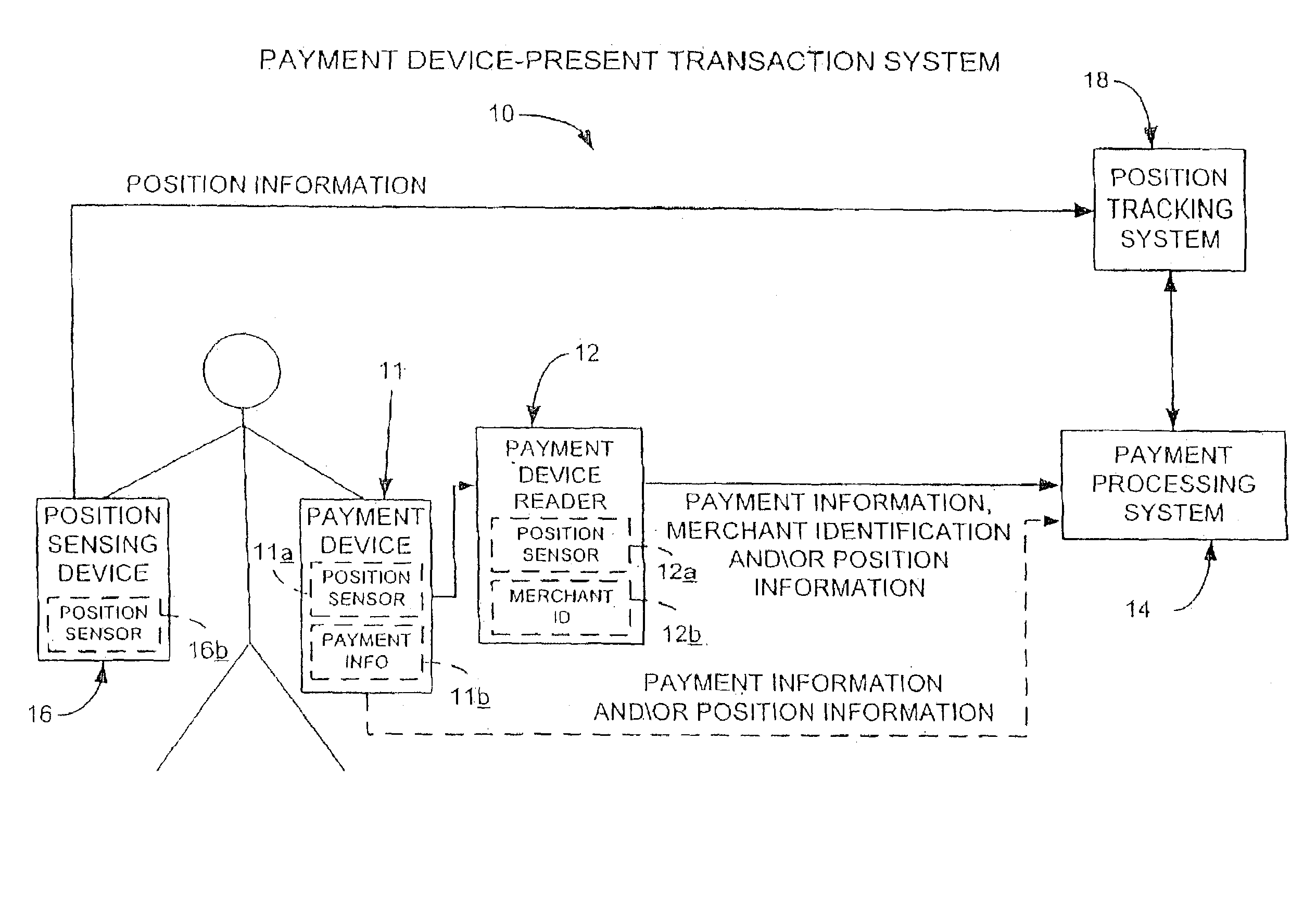
Location based fraud reduction system and method
ActiveUS7376431B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCredit cardTelecommunications
Likelihood of fraud is reduced by having at least one of an identifier of a location from where a request is submitted or information that can lead to identification of the location, submitted with or in addition to a request. Then, determination is made to whether to service the request, based at least in part on the location from where the request is submitted. In various embodiments, the location may be compared against predetermined permissible location(s) or a current user location. The request may be a request to charge an amount against an account, such as a credit card account, a request to access a physical resource, such as a VPN, or an informational resource, such as account information, or a request to access a secured area.
Owner:BLOCK INC
Search engine system and method utilizing context of heterogeneous information resources
InactiveUS6490579B1Data processing applicationsWeb data indexingInformation recoveryInformation resource
A system and method for facilitating the retrieval of information from a system of distributed computers or information resources is disclosed. In particular, the system and method of the present invention improves upon metasearch techniques by including information resource profiles that provide directives to the metasearch engine for facilitating information recovery. These information resource profiles additionally allow for metasearches to recover information from non-indexed information resources such as when browsing the web. Contextual searching is further provided via a grouping of the information resource profiles. The present invention is further directed to tools for the creation and management of the information resource profiles.
Owner:PEROT SYSTEMS
System and method for composing menus of URL-encoded bar code symbols while using internet browser program
InactiveUS6068188AEasy to visitDigital data information retrievalCharacter and pattern recognitionInformation resourceBarcode
A computer-based system is provided for composing menus of URL-encoded bar code symbols specifying the location of Internet-based information resources on the Internet. In the illustrative embodiment, the system comprises a computer system operably connectable to the Internet and including a visual display screen, a keyboard, and printer. The system also includes a GUI-based Internet browser program and a URL-menu composition program supported by the computer system. The function of the GUI-based Internet browser program is to enable a user to access and display Internet-based information resources stored on an Internet information server at a location specified by a Uniform Resource Locator (URL). The function of the URL-menu composition program is to enable the user to compose a menu of URL-encoded bar code symbols while using the GUI-based Internet browser program. After the menu of URL-encoded bar code symbols has been composed, it may be edited and then printed on a selected print medium. By virtue of the present invention, any Internet-based information resource can be automatically accessed and displayed by reading its URL-encoded bar code symbol from the printed menu using a bar code symbol reader operably connected to an Internet-enabled computer system supporting a bar code driven Internet browser program.
Owner:METROLOGIC INSTR
Enhanced video programming system and method for incorporating and displaying retrieved integrated Internet information segments
InactiveUS7409437B2Information receivedTelevision system detailsRecording carrier detailsWeb siteInformation resource
A system for integrating video programming with the vast information resources of the Internet. A computer-based system receives a video program with embedded uniform resource locators (URLs). The URLs, the effective addresses of locations or Web sites on the Internet, are interpreted by the system and direct the system to the Web site locations to retrieve related Web pages. Upon receipt of the Web pages by the system, the Web pages are synchronized to the video content for display. The video program signal can be displayed in a video window on a conventional personal computer screen. The actual retrieved Web pages are time stamped to also be displayed, on another portion of the display screen, when predetermined related video content is displayed in the video window. As an alternative, the computer-based system receives the URLs directly through an Internet connection, at times specified by TV broadcasters in advance. The system interprets the URLs and retrieves the appropriate Web pages. The Web pages are synchronized to the video content for display in conjunction with a television program being broadcast to the user at that time. This alternative system allows the URLs to be entered for live transmission to the user.
Owner:OPEN TV INC
Web-Based User-Dependent Customer Service Interaction with Co-Browsing
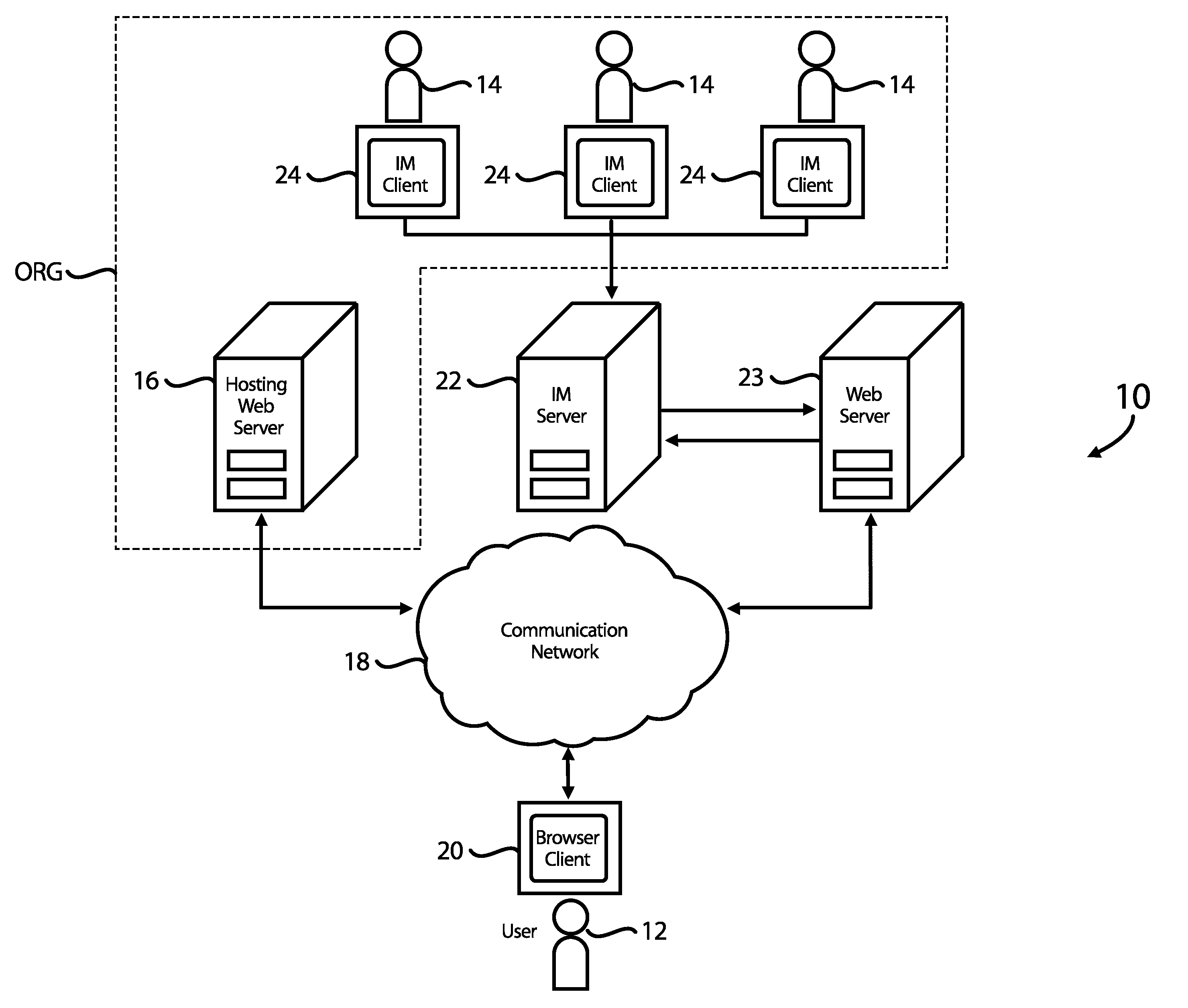
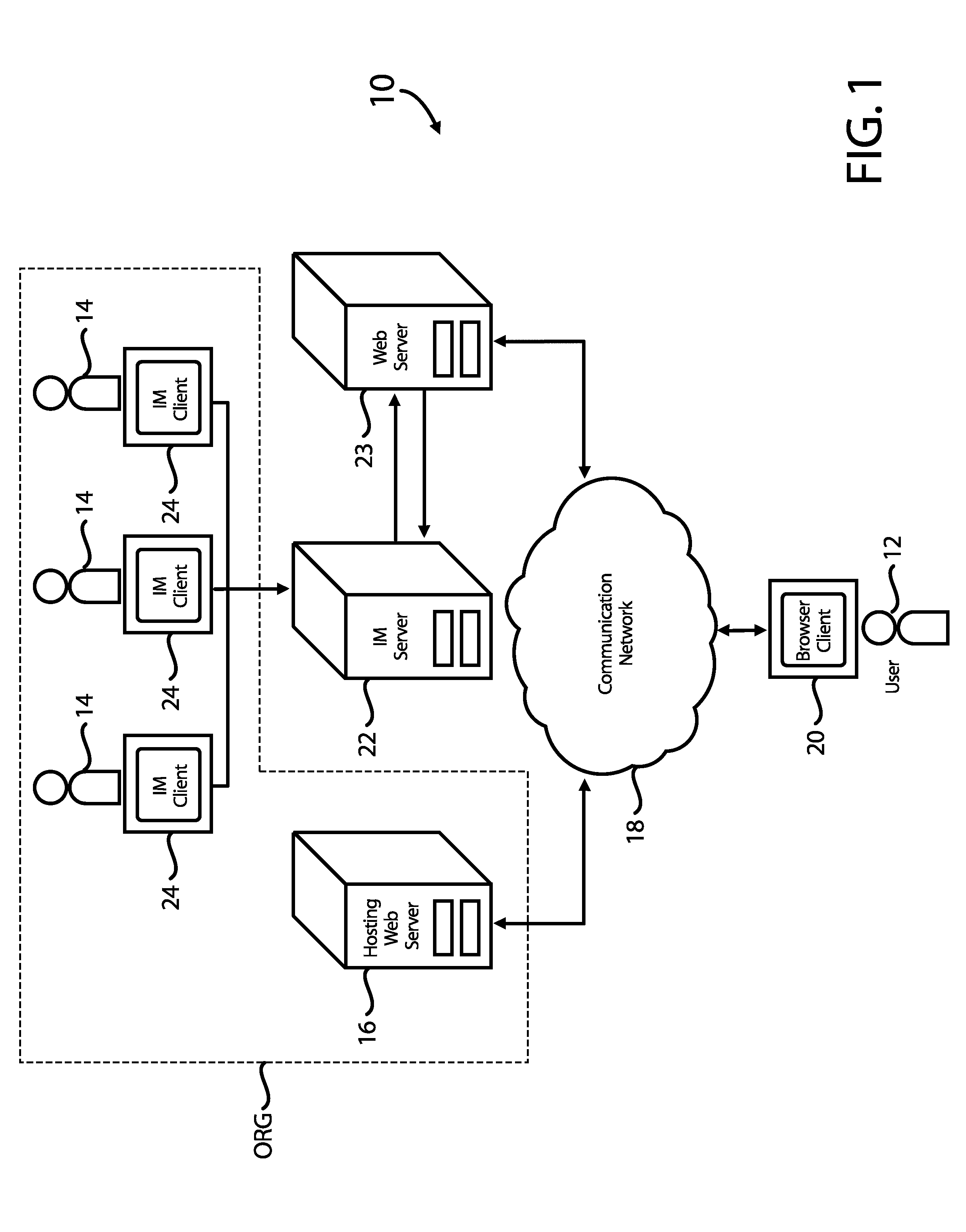
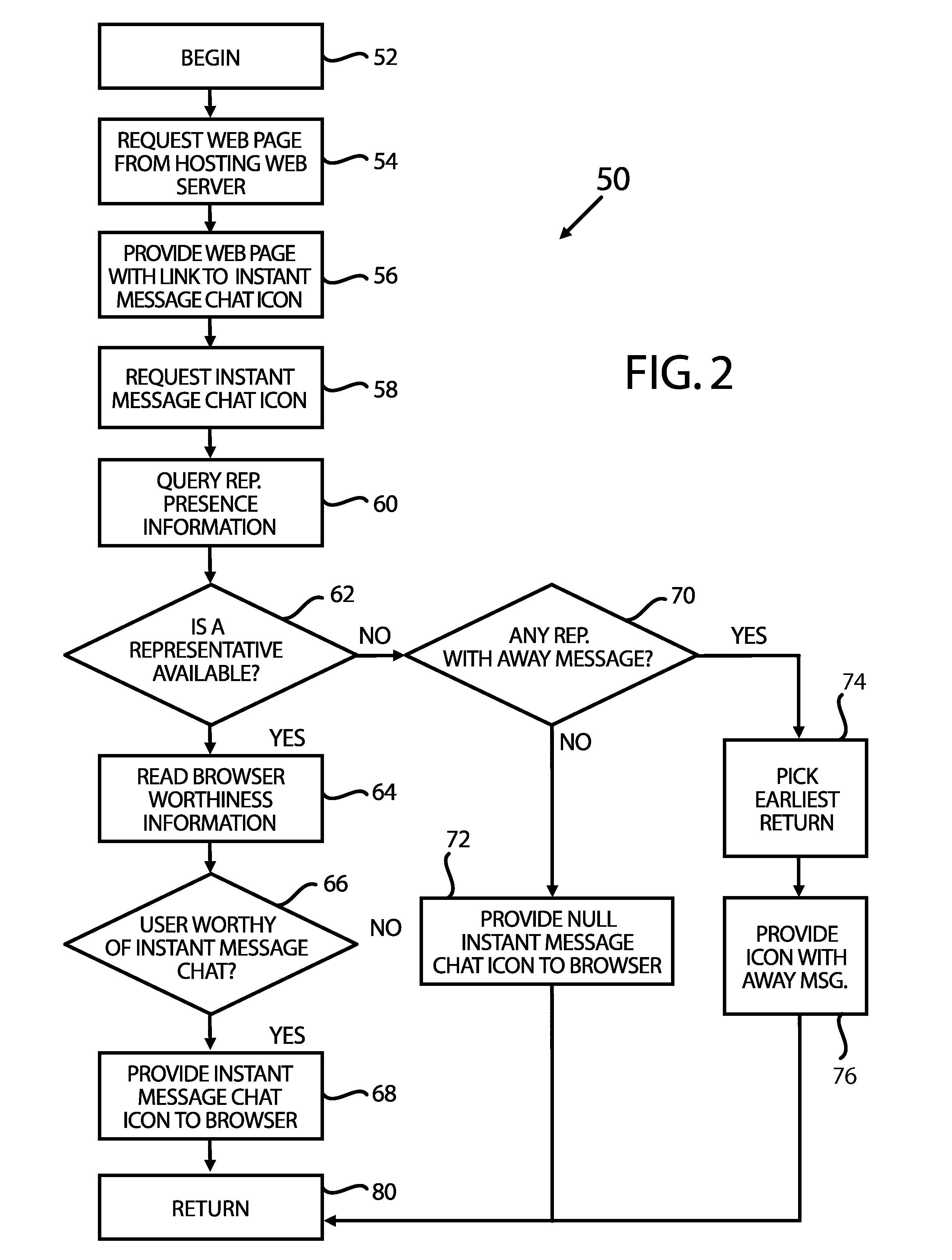
InactiveUS20080052377A1Multiple digital computer combinationsData switching networksWeb siteInformation resource
Systems and methods for communication between customer service representatives and users, for example, users of a website, are disclosed. In connection with rendering an informational resource, such as a World Wide Web page, on a browser, a user is provided with an indication that communication between a representative and the user is possible only if presence information for the representative indicates that the representative is available. If no representative is available, the user is provided with a null image, although the user may instead be shown the presence information for the representative expected to be available soonest. The ability to communicate with a representative may depend on the user's characteristics and history. The mode of communication offered to the user may vary, and may also depend on user characteristics, organizational preferences, and other factors. Users and representatives can also collaboratively co-browse web pages.
Owner:LIGHT ROBERT
Visual electronic library
InactiveUS20050102610A1Digital computer detailsNatural language data processingDocumentation procedureInformation resource
A method and system of generation, organization and presentation of web pages or computer graphic user interfaces on computer, computer peripheral devices, electronic equipment, digital processing systems, and other information resources are disclosed. Modeling physical books, bookshelves and libraries, Visual Library comprises Visual Bookshelves, while Visual Bookshelf comprises Visual Book Covers that represent and link to Visual Books, and Visual Books comprise a set of Visual Navigation Tabs that represent and link a set of web pages or a set of graphic user interfaces. With look-and-feel, the linked Visual Library, Visual Bookshelves and Visual Books in hierarchical structures provide a friendly environment in which the documents, contents can be well organized and easily navigated.
Owner:JIE WEI
Consumer product information request (CPIR) enabling servlets and web-based consumer product information catalogs employing the same
InactiveUS6961712B1High acceptanceEasy to disassembleDigital data information retrievalAdvertisementsInformation resourceInformation networks
A consumer product information requesting (CPIR) enabling Servlet for execution on the server-side of an information network such as the Internet. The CPIR-enabling Servlet comprises a Universal Product Number (UPN) a uniquely associated with a particular consumer product on which an information search is to be carried out within a database management subsystem. One or more classes are loaded on a an Internet-enabled information server. When the consumer selects a CPIR-enabling Servlet tag embedded within the WWW and corresponding CPIR-enabling Servlet, a UPN-directed-search is automatically carried out within the database management subsystem, the a graphical user interface (GUI) is displayed within the Internet-enabled browser program used by the consumer, and the results from the UPN-directed search are displayed within the GUI in the form of a menu of categorized URLs pointing to consumer product related information resources published on the WWW, without disturbing the consumer's point of presence thereon. The CPIR-enabling Servlets can be used to build various types of consumer product information systems for operation on the WWW.
Owner:PERKOWSKI THOMAS J
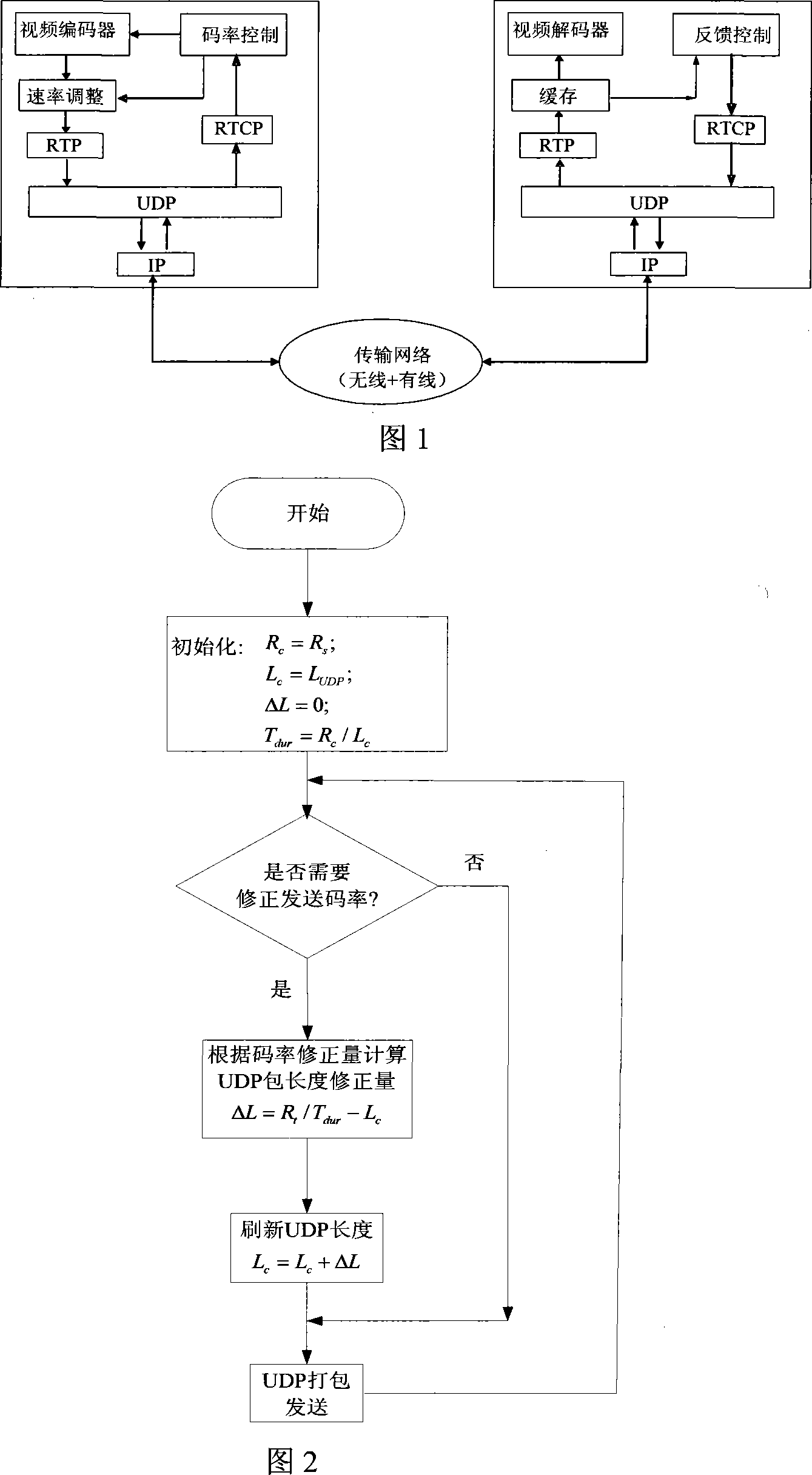
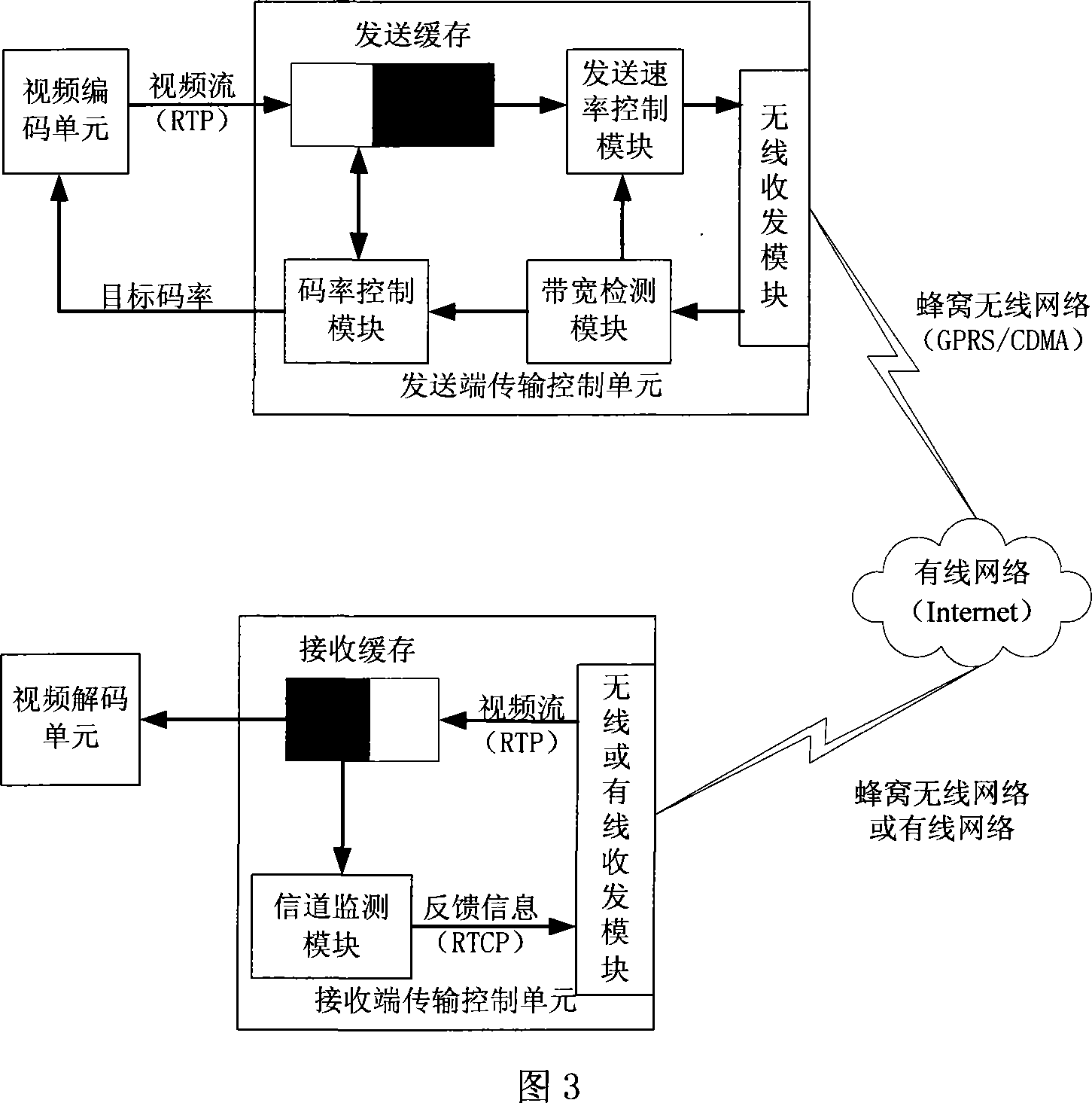
Self-adapting transmission method and system in ascending honeycomb video communication
InactiveCN101222296AImprove playback qualityReduce packet loss eventsError preventionData streamPacket loss
The invention discloses a self-adaptive transmission method and a self-adaptive transmission system in the uplink cellular video communication of the wireless multimedia communication technical field. The method is that: a feedback-based channel effectively transmits bandwidth perceiving; the sending speed of a data flow is adjusted according to the perceived effective transmission bandwidth, the adjustment of the sending rate is realized by changing the packet length of the data flow; two-stage information resource rate control based on cache cleaning and rate control of an encoder is used. The device comprises a sending end, a transmission network and a receiving end, wherein the sending end comprises a video encoding unit and a transmission control unit, the receiving end comprises a transmission control unit and a video decoding unit, the sending end and the receiving end transmit messages through the transmission network. The sending rate of the invention can automatically adapt to the change of the channel bandwidth, decreases the probability of packet loss caused by the fluctuation of the wireless channel bandwidth, and realizes that the customer side can obtain the best possible playing quality under the condition of constant change of network operation conditions.
Owner:SHANGHAI JIAO TONG UNIV
Image processing device and control method of image processing device
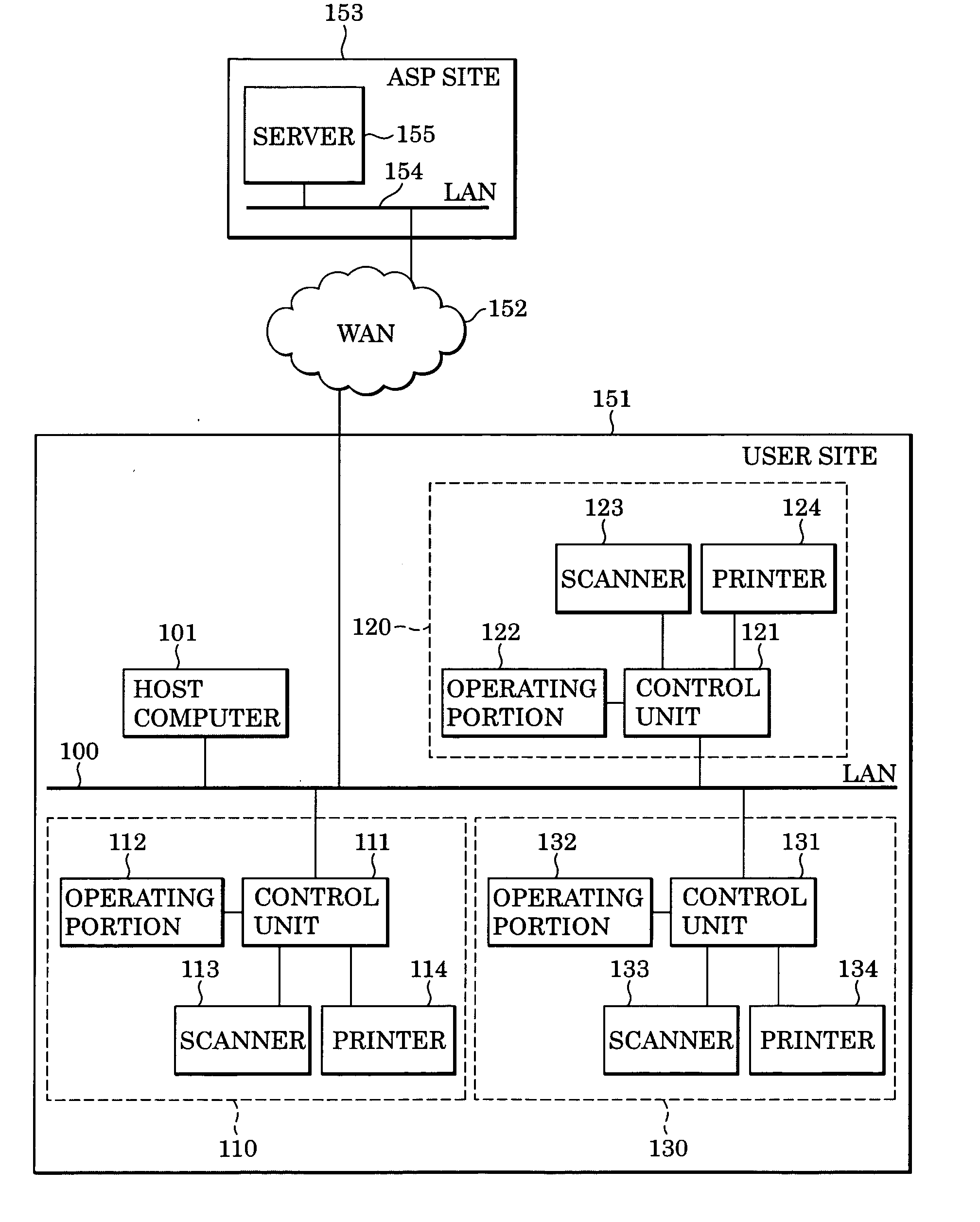
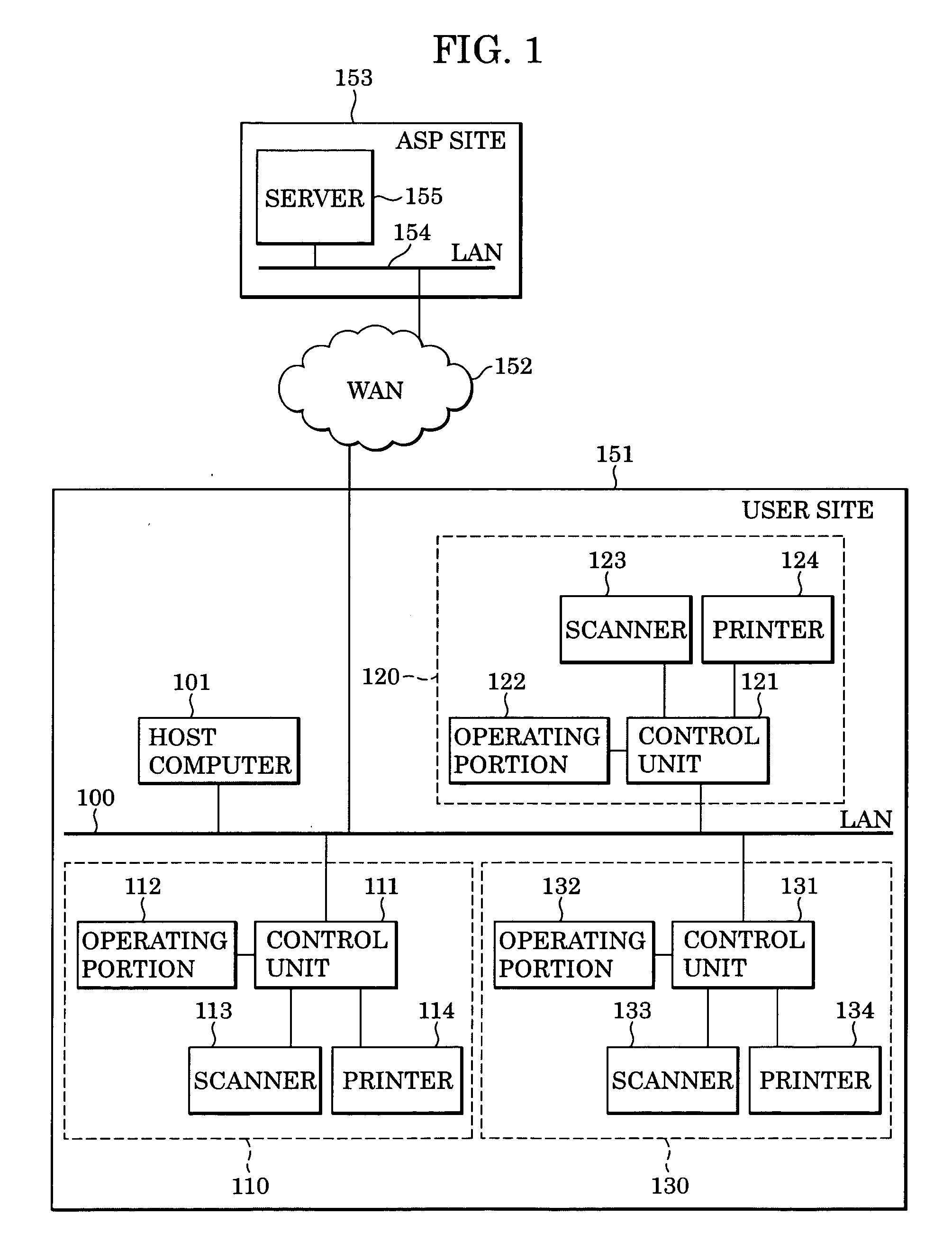
InactiveUS20050108353A1Multiple digital computer combinationsElectrography/magnetographyInformation resourcePaper document
An image processing device communicable with a server on a LAN includes a scanner that inputs image information, a user interface that inputs a URL for specifying an information resource on the server, a web browser module which receives, from the server, an HTML document for sending image data to the information resource, an operating portion that displays a display screen for starting data transmission to the information resource based on the HTML document, and a control unit that starts input of the image data to the scanner and starts the transmission of the image data in accordance with an operation of the display screen.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com