Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2972 results about "Access time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Access time is the time delay or latency between a request to an electronic system, and the access being completed or the requested data returned...
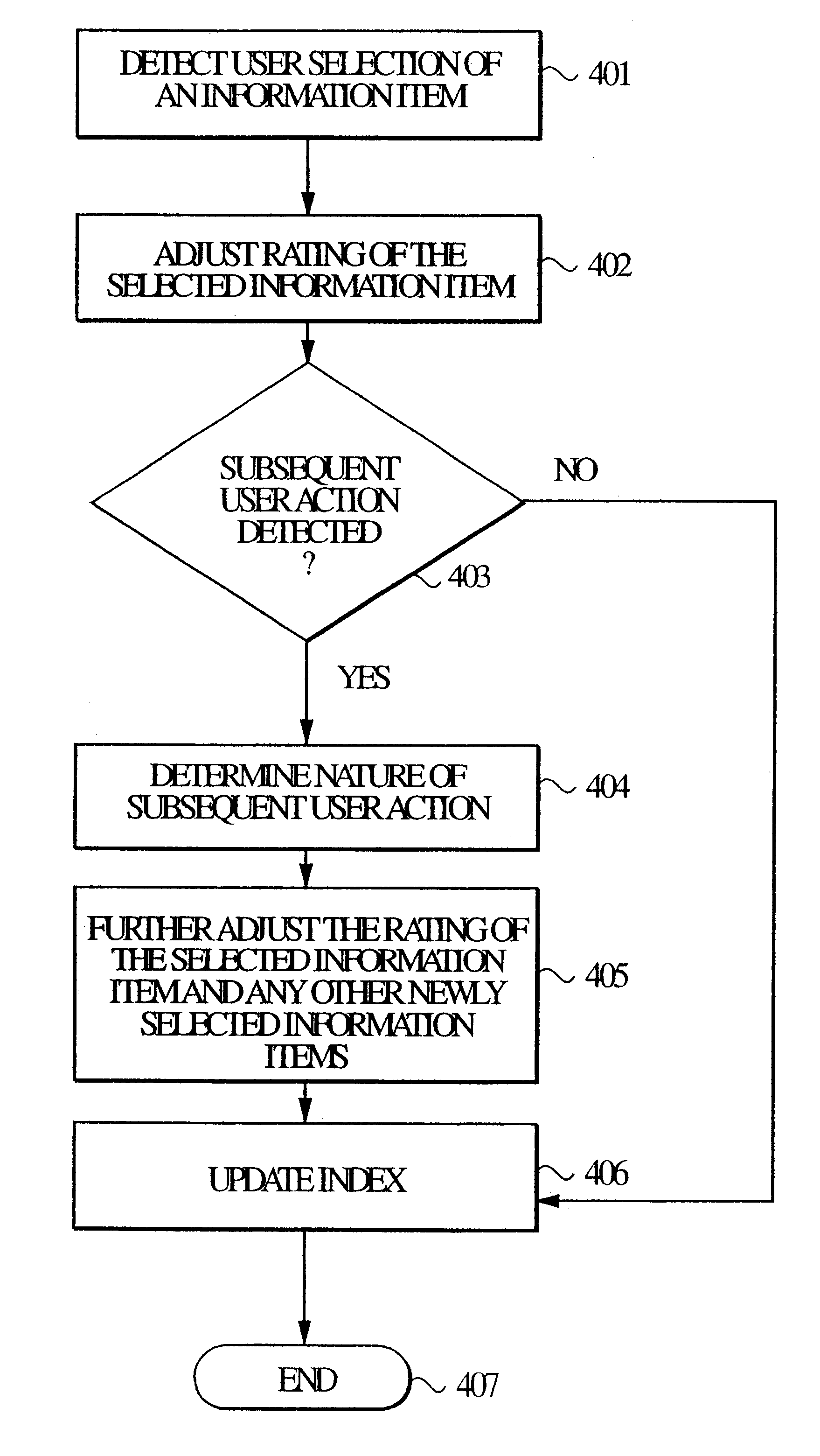
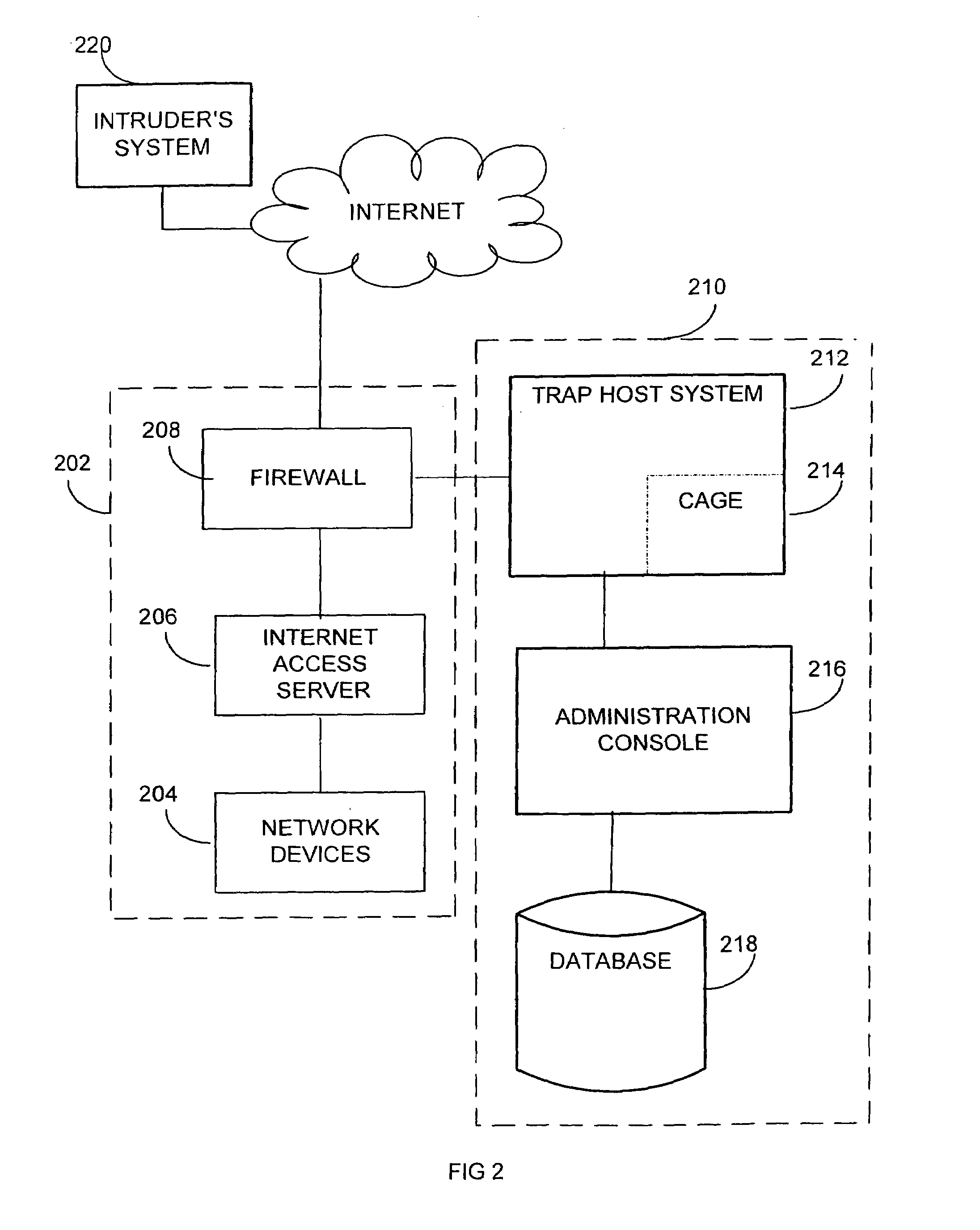
Implicit rating of retrieved information in an information search system
InactiveUS6665655B1Data processing applicationsUnstructured textual data retrievalUser inputAccess time
An information retrieval system allows a user to search a database of informational items for a desired informational item, and presents the search result in the form of matching index entries in the order of relevance. The information retrieval system in accordance with the principles of the present invention assigns a relevance rating to each of the index entries without requiring an explicit input from the user with respect to the usefulness or the relevance of the retrieved information corresponding to the respective index entries. When the user selects and retrieves an informational item through a list of index entries presented by the retrieval system, as a result of a search, the relevance rating of the selected informational item is increased by a predetermined amount. The relevance rating of the selected informational item is further adjusted based on any actions the user takes subsequent to the initial selection of the informational item if the subsequent act indicates that the relevance of the selected informational item may be less than what is reflected by the rating increase by the predetermined amount. Ratings of the informational items in the database are determined from implicit suggestions from the usage of the retrieval system and the database by the user rather than from an explicit user input. In another aspect of the present invention, the ratings are allowed to decay over time to minimize the tendencies for historical usage biased rating, and to provide more temporally accurate ratings. The most recently accessed time of each of the informational items in the database is compared to a predetermined stale access time threshold, and if the most recently accessed time is older than the threshold, than the rating of the corresponding informational item is decreased to reflect the dated nature of the information contained within the item.
Owner:ORACLE OTC SUBSIDIARY
Scheduling and planning maintenance and service in a network-based supply chain environment
InactiveUS7716077B1Simple personalization processTechnology managementResourcesData synchronizationExternal data
A system, method and article of manufacture are provided for administrating a network-based supply chain on a network. Operation of entities is monitored. Entities include server processes, disk space, memory availability, CPU utilization, access time to a server, and / or a number of connections in a network-based supply chain. Items including merchandising content, currency exchange rates, tax rates, and / or pricing in the network-based supply chain are updated at predetermined intervals. In addition, external data stored separately from the network-based supply chain is synchronized with internal data stored on the network-based supply chain. Contact information received from users of the network-based supply chain is also managed. Users include service providers and manufacturer utilizing the network-based supply chain. The items are altered based on profiles of the users of the network-based supply chain.
Owner:ACCENTURE GLOBAL SERVICES LTD
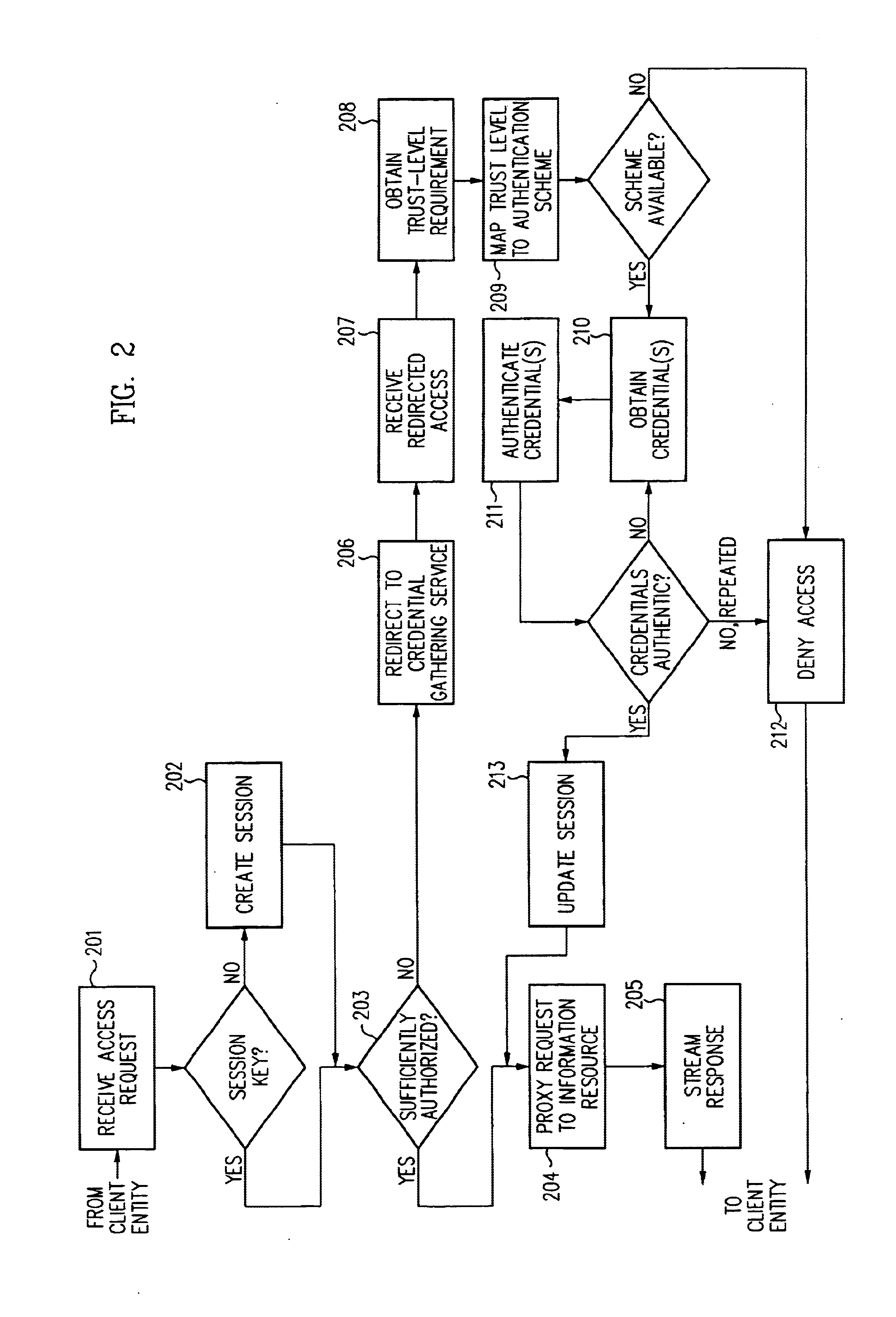
Security architecture with environment sensitive credential sufficiency evaluation
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
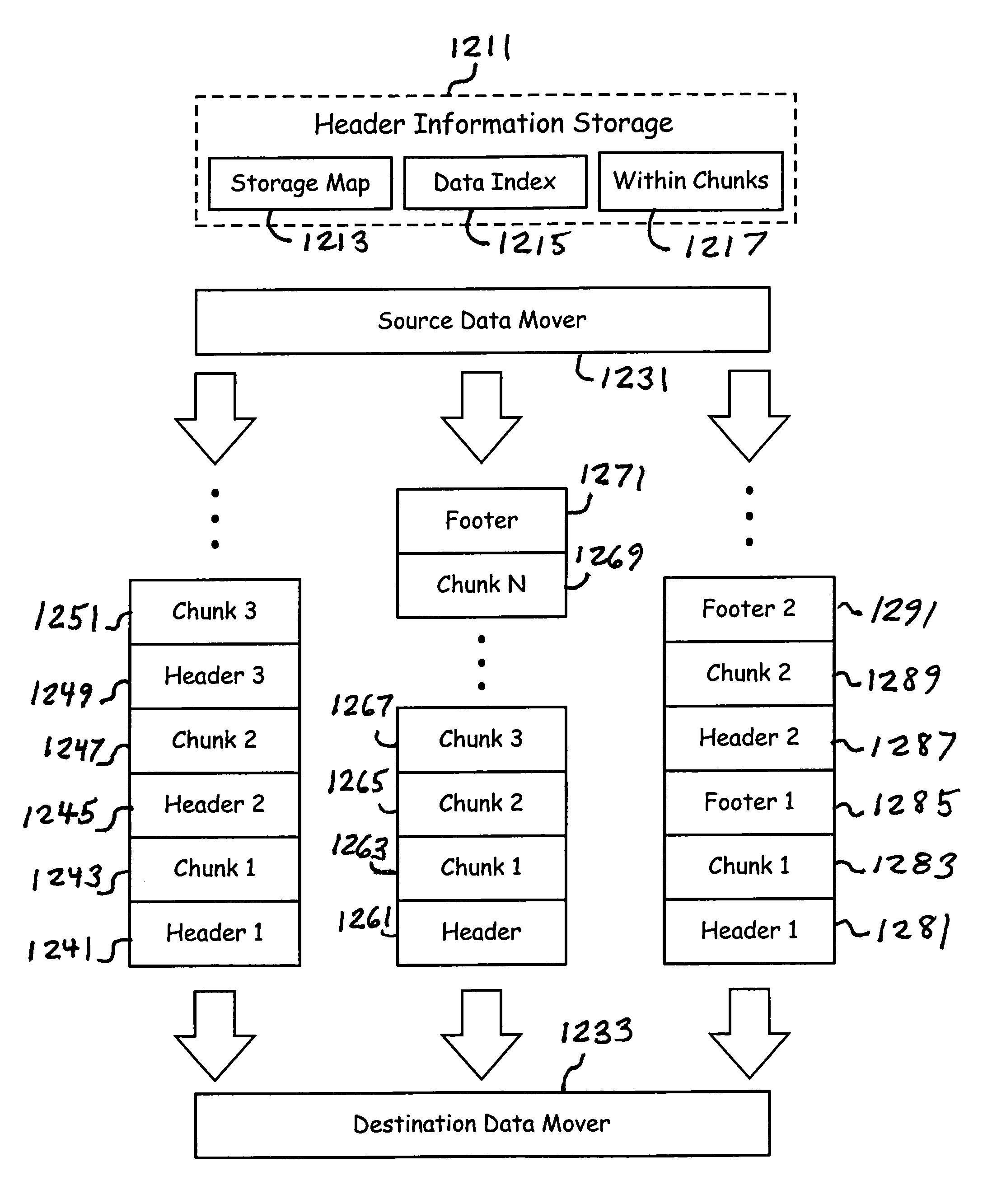
High speed data transfer mechanism
InactiveUS7209972B1Input/output to record carriersData switching by path configurationMedia typeOperational system
A storage and data management system establishes a data transfer pipeline between an application and a storage media using a source data mover and a destination data mover. The data movers are modular software entities which compartmentalize the differences between operating systems and media types. In addition, they independently interact to perform encryption, compression, etc., based on the content of a file as it is being communicated through the pipeline. Headers and chunking of data occurs when beneficial without the application ever having to be aware. Faster access times and storage mapping offer enhanced user interaction.
Owner:COMMVAULT SYST INC
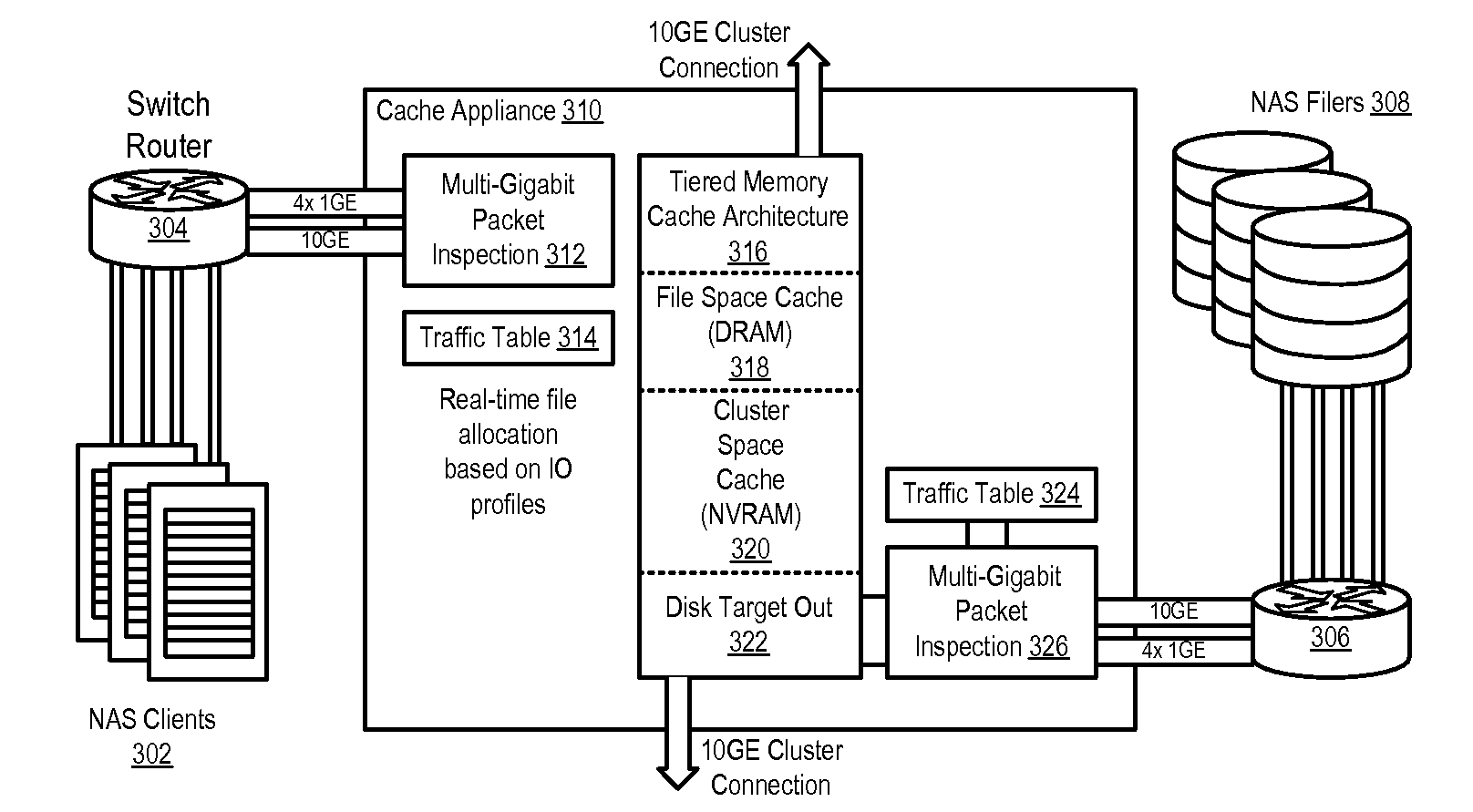
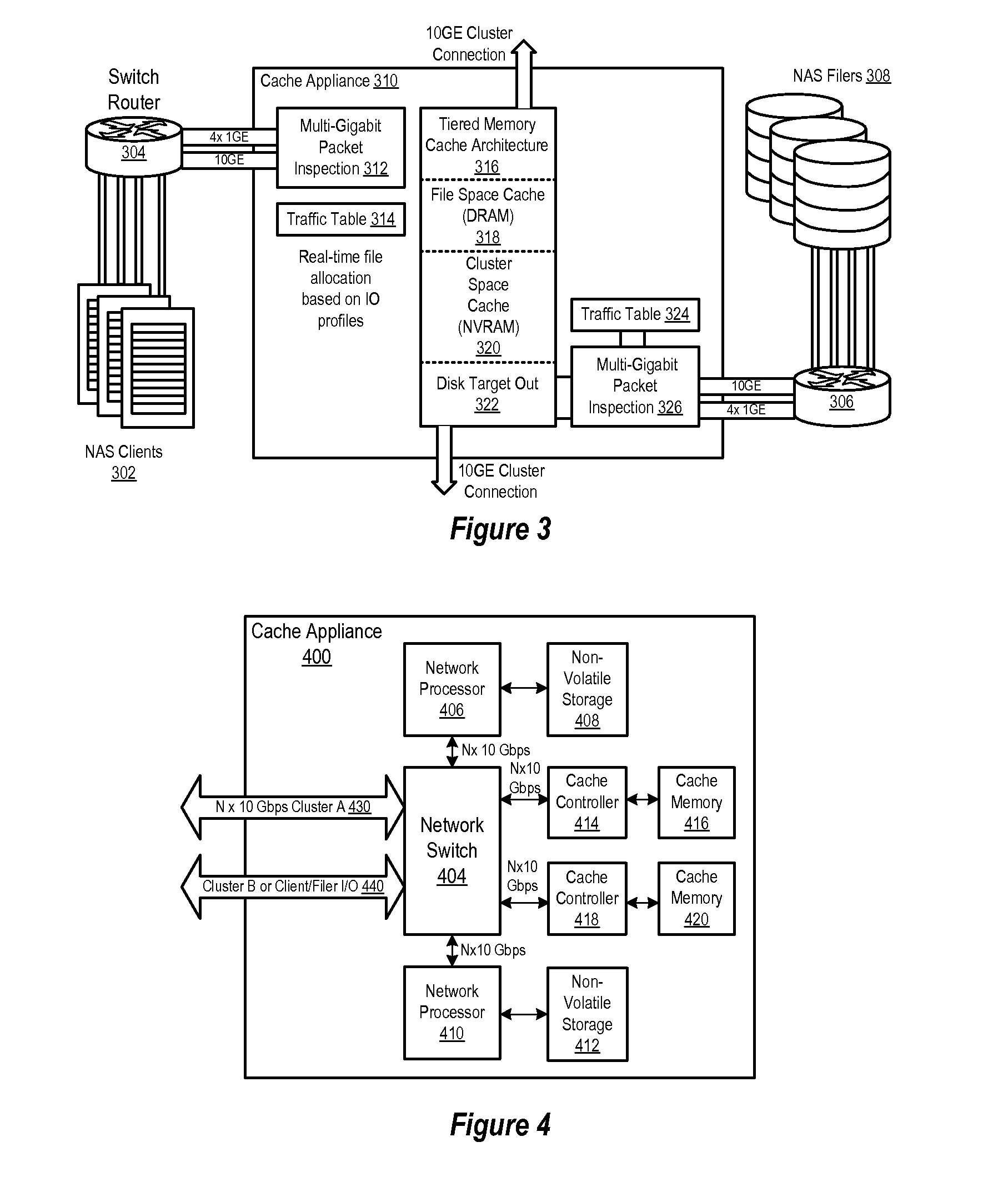
Clustered cache appliance system and methodology
ActiveUS20090182945A1Memory adressing/allocation/relocationTransmissionAccess timeLatency (engineering)
A method, system and program are disclosed for accelerating data storage by providing non-disruptive storage caching using clustered cache appliances with packet inspection intelligence. A cache appliance cluster that transparently monitors NFS and CIFS traffic between clients and NAS subsystems and caches files using dynamically adjustable cache policies provides low-latency access and redundancy in responding to both read and write requests for cached files, thereby improving access time to the data stored on the disk-based NAS filer (group).
Owner:NETWORK APPLIANCE INC
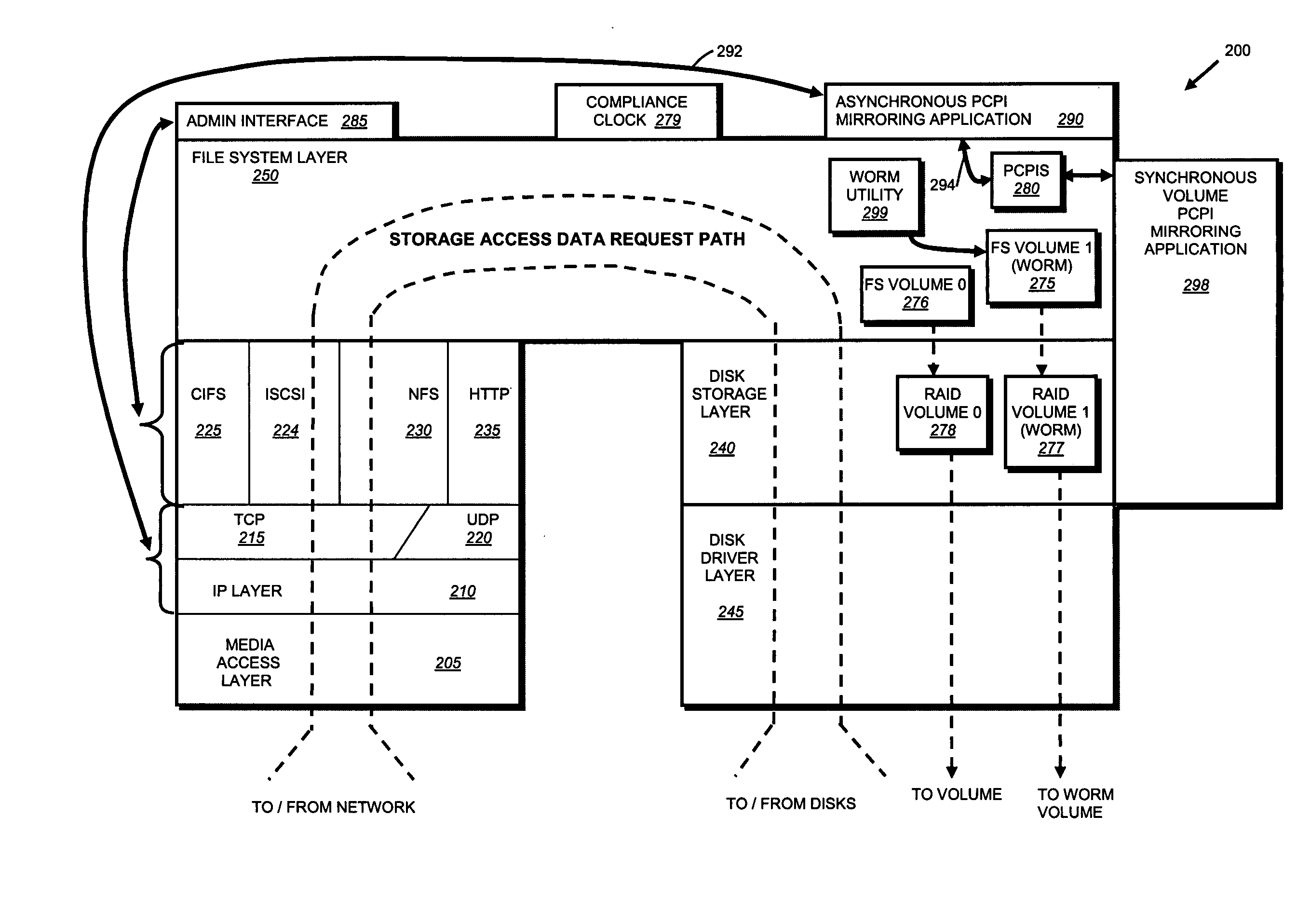
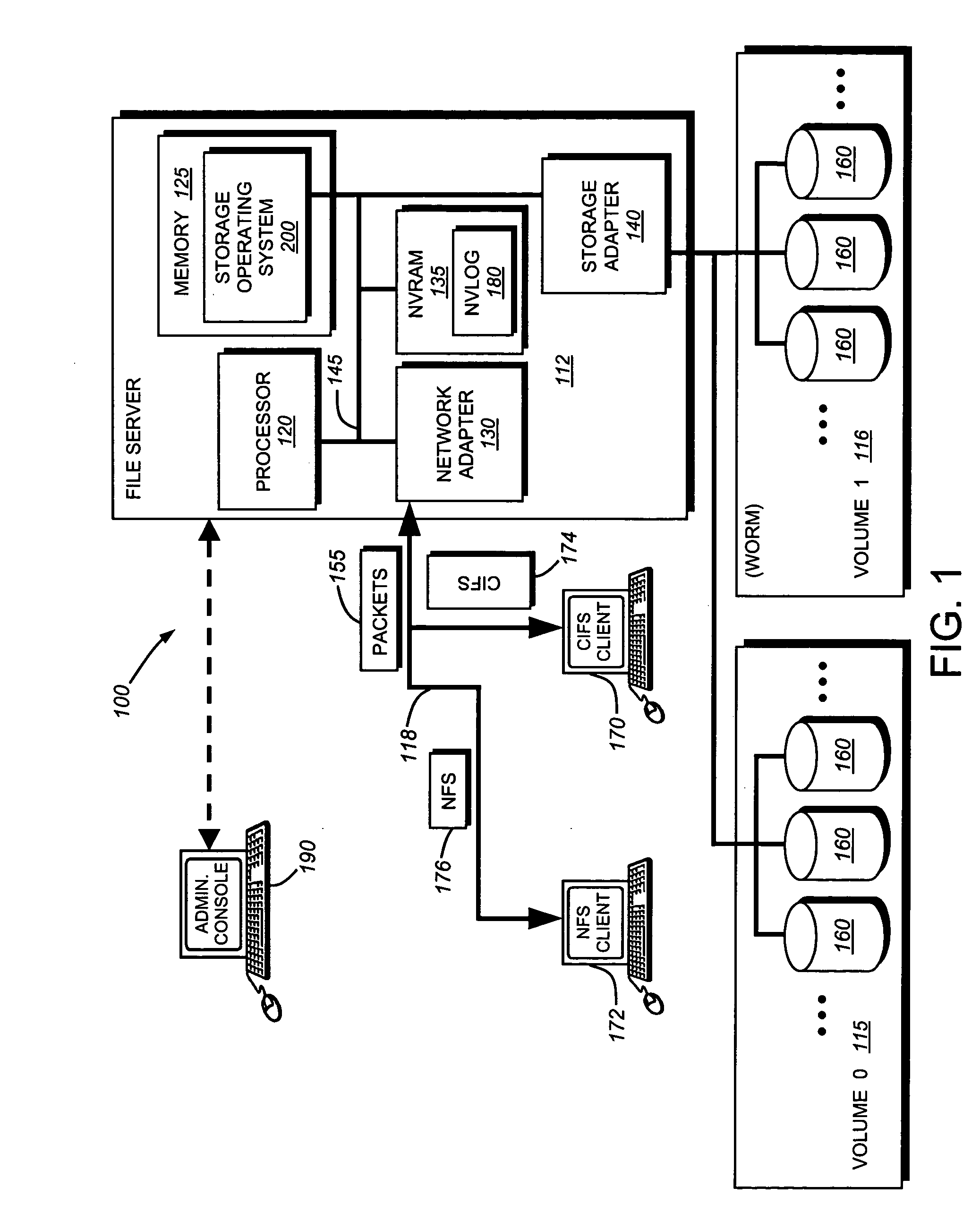
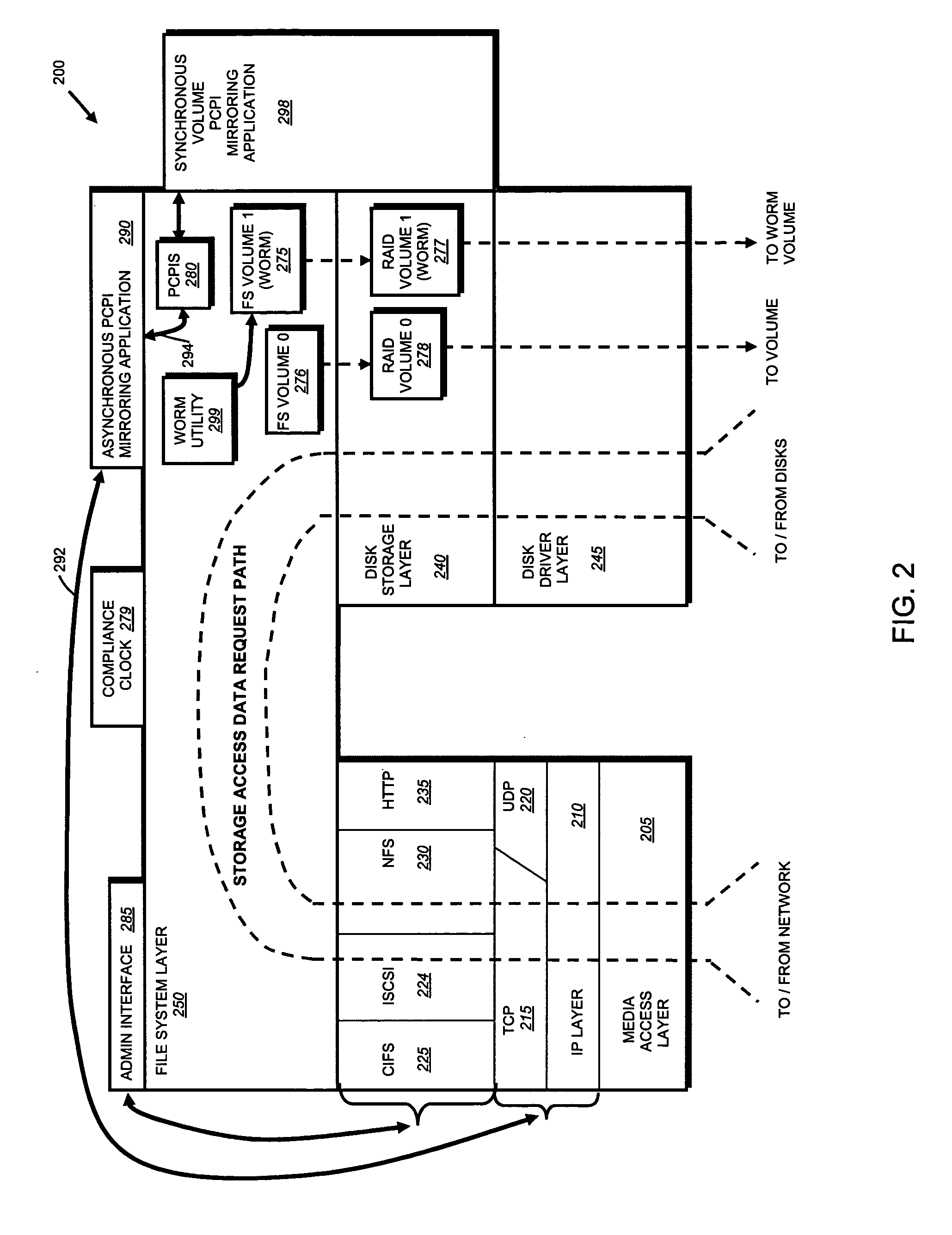
System and method for record retention date in a write once read many storage system
ActiveUS20050097260A1Improve performanceInput/output to record carriersData processing applicationsRetention periodData set
This invention provides a specified retention date within a data set that is locked against deletion or modification within a WORM storage implementation. This retention date scheme does not utilize any proprietary application program interfaces (APIs) or protocols, but rather, employs native functionality within conventional file (or other data containers, data sets or block-based logical unit numbers) properties available in commonly used operating systems. In an illustrative embodiment, the retention date / time is calculated by querying the file's last-modified time prior to commit, adding the retention period to this value and thereby deriving a retention date after which the file can be released from WORM. Prior to commit, the computed retention date is stored in the file's “last access time” property / attribute field, or another metadata field that remains permanently associated with the file and that, in being used for retention date, does not interfere with file management in a WORM state. Since this field is not utilized in a WORM context, it can be adapted to store this date. Once stored, the retention date in this field is locked against modification. Where extension (never reduction) of a retention period is desired, the last access time field be updated, wherein the new retention period is added to the existing last access time value to derive a new, later retention date for the file. Upon expiry of the retention date, the system allows deletion of the expired WORM file / data set.
Owner:NETWORK APPLIANCE INC
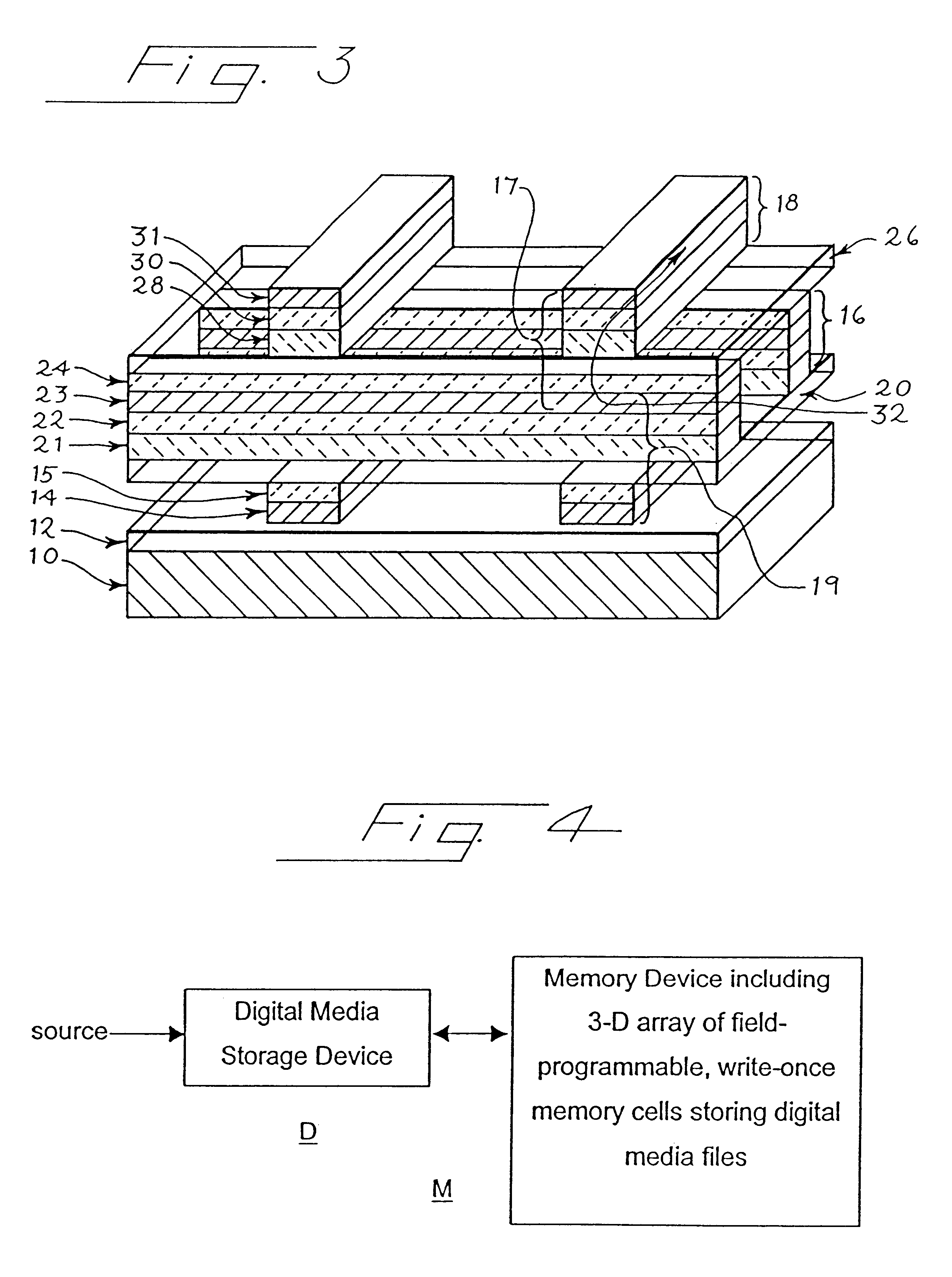
Low cost three-dimensional memory array
InactiveUS6515888B2Reduce areaReduce manufacturing costSolid-state devicesRead-only memoriesDopantAccess time
A low-cost memory cell array includes multiple, vertically-stacked layers of memory cells. In one form, each memory cell is characterized by a small cross-sectional area and a read current less than 6.3 microamperes. The resulting memory array has a slow access time and is well-suited for digital media storage, where access time requirements are low and the dramatic cost reductions associated with the disclosed memory arrays are particularly attractive. In another form, each memory cell includes an antifuse layer and diode components, wherein at least one diode component is heavily doped (to a dopant concentration greater than 1019 / cm3), and wherein the read current is large (up to 500 mA).
Owner:SANDISK TECH LLC
Scheduling with reverse direction grant in wireless communication systems
ActiveUS20070058605A1Reduce power consumptionReduce wasteNetwork topologiesTime-division multiplexComplete dataCommunications system
Systems and methodologies are described that facilitate increased communication channel bandwidth efficiency in association with scheduled time periods that allocate channel access to particular stations. According to various aspects, systems and methods are described that facilitate providing and / or utilizing reverse direction grants in connection with scheduled channel access. Such systems and / or method can mitigate an amount of unused channel access time after a station completes data transmission prior to an end of the allocated period.
Owner:QUALCOMM INC
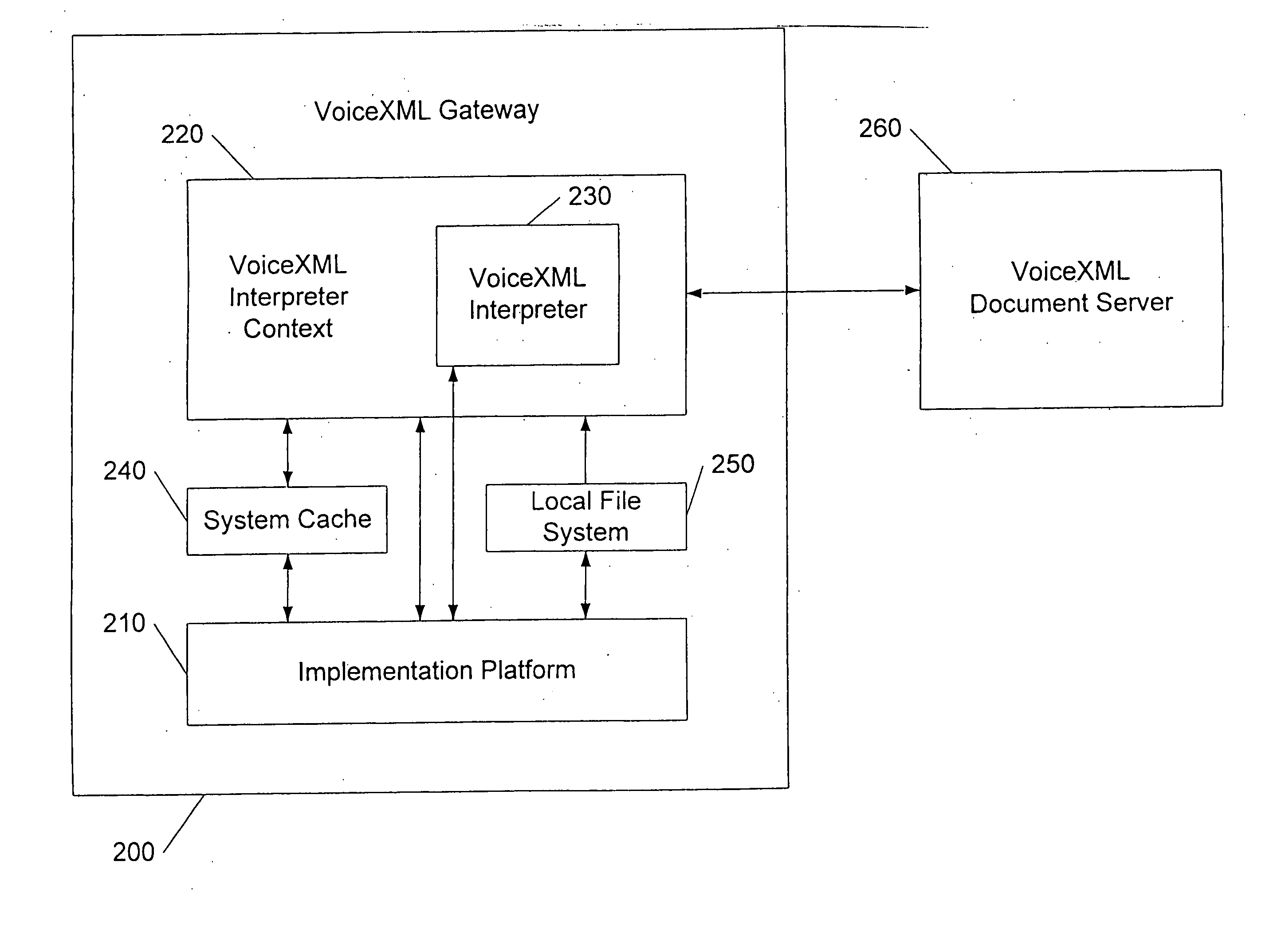
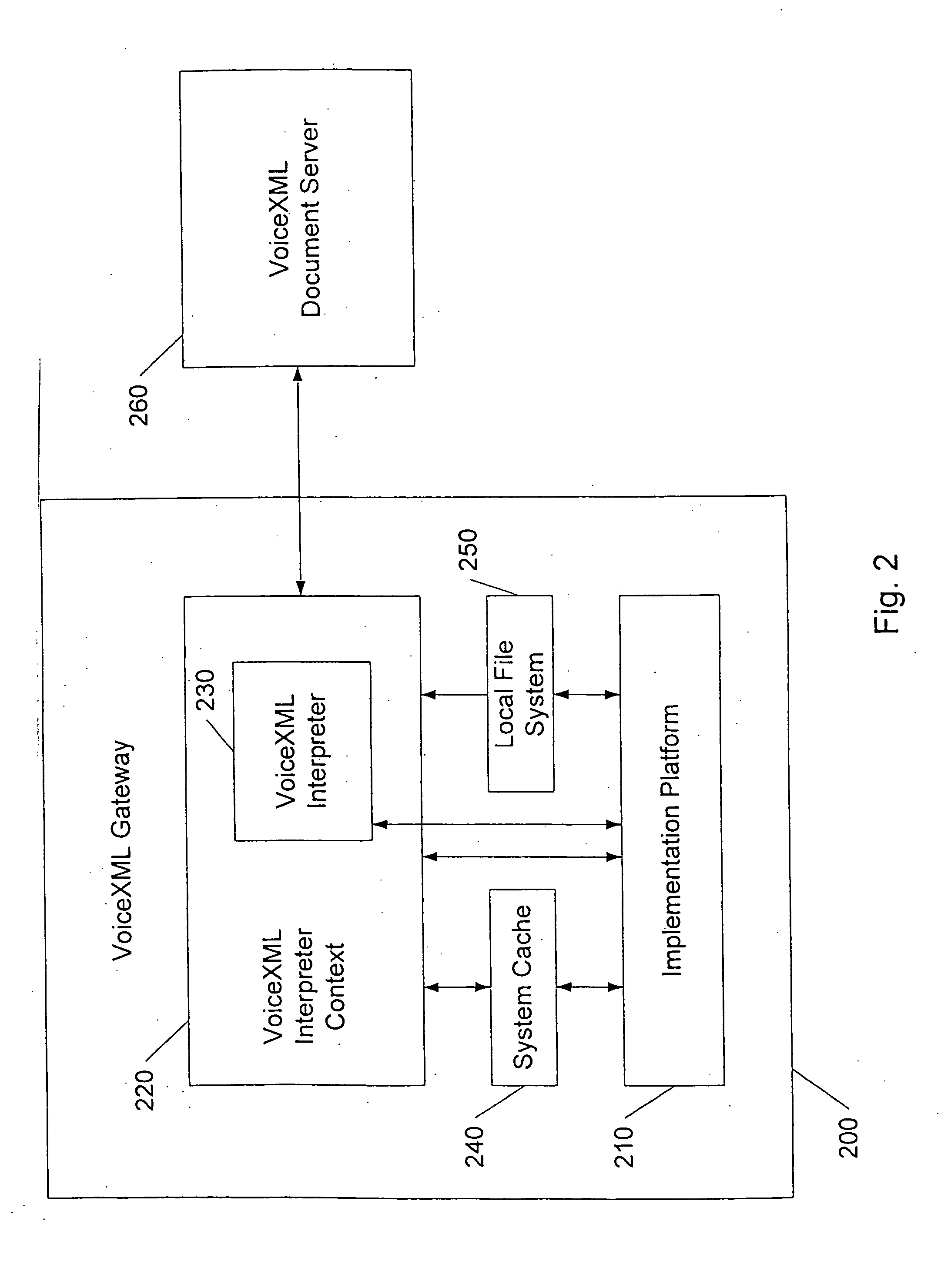
System and method for enhancing performance of VoiceXML gateways
A system and method are disclosed for managing frequently used VoiceXML documents. In particular, a VoiceXML gateway is provided having an administrator-managed and provisioned local file system. Specifically, the administrator provisions the files that are to be stored on the local file system. Importantly, neither the VoiceXML interpreter nor the VoiceXML interpreter context manage the local file system. Accordingly, the local file system is not subject to the cache control directives that requires regular retransmission of frequently used VoiceXML documents and other files from the remote documents servers. To that end, administrator-provisioned files may be permanently stored on the local file system thereby minimizing their search and access time.
Owner:LUCENT TECH INC
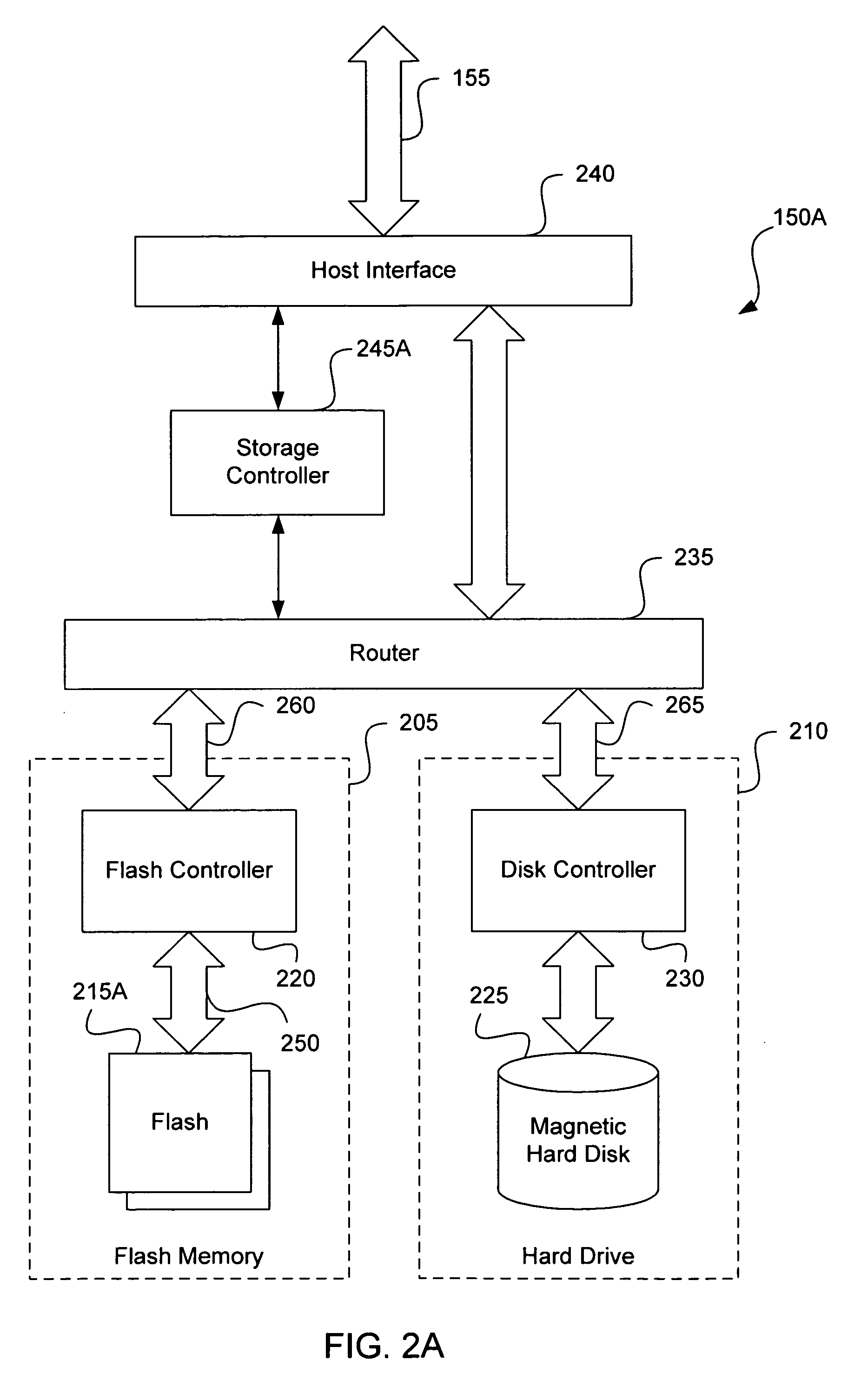
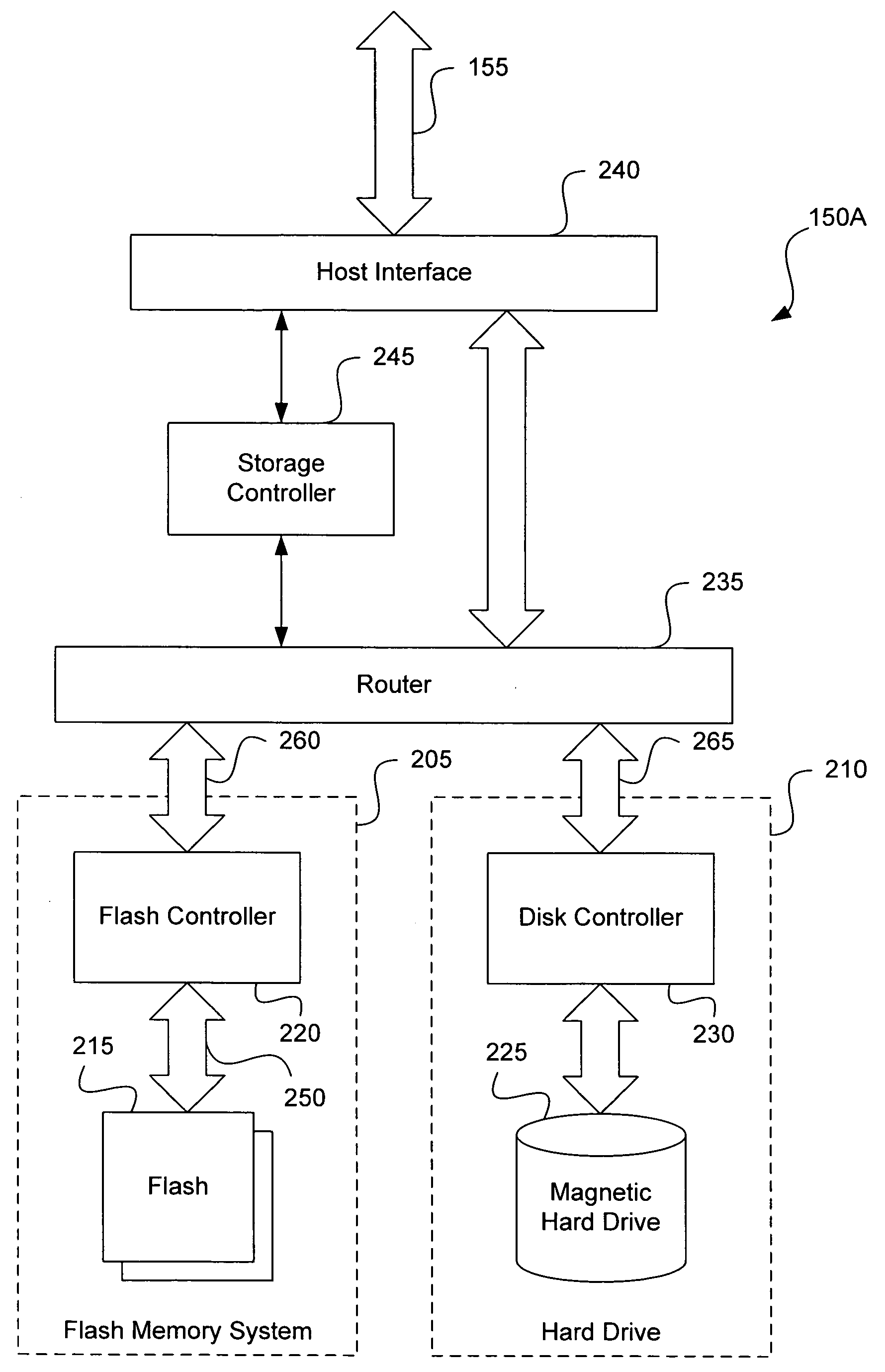
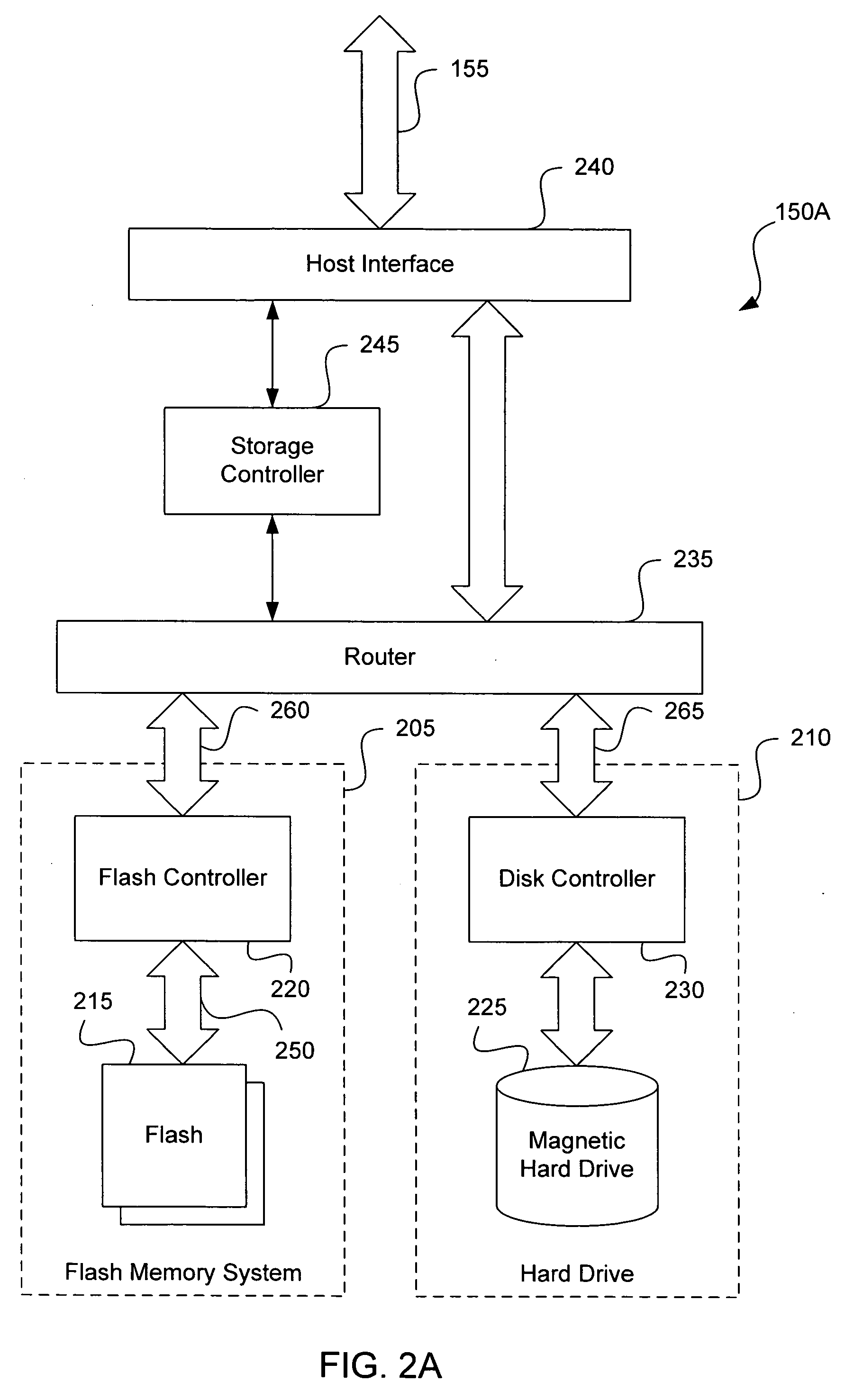
Mass storage accelerator
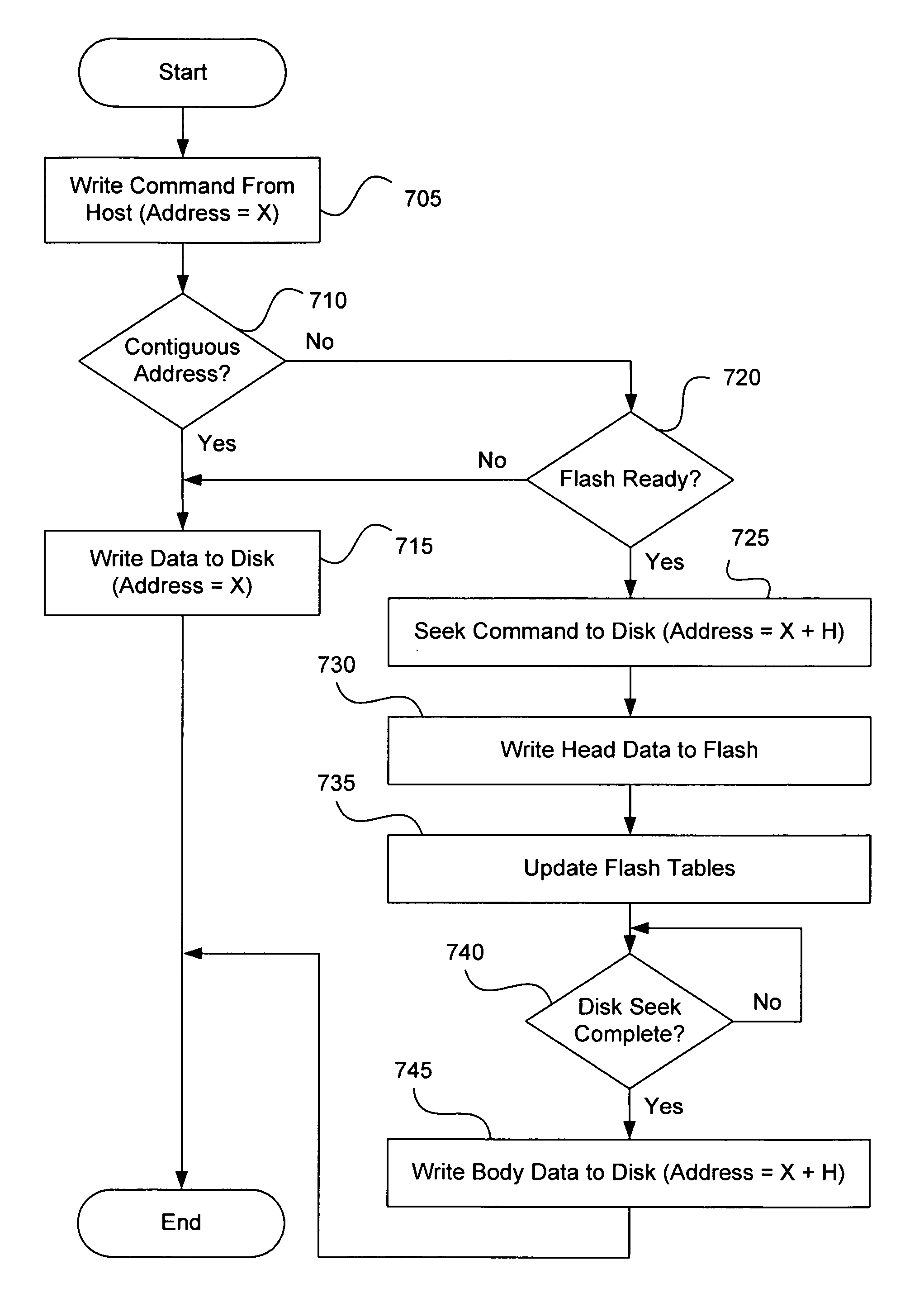
A data storage device is provided. A disk device is combined with a non-volatile memory device to provide much shorter write access time and much higher data write speed than can be achieved with a disk device alone. Interleaving bursts of sector writes between the two storage devices can effectively eliminate the effect of the seek time of the disk device. Following a non-contiguous logical address transition from a host system, the storage controller can perform a look-ahead seek operation on the disk device, while writing current data to the non-volatile memory device. Such a system can exploit the inherently faster write access characteristics of a non-volatile memory device, eliminating the dead time normally caused by the disk seek time.
Owner:SANDISK TECH LLC
Extensible intrusion detection system
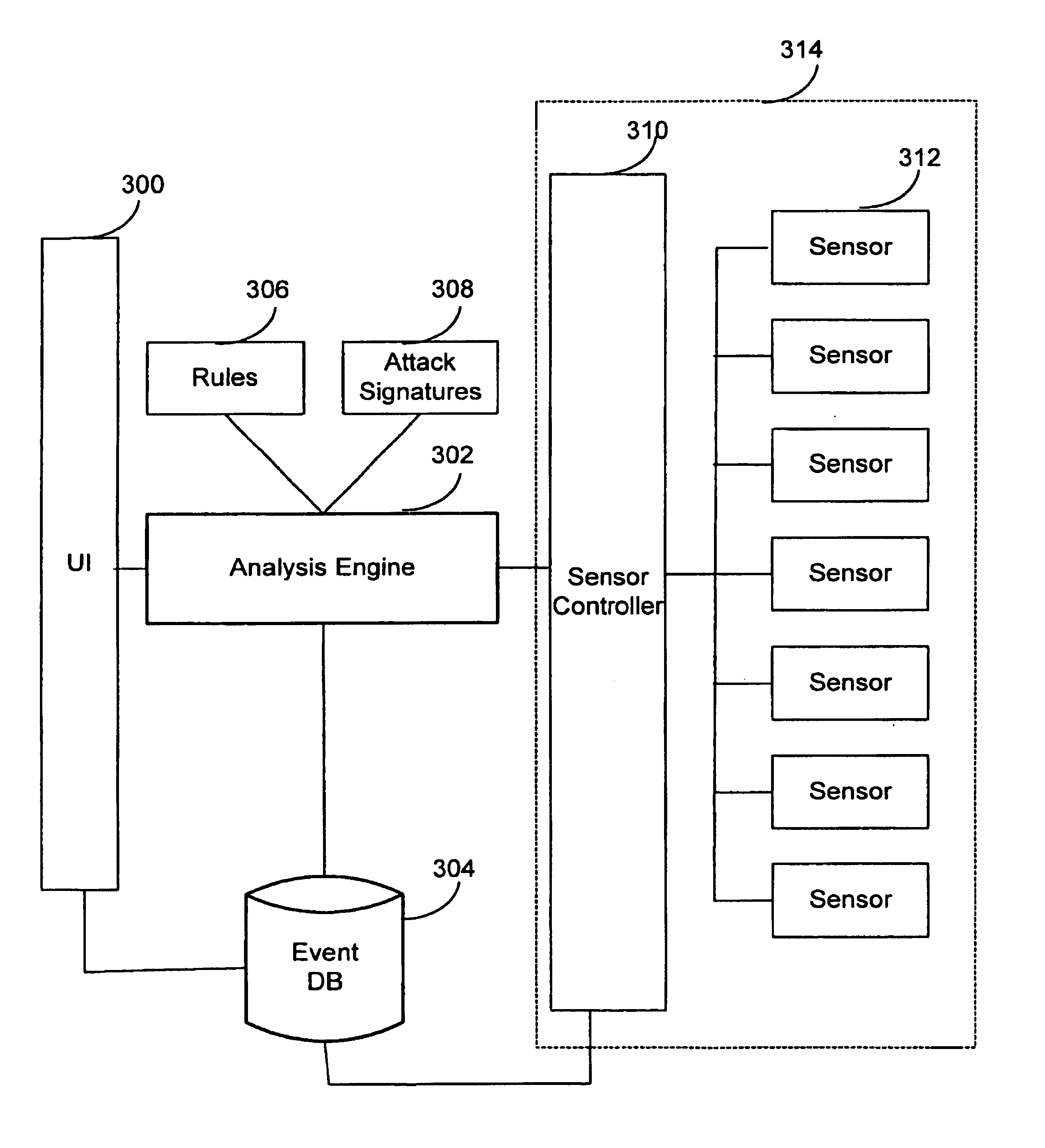
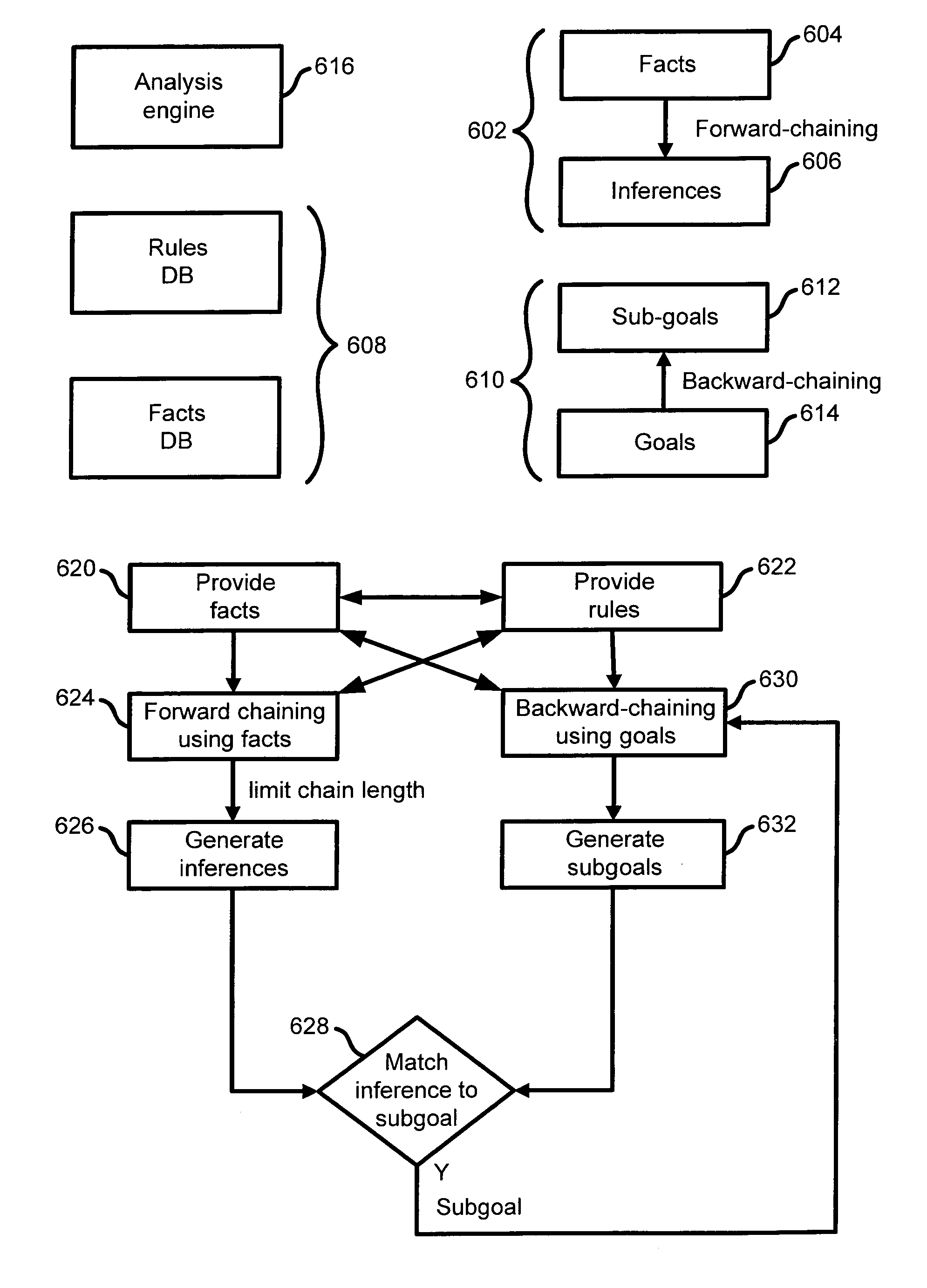
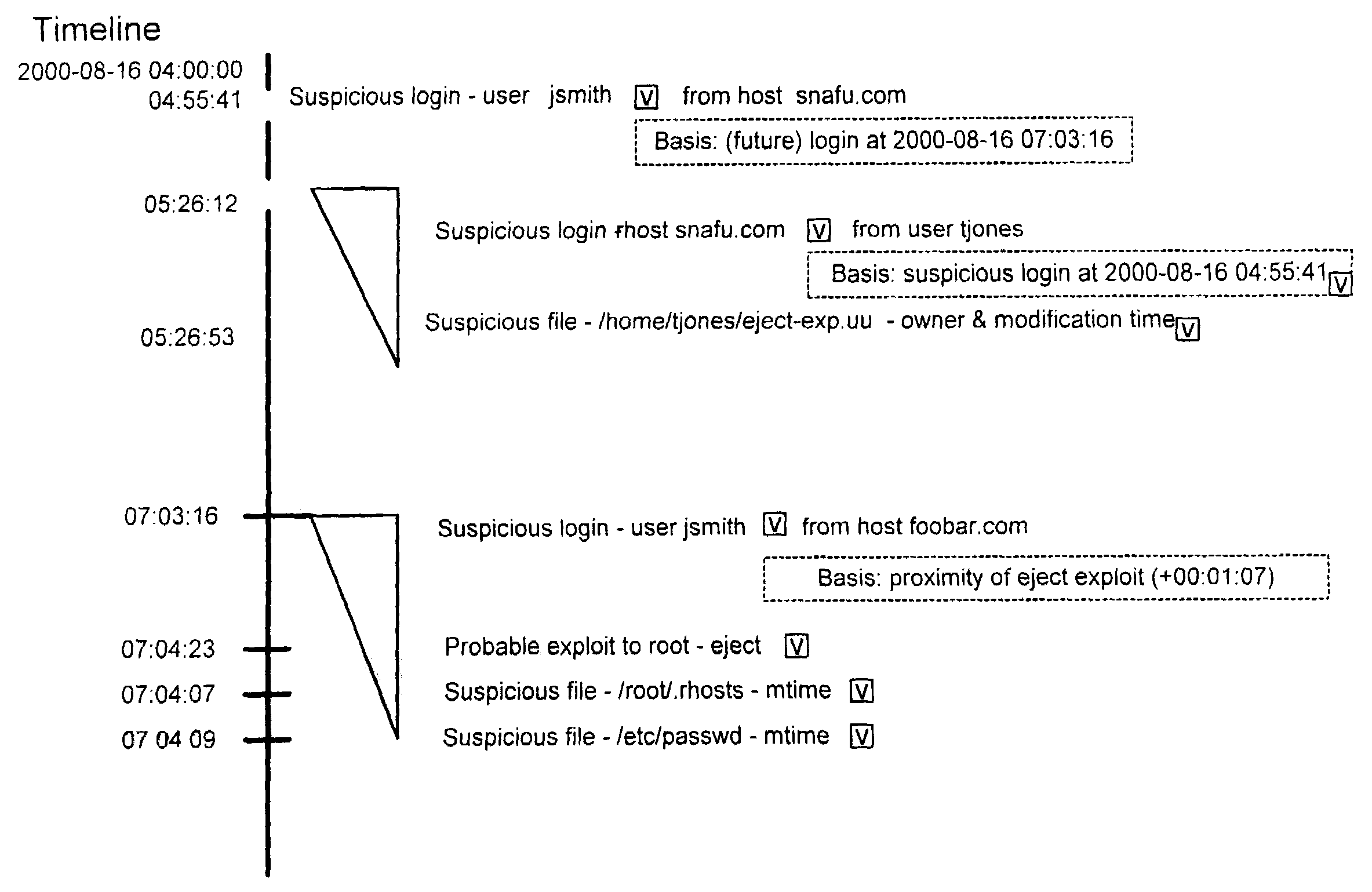
InactiveUS7065657B1Overcome problemsEnabling detectionDigital data processing detailsHardware monitoringTimestampAccess time
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
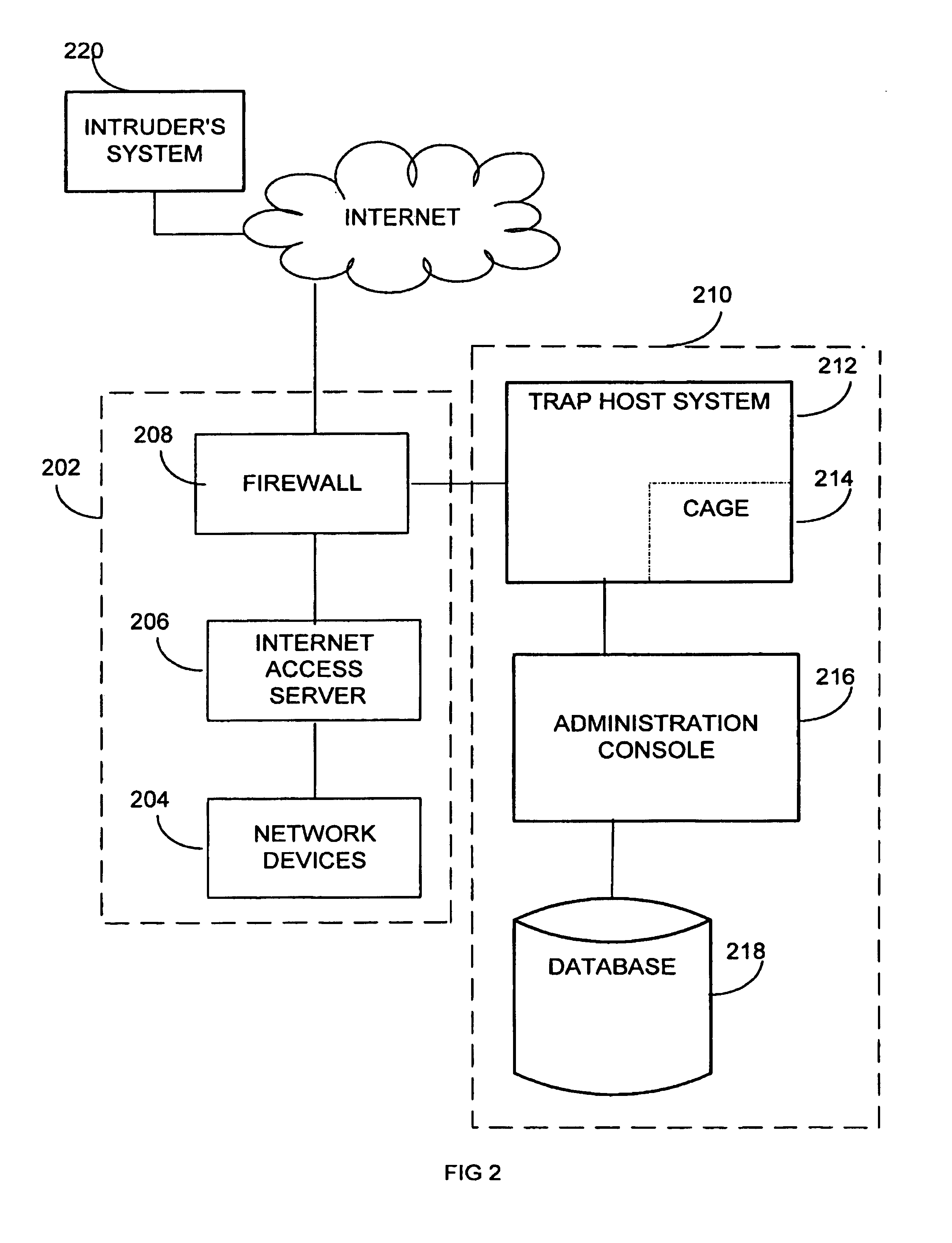
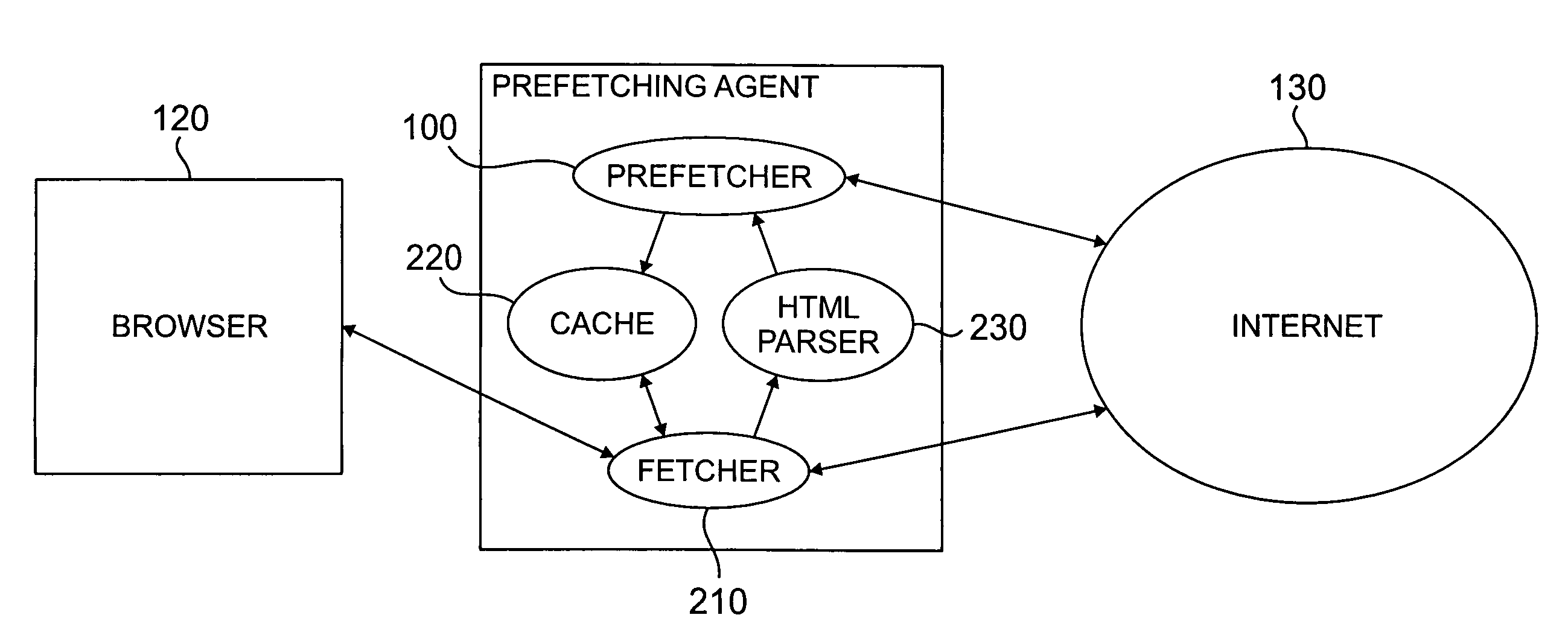
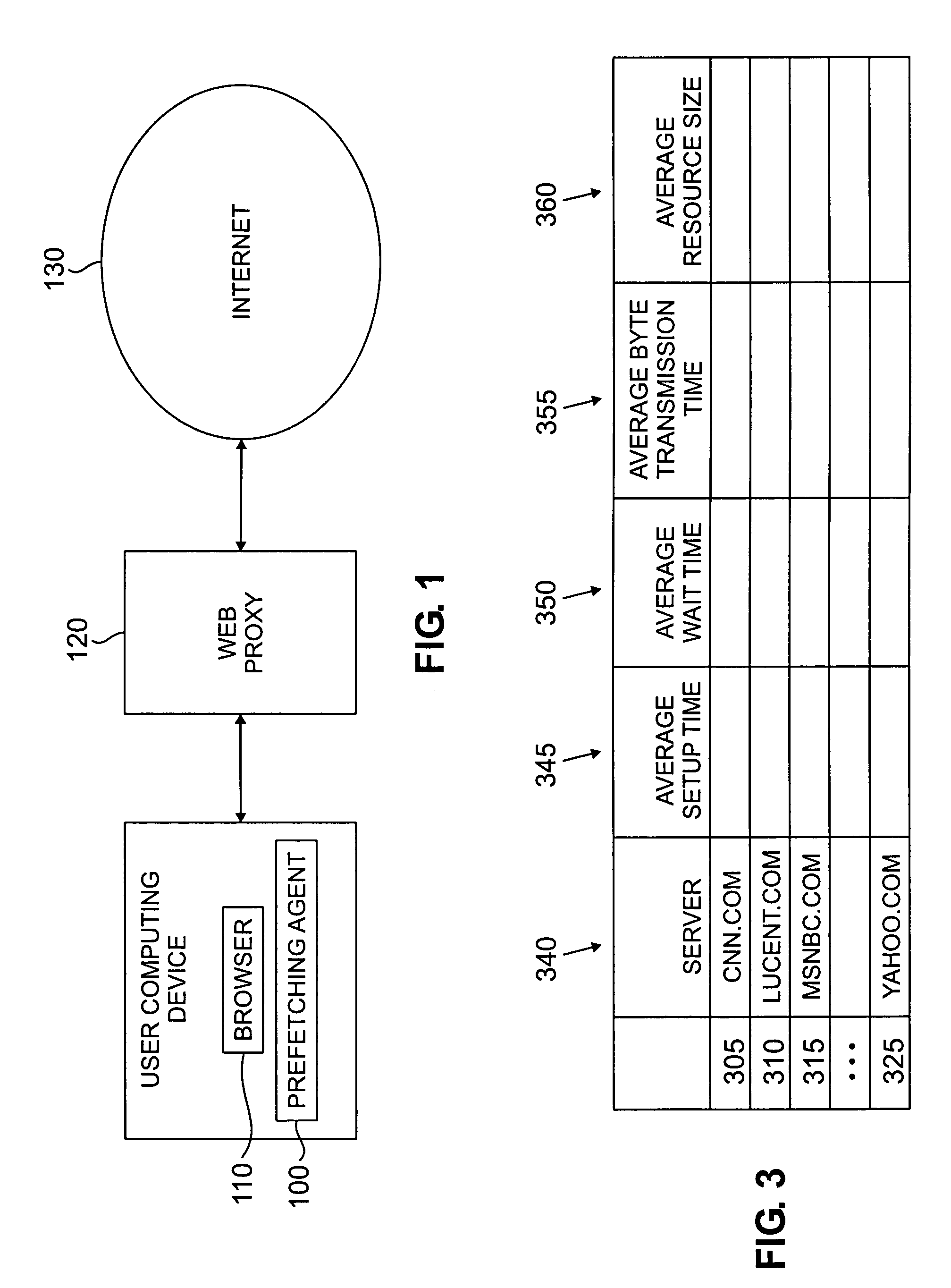
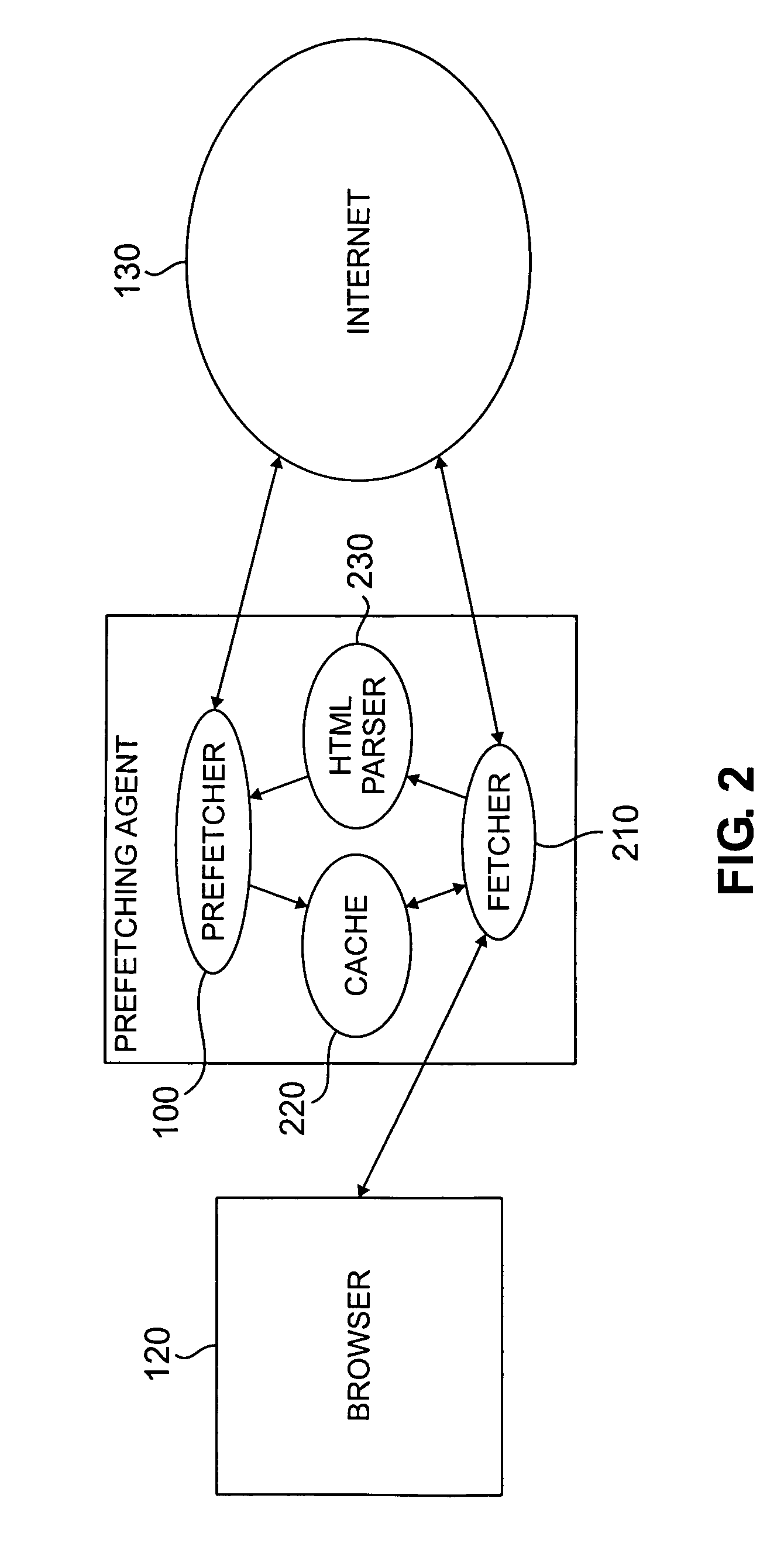
Method and apparatus for prefetching internet resources based on estimated round trip time
InactiveUS6993591B1Shorten access timeMinimizing networkData processing applicationsMultiple digital computer combinationsHyperlinkTTEthernet
A method and apparatus are disclosed for prefetching Internet resources based on the estimated round trip time of the resources. Whenever a user clicks on an embedded hyperlink, the prefetching strategy aims to ensure that the corresponding document has been prefetched or can be fetched very quickly from its origin server. Web access time as perceived by the user is reduced, while also minimizing the network, server and local resource overhead due to prefetching. The estimated round trip time is obtained or approximated for all referenced documents. The “round trip” time or access time of a resource is the time interval between the sending of the first byte of an HTTP request for the resource until the last byte of the server response has arrived at the requesting Web client. Documents with the longest access times are prefetched first and prefetching generally continues until the estimated round trip time falls below a predefined threshold. An HTTP HEAD request may be used to determine the estimated round trip time of a Web resource. The prefetching agent can be configured to prevent prefetching of those documents that are quickly fetchable, dynamically generated or non-HTTP based resources, or those documents whose size exceed a certain limit, to minimize the network, server and local resource overhead due to prefetching. The thresholds applied to the list of documents to be prefetched can be dynamically adjusted by the agent, based on changing network and server conditions.
Owner:SOUND VIEW INNOVATIONS
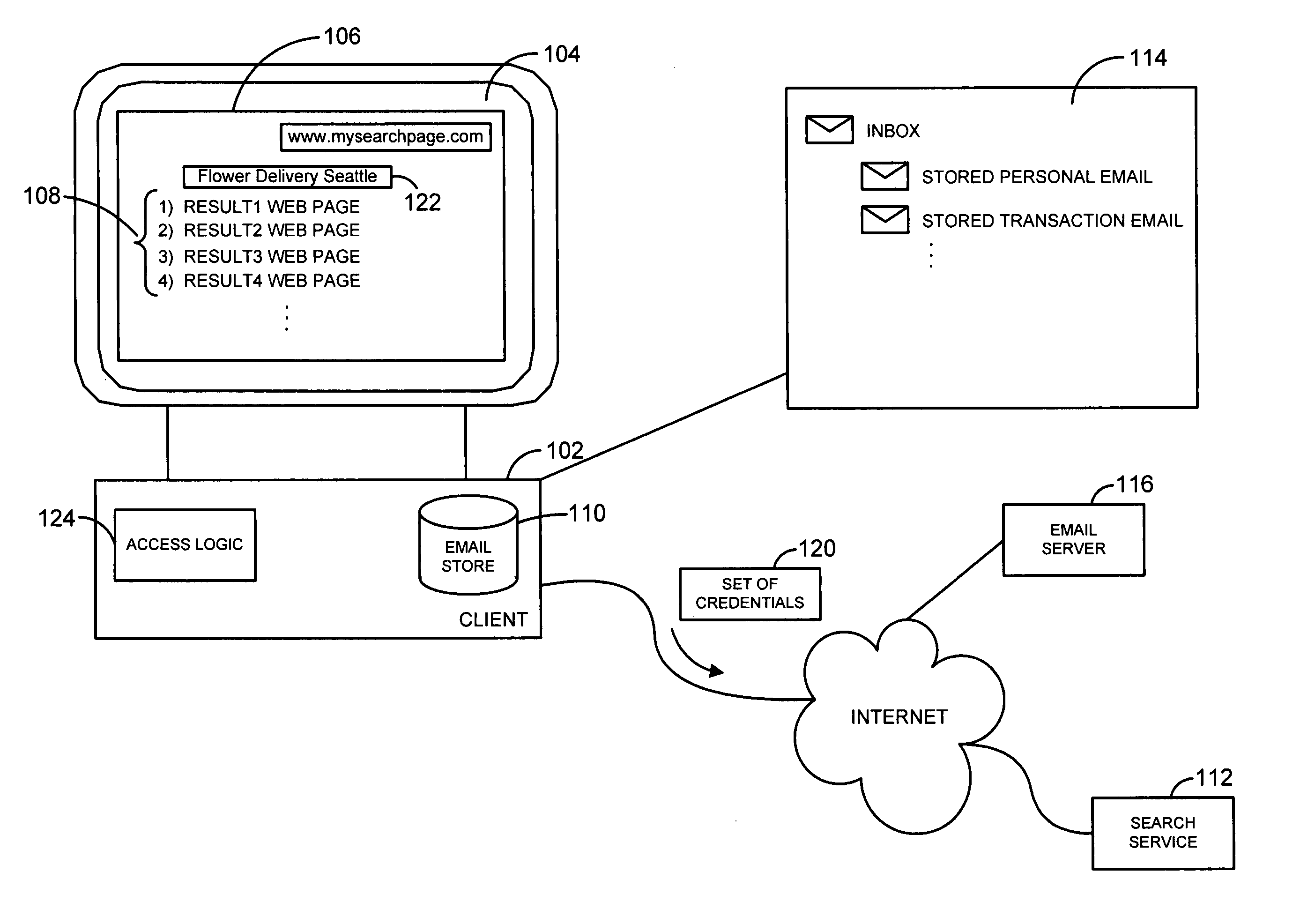
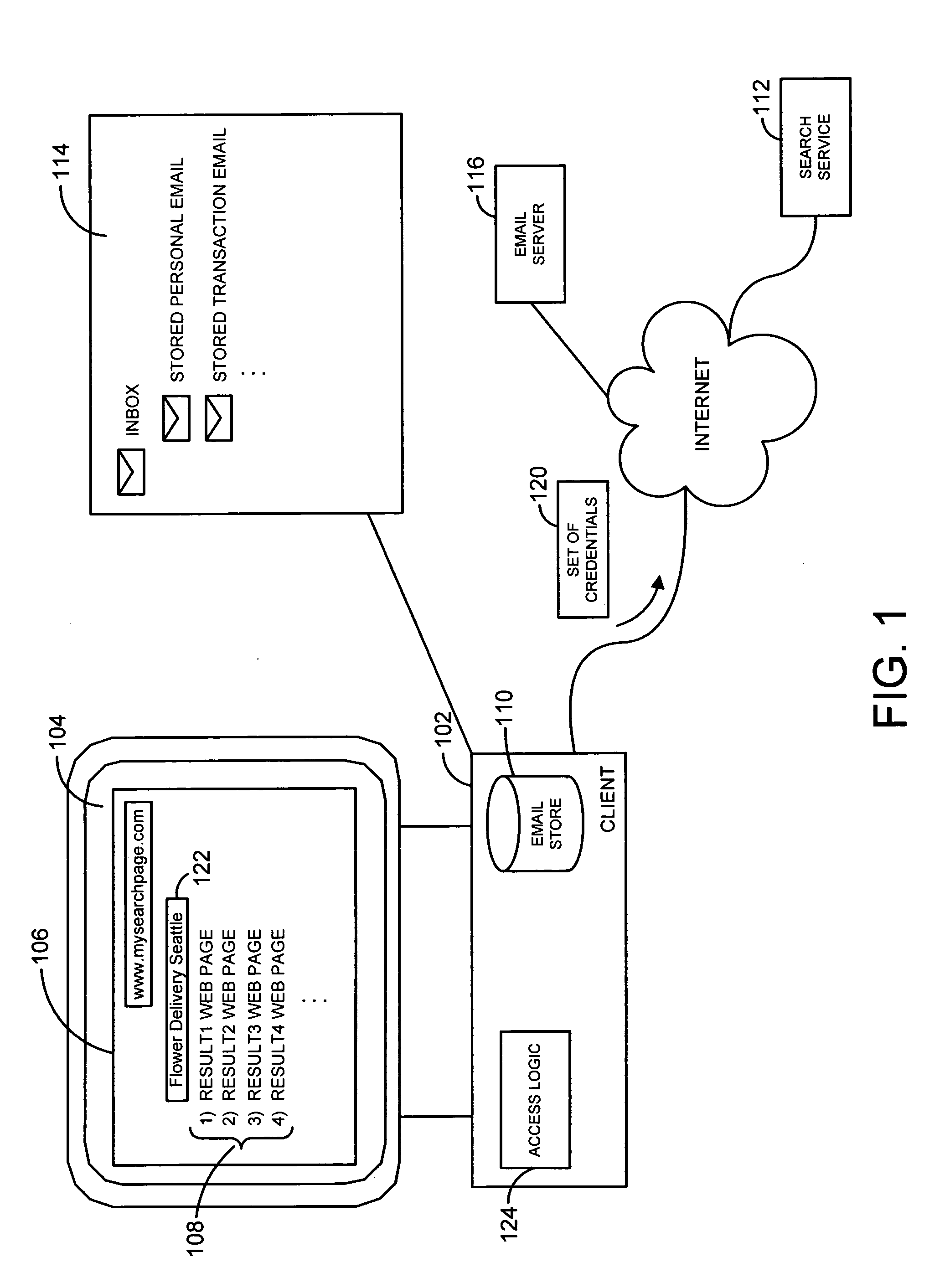
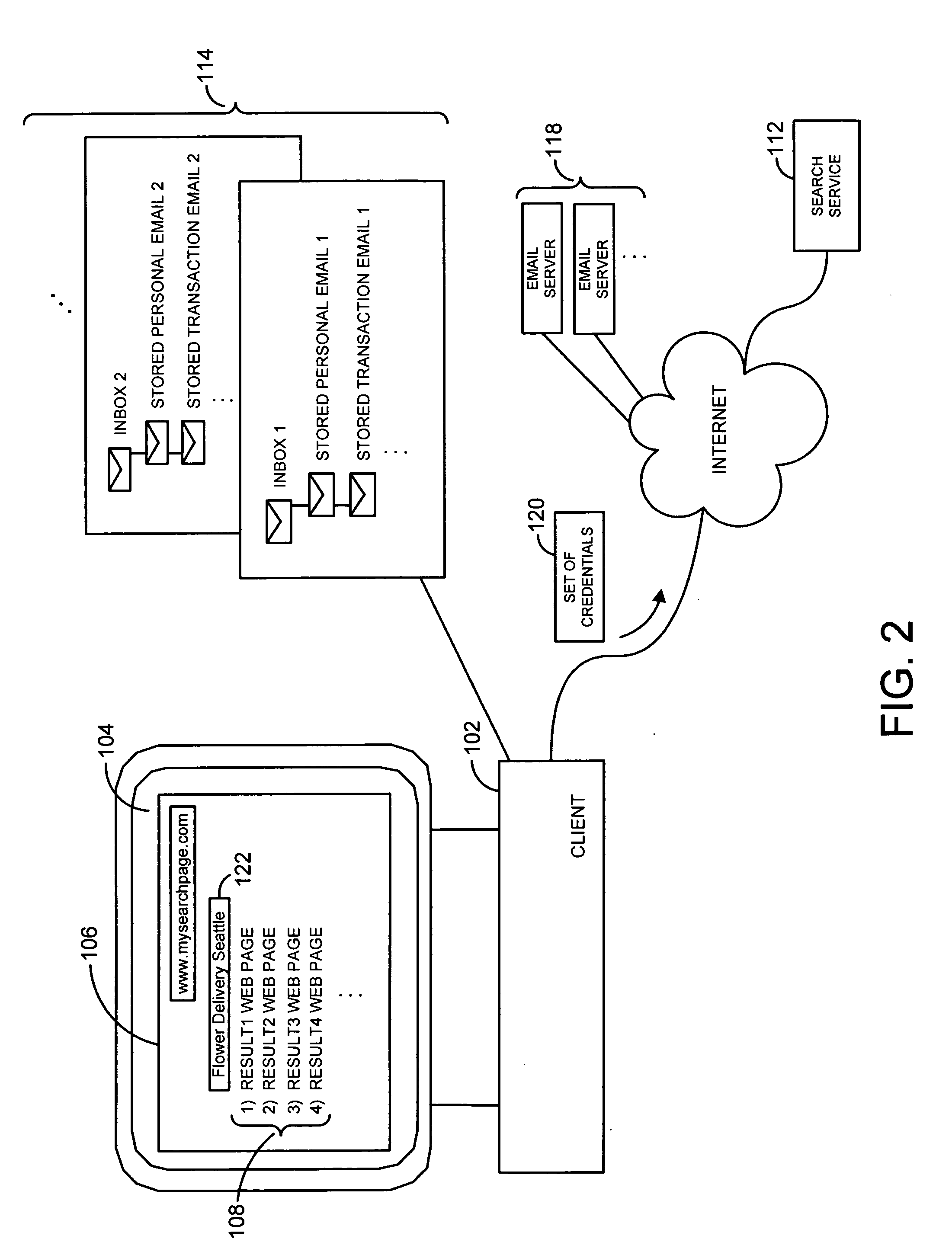
System and method for simultaneous search service and email search
InactiveUS20060259494A1Improve search capabilitiesWeb data indexingSpecial data processing applicationsWeb siteAccess time
A system and related techniques execute search queries against both remote Internet or other search services, as well as local or remote email stores. A user may access a search service Web site or other search interface, and enter search inputs or terms. That search input may be transmitted to a remote search service via the Internet or other network, as well as through access logic which communicates the same search inputs to the user's local or remote email store. Web sites as well as email messages or other content that matches the search input may be retrieved both from the remote search service as well as the email store, and presented to the user in combined or separate fashion. The access logic may manage the transmission of necessary authentication credentials to remote servers or otherwise to access and retrieve the email portion of the results. According to embodiments, email search results may be cached to improve access time and integration with results retrieved from the search service.
Owner:MICROSOFT TECH LICENSING LLC
Adjusting access of non-volatile semiconductor memory based on access time
ActiveUS20100250793A1Memory architecture accessing/allocationRead-only memoriesAccess timeControl circuit
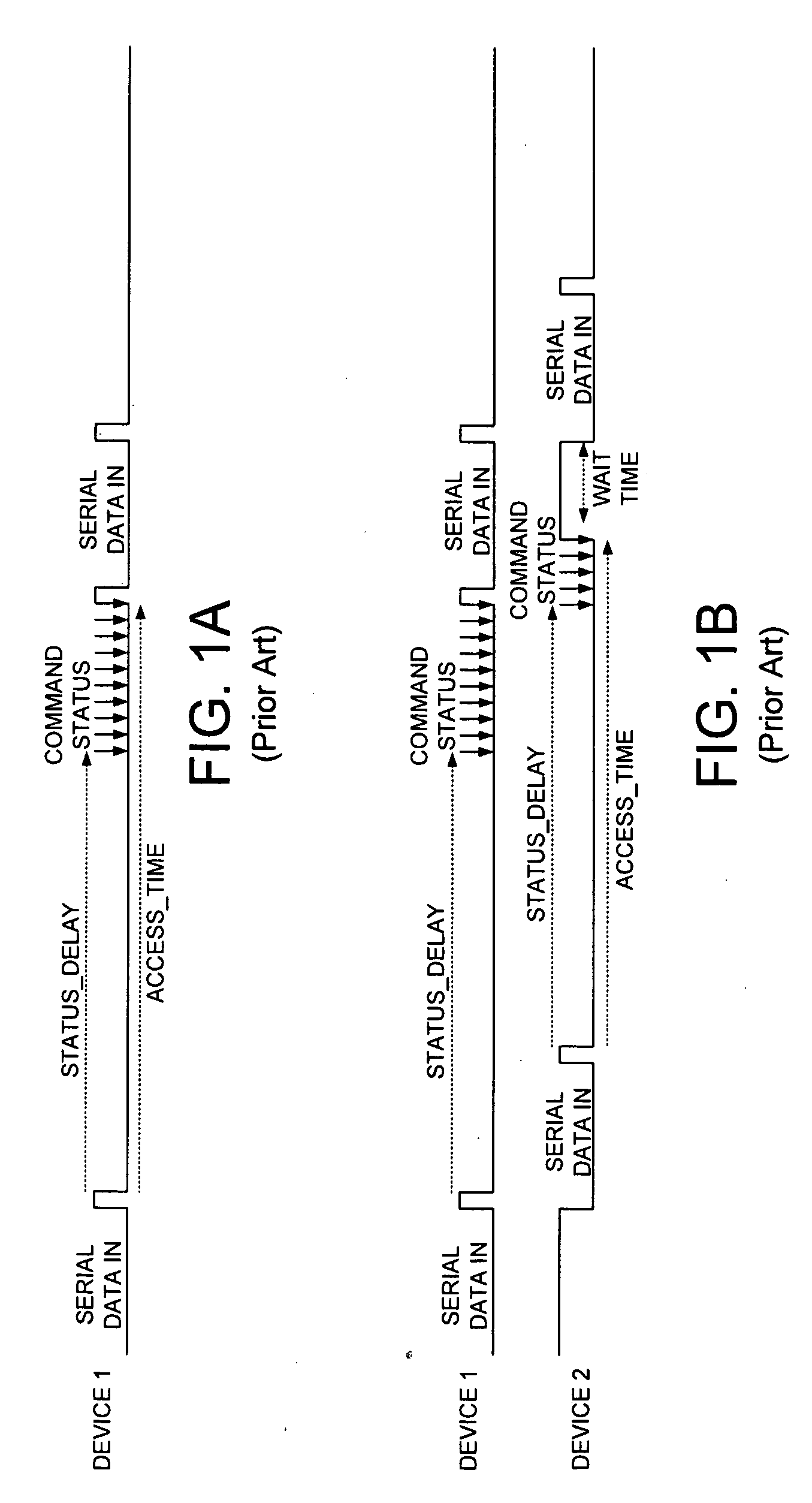
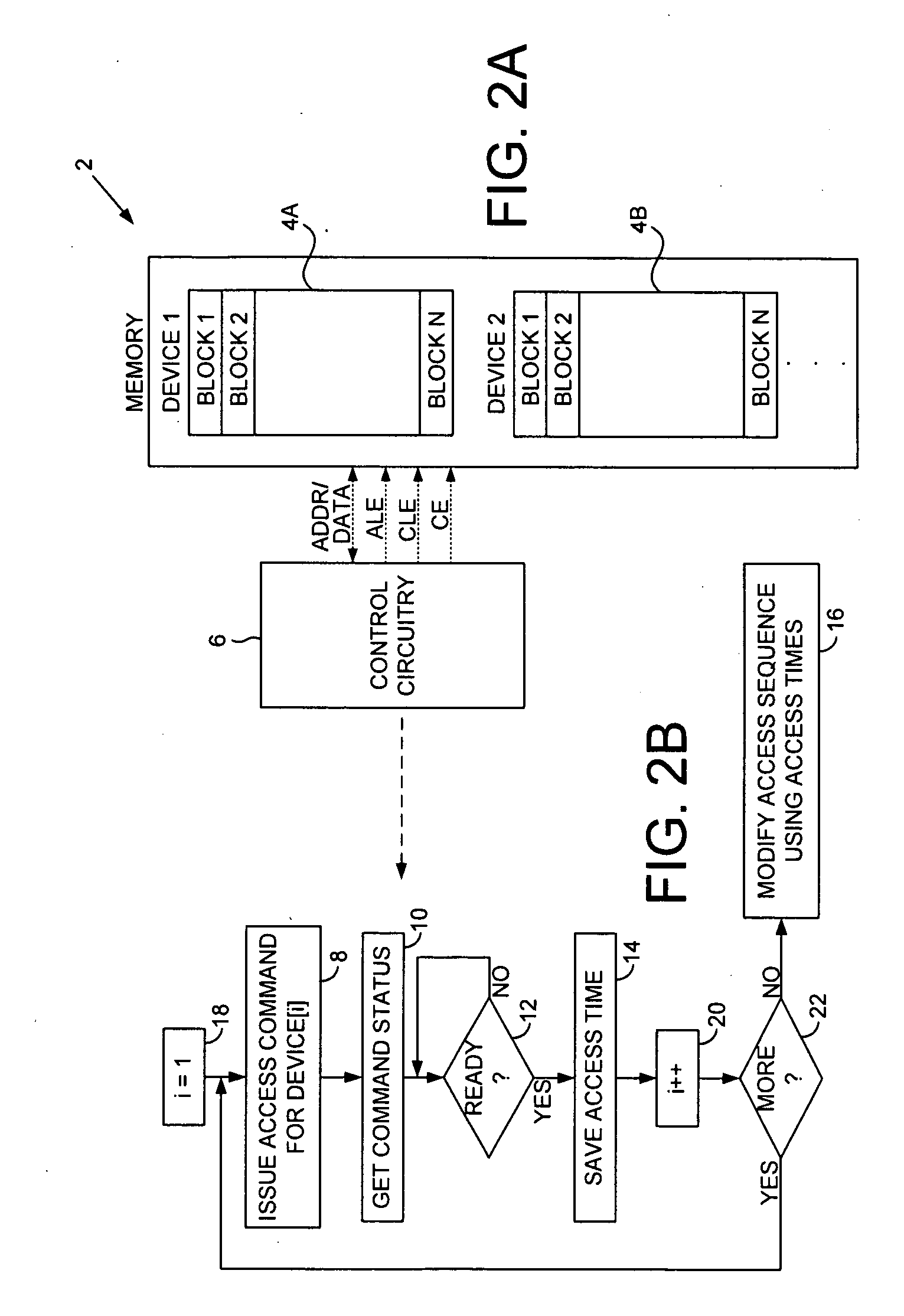
A non-volatile semiconductor memory is disclosed comprising a first memory device and control circuitry operable to issue an access command to the first memory device. A command status is requested from the first memory device after a status delay. When the command status indicates the first memory device has completed the command, a first access time of the memory device is measured. An access sequence of the first memory device is then modified in response to the access time.
Owner:WESTERN DIGITAL TECH INC
Mass storage accelerator
ActiveUS20050172067A1Slow access timeLarge capacityInput/output to record carriersMemory systemsMass storageDead time
A data storage device is provided. A disk device is combined with a non-volatile memory device to provide much shorter write access time and much higher data write speed than can be achieved with a disk device alone. Interleaving bursts of sector writes between the two storage devices can effectively eliminate the effect of the seek time of the disk device. Following a non-contiguous logical address transition from a host system, the storage controller can perform a look-ahead seek operation on the disk device, while writing current data to the non-volatile memory device. Such a system can exploit the inherently faster write access characteristics of a non-volatile memory device, eliminating the dead time normally caused by the disk seek time.
Owner:SANDISK TECH LLC
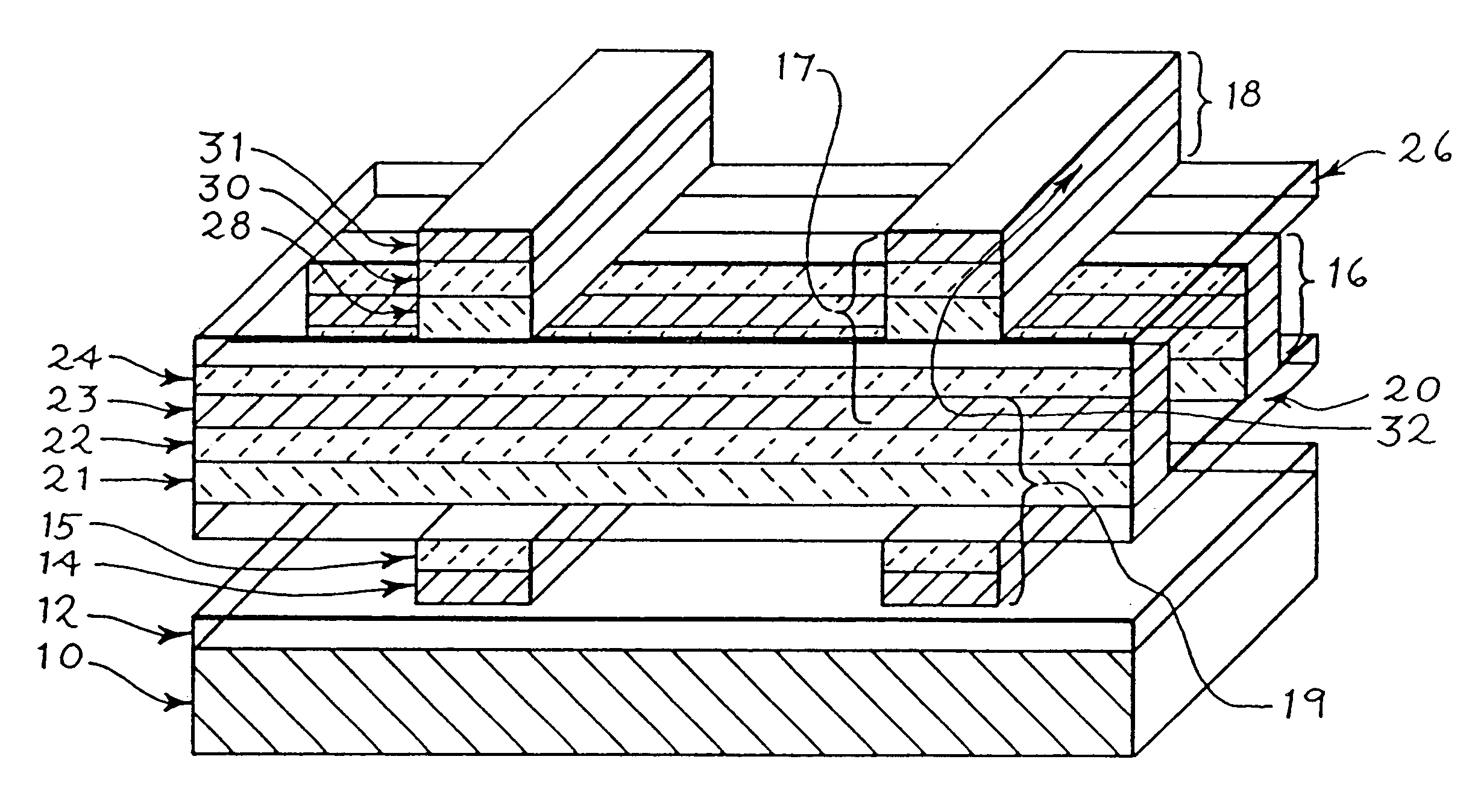
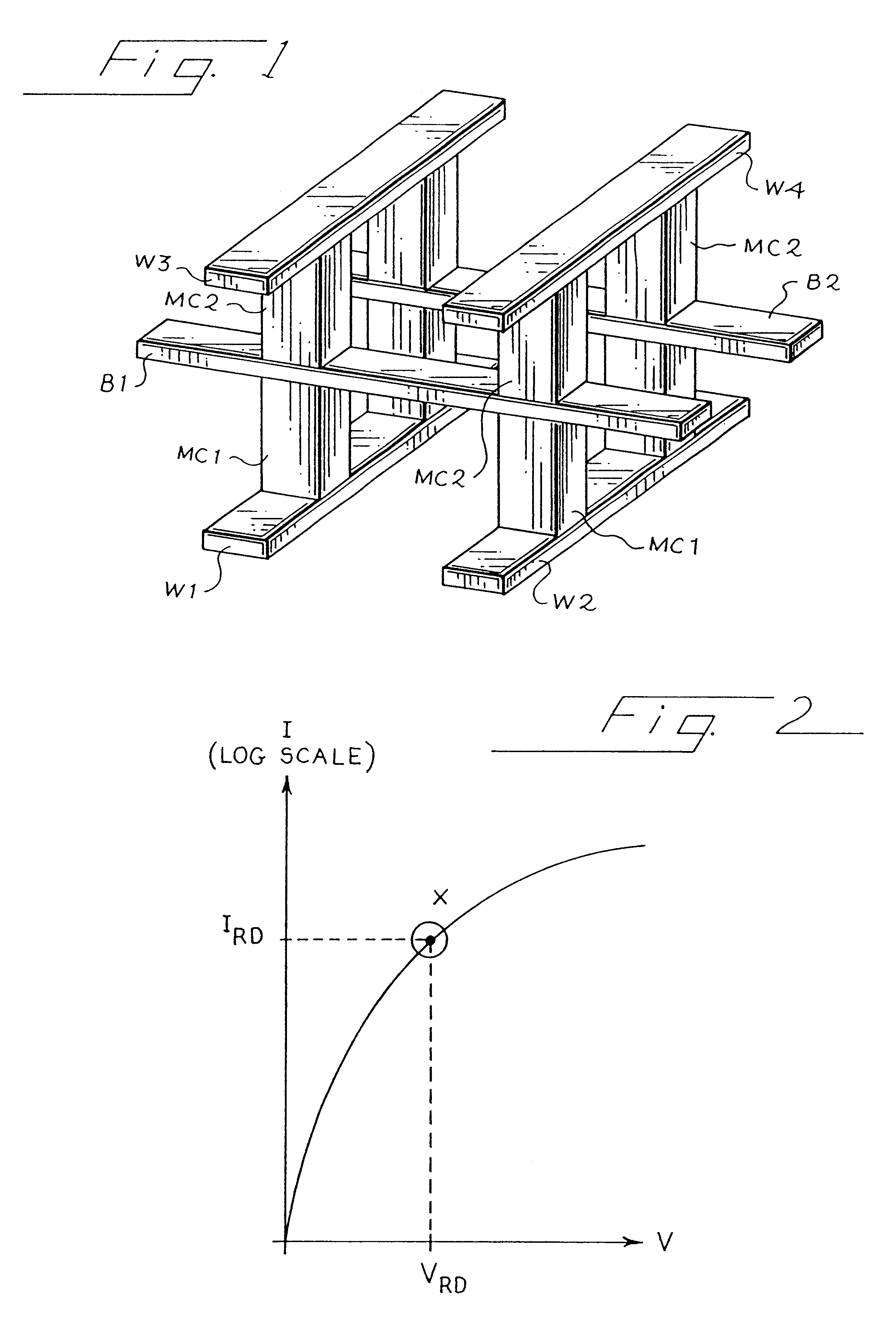
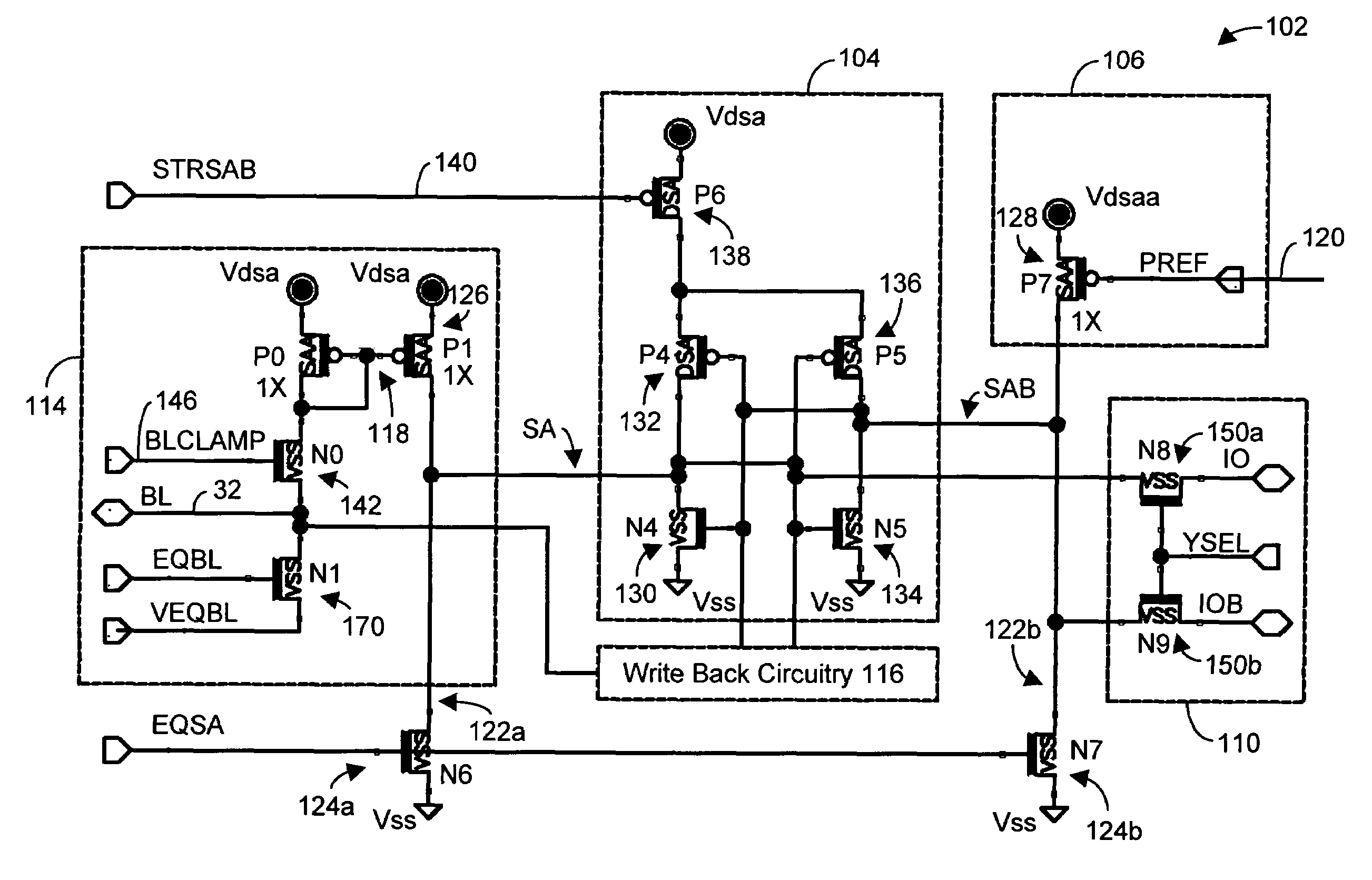
Sense amplifier circuitry and architecture to write data into and/or read from memory cells
A technique of, and circuitry for sampling, sensing, reading and / or determining the data state of a memory cell of a memory cell array (for example, a memory cell array having a plurality of memory cells which consist of an electrically floating body transistor). In one embodiment, sense amplifier circuitry is relatively compact and pitched to the array of memory cells such that a row of data may be read, sampled and / or sensed during a read operation. In this regard, an entire row of memory cells may be accessed and read during one operation which, relative to at least architecture employing multiplexer circuitry, may minimize, enhance and / or improve read latency and read access time, memory cell disturbance and / or simplify the control of the sense amplifier circuitry and access thereof. The sense amplifier circuitry may include write back circuitry to modify or “re-store” the data read, sampled and / or sensed during a read operation and / or a refresh operation in the context of a DRAM array. The sense amplifier circuitry of this embodiment restores and / or refreshes data in an entire row of volatile and / or destructive read type memory cells in parallel. This architecture may minimize, enhance and / or improve write back and read latency parameters, relative to at least architecture employing multiplexer circuitry. Also, data that has been read, sampled and / or sensed by the sense amplifier circuitry during a read operation may be modified before being written back to one or more of the memory cells of the selected row of the array of memory cells.
Owner:MICRON TECH INC
Single-chip microcomputer using adjustable timing to fetch data from an external memory
InactiveUS6125431AIncrease costEasy to operateMemory adressing/allocation/relocationProgram controlMicrocontrollerInternal memory
It is an object of the present invention to provide a one-chip microcomputer which permits the access time for an external memory to be equal to that for an internal memory. The one-chip microcomputer 10 includes an internal ROM 11, control circuit 12, output terminals 13, input terminals 14, control circuit 15, selector 16, instruction register 17, delay circuit 18, and fetch control signal select gate 19. For selection of the external ROM 30, a control arrangement 20 and a delay circuit 18 are employed in one embodiment to adjust the time at which ROM data is fetched by the instruction register 17, based on the delay time for accessing the external ROM 30.
Owner:LAPIS SEMICON CO LTD
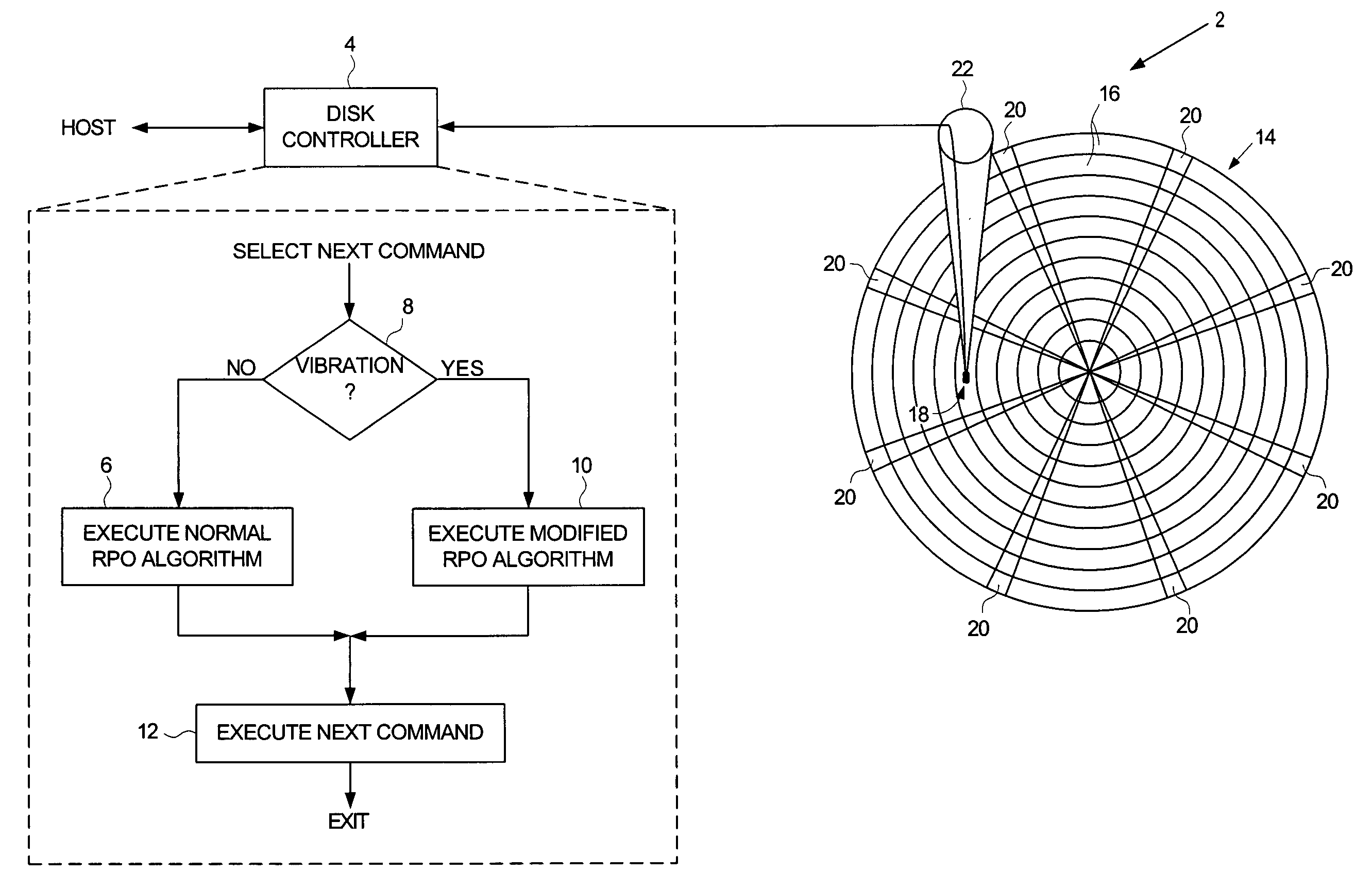
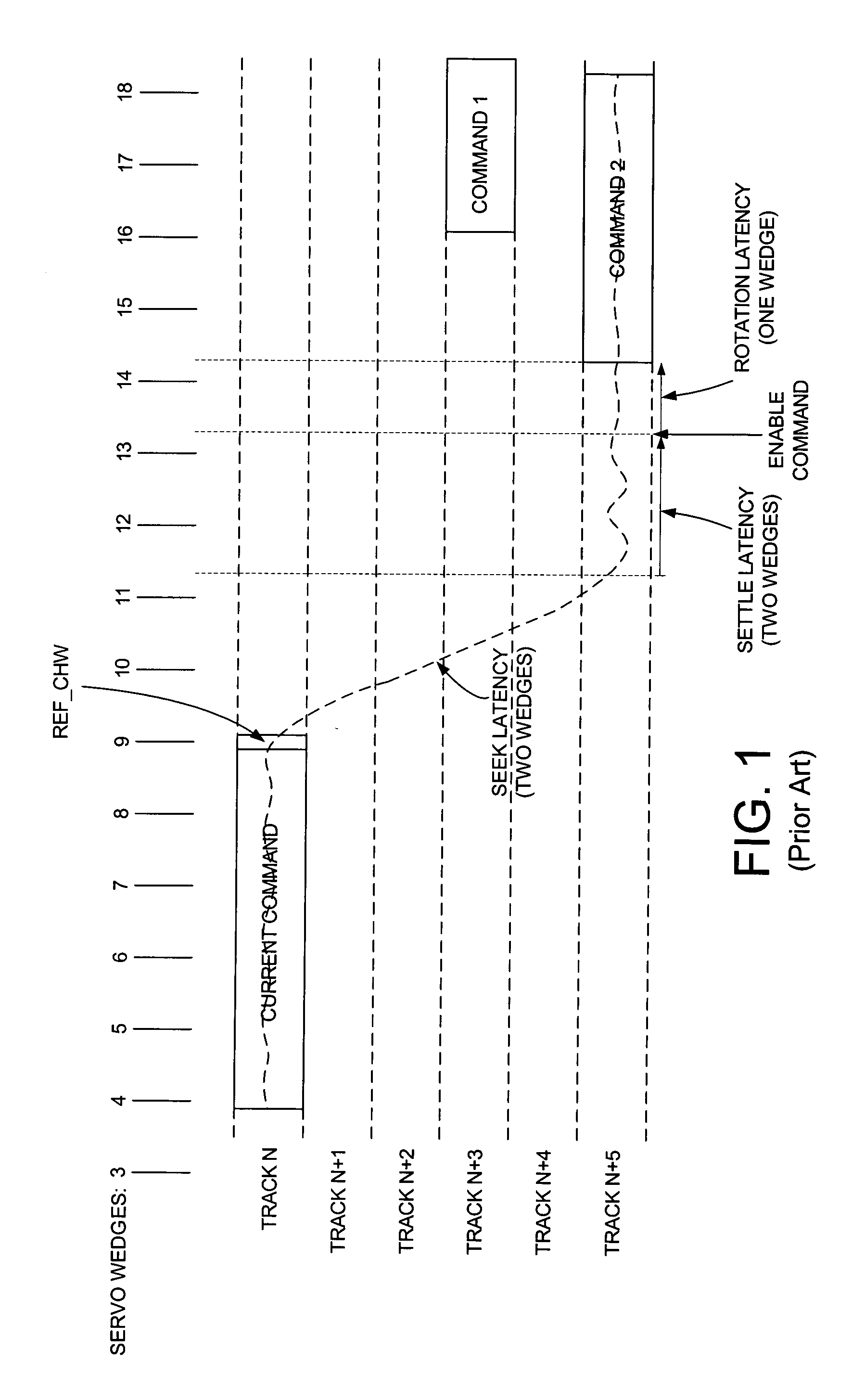
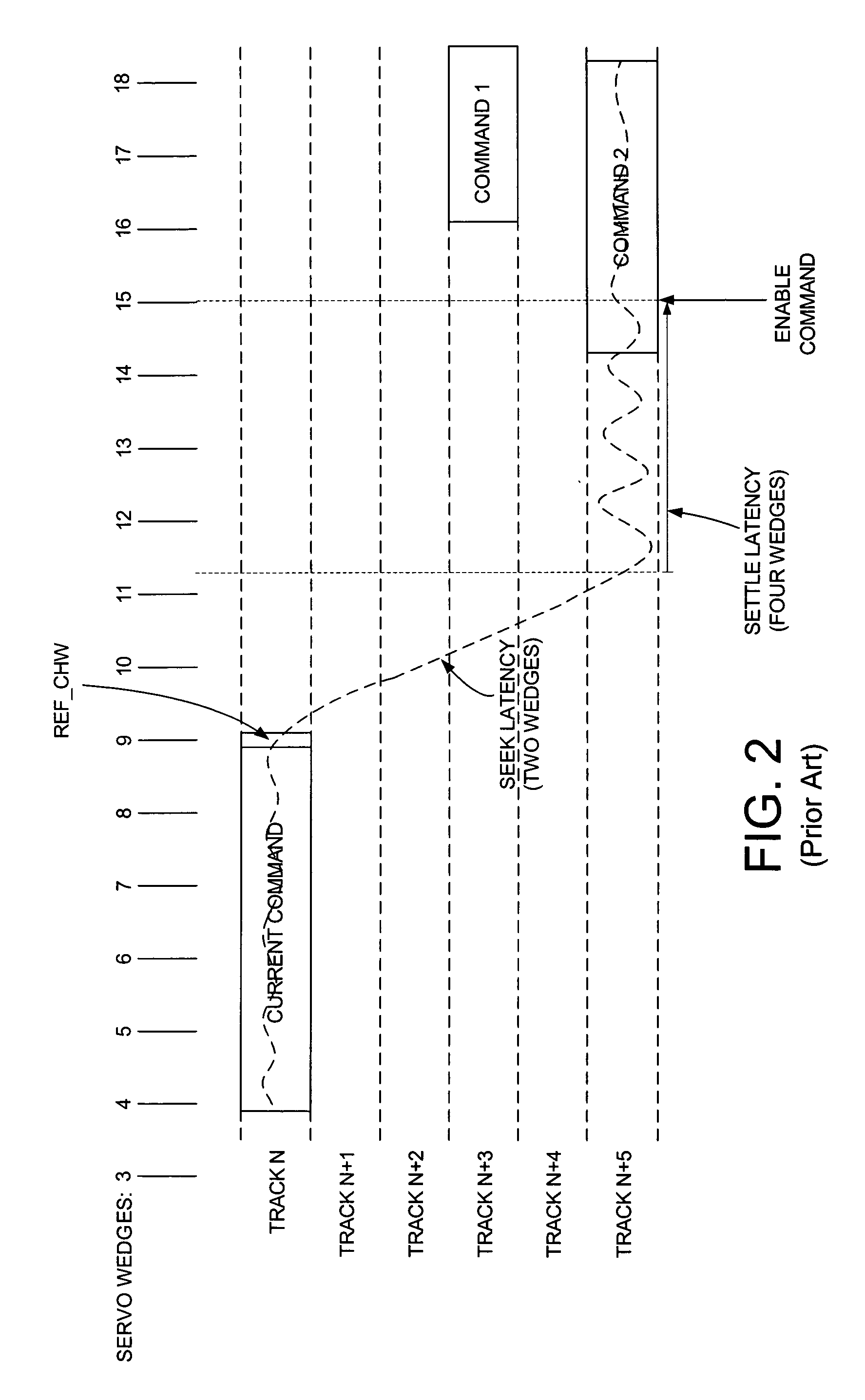
Disk drive employing a modified rotational position optimization algorithm to account for external vibrations
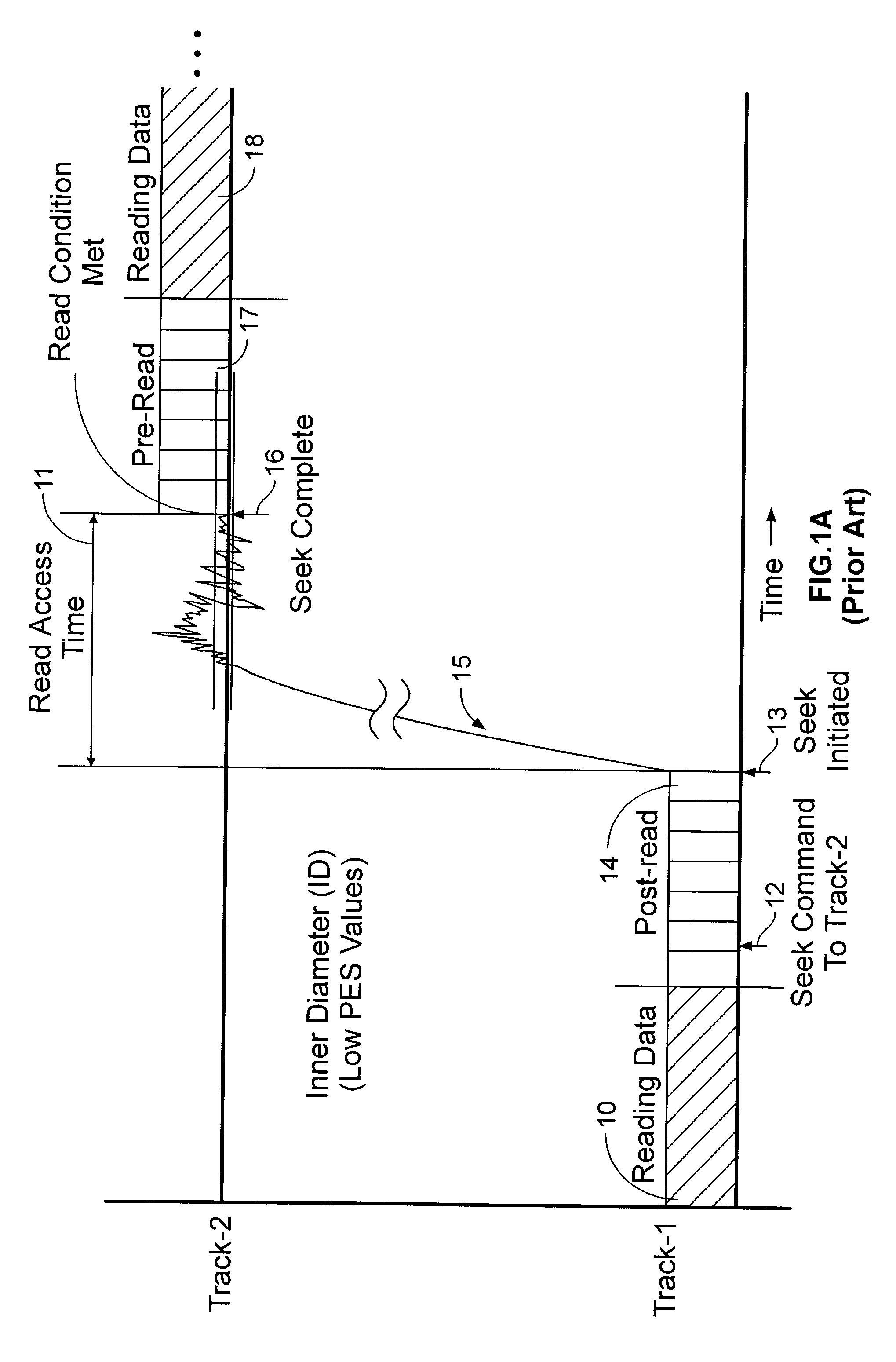
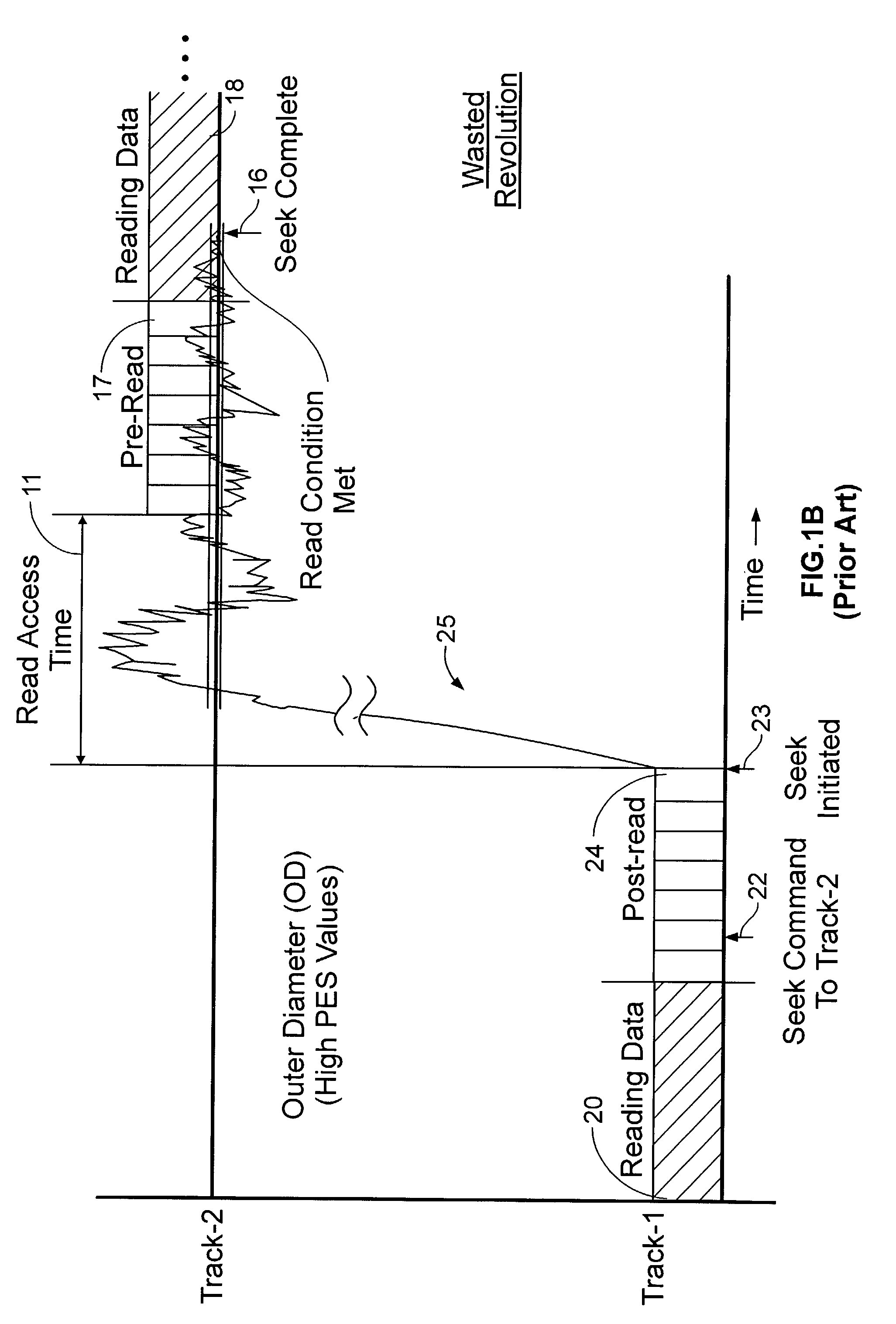
InactiveUS6968422B1Increases estimated rotational latencyImprove latencyDisposition/mounting of recording headsInput/output to record carriersAccess timeComputer science
A disk drive is disclosed which executes a rotational position optimization (RPO) algorithm to select a next command to execute from a command queue relative to an estimated access time. If an external vibration is detected, the RPO algorithm increases at least one of an estimated seek latency, an estimated settle latency, and an estimated rotational latency for each command in the command queue.
Owner:WESTERN DIGITAL TECH INC
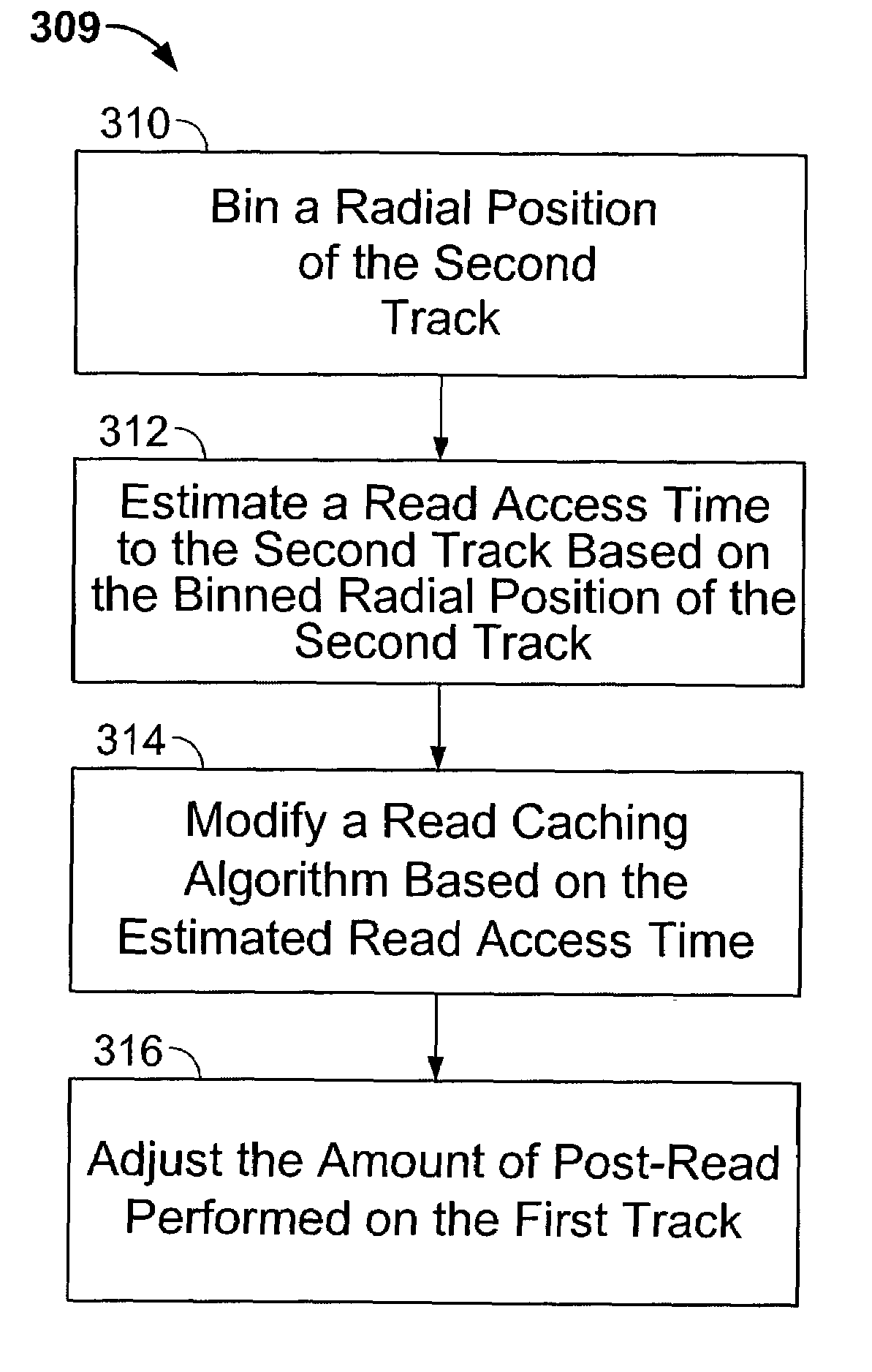
Adaptively estimating a read access time to a second track based upon the binned radial position of the second track within a rotating media storage device
InactiveUS7088538B1Reduce the amount requiredIncrease volumeFilamentary/web record carriersRecord information storageRadial positionAccess time
A rotating media storage device (RMSD) to adaptively estimate a read access time to a second track based on the radial position of the second track is disclosed. The RMSD includes a disk having at least a first track and a second track and a microprocessor for controlling operations in the RMSD including seek operations. During a seek operation, the microprocessor bins a radial position of the second track and estimates a read access time to the second track based on the binned radial position of the second track.
Owner:WESTERN DIGITAL TECH INC
System and method for detecting computer intrusions
InactiveUS6996843B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampAccess time
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
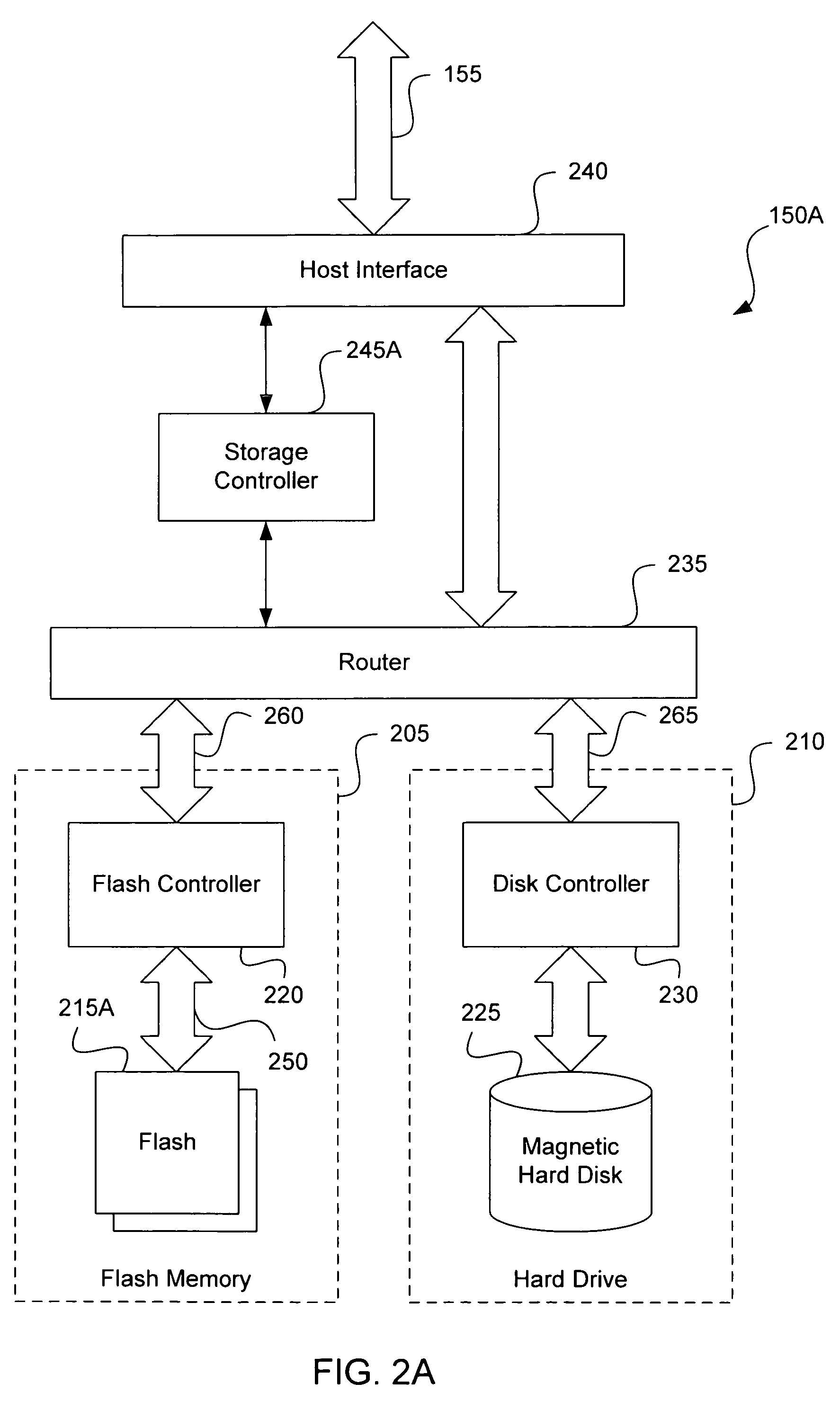
Dual media storage device
ActiveUS20050172074A1Memory architecture accessing/allocationEnergy efficient ICTMass storageData stream
A dual media storage device is provided. Two separate non-volatile mass storage devices, one having a faster access time and a lower capacity than the other, are combined into a single system. A storage controller can direct the flow of data into one device or the other, depending upon various conditions, which might include one mass storage device being unavailable or for certain caching schemes.
Owner:SANDISK TECH LLC
Resource browser sessions search
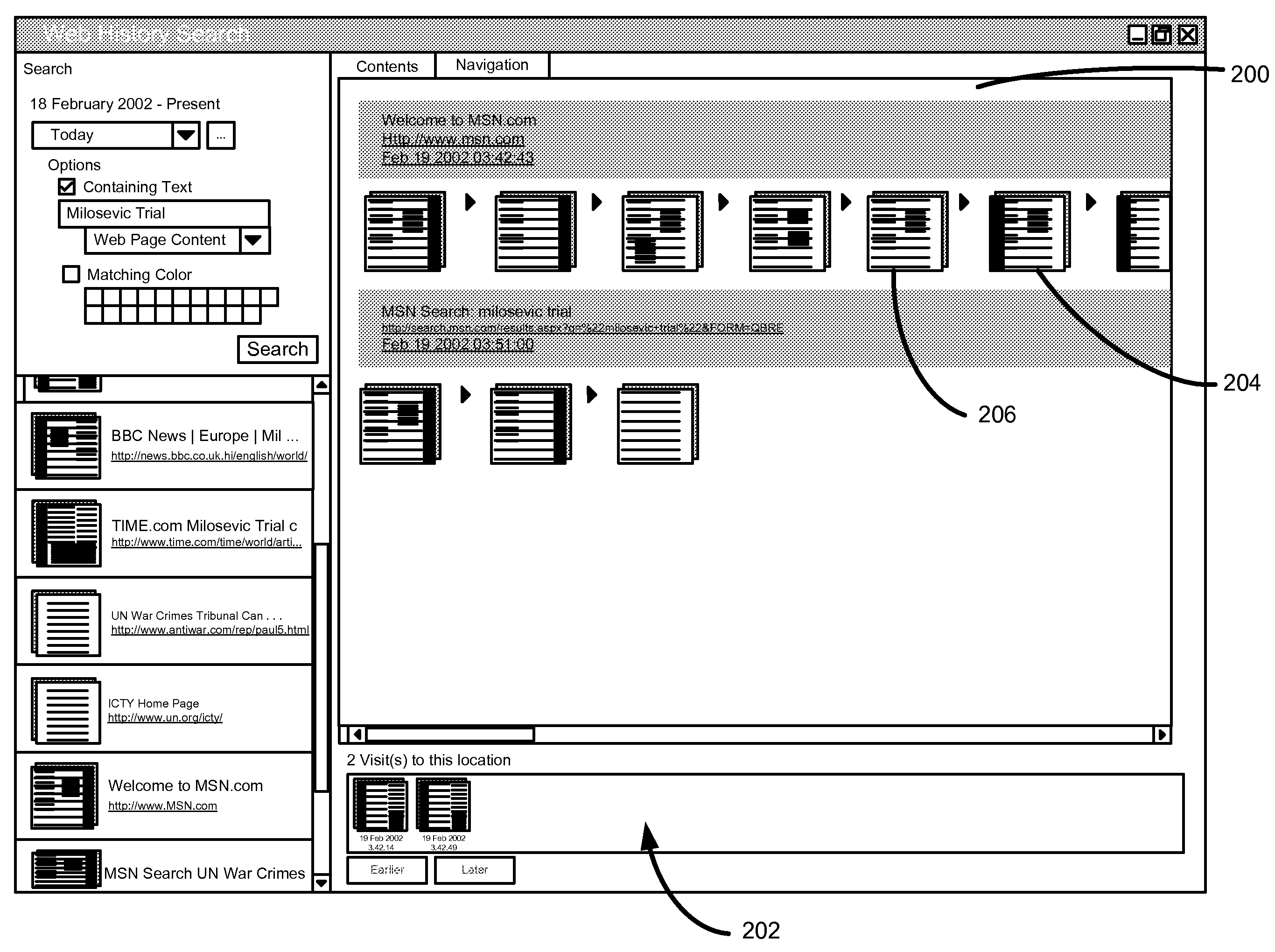
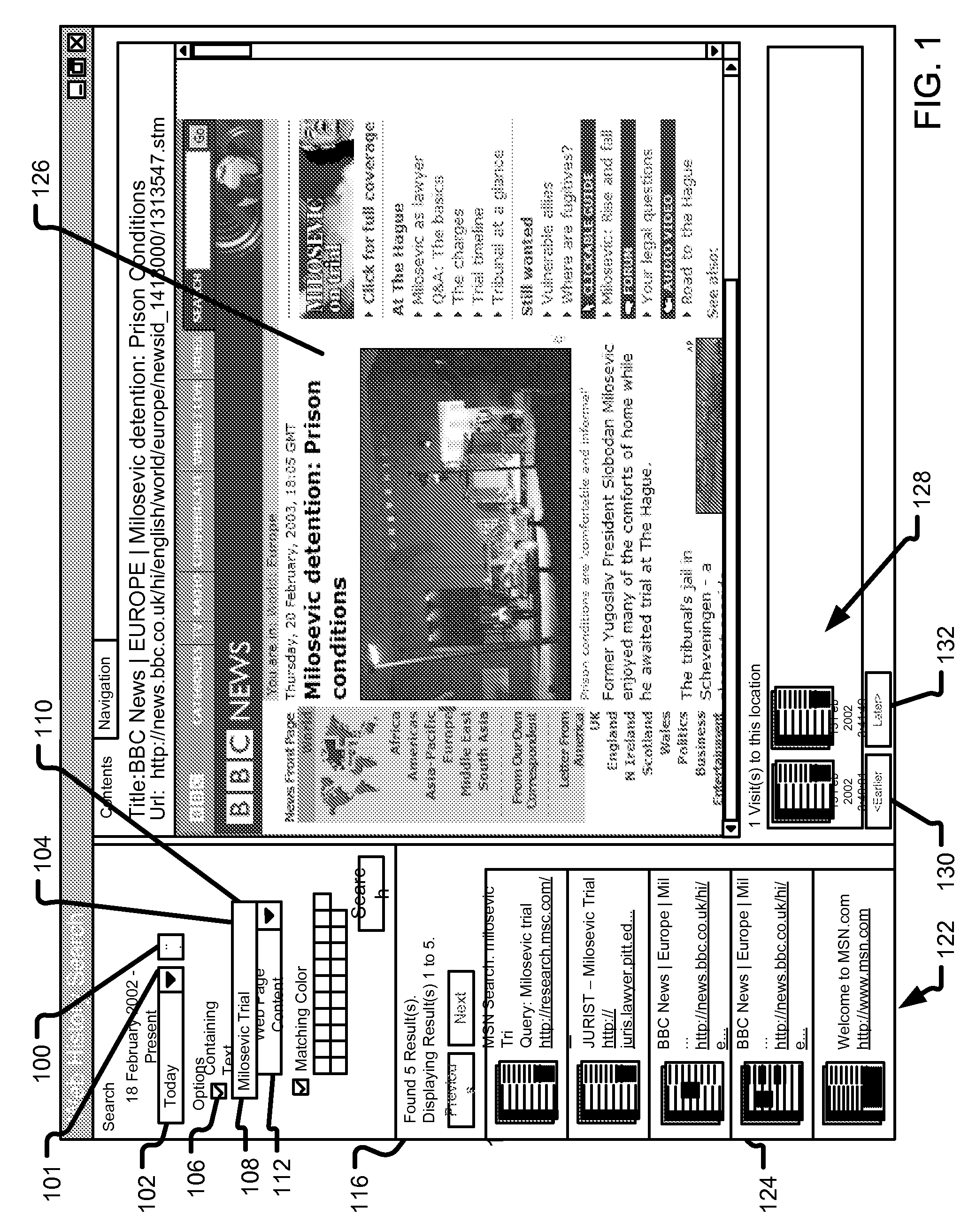
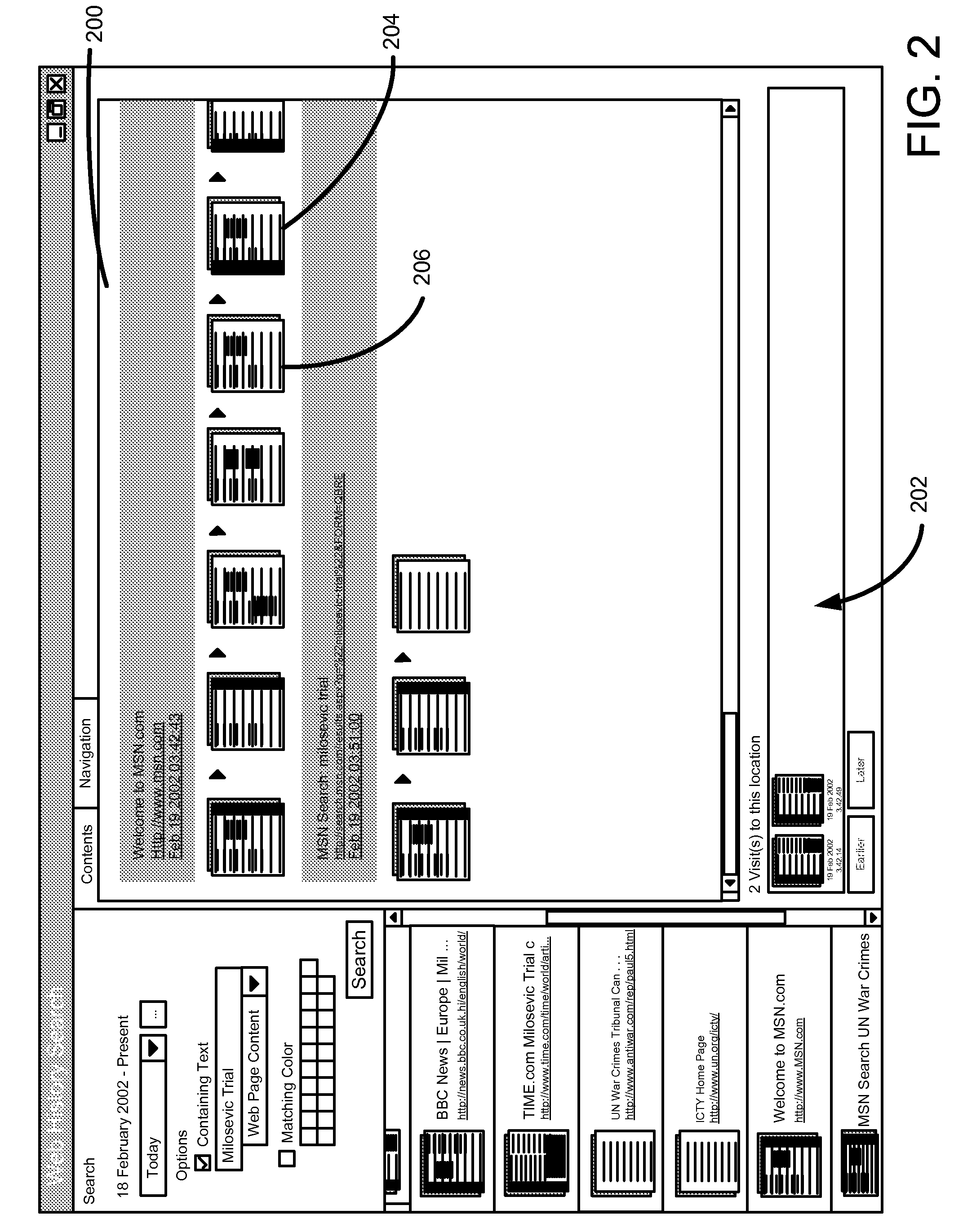
ActiveUS7225407B2Easy accessData processing applicationsCathode-ray tube indicatorsAccess timeVisual perception
A browser sessions search tool allows a user to search through records of previously viewed resource pages, even across multiple browser sessions. Each visit to a resource page results in creation of a visit data structure that references the resource page content. A rich assortment of data is recorded for each visited resource page, such as full text and layout data, time of access and navigation type that lead to the page. In one embodiment, color aspects of each resource page are stored to assist in a search, although other recorded resource page characteristics may additionally or alternatively include without limitation other visual, audio, navigational, or metadata aspects.
Owner:MICROSOFT TECH LICENSING LLC
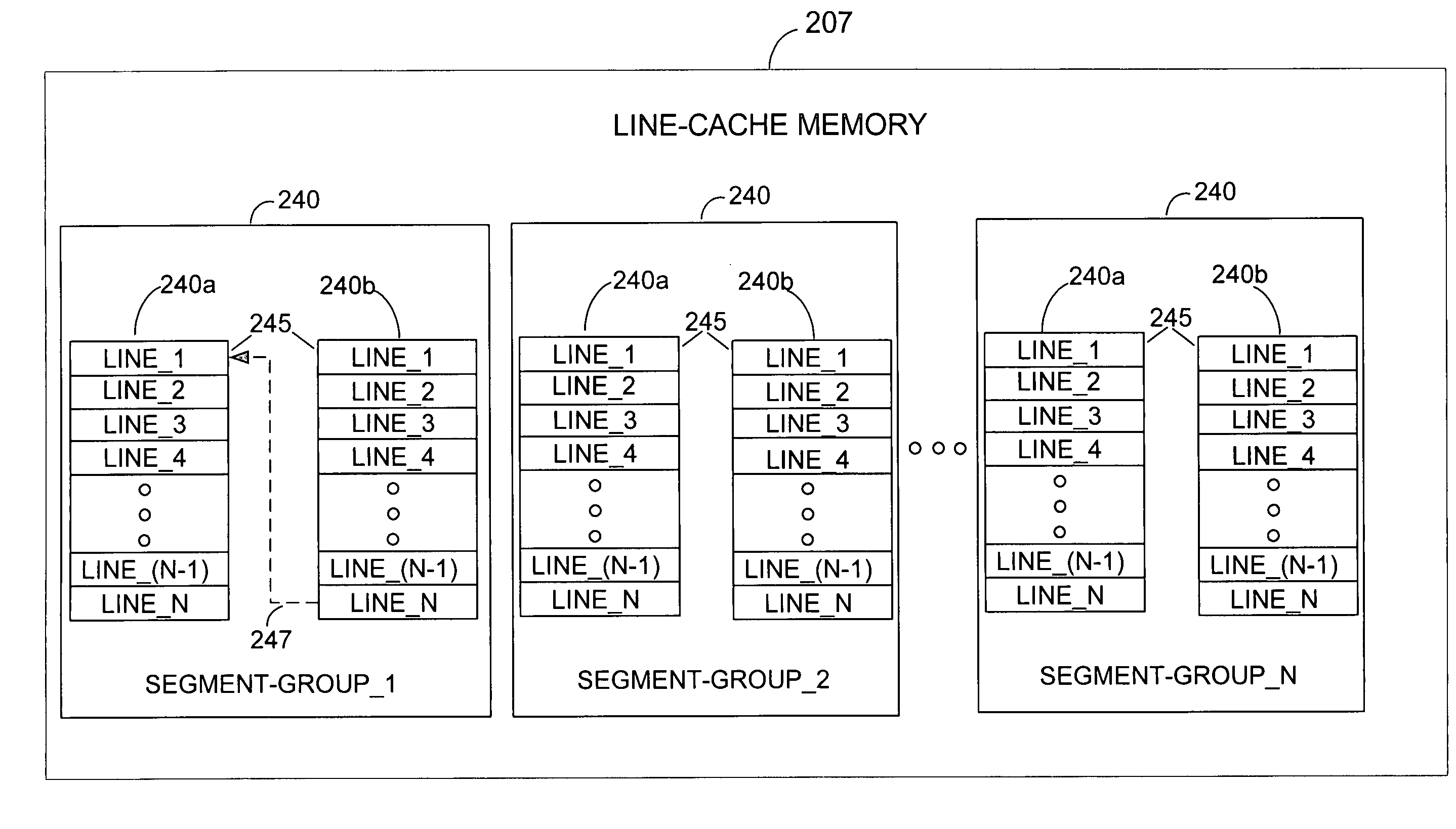
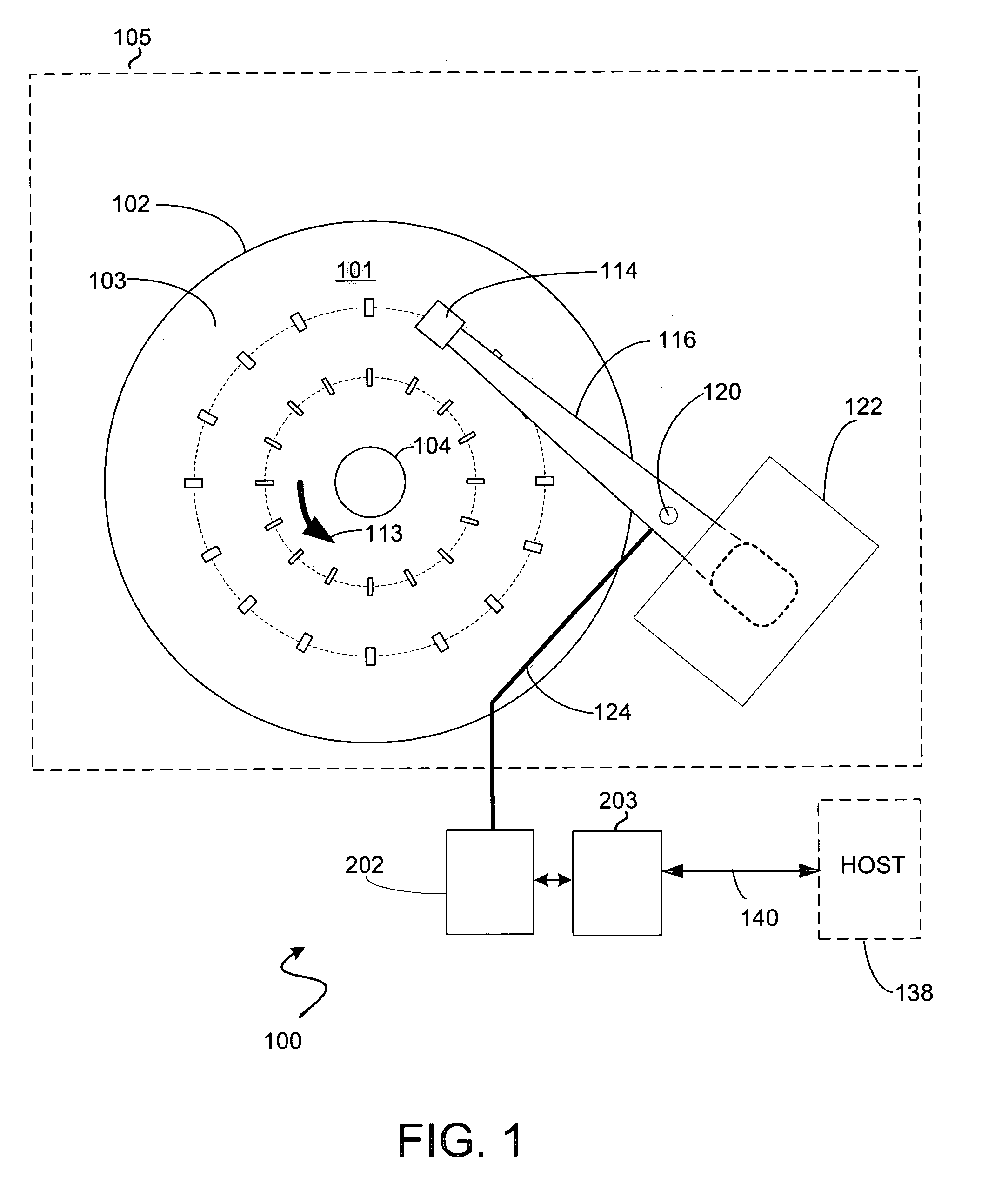
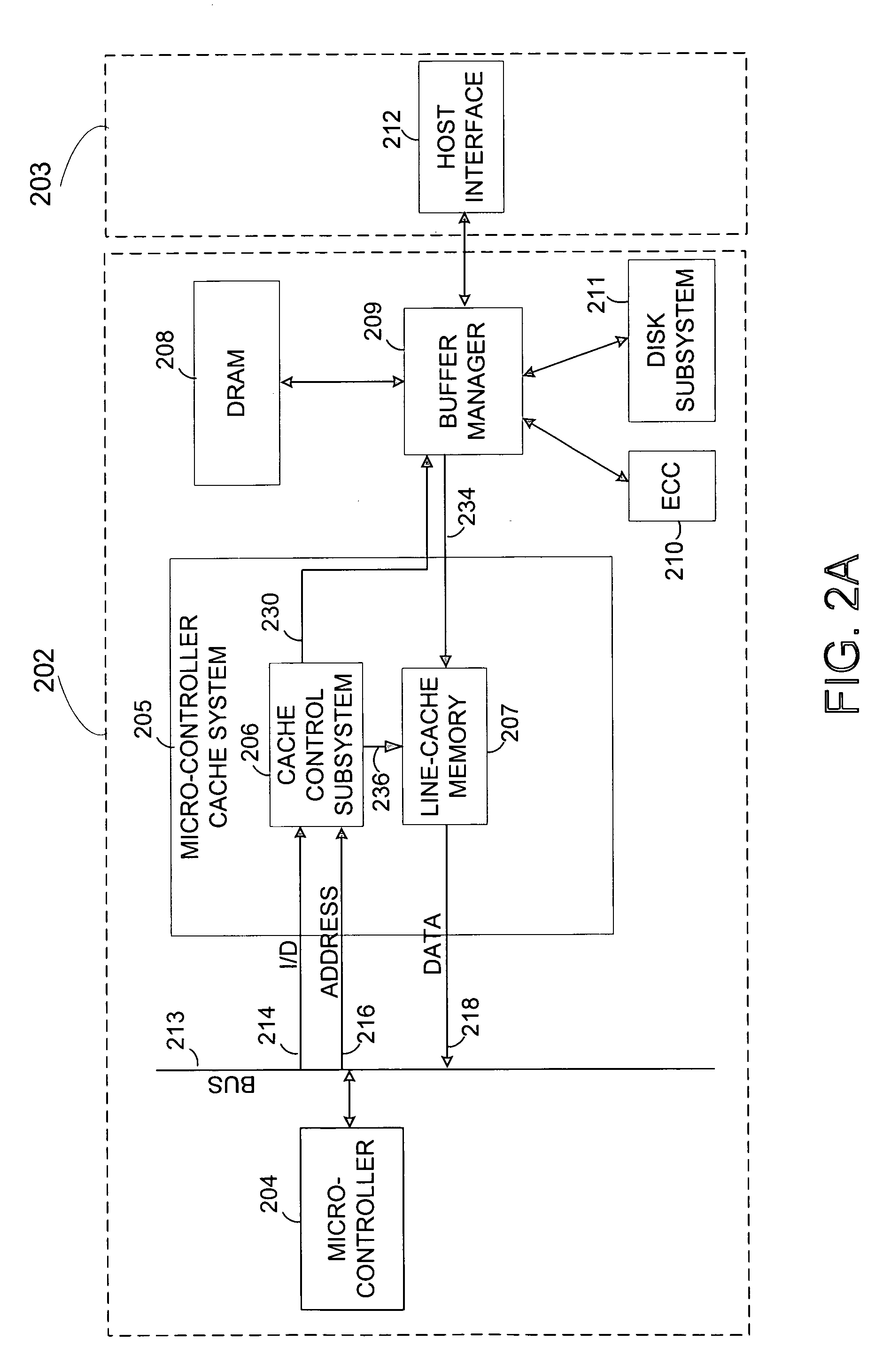
Reducing micro-controller access time to data stored in a remote memory in a disk drive control system
InactiveUS7111116B1Shorten access timeReducing micro-controller access timeMemory adressing/allocation/relocationControl systemAccess time
A method and system for reducing micro-controller access time to information stored in the remote memory via the buffer manager in a disk drive control system comprising a micro-controller, a micro-controller cache system having a plurality of line-cache segments grouped into at least one line-cache segment-group, and a buffer manager communicating with the micro-controller cache system and a remote memory. The method and system includes receiving in the micro-controller cache system a current data-request from the micro-controller, providing the current requested data to the micro-controller if the current requested data resides in a first line-cache segment of a first segment-group, and automatically filling a second line-cache segment of the first segment-group with data retrieved from the remote memory wherein the retrieved data is sequential in the remote memory to the provided current requested data.
Owner:WESTERN DIGITAL TECH INC
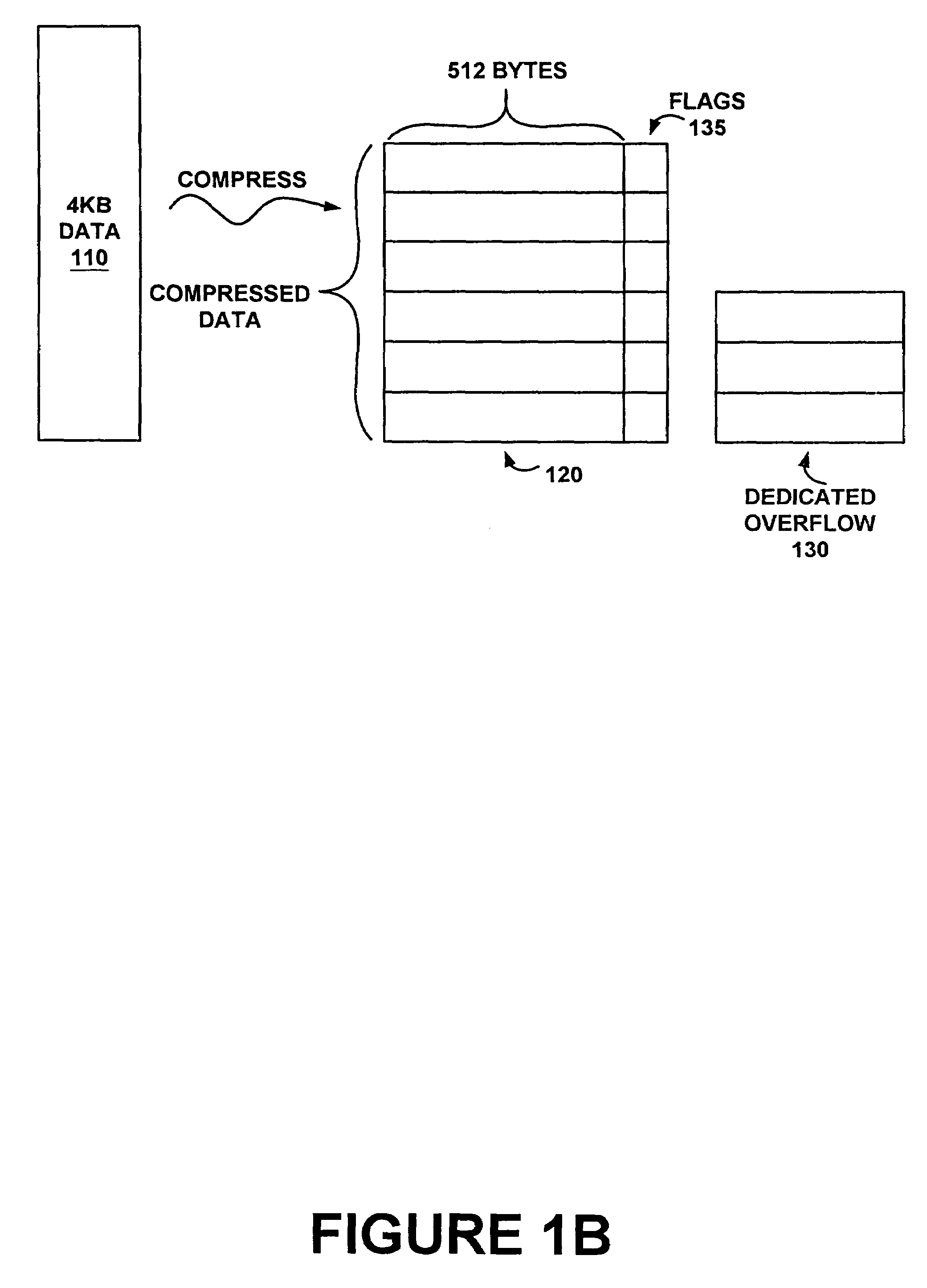
Method and system of improving disk access time by compression
InactiveUS7058769B1Reduce heatImprove hard drive access timeRecording carrier detailsCode conversionData compressionAccess time
Owner:NVIDIA CORP
System and method for using timestamps to detect attacks
InactiveUS7203962B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampContinuation
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
Method and apparatus for improving update performance of non-uniform access time persistent storage media
InactiveUS7328307B2Improve performanceImprove random access performanceInput/output to record carriersMemory adressing/allocation/relocationRAIDAccess time
A high volume storage system is described which continuously remaps where data is stored. The remapping is designed so that writing occurs on an optimum speed basis tuned to the storage system being utilized, e.g., the writes occur in substantially sequential disk storage locations to the extent possible. By remapping data on a substantially continuous basis writes advantageously occur nearer the sequential performance limits of the particular drive or devices being utilized. A methodology is described which improves the external performance of a random access storage system, such as a RAID array. The illustrative embodiments introduce a continuous, optimized dynamic reorganization of the storage media that converts concurrent updates from one or more logical volumes to one or more sequential streams, as appropriate to the number of physical devices and channels over which the updates can be dispersed and thereby minimize the number of seek operations necessary on each physical device.
Owner:UNIFIED PATENTS
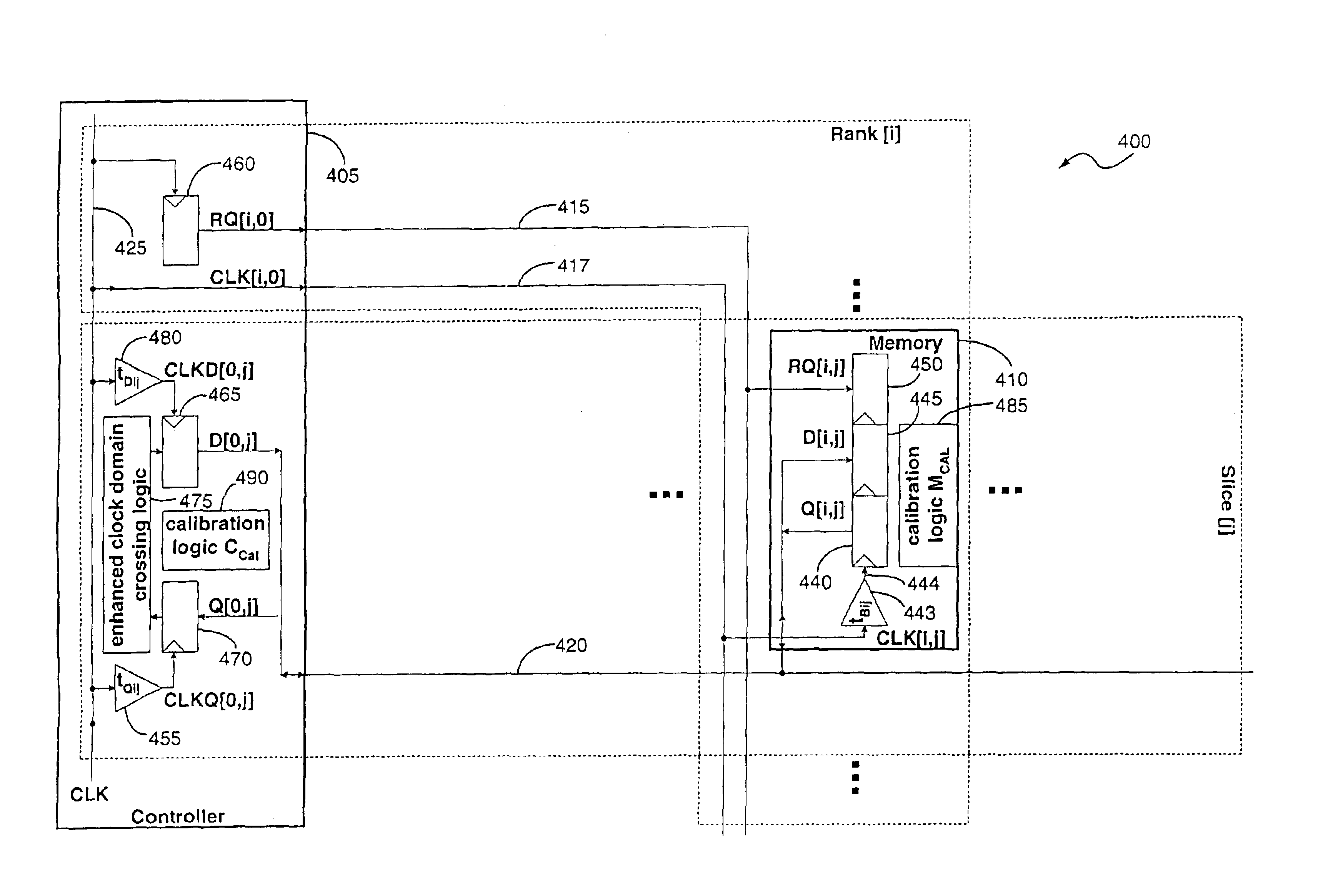
Timing calibration apparatus and method for a memory device signaling system
A memory system includes a memory controller and a memory component coupled to each other. An interface of the memory component is configured to receive a first signal from the memory controller with read request information, retrieve the read data information from the memory core in response to the request information, and transmit to the memory controller a second signal containing the read data information. The read data information includes read data symbols, where the average duration of the read data symbols, measured at the interface, defines a symbol time interval. A first external access time is measured at the interface between a first read request and read data transmitted by the interface in response to the first read request. A second external access time interval is measured at the interface between a second read request and read data transmitted by the interface in response to the second read request. The difference between the first external access time and the second external access time is greater than one-half of the symbol time interval.
Owner:RAMPART ASSET MANAGEMENT LLC
Disk acceleration using first and second storage devices
A data storage device is provided. A disk device is combined with a non-volatile memory device to provide much shorter write access time and much higher data write speed than can be achieved with a disk device alone. Interleaving bursts of sector writes between the two storage devices can effectively eliminate the effect of the seek time of the disk device. Following a non-contiguous logical address transition from a host system, the storage controller can perform a look-ahead seek operation on the disk device, while writing current data to the non-volatile memory device. Such a system can exploit the inherently faster write access characteristics of a non-volatile memory device, eliminating the dead time normally caused by the disk seek time.
Owner:SANDISK TECH LLC
Hierarchically structured mass storage device and method
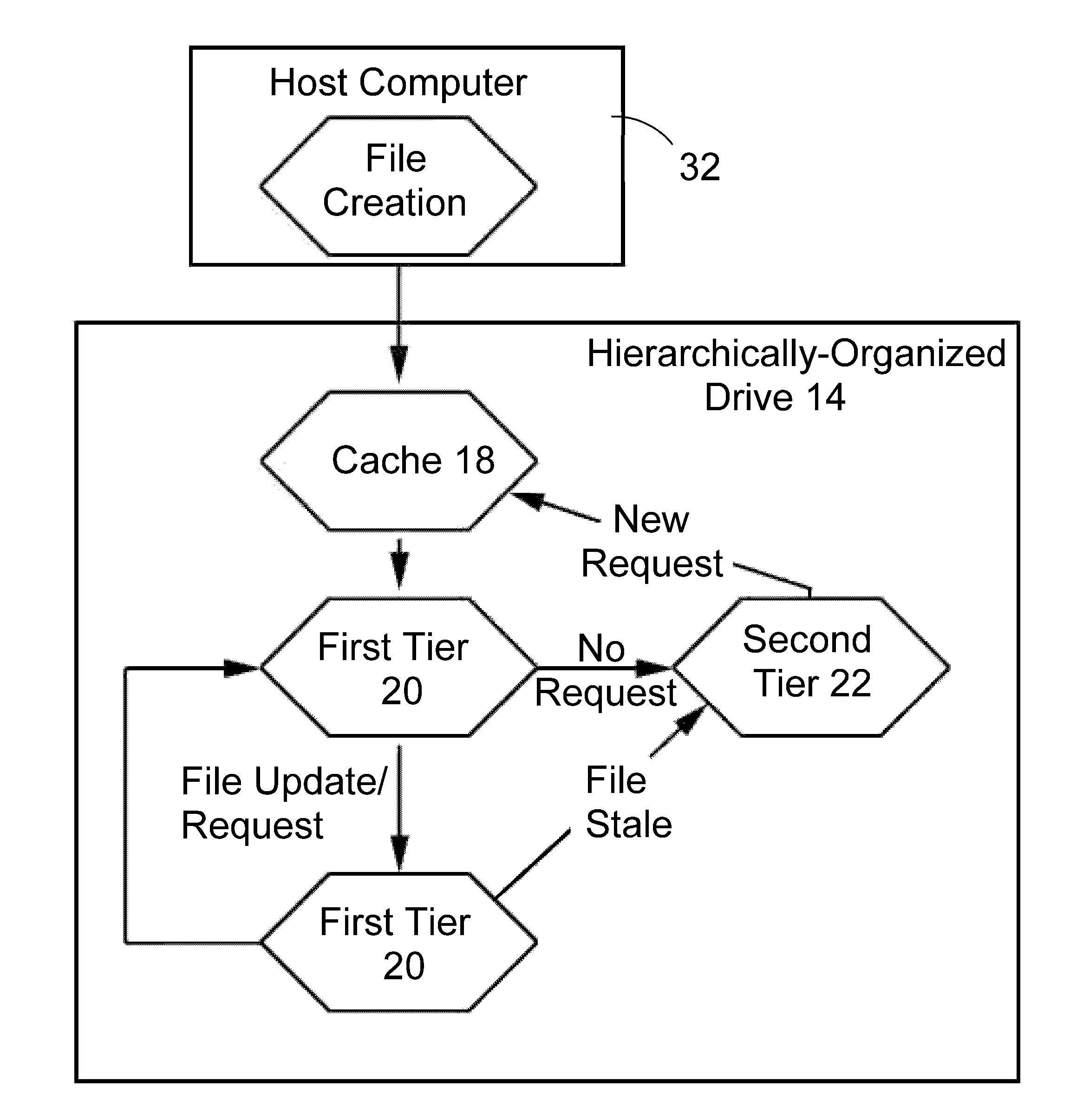
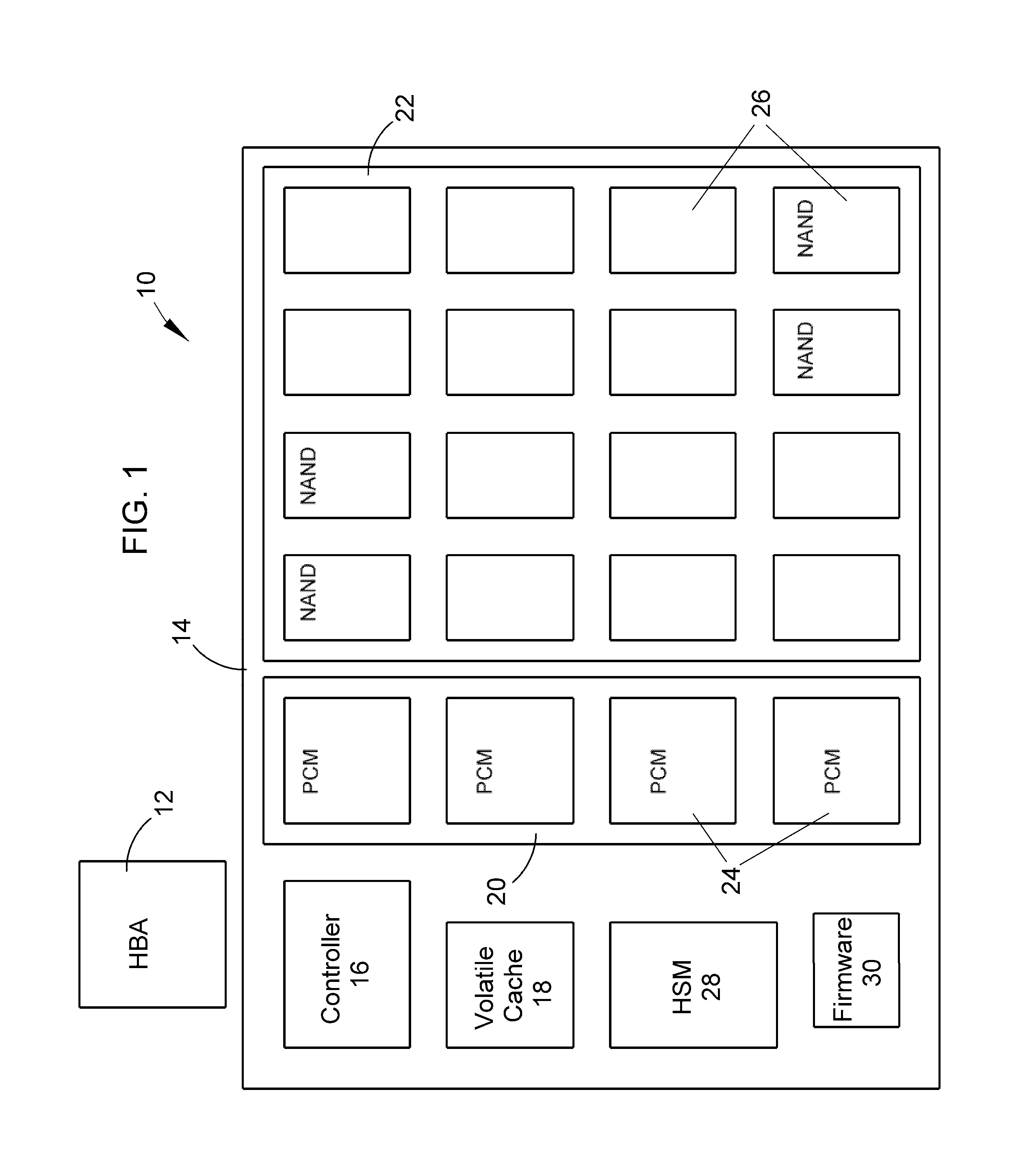
InactiveUS20100325352A1Faster access timeHigh write enduranceMemory architecture accessing/allocationMemory adressing/allocation/relocationAccess timeStorage management
A hierarchically-structured computer mass storage system and method. The mass storage system includes a mass storage memory drive, control logic on the mass storage memory drive that includes a controller and one or more devices for executing a hierarchical storage management technique, a volatile memory cache configured to be accessed by the control logic, and first and second non-volatile storage arrays on the mass storage memory drive and comprising, respectively, first and second non-volatile memory devices. The first and second non-volatile memory devices have properties including access times and write endurance, and at least one of the access time and the write endurance of the first non-volatile memory devices is faster or higher, respectively, than the second non-volatile memory devices. Desired data storage localities on the storage arrays are determined through access patterns and selectively utilizing the properties of the memory devices to match the data storage requirements.
Owner:OCZ STORAGE SOLUTIONS
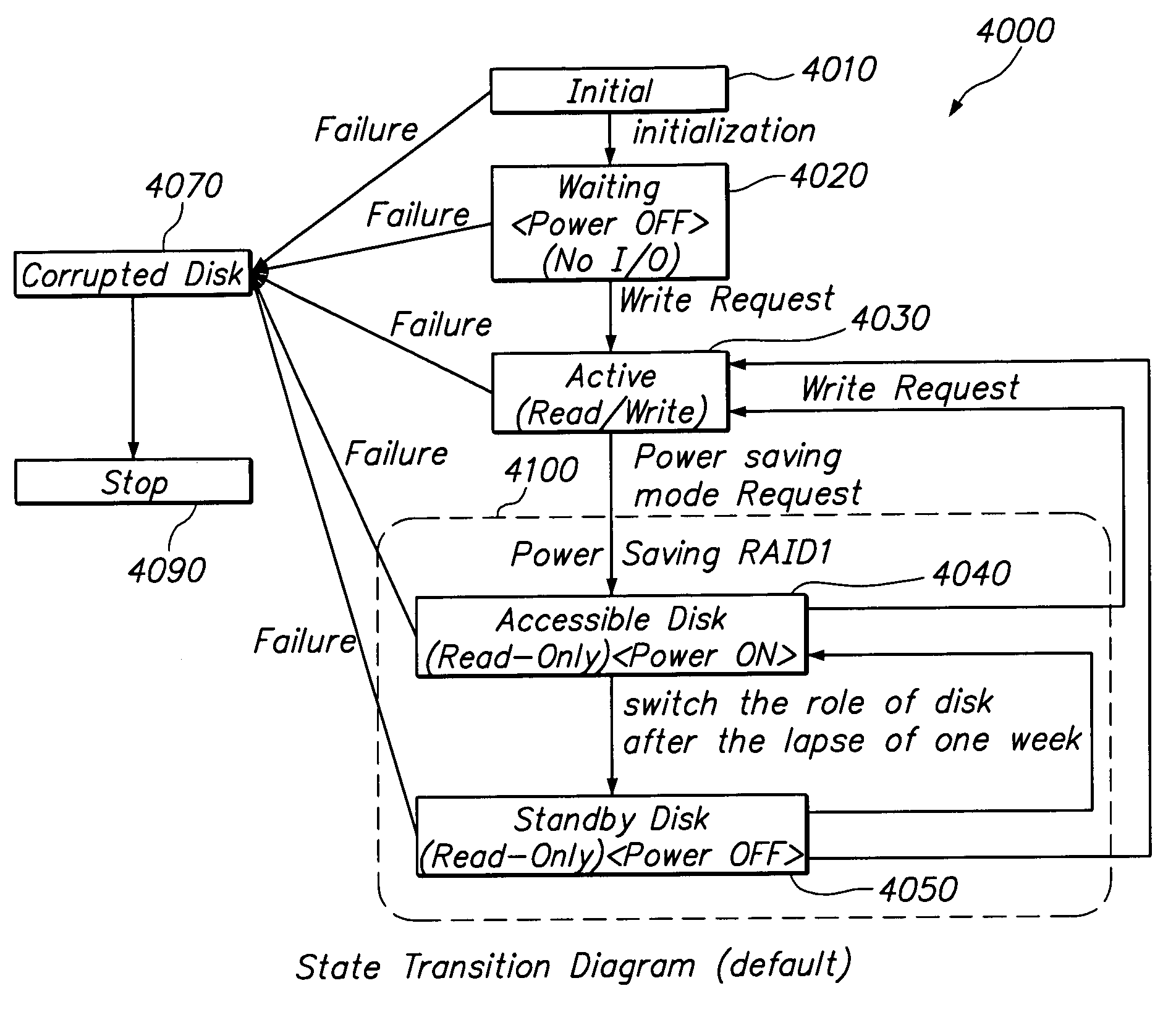
Data storage system with redundant storage media and method therefor
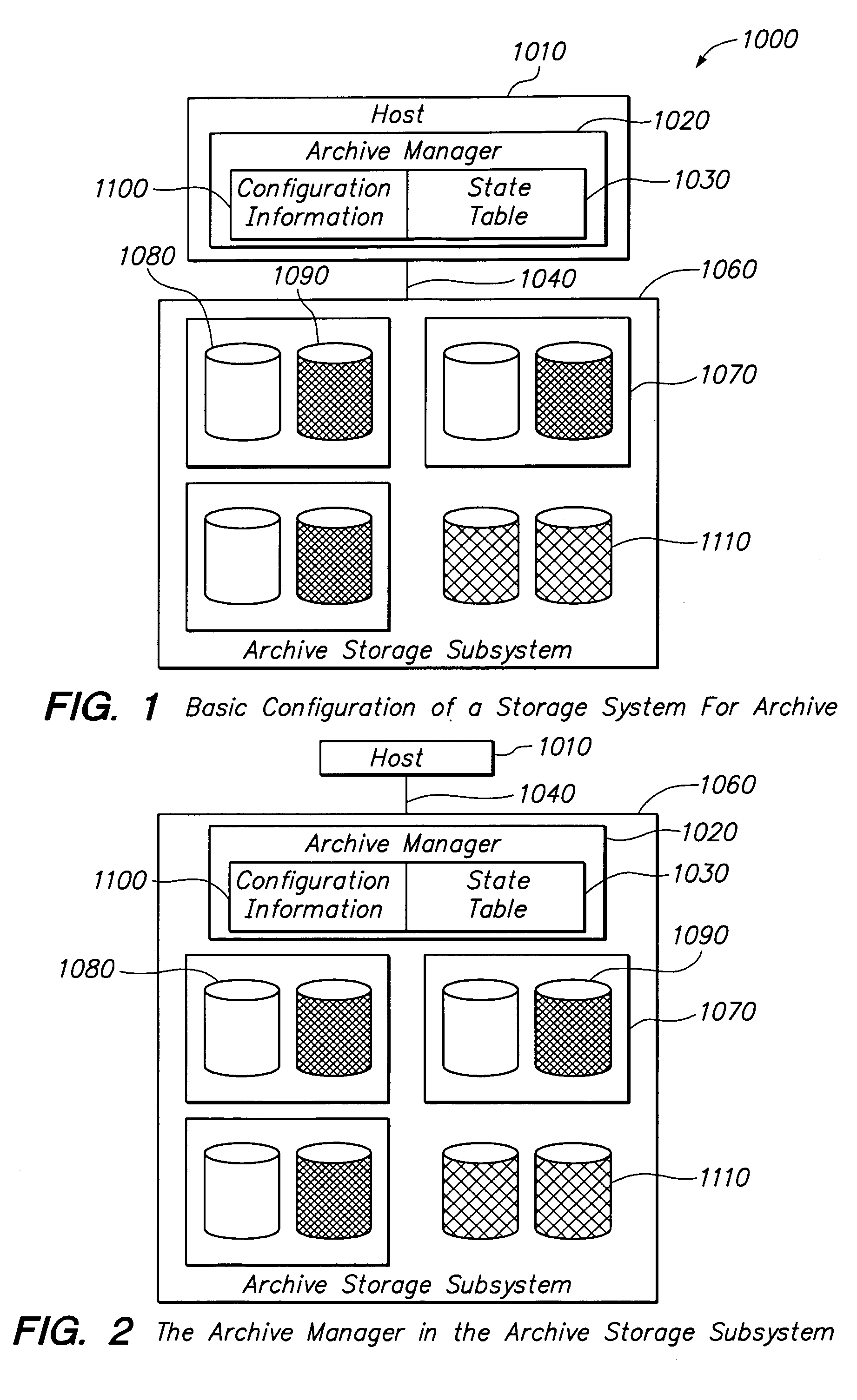
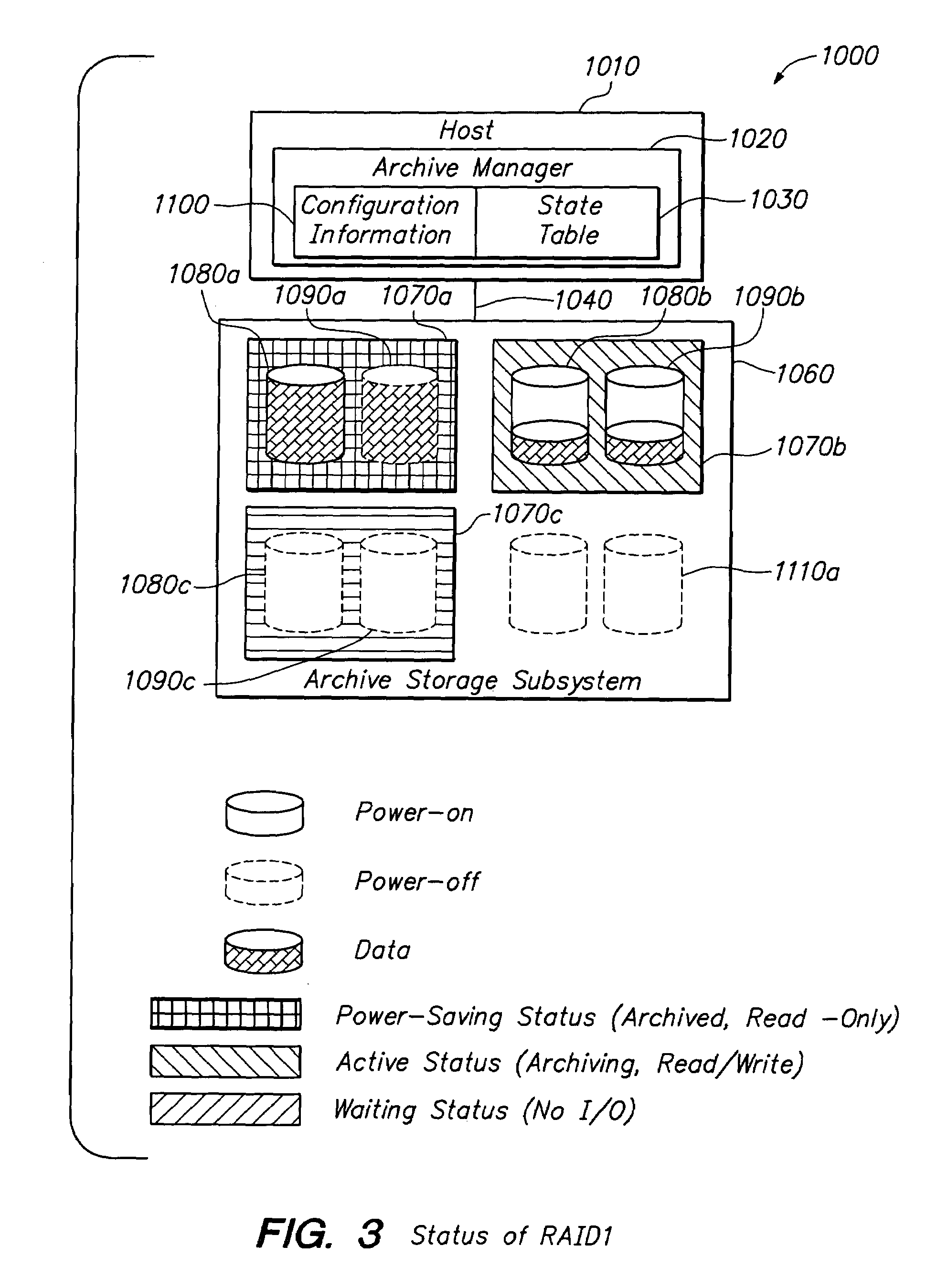
A data storage system includes a first data storage medium for storing data, the first data storage medium currently configured as an accessible medium; a second data storage medium for storing a copy of the data, the second data storage medium currently configured as a standby medium; first configuration information defining a switching trigger when the first data storage medium currently configured as the accessible medium becomes the standby medium and when the second data storage medium currently configured as the standby medium becomes the accessible medium; and a data storage system manager using the first configuration information to control the switching. The first data storage medium and second data storage medium may each be in a power-saving state. The accessible medium thus may be in a power-saving mode. The standby medium thus may be in a power-saving mode or in a power-off mode. The accessible medium may be read-only. The switching trigger may be a time period, an equation of access time or an administrative request. There data storage system may include additional data storage media for storing additional copies of the data, the additional data storage media also configured as standby media.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com