Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
66 results about "Hash tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
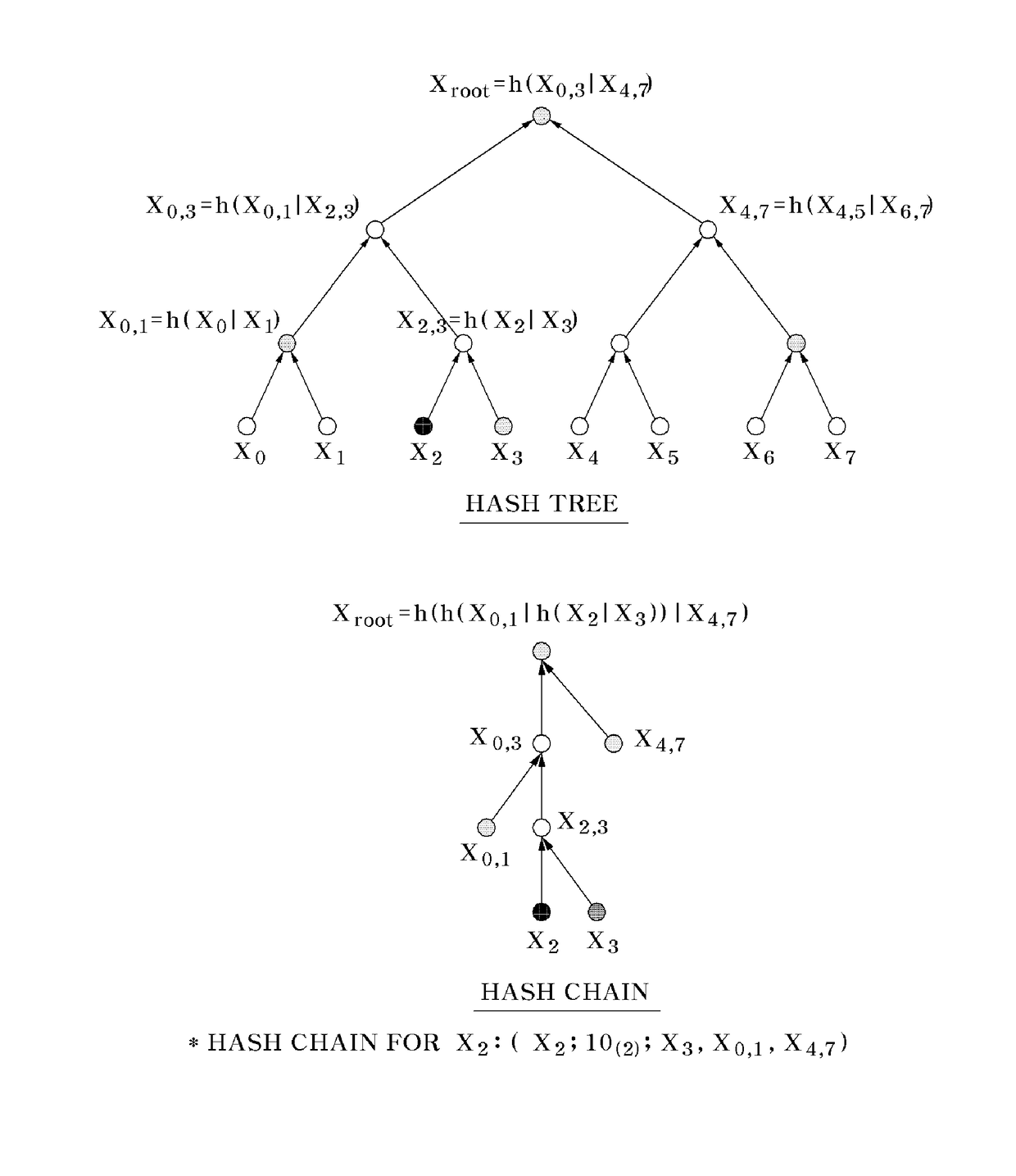
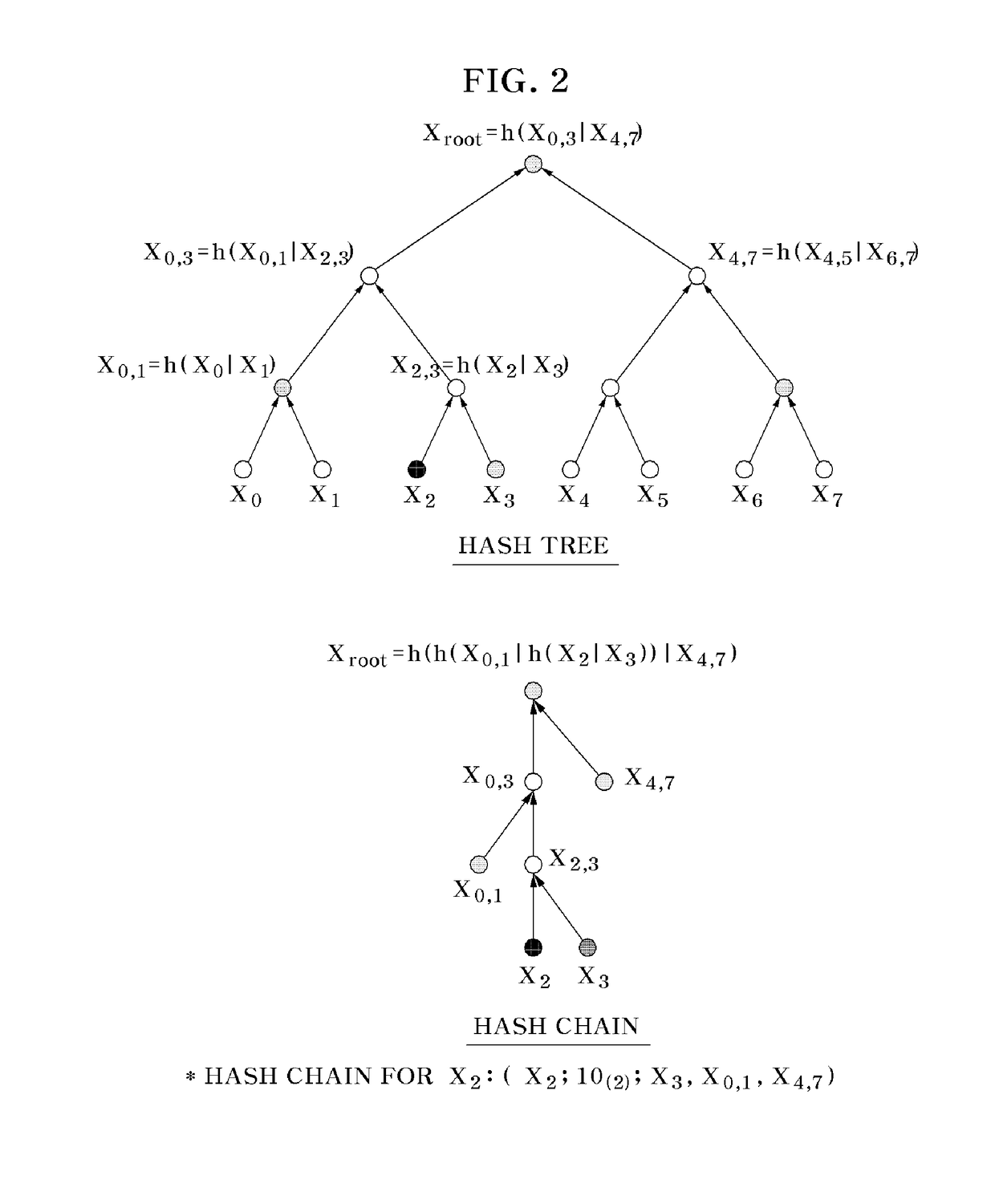
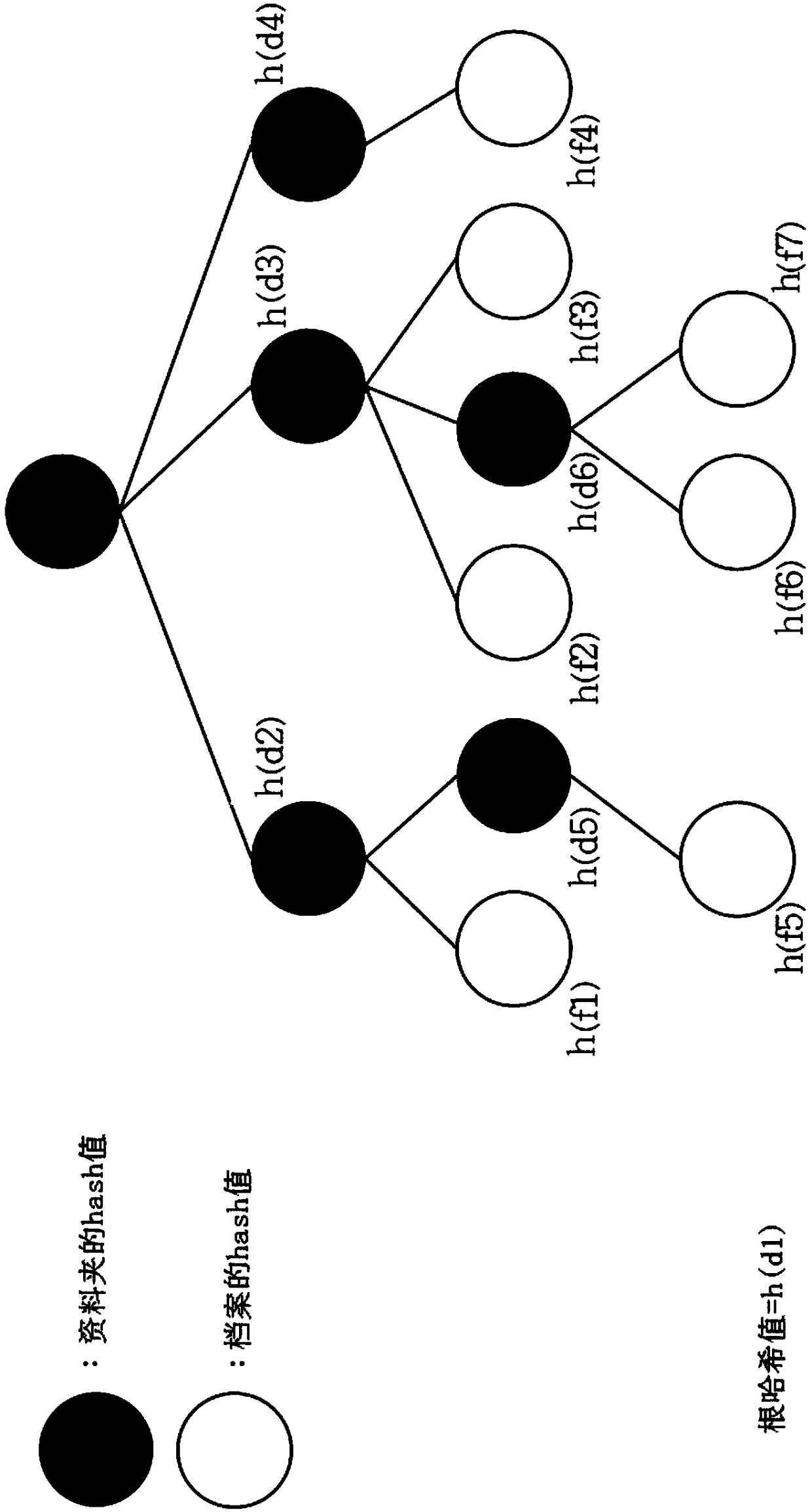
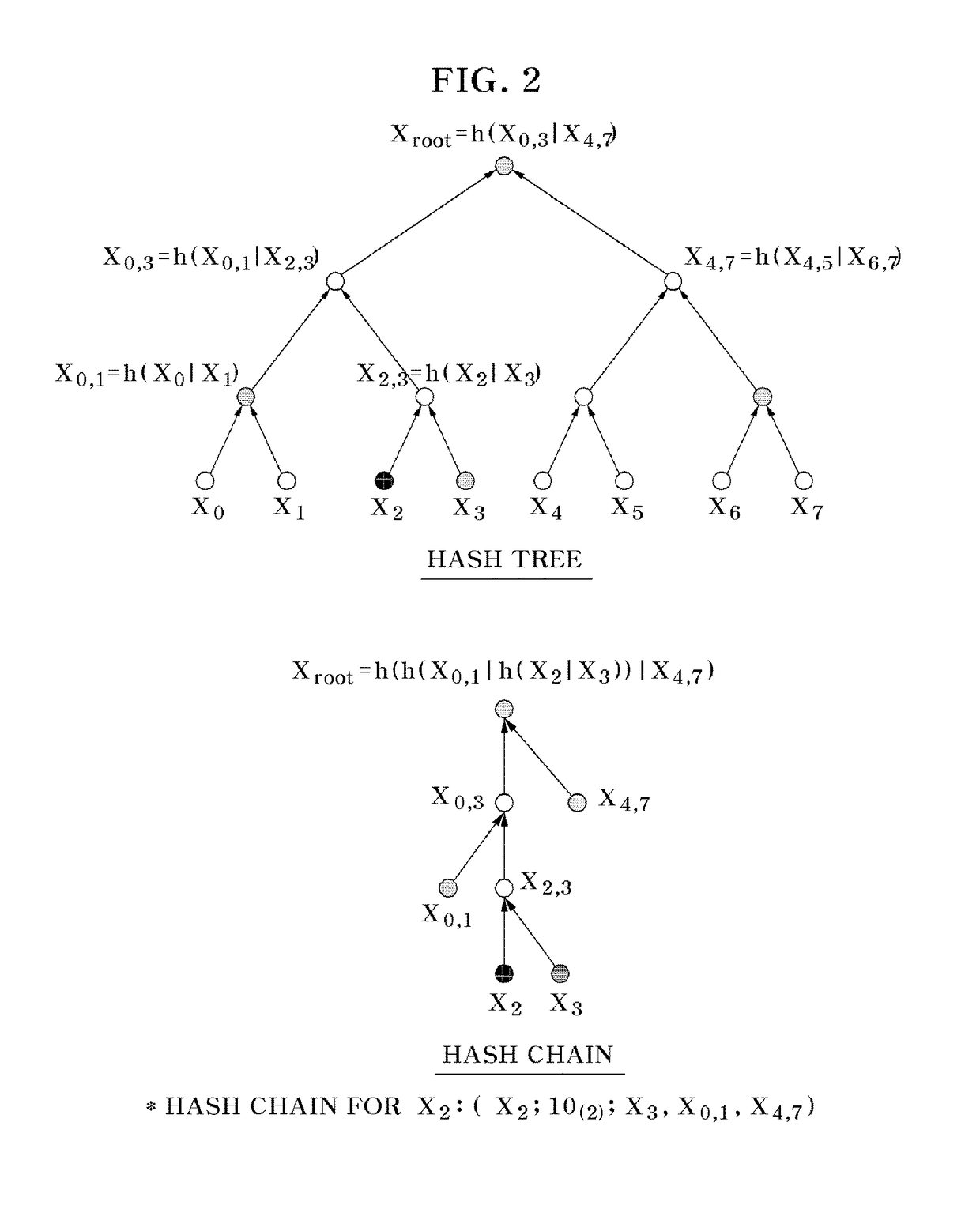
In computer science, a hash tree (or hash trie) is a persistent data structure that can be used to implement sets and maps, intended to replace hash tables in purely functional programming. In its basic form, a hash tree stores the hashes of its keys, regarded as strings of bits, in a trie, with the actual keys and (optional) values stored at the trie's "final" nodes.
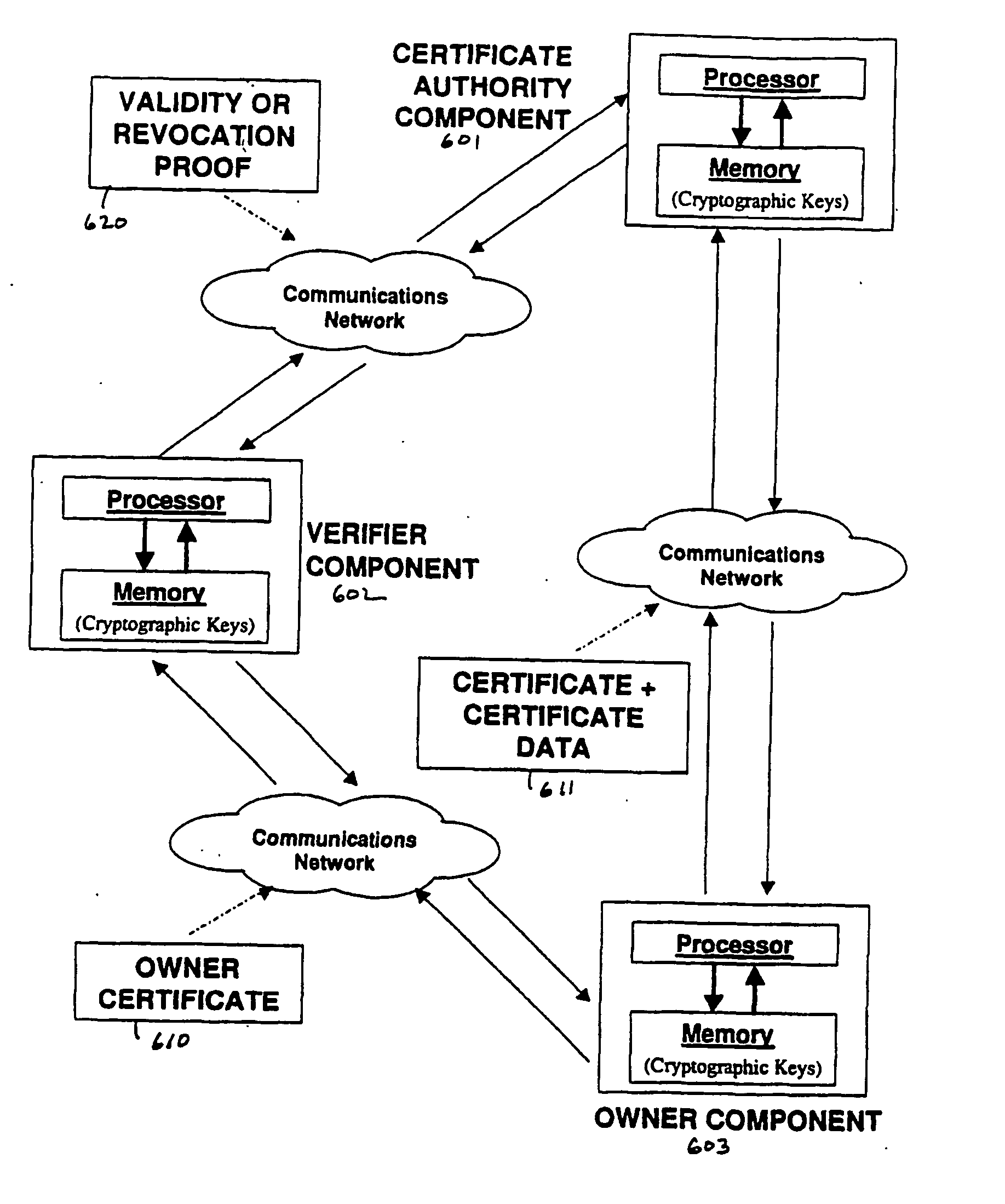
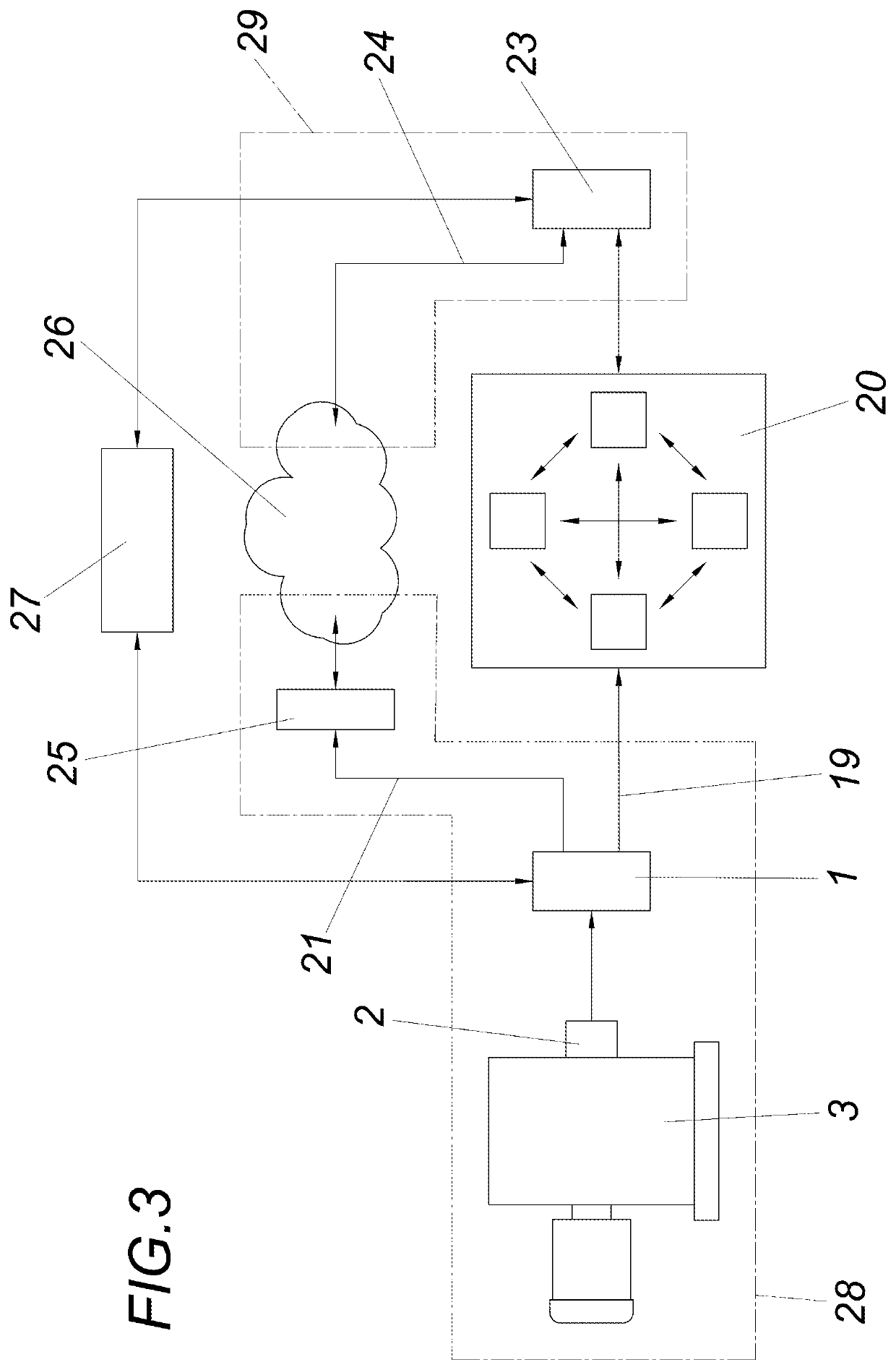
Method and apparatus for efficient certificate revocation
ActiveUS20060129803A1Digital data processing detailsUser identity/authority verificationMerkle treeRevocation
Revocation of digital certificates in a public-key infrastructure is disclosed, particularly in the case when a certificate might need to be revoked prior to its expirations. For example, if an employee was terminated or switched roles, his current certificate should no longer be valid. Accordingly, novel methods, components and systems are presented for addressing this problem. A solution set forth herein is based on the construction of grounded dense hash trees. In addition, the grounded dense hash tree approach also provides a time-communication tradeoff compared to the basic chain-based version of NOVOMODO, and this tradeoff yields a direct improvement in computation time in practical situations.
Owner:NTT DOCOMO INC
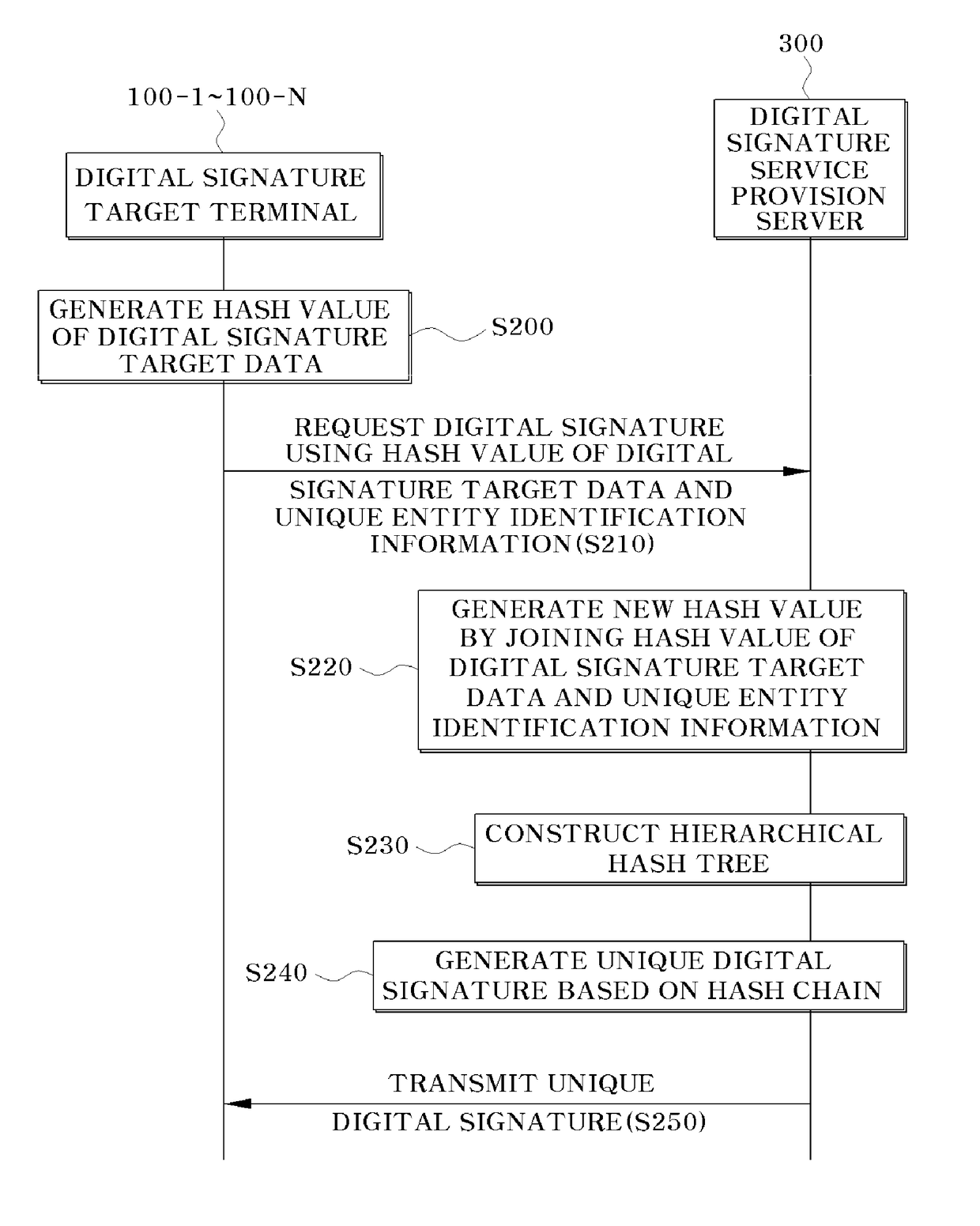
Digital signature service system based on hash function and method thereof
ActiveUS20170070350A1Stable generationIntegrity guaranteedUser identity/authority verificationPublic key infrastructure trust modelsElectronic documentDigital data
Disclosed is a digital signature service system and method based on a hash function in which a main agent, who requires the generation of a digital signature, does not personally generate the digital signature, and wherein digital signatures may be simultaneously and stably generated for large-scale data such as multiple electronic documents and digital data using a hash function and a hash tree, which are known as a simple and secure method, to guarantee the integrity of the data in a digital signature-based structure based on a server.
Owner:MARKANY
Security protocols for hybrid peer-to-peer file sharing networks
ActiveUS20090259847A1User identity/authority verificationMultiple digital computer combinationsComputer networkDigital signature
In a hybrid peer-to-peer file sharing network including a receiver peer and a provider peer, the receiver sends the provider a ticket [710] obtained from a server authorizing the receiver to obtain a data object O. The receiver obtains a root value of a hash tree for the object, verifies its digital signature, and sends the provider peer a request for a block of data object O and a request for a corresponding set of hash tree of hash values from the hash tree [714]. The receiver receives from the provider peer the block of O and the corresponding set of hash values of the hash tree [716] that do not contain any hash value in the local hash tree. The receiver sends the provider an acknowledgement of receipt [718], obtains a block key from the provider [720], decrypts the block, verifies the integrity of the block using the subset of hash values and the local hash tree for O, and updates the local hash tree by adding the subset of hash values to the local hash tree, as well as any newly calculated hash values [722]. The provider may submit to a server the acknowledgements as proof of its service to the receiver.
Owner:OREGON HEALTH & SCI UNIV
Compact recordation protocol
A method for efficiently storing and verifying records is disclosed. The method may comprise receiving a first hash of first interaction data and determining an interaction identifier associated with the first hash, then storing the first hash in a database along with the interaction identifier and determining a root hash of a hash tree. In addition, the method may also comprise providing the root hash of the hash tree to a public blockchain. Embodiments of the invention also allow users to easily present records to a third party or inquiring entity. Furthermore, interactions may be processed more quickly than previous blockchain methods that publish to a block during each individual interaction.
Owner:VISA INT SERVICE ASSOC
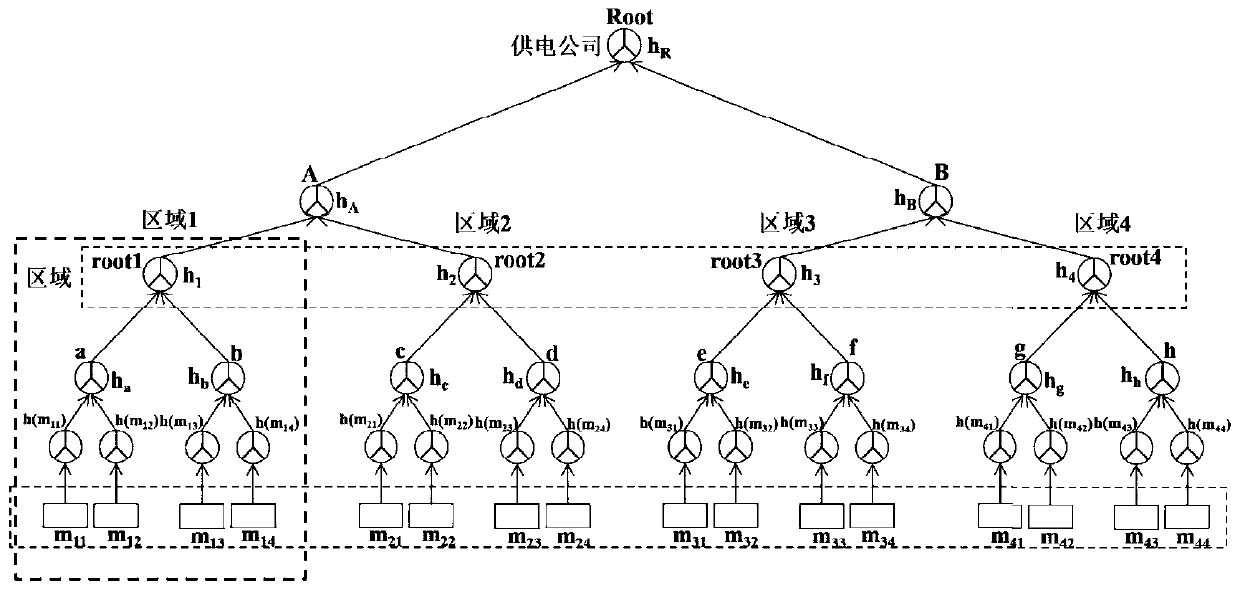
Security data reporting method and security data reporting system on basis of Hash trees and anonymity technologies
ActiveCN104636672AImprove reporting efficiencyData processing applicationsUser identity/authority verificationTrusted authorityData integrity
The invention discloses a security data reporting system on the basis of Hash trees and anonymity technologies. The security data reporting system comprises four parties and seven modules. The four parties include a trusted authority (TA), a control center (CC), a gateway (GW) and a residential area (RA), and the gateway (GW) is connected with the trusted authority (TA) and the residential area (RA); the seven modules include a system initialization module, a session key agreement module, an autonomous aggregation forming module, an offline pre-computation module, an online power consumption data reporting module, a security data collecting module and a security data reading module. The security data reporting system has the advantages that the light-weight security data reporting system can be applied to intelligent power grids, accordingly, the privacy can be protected, and the integrity of communication data can be guaranteed.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Lightweight multi-copy data cloud auditing method and device supporting justice
PendingCN111783148AEnsure information securitySupport batch auditDigital data protectionThird partyData integrity
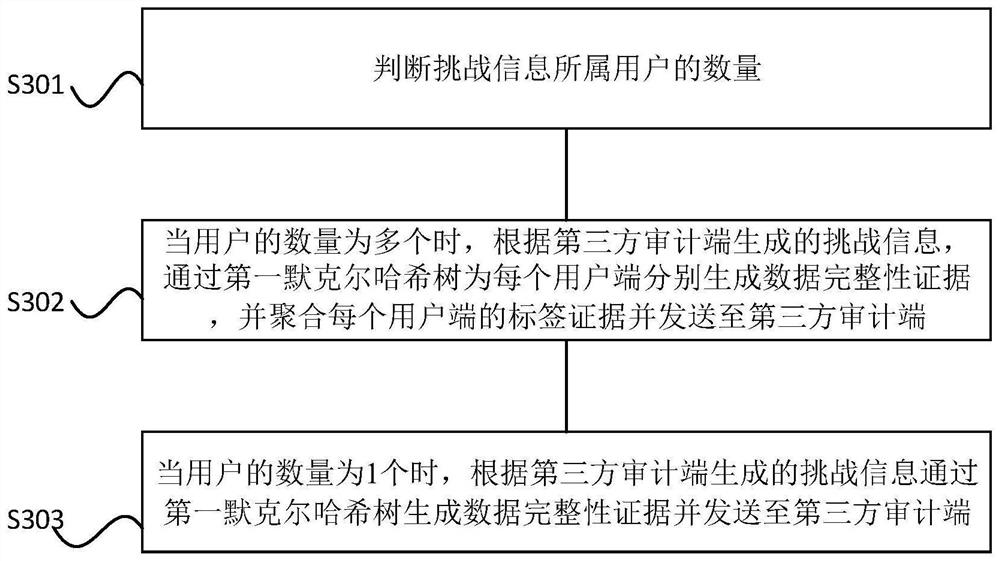
The invention provides a lightweight multi-copy data cloud auditing method and device supporting justice. The lightweight multi-copy data cloud auditing method comprises the steps of constructing a first Merkel hash tree according to hash values of data block tags generated by a user side based on data blocks of a to-be-audited file; and generating data integrity evidence information through the first Merkel hash tree according to challenge information obtained from a third-party auditing end, and sending the data integrity evidence information to the third-party auditing end so as to allow the third-party auditing end to verify the data integrity evidence information, wherein the data integrity evidence information comprises label evidence and a data block evidence set. Compared with an existing cloud auditing scheme, a data block mask label is adopted to replace a data block mask, so the risk that the data block mask is leaked is avoided; and the Merkel hash tree is adopted to authenticate the data block label, so it is ensured that the data block label cannot be forged, and the calculation complexity of the data block label is simplified.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Software micro-service combination optimization method for edge cloud system
ActiveCN112398899AReduce combo reduceImprove search efficiencyTransmissionLocal search (optimization)Service composition
The invention discloses a software micro-service combination optimization method for an edge cloud system. The method resets a step length factor and an attraction degree formula, gives full play to the detection capability of the step length factor at the early stage of an algorithm, and balances the local search and global search; micro-services are classified by utilizing the characteristics ofthe micro-services, and the services with the same input and output are classified into the same class, so that the number of combinations is reduced, and all combination schemes can be enumerated completely; in a combination algorithm, residual tangent initialization and residual tangent disturbance are adopted to replace random initialization and random disturbance, initialization and updatingof a micro-service combination scheme are improved, and the diversity of a final combination scheme is greatly improved; meanwhile, service attribute values stored in a service registration center arehashed and stored as a hash root through the concept of a hash tree, and therefore it is guaranteed that all the service quality attribute values stored in the service registration center are safe and reliable.
Owner:NANJING UNIV OF POSTS & TELECOMM
Data processing method and device based on block chain, terminal and storage medium
PendingCN110675145AImprove accounting efficiencyReduce error loggingFinancePayment protocolsBusiness enterpriseTransaction data
The invention provides a data processing method based on a block chain. The data processing method comprises the steps that a block chain system receives a transaction request; the blockchain system generates a transaction contract and transmits the transaction contract to both transaction parties; after the blockchain system detects that the two transaction parties sign the transaction contract,the blockchain system confirms that the transaction is completed and writes transaction information into the blockchain system; the enterprise data processing terminal obtains transaction informationfrom the block chain system and obtains preset transaction data; the enterprise data processing terminal uploads the financial data to the block chain system according to the determined financial data; the block chain system assembles the financial data in the form of a Hash tree and returns a Hash value to the tax node; and the tax node acquires financial data according to the Hash value. The invention further provides a data processing device based on the block chain, a terminal and a storage medium. By utilizing the embodiment of the invention, for one piece of transaction information, theaccounting operation is automatically completed, the accounting efficiency is improved, a manual account checking link is not needed, wrong records are reduced, and the auditing difficulty is reduced.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
Request processing method and device, computer readable storage medium and electronic equipment
PendingCN112799839AImprove processing efficiencyReduce data processingResource allocationSpecial data processing applicationsComputer networkService set
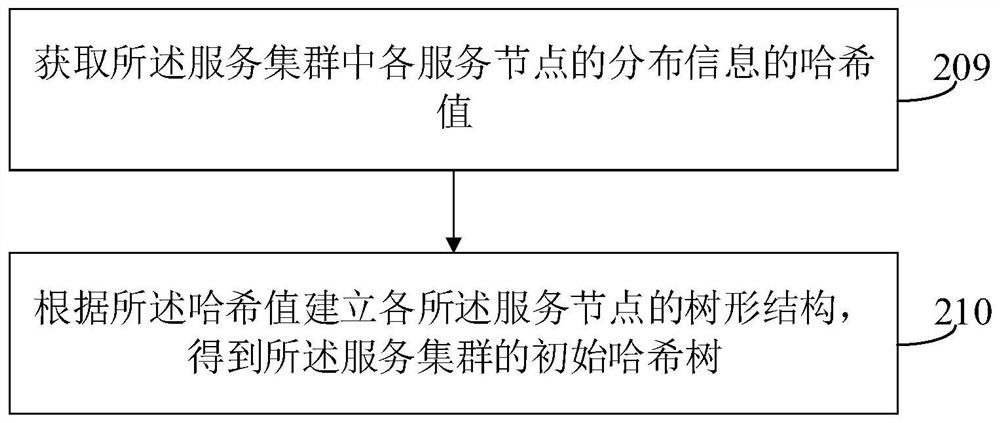
The invention provides a request processing method and device, a computer readable storage medium and electronic equipment, and belongs to the technical field of computers. The method comprises the steps: when request information is received, acquiring a target hash tree of a service cluster, wherein the score of each service node in the target hash tree is related to the operation information of the service node; traversing the target hash tree, and querying target service nodes with scores meeting score requirements; and sending the request information to the target service node for processing. According to the scheme, the request information is distributed through the Hash tree obtained by calculating the scores of the service nodes based on the Hash algorithm, under the condition that individual service nodes are unavailable, only the service nodes and the corresponding sub-nodes can be influenced, and the whole Hash tree does not need to be reconstructed, so that the time for updating a downstream list is shortened, and in addition, due to the fact that no virtual node exists, the data processing amount needed by query of the service node during request processing is reduced, and the request processing efficiency is improved.
Owner:BIGO TECH PTE LTD
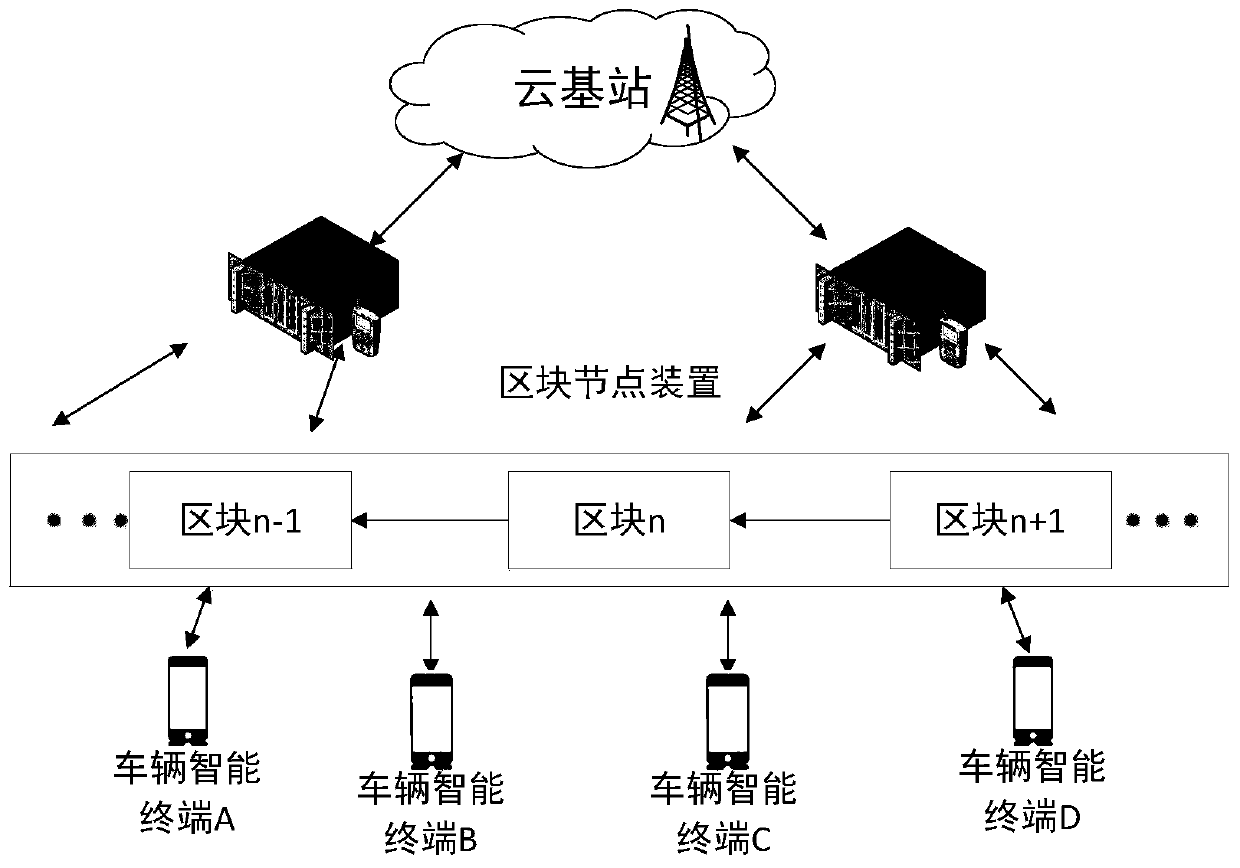
Intelligent Internet of Vehicles credible data encryption method and system based on block chain
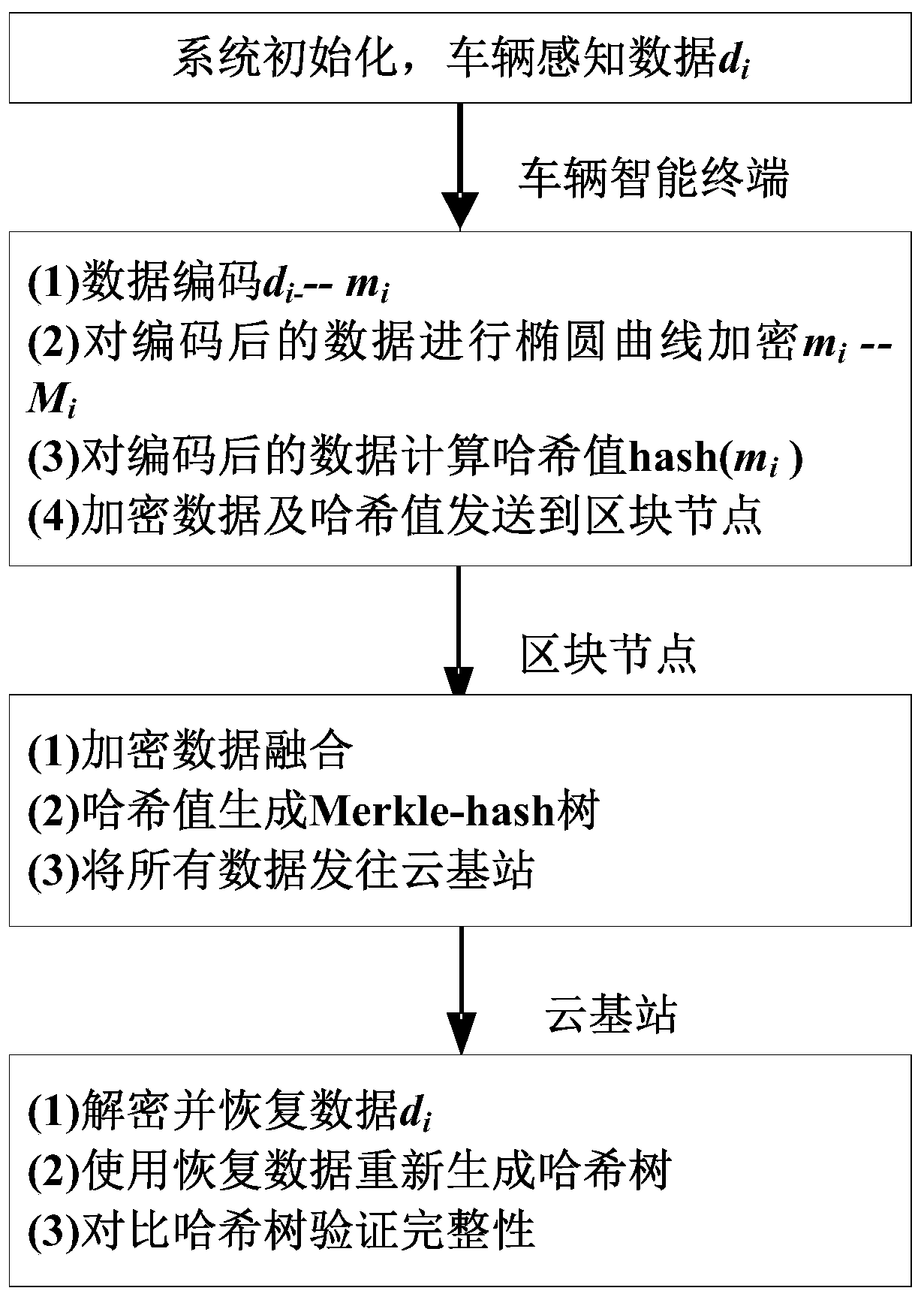
ActiveCN110830235AMeet security requirementsSatisfy latency requirementsEncryption apparatus with shift registers/memoriesPublic key for secure communicationData integrityConfidentiality
The invention discloses an intelligent Internet of Vehicles credible data encryption method and system based on a block chain, and designs a privacy protection method with low power consumption and credible data integrity verification by adopting Merkle-hash authentication in the block chain and a homomorphic encryption technology of an elliptic curve. On one hand, the distributed characteristicsof the Merkle-hash tree are adopted to achieve integrity verification of the Internet of Vehicles trusted data and the function of positioning the wrong vehicle intelligent terminal; on the other hand, a homomorphic encryption technology based on an elliptic curve is adopted to map data transmitted by the vehicle intelligent terminal into encrypted data points, so that lower energy consumption isrealized, and encryption from the vehicle terminal to the vehicle terminal is realized. The method has the advantages of high confidentiality, low calculation amount and low communication traffic overhead, can meet the requirements of the Internet of Vehicles for trusted data security and transmission delay, and is suitable for large-scale Internet of Vehicles intelligent terminal data transmission and instant messaging.
Owner:HUAQIAO UNIVERSITY +1
Dynamic social outsourcing data keyword query and verification method and device based on block chain
ActiveCN110971393AImprove securityAccurate and completeSpecial service provision for substationKey distribution for secure communicationData providerChain network
The invention discloses a dynamic social outsourcing data keyword query and verification method based on a block chain, and the method comprises the steps that an OSN operator outsources social data to a data provider, and the data provider provides data for a data consumer; the OSN operator constructs an auxiliary information block chain network and issues auxiliary information to the auxiliary information block chain network, wherein the auxiliary information block chain network constructs a block chain by nodes in an auxiliary information block chain; the data consumer verifies the authenticity of the query data through the auxiliary information block chain. The invention provides an efficient self-balancing Merkle hash tree data structure. The dynamic change of social data is supported, an updating algorithm supporting a self-balancing Merkle hash tree data structure is provided, a data consumer is allowed to efficiently check the authenticity of a queried data result, the decentralization of stored auxiliary information is realized, and the safety of the stored auxiliary information is improved; according to the invention, the social data is allowed to change dynamically, andthe expandability of the system is improved.
Owner:CENT SOUTH UNIV
Data synchronization method and device, storage medium and computer equipment
PendingCN111917834AImprove synchronization efficiencyQuick fixTransmissionData synchronizationData set
The embodiment of the invention discloses a data synchronization method and device, a storage medium and computer equipment. The embodiment of the invention is related to file storage and database synchronization of cloud storage, and the method comprises the steps: obtaining a first hash tree of a data set on a first server, and obtaining a second hash tree of a to-be-synchronized target data seton a second server; starting traversal comparison based on the root nodes of the first hash tree and the second hash tree, and determining target identifiers corresponding to different target leaf nodes; determining first data and second data, corresponding to the data set and the target data set, of the target identifier; and performing data synchronization according to the difference between the version information of the first data and the version information of the second data. The data synchronization efficiency can be effectively improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Light dynamic data integrity auditing method based on hierarchical Merkel hash tree
ActiveCN110958109AImprove update efficiencyIncrease profitEncryption apparatus with shift registers/memoriesDigital data protectionData integrityData information
The invention discloses a light dynamic data integrity auditing method based on a hierarchical Merkel hash tree, which comprises the following steps that: 1) a data owner constructs the hierarchical Merkel hash tree for data, stores data information on a node, and introduces a local root node; 2) a cloud database stores the data of the data owner by using a position sensitive hash technology; 3) the cloud database generates challenge evidence according to the challenge information audited by a trusted third party; 4) the trusted third-party audits the integrity of the evidence ; and 5) when dynamic operation is performed on the data, the cloud database generates evidence, and the trusted third-party performs integrity auditing on the dynamic data. Compared with the prior art, the method ishigh in the auditing efficiency, can be effectively reduce the communication and calculation expenditure, and supports efficient data updating.
Owner:SHANGHAI UNIVERSITY OF ELECTRIC POWER
Integrity verification method and device, terminal equipment and verification server
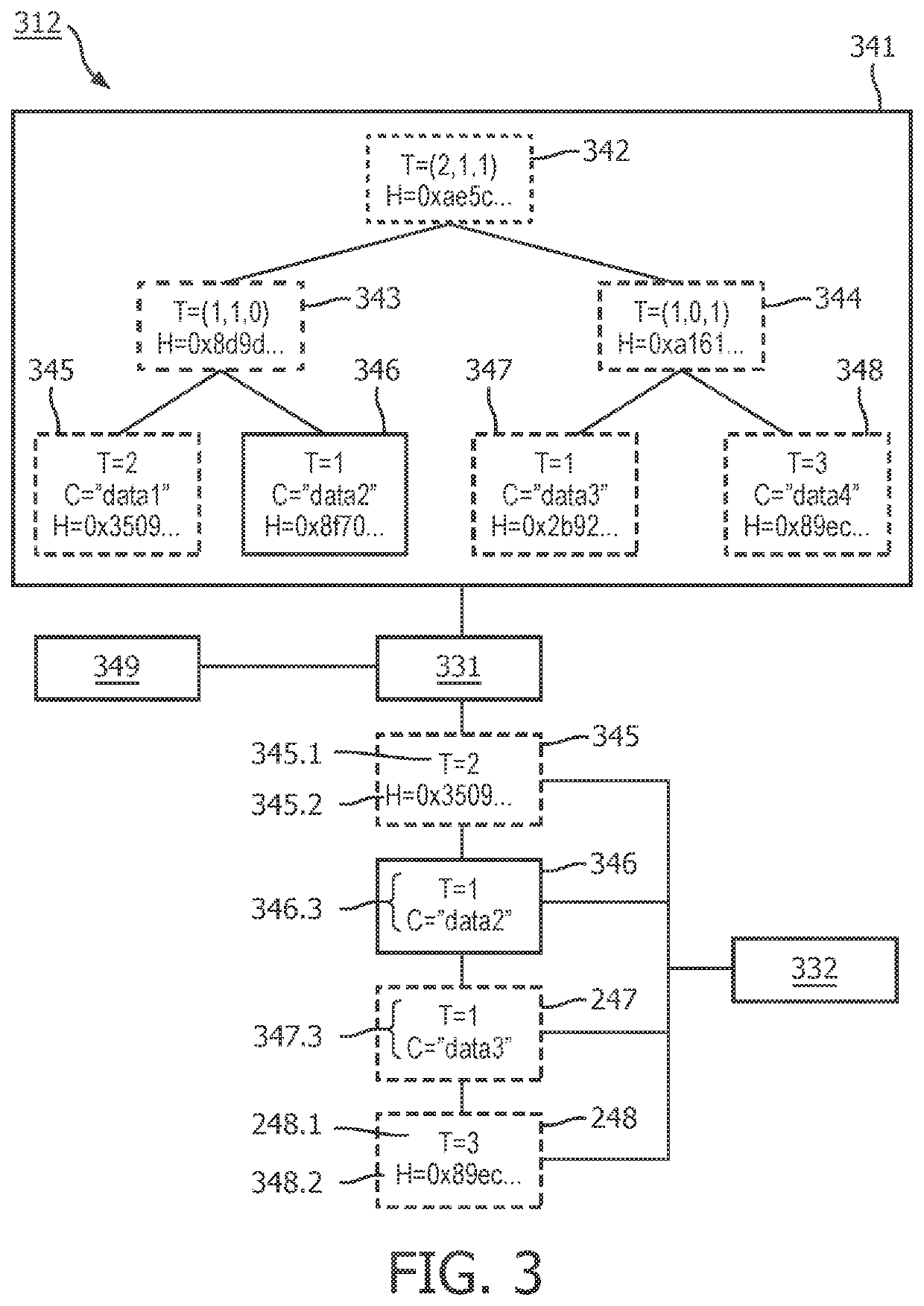
The invention is suitable for the technical field of terminals, and particularly relates to an integrity verification method and device, terminal equipment and a verification server. The method comprises the steps of obtaining a to-be-verified file sent by a file server and integrity verification information of the to-be-verified file, wherein the integrity verification information comprises root node signature information obtained by using a first signature private key to sign a target root node of a target Hash tree, child nodes related to the to-be-verified file in the target Hash tree and a first signature public key corresponding to the first signature private key, and the target hash tree is a hash tree constructed according to all files in the file server; verifying the root node signature information by using the first signature public key; and when the root node signature information passes verification, constructing a current root node corresponding to the target hash tree according to the to-be-verified file and the child nodes, and verifying the integrity of the to-be-verified file according to the current root node and the target root node, thereby solving the problem of large calculation amount caused by the need of respectively signing all files at present.
Owner:HUAWEI TECH CO LTD
Method for auditing cloud access in real time
InactiveCN108243004AEncryption apparatus with shift registers/memoriesUser identity/authority verificationTheoretical computer scienceIndex function
A method for auditing cloud access in real time includes steps of Step 1: client obtains necessary information from a synchronization server (SYS), by executing a library comprising index function [gamma] required by program, and saving a root hash value R of a fully binary hash tree (FBHTREE) in SYS; Step 2: the client obtains leave node position corresponding to FBHTREE and corresponding tree node position by inputting an index function [gamma] via file absolute path; Step 3: obtaining slice of FBHTREE based on the leave node position in Step 2; Step 4: performing a hash computation on treenode position in the slice and hash value saved at another tree node position to obtain hash value of tree node position of one previous level till root hash value Y is obtained; Step 5: comparing thehash value Y and the root hash value R saved by the client.
Owner:TIDETIME SUN LTD
Anti-replay method for radio frequency identification system based on time slot ALOHA protocol of frame
ActiveCN112867008ADefense against replay attacksImplement replay detectionEncryption apparatus with shift registers/memoriesSecurity arrangementFrame timeSequence search
Owner:ZHEJIANG UNIV
Cloud storage data security deduplication method based on block chain
ActiveCN112732695AReduce computational overheadGuaranteed privacy and securityFinanceDatabase distribution/replicationCloud userCiphertext
The invention discloses a cloud storage data security deduplication method based on a block chain. The method comprises the following steps: sending a generated file label to a cloud storage service provider for repeatability detection; if the result is file repetition, enabling the user to generate a file repetition storage log, executing the intelligent contract through the intelligent contract management center to integrate the storage log into a transaction and uploading the transaction to the block chain for storage, so that the current storage state information is safely stored; if the result is that the file is not repeated, enabling the secret key server to generate an authority secret key of the user by constructing a role hierarchical hash tree, executing safe encryption operation on the data by using the authority secret key, and uploading a ciphertext to the cloud storage server for storage; and generating a file non-repeated storage log and transaction under the assistance of the intelligent contract management center. According to the method, data security deduplication and storage of the cloud user can be achieved, malicious behaviors of stealing and tampering of a cloud storage service provider are resisted, the computing overhead of the cloud storage server is greatly reduced, and the privacy security is ensured.
Owner:GUANGDONG UNIV OF TECH
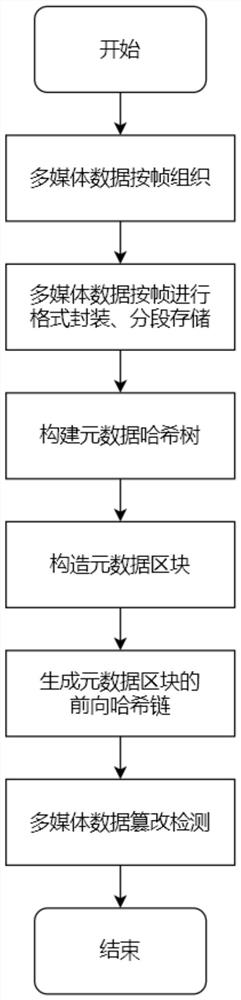
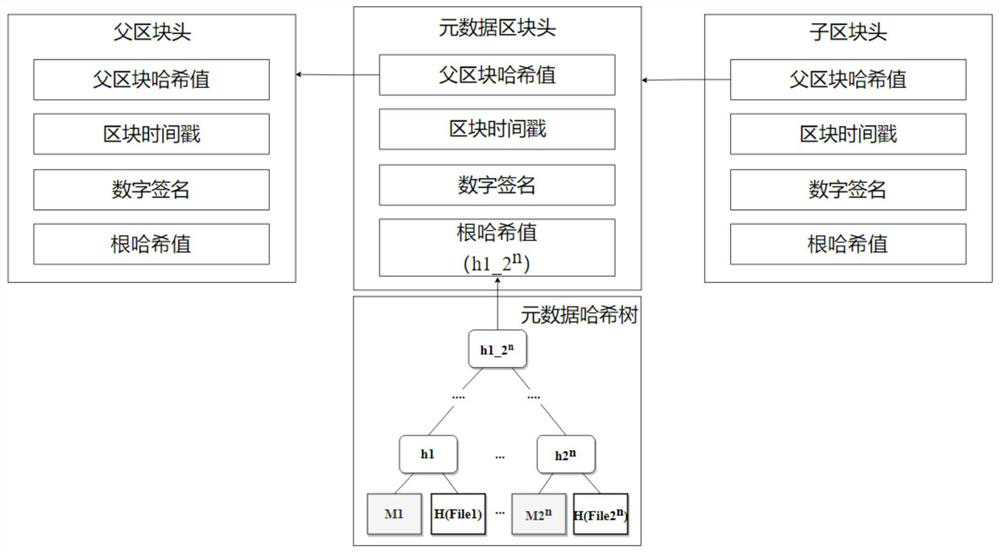
Multimedia data tampering detection method
ActiveCN113536956AGuaranteed credibilityEasy to implement in real timeCharacter and pattern recognitionDigital data protectionDigital signatureData file
The invention discloses a multimedia data tampering detection method. The method comprises the following steps of packaging audio and video multimedia data needing to be recorded on a storage medium and storing the data in a segmented mode; constructing a metadata hash tree according to the hash values of the multi-segment grouped multimedia data files and the corresponding metadata information, and constructing corresponding metadata blocks; recording the generated metadata blocks, and linking the metadata blocks by using a forward hash chain structure; and carrying out tampering detection on the multimedia data file by the verifier according to the recorded metadata block forward hash chain. According to the method, tampering detection is carried out on the grouped multimedia data files by utilizing the metadata blocks, and multiple verification is carried out on the metadata blocks by utilizing the forward hash chains and the block timestamps of the metadata blocks, so that the credibility of the multimedia data files is ensured; meanwhile, only the metadata block head is digitally signed, so that the calculation overhead is reduced, and real-time implementation is facilitated.
Owner:SOUTH CHINA UNIV OF TECH +1
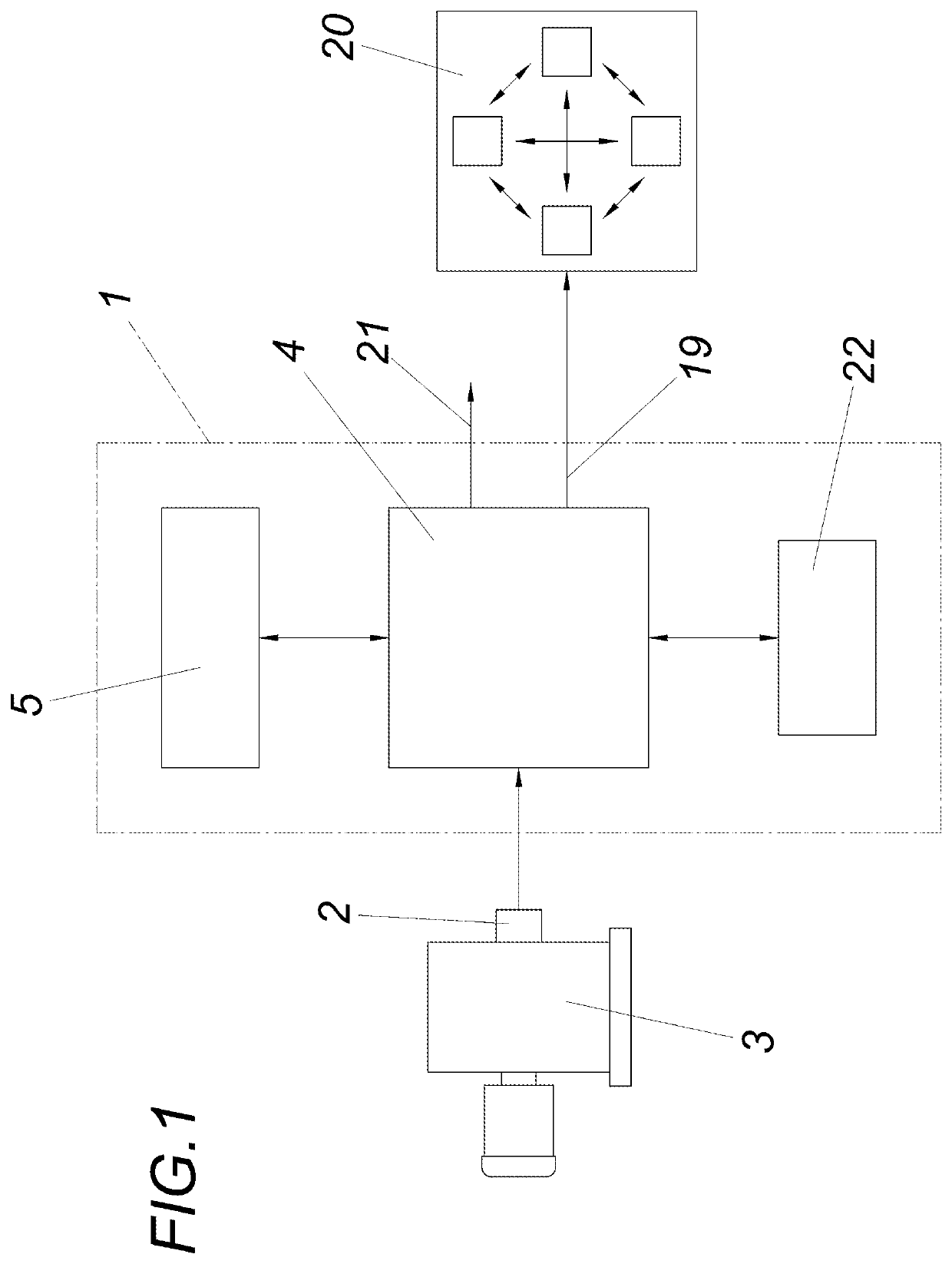
Apparatus and method for checking the integrity of sensor-data streams
PendingUS20220179998A1Reduce resource consumptionAvoid authenticityUser identity/authority verificationDigital data protectionData streamResource consumption
The invention relates to an apparatus for checking the integrity of sensor-data streams (15) with a detection unit (1) having a sensor-data input. In order that individual sensor-data stream sections (11, 12, 13, 14) of a sensor-data stream (15) can also be checked for integrity independently of further processing in existing infrastructures (26), in particular in the case of transmission across a plurality of infrastructure nodes, with low resource consumption, it is proposed in that the detection unit (1) comprises a control device (4), connected to the sensor-data input and to a hash tree memory (5), for calculating and storing hash values on the basis of individual sensor-data stream sections (11, 12, 13, 14) and on the basis of subordinate hash values of the hash tree, and in that the control device (4) has a root hash output (19) for outputting the most recently calculated root hash value.
Owner:TRIBUTECH SOLUTIONS GMBH
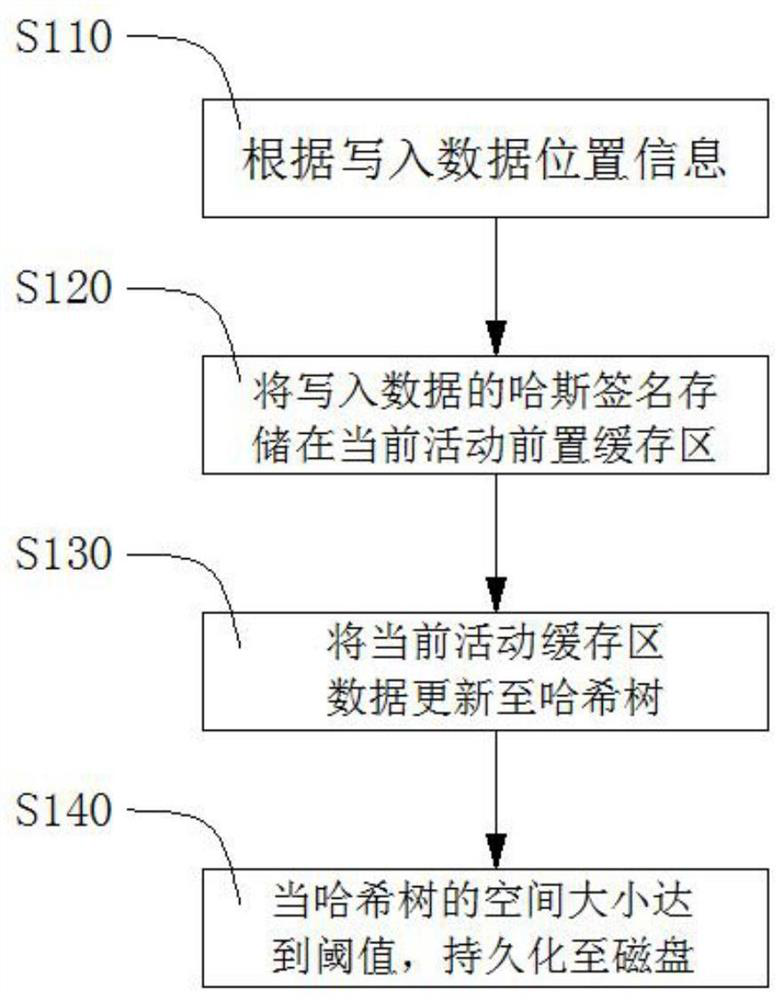
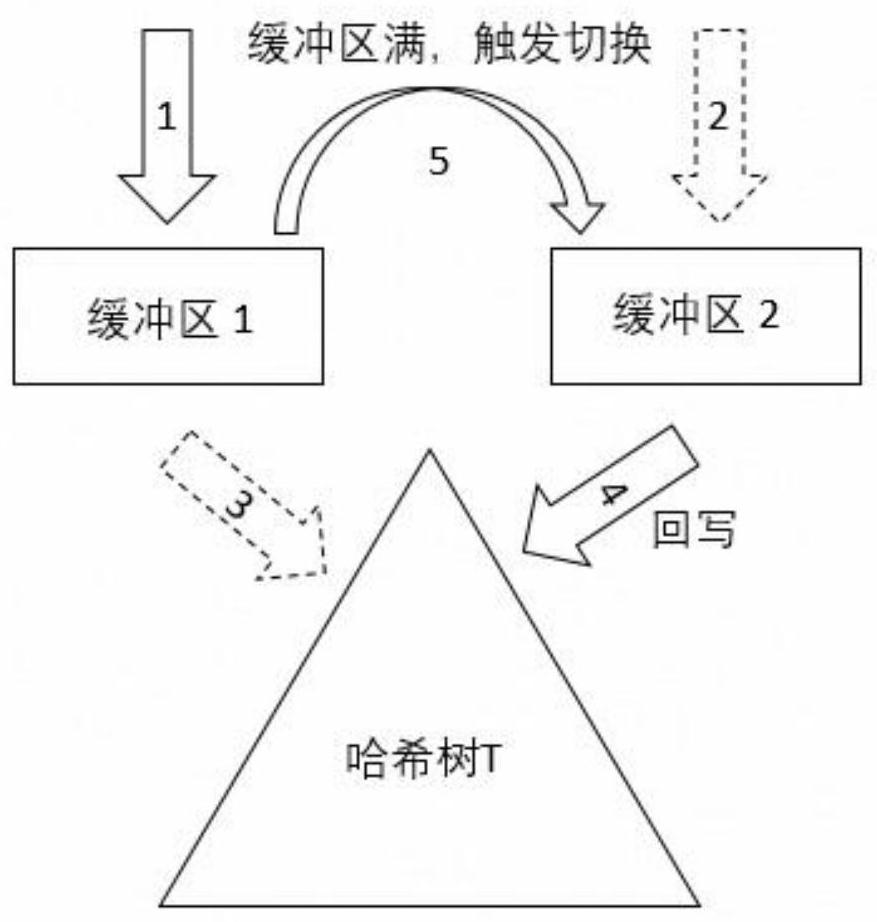
Hash tree caching method and device
PendingCN112286873AQuarantine operationIncreased complexityFile access structuresFile system functionsParallel computingTheoretical computer science
The invention discloses a hash tree caching method and device, and the method comprises the steps: determining the position information of written data in a hash tree according to the logic position of the written data, and storing a hash signature and the position information of the written data in a first front buffer region; when the first preposed buffer area is full, taking the first preposedbuffer area as a current standby preposed buffer area, and updating internal data of the first preposed buffer area to the hash tree; when the space size of the hash tree reaches a threshold value, persisting the hash tree to a disk. According to the method, the first front buffer area and the second front buffer area are introduced, so that the read-write data corresponds to the front buffer areas, the two inverse hash tree operations are effectively isolated, the complexity of the hash tree operations is improved, persistent concurrent execution of the user read-write task and the hash treecan be realized, and the user experience is improved. And the determination writing performance of the distributed storage system is effectively improved.
Owner:西安奥卡云数据科技有限公司
Digital signature service system based on hash function and method thereof
ActiveUS9819494B2Stable generationIntegrity guaranteedUser identity/authority verificationPublic key infrastructure trust modelsElectronic documentDigital data
Disclosed is a digital signature service system and method based on a hash function in which a main agent, who requires the generation of a digital signature, does not personally generate the digital signature, and wherein digital signatures may be simultaneously and stably generated for large-scale data such as multiple electronic documents and digital data using a hash function and a hash tree, which are known as a simple and secure method, to guarantee the integrity of the data in a digital signature-based structure based on a server.
Owner:MARKANY
Hash tree computation device
ActiveUS20200007341A1Accurate performanceUser identity/authority verificationAlgorithmTheoretical computer science
Some embodiments are directed to a hash tree computation device. The hash tree computation device computes a top hash of a hash tree. A hash preimage of a leaf node of the hash tree comprises a type of the leaf node. A hash preimage of an internal node of the hash tree comprises a type count comprising a number of descendants of the internal node having a given type. The hash tree computation device computes the top hash by computing hashes of a current node and of its ancestors, where a hash of an ancestor is computed based on its type count, the type count being computed from types or type counts of its descendants.
Owner:KONINKLJIJKE PHILIPS NV
Data processing method and device, computer equipment and storage medium
ActiveCN113901395AImprove verification efficiencyReduce storage pressureComplex mathematical operationsComputer hardwareComputation complexity
The invention relates to a data processing method and device, computer equipment and a storage medium. The method comprises the following steps: enabling a terminal to send a data reading request; according to a storage file corresponding to the data reading request, selecting a verification data block through a random algorithm; acquiring a target hash tree corresponding to the storage file, wherein the target hash tree comprises data from a layer where a root node is located to an M-th layer, M is a positive integer, a first hash value is stored in the root node, and each leaf node corresponds to a data block of the storage file; calculating a second hash value corresponding to a root node of the target hash tree according to the verification data block and the target hash tree; and if the first hash value is the same as the second hash value, returning data corresponding to the data reading request in the storage file to the terminal. According to the method, the authenticity of the storage file is verified by randomly selecting the verification data block, so that the storage pressure of the CDN node can be reduced, the verification calculation complexity is reduced, and the verification efficiency of the security of the data requested to be read by a user is greatly improved.
Owner:深圳市名竹科技有限公司
Backup method and system of NAS file system and storage medium
ActiveCN114546980AEfficient backupDigital data information retrievalSpecial data processing applicationsFile systemEngineering
The invention relates to a backup method and system of an NAS file system and a storage medium, and belongs to the field of file system backup. The method comprises the following steps: a mounting step; a directory and file metadata acquisition step; a file directory tree construction step; a file hash tree construction step; and an incremental file obtaining step. The system comprises a mounting module; a directory and file metadata acquisition module; a file directory tree construction module; a file hash tree construction module; and an incremental file acquisition module. According to the method, depth-first traversal is carried out on the NAS file system, the file directory tree is constructed, the file hash tree is constructed based on the file directory tree, then the file hash tree constructed by the current backup and the file hash tree constructed by the last backup are compared step by step, nodes containing incremental files are quickly positioned, and the incremental files are quickly positioned. The incremental file between the two backup time points is obtained, and efficient backup of the NAS file system is achieved.
Owner:成都云祺科技有限公司
Method and system to validate uniqueness in a data store
PendingUS20210075617A1User identity/authority verificationSpecial data processing applicationsTheoretical computer scienceEngineering
A method, system and apparatus of for validating uniqueness of a non-disclosed element of data, including in response to receiving a plurality of elements, generating an index of the plurality of elements of data received from a data store to create uniquely indexed data, generating filters from the index, generating a hash tree for the uniquely indexed data using the index, and validating a unique element of data from the hash tree and filters.
Owner:IBM CORP
Method and system for operating a cache in a trusted execution environment
ActiveUS10204229B2Memory architecture accessing/allocationKey distribution for secure communicationData processing systemData treatment
Owner:NXP BV
Data resource authorization and authentication method, device and system based on Hash tree
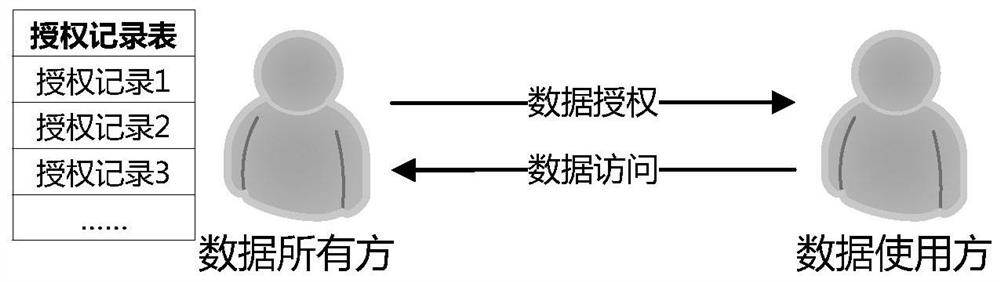
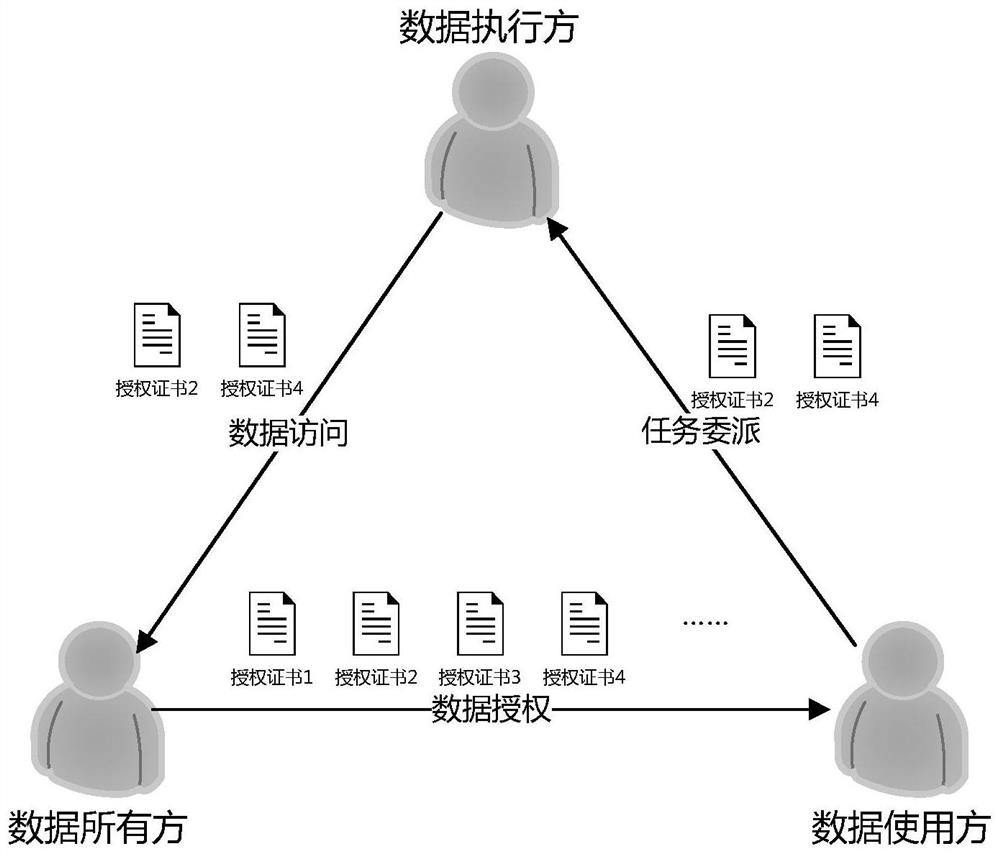
PendingCN114362974ANot easy to tamper withResists unauthorized tamperingUser identity/authority verificationAuthorization certificateAuthorization
The invention at least relates to a data resource authorization and authentication method, device and system based on a hash tree. The data resource authorization method based on the hash tree comprises the following steps: constructing the hash tree based on each permission record in a plurality of permission records of a plurality of data resources; and forming an authorization certificate, wherein the authorization certificate at least comprises a root node value of the constructed hash tree.
Owner:CHINA TELECOM CORP LTD
Compact recordation protocol
ActiveCN110383752AImprove securitySafe and Efficient RecordsEncryption apparatus with shift registers/memoriesThird partyComputer network
A method for efficiently storing and verifying records is disclosed. The method may comprise receiving a first hash of first interaction data and determining an interaction identifier associated withthe first hash, then storing the first hash in a database along with the interaction identifier and determining a root hash of a hash tree. In addition, the method may also comprise providing the roothash of the hash tree to a public blockchain. Embodiments of the invention also allow users to easily present records to a third party or inquiring entity. Furthermore, interactions may be processedmore quickly than previous blockchain methods that publish to a block during each individual interaction.
Owner:VISA INT SERVICE ASSOC
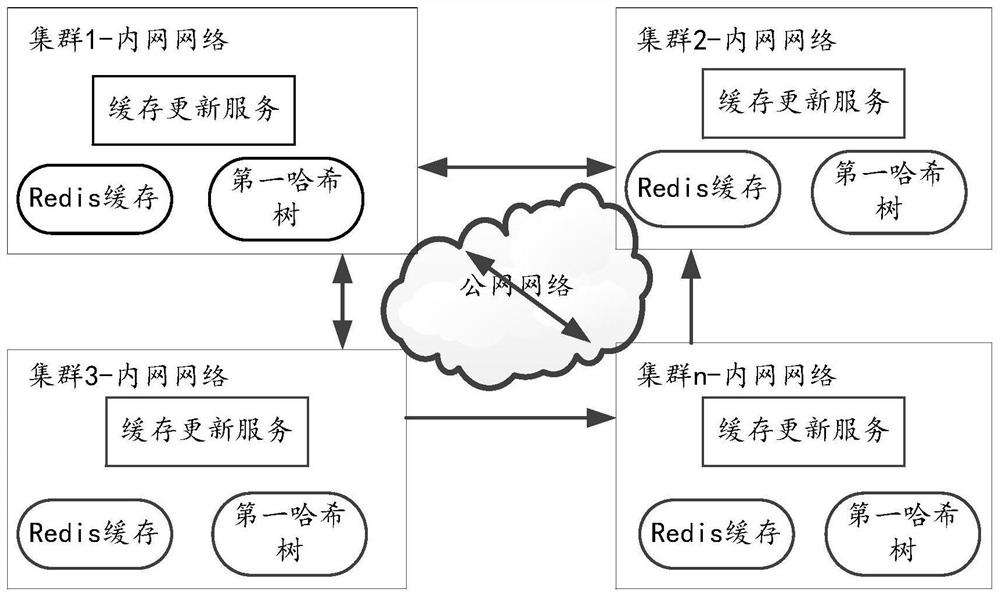
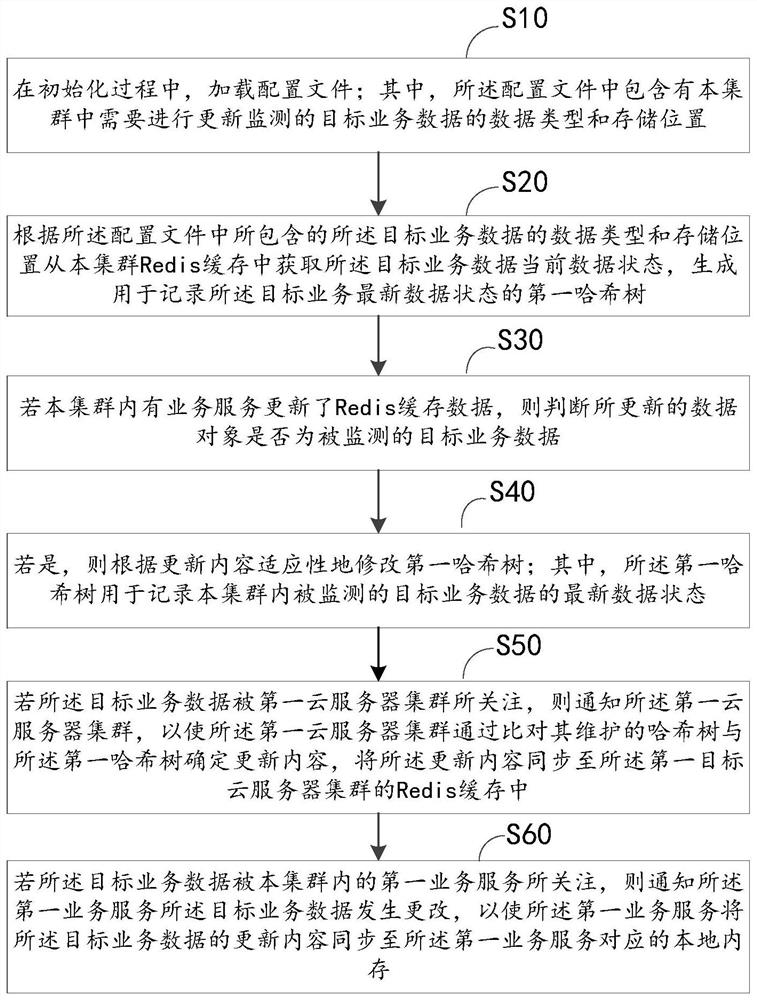
Data synchronization method and device between cloud server clusters
PendingCN112765182AImprove data securityDatabase updatingDatabase distribution/replicationData synchronizationBusiness data
The invention provides a data synchronization method and device between cloud server clusters. The method comprises the following steps: if a business service in a cluster updates Redis cache data, judging whether an updated data object is monitored target business data or not; if yes, adaptively modifying the first hash tree according to the updated content, wherein the first hash tree is used for recording the latest data state of the monitored target service data in the cluster; if the target service data is concerned by the first cloud server cluster, notifying the first cloud server cluster that the target service data is changed, enabling the first cloud server cluster to determines update content by comparing a Hash tree maintained by the first cloud server cluster with a first Hash tree, and synchronizing the update content to a Redis cache of the first cloud server cluster. According to the method and the device, the data sharing efficiency and security among the cloud server clusters are improved.
Owner:BEIJING CYBER CLOUD TECH
Local sensitive hash-based adaptive random test method
ActiveCN111352834AImprove performanceReduce computational overheadSoftware testing/debuggingFailure rateAlgorithm
The invention discloses a local sensitive hash-based adaptive random test method. The method comprises the steps of 1, determining an input domain range; 2, randomly generating a first test case in the input domain and executing the first test case; 3, randomly generating k candidate test cases to form a candidate test case set; 4, selecting a next test case by adopting FSCS-ART, executing the next test case and inserting the next test case into the hash tree; and 5, repeatedly executing the steps 3 and 4 until m executed test cases are obtained or errors are found. 6, randomly generating k candidate test cases to form a candidate test case set; and 7, selecting a next test case by adopting an improved locality sensitive hash algorithm, executing and inserting the next test case into the hash tree. And repeating the steps 6 and 7 until a program error is found. Compared with the existing FSCS-ART, the LSH-ART provided by the invention has the advantages that in performance, the LSH-ARTis slightly similar to the FSCS-ART in low dimension, but the LSH-ART is better than the FSCS-ART in high dimension; in terms of time expenditure, the LSH-ART is less than the FSCS-ART in both low dimension and high dimension, and particularly, the time expenditure of the LSH-ART is even less than 10% of the time expenditure of the FSCS-ART under low failure rate.
Owner:JIANGSU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com