Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1328 results about "Scanner" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A scanner (also referred to a police scanner, police scanner radio or radio scanner) is a radio receiver that can automatically tune, or scan, two or more discrete frequencies, stopping when it finds a signal on one of them and then continuing to scan other frequencies when the initial transmission ceases.
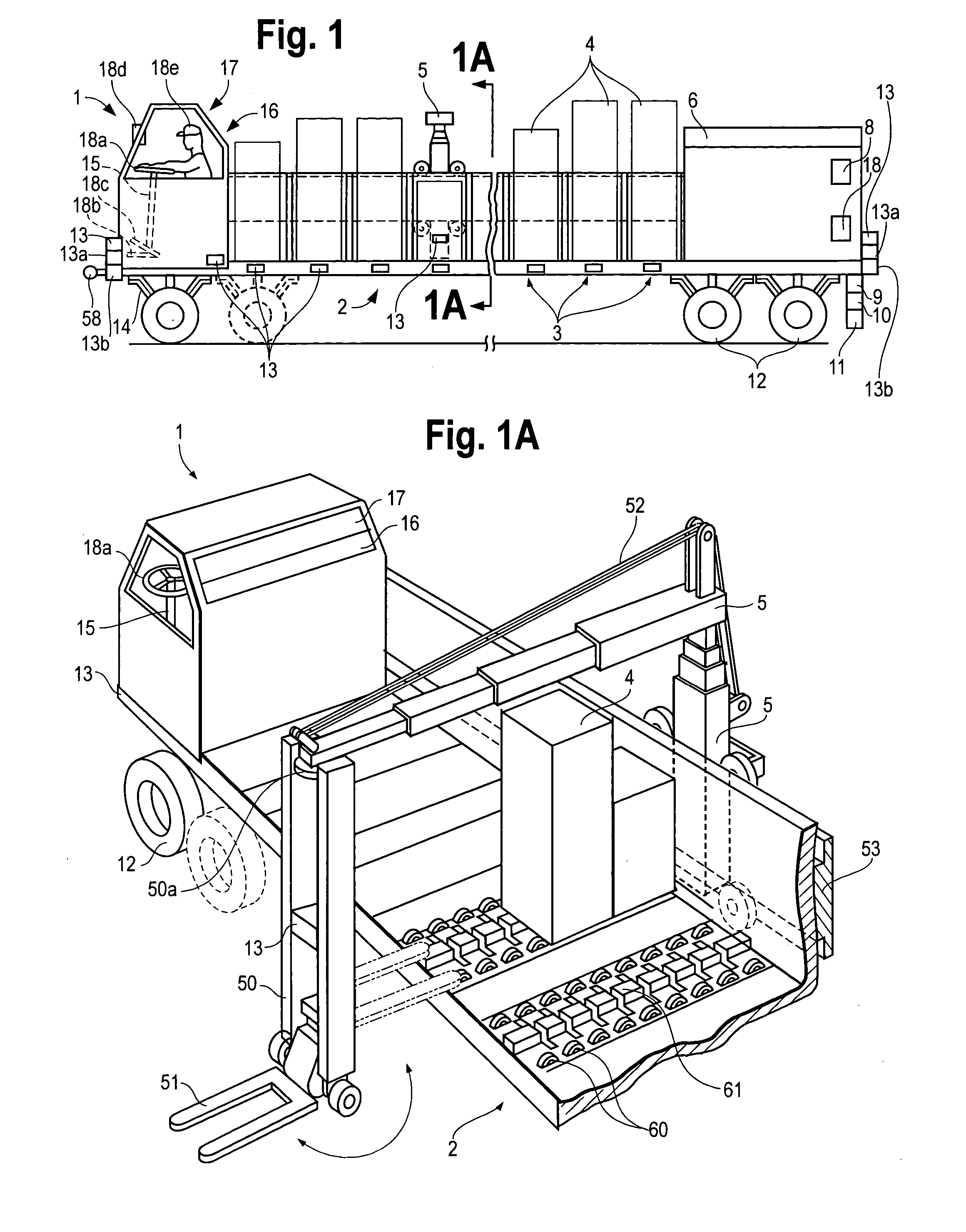
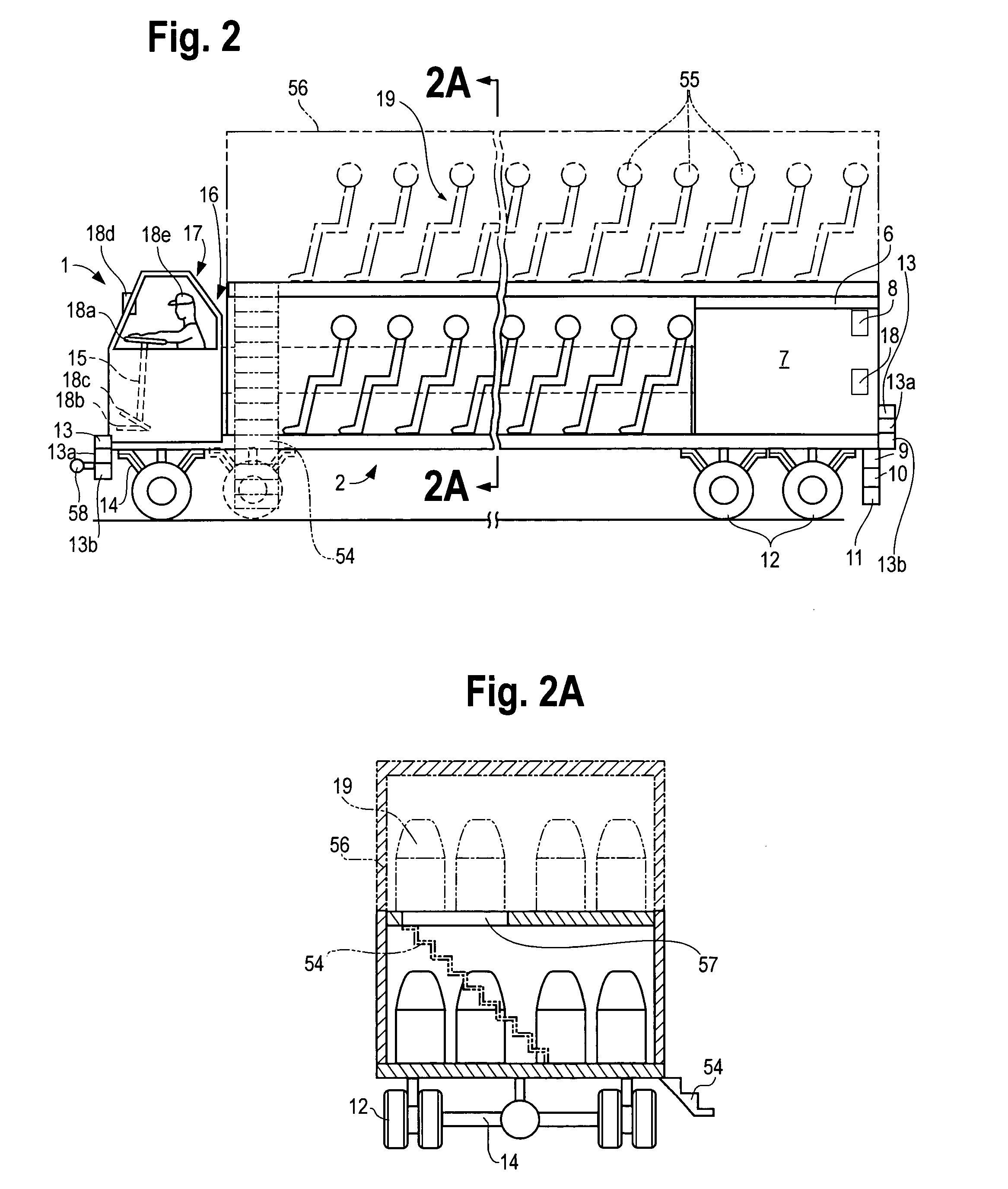
Machine having automatic transport with scanning and GPS functions
InactiveUS20050131645A1Drawn preciselyInstruments for road network navigationVehicles with cranesTransport systemEngineering
A automatic-transport system with scanning and GPS functions for moving people or objects, on platforms or items placed on an automatic-transport system that can be ejected from it and delivered from one location to another and to return automatically or to proceed to other destination(s) by following GPS coordinates, and or by following a line painted or taped to a floor through forward looking scanners built into the automatic-transport system. The automatic-transport system can arrive at a destination and give an alert when it has arrived. Electromechanical system(s) aboard the unit can drop off contents automatically at destinations and load or unload cargo. The transport unit can proceed from one location to another stored in its memory and or it may be redirected by its circuitry or remotely through a wireless port, or directed by GPS or radio control circuits to a further destination.
Owner:PANOPOULOS PETER JOHN
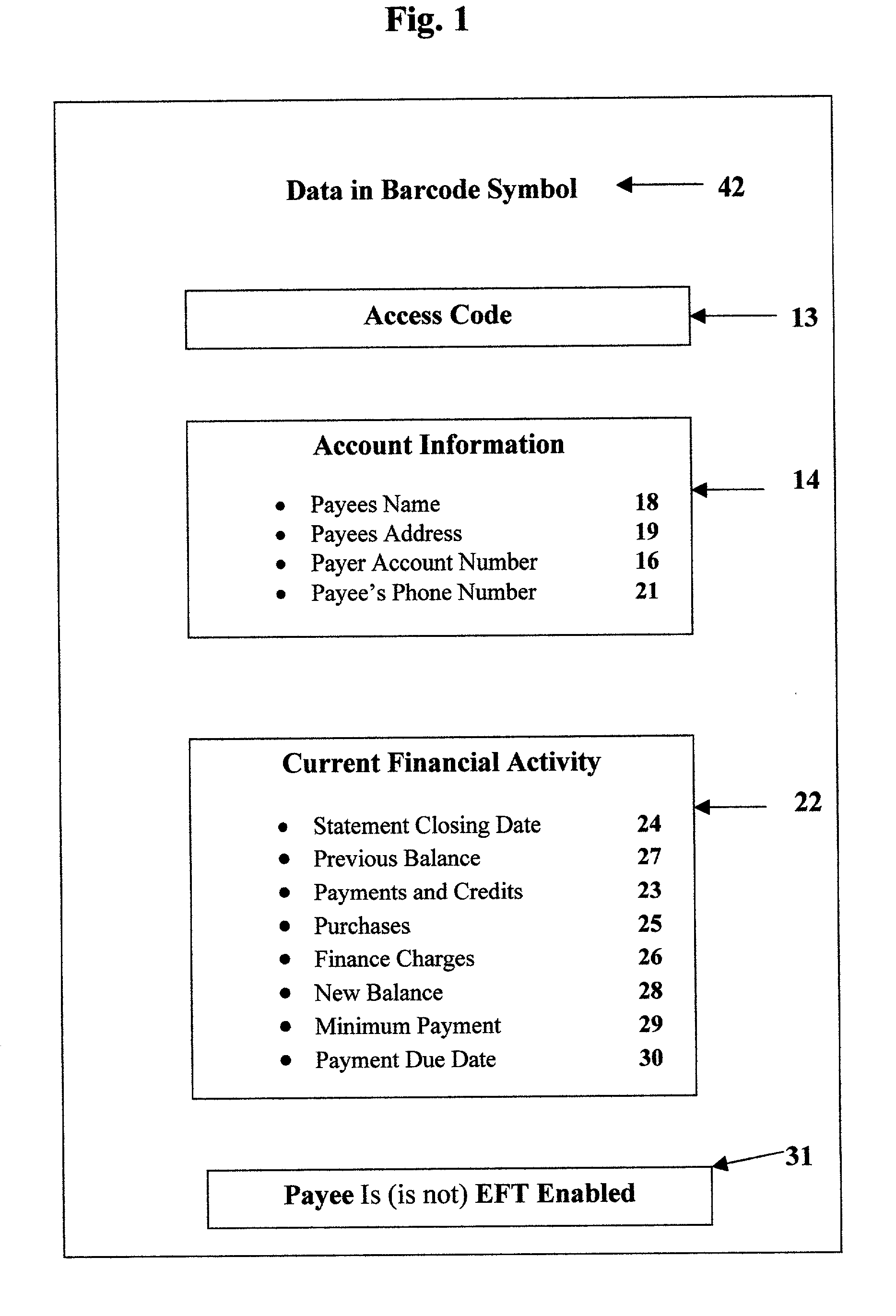
Bill paying with the aid of a scanner
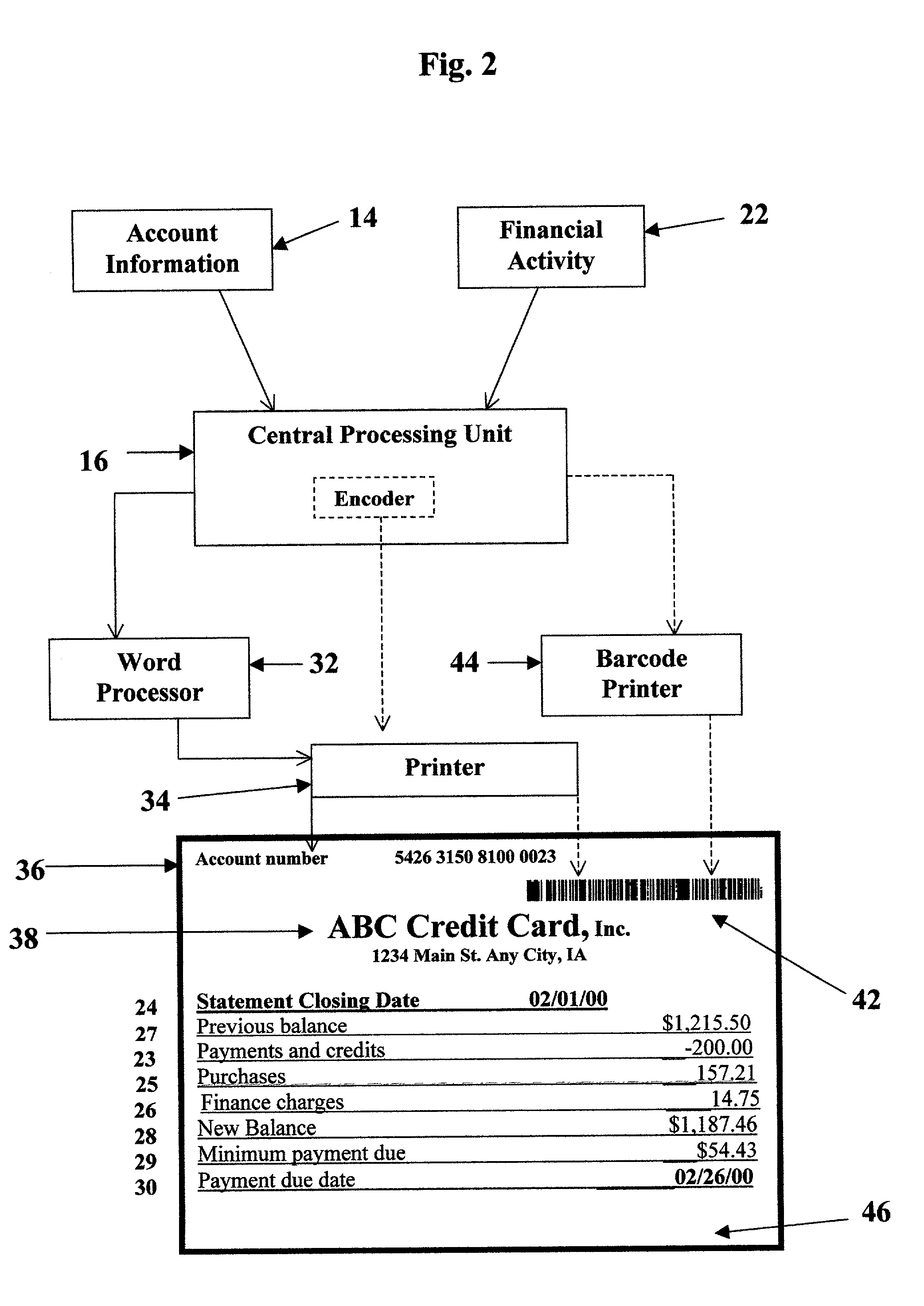
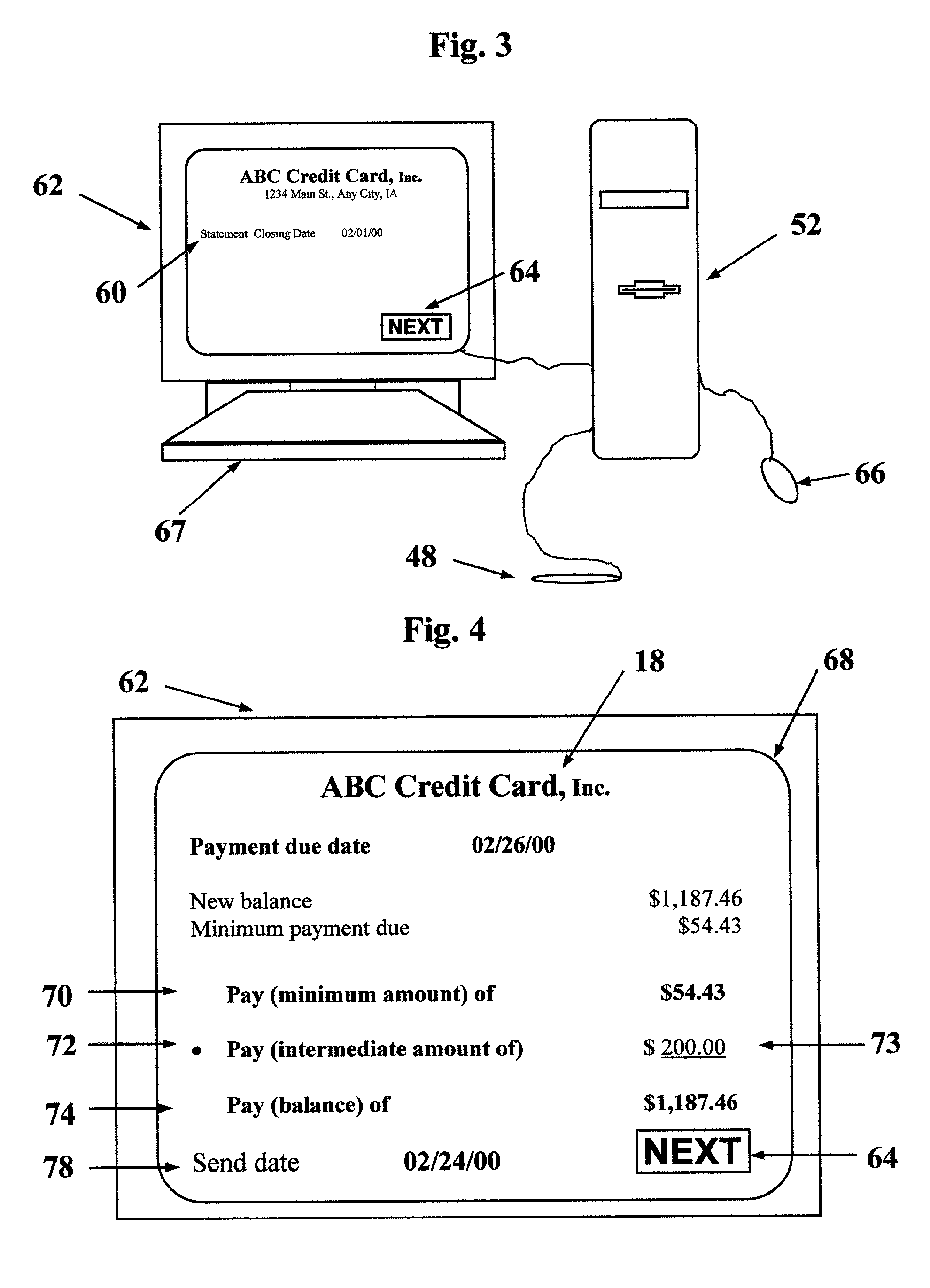
A payee (a vendor) creates bill 46 with account information 14 and activity 22 printed in alphanumeric characters and in a barcode symbol 42. Bill 46 is sent in the mail to a payer (a customer). The payer scans symbol 42 into a PC 52 (personal computer). Scanning wand 48 decodes symbol 42 and transmits it to PC 52. An editor 54 is installed on PC 52. Editor 54 interprets signals and displays interactive visual image 60 on a display terminal 62. The payer verifies that the information on image 60 is the same as on bill 46. The payer clicks the next button with a mouse 66 to show a transaction display 68 on terminal 62. The payer determines that he or she wishes to pay amount 73 and enters amount 73 on display 68. The payer instructs editor 54 to transfer a payment order 82 either to an electric banking software program 58 installed on PC 52 or to an online program 59 accessible through a modem 55 of PC 52.
Owner:MCNAIR EDWARD PARRY
Method and apparatus for extending operating range of bar code scanner
InactiveUS6969003B2Increase working depthReduce the impactImage enhancementImage analysisPhotodetectorOpto electronic
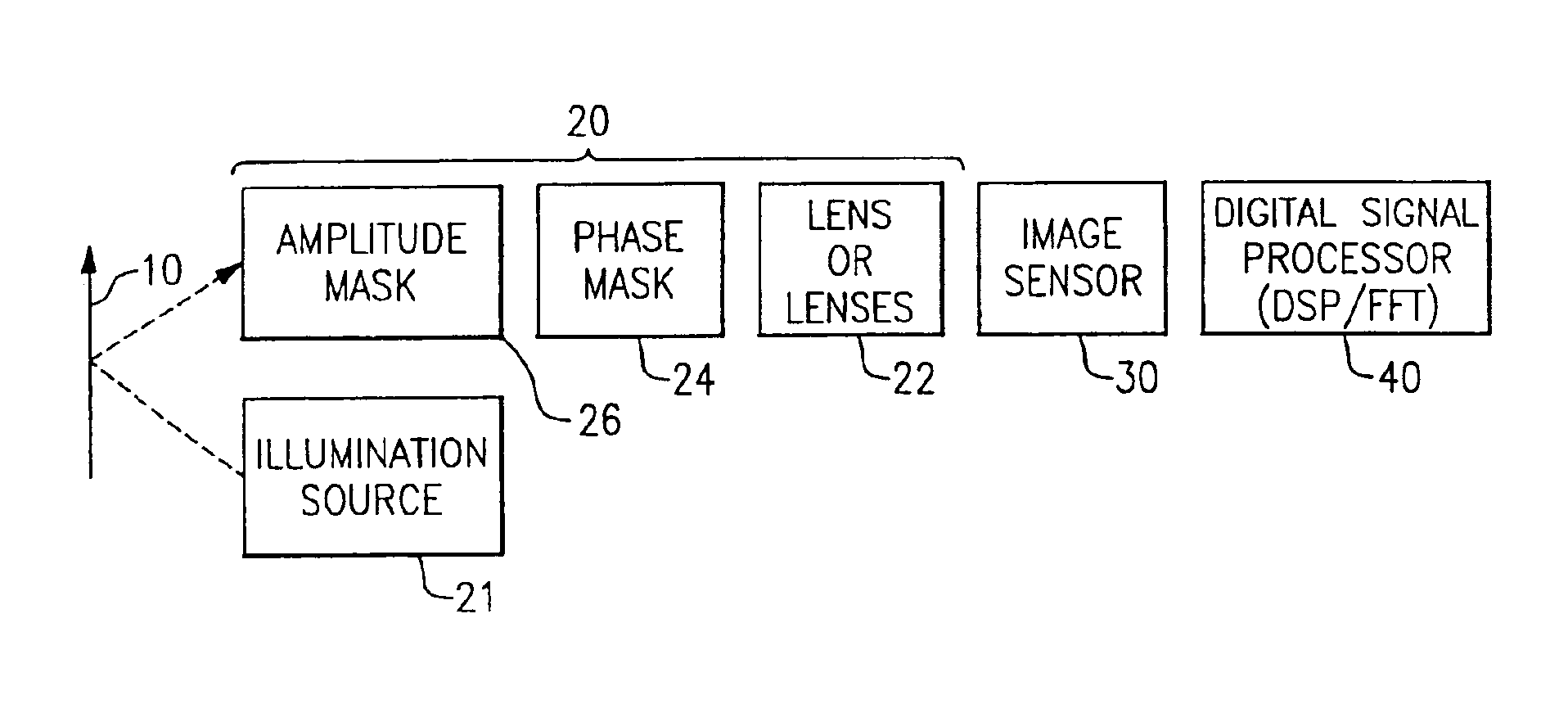
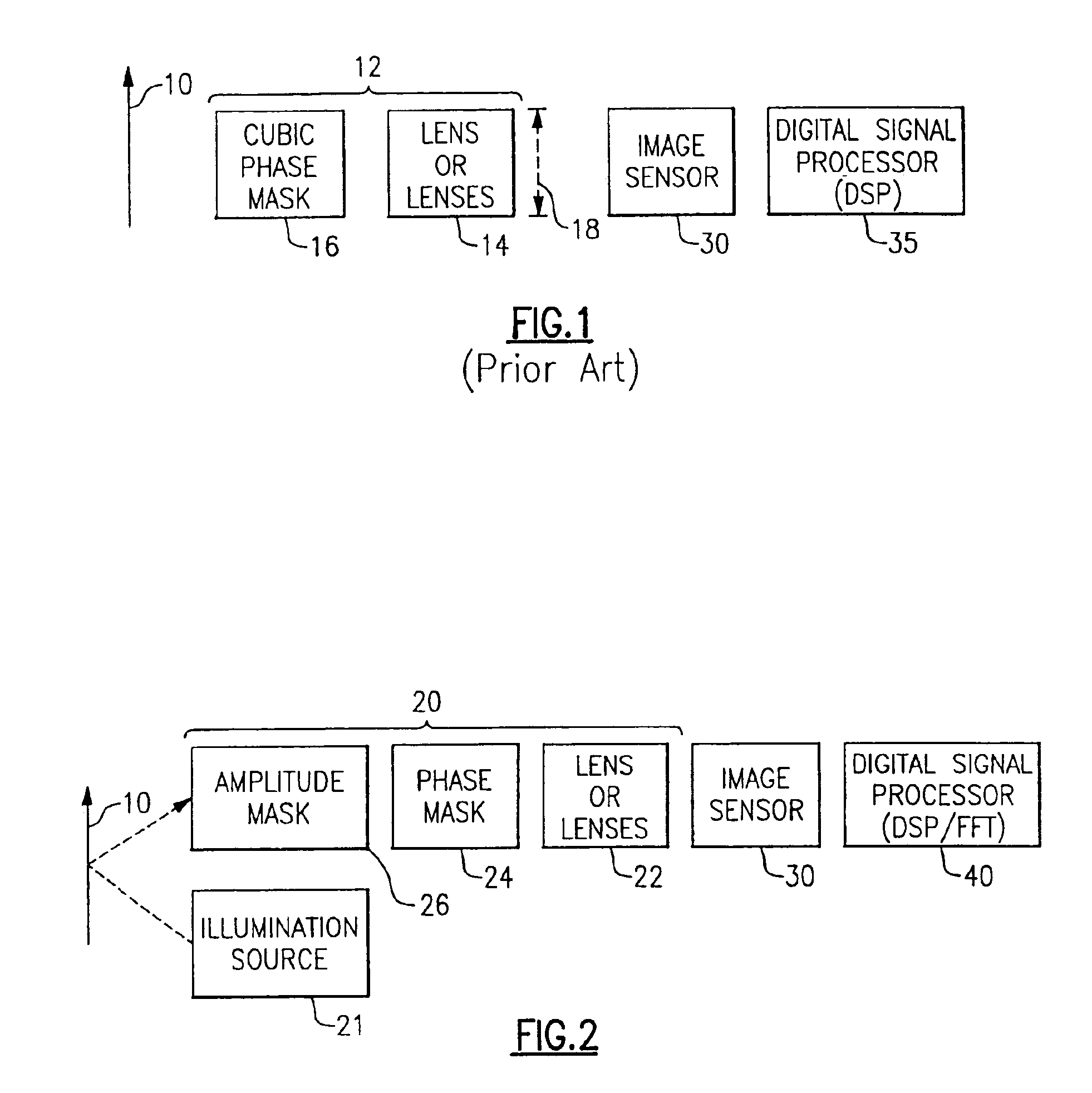
Briefly stated, the operating depth of field for a bar code scanner, preferably a laser scanner, is increased by placing a cubic phase mask (CPM) in the scanning beam. The masked beam is then scanned and reflected off a bar code and received by a photodetector. The received signal is then processed to recover the original unperturbed representation of the bar code pattern. The processed signal has an increased depth of field over an unmasked scanner signal.
Owner:HAND HELD PRODS
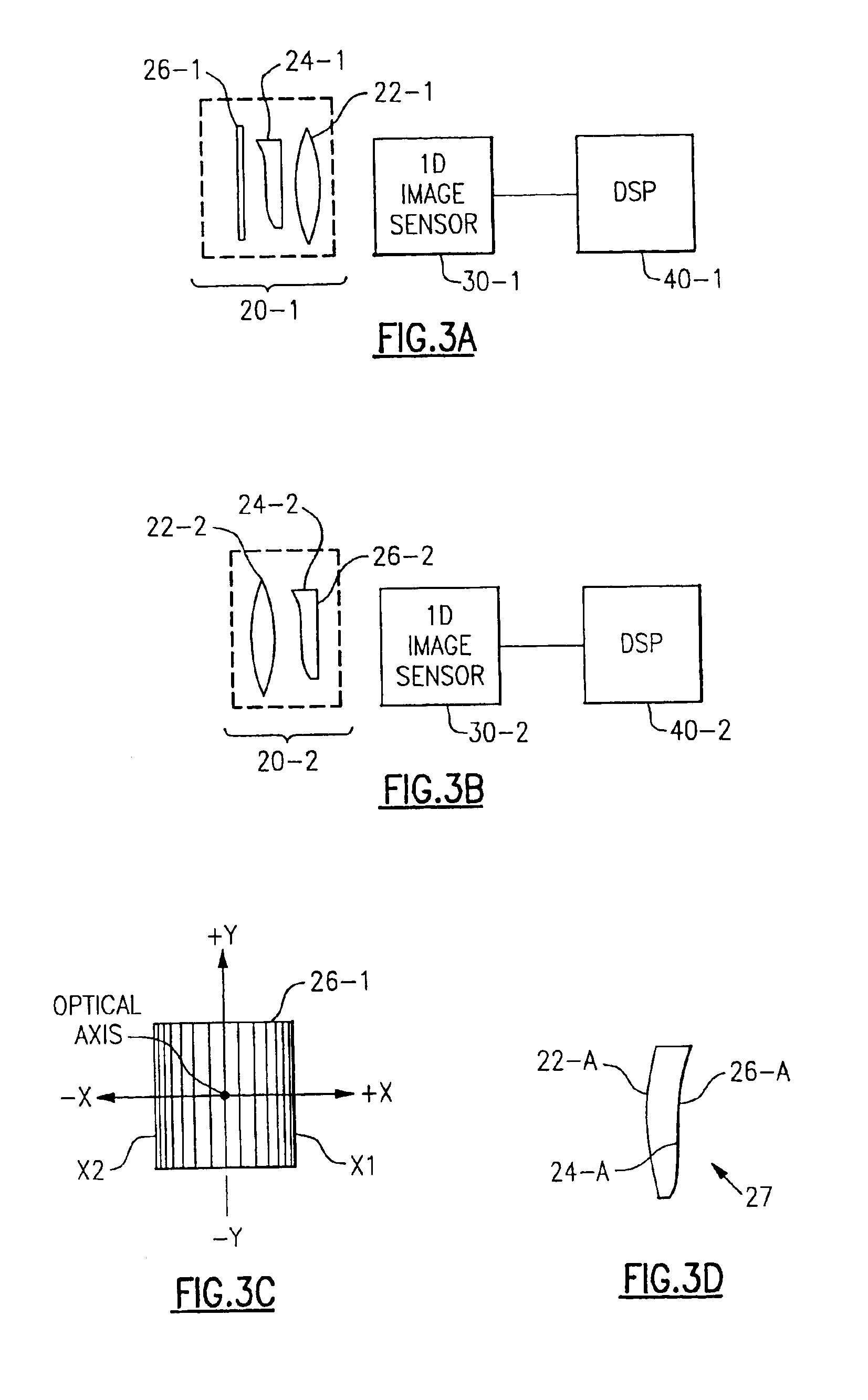
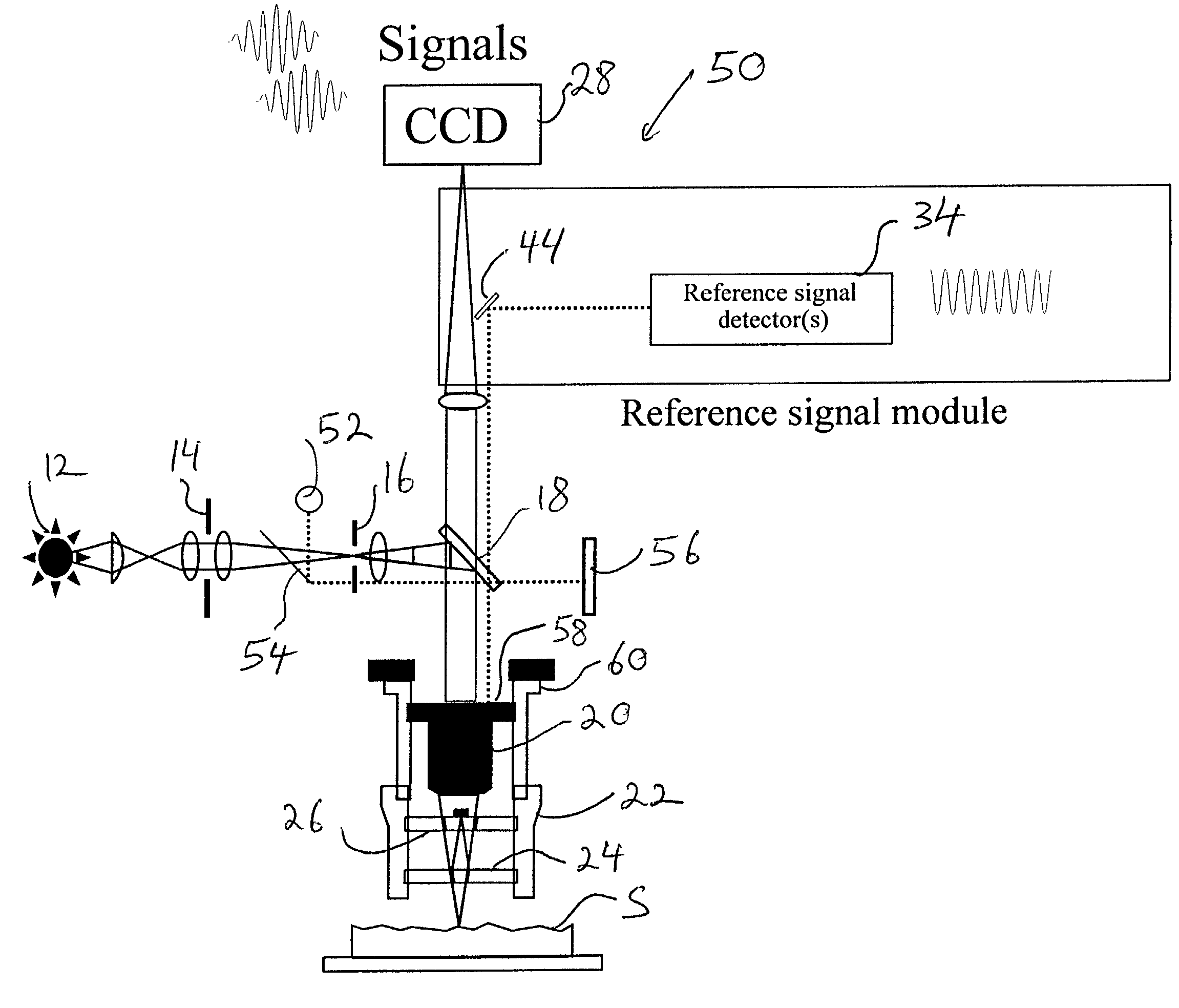
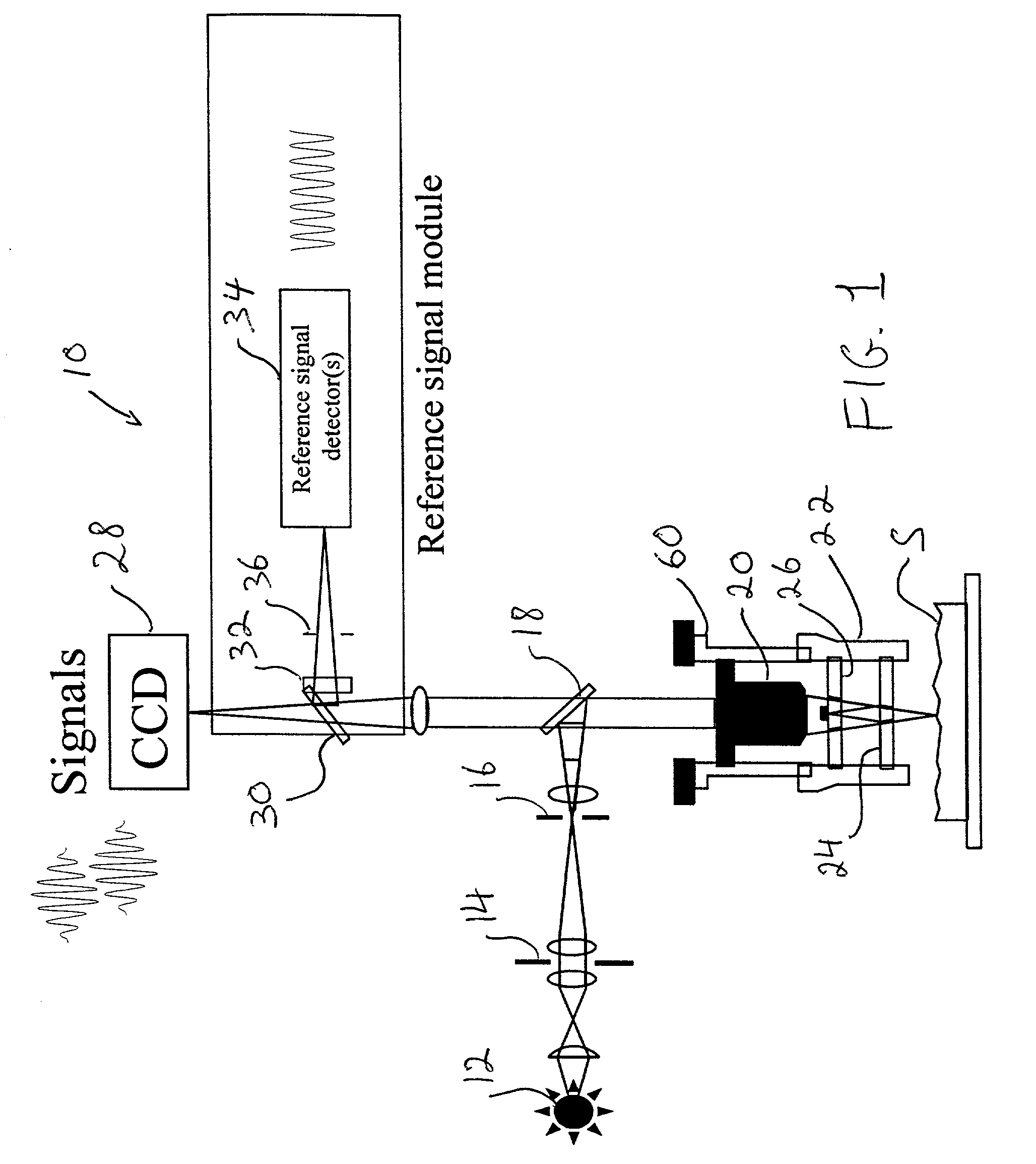
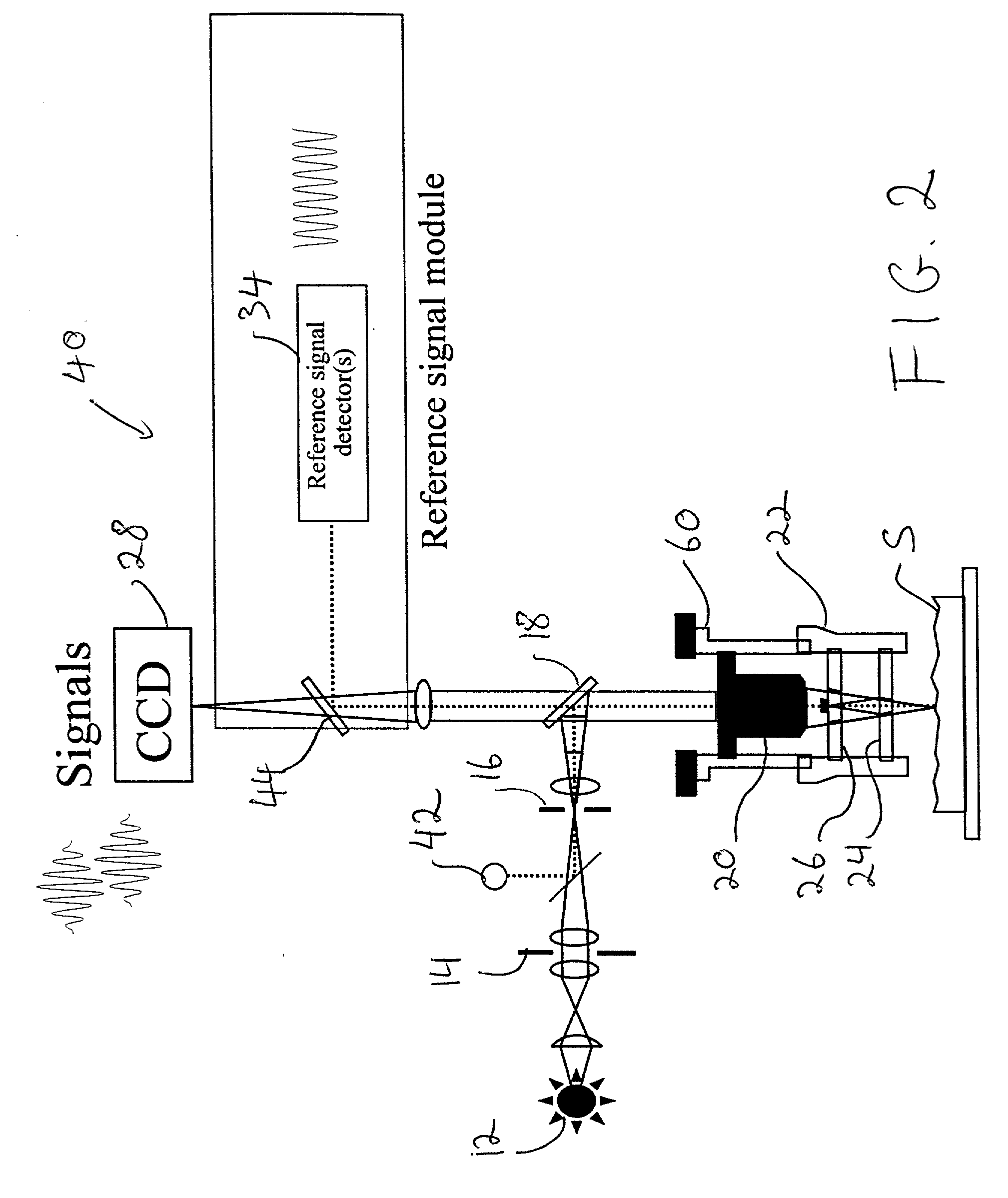
Scanning interferometry with reference signal
A reference signal is used to track the actual behavior of the scanner in an interferometer to produce scanner-position data that can be used to correct errors introduced by scanner nonlinearities and other error sources. A narrow-band light source is advantageously utilized to cover the entire range of operation of the scanner. Because of the independent reference channel, the invention is suitable for implementation with all types of conventional interferometric techniques. The concept is preferably implemented by utilizing an additional light source and the same scanner and detector used for the measurement, so that the OPD varies in synchronization of both the reference-signal and data-collection procedures. Alternatively, a high temporal-coherence filter may be used with the same light source and optical path used for the interferometric measurement.
Owner:BRUKER NANO INC
Detecting the locations of a plurality of objects on a touch surface
ActiveUS20110074735A1Overcome limitationsInput/output processes for data processingUltrasound attenuationLight beam
An apparatus is controlled to detect locations of a plurality of objects on a touch surface of a panel. An input scanner arrangement introduces at least three beams of radiation into the panel for propagation by internal reflection, and sweeps the beams inside the panel across a sensing area, preferably in at least two different principal directions. At least one radiation detector is arranged to receive the beams from the input scanner arrangement while they are swept across the sensing area. A data processor is connected to the radiation detector(s) and operated to identify the locations based on an attenuation of the beams caused by the objects touching the touch surface within the sensing area, the attenuation being identifiable from an output signal of the radiation detector(s). Each output signal may be further processed to generate a transmission signal, by dividing the output signal by a background signal which represents the output signal without any object on the touch surface.
Owner:FLATFROG LAB
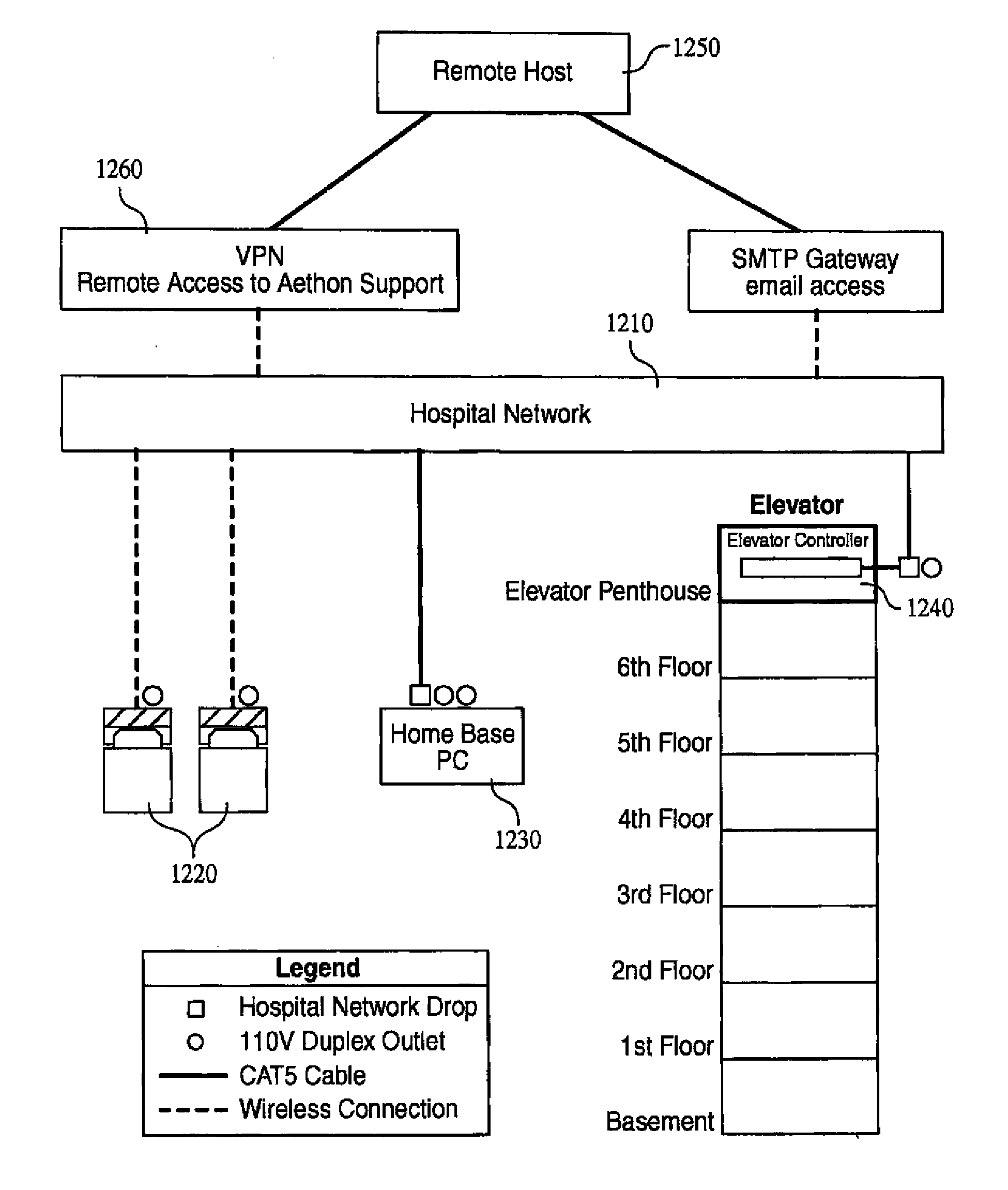
Robotic ordering and delivery apparatuses, systems and methods
Systems, methods and devices for the automated retrieval / delivery of goods from one location to another using a robotic device such as a tug and accompanying cart. A computer within the tug / cart stores a map of the building floor plan and intended paths for the tug to take when traversing from one location to the next. During the delivery, a variety of different sensors and scanners gather data that is used to avoid obstacles and / or continuously adjust the movement of the tug in order to more closely follow the intended path. The system preferably includes wireless networks that allow one or more tugs to communicate with a tug base station, a primary network located at the site of the delivery and a remote host center that monitors the status and data collected by the tugs.
Owner:ST ENG AETHON INC
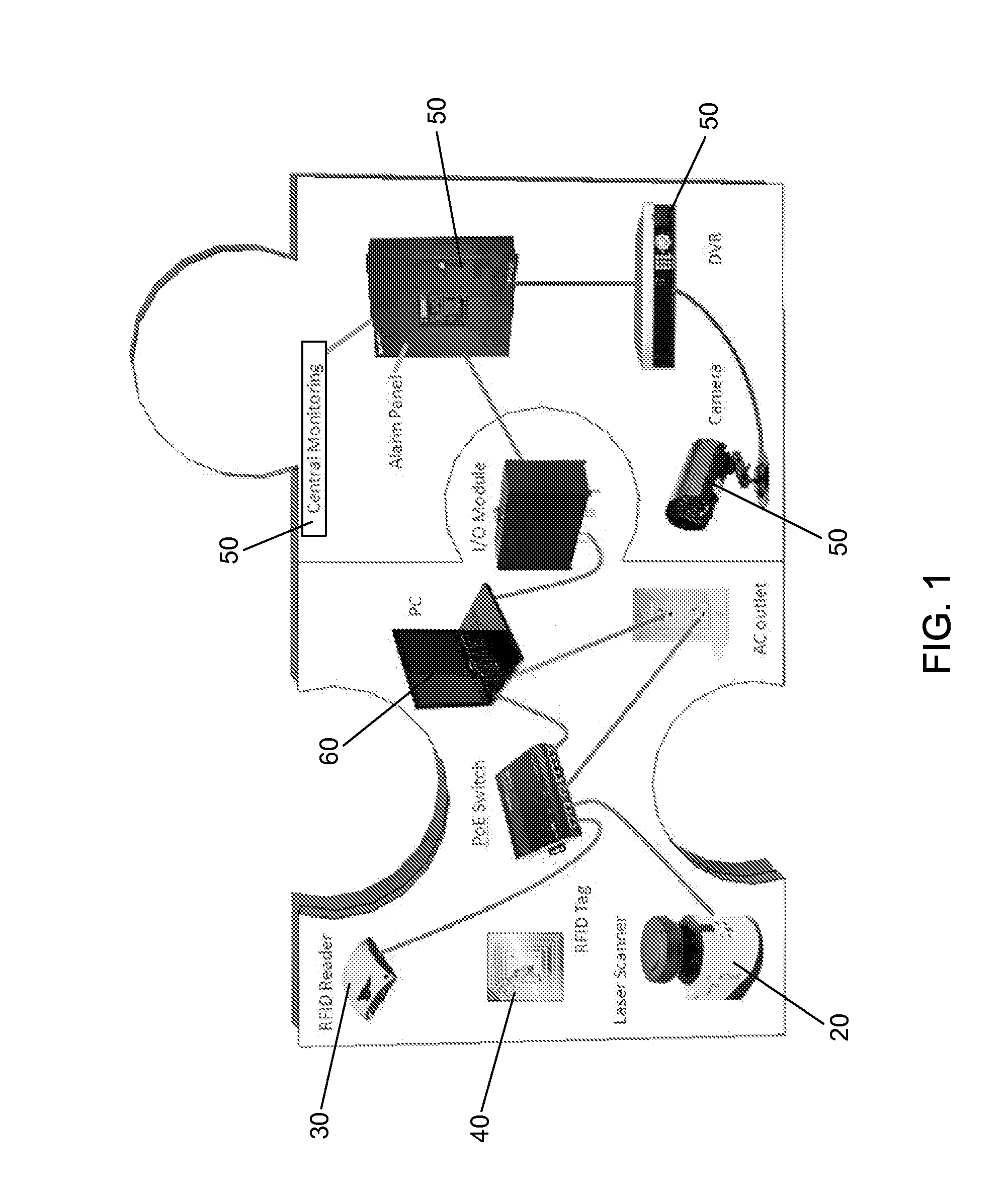
Multimedia network appliances for security and surveillance applications
ActiveUS7228429B2Improve functionalityStable supportComputer security arrangementsMultiple digital computer combinationsMotion detectorGeolocation
Network appliances for use in combination with a network based full service, multi-media surveillance system provide a wide range of monitoring techniques utilizing digital network architecture. The appliances may be connected to the surveillance system for transmitting event data, video and / or image monitoring information, audio signals and other data over significant distances using digital data transmission over networks such as a local area network (LAN), a wireless LAN (WLAN), a wide area network such as the Internet for other networks, permitting remote manual and / or automatic assessment and response. The wireless LAN connectivity permits local distribution of sensor information audio, video and image data with relatively high bandwidth without requirement of a license and without relying on a common carrier and the fees associated therewith. The surveillance system may be interfaced with a WAN (wide area network) such as frame relay or the Internet for providing a worldwide, low cost surveillance system with virtually unlimited geographic application. Multiple sensors and appliances may be accommodated, as required. The topology of the network will be established by the geographic situation of the specific installation. Appropriate firewalls may be set up as desired to protect unauthorized access to the system or collected data. The server based system permits a security provider to have access to the appliance, related sensor and surveillance data or to configure or reconfigure the system from any station on the Intranet or Internet. The use of power supplied over LAN wiring to various configurations of security network appliances provides an important simplification and cost reduction of the installation of various alarm and security system devices, such as card readers and scanners, audible devices, strobe enunciators, keypads, motion detectors, and the like. The use of networked sensors in the form of network appliances allows various servers and monitors to share common sensors, further reducing installation costs and greatly increased flexibility.
Owner:PR NEWSWIRE
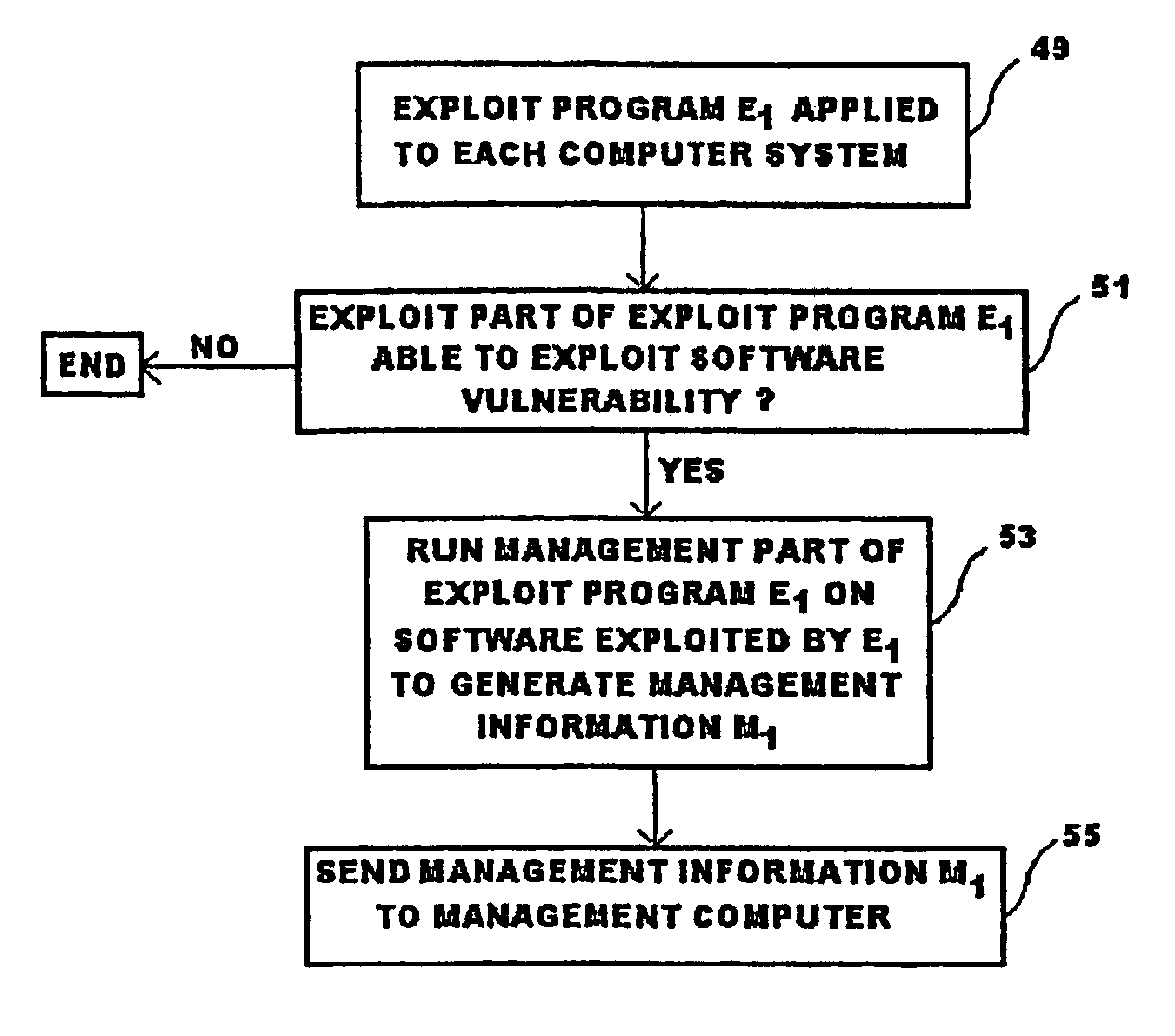
Method and system for identifying, fixing, and updating security vulnerabilities
InactiveUS6907531B1Easy to useError preventionMemory loss protectionOperational systemSystem identification
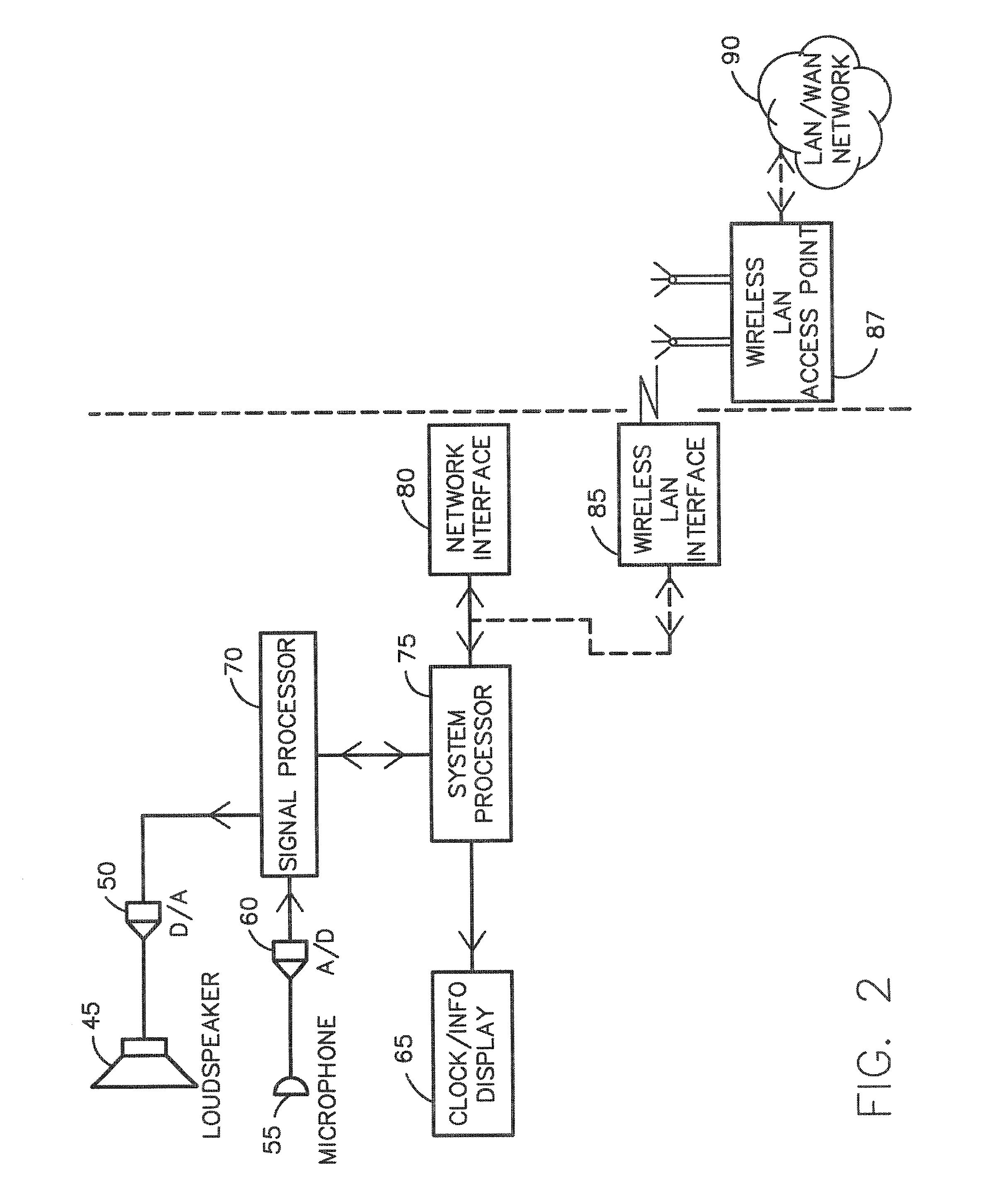
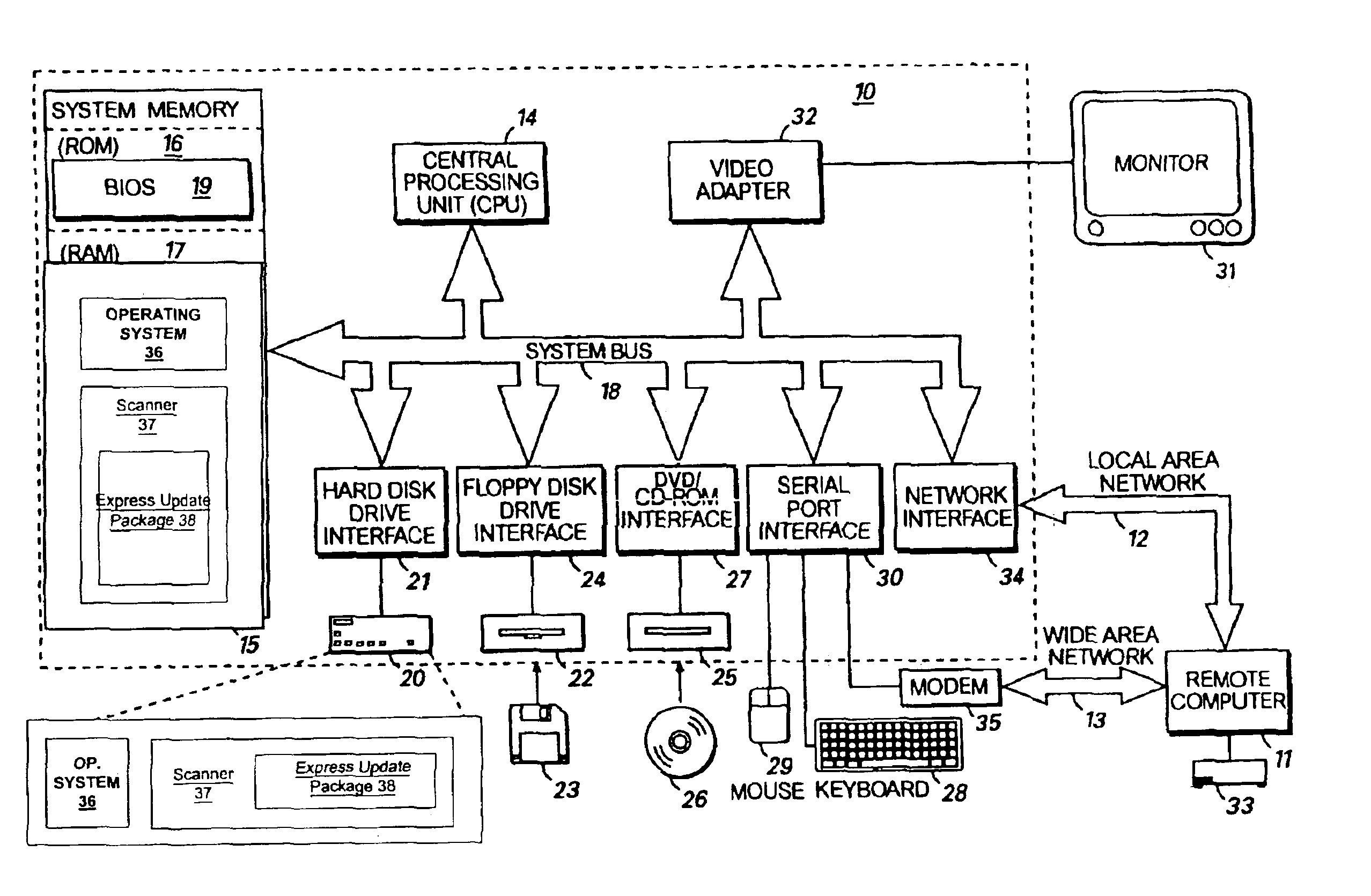
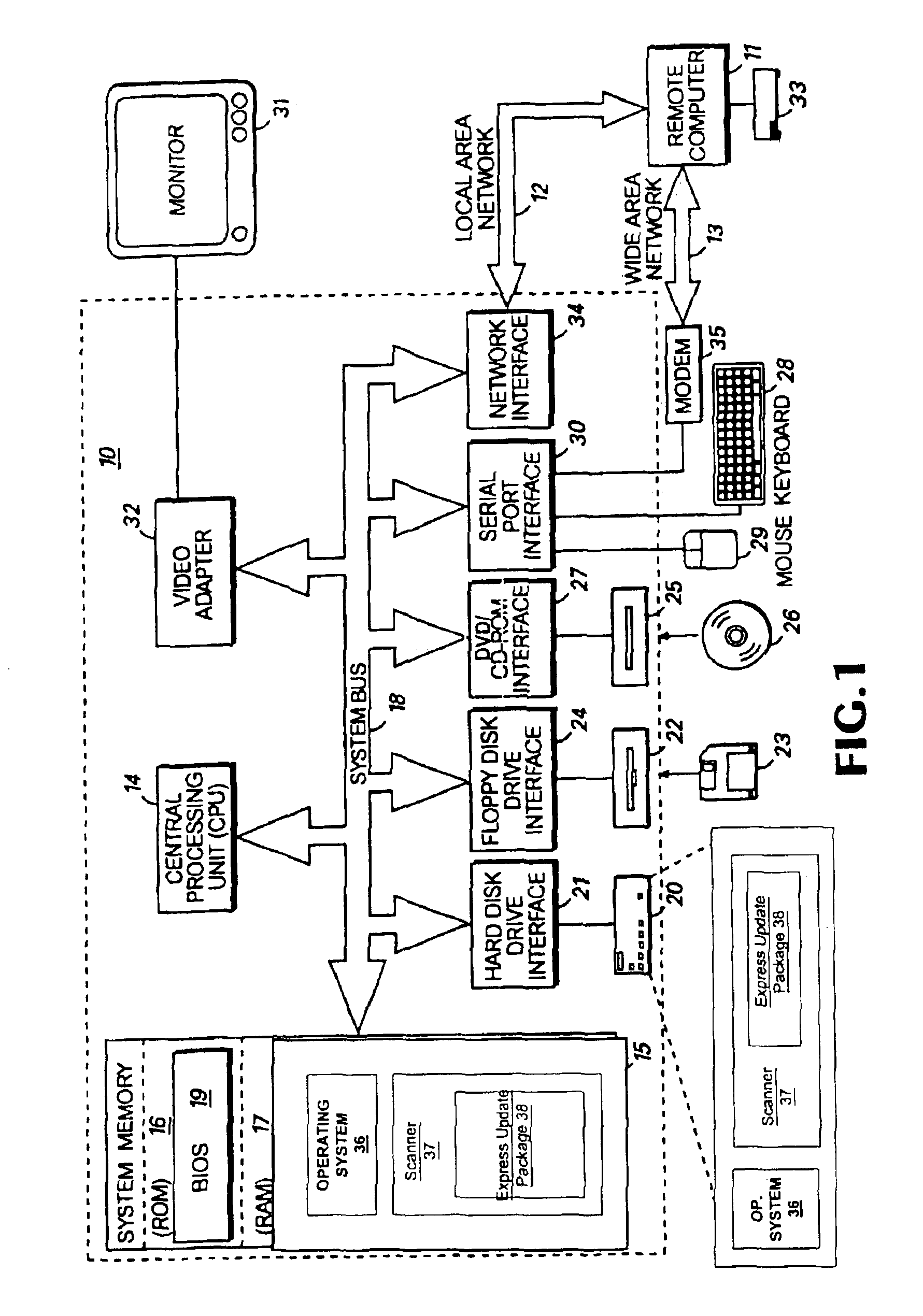
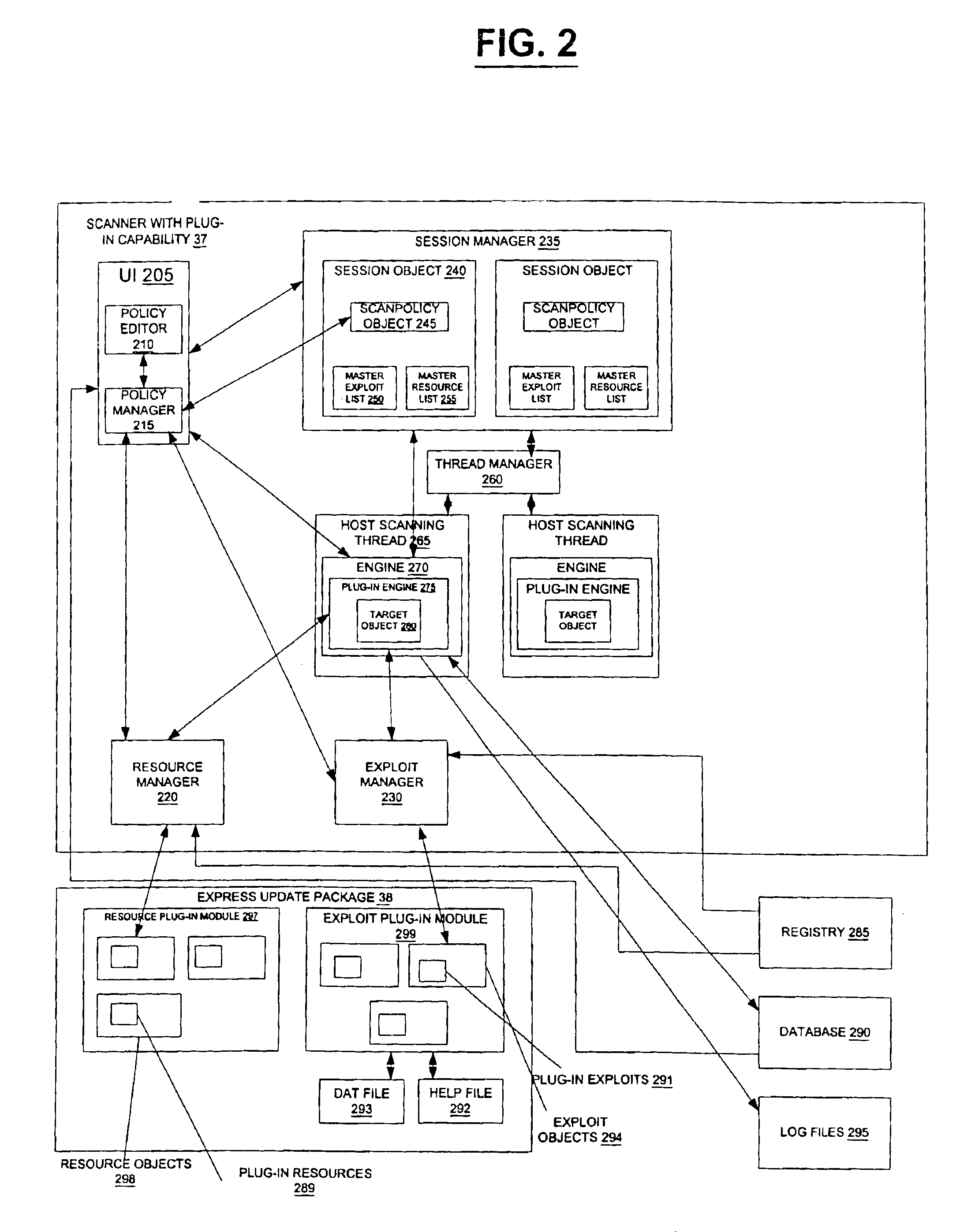
A method and system identifies, fixes, and updates security vulnerabilities in a host computer or host computers. The present invention can communicate between a scanner with plug-in capability, an operating system, and an express update package.The architectural set-up can allow exploits within the scanner and exploits in the express update package to function with no knowledge of each other. The user also needs no knowledge of whether the exploits are within the scanner or the express update package. Mutual authentication procedures can enable the scanner to load only legitimate express update packages, and can provide that express update packages can only be loaded into legitimate scanners.
Owner:FINJAN BLUE INC
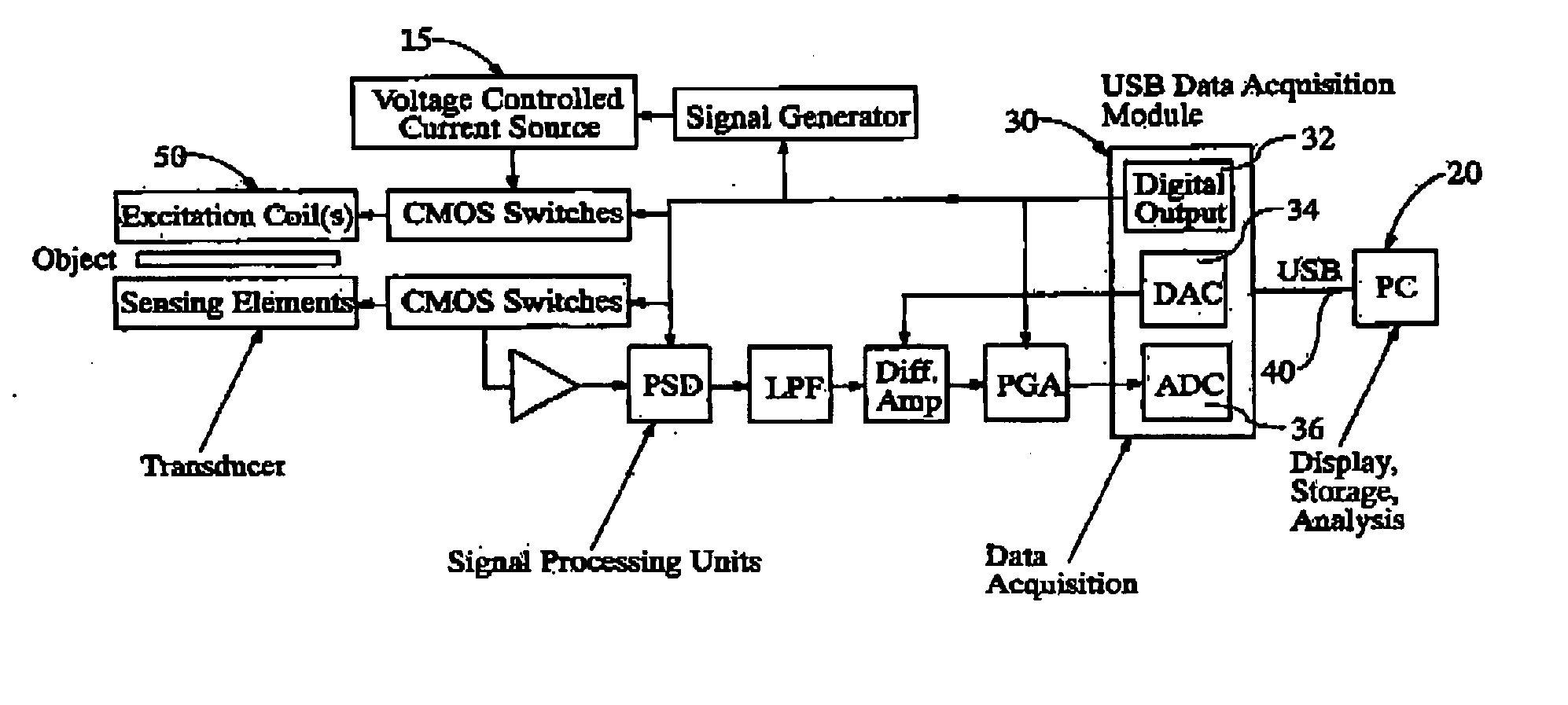
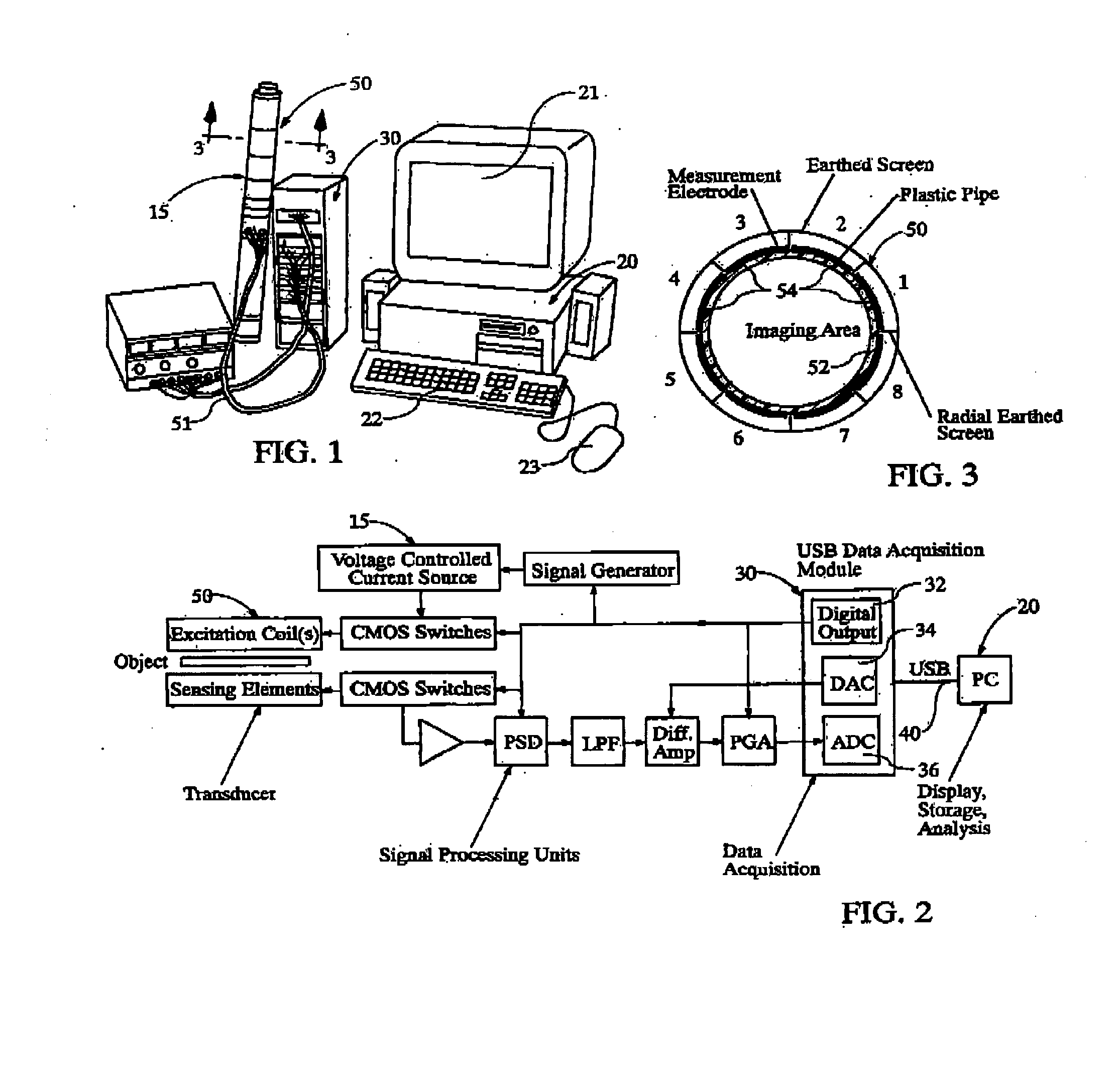
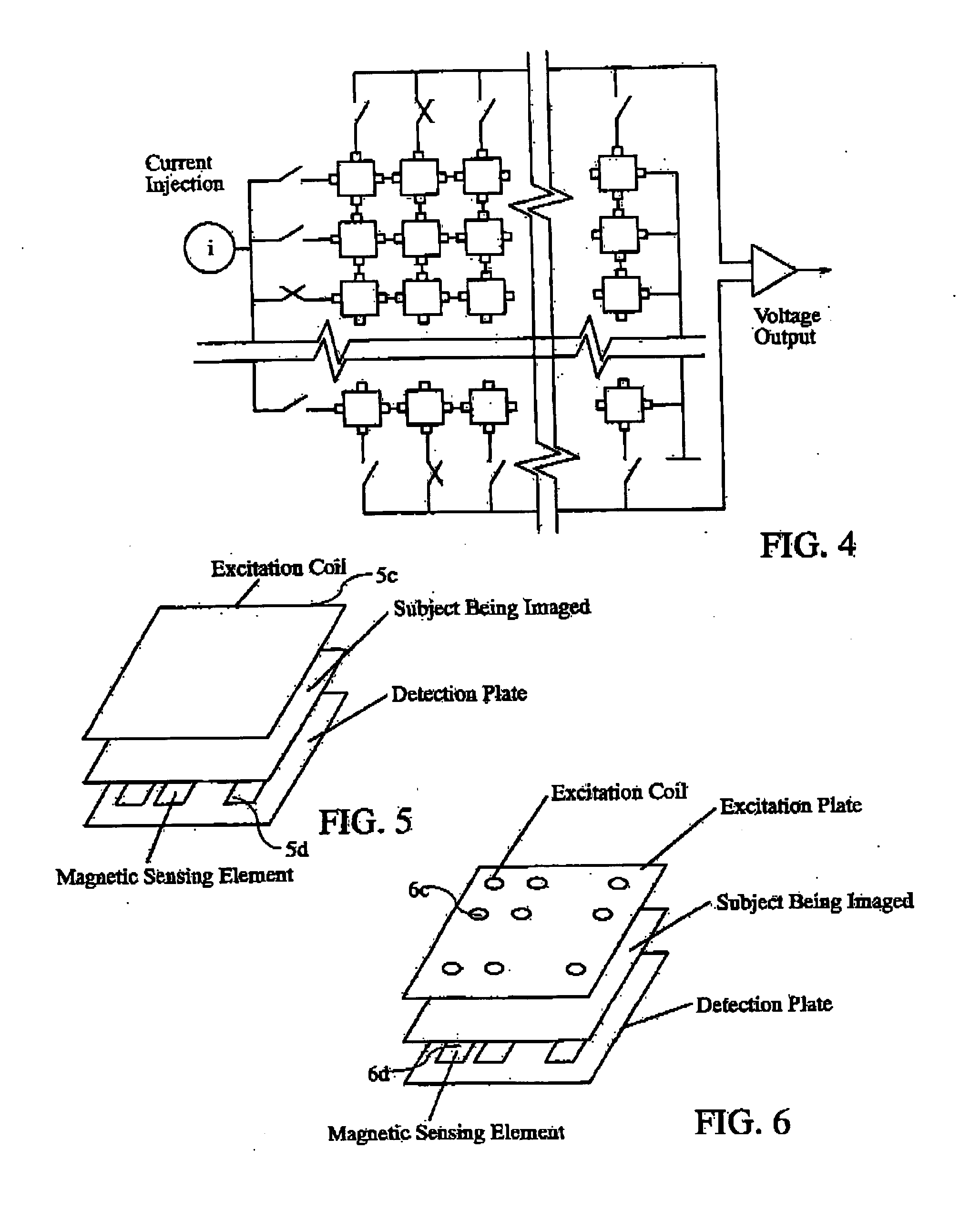
Security scanners with capacitance and magnetic sensor arrays
InactiveUS20060176062A1Facilitate creating imageImprove performanceResistance/reactance/impedenceMaterial analysis by electric/magnetic meansSensor arrayMultiple sensor
Security scanning devices based on electrical tomography, including tomography systems based on the measurement of capacitance (ECT) and electromagnetic tomography (EMT), in combination with knowledge-based image analysis and understanding. Each device includes a sensing head or transducer, sensing electronics, image reconstruction and image analysis microprocessor, a display unit and accompanying software for identifying dangerous materials and items. The security scanning devices are employed for obtaining multiple independent measurements and enable implementation of data fusion to combine the complementary sensitivity of ECT and EMT to different material properties, while providing architecture to implement image knowledge bases, which characterize objects, whose image attributes are acquired from multiple sensors.
Owner:KONSULTEURO LIMITED LIMITED UK
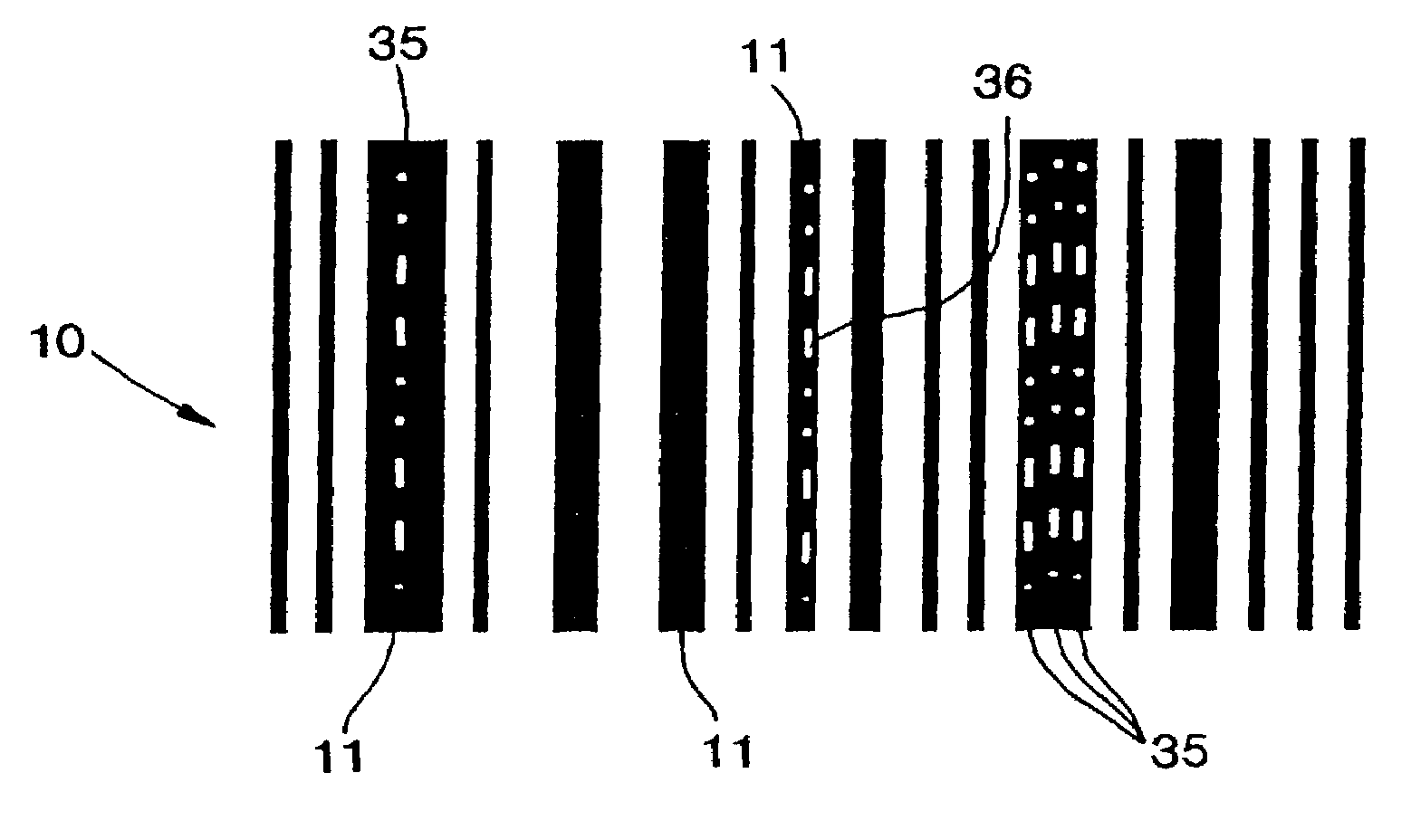
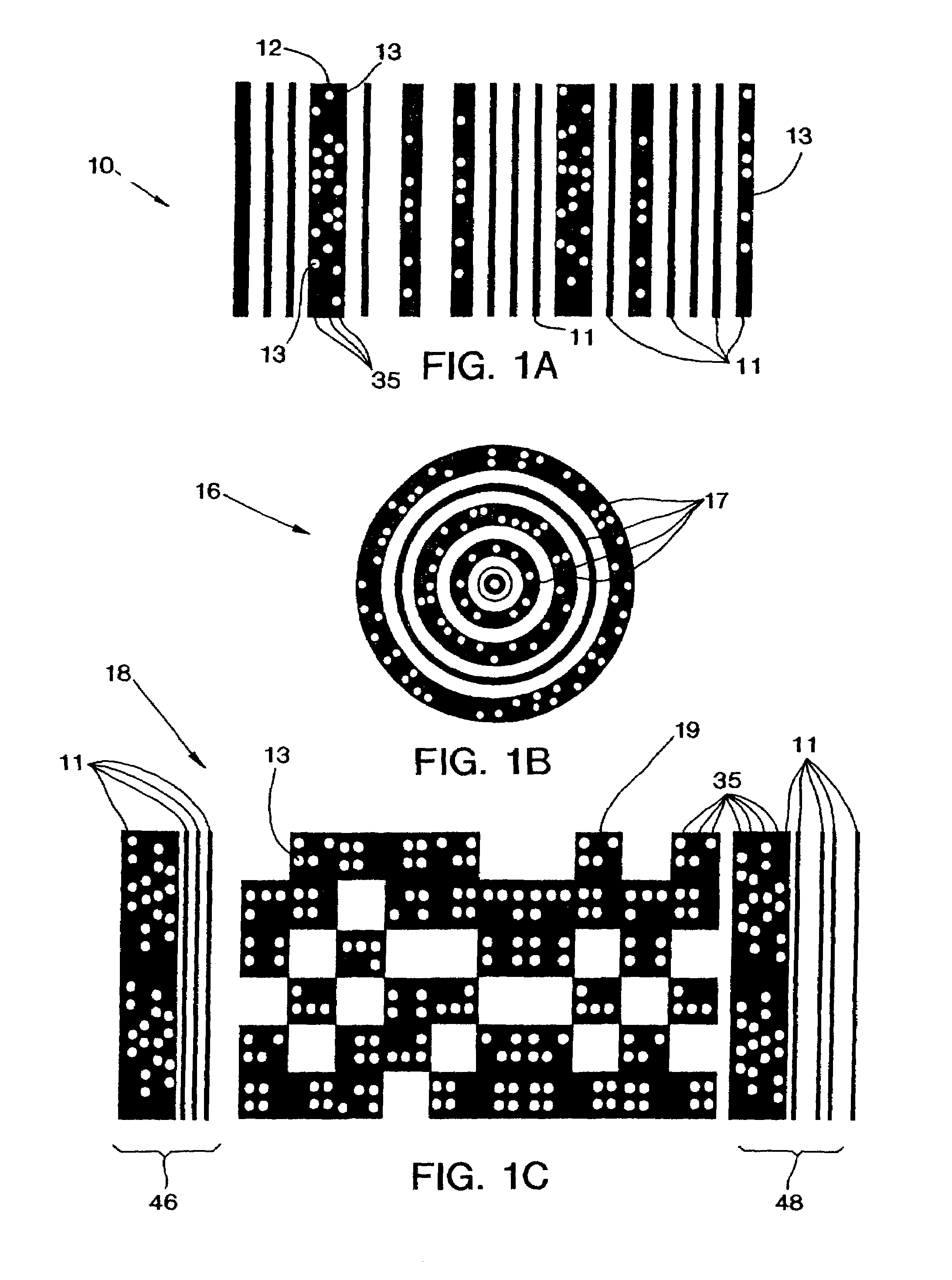
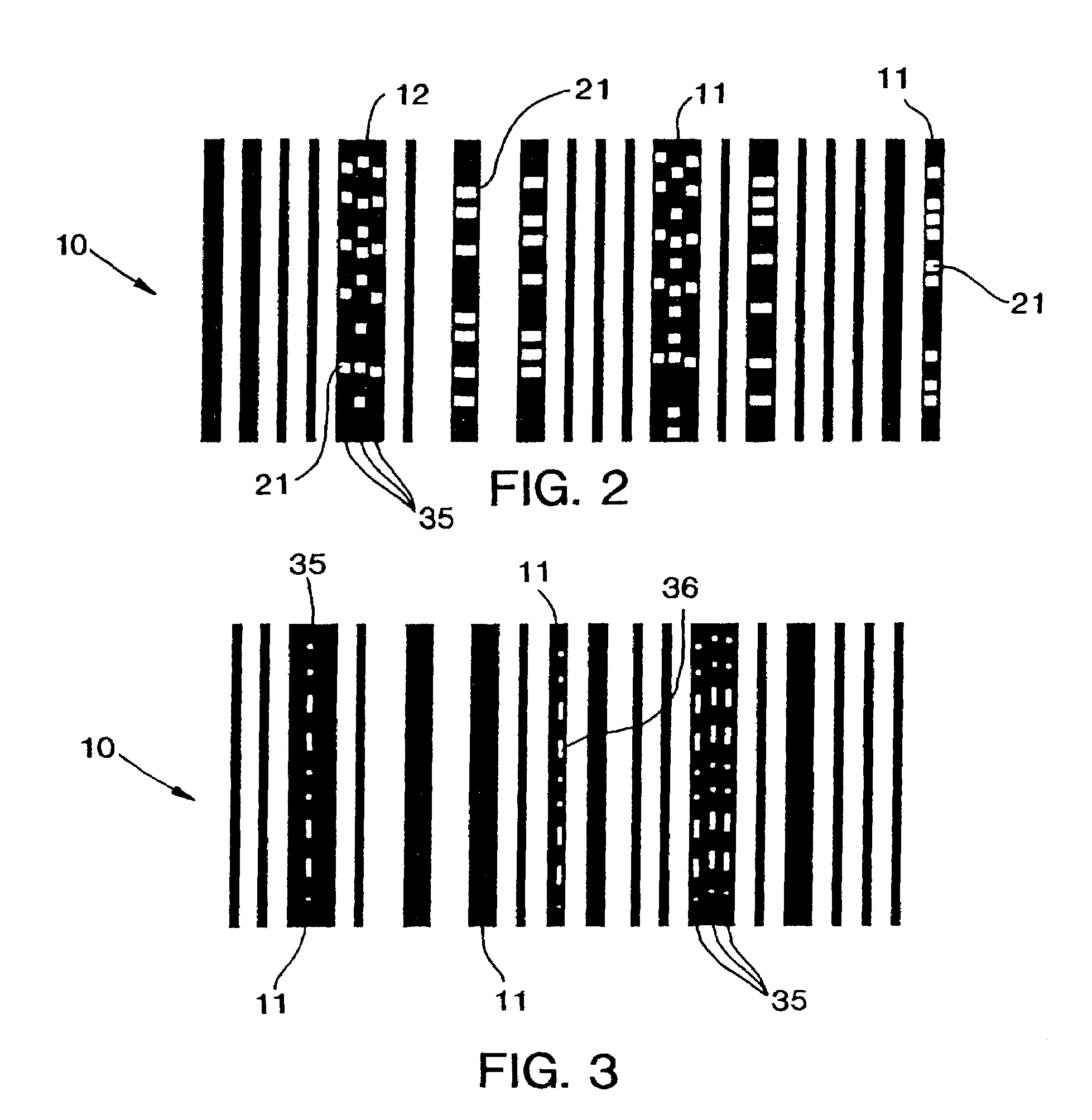
Method and apparatus for encoding and decoding bar codes with primary and secondary information and method of using such bar codes
InactiveUS6991164B2Character and pattern recognitionRecord carriers used with machinesScannerIn plane
A bar code (10) has primary information (46, 48, 50, 51) encoded in one direction (e.g., horizontally) and secondary information (13, 21, 36) encoded in another direction (e.g., vertically) in single (11) or multiple tracks (35) in selected ones of the vertical bars (11) of a bar code (10). Using a non-linear, variable amplitude scanner, all of the bars are scanned in the one direction to obtain all of the primary information and all of those vertical bars having secondary information are scanned in the other direction to obtain all of the secondary information. The one direction which is perpendicular to the vertical bars (11), is determined by first rotating the scan path axis (86, 87) until both start (46) and end (48) code bars are read thereby placing the scan path entirely within the total bar code, and, then, further rotating the scan path (88, 89) to determine the direction of the minimum crossing width (Lsc 80) of the total bar code (10). Secondary information is scanned in planes orthogonal to the one direction after those vertical bars (11) having such information are first identified and selected. In a preferred embodiment, the decoded secondary information may be used to control selected station process operations for selected products in a continuous manufacturing assembly line.
Owner:LEMELSON MEDICAL EDUCATION & RES FOUND PARTNERSHIP
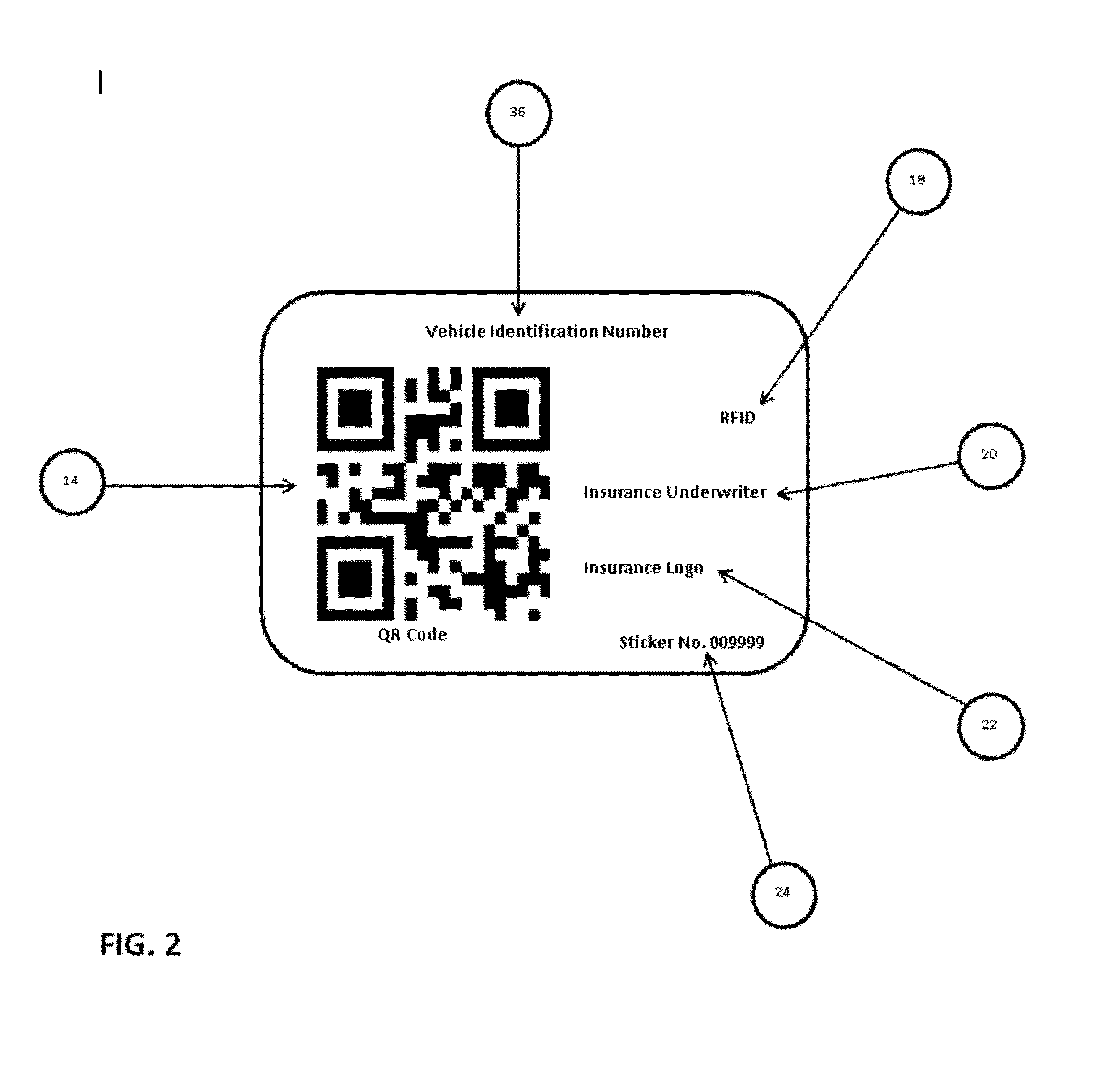
e-Sure Insurance Quick Verification System
InactiveUS20130197945A1Eliminate fraudEliminate falsified documentFinanceOffice automationScannerBarcode
System and method for providing instant access to information about a vehicles insurance coverage. The linking element physically located on the vehicle body which includes vehicle license plate, or can be installed on vehicle for the specific purpose of retrieving insurance information. Linking element can be, radio frequency identification (RFID) or barcode, or quick response code (QRC) affixed anywhere on vehicle. Authorized users immediately access and retrieve current vehicle insurance coverage from a plurality of information retrieval systems including portable and fixed scanning systems, smart phone or other portable devices based on the linking element. The RFID scanner or smart phone transmit information over a communication link to a database / fileserver containing the most current vehicle insurance information associated with vehicle's vehicle identification number. The RFID reader or smart phone then receives information from the database / fileserver on the specific VIN queried where it is reviewed by an authorized user.
Owner:ANDERSON THEODRIC
Method for measuring volume of large irregular bulk grain pile based on dynamic three-dimensional laser scanning
The invention relates to a method for measuring the volume of a large irregular bulk grain pile based on dynamic three-dimensional laser scanning. The method comprises the following steps of: arranging a guide rail in the middle of the top of a barn along the width direction, wherein the guide rail is provided with a slide block controlled by a stepping motor, and a laser radar scanner is installed on the slide block; moving the slide block from one end to the other end of the top of the barn at a constant speed to drive the laser radar scanner by the slide block to finish scanning on the surface of the whole bulk grain pile, wherein the laser radar device is a one-dimensional scanning device to realize linear scanning and returning coordinate data, and the master control computer is used for transmitting pulses to the stepping motor and processing the signal; acquiring point cloud data of the surface of the bulk grain pile through the master control computer, determining the distribution density of scanned points for calculating the volume according to an allowed error value of the grain pile measured by the user, and calculating the weight of the grain pile according to the grain density provided by the user; and generating a point cloud graphic matrix attached with coordinates through scanning space morphology by guide rail moving type three-dimensional laser, performing surface fitting to form an irregular bulk grain pile appearance, and thus obtaining the volume of the irregular bulk grain pile. The volume of the large irregular bulk grain pile can be rapidly and effectively measured at high precision, and remote monitoring can be realized; and moreover, the method is low in cost and easy to implement.
Owner:MENG FAN'GANG
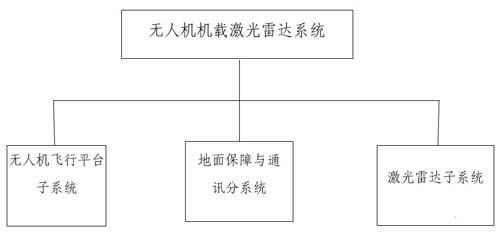
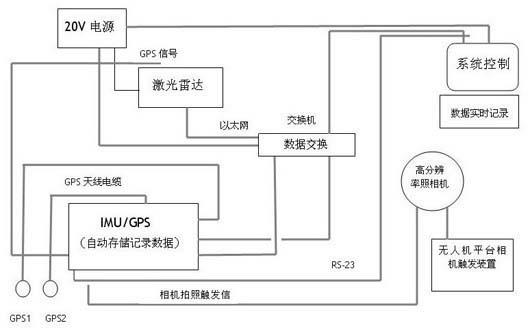
Unmanned aerial vehicle-mounted laser radar system
InactiveCN102381481AEasy to transportLow running costAircraft componentsInertial measurement unitImage resolution
The invention relates to an unmanned aerial vehicle-mounted laser radar system, which consists of an unmanned aerial vehicle flying platform subsystem, a laser radar subsystem and ground protection and communication subsystems, wherein the unmanned aerial vehicle flying platform subsystem takes an unmanned helicopter as a carrying platform, the laser radar subsystem is used for acquiring three-dimensional spatial information and digital image data and consists of a laser scanner, an IMU (Inertial Measurement Unit), and a high-resolution aerially-photographing digital camera, and the ground protection and communication subsystems are used for protecting flying safety and timely returning working state information of the system. With the adoption of the unmanned aerial vehicle-mounted laser radar system, the patrol efficiency can be increased, the patrolling means is scientific, intuitive and accurate, the potential problems can be timely discovered so as to ensure safe operation and reduce economic losses, and thus, the unmanned aerial vehicle-mounted laser radar system has the characteristics of low cost, simplicity for operating, high accuracy of data and the like.
Owner:MIANYANG SKYEYE LASER TECH
Scanner having connected and unconnected operational behaviors
InactiveUS20110075228A1Buying/selling/leasing transactionsSpecial data processing applicationsOperational behaviorWorld Wide Web
Owner:GOOGLE LLC
Surgical procedures
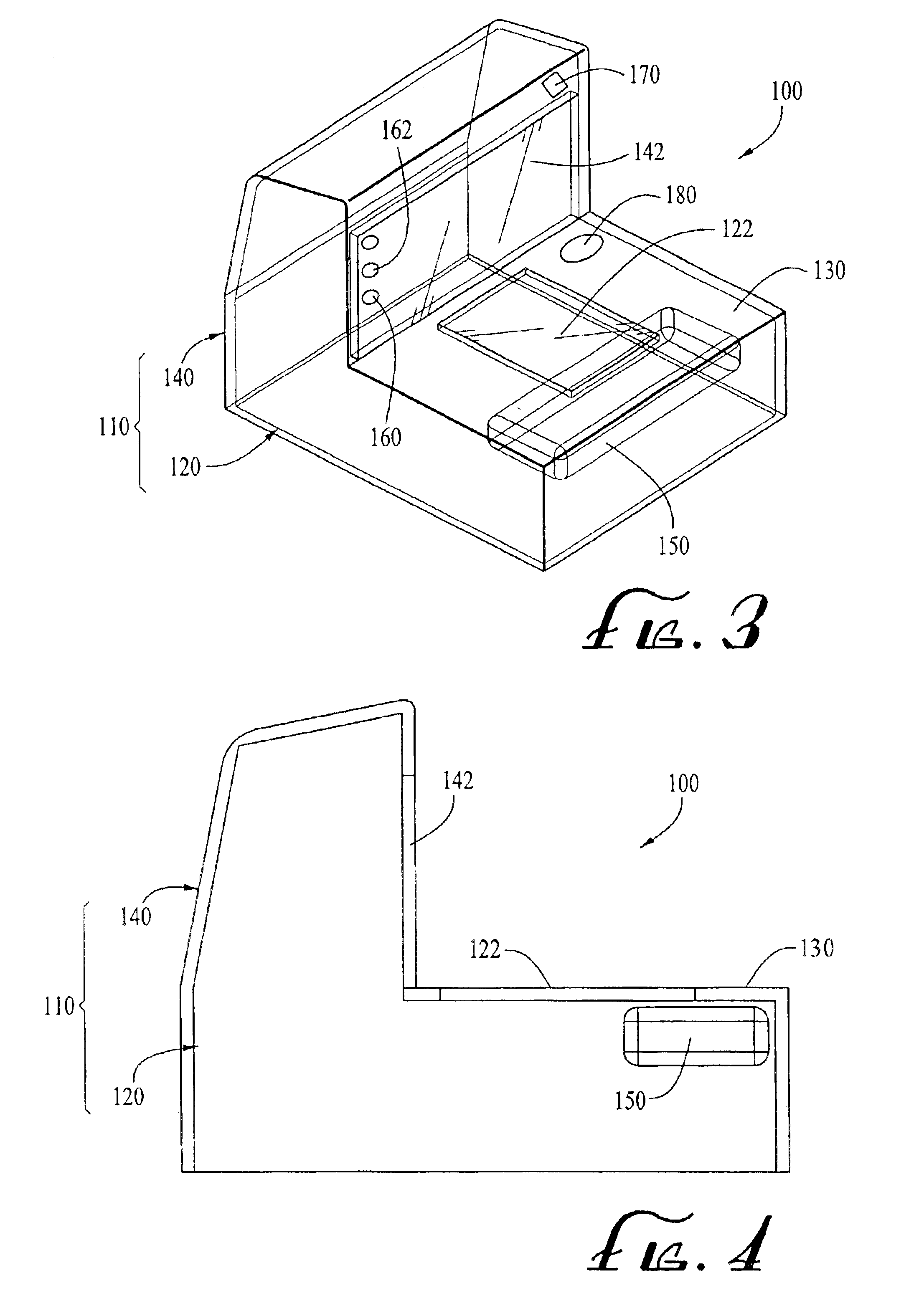
InactiveUS20080281190A1Efficient and reliable and identificationEfficient and reliable locationSurgeryDiagnostic markersSurgical operationScanner
A method of locating and identifying, during surgery, target regions within a body intended for excision of suspect tissue and / or removal of diseased organs or foreign objects, resides in implantation within the body proximate the suspect tissue or object prior to surgery of one or more passive integrated transponder tags and, at the time of and / or during surgery, scanning of the body with a radio frequency scanner or reader that activates the tag or tags and provides the surgeon with one or more signals indicative of the approximate location and unique identification of each of the tags, thereby to aid the surgeon in performance of the surgery. Verification of the success of the surgical procedure is obtained following surgery by scanning the site for absence of the tag or tags and / or by scanning the excised tissue for presence of the tag or tags.
Owner:HEALTH BEACONS
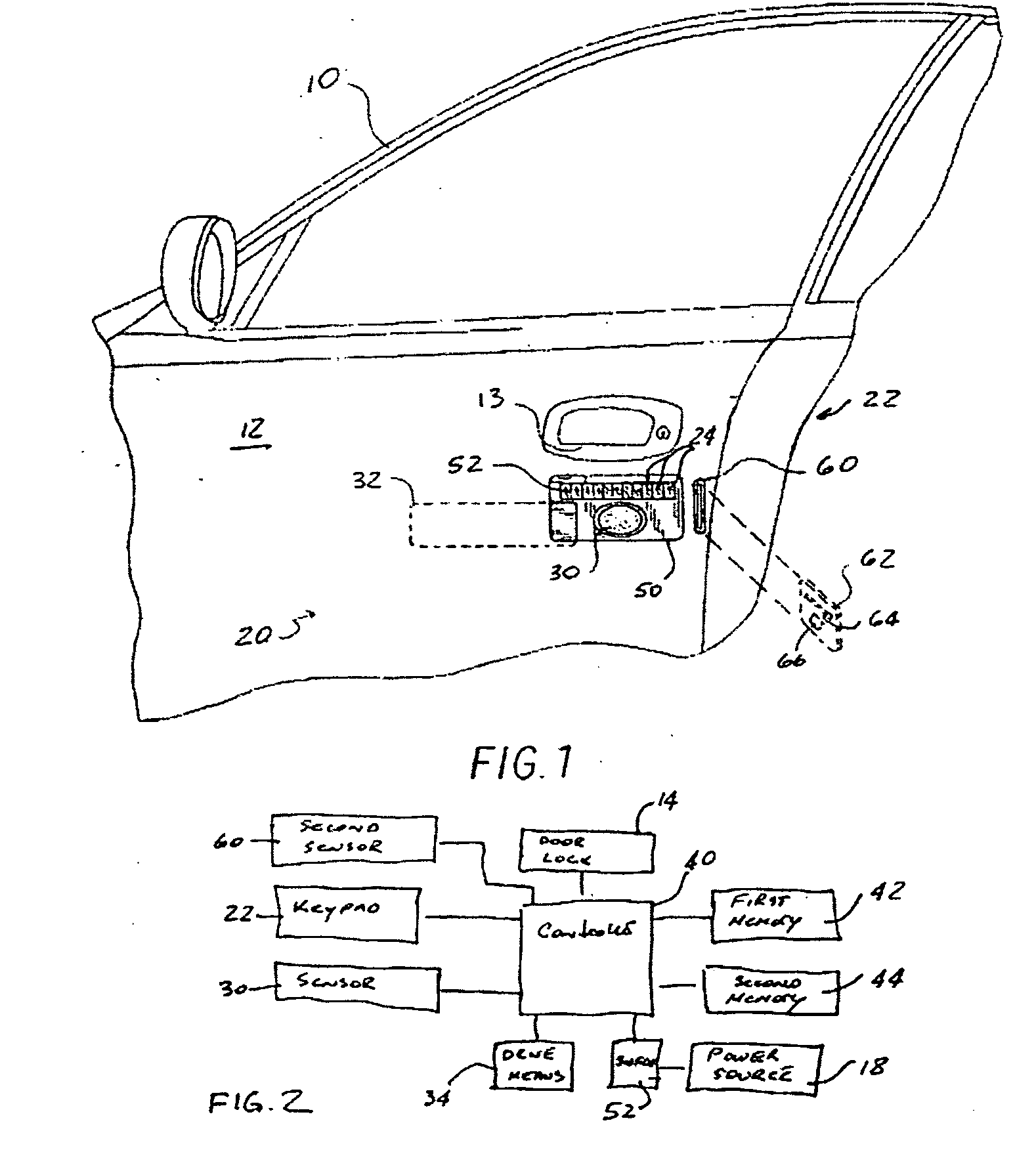
Keyless security system
InactiveUS20060186987A1Increase entryElectric signal transmission systemsImage analysisControl signalUser input
A keyless security system for enabling a user to gain entry into or start a vehicle includes a keypad for providing a first signal when the user inputs a predetermined character string. A fingerprint scanner provides a second signal characterizing a finger placed in close proximity to such sensor. A controller is coupled to the keypad and to the fingerprint scanner for receiving the first signal and the second signal for comparing each of the first signal and the second signal with a respective default signal stored in a memory and for providing a control signal when each of the first signal and the second signal is substantially identical to its respective default signal, whereby operation of the fingerprint sensor is enabled only when the first signal is substantially identical to its respective default signal.
Owner:WILKINS DEBBIE L
Theft prevention system and method
A theft prevention system includes an RFID reader configured to read an RFID tag to authenticate access to a predefined area, a laser scanner configured to scan the predefined area and detect an object in the predefined area, and a security component configured to initiate a security action when the detected object is at least one of an unauthenticated object and an unauthorized object.
Owner:PEPPERL FUCHS GMBH
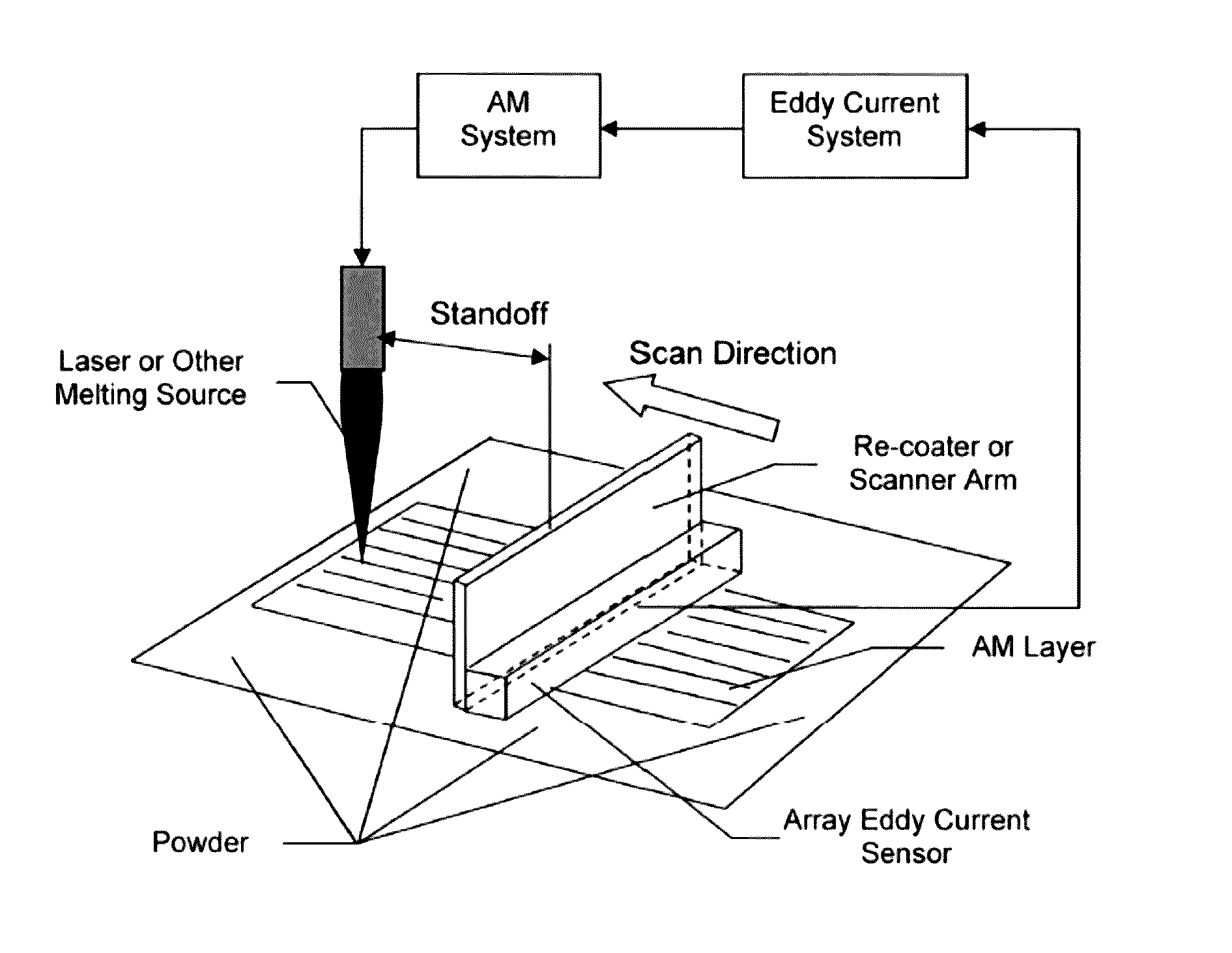
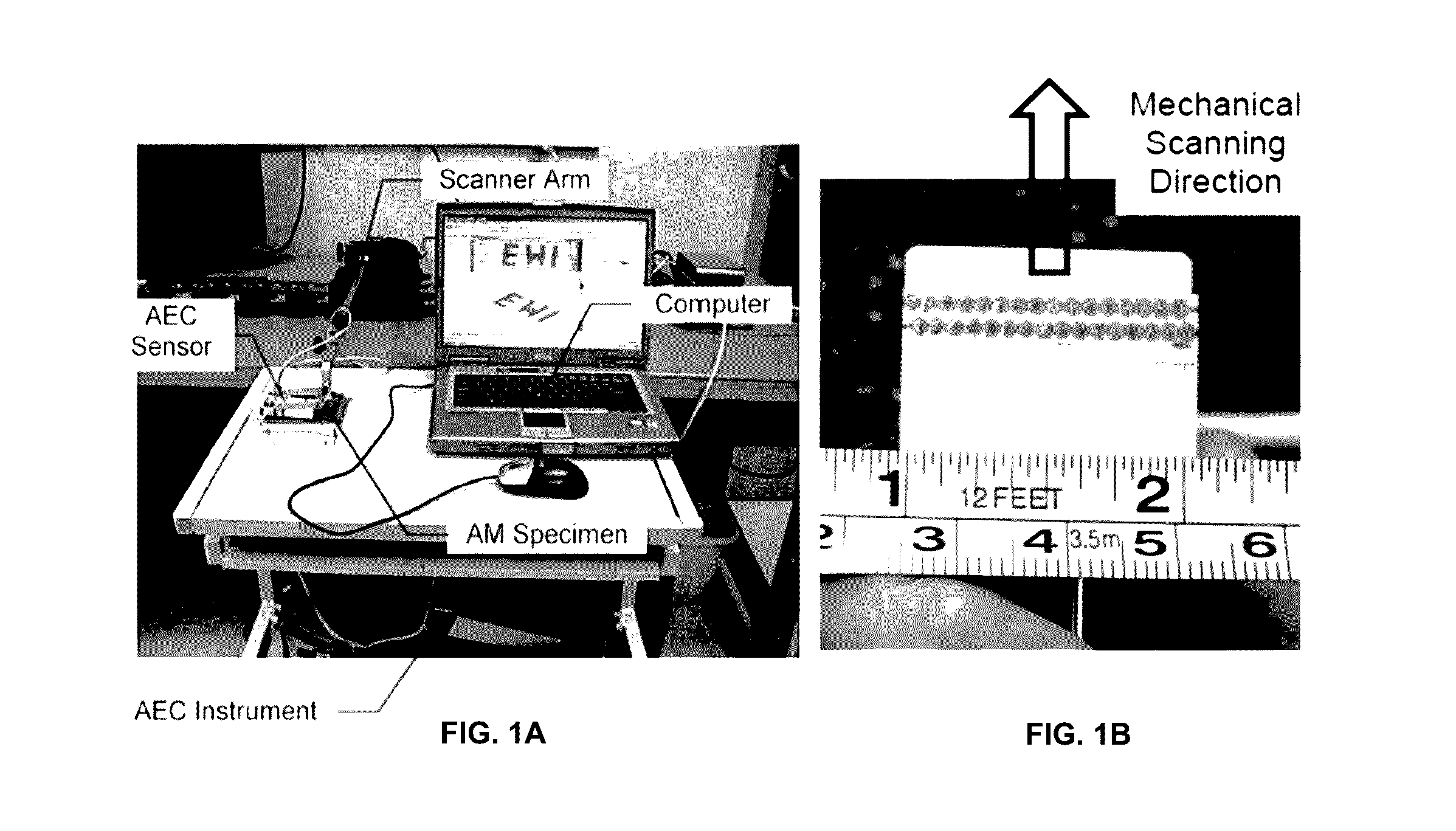
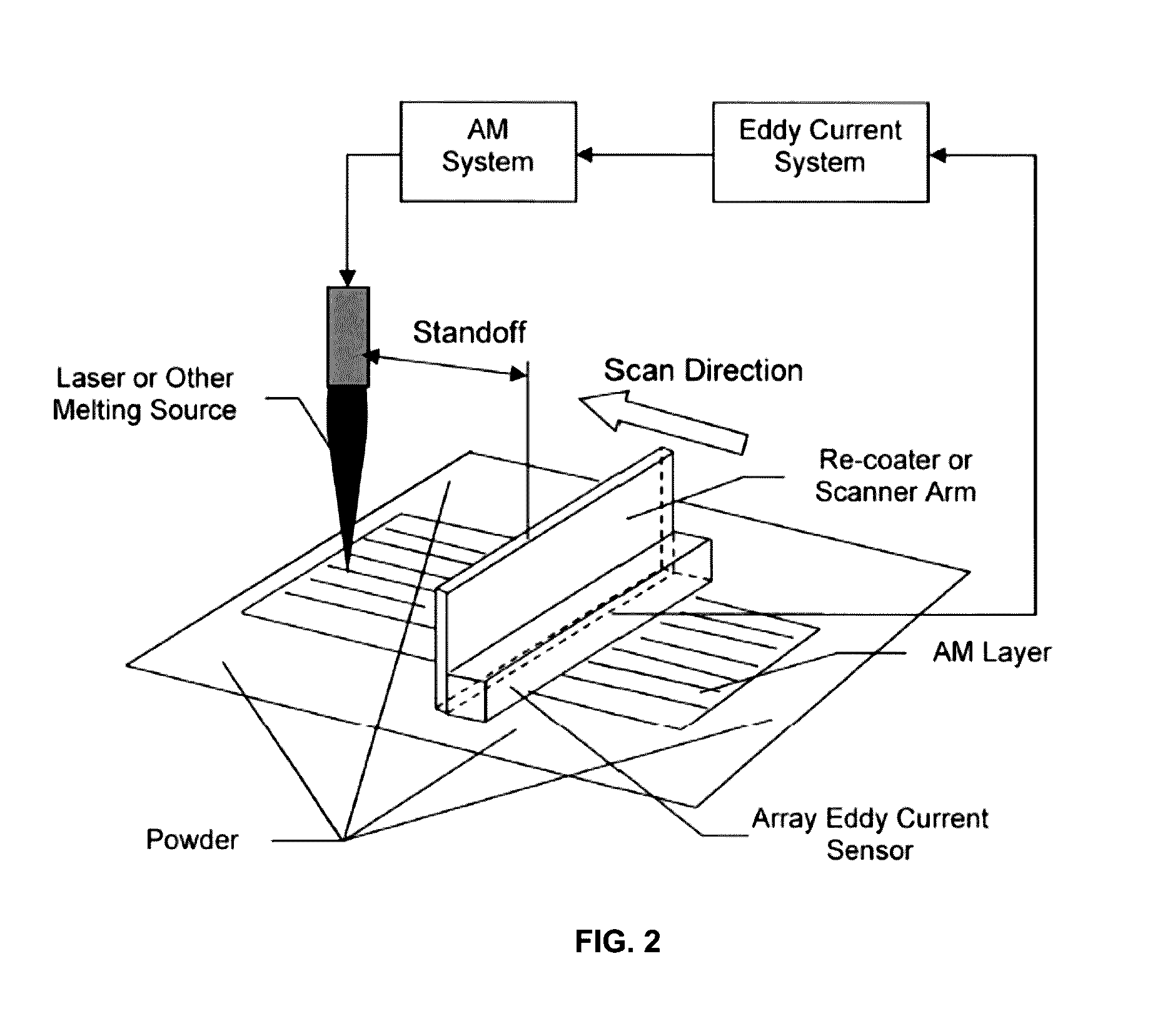
Non-destructive evaluation of additive manufacturing components using an eddy current array system and method
InactiveUS20160349215A1Additive manufacturing apparatusAdditive manufacturing with solidsNon destructiveSensor array
A system for non-destructively evaluating components fabricated by additive manufacturing, comprising a sensor array that includes a plurality of individual elements arranged in a predetermined pattern for allowing uniform coverage of an area of an electrically conductive component to be evaluated, wherein each element in the plurality of elements further includes at least one coil that acts as an exciter coil for generating an alternating electromagnetic field when activated or a receiver coil for measuring a change in impedance of the at least one coil or both an exciter coil and receiver coil, wherein the alternating electromagnetic field generates eddy currents in the component to be evaluated, and wherein the individual elements in the sensor array are excited in a predetermined sequence during a single pass of the array over the area to be evaluated; and an XY-scanner arm adapted to receive the sensor array, wherein the XY-scanner arm is operative to generate a C-scan of the area being evaluated during the single pass.
Owner:EDISON WELDING INSTITUTE INC
Modifying RFID system operation using movement detection
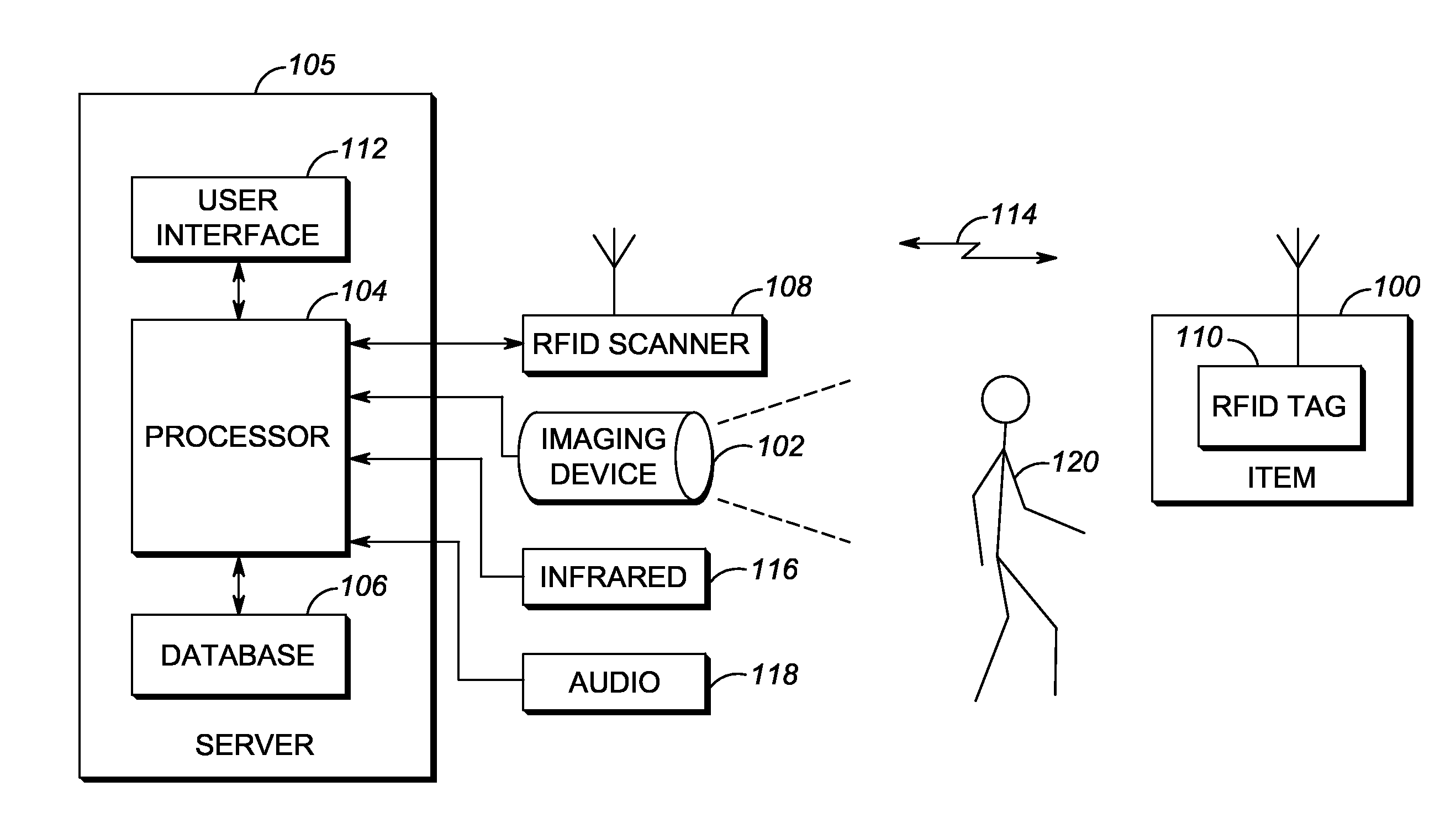
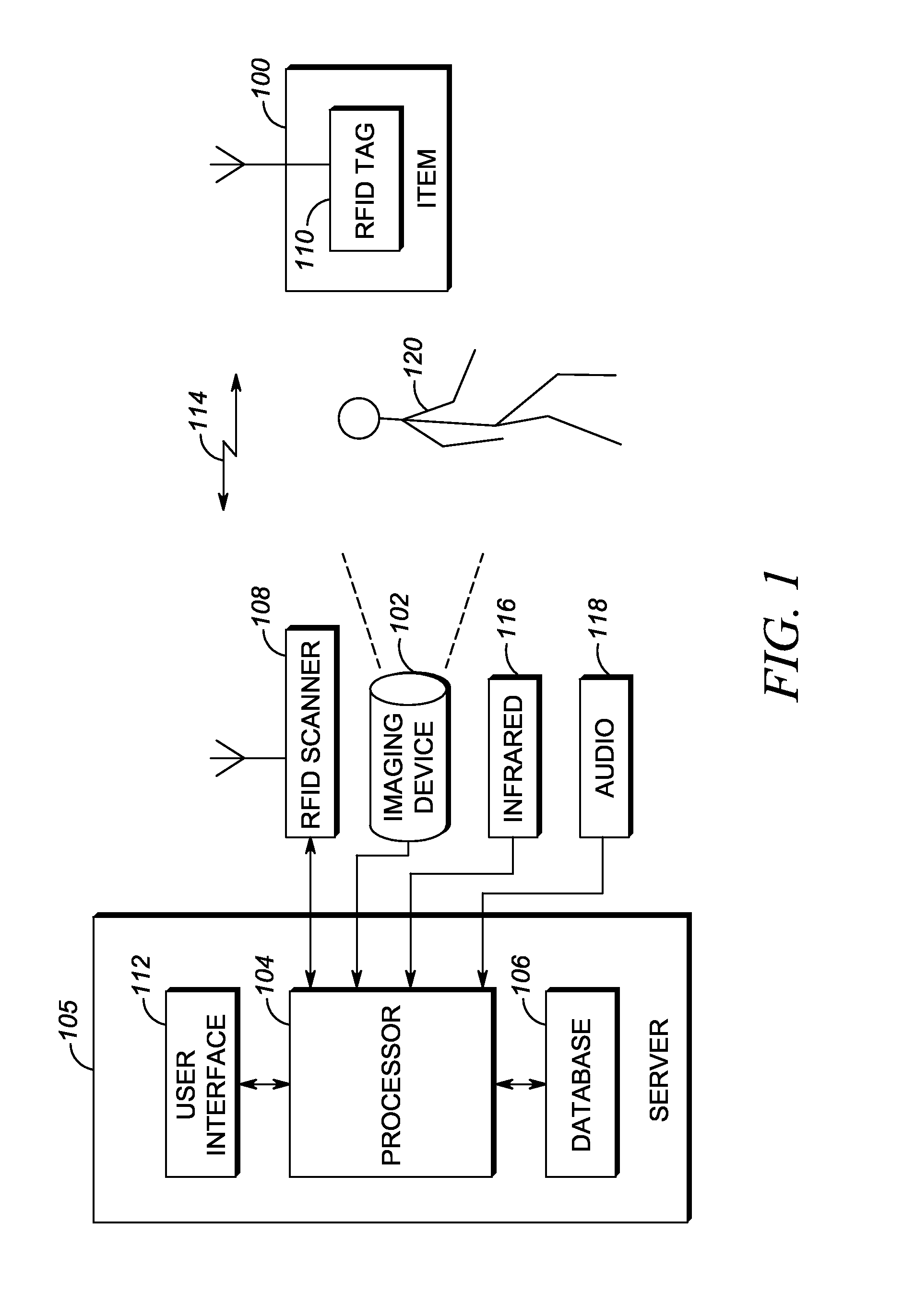
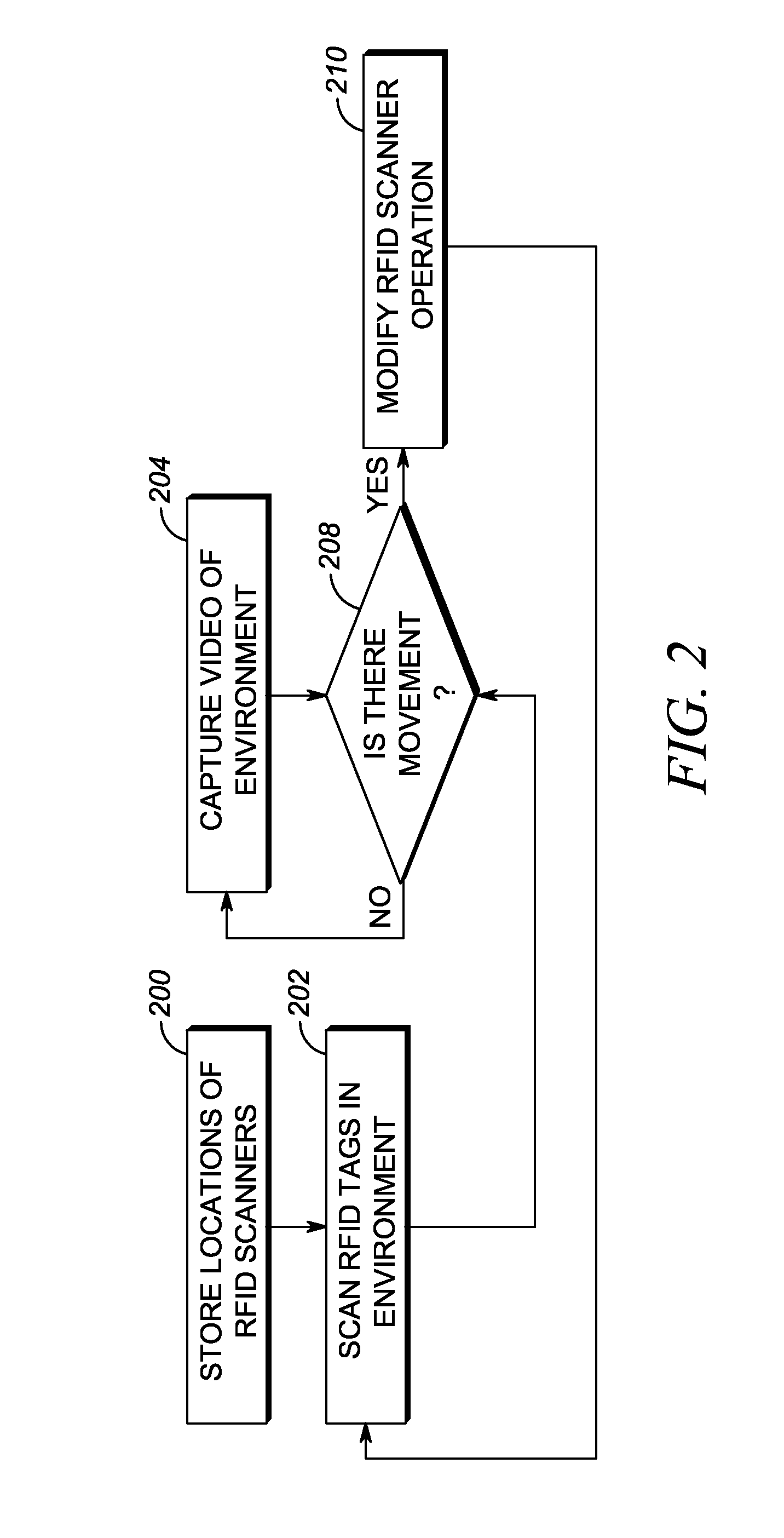
ActiveUS20150269818A1Sensing record carriersBurglar alarm by hand-portable articles removalScannerVideo processing
A technique for modifying radio frequency identification (RFID) system operation using movement detection includes an RFID scanner disposed within an environment and operable to obtain RFID data from RFID tags located within the environment. An imaging device captures video of the environment, and a processor analyzes the captured video from the imaging device to detect and locate movement within the environment. If movement is detected within the environment, the processor modifies operation of the RFID scanner that is proximal to the location of the movement, increasing or decreasing interrogation rate, for example.
Owner:SYMBOL TECH LLC
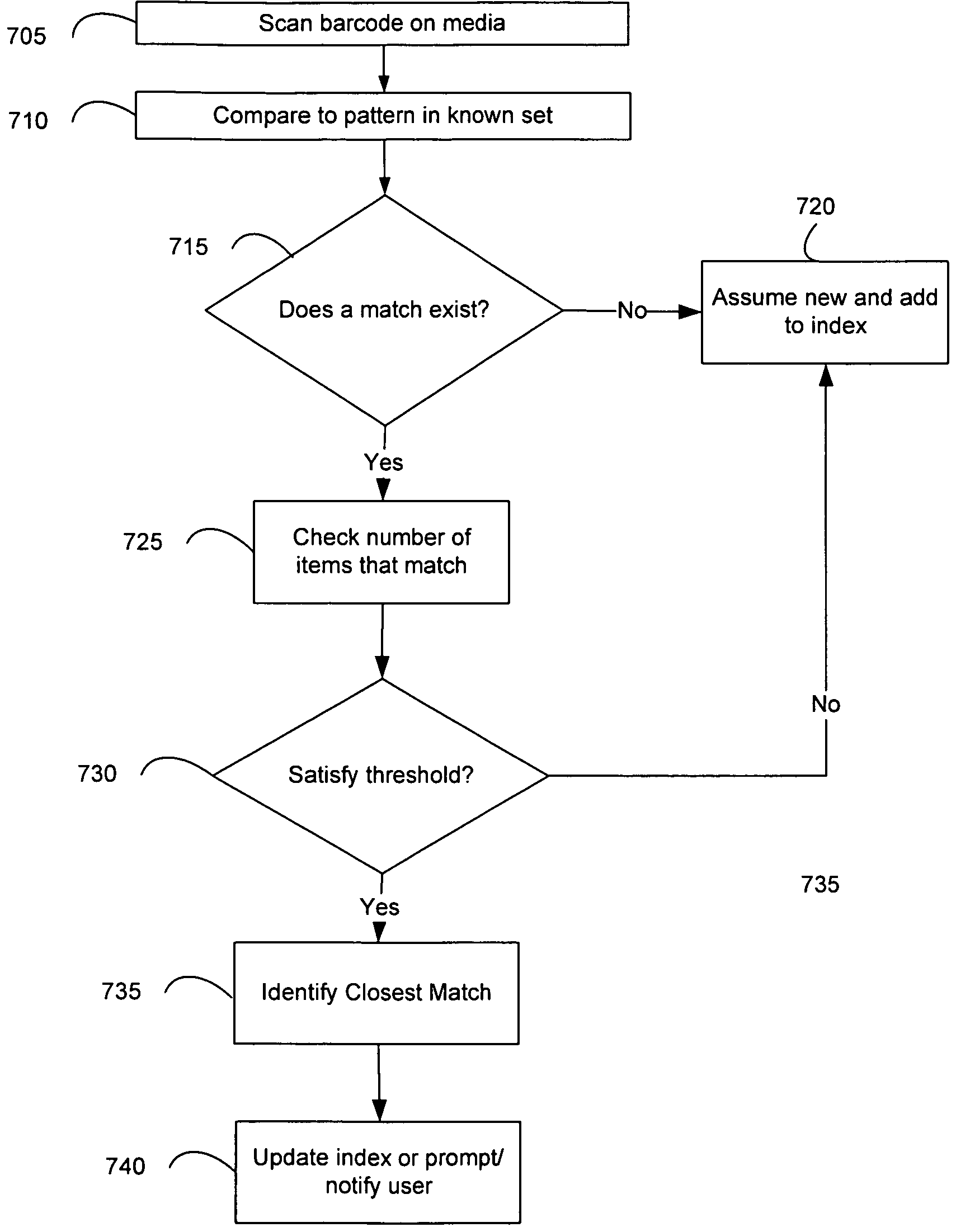
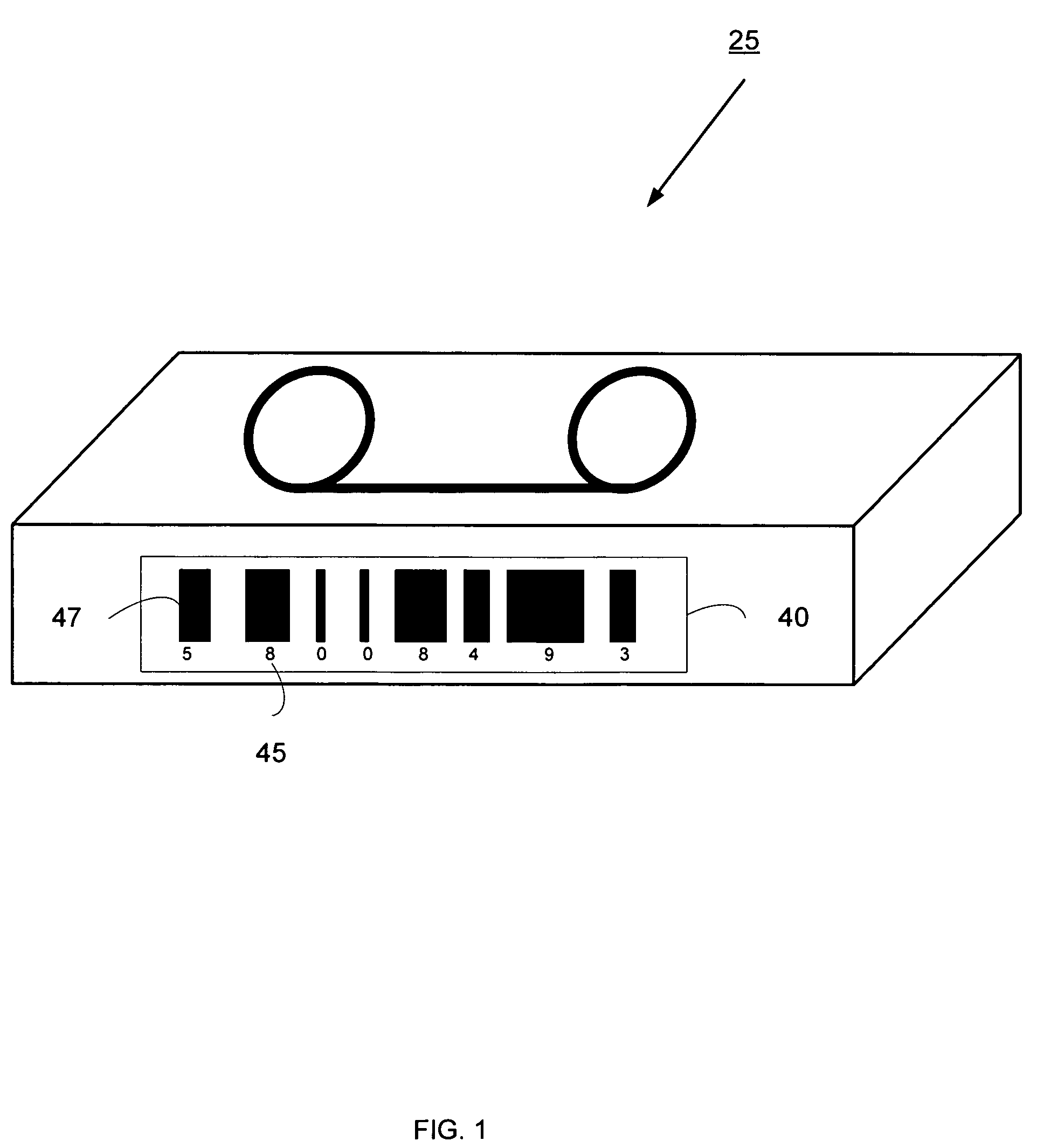
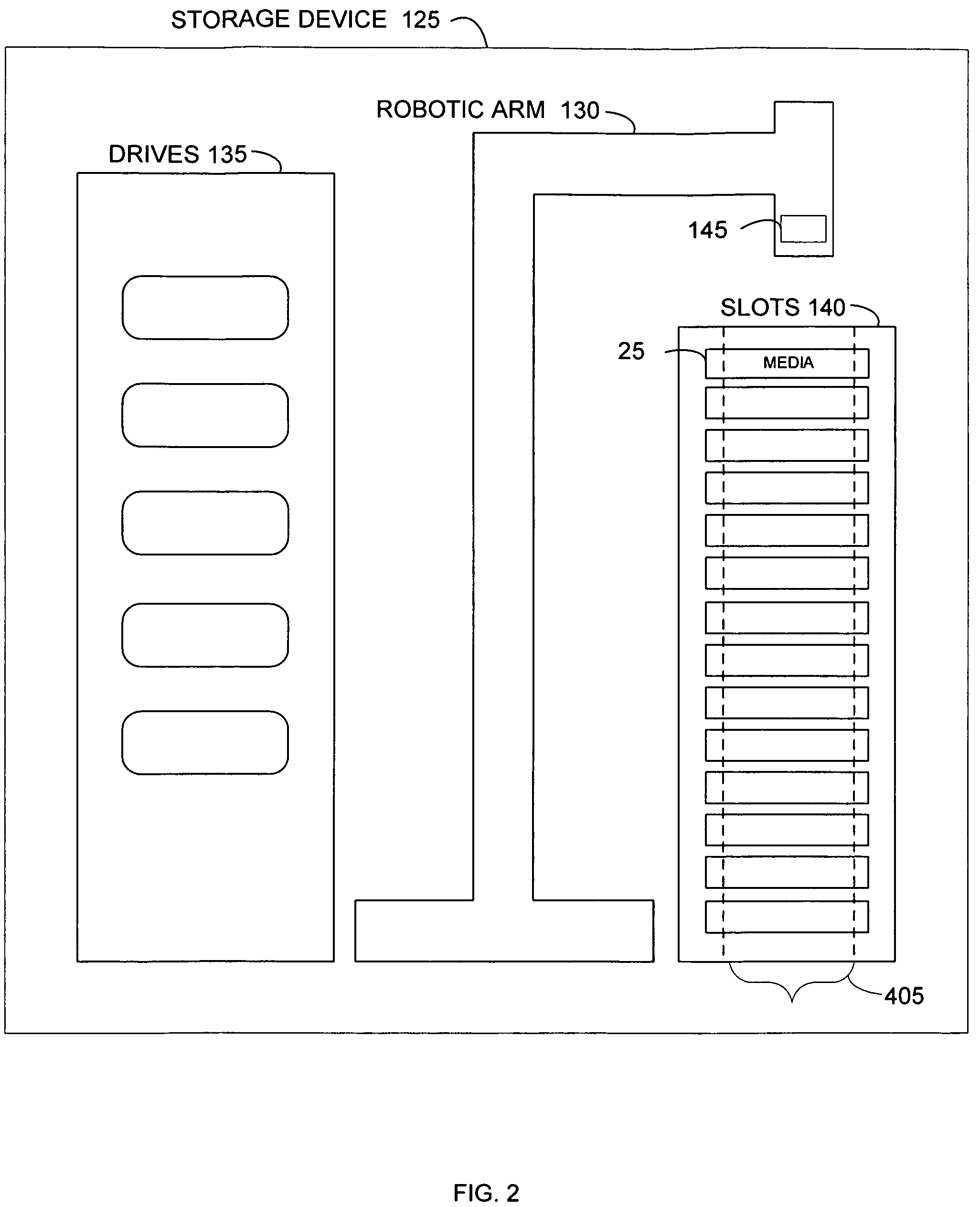
System and method for improved media identification in a storage device
Systems and methods are provided for improved identification of removable storage media. A scanner may be used to read an identifier, such as a barcode, on a removable storage media. In the event that the scanner reads the identifier incorrectly due to a defect in the barcode, such as a damaged label, misaligned identifier, or because the scanner is incapable of reading the identifier type or the scanner's field of view is incorrect, a media management component receives the scanned identifier data and matches it to a known set of media identifiers to create a subset of matching identifier data. A closest matching media identifier may be identified from the subset of matching identifier data. An index may be updated with information indicating the closest matching media identifier and a location of the removable storage media.
Owner:COMMVAULT SYST INC
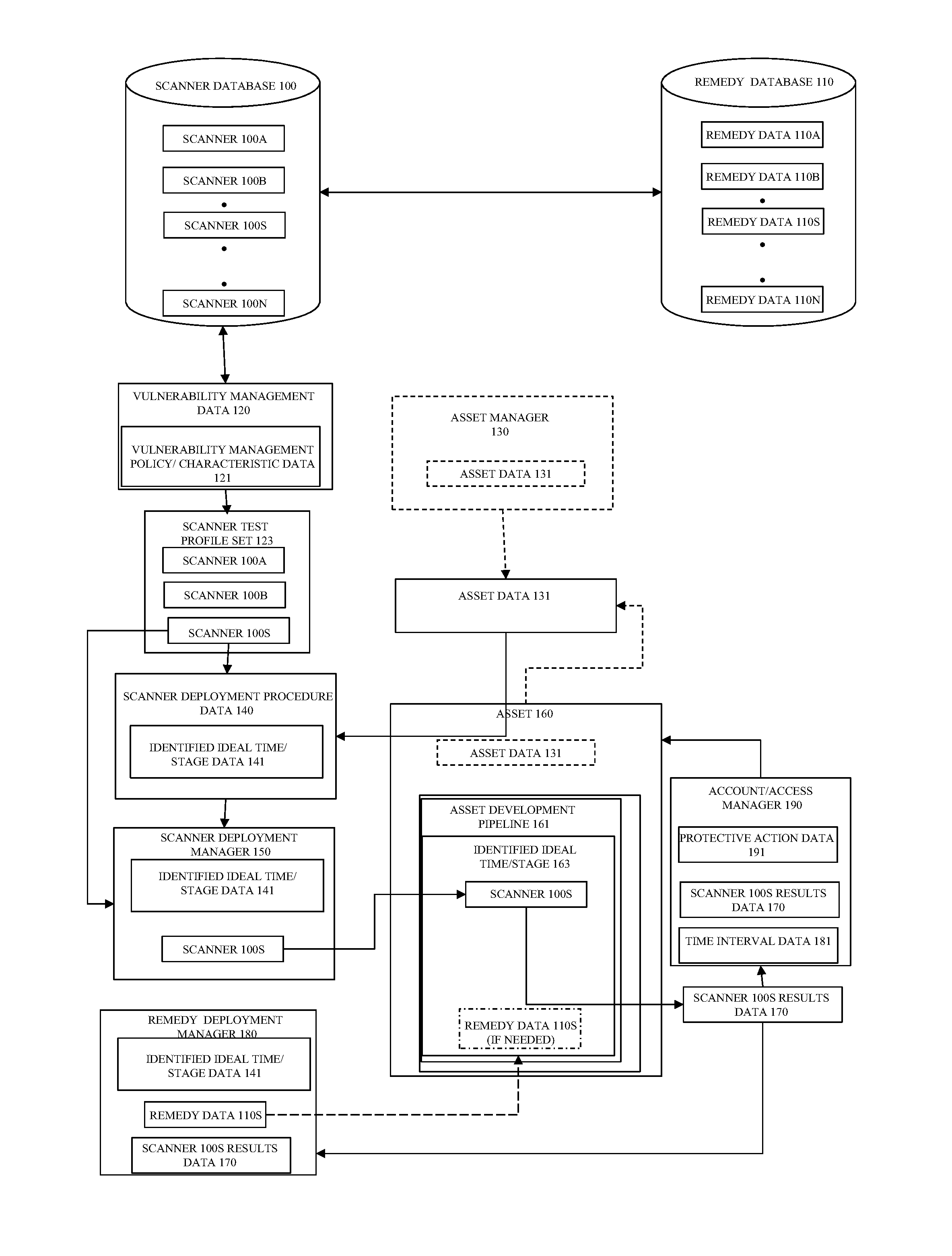
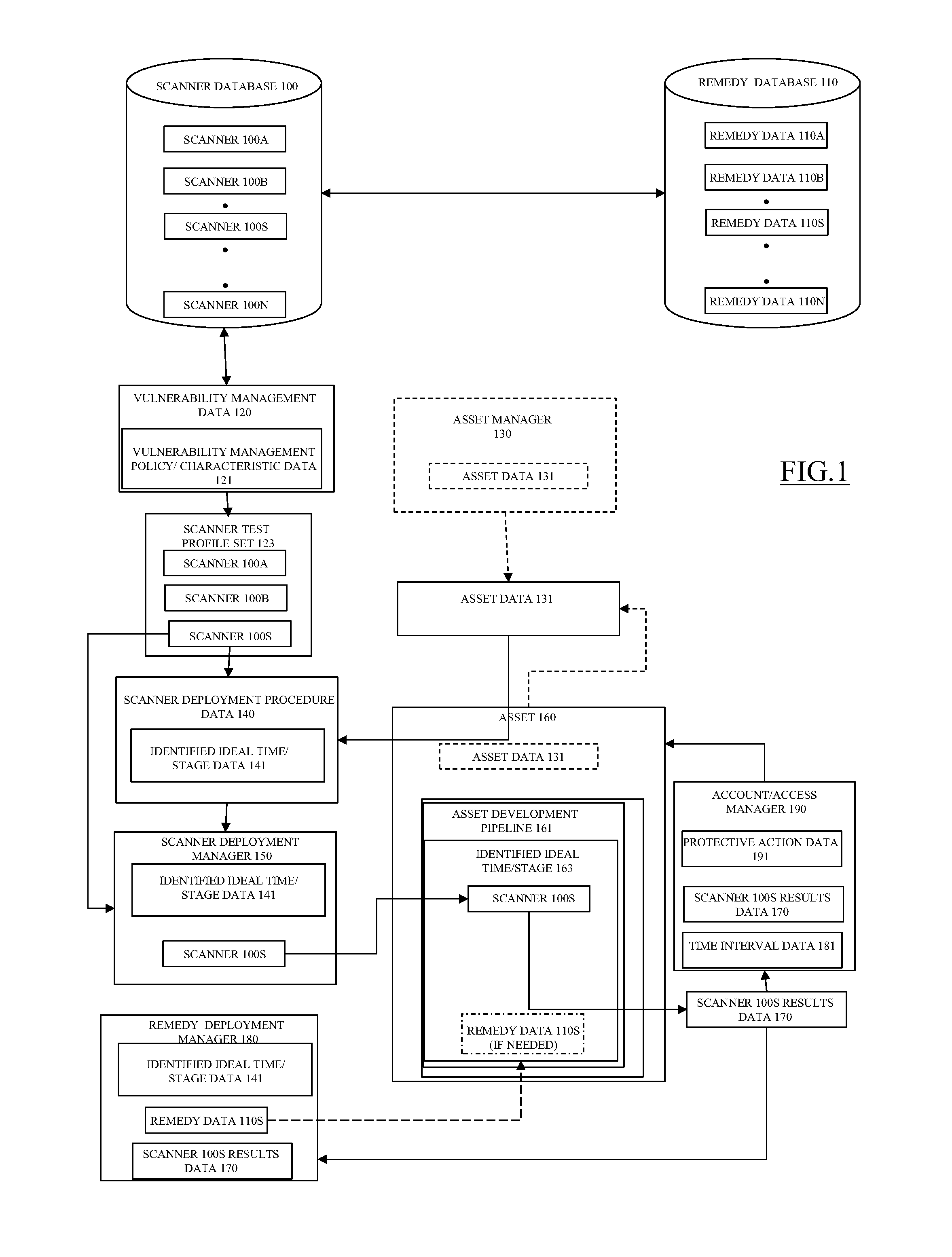
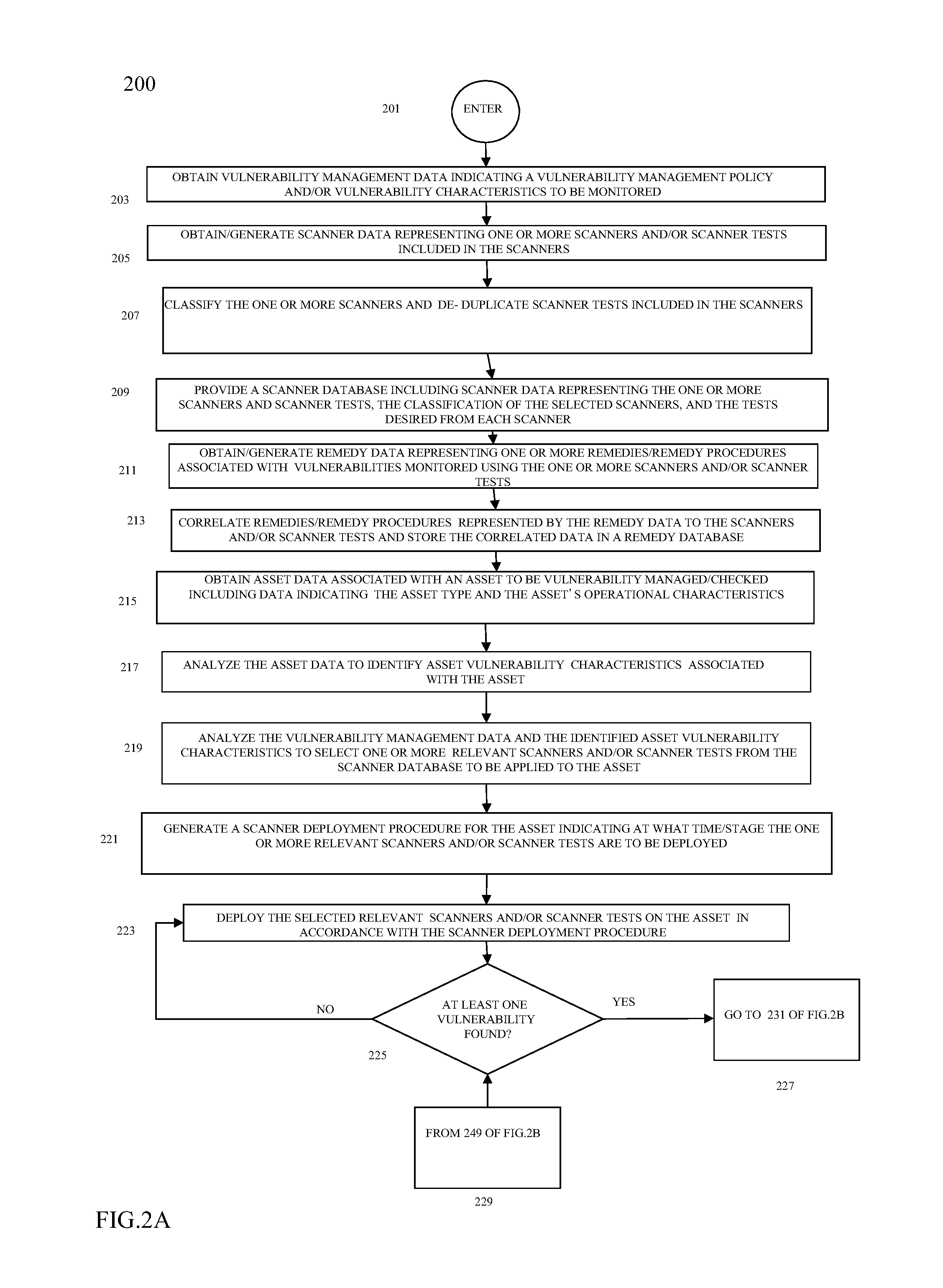
Method and system for dynamic and comprehensive vulnerability management
ActiveUS20150106939A1Reduce vulnerabilityMemory loss protectionError detection/correctionVulnerability managementRemedial action
One or more relevant scanners used to identify asset vulnerabilities are identified, obtained, and logically arranged for deployment on an asset in accordance with a vulnerability management policy and a scanner deployment policy such that the relevant scanners are deployed at, or before, a determined ideal time to minimize the resources necessary to correct the vulnerabilities, if found. The relevant scanners are then automatically deployed in accordance with the scanner deployment policy and, if a vulnerability is identified, one or more associated remedies or remedy procedures are applied to the asset. At least one of the one or more relevant scanners are then re-deployed on the asset to determine if the identified vulnerability has been corrected and, if the vulnerability is not corrected at, or before, a defined time, protective measures are automatically taken.
Owner:INTUIT INC
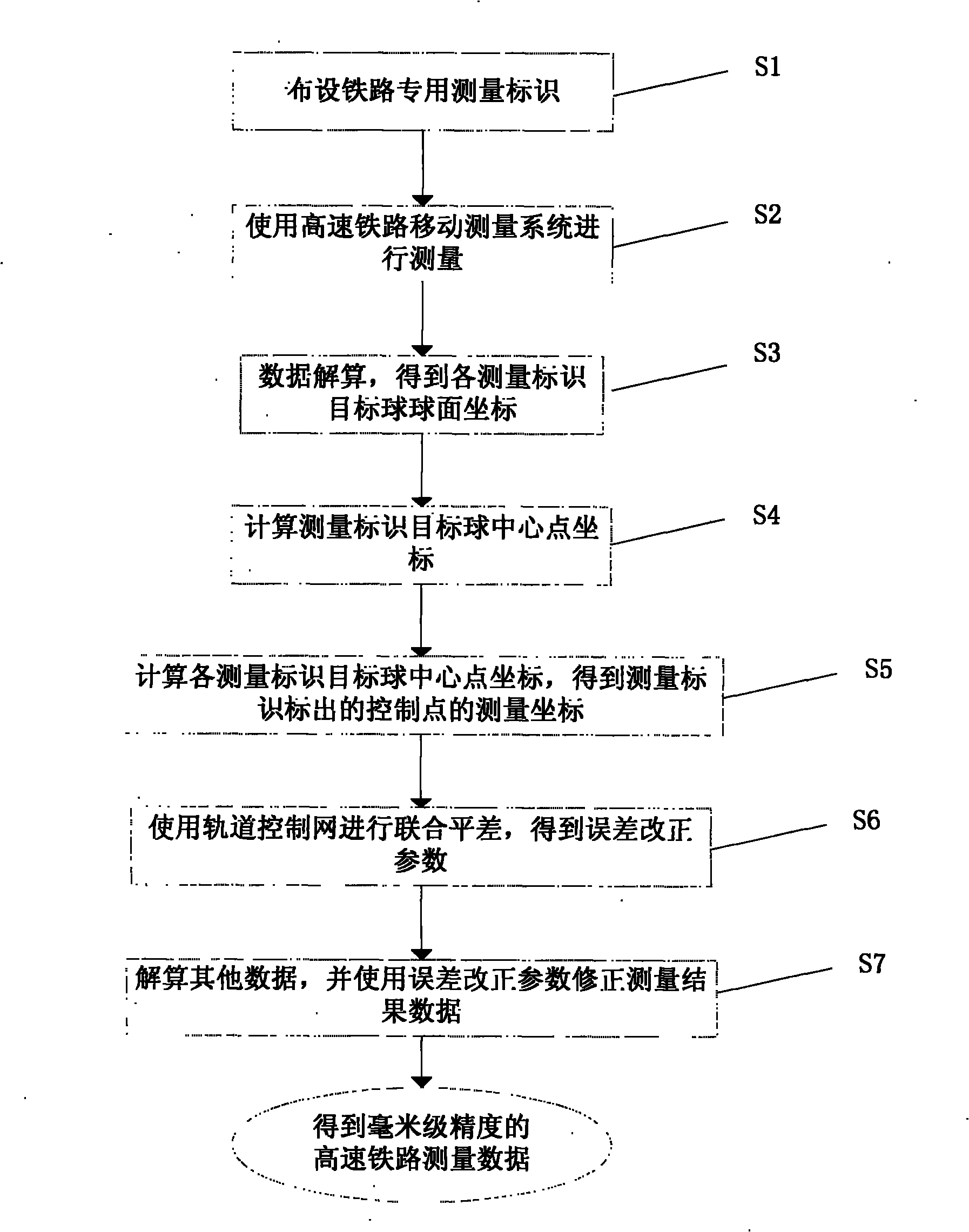
System and method for fast precise measurement and total factor data acquisition of high speed railway
InactiveCN101913368AGuaranteed safe operationMeasuring points markingRailway auxillary equipmentMeasurement deviceData acquisition
The invention relates to the field of precise railway measurement, high speed railway rail detection and security and digital railway, in particular to a system and a method for carrying out movable precise measurement of the high speed railway and synchronously obtaining total factor data along the line of the railway on the basis of GPS (Global Positioning System) / IMU (Inertia Measurement Unit) positioning and orientation, laser scan and digital imaging technologies. The invention further relates to a special railway measurement mark. The system consists of a laser scanner (1), a digital imaging device (2), a GPS receiver (3), an IMU (4), an industrial computer (5) and a power supply unit (6), and the system can obtain three-dimensional point clouds of rail, roadbed and peripheral environment of the high speed railway and digital images oriented by the earth. The method comprises a method for carrying out movable precise measurement movable precise measurement of the high speed railway and a method for improving the measurement precision by carrying out the simultaneous adjustment with a control point of a rail control network (such as a CPIII foundation pile control network). The system has high integration degree and has the characteristics of high efficiency and high precision, and the precision of the data can reach millimeter level.
Owner:扬州德可达科技有限公司
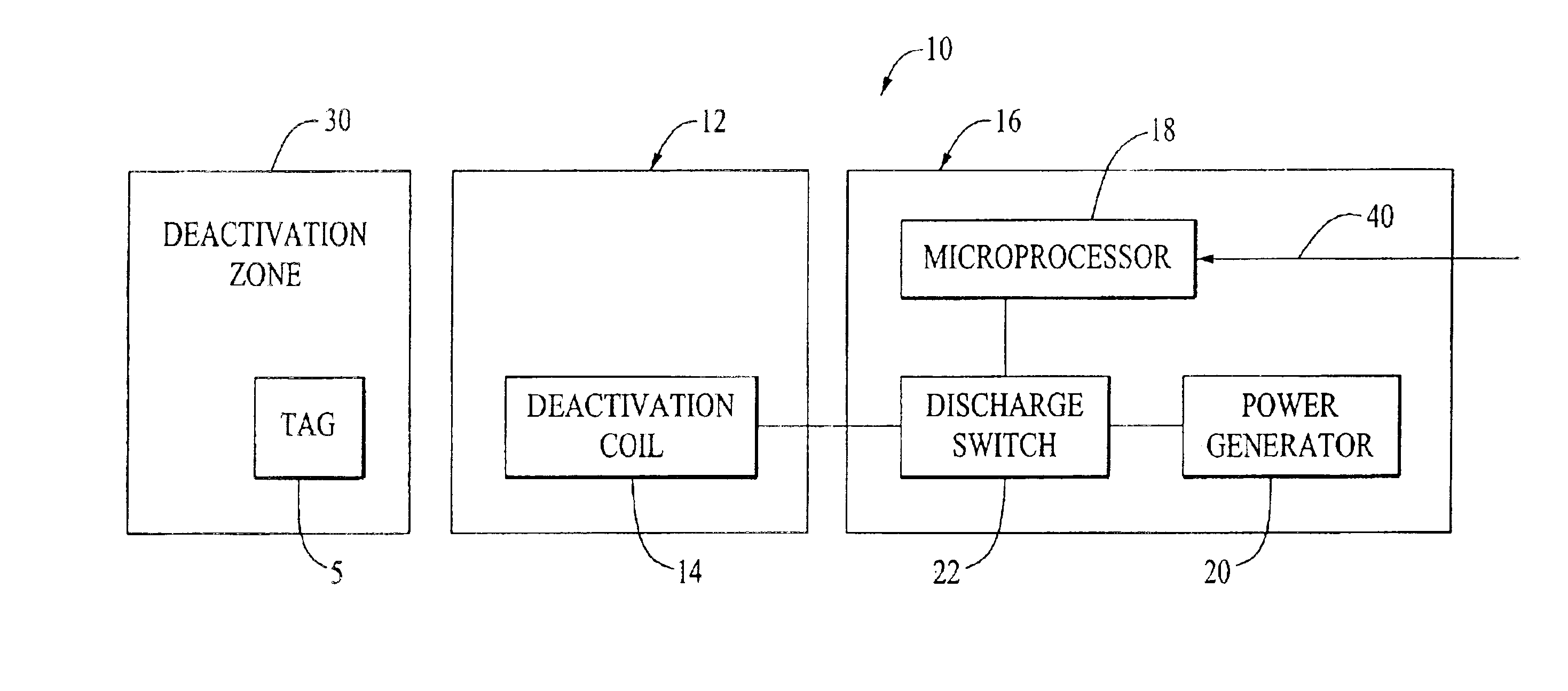
Systems and methods for data reading and EAS tag sensing and deactivating at retail checkout
Methods of operation of a data reader and security tag deactivation system whereby a data reader such as a barcode scanner is equipped with EAS deactivation coils or modules disposed in the vicinity of the read volume or generally proximate thereto and the system is operable to permit reading of the ID tag (such as the barcode label) on an item, and upon a successful read, the deactivation unit is operable to (1) sense the presence of an EAS tag; (2) if presence of an EAS tag is sensed, energize the deactivation coil / module to deactivate the EAS tag; and (3) sense if the EAS tag is deactivated. If the EAS tag is sensed to have been deactivated, the system signals as such and a next item may be scanned. If the EAS tag is sensed to have not been deactivated, the system proceeds to alternate operational steps to handle the exception. In another function, the system is operable to urge the operator to return the item to the read volume to enhance EAS tag deactivation, one method being by delaying a good read acknowledgment until the system determines that the EAS tag which may have been previously detected has subsequently been deactivated.
Owner:SENSORMATIC ELECTRONICS CORP +1
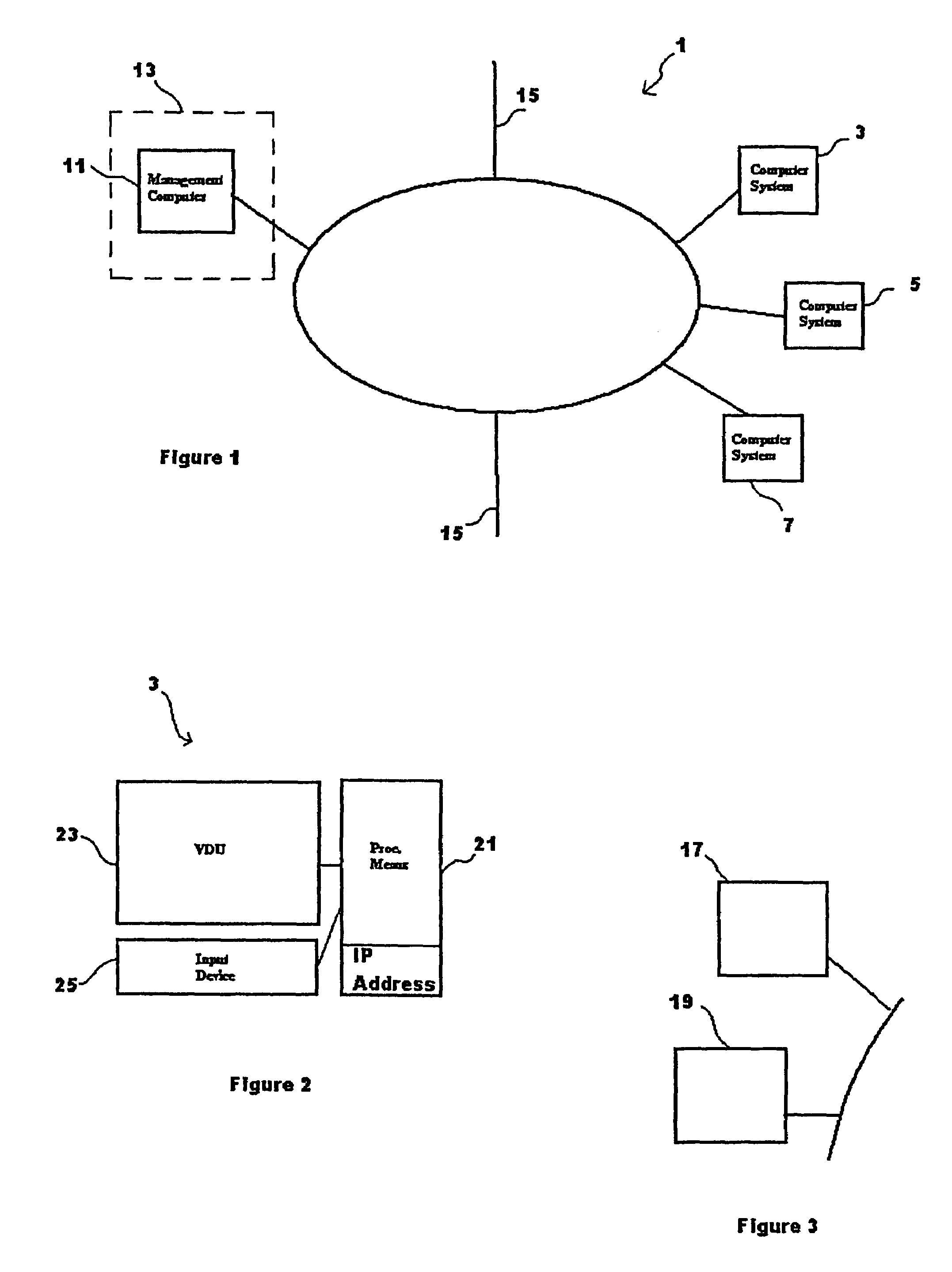
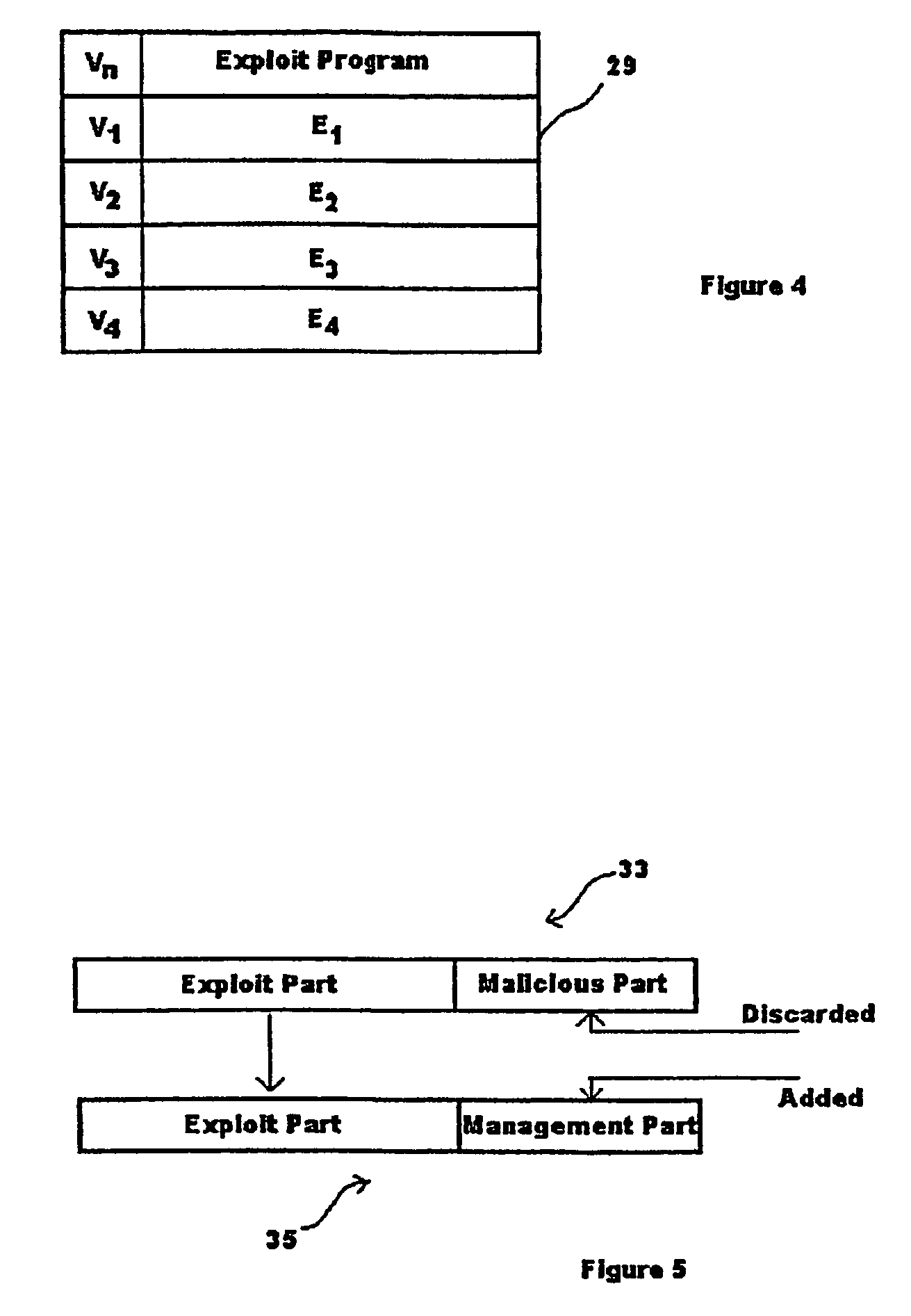
Signal level propagation mechanism for distribution of a payload to vulnerable systems
ActiveUS7353539B2Memory loss protectionUser identity/authority verificationScannerNetwork addressing
A method of identifying a software vulnerability in computer systems in a computer network includes a multiple level scanning process controlled from a management system connected to the network. The management system runs a root scanner which applies an interrogation program to remote systems having network addresses in a predefined address range. When a software vulnerability is detected, the interrogation program causes the respective remote system to scan topologically local systems, the remote system itself applying a second interrogation program to the local systems to detect and mitigate the vulnerability using an associated mitigation payload. Whilst that local scanning process is in progress, the root scanner can be applied to remote systems in other predefined address ranges.
Owner:QUEST PATENT RES
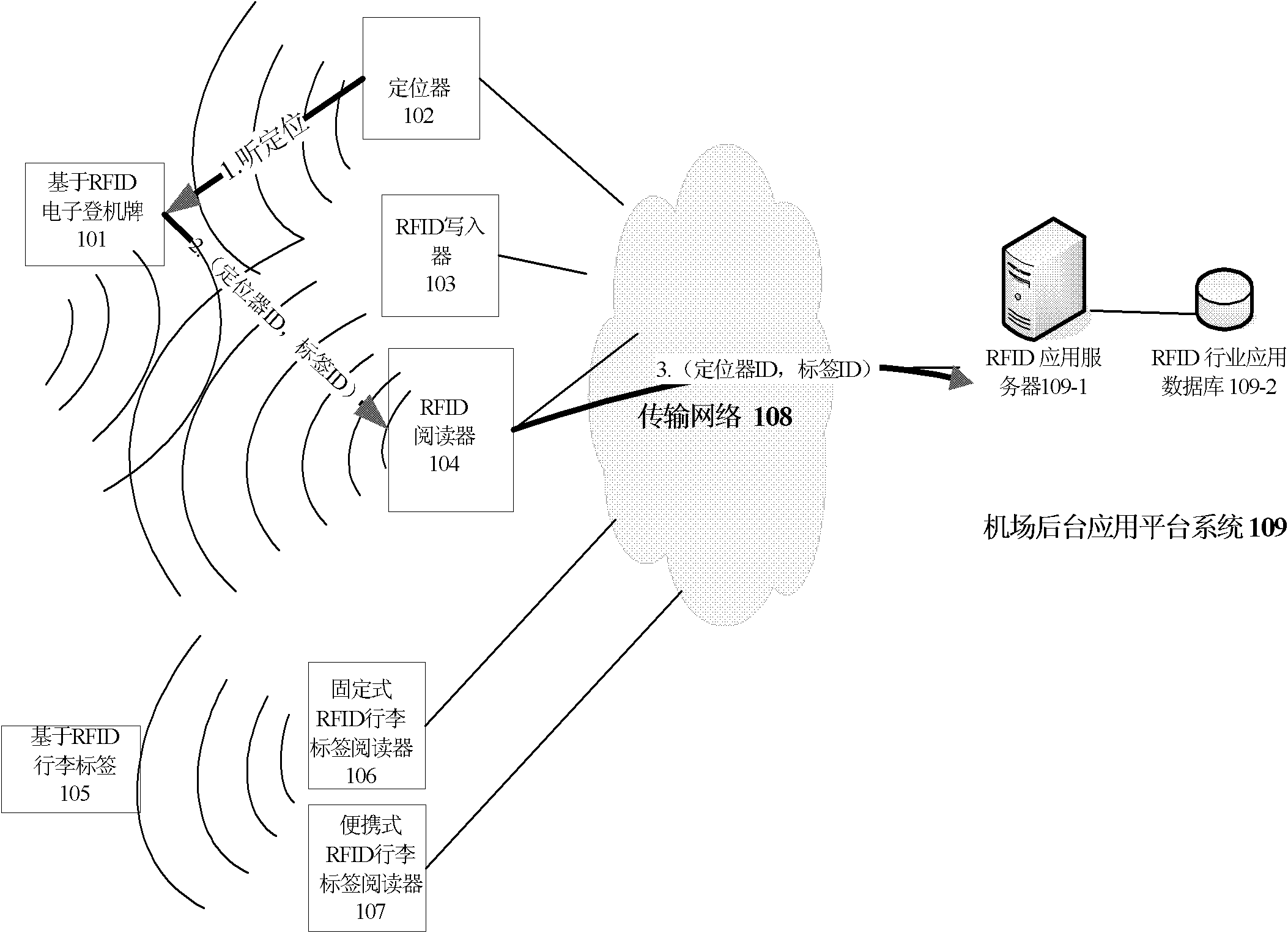
Airport application method and system based on radio frequency identification
InactiveCN102324054APrevent getting lostCo-operative working arrangementsInformation processingFixed position
The invention discloses an airport application method and a system based on radio-frequency identification. Based on the RFID, in an airport application scene, the method and the system can realize the automatic identification and tracking functions of one or a plurality of passengers and / or luggage, further correlations such as matching, correlation and the like among one or a plurality of identified passengers and / or luggage, further linking functions such as reminding, alarming and the like of one or a plurality of identified passengers and / or luggage, and the functions such as data statistics, mining, information processing and the like of one or a plurality of identified passengers and / or luggage. The system comprises boarding cards with RFID tags, readers which are installed at fixed positions and are used for reading the boarding cards with the RFID tags, RFID locators which are used for locating accurately, handheld scanners for the boarding cards with the RFID tags, luggage labels with RFID tags, counting and scanning equipment for the luggage labels with the RFID tags, handheld scanners for the luggage labels with the RFID tags, a transmission network and a background application system.
Owner:BEIJING RIYUE TIANDI TECH
Robotic ordering and delivery apparatuses, systems and methods
Systems, methods and devices for the automated retrieval / delivery of goods from one location to another using a robotic device such as a tug and accompanying cart. A computer within the tug / cart stores a map of the building floor plan and intended paths for the tug to take when traversing from one location to the next. During the delivery, a variety of different sensors and scanners gather data that is used to avoid obstacles and / or continuously adjust the movement of the tug in order to more closely follow the intended path. The system preferably includes wireless networks that allow one or more tugs to communicate with a tug base station, a primary network located at the site of the delivery and a remote host center that monitors the status and data collected by the tugs.
Owner:ST ENG AETHON INC
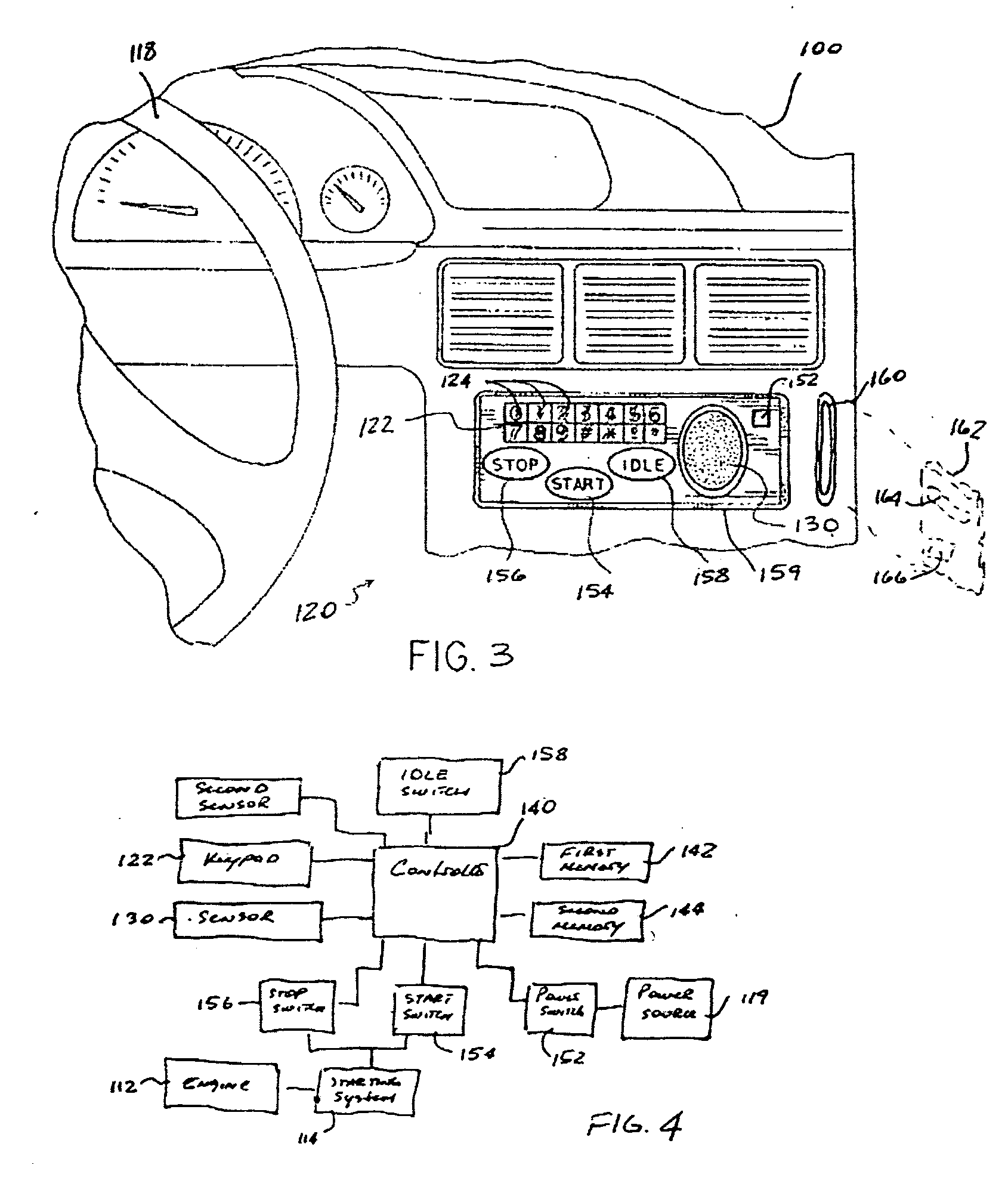
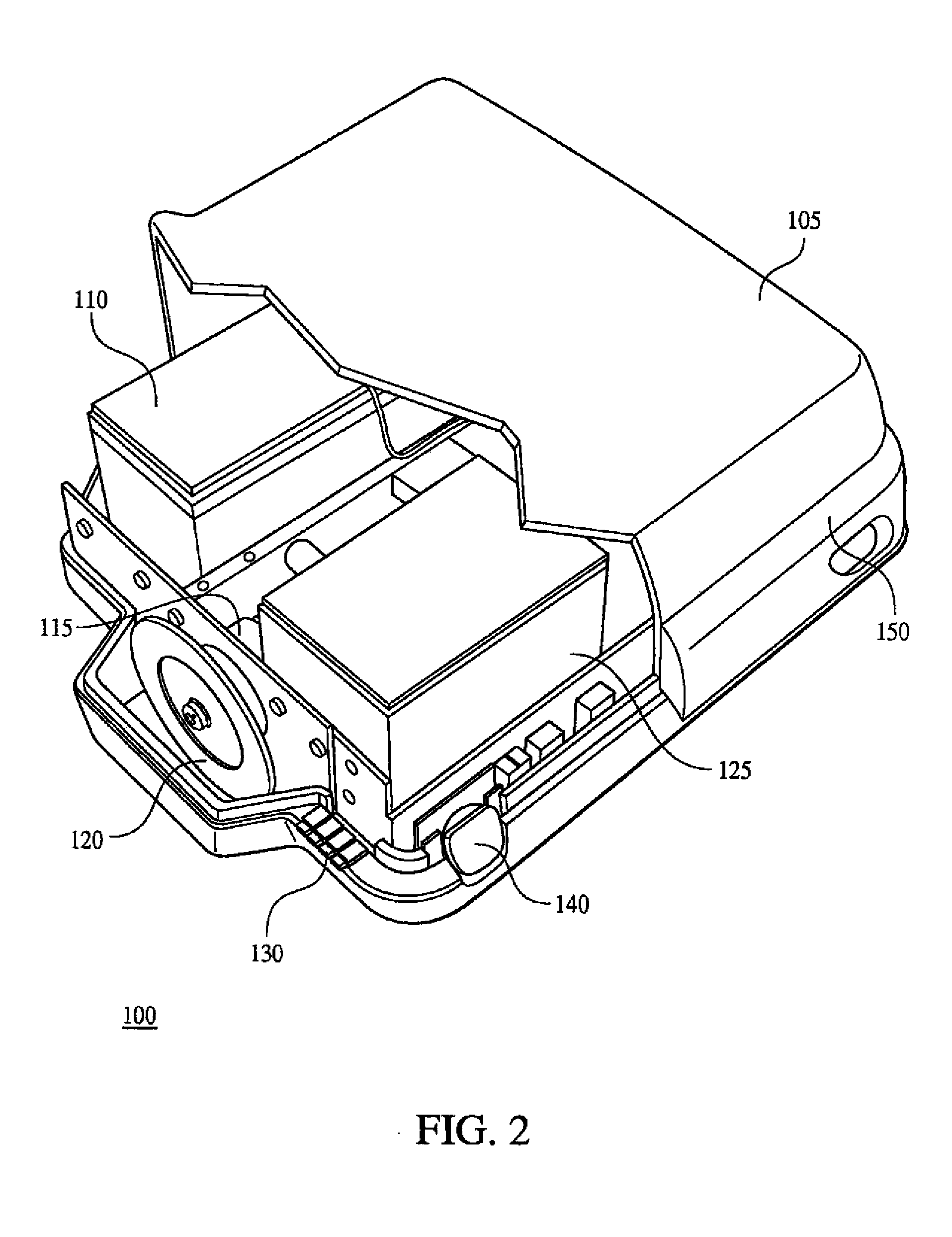
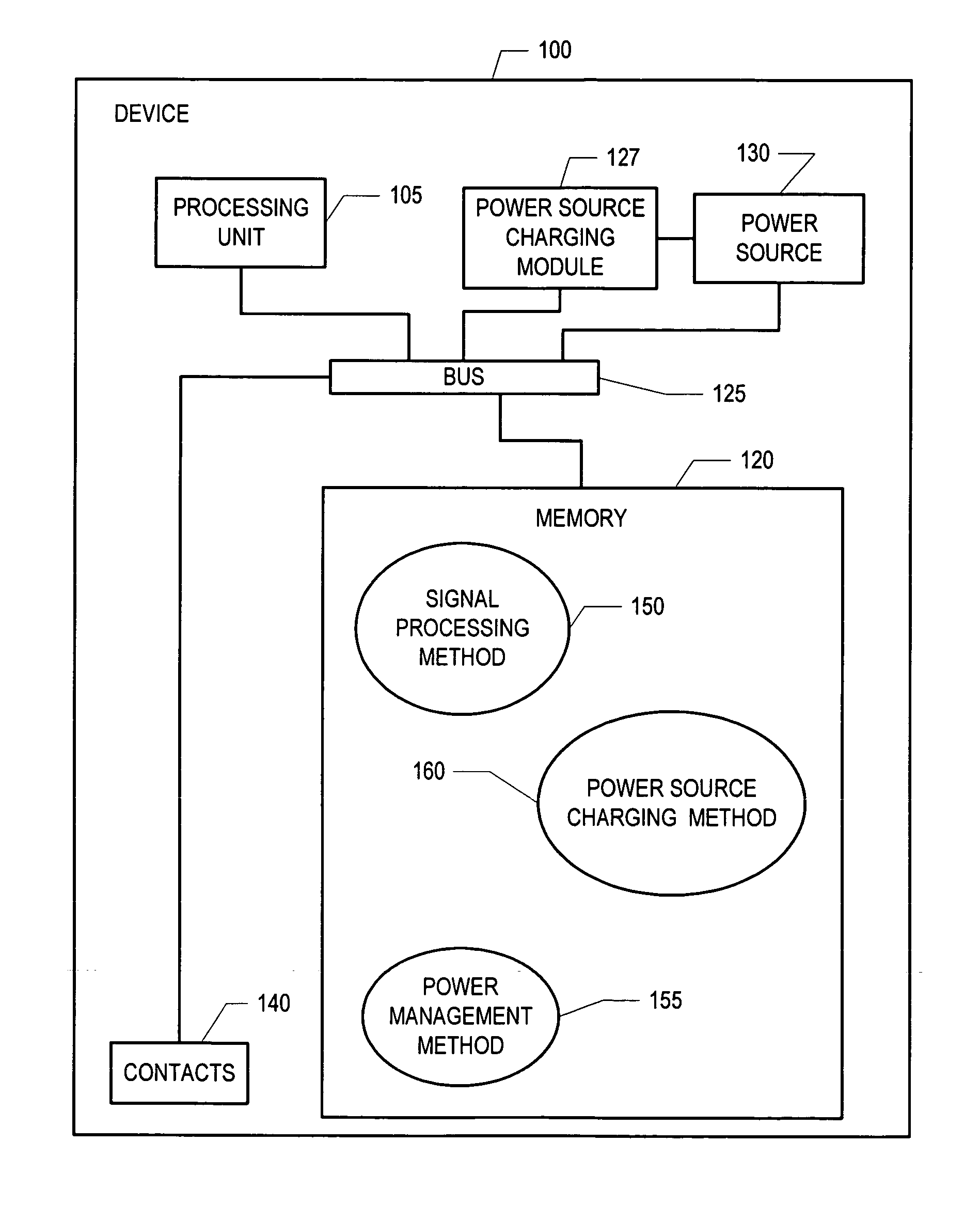
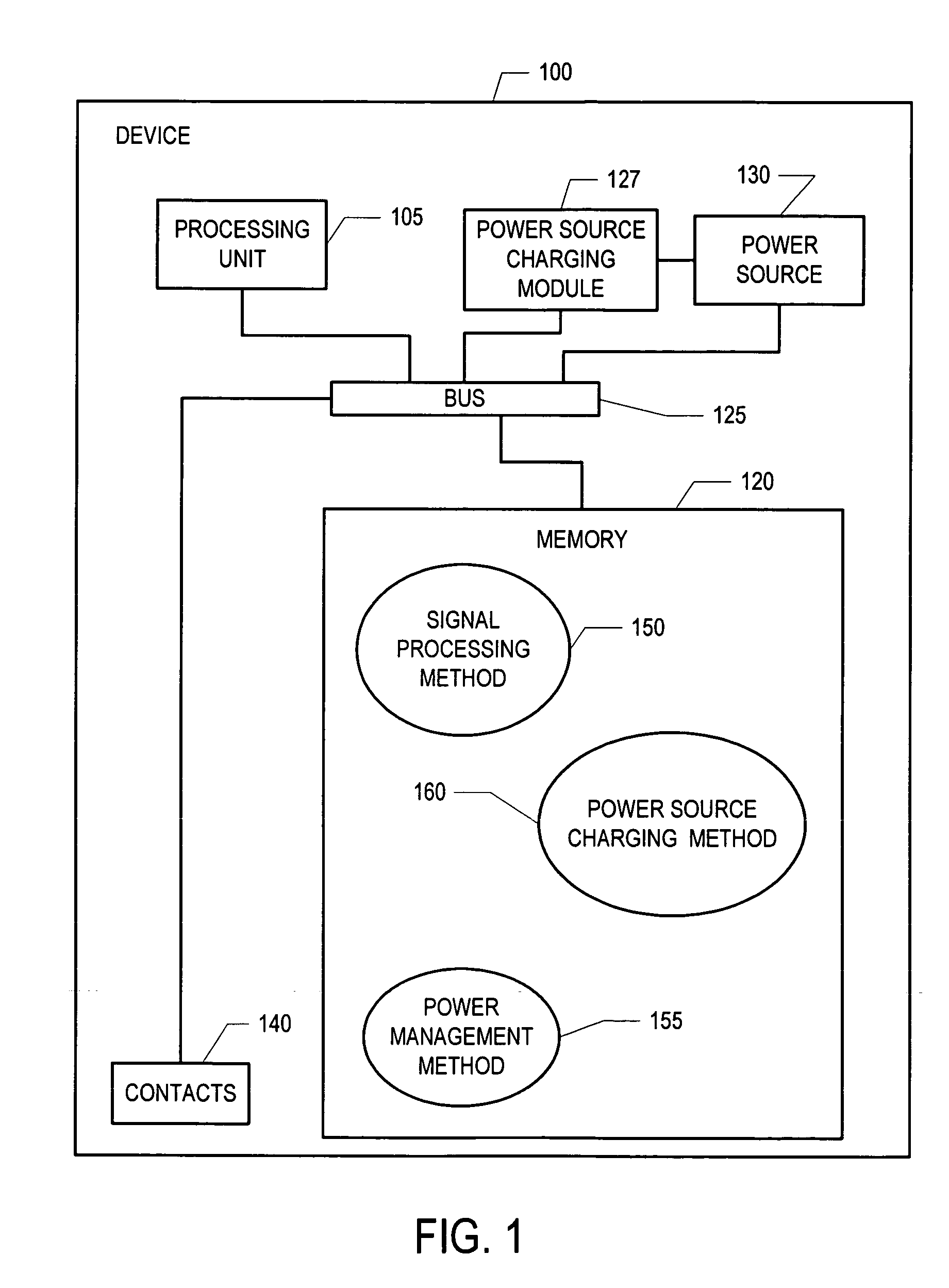
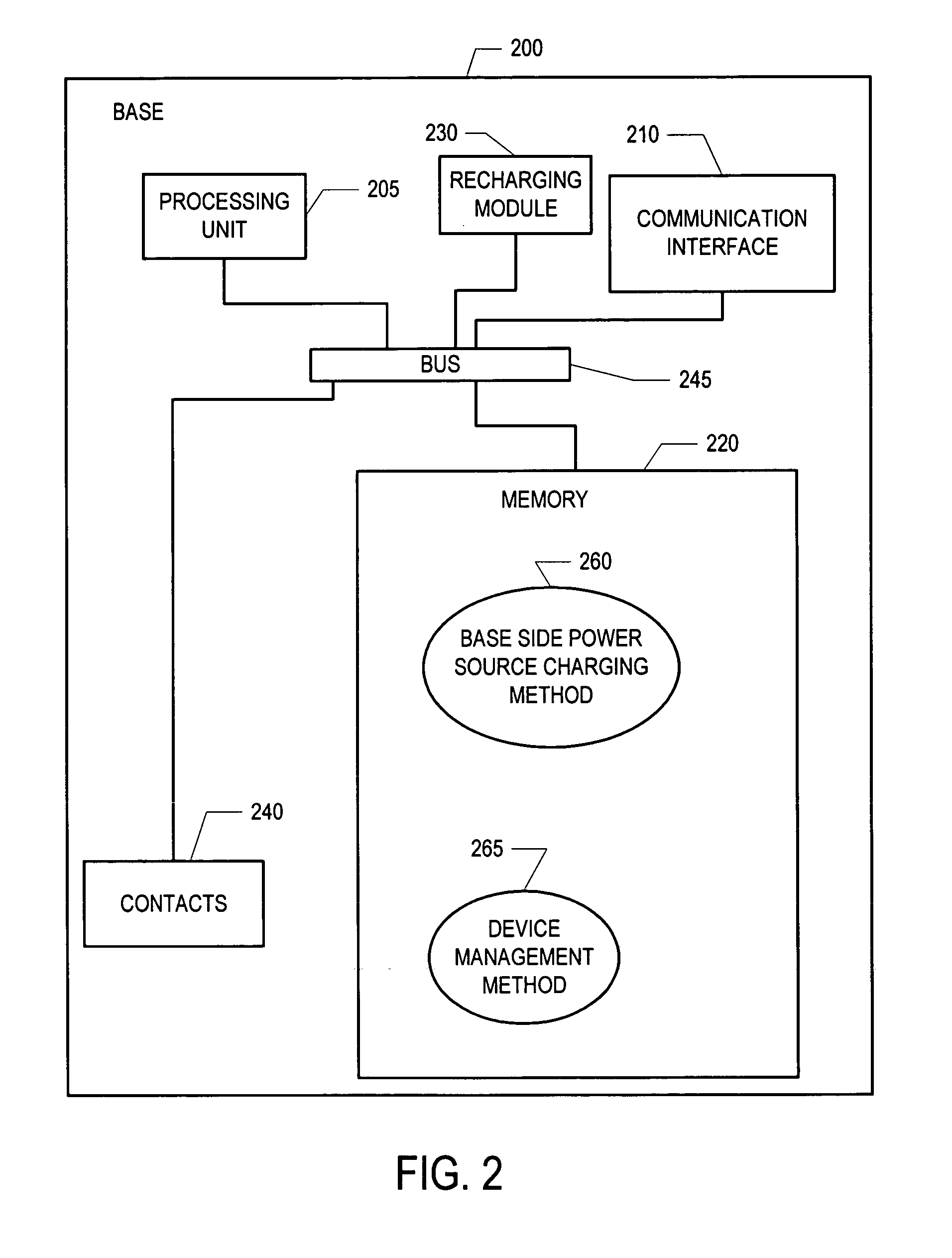
Methods and apparatus for charging a power source
InactiveUS20060244422A1Batteries circuit arrangementsDigital data processing detailsScannerCharge rate
Methods and apparatus for charging a power source comprising determining a type of power supply used by a base, communicating a charge rate to a power source charging module and providing power to the power source at a charge rate. In one embodiment, a scanner can recharge from a cradle that receives power from either a dedicated external power source or through USB by adjusting its charge rate based on a communication from the base.
Owner:SYMBOL TECH INC
Flash drive-radio combination
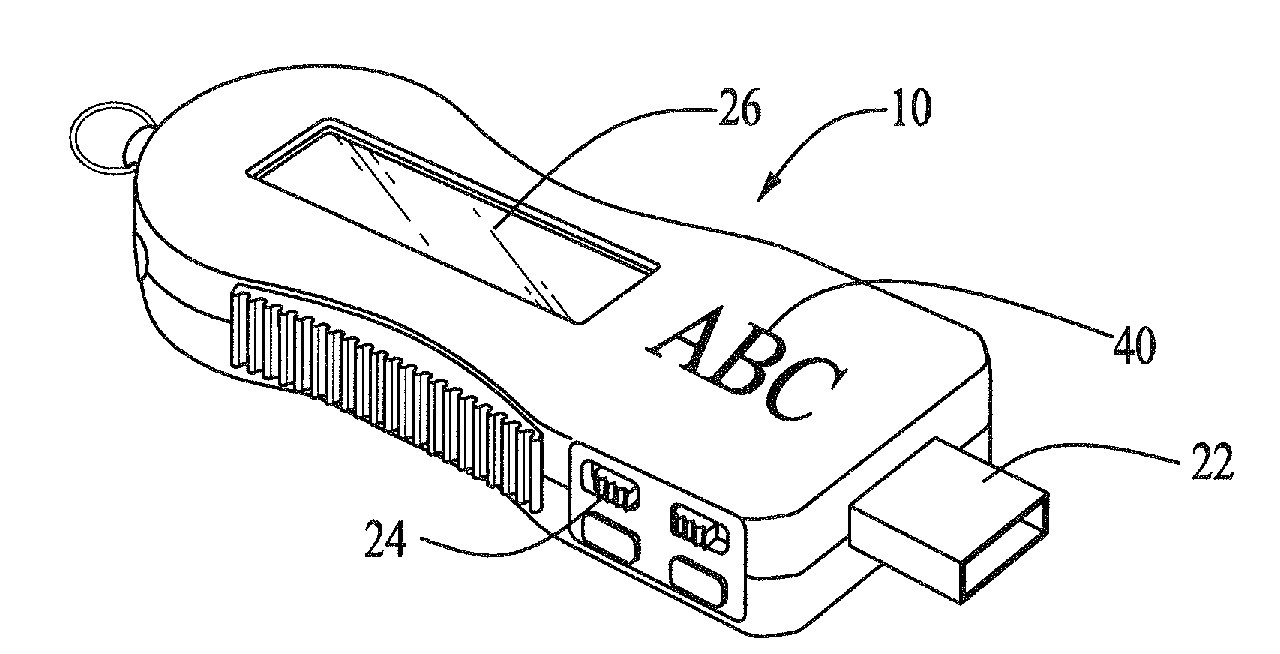
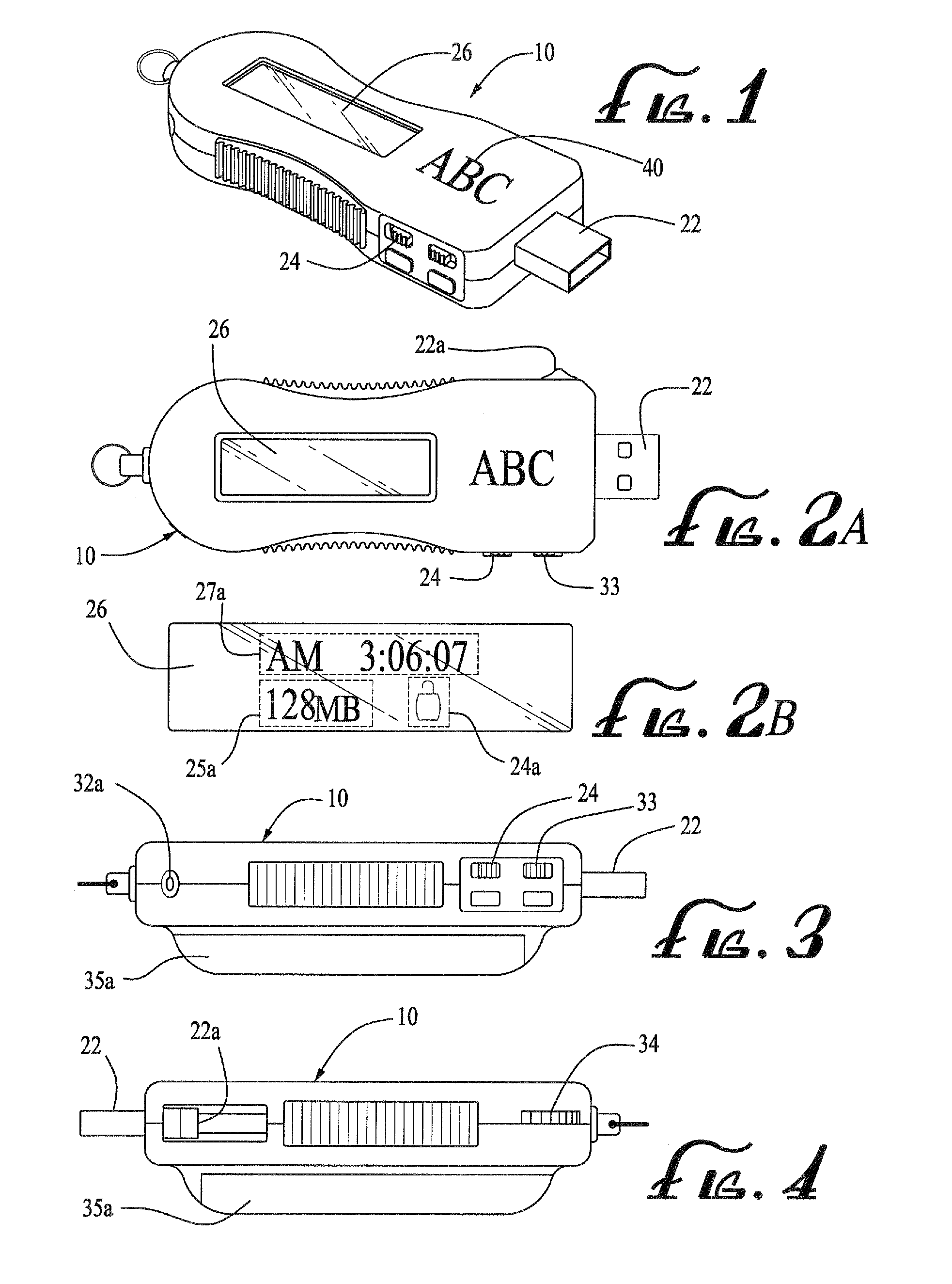
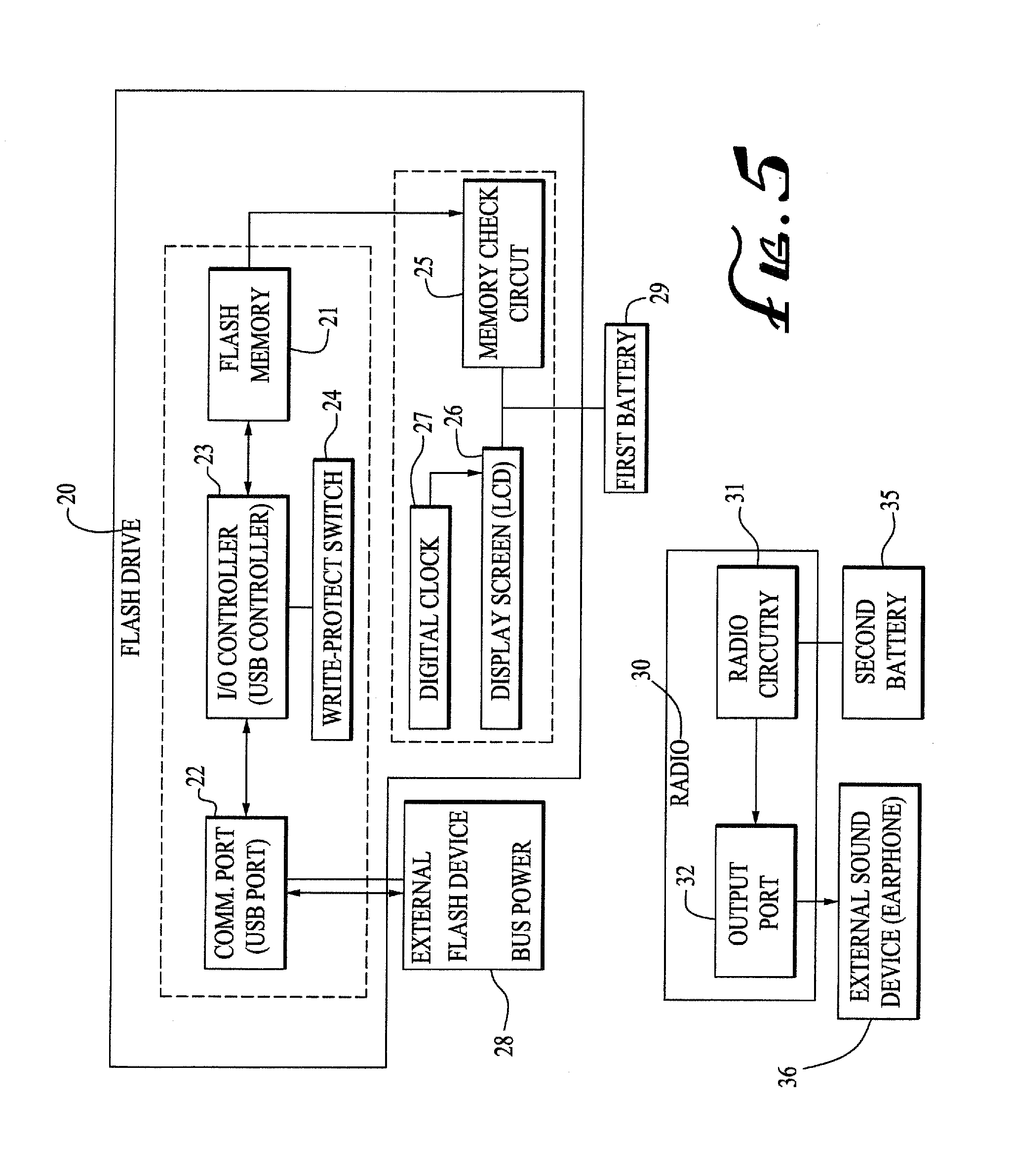
InactiveUS20080133832A1Low production costSmall sizeRecord carriers used with machinesMemory systemsElectricityDigital clock
A flash drive incorporating a FM scanner radio, of which the circuitry is electrically isolated from each other and separately powered to reduce production cost and size. The flash drive-radio combination comprises a radio and a flash drive encased in a housing. The radio is configured only to search, receive, and convert to audio signals, radio signals that lies within only the broadcast FM bands, and the flash drive comprises a flash memory, a bidirectional communication port, a controller, and preferably, a display unit for displaying used and available memory in the flash memory. A write protect switch, a channel scan button, a digital clock may be further included in the present invention.
Owner:SUN COAST MERCHANDISE
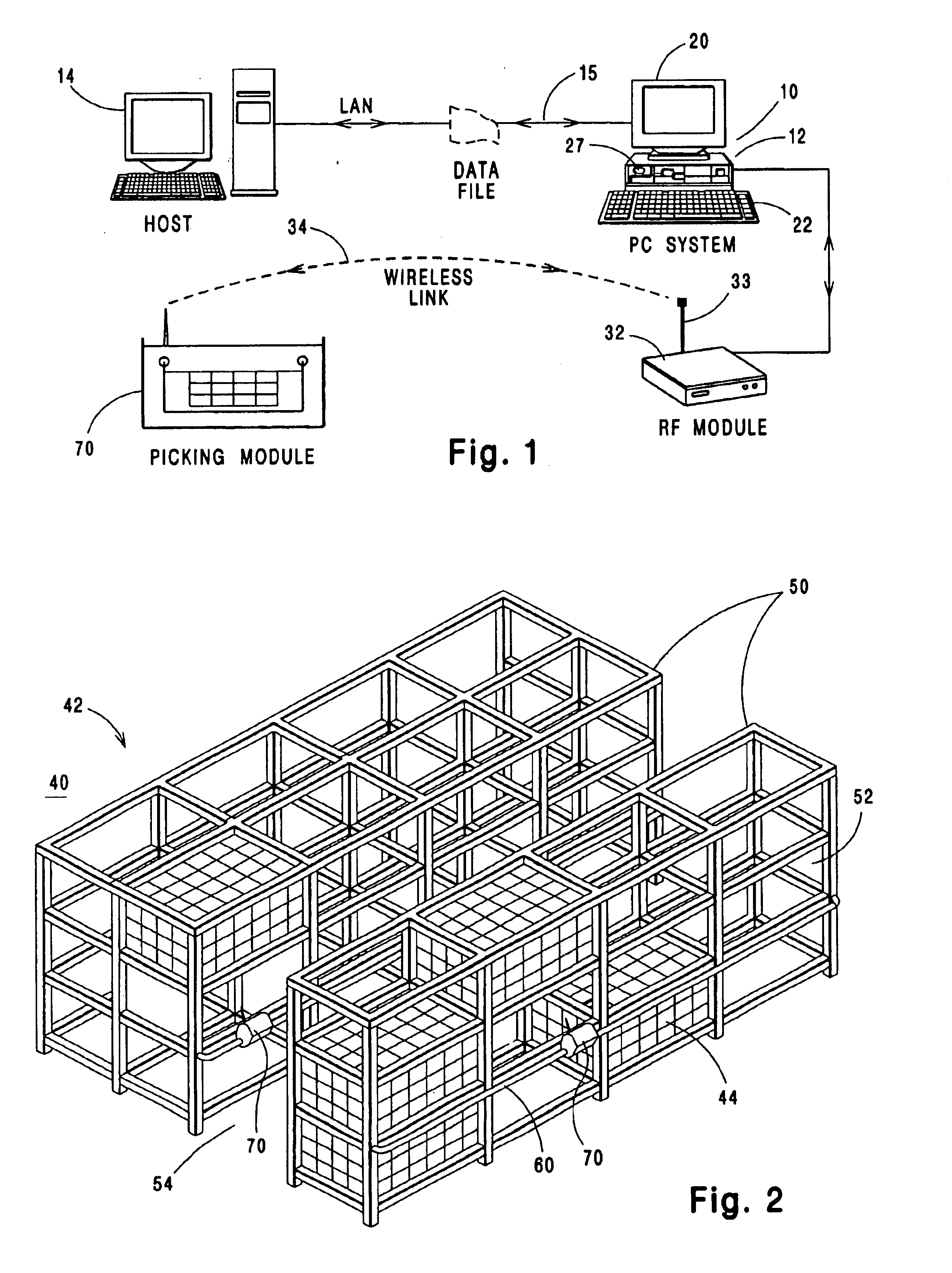
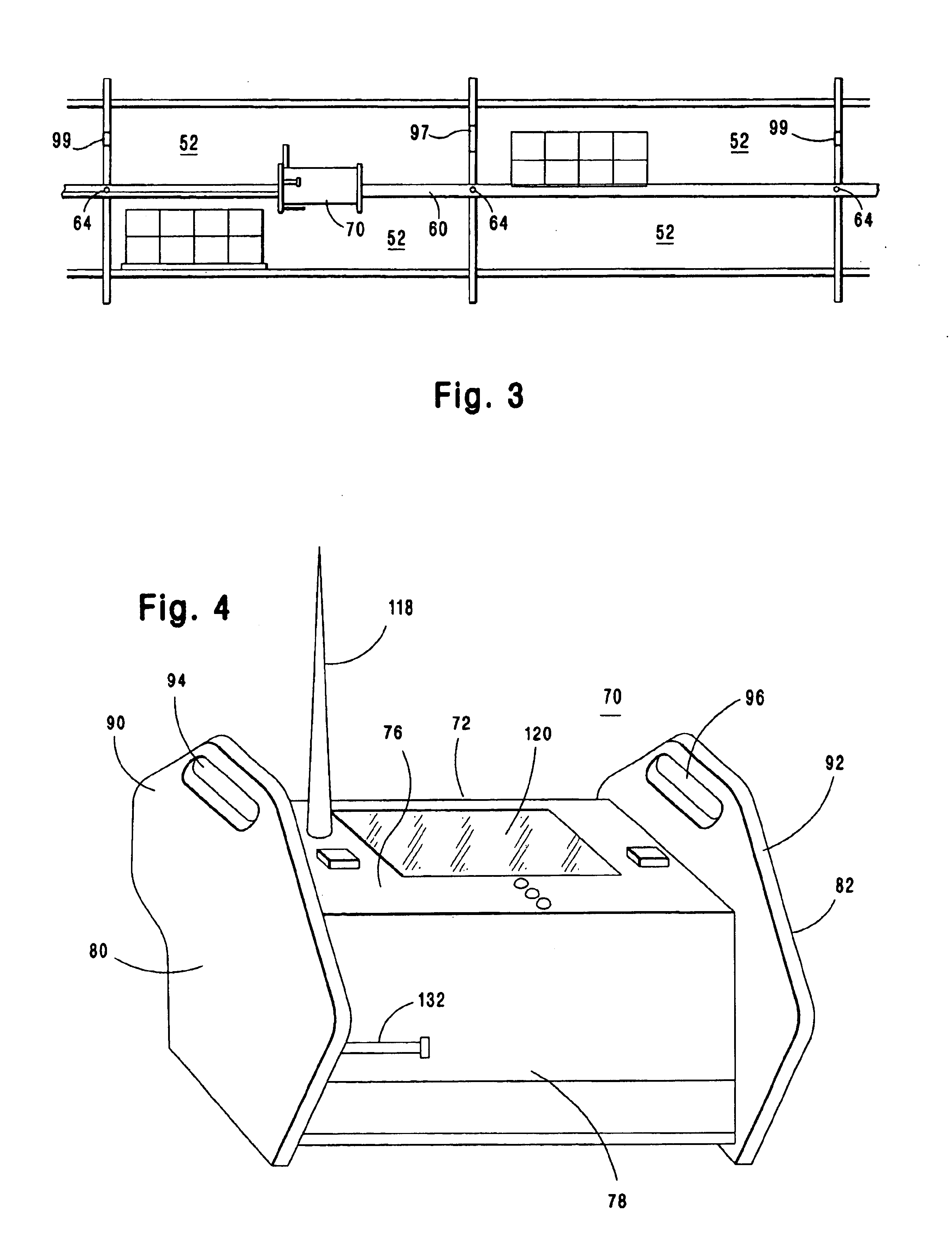
Automated paperless order selection system
InactiveUS6873881B1Reduce in quantityAccurate locationDigital data processing detailsOrder reductionBarcode
Provided is an automated paperless order selection system of the type wherein an electronic order picking unit moves horizontally along a rail directly to a product storage location, thereby decreasing the distance traveled by the order picker and improving the accuracy of the order picking process, such order picking unit having an incremental encoder means for determining its exact location on the rail, and having a wireless radio frequency data communication (RF / DC) capability, and preferably including a printer, bar code scanner as well as audit and inventory report features.
Owner:SCHNEIBLE SR SETH R
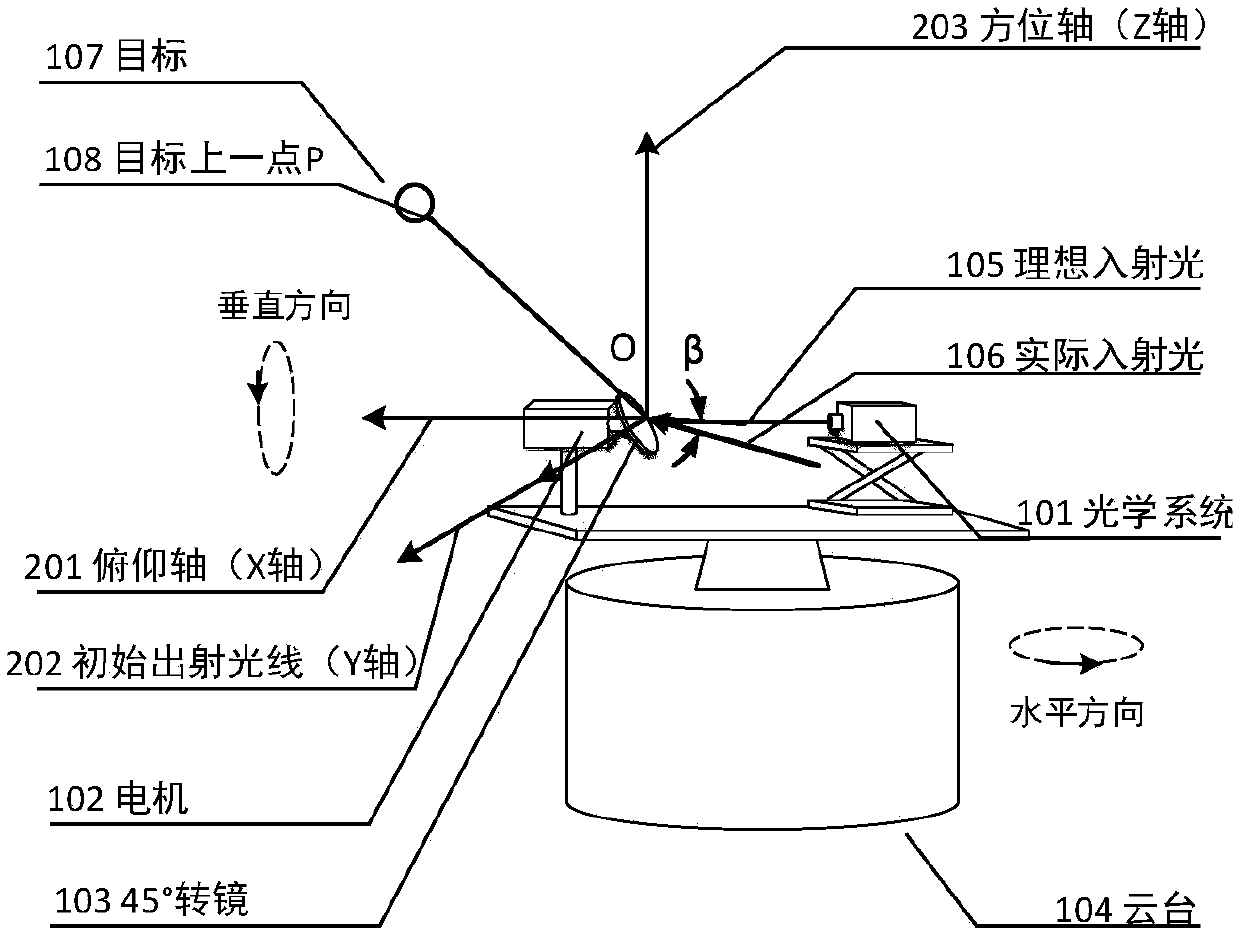
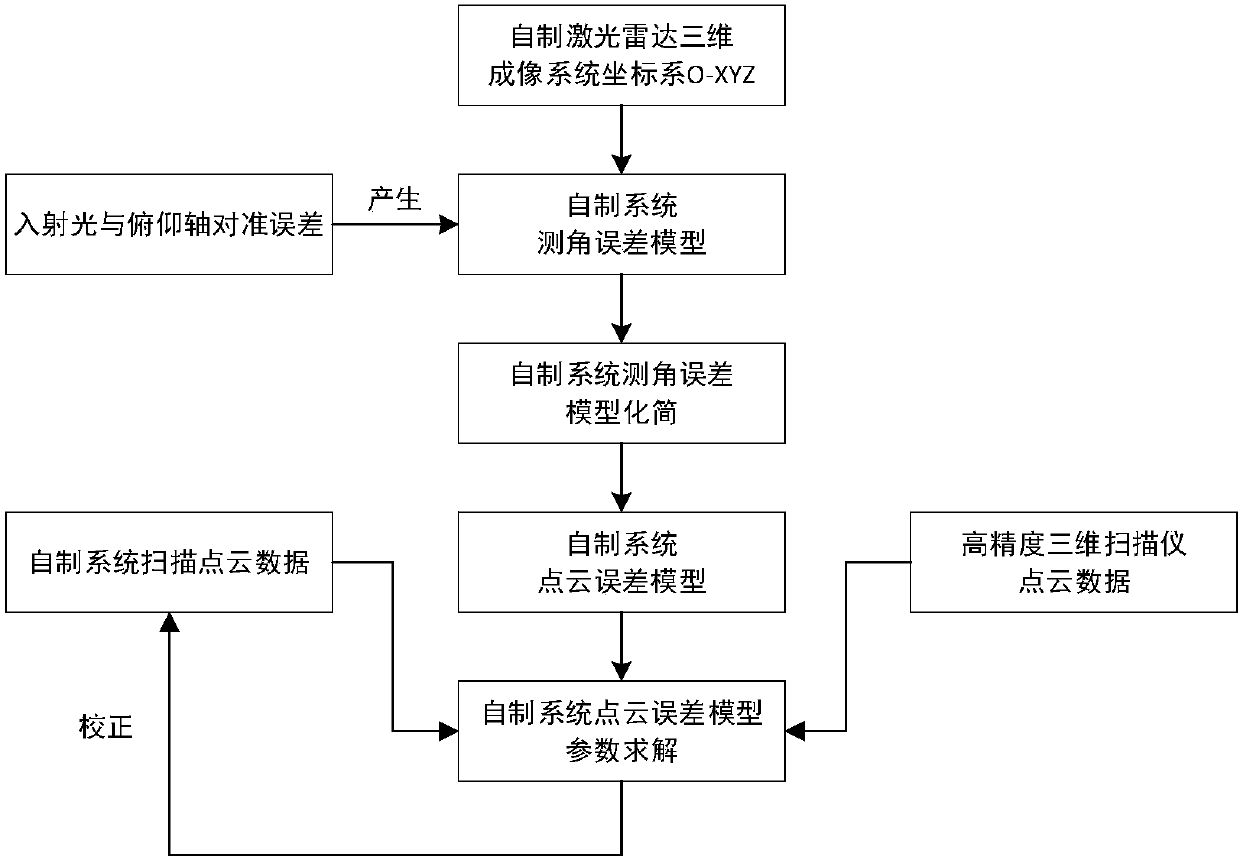
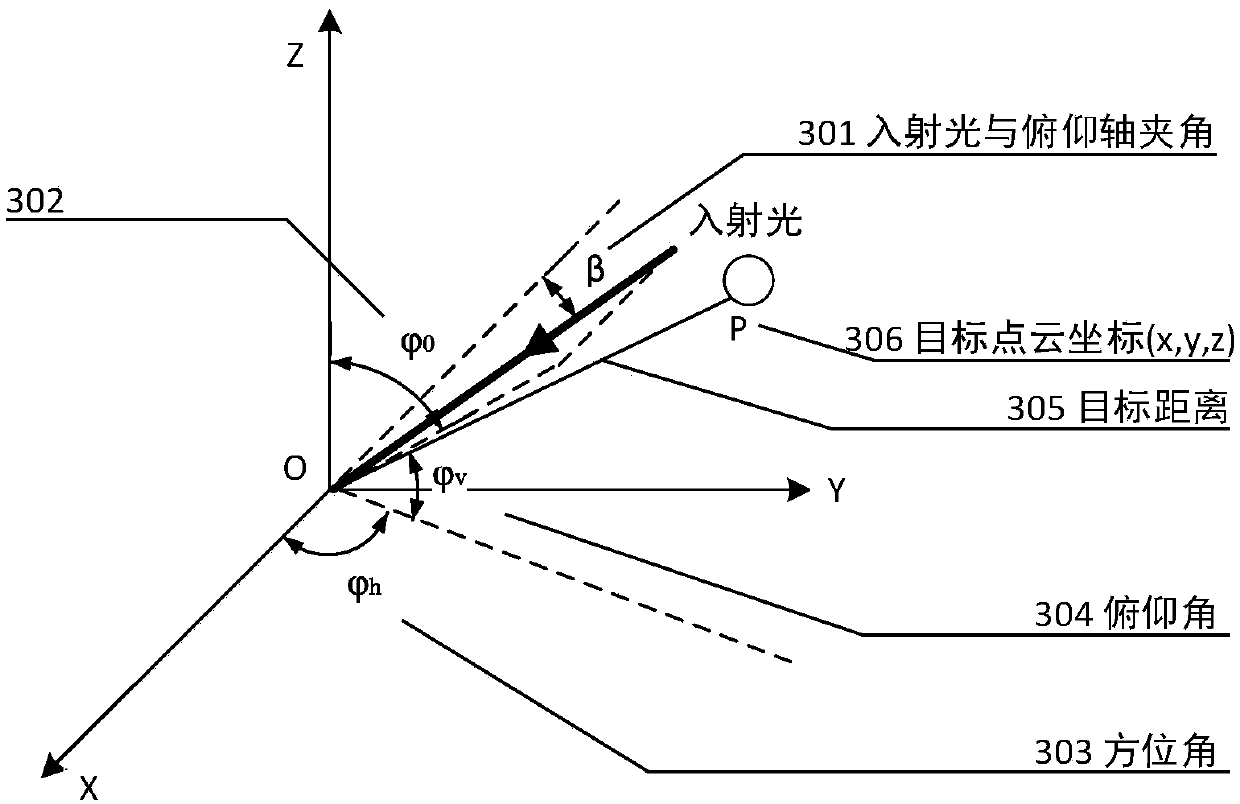
Homemade foundation laser radar alignment error-based point cloud error correction method
The present invention discloses a homemade foundation laser radar alignment error-based point cloud error correction method. The method mainly aims at a scanning mode that a 45-degree rotating mirrorof a homemade laser radar system cooperates with a pan-tilt to rotate, establishes a homemade laser radar system point cloud error correction model by calculating the influence of an alignment error between the incident light and a pitch axis on a homemade system angle measurement error, and adopts the scanned point cloud coordinate of a high-precision three-dimensional scanner to a target as a real value solution alignment error, so that the error correction of the homemade laser radar system alignment error to the target point cloud is realized. The method mainly comprises the following three steps of 1) establishing and simplifying a homemade laser radar three-dimensional imaging system angle measurement error model caused by the alignment error; 2) obtaining a homemade laser radar three-dimensional imaging system point cloud error model; 3) solving the alignment error in the homemade laser radar three-dimensional imaging system point cloud error model, and correcting the homemade laser radar system target point cloud according to the model.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com