Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
388results about How to "Avoid deletion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
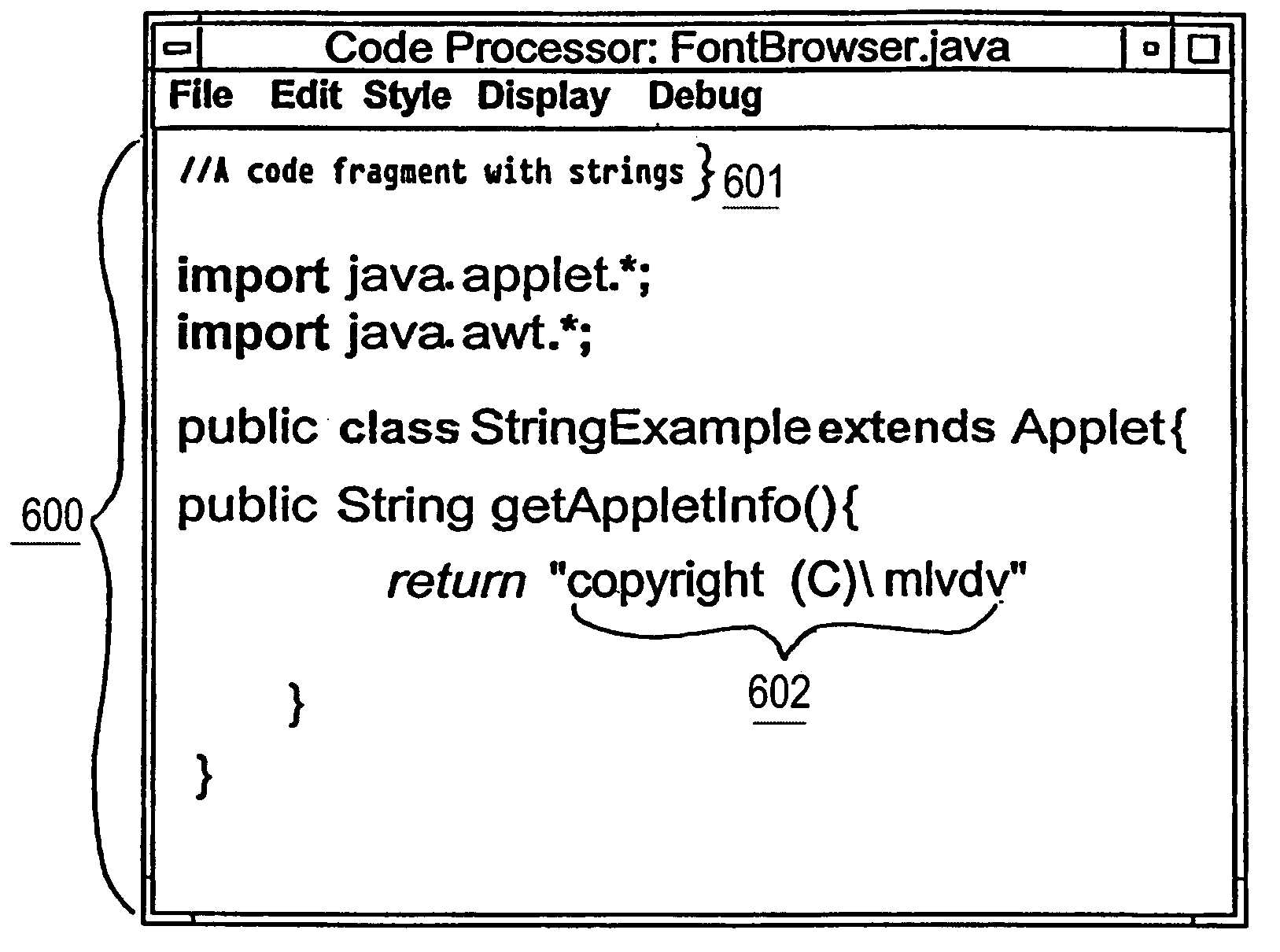
Interactive software engineering tool with support for embedded lexical contexts
InactiveUS7127704B2Avoid deletionIntelligent editorsSpecial data processing applicationsInteractive softwareProgramming language
In response to programmer input of a trigger token, a program editor creates a pair of boundary tokens encapsulating an embedded lexical context and positions an insertion point within the embedded lexical context. The operations on the embedded lexical context are preferably performed using an embeddable sub-editor specialized to the task at hand. Since boundary tokens are generated in pairs, stability of lexical boundaries is enforced. Accordingly, stable implementations of certain desirable behaviors, including language-oriented advanced program typography that is robust to user edits, are facilitated using the invented techniques.
Owner:ORACLE INT CORP
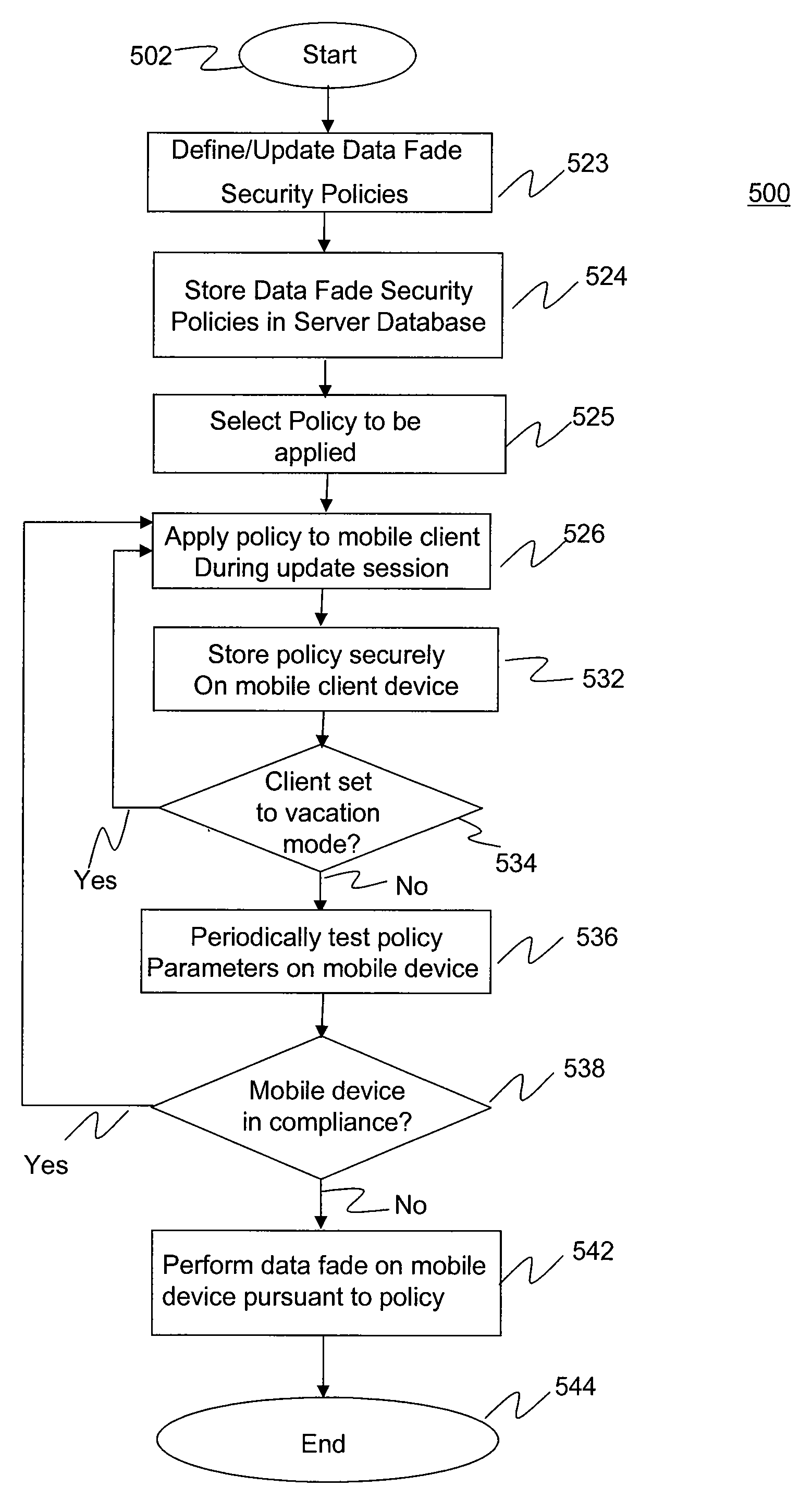
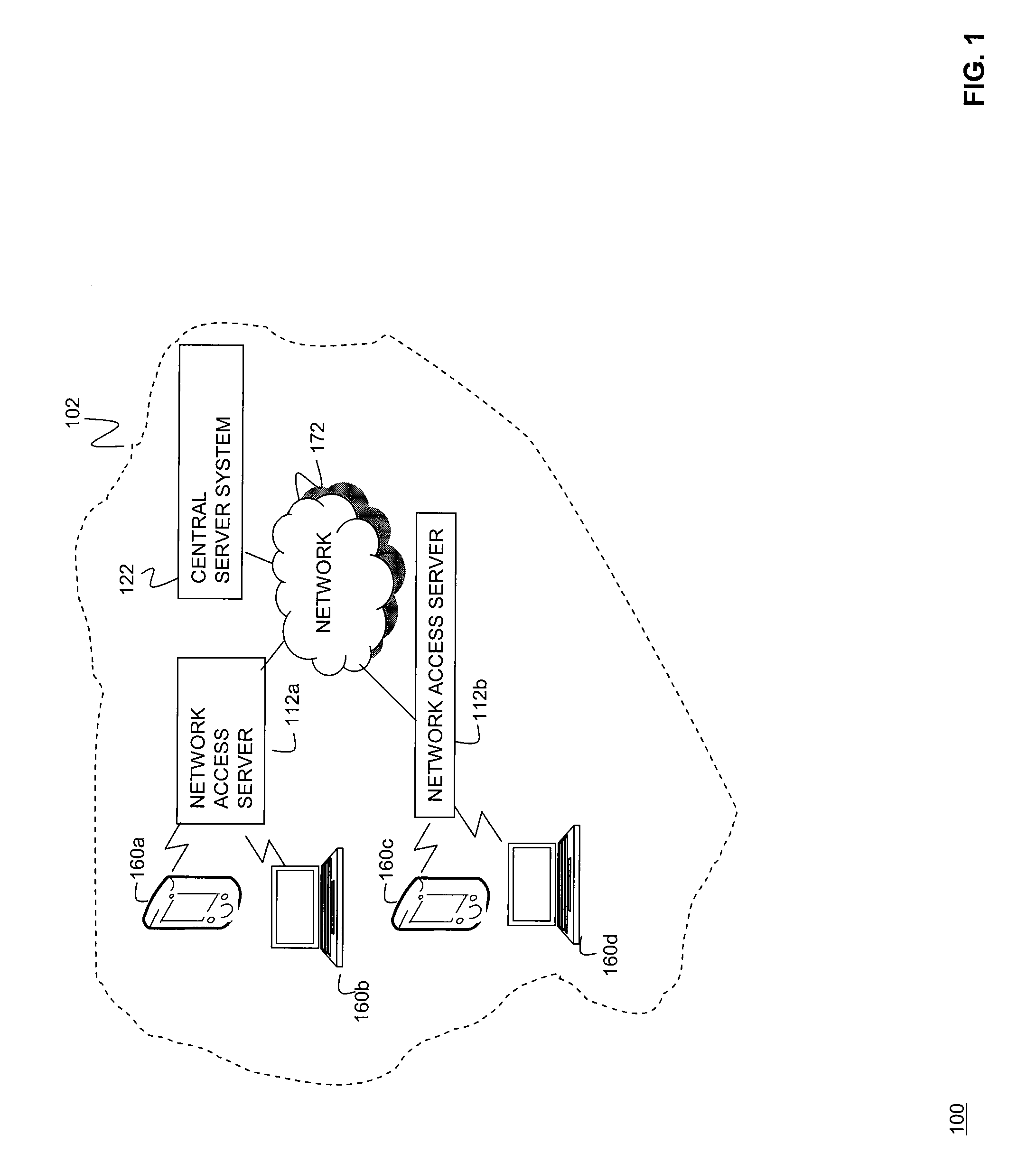
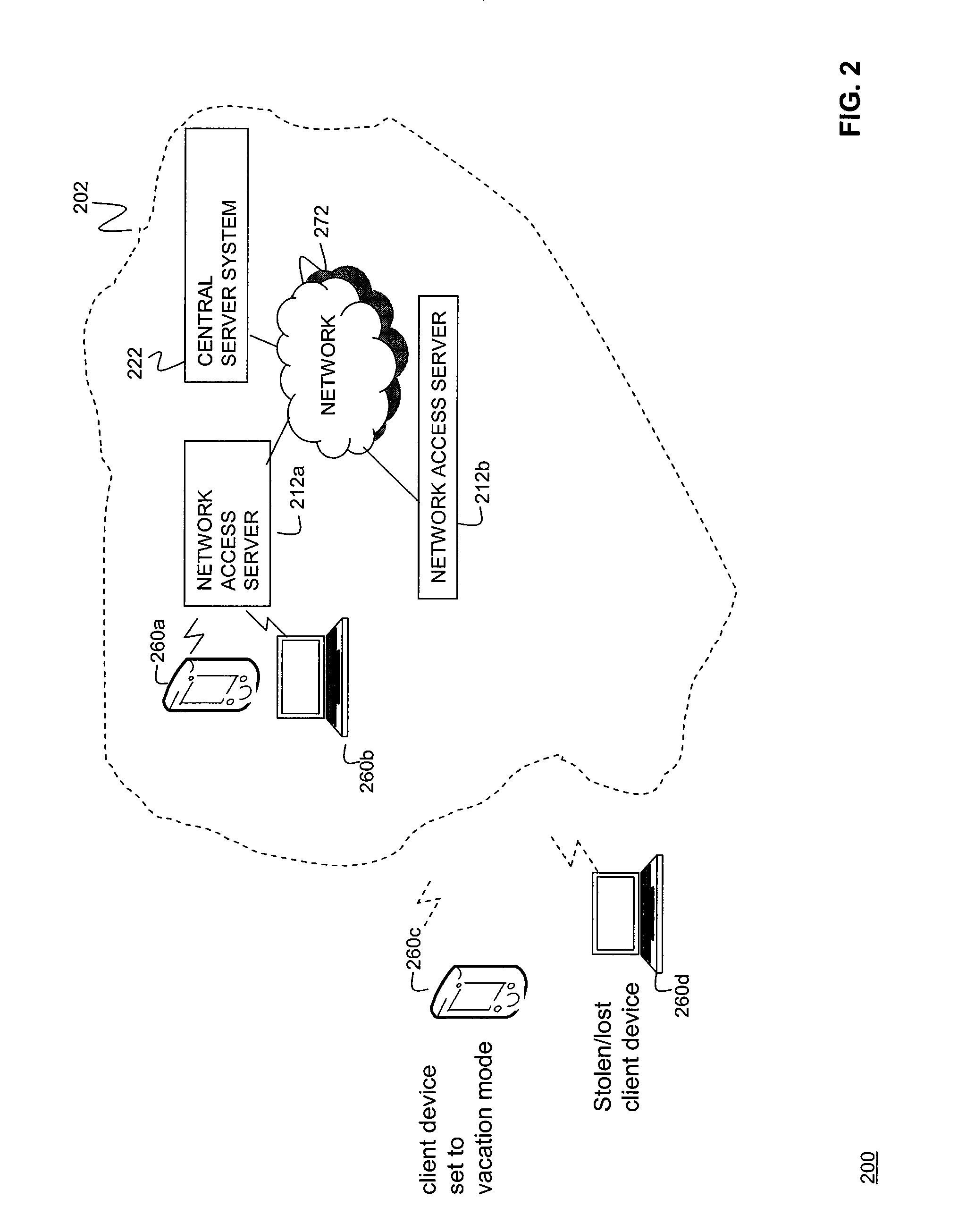
Data Fading to Secure Data on Mobile Client Devices
InactiveUS20090150970A1Protect dataEliminate needInternal/peripheral component protectionTransmissionNetwork security policyClient-side
Methods, systems, and computer program products to secure data stored on mobile client devices are provided. In an embodiment, the method operates by defining one or more security policies. Each security policy comprises a plurality of security policy parameters. The method stores the security policies in a data store, and selects a security policy from among the stored security policies for a mobile client device. The selected security policy is applied to the mobile client device. The mobile client device determines whether it is compliance with parameters of said selected security policy, and performs data fade actions if it is determined that it is out of compliance with said security policy parameters.
Owner:IANYWHERE SOLUTIONS
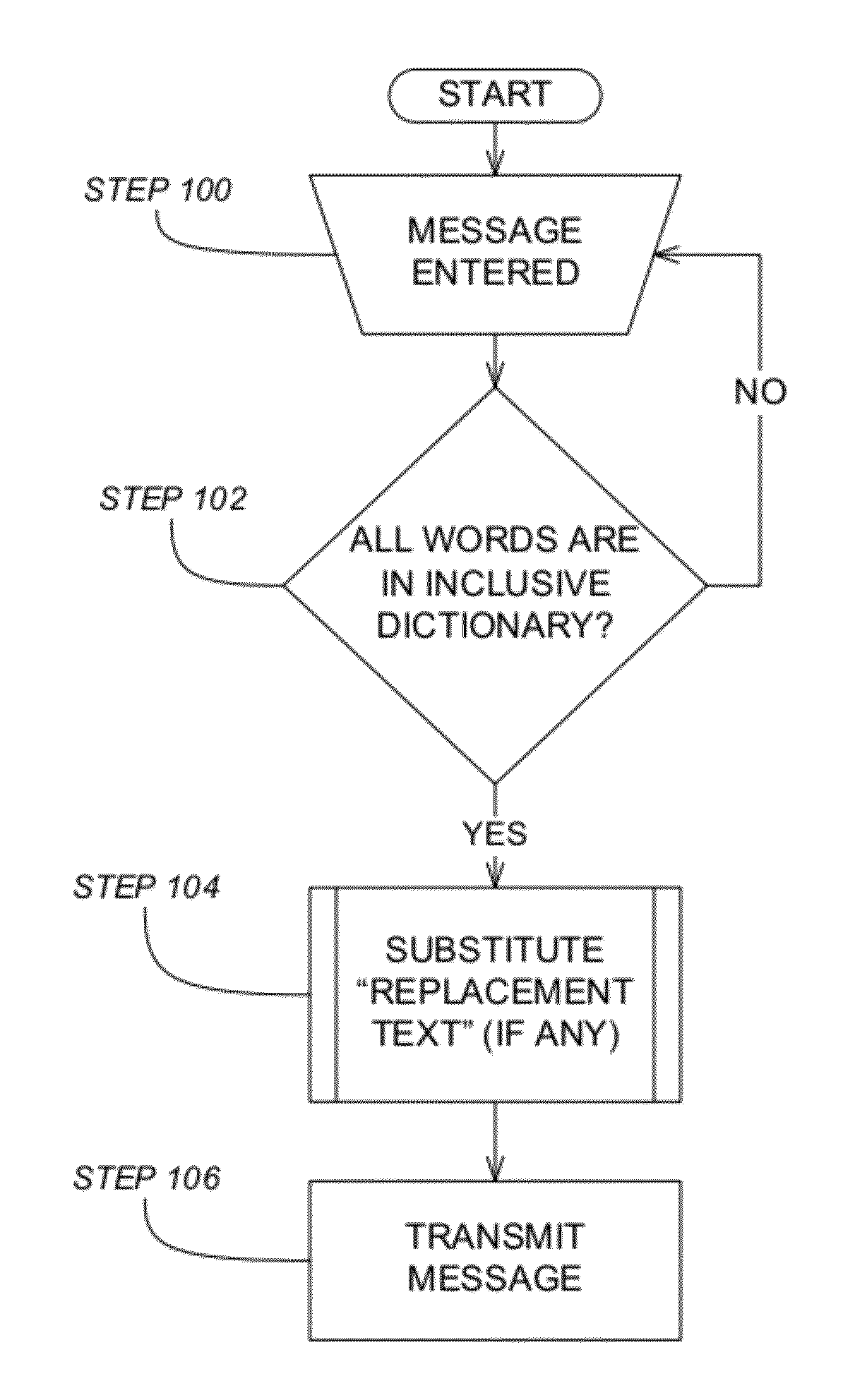
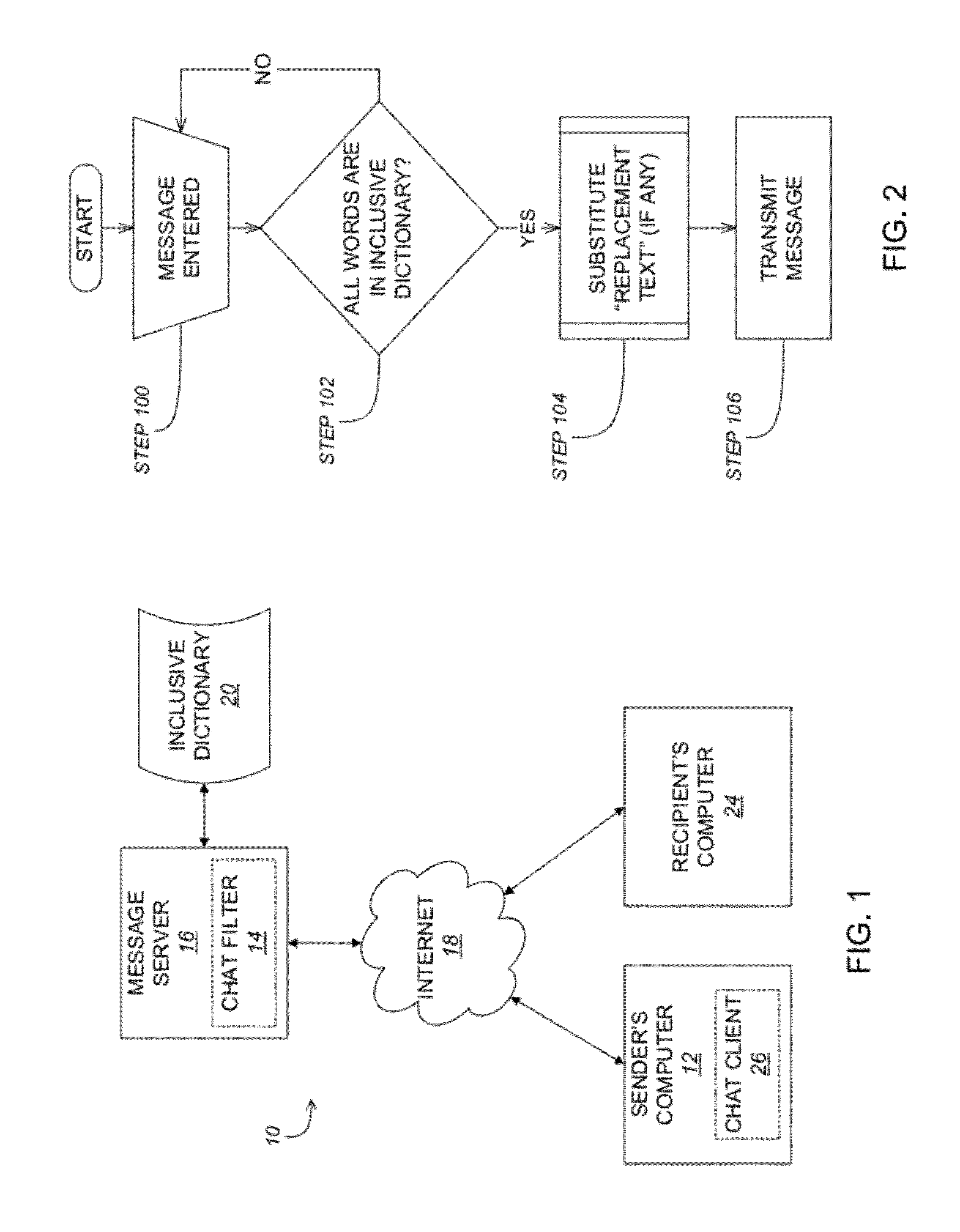
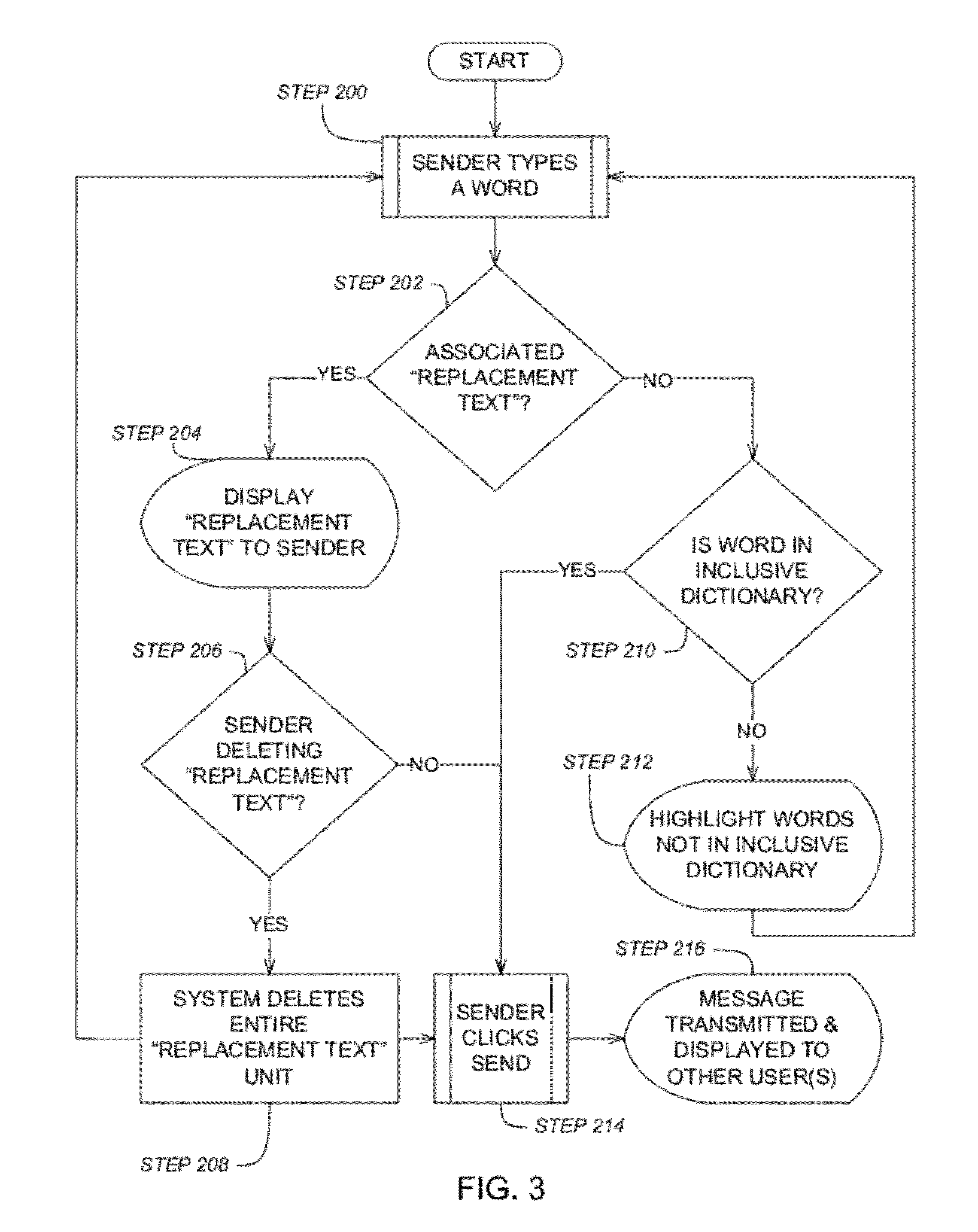
Message filter with replacement text
ActiveUS20120036147A1Avoid deletionDigital data processing detailsMultiple digital computer combinationsWorld Wide WebPhrase
A computer network-based messaging system controls the content of messages sent by users. A database includes permitted words and replacement text elements corresponding to at least one permitted word. A message filter receives an entered word or phrase input by a user on a messaging device as part of a message. The message filter replaces the entered word in the message with a corresponding replacement text element stored in the database. A message sending part transmits the message including the replacement text element over a data network for viewing by other users only if every entered word in the message is included in the database. The message sending part transmits the message even though one or words contained in the replacement text element are not permitted words in the database. The system may allow deletion of a replacement text element from a message only in its entirety.
Owner:GANZ
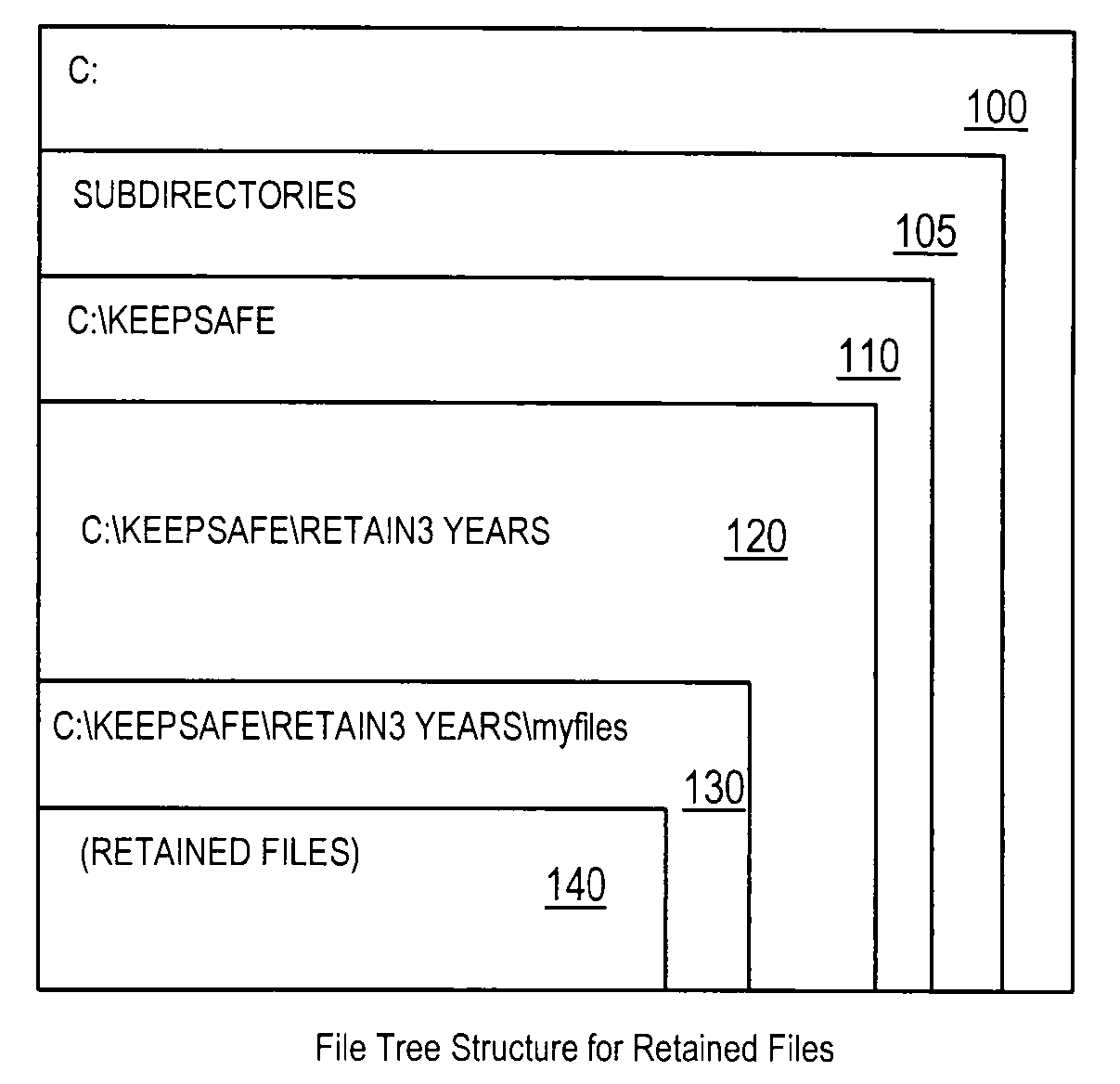
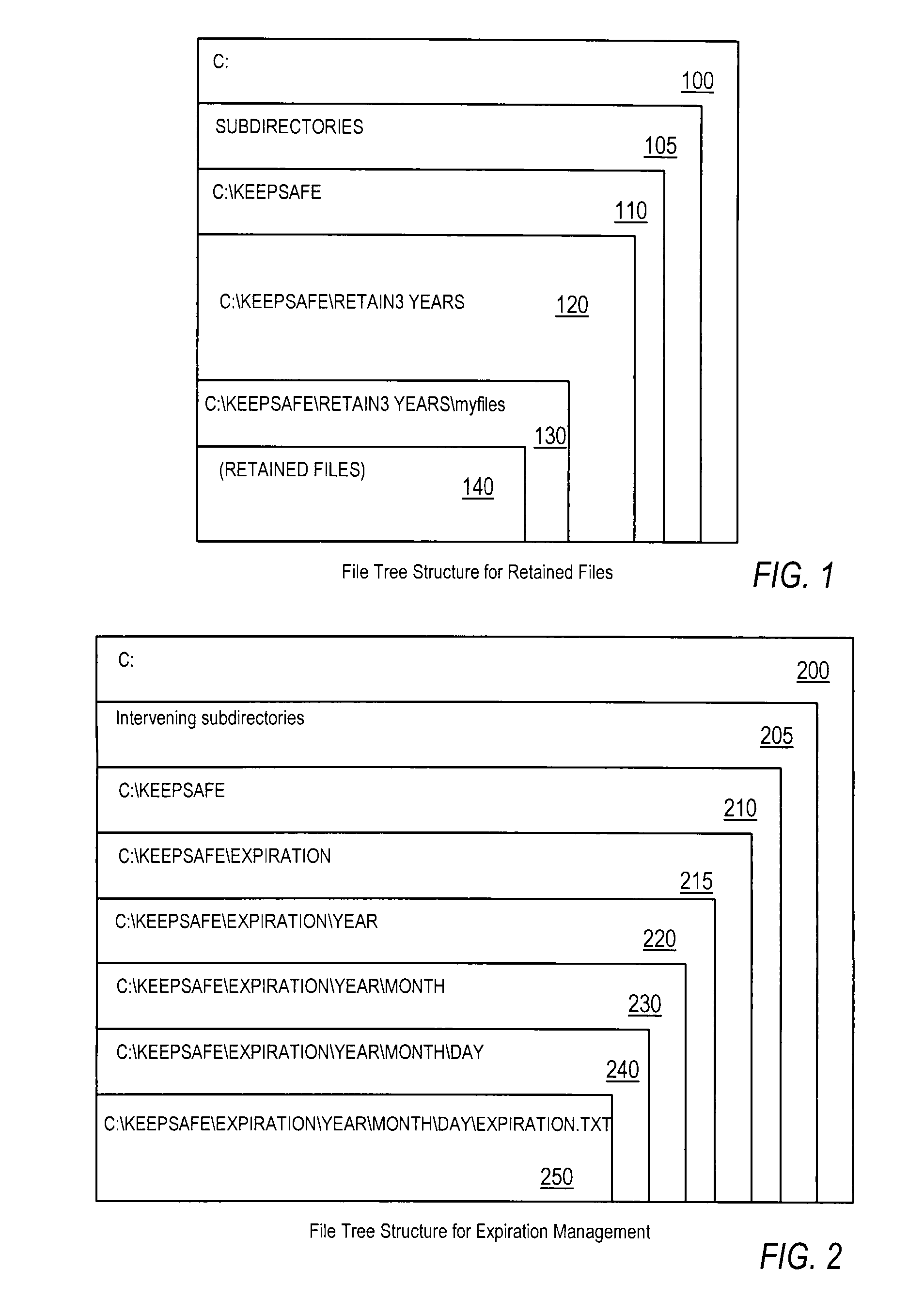
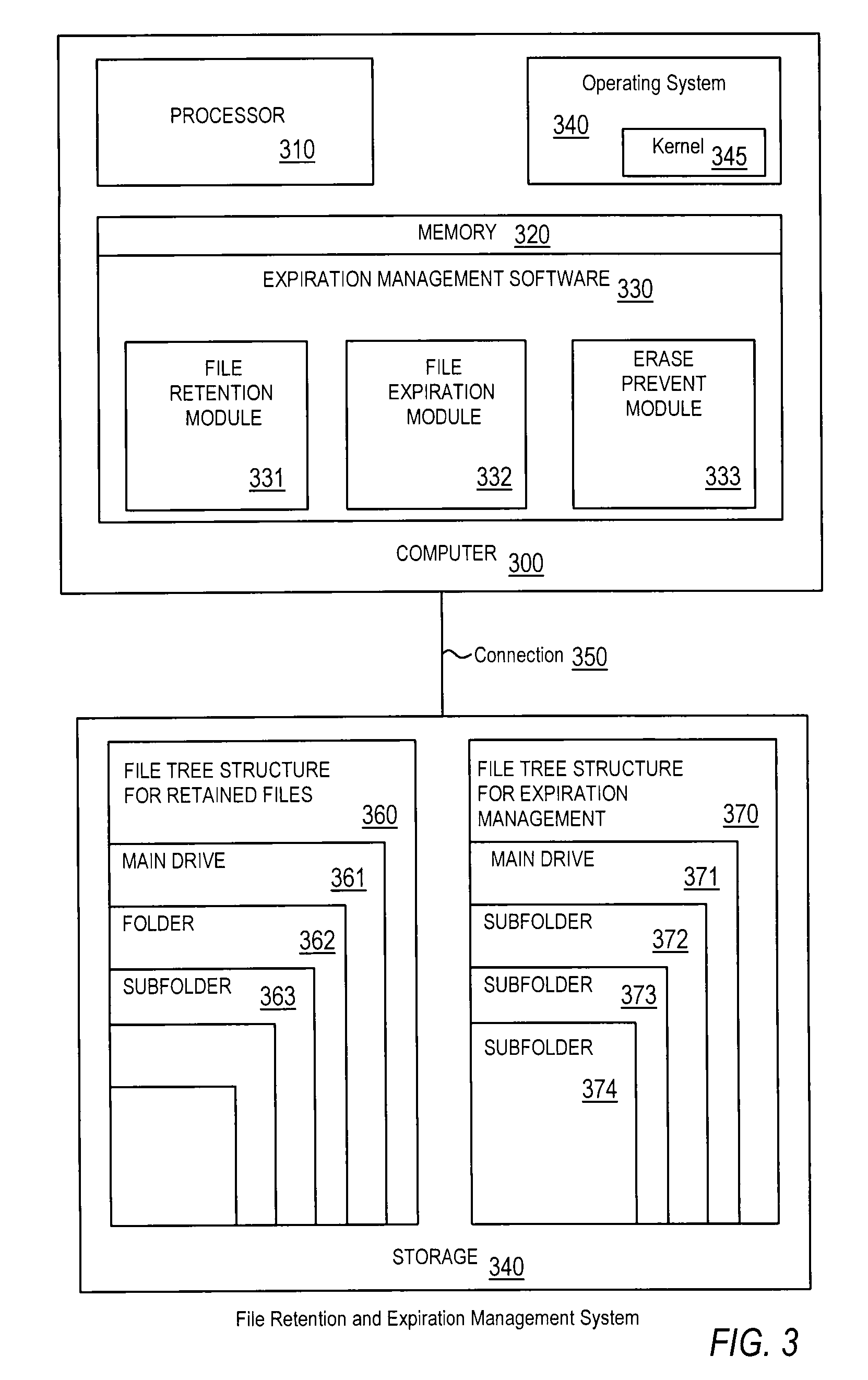
Efficient non-database file-expiration management for document retention
ActiveUS20080034003A1Efficiently performing functionEffective functionObsolescenceSpecial data processing applicationsRetention periodOperational system
Disclosed are a method, system, program and data structure for implementing a records retention policy by storing selected files for designated lengths of time and then deleting them only when that time has passed. Embodiments of the invention perform this function in an efficient database-free manner. Embodiments of the invention can perform this function by utilizing existing storage directory tree functionality provided by any computer operating system organized under a retention directory coupled with a mechanism for preventing unauthorized deletions of files designated for retention. Expiration of retained files may be managed through directory structure using directory names corresponding to expiration dates determined from identified retention periods for retained files. Files may be further protected from erasure by a kernel mode process which prevents erasure of any files contained in the retention directory.
Owner:IBM CORP
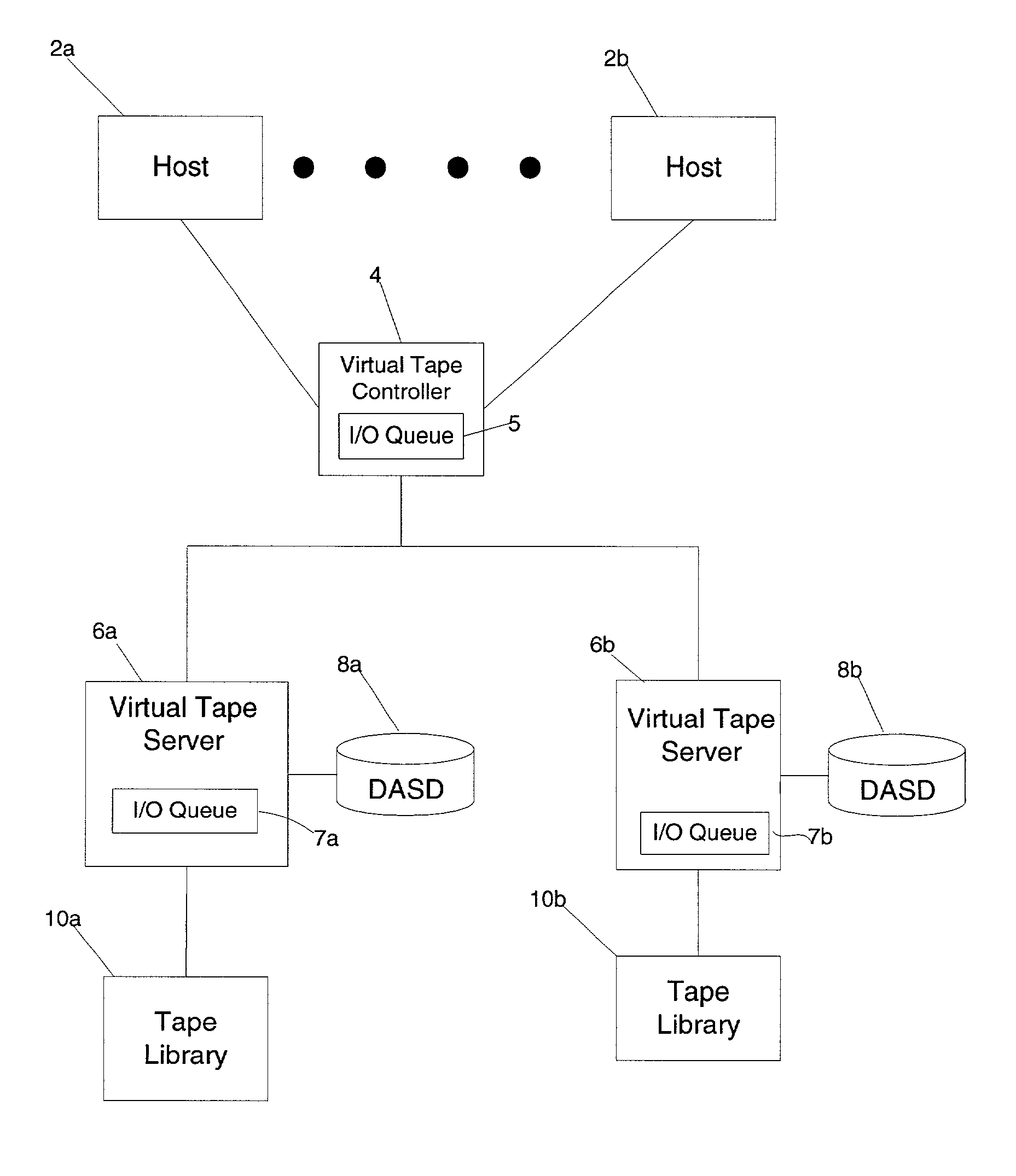
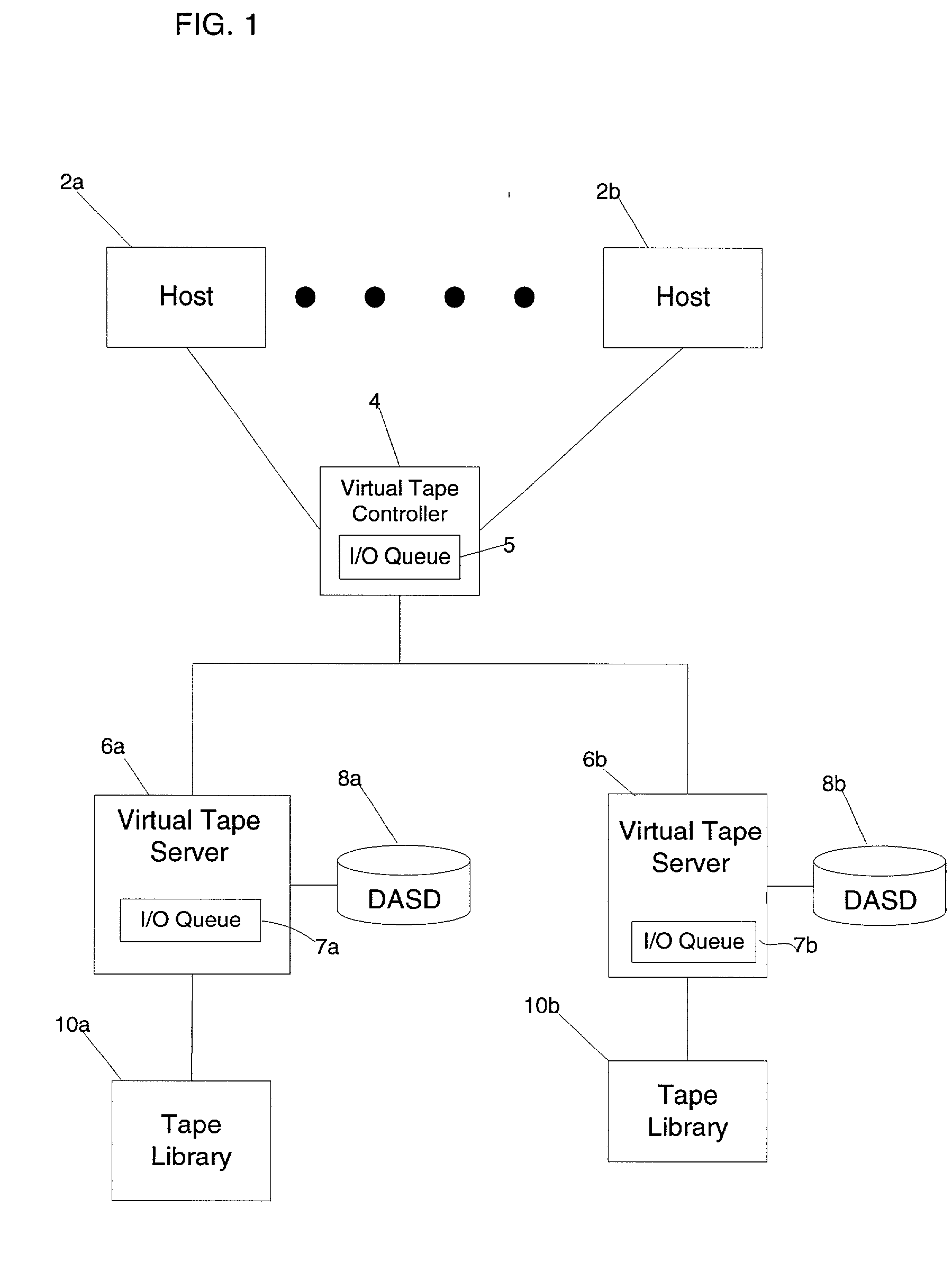
Method, system, and program for transferring data between storage devices
InactiveUS20030014568A1Increase ratingsIncrease transfer rateData processing applicationsError detection/correctionData setOperating system
Provided is a method, system, and an article of manufacture for maintaining data accessible by a host in two storage devices, wherein the data is comprised of a plurality of data sets. A determination is made of a percentage of uncopied data at the first storage device, wherein uncopied data comprises data sets to be copied from the first storage device to the second storage device. If the calculated percentage is greater than a threshold amount, a rate at which uncopied data sets are transferred from the first storage device to the second storage device is increased.
Owner:IBM CORP
Data stand-by system based on finger print
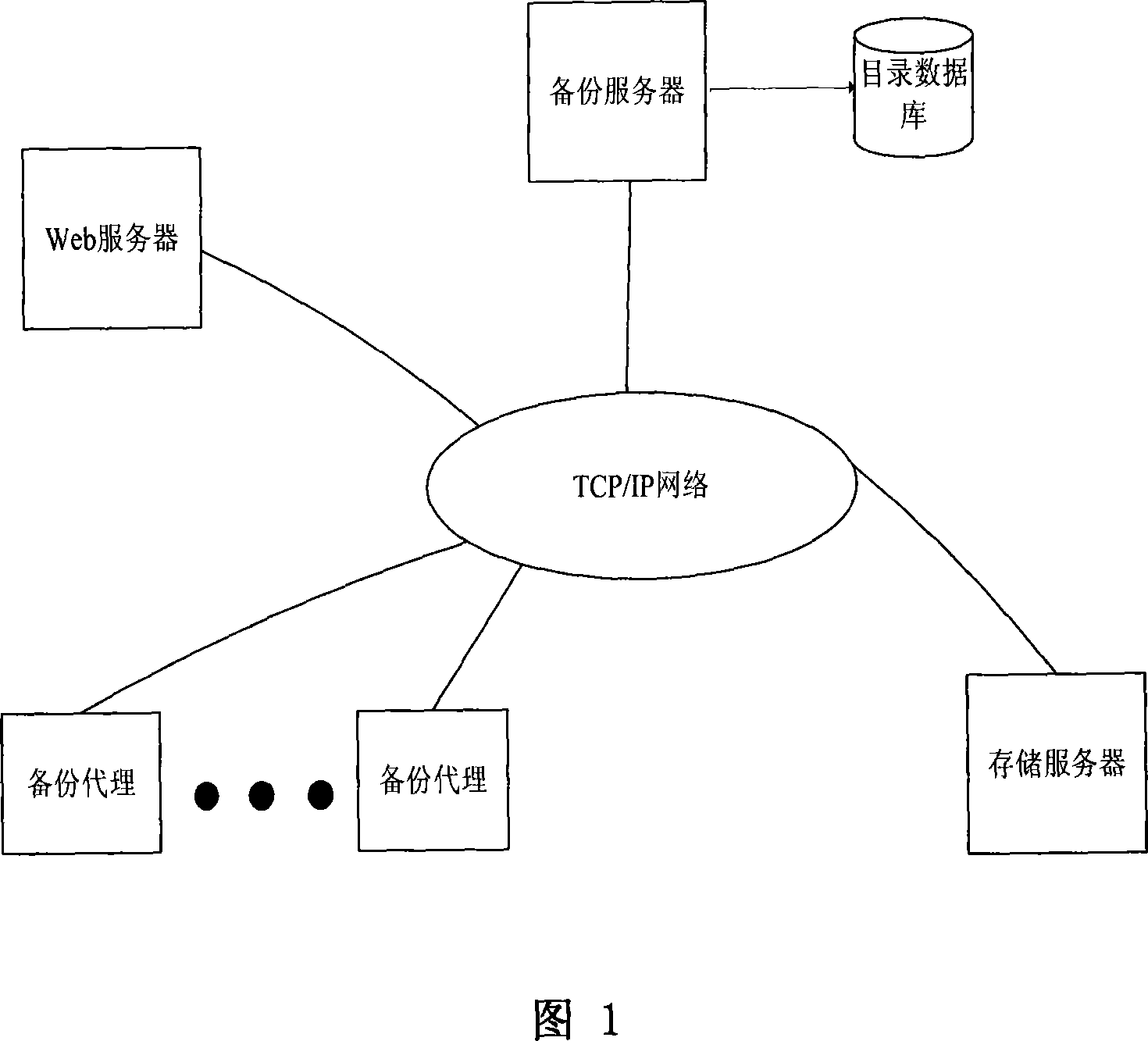
InactiveCN101183323AReduce computational overheadHas modification stabilityMultiprogramming arrangementsTransmissionComplete dataApplication server
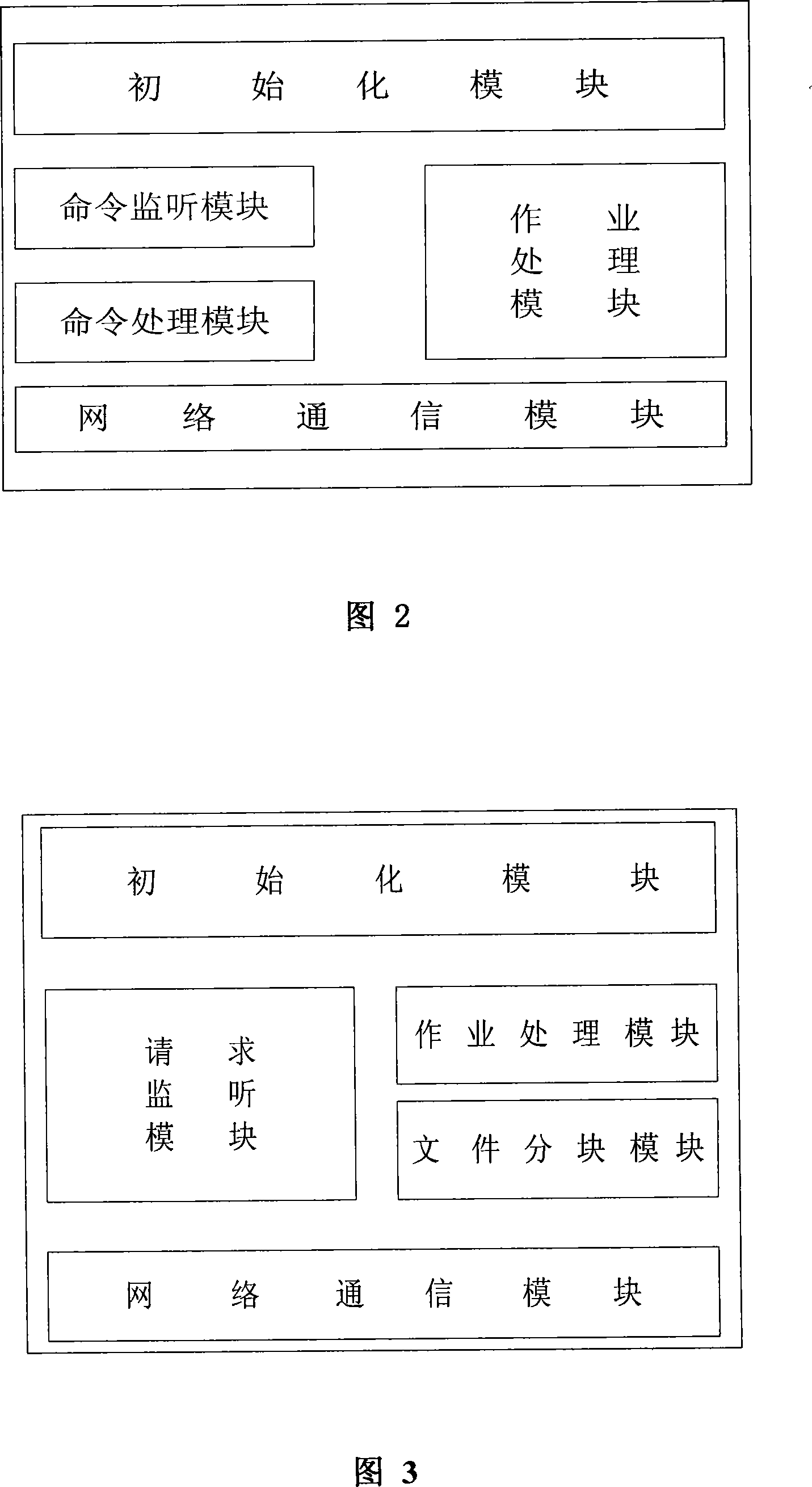
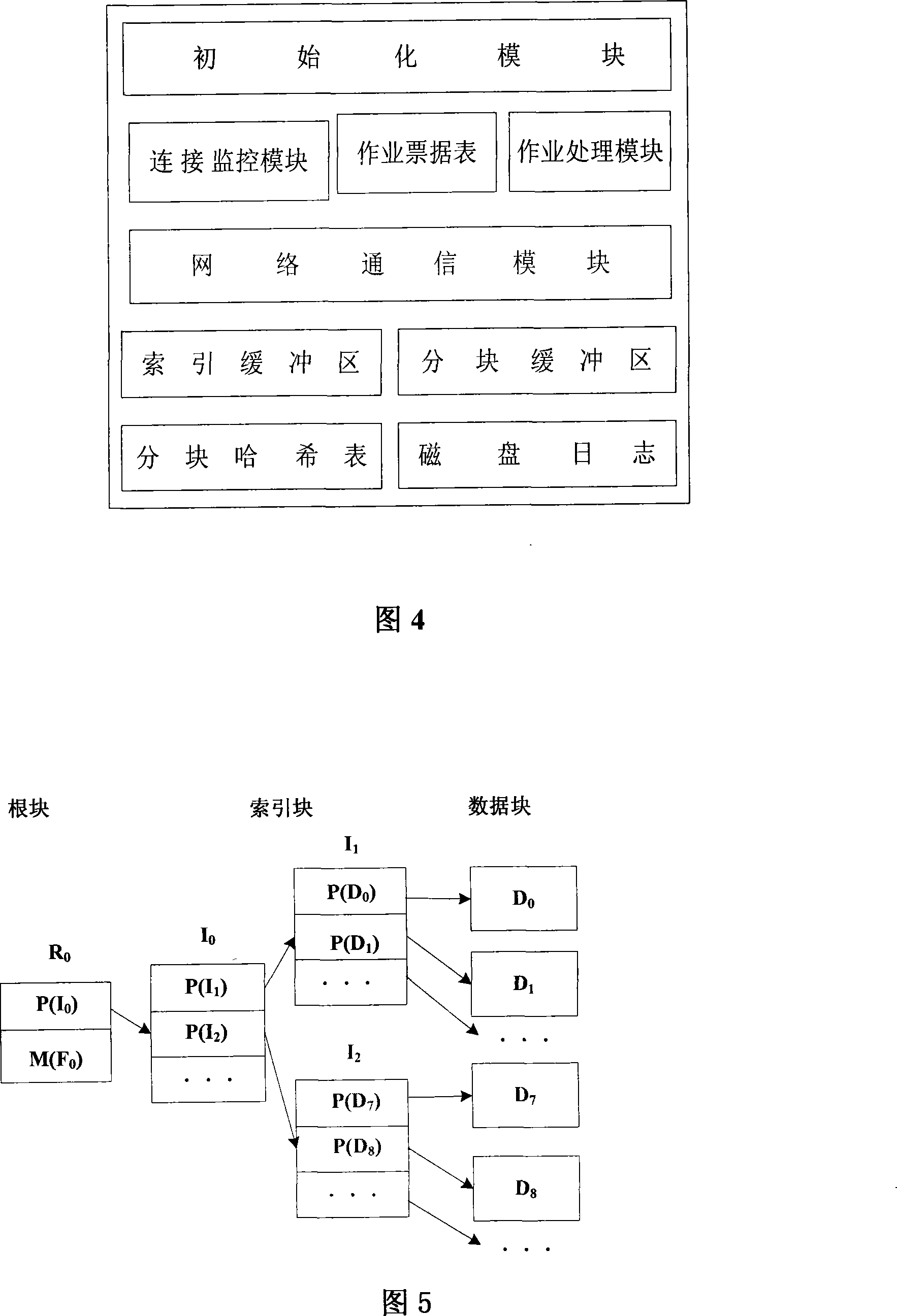
The invention relates to a data backup system based on fingerprints, belonging to the technical field of computer storage backup, which aims at reducing management, storage and network overhead of data backup and improving backup performance. The invention comprises a backup server, a backup agent, a storage server and a Web server which complete data backup and recovery through mutual network communication. The invention is characterized in that redundant data of backup files is recognized with the file segmentation technology based on anchors, thus the invention has the advantages that the modification stability is good and computation cost is low; data segmentations with fingerprints as the index are stored on a plurality of disk arrays of the storage server so as to eliminate backup of redundant data and save disk storage space; the data segmentations are not erased once stored and can be continuously appended on the disk so as to eliminate disk storage fragments; since the effective backup buffer strategy is adopted, the invention also has the advantages of reduced network overhead of backup, increased data backup speed and lowered backup influence to application servers.
Owner:HUAZHONG UNIV OF SCI & TECH
Electronic mail processing method and electronic mail processing system
InactiveUS20080208995A1Avoid deletionReliable judgmentMultiple digital computer combinationsData switching networksSpammingWorld Wide Web
Even when setting a complicated spam judging condition, it is possible to reliably determine a necessary electronic mail in reality (i.e a mail that is not a spam mail), without deleting a necessary electronic mail or the like. Based on the assumption that an electronic mail from a mail address to which transmission was performed in the past has a high possibility of not being a spam mail, a transmission destination mail address of an electronic mail transmitted to outside the organization is recorded as a permitted mail address (Step 506-Step 510), and when a transmission source address of an electronic mail destined to inside the organization matches a mail address registered in a permitted mail address database (Step 511: Yes), processing is performed to unconditionally receive this electronic mail (Step 504).
Owner:DIGITAL ARTS
Internet of things security access gateway
InactiveCN103139058ARealize security border controlMeeting Multi-Protocol Complexity RequirementsNetwork connectionsGate arrayThe Internet
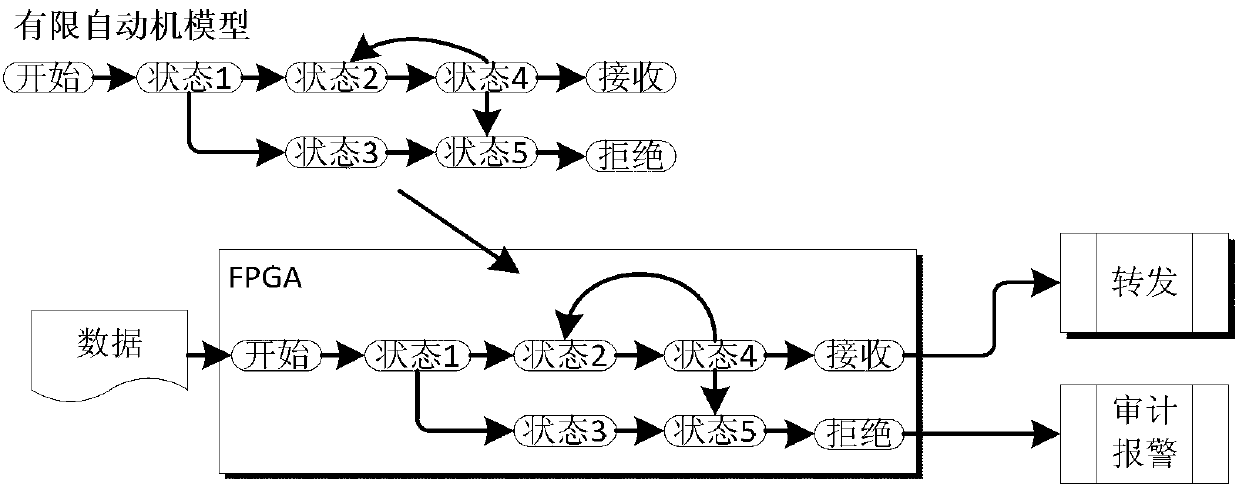
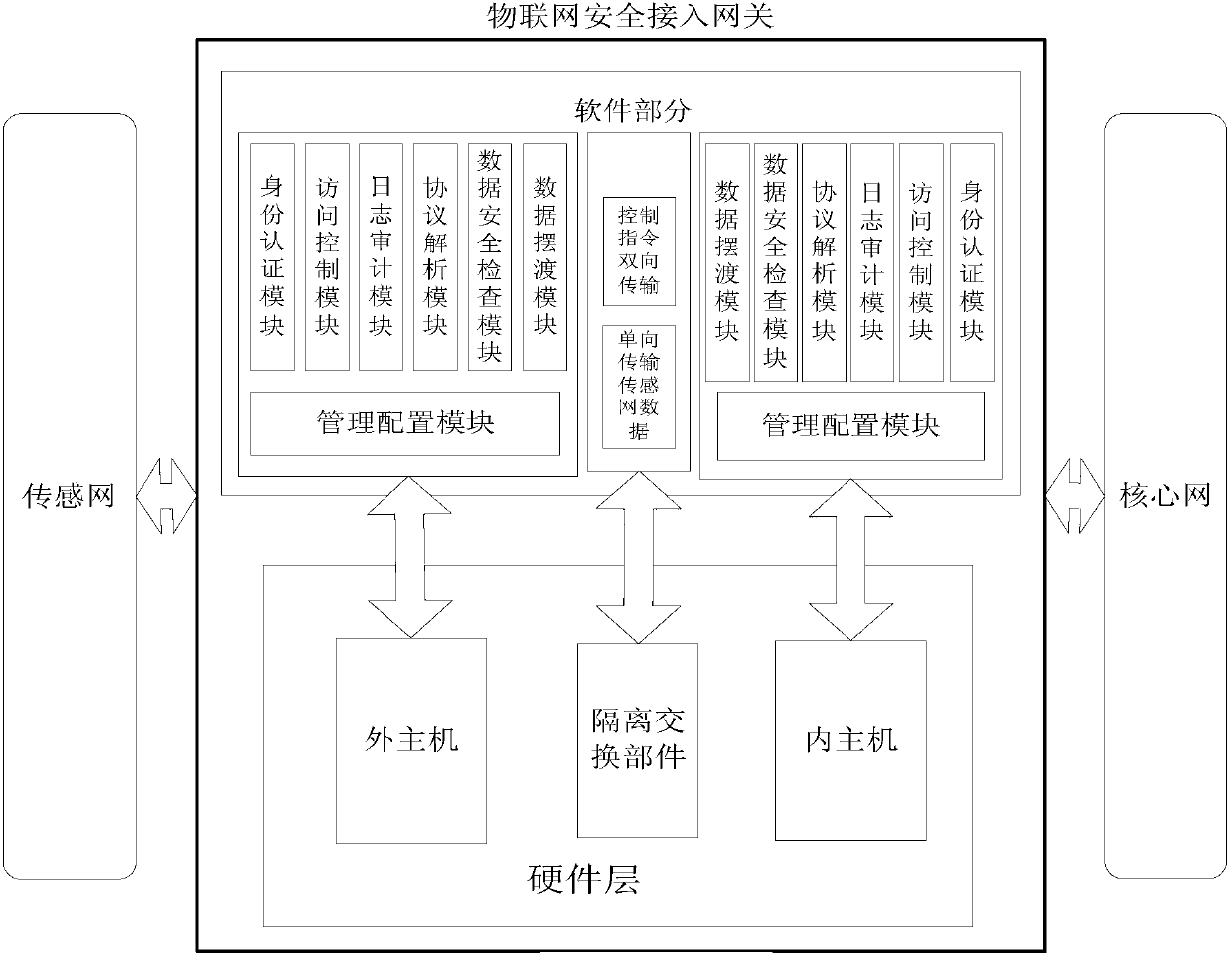
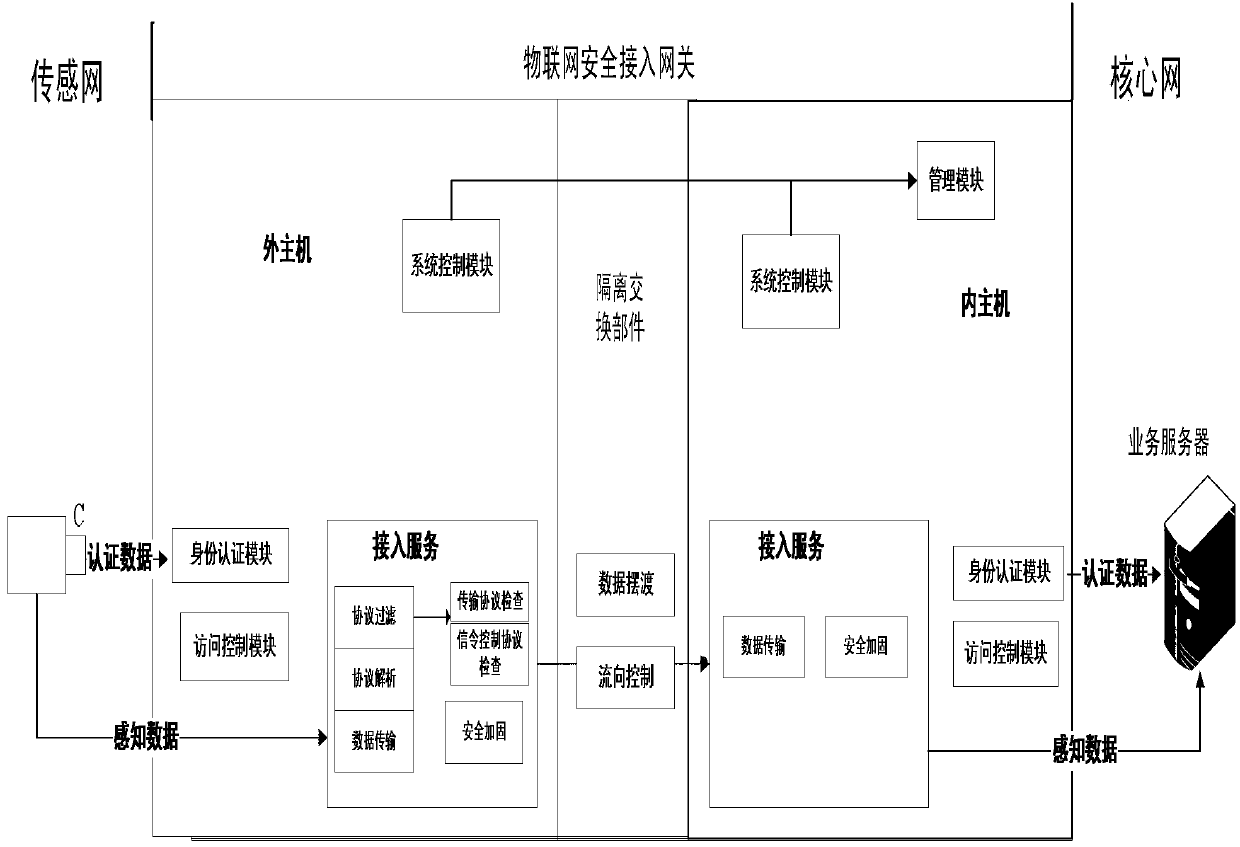
The invention discloses an internet of things security access gateway. A three component framework of 2+1 is adopted in a hardware layer of the gateway. The three component framework comprises an outer host machine, an isolation exchange component and an inner host machine. A filed programmable gate array (FPGA) card based on hardware serves as the isolation exchange component so that isolation of a network and safe and rapid exchange of data are achieved. Device certification, access control, protocol analysis, data security check, data ferry service and audit service are achieved through software layers on the inner host machine and the outer host machine and action of the services can be traced. The internet of things security access gateway has the advantages that relative requirements that data collected by an internet of things perception terminal is introduced to a core network safely are satisfied, network attack, Trojan horse virus transmission and denial of service attack are prevented from being launched through a sensing layer network with weak safety protection to the core network, safe exchange of data is achieved under the condition that the sensing network and the core network are in network isolation, and practical application of the internet of things is achieved under the condition that safety is guaranteed.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
Method and apparatus for performing electronic data file protection based on encrypted partition
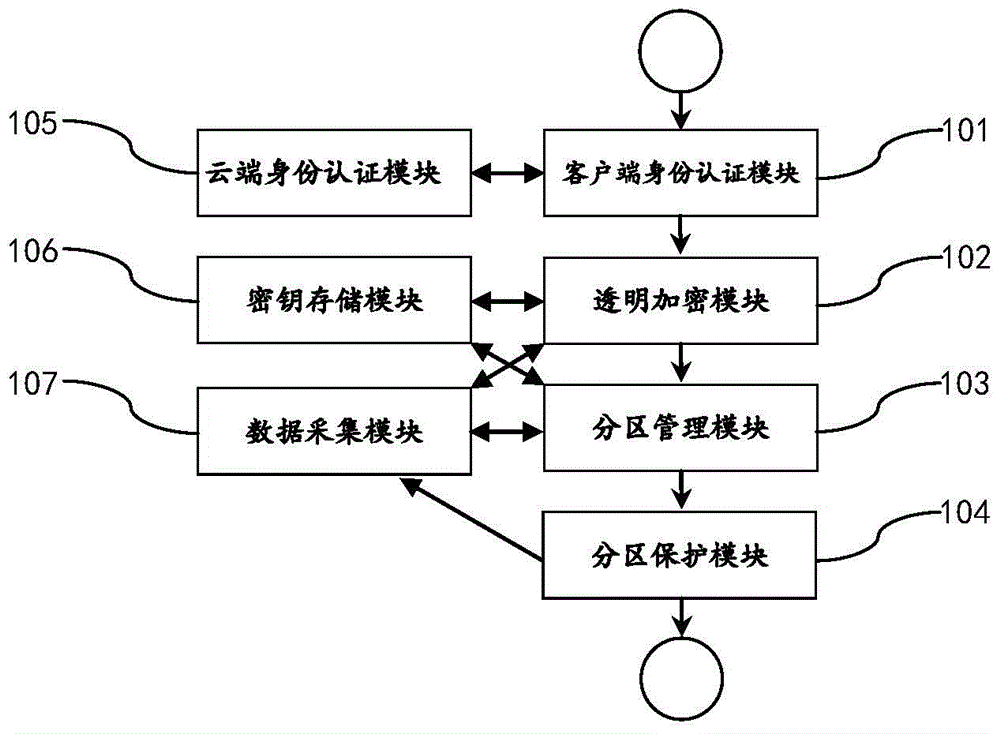
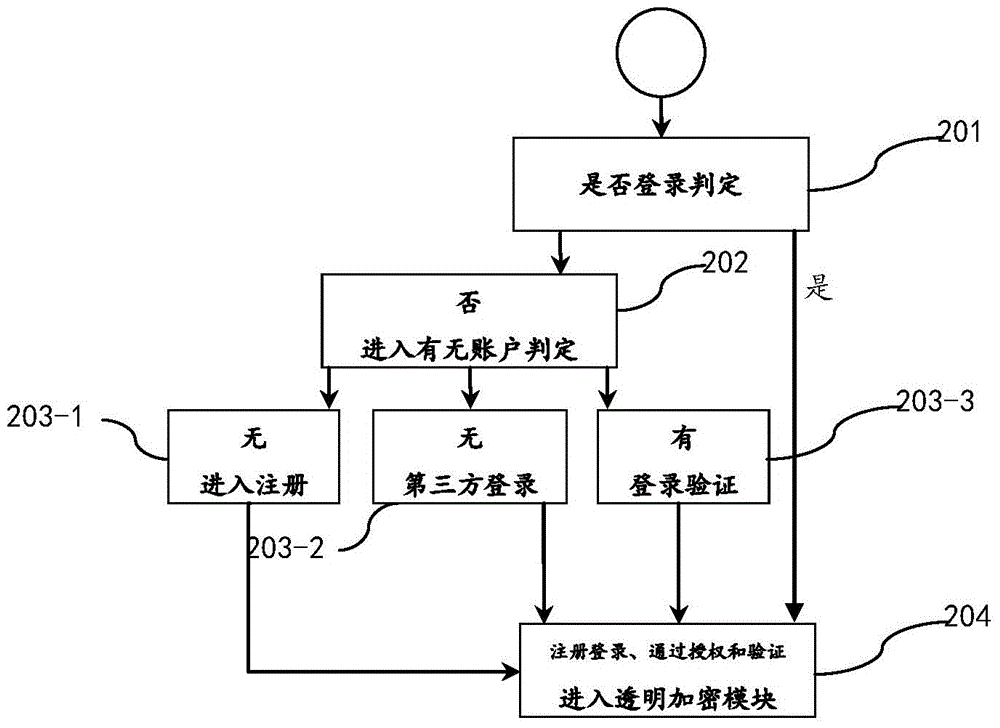
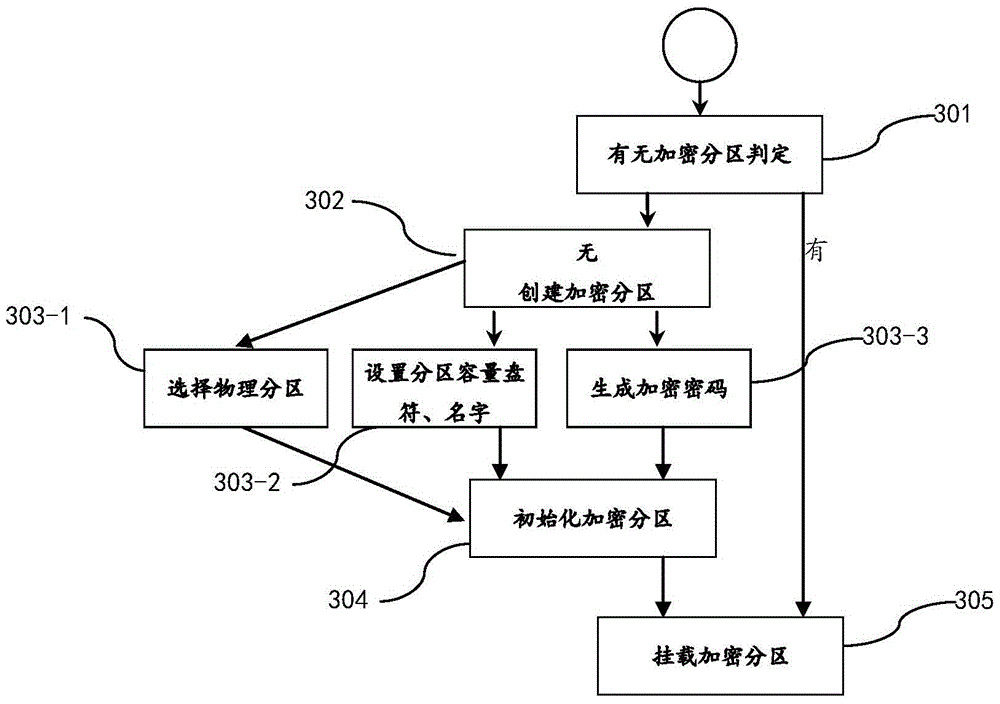
The present invention discloses a method and an apparatus for performing electronic data file protection based on an encrypted partition, and belongs to the field of electronic data file protection. The apparatus disclosed by the present invention adopts an overall design of ''a cloud server+a client''. The cloud server comprises a data acquisition module, a key storage module and a cloud identity authentication module. The client comprises a client identity authentication module, a transparent encryption module, a partition management module and a partition protection module. According to the method and apparatus disclosed by the present invention, ''a cloud server+a client'' dynamic authentication and transparent encryption / decryption are combined, so that files and folders can be effectively prevented from being freely accessed, duplicated or deleted by others, and the security of privacy data is ensured.
Owner:XLY SALVATIONDATA TECHNOLOGY INC
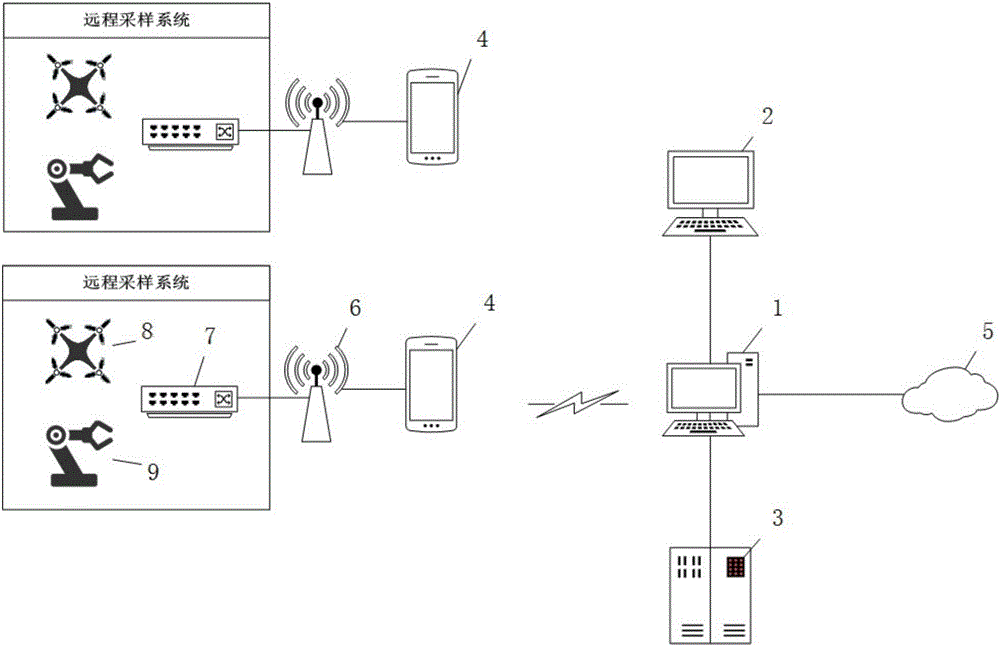
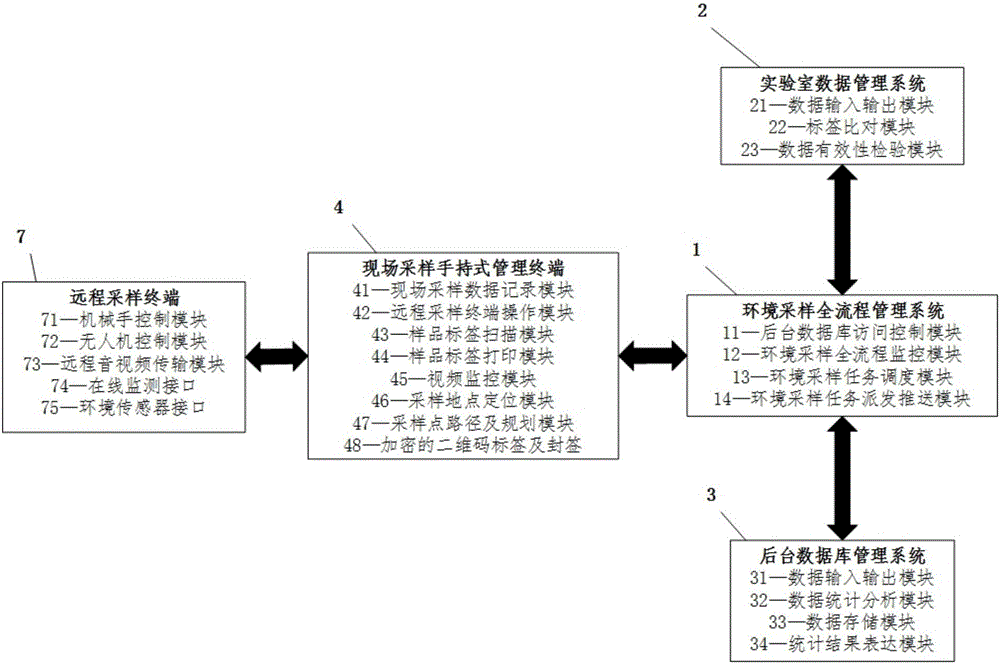
Whole process management and control-based environment sampling management system and method
The invention discloses a whole process management and control-based environment sampling management system and method. The system comprises an environment sampling whole process management system, a laboratory data management system, a background database management system, one or more embedded system secondary development-based field sampling handheld management terminals, one or more cloud information distribution systems, one or more directed wireless data reception / transmission ends, one or more remote sampling terminals and one or more remote sampling tools, wherein the one or more cloud information distribution systems are supplied to the public for accessing environment sampling test data and reports, and the one or more directed wireless data reception / transmission ends are used for field short-distance data transmission. According to the system and method disclosed by the invention, the whole process management and control in an environment sampling process can be realized by utilizing technological means such as real-time video uploading, two-dimensional code encryption and task pushing.
Owner:北京南科大蓝色科技有限公司 +1
File management method of electronic equipment and electronic equipment
InactiveCN105653582ANormal accessRealize temporary storageSpecial data processing applicationsElectronic equipmentFile storage
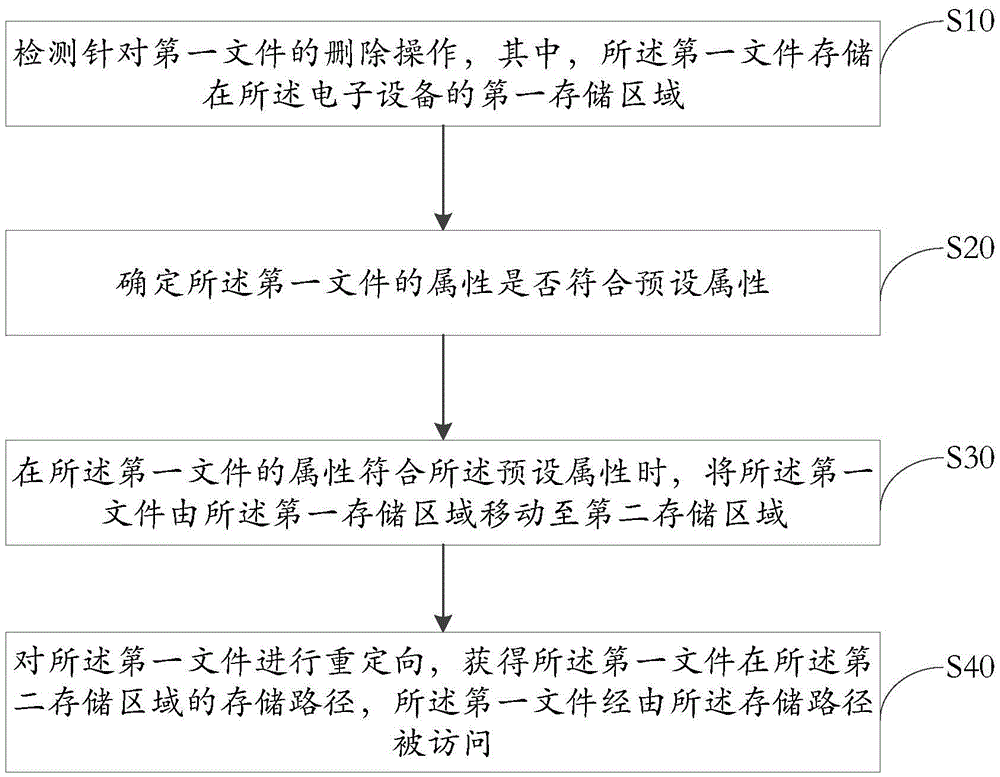
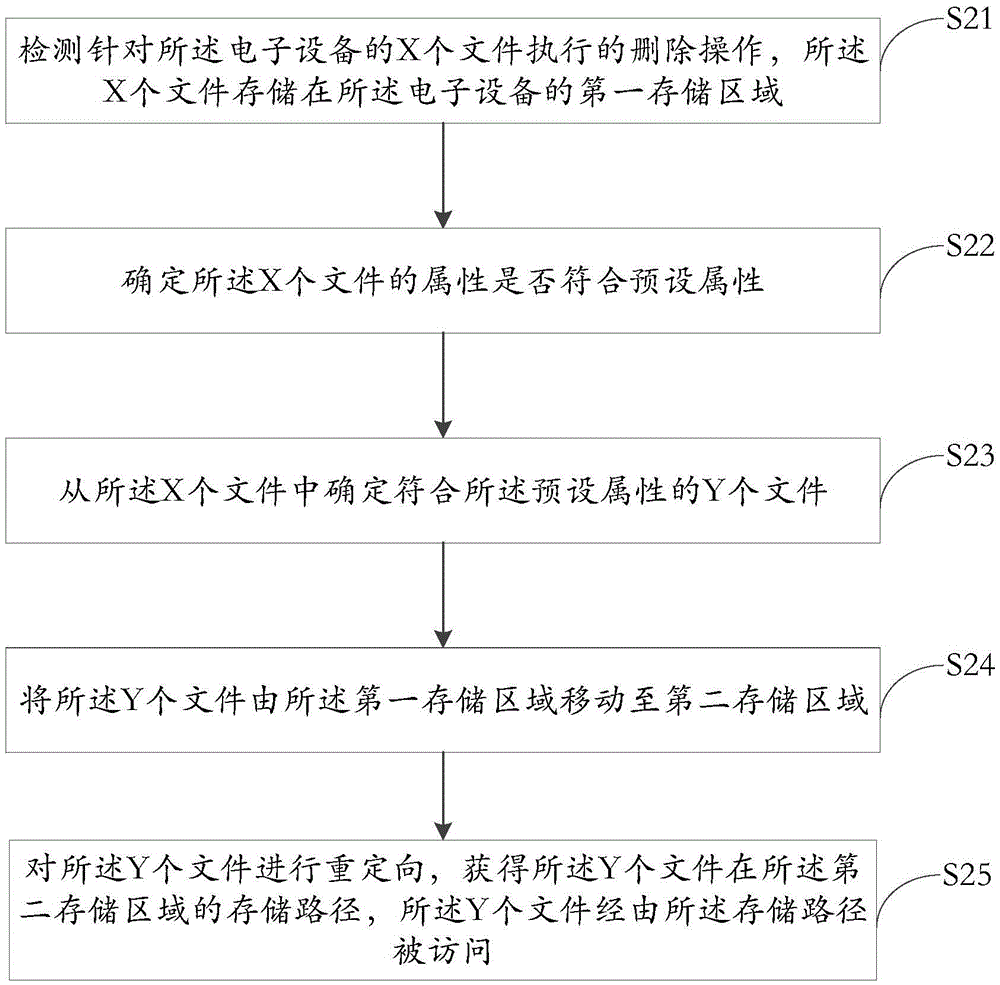
The invention discloses a file management method of electronic equipment and the electronic equipment. The method comprises the following steps: detecting a deletion operation in allusion to a first file, wherein the first file is stored in a first storage area of the electronic equipment; determining whether the attribute of the first file accords with a preset attribute; when the attribute of the first file accords with the preset attribute, moving the first file from the first storage area to a second storage area; and redirecting the first file to obtain a storage path of the first file in the second storage area, wherein the first file is accessed through the storage path. The method provided by the invention is used for solving the technical problem that related applications cannot run normally as the files cannot be accessed after being deleted, so that the technical effect that the deleted files are temporarily stored and then the related applications still can normally access to the files is realized.
Owner:LENOVO (BEIJING) CO LTD
Fluid conveyance system and fluid conveyance device
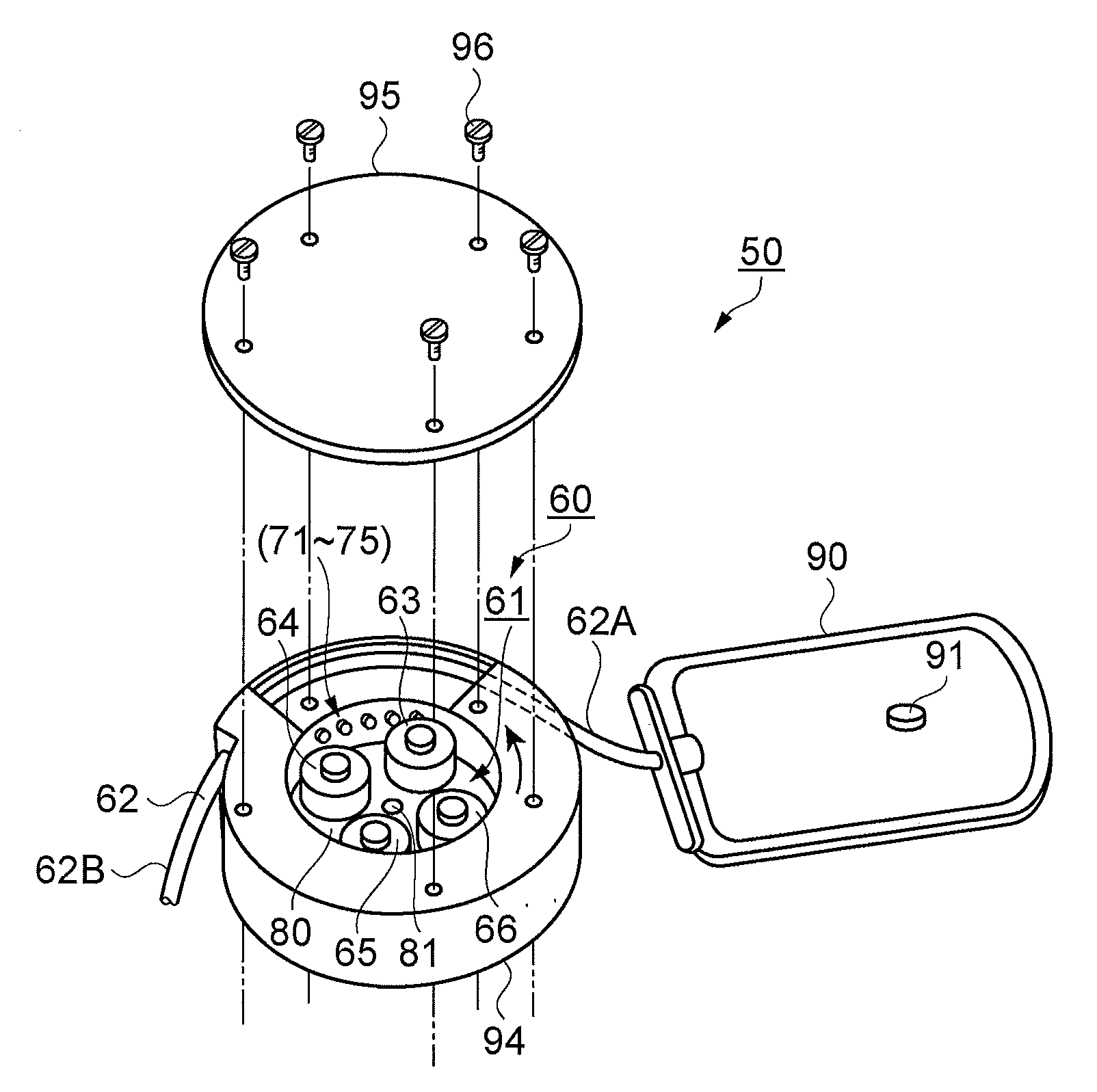
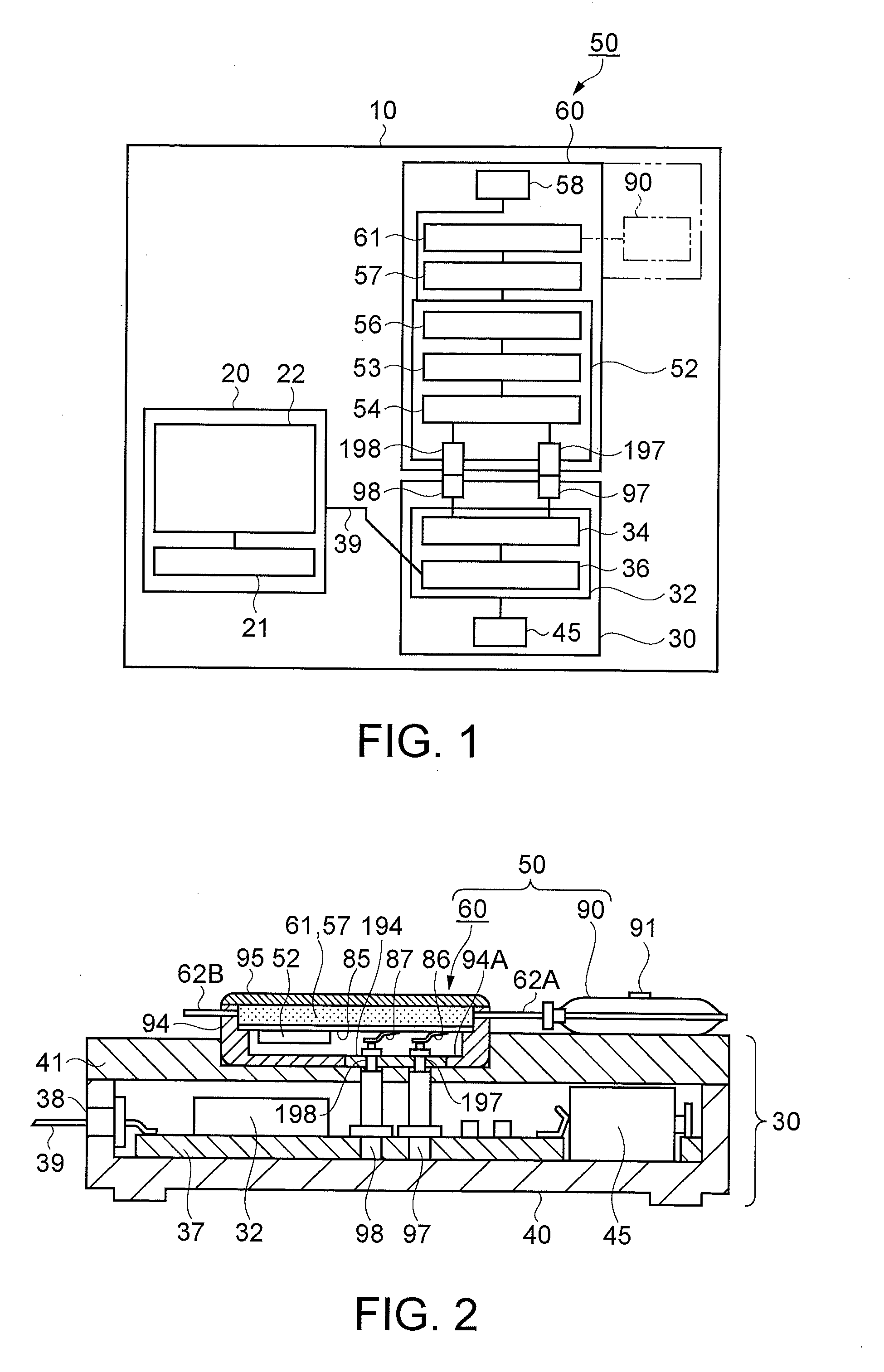
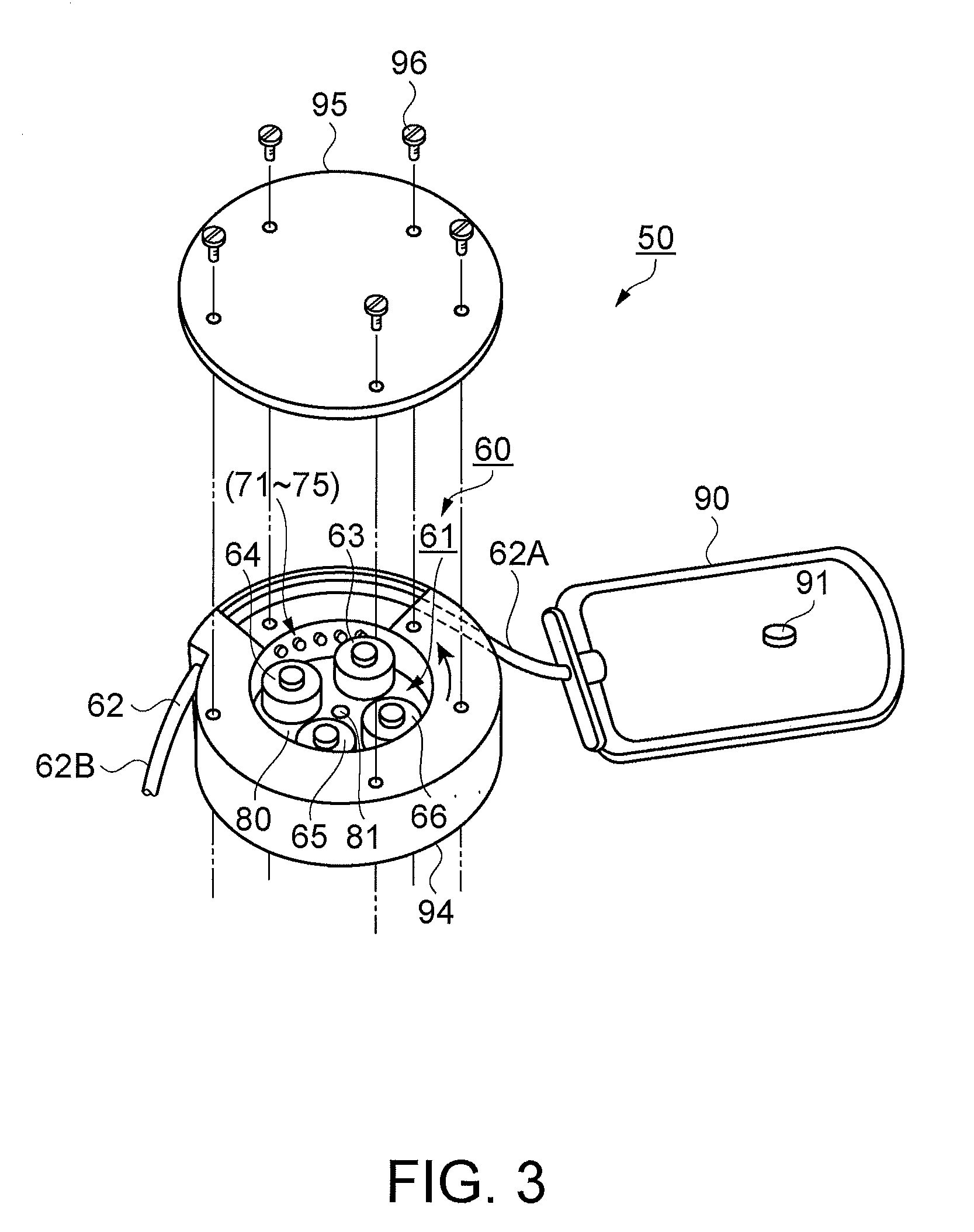
InactiveUS20080031740A1Eliminate the effects ofAvoid deletionFlexible member pumpsMedical devicesCommunication unitDischarge data
A fluid conveyance system includes: a fluid conveyance device including a micro pump module which compresses a flexible tube communicating with a fluid containing receptacle and discharges a fluid, a memory device furnished on the micro pump module which stores individual identification data of the micro pump module, and a power source; a discharge data processing device which stores basic data for driving the fluid conveyance device; and a communication device having a communication unit which interconnects the fluid conveyance device and the discharge data processing device, wherein the discharge data processing device inputs discharge data, for discharging a desired discharge amount of a fluid, calculated from the identification data and the basic data read via the communication device, into the memory device via the communication device, and the fluid conveyance device is driven based on the discharge data.
Owner:SEIKO EPSON CORP
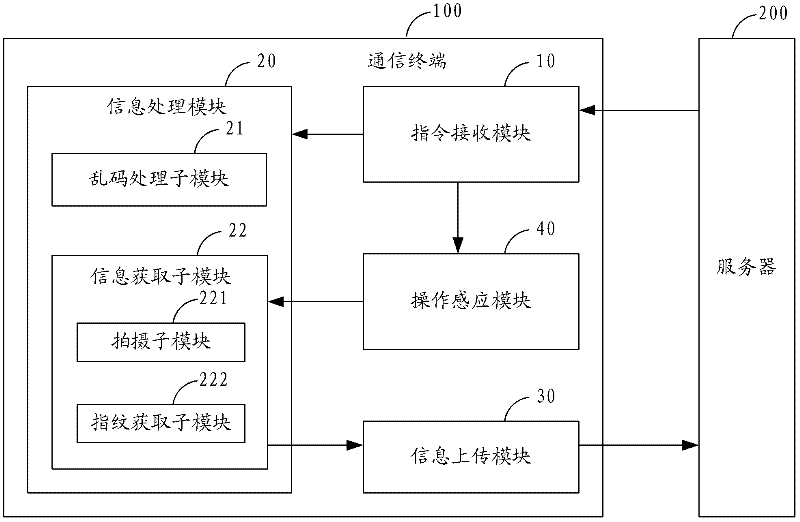
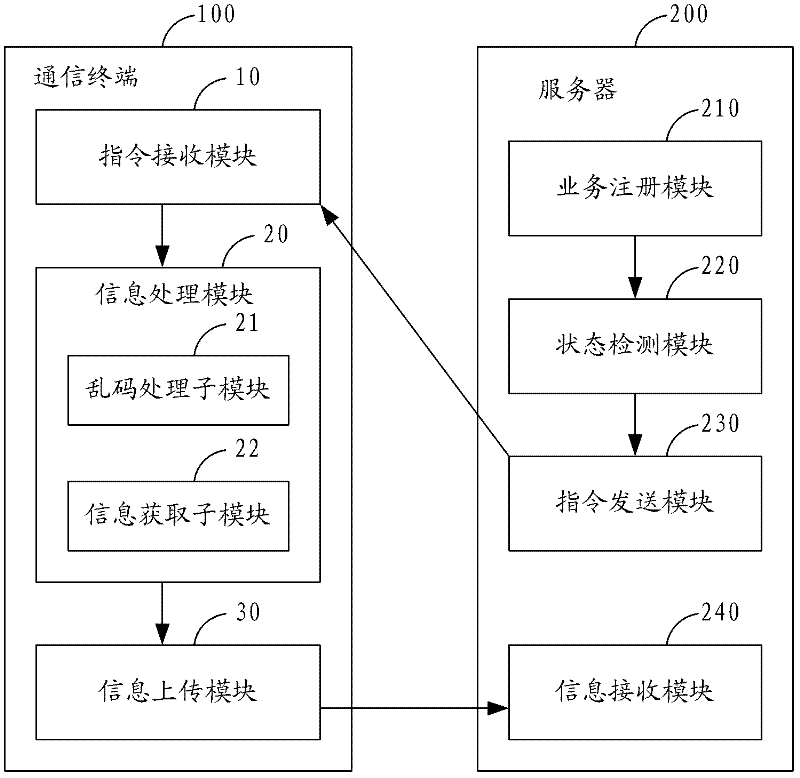
Processing method of communication terminal after being stolen and communication terminal
InactiveCN102509033AImprove securityProtection securityInternal/peripheral component protectionWireless commuication servicesComputer terminalAnti theft
The invention is suitable for the technical field of communication and provides a processing method of a communication terminal after being stolen and the communication terminal. The processing method comprises the following steps of: sending an anti-theft processing command to the communication terminal through a server; and carrying out messy code processing on data in the communication terminal by the communication terminal according to the anti-theft processing command. Therefore, after the communication terminal disclosed by the invention is stolen, when other people read the data of the communication terminal, the data is displayed in a messy code state, then the other people can be further prevented from illegally viewing or using private information of a user and safety of the information of the user can be effectively protected. In a better way, the communication terminal can automatically acquire physiological information of a suspected object according to the anti-theft processing command and uploads the physiological information of the suspected object to the server, so that possibility of getting the stolen communication terminal back by the user is increased.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
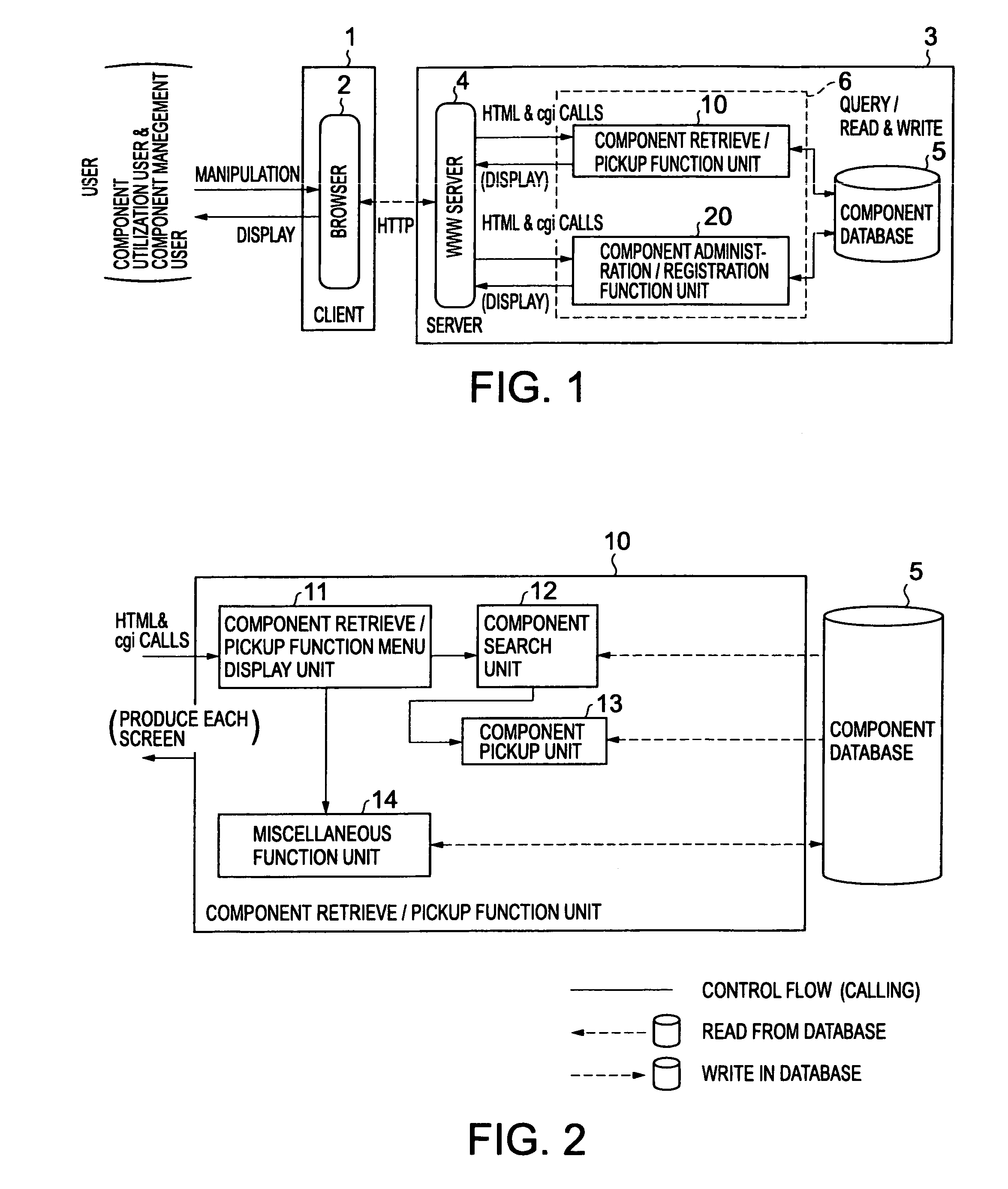
Software component library management system
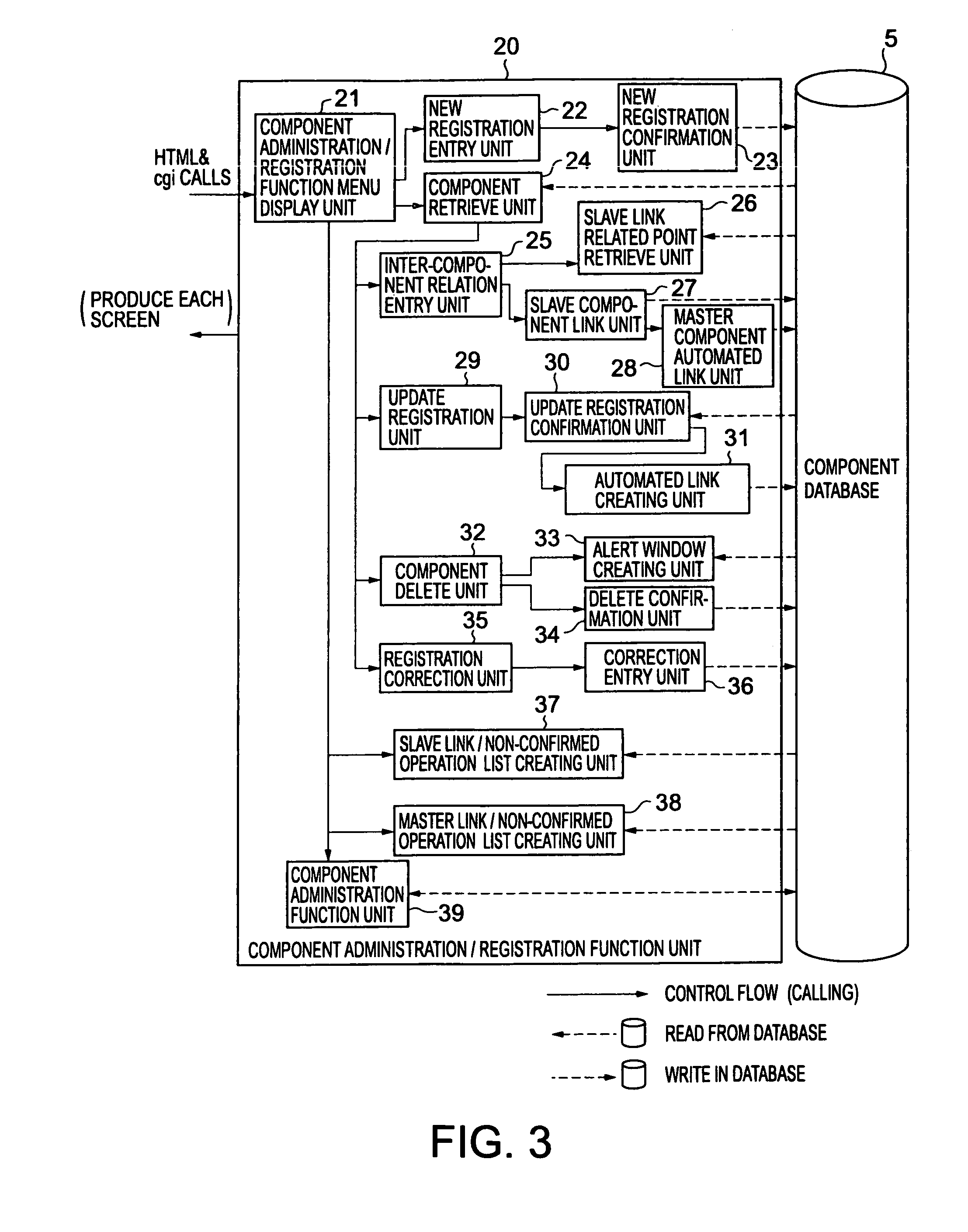
InactiveUS7676792B2Effective supportEasy to operateSoftware reuseSpecific program execution arrangementsManagement toolSoftware engineering
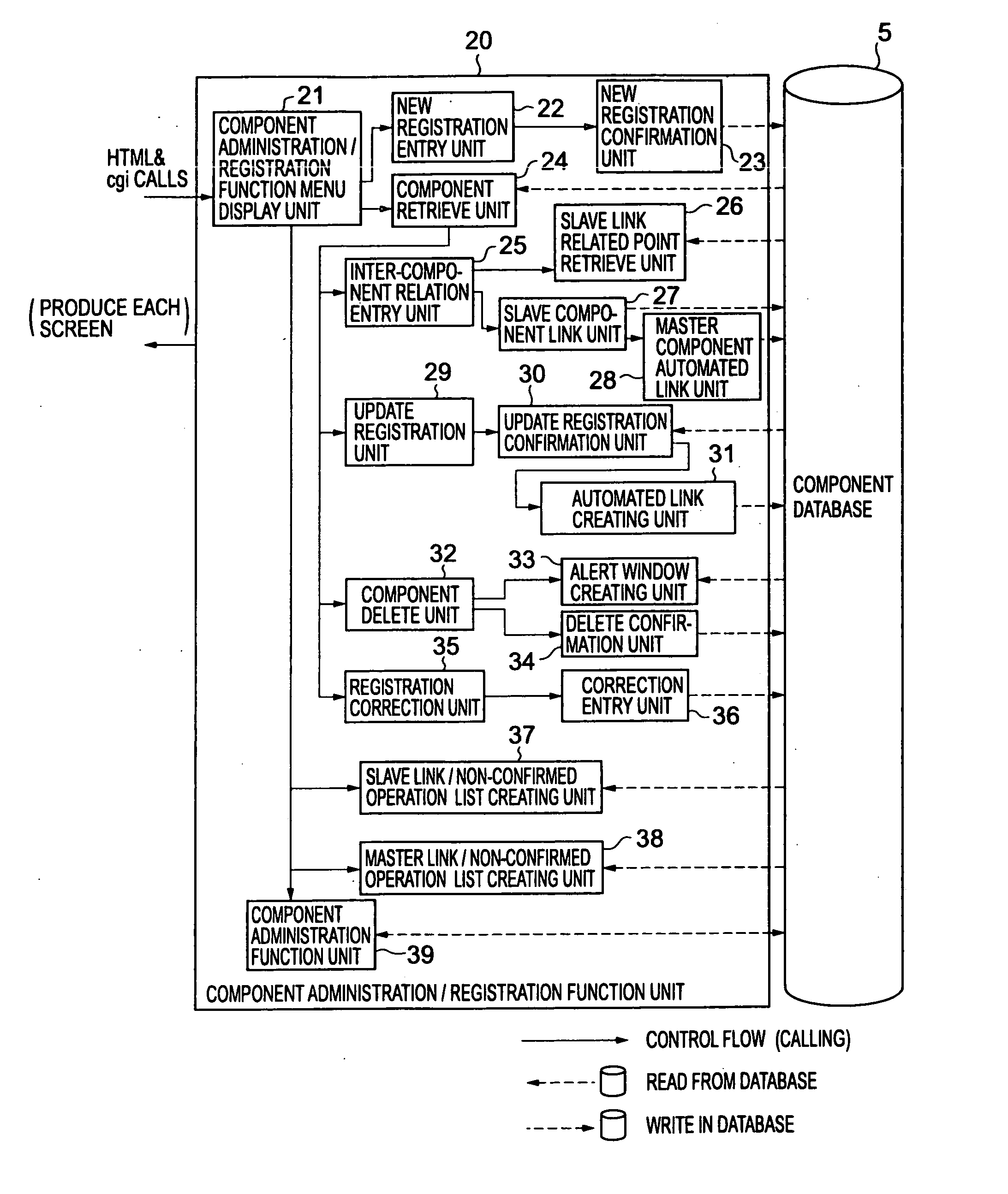
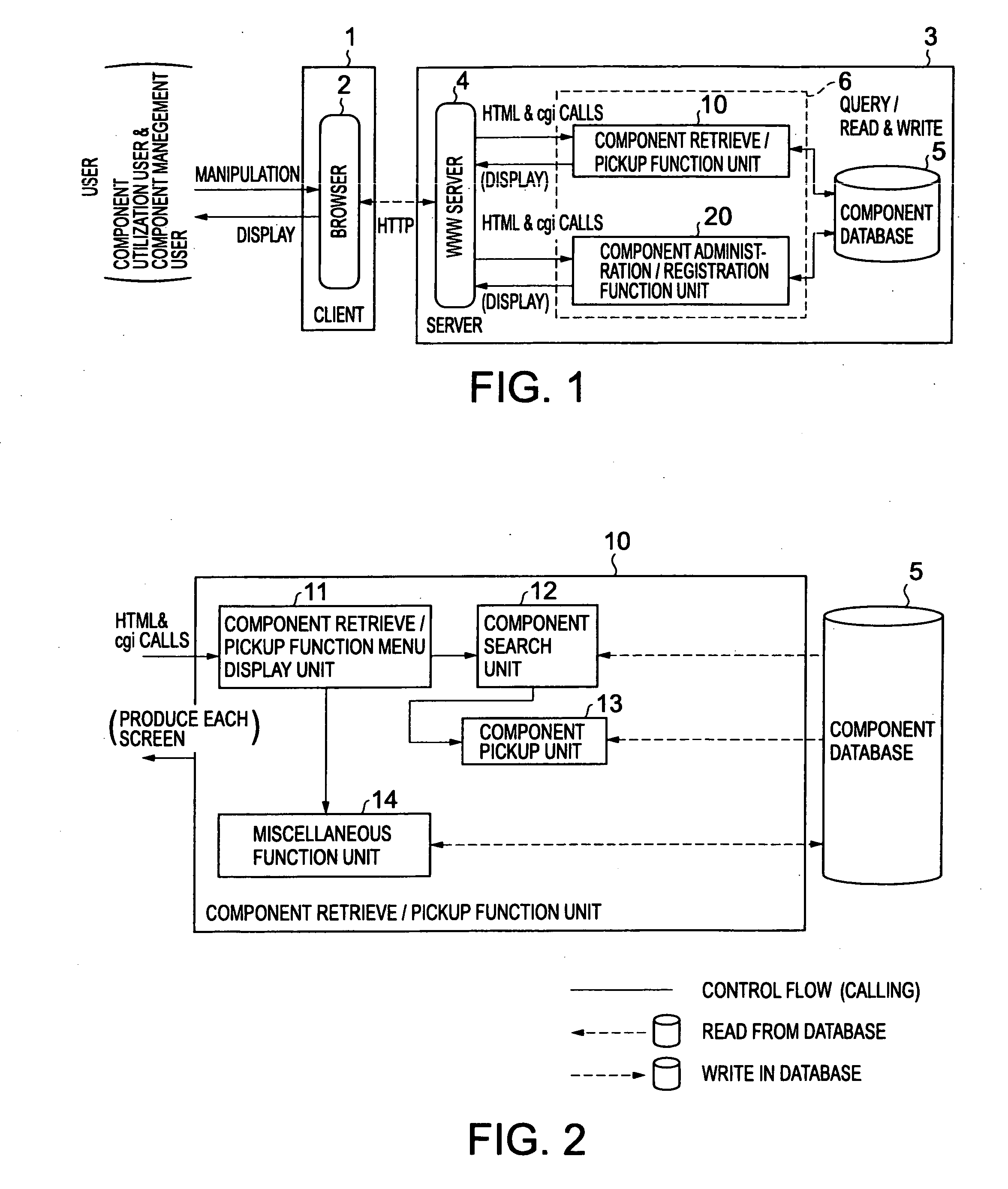
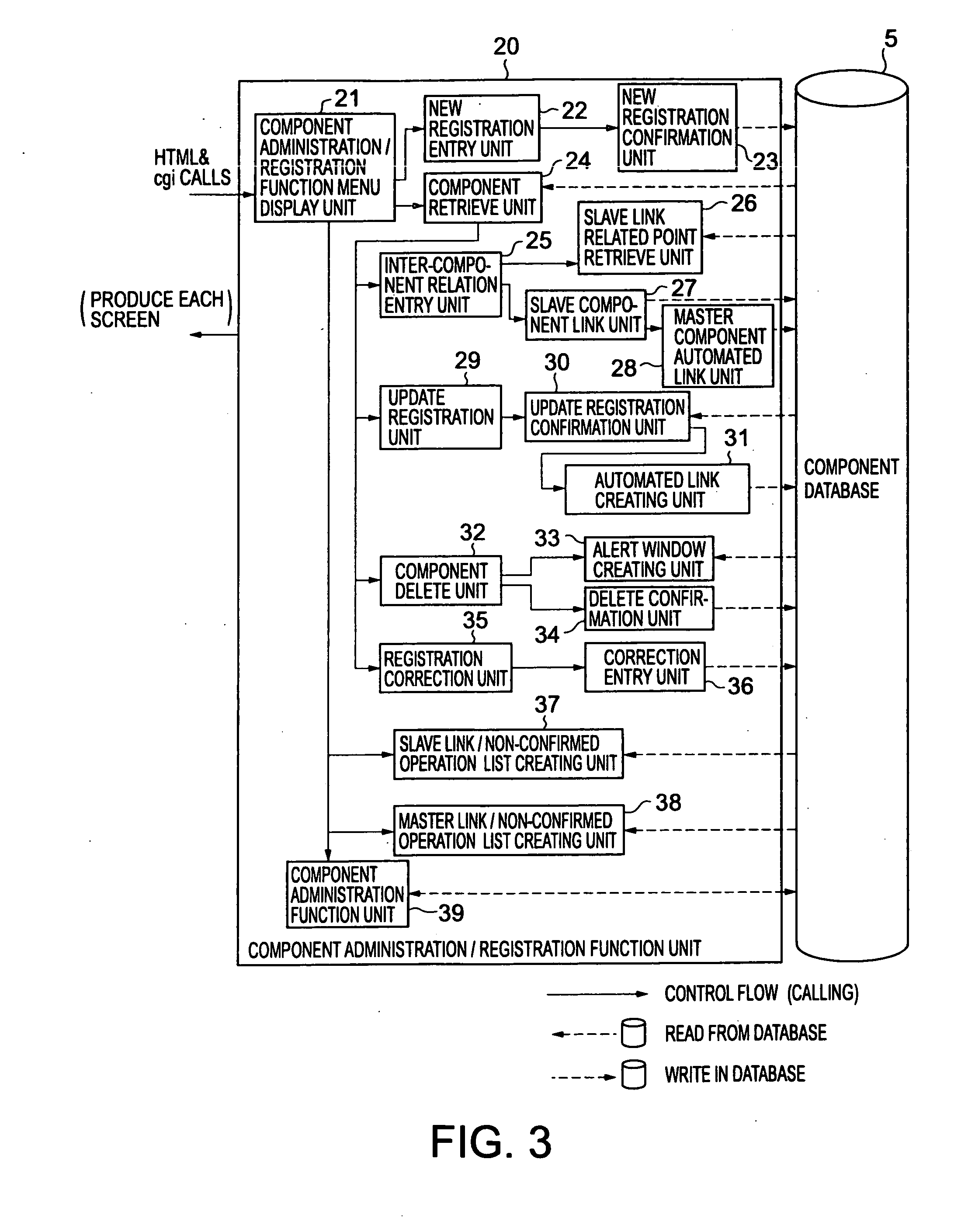
A software component library management system is provided, which can effectively support both a component utilization user and a component management user in carrying out their business tasks. The component management tool 6 includes a component retrieve / pickup function unit 10 and a component administration / registration function unit 20. The component administration / registration function unit 20 is adapted to make registrations of attribute information on software components stored in the component database 5, such as relation information items representing relations between the software component and other software components. The component retrieve / pickup function unit 10 can retrieve and pickup a batch of software components related to a specific software component, based on the relation information items. The relation information item includes a slave link used to identify a slave component which a certain software component uses (slave information item), and a master link used to identify a master component by which a certain software component is used (master information item).
Owner:KK TOSHIBA
Apparatus and method for canceling SMS message transmission and retaining received SMS message
InactiveUS20060063541A1Avoid spreadingAvoid deletionRadio/inductive link selection arrangementsAutomatic exchangesComputer hardware
Owner:SAMSUNG ELECTRONICS CO LTD
Software component library management system
InactiveUS20060037001A1Effective supportEasy to operateSoftware reuseSpecific program execution arrangementsManagement toolSoftware engineering
A software component library management system is provided, which can effectively support both a component utilization user and a component management user in carrying out their business tasks. The component management tool 6 includes a component retrieve / pickup function unit 10 and a component administration / registration function unit 20. The component administration / registration function unit 20 is adapted to make registrations of attribute information on software components stored in the component database 5, such as relation information items representing relations between the software component and other software components. The component retrieve / pickup function unit 10 can retrieve and pickup a batch of software components related to a specific software component, based on the relation information items. The relation information item includes a slave link used to identify a slave component which a certain software component uses (slave information item), and a master link used to identify a master component by which a certain software component is used (master information item).
Owner:KK TOSHIBA
Method and apparatus for garbage collection using advanced marking techniques and restricted barrier to protect the data
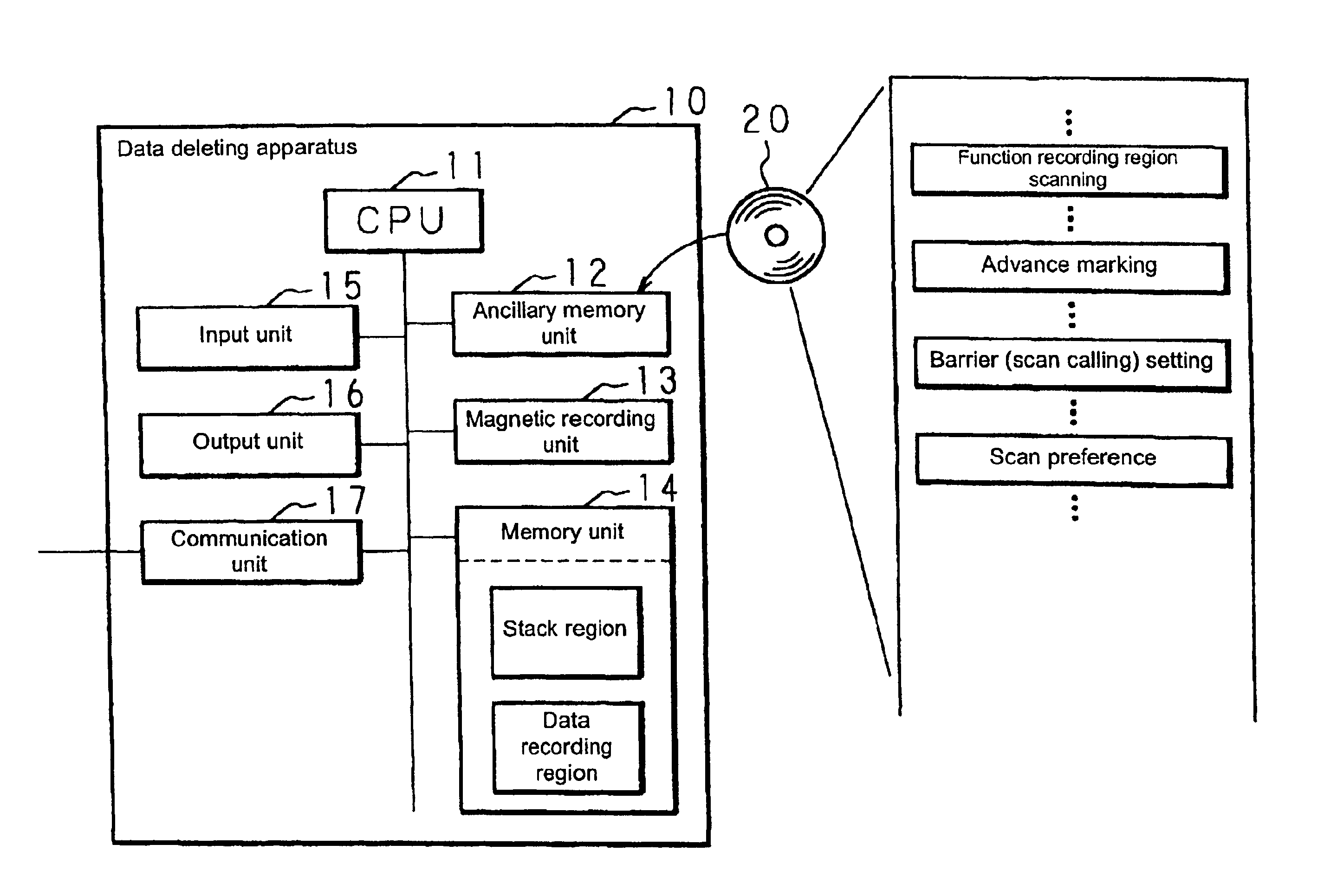
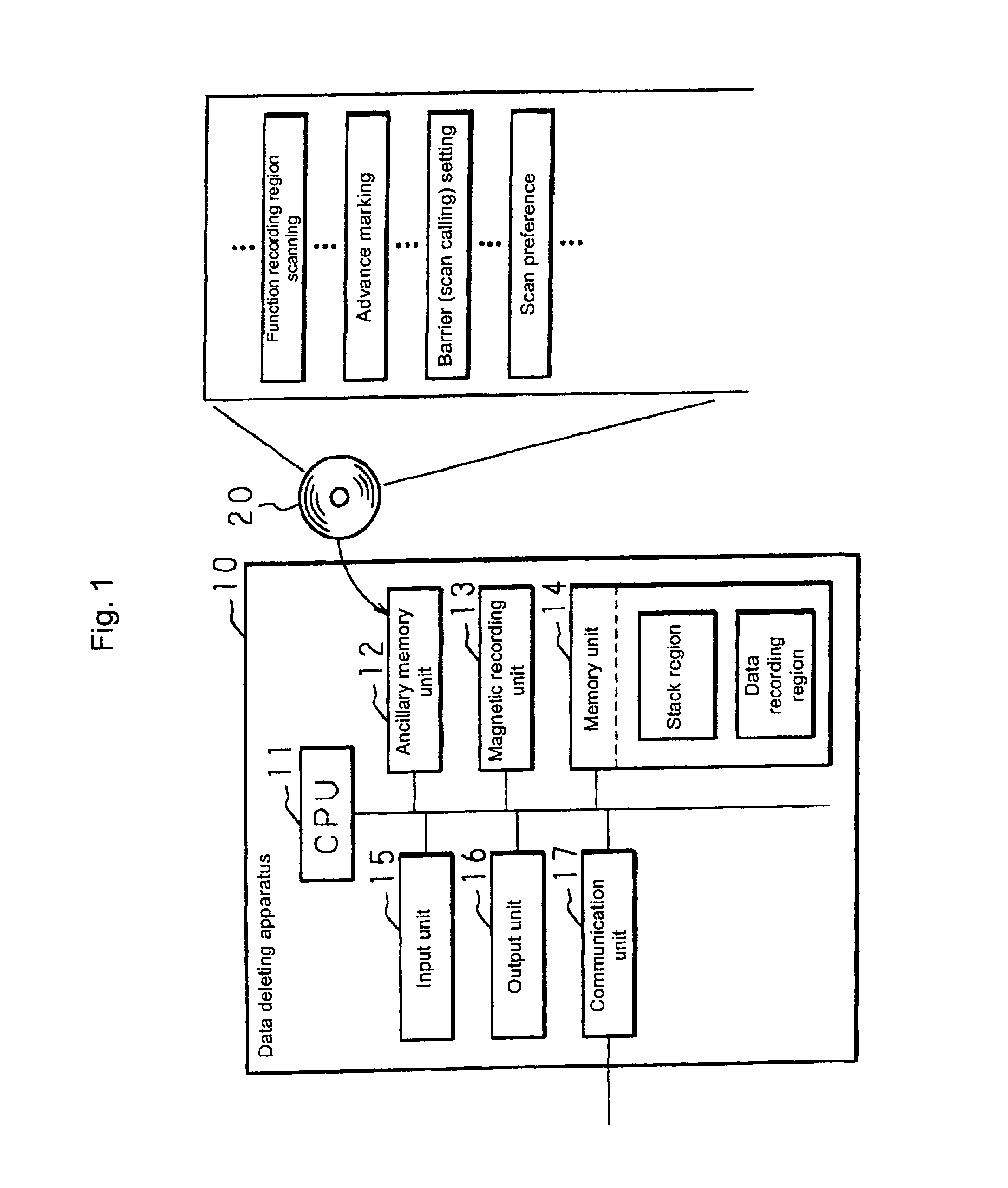
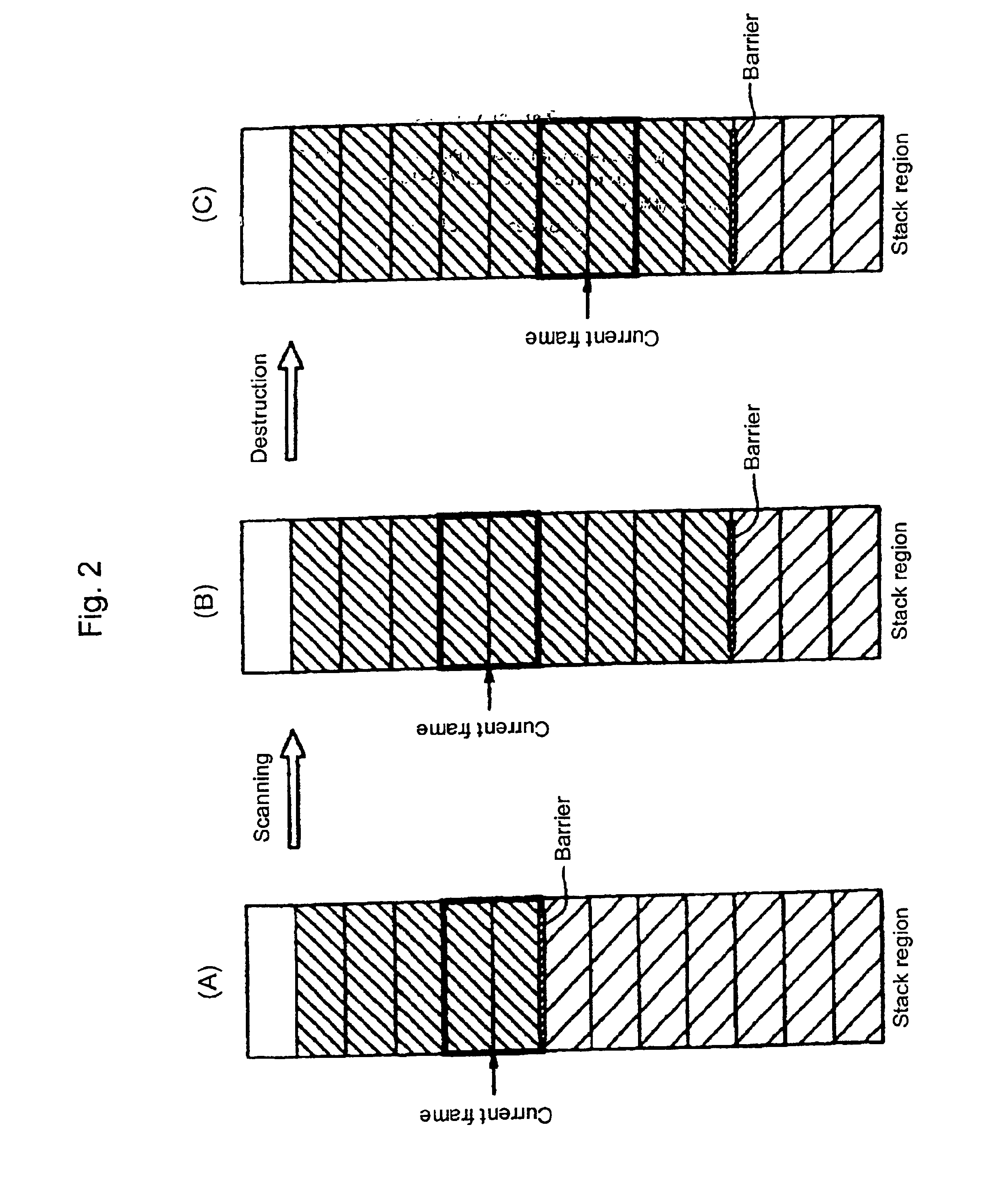
InactiveUS6912554B2Process abnormalityAvoid deletionData processing applicationsMemory adressing/allocation/relocationWaste collectionData recording
A method for deleting data, a data deleting apparatus and a recording medium involve a process for deleting unnecessary data generated during the processing of a main program which is created using programming languages which create data dynamically, wherein revisions of the main program are unnecessary and the overhead cost for that process is controlled without losing the real time property of the main program. While the main program is interrupted, the function recording region is scanned and advance marking to identify data for protection is carried out in the data recording region which is directly or indirectly indicated by the pointer which has been recorded in the functional recording region which has been scanned.
Owner:ORMON CORP
Cross-correlation mitigation method and apparatus for use in a global positioning system receiver
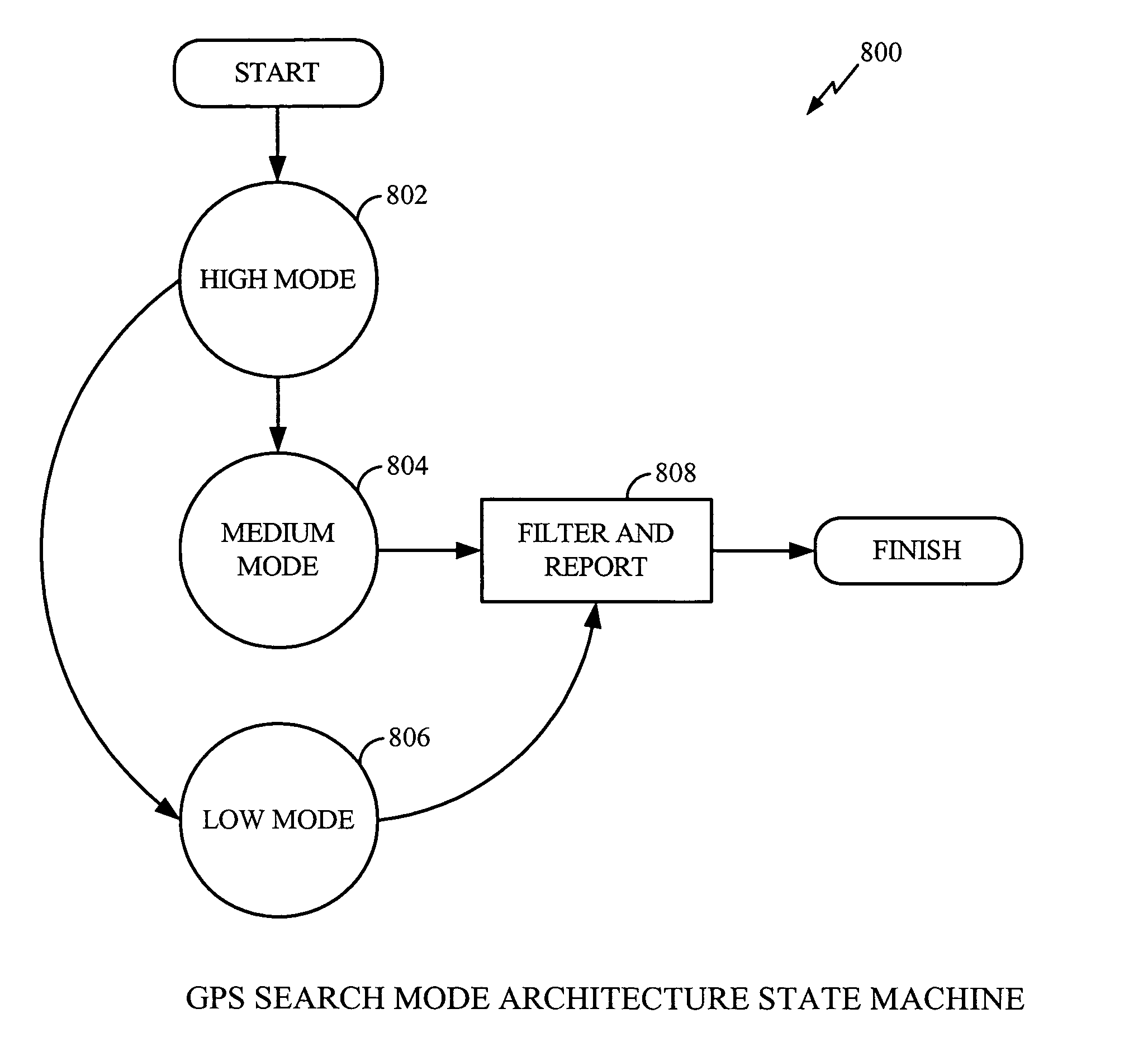
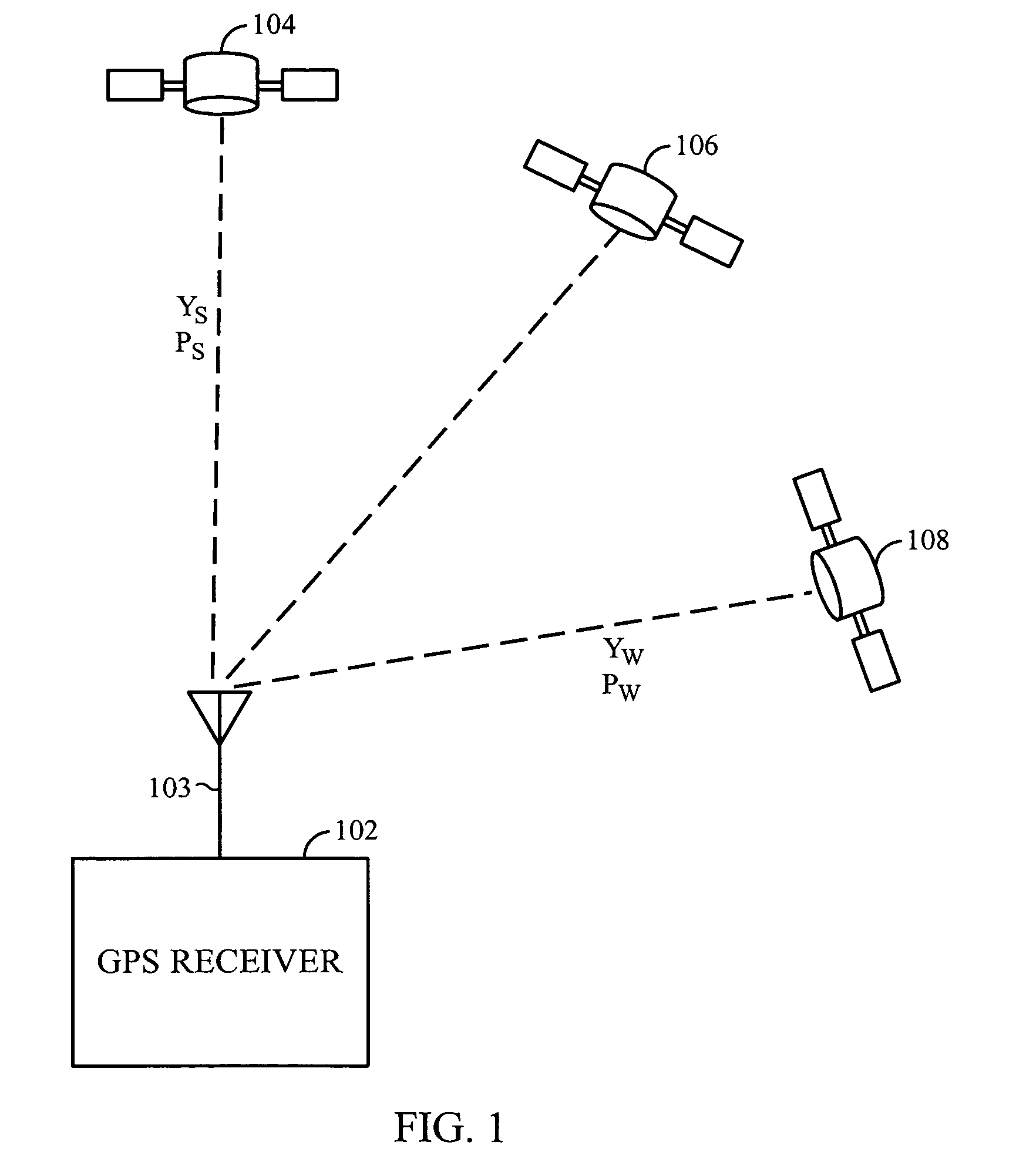
A method and apparatus mitigating the effects of cross-correlation signals on received satellite signals in a Global Positioning System (GPS) receiver is described. MS-Assisted and MS-Based cross-correlation detection and mitigation methods and apparatus are described. A GPS search mode architecture is used to detect SV signals and identify potential cross-correlations. The GPS search modes have different coherent integration lengths and different degrees of sensitivity. After detection, measurements are logged into a database for further processing. Several cross-correlation tests are described. For example, a “Mainlobe” cross-correlation test is described that identifies the most significant cross-correlations that occur when the Doppler difference between the interfering SV signal and the target SV signal is nonzero and a multiple of 1 kHz. Appropriate C / No and Doppler thresholds, or masks, are selected and used to identify the mainlobe cross-correlations. A wide Doppler mask is used to account for the effects on cross-correlations caused by BPSK data bit modulation. Appropriate MS-Assisted and MS-Based cross-correlation masks are described. Other cross-correlation tests include “variable C / No”, “strong”, “wide Doppler” and “pre-emptive” cross-correlation detection tests.
Owner:QUALCOMM INC
Static object detecting method and system
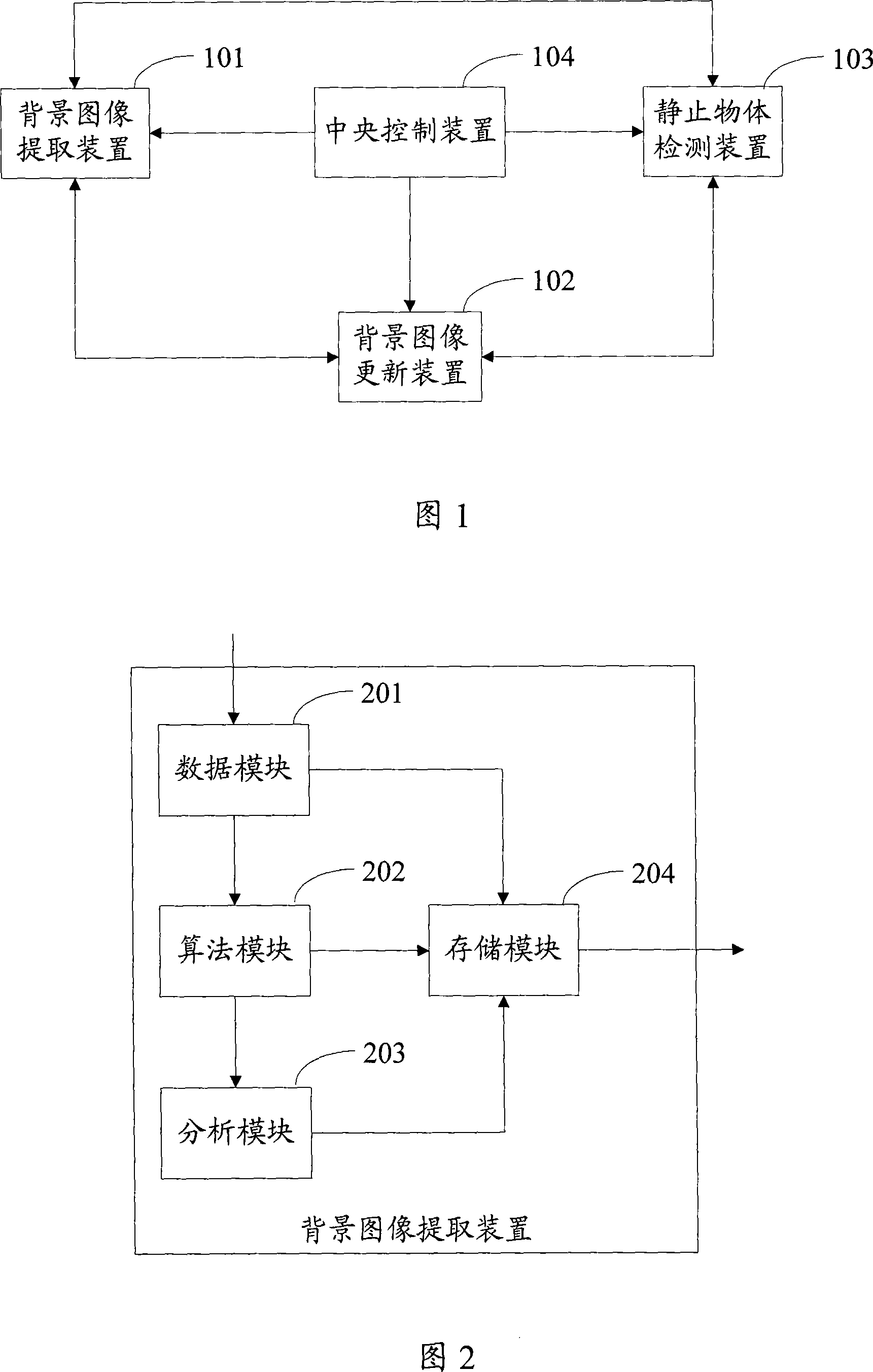
ActiveCN101026685AAccurate gray valueAccurately getTelevision system detailsColor television detailsAlgorithmStationary object
Being in use for solving issue that still object cannot be detected precisely currently. The method includes steps: comparing each target foreground (TF) in current image frame with each historical foreground (HF); when determining it is existed that both ratios of crossed area between a TF and a HF to first area of the TF, and to second area of the HF respectively are not smaller than prearranged first threshold value, the method updates parameter value, which is in use for marking a HF is matched; when determining that second area ratio is not smaller than first threshold value, first area ratio is smaller than first threshold value, and crossed area is as area of HF, and the first area ratio is not larger than prearranged second threshold value, the method considers a TF as a HF; ensuring that a HF corresponding matched parameter value reaching to third threshold value is as a still object. The invention also discloses devices and system for detecting still object.
Owner:中星智能系统技术有限公司
Framework system
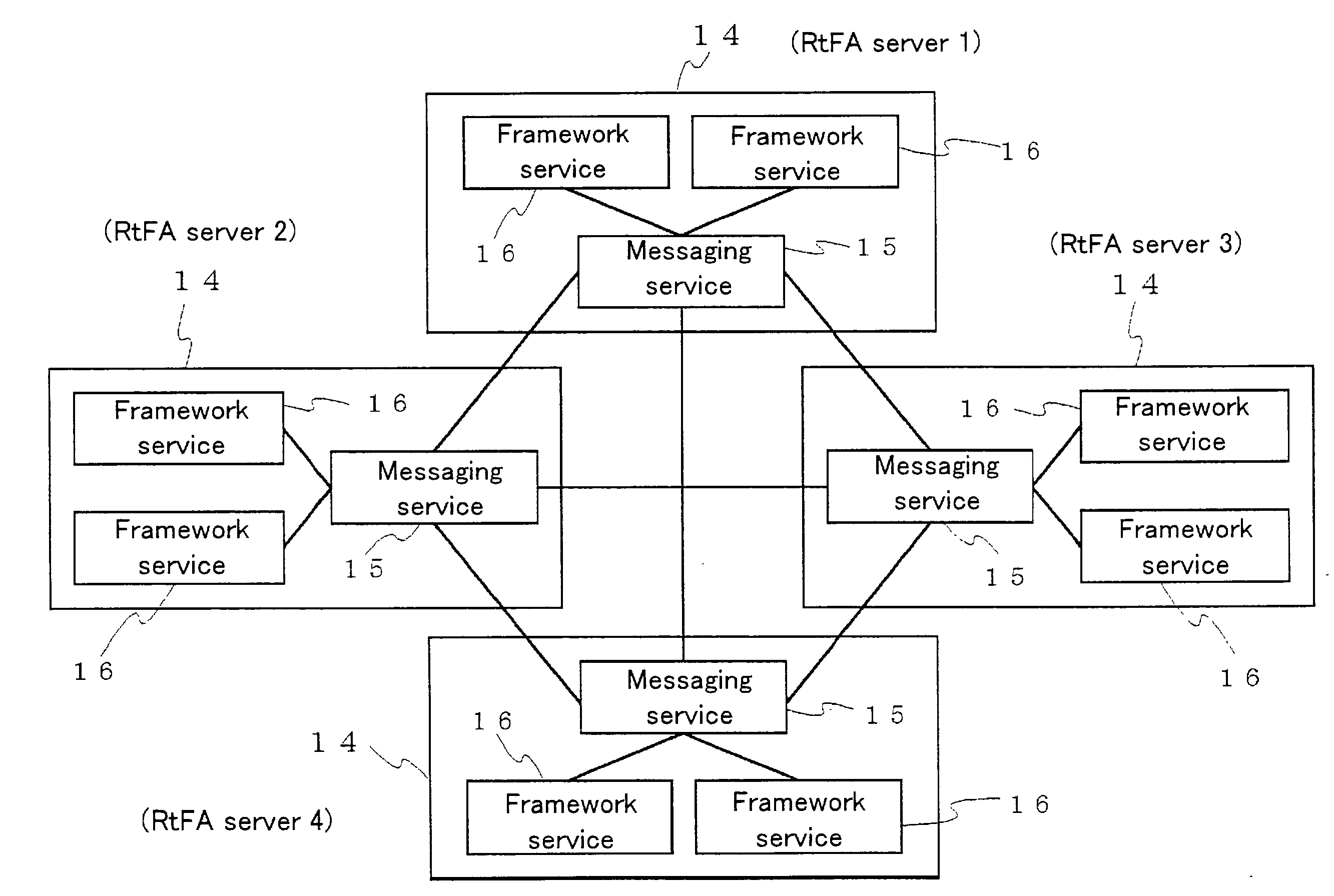
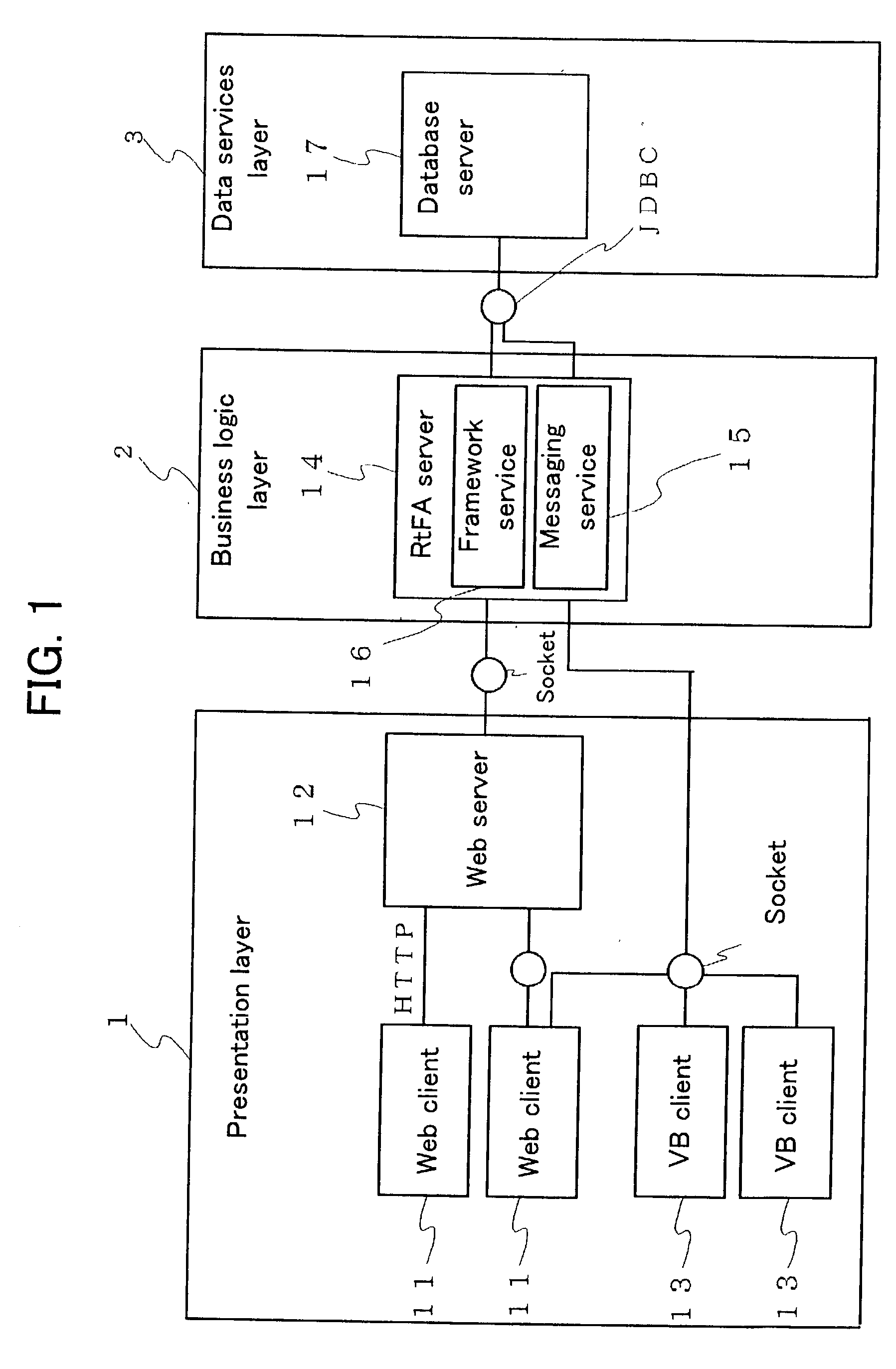
ActiveUS20030014551A1Easy to changeEasily definedInterprogram communicationMultiple digital computer combinationsTime scheduleMessage flow
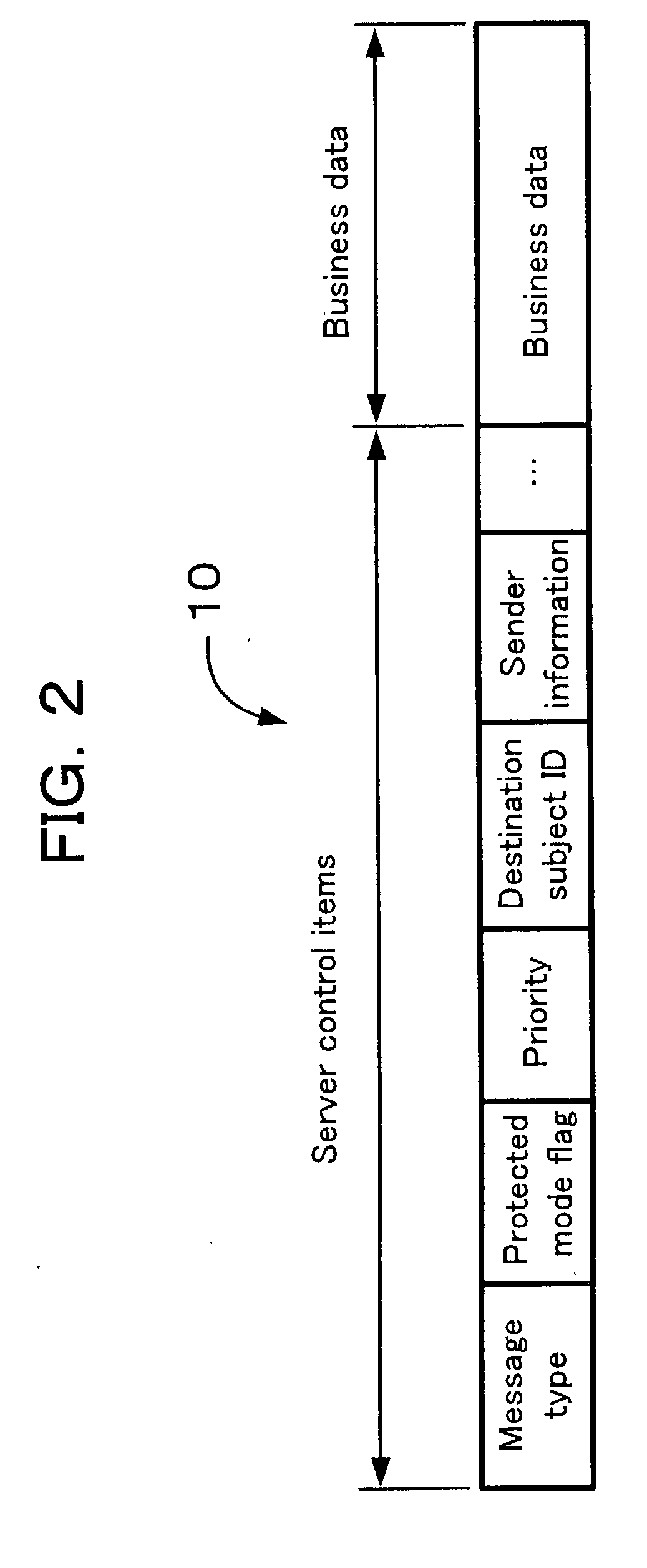
Disclosed is a framework system improved such that flow of complex business logic for processing a variety of messages may be easily defined and changed without need for programming. Messaging service(s) 15 may relay message(s) between client(s) 11, 13 and framework service(s) 16. Among request message(s) relayed from client(s) 11, 13 to framework service(s) 16 there may be message(s) comprising subject ID(s) associated with subject(s) of such message(s). Framework service(s) 16 may possess a plurality of sets of business logic 22 and flow definition file(s) 23. Flow definition file(s) 23 may comprise a plurality of definition sentences respectively corresponding to various subject IDs, and each such definition sentence may indicate schedule(s) for execution of business logic. Framework service(s) 16, upon receiving request message(s) from messaging service(s) 15, may select one or more sets of business logic for execution in accordance with execution schedule(s) corresponding to subject ID(s) of such message(s) indicated in definition file(s). Flow definition file(s) 23 can be rewritten at desired time or times notwithstanding the fact that framework service(s) 16 may be operational at such time(s). In the event that a plurality of sets of business logic are to be executed in linked fashion, framework service(s) 16 may execute subsequent business logic synchronously and / or asynchronously with respect to first business logic pursuant to execution schedule(s) indicated in definition sentence(s).
Owner:FUTURE SYST CONSULTING
Method for managing mobile terminal software and mobile terminal
InactiveCN103389898AAvoid erratic or even severe crashesAvoid deletionSpecific program execution arrangementsInstabilitySoftware engineering
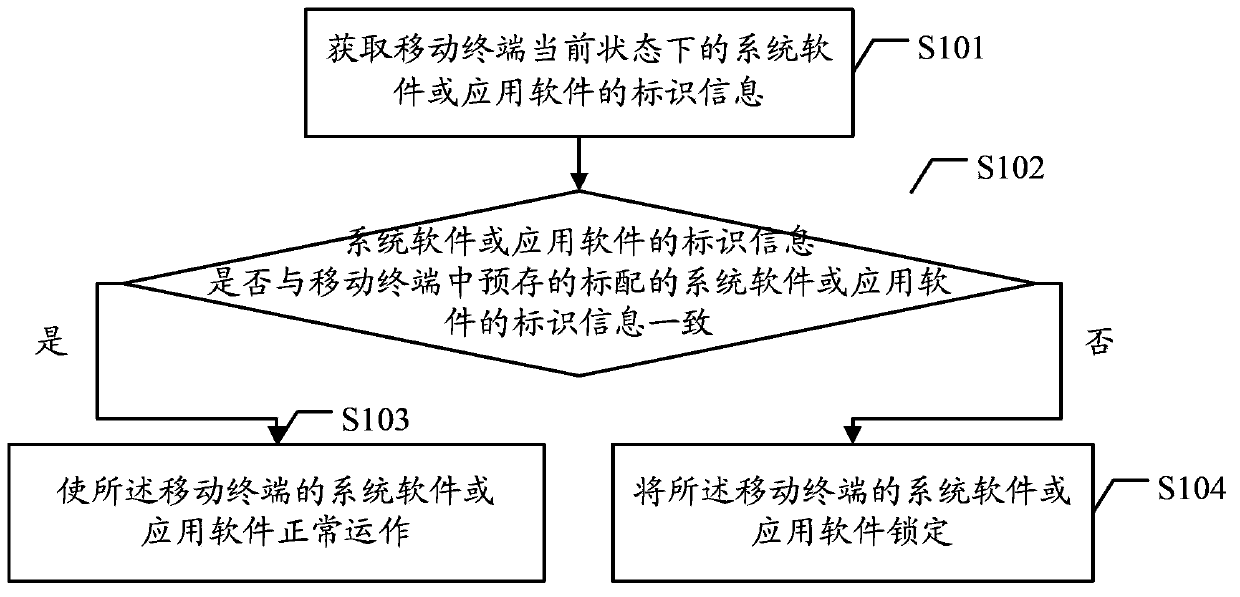
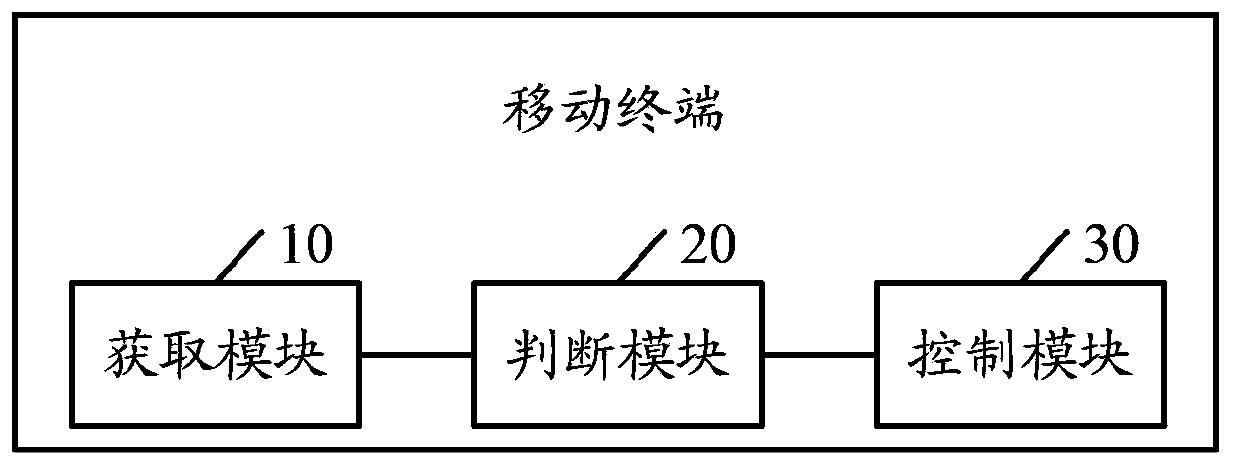
The embodiment of the invention discloses a method for managing mobile terminal software, which includes the following steps: the identification information of the system software or application software of a mobile terminal under the current state is acquired; whether the identification information of the system software or application software is the same as the identification information of standard system software or application software prestored in the mobile terminal is judged; if a judgment result is yes, then the system software or application software of the mobile terminal is enabled to normally operate, and if the judgment result is no, then the system software or application software of the mobile terminal is locked. The embodiment of the invention also discloses a mobile terminal. The method and the mobile terminal have the advantage that the unauthorized reinstallation of the mobile terminal by a user can be limited, so that the instability of the operation of the mobile terminal as the result of unauthorized reinstallation by the user is prevented, and thereby the stability of the operation of the mobile terminal is guaranteed.
Owner:SHENZHEN GIONEE COMM EQUIP
User terminal detaching method, system and device
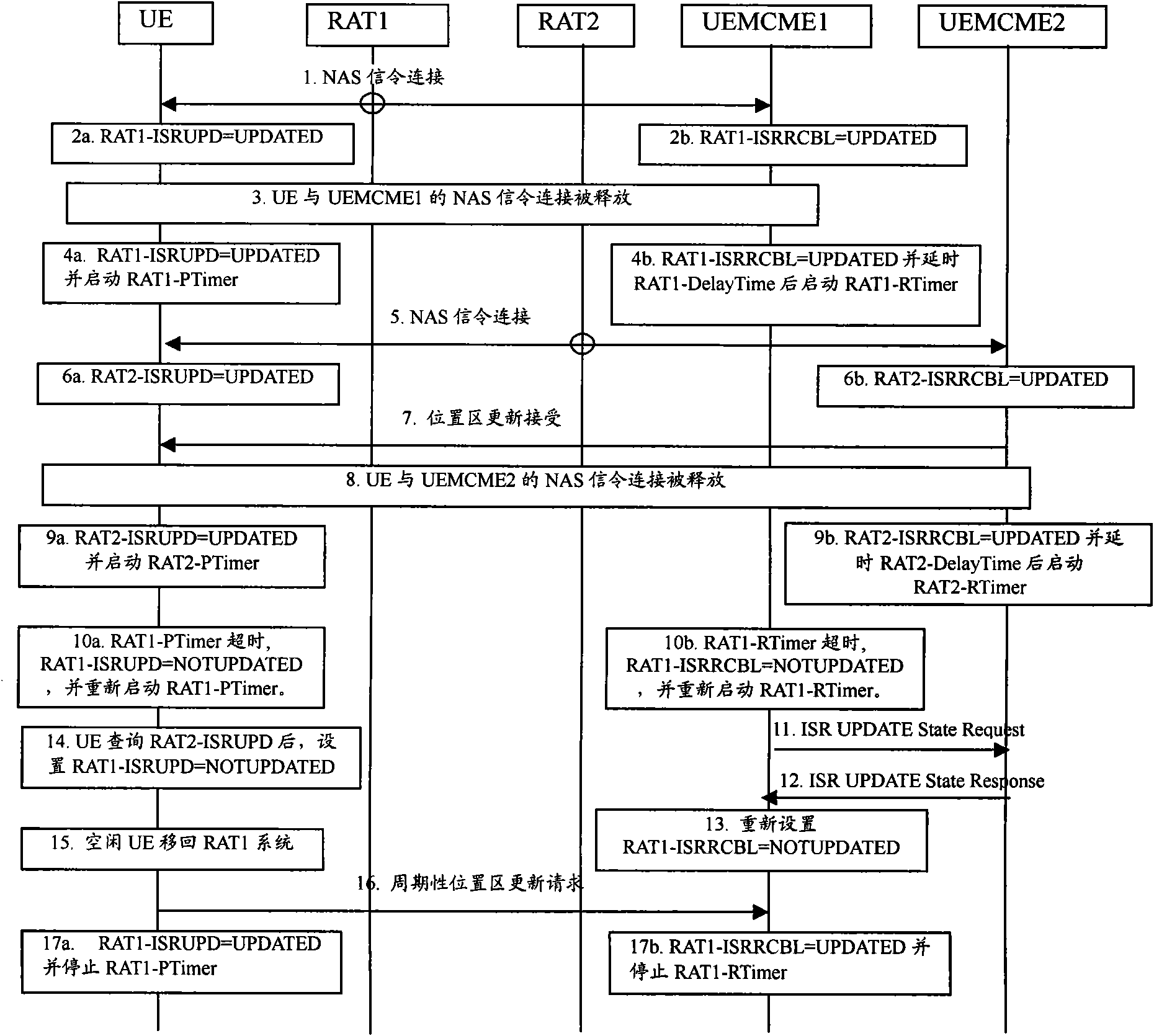
The invention discloses a user terminal detaching method, which comprises that: when a first user mobile control management entity of a first radio access type RAT system registered by a user terminal in an idle state does not receive a periodic position update request sent by the user terminal before a first user reachable timer overtimes, the first user mobile control management entity sets a first reachable state parameter value used for recording the update state of a periodic position area as nonupdated; the first user mobile control management entity checks the activation state of an idle state signaling optimization ISR function of the user terminal according to the context of the user terminal; and when the ISR function of the user terminal is activated and a second reachable state parameter value used for recording update state of the periodic position area in a second user mobile control management entity of a second RAT system registered by the user terminal is not updated, the first user mobile control management entity detaches the user terminal.
Owner:DATANG MOBILE COMM EQUIP CO LTD
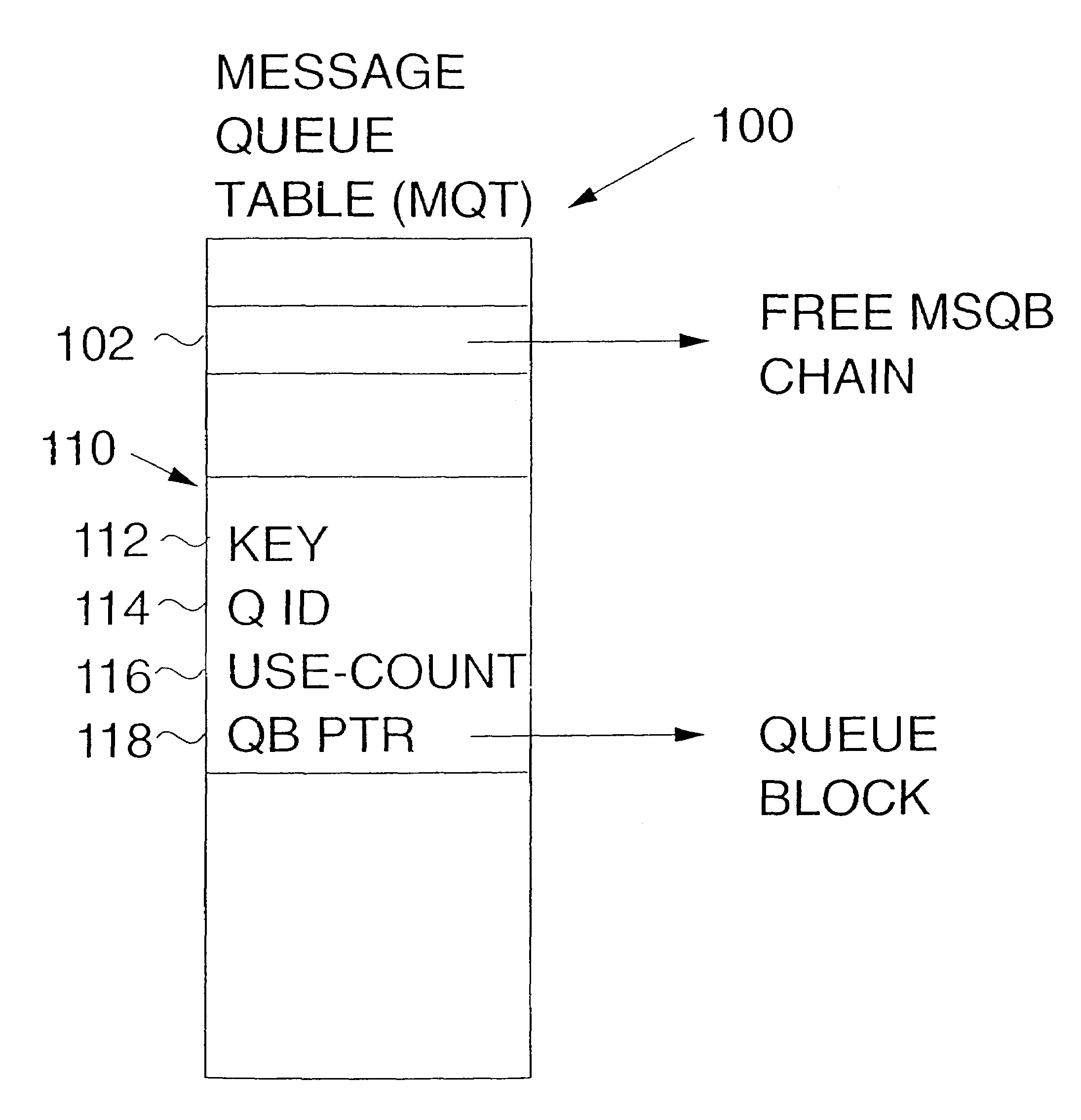
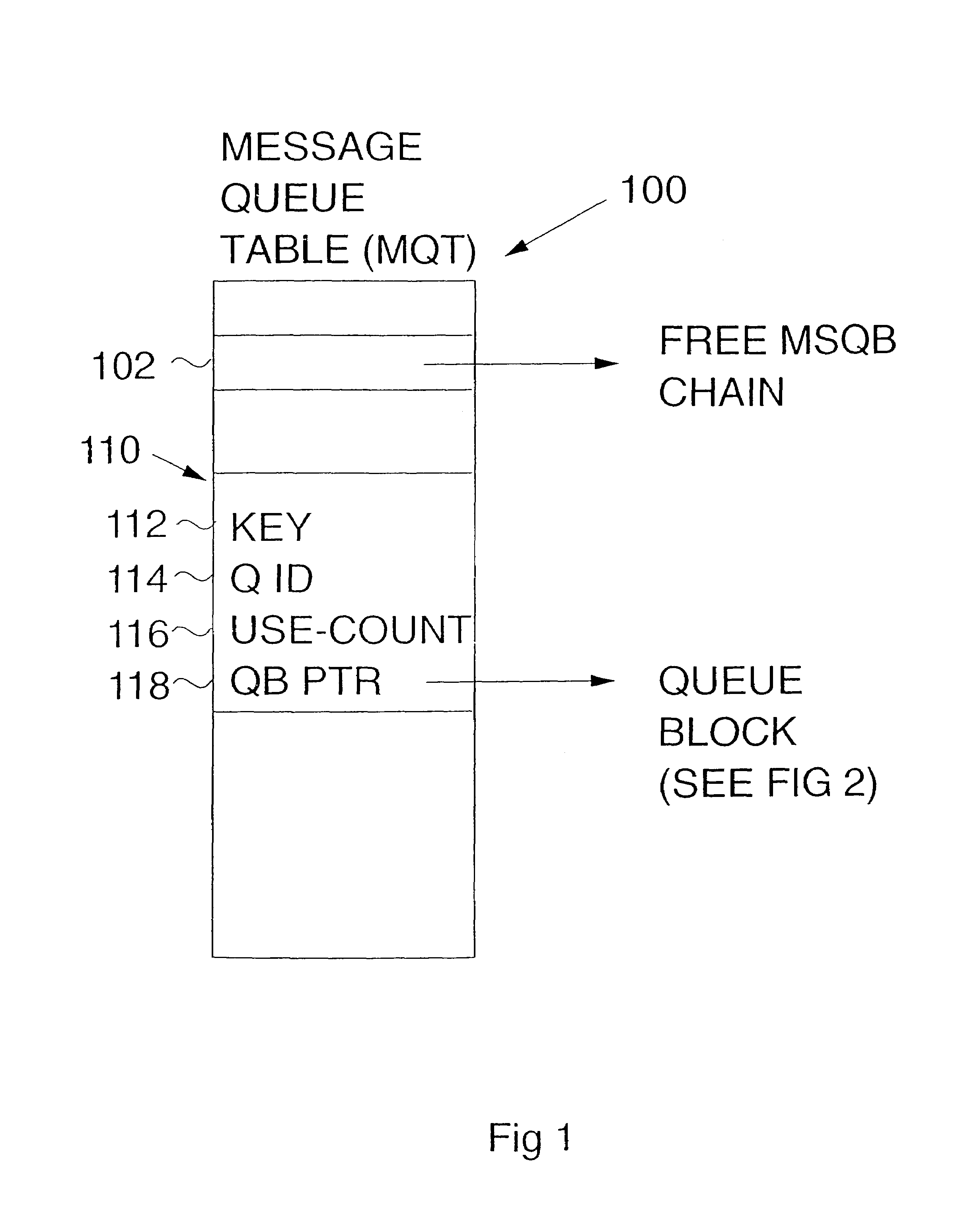
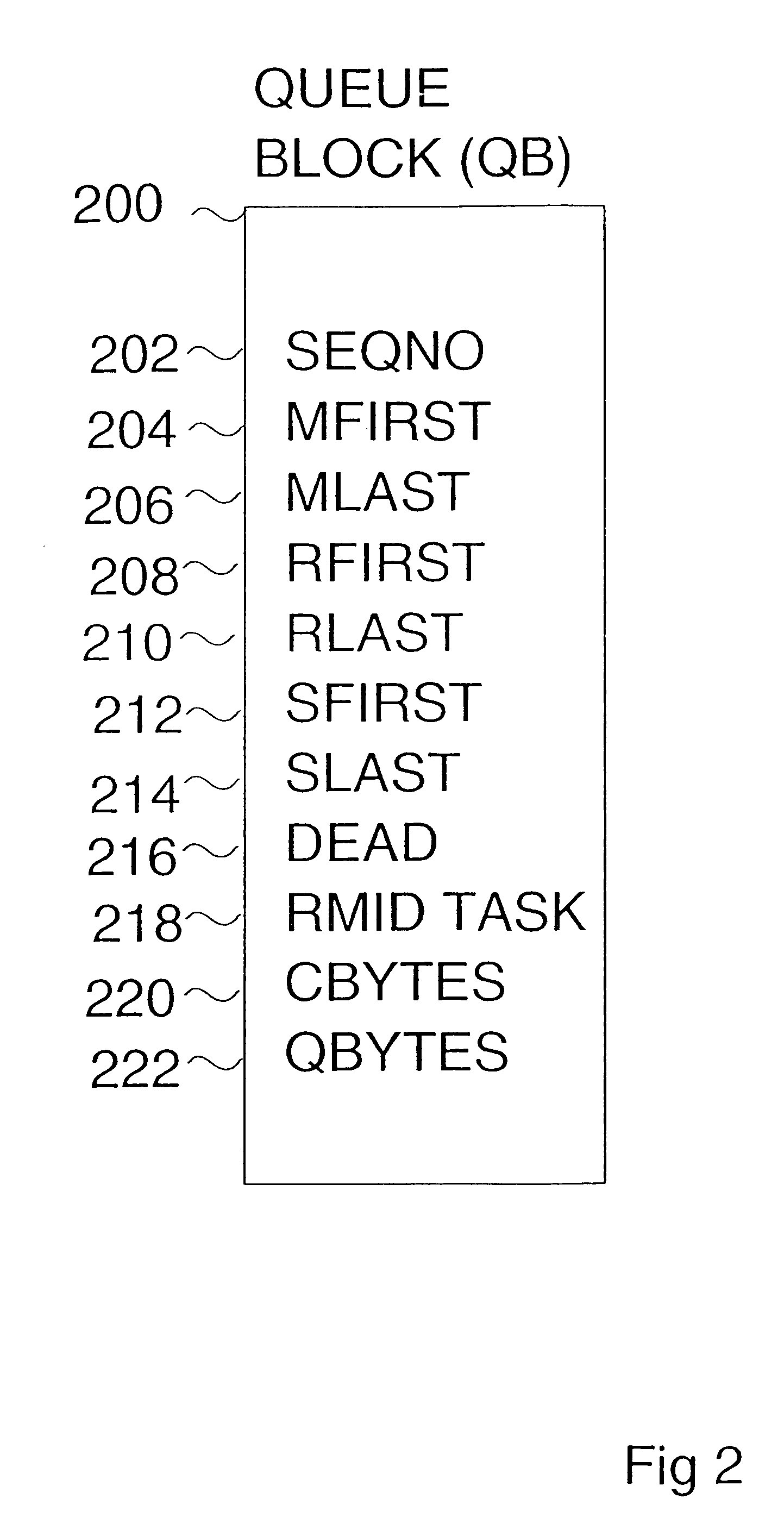
Method and apparatus for serializing a message queue in a multiprocessing environment
InactiveUS6976260B1Possible to recoverAvoid deletionMultiprogramming arrangementsInput/output processes for data processingFootprintingMessage queue
A single atomic instruction is used to change up to four disjoint areas in memory concurrently in an extended compare and swap operation, replacing traditional locks for serialization and providing recovery for all queue manipulations. Use count-based responsibility passing is employed so that any number of tasks can read the various message queue chains, concurrent with queue updates being made. A summary queue update sequence number is maintained to provide concurrent chain update detection, so that any number of tasks can add elements to the end, or remove elements from the middle (i.e. any where in the chain) concurrently. Concurrent footprinting is used with chain manipulation, so that all (or none) of the chaining indicators and a footprint are set with a single, non-interruptible instruction, making it possible for recovery to always take the correct action. One such use of concurrent footprinting is the concurrent footprinting of use count changes, while another is the transfer of ownership of message queue control blocks. In a preferred embodiment on an IBM S / 390 platform, the Perform Locked Operation (PLO) instruction is used to perform the extended compare and swap operations.
Owner:IBM CORP
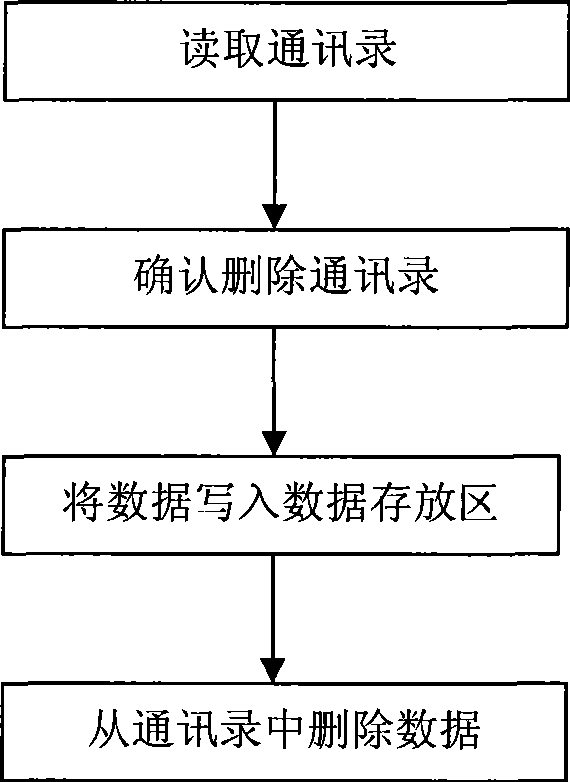
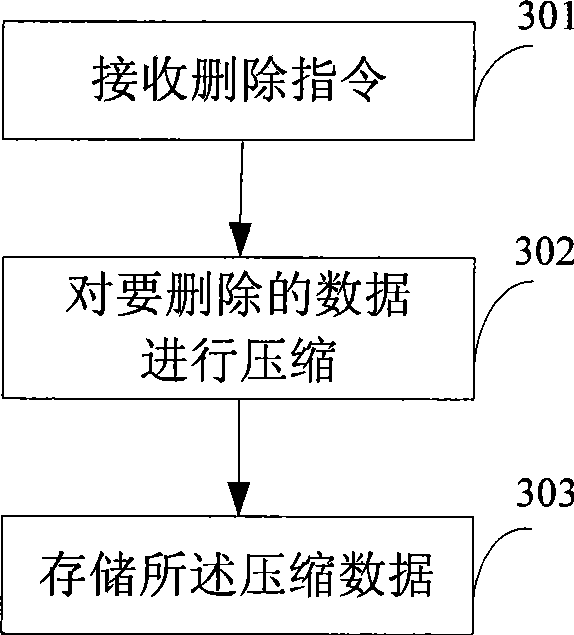
Data processing method and apparatus
InactiveCN101370212AAvoid deletionReduce occupancySubstation equipmentRadio/inductive link selection arrangementsData storeData processing
The embodiment of the invention relates to a data processing method, comprising the steps of: receiving a data deletion instruction to delete the data from a user-visible storage region, recording the current storage location of the data and compressing the data to be deleted, and storing the compressed deleted data to a backup storage region. The embodiment of the invention further comprises a method for recovering the deleted data and a device for data processing. With the method and the device, a user is able to compress and store the backup data in a cell phone, like address list or other information, and delete the data when necessary in order to reduce occupation of the backup data in memory space of the cell phone.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
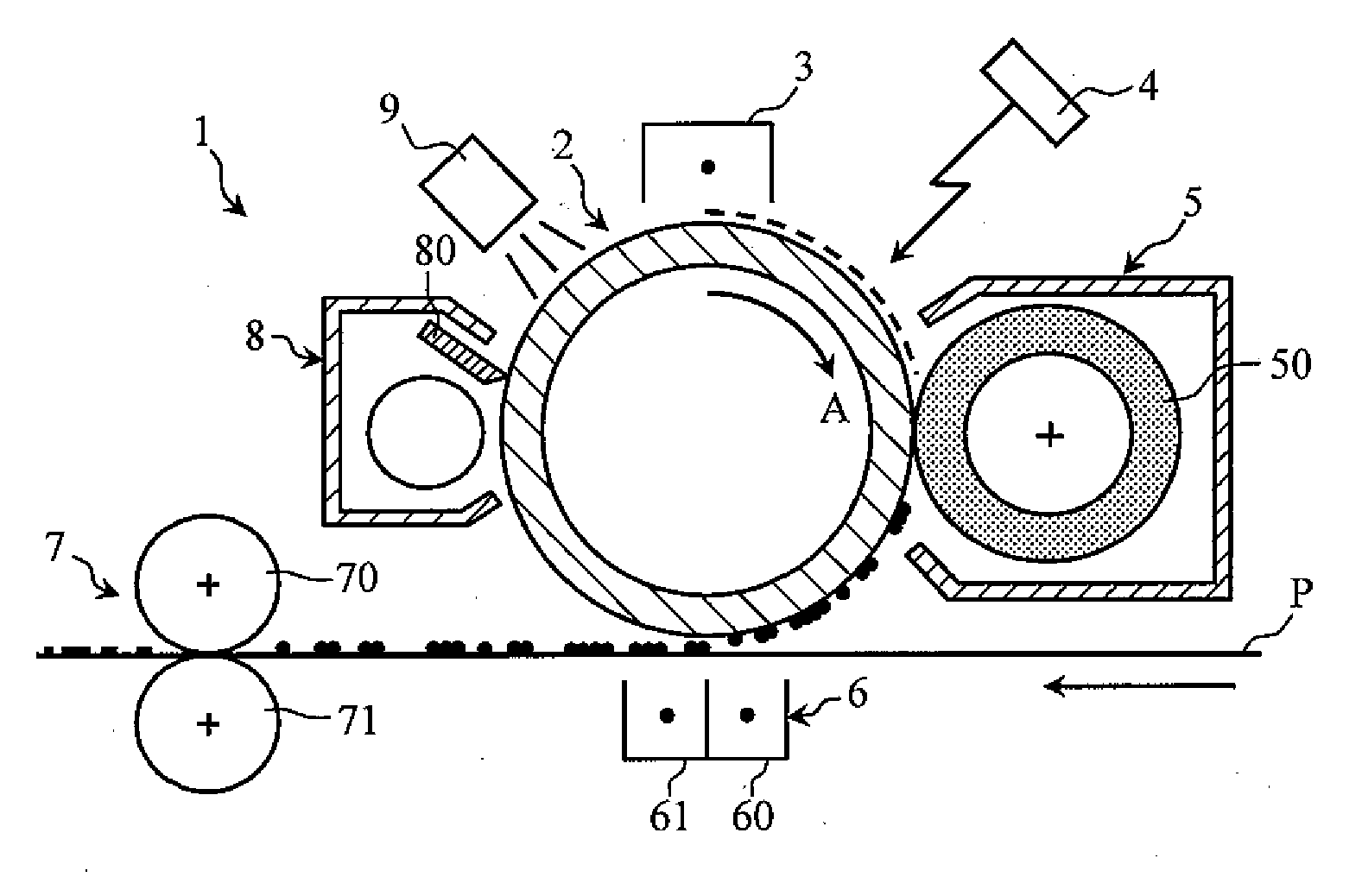
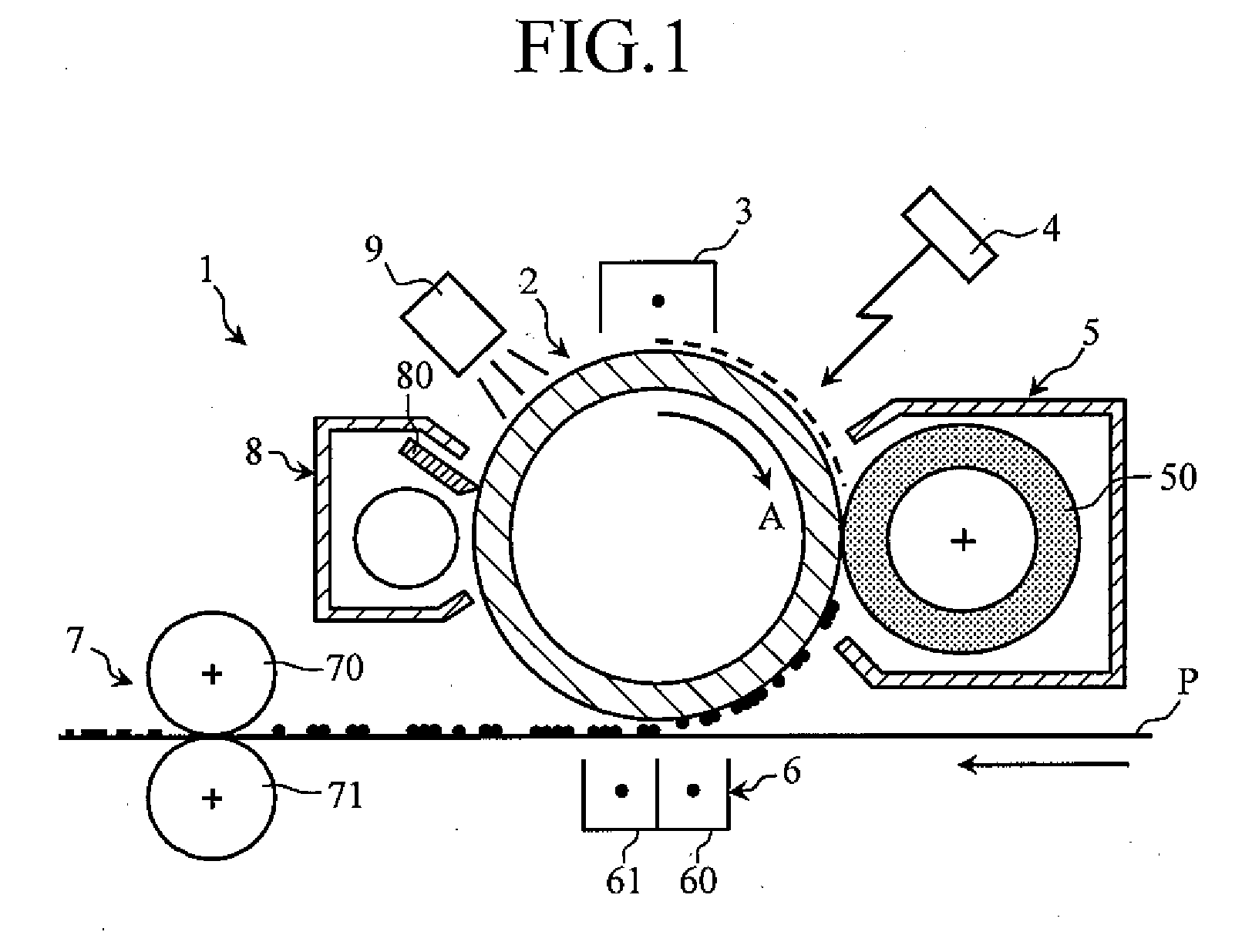
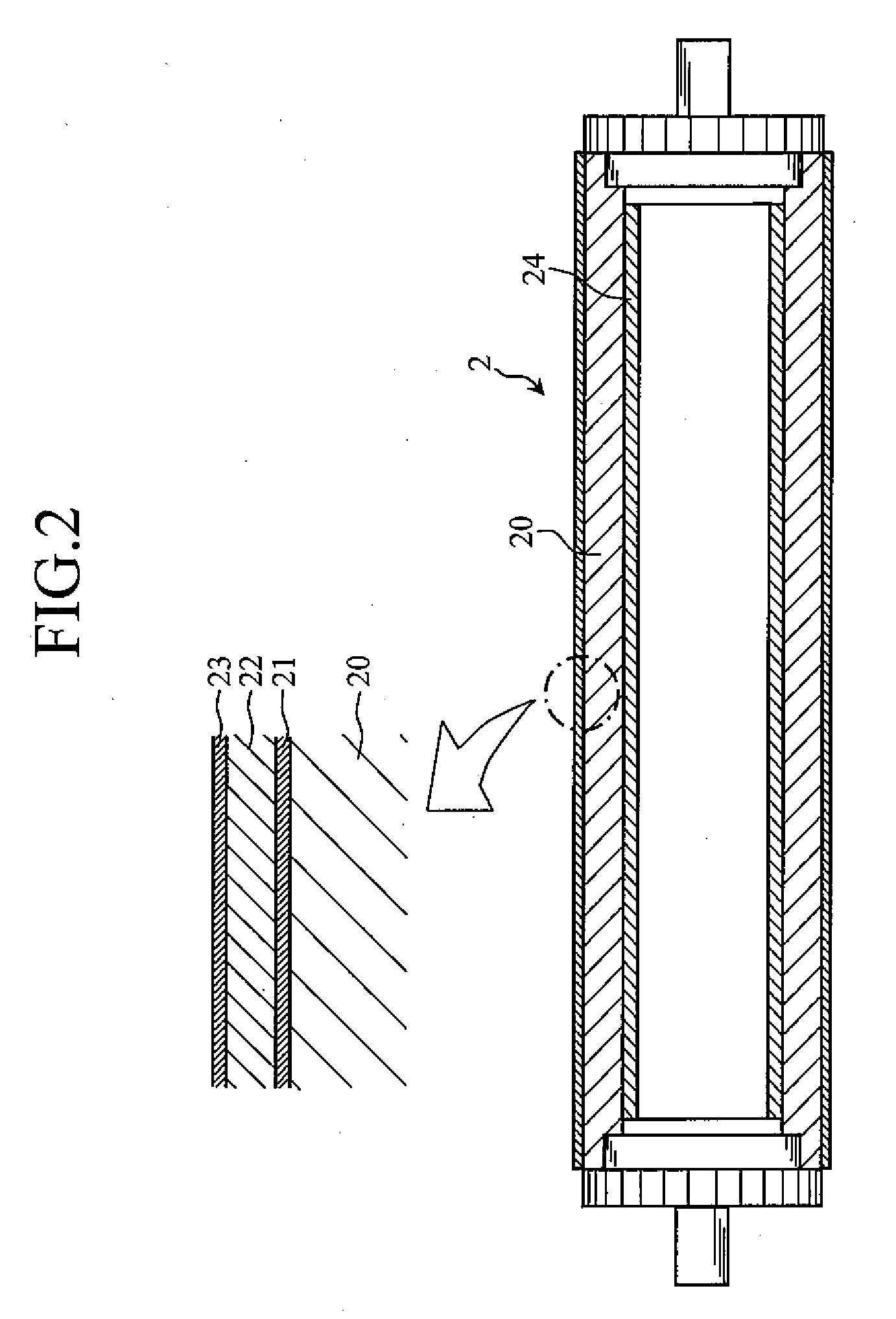
Electrophotographic Photosensitive Member and Image Forming Apparatus Provided with the Same
InactiveUS20100014888A1High durabilityHigh qualityElectrographic process apparatusCorona dischargeEngineeringSurface layer
The present invention relates to an electrophotographic photosensitive member 2 including a conductive body 20, a photoconductive layer 22 formed on the conductive body 20 using amorphous silicon, and a surface layer 23 formed on the photoconductive layer using amorphous silicon. The present invention further relates to an image forming apparatus provided with the electrophotographic photosensitive member 2. The photoconductive layer 22 has a mean roughness Ra of not more than 10 nm per 10 μm square. The surface layer 23, without undergoing grinding process, has a mean roughness Ra of not more than 10 nm per 10 μm square.
Owner:KYOCERA CORP
Image forming apparatus, data processing method, computer-readable storage medium on which a program is stored, and program
InactiveUS20050257275A1Easy to operateAvoid deletionDigital data processing detailsAnalogue secracy/subscription systemsData processingUser information
In an image forming apparatus, a user of the image forming apparatus is authenticated, and a search is performed for user information stored in the storage unit by the authenticated user. Of all user information detected in the searching, deletable user information is displayed on a category-by-category basis on a display unit. In a mode selected from a plurality of modes, user information displayed on a category-by-category basis on the display unit is deleted from the storage unit.
Owner:CANON KK
Electronic image processing device and system for image data transfer operation
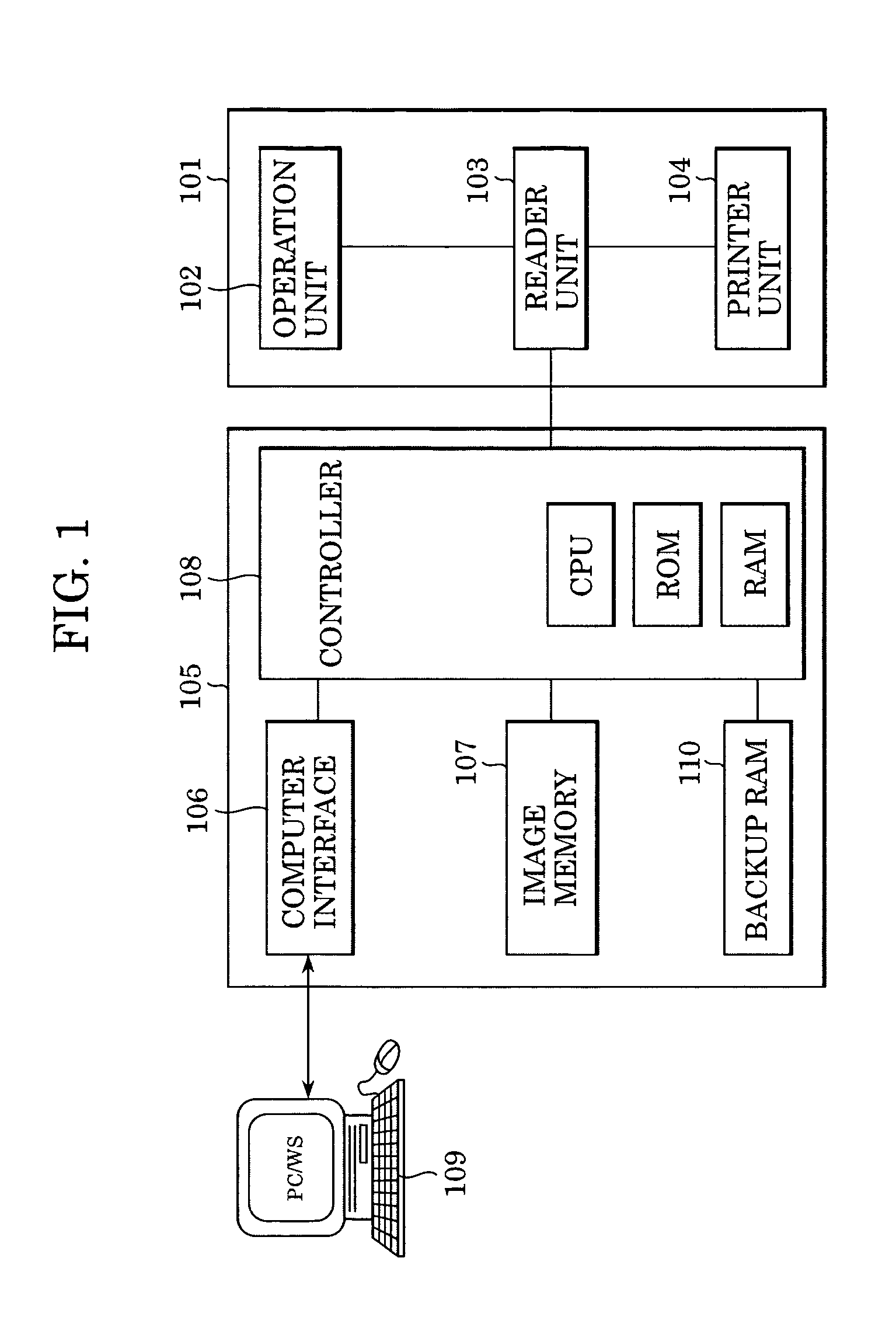
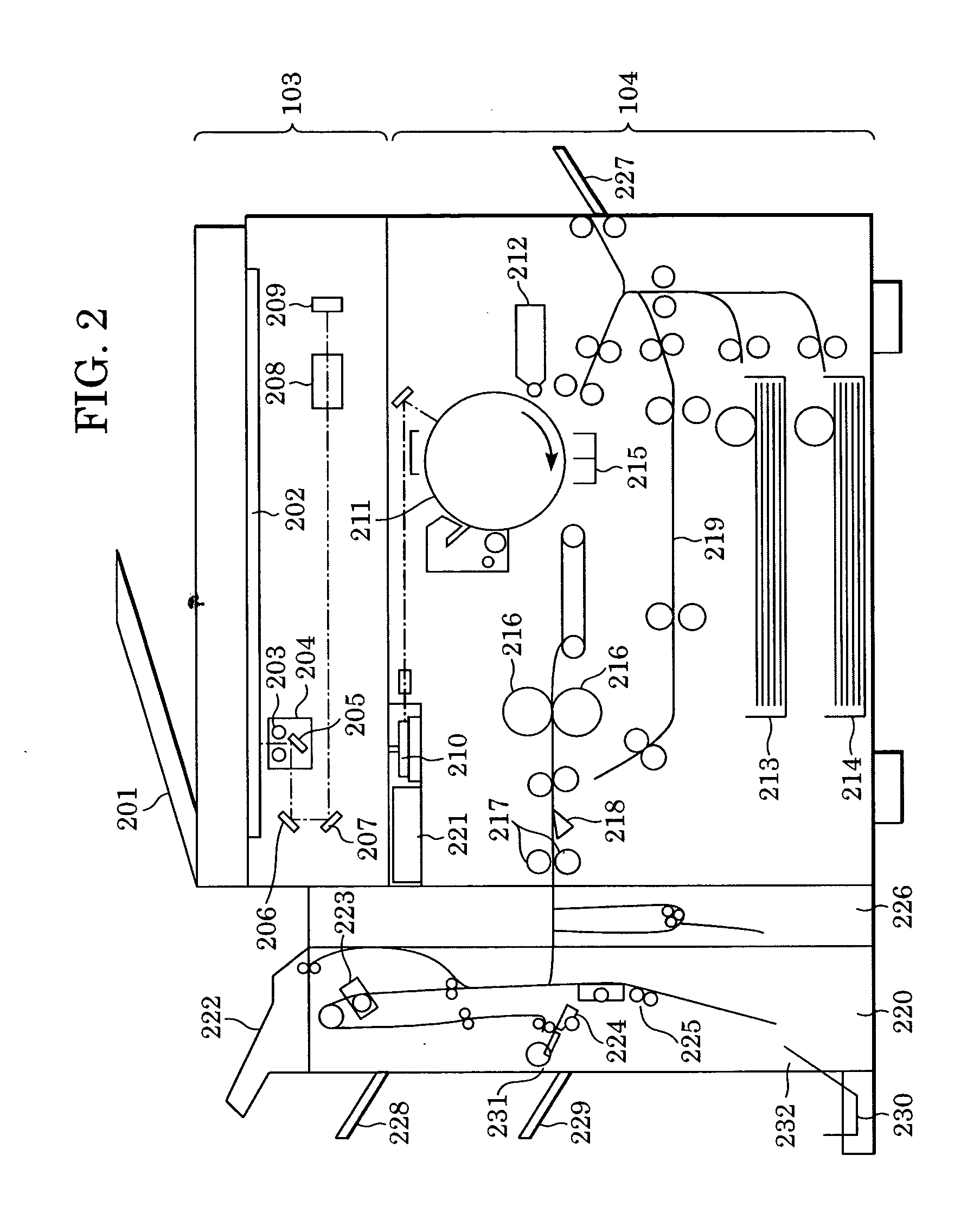
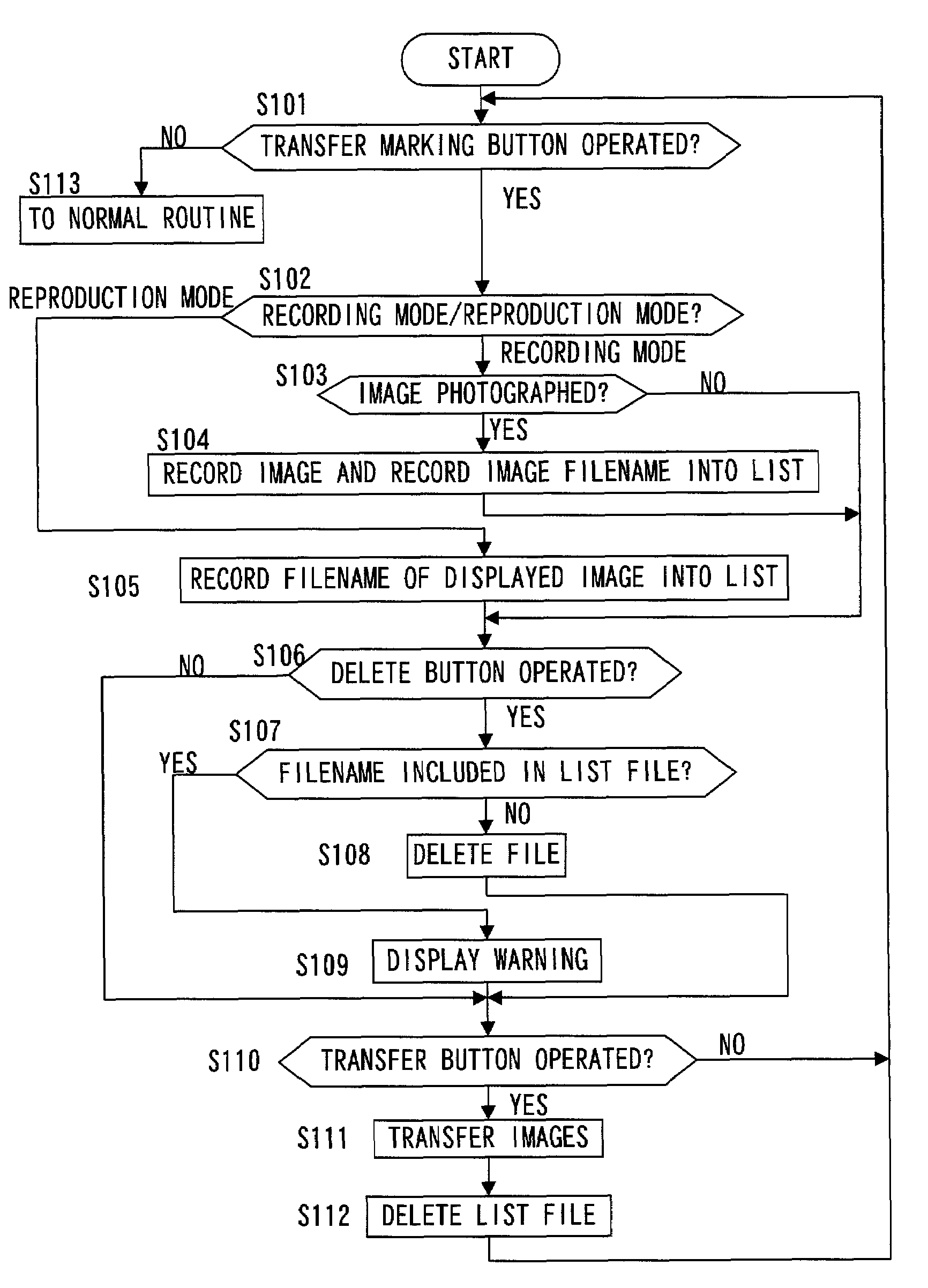
InactiveUS7385635B2Avoid deletionTelevision system detailsColor television detailsComputer hardwareImaging processing
An electronic device comprises an image-capturing device that captures an image of a subject, a recording device that records image files of images captured by the image-capturing device into a recording medium, a specifying information forming device that forms image specifying information for specifying an image file in the recording medium separately from the image files, a communication device that transfers image files recorded in the recording medium to an external recording device, a transfer instruction operation unit that issues an instruction for the communication device to transfer the image file specified in the image specifying information and a processing device that processes the image files differently depending upon whether or not image specifying information has been formed in the recording medium with respect to the recorded image files.
Owner:NIKON CORP
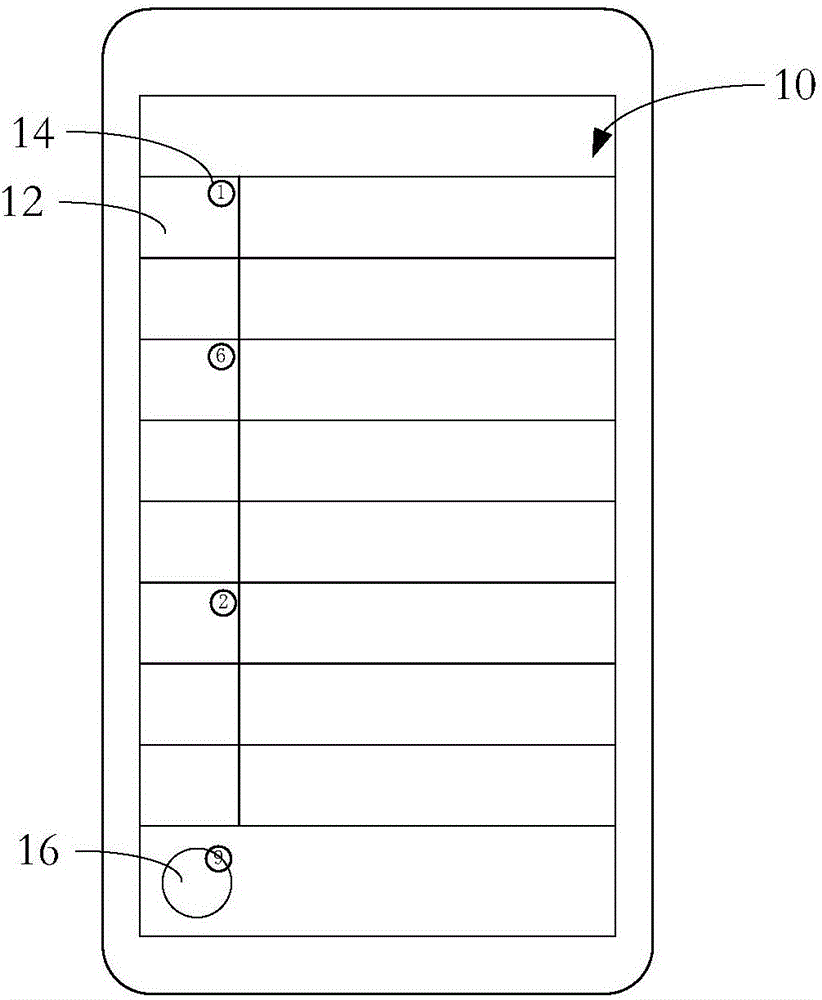
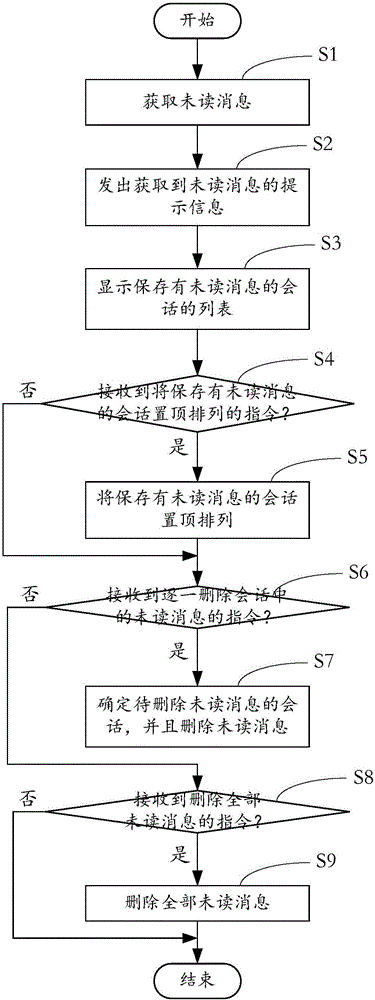
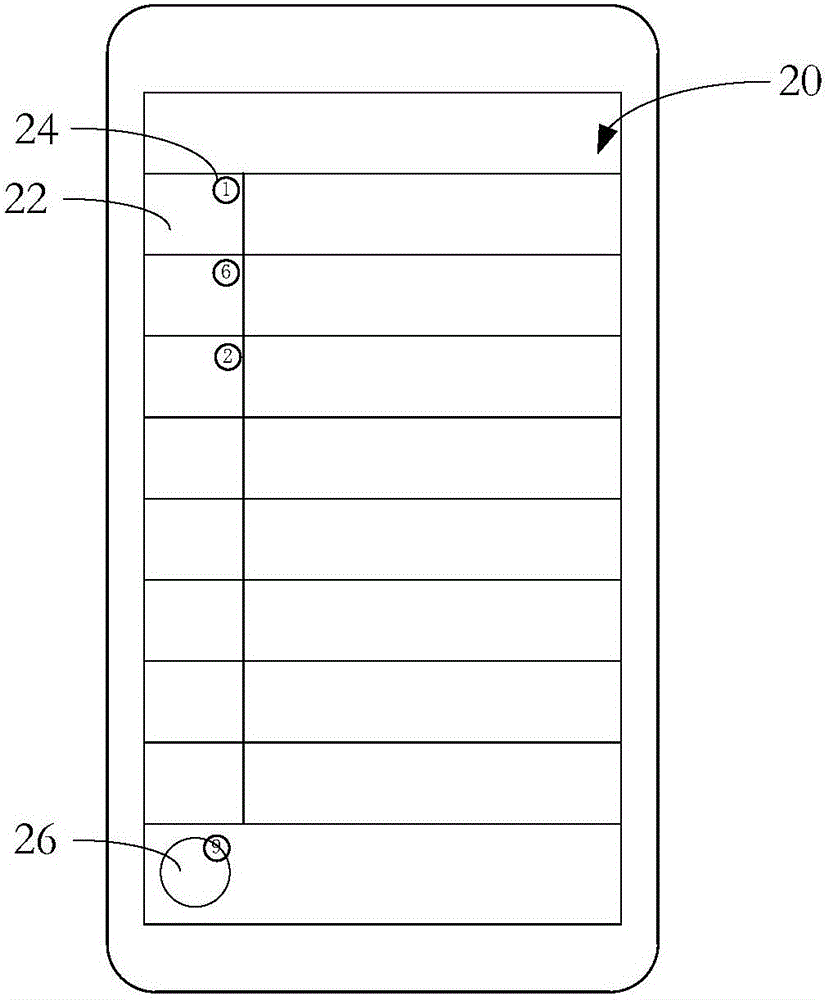
Message display method and apparatus
InactiveCN106484423AAvoid rummaging through a large number of sessionsEasy to viewExecution for user interfacesInput/output processes for data processingComputer hardware
The invention provides a message display method and apparatus. The method comprises the following steps: obtaining unread messages; obtaining an instruction of checking a list of sessions storing the unread messages, and displaying the list of the sessions storing the unread messages; and obtaining an instruction of deleting the unread messages, and deleting the unread messages. The apparatus comprises an unread message obtaining module used for obtaining the unread messages and sending a prompt message of obtaining the unread messages; the apparatus further comprises a session list display module used for obtaining the instruction of checking the list of the sessions storing the unread messages and displaying the list of the sessions storing the unread messages; and the apparatus further comprises an unread message deleting module used for obtaining the instruction of deleting the unread messages and deleting the unread messages. By adoption of the message display method and apparatus provided by the invention, a user can quickly check the sessions storing the unread messages and quickly execute a deletion operation of the unread messages.
Owner:MEIZU TECH CO LTD
Block chain based key infrastructure information management method
ActiveCN108805409APrevent tamperingAvoid deletionDigital data protectionResourcesData informationChain network
The invention discloses a block chain based key infrastructure information management method. A decentralized shared data pool, including, equipment foundation information, monitoring information, fault diagnosis and state overhaul scheme is built based on a block chain network; and a just, fair and open key infrastructure information management system is built. The method is to guarantee a creditfoundation in a sharing process by building a consensus mechanism, to guarantee information security in an information transaction process by adopting a public / private key verification way and to improve participation enthusiasm of all parties involved by using a paid mechanism for jobs such as maintenance and evaluation of information in the data pool. The block chain based key infrastructure information management method can realize multi-backup and multi-party supervision for a plenty of data information of the equipment in the whole process from research and production, delivery for application to scrapping out of operation and can prevent data loss and data tempering or deletion caused by physical reasons; and as the platform which each party can participate in data analysis and sharing, research work in all aspects of the key infrastructure is speeded up.
Owner:WUHAN UNIV
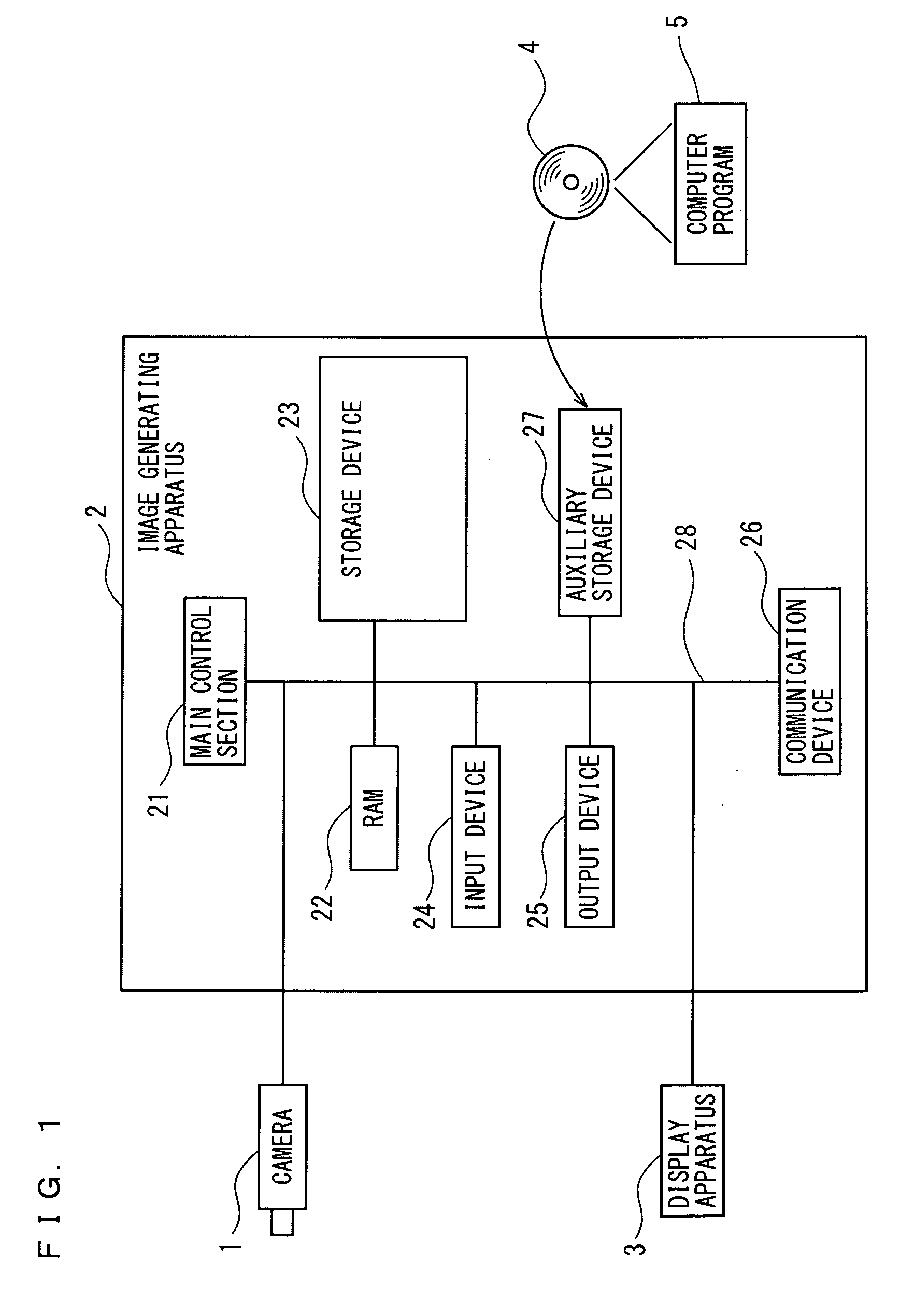
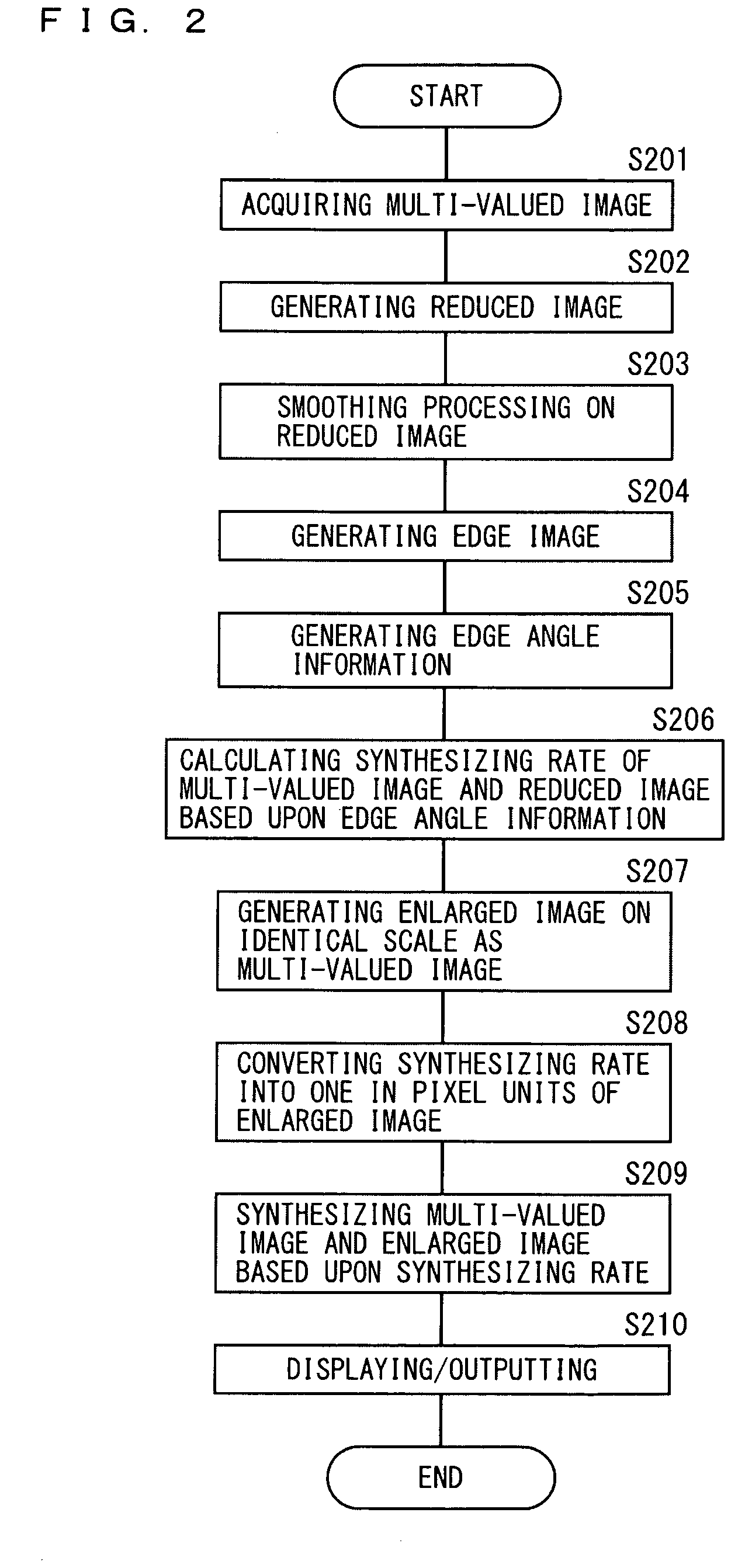
Image Generating Apparatus and Method
InactiveUS20090208129A1High synthesis rateReliable deletionImage enhancementImage analysisImage generationImage based
There are provided an image generating apparatus and an image generating method, which are capable of generating an image with only a noise portion reliably deleted. A reduced image is generated by reducing the multi-valued image, smoothing processing is executed on the reduced image, an edge image is generated from the reduced image, edge angle information concerning edge angles is generated in pixel units from the edge image, a synthesizing rate of the multi-valued image and the smoothed reduced image is calculated in pixel units of the reduced image based upon the edge angle information. An enlarged image is generated by enlarging the smoothed reduced image to an identical scale, the synthesizing rate calculated in pixel units of the reduced image is converted into a synthesizing rate in pixel units of the enlarged image, and the multi-valued image and the enlarged image are synthesized based upon the converted synthesizing rate.
Owner:KEYENCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com