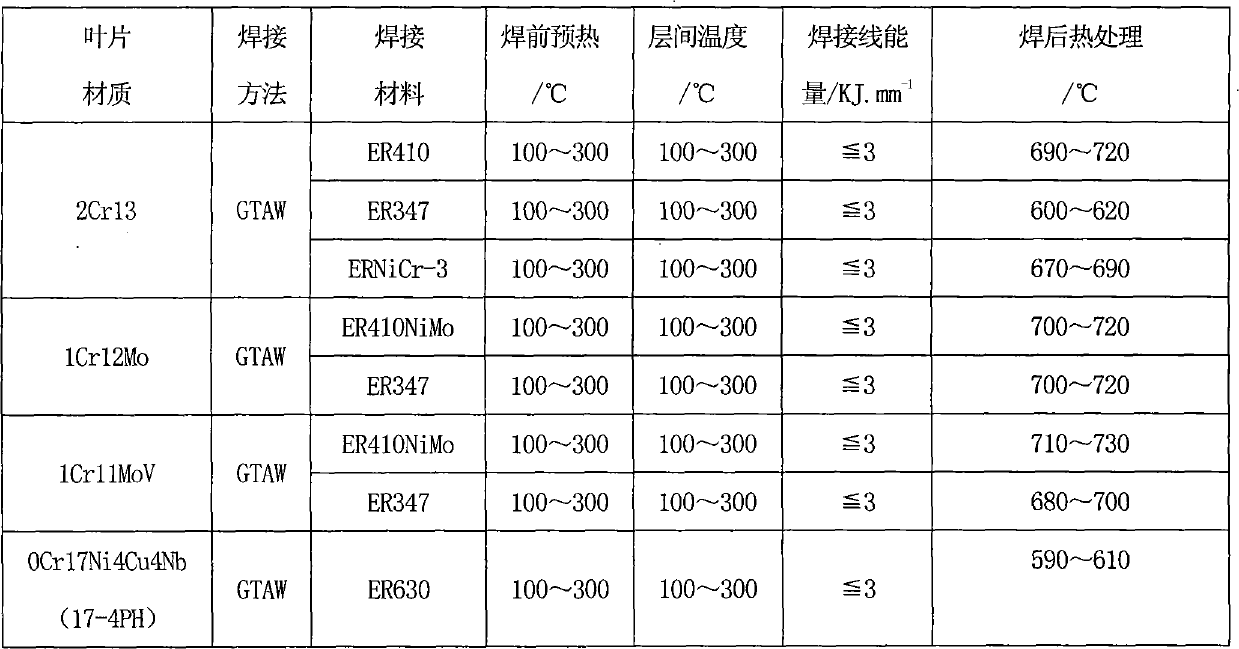
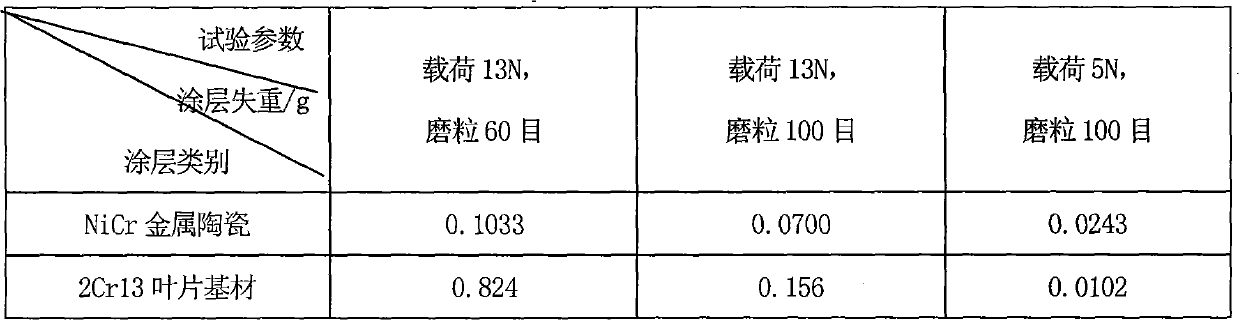
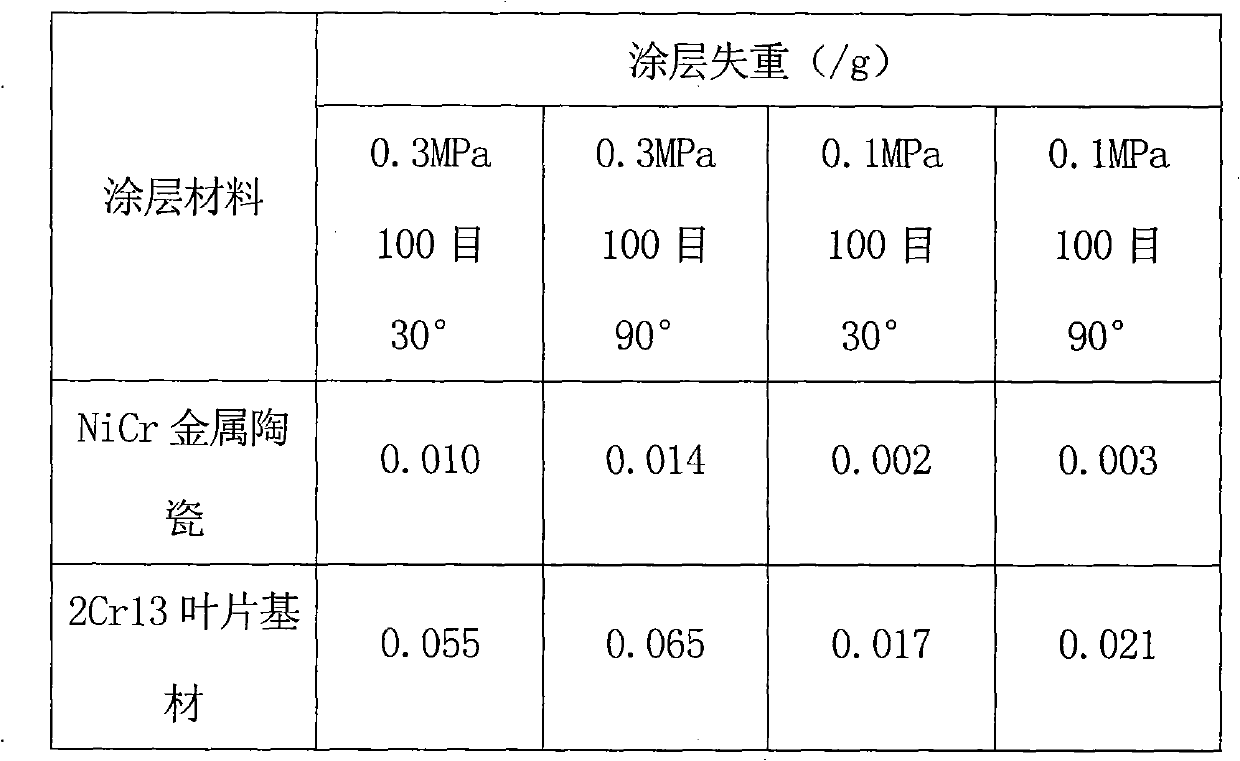
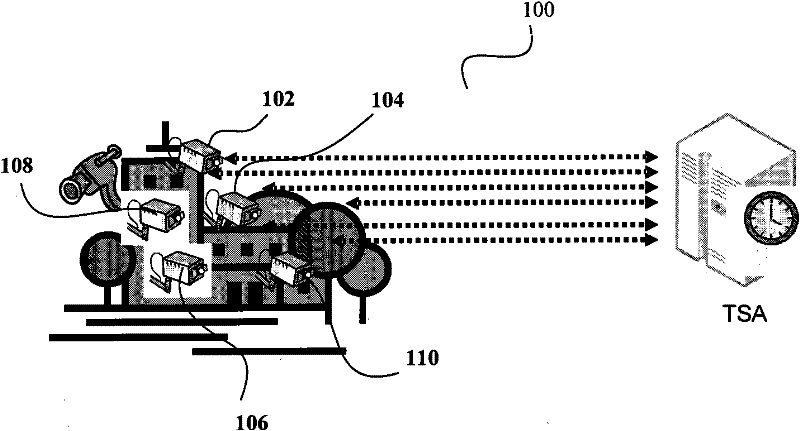
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
8369results about How to "Achieve protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
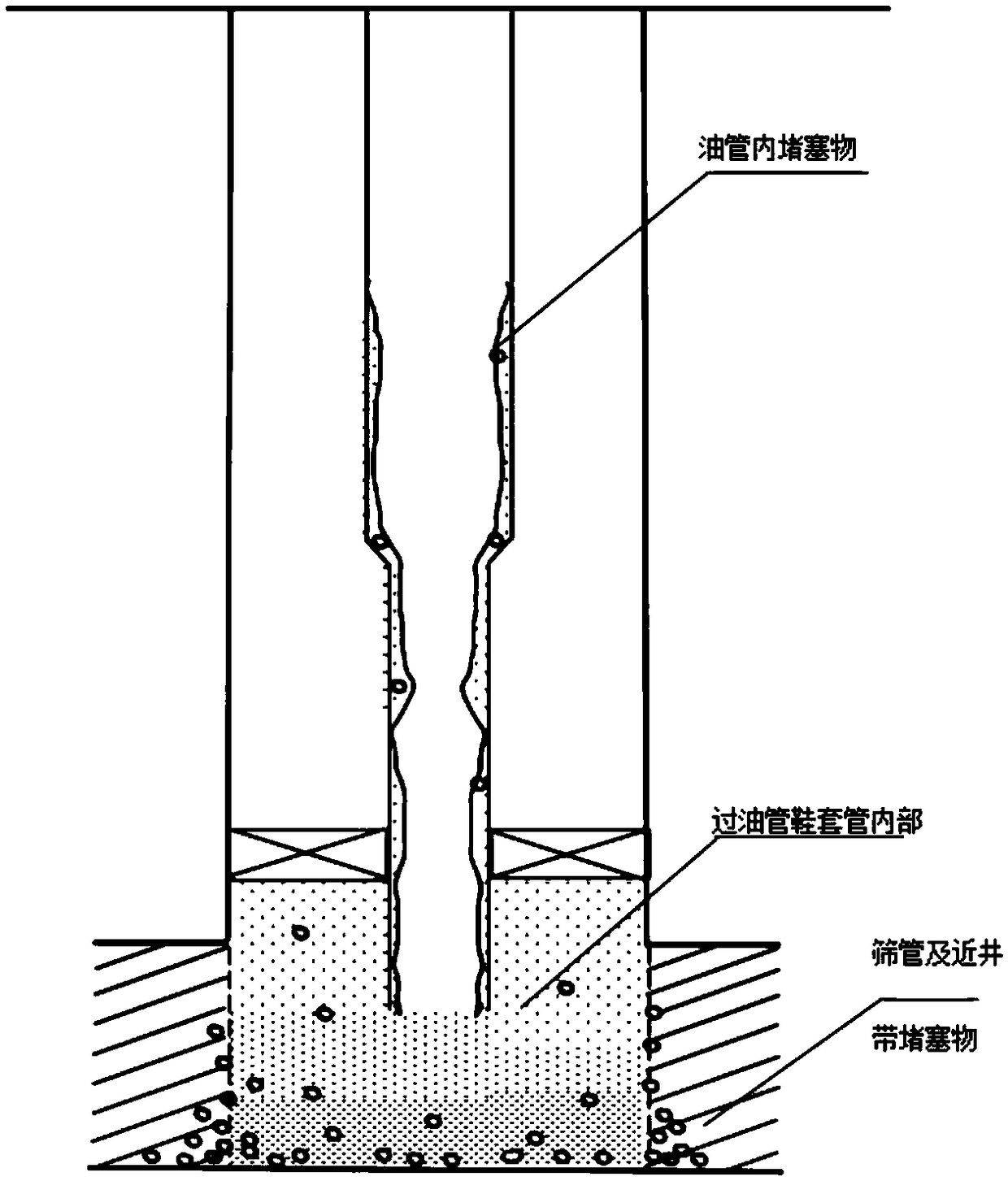
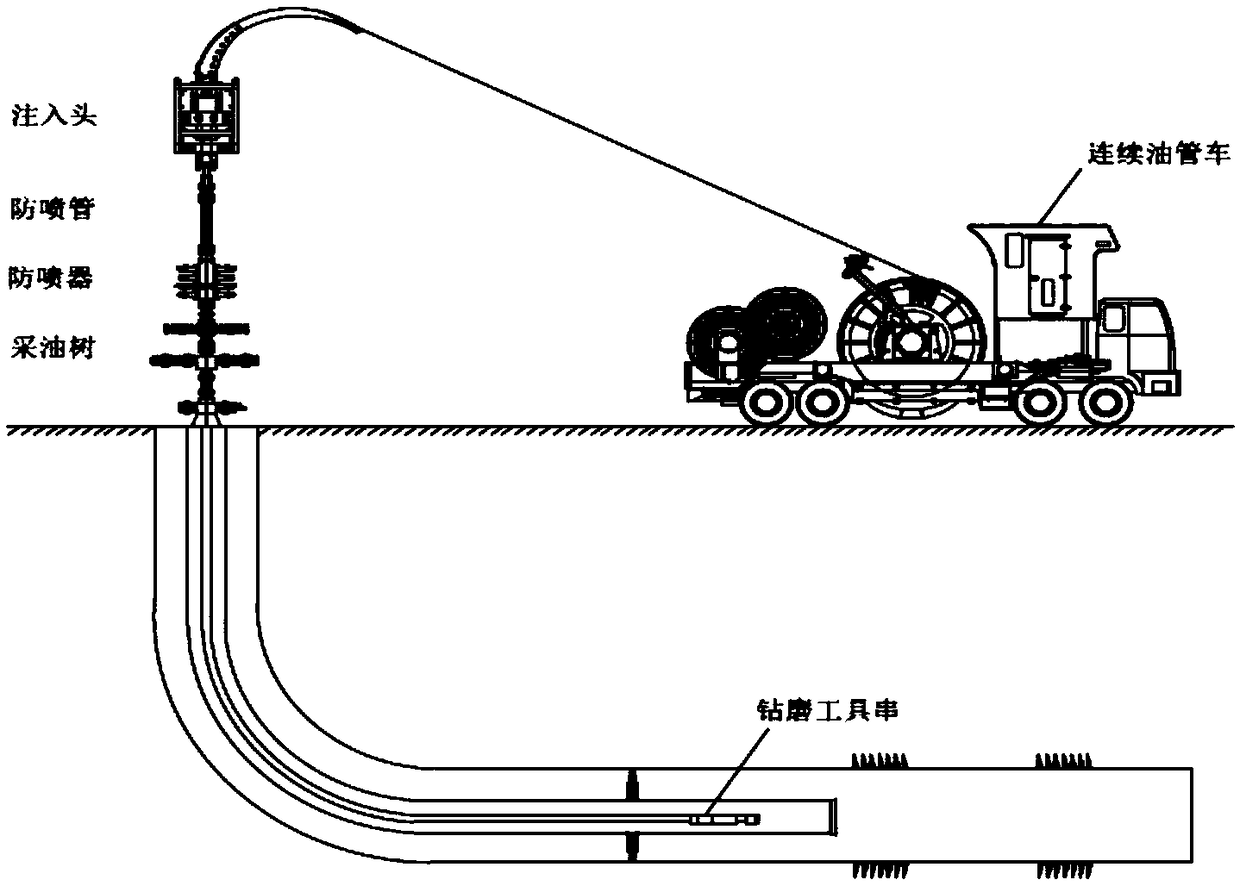
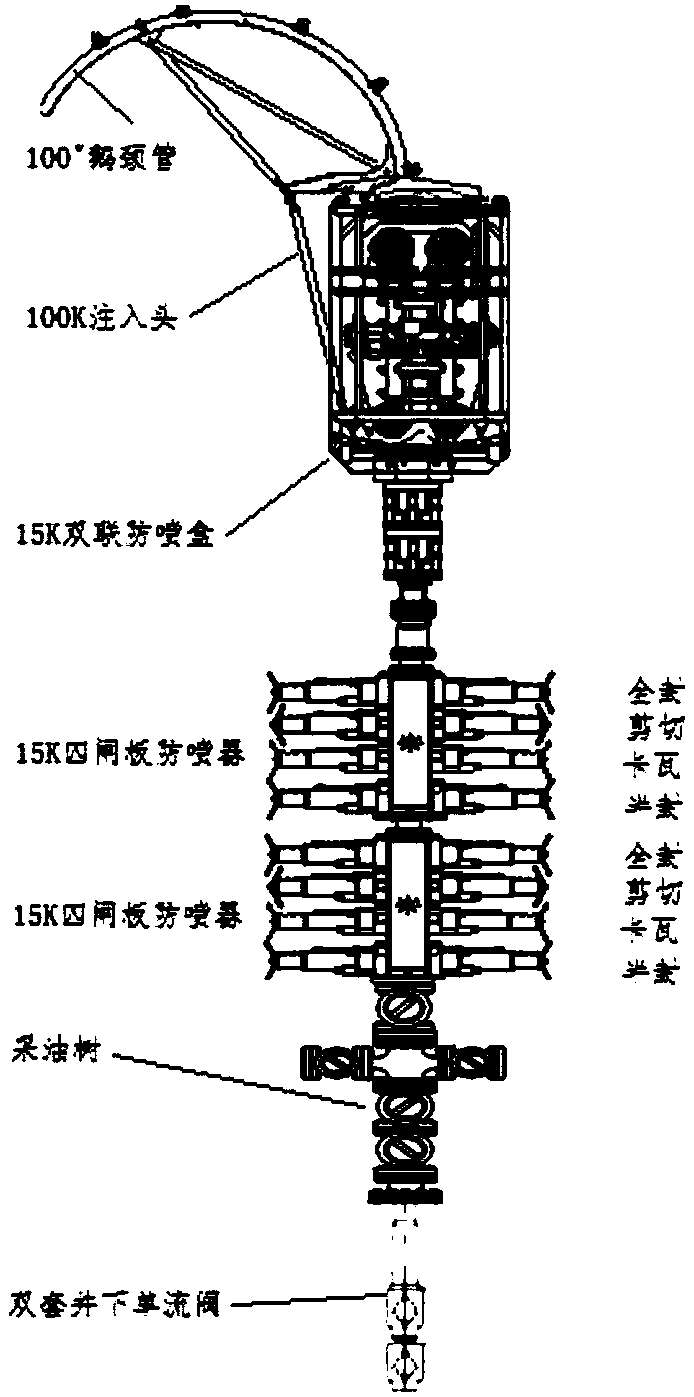
Method for three-layer unblocking for immovable string
InactiveCN108979569AEasy constructionLow costCleaning apparatusFluid removalCoiled tubingEngineering
The invention relates to the technical field of unblocking of oilfield gas wells, in particular to a method for three-layer unblocking for an immovable string. The three-layer unblocking includes oiltube internal unblocking, through-tubing casing internal unblocking and unblocking of immediate vicinity of a wellbore. The method comprises the following specific steps: arranging coiled tubing wellcontrol equipment at the position of an inlet of a high-pressure gas well; arranging a circulating working liquid sand removal system on the ground; and carrying downhole tools and delivering unblocking liquid by coiled tubing to realize three-layer unblocking. The method is proposed for a blocked gas well of an oilfield, the coiled tubing is used as a carrier of unblocking tools, and used as a deliverer for unlocking liquid. The method is simple to construct, the cost is saved, well control is safe, reservoir protection is implemented, occupied area is small, the method runs safely and reliably, and the requirements for unblocking operation of a high-pressure gas well of an oilfield can be met completely.
Owner:JEREH ENERGY SERVICES
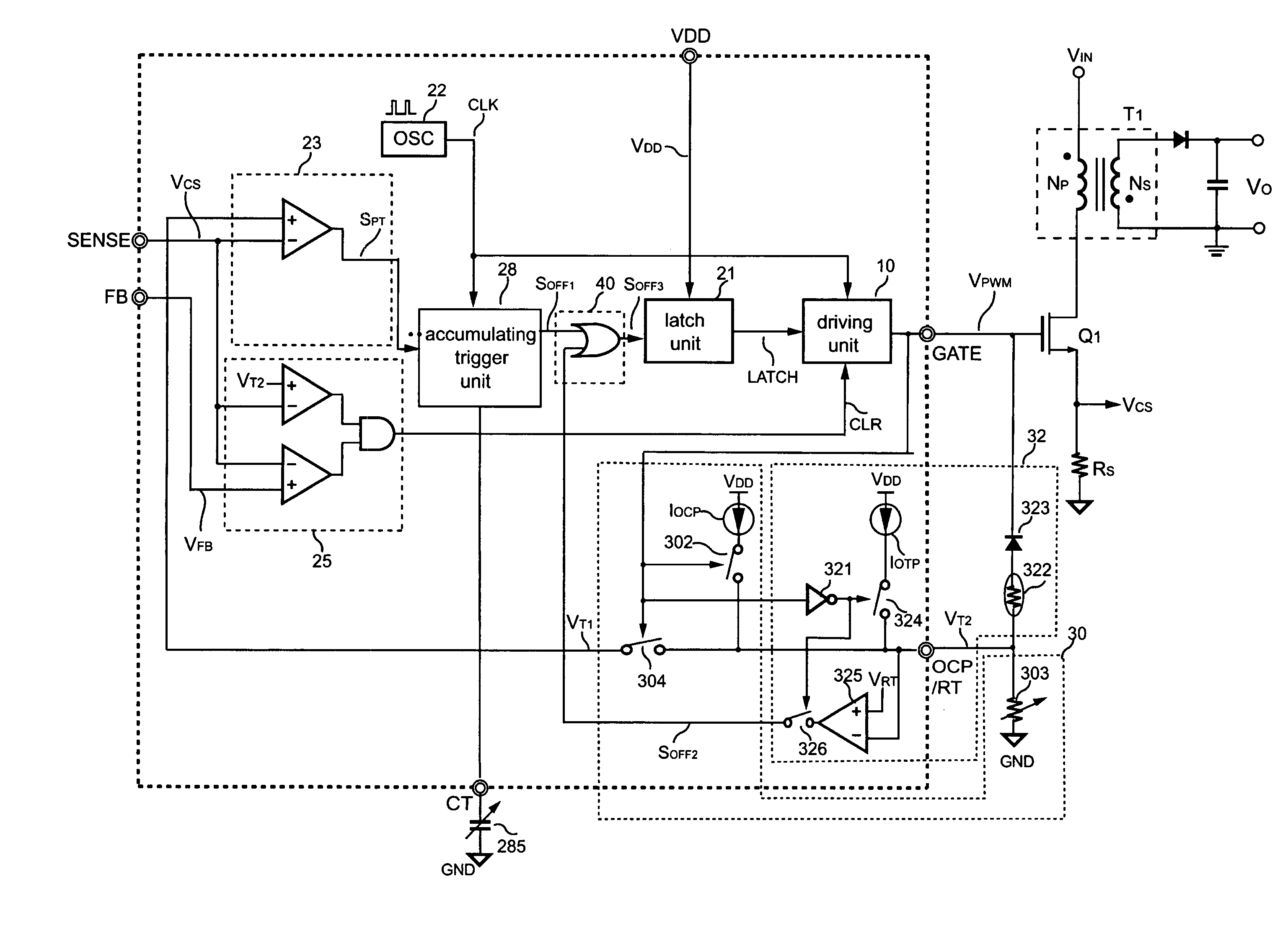
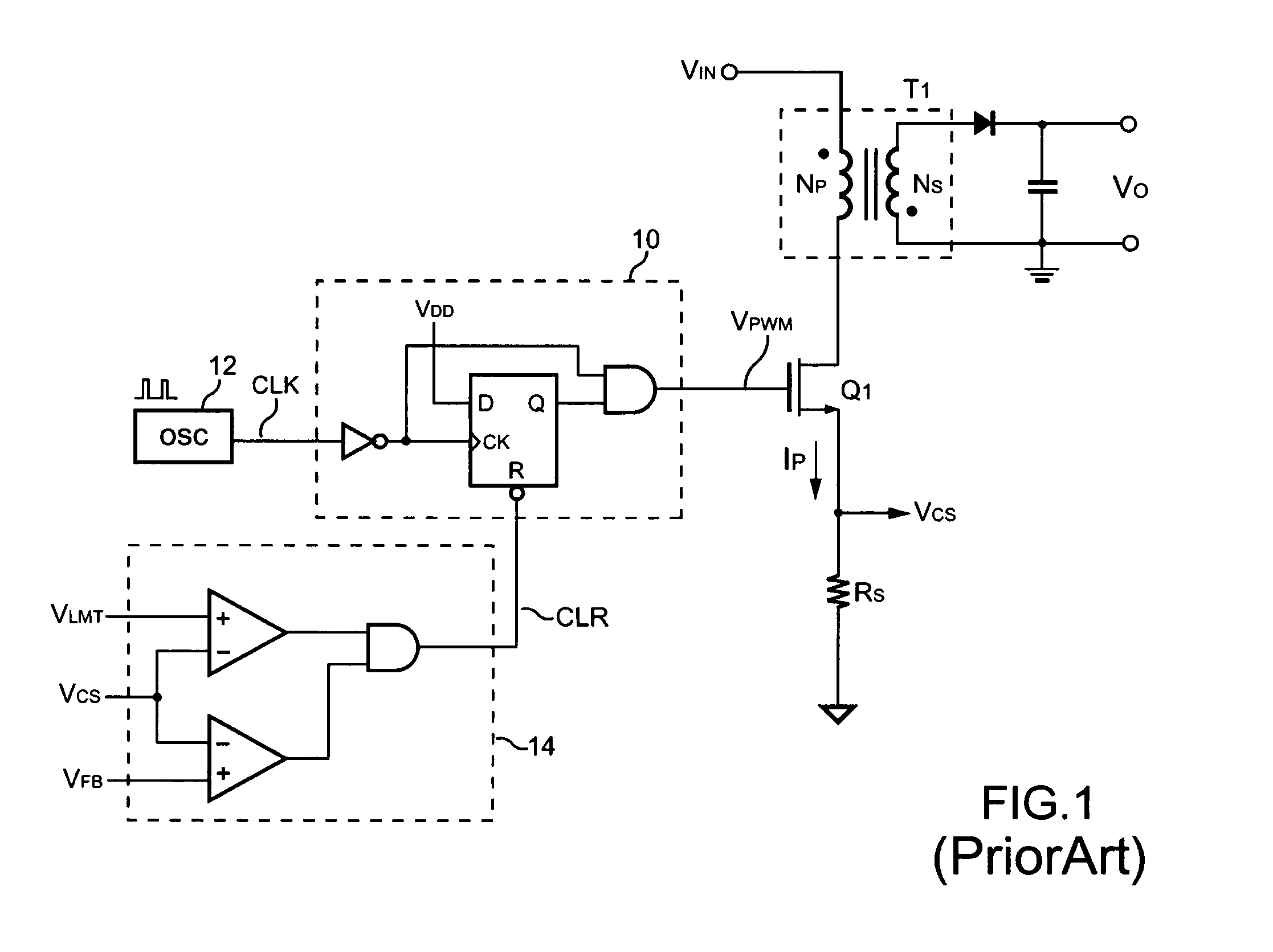
Over-power protection apparatus with programmable over-current threshold
ActiveUS7149098B1Achieve protectionParameter calibration/settingDc-dc conversionCurrent thresholdEngineering
An over-power protection apparatus with programmable over-current threshold for a power converter is provided. The over-power protection apparatus further provides an over-temperature threshold for protection purposes. The over-power protection apparatus is able to achieve over-power and over-temperature protection in response to the level of the driving signal of the power converter. In addition, the programmable over-current threshold of the present invention can be adjusted in response to various load conditions.
Owner:SEMICON COMPONENTS IND LLC
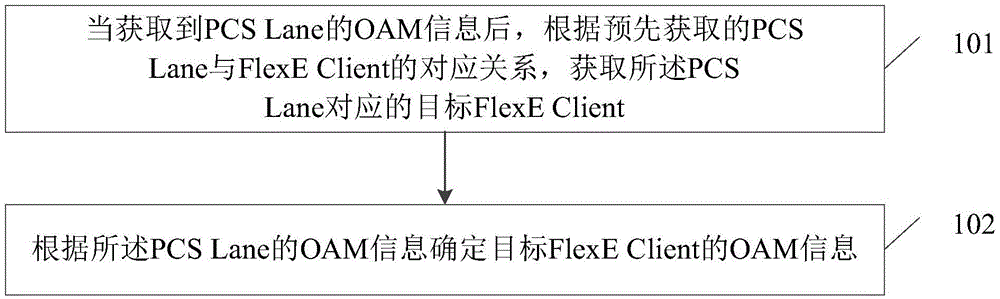
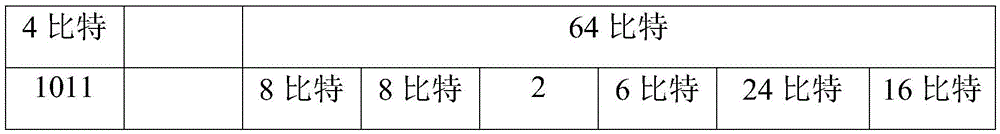
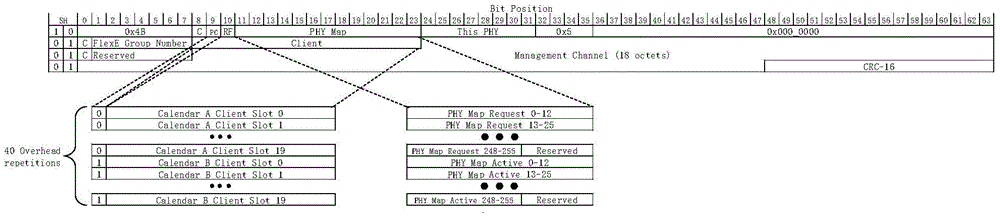
Flexible Ethernet lane management method and apparatus
InactiveCN106612220ARealize managementDoes not cause paralysisData switching by path configurationEthernetPhysical Coding Sublayer
The present invention provides a flexible Ethernet lane management method and apparatus. The method comprises the steps of when OAM information of a PCS Lane is acquired, acquiring a target FlexE Client corresponding to the PCS Lane according to a pre-acquired correspondence between the PCS Lane and the FlexE Client; and determining OAM information of the target FlexE Client according to the OAM information of the PCS Lane.
Owner:ZTE CORP
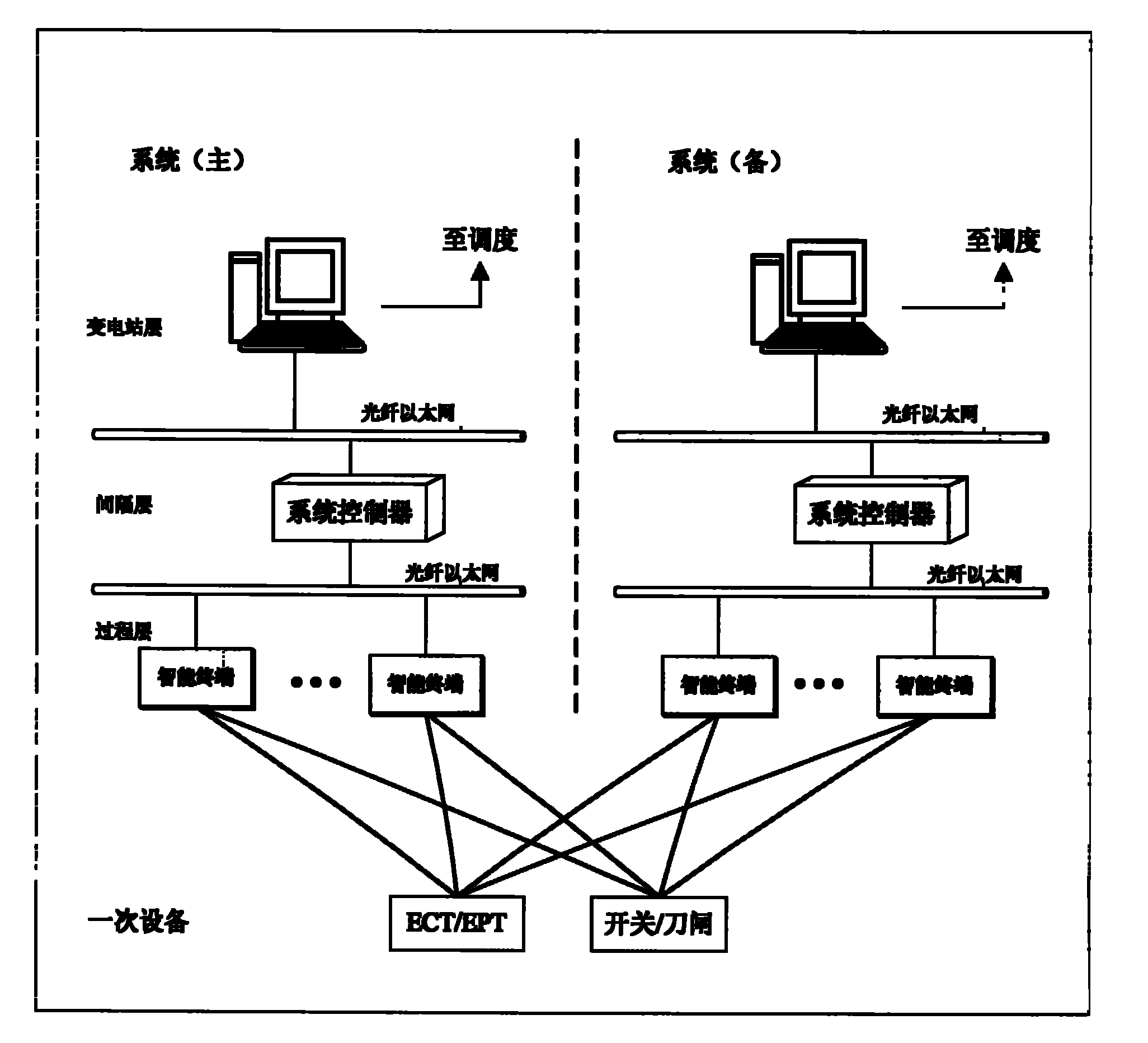
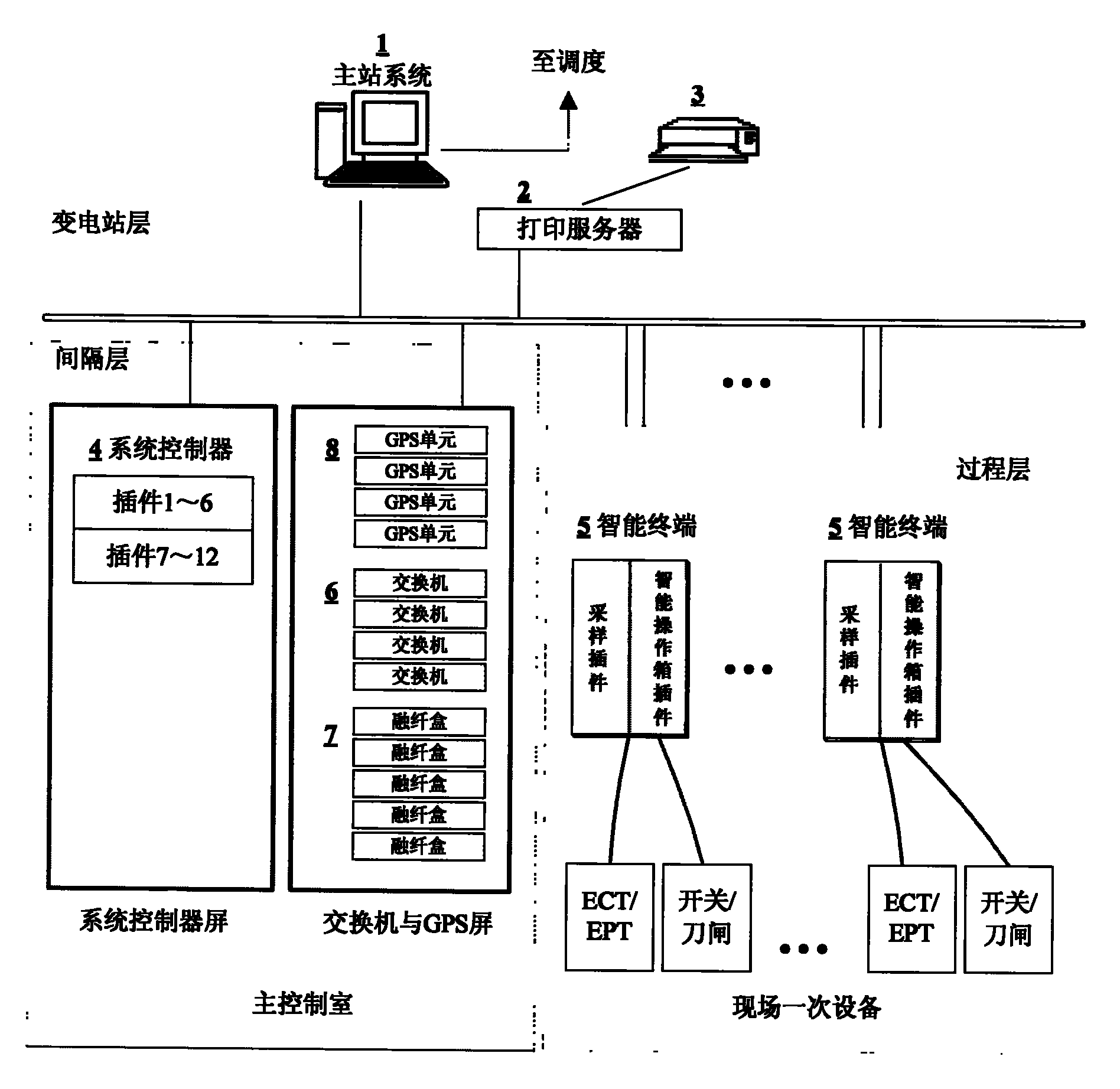
Centralized digital transformer substation system
ActiveCN101789624AFully configuredComprehensive testCircuit arrangementsInformation technology support systemElectric networkEmbedded system
The invention provides a centralized digital transformer substation system. By adopting various new technologies and new devices, a new level centralized multifunctional intelligent device and a system are realized, thereby laying the foundation for the construction of a digital electric network. Based on an IEC 61850 standard, high speed Ethernet exchange and a virtual local area network (VLAN) technology, the system constructs a digital transformer substation information model and a communication network, and realizes sharing of information of the whole substation. On the basis, function integration of a digital transformer substation is realized and a system structure is simplified. A bay level multifunctional intelligent electronic device, i.e. a system controller integrates the functions of protection, measurement and control, wave recording and the like into a whole, and greatly simplifies the bay level device and wire connection; a process level intelligent terminal integrates the functions of a merging unit and an intelligent operation box into a whole; and all devices of each level provide models and interfaces conforming to the IEC 61850 standard.
Owner:CHINA ELECTRIC POWER RES INST +1
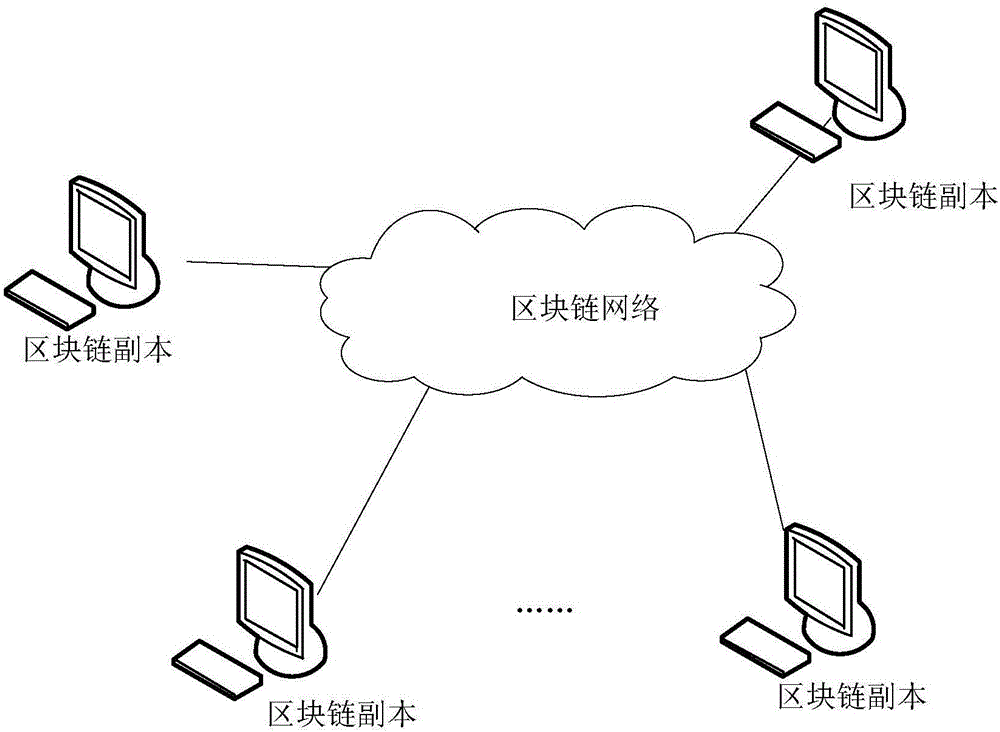
Right control method, apparatus, system and node device of block chain
ActiveCN106796688AEnsure safetyGuaranteed privacySecuring communicationProtocol authorisationChain networkBlockchain
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
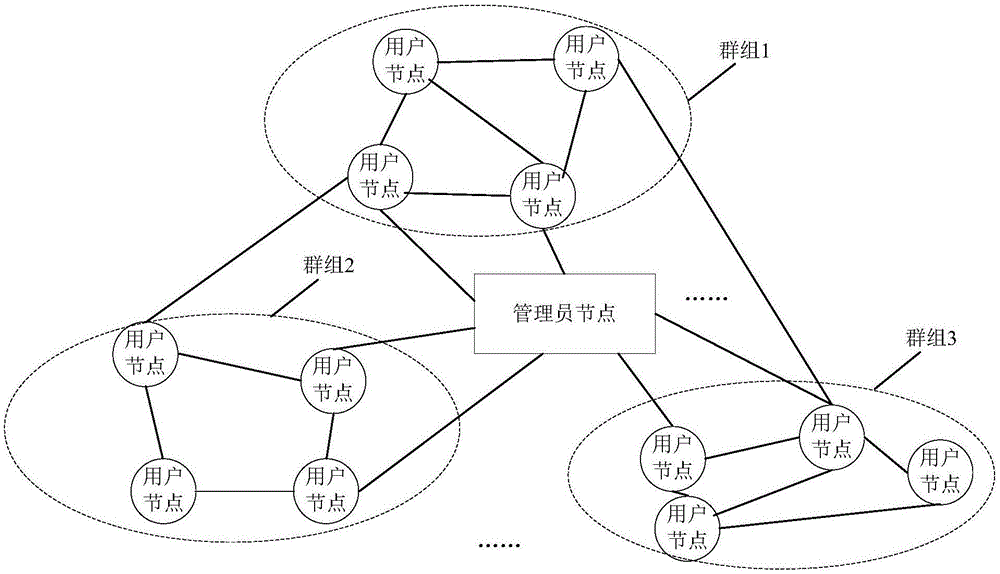
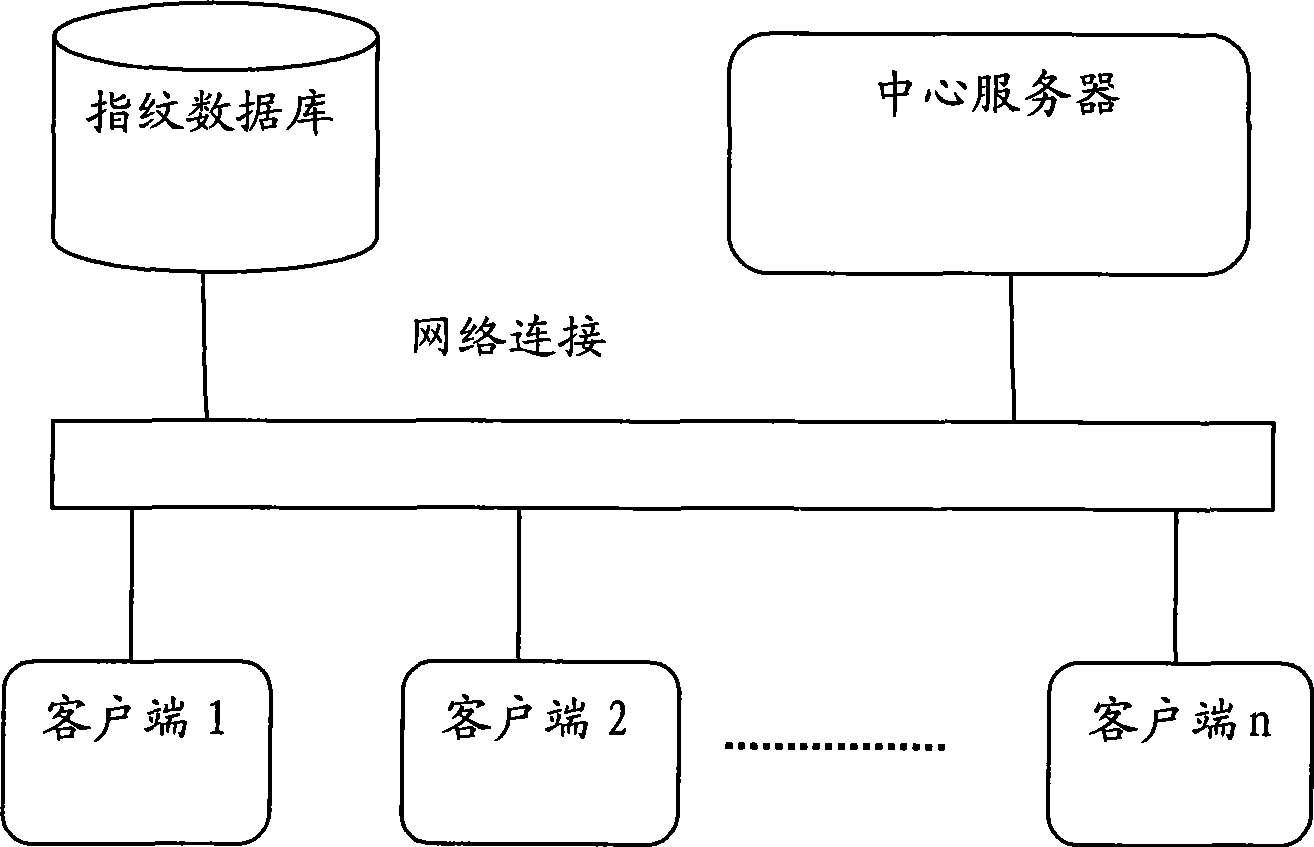
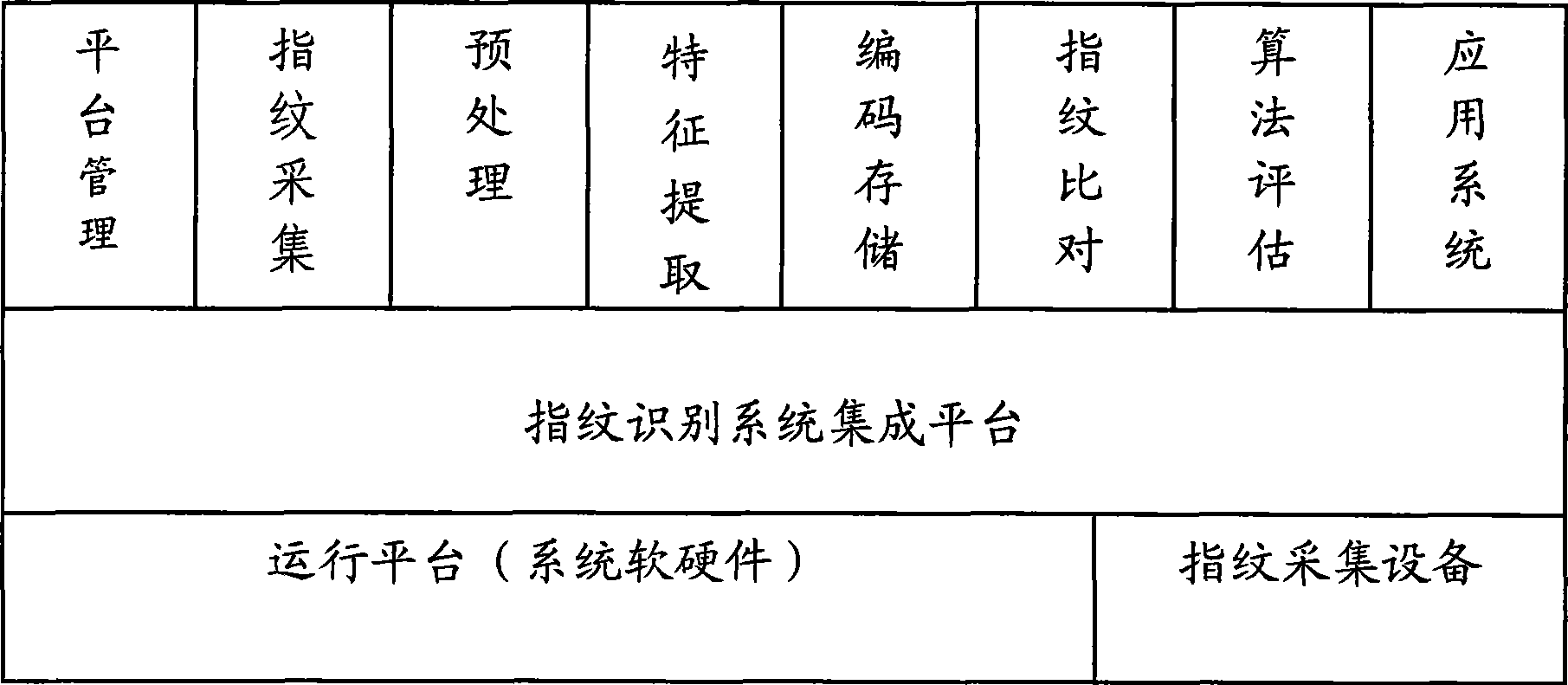
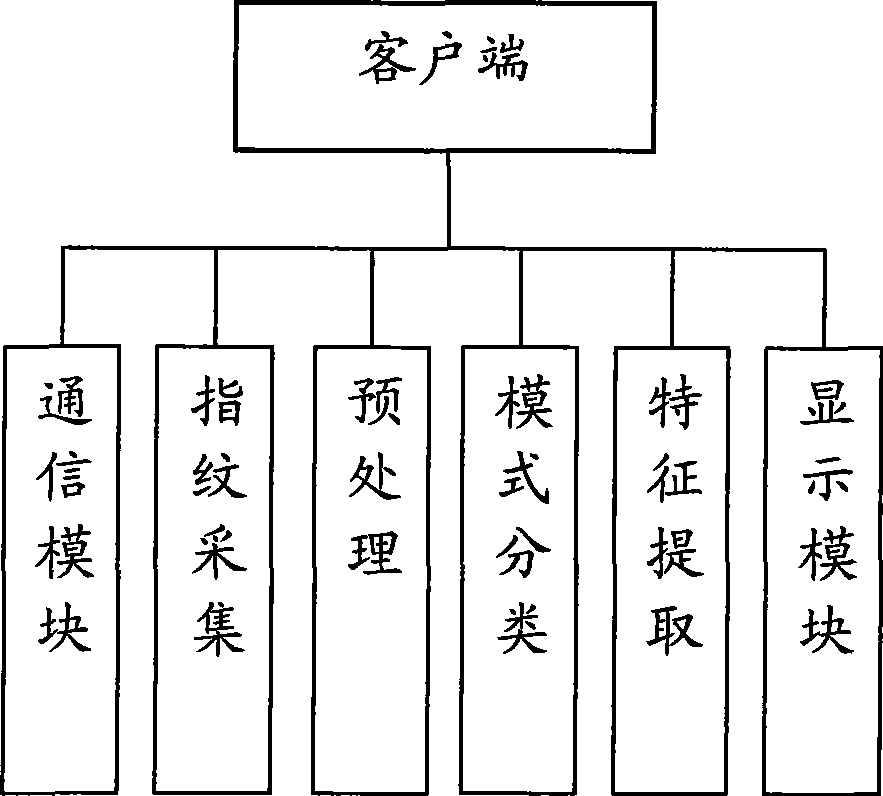
Fingerprint recognition system and control method
InactiveCN101414351AAvoid accessEasy constructionUser identity/authority verificationCharacter and pattern recognitionCapital investmentFingerprint database
The invention discloses a fingerprint identifying system which comprises three large parts of a fingerprint database, a central server and a client terminal; the fingerprint database is mainly used for memorizing the fingerprint characteristic information after digital coding; the central server is mainly responsible for validating the validity of the client terminal, receiving the fingerprint characteristic data, comparing the characteristics and returning the fingerprint identifying result; the client terminal is mainly responsible for collecting the fingerprint, extracting and uploading the fingerprint characteristic data. The system overcomes the defects of the prior art, can provide an online / offline fingerprint identifying system the basic algorithm library of which can be seamlessly expanded and the functions of which can be selected and matched. The fingerprint identifying system can lead a user to obtain the ID identification and authentication services with high quality under the situation of not needing a great amount of capital investment.
Owner:章毅 +2
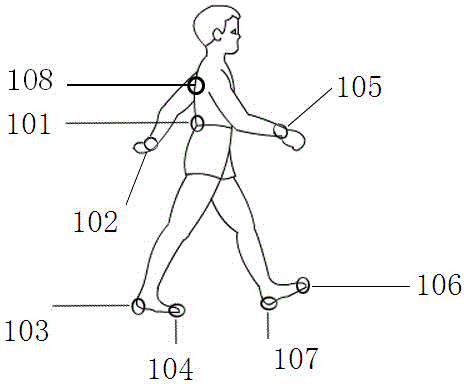
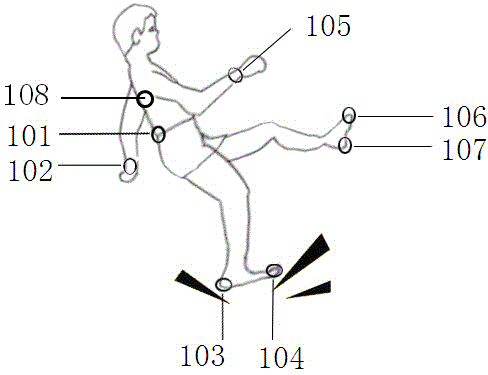
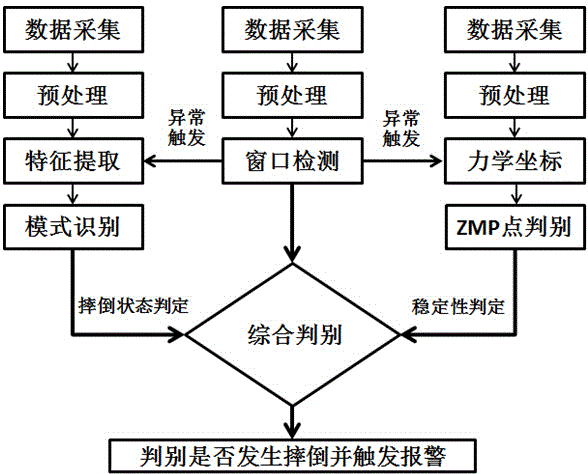
Wearing type dynamic real-time fall detection method and device
ActiveCN103976739AAchieve protectionHigh precisionCharacter and pattern recognitionDiagnostic recording/measuringHuman bodyHardware structure
The invention discloses a wearing type dynamic real-time fall detection method and device. The wearing type detection device comprises a specific hardware structure consisting of a foot part, a waist part, a wrist part and a back part. According to the dynamic real-time fall detection method, real-time judgment of the fall of human body in any state can be finished. The core algorithm of the detection device comprises a threshold opening logic structure caused by sudden change of gait acceleration, a human body posture dynamic stability judgment algorithm based on zero moment point (ZMP), and a fall mode identification algorithm based on a human body motion database. A complete dynamic real-time detection system is constructed, and the aims of wide application field, low dependence on the application environment and real-time detection are fulfilled. Moreover, the detection method and the detection device are high in accuracy, and have the advantages of low system cost, small system size and good convenience in wearing.
Owner:BEWIS TECH
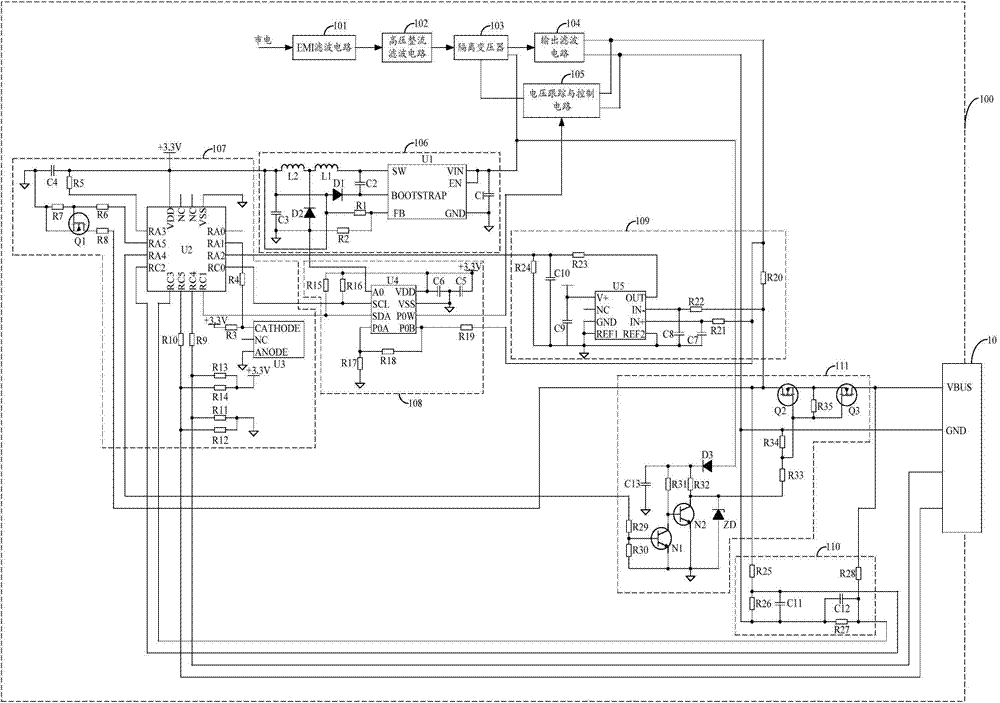
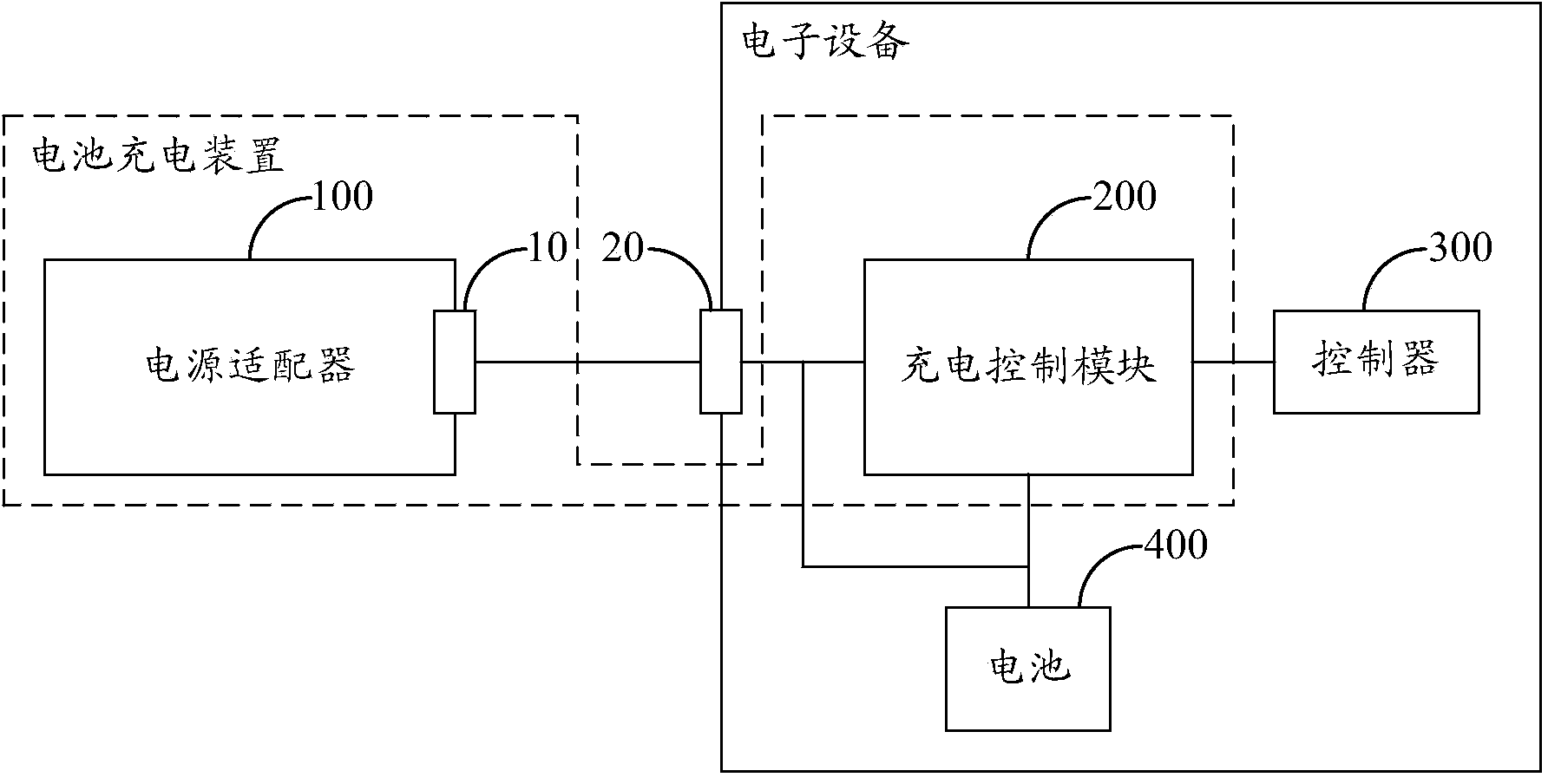
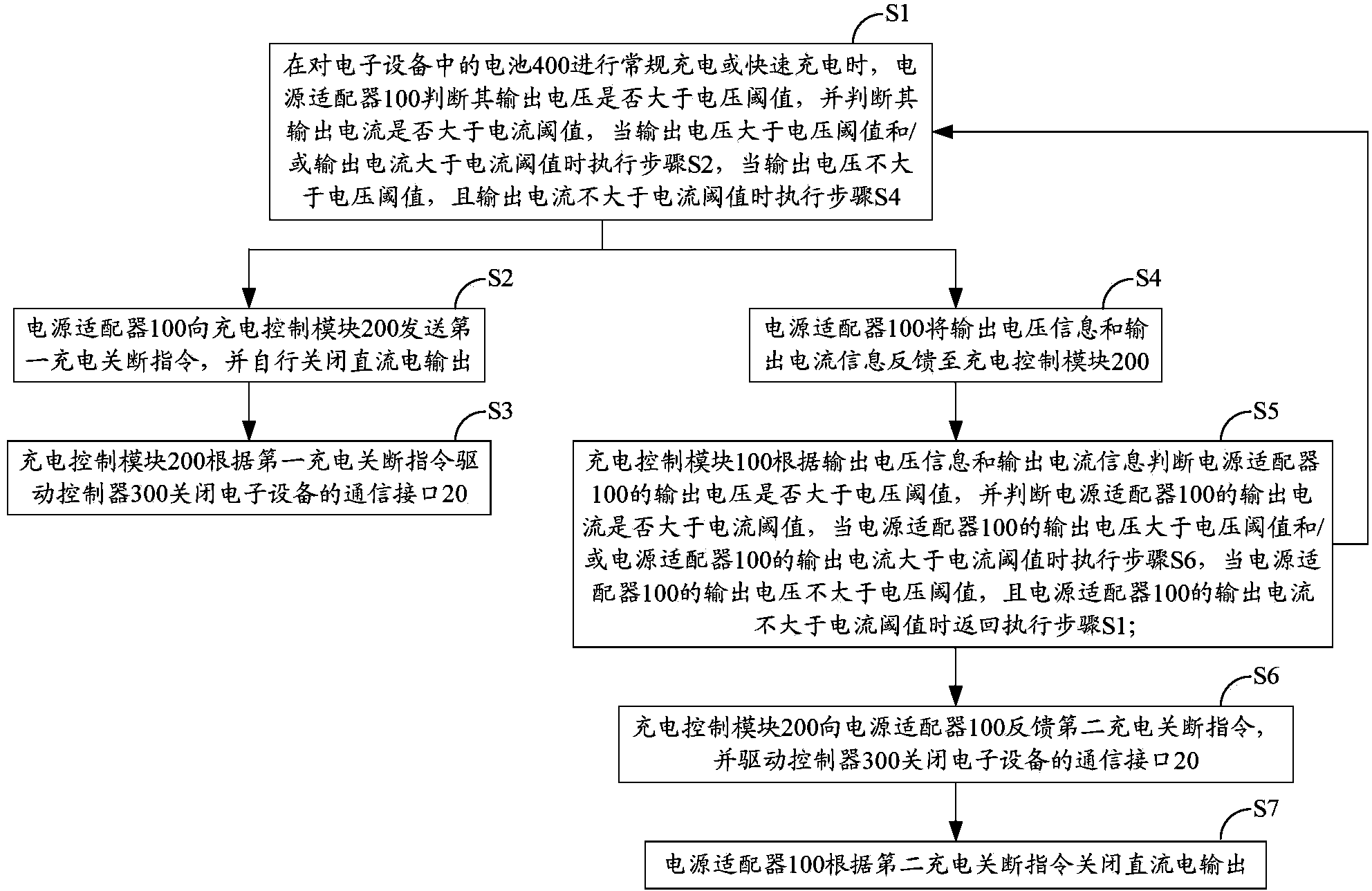
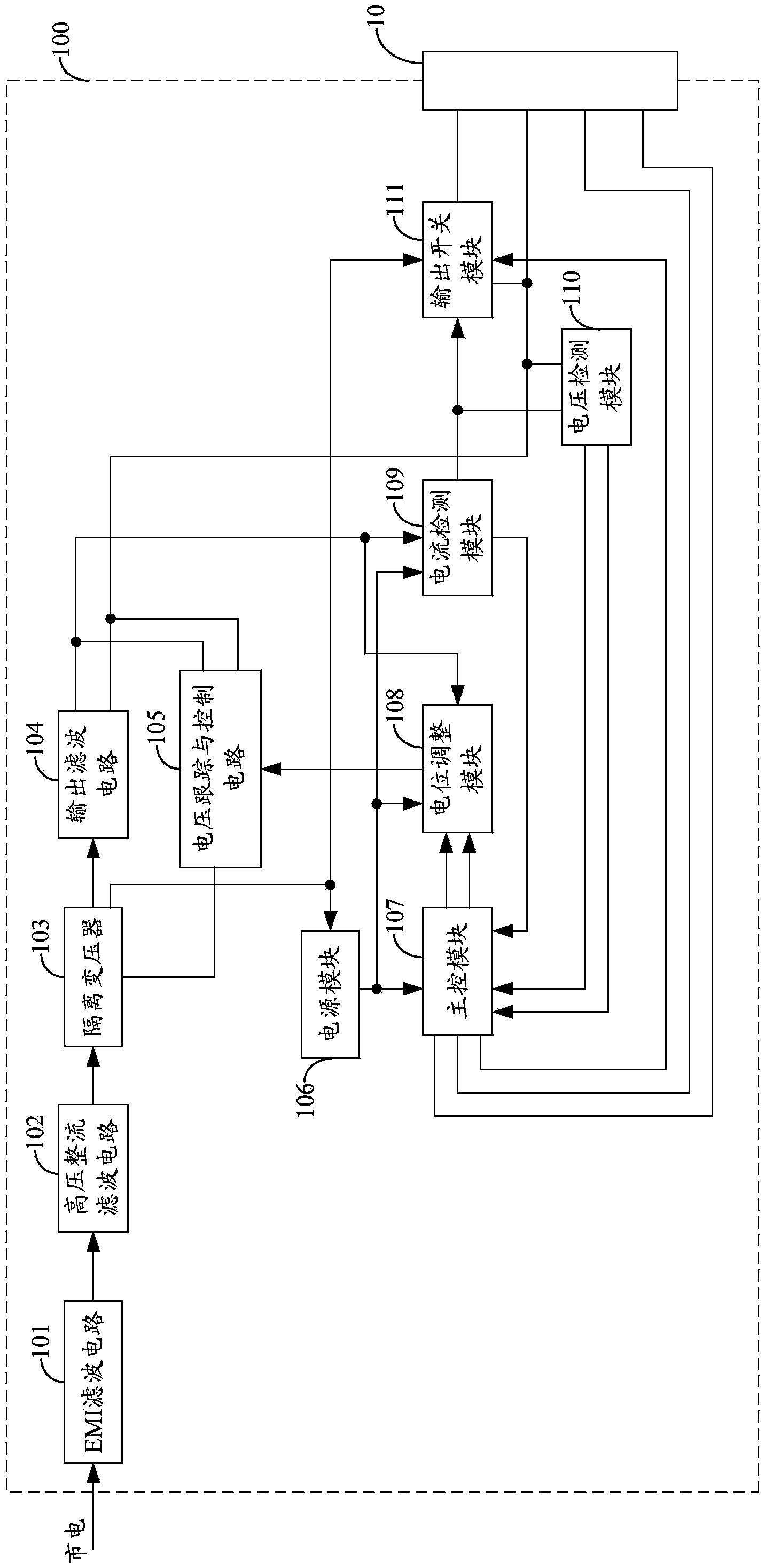
Electronic device and power adapter thereof
ActiveCN103795040AAchieve protectionEmergency protective circuit arrangementsElectric powerElectricityComputer module
The invention belongs to the technical field of charging, and provides an electronic device and a power adapter of the electronic device. The power adapter comprising a power source module, a master control module, an electric level adjustment module, a current detection module, a voltage detection module and an output switch module is provided for the electronic device, the master control module judges whether the output current of the power adapter is larger than a current threshold and whether the output voltage of the power adapter is larger than a voltage threshold, and if the output current is larger than the current threshold and / or the output voltage is larger than the voltage threshold, the master control module controls the output switch module to close direct current electricity output of the power adapter. In addition, if the electronic device judges that the output of the power adapter has an overcurrent and / or overvoltage phenomenon and feeds a charging closing instruction back to the master control module, the master control module controls the output switch module to close the direct current electricity output of the power adapter according to the charging closing instruction, and therefore the purpose of achieving overcurrent and / or overvoltage protection is achieved for a battery.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Sensitive data protection system and method of data circulation and transaction of big data platform
ActiveCN105653981AEffective measureAchieve protectionDigital data protectionData acquisitionData file
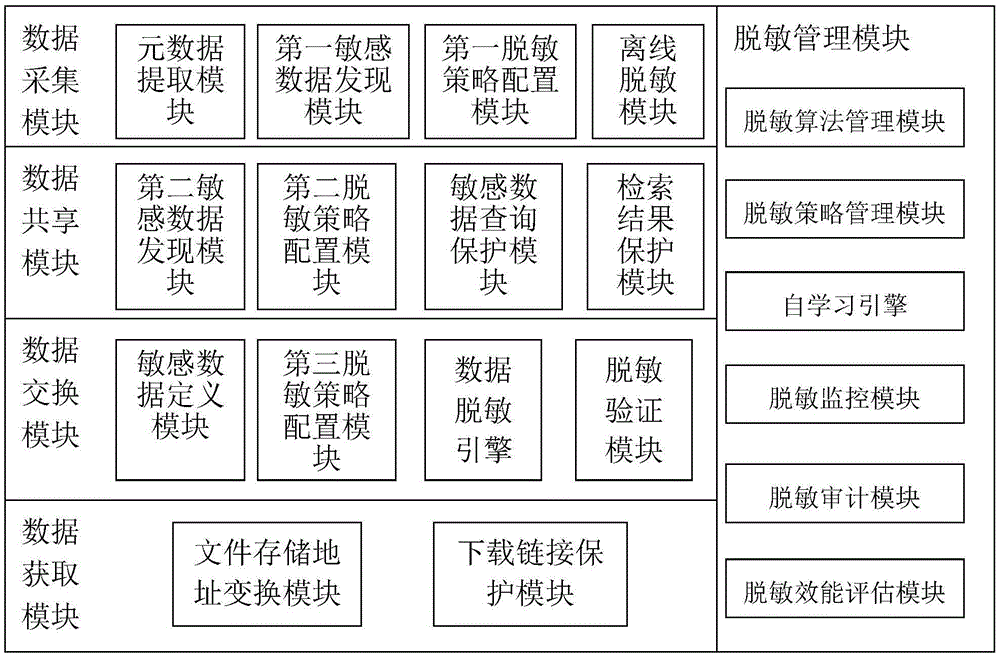
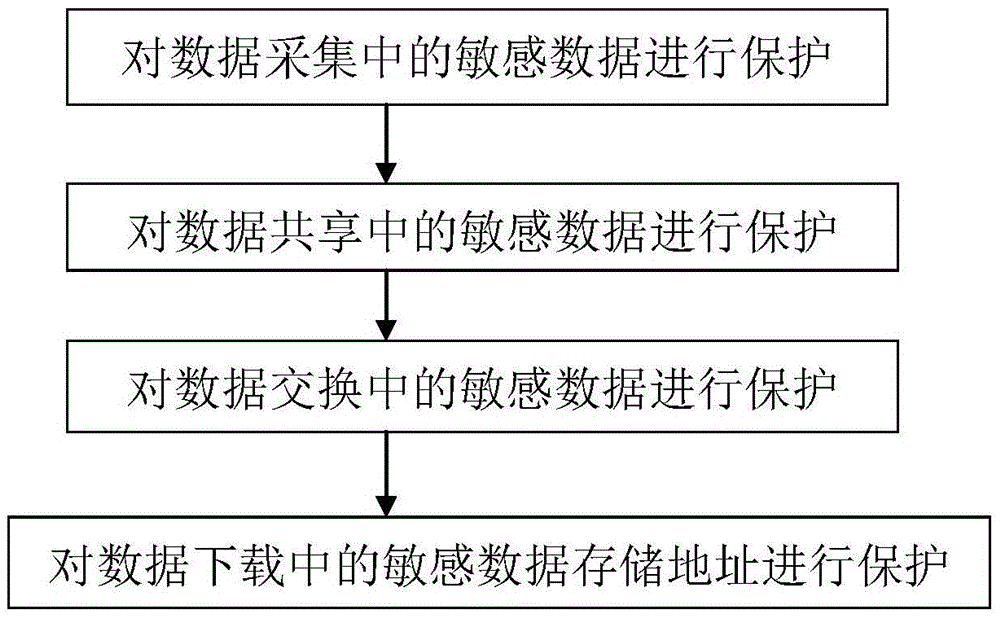
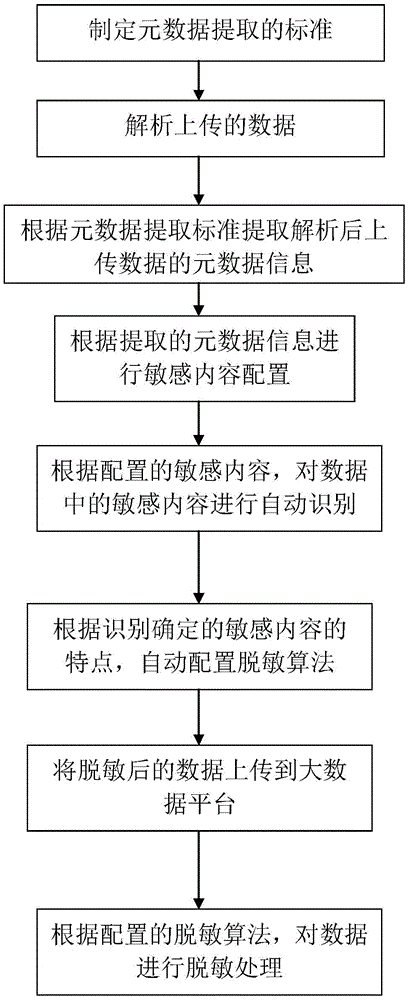
The invention discloses a sensitive data protection system of the data circulation and transaction of a big data platform. The sensitive data protection system is characterized in that the sensitive data protection system of the data circulation and transaction of the big data platform comprises a data collection module, a data sharing module, a data exchange module, a data acquisition module and a desensitization management module, wherein the data collection module discovers sensitive contents in data collection and carries out protection processing on the sensitive contents; the data sharing module carries out the protection processing on the sensitive data in a data sharing process; the data exchange module carries out desensitization processing on a relative sensitive data configuration desensitization strategy in a data exchange process; the data acquisition module protects a data file downloading link and a storage address in a data acquisition process; and the desensitization management module manages, monitors and audits the desensitization and the protection processing of the sensitive data. The invention also discloses a sensitive data protection method of the data circulation and transaction of the big data platform.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
Biomass pyrolysis liquefied technique and double tower apparatus system thereof
InactiveCN1730177AImprove pyrolysis efficiencyWell mixedSolid waste disposalGas phaseProcess engineering
The invention relates to a biomass analgesic liquidation method and its twin-tower set system, the processes of which comprise the following steps: sending biomass to pyrolytic reaction tower and blending it with high-heat fluidized gas to subject biomass to pyrolytic cracking; separating thermal cracking gas with carbon residue and ash content in separator; and condensing thermal cracking gas to biological oil in condenser. In the process, heat-carrying agent is exported from pyrolytic reaction tower along with thermal cracking gas, carbon residue and so on, and carbon residue is used to preheat heat-carrying agent. The invention is special for heat-carrying agent heating tower to burn carbon residue and primary separator to separate heat-carrying agent, carbon residue and other materials. The invention can not only increase circulation rate to ensure uniform and stable temperature field in pyrolytic reaction tower, higher heating rates and shorter detention period of gas phase, but also make use of carbon residue as heat source by using existing apparatus.
Owner:CHONGQING UNIV
Terminal and battery charging control device and method
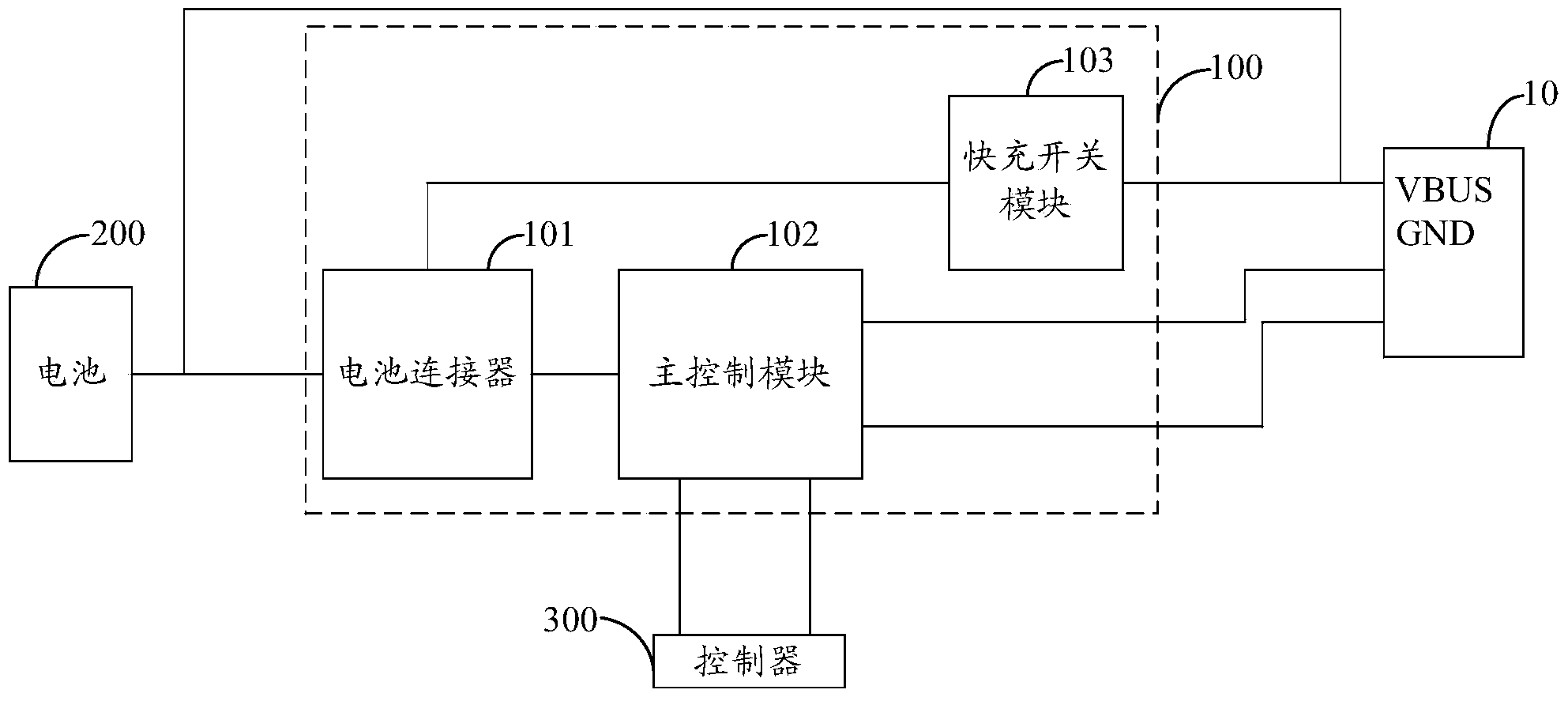
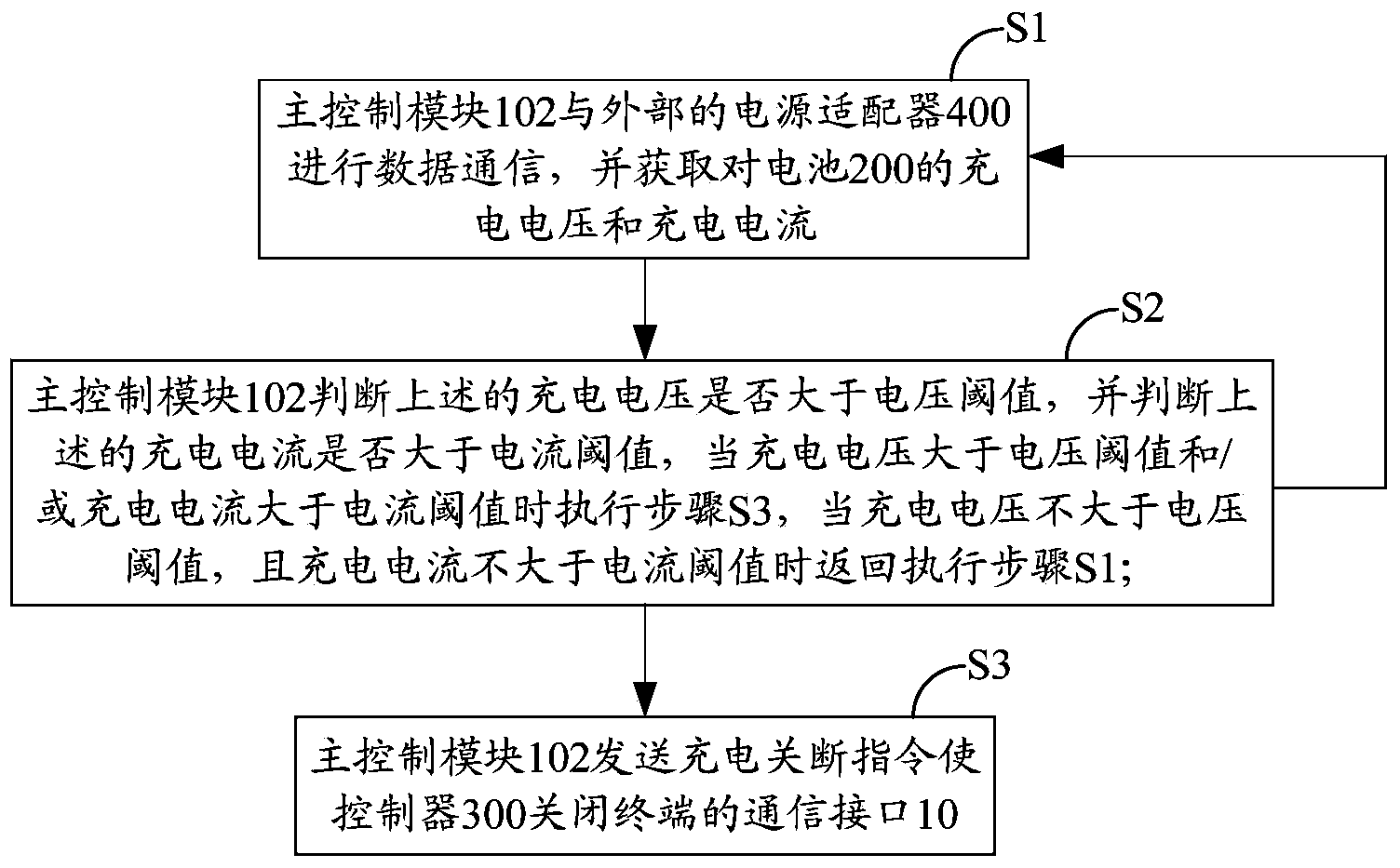
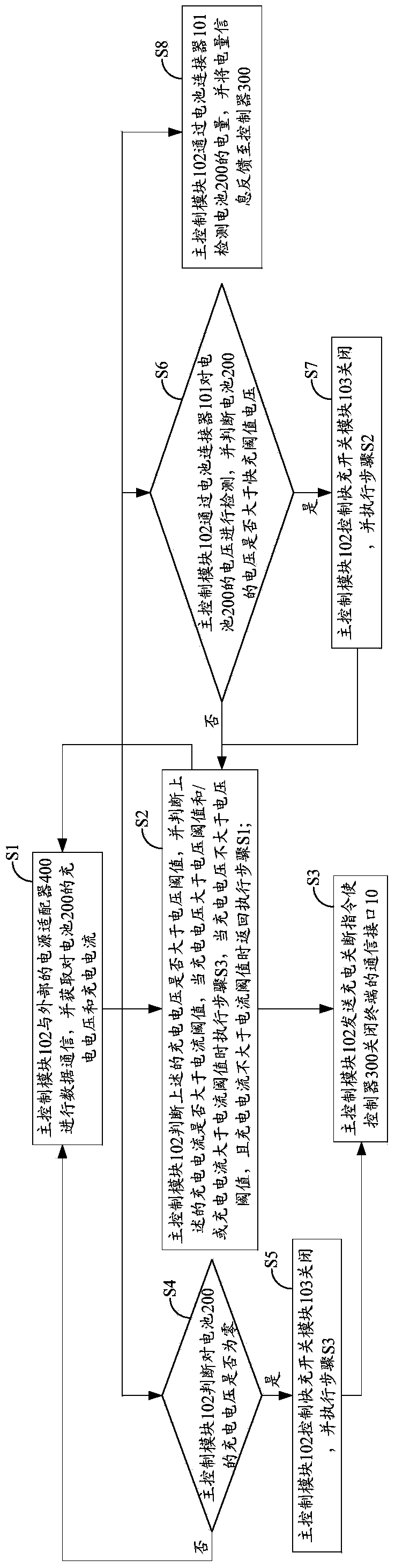
ActiveCN103779907AAchieve overvoltageAchieve protectionEmergency protective circuit arrangementsSecondary cells charging/dischargingOvervoltageCommunication interface
The invention belongs to the technical field of charging and provides a terminal, and a battery charging control device and method. The battery charging control device comprising a battery connector, a master control module and a rapid charging switch module is adopted, in the process of carrying out conventional charging or quick charging on a battery in the terminal, data communication is carried out between the master control module and an external power adapter through a communication interface of the terminal, and the charging voltage and the charging current of the battery are obtained. If the charging voltage is larger than the voltage threshold value and / or the charging current is larger than the current threshold value, the master control module sends a charging cut-off instruction to enable a controller of the terminal to shut down the communication interface of the terminal, so the purpose of overvoltage and / or overcurrent protection on the battery is achieved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
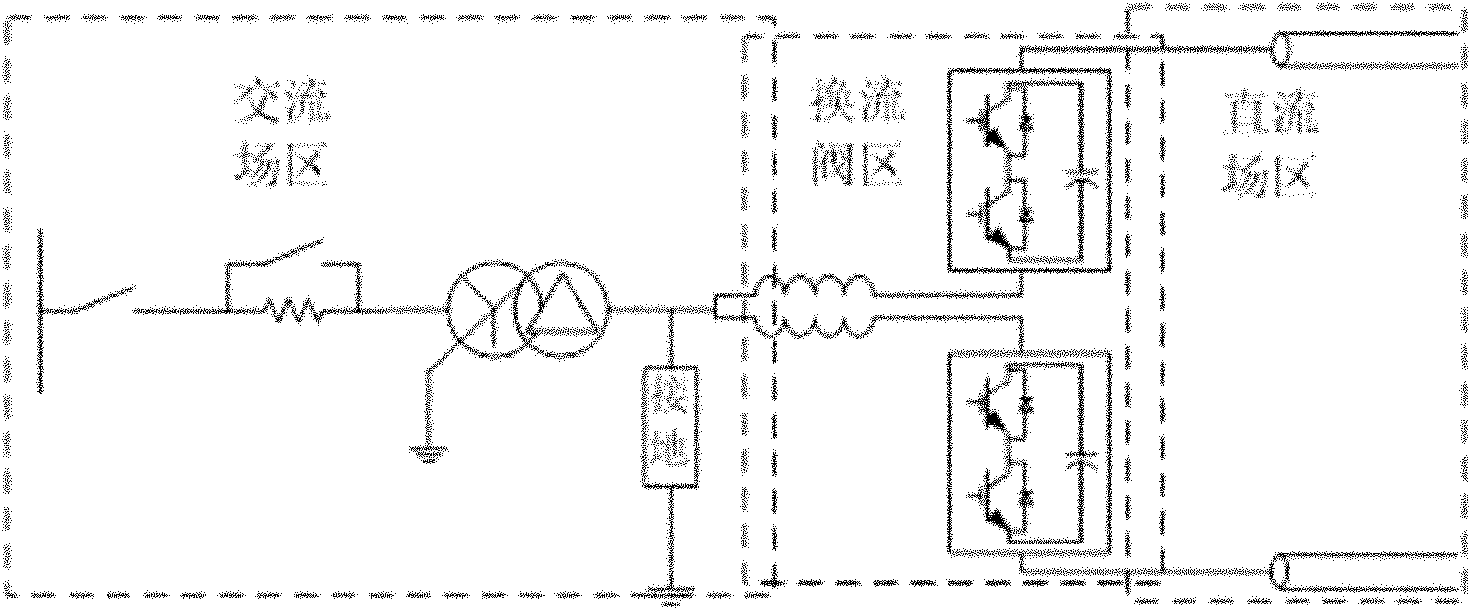
Protection configuration method of flexible direct-current (DC) transmission system of modular multiple-level converter
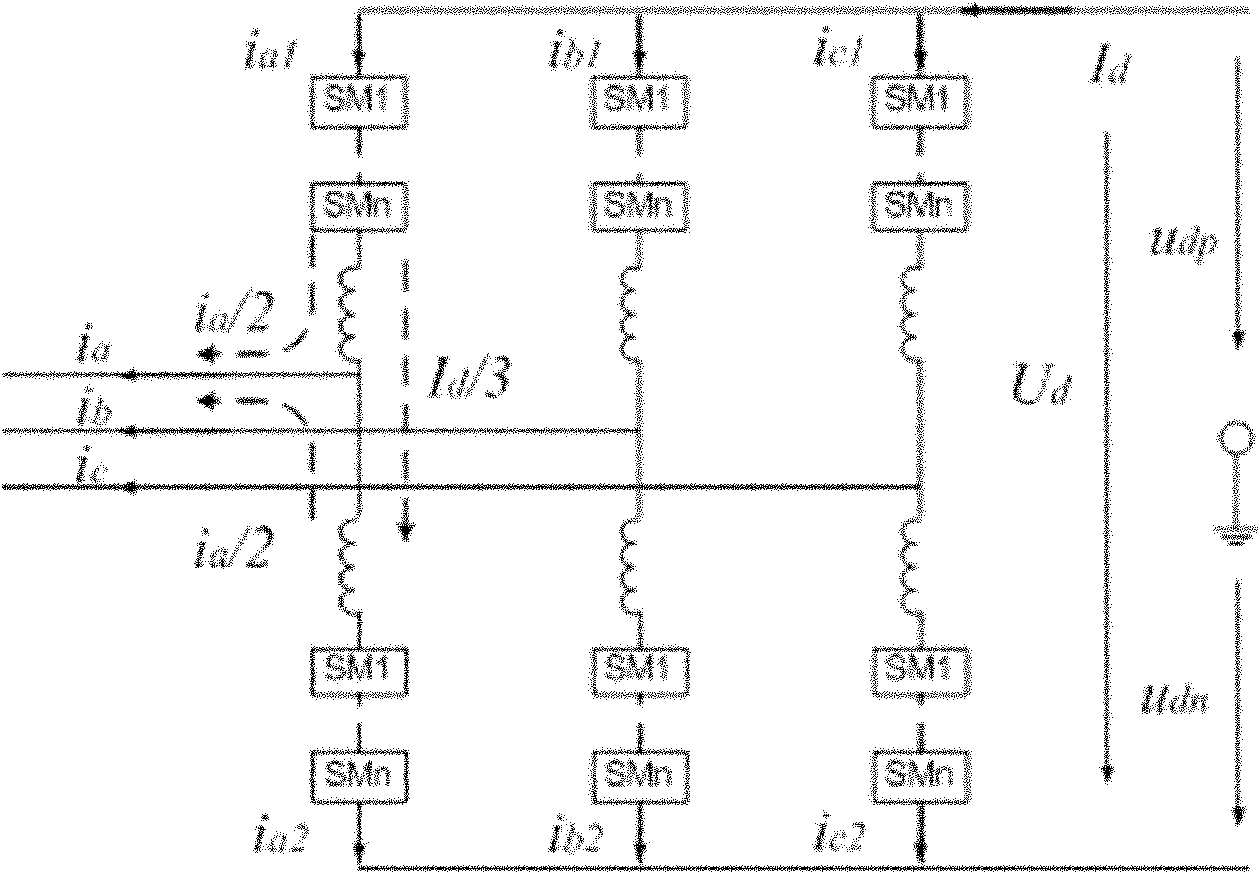
ActiveCN102130441ARapid isolationAccurate isolationEmergency protective circuit arrangementsAc-dc conversionComputer moduleEngineering
The invention relates to a protection configuration method of a flexible direct-current (DC) transmission system of a modular multiple-level converter, which comprises the steps of: using three layers of protection configuration, i.e., a submodule layer, a converter valve layer and a convertor station layer; setting a submodule layer protection function in a submodule controller; setting in a valve based controller (VBC) by the converter valve layer aiming at a failure protection function of a single converter valve; and realizing functions of failure protection of the converter station layer and a DC system in a system control protection equipment PCP (Primary Control Program). The method provided by the invention ensures that the flexible DC transmission system can rapidly carry out a protection action under an abnormal working condition, prevents overstress from continuously developing and isolates a failure assembly.
Owner:CHINA ELECTRIC POWER RES INST +1
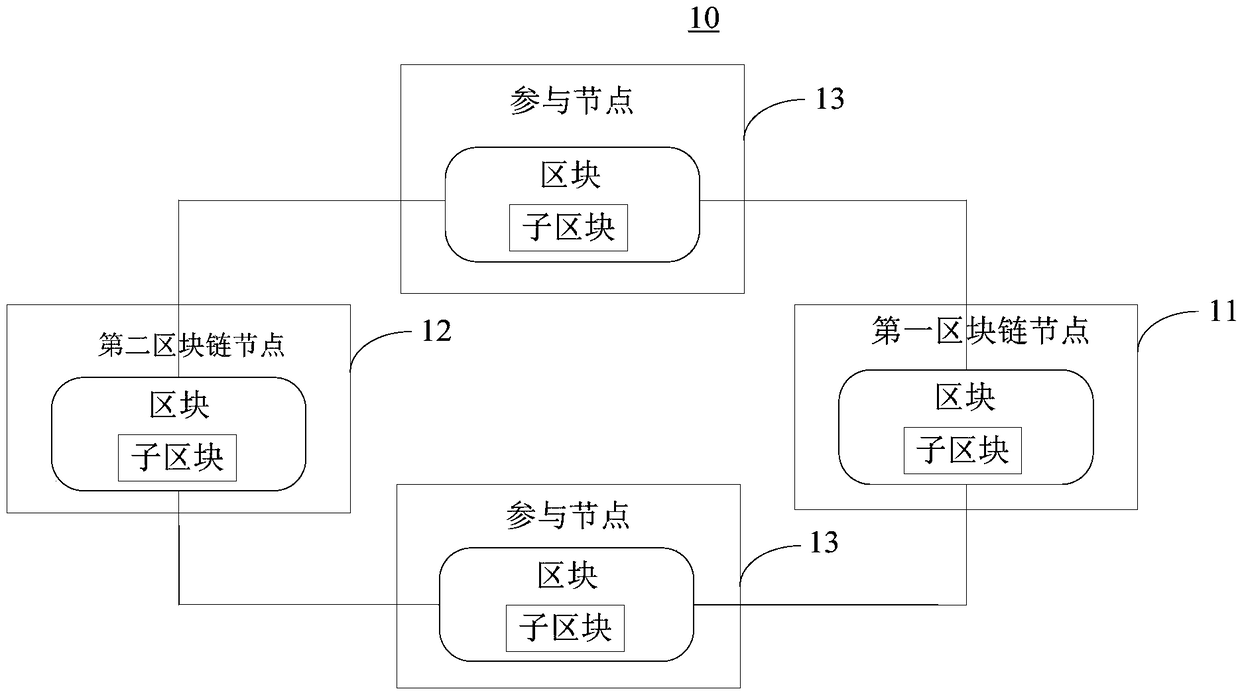
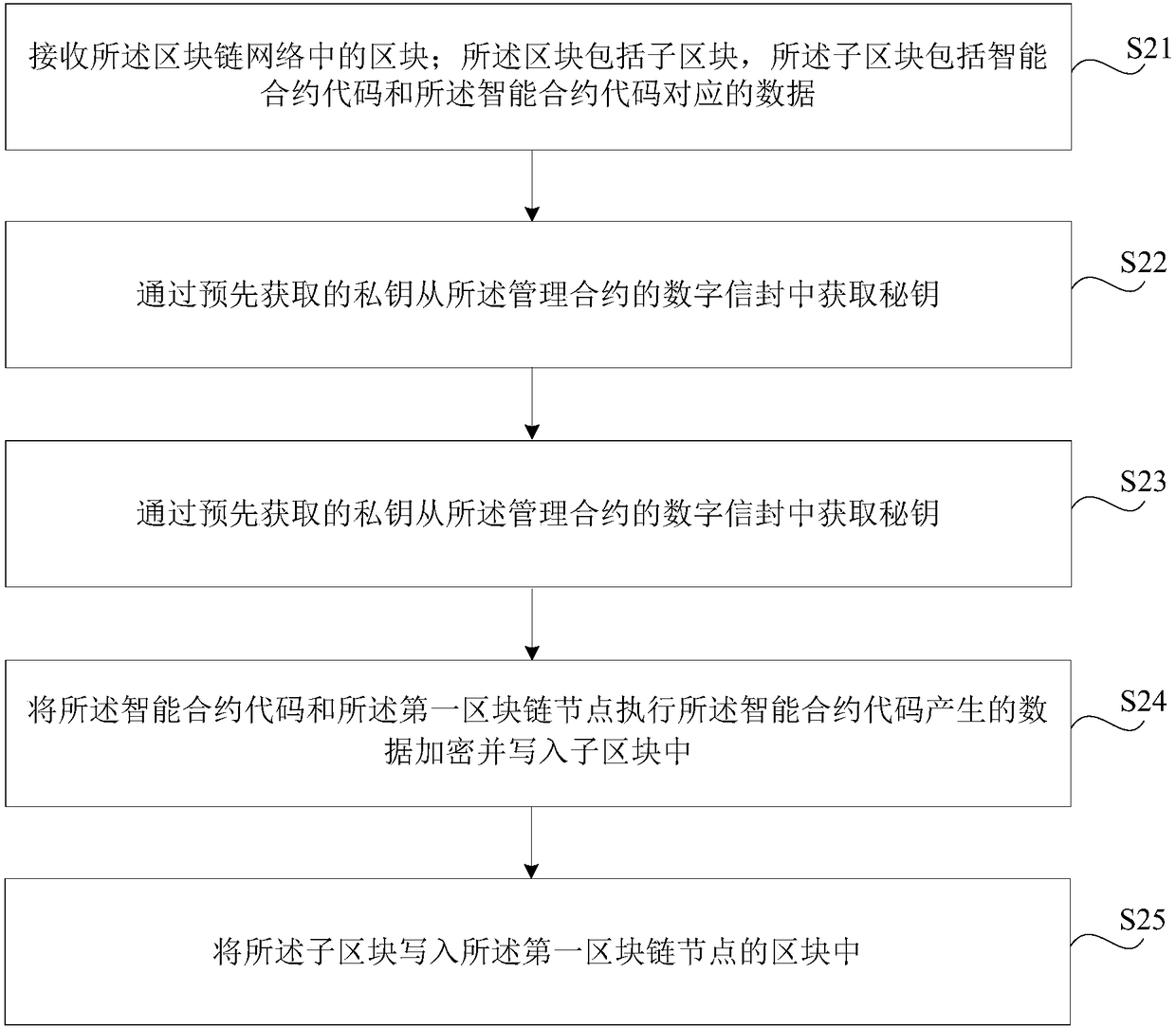
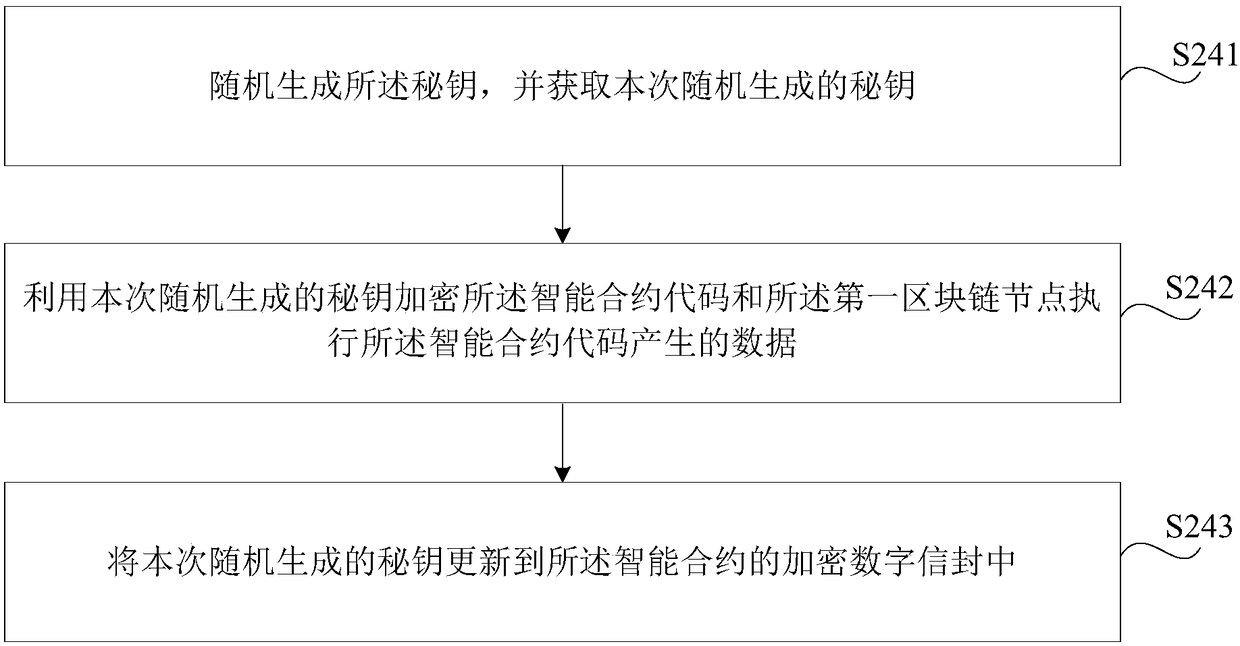
Block chain-based data processing method, apparatus, storage medium, and electronic device
ActiveCN108235772AAchieve protectionDoes not affect effectivenessProtocol authorisationManagement contractData processing
The present disclosure proposes a block chain-based data processing method, apparatus, storage medium, and electronic device for protecting a private transaction of a block chain node. The method includes: receiving a block in a blockchain network; the block includes a sub-block, the sub-block includes data corresponding to the smart contract code and the smart contract code; and obtaining the private key from the management contract by using a pre-acquired private key a secret key; obtaining a smart contract code in the sub-block according to the secret key, so that the first block chain nodeexecutes the smart contract code; encrypting and writing the data generated by the smart contract code and the block chain node to execute the smart contract code In the block; the sub-block is written into the block of the block chain node.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
Battery charging device and battery charging protection control method
ActiveCN103762691AAchieve overvoltageAchieve protectionEmergency protective circuit arrangementsElectric powerCommunication interfaceOvervoltage
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
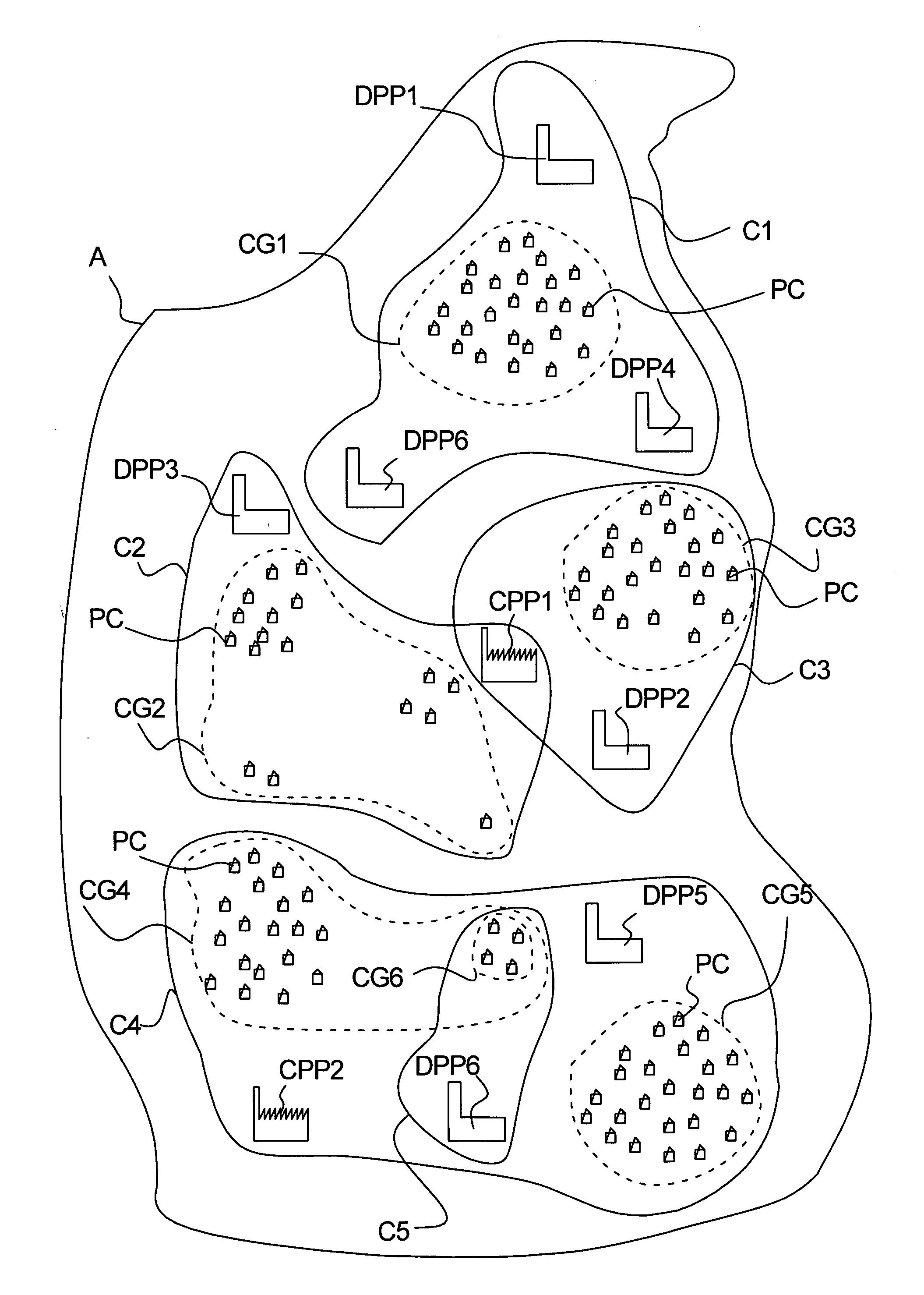
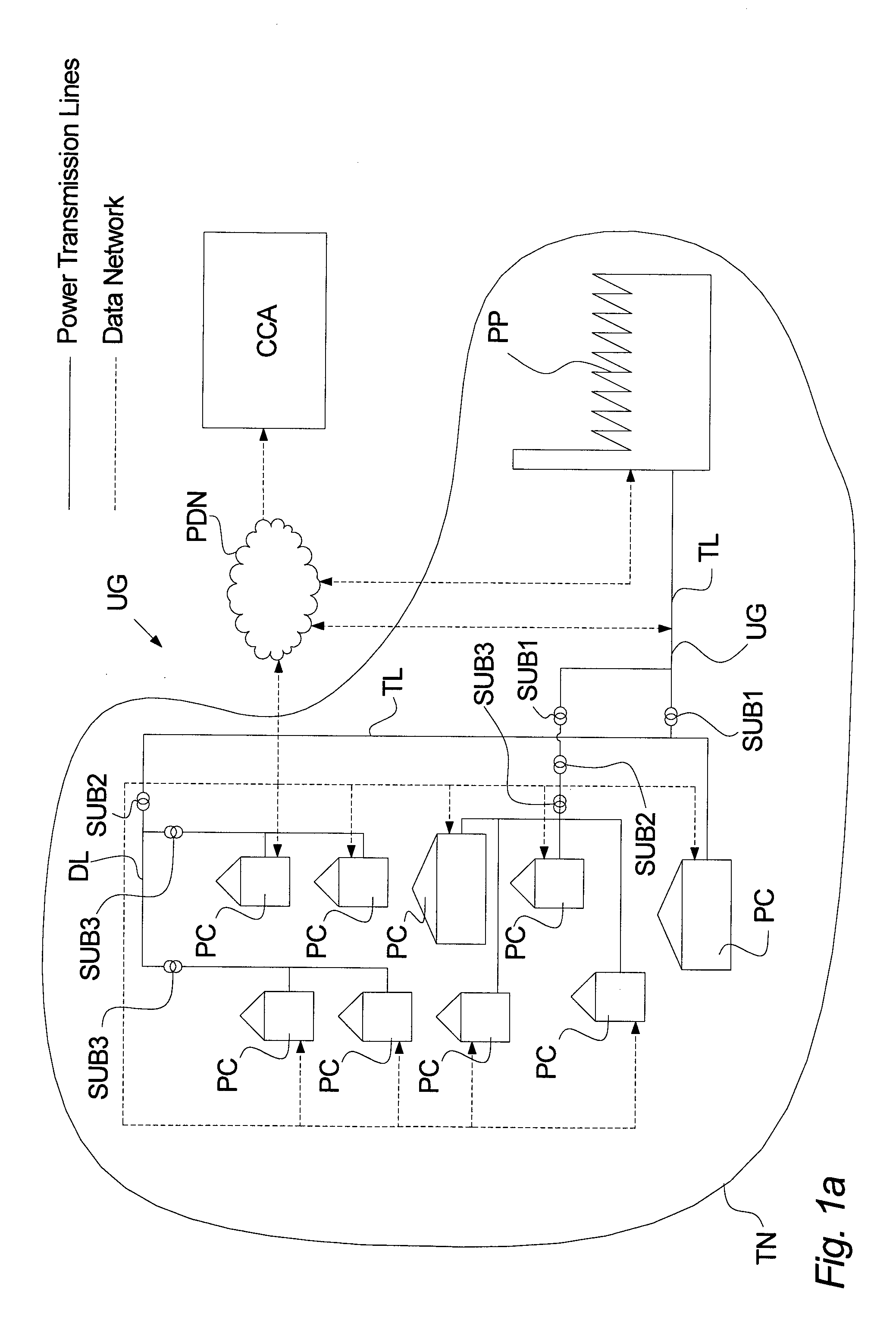
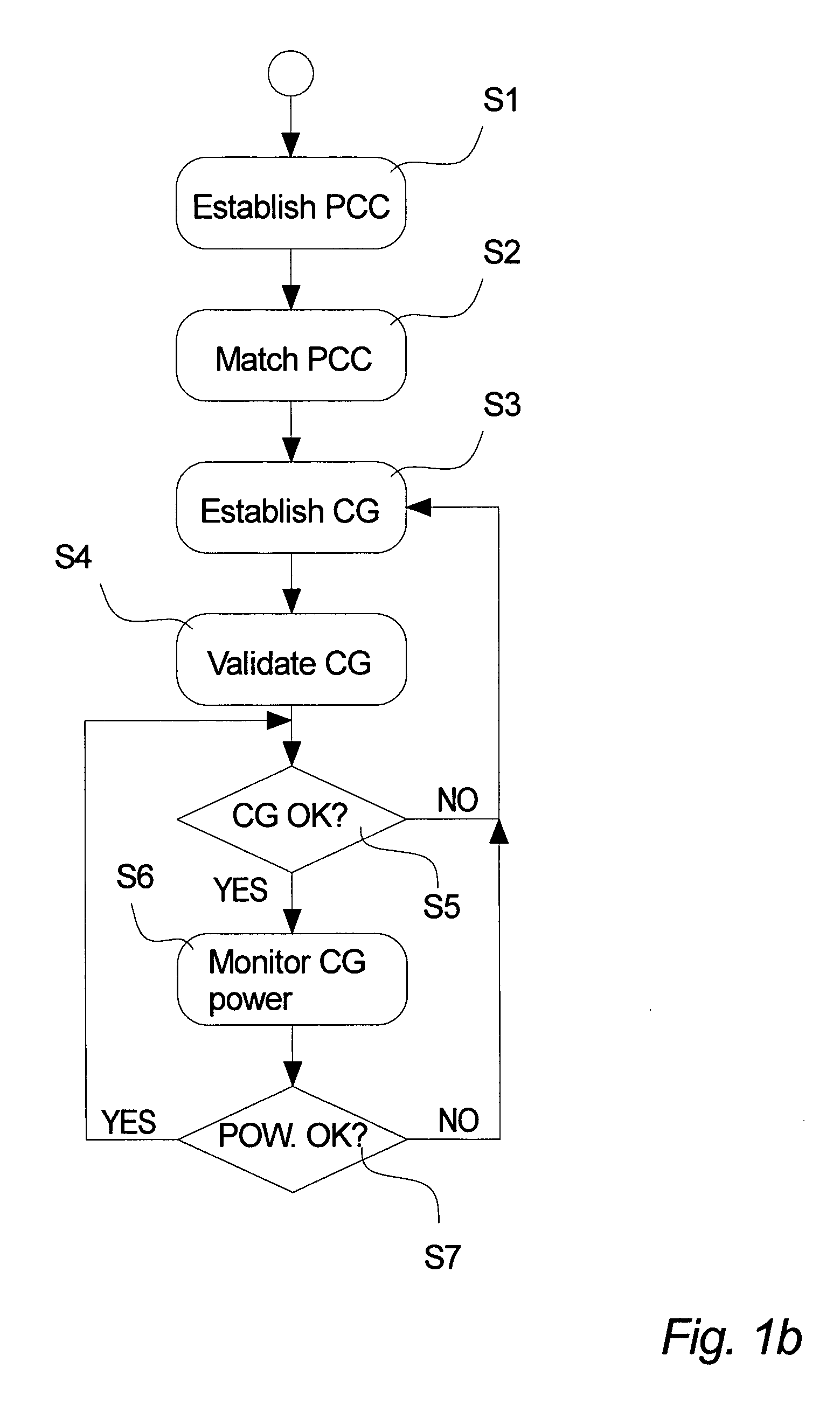
Method and Apparatus for Managing Transmission of Power in a Power Transmission Network
InactiveUS20130043725A1Reduce riskCost expensive and time-consumePower network operation systems integrationLoad forecast in ac networkElectric power transmissionControl power
The invention relates to a method of managing transmission of power in a power transmission network, said method comprising the steps of: establishing utility grid characteristic comprising at least one reference value based on at least one parameter reflecting the state of said transformer, continuously monitoring said at least one parameter reflecting the state of said transformer, and continuously controlling power consumption and / or power production at the lower voltage side of said transformer based on said monitoring of said at least one parameter reflecting the state of said transformer, said controlling of said power consumption and / or said power production comprising regulating said power consumption of one or more of said plurality of power consumers and / or regulating said power production of one or more decentralized power producers located at said lower voltage side of said transformer, so as to comply with said established reference value.
Owner:GRIDMANAGER
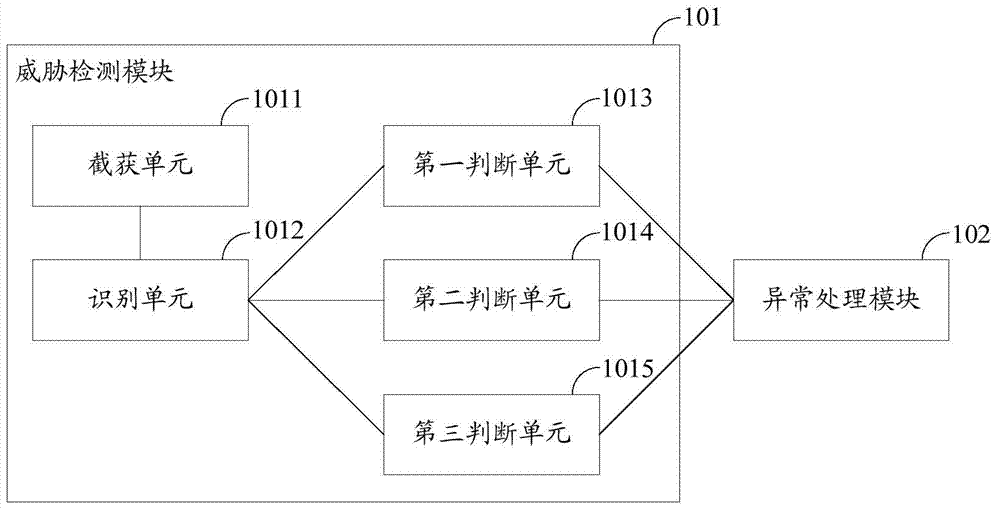
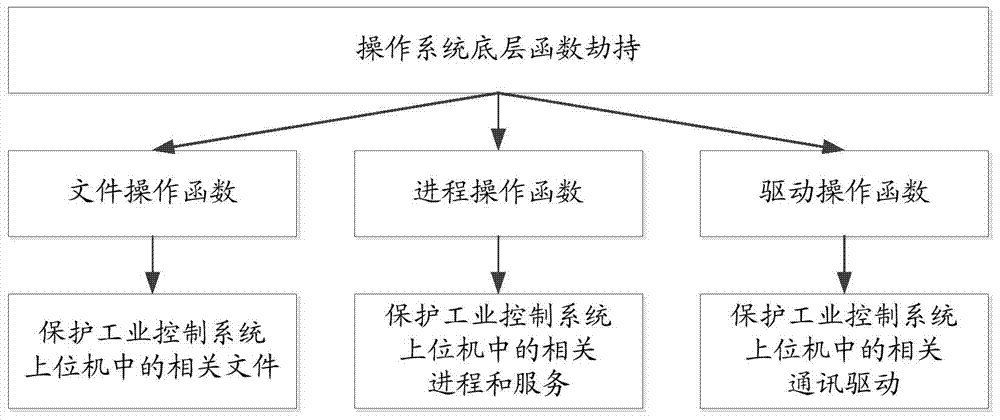
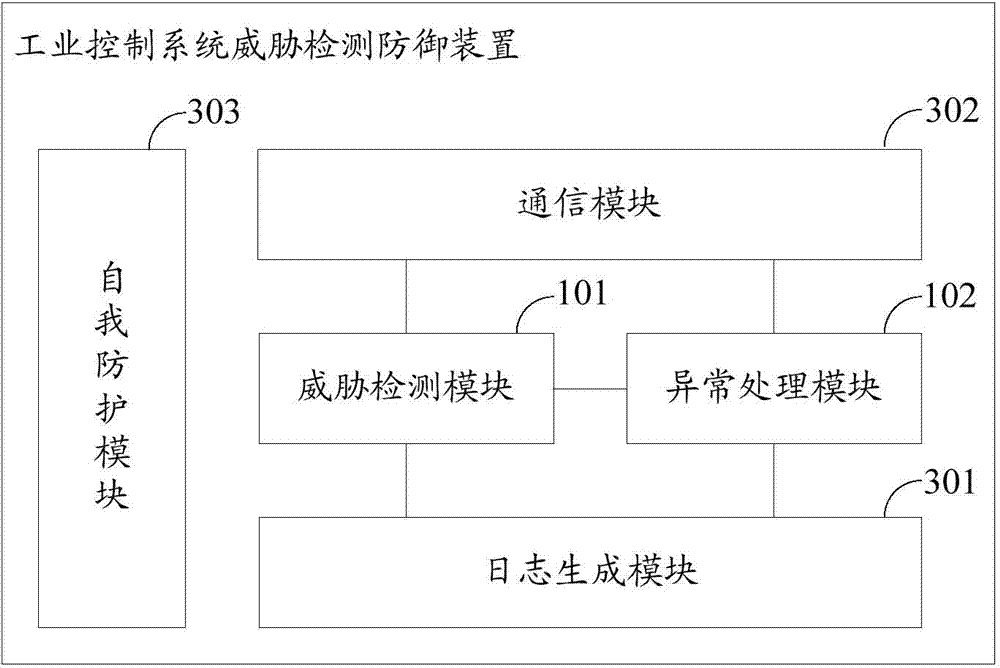
Threat detection and defense device, system and method for industrial control system
InactiveCN103944915AWill not affect normal workEasy to detectTransmissionIndustrial control systemSafe operation
The invention discloses a threat detection and defense device, system and method for an industrial control system. The threat detection and defense device, system and method is used for protecting safety of the industrial control system. The threat detection and defense device comprises a threat detection module and an exception handling module, wherein the threat detection module is used for intercepting and capturing a communication data message, identifying message field information in the communication data message, judging whether the communication data message is the malicious message according to the message field information, judging whether malicious act against a local upper computer or malicious act initiated by the local upper computer exists according to the message field information and message field information in a communication massage recorded in a local communication log database and detecting whether malicious operation against a control program in the local upper computer exists; the exception handling module is used for triggering and performing corresponding safety operation according to safety configuration files if one or more of the malicious message, the malicious act against the local upper computer, the malicious act initiated by the local upper computer and the malicious operation against the control program in the local upper computer exist.
Owner:ZHEJIANG UNIV
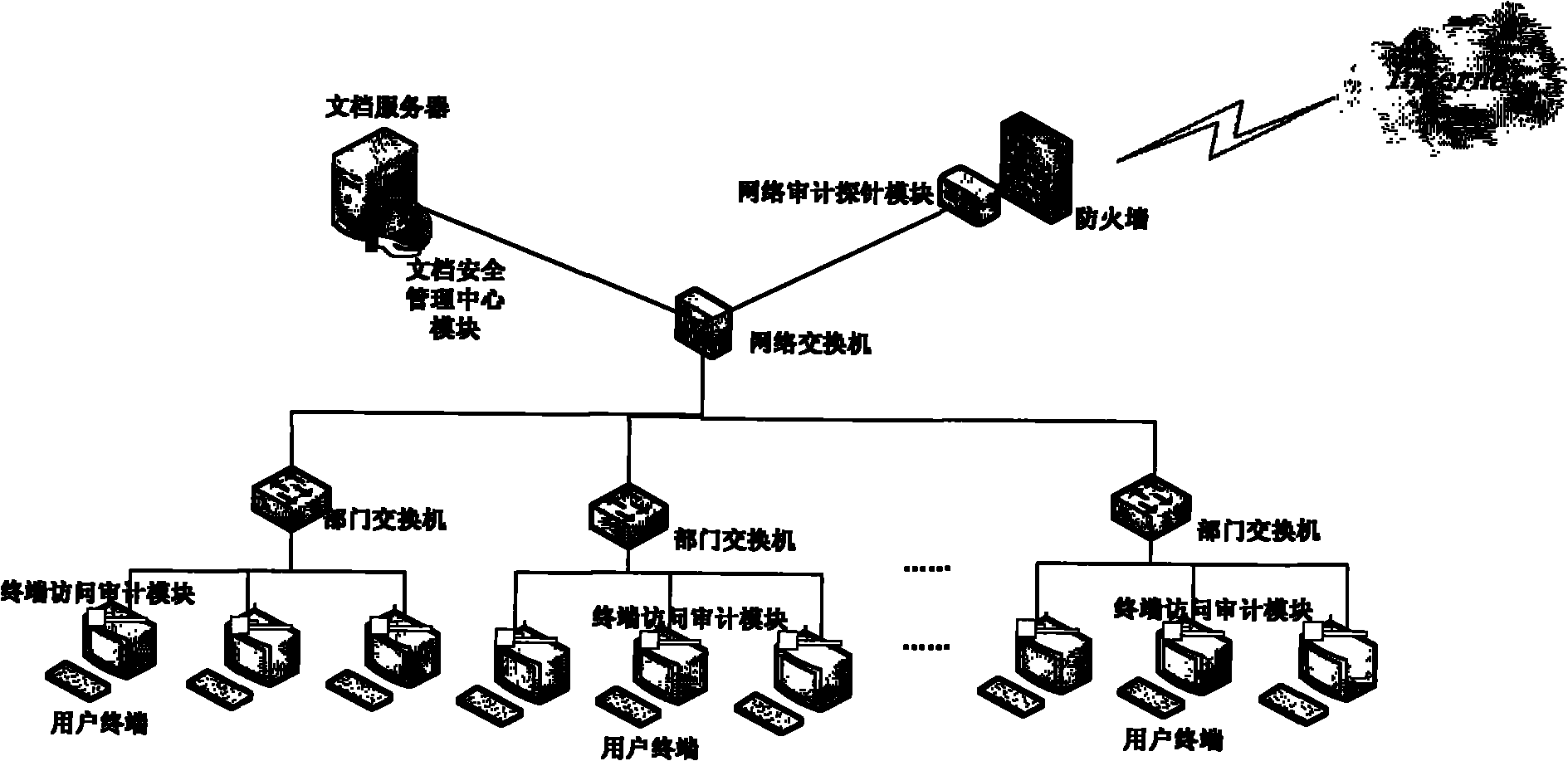
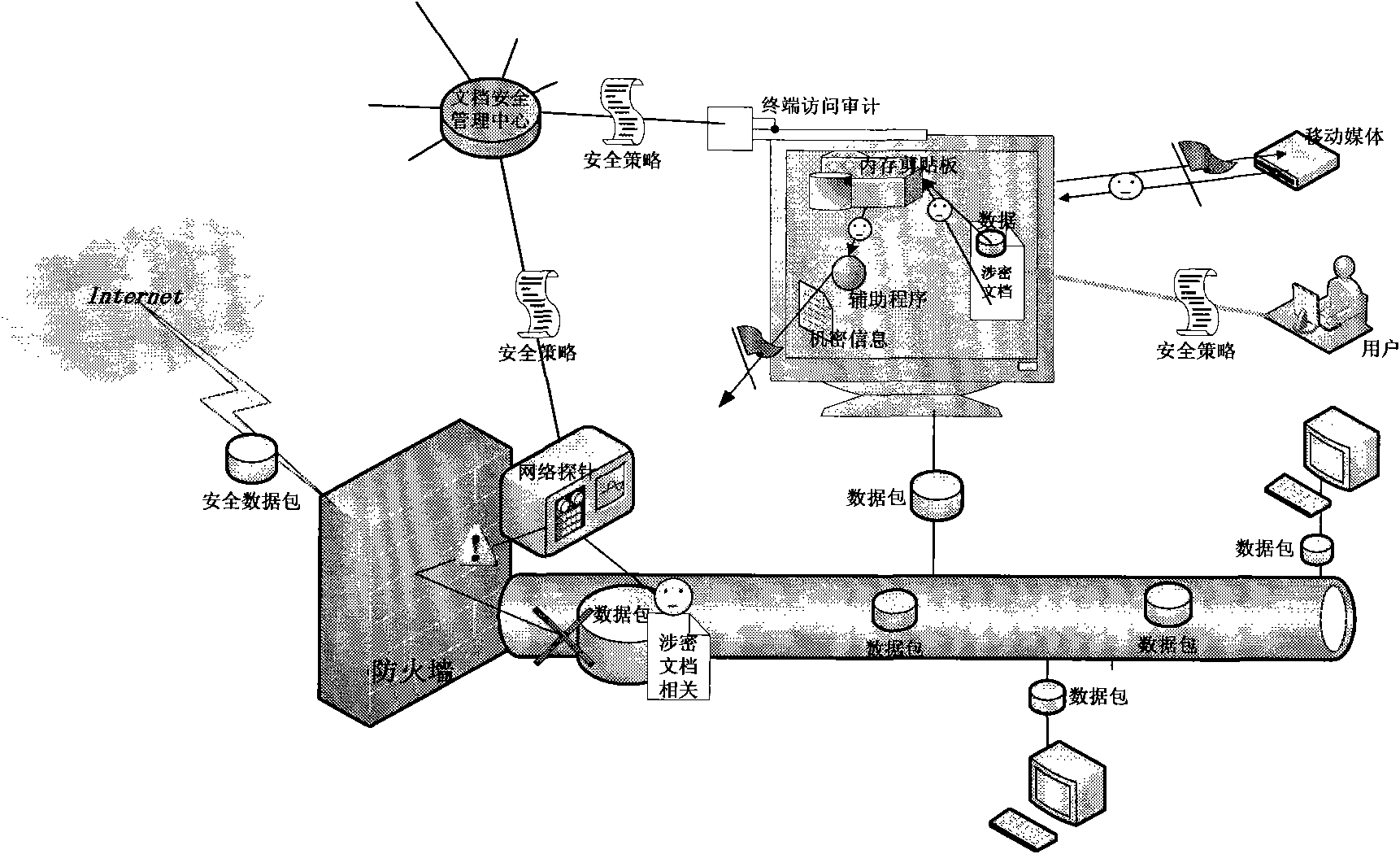
Document monitor and management system based on comprehensive safety audit
InactiveCN101895578AAchieve protectionDigital data protectionTransmissionComputer moduleDocumentation
The invention discloses a document monitor and management system based on comprehensive safety audit, comprising a document safety management center module, a network probe auditing module, a terminal accessing and auditing module and a linkage module. In the system, a core switch is connected with a plurality of secondary switches; each secondary switch is connected with a plurality of user terminals; and the terminal accessing and auditing module is provided in each user terminal. Based on the invention, the defect of the prior art is overcome and the safety of the document is ensured effectively.
Owner:国都兴业信息审计系统技术(北京)有限公司
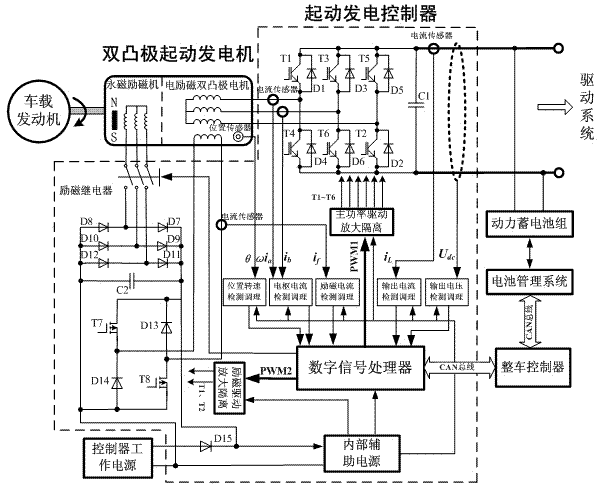
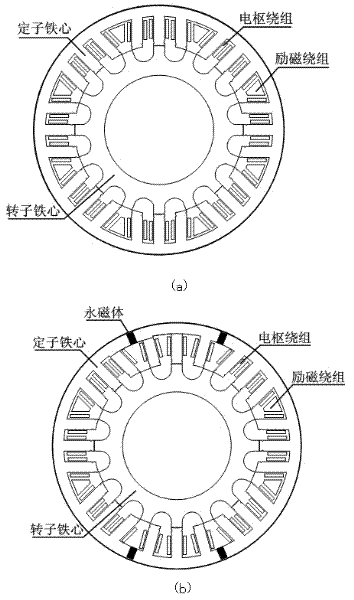
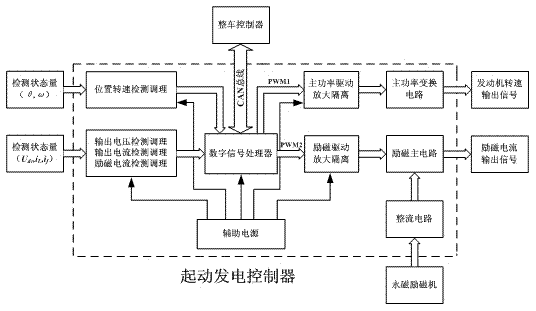
Starting power generation system for electric automobile
ActiveCN102386829ASimple structureImproved power to weight ratioBatteries circuit arrangementsPropulsion using engine-driven generatorsStarter generatorEngineering
The invention discloses a starting power generation system for an electric automobile, which comprises a double salient pole starting power generator, a starting power generation controller and controller working power; the starting power generation controller comprises a bidirectional power conversion circuit, an exciting current detection unit, an output current detection unit, an output voltage detection unit, a position rotation speed detection unit, an armature current detection unit, an exciting main circuit and a digital signal processor, wherein the exciting main circuit includes an exciting relay, a rectification filter unit and a chopper circuit which are connected in series in turn; and the digital signal processor is connected with the exciting current detection unit, the output current detection unit, the output voltage detection unit, the armature current detection unit, the position rotation speed detection unit, and the control ends of the bidirectional power conversion circuit, the exciting relay and the rectification filter unit by signals respectively. The invention also discloses an electric automobile and a control method thereof. Compared with the prior art, the starting power generation system is simple in structure, low in cost and flexible to control.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Process for repairing water erosion damage of flow passage component of steam turbine and protecting flow passage component of steam turbine
ActiveCN101767261AExtended service lifeNo change in vibration characteristicsMolten spray coatingPolishing machinesPower stationEconomic benefits
The invention discloses a process for repairing water erosion damage of a flow passage component of a steam turbine and protecting the flow passage component of the steam turbine. In the process, molded lines of the flow passage component of the steam turbine are repaired by adopting copy overlaying of manual argon tungsten arc welding aiming at the phenomenon of the water erosion damage existing in the flow passage component of the steam turbine. A water erosion resistant coating is prepared by supersonic speed flame spraying so as to achieve the purposes of repairing the molded lines of the flow passage component of the steam turbine and protecting the molded lines at large area on line and prolonging the service life of the flow passage component of the steam turbine. Through the process of the invention, the flow passage component of the steam turbine can be repaired and protected at large area on line in a short time without changing vibration characteristic, steam-driven characteristic and strength characteristic of the flow passage component of the steam turbine, so that the process has the advantages of high on-site operability, small deformation of the repaired workpiece, remarkable improvement on water erosion resistance and the like, can solve the common problem of water erosion in the flow passage component of the power station steam turbine in service on site, improves the running safety and efficiency of units and increases economic benefit of a power plant.
Owner:XIAN THERMAL POWER RES INST CO LTD
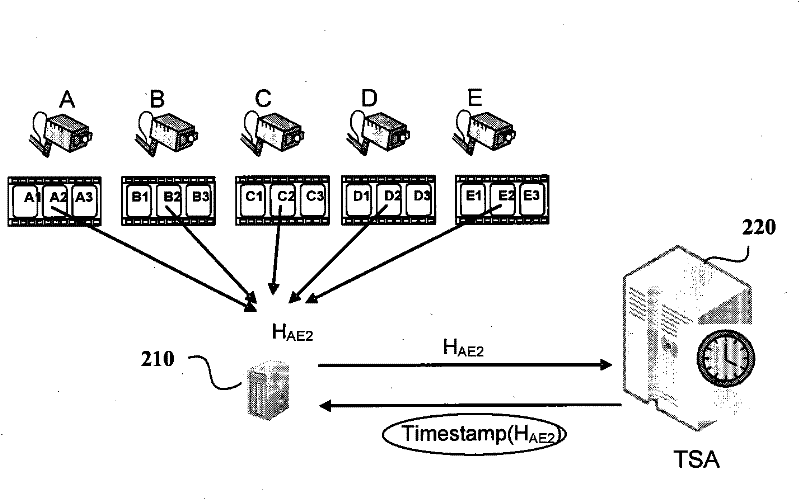
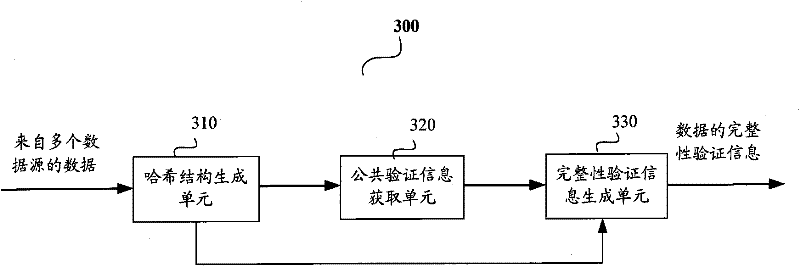
Data integrity authentication information generation method and device as well as data integrity authentication method and device
InactiveCN102413313AEffective Integrity ProtectionAchieve protectionTelevision system detailsColor television detailsComputer hardwareData integrity
The invention provides a data integrity authentication information generation method and device. The device comprises a Hash structure generation unit, a common authentication information acquisition unit and an integrity authentication information generation unit, wherein the Hash structure generation unit can generate a Hash structure corresponding to a specific time period according to Hash values of data sections contained in multiple data sources in the specific time period, so that the Hash value in each data section can respectively represent a child node at the lowest level of the Hash structure in order to calculate a root Hash value of the child node; the common authentication information acquisition unit can acquire the common authentication information according to the root Hash values; the integrity authentication information generation unit can generate the integrity authentication information of the data sections contained in the multiple data sources in the specific time period for the multiple data sources, wherein the integrity authentication information of each data section comprises common authentication information, path information containing from the Hash value of the data section of the leaf node at the lowest level in the Hash structure to the root node, and the relevant node Hash value of the child node in the path. The invention also provides a data integrity authentication device and method.
Owner:SONY CORP
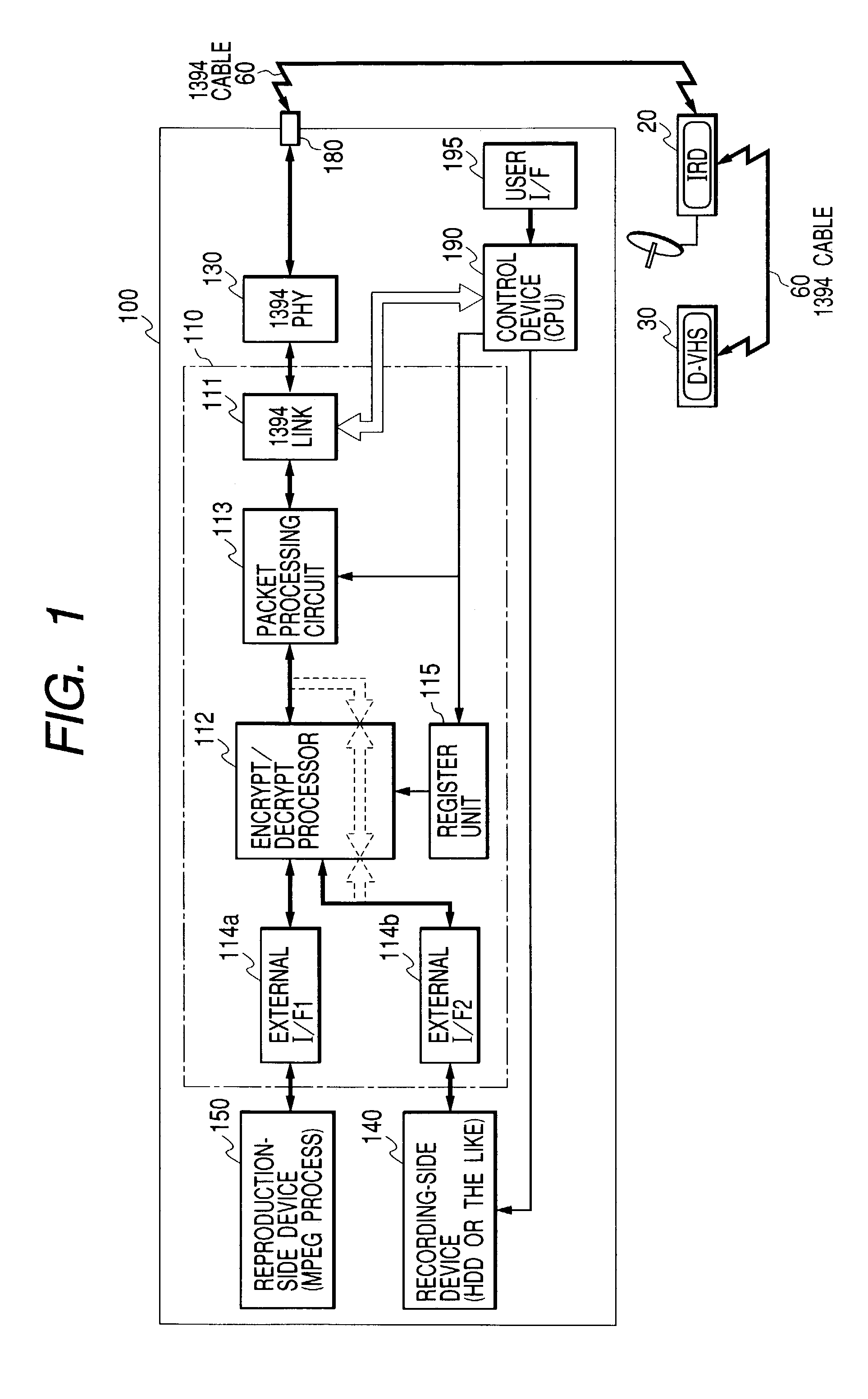
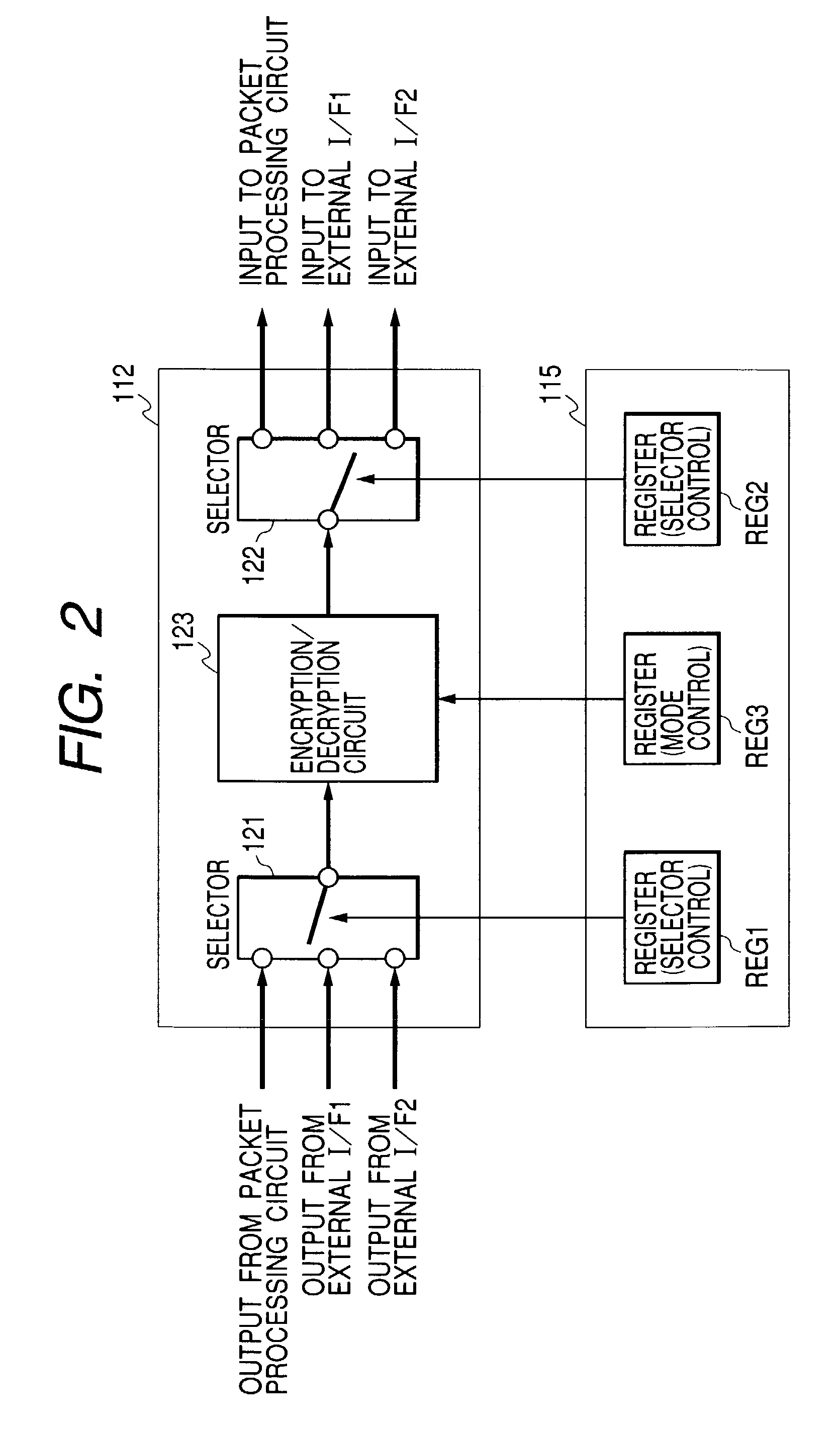
Encryption and decryption communication semiconductor device and recording/reproducing apparatus
InactiveUS7290148B2Reduce in quantityAchieve protectionTelevision system detailsDigital data processing detailsCommunication interfaceCommunications system
Disclosed herein is an encryption and decryption communication semiconductor device comprising at least, a communication interface for performing a transfer of data according to a predetermined communication system, one or two or more encryption / decryption circuits which encrypt or decrypt input data in accordance with a predetermined algorithm, and a plurality of external interfaces for performing the input / output of data from and to external devices. The communication interface, the encryption / decryption circuits and the plurality of external interfaces are formed on one semiconductor chip. In the cryption and decryption communication semiconductor device, input data sent from any one of the plurality of external interfaces is encrypted or decrypted by at least one of the encryption / decryption circuits and is capable of being outputted to any different one of the plurality of external interfaces.
Owner:RENESAS ELECTRONICS CORP
Positional information providing method and positional information providing system
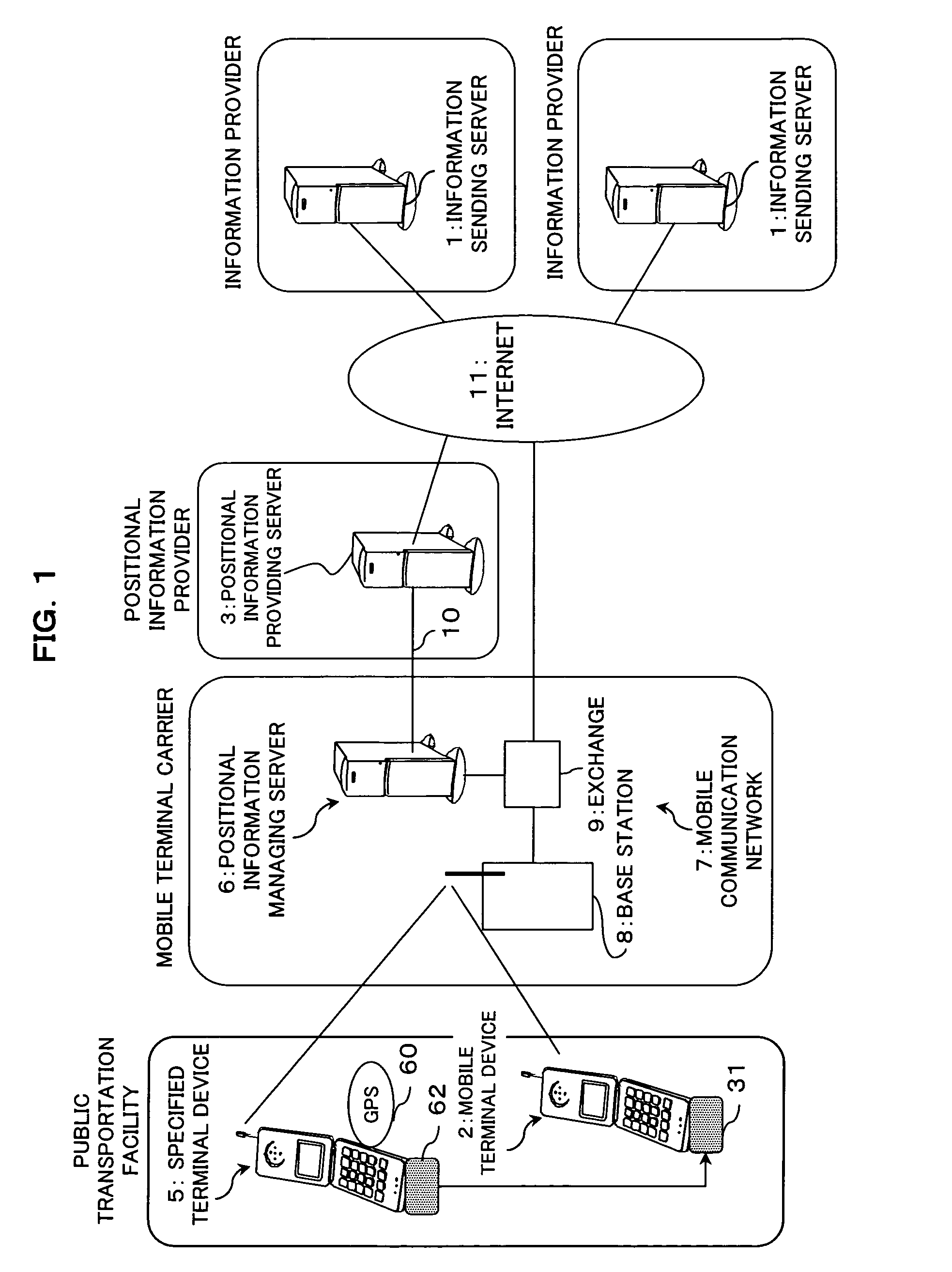
InactiveUS20050032529A1Privacy protectionAvoid abuseInstruments for road network navigationNetwork topologiesTerminal equipmentLibrary science
In a positional information providing method, an information sending server transmits desired decision positional information and unique information on a designated mobile terminal device to a positional information providing server, and a mobile terminal device transmits unique information thereon to the positional information providing server, and when the designated unique information and the unique information agree with each other, the positional information providing server makes a decision as to whether or not there is a point of agreement between the decision positional information and the positional information on the mobile terminal device and, when the decision indicates that there is a point of agreement between the decision positional information and the positional information on the mobile terminal device, the positional information providing server notifies the decision result through a network to the information sending server, thereby providing the positional information.
Owner:FUJITSU LTD
Data security control method and data security control platform
ActiveCN104796290AReflect business valueIncrease profitData switching networksSpecial data processing applicationsFull life cycleEncryption
The invention discloses a data security control method and a data security control platform. The method includes S1, partitioning data according to type and security classification; S2, performing encryption, identity authentication, access control, security audit, tracking and forensics on the data according to a data partitioning result, and distributing corresponding security protection tools for security protection; S3, collecting and normalizing log information generated by the security protection tools, and creating a full-life-cycle security view of the data. The data security control method and the data security control platform have the advantages that fine-grained differential full-life-cycle protection of big data can be achieved, utilization rate of the security protection tools can be increased, and the big data can be subjected to tracking and forensics.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
Mutual authentication method between terminal and server
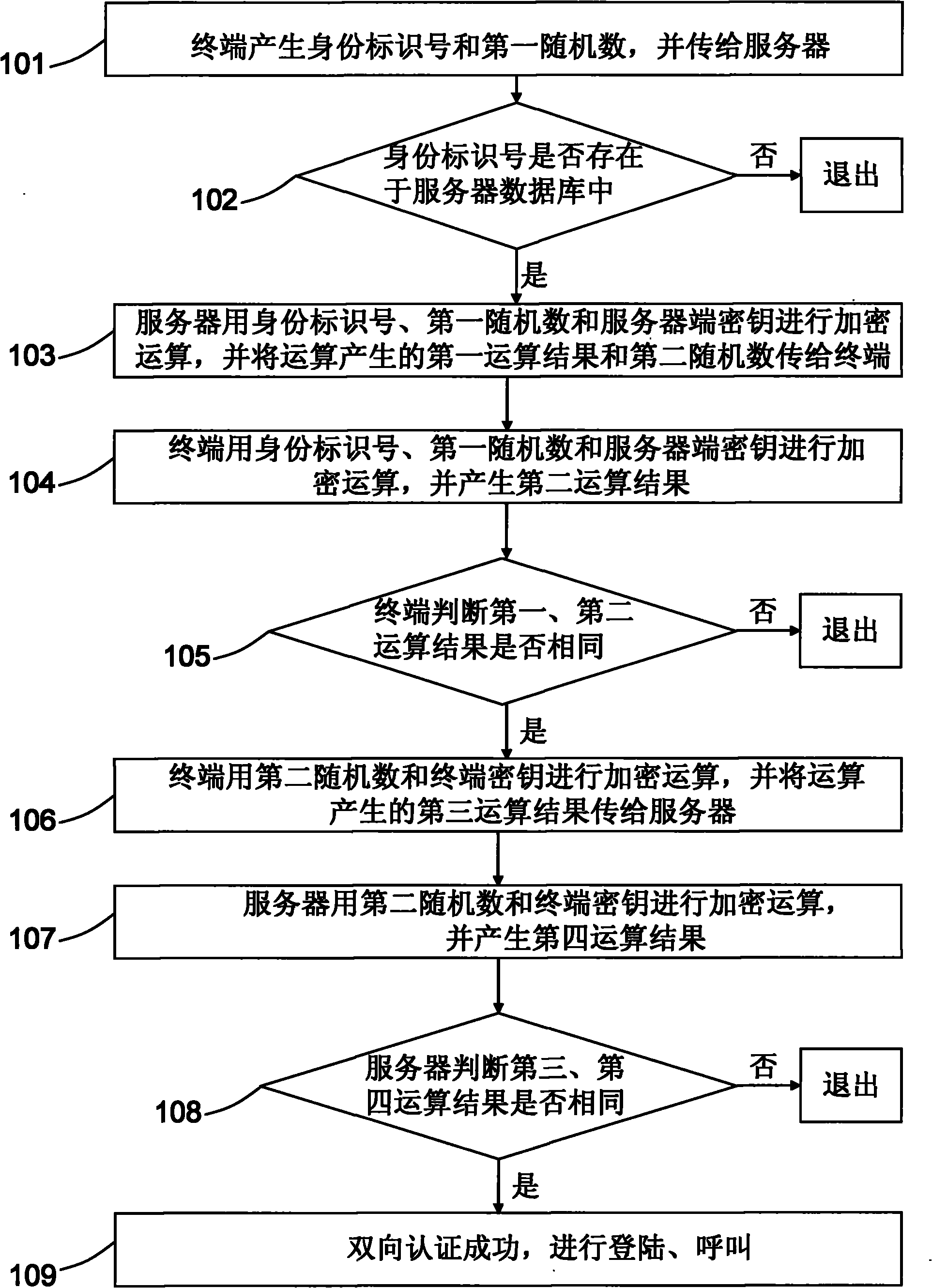
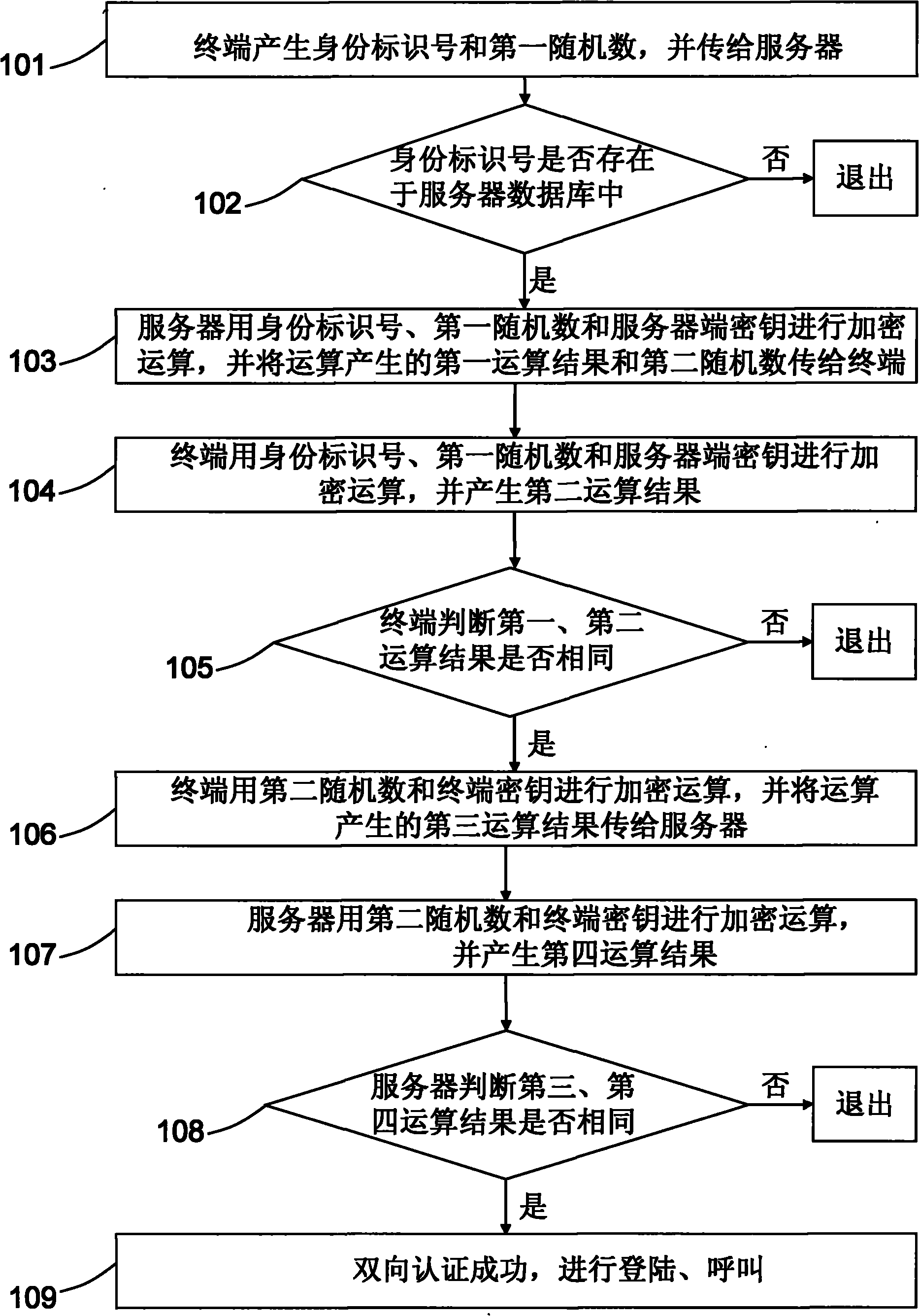
InactiveCN101771535AEnsure safetyGuaranteed privacyKey distribution for secure communicationUser identity/authority verificationMutual authentication
The invention relates to a mutual authentication method between a terminal and a server. The method comprises that: the terminal generates an identity number and a first random number and sends the identity number and the first random number to the server; the server verifies whether the identity number exists in a database of the server; the server generates a first operation result according to the identity number, the first random number and a server secret key, and the first operation result and a second random number are transmitted to the terminal; the terminal generates a second operation result according to the identity number, the first random number and the server secret key and carries out authentication on the server according to the first and second operation results; the terminal generates a third operation result according to the second random number and a terminal secret key and sends the third operation result to the server; and the server generates a fourth operation result according to the second random number and the terminal secret key and carries out authentication on the terminal according to the third and fourth operation results.
Owner:上海茂碧信息科技有限公司
Air bag device
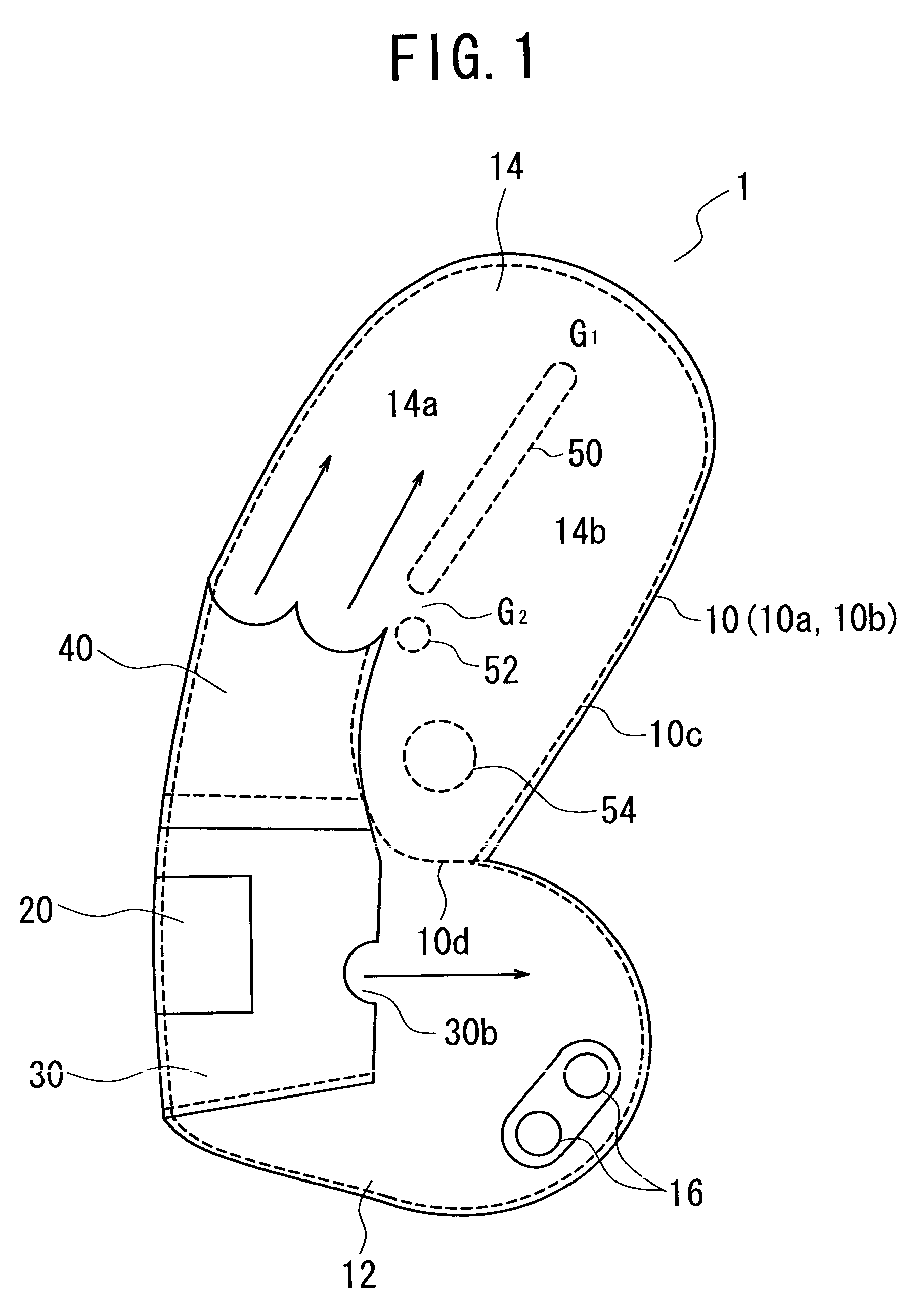
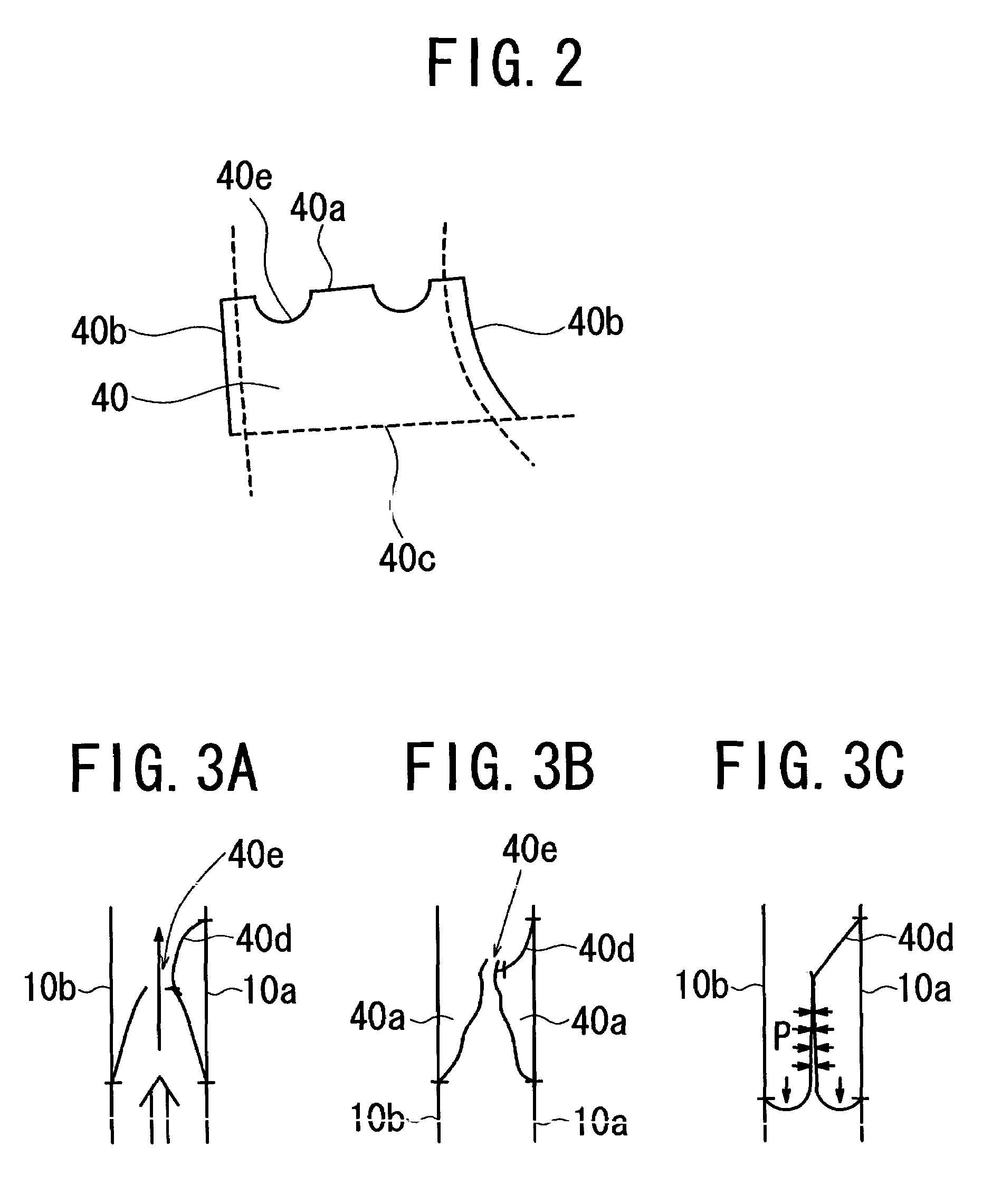
ActiveUS7431329B2Quick implementationRelieve stressPedestrian/occupant safety arrangementEngineeringAir chamber
Expansion of an air bag can be smoothly effected even in a small space by controlling the air bag in thickness and introduction of the gas for expansion, and the protection of an occupant can be rapidly implemented with a relatively small volume of the gas. An air bag device comprises a first air chamber 12 for protection of the chest or the waist of an occupant, a second air chamber 14 for protection of the head of the occupant, and a lower portion of the diffuser bag 30 interposed therebetween for portioning out gas from an inflator 20, wherein the second air chamber 14 has a first tether 50 forming a gas passage 14a for guiding gas jetted from gas outlets of the lower portion of the diffuser bag 30 into the second air chamber 14 so as to go around the tether of a head protection region of an air bag 1, from the back side thereof toward the front side thereof, and has a second tether 52 for forming a gap provided at the lower end of the first tether 50 in the vicinity of the gas outlets, for letting a portion of the gas escape into a front part of the second air chamber 14.
Owner:MAZDA MOTOR CORP +1
Method, equipment and system for forwarding message as well as equipment for receiving message
InactiveCN101257441AAchieve protectionReduce consumptionNetworks interconnectionTraffic capacityPseudo-wire
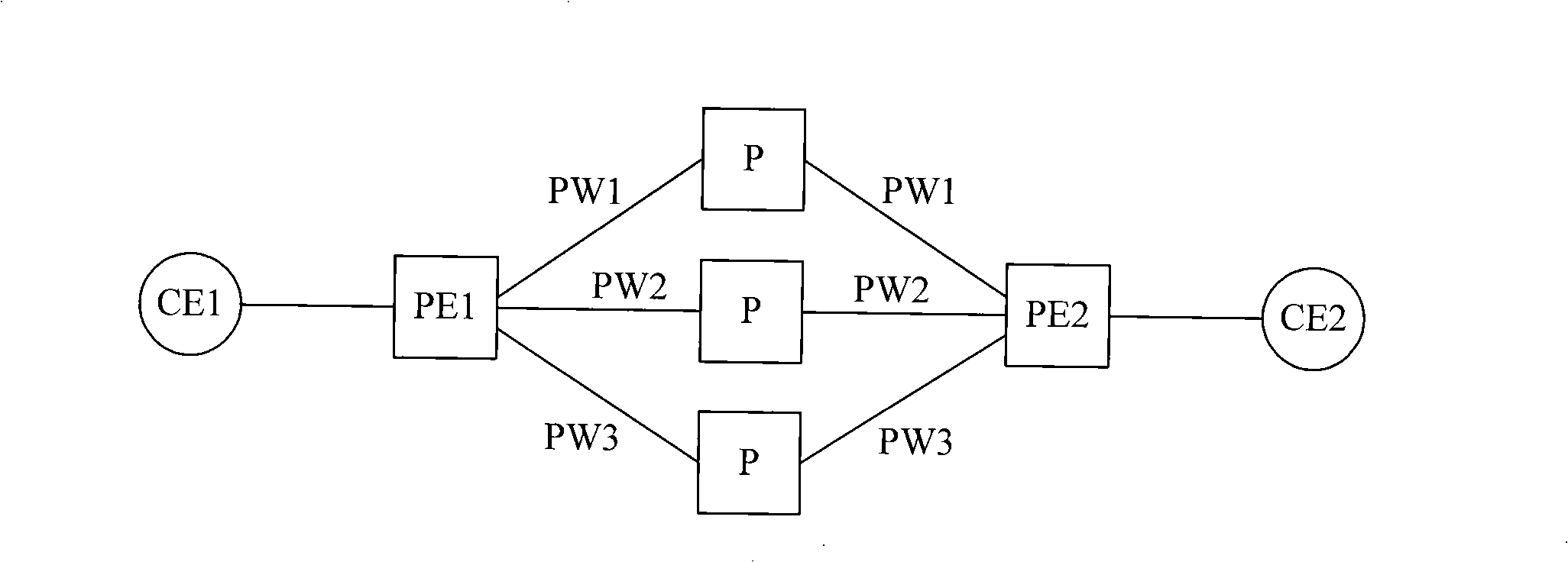
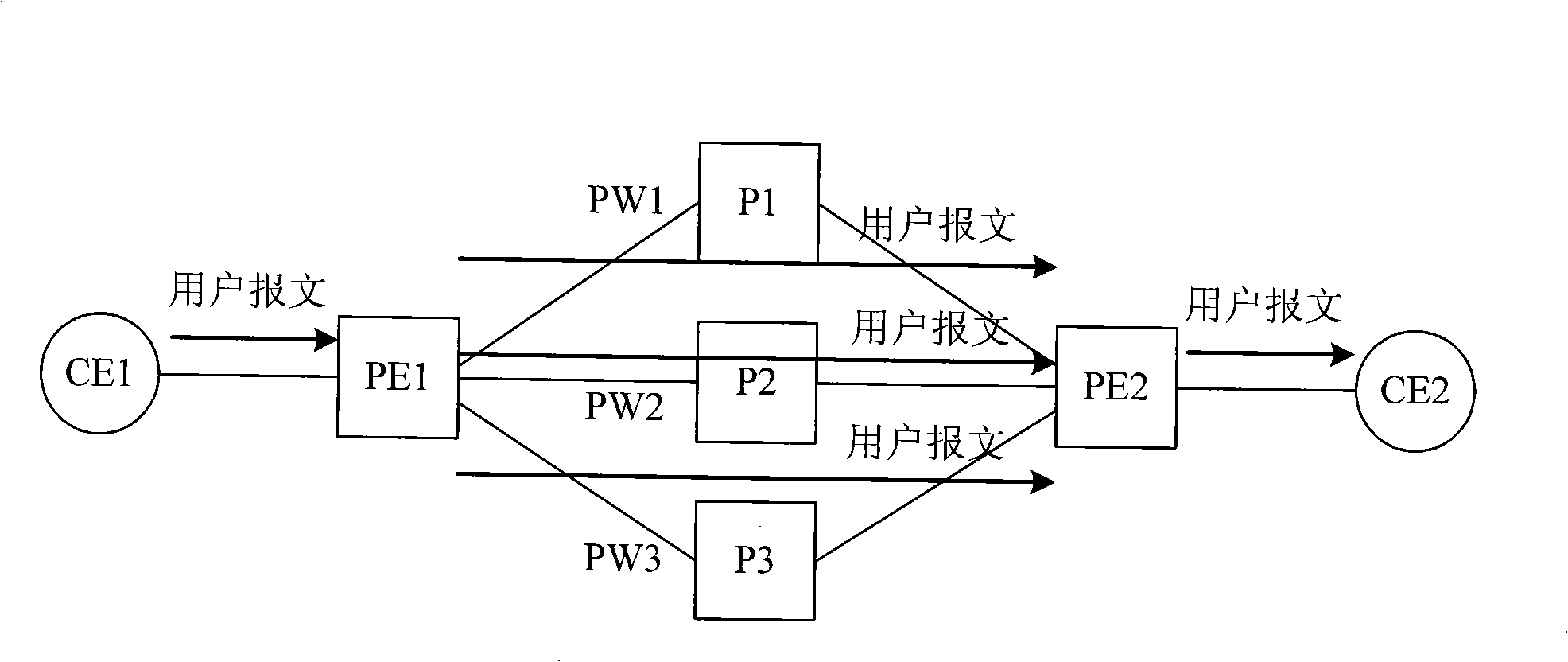
The invention discloses method, device, system for transferring message and a device for receiving message, belonging to the communication technology art. The method comprises: receiving message; obtaining at least one message by copying the message; and transferring the received message and the copied message to a receiving end PE by presetting at least two pseudowires from a plurality of pseudowires, according to the principle that each pseudowire only transfers one message. The transferring device includes: a receiving module and a transferring module. The receiving device comprises: a receiving module and a processing module; or receiving module, a recombining module and a processing module. The system contains a sending end equipment and a receiving end equipment. Due to the plurality of pseudowires simultaneously bears the user traffic, when any link goes wrong, the other links can continuously transfer the traffic to protect the links and avoid the situation of user traffic lost in the transferring and failback process caused by protecting the links using a backup link, thereby, the invention can provide higher level reliability assurance.
Owner:JIANGSU HENGBO PNEUMATIC CONVEYING EQUIP MFG CO LTD
Intelligent vending machine
ActiveCN105825583AImprove experienceImplement encryptionCoin-freed apparatus detailsApparatus for dispensing discrete articlesSystems managementIntelligent city
The invention discloses an intelligent vending machine. A payment module, a cargo transmission module, a commodity management module, an environment sensing module, a commodity state display module, an advertisement management module and an intelligent city module are arranged inside a machine body, wherein the commodity management module comprises a system management and communication center, a mobile display hand set and a remote vending machine operation terminal; the payment module comprises a mobile payment module, an iris payment module and a face payment module; the intelligent city module and the advertisement management module are used for displaying and inquiring relevant city information. The intelligent vending machine has the advantages that a manager can be timely notified to supplement cargos in time; the function of reminding the concrete position of the vending machine with the short lacked commodity distance is achieved; the cloud server can recommend buying commodity to the user according to the weather, temperature, geographic position and health preserving information sensed by the vending machine according to seasons; the user experience is enhanced; various payment functions are realized; convenience and high speed are realized.
Owner:永州巨米智能科技有限公司
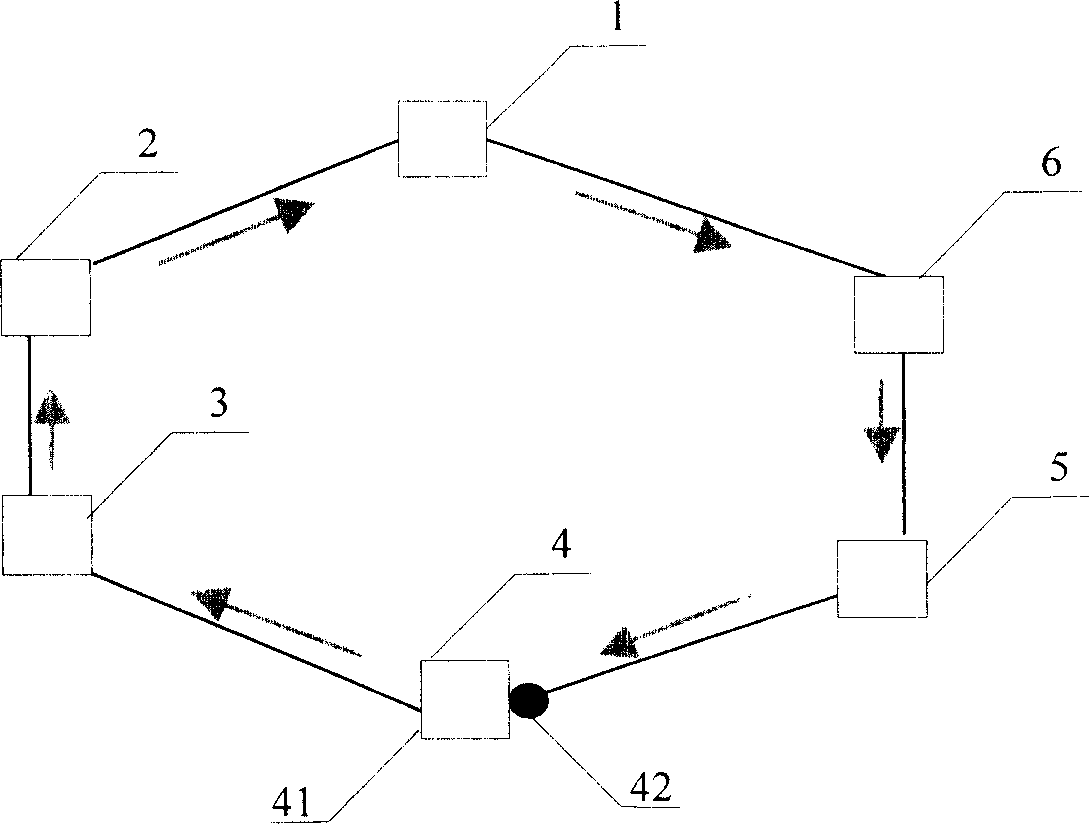
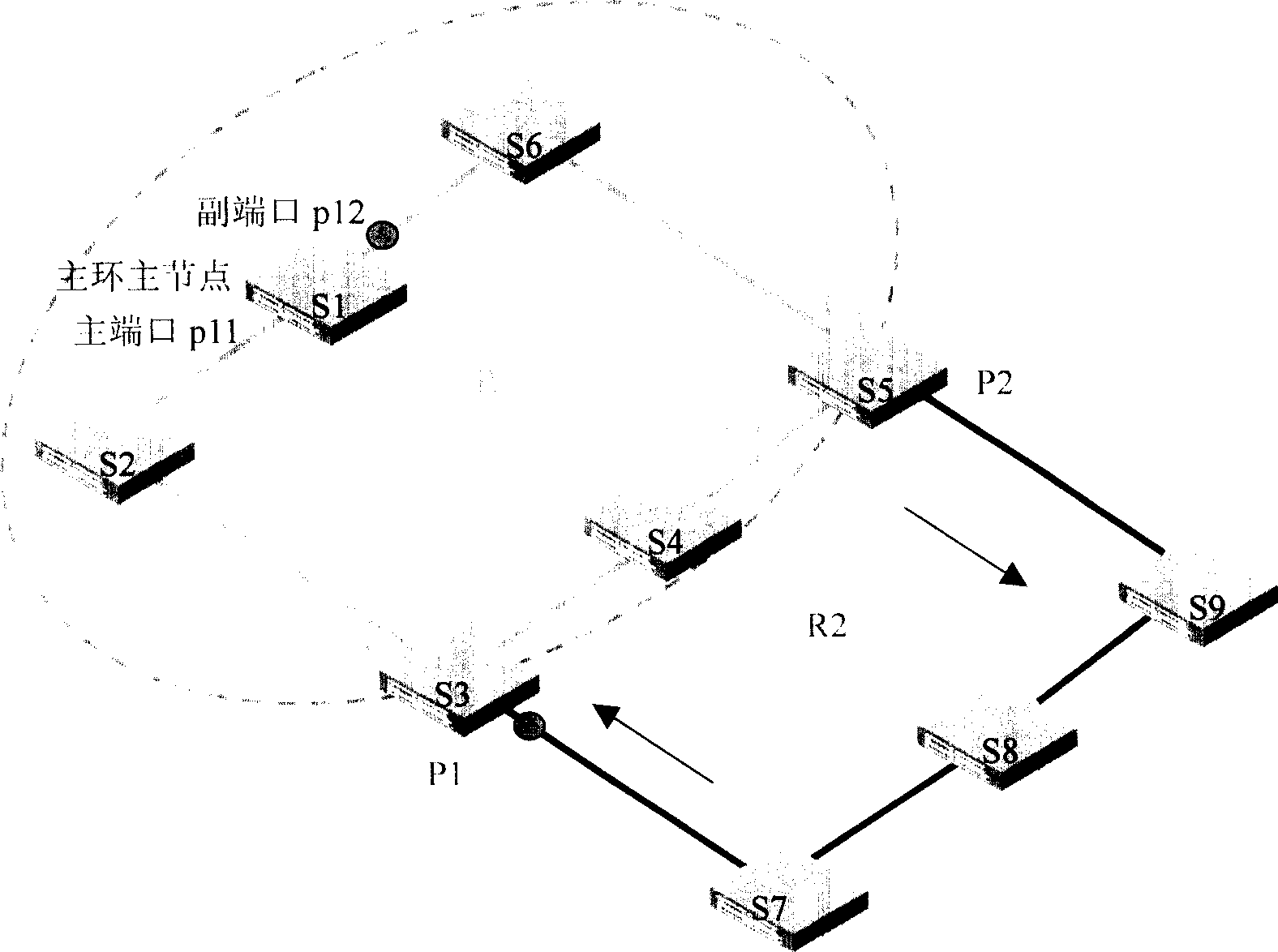
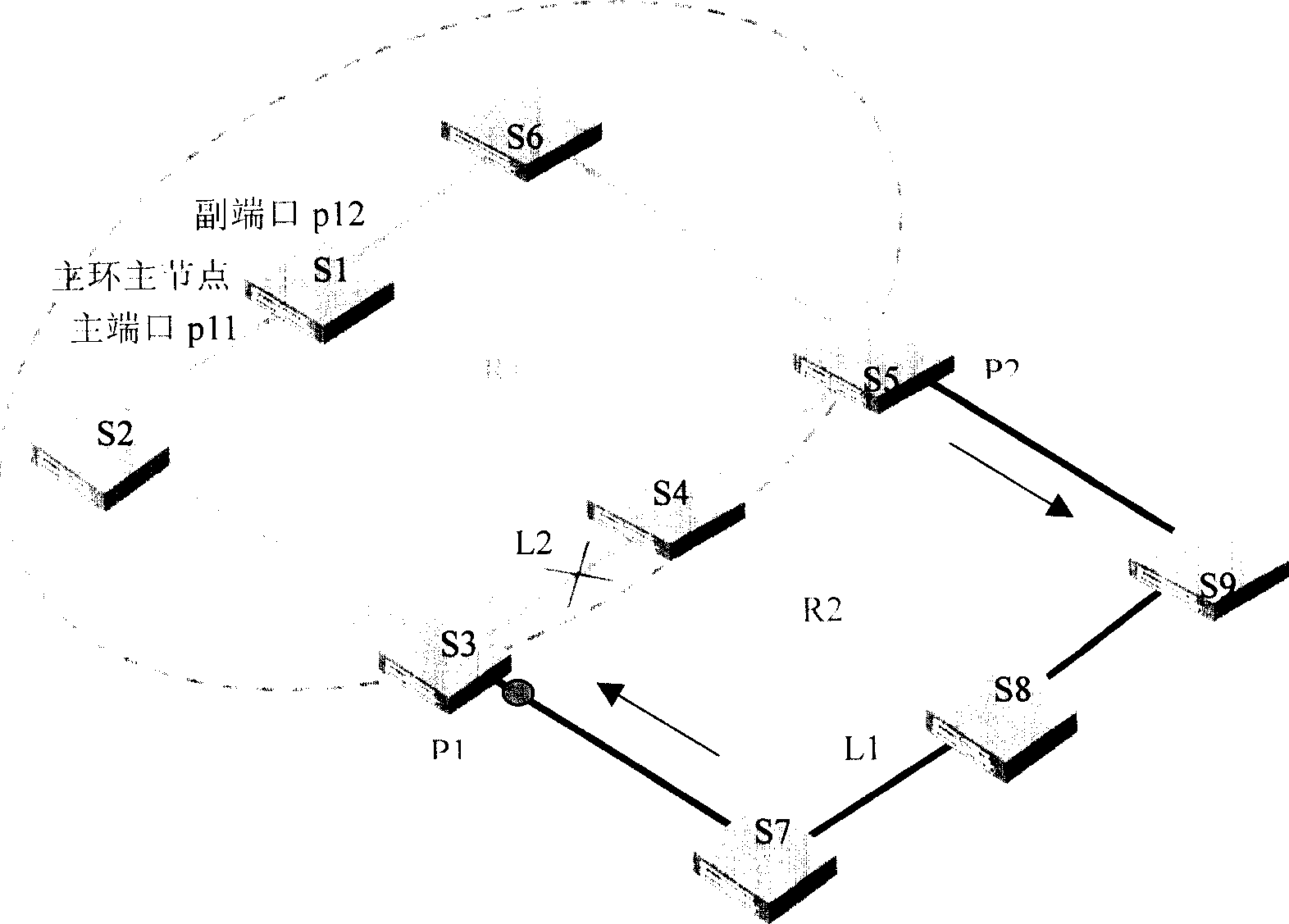
Intersecting Ether ring net and its automatic protecting method, node device for Ether ring net
The invention relates to a method for protecting crossed Ethernet network, wherein said network is arranged with quick annular network protective region; said region comprises a main ring and a sub ring; main ring is the virtual main node of sub ring; the main ring via the first and second edge nodes is crossed with sub ring; the port of first edge node connected to the sub ring is the first port of virtual main node; the port of second edge node connected to the sub ring is the second port of virtual main node. And said method comprises following steps: setting the second port of virtual main node as transfer mode; the first port of virtual main node is block mode; checking if the sub ring has chain accidence; if it is, setting the first port of virtual main node as transfer mode, and initializing the refresh transfer list information; when the accidence of sub ring is recovered, setting the first port of virtual main node as block mode, to initialize the refresh transfer list.
Owner:XINHUASAN INFORMATION TECH CO LTD
Method and apparatus for controlling smart home appliance
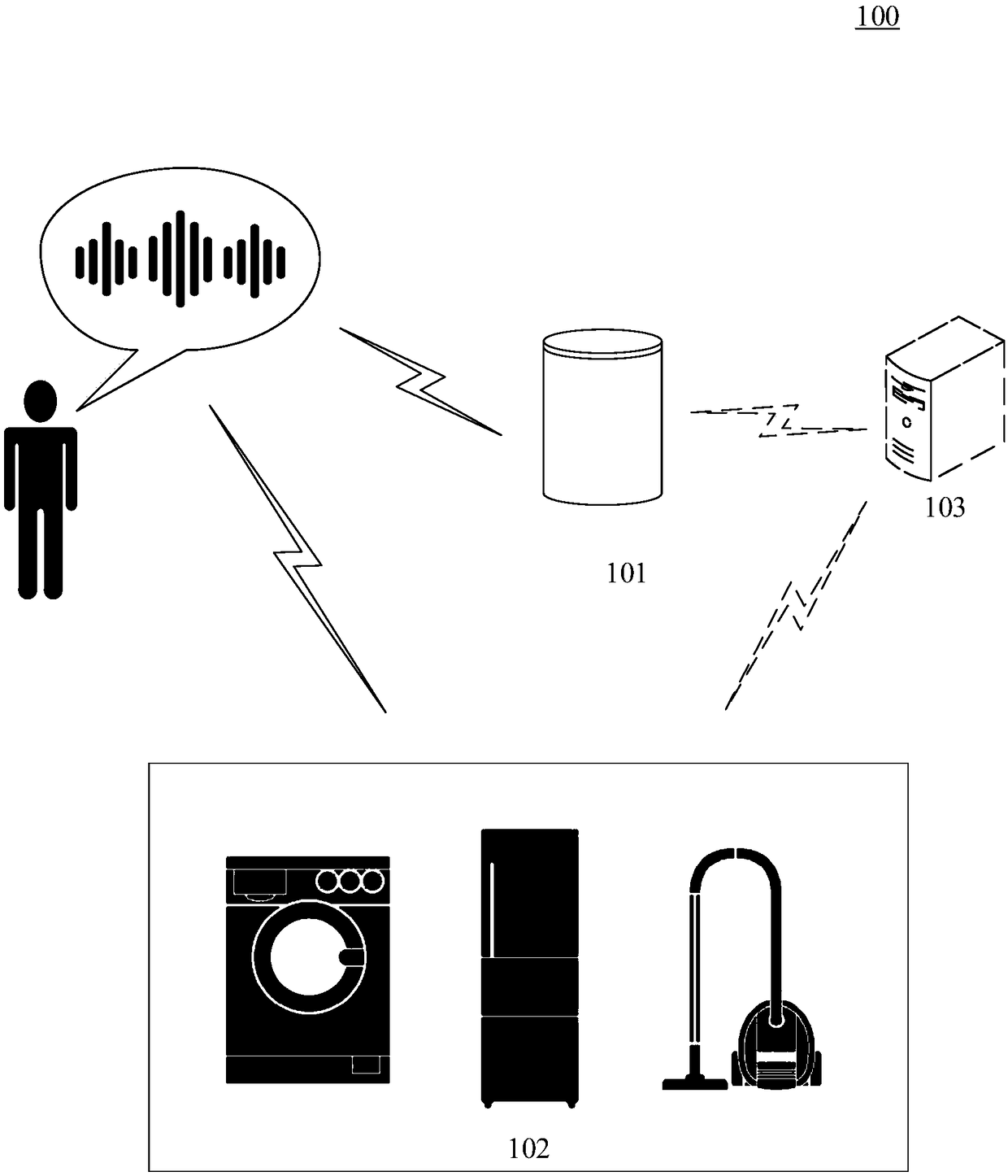
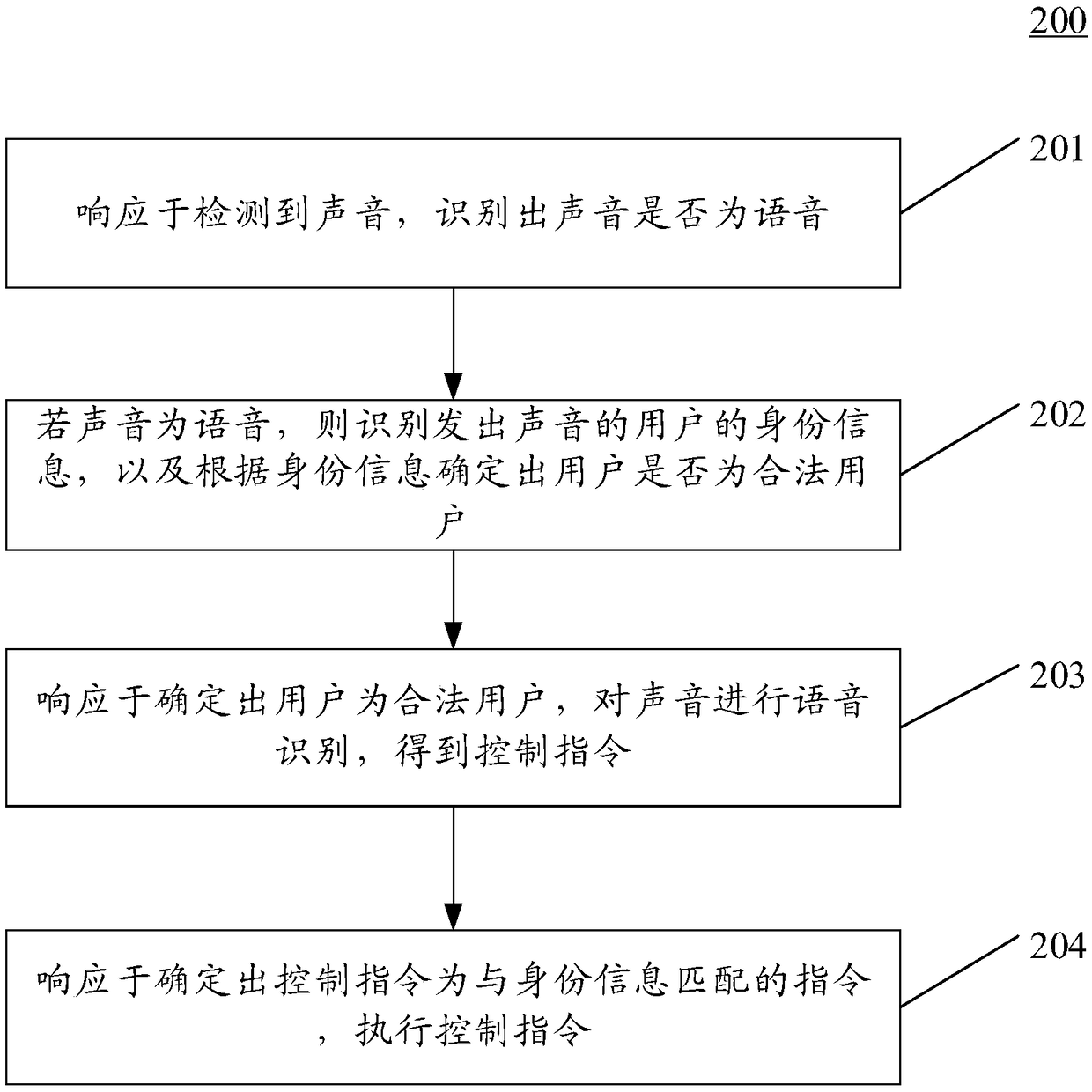
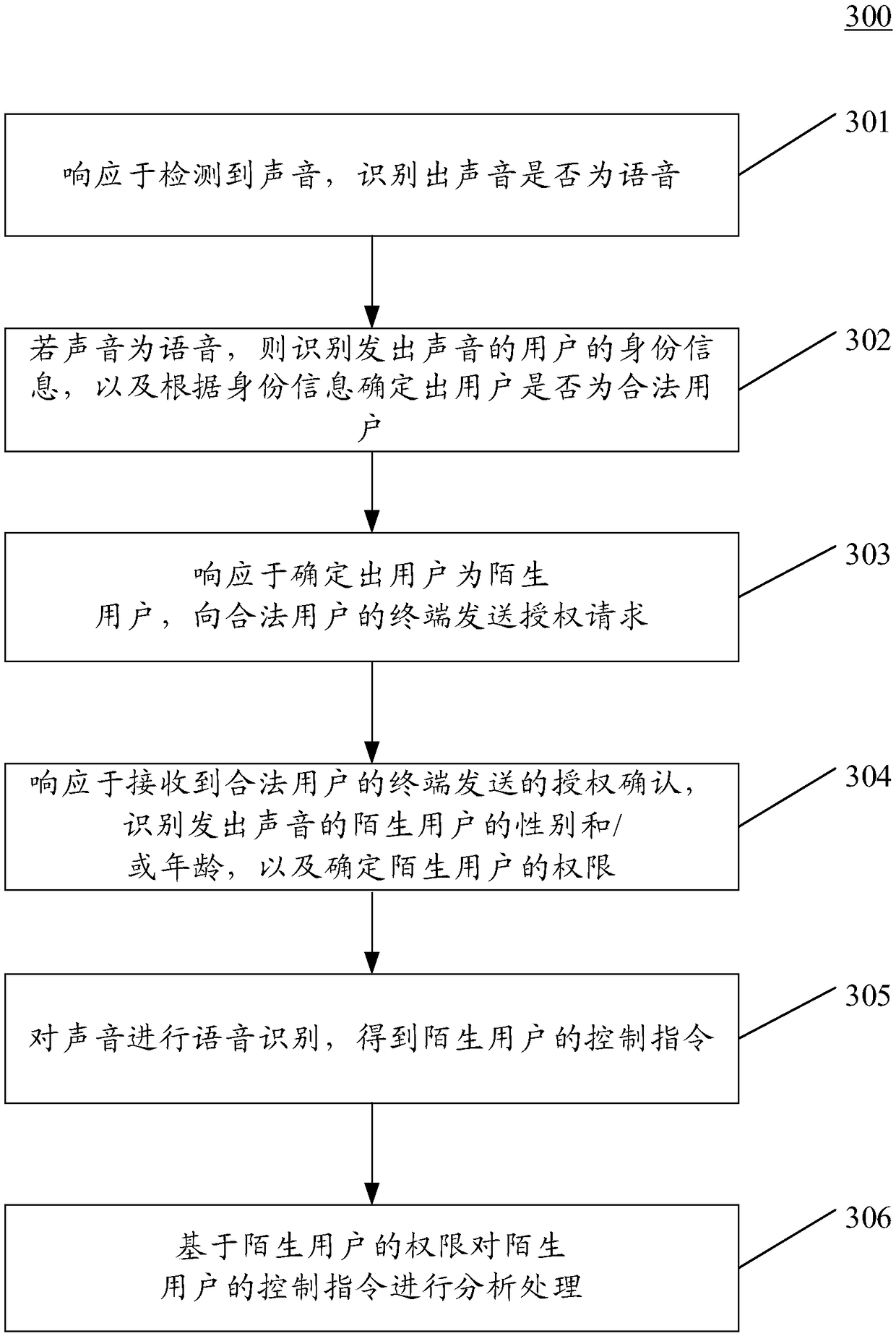
InactiveCN109412910ARealize security management and controlAchieve securitySpeech analysisHome automation networksExecution controlSpeech identification
The embodiment of the application discloses a method and apparatus for controlling a smart home appliance. One specific embodiment of the method includes steps: recognizing whether a sound is a voicein response to detection of the sound; if yes, recognizing identity information of a user emitting the sound, and determining whether the user is a legal user according to the identity information; performing speech recognition on the sound in response to determination that the user is the legal user, and obtaining a control instruction; and executing the control instruction in response to determination that the control instruction is an instruction matched with the identity information. According to the method and apparatus, security management and control of the smart home appliance and security management and security protection of a speaker can be realized.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
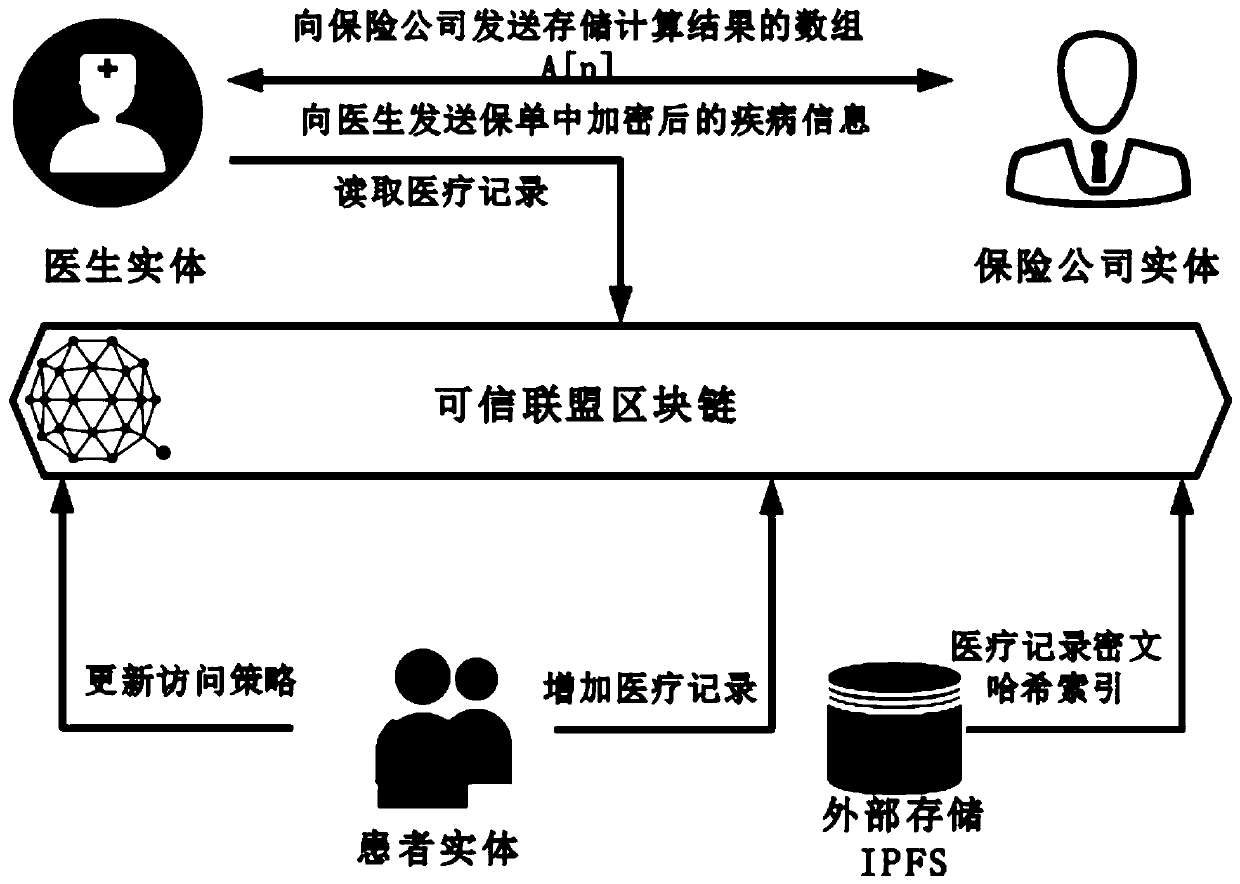
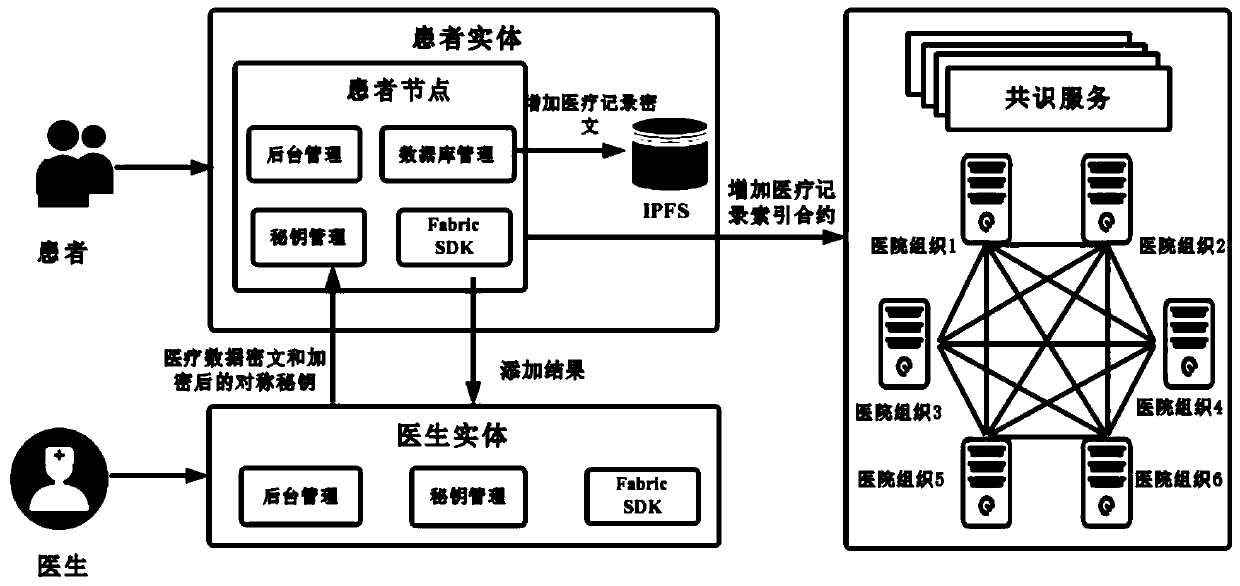
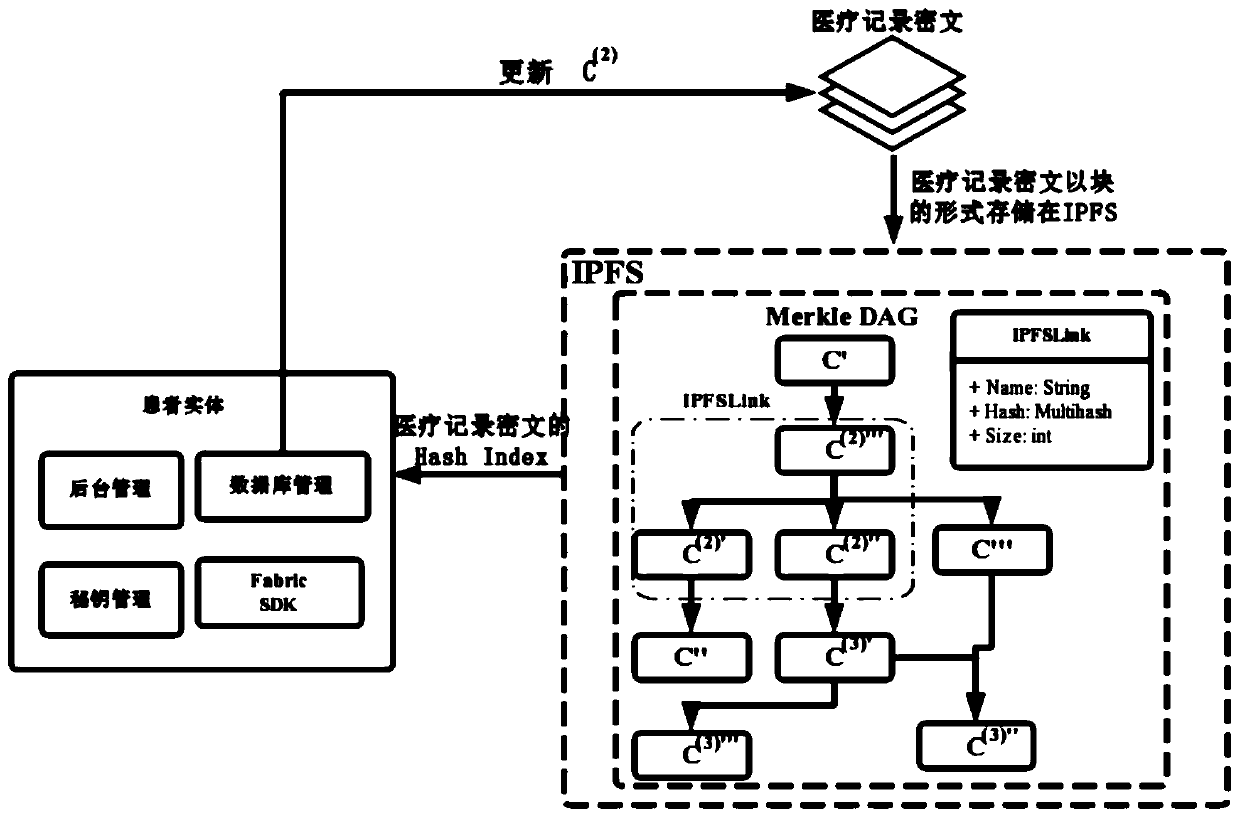
Medical record storage, sharing and security claim settlement model and method based on a block chain
ActiveCN110008746AGuaranteed privacyIncrease resistanceDigital data protectionPatient healthcareMedical recordThird party
The invention belongs to the technical field of medical data management, and relates to a medical record storage, sharing and security claim settlement model and method based on a block chain. Firstly, credible sharing of medical data of patients among medical institutions is achieved through the blockchain technology, and a lifelong medical record is established for the patients; based on a Hashchain type storage structure, the medical data cannot be tampered; secondly, an improved CP-ABE-based cryptographic primitive SHDPCPC-CP-ABE is proposed, security encryption and fine-grained access control on the medical data are realized, and a patient can conveniently and efficiently access and authorize a medical institution to read the medical data; and finally, a Paillier homomorphic encryption technology is utilized to realize safe medical insurance claim settlement, and the privacy of the patient is protected when the patient interacts with a third-party non-medical institution. According to the invention, security, confidentiality, reliability and integrity of medical data can be realized, and confidential sharing of private data is supported.
Owner:DALIAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com