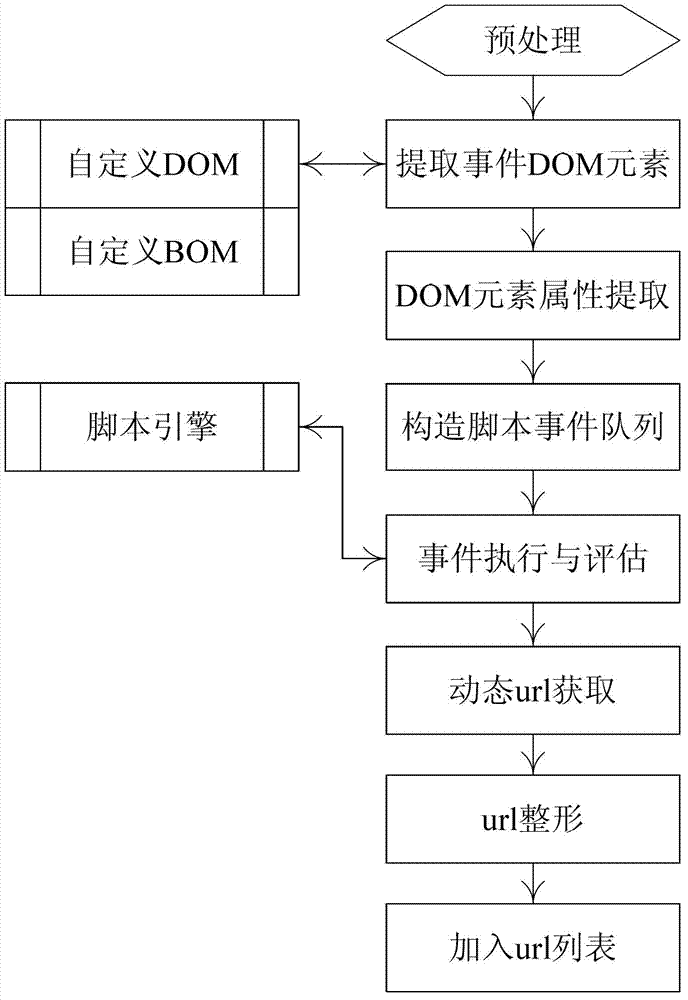
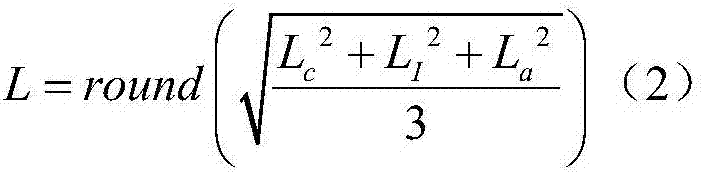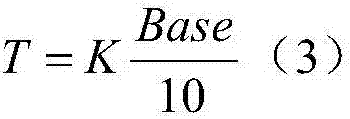Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1375 results about "Vulnerability detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
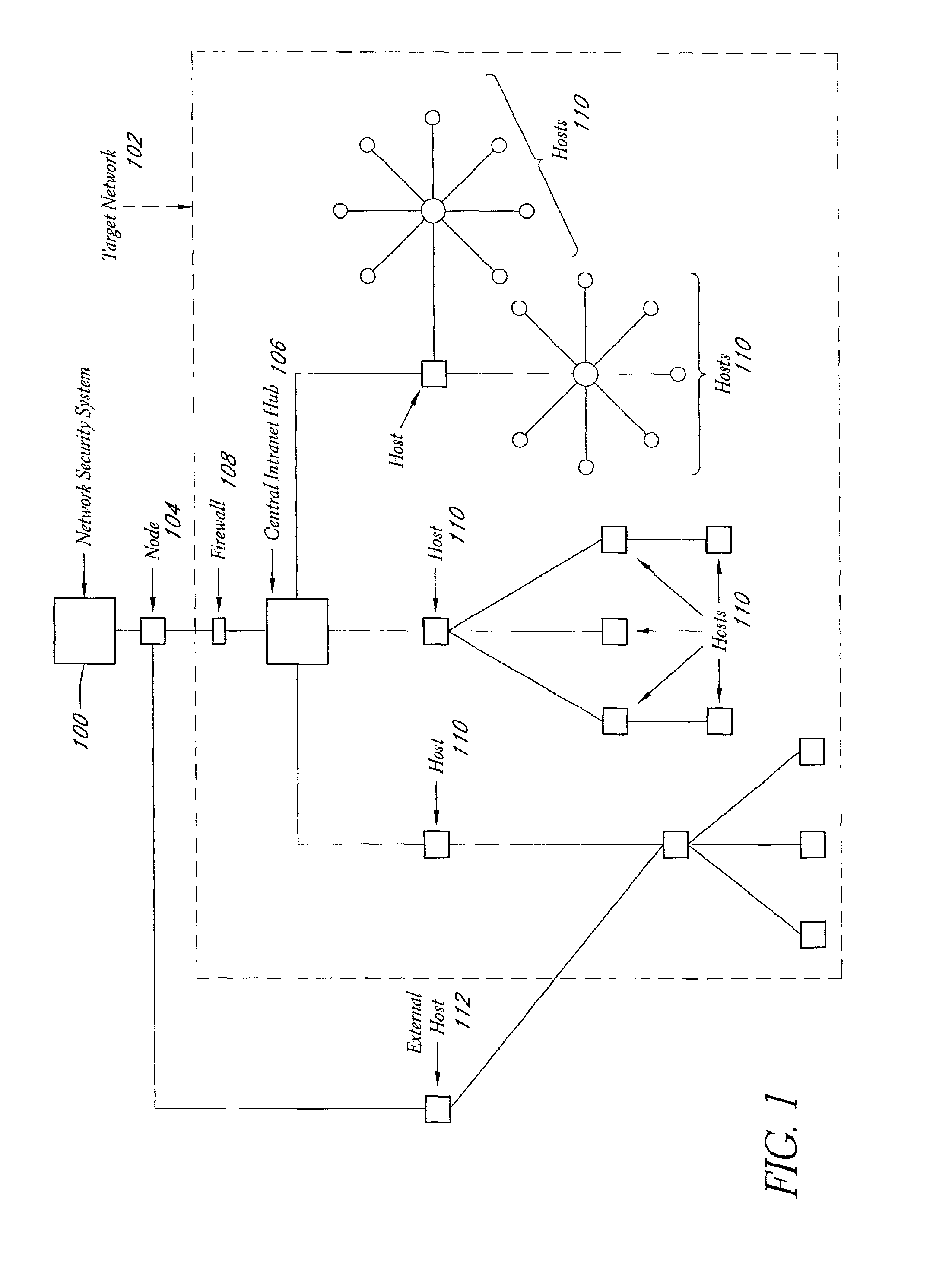
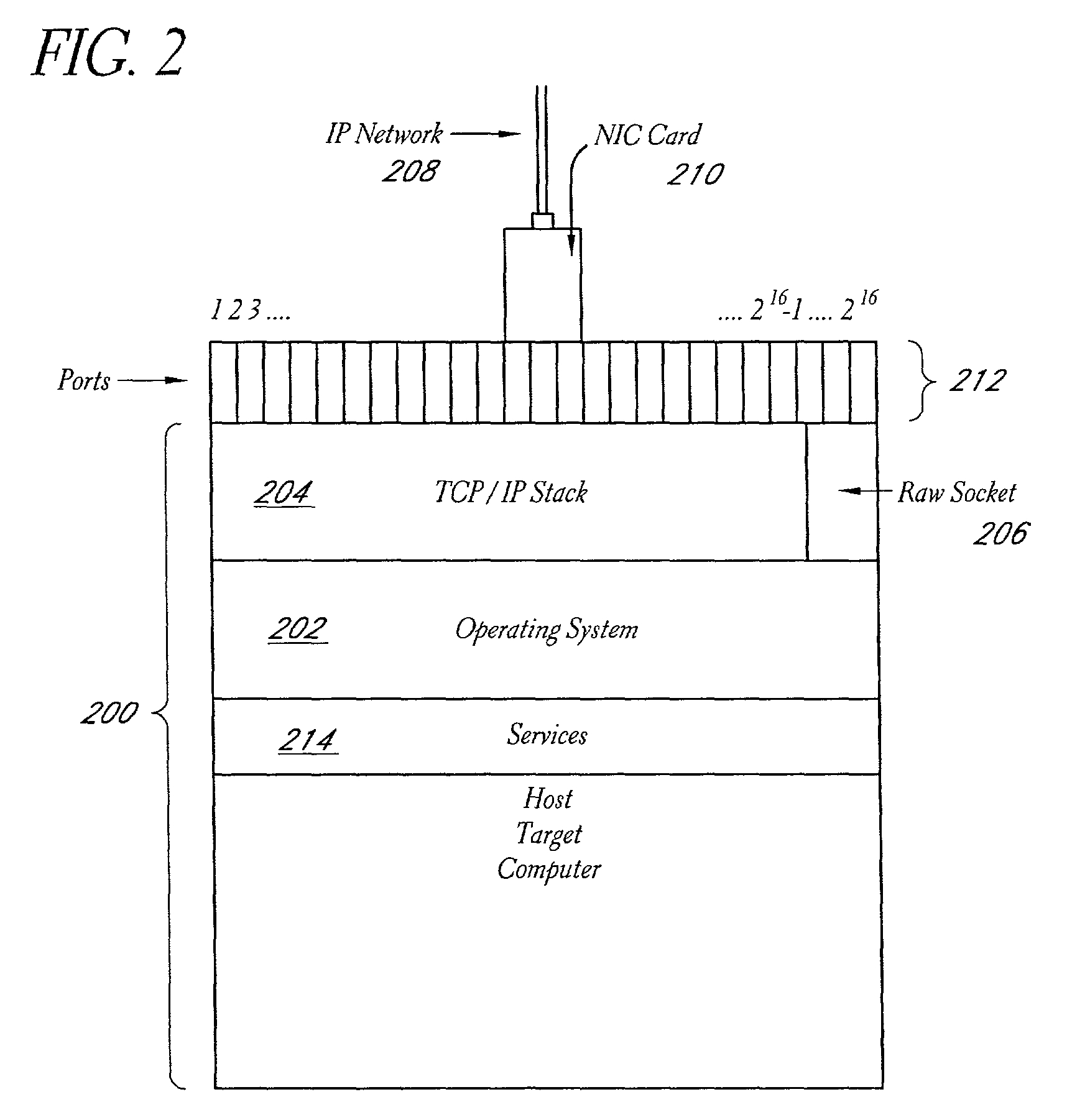
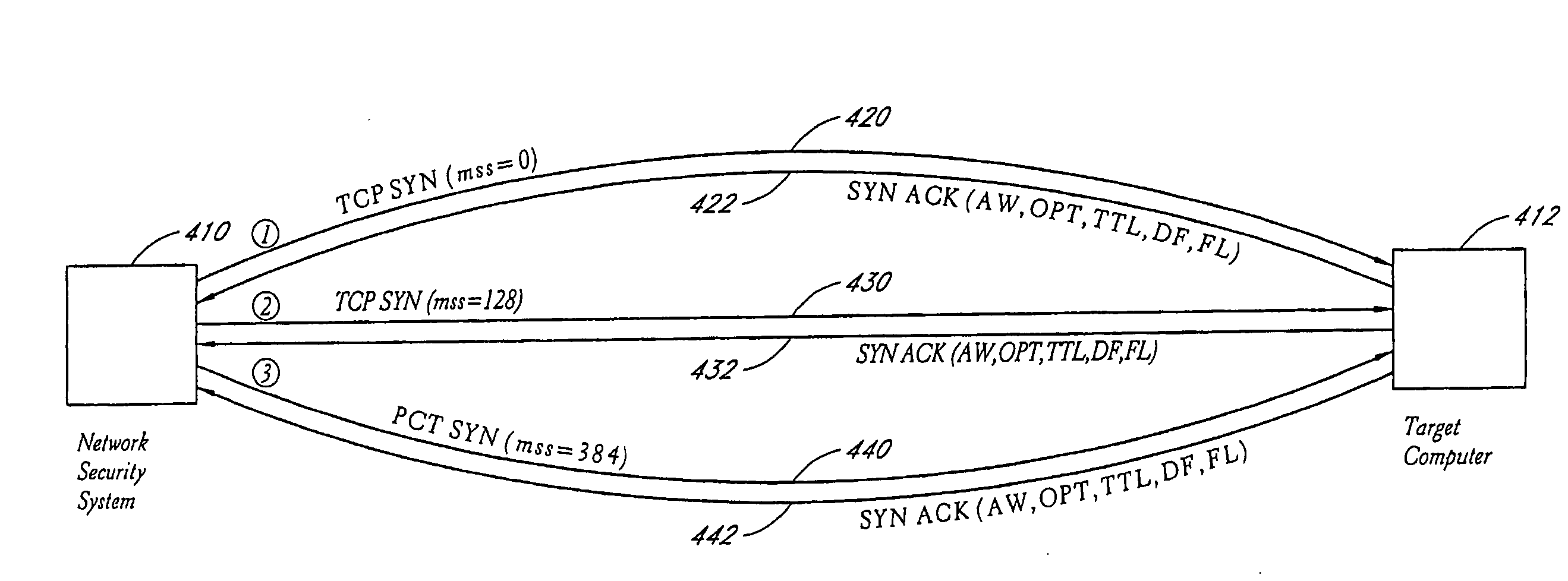
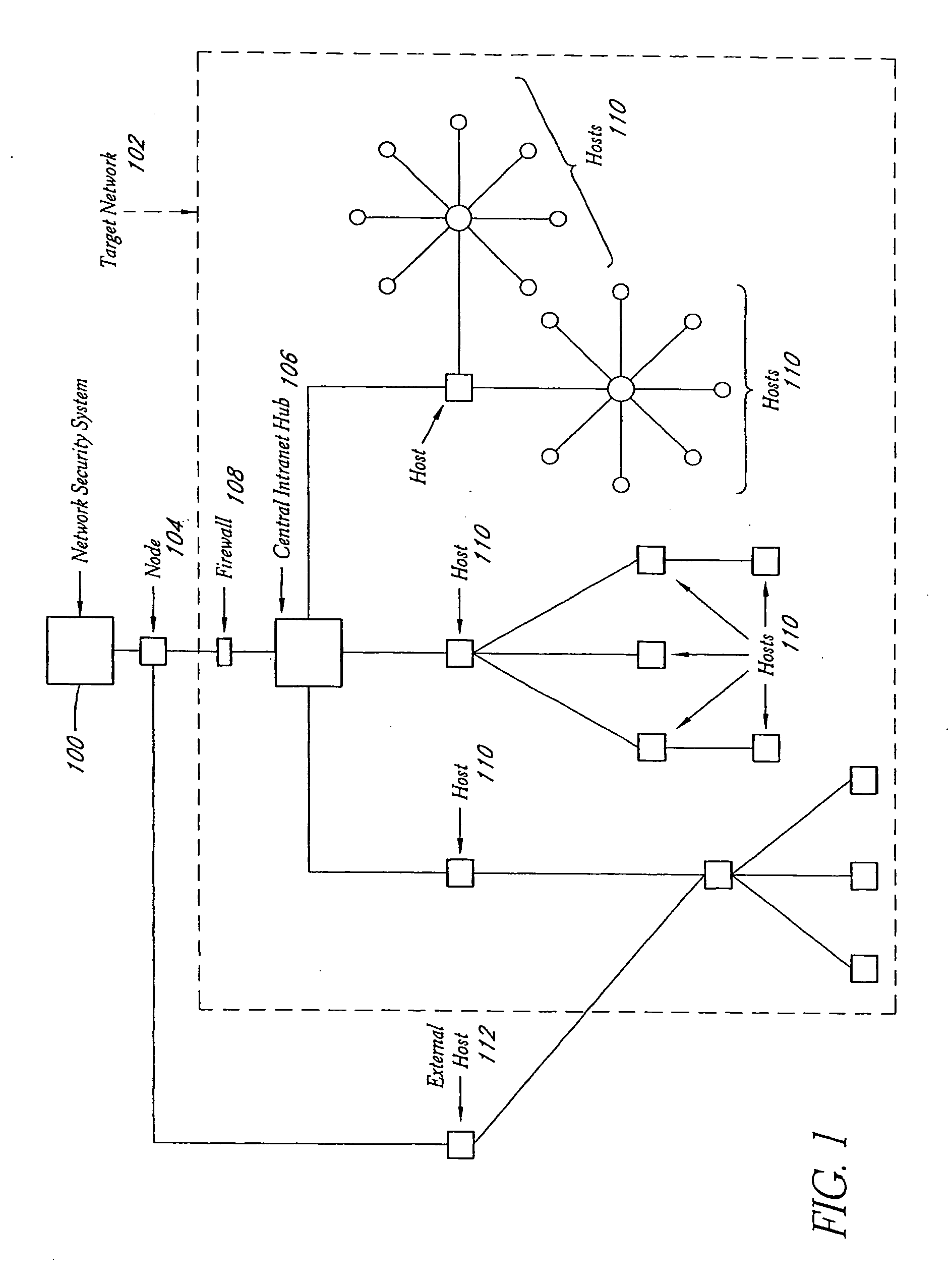
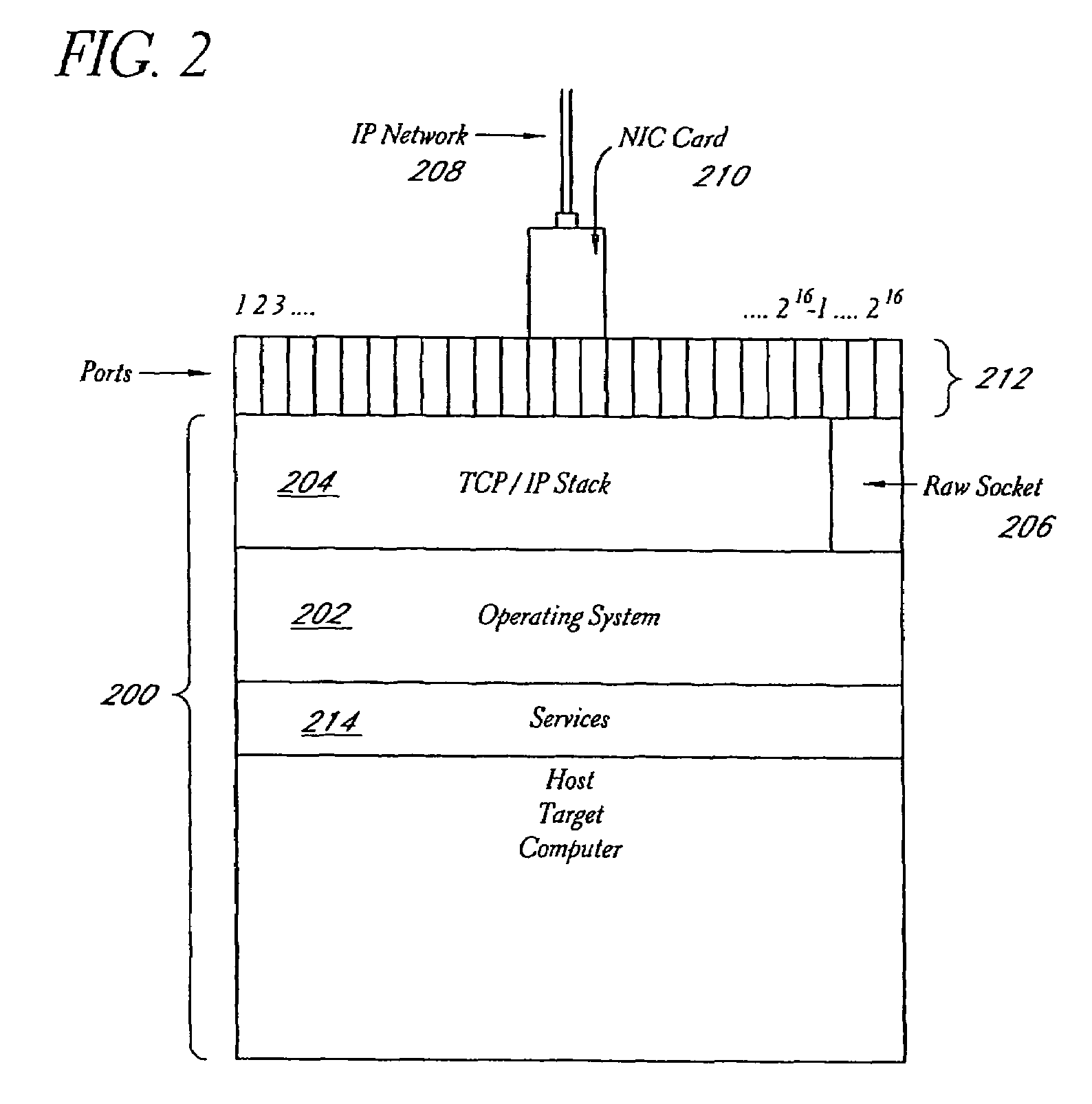
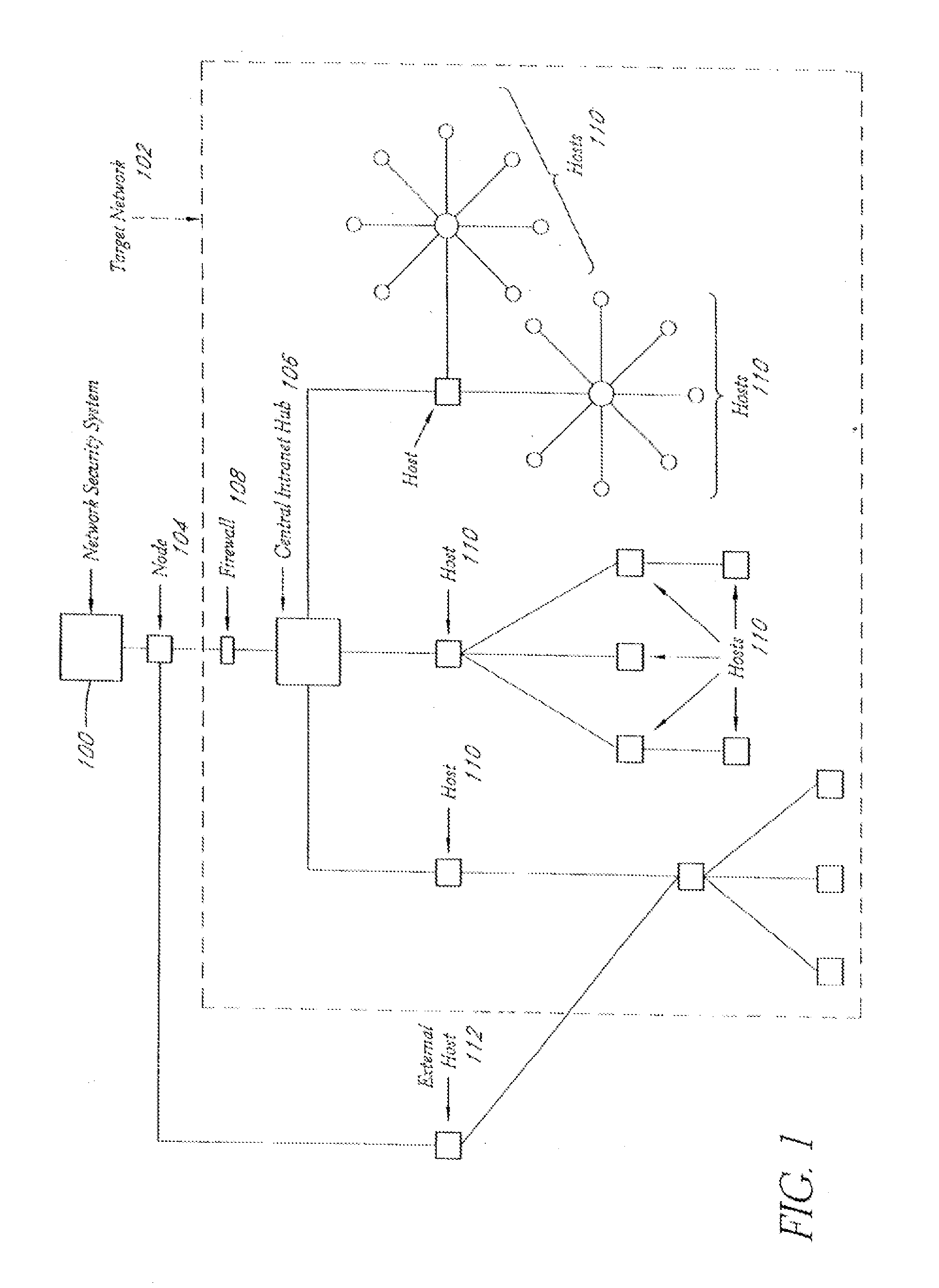
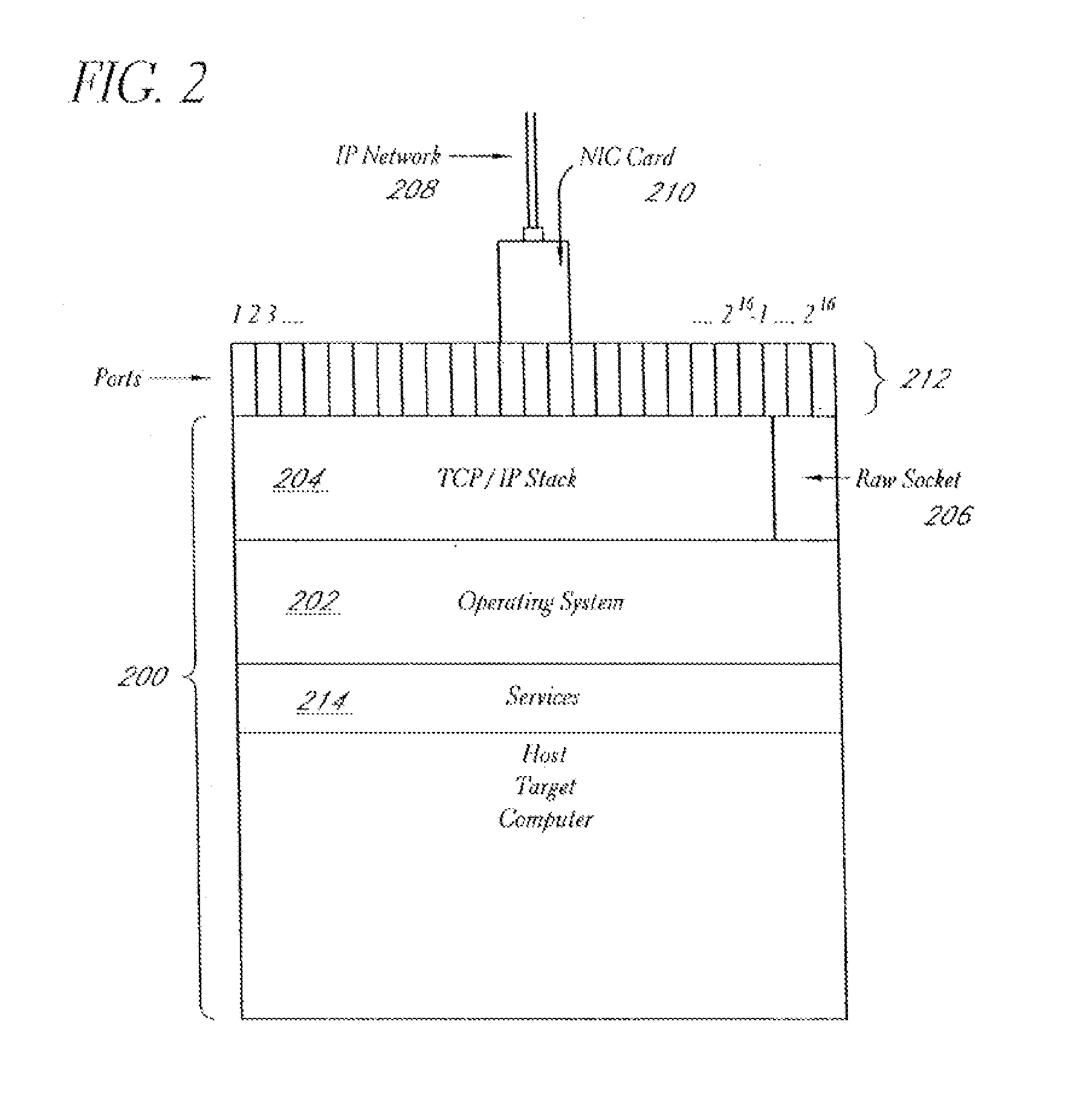
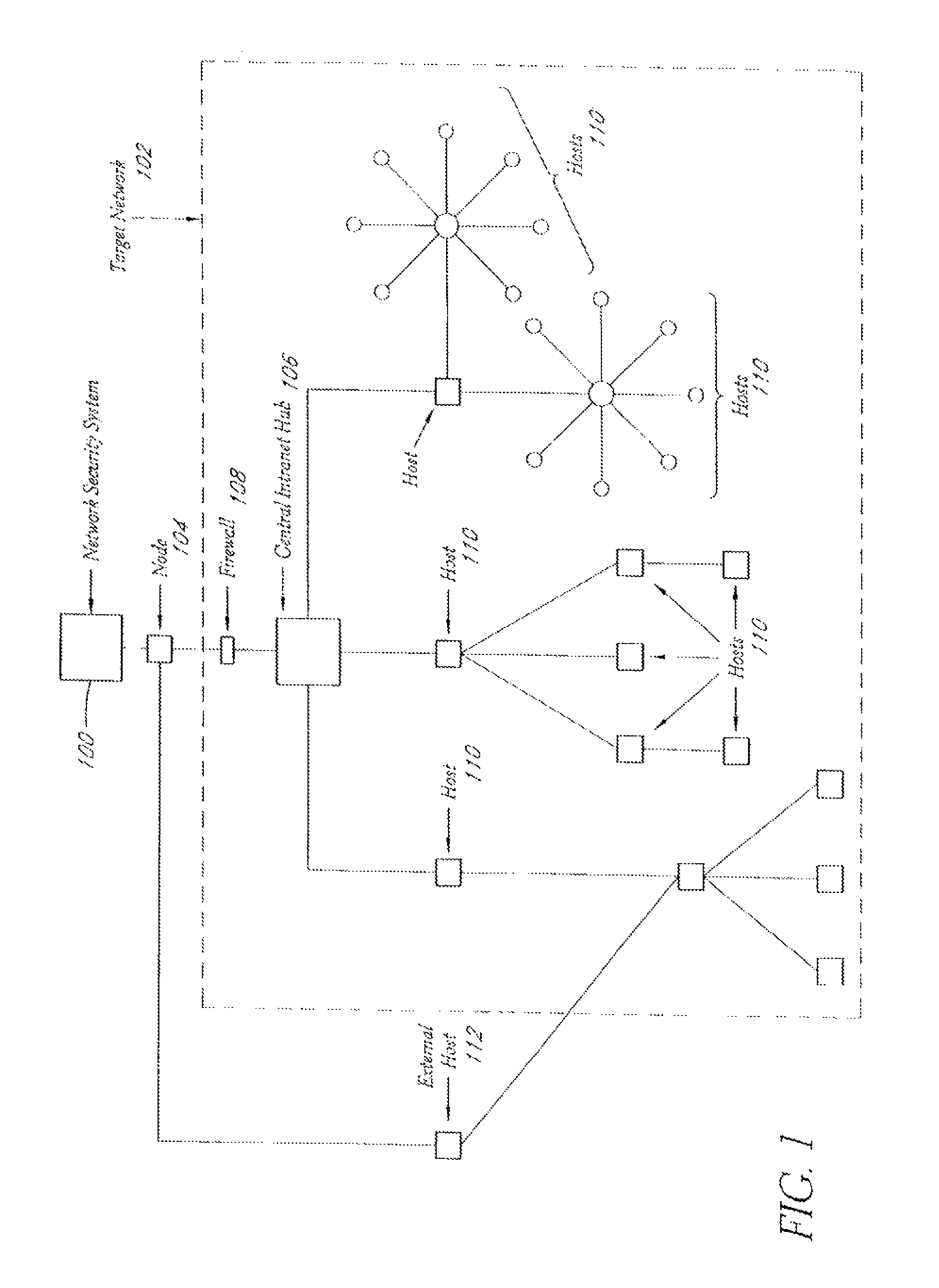
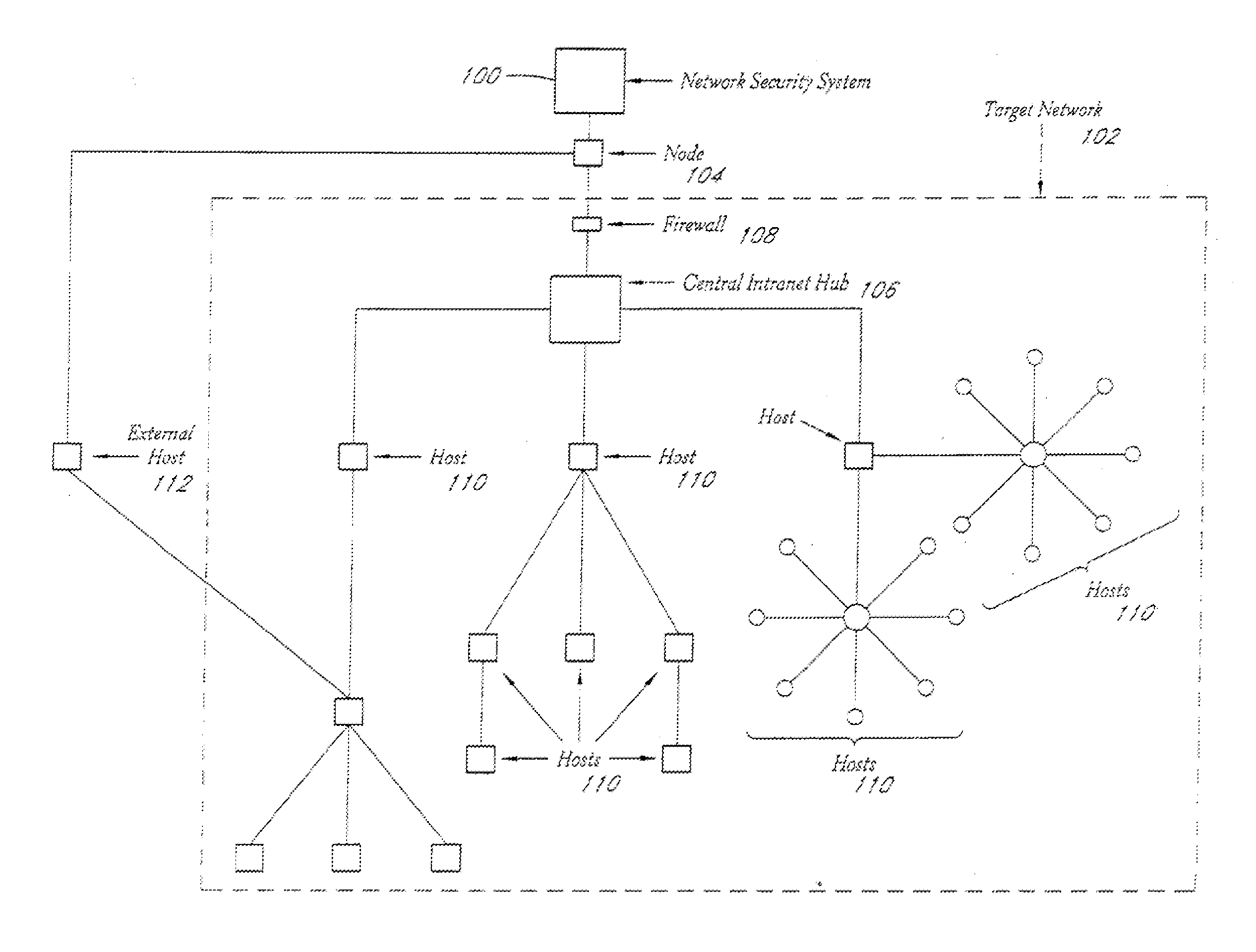
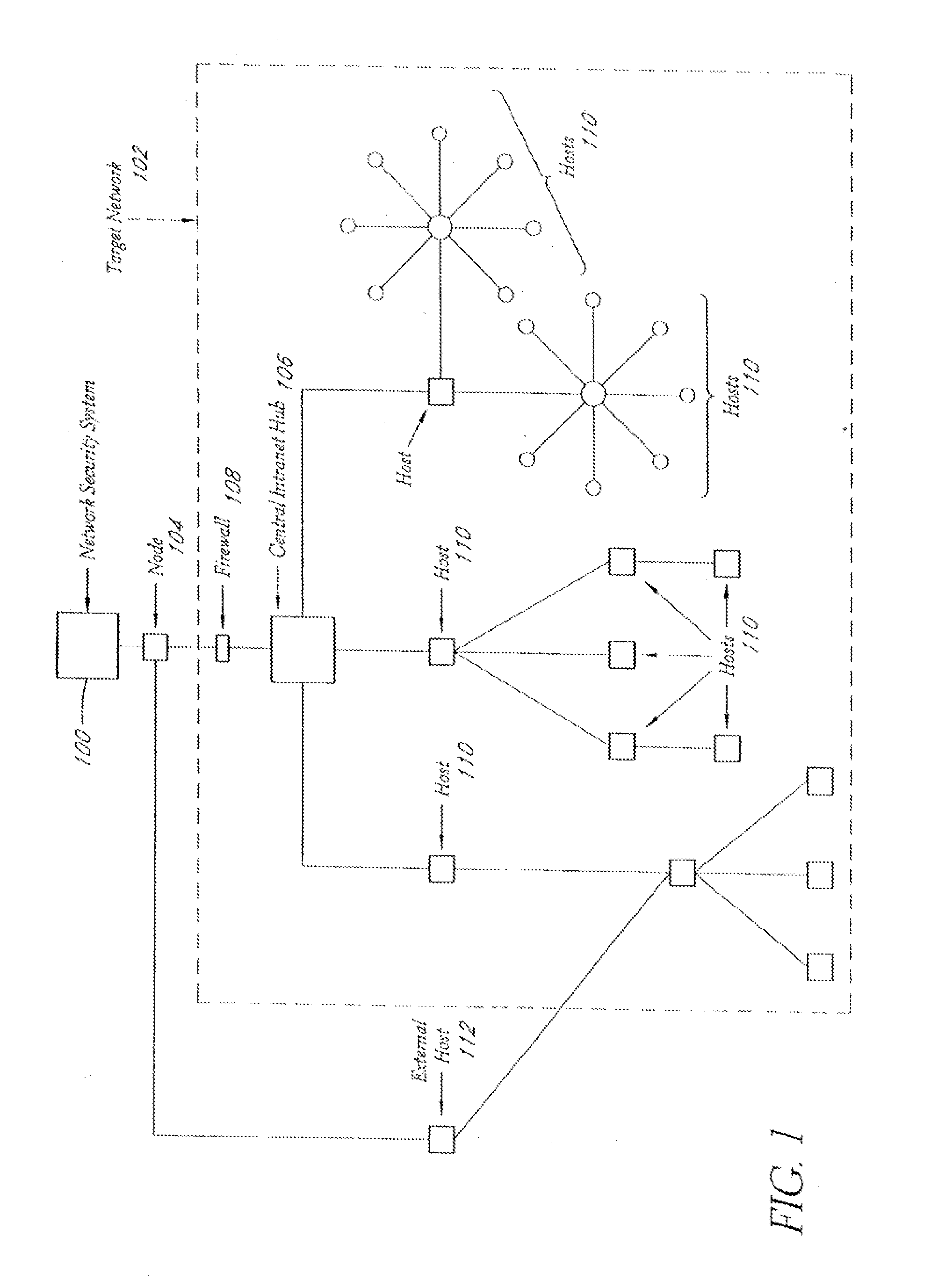
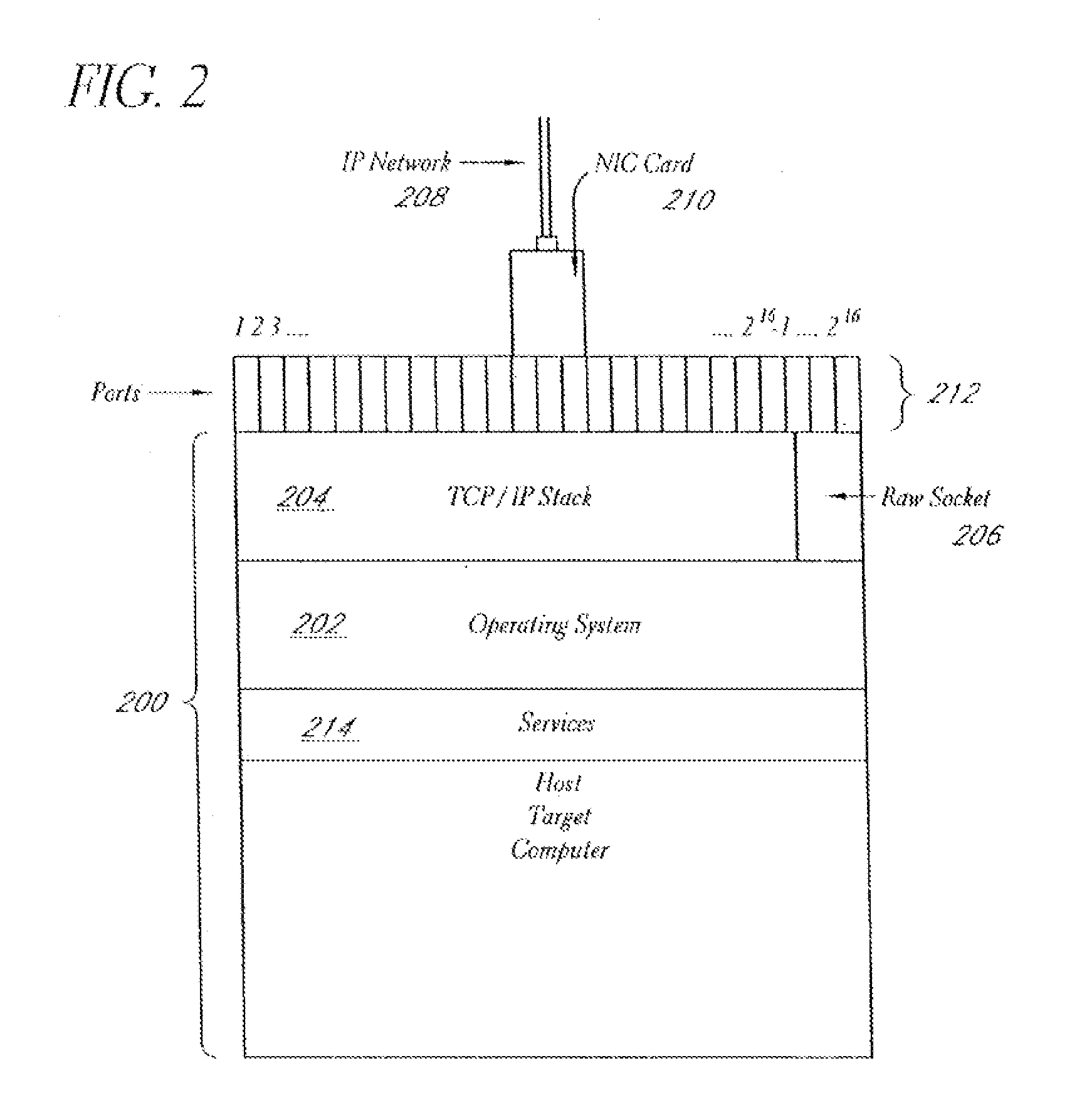
System and method for network vulnerability detection and reporting
ActiveUS7257630B2Reduce the possibilityReliably determinedMemory loss protectionError detection/correctionGraphicsOperational system
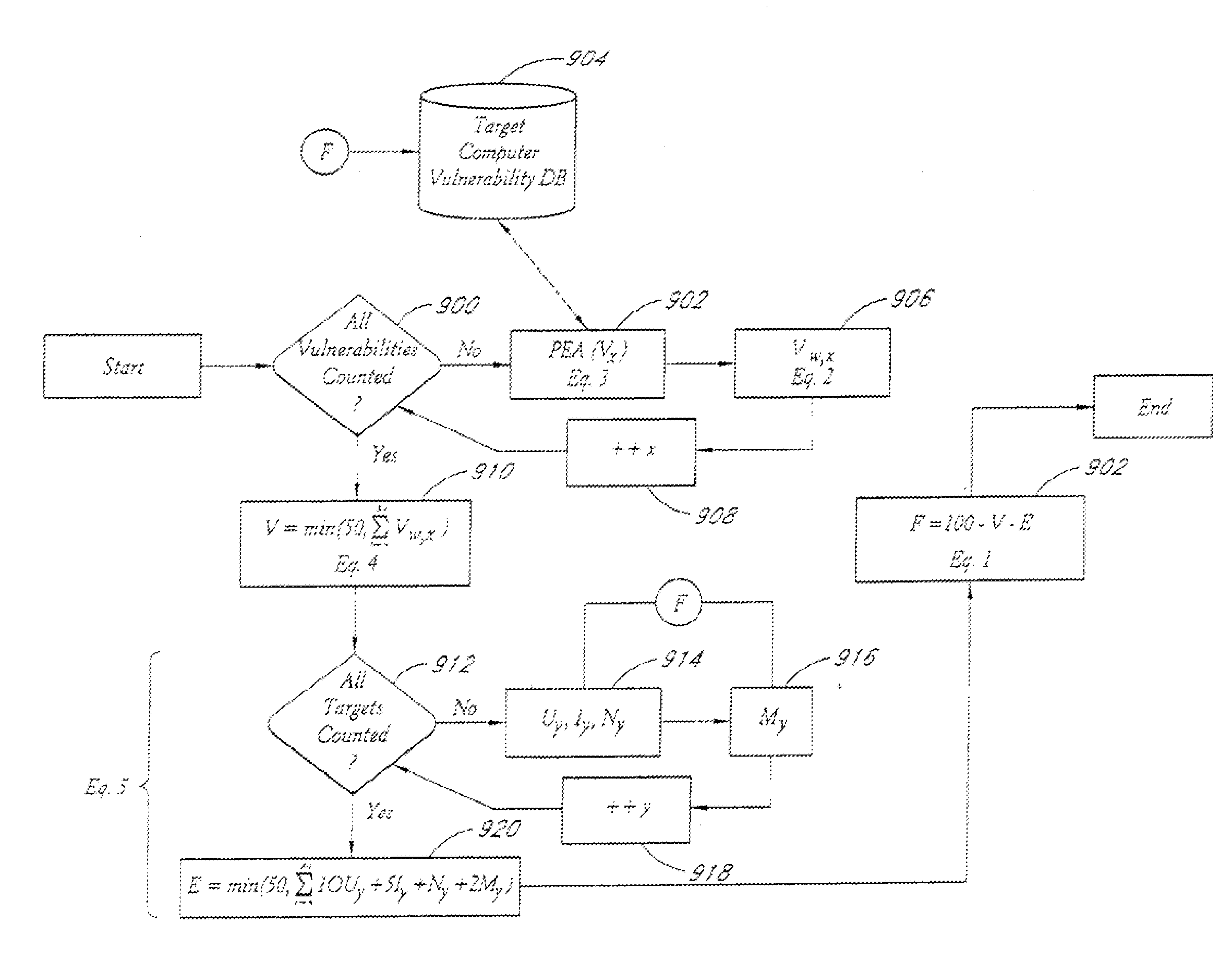
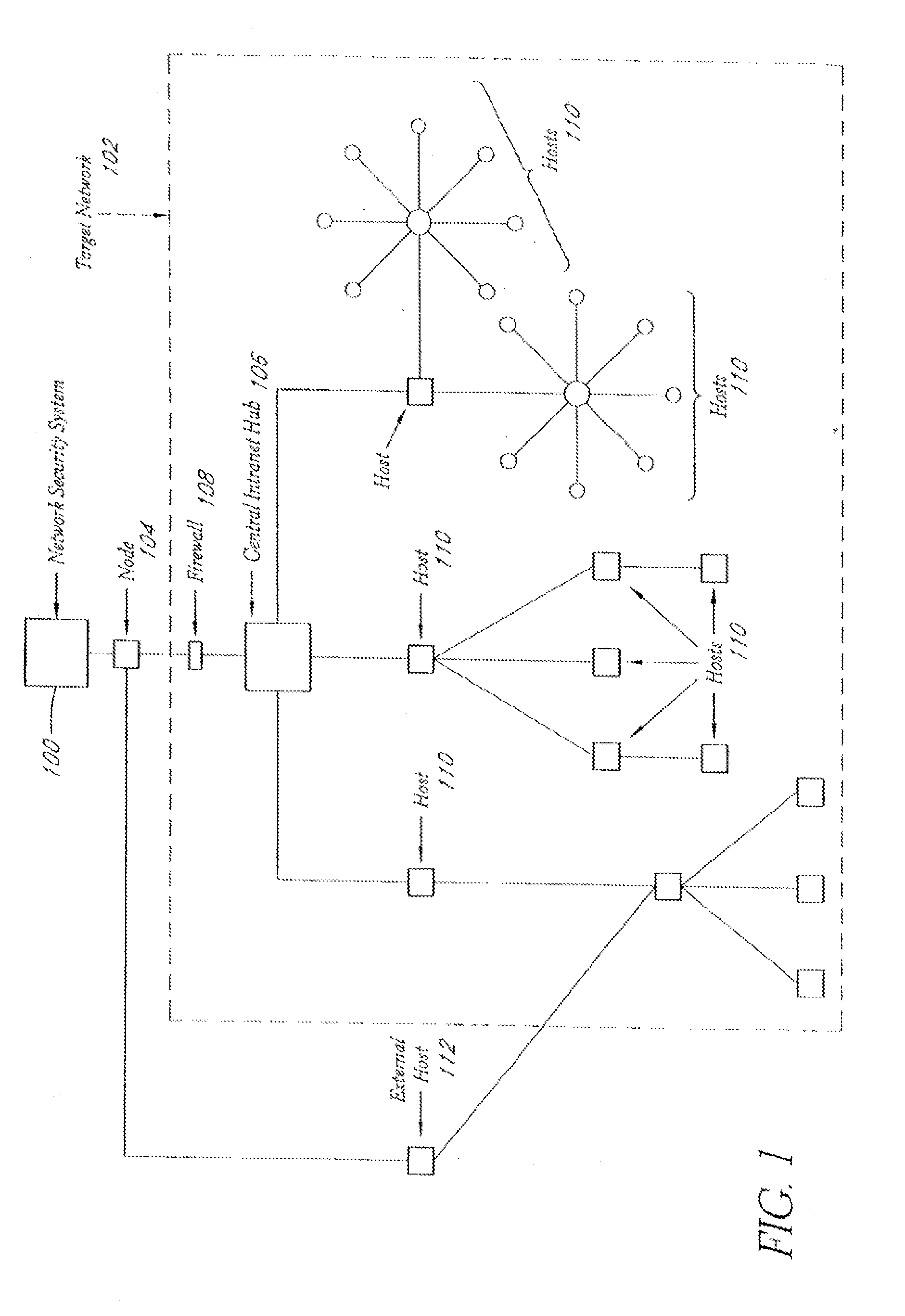
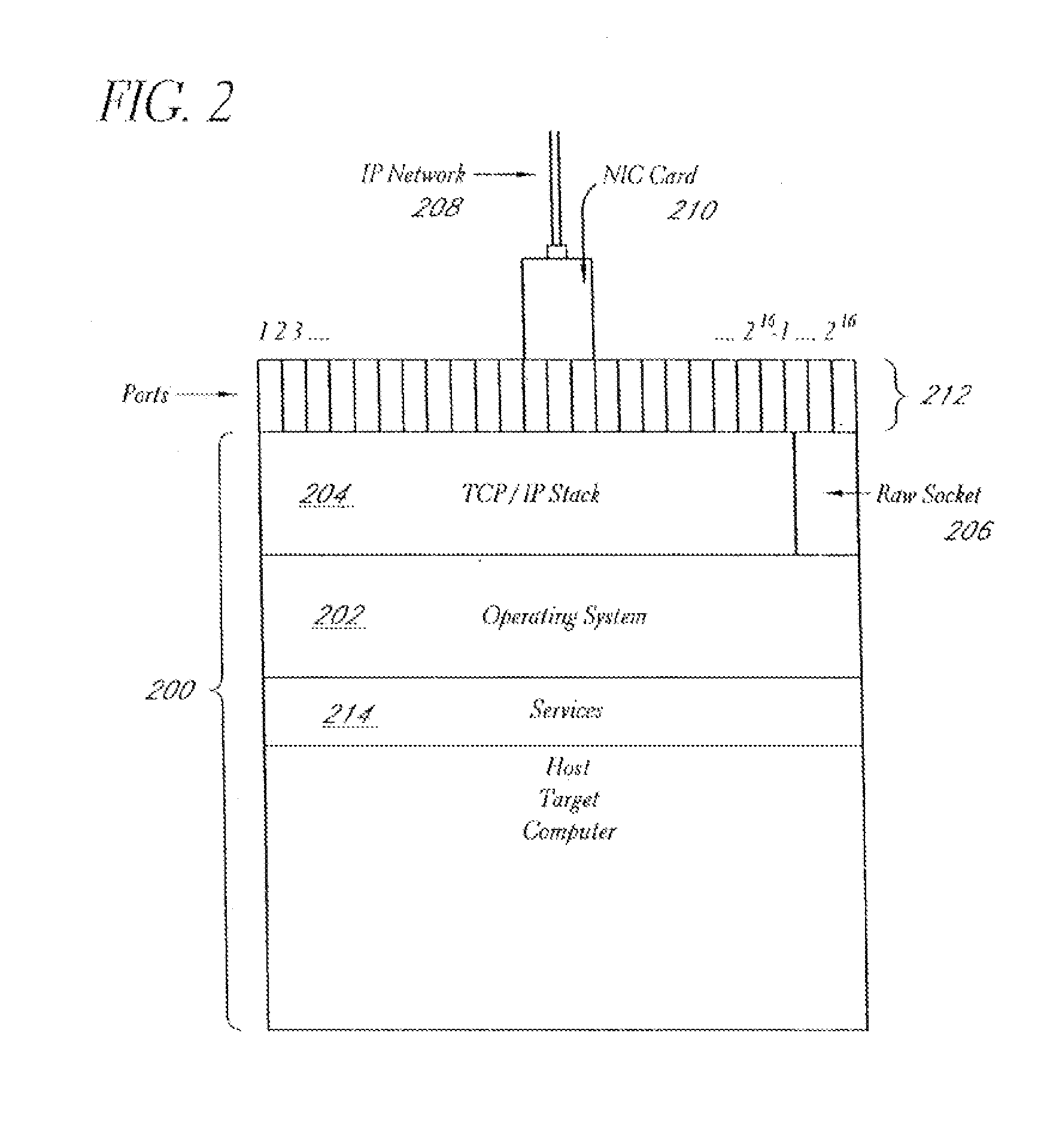
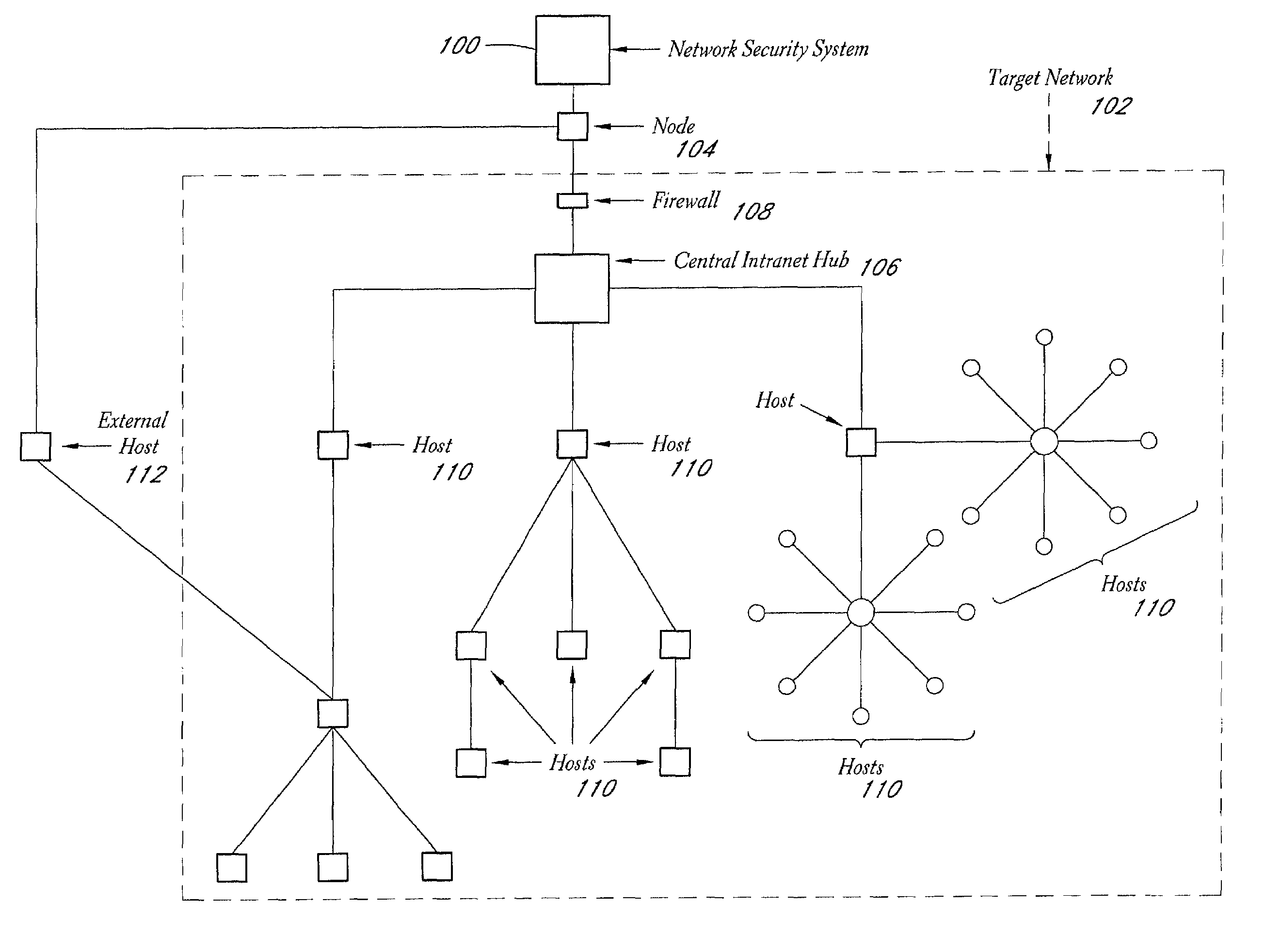
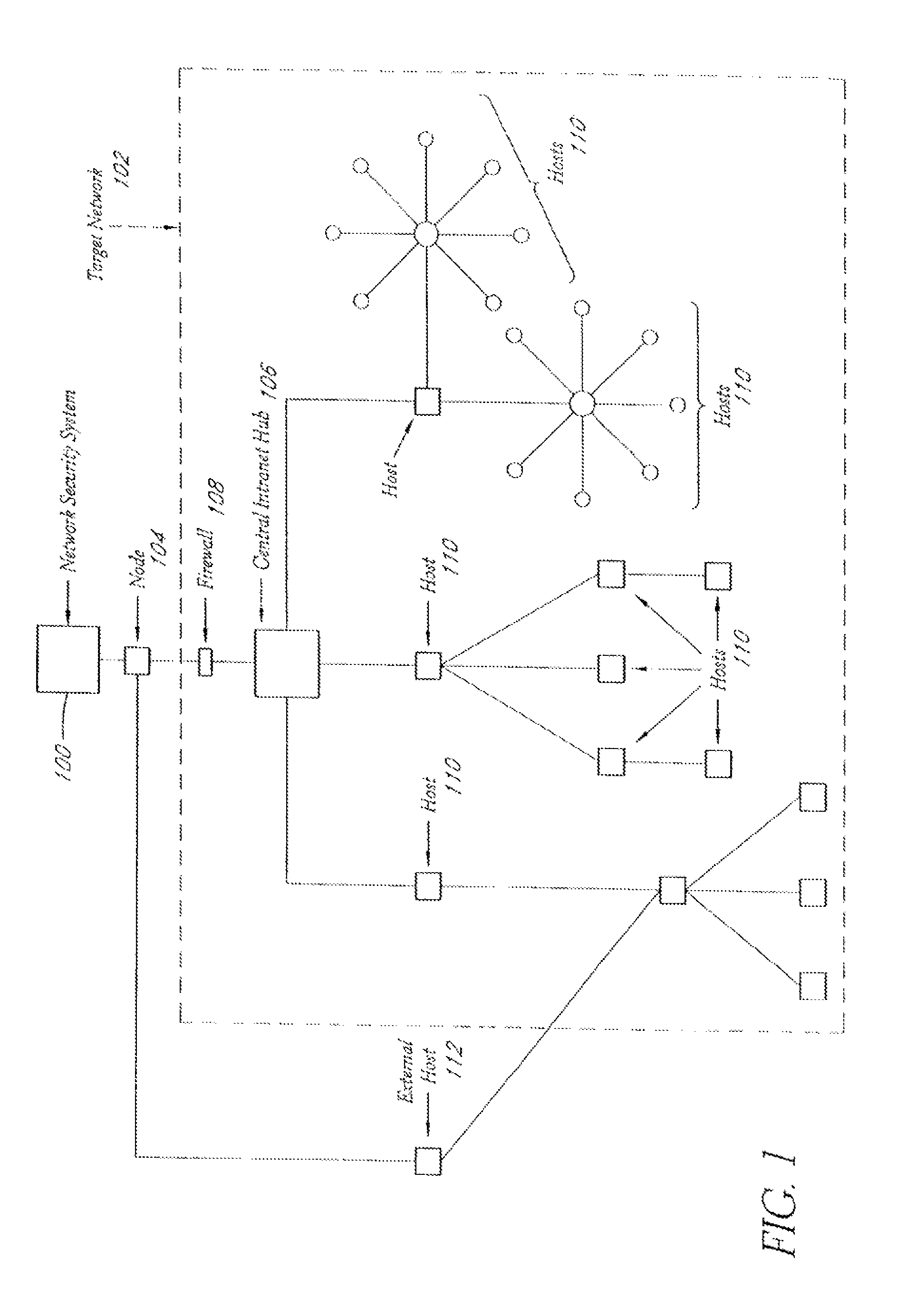
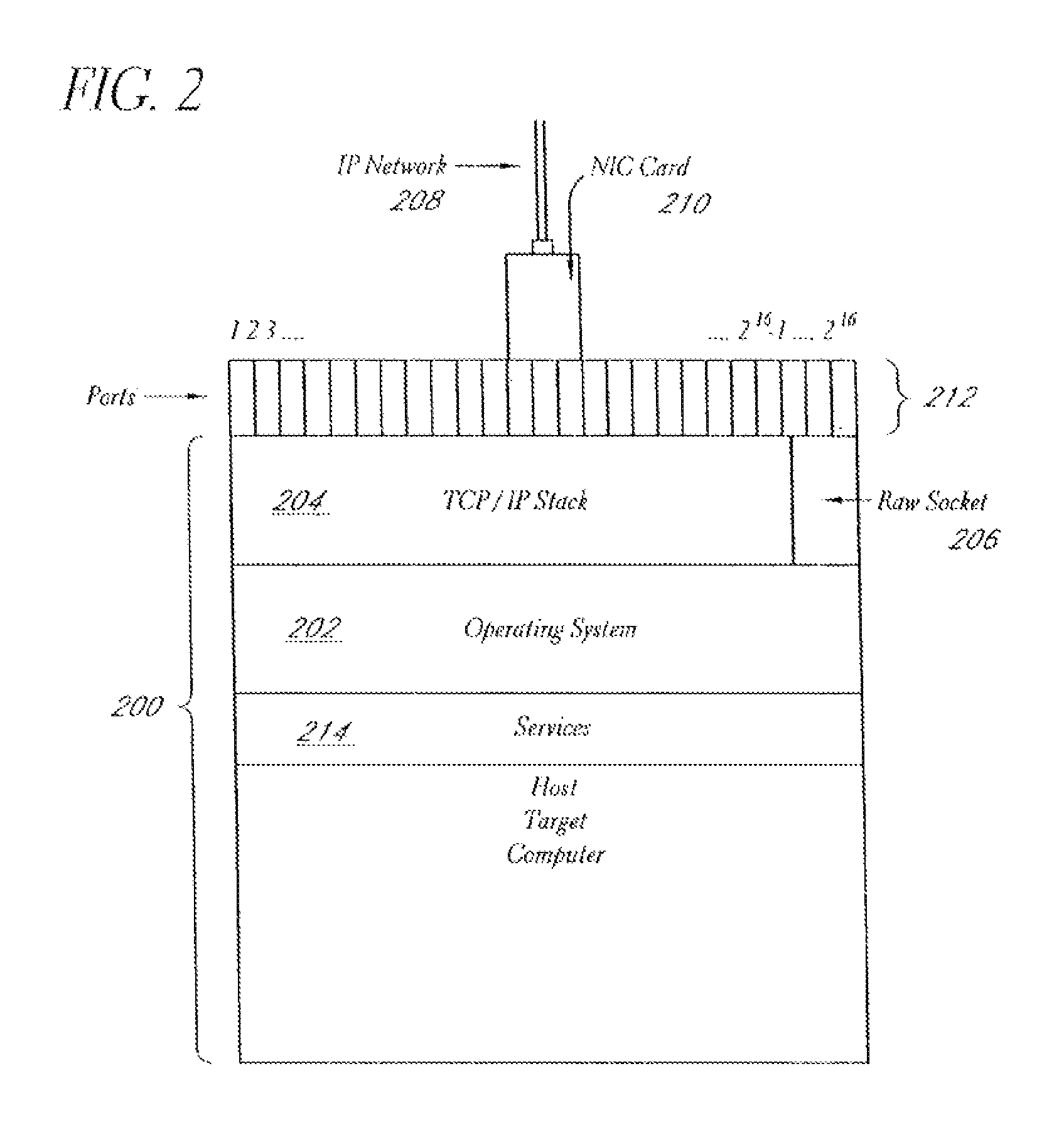
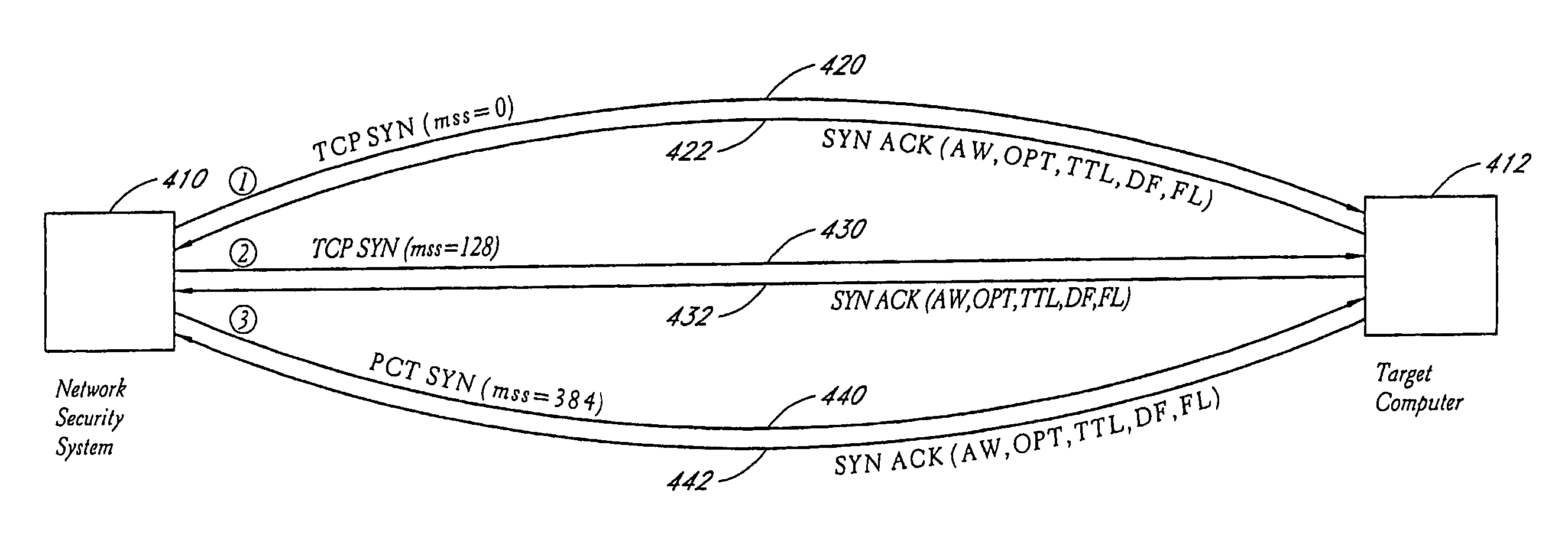
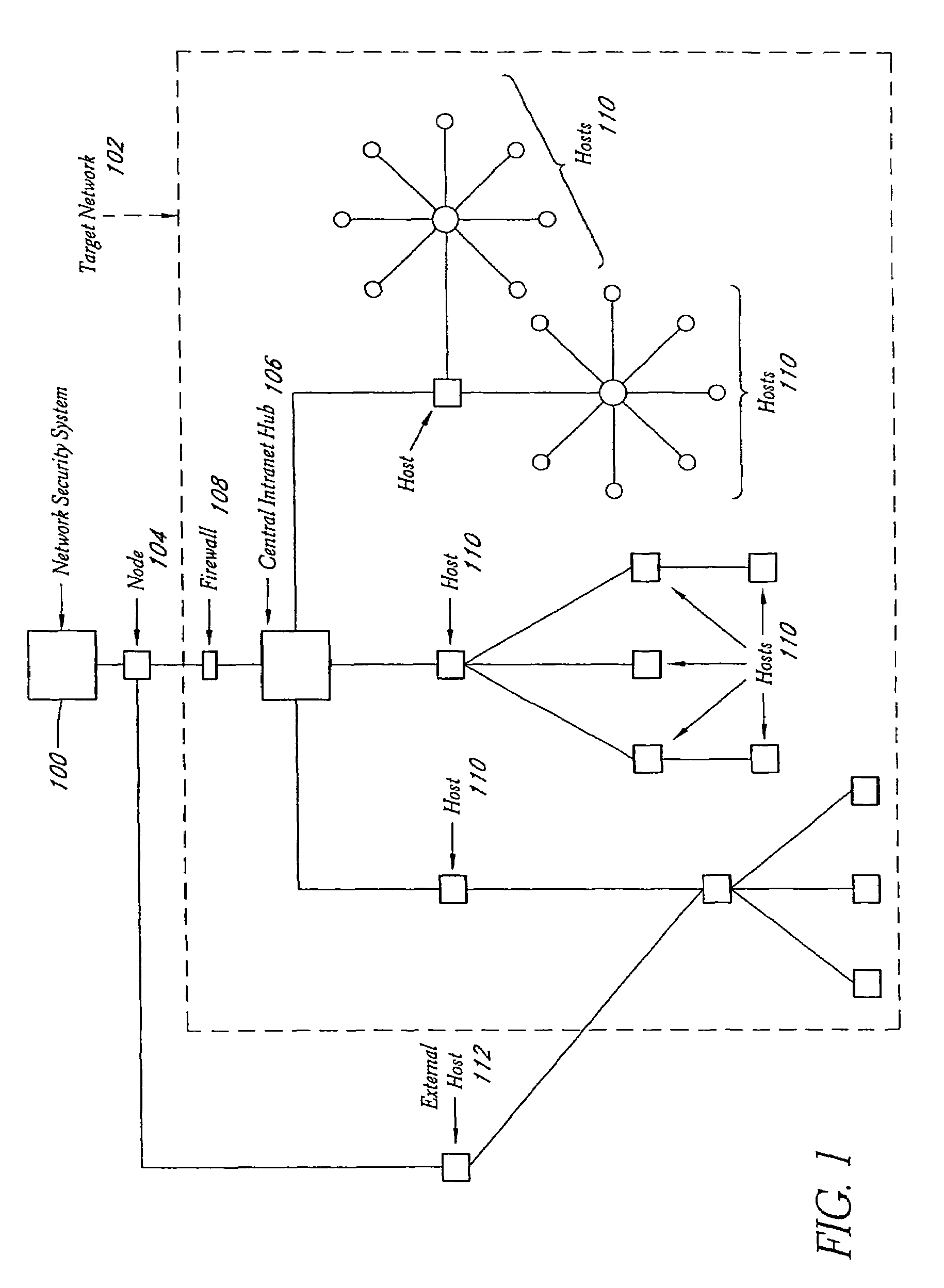
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
System and method for network vulnerability detection and reporting
ActiveUS7152105B2Easy to useReliably determinedElectric signal transmission systemsImage analysisGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
System and method for network vulnerability detection and reporting
InactiveUS20070011319A1Easy to useReliably determinedDigital computer detailsPolarising elementsGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
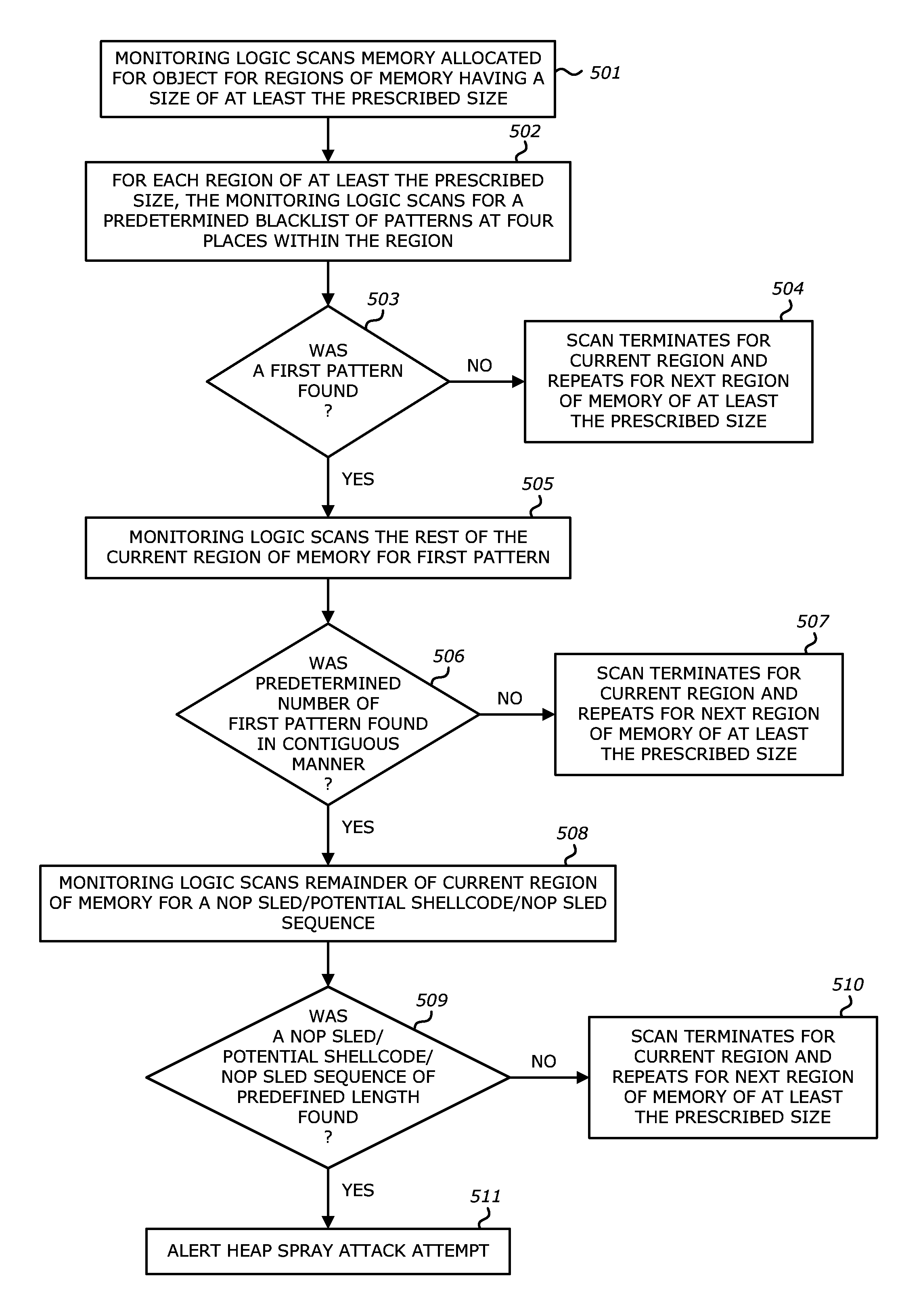
Computer exploit detection using heap spray pattern matching
ActiveUS9438623B1Analogue secracy/subscription systemsPlatform integrity maintainancePattern matchingTheoretical computer science
According to one embodiment, a threat detection system is integrated with at least a dynamic analysis engine. The dynamic analysis engine is configured to automatically to detect potential shellcode at a first storage location within a region of memory allocated for an application, conduct a first search at one or more storage locations prior to the first storage location within the region of allocated memory for at least one or more patterns, conduct a second search at one or more storage locations subsequent to the first storage location within the region of allocated memory for at least one or more patterns, detect a first pattern at one or more storage locations prior to the first storage location within the region of allocated memory, and detect a second pattern at one or more storage locations subsequent to the first storage location with the region of allocated memory, wherein at least one of the first pattern or the second pattern is absent from a predefined list of patterns.
Owner:FIREEYE SECURITY HLDG US LLC
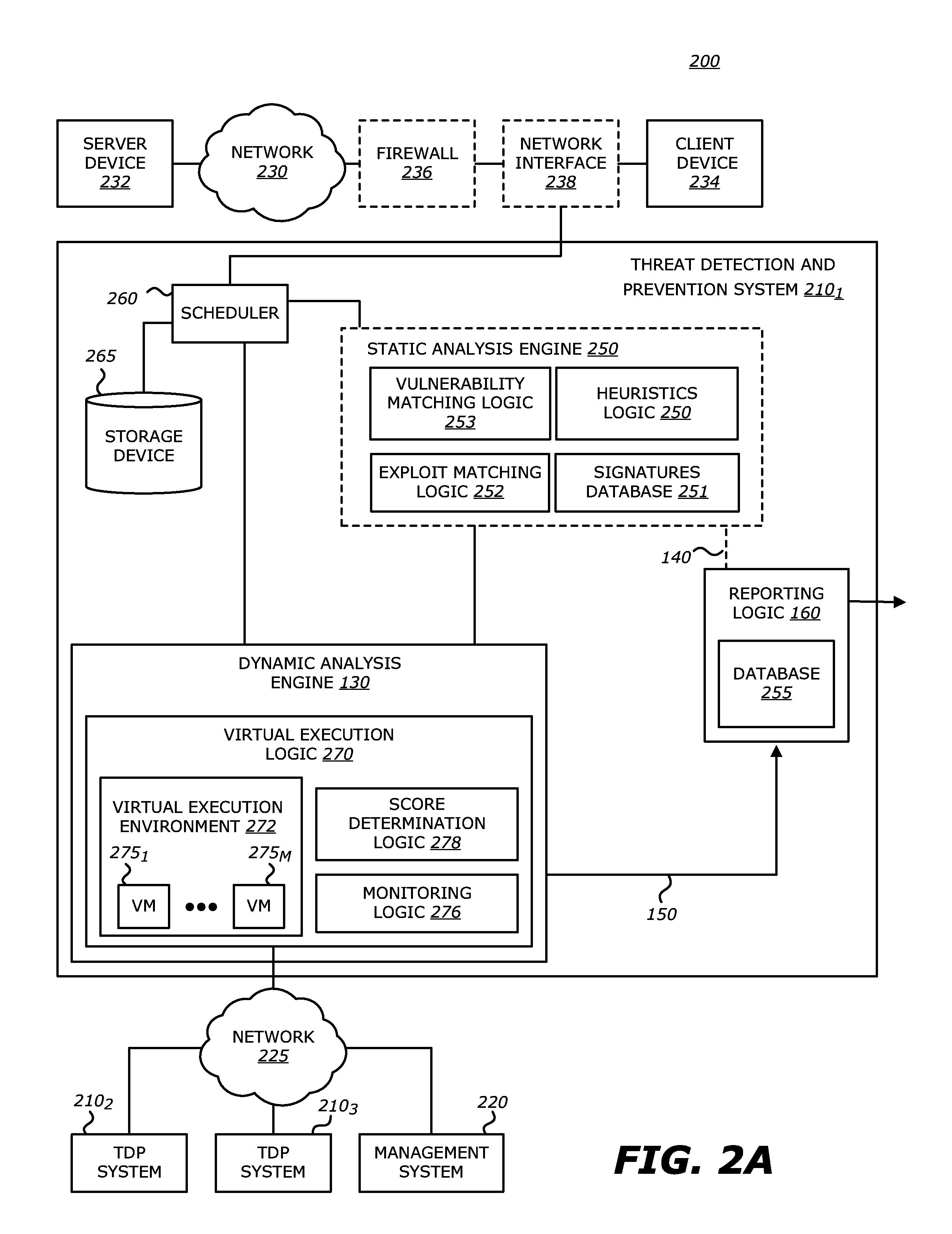
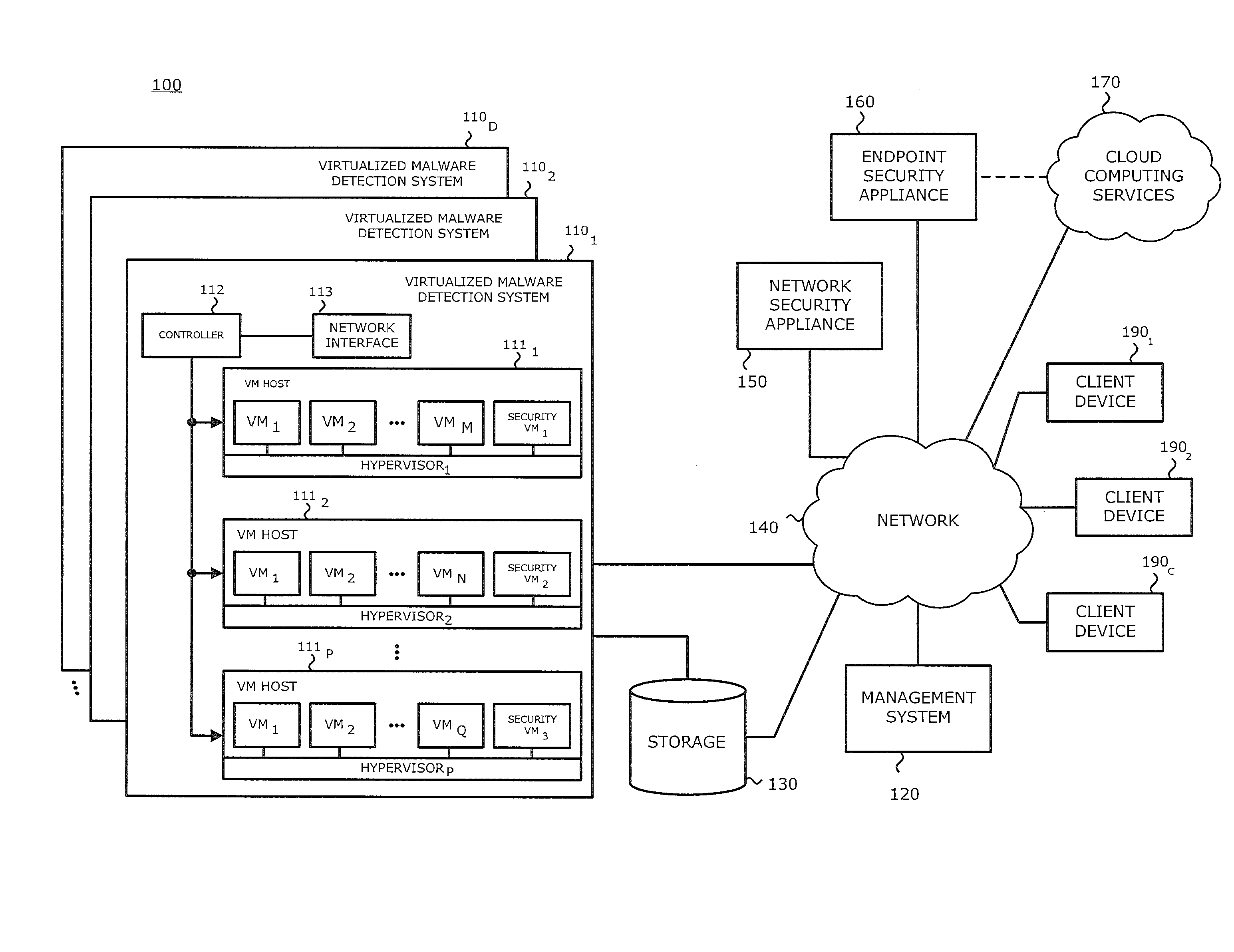
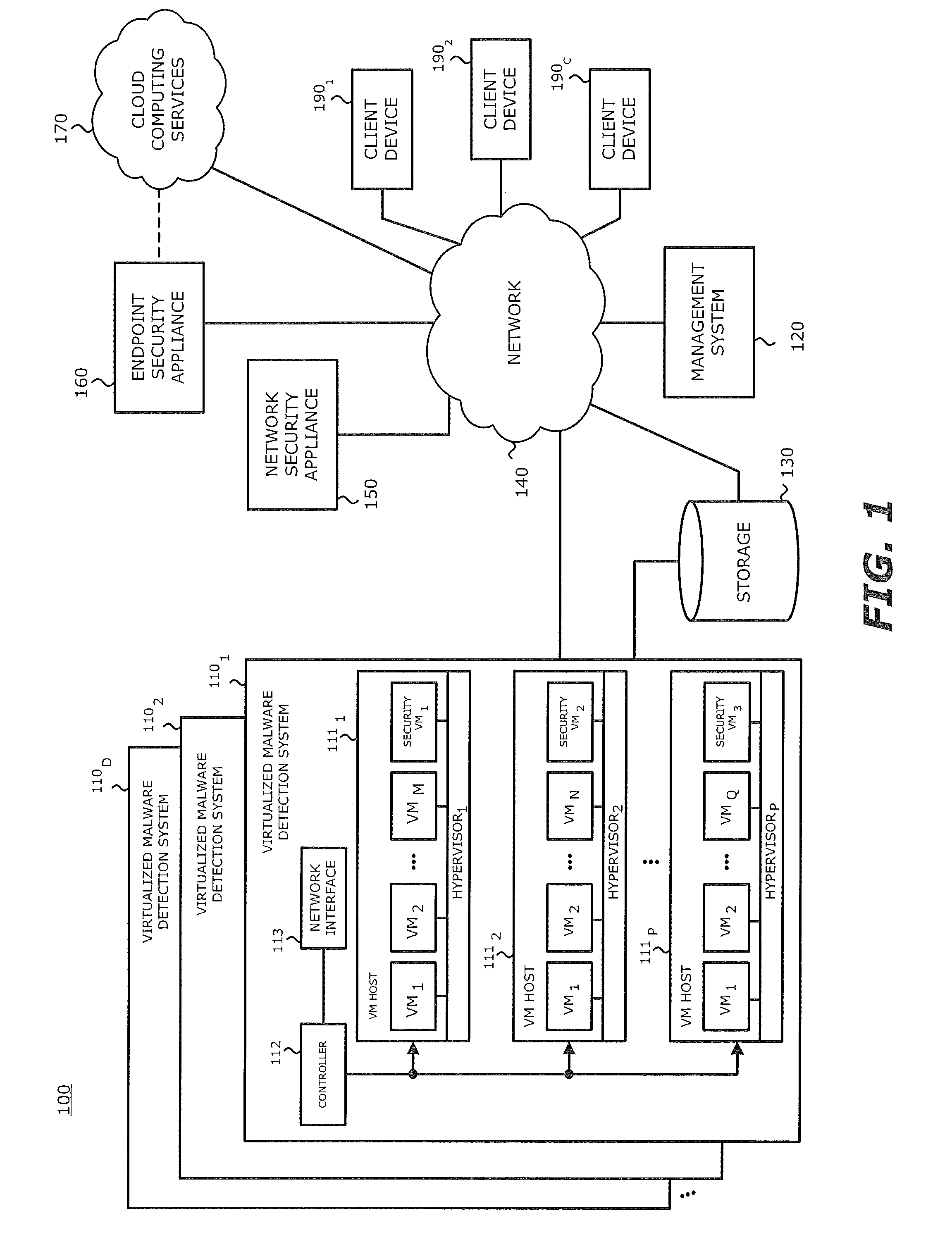
Exploit detection system
According to one embodiment, a virtualized malware detection system is integrated with a virtual machine host including a plurality of virtual machines and a security virtual machine. Logic within the virtual machines are configured to perform a dynamic analysis of an object and monitor for the occurrence of a triggering event. Upon detection of a triggering event within a virtual machine, the logic within the virtual machine provides the security virtual machine with information associated with the triggering event for further analysis. Based on the further analysis, the object may then be classified as “non-malicious,” or “malicious.”
Owner:FIREEYE SECURITY HLDG US LLC
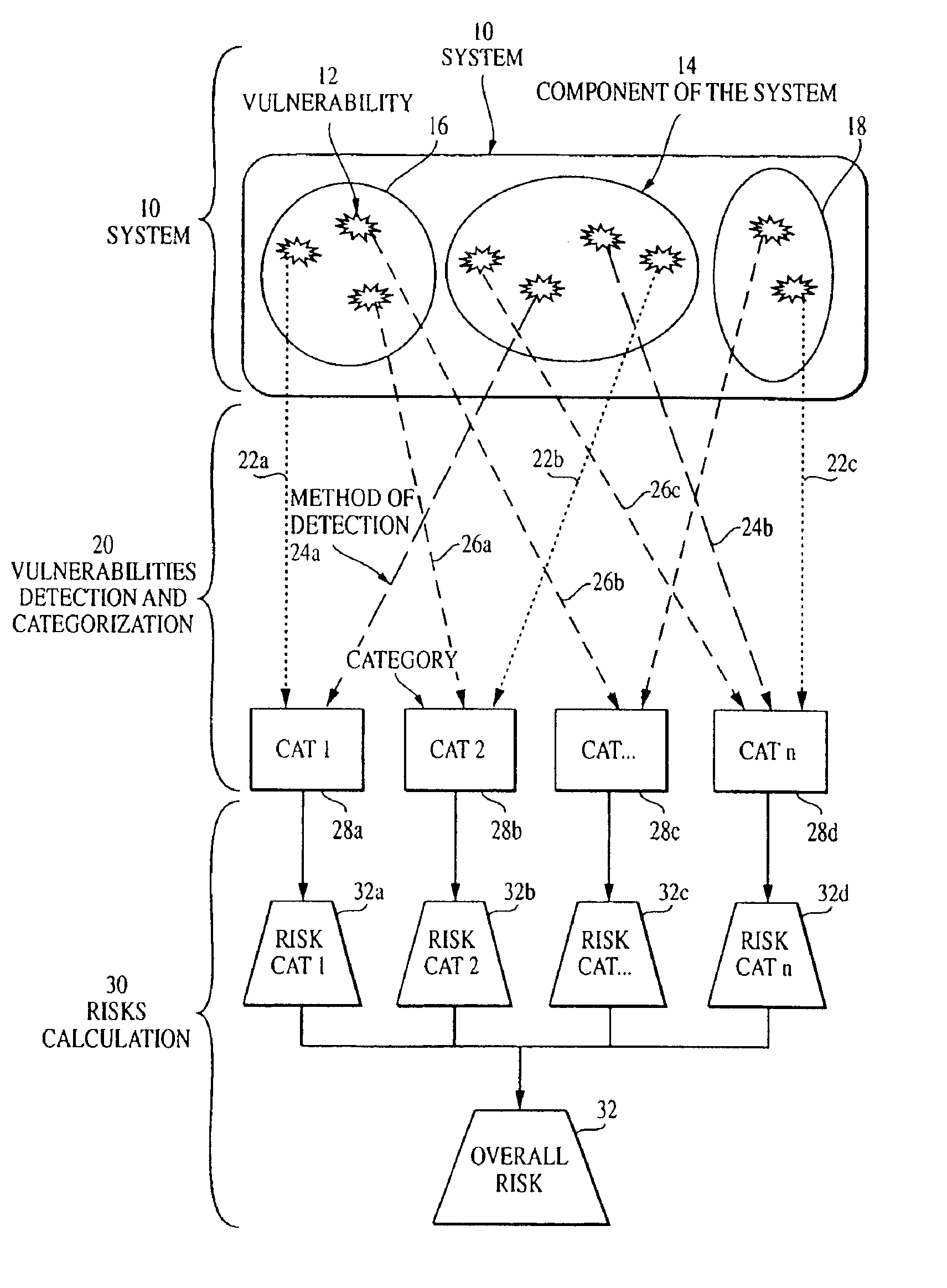
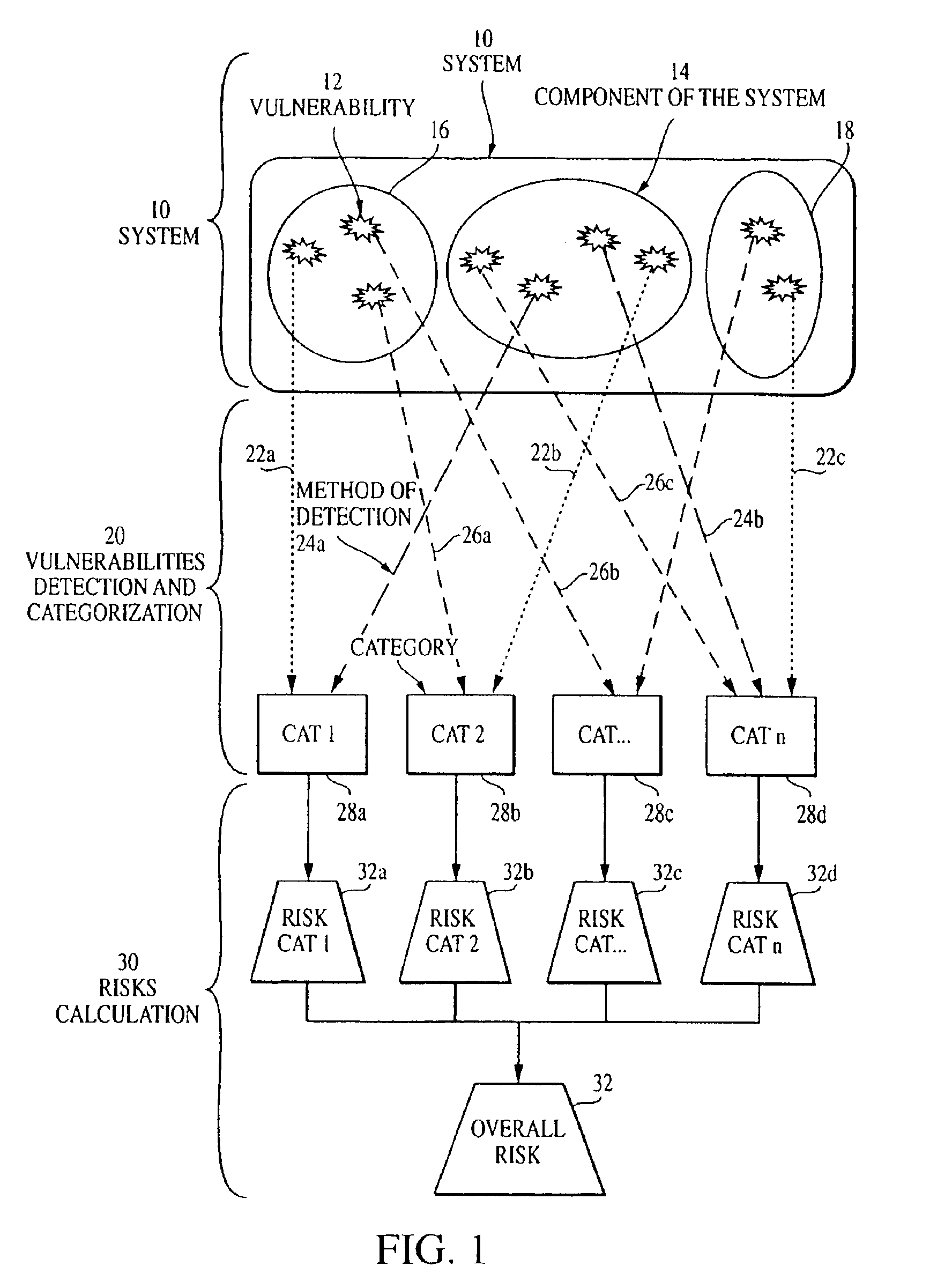
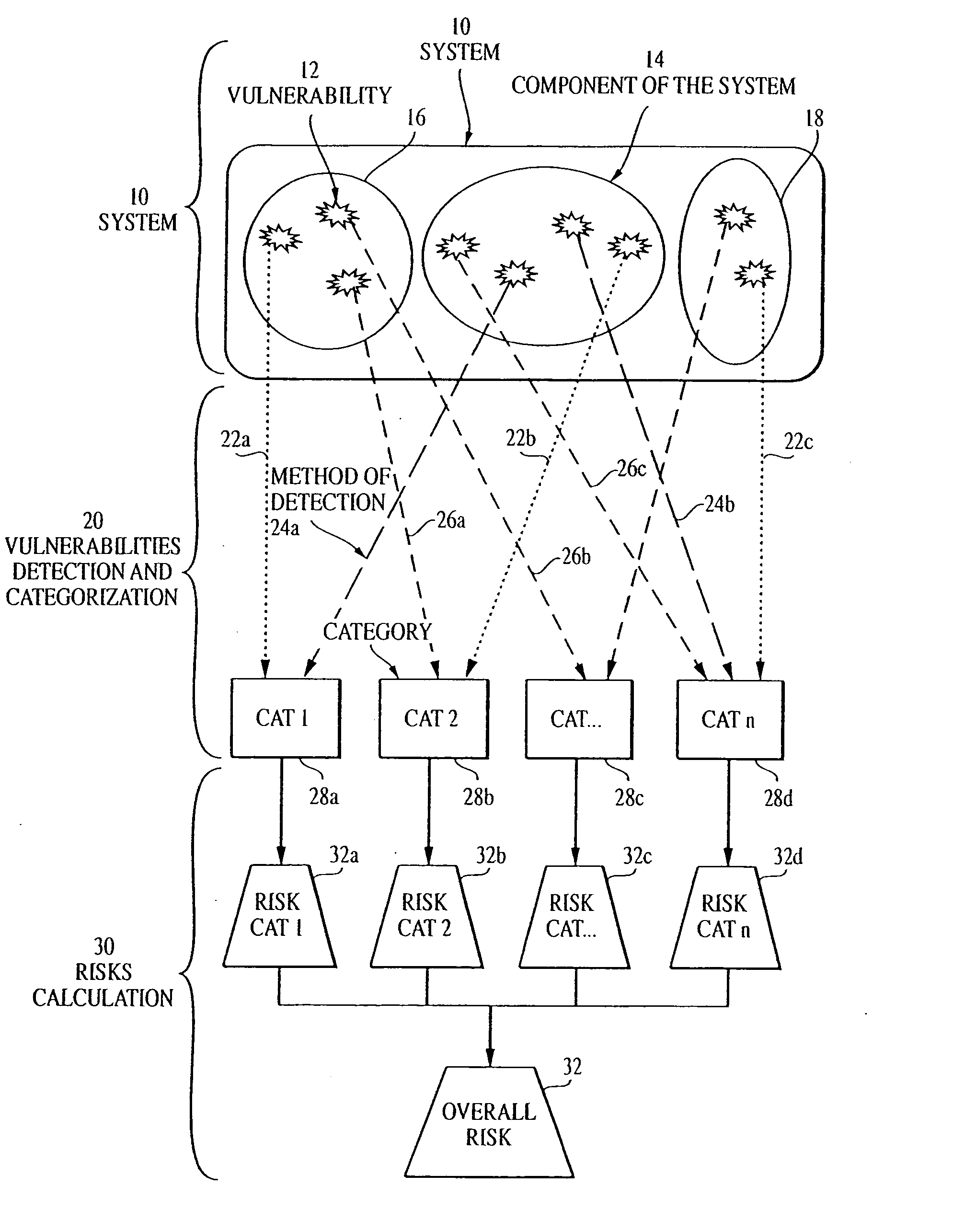
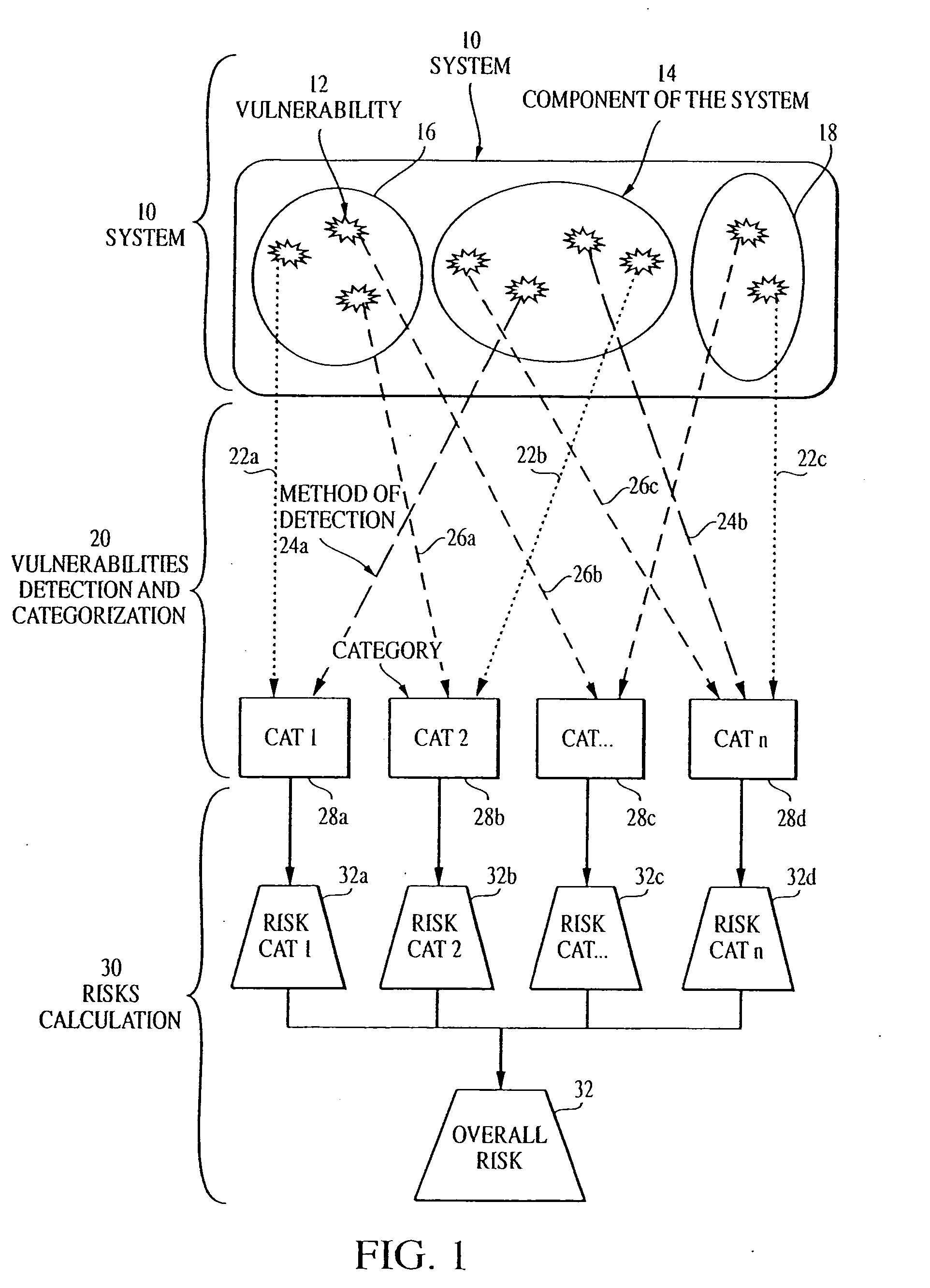
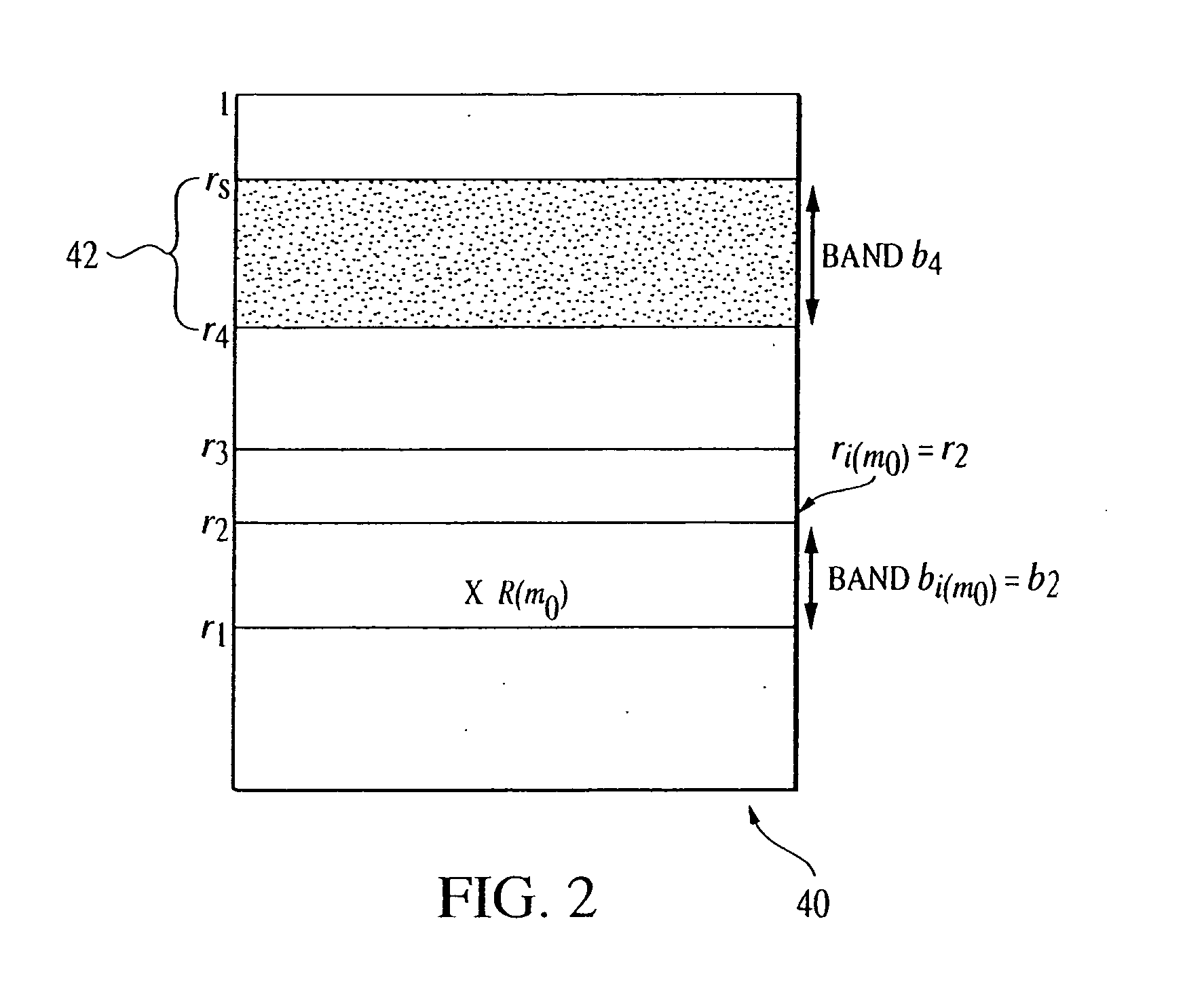
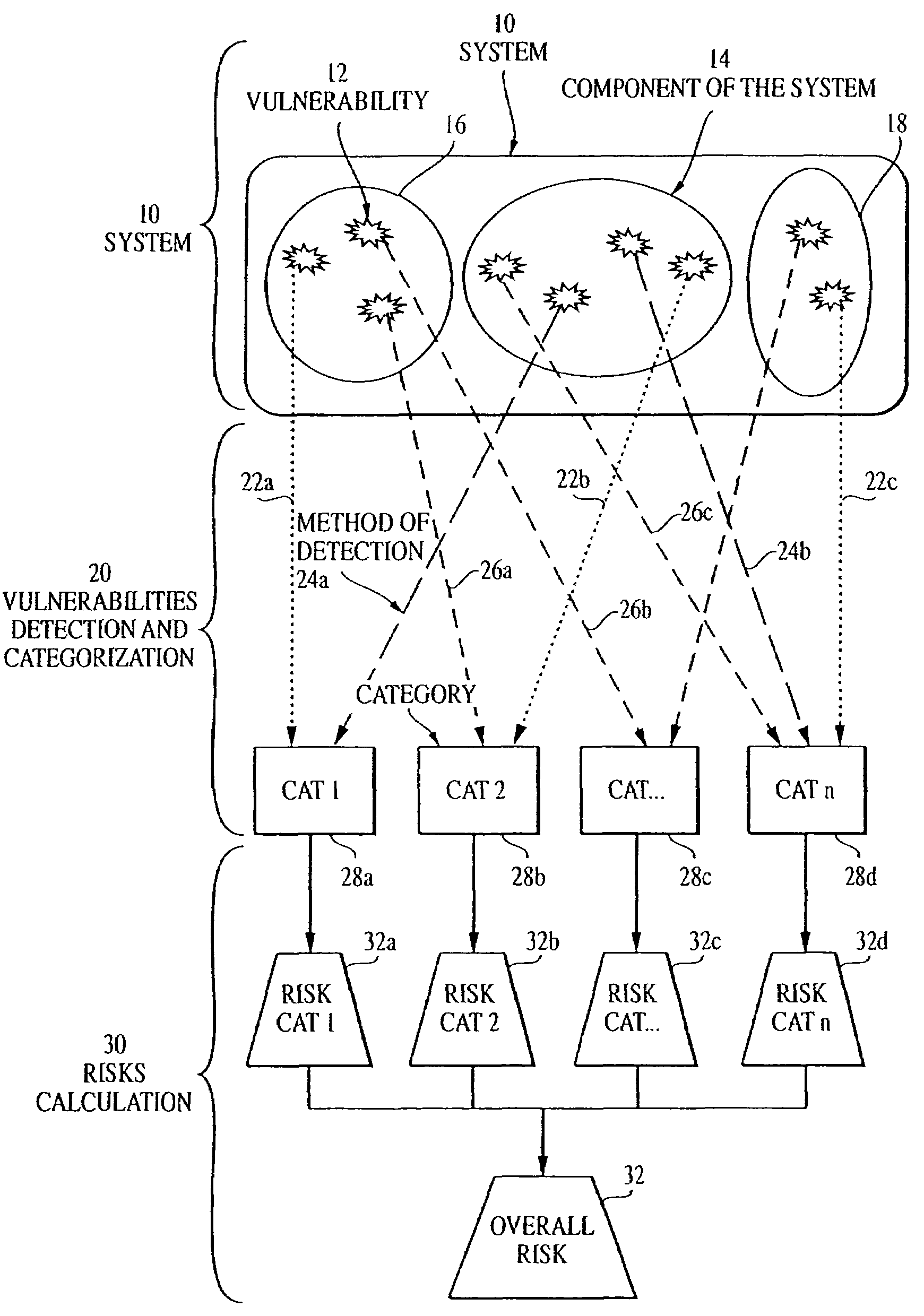
Overall risk in a system
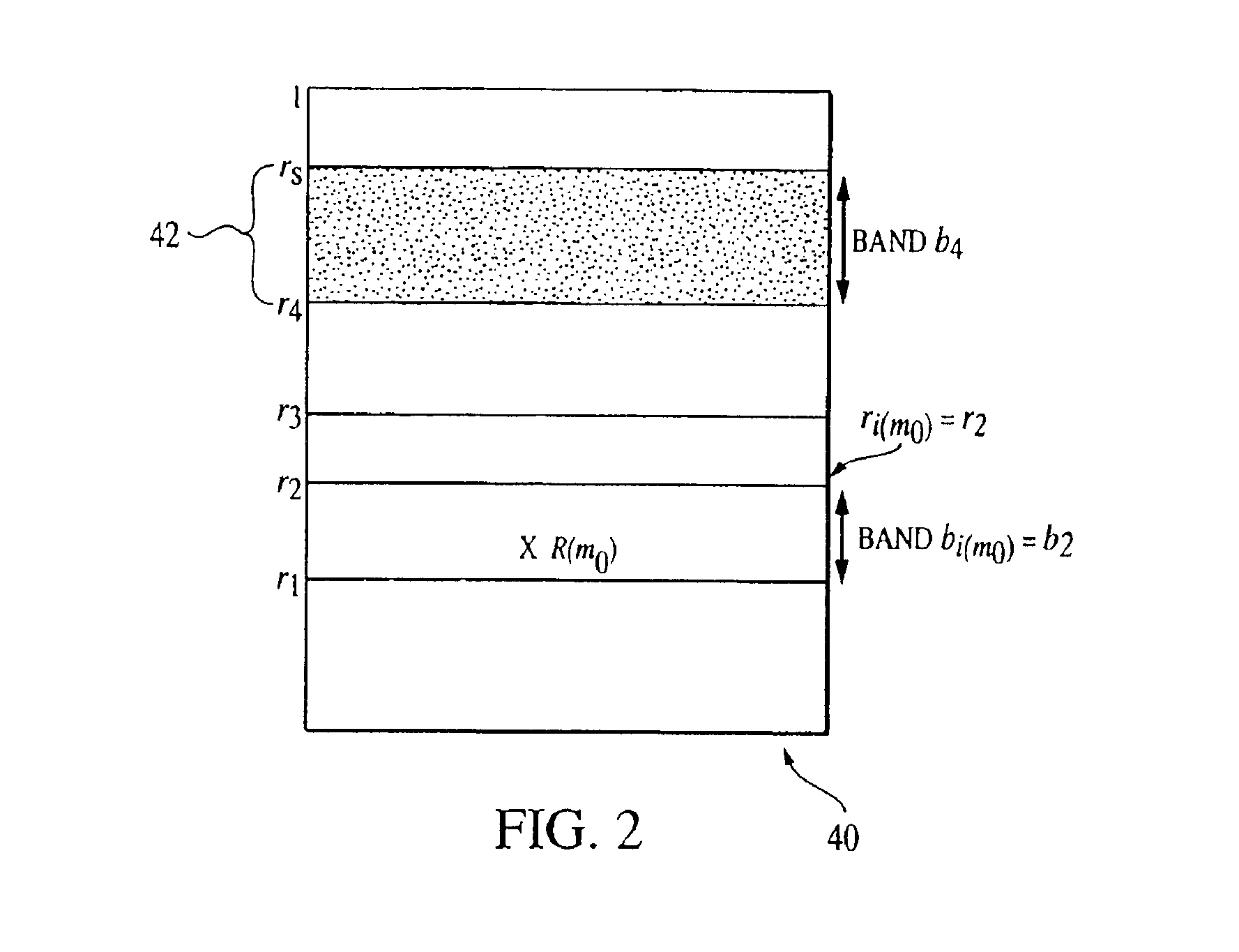
A computer-implemented method and system for assessing the overall risk in at least part of an information technology system includes inputting into a risk assessment database a plurality of identified risks in a system; associating the risks to at least one severity band in a risk echelon; assigning a value to each risk; multiplying each risk value by a coefficient factor; and summing the factored risk values to determine the overall risk. The method preferably includes modifying the security implementation of the information technology system and determining the modified overall risk. The system preferably includes an automated vulnerability detection scanner to gather risk information, which is stored on a database and used in calculating the overall risk.
Owner:ACCENTURE GLOBAL SERVICES LTD
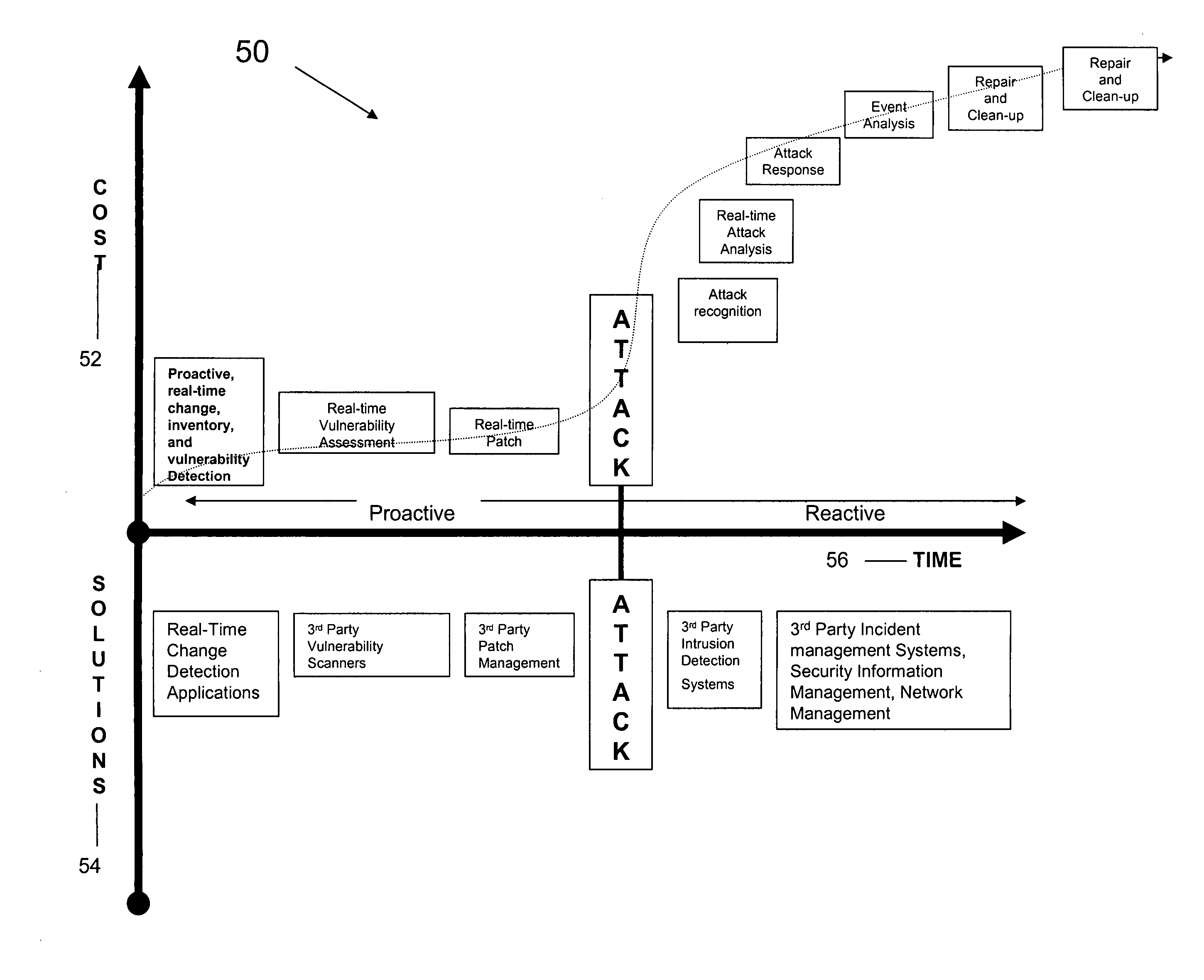
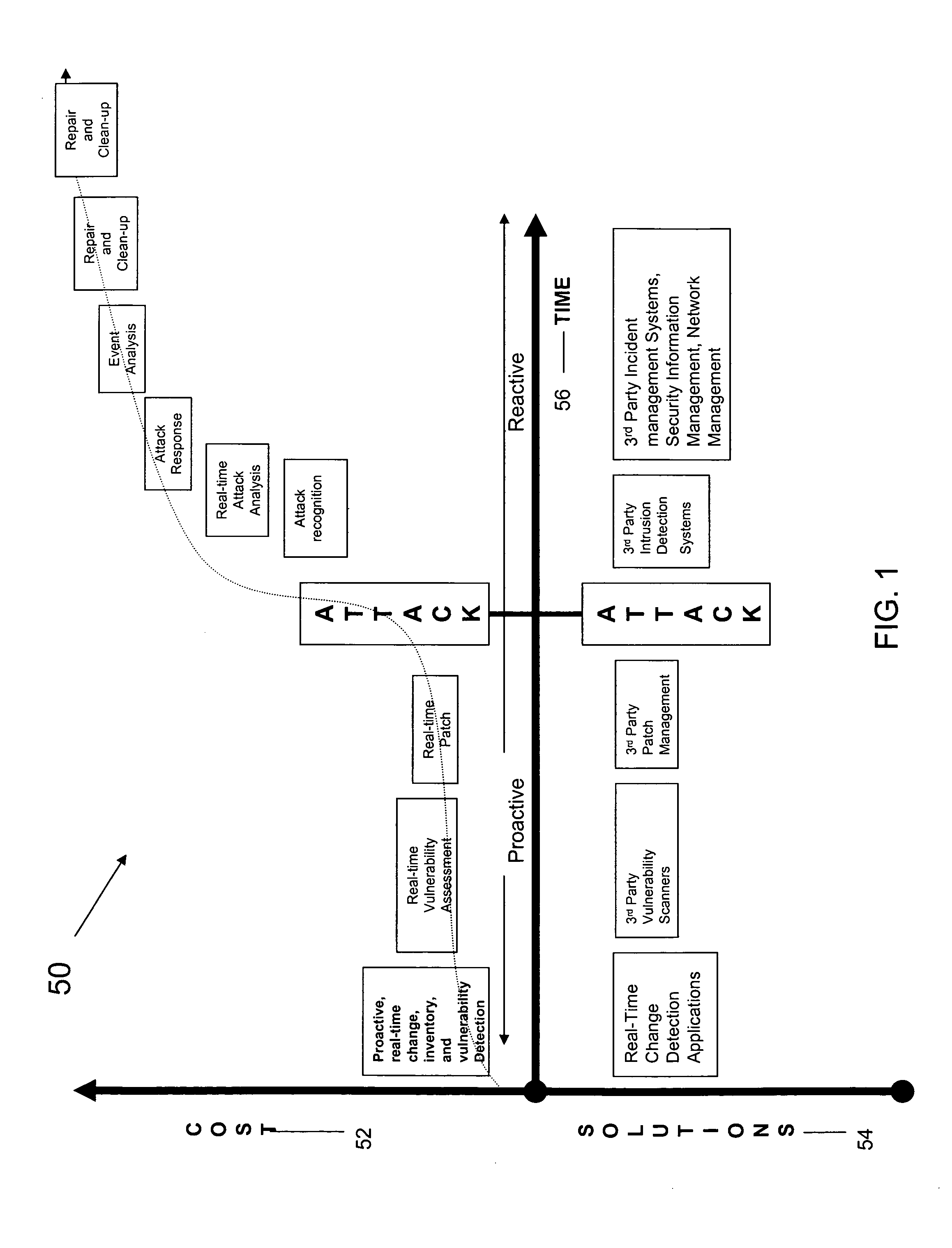
Systems and Methods for Vulnerability Detection and Scoring with Threat Assessment
InactiveUS20080028470A1Memory loss protectionUnauthorized memory use protectionSeverity levelComputer science
Certain embodiments of the present invention provide a system for vulnerability detection and scoring with threat assessment including an analysis engine adapted to perform at least one of automated and semi-automated analysis of a computing system of at least one of known threats, vulnerabilities, and risk factors. The analysis engine is further adapted to determine a security score for the computing system based on the analysis and a schedule indicating a severity level for each threat, vulnerability, and risk factor.
Owner:REMINGTON MARK +3
System and method for network vulnerability detection and reporting
ActiveUS7664845B2Reduce the possibilityReliably determinedMemory loss protectionError detection/correctionGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
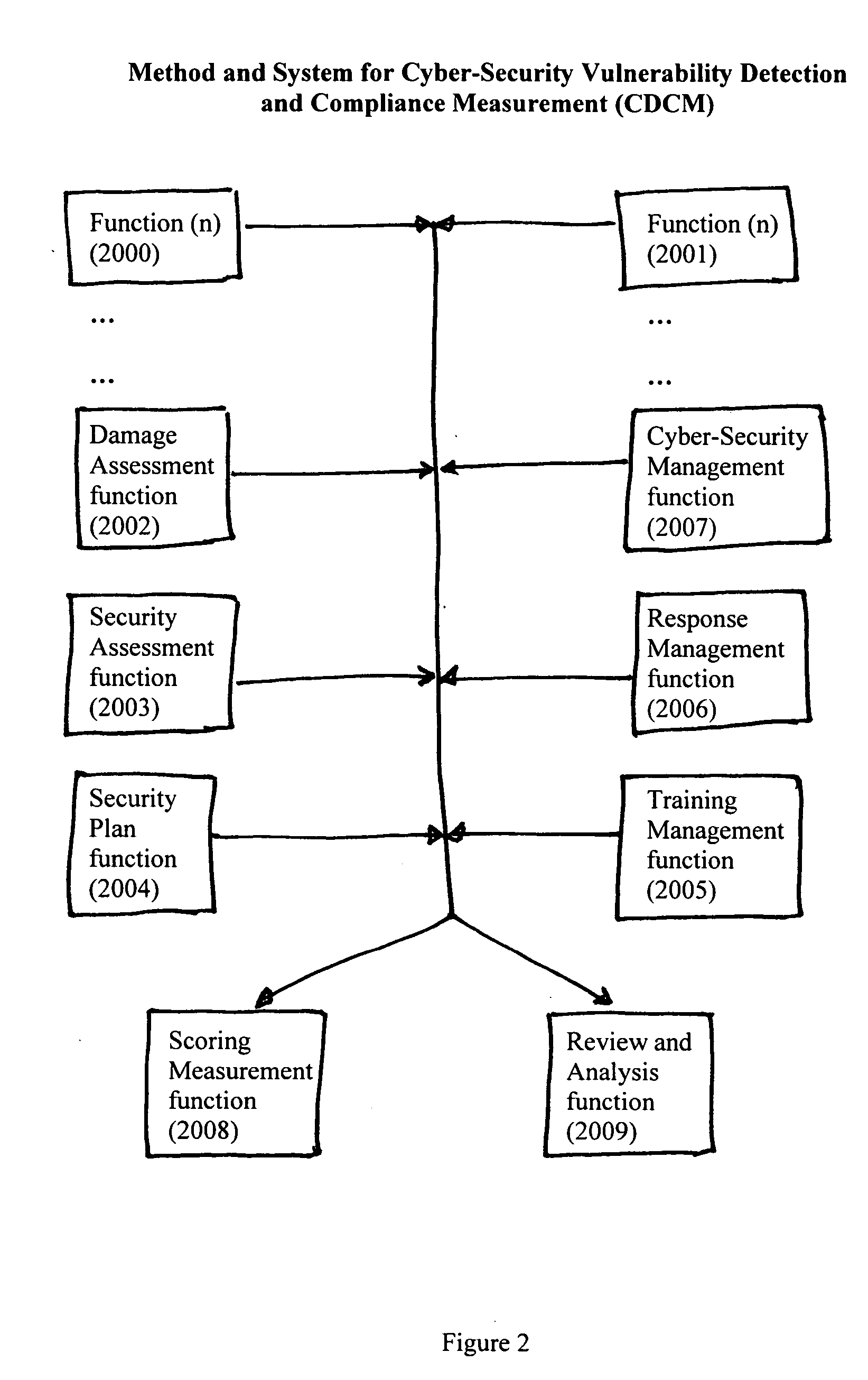
Method and system for cyber-security vulnerability detection and compliance measurement (CDCM)
InactiveUS20050132225A1Improve abilitiesDigital data processing detailsUser identity/authority verificationProgram planningHandling system
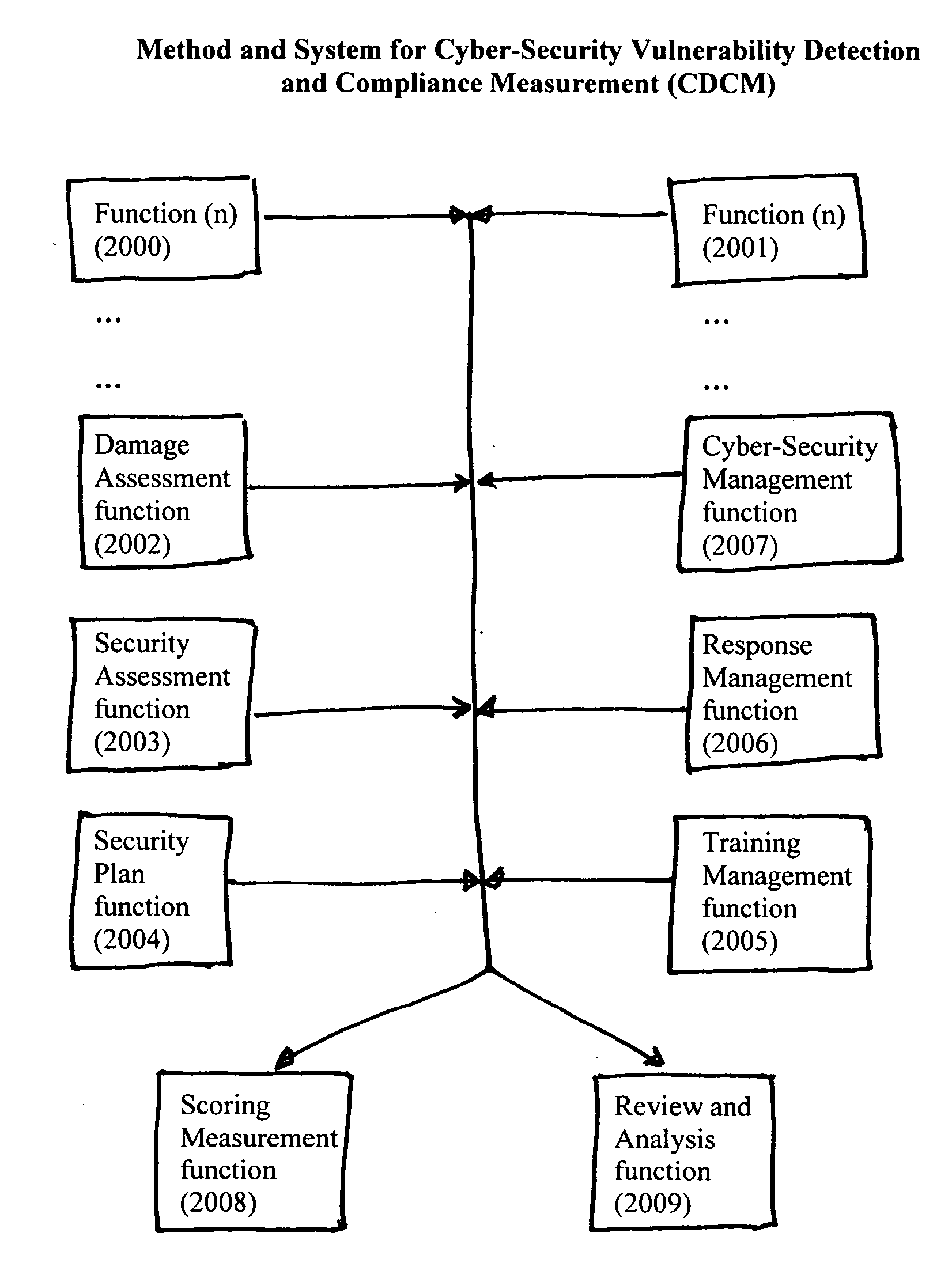
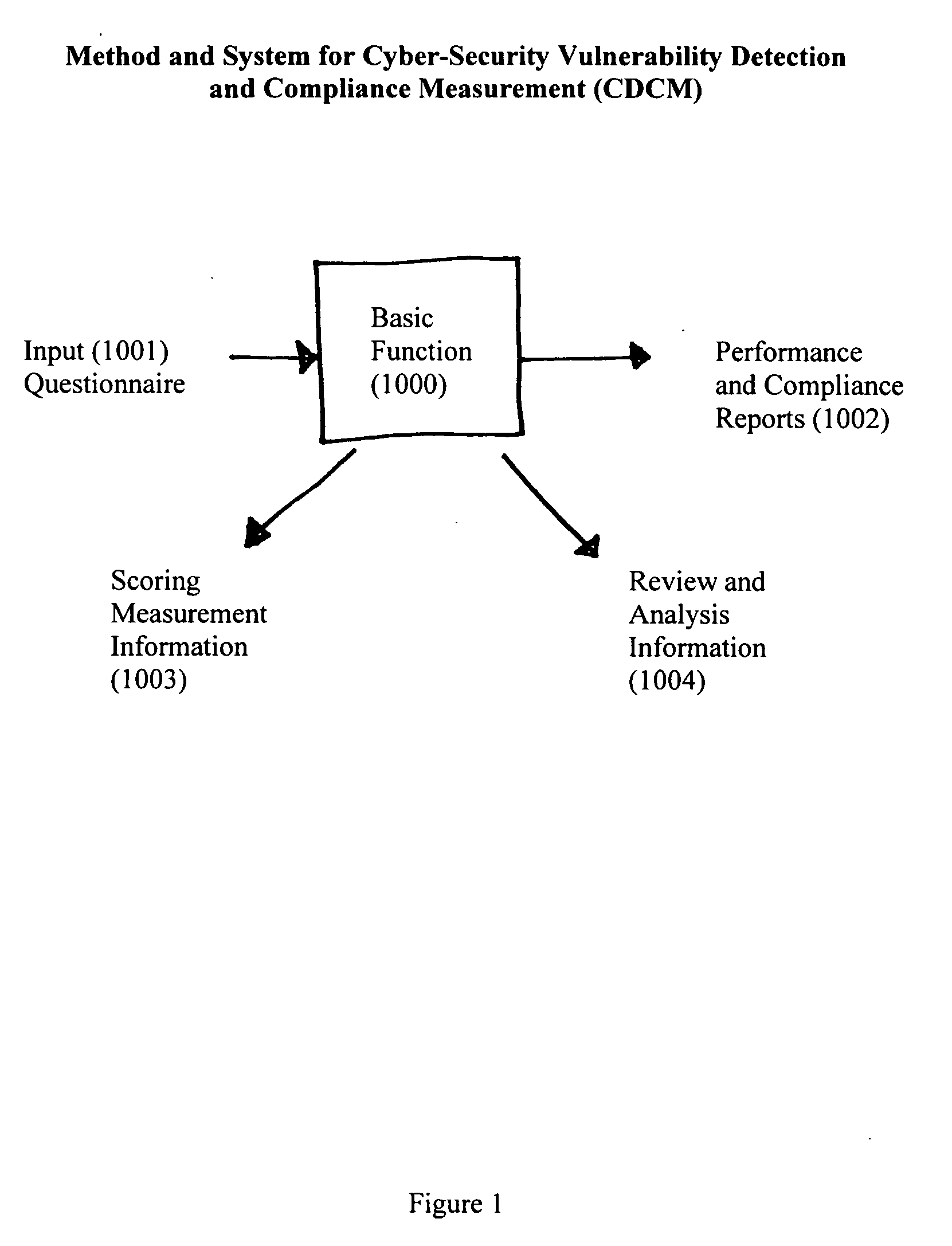
Method and System for Cyber-Security Vulnerability Detection and Compliance Measurement (CDCM) provides any entity, organization or individual with access to or possession of sensitive, confidential or secret information, defined as “protected information,” in digital format that is received, processed, stored or distributed by a computer, computer system or digital processing equipment with the capability to detect and respond to cyber security vulnerabilities and to measure compliance with cyber-security requirements as established by the Federal Security Information Management Act (FISMA) for the security of protected information and certain additional related desirable or mandatory cyber-security requirements. In one sample embodiment of the invention, the method utilizes a damage assessment function; a security assessment function; a security plan or planning function; a training management function; a response management function; a cyber-security management function; a scoring measurement function; and a review and analysis function; to establish a quantifiable and definitive numerical measurement of the relative compliance of a specific processing system, at a specific point in time, to a defined and established threshold value of performance, or compliance acceptance, and to provide, assemble and be capable of archiving the supporting parameters, status, states and analysis that is specifically associated with the numerical value which represents the specific processing system's state of compliance at the specified time and to utilize various intermediate values and parameters to manage and enhance the performance of the specific system thereby improving the systems compliance score and numerical performance measurement value.
Owner:GEARHART GLENN
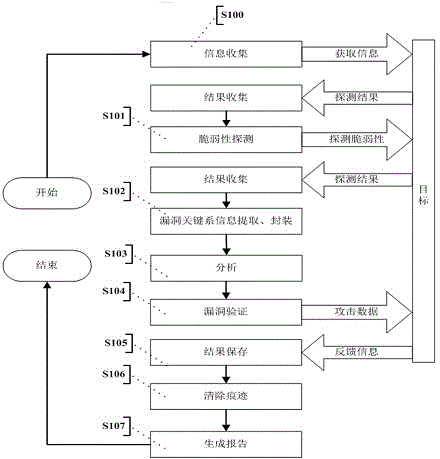
Automatic vulnerability validation method
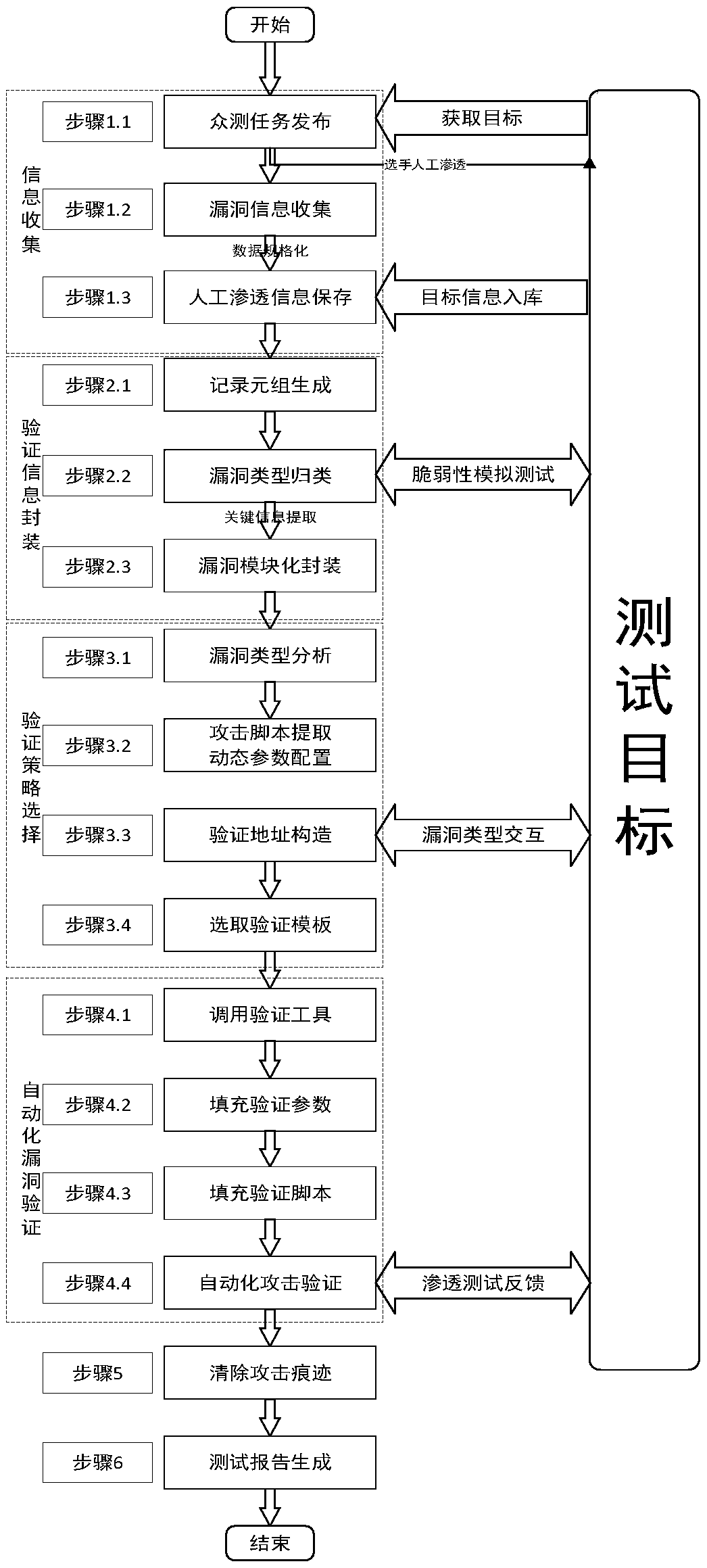
InactiveCN104363236AAutomated verificationUnderstand the dangers of vulnerabilitiesPlatform integrity maintainanceTransmissionValidation methodsModularity
The invention provides an automatic vulnerability validation method. The method comprises the steps that firstly, validation information is collected, wherein an active detection way is adopted for carrying out information detection, topological detection, vulnerability detection and website directory structure detection on a target; secondly, the validation information is packaged, wherein suspicious vulnerability key information in vulnerability detection results is extracted, uniform-interface modularized packaging is carried out on the data; thirdly, a validation strategy is searched for, wherein according to the suspicious vulnerability identity and variety information, an appropriate attack script template and a vulnerability utilizing tool are selected; vulnerability validation is carried out, wherein scripts are called to be loaded into the packaged vulnerability information to carry out validation attack, and an utilization voucher is obtained and stored; fifthly, validation traces are removed, wherein validation attack traces are removed, sessions are recycled; finally, a scanning report is generated. The automatic vulnerability validation method solves the problem that an existing vulnerability scanning system is high in false alarm rate and cannot carry out effective validation, is automatic and procedural, can automatically recognize and validate vulnerabilities, lowers the requirement for the ability of non-professional staff and improves the vulnerability validation efficiency.
Owner:XIAN UNIV OF POSTS & TELECOMM +1
Systems, methods and computer program products for string analysis with security labels for vulnerability detection
InactiveUS7530107B1Suppress false detectionDetailed analysisMemory loss protectionError detection/correctionLocation detectionPre-condition
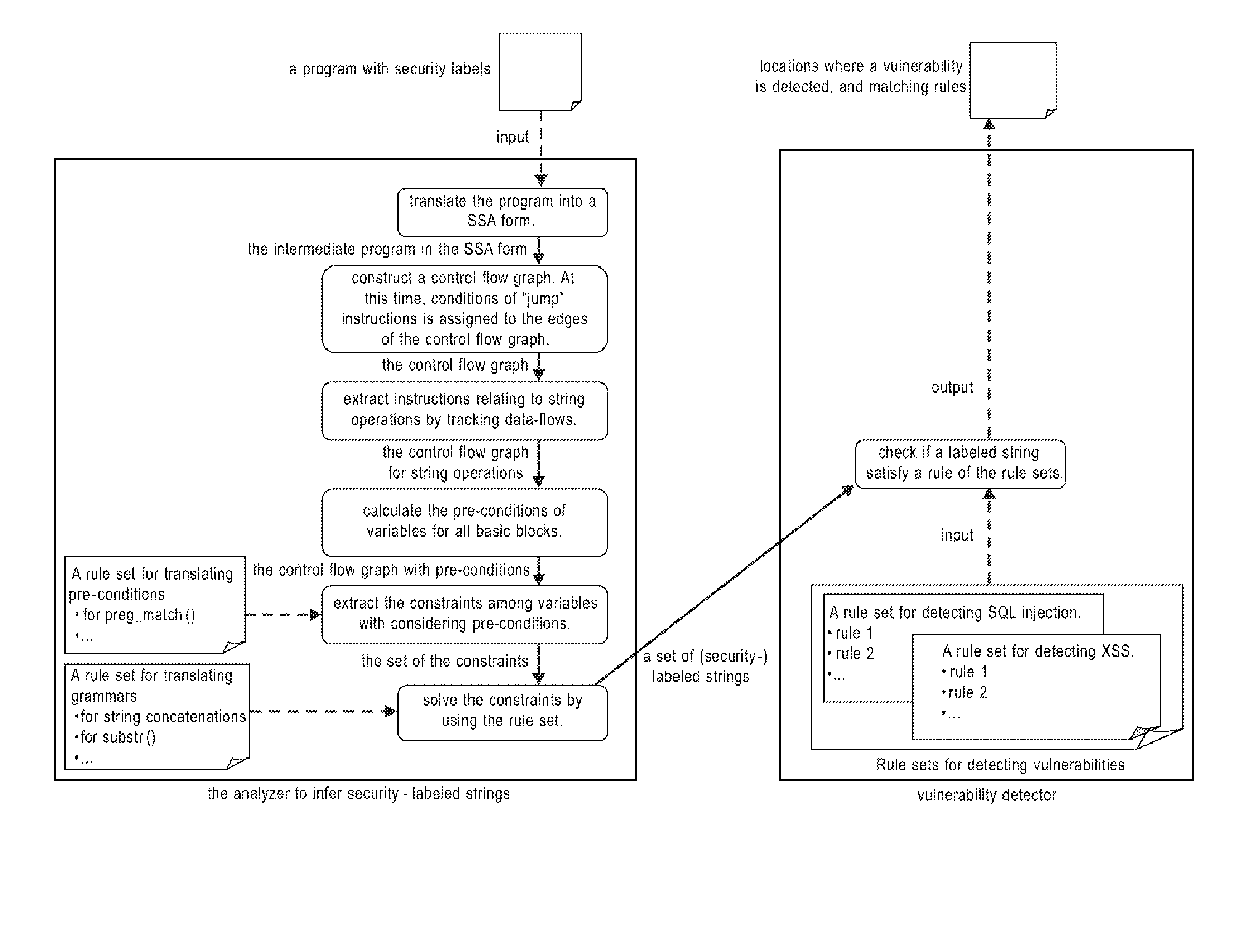
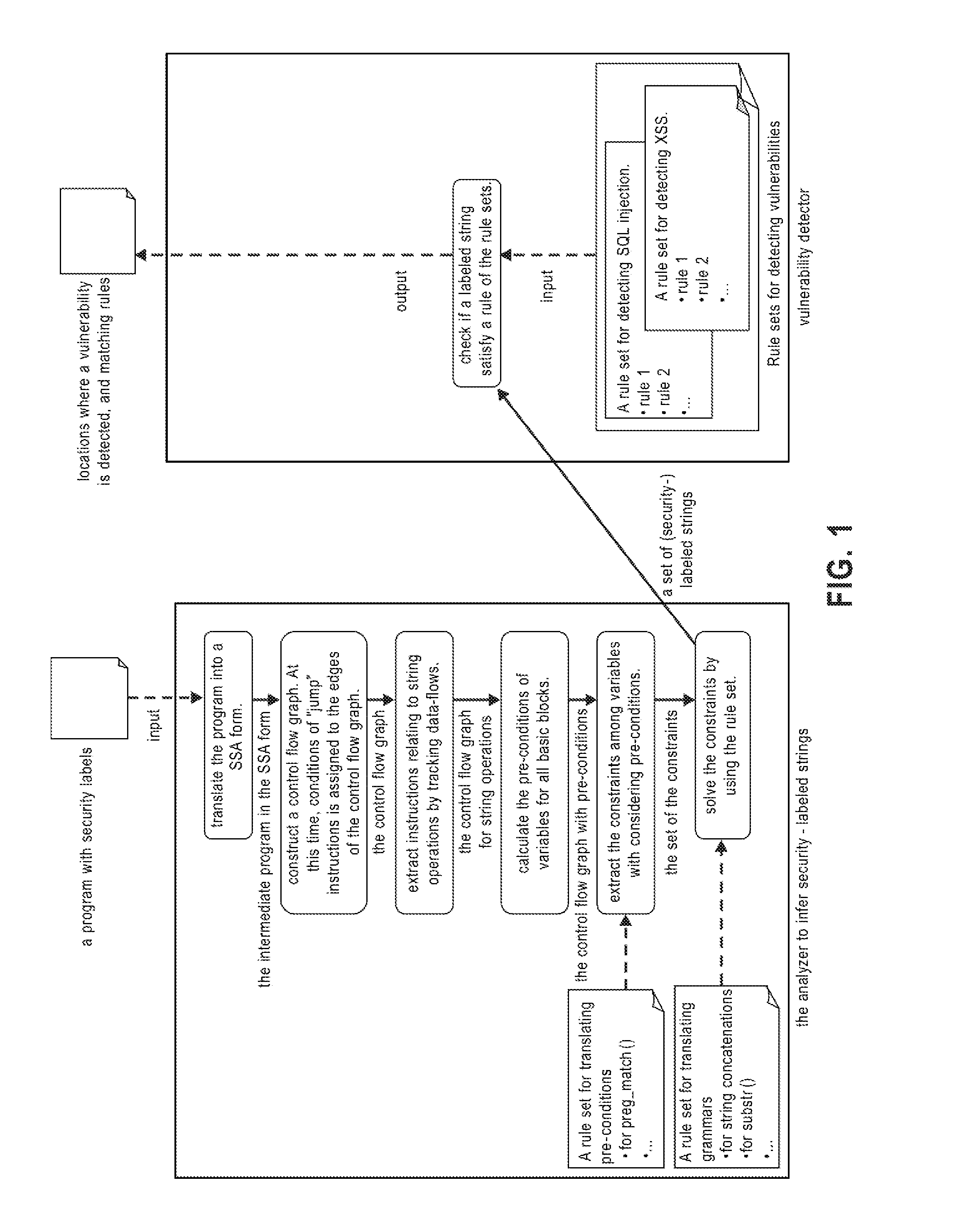
Systems, methods and computer program products for string analysis with security labels for vulnerability detection. Exemplary embodiments include a method in a computer system configured to analyze security-labeled strings and to detect vulnerability, the method including receiving a program with security labels, translating the program into a static single assignment form, constructing a control flow graph having basic blocks as nodes, extracting instructions relating to string functions and object variables, calculating pre-conditions of variables for the basic blocks, extracting constraints among the variables subject to a rule set for translating pre-conditions, solving the constraints and obtaining a set of strings that he object variables form as a context-free grammar to obtain a set of security-labeled strings, checking if the set of security-labeled strings satisfies a rule of the rule set for translating pre-conditions and identifying locations in the program where a vulnerability is detected.
Owner:IBM CORP
System and method for network vulnerability detection and reporting
InactiveUS7543056B2Reliably determinedSimple methodMemory loss protectionError detection/correctionGraphicsOperational system
Owner:MCAFEE LLC
Overall risk in a system
A computer-implemented method and system for assessing the overall risk in at least part of an information technology system includes inputting into a risk assessment database a plurality of identified risks in a system; associating the risks to at least one severity band in a risk echelon; assigning a value to each risk; multiplying each risk value by a coefficient factor; and summing the factored risk values to determine the overall risk. The method preferably includes modifying the security implementation of the information technology system and determining the modified overall risk. The system preferably includes an automated vulnerability detection scanner to gather risk information, which is stored on a database and used in calculating the overall risk.
Owner:ACCENTURE GLOBAL SERVICES LTD
Network security risk assessment method
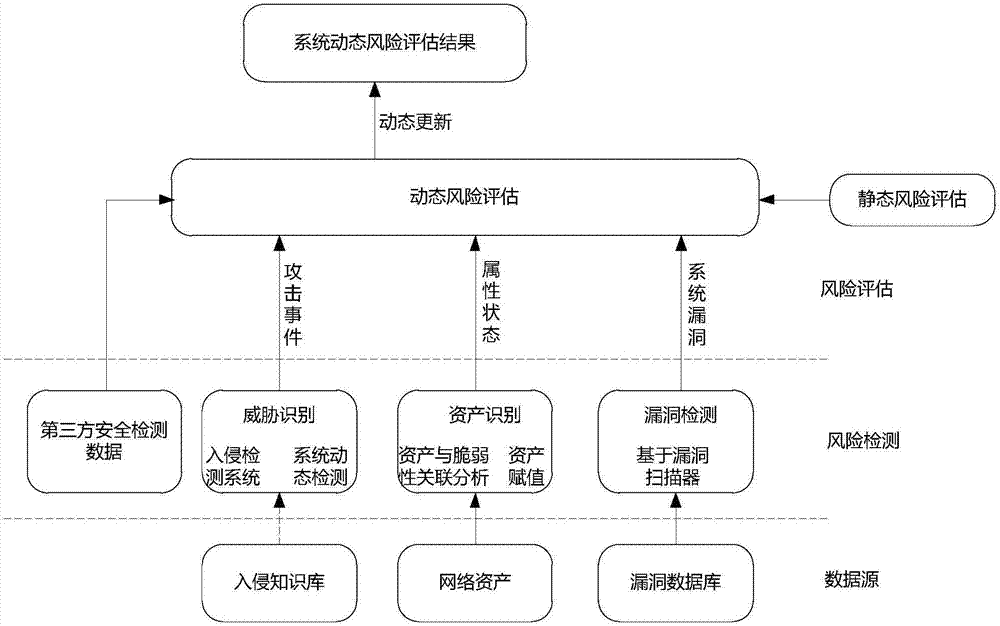
InactiveCN107204876AImprove real-time performanceImprove accuracyData switching networksThird partyMonitoring system
The invention discloses a network security risk assessment method. The security of a target network is assessed dynamically by combining an intrusion detection system, vulnerability detection and real-time attack events obtained by a third party on the basis of static risk assessment. With regard to risk assessment, the asset value is usually defined by specialists or managers during static assessment and no great change occurs in a certain period; dynamic changes of threatening and vulnerable information can be assessed by aid of corresponding tools; the intrusion detection system and a firewall are taken as monitoring systems and can warn of anomalous events at any time, and warning information is possible threats to a system and is also an important basis for assessment of a system risk condition. With the adoption of the network security risk assessment method, the accuracy and instantaneity of network risk assessment can be improved effectively, security defense measures can be carried out according to risk assessment results, and risks can be controlled effectively in time.
Owner:成都网络空间安全技术有限公司
Deep learning-based vulnerability detection method and system
ActiveCN107885999AUnlimited Vulnerability TypeImprove accuracyPlatform integrity maintainanceLearning basedTraining program
The invention discloses a deep learning-based vulnerability detection method and system. The method comprises an offline vulnerability classifier training part and an online vulnerability detection part. The offline vulnerability classifier training part comprises the following steps of: calling candidate code sections for a training program extraction library / API function; adding type label for the candidate code sections; converting the candidate code sections into vectors; inputting the vectors into a neural network model to carry out training; and finally outputting a vulnerability classifier. The online vulnerability detection part comprises the following steps of: calling candidate code sections for a target program extraction library / API function; converting the candidate code sections into vectors; classifying the candidate code sections by adoption of the trained vulnerability classifier; and finally outputting the code sections which contain online vulnerabilities in the classification result. According to the method and system, vulnerability features aiming at library / API function calling can be automatically generated, and the operation does not depend on expert knowledges and is not restricted to vulnerability types, so that the false report rate and missing report rate of vulnerability detection in target programs can be remarkably reduced and vulnerability positions can be given.
Owner:HUAZHONG UNIV OF SCI & TECH
System And Method For Network Vulnerability Detection And Reporting
ActiveUS20070283441A1Reliably determinedSimple methodMemory loss protectionError detection/correctionGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
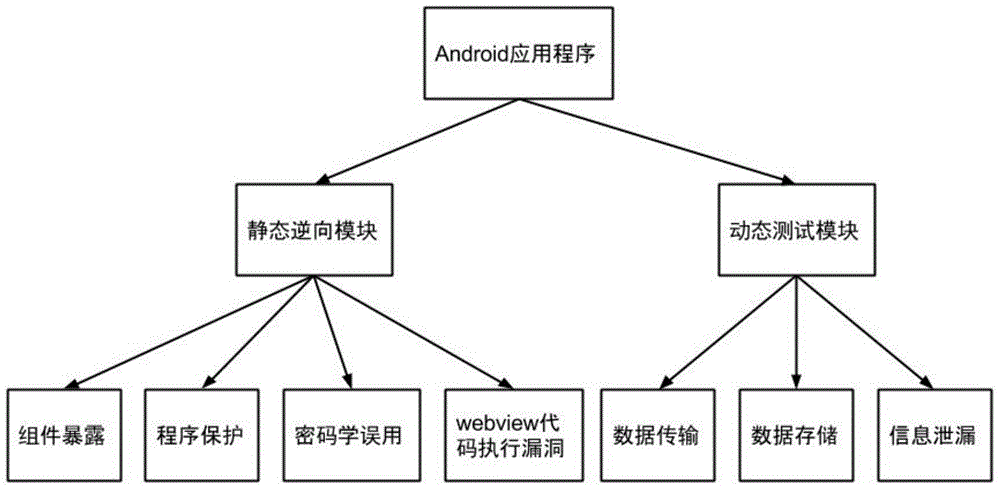
Universal method and universal system for performing safety testing on Android application programs
InactiveCN104484607AReduce false alarm ratePlatform integrity maintainanceApplication softwareSafety testing
The invention discloses a universal method and a universal system for performing safety testing on Android application programs. The universal method comprises the following steps of unpacking and decompiling a to-be-tested program to obtain an XML (extensive markup language) source code; then, through static analysis on configuration files and the code of the to-be-tested program, performing vulnerability detection and safety testing on the aspects of component exposed vulnerability, cryptology misuse, webview code execution vulnerability and code protection; then, performing actual running on the to-be-tested program, and configuring a network detection environment; finally, performing dynamic analysis, and performing dynamic vulnerability detection and the safety testing on three aspects of information leakage, data transmission safety and data storage safety, thus obtaining a vulnerability detection and safety testing report. According to the universal method and the universal system disclosed by the invention, by performing a static analysis and dynamic analysis combination mode on an optional Android application program and through a series of steps of detection and estimation, safety flaws and potential safety hazards existing in the aspects of design and implementation of the application program can be finally given out.
Owner:SHANGHAI JIAO TONG UNIV +1
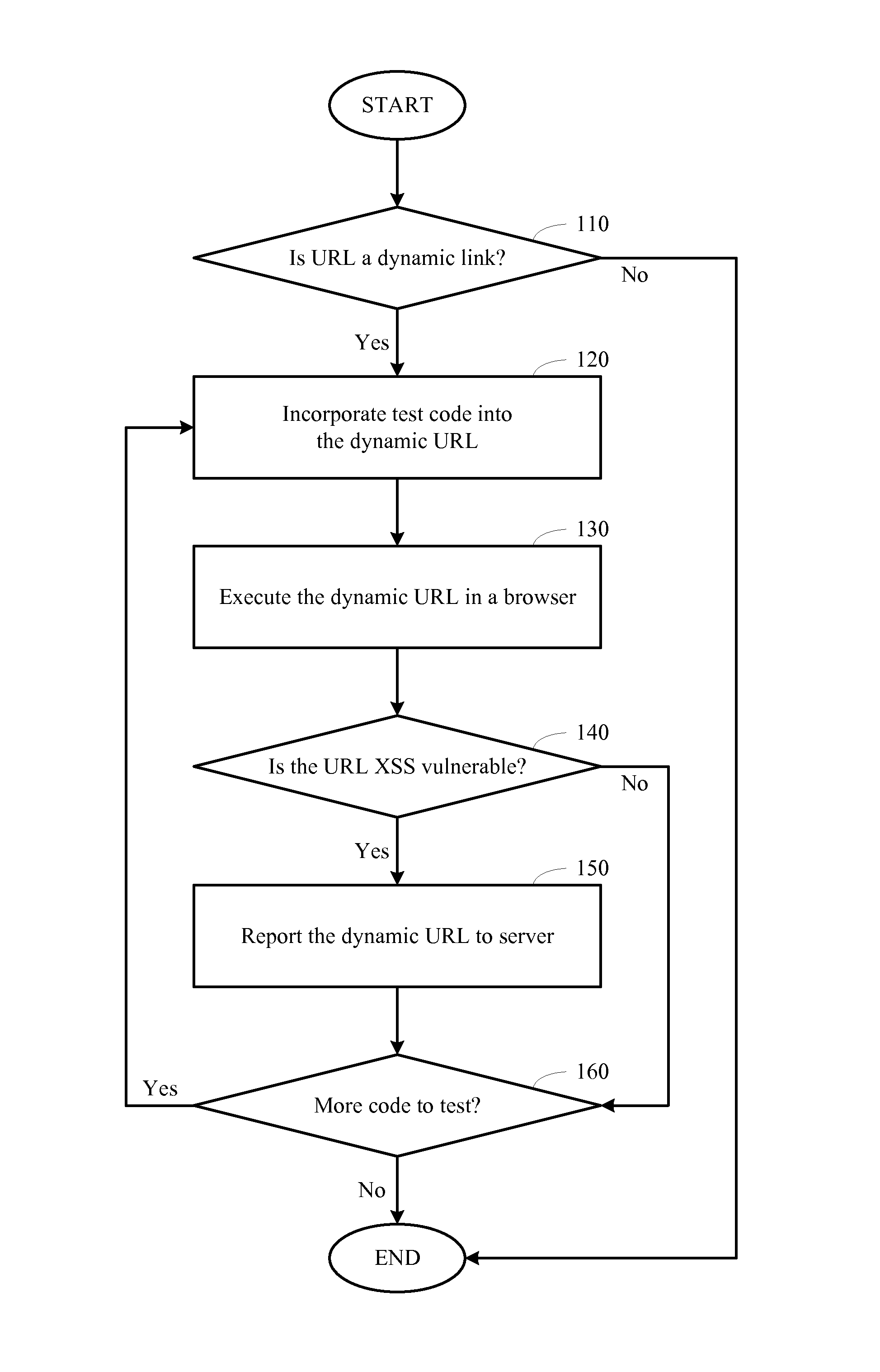
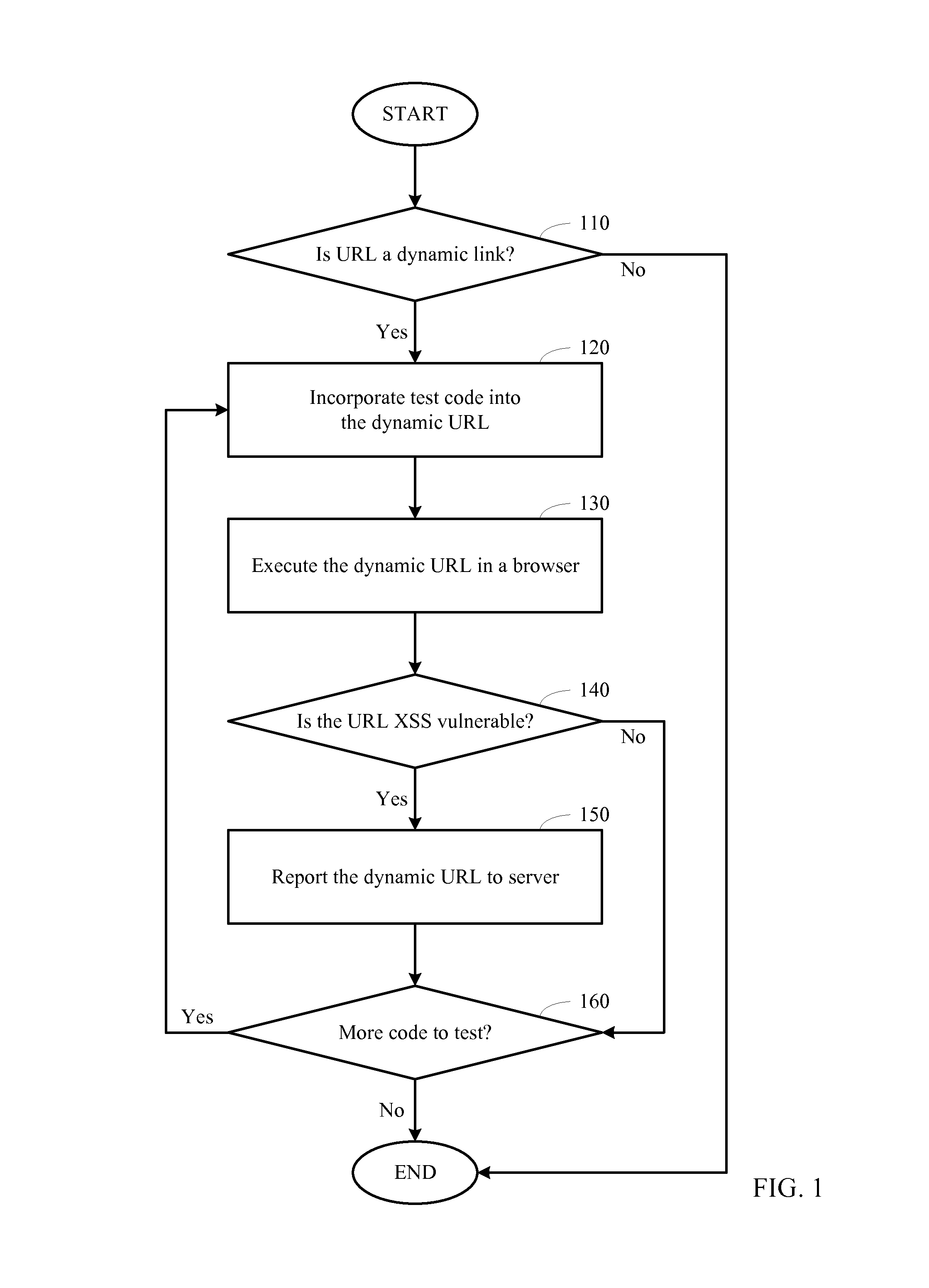
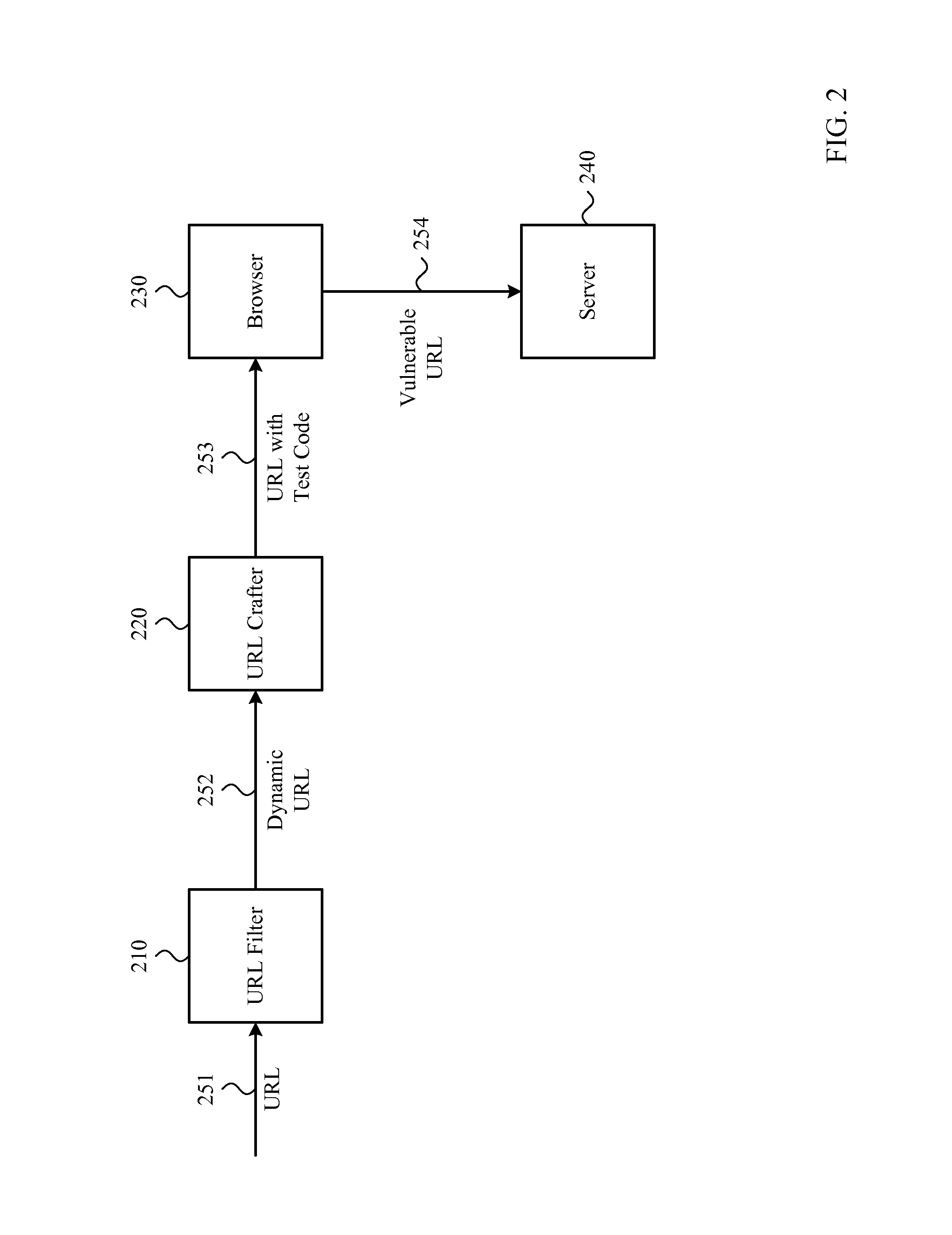
Script-based XSS vulnerability detection
ActiveUS8949990B1Avoid attackMemory loss protectionError detection/correctionWeb serviceUniform resource locator
Detection of dynamic URLs that are vulnerable to XSS attacks is described. First, a dynamic URL is crafted by incorporating a piece of test code designed to expose an instance of XSS vulnerabilities. Next, the crafted URL is loaded into a browser, which causes a web page to be generated that may include the piece of test code. If, upon loading the web page into the browser, the piece of test code is executed by the browser and the browser sends a request to a web server as a result, then the URL is reported as XSS vulnerable. Others, the URL is not vulnerable to this instance of XSS attack. The test may be repeated multiple times for different pieces of test code, each piece designed to expose a different instance of XSS vulnerabilities.
Owner:TREND MICRO INC
System and method for network vulnerability detection and reporting
InactiveUS8135823B2Reliably determinedSimple methodDigital computer detailsPolarising elementsGraphicsOperational system
Owner:MCAFEE LLC
System And Method For Network Vulnerability Detection And Reporting
InactiveUS20070283007A1Reliably determinedSimple methodError detection/correctionDigital computer detailsGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
Vulnerability detection method and device
ActiveCN106302337AAvoid situations where vulnerability detection is impossibleIncrease coverageTransmissionUser needsComputer terminal
The invention relates to a vulnerability detection method and device, and the method comprises the steps: receiving a user network access request transmitted by a terminal in a forward proxy mode; recording the user network access request; generating a vulnerability detection network request according to the recorded user network access request; transmitting the vulnerability detection network request to a to-be-detected server corresponding to the user network access request; receiving the vulnerability detection response information fed back by the to-be-detected server according to the vulnerability detection network request; detecting whether the vulnerability detection response information has the preset vulnerability features in a preset vulnerability feature database or not, and obtaining the vulnerability detection result. The method and device provided by the invention employ the user network access requests, generated in various types of scenes, of users to carry out the vulnerability detection, avoids a condition that the vulnerability detection cannot be carried out because the users need to log in a system, and is high in vulnerability detection coverage rate.
Owner:TENCENT TECH (SHENZHEN) CO LTD
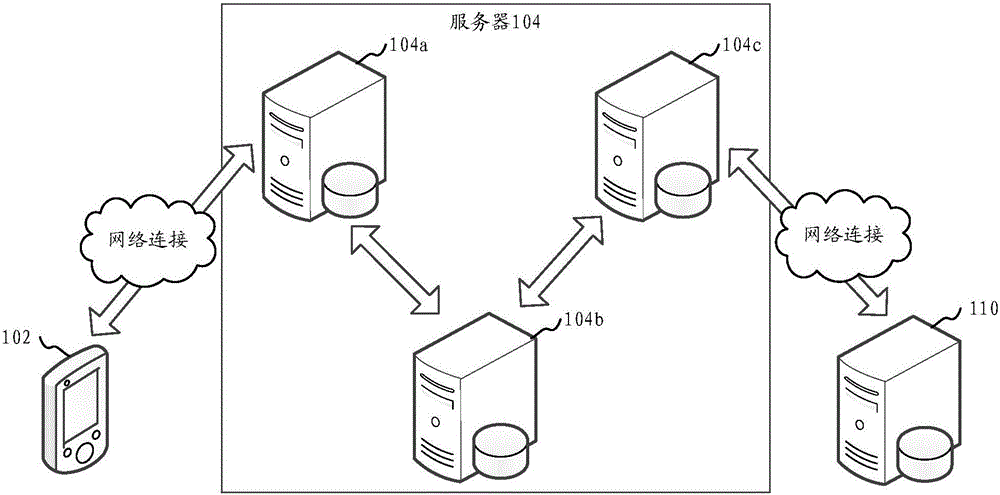
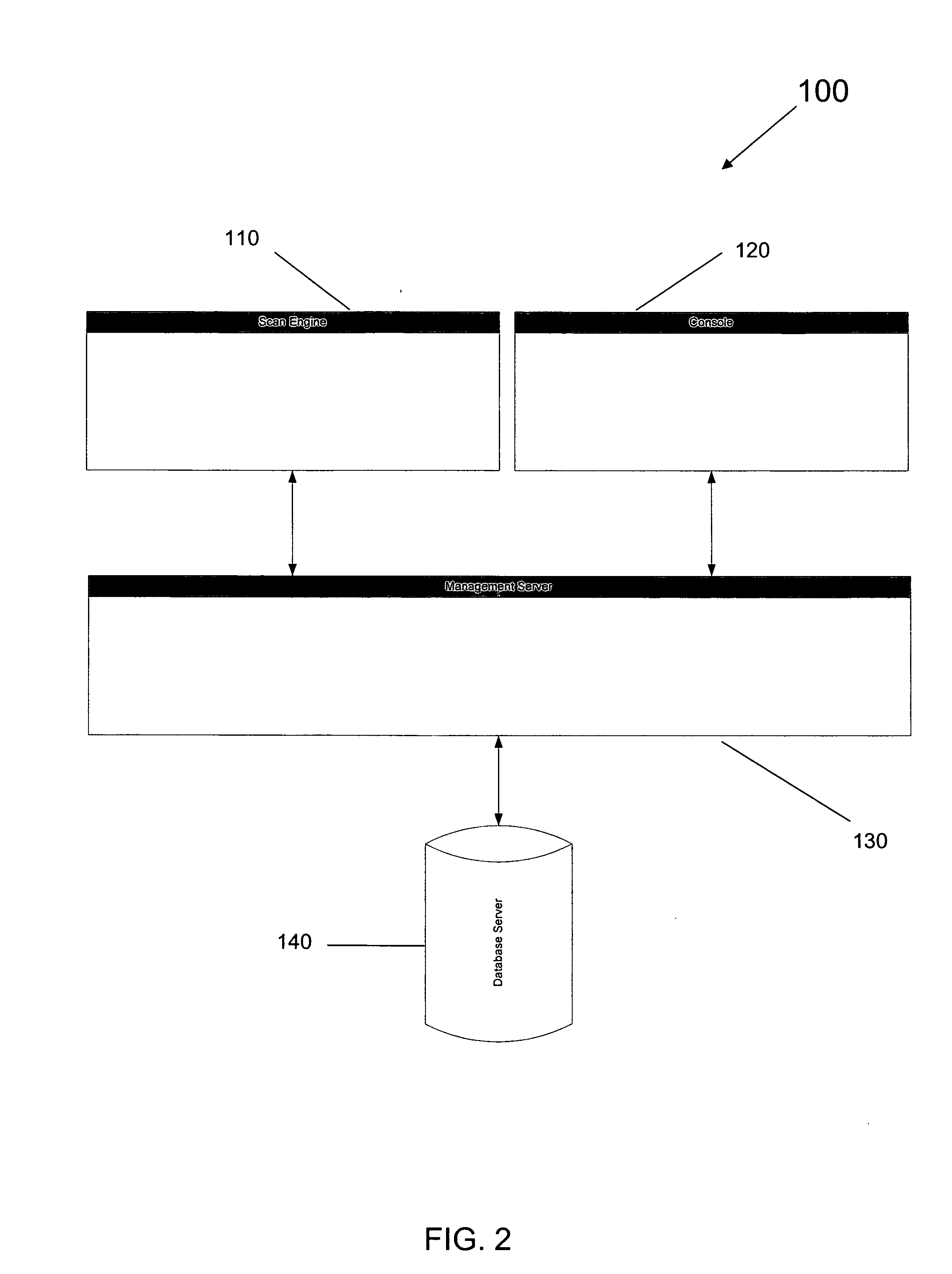
Real-time change detection for network systems
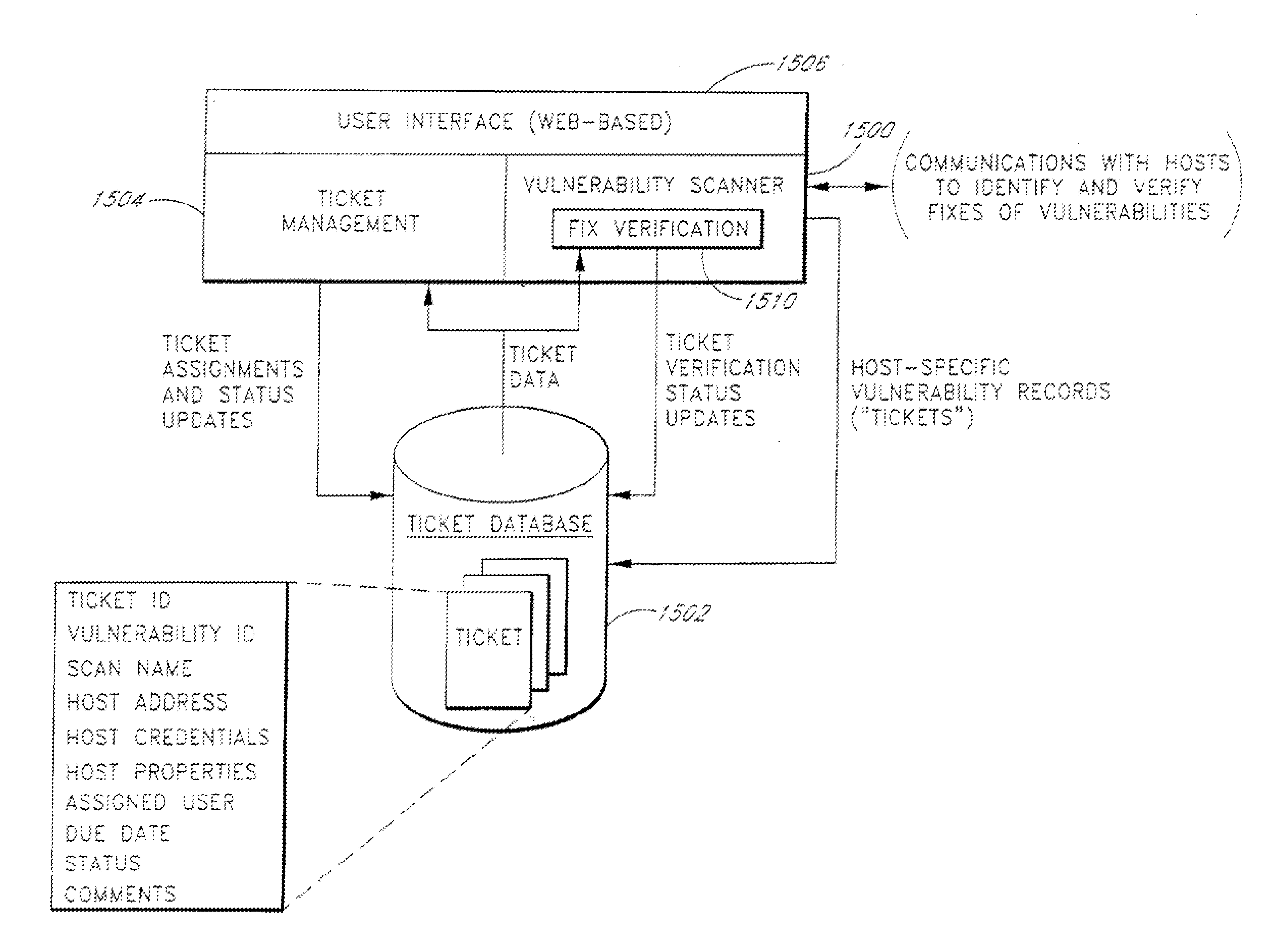
InactiveUS20050154733A1Digital data processing detailsComputer security arrangementsContinuous scanningTime changes
A system for conducting continuous, real-time vulnerability detection of computer networks. The system includes a user interface, a scan engine and a database for obtaining and storing information concerning a network in general and devices and services that may interact with the network. The system provides continuous scanning of the network, each scan being compared with a predetermined baseline network configuration to determine if a change to the network has occurred. If a change has occurred, the system issues an alert informing a network administrator of the where and how the network has changed so appropriate action may be taken by the network administrator.
Owner:TRIPWIRE
Android application vulnerability detection method and Android application vulnerability detection system
InactiveCN103984900AAvoid false positivesEfficient discoveryPlatform integrity maintainanceSQL injectionUniform resource identifier
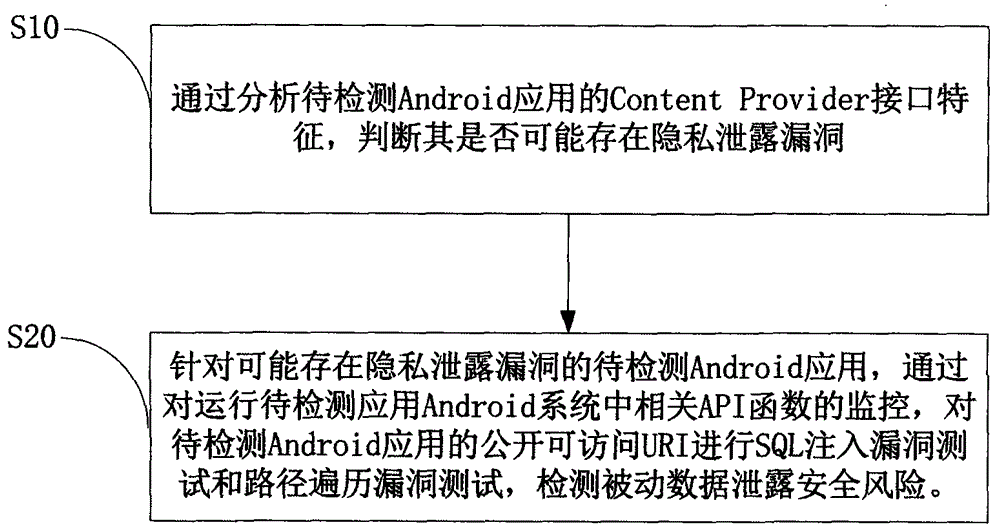
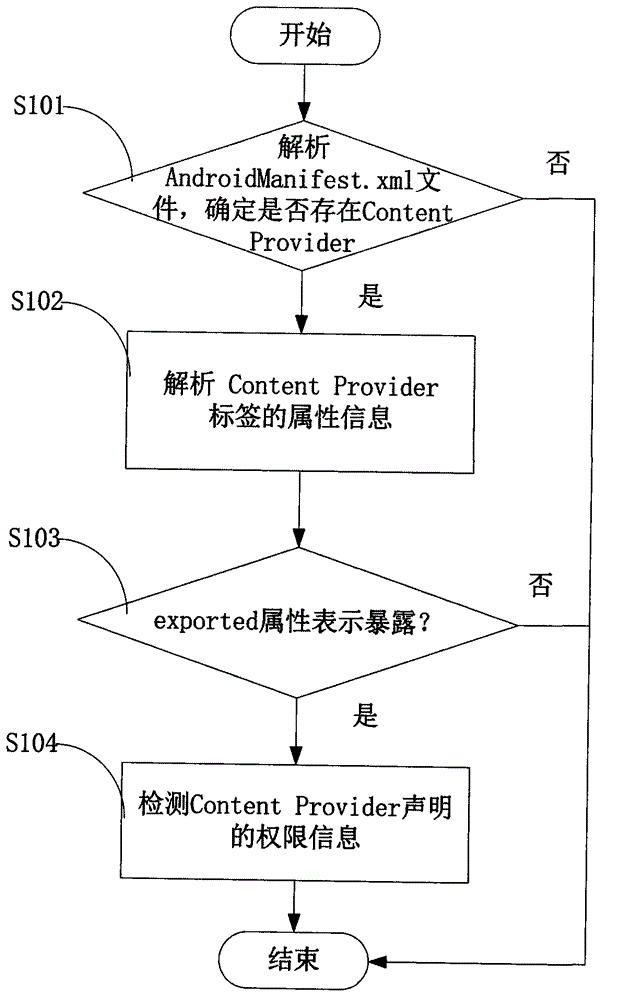
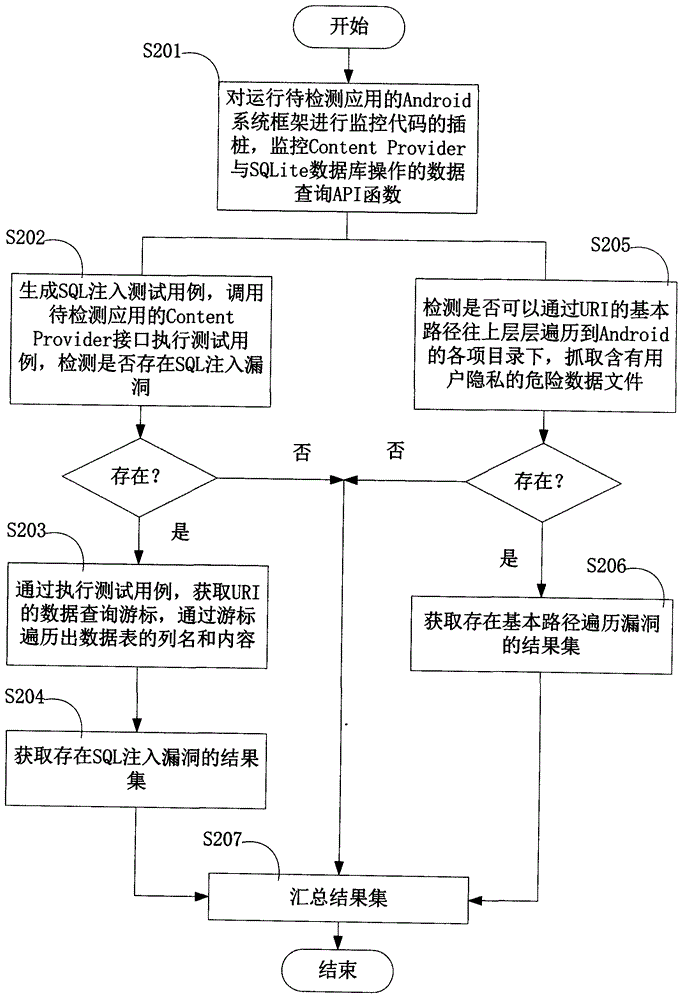
The invention provides an Android application vulnerability detection method which comprises the following steps: 1, judging whether a privacy leakage vulnerability possibly exists or not by virtue of analyzing Content Provider interface characteristics of a to-be-detected Android application; 2, if the privacy leakage vulnerability possibly exists, performing an SQL (Structured Query Lanaguge) injection vulnerability test and a path traversal vulnerability test on a public accessible URI (Uniform Resource Identifier) of the to-be-detected Android application which possibly has the privacy leakage vulnerability by virtue of monitoring a related API (Application Program Interface) function in an Android system, and then detecting passive data leakage safety risks. The invention also provides an Android application vulnerability detection system. The method and the system can be used for rapidly discovering privacy leakage and data pollution vulnerabilities possibly existing in the Android application, avoiding misdeclaration, and providing a powerful support for discovering the privacy leakage and data pollution vulnerabilities in the Android application on a large scale.
Owner:南京赛宁信息技术有限公司 +1
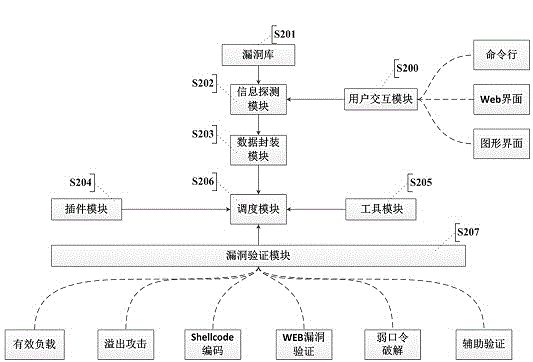
A security vulnerability automatic verification system based on a crowd test platform
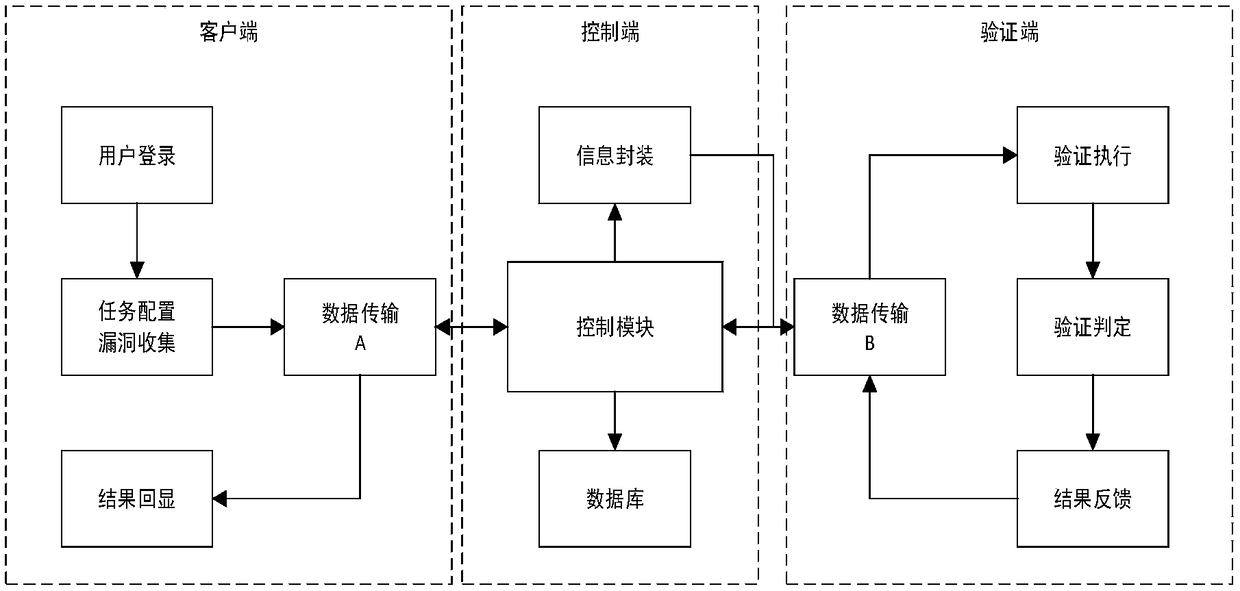
ActiveCN109325351AGuaranteed accuracyGuaranteed availabilitySoftware testing/debuggingPlatform integrity maintainanceModularityField data
The invention discloses a security vulnerability automatic verification system based on a crowd testing platform. The system executes the following steps of 1, collecting the verification information;2, implementing the authentication information encapsulation, classifying all kinds of vulnerabilities collected by security vulnerability automatic verification system according to their types, extracting the key information from vulnerability detection results for each type of vulnerabilities, taking the key information as the necessary field data to submit the vulnerabilities, collecting the required data according to the fields, and packaging the data in a unified interface modularly; 3, searching for an authentication strategy, and selecting an appropriate attack script template and a vulnerability utilization tool according to suspicious vulnerability identification and type information; 4, carrying out automatic vulnerability verification; 5, clearing the verification trace; 6, generating a scanning report.
Owner:CHINA INFOMRAITON CONSULTING & DESIGNING INST CO LTD
Overall risk in a system
A computer-implemented method and system for assessing the overall risk in at least part of an information technology system includes inputting into a risk assessment database a plurality of identified risks in a system; associating the risks to at least one severity band in a risk echelon; assigning a value to each risk; multiplying each risk value by a coefficient factor; and summing the factored risk values to determine the overall risk. The method preferably includes modifying the security implementation of the information technology system and determining the modified overall risk. The system preferably includes an automated vulnerability detection scanner to gather risk information, which is stored on a database and used in calculating the overall risk.
Owner:ACCENTURE GLOBAL SERVICES LTD
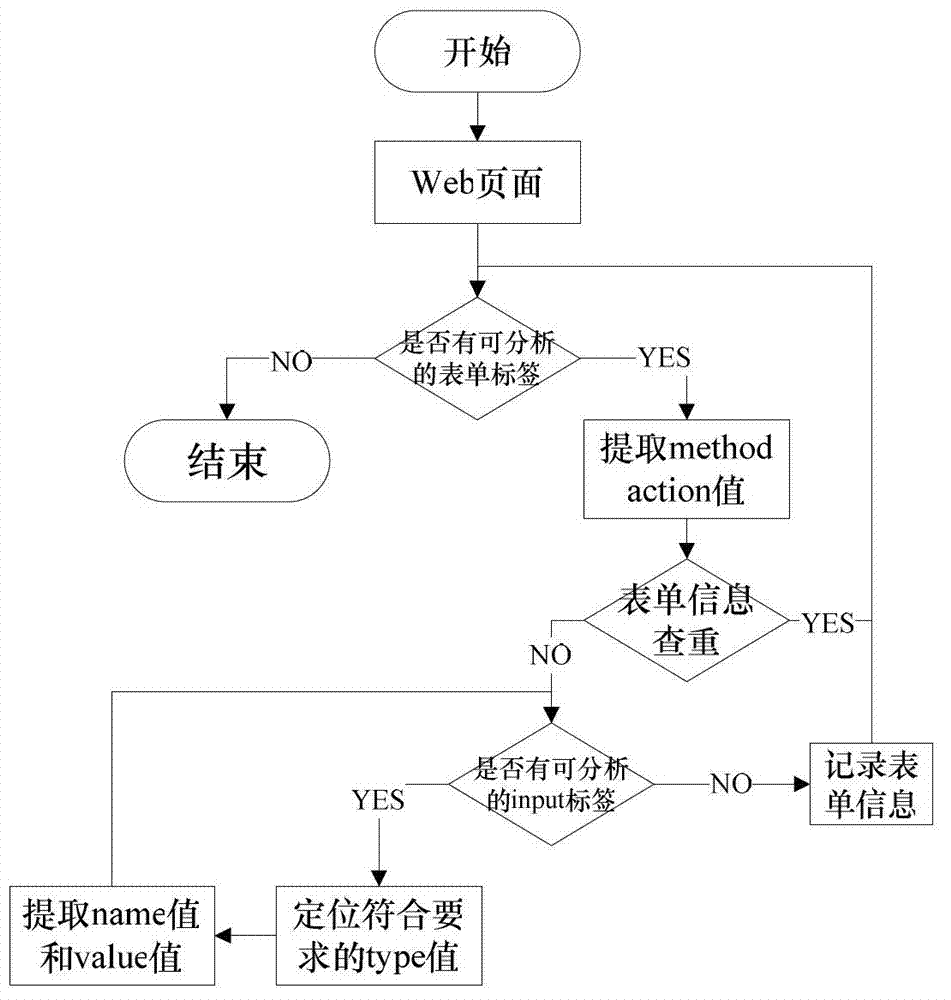
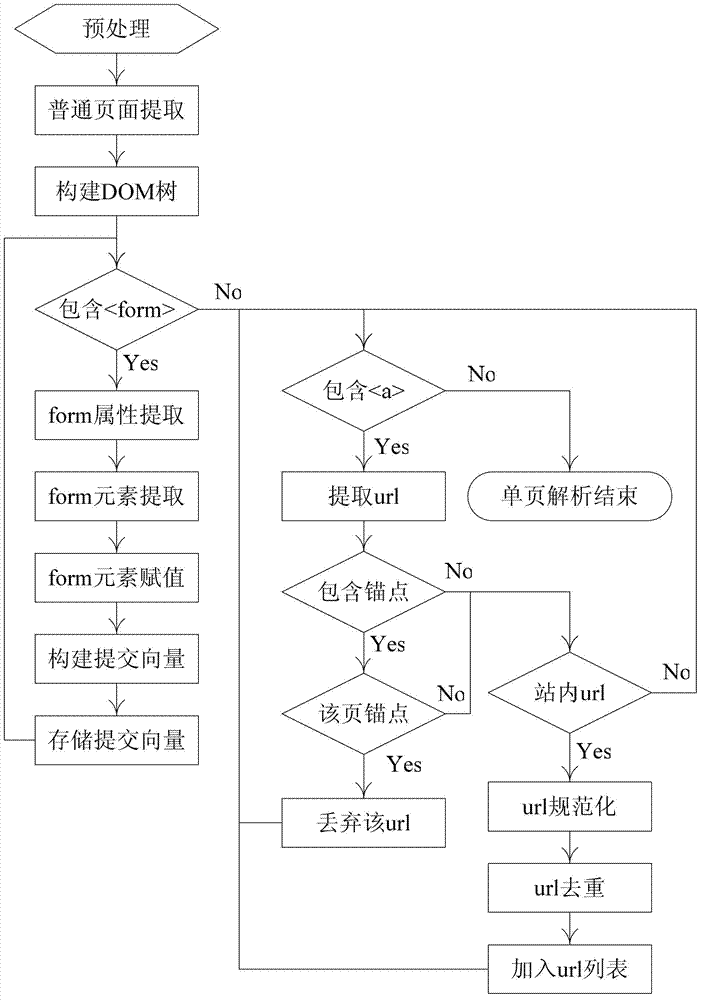
Cross-site script vulnerability detection method based on percolation test
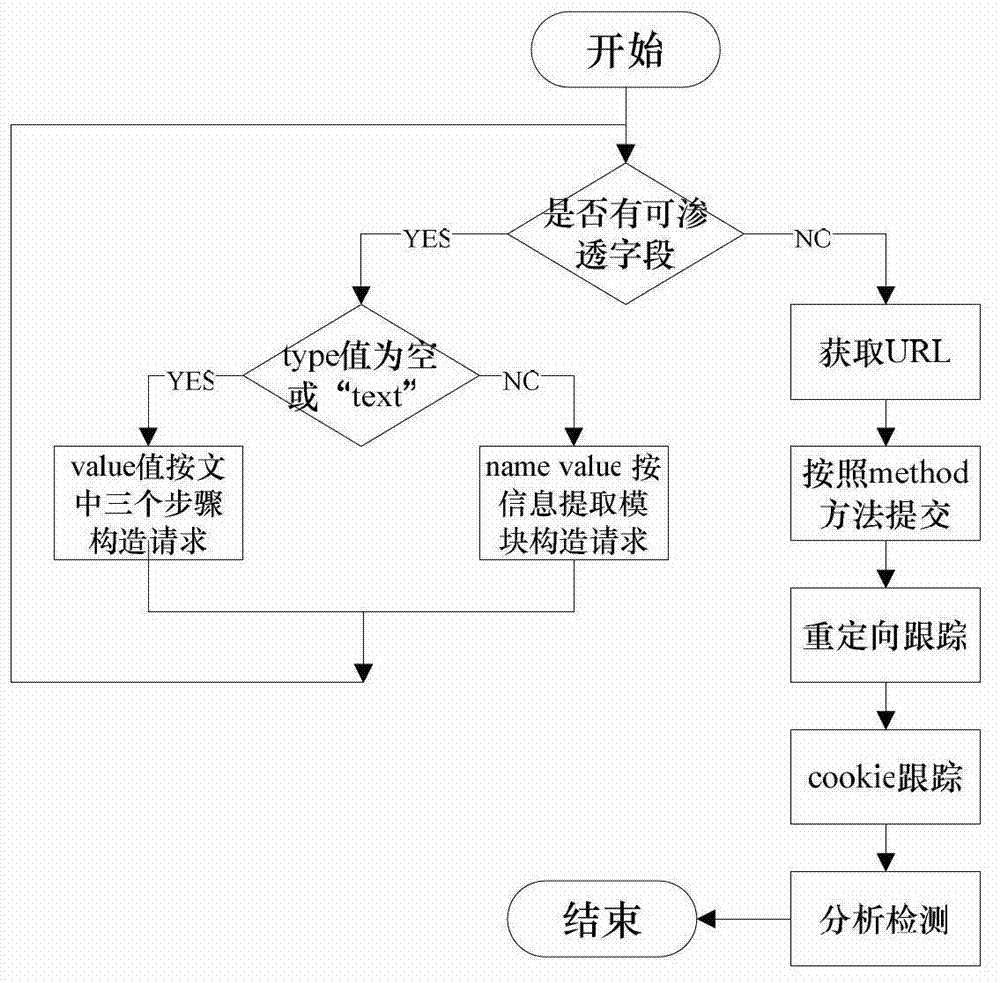
InactiveCN102819710AReduce incomplete analysisImprove detection efficiencyComputer security arrangementsSoftware testing/debuggingWeb siteComputer science
The invention discloses a cross-site script vulnerability detection method based on a percolation test. According to the cross-site script vulnerability detection method, the technical problem of low detection efficiency in a traditional cross-site script vulnerability detection method is solved. The technical scheme provided by the invention is that the cross-site script vulnerability detection method comprises the following steps of: firstly, acquiring a page; secondly, extracting form information and carrying out the percolation test on the extracted form; and finally, carrying out session retaining and redirection tracking. Due to the adoption of a session retaining and redirection tracking method, the conditions that the analysis for Web pages is incomprehensive are reduced, all pages of a Web site are analyzed and detected and further the automatic detection capability is improved. According to a percolation test strategy, the detection range of the XSS (Cross-Site Script) is gradually narrowed and the depth detection for the safe pages is avoided. While test statements are injected, test statements for closing HTML (Hypertext Markup Language) statements are actively constructed according to the returned page information, so that interaction frequencies with a server are reduced and the detection efficiency of the XXS vulnerabilities of large complex Websites is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and evaluation system based on the model
ActiveCN105763562AImprove accuracyImprove timelinessPlatform integrity maintainanceTransmissionDistributed structureStructure of Management Information
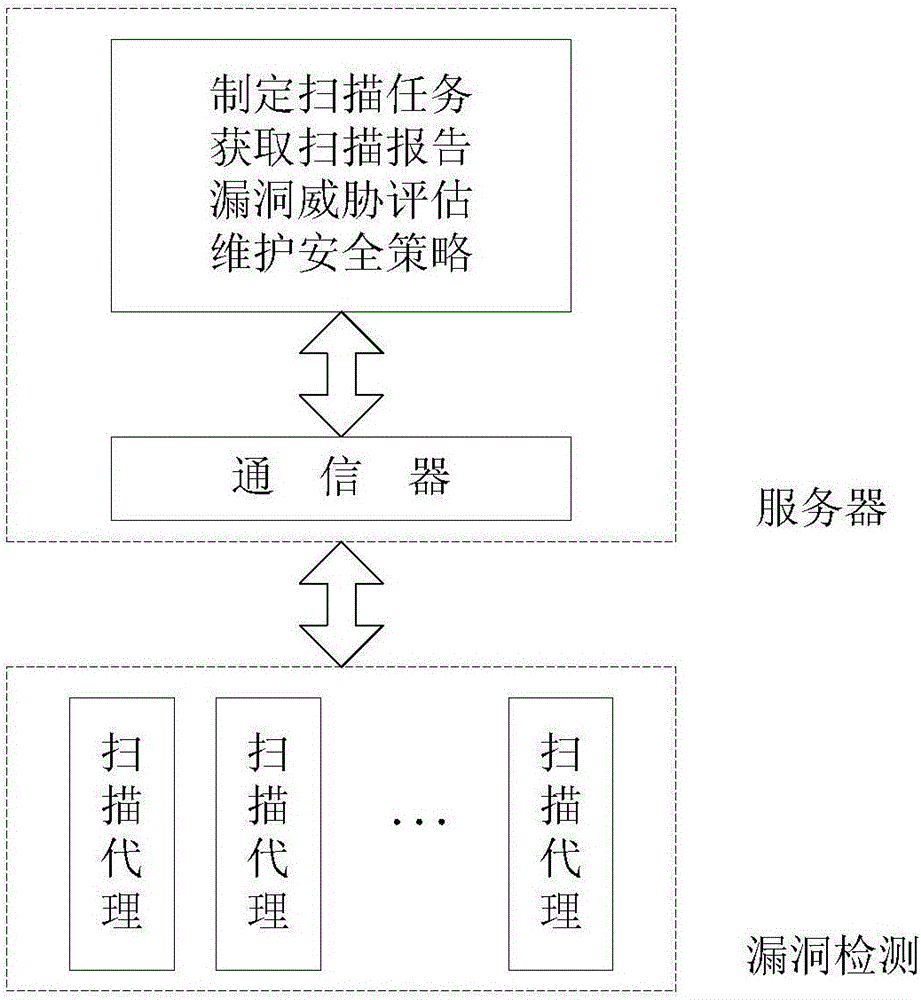
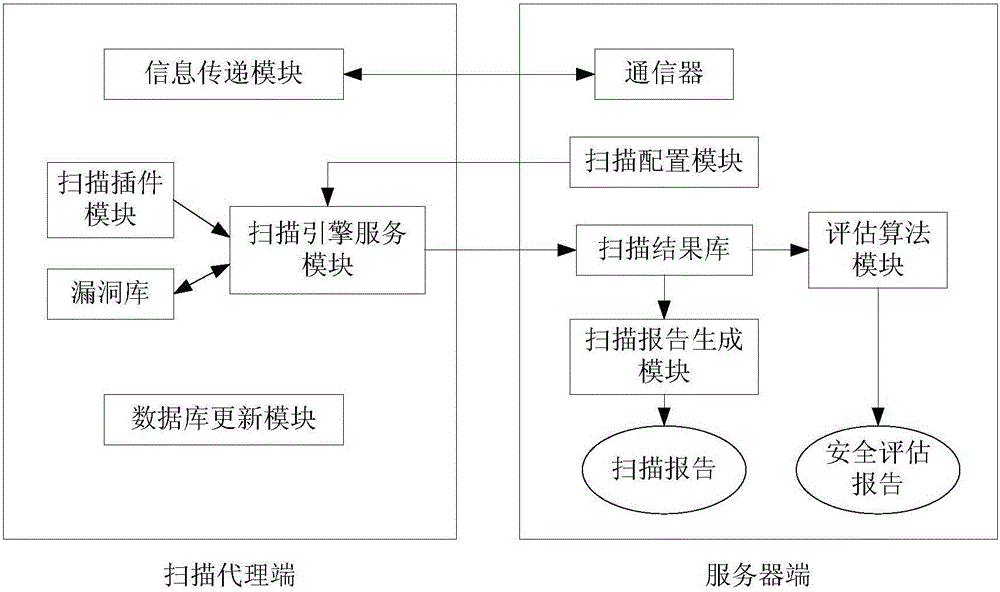
The invention discloses an electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and an evaluation system based on the model, the model selects three groups of security vulnerability evaluation factors including vulnerability distribution threat degree, access approach and utilization complexity; an analytic hierarchy process is adopted to establish a vulnerability threat degree evaluation model, and a parameter construction method is provided; on the basis of quantitative evaluation, the evaluation result defines a vulnerability threat level, and the objectivity of quantitative evaluation and visibility of qualitative evaluation are considered; and the system related to the invention comprises a vulnerability detection part and a server part which adopt distributed structure. According to the invention, a vulnerability scanning system and a security area of the electric power information network are combined, an electric power information network vulnerability threat evaluation algorithm based on CVSS and analytic hierarchy process is adopted to perform vulnerability threat evaluation, so that the system can be safer and more accurate for performing vulnerability scanning and safety evaluation on the electric power information network.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
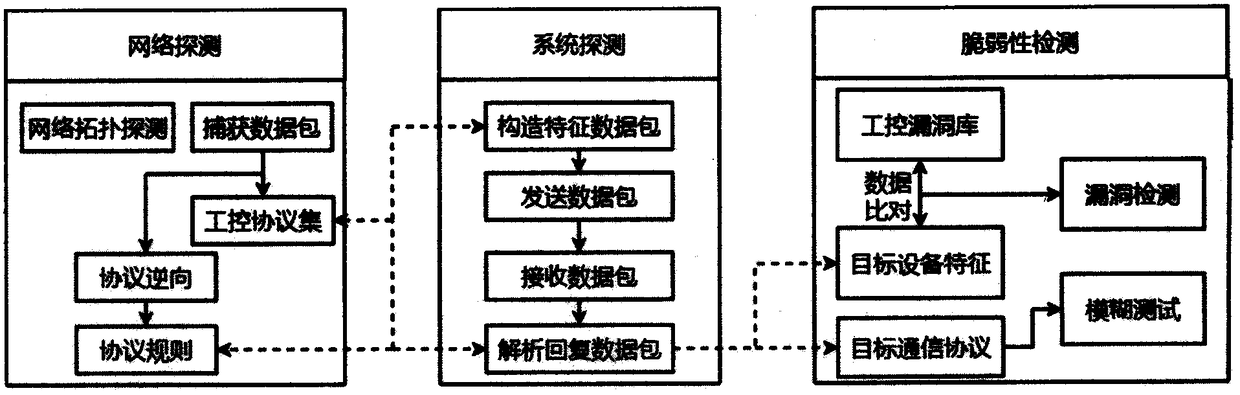
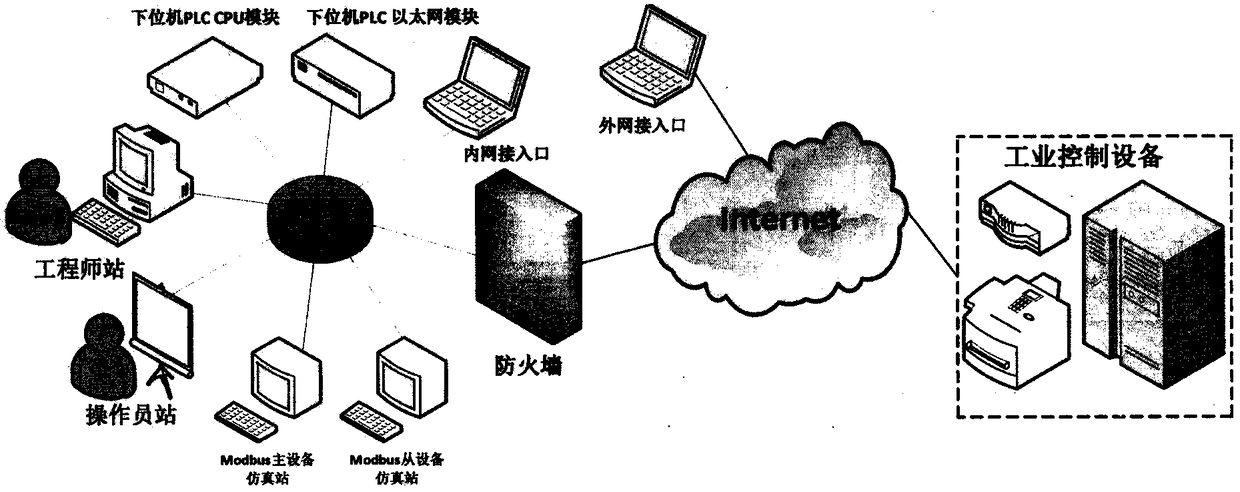
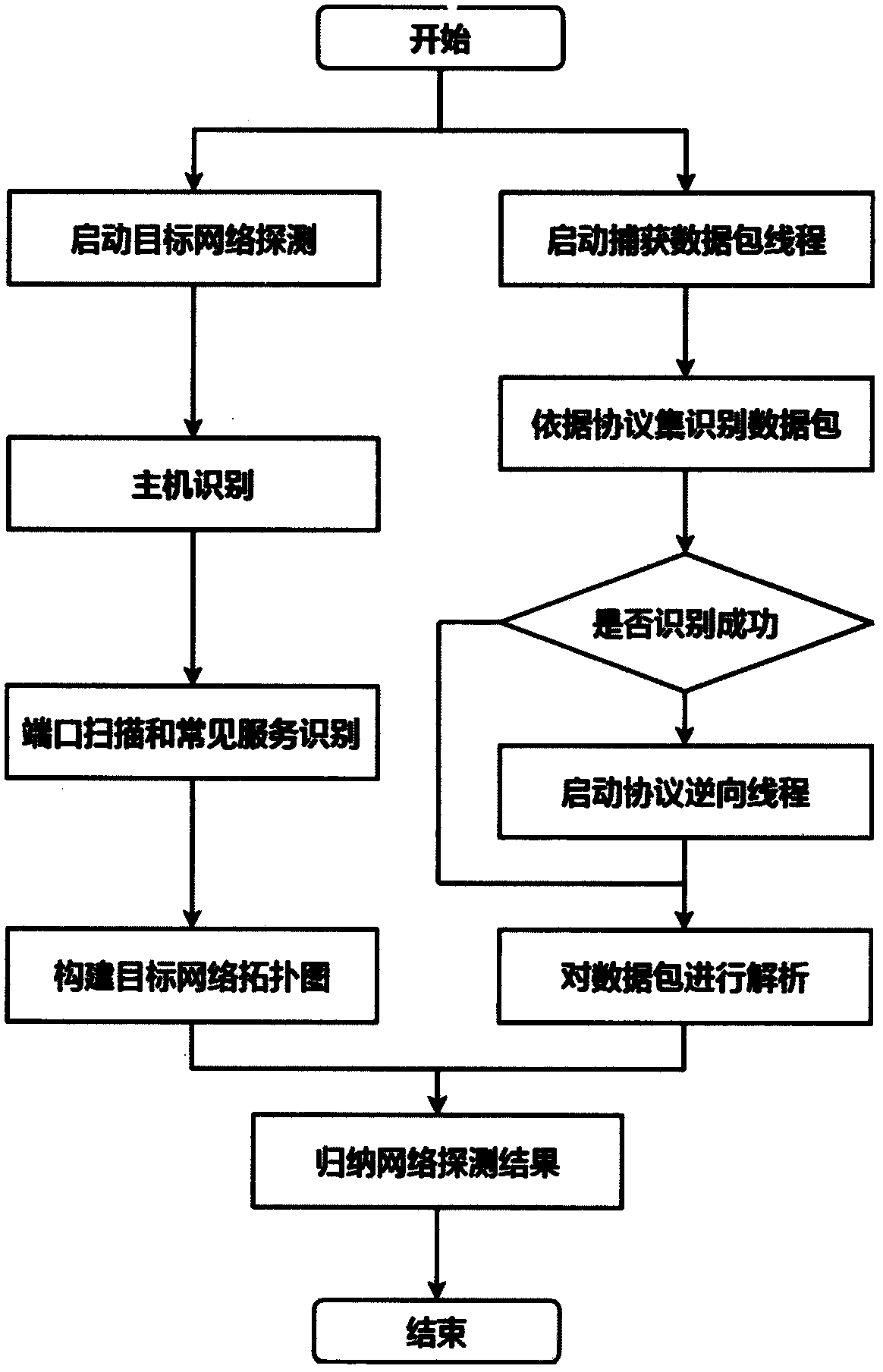
Vulnerability detection method for industrial control system
InactiveCN108737417AGain advantageImprove applicabilityTransmissionIndustrial EthernetNetwork packet
The invention provides a vulnerability detection method for an industrial control system. The method comprises the following steps: performing network detection on a target environment based on industrial Ethernet features, identifying an industrial control device, and capturing a session data packet; parsing the data packet according to the industrial control protocol specification and the private protocol reverse technology, and constructing a feature code data packet to perform further system detection to obtain specific fingerprint information; comparing the vulnerability information of amatching target based on the features of an industrial control dedicated vulnerability database, and performing related vulnerability detection based on strategy drive; and performing a fuzzy test based on the industrial control protocol vulnerability, and mining the security vulnerabilities of the industrial control system network, and detecting the security vulnerability. According to the vulnerability detection method provided by the invention, the vulnerability detection is performed on the industrial control target to detect the security vulnerabilities before the network attackers so asto improve the security and reliability of the industrial control system.
Owner:NANJING UNIV +3
Injection point extracting method in SQL (Structured Query Language) injection vulnerability detection
InactiveCN102831345AIncrease the analysis processSolve the problem of false positivesComputer security arrangementsSoftware testing/debuggingFiltrationSQL injection
The invention discloses an injection point extracting method in SQL (Structured Query Language) injection vulnerability detection, which is used for solving the technical problem of poor accuracy of the traditional method in the SQL injection vulnerability detection under a Web environment. According to the technical scheme, the injection point extracting method comprises the steps of: firstly, preprocessing a downloaded webpage, dividing the webpage into a simple webpage and a complex webpage, extracting a data injection point of the simple webpage, extracting a data injection point of the complex webpage, extracting a test case through constructing the test case, analyzing service response, and establishing a decision rule of an SQL injection vulnerability. According to the invention, starting from obtaining the data injection points of a Web application system, through constructing the targeted test case, the used test case is used for carrying out character string, numerical value, annotation and delay testing according to the types and the parameter compositions of the data injection points, thus the test of the injection vulnerability caused by simple filtration of URL (Uniform Resource Locator) parameters and table submitted data is effectively dealt; and through analysis response, the established decision rule of the SQL injection vulnerability is improved in testing accuracy.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
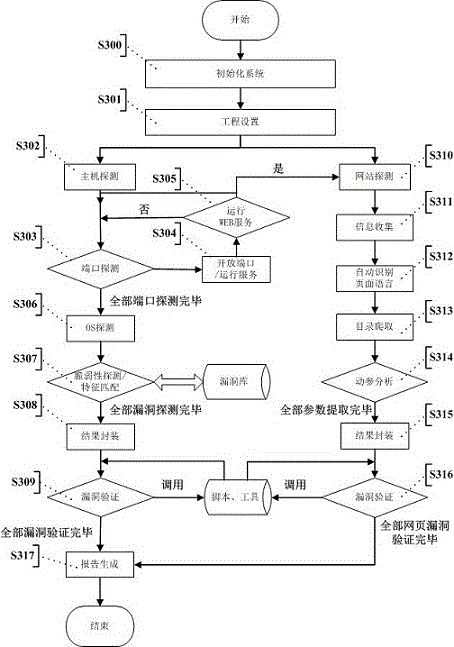
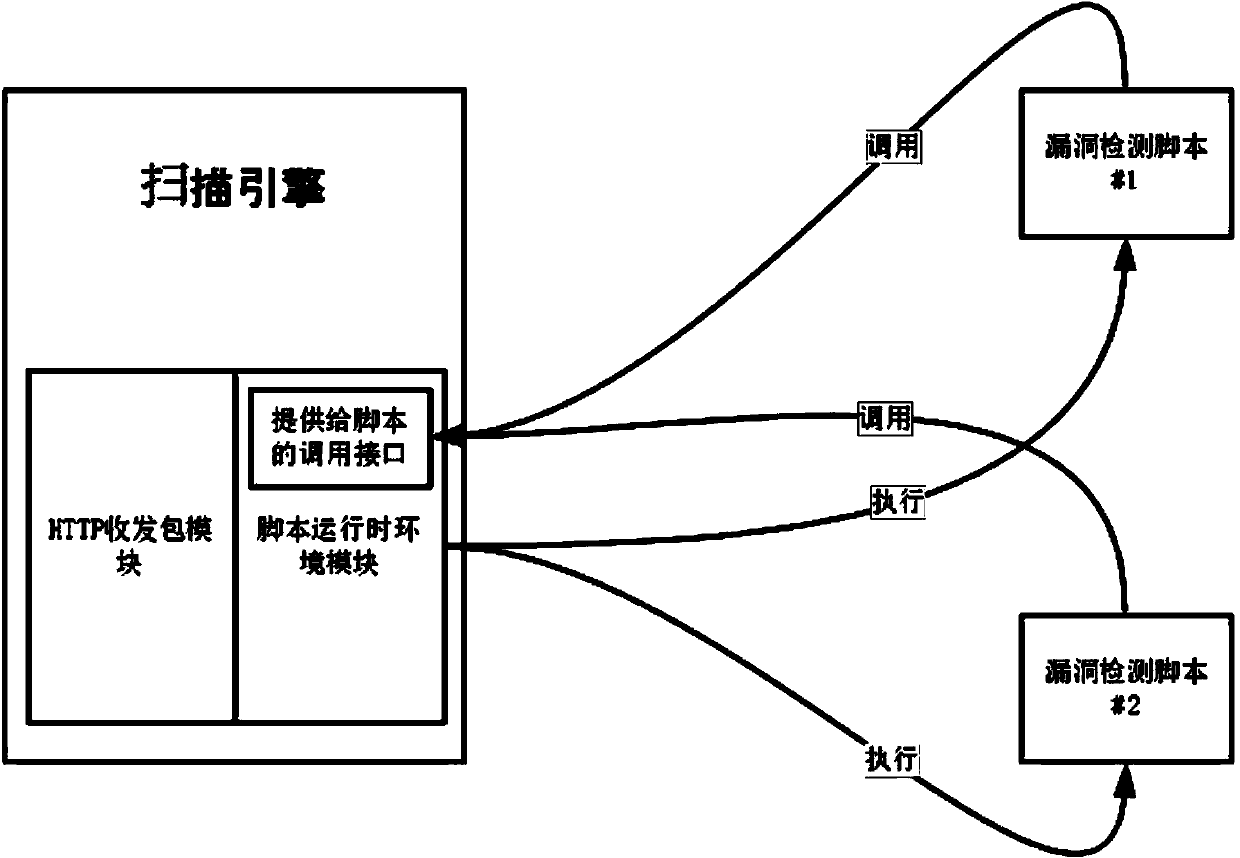
Script-based website vulnerability scanning method and system
The invention relates to the field of network application security, and provides a script-based website vulnerability scanning method and system. The script-based website vulnerability scanning method comprises the steps of setting a website URL to be scanned, selecting security vulnerability types needing to be detected by a website, starting a scanning engine module, constructing and sending an HTTP request to the URL needing to be detected, receiving an HTTP response, storing all data into the scanning engine module, and respectively executing corresponding vulnerability detection script modules according to the security vulnerability types selected by a user. The website vulnerability scanning system comprises the scanning engine module and the vulnerability detection script modules. According to the script-based website vulnerability scanning method and system, vulnerability detection logic is separated from a scanning engine, the coupling degree of the vulnerability detection logic and the scanning engine is reduced, the vulnerability detection logic is achieved through a vulnerability detection script, and the scanning engine has the general basic function not special for vulnerabilities of a certain kind.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com