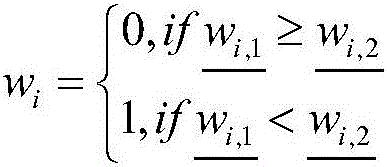Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
29999 results about "Network model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The network model is a database model conceived as a flexible way of representing objects and their relationships. Its distinguishing feature is that the schema, viewed as a graph in which object types are nodes and relationship types are arcs, is not restricted to being a hierarchy or lattice.
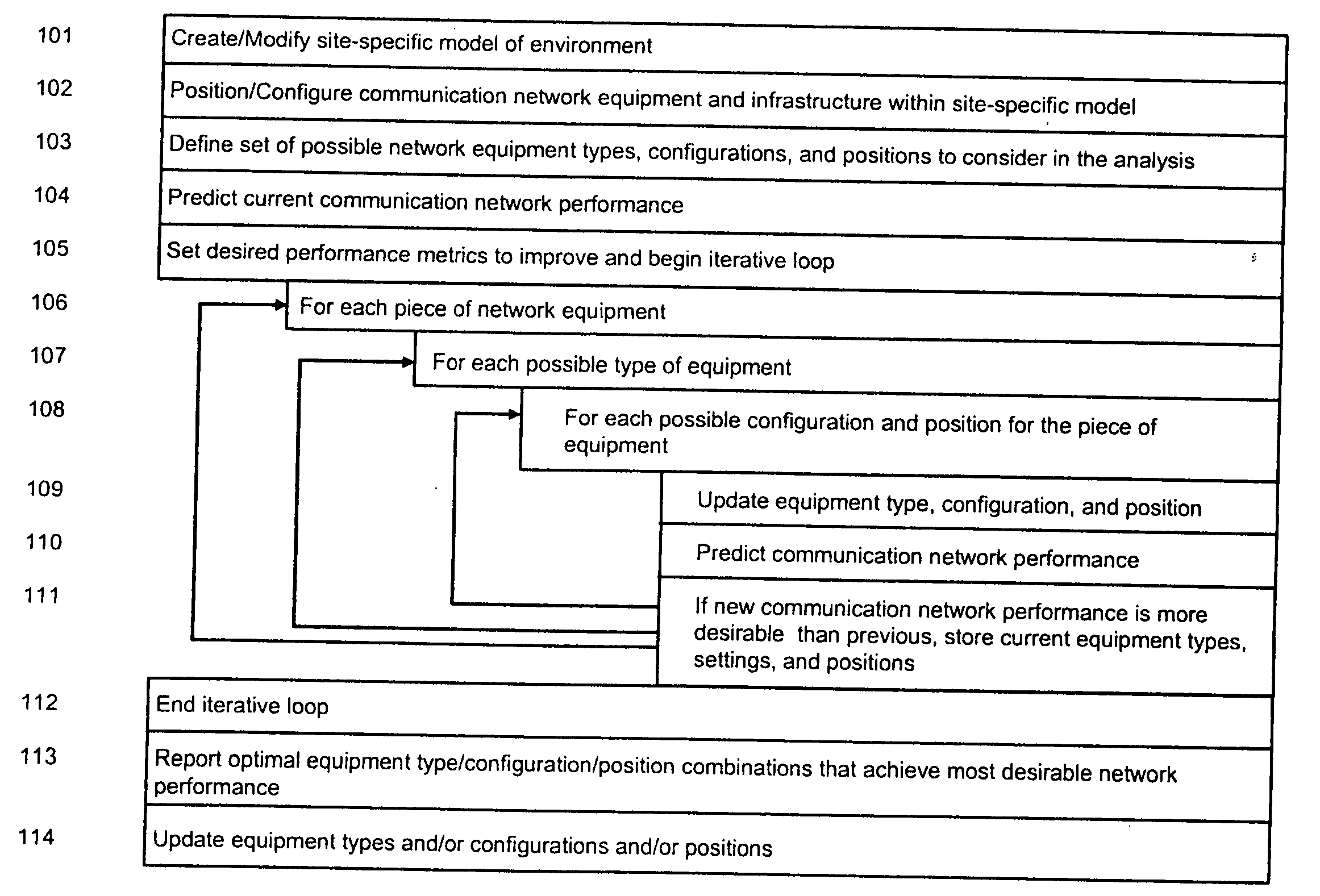
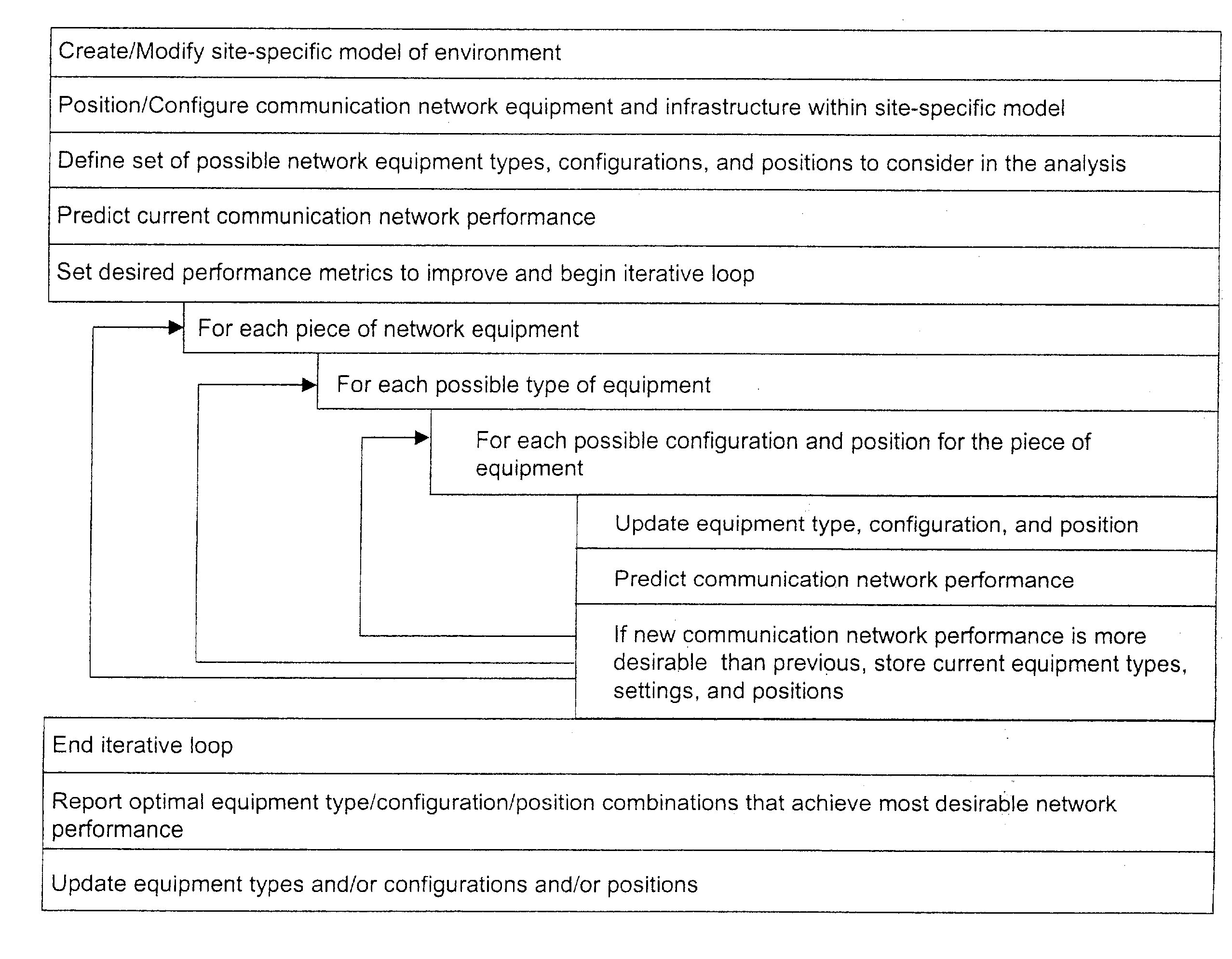
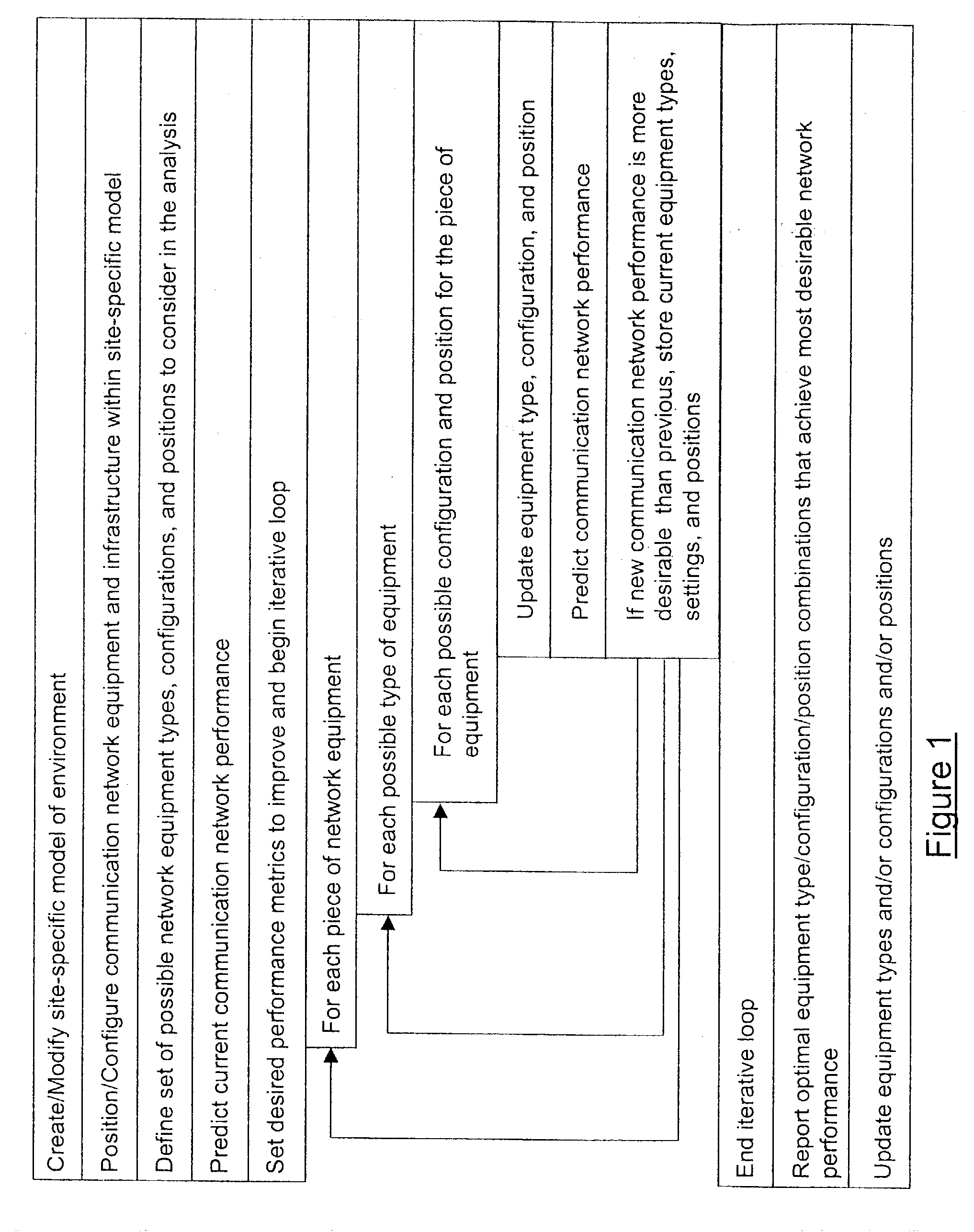
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
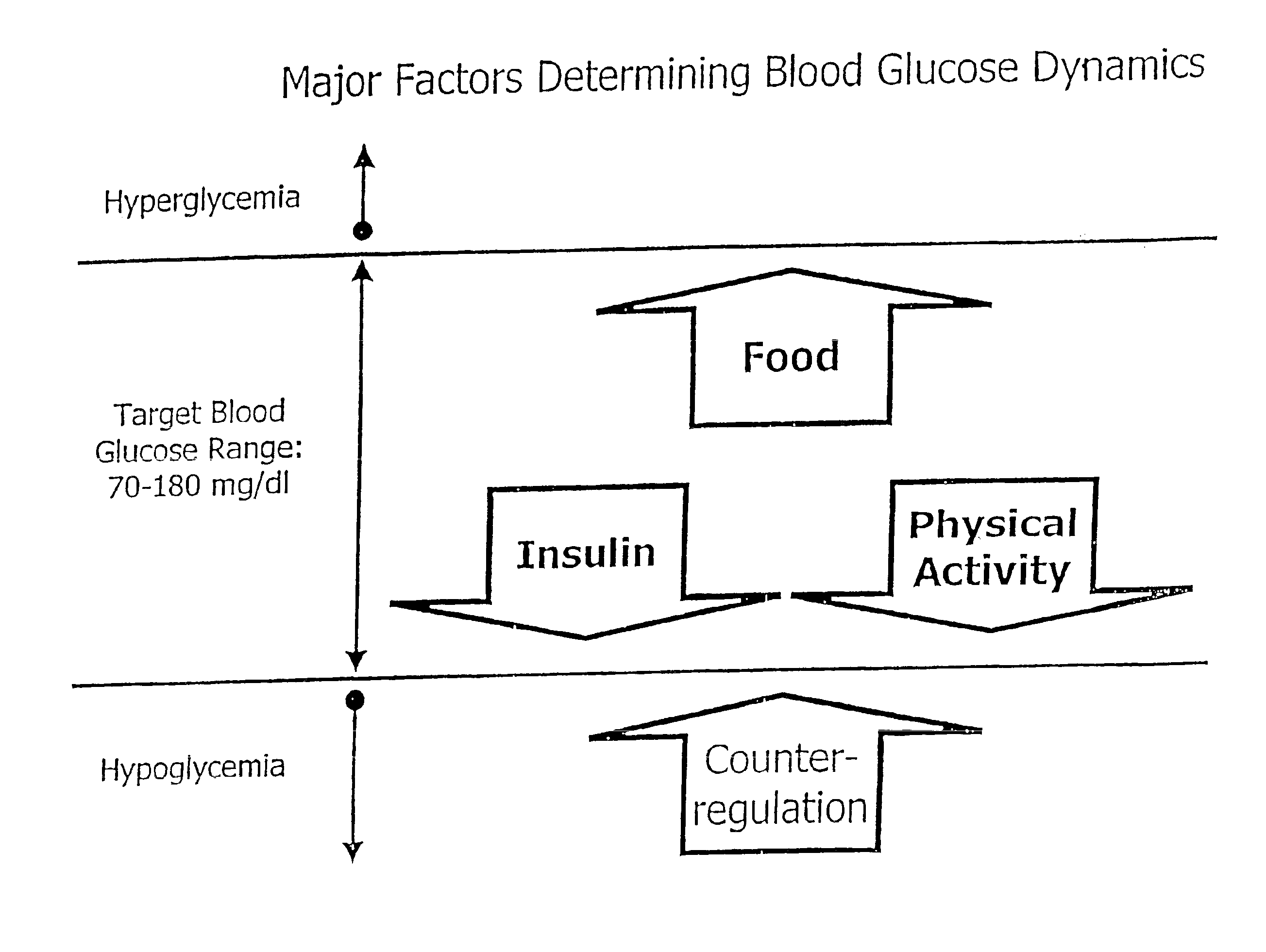
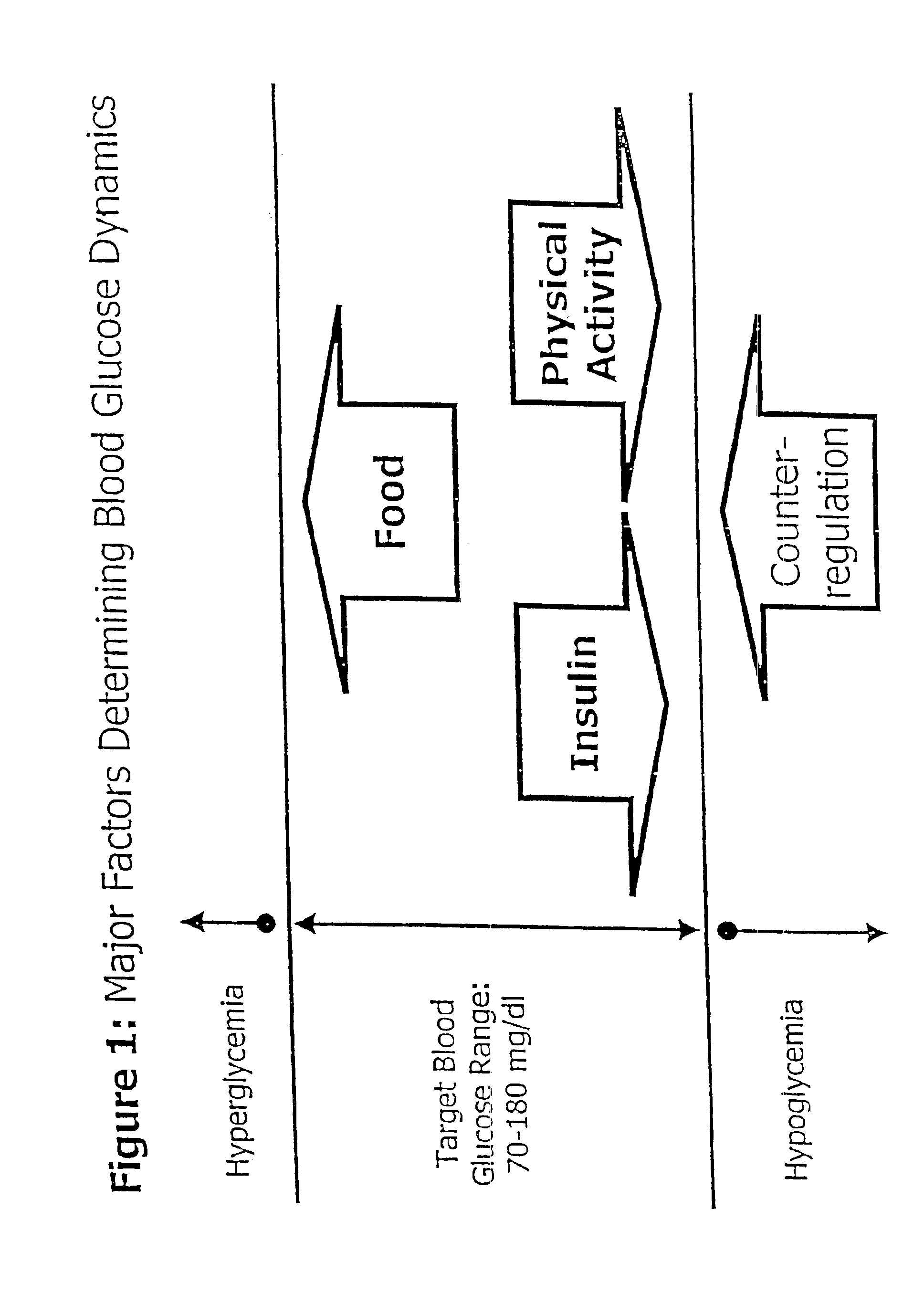
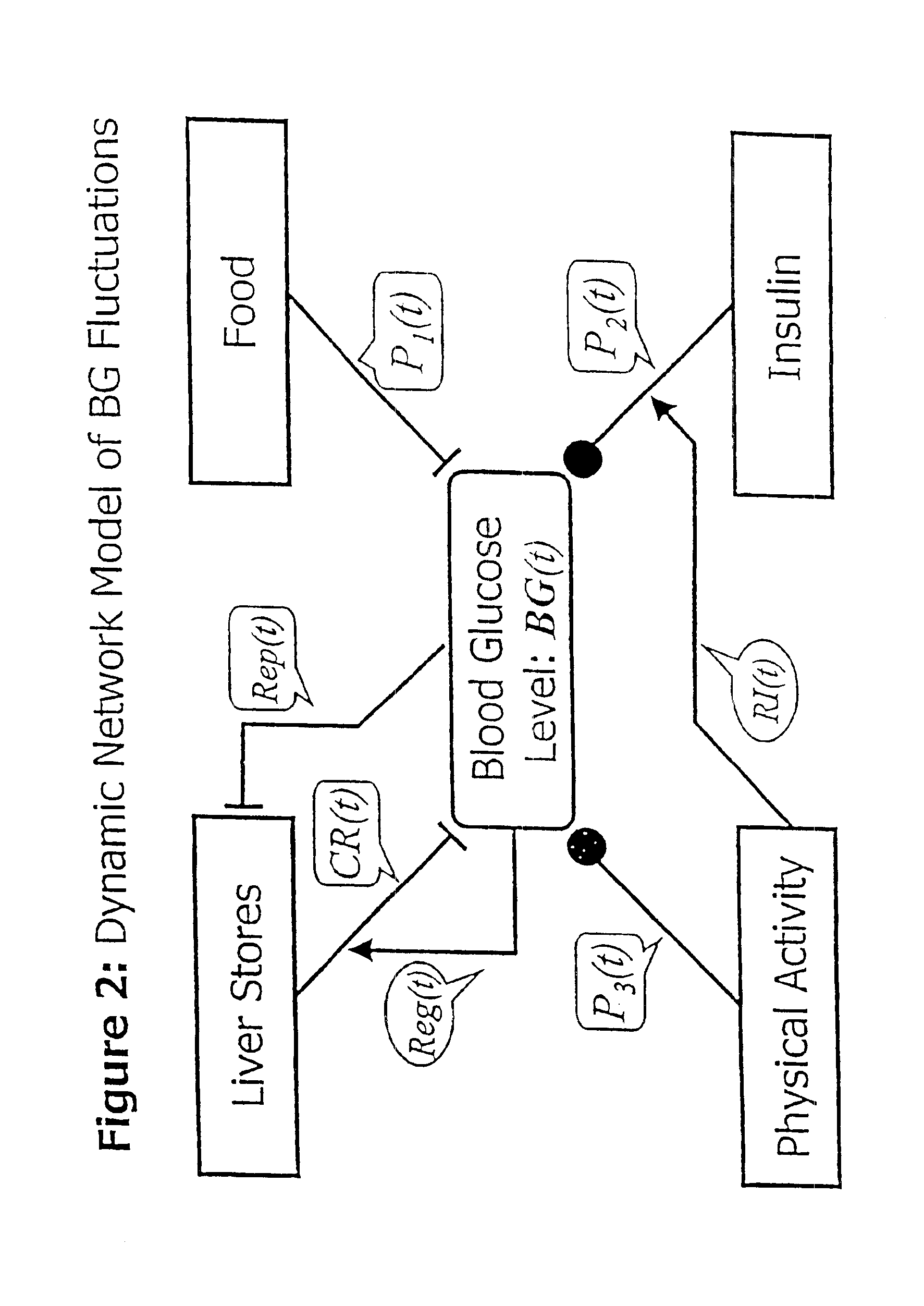
Method and apparatus for predicting the risk of hypoglycemia
InactiveUS6923763B1Reduced responseOptimal glucose controlMedical simulationHealth-index calculationInsulin infusionMedicine
The invention relates to a method which utilizes blood glucose (“BG”) sampling, insulin infusion / injection records, heart rate (“HR”) information and heart rate varability (“HRV”) information to estimate BG in the near future and to estimate of the risk of the onset of hypoglycemia. The invention also relates to an apparatus for predicting BG levels and for assessing the risk of the onset of hypoglycemia in the near future. The invention is based on two predetermined bio-mathematical routines: a network model of BG fluctuations and a BG profile for assessment of the risk of hypoglycemia.
Owner:UNIV OF VIRGINIA ALUMNI PATENTS FOUND
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives
ActiveUS20040143428A1Significant valueEasy to explainGeometric CADProgram controlHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
Multi-reservoir pressure control system
InactiveUS6915679B2Sufficient oscillationAccurate and stable and reliable assayAnalysis by electrical excitationLaboratory glasswaresFluid transportFlow resistivity
Improved microfluidic devices, systems, and methods allow selective transportation of fluids within microfluidic channels of a microfluidic network by applying, controlling, and varying pressures at a plurality of reservoirs. Modeling the microfluidic network as a series of nodes connected together by channel segments and determining the flow resistance characteristics of the channel segments may allow calculation of fluid flows through the channel segments resulting from a given pressure configuration at the reservoirs. To effect a desired flow within a particular channel or series of channels, reservoir pressures may be identified using the network model. Viscometers or other flow sensors may measure flow characteristics within the channels, and the measured flow characteristics can be used to calculate pressures to generate a desired flow. Multi-reservoir pressure modulator and pressure controller systems can optionally be used in conjunction with electrokinetic or other fluid transport mechanisms.
Owner:CAPLIPER LIFE SCI INC
Method and system for modelling a communications network
ActiveUS7392300B2Analogue computers for electric apparatusDigital computer detailsOrder of operationsNetwork model
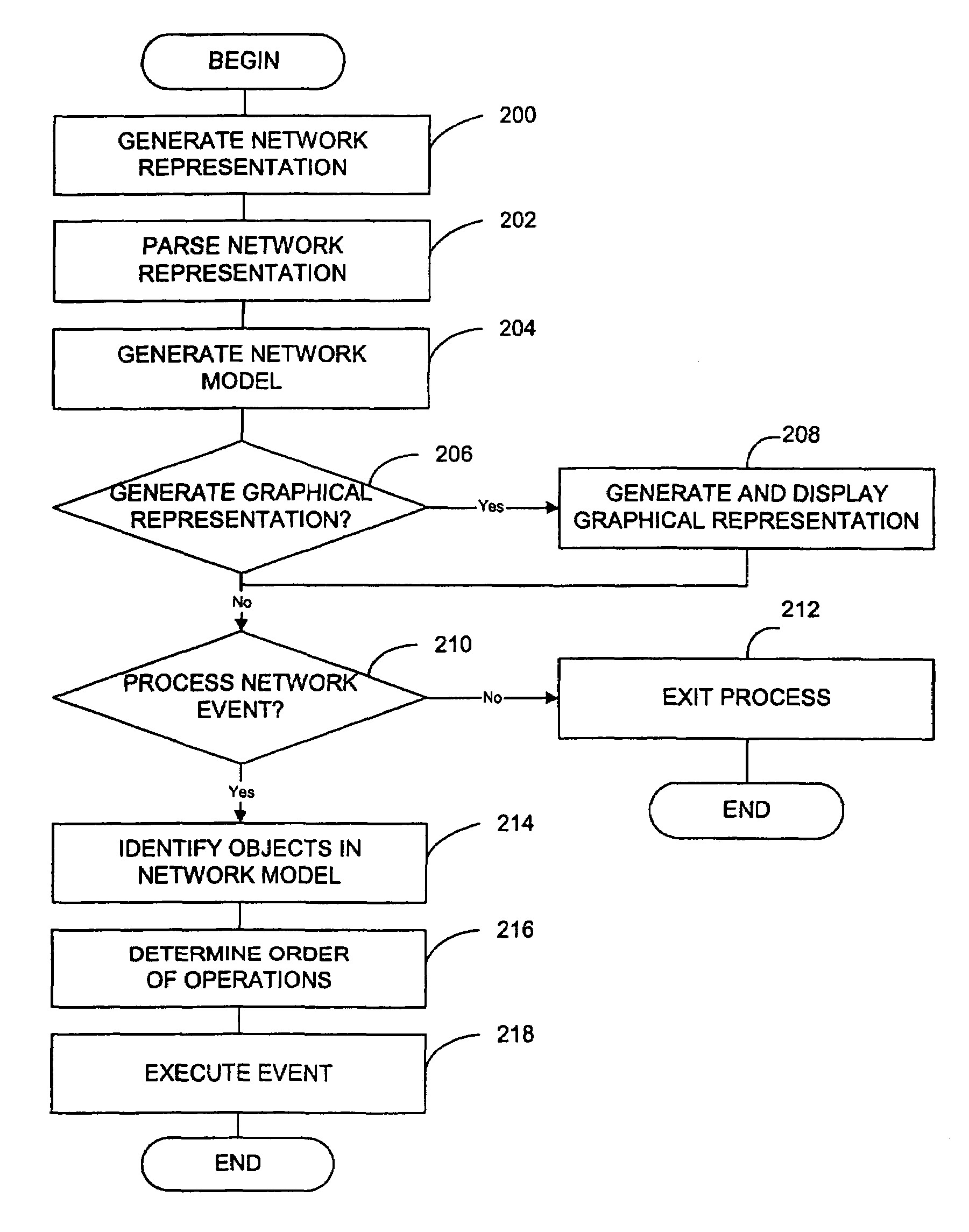
A system and method of modelling a communications network using a computer system is disclosed, the method including generating a network representation using computer-readable code that represents structured information; parsing the network representation; generating a network model using the parsed network representation, the network model including a plurality of network objects and relationships between the plurality of network objects; and storing the network model in memory. Any type of network may be modeled. The computer-readable code may be any suitable language or instructions for representing structured information such as, for example, extensible mark-up language (XML). A network inventory adapter receives the network representation from the network. The network inventory adapter is a software component that may be used to connect applications to the network. The network inventory adapter receives the network representation from the network and reads and parses the network representation to determine which network objects are to be operated on and the order of operation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Methods for testing biological network models
InactiveUS6132969AModel is bulkyLow costMicrobiological testing/measurementLibrary screeningBiological pathwayNetwork model
The present invention provides methods and systems for testing and confirming how well a network model represents a biological pathway in a biological system. The network model comprises a network of logical operators relating input cellular constituents (e.g., mRNA or protein abundances) to output classes of cellular constituents, which are affected by the pathway in the biological system. The methods of this invention provide, first, for choosing complete and efficient experiments for testing the network model which compare relative changes in the biological system in response to perturbations of the network. The methods also provide for determining an overall goodness of fit of the network model to biological system by: predicting from the network model how output classes behave in response to the chosen experiments, finding measures of relative change of cellular constituents actually observed in the chosen experiments, finding goodnesses of fit of each observed cellular constituent to an output class with which the cellular constituent has the strongest correlation, and determining an overall goodness of fit of the network model from the individual goodnesses of fit of each observed cellular constituent. Additionally, these methods provide for testing the significance of the overall goodness of fit according to a nonparametric statistical test using an empirically determined distribution of possible goodnesses of fit. This invention also provides for computer systems for carrying out the computational steps of these methods.
Owner:MICROSOFT TECH LICENSING LLC
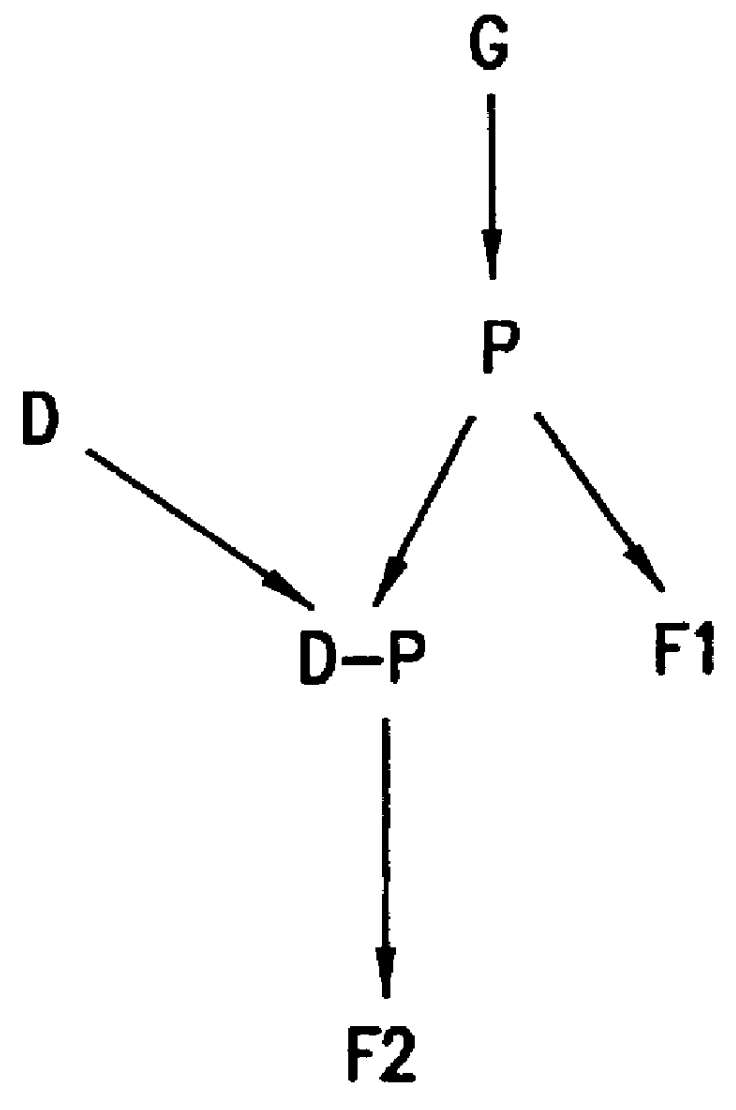
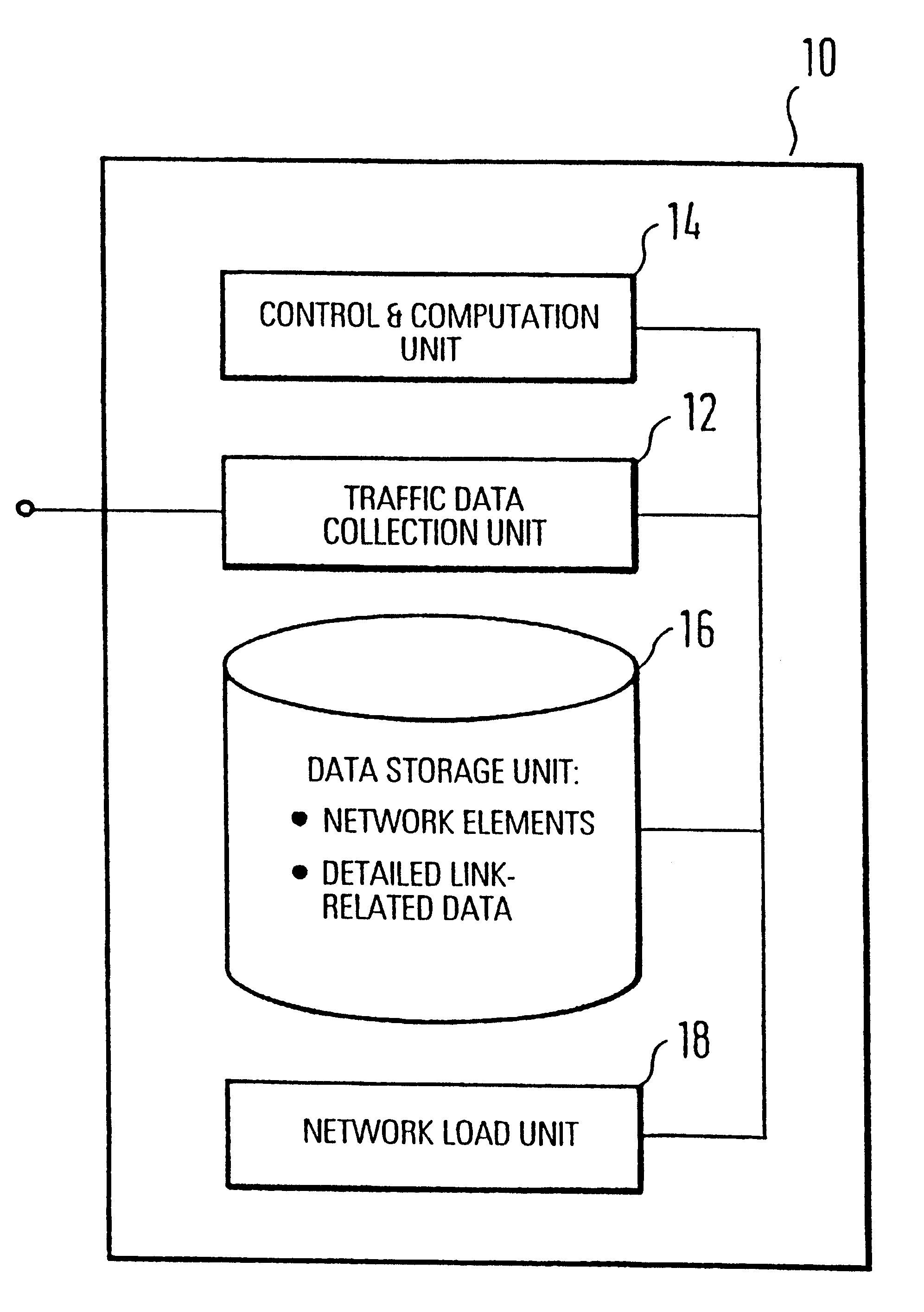
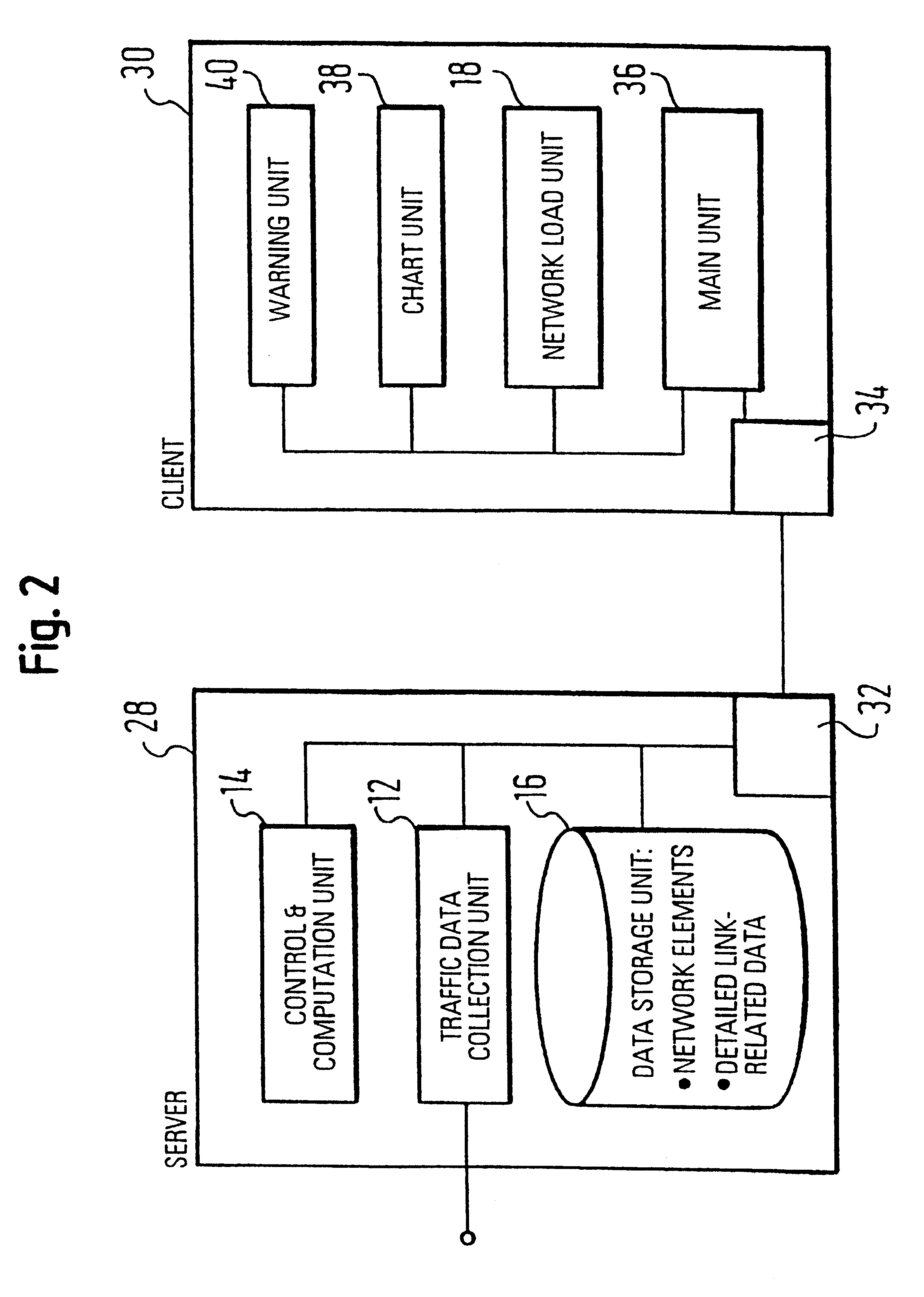
System for traffic data evaluation of real network with dynamic routing utilizing virtual network modelling
InactiveUS6442615B1Multiple digital computer combinationsData switching networksNetwork modelAdaptive routing
To provide an improved approach to traffic data evaluation in a network using dynamic routing there is provided a traffic data evaluation apparatus for a network using dynamic routing comprising traffic data collection means (12) to collect data with respect to a real traffic flow in the network. Further, the traffic data evaluation apparatus comprises a network modelling unit (14, 16) to model the network through a virtual network having virtual links without capacity restrictions imposed thereon. Still further, there is provided a network load evaluation means (18) to map the real traffic flow onto the virtual network assuming optimal routing and to compare the capacity used for each virtual link with the capacity assigned thereto. Thus, it is possible to draw conclusions on the network load by real network measurements also for a network using a dynamic routing protocol.
Owner:TELEFON AB LM ERICSSON (PUBL)
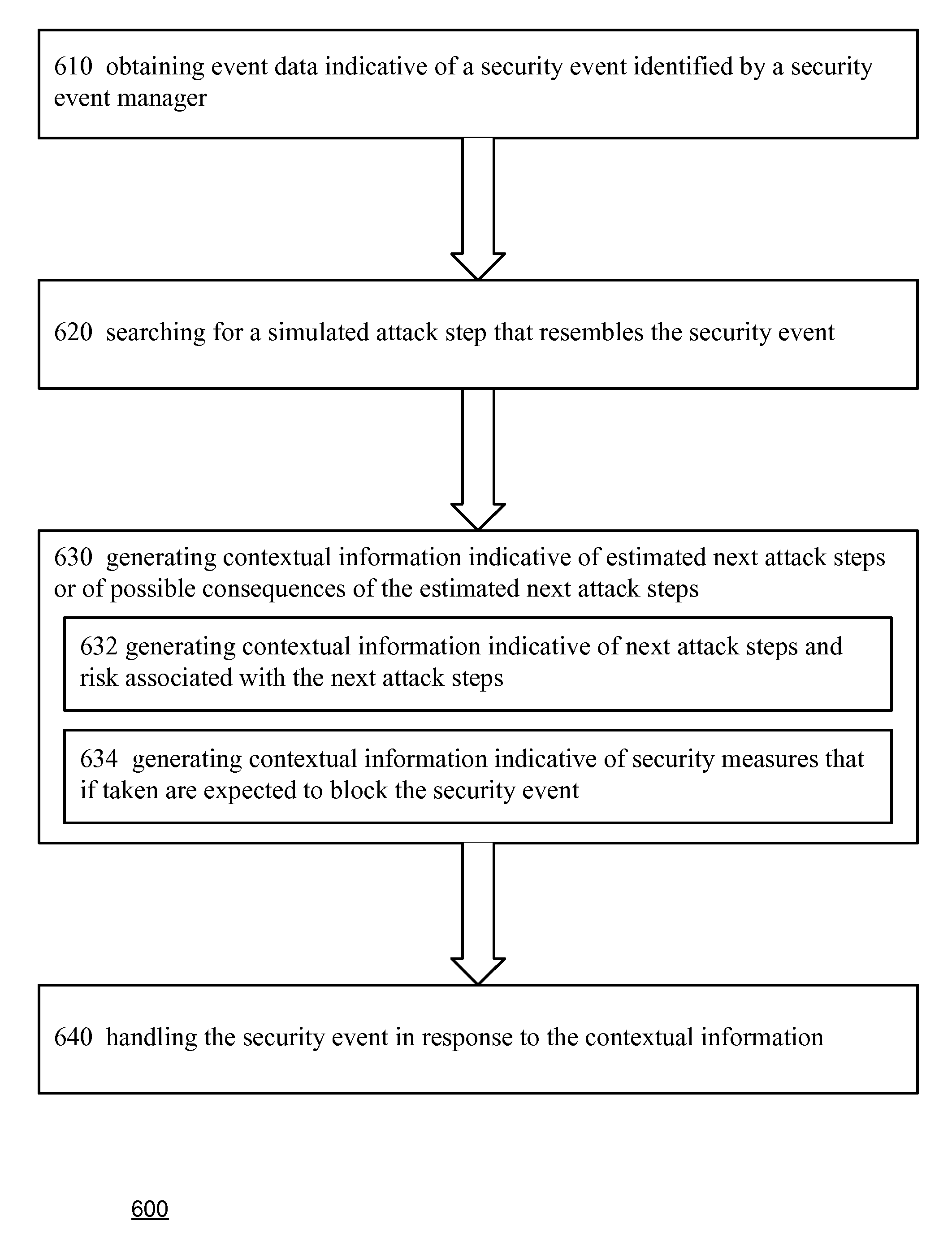
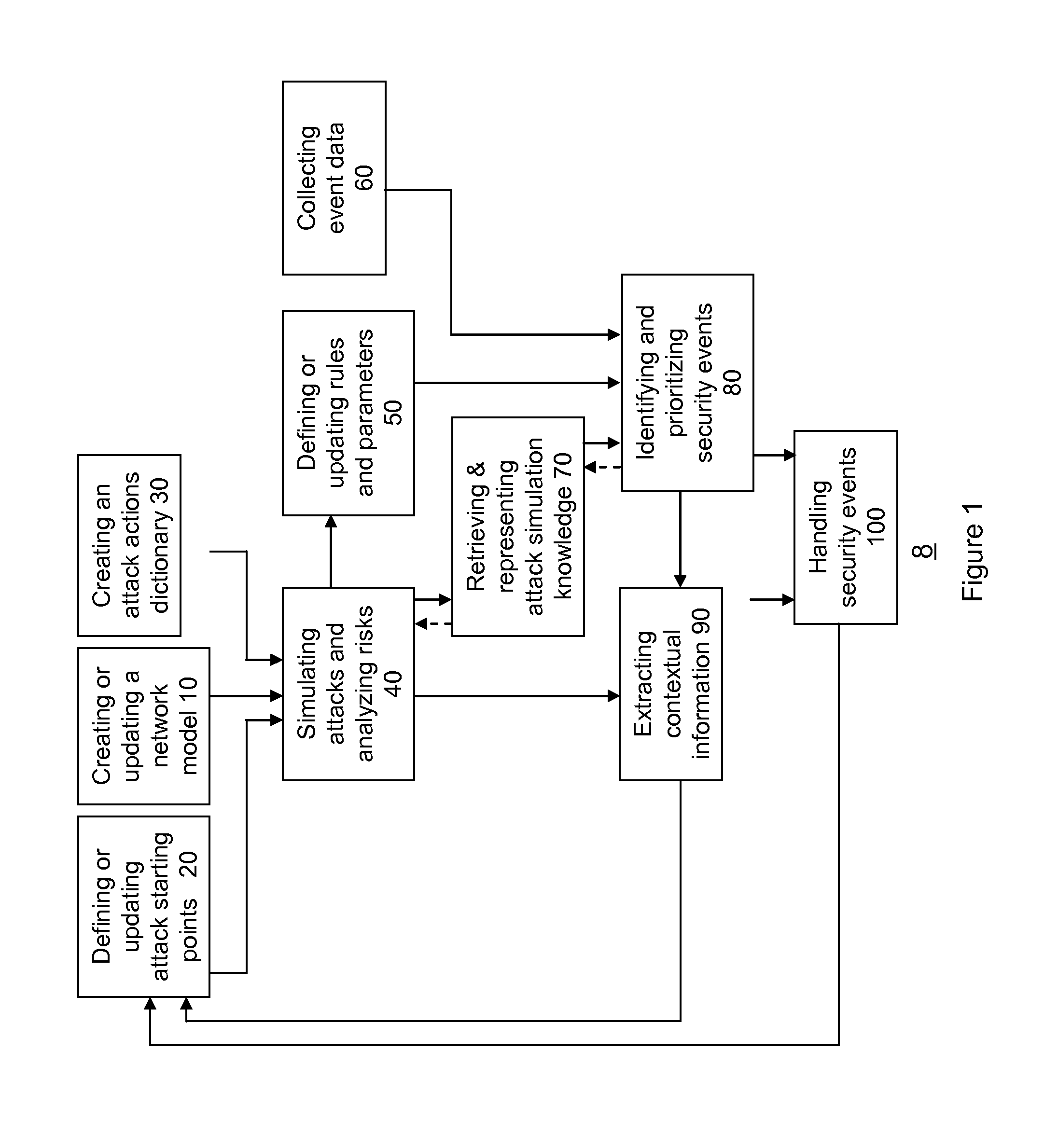
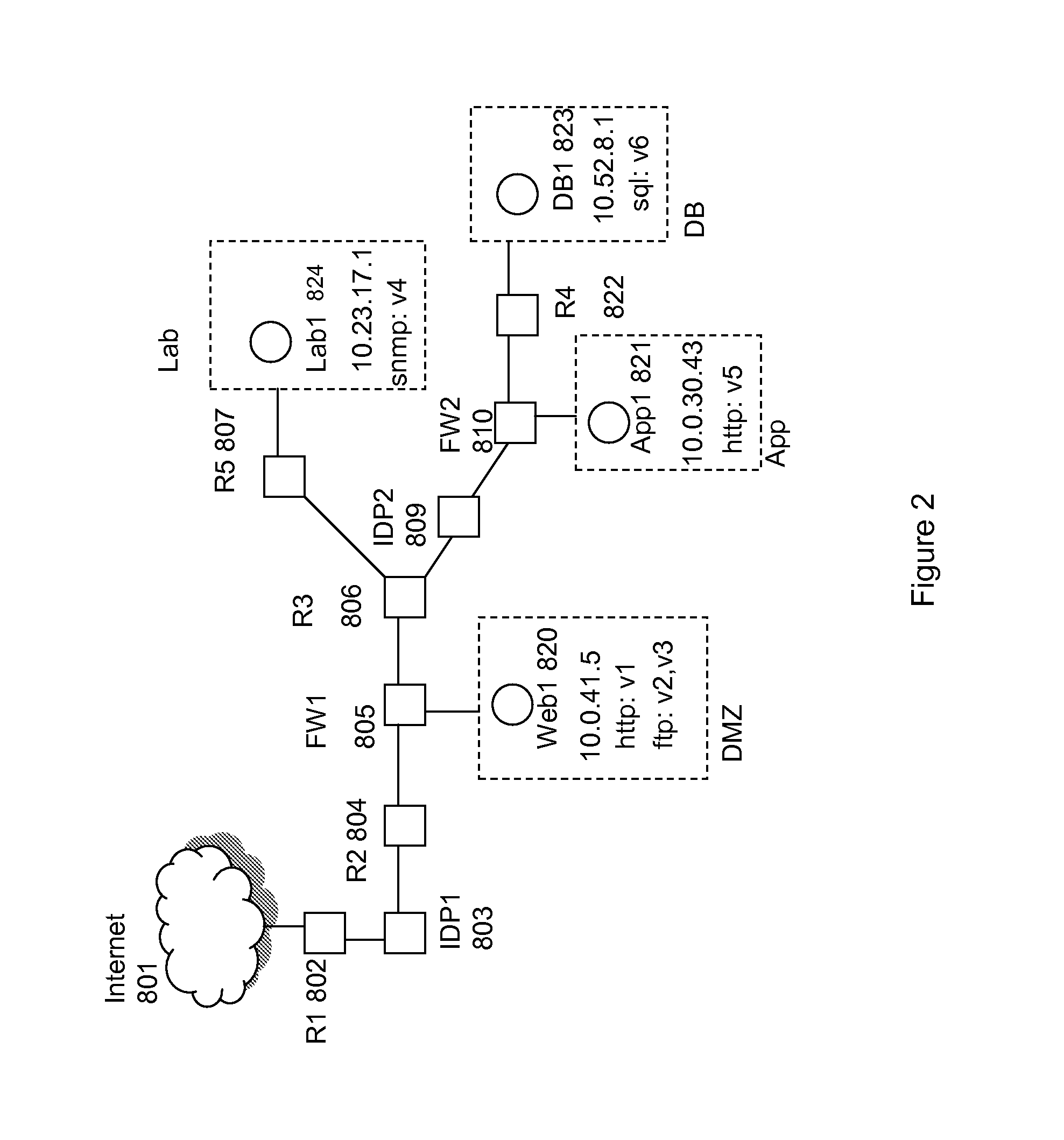
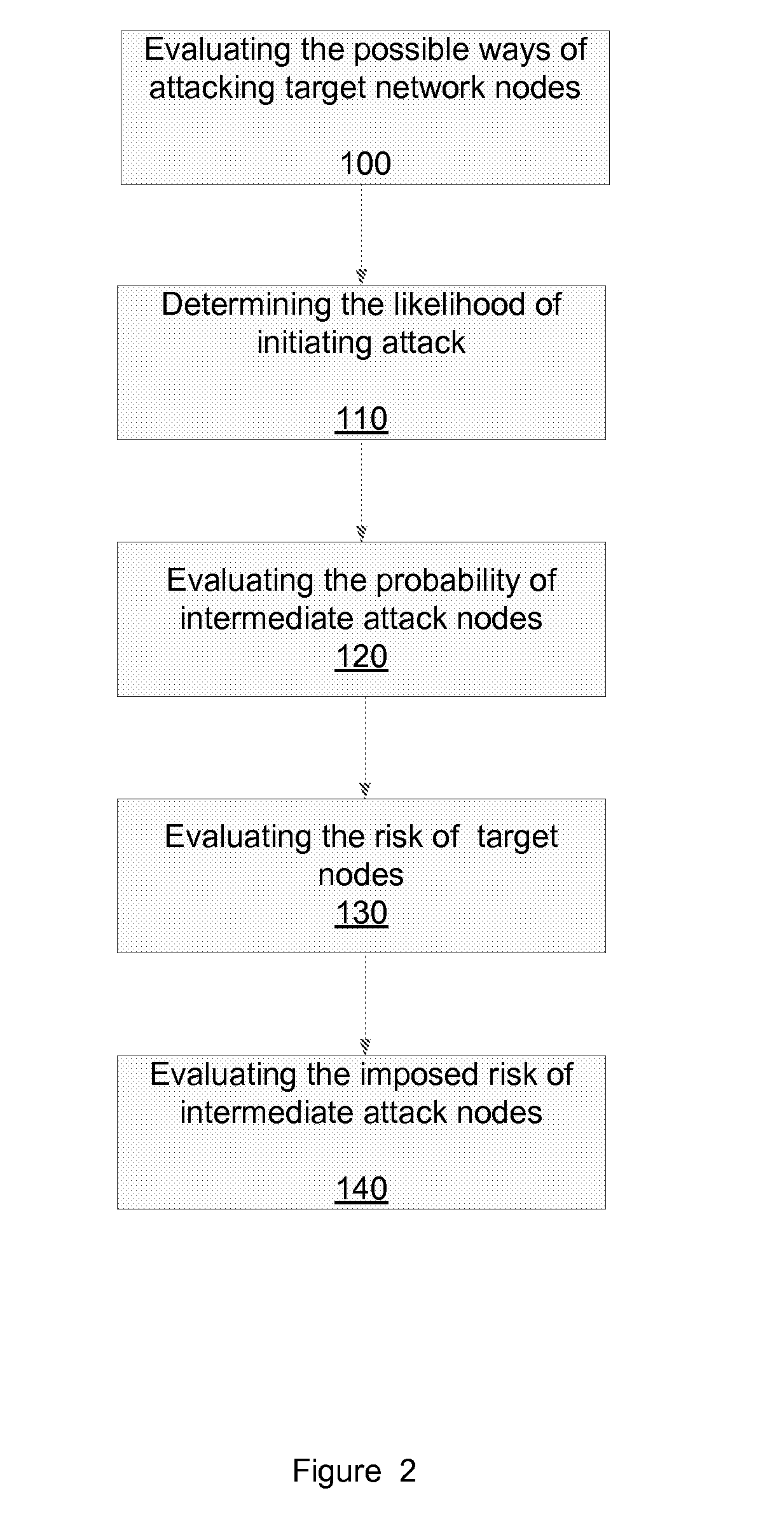
Method for simulation aided security event management
A method for simulation aided security event management, the method includes: generating attack simulation information that comprises multiple simulation data items of at least one data item type out of vulnerability instances data items, attack step data items and attack simulation scope data items; wherein the generating of attack simulation information is responsive to a network model, at least one attack starting point and attack action information; identifying security events in response to a correlation between simulation data items and event data; and prioritizing identified security events.
Owner:SKYBOX SECURITY
Method for Configuring an Optical Network
InactiveUS20090296719A1Huge complexityHuge timeData switching by path configurationOptical multiplexObject definitionNetwork model
A network model for the planning and / or the provisioning of traffic flows in a communication network includes nodes interconnected with each other by links according to a given network topology. The network model uses a graph defined by arc objects storing information related to both the links and adjacent nodes thereof.
Owner:TELECOM ITALIA SPA
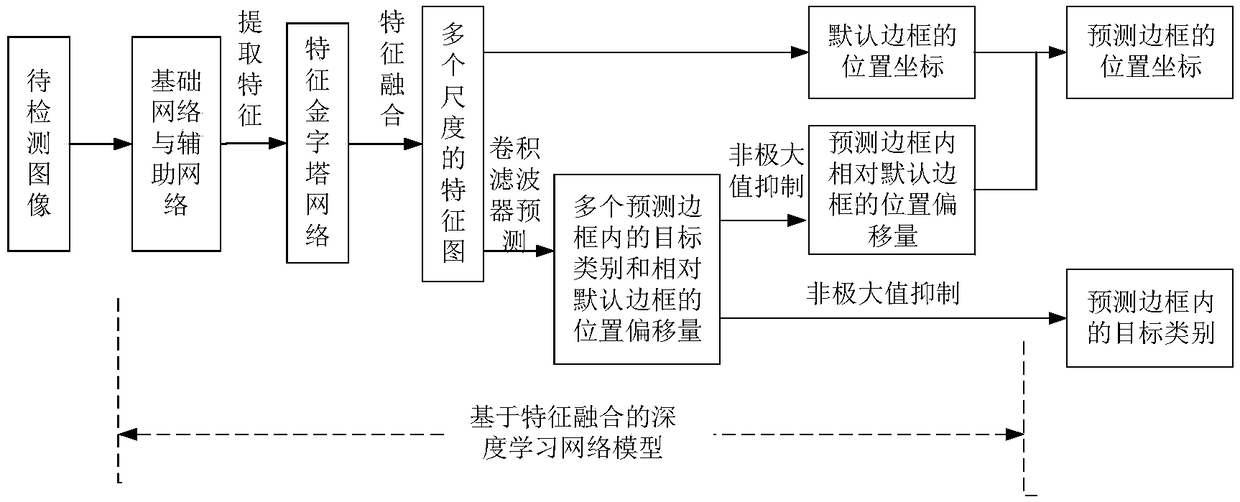
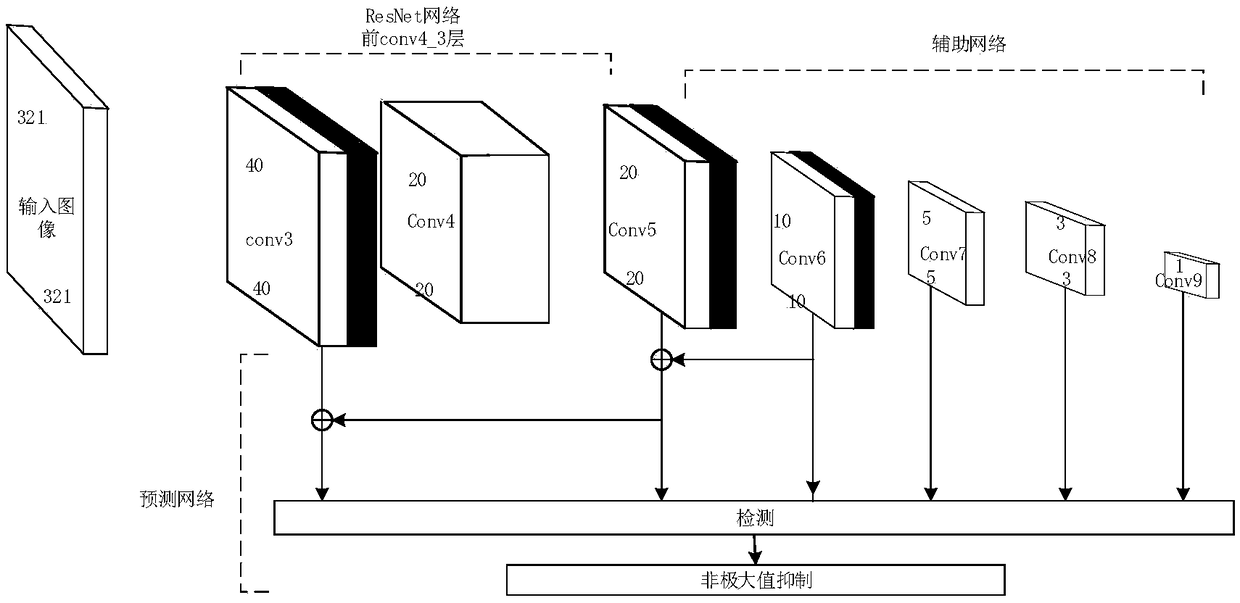
Small target detection method based on feature fusion and depth learning
InactiveCN109344821AScalingRich information featuresCharacter and pattern recognitionNetwork modelFeature fusion
The invention discloses a small target detection method based on feature fusion and depth learning, which solves the problems of poor detection accuracy and real-time performance for small targets. The implementation scheme is as follows: extracting high-resolution feature map through deeper and better network model of ResNet 101; extracting Five successively reduced low resolution feature maps from the auxiliary convolution layer to expand the scale of feature maps. Obtaining The multi-scale feature map by the feature pyramid network. In the structure of feature pyramid network, adopting deconvolution to fuse the feature map information of high-level semantic layer and the feature map information of shallow layer; performing Target prediction using feature maps with different scales and fusion characteristics; adopting A non-maximum value to suppress the scores of multiple predicted borders and categories, so as to obtain the border position and category information of the final target. The invention has the advantages of ensuring high precision of small target detection under the requirement of ensuring real-time detection, can quickly and accurately detect small targets in images, and can be used for real-time detection of targets in aerial photographs of unmanned aerial vehicles.
Owner:XIDIAN UNIV
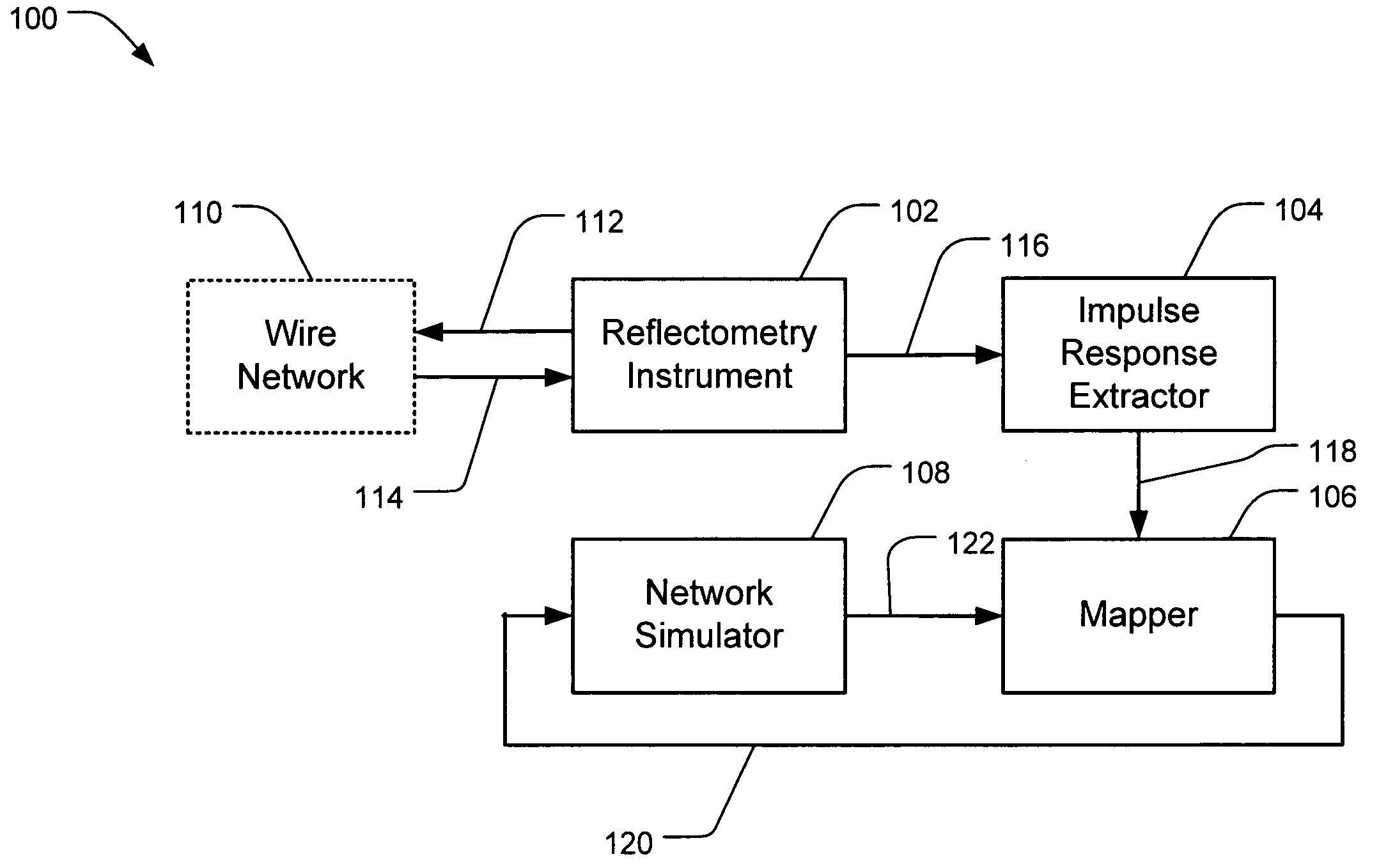
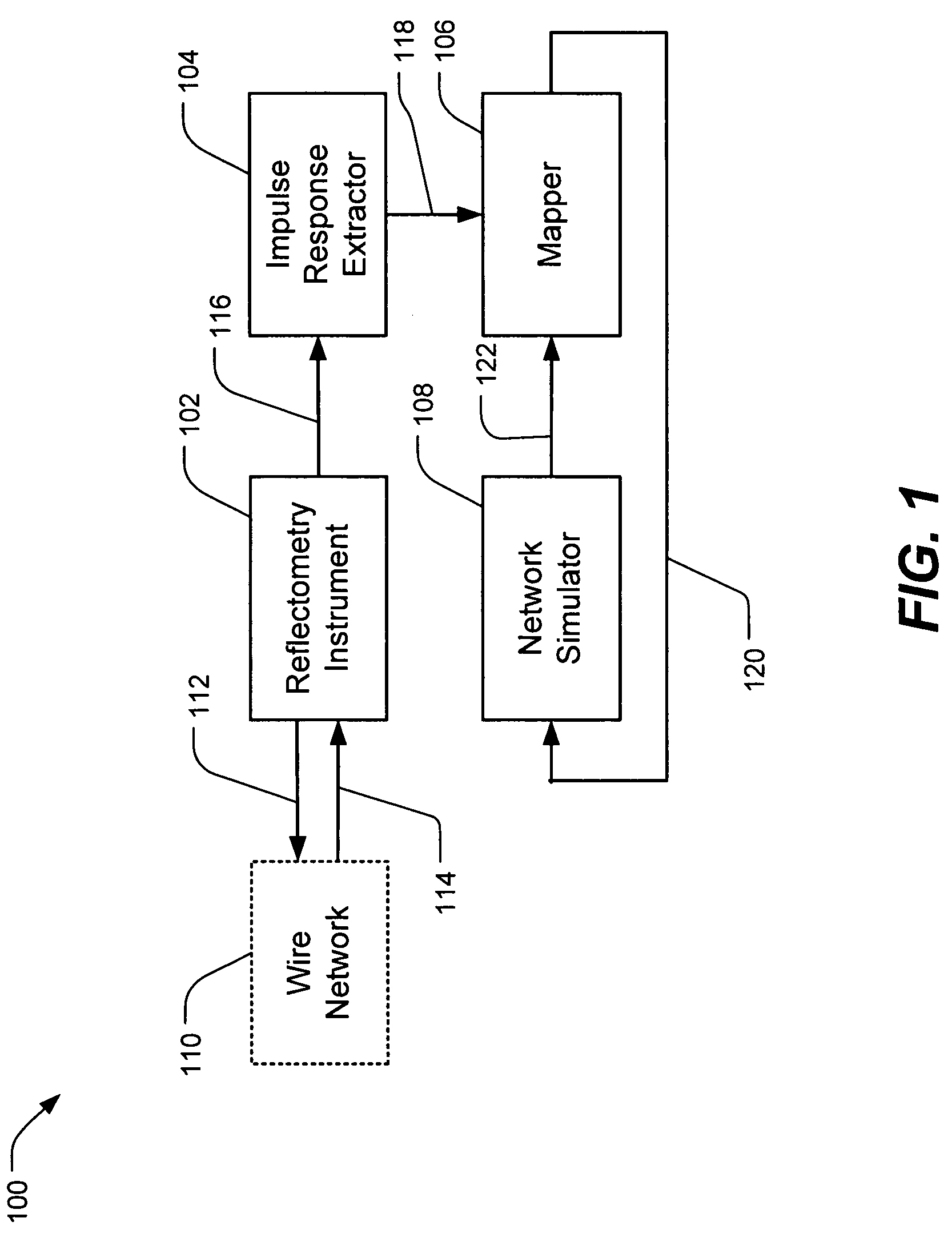
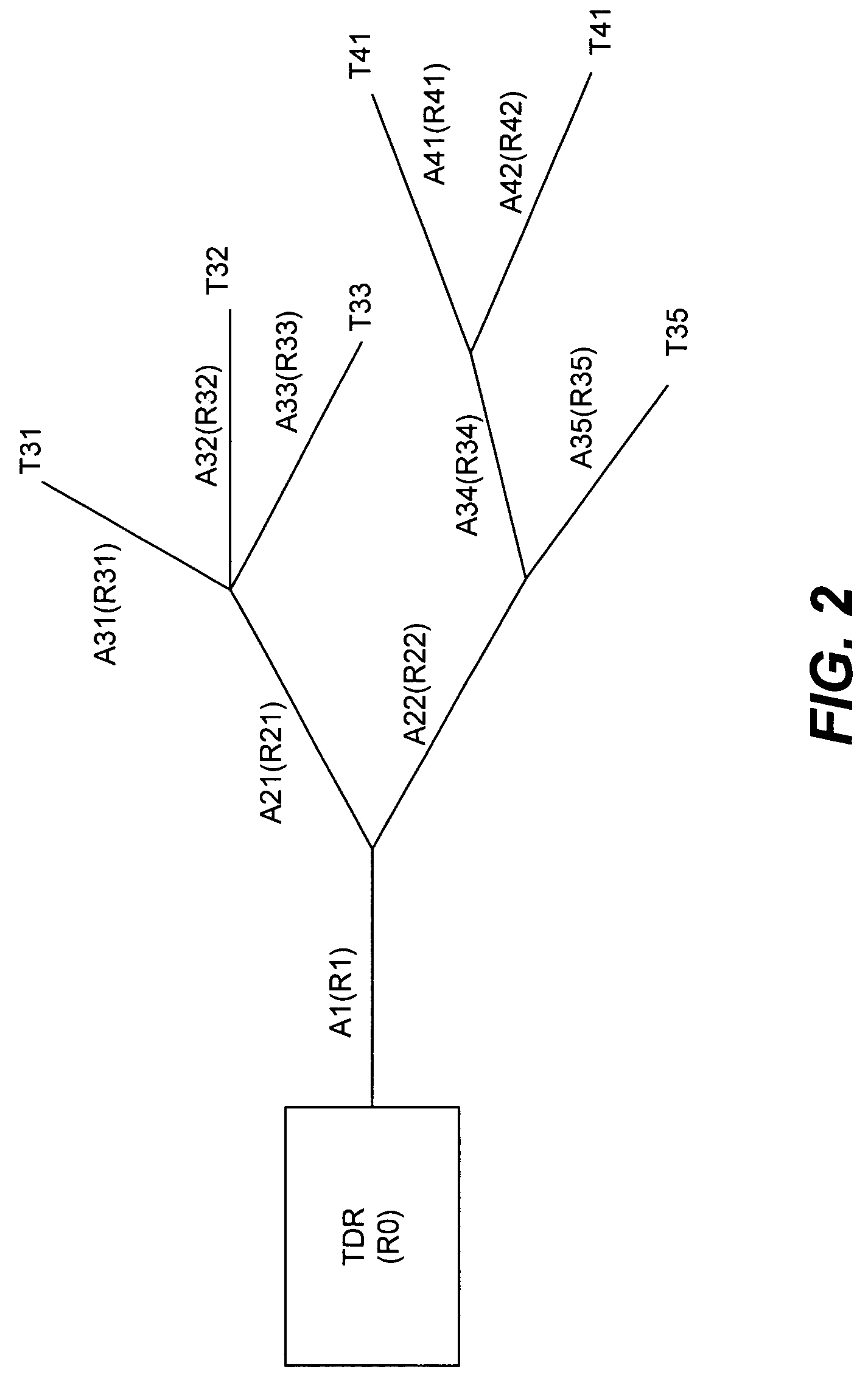
Wire network mapping method and apparatus using impulse responses
ActiveUS7282922B2Reduce the differenceFault location by pulse reflection methodsFinite impulse responseNetwork model
A method and apparatus for mapping a wire network is disclosed. The method includes obtaining a reflectometry test signal of the wire network. An estimated network impulse response is estimated from the reflectometry response. A wire network model is then initialized, and iteratively improved by simulating an impulse response of the wire network model and adjusting the wire network model to reduce differences between the simulated impulse response and estimated network impulse response.
Owner:UNIV OF UTAH RES FOUND
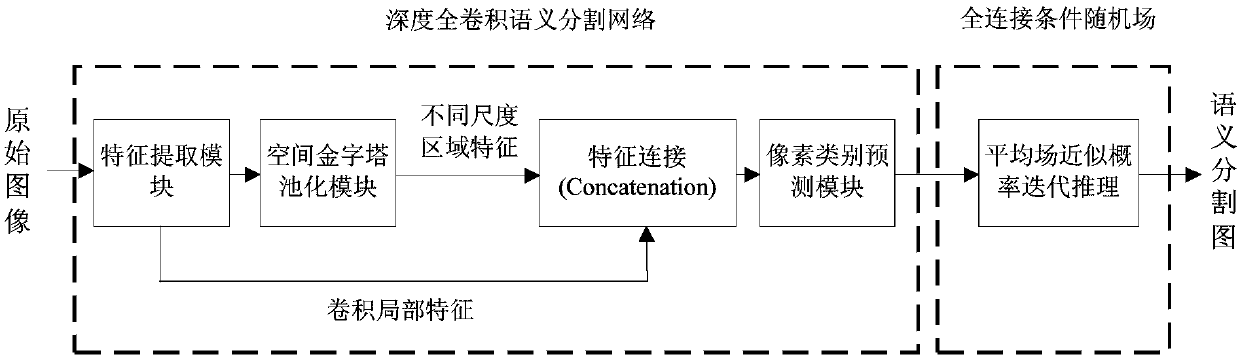
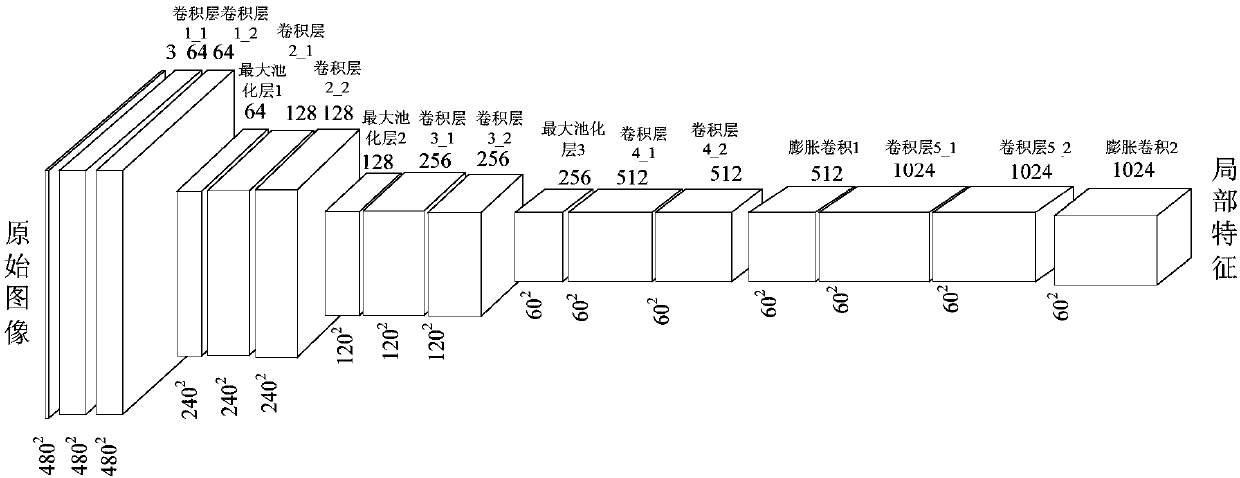
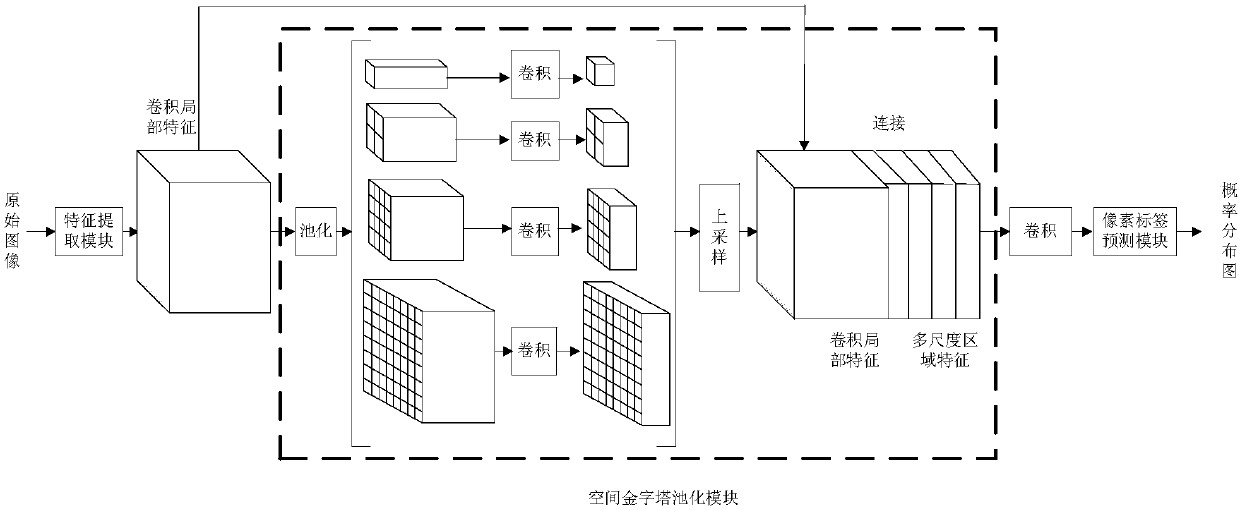
Image semantic division method based on depth full convolution network and condition random field
InactiveCN108062756ADoes not reduce dimensionalityHigh-resolutionImage enhancementImage analysisConditional random fieldImage resolution
The invention provides an image semantic division method based on a depth full convolution network and a condition random field. The image semantic division method comprises the following steps: establishing a depth full convolution semantic division network model; carrying out structured prediction based on a pixel label of a full connection condition random field, and carrying out model training, parameter learning and image semantic division. According to the image semantic division method provided by the invention, expansion convolution and a spatial pyramid pooling module are introduced into the depth full convolution network, and a label predication pattern output by the depth full convolution network is further revised by utilizing the condition random field; the expansion convolution is used for enlarging a receptive field and ensures that the resolution ratio of a feature pattern is not changed; the spatial pyramid pooling module is used for extracting contextual features of different scale regions from a convolution local feature pattern, and a mutual relation between different objects and connection between the objects and features of regions with different scales are provided for the label predication; the full connection condition random field is used for further optimizing the pixel label according to feature similarity of pixel strength and positions, so that a semantic division pattern with a high resolution ratio, an accurate boundary and good space continuity is generated.
Owner:CHONGQING UNIV OF TECH
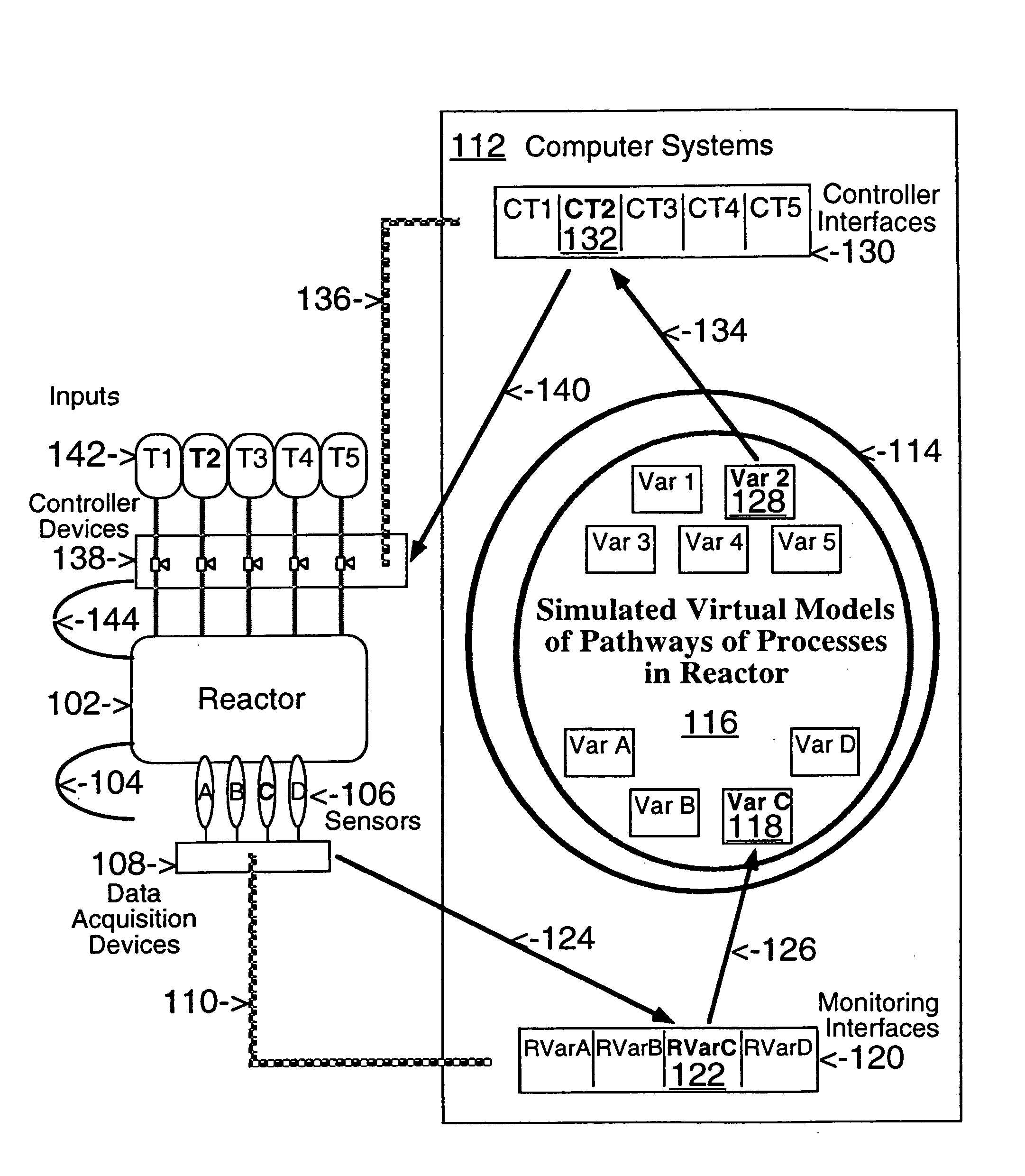
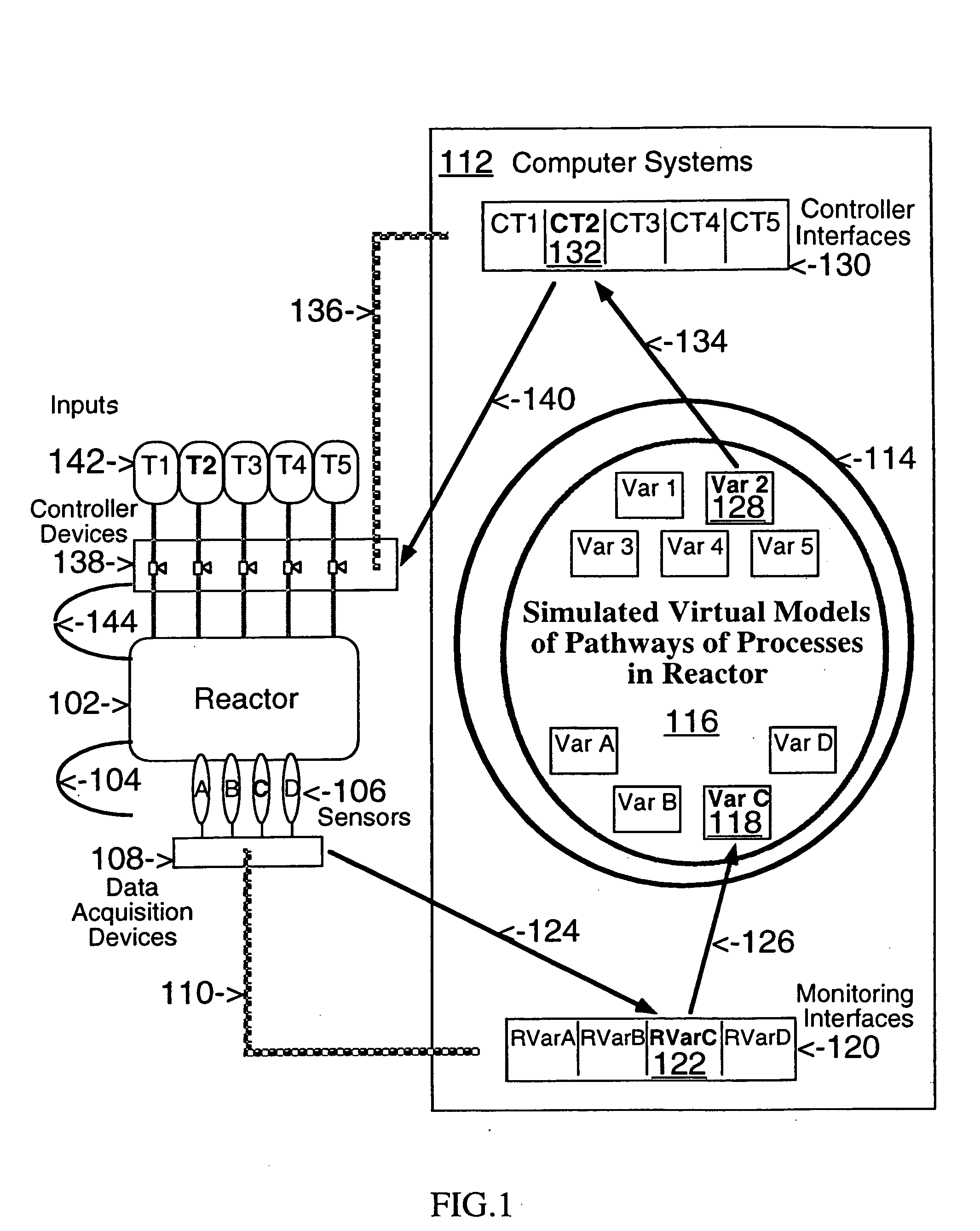
Network models of complex systems
This invention describes computer based virtual models of complex systems, together with integrated systems and methods providing a development and execution framework for visual modeling and dynamic simulation of said models. The virtual models can be used for analysis, monitoring, or control of the operation of the complex systems modeled, as well as for information retrieval. More particularly, the virtual models in the present implementation relate to biological complex systems. In the current implementation the virtual models comprise building blocks representing physical, chemical, or biological processes, the pools of entities that participate in those processes, a hierarchy of compartments representing time-intervals or the spatial and / or functional structure of the complex system in which said entities are located and said processes take place, and the description of the composition of those entities. The building blocks encapsulate in different layers the information, data, and mathematical models that characterize and define each virtual model, and a plurality of methods is associated with their components. The models are built by linking instances of the building blocks in a predefined way, which, when integrated by the methods provided in this invention, result in multidimensional networks of pathways. A number of functions and graphical interfaces can be selected for said instances of building blocks, to extract in various forms the information contained in said models. Those functions include: a) on-the-fly creation of displays of interactive multidimensional networks of pathways, according to user selections; b) dynamic quantitative simulations of selected networks; and c) complex predefined queries based on the relative position of pools of entities in the pathways, the role that the pools play in different processes, the location in selected compartments, and / or the structural components of the entities of those pools. The system integrates inferential control with quantitative and scaled simulation methods, and provides a variety of alternatives to deal with complex dynamic systems and with incomplete and constantly evolving information and data.
Owner:INTERTECH VENTURES
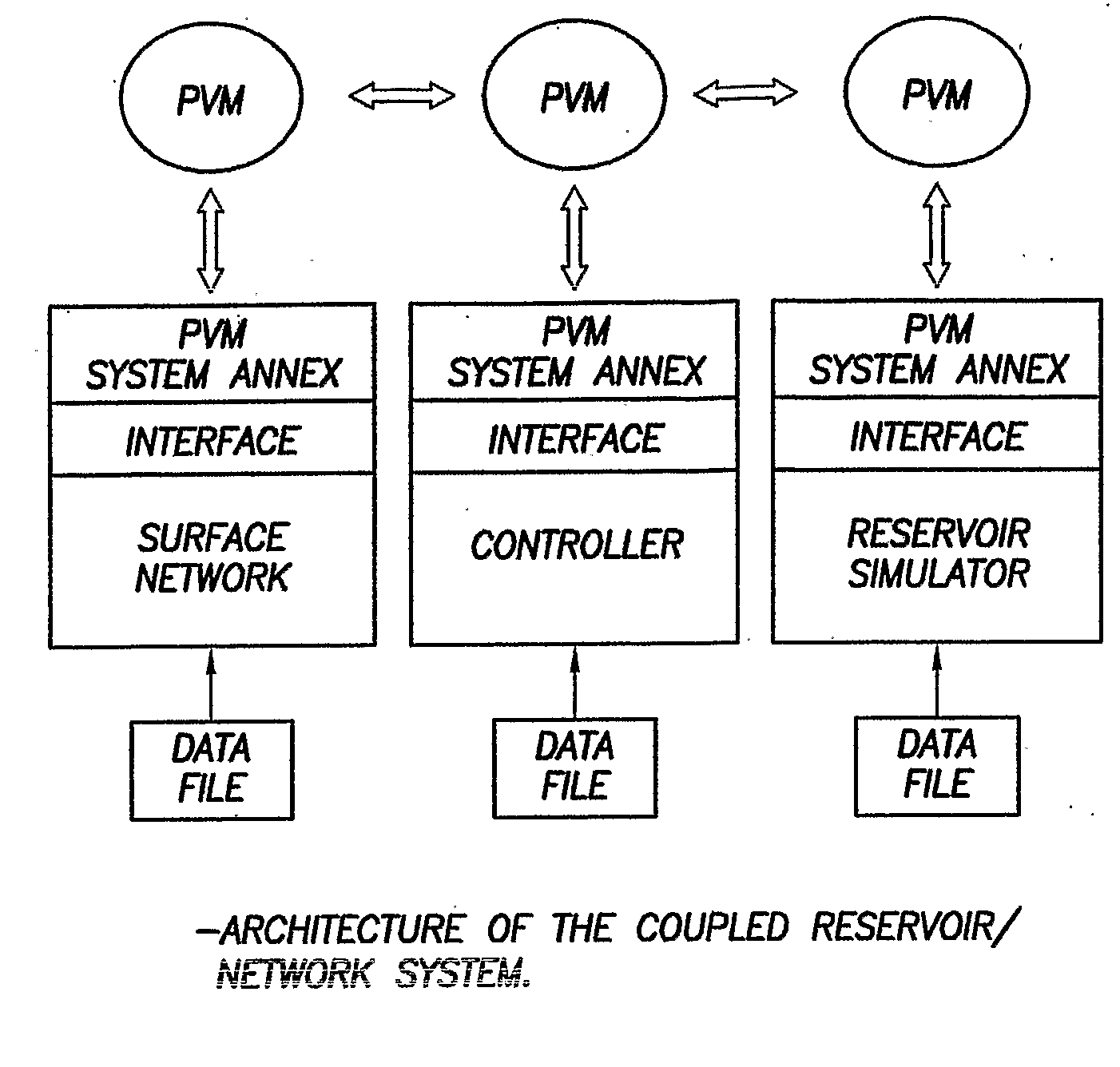
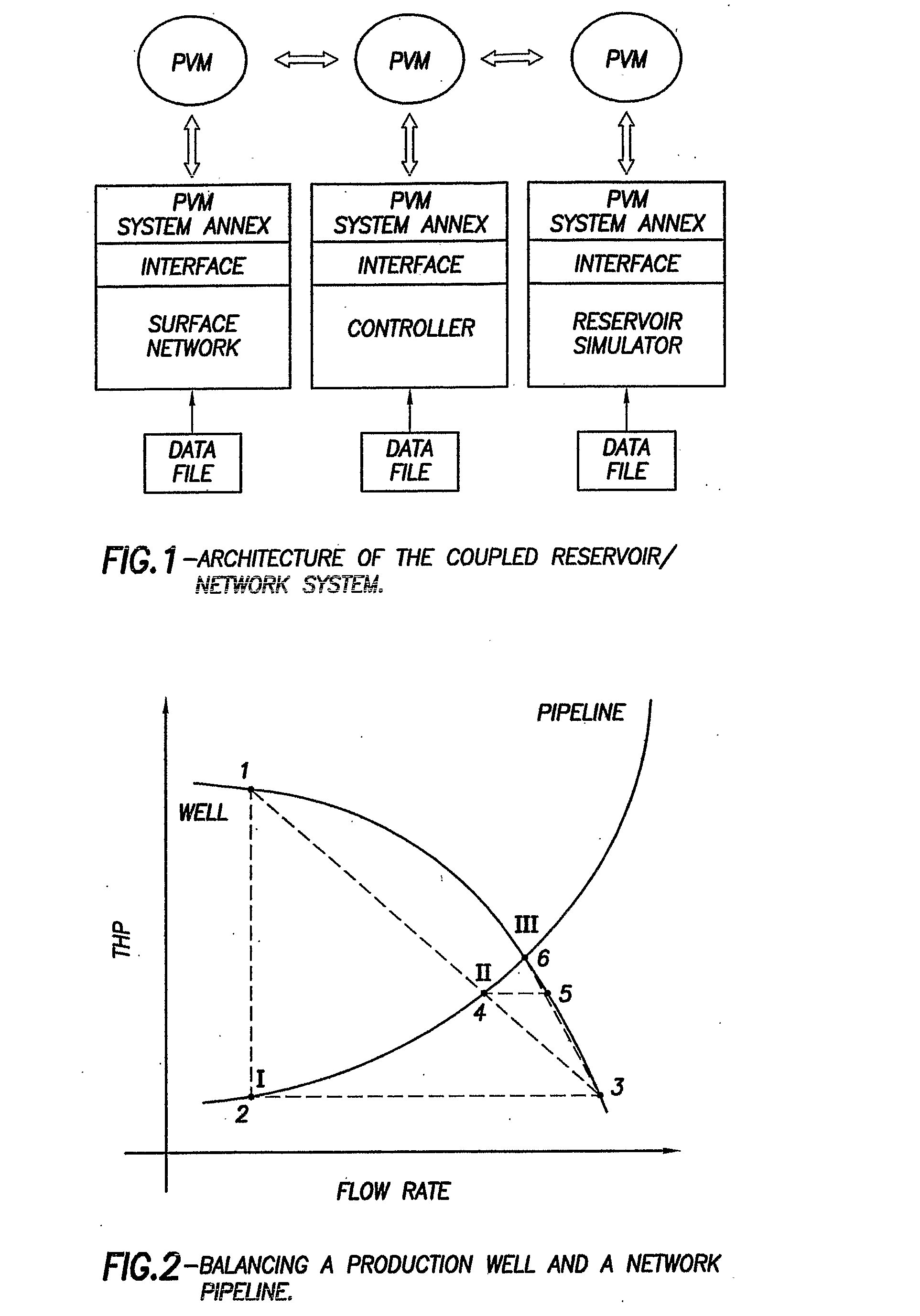
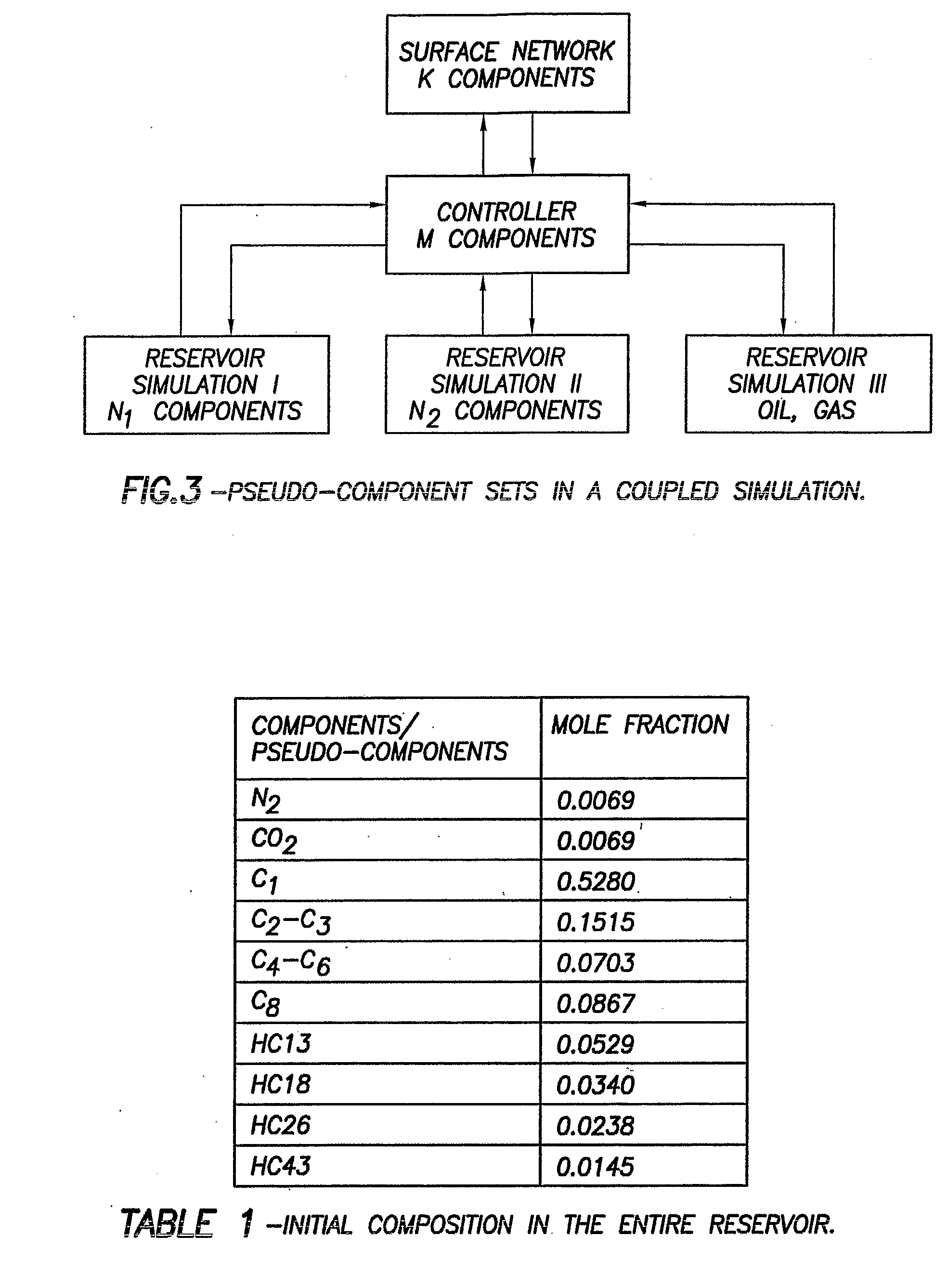
Method and system for integrated reservoir and surface facility networks simulations
InactiveUS20070112547A1Design optimisation/simulationConstraint-based CADMulti platformNetwork model
Integrated surface-subsurface modeling has been shown to have a critical impact on field development and optimization. Integrated models are often necessary to analyze properly the pressure interaction between a reservoir and a constrained surface facility network, or to predict the behavior of several fields, which may have different fluid compositions, sharing a common surface facility. The latter is gaining a tremendous significance in recent deepwater field development. These applications require an integrated solution with the following capabilities: * to balance a surface network model with a reservoir simulation model in a robust and efficient manner. * To couple multiple reservoir models, production and injection networks, synchronising their advancement through time. * To allow the reservoir and surface network models to use their own independent fluid descriptions (black oil or compositional descriptions with differing sets of pseudo-components). * To apply global production and injection constraints to the coupled system (including the transfer of re-injection fluids between reservoirs). In this paper we describe a general-purpose multi-platform reservoir and network coupling controller having all the above features. The controller communicates with a selection of reservoir simulators and surface network simulators via an open message-passing interface. It manages the balancing of the reservoirs and surface networks, and synchronizes their advancement through time. The controller also applies the global production and injection constraints, and converts the hydrocarbon fluid streams between the different sets of pseudo-components used in the simulation models. The controller's coupling and synchronization algorithms are described, and example applications are provided. The flexibility of the controller's open interface makes it possible to plug in further modules (to perform optimization, for example) and additional simulators.
Owner:SCHLUMBERGER TECH CORP
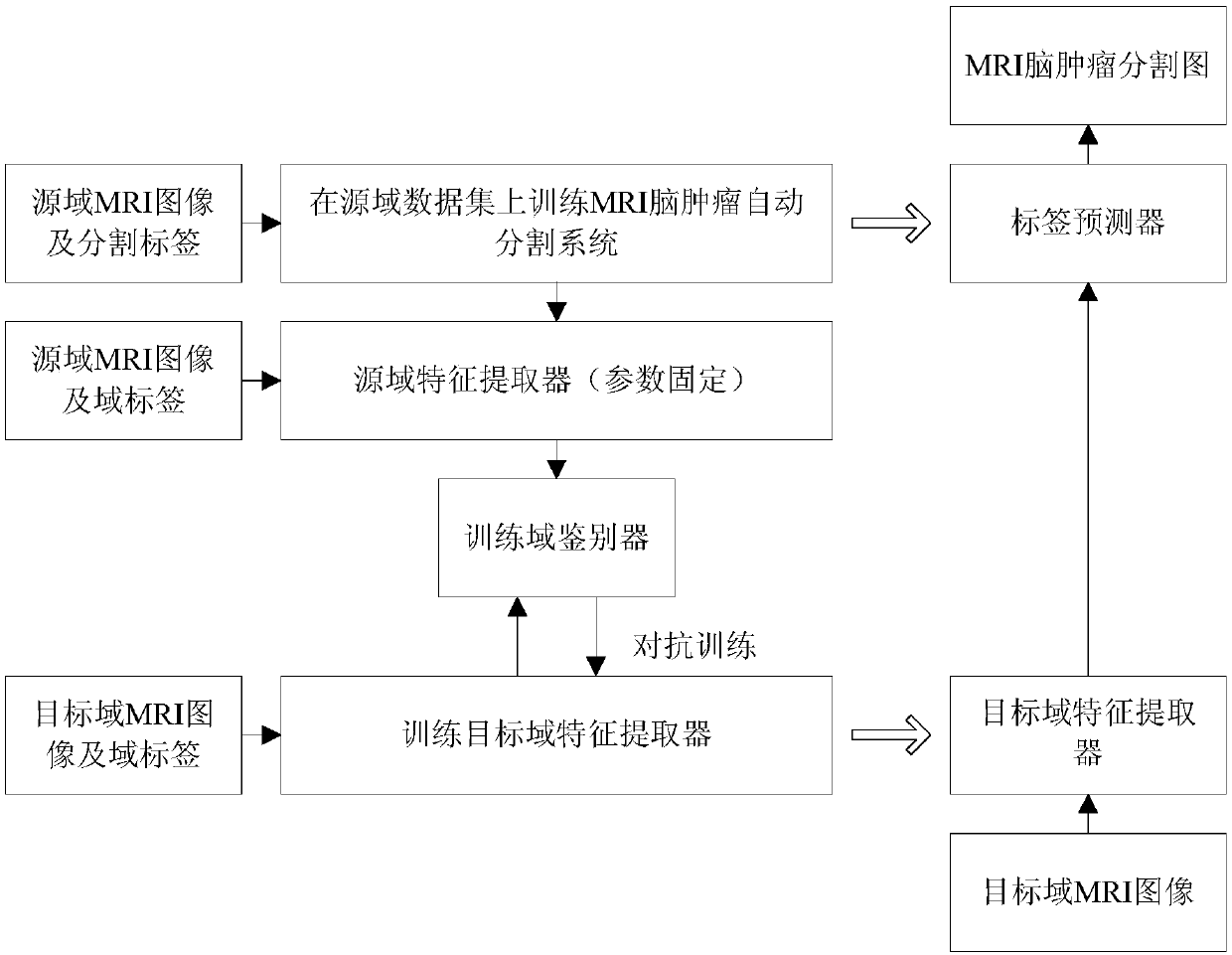
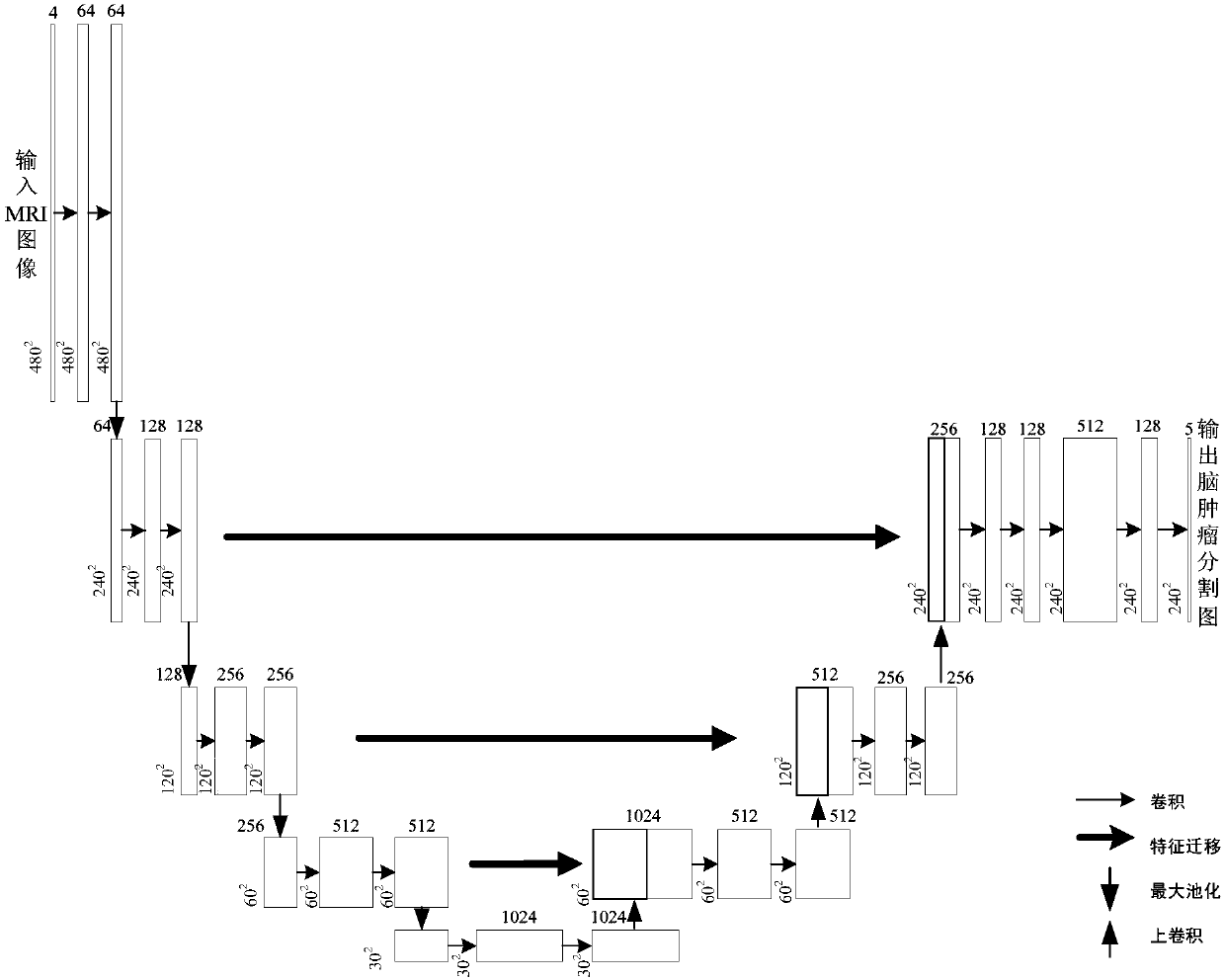
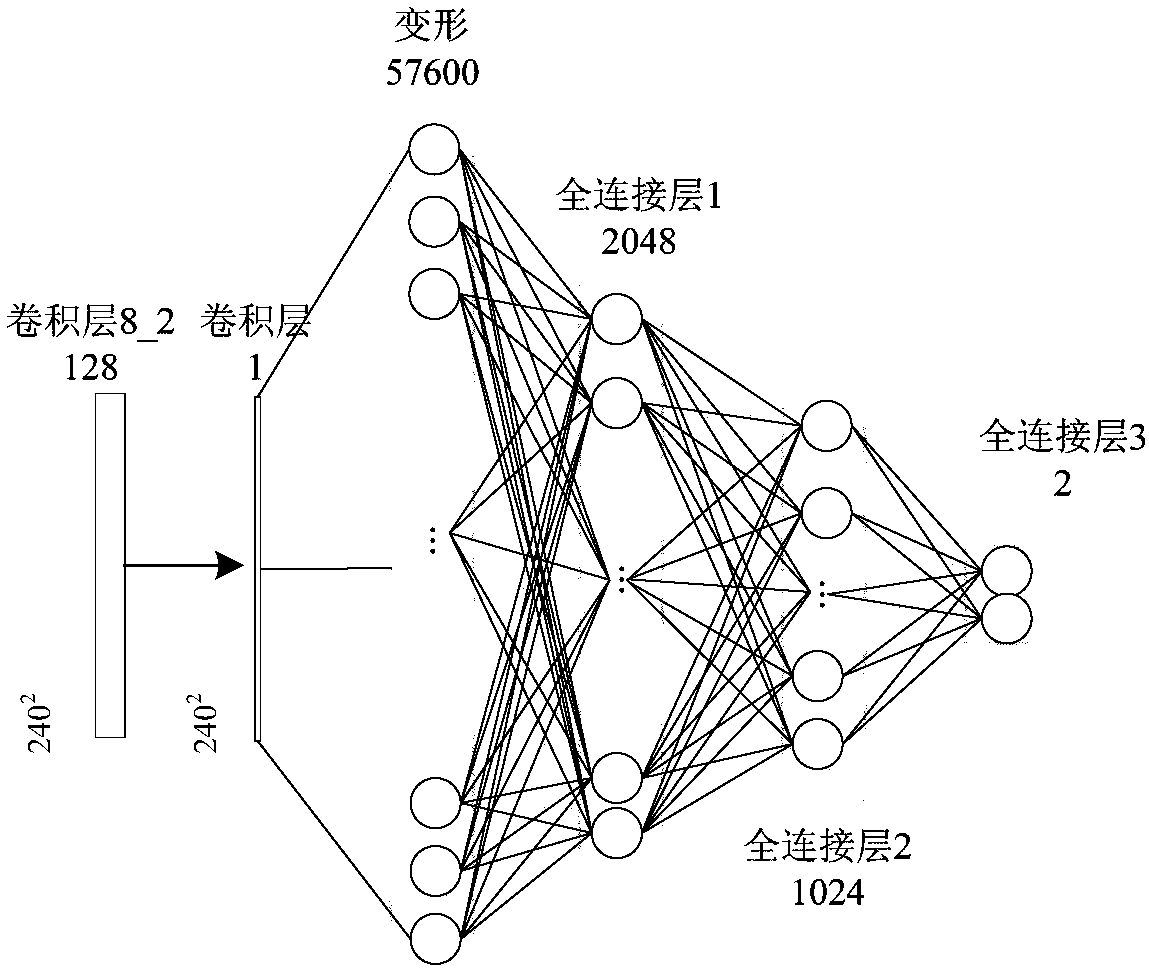
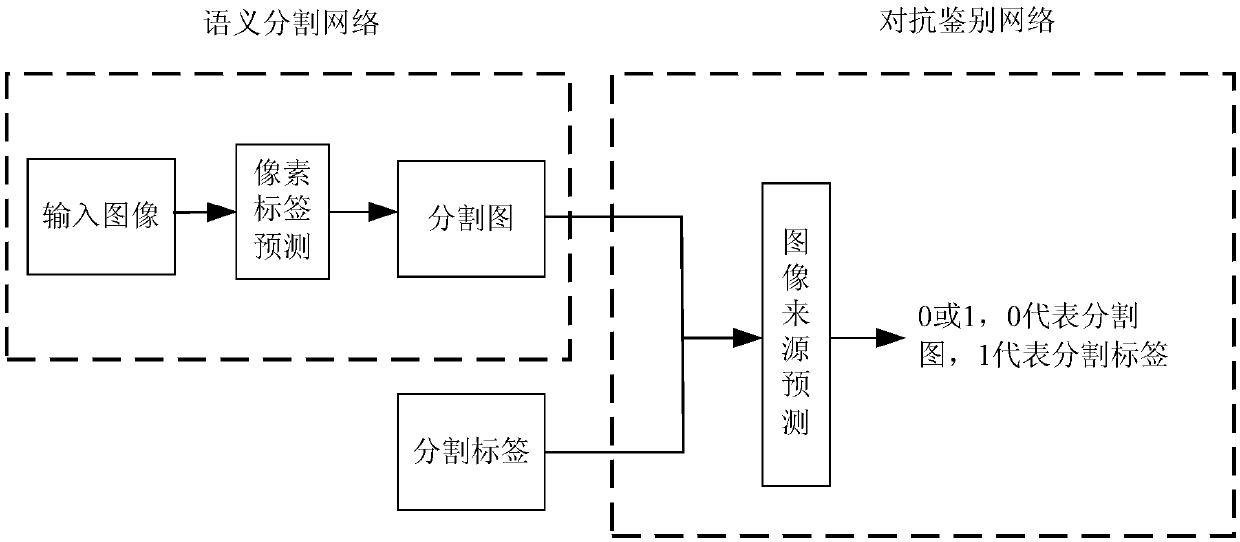
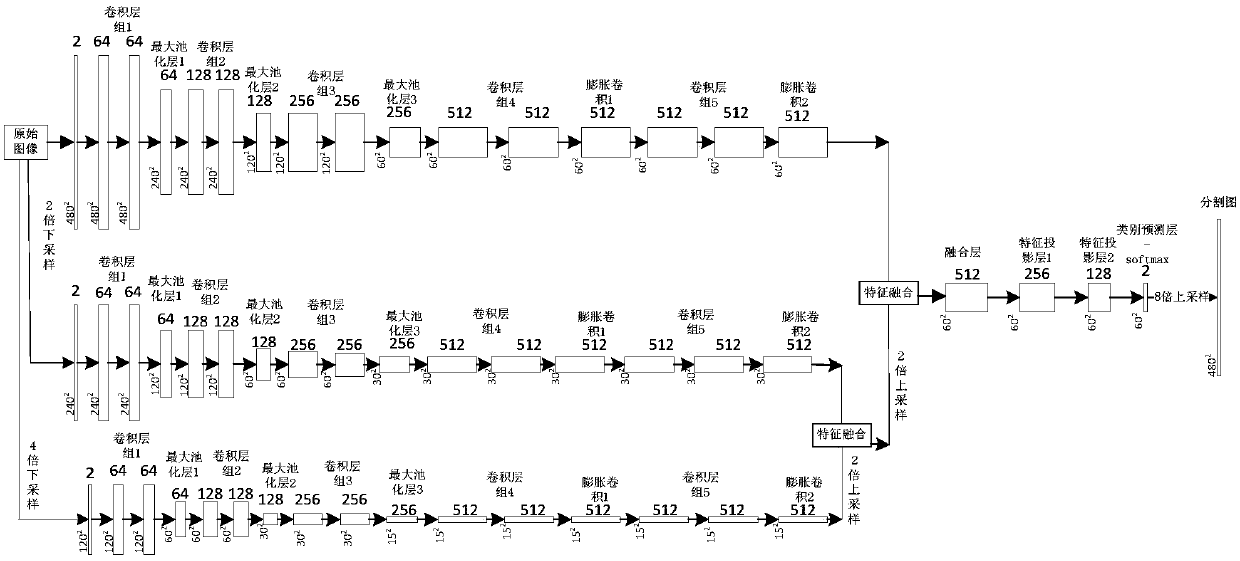
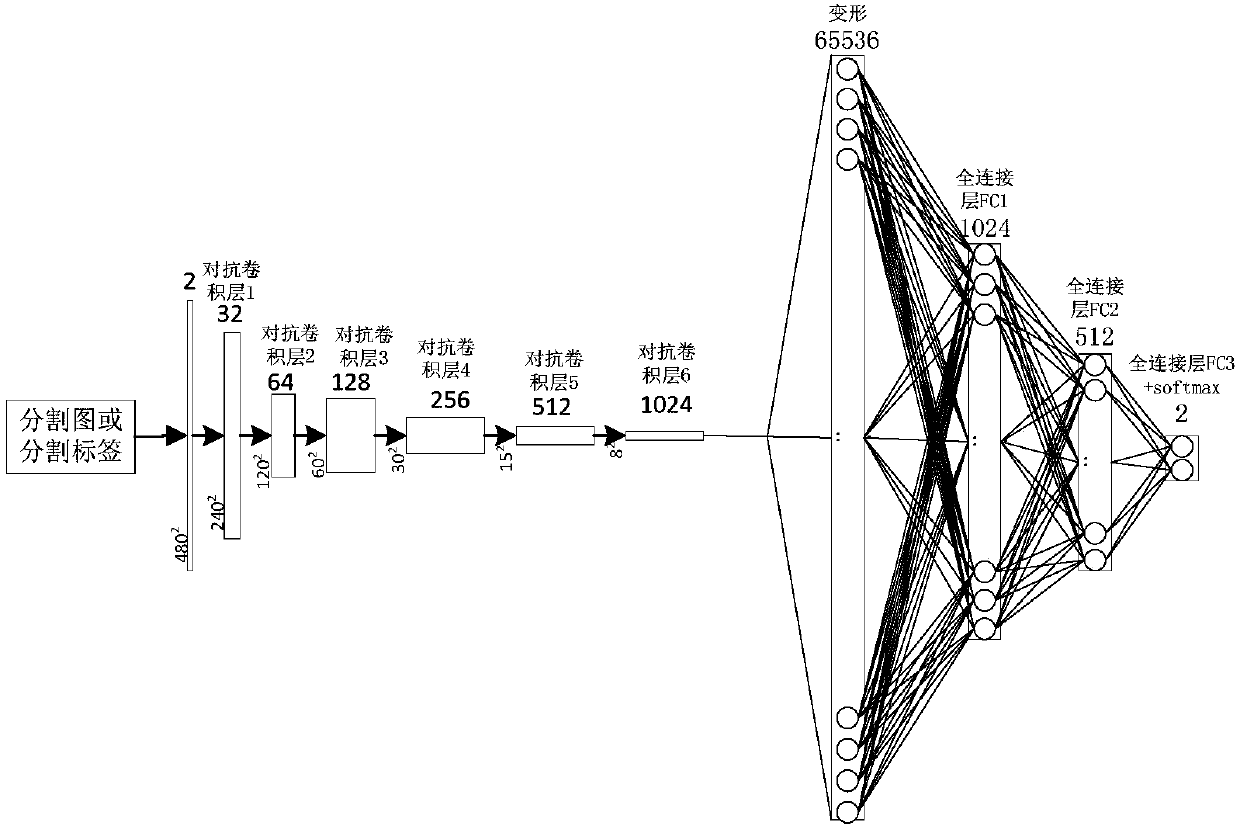
Unsupervised domain-adaptive brain tumor semantic segmentation method based on deep adversarial learning
InactiveCN108062753AAccurate predictionEasy to trainImage enhancementImage analysisDiscriminatorNetwork model
The invention provides an unsupervised domain-adaptive brain tumor semantic segmentation method based on deep adversarial learning. The method comprises the steps of deep coding-decoding full-convolution network segmentation system model setup, domain discriminator network model setup, segmentation system pre-training and parameter optimization, adversarial training and target domain feature extractor parameter optimization and target domain MRI brain tumor automatic semantic segmentation. According to the method, high-level semantic features and low-level detailed features are utilized to jointly predict pixel tags by the adoption of a deep coding-decoding full-convolution network modeling segmentation system, a domain discriminator network is adopted to guide a segmentation model to learn domain-invariable features and a strong generalization segmentation function through adversarial learning, a data distribution difference between a source domain and a target domain is minimized indirectly, and a learned segmentation system has the same segmentation precision in the target domain as in the source domain. Therefore, the cross-domain generalization performance of the MRI brain tumor full-automatic semantic segmentation method is improved, and unsupervised cross-domain adaptive MRI brain tumor precise segmentation is realized.
Owner:CHONGQING UNIV OF TECH
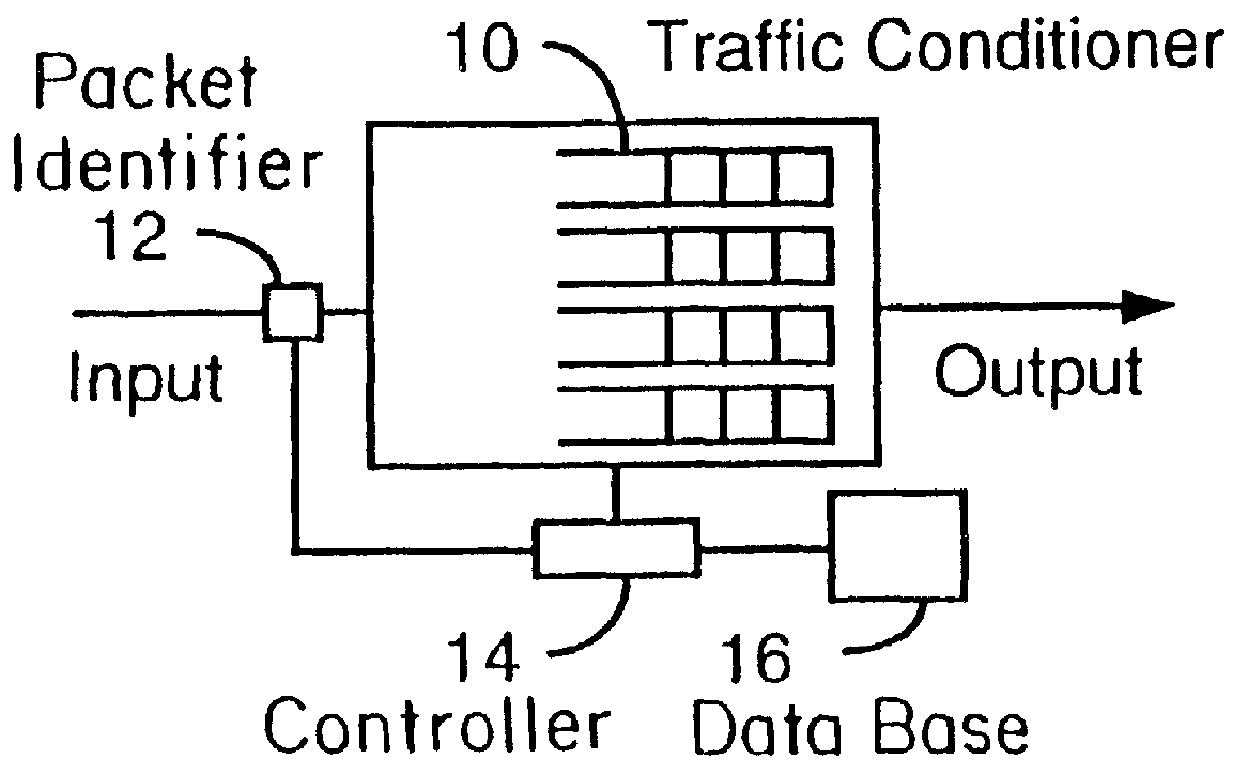
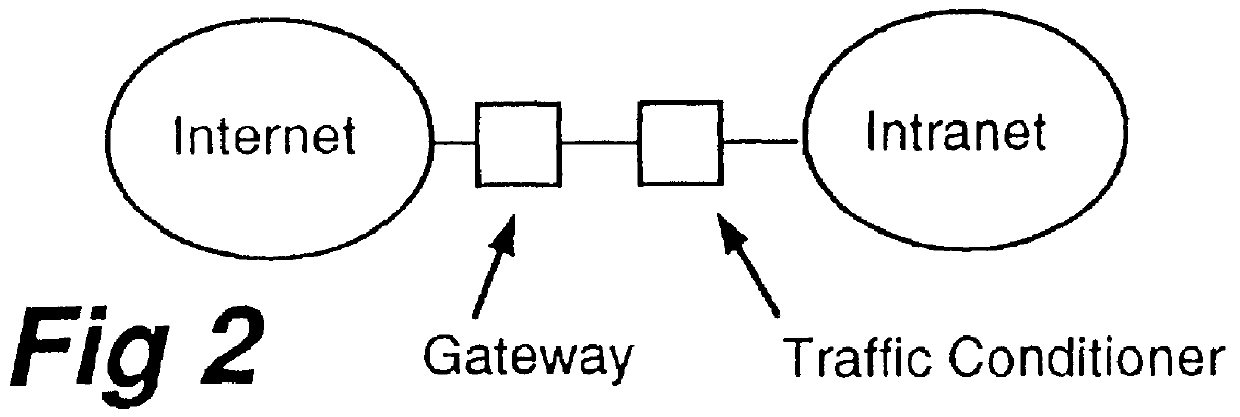
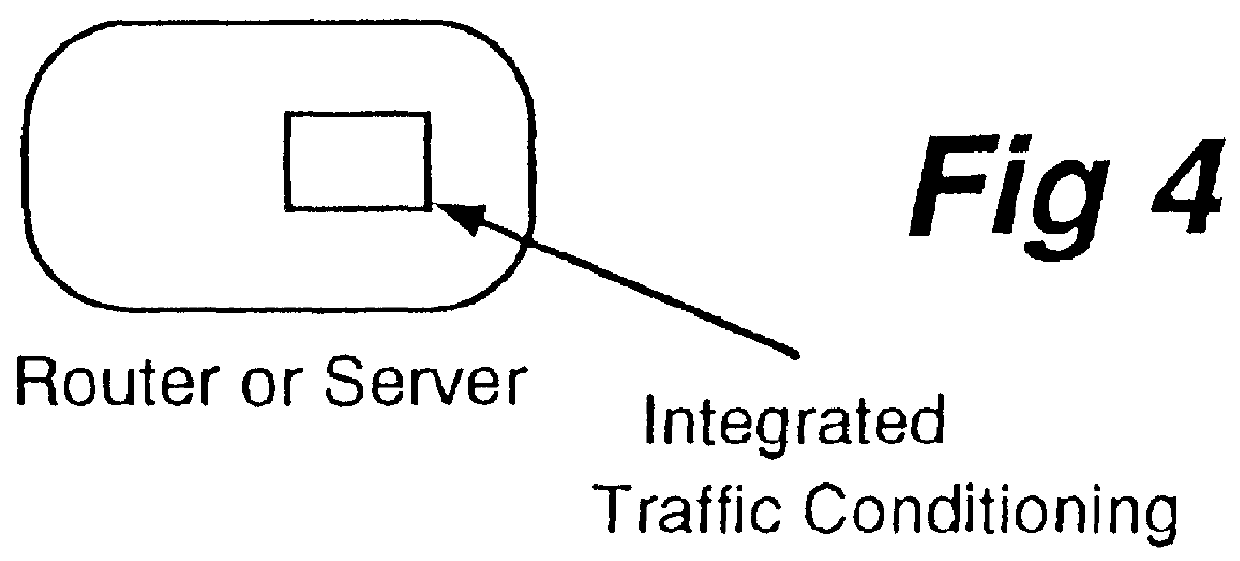
Dynamic traffic conditioning
Multi-media networks will require that a data flow be given certain quality-of-service (QOS) for a network connection but pre-negotiation of this sort is foreign to the current data networking model. The real time traffic flow in the data network requires distinct limits on the tolerance to delay, and the variations in that delay. Interactive voice and video demand that the total delay does not exceed the threshold beyond which human interaction is unacceptably impaired. The present invention allows the network to discover the nature of the service for each traffic flow, classifies it dynamically, and exercises traffic conditioning by means of such techniques as admission control and scheduling when delivering the traffic downstream to support the service appropriately.
Owner:RPX CLEARINGHOUSE
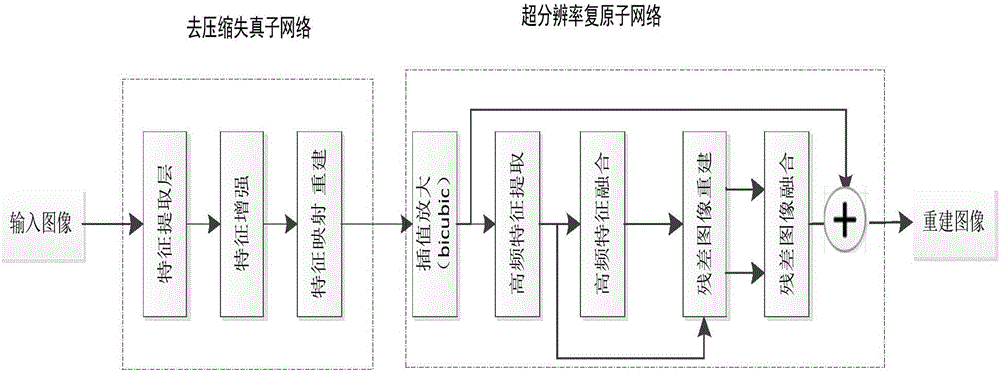
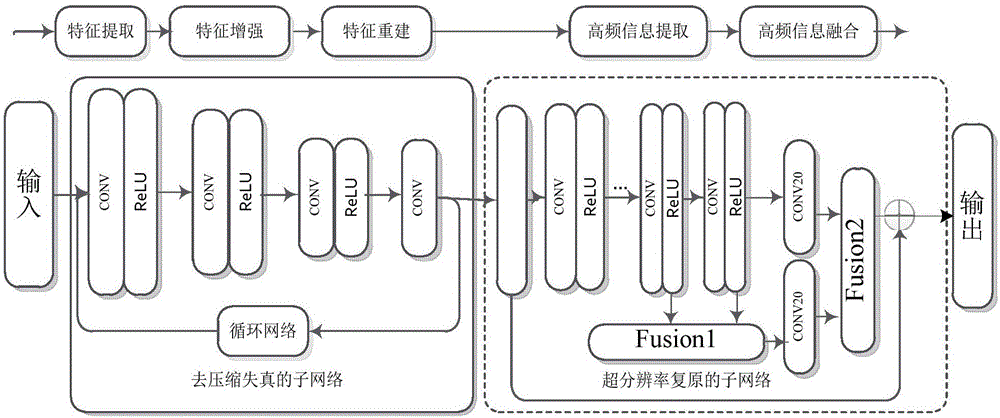
Compressed low-resolution image restoration method based on combined deep network
The present invention provides a compressed low-resolution image restoration method based on a combined deep network, belonging to the digital image / video signal processing field. The compressed low-resolution image restoration method based on the combined deep network starts from the aspect of the coprocessing of the compression artifact and downsampling factors to complete the restoration of a degraded image with the random combination of the compression artifact and the low resolution; the network provided by the invention comprises 28 convolution layers to establish a leptosomatic network structure, according to the idea of transfer learning, a model trained in advance employs a fine tuning mode to complete the training convergence of a greatly deep network so as to solve the problems of vanishing gradients and gradient explosion; the compressed low-resolution image restoration method completes the setting of the network model parameters through feature visualization, and the relation of the end-to-end learning degeneration feature and the ideal features omits the preprocessing and postprocessing; and finally, three important fusions are completed, namely the fusion of the feature figures with the same size, the fusion of residual images and the fusion of the high-frequency information and the high-frequency initial estimation figure, and the compressed low-resolution image restoration method can solve the super-resolution restoration problem of the low-resolution image with the compression artifact.
Owner:BEIJING UNIV OF TECH
Multi-scale feature fusion ultrasonic image semantic segmentation method based on adversarial learning
ActiveCN108268870AImprove forecast accuracyFew parametersNeural architecturesRecognition of medical/anatomical patternsPattern recognitionAutomatic segmentation
The invention provides a multi-scale feature fusion ultrasonic image semantic segmentation method based on adversarial learning, and the method comprises the following steps: building a multi-scale feature fusion semantic segmentation network model, building an adversarial discrimination network model, carrying out the adversarial training and model parameter learning, and carrying out the automatic segmentation of a breast lesion. The method provided by the invention achieves the prediction of a pixel class through the multi-scale features of input images with different resolutions, improvesthe pixel class label prediction accuracy, employs expanding convolution for replacing partial pooling so as to improve the resolution of a segmented image, enables the segmented image generated by asegmentation network guided by an adversarial discrimination network not to be distinguished from a segmentation label, guarantees the good appearance and spatial continuity of the segmented image, and obtains a more precise high-resolution ultrasonic breast lesion segmented image.
Owner:CHONGQING NORMAL UNIVERSITY
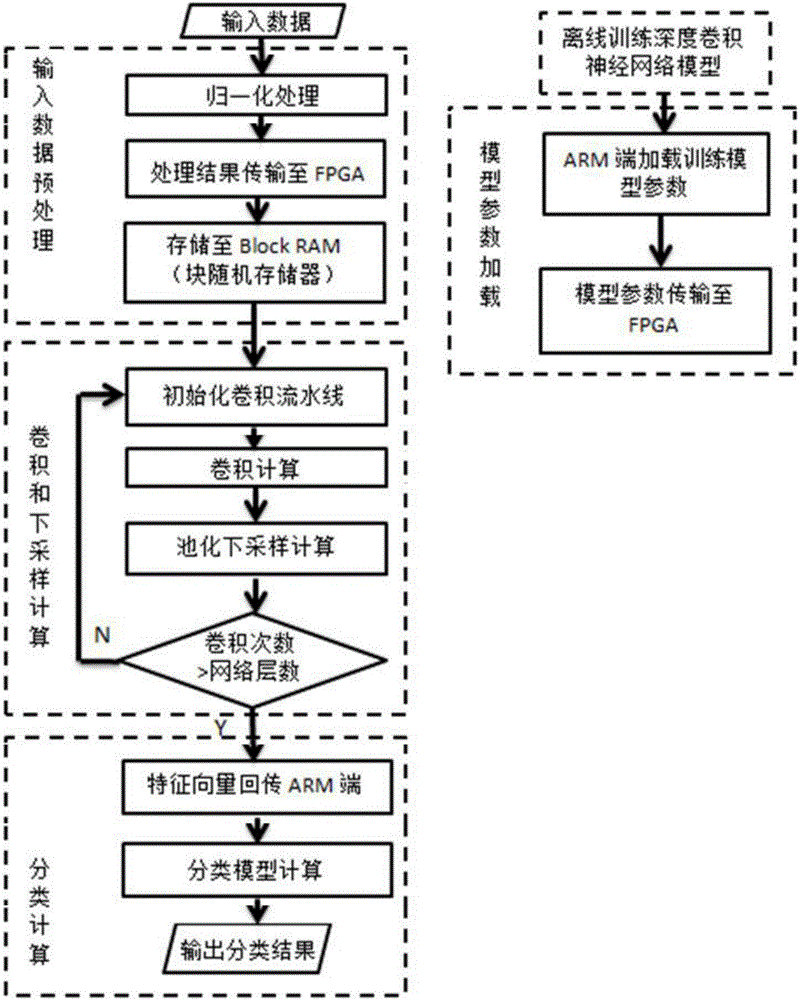
FPGA-based deep convolution neural network realizing method
ActiveCN106228240ASimple designReduce resource consumptionCharacter and pattern recognitionSpeech recognitionFeature vectorAlgorithm
The invention belongs to the technical field of digital image processing and mode identification, and specifically relates to an FPGA-based deep convolution neural network realizing method. The hardware platform for realizing the method is XilinxZYNQ-7030 programmable sheet SoC, and an FPGA and an ARM Cortex A9 processor are built in the hardware platform. Trained network model parameters are loaded to an FPGA end, pretreatment for input data is conducted at an ARM end, and the result is transmitted to the FPGA end. Convolution calculation and down-sampling of a deep convolution neural network are realized at the FPGA end to form data characteristic vectors and transmit the data characteristic vectors to the ARM end, thus completing characteristic classification calculation. Rapid parallel processing and extremely low-power high-performance calculation characteristics of FPGA are utilized to realize convolution calculation which has the highest complexity in a deep convolution neural network model. The algorithm efficiency is greatly improved, and the power consumption is reduced while ensuring algorithm correct rate.
Owner:FUDAN UNIV
Convolution neural network parallel processing method based on large-scale high-performance cluster
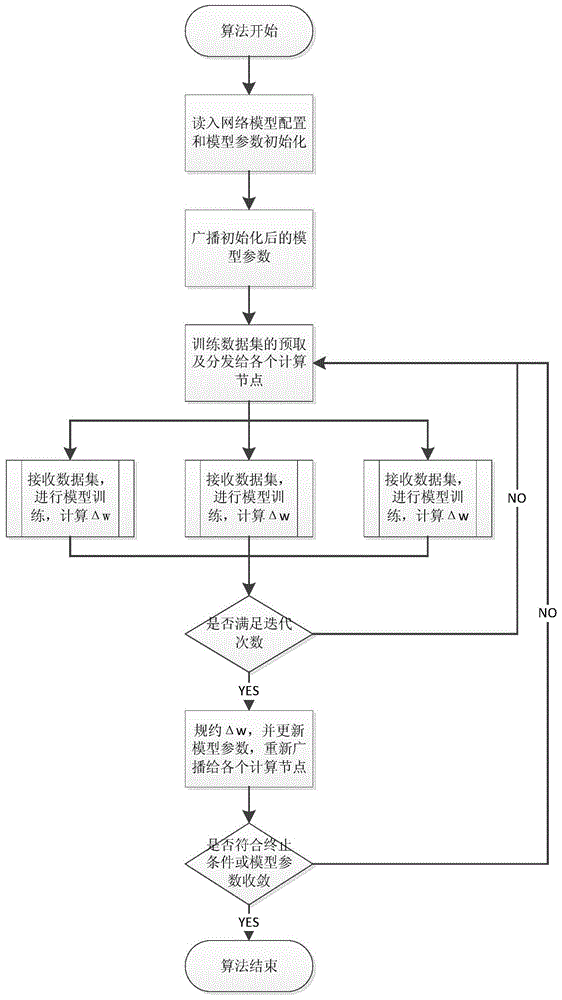
InactiveCN104463324AReduce training timeImprove computing efficiencyBiological neural network modelsConcurrent instruction executionNODALAlgorithm
The invention discloses a convolution neural network parallel processing method based on a large-scale high-performance cluster. The method comprises the steps that (1) a plurality of copies are constructed for a network model to be trained, model parameters of all the copies are identical, the number of the copies is identical with the number of nodes of the high-performance cluster, each node is provided with one model copy, one node is selected to serve as a main node, and the main node is responsible for broadcasting and collecting the model parameters; (2) a training set is divided into a plurality of subsets, the training subsets are issued to the rest of sub nodes except the main mode each time to conduct parameter gradient calculation together, gradient values are accumulated, the accumulated value is used for updating the model parameters of the main node, and the updated model parameters are broadcast to all the sub nodes until model training is ended. The convolution neural network parallel processing method has the advantages of being capable of achieving parallelization, improving the efficiency of model training, shortening the training time and the like.
Owner:CHANGSHA MASHA ELECTRONICS TECH
Method for optimizing an artificial neural network (ANN)
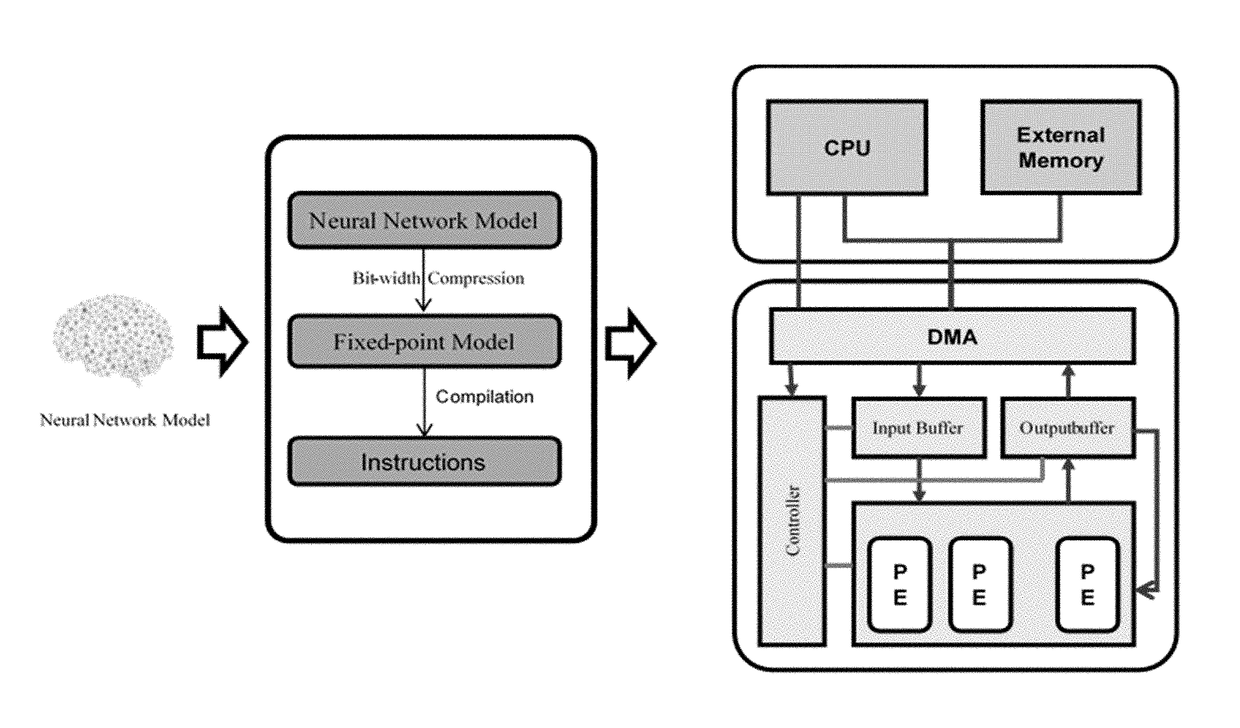
ActiveUS20180046894A1Digital data processing detailsSpeech analysisNetwork modelArtificial neural network
The present invention relates to artificial neural network, for example, convolutional neural network. In particular, the present invention relates to how to implement and optimize a convolutional neural network based on an embedded FPGA. Specifically, it proposes an overall design process of compressing, fix-point quantization and compiling the neural network model.
Owner:XILINX TECH BEIJING LTD
System and method for predicting power plant operational parameters utilizing artificial neural network deep learning methodologies
A system and method of predicting future power plant operations is based upon an artificial neural network model including one or more hidden layers. The artificial neural network is developed (and trained) to build a model that is able to predict future time series values of a specific power plant operation parameter based on prior values. By accurately predicting the future values of the time series, power plant personnel are able to schedule future events in a cost-efficient, timely manner. The scheduled events may include providing an inventory of replacement parts, determining a proper number of turbines required to meet a predicted demand, determining the best time to perform maintenance on a turbine, etc. The inclusion of one or more hidden layers in the neural network model creates a prediction that is able to follow trends in the time series data, without overfitting.
Owner:SIEMENS AG
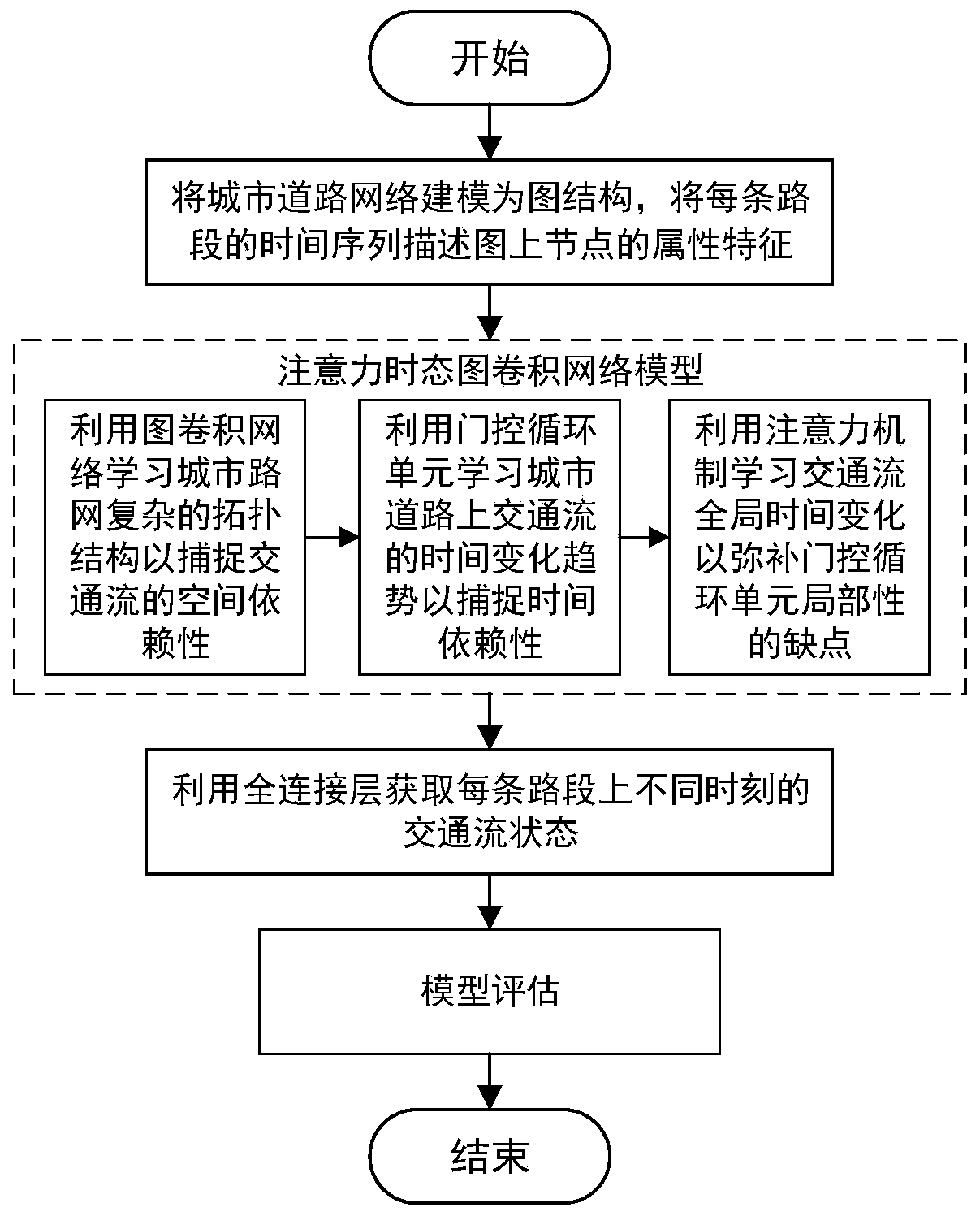
Traffic prediction method based on attention temporal graph convolutional network
ActiveCN109754605AGain spatial dependenceGood forecastDetection of traffic movementForecastingTraffic predictionNetwork model
The invention belongs to the field of intelligent transportation, and discloses a traffic prediction method based on an attention temporal graph convolutional network. The method includes the following steps that: firstly, an urban road network is modeled as a graph structure, nodes of the graph represent road sections, edges are connection relationships between the road sections, and the time series of each road section is described as attribute characteristics of the nodes; secondly, the temporal and spatial characteristics of the traffic flow are captured by using an attention temporal graph convolutional network model, the temporal variation trend of the traffic flow on urban roads is learned by using gated cycle units to capture the time dependence, and the global temporal variation trend of the traffic flow is learned by using an attention mechanism; and then, the traffic flow state at different times on each road section is obtained by using a fully connected layer; and finally,different evaluation indexes are used to estimate the difference between the real value and the predicted value of the traffic flow on the urban roads and further estimate the prediction ability of the model. Experiments prove that the method provided by the invention can effectively realize tasks of predicting the traffic flow on the urban roads.
Owner:CENT SOUTH UNIV
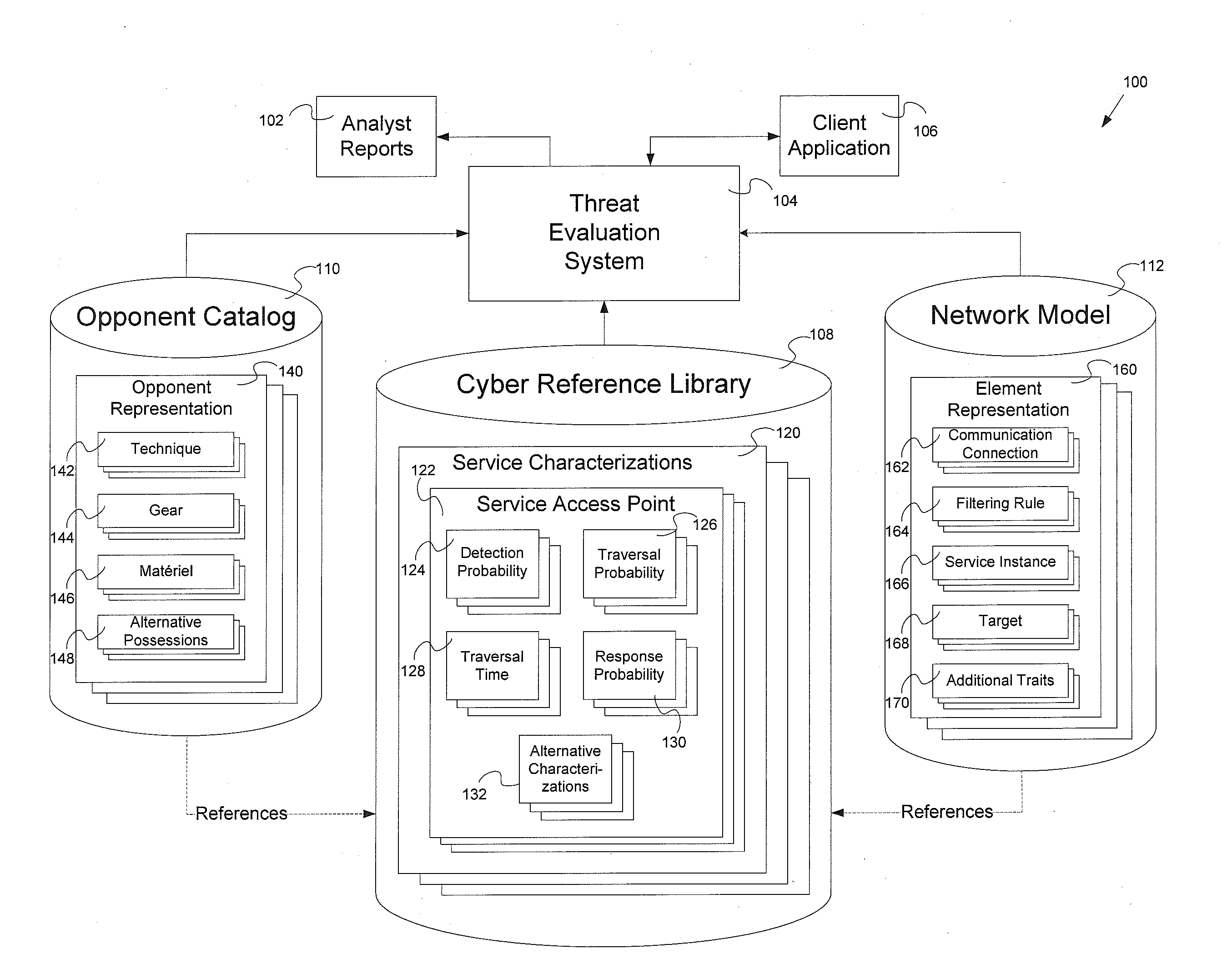
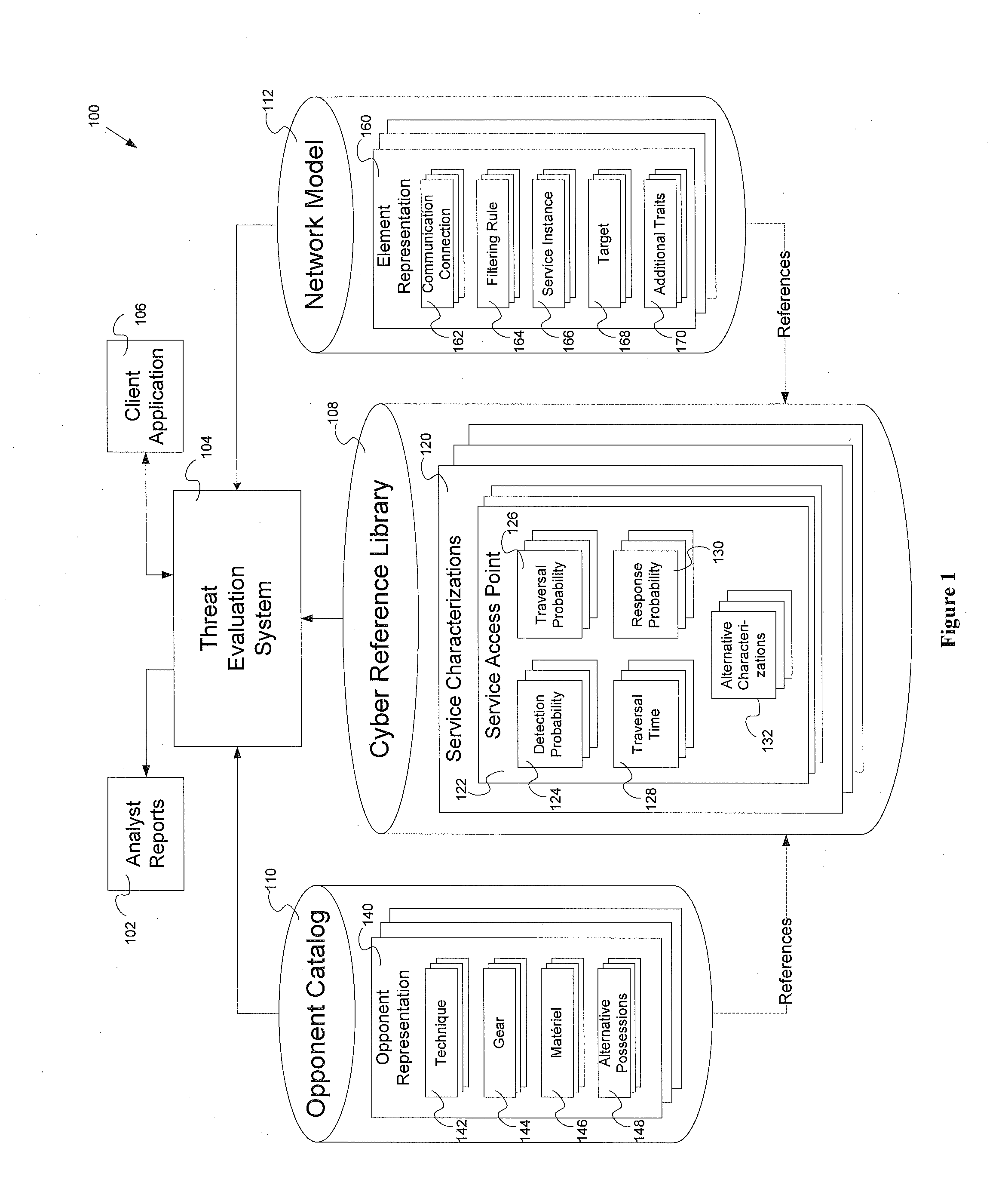
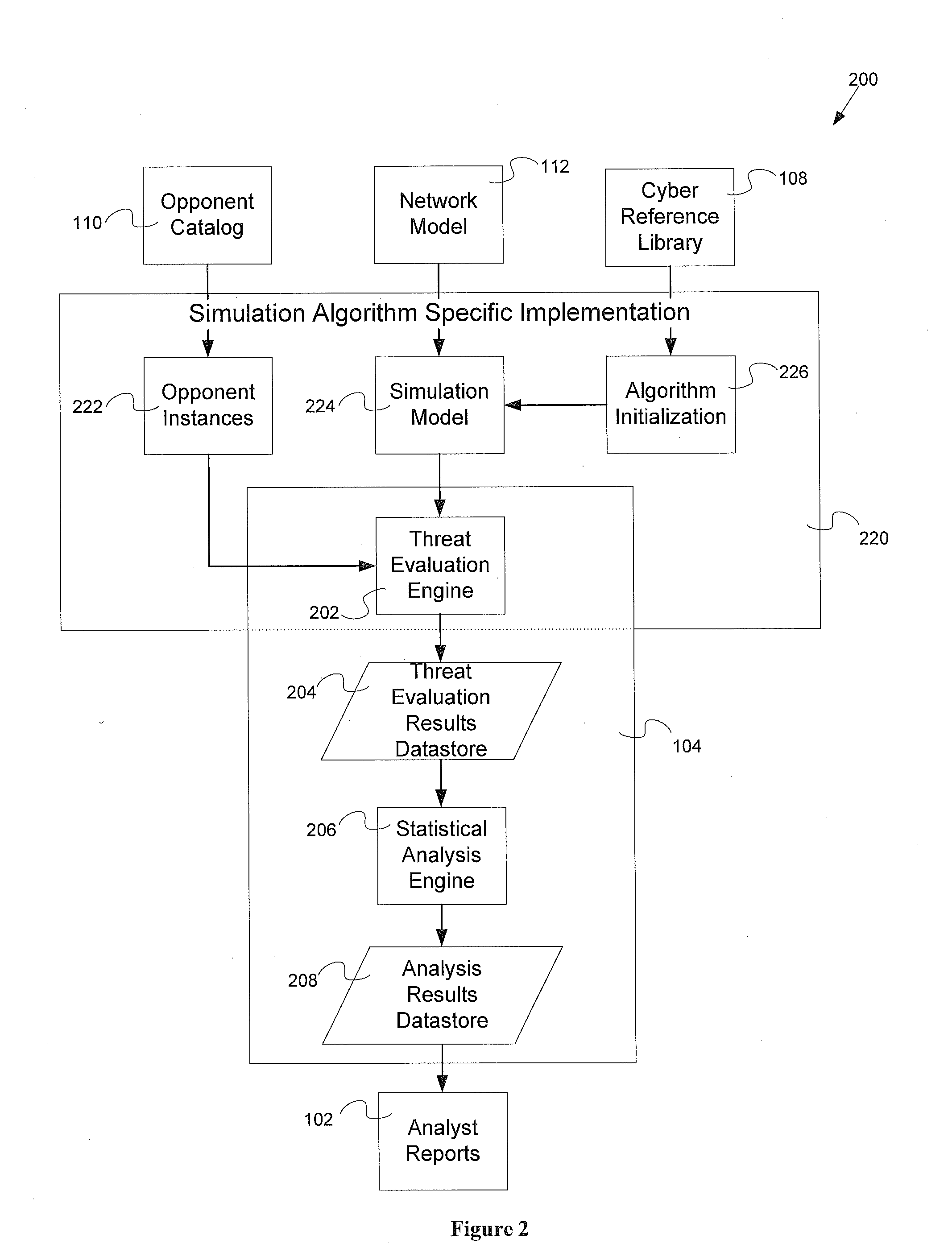
Threat evaluation system and method
InactiveUS20130347116A1Memory loss protectionError detection/correctionStatistical analysisNetwork model
Systems and methods of evaluation of threats to elements of a client computer application having a cyber reference library, an opponent catalog and a network model. The systems and methods produce a set of analyst reports evaluating the threats to the client computer application. One embodiment of the system for evaluating at least one threat to a client computer application has a threat evaluation engine which performs a plurality of algorithms, where each algorithm of has implementation specific needs for input into the individual algorithm, a threat evaluation results data store, a statistical analysis engine, and an analysis results data store.
Owner:OPPLEO SECURITY
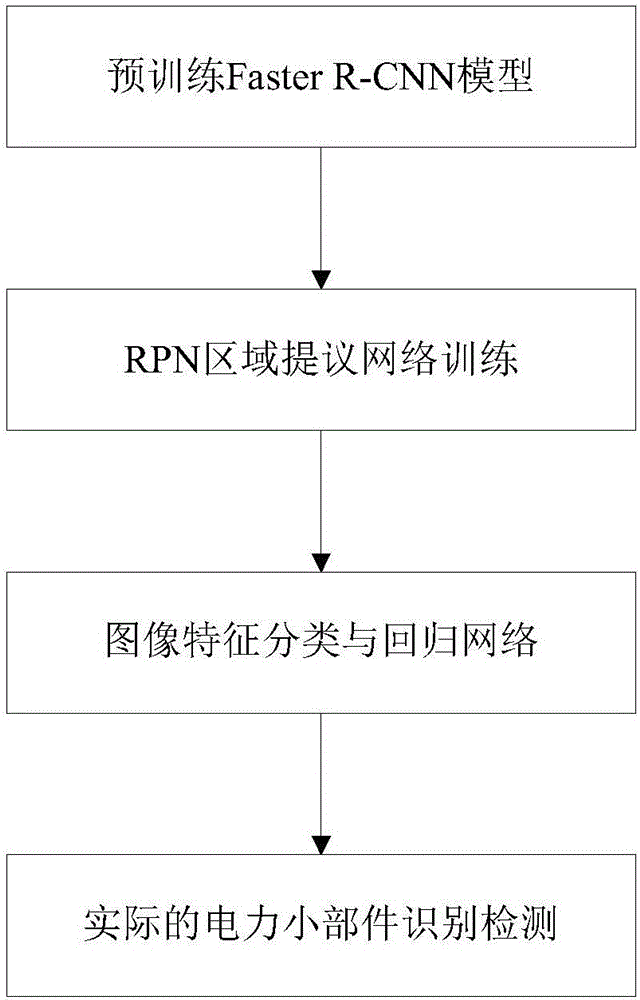
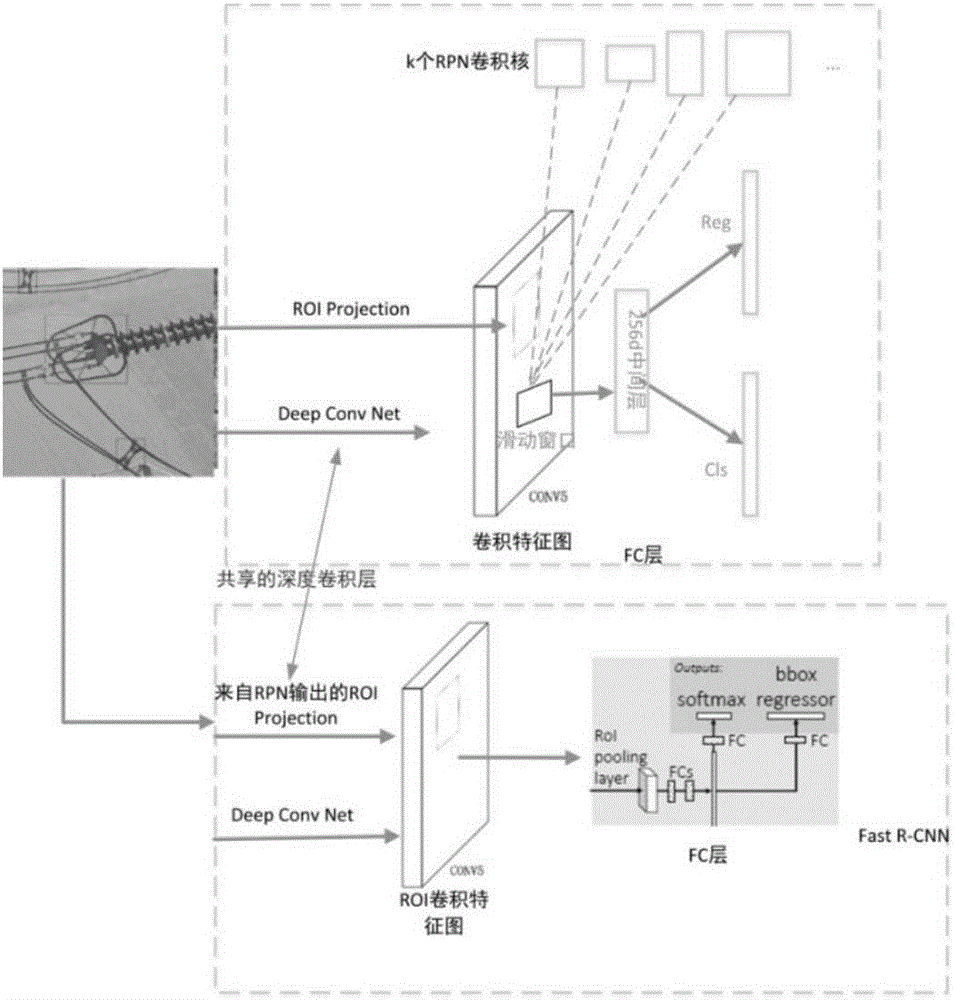
Unmanned aerial vehicle patrol detection image power small component identification method and system based on Faster R-CNN
ActiveCN106504233ABreak through the time bottleneckImprove recognition rateImage enhancementImage analysisFeature extractionUncrewed vehicle
Owner:STATE GRID INTELLIGENCE TECH CO LTD
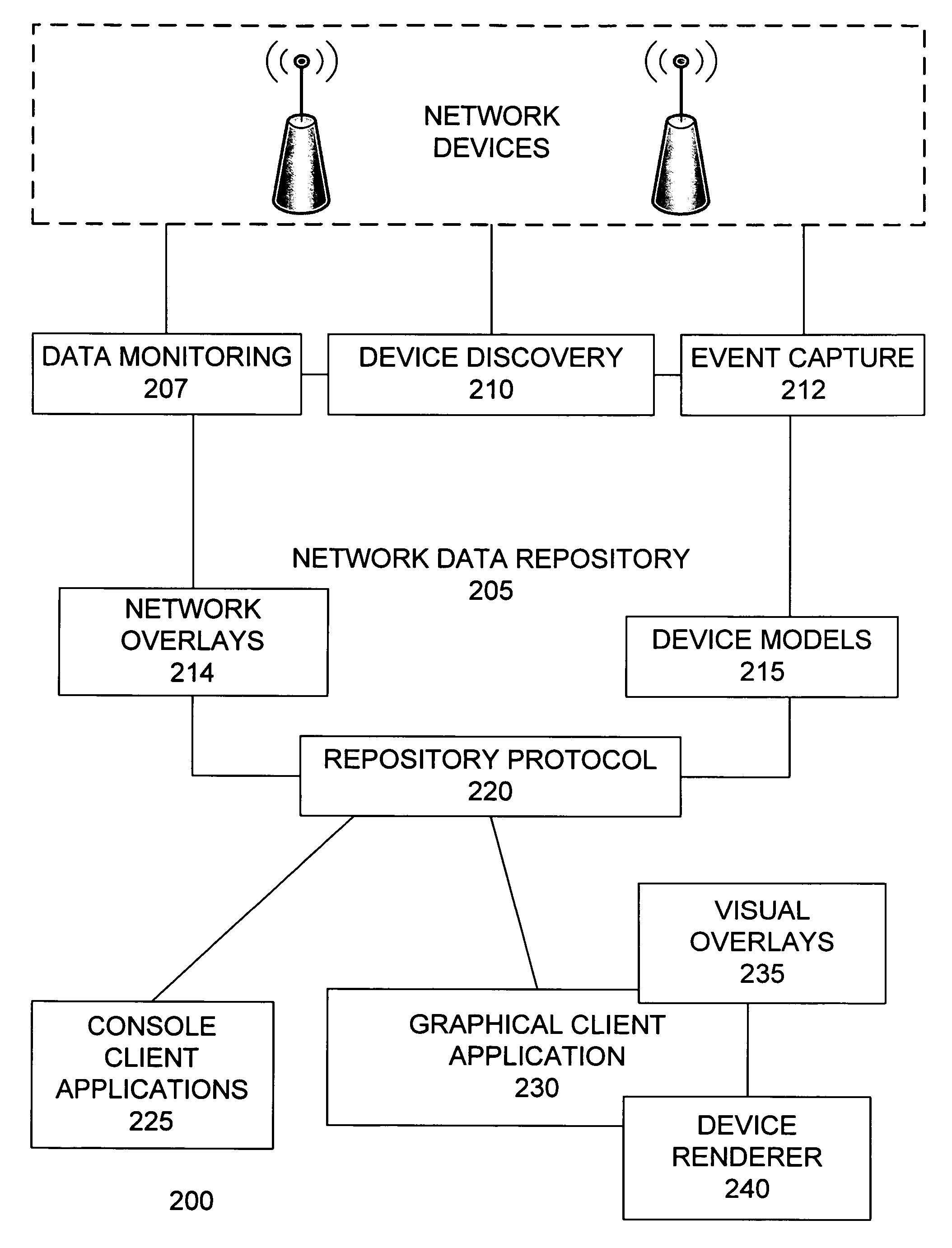
Network monitoring device
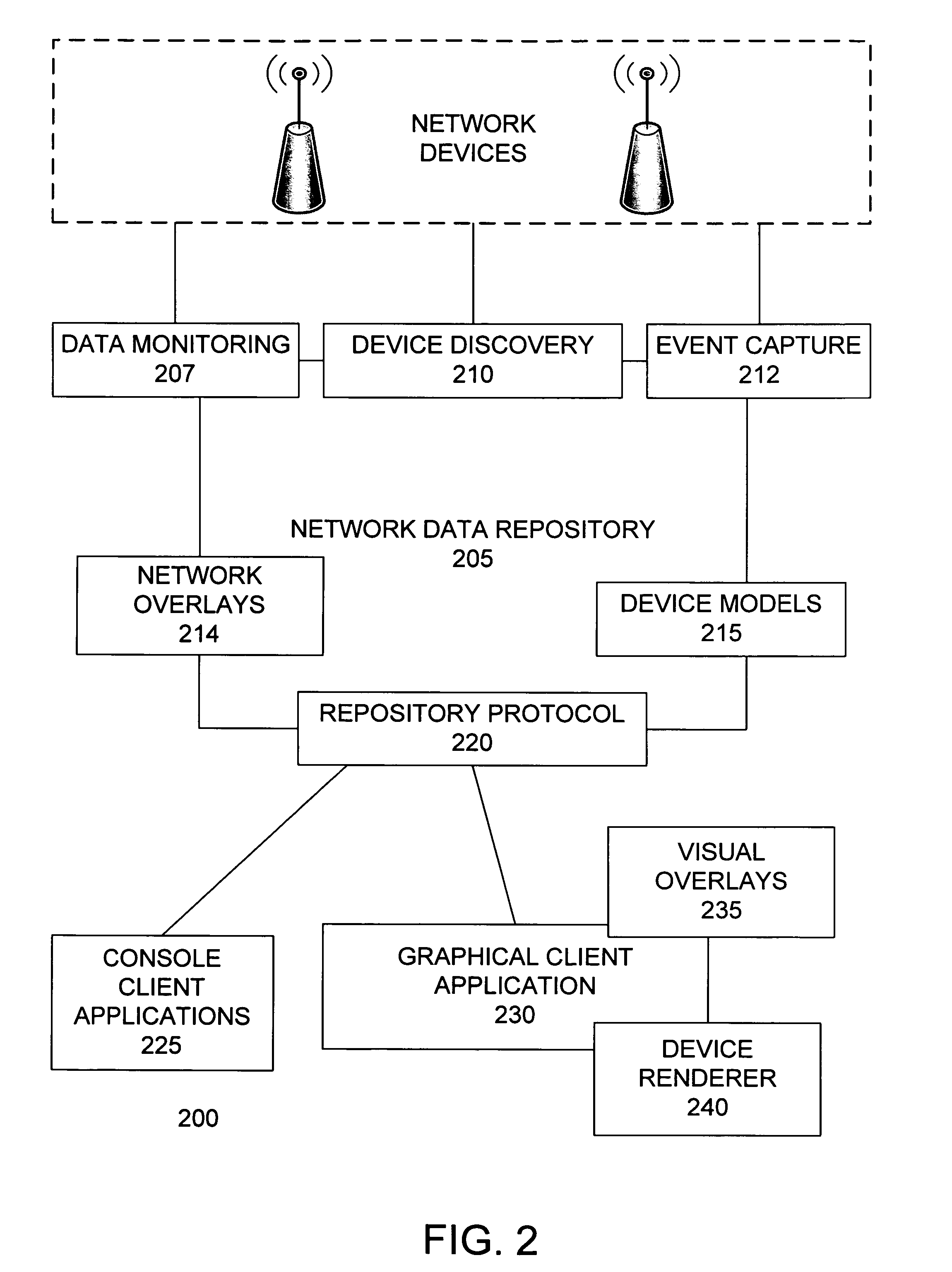
ActiveUS20070014248A1CommunicationData switching by path configurationMonitoring systemSystem maintenance
A network monitoring system monitors a data network and enables observation of the data network state in the present or any arbitrary previous time. The system maintains an object-oriented network model that mirrors the state of network devices. A network data repository stores and maintains the network model. The network model retains a history of network events, enabling the system to reconstruct the state of all or a portion of the devices in the network at any previous time. The network data repository detects network devices on the data network to be monitored, communicates with network devices, monitors the state of network devices, receives and records network events, provides device and network state information to client applications, and manages data storage. Client applications can rewind and replay the history of the network model, allowing the observation of network devices and all of their state data at any prior time.
Owner:CHANNEL IP BV
Application integration system and method using intelligent agents for integrating information access over extended networks
InactiveUS20050027495A1Easy to readDigital computer detailsCathode-ray tube indicatorsInformation accessProblem statement
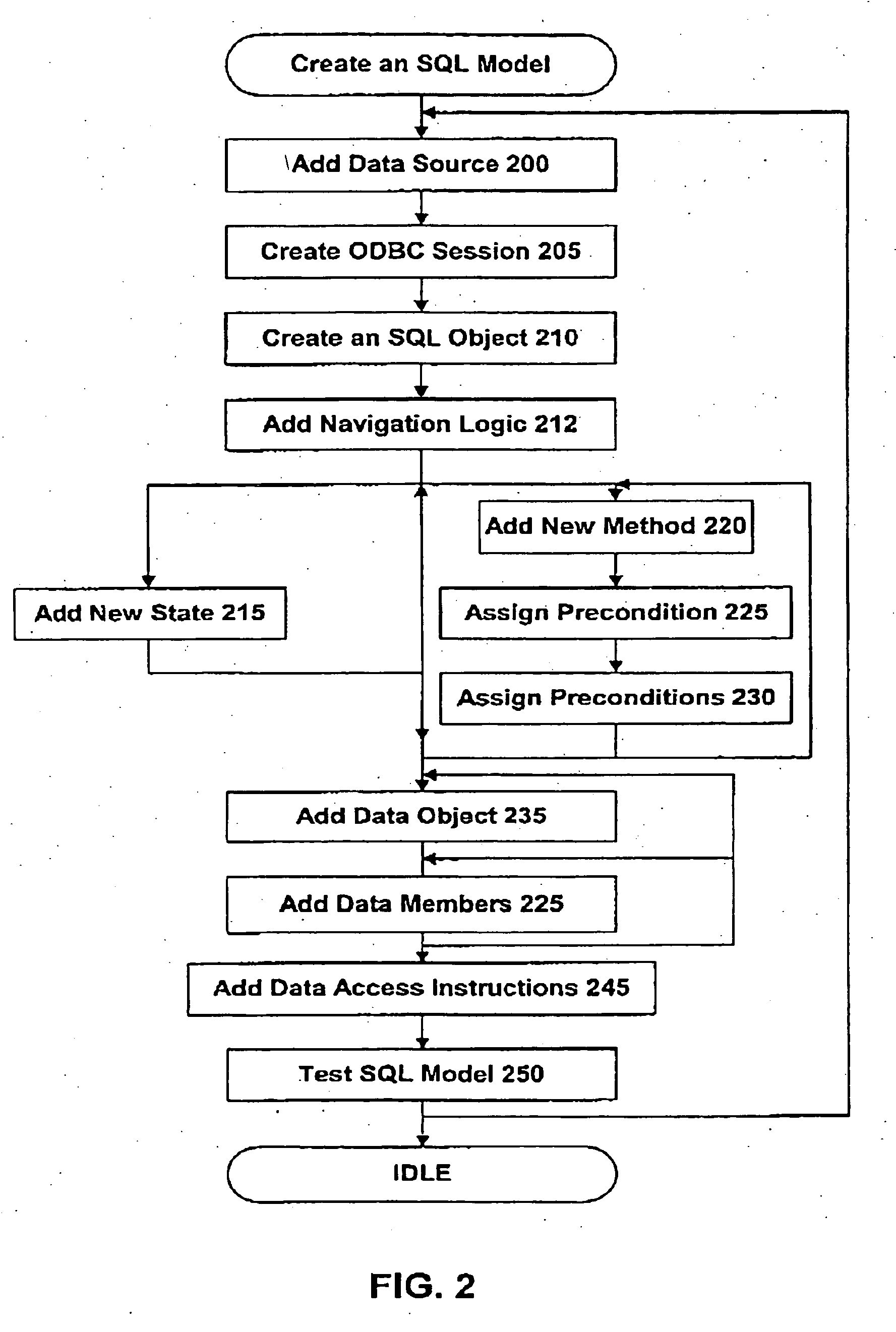
Models that encapsulate information on how remote applications are controlled and data is accessed are created to be used by a runtime agent that intelligently reasons out goal-oriented plans and execute tasks to solve problem statements generated by a user interface or other software agents. The models may be used to assemble workflows using a reasoning process. In particular, the models of the present invention include a state that includes a planning state and a navigational value. In embodiments of the invention, the models may include intelligent agents, a loop state, submodel invocation that allows the models to invoke agents over a network, and the ability to integrate the three application layers in a computer.
Owner:CELCORP
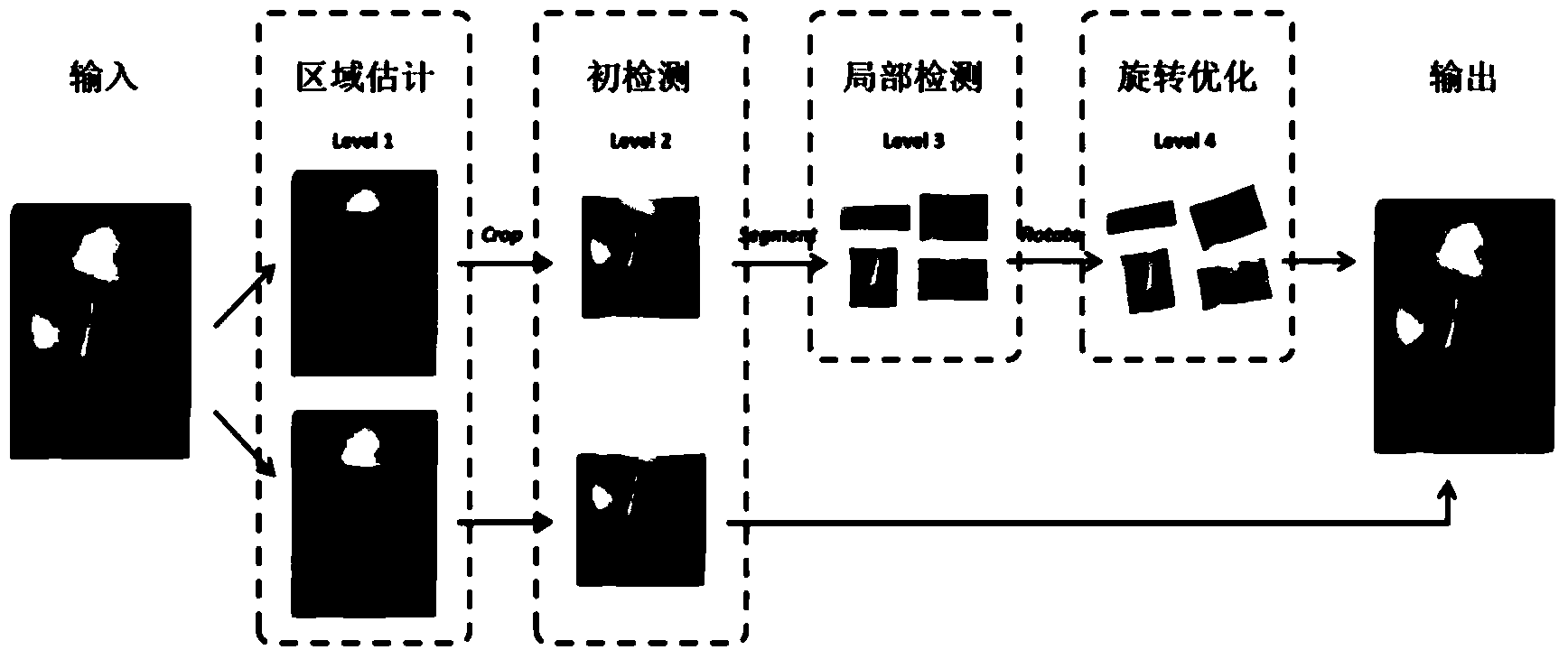
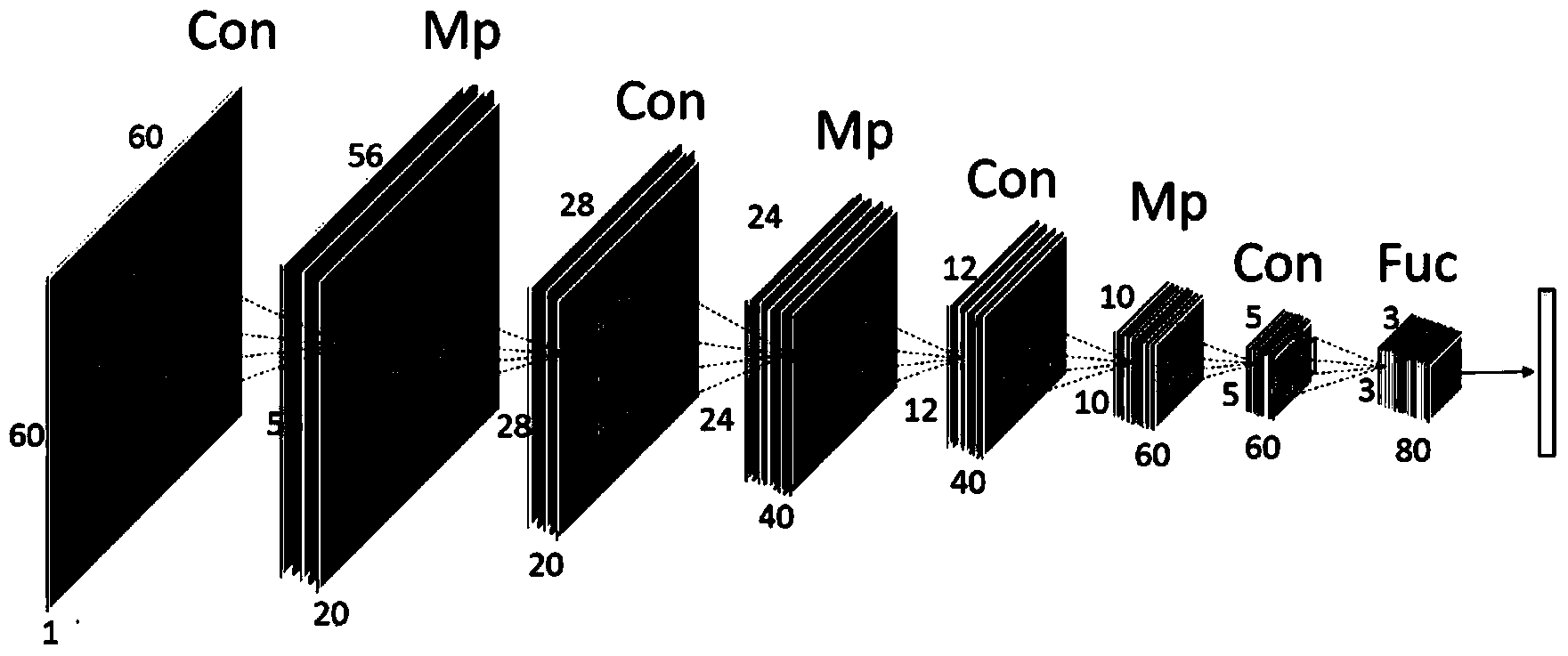
Cascaded neural network-based face key point detection method
InactiveCN103824049AAvoid mutual interferenceOptimize outputBiological neural network modelsCharacter and pattern recognitionPattern recognitionData set
The invention relates to a cascaded neural network-based face key point detection method. The method includes the following steps that: a) a training-used face image set is established, and a key point position requiring detection is marked; b) a first-layer depth neural network is constructed and is used to train a face region estimation model; c) a second-layer depth neural network is constructed and is used to perform face key point preliminary detection; d) local region division is continued to be performed on an inner face region; e) a third-layer depth neural network is constructed for each local region respectively; f) the rotation angle of each local region is estimated; g) correction is performed according to the estimated rotation angles; h) a fourth-layer depth neural network is constructed for the correction data set of each local region; and i) any face image is given, and the above four-layer depth neural network model is adopted to perform key point detection, such that final face key point detection results can be obtained. With the cascaded neural network-based face key point detection method of the invention adopted, face key point detection can be improved, and especially the accuracy and real-time property of dense face key point detection.
Owner:BEIJING KUANGSHI TECH
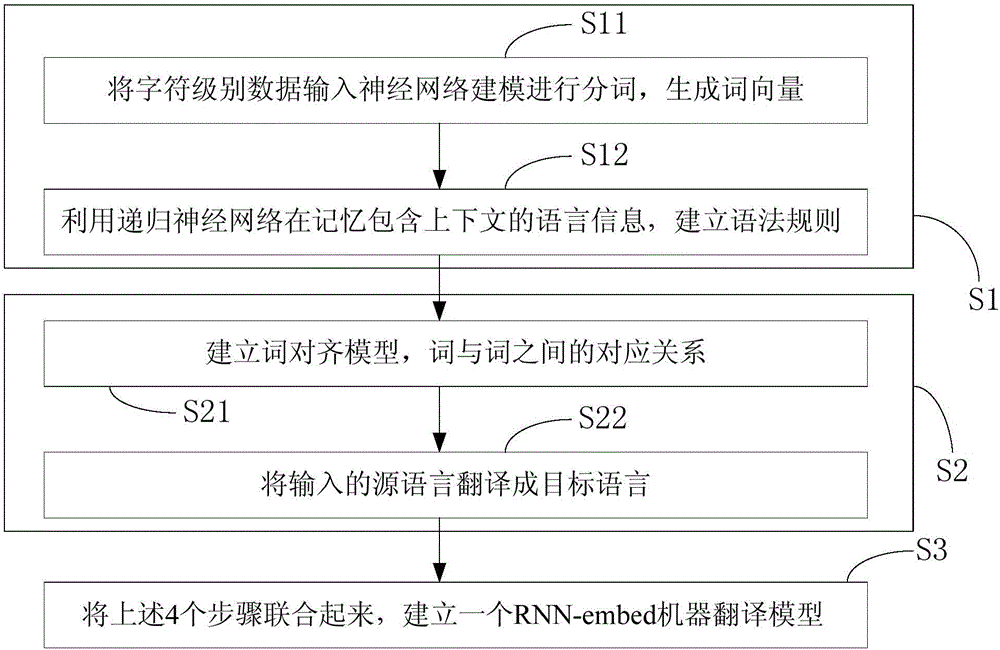
Method and system for deep nerve translation based on character encoding
ActiveCN106126507AReduce feature dimensionExcellent translation resultNatural language translationSpecial data processing applicationsNerve networkEncoder decoder
The invention provides a method and a system for deep nerve translation based on character encoding. A combined nerve network model is established by using an RNN to cover the whole translation process, and translation tasks are directly completed from the perspective of an encoder-decoder framework. The method comprises the following steps: A, word vector generation: performing word segmentation on character-level input data through neural network modeling and generating a word vector; B, language model generation: establishing grammar rules by utilizing the characteristic of memory of the recurrent neural network in time; C, word alignment model generation: obtaining the probability of translating multiple words in a source language statement into target language words; D, output: translating an inputted source language into a target language; E, translation model combination: establishing a deep nerve translation model (RNN-embed) based on character encoding in combination with neural network models in the four steps and accelerating model training by using CPU parallel computation.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
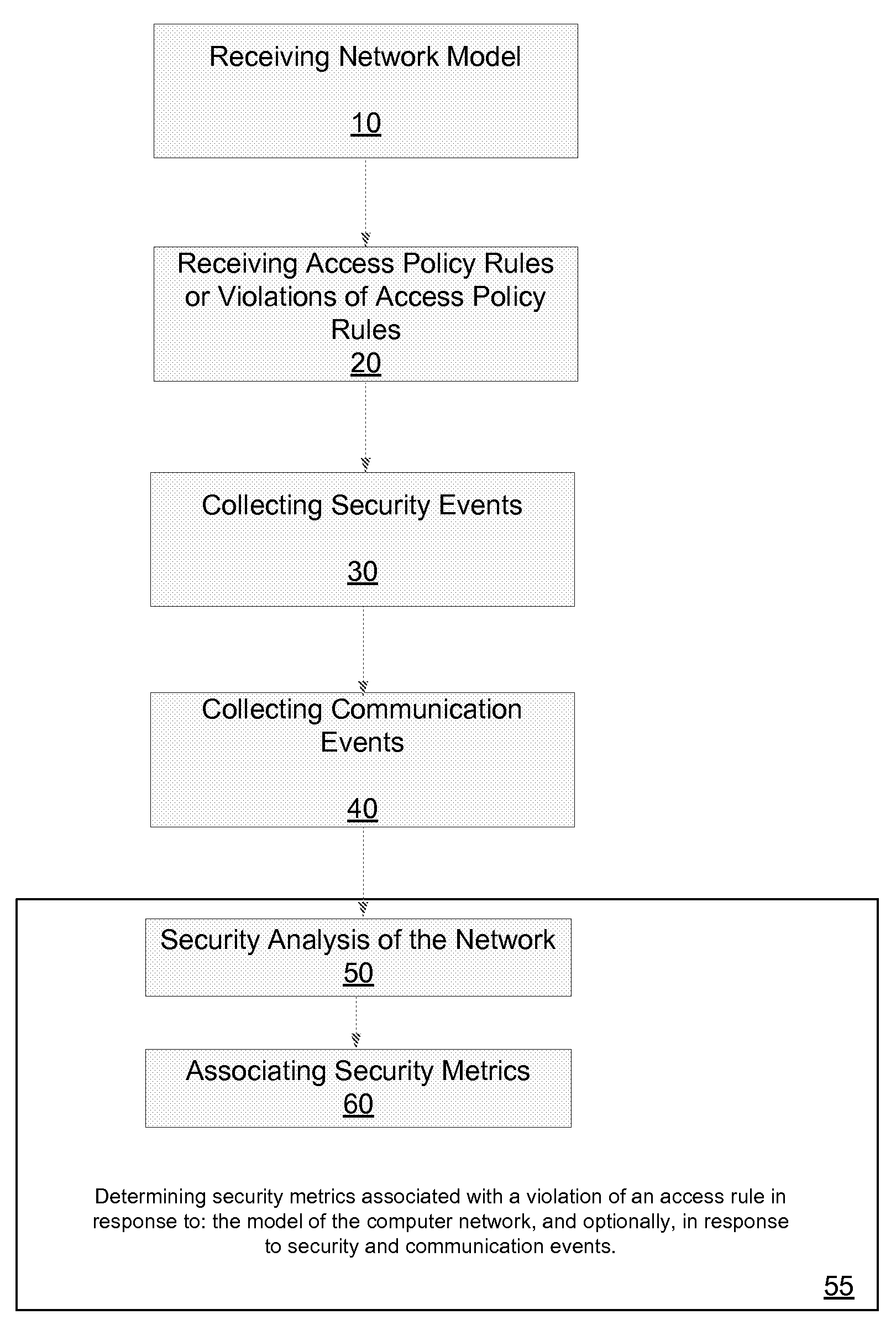
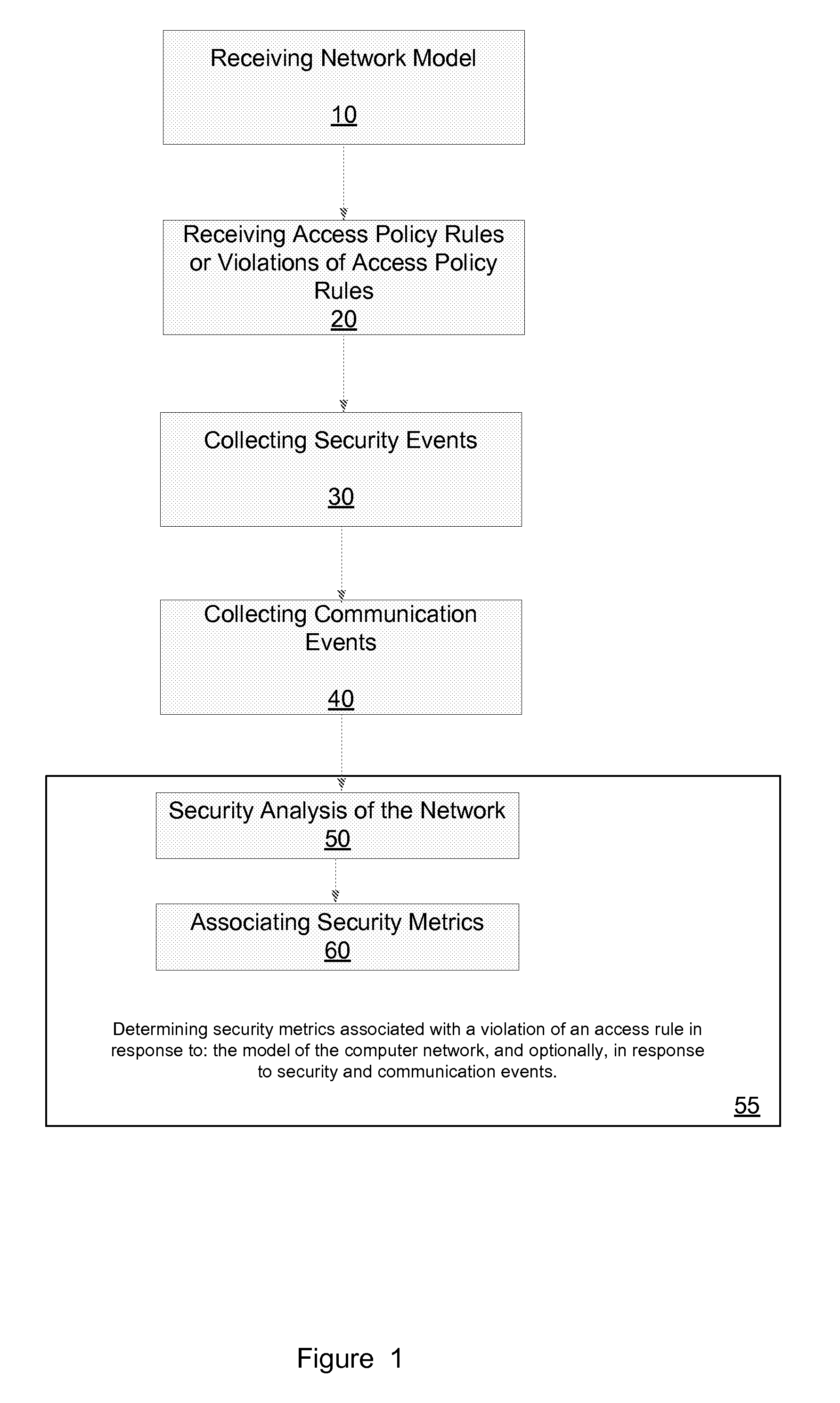
Method for evaluating a network
A method for evaluating access rules violations, the method includes: receiving, a model of a computer network; and determining security metrics associated with a violation of an access rule in response to: the model of the computer network, multiple network nodes of the computer network accessible according to at least one violated access rule or according to the network model, at least one vulnerability associated with the multiple network nodes, and damage associated with an exploitation of the at least one vulnerability.
Owner:SKYBOX SECURITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com