Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
9185 results about "False alarm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A false alarm, also called a nuisance alarm, is the deceptive or erroneous report of an emergency, causing unnecessary panic and/or bringing resources (such as emergency services) to a place where they are not needed. False alarms may occur with residential burglary alarms, smoke detectors, industrial alarms, and in signal detection theory. False alarms have the potential to divert emergency responders away from legitimate emergencies, which could ultimately lead to loss of life. In some cases, repeated false alarms in a certain area may cause occupants to develop alarm fatigue and to start ignoring most alarms, knowing that each time it will probably be false.
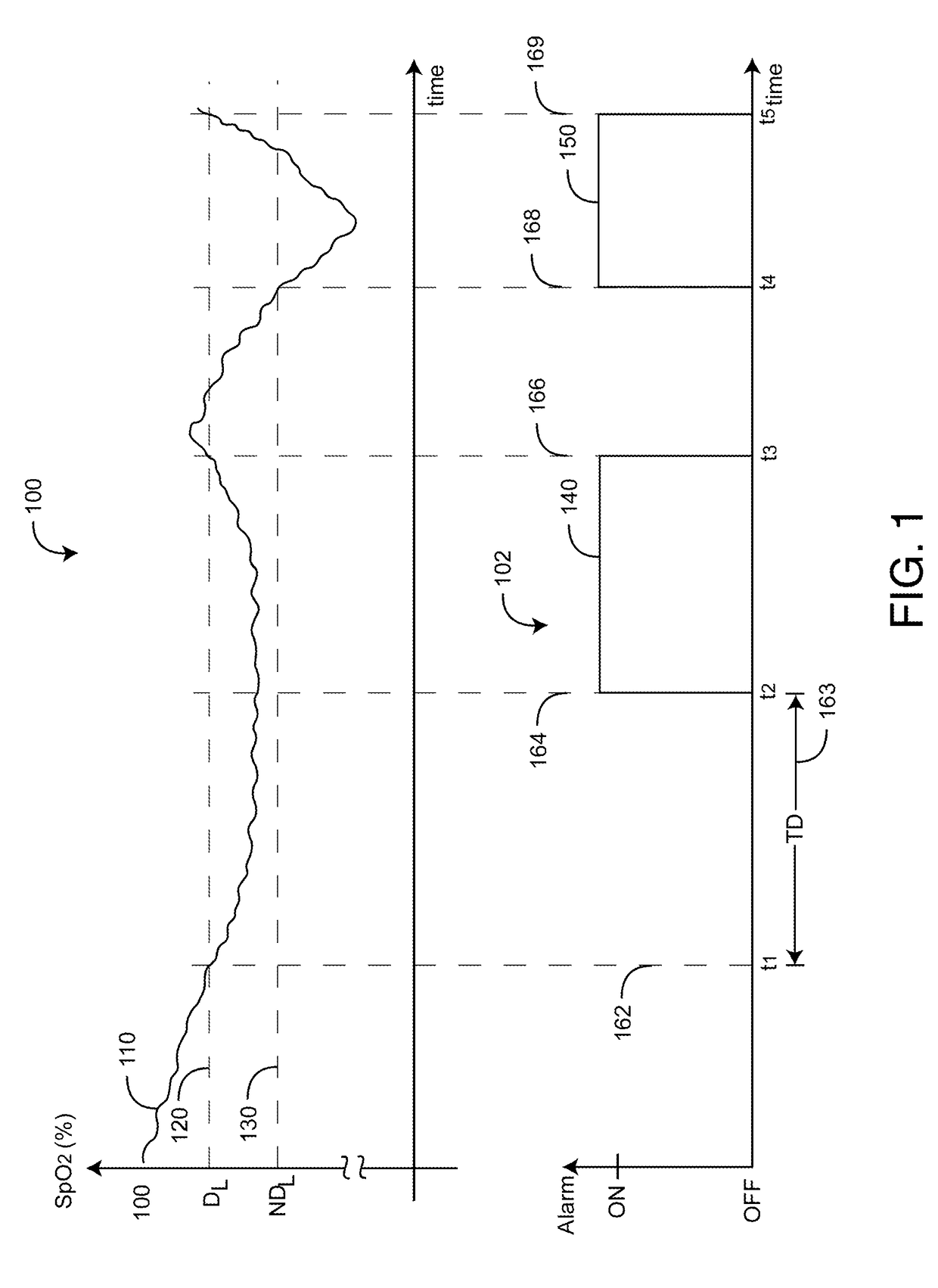
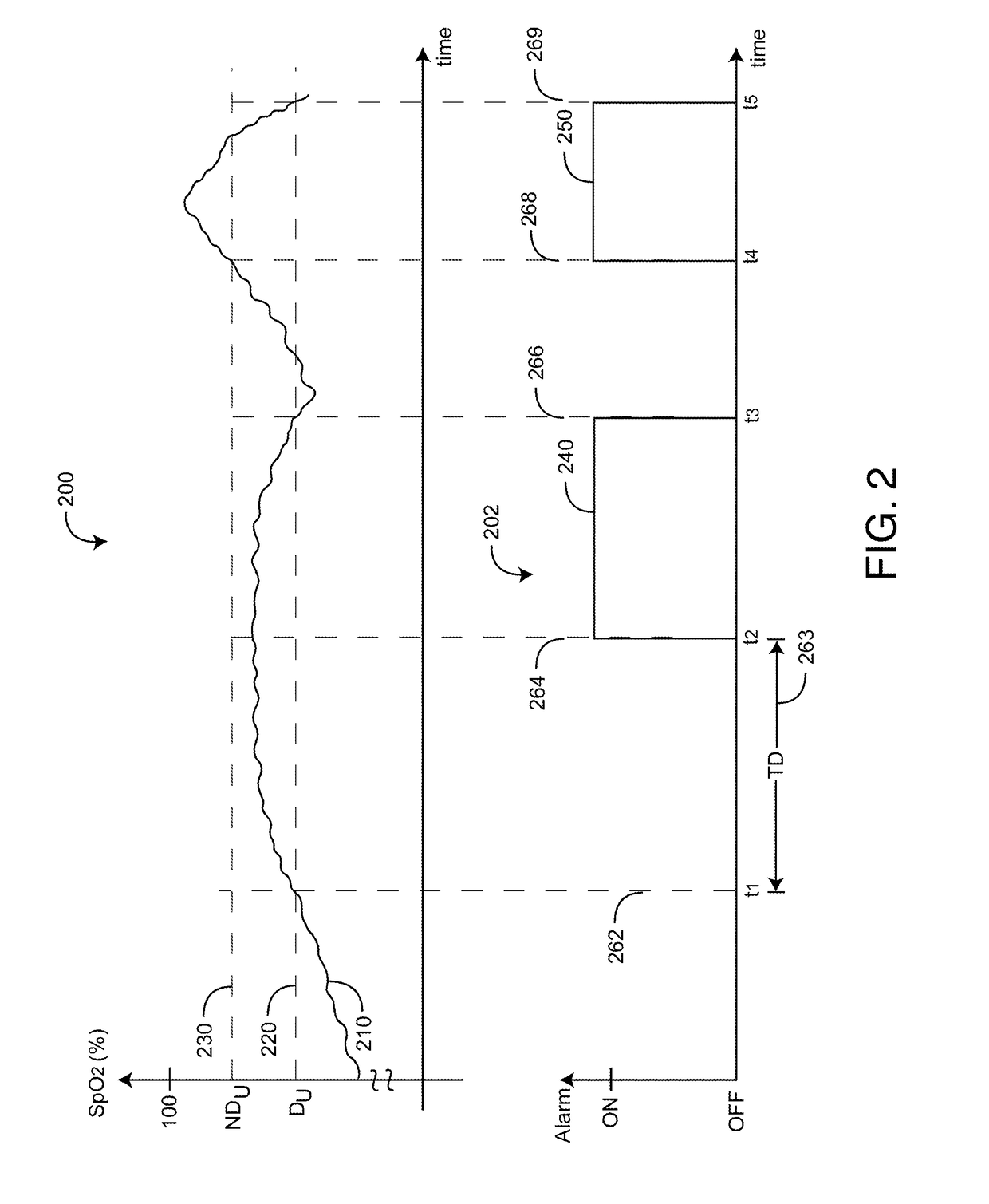
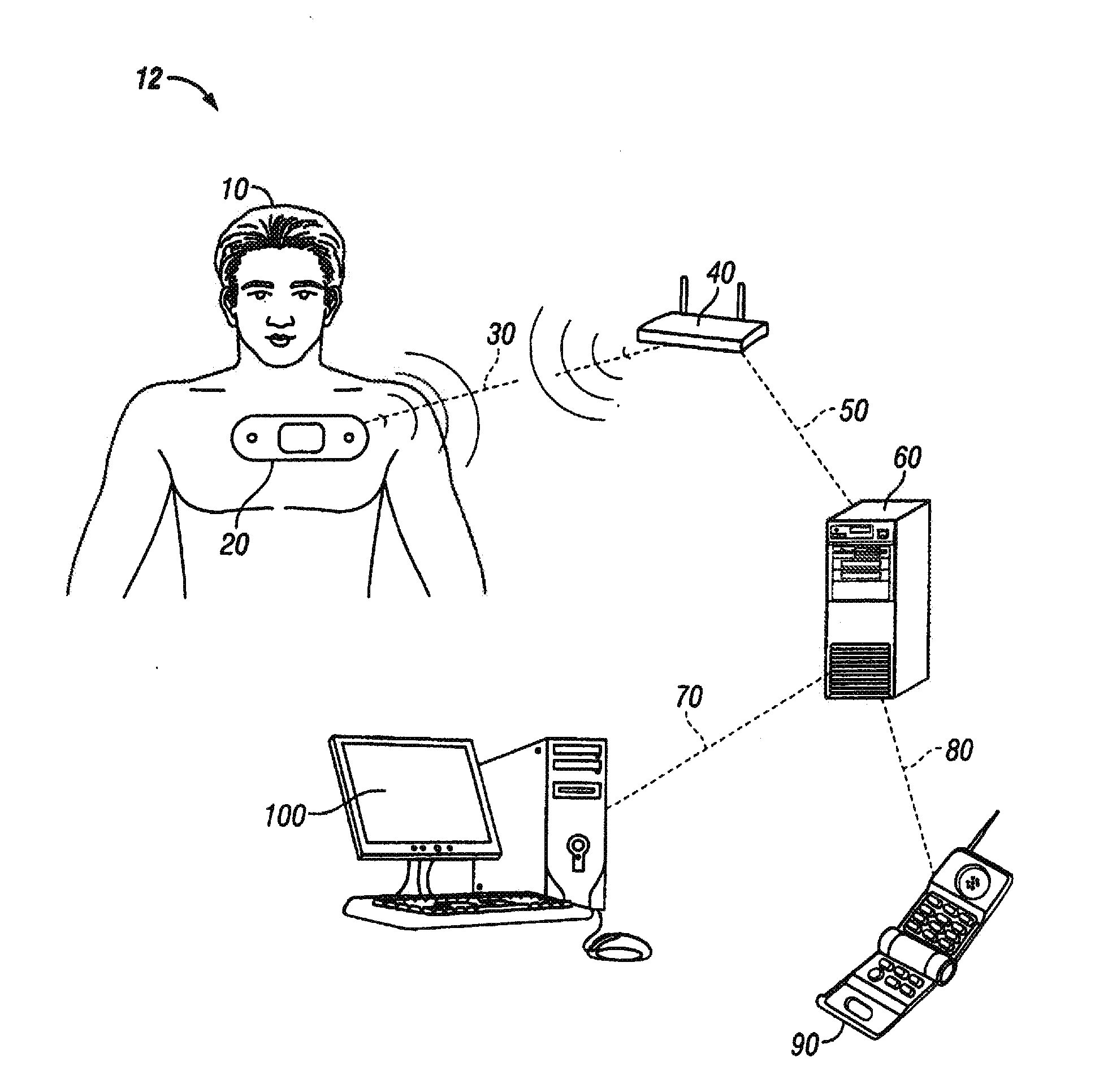
Pulse oximetry data confidence indicator
InactiveUS6996427B2Reduce probabilitySensorsMeasuring/recording heart/pulse rateSignal qualityPulse rate
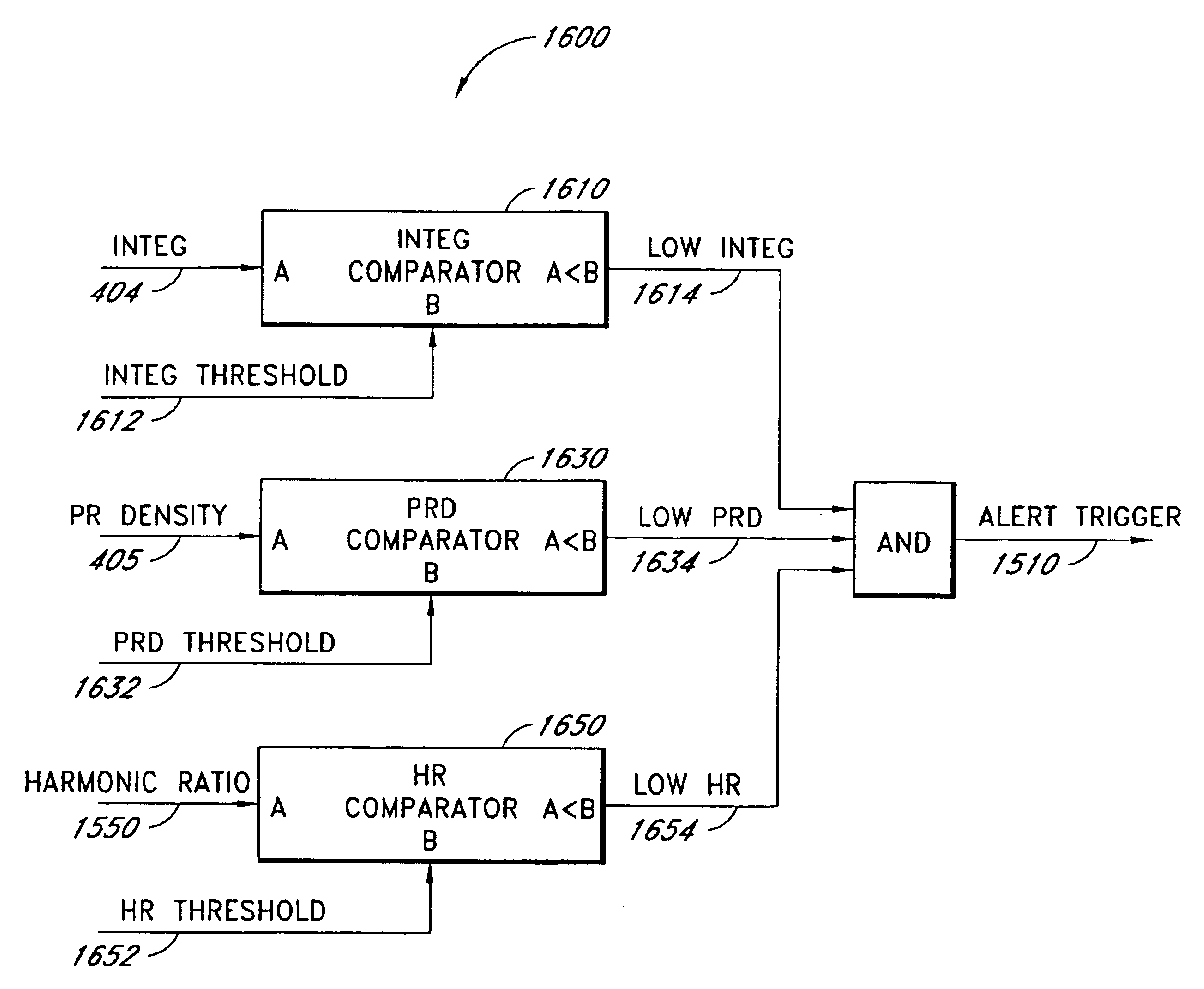
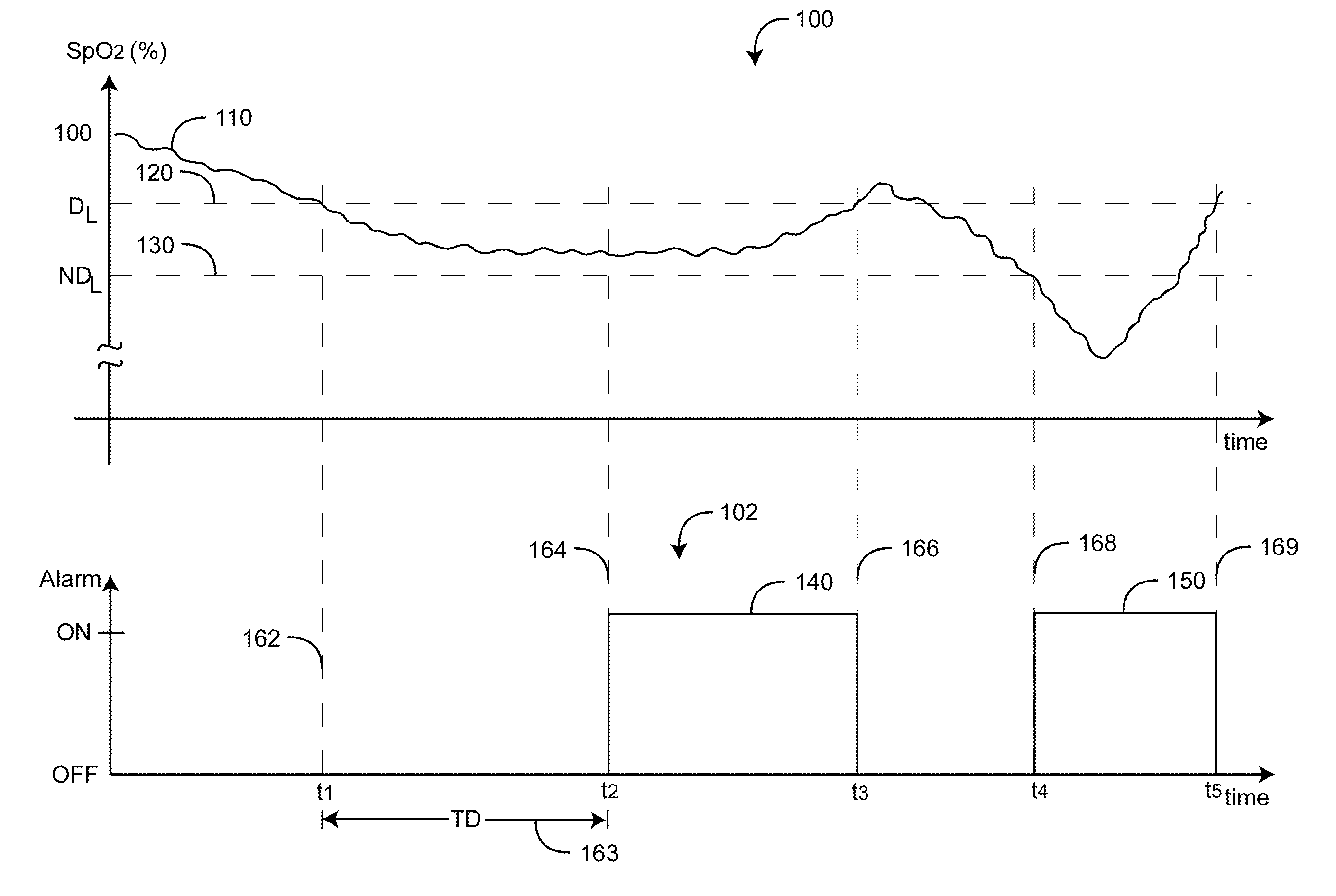
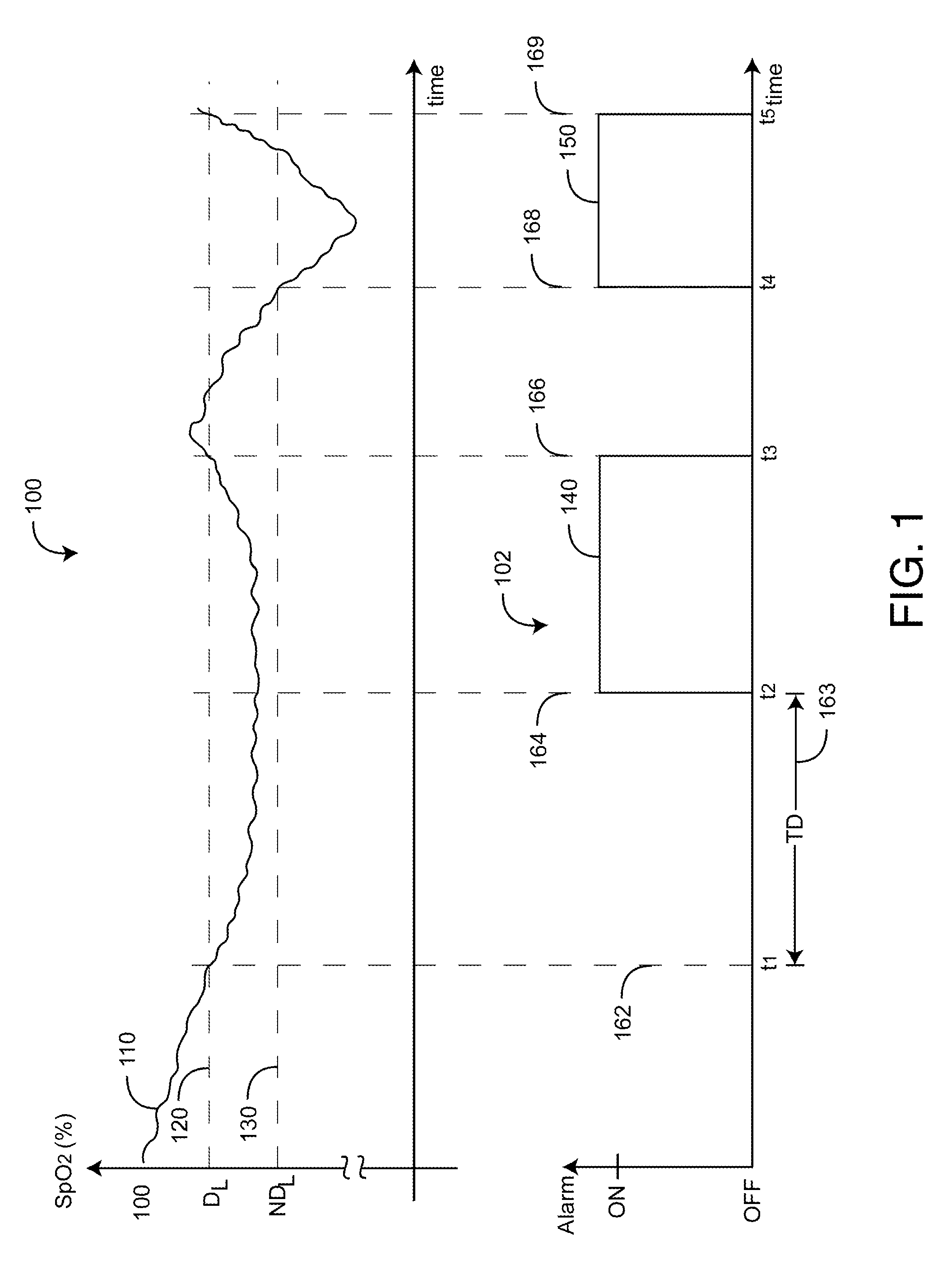
A data confidence indicator includes a plurality of physiological data and a plurality of signal quality measures derived from a physiological sensor output, and a plurality of comparator outputs each responsive to one of the measures and a corresponding one of a plurality of thresholds. An alert trigger output combines the comparator outputs. A low signal quality warning is generated in response to the alert trigger output, wherein the thresholds are set so that the warning occurs during a time period when there is low confidence in the data. The alert may be in the form of a message generated on the pulse oximeter display to warn that the accuracy of saturation and pulse rate measurements may be compromised. A confidence-based alarm utilizes signal quality measures to reduce the probability of false alarms when data confidence is low and to reduce the probability of missed events when data confidence is high.
Owner:JPMORGAN CHASE BANK NA
Adaptive alarm system
ActiveUS9724024B2Control rateSmall sizeUser/patient communication for diagnosticsSensorsEngineeringSelf adaptive
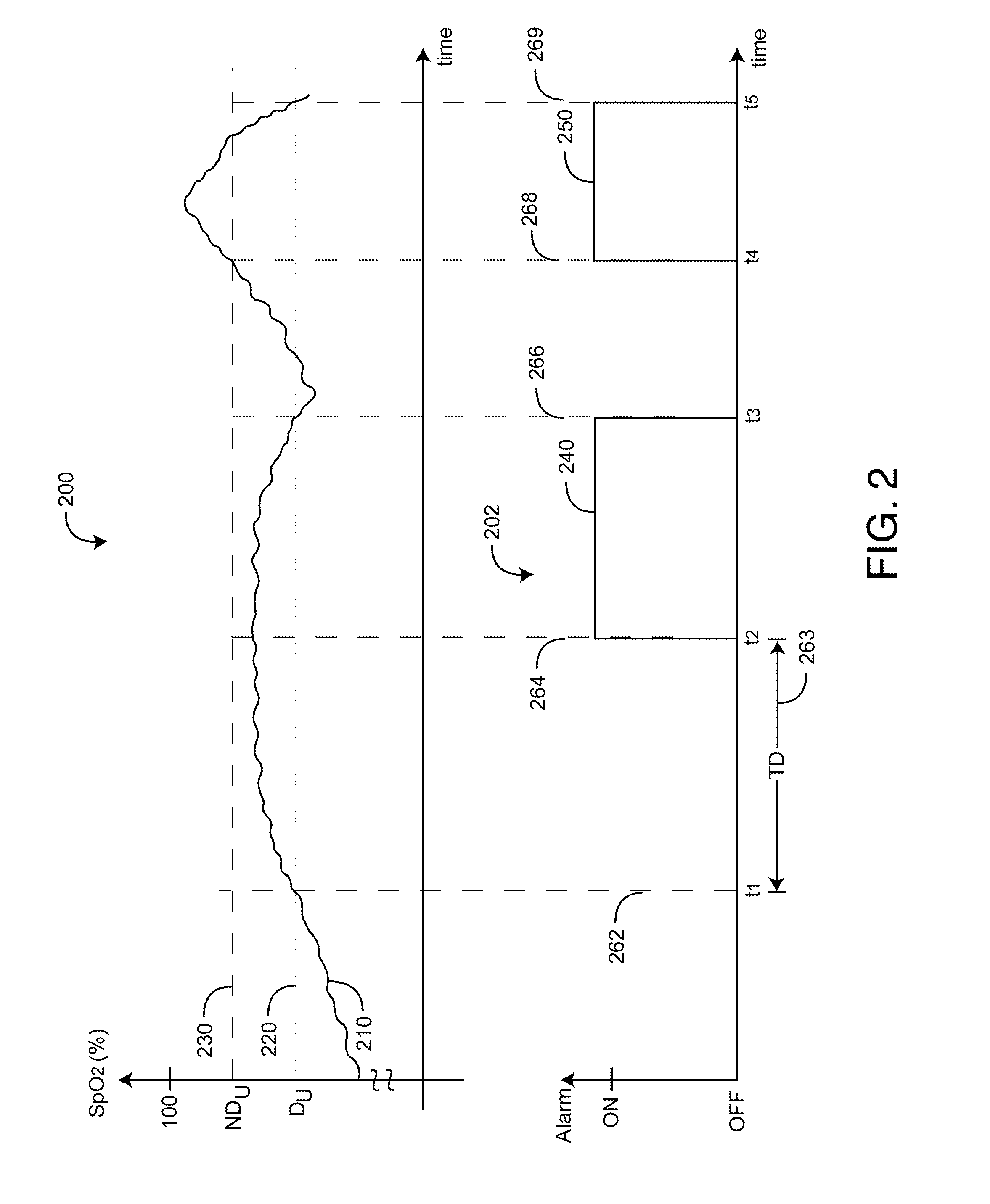
An adaptive alarm system is responsive to a physiological parameter so as to generate an alarm threshold that adapts to baseline drift in the parameter and reduce false alarms without a corresponding increase in missed true alarms. The adaptive alarm system has a parameter derived from a physiological measurement system using a sensor in communication with a living being. A baseline processor calculates a parameter baseline from a parameter trend. Parameter limits specify an allowable range of the parameter. An adaptive threshold processor calculates an adaptive threshold from the parameter baseline and the parameter limits. An alarm generator is responsive to the parameter and the adaptive threshold so as to trigger an alarm indicative of the parameter crossing the adaptive threshold. The adaptive threshold is responsive to the parameter baseline so as to increase in value as the parameter baseline drifts to a higher parameter value and to decrease in value as the parameter baseline drifts to a lower parameter value.
Owner:JPMORGAN CHASE BANK NA
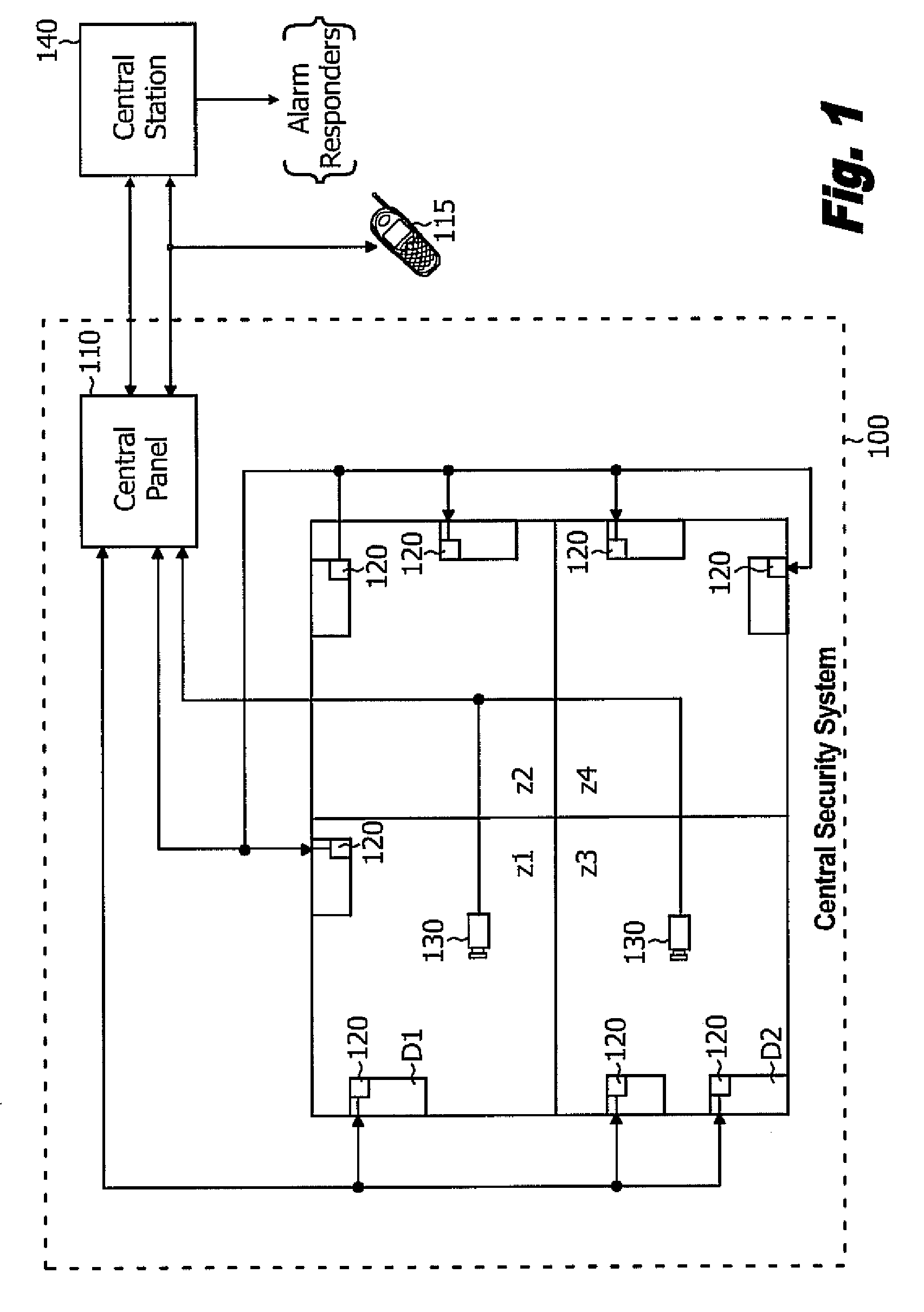
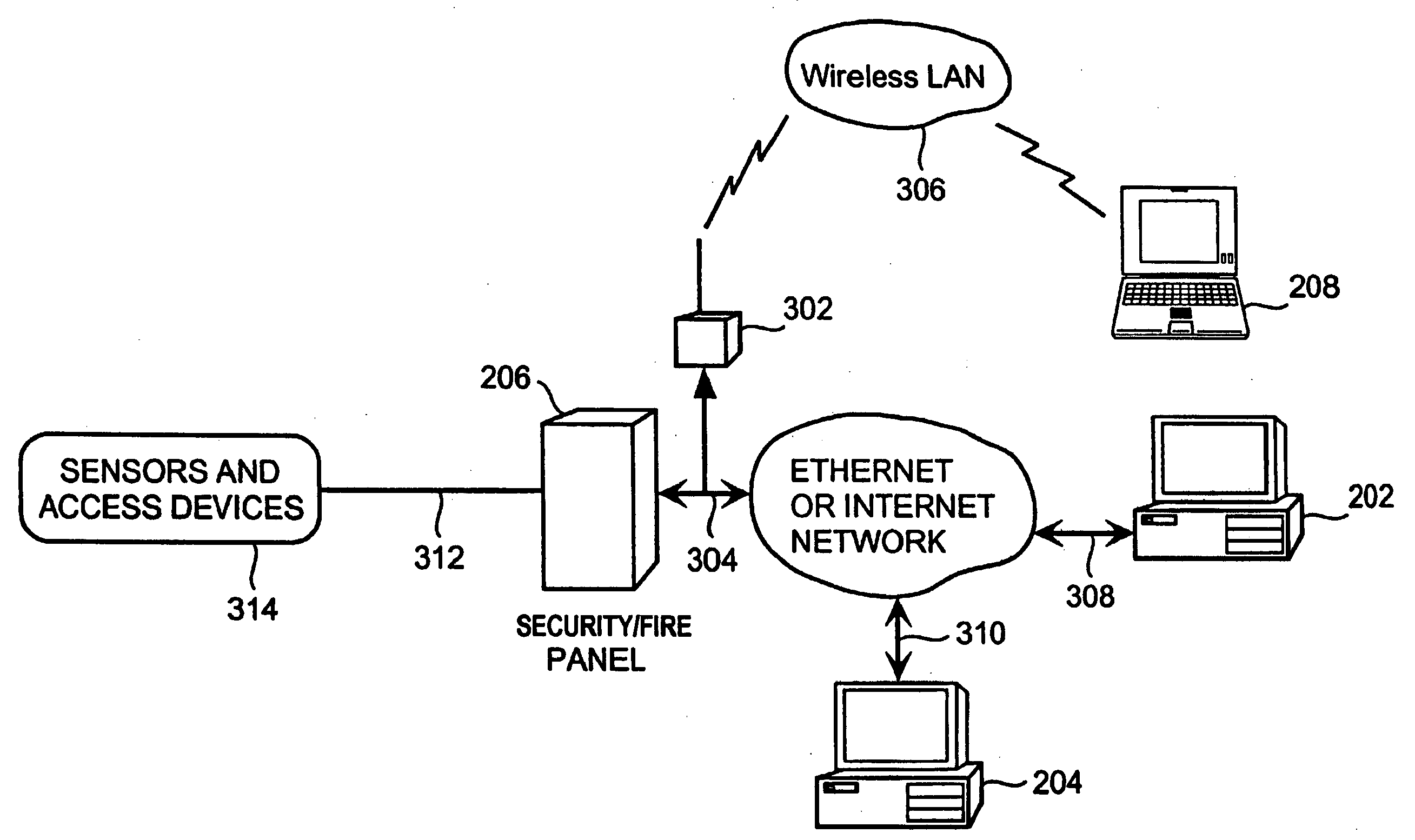
Security system
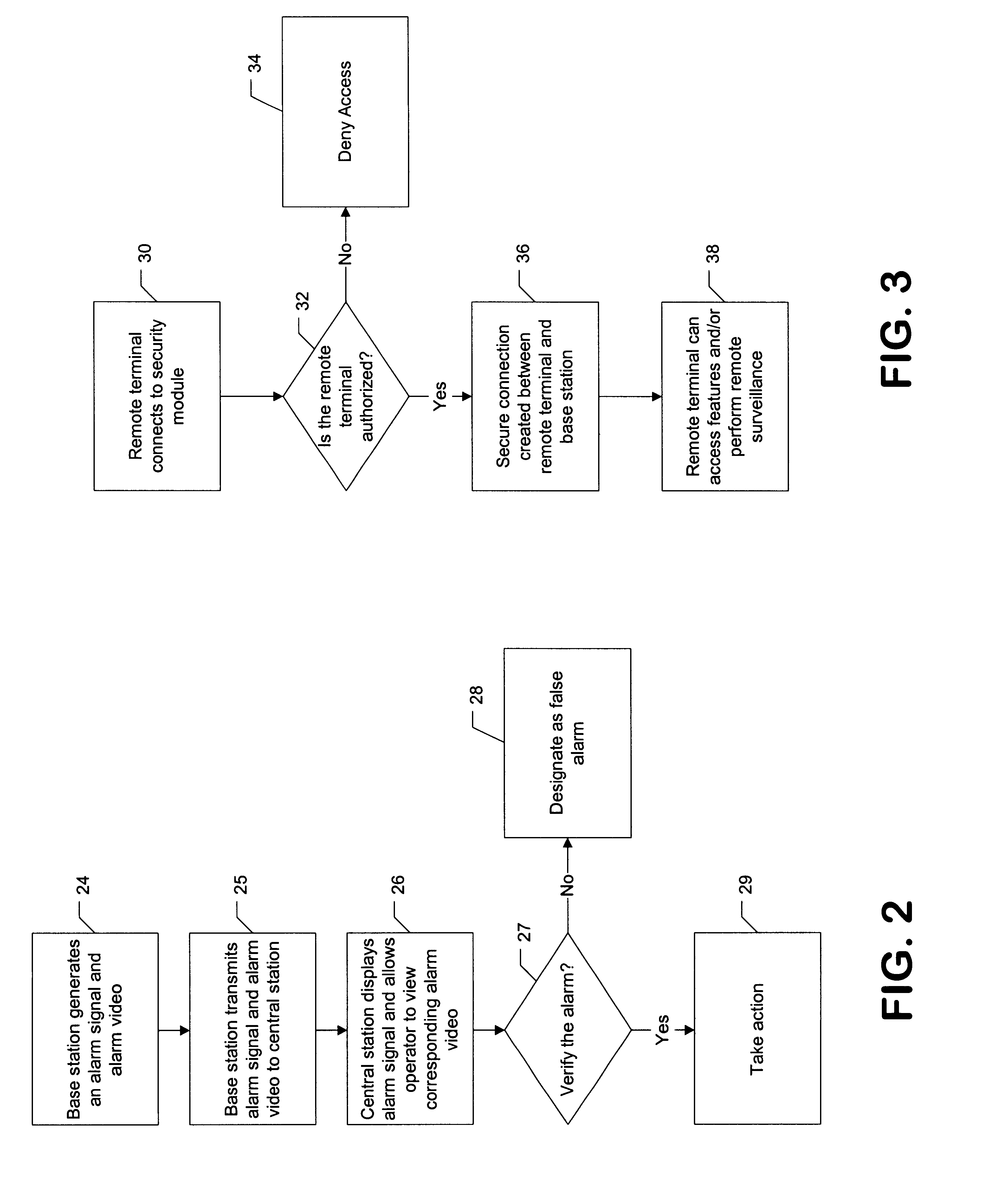
InactiveUS6690411B2Color television detailsClosed circuit television systemsGuard - securityEngineering
A system and method for enabling a central station to accurately verify in real-time whether an alarm signal generated by a security base station is a false alarm, and for enabling remote users to securely access features of the security base station such as remote surveillance, activating and deactivating the system, and adjusting alarm sensitivities.
Owner:COMCAST CABLE COMM LLC
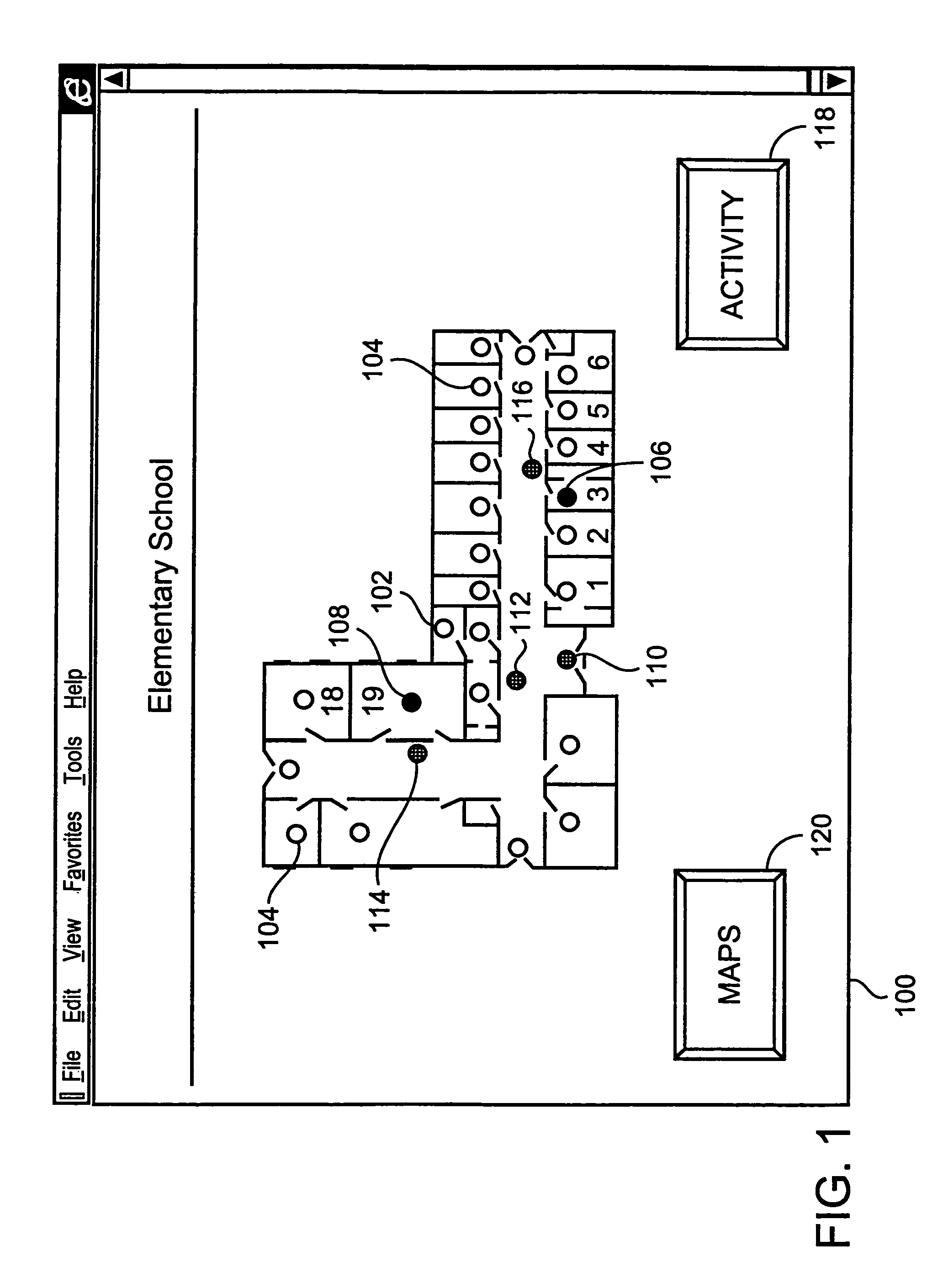
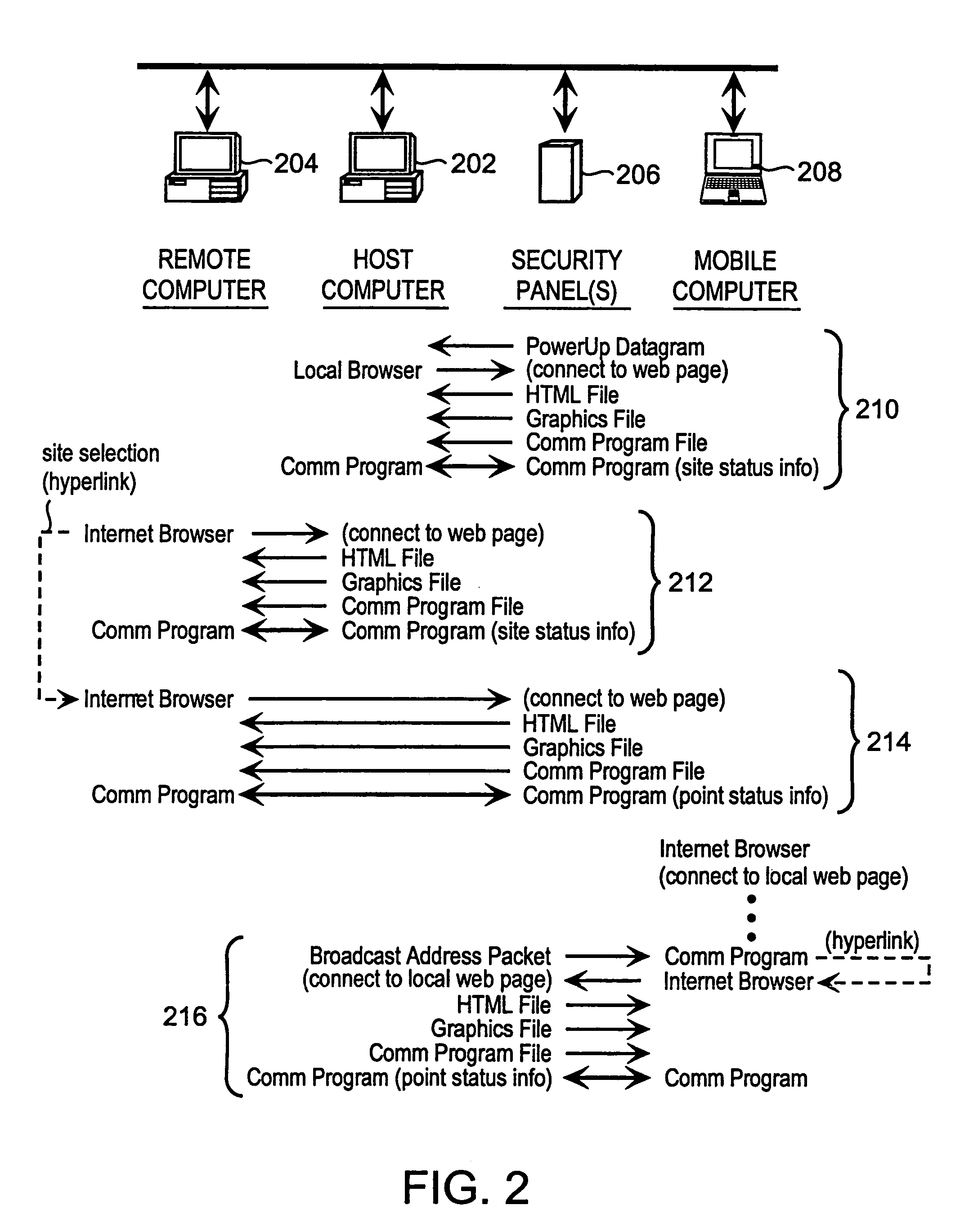
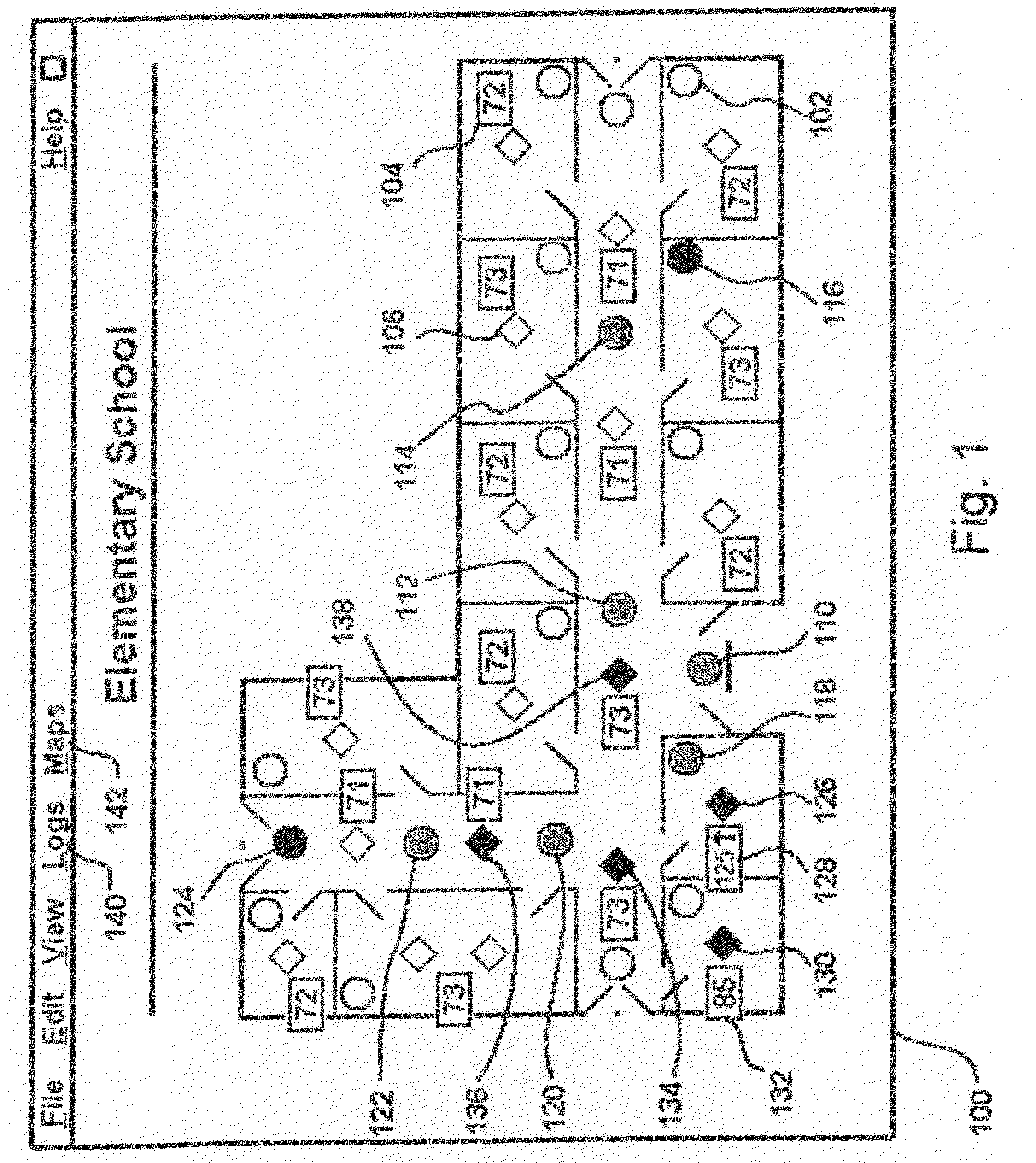
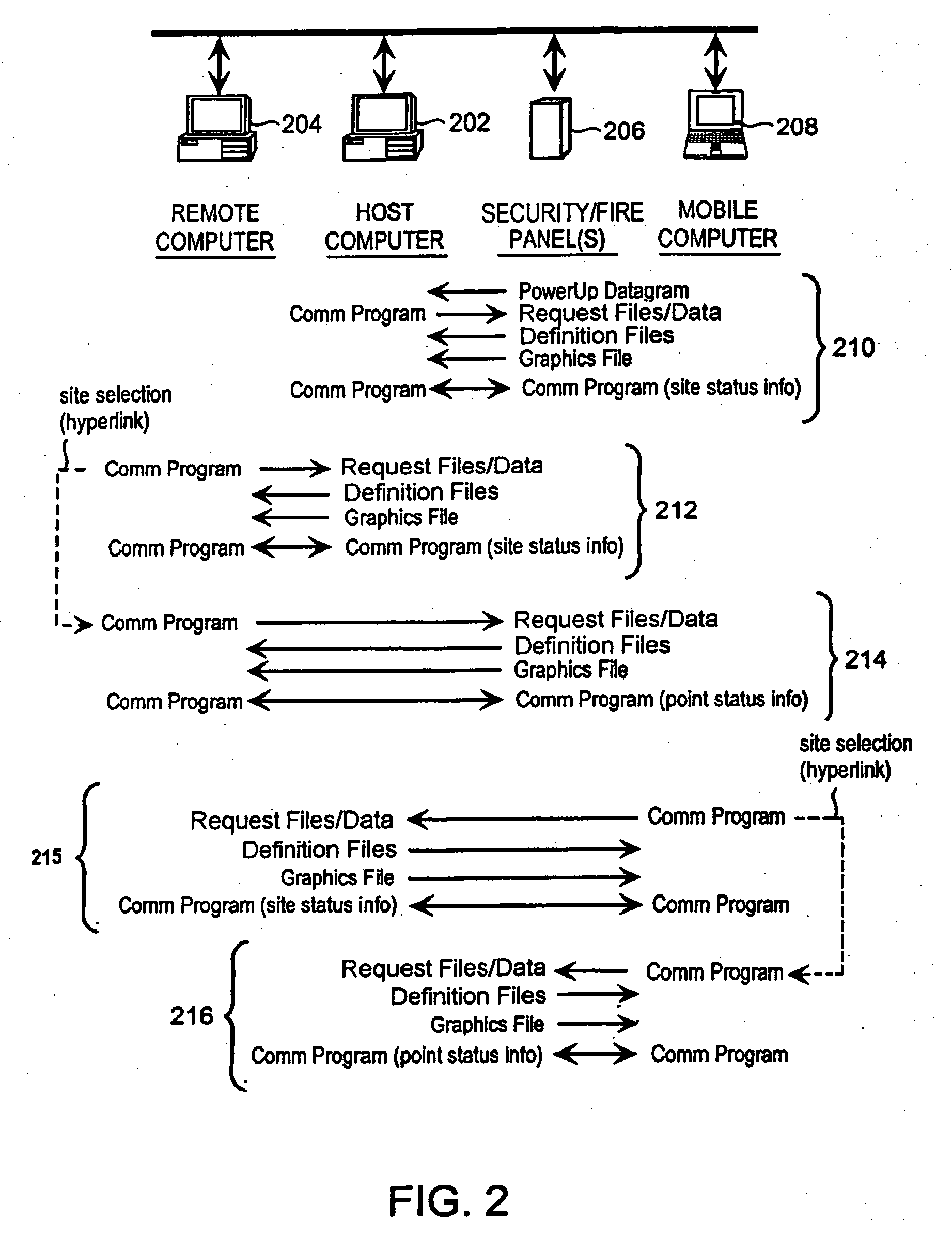
Method and apparatus for remotely monitoring a site
InactiveUS20070008099A1Maximum precisionEasy to distinguishFire rescueFire alarmsTime informationSprinkler system
The present invention is directed to providing systems and methods for remotely monitoring sites to provide real-time information which can readily permit distinguishing false alarms, and which can identify and track the precise location of an alarm. In embodiments, monitoring capabilities such as intrusion / fire detection and tracking capabilities, can be implemented through the use of multistate indicators in an interface which permits information to be transmitted using standard network protocols from a remote site to a monitoring station in near real-time. In embodiments, communications can be handed from the centrally located host monitoring station to a mobile monitoring station (for example, a laptop computer in a responding vehicle, such as a police or fire vehicle). Additional embodiments include the measurement of environmental parameters such as temperature, carbon monoxide and differential air pressure to detect, monitor and manage a fire event. These measurements along with selected controllable output devices deployed in a space, such as sprinkler control valves and individually or zoned sprinkler heads, are used to initiate and control fire suppression technology both locally and remotely. For instance, a system of the present invention may detect a fire and cause a sprinkler system to disburse water in a facility.
Owner:NETTALON SECURITY SYST
Adaptive alarm system
ActiveUS20110213212A1Small sizeReduces baseline movementUser/patient communication for diagnosticsSensorsEngineeringSelf adaptive
An adaptive alarm system is responsive to a physiological parameter so as to generate an alarm threshold that adapts to baseline drift in the parameter and reduce false alarms without a corresponding increase in missed true alarms. The adaptive alarm system has a parameter derived from a physiological measurement system using a sensor in communication with a living being. A baseline processor calculates a parameter baseline from a parameter trend. Parameter limits specify an allowable range of the parameter. An adaptive threshold processor calculates an adaptive threshold from the parameter baseline and the parameter limits. An alarm generator is responsive to the parameter and the adaptive threshold so as to trigger an alarm indicative of the parameter crossing the adaptive threshold. The adaptive threshold is responsive to the parameter baseline so as to increase in value as the parameter baseline drifts to a higher parameter value and to decrease in value as the parameter baseline drifts to a lower parameter value.
Owner:JPMORGAN CHASE BANK NA
Method and apparatus for remotely monitoring a site
InactiveUS6972676B1Easy to distinguishAccurate locationElectric testing/monitoringElectric/electromagnetic visible signallingTime informationOperating energy
The present invention is directed to providing systems and methods for remotely monitoring sites to provide real time information which can readily permit false alarms to be distinguished, and which can identify and track the precise location of an alarm. In exemplary embodiments, monitoring capabilities such as intrusion / fire detection and tracking capabilities, can be implemented through the use of multistate indicators in a novel interface which permits information to be transmitted using standard network protocols from a remote site to a monitoring station in real-time over preexisting communication networks, such as the Internet. A wireless network can also be established using browser encapsulated communication programs (for example, active X control, Java applets, and so forth) to transmit data packets which comply with any standard wireless local area network protocol. Communications can thereby be established between a web server embedded in a centrally located host monitoring station and a separate security panel deployed in each of the buildings to be remotely monitored. In exemplary embodiments, communications can be handed off from the centrally located host monitoring station to a mobile monitoring station (for example, to a laptop computer in a responding vehicle, such as a police or fire vehicle). The handoff can be such that direct communications are established between a security panel site being monitored and the laptop, or over, for example, a cellular network or indirect communications can be established via the host monitoring station.
Owner:NETTALON SECURITY SYST
Mapping defects or dirt dynamically affecting an image acquisition device
Defects such as dirt, dust, scratches, blemishes, pits, or defective elements or pixels in a CCD, scanner, photocopier, or image acquiring device are dynamically detected by processing a plurality of images via a computer. A pristine object of calibration is not required. Stationary components of the video images are found and detected so as to produce a low false alarm probability. Text segmentation and measurement of total deviation based on variability related to high-frequency components of the video image are employed to prevent applying the process or method to printed text or graphics. Additional techniques optionally employed are median filtering, sample area detection, and dynamic adjustment of scores. In special cases, only moderately blank documents are used. The dynamic defect detection allows defect compensation, defect correction, and alerting the operator of defects.
Owner:FOTONATION LTD
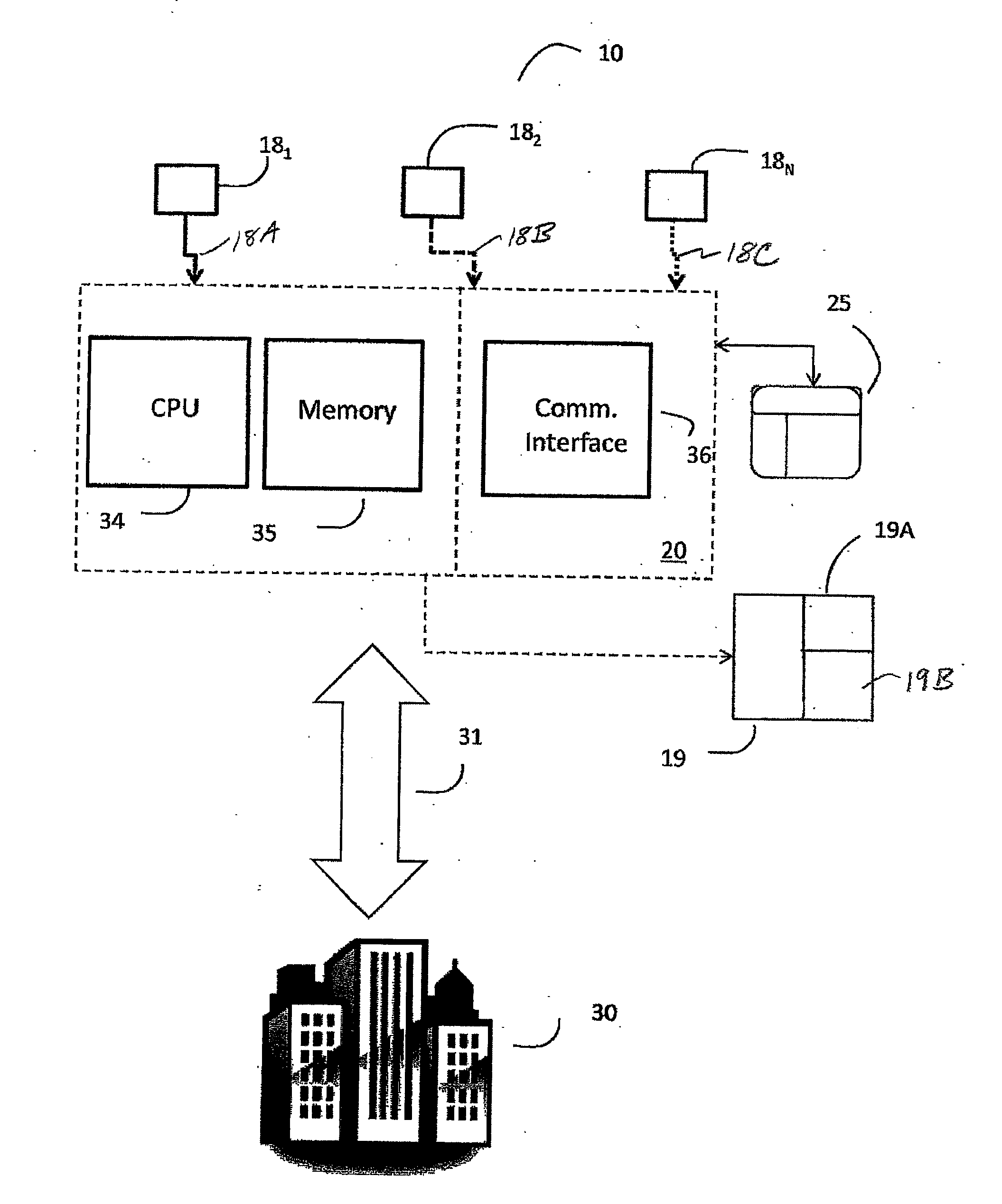
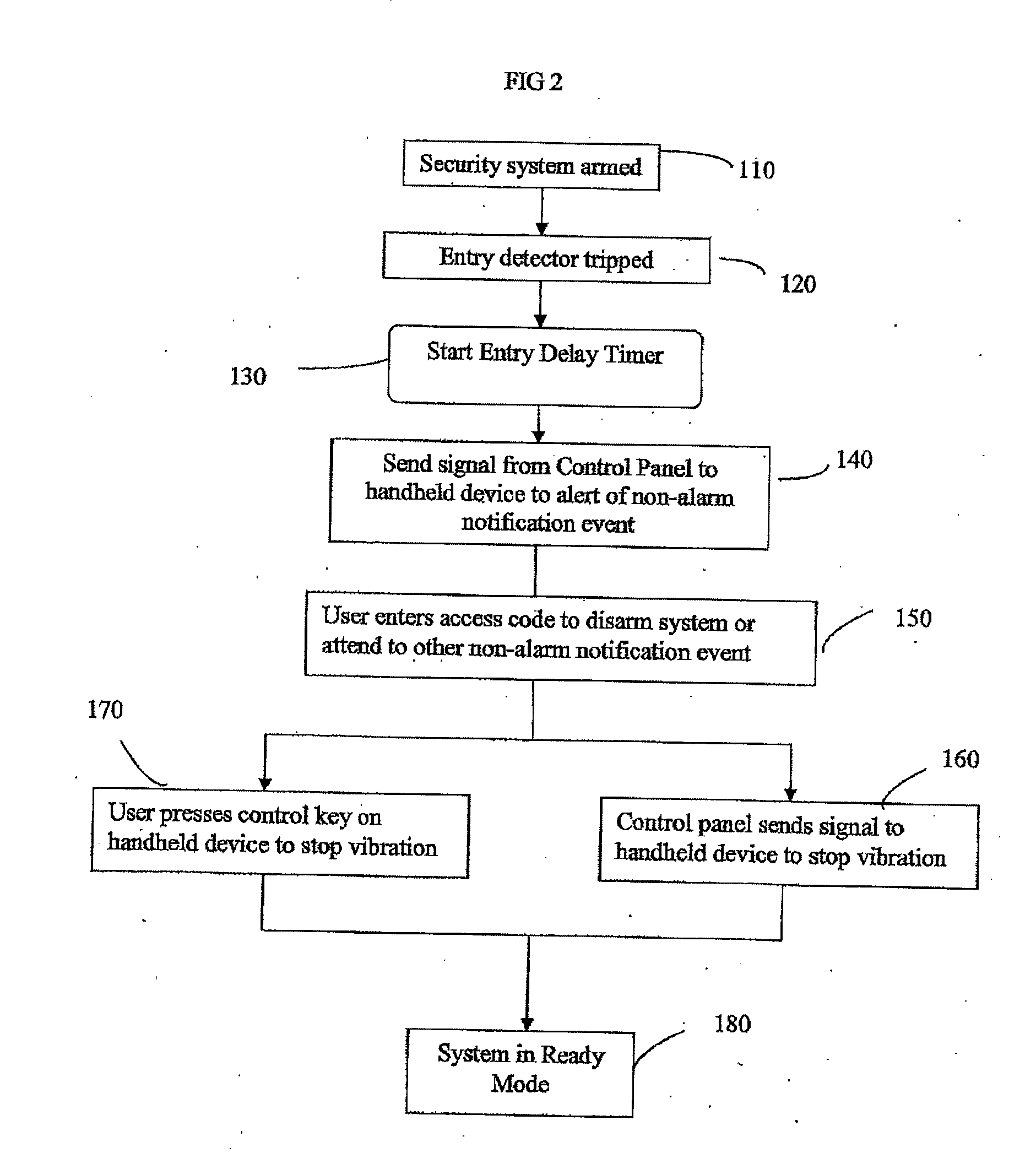
Security system with keyfob alert notification
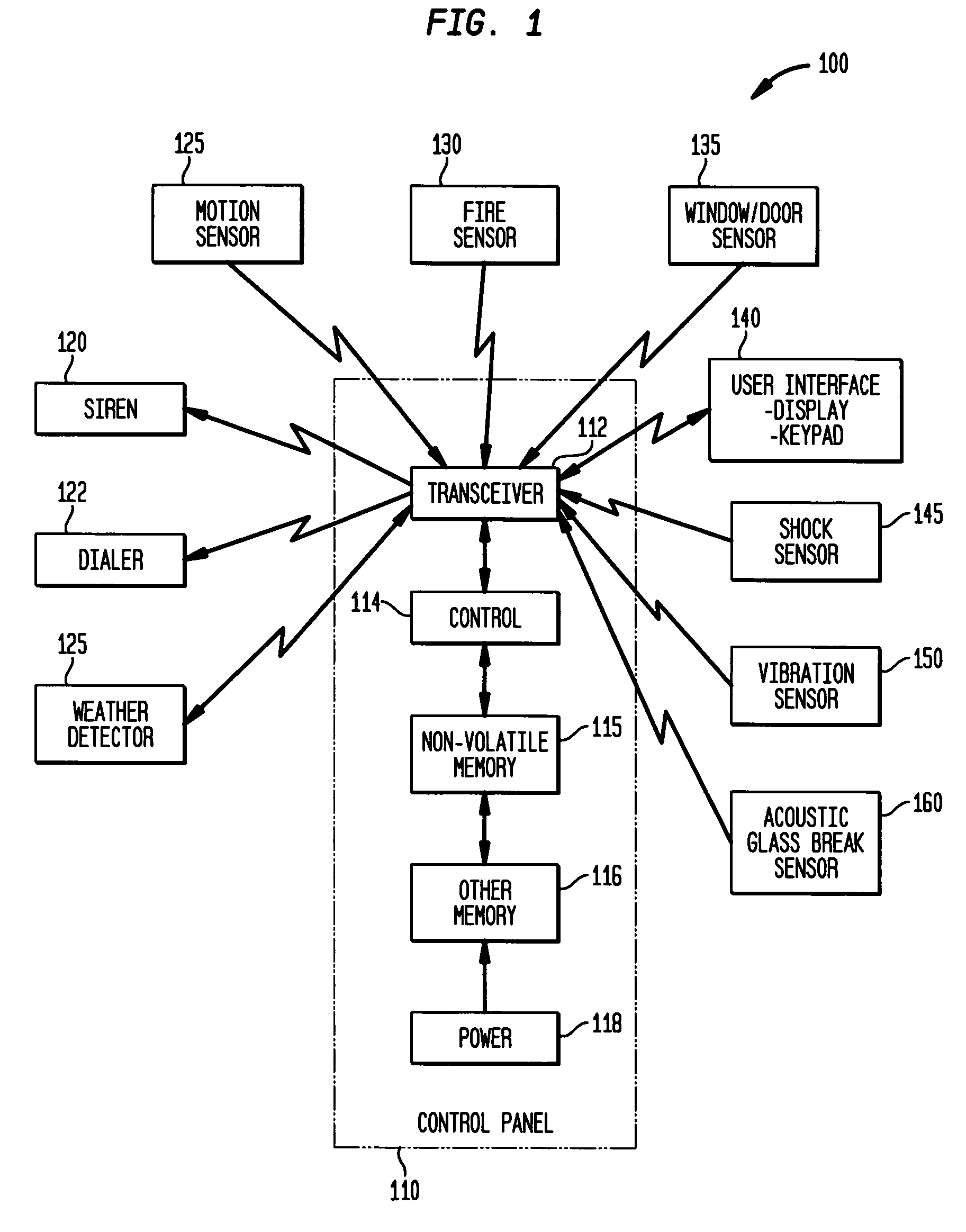
A system and method are provided for notifying a hearing impaired user of one of a plurality of qualified events via a personal device rather than an audible alert to avoid unnecessary false alarms. The security system includes at least one detection device for monitoring a portion of the premises and a control panel configured to communicate with the at least one detection device. A personal device communicates with the control panel where the personal device is configured to mechanically vibrate upon receipt of a signal from the control panel representing a qualified event associated with the security system.
Owner:TYCO SAFETY PRODS CANADA
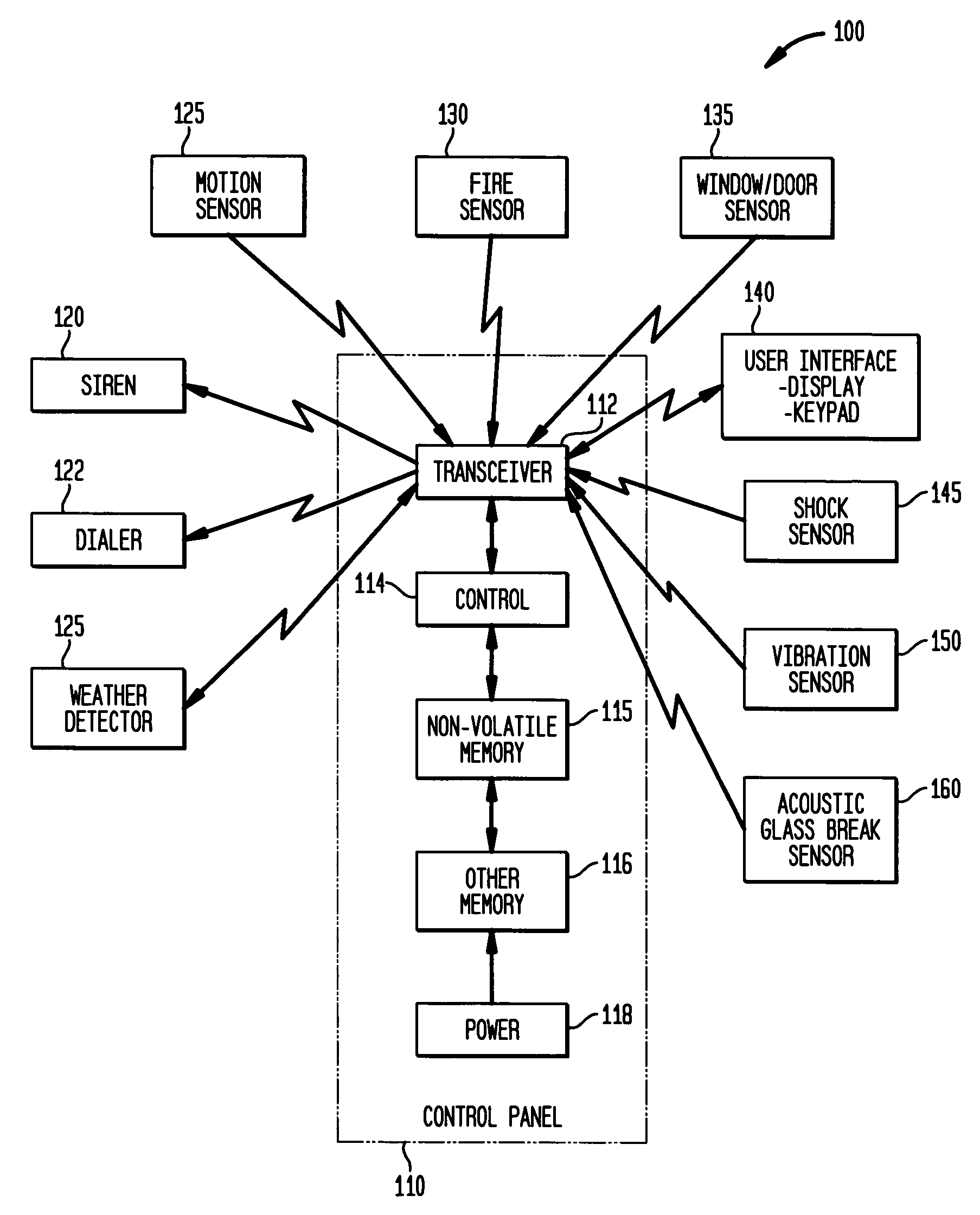
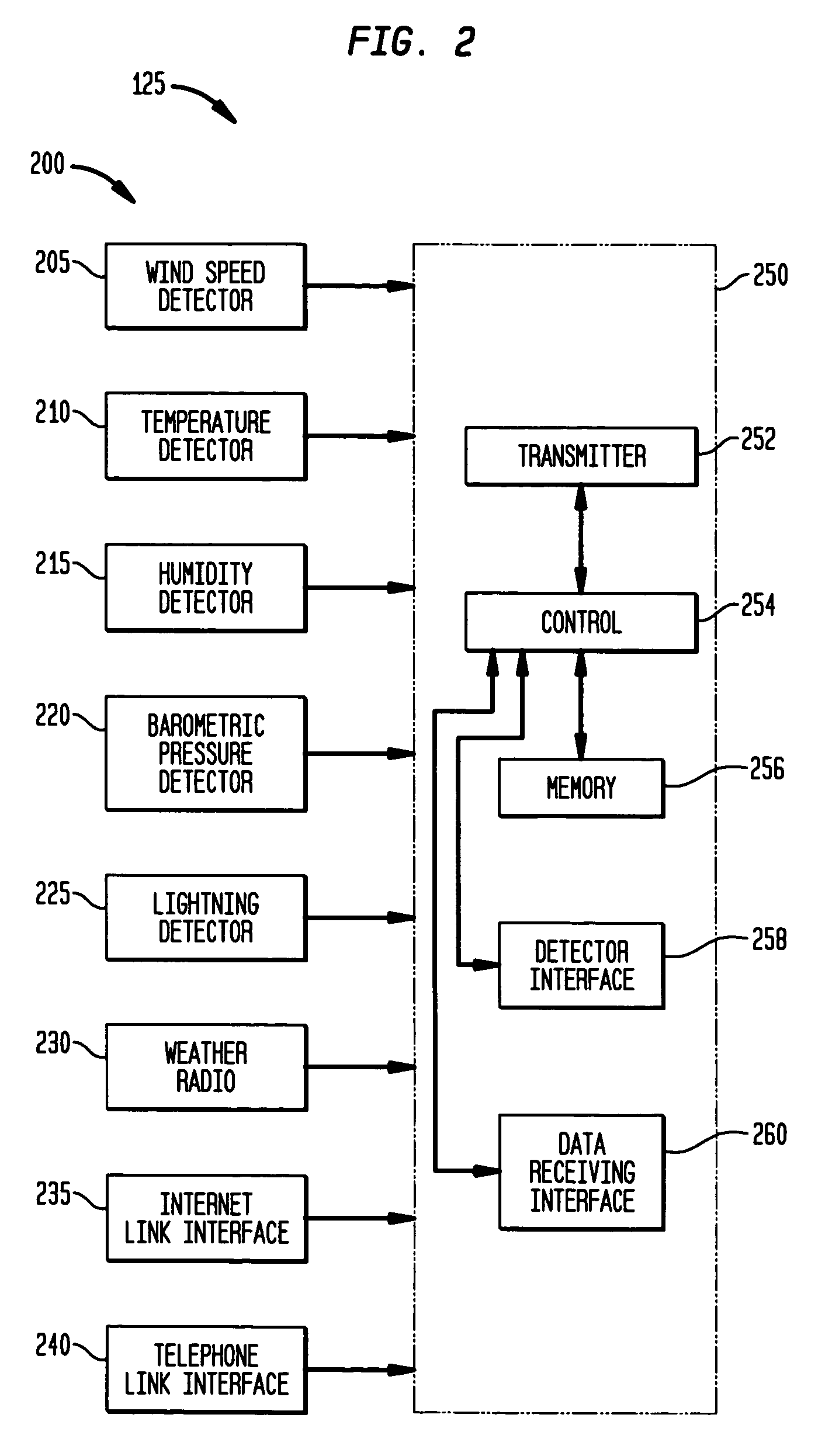
False alarm reduction in security systems using weather sensor and control panel logic
InactiveUS7218217B2Burglar alarm by glass breakingElectric signalling detailsThe InternetFalse alarm
Owner:HONEYWELL INT INC
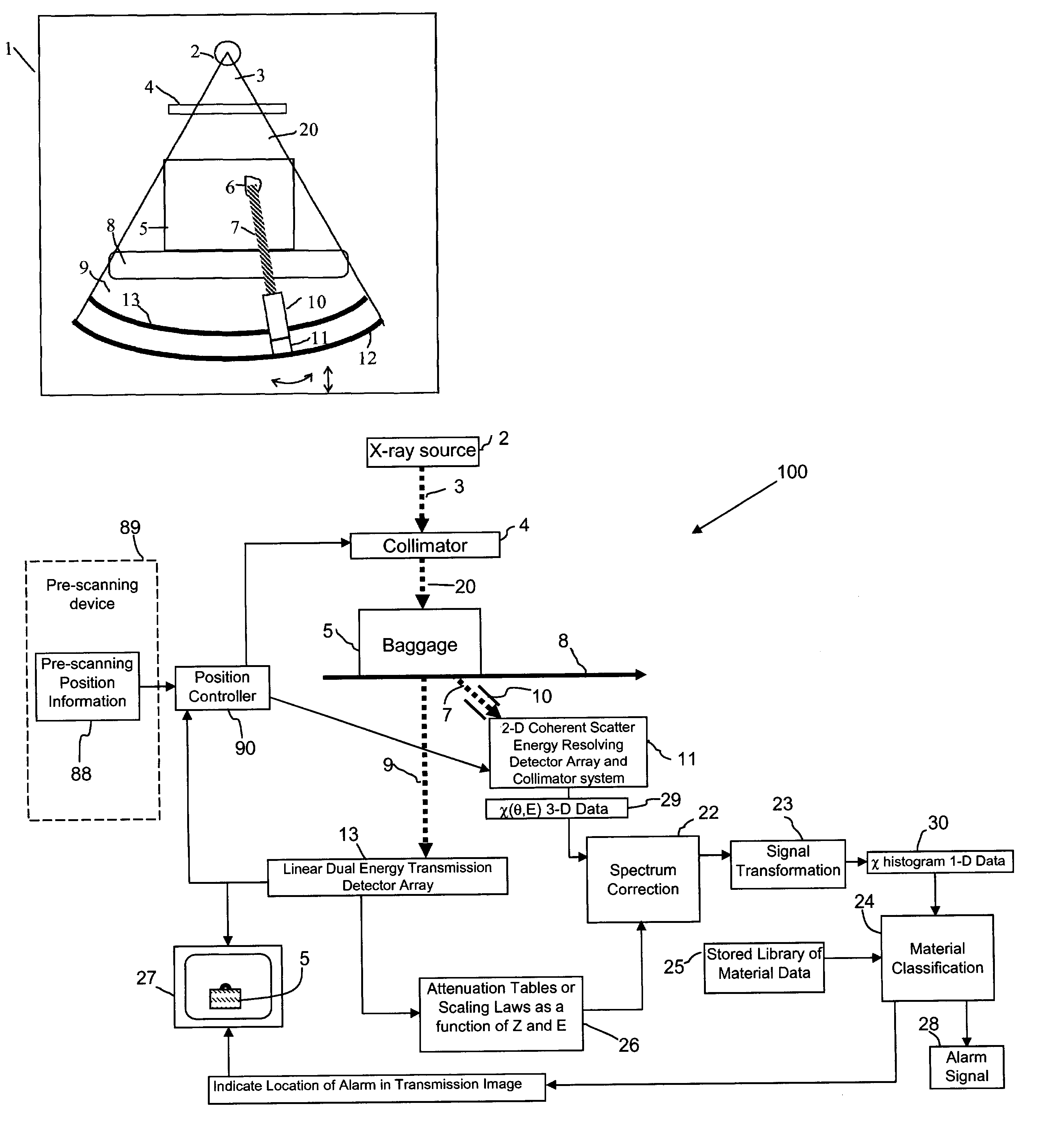
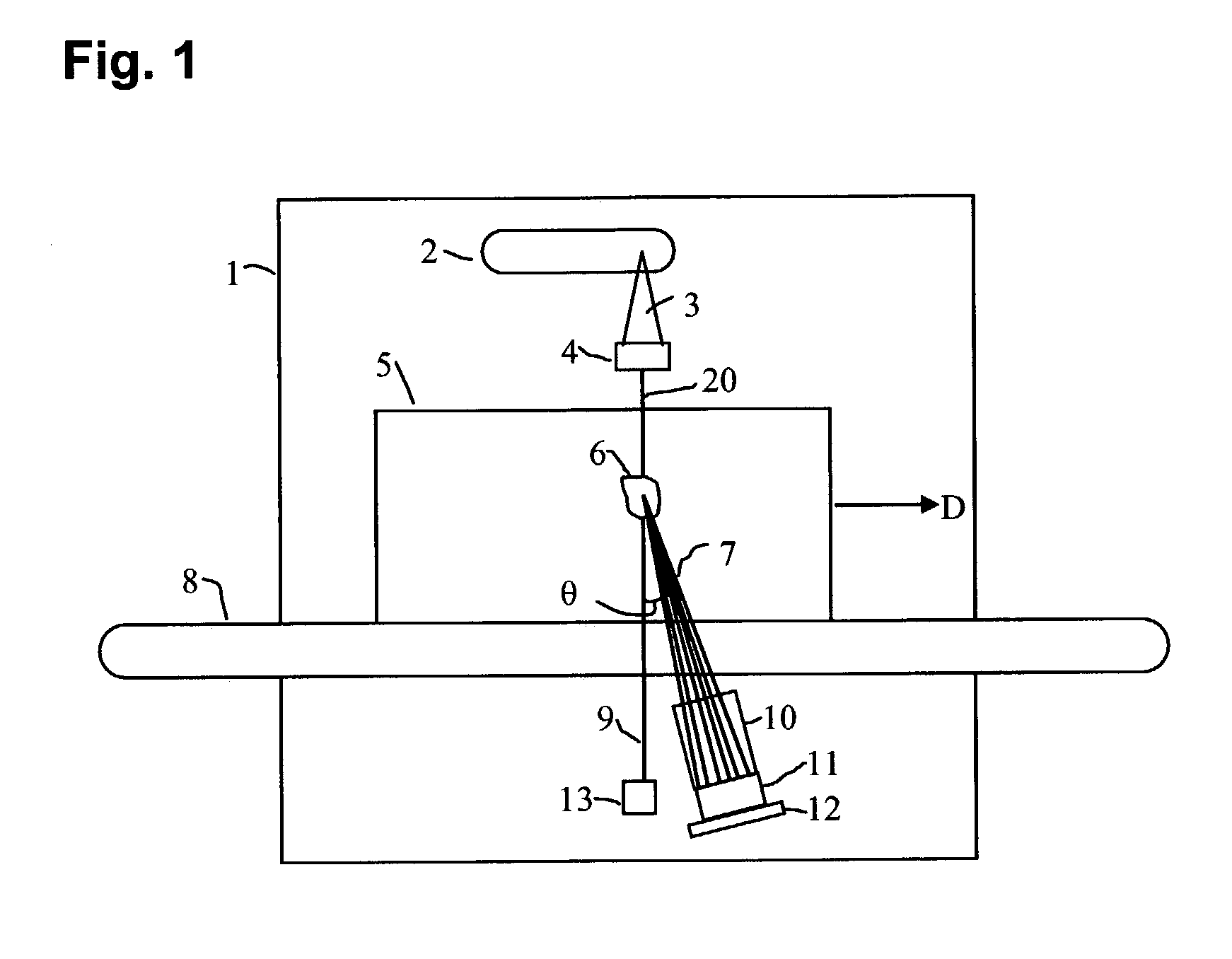
X-ray inspection system for detecting explosives and other contraband
InactiveUS7092485B2Rapidly and accurately discriminates among different substancesQuick checkUsing wave/particle radiation meansMaterial analysis by transmitting radiationX-rayExplosive material
A baggage scanning system and method employ combined angular and energy dispersive x-ray scanning to detect the presence of a contraband substance within an interrogation volume of a baggage item. The interrogation volume is illuminated with penetrating, polychromatic x-rays in a primary fan beam from a source such as a tungsten-anode x-ray tube. An energy-dependent absorption correction is determined from measurement of the attenuation of the fan beam at a plurality of different energies. Radiation coherently scattered by substances in the interrogation volume is detected by an energy-resolved x-ray detector operated at a plurality of scattering angles to form a plurality of scattering spectra. Each scattering spectrum is corrected for energy-dependent absorption and the corrected spectra are combined to produce a scattering pattern. The experimental scattering pattern is compared with reference patterns that uniquely characterize known contraband substances. The system and method can locate and identify a wide variety of contraband substances in an accurate, reliable manner. The system provides for automated screening, with the result that vagaries of human performance are virtually eliminated. False alarms and the need for hand inspection are reduced and detection efficacy is increased.
Owner:CONTROL SCREENING
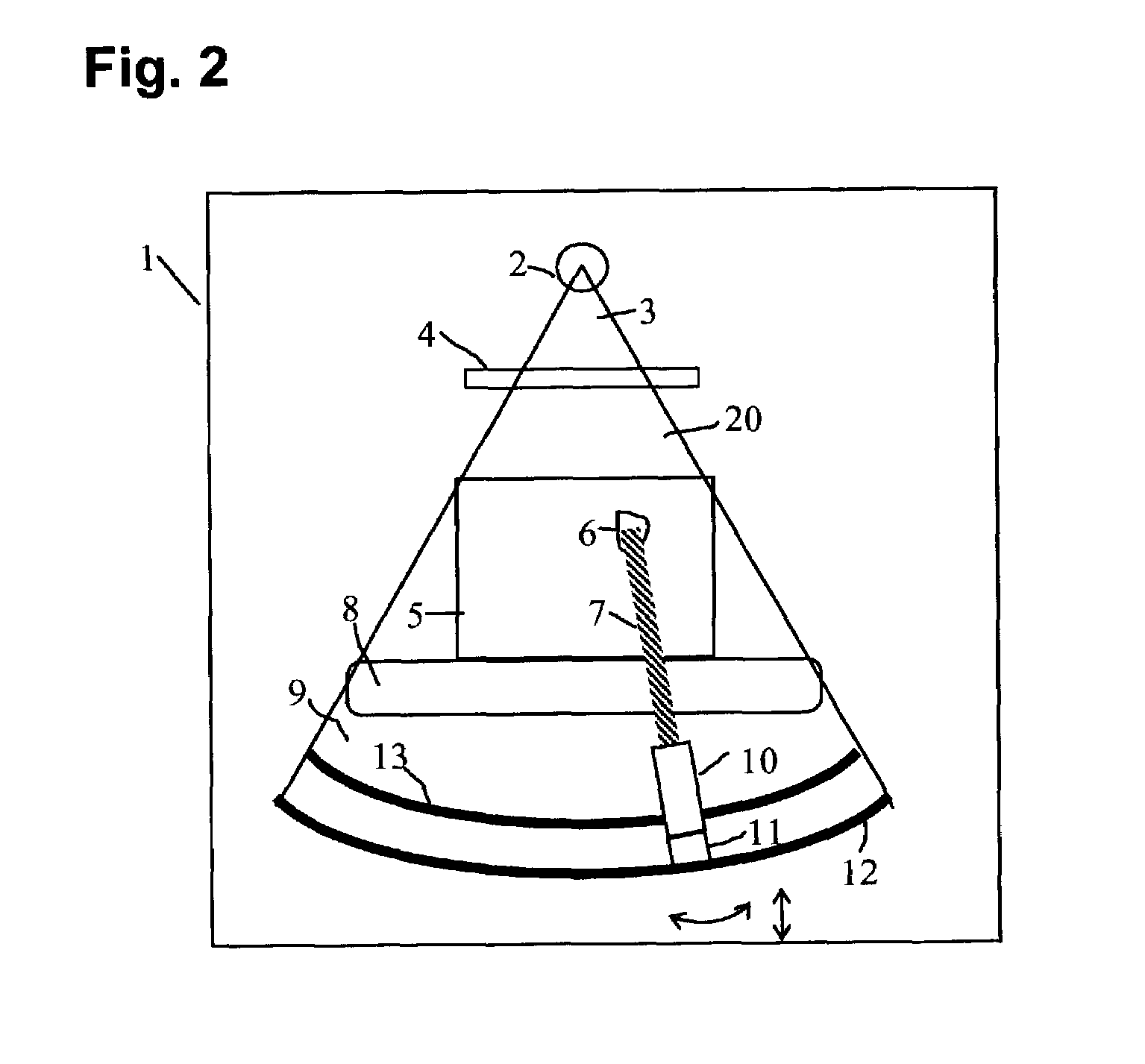
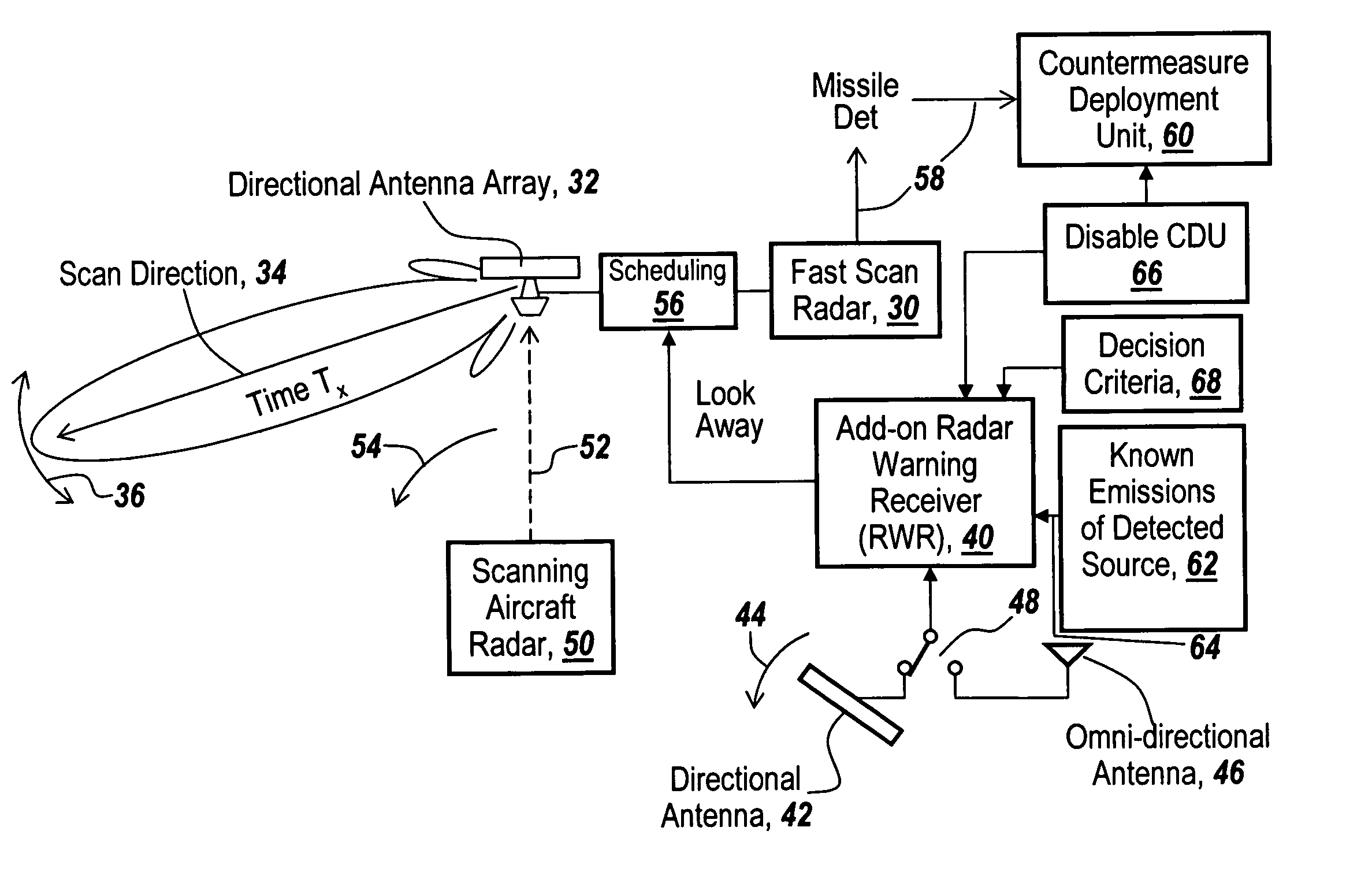
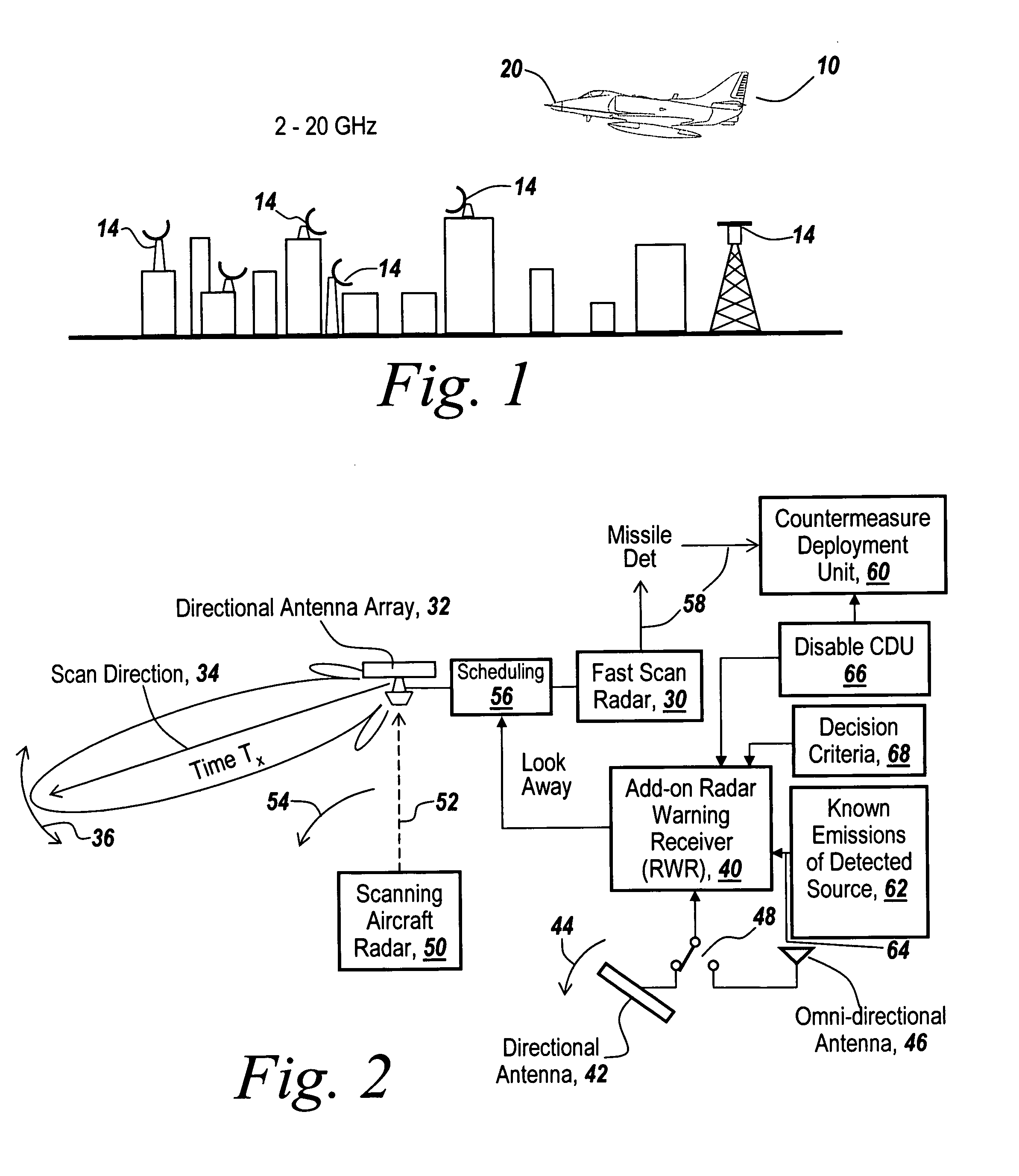
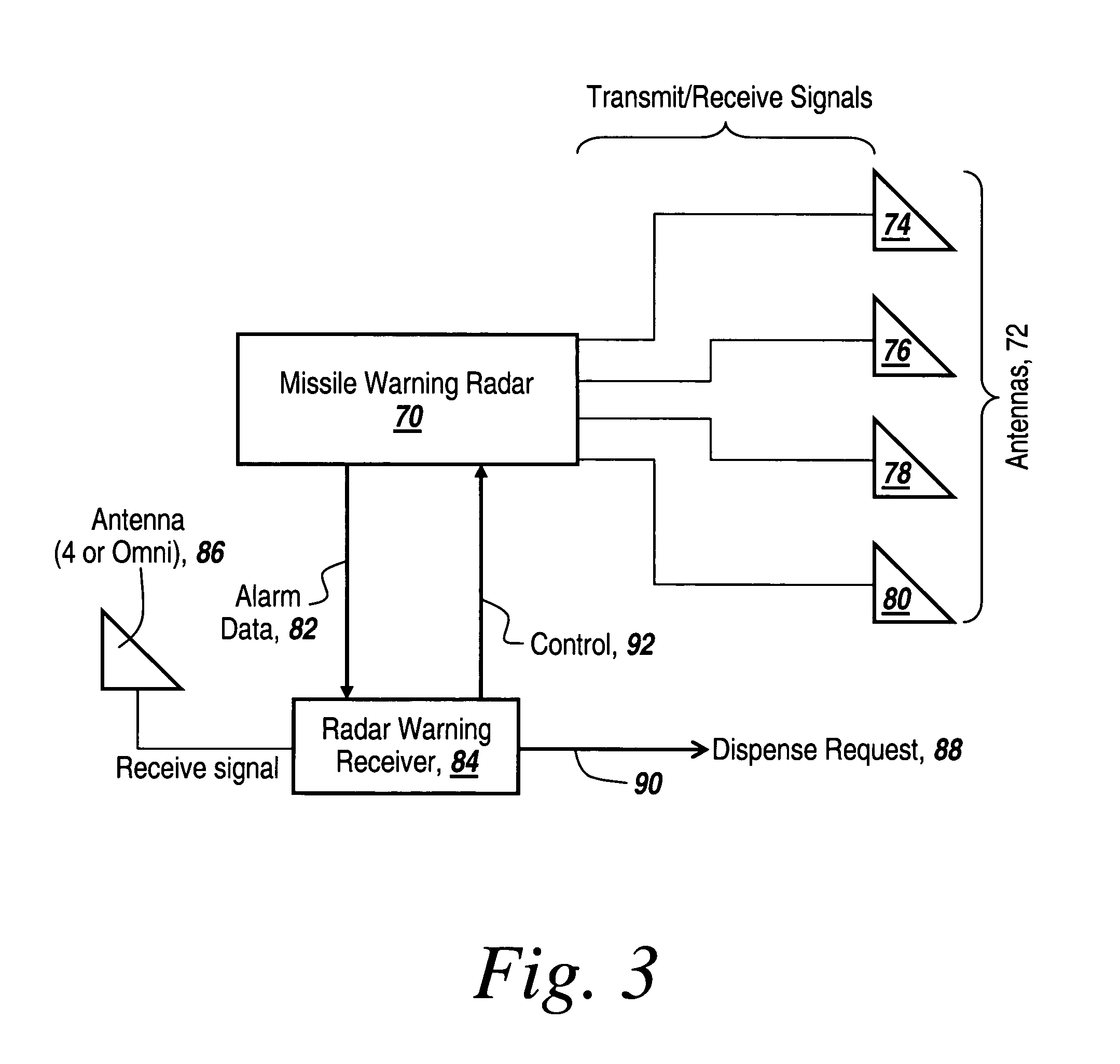
Method and apparatus for monitoring the RF environment to prevent airborne radar false alarms that initiate evasive maneuvers, reactionary displays or actions
InactiveUS7843375B1Accurate predictionLower false alarms without degrading system performanceCommunication jammingRadio wave reradiation/reflectionRadarFalse alarm
Rather than costly modifications to existing radars, a small, low cost radar warning receiver is used to monitor the RF environment. This add-on receiver can provide situational awareness including RF signal levels and angle of arrival, and recommend or provide antenna scanning synchronization, blanking inputs or gated reactionary outputs to or for the airborne radar. Utilization of this information can be used to reduce false alarms and improve system performance.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
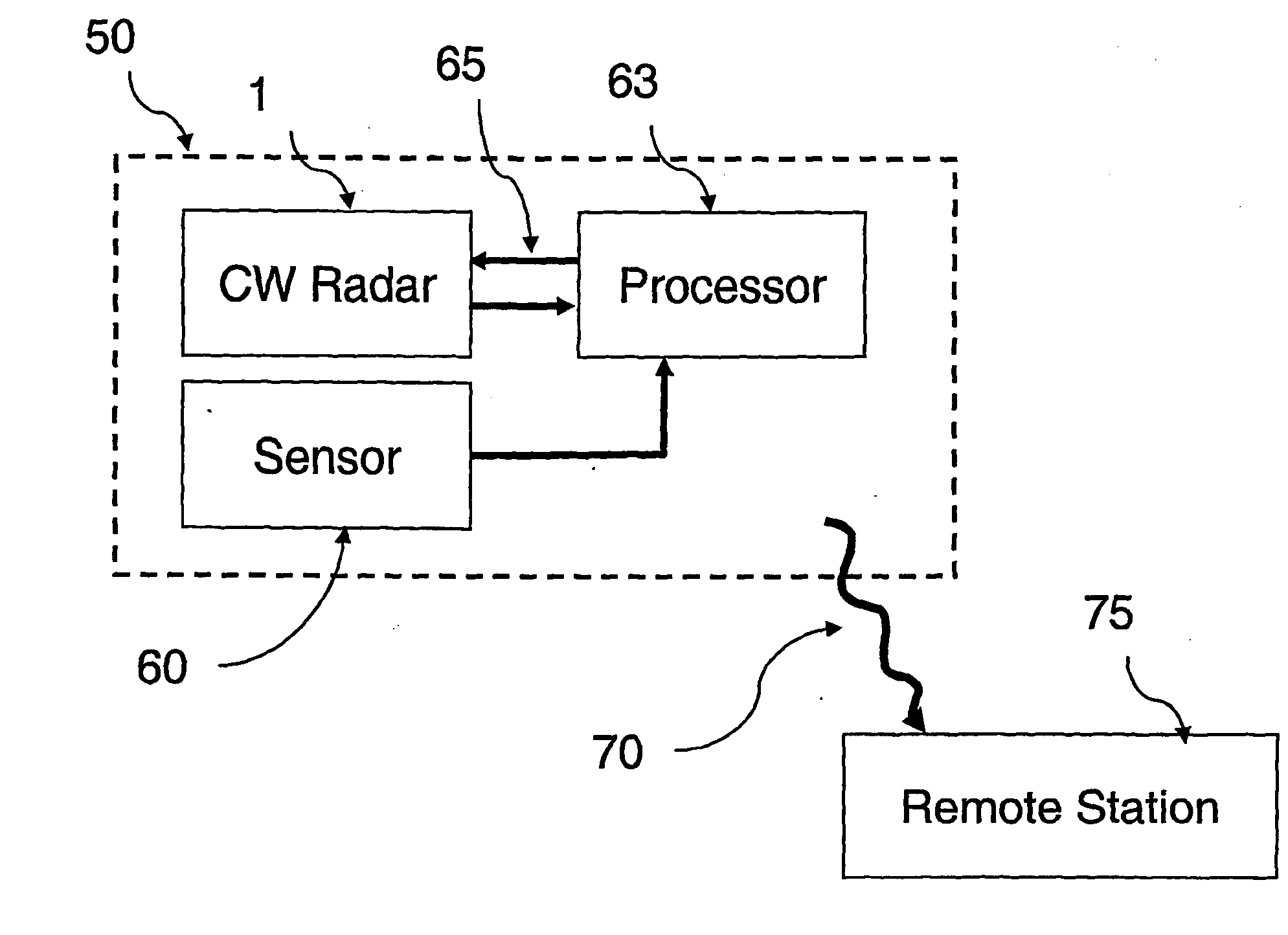
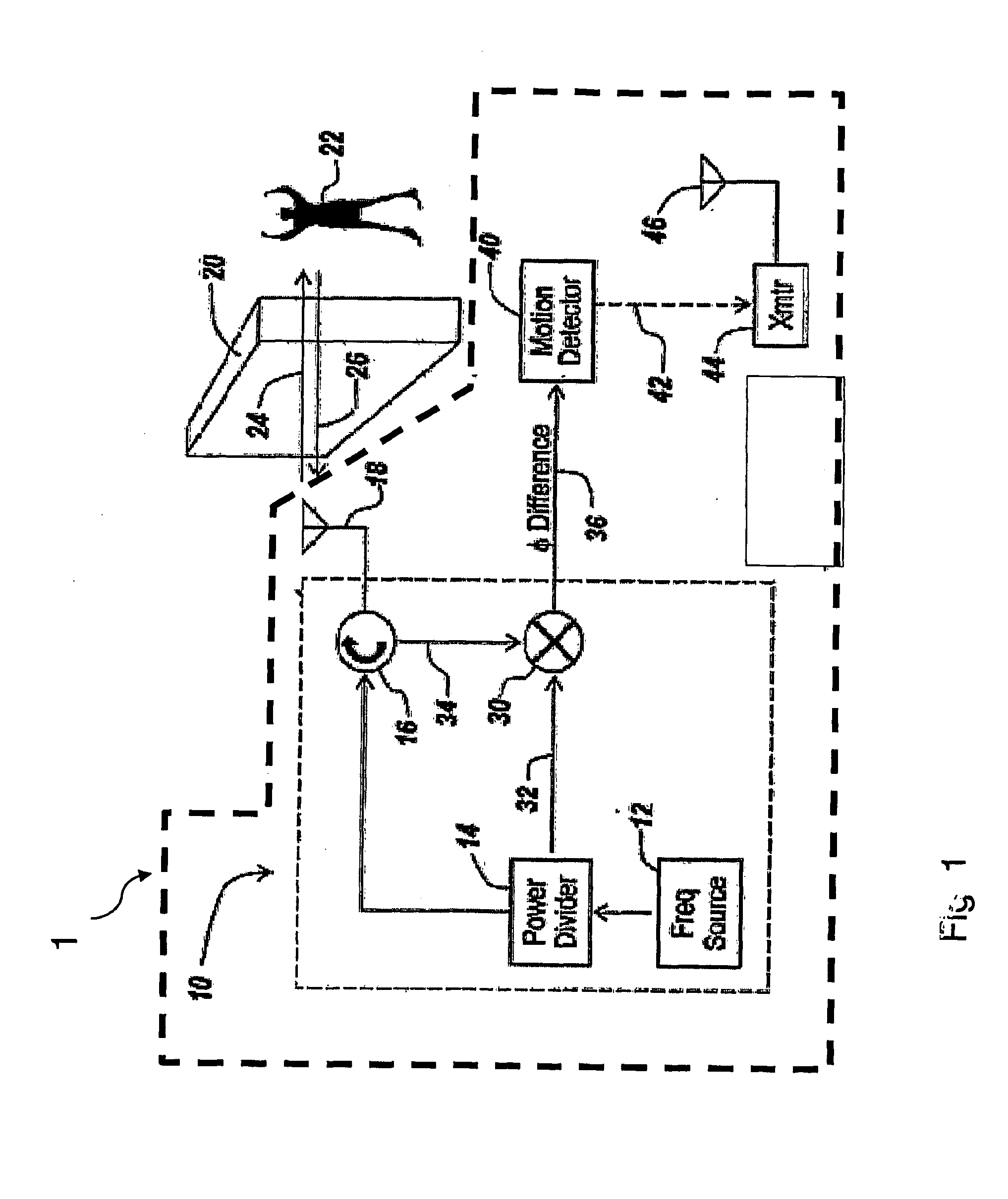
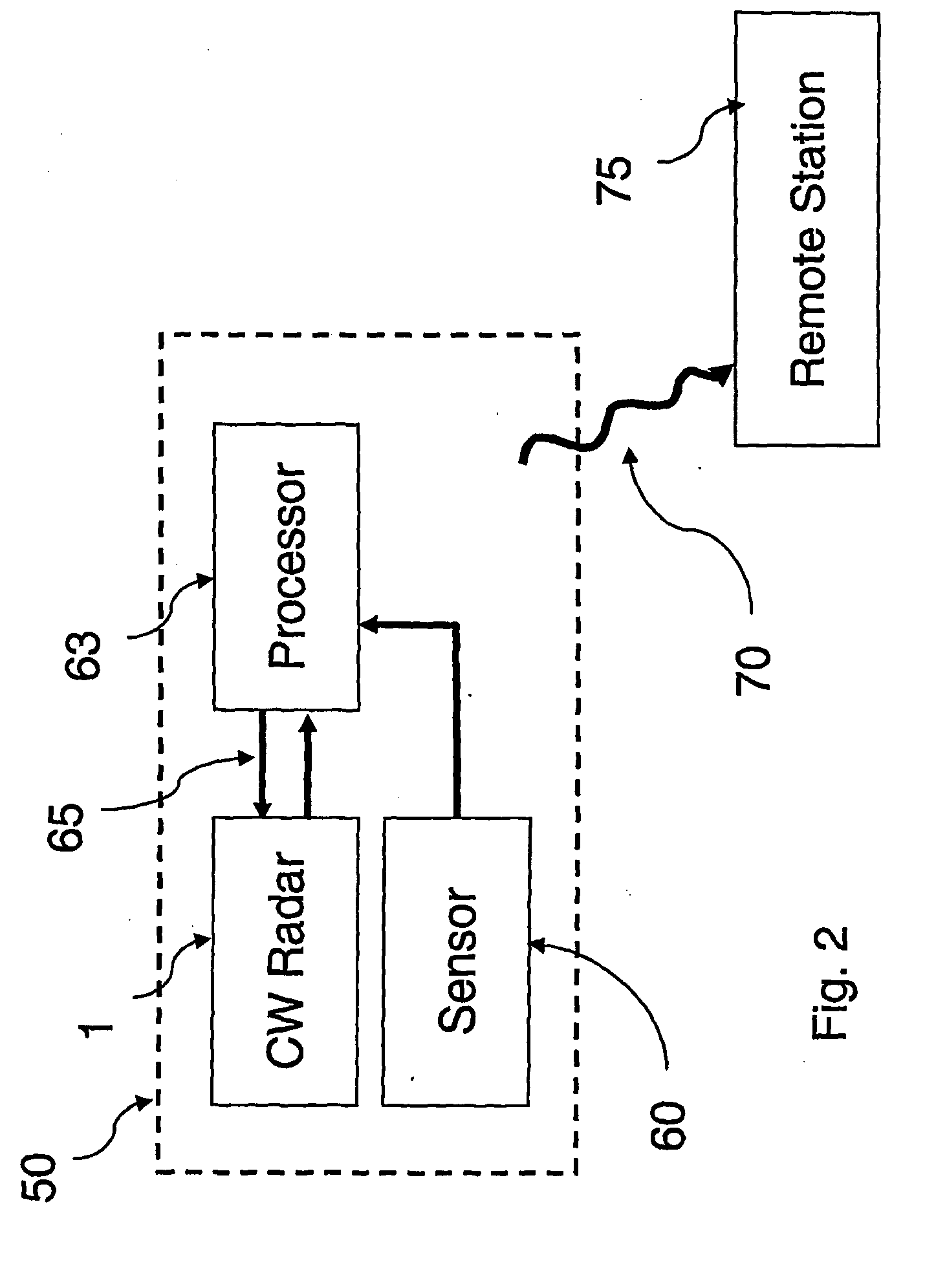
Motion Detection Systems Using CW Radar in Combination With Additional Sensors
ActiveUS20090303100A1Reduce power consumptionImprove discriminationRadio wave reradiation/reflectionRadarFalse alarm
Whether or not the CW radar is utilized for through-the-wall detection, additional one or more sensors are used with the CW radar to confirm the motion detection result or to in fact turn on the CW radar once motion or the physical presence of an individual has been sensed, thereby to provide confirmation of a less-reliable sensor with the use of the more reliable CW radar. Thus, the addition of other sensors provides lower power consumption, lower false alarm rates and better discrimination and classification of moving objects.
Owner:III HLDG 1
Alarm with remote monitor and delay timer
InactiveUS7075429B2Easy to installEasy maintenanceBurglar alarm by openingATM surveillanceFiberEngineering
An alarm apparatus for detecting an intrusion or compromise situation upon critical equipment or private areas. The apparatus detects an unauthorized radio transmitter (like a wireless camera), or the covering of a critical piece of equipment. Fiber optics, solar cells and special radio antennas are used to detect intrusion remotely and a delay timer will allow normal activity to occur, while reducing false alarms. This alarm apparatus will notify an existing system of the intrusion or compromise when limits are exceeded. This alarm apparatus also addresses privacy concerns of wireless cameras and recording devices in areas like changing rooms, bathrooms, or boardrooms. The apparatus addresses security issues for critical devices like smoke alarms and ATM machines.
Owner:MARSHALL CRANBROOK
Two-way voice and voice over IP receivers for alarm systems
ActiveUS7734020B2Reduce errorsShort response timeInterconnection arrangementsSupervisory/monitoring/testing arrangementsVoice communicationVoice over IP
Security systems typically communicate with alarm monitoring centers using a telephone connection. The present invention offers a system and technique for monitoring a security system connected using a Voice-over-IP connection, in real time, and alerting the owner of the security system, or the alarm-monitoring center, when the connection is broken. This alert can be used, for example, to issue a telephone call to the police, informing them of the breach of line integrity and possible compromise of the premise. In addition, the present invention allows for one-way or two-way voice communication between the alarm panel and an alarm operator and / or a 3rd party. Such voice communication helps the alarm operator and / or 3rd party to determine whether an alarm is a real alarm or a possible false alarm.
Owner:SIERRA WIRELESS AMERICA
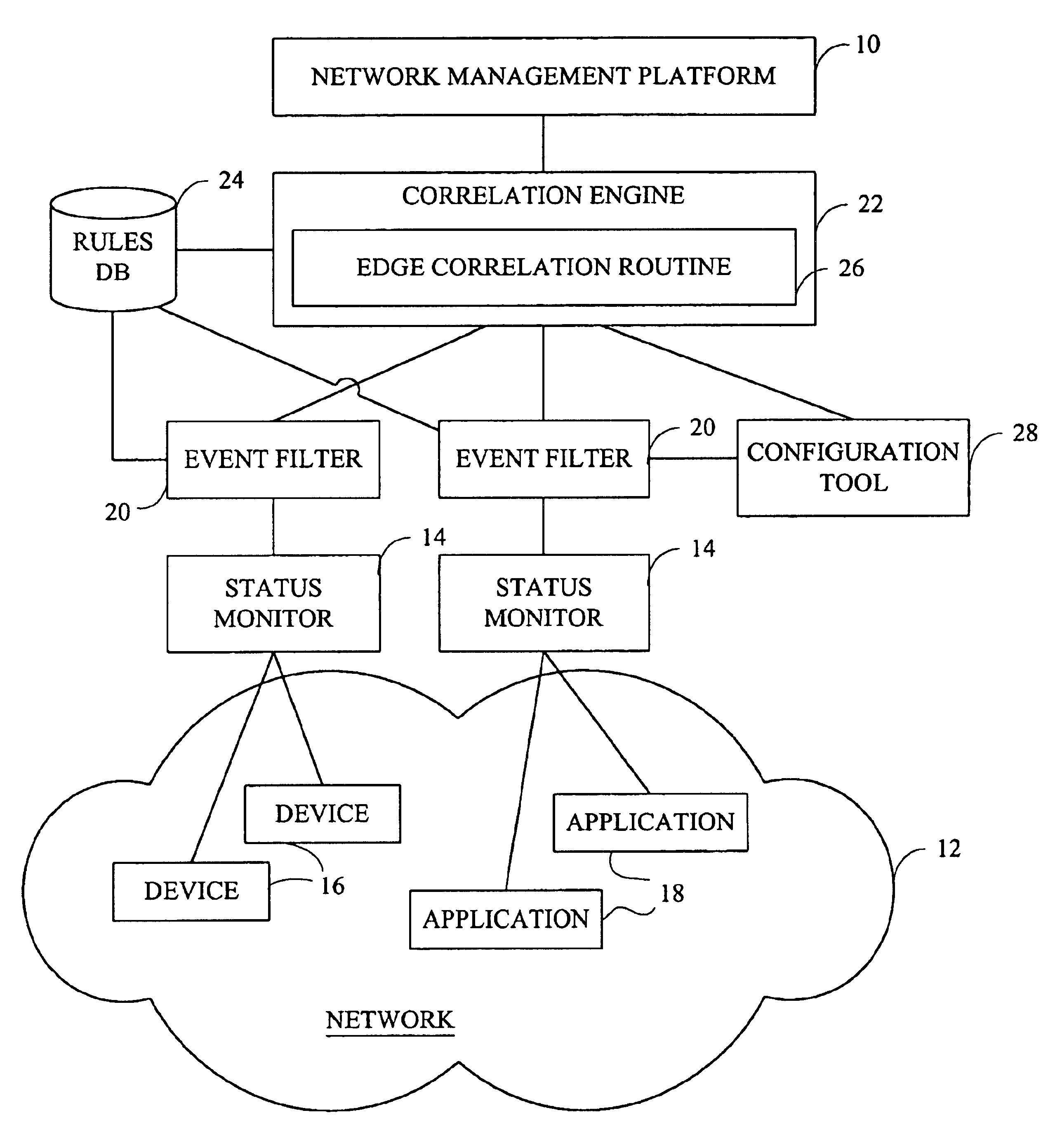
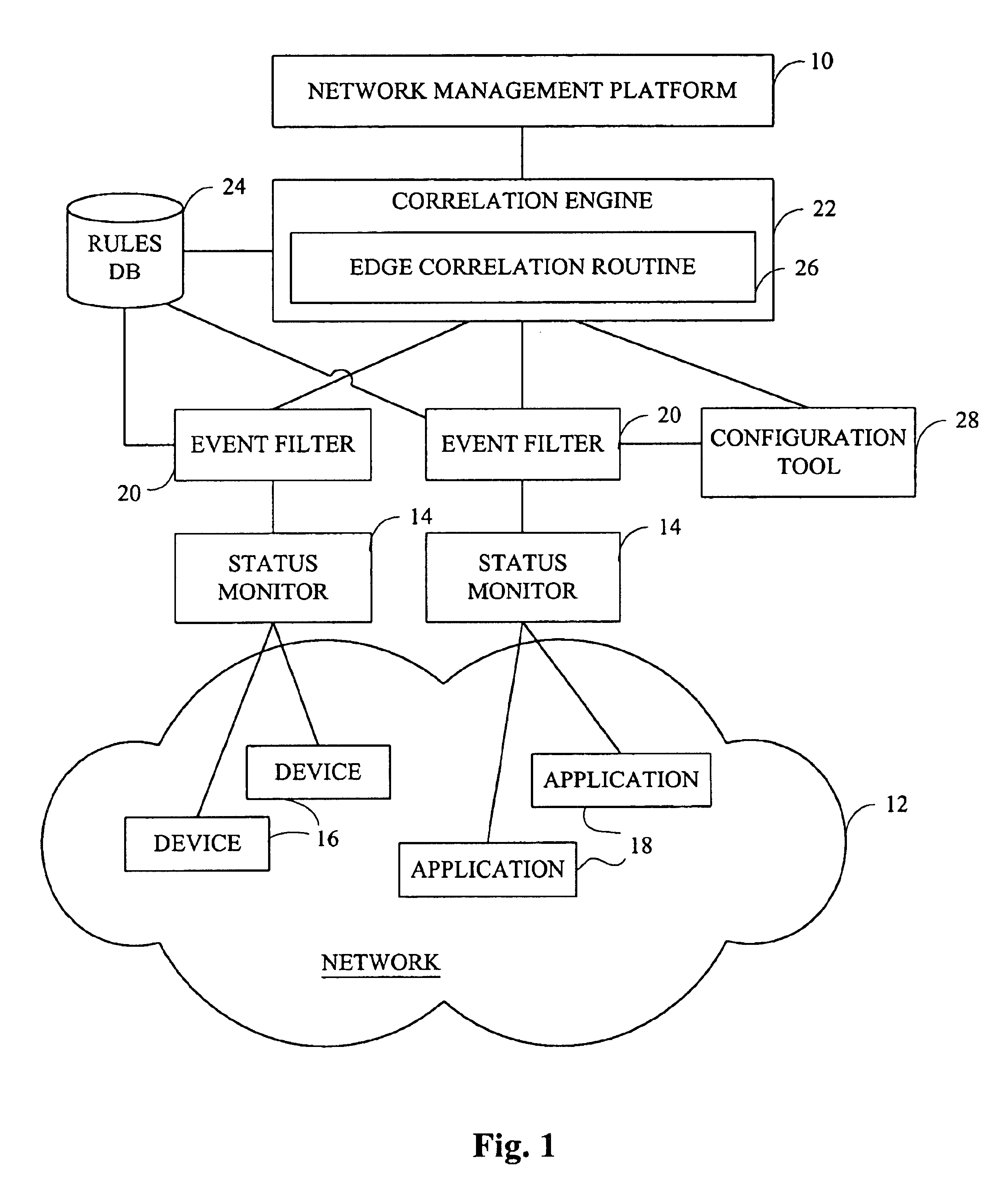
Method and system for reducing false alarms in network fault management systems
InactiveUS6966015B2Reducing false alarmReduce the possibilityError detection/correctionData switching networksFault managementRule-based system
Methods and systems are described for reducing the number of false alarms in fault correlation software used to detect and diagnose faults in computer networks and similar systems. The fault correlation software includes rules that monitor a number of indicators that, if occurring together over a window of time, are known to cause or reflect the occurrence of a fault. The method involves monitoring the transition of these indicators from one state to another over the time window and determining the extent of the correlation of the transitions of the indicators. The determination that indicators monitored by a rule do not correlate closely in their transitions is used to reduce the likelihood of the rule finding correlation of the indicators as a whole. This in turn reduces the number of false alarms which the rule-based system might otherwise have transmitted.
Owner:IBM CORP
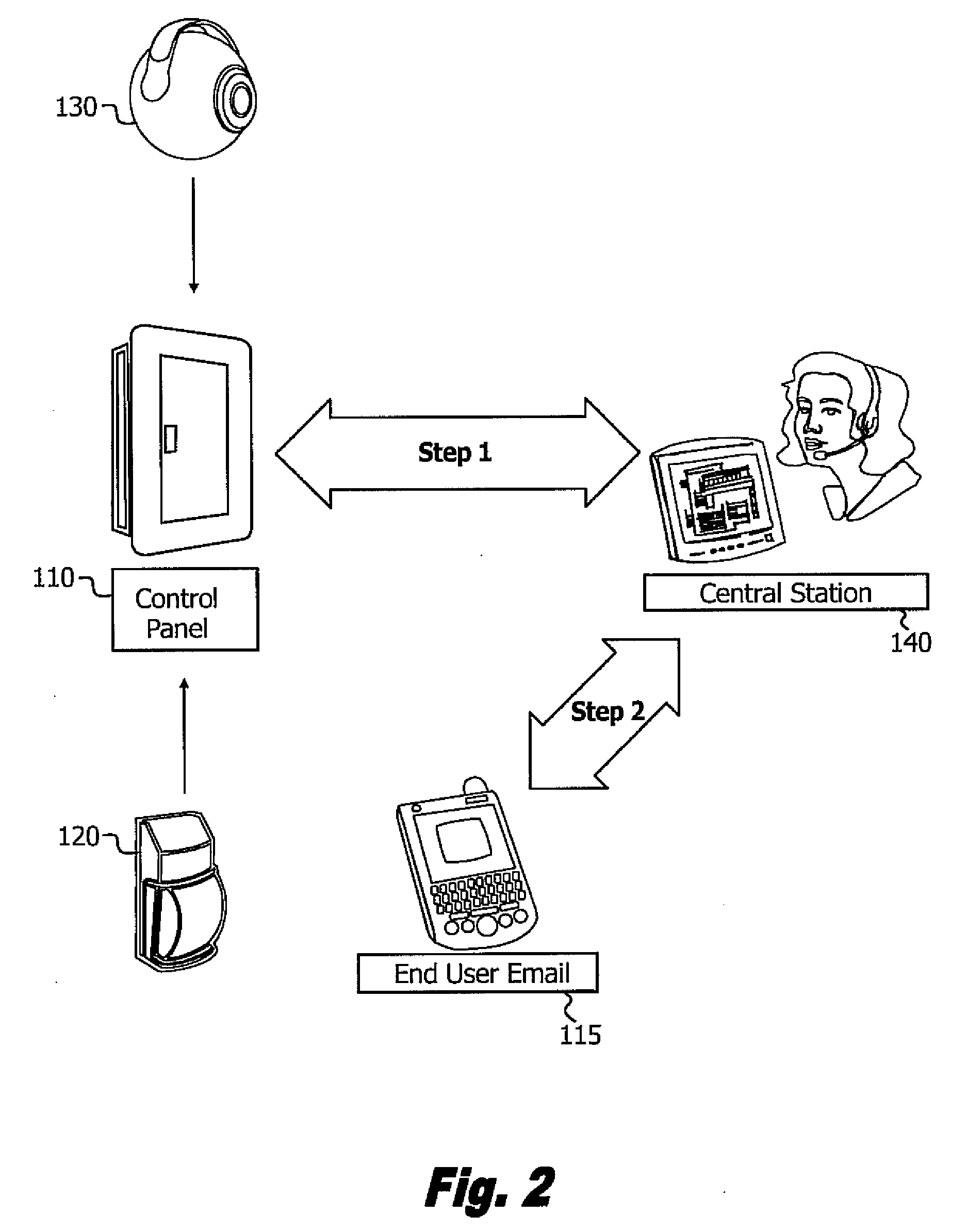
Video alarm verification
ActiveUS20080284580A1Increase delayColor television detailsClosed circuit television systemsVideo imageFalse alarm
A method for monitoring an alarm zone within a perimeter, border and / or building includes capturing video image data of an alarm event detected in the alarm zone, and automatically establishing a cell phone session with an end-user to verify a true or false nature of the detected alarm. The end-user may use the cell phone display to review the video during the cell phone session, and may use the cell phone's key for the verifying. The novel monitoring method with end-user alarm event verification avoids false alarms being raised where the nature of the detected alarm event is false, and the verifying occurs before a false alarm is raised / communicated.
Owner:ADEMCO INC
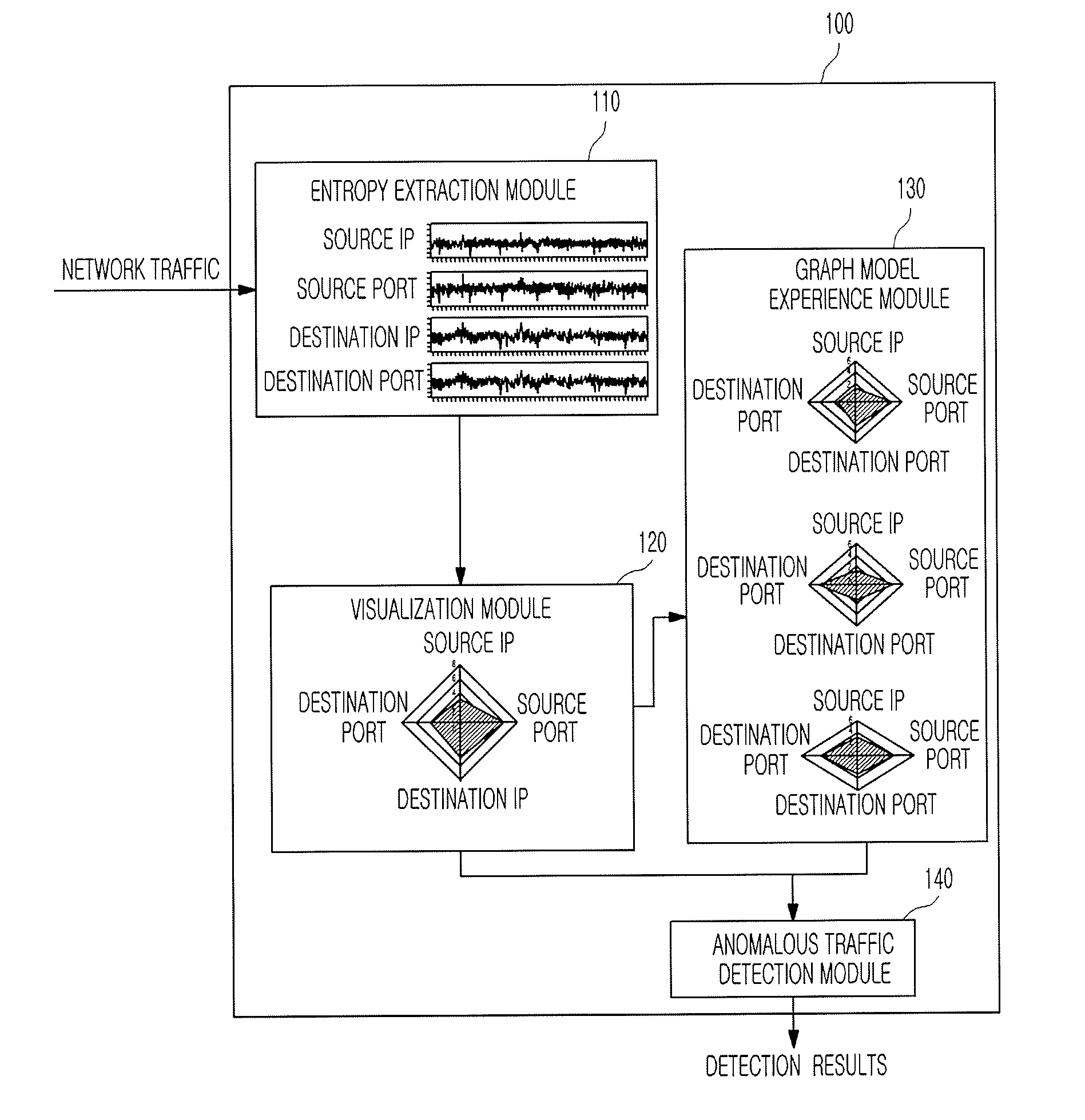
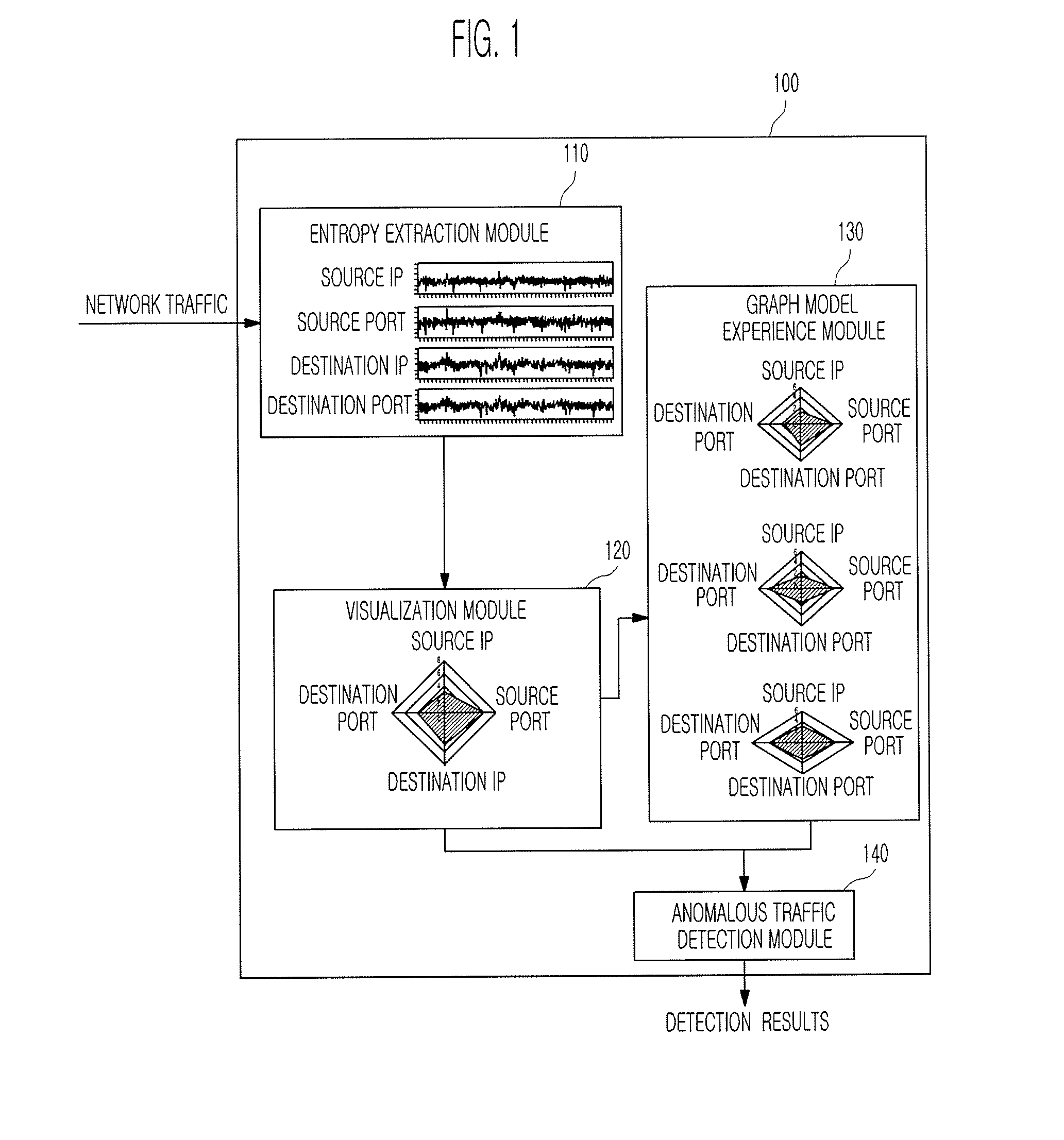
Apparatus and method for detecting anomalous traffic
InactiveUS20090138590A1Efficient and accurate detectionDetect anomalous traffic more accurately and efficientlyMultiple digital computer combinationsTransmissionNetwork entropyNetwork attack
An apparatus and method for detecting anomalous traffic are provided. More particularly, an apparatus and method for detecting anomalous traffic based on entropy of network traffic are provided. The apparatus of detecting anomalous traffic includes: an entropy extraction module for extracting entropy from network traffic; a visualization module for generating an entropy graph based on the entropy; a graph model experience module for updating a graph model for each network attack based on the entropy graph; and an anomalous traffic detection module for detecting anomalous traffic based on the entropy graph and the graph model for each network attack and outputting the detection results to a user. In the apparatus and method, anomalous traffic is detected based on network entropy rather than simple statistics based on the amount of traffic, so that a false alarm rate of the apparatus for detecting anomalous traffic can be reduced.
Owner:IZEX +1
Method and apparatus for remotely monitoring a site
InactiveUS6917288B2Easy to distinguishAccurate locationDigital data processing detailsTelephonic communicationTime informationFalse alarm
The present invention is directed to providing systems and methods for remotely monitoring sites to provide real time information which can readily permit distinguishing false alarms, and which can identify and track the precise location of an alarm. In embodiments, monitoring capabilities such as intrusion / fire detection and tracking capabilities, can be implemented through the use of multistate indicators in a novel interface which permits information to be transmitted using standard network protocols from a remote site to a monitoring station in real-time. In embodiments, communications can be handed from the centrally located host monitoring station to a mobile monitoring station (for example, a laptop computer in a responding vehicle, such as a police or fire vehicle). Additional embodiments include high, low, and rate-of-change alarms; chromagraphic representation of the value of an environmental or other parameter measured in a space; and detection and location of portable interface devices in a space.
Owner:NETTALON SECURITY SYST
System and method for reducing false alarms and false negatives based on motion and position sensing
InactiveUS20120029300A1Reduce and eliminate false positiveAvoid unnecessary trips or other actionsTelemedicineMedical automated diagnosisAccelerometerComputer science
Systems and methods of reducing false alarms associated with vital-sign monitoring are disclosed. One or more vital-sign readings of a patient are received. One or more acceleration readings from an accelerometer attached to the patient are received. At least one of motion and position of the patient are determined based at least in part on the one or more acceleration readings. An alarm condition determination procedure is modified if at least one of the motion and the position satisfies a predefined condition.
Owner:CAREFUSION 303 INC
Method and apparatus for remotely monitoring a site
InactiveUS20090121860A1Maximum precisionEasy to distinguishFire rescueBurglar alarm electric actuationTime informationSprinkler system
The present invention is directed to providing systems and methods for remotely monitoring sites to provide real-time information which can readily permit distinguishing false alarms, and which can identify and track the precise location of an alarm. In embodiments, monitoring capabilities such as intrusion / fire detection and tracking capabilities, can be implemented through the use of multistate indicators in an interface which permits information to be transmitted using standard network protocols from a remote site to a monitoring station in near real-time. In embodiments, communications can be handed from the centrally located host monitoring station to a mobile monitoring station (for example, a laptop computer in a responding vehicle, such as a police or fire vehicle). Additional embodiments include the measurement of environmental parameters such as temperature, carbon monoxide and differential air pressure to detect, monitor and manage a fire event. These measurements along with selected controllable output devices deployed in a space, such as sprinkler control valves and individually or zoned sprinkler heads, are used to initiate and control fire suppression technology both locally and remotely. For instance, a system of the present invention may detect a fire and cause a sprinkler system to disburse water in a facility.
Owner:NETTALON SECURITY SYST
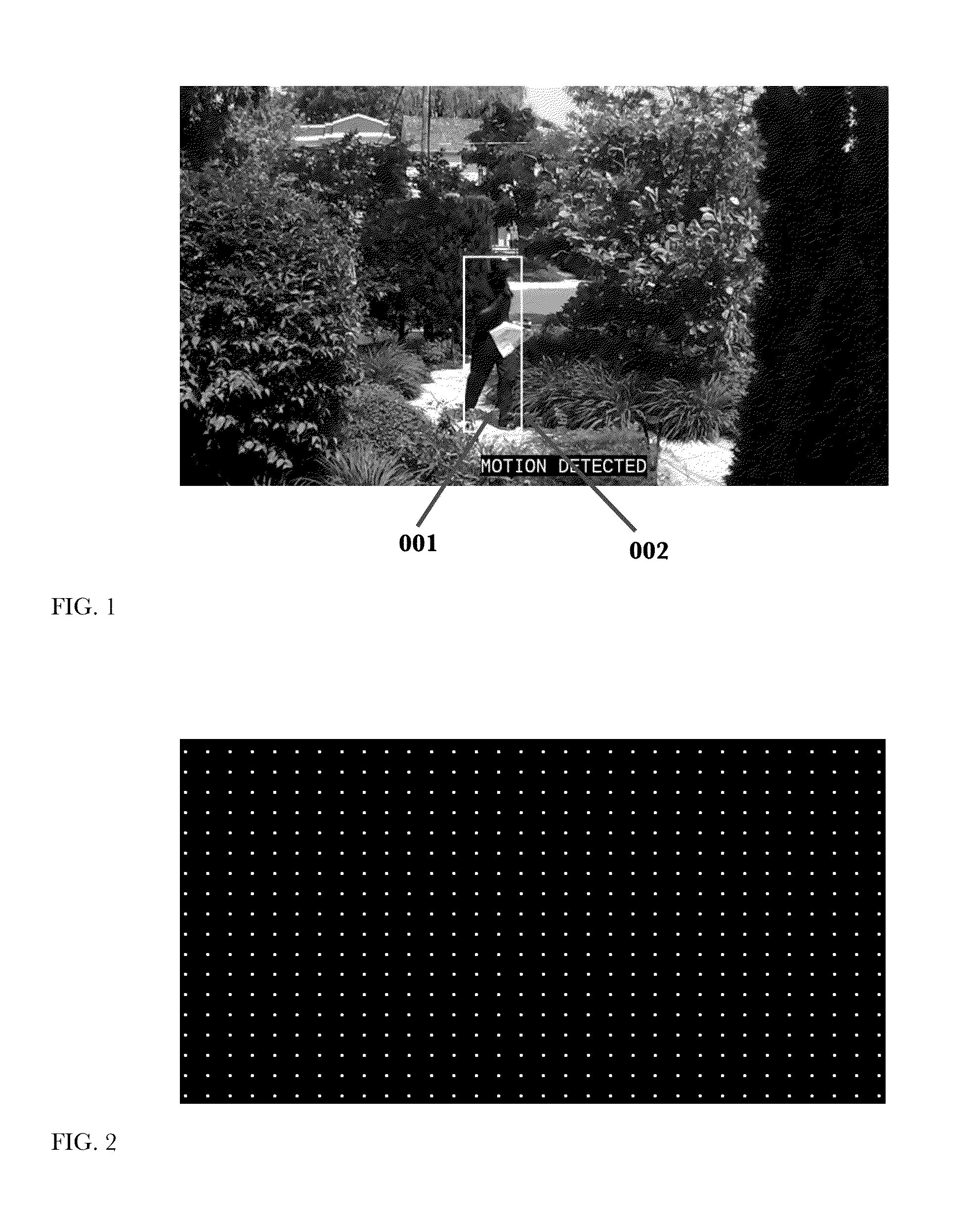
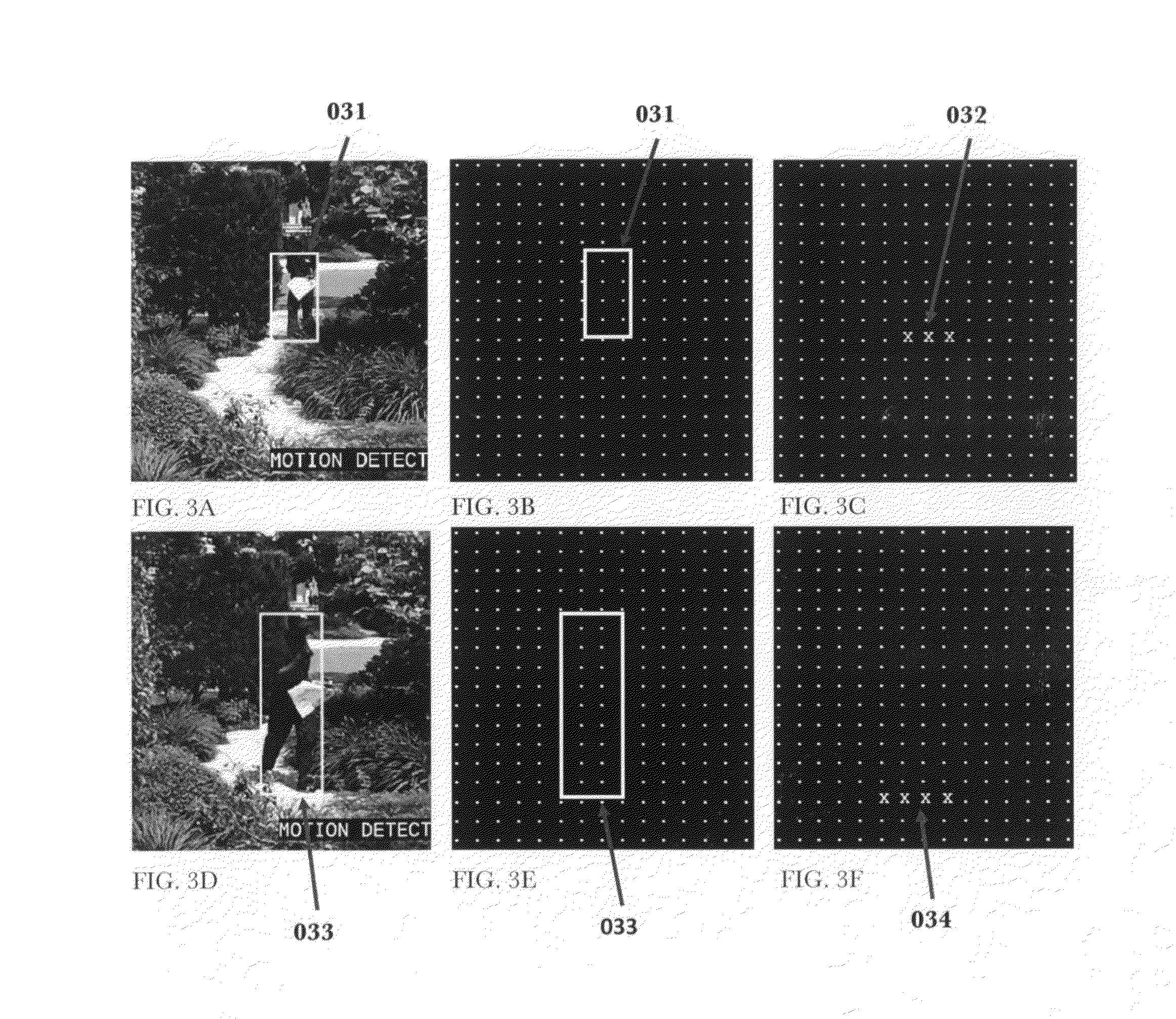
Video Motion Detection Method and Alert Management
InactiveUS20160042621A1Reduce in quantityImprove abilitiesImage enhancementTelevision system detailsMathematical modelComputer graphics (images)
This invention describes a method and apparatus for security monitoring with a video camera. A mathematical model consisting of an array of cells, or learning map, is used to describe the motion of any object(s) detected by the camera. When an object(s) is detected, its positional location(s) for a period of time, or motion event, is recorded in a learning map. This learning map is then compared to a reference learning map where the camera determines whether to alert the user or not that an object of interest was detected. After viewing the video of the motion event, the user provides feedback that impacts how the reference learning map is updated by information in the motion event learning map. Through this user feedback mechanism, the camera learns to more accurately determine whether or not to alert the user about future motion events, thus reducing the number of false alarms.
Owner:HOGG WILLIAM DAYLESFORD +1
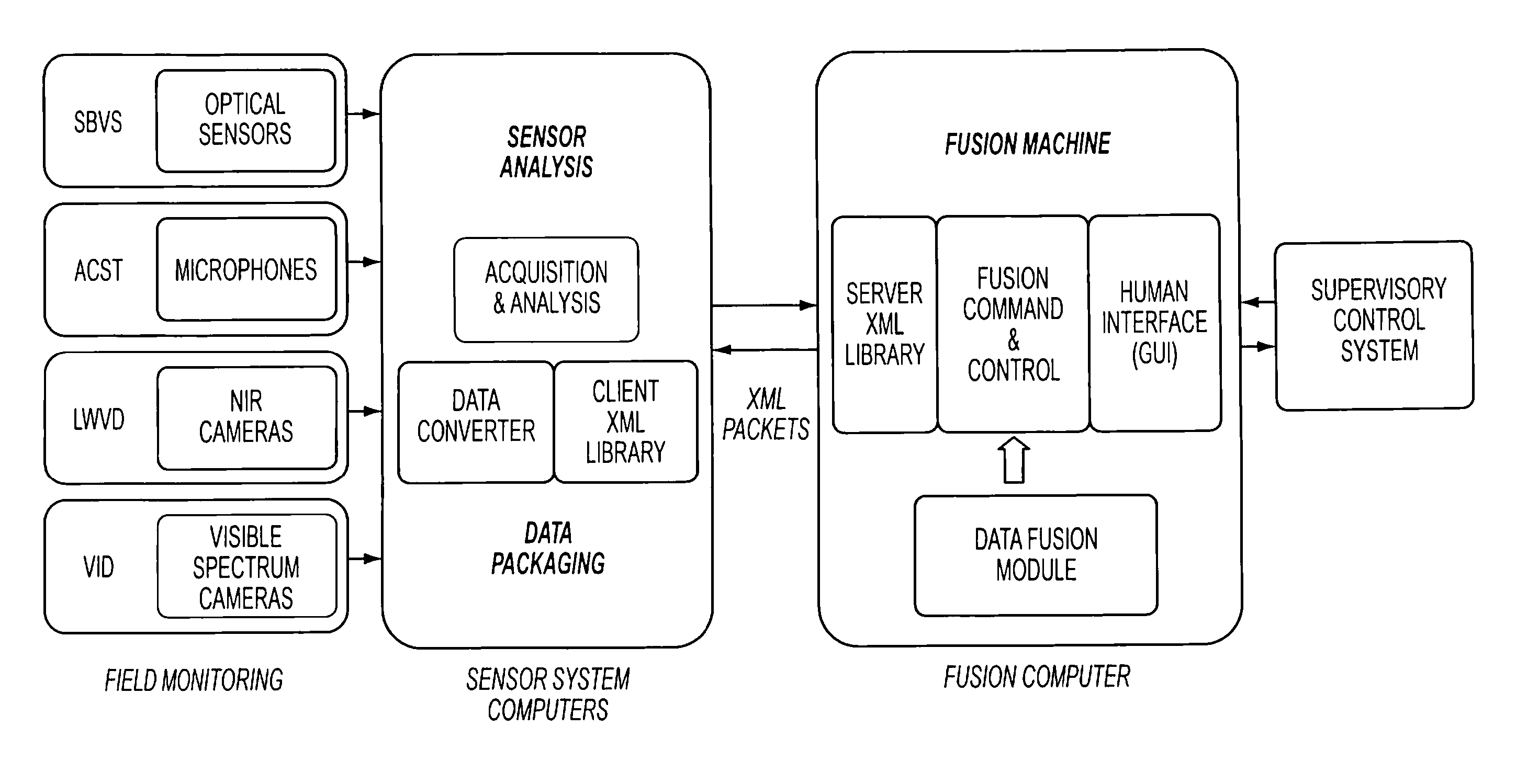
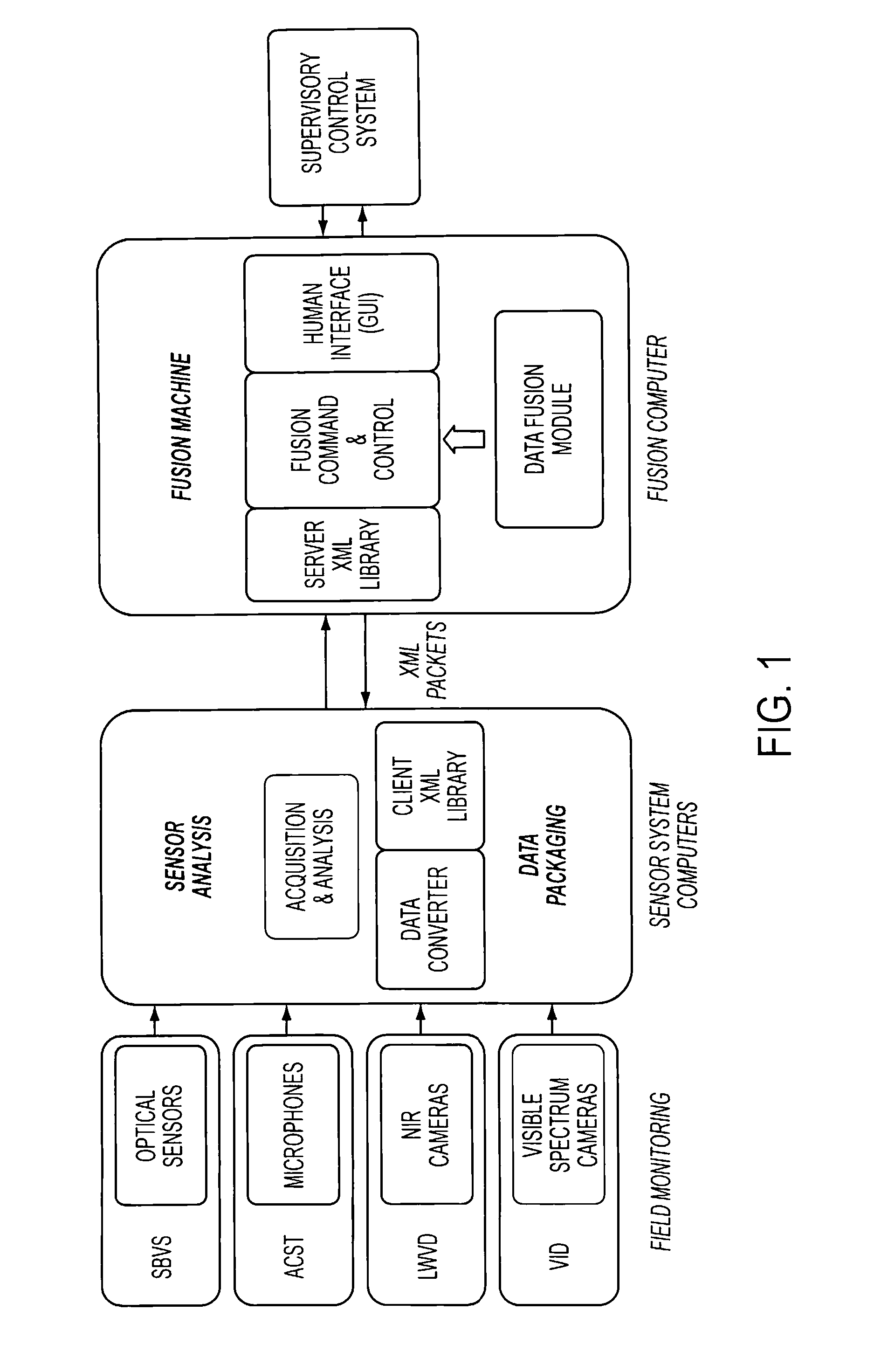
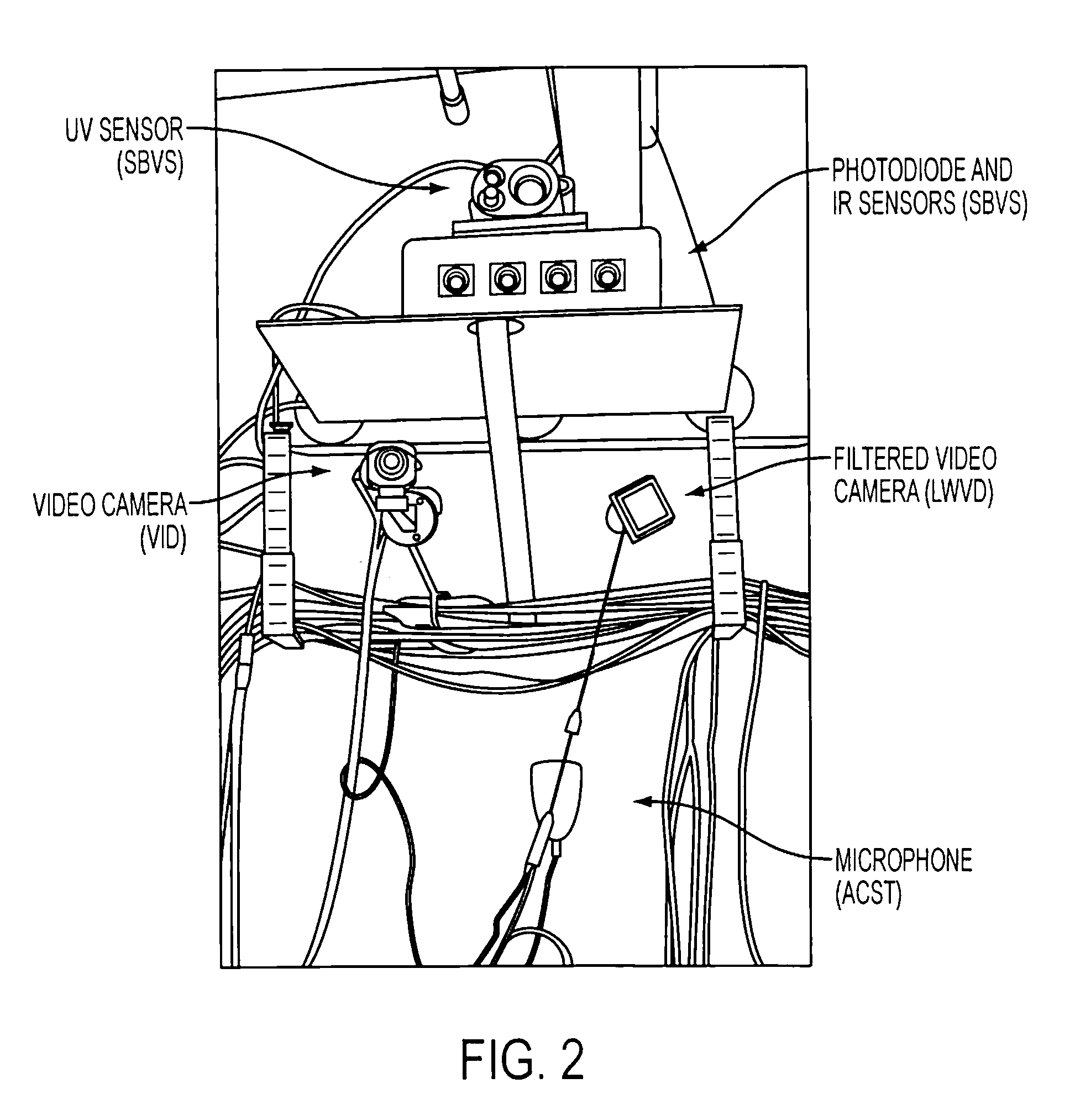
Volume sensor: data fusion-based, multi-sensor system for advanced damage control
Provided a system and method for detecting an event while discriminating against false alarms in a monitored space using at least one sensor suite to acquire signals, transmitting the signals to a sensor system device where the signal is processed into data packets, transmitting the data packets to a data fusion device, where the data packets are aggregated and algorithmic data fusion analysis is performed to generate threat level information. The threat level information is distributed to a supervisory control system where an alarm level can be generated when predetermined criteria are met to indicate the occurrence of an event in the monitored space.
Owner:UNITED STATES OF AMERICA
Method for preventing evacuation of plunger pump based on monitoring of output pressure
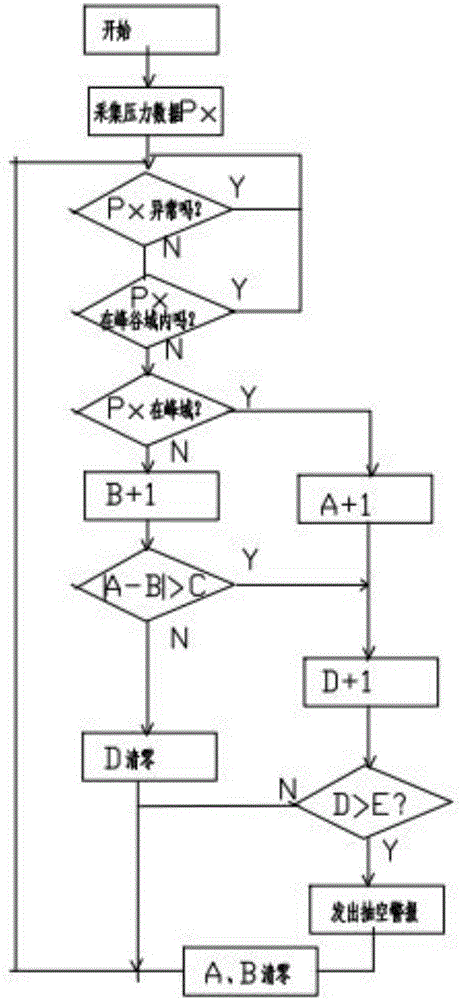
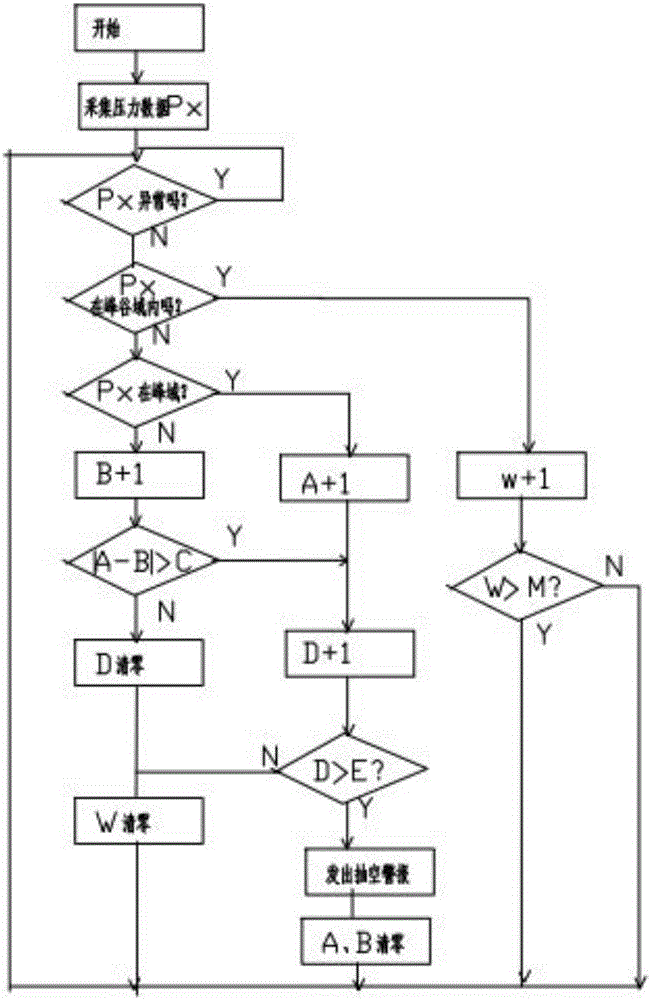
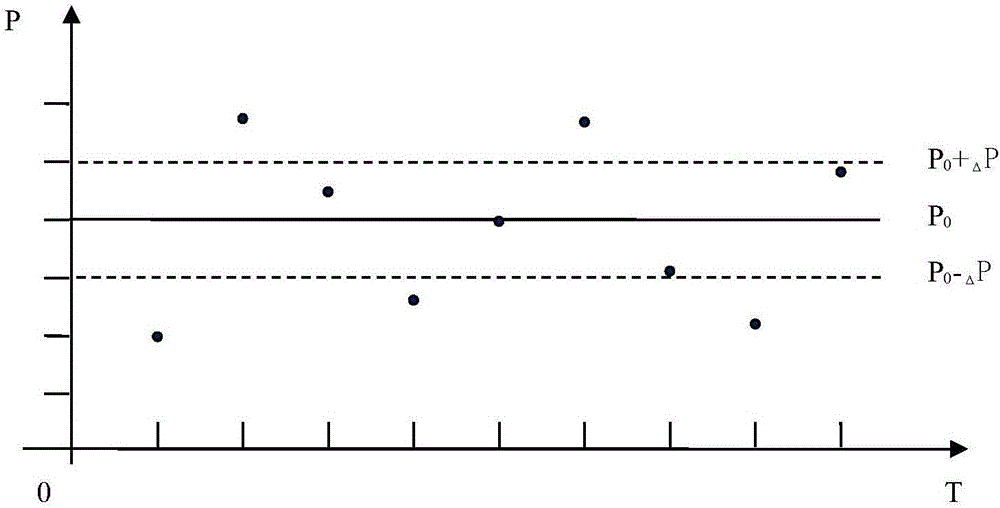
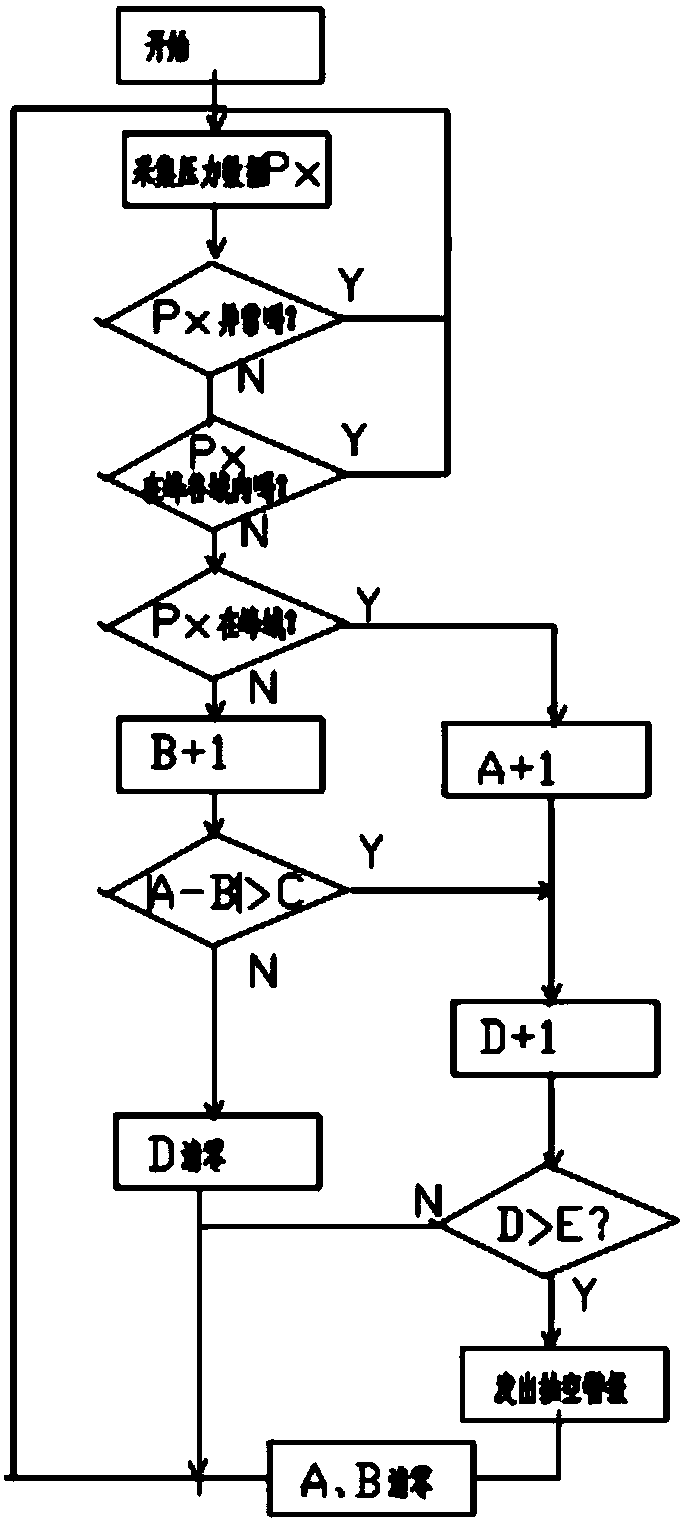
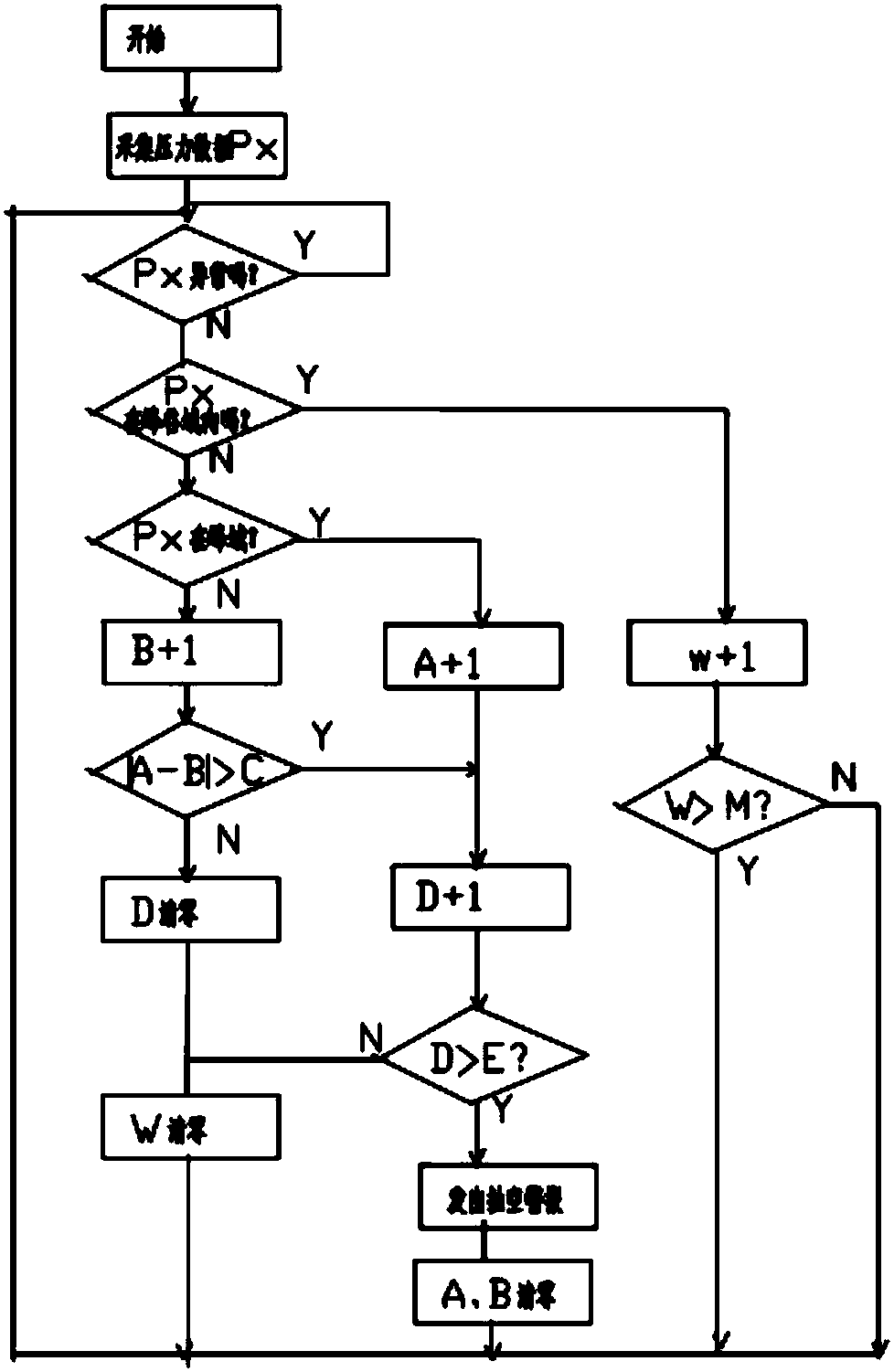
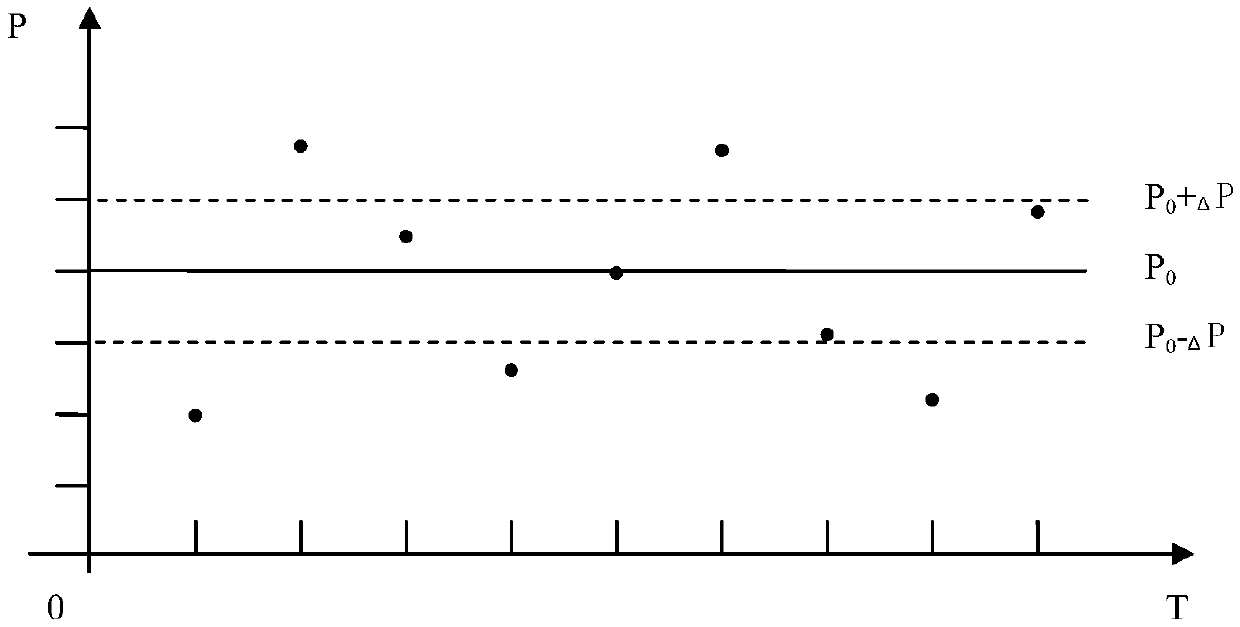
ActiveCN106438310AImprove protectionThe detection method is accuratePump testingPump controlData acquisitionEngineering
The invention relates to the technical field of monitoring of plunger pumps, in particular to a method for preventing evacuation of a plunger pump based on monitoring of the output pressure. The method relates to the plunger and an output pipeline, and is characterized in that a pressure data acquisition control device is arranged on the outlet pipeline; and a data processing method comprises the following steps that (1) the average value P0 of the output pressure is obtained, specifically, the output pressure setting tolerance delta P is set, the domain above a P0+delta P line is called a peak domain, and the domain below a P0-delta P line is called a valley domain; a peak domain counter A and a valley domain counter B are set correspondingly; the allowable difference value between the peak domain counter A and the valley domain counter B is the numerical value C; and an out-of-tolerance time counter D and an upper limit E are set; (2) pressure data Px is acquired; (3) abnormal data are removed; (4) the number of times of Px falling into the peak domain and the valley domain is calculated; and (5) whether the out-of-tolerance time D of the difference value between the peak domain counter A and the valley domain counter B exceeds a preset value E or not is judged, and if yes, an evacuation alarm is given out. Compared with a detection method in the prior art, the method is accurate and reliable, and false alarms are avoided.
Owner:JEREH OIL & GAS ENG
A method for preventing plunger pump from pumping out based on monitoring output pressure
ActiveCN106438310BImprove protectionThe detection method is accuratePump testingPump controlData acquisitionEngineering
Owner:JEREH OIL & GAS ENG
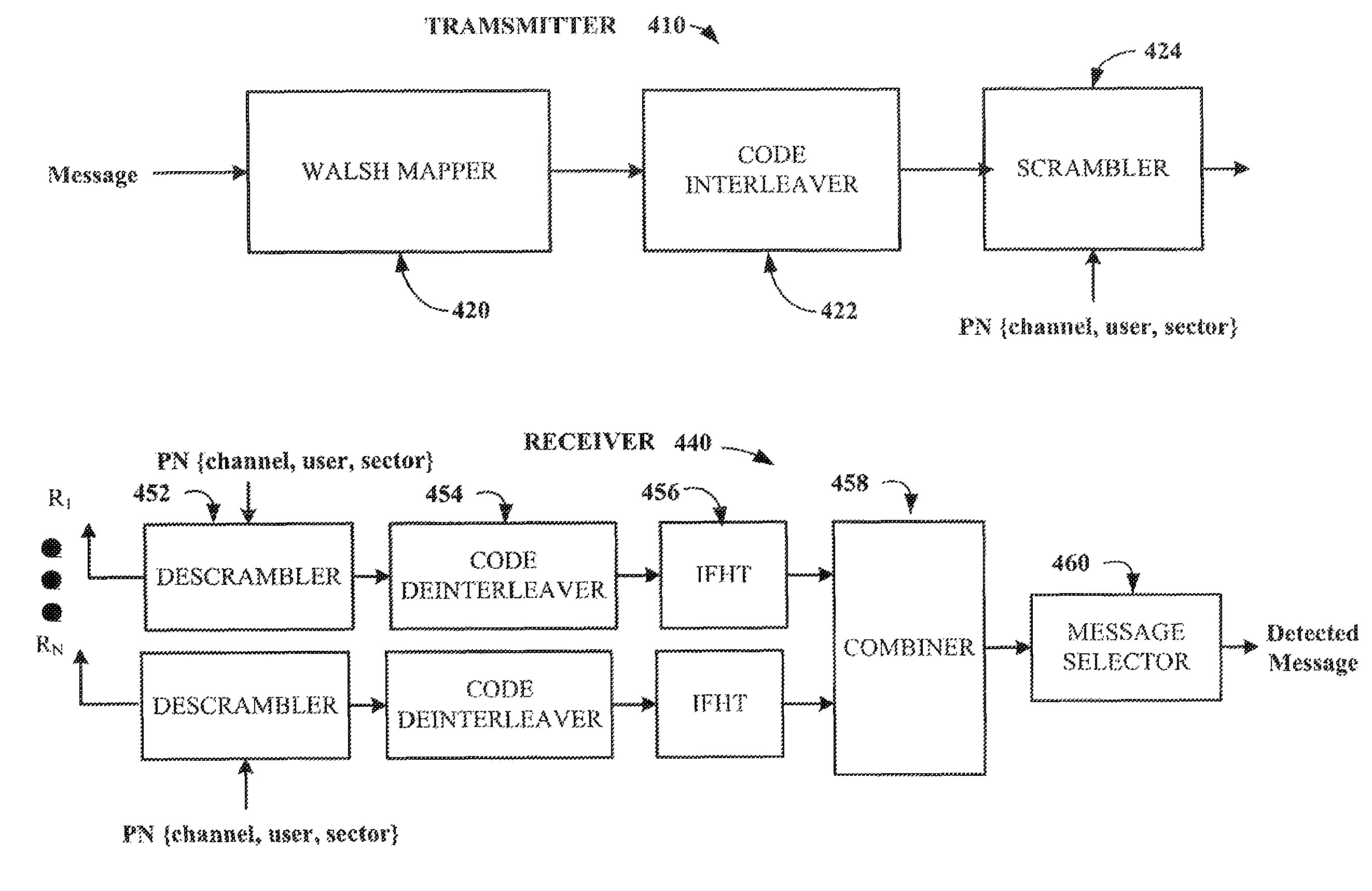
Code interleaving for a structured code
ActiveUS8295250B2Higher false alarmsRadio transmissionError correction/detection using interleaving techniquesComputer hardwareCommunications system
Communication systems and methods that mitigate false alarms due to Doppler shift are disclosed. Received message data is mapped to orthogonal Walsh codes, interleaved and scrambled with appropriate PN sequence prior to transmission. The transmitted message data is descrambled and deinterleaved upon reception. The energies associated with each of the Walsh code from various antennas and / or signal paths are combined to obtain a total energy for each Walsh code. If the total energy of the Walsh code exceeds a certain threshold it is declared as the received message else an erasure is indicated. As the data is interleaved prior to transmission, any phase ramp introduced due to Doppler is transformed into random phase errors upon deinterleaving at the receiver thereby mitigating false alarms.
Owner:QUALCOMM INC
Theft detection system and method
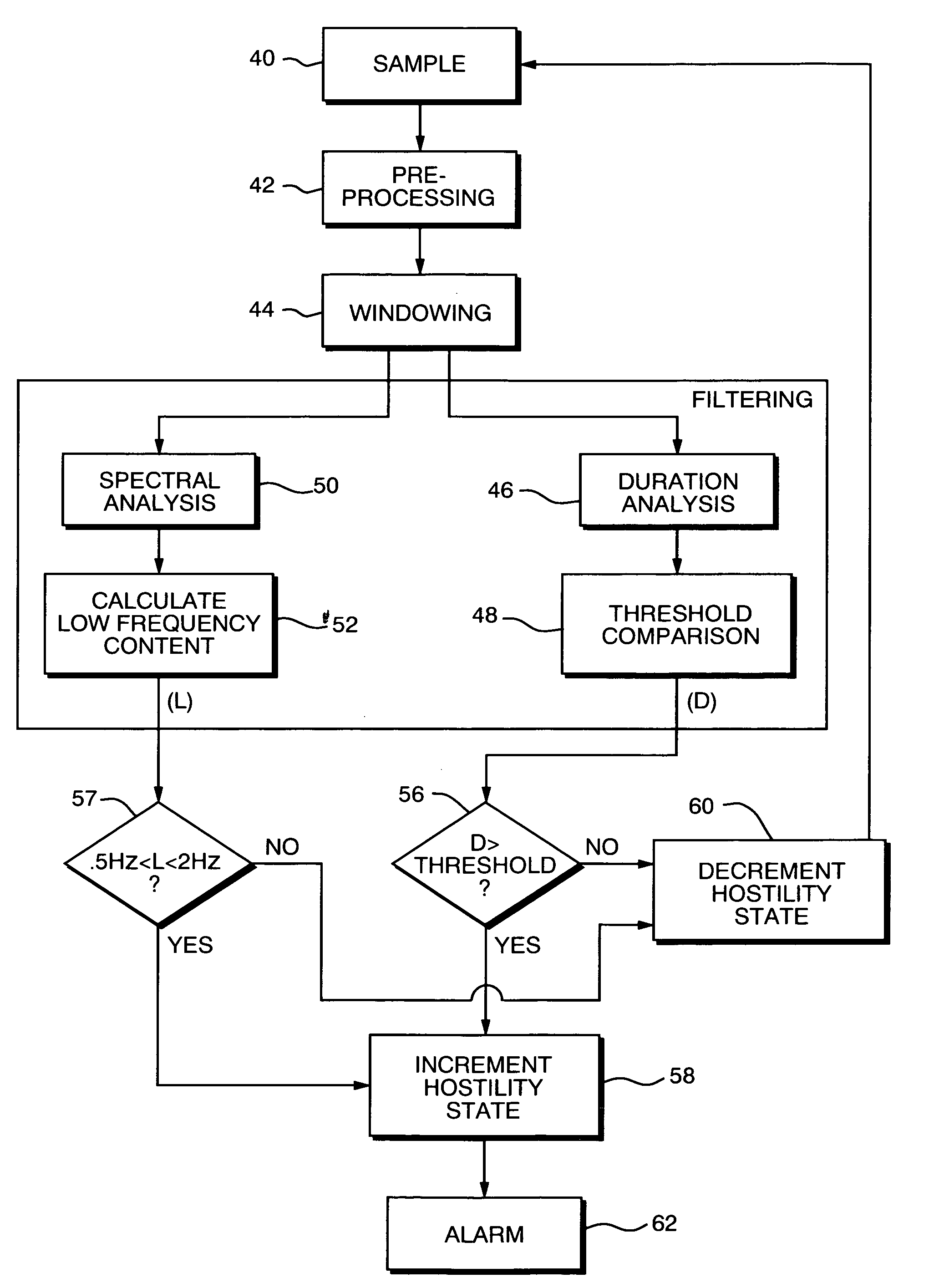
InactiveUS6970095B1Good adhesionEliminating false alarmsBurglar alarm by hand-portable articles removalAccelerometerFalse alarm
A theft detection system includes an accelerometer attachable to an object, the accelerometer providing an acceleration signal in response to movement of the object; an alarm mechanism for providing a signal in response to movement of the object; and for preventing false alarms, a filter programmed to determine the frequency of the acceleration signal and to provide an output to activate the alarm mechanism only when the frequency of the acceleration signal meets a predetermined criteria.
Owner:CAVEO INVESTMENTS
Method and system for man-made noise rejection detector
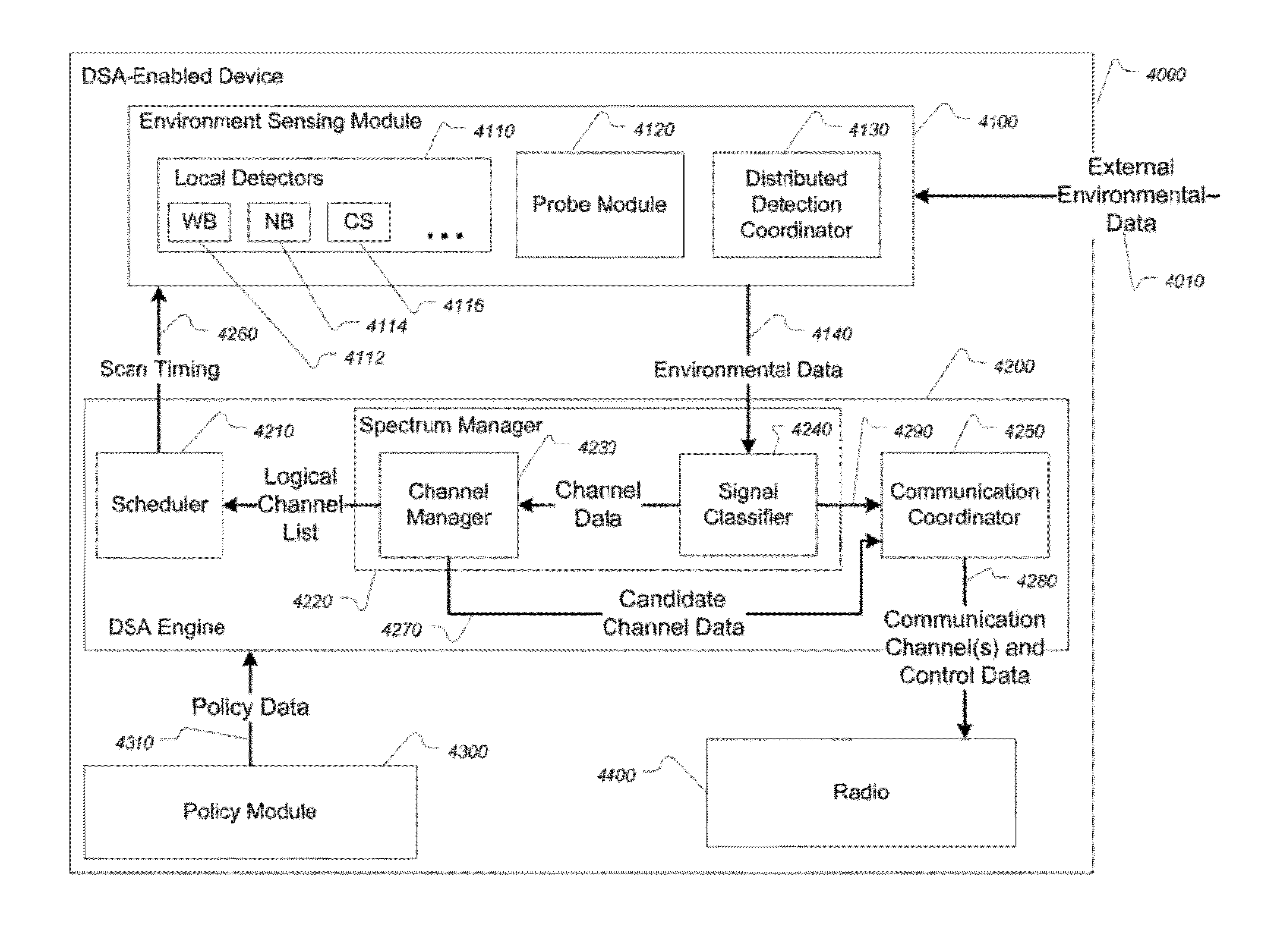
InactiveUS20120302190A1Improve performanceIncrease choiceTransmission monitoringFrequency spectrumNoise suppression
Methods and systems for dynamic spectrum access (DSA) in a wireless network are provided. A DSA-enabled device may sense spectrum use in a region and, based on the detected spectrum use, select one or more communication channels for use. The devices also may detect one or more other DSA-enabled devices with which they can form DSA networks. A DSA network may monitor spectrum use by cooperative and non-cooperative devices, to dynamically select one or more channels to use for communication while avoiding or reducing interference with other devices. A man-made noise rejection sub-system is used to permit signal detection while maintaining a low false alarm rate.
Owner:SHARED SPECTRUM
Method and arrangement for detecting a watermark using statistical characteristics of the information signal in which the watermark is embedded
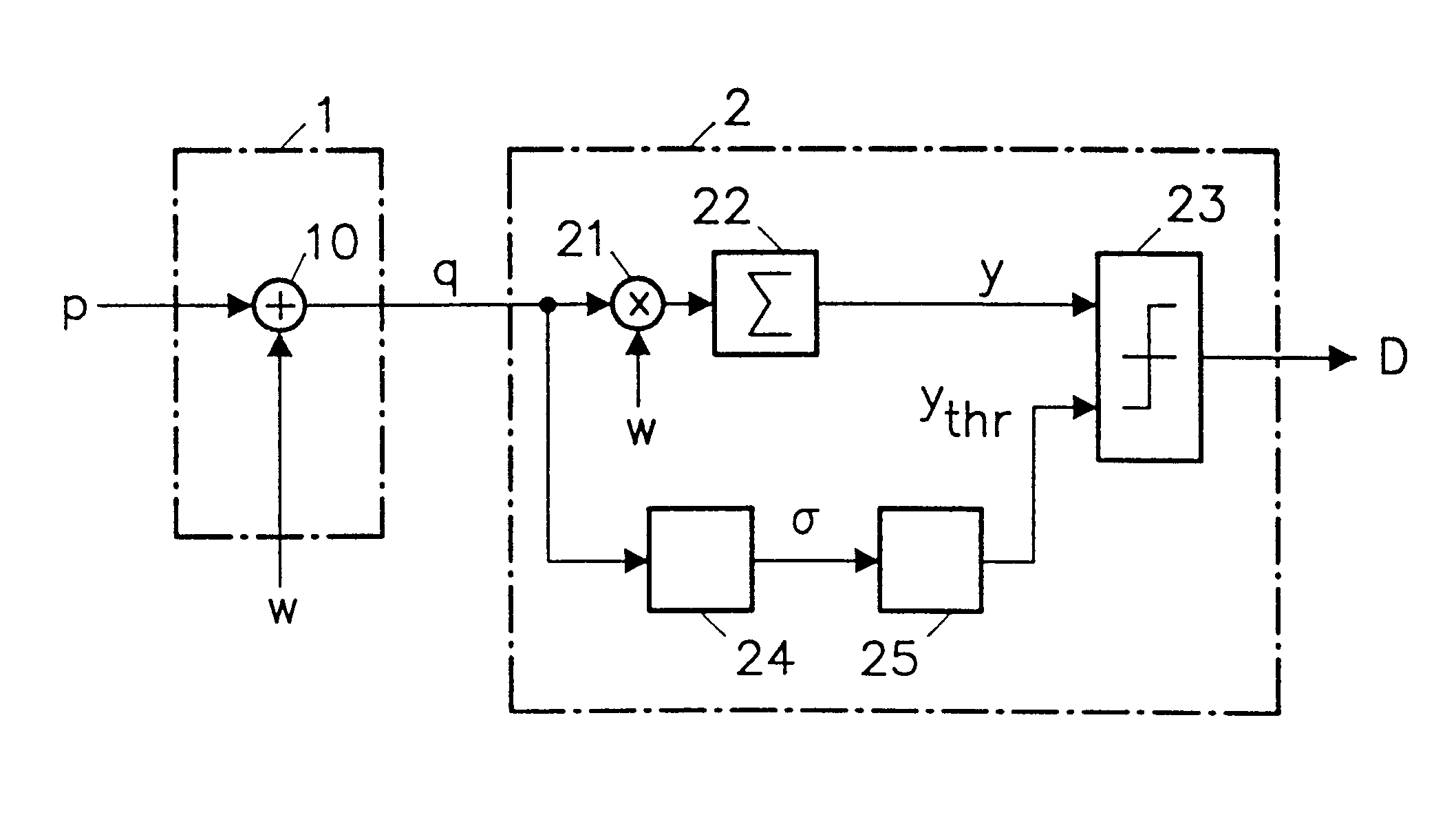
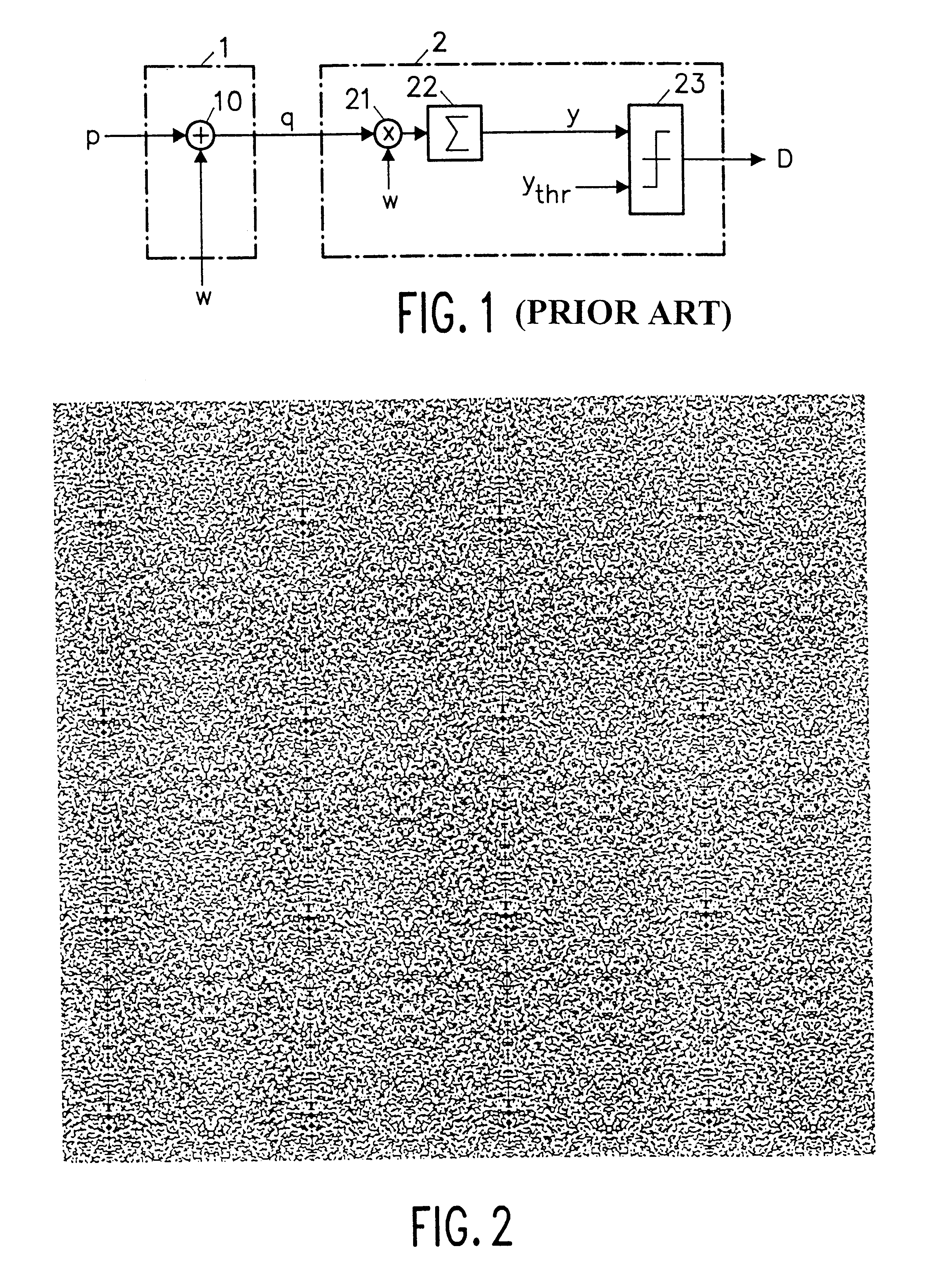
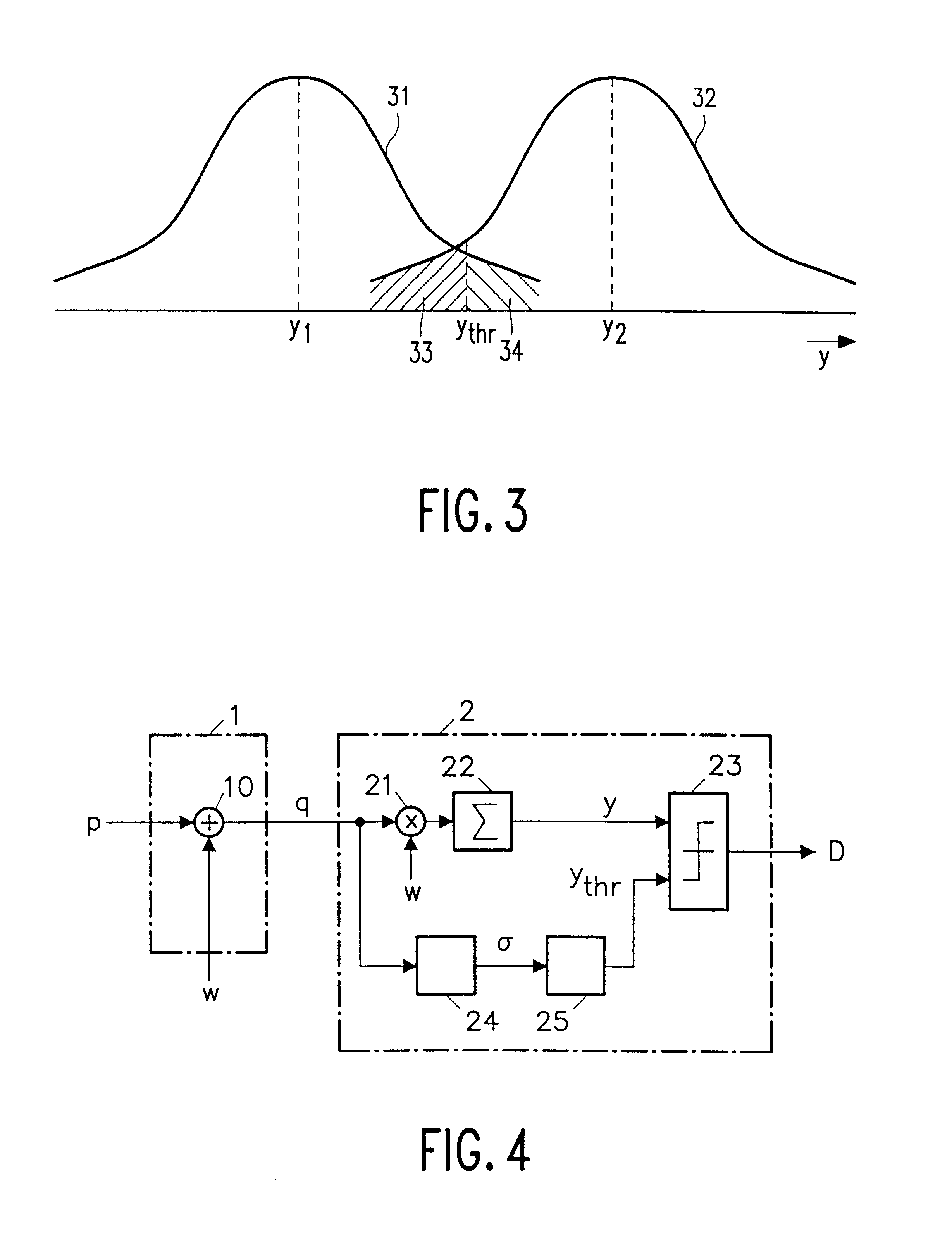
Recently developed methods for copy protection rely on a watermark detector to judge whether multimedia content can be copied or not. In such copy protection schemes, a watermark detector examines the multimedia content and outputs a signal (D) indicating whether a watermark is present or not. Known watermark detectors determine a decision variable (y) indicating to which extent the watermark is present, for example, the amount of correlation between input signal and a reference copy of the watermark to be detected. The watermark is detected if the decision variable exceeds a predetermined threshold (ythr)In accordance with the invention, the threshold value (ythr) is adaptively controlled in dependence upon statistical characteristics of the information signal and a desired probability of false alarms (watermark detected whereas the signal is not watermarked). In an embodiment, the watermark detector determines the standard deviation (sigma) of the pixel values threshold level and calculates the threshold value in accordance with the relationin which erfc is the error function and sigma is said standard deviation of the information signal values.
Owner:U S PHILIPS CORP +1
Physiological event detection systems and methods
Systems and methods using constant false alarm rate techniques for event detection. One example of an event detection method includes collecting a first distribution of measurements for a first physiological parameter. In another example, the first distribution of measurements includes only non-event measurements. One or more values are determined corresponding to at least a first tail area of the first distribution from at least one measurement of the first physiological parameter toward an end point of the distribution. A threshold is established based on a specified false alarm rate. The one or more values are compared to the threshold. The method includes determining if the measurement is representative of a detected event using the comparison.
Owner:CARDIAC PACEMAKERS INC
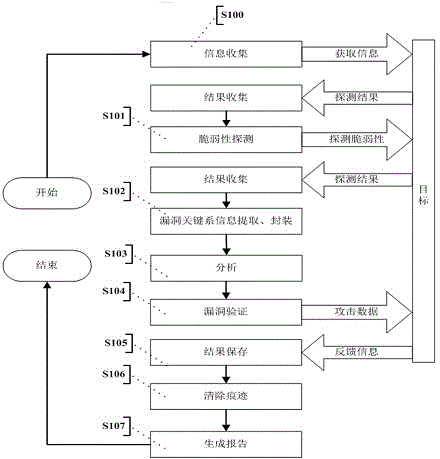
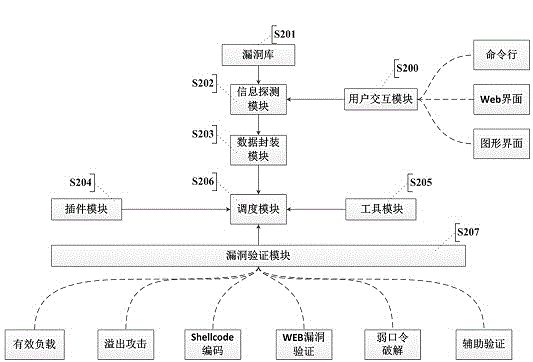
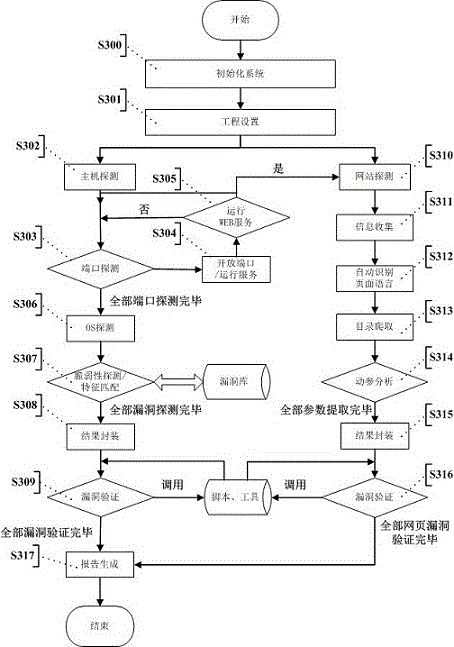
Automatic vulnerability validation method
InactiveCN104363236AAutomated verificationUnderstand the dangers of vulnerabilitiesPlatform integrity maintainanceTransmissionValidation methodsModularity
The invention provides an automatic vulnerability validation method. The method comprises the steps that firstly, validation information is collected, wherein an active detection way is adopted for carrying out information detection, topological detection, vulnerability detection and website directory structure detection on a target; secondly, the validation information is packaged, wherein suspicious vulnerability key information in vulnerability detection results is extracted, uniform-interface modularized packaging is carried out on the data; thirdly, a validation strategy is searched for, wherein according to the suspicious vulnerability identity and variety information, an appropriate attack script template and a vulnerability utilizing tool are selected; vulnerability validation is carried out, wherein scripts are called to be loaded into the packaged vulnerability information to carry out validation attack, and an utilization voucher is obtained and stored; fifthly, validation traces are removed, wherein validation attack traces are removed, sessions are recycled; finally, a scanning report is generated. The automatic vulnerability validation method solves the problem that an existing vulnerability scanning system is high in false alarm rate and cannot carry out effective validation, is automatic and procedural, can automatically recognize and validate vulnerabilities, lowers the requirement for the ability of non-professional staff and improves the vulnerability validation efficiency.
Owner:XIAN UNIV OF POSTS & TELECOMM +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com