Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
809 results about "Virtual link" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
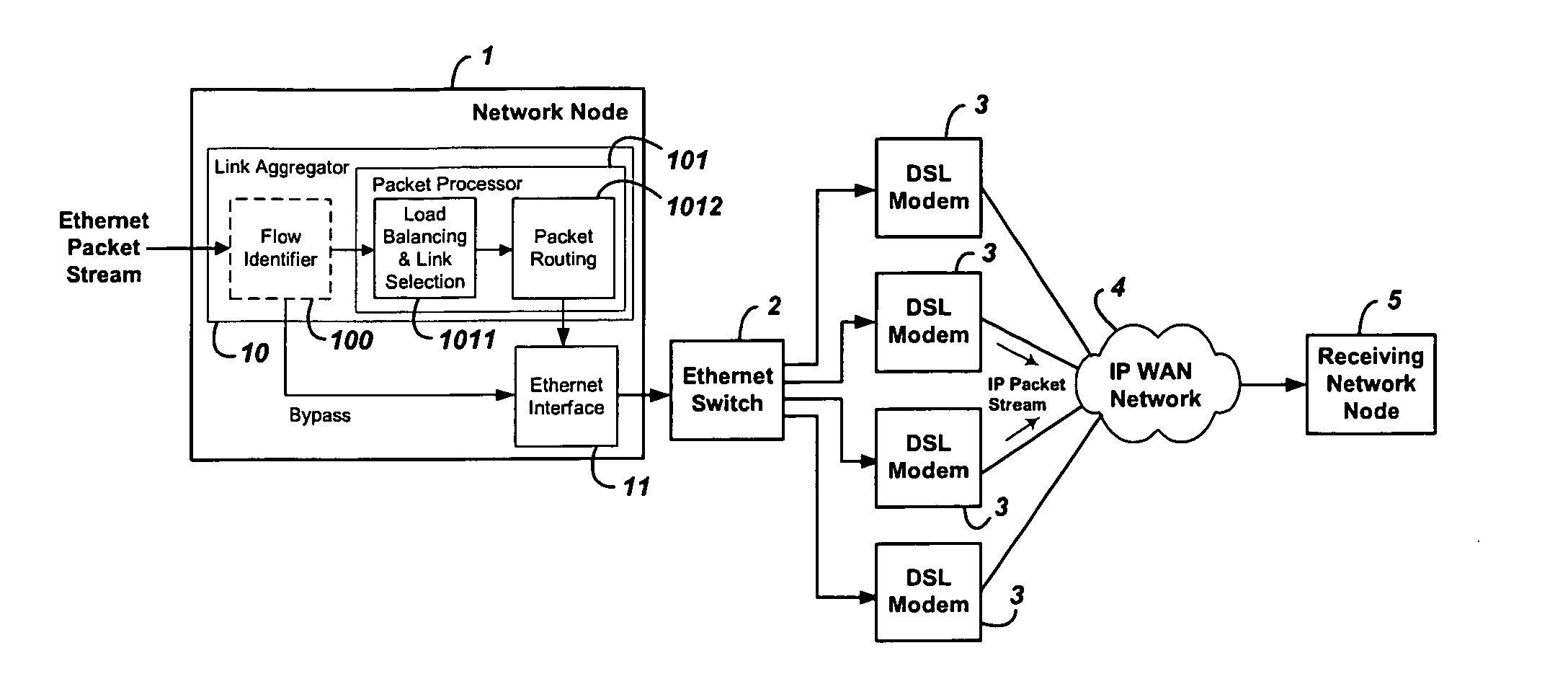
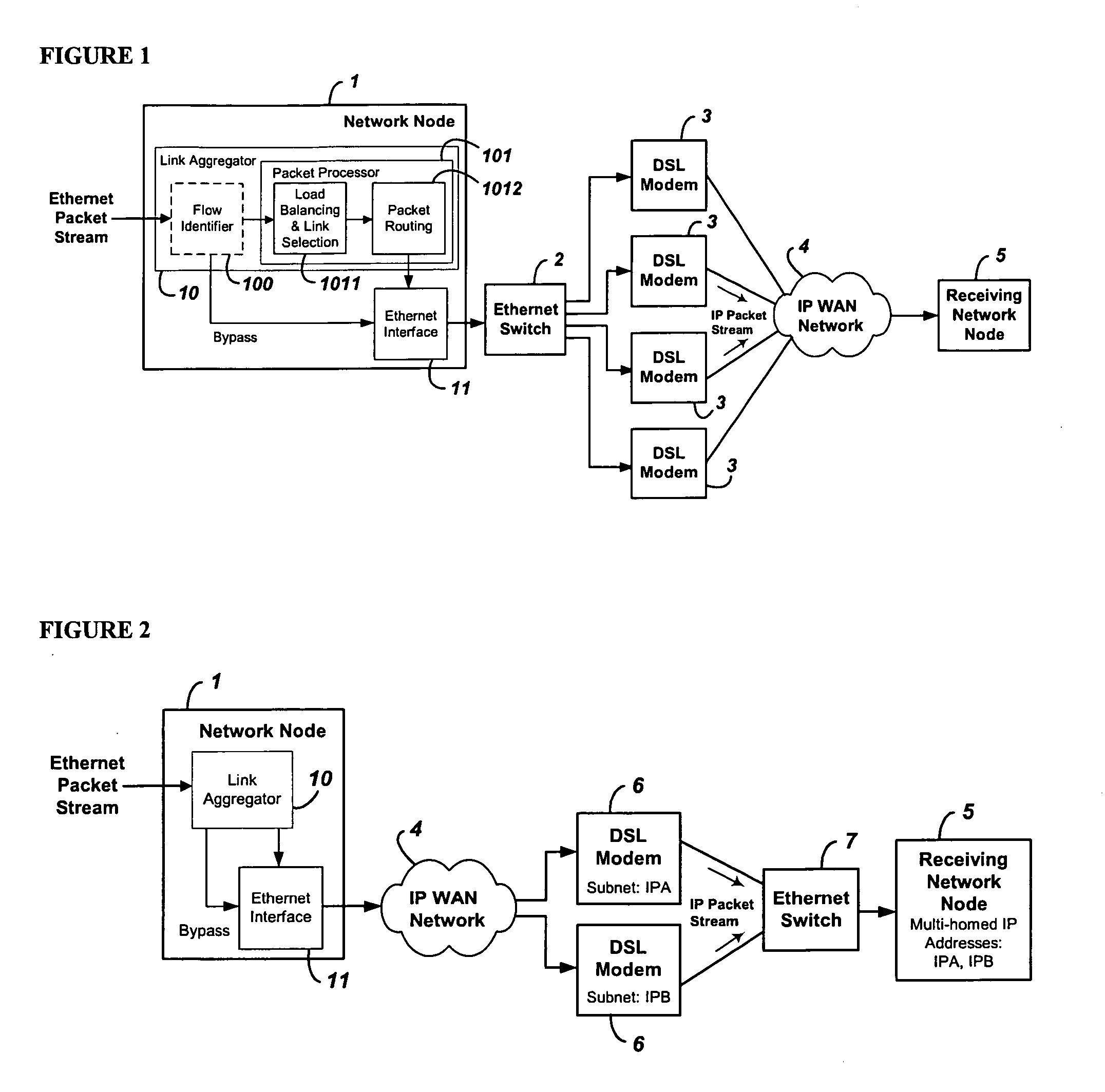
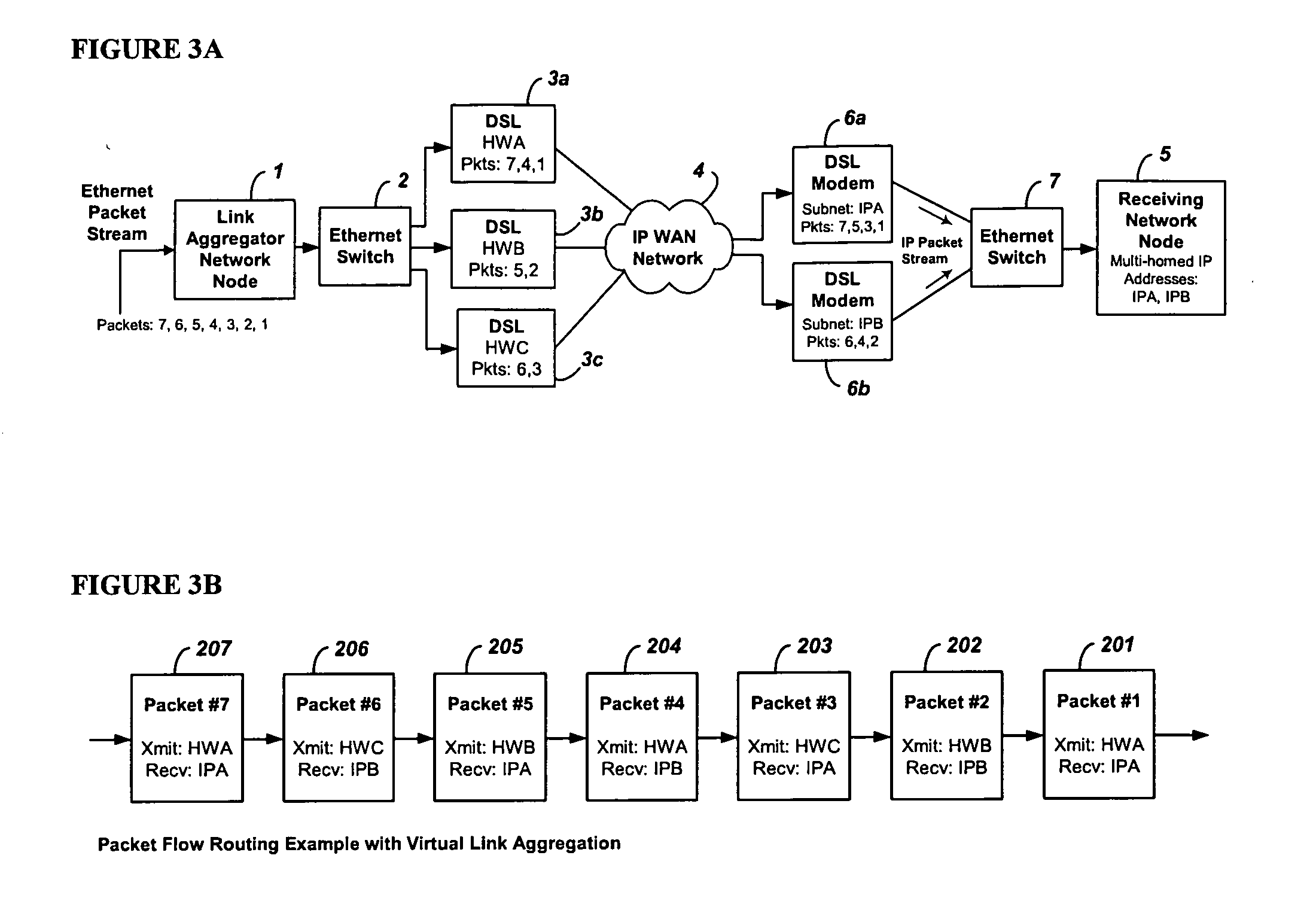
System and method for the virtual aggregation of network links
InactiveUS20060098573A1Improve throughputImprove reliabilityEnergy efficient ICTError preventionNetwork linkRewriting
A system and method for virtual link aggregation for combining network links of various types and speeds to increase throughput and reliability for packetized transport. In contrast with physical port trunking, the system does not require direct control over ports or network interfaces. Instead, the system rewrites packet addresses and works through existing networking equipment, without requiring any new or special protocols, processing, or equipment within the network. The system works through low-level rerouting by rewriting hardware addresses and / or high-level routing by rewriting logical addresses. Thus packets are redirected through multiple routes to a common destination via alternate gateways and links. Different algorithms may be employed to balance the load on each link and determine an optimal route for each packet. Embodiments may also employ packet flow or stream identification and thereby only provide link aggregation for a specified set of packet flows.
Owner:QVIDIUM TECH
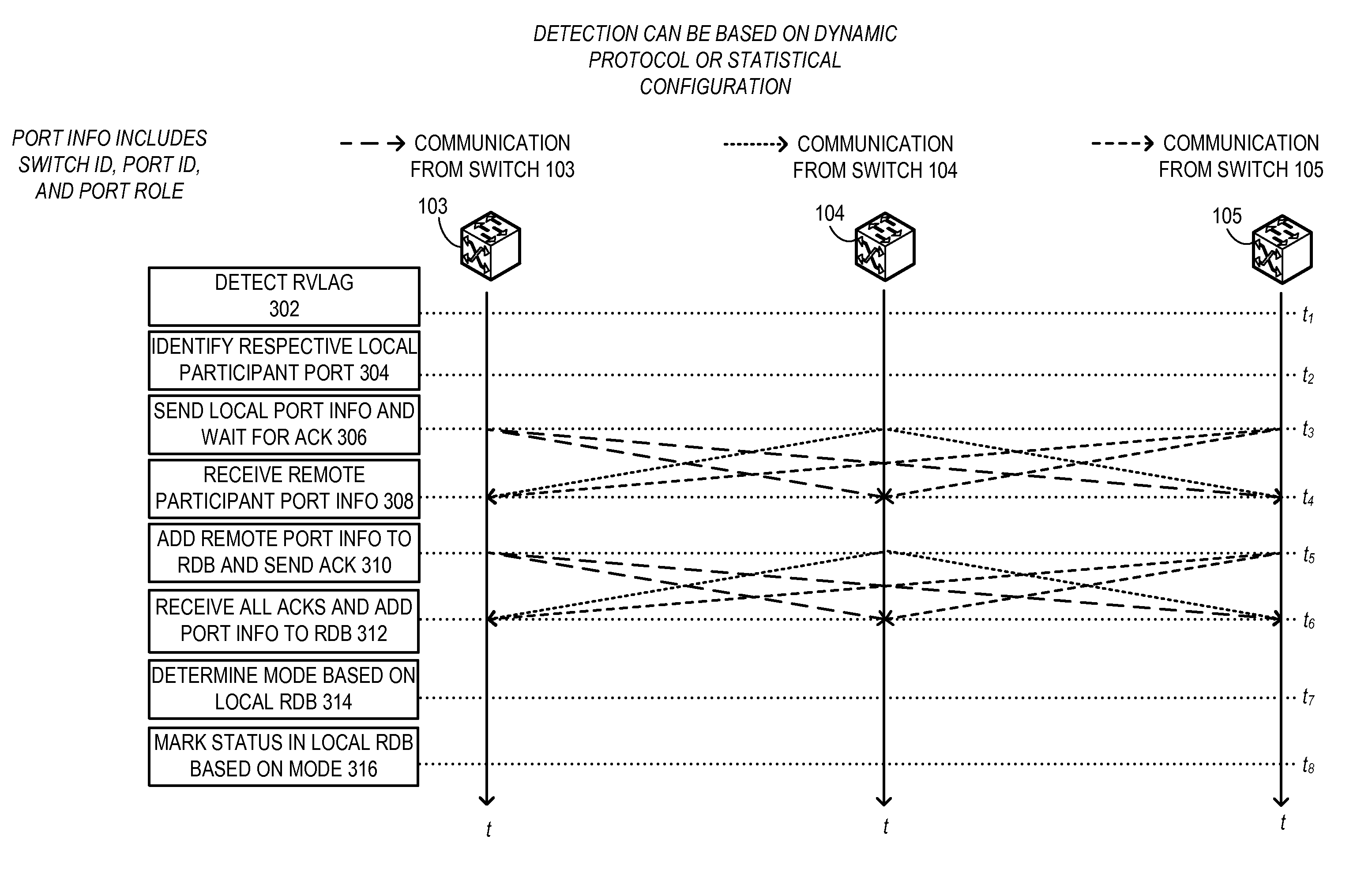
Redundent virtual link aggregation group
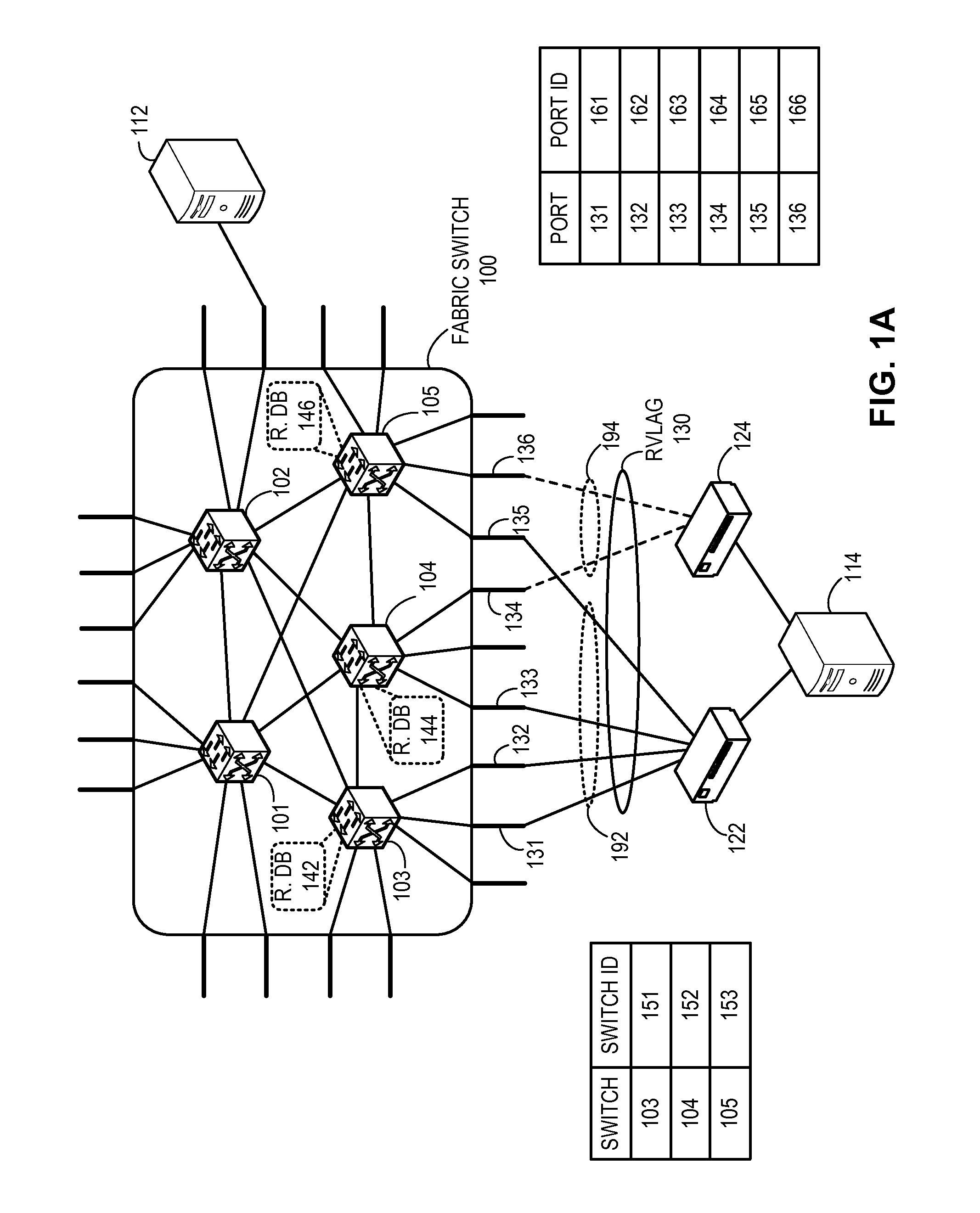
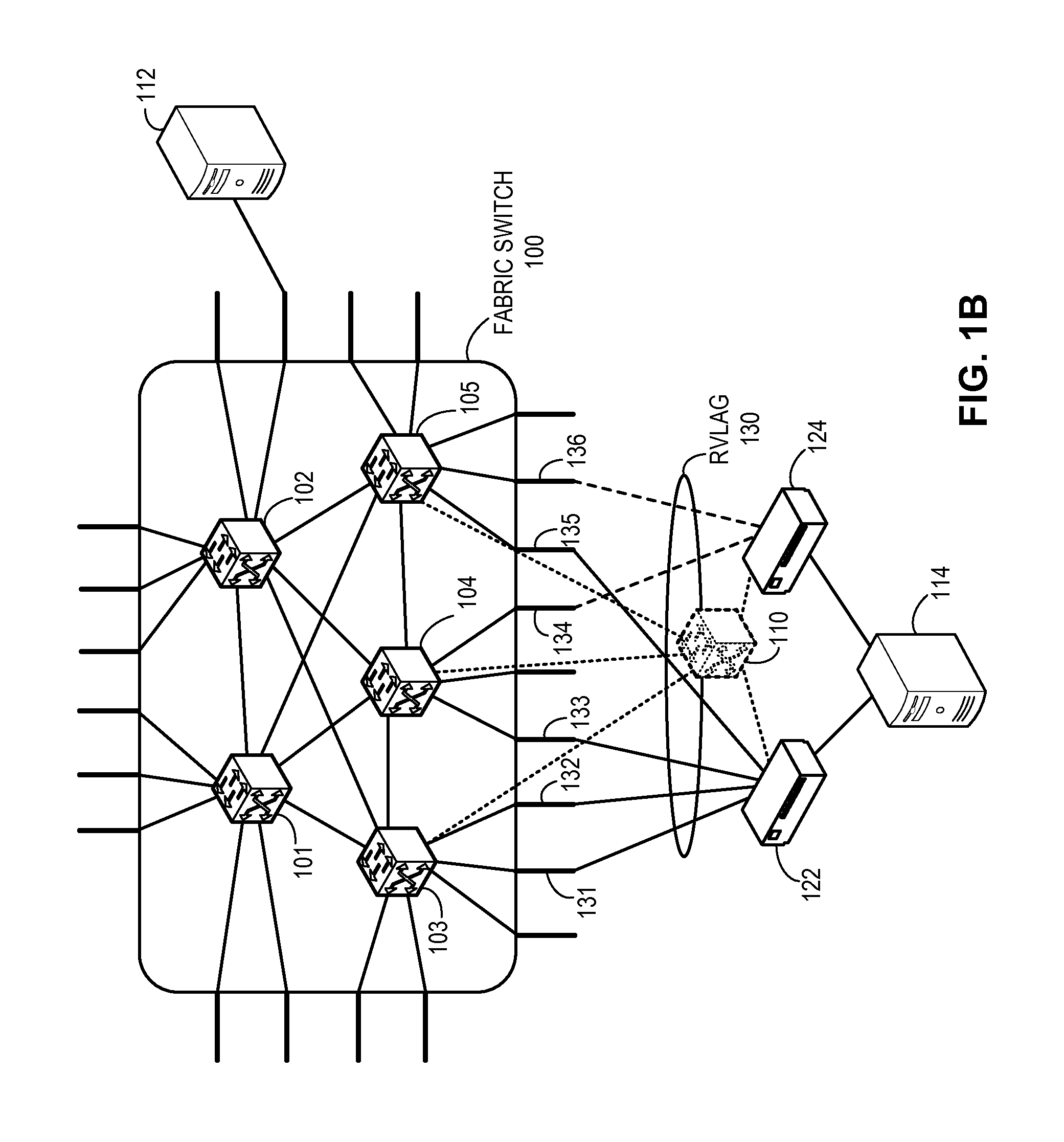
One embodiment of the present invention provides a switch. The switch includes a link aggregation module and a link management module. The link aggregation module establishes a virtual link aggregation group comprising a plurality of links coupled to the switch and one or more other switches. The plurality of links includes a first and a second sets of links coupling a first and a second end devices, respectively. The link management module determines a current mode which indicates which of the sets of links is currently active, and operates the first and the second sets of links as active and standby links, respectively, for the virtual link aggregation group based on the current mode and a port role for a port participating in the virtual link aggregation group. The port role indicates whether the port is coupled to an active link or a backup link.
Owner:AVAGO TECH INT SALES PTE LTD
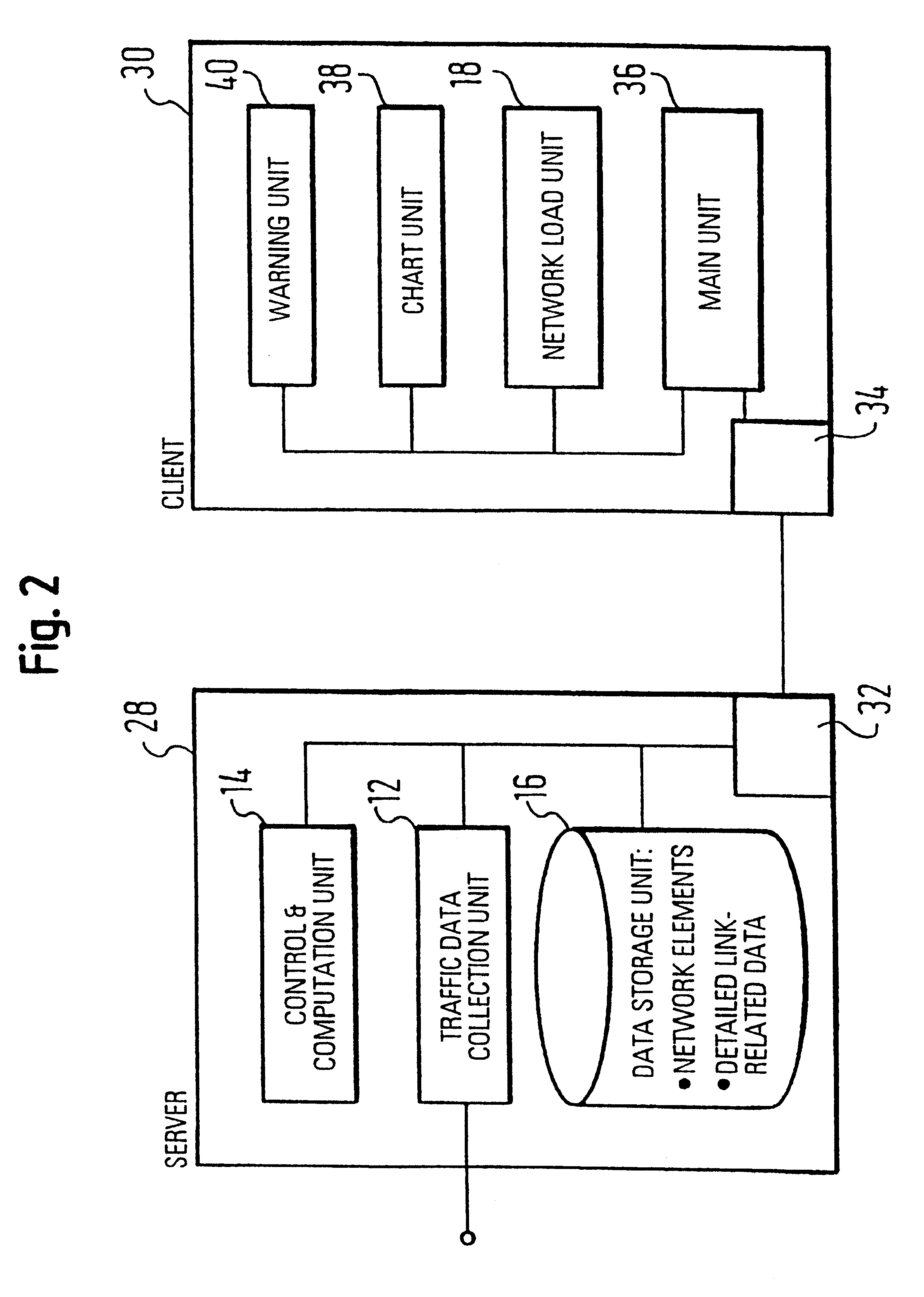
System for traffic data evaluation of real network with dynamic routing utilizing virtual network modelling
InactiveUS6442615B1Multiple digital computer combinationsData switching networksNetwork modelAdaptive routing
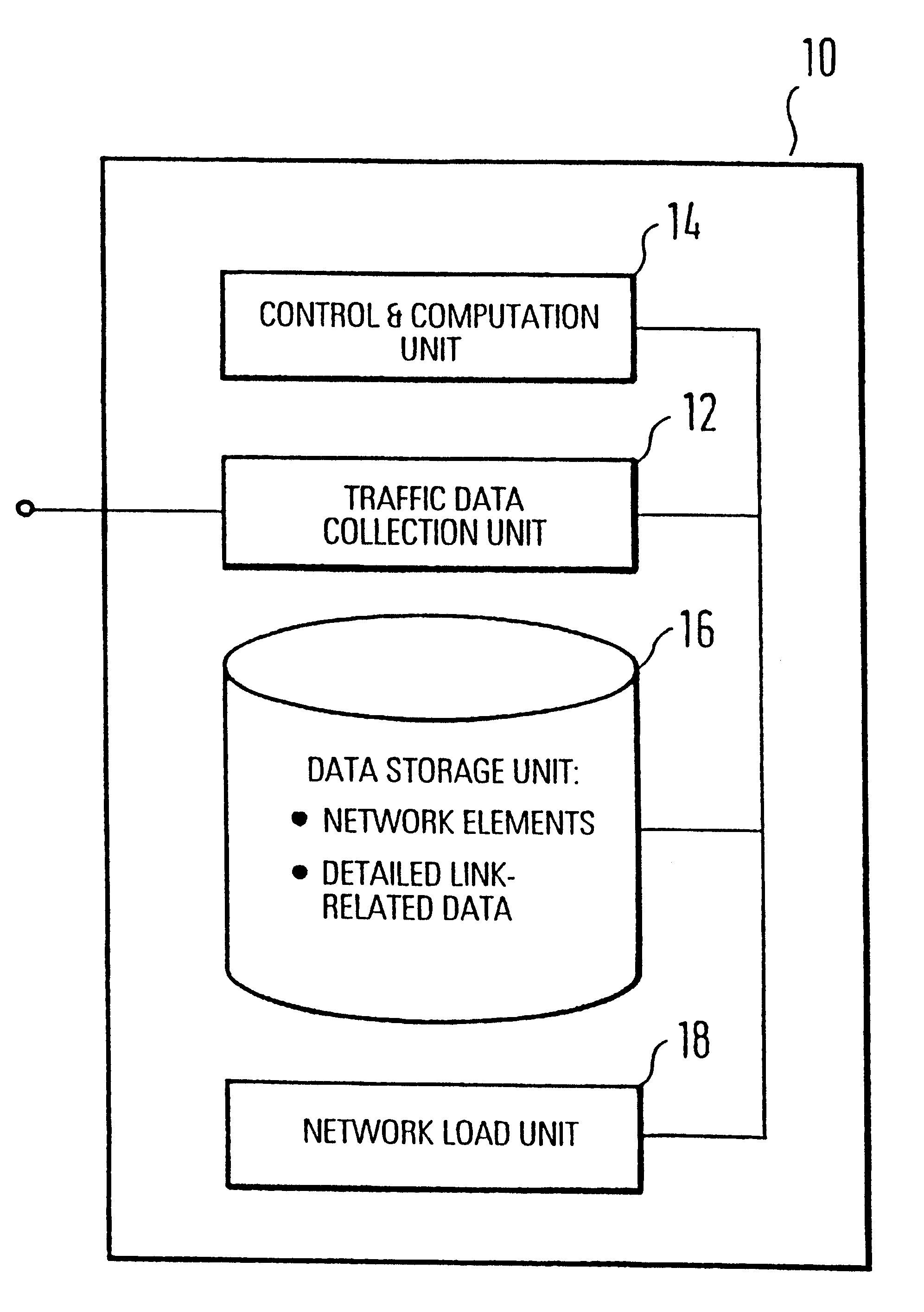
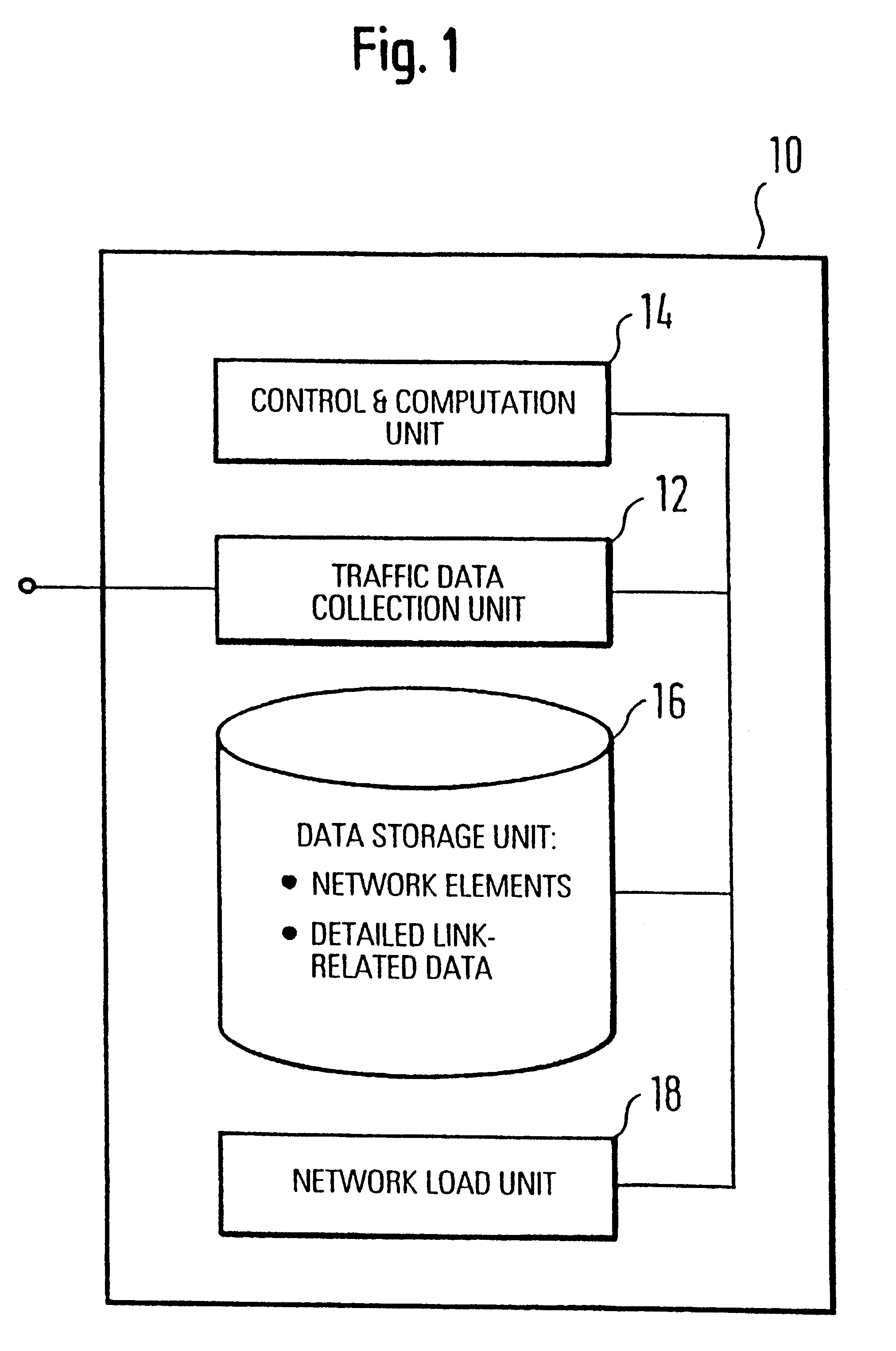
To provide an improved approach to traffic data evaluation in a network using dynamic routing there is provided a traffic data evaluation apparatus for a network using dynamic routing comprising traffic data collection means (12) to collect data with respect to a real traffic flow in the network. Further, the traffic data evaluation apparatus comprises a network modelling unit (14, 16) to model the network through a virtual network having virtual links without capacity restrictions imposed thereon. Still further, there is provided a network load evaluation means (18) to map the real traffic flow onto the virtual network assuming optimal routing and to compare the capacity used for each virtual link with the capacity assigned thereto. Thus, it is possible to draw conclusions on the network load by real network measurements also for a network using a dynamic routing protocol.
Owner:TELEFON AB LM ERICSSON (PUBL)
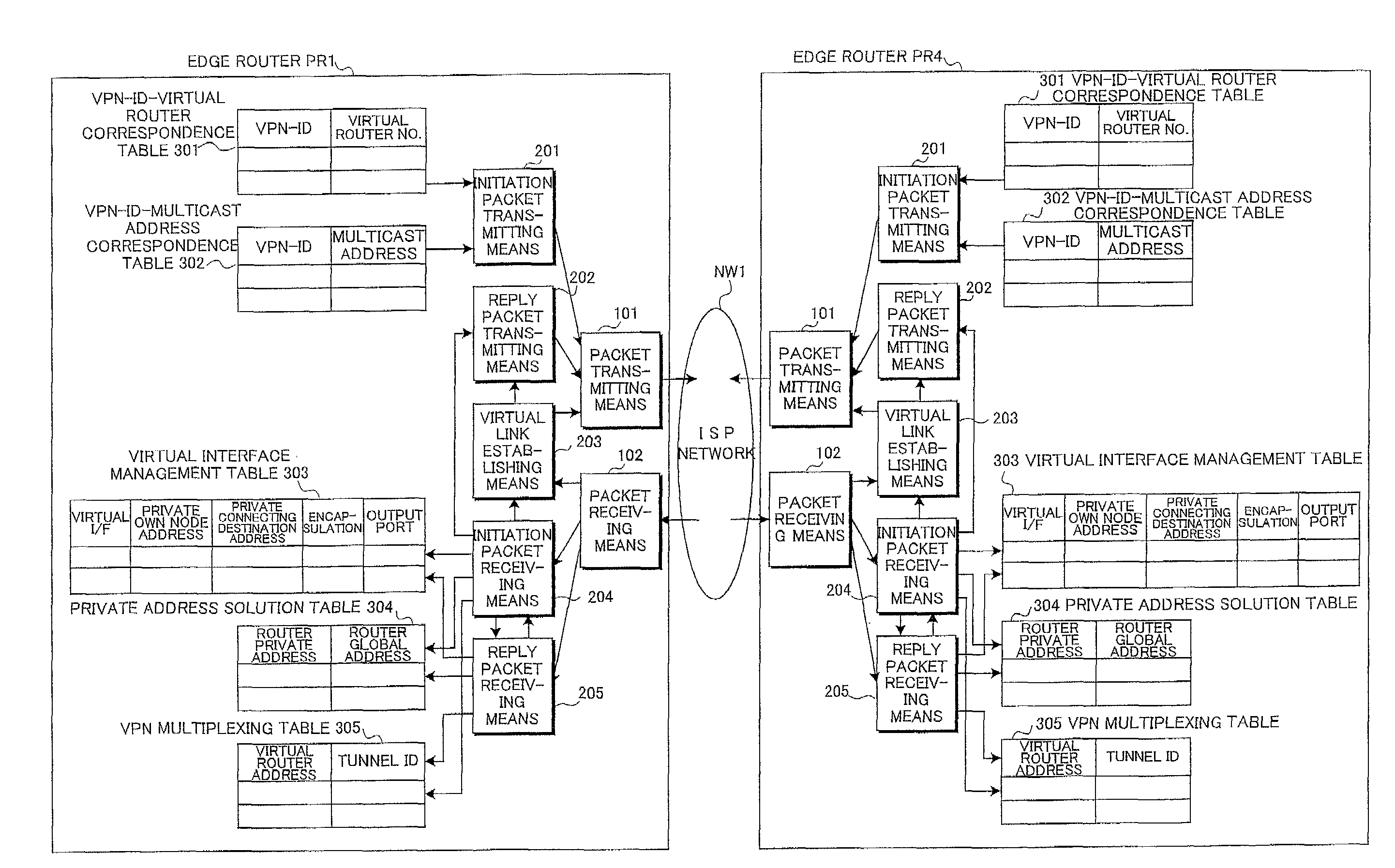
Virtual network construction method, system, and relaying apparatus
InactiveUS7660324B2Error preventionFrequency-division multiplex detailsMulticast addressVirtual network
In a virtual network construction method, a virtual network construction system, and a relaying apparatus within a public data communication network, control packets each having set a multicast address are multicast, and upon reception of the control packets by the relaying apparatuses belonging to the multicast address group, virtual links to the transmitting sources of the control packets are established and reply packets are returned through the virtual links, whereby the virtual links are established between all of the relaying apparatuses belonging to the multicast address group to establish the virtual network.
Owner:FUJITSU LTD
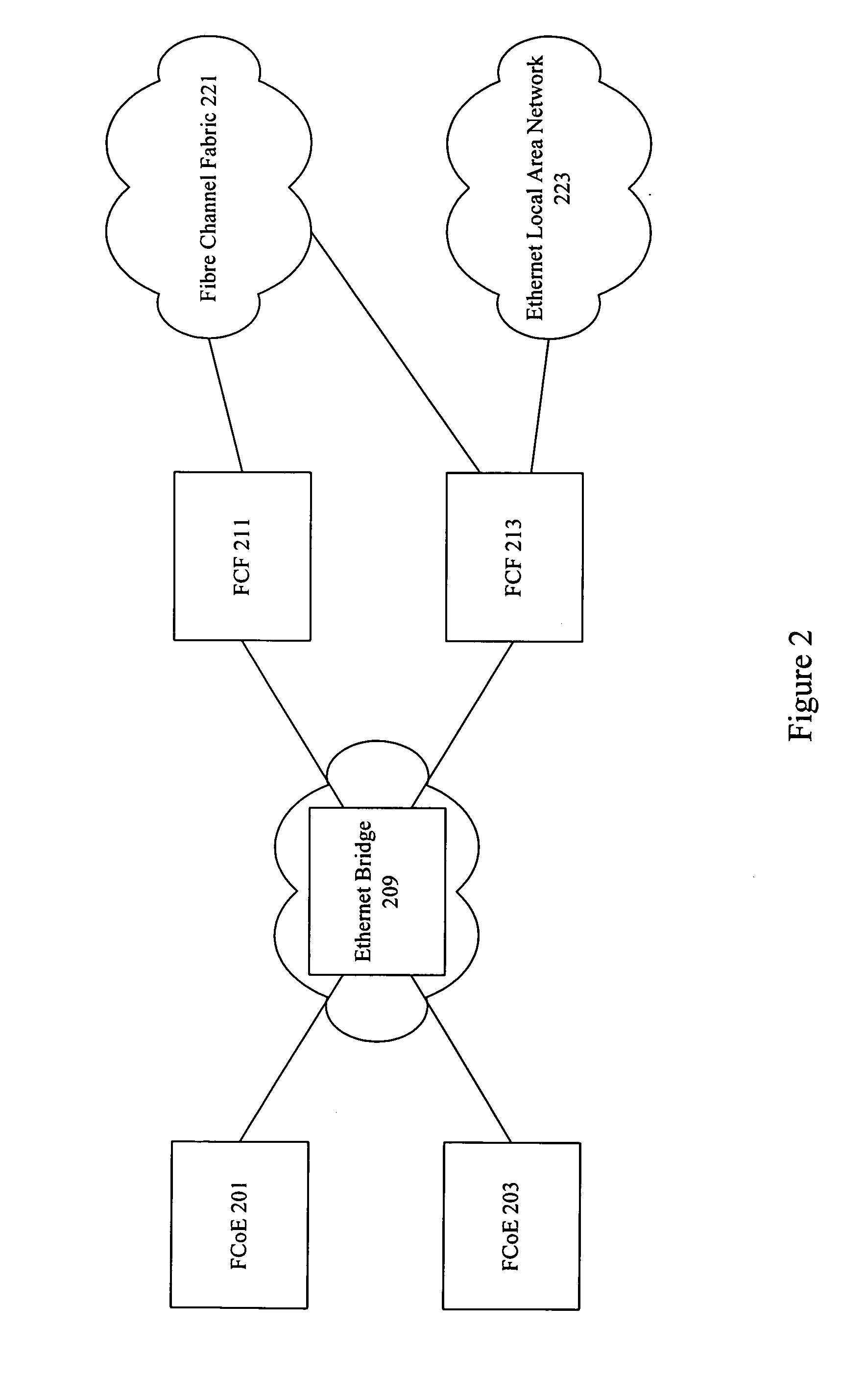
Methods, systems and apparatus for converged network adapters
InactiveUS20120177039A1Data switching by path configurationStore-and-forward switching systemsFibre Channel over EthernetVirtual link
Methods, apparatus and systems are provided for creating virtual links between Fibre Channel over Ethernet (FCoE) nodes. FIP Discovery Advertisement frames are received from multiple FCoE device interconnection apparatus (FIA). The FIP Discovery Advertisement frames comprises source Ethernet MAC addresses, a destination Ethernet MAC address of All-ENode-MACs, Fabric FIP descriptor, and a Priority FIP descriptor. A list is stored of one or more of the source Ethernet MAC address, FIP Priority descriptor, and FIP Fabric descriptor for each unique FIP Discovery Advertisement frame received as indicated by the Fabric descriptor. The Name Server is queried for each source Ethernet MAC address in said storage. For all FCoE devices that match in more that one Name Server, connect to those FCoE devices using the highest priority Ethernet MAC address from matching list items.
Owner:JEDA NETWORKS
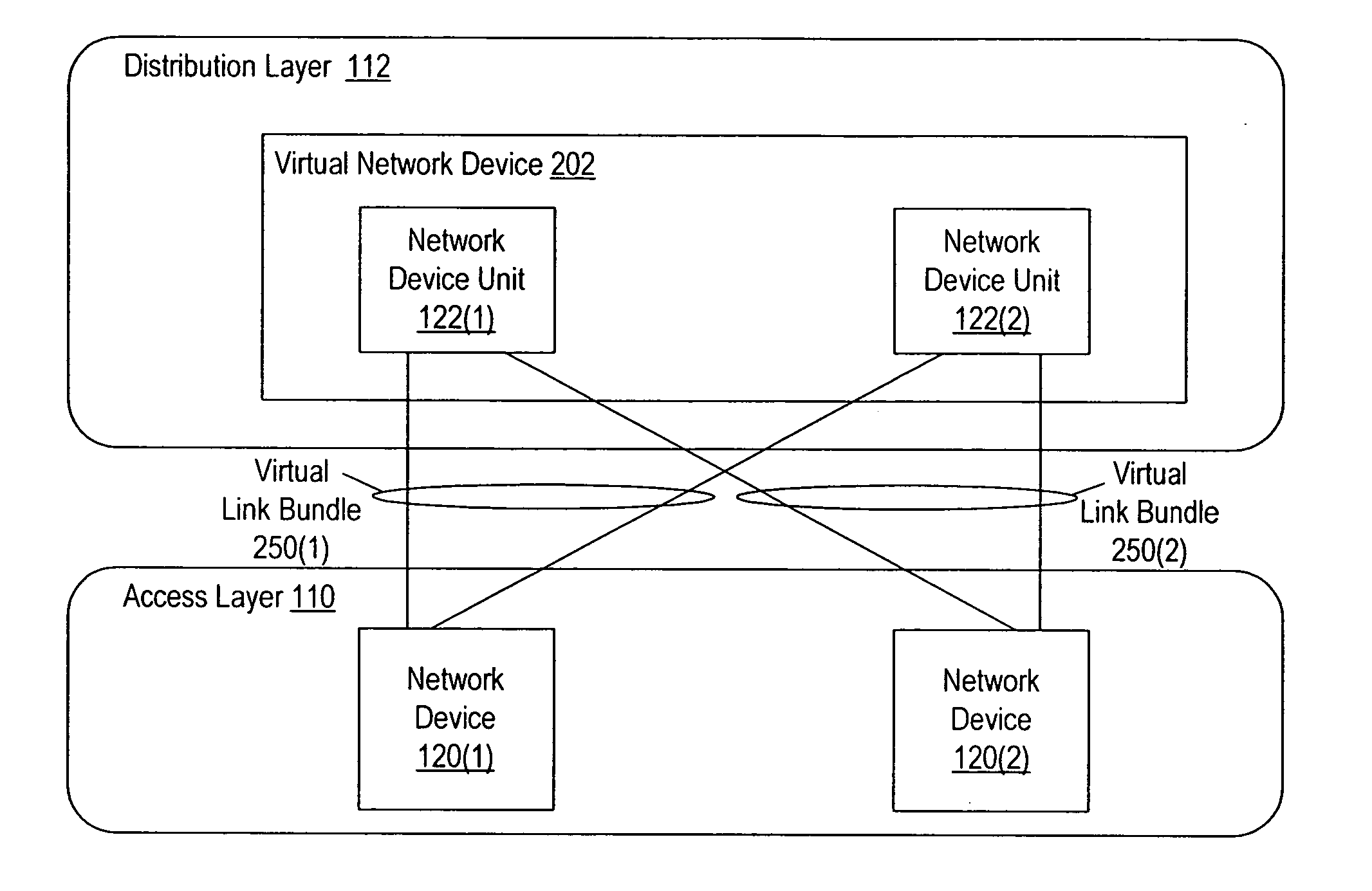
Interface bundles in virtual network devices
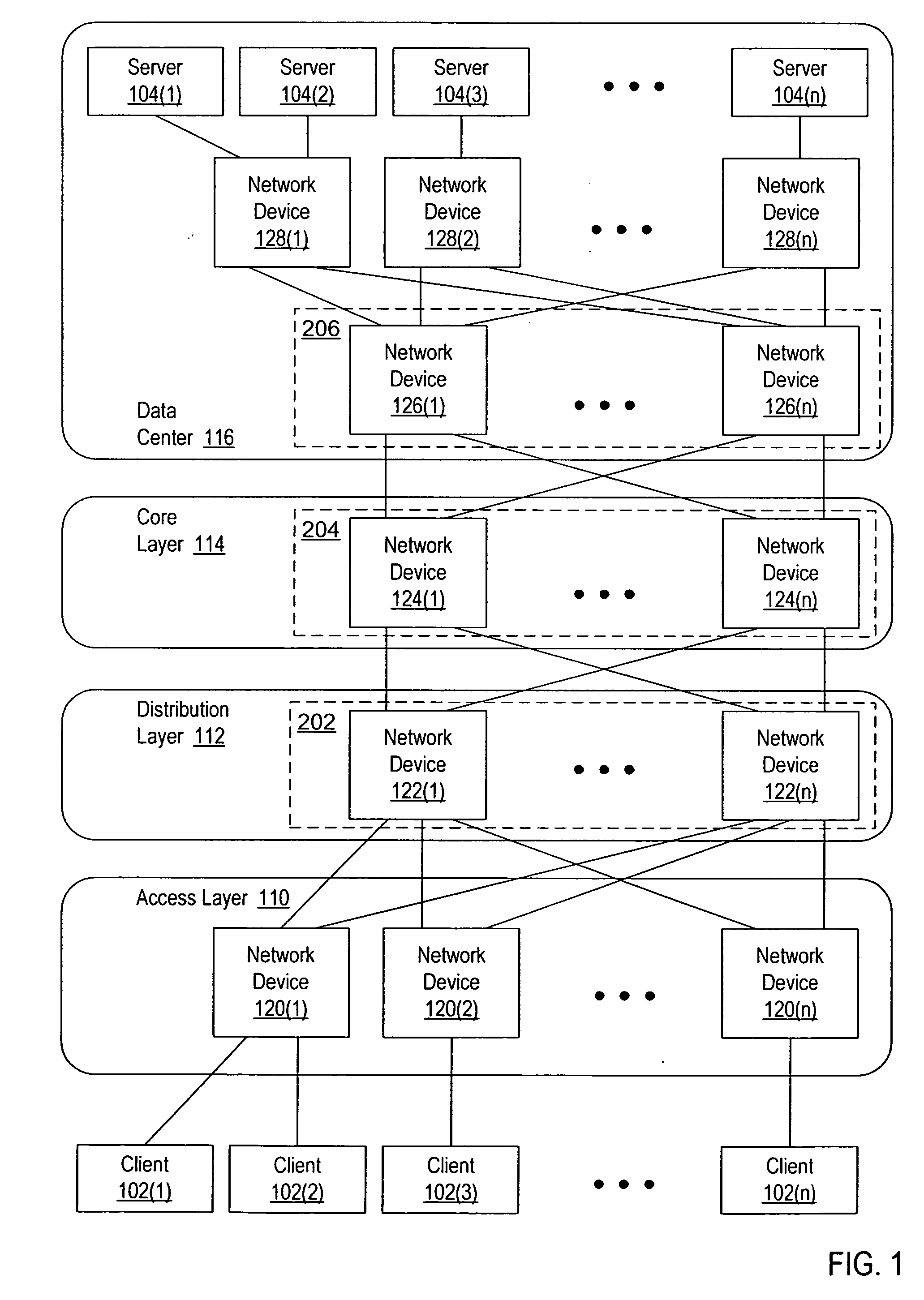
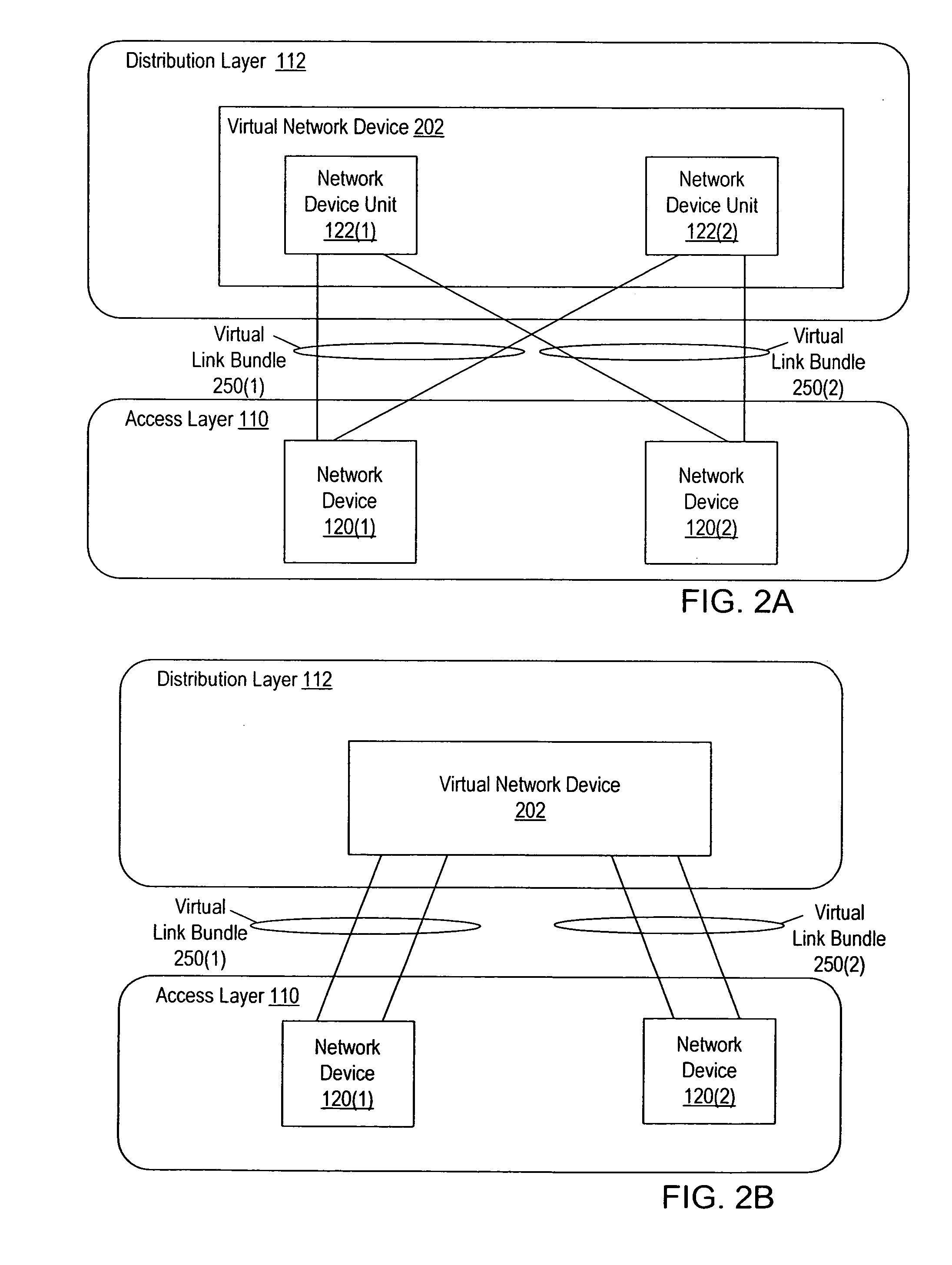
A virtual network device includes several different virtual network device sub-units, which collectively operate as a single logical network device. An interface bundle includes interfaces in more than one of the different virtual network device sub-units included in the virtual network device. The interface bundle is coupled to a virtual link bundle, which connects the virtual network device to another device. The interface bundle is managed as a single logical interface.
Owner:CISCO TECH INC
Virtual network construction method, system, and relaying apparatus
InactiveUS20020067725A1Error preventionFrequency-division multiplex detailsMulticast addressVirtual network
In a virtual network construction method, a virtual network construction system, and a relaying apparatus within a public data communication network, control packets each having set a multicast address are multicast, and upon reception of the control packets by the relaying apparatuses belonging to the multicast address group, virtual links to the transmitting sources of the control packets are established and reply packets are returned through the virtual links, whereby the virtual links are established between all of the relaying apparatuses belonging to the multicast address group to establish the virtual network.
Owner:FUJITSU LTD
Route search method and apparatus for navigation system utilizing map data of XML format
ActiveUS20100262359A1Efficient searchImprove accuracyInstruments for road network navigationRoad vehicles traffic controlCost effectivenessRoute search
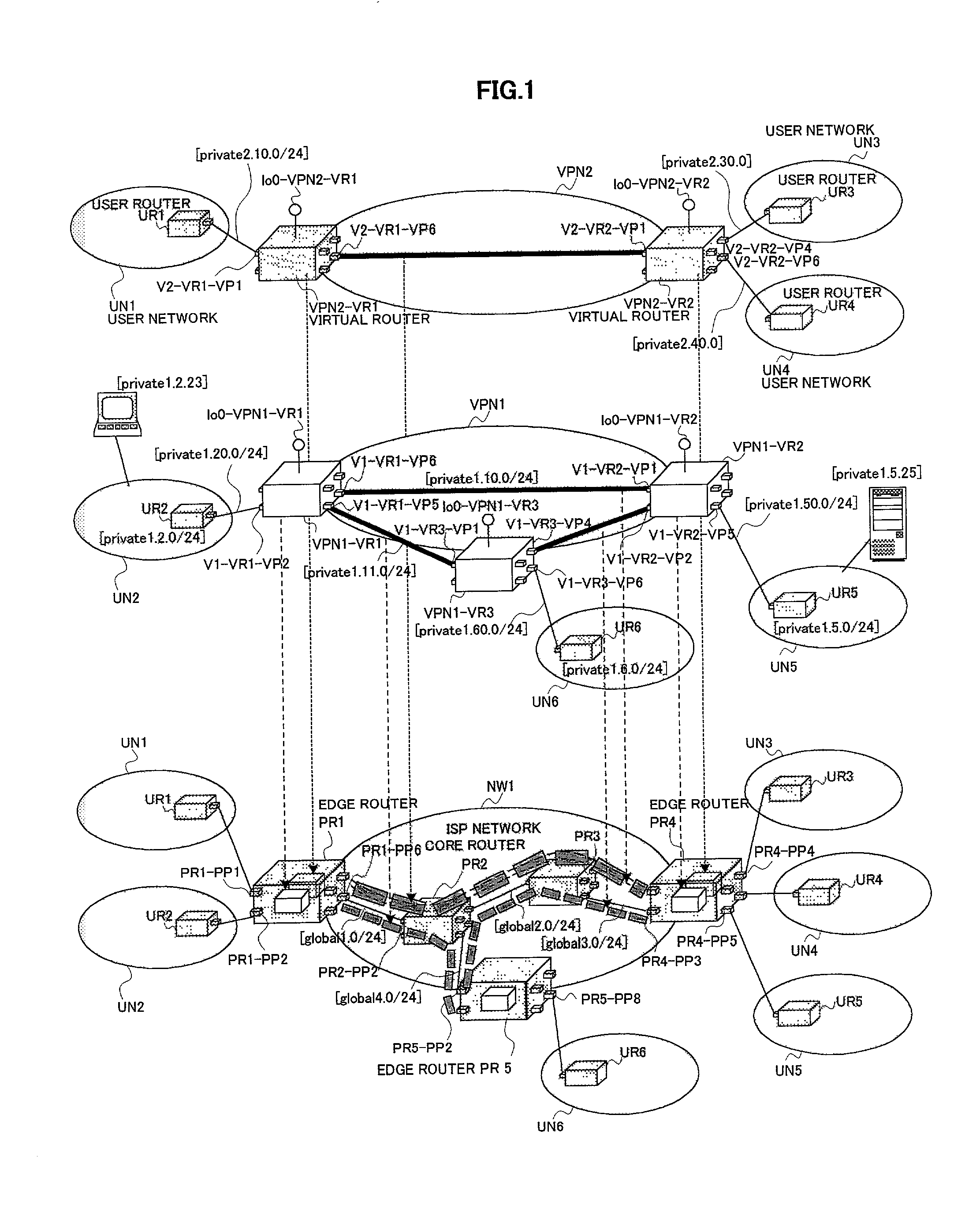
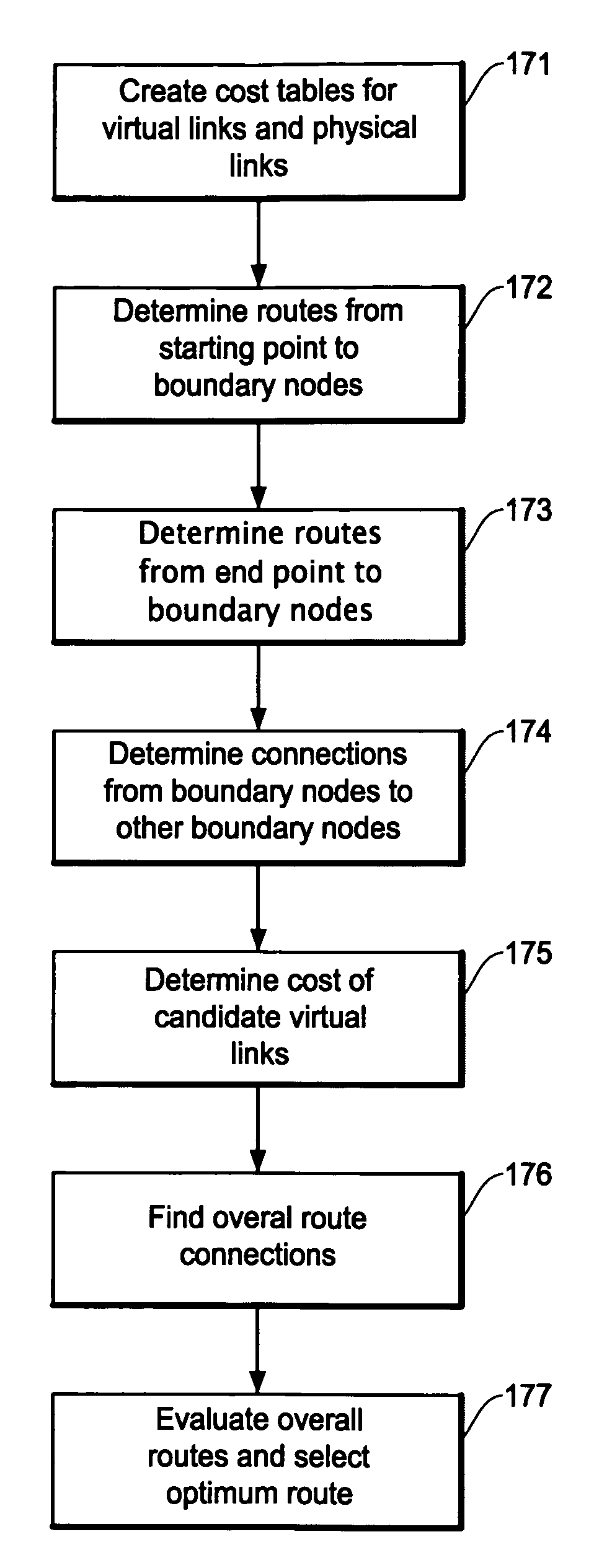
A route search method for a navigation system using the XML map data that is layered based on administrative regions improves efficiency and accuracy of finding an optimum route. The method includes the steps of establishing boundary nodes on boundaries of administrative regions, creating cost information on virtual links that connect the boundary nodes on the administrative regions and physical links on a base layer, selecting candidate virtual links regions by evaluating the cost information, detecting candidate total routes between the start point and destination by connecting the candidate virtual links and other routes, and applying physical links in the base layer to the candidate total routes for further evaluating the costs of the total routes to select the most cost effective total route.
Owner:ALPINE ELECTRONICS INC
Credit-based flow control in lossless ethernet networks
In one embodiment, a system includes a hardware processor and logic integrated with and / or executable by the processor or media access control (MAC) functionality of a network port, the logic being adapted to initialize a link between a receiving endpoint and a sending endpoint, the receiving and sending endpoints being connected in a network fabric, wherein at least one virtual link is created within the link, receive an amount of available flow credits from the receiving endpoint, wherein the amount of available flow credits are used to determine a capacity to process packets at the receiving endpoint, and transmit one or more packets to the receiving endpoint until all packets are sent or the amount of available flow credits is insufficient to process additional packets, wherein exchange of flow credits is performed on a per virtual link basis.
Owner:KYNDRYL INC
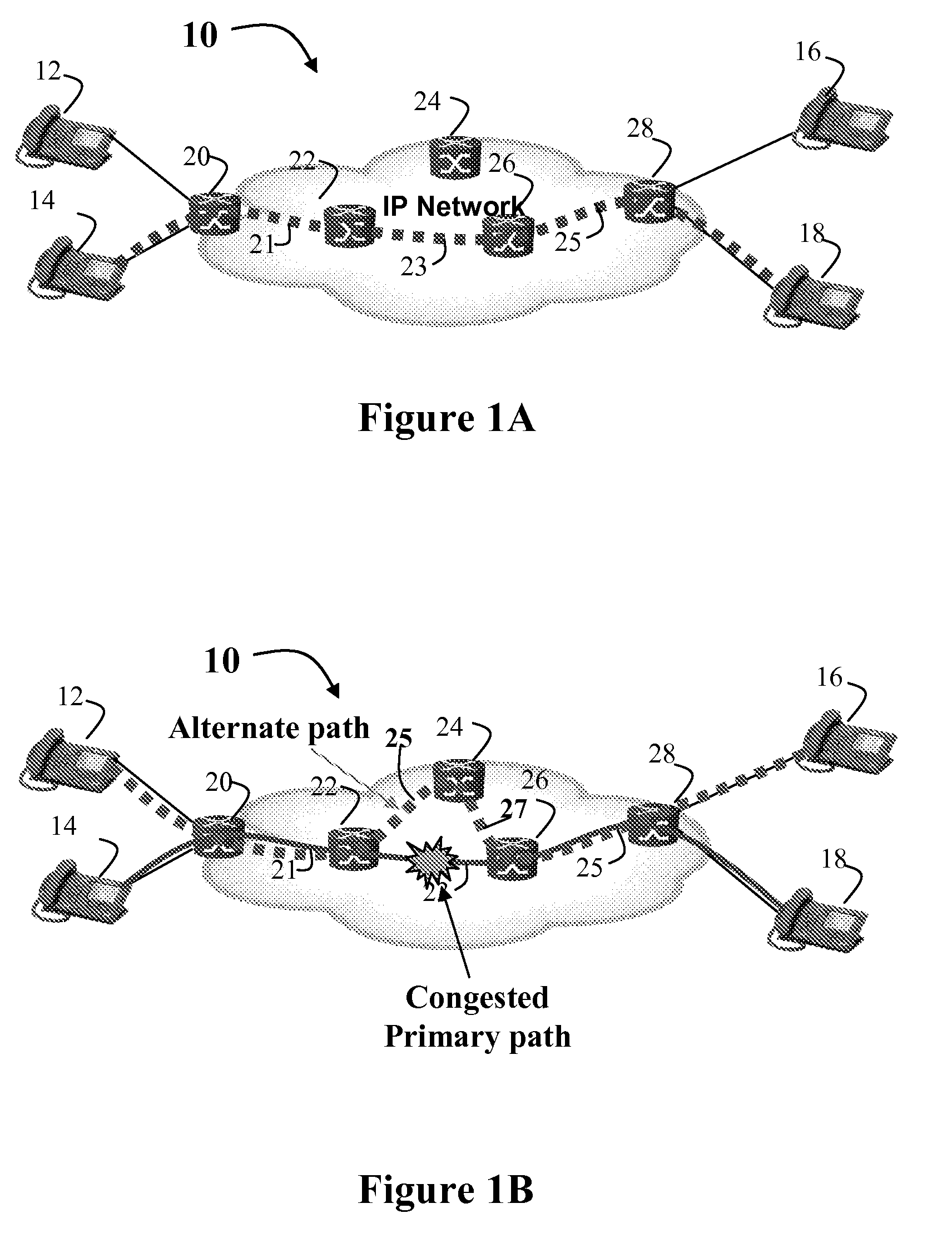
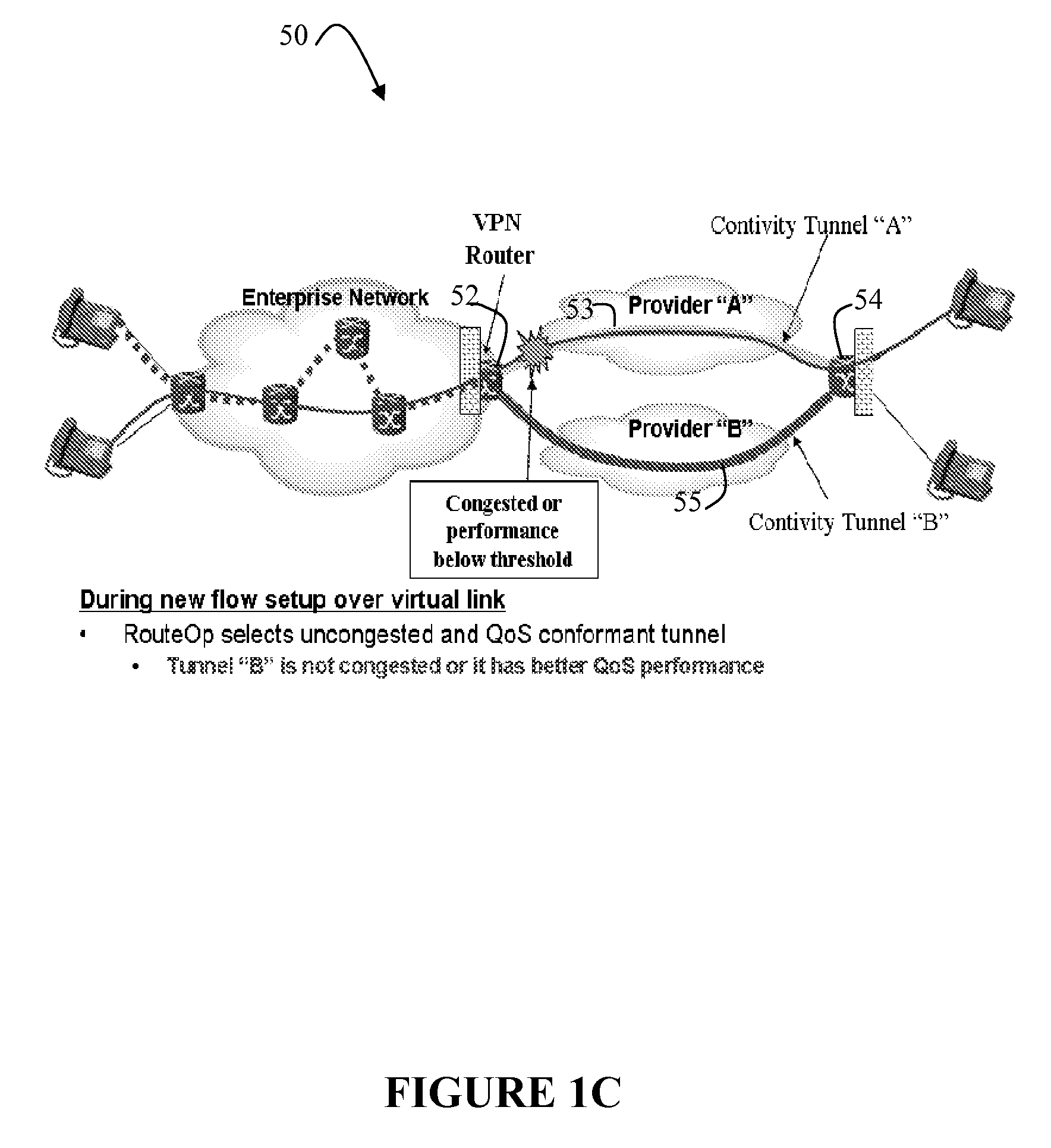
Route Optimization Using Measured Congestion
A flow based routing method and apparatus selects a path from a plurality of different paths for assignment to a flow. The path is selected based on a traffic performance measurements which identify relative congestion and performance of the different paths, so that traffic flows can be diverted away from network congestion points, thereby allowing network resources to be load balanced at a flow granularity. The present invention may be configured on physical or virtual links on an NE to enhance the forwarding of packets using the primary link and one or more alternate links to any given destination.
Owner:AVAYA INC
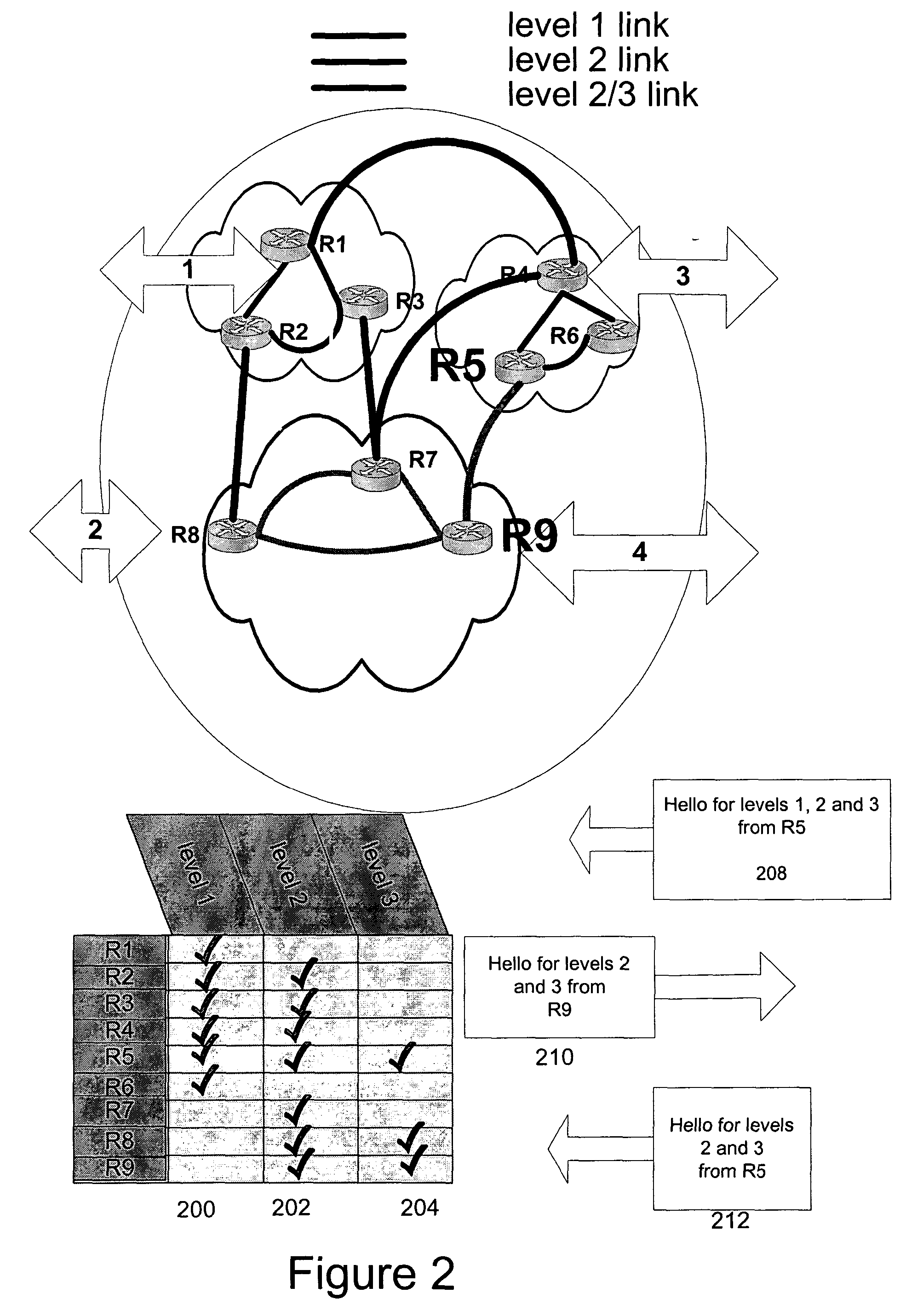
Virtual Links in a Routed Ethernet Mesh Network
ActiveUS20100272110A1Broad spectrum of traffic manipulationSame costData switching by path configurationTraffic capacityLogical view
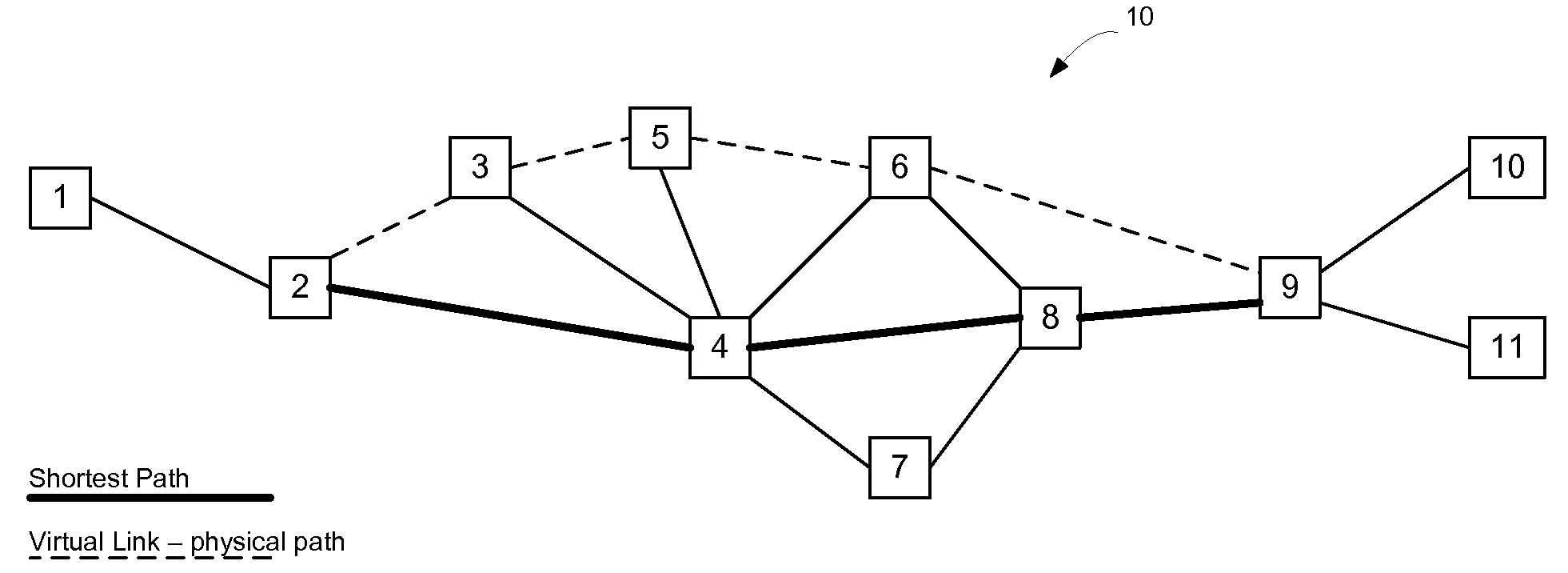
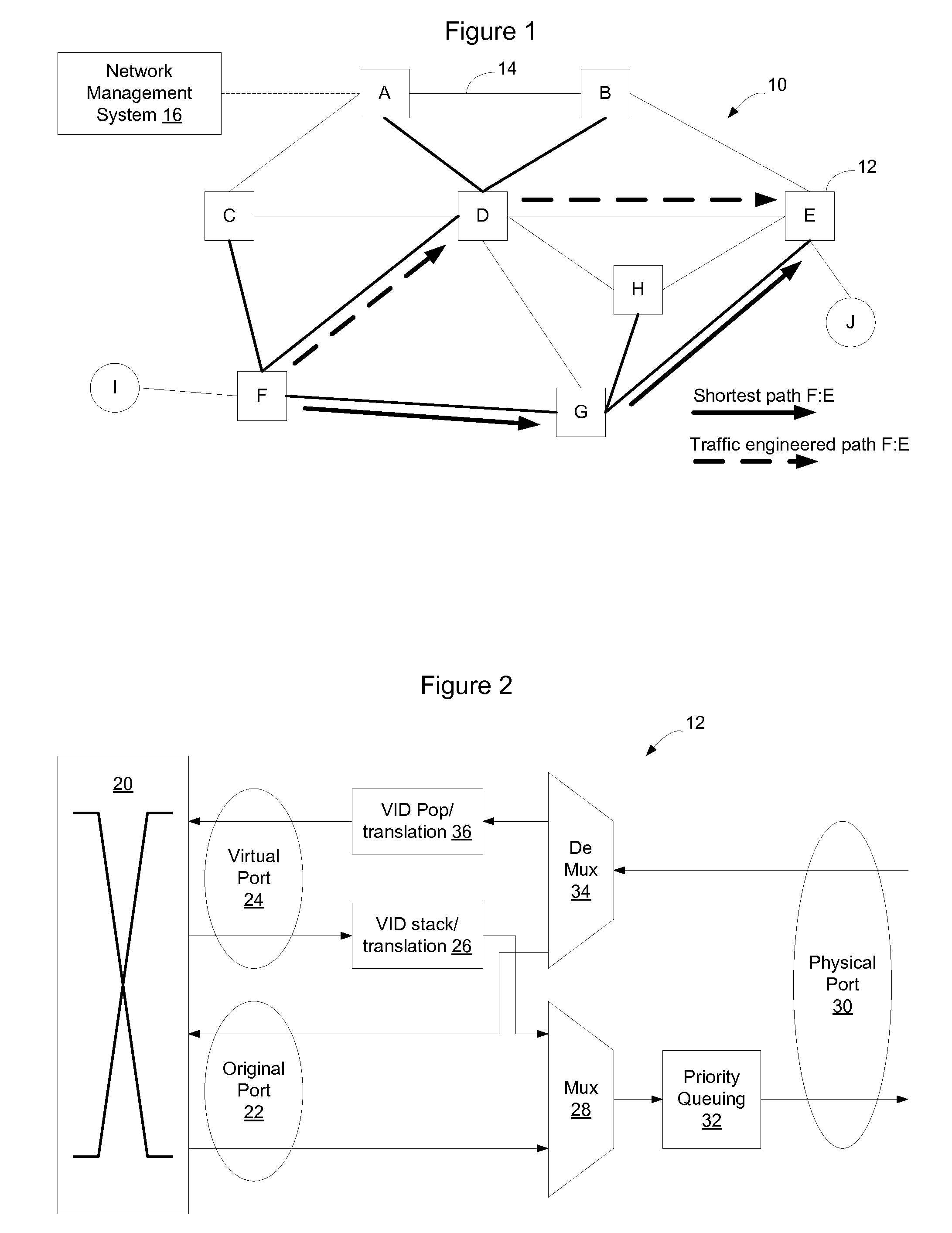
Virtual links may be used to divert traffic within an Ethernet network without affecting overall traffic patterns on the Ethernet network. In one embodiment, the virtual link may be established on the network via a routing system in use on the network. Nodes on a defined path for the virtual link will install forwarding state for the virtual link so that traffic may follow the defined path through the network. The logical view of the virtual link, from a routing perspective however, has the same cost as the shortest path between the endpoints of the virtual link and, accordingly, does not affect other traffic patterns on the network. Once established, the end nodes on the virtual path will have two equal cost paths through the network—one following the shortest path tree and one along the path for the virtual link. The end nodes may use a tie breaking process in an Equal Cost Multi Path (ECMP) selection process to preferentially select the virtual link over the shortest path.
Owner:CIENA
Network communications over shared links in a virtualized environment
A method of data processing includes a physical host executing a virtual machine monitor (VMM) that instantiates a plurality of virtual machines (VMs). The VMM supports processing of a virtual link manager (VLM) that deploys and configures a plurality of Layer 2 virtual links sharing bandwidth of a Layer 2 physical link between the physical host and an access switch. The VMM communicates parameters of the plurality of virtual links with the access switch.
Owner:IBM CORP
Systems and methods for routing employing link state and path vector techniques
InactiveUS20050047353A1Minimize floodingTime-division multiplexData switching by path configurationNetwork strategyNetwork routing
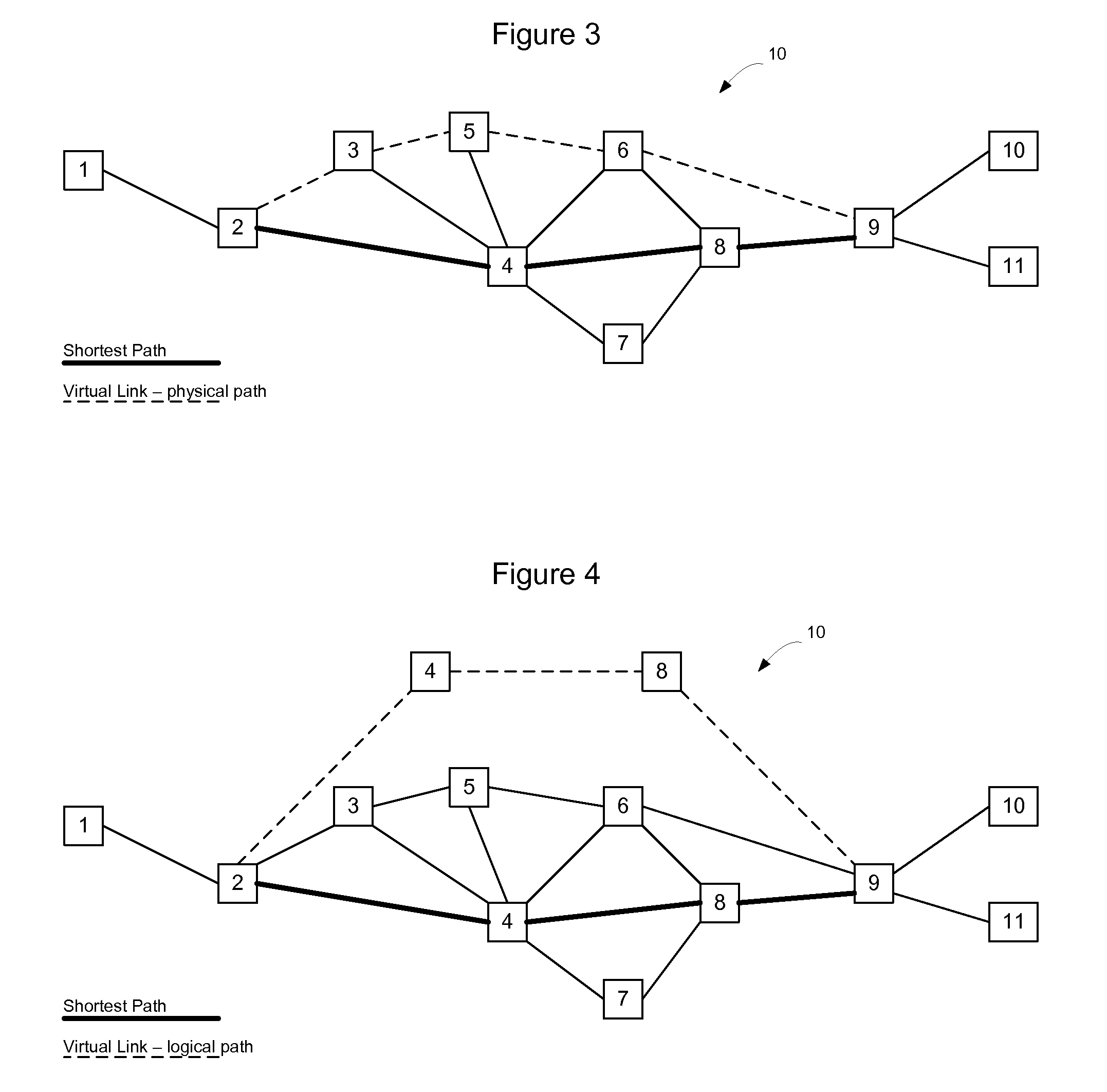
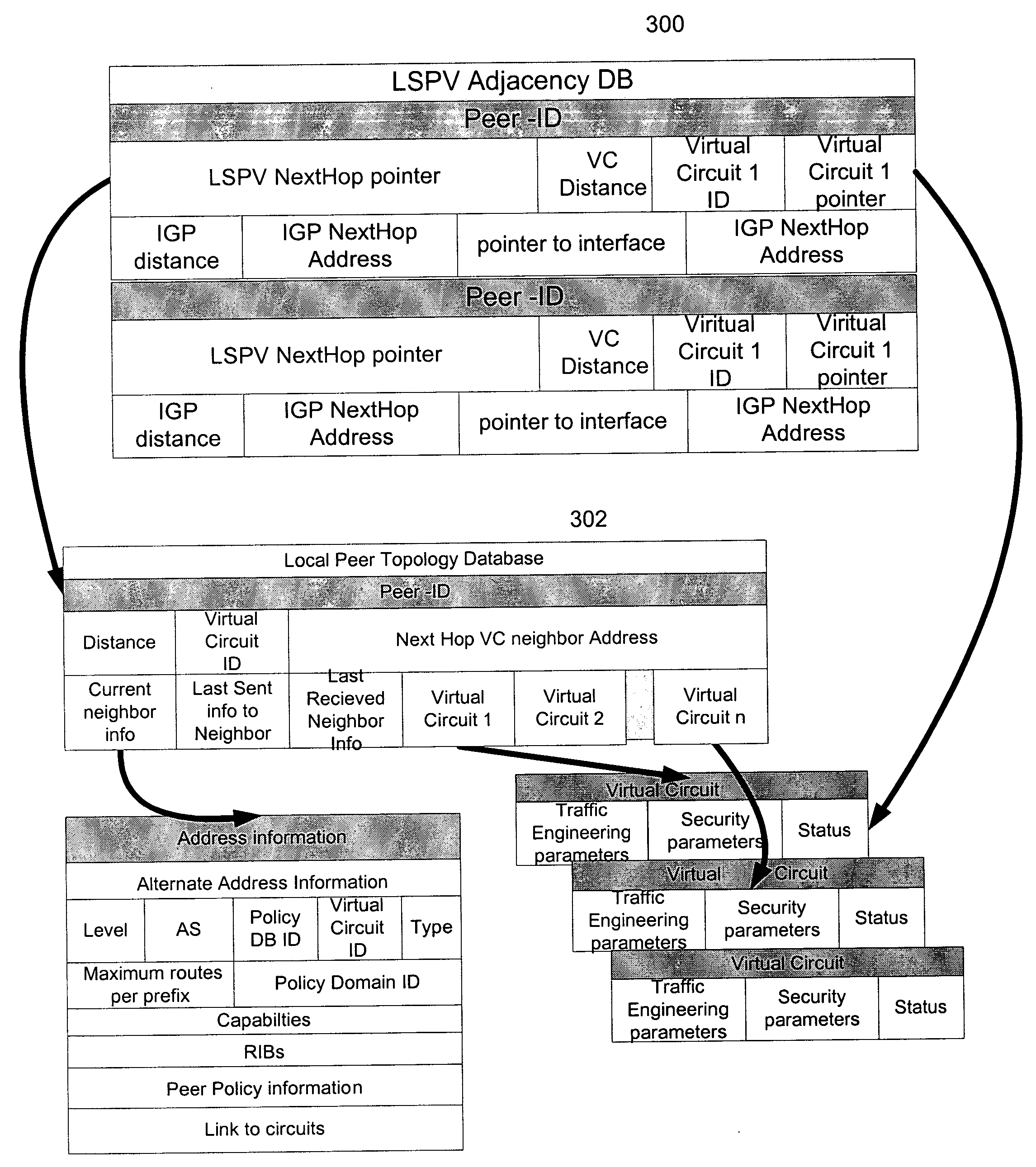
Routing protocols and algorithms, referred to collectively as “Link State Path Vector” (LSPV) techniques, are described. The LSPV allows the application of link-state techniques, such as flooding, to path vector protocols. Routing peers may be organized to form multiple levels of hierarchy. The LSPV mechanisms enable these peers to (1) exchange routing information via virtual links and (2) calculate the best network routes in light of the routing information. Routes may be selected on the basis of both topological distance and network policy. Such metrics may be determined by combining otherwise orthogonal metrics for IGPs and EGPs.
Owner:NEXTHOP TECH INC
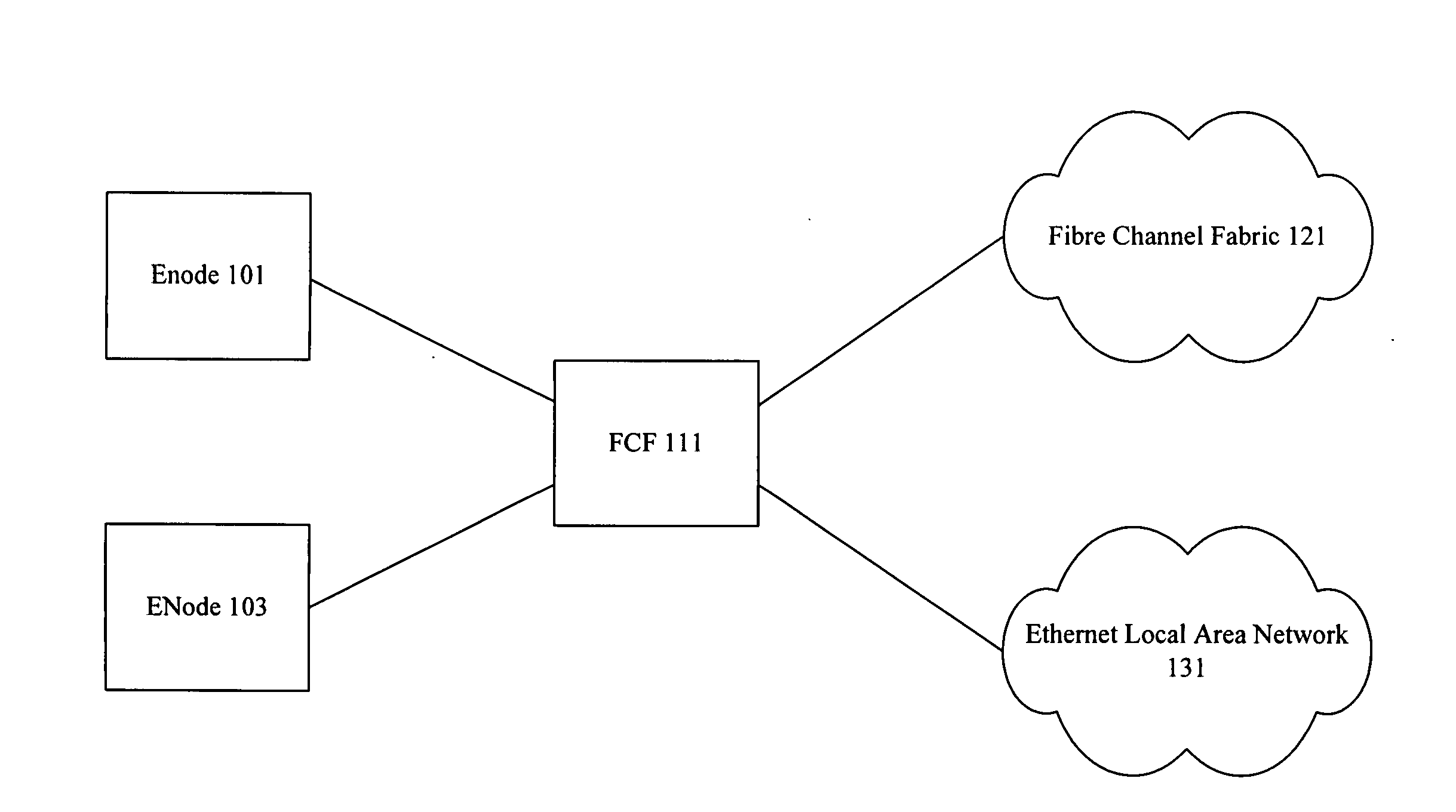
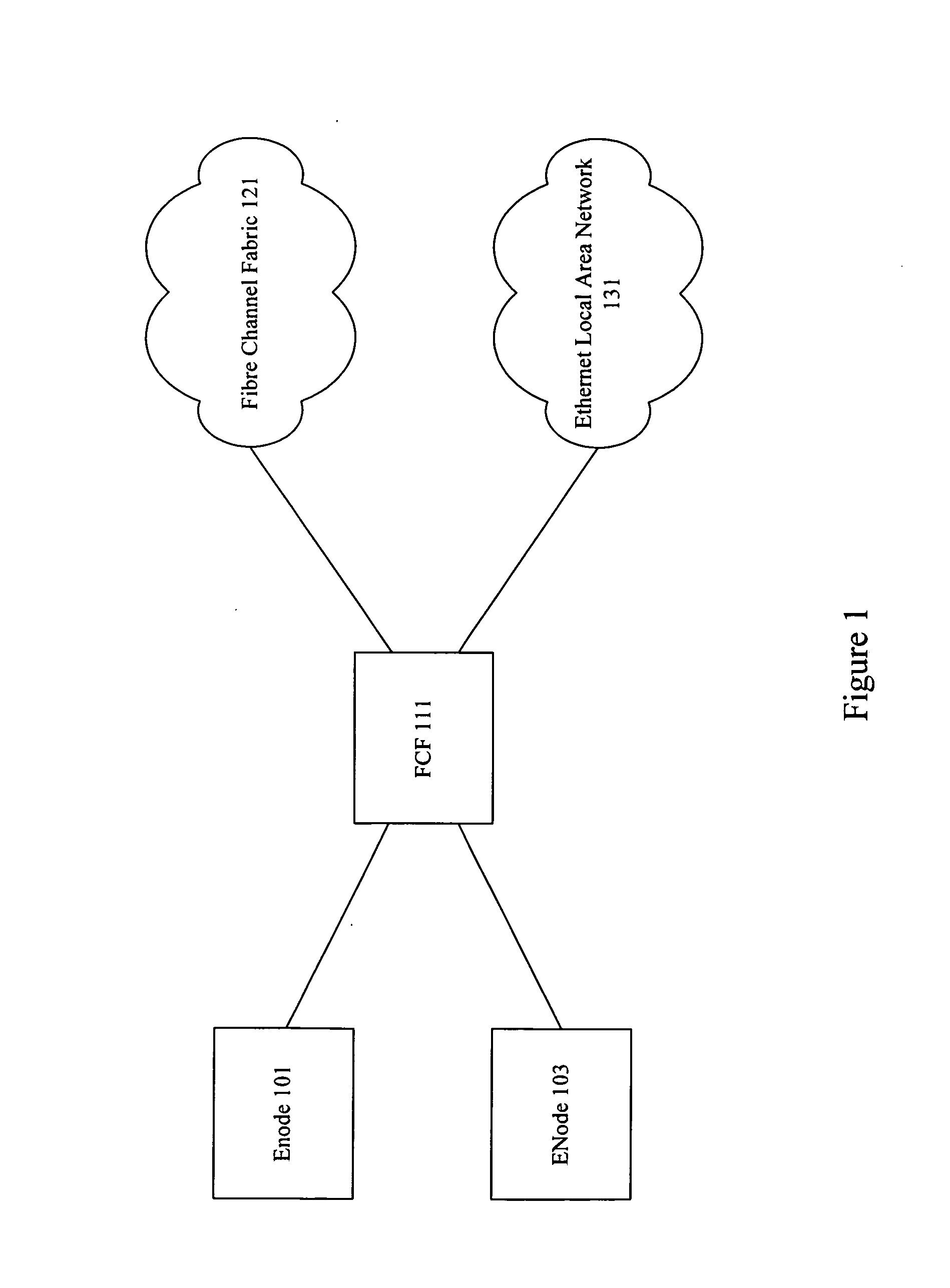
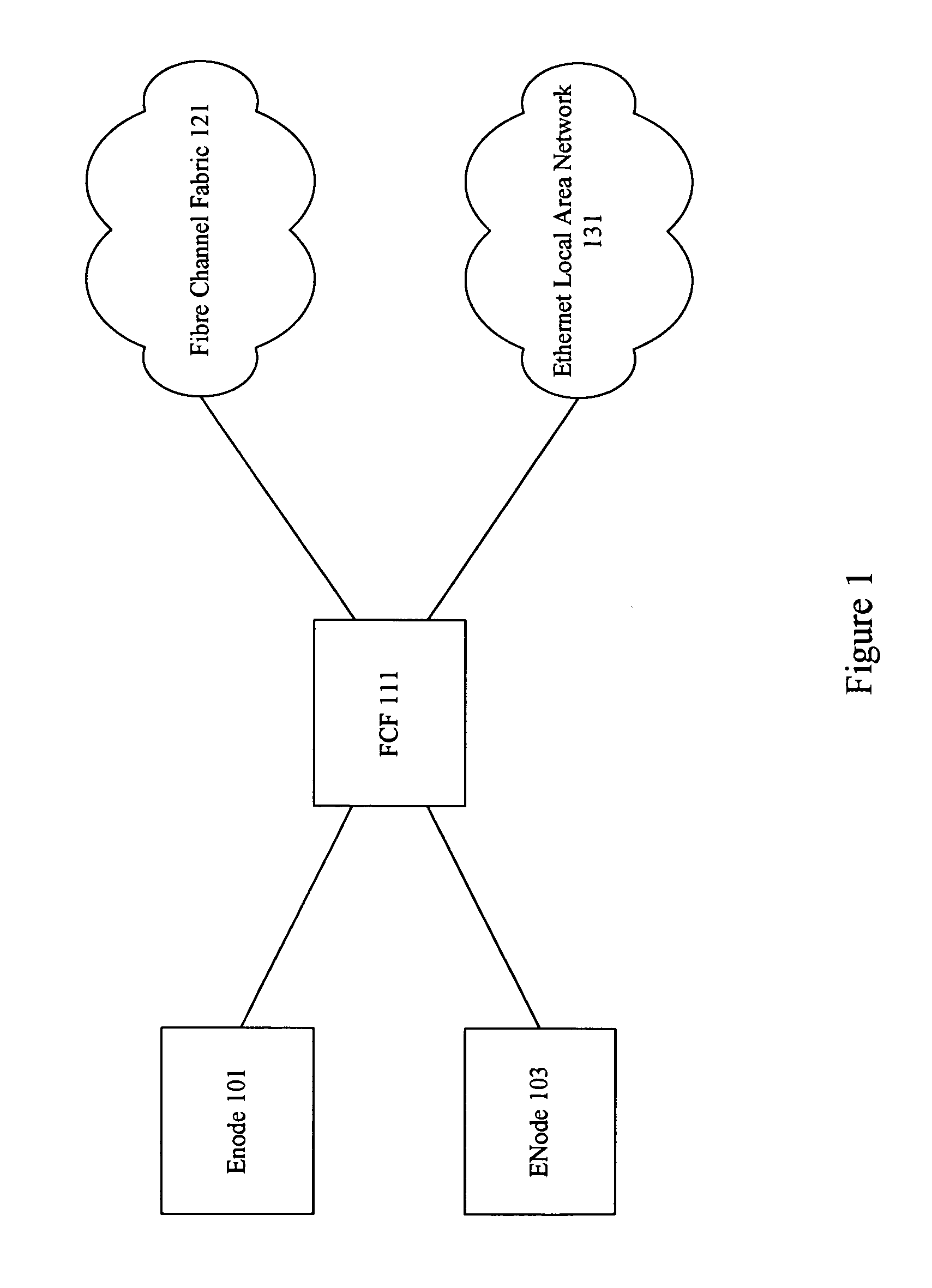
Discovery for fibre channel over ethernet devices
ActiveUS20090252181A1Time-division multiplexData switching networksNetwork packetFibre Channel over Ethernet
Techniques are provided for performing discovery in a Fibre Channel over Ethernet (FCoE) network. An FCoE Node (ENode) discovers the FCoE Forwarders (FCFs) connected to its network segment by transmitting a solicitation message to the multicast MAC address “All-FCF-MACs”. All FCFs receive packets with this multicast MAC address including the solicitation message that announces the presence of the ENode. Each FCF replies with a unicast advertisement message that provides the ENode with a MAC address of the responding FCF. The ENode builds a list of the FCFs available on its network segment and may then establish a virtual link with one or more of the FCFs through a Fabric Login (FLOGI) exchange.
Owner:CISCO TECH INC
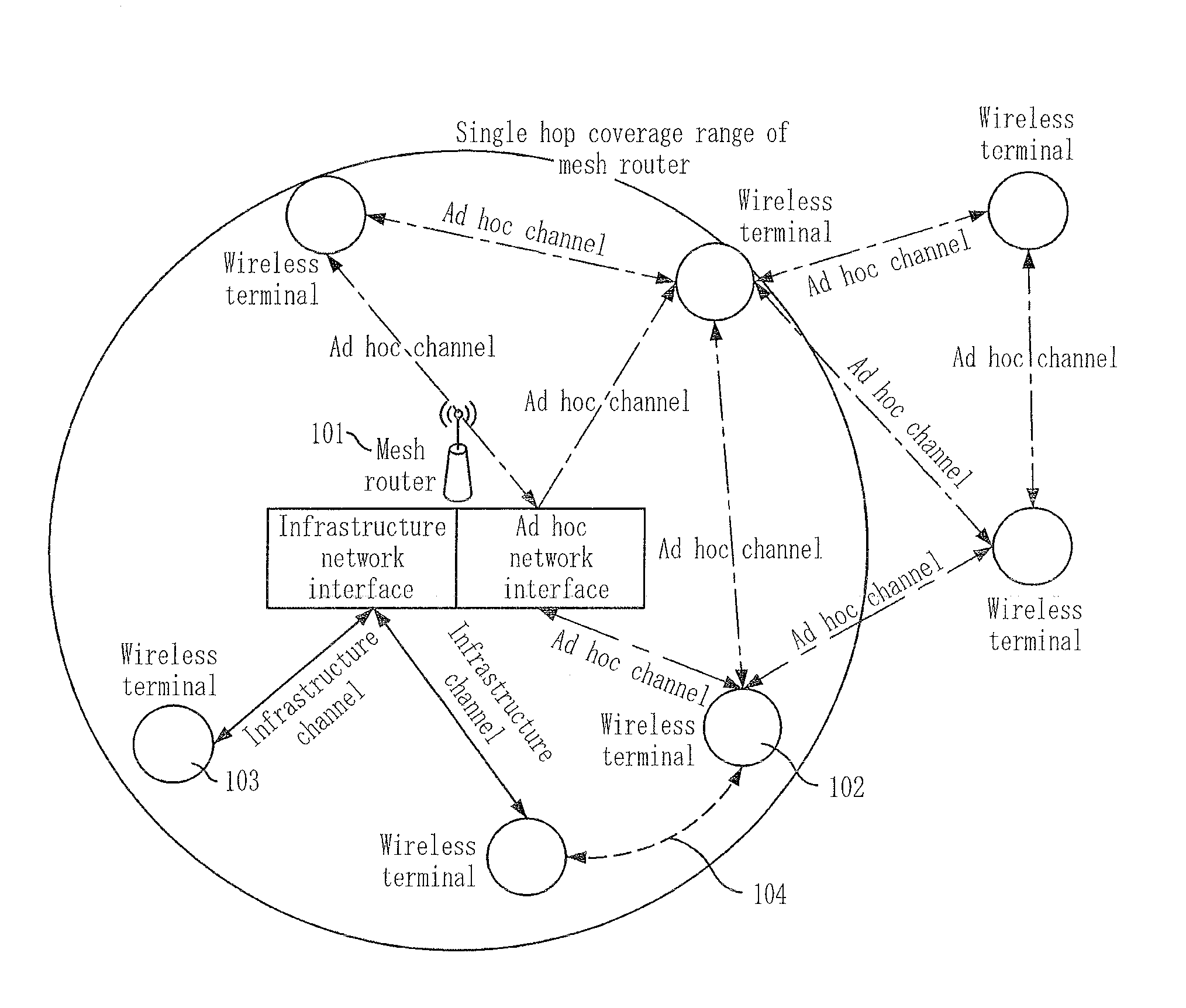
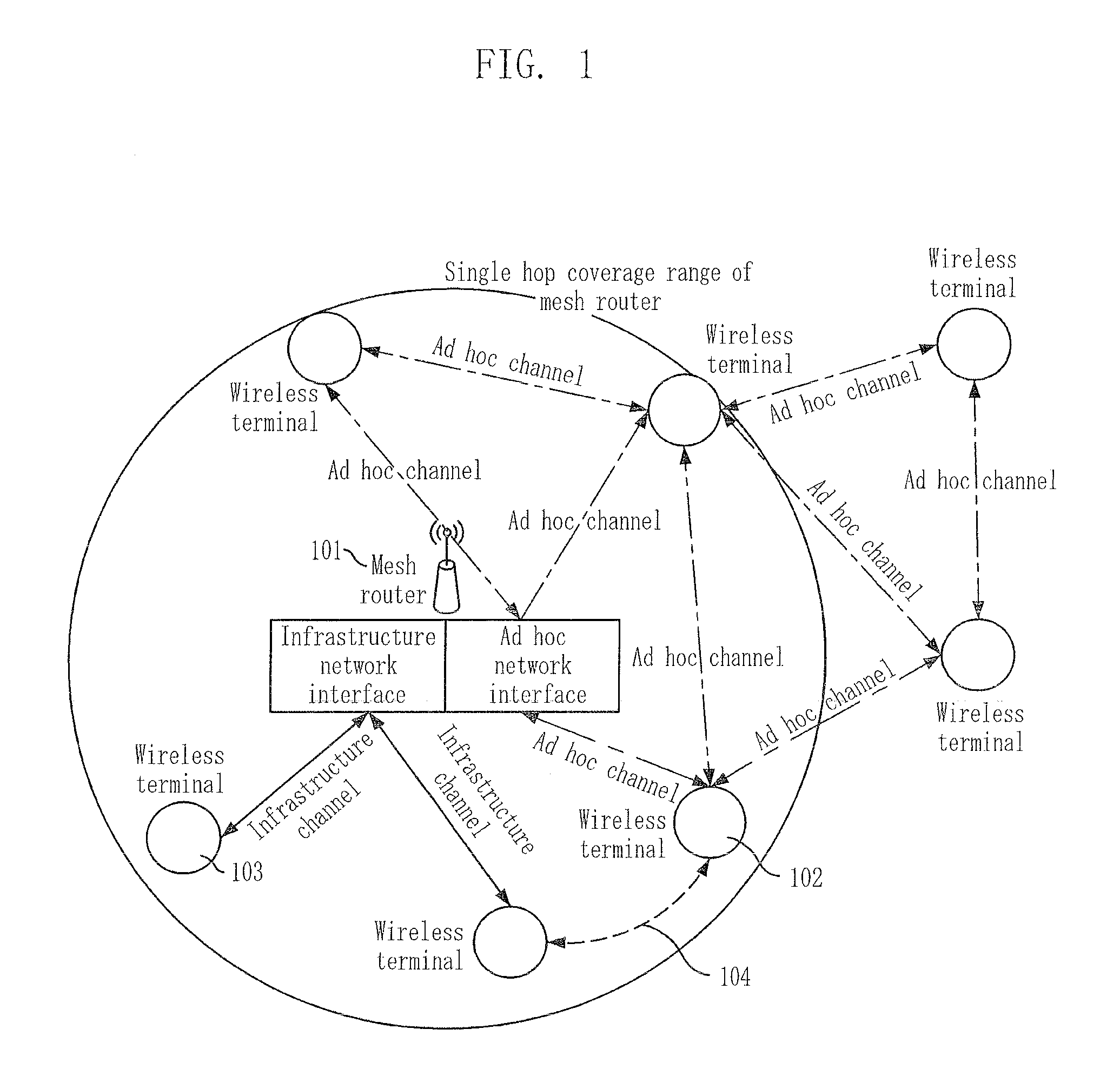
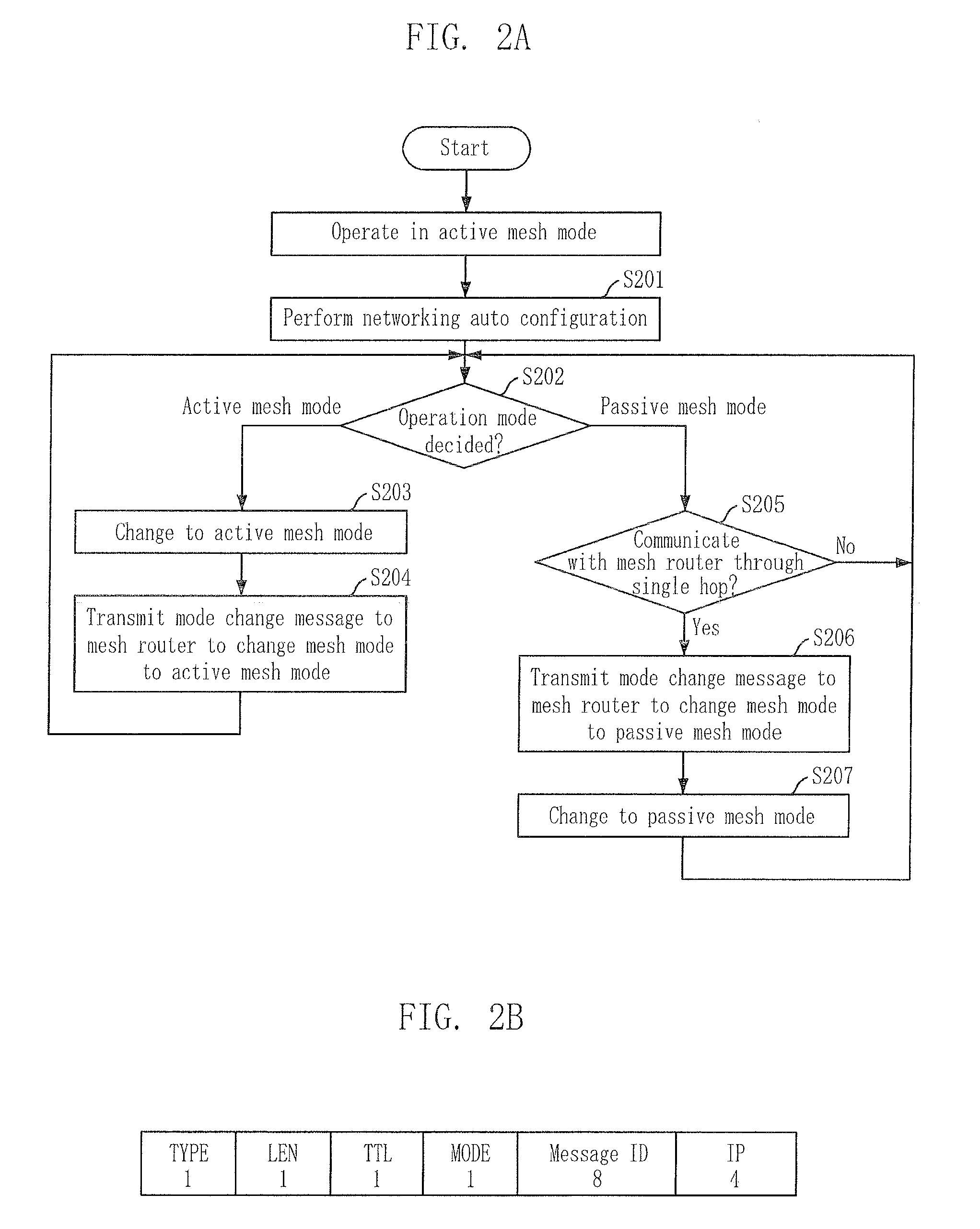
Mesh networking auto configuration method, virtual link setting method, packet transmission method in multi-hop wireless lan, and terminal thereof
InactiveUS20080137556A1Supporting connectivitySupport mobilityNetwork topologiesDigital computer detailsAuto-configurationWireless lan
Provided are a mesh networking auto configuration method, a virtual link setting method, and a packet transmission method in a multi-hop wireless local area network (LAN), and a terminal thereof. According to the provided methods and terminal, the mobility and connectivity of a wireless terminal is guaranteed in a multi-hop wireless LAN, and a seamless service can be provided. Also, a wireless terminal can be enabled to operate in a home gateway in a home networking field according to the present invention.
Owner:ELECTRONICS & TELECOMM RES INST +1
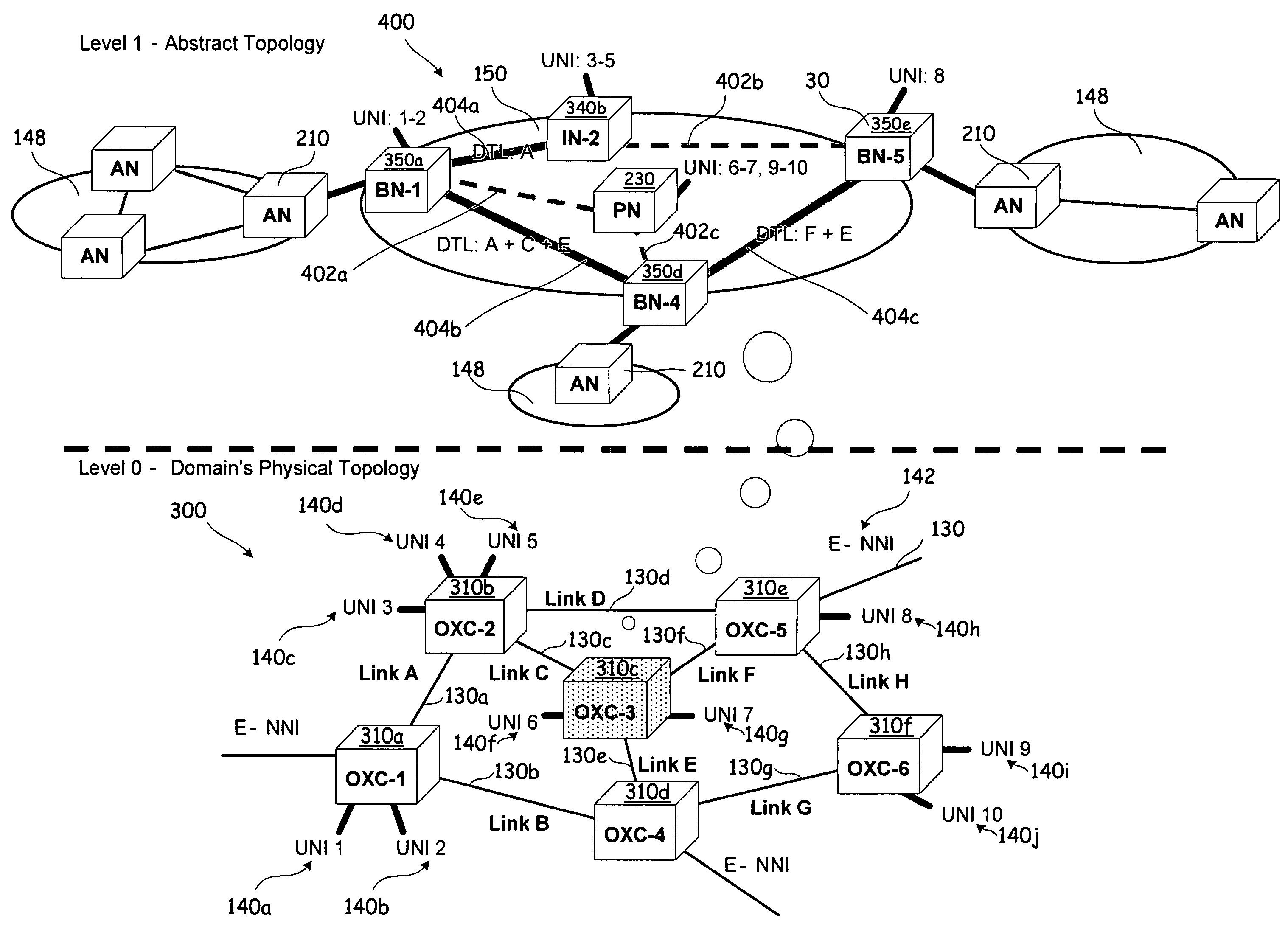
System and method for supporting virtualized links at an exterior network-to-network interface
ActiveUS20080095176A1Reduce complexityProvide controlData switching by path configurationNetwork-to-network interfaceVirtualization
The present invention provides systems and methods for abstracting a network topology into virtual links and supporting both generic and instantiated virtualized links for linking a virtualized topology with actual resources within a domain, providing security over network topology information, providing control over the allocation of resources, and reducing the complexity of advertising.
Owner:CIENA
Discovery for fibre channel over ethernet devices
Techniques are provided for performing discovery in a Fibre Channel over Ethernet (FCoE) network. An FCF discovers other FCoE Forwarders (FCFs) connected to its network segment by transmitting a solicitation message to the multicast MAC address “All-FCF-MACs”. All FCFs receive packets with this multicast MAC address including the solicitation message that announces the presence of the FCF. Each FCF replies with a unicast advertisement message that provides the new FCF with a MAC address of the responding FCF. The FCF builds a list of the FCFs available on its network segment and may then establish a virtual link with one or more of the FCFs through an exchange link parameter (ELP) exchange.
Owner:CISCO TECH INC
Network visible inter-logical router links
InactiveUS20070140235A1Reduce in quantityProvide efficiencyData switching by path configurationNetwork connectionsVisibilityDatapath
A scheme for allowing logical routers to achieve data path efficiency and still maintain network visible virtual links is provided by allowing logical routers in the same physical router to share routing information using standard protocols in place of proprietary route leaking, and by analyzing received data packets to determine if they are tandem data packets or terminating data packets. Tandem data packets are routed directly to egress ports with a single pass through the switch fabric to achieve efficiency, while the TTL value of the packet is decremented twice to maintain the external appearance of the separation of the logical routers. Terminating data packets are routed to other logical routers over virtual links to allow network visibility of the inter-logical router links.
Owner:AVAYA HLDG
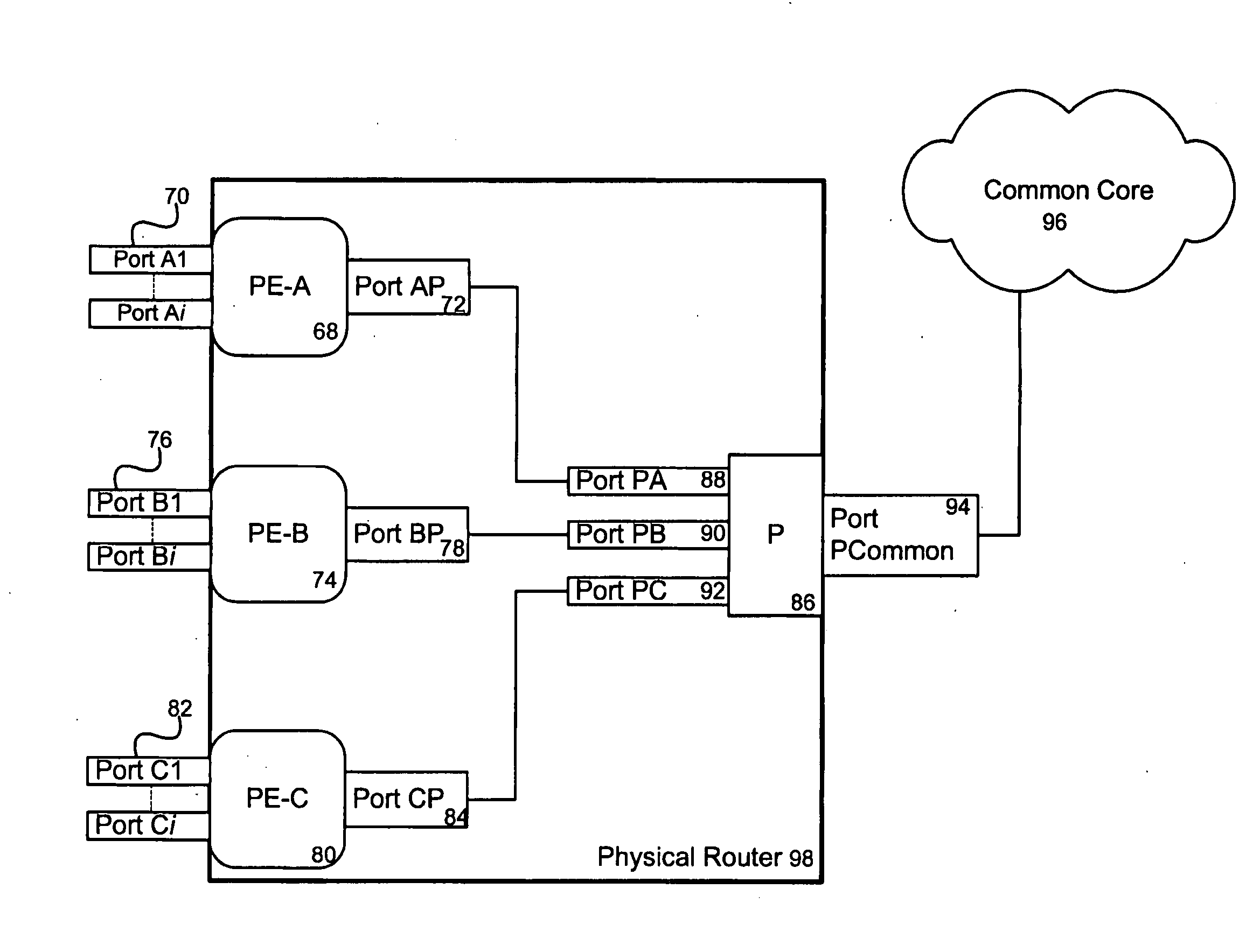
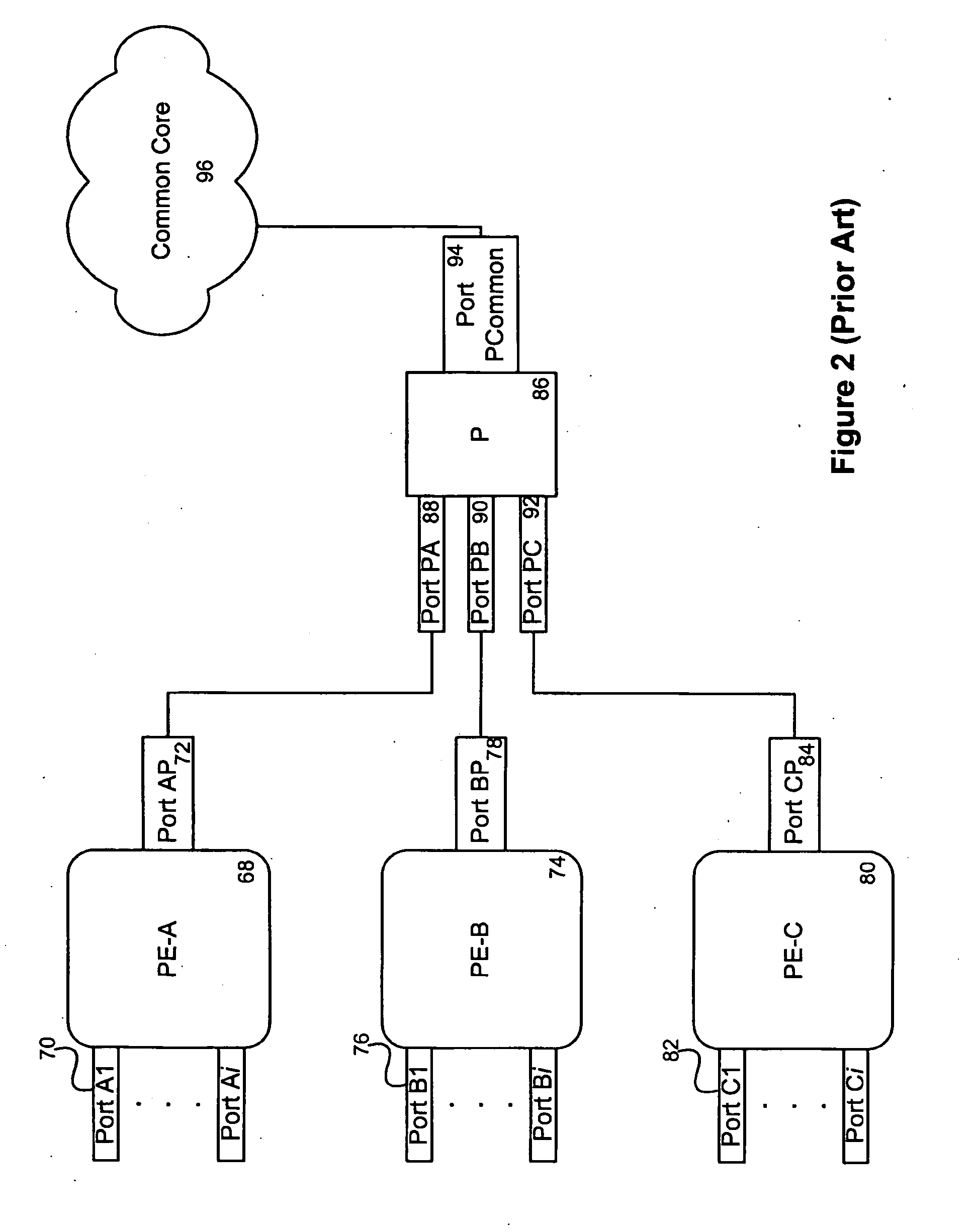
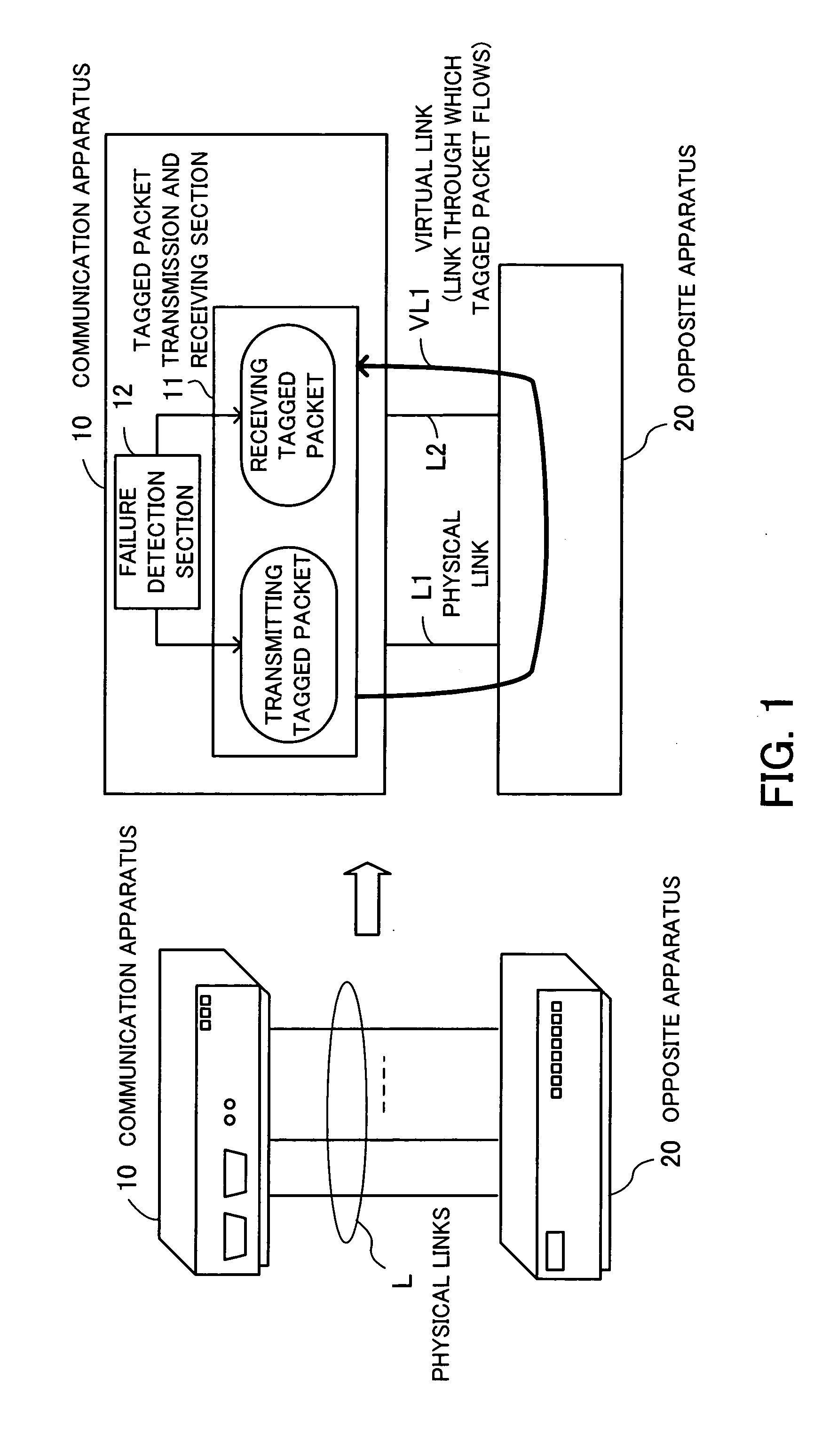
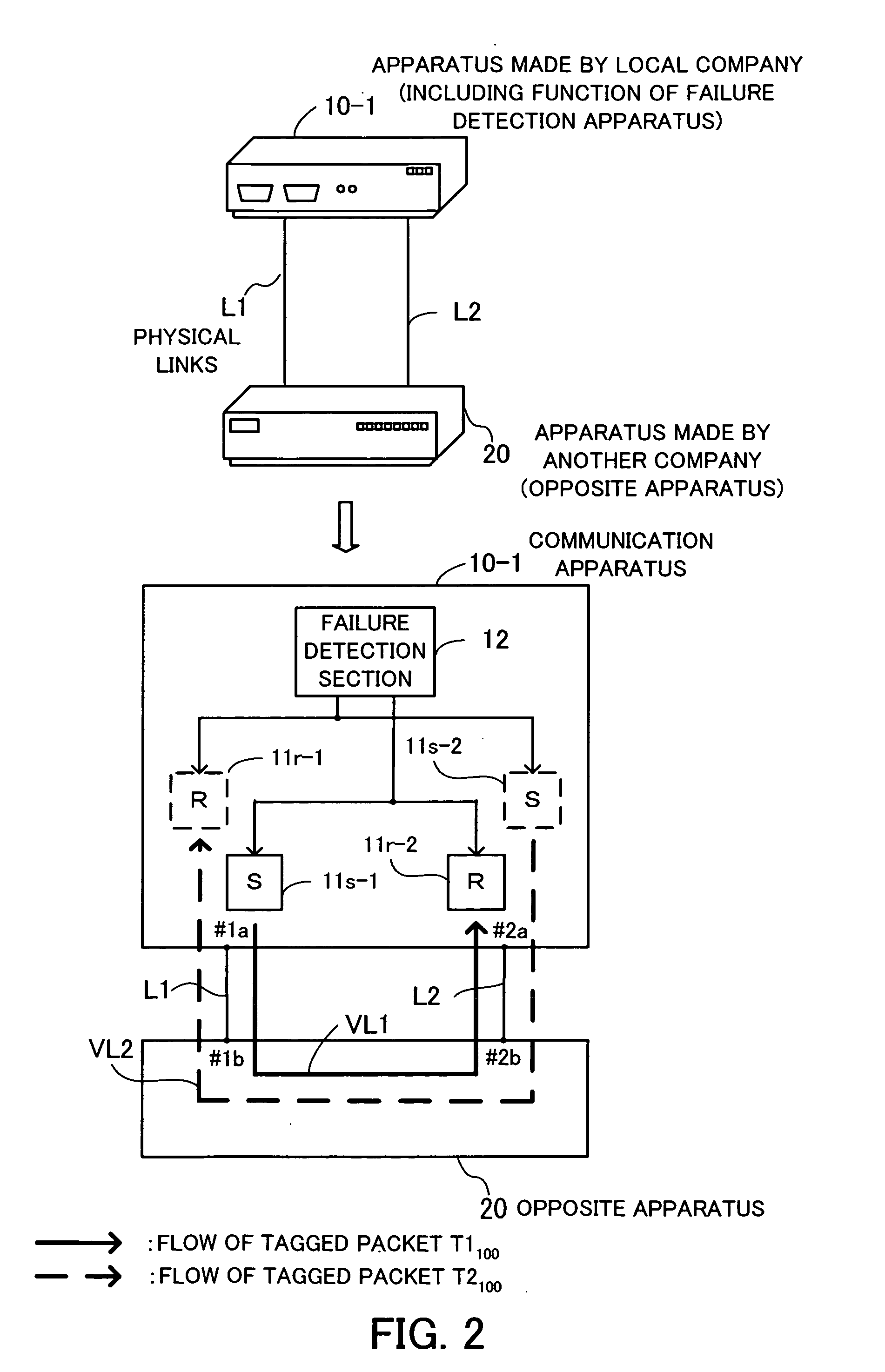
Communication apparatus
InactiveUS20060198315A1Error preventionFrequency-division multiplex detailsVirtual LANCommunication device
A communication apparatus that detects a network failure by itself, without using any particular protocol to interact with other apparatuses in a multivendor virtual LAN (VLAN) environment. The communication apparatus has a group of physical link ports, including first and second ports, to provide physical link connections to an opposite apparatus. A virtual link from the first port to the second port is formed by tunneling through the opposite apparatus. A tagged packet transmission and receiving section transmits outgoing tagged packets from the first physical link port, while receiving incoming tagged packets arriving at the second physical link port. A failure detection section detects a failure on the VLAN by checking whether every tagged packet sent out of the first port can return to the second port via the virtual link that tunnels through the opposite apparatus.
Owner:FUJITSU LTD
System and method for reducing information loss in an aggregated information handling system
ActiveUS20130268590A1Energy efficient ICTMultiple digital computer combinationsInformation handling systemInformation loss
A provided information handling system includes a plurality of aggregation devices configured to distribute information in a virtual link trunk and a plurality of nodes coupled to the aggregation devices. When an aggregation device receives a reboot command, that aggregation device is configured to transmit a first message to the nodes indicating that the aggregation device is rebooting, and receive a first acknowledgement message from the nodes indicating that they will not send any information to the rebooting aggregation device. The aggregation device is then configured to reboot, receive a second message from the nodes indicating the nodes are ready to receive information from the rebooted aggregation device, transmit a second acknowledgement message to the nodes indicating that the rebooted aggregation device has rebooted and is capable of receiving information, and receive information from one of the nodes for transmission to another node.
Owner:DELL PROD LP
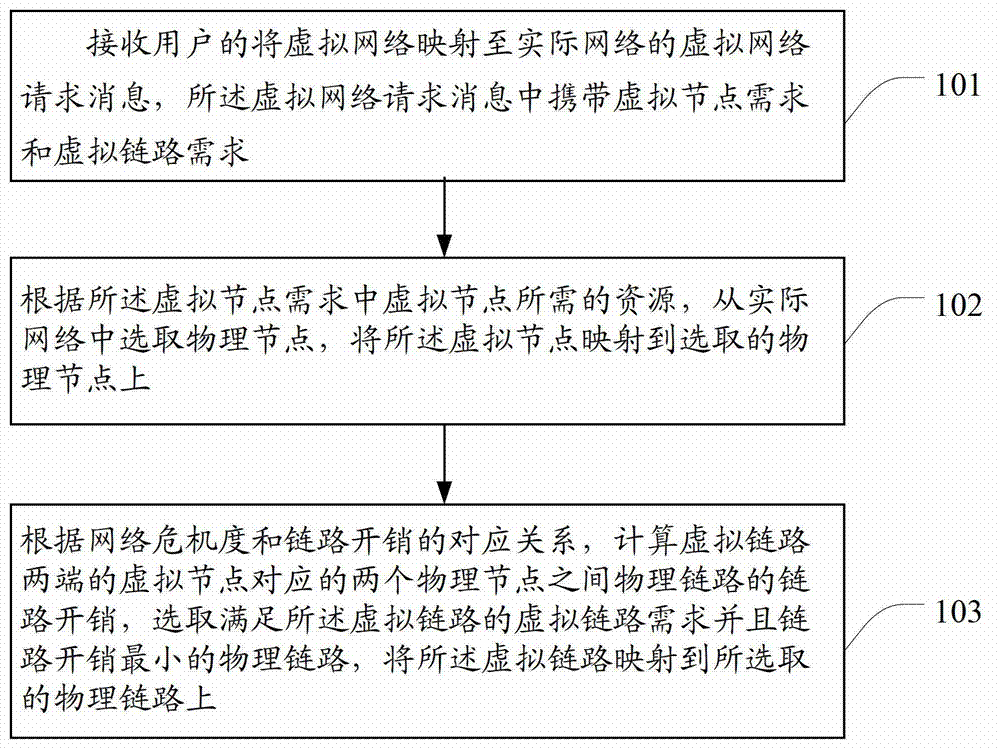
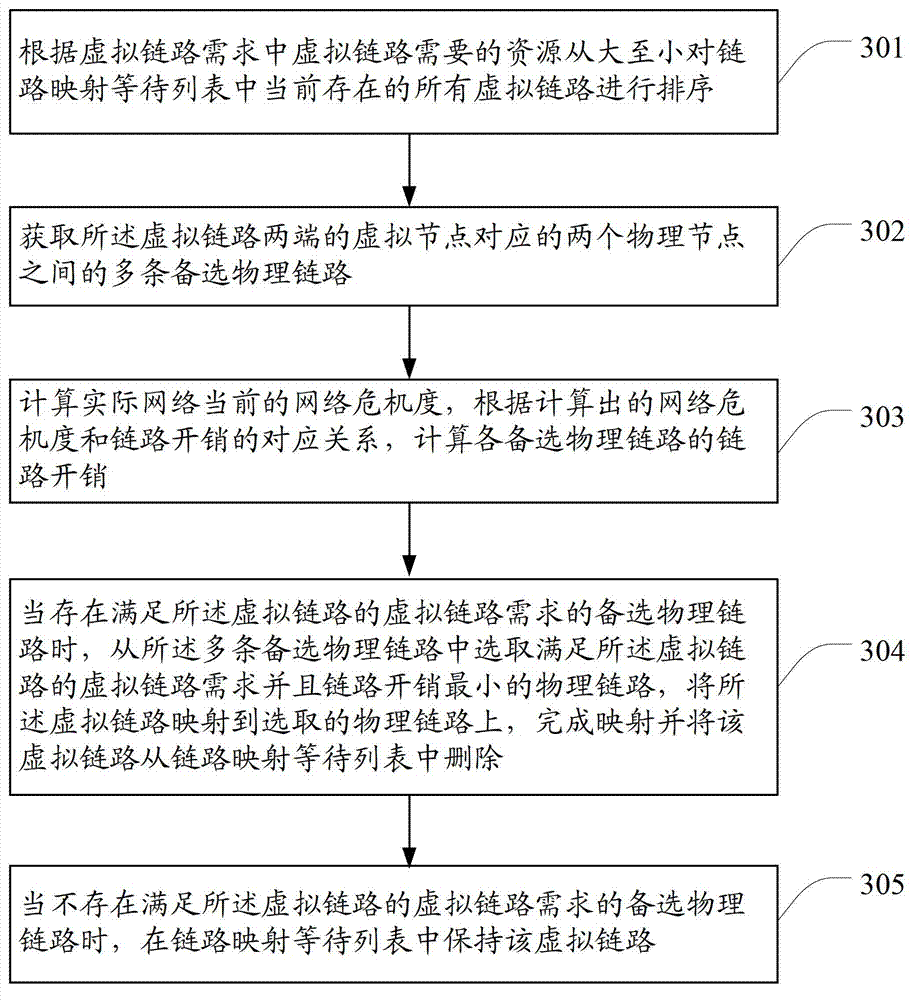
Method and device for mapping virtual network
InactiveCN102904794AReduce the impactImprove robustnessNetworks interconnectionVirtual network mappingVirtual network
The invention discloses a method and a device for mapping a virtual network. The method comprises the steps of receiving a virtual network request message of a user for mapping the virtual network to an actual network, wherein virtual node demands and virtual link demands are carried in the virtual network request message; selecting physical nodes from the actual network according to the resource needed by the virtual nodes in the virtual node demands; mapping the virtual nodes to the selected physical nodes; calculating the link expenditure of a physical link between the two physical nodes corresponding to the virtual nodes at the two ends of the virtual link according to the corresponding relation between the network criticality and the link expenditure; selecting the physical link meeting the virtual link demands of the virtual link and having the lowest link expenditure; and mapping the virtual link to the selected physical link. According to the technical scheme provided by the invention, the problem that the existing method for building the virtual network is low in robustness is solved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method, Device, and Routing System for Data Transmission of Network Virtualization
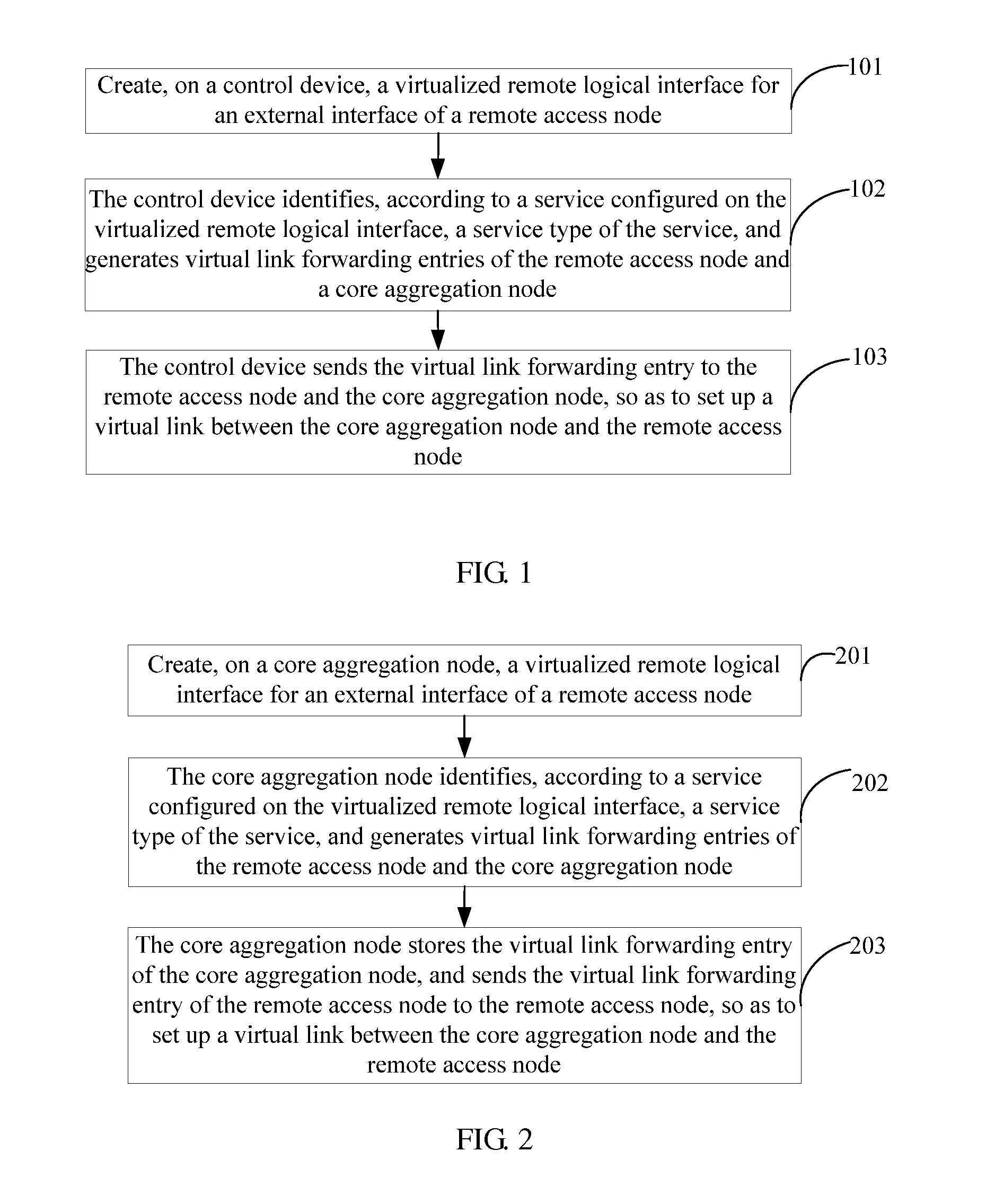
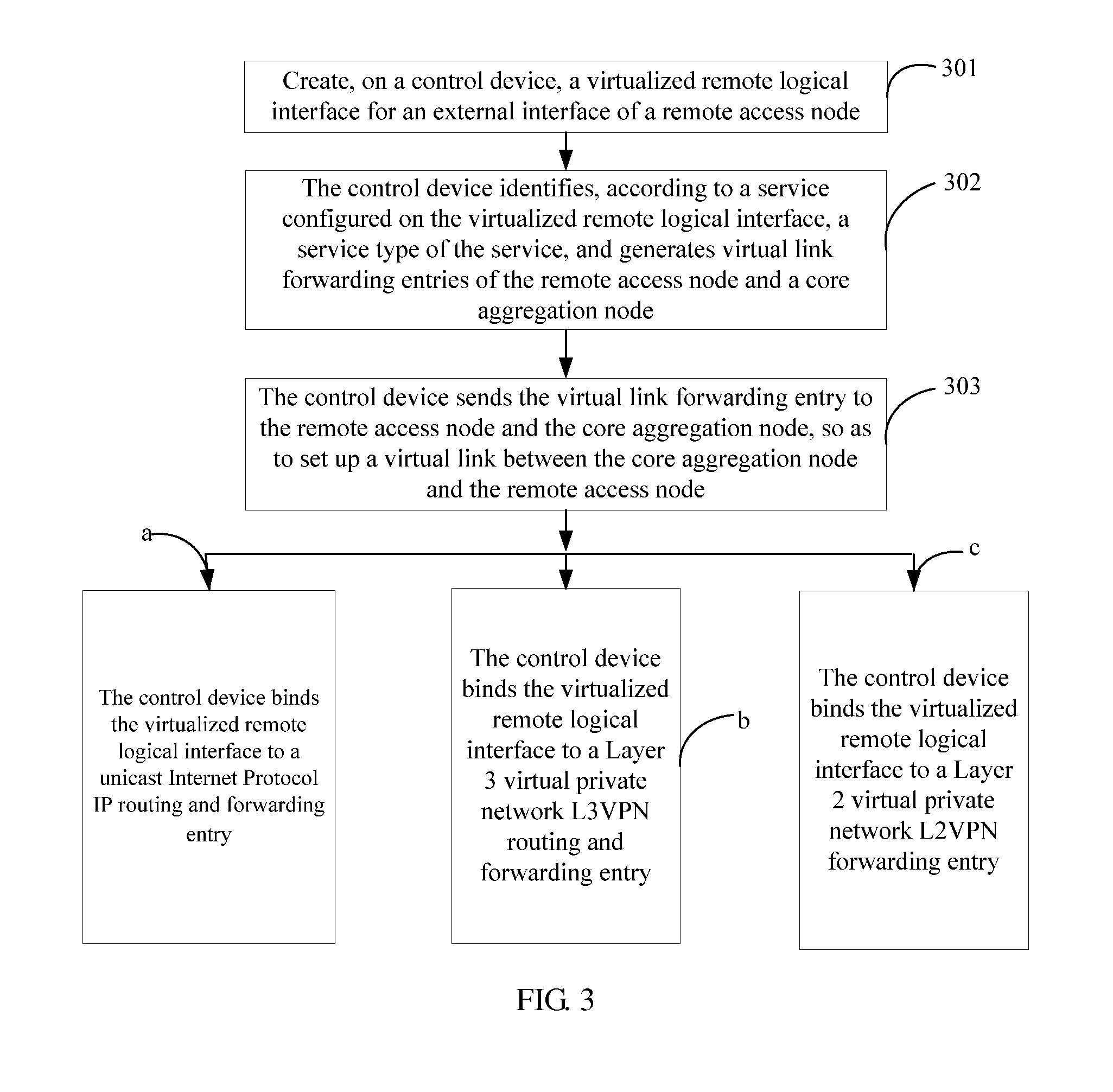
A method resolves connectivity of services inside a network virtualization system when a virtual cluster system supports unicast IP, L2VPN, and L3VPN services, so that the software network virtualization system can support various types of services efficiently and with high quality. The method includes: creating, on a control device, a virtualized remote logical interface for an external interface of a remote access node; identifying, by the control device according to a service configured on the virtualized remote logical interface, a service type of the service, and generating virtual link forwarding entries of the remote access node and a core aggregation node; and sending, by the control device, the virtual link forwarding entry to the remote access node and the core aggregation node, so as to set up a virtual link between the core aggregation node and the remote access node.
Owner:HUAWEI TECH CO LTD
RFID auto-connect for wireless devices
InactiveUS20060061482A1Flexible performanceEliminate needCircuit arrangementsMemory record carrier reading problemsComputer hardwareUnique identifier
A set of wireless devices can be coupled together using a radio frequency identification (RFID) system. The system includes an RFID writer for writing a unique identifier to an RFID tag stored in a transmitter device. The unique identifier can then be used to identify a wireless signal sent from the transmitter device to a receiver device. The receiver may also include an RFID tag, and the two devices may share a secret encryption key for use in creating an encrypted link between the transmitter and receiver. Virtual links may also be established at a distribution center by writing an address through a closed box into each device RFID. One or more RFID writers may be used to verify the identifier written to the RFID tags, carry out quality control checks, and track products to prevent inventory leaks and verify that sold products are certified.
Owner:LOGITECH EURO SA
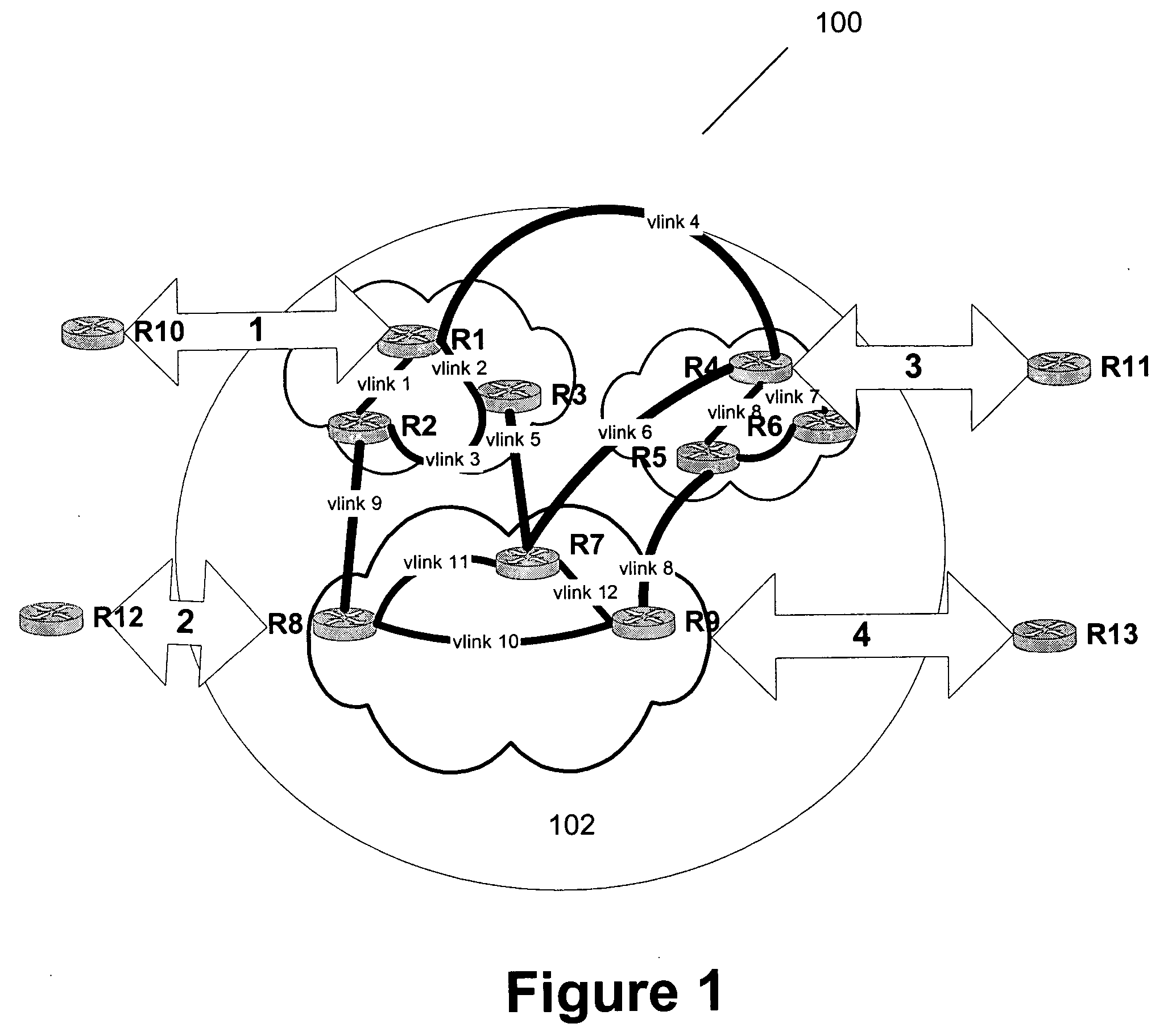
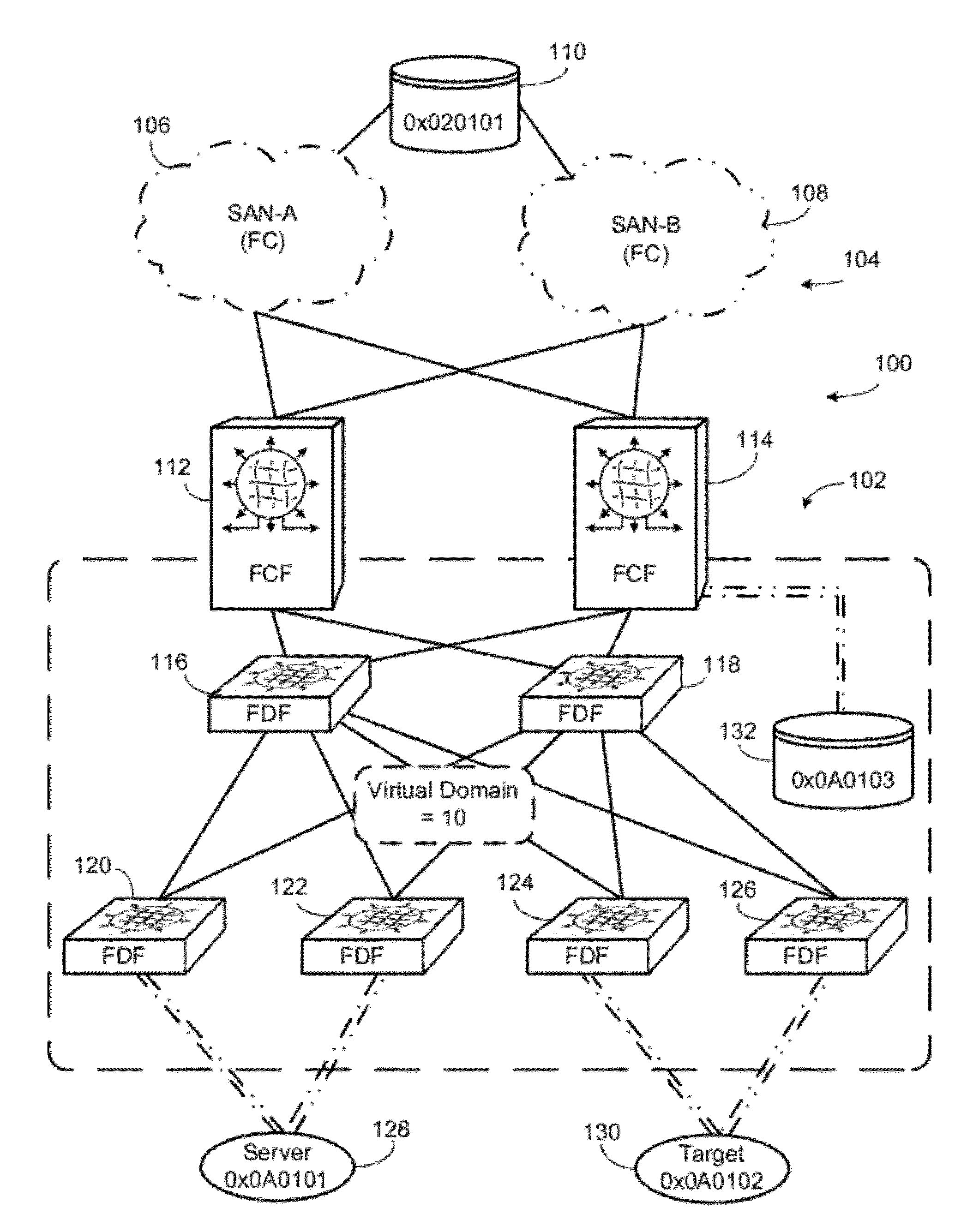
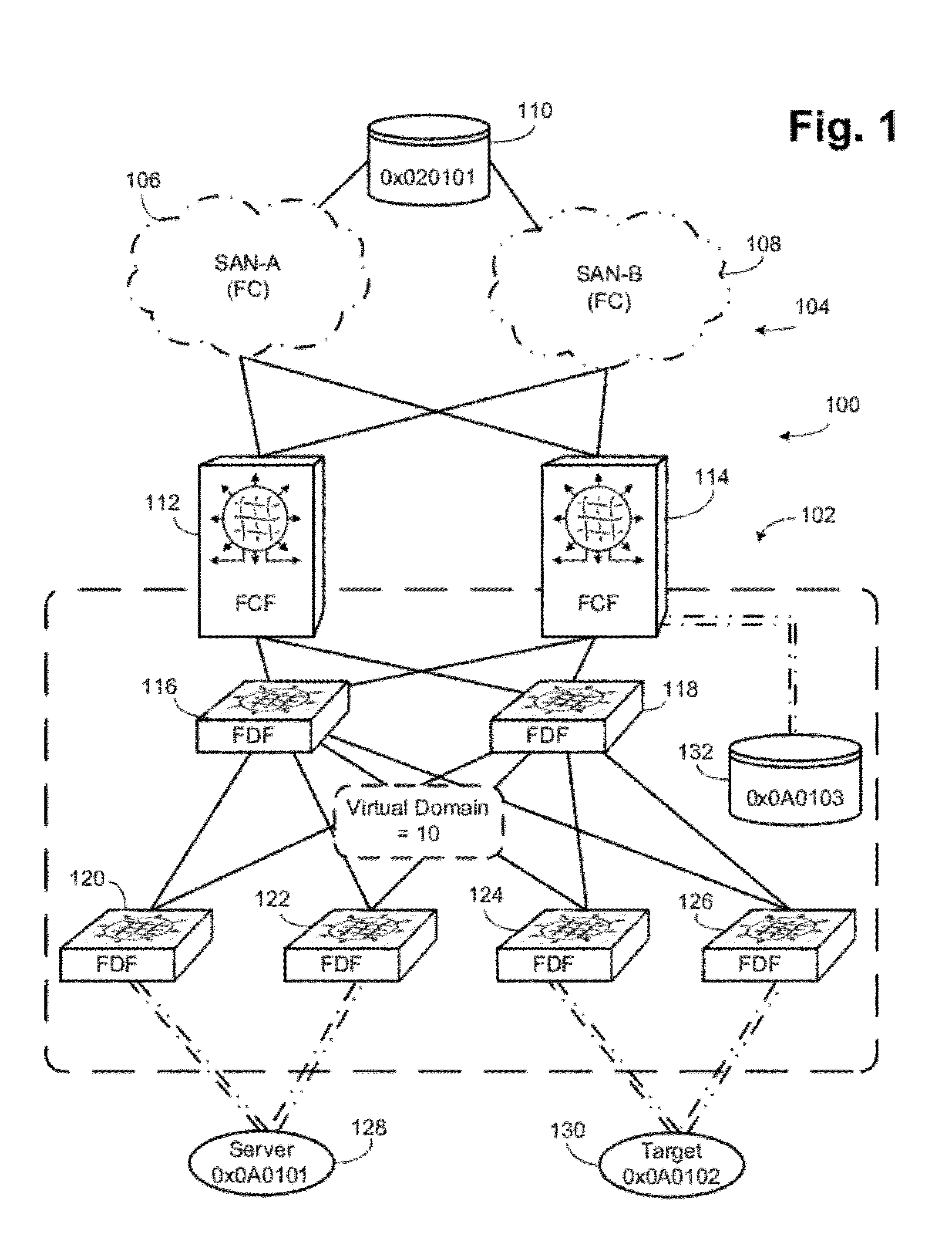
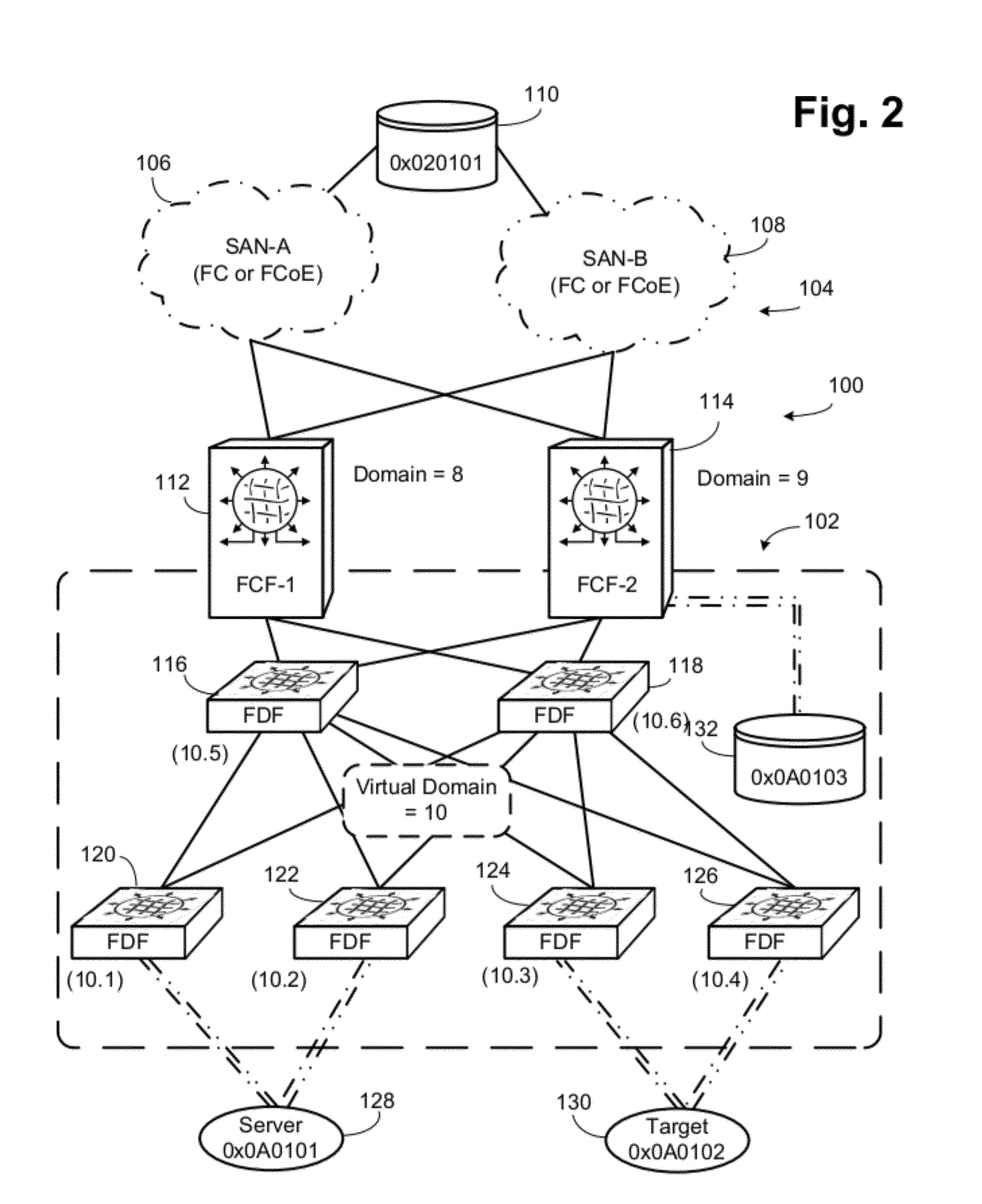
Single Virtual Domain Fibre Channel over Ethernet Fabric
ActiveUS20120106957A1Simplify the development processOptical multiplexElectromagnetic transmissionFibre Channel over EthernetComputer science
The entire FCoE fabric is a single virtual domain, even though there may be multiple FCFs and FDFs. The virtual domain is a different Domain_ID than any of the FCFs. In certain embodiments there are multiple FCFs, of which one is selected as the master or designated FCF. The master FCF performs normal fabric configuration in conjunction with the Fibre Channel fabric. The master FCF assigns the virtual domain FC node IDs and controls development of subdomain IDs. Virtual links are instantiated between the master FCF and other FCFs, between top level FDFs and the FCFs and between the FDFs at each of various levels. FDFs connected to ENodes proxy the master FCF for most FIP operations. FIP FLOGI and FDISC operations are handled by the master FDF, but the FDFs convert the FIP FLOGI requests to VD_FLOGI requests, which include information about the FDF handling the transaction.
Owner:AVAGO TECH INT SALES PTE LTD
Method, device, system and host for three-layer switching
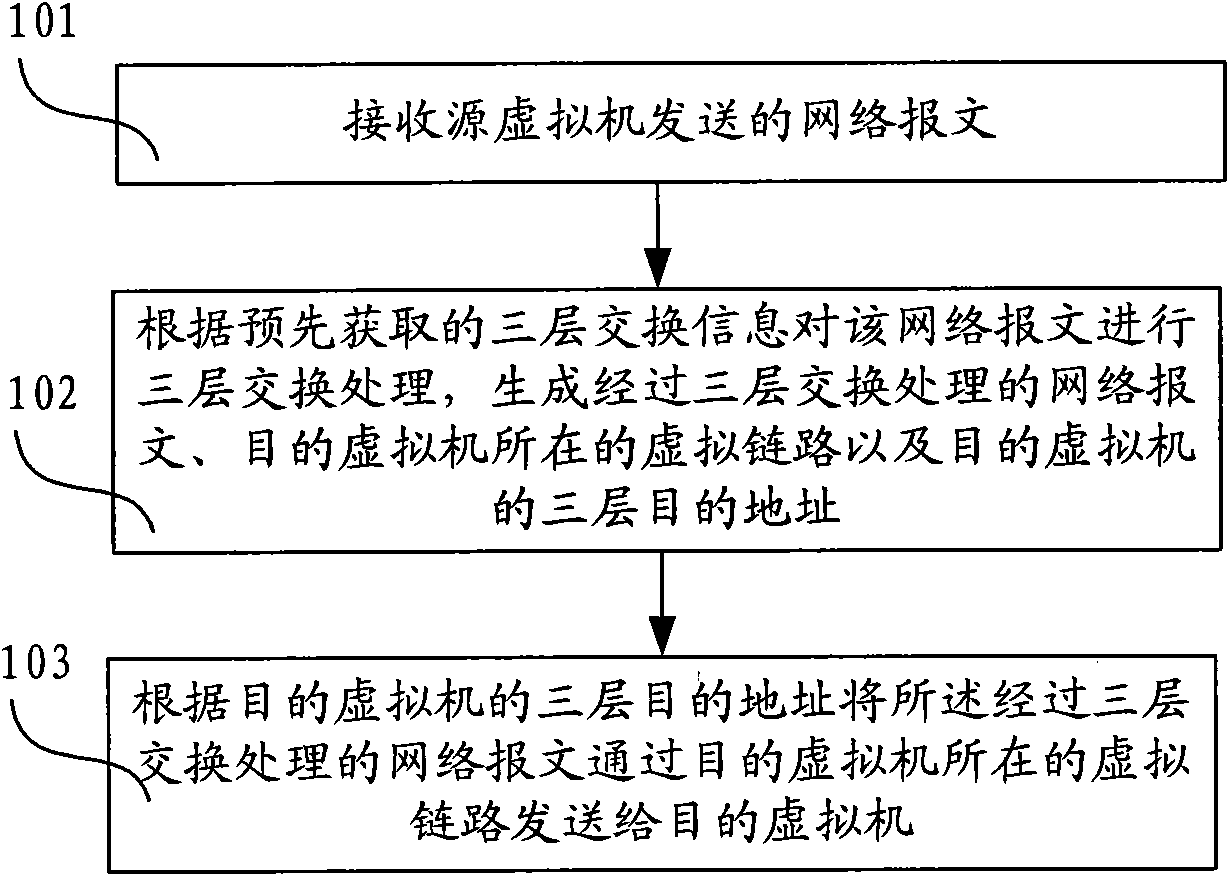
InactiveCN101594358AAvoid the problem of low efficiency of Layer 3 switchingData switching networksLabel switchingVirtual machine
The invention discloses a method, a device, a system and a host for three-layer switching. The method comprises the following steps of: receiving a network message sent by a source virtual machine; according to three-layer switching information acquired in advance, carrying out the three-layer switching treatment of the network message, and generating the network message undergoing the three-layer switching treatment, a virtual link of a destination virtual machine and a three-layer destination address of the destination virtual machine; and according to the three-layer destination address of the destination virtual machine, sending the network message undergoing the three-layer switching treatment to the destination virtual machine by the virtual link of the destination virtual machine. In the technical proposal, the host completes the three-layer switching treatment of the network message according to the three-layer switching information acquired in advance, and sends the network message undergoing the three-layer switching treatment to the destination virtual machine according to the three-layer destination address of the destination virtual machine, so that the three-layer switching efficiency of a virtual machine network is effectively improved.
Owner:BEIHANG UNIV
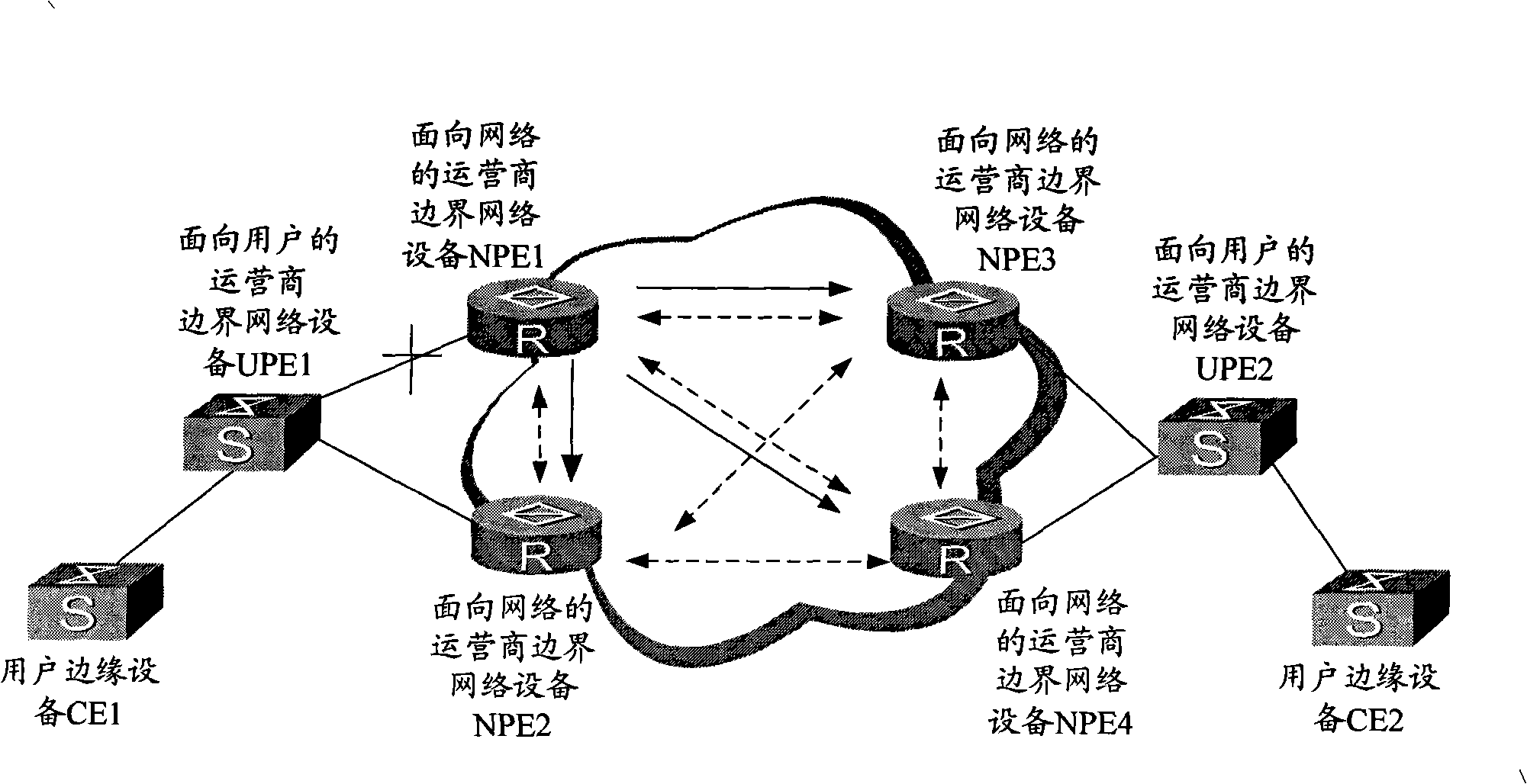
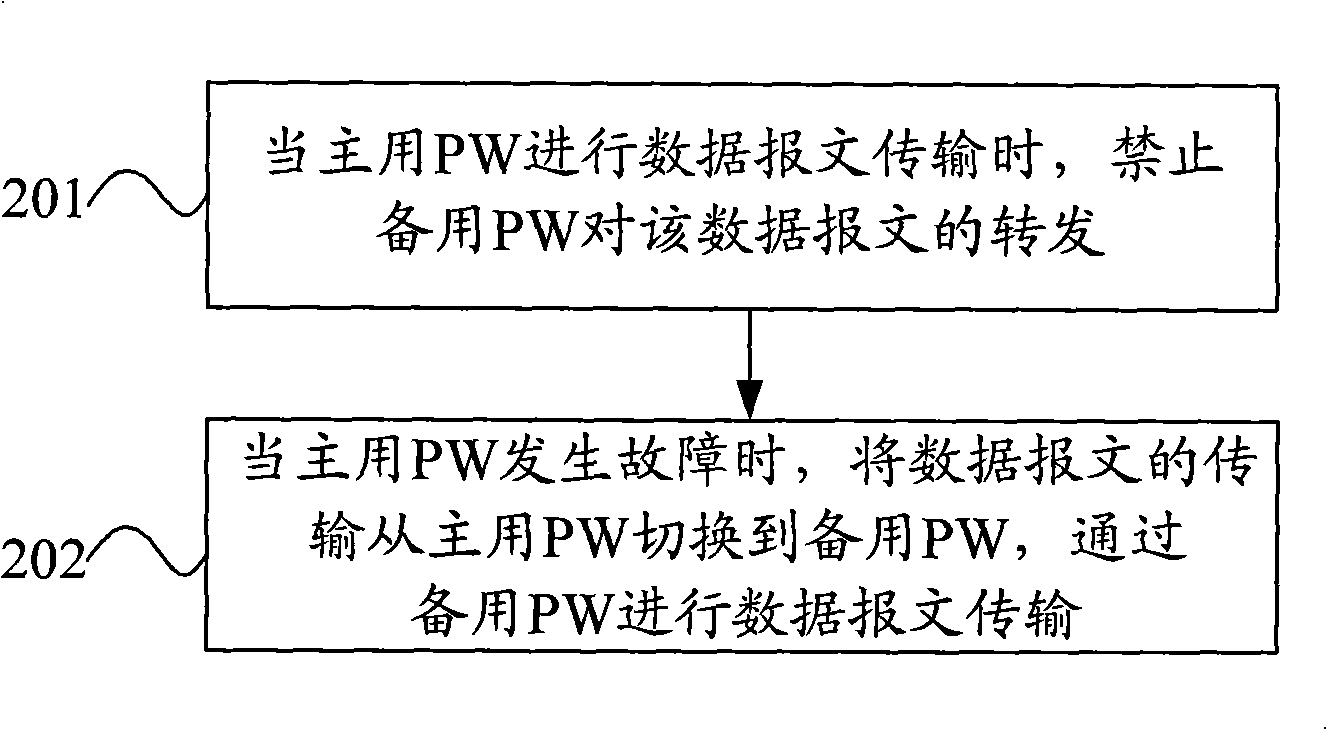
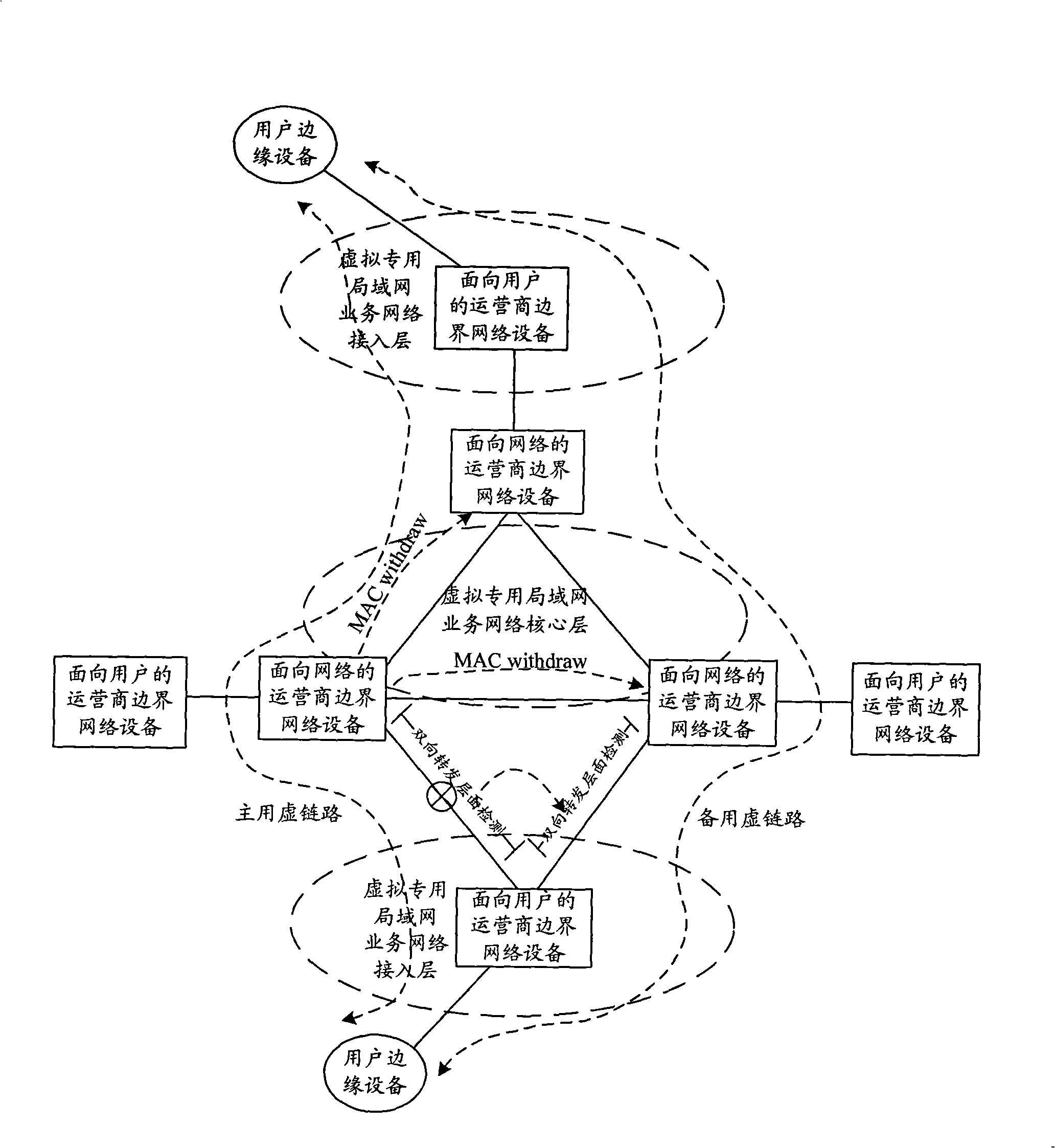
Data transmission method, apparatus and system in VPLS network
InactiveCN101340351AReduce the burden onImprove QoSError preventionNetworks interconnectionRing circuitData transmission
The embodiment of the invention discloses a method for transmitting data in a virtual special LAN service (VPLS) network, a device and a system thereof. A main virtual link circuit PW and a ready-for-use virtual link circuit PW are arranged in the VPLS network. The method for transmitting data comprises that: when the main virtual link circuit PW transmits the data message, the forwarding of the data message by the ready-for-use virtual link circuit PW is prohibited; when the main PW goes wrong, the transmission of the data message is switched to the ready-for-use PW from the main PW, and the data message is transmitted by the ready-for-use PW. Due to the embodiment of the invention, the forming of a ring circuit between UPE and NPE which are accessed in a way of double-returning is avoided; when the main PW goes wrong, the link circuits can be switched quickly, and the convergence of the link circuits is accelerated, therefore, QoS of the VPLS network is improved.
Owner:HUAWEI TECH CO LTD
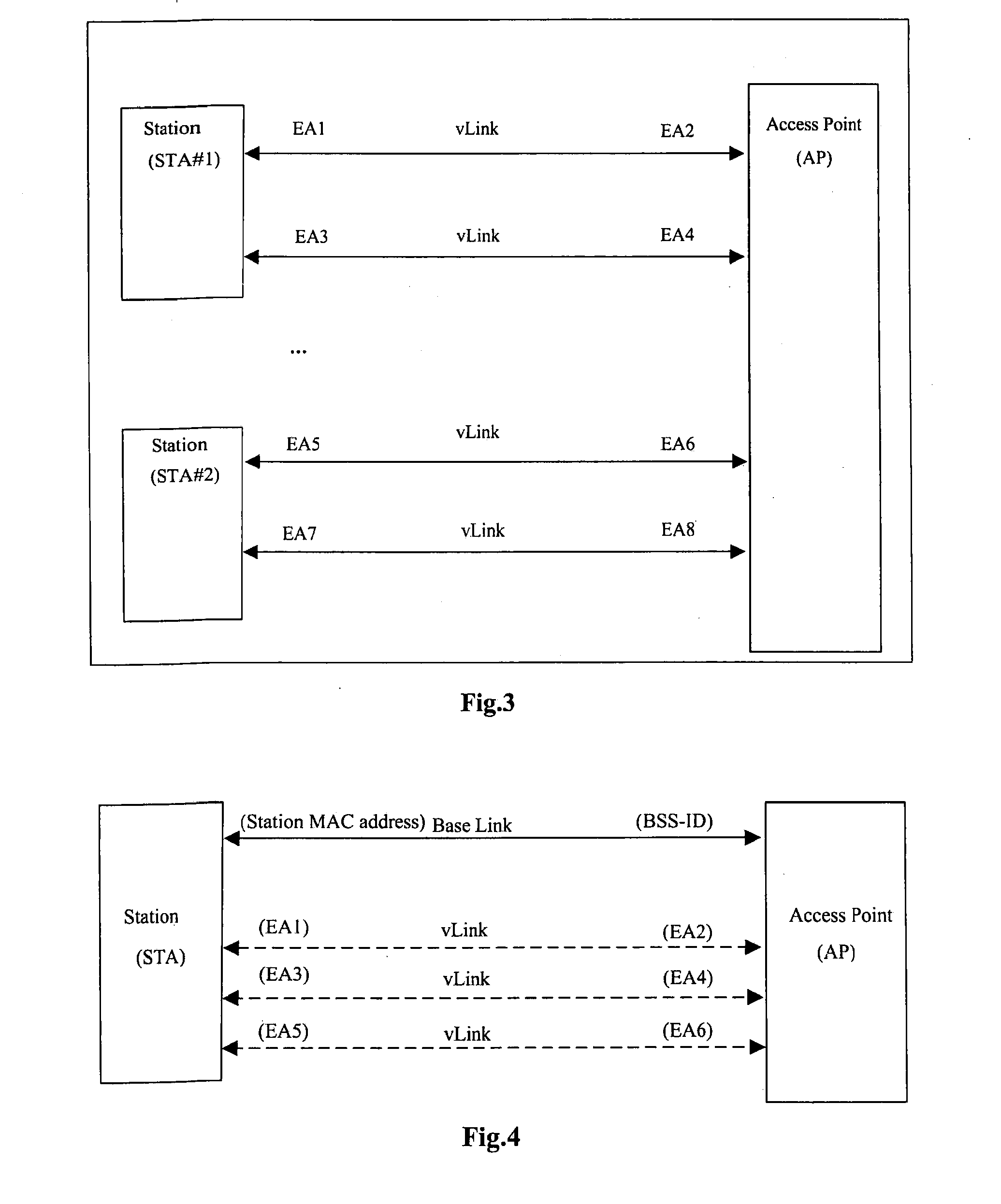
Method and Apparatus for Establishing a Virtual Link, Wireless Lan, and Method for Transmitting Data
InactiveUS20070189168A1Improve service capabilitiesStable supportError preventionTransmission systemsWireless lanComputer science
The embodiments of the present invention provide a method and an apparatus for establishing a virtual link. The method includes the following steps: a virtual link establishment requesting end initiates a virtual link establishment request which contains virtual link negotiation parameters of the requesting end to a requested end through a base link; the requested end receives the virtual link establishment request, parses the request and obtains the virtual link negotiation parameters of the requesting end, and negotiates between the obtained parameters with the virtual link parameters of local end to obtain negotiated virtual link parameters; the requested end determines the virtual link end-point address identifications; the requested end sends a virtual link establishment response which contains the negotiated virtual link parameters and the virtual link end-point address identifications to the requesting end through the base link; the requesting end receives the response, parses the response and obtains the negotiated virtual link parameters and the virtual link end-point address identifications; the identification of the virtual link is accomplished for the requesting end and the requested end.
Owner:HUAWEI TECH CO LTD
Resilient provider link state bridging (PLSB) virtual private LAN service (VPLS) interworking
A method of peer interfacing a Link-State controlled network domain with an Ethernet Bridging controlled network domain. A pair of peer attachment points are provided between the Link-State controlled network domain and the Ethernet Bridging domain. The peer attachment points are respective endpoints of a set of one or more LAN segments defined within the Ethernet Bridging domain. The set of LAN segments are represented as a virtual node in the Link-State controlled network domain. The virtual node is represented in the Link-State controlled network domain as connected to each of the peer attachment points via a respective virtual link. The virtual links are configured such that frames to or from an address in the Link-State controlled network domain are forwarded over a tree passing through only one of the peer attachments points.
Owner:RPX CLEARINGHOUSE
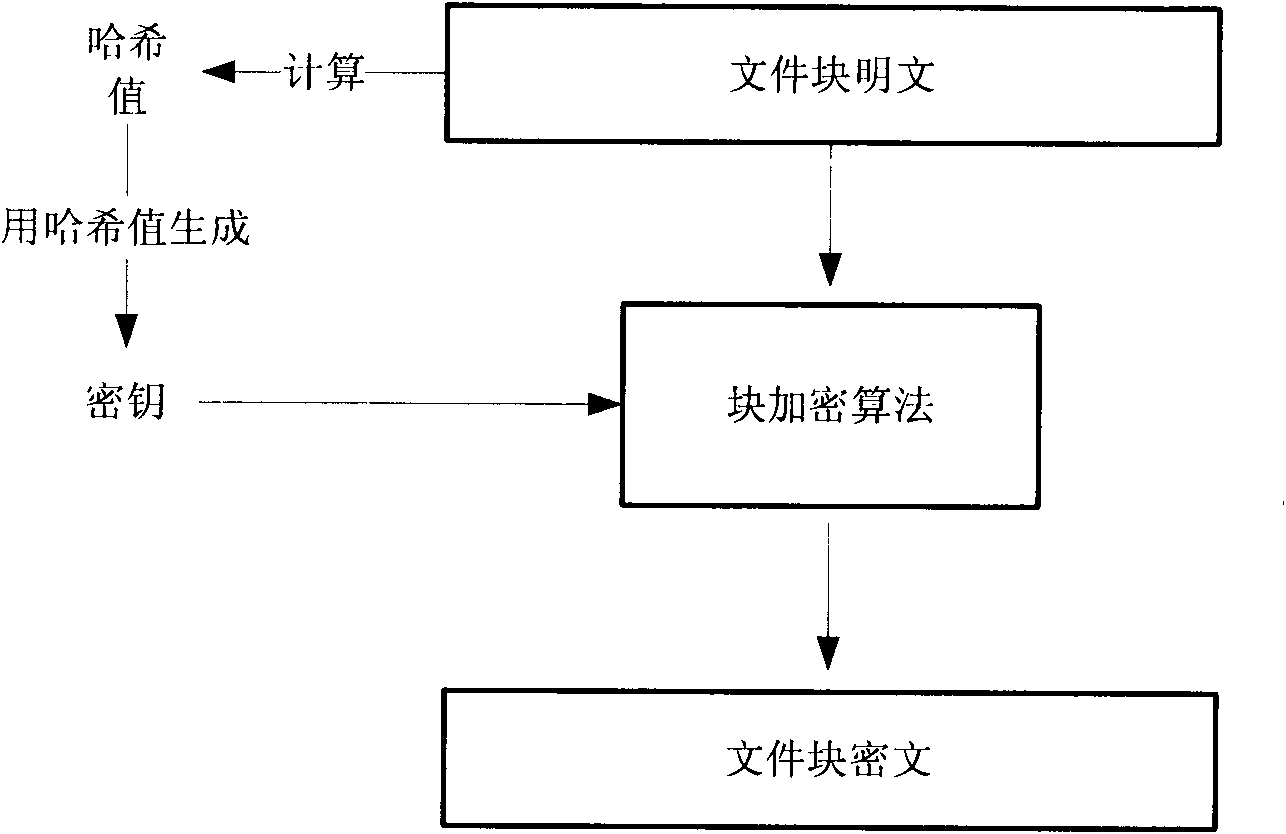
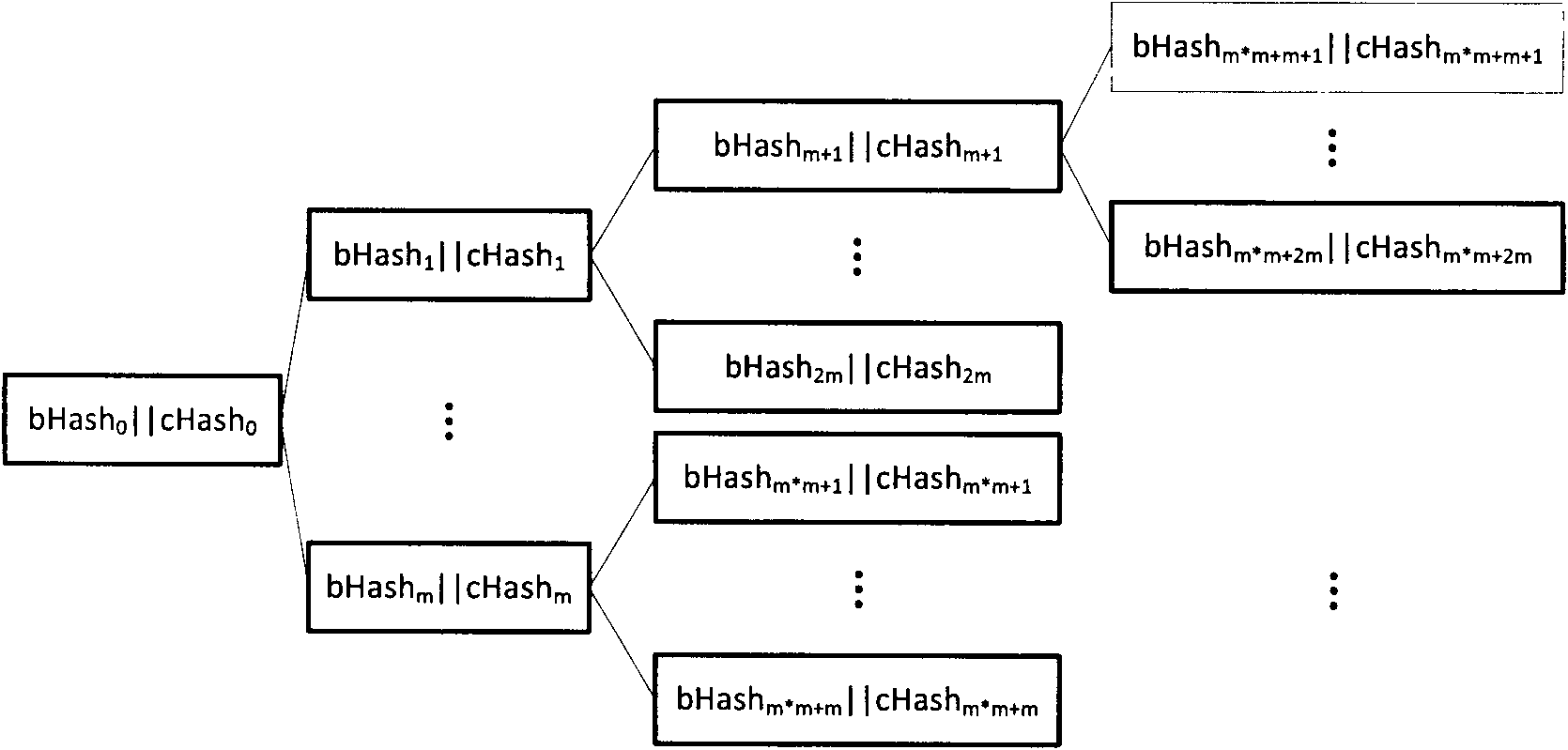
Safety metadata management method based on integrality checking
InactiveCN101976322AGuaranteed confidentialityWarranty requirementsDigital data protectionSpecial data processing applicationsMetadata managementData management
The invention relates to a safety metadata management method based on integrality checking, belonging to the field of storage safety. The method is characterized in that a self encryption technology for file data is used at a client to encrypt the file data, thereby improving the storage efficiency; a 64-heap hash tree is used at a safety metadata management server end to maintain the hash value of a file block, thereby providing integrality protection on the hash value of the file data block and realizing the high-efficiency verification on the user's access to file and the high-efficiency data updating; and simultaneously a root hash virtual linked list technology is used, thereby ensuring the integrality of root hash values of multiple 64-heap hash trees belonging to one file and supporting the user's concurrent access to the file to a certain extent.
Owner:TSINGHUA UNIV
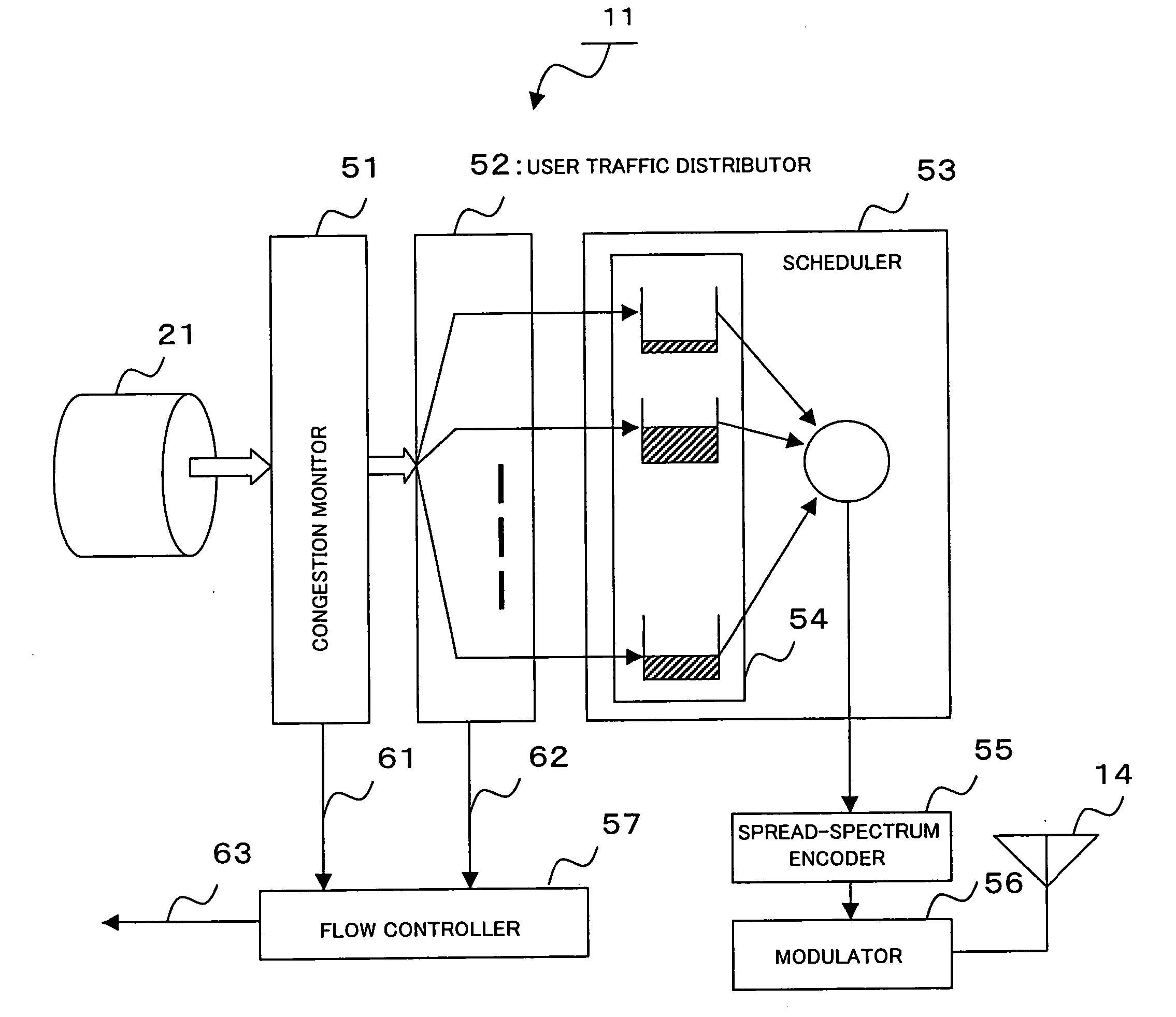
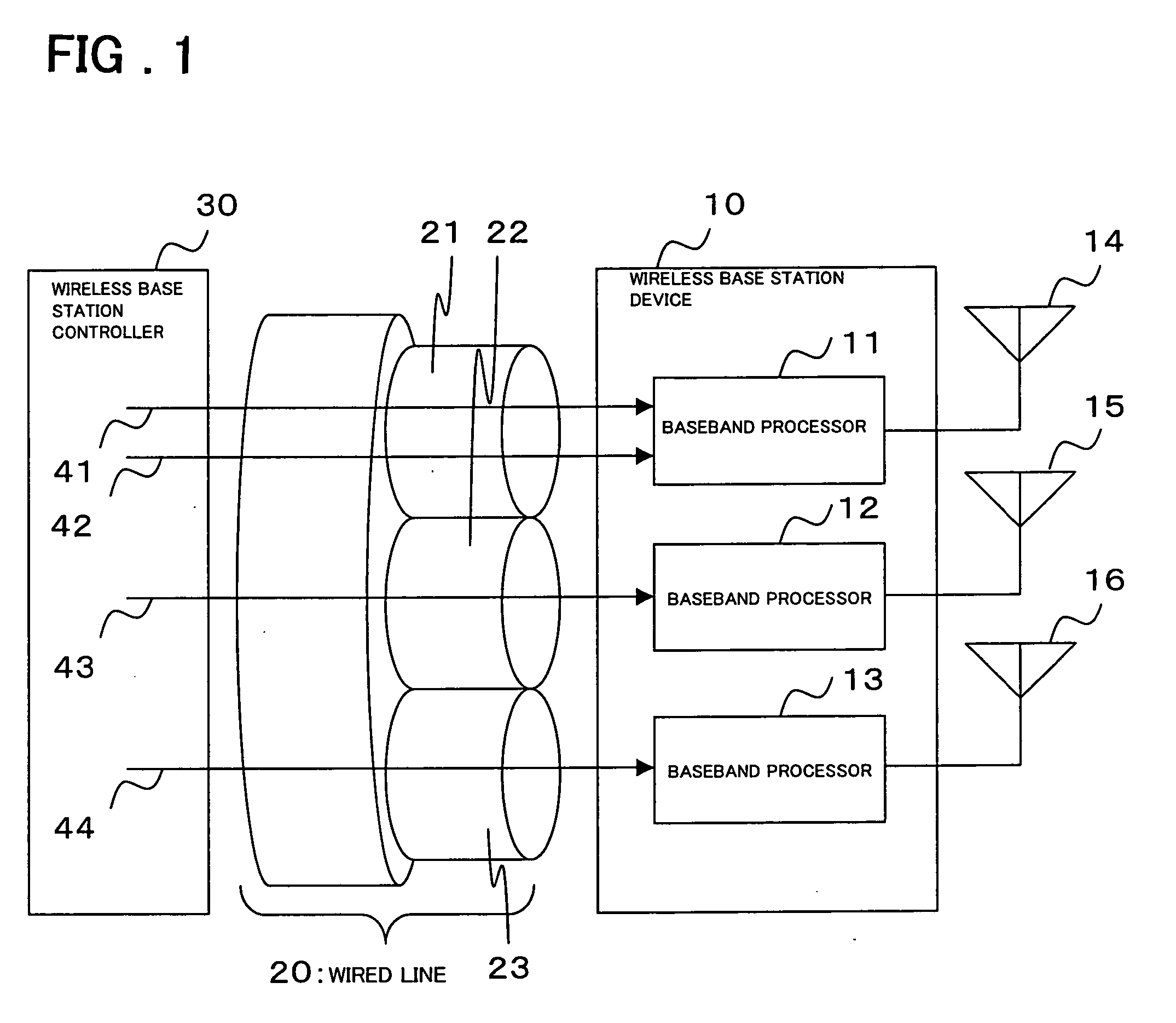
Wireless base station device and rate control method thereof
InactiveUS20060126507A1Increase profitLow costError preventionFrequency-division multiplex detailsData streamStation
A wireless base station device, connected to a higher-level station device via a wired line, comprises baseband processors 11, one for each virtual link 21 to which user data flows belong. In the baseband processor 11, a congestion monitor 51 monitors the reception bandwidth usage rate of a virtual link allocated to each cell for detecting congestion and, upon detecting congestion, sends a notification to a flow controller 57. A user traffic distributor 52 distributes a received user traffic into the traffic flow of each user and, at the same time, extracts, for each user data flow, the buffer holding amount in the higher-level station device where user data flows are multiplexed and sends a notification to the flow controller 57. The flow controller 57 manages the data flow of each user and, in response to a congestion notification from the congestion monitor 51, requests the higher-level station device to reduce the rate of a user data flow in descending order of rates beginning with a data flow with a highest rate.
Owner:NEC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com