Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
23366 results about "Fingerprint" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
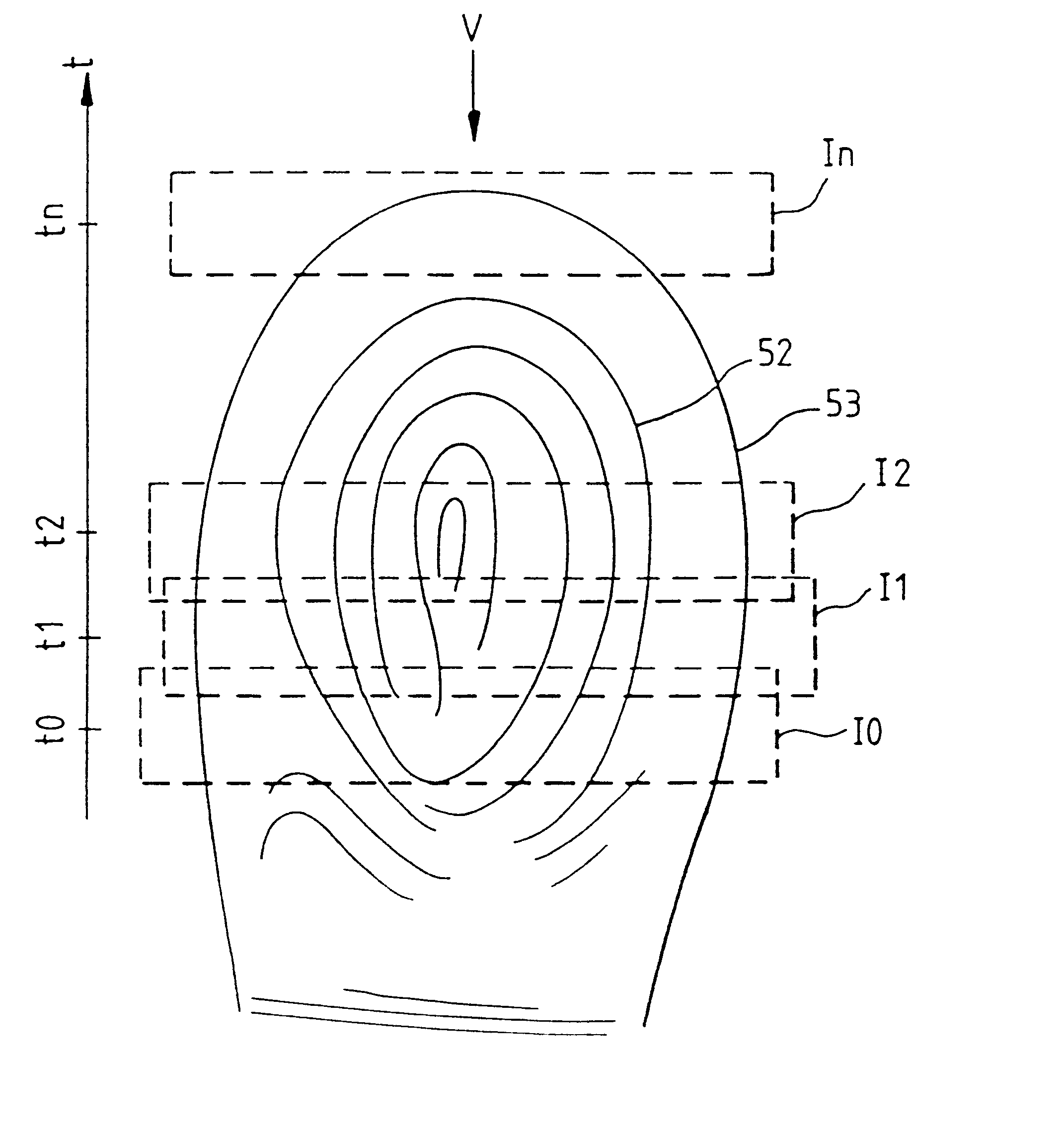
A fingerprint is an impression left by the friction ridges of a human finger. The recovery of partial fingerprints from a crime scene is an important method of forensic science. Moisture and grease on a finger result in fingerprints on surfaces such as glass or metal. Deliberate impressions of entire fingerprints can be obtained by ink or other substances transferred from the peaks of friction ridges on the skin to a smooth surface such as paper. Fingerprint records normally contain impressions from the pad on the last joint of fingers and thumbs, although fingerprint cards also typically record portions of lower joint areas of the fingers.
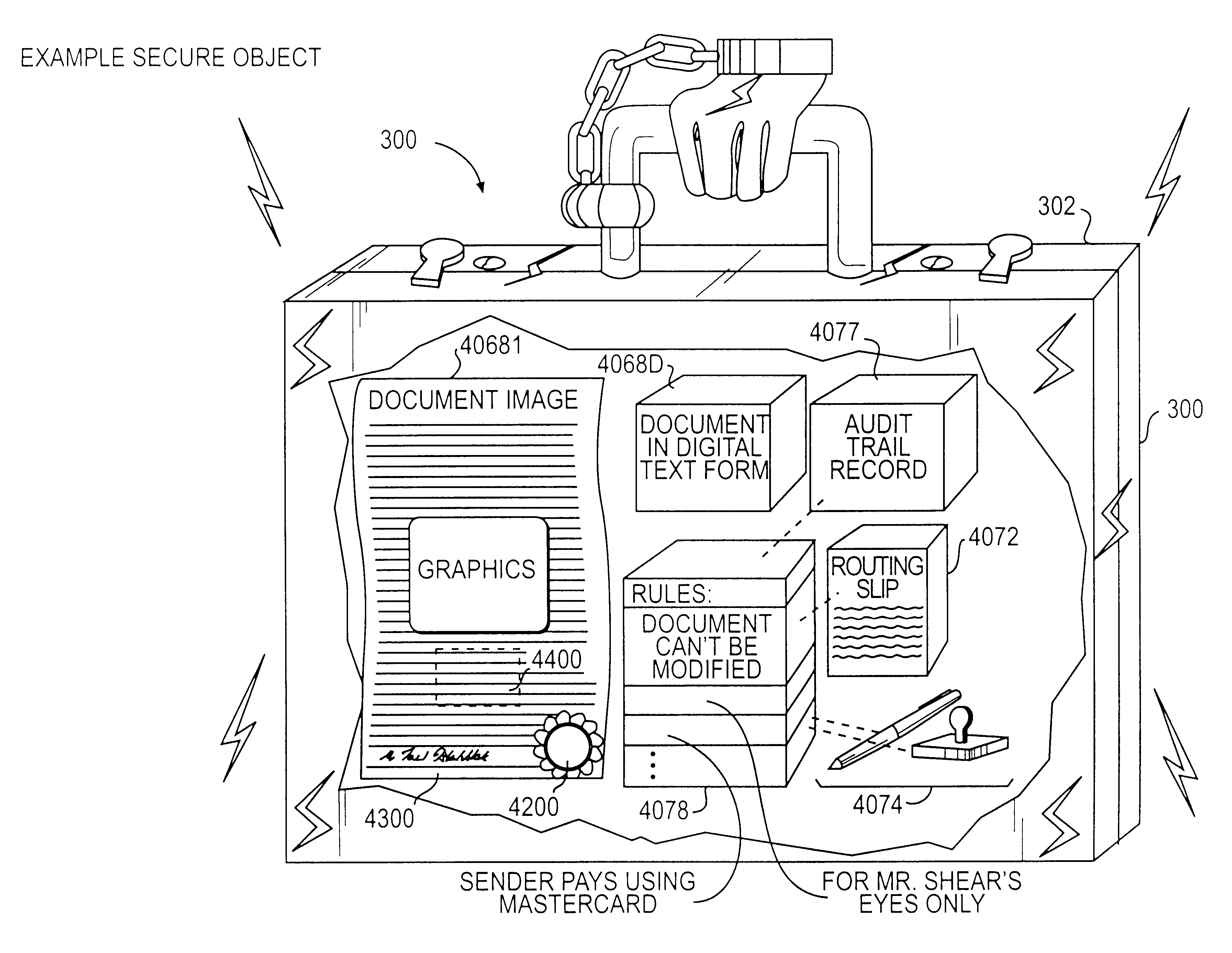
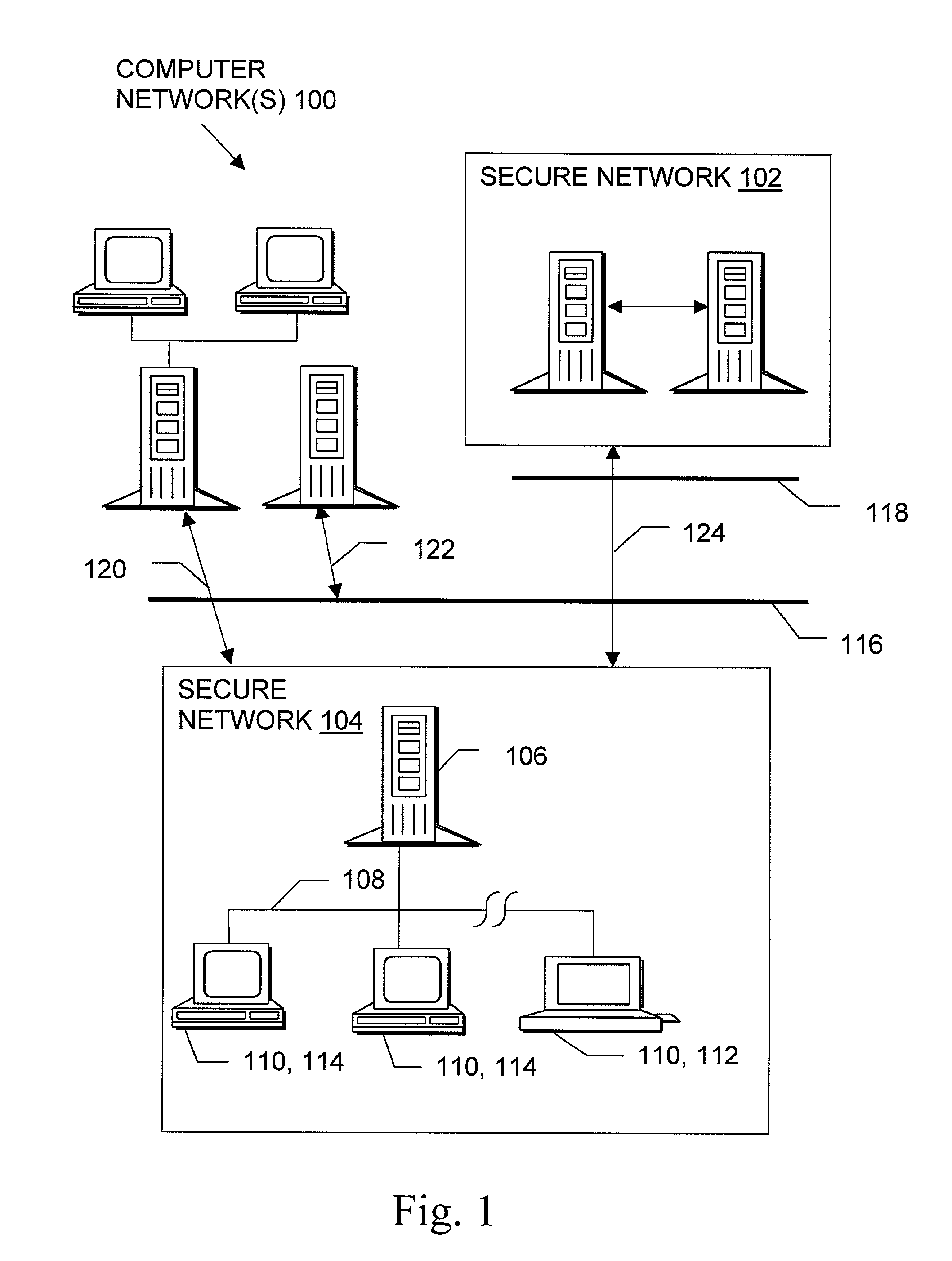
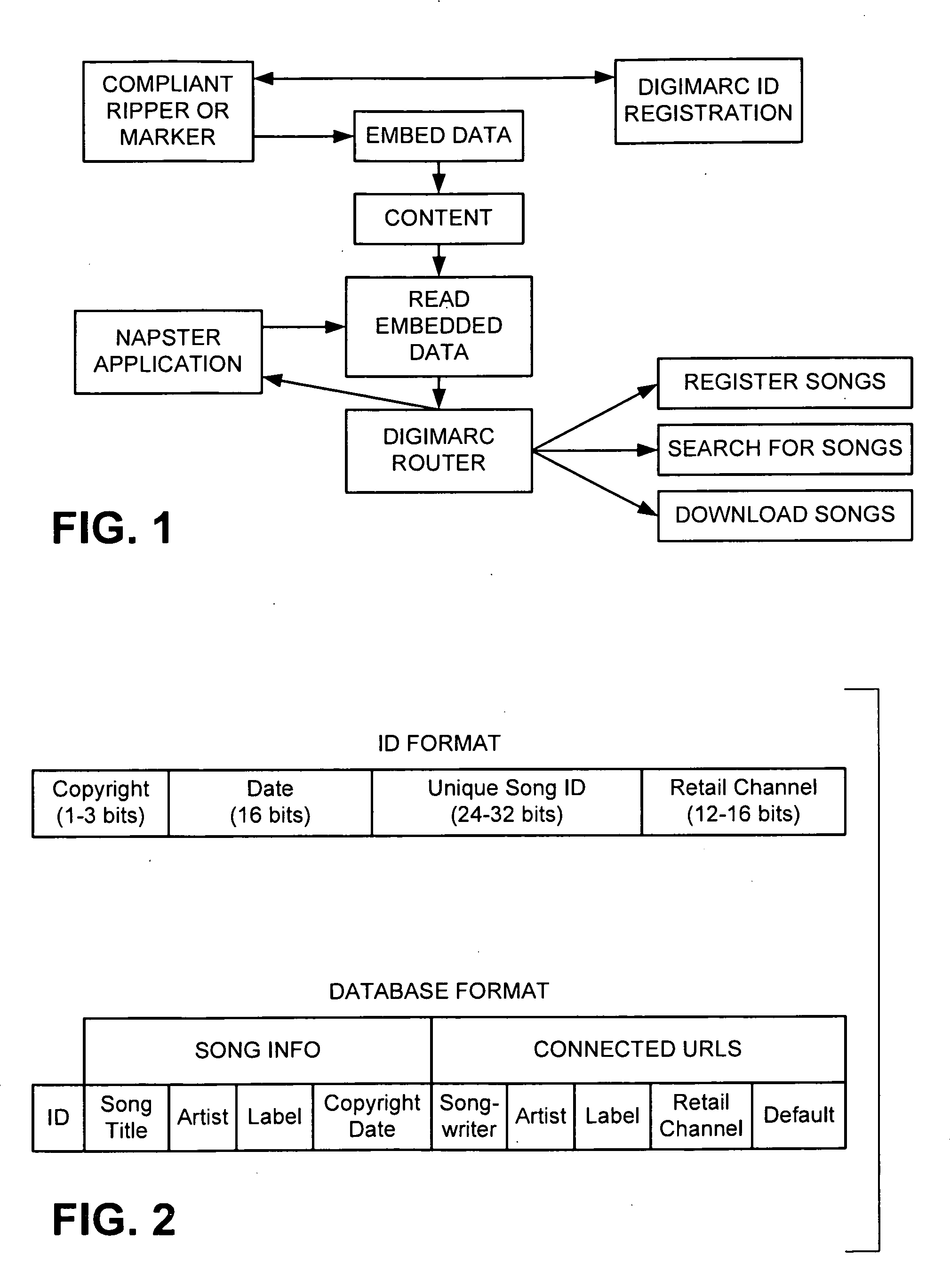
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
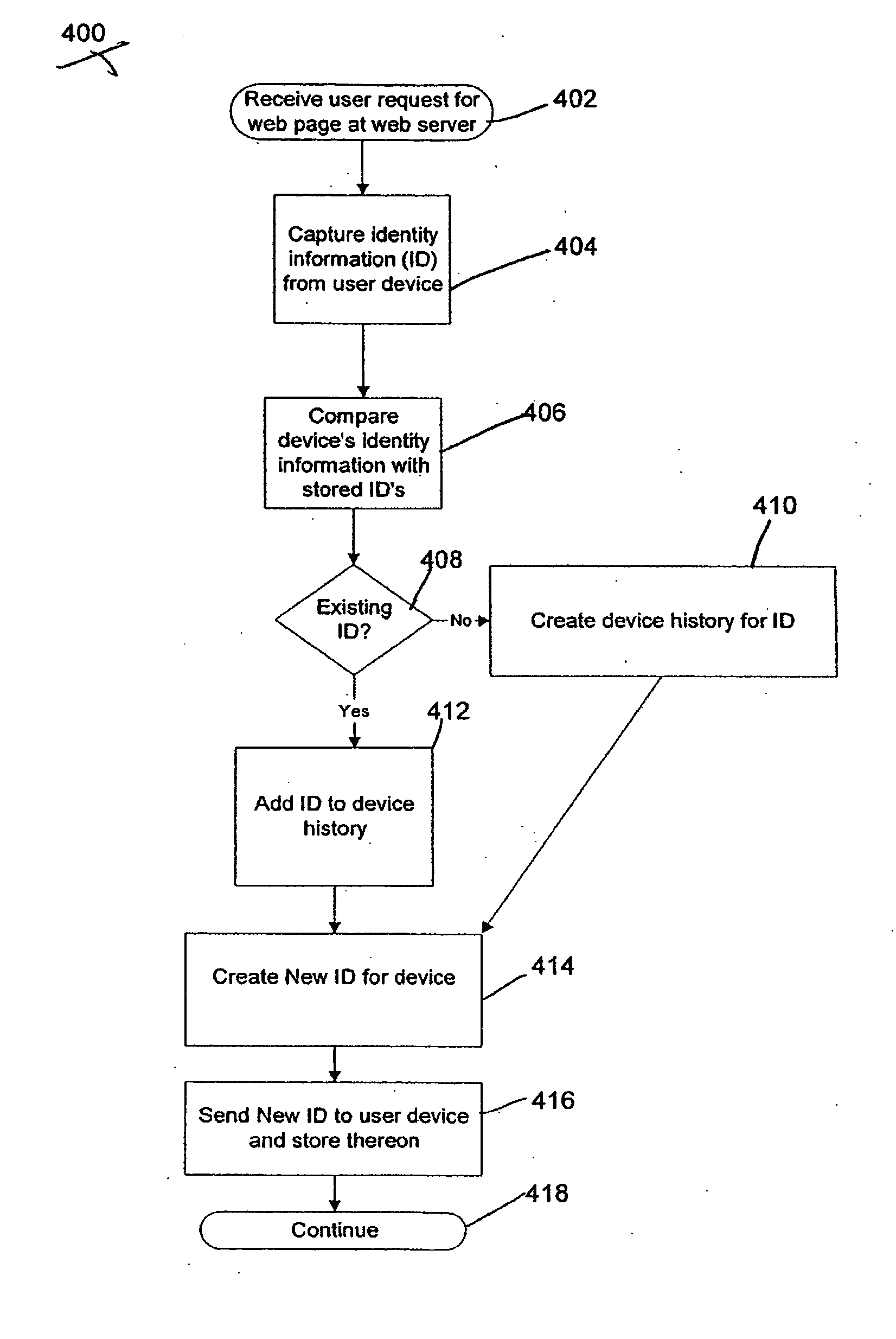
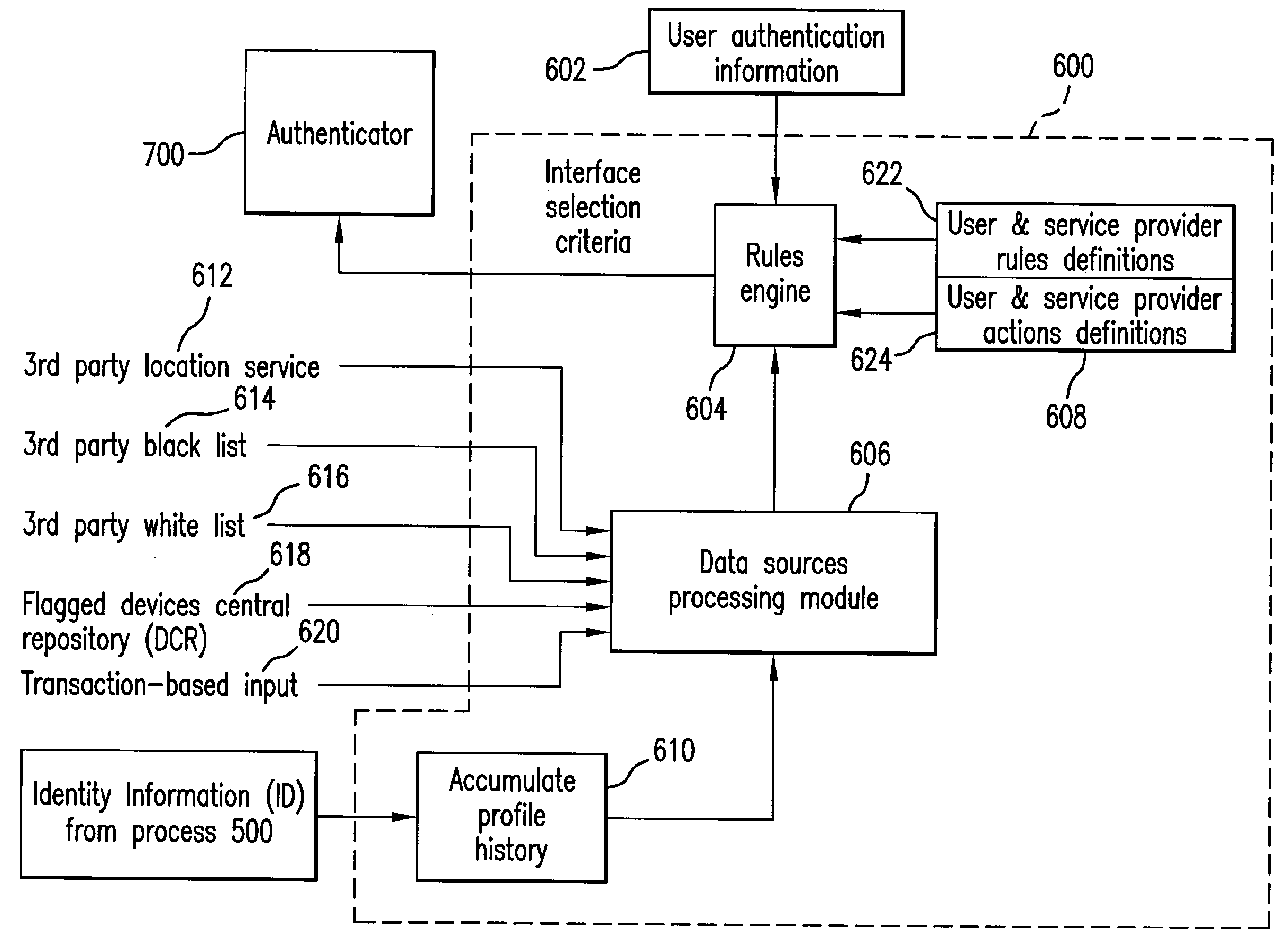
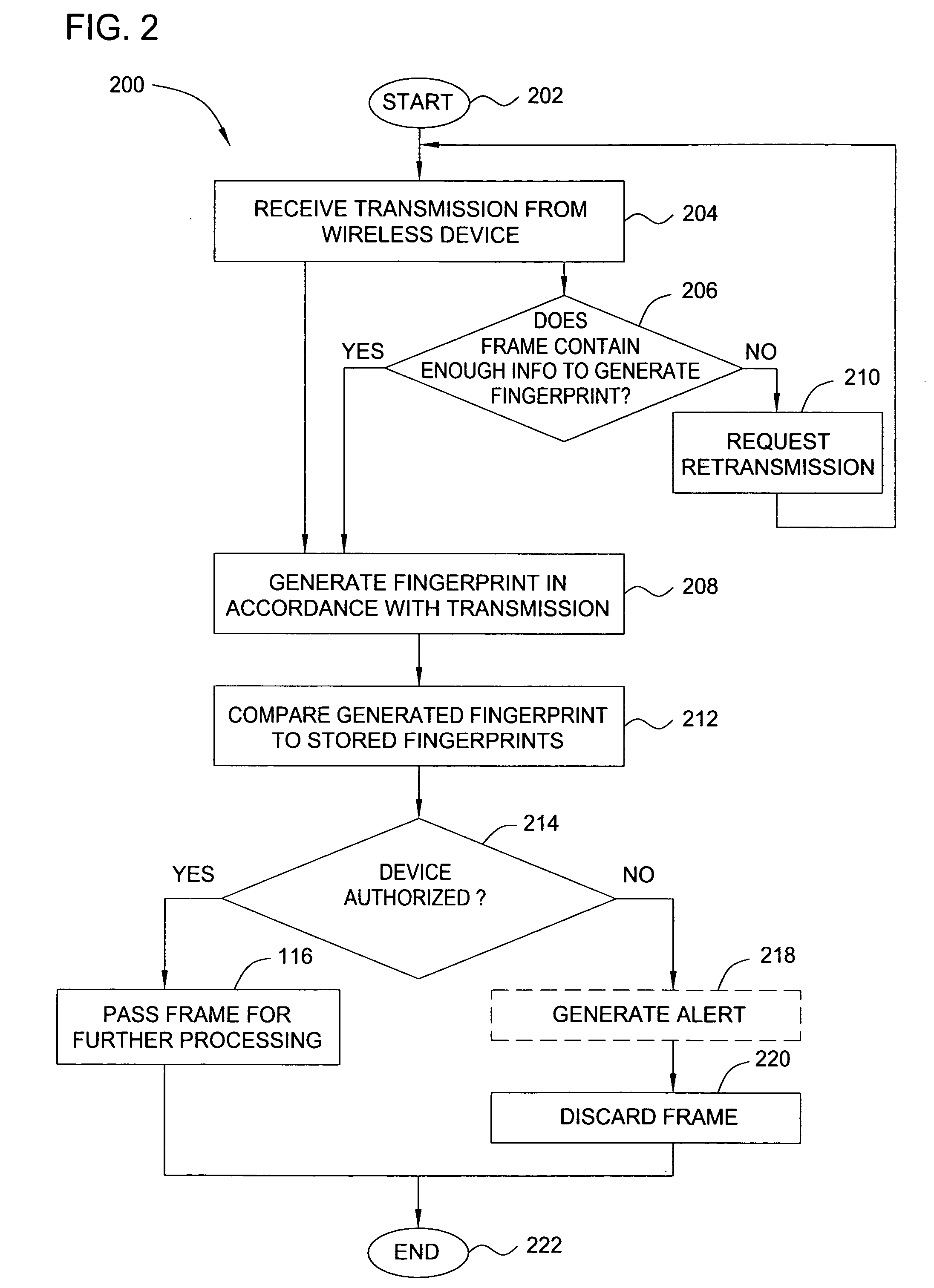
System and method for fraud monitoring, detection, and tiered user authentication
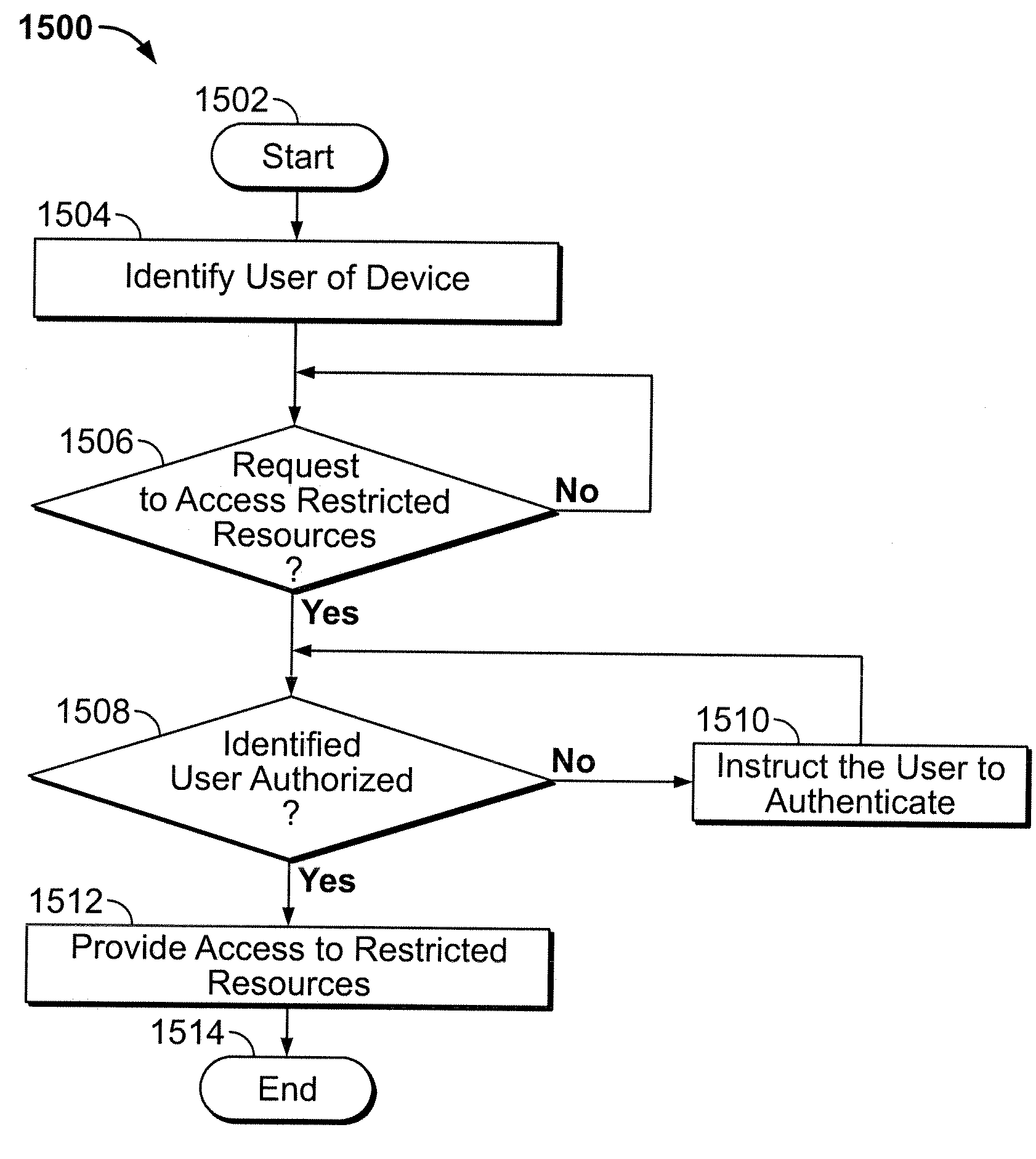
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
System and methods for recognizing sound and music signals in high noise and distortion
ActiveUS6990453B2High of distortionHigh levelGearworksMusical toysNonlinear distortionLinear correlation
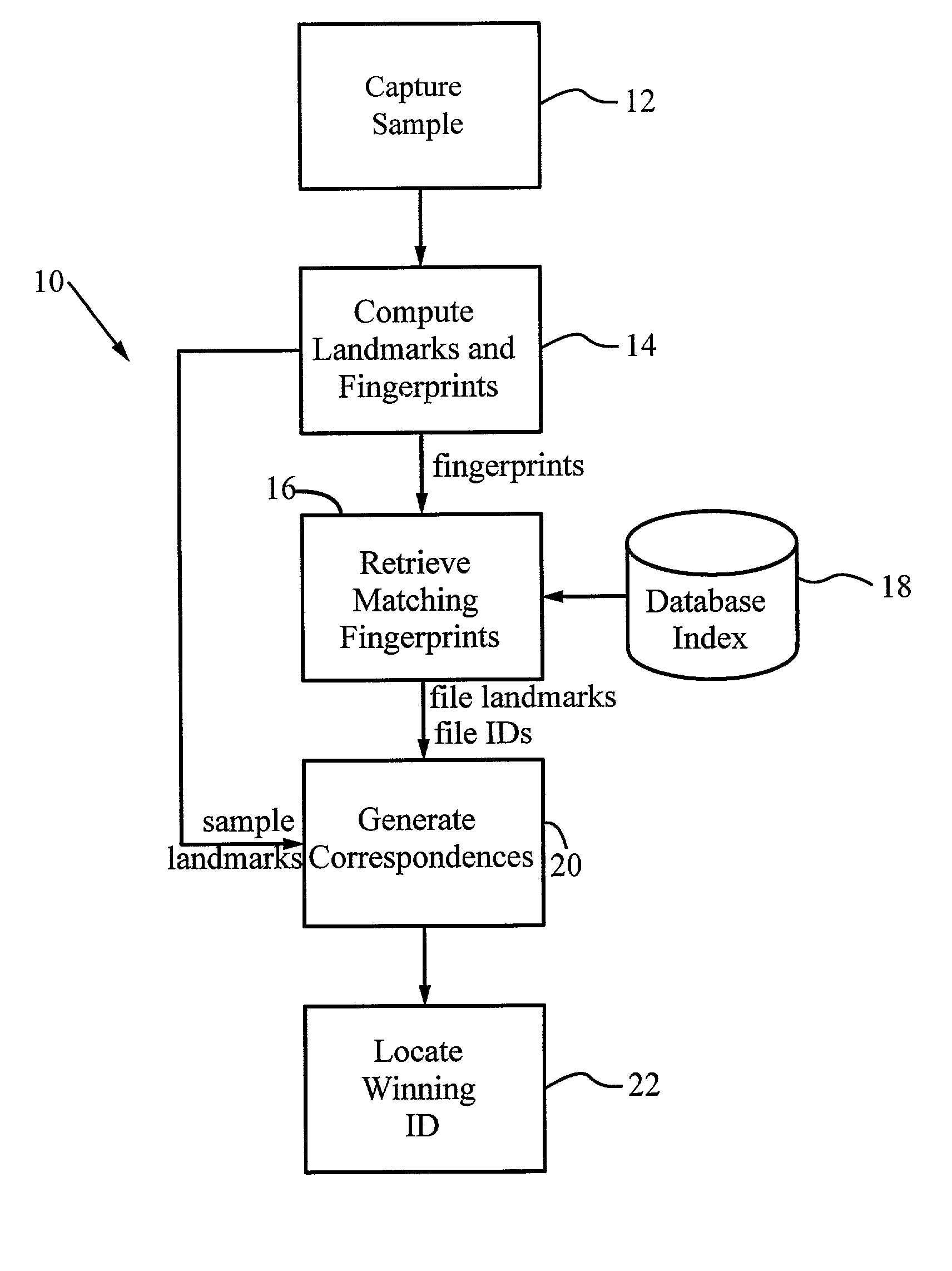
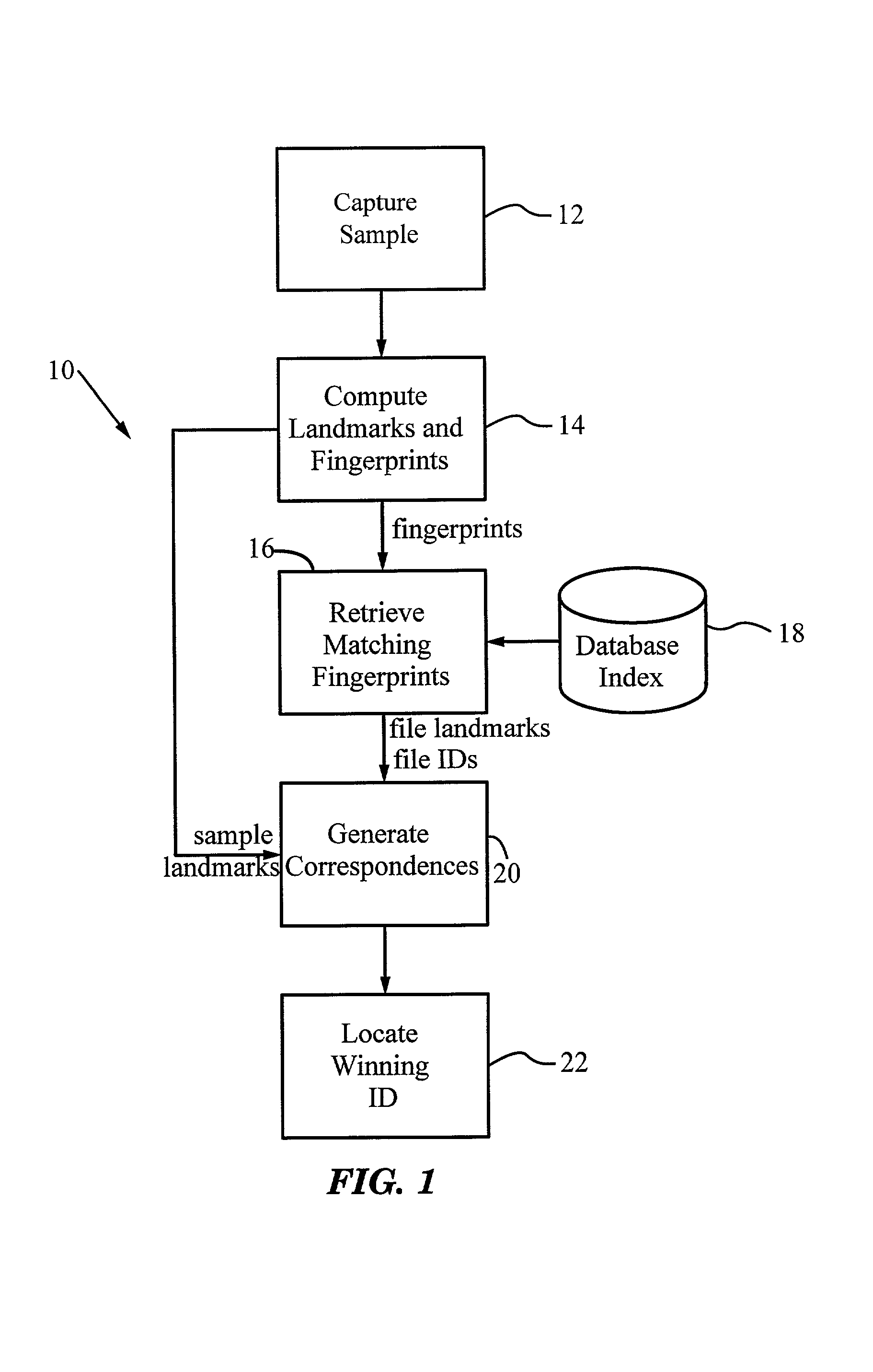
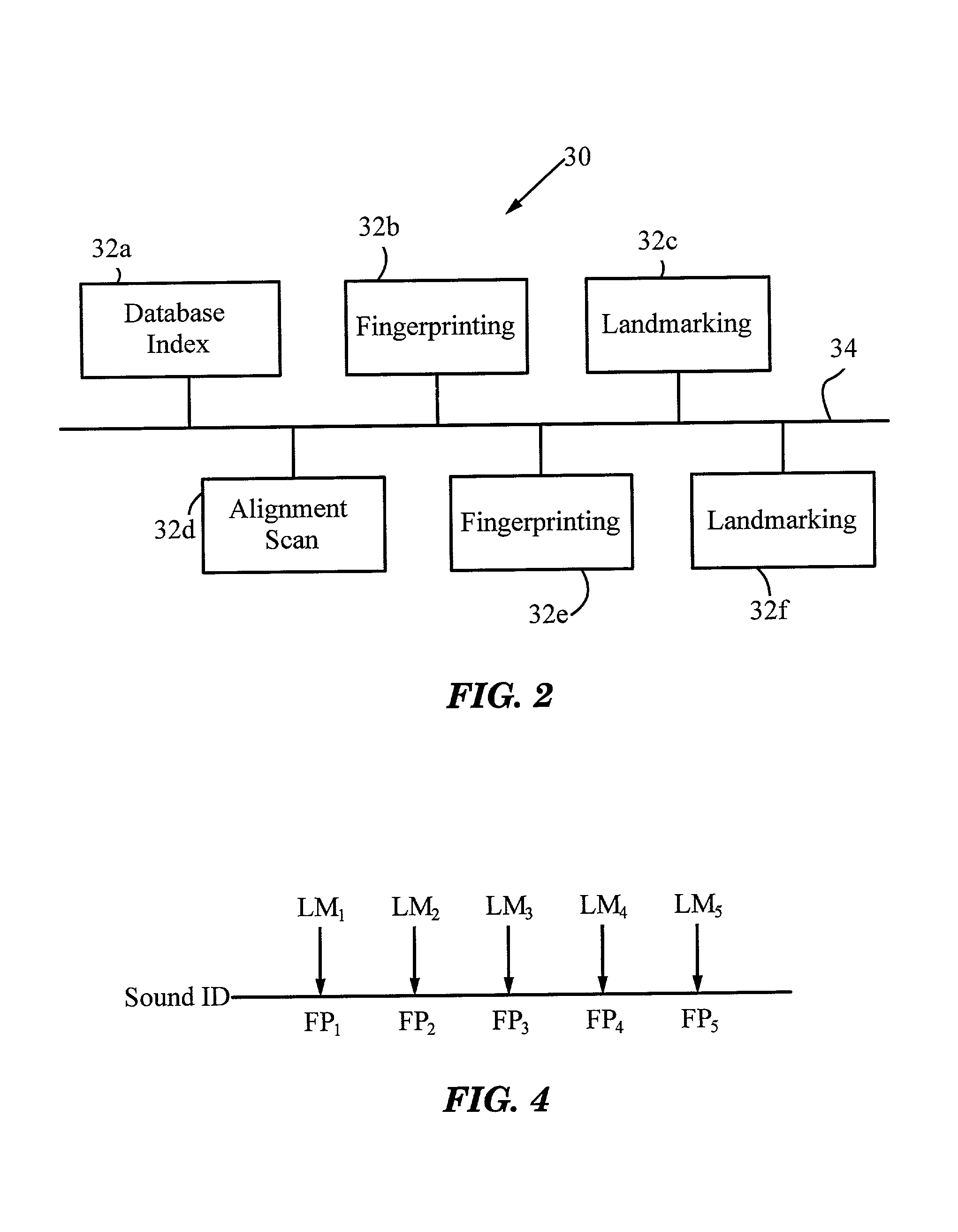
A method for recognizing an audio sample locates an audio file that most closely matches the audio sample from a database indexing a large set of original recordings. Each indexed audio file is represented in the database index by a set of landmark timepoints and associated fingerprints. Landmarks occur at reproducible locations within the file, while fingerprints represent features of the signal at or near the landmark timepoints. To perform recognition, landmarks and fingerprints are computed for the unknown sample and used to retrieve matching fingerprints from the database. For each file containing matching fingerprints, the landmarks are compared with landmarks of the sample at which the same fingerprints were computed. If a large number of corresponding landmarks are linearly related, i.e., if equivalent fingerprints of the sample and retrieved file have the same time evolution, then the file is identified with the sample. The method can be used for any type of sound or music, and is particularly effective for audio signals subject to linear and nonlinear distortion such as background noise, compression artifacts, or transmission dropouts. The sample can be identified in a time proportional to the logarithm of the number of entries in the database; given sufficient computational power, recognition can be performed in nearly real time as the sound is being sampled.
Owner:APPLE INC
Analying polynucleotide sequences
InactiveUS6054270AStable duplexReduce impactSequential/parallel process reactionsSugar derivativesHybridization reactionSequence determination
This invention provides an apparatus and method for analyzing a polynucleotide sequence; either an unknown sequence or a known sequence. A support, e.g. a glass plate, carries an array of the whole or a chosen part of a complete set of oligonucleotides which are capable of taking part in hybridization reactions. The array may comprise one or more pair of oligonucleotides of chosen lengths. The polynucleotide sequence, or fragments thereof, are labelled and applied to the array under hybridizing conditions. Applications include analyses of known point mutations, genomic fingerprinting, linkage analysis, characterization of mRNAs, mRNA populations, and sequence determination.
Owner:OXFORD GENE TECH
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
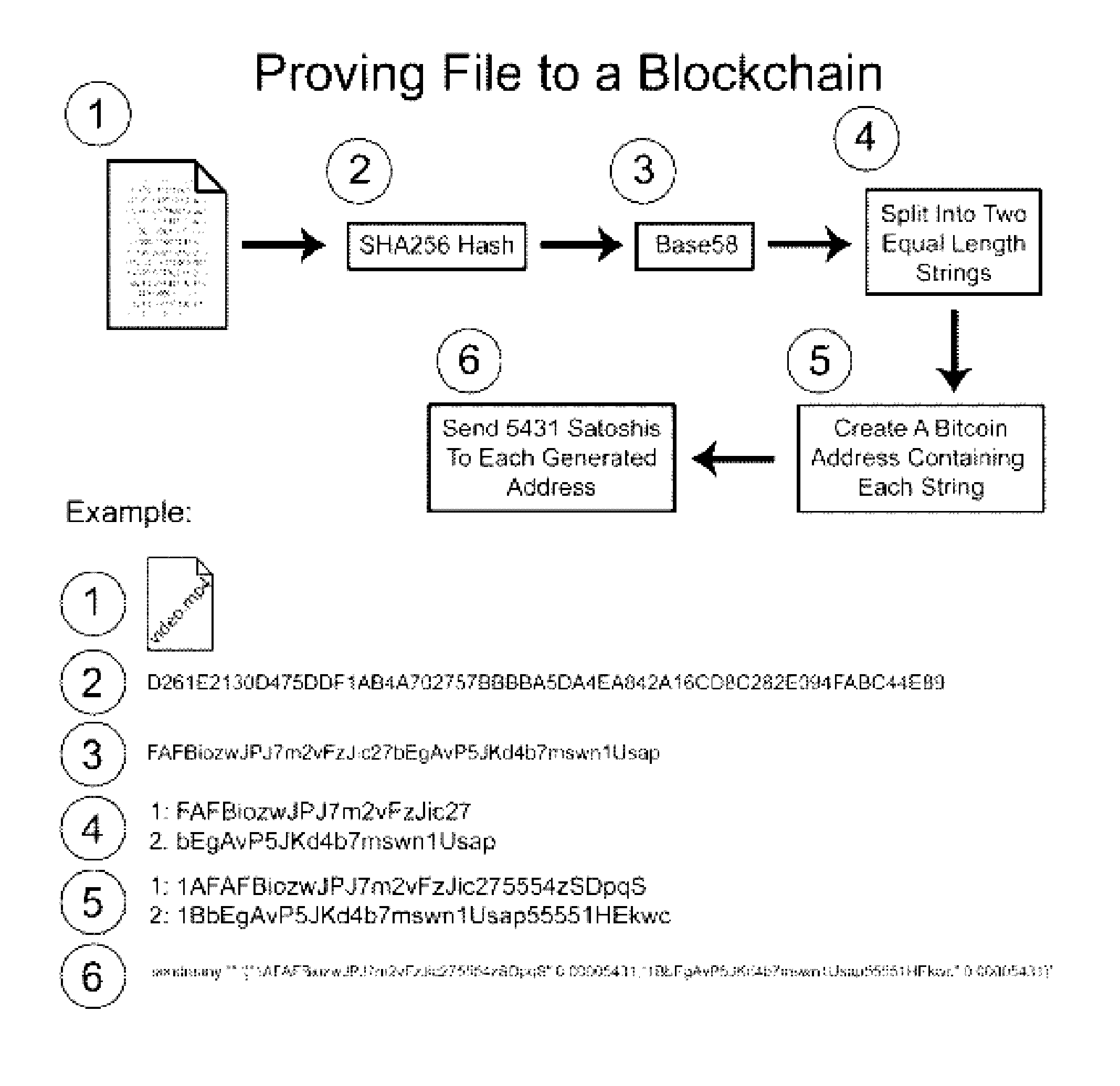
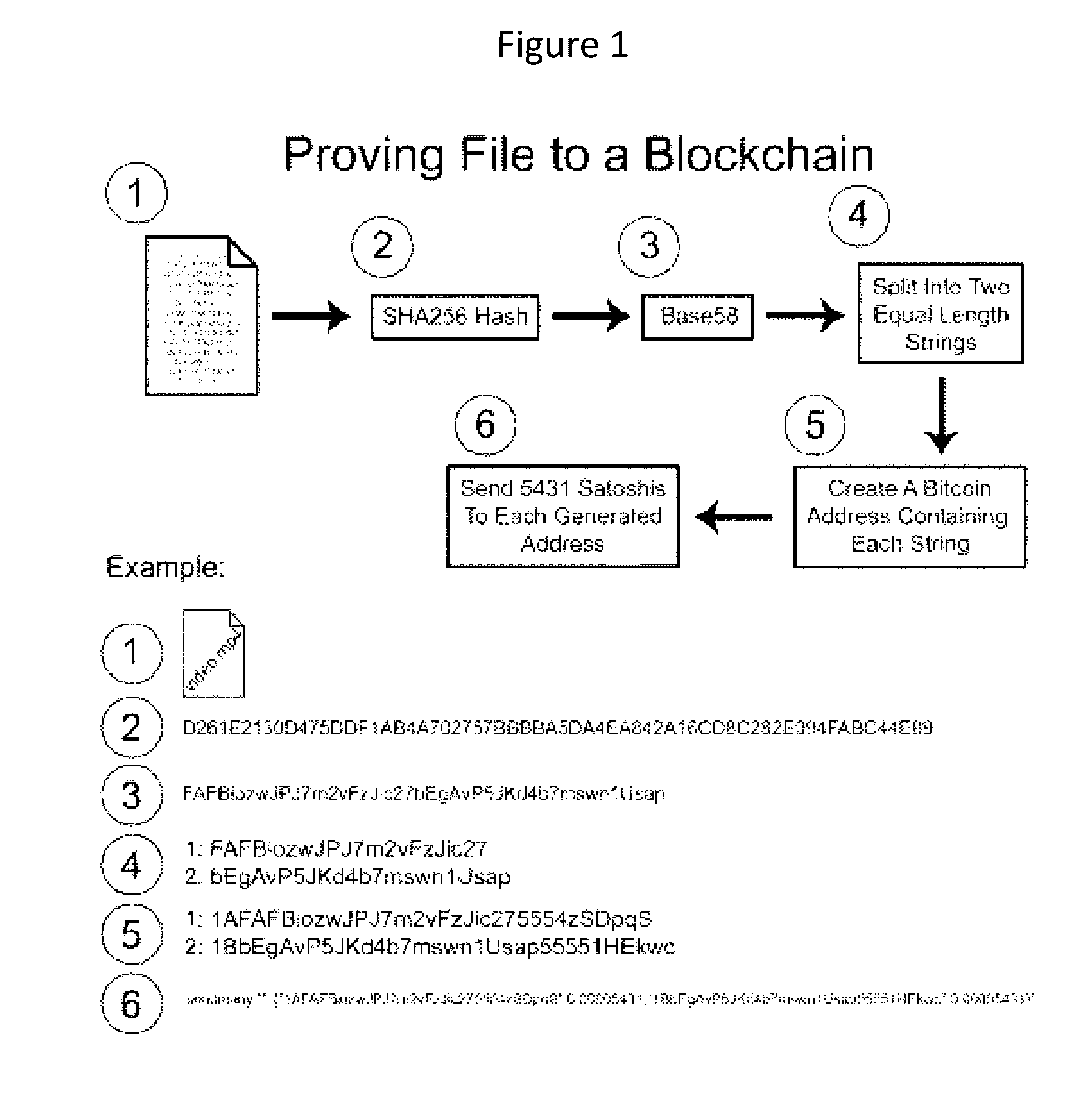
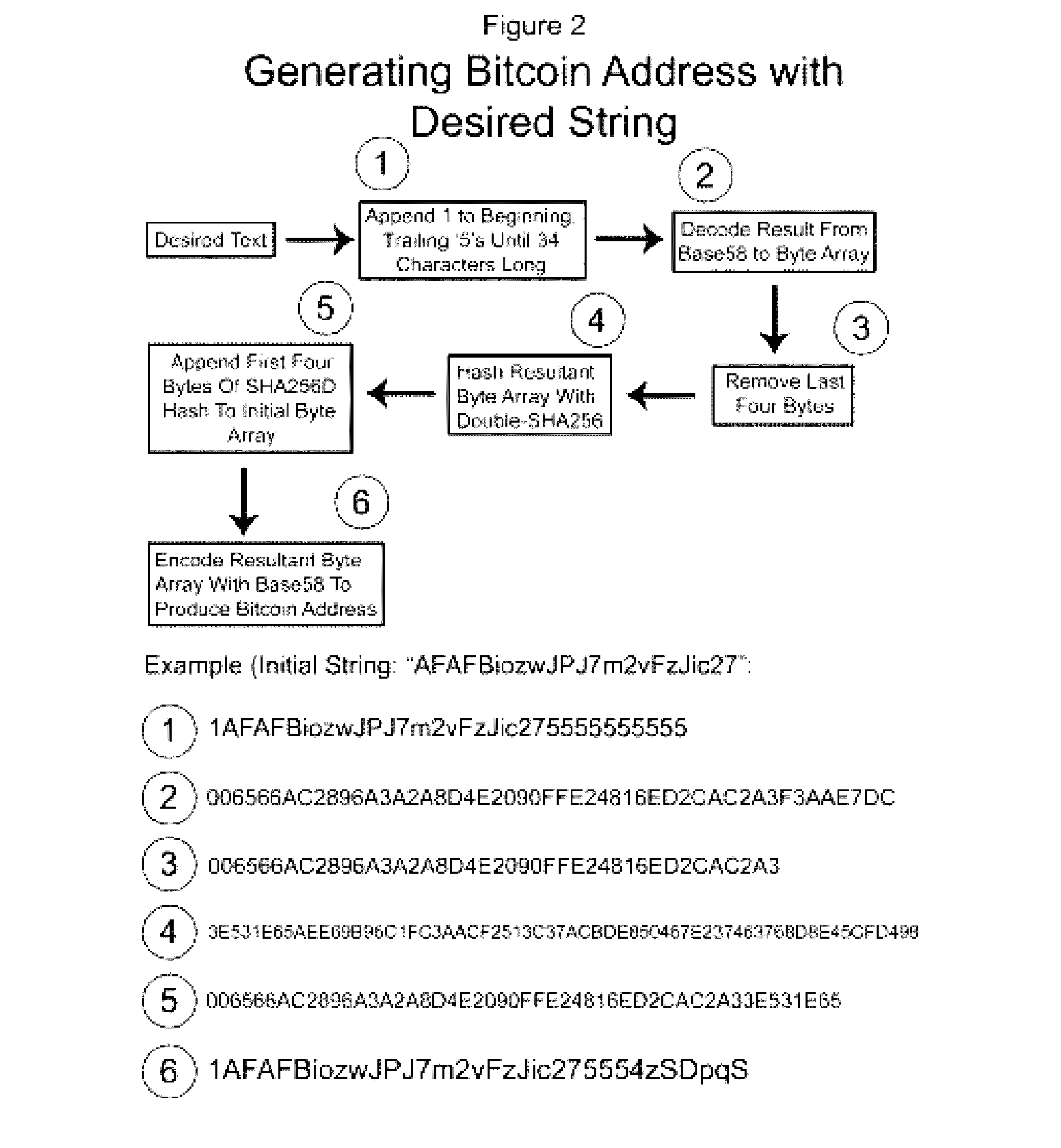
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
Techniques for fraud monitoring and detection using application fingerprinting
ActiveUS20090089869A1Acutation objectsDigital data processing detailsMultiple contextApplication software
Techniques for fraud monitoring and detection using application fingerprinting. As used herein, an “application fingerprint” is a signature that uniquely identifies data submitted to a software application. In an embodiment, a plurality of historical application fingerprints are stored for data previously submitted to a software application. Each historical application fingerprint is associated with one or more contexts in which its corresponding data was submitted. When new (i.e., additional) data is subsequently submitted to the application, a new application fingerprint is generated based on the new data, and the new application fingerprint is associated with one or more contexts in which the new data was submitted. The new application fingerprint is then compared with one or more historical application fingerprints that share the same, or substantially similar, context(s). Based on this comparison, a risk score is generated indicating a likelihood that the new data was submitted for a fraudulent / malicious purpose.
Owner:ORACLE INT CORP
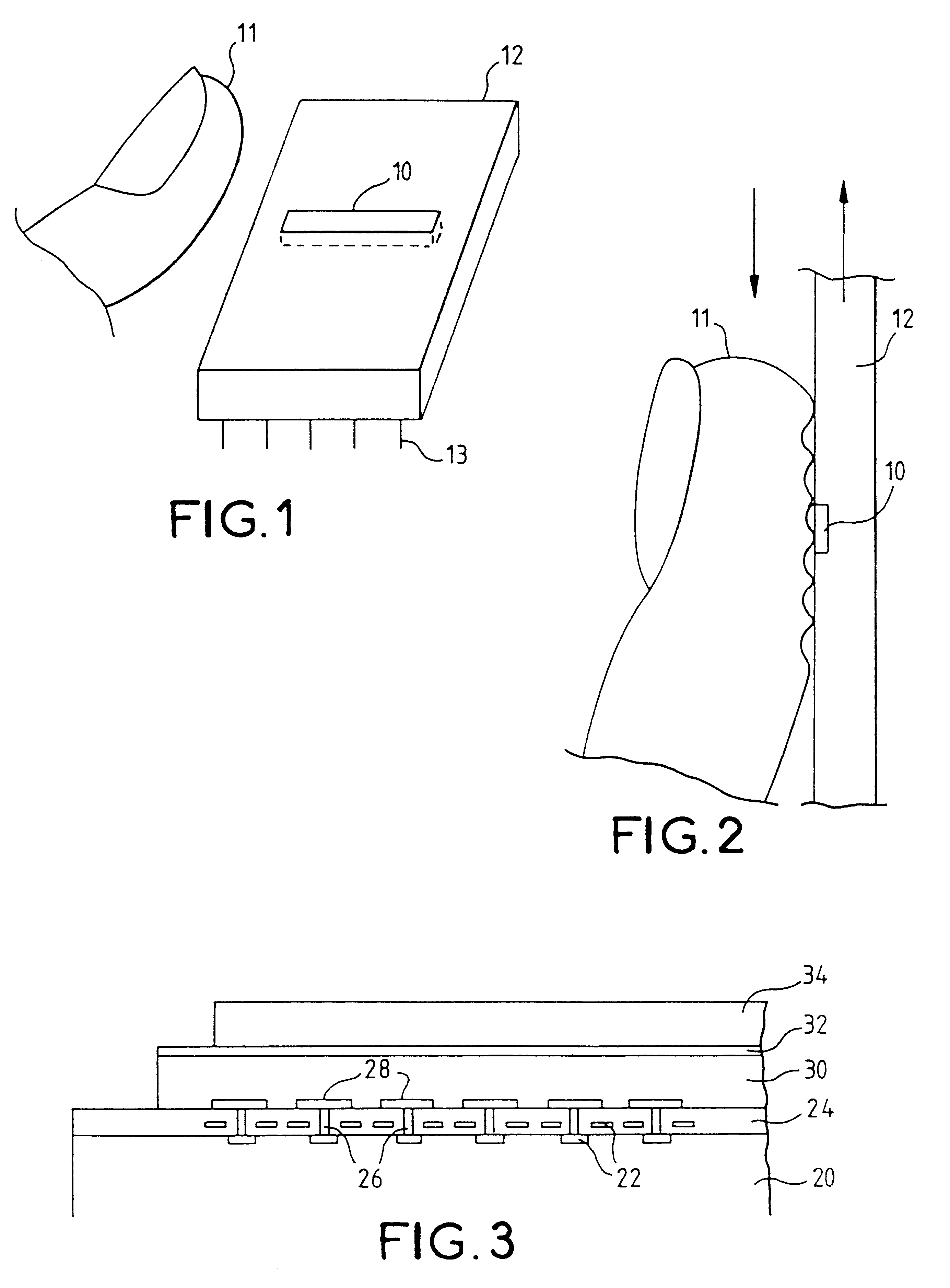
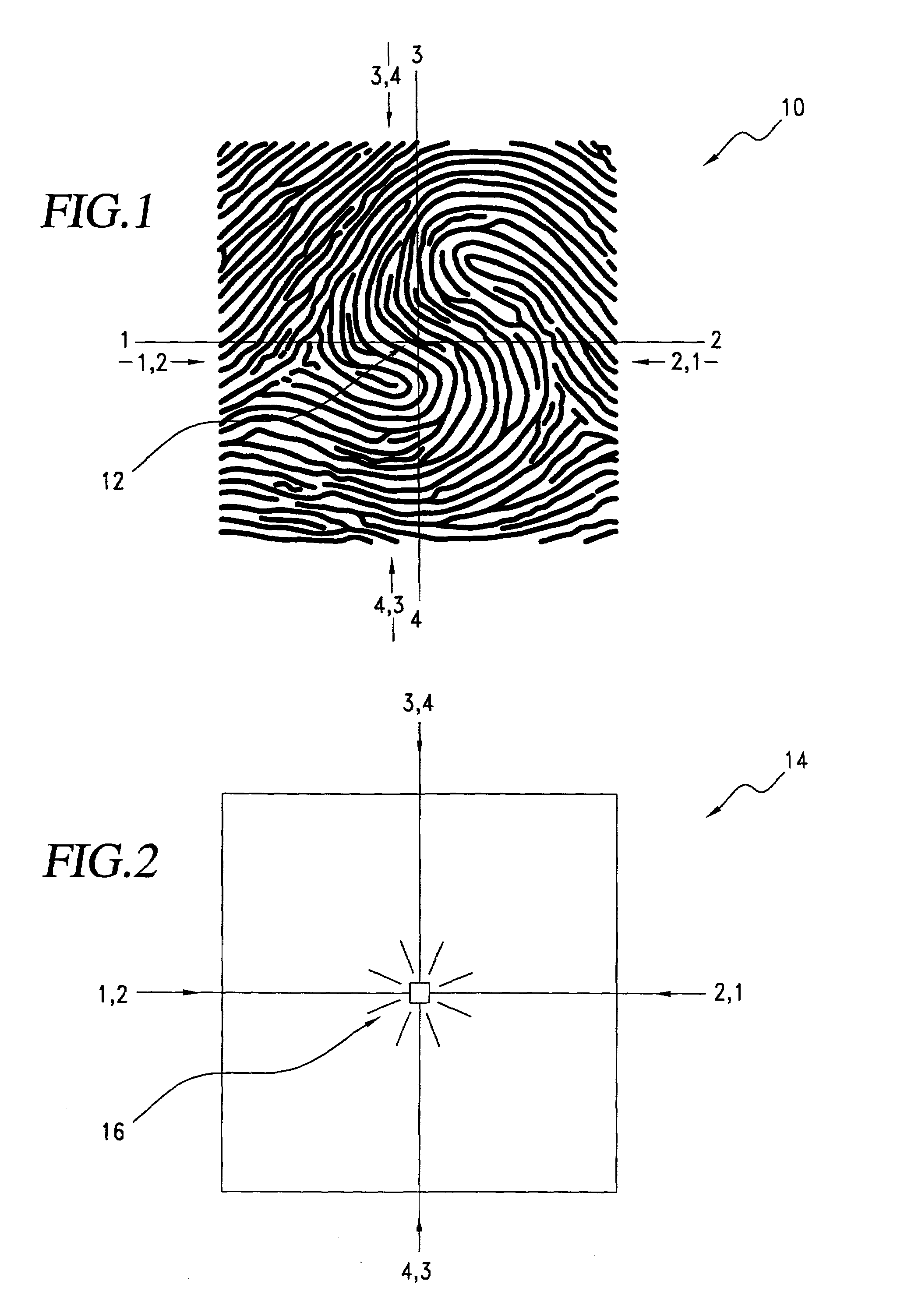
Fingerprint-reading system
InactiveUS6289114B1Image analysisElectric/magnetic contours/curvatures measurementsEffective surfaceRelative motion
A fingerprint-reading system includes a fingerprint sensor having an active surface sensitive to the pressure and temperature of a finger. The surface area of this sensor is far smaller than the surface area of the fingerprint to be read. The reading is done when the sensor and the finger are in contact and in a relative motion of sliding of the sensor and the finger with respect to each other. The system reconstitutes a complete image of the fingerprint from the partial images given by the sensor during this motion.
Owner:APPLE INC
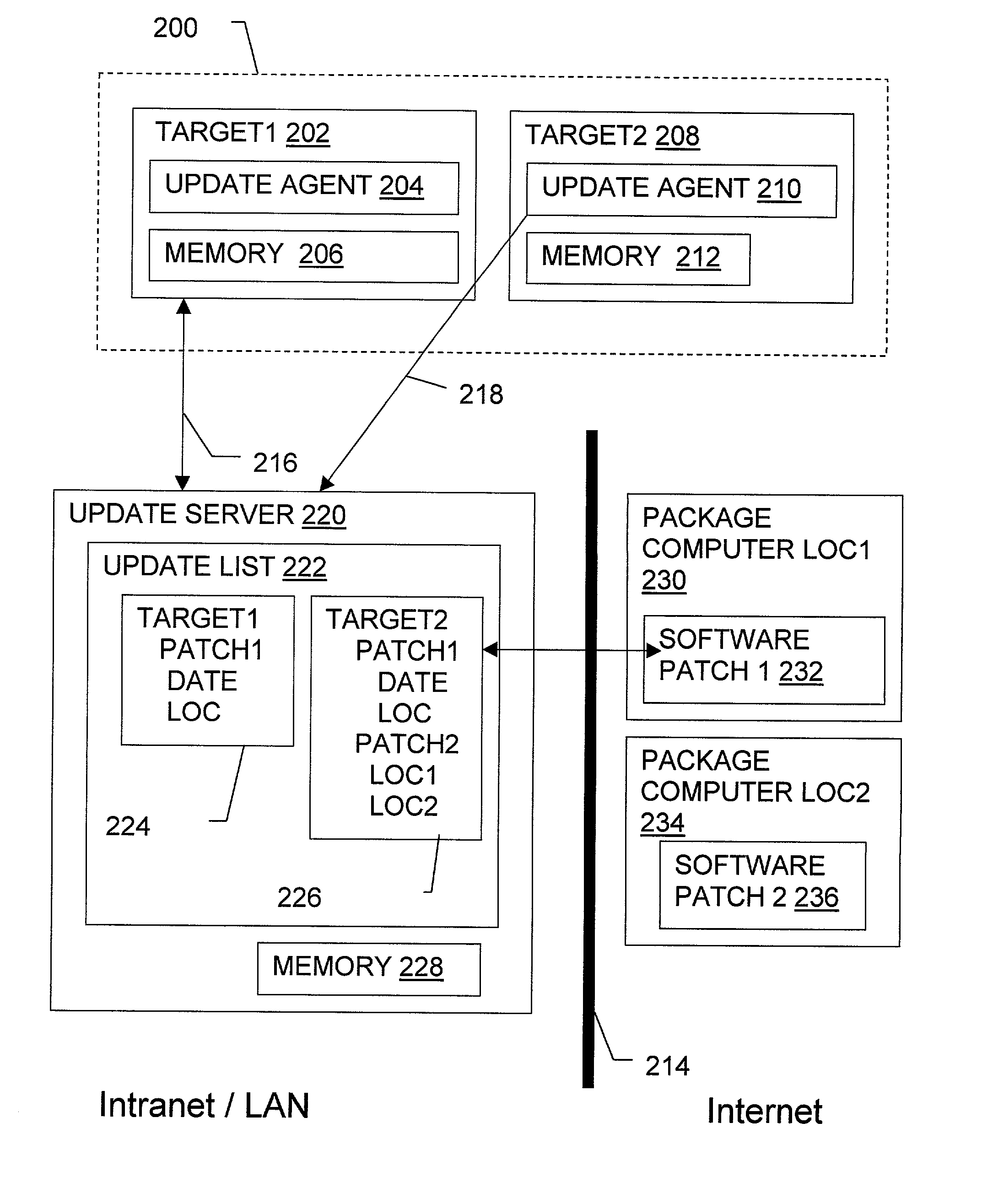
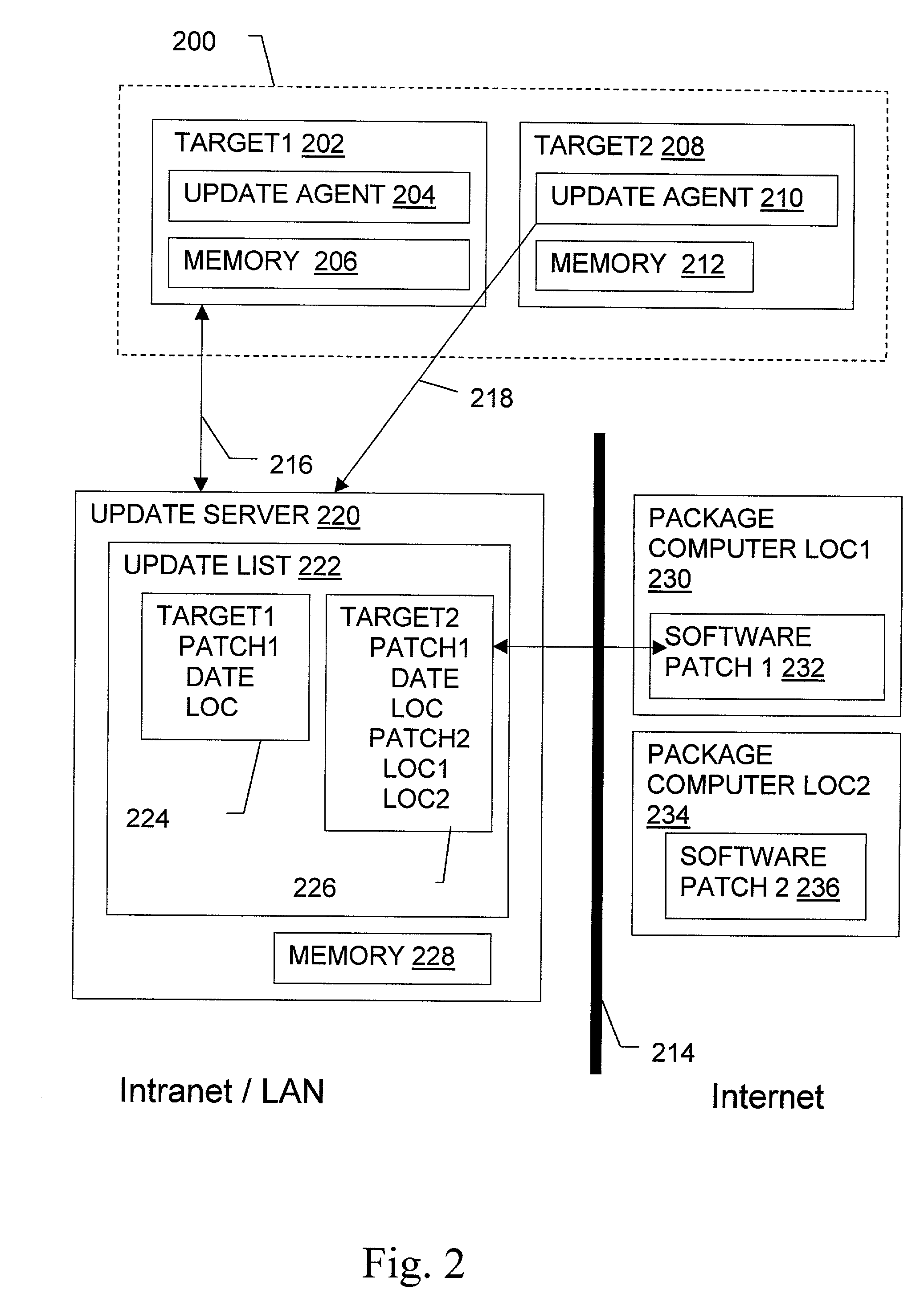
Non-invasive automatic offsite patch fingerprinting and updating system and method
InactiveUS20020100036A1Error detection/correctionDigital computer detailsSoftware updateNon invasive
Methods, systems, and configured storage media are provided for discovering software updates, discovering if a given computer can use the software update, and then updating the computers with the software as needed automatically across a network without storing the updates on an intermediate machine within the network. Furthermore, when a failure is detected, the rollout is stopped and the software can be automatically removed from those computers that already were updated. The software update can be stored originally at an address that is inaccessible through the network firewall by intermediately uploading the software update to an update computer which is not a part of the network but has access through the firewall, which is then used to distribute the update.
Owner:HEAT SOFTWARE USA
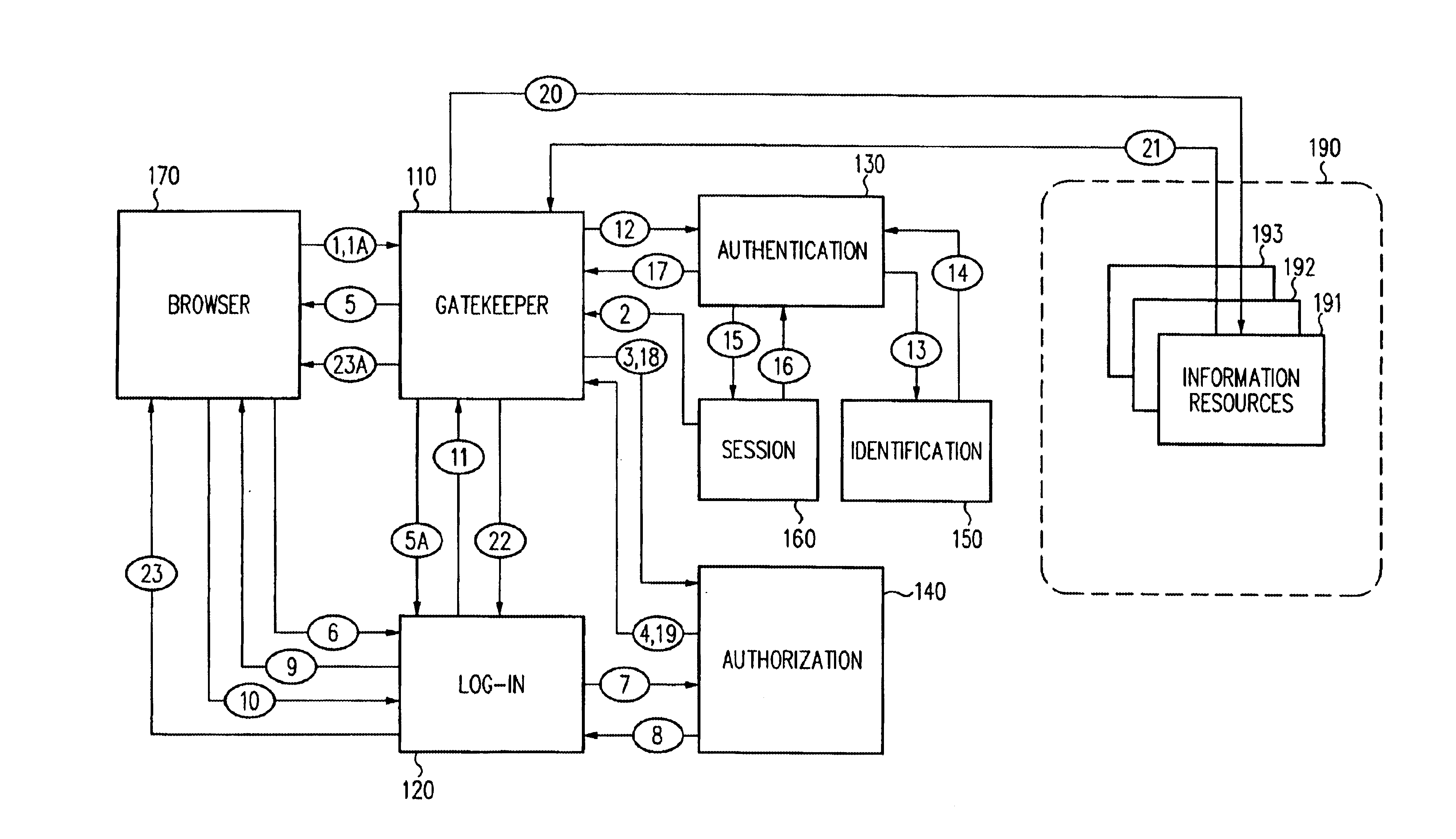
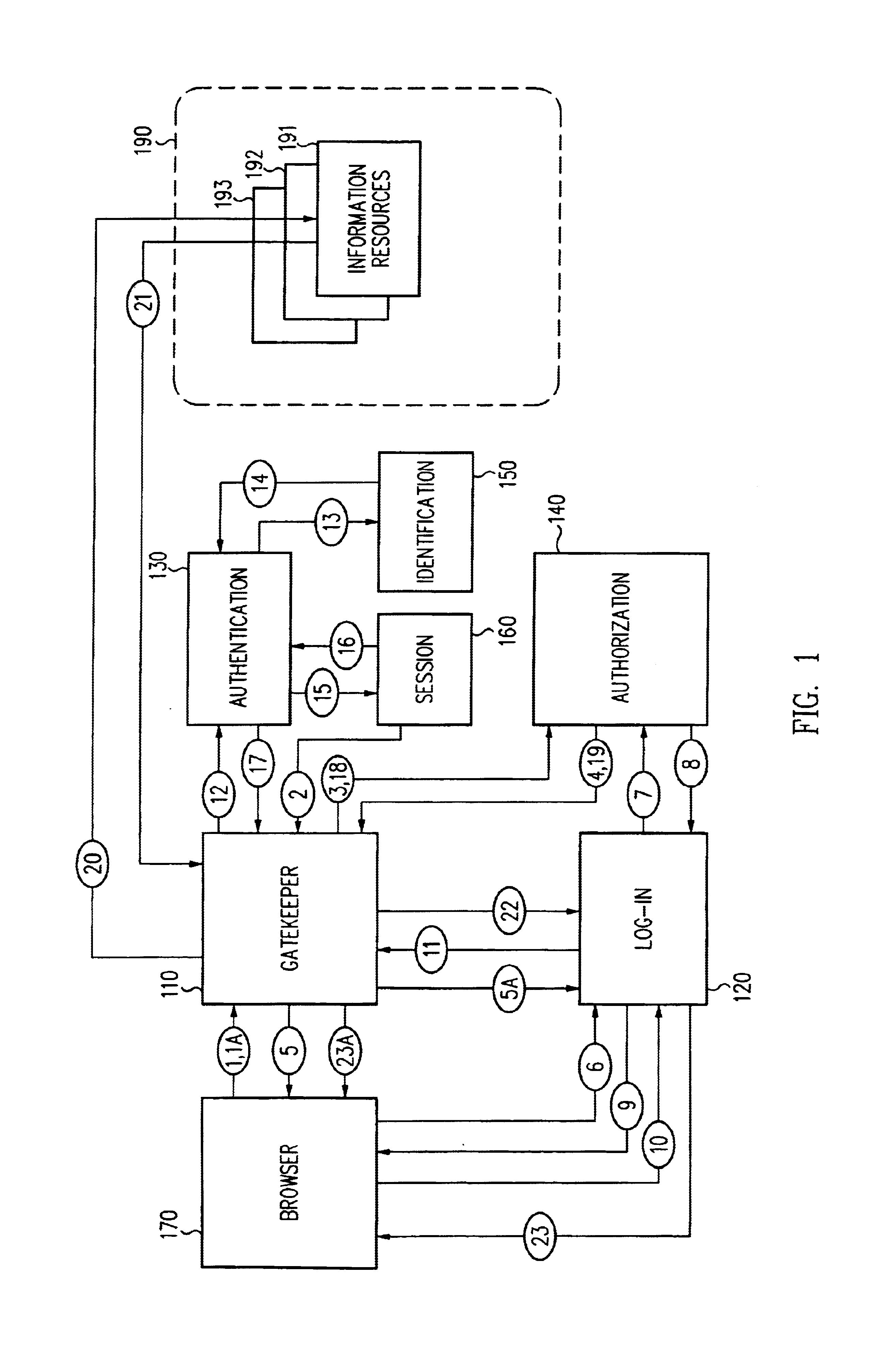
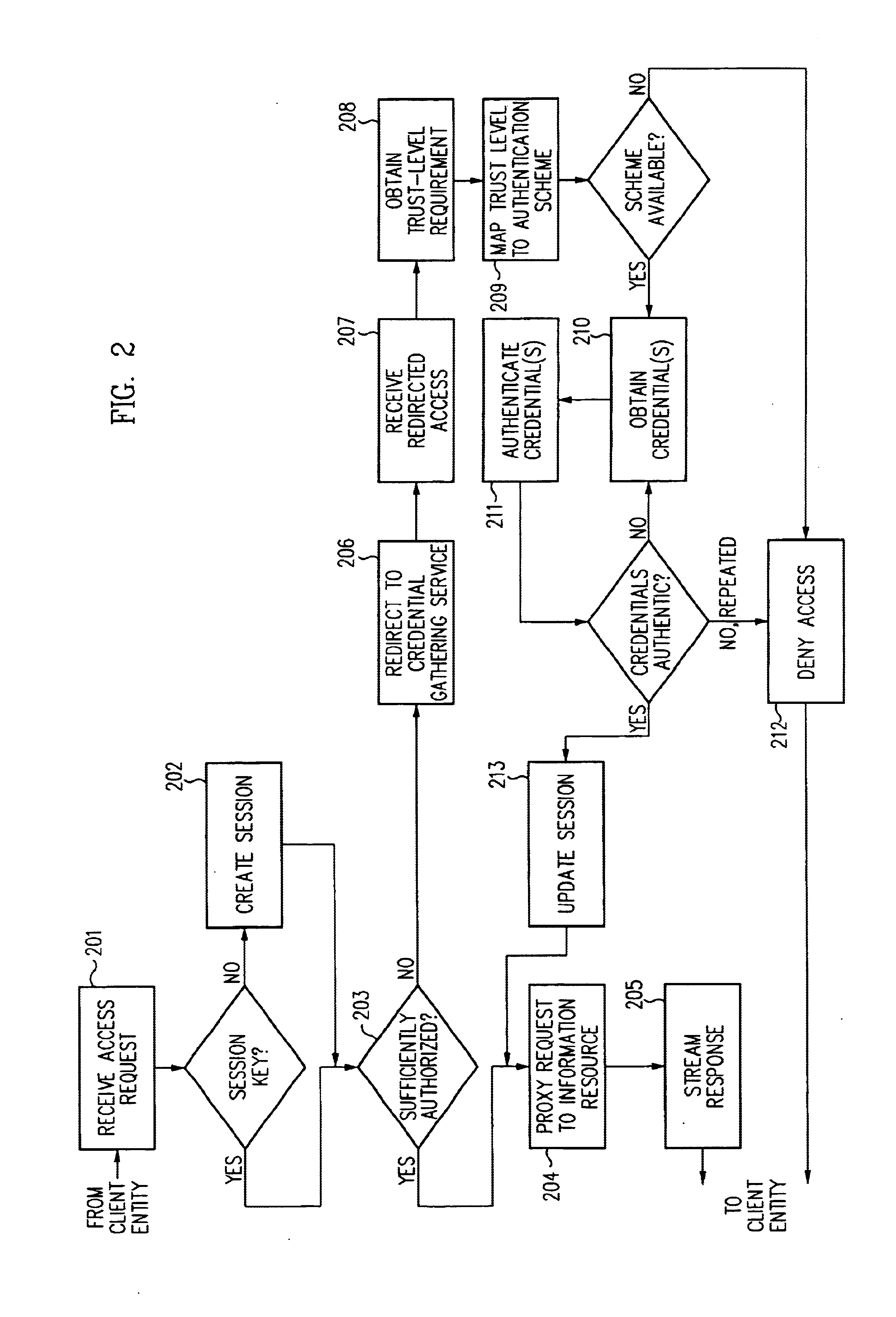
Security architecture with environment sensitive credential sufficiency evaluation
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
Method and apparatus for wireless network security
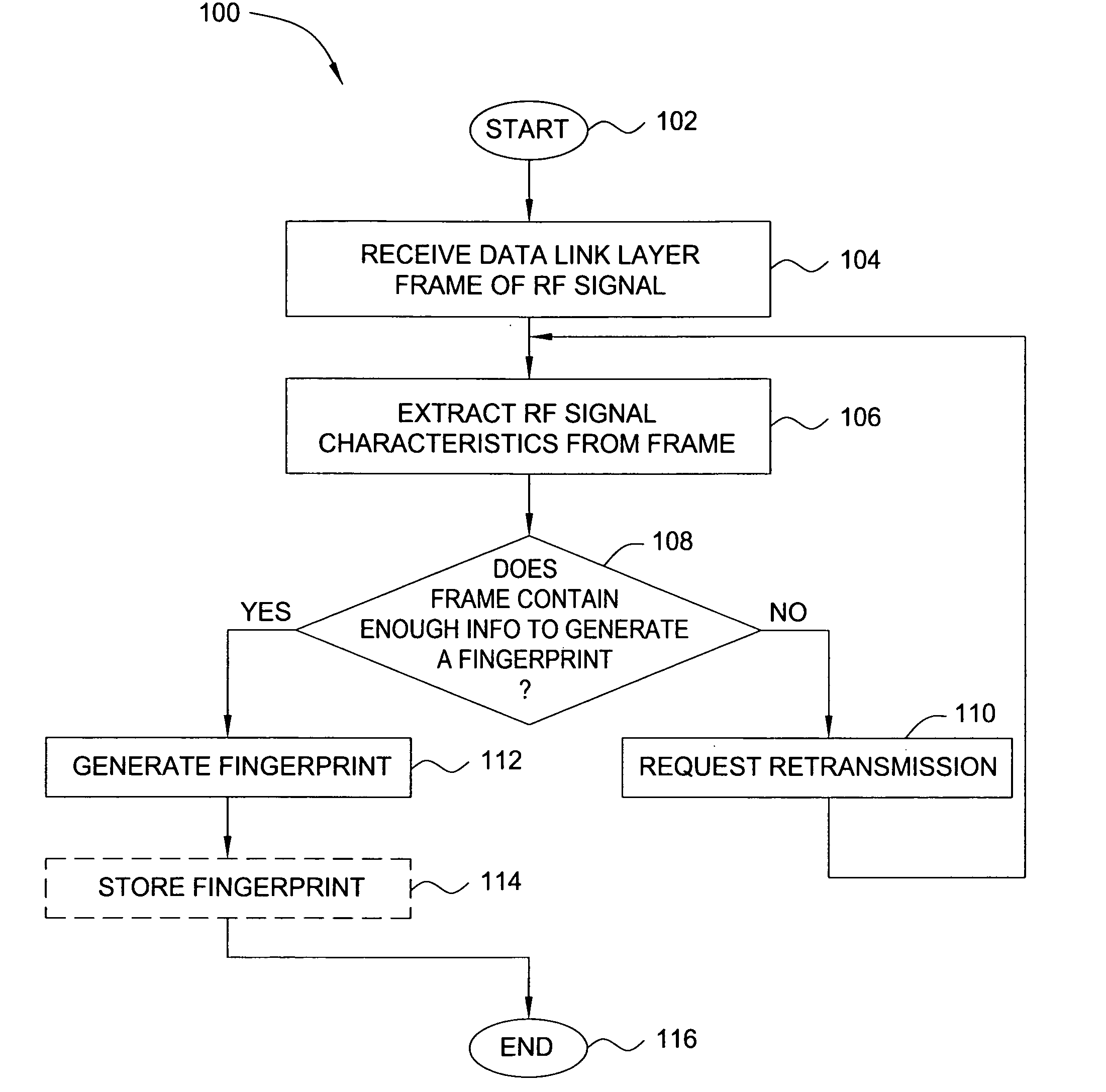
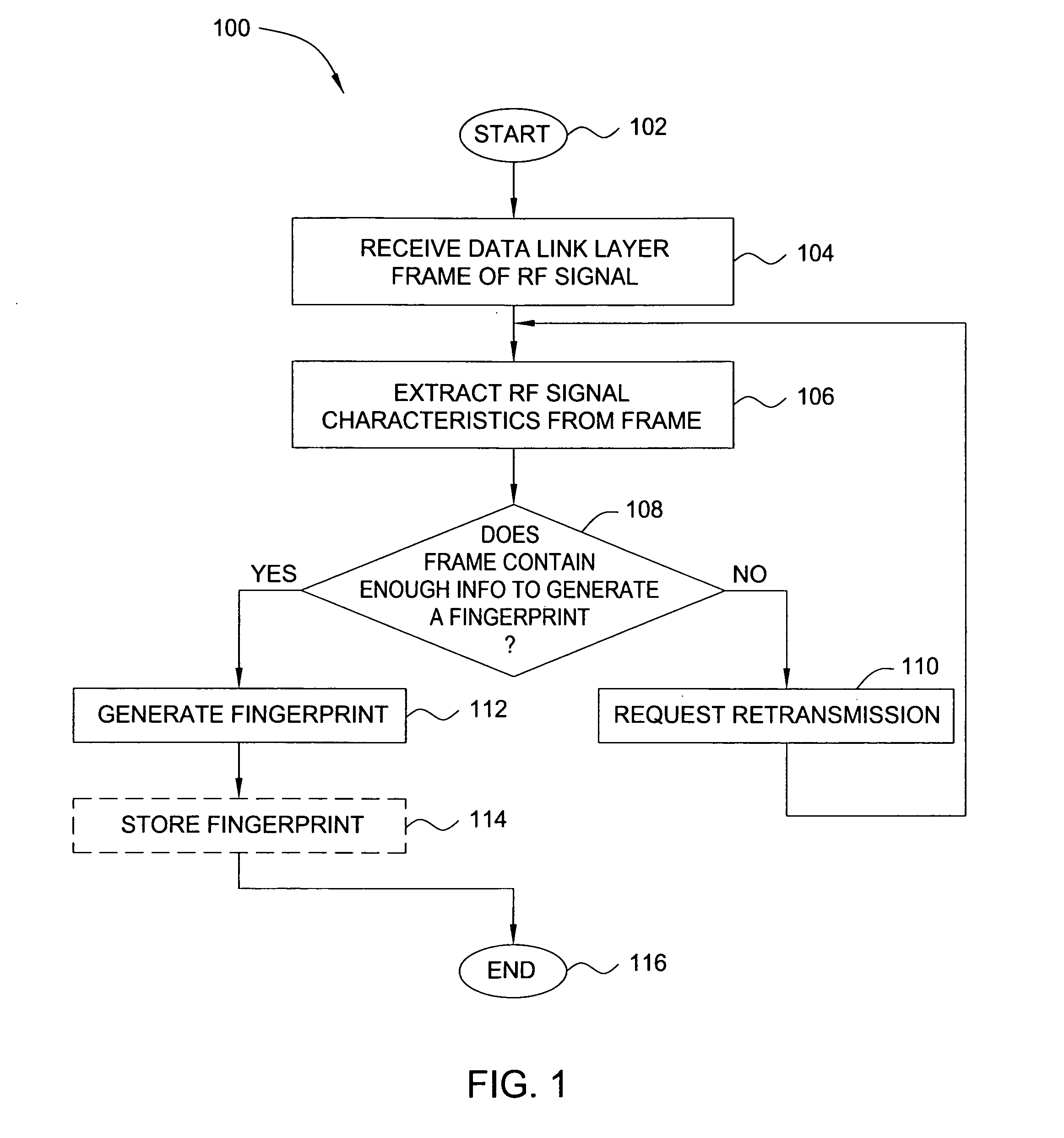
ActiveUS20070025265A1Error preventionFrequency-division multiplex detailsRadio frequency signalEngineering
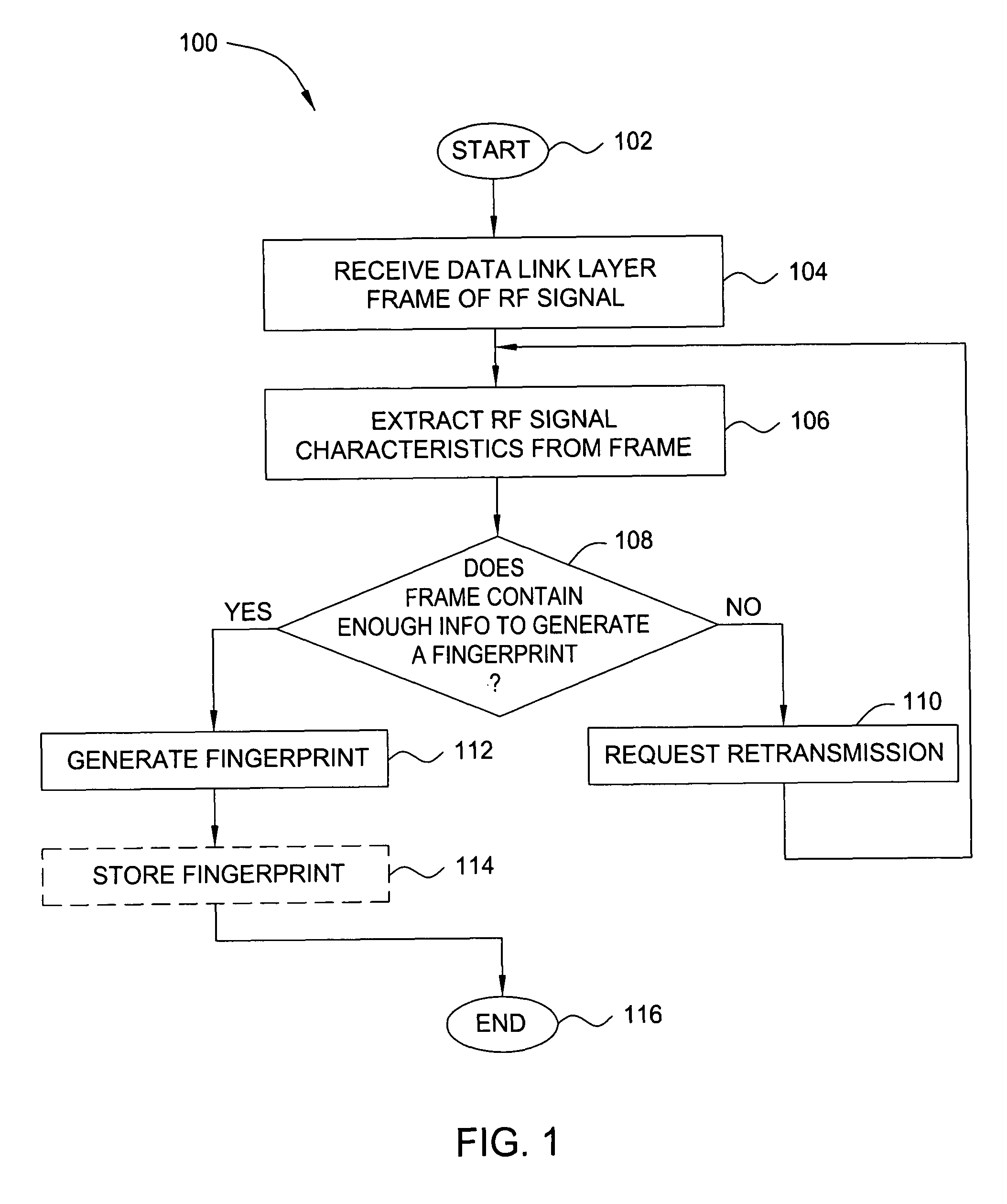
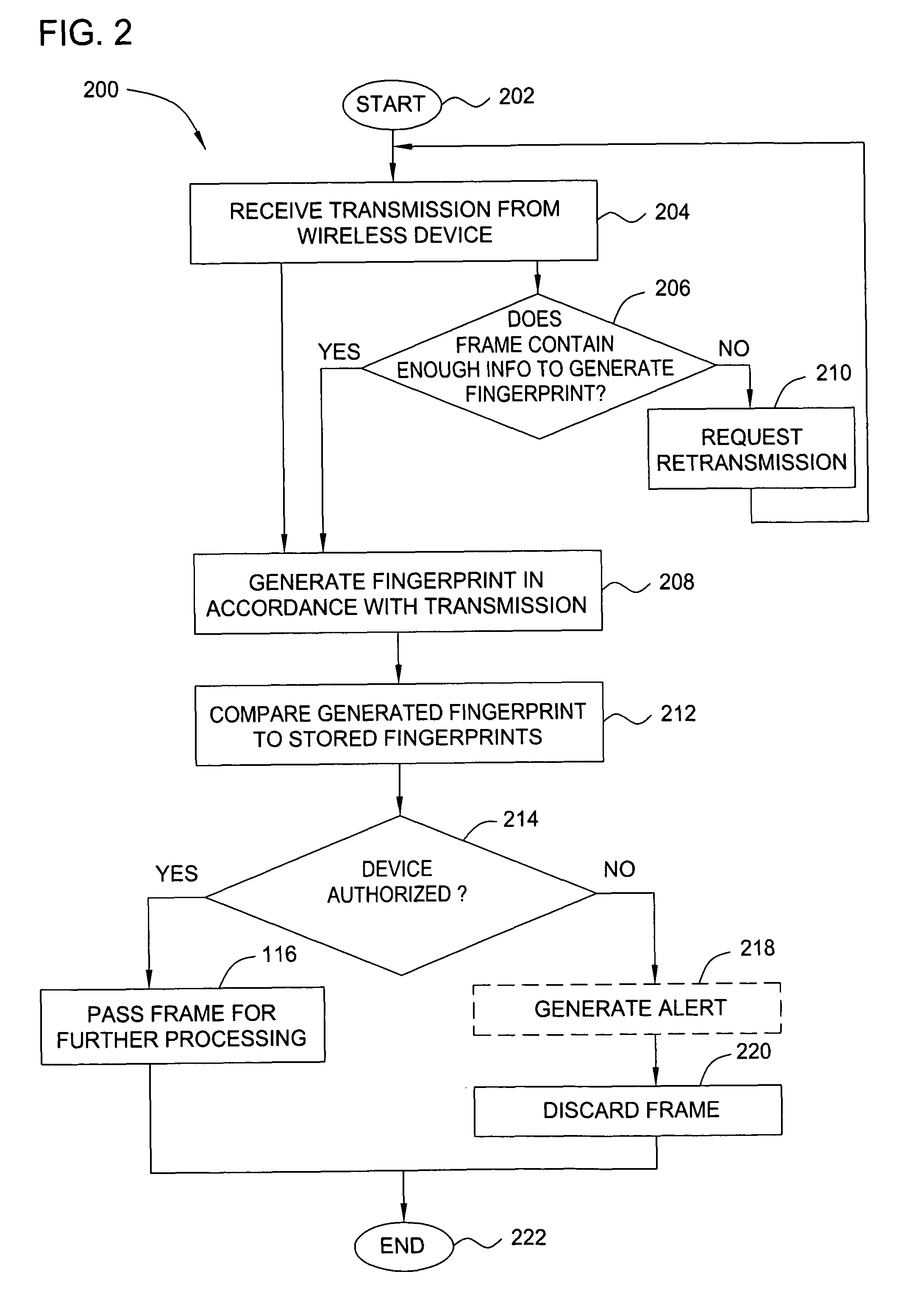
In one embodiment, the present invention is a method and apparatus for wireless network security. In one embodiment, a method for securing a wireless computing network includes receiving a communication from an unidentified transmitter, identifying the transmitter in accordance with a fingerprint generated from one or more radio frequency signal characteristics extracted from the communication, and taking action in response to an identity of the transmitter.
Owner:SRI INTERNATIONAL
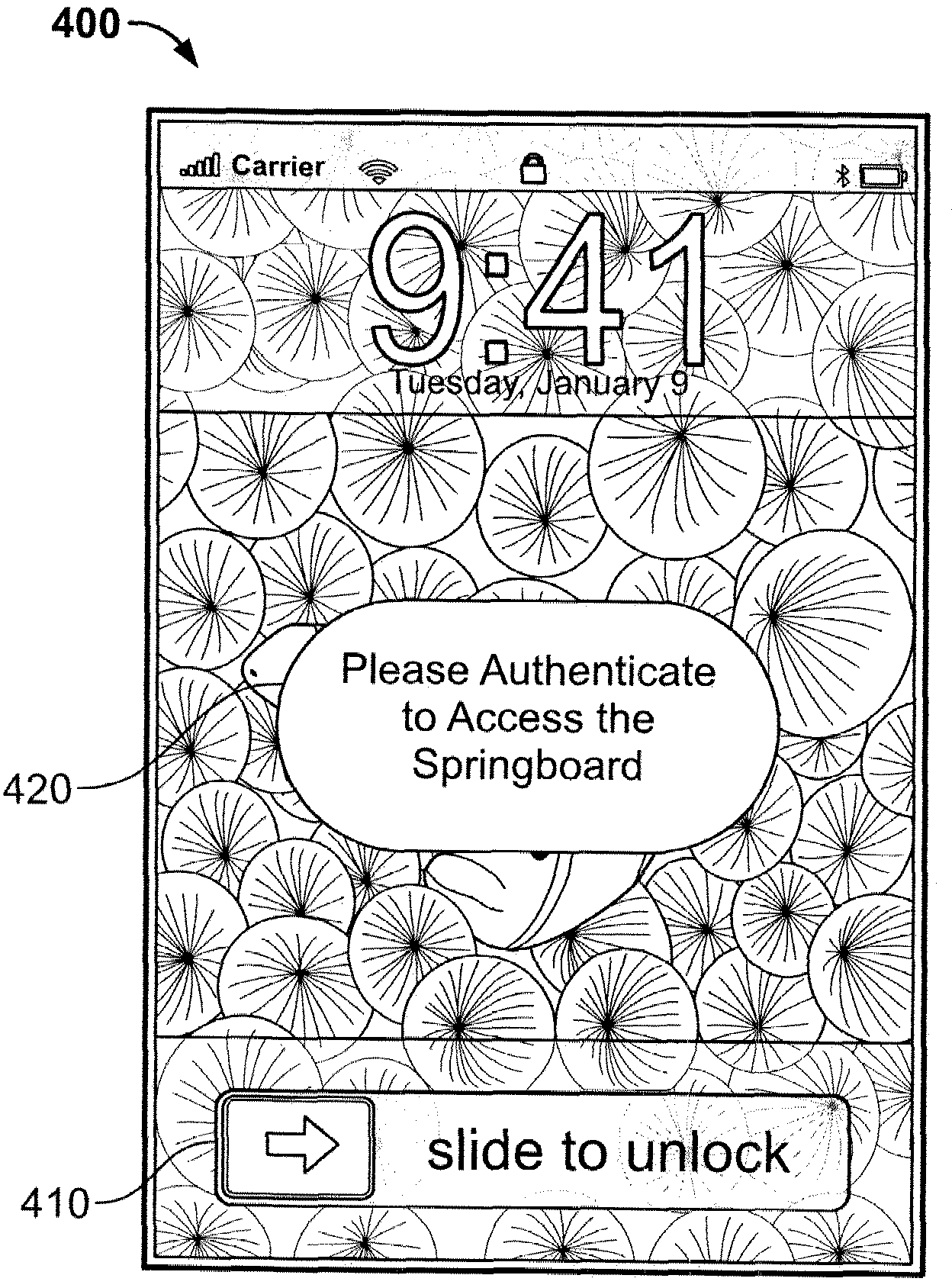
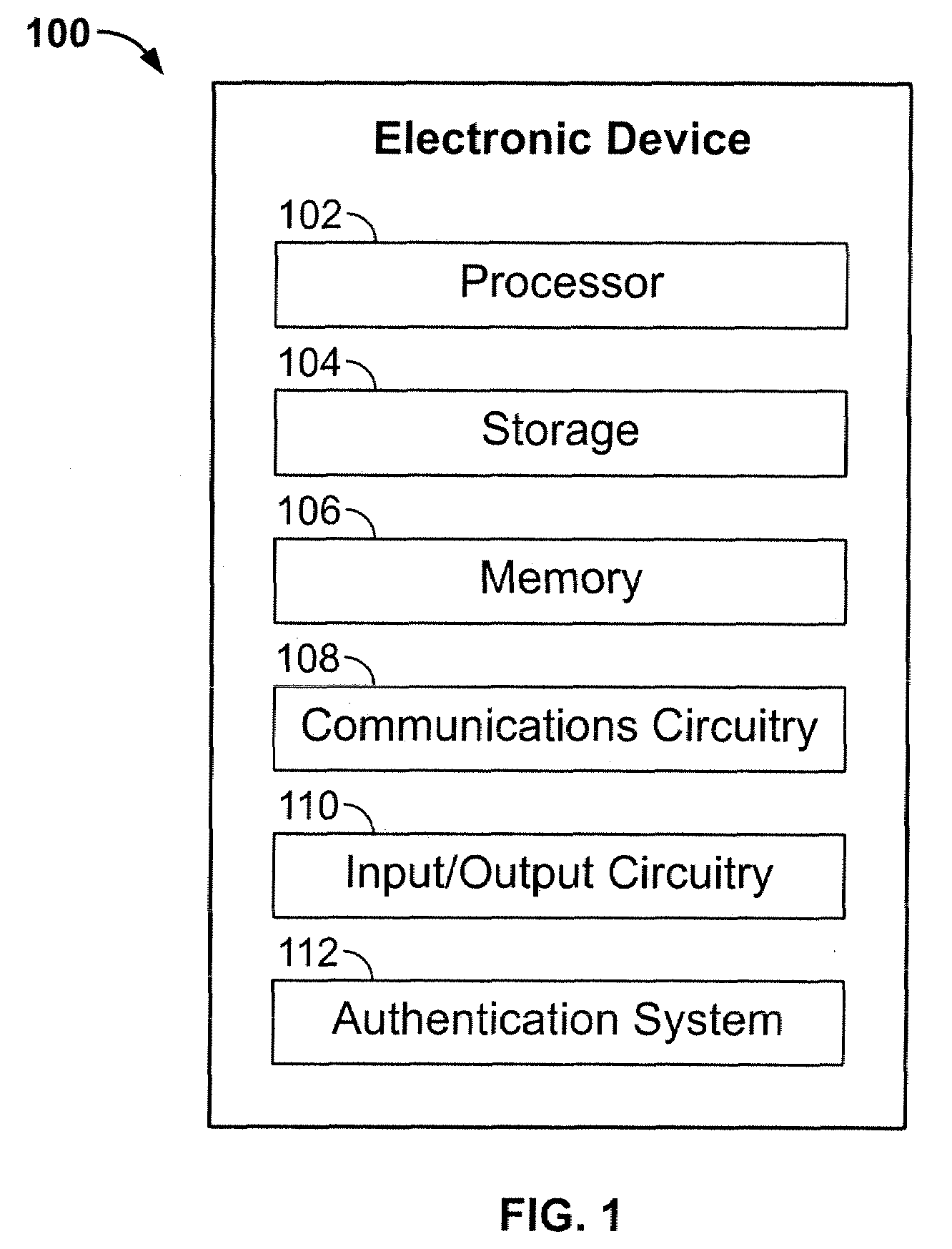
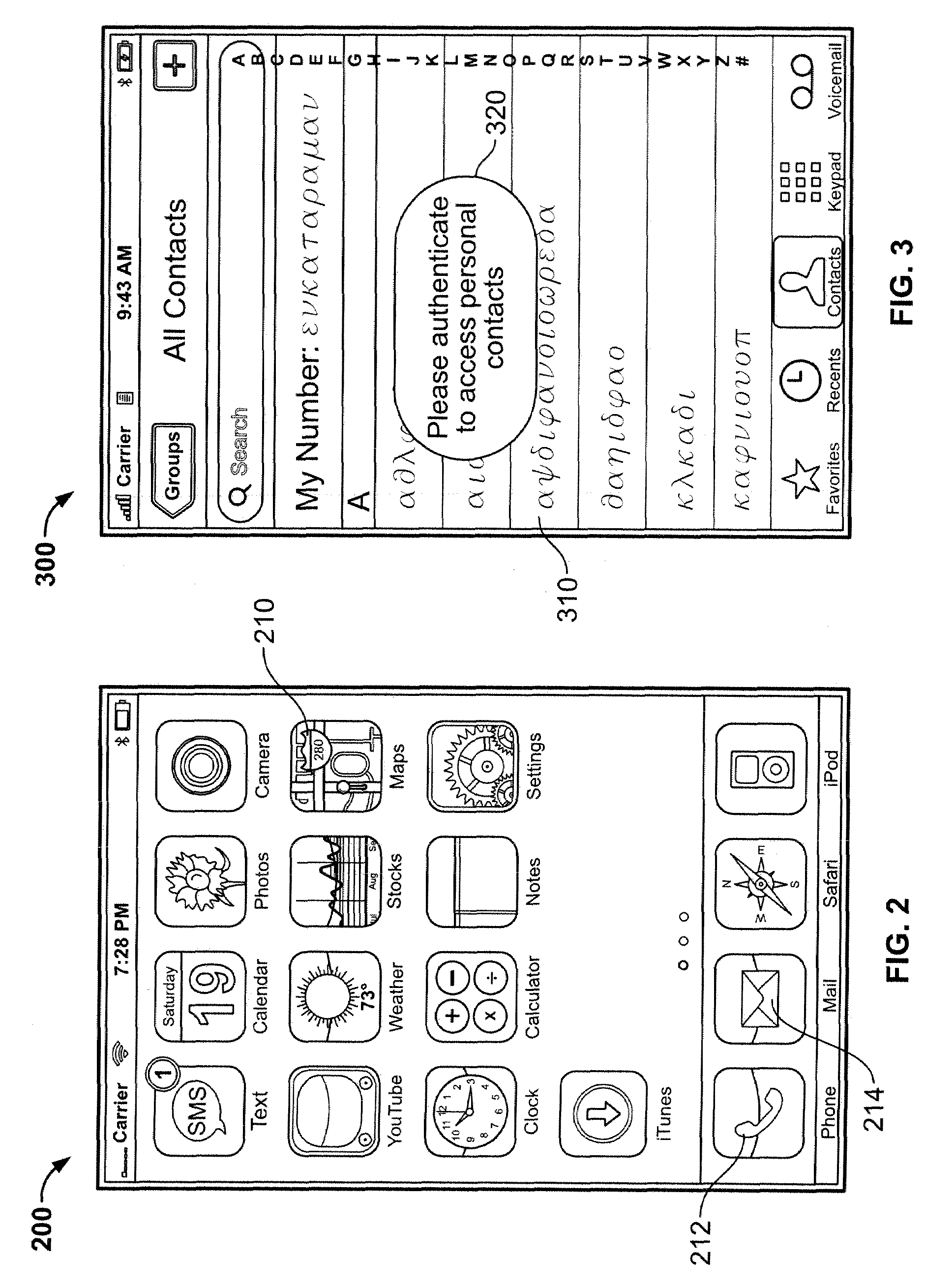
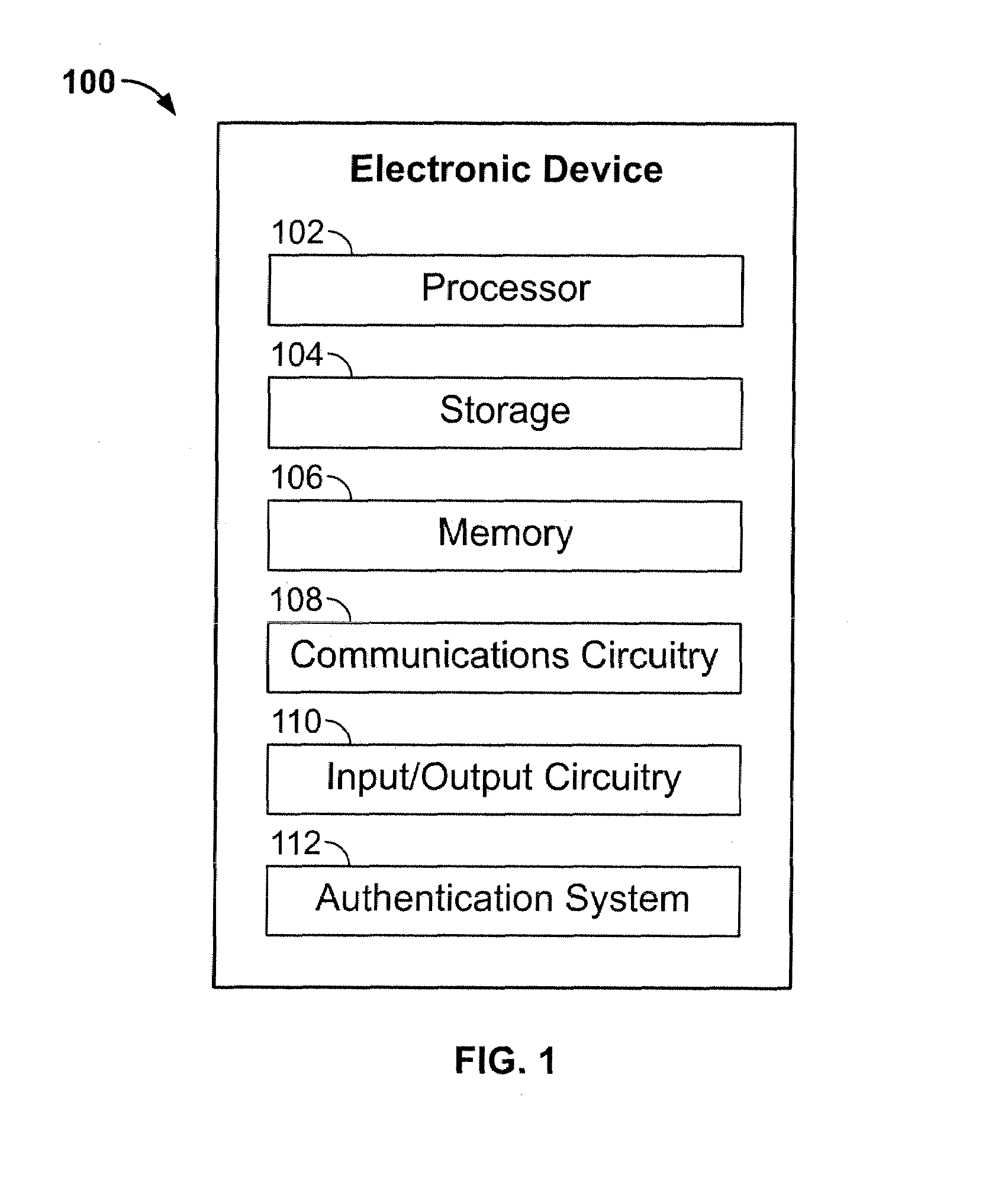
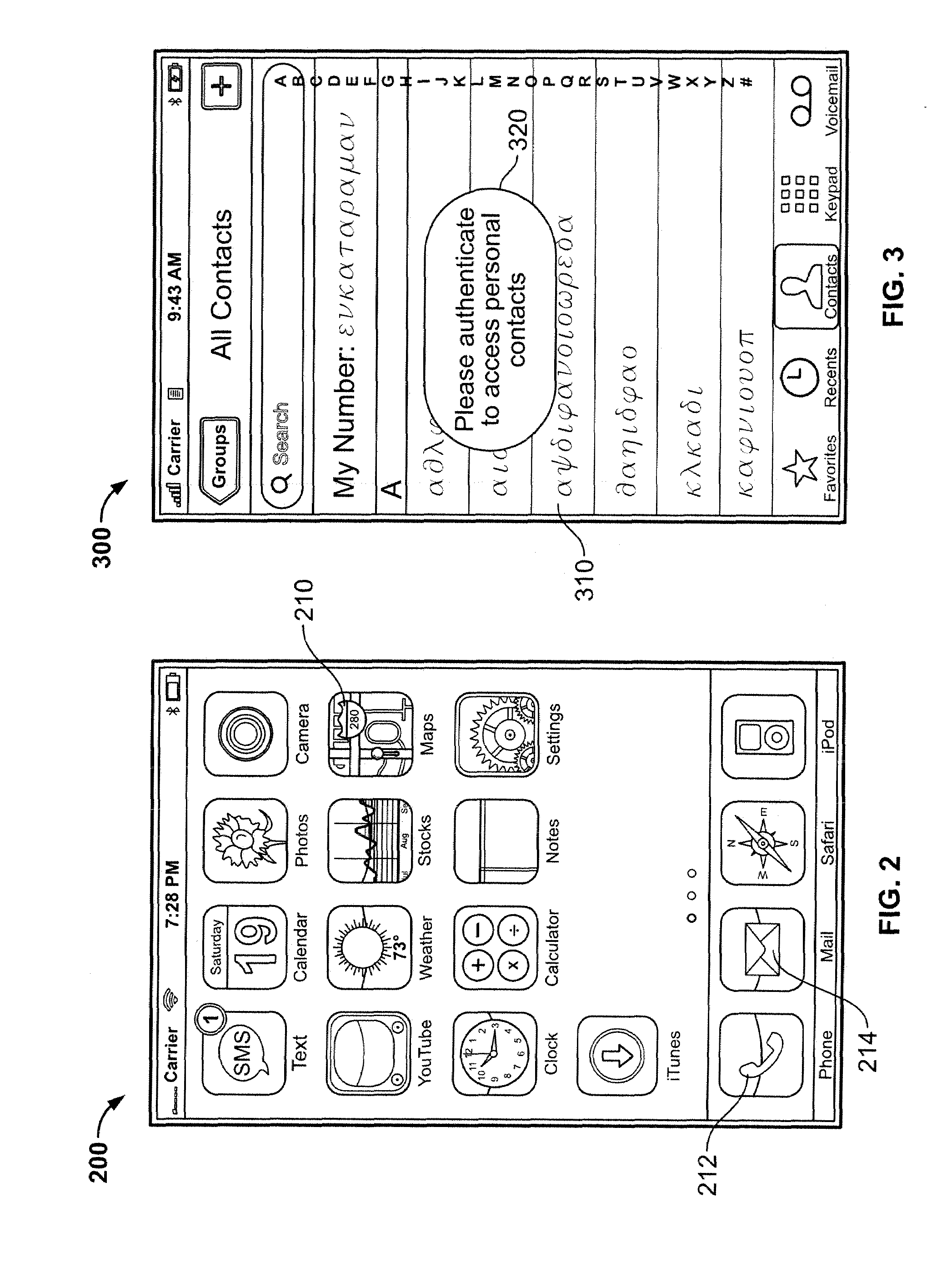
Embedded authentication systems in an electronic device
ActiveUS20090083847A1Digital data processing detailsUser identity/authority verificationAuthentication systemVisual perception
This invention is directed to an electronic device with an embedded authentication system for restricting access to device resources. The authentication system may include one or more sensors operative to detect biometric information of a user. The sensors may be positioned in the device such that the sensors may detect appropriate biometric information as the user operates the device, without requiring the user to perform a step for providing the biometric information (e.g., embedding a fingerprint sensor in an input mechanism instead of providing a fingerprint sensor in a separate part of the device housing). In some embodiments, the authentication system may be operative to detect a visual or temporal pattern of inputs to authenticate a user. In response to authenticating, a user may access restricted files, applications (e.g., applications purchased by the user), or settings (e.g., application settings such as contacts or saved game profile).
Owner:APPLE INC
Pointing device with biometric sensor
InactiveUS6148094ACathode-ray tube indicatorsInternal/peripheral component protectionComputerized systemPointing device
A pointing device incorporates a biometric sensor at a location such that when operating the pointing device in a normal manner, a user's hand rests naturally in a position to place a finger of the user's hand in proximity to and readable by the biometric sensor. In one embodiment, a computer trackball pointing device includes a fingerprint sensor which is equally well suitable for use by either a right-handed or a left-handed user. Along with positional information from a position sensor and user selection information from at least one user-depressable button, the pointing device also conveys to an attached computer system information associated with the user's identity detected by the fingerprint sensor. Such a pointing device is well suited to both transparent verification as well as continuous verification, for if a user removes his or her hand from the natural position when using the device, the user's fingerprint will no longer be detectable by the fingerprint sensor, and the computer system to which the pointing device is attached can be alerted as to the need to re-authenticate any additional attempts at using the pointing device.
Owner:DALTON PATRICK ENTERPRISES
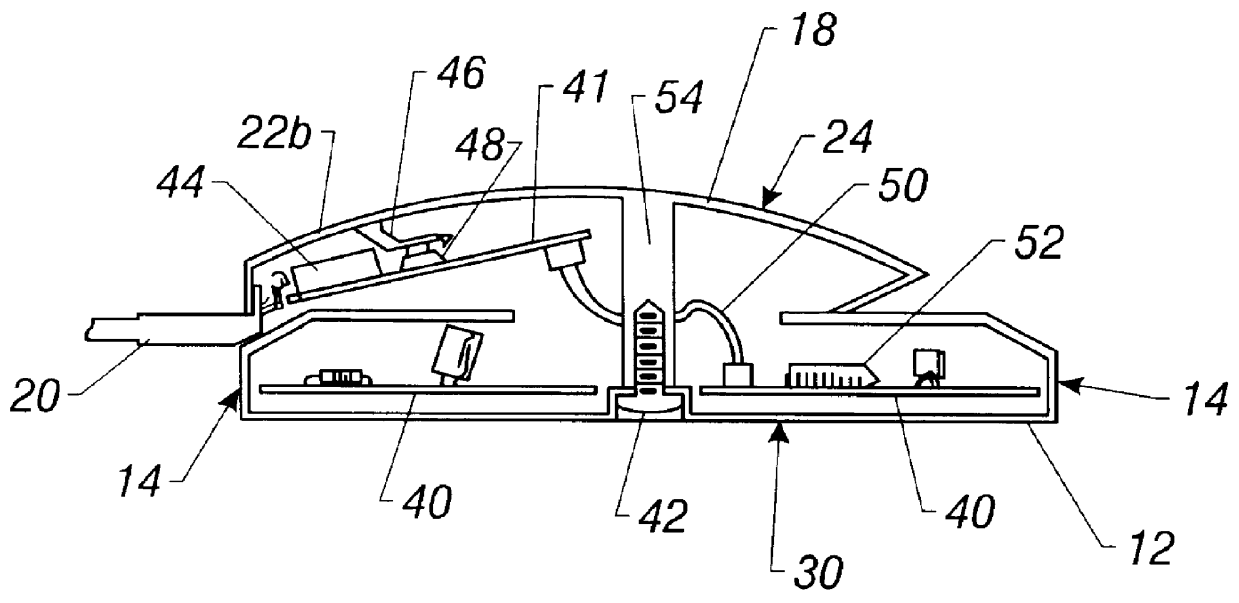
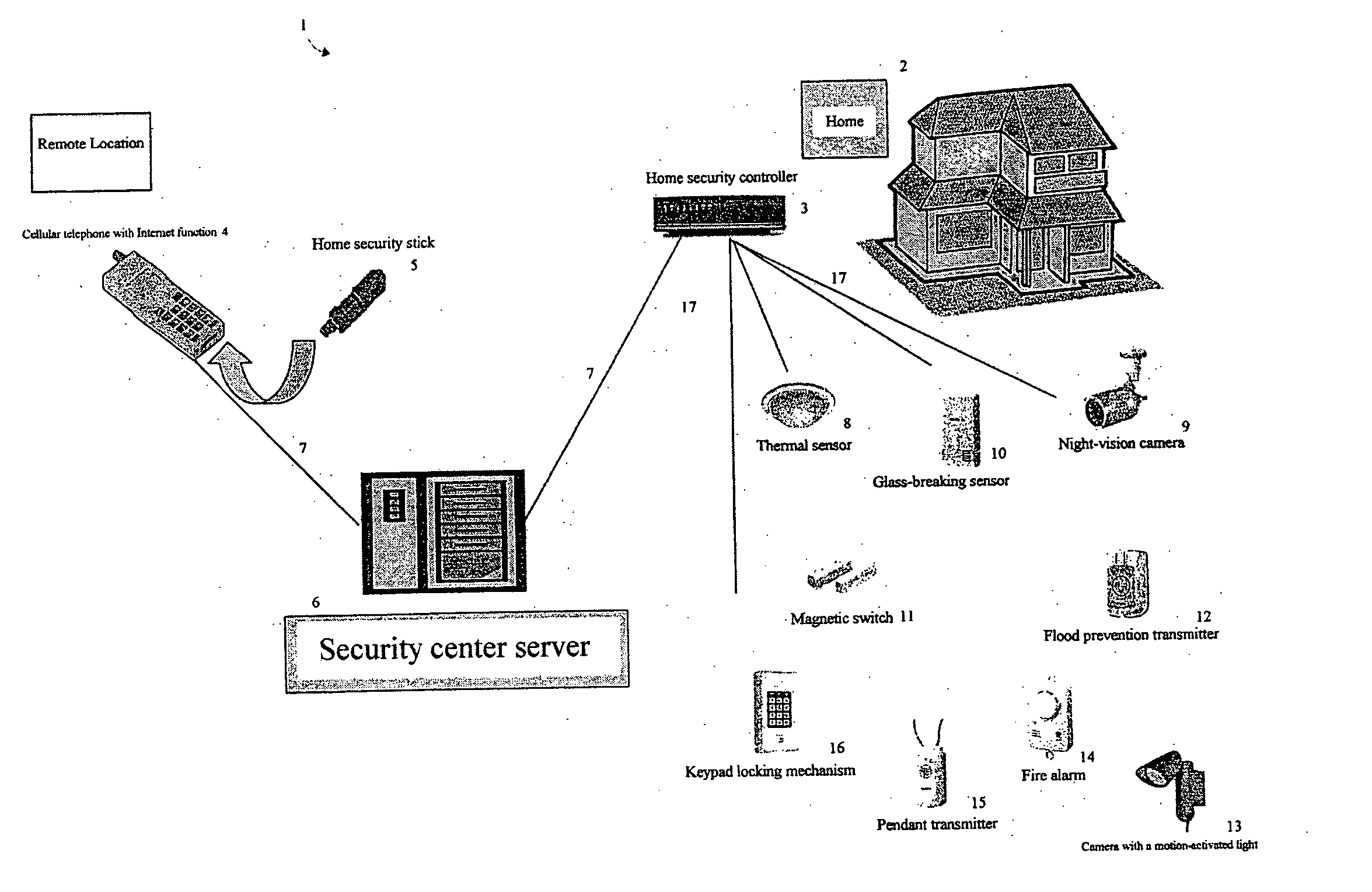
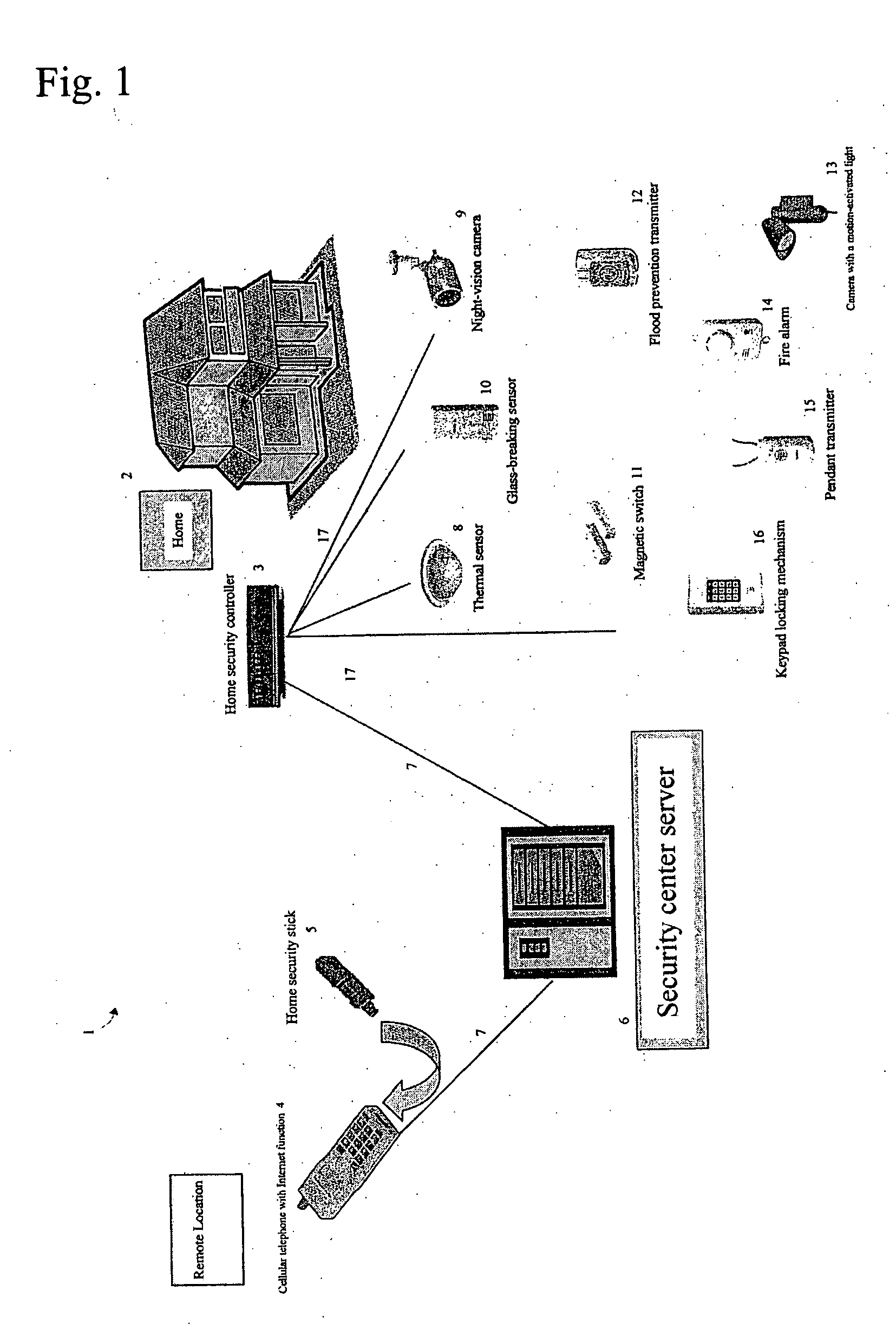
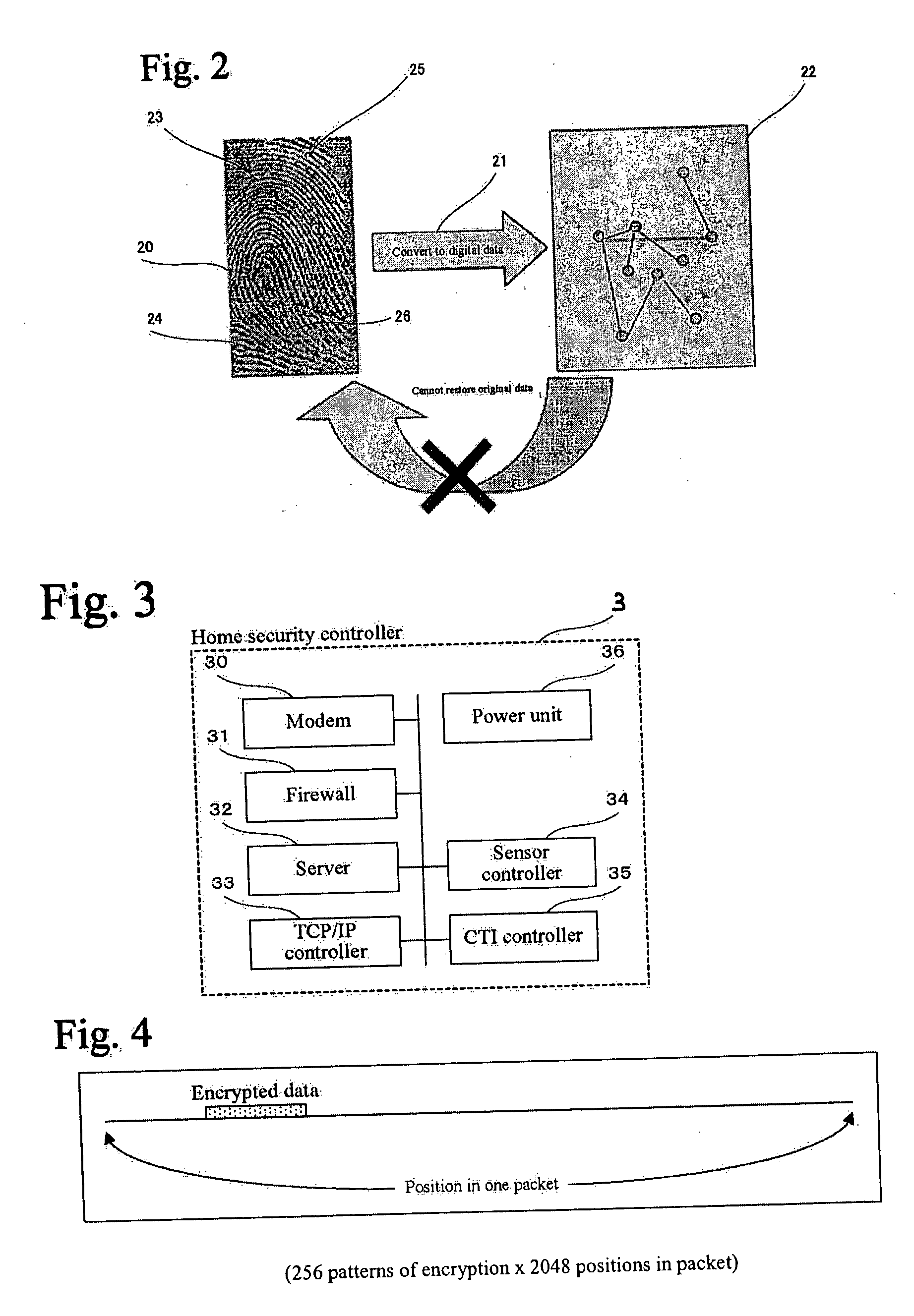
Home security system
InactiveUS20060022816A1Prevent intrusionEasy to operateElectric signal transmission systemsImage analysisRemote controlEngineering
The present invention provides a home security system that includes a home security controller for collecting monitor data from various crime prevention and disaster prevention sensors installed in a home via a home network and notifying the portable terminal when a state of emergency occurs. The home security controller also enables devices in the home to be operated through remote control signals via an external network. The home security system further includes a portable terminal capable of connecting to the external network and having fingerprint data inputting means mounted on the body of the portable terminal for inputting fingerprints used for authentication. The fingerprint data inputting means has an assigned ID number. The home security system further includes a security center server having fingerprint authenticating means for receiving fingerprint data from the portable terminal via the external network and authenticating the fingerprint data through comparisons with registered fingerprint data. The fingerprint authenticating means completes authentication by checking the assigned ID number of the fingerprint data inputting means and matching the received fingerprint data with fingerprint data registered in association with the ID number. The security center server allows a connection between the portable terminal and the home security controller and controls bi-directional communications between the two after the security center server has completed authentication, enabling the portable terminal to receive monitor data from and transmit remote control signals to the home security controller via the external network.
Owner:AMERICAN TECH GRP JAPAN
Second screen interactive platform
InactiveUS20130111514A1Broadcast systems characterised by additional dataAnalogue secracy/subscription systemsData storeSocial web
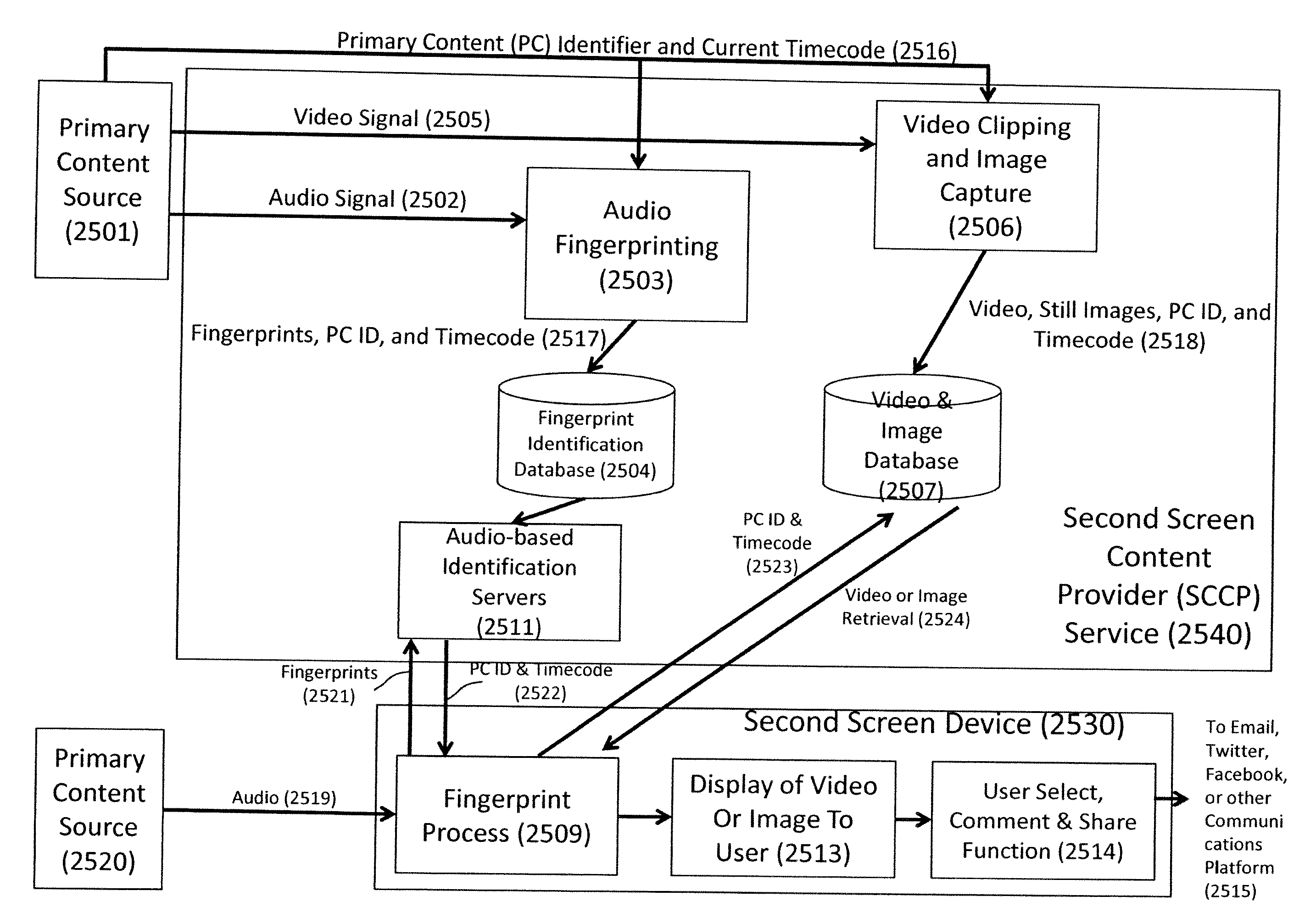
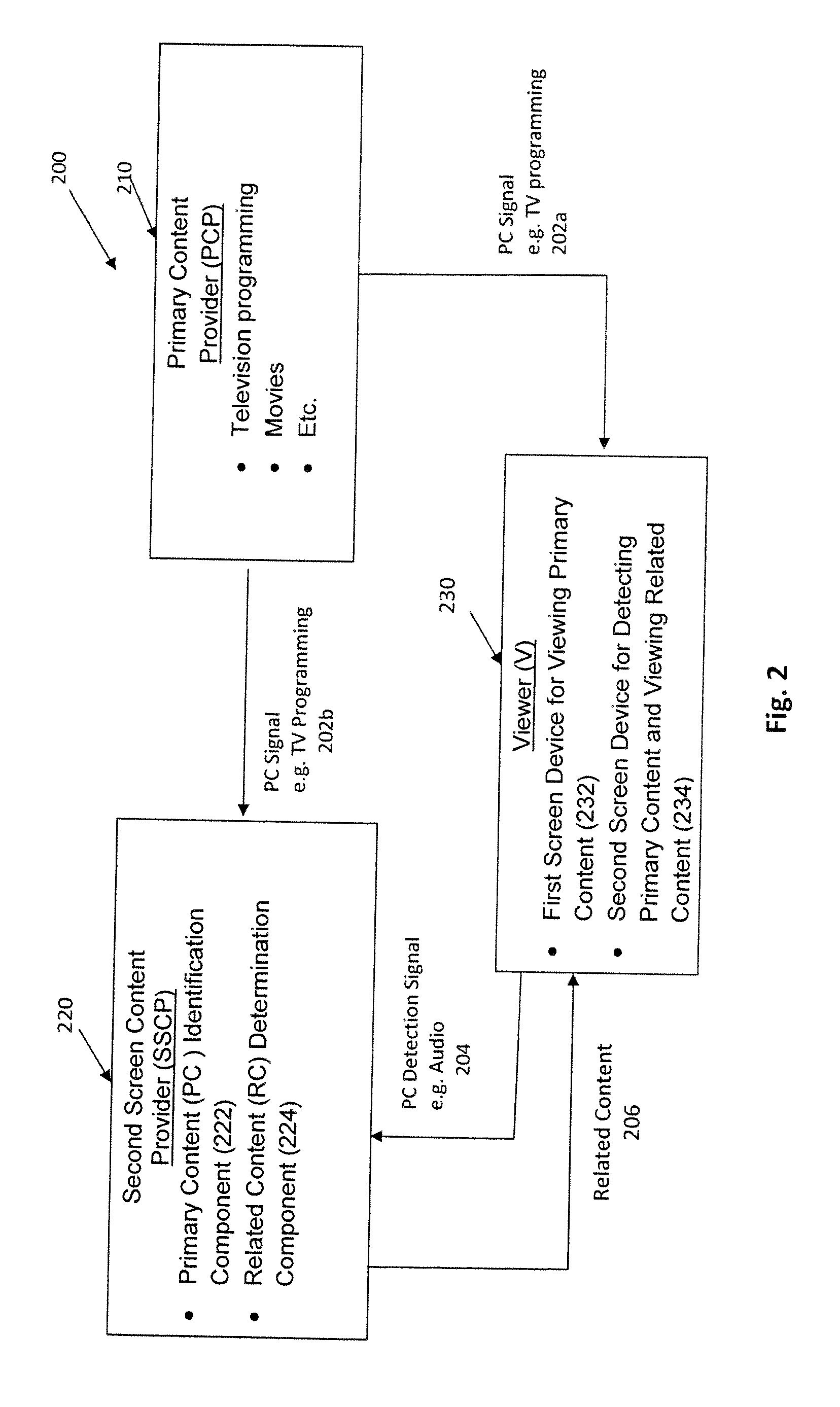
Interactive digital media platform, methods and apparatus for detecting and dynamically synchronizing to media content (e.g., television (TV) programs or movies) that a viewer is watching while providing related content on a second screen for enhancing the viewer experience. In one embodiment, the primary content is determined by detecting an audio signal of the primary content via the second screen device; the audio signal may then be processed to generate a fingerprint for comparison with a data store of primary content. The primary content can be classified by various categories (e.g., unique program, advertising, repeat airing, theme song . . . ) and the classification used to aid in the identification and / or in selection of the content to be presented on the interactive second screen device. The system allows a substantially real time comparison and recognition of what primary content a viewer is watching on a first screen device and presentation to the user of content that is substantially synchronous to the viewer's location in the primary content. The viewer can actively engaged with the content presented and can share the content with others via social networking and the like.
Owner:UMAMI
Embedded authentication systems in an electronic device
ActiveUS20090083850A1Digital data processing detailsUser identity/authority verificationAuthentication systemVisual perception
This invention is directed to an electronic device with an embedded authentication system for restricting access to device resources. The authentication system may include one or more sensors operative to detect biometric information of a user. The sensors may be positioned in the device such that the sensors may detect appropriate biometric information as the user operates the device, without requiring the user to perform a step for providing the biometric information (e.g., embedding a fingerprint sensor in an input mechanism instead of providing a fingerprint sensor in a separate part of the device housing). In some embodiments, the authentication system may be operative to detect a visual or temporal pattern of inputs to authenticate a user. In response to authenticating, a user may access restricted files, applications (e.g., applications purchased by the user), or settings (e.g., application settings such as contacts or saved game profile).
Owner:APPLE INC
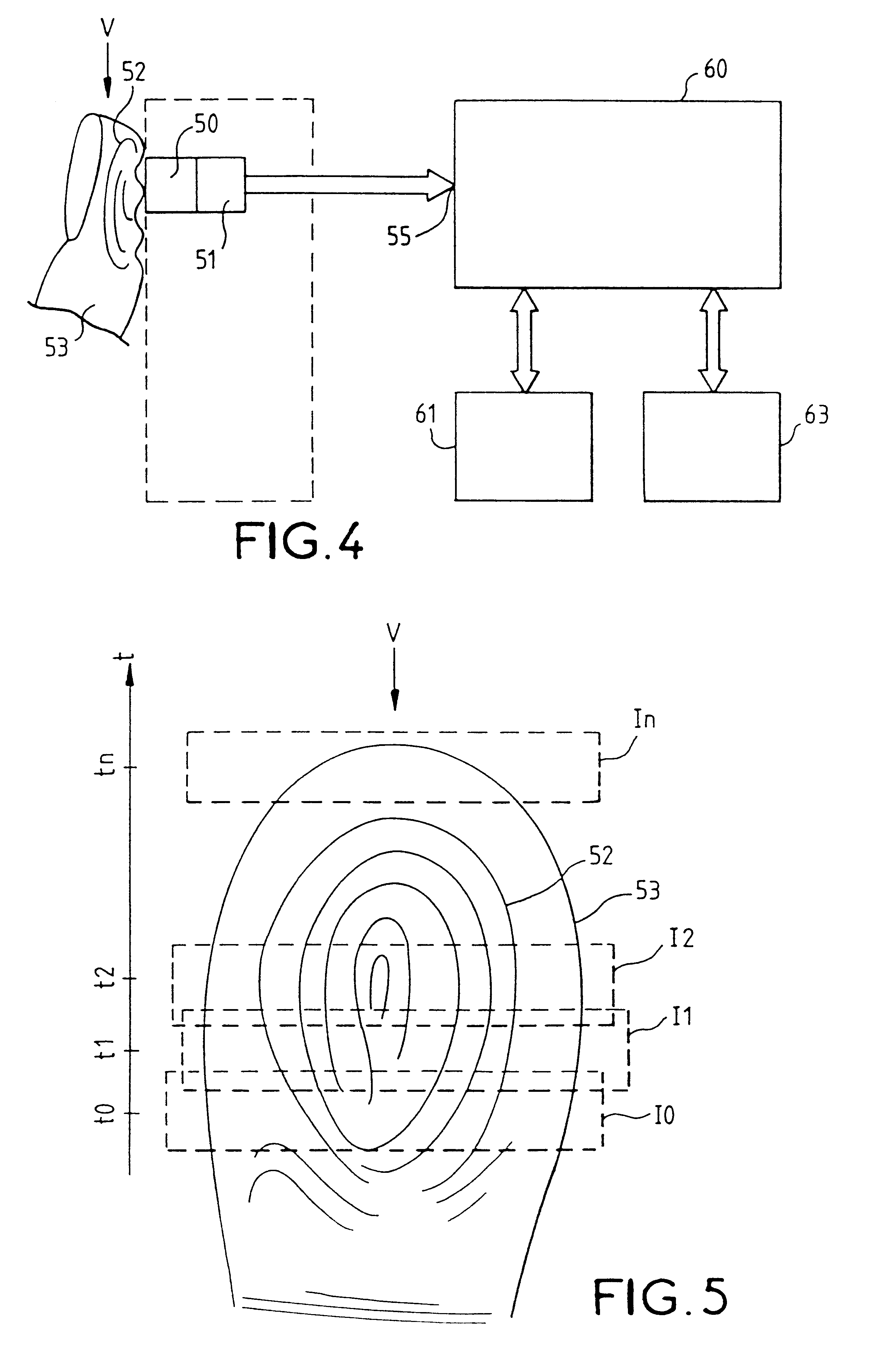
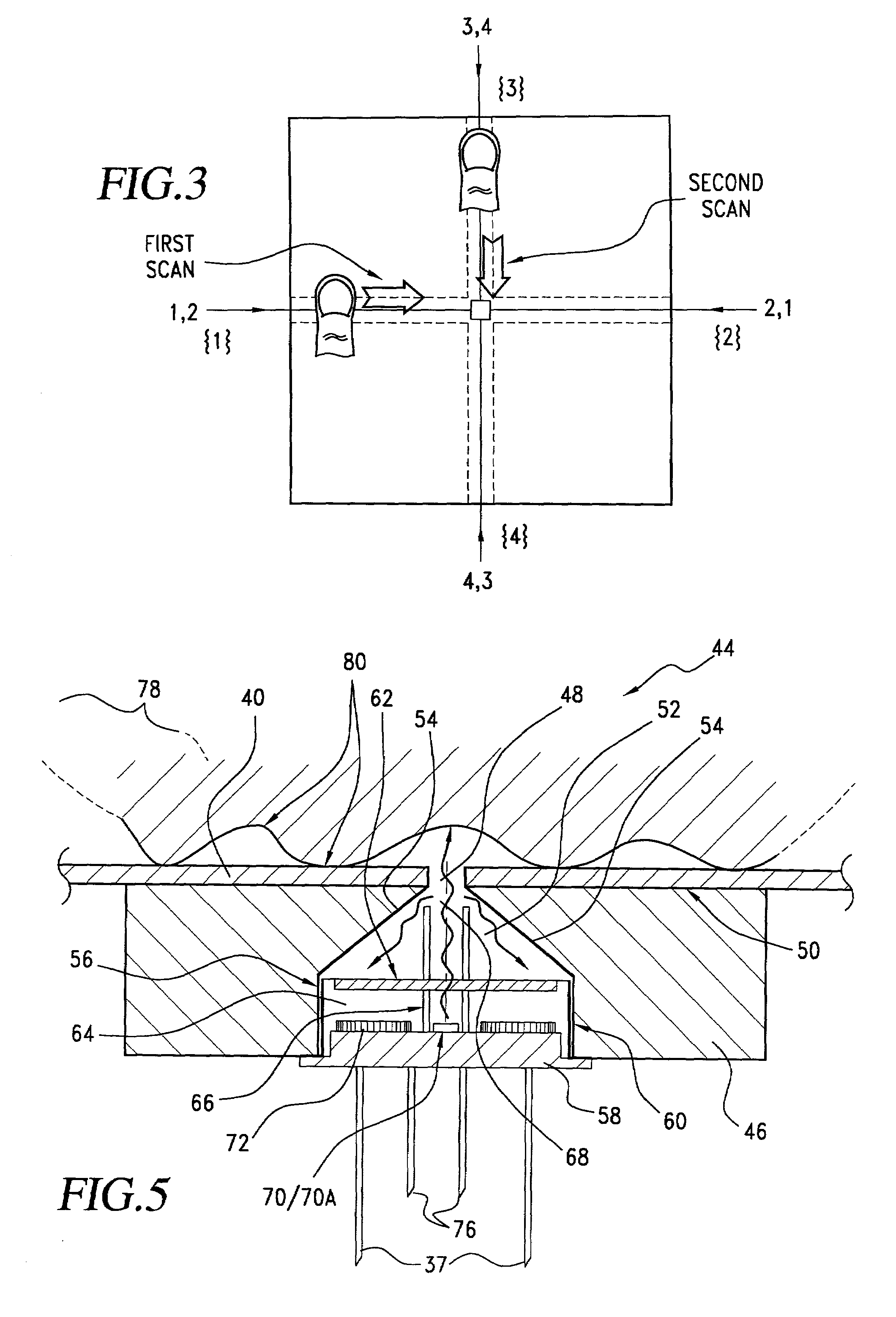
Method for authenticating an individual by use of fingerprint data
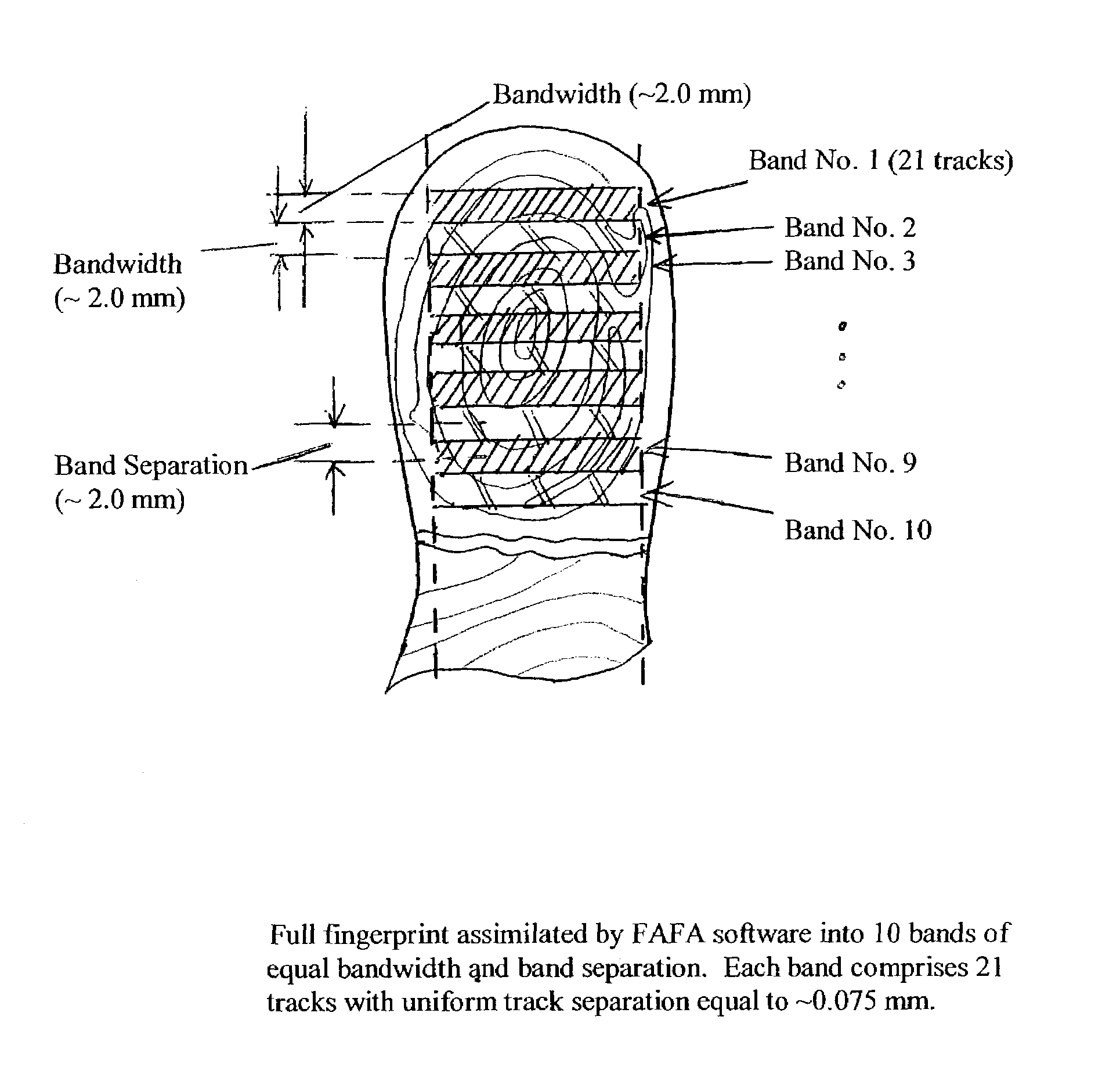
InactiveUS7136514B1Simple methodElectric signal transmission systemsImage analysisFast Fourier transformBiometrics
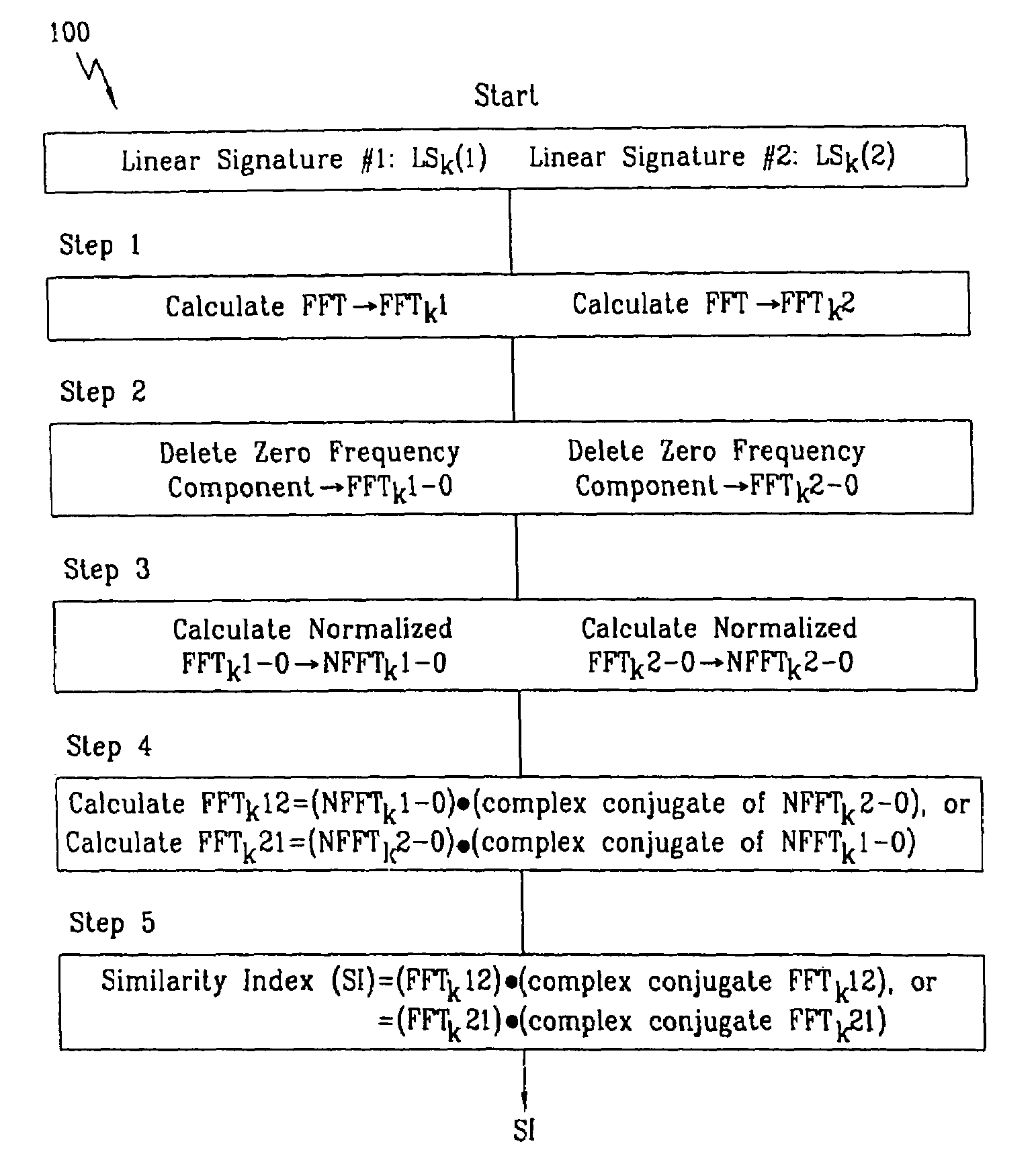
A method for authenticating an individual by use of fingerprint data that involves two different broad steps. The first step is to obtain a biometrics fingerprint signature template (“BFST”) for an individual in an enrollment process by selecting a plurality of bands for the BFST and obtaining a plurality of tracks corresponding to each of the plurality of bands by use of an enrollment frame of a selected finger of the individual, wherein the plurality of bands are spatially referenced to the enrollment frame and can be spatially referenced to a reference barrier. The second step is to authenticate (or not) a candidate finger against one or more BFST in an authentication process in which a swipe direction and an access code for the individual are selected, a plurality of candidate tracks are obtained from the candidate finger through use of the reference barrier in an authentication unit so that each of the plurality of candidate tracks is spatially referenced so as to be within a corresponding one of the plurality of bands, calculating a similarity index for each of the plurality of candidate tracks and each of the plurality of tracks for the band to which the candidate track corresponds by use of a Fast Fourier-transform fingerprint algorithm, and multiplying each maximum similarity index obtained for each of the plurality of candidate tracks to obtain a match index which indicates a match if it exceeds a preselected threshold.
Owner:WONG JACOB Y
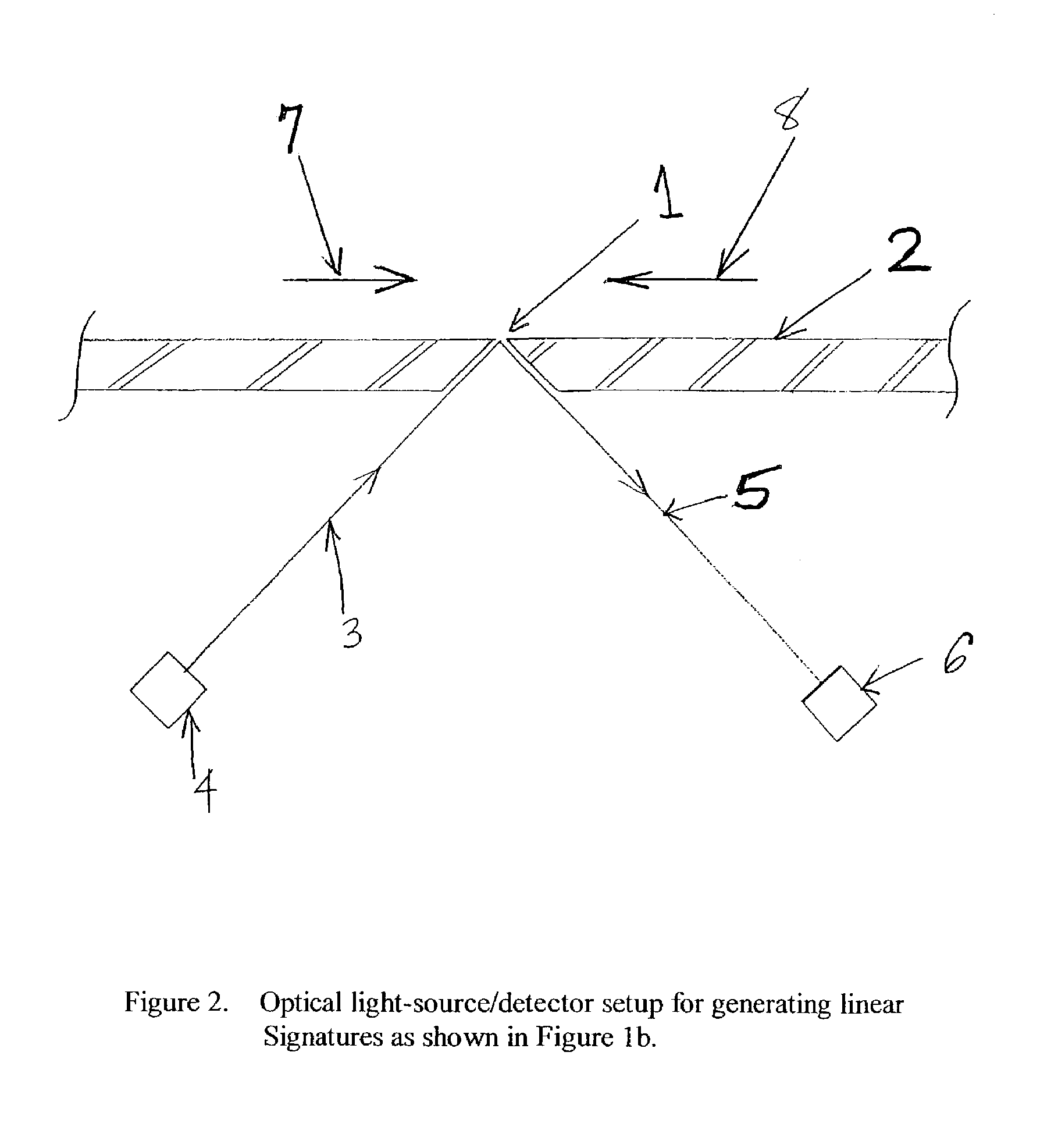
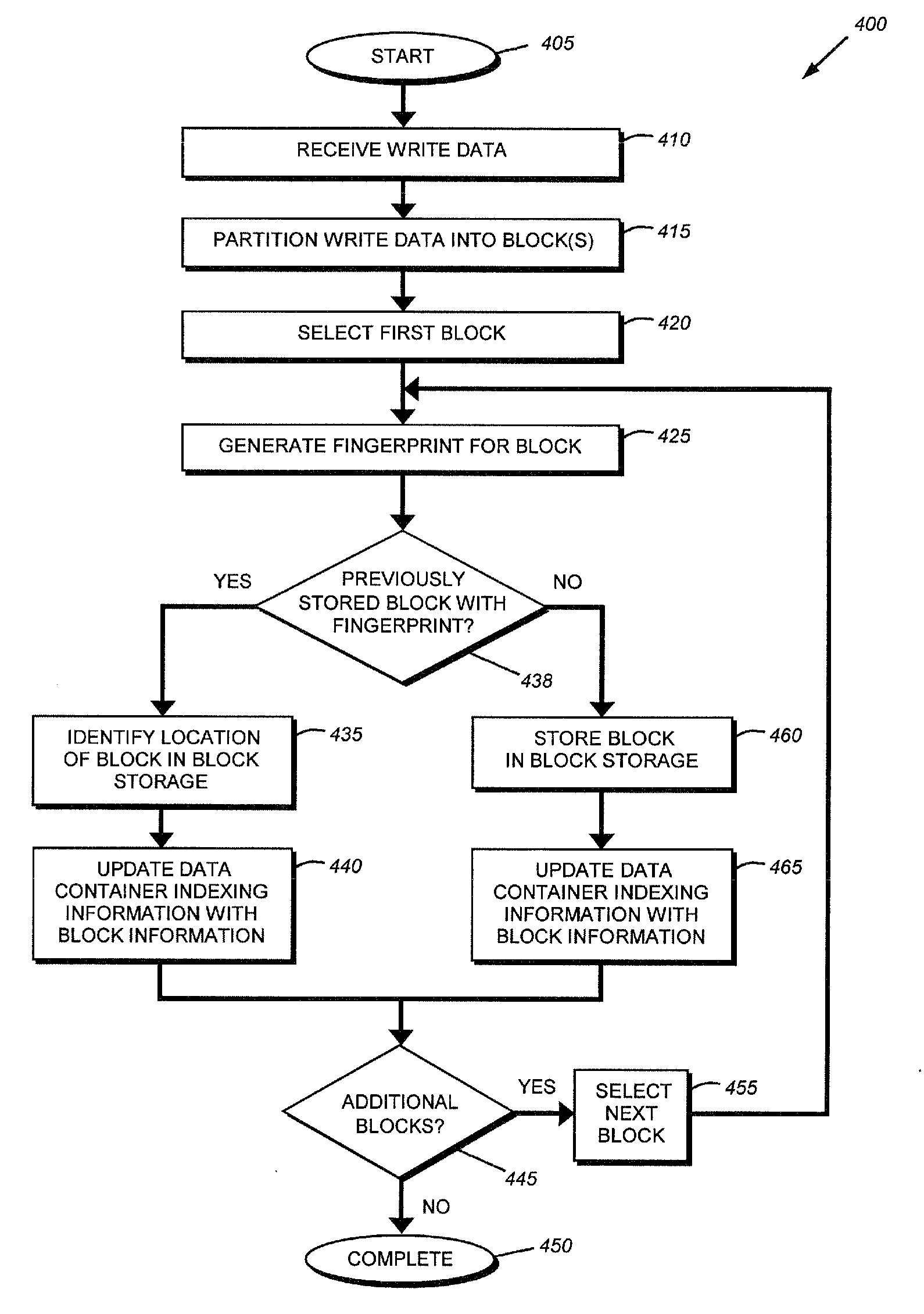
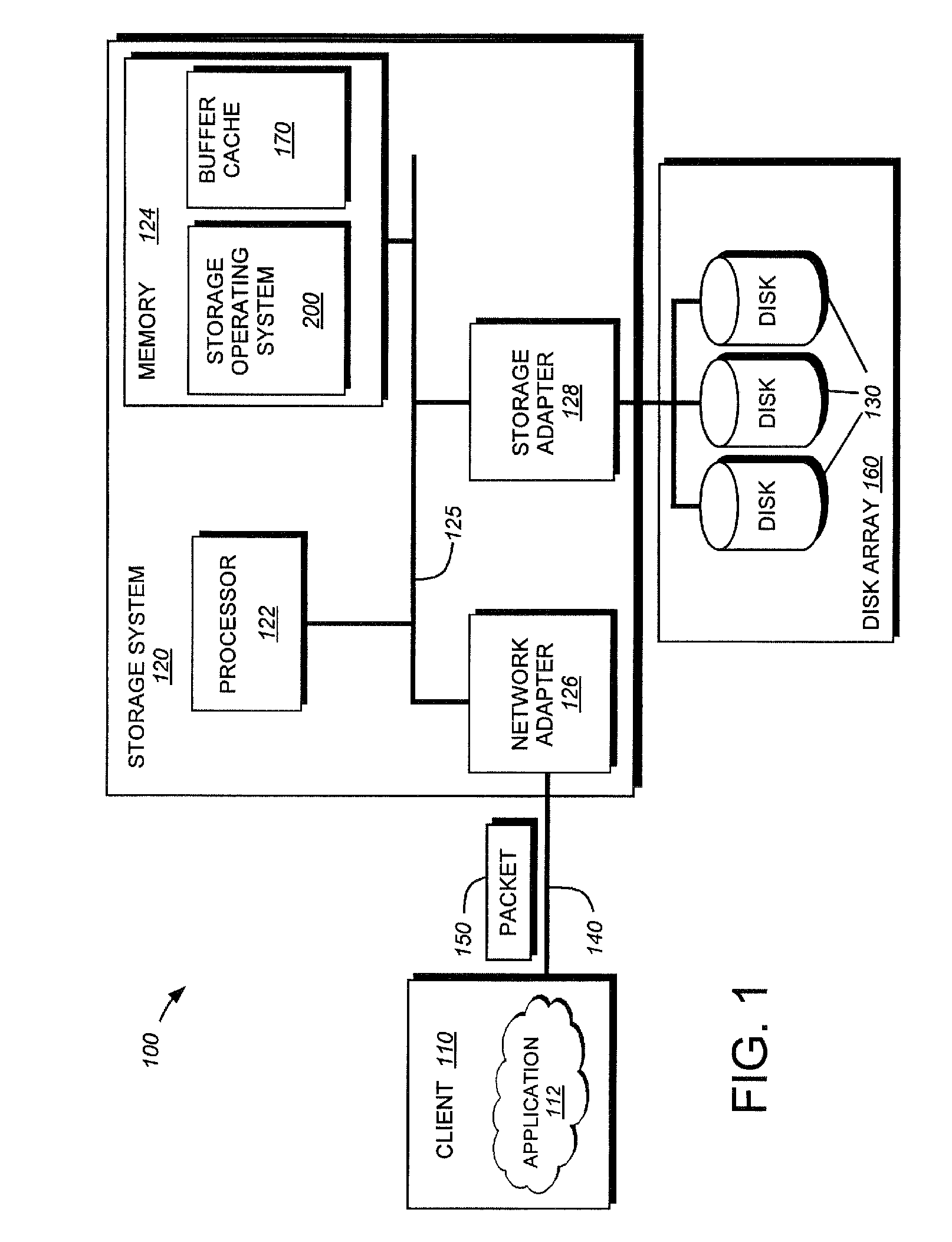
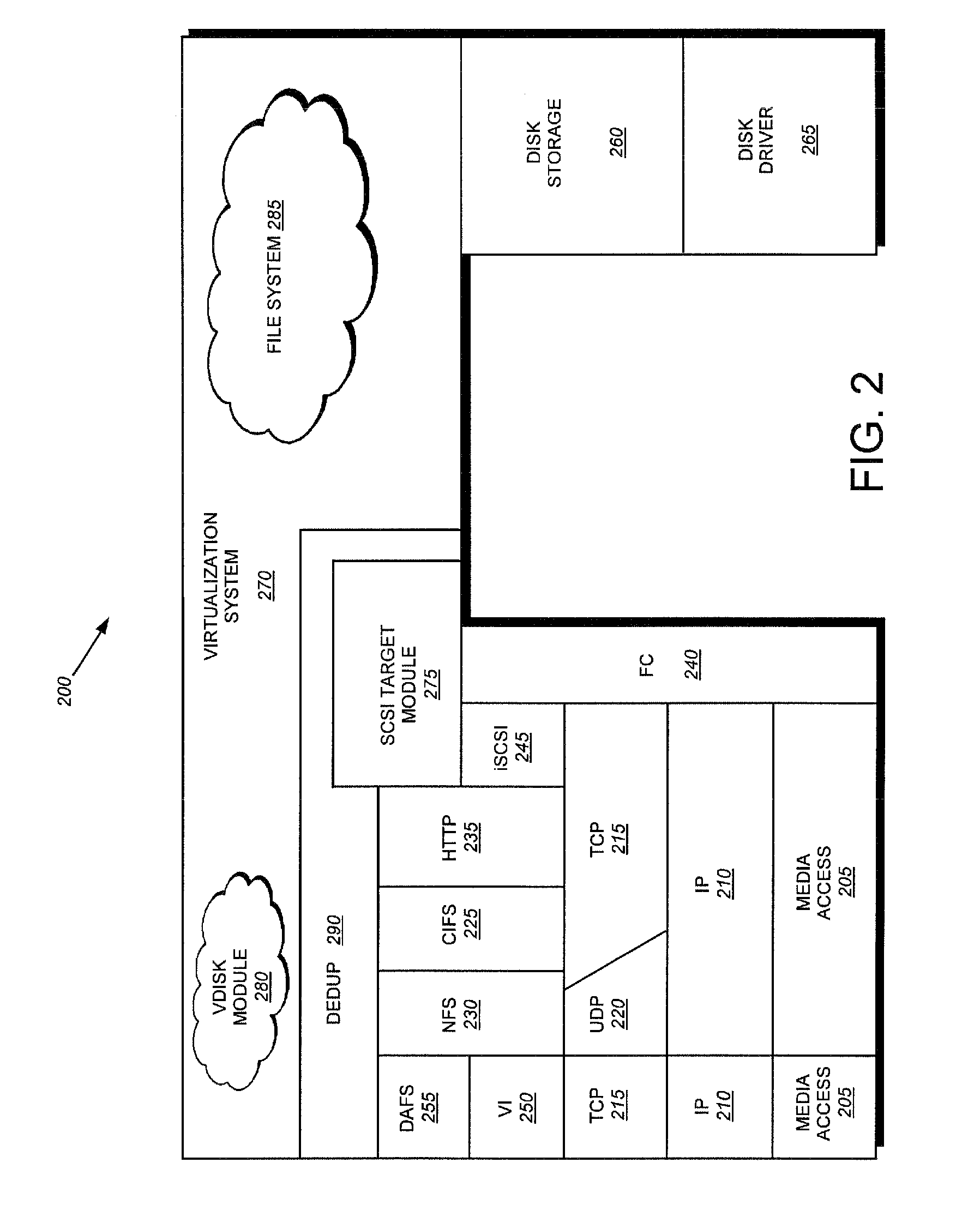
System and method for on-the-fly elimination of redundant data
ActiveUS20080294696A1Digital data information retrievalDigital data processing detailsOperational systemFile system
Owner:NETWORK APPLIANCE INC
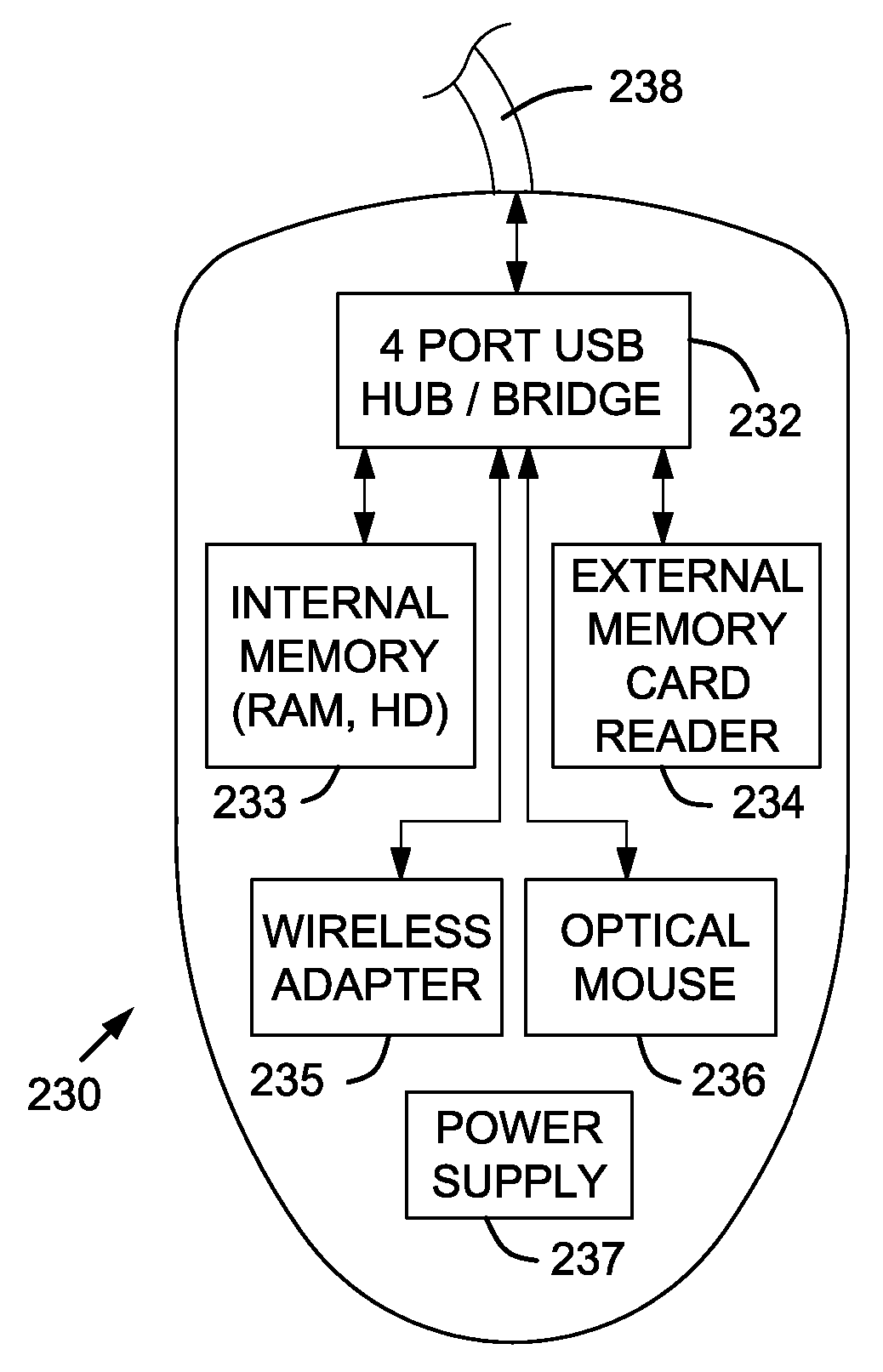
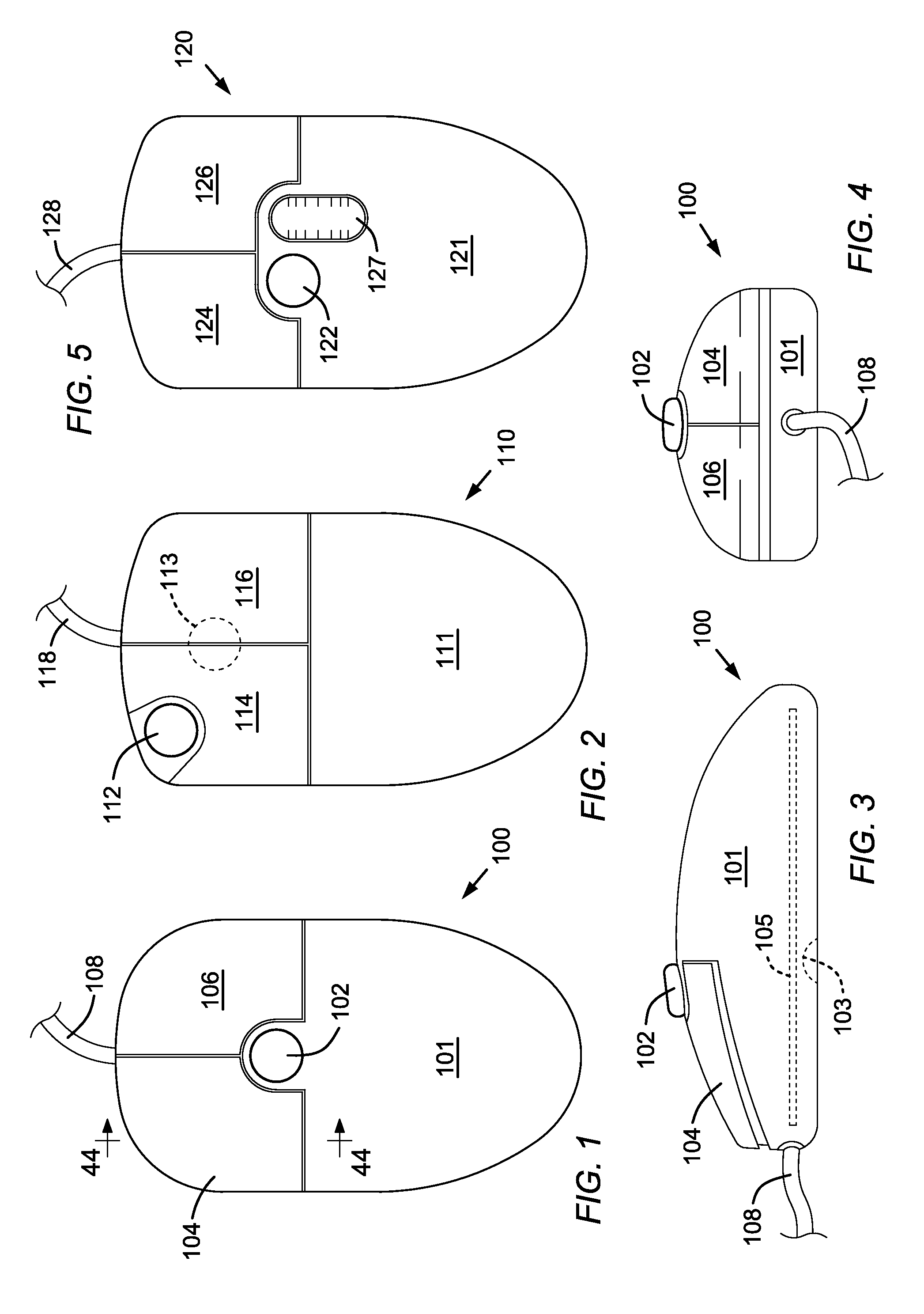
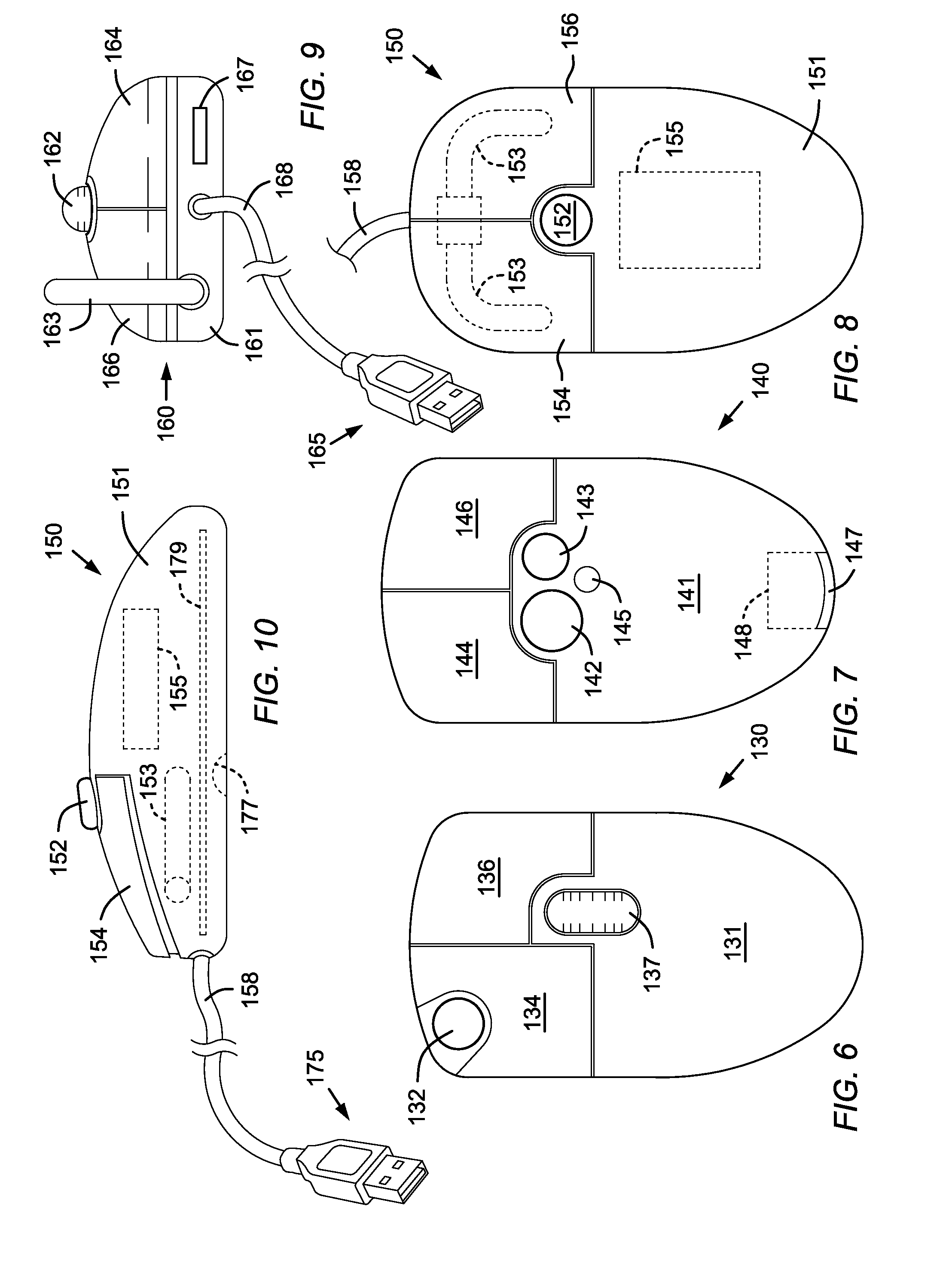
Computer Apparatus with added functionality
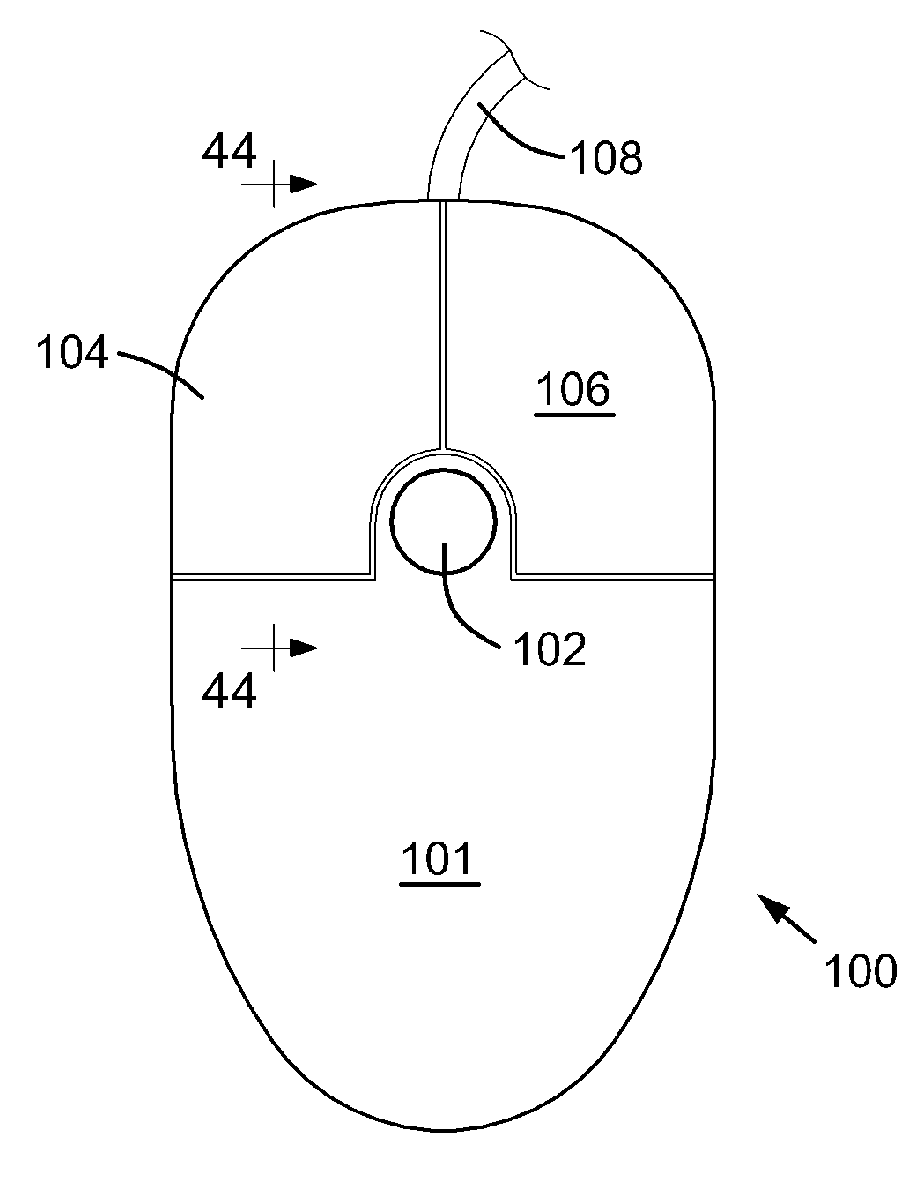
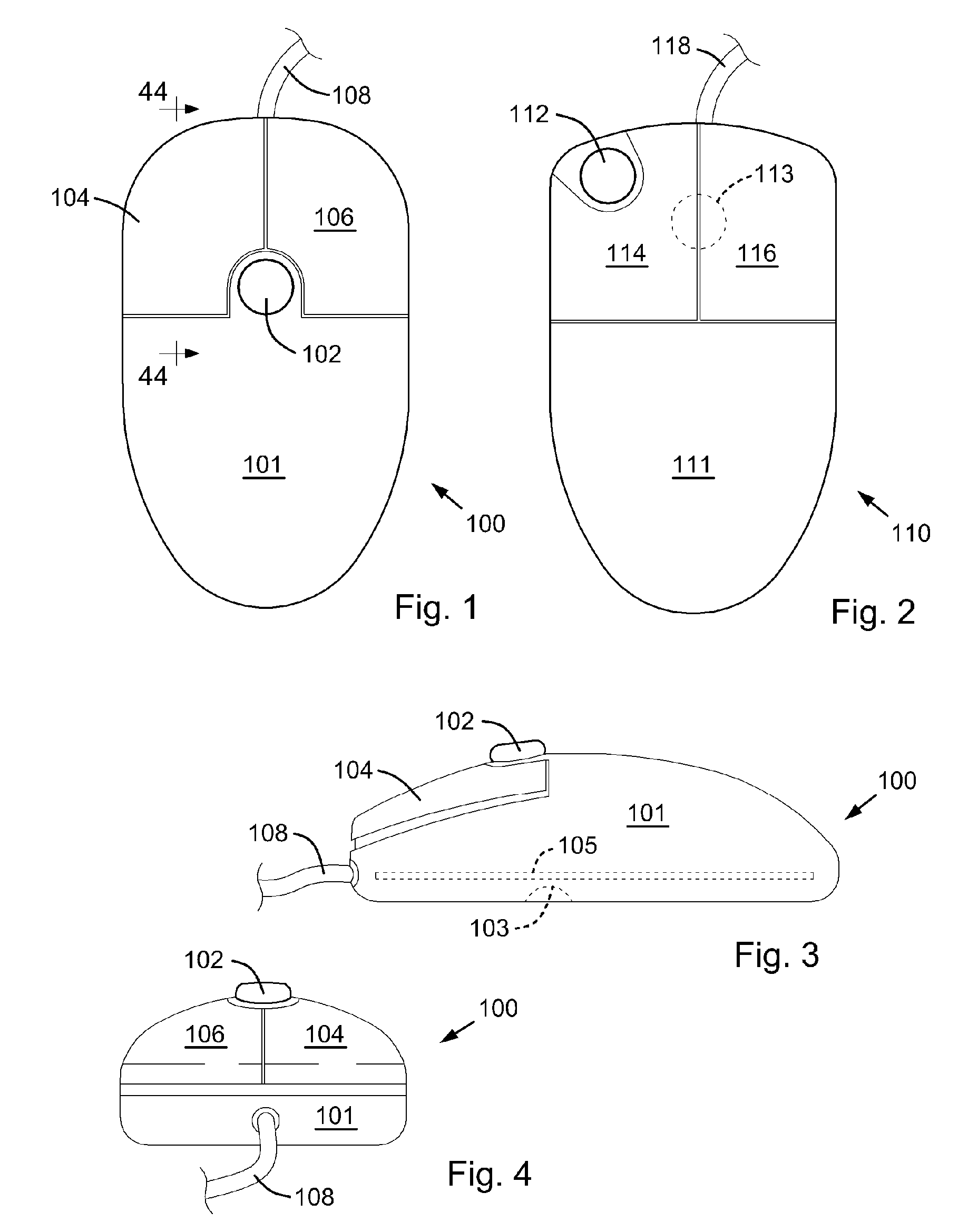
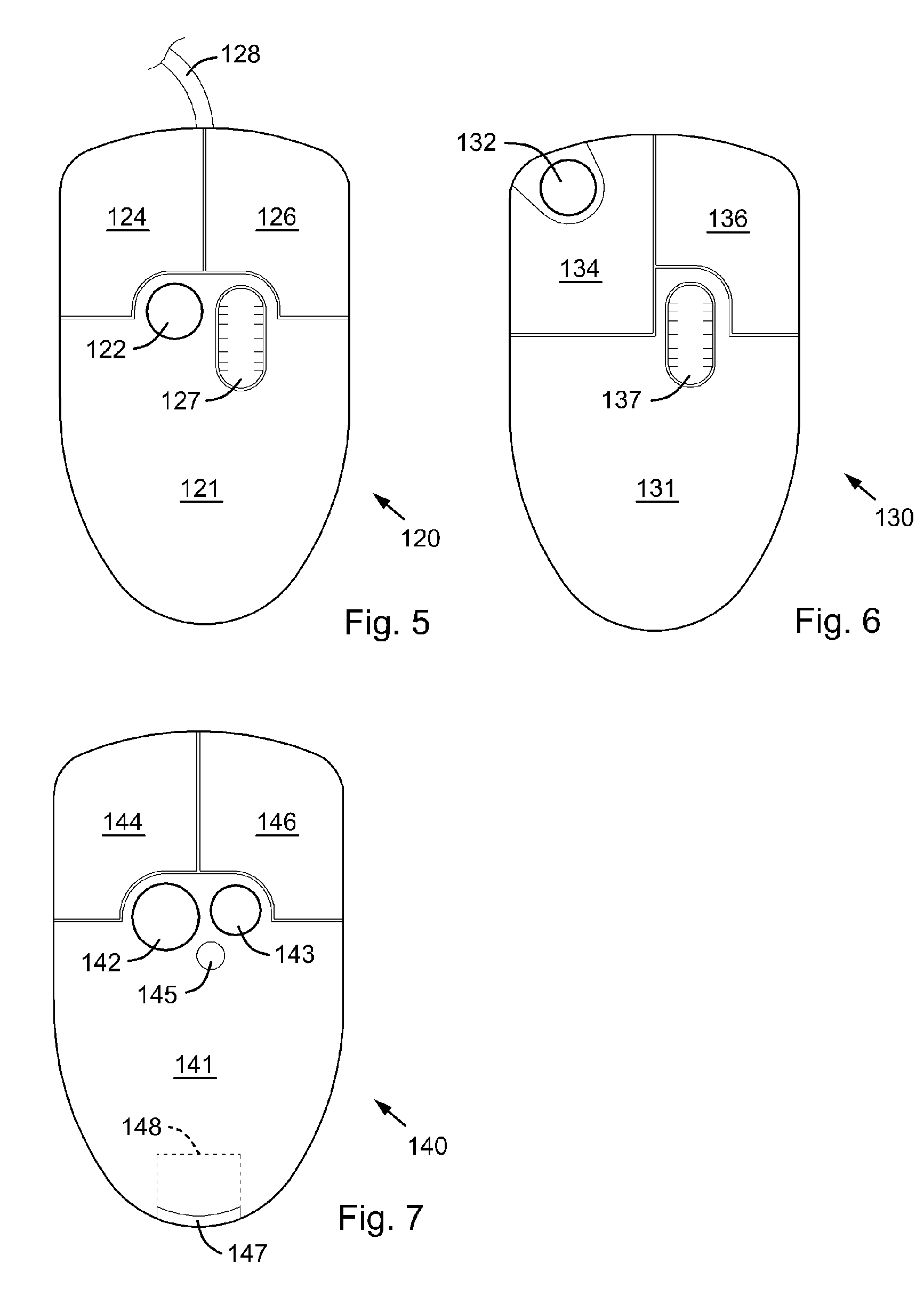
InactiveUS20070132733A1Function increaseLow costCathode-ray tube indicatorsInput/output processes for data processingEmbedded systemFingerprint
A computer apparatus such as a mouse apparatus or a keyboard apparatus with additional functionality or features disposed within the apparatus enclosure. Each additional functionality enhances the overall functionality of the computer apparatus. In the preferred embodiments, the additional devices include a remote control, a multiple host mouse apparatus, a multiple host keyboard apparatus, various trackpoint-style devices and other control devices, mouse apparatus with various integrated displays and various means of extending or retracting said integrated displays, fingerprint readers, USB receptacles and hub devices, various mouse apparatus enclosure covers with various devices disposed within said enclosure cover, a fuel cell, a dual sensor mouse apparatus, miniature mouse apparatus and their associated wireless transmitters, keyboard apparatus with IR and IrDA remote control ports, solar panels as a power source, and the like.
Owner:RAM PRANIL
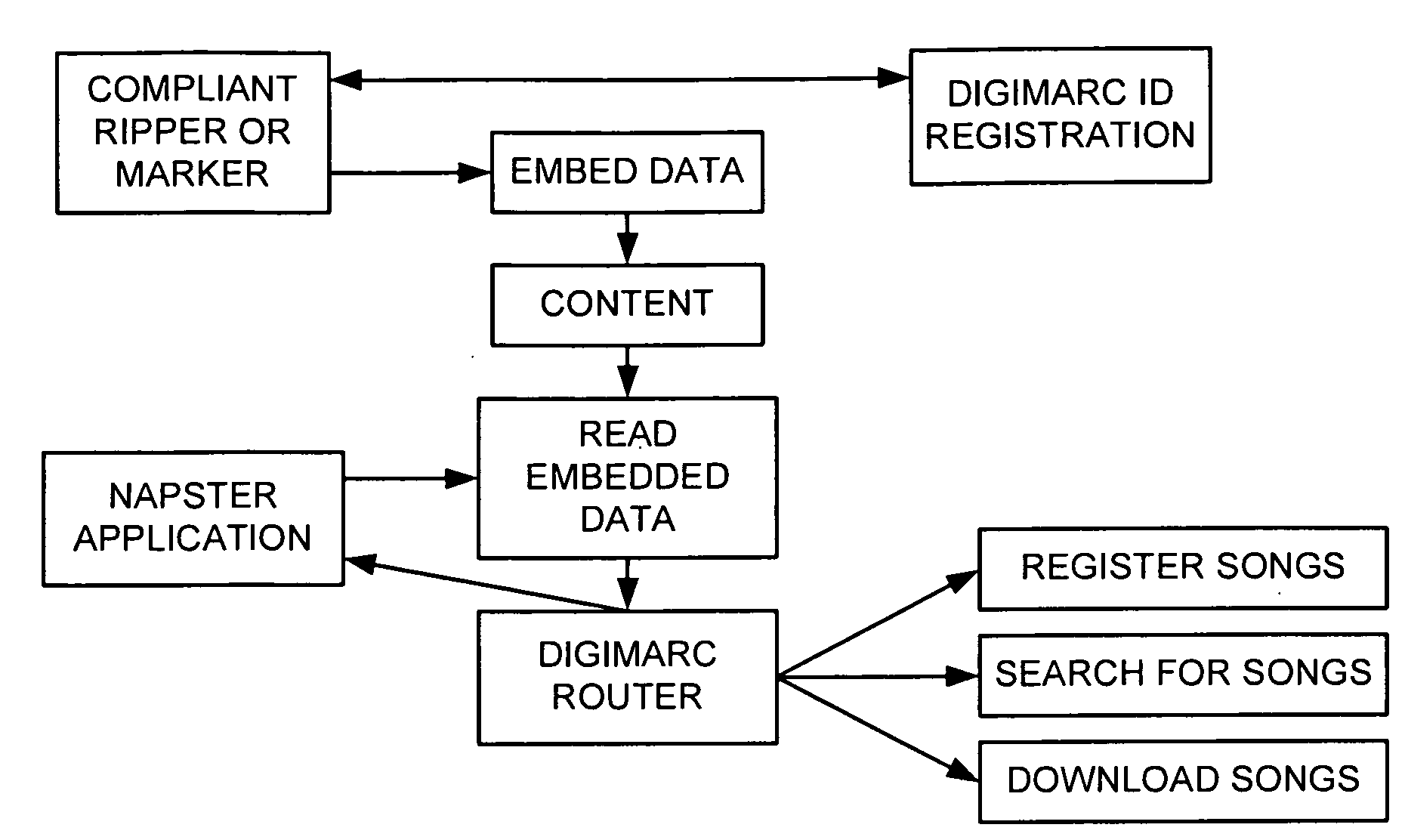
Media Methods and Systems
InactiveUS20090158318A1Good effectImprove service reliabilityTelevision system detailsDigital data authenticationBroadcastingFingerprint
Several novel watermarking and fingerprinting applications—and related improvements—are disclosed. Some relate to advertising. These include techniques for replacing broadcast advertising with other advertising; inserting advertising based on a viewer's ad-viewing history; triggering insertion of advertising based on fingerprint data derived from compressed video content; and discontinuing advertising when a threshold amount of advertising has apparently been viewed. A great number of other features and technologies are also detailed.
Owner:DIGIMARC CORP
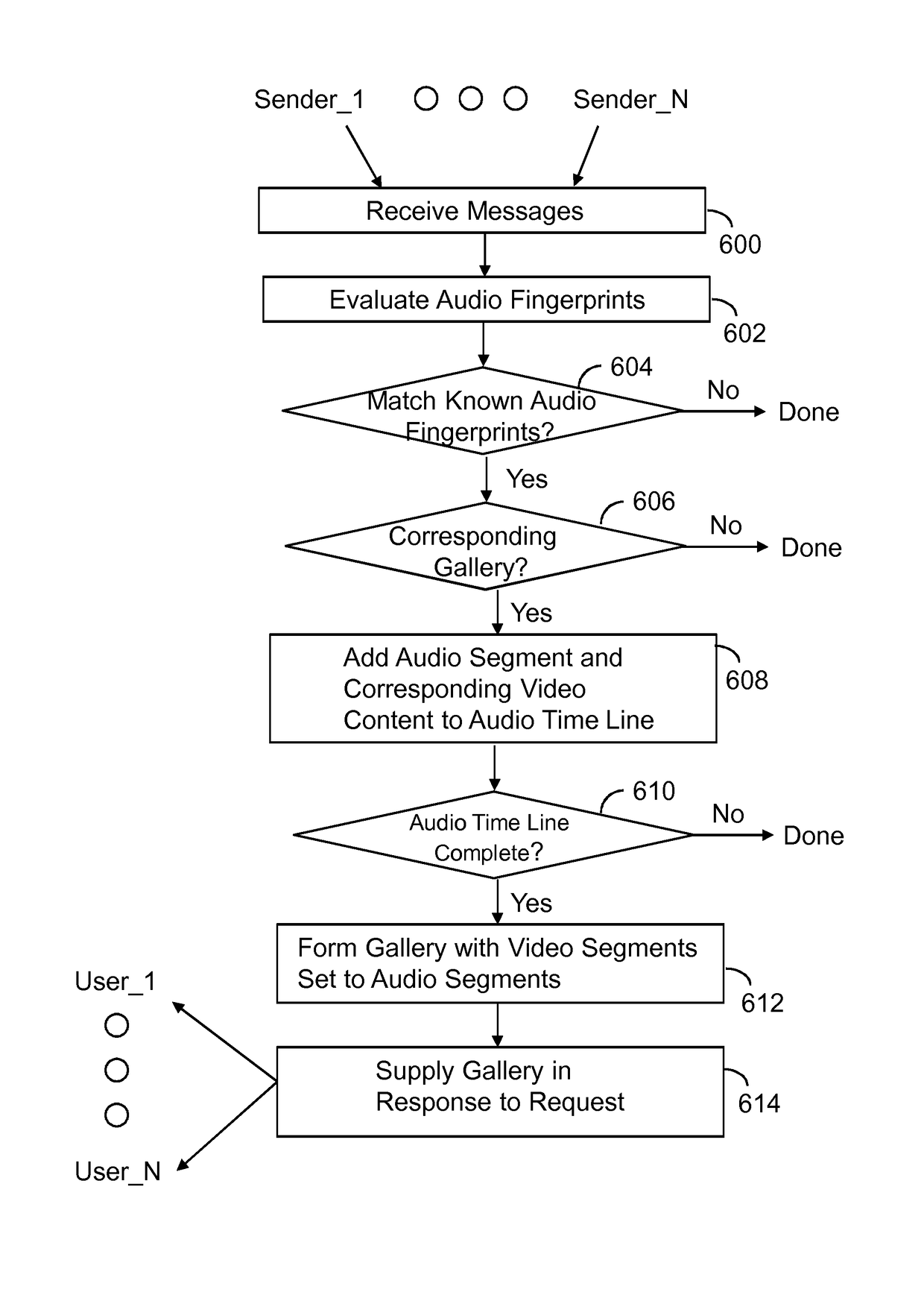
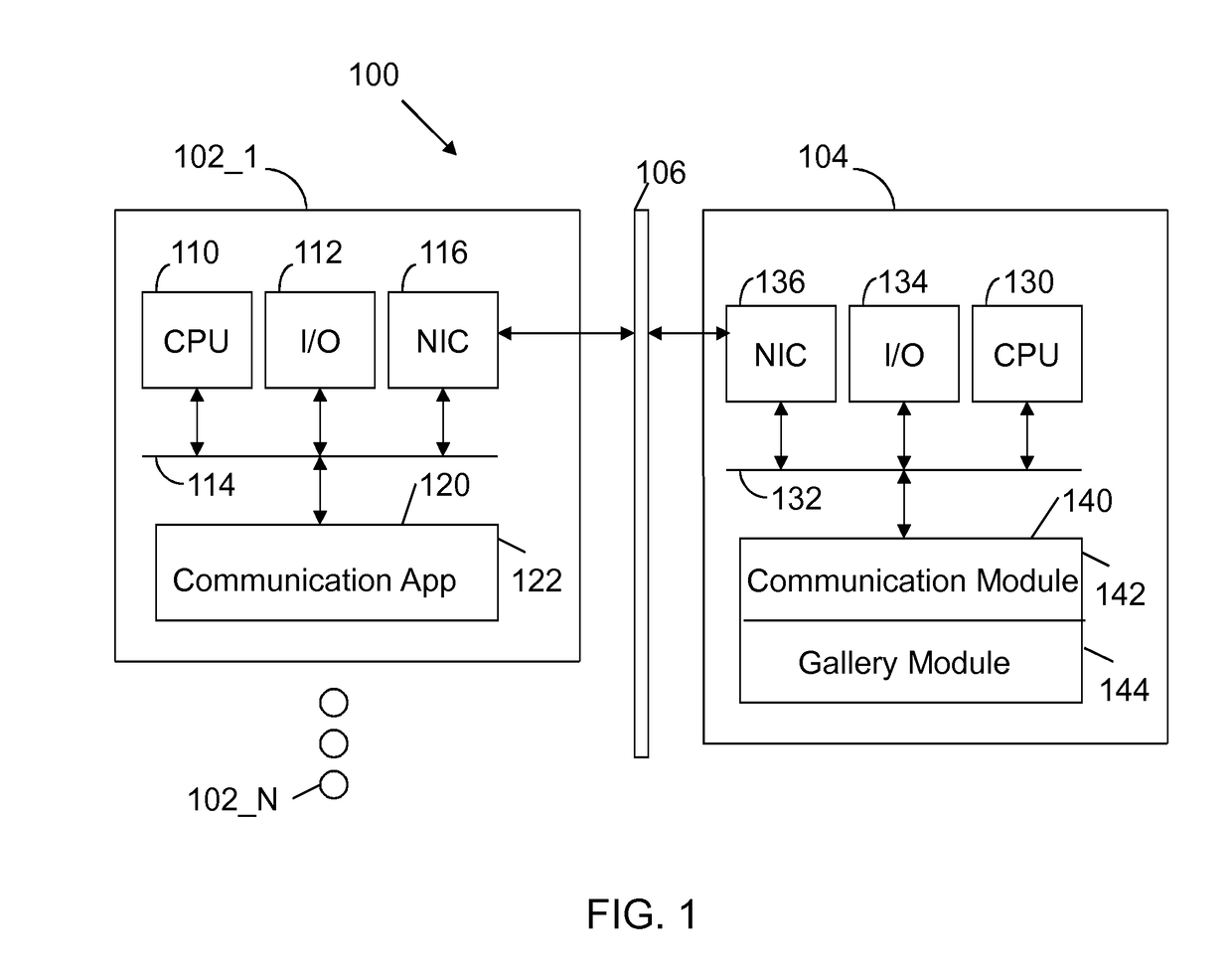
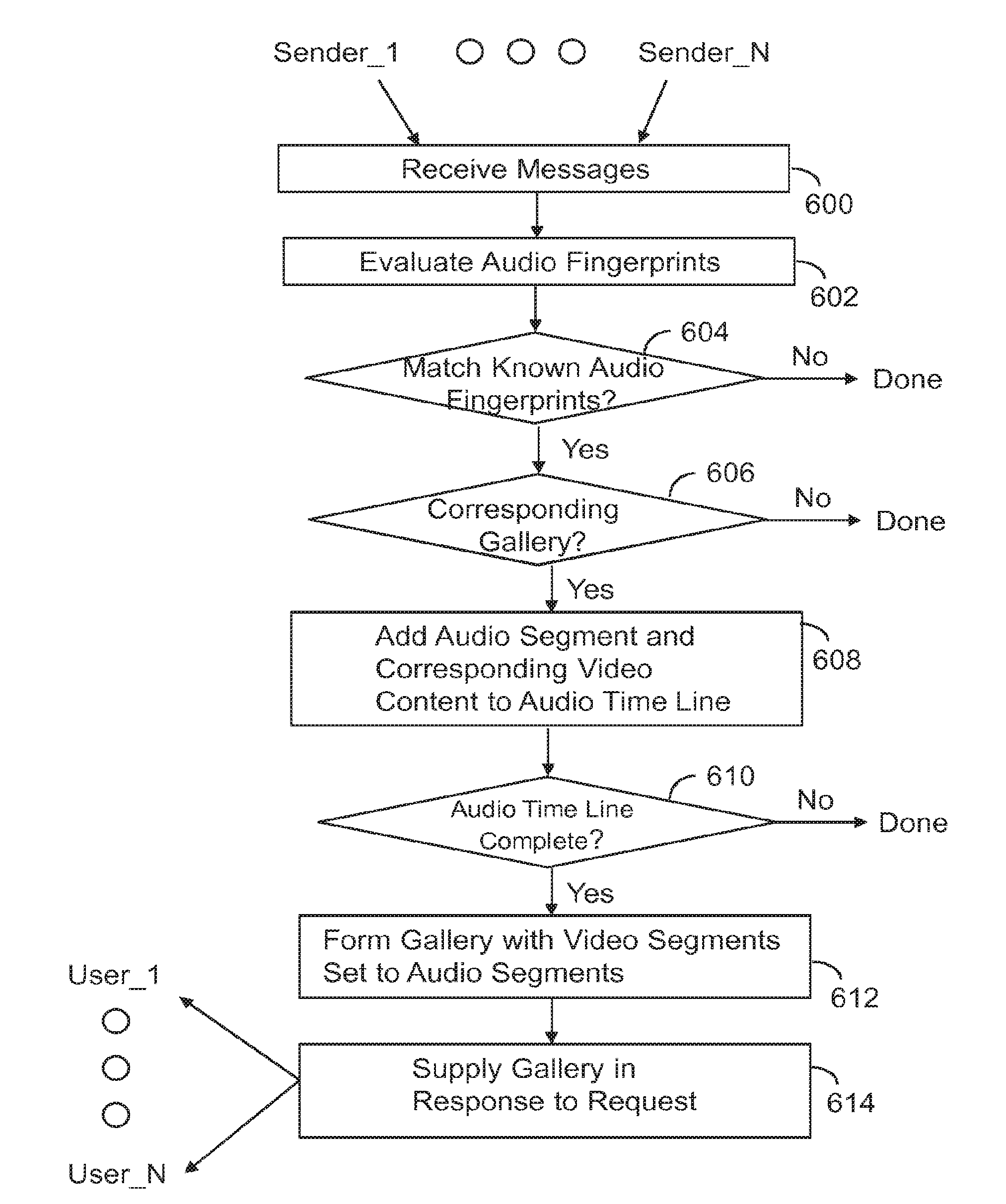
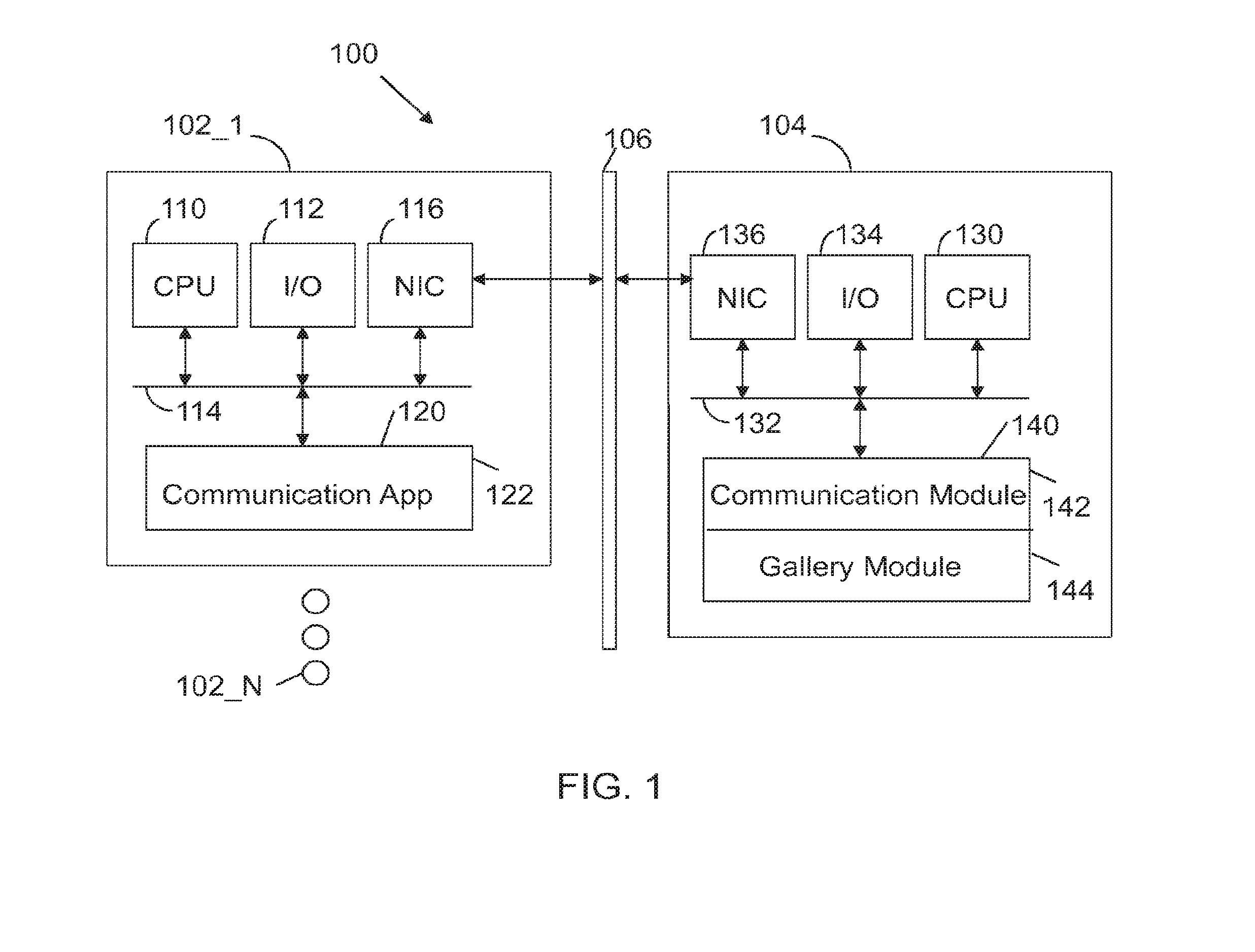
Gallery of videos set to an audio time line
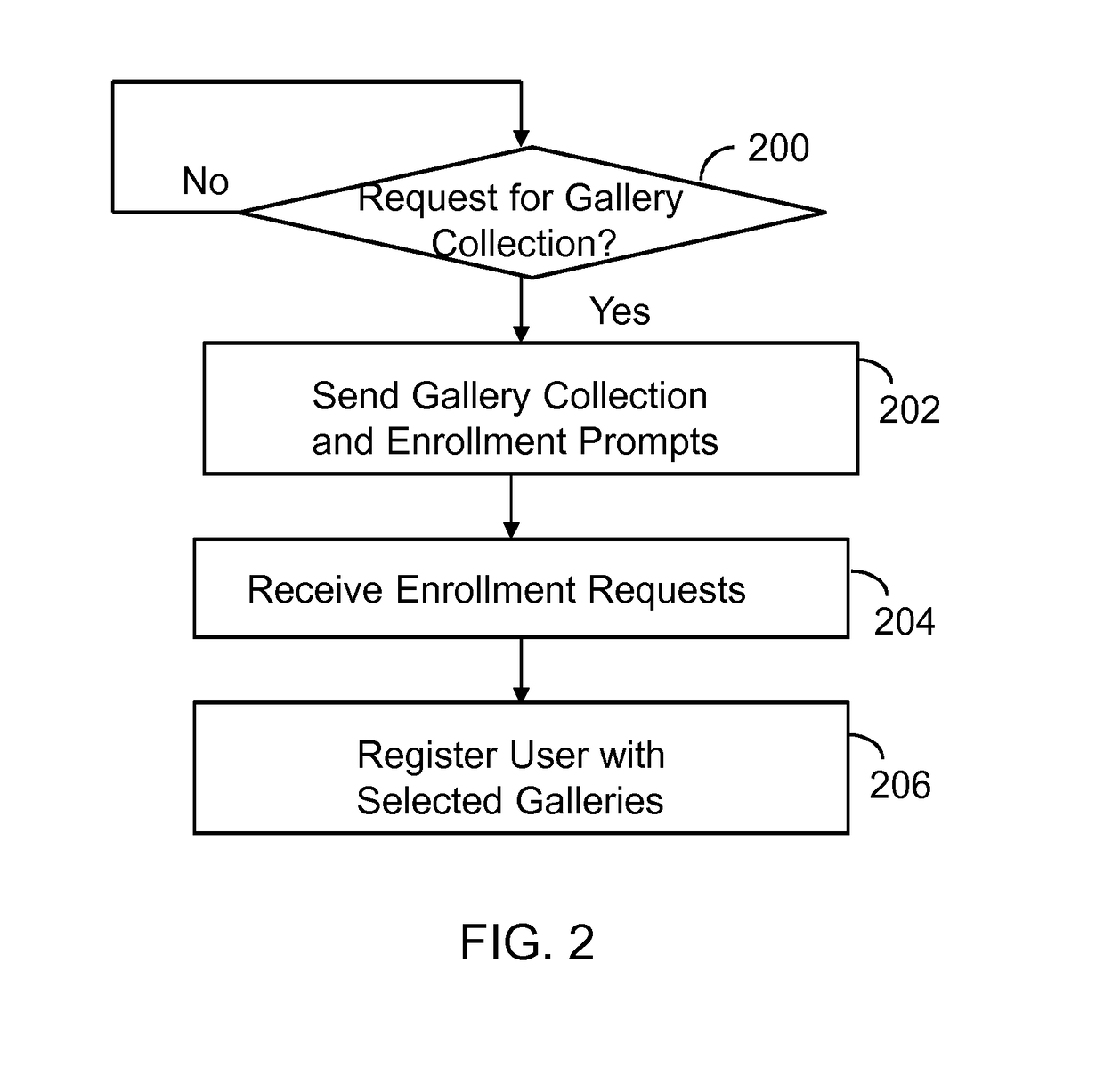
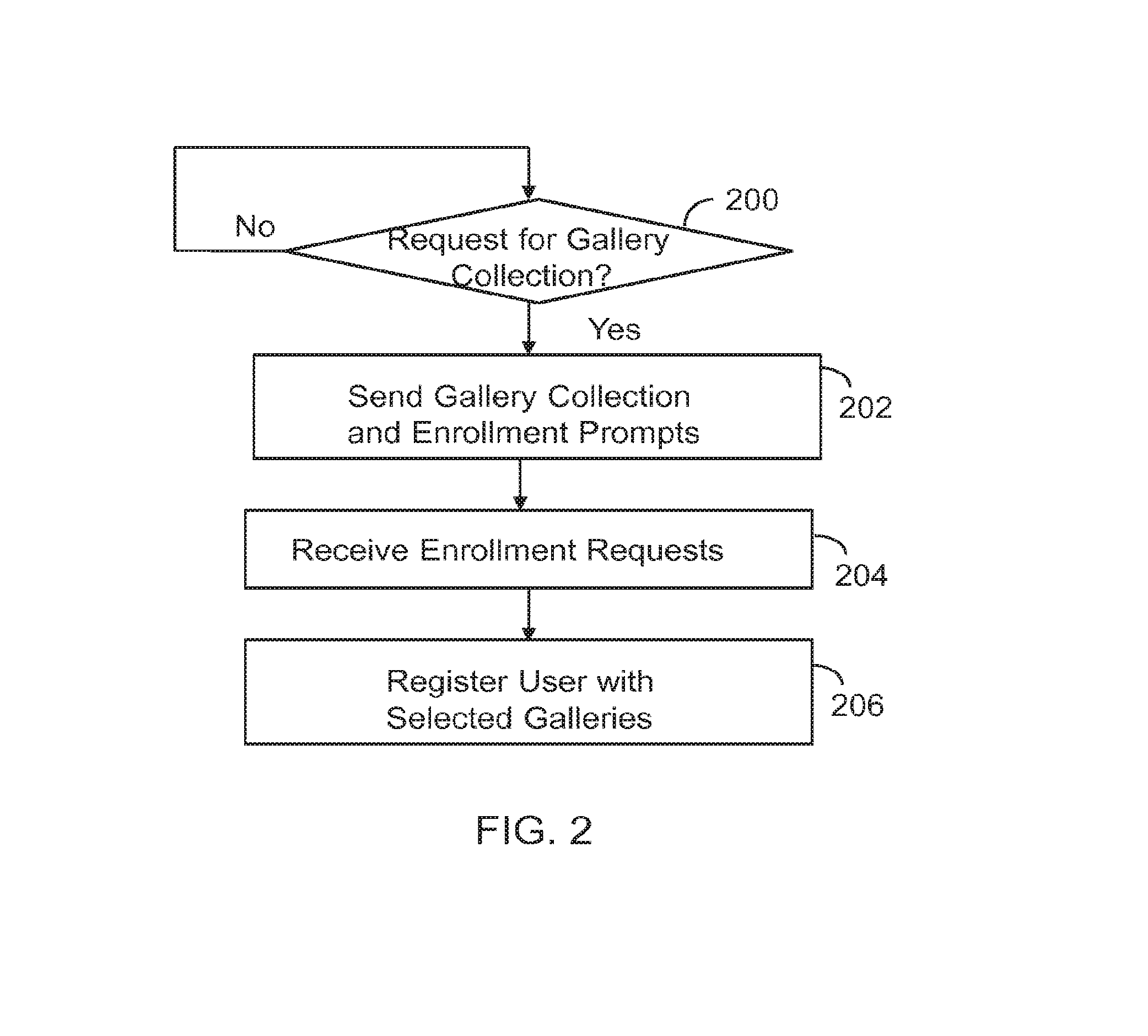
ActiveUS9854219B2Electronic editing digitised analogue information signalsRecord information storageVideo sequenceTime line
A machine includes a processor and a memory connected to the processor. The memory stores instructions executed by the processor to receive a message with audio content and video content. Audio fingerprints within the audio content are evaluated. The audio fingerprints are matched to known audio fingerprints to establish matched audio fingerprints. A determination is made whether the matched audio fingerprints correspond to a designated gallery constructed to receive a sequence of videos set to an audio time line. The matched audio fingerprints and corresponding video content are added to the audio time line. The operations are repeated until the audio time line is populated with corresponding video content to form a completed gallery with video segments set to audio segments that constitute a complete audio time line. The completed gallery is supplied in response to a request.
Owner:SNAP INC
Smart card with random temporary account number generation
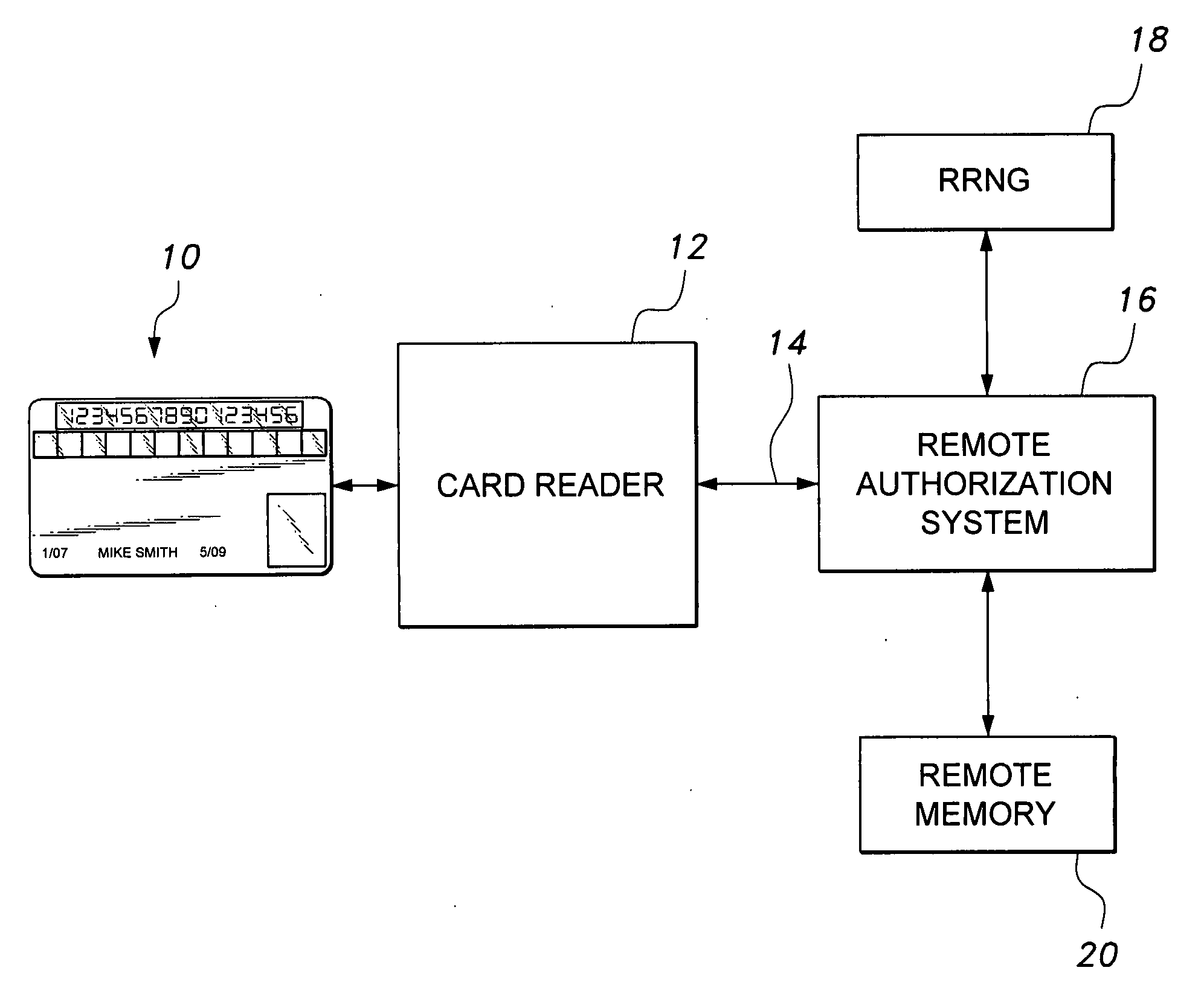
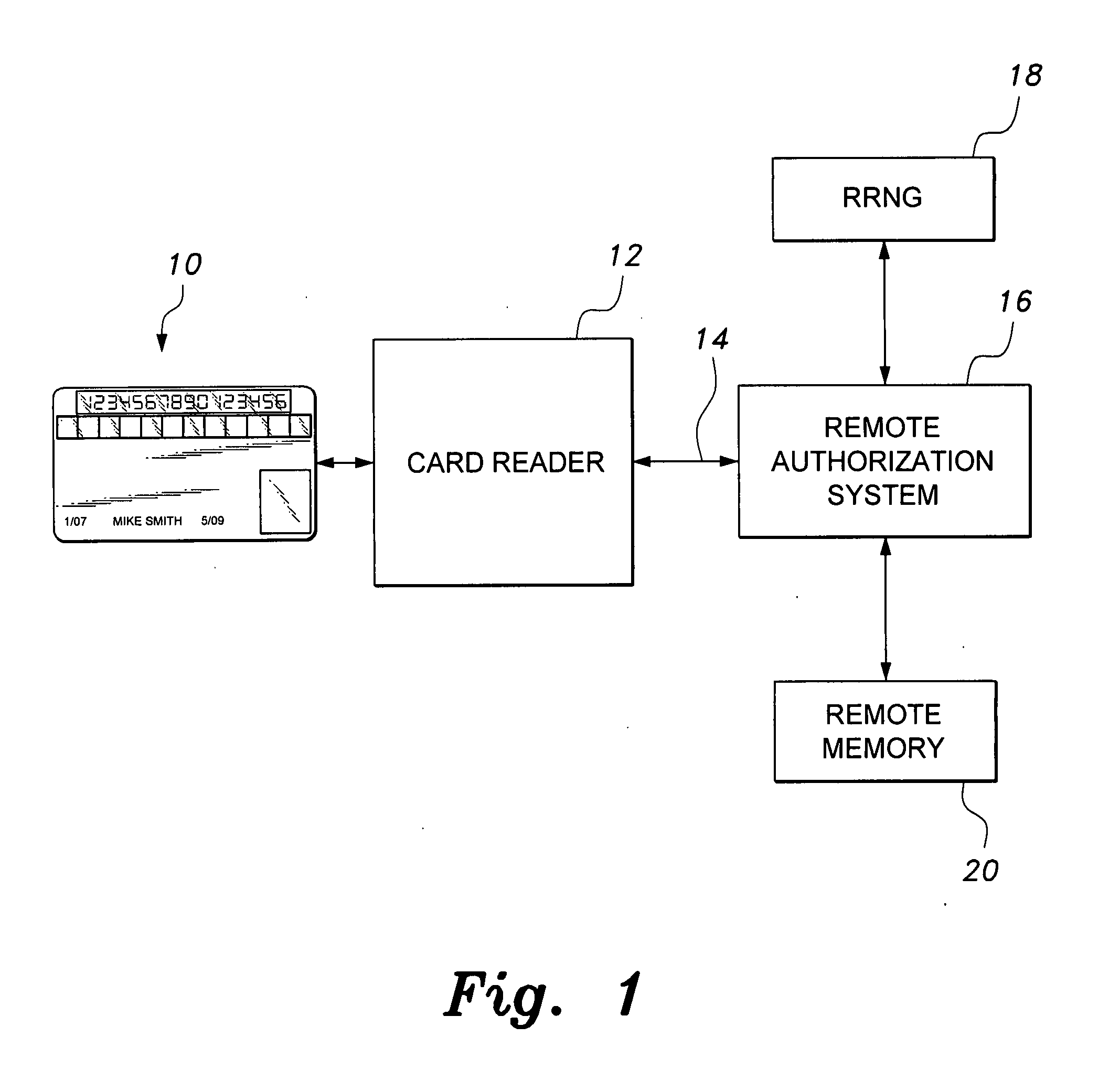
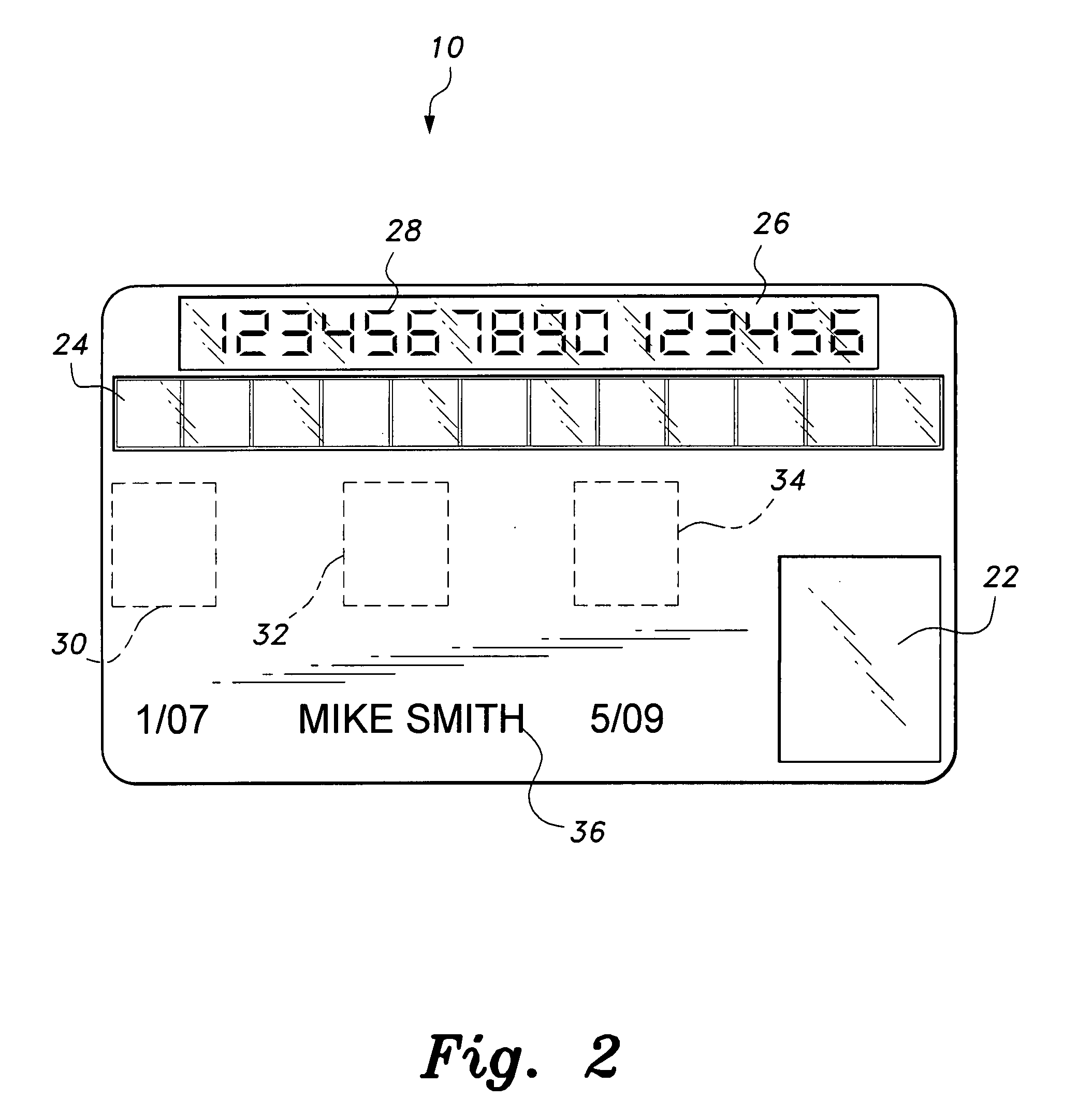
The smart card with random temporary account number generation provides an authenticating system coupled with an access or transaction card, such as a credit card. The card includes first and second memory storage media, with the first memory medium containing a plurality of temporary account or authentication numbers. The card also has a biometric sensor, such as a fingerprint scanner, and the second memory stores the biometric parameters of the authorized user. A processor compares the biometric parameters with the measured biometric readings to enable the card. The processor has a random number generator, allowing for the randomized selection of one of the account numbers stored in the first memory, thus providing a temporary account number for the transaction. A remote site includes an identical random number generator and set of account numbers, allowing the temporary account number to be verified and then discarded, following the transaction.
Owner:HEWTON ALFRED
Computer Apparatus with added functionality
InactiveUS20060007151A1Add to and enhance functionLow costCathode-ray tube indicatorsInput/output processes for data processingHard disc driveWi-Fi
A computer apparatus such as a mouse, keyboard, or PC headset with additional devices disposed within the apparatus enclosure, which can enhance the functionality of such computer apparatus. In the preferred embodiment, the additional devices are disposed within or along the length of a mouse apparatus. The additional devices typically function independently of the mouse apparatus. However, the additional components may share one or more wired or wireless paths to a host PC and to other devices, or to a network. The additional devices either integrated within the mouse enclosure or removable from the mouse enclosure, include a wireless adapter (Wi-Fi, Bluetooth, 3G, GSM, etc. . . . ), RAM, ROM, a mini hard drive, a GPS receiver module, a flash memory, flash memory drive reader, a USB Hub, a Trackpoint™ device, a keyboard or keypad, a fingerprint reader, or a SIM card reader. Also disclosed, are software controls for mapping the mouse velocity to a cursor velocity and for controlling the function and settings of the Trackpoint device. Further disclosed is a method for assigning the mouse's data output to a variety of devices connected to a wired or wireless network.
Owner:RAM PRANIL
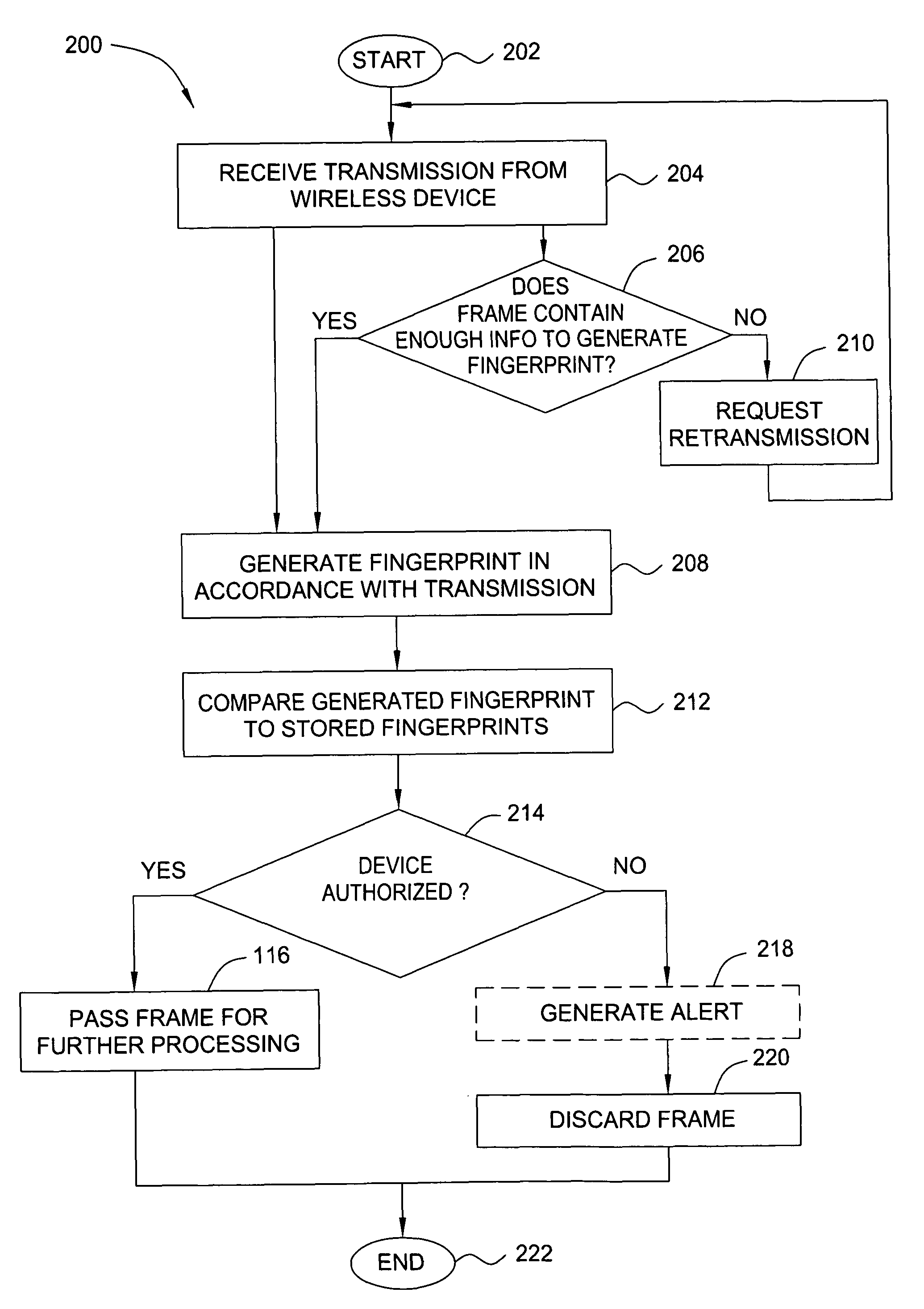
Method and apparatus for identifying wireless transmitters
ActiveUS8249028B2Error preventionFrequency-division multiplex detailsRadio frequency signalWireless computing
In one embodiment, the present invention is a method and apparatus for identifying wireless transmitters. In one embodiment, a method for identifying a transmitter in a wireless computing network includes extracting one or more radio frequency signal characteristics from a communication from the transmitter and generating a fingerprint of the transmitter in accordance at least one of the extracted radio frequency signal characteristics.
Owner:SRI INTERNATIONAL
Personal choice biometric signature
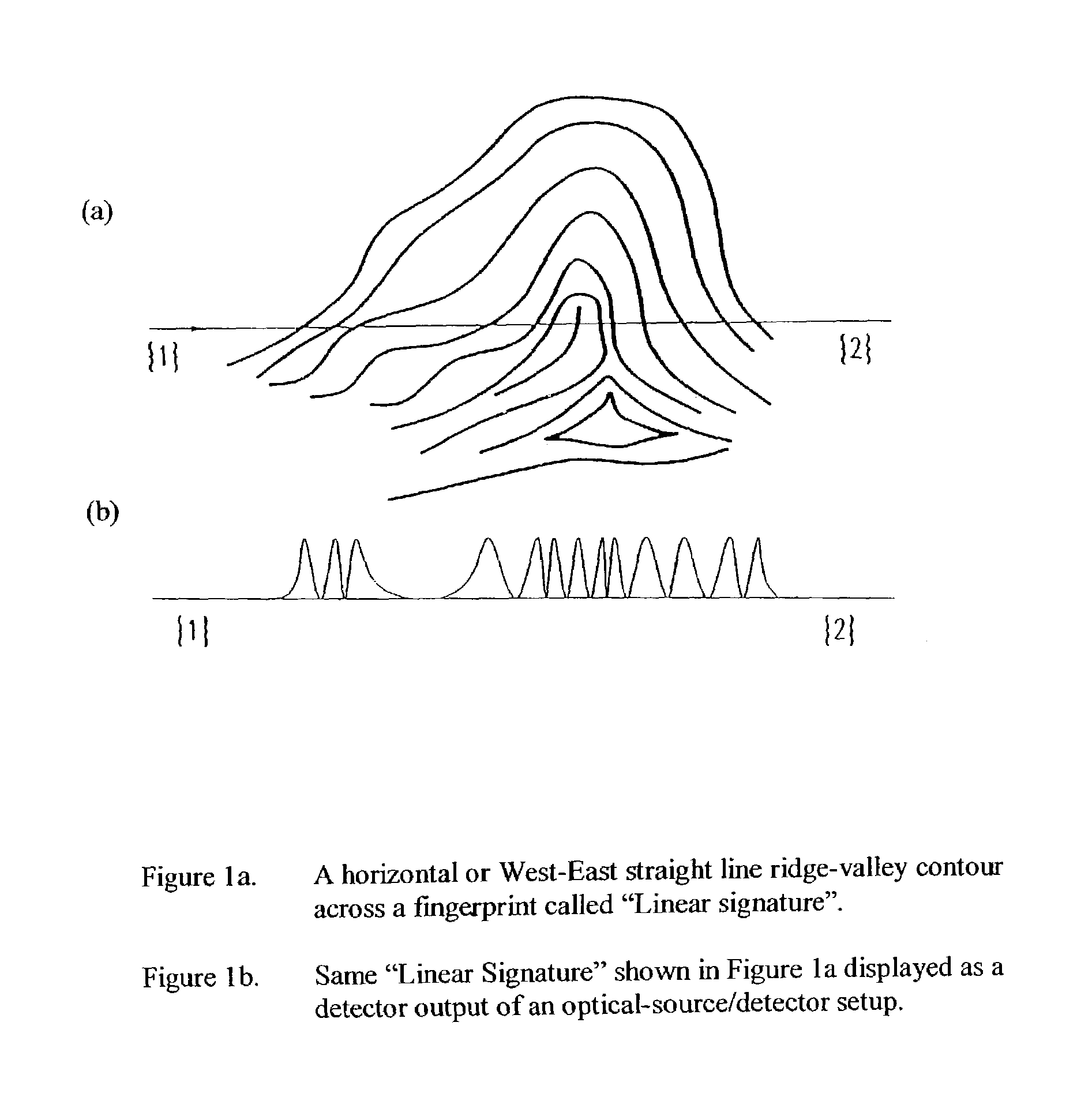
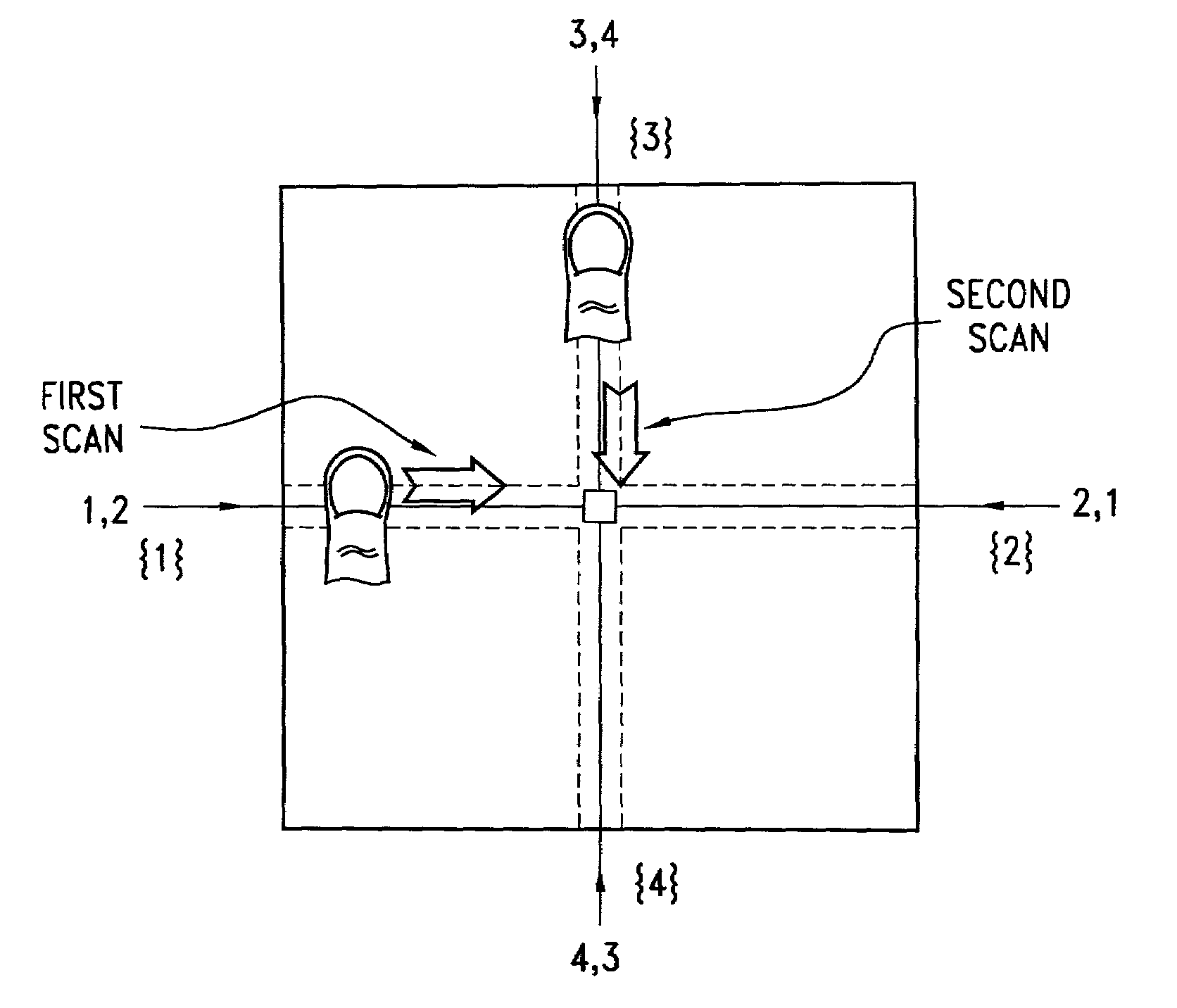
InactiveUS7013030B2Improved high security method and systemEasy to useElectric signal transmission systemsImage analysisCombined useLinearity
A biometric method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. This approach is further enhanced by employing a frequency domain technique for calculating a Similarity Index of the partial fingerprint signatures. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains four (illustratively) linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. In an advanced embodiment, the same two candidate signatures in the chosen sequence are processed in a unique FFT / DFT process to produce a highly reliable Similarity Index to authenticate or verify the identity of individuals. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y +1
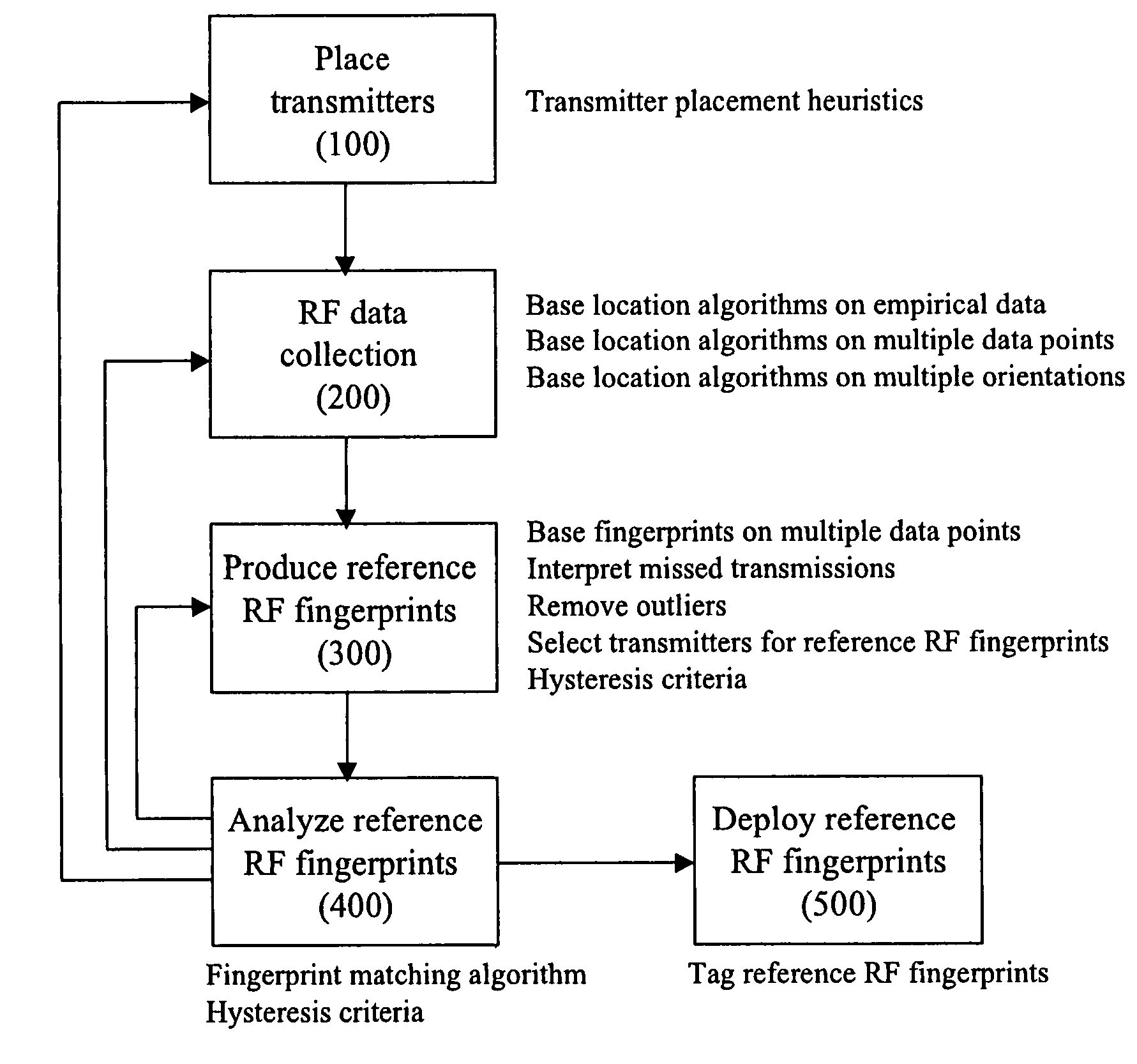
Method for RF fingerprinting
InactiveUS7346359B2Improve accuracyAccurate locationElectric signal transmission systemsImage analysisEngineeringLocation determination
The invention provides a novel method for preparing a wireless environment for location determination of a wireless mobile unit, and for location determination of a wireless mobile unit. In preparing the physical environment, the invention utilizes novel techniques, including novel techniques to place transmitters, the removal of outlying data in the creation of reference RF fingerprints, and algorithms to obtain accurate reference RF fingerprints. In determining the location of a wireless mobile unit, the invention utilizes novel techniques, including novel techniques to select transmitters, the removal of outlying data in the creation of reference RF fingerprints, and algorithms to obtain accurate reference RF fingerprints.
Owner:INNERWIRELESS
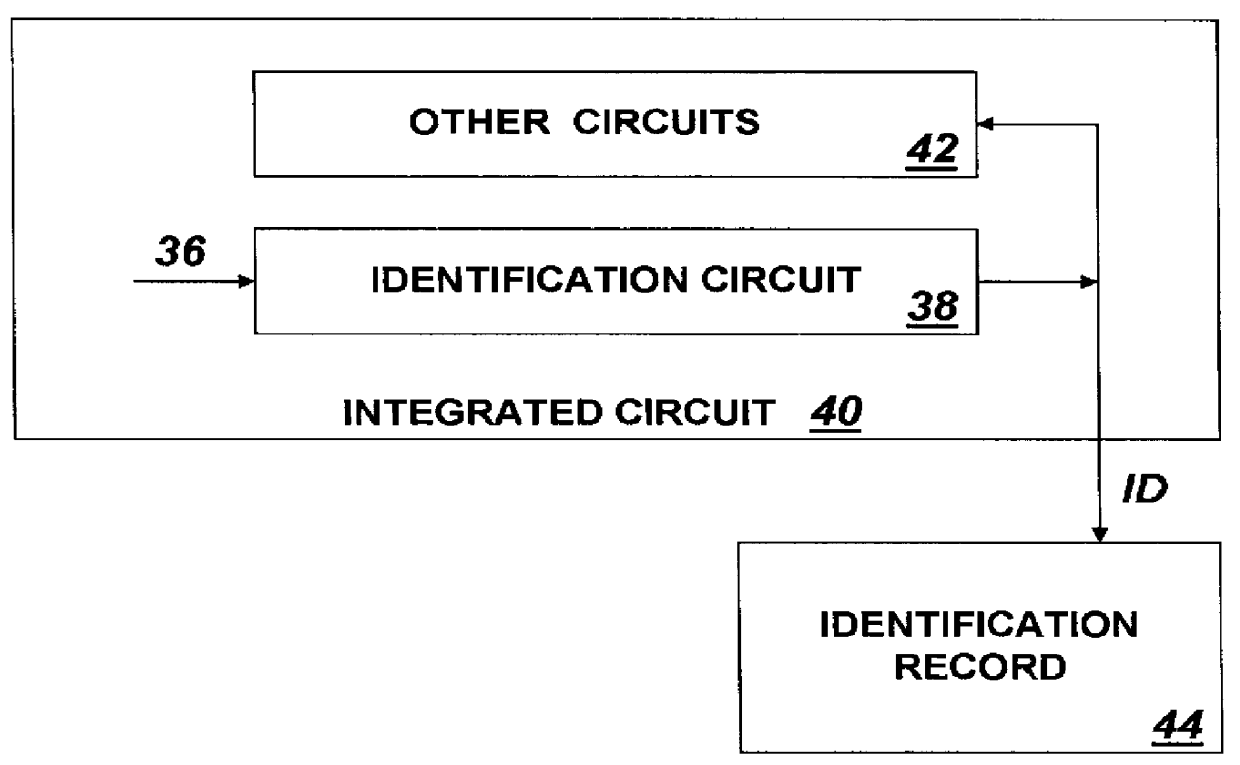
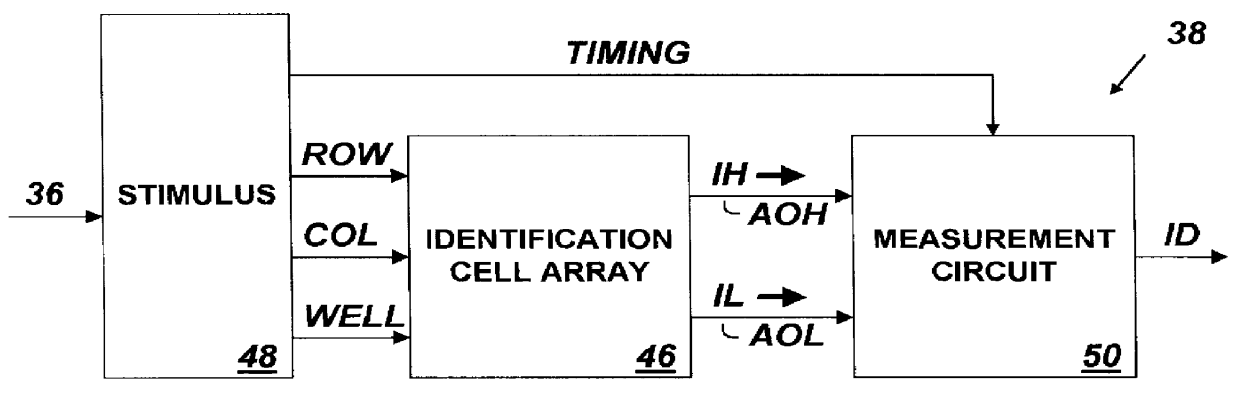
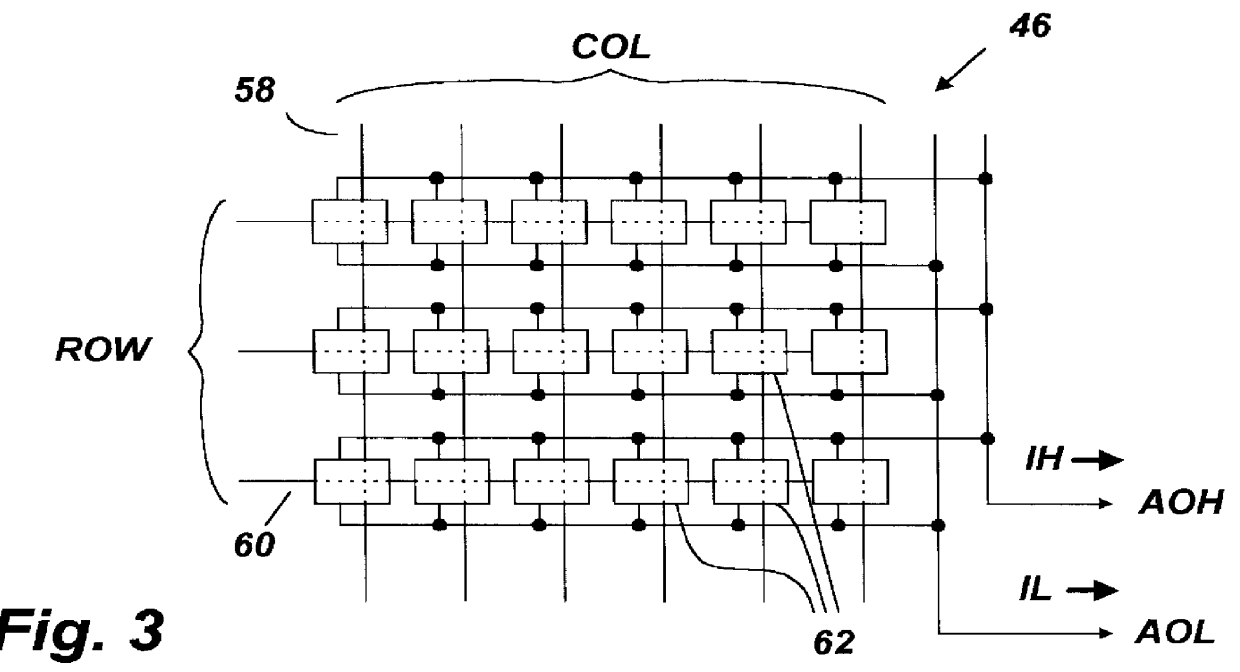
System for providing an integrated circuit with a unique identification
InactiveUS6161213ANoise figure or signal-to-noise ratio measurementSemiconductor/solid-state device detailsIdentification deviceIntegrated circuit
An integrated circuit identification device (ICID) to be incorporated into an integrated circuit (IC) includes an array of electronic cells in which the magnitude of an output signal of each cell is a function of randomly occurring parametric variations which vary from cell-to-cell. The ICID also includes a circuit for measuring the output of each cell and for producing output data having a value reflecting the particular combination of measured characteristics of all of the elements of the array. When we make the number of elements in the array large enough, we insure that to a high degree of probability, the pattern of measured array cell characteristics for an ICID embedded in any one IC will be unique and distinguishable from such patterns measured by ICIDs embedded in millions of other ICs. Thus the value of the output data produced by an ICID circuit acts as a unique "fingerprint" for the IC in which it is installed, and can be used as a unique identification (ID) for that IC.
Owner:ICID
Personal choice biometric signature
InactiveUS7035443B2Complicated processSpatial variation is minimizedElectric signal transmission systemsImage analysisPattern recognitionProximity sensor
A biometric method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. This approach is further enhanced by employing a frequency domain technique for calculating a Similarity Index of the partial fingerprint signatures. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains a reference set of linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. In an advanced embodiment, a pair of proximity sensors located along each of the linear tracks used for developing the linear partial signatures produce finger sensing signals which compensate for finger movement speeds and hence significantly improves the calculated Similarity Index values. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y
Gallery of videos set to an audio time line
ActiveUS20160180887A1Television system detailsElectronic editing digitised analogue information signalsVideo sequenceTime line
A machine includes a processor and a memory connected to the processor. The memory stores instructions executed by the processor to receive a message with audio content and video content. Audio fingerprints within the audio content are evaluated. The audio fingerprints are matched to known audio fingerprints to establish matched audio fingerprints. A determination is made whether the matched audio fingerprints correspond to a designated gallery constructed to receive a sequence of videos set to an audio time line. The matched audio fingerprints and corresponding video content are added to the audio time line. The operations are repealed until the audio time line is populated with corresponding video content to form a completed gallery with video segments set to audio segments that constitute a complete audio time line. The completed gallery is supplied in response to a request.
Owner:SNAP INC
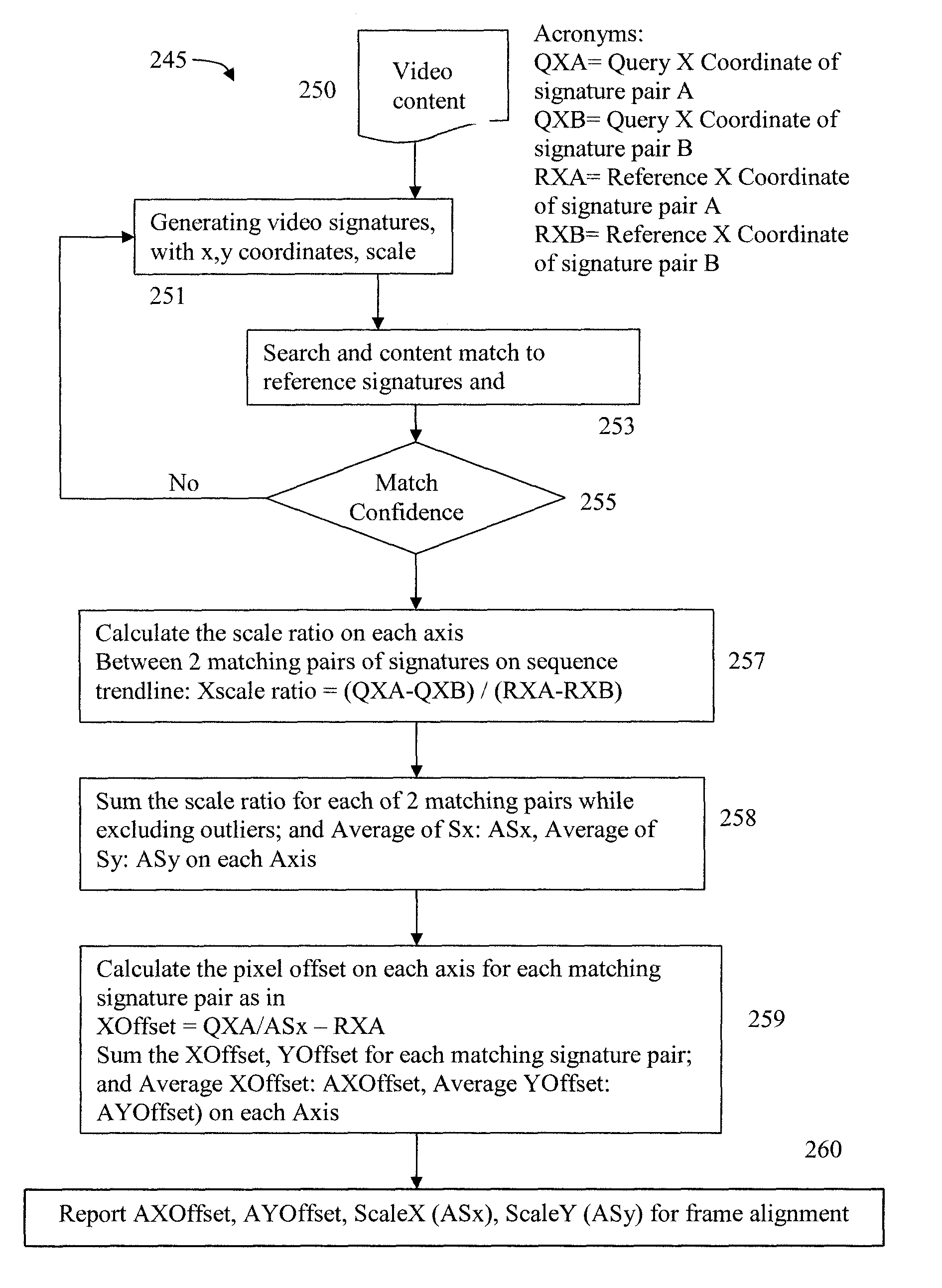
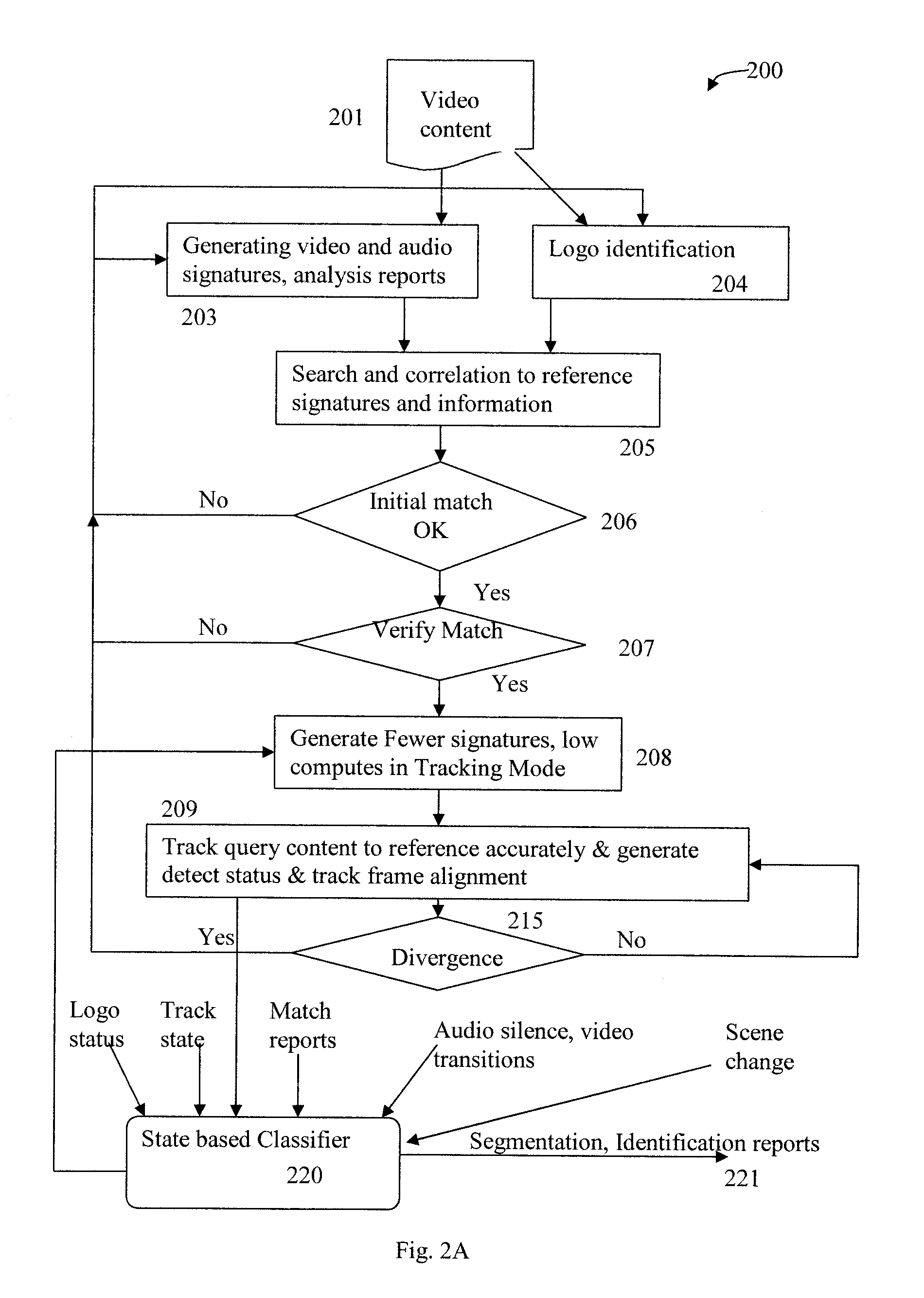
TV content segmentation, categorization and identification and time-aligned applications
ActiveUS9510044B1Receiver side switchingCharacter and pattern recognitionMulti languageDisplay device
Content segmentation, categorization and identification methods are described. Content tracking approaches are illustrated that are suitable for large scale deployment. Time-aligned applications such as multi-language selection, customized advertisements, second screen services and content monitoring applications can be economically deployed at large scales. A client performs fingerprinting, scene change detection, audio turn detection, and logo detection on incoming video and gathers database search results, logos and text to identify and segment video streams into content, promos, and commercials. A learning engine is configured to learn rules for optimal identification and segmentation at each client for each channel and program. Content sensed at the client site is tracked with reduced computation and applications are executed with timing precision. A user interface for time-aligned publishing of content and subsequent usage and interaction on one or more displays is also described.
Owner:ROKU INCORPORATED
Transaction automation and archival system using electronic contract and disclosure units
ActiveUS8228299B1Shorten the timeEliminate mistakesImage analysisFinanceDisplay deviceFinancial transaction
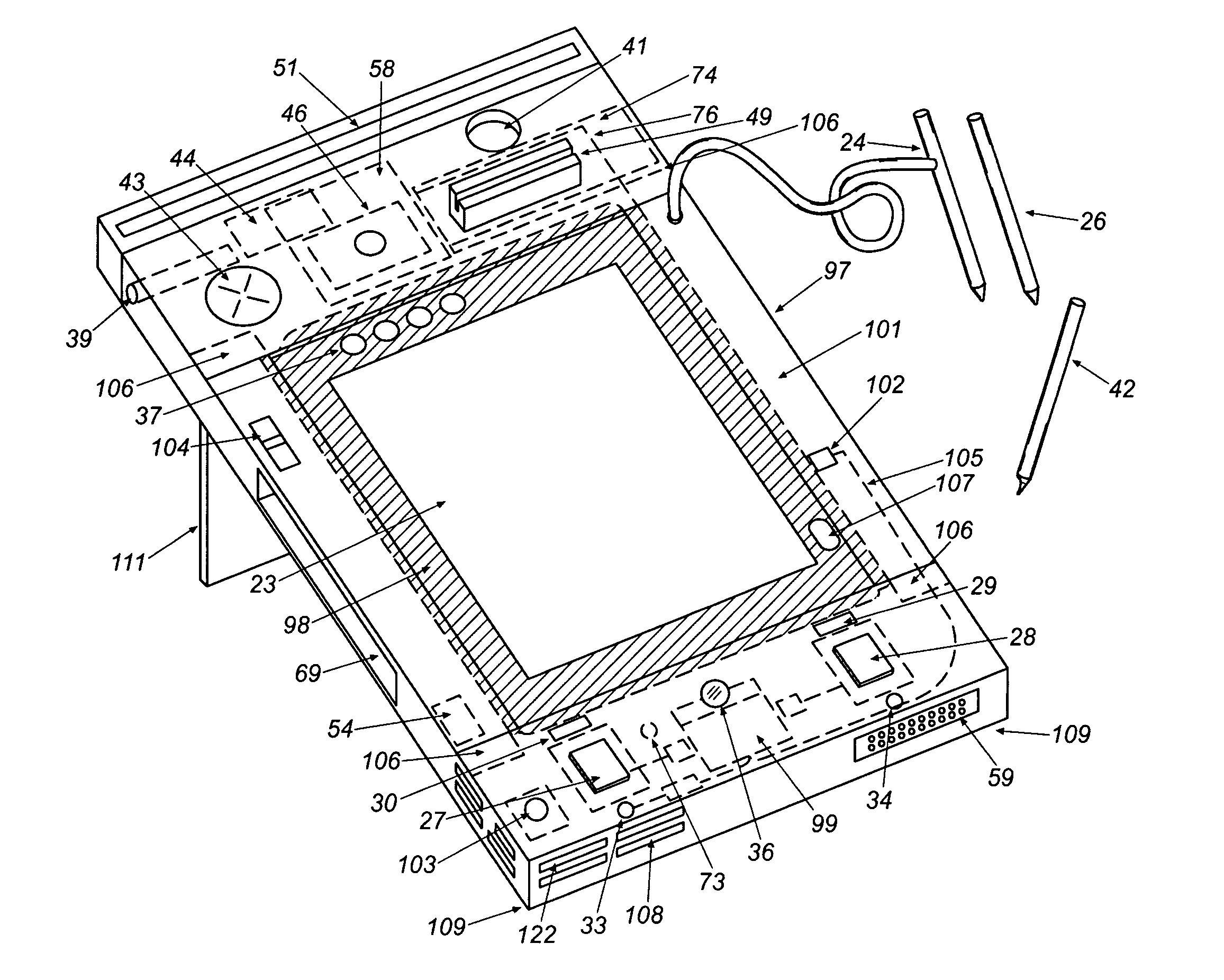
A transaction automation and archival system is provided for controlling, real-time logging, and archiving complex commercial transactions such as the purchase and financing of an automobile. The heart of the system is an electronic contract disclosure unit, or ECDU. The ECDU includes a digitizing display that includes a video display for imaging to participants the various documents involved in the transaction and a digitizer for allowing participants to sign, indicate choices, and otherwise interact directly on documents and images presented on the display. A computer controls the entire progress of the transaction, and thus controls the collaborative space occupied by the participants to the transaction. The computer, for instance, controls the order of presentation of documents to a vehicle purchaser, receives the purchaser's signature on the displayed documents when required, offers choices of various packages that can be accepted or declined by the purchaser, and insures that the entire transaction is carried out properly. The ECDU further logs the transaction for future review and preferably includes a video camera and microphone for logging images and sounds of the participants during the transaction. One or more fingerprint readers are associated with the digitizing display for allowing participants to select between options by pressing their thumb or finger on the reader, which simultaneously verifies the identity of the individual making the selection through the fingerprint.
Owner:REYNOLDS AND REYNOLDS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com