Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30results about "Obsolescence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
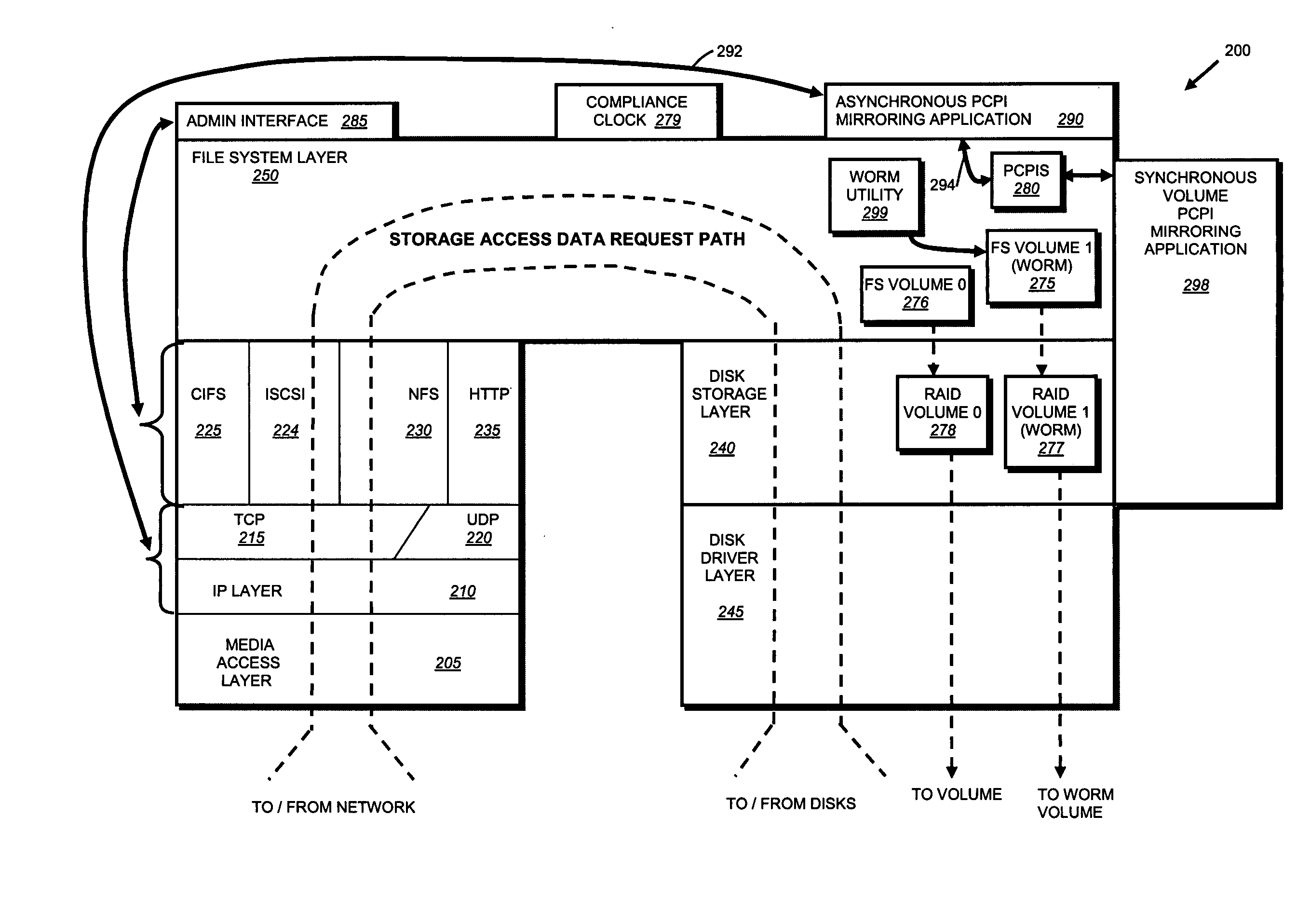
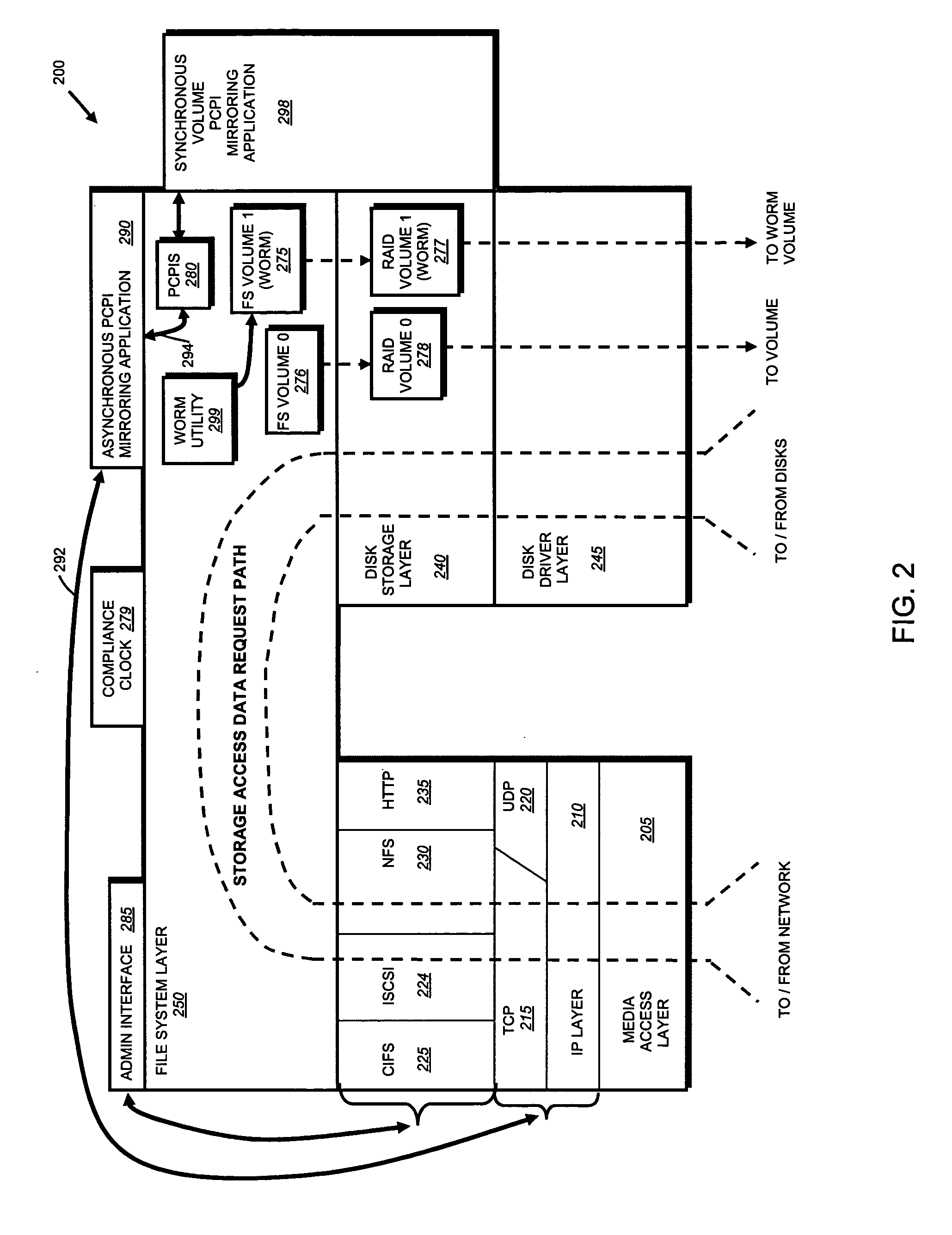
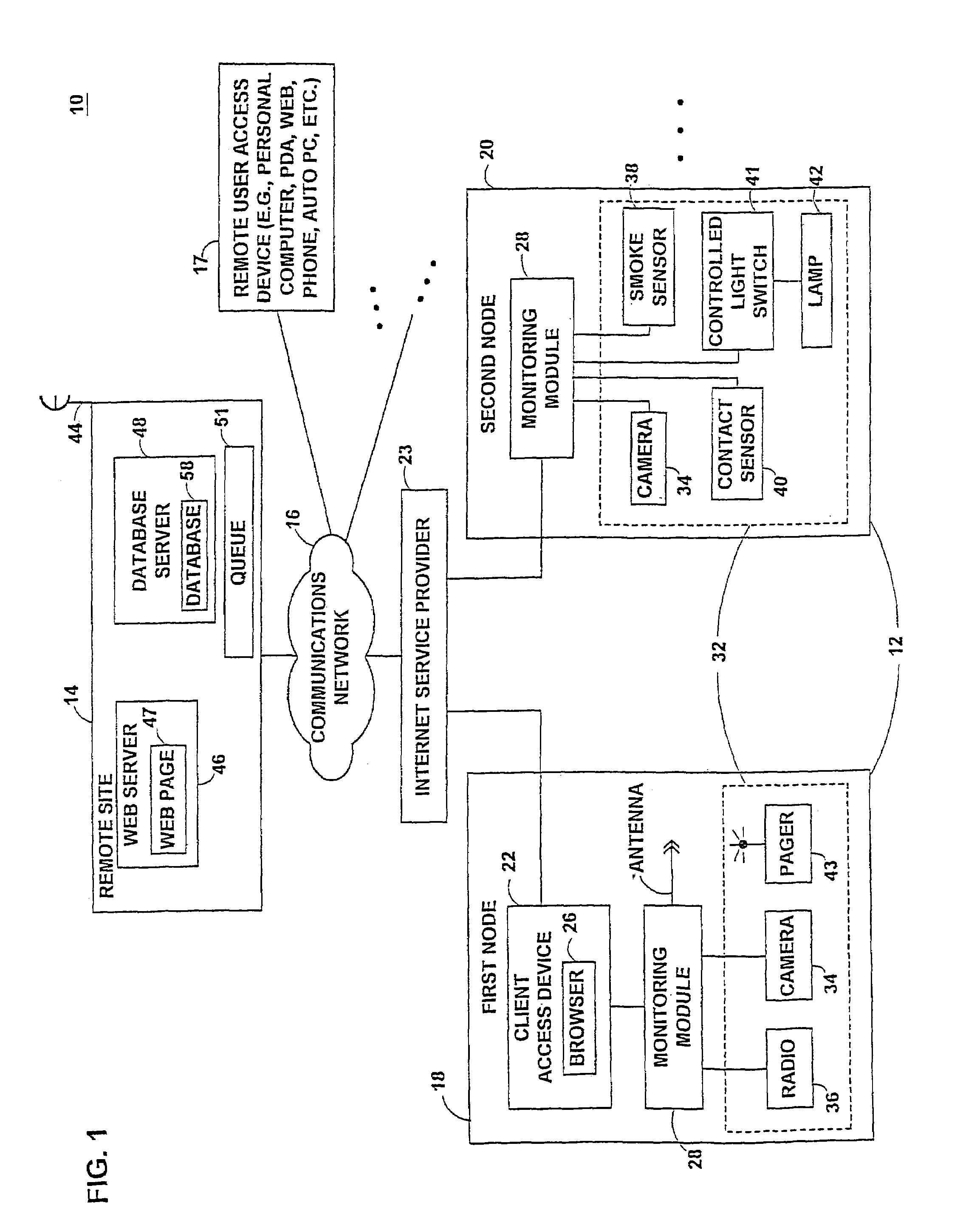
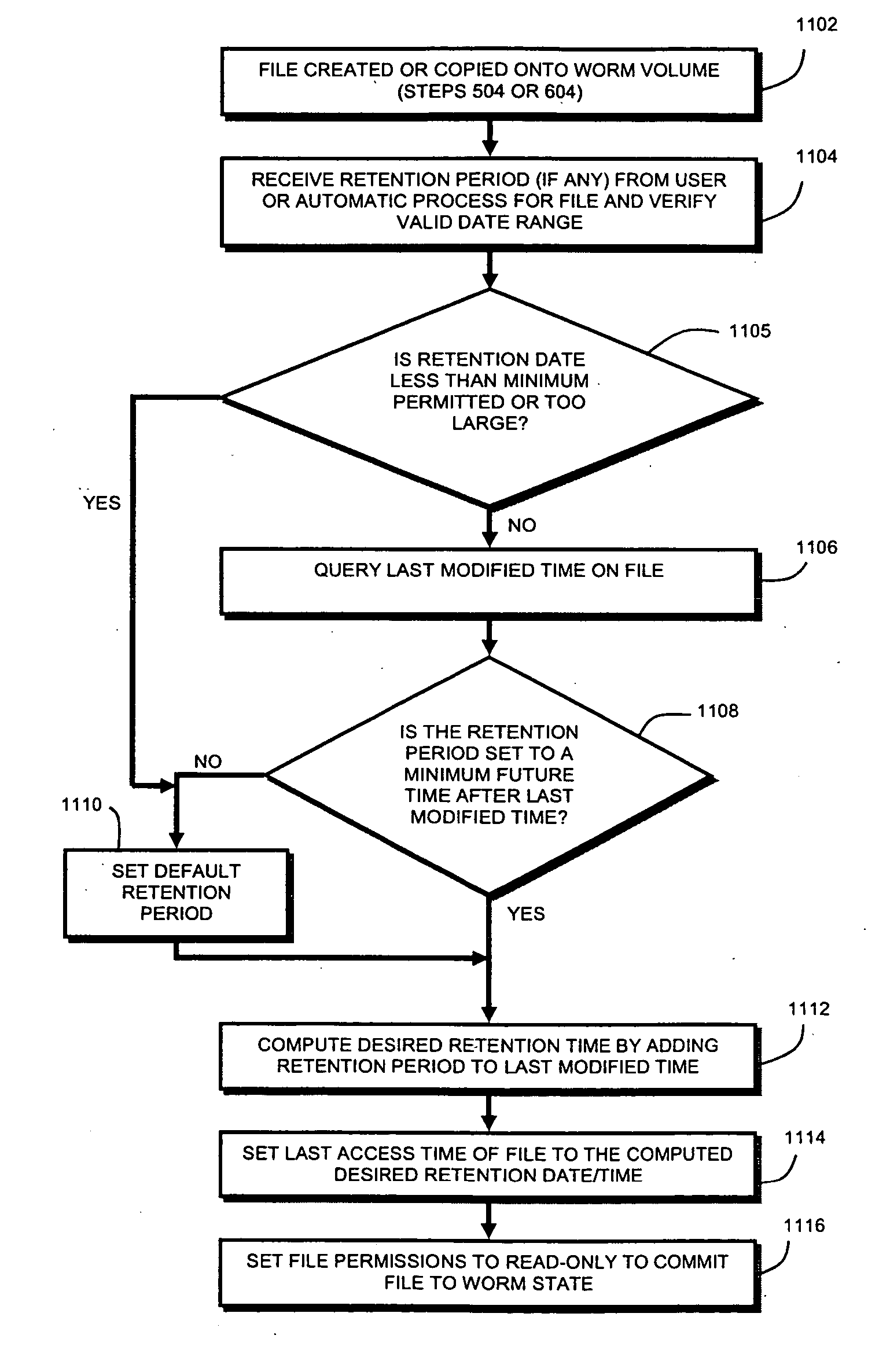
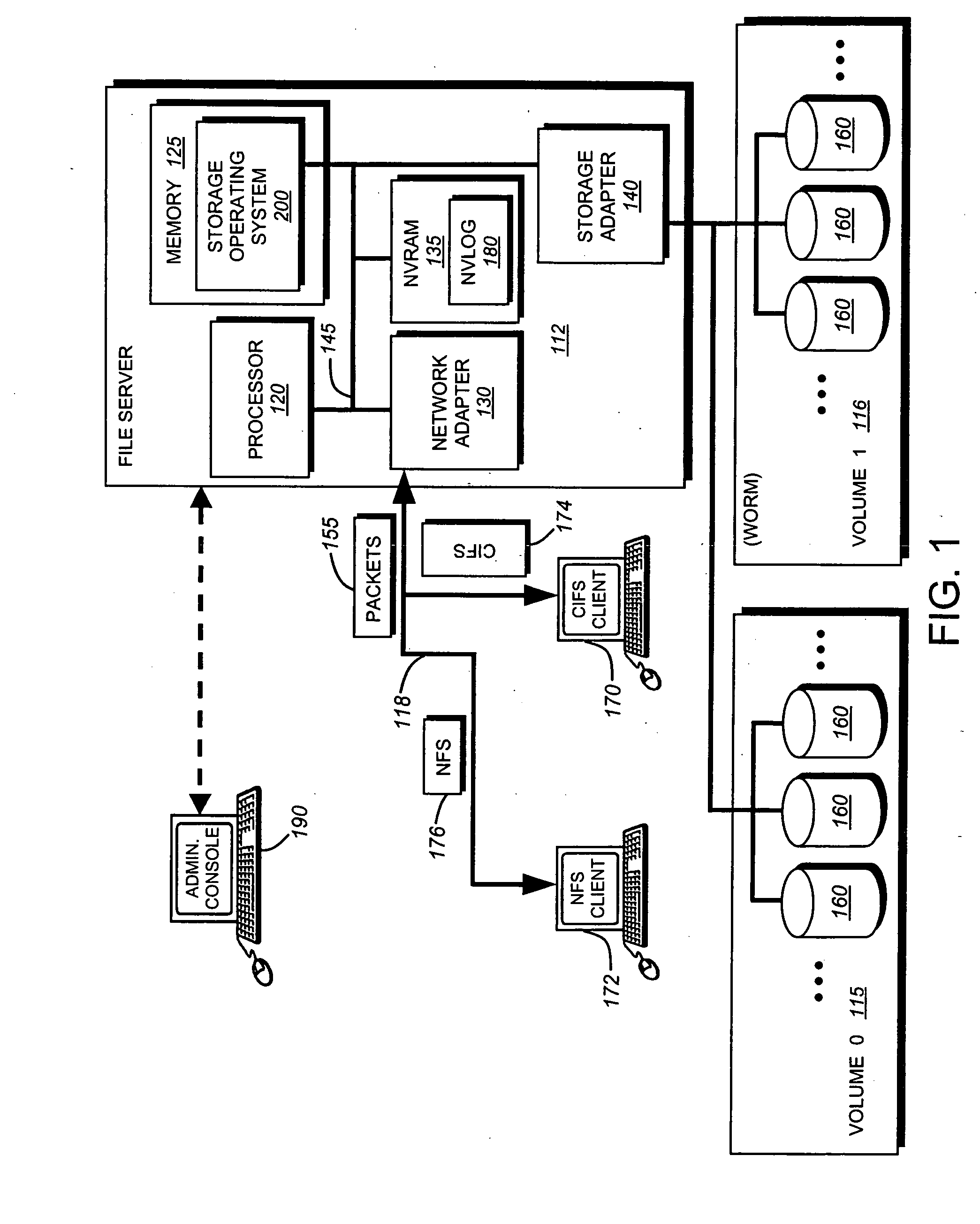
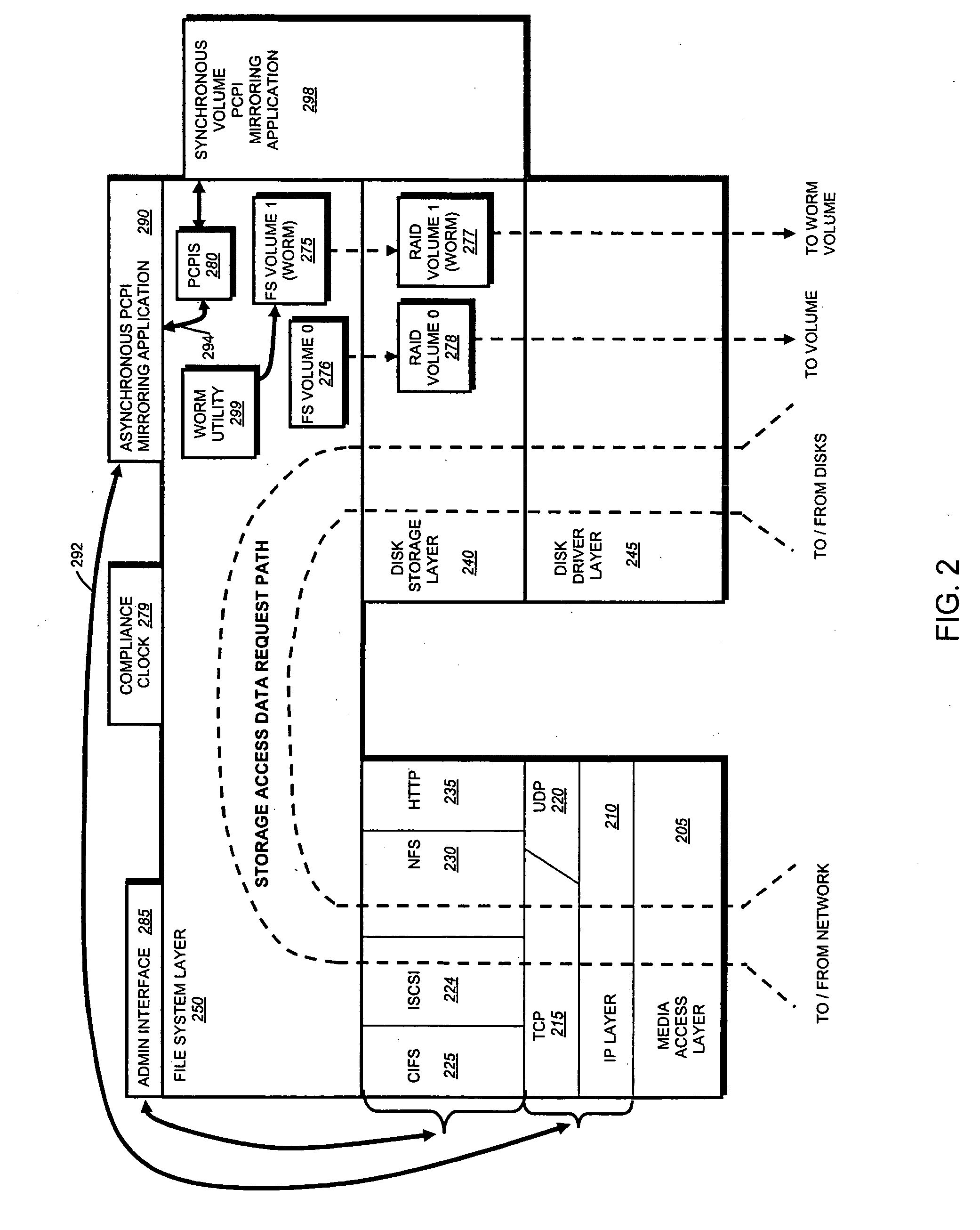
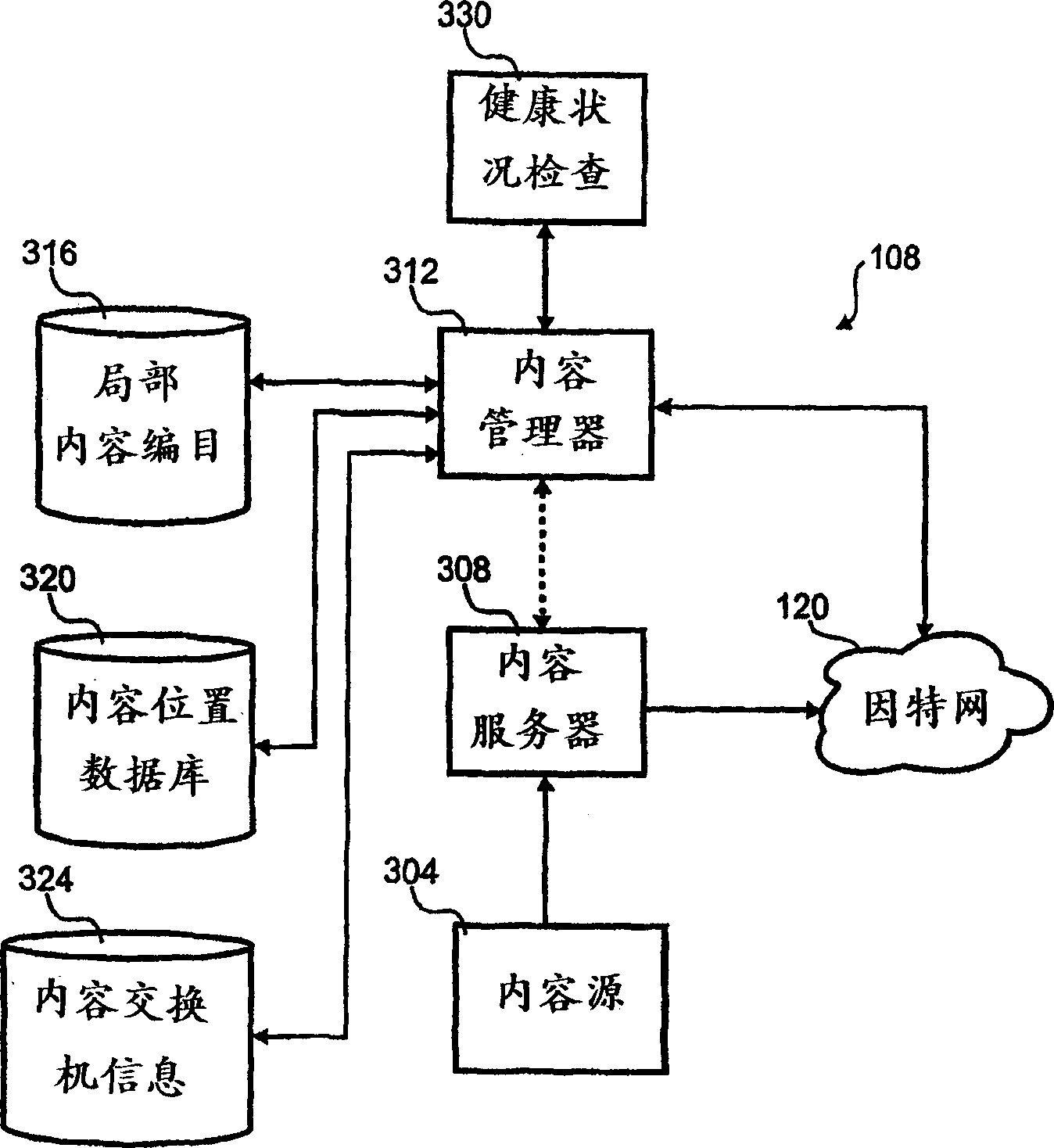
System and method for record retention date in a write once read many storage system
ActiveUS20050097260A1Improve performanceInput/output to record carriersData processing applicationsRetention periodData set
This invention provides a specified retention date within a data set that is locked against deletion or modification within a WORM storage implementation. This retention date scheme does not utilize any proprietary application program interfaces (APIs) or protocols, but rather, employs native functionality within conventional file (or other data containers, data sets or block-based logical unit numbers) properties available in commonly used operating systems. In an illustrative embodiment, the retention date / time is calculated by querying the file's last-modified time prior to commit, adding the retention period to this value and thereby deriving a retention date after which the file can be released from WORM. Prior to commit, the computed retention date is stored in the file's “last access time” property / attribute field, or another metadata field that remains permanently associated with the file and that, in being used for retention date, does not interfere with file management in a WORM state. Since this field is not utilized in a WORM context, it can be adapted to store this date. Once stored, the retention date in this field is locked against modification. Where extension (never reduction) of a retention period is desired, the last access time field be updated, wherein the new retention period is added to the existing last access time value to derive a new, later retention date for the file. Upon expiry of the retention date, the system allows deletion of the expired WORM file / data set.
Owner:NETWORK APPLIANCE INC
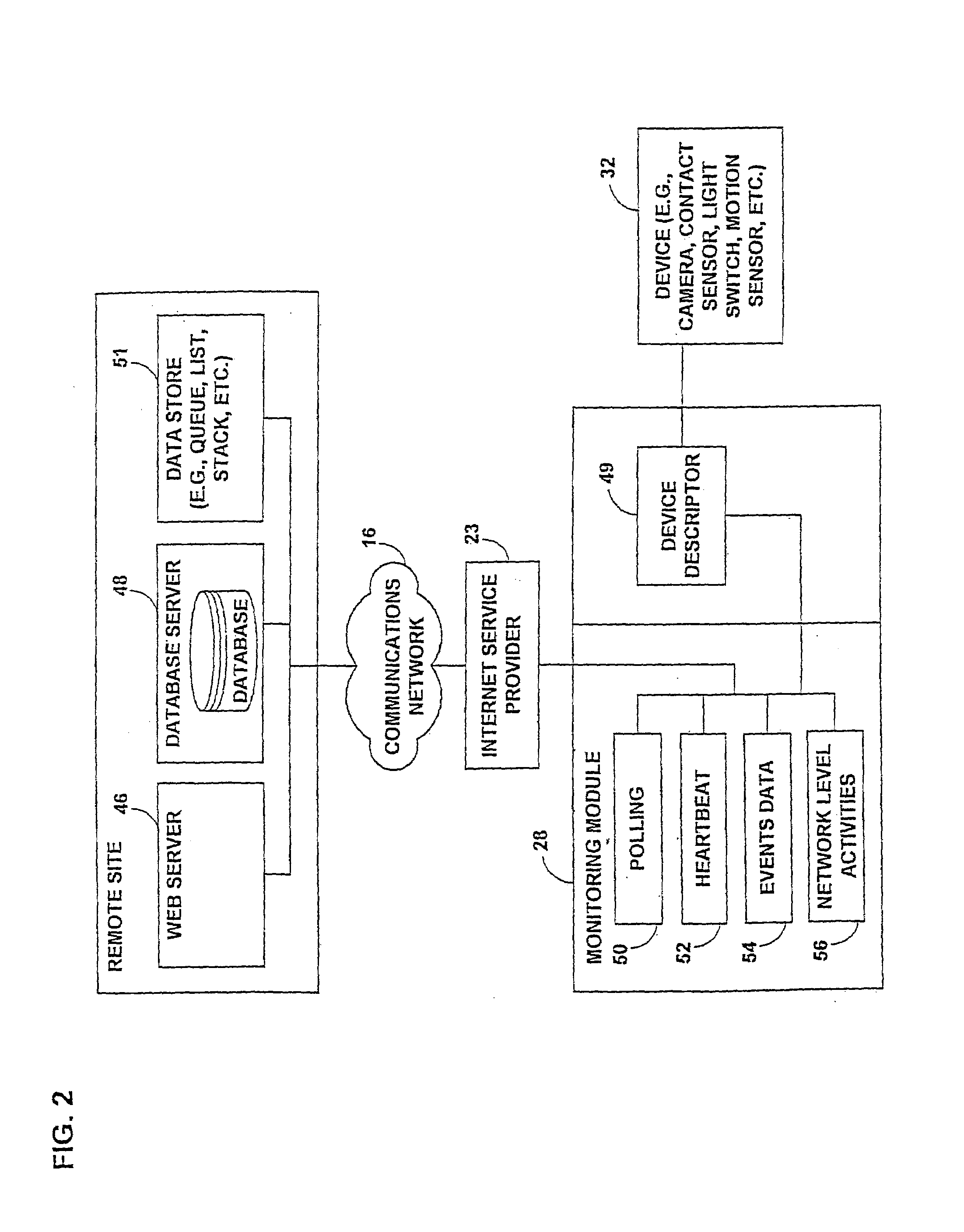
Method and system for adaptively setting a data refresh interval
InactiveUS7149798B2Digital computer detailsAnalogue secracy/subscription systemsTelecommunications linkData source
A method and system is disclosed for adaptively refreshing a data using system. The data using system includes a data source and a data using device for utilizing data from the data source. The data using device has an initial refresh interval. A communication link is provided between the data source and the data using device. A criteria monitor is provided for monitoring at least one criteria related to the refresh interval. A processor is provided for generating an updated data refresh interval based at least in part on the monitored criteria. The updated data refresh interval is transferred to the data using device. The data using device is also updated based on the data refresh interval.
Owner:AT&T DIGITAL LIFE
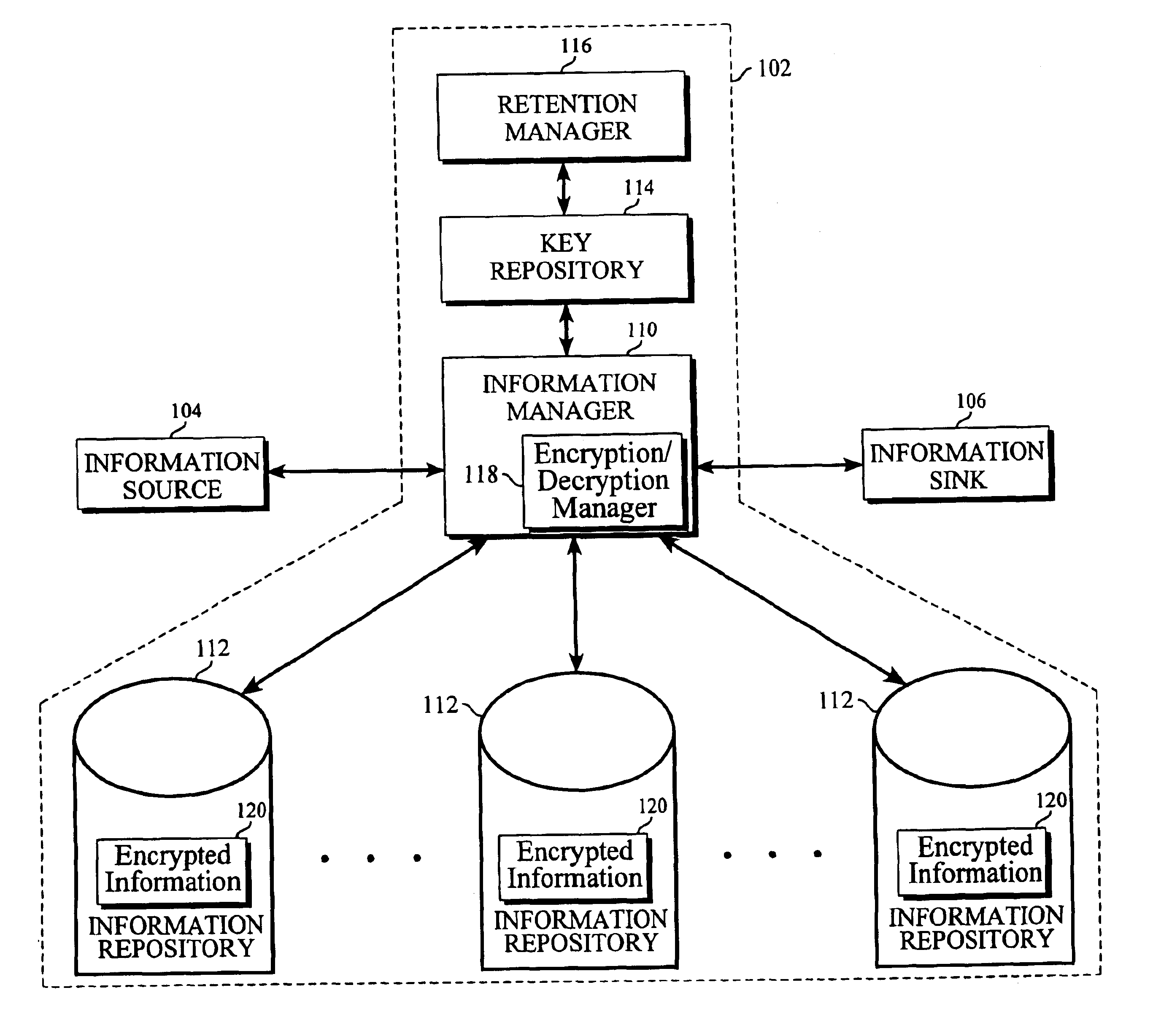
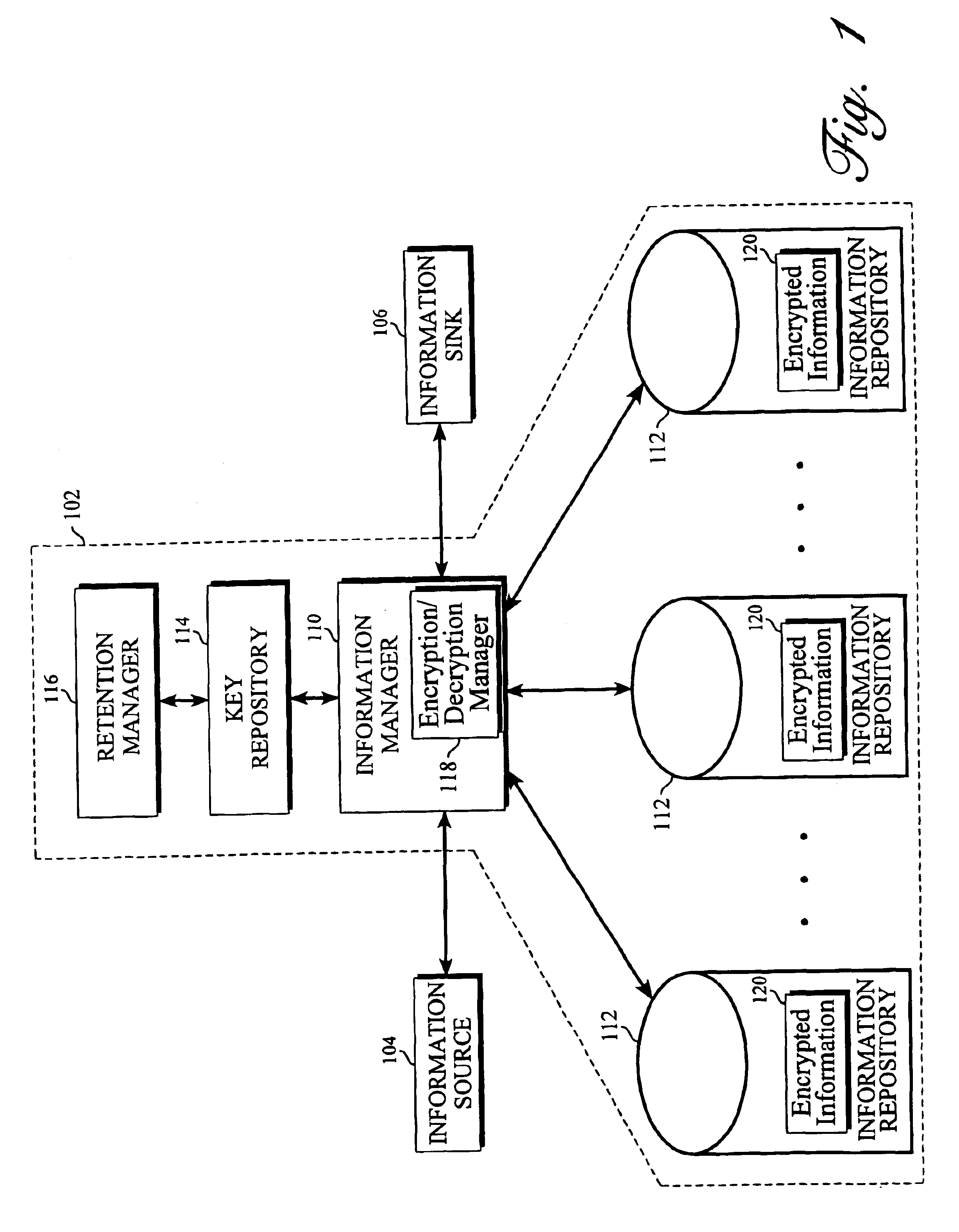
Method and system for managing information retention
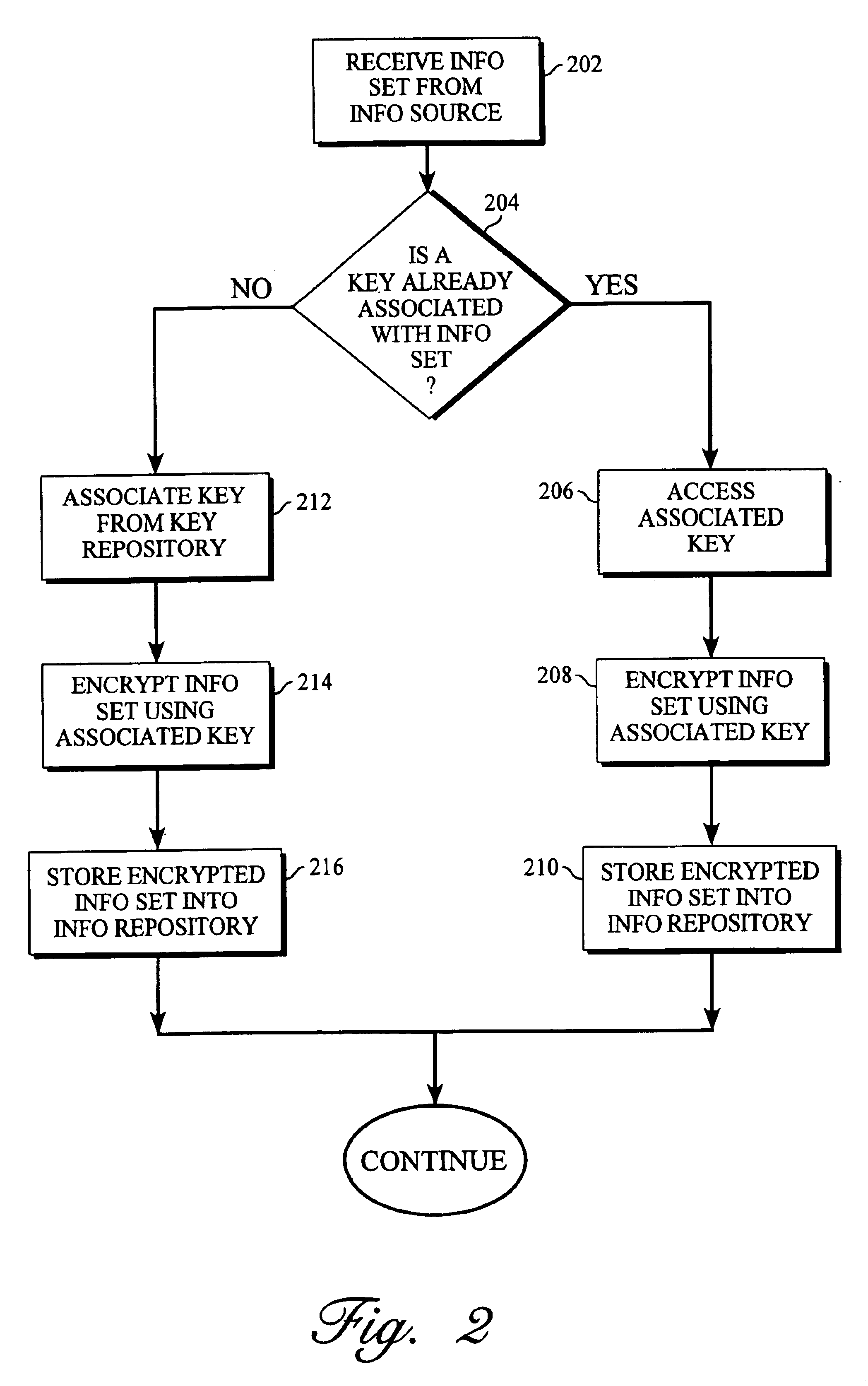
InactiveUS6915435B1Improved information retention mechanismSimple processKey distribution for secure communicationDigital data processing detailsWorld Wide WebInformation system
An improved information retention management mechanism is disclosed wherein an information set may be purged from an information system without having to delete the information set from the system. Whenever an information set enters an information system, a key is associated with the information set. The information set is encrypted using the associated key, and the encrypted form of the information set is stored in the information system. The unencrypted form of the information set is not stored. To render the information set to a user, the encrypted form of the information set is accessed along with the associated key, and then decrypted using the associated key to derive the original information set. Once derived, the information set is rendered to the user. So long as the associated key remains in the system, this process may be carried out to render the information set to a user. At some point, in accordance with an information retention policy, the information set is selected for purging. To purge the information set, all that needs to be done is to delete the associated key. By deleting the associated key, all copies of the encrypted information set stored within the information system are made unrenderable; as a result, the information set is effectively “purged” from the system. This purging is achieved without having to delete the encrypted information set from the system.
Owner:ORACLE INT CORP
Reverse content harvester
The invention relates to gathering information for a networked directory. In one embodiment, a method for gathering information for a directory on a packet switched network is disclosed. In one step, a directory is determined for a first web site. The directory is reported to a second web site a first time. After detecting changes on the first web site, the directory is updated with the changes. The directory is reported to a second web site a second time.
Owner:GOOGLE TECH HLDG LLC
Method for learning and combining global and local regularities for information extraction and classification
InactiveUS6892189B2Digital data processing detailsDigital computer detailsPattern recognitionData set
A method is provided for information extraction and classification which combines aspects of local regularities formulation with global regularities formulation. A candidate subset is identified. Then tentative labels are created so they can be associated with elements in the subset that have the global regularities, and the initial tentative labels are attached onto the identified elements of the candidate subset. The attached tentative labels are employed to formulate or “learn” initial local regularities. Further tentative labels are created so they can be associated with elements in the subset that have a combination of global and local regularities, and the further tentative labels are attached onto the identified elements of the candidate subset. Each new dataset is processed with reference to an increasingly-refined set of global regularities, and the output data with their associated confidence labels can be readily evaluated as to import and relevance.
Owner:WHIZBANG LABS
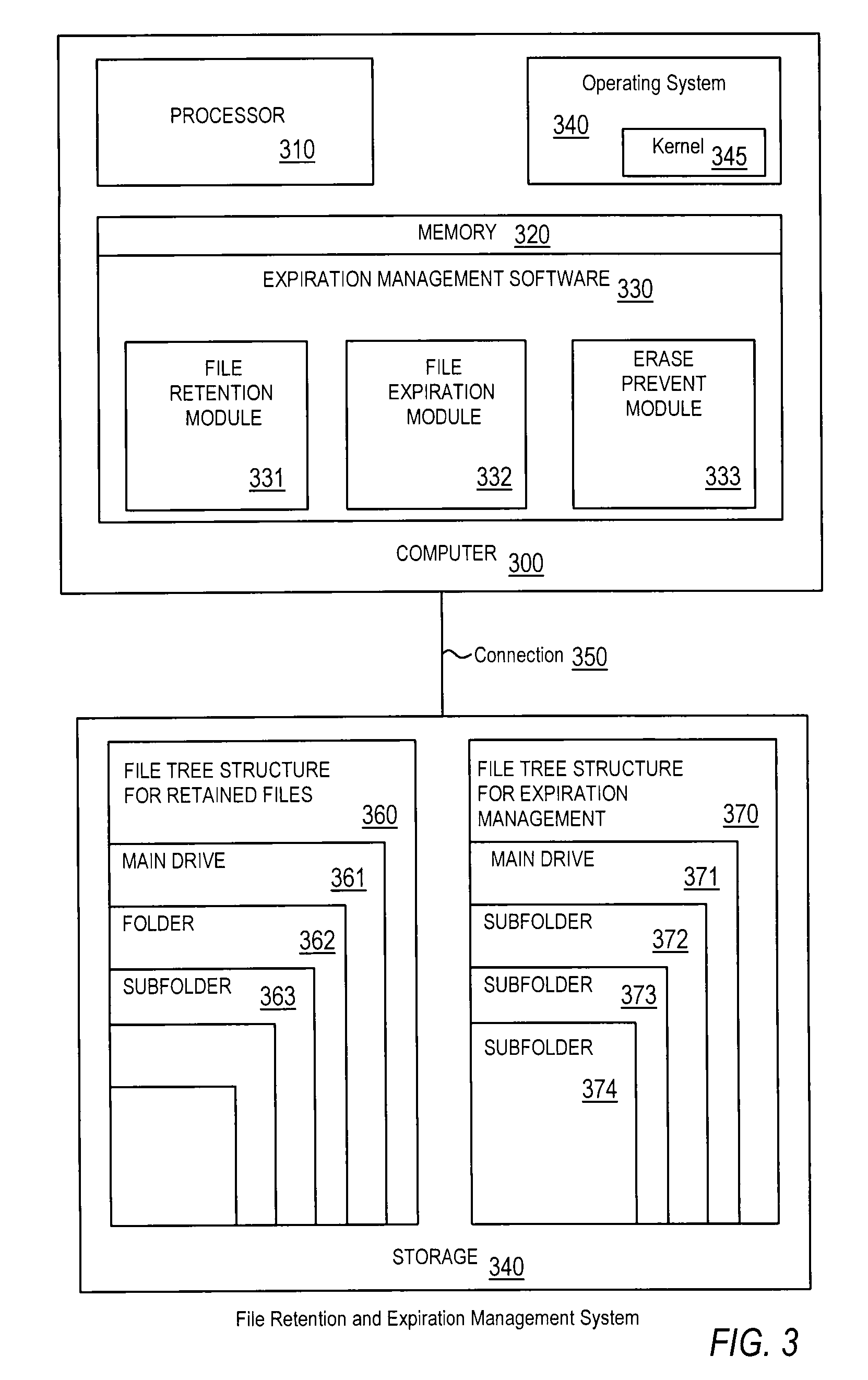
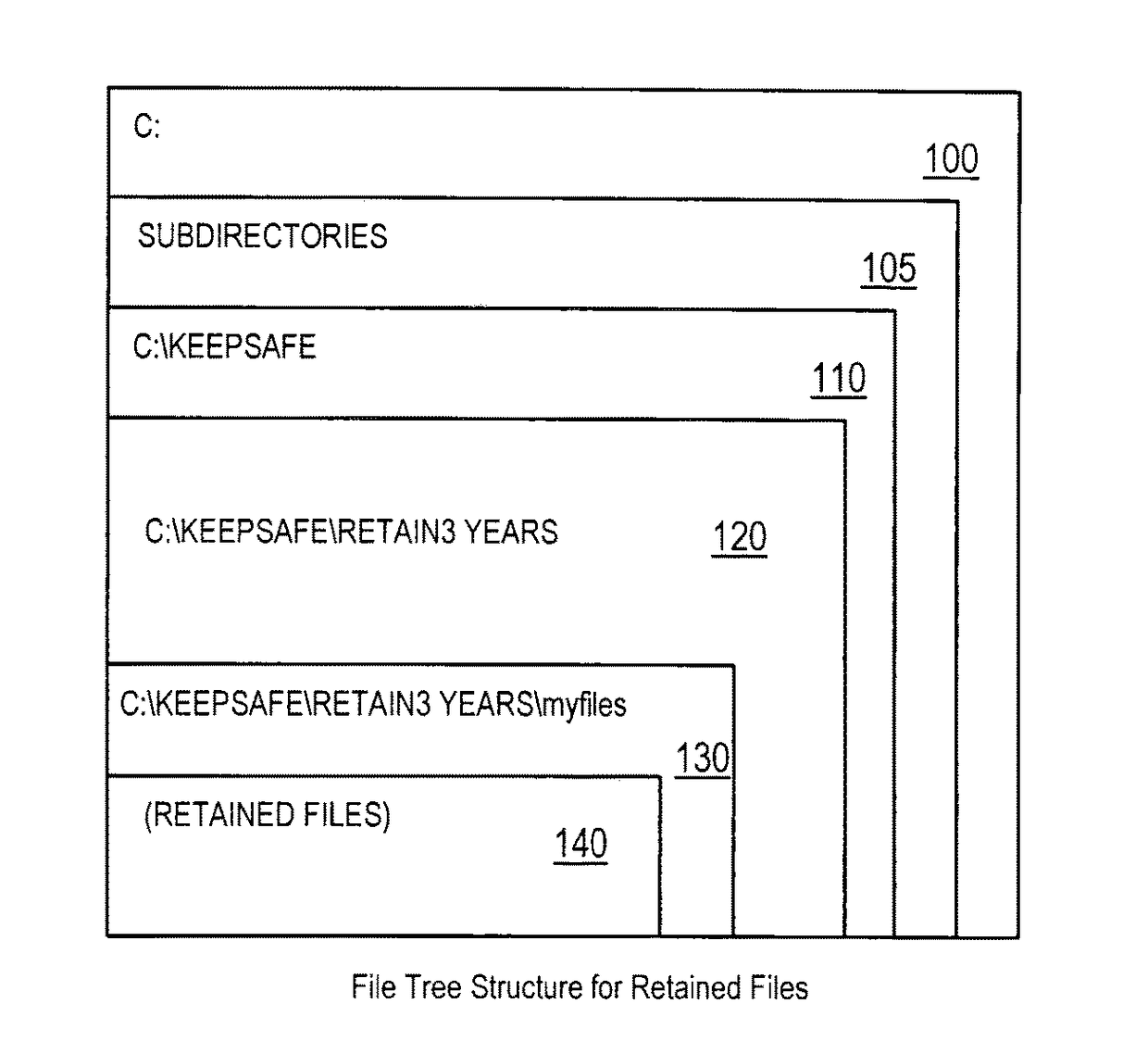
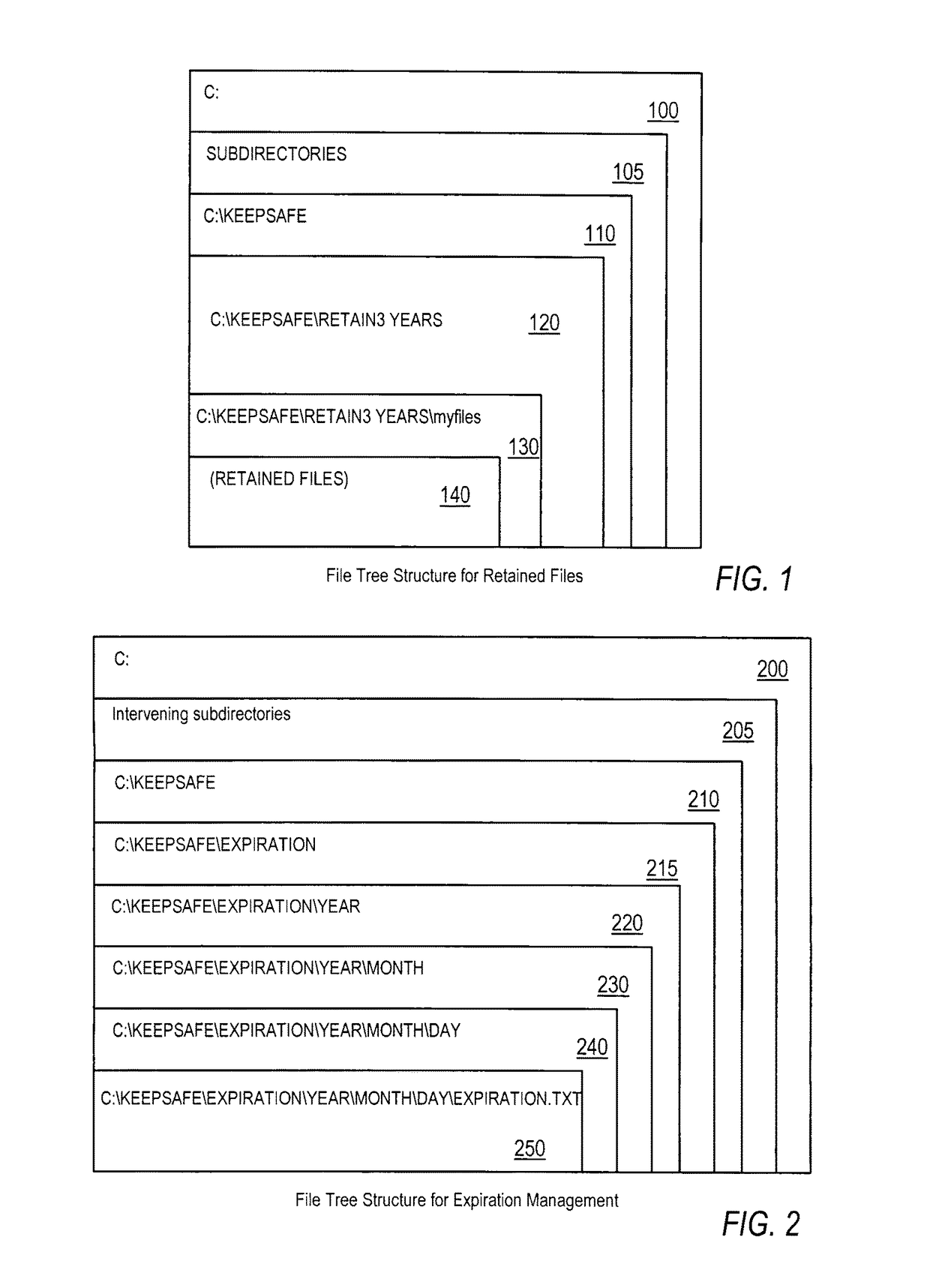
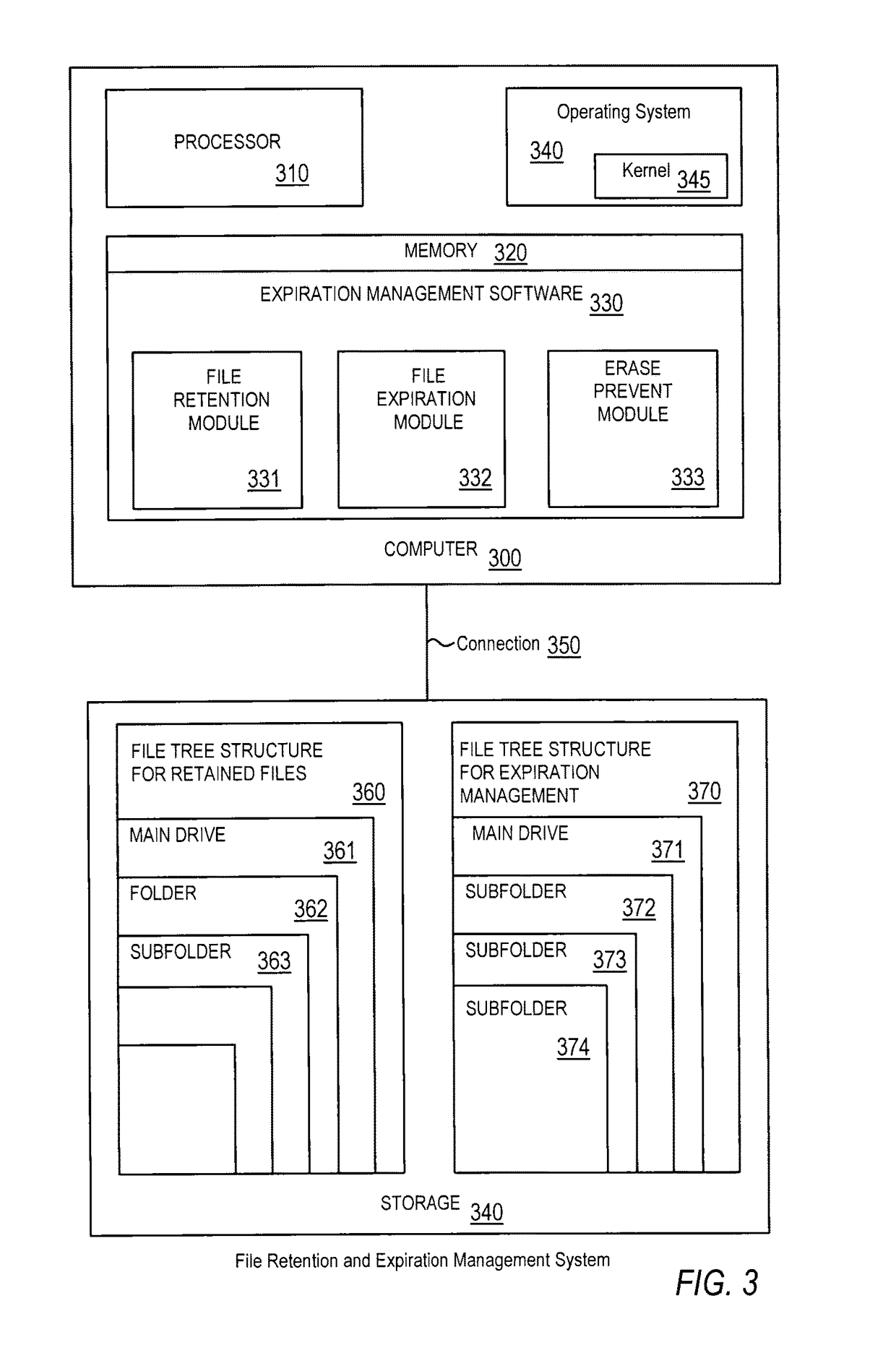
Efficient non-database file-expiration management for document retention
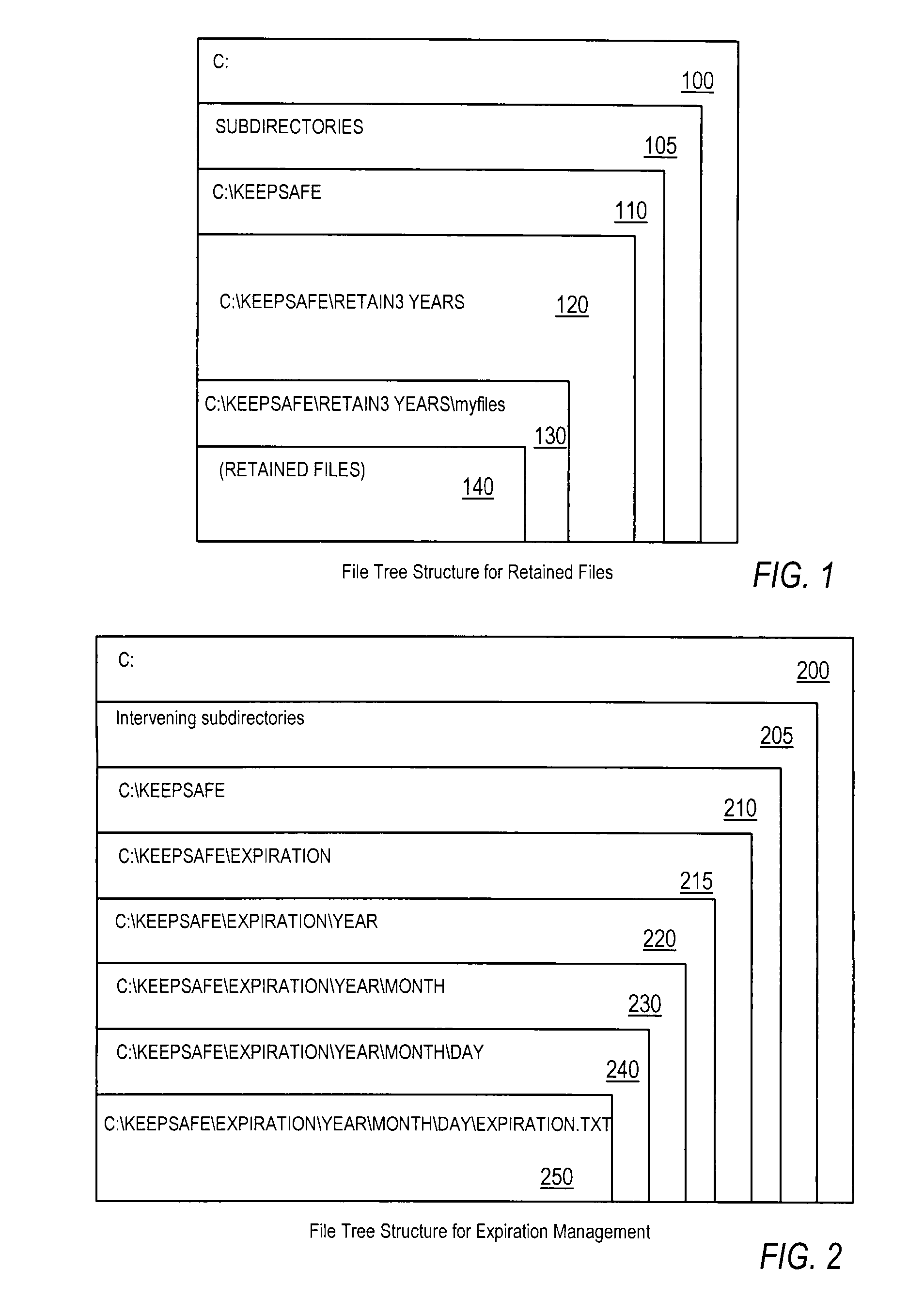
ActiveUS20080034003A1Efficiently performing functionEffective functionObsolescenceSpecial data processing applicationsRetention periodOperational system
Disclosed are a method, system, program and data structure for implementing a records retention policy by storing selected files for designated lengths of time and then deleting them only when that time has passed. Embodiments of the invention perform this function in an efficient database-free manner. Embodiments of the invention can perform this function by utilizing existing storage directory tree functionality provided by any computer operating system organized under a retention directory coupled with a mechanism for preventing unauthorized deletions of files designated for retention. Expiration of retained files may be managed through directory structure using directory names corresponding to expiration dates determined from identified retention periods for retained files. Files may be further protected from erasure by a kernel mode process which prevents erasure of any files contained in the retention directory.
Owner:IBM CORP
Viewer object proxy
InactiveUS6879998B1Improve transfer qualityEvaluating transfer qualityData processing applicationsError preventionContent distributionWorld Wide Web
A method for increasing transfer quality between a content requestor and a content source on a content distribution system. The method involves determining transfer quality between the requestor and various content sources. The determination is made from the requestor's perspective. After determining transfer qualities for the various content sources, the requester provides the transfer qualities to a selector on the content distribution system. The selector uses the determined transfer qualities select a content source to supply the requestor.
Owner:GOOGLE TECH HLDG LLC
Viewer object proxy
InactiveUS20050160154A1Improve transfer qualityEvaluating transfer qualityData processing applicationsError preventionContent distributionDistributed computing
A method for increasing transfer quality between a content requestor and a content source on a content distribution system. The method involves determining transfer quality between the requestor and various content sources. The determination is made from the requestor's perspective. After determining transfer qualities for the various content sources, the requester provides the transfer qualities to a selector on the content distribution system. The selector uses the determined transfer qualities select a content source to supply the requestor.
Owner:GOOGLE TECH HLDG LLC
System and method for record retention date in a write once read many storage system
InactiveUS20070118687A1Input/output to record carriersData processing applicationsRetention periodData set
This invention provides a specified retention date within a data set that is locked against deletion or modification within a WORM storage implementation. This retention date scheme does not utilize any proprietary application program interfaces (APIs) or protocols, but rather, employs native functionality within conventional file (or other data containers, data sets or block-based logical unit numbers) properties available in commonly used operating systems. In an illustrative embodiment, the retention date / time is calculated by querying the file's last-modified time prior to commit, adding the retention period to this value and thereby deriving a retention date after which the file can be released from WORM. Prior to commit, the computed retention date is stored in the file's “last access time” property / attribute field, or another metadata field that remains permanently associated with the file and that, in being used for retention date, does not interfere with file management in a WORM state. Since this field is not utilized in a WORM context, it can be adapted to store this date. Once stored, the retention date in this field is locked against modification. Where extension (never reduction) of a retention period is desired, the last access time field be updated, wherein the new retention period is added to the existing last access time value to derive a new, later retention date for the file. Upon expiry of the retention date, the system allows deletion of the expired WORM file / data set.
Owner:NETWORK APPLIANCE INC
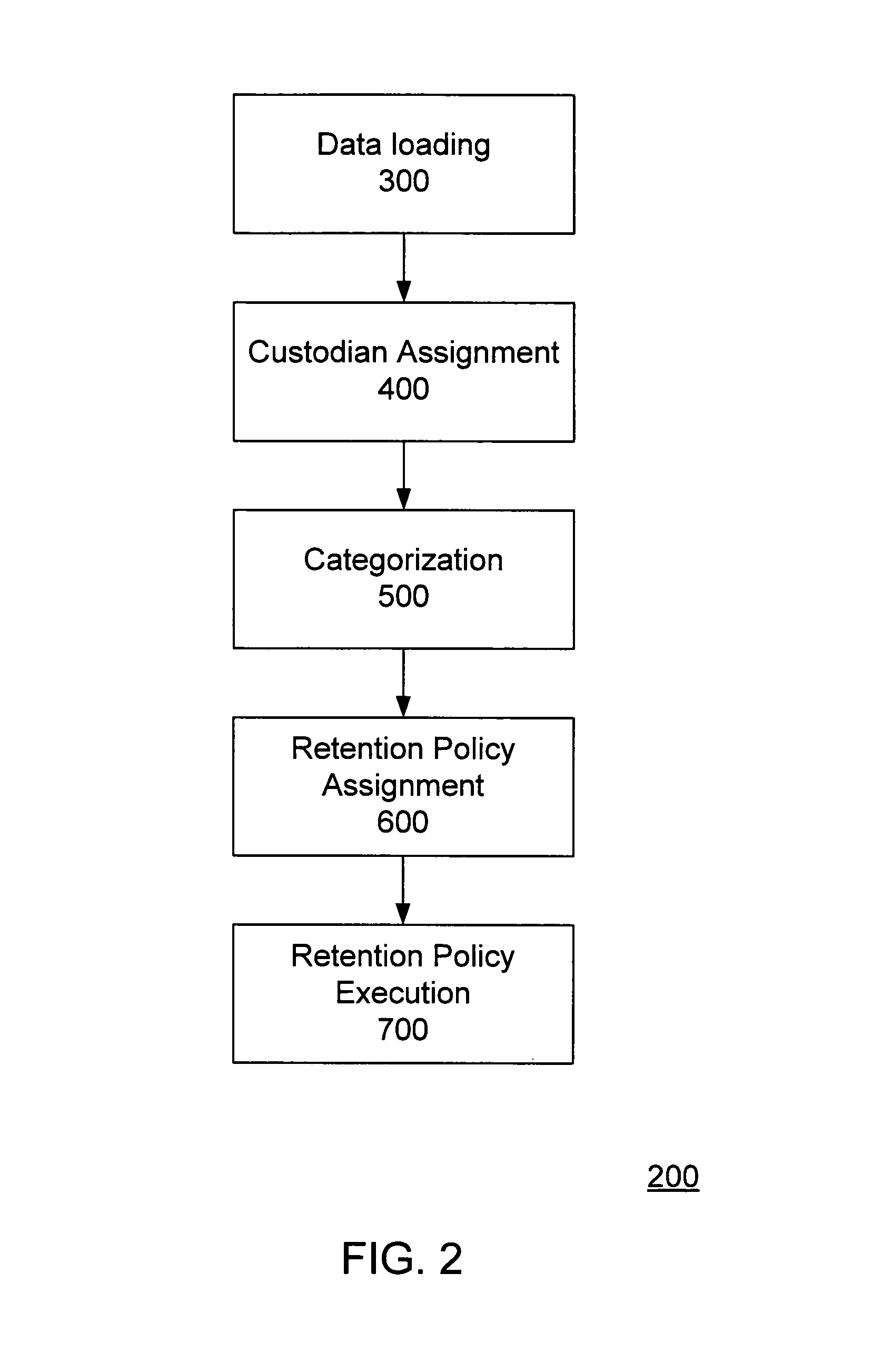
System and method for management of retention periods for content in a computing system
ActiveUS8527468B1Digital data processing detailsObsolescenceRetention periodDistributed Computing Environment
Disclosed are embodiments of a system and method for establishing and managing document retention policy in a distributed computing environment. One embodiment comprises the steps of loading documents into a database as individual components or items; establishing a custodian for each document instance; categorizing its content into a plurality of categories; assigning retention periods to the content by category; and continuously monitoring retention policies according to the assigned retention periods. Any database capable of storing de-duplicated data can be adapted to implement embodiments of the invention. One embodiment utilizes codified algorithms to cross-match one or more retention policies with each document instance in the system based on the role of the custodian held at the time the instance was created and retained and / or the content or category of the content to which the document refers. If multiple policies apply, the retention period is set to the furthest in the future.
Owner:COMERICA BANK
Method and system for adaptively setting a data refresh interval
A method and system is disclosed for adaptively refreshing a data using system. The data using system includes a data source and a data using device for utilizing data from the data source. The data using device has an initial refresh interval. A communication link is provided between the data source and the data using device. A criteria monitor is provided for monitoring at least one criteria related to the refresh interval. A processor is provided for generating an updated data refresh interval based at least in part on the monitored criteria. The data using device is updated based on the data refresh interval.
Owner:XANBOO
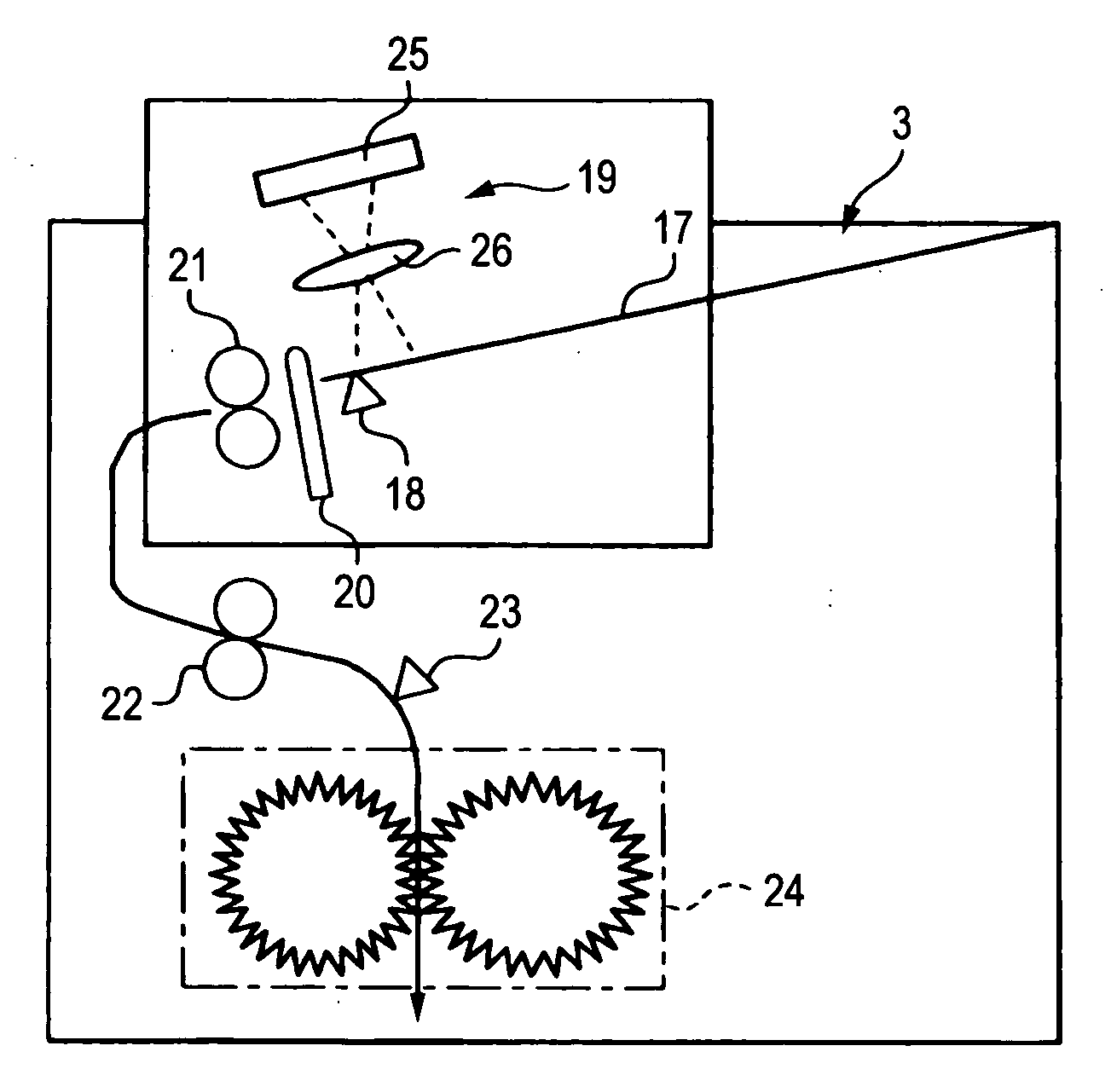
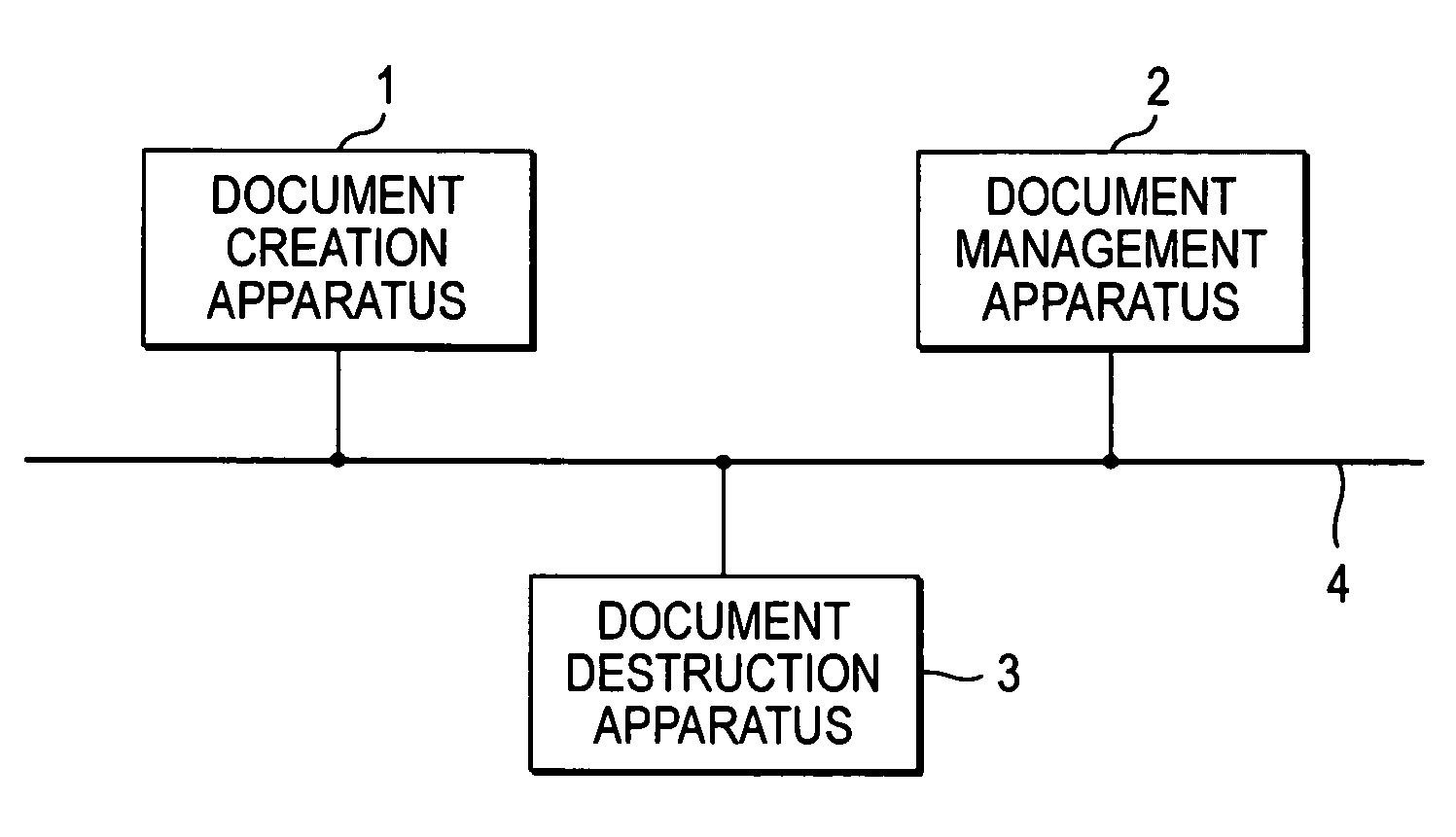
Document management system and document destruction apparatus
A document management system comprises a document management apparatus that manages a document ID by associating the document ID with a storage time of the document, and checks the storage time in response to an inquiry about a permission of destroying the document and gives a permission of destroying the document when the storage time has expired, and a document destruction apparatus including a mode selection unit that selects one of a first destruction mode and a second destruction mode and an execution unit that destroys the document according to a destruction mode selected by the mode selection unit. The execution unit destroys the document without reading the document ID in the first destruction mode, and reads the document ID to inquire the permission of destroying the and destroys the document when the document management apparatus gives the permission of destroying the document in the second destruction mode.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Clean-up of files in a network system
InactiveUS6418456B1Minimize network trafficMinimization requirementsData processing applicationsObsolescenceData structureUnit process
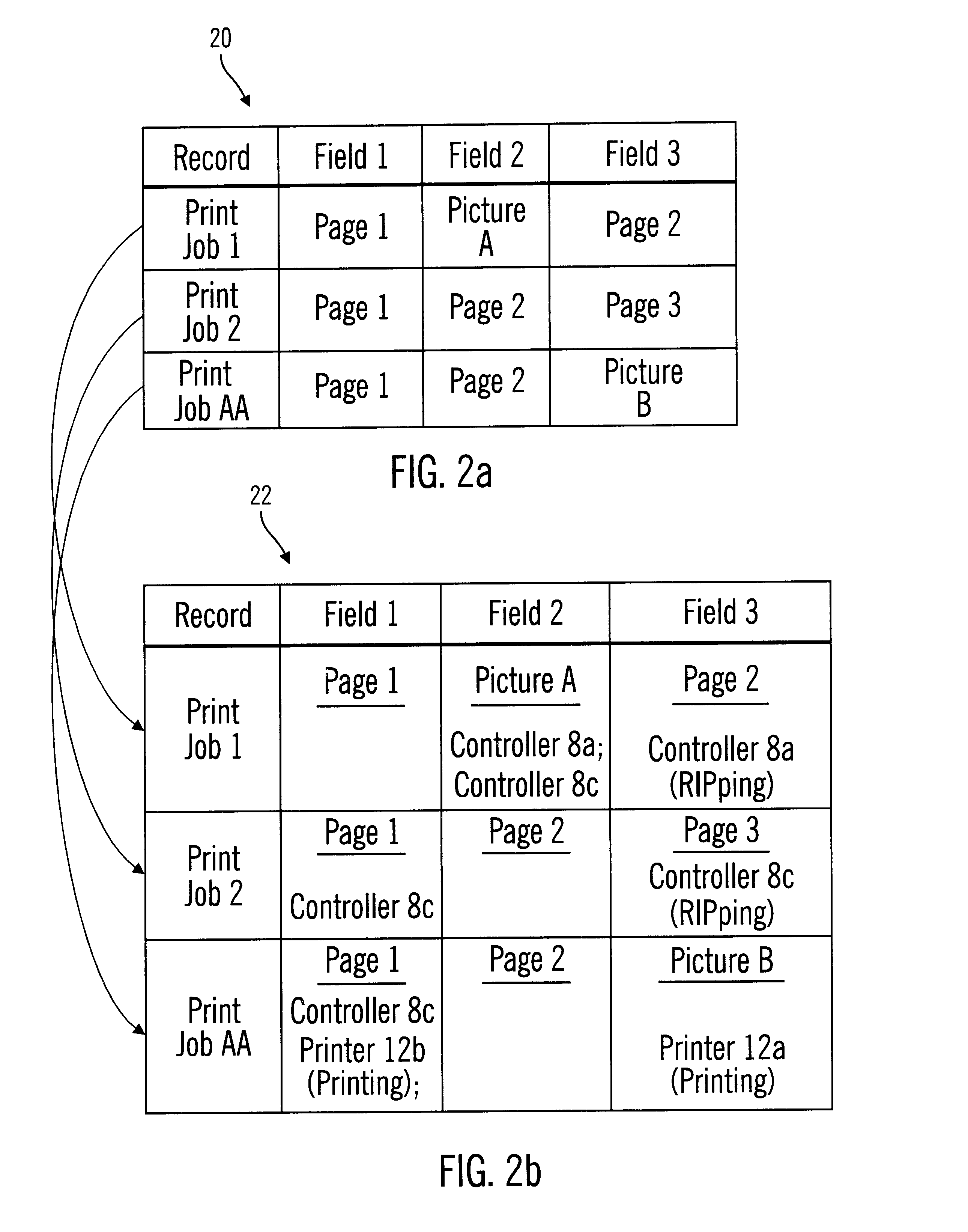
Disclosed is a system and method for managing files in a network system and, in particular, a network printing system. A processing unit, such as a printer manager detects an update to a file, such as a print file, maintained in a storage unit. At least one network device, such as a printer controller, maintains a copy of the file to update that is a previous version of the file to update maintained at the storage unit. The processing unit processes a data structure indicating network devices that include previous versions of the file and determines the network devices that include at least one previous version of the file. The processing unit then transmits a message to the network devices that include at least one previous version of the file to delete the previous versions of the file.
Owner:RICOH KK
Document management system and document destruction apparatus
A document management system comprises a document management apparatus that manages a document ID by associating the document ID with a storage time of the document, and checks the storage time in response to an inquiry about a permission of destroying the document and gives a permission of destroying the document when the storage time has expired, and a document destruction apparatus including a mode selection unit that selects one of a first destruction mode and a second destruction mode and an execution unit that destroys the document according to a destruction mode selected by the mode selection unit. The execution unit destroys the document without reading the document ID in the first destruction mode, and reads the document ID to inquire the permission of destroying the and destroys the document when the document management apparatus gives the permission of destroying the document in the second destruction mode.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Selective routing
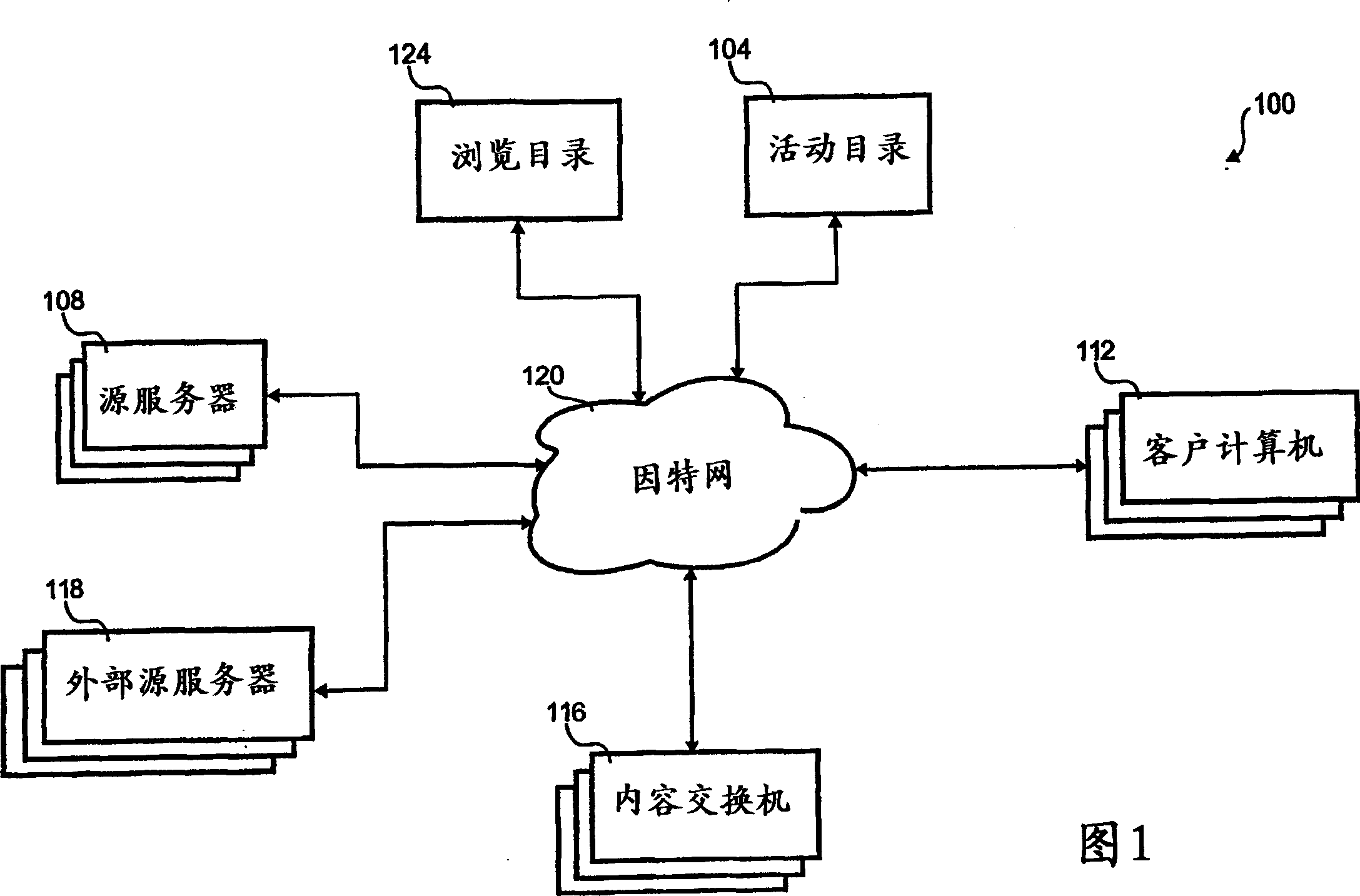
The present invention relates to routing content from a network. In one implementation, a method of client-side routing of content objects among multiple data paths to a server is disclosed. The first data path of the server is associated with the first party. The second data path of the server is associated with the second party. The client computer is operable to automatically determine which of the first and second data paths to receive the content object from.
Owner:AEROCAST COM INC
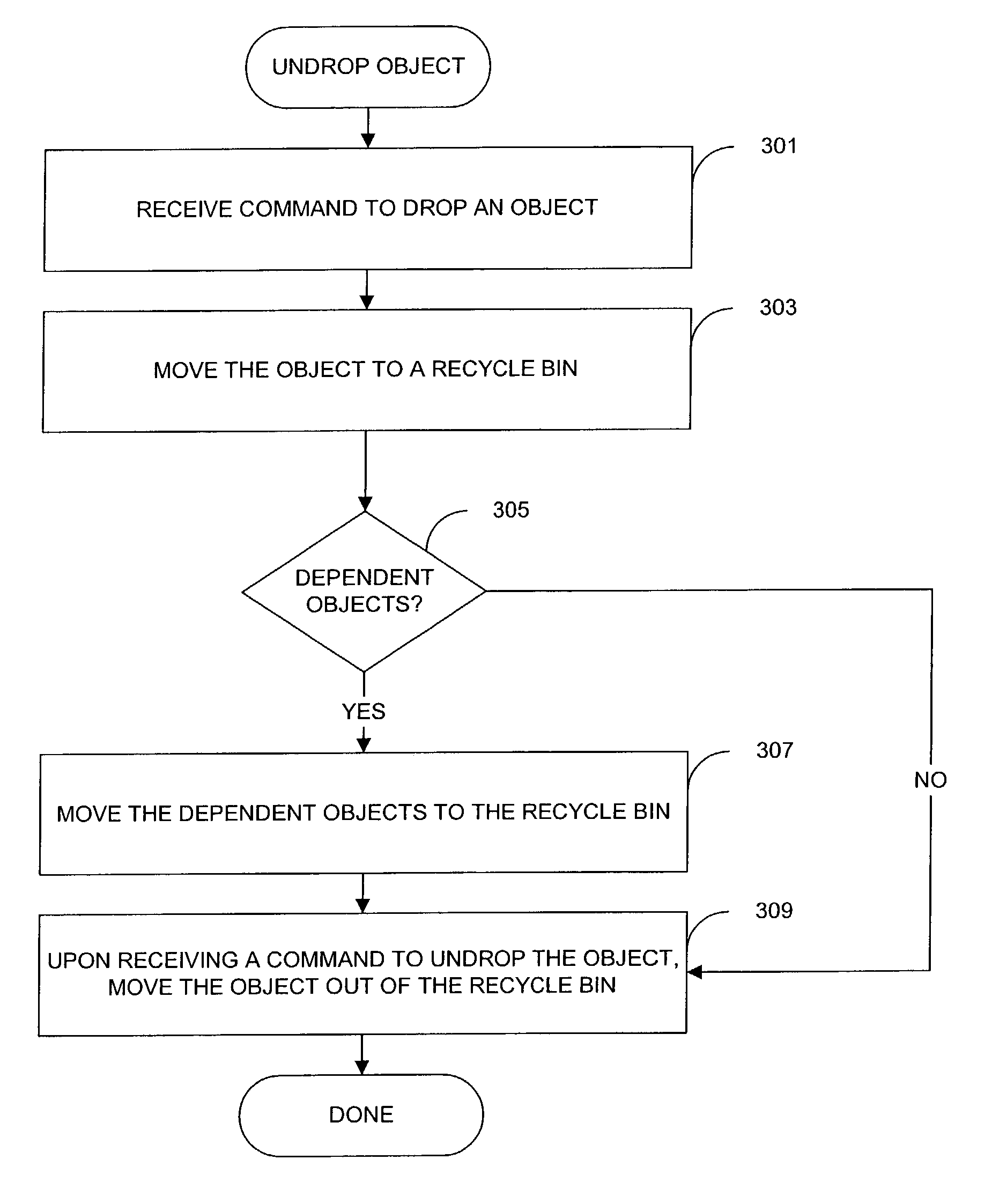
Undrop objects and dependent objects in a database system
Techniques for undropping objects (e.g., tables) and dependent objects in a database systems are provided. When an object is dropped, the object is moved to a recycle bin where it resides until the user undrops the objects or the object is purged. Dependent objects are also moved into the recycle bin with the object to which they depend. The object can be purged from the recycle bin explicitly by a user or when more storage space is needed. Purging of dependent objects and partitions can be deferred if not required to obtain more storage space.
Owner:ORACLE INT CORP
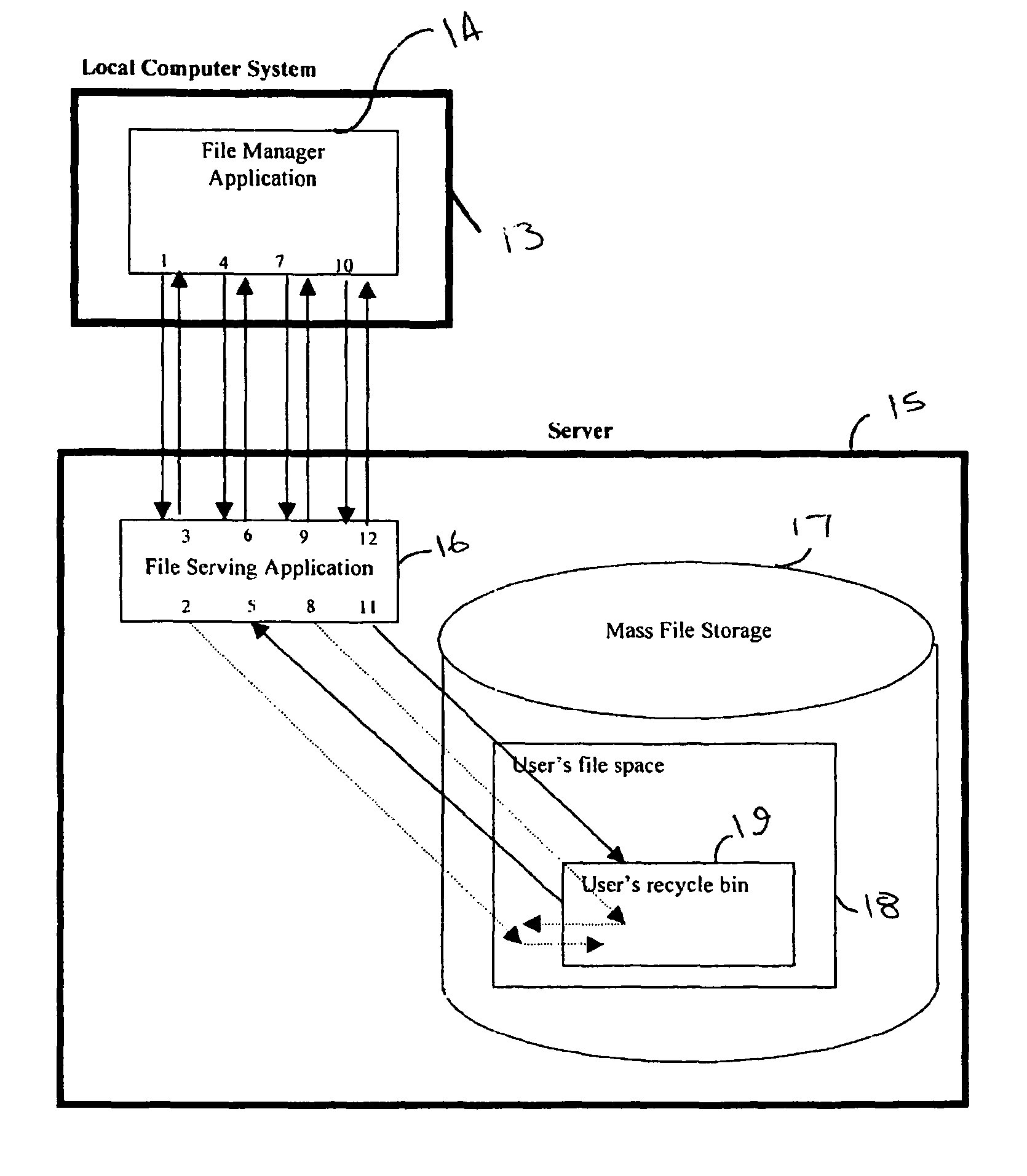
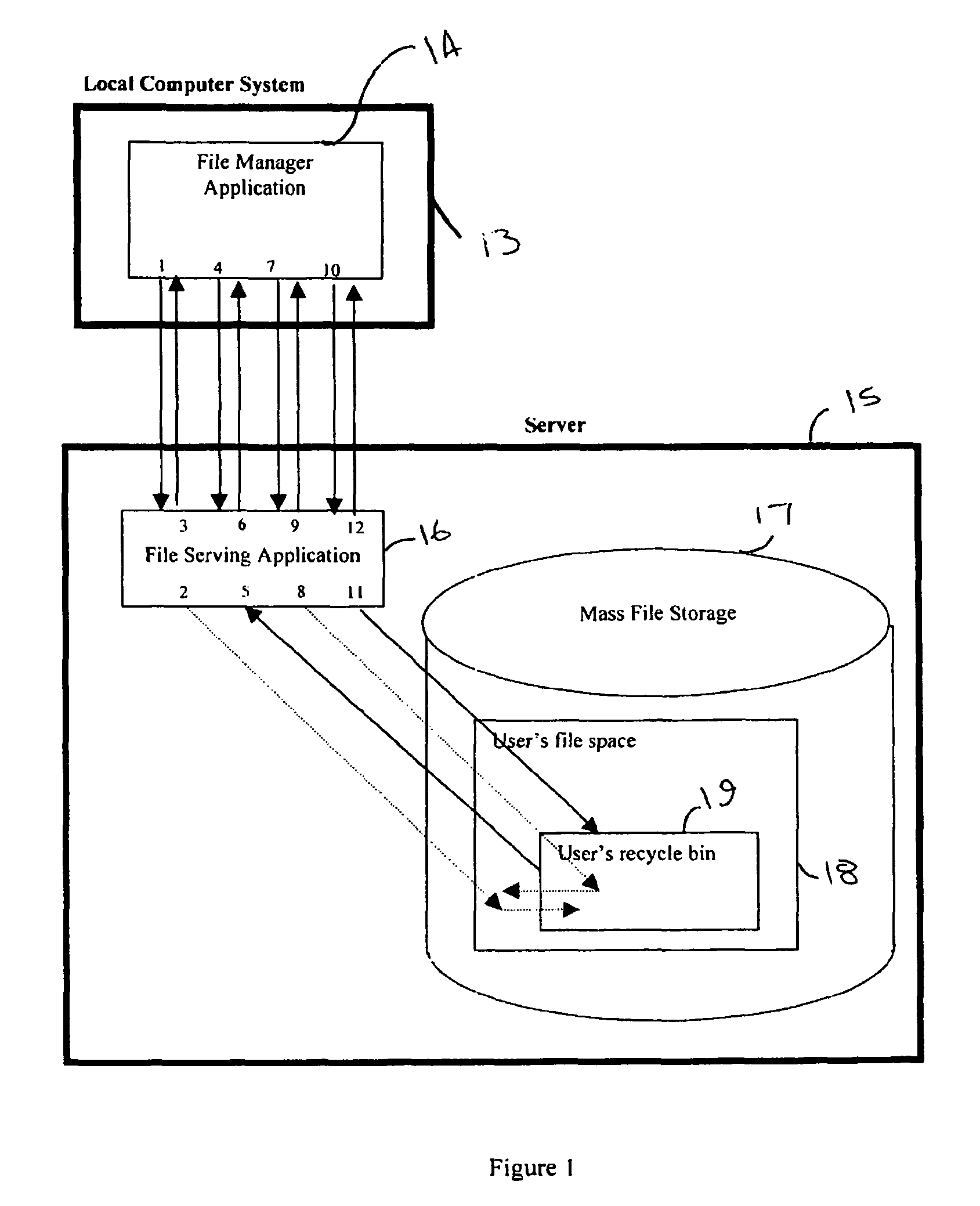
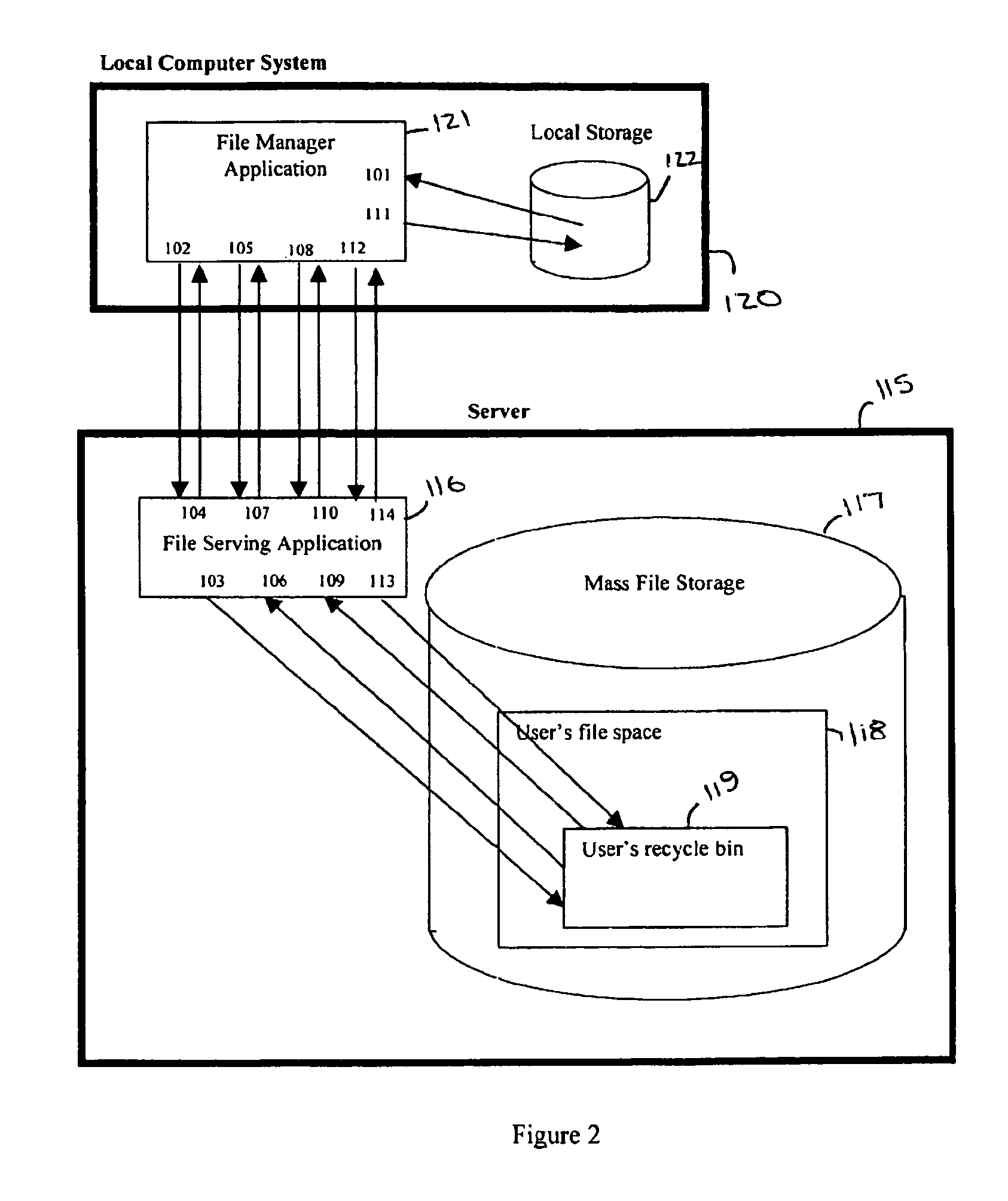
Server-side recycle bin system
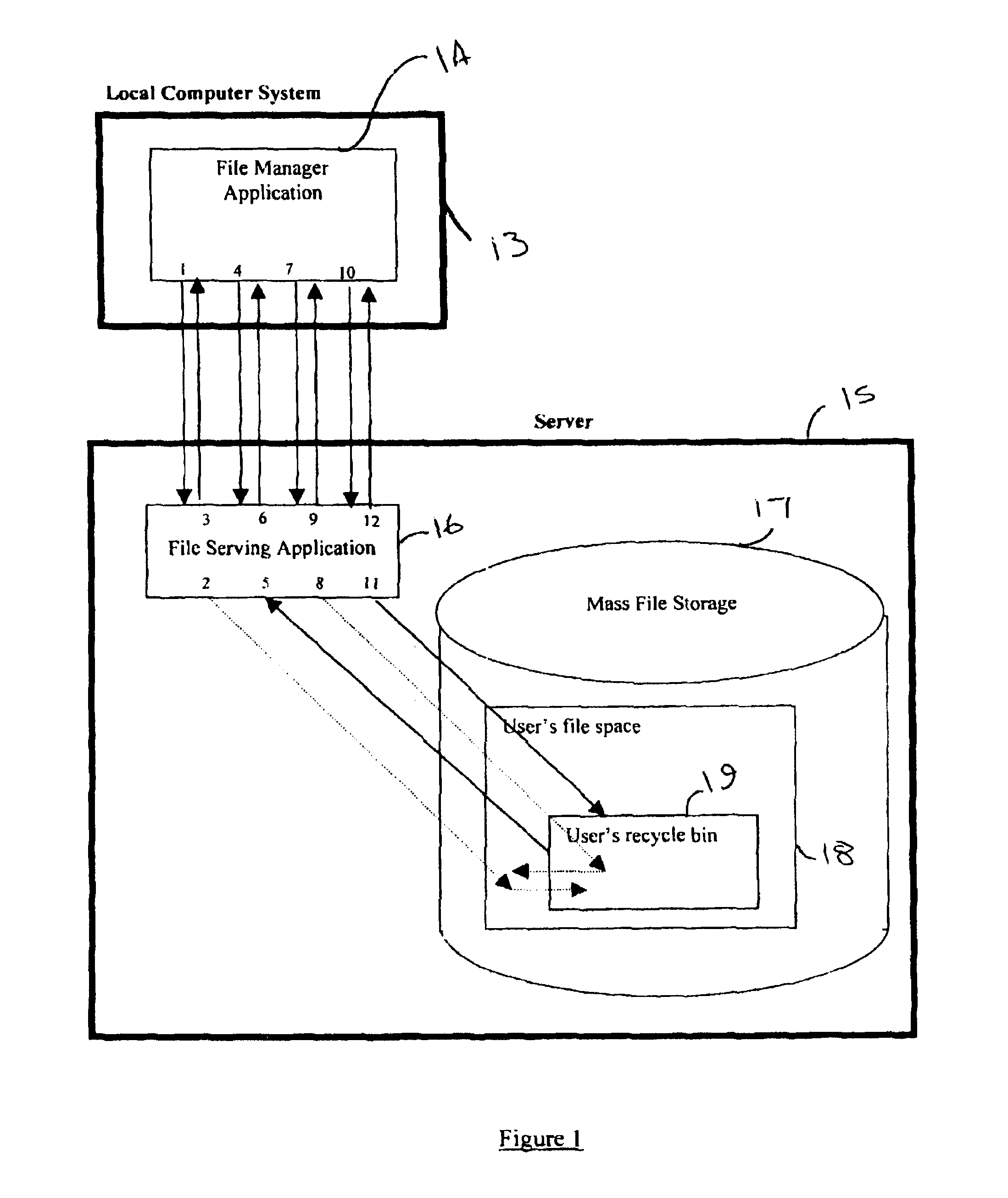
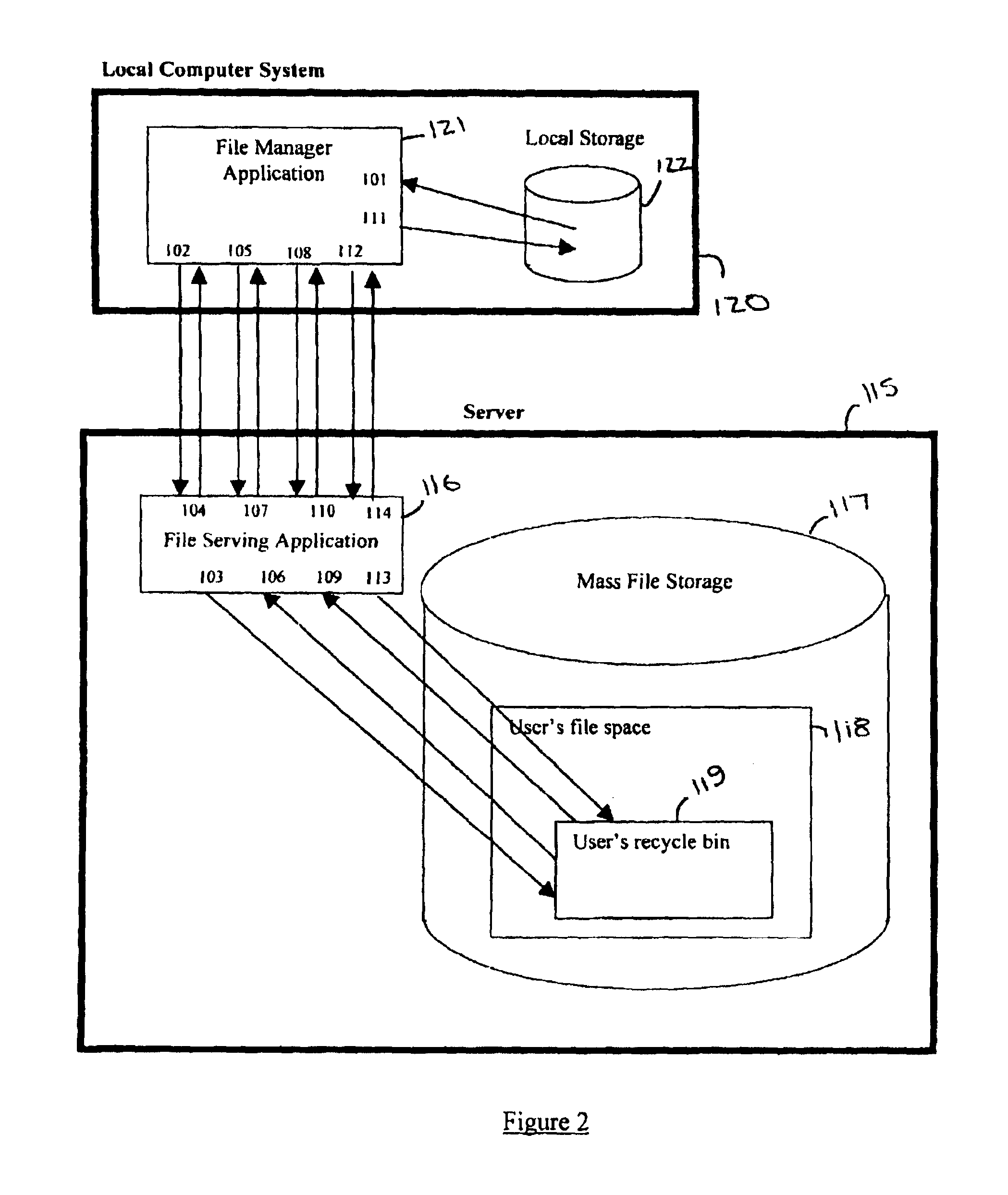
A server-side recycle bin system for retaining computer files and information is disclosed. The system comprises a local computer system, and a server including a server-side recycle bin. One or more persistent storage devices, providing the files and directories to be protected, are present either as part of the local computer system or as part of the server. The local computer system and the server may be connected via a wide area computer network, a local area network, the Internet, of any other method or combination of methods. A file manager application running on the local computer system interacts with a file serving application on the server such that there is generated a retained file in the server-side recycle bin.
Owner:SYNACOR
Active directory for content objects
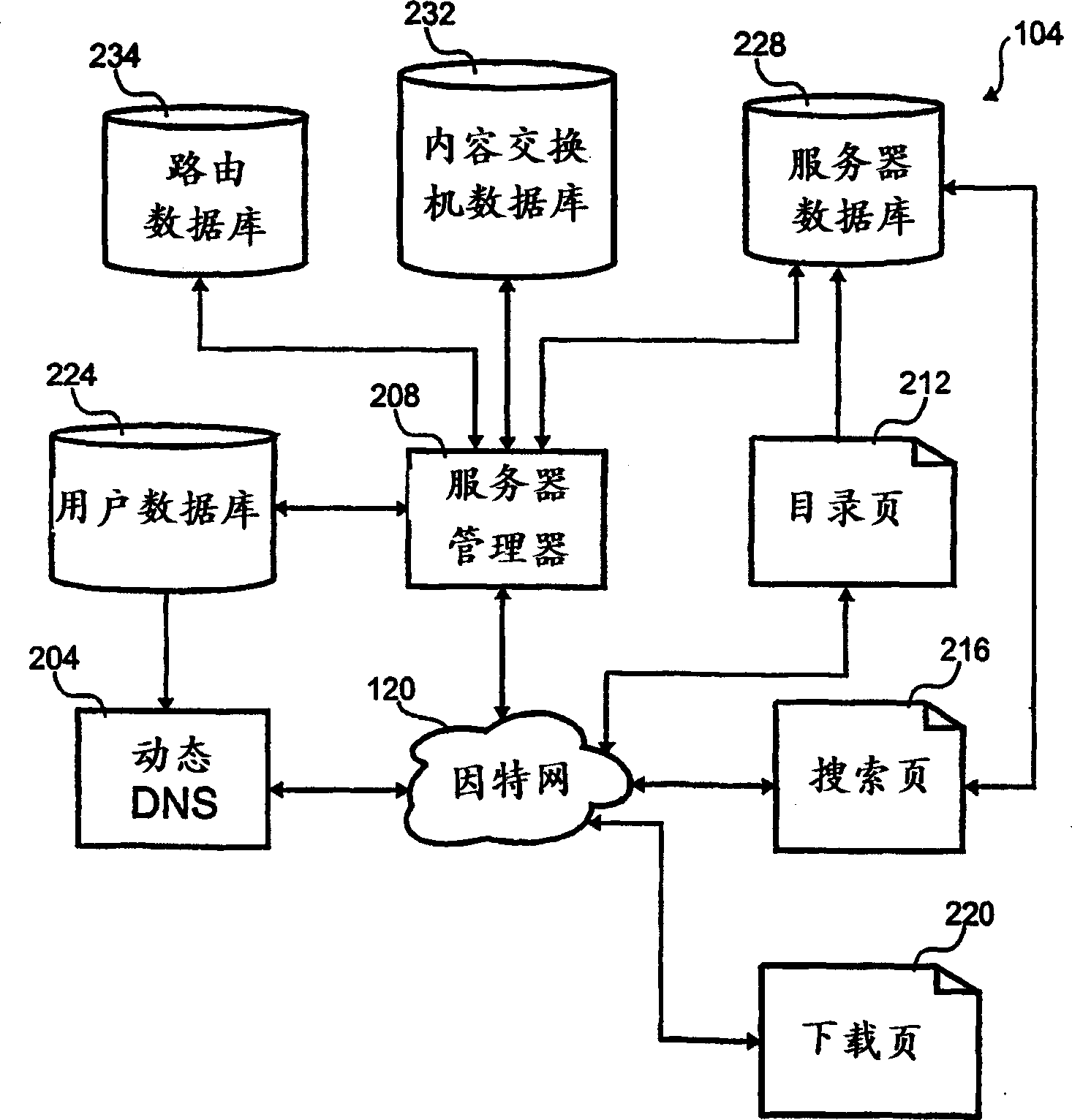
The present invention relates to maintaining information in a networked directory. In one implementation, a method for updating a networked directory of content objects is disclosed. In one approach, a first catalog of first content objects associated with a first server is received. The first catalog is stored in the information store. A second catalog of second content objects associated with a second server is received. Store the second catalog in the information store. A first elapsed time associated with the first server is detected. When the first elapsed time is detected, the first catalog is marked for deletion from the information store.
Owner:AEROCAST COM INC
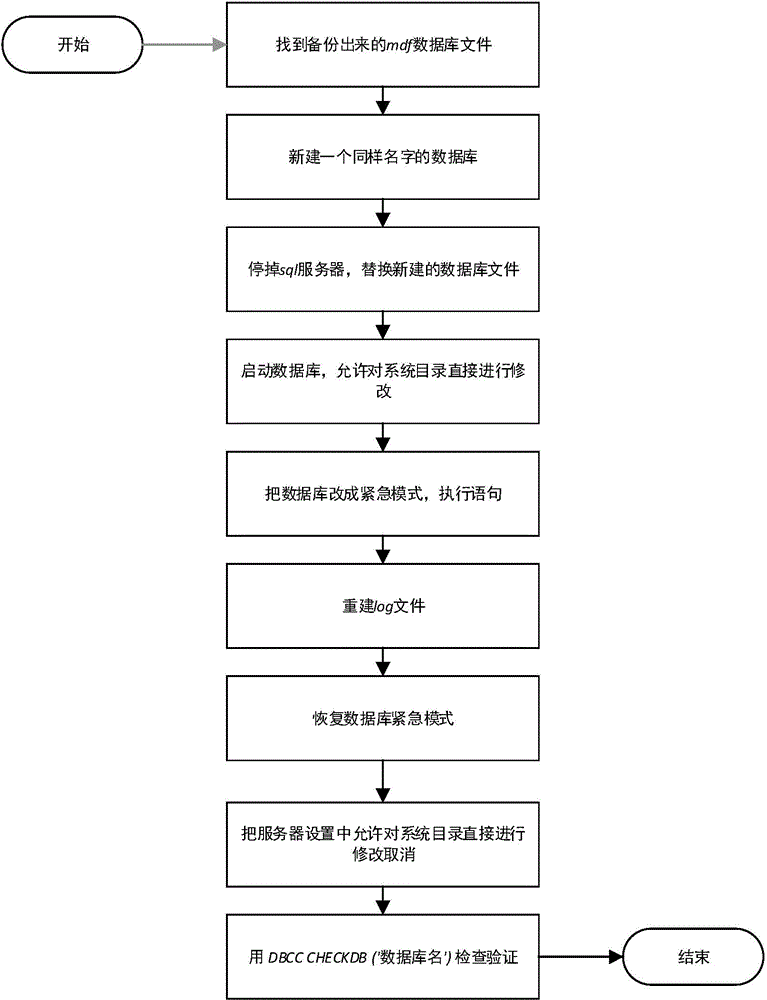
Method for making only MDF attached to restore database
InactiveCN104462261AAchieve restorationObsolescenceRedundant operation error correctionSql serverDatabase file
The invention relates to the technical field of SQL Server databases, in particular to a method for making only an MDF attached to a restore database. The method includes the steps of firstly, finding a backup MDF database file; secondly, creating a new database with the same name in an enterprise manager; thirdly, stopping an SQL server, and deleting the created new MDF and log files; fourthly, starting the database, setting the server to a state that a system catalog can be directly modified; fifthly, changing the mode of the database into an emergency mode; sixthly, restoring the emergency state of the database by executing update sysdatabases set status=0where name='database name'; seventhly, setting the server to a state that the system catalog can be directly modified and deleted. By means of the method, the technical problem that report errors happen when only the MDF without an LDF is attached to the restore database is solved; the method can be used for restoring the SQL Server database.
Owner:G CLOUD TECH
Reverse content harvester
The present invention relates to collecting information for networked directories. In one implementation, a method for gathering information for a directory on a packet-switched network is disclosed. In one measure, a directory of the first web site is determined. The directory is reported to the second web site for the first time. After detecting changes in the first web site, the directory is updated according to the changes. The directory is reported to the second web site a second time.
Owner:AEROCAST COM INC
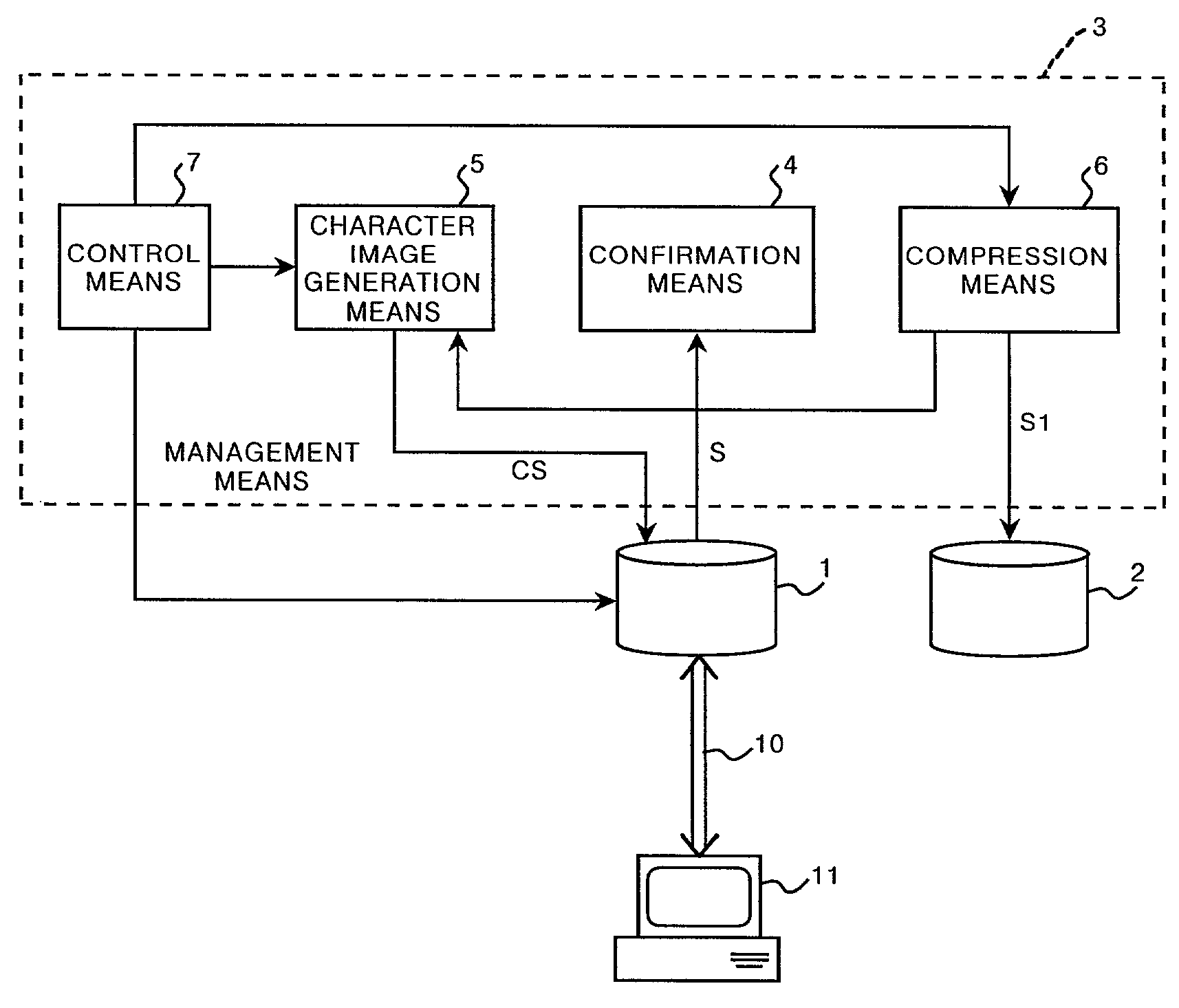
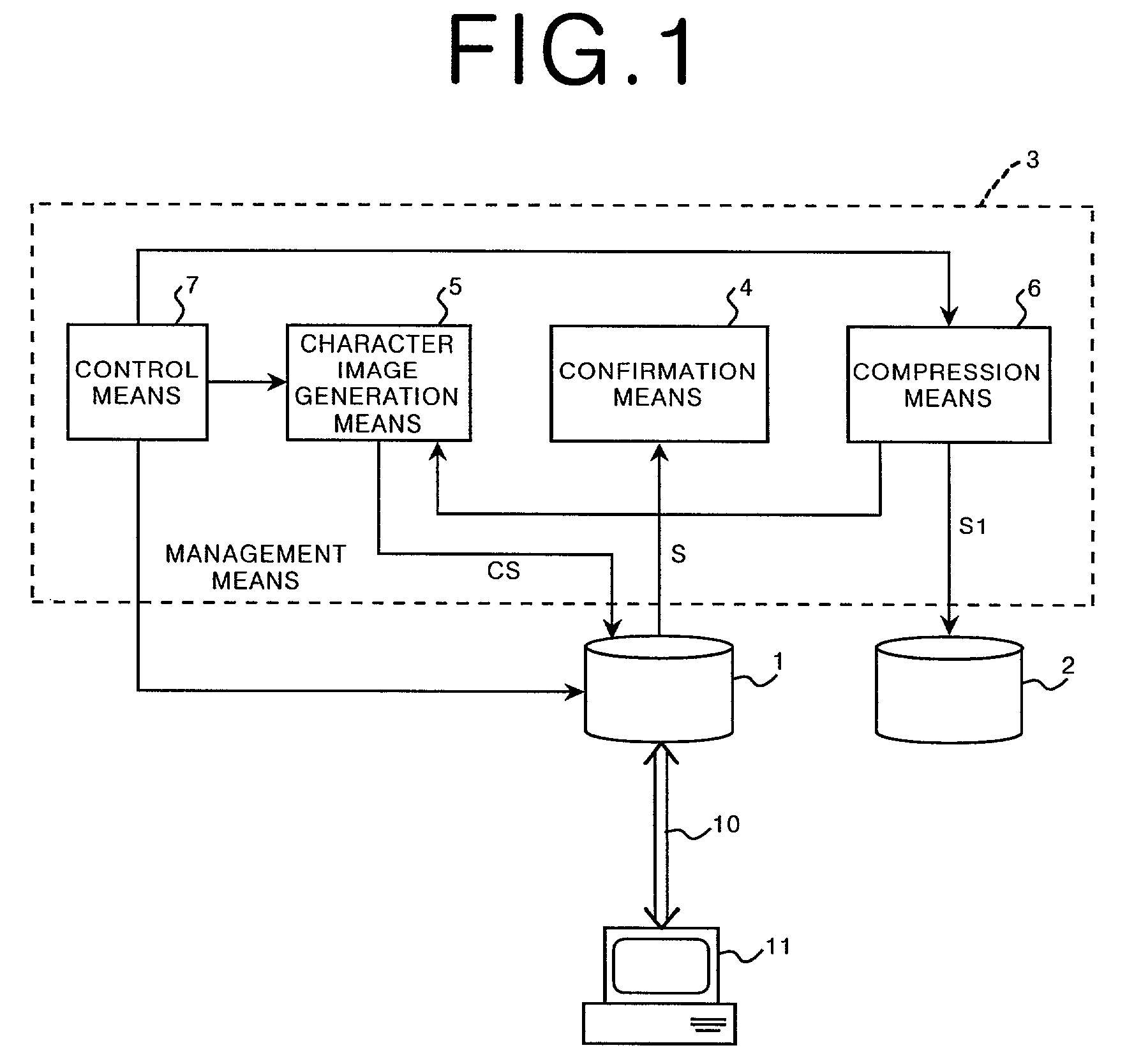
Method, apparatus, and program for image filing
In the case where an image data set stored in a recording medium of an image server or the like is linked to a Web page, an error message is prevented from being shown even if the image data set is deleted. Confirmation means confirms a storage period for the image data set. If the storage period has expired, character image generation means generates a character image data set of the same format and having the same file name as the image data set. The character image represented by the character image data set indicates deletion of the image data set. Compression means compresses the image data set and the compressed image data set is stored in another recording medium. The image data set is then deleted. When an access to the image data set is attempted, the character image data set is referred to.
Owner:FUJIFILM HLDG CORP +1
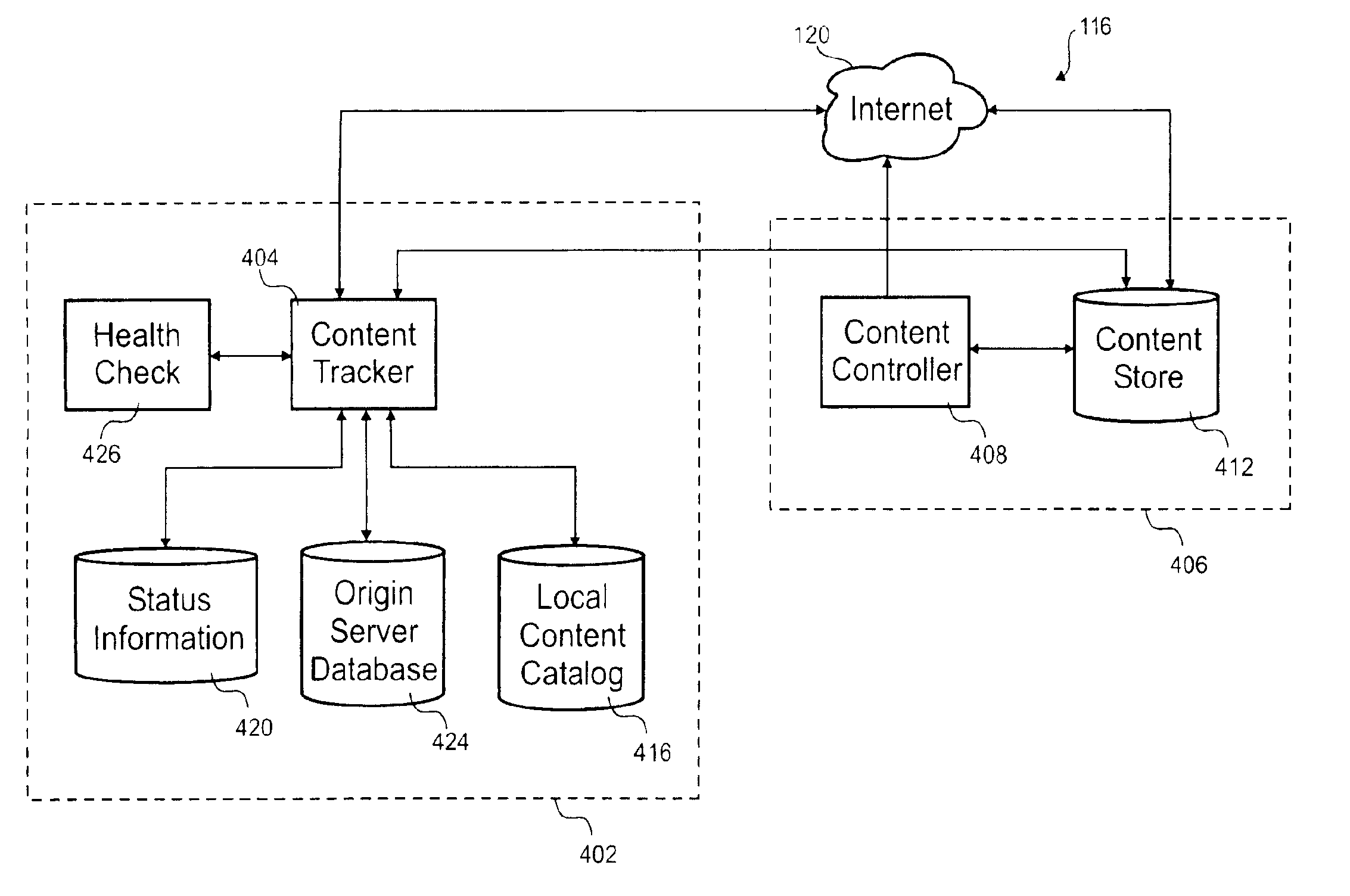
Content tracing
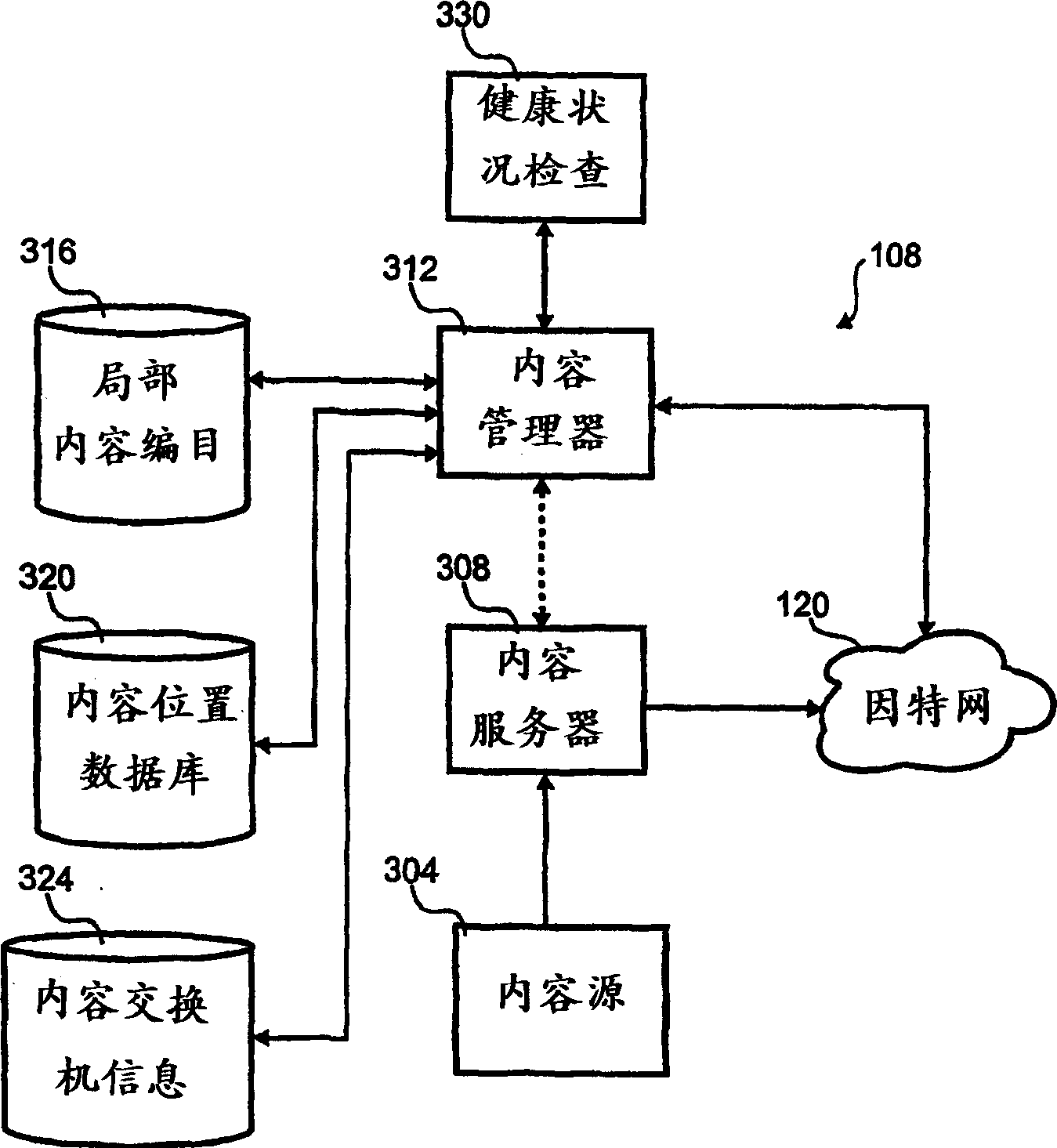
The invention relates to tracking content objects when distributing content on a network. One embodiment of the invention reports status information from a plurality of content exchanges to a remote location and includes a first and second content exchanges, a remote server, and a first and second datalinks. The first content exchange includes a first plurality of content object portions and the second content exchange includes a second plurality of content object portions. The remote server includes a first subset of the first plurality of content object portions and a second subset of the second plurality of content object portions. The first datalink transports a first catalog of the first subset between the first content exchange and the server and the second datalink transports a second catalog of the second subset between the second content exchange and the server.
Owner:AEROCAST COM INC
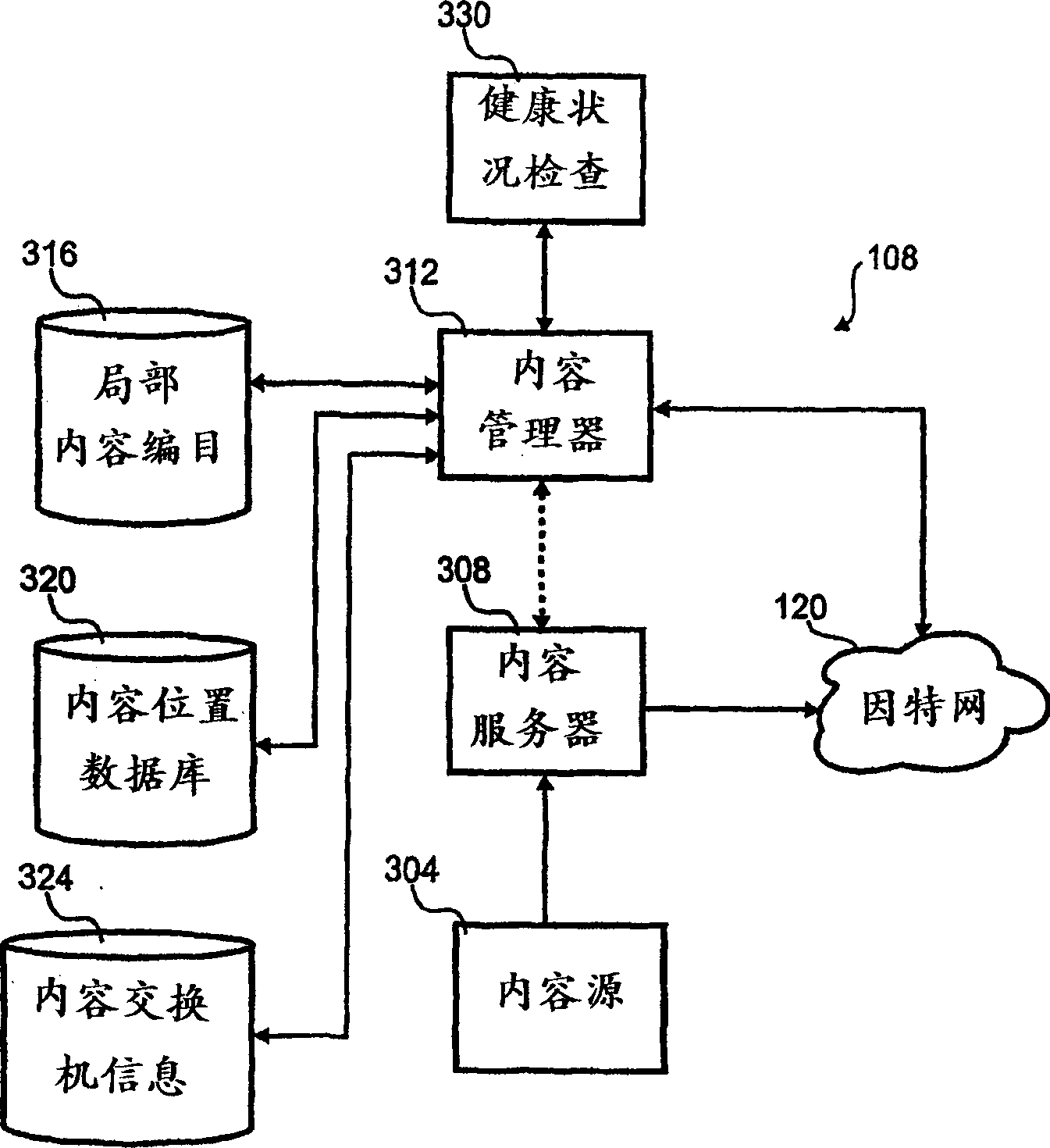
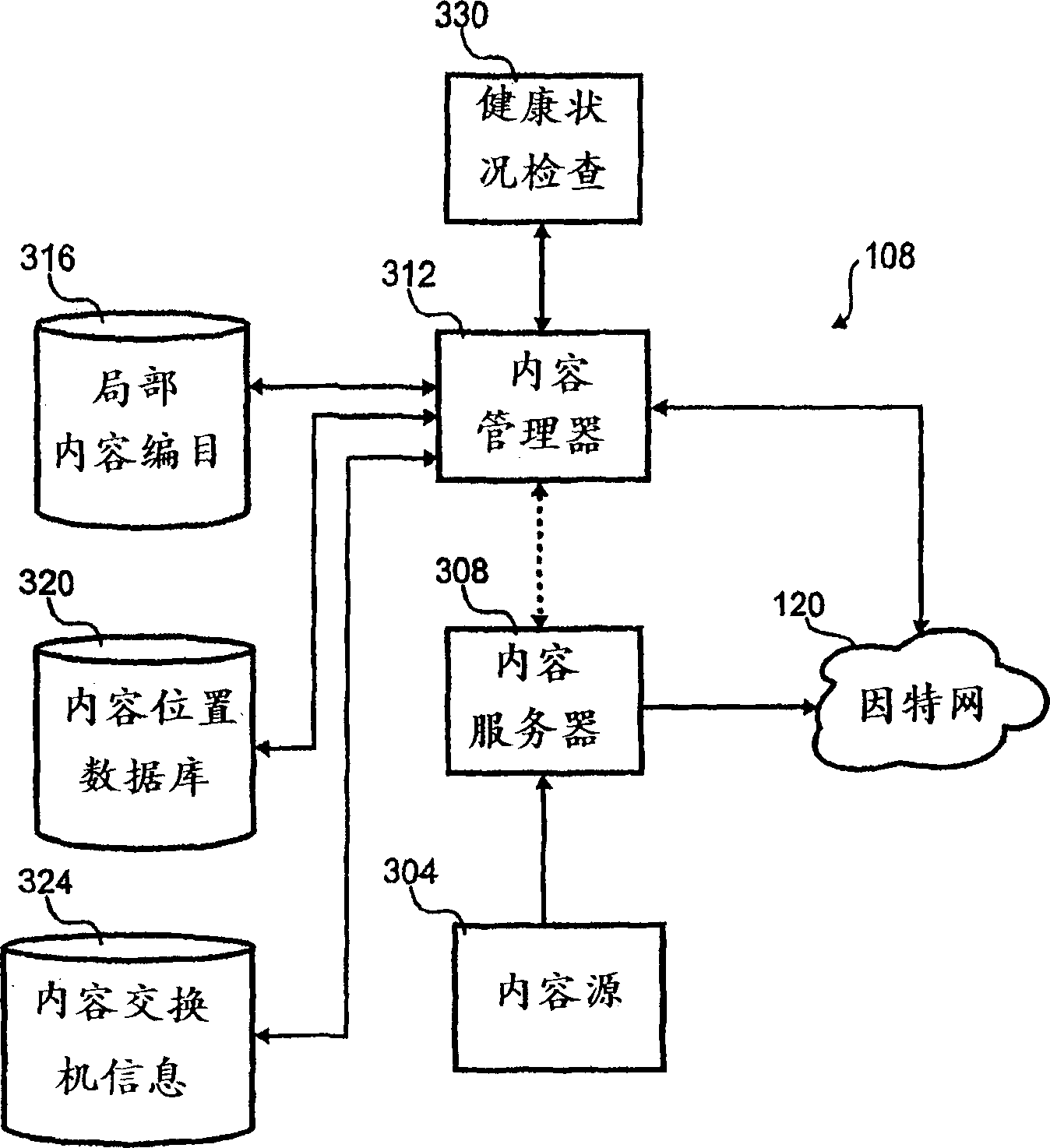
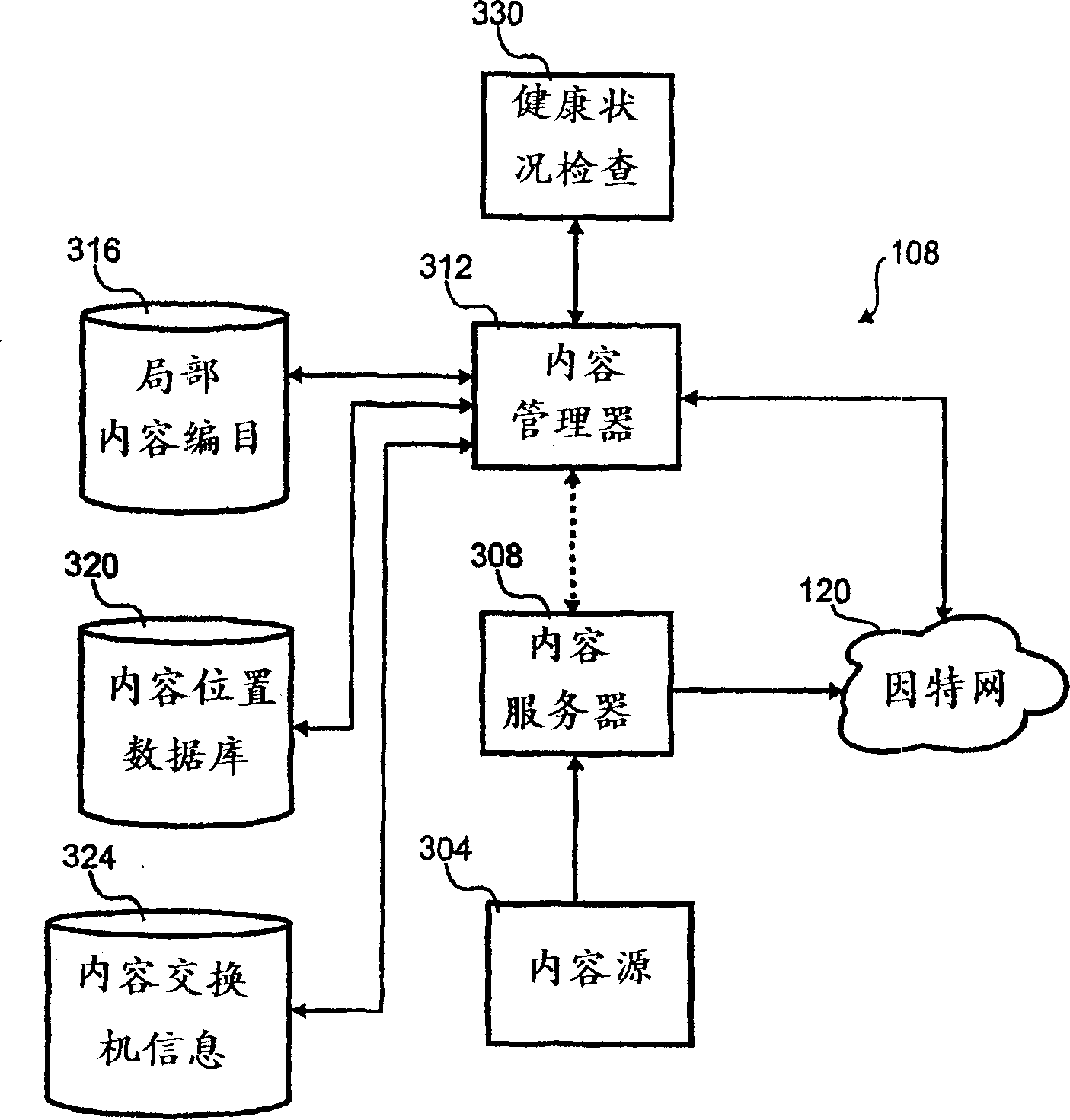
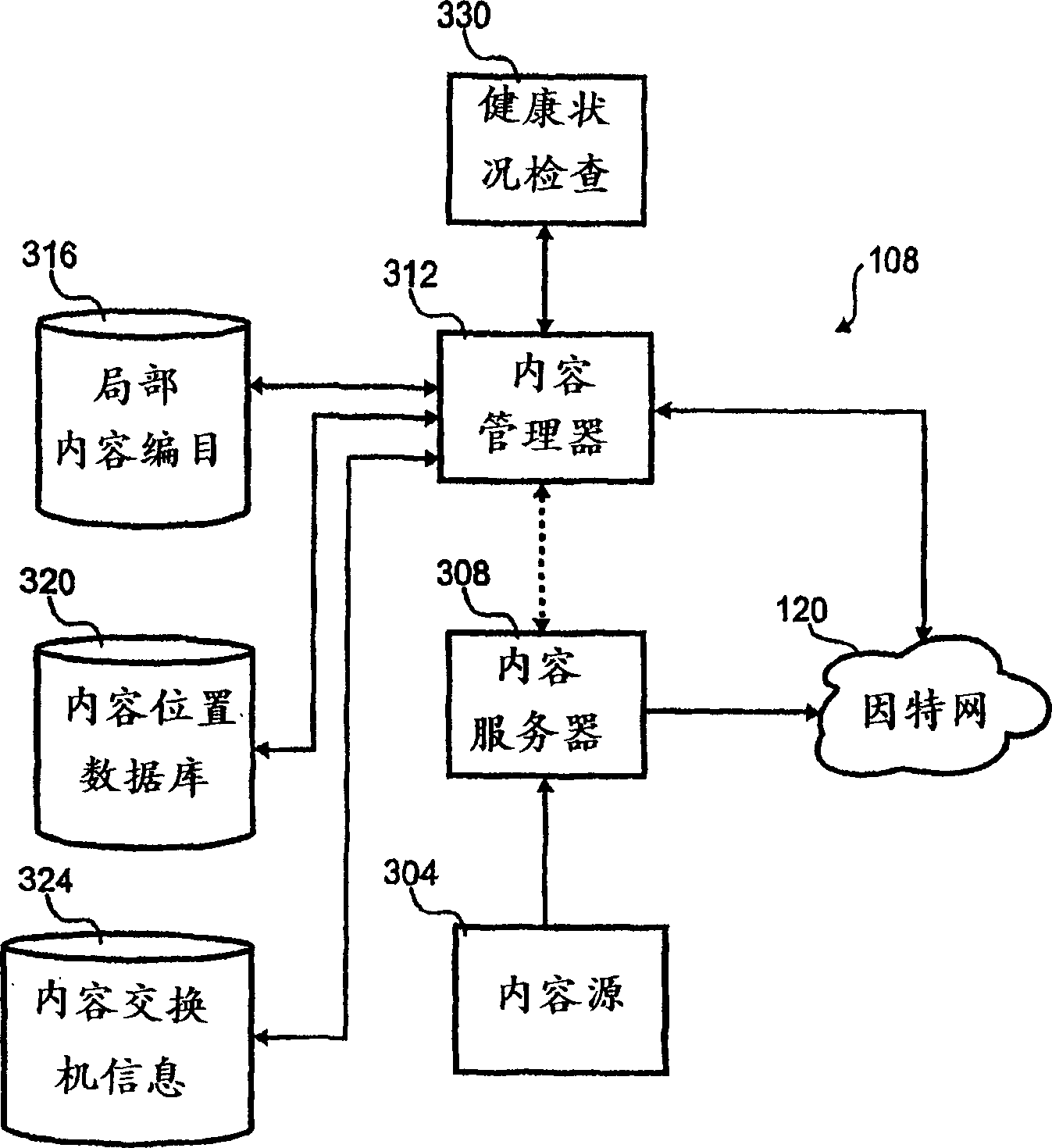
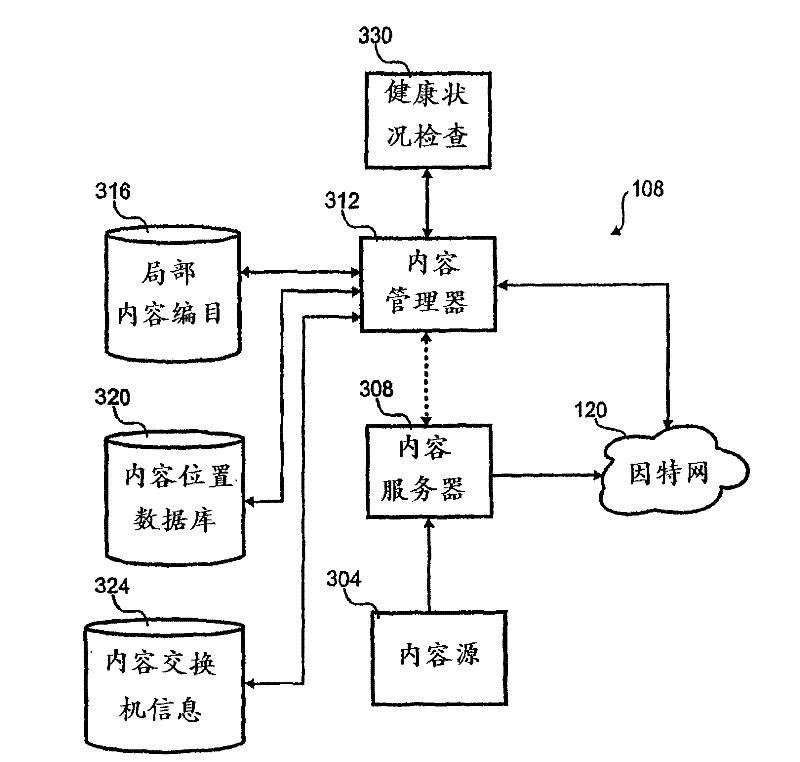
Client side holistic health check
A method for indicating holistic health of a server to various client computers in a content distribution system. The method includes monitoring various status indicia of the server and combining the various indicia into a single indicia. The single indicia is then distributed to various client computers. The client computers use the single indicia to influence routing of content from the content distribution to the client computer.
Owner:AEROCAST COM INC
A QOS based content distribution network
InactiveCN1454426AImprove QoSWeb data indexingDigital computer detailsContent distributionDistributed computing
The present invention relates to distributing content objects to client computers. One implementation includes a server, a first content cache, a second content cache, and a preference table. The first server is at a first address and the second server is at a second address. The server includes content objects to be copied into the first and second content caches. The preference list sent from the client computer includes at least one of the first and second addresses.
Owner:AEROCAST COM INC
Efficient non-database file-expiration management for document retention
ActiveUS9984080B2Effective functionLighten the computational burdenObsolescenceSpecial data processing applicationsRetention periodOperational system
Owner:INT BUSINESS MASCH CORP
Undrop objects and dependent objects in a database system
The present invention provides techniques for restoring objects (eg, tables) and dependent objects in a database. When an object is discarded, the object is moved to the recycle bin, where the object resides until the user restores the object or the object is cleared. Dependent objects are also moved to the recycle bin along with the object they are dependent on. Objects can be cleared from the recycle bin explicitly by the user, or when more storage space is needed. Slave object and partition cleanup can be delayed if there is no need to acquire more storage space.
Owner:ORACLE INT CORP
Server-side recycle bin system
A server-side recycle bin system for retaining computer files and information is disclosed. The system comprises a local computer system, and a server including a server-side recycle bin. One or more persistent storage devices, providing the files and directories to be protected, are present either as part of the local computer system or as part of the server. The local computer system and the server may be connected via a wide area computer network, a local area network, the Internet, of any other method or combination of methods. A file manager application running on the local computer system interacts with a file serving application on the server such that there is generated a retained file in the server-side recycle bin.
Owner:SIMDESK ACQUISITION +1
Database with aging mechanism and method for managing database
Methods of managing databases and corresponding database systems are disclosed. A method of managing a database comprising determining, prior to removal, a time interval corresponding to said maximum time span across database entries to be retained in the database; dividing said time interval into at least first and second time slices; and updating at least the first and second slice databases with database events. After the time span corresponding to the duration of the first time slice, the method includes replacing the first slice database with the second slice database and creating a new second slice database as the former Two copies of the database.
Owner:HUAWEI TECH CO LTD
Content manager
InactiveCN1444747BImprove QoSData processing applicationsWeb data indexingContent distributionContent management
The invention relates to tracking content objects in a content distribution system. In one embodiment, a content serving system for tracking content objects stored on a plurality of remotely-located content exchanges includes a content source, a content server, a local content catalog and location information. The content source provides a content object to the system. The content server is coupled to the content source and comprises one or more content objects. The content server provides copies and partial copies of the one or more content objects. Included in the local content catalog is information on the one or more content objects stored on the content server. The location information is for the plurality of remotely-located content exchanges.
Owner:MOTOROLA MOBILITY LLC
Method for searching and analyzing information in data networks
InactiveCN1279475CIncrease the totalIncrease percentageWeb data indexingObsolescenceData streamConfidentiality
Methods are disclosed for providing search and alert capabilities in traffic content at an access point of a data network. This invention teaches how appropriate privacy and content filters can be applied to traffic sources. Filtered data streams from service streams can be used to improve the quality of existing search and alert services. The present invention also teaches how to develop caches to optimally maintain fresh searchable information captured in traffic flows. Also disclosed is how the cache described above can be converted into a searchable index, and how it can be used as a basis for improved search operations, either separately or in conjunction with external search indexes. The present invention also discloses how to analyze business flows to derive additional information used to measure document relevance, access similarity between documents, personalization level ratings of search results, and regional differences in document access.
Owner:JOLLIFY MANAGEMENT
Popular searches
Unauthorized memory use protection Internal/peripheral component protection Broadcast information monitoring Website content management Securing communication Error detection/correction Digital data protection Multiple digital computer combinations Machine learning Vehicle position/course/altitude control
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com