Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3673results about "Burglar alarm electric actuation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
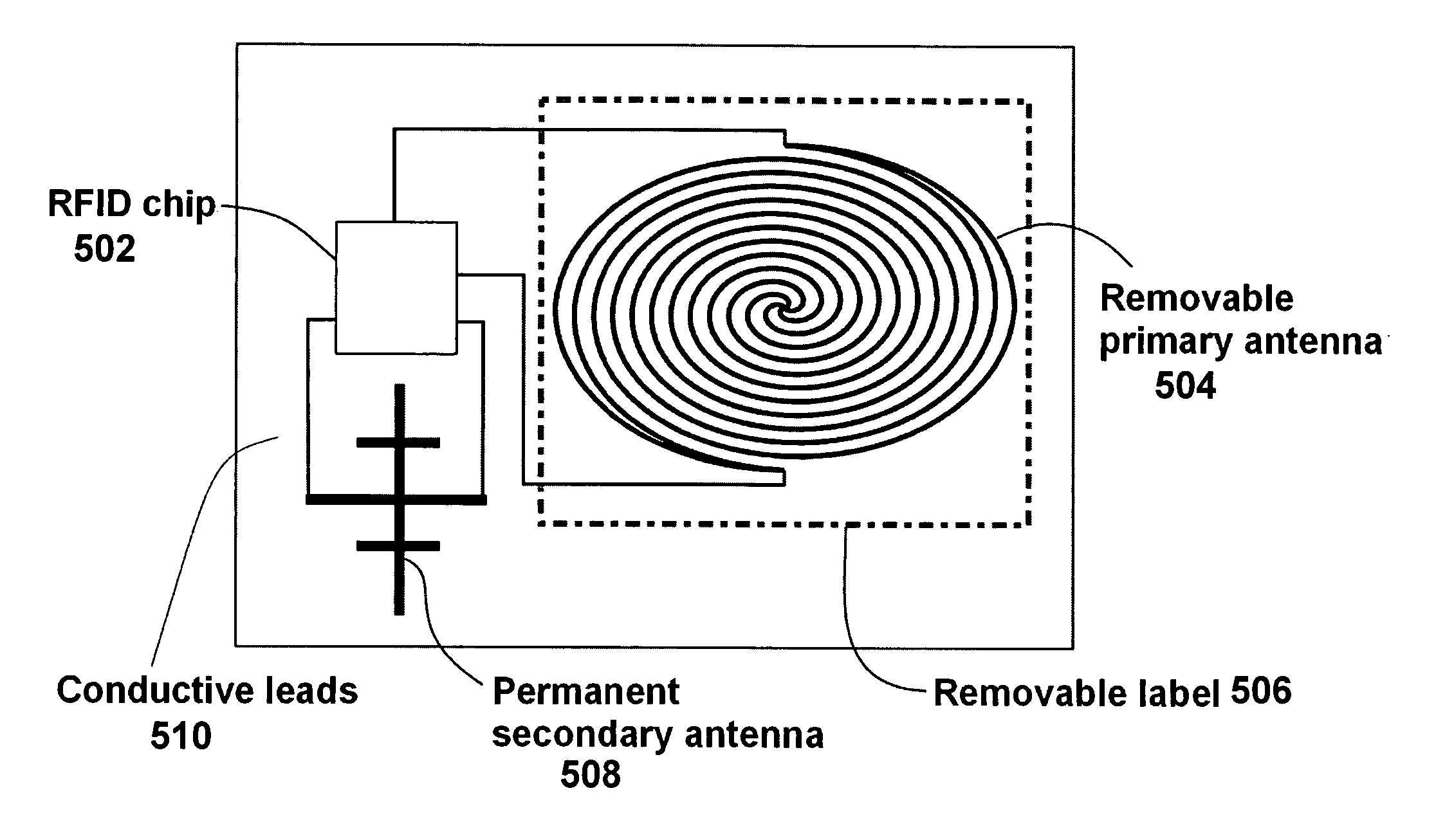
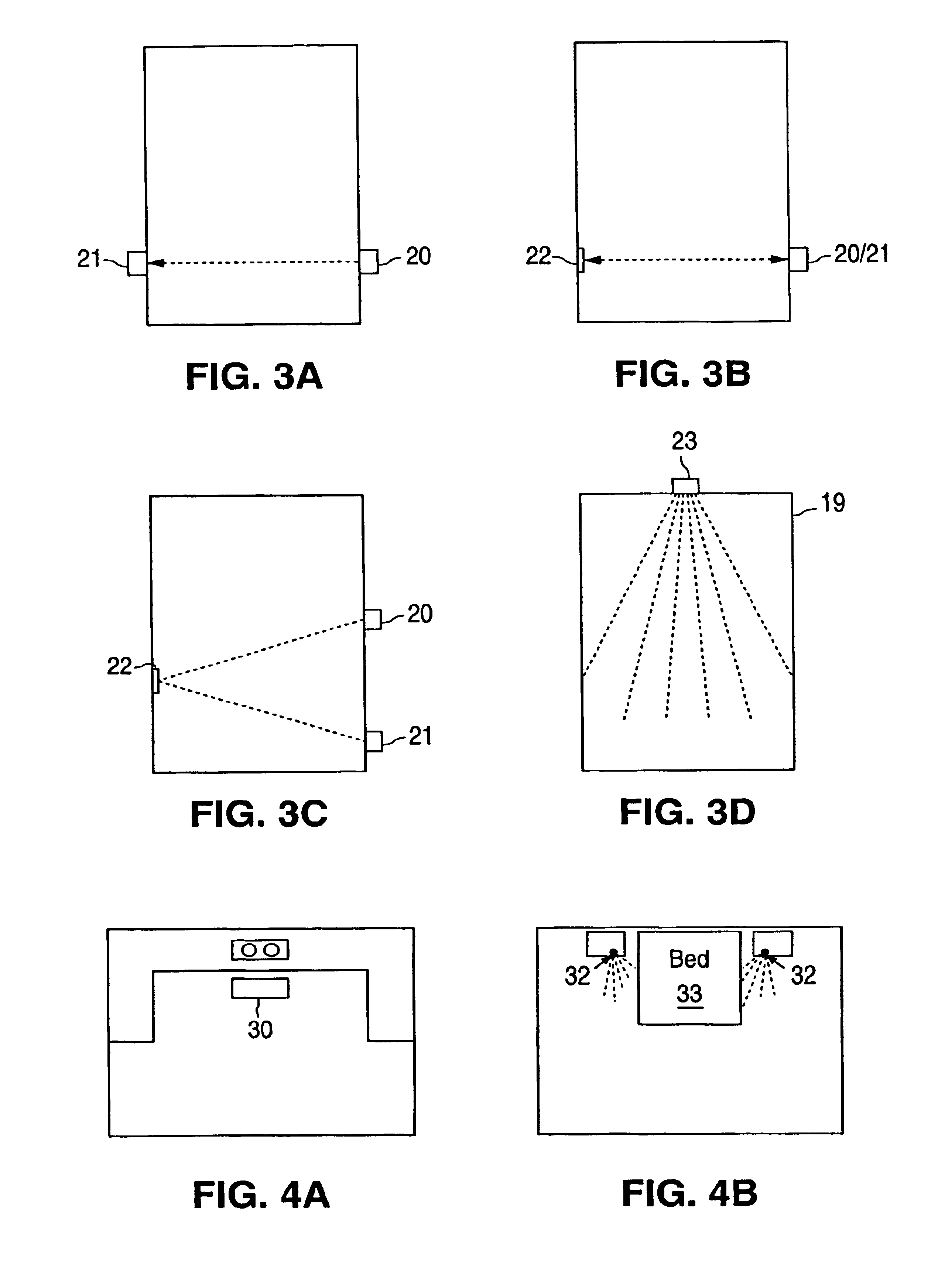
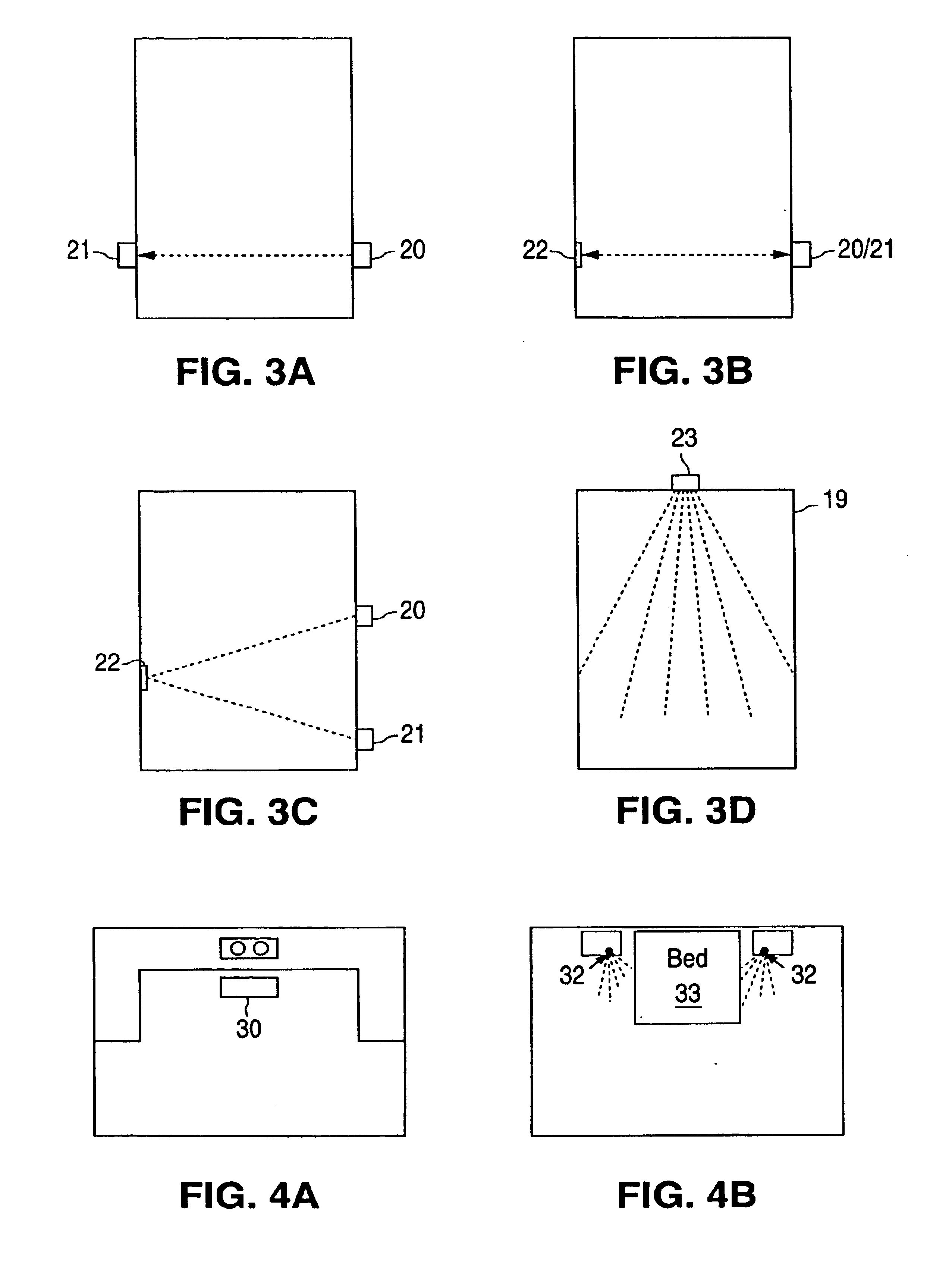
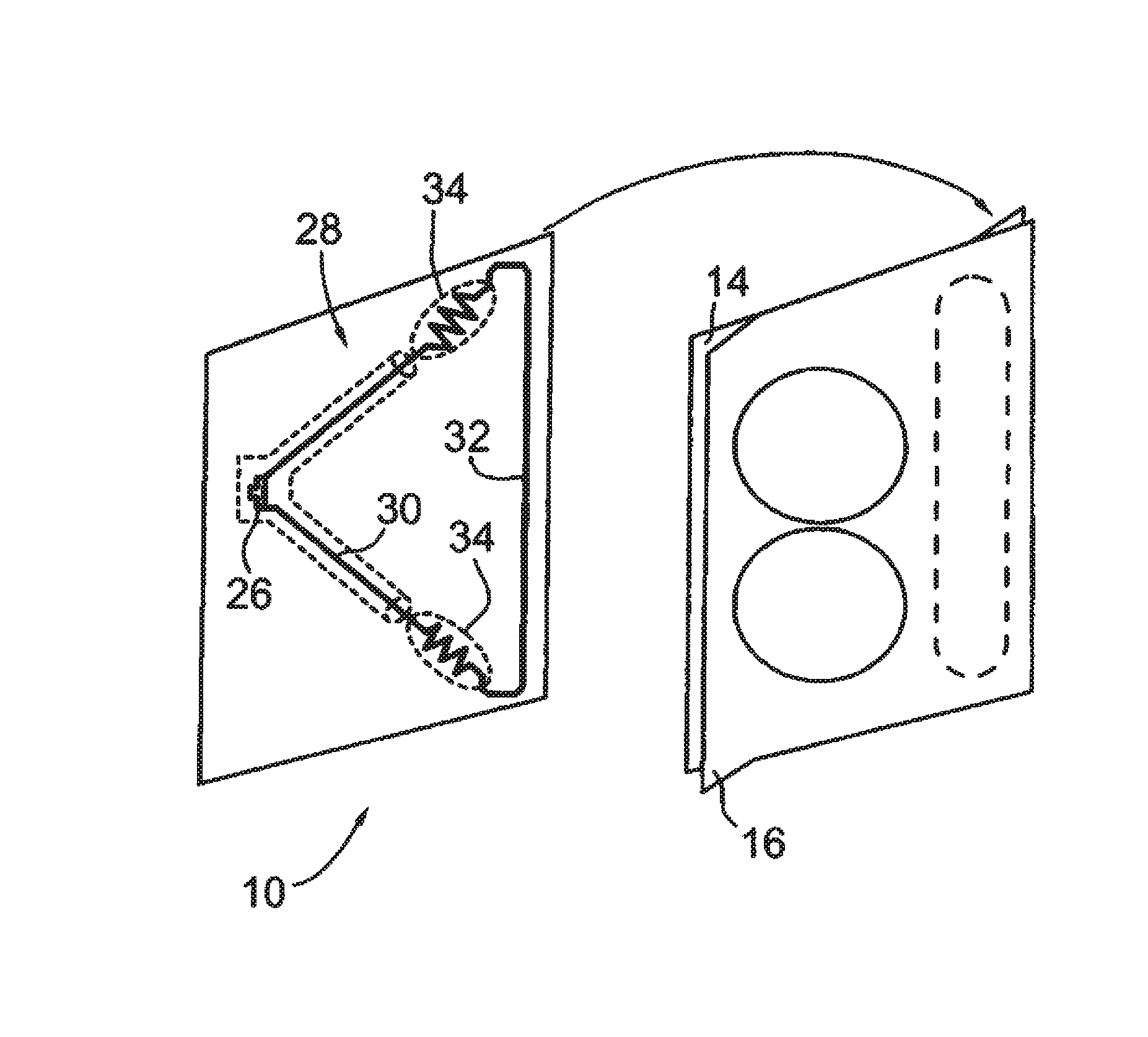
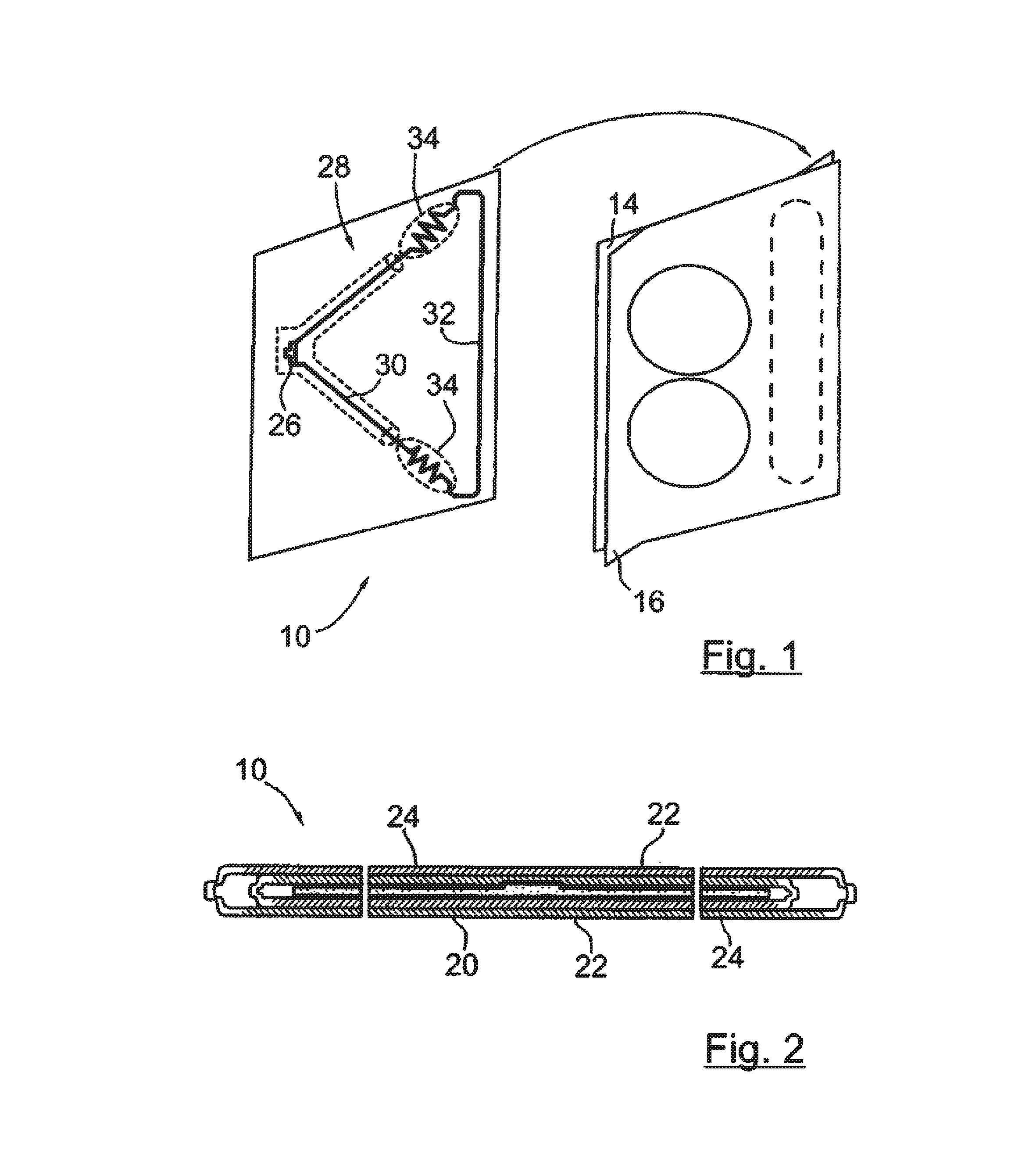
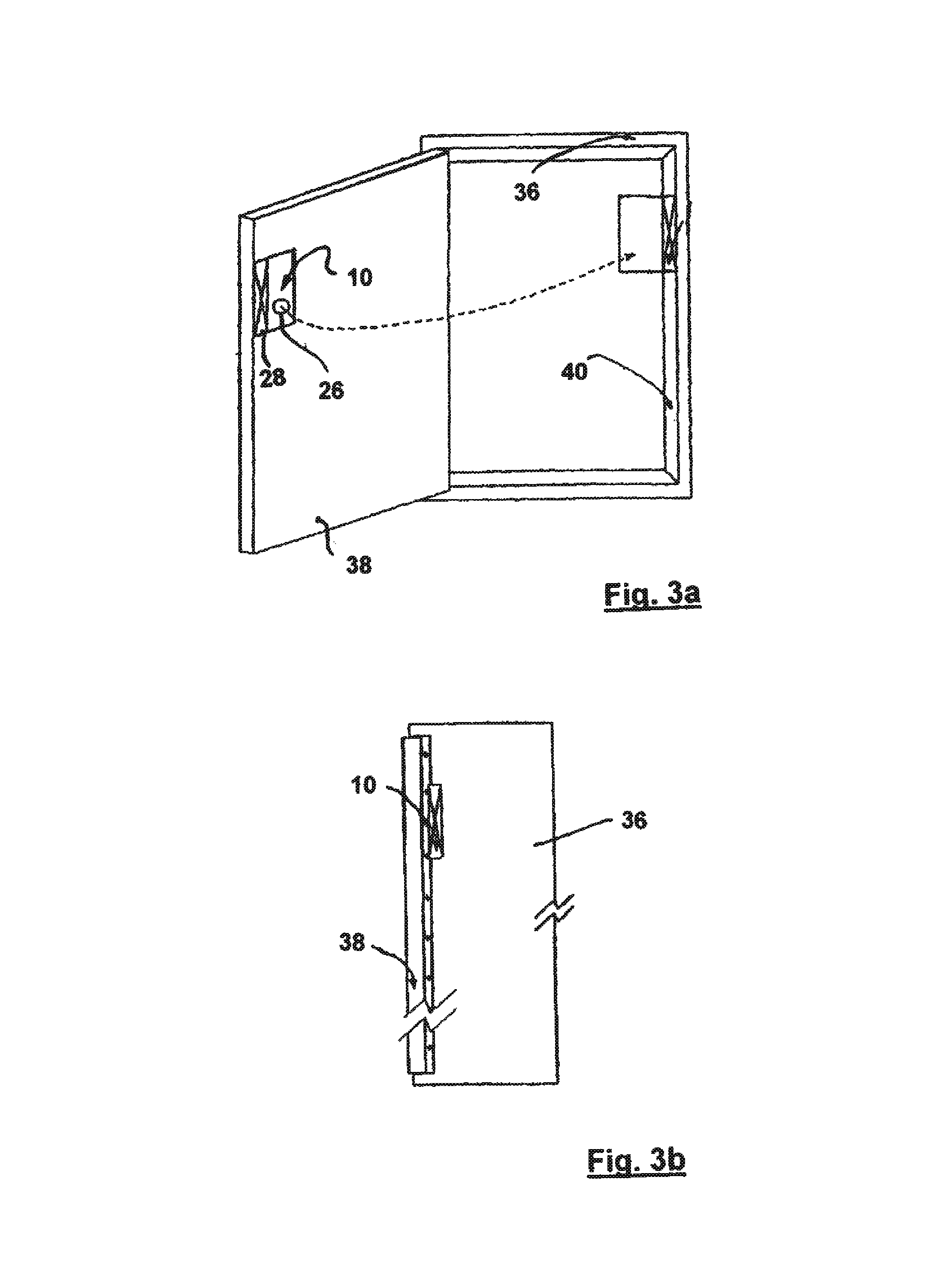
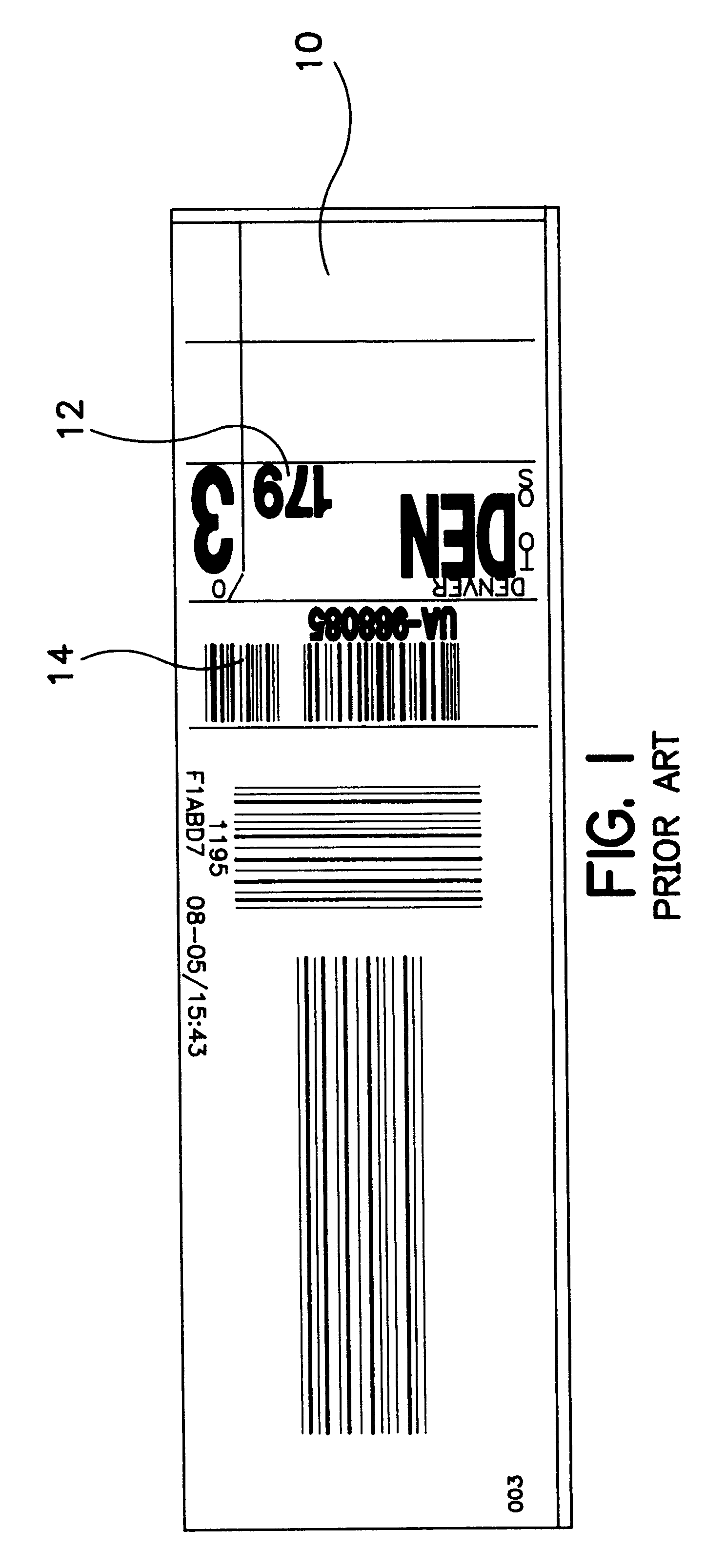
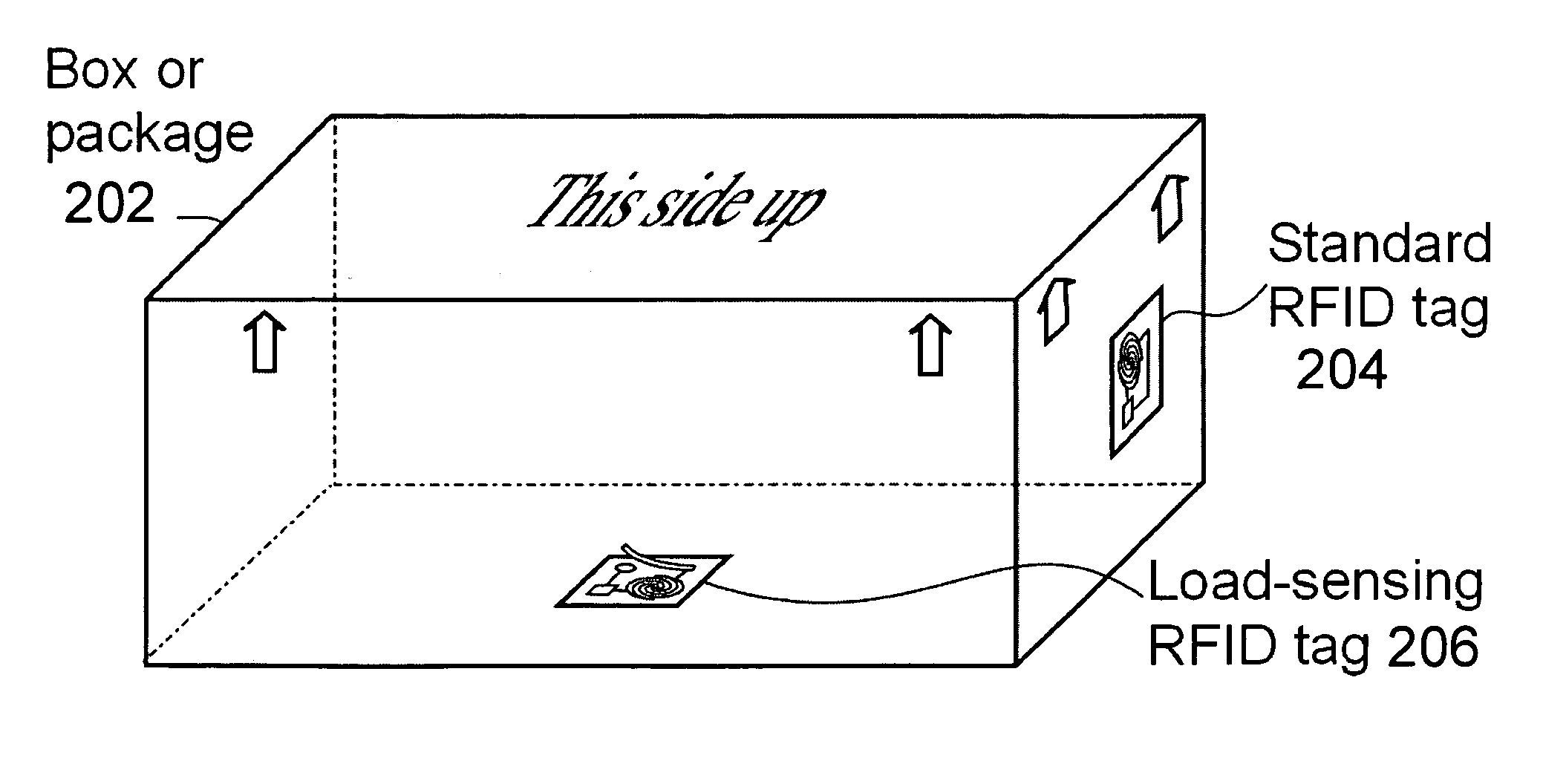
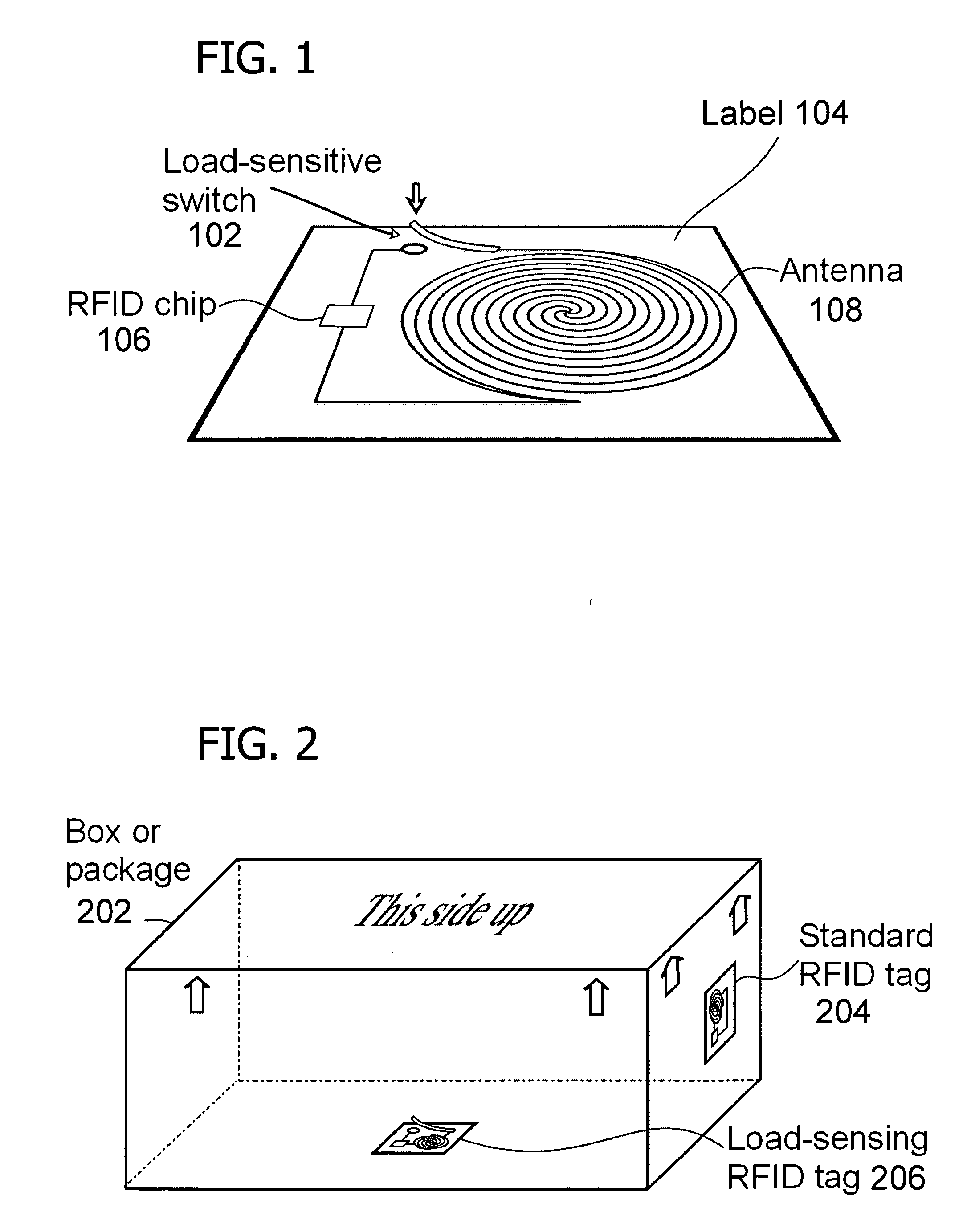
Deactivating a data tag for user privacy or tamper-evident packaging
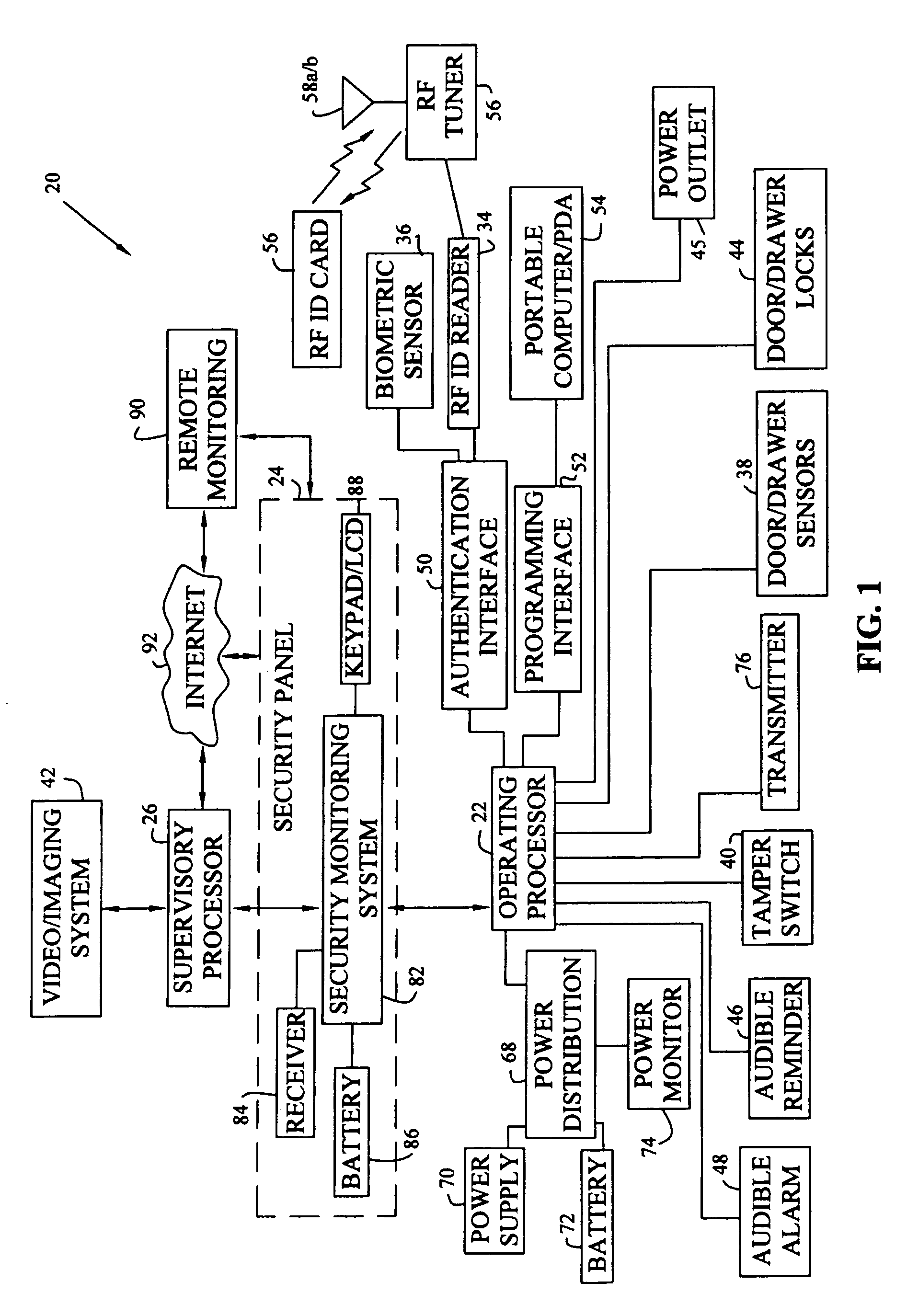
ActiveUS7098794B2Facilitate communicationBurglar alarm by openingLocks for portable objectsUser privacyVIT signals
Deactivating a data tag attached to packaging for user privacy or tamper-evident reasons. A data circuit stores identification information. A plurality of antennas is coupled to the data circuit. At least one antenna of the plurality of antennas is a removable antenna capable of wireless signal transmission at a first range such that removal of the antenna substantially prevents communication of the identification information via the removed antenna and permits communication of the identification information via another antenna of the plurality of antennas at a second range relatively smaller than the first range.
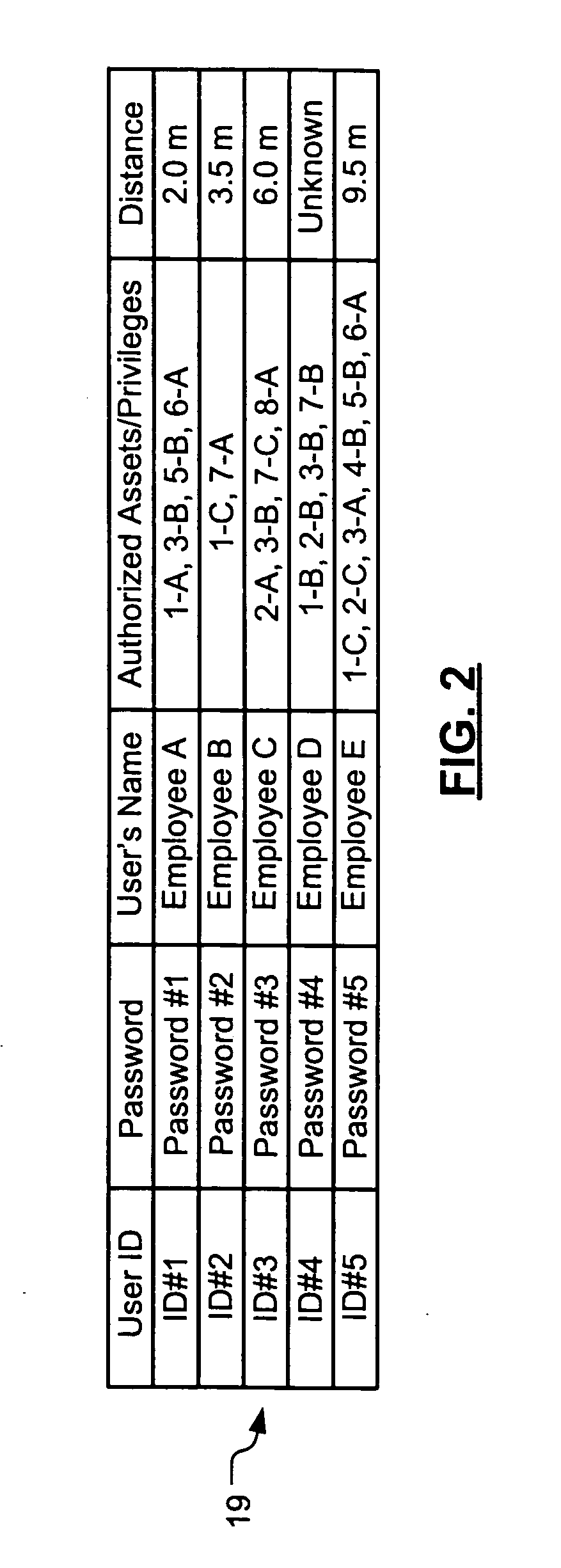
Owner:BUFFALO PATENTS LLC
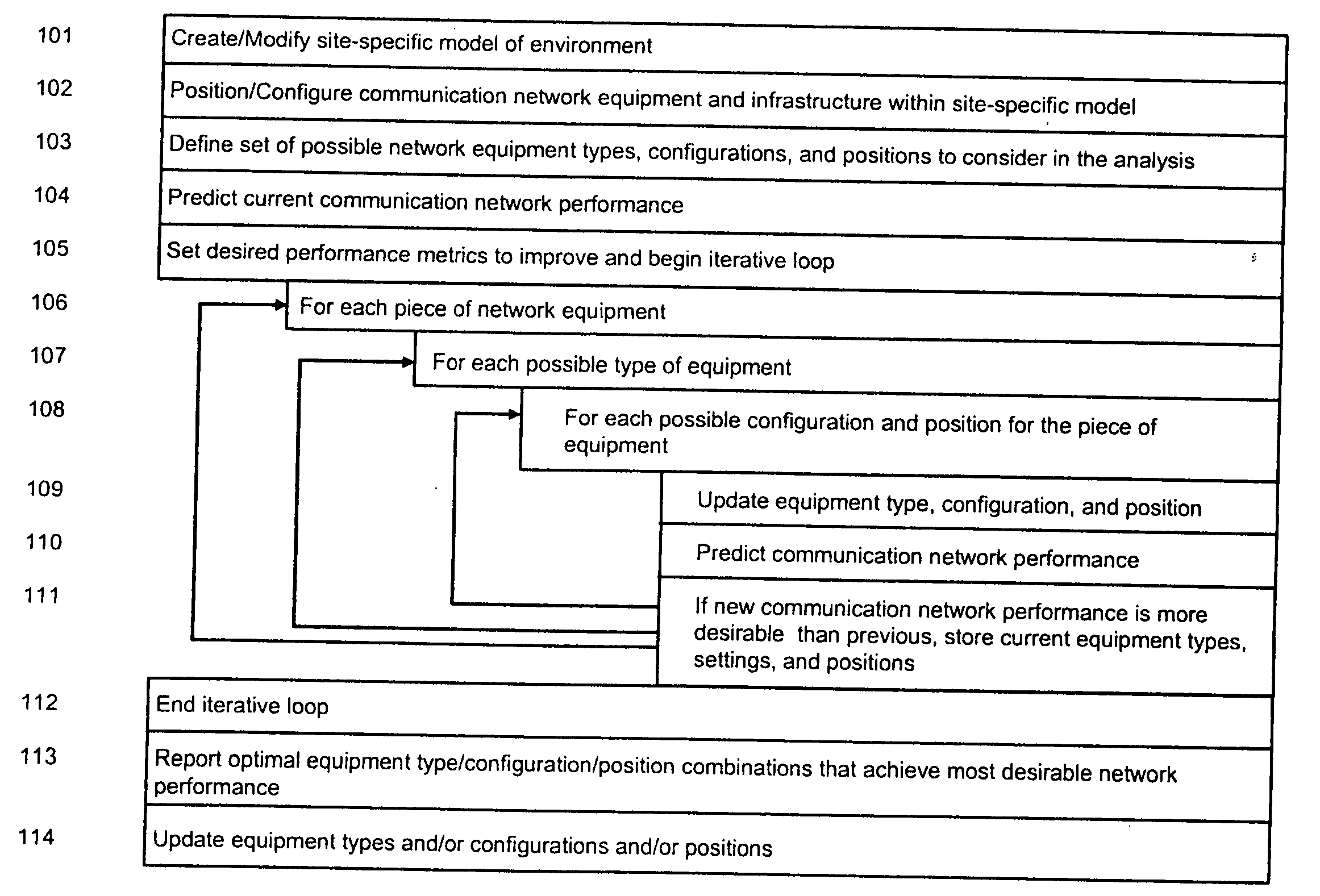
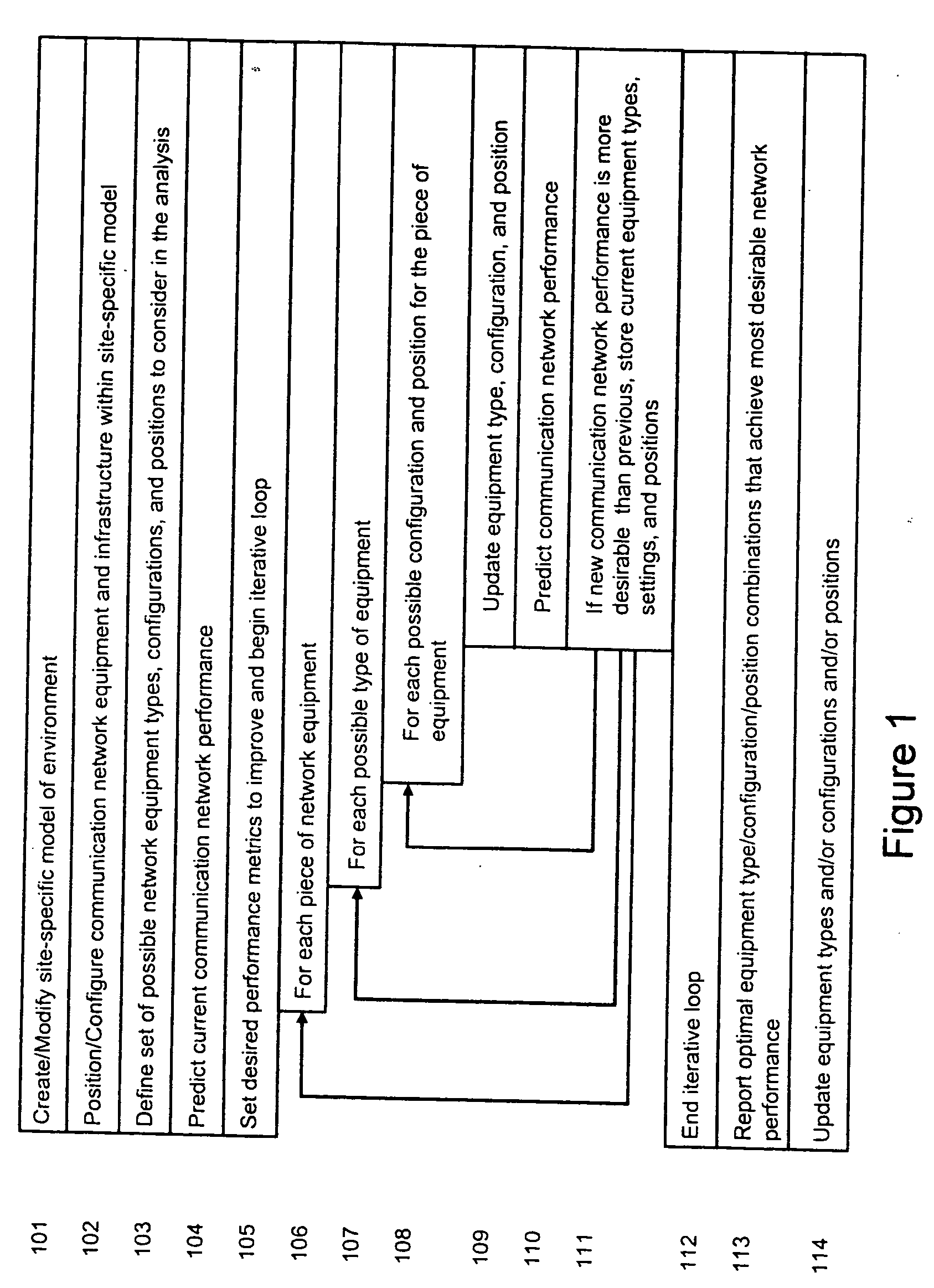
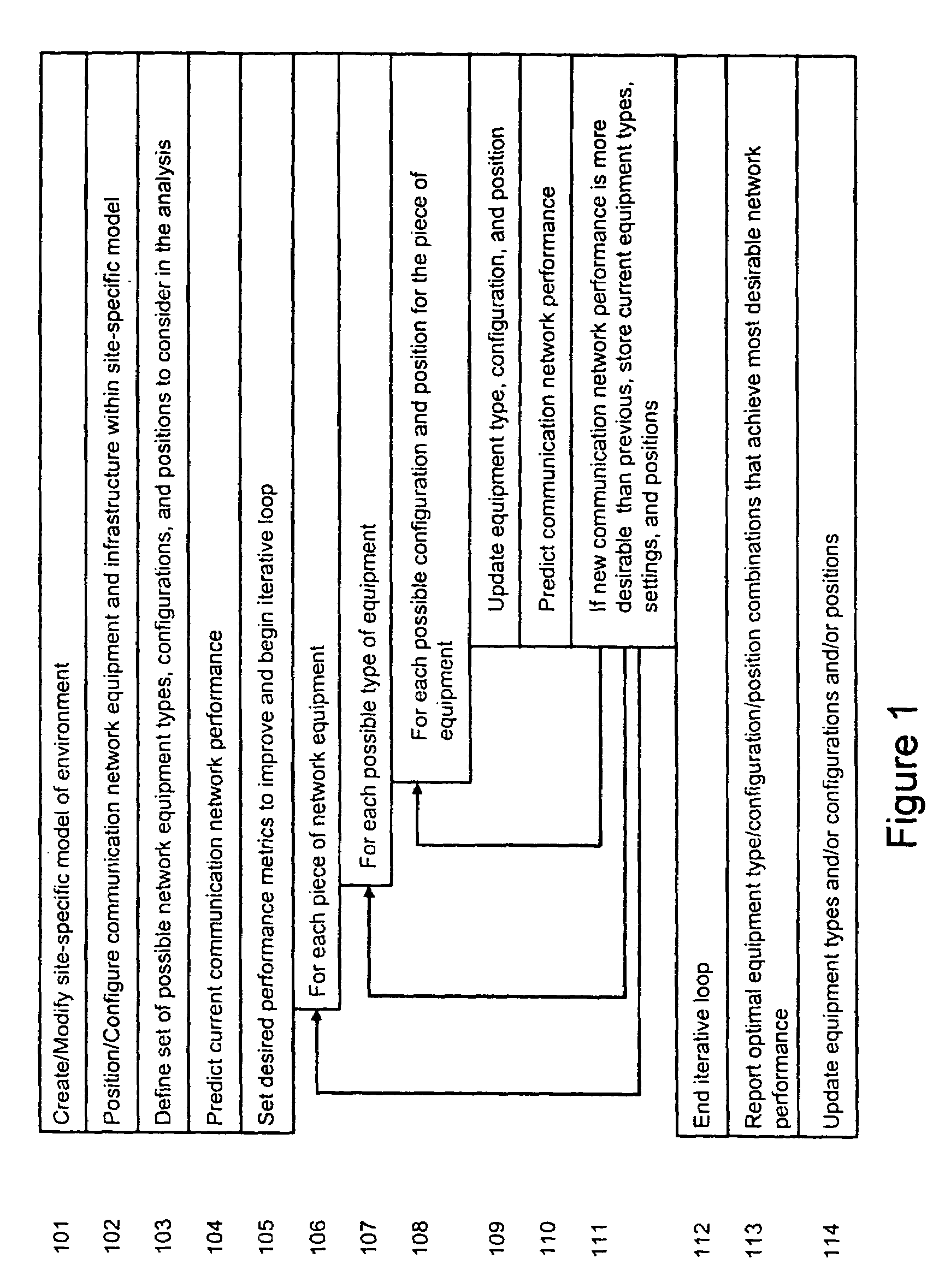
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
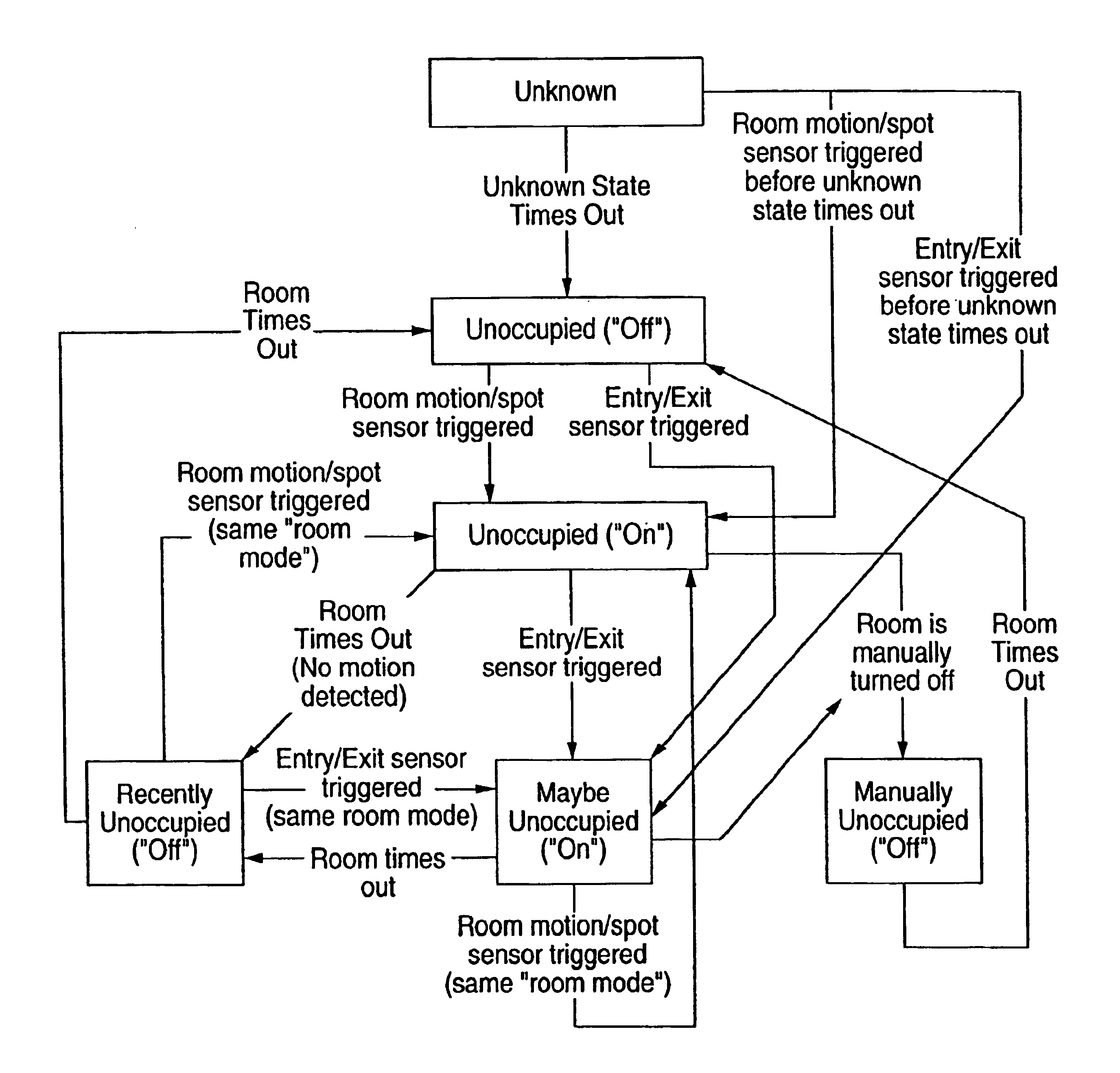
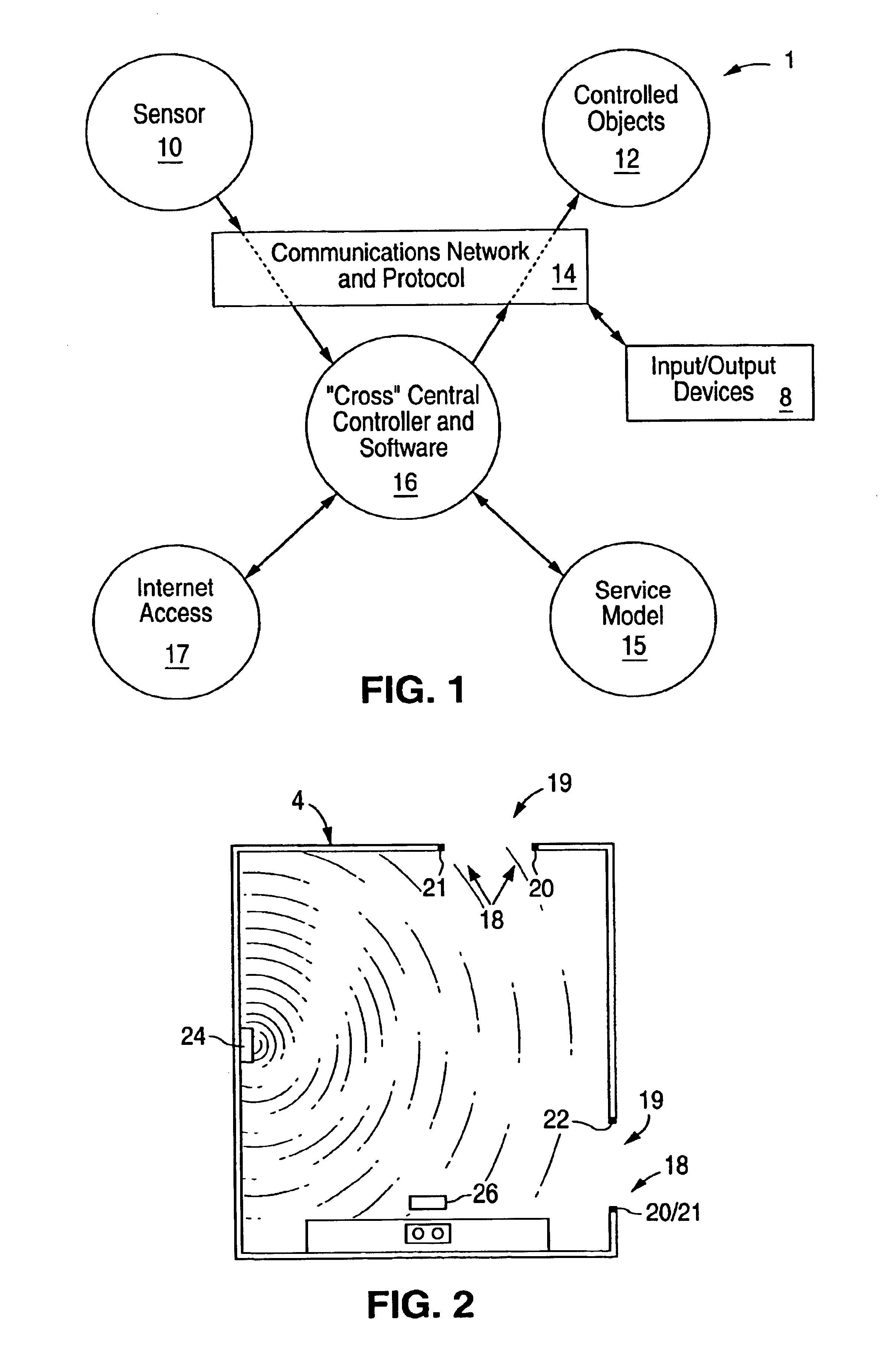
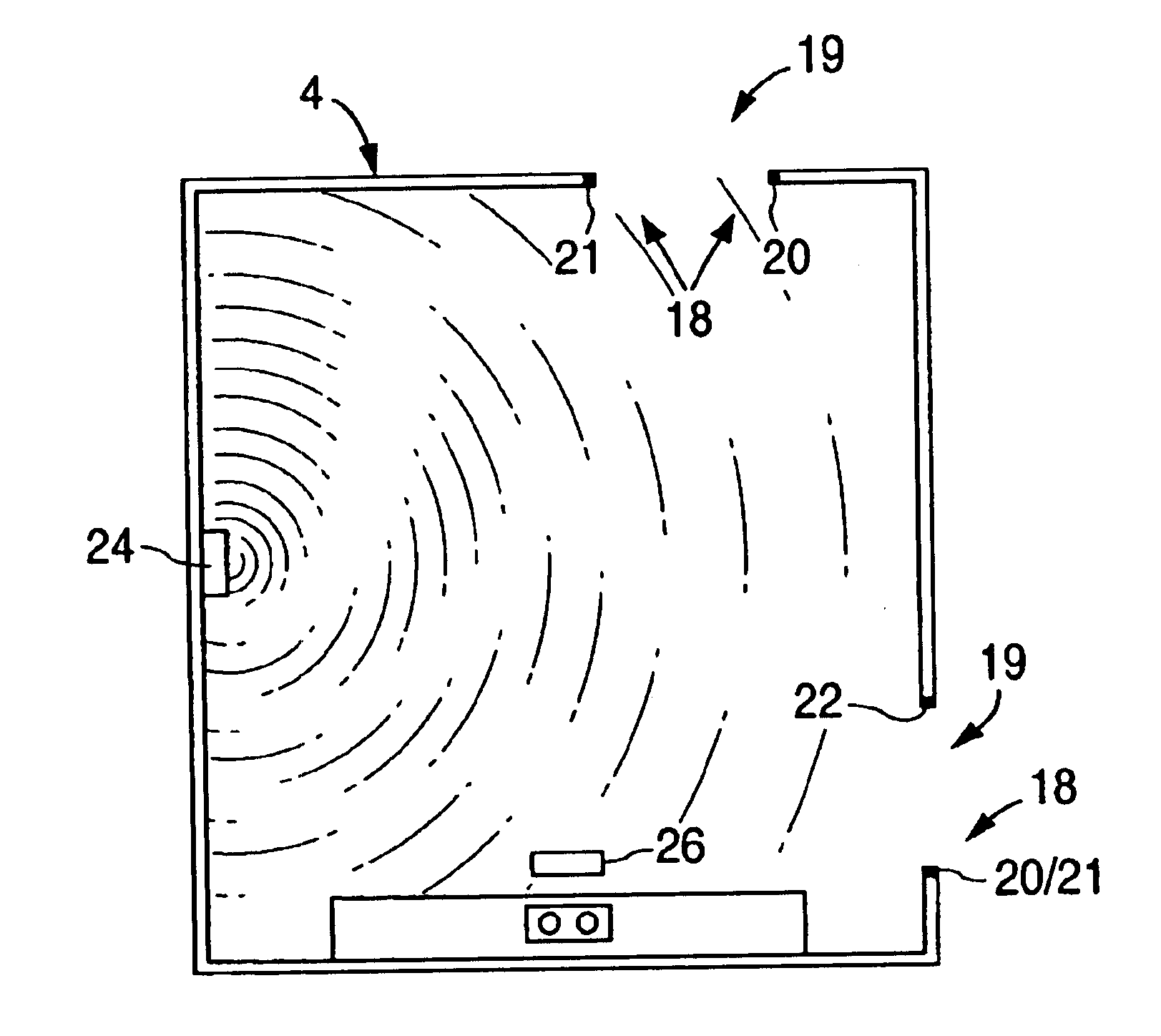
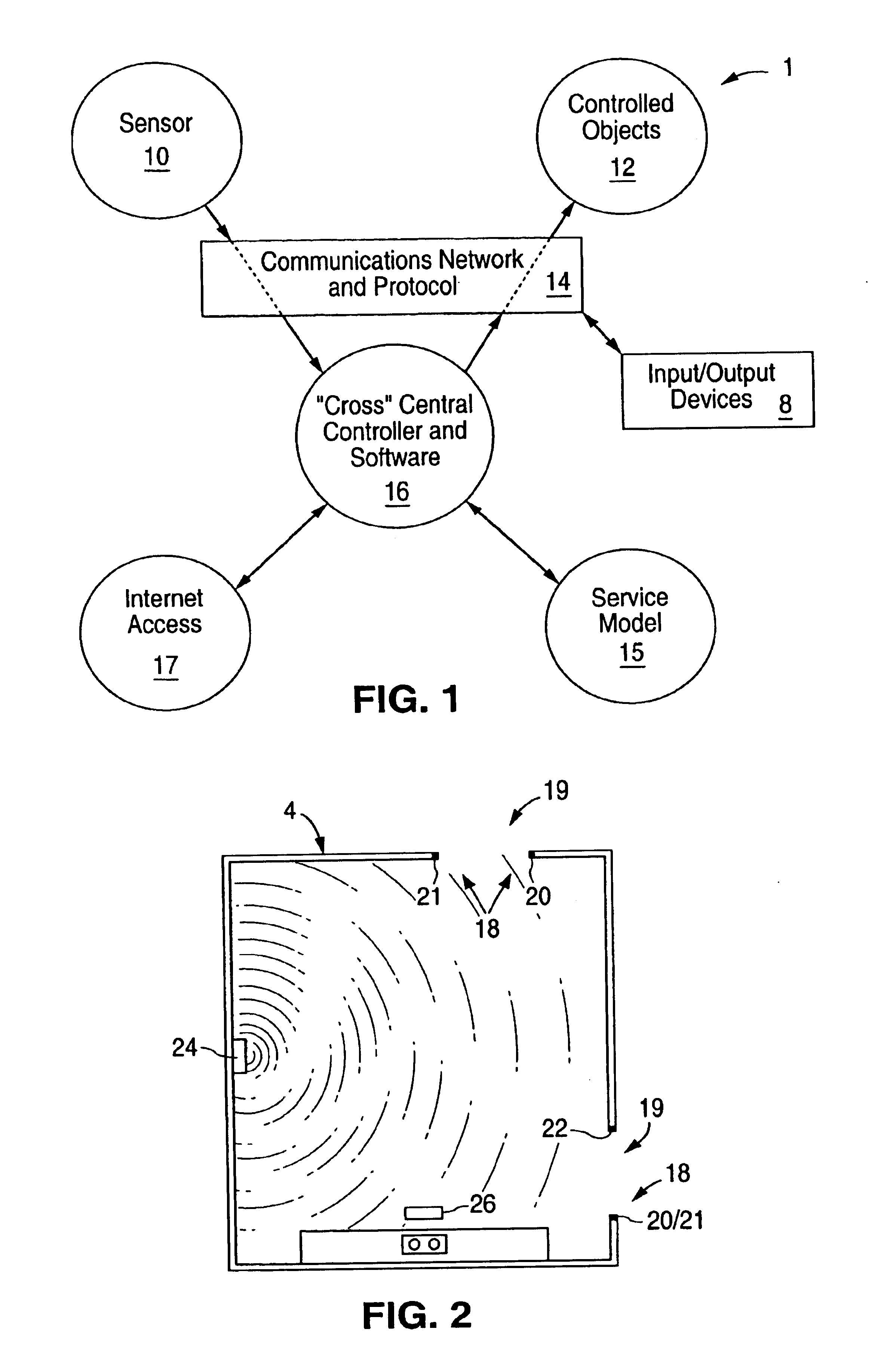
Home automation system and method
InactiveUS6912429B1Matches need and abilityImprove automationSpace heating and ventilationTemperatue controlAutomatic controlEngineering
A home automation system and method for automatic control of controlled devices throughout a home. A unique architecture of occupancy sensors includes entry / exit sensors for detecting movement through doorways that separate rooms in the home, room motion sensors for detecting room occupancy, spot sensors to detect occupancy of specific locations within the rooms, and house status sensors to detect the status of certain parameters of the home. A central controller communicates with the sensors and controlled objects over a communications network, where the sensors and controlled objects can be added to the system in a ‘plug and play’ manner. The central controller controls the controlled objects in response to the entry / exit sensors, room motion sensors, spot sensors and the house status sensors. This control is accomplished by assigning each room to one of a plurality of room occupancy states, and to one of a plurality of room modes for creating desired room atmospheres using the controlled objects, which both dictate how the controlled objects are controlled by the central controller. The room modes travel from room to room as the occupant moves throughout the home, and multiple occupants can be using different room modes as they move about the home. The controlled objects also have controlled object states, which are used by the central controller to control the controlled objects.
Owner:HOME DIRECTOR
Occupancy sensor and method for home automation system
InactiveUS6909921B1Good roomTemperatue controlStatic/dynamic balance measurementAuto regulationAutomatic control
A room occupancy sensor, a home automation system and a method for automatic control of controlled devices throughout a home. A unique architecture of occupancy sensors includes entry / exit sensors for detecting movement through doorways that separate rooms in the home, room motion sensors for detecting room occupancy, spot sensors to detect occupancy of specific locations within the rooms, and house status sensors to detect the status of certain parameters of the home. A central controller communicates with the sensors and controlled objects over a communications network, where the sensors and controlled objects can be added to the system in a ‘plug and play’ manner. The central controller controls the controlled objects in response to the entry / exit sensors, room motion sensors, spot sensors and the house status sensors. This control is accomplished by assigning each room to one of a plurality of room states, which dictate how the controlled objects are controlled by the central controller. The controlled objects also have controlled object states, which are used by the central controller to control the controlled objects. The room occupancy sensors have a sensitivity that is automatically adjusted based upon temperature measurements, and the number and timing of occupancy detections.
Owner:HOME DIRECTOR
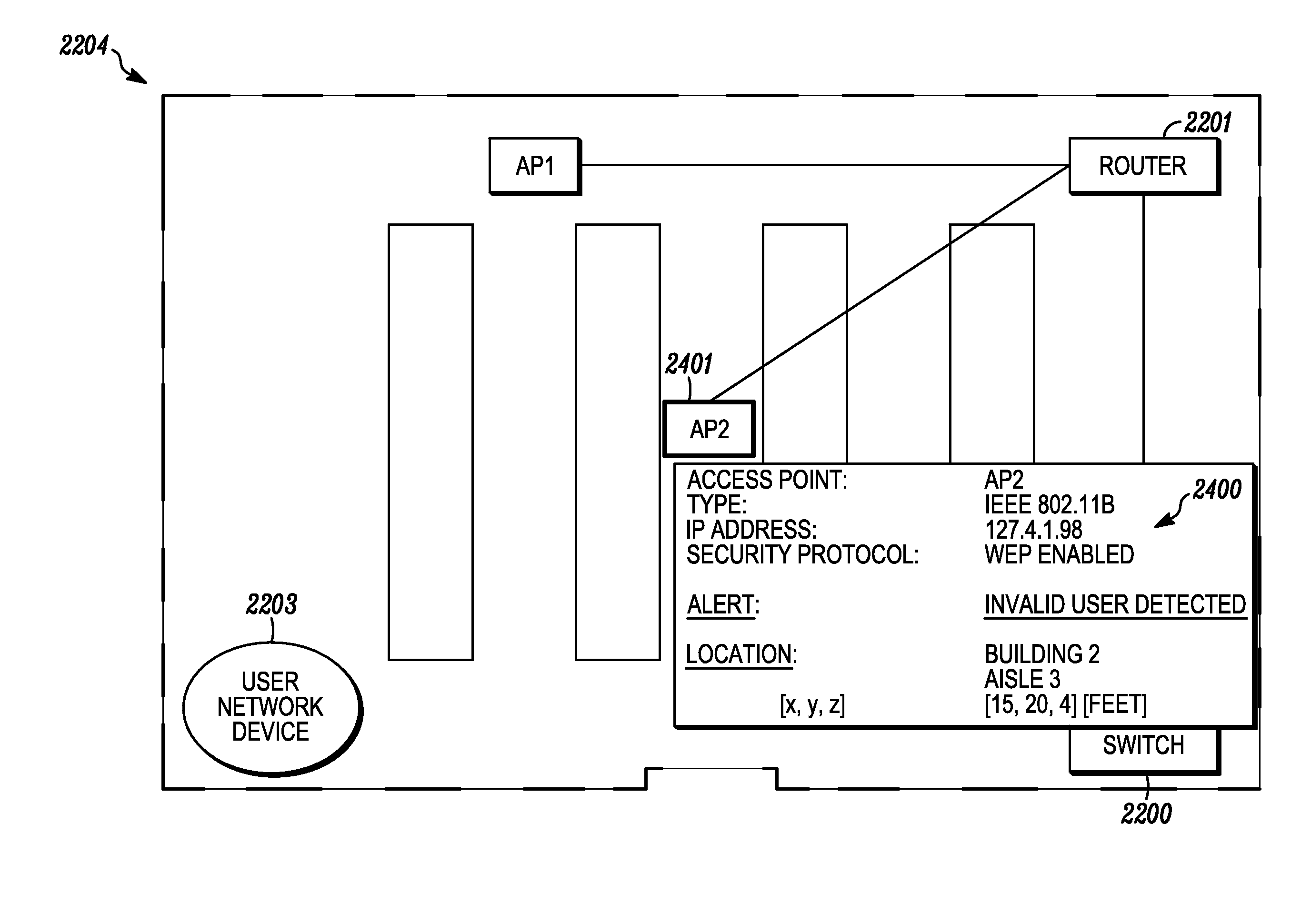
System and method for indicating the presence or physical location of persons or devices in a site specific representation of a physical environment
ActiveUS7295119B2Significant valueEasy to explainDigital data processing detailsBurglar alarm mechanical actuationCommunications systemDisplay device
A system and method for providing security to a wireless communication system having wireless communication components positioned at different locations within a physical environment are provided. The wireless communication components include an access point and a network device. A site-specific computerized representation of the physical environment displays the location of the wireless communication components including the access point and network device. The access point and network device identify the presence or a physical location of a possible intruder or intruder devices. An indicator is presented in the site-specific representation on the display when an erroneous authentication request or other undesired transmission is received by the network device or the access point.
Owner:EXTREME NETWORKS INC
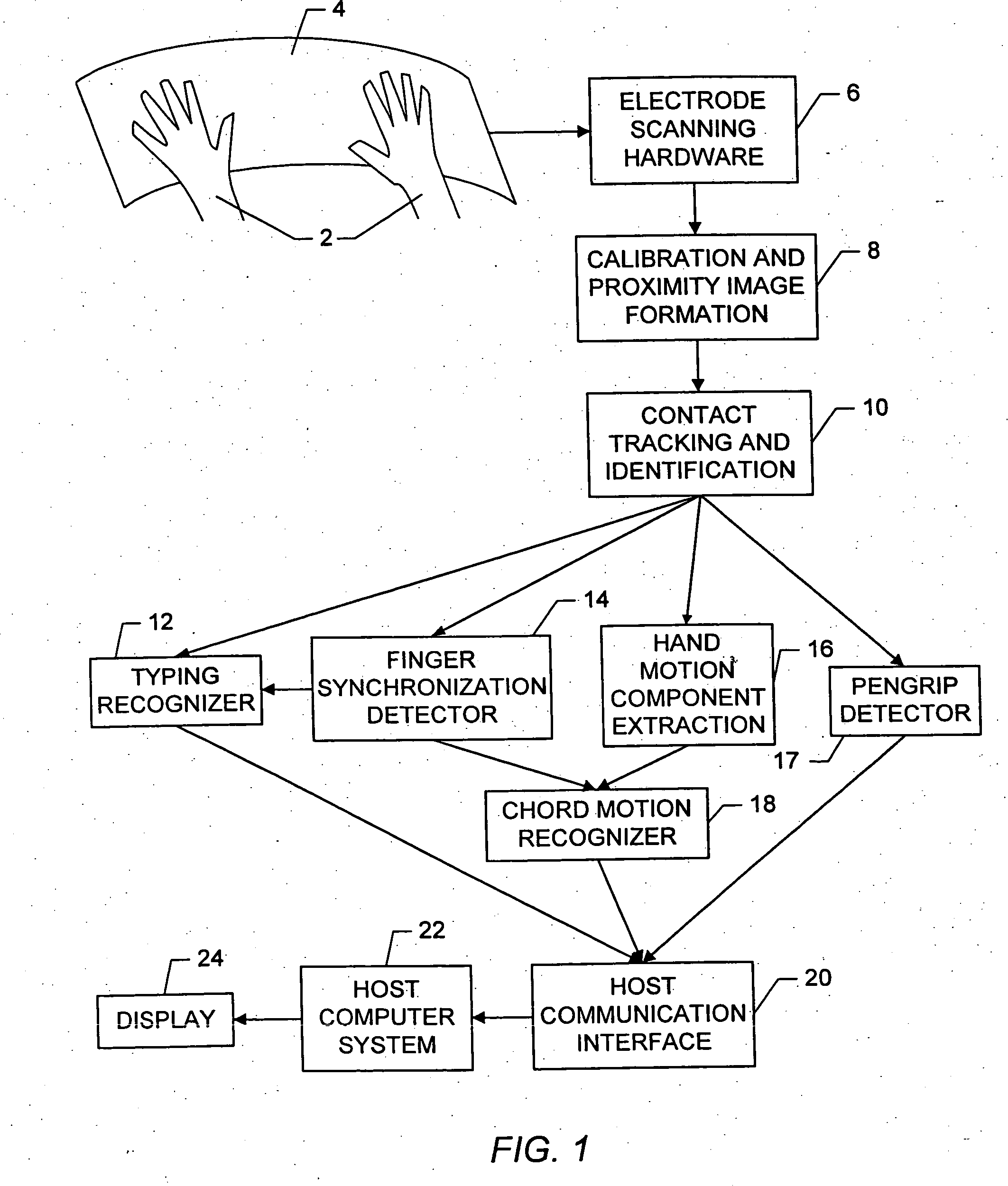
Method and apparatus for integrating manual input
InactiveUS20050104867A1Easy to learnEasy to identifyInput/output for user-computer interactionImage analysisLow noiseDielectric
Owner:APPLE INC
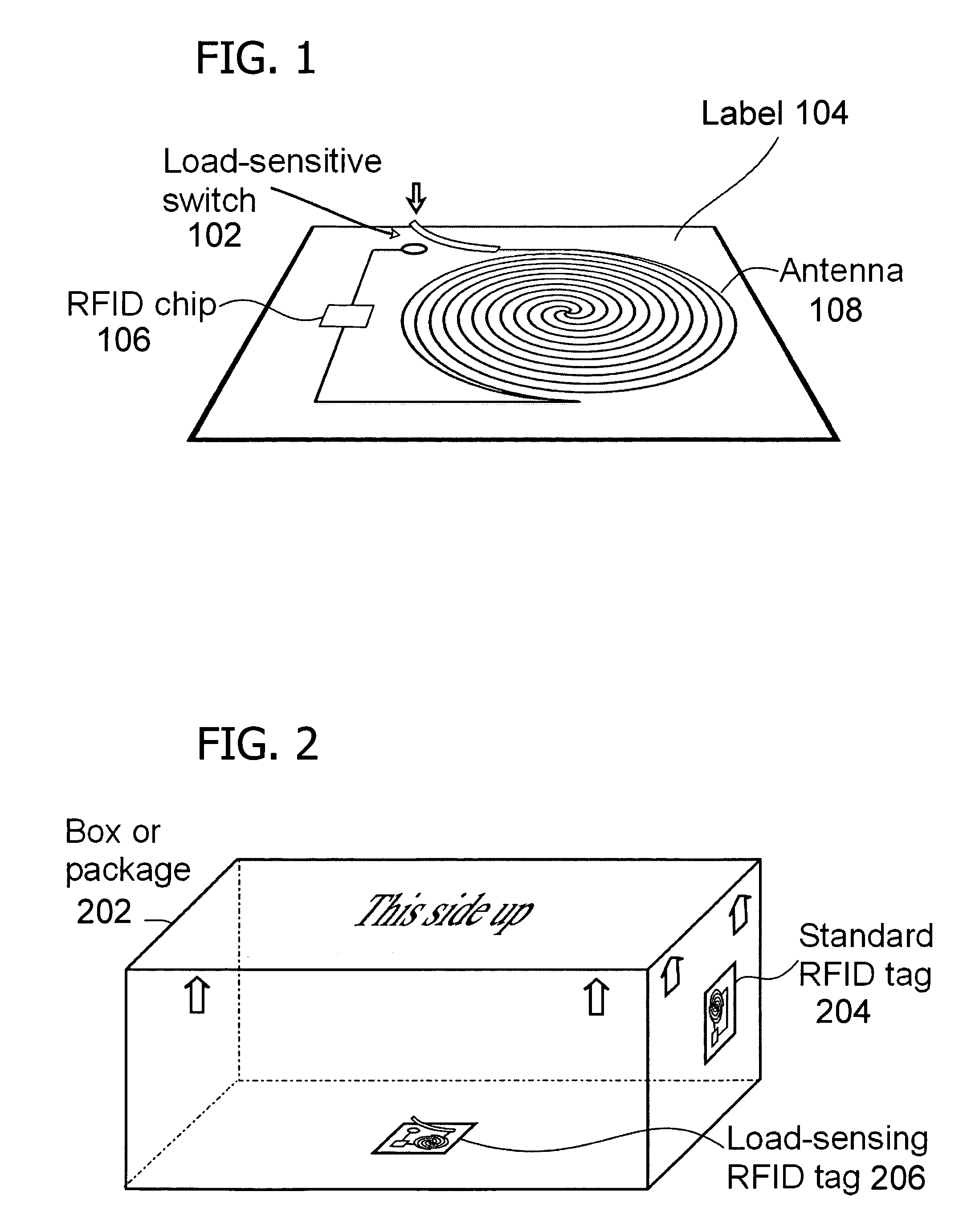
Wireless asset monitoring and security system
InactiveUS20050128083A1Electric signal transmission systemsMultiple keys/algorithms usageLocking mechanismUnique identifier
An asset monitoring and security system includes at least one asset assigned a unique identifier and operable wirelessly transmit an identification signal embodying the identifier. A data store maintains a list of the assets and privileges associated with the assets for authorized users of the assets. A control unit is adapted to receive identification signals from the assets and monitor positions of the assets within a defined area. The control unit communicates with the data store and is further operable to initiate an alarm event when privileges associated with a given asset for authorized users of the asset are exceeded. Each of the assets includes a lock-out mechanism that impedes use of the asset when the lock-out mechanism is activated. The control unit activates the lock-out mechanism of a given asset when the privileges associated with the asset for authorized users of the asset are exceeded.
Owner:BLACK & DECKER INC
Method and apparatus for remotely monitoring a site
InactiveUS20070008099A1Maximum precisionEasy to distinguishFire rescueFire alarmsTime informationSprinkler system
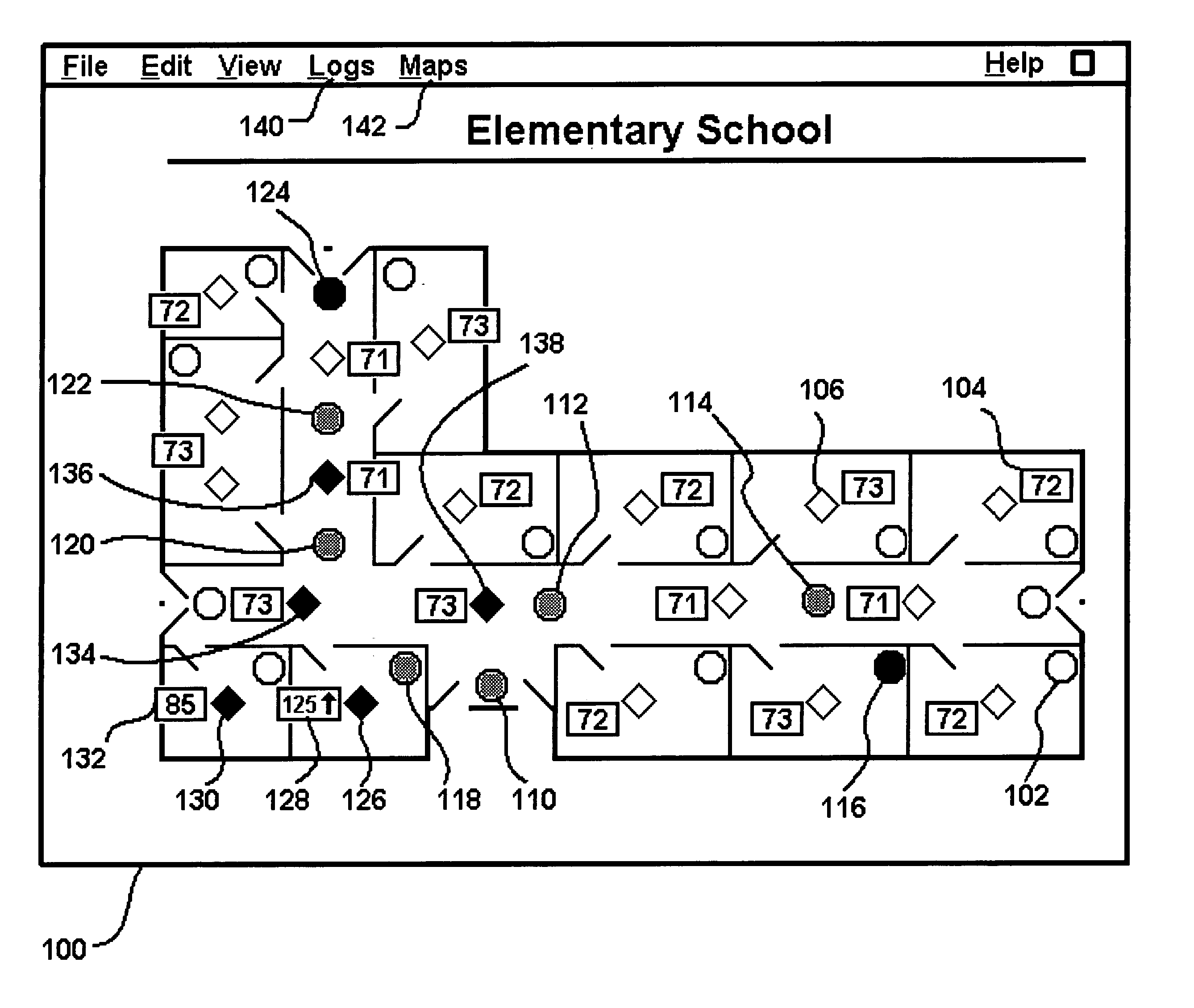
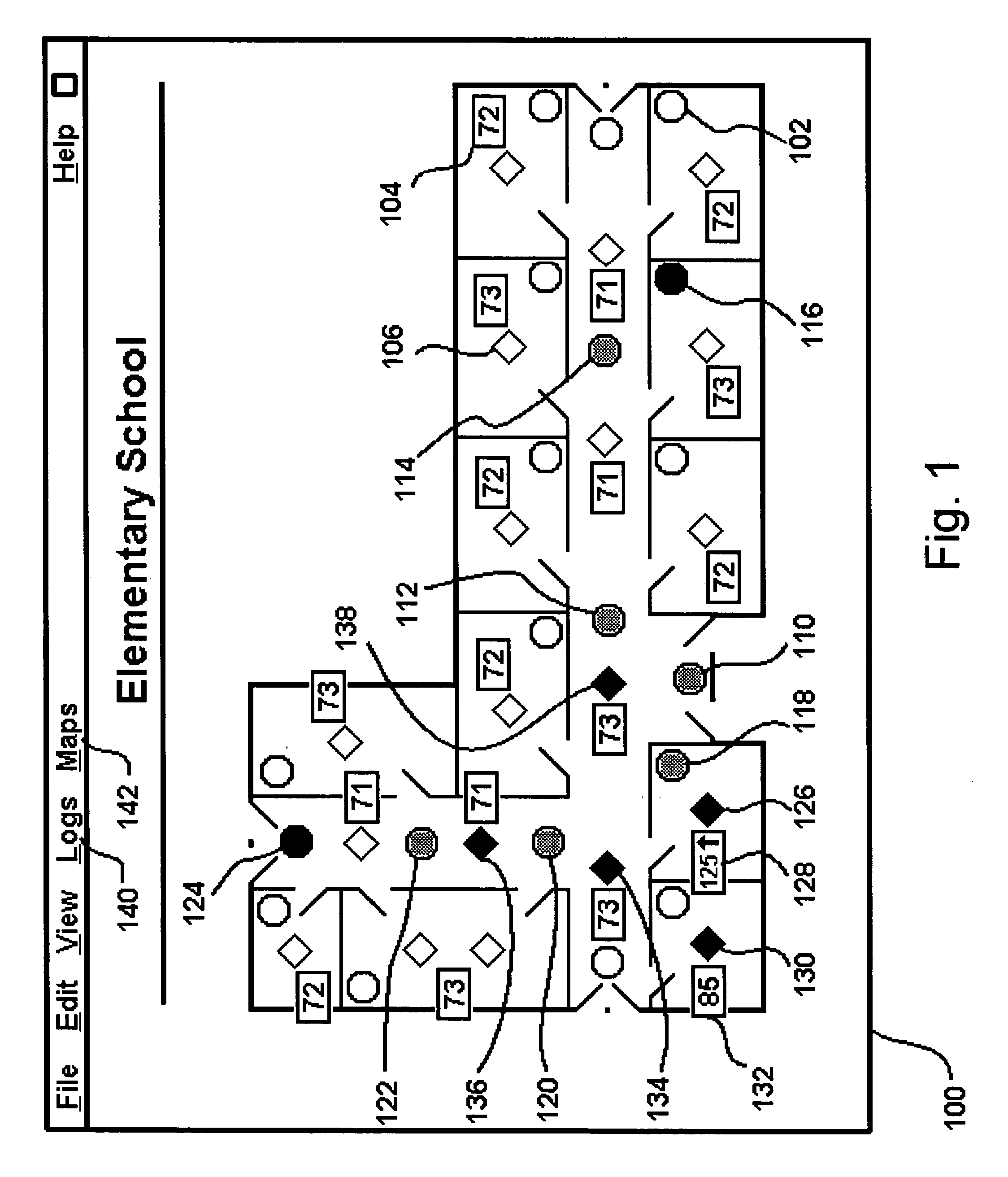
The present invention is directed to providing systems and methods for remotely monitoring sites to provide real-time information which can readily permit distinguishing false alarms, and which can identify and track the precise location of an alarm. In embodiments, monitoring capabilities such as intrusion / fire detection and tracking capabilities, can be implemented through the use of multistate indicators in an interface which permits information to be transmitted using standard network protocols from a remote site to a monitoring station in near real-time. In embodiments, communications can be handed from the centrally located host monitoring station to a mobile monitoring station (for example, a laptop computer in a responding vehicle, such as a police or fire vehicle). Additional embodiments include the measurement of environmental parameters such as temperature, carbon monoxide and differential air pressure to detect, monitor and manage a fire event. These measurements along with selected controllable output devices deployed in a space, such as sprinkler control valves and individually or zoned sprinkler heads, are used to initiate and control fire suppression technology both locally and remotely. For instance, a system of the present invention may detect a fire and cause a sprinkler system to disburse water in a facility.
Owner:NETTALON SECURITY SYST
Passive tamper-resistant seal and applications therefor
A radio frequency identification seal comprises an antenna including a main antenna portion and at least one break-away portion and an RFID tag coupled and tuned to the antenna. The RFID tag outputs a signature in response to a scanning signal when tuned to the antenna.
Owner:COVELEY SOLBYUNG
Electronic identification tag
An electronic identification tag is made up of at least one cover strip and a carrier strip having an antenna and transponder mounted thereon, and an adhesive to secure the strips together such that the antenna is interposed between the strips, the transponder being pre-programmed to generate a signal having a unique code correlated with indicia on the tag to identify a passenger or luggage. The tag further lends itself well to a novel method of tracking luggage and passengers in a transportation facility.
Owner:TIMESTAMP
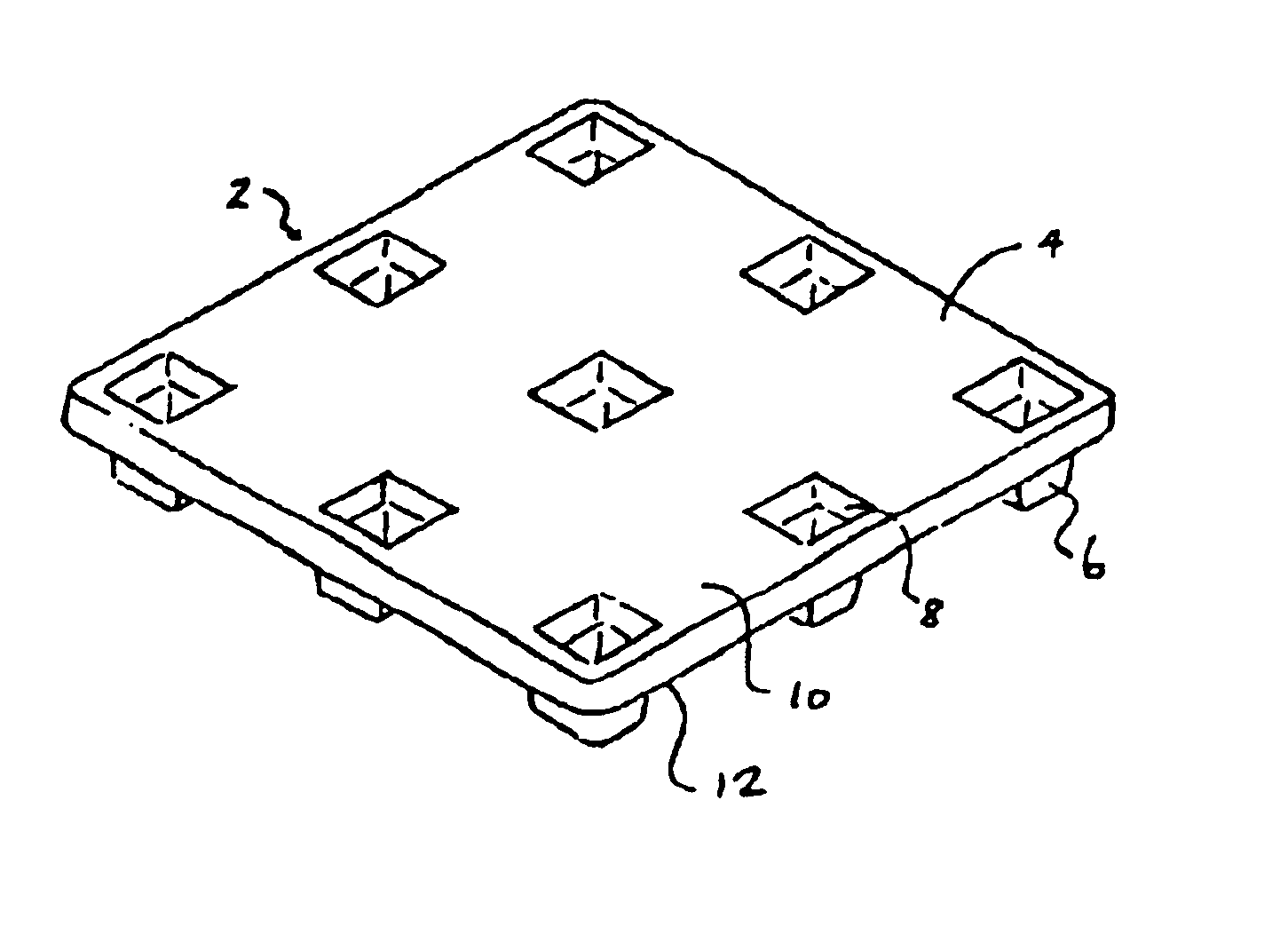
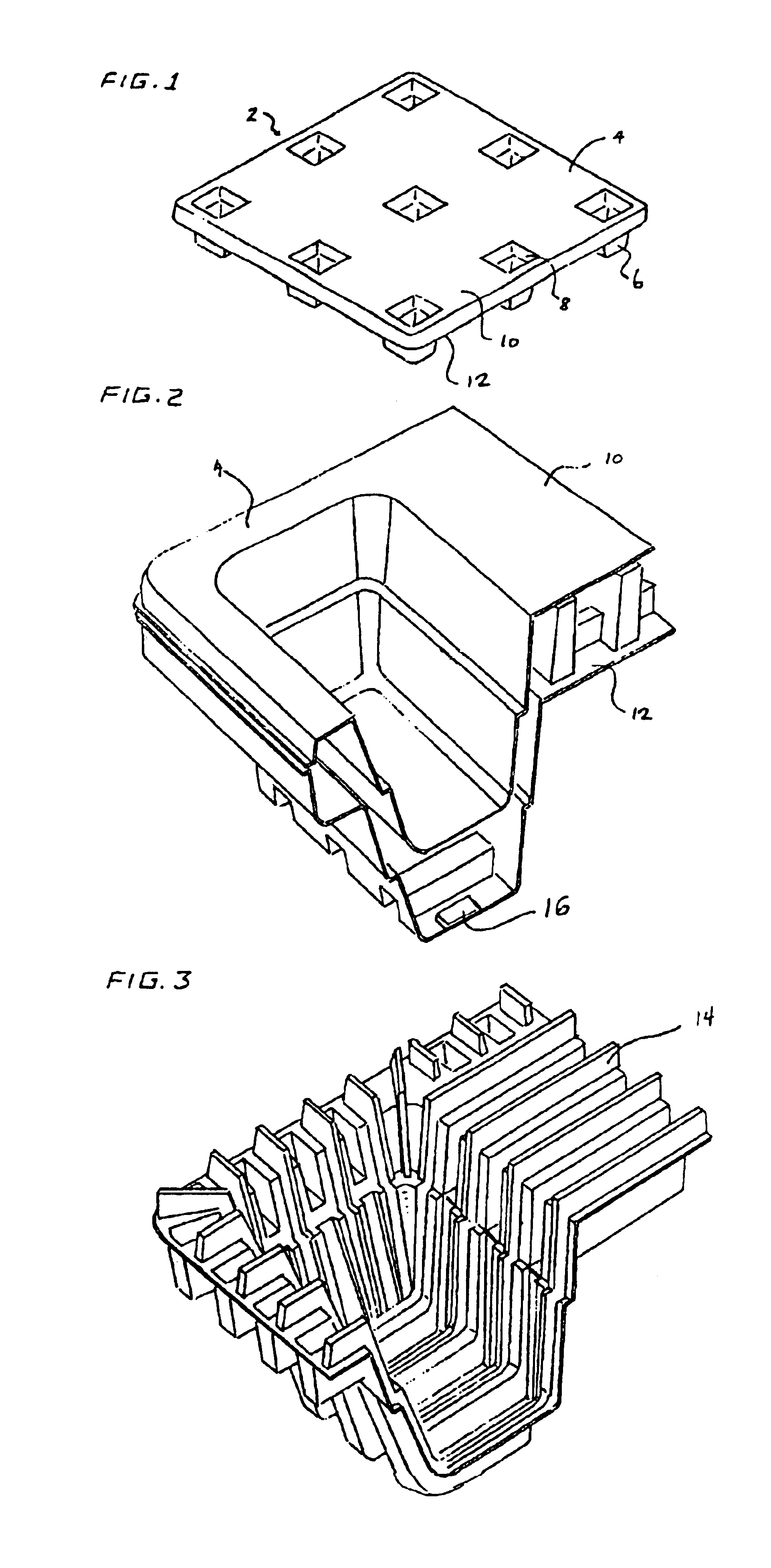
Thermoformed apparatus having a communications device
InactiveUS6943678B2Improve protectionIncreased durabilityRecord carriersDigital data processing detailsThermoformingEngineering
An apparatus has a communications device associated therewith. In another aspect of the present invention, a pallet is made from thermoformed polymeric sheets with an attached communications device. A further aspect of the present invention provides a radio frequency identification device attached to an apparatus. In still another aspect of the present invention, a communications device is incorporated into one or more sheets of a pallet or other container prior to forming. Methods of making and using a thermoformed pallet and container, having a communications device, are also provided.
Owner:NEXTREME
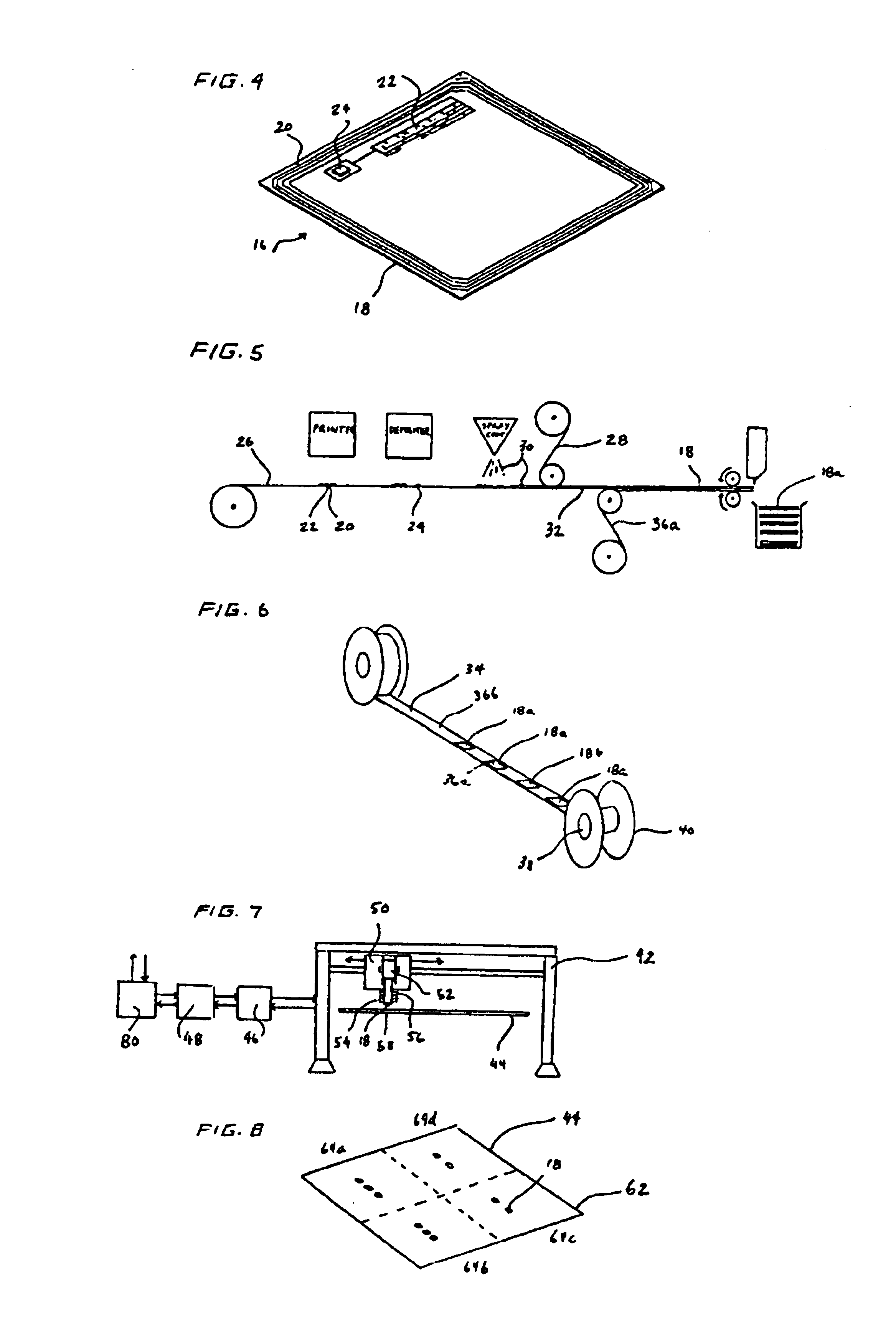
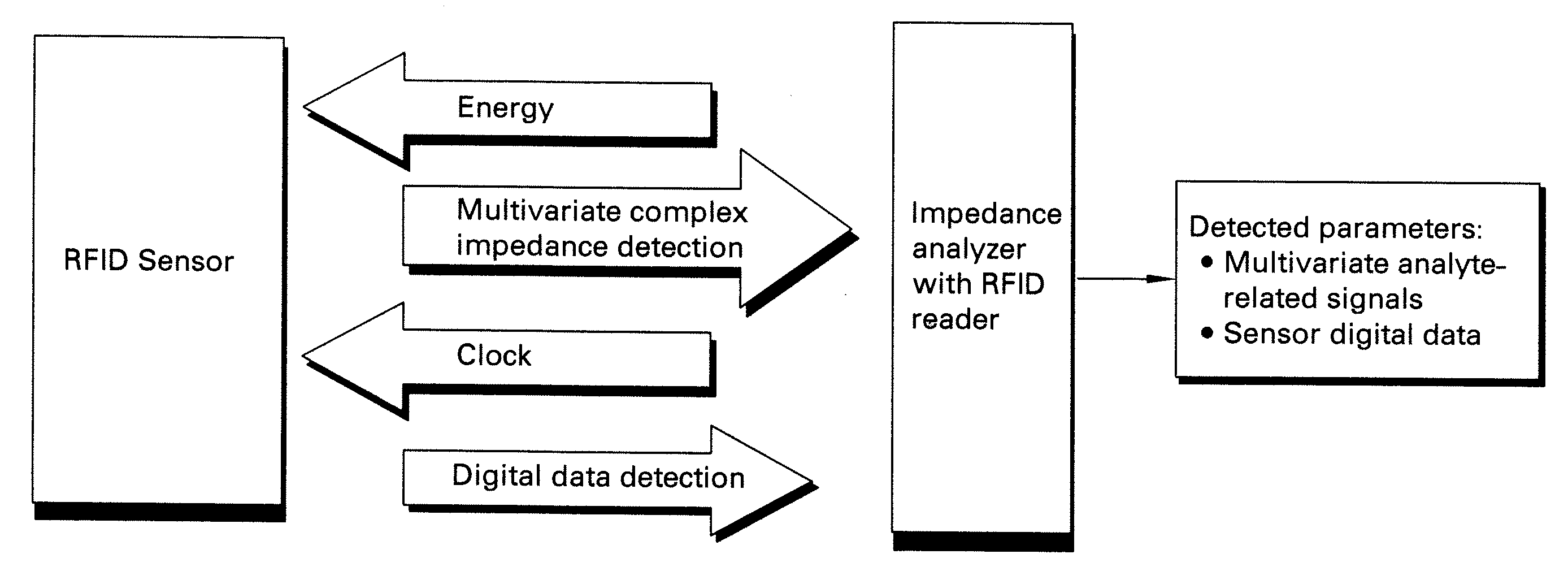
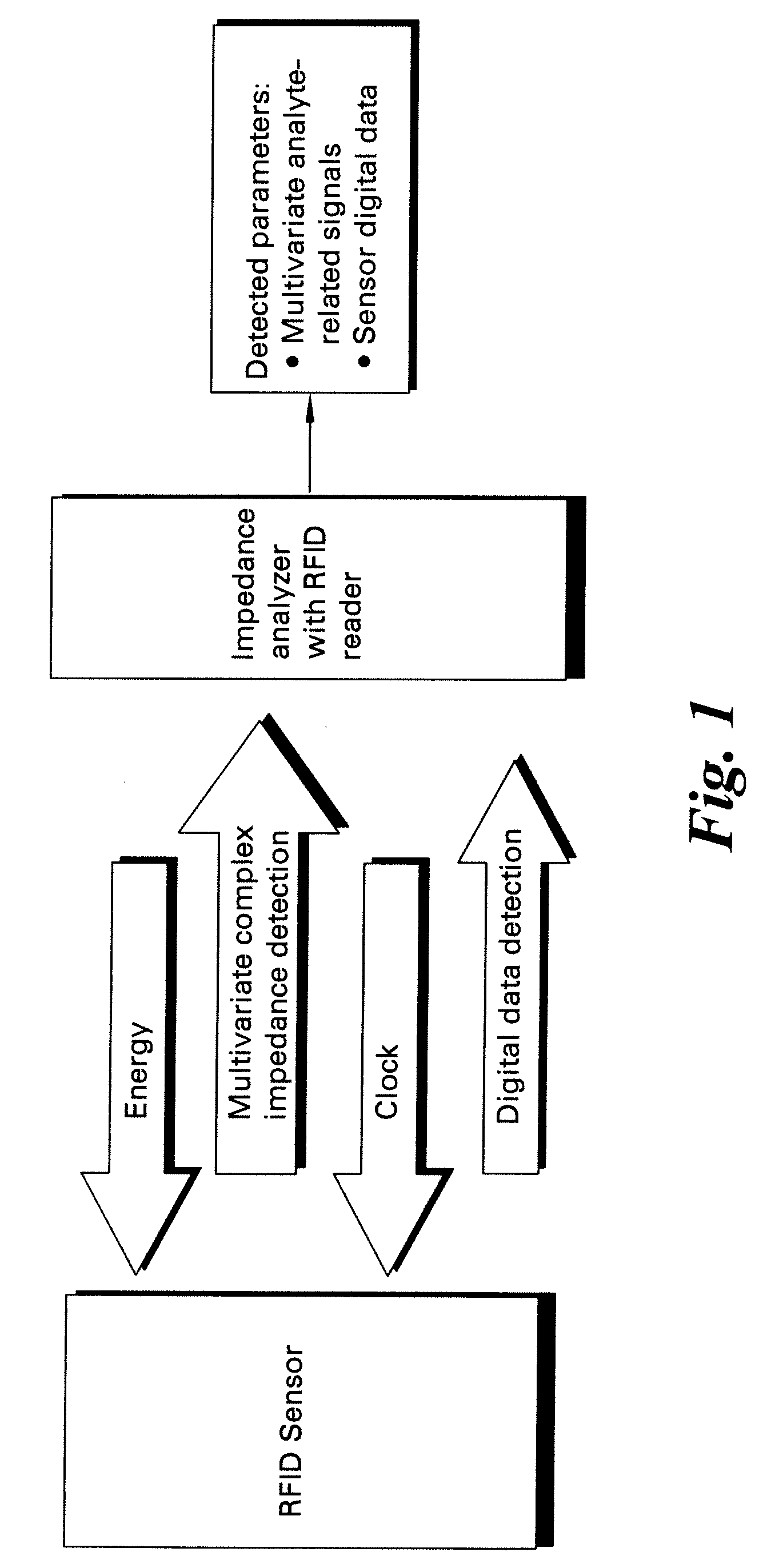
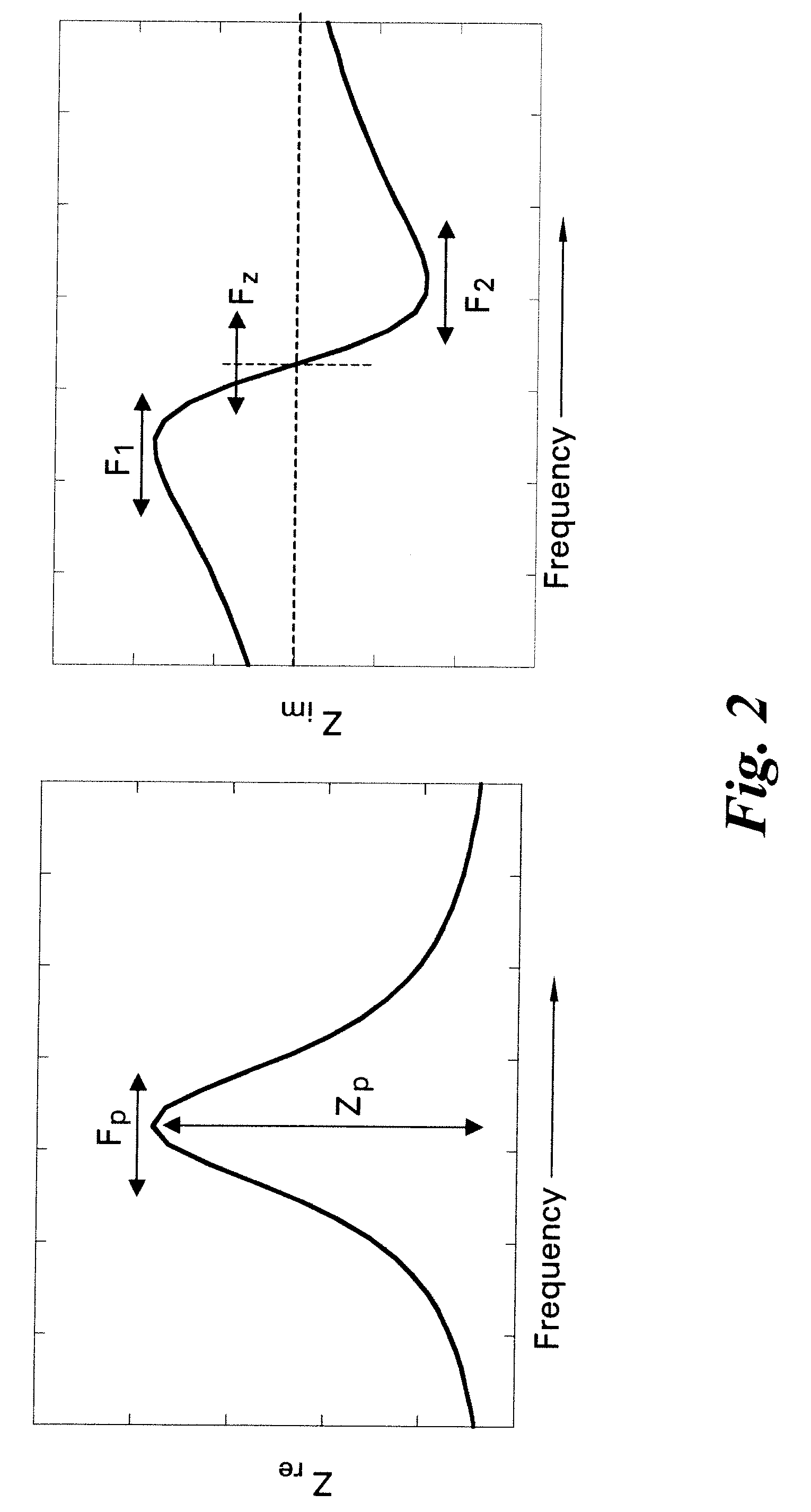
Methods and systems for calibration of RFID sensors
ActiveUS20090278685A1Testing sensing arrangementsGas analyser calibrationMemory chipComplex impedance spectra
Methods and systems for calibration of RFID sensors used in manufacturing and monitoring systems are provided. The methods include measuring impedance of an RFID sensor antenna, relating the measurement of impedance to one or more parameters (such as physical, chemical and biological properties), computing one or more analytical fit coefficients, and storing the one or more analytical fit coefficients on a memory chip of the RFID sensor. Measuring impedance of the RFID sensor may comprise measuring complex impedance which involves measuring complex impedance spectrum, phase angle and magnitude of the impedance, at least one of frequency of the maximum of the real part of the complex impedance, magnitude of the real part of the complex impedance, zero-reactance frequency, resonant frequency of the imaginary part of the complex impedance, and antiresonant frequency of the imaginary part of the complex impedance. Also provided are manufacturing or monitoring systems comprised of an RFID sensor wherein the RFID sensor comprises, a memory chip, an antenna, and a sensing film wherein analytical fit coefficients are stored on the memory chip to allow calibration of the RFID sensor. Also provided are manufacturing or monitoring systems comprised of an RFID sensor wherein the RFID sensor comprises, a memory chip, an antenna, and a complementary sensor attached to the antenna where the complementary sensor in a pre-calibrated fashion predictably affects the impedance of the antenna.
Owner:WESTINGHOUSE AIR BRAKE TECH CORP
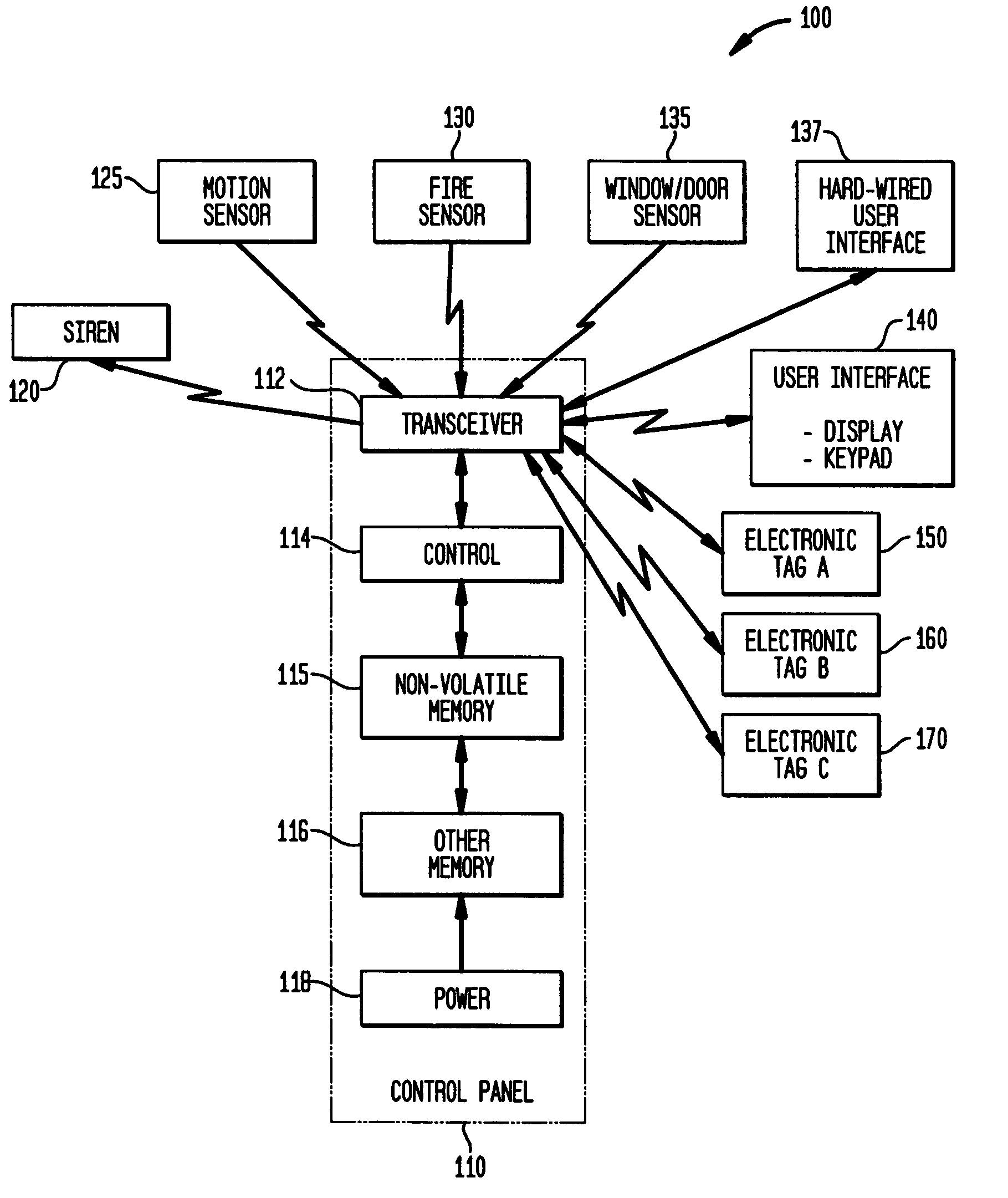
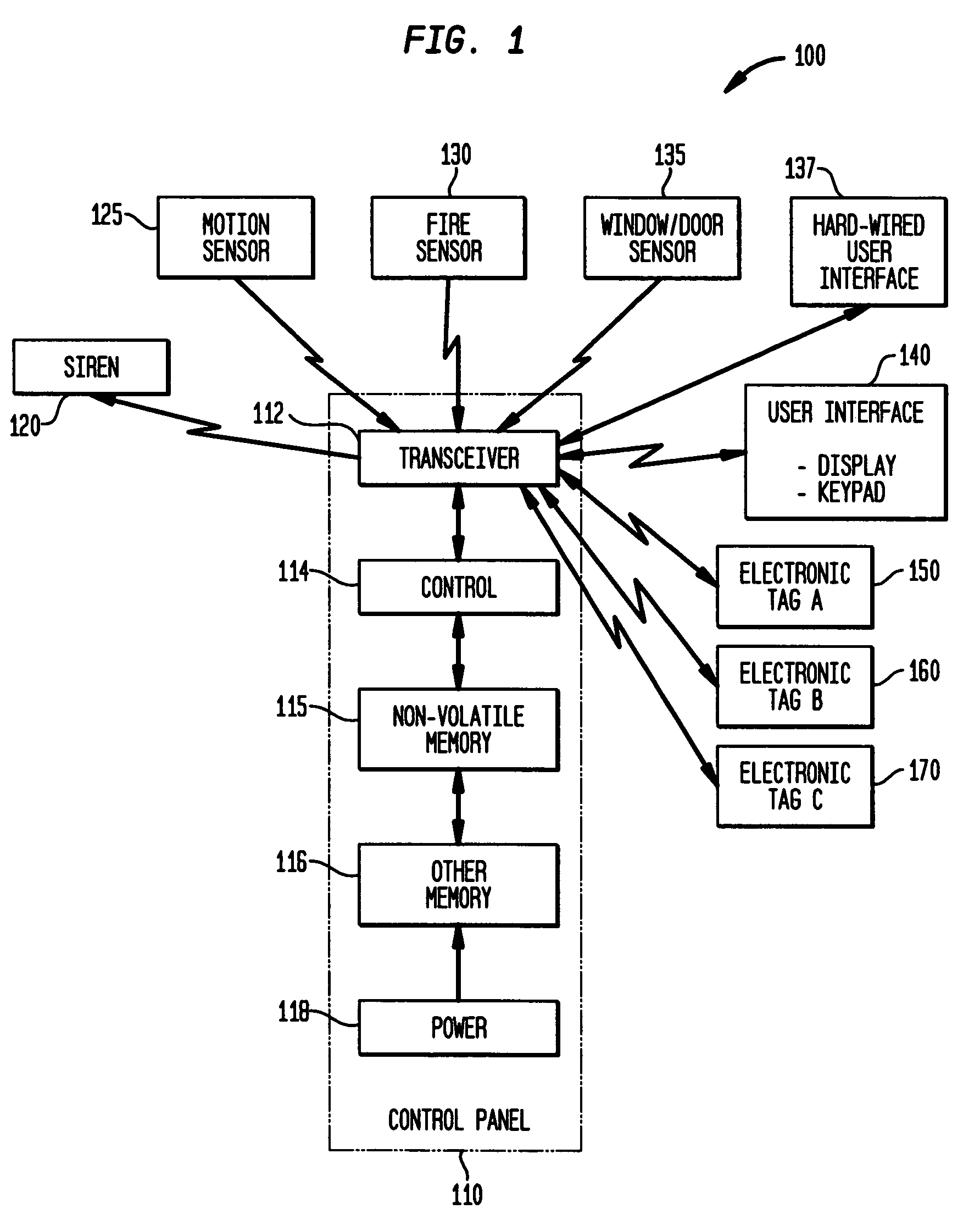
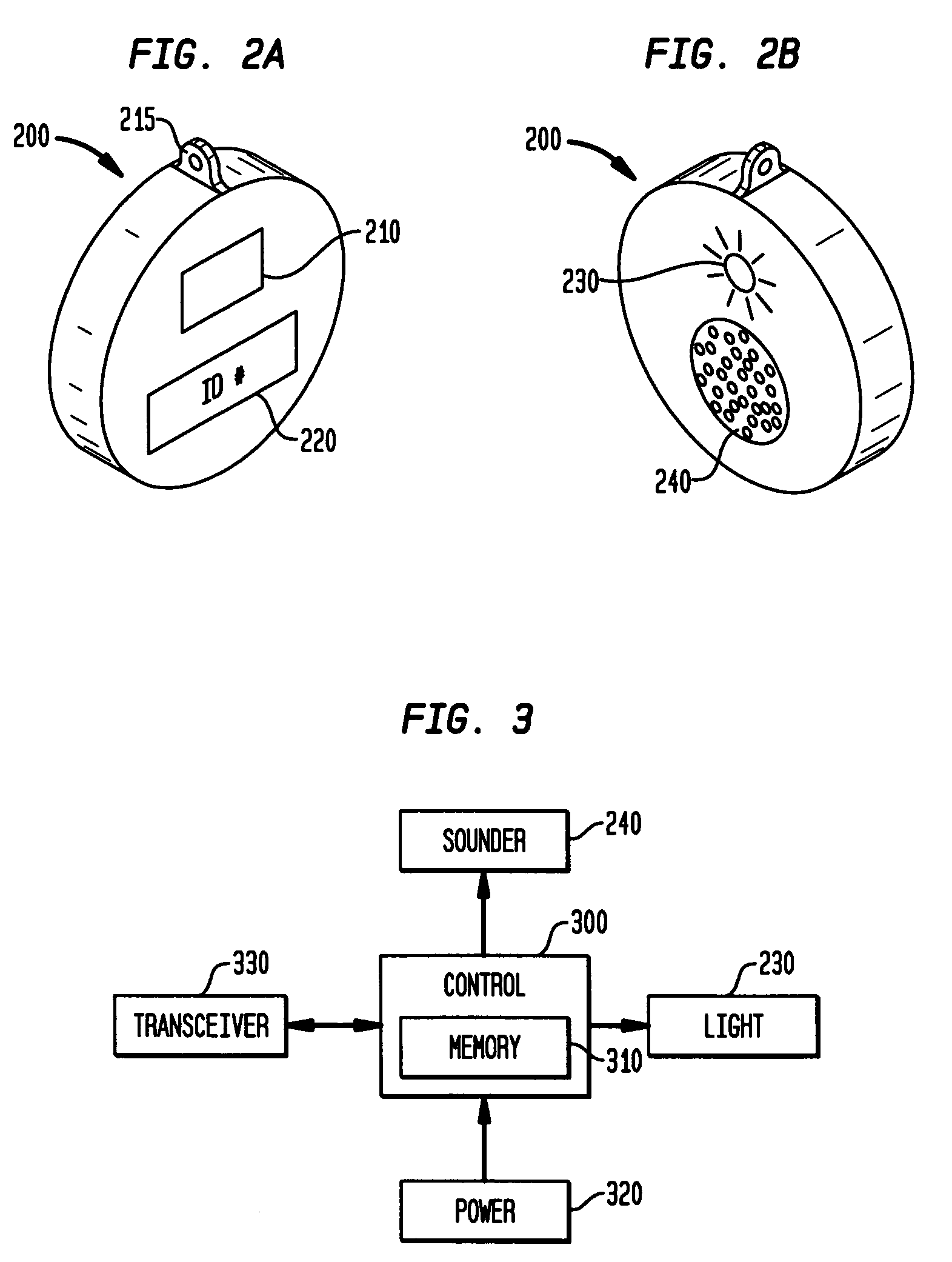
Tracking, presence verification and locating features as part of a security system
ActiveUS7113099B2More user-friendlyElectric/electromagnetic visible signallingSensing record carriersTransceiverDisplay device
Tracking, presence verification, and locating features are incorporated into a security system that includes a user interface device with a display, keypad and associated transceiver. Wireless RF electronic tags are attached to different objects, e.g., an inanimate object, or a living being such as a child or pet. To verify the presence of an object associated with a tag, the user instructs the user interface device to transmit a wireless signal to the tag. The tag responds, when within range, by returning a wireless signal. In another aspect, a person is detected such as at the entry to a home, and a low-power transmitter at the entry sends a signal to the electronic tag. The electronic tag responds by transmitting data to the security system to cause it to take a desired action. The presence of a person, such as a child, in an unauthorized area can trigger an alarm.
Owner:ADEMCO INC
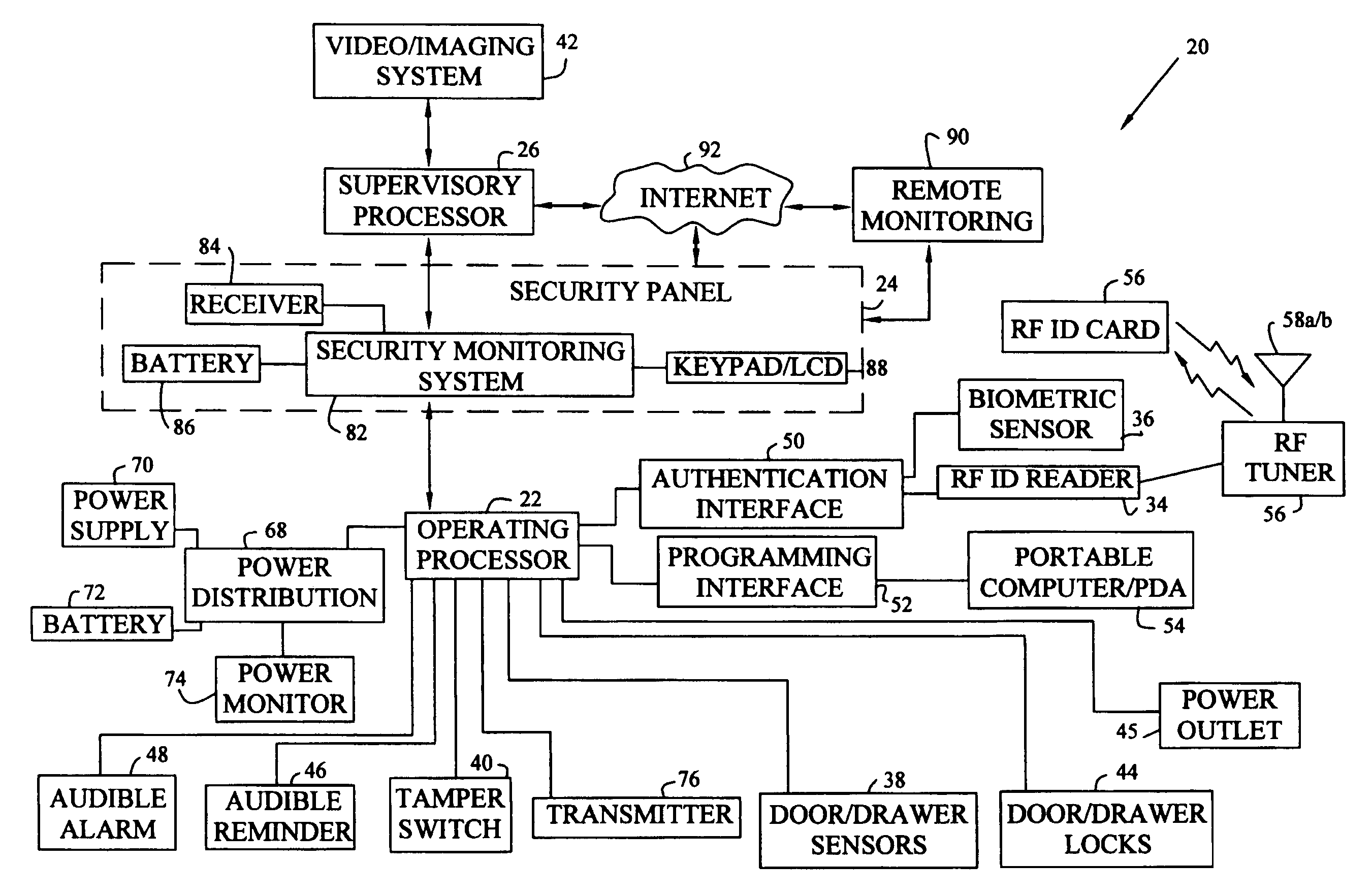
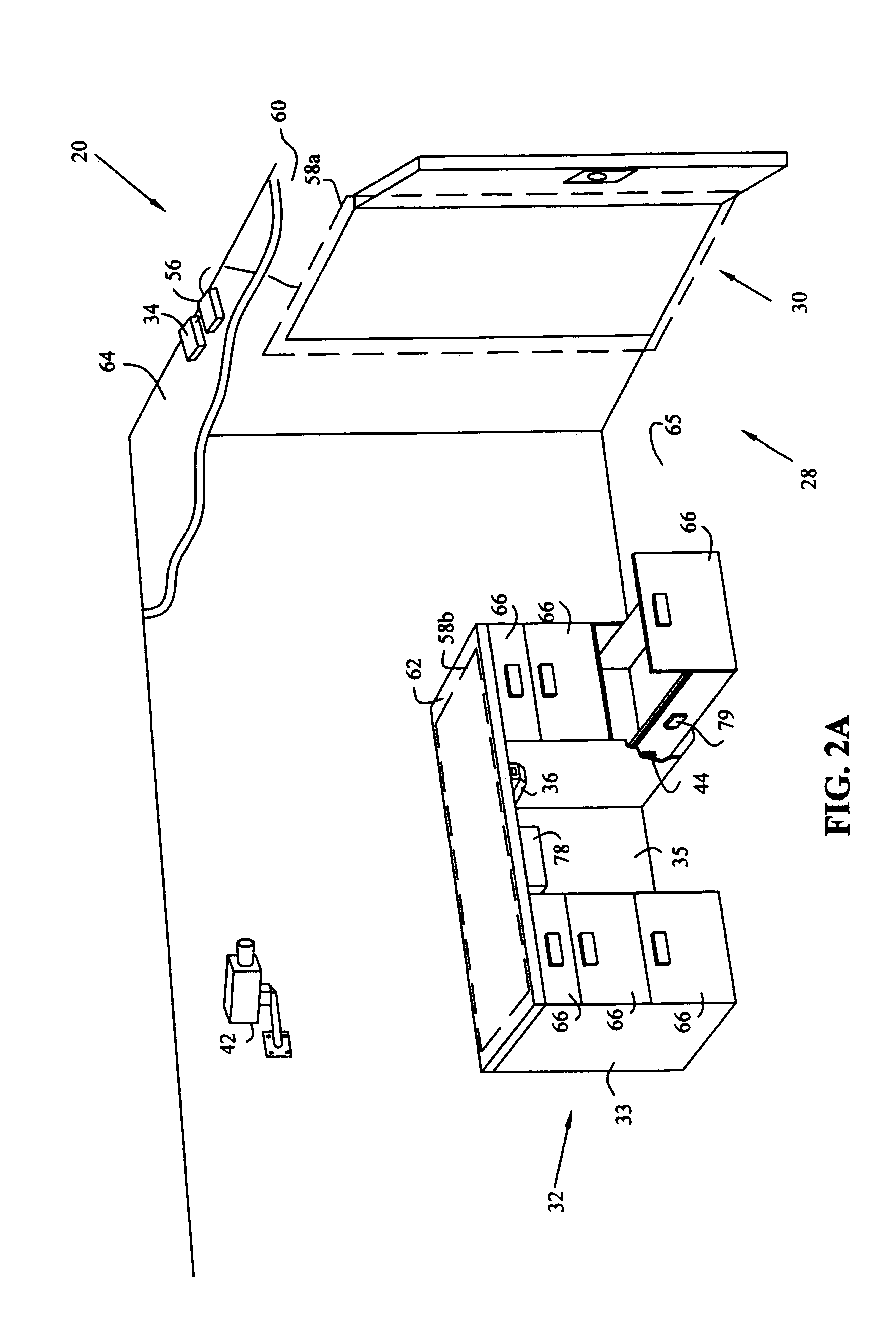
Workspace security system
InactiveUS6965294B1Effectively eliminate most false security alarmsElectric signal transmission systemsMultiple keys/algorithms usageProduction rateWorkspace
A workspace security system having processors, sensors, and actuators for local and remote monitoring, control, and automation of physical and environmental security, safety, efficiency, and productivity. The system includes passive and active access authentication devices and active or passive unlocking and lockdown of office furniture components, work sites, and facilities. The system may include multilevel authentication credentials, automatic lockdown of office furniture and other components based on the proximity of credentials, and video or other imaging systems to detect and record motion.
Owner:KIMBALL INTERNATIONAL
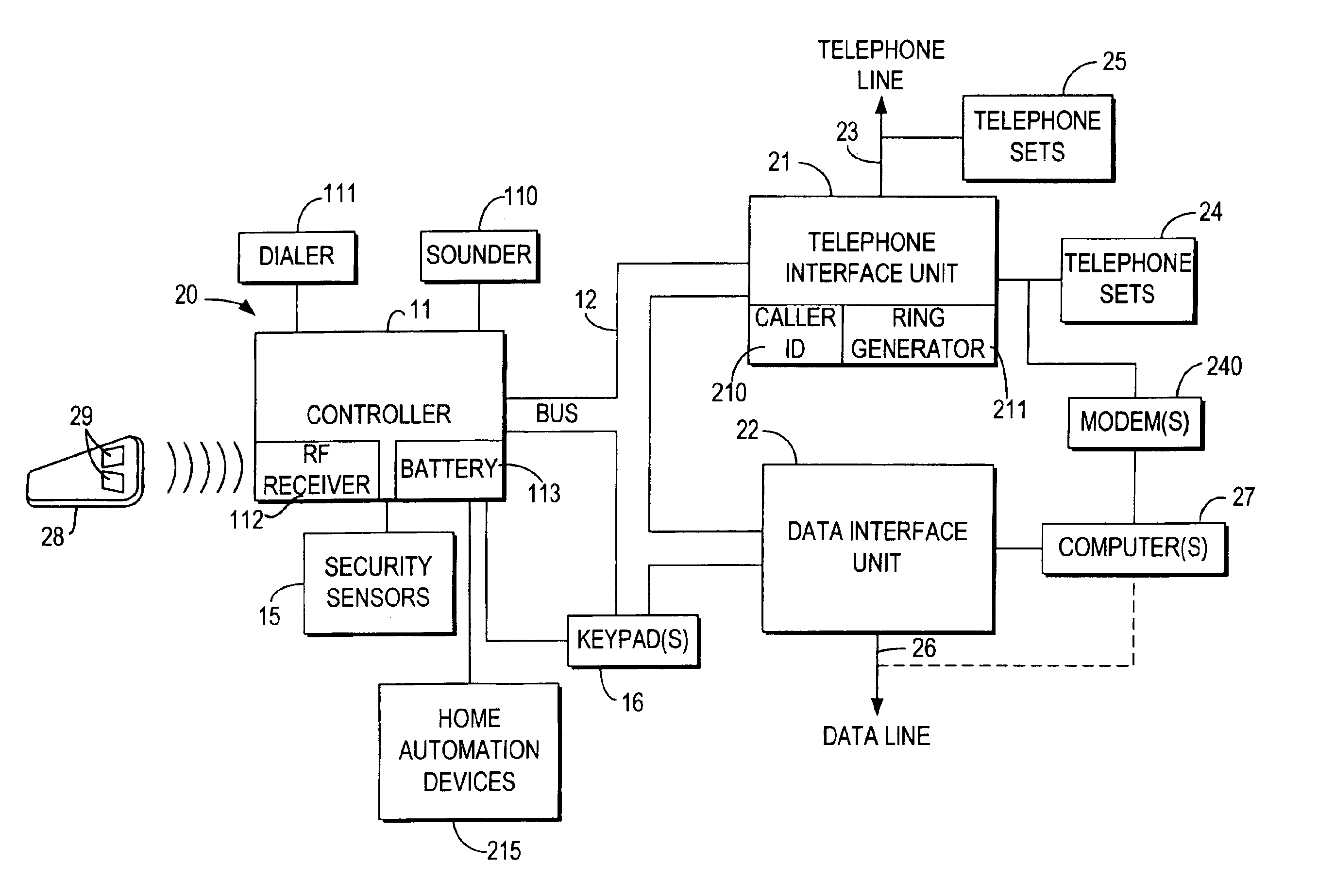
Integrated security and communications system with secure communications link
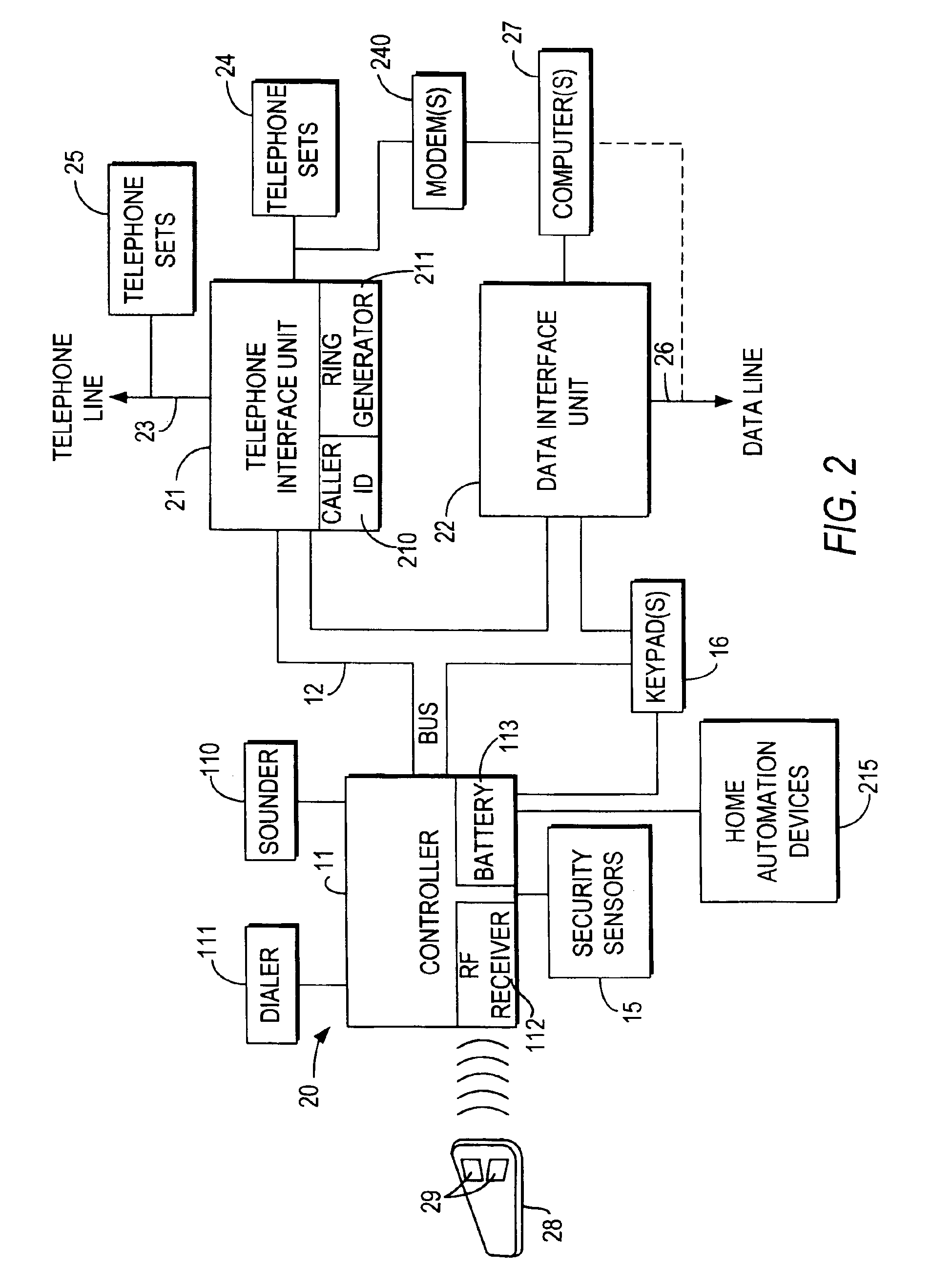
InactiveUS6928148B2Minimize the numberImprove securitySpecial service for subscribersCalled number recording/indicationData interfaceSecurity system
An integrated security and communications system combines a security system to either or both of a telephone system interface and a data interface. Users have access to voice-mail or other PBX-type telephone functions, many or all of which can be accessed not only at telephone sets, but also at keypads of the security system. Data functions such as electronic mail and possible partial or full World Wide Web access may also be provided at the keypads, as well as at connected personal computers or computer terminals. The system keypads may be enhanced to better accommodate some of the added functions. A central communications station could be used to maintain secure, shared private key encrypted communications with each premises system, using a redirector arrangement or relay to allow each premises system to communicate securely with a central monitoring station and with other systems. The secure communications system could be used without a security system to allow secure computer-to-computer communications.
Owner:ADEMCO INC
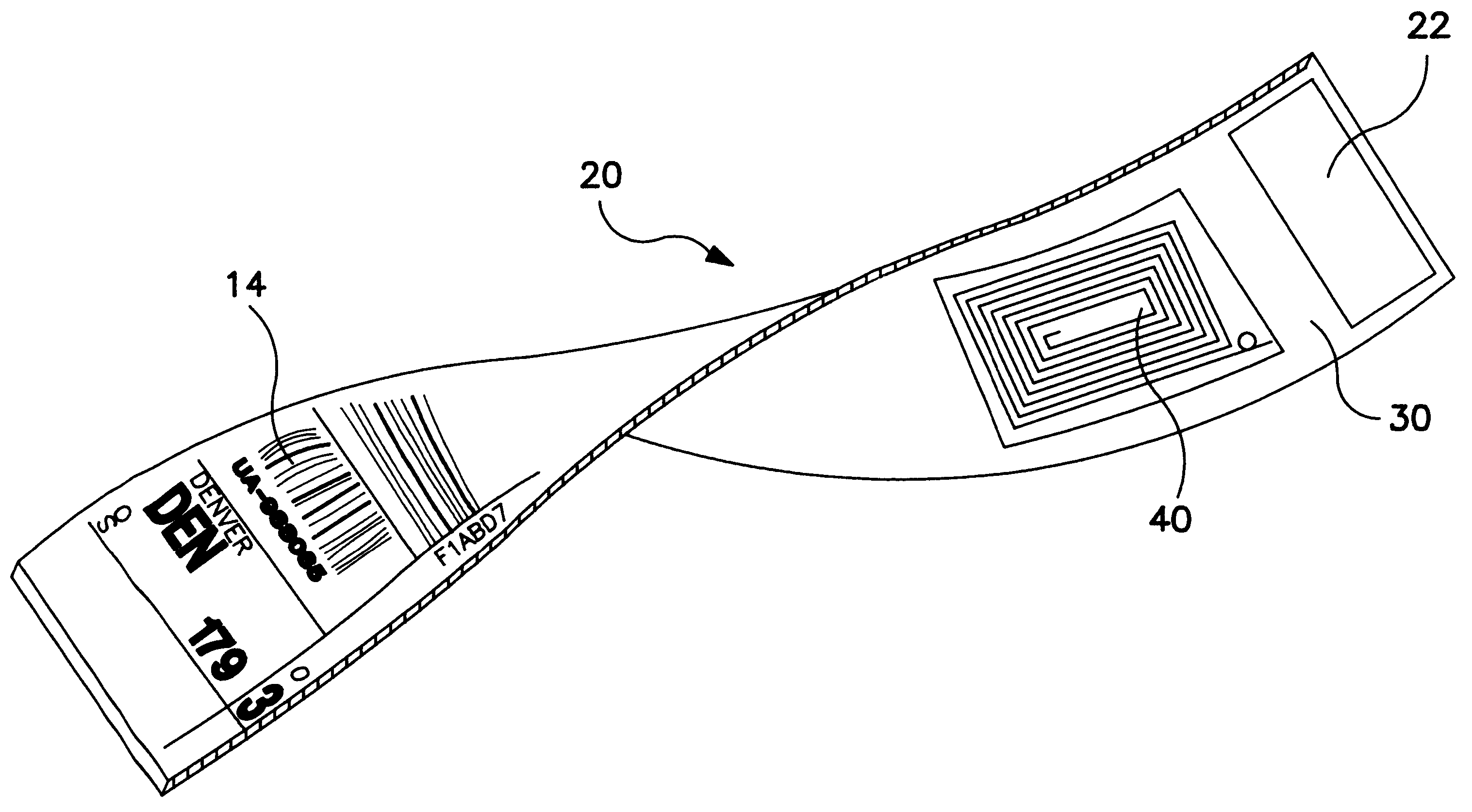
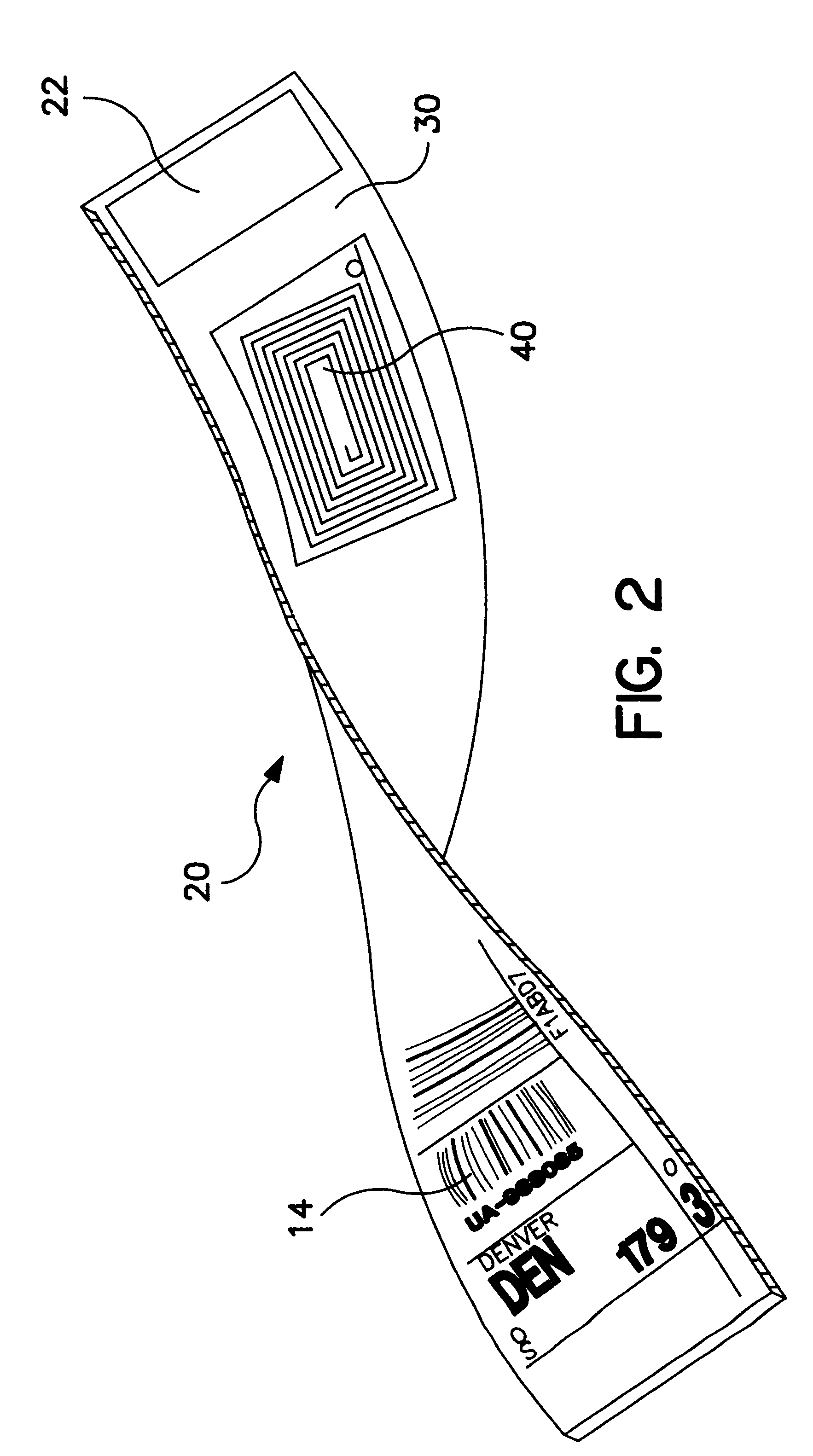
Deactivating a data tag for user privacy or tamper-evident packaging
ActiveUS20050242957A1Facilitate communicationBurglar alarm by openingAntenna arraysUser privacyComputer science
Deactivating a data tag attached to packaging for user privacy or tamper-evident reasons. A data circuit stores identification information. A plurality of antennae is coupled to the data circuit. At least one antenna of the plurality of antennae is a removable antenna capable of wireless signal transmission at a first range such that removal of the antenna substantially prevents communication of the identification information via the removed antenna and permits communication of the identification information via another antenna of the plurality of antennae at a second range relatively smaller than the first range.
Owner:BUFFALO PATENTS LLC
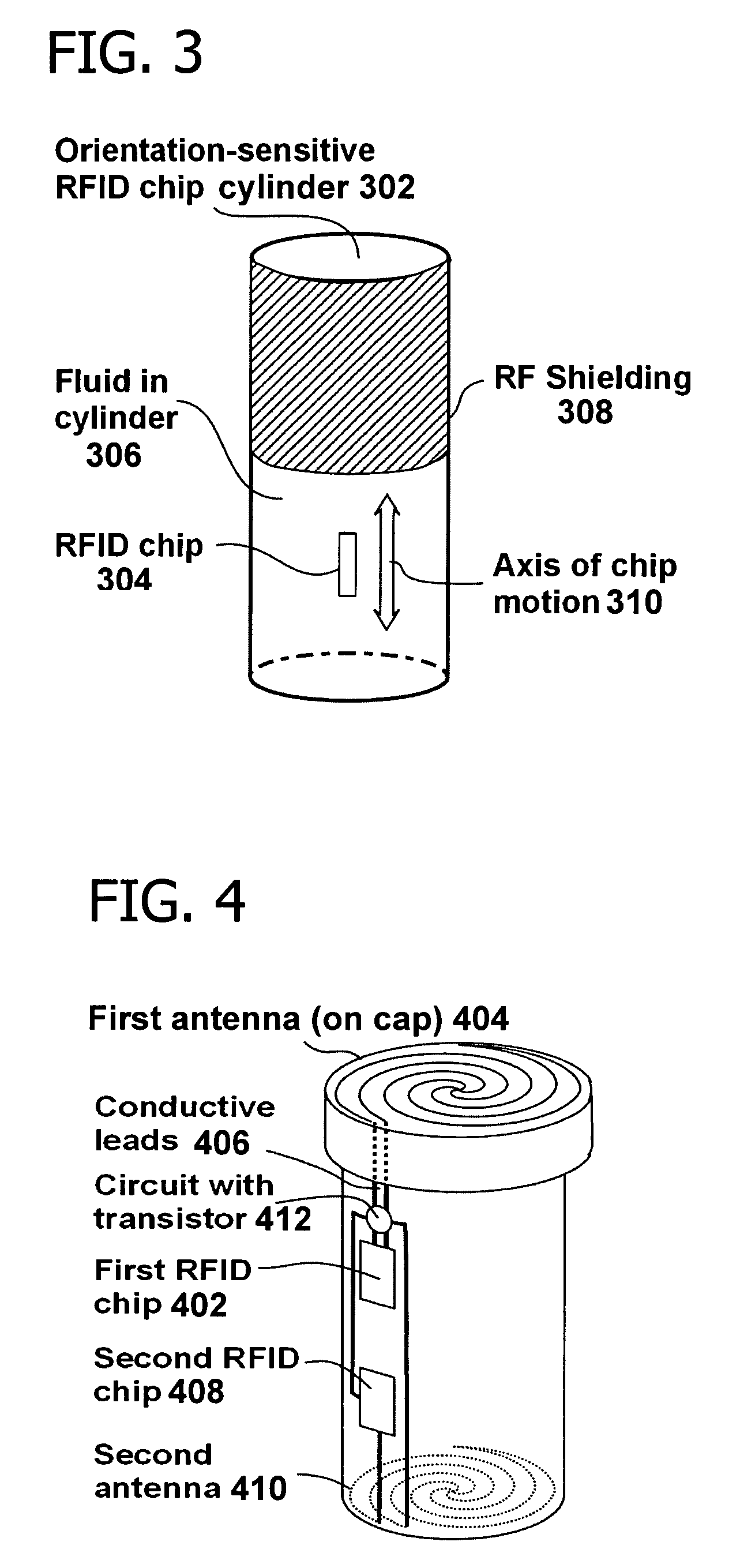
Wireless IC tag, and method and apparatus for manufacturing the same
InactiveUS20050140512A1Reduced durabilityImprove communication distanceSimultaneous aerial operationsAntenna supports/mountingsDielectricWireless
In a wireless IC tag, metallic antennas are deposited as thin films on the front and back surfaces of a spacer, made of a heat-resistant glass epoxy material having a desired dielectric constant, to form a first antenna and a second antenna. An IC chip is mounted in the center of the first antenna. The second antenna functions as an auxiliary antenna for resonating to a desired frequency of a transmission radio wave of the first antenna to strengthen the intensity of the radio wave. Accordingly, even when the IC tag is mounted to a cable or the like, the tag can be mounted in the interior of the enclosure of the cable and thus the radio wave intensity of the first antenna can be prevented from being weakened by a metallic member in the cable.
Owner:HITACHI LTD
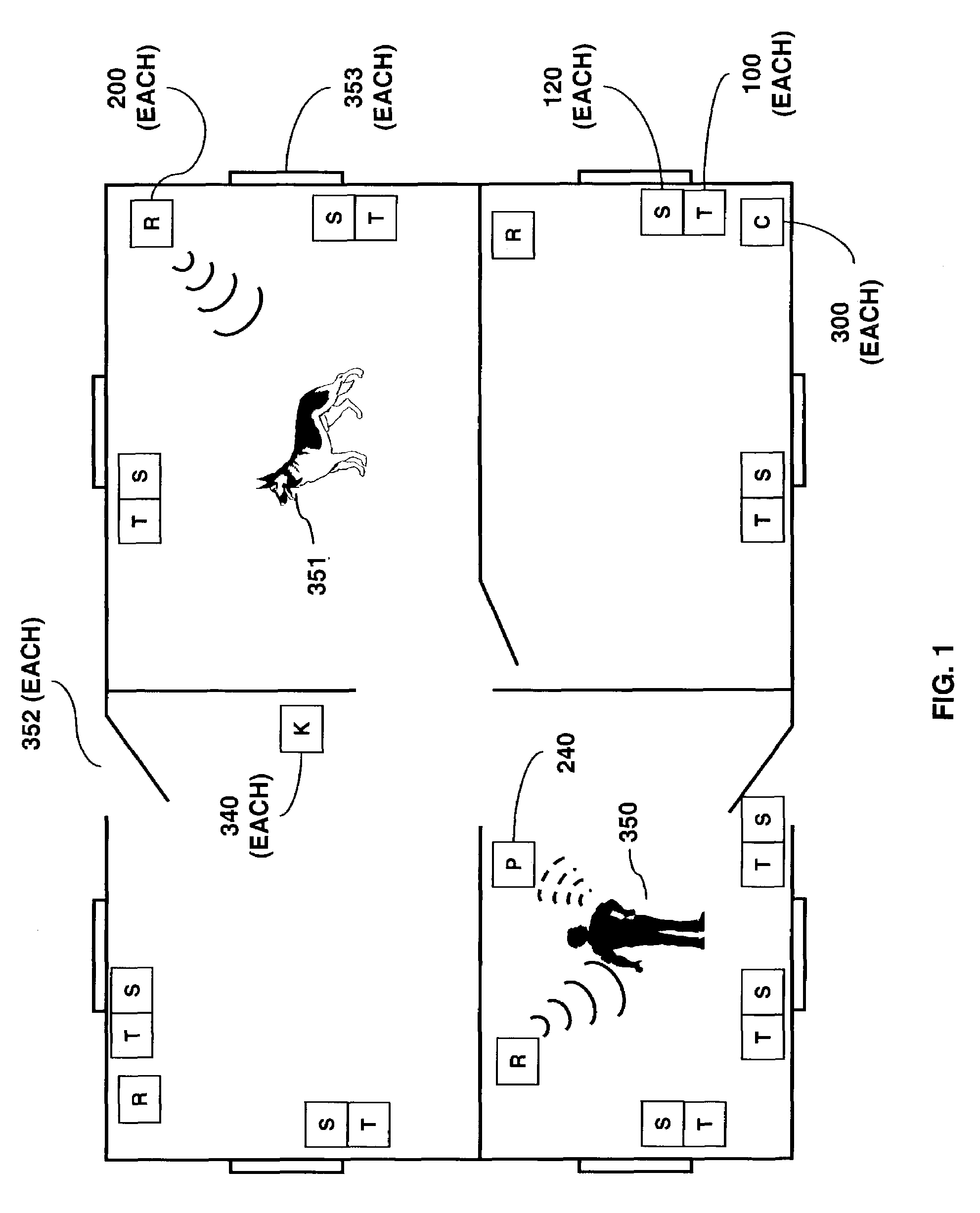
Facilities management system
InactiveUS20050078006A1Improve securityEffective time managementIndividual entry/exit registersBurglar alarm electric actuationActive monitoringSystems management
A system is described for management of an operations area. The management system includes a central processing component with one or more central processors. An active monitoring system component is connected to the central processor. The active monitoring system includes tags and readers for individual identification of one or more tagged entities. The active monitoring system component is arrayed to create a management zone. The tags and readers are linked to the central processing component such that information from the tags and readers is received and analyzed by the central processing component. A passive monitoring system component is connected to the central processor. The passive monitoring system identifies non-tagged entities entering the management zone and additional information is communicated to the central processing component for analysis.
Owner:HUTCHINS J MARC +1
Safety detection and protection system for power tools
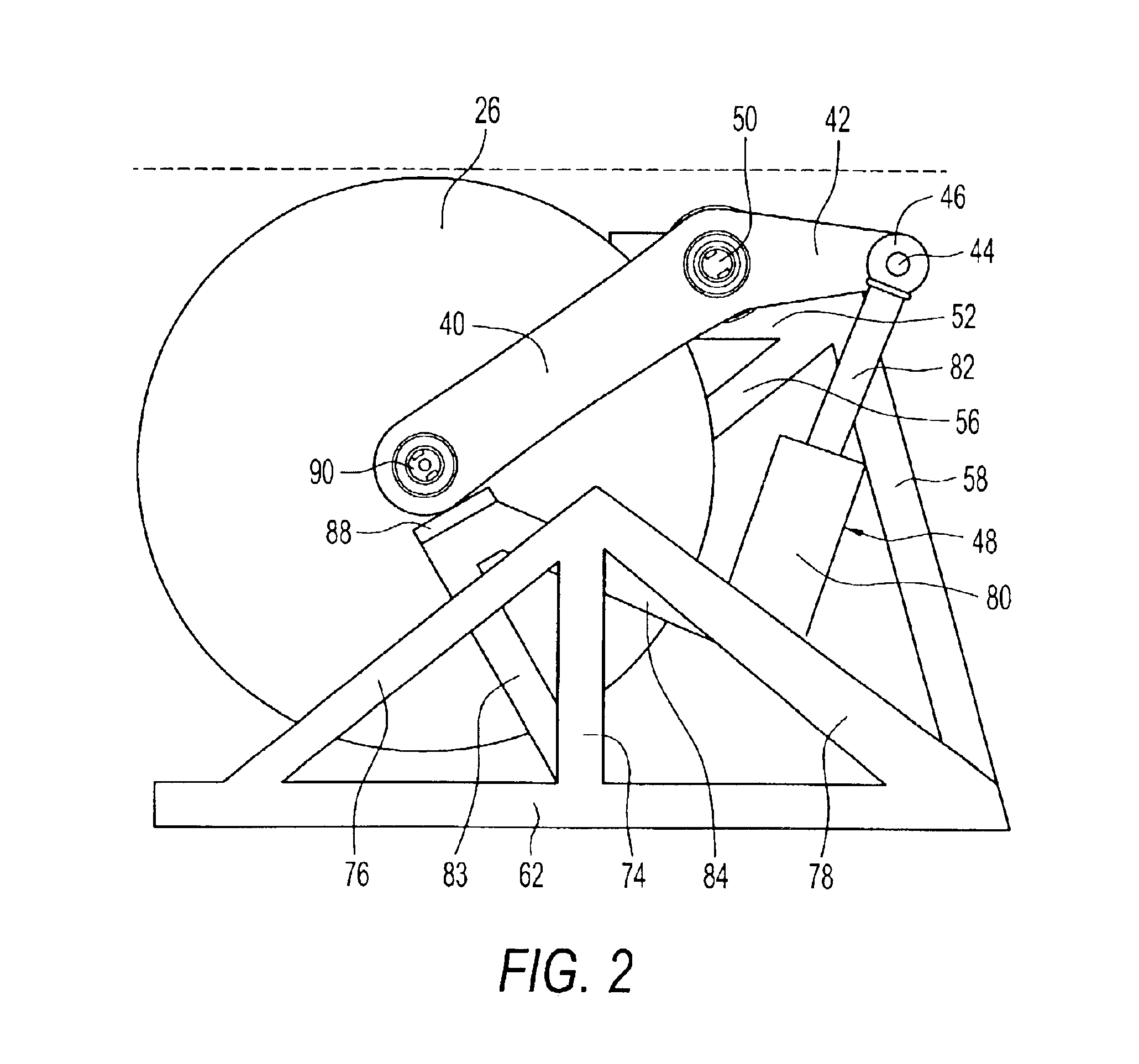
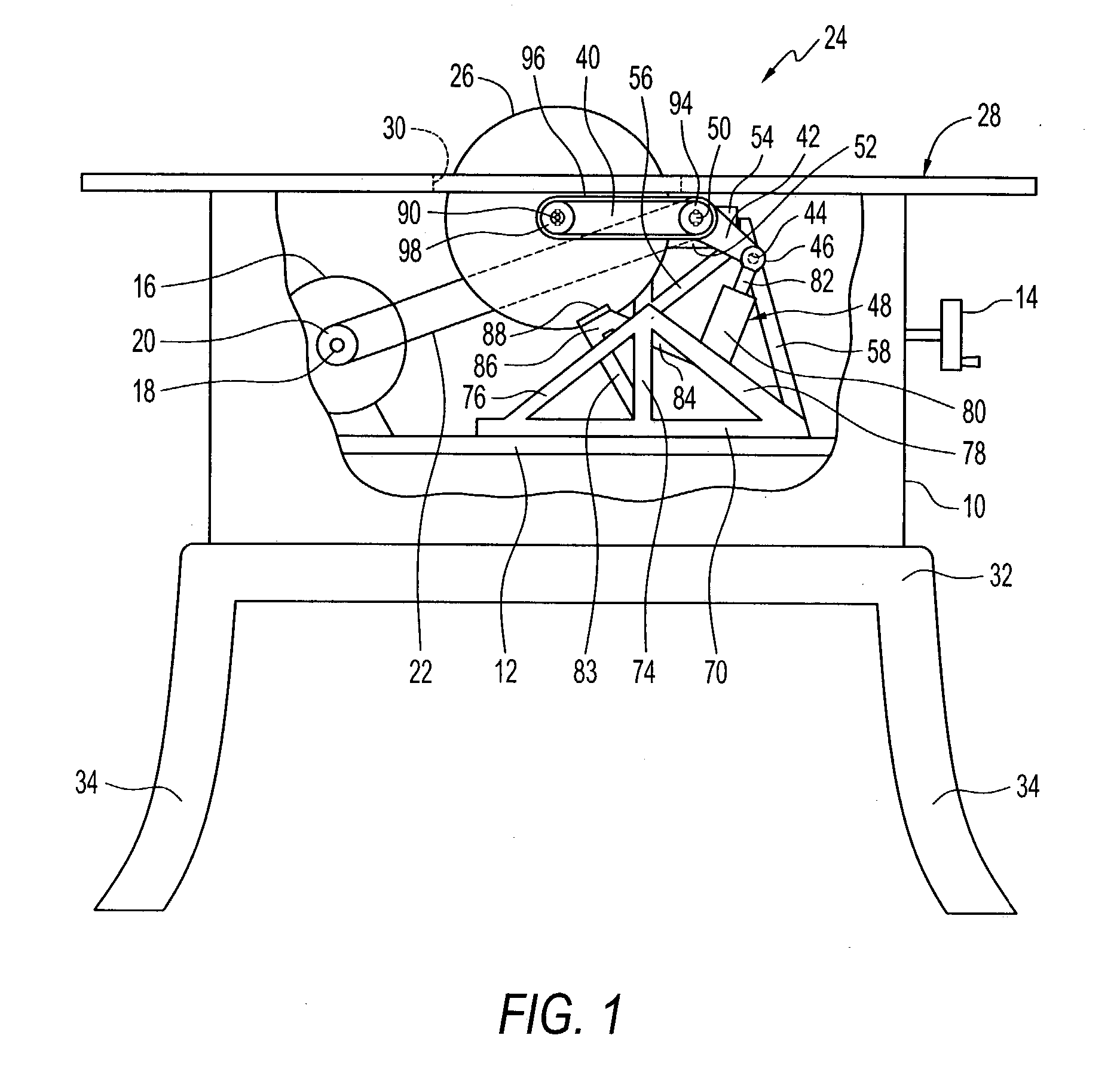
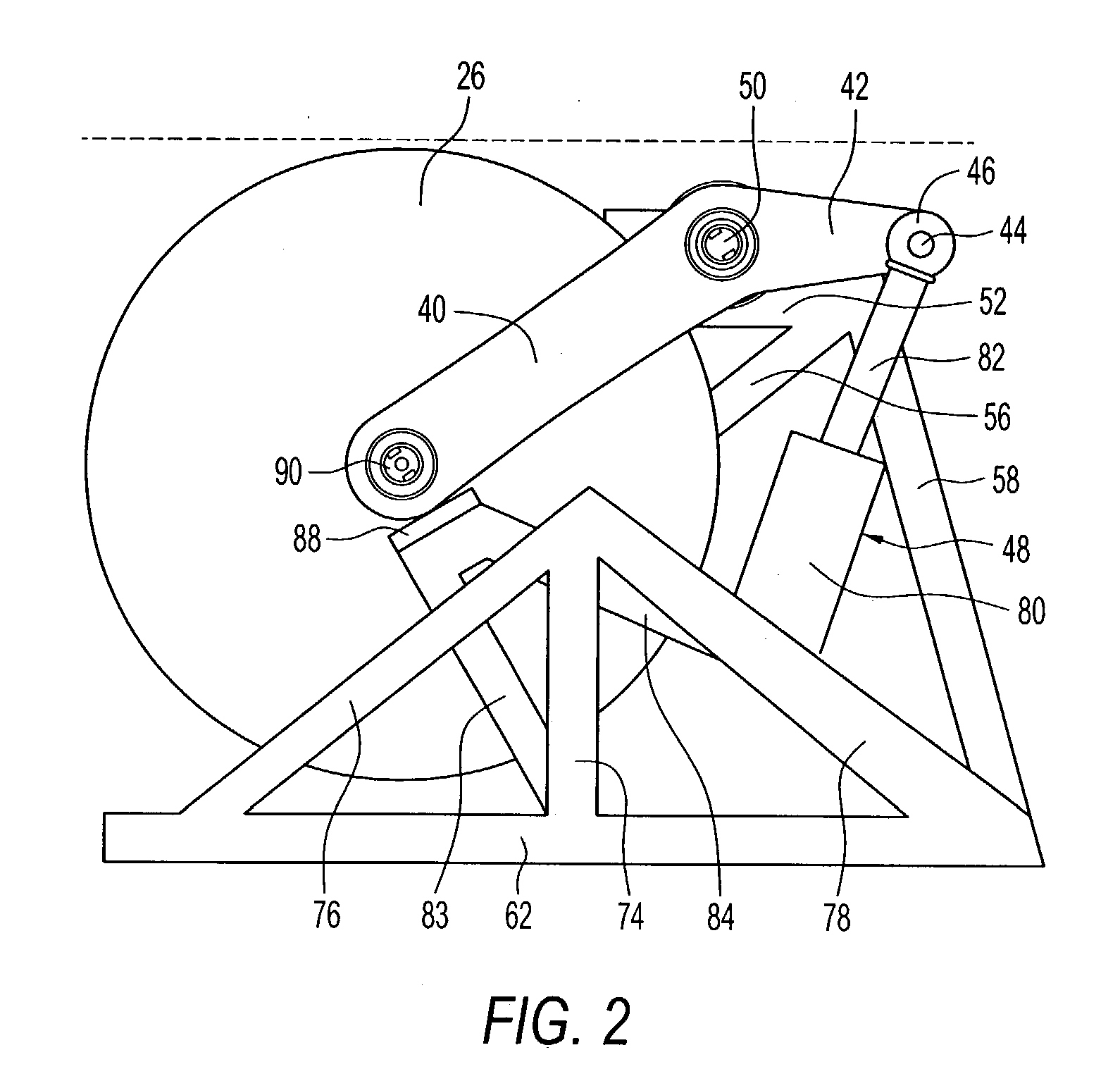
InactiveUS6922153B2Quick stopRule out the possibilityDC motor speed/torque controlEmergency protective circuit arrangementsPower toolProtection system
A detection system for detecting a dangerous condition for an operator using a power tool of the type which has an exposed blade relative to a work surface and a protection system for minimizing, if not eliminating the possibility of a user being injured by contacting the blade. In one preferred embodiment of the present invention, a proximity detection system is capable of detecting the presence of a user near the blade of a table saw and a protection system that can either retract the blade below the work surface of the table saw or terminate the drive torque to the blade which can result in rapid stopping of the saw blade by a work piece that is being cut.
Owner:CREDO TECH CORP +1
Safety detection and protection system for power tools
InactiveUS20040226800A1Quick stopQuick pullDC motor speed/torque controlEmergency protective circuit arrangementsPower toolProtection system
A detection system for detecting a dangerous condition for an operator using a power tool of the type which has an exposed blade relative to a work surface and a protection system for minimizing, if not eliminating the possibility of a user being injured by contacting the blade. In one preferred embodiment of the present invention, a proximity detection system is capable of detecting the presence of a user near the blade of a table saw and a protection system that can either retract the blade below the work surface of the table saw or terminate the drive torque to the blade which can result in rapid stopping of the saw blade by a work piece that is being cut.
Owner:CREDO TECH CORP +1
RFID based security system
InactiveUS6888459B2Improve reliabilityLow costSafety arrangmentsBurglar alarm by openingElectric power transmissionNetwork Communication Protocols
A system and method for constructing a security system for a building using at least one RFID reader to communicate with at least one RFID transponder to provide the radio link between each of a number of openings and a controller capable of causing an alert in the event of an intrusion. The RFID transponder is connected to an intrusion sensor. The controller preferably communicates with the RFID reader using a power line communications protocol. The RFID transponder can contain a battery. The RFID reader contains means for transferring power to an RFID transponder for the purpose of charging any battery. The security system can contain more than one controller, whereby the RFID reader can communicate with more than one controller.
Owner:ADT US HLDG INC
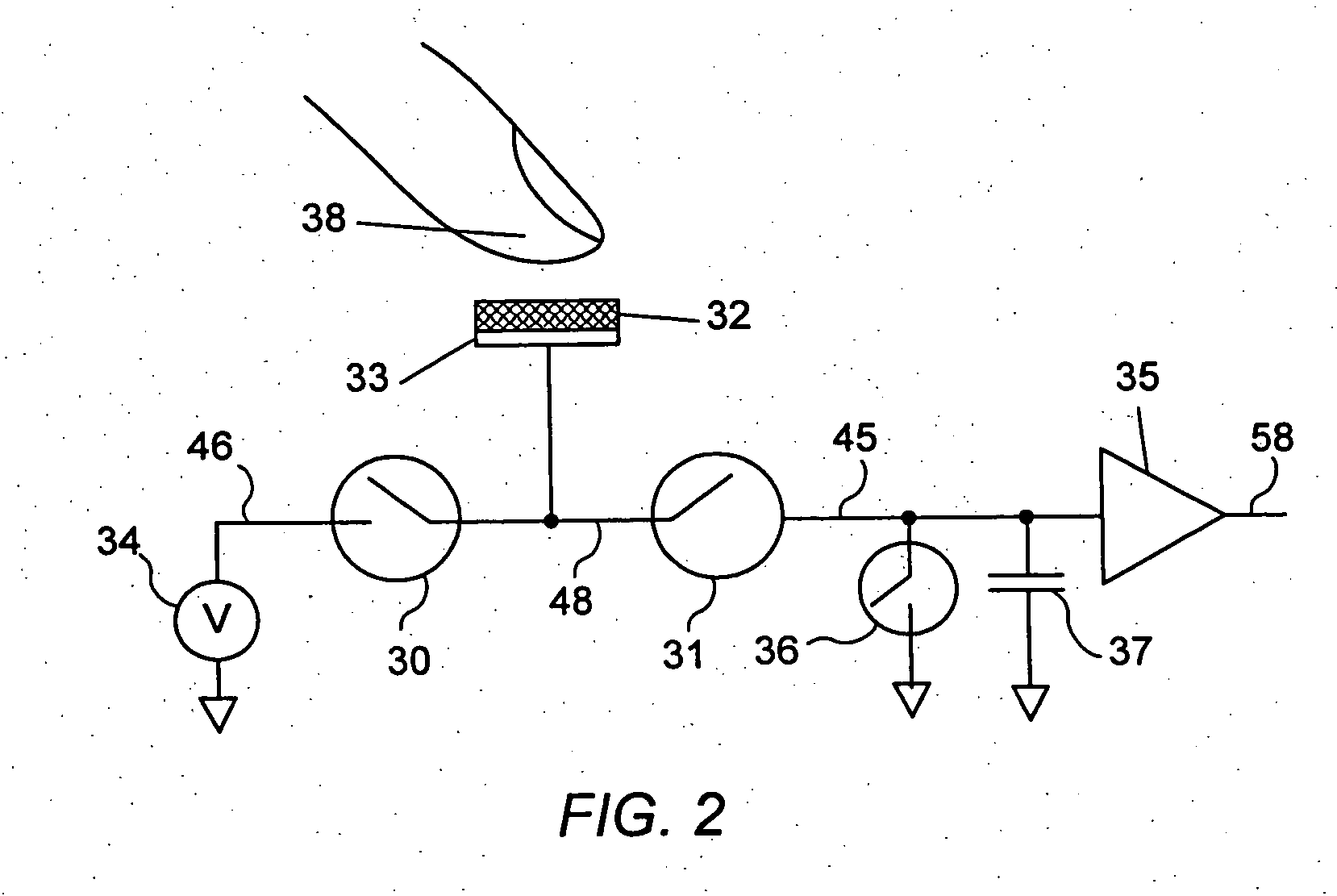
Sensor apparatus and safety apparatus for protecting approach to machines
InactiveUS6376939B1Improve securityPossibility is mitigated and suppressedBoards/switchyards circuit arrangementsEmergency protective arrangement detailsCapacitanceElectricity
A sensor apparatus and a safety apparatus which can ensure significantly enhanced safety by monitoring constantly whether the sensor apparatus is operating normally. An auxiliary electrode plate of a small area is disposed in parallel and in opposition to an electrode plate with a short distance therefrom. A switching element is turned on every second for a period of milliseconds repetitively. When the switching element is turned on under the control of a central processing unit, the auxiliary electrode plate is connected to the ground potential, as a result of which a capacitance DELTAC effective between the auxiliary electrode plate and the electrode plate is electrically connected in parallel with a capacitor C0 effective between the electrode plate and a machine component, resulting in that the capacitance C0 is increased by a proportion corresponding to the capacitance DELTAC. Consequently, change of the capacitance C0 comparable to that brought about upon detection of the human body takes place, whereby a substantially similar detection signal as the human body detection signal is made available. On the basis of this detection signal, it is possible to monitor whether or not the sensor apparatus is operating normally.
Owner:SUMITOMO CHEM CO LTD
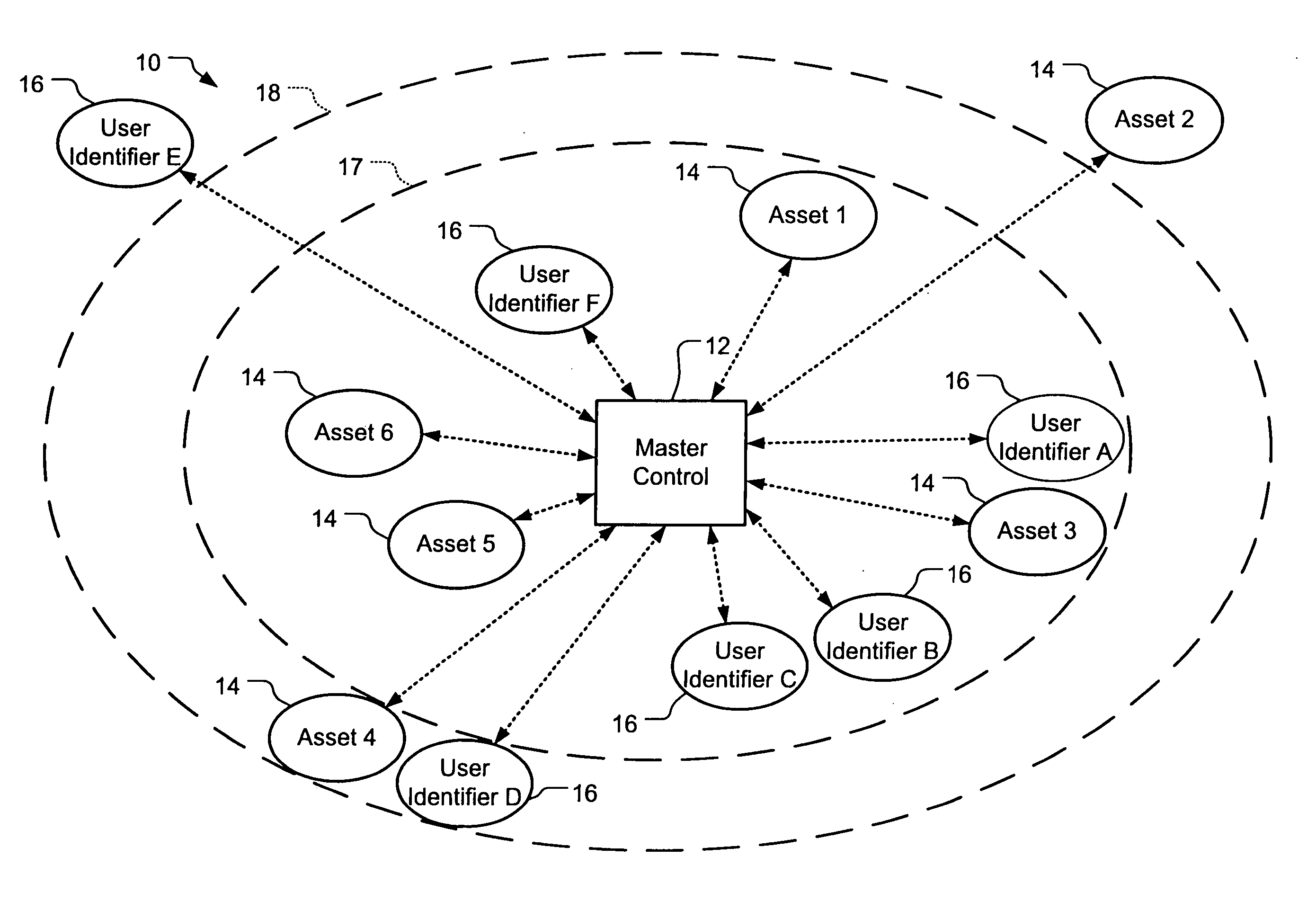
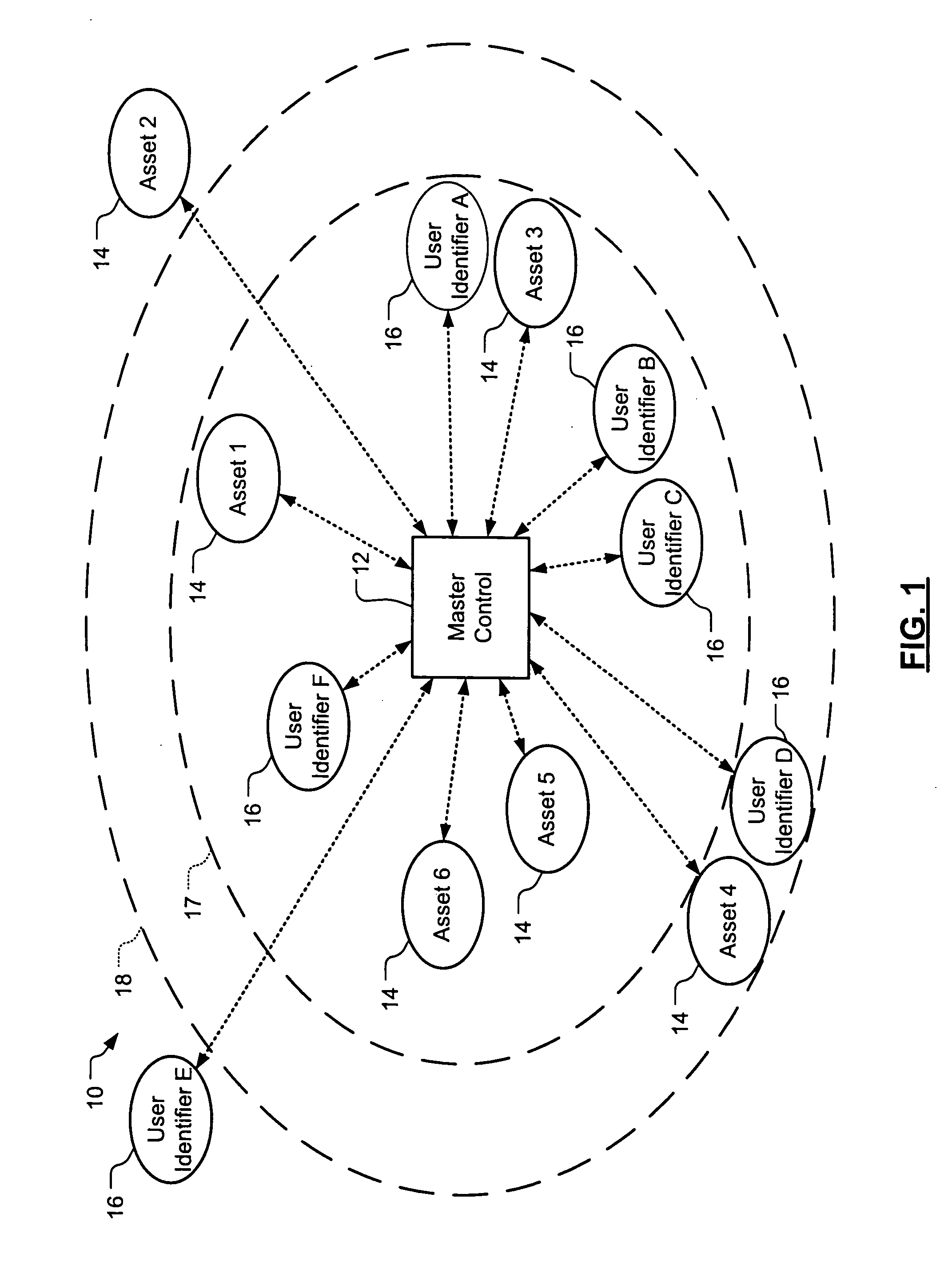
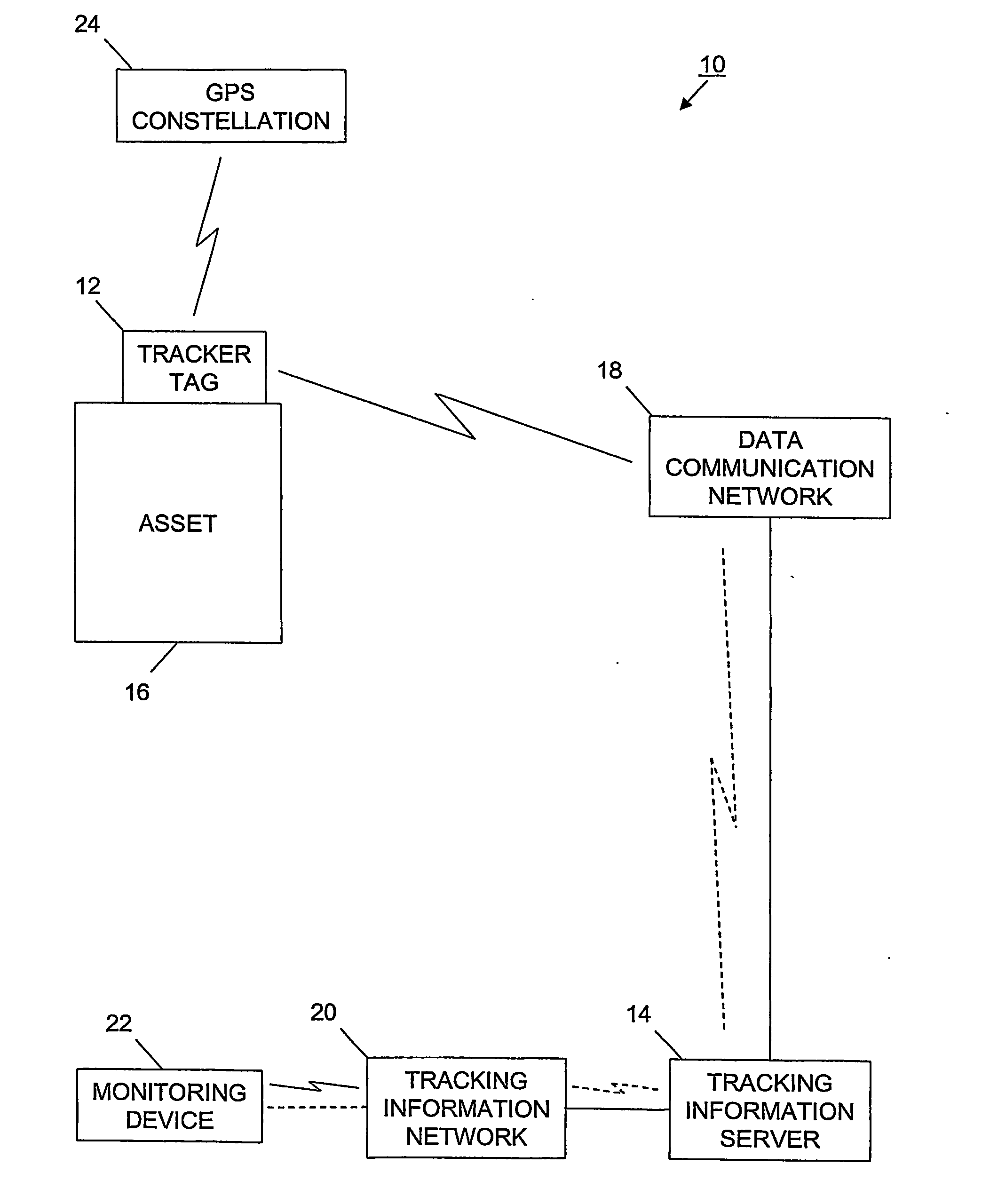
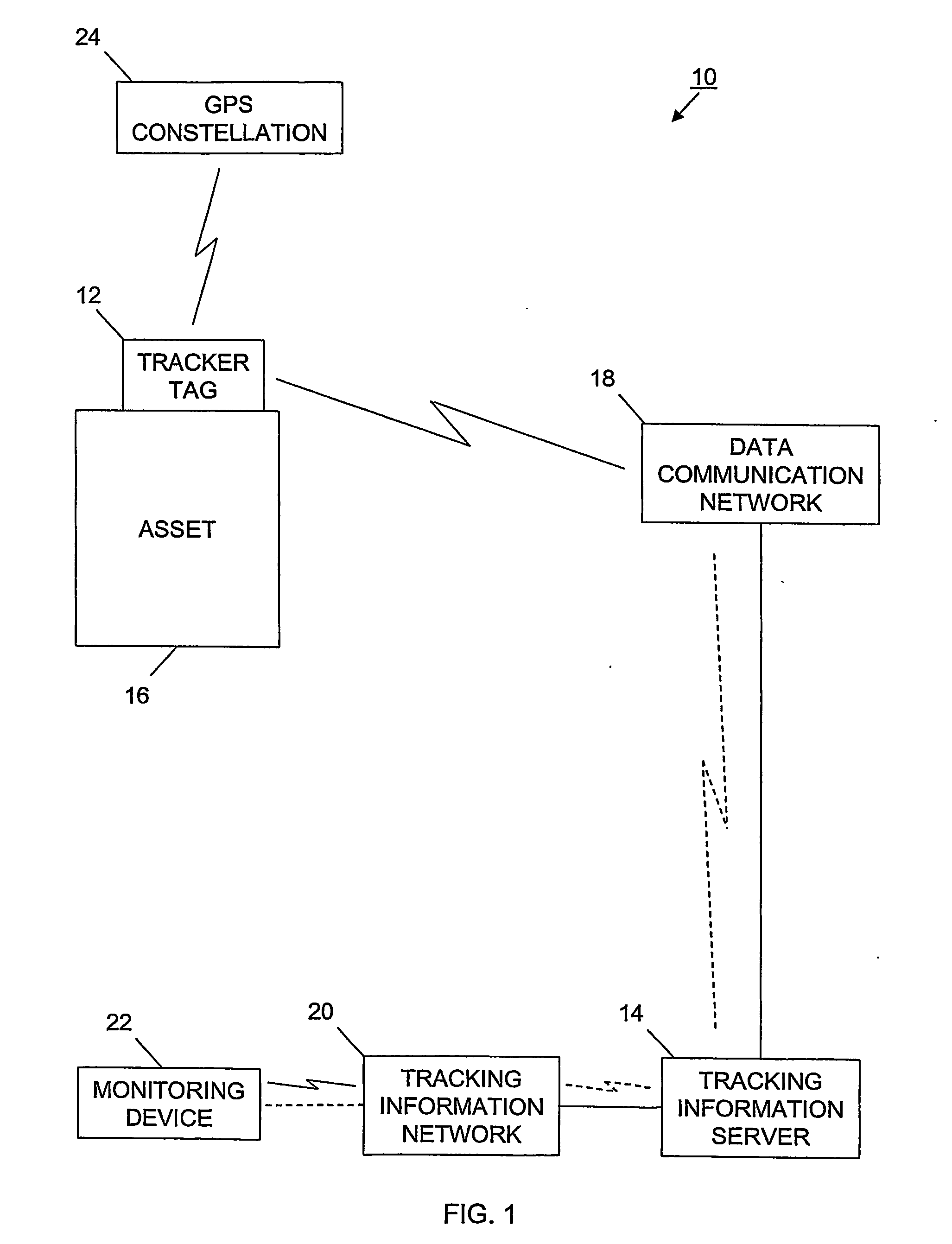
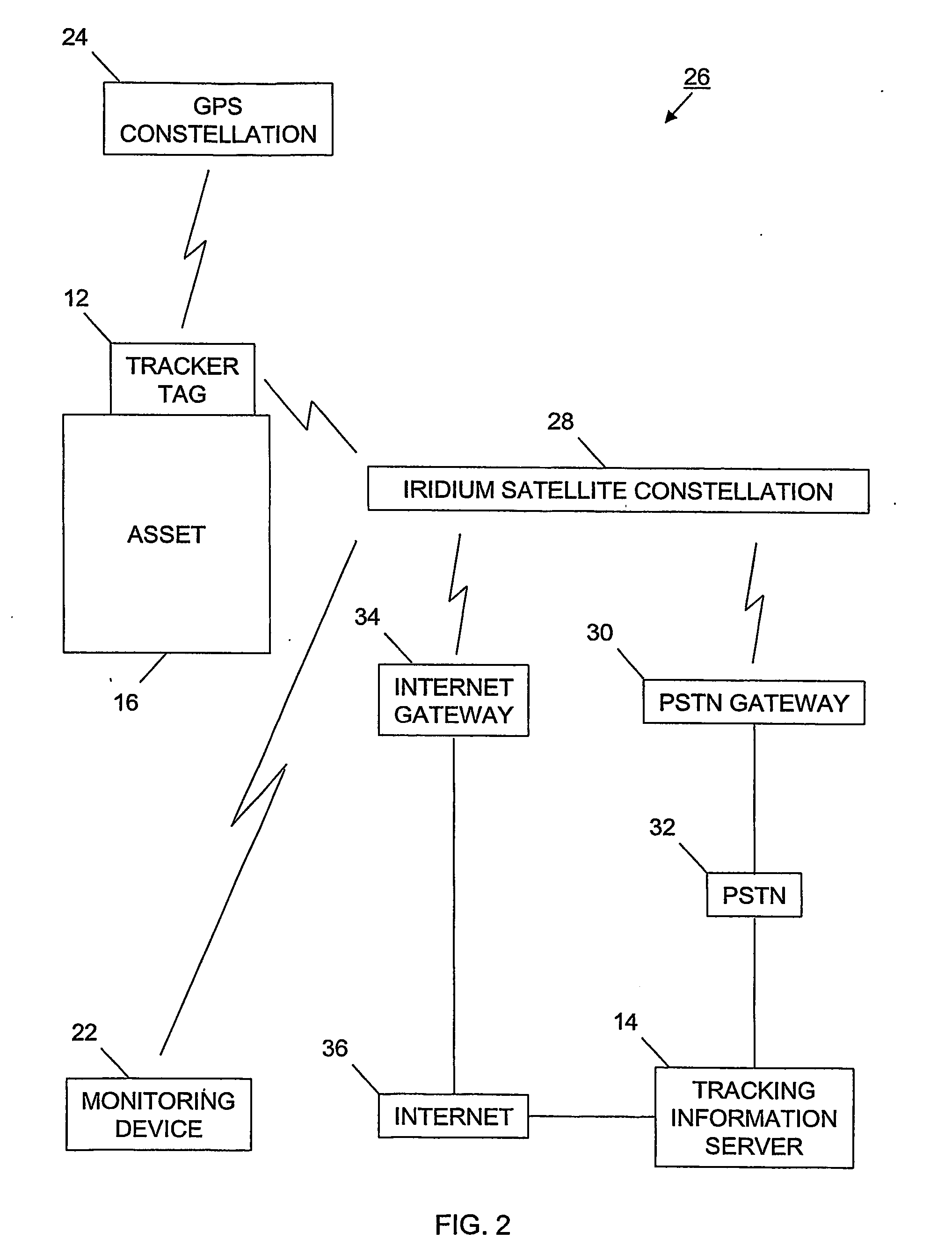
Tracking system and associated method
InactiveUS20060187026A1Easy to receiveVehicle testingRegistering/indicating working of vehiclesProgram instructionIridium satellite constellation
A tracking system (10) for tracking movable assets (16) and several methods for using the system are provided. The tracking system includes a monitoring device (22), a tracking information network (20), a data communication network (18), a tracker tag (12), and a tracking information server (14). The tracker tag uses GPS technology. The tracking information server provides programmed instructions to the tracker tag in messages via a messaging system. The tracker tag selectively retrieves the messages from the messaging system. The tracking information server provides tracking information and related information to a subscriber. In one embodiment, the tracker tag is in communication with an Iridium satellite constellation (28) and tracking information is displayed to the subscriber when the asset is substantially anywhere in the world. In another embodiment, the monitoring device is in communication with the Iridium satellite constellation and tracking information is displayed to the subscriber when the subscriber is substantially anywhere in the world, preferably via the Internet (36).
Owner:ARGO TECH CORP
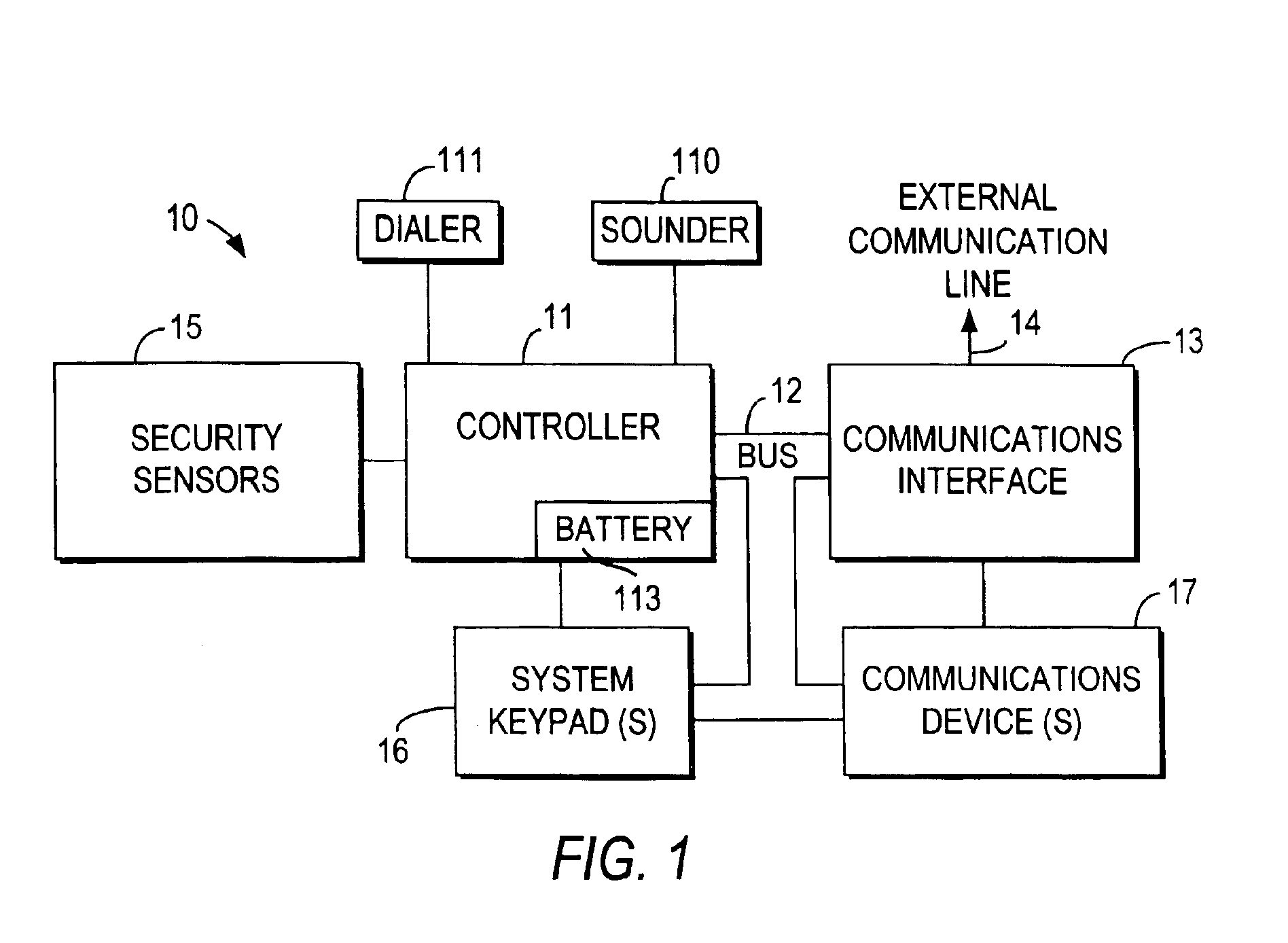
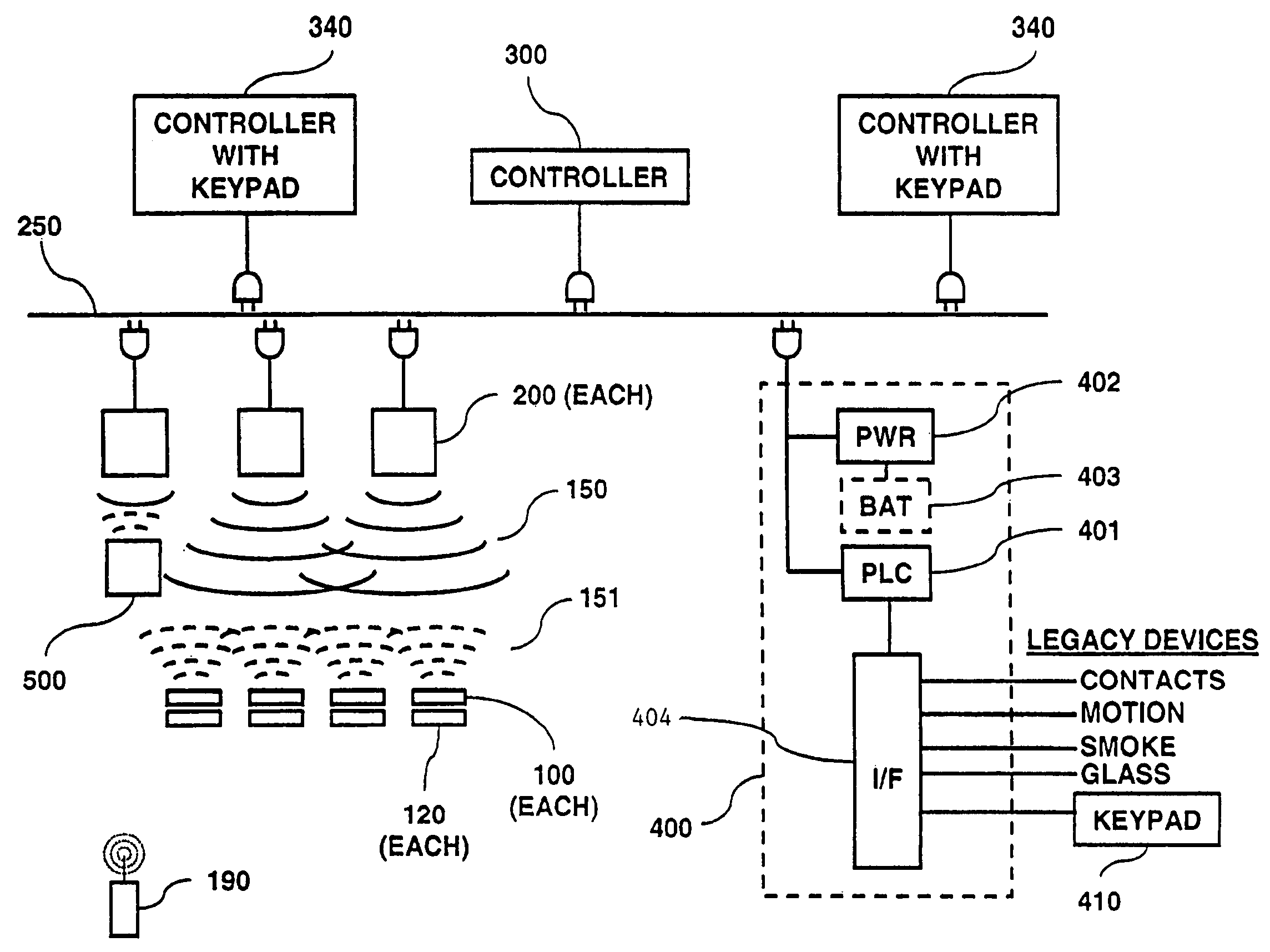
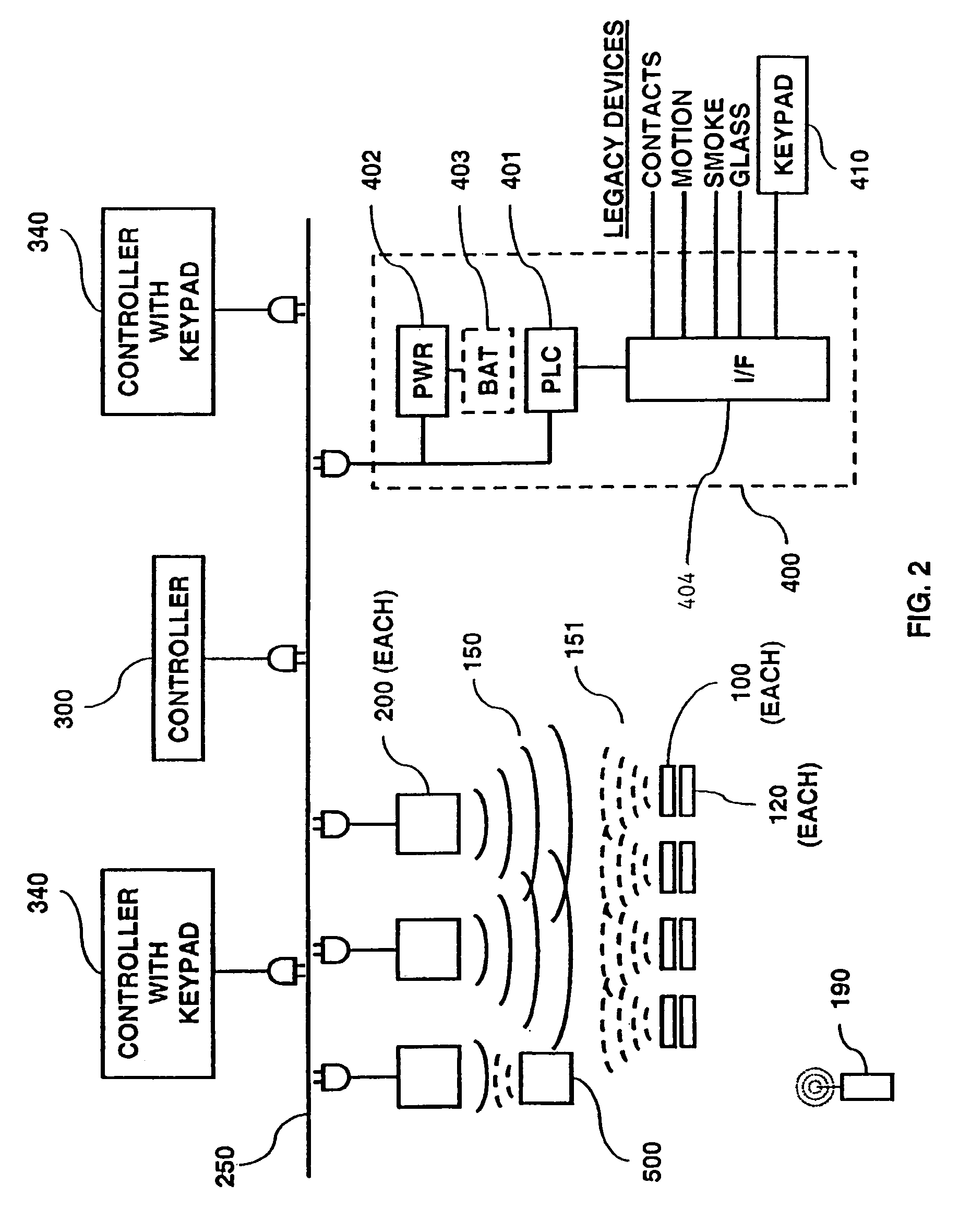
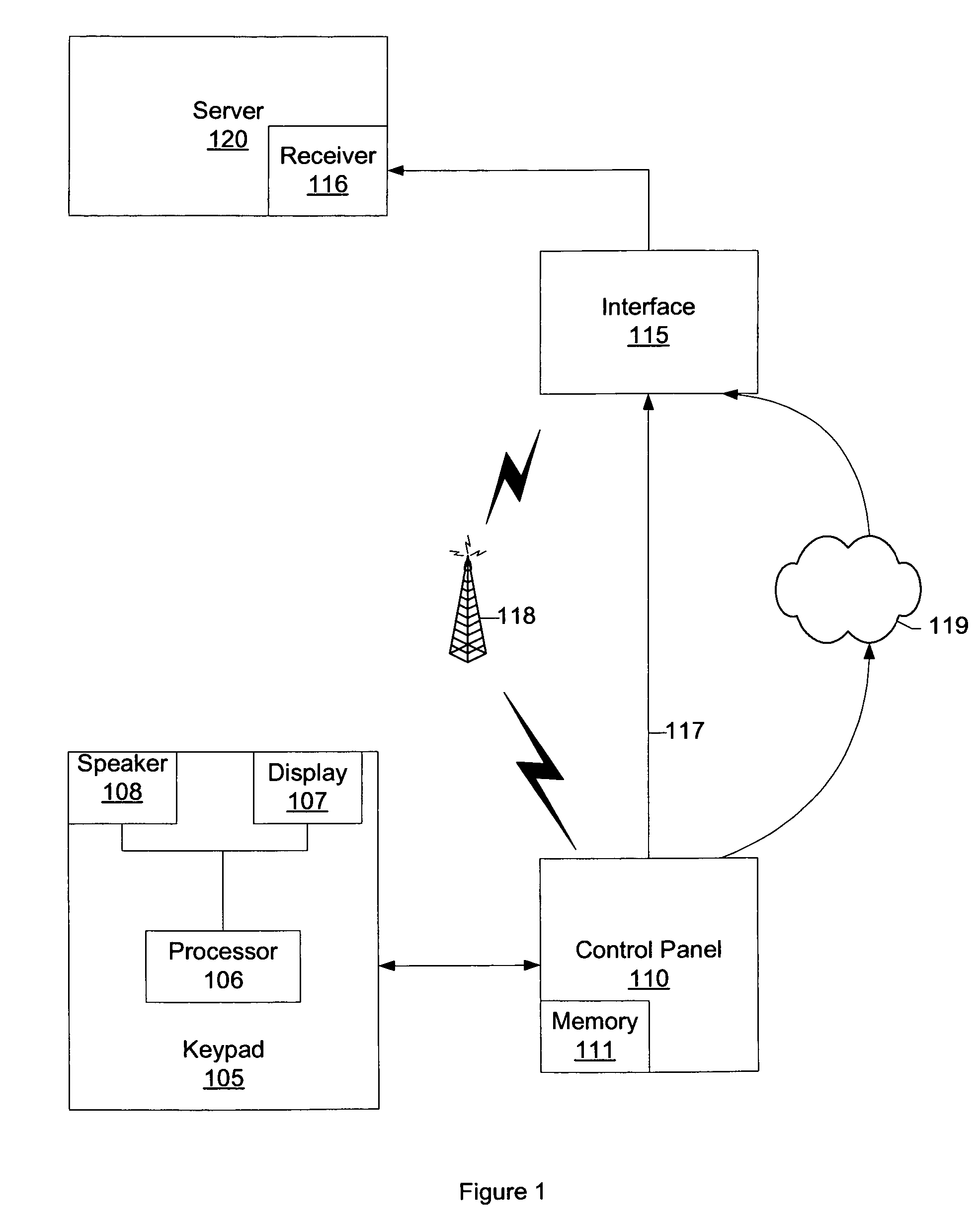
Controller for a security system
InactiveUS7053764B2Improve reliabilityLow costFrequency-division multiplex detailsTelephonic communicationModem deviceMaster controller
A controller for use in a security system based upon RFID techniques. The controller can use power line carrier communications to communicate with other devices in the security system. The controller can use a modem or wireless module to connect to public networks. Multiple controllers can be used in a system, and the controllers can arbitrate to determine a master controller. The controller contains configuration data and tables that define the relationships between devices in the security system. The controller can receive communications from other devices in the system and can interface with legacy devices previously used with wired security systems. The controller can send messages based upon predetermined events, and can support a remote alerting function.
Owner:LIFESHIELD LLC
Cargo theft prevention using text messaging
InactiveUS20130033381A1Reducing and eliminating theftEfficient powerBraking element arrangementsBuilding locksDriver/operatorCargo container
Method for monitoring a cargo container in which a transmitter is arranged on the container and periodically transmits messages to a remote site or location according to a schedule of messages. When a message is not received according to the schedule, which may be the result of tampering with the transmitter or another nefarious action involving the container, it may be considered that the container has been stolen. A rate of transmission of the messages may be modified based on a condition of the vehicle, such as the presence of a driver inside the vehicle, a distance between a driver inside the vehicle and the vehicle, the vehicle being at rest after motion of the vehicle stops, a location of the vehicle, biometric identification of a driver of the vehicle and deviation of the vehicle from an expected route, and / or based on current time and weather around the vehicle.
Owner:INTELLIGENT TECH INT
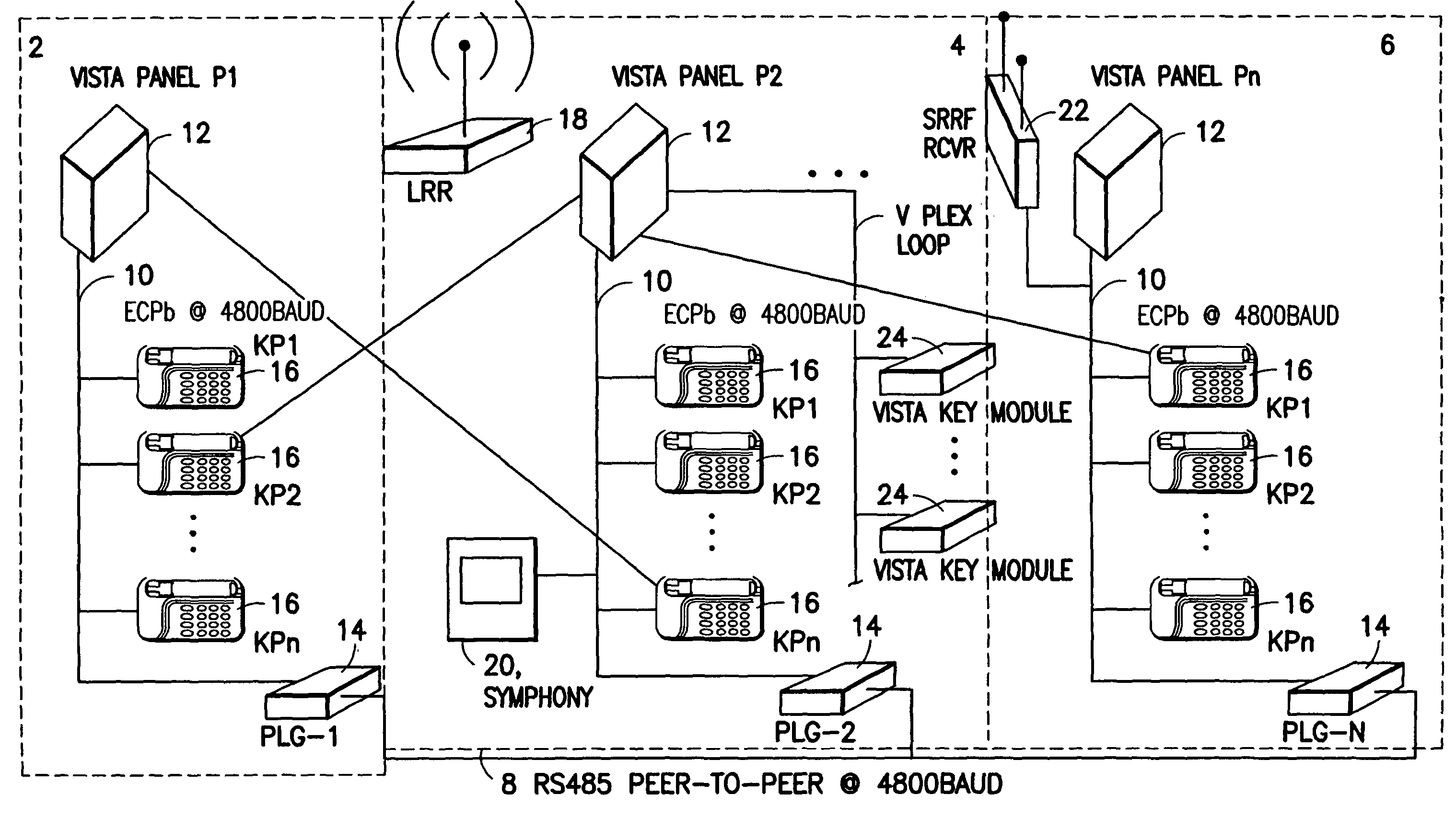
System and method for panel linking in a security system
InactiveUS7734906B2Low costLimited accessDigital data processing detailsTelephonic communicationEngineeringSecurity system
A security system comprising a plurality of security subsystems each of the security subsystems being discretely located, typically in separate buildings. The security subsystems are interconnected by a system communications bus to enable bi-directional communication between the security subsystems. Each of the security subsystems comprises a user interface, a control panel, a plurality of security devices, a local communications bus, and a panel linking gateway. The panel linking gateway allows data on the local communications bus of each security subsystem to be transmitted to and received from the system communications bus. The security system allows a keypad or other user interface from one security subsystem to access and control a second remote security subsystem.
Owner:ADEMCO INC
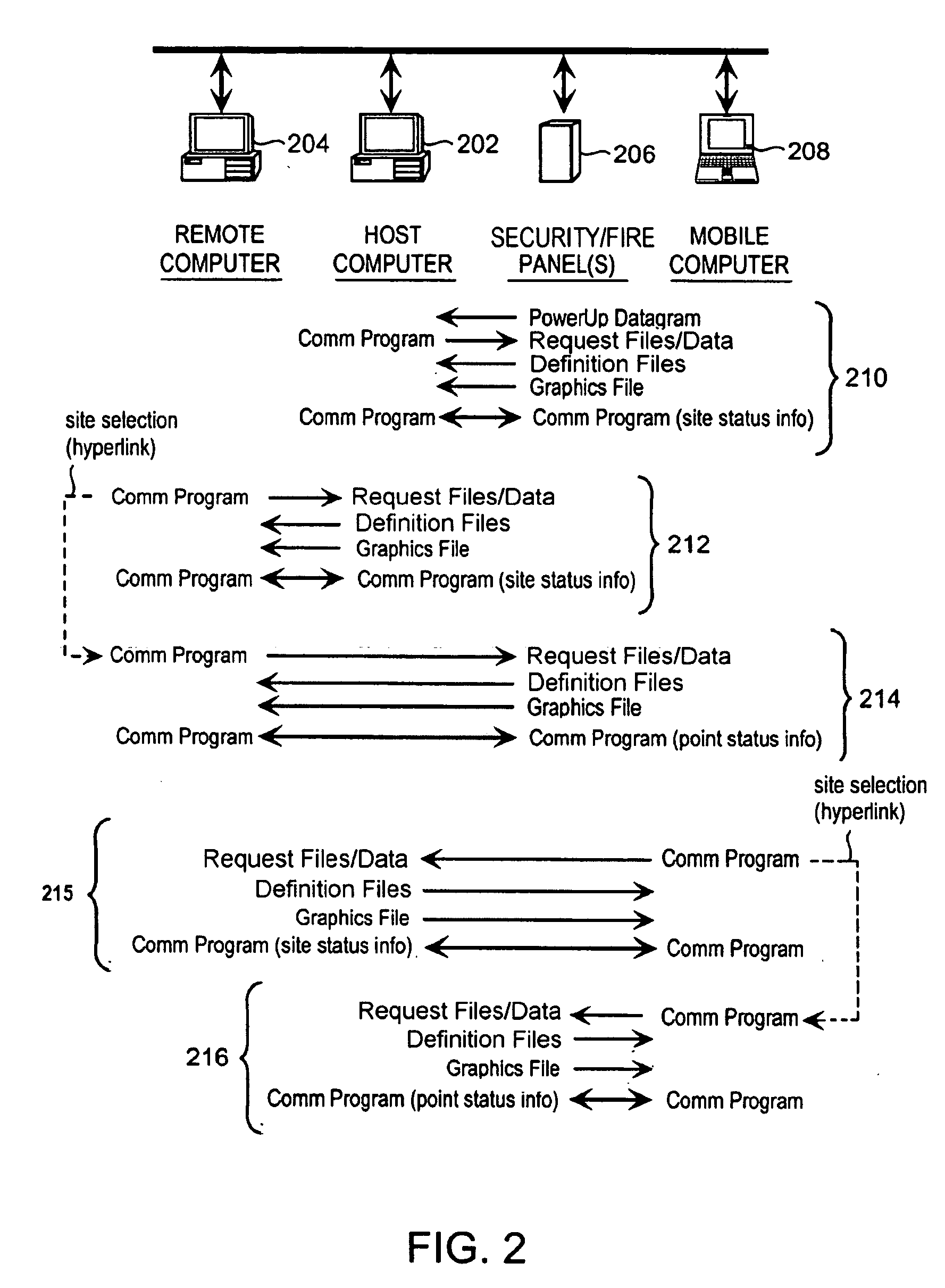
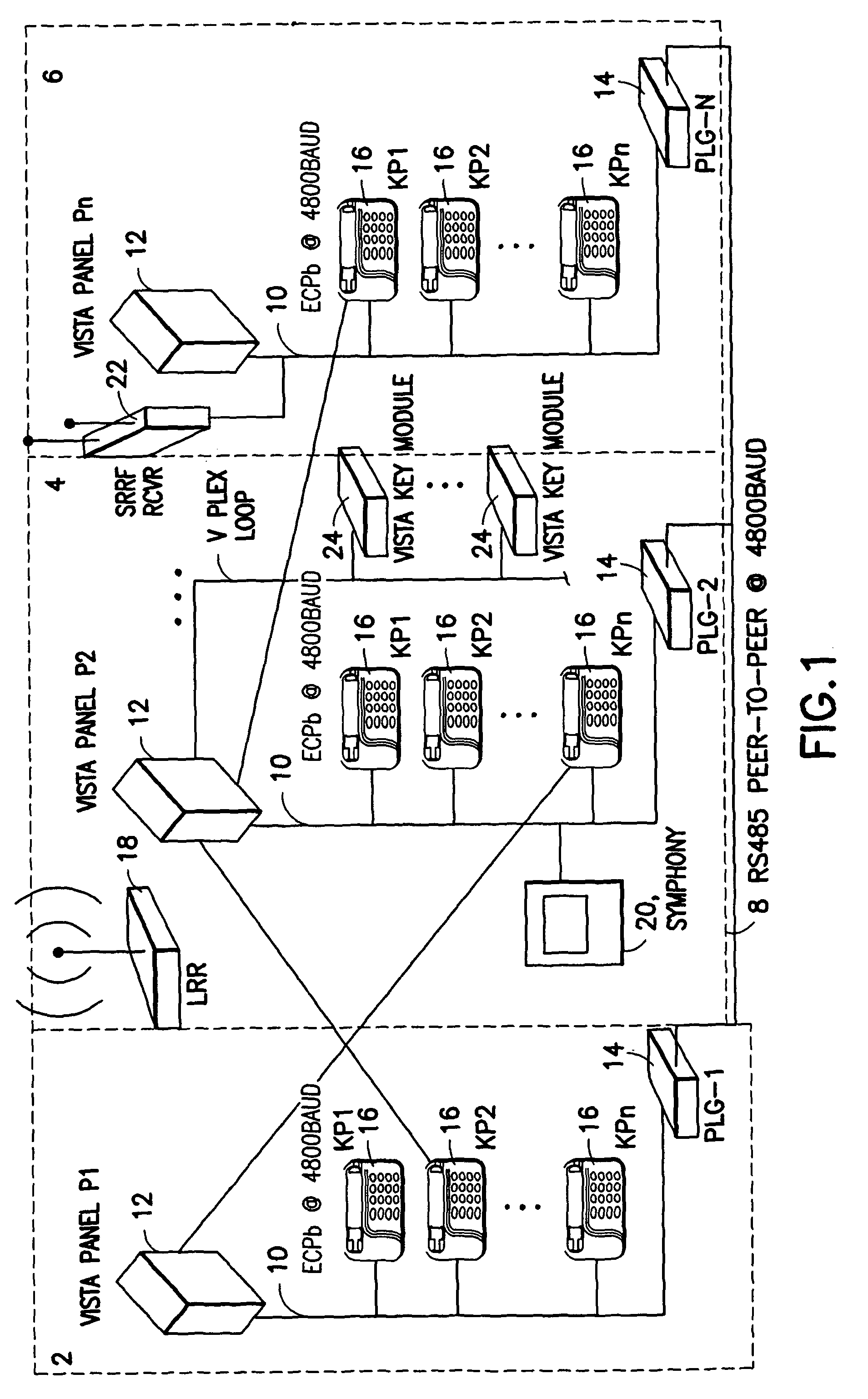
Automatic panel configuration upload to a central station automation system
A method and system for automatically uploading the configuration of a security system to a central station automation system via telephonic lines, long-range radio (e.g., cellular), or Internet. The end result is that the automation system has sufficient information regarding the type and configuration of the system installed at the protected premises to properly handle alarms reports from that system.
Owner:ADEMCO INC
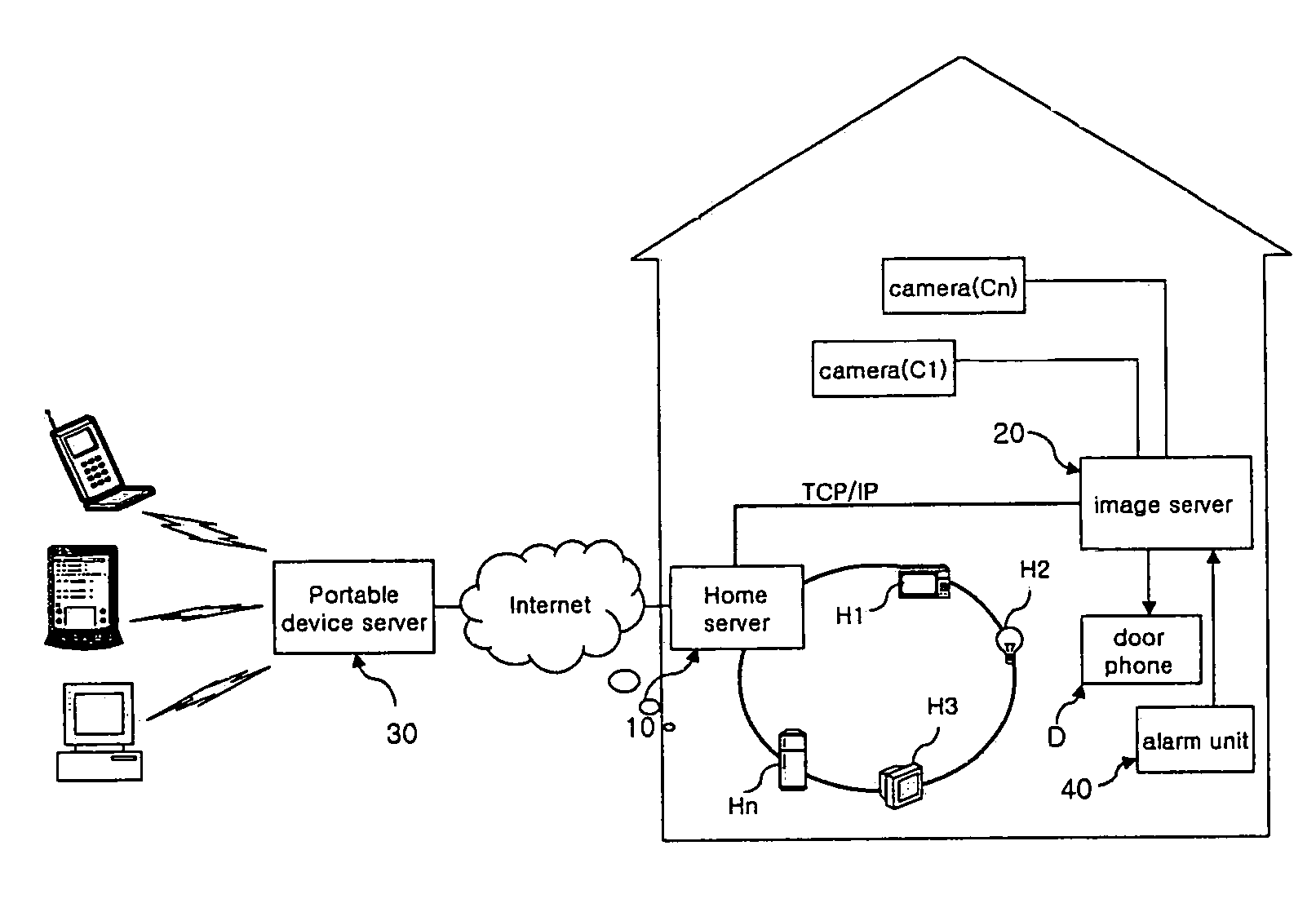
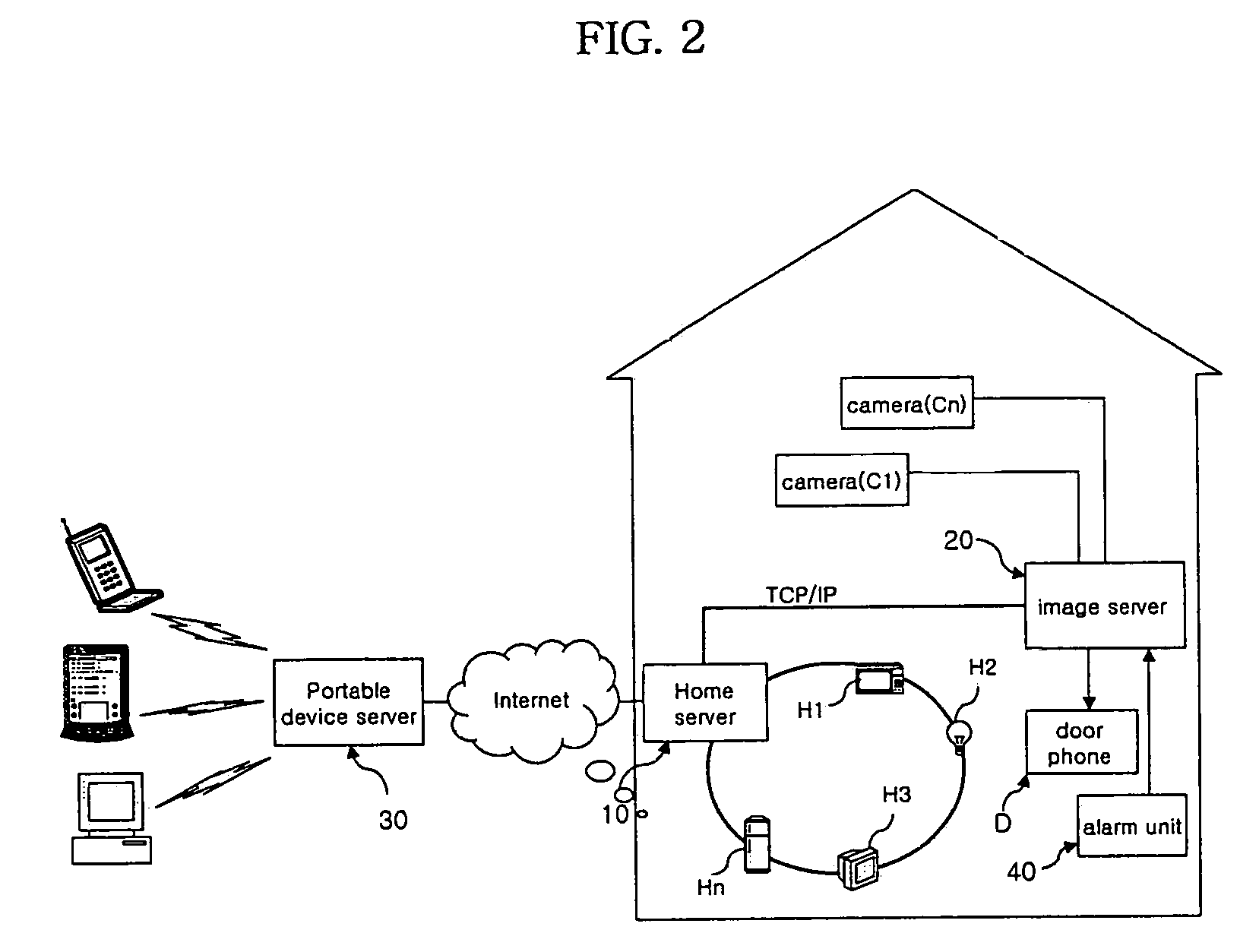
Portable device-interoperable home network system
InactiveUS7106176B2Reducing the user's anxietyFrequency-division multiplex detailsTime-division multiplexImage serverHome appliance
A portable device-interoperable home network system includes a home server controls data transmission and reception of an internal network to which a plurality of home appliances are connected in a home. An image server outputs information regarding at least one image in the home to the home server. A portable device server receives the image information from the image server via the home server and transfers it to a portable electronic device. Therefore, a user can recognize a situation in the home through the portable electronic device from anywhere outside of the home, resulting in an increase in convenience of use.
Owner:LG ELECTRONICS INC
Integrated circuit with enhanced coupling
InactiveUS7119693B1Coupling efficiency is improvedEnhanced couplingMemory record carrier reading problemsNear-field systems using receiversCouplingEngineering
A system for conveying a radio frequency (RF) signal from a base station to a detached integrated circuit (IC) has an intermediate resonant circuit and an IC. The intermediate resonant circuit is configured to resonate in response to the RF signal from the base station, reproducing the RF signal. The IC has an integral resonant circuit configured to resonate in response to the reproduced RF signal. The IC and the intermediate resonant circuit are affixed proximate each other. Both are separate from the base station and each other. Either or both of the intermediate resonant circuit and the integral resonant circuit may contact a high magnetic permeability layer. The intermediate resonant circuit may be formed of conductive ink.
Owner:CELIS SEMICONDUCTOR CORP
Bed exit and patient detection system
InactiveUS20080169931A1Accurate and reliable positioningEasy to useBedsMeasuring/recording heart/pulse rateMultiple inputSpeech sound
A bed exit and patient detection system especially adapted for use in the general medical or surgical floor area of a hospital or other healthcare facility as part of a vital signs monitoring and remote warning system includes a plurality of pressure sensors disposed in the patient's bed in a series of rectangular strips or zones that run laterally across the bed in the area of the patient's mid-back, hips and mid-legs, respectively. Each zone contains a plurality of sensors, arranged symmetrically about the centerline of the bed, with the corresponding sensors on opposite sides of the centerline in each zone being connected in parallel. The sensors are connected to a processor with multiple input channels that continuously monitors the sensor states to determine, from the pattern of sensor states observed, whether the patient is in bed, out of bed or is actively attempting to ext the bed at the sides or foot of the bed. At least three different sets of bed exit logic rules are available for user selection to configure the system for high, medium or low sensitivity, or bed exit privileges, for any particular patient. In some embodiments, the system also is capable of detecting when a patient is attempting to assume certain prohibited in-bed positions, such as sitting positions or slumping positions. An alarm in the form of a pre-recorded voice announcement or an alarm over a pre-existing nurse call system is provided when the sensor states are indicative of an out-of-bed or an exiting bed condition, or other prohibited in-bed positions, for a predetermined minimum period of time.
Owner:HOANA MEDICAL
Popular searches
Co-operative working arrangements Electric signalling details Burglar alarm by hand-portable articles removal User identity/authority verification Data switching by path configuration Computation using non-denominational number representation Program control Electric/magnetic detection Complex mathematical operations Nuclear radiation detection
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com