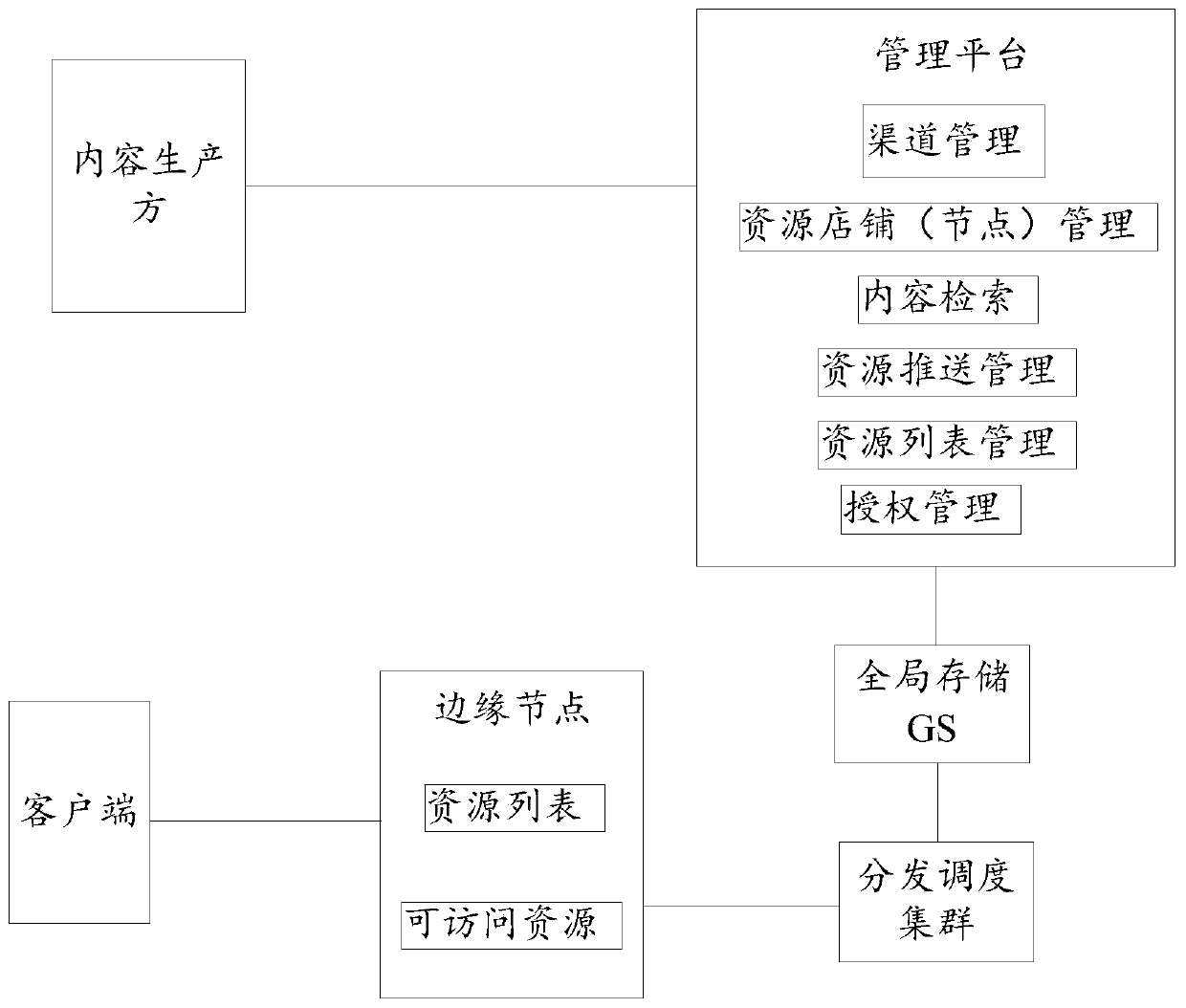
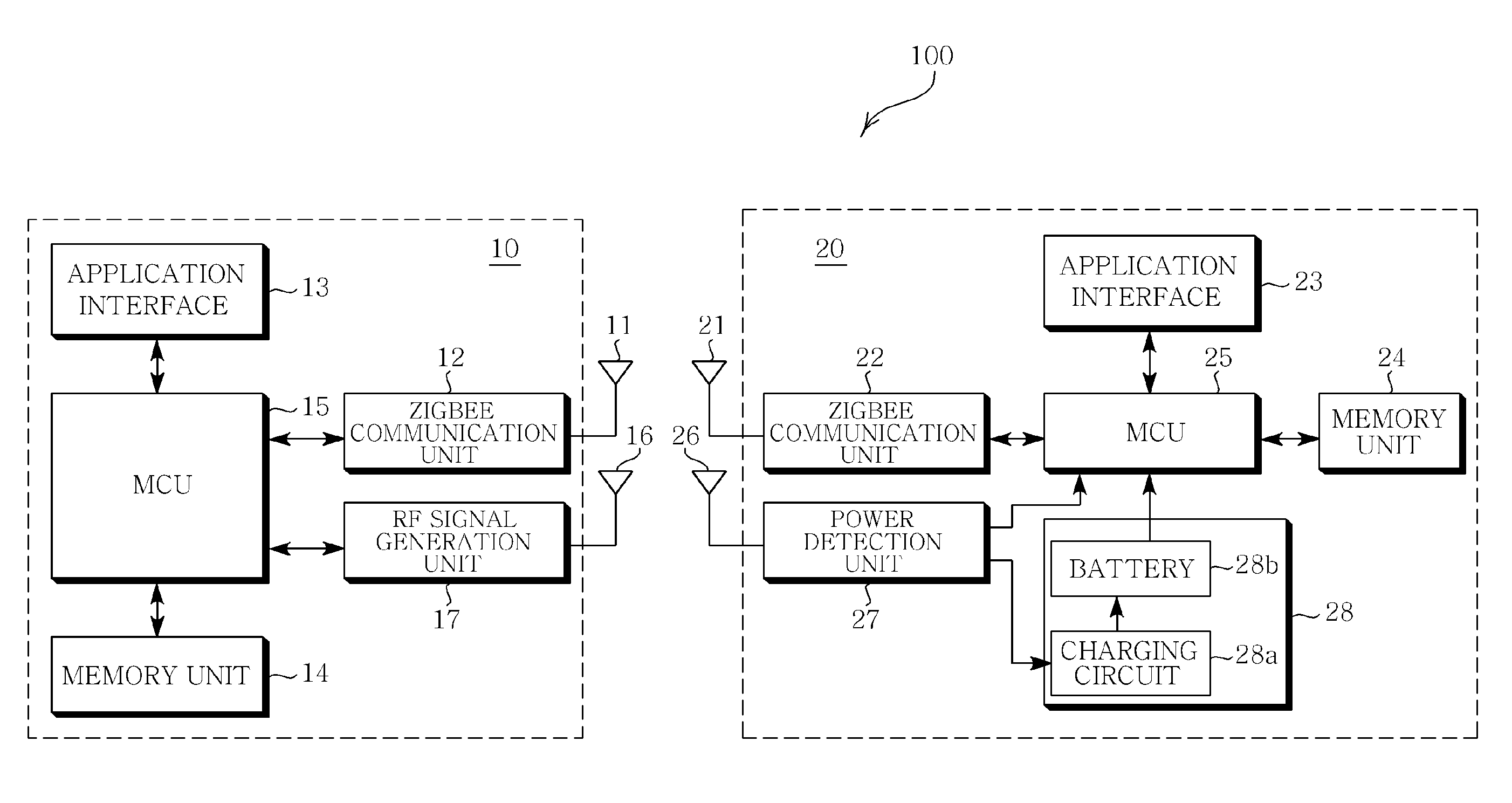
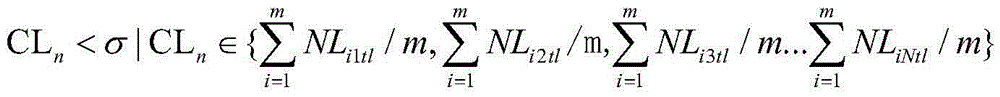Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
751 results about "Service set" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
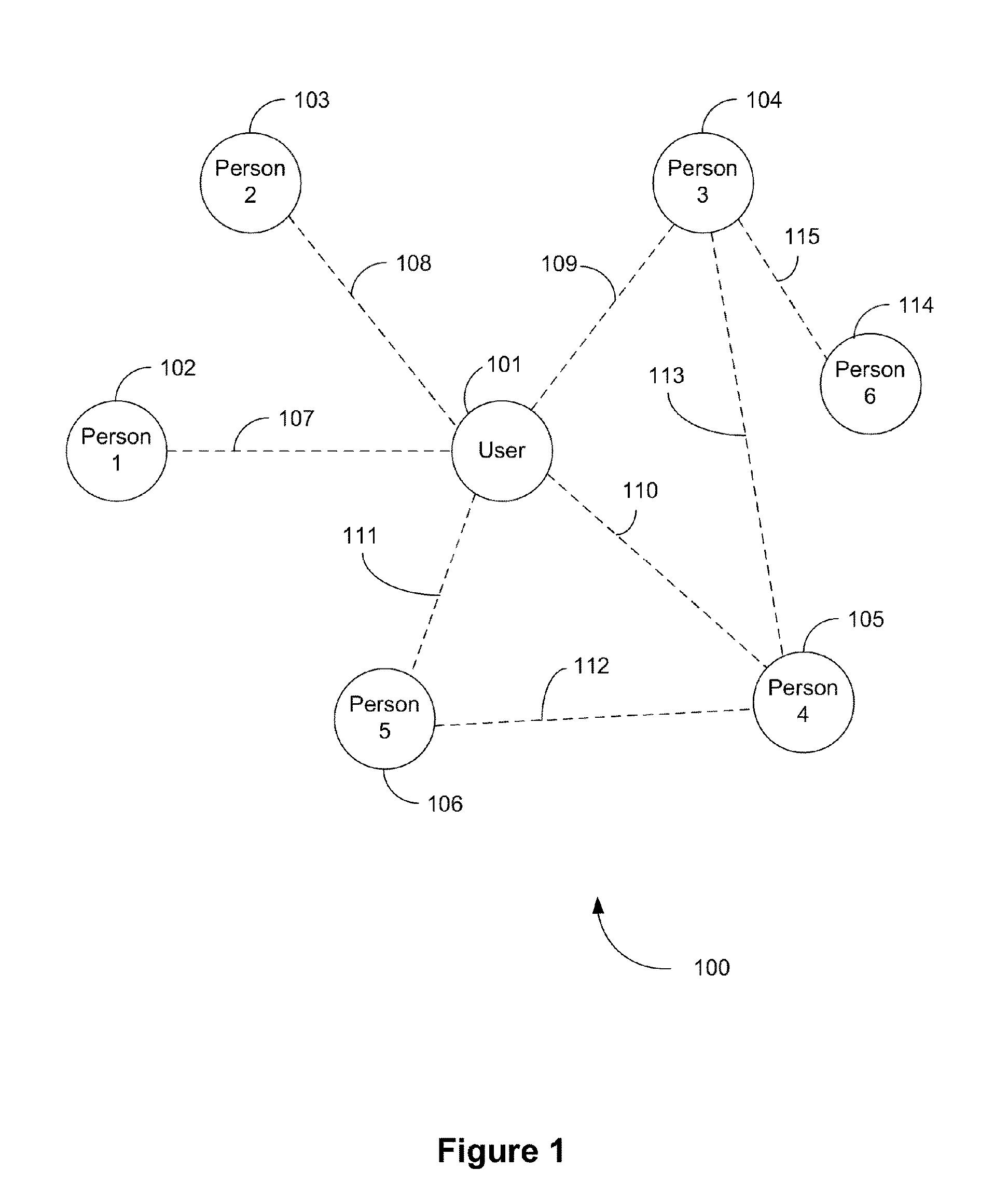
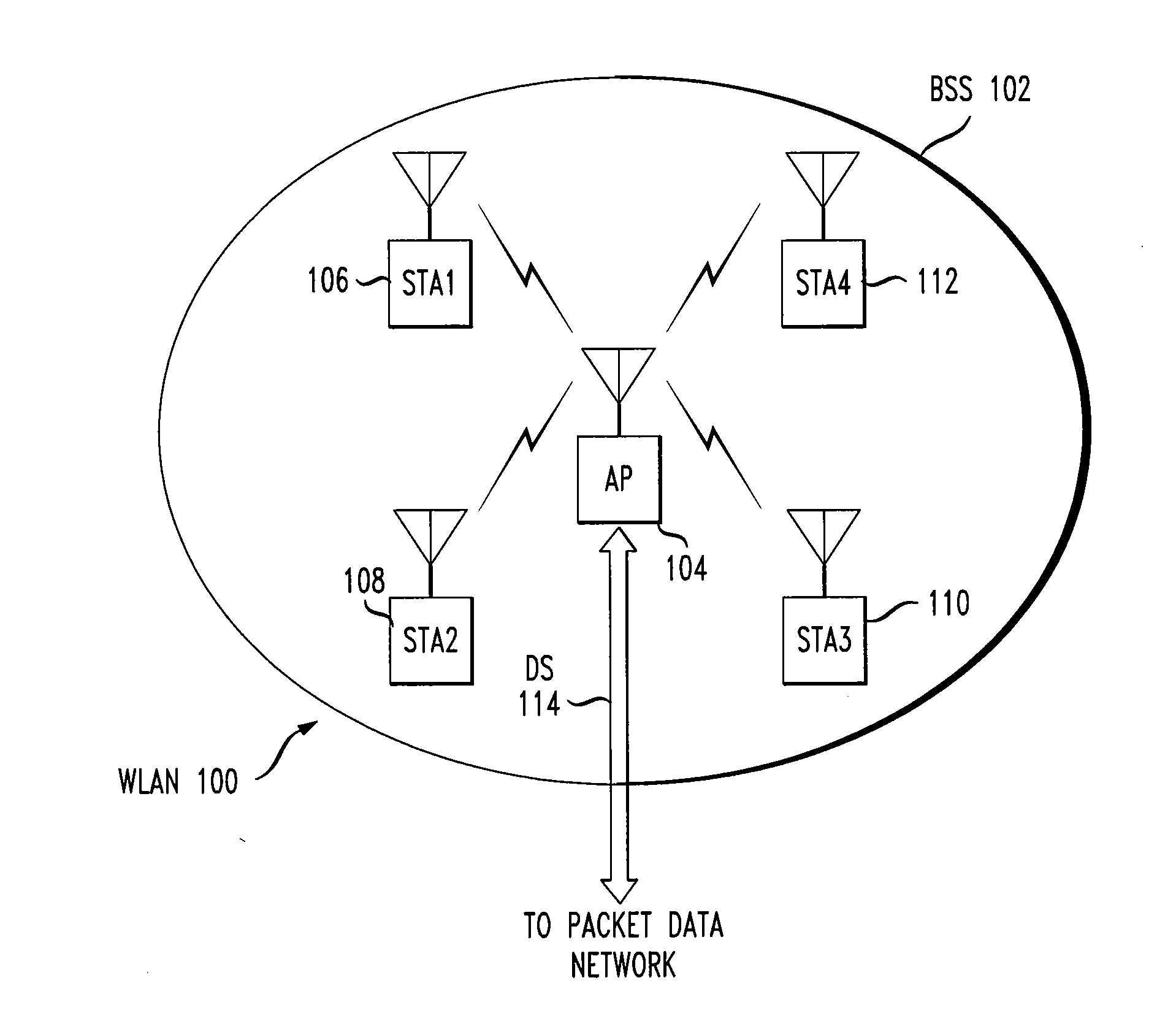
In IEEE 802.11 wireless local area networking standards (including Wi-Fi), a service set is a group of wireless network devices that are operating with the same networking parameters. Service sets are arranged hierarchically,: basic service sets (BSS) are units of devices operating with the same medium access characteristics (i.e. radio frequency, modulation scheme etc.), while extended service sets (ESS) are logical units of one or more basic service sets on the same logical network segment (i.e. IP subnet, VLAN etc.). There are two classes of basic service sets: those that are formed by infrastructure mode redistribution points (access points or mesh nodes), and those that are formed by independent stations in a peer-to-peer ad hoc topology. Basic service sets are identified by BSSIDs (basic service set identifiers), which are 48-bit labels that conform to MAC-48 conventions. Logical networks (including extended service sets) are identified by SSIDs (service set identifiers), which serve as "network names" and are typically natural language labels.
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
Service-oriented architecture
InactiveUS20070011126A1ModificationEasy to adaptData processing applicationsKnowledge representationService implementationReusability
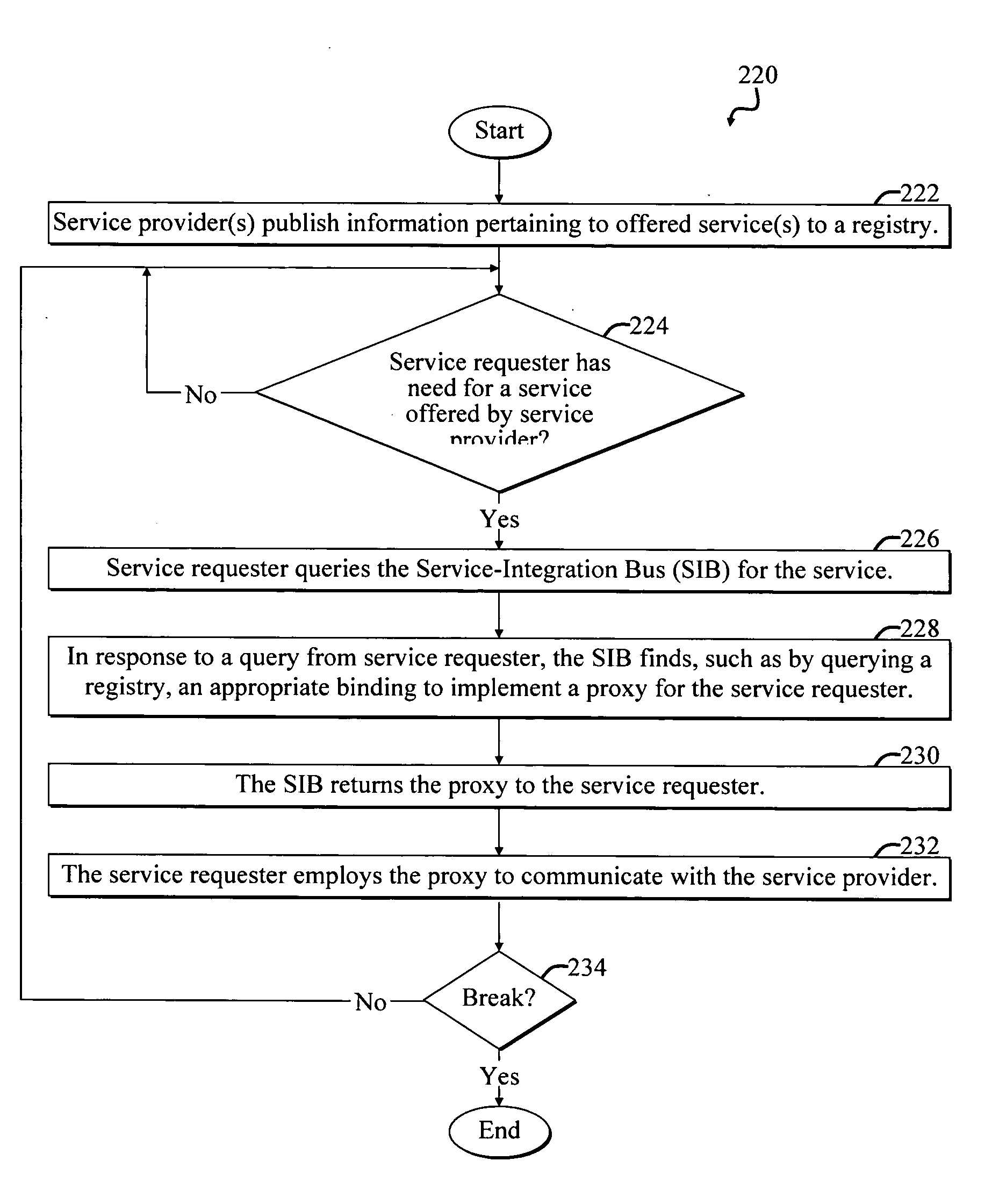
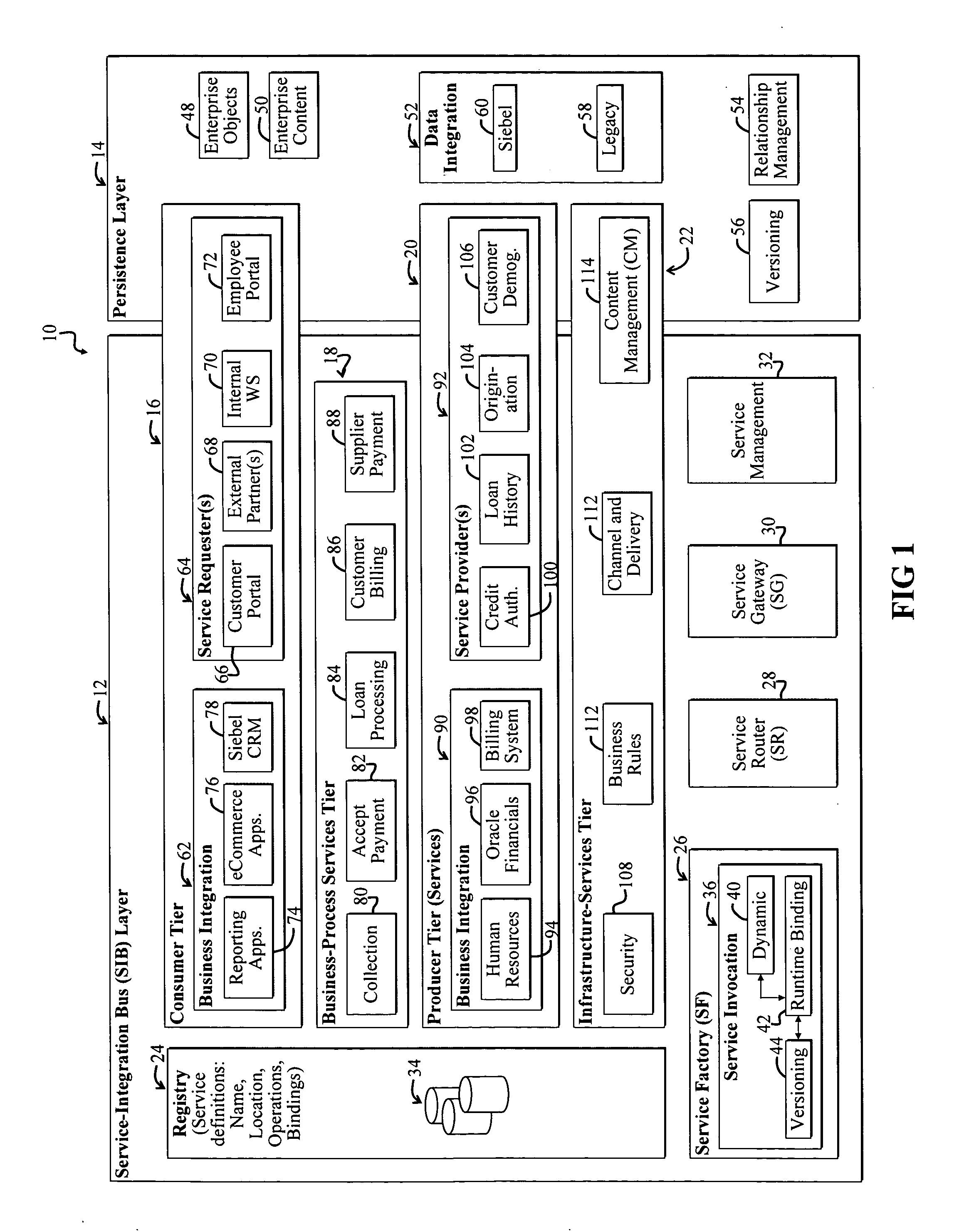
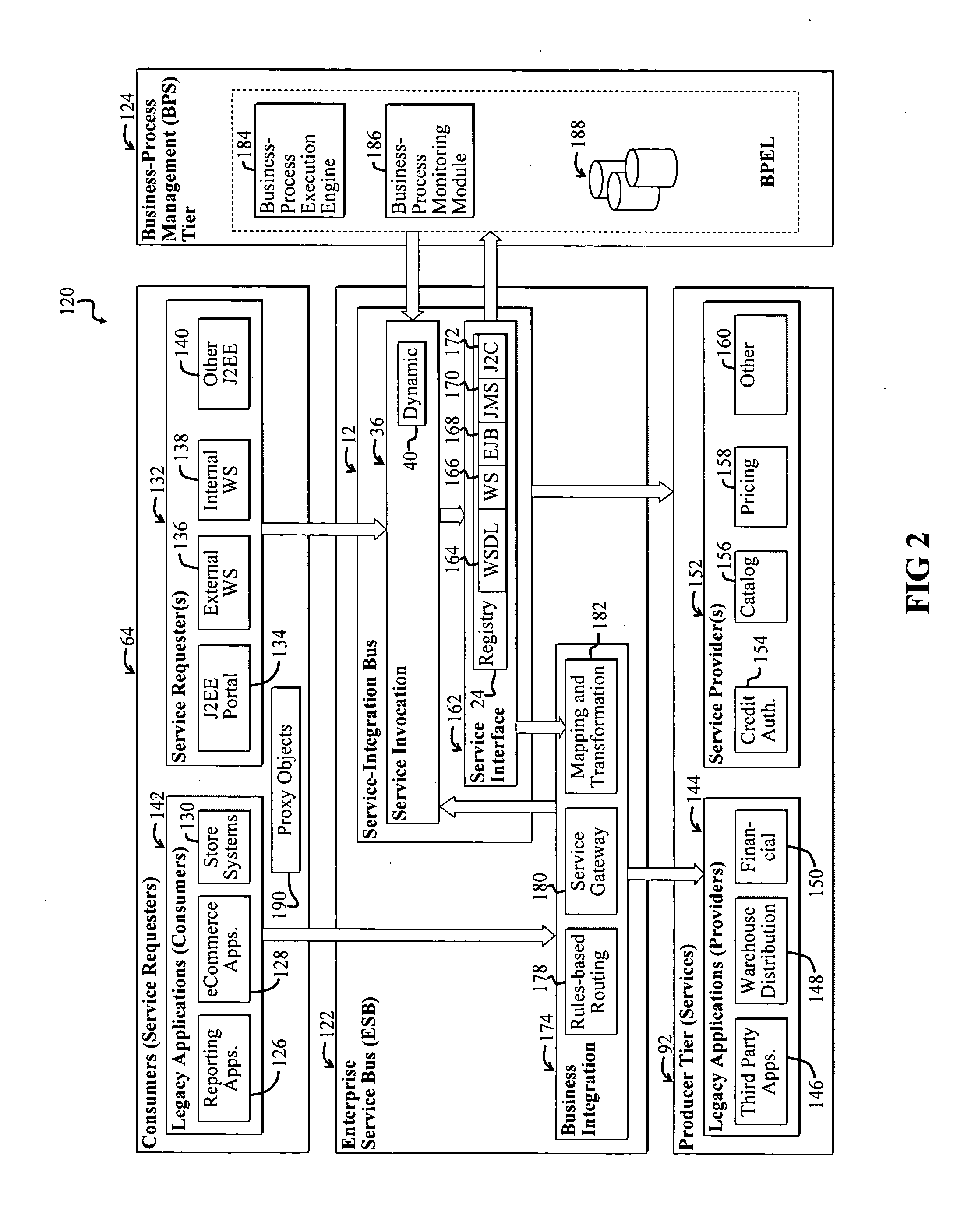
A Service-oriented architecture (SOA) and accompanying method. In one embodiment, the SOA includes one or more service requesters coupled to one or more service providers via a bus. The bus includes runtime-binding functionality to facilitate interaction between the one or more service requesters and the one or more service providers. A registry, which stores information pertaining to a service provided by the one or more service providers, communicates with one or more service providers and / or requesters and the bus. In a more specific embodiment, bus includes a Service-Integration Bus (SIB) that includes a Service-Factory (SF) module for facilitating implementing the runtime binding functionality and for selectively invoking the service. Functionality of the SOA is strategically organized into various tiers and layers, including a requester tier, a provider tier, a business-process services tier, an infrastructure-services tier, an SIB layer, a persistence layer, and so on, to optimize system reusability, adaptability, and other desirable properties. A service interface pattern is described whereby a change in service implementation does not require modification to the manner in which the service is invoked by a requester
Owner:PRIMITIVE LOGIC
System and method for providing video services
InactiveUS6961955B1High bandwidthGreater storage savingsTelevision system detailsAnalogue secracy/subscription systemsComputer networkData stream
Set top boxes are provided with access to full EIT data streams without having to off-tune from one transport to another. If off-tuning is required, however, a locking mechanism substantially reduces or eliminates service interruption. Data in the additional EIT data streams in the non-home transports is reorganized to be sent by time rather than by service. EIT data is stored in the set top box in an architecture which significantly reduces the redundancy inherent in EIT data, allowing a full 7 days of EIT data to be stored in the set top box memory. The set top box of the present invention is backward compatible with conventional set top boxes.
Owner:BELLSOUTH INTPROP COR
Service clusters and method in a processing system with failover capability
InactiveUS20060107108A1Special service provision for substationError detection/correctionComputer architectureHandling system
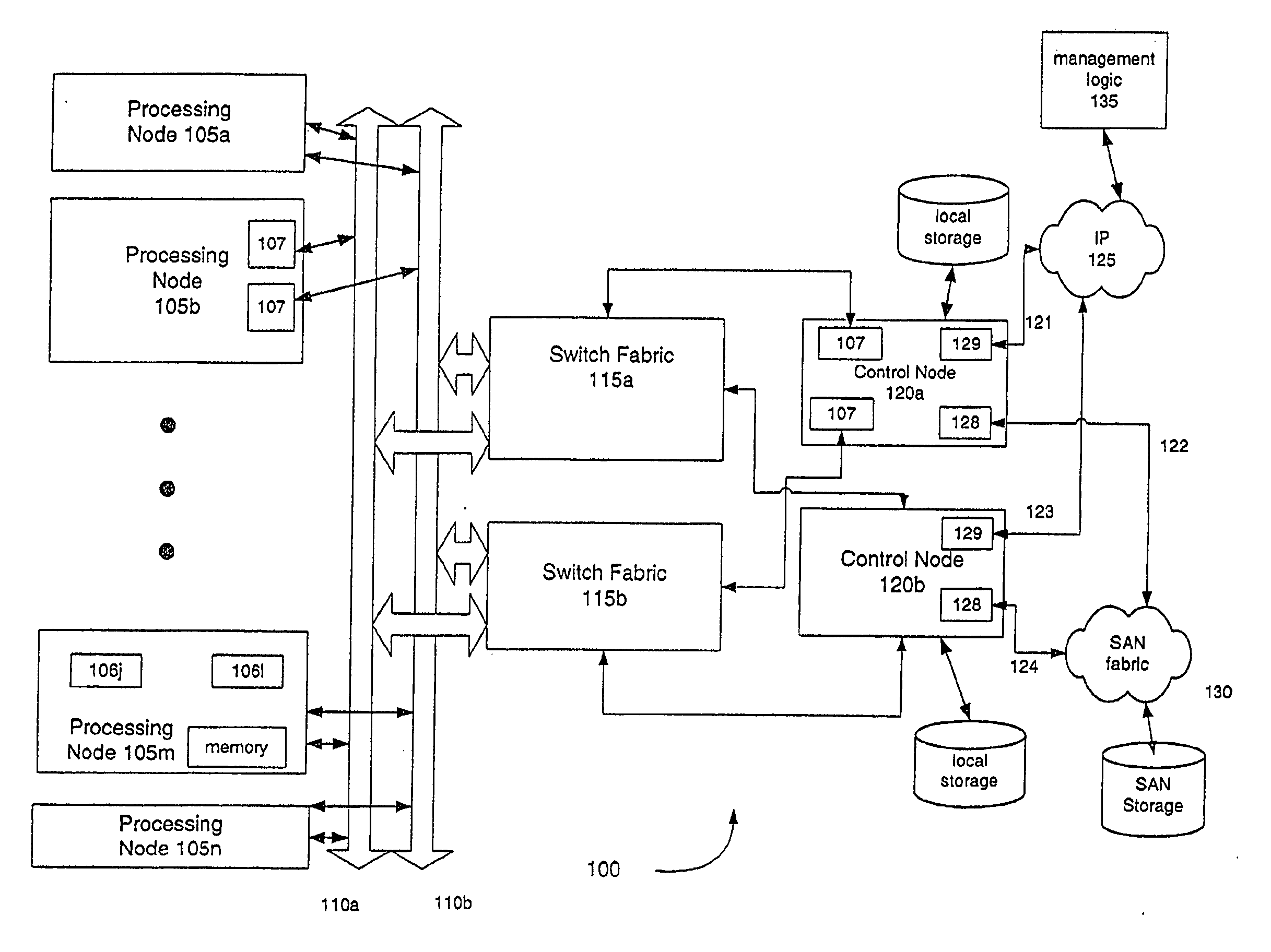
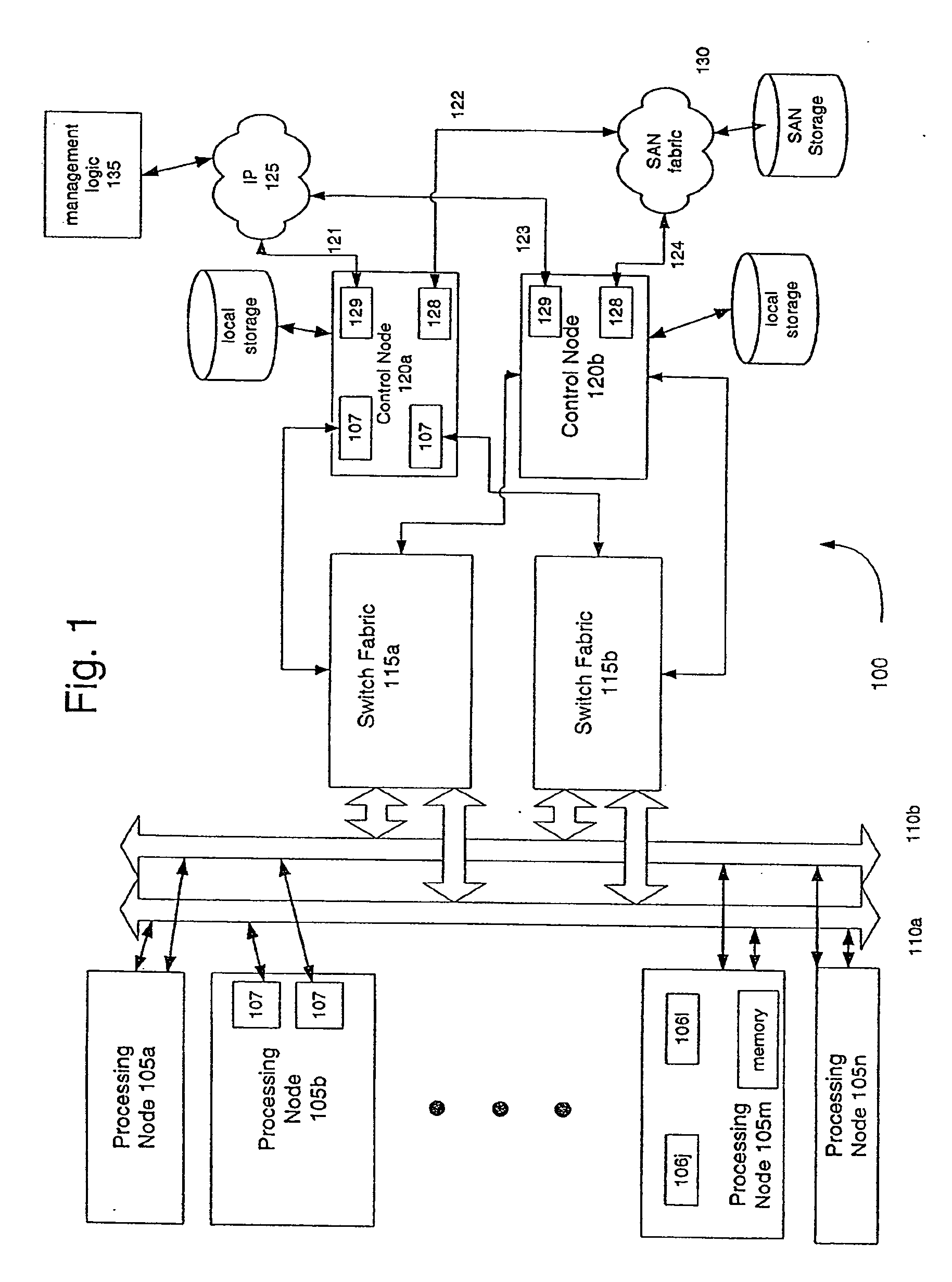
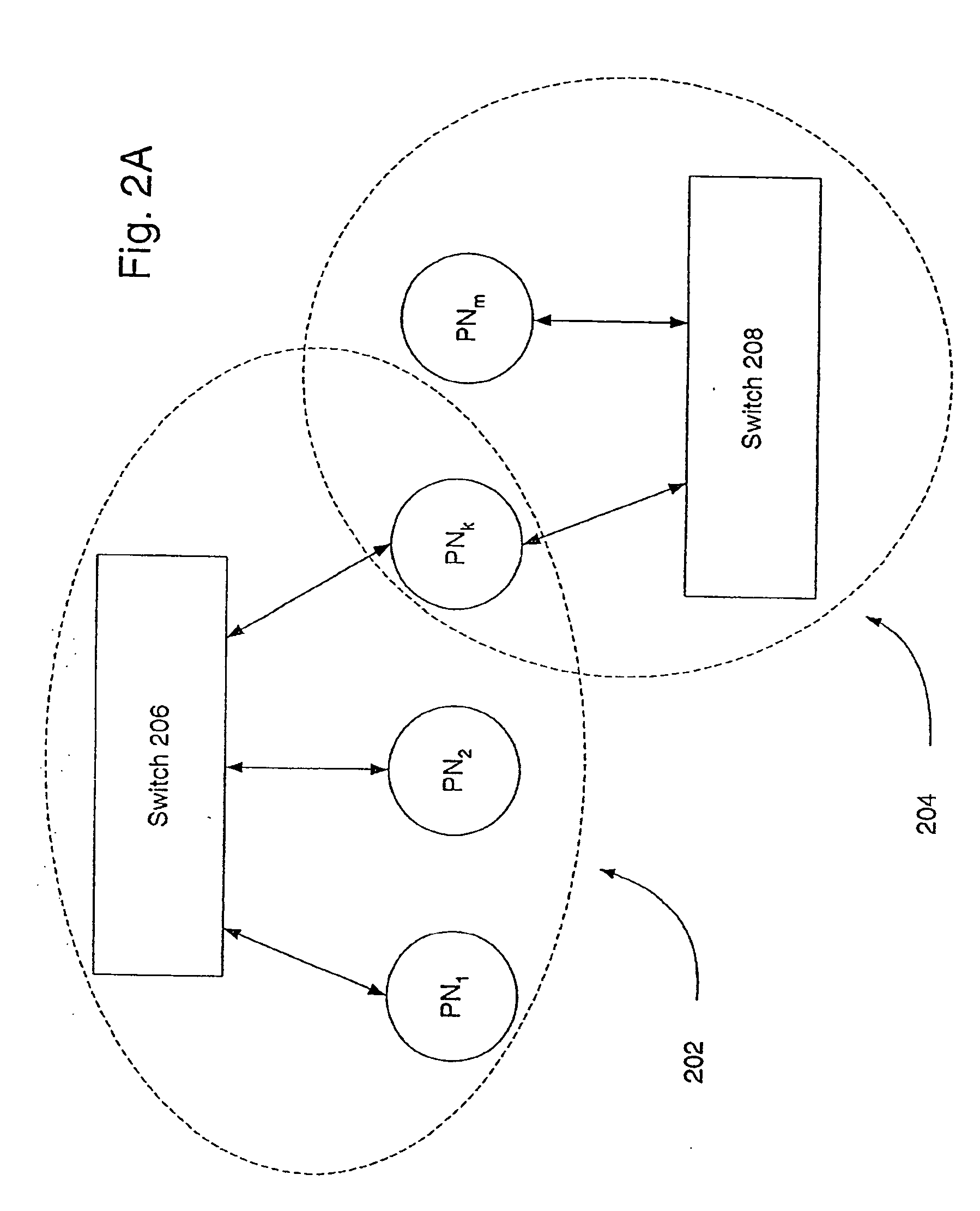
A platform for and method of computer processing to support processor failover are disclosed. A plurality of computer processors are connected to an internal communication network. A virtual local area communication network over the internal network is defined and established. Each computer processor in the virtual local area communication network has a corresponding virtual MAC address and the virtual local area network provides communication among a set of computer processors but excludes the processors from the plurality not in the defined set. A virtual storage space is defined and established with a defined correspondence to the address space of the storage network. In response to a failure by a computer processor, a computer processor from the plurality is allocated to replace the failed processor. The MAC address of the failed processor is assigned to the processor that replaces the failed processor. The virtual storage space and defined correspondence of the failed processor is assigned to the processor that replaces the failed processor. The virtual local area network is reestablished to include the processor that replaces the failed processor and to exclude the failed processor.
Owner:EGENERA
Communication Control Method and Wireless Communication Apparatus
ActiveUS20080261640A1Assure compatibilityNetwork traffic/resource managementAssess restrictionCommunication controlCommunication device
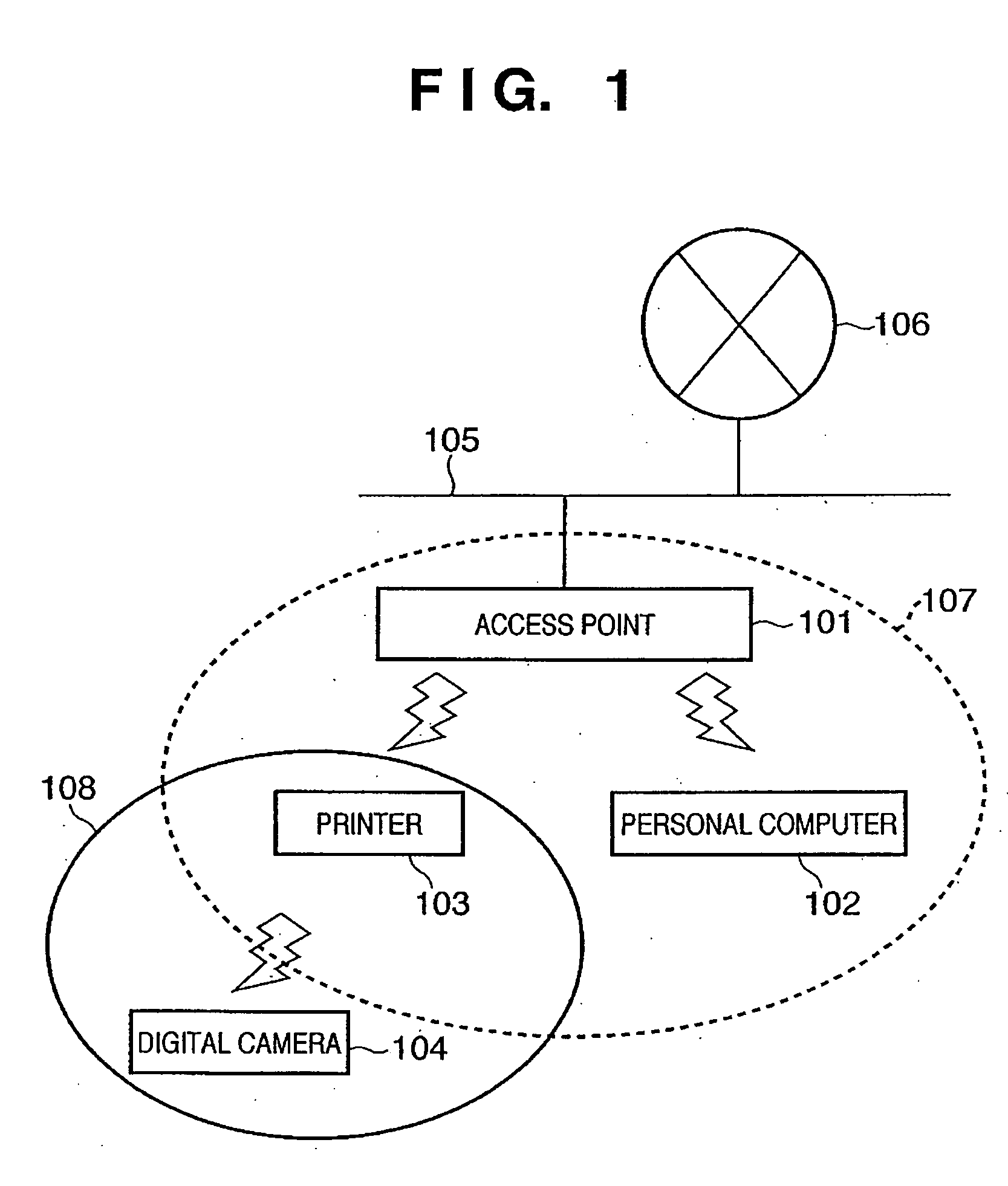
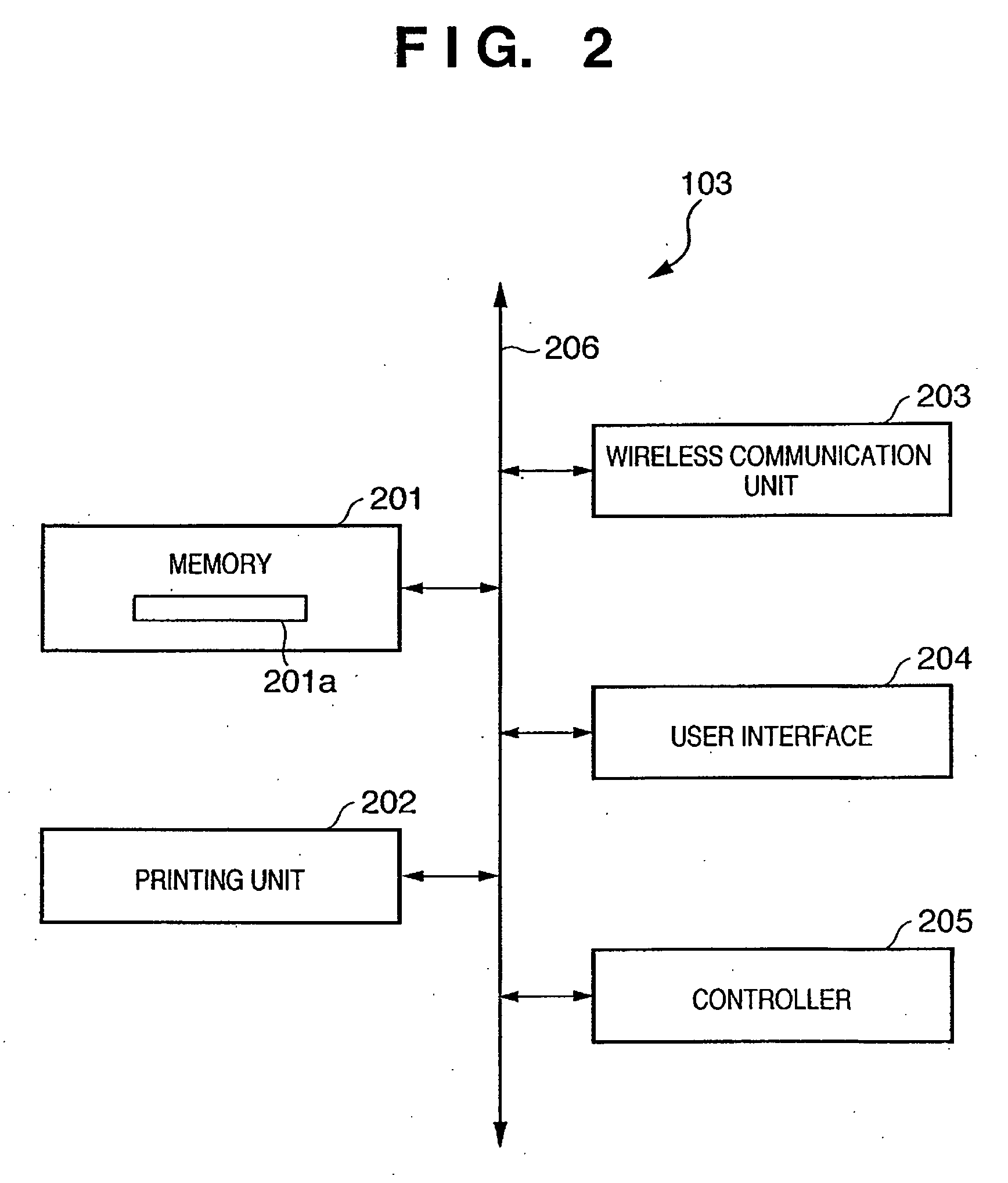
A printer (103) belongs to a service set (107) and communicates via an access point (101) in the infrastructure mode. The printer (103) searches for a beacon periodically. If a beacon is received from a terminal such as a digital camera (104), the printer registers the terminal address, service-set identifier and communication mode, which are contained in the beacon, in a function table. The printer sends each terminal, which has been registered in the function table, a frame that is for searching for a terminal that has a required function. If the response to the frame is positive, then the printer registers the fact that the search succeeded in the function table. A similar function search is conducted also by a digital camera (104) for which a print command has been issued, and the digital camera creates a function table. If there is a terminal (a printer) having the required function, the digital camera (104) transmits print data to this terminal.
Owner:CANON KK
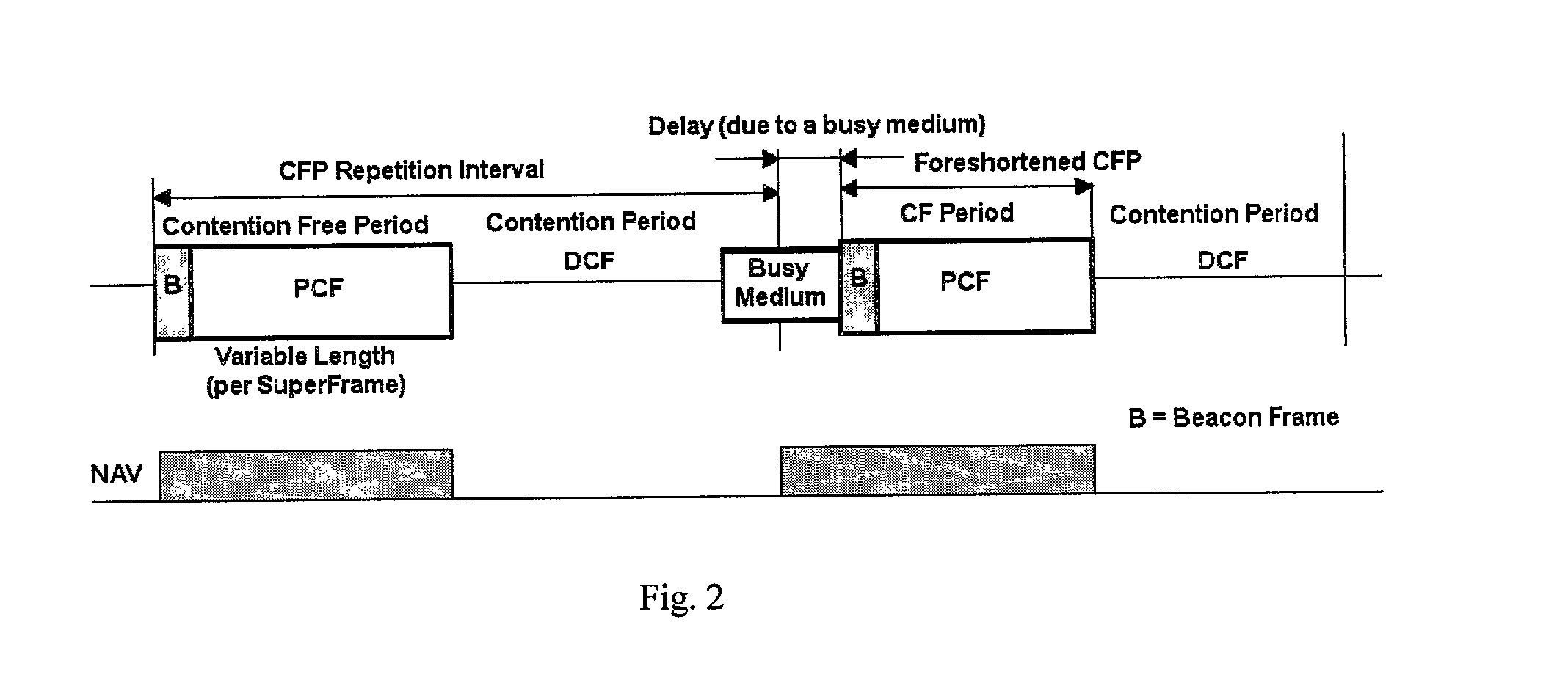
Collision avoidance in IEEE 802.11 contention free period (CFP) with overlapping basic service sets (BSSs)
InactiveUS7054329B2Improve efficiencyAvoid contentionNetwork topologiesTime-division multiplexClear to sendTelecommunications
Owner:KONINK PHILIPS ELECTRONICS NV
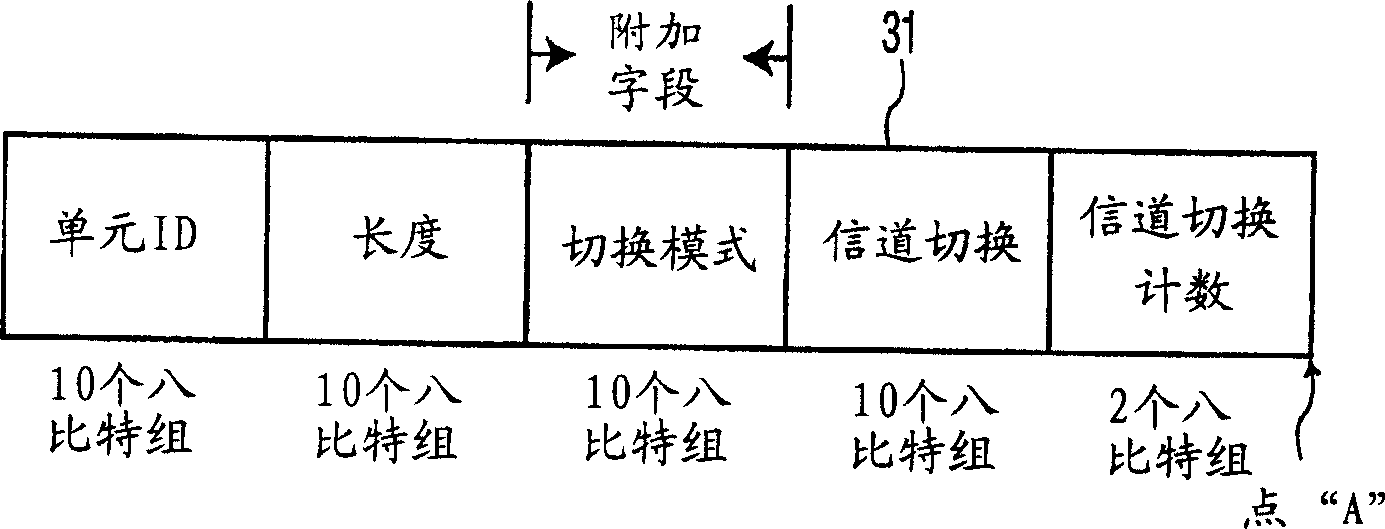
Fast switching method for WLAN
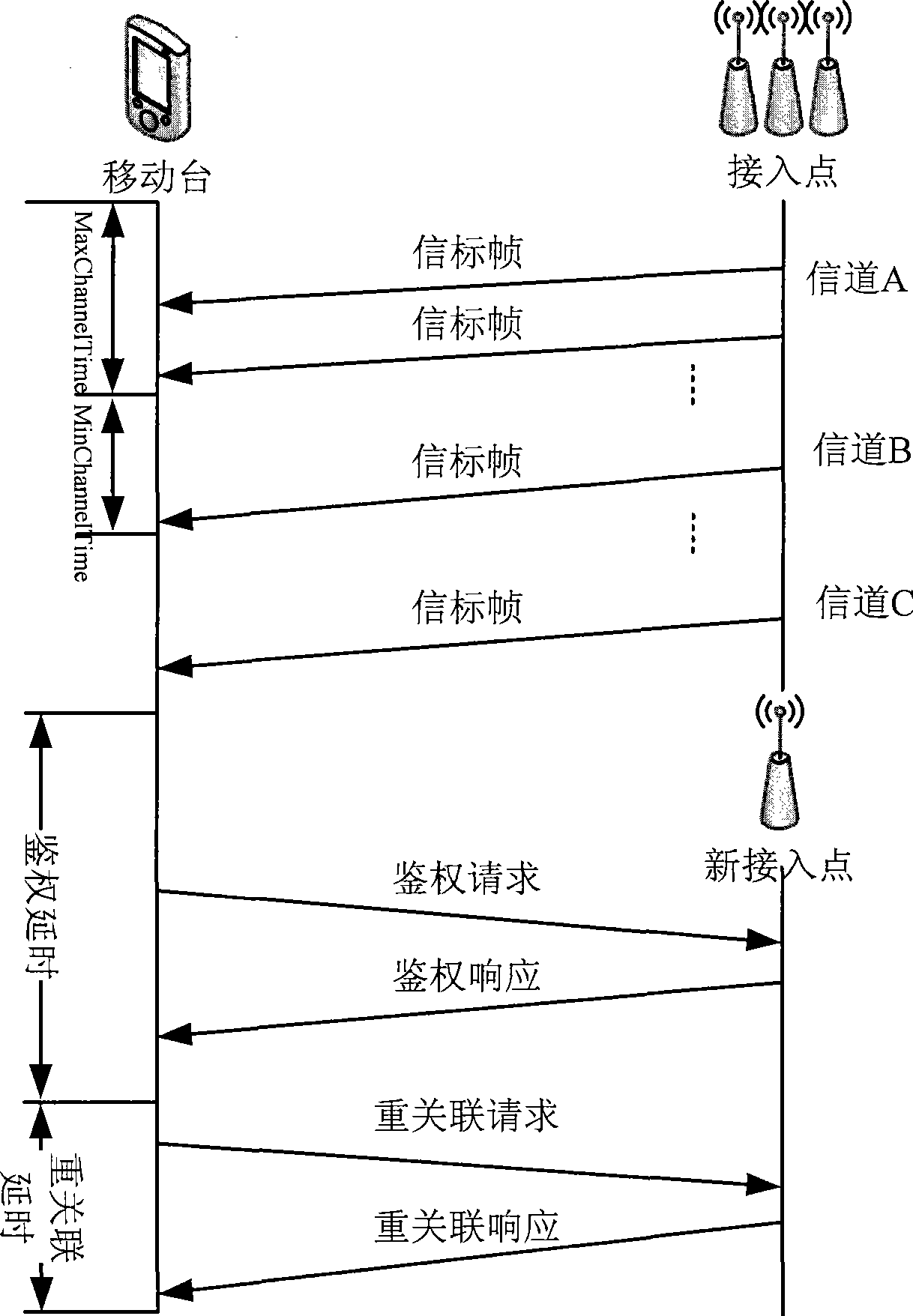
The invention relates to a rapid switching method for a wireless local area network, wherein, in a beacon frame being sent, an access point contains a channel used by an adjacent access point, SSID (service set identifier) and BSSID (basic service set identifier) information; a mobile station receives and stores the information of a target access point in the beacon frame, and when switching condition is satisfied, the information is used as a reference for selecting the target access point in switching. The mobile station preferentially searches the beacon frame or sends a polling request frame on a channel appointed by the information, and selects a next access point needing to be switched according to the RSSI (received signal quality indication) of the beacon frame or a polling response frame. Through the rapid switching algorithm of the invention, the mobile station does not need to scan all channels in the wireless local area network, thus greatly reducing switching delay.
Owner:TRAFFIC CONTROL TECH CO LTD
Container-based service multi-version coexistence implementation method
ActiveCN106789250AReduce time to release or stopImprove work efficiencyData switching networksClient-sideType of service
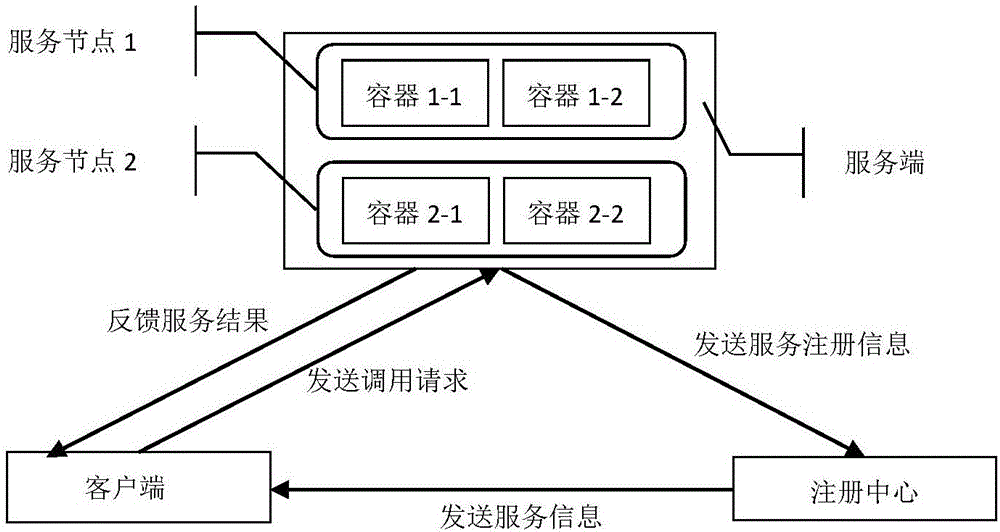
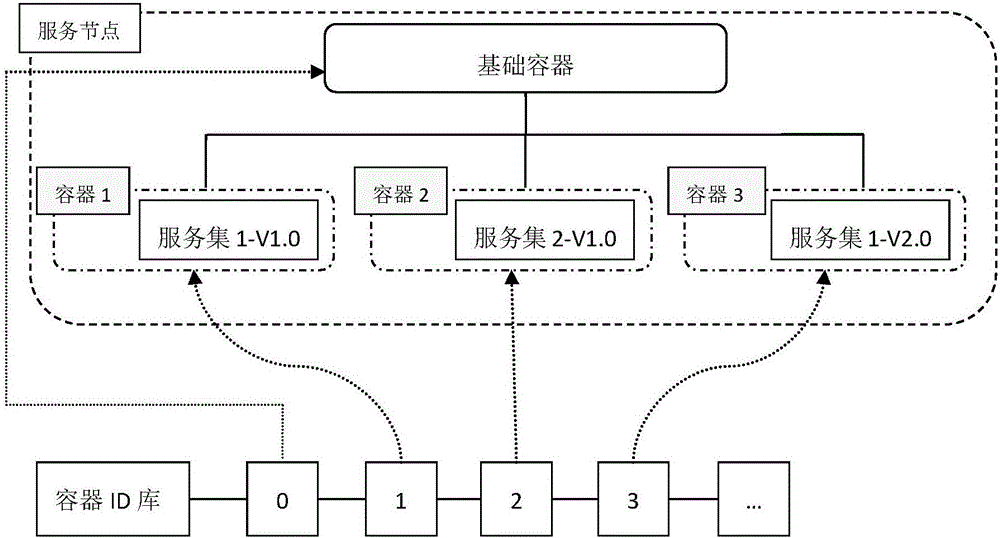
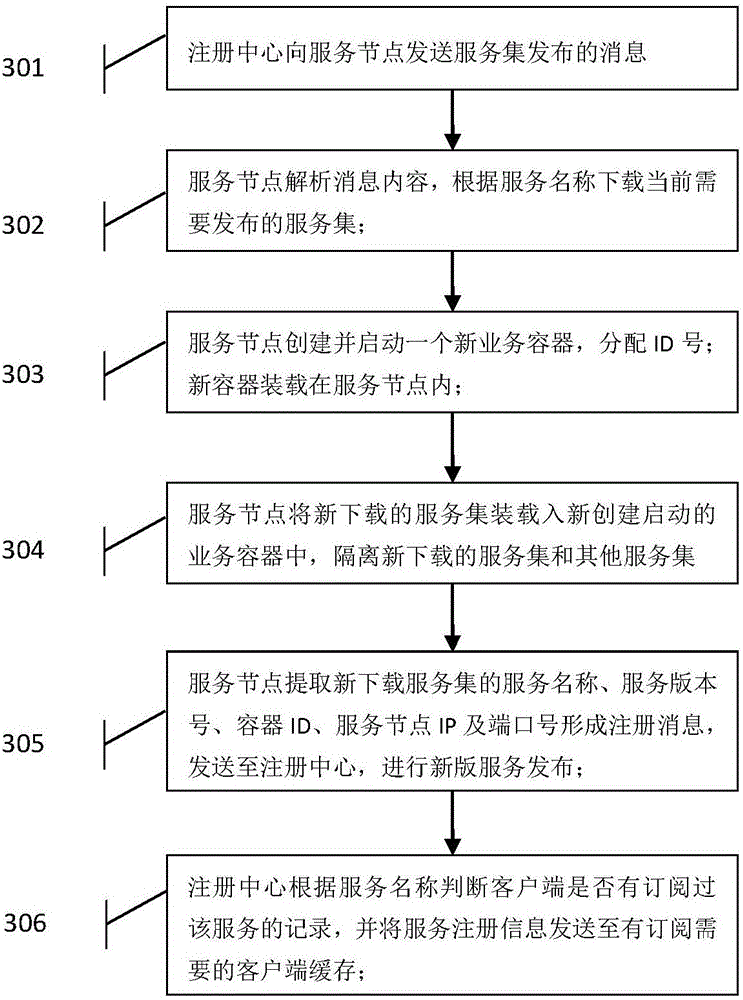
The invention provides a container-based service multi-version coexistence implementation method. The method comprises the following steps: configuring a plurality of service nodes in a server, configuring a plurality of containers in each service node and loading different service sets in each container, thereby not only realizing the multi-version coexistence of the service, but also clearly distinguishing different service types and different versions of the same service type in a service coexistence environment; services of old and new versions are distinguished by the containers, after new services are added or old services are stopped, a client can automatically screen a to-be-called service version according to its own version and obtains a service call result from the corresponding container, thereby reducing the manual controlled call when the client is inconsistent with the called service version; and due to the coexistence of multiple versions of services, the new services do not need to be restarted and loaded in an upgrading process of a service application, thereby simplifying the cumbersome process of service upgrade and realizing hot deployment of services in a distributed environment.
Owner:FOCUS TECH
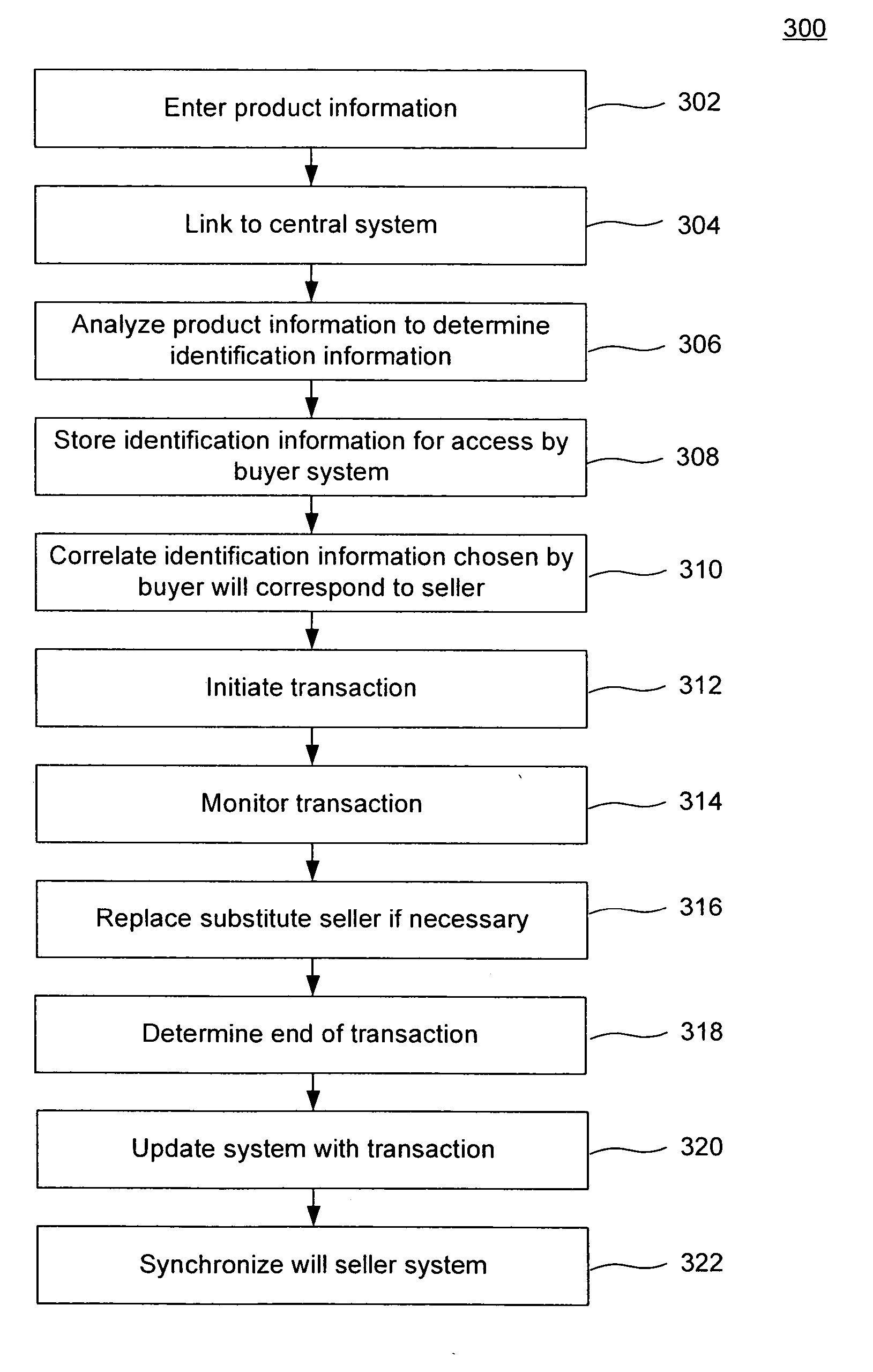
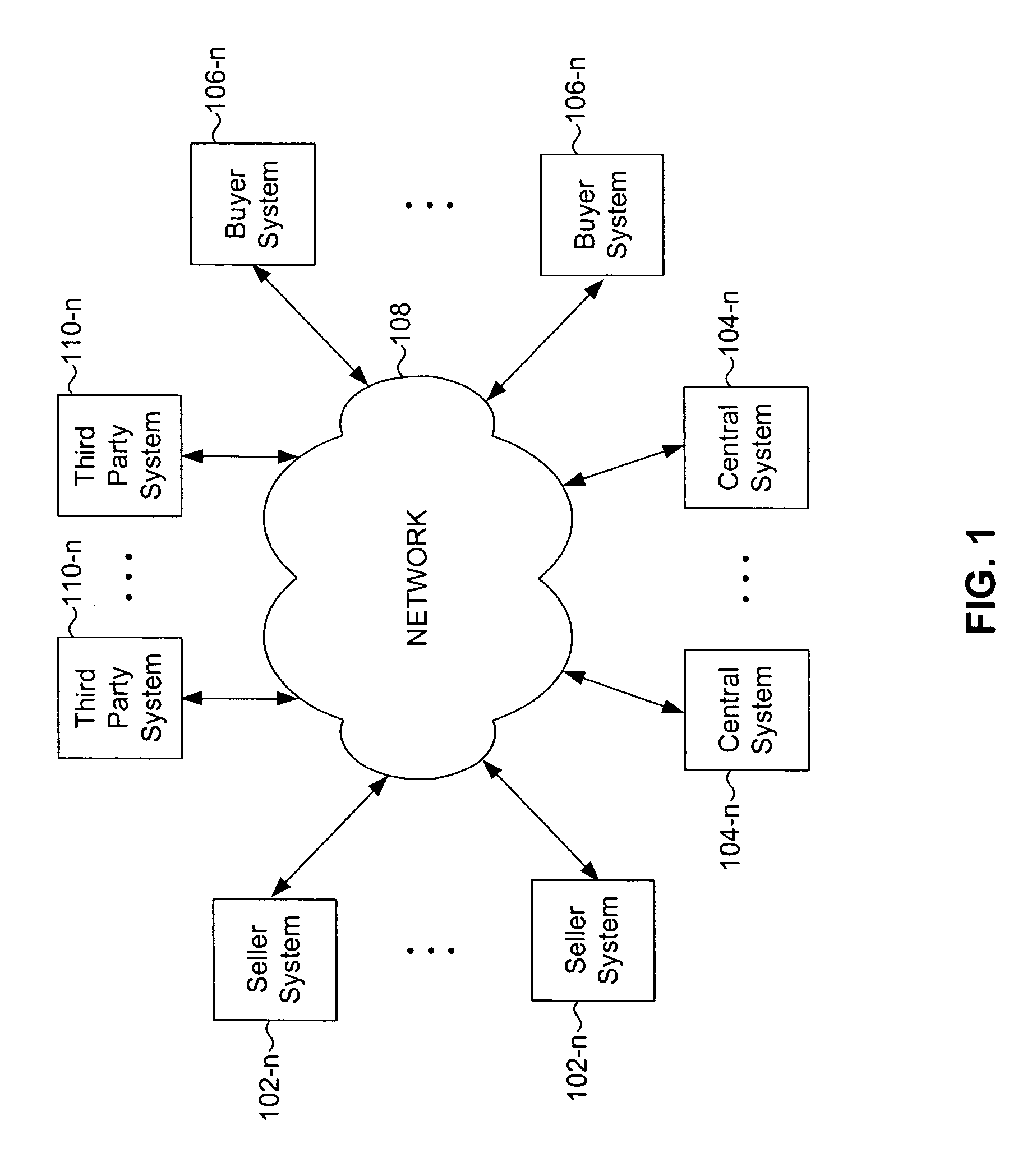
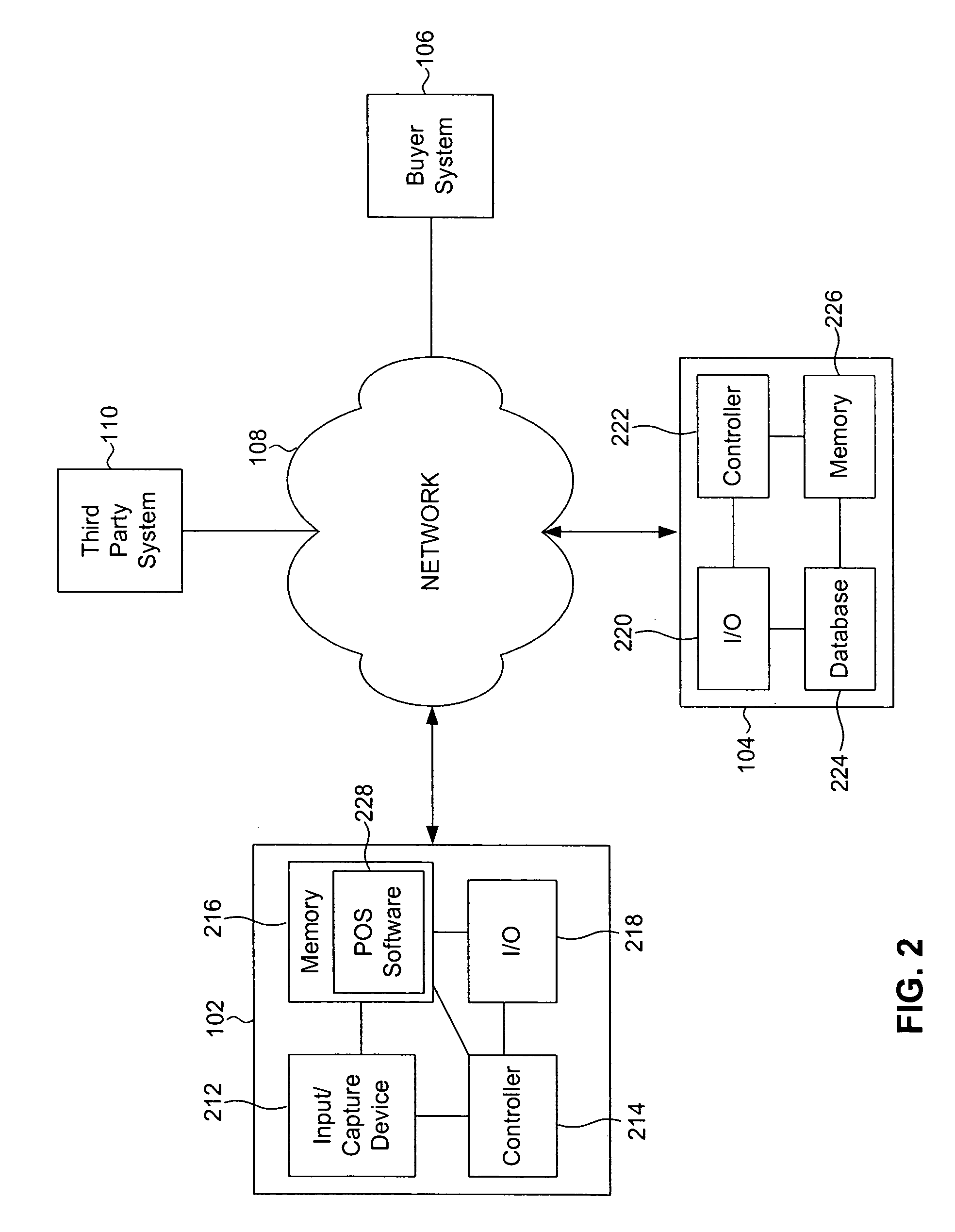
System, method, and computer program product for automated consolidating and updating of inventory from multiple sellers for access by multiple buyers
InactiveUS20060111986A1Buying/selling/leasing transactionsElectronic transmissionCommunications system
A system and method that allow for collection of available and sellable goods or services in a real-time or near real-time environment from a network of retail or a chain of retail stores, wholesalers, distributors, or service providers. The collective database is made available to the general public via a network or communications system (e.g., the world wide web, an intranet, a respective virtual private network (VPN), or any other form of electronic transfer) for purchase utilizing best price available for both parties.
Owner:YORKE KEVIN S +1
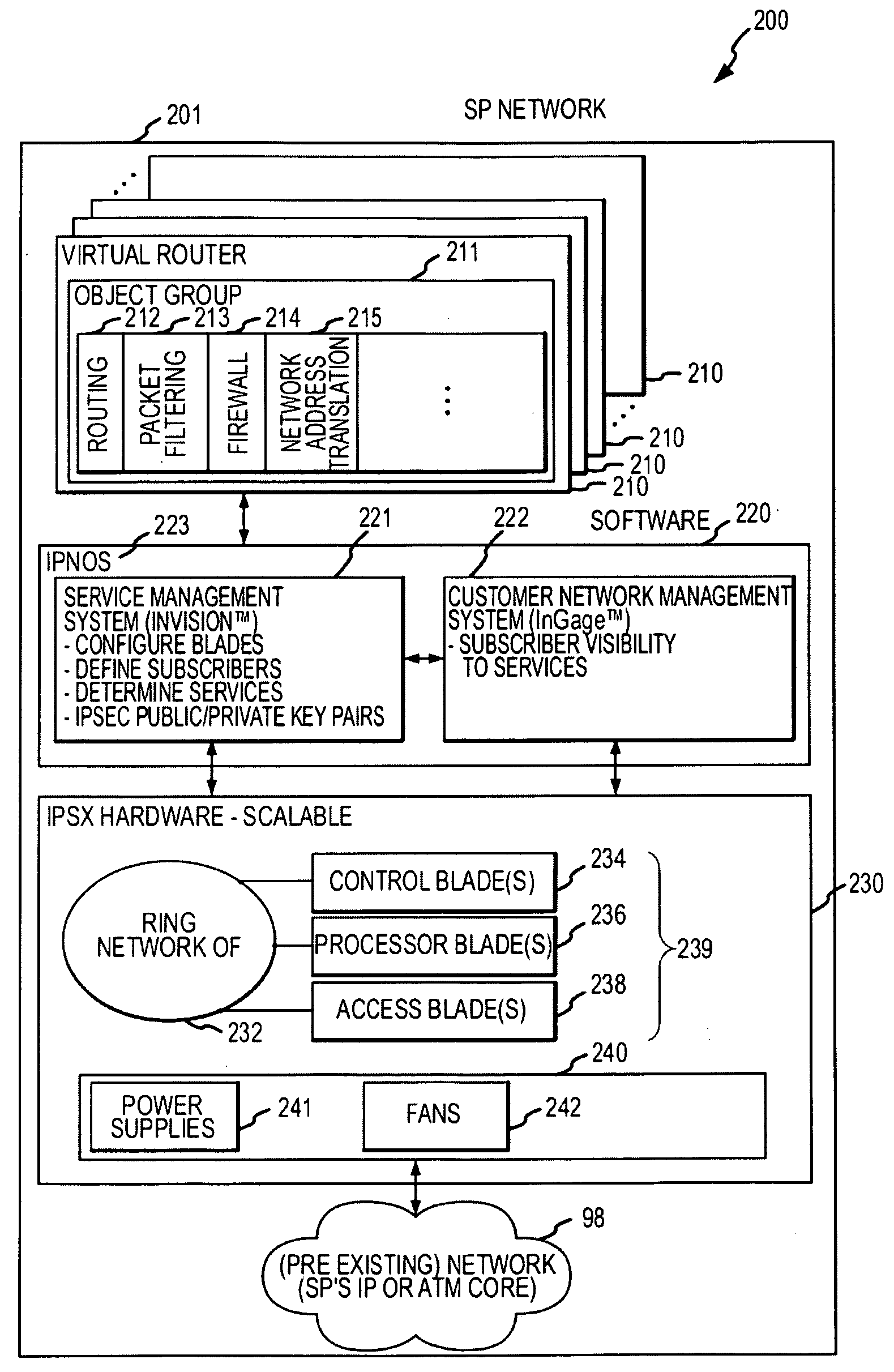
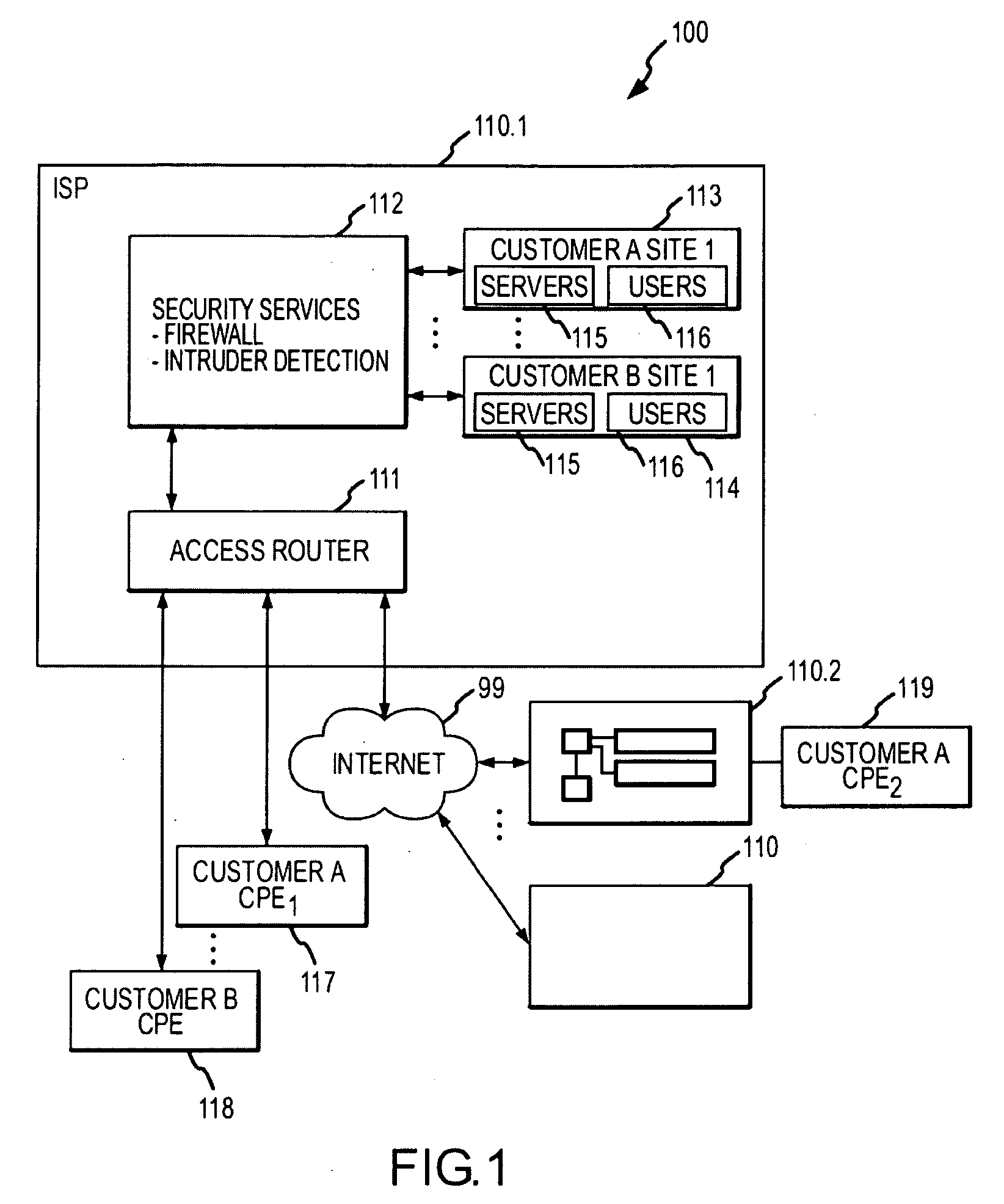
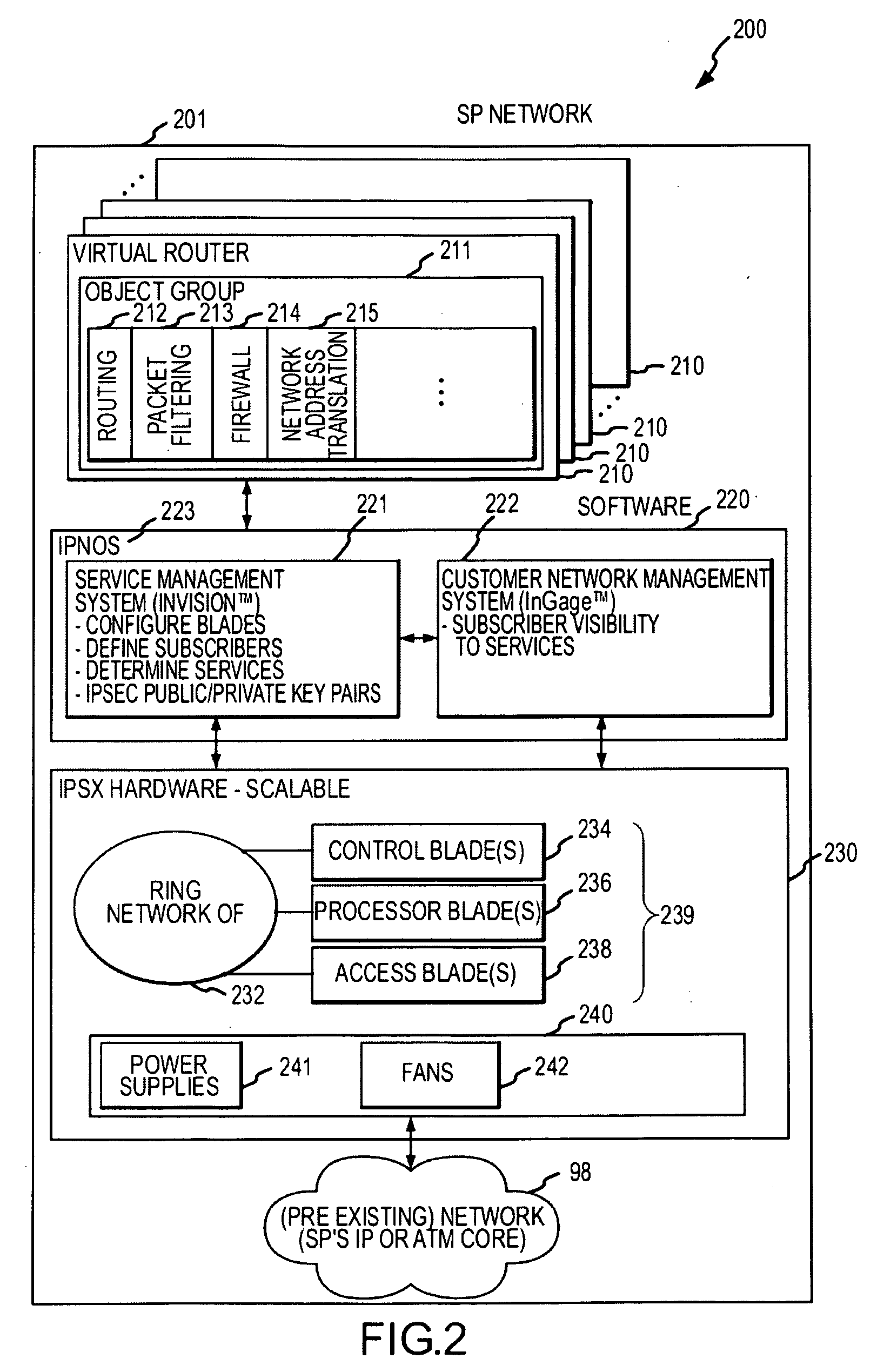
System and method for delivering security services
InactiveUS20090046728A1Data switching by path configurationNetwork connectionsResource isolationEngineering
Systems and methods are provided for delivering security services. According to one embodiment, multiple virtual routers are established within a service processing switch, which is operable to be logically interposed between a public communications network and multiple subscriber sites. Each of the virtual routers has associated therewith a subset of processing and storage resources of the service processing switch. Subscribers are provided with respective sets of customized application layer services. Subscriber resource isolation is provided by partitioning the virtual routers between the subscribers including allocating and configuring partitions, having subsets of the virtual routers, to the subscribers. Changeable provisioning of processing capacity between the subscribers is provided by dynamically reallocating resources of the service processing switch between the partitions based on comparative processing demands of the customized application layer services.
Owner:FORTINET
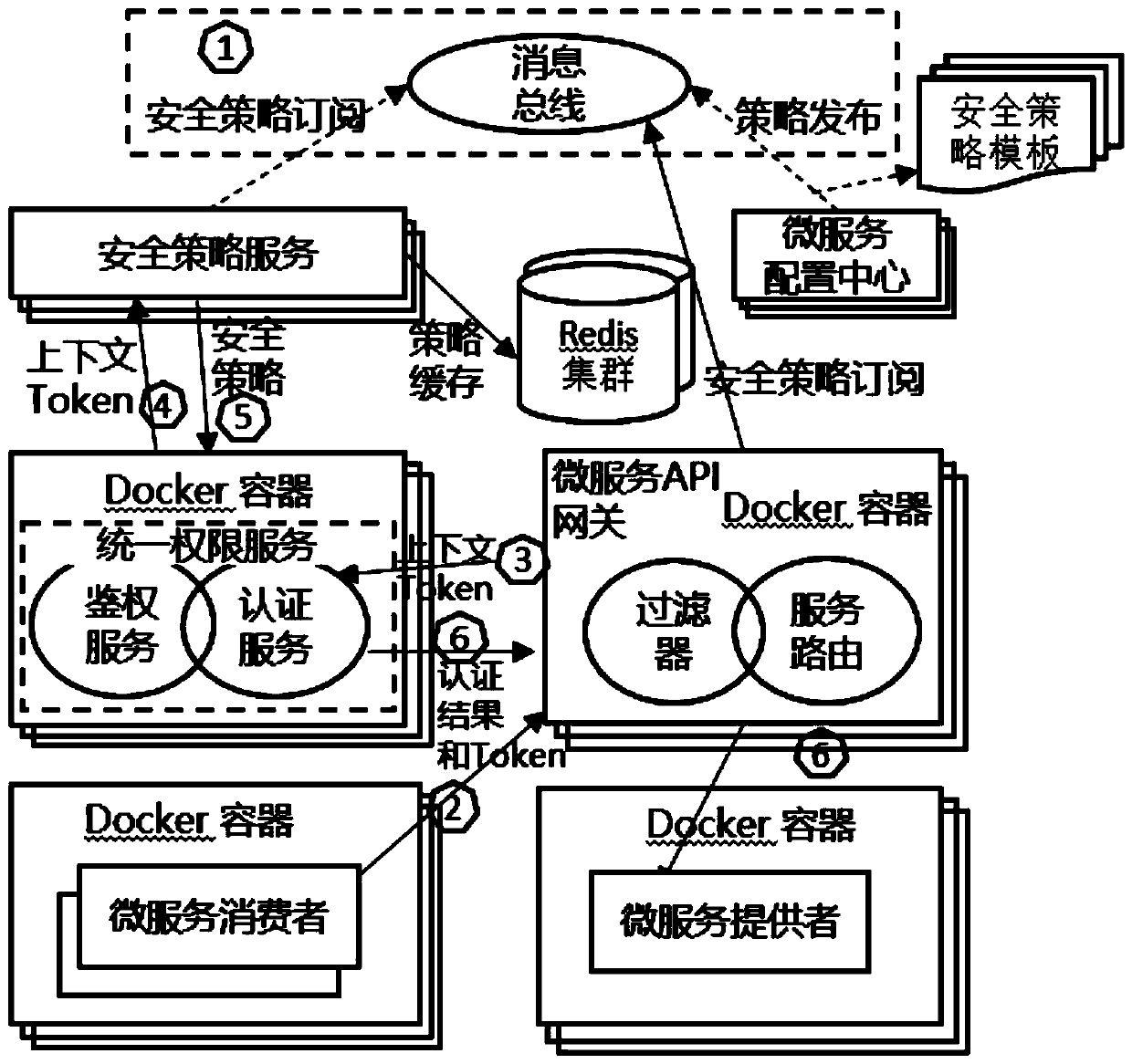
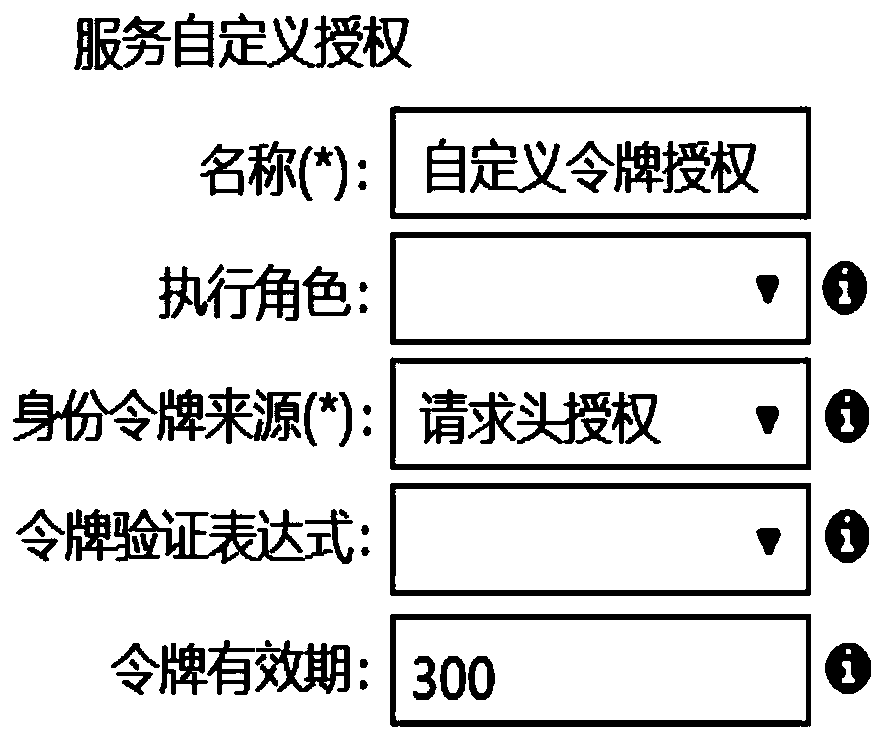
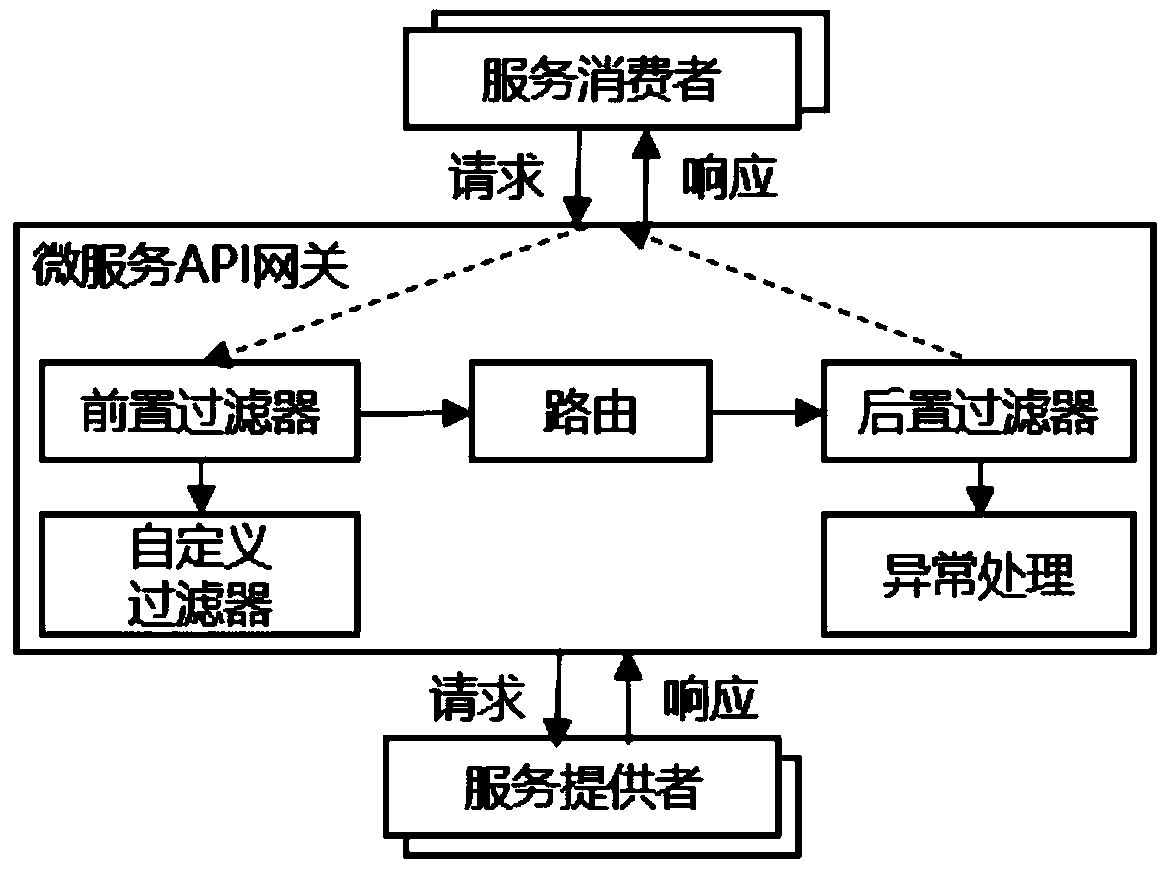
Flexible micro-service security access control method and system
PendingCN110781476AImplement secure access controlImprove flexible security control capabilitiesDigital data authenticationFault toleranceService configuration
The invention discloses a flexible micro-service security access control method and system. The system is composed of a micro-service API gateway, a lightweight micro-service access token, a securitypolicy service and policy template, a unified permission service, a Redis cluster, a micro-service configuration center and a Docker container security policy. A security policy template supporting aconventional security policy and a self-defined security policy is flexibly defined, flexible security access control is better realized, and instant release and application of the security policies are realized through unified configuration service and message bus service. A layered interception filtering mode is adopted in the micro-service API gateway, and safety access control and fault tolerance are better achieved through combination of links such as pre-filtering, routing, post-filtering and exception handling and a safety strategy. In the aspect of the service access token, the lightweight service access token is dynamically generated in combination with a security access control strategy, so that the operability and performance of security access control are enhanced, and meanwhile, the flexibility of micro-service security access control is improved.
Owner:NARI INFORMATION & COMM TECH
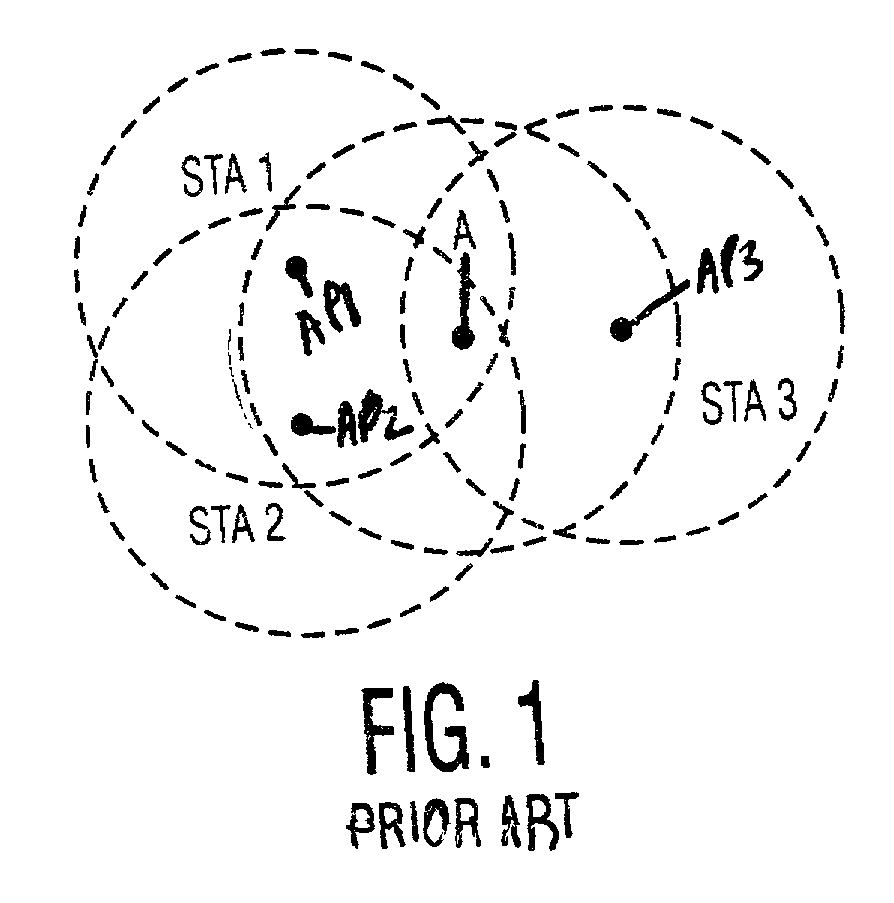
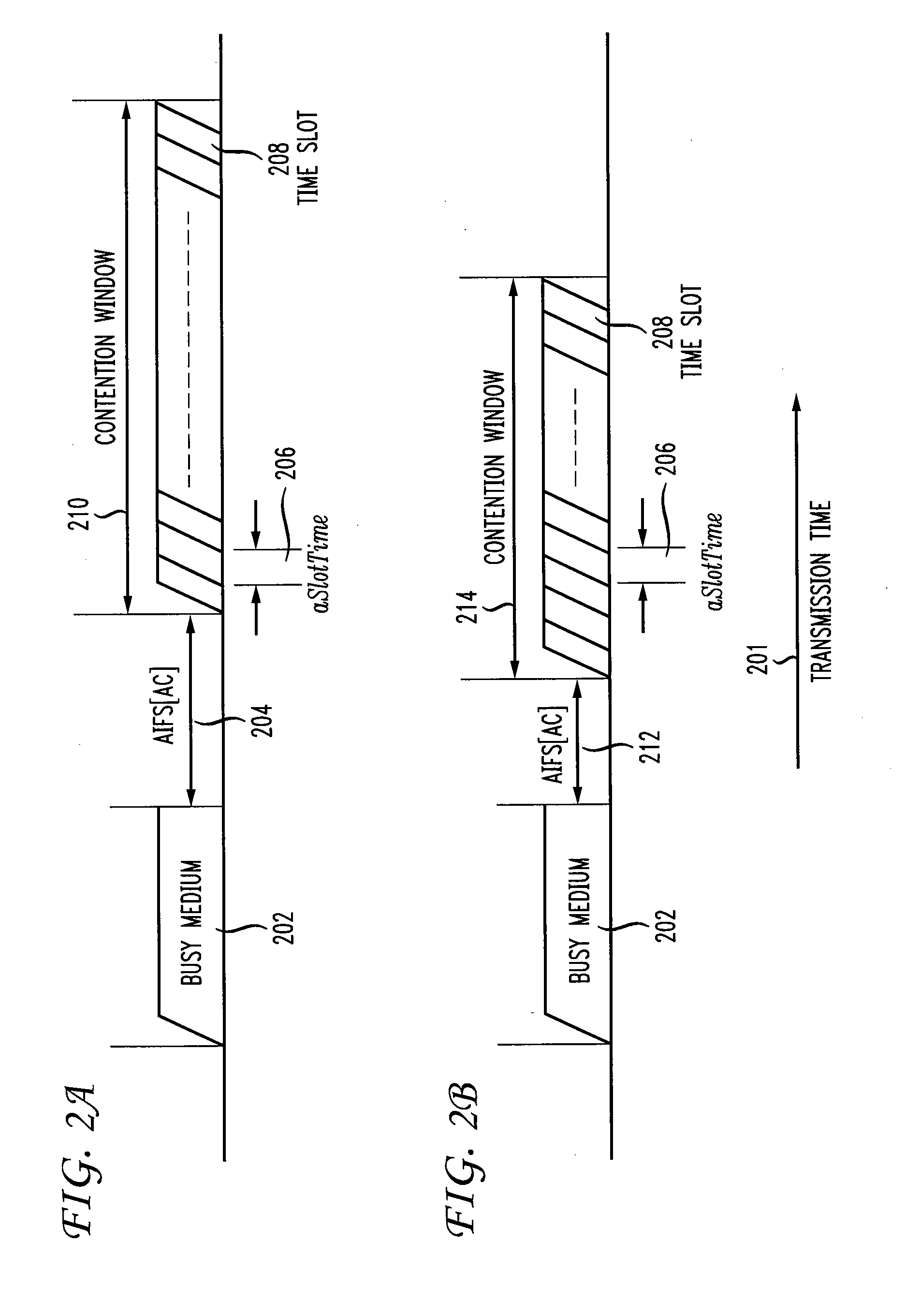
Control of Quality of Service in Overlapping Basic Service Sets in Wireless Local Area Networks
InactiveUS20130064236A1Network topologiesWireless commuication servicesQuality of serviceWireless lan
Access priority for wireless devices located in an area in which radiofrequency (RF) coverage areas of a first wireless access point and a second wireless access point overlap is controlled by coordinating operation of the first wireless access point and the second wireless access point. The wireless devices access a common RF channel via a collision sense multiple access / collision avoidance mechanism. The probability of accessing the RF channel may be varied by adjusting the length of interframe spacings and the length of contention windows. The length of the interframe spacings and the length of the contention windows associated with the first access point and associated with the second access point are configured such that the probability of wireless devices associated with the first wireless access point accessing the RF channel is greater than the probability of wireless devices associated with the second wireless access point accessing the RF channel.
Owner:LYFT INC
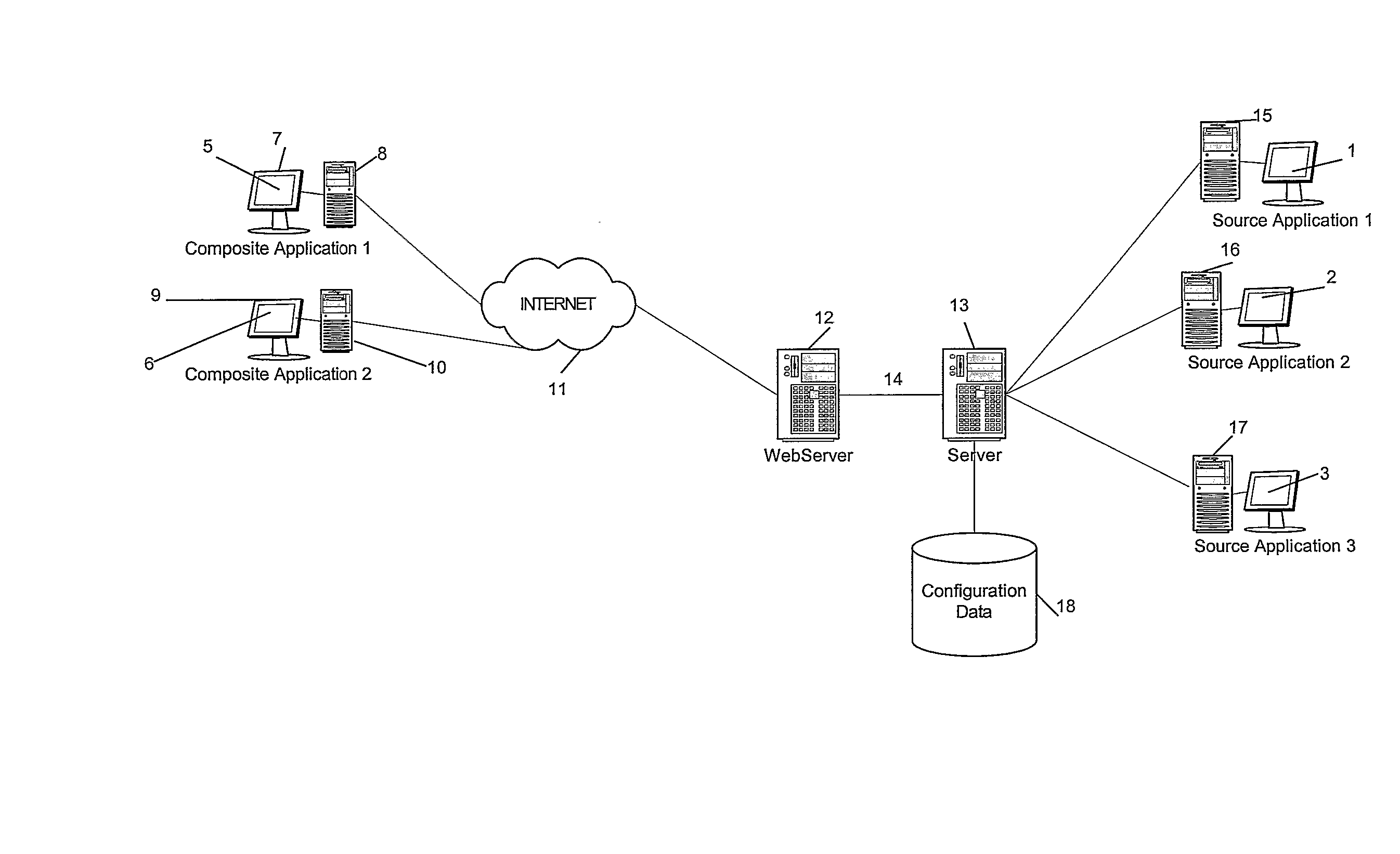
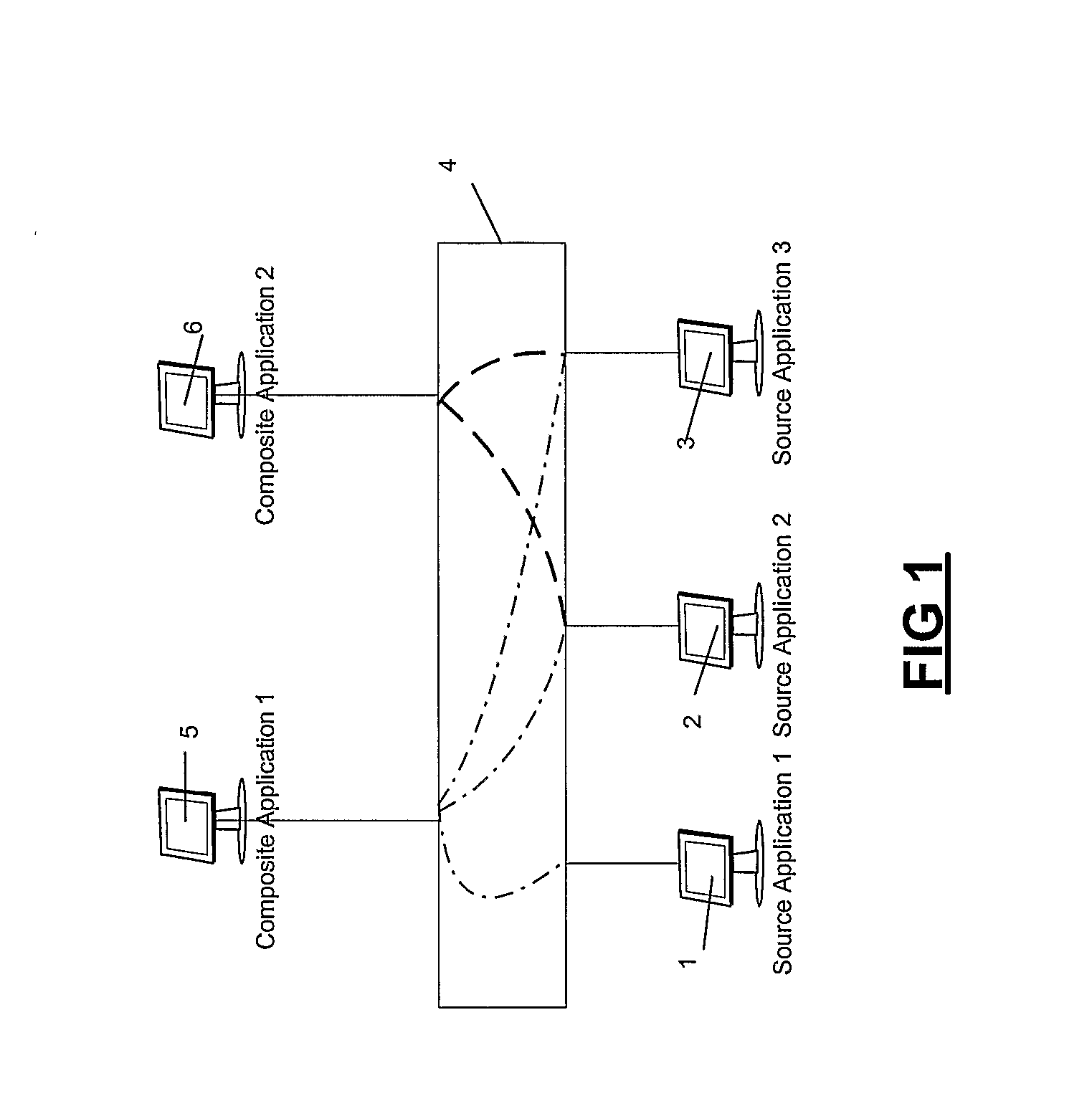
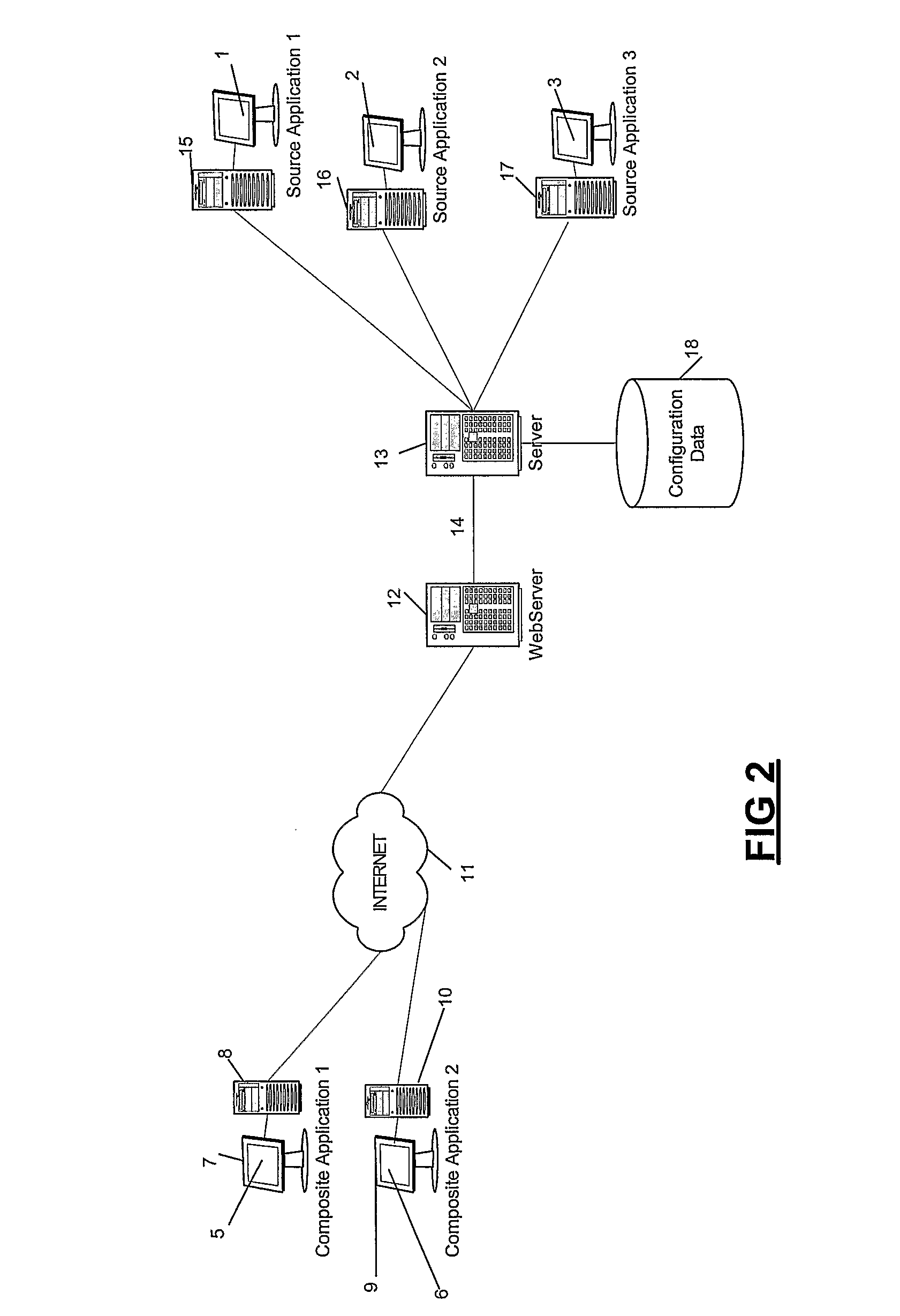
Method and Apparatus for Composite User Interface Generation
ActiveUS20070250839A1The process is convenient and fastEfficient combinationInterprogram communicationMultiple digital computer combinationsApplication softwareComputer science
A method for directing messages between a composite user interface and at least one source application. A message is to be directed to a predetermined set of services, each service executes a command specified by the message and the message comprises details of the predetermined set of services. Each service in the predetermined set of services uses said details to determine whether the message should be sent to another service, and if it is determined that the message should be sent to another service transmits the message to an appropriate service.
Owner:VERSATA FZ
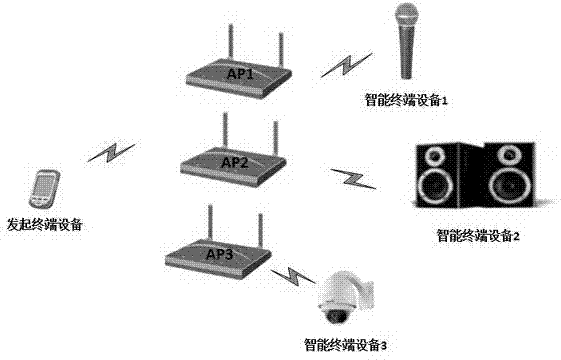
Method for connecting WI-FI network by intelligent hardware terminal based on sound waves and system for realizing same
InactiveCN104796888ALow costFirmly connectedAssess restrictionConnection managementComputer hardwareAccess network
The invention provides a method for connecting a WI-FI network by an intelligent hardware terminal based on sound waves. The method comprises the following steps: intelligent equipment obtains an SSID (Service Set Identifier) and a password to be accessed into the WI-FI network of the intelligent hardware terminal, and converts the obtained SSID and password into a byte stream; the byte stream is converted into a sound wave signal according to an encoding rule and is transmitted by a loudspeaker; the intelligent hardware terminal receives the sound wave signal and converts the sound wave signal into a byte stream according to the encoding rule; then, the SSID and password to be accessed into the WI-FI network are analyzed, and obtained SSID and password information is connected with the WI-FI network. The method and the system can be effectively realized without additionally arranging other hardware modules on the intelligent hardware terminal, so that the method and the system have strong adaptability and are portable and easy to use.
Owner:深圳声联网科技有限公司
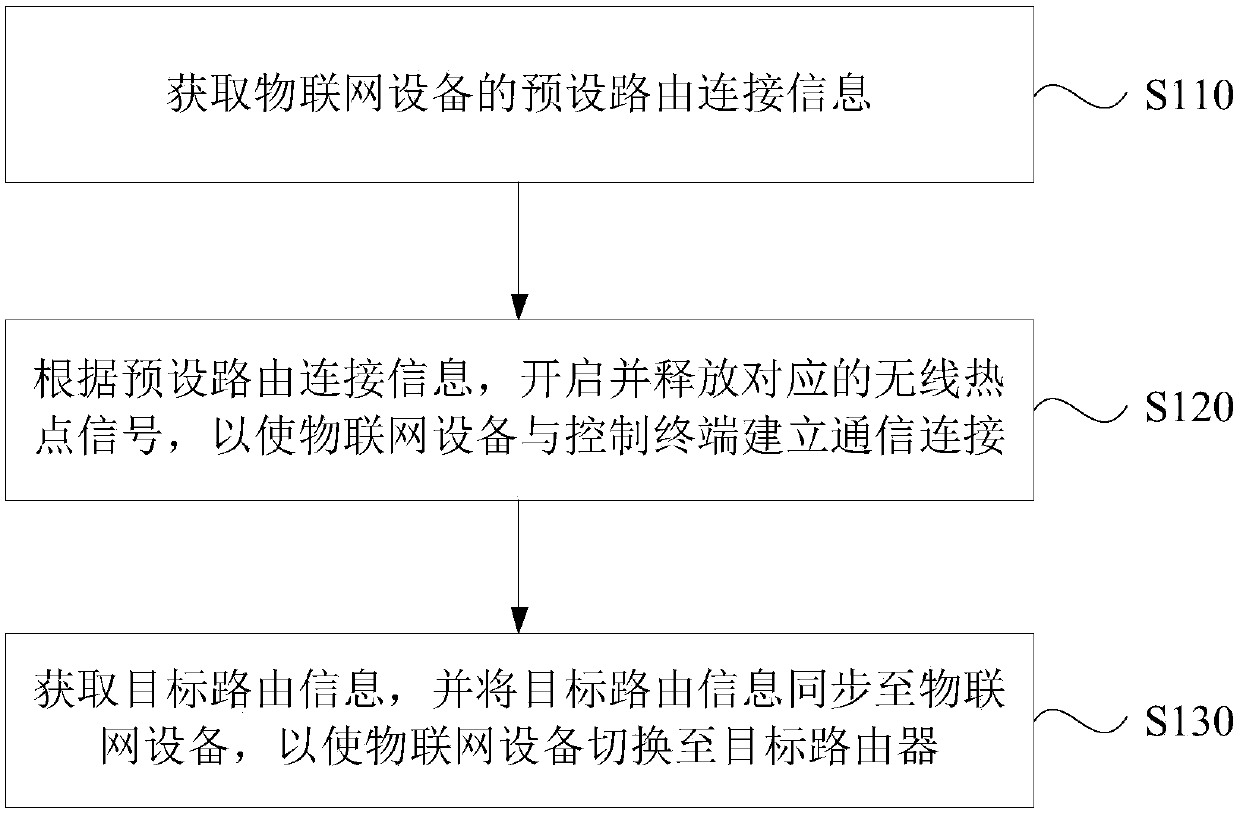
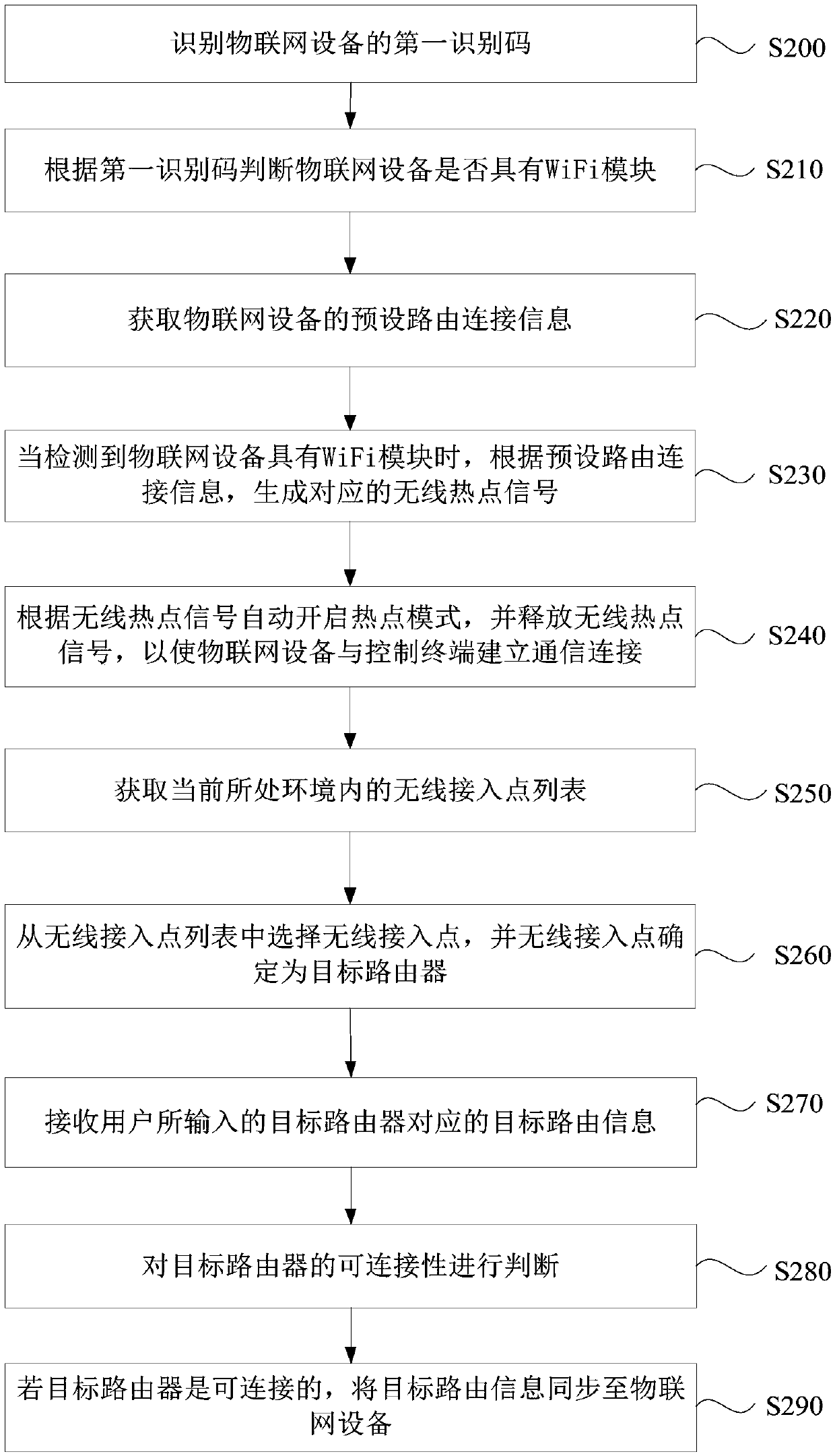
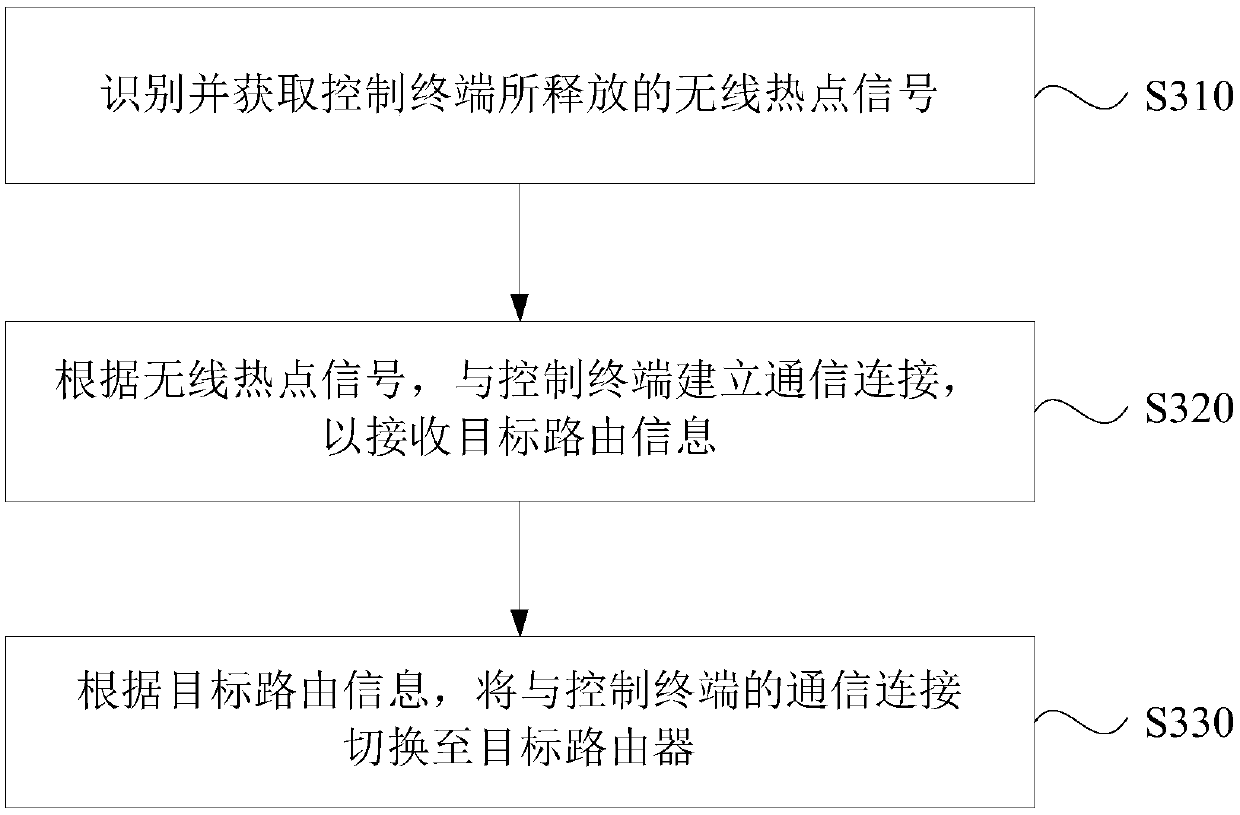
Network configuration method and device, terminal equipment and storage medium
ActiveCN110798493AImprove user experienceConnection managementTransmissionTerminal equipmentThe Internet
The invention discloses a network configuration method and device, terminal equipment and a storage medium. The method comprises: acquiring preset routing connection information of the Internet of Things device, wherein the preset routing connection information comprises a service set identifier SSID and a login password; starting and releasing a corresponding wireless hotspot signal according topreset routing connection information so as to enable the Internet of Things equipment to establish communication connection with the control terminal; and acquiring target routing information, and synchronizing the target routing information to the Internet of Things device, so as to enable the Internet of Things device to be switched to the target router. According to the invention, the technical problems that the communication connection process between the Internet of Things equipment and the control terminal is tedious and the user experience is reduced in the prior art are solved, the communication connection between the Internet of Things equipment and the control terminal is realized simply and conveniently in a scene without a target router, and the technical effect of improving the user experience is improved.
Owner:QINGDAO ECONOMIC & TECHN DEV ZONE HAIER WATER HEATER
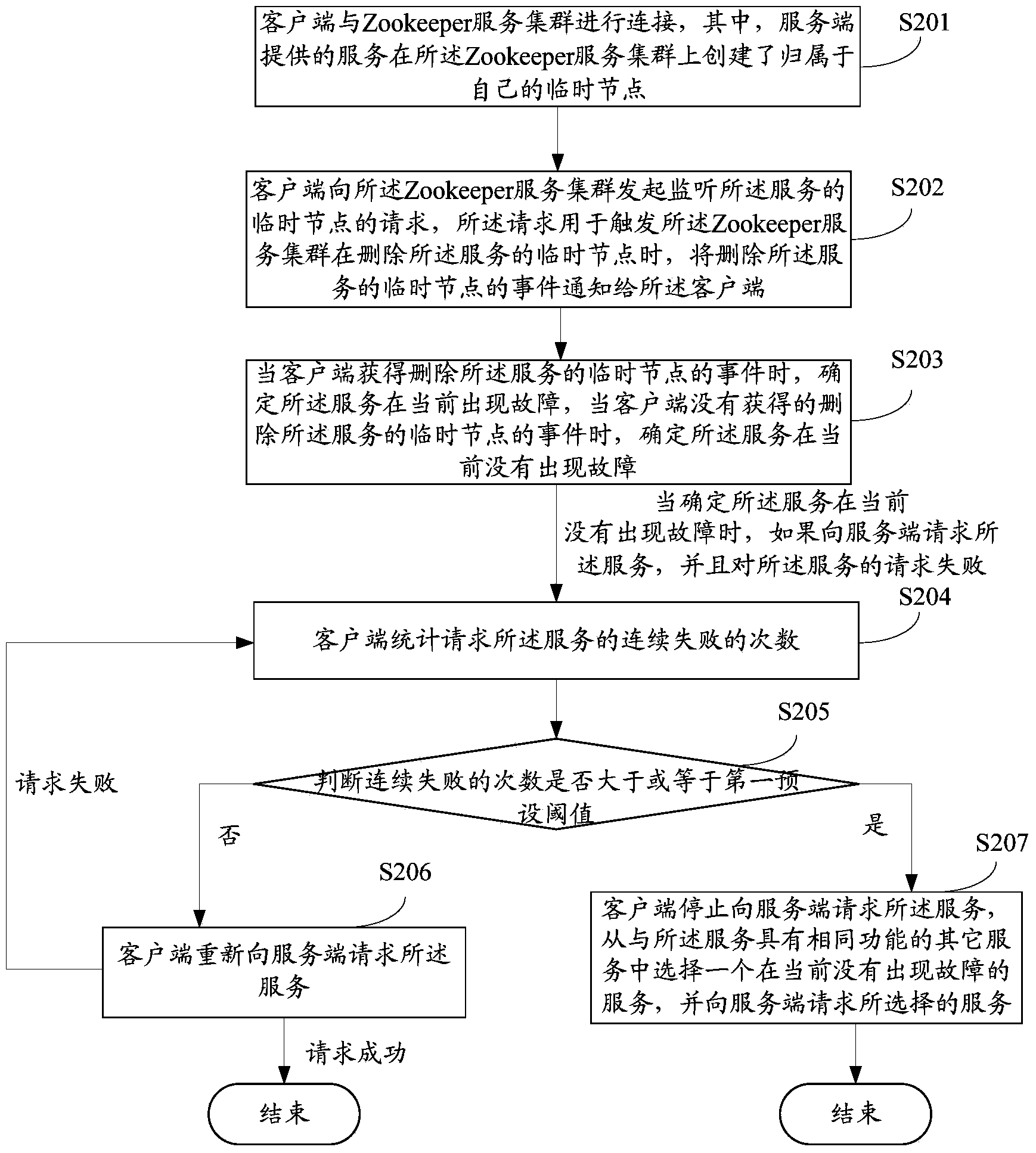
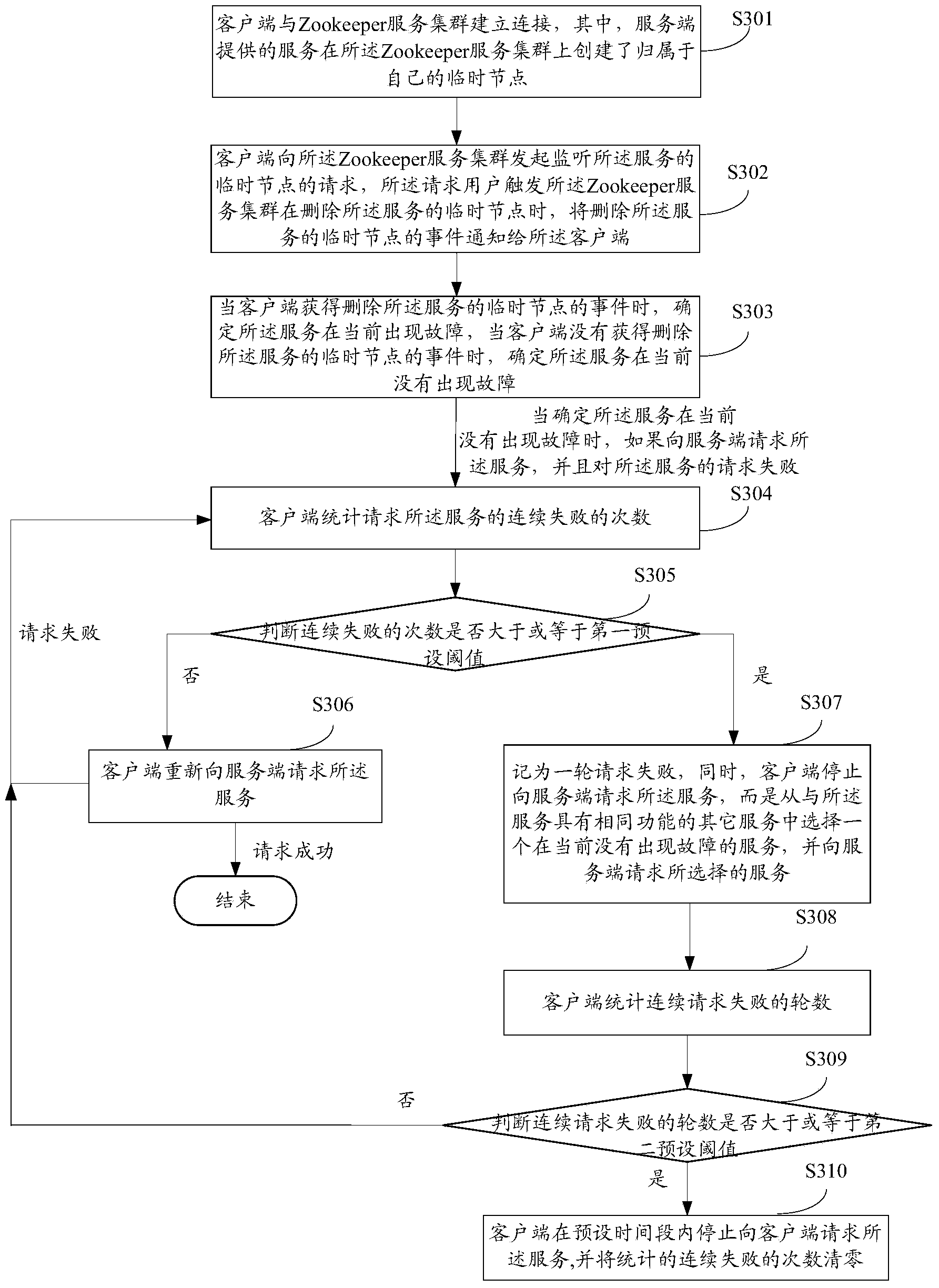
Method and apparatus for performing failure checking on service of remote method invocation
The embodiment of the invention discloses a method and apparatus for performing failure checking on a service of remote method invocation. The method is follows: a client is connected with a Zookeeper service cluster, a service provided by a server creates a temporary node to which the service end belongs on the Zookeeper service cluster; the client initiates a request of the temporary node of monitoring the service to the Zookeeper service cluster, wherein the request is used for informing the client of a delete event when being used for triggering the Zookeeper service cluster to delete the temporary node of the service; when the client obtains the delete event, the client determines that the service fails currently, and when the client does not obtain the delete event, the client determines that the service does not fail currently. According to the embodiment of the invention, the client senses whether the service requested by the client fails or not, furthermore, when the client senses that the service requested by the client fails, a series of disaster recovery treatment measures are taken specific to a condition of request failure, and the stability and reliability of the service can be improved.
Owner:FLYING FOX INFORMATION TECH TIANJIN CO LTD
Fast channel switching scheme for IEEE 802.11 WLANs
Disclosed is a method for switching at least one wireless node located within the coverage of a basic service set (BSS) or an basic basic service set (IBSS) from a first communication channel to a second communication channel in a wireless local area network (WLAN). methods and systems. In one embodiment, the method includes the following steps: determining whether a second communication channel to be used by at least one wireless node is required; when it is determined that the second communication channel is required, broadcasting a management frame by the source node to the at least one wireless node, the The management frame includes a channel switching time and a second communication channel identifier; and switching at least one wireless node that receives the management frame from the first communication channel to the second communication channel within a countdown time corresponding to the channel switching time, The channel switching time is less than the beacon interval. In an alternative embodiment, the method includes the steps of: determining whether a second communication channel to be used by at least one wireless node is required; and when it is determined that the second communication channel is required, broadcasting, by the source node, a first management frame to the at least one wireless node , the first management frame includes the channel switching time and the second communication channel identifier; and upon receiving the broadcast first management frame on the at least one wireless node, suspending all further frame exchanges in the first communication channel to mute the second communication channel. A communication channel.
Owner:KONINK PHILIPS ELECTRONICS NV
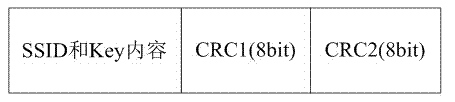
Correlation method applied to intelligent terminal
InactiveCN104735260AImprove compatibilityEffective encodingSubstation equipmentTerminal equipmentNetwork management
The invention discloses a correlation method applied to an intelligent terminal. The correlation method includes the steps that S10, launching terminal equipment encodes server set identifiers (SSID) and Keys of input APs, and broadcast frames are established according to the length field of a WiFi frame protocol data unit (PDU) and broadcast; S20, the APs receive the broadcast frames of the launching terminal equipment and forward the broadcast frames to all intelligent terminal equipment within the coverage range; S30, the intelligent terminal equipment conducts frame recognition and decode frame content through the broadcast frames forwarded by the APs and received through scanning, and the SSIDs and the Keys are acquired; S40, the intelligent terminal equipment is correlated to the designated APs according to the SSIDs and the Keys. The correlation method has the advantages of being high in compatibility, good in expandability, high in efficiency, low in cost and high in reliability, the intelligent equipment can be quickly configured by network administrators, and high practical value and promotional value are achieved.
Owner:SHENZHEN FENGLIAN TECH
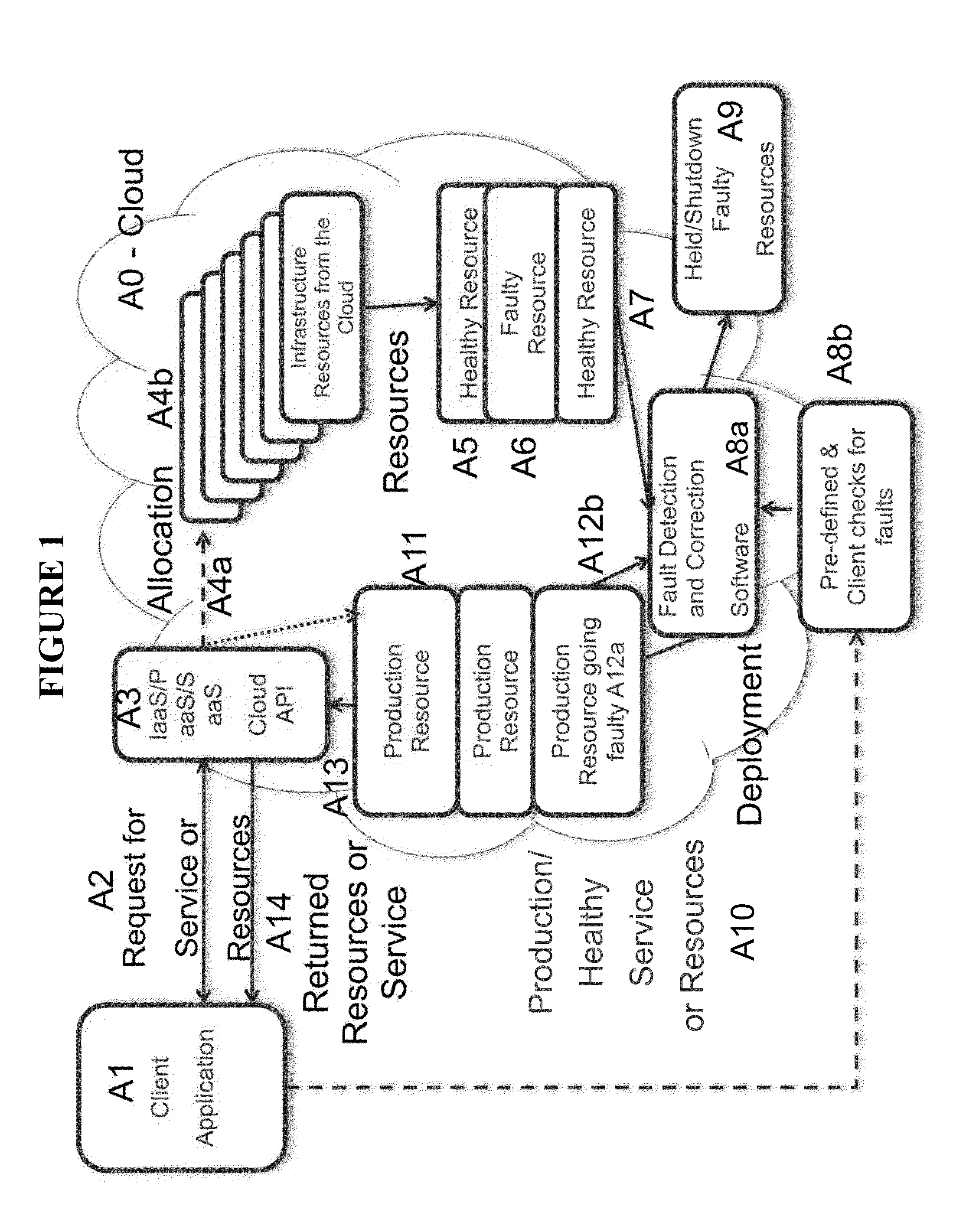
Method and system for automatically detecting and resolving infrastructure faults in cloud infrastructure
ActiveUS20140006844A1Eliminate needStay healthySoftware testing/debuggingNon-redundant fault processingCloud providerWorkload
Systems and methods are provided for any party in a cloud ecosystem (cloud providers of such resources, the intermediate management software for such resources, and the end user of such resources) to detect and resolve faulty resources synchronously or asynchronously, before said faults adversely affect the users' workloads. The system requests a service or set of one or more resources within a cloud, automatically checking the infrastructure for various faults that would cause it to be non-functional, including pre-defined and user-defined checks, and resolving them before including the infrastructure in the working service cluster of resources. The system presents an API to the user that returns only functional, production-quality resources that are not in a faulty state. An API that tests and resolves bad infrastructure can be registered during the request or a preceding / subsequent API call, removing the need for the end-user to deal with various types of infrastructure faults.
Owner:CYCLE COMPUTING
Method and system for constructing platform system infrastructure in government affair service
InactiveCN111045656AEasy to reinforceAvoid wastingData processing applicationsSoftware designBasic serviceMiddleware
The invention discloses a method and a system for constructing a platform system infrastructure in government affair service, and belongs to the technical field of middle platform systems. The systemcomprises: middle platform services which are specific products realized on the basis of a middle platform support technology framework and are mainly divided into basic services, general services andbusiness services; middle platform support, wherein the support service of a content middle platform integrates four services of micro-service governance, an interface management platform, application management and basic support, and the internal service of the content middle platform is registered to the registration center and the configuration center of the micro-service governance platform;and middleware service, wherein the technical architecture of the content middle platform is specially used for adaptively developing various open-source middleware, and a user can select according toown conditions. Through service reuse, repeated car making is avoided, public functions of all products are independent and non-uniform in interaction, the communication cost is reduced, and the cooperation efficiency is improved.
Owner:大汉软件股份有限公司
Network connection method, smart home device, smart gateway and electronic device
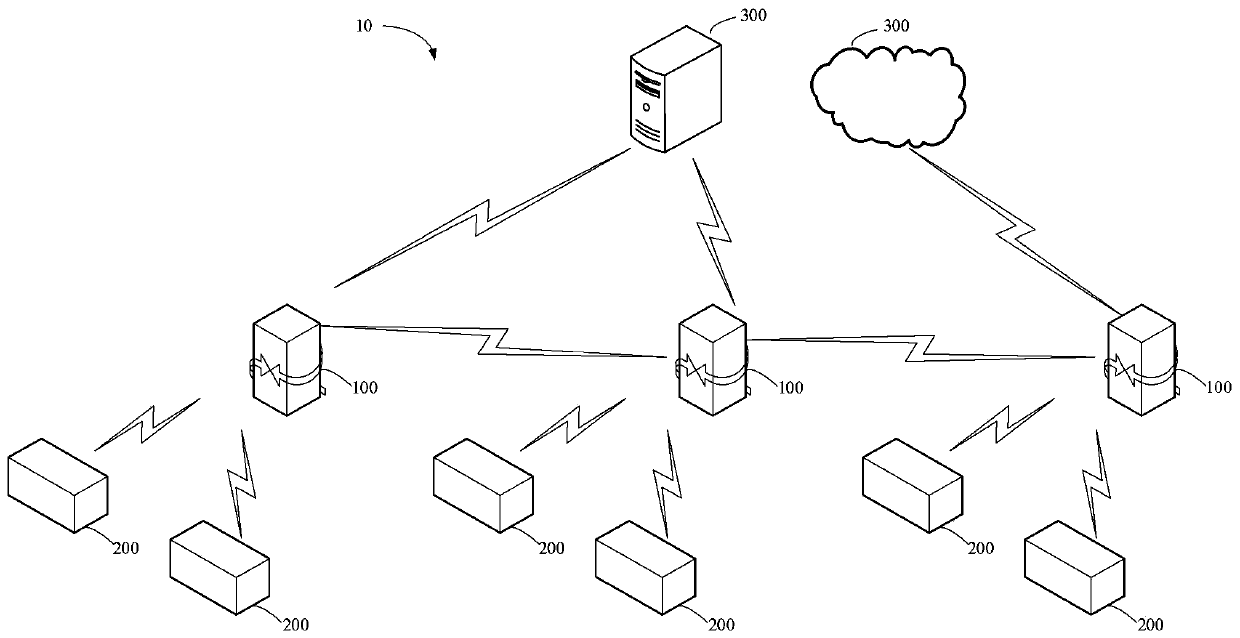
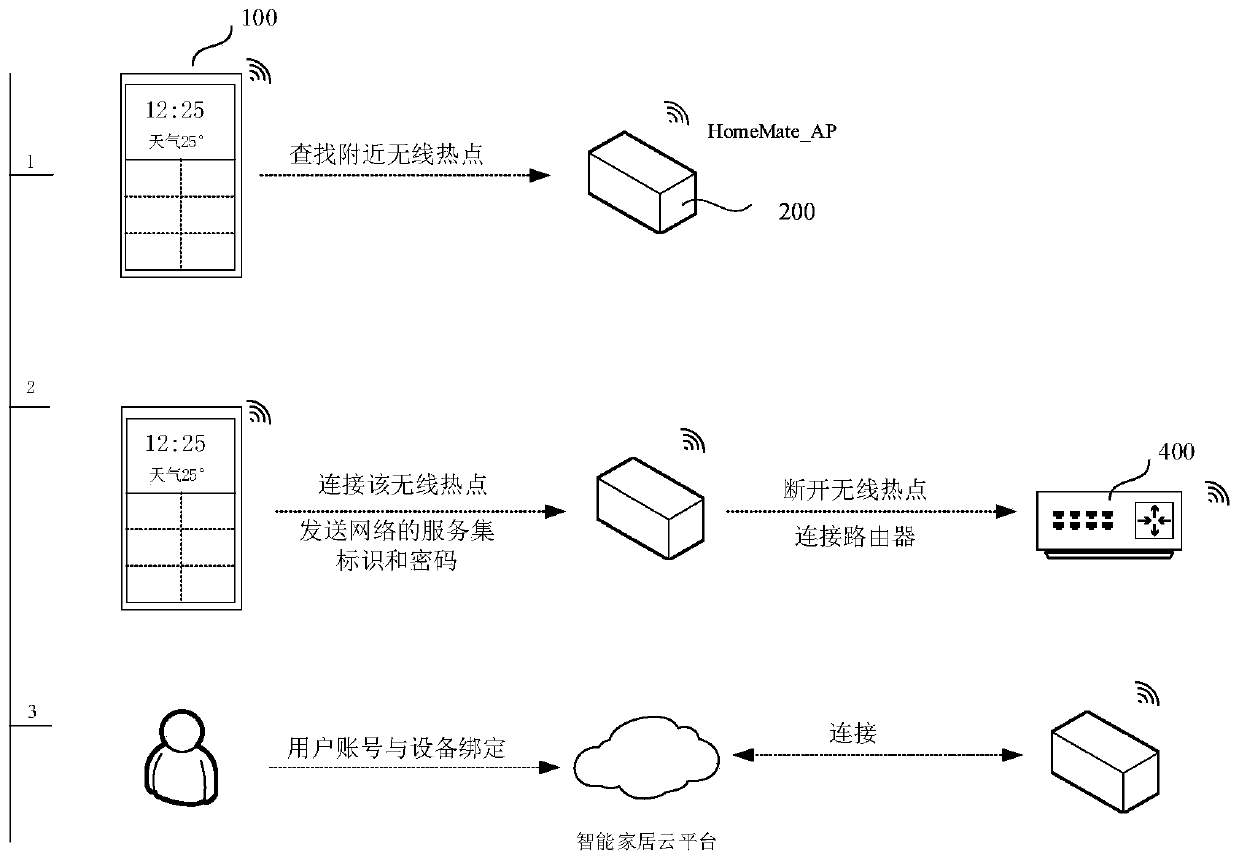
ActiveCN110831112AEasy accessSimplify the network distribution processAssess restrictionConnection managementIntelligent NetworkNetwork connection
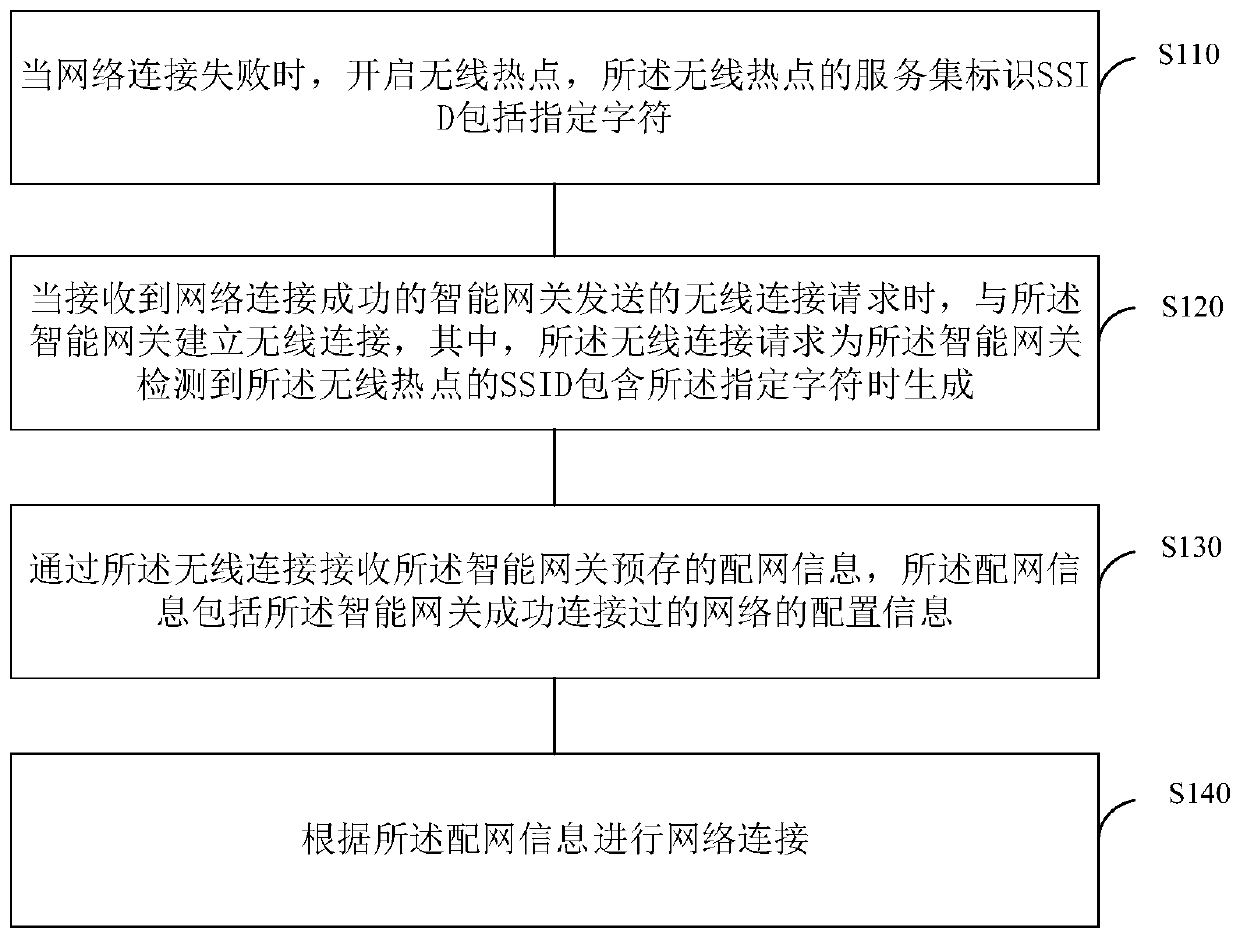
The invention discloses a network connection method and device of a smart home device, electronic equipment and a storage medium, and relates to the technical field of smart home. The method comprisesthe steps that when network connection fails, a wireless hotspot is started, and a service set identifier SSID of the wireless hotspot comprises a specified character; when a wireless connection request sent by an intelligent gateway with successful network connection is received, wireless connection with the intelligent gateway is established, and the wireless connection request is generated when the intelligent gateway detects that the SSID of the wireless hotspot contains the specified character; the network distribution information pre-stored by the intelligent gateway is received throughthe wireless connection, wherein the network distribution information comprises configuration information of a network successfully connected by the intelligent gateway; and the network connection iscarried out according to the distribution network information. The method can achieve the quick network access of the smart home device through the intelligent gateway, and improves the convenience and success rate of the network access of the smart home device.
Owner:SHENZHEN OURUIBO ELECTRONICS
Resource access method and device, resource access system, equipment and storage medium
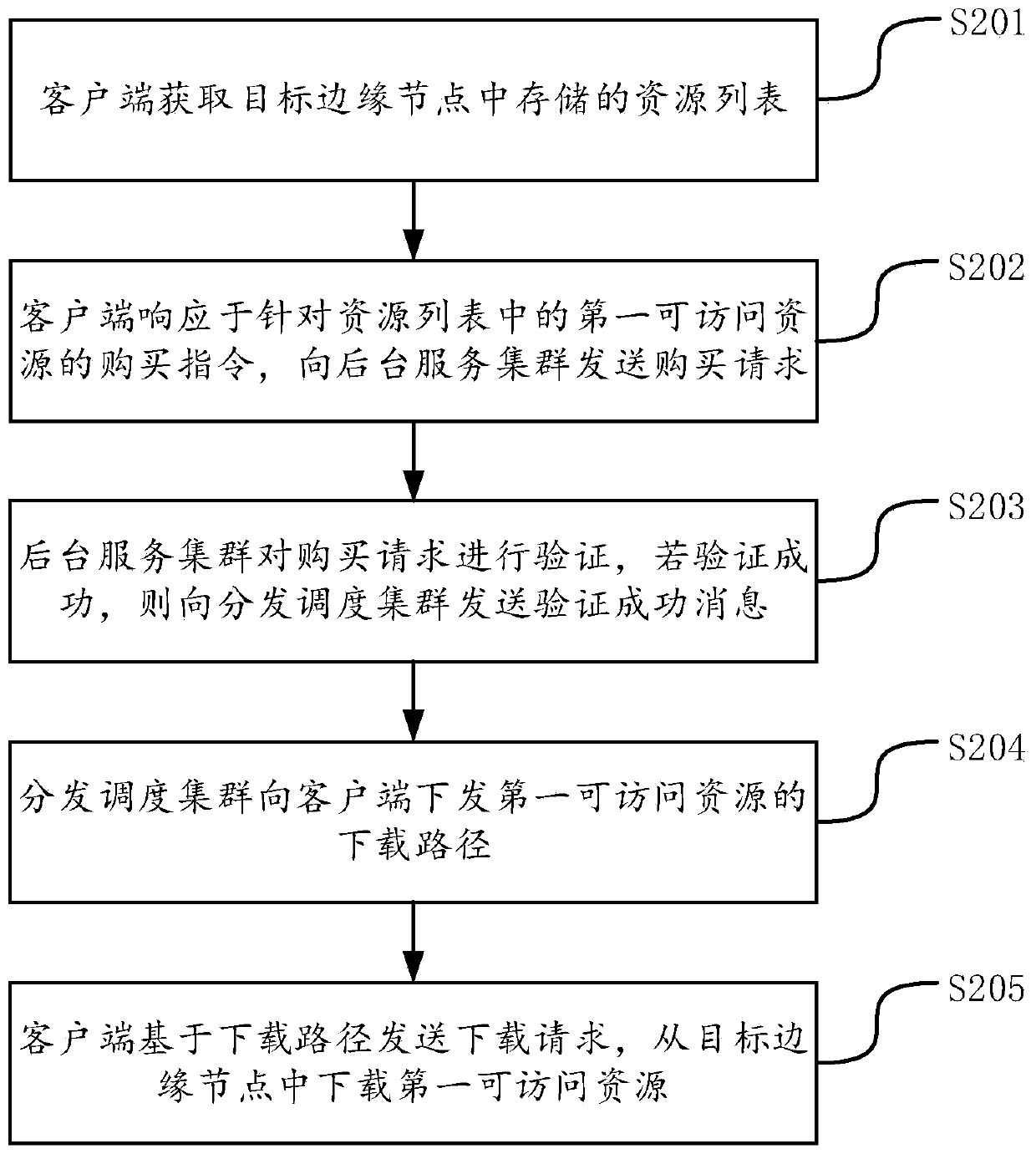
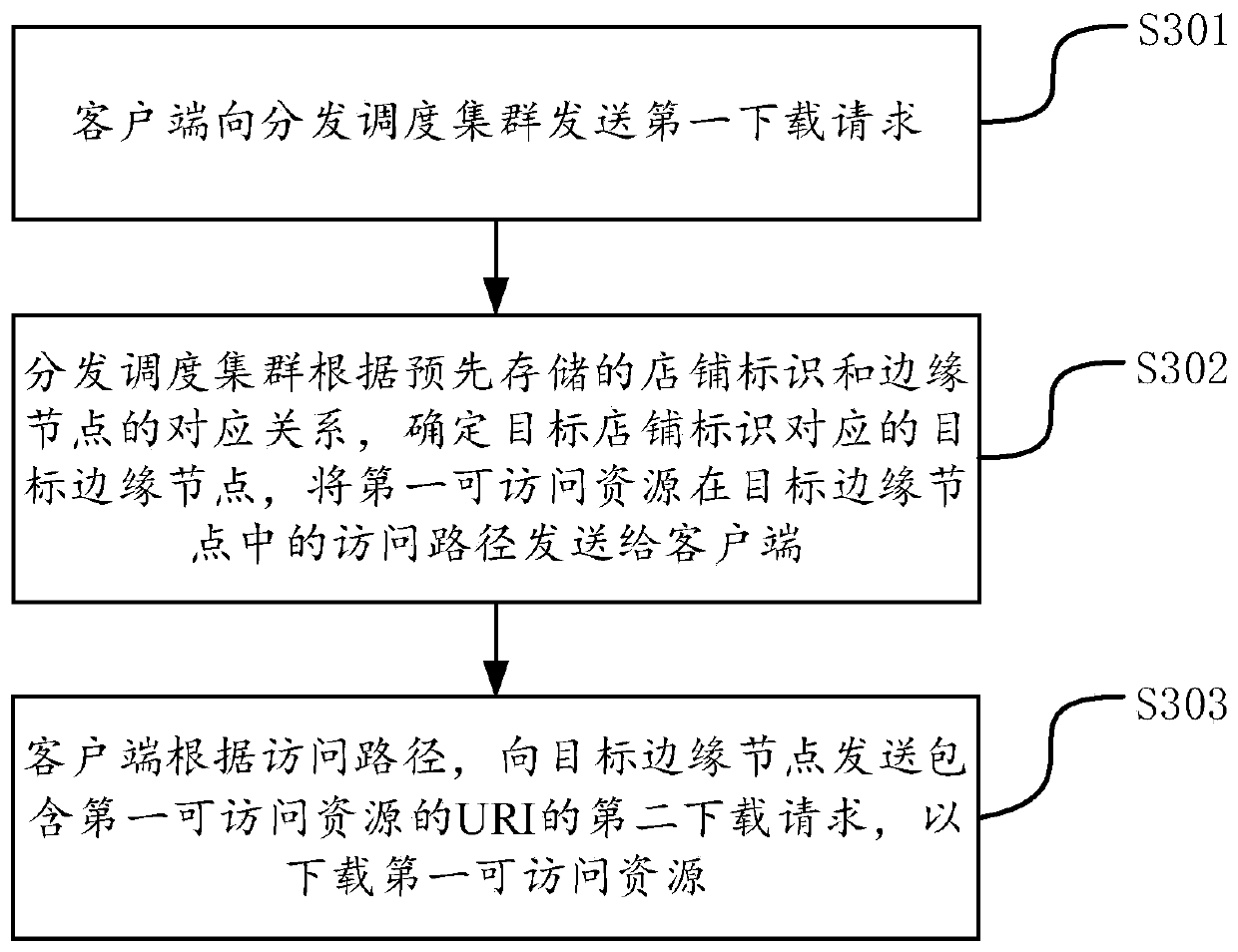
ActiveCN111355731AImprove the efficiency of downloading resourcesTransmissionSpecial data processing applicationsPathPingAccess method
The embodiment of the invention provides a resource access method and device, a resource access system, equipment and a storage medium, and belongs to the technical field of the Internet. The method comprises the following steps: a client acquires a resource list stored in a target edge node, the target edge node is an edge node belonging to the same local area network as the client in the edge nodes, and the resource list comprises information of accessible resources stored in the target edge node; the client sends a purchase request to the background service cluster in response to a purchaseinstruction for the first accessible resource in the resource list; the background service cluster verifies the purchase request, and if verification succeeds, a verification success message is sentto the distribution scheduling cluster; the distribution scheduling cluster issues a downloading path of the first accessible resource to the client; and the client sends a downloading request based on the downloading path, and downloads the first accessible resource from the target edge node. By adopting the method and the device, the resource downloading efficiency can be improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
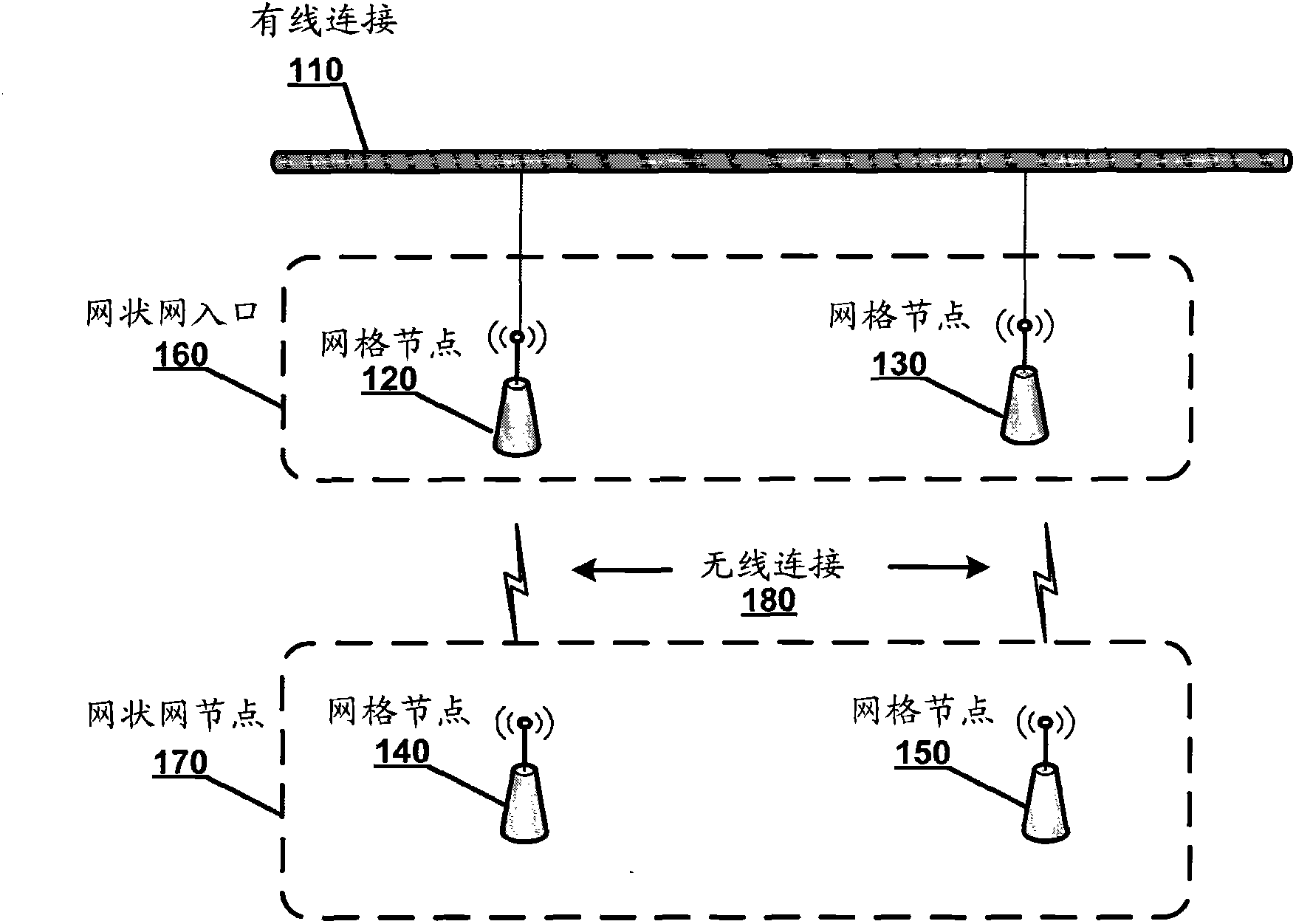
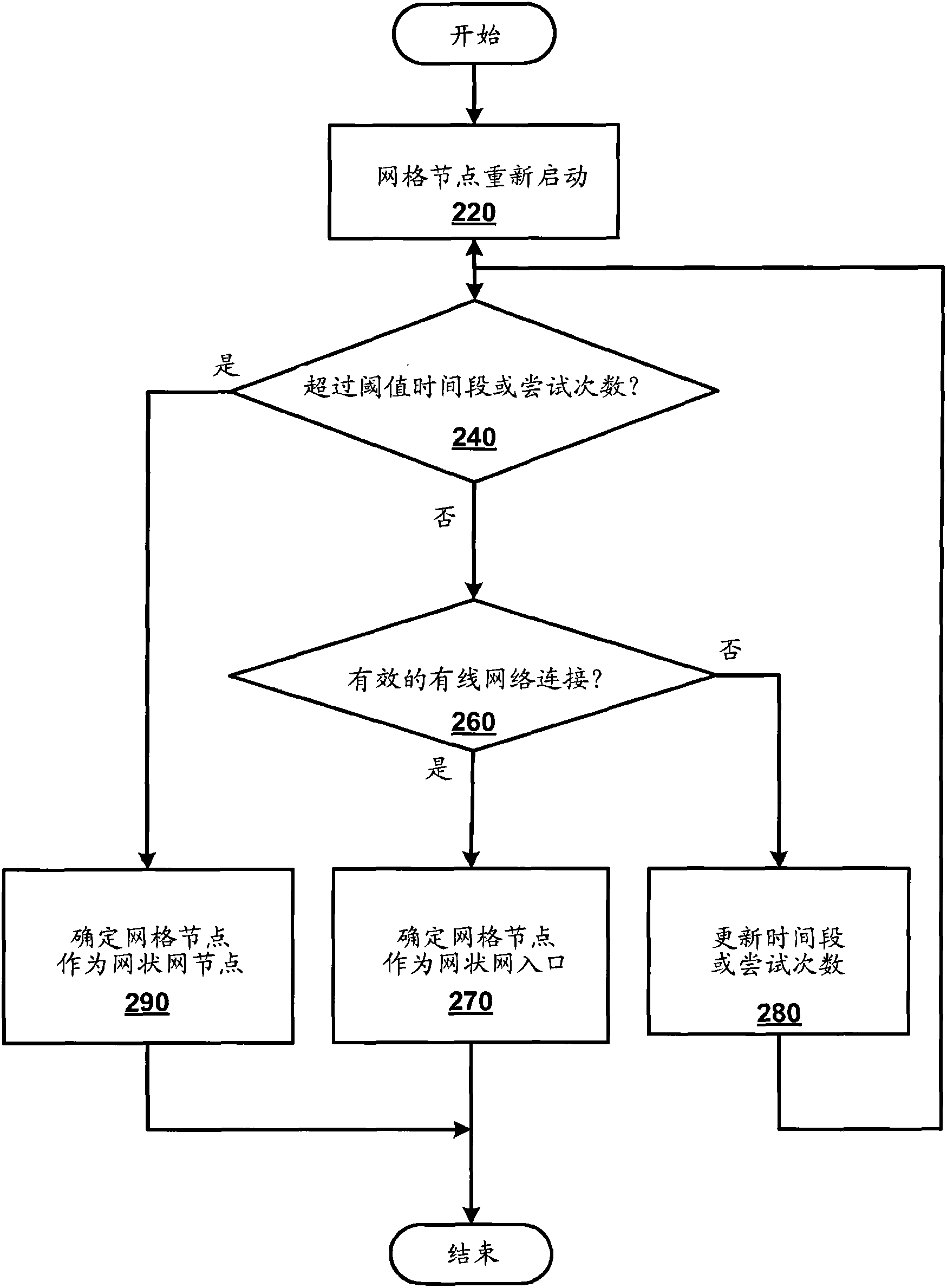
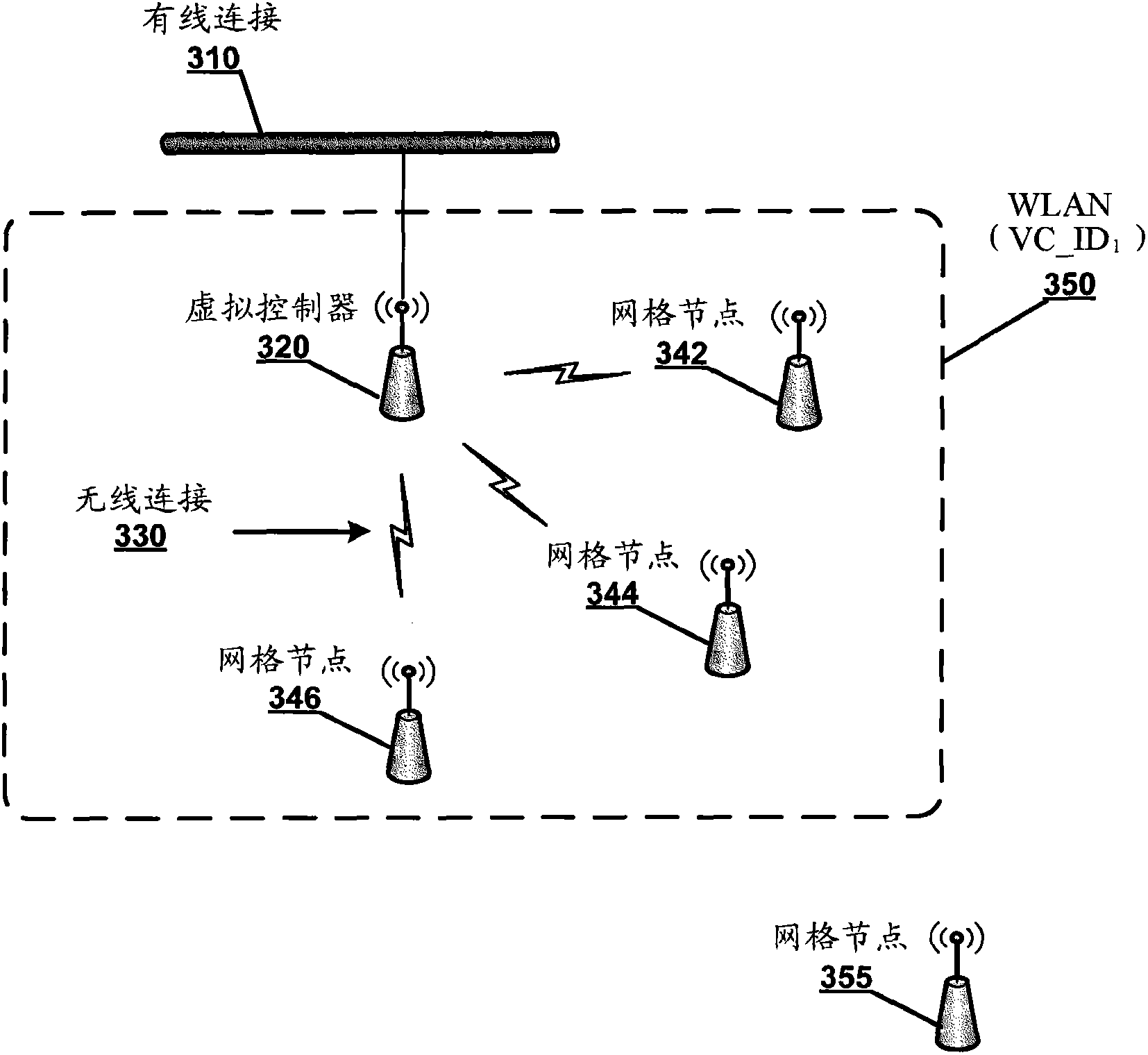
Method and equipment for role discovery and automatic wireless configuration of grid nodes
The invention discloses a method and equipment for role discovery and automatic wireless configuration of grid nodes. The method and the equipment are used for configuring and managing the grid nodes when the grid nodes fail occasionally or new grid nodes are added. The method includes: determining that the grid nodes serve as a mesh portal or a mesh point; if the grid nodes serve as the mesh portal, enabling the grid nodes to inform other grid nodes in the network of the capability of the grid nodes serving as the mesh portal; if the grid nodes serve as the mesh point, when the grid nodes recognize a unique wireless mesh network based on an associated network identifier such as a VC_ID (virtual controller identifier) or an SSID (service set identifier), enabling the grid nodes to attempt automatic wireless configuration to be connected with the corresponding wireless mesh network; and if more than one network identifier is discovered, delaying the grid nodes to be connected with the wireless mesh network until a selection is received.
Owner:ARUBA NETWORKS
Method for protecting wireless network
ActiveCN103442351AReduce riskAchieve protectionAssess restrictionNetwork topologiesWork patternNetwork packet
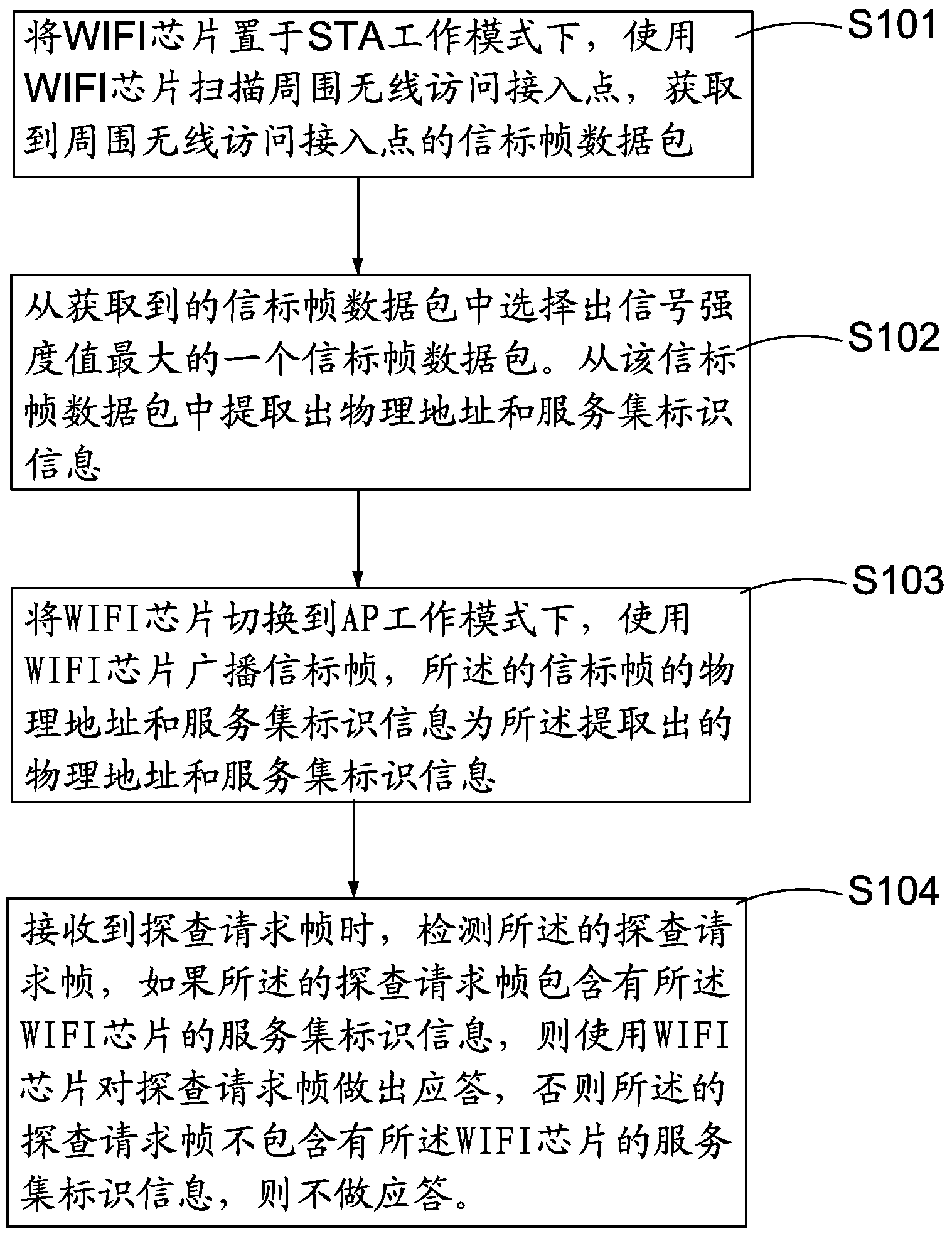
The invention provides a method for protecting a wireless network. The method for protecting the wireless network comprises the steps that a WIFI module is arranged in an STA working pattern, the WIFI module is used for scanning wireless access points around, and the beacon frame data packages of the wireless access points are obtained; one beacon frame data package is selected from the beacon frame data packages of the wireless access points around, and physical address and service set identification information are extracted from the beacon frame data package; the WIFI module is switched to an AP working pattern, the WIFI module is used for broadcasting the beacon frame, and the physical address and the service set identification information of the beacon frame are the extracted physical address and the extracted service set identification information. According to the method for protecting the wireless network, the physical addresses and the service set identification information of other equipment are used for achieving the purpose that the self information of the WIFI module is not broadcasted, self information leakage of the WIF module is prevented, and the protection of the wireless network is achieved.
Owner:FUZHOU ROCKCHIP SEMICON
Method and system for enabling discovery of services and automated exchange of data between bluetooth devices
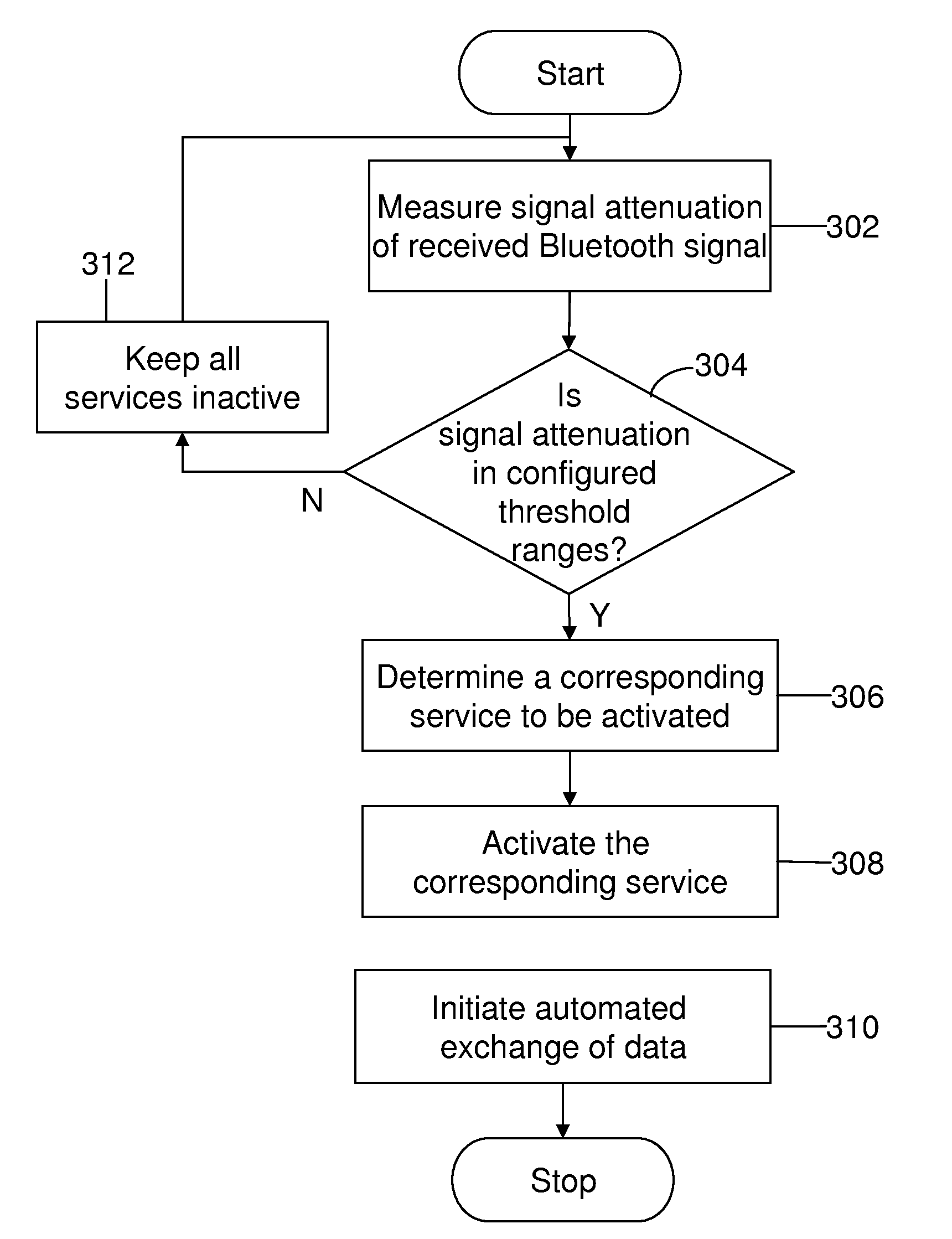
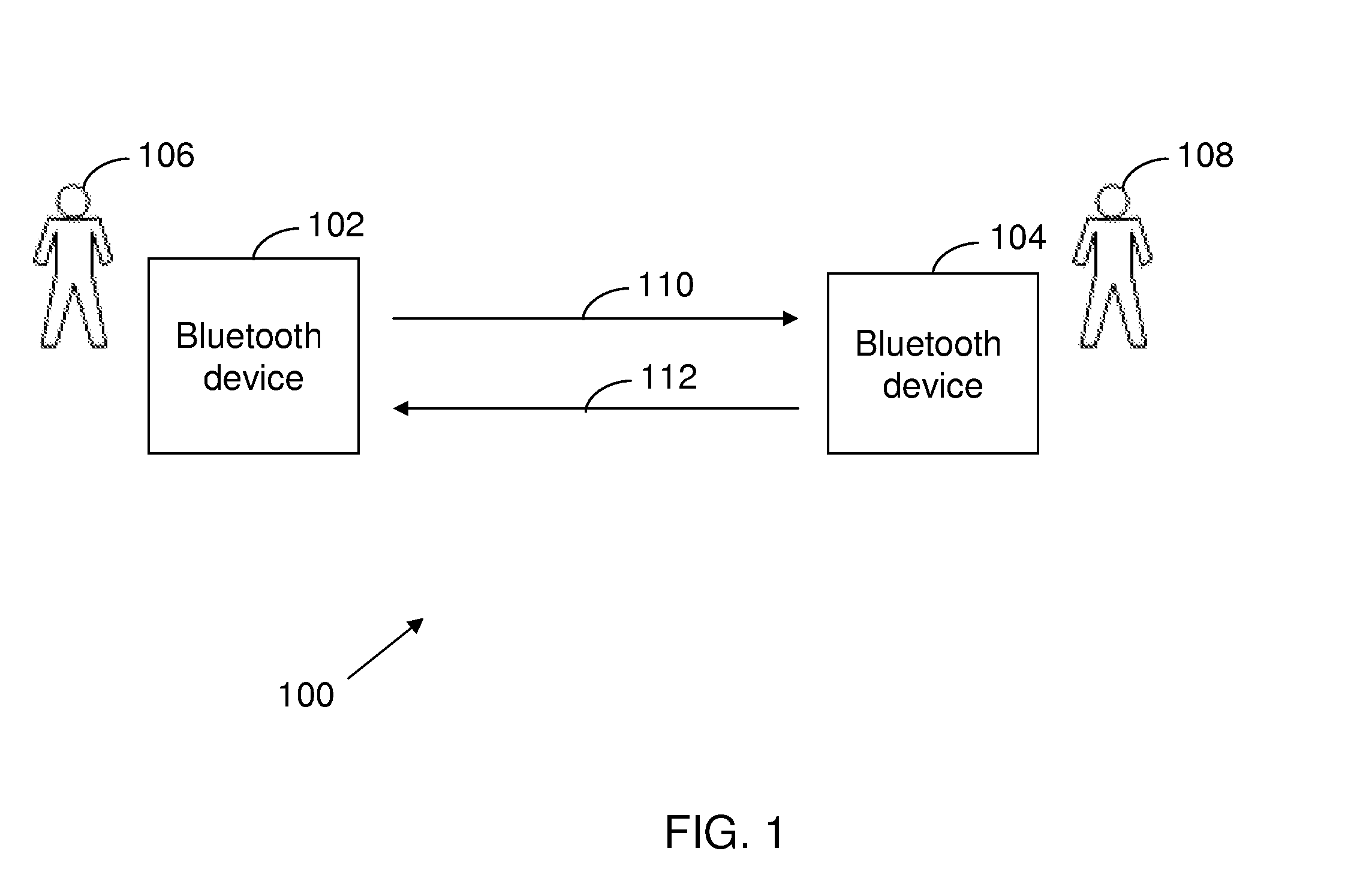
A method and system for enabling discovery of services and automated exchange of data between multiple Bluetooth devices are disclosed. The method includes measuring signal attenuation of a Bluetooth signal between a first Bluetooth device and a second Bluetooth device. The method further includes comparing the signal attenuation with a set of predefined threshold values. The set of predefined threshold values is associated with a set of services. The method also includes activating a corresponding service from among the set of services based on the comparison. Activating the corresponding service enables discovery of the service and automated exchange of data between the first Bluetooth device and the second Bluetooth device.
Owner:INFOSYS LTD
Democratic and autonomous cluster management method and system
ActiveCN104917792AContinuous service quality requirements are highLarge number of nodesData switching networksQuality of serviceFault tolerance
The invention provides a democratic and autonomous cluster management method. The democratic and autonomous cluster management method includes the following steps of: step 1, cluster startup; step 2, cluster operation autonomy; step 3, cluster split autonomy; step 4, cluster merged autonomy; step 5, cluster dynamic elastic autonomy; and step 6, cluster administrator governance. The invention also provides a corresponding system. With the democratic and autonomous cluster management method and system of the invention adopted, a cluster can have continuous external service and cluster management service providing ability when any single node is abnormal or a plurality of nodes are abnormal; at any state, maintenance upgrade can be performed on nodes in the cluster, and service nodes can be added into the cluster; third-party services are not required as for the selection of a master; and democratic and autonomous selection and generation of the master can be competed; split autonomy of the cluster is supported; fault tolerance and management performance can be improved; the highest administrative authority of the administrator is supported. The democratic and autonomous cluster management method can be widely applied to cluster management systems which require elastic flexibility, have high requirements for continuous service quality and have a large number of nodes in clusters.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
Intelligent gateway capable of automatically adding https portal and working method thereof
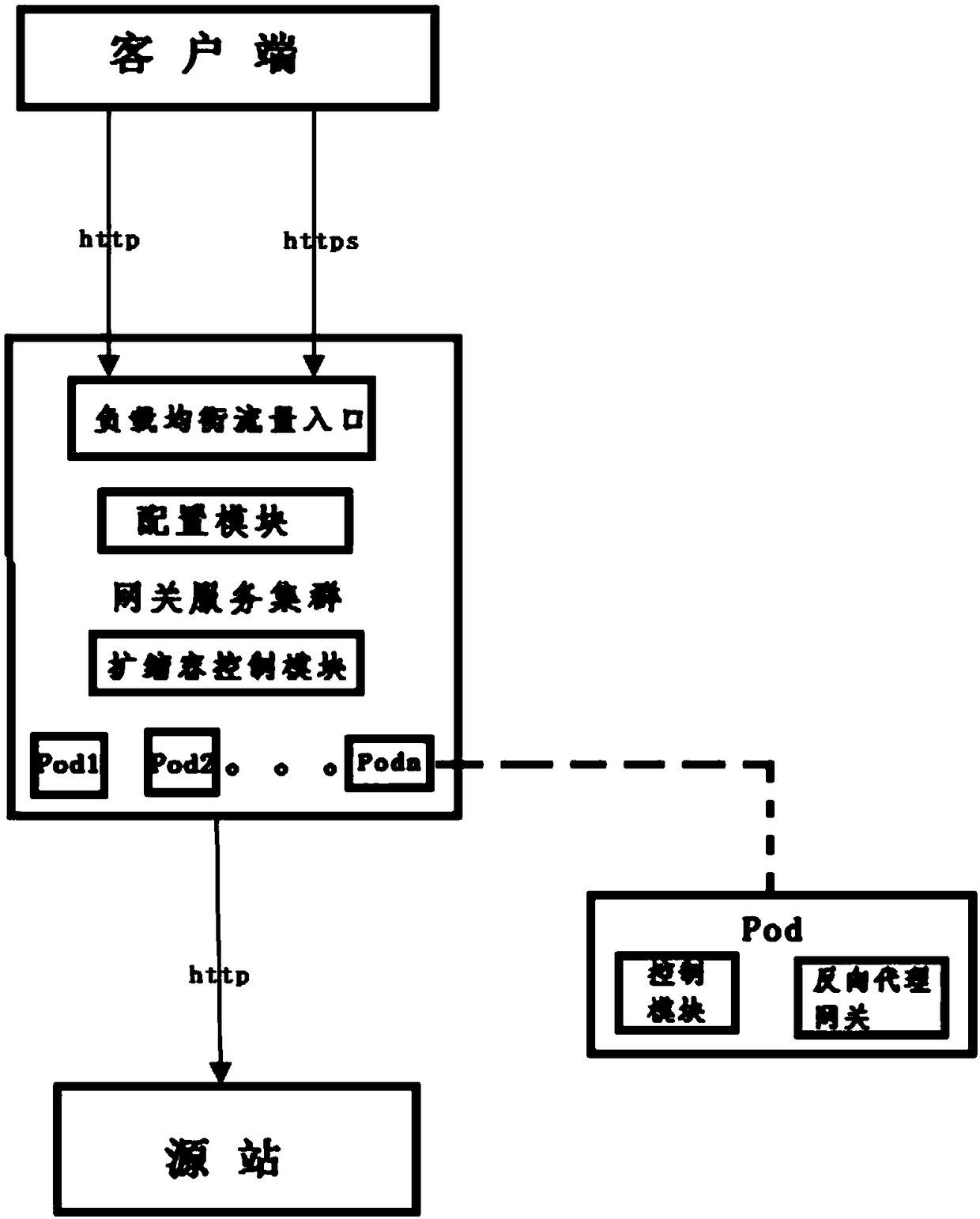
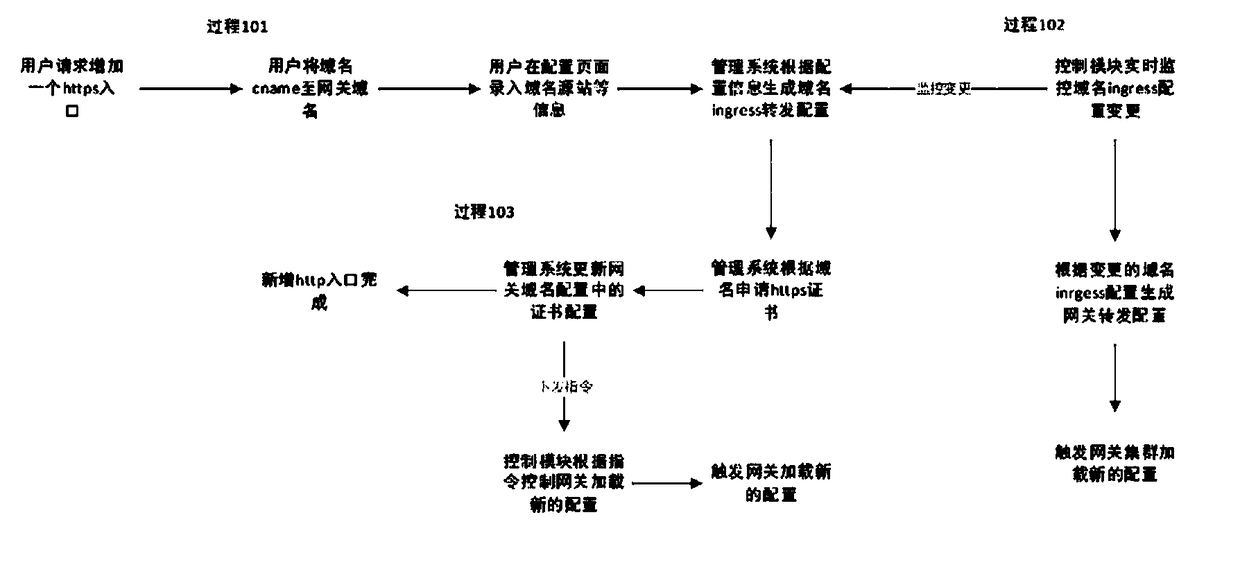
ActiveCN109150616ASolve centralized configuration managementImprove securityNetwork connectionsReverse proxyHypertext Transfer Protocol over Secure Socket Layer
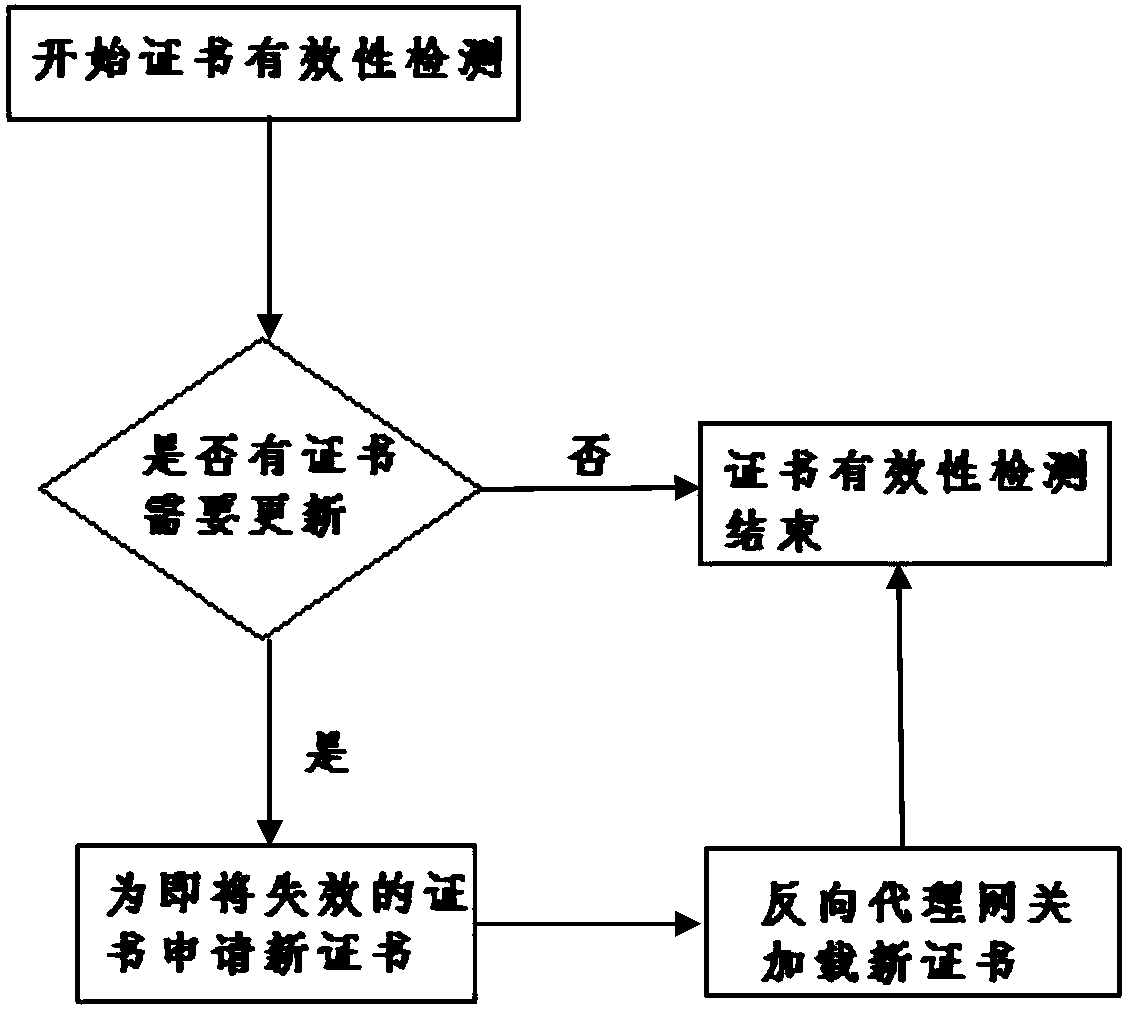
The invention discloses an intelligent gateway capable of automatically adding an https portal and a working method thereof. The intelligent gateway comprises a gateway service cluster including a load balancing flow inlet, a configuration module and a plurality of container groups. Each container group includes a control module and a reverse proxy gateway. The gateway service cluster is in communication connection with a client through the load balancing flow inlet and is in communication connection with a source station. According to the invention, with the configuration module and the plurality of container groups, a centralized configuration management problem of http ports is solved; an https port with high safety is provided; the effectiveness of the https certificate is kept automatically for long time by a certificate detection module, so that the service interruption during the certificate updating process is prevented; and with an expansion and shrinkage control module, loadsof all reverse proxy gateways are balanced, so that the smooth expansion and shrinkage of the reverse proxy gateway are realized.
Owner:成都潜在人工智能科技有限公司
Apparatus and method for low power local area communication using event signal control
ActiveUS8605693B2Maintaining low-power characteristicsPower managementEnergy efficient ICTStructure of Management InformationCommunication device
Disclosed herein is an apparatus and method for low power local area communication using event signal control. The low power local area communication apparatus includes at least one coordinator and a plurality of network device. The network coordinator transmits a periodic beacon signal based on the preset beacon period of a superframe and a continuous RF event signal, receives a first signal including a Service Set Identifier (SSID) and a second signal including the SSID and an event detection code, and performs the transmission or reception of data when authentication has been completed. Each of the network devices generates and transmits the first and second signals, performs the transmission and reception of data after authentication has been completed, and is thereafter switched to power saving mode or OFF mode. Accordingly, the construction of the system is simplified, and the cost of the system is reduced.
Owner:SAMSUNG ELECTRO MECHANICS CO LTD
Base station cooperation dormancy method and system applied to cellular heterogeneous network
ActiveCN104602329AImprove energy efficiencyReduce energy consumptionPower managementHigh level techniquesCurrent channelTime delays
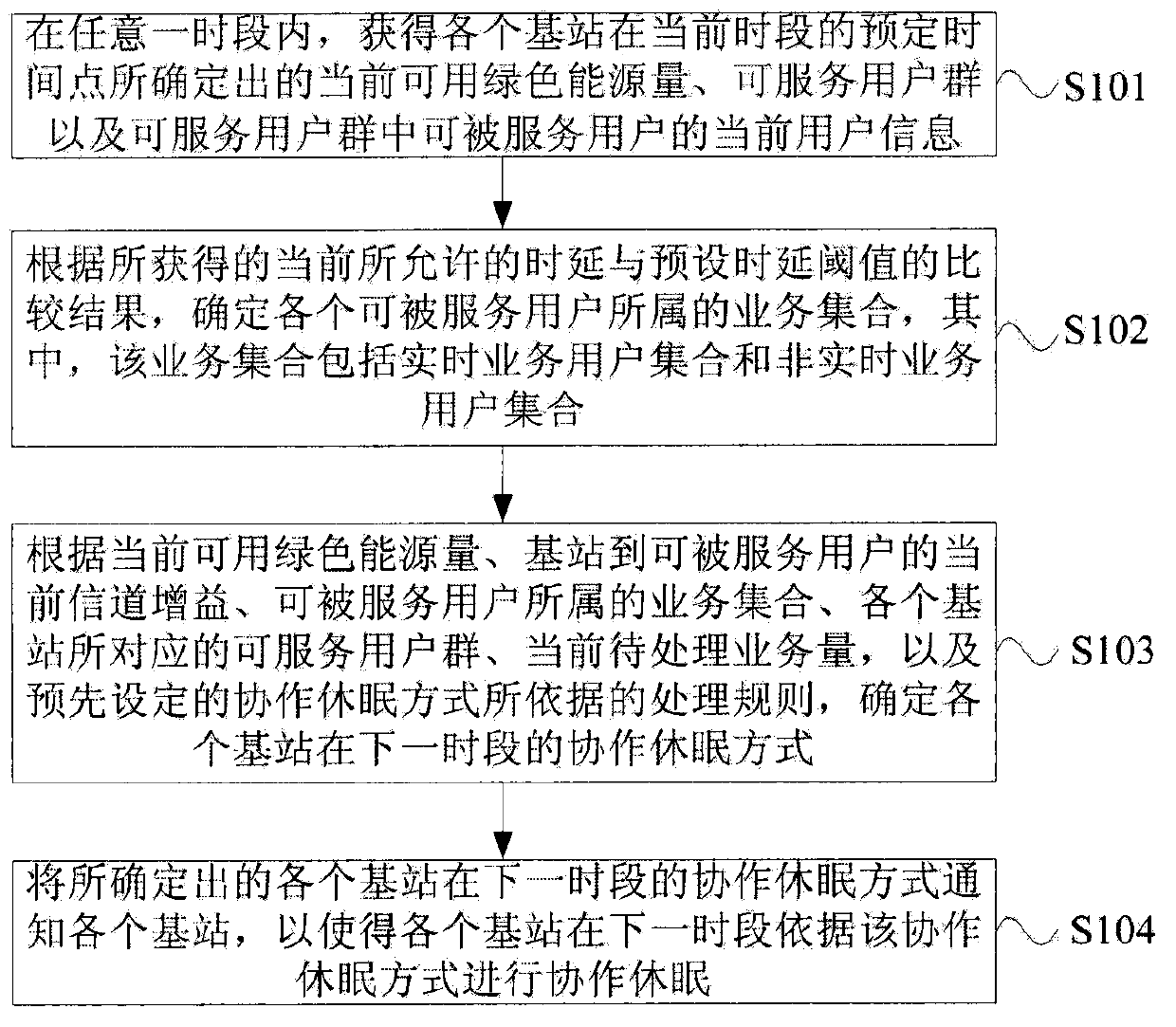
The embodiment of the invention provides a base station cooperation dormancy method and system applied to a cellular heterogeneous network. The method includes the steps of obtaining the current available green energy amount, user groups capable of conducting serving, and current user information of users capable of being served in the user groups capable of conducting serving with any time period, wherein the available green energy amount, the user groups capable of conducting serving and the current user information are determined through all base stations at a preset time point of the current time period; determining a service set which all the users capable of being served belong to according to the comparison result of the current allowable time delay in the current user information and the preset time delay threshold value; determining the cooperation dormancy mode of all the base stations in the next time period and noticing all the base stations to conduct cooperation dormancy according to the current available green energy amount, the current channel gain from the base stations to the users capable of being served in the current user information, the service set which the users capable of being served belong to, the user groups which correspond to the base stations and can conduct serving, the current to-be-processed service amount and processing rules which the preset coordination dormancy method based on.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Network distribution method and system
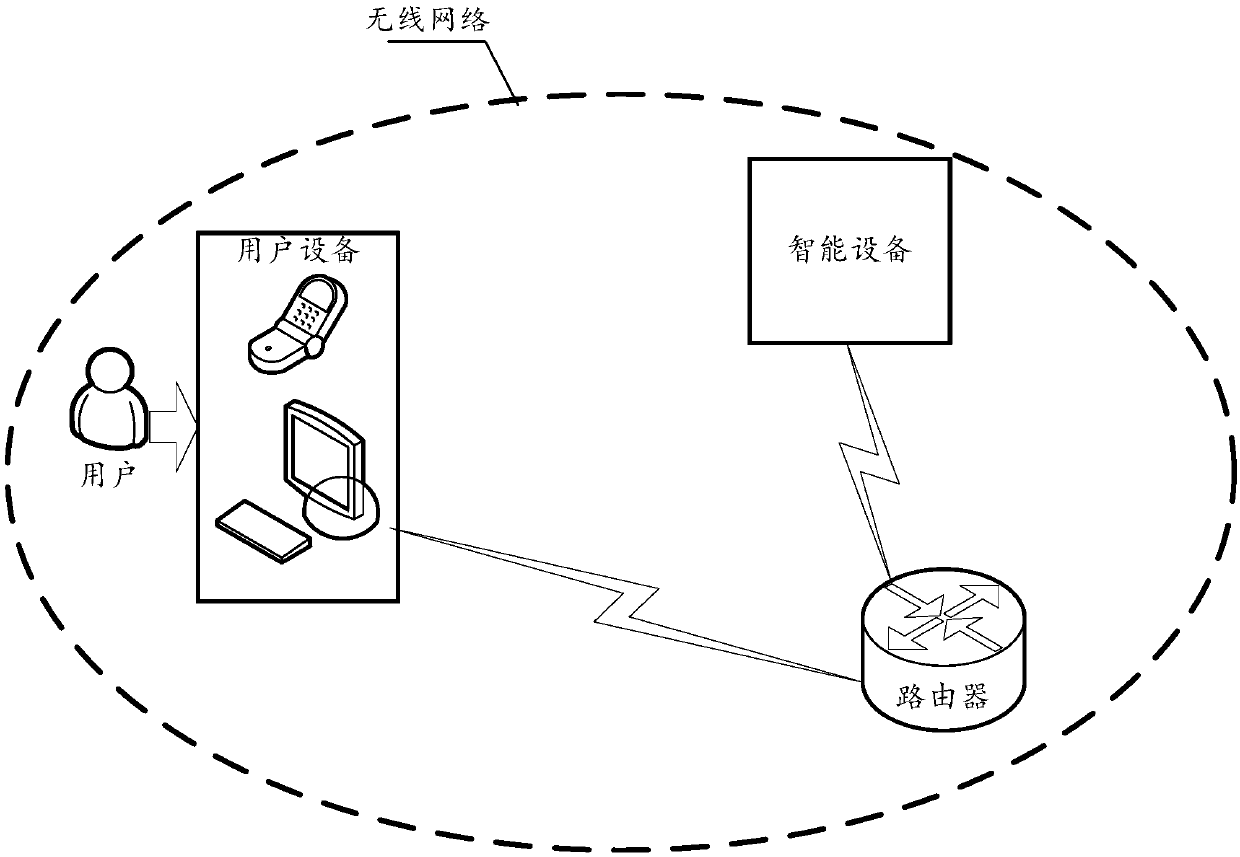
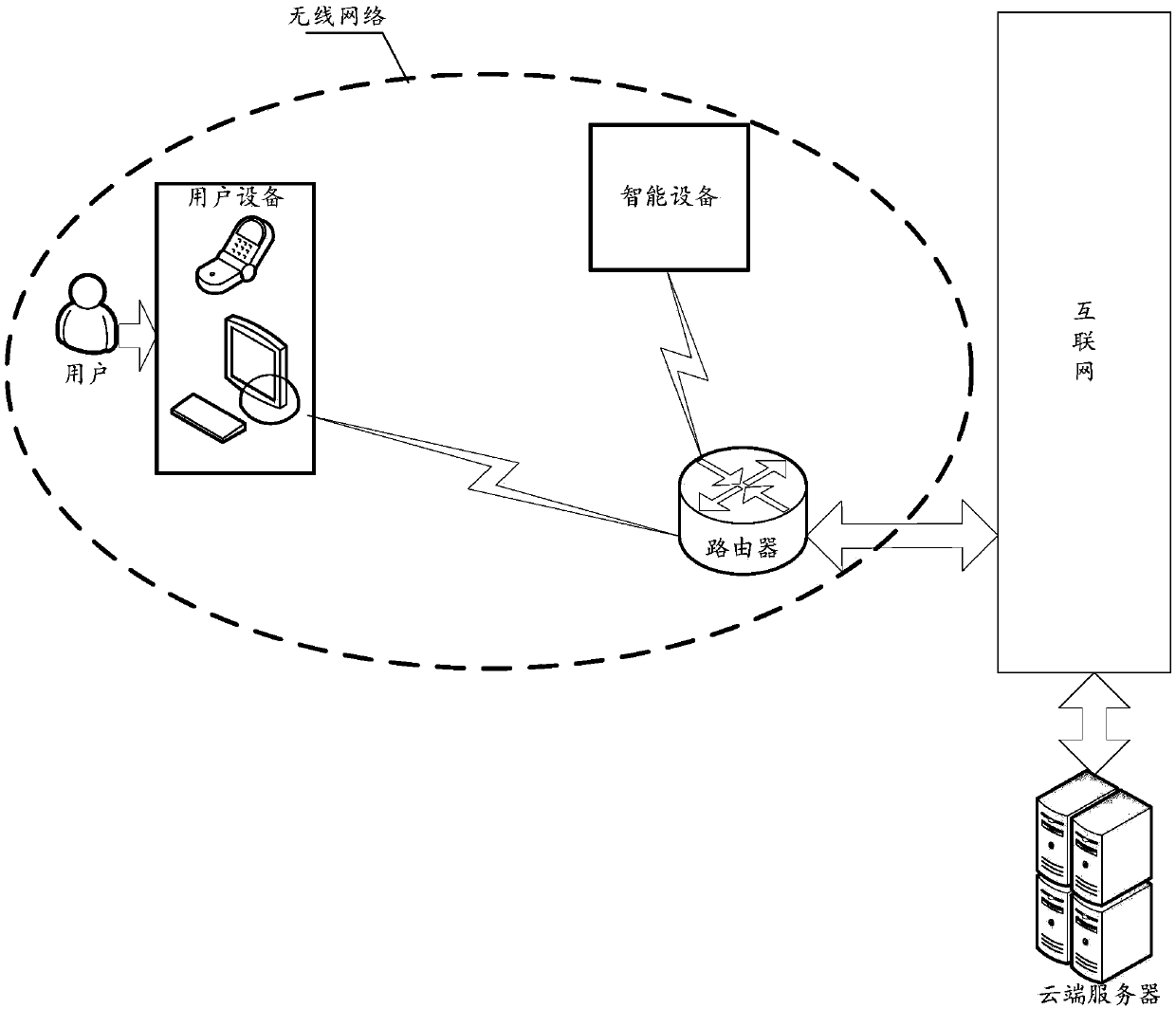
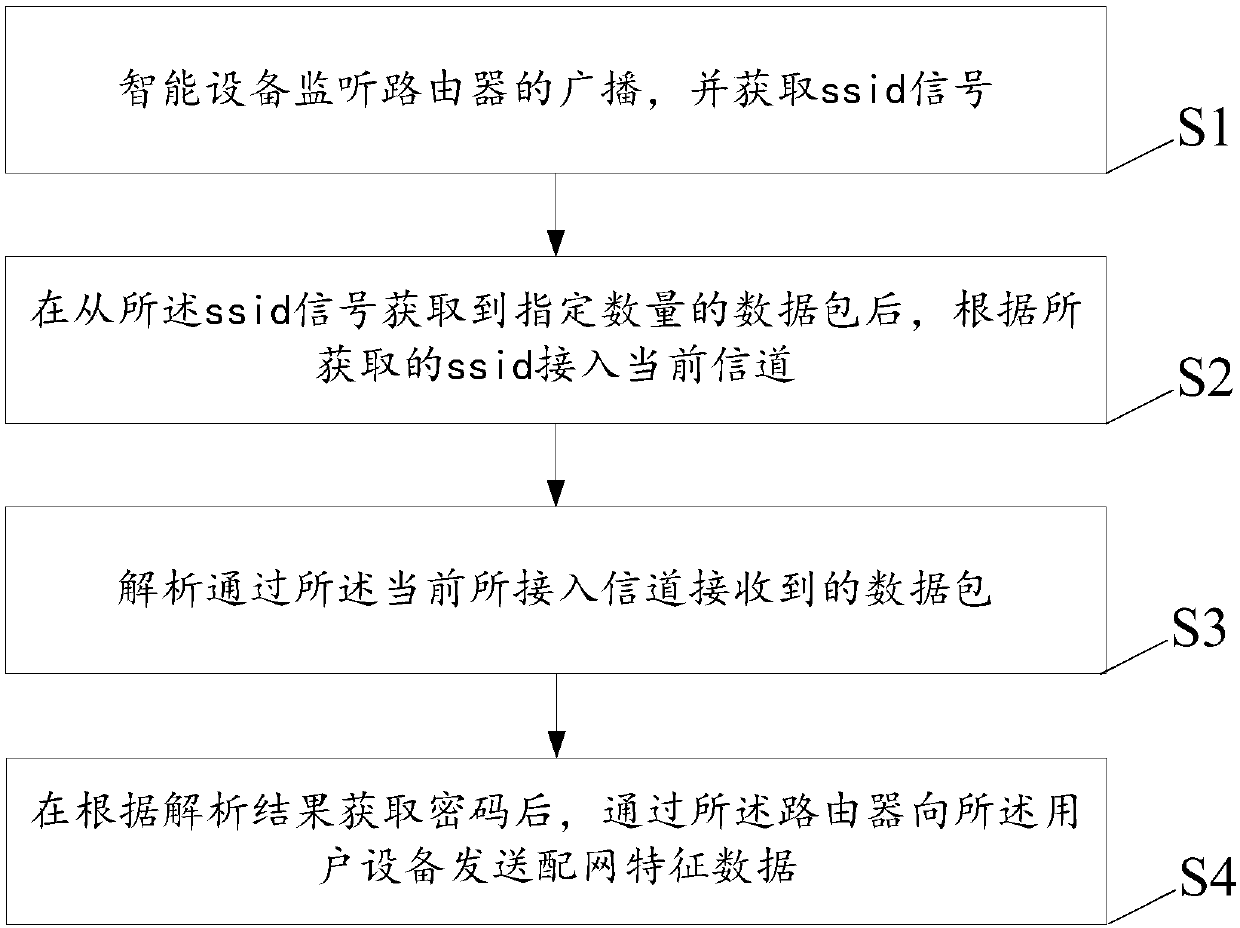
ActiveCN109548019AShort timeAvoid restartAssess restrictionConnection managementBroadcast packetCurrent channel
The embodiment of the invention discloses a network distribution method and system, and relates to the field of smart home. The time consumption of network distribution can be reduced. The method comprises the following steps: monitoring, by a smart device, the broadcast of a router, and obtaining a service set identifier (ssid) signal; after a specified number of data packets are obtained from the ssid signal, accessing a current channel according to the obtained ssid, wherein the specified number of data packets comprise the same address flag, and the address flag points to user equipment;parsing the data packet received through the currently accessed channel, wherein the data packet comprises a multicast packet and a broadcast packet sent by the user equipment to the router; after a password is obtained according to the parsing result, sending network distribution feature data to the user equipment through the router, wherein the network distribution feature data are used for notifying the user equipment of network distribution success. The network distribution method and system disclosed by the invention are suitable for rapid network distribution in the field of smart home.
Owner:SUNING COM CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com