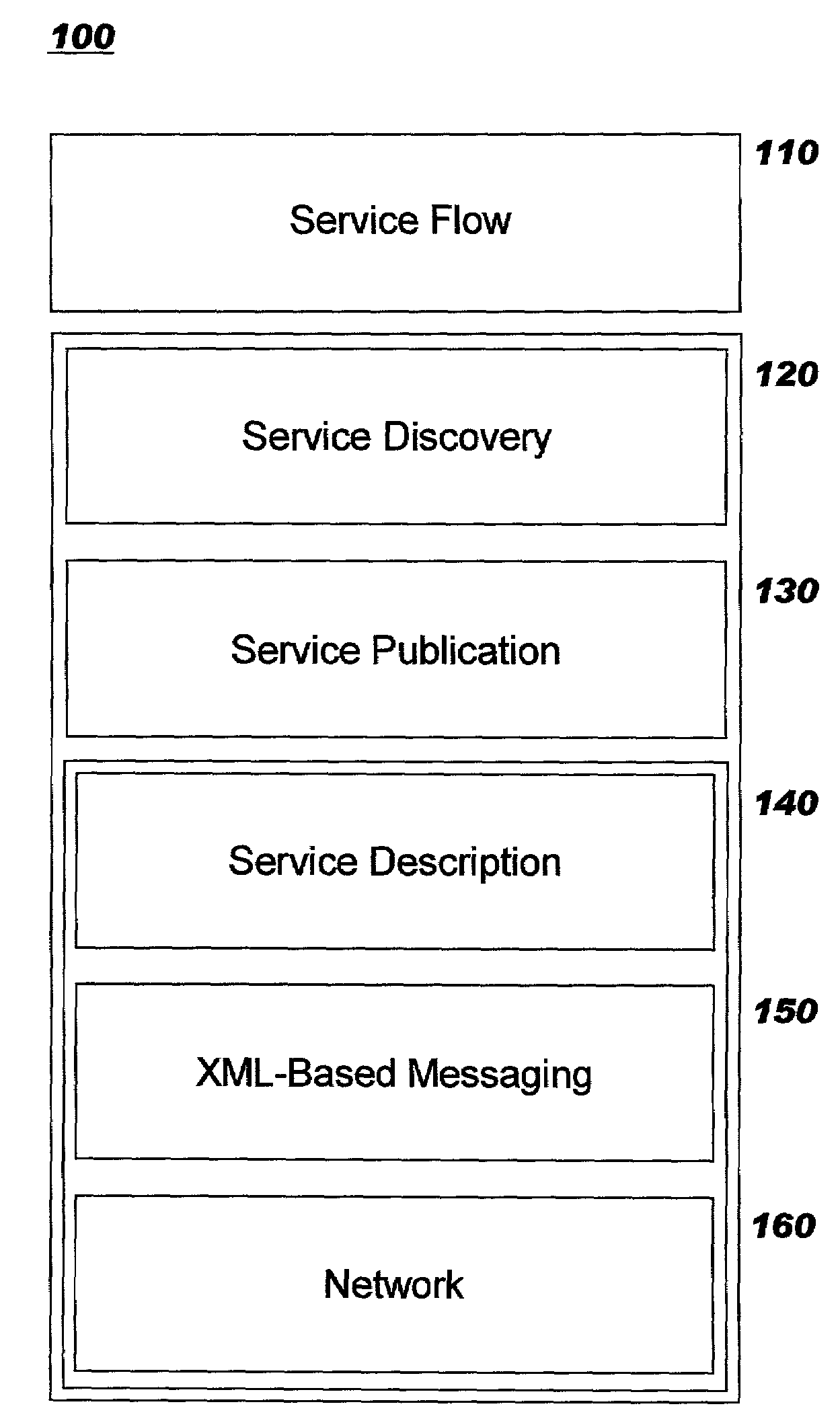
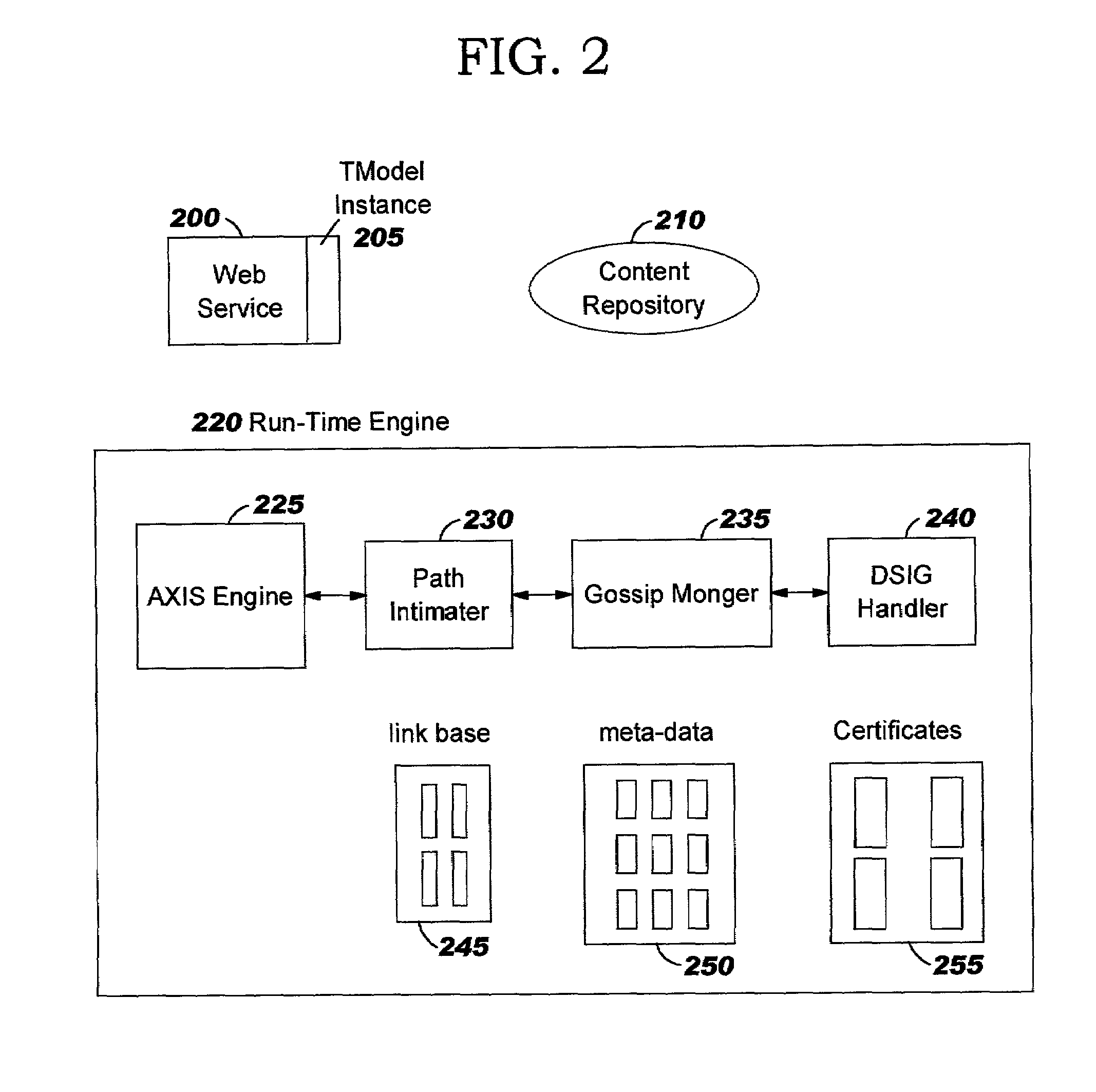
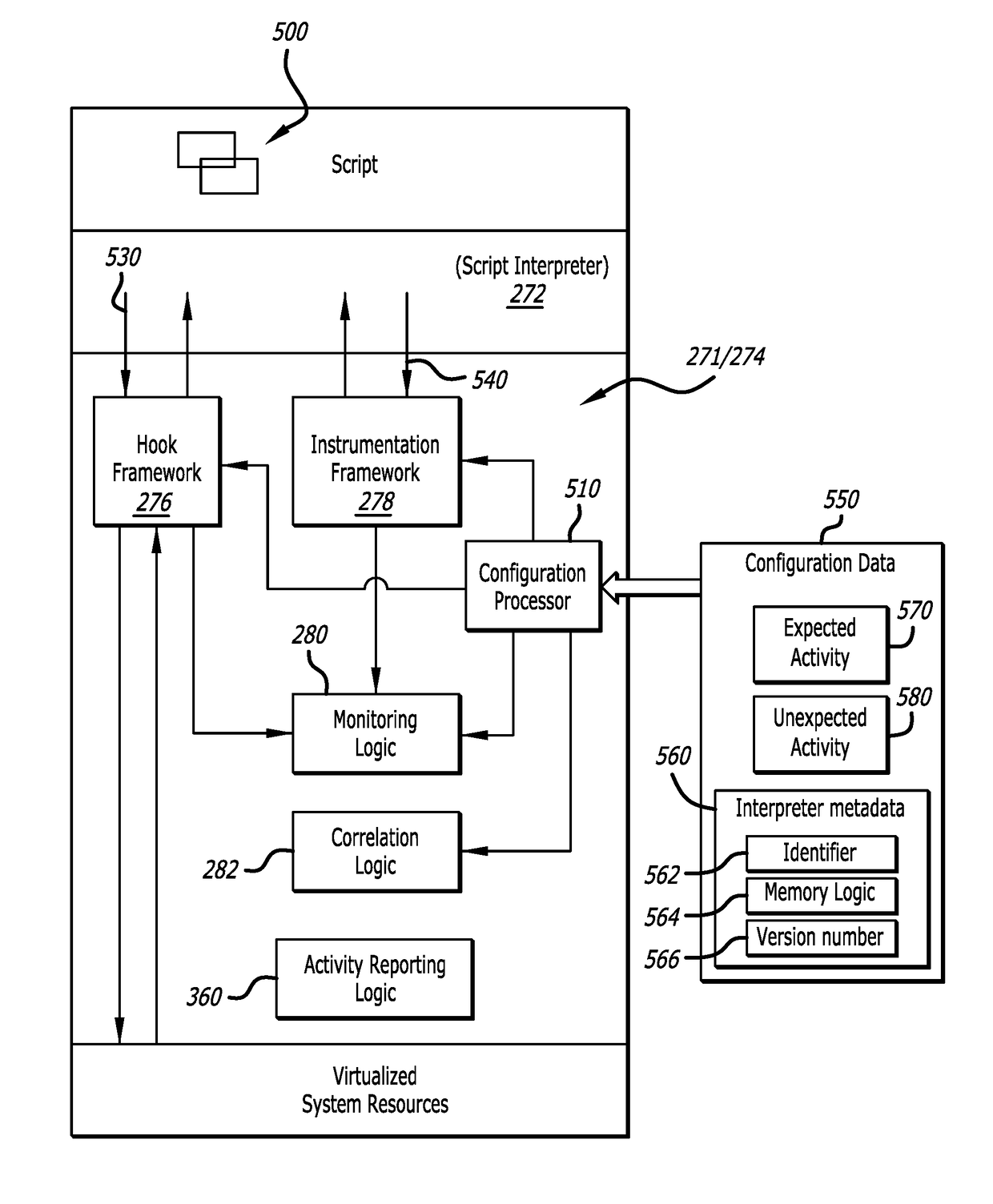
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6766 results about "Exploit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
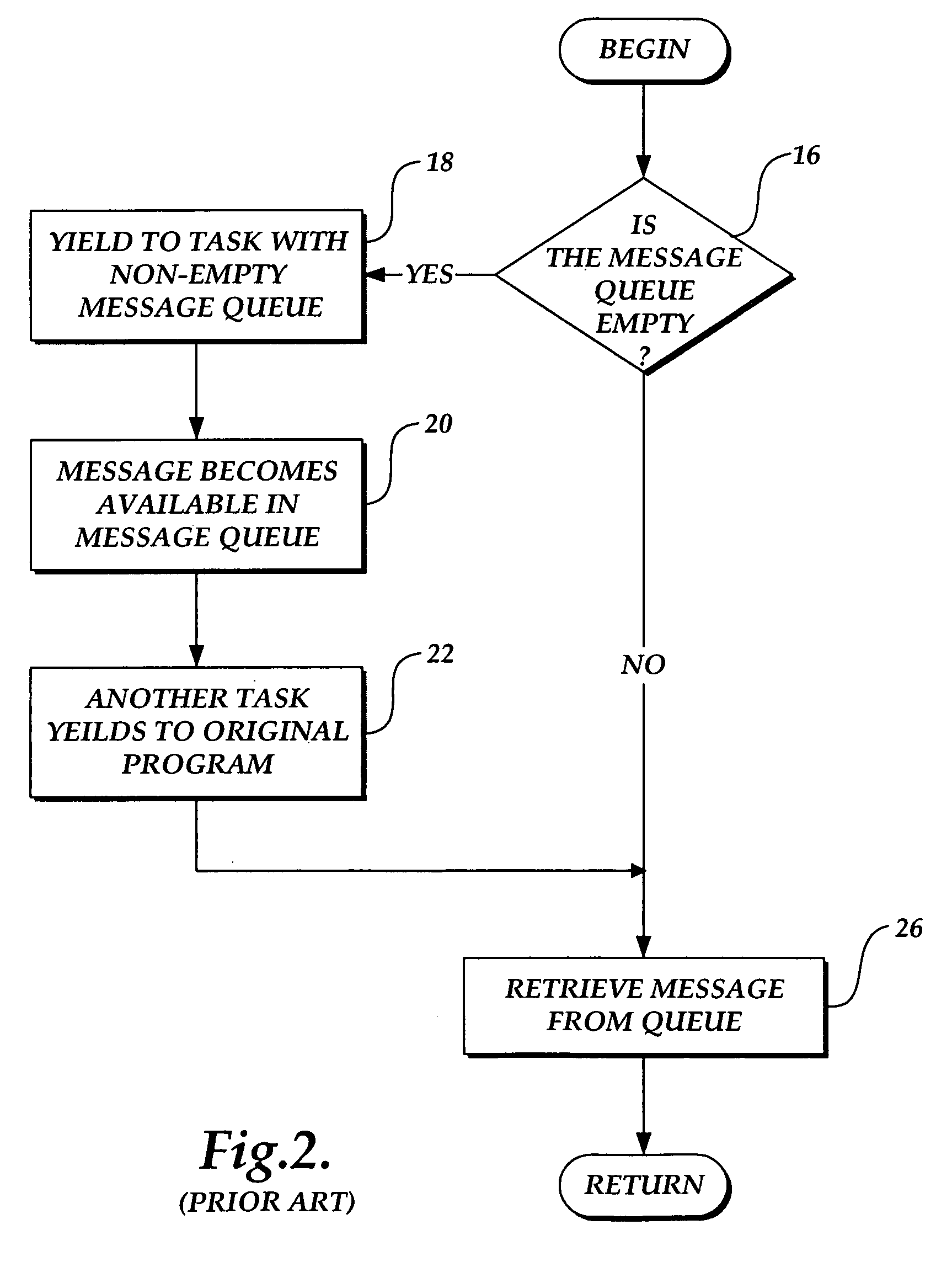
An exploit (from the English verb to exploit, meaning "to use something to one’s own advantage") is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerized). Such behavior frequently includes things like gaining control of a computer system, allowing privilege escalation, or a denial-of-service (DoS or related DDoS) attack.
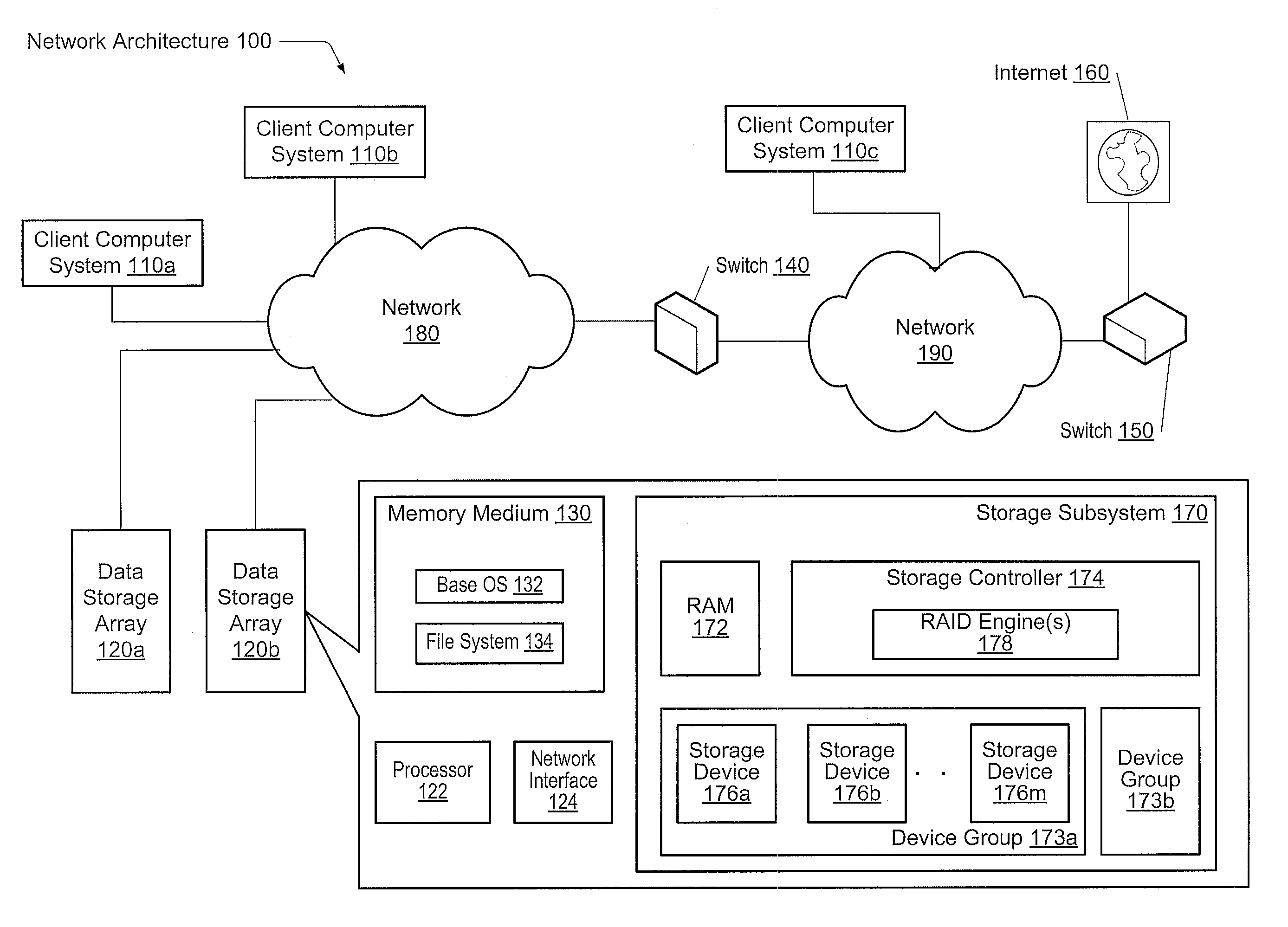
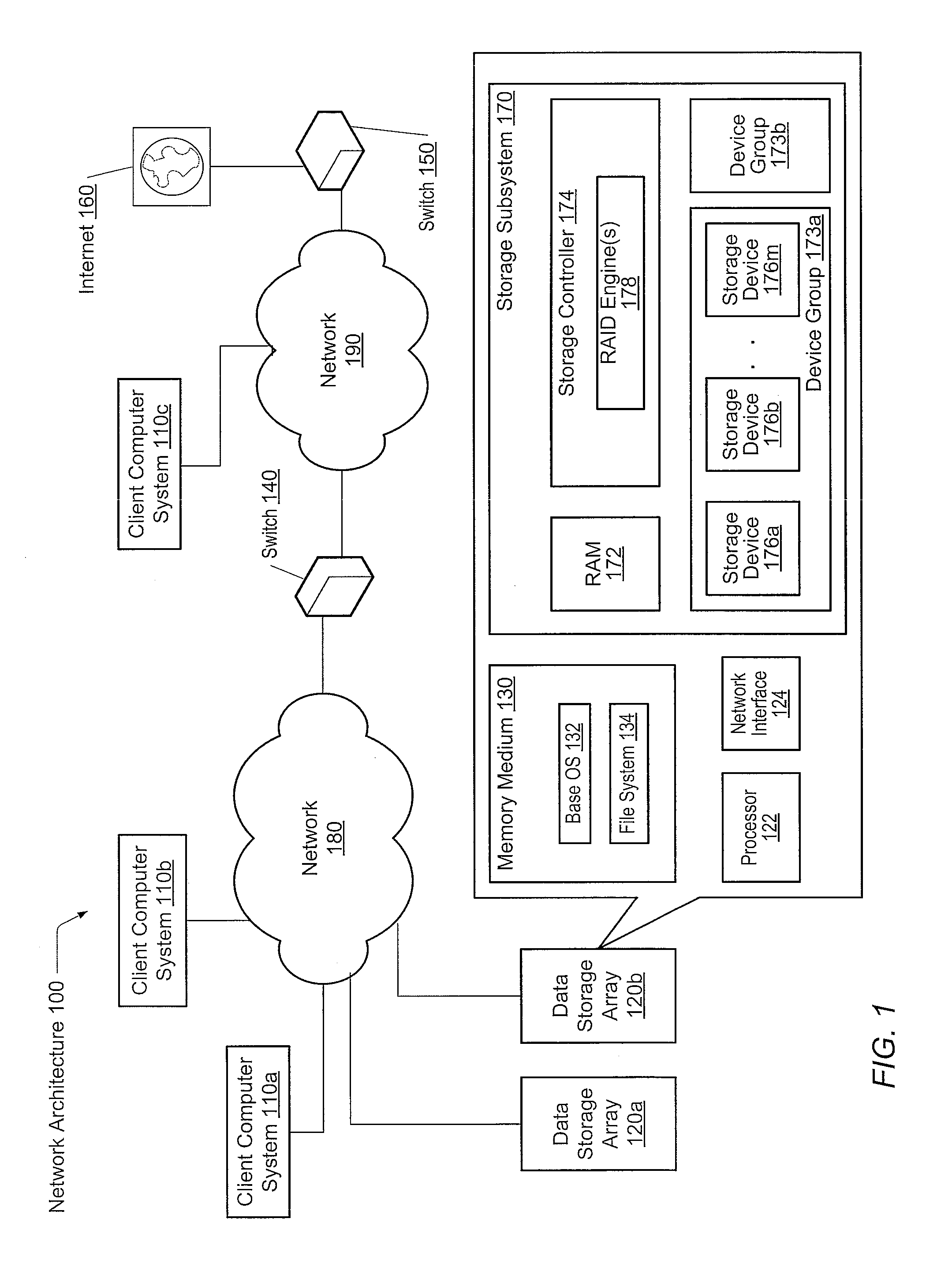
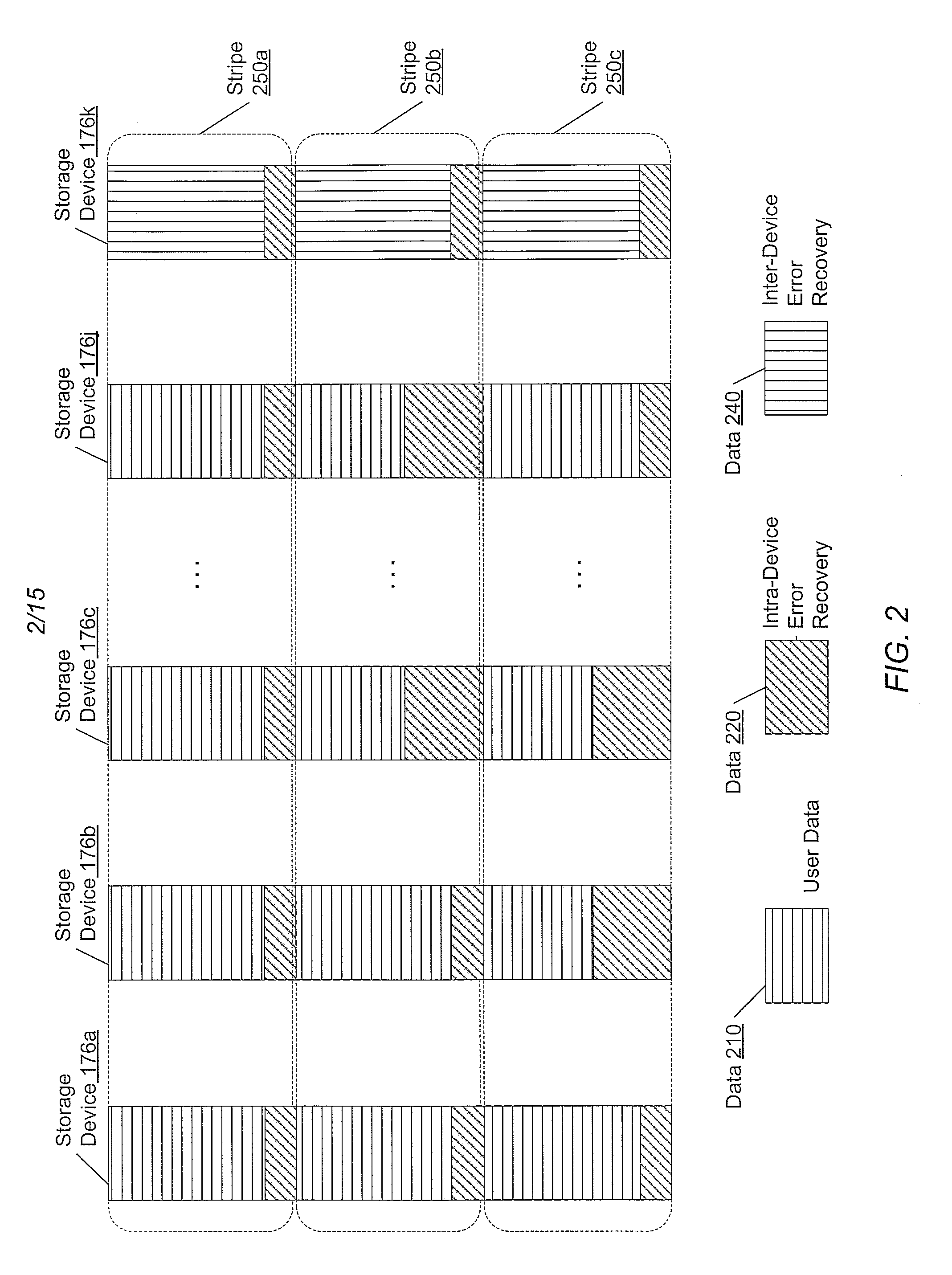
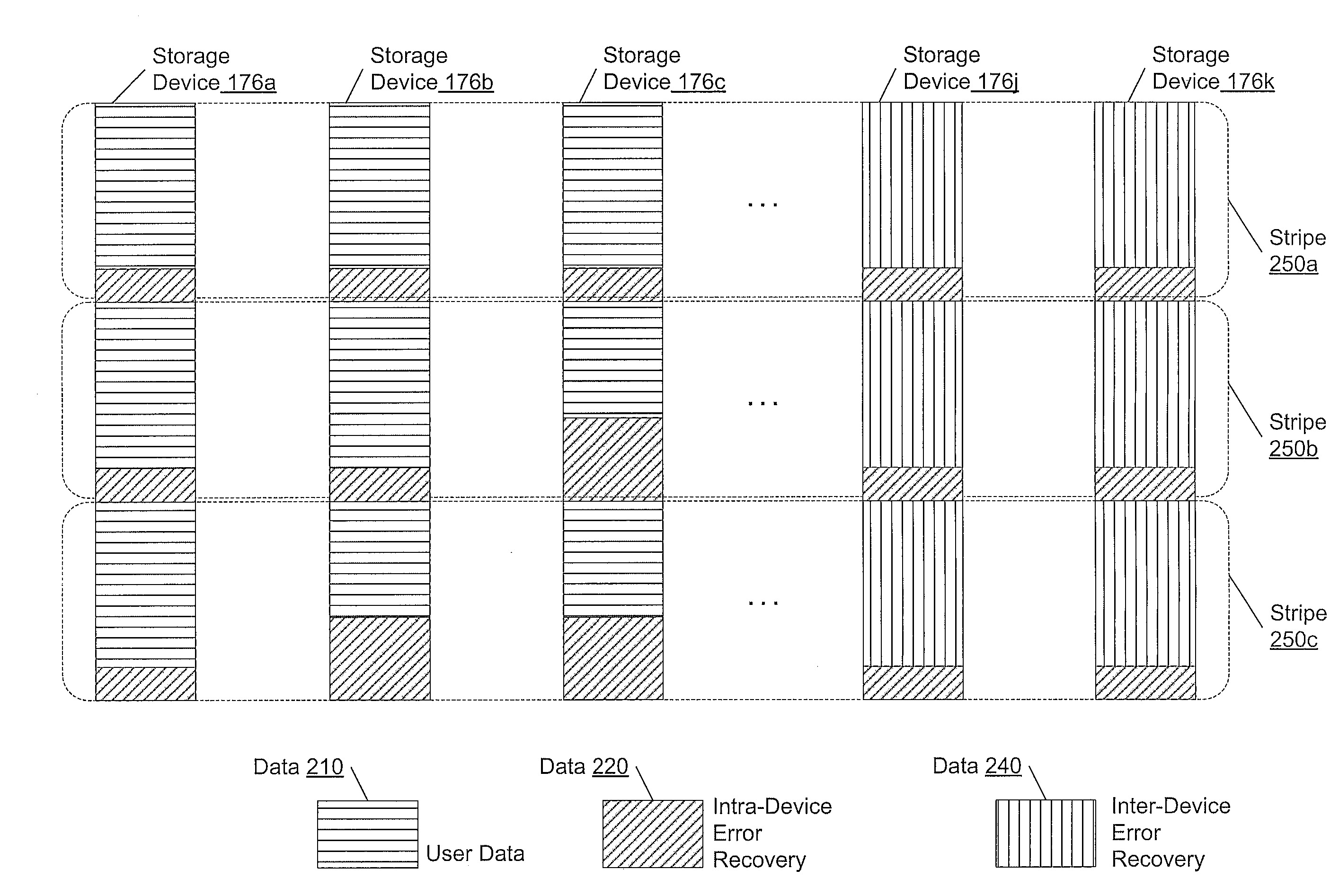
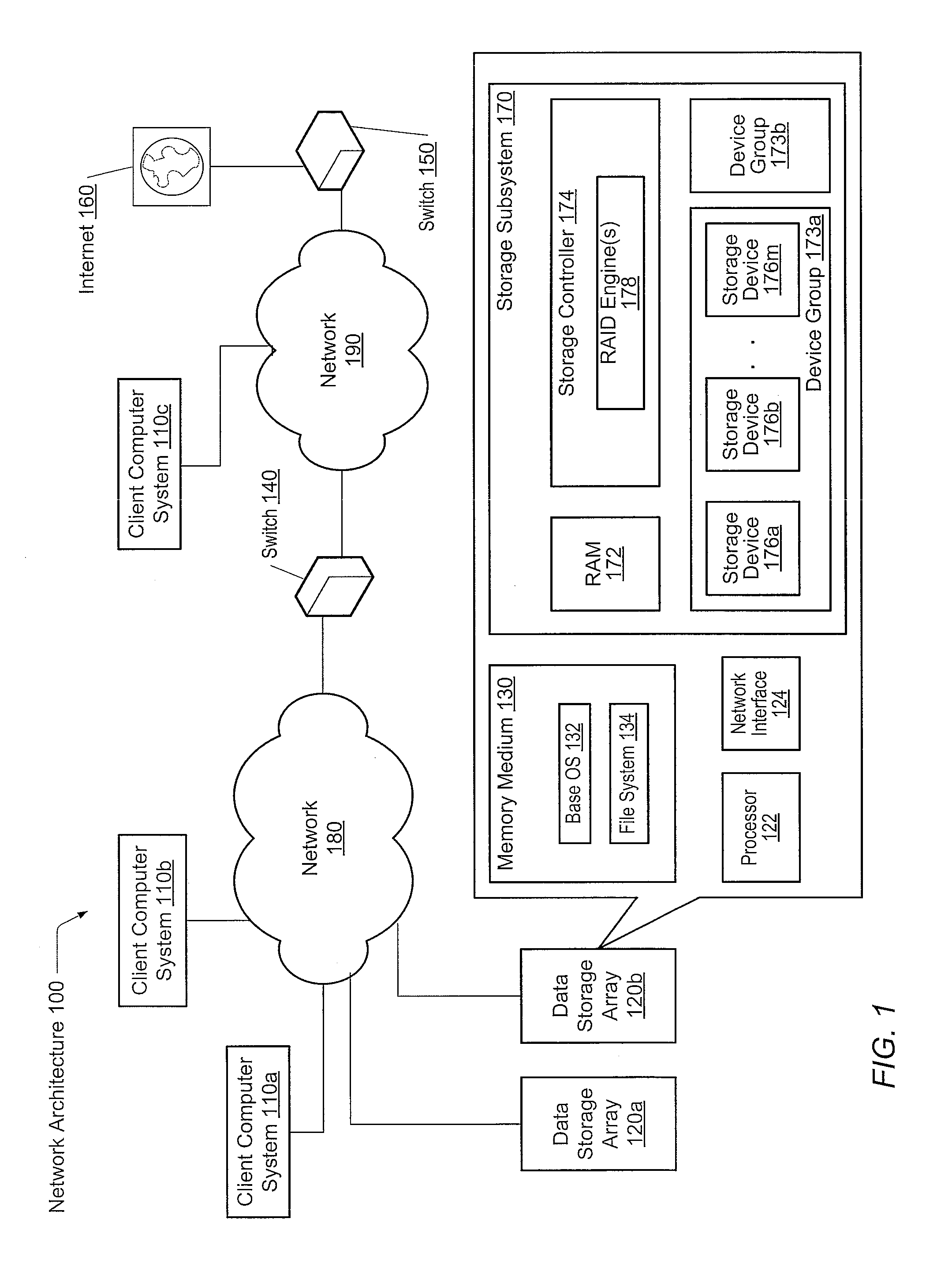
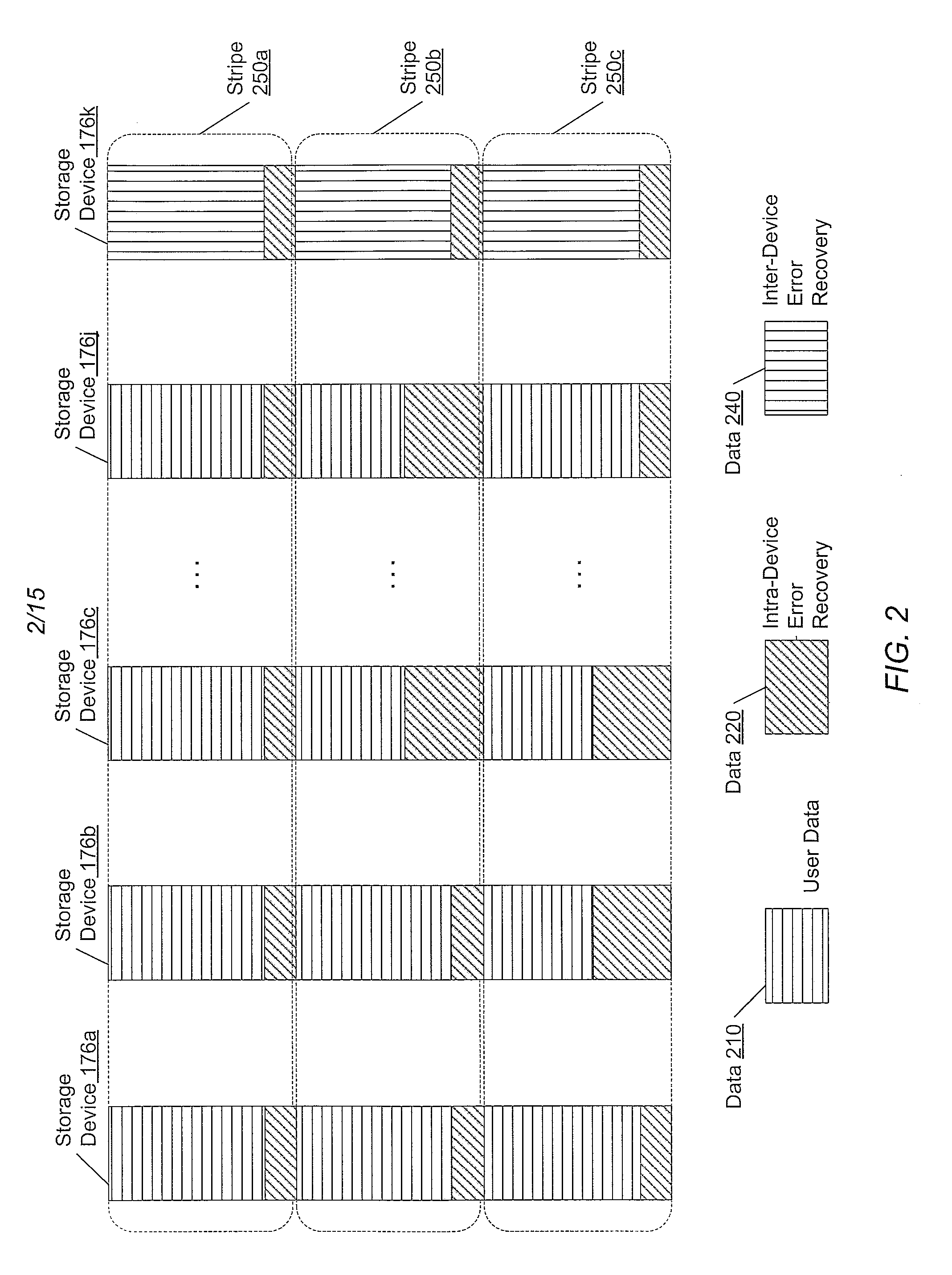
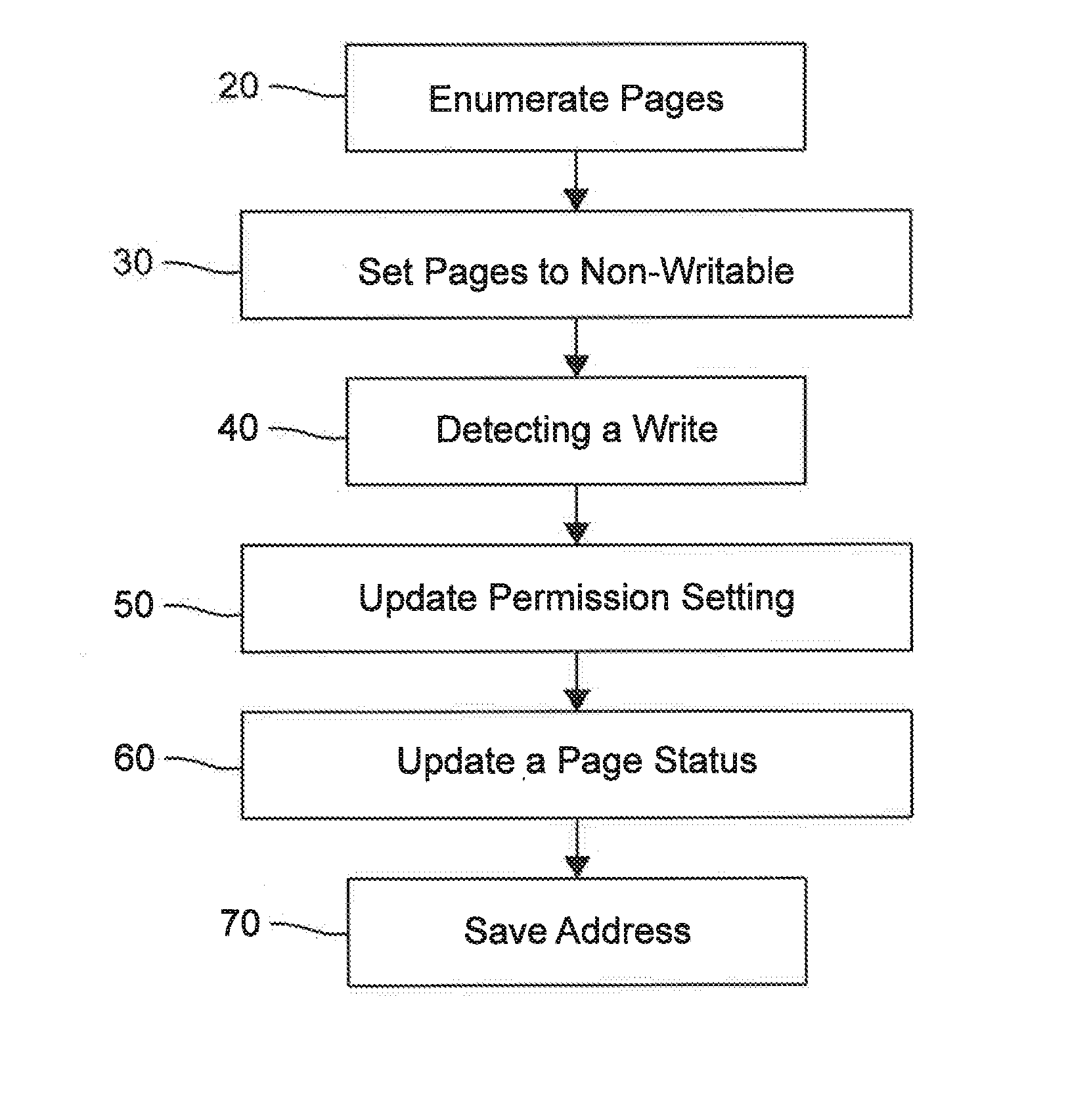
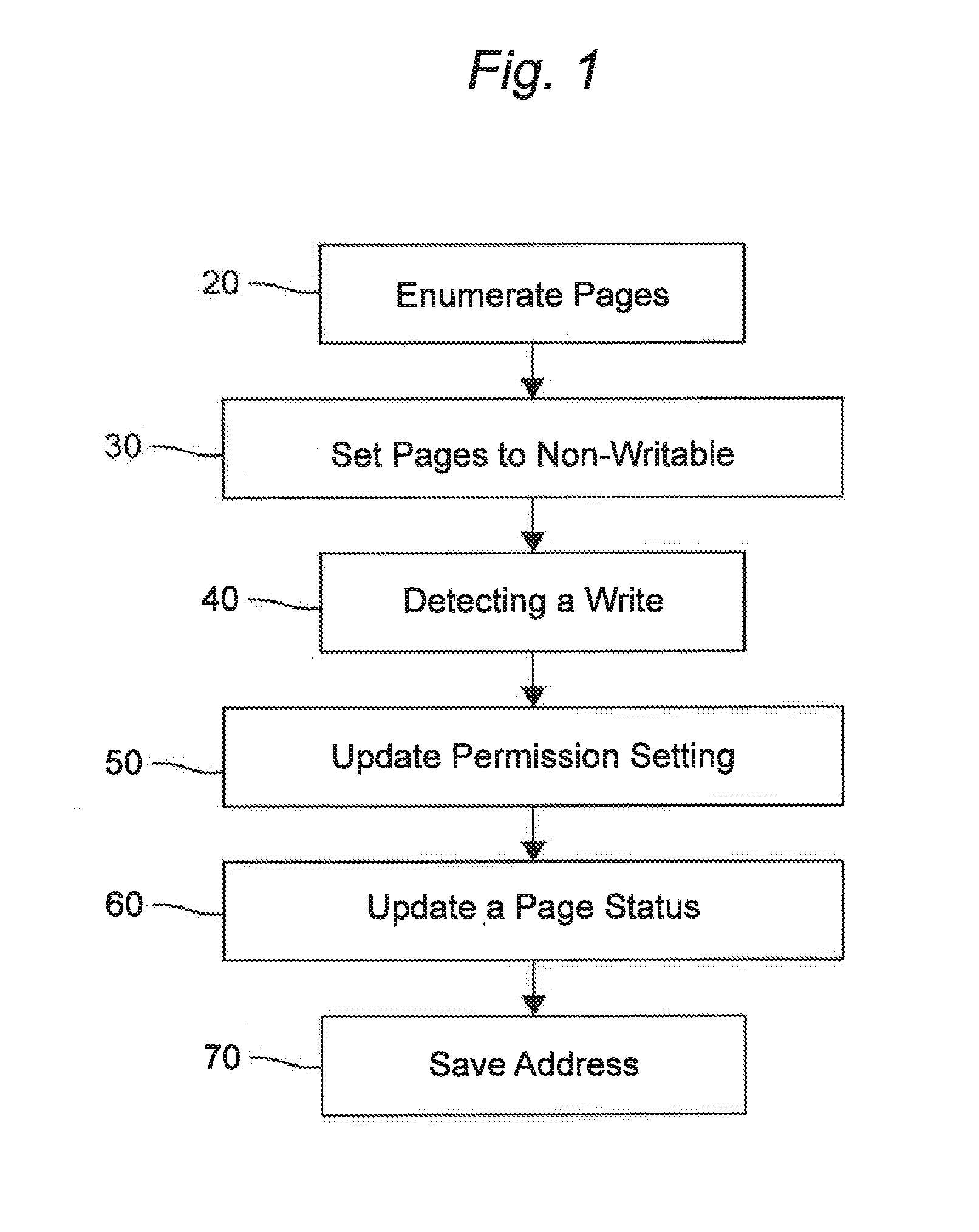
Adaptive raid for an SSD environment
A system and method for adaptive RAID geometries. A computer system comprises client computers and data storage arrays coupled to one another via a network. A data storage array utilizes solid-state drives and Flash memory cells for data storage. A storage controller within a data storage array is configured to determine a first RAID layout for use in storing data, and write a first RAID stripe to the device group according to the first RAID layout. In response to detecting a first condition, the controller is configured to determine a second RAID layout which is different from the first RAID layout, and write a second RAID stripe to the device group according to the second layout, whereby the device group concurrently stores data according to both the first RAID layout and the second RAID layout.
Owner:PURE STORAGE
Practical platform for high risk applications
InactiveUS20070180509A1Safe and reliable and easy to use practicalIncrease system complexityDigital data processing detailsUser identity/authority verificationSystem integrationComputer hardware
The present invention is a portable device that a computer can boot from, containing a prefabricated independent operating system environment which is engineered from the ground up to prioritize security while maximizing usability, in order to provide a safe, reliable and easy to use practical platform for high risk applications. An embodiment of the present invention may temporarily transform an ordinary computer into a naturally inexpensive logical appliance which encapsulates a turn-key functional solution within the digital equivalent of a military grade security fortress. This allows existing hardware to be conveniently leveraged to provide a self contained system which does not depend on the on-site labor of rare and expensive system integration and security experts.
Owner:SWARTZ ALON R +1
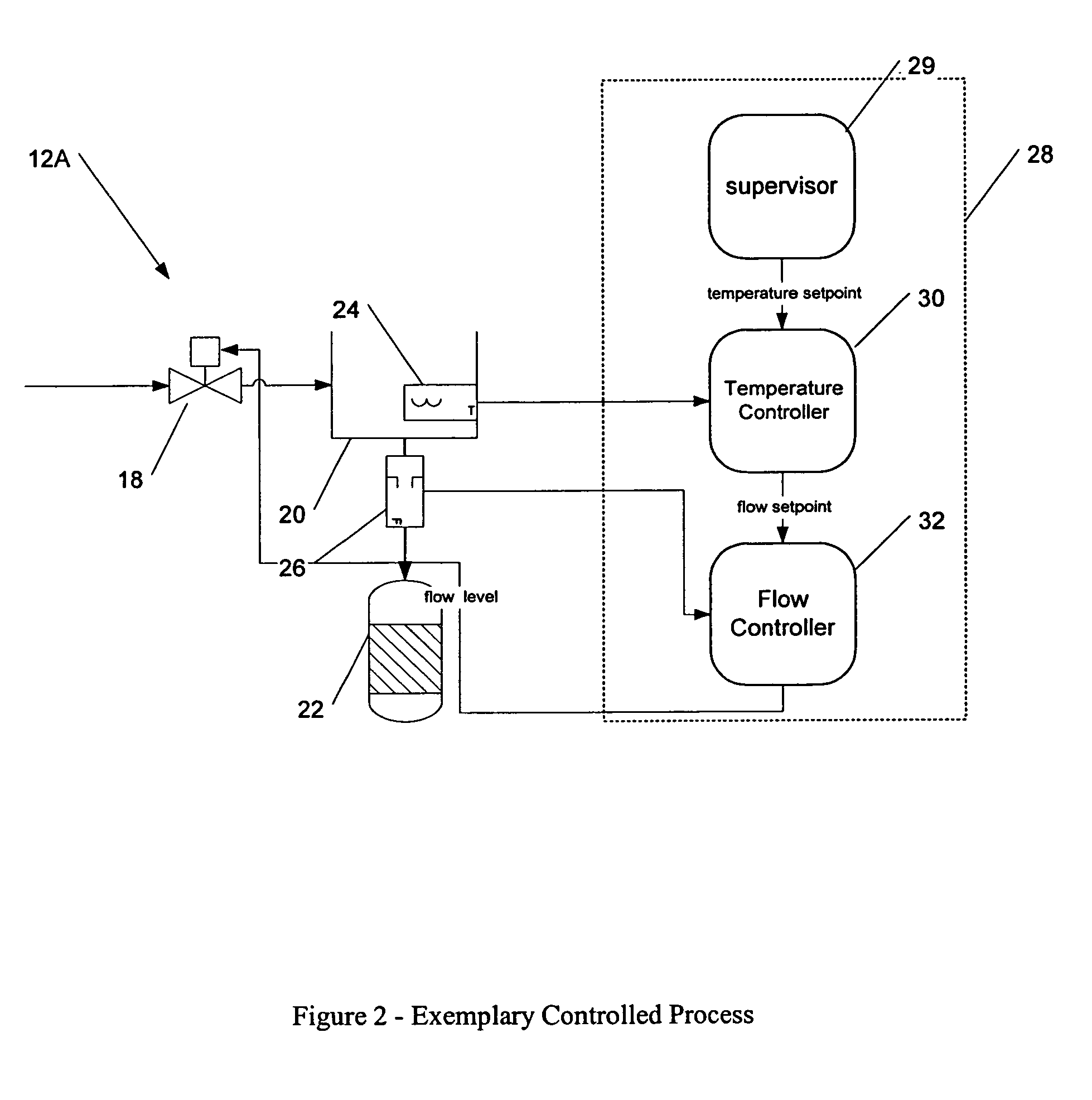
Methods and apparatus for control configuration with versioning, security, composite blocks, edit selection, object swapping, formulaic values and other aspects
InactiveUS7272815B1OptimizationOptimize system configurationData processing applicationsDigital data processing detailsGraphical user interfaceComposite object
Methods and apparatus for configuring process, environmental, industrial and other control systems generate and / or utilize models representing configurations of control systems and / or the systems controlled by them. Records of changes to the models or the configurations represented by them are maintained, thereby, for example, providing bases for determining current states, prior states and histories of changes. Objects in the model have characteristics, such as an object type characteristic and an area characteristic. Users can have corresponding permissions. A security mechanism apparatus controls access by users to the objects. Composite objects are defined by definition objects and are displayed in encapsulated or expanded formats. Objects can include an edit control type identifier that determines how they are presented for editing. Functionality responds to user commands by transferring characteristics of a first object depicted by the graphical user interface to a second object. Configuration-time formulas contained objects are evaluated to constants prior to downloading to the control system.
Owner:SCHNEIDER ELECTRIC SYST USA INC
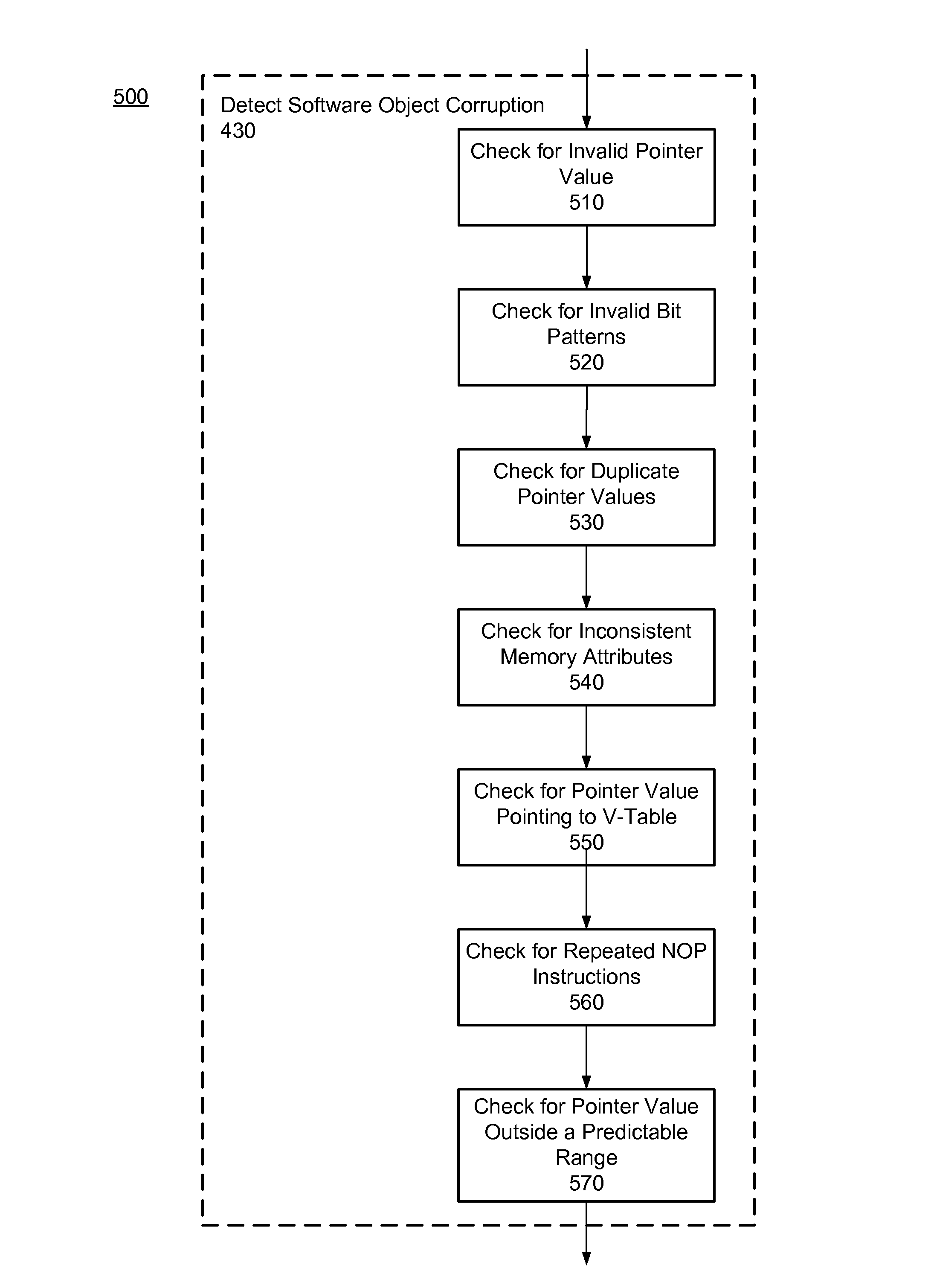
Software object corruption detection
ActiveUS8307435B1Memory loss protectionError detection/correctionSoftware engineeringApplication software
The execution of a software application is diverted to detect software object corruption in the software application. Software objects used by the software application are identified and their pointers are inspected. One or more tests are applied to pointers pointing to the virtual method tables of the software objects, addresses (or pointers) in the virtual method tables, and memory attributes or content of the memory buffer identified by the addresses for inconsistencies that indicate corruption. A determination of whether the software objects are corrupted is made based on the outcome of the tests. If software object corruption is detected, proper corrective actions are applied to prevent malicious exploitation of the corruption.
Owner:CA TECH INC
Adaptive RAID for an SSD environment
A system and method for adaptive RAID geometries. A computer system comprises client computers and data storage arrays coupled to one another via a network. A data storage array utilizes solid-state drives and Flash memory cells for data storage. A storage controller within a data storage array is configured to determine a first RAID layout for use in storing data, and write a first RAID stripe to the device group according to the first RAID layout. In response to detecting a first condition, the controller is configured to determine a second RAID layout which is different from the first RAID layout, and write a second RAID stripe to the device group according to the second layout, whereby the device group concurrently stores data according to both the first RAID layout and the second RAID layout.
Owner:PURE STORAGE
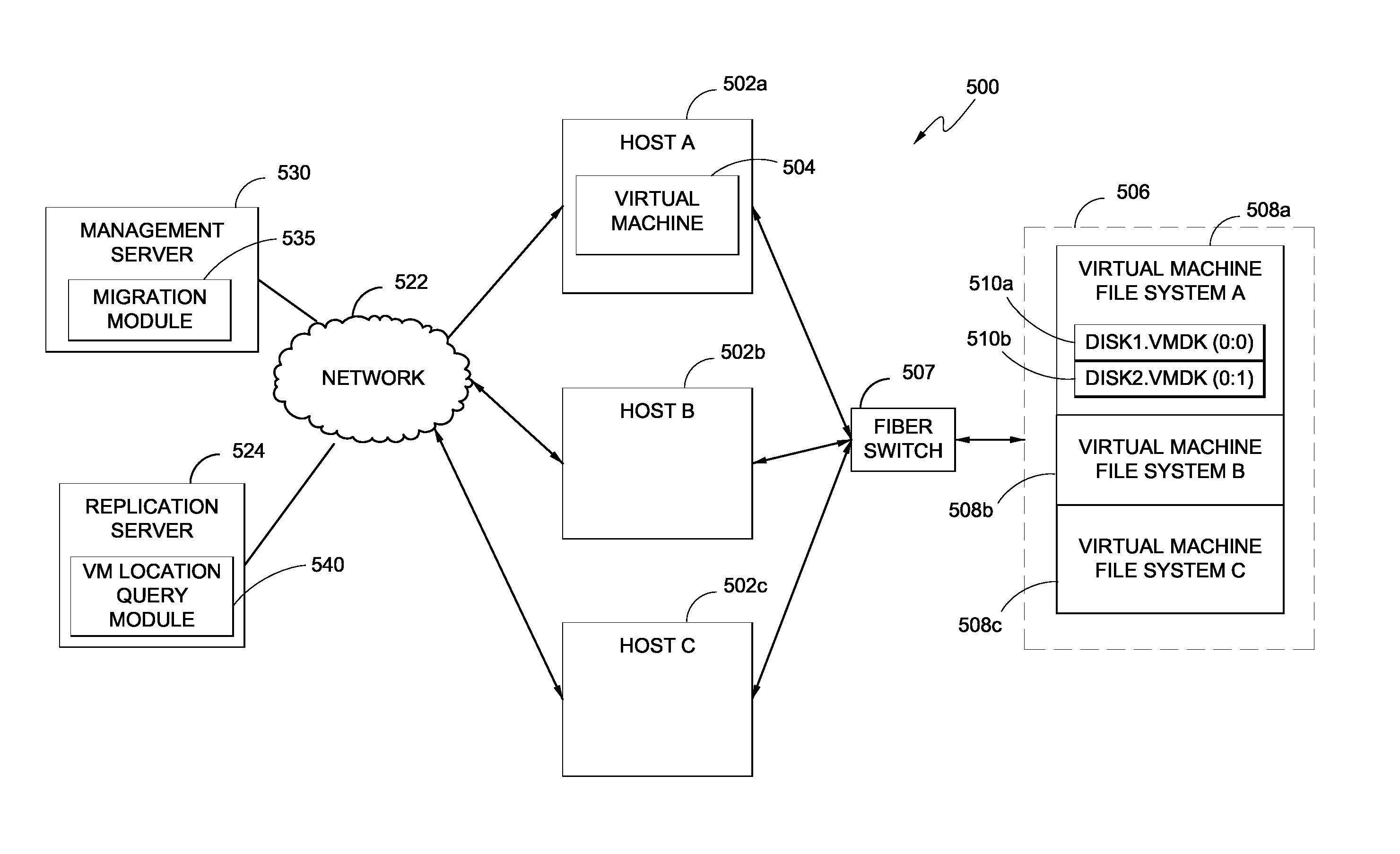
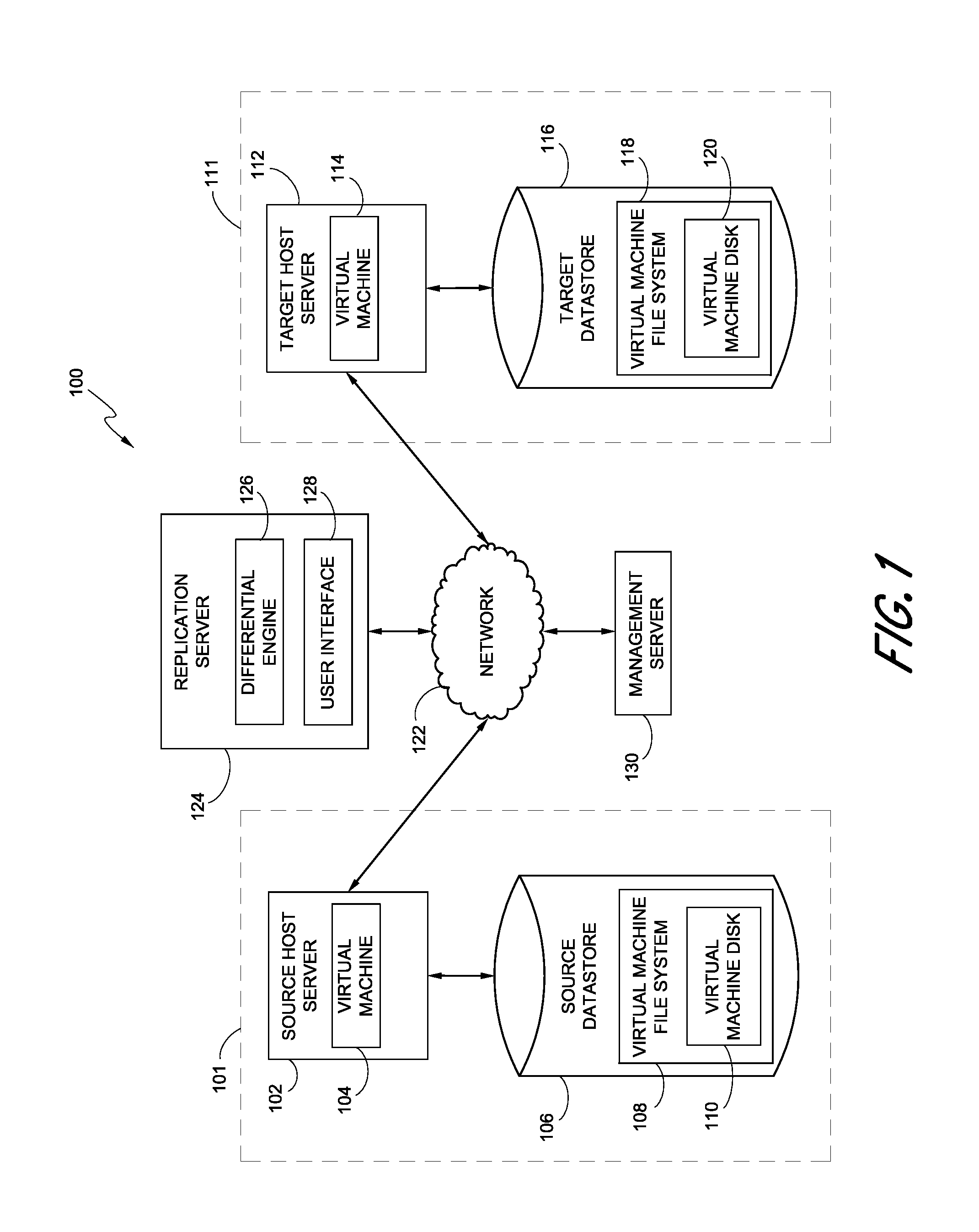
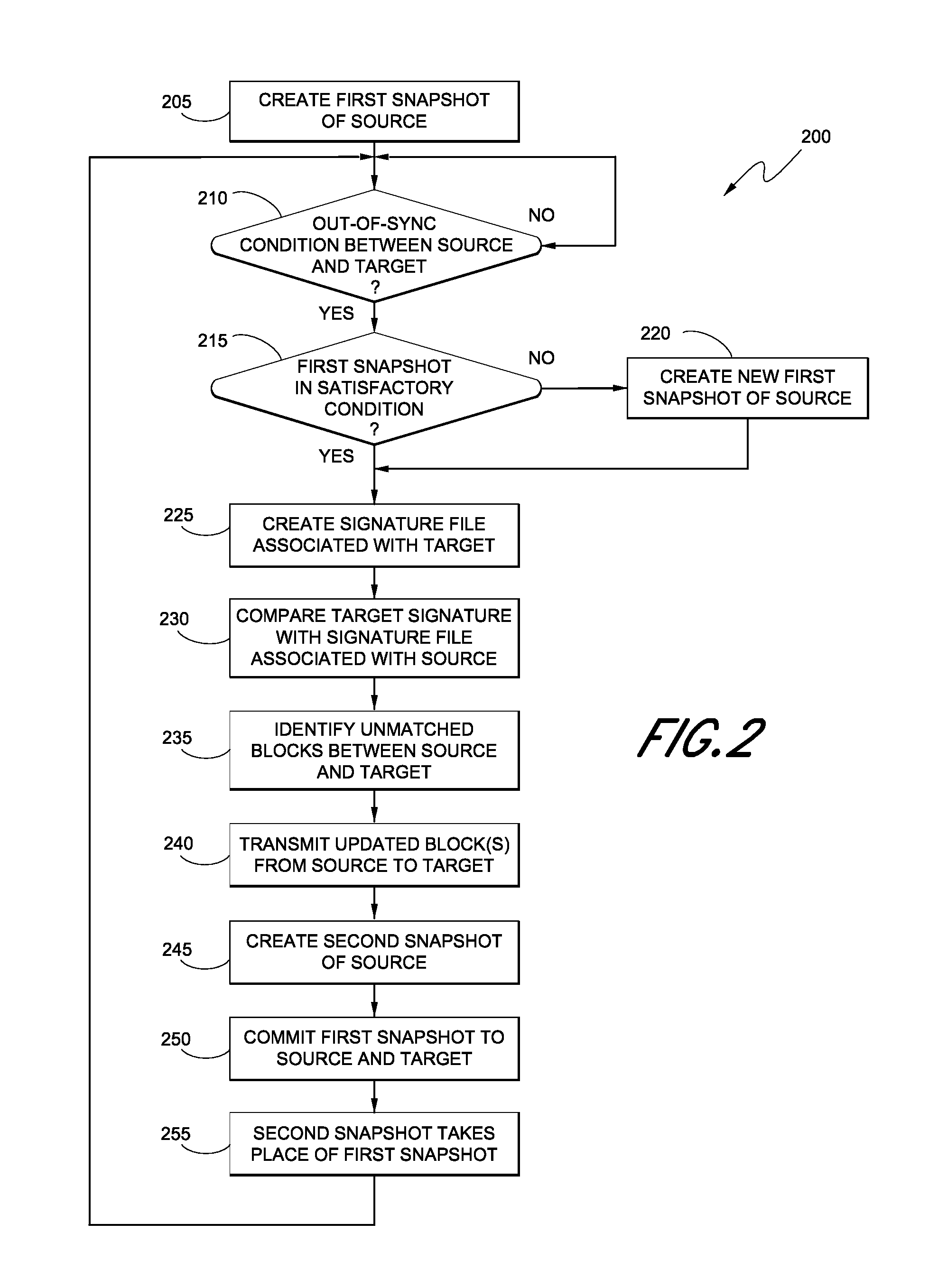
Replication systems and methods for a virtual computing environment
Hybrid replication systems and methods for a virtual computing environment utilize snapshot rotation and differential replication. During snapshot rotation, data modifications intended for a source virtual machine disk (VMDK) are captured by a primary snapshot. Once a particular criterion is satisfied, the data modifications are redirected to a secondary snapshot while the primary snapshot is committed to both source and target VMDKs. The secondary snapshot is then promoted to primary, and a new secondary snapshot is created with writes redirected thereto. If the VMDKs become out-of-sync, disclosed systems can automatically perform a differential scan of the source data and send only the required changes to the target server. Once the two data sets are synchronized, snapshot replication can begin at the previously configured intervals. Certain systems further provide for planned failover copy operations and / or account for migration of a virtual machine during the copying of multiple VMDKs.
Owner:QUEST SOFTWARE INC
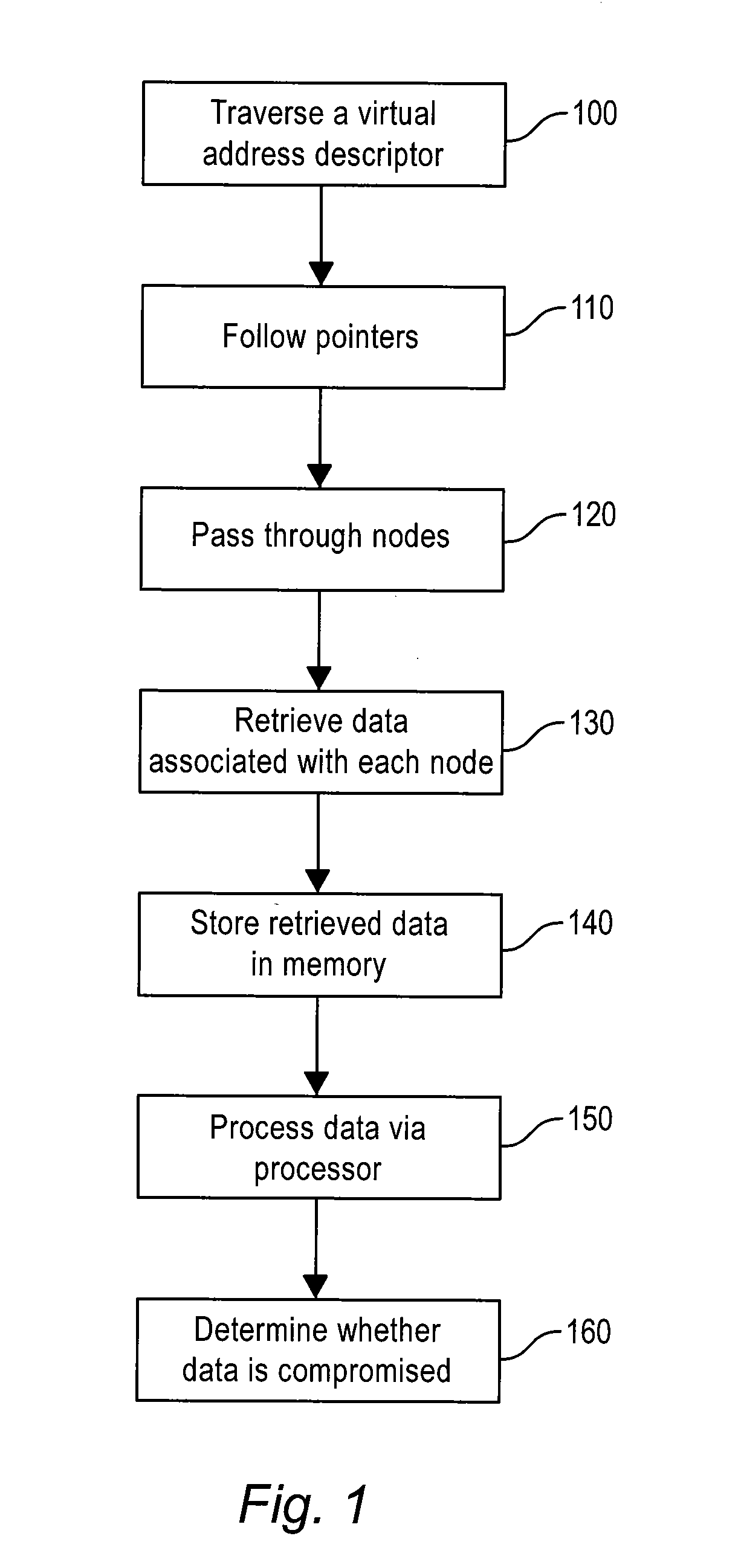
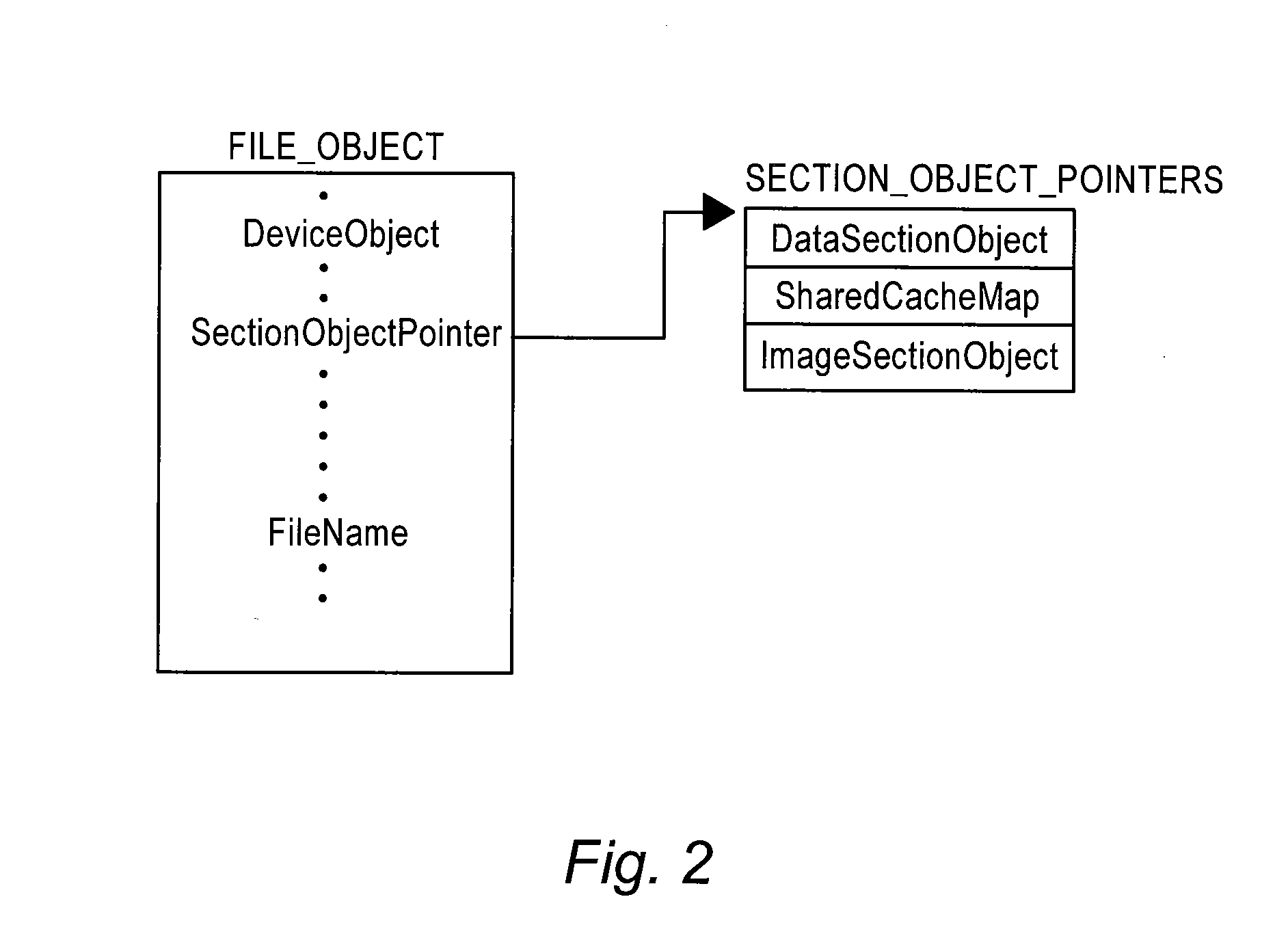
Physical Memory Forensics System and Method
ActiveUS20140032875A1Accurate reconstructionMemory adressing/allocation/relocationDigital data protectionMemory forensicsData pack
The method of the present inventive concept is configured to utilize Operating System data structures related to memory-mapped binaries to reconstruct processes. These structures provide a system configured to facilitate the acquisition of data that traditional memory analysis tools fail to identify, including by providing a system configured to traverse a virtual address descriptor, determine a pointer to a control area, traverse a PPTE array, copy binary data identified in the PPTE array, generate markers to determine whether the binary data is compromised, and utilize the binary data to reconstruct a process.
Owner:FIREEYE SECURITY HLDG US LLC
System and method for the programmatic runtime de-obfuscation of obfuscated software utilizing virtual machine introspection and manipulation of virtual machine guest memory permissions
ActiveUS20140189882A1Digital data processing detailsAnalogue secracy/subscription systemsObfuscationVirtual machine introspection
A system and method operable to programmatically perform runtime de-obfuscation of obfuscated software via virtual machine introspection and manipulation of virtual machine guest memory permissions.
Owner:FIREEYE SECURITY HLDG US LLC
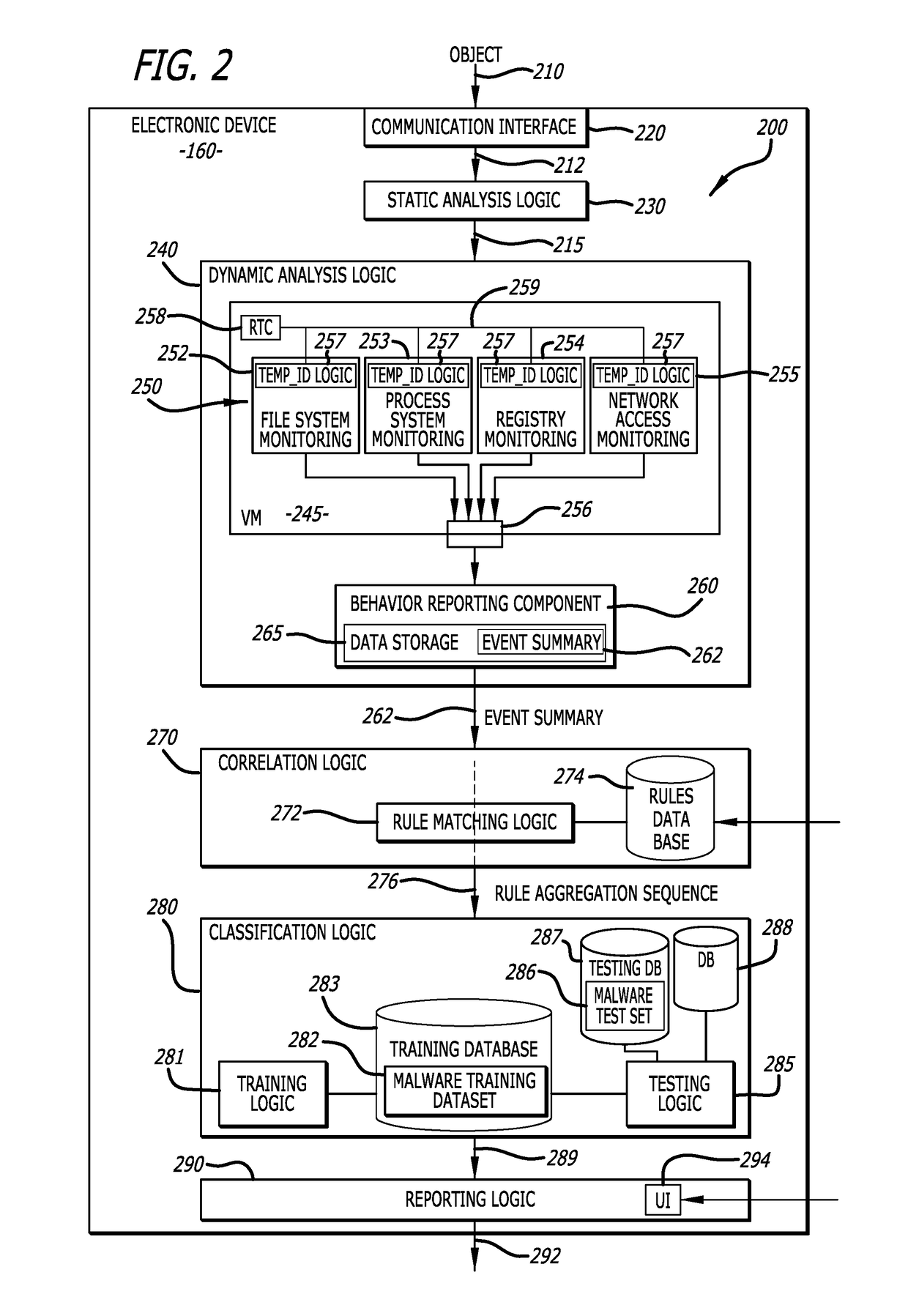
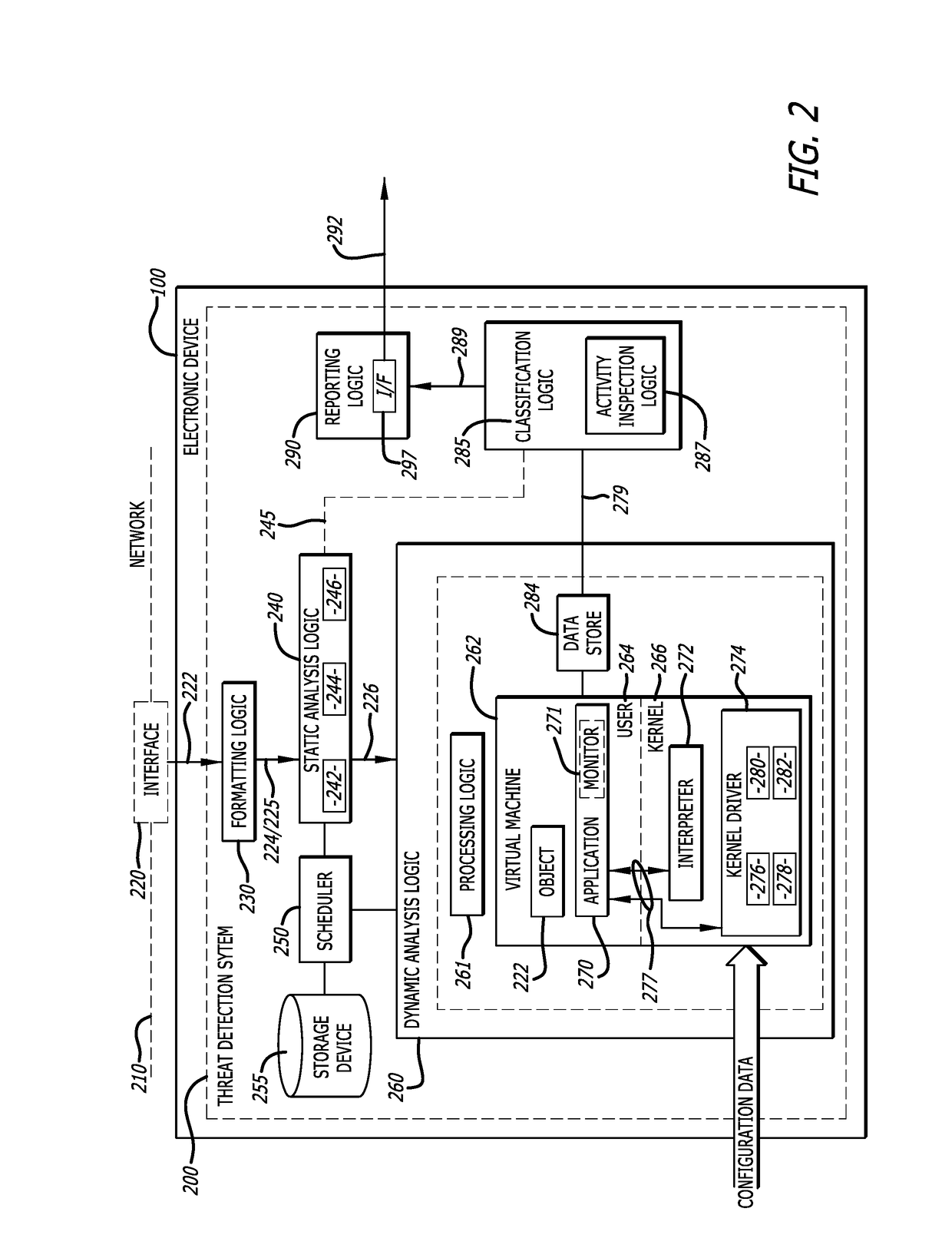
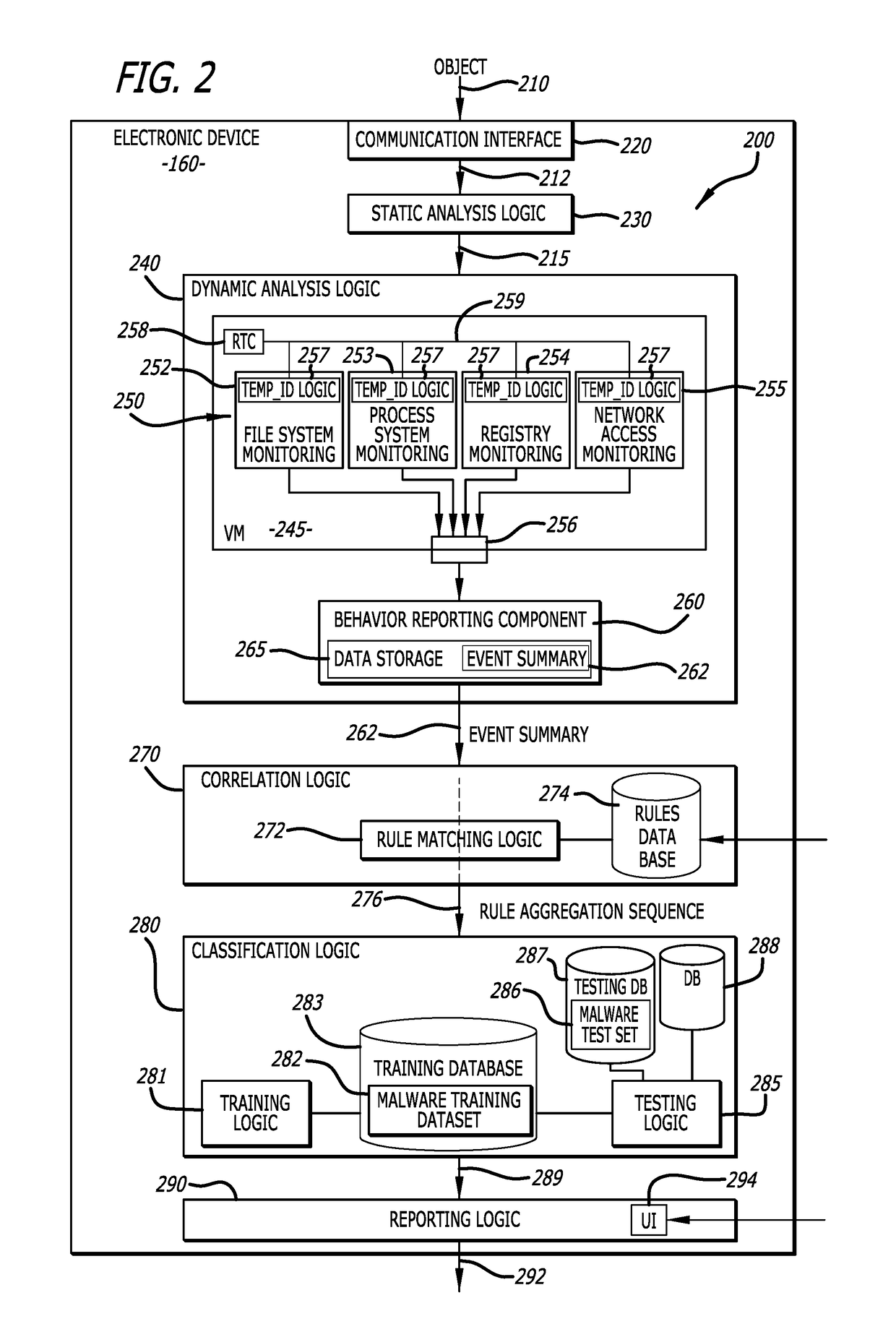
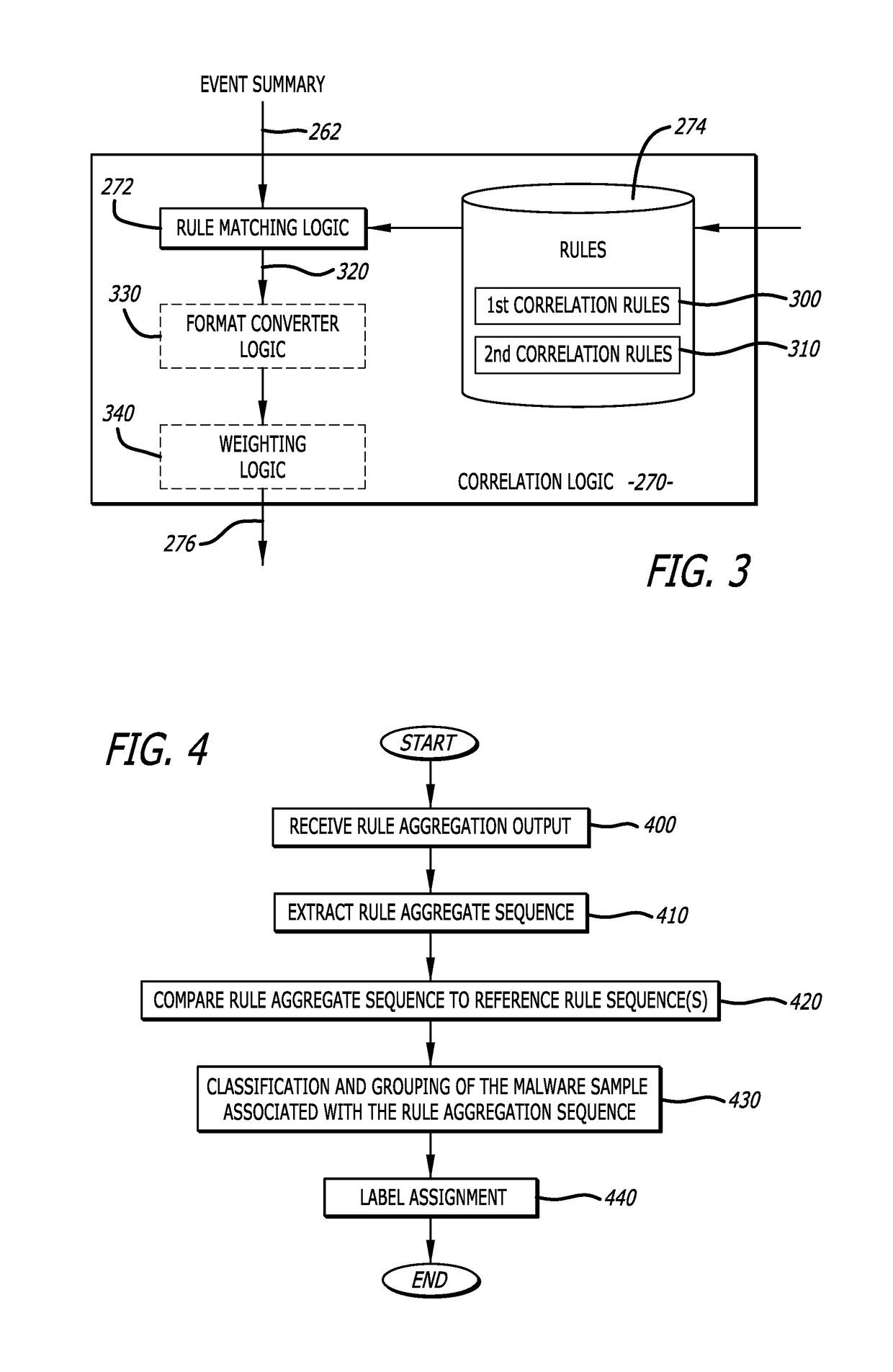
Leveraging behavior-based rules for malware family classification
According to one embodiment, a malware classification scheme operating with an electronic device, configured with one or more hardware processors and a memory that stores the software handling the malware classification scheme that is conducted through analysis of behavior-based rules, is described. This malware classification scheme (i) conducts a determination whether a sequence of rules correspond to potential malicious behaviors detected during analysis of a malware sample within one or more virtual machines, and in response to determining that the sequence of rules corresponds to potential malicious behaviors, (ii) conducts an attempt to classify the malware sample to at least one known malware family based on an analysis of the sequence of rules.
Owner:FIREEYE SECURITY HLDG US LLC
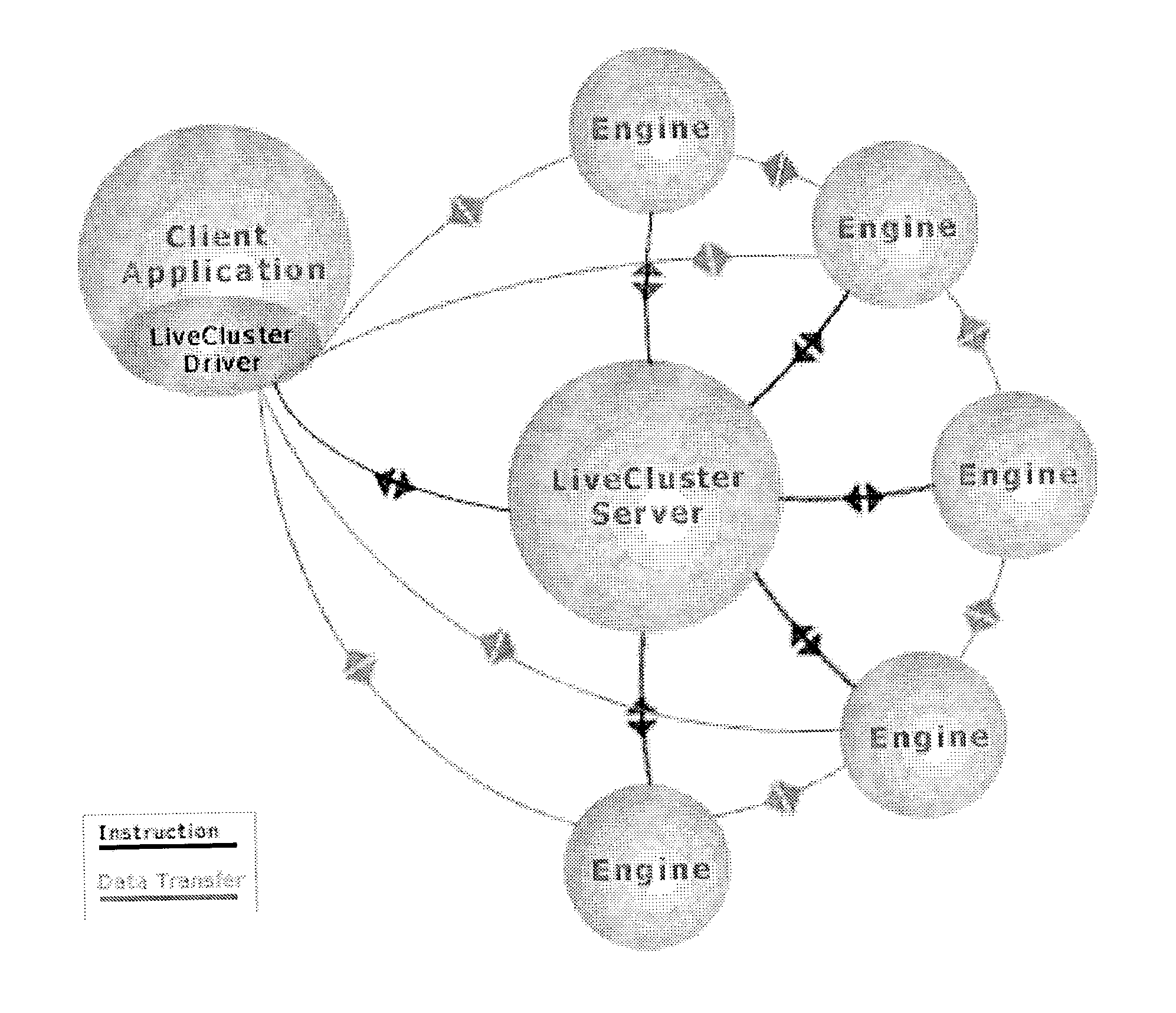
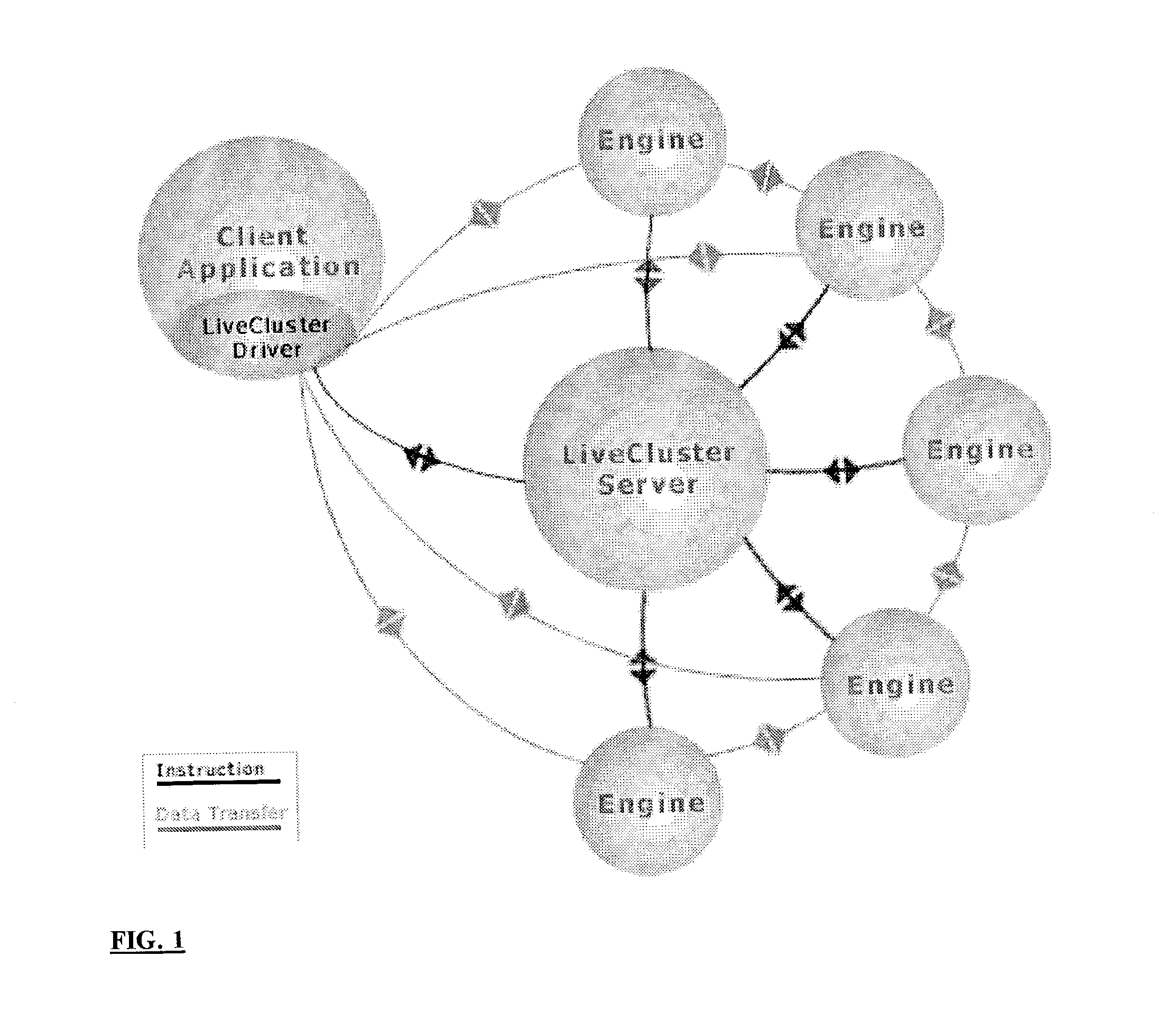
Using execution statistics to select tasks for redundant assignment in a distributed computing platform
InactiveUS7093004B2Minimizes unnecessary network congestionImprove deploymentResource allocationMultiple digital computer combinationsOff the shelfSelf adaptive
The invention provides an off-the-shelf product solution to target the specific needs of commercial users with naturally parallel applications. A top-level, public API provides a simple “compute server” or “task farm” model that dramatically accelerates integration and deployment. A number of described and claimed adaptive scheduling and caching techniques provide for efficient resource and / or network utilization of intermittently-available and interruptible computing resource in distributed computing systems.
Owner:DATASYNAPSE
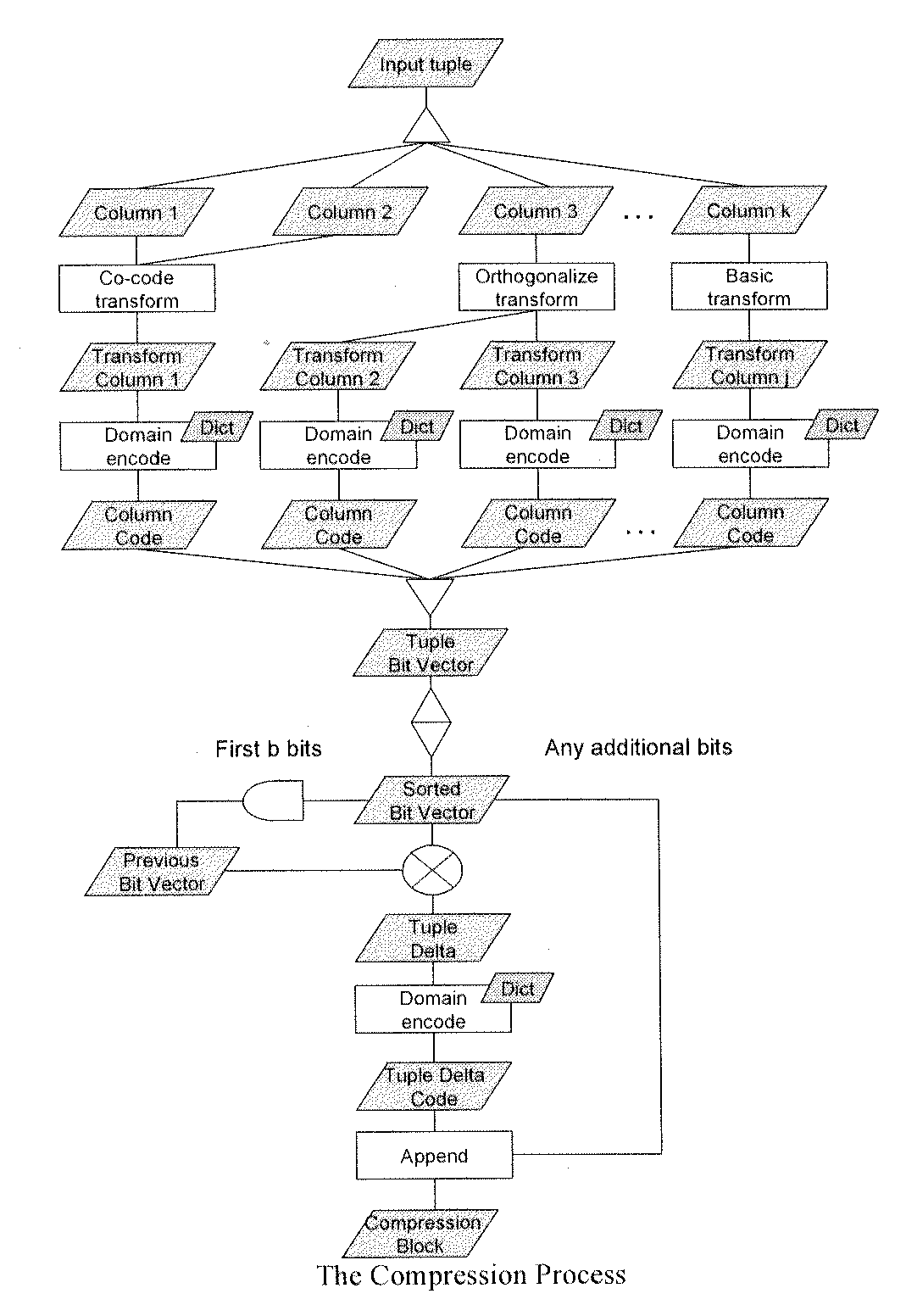
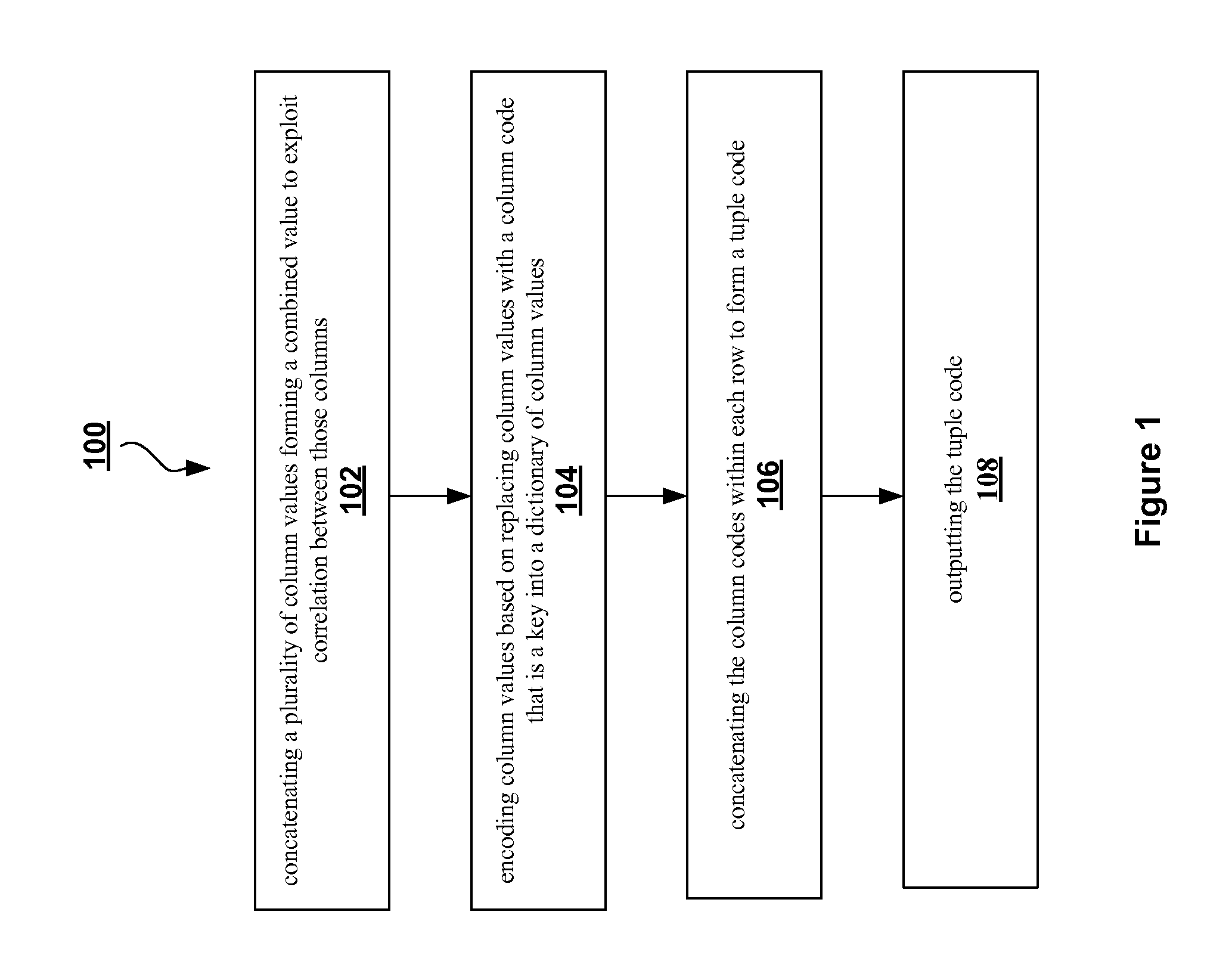
Compression method for relational tables based on combined column and row coding
InactiveUS20090006399A1Digital data information retrievalDigital data processing detailsVariable-length codeTheoretical computer science
A robust method to compress relations close to their entropy while still allowing efficient queries. Column values are encoded into variable length codes to exploit skew in their frequencies. The codes in each tuple are concatenated and the resulting tuplecodes are sorted and delta-coded to exploit the lack of ordering in a relation. Correlation is exploited either by co-coding correlated columns, or by using a sort order that can leverage the correlation. Also presented is a novel Huffman coding scheme, called segregated coding, that preserves maximum compression while allowing range and equality predicates on the compressed data, without even accessing the full dictionary. Delta coding is exploited to speed up queries, by reusing computations performed on nearly identical records.
Owner:IBM CORP
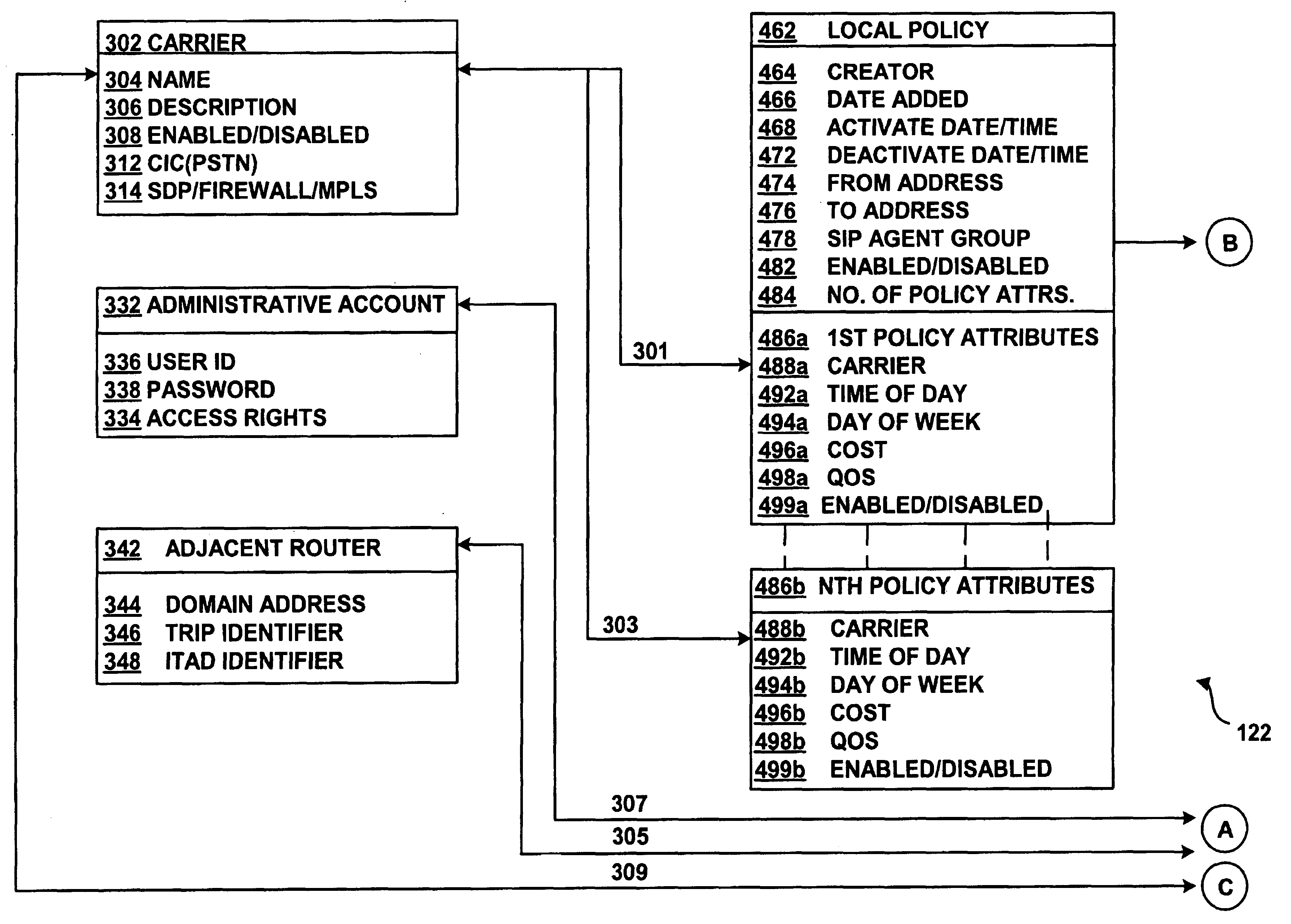
System and method for assisting in controlling real-time transport protocol flow through multiple networks via media flow routing
InactiveUS7028092B2Not easy to changeMultiplex system selection arrangementsInterconnection arrangementsTransceiverReal-time Transport Protocol
A system and method for assisting in controlling real-time transport protocol flow through multiple networks via media flow routing is disclosed. The system utilizes a first computer and a second computer connected to the first computer, via a group of associated computers, wherein each of the first computer, second computer, and group of associated computers comprise a transceiver, a memory, and a processor. The processor is configured by the memory to perform the functions of: performing an inbound screen on route information received from the first computer, to determine if the received route information should be discarded; if the route information is not discarded, comparing the received and screened route information to a local policy defined within the second computer; performing an outbound screen on the received and screened information prior to transmitting the received and screened route information to the first computer; and selecting a primary route from the received route information and local route information in accordance with the local policy, wherein the primary route is a path from the second computer to the first computer via the group of associated computers.
Owner:ACME PACKET +1
Language for performing high level actions using hardware registers
InactiveUS20050060525A1Easy to useDigital computer detailsProgram loading/initiatingComputer hardwareHuman language
A system and method that utilizes a common hardware register pseudo-language are disclosed. The present invention employs a common platform to specify hardware functionality and to execute hardware action(s). Hardware actions can be effectuated by performing a series of instructions, which comprise hardware register primitives and resources utilized by the primitives. The hardware register primitives are operations defined according to the common hardware register pseudo-language. The series of instructions can be loaded prior to boot or during initialization.
Owner:MICROSOFT TECH LICENSING LLC
Managing storage resources in decentralized networks
InactiveUS7251689B2Avoiding drawback and limitationMultiple digital computer combinationsSecuring communicationPersistent identifierWeb service
Methods, systems, and computer program products are disclosed for managing storage resources in decentralized networks. Persistent identifiers are defined for nodes, allowing nodes to be identified across sessions and invocations, even though they re-enter the network with a different network address. Paths taken by content resources as they traverse the network (e.g. which nodes forwarded the content) are persisted, along with reputation information about nodes (e.g. indicating how successful they are at answering queries from peers). Trust relationships can be derived using the persisted information. A tiered broadcast strategy is defined for reducing the number of messages exchanged. Preferred embodiments leverage a web services implementation model.
Owner:IBM CORP
System and method for detecting interpreter-based exploit attacks
For one embodiment, a computerized method for detecting exploit attacks on an interpreter comprises configuring a virtual machine including a user mode and a kernel mode and processing an object by an application operating in the user mode of the virtual machine. Responsive to the processing of the object, detecting a loading of an interpreter. Furthermore, responsive to the loading of the interpreter, inserting one or more intercept points for detecting one or more types of software calls from the interpreter or for detecting a certain type or certain types of activities occurring within the interpreter. Thereafter, an exploit attack is detected as being conducted by the object in response to the interpreter invoking a software call that corresponds to the one or more types of software calls that is considered anomalous when invoked by the interpreter or an anomalous activity being conducted within the interpreter.
Owner:FIREEYE SECURITY HLDG US LLC
Leveraging behavior-based rules for malware family classification
According to one embodiment, a malware classification scheme operating with an electronic device, configured with one or more hardware processors and a memory that stores the software handling the malware classification scheme that is conducted through analysis of behavior-based rules, is described. This malware classification scheme (i) conducts a determination whether a sequence of rules correspond to potential malicious behaviors detected during analysis of a malware sample within one or more virtual machines, and in response to determining that the sequence of rules corresponds to potential malicious behaviors, (ii) conducts an attempt to classify the malware sample to at least one known malware family based on an analysis of the sequence of rules.
Owner:FIREEYE SECURITY HLDG US LLC
Exploit detection system with threat-aware microvisor
ActiveUS20150199531A1Digital data processing detailsAnalogue secracy/subscription systemsVulnerability detectionThreat intelligence
An exploit detection system deploys a threat-aware microvisor to facilitate real-time security analysis, including exploit detection and threat intelligence, of an operating system process executing on a node of a network environment. The microvisor may be organized as a main protection domain representative of the operating system process. In response to the process attempting to access a kernel resource for which it does not have permission, a capability violation may be generated at the main protection domain of the microvisor and a micro-virtual machine (VM) may be spawned as a container configured to encapsulate the process. The main protection domain may then be cloned to create a cloned protection domain that is representative of the process and that is bound to the spawned micro-VM. Capabilities of the cloned protection domain may be configured to be more restricted than the capabilities of the main protection domain with respect to access to the kernel resource. The restricted capabilities may be configured to generate more capability violations than those generated by the capabilities of the main protection domain and, in turn, enable further monitoring of the process as it attempts to access the kernel resource.
Owner:FIREEYE SECURITY HLDG US LLC
Intrusion protection system utilizing layers and triggers
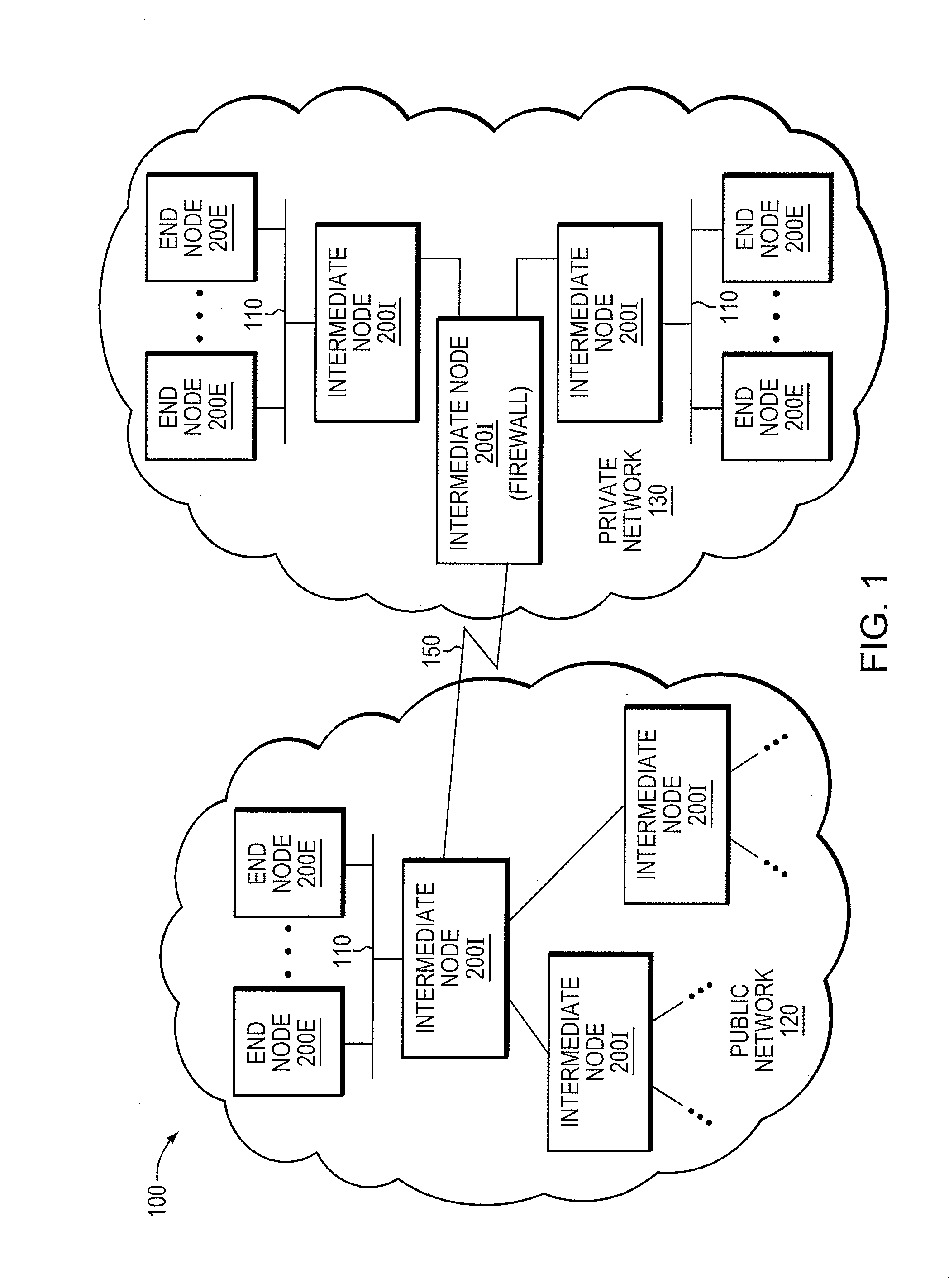
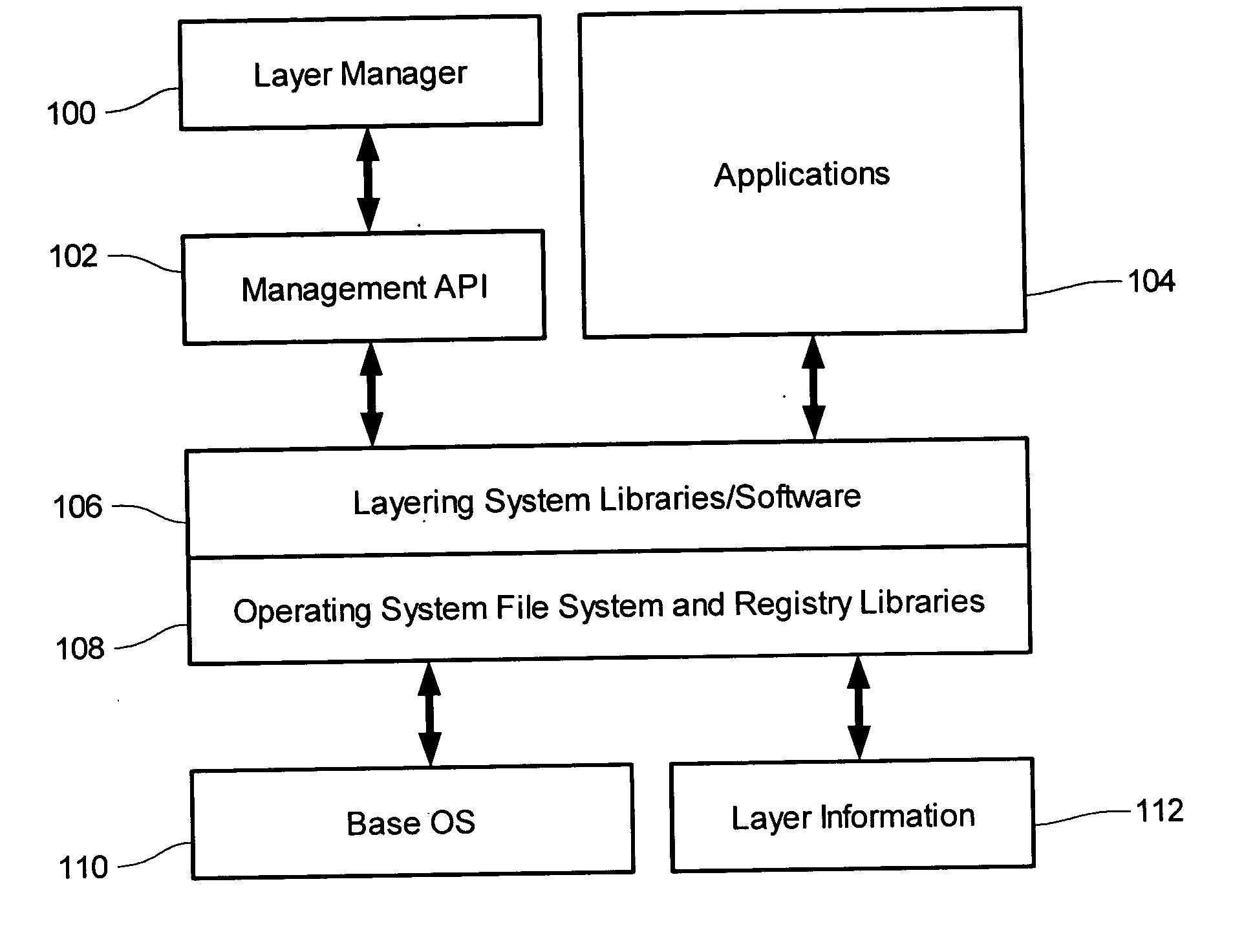
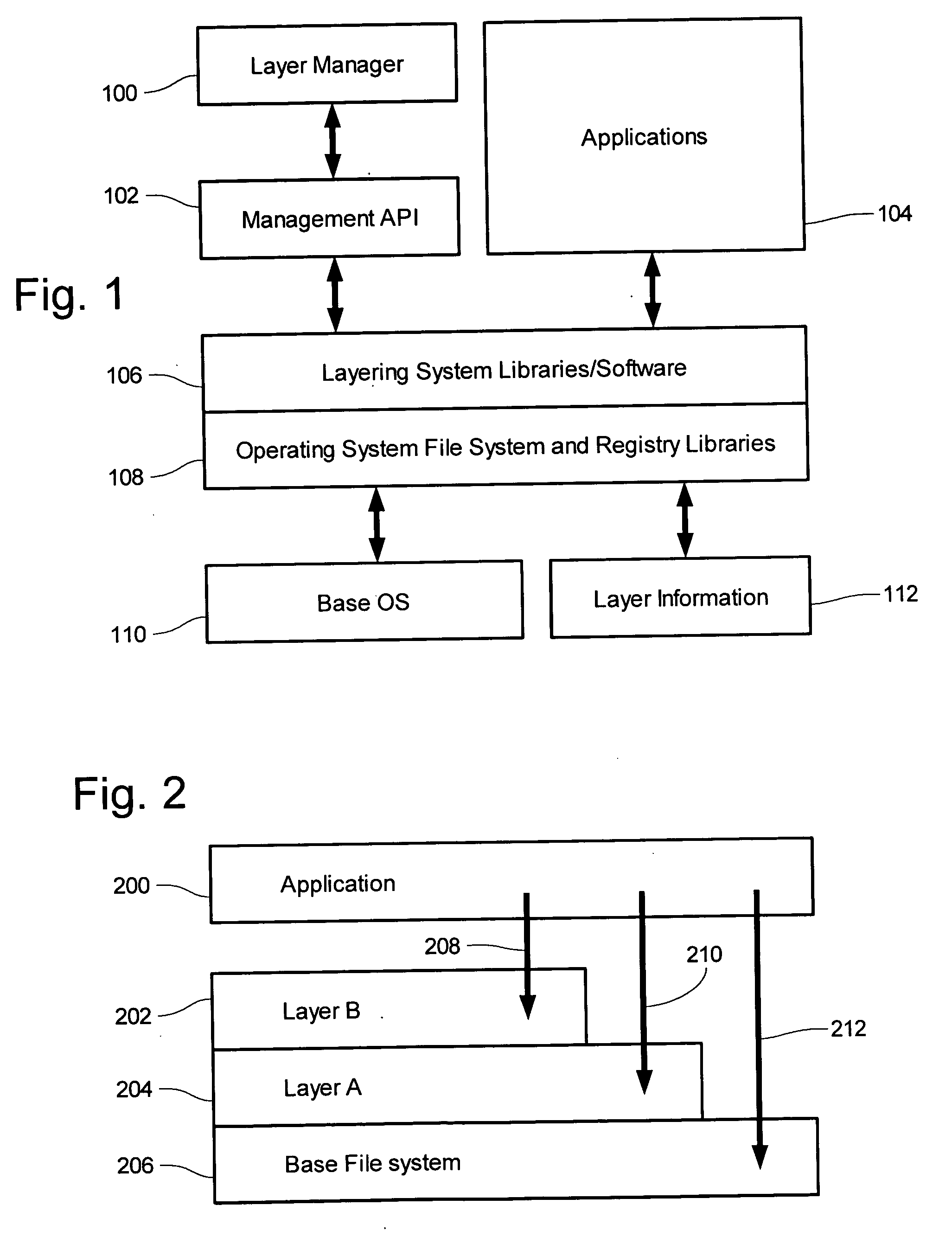
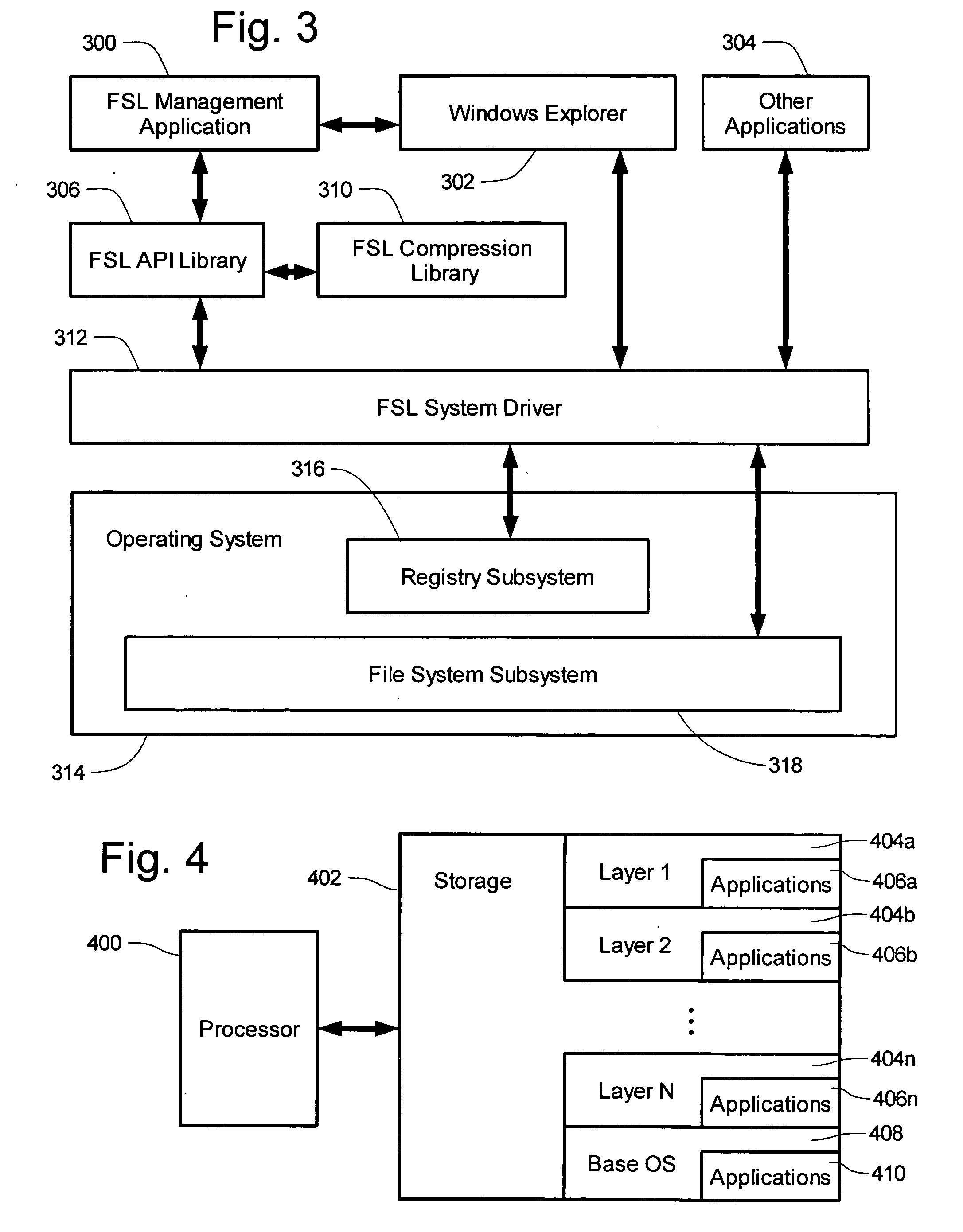
The inventions relate generally to protection of computing systems by isolating intrusive attacks into layers, those layers containing at least file objects and being accessible to applications, those layers further maintaining potentially intrusive file objects separately from regular file system objects such that the regular objects are protected and undisturbed. Also disclosed herein are computing systems which use layers and / or isolation layers, and various systems and methods for using those systems. Detailed information on various example embodiments of the inventions are provided in the Detailed Description below, and the inventions are defined by the appended claims.
Owner:CA TECH INC
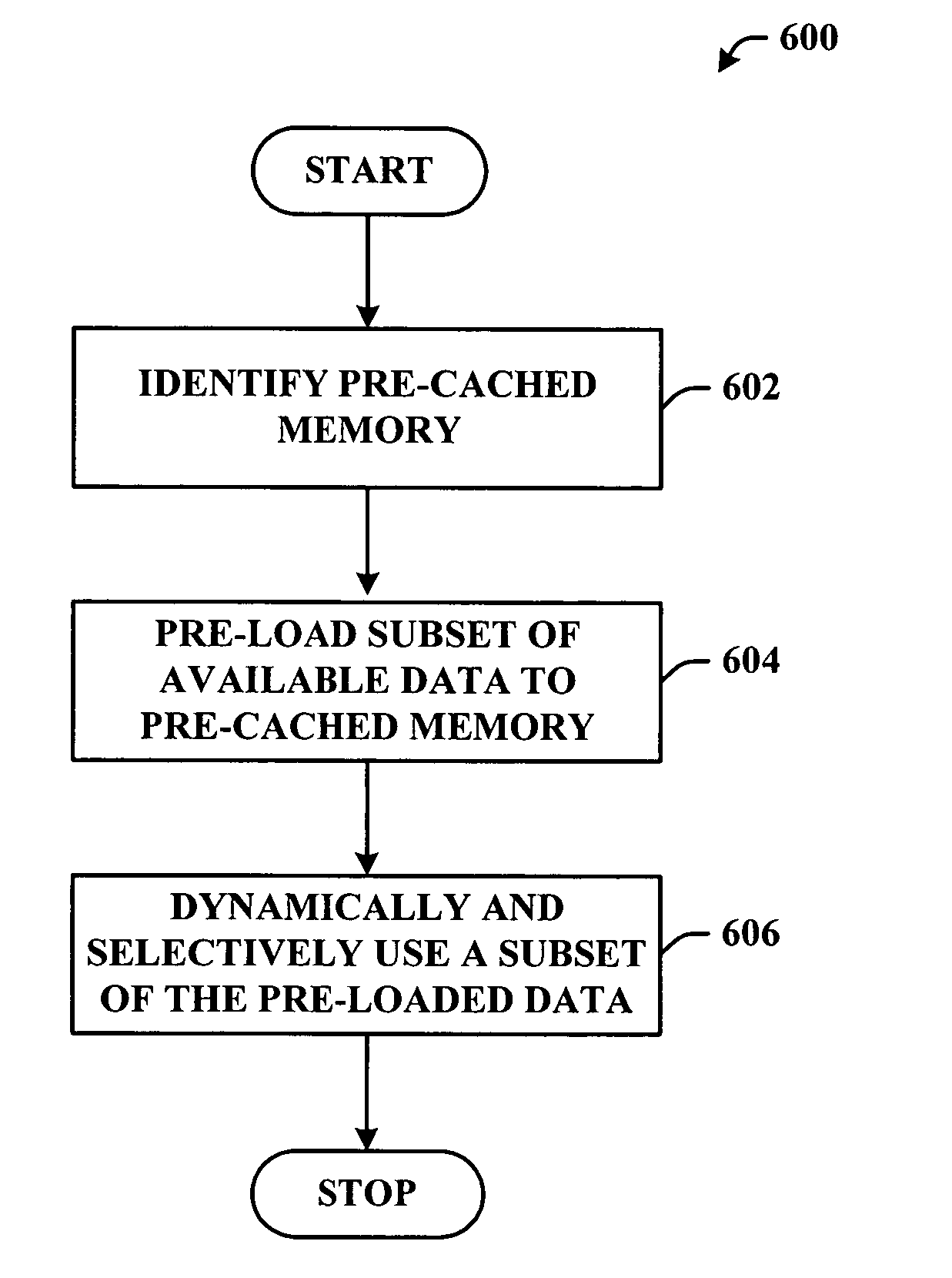
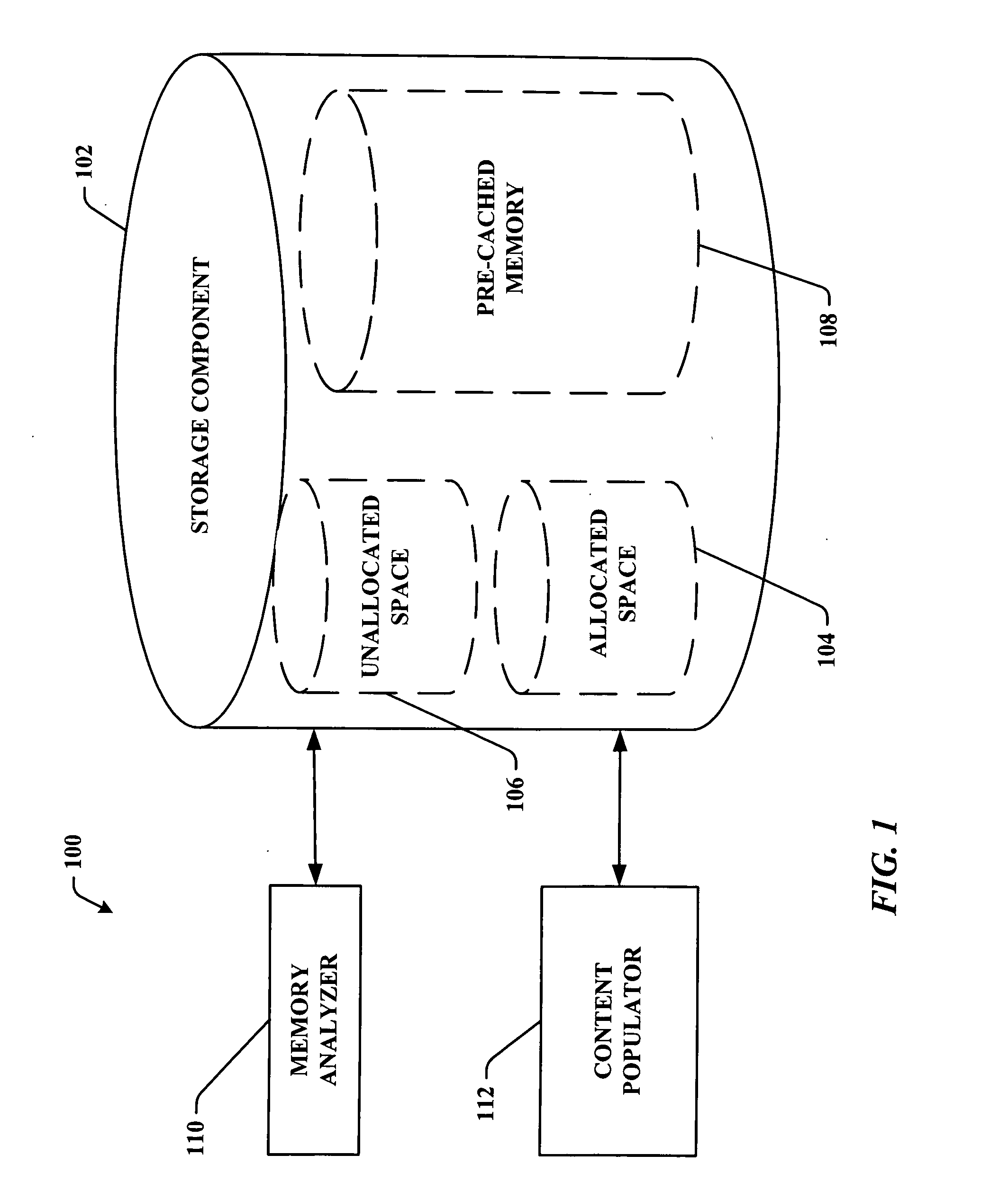
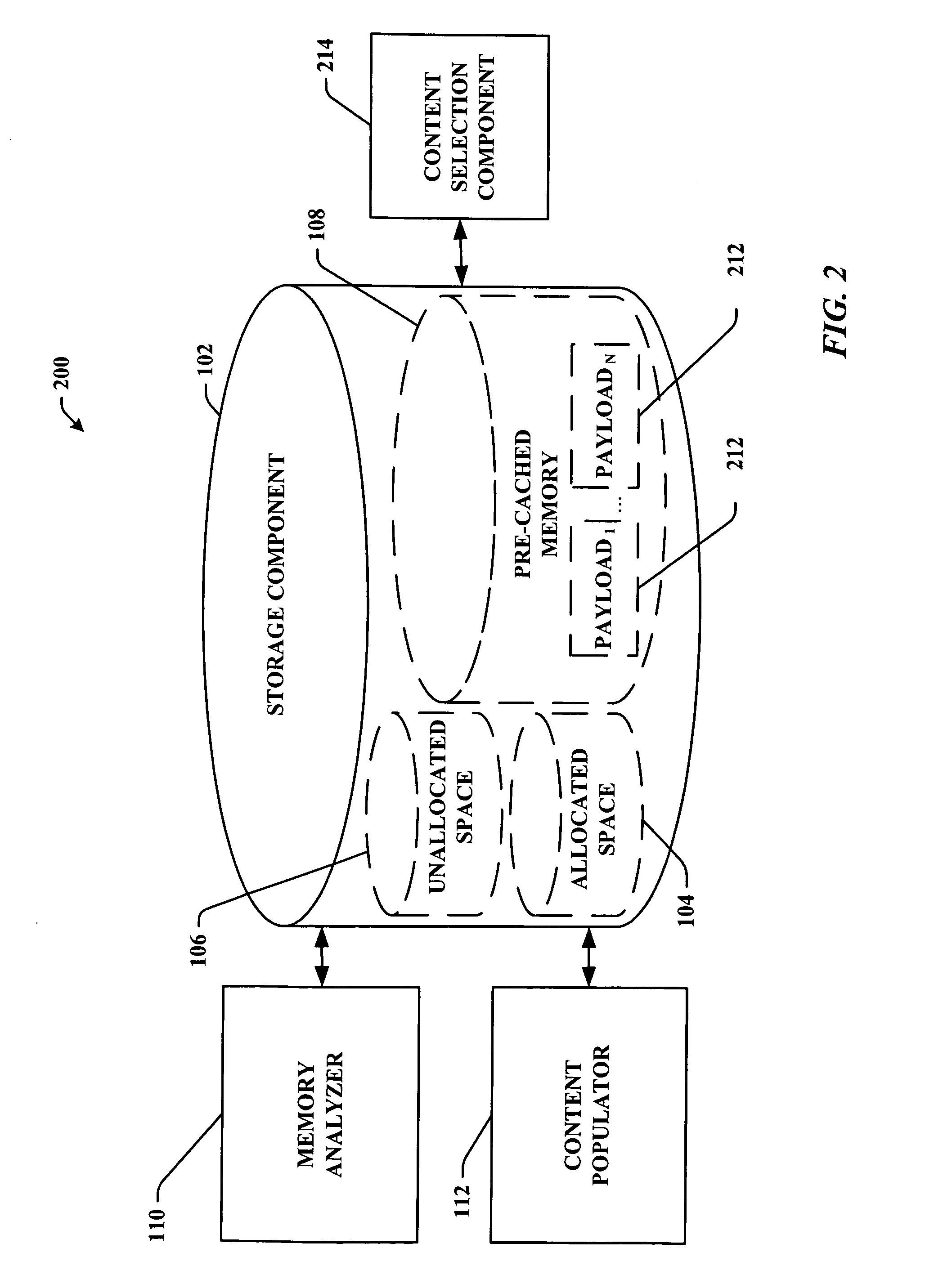
Pre-storage of data to pre-cached system memory
ActiveUS20070136533A1Improve utilizationImprove computing powerAdvertisementsTransmissionOperational systemData access
System(s) and method(s) that facilitate utilizing pre-cached disk space. Pre-cached memory space within a storage device is identified, and a subset of the pre-cached memory space is pre-populated with data so that the data can be selectively and dynamically accessed. During use of a computer (e.g., in a web-browsing session) a subset of the pre-stored data can be dynamically and selectively exposed to the user as a function of user and / or computer application state. Pre-storage of the data on pre-cached memory of the computer mitigates delayed data access (e.g., due to insufficient transmission bandwidth) thereby enhancing user computing experience. The user can utilize the device without having to distinguish between pre-cached and free memory. In other words, the operating system can present the cached memory to the user so that it appears as free memory without the user having to direct the system to do so.
Owner:MICROSOFT TECH LICENSING LLC
Data security
InactiveUS20060277413A1Reduce theftPrevent theftUnauthorized memory use protectionHardware monitoringComputer hardwareData field
Data Security methods, computer programs, and systems for encrypting and decrypting data, process sharing, and redundancy. The invention provides techniques for encryption including the encryption of a structured data file where each smallest unit of the data file (e.g., a field in a database record) is encrypted separately. The invention also provides techniques for decrypting such an encrypted data file. Requested fields of data are decrypted, stored in temporary memory, and displayed to the user or used to complete a task. Once the display is over or the task is completed, the decrypted data in temporary memory is deleted. The invention also provides techniques for real time process sharing and redundancy that utilize system characteristics to determine the apportionment of processes.
Owner:DREWS DENNIS T
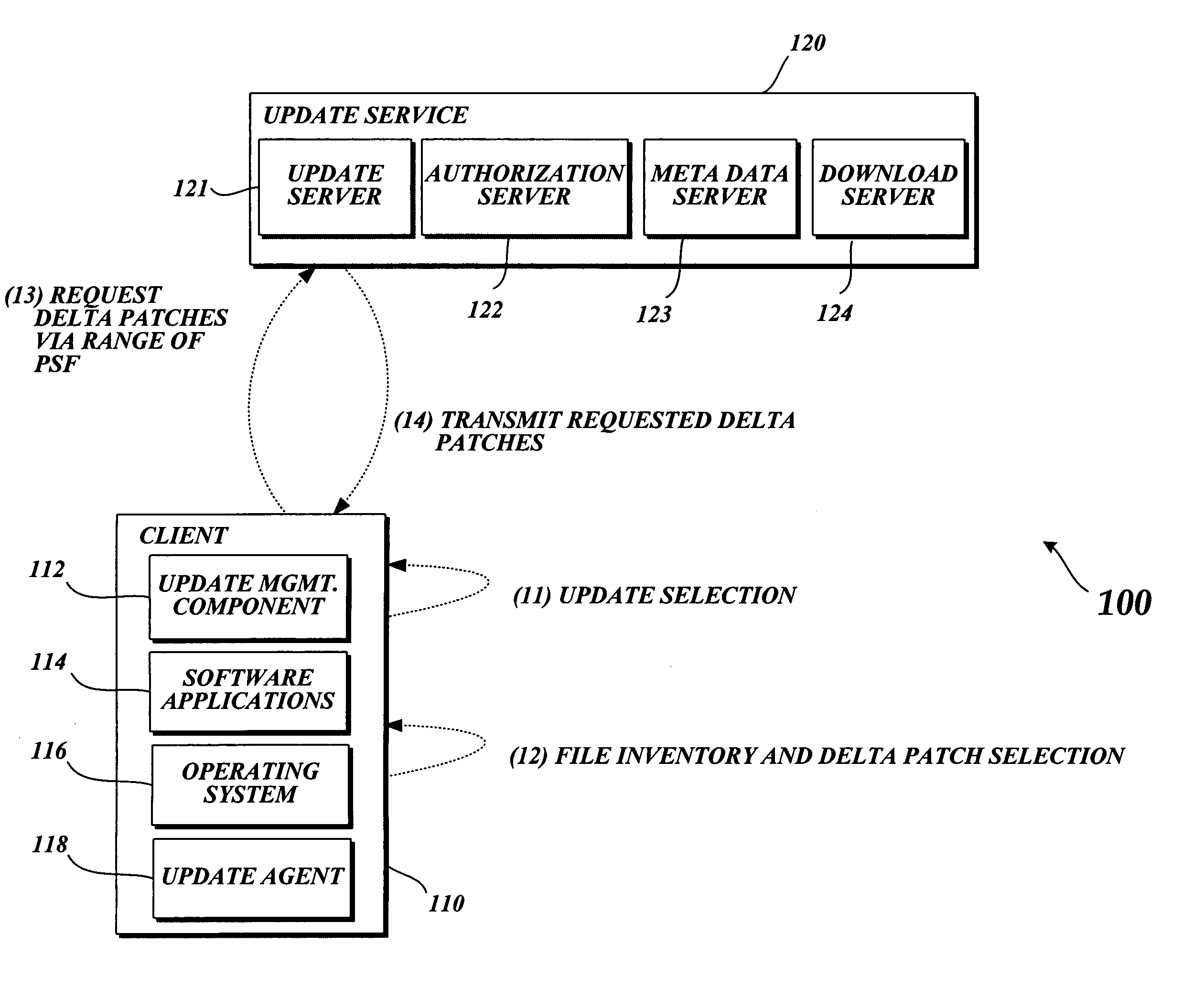
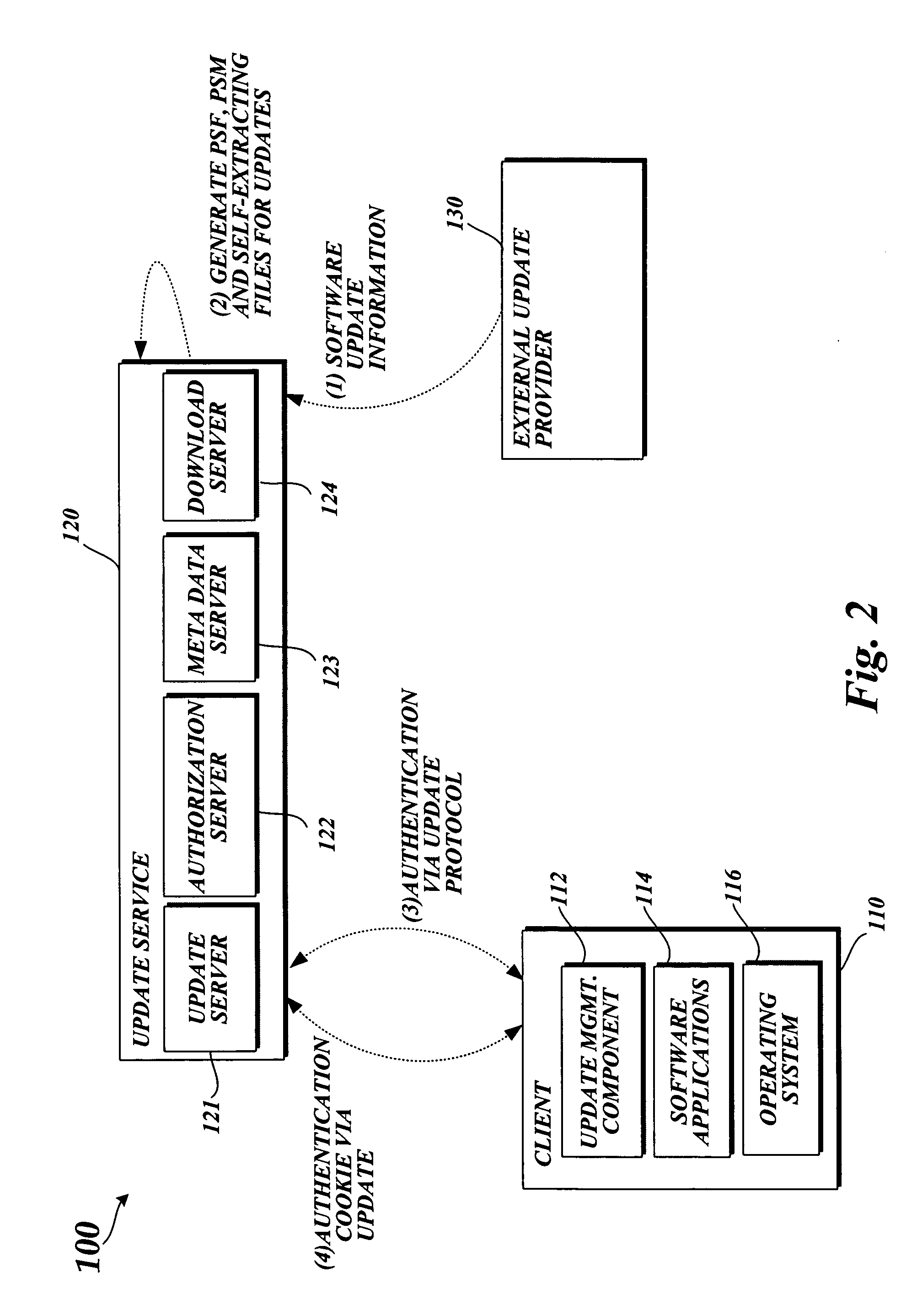
System and method for updating files utilizing delta compression patching
A system and method for updating one or more files on a computing device are provided. A client computing device obtains update information including an index identifying particular delta patches with specific versions of installed files. Upon selecting which of the applicable updates will be implemented, an update agent on the client computing device performs an inventory to identify which version a file to be updated is installed on the machine. The update agent selects a corresponding delta patch and transmits the request to an update service.
Owner:MICROSOFT TECH LICENSING LLC
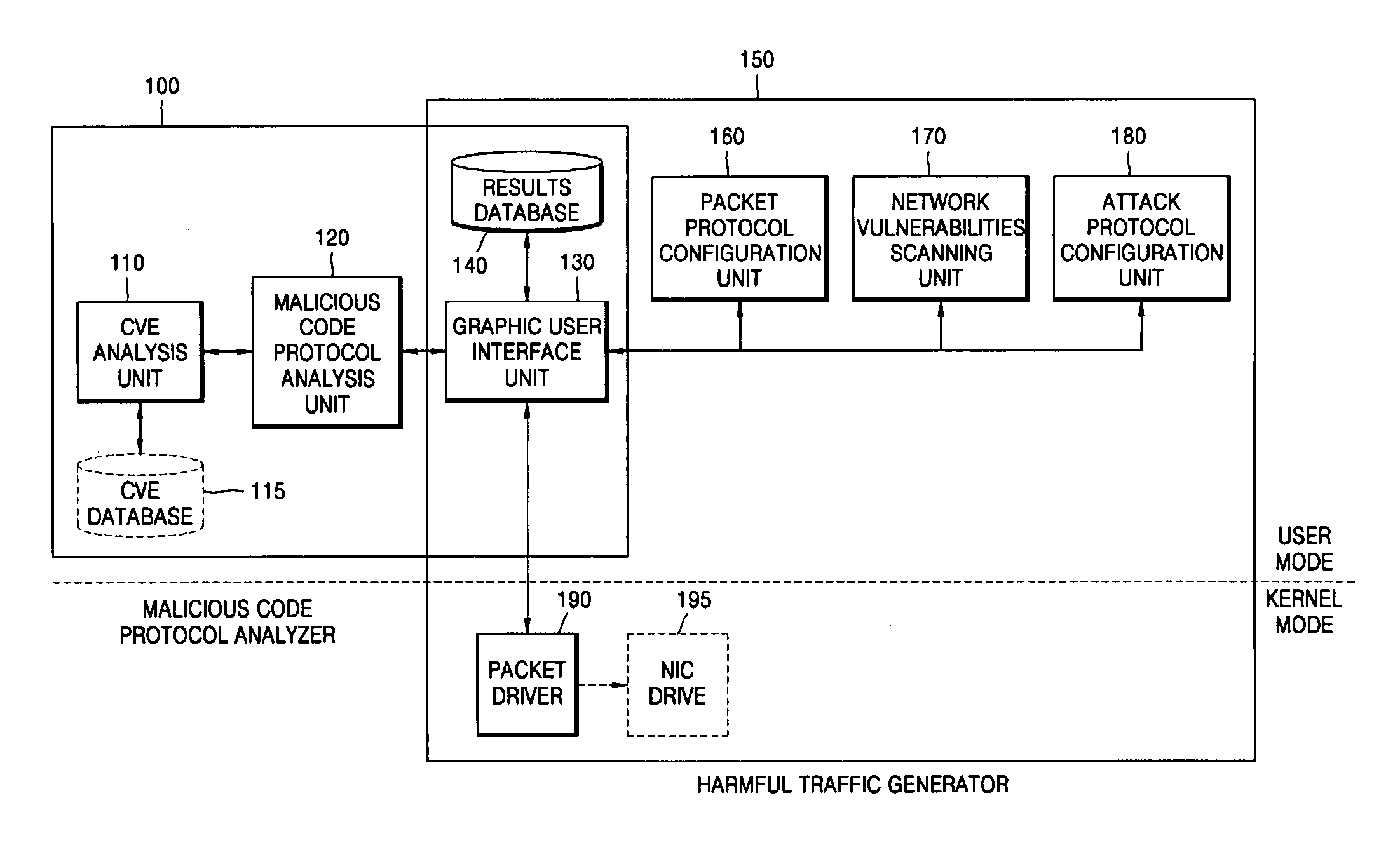
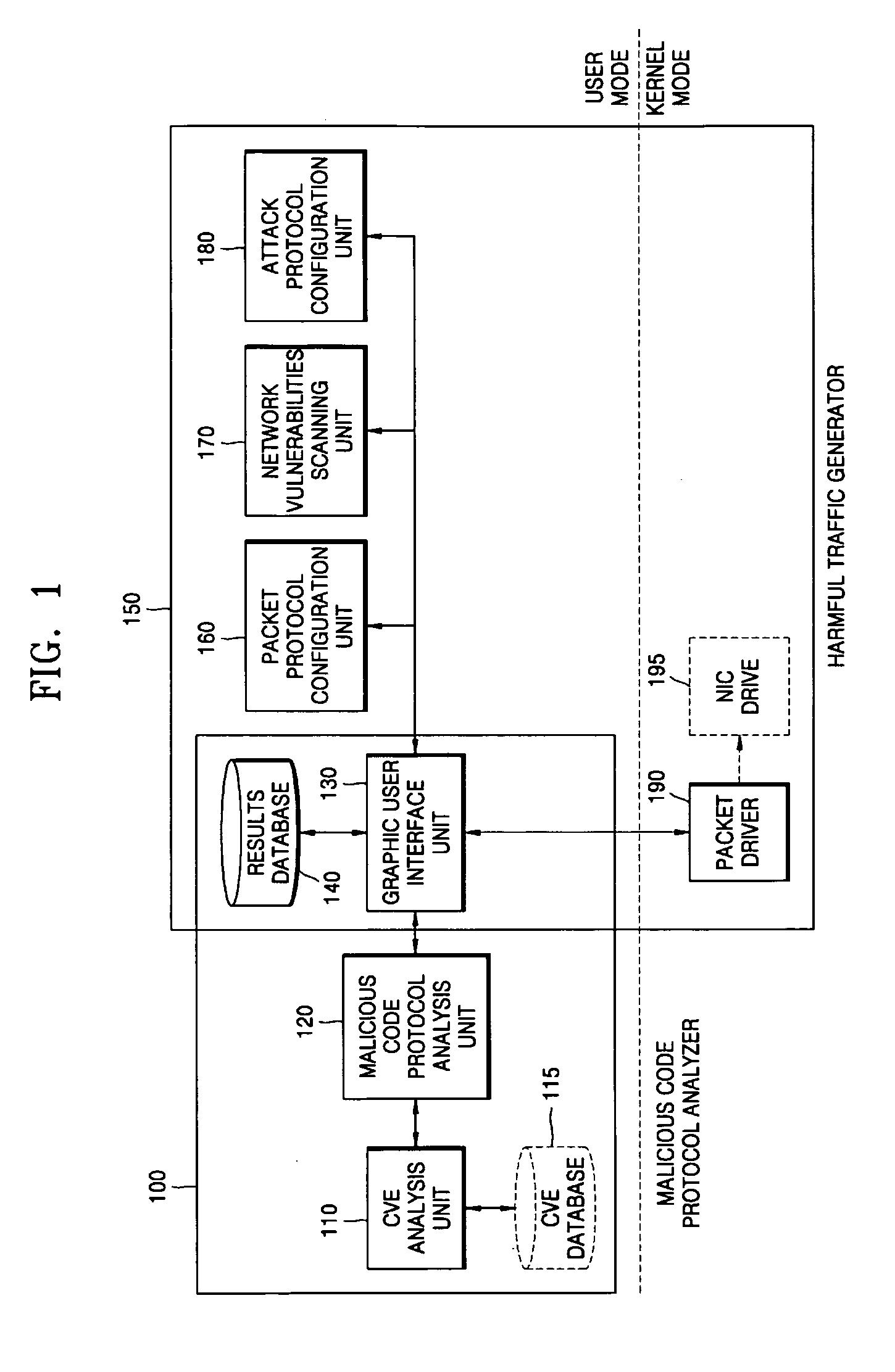
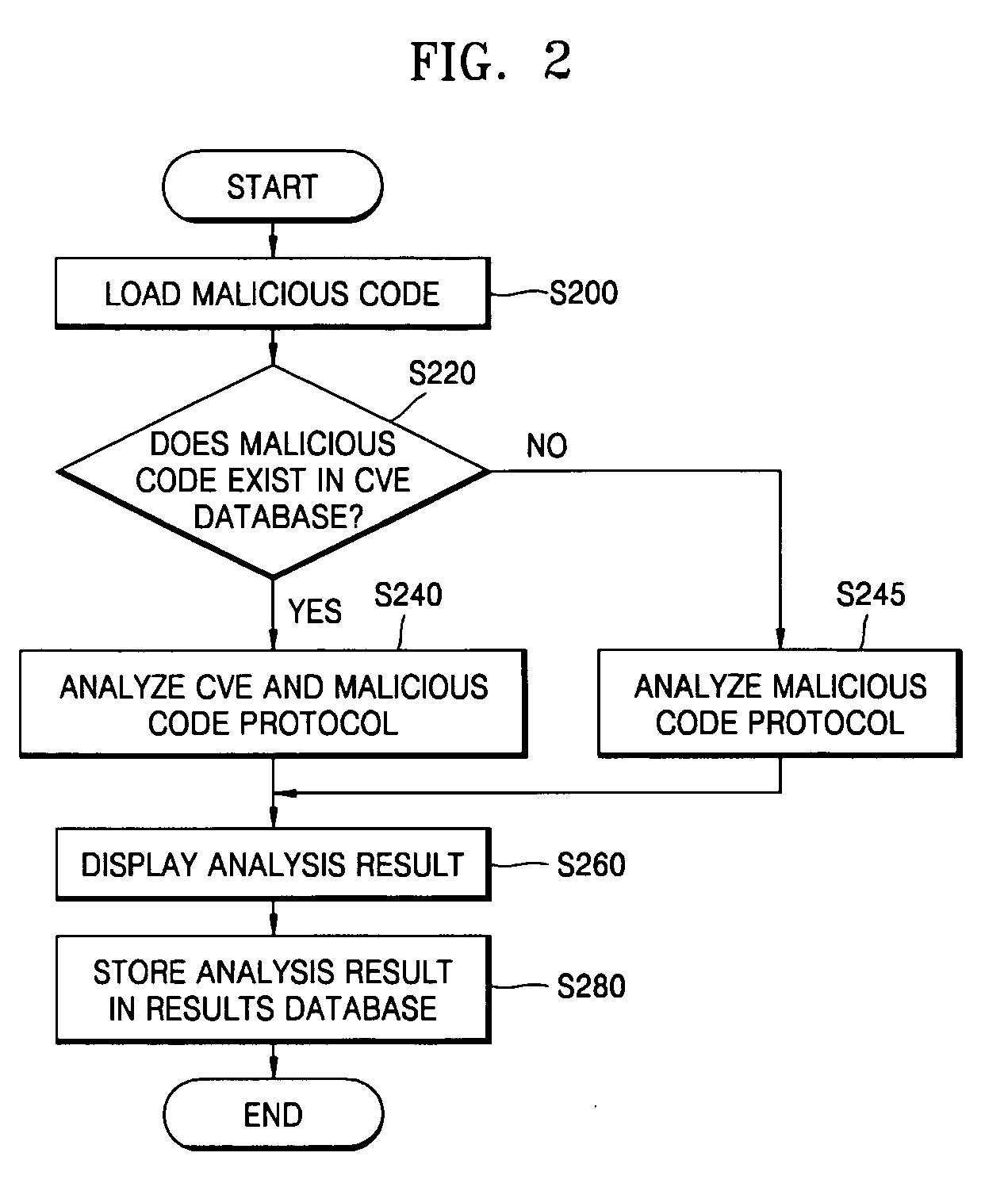
System and method for analyzing malicious code protocol and generating harmful traffic
The provided method and system is a method and system for analyzing the malicious code protocol and generating harmful traffic. The harmful traffic generating method constructs packet protocol information for generating a first attack packet corresponding to the TCP / IP protocol for generating network traffic, and then sets network vulnerability scanning for generating a second attack packet for carrying out network vulnerability scanning. Subsequently, the method constructs attack information for generating a third attack packet in the form of denial of service, and generates harmful traffic using the packet protocol information, network vulnerability scanning and attack information. Accordingly, performance testing of the network security system against malicious code attacks such as the Internet worm can be performed.
Owner:CHOI BYEONG CHEOL +1
Preemptive multi-tasking with cooperative groups of tasks
An operating system combines preemptive scheduling with cooperative or non-preemptive scheduling. In particular, tasks are divided into groups of interdependent tasks. Interdependent tasks are tasks that utilize the same modules of code or resources Each group includes tasks that should not be run asynchronously relative to each other. The scheduler in the operating system provides each group with a time slot of processor time. The tasks within the group are cooperatively scheduled to exploit the time slot assigned to the group. Dependencies between modules and tasks are maintained to assure that no difficulties arise amongst preemptively scheduled groups.
Owner:MICROSOFT TECH LICENSING LLC
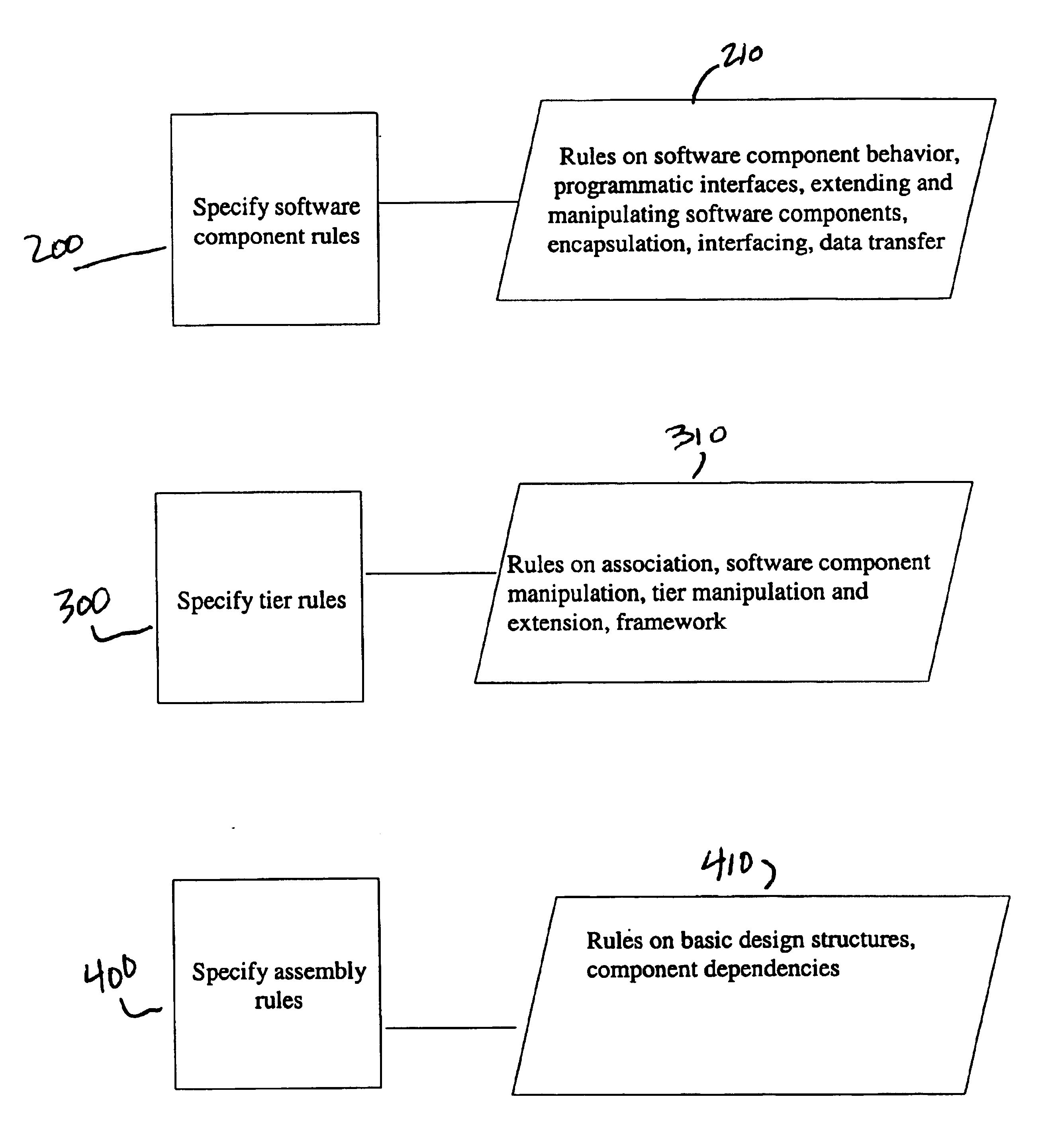
Method of and system for designing an N-tier software architecture for use in generating software components
InactiveUS6854107B2Low costMultiple digital computer combinationsSoftware designSoftware architectureSoftware engineering
A system and method for designing a software architecture for utilizing software components in building extensible N-tier software applications is described, the method comprising specifying a set of software component rules for creating software components; specifying a set of tier rules for creating tiers; and specifying a set of assembly rules further comprising association rules by which each tier may be associated with at least one software component and linkage rules by which each tier may be linked to at least one other tier. The tier rules may further comprise a set of association rules by which each tier created with the set of tier rules may be associated with at least one software component created using the software component rules; a set of tier framework rules to provide an architected context for software components within a tier; and a set of package rules to provide for logical grouping of interfaces within a framework defined by the tier framework rules to provide a set of specific behaviors for the tier.
Owner:BAKER HUGHES INC
Fault tolerant operation of reconfigurable devices utilizing an adjustable system clock
A method of fault tolerant operation of an adaptive computing system includes identifying a faulty resource in a signal path of the adaptive computing system, reconfiguring the signal path to avoid the faulty resource, estimating a time delay created by reconfiguring the signal path, and adjusting a system clock period to accommodate the time delay. In a preferred embodiment, an FPGA is configured into an initial self-testing area and a working area. Resources located within the self-testing area are tested and faulty resources identified. The FPGA is then reconfigured to avoid the identified faulty resources. When the resources are reconfigured for fault tolerant operation, signal path delays may be introduced into the system. If the signal path delays are in a critical path, a period of a system clock may be adjusted in order to insure proper fault tolerant operation.
Owner:JUNIVERSITI OF NORT KAROLINA EHT SHARLOTT +1
Off-heap direct-memory data stores, methods of creating and/or managing off-heap direct-memory data stores, and/or systems including off-heap direct-memory data store
ActiveUS20120222005A1Fast timeReduce the amount requiredMemory architecture accessing/allocationSpecific program execution arrangementsRefuse collectionJava
Certain example embodiments relate to a highly-concurrent, predictable, fast, self-managed, in-process space for storing data that is hidden away from the garbage collector and its related pauses. More particularly, certain example embodiments relate to improved memory management techniques for computer systems that leverage an off-heap direct-memory data store that is massively scalable and highly efficient. The off-heap store may be provided in connection with a Java-based environment, and garbage collection may be completely or nearly completely avoided for the off-heap store. The off-heap store may be integrated into a tiered storage solution in certain example embodiments.
Owner:SOFTWARE AG USA
Data processing apparatus
ActiveUS20070113079A1Reduce memorySmall sizeSpecific access rightsProgram initiation/switchingComputer hardwareProtection mechanism
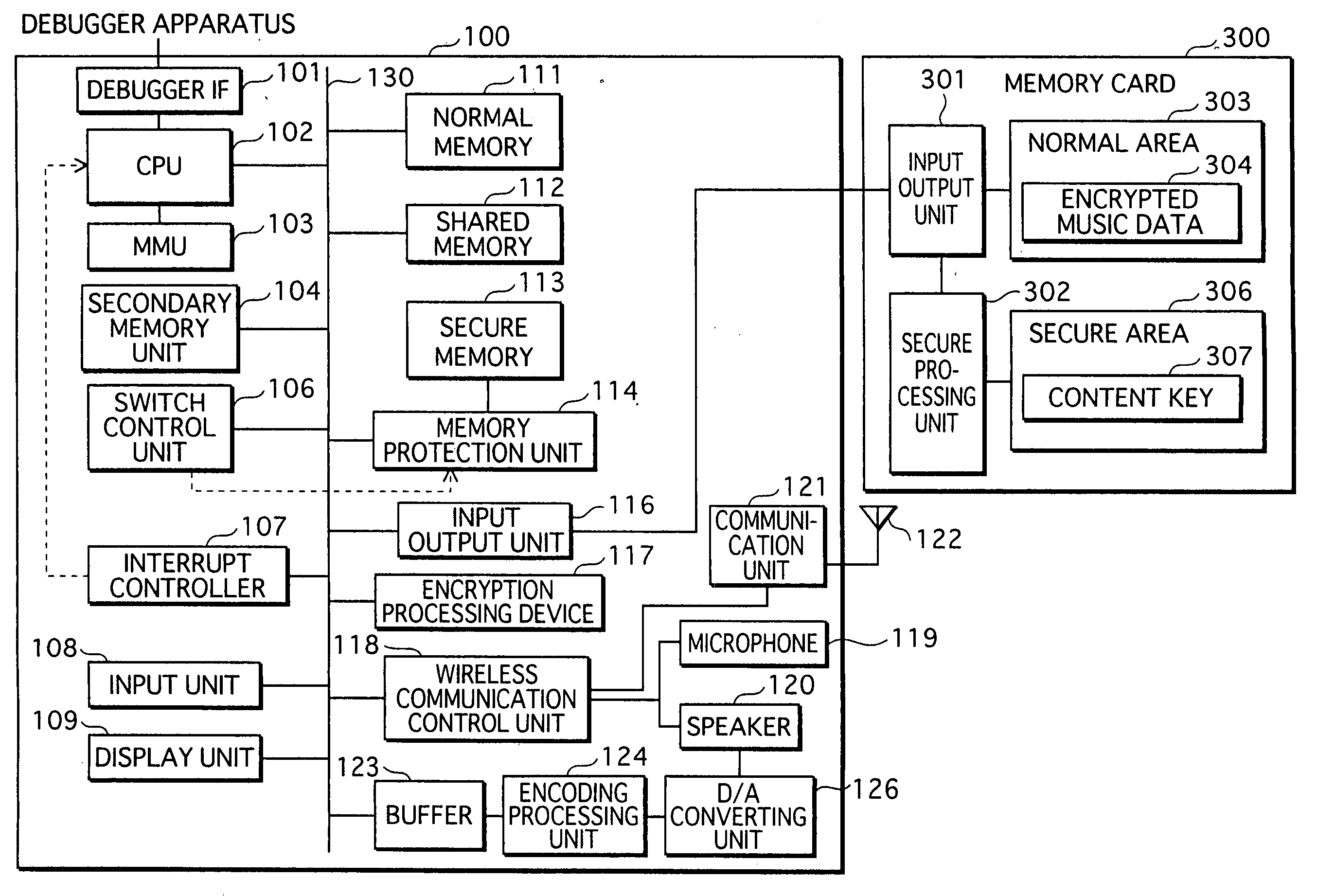
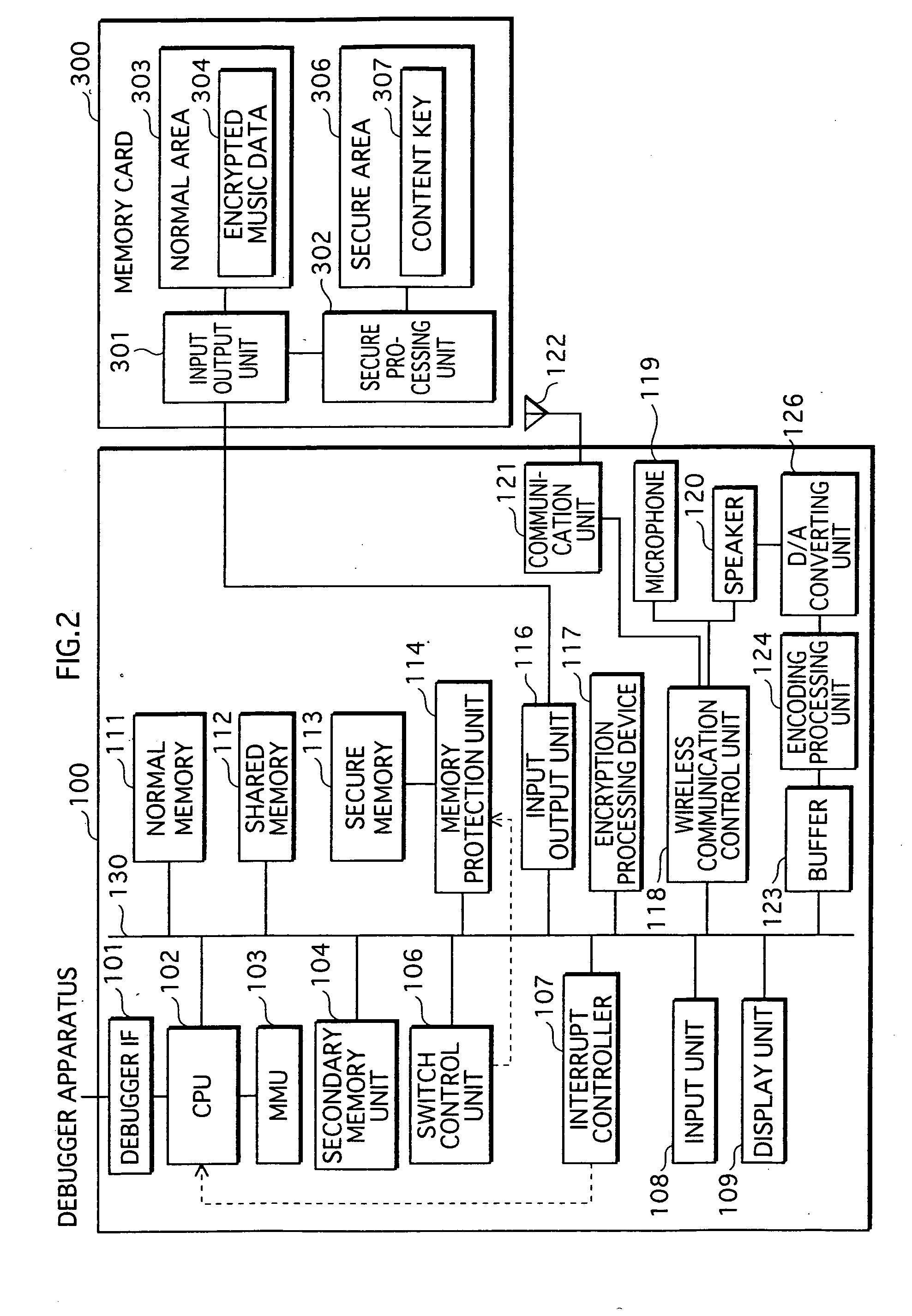
In a data processing apparatus that switches between a secure mode and a normal mode during execution, the secure mode allowing access to secure resources to be protected, the normal mode not allowing access to the secure resources, when the secure resources increase in the secure mode, the load on a protection mechanism for protecting the resources becomes large. Thus, there is a demand for data processing apparatuses that are able to reduce secure resources. The present invention relates to a data processing apparatus that stores therein a secure program including one or more processing procedures which use secure resources and a call instruction for calling a normal program to be executed in a normal mode. While executing the secure program, the data processing apparatus calls the normal program with the call instruction and operates according to the called normal program.
Owner:SK HYNIX INC
Distributed software architecture for implementing BGP
InactiveUS20050074003A1Improve fault toleranceRecover simplyData switching by path configurationRouting protocolDistributed software architecture
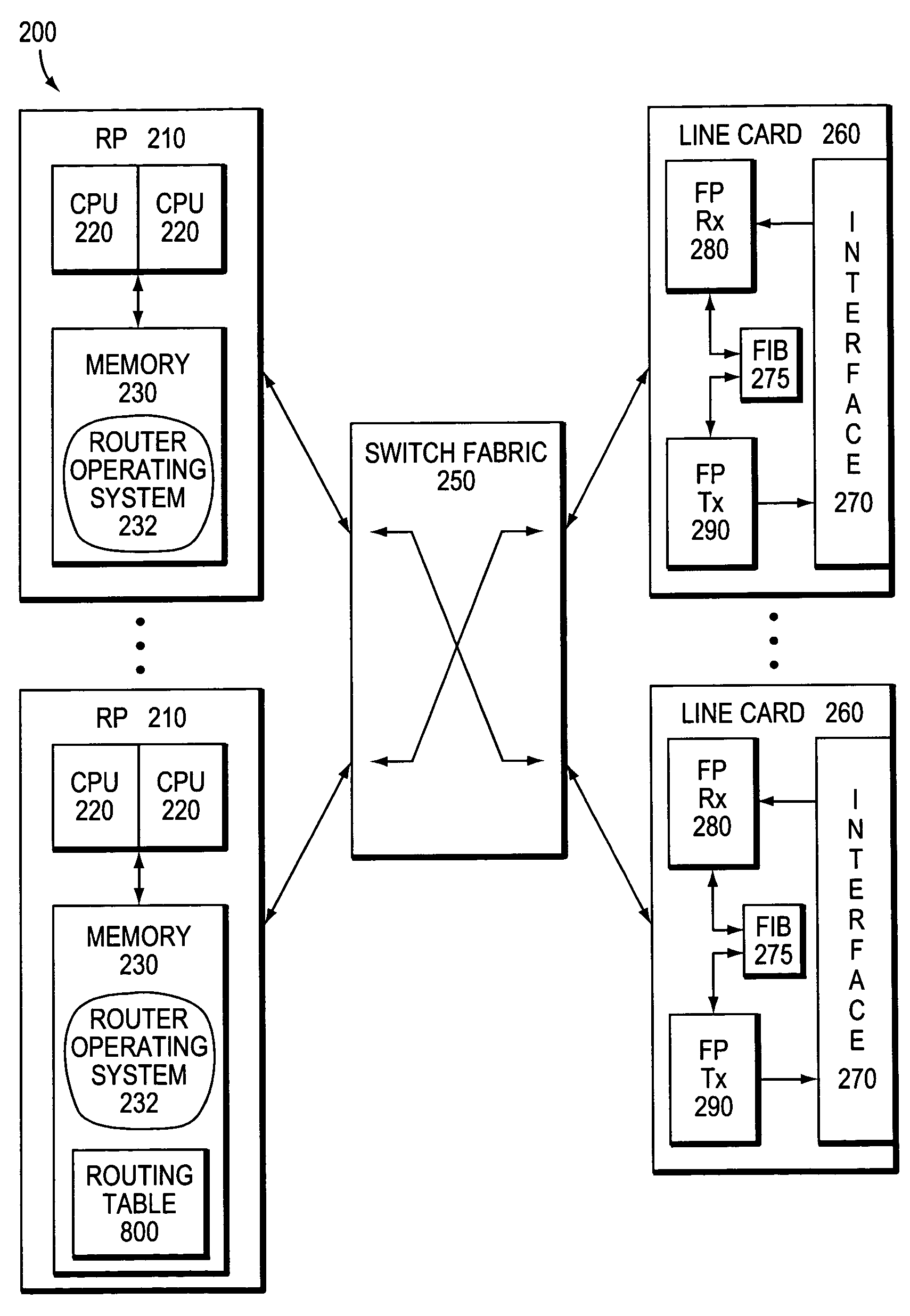
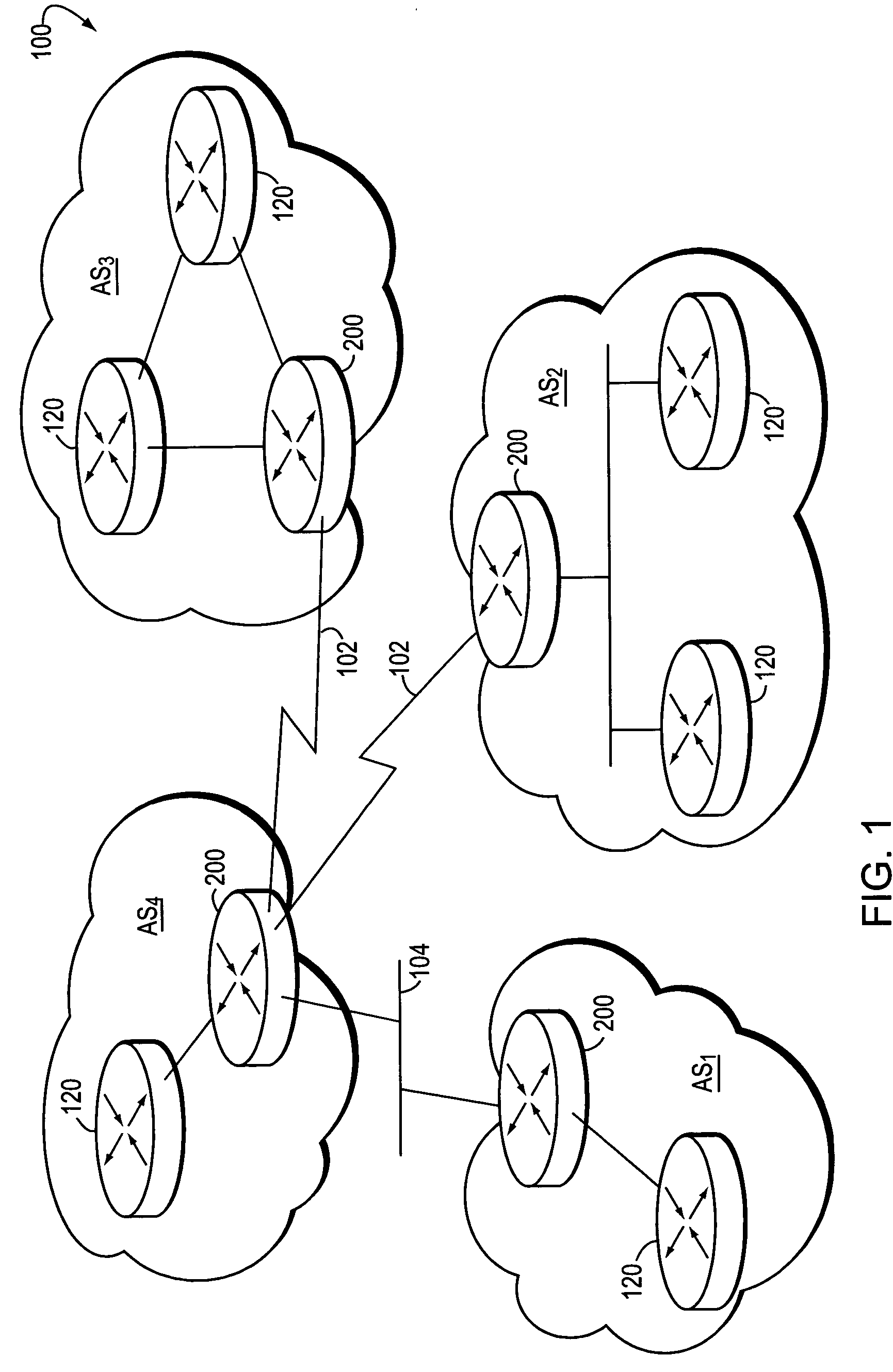
A distributed software architecture implements a routing protocol as a set of processes running on a set of processors of a router. The distributed processes cooperate in a manner that internally exploits the distributed set of processors, yet externally presents an appearance / behavior of a single routing protocol process communicating with its peers in the network. The distributed nature of the architecture is achieved without altering the fundamental routing protocol, but by apportioning certain functions / tasks of the protocol among various processes in the multiprocessor router.
Owner:CISCO TECH INC
System and method for constraint-based rule mining in large, dense data-sets
InactiveUS6278997B1Data processing applicationsDigital data information retrievalData setConfidence metric
A dense data-set mining system and method is provided that directly exploits all user-specified constraints including minimum support, minimum confidence, and a new constraint, known as minimum gap, which prunes any rule having conditions that do not contribute to its predictive accuracy. The method maintains efficiency even at low supports on data that is dense in the sense that many items appear with high frequency (e.g. relational data).
Owner:IBM CORP
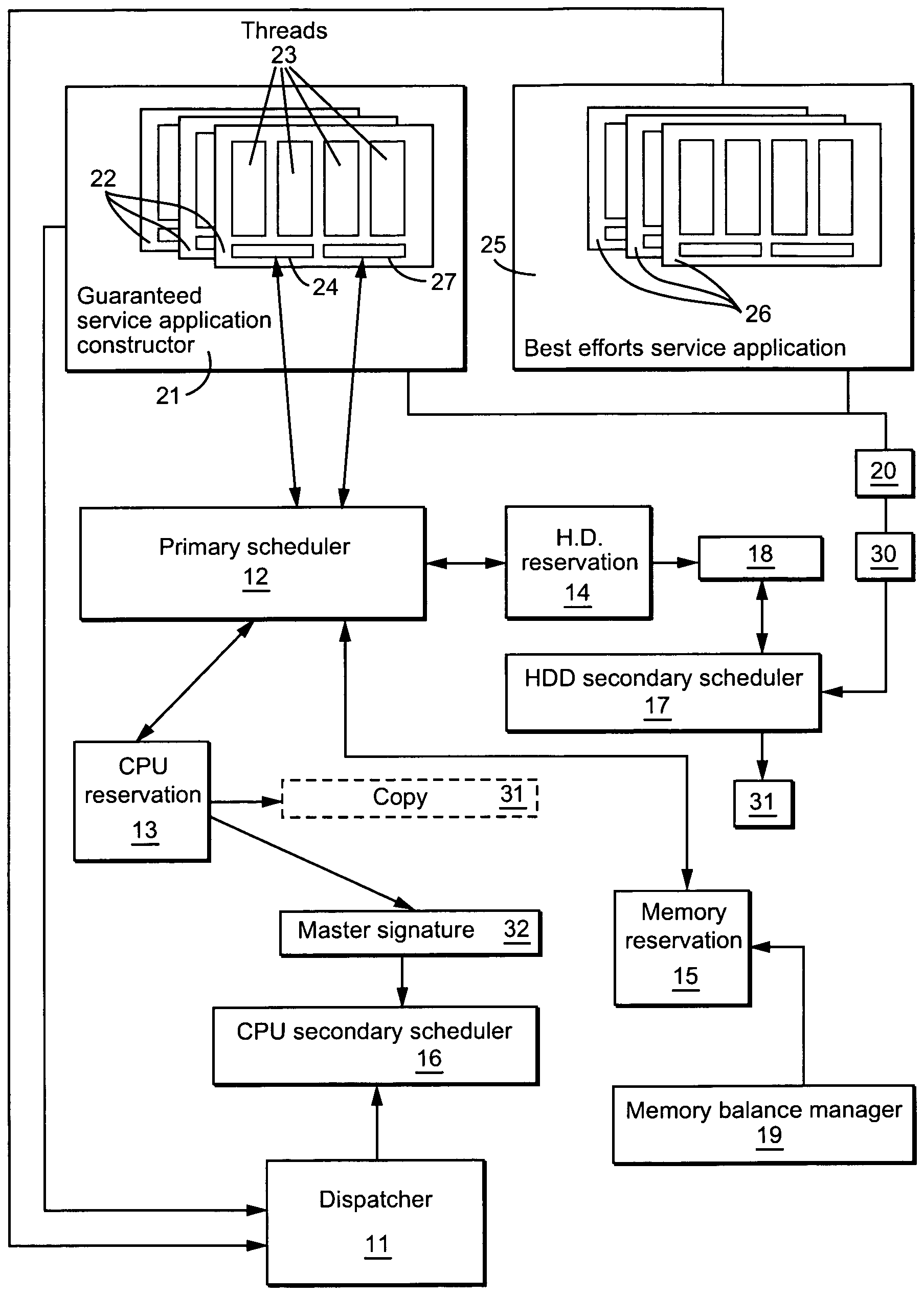
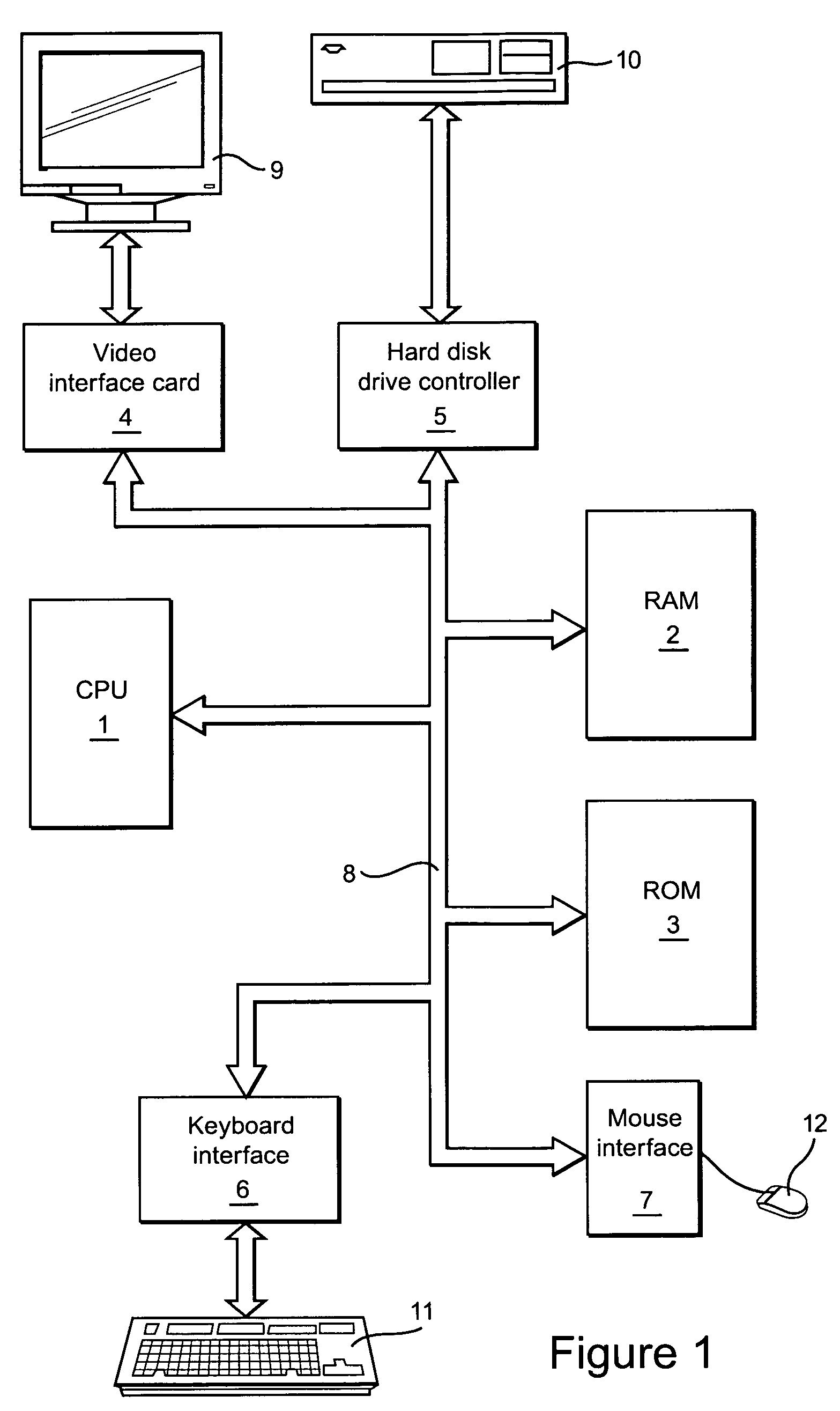
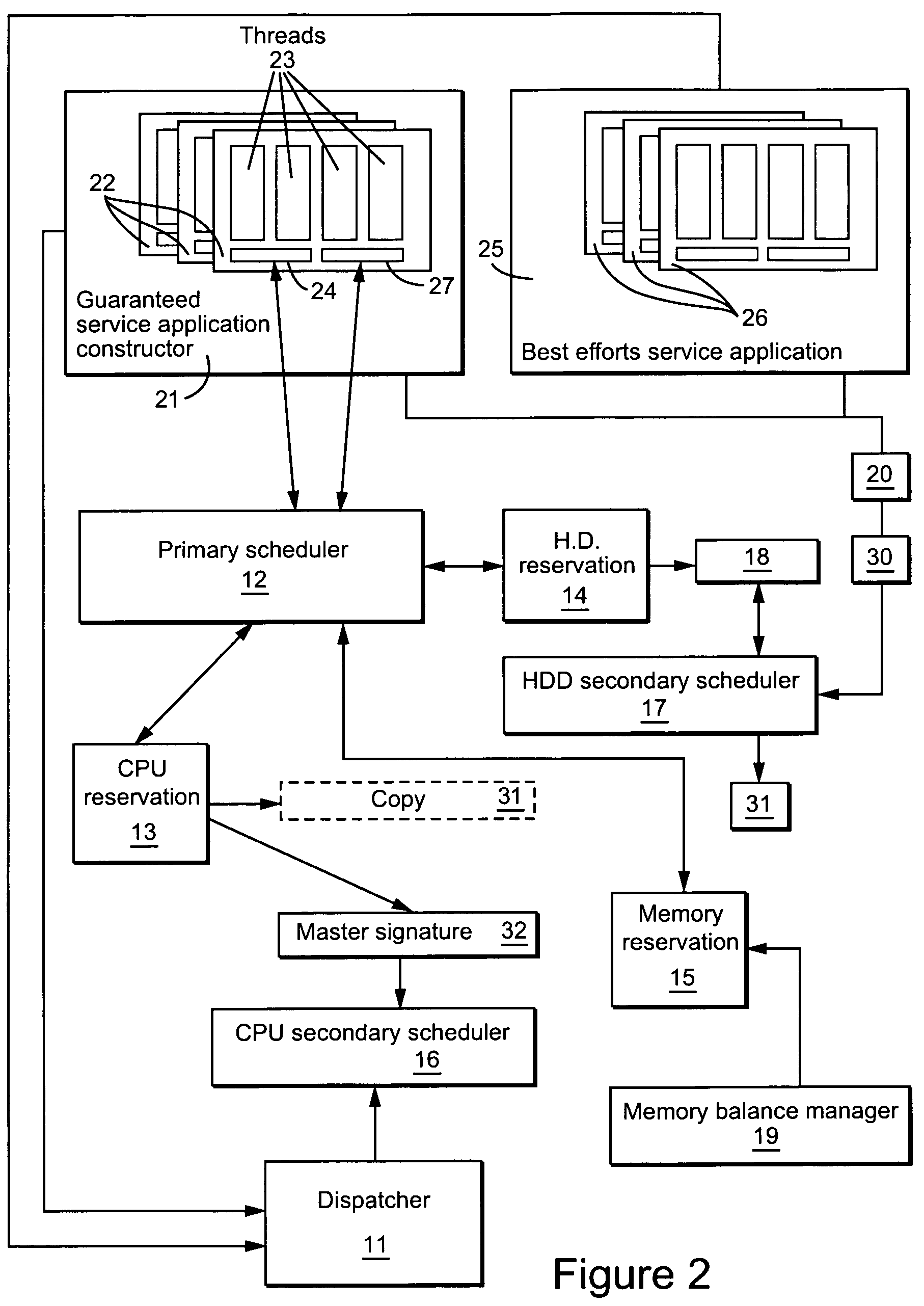
Resource scheduling
InactiveUS7219347B1Avoid hungerRaise priorityProgram initiation/switchingResource allocationPublic interfaceResource utilization
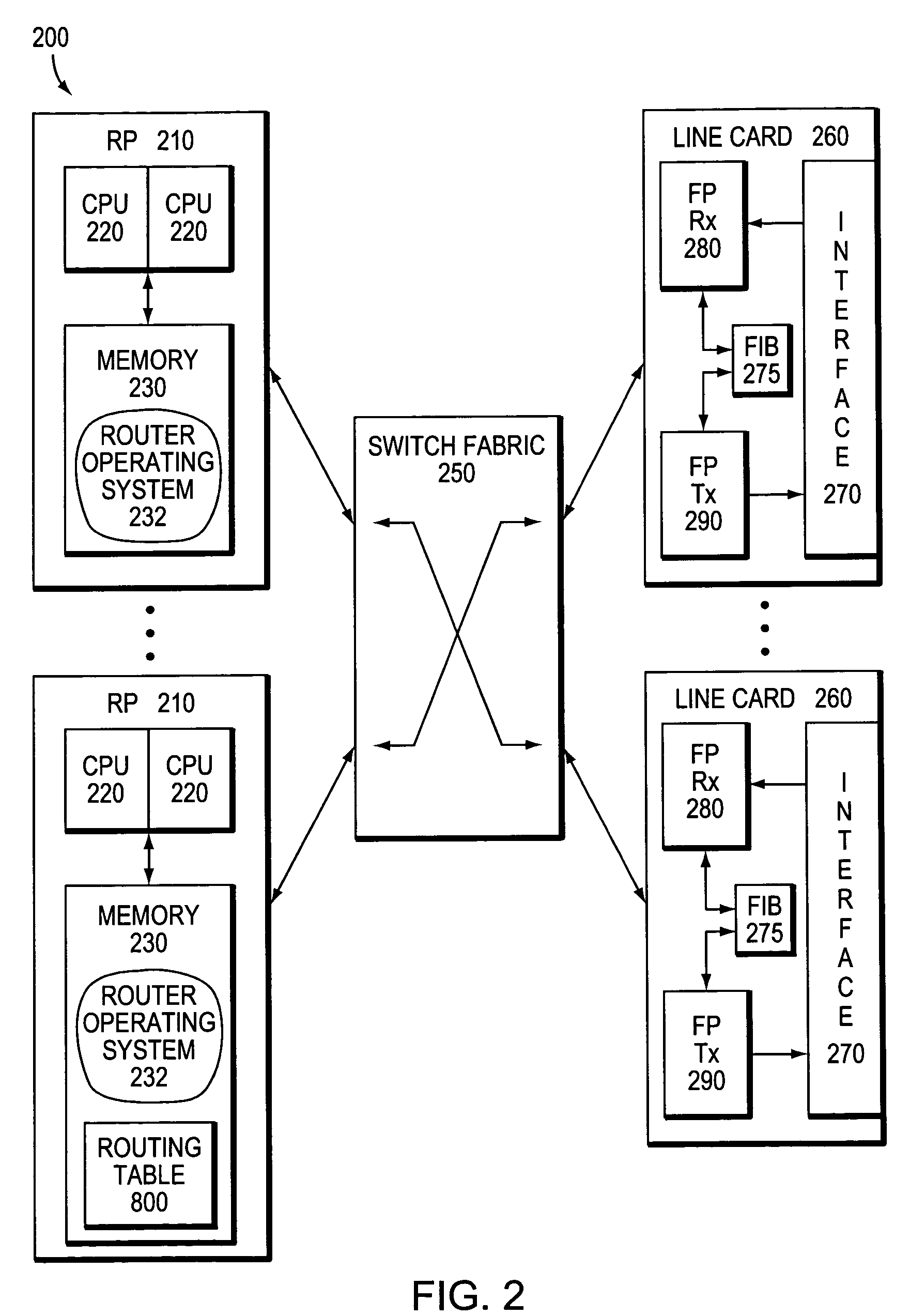
Resource utilization in a computer is achieved by running a first process to make a reservation for access to a resource in dependence on a resource requirement communication from an application and running a second process to grant requests for access to that resource from that application in dependence on the reservation. A further process provides a common interface between the first process for each resource and the application. The further process converts high-level abstract resource requirement definitions into formats applicable to the first process for the resource in question. The processes are preferably implemented as methods of software objects.
Owner:BRITISH TELECOMM PLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com