Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
24260 results about "Third party" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
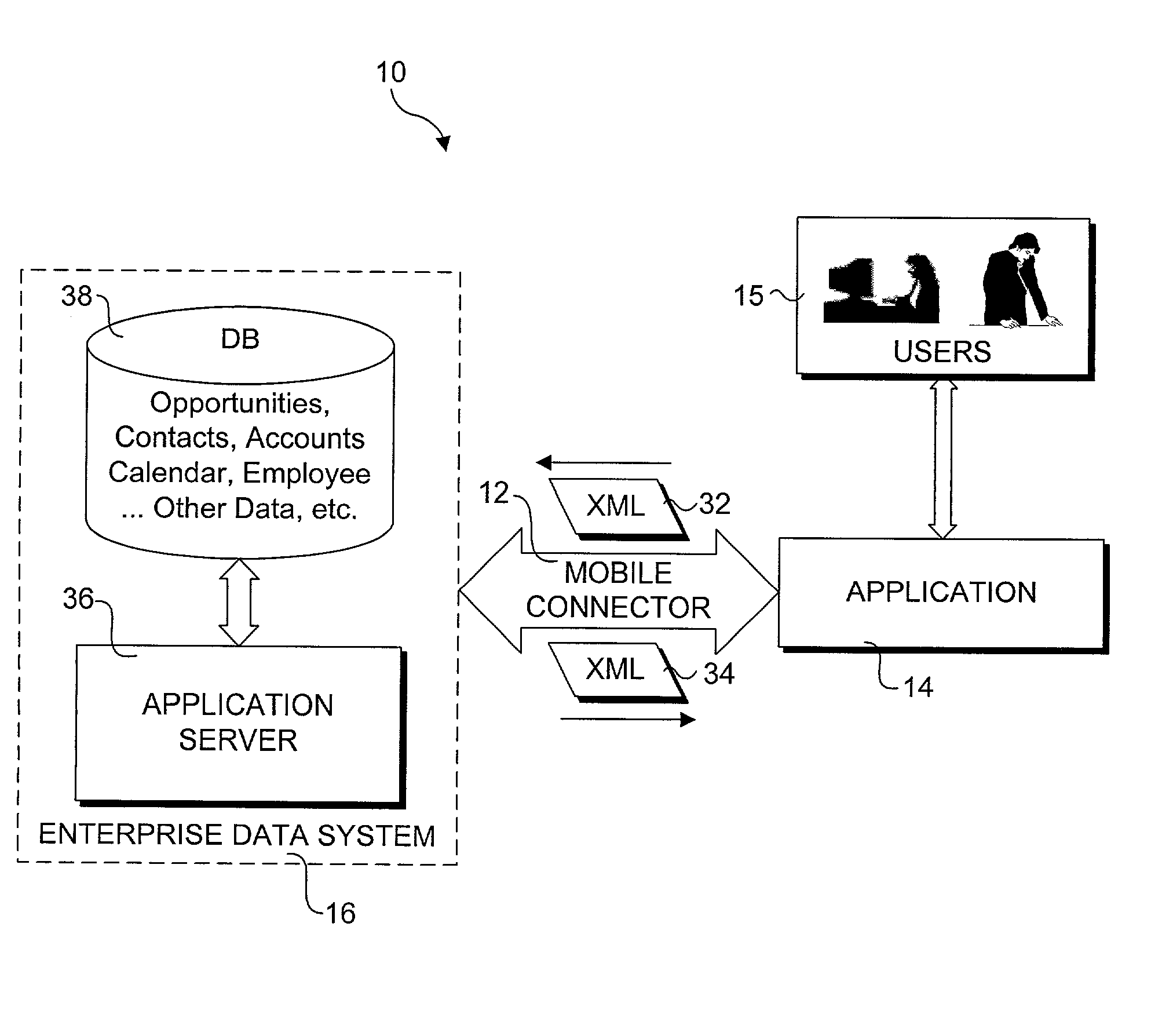
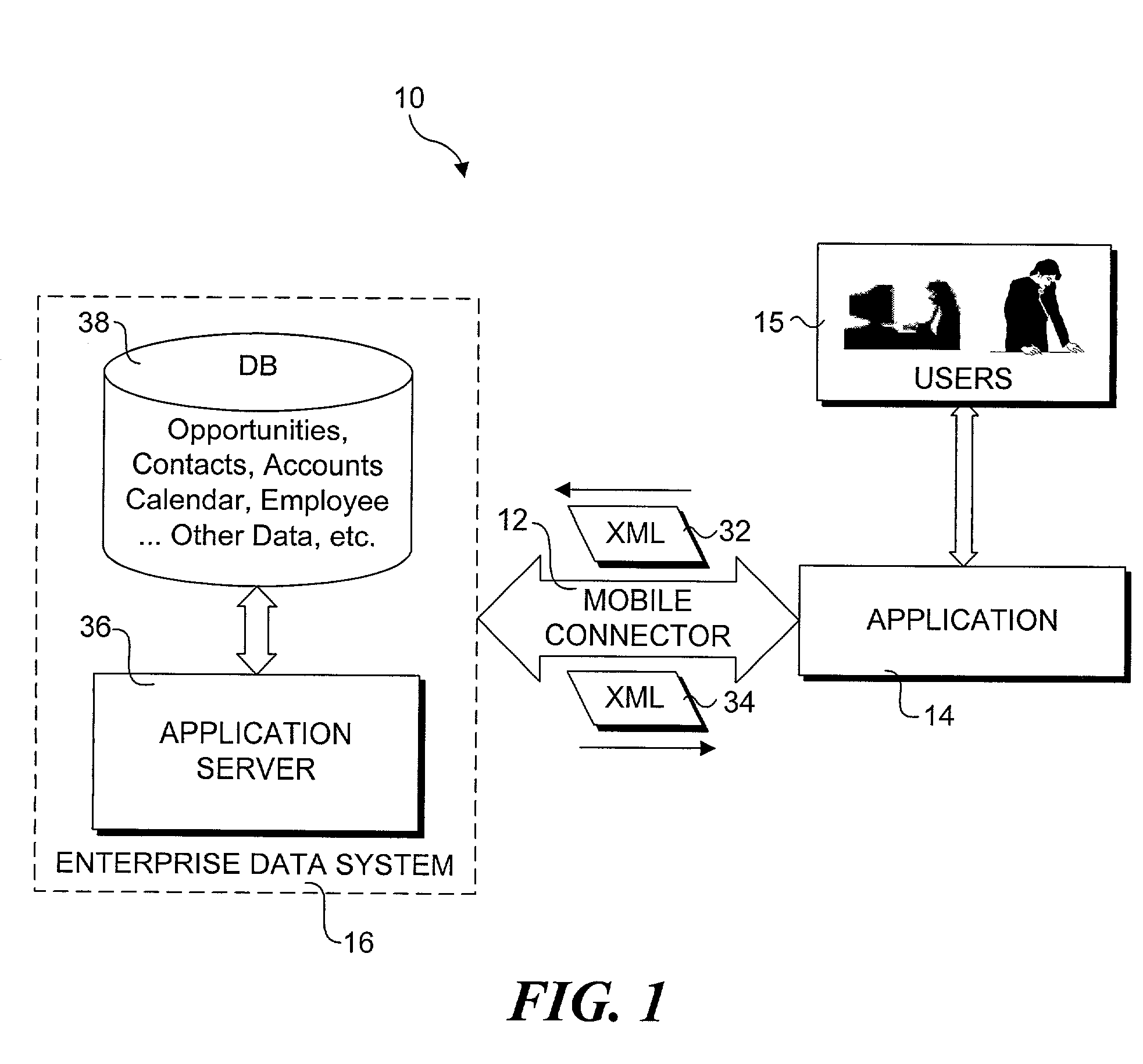
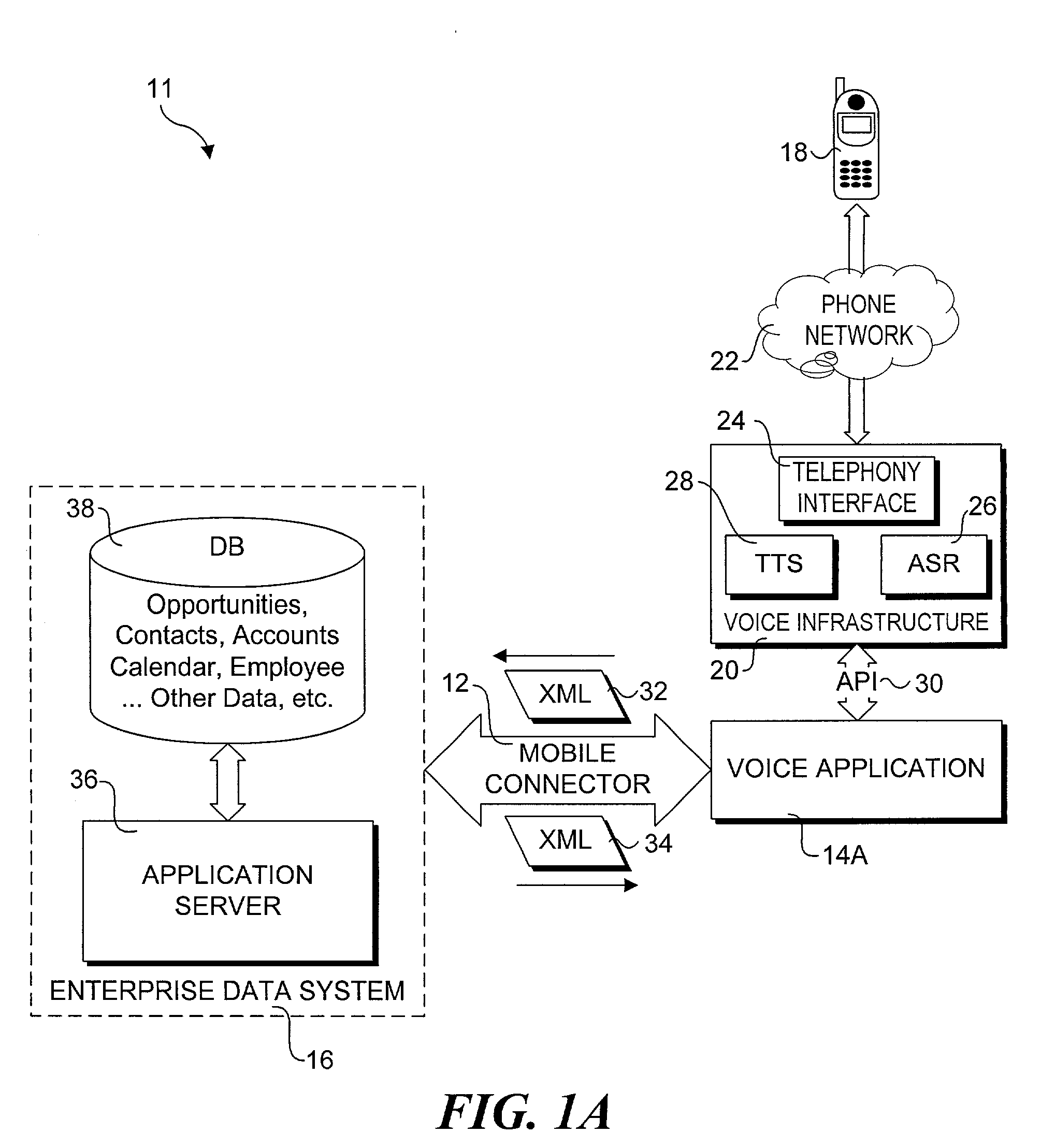
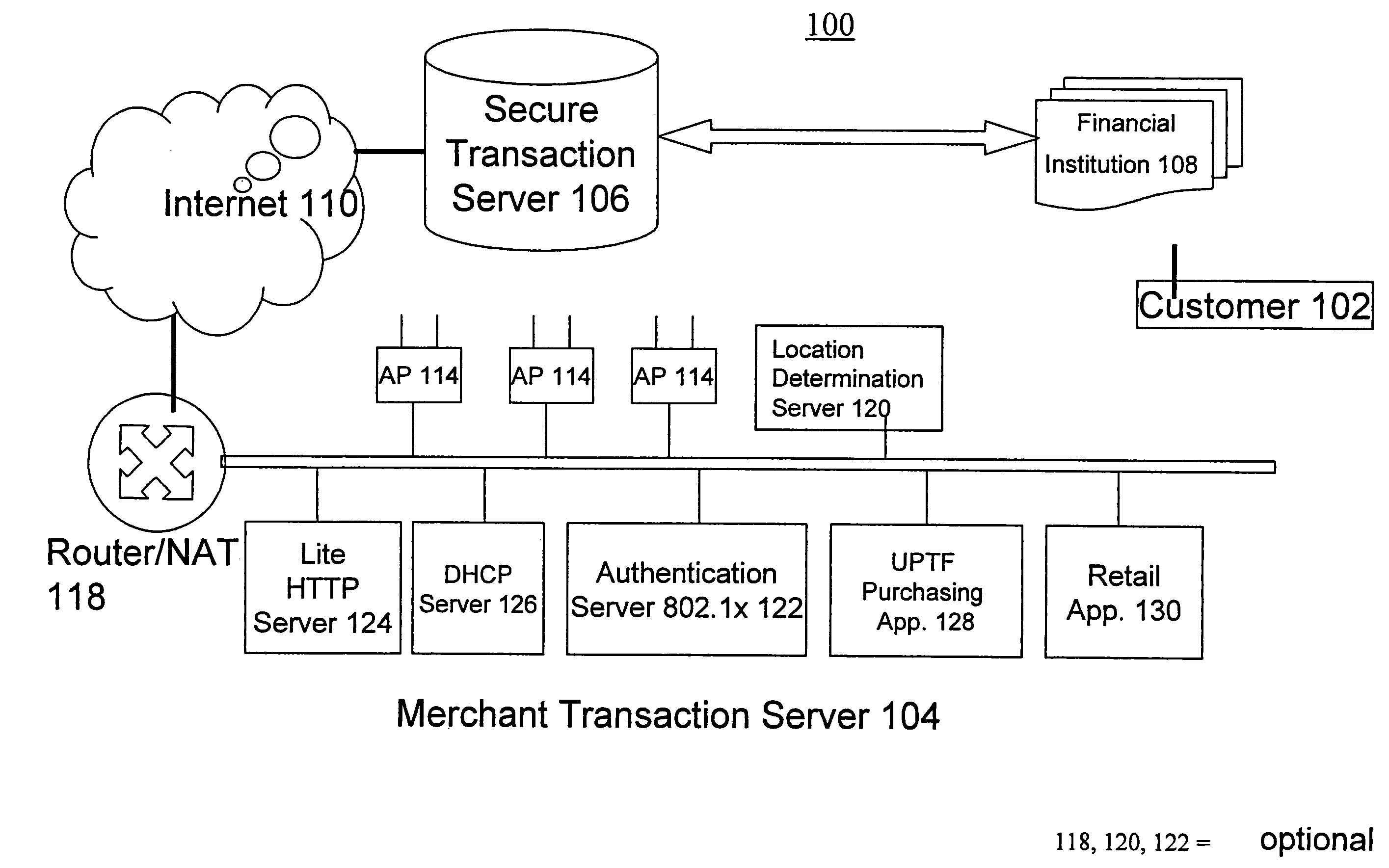
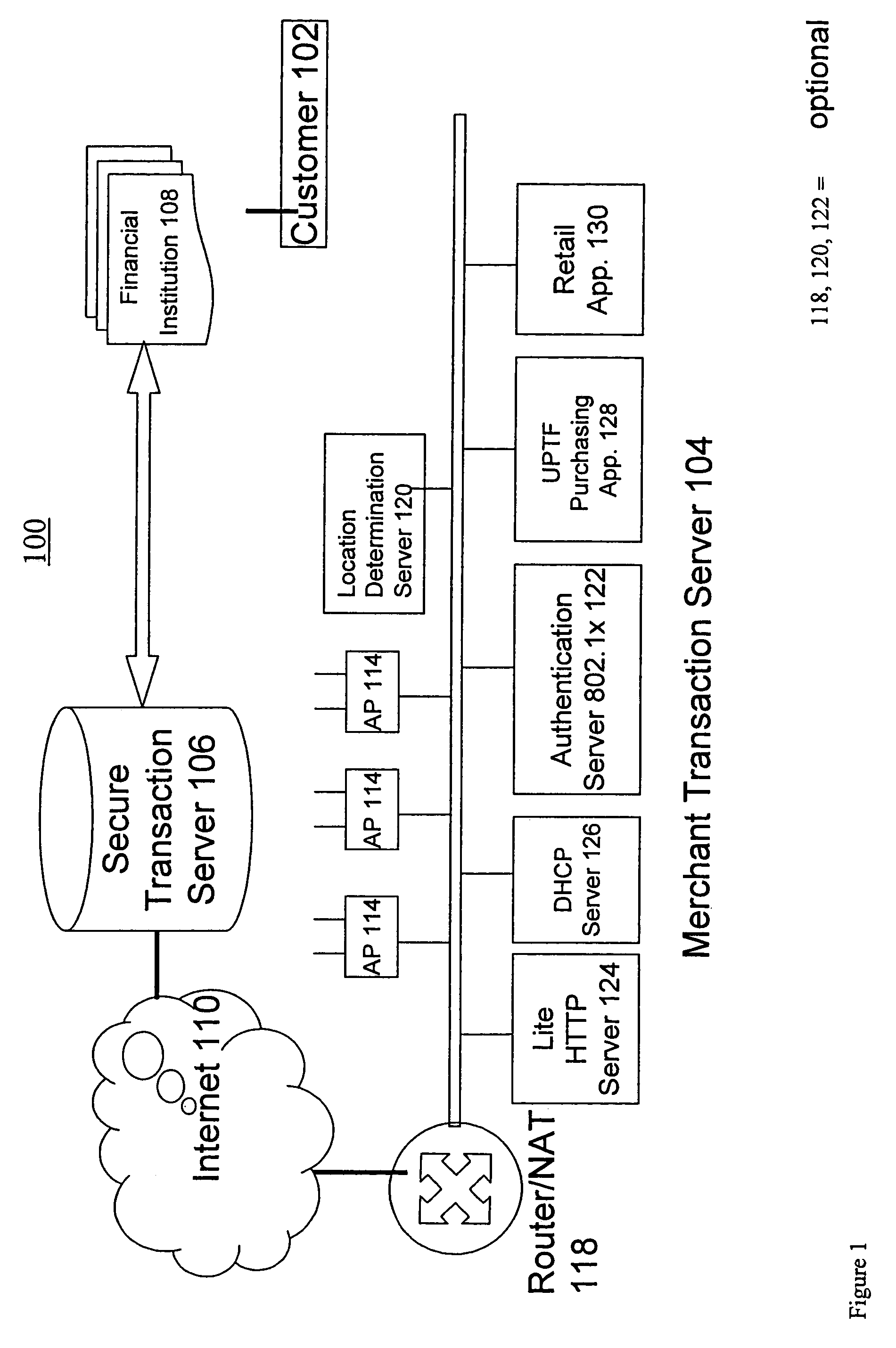
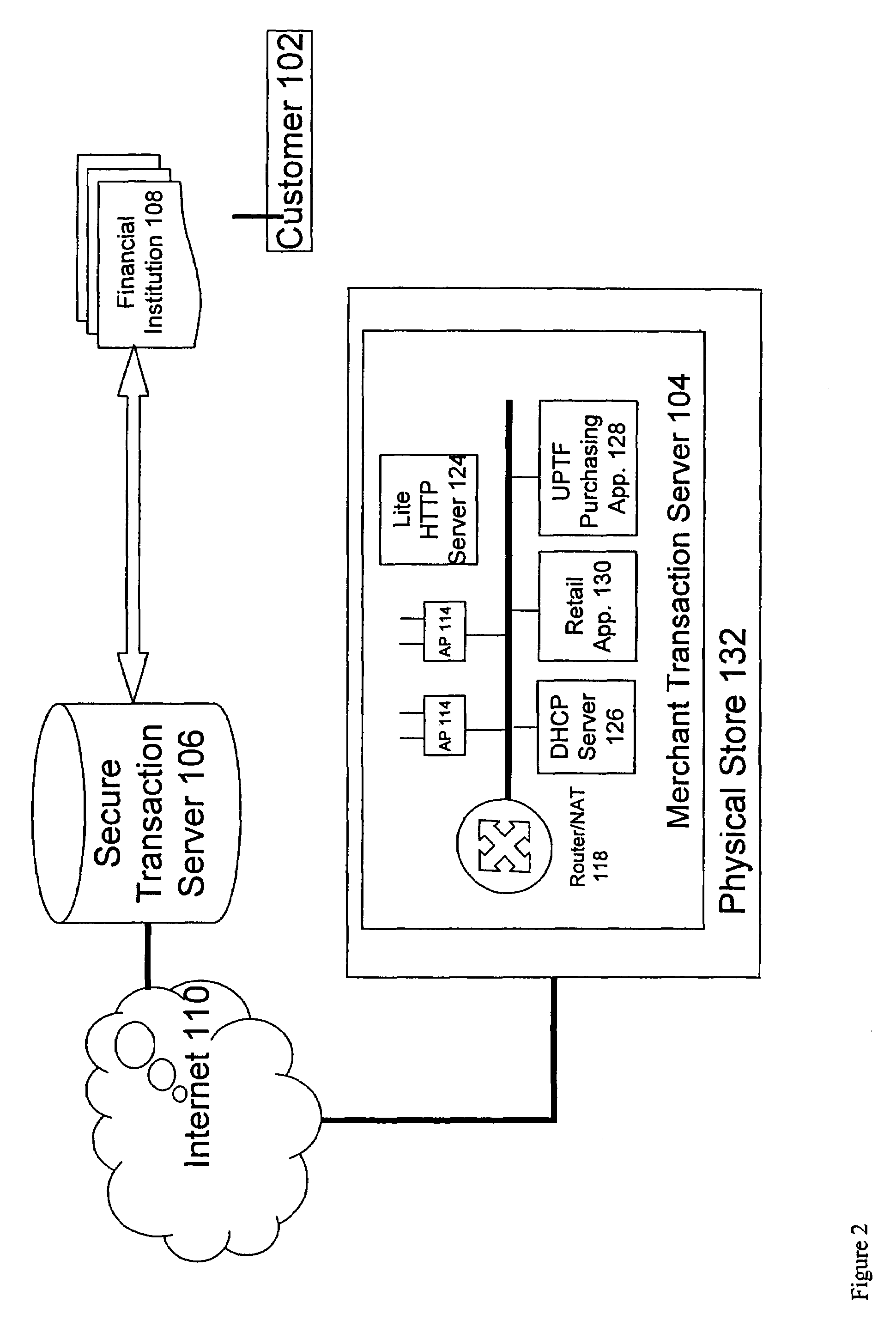
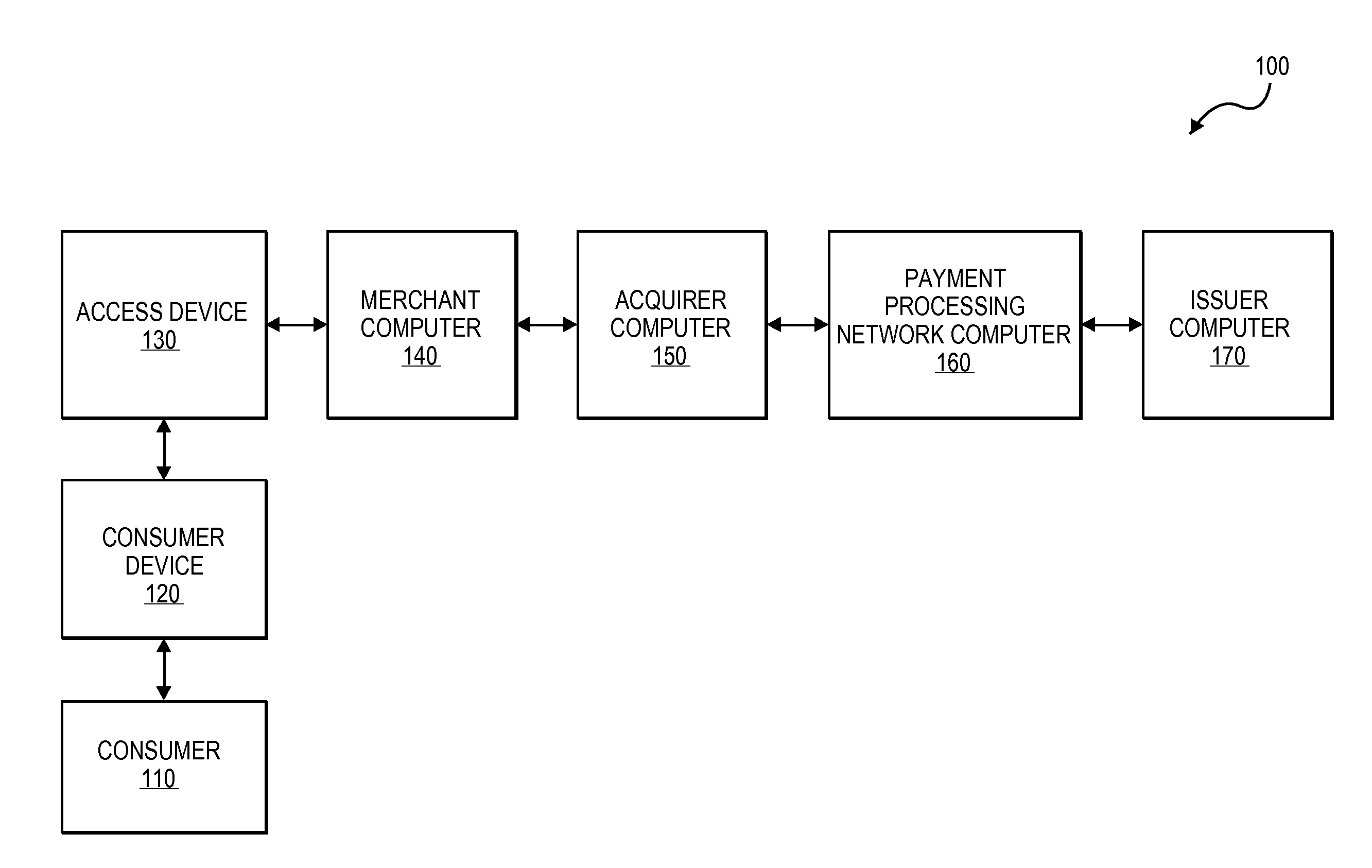
Method and system for enabling connectivity to a data system
A method and system that provides filtered data from a data system. In one embodiment the system includes an API (application programming interface) and associated software modules to enable third party applications to access an enterprise data system. Administrators are enabled to select specific user interface (UI) objects, such as screens, views, applets, columns and fields to voice or pass-through enable via a GUI that presents a tree depicting a hierarchy of the UI objects within a user interface of an application. An XSLT style sheet is then automatically generated to filter out data pertaining to UI objects that were not voice or pass-through enabled. In response to a request for data, unfiltered data are retrieved from the data system and a specified style sheet is applied to the unfiltered data to return filtered data pertaining to only those fields and columns that are voice or pass-through enabled.
Owner:ORACLE INT CORP
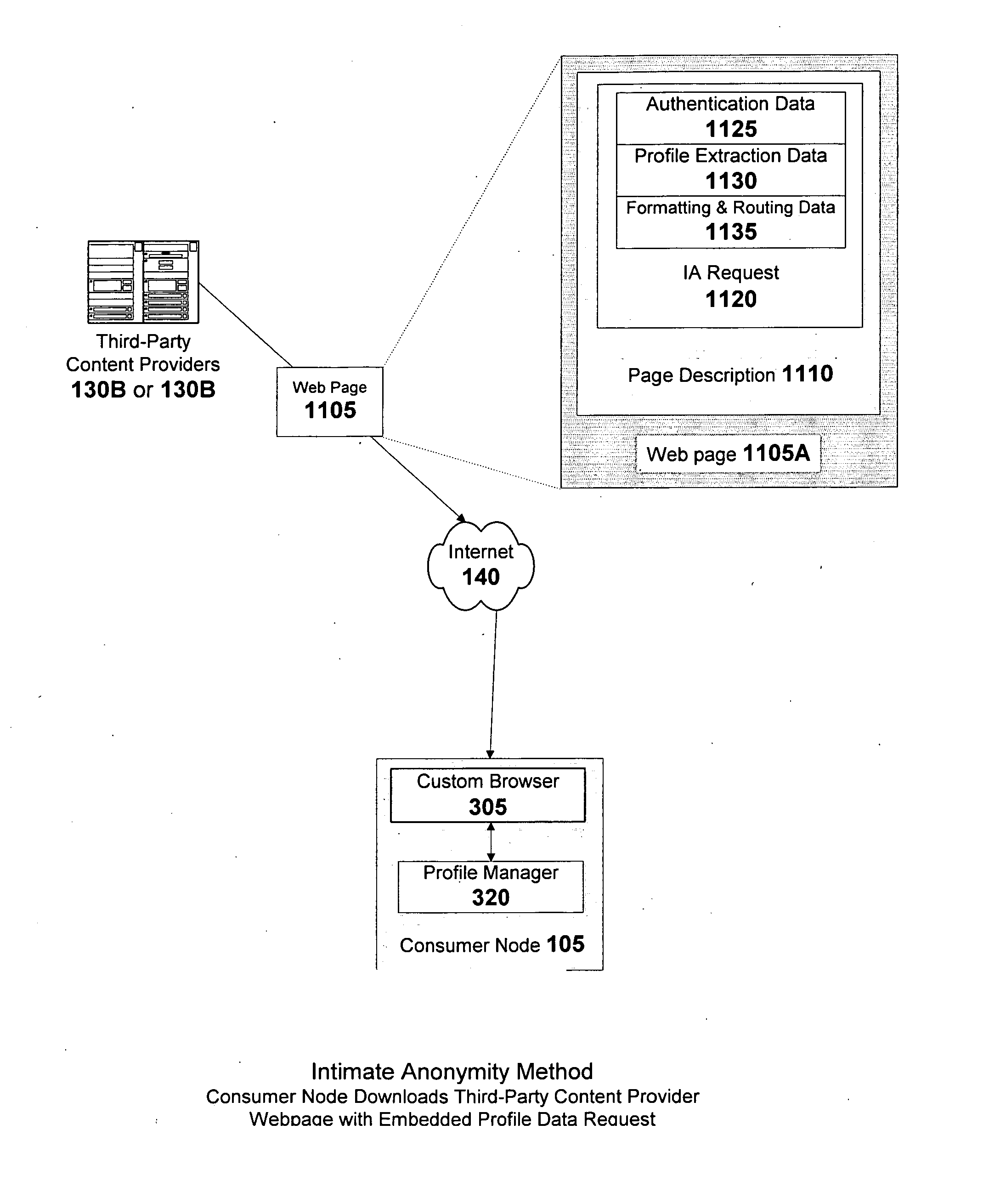
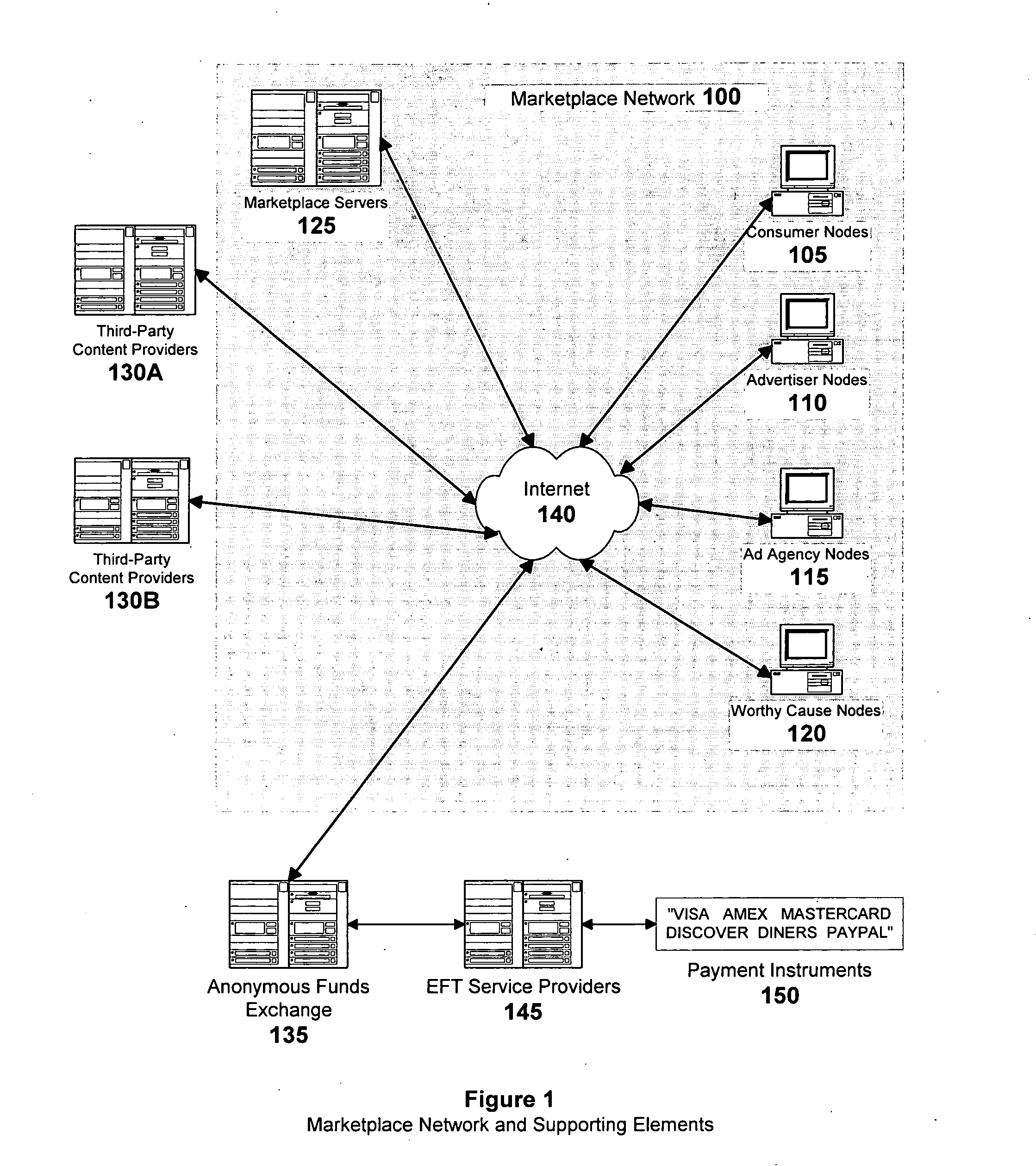
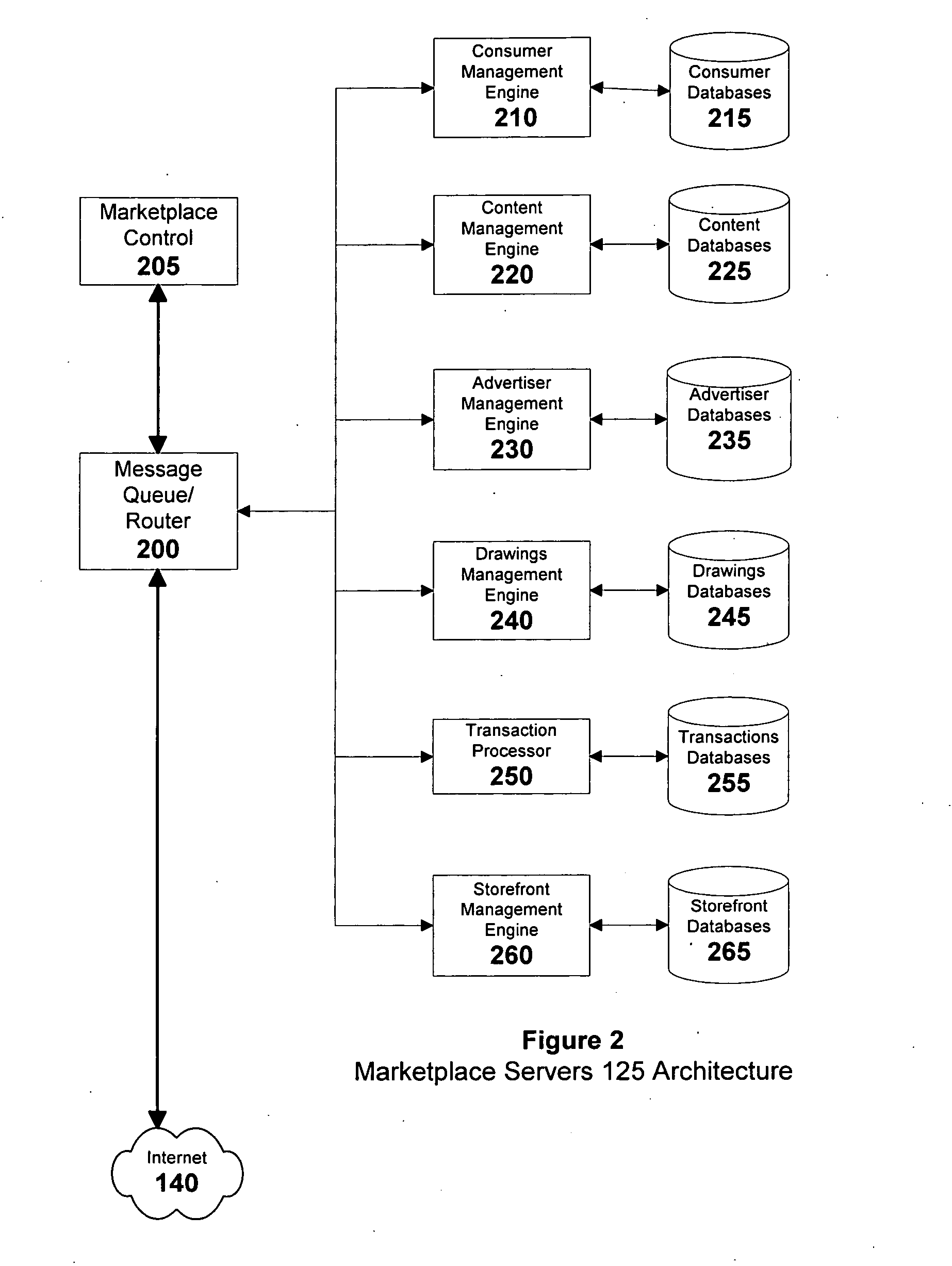
System and methods for a micropayment-enabled marketplace with permission-based, self-service, precision-targeted delivery of advertising, entertainment and informational content and relationship marketing to anonymous internet users
InactiveUS20070067297A1Payment architectureSpecial data processing applicationsPersonalizationThird party
A method of enabling anonymous Internet users to publish and manage extensive, non-identifying personal data, including demographic, psychographic, needs, wants, interests, propensities, means to purchase, credibility and other data which in turn, enables a marketplace wherein such users, advertisers, websites, and other third-parties can mutually benefit from the commercial exploitation of such data. Advertisers can directly use the data to segregate the users into highly differentiated anonymous audiences for the purposes of targeting them with individualized marketing campaigns and then monitor user responses in near real-time. Websites can individualize their content to the profiles of visiting users. Users can share surface and deep web links with other users having similar profiles. Consumers participating in good faith are proportionately rewarded via revenue sharing, which they may withdraw from the marketplace or use to purchase and rent digital content offered in the marketplace's micropayment-enabled storefronts by other users and third-party content providers.
Owner:KUBLICKIS PETER JOSEPH
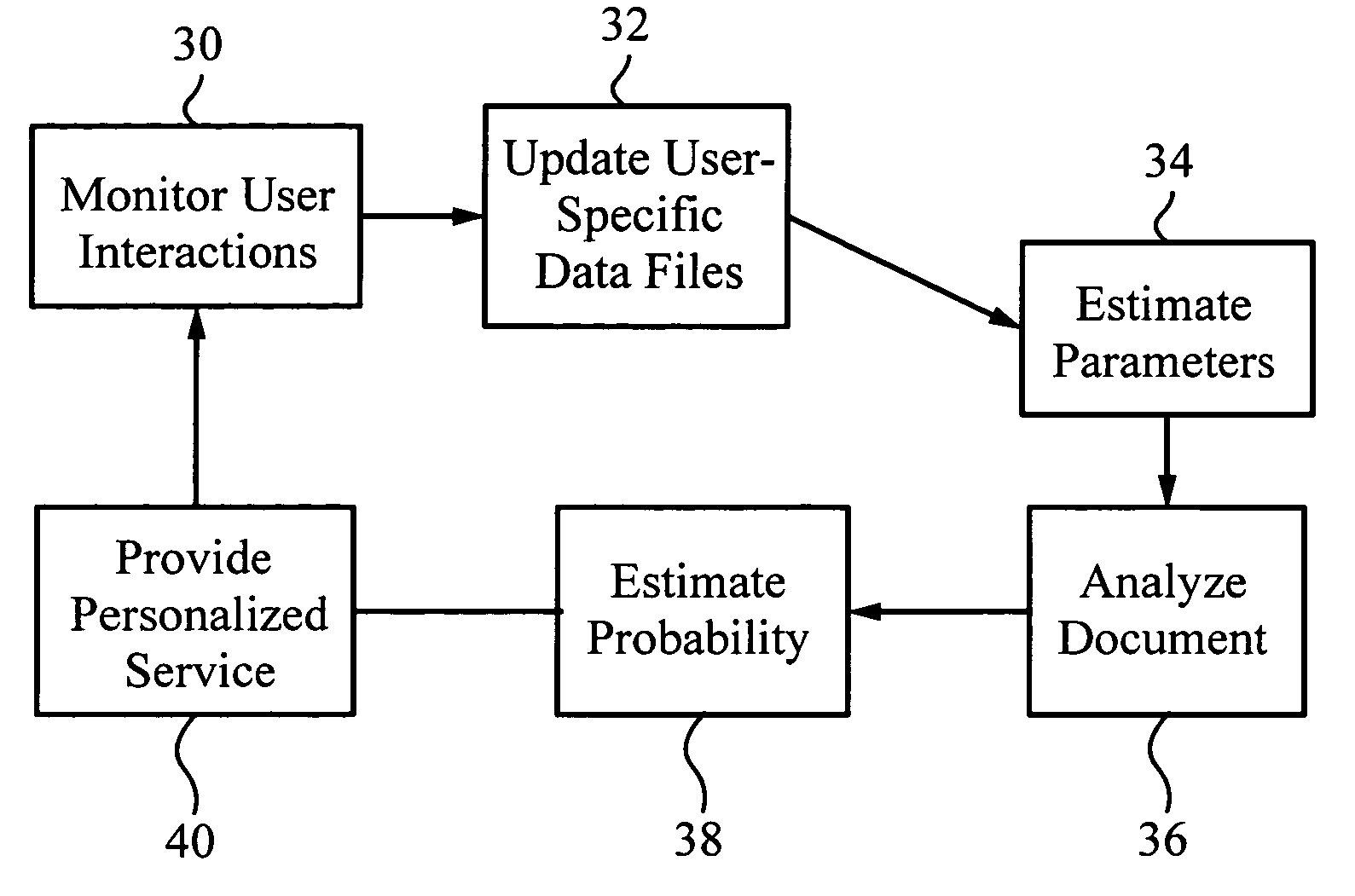
Automatic, personalized online information and product services
InactiveUS6981040B1Improve performanceManage efficiently enormousDigital data information retrievalMultiple digital computer combinationsLearning machinePersonalized search
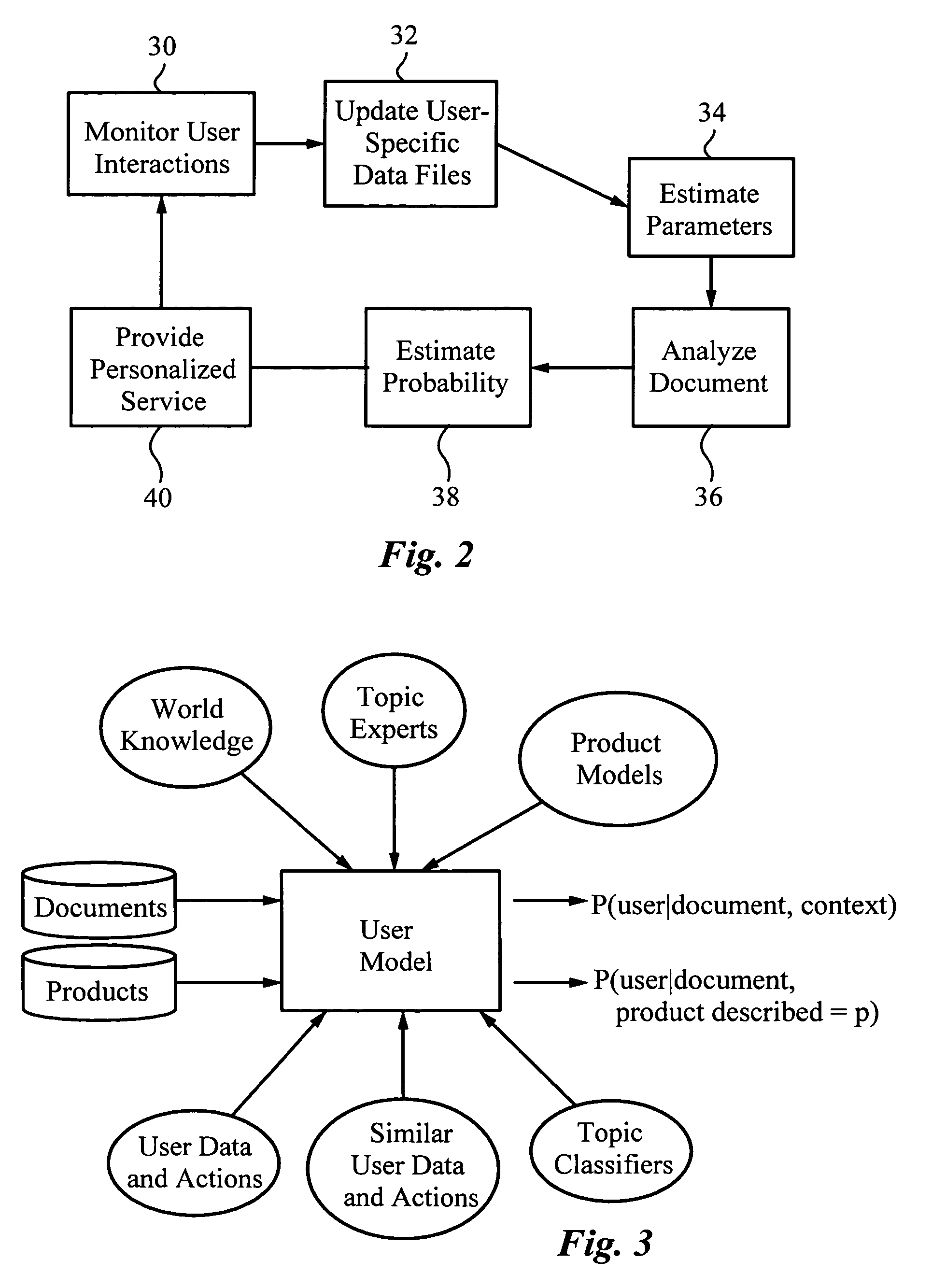
A method for providing automatic, personalized information services to a computer user includes the following steps: transparently monitoring user interactions with data during normal use of the computer; updating user-specific data files including a set of user-related documents; estimating parameters of a learning machine that define a User Model specific to the user, using the user-specific data files; analyzing a document to identify its properties; estimating the probability that the user is interested in the document by applying the document properties to the parameters of the User Model; and providing personalized services based on the estimated probability. Personalized services include personalized searches that return only documents of interest to the user, personalized crawling for maintaining an index of documents of interest to the user; personalized navigation that recommends interesting documents that are hyperlinked to documents currently being viewed; and personalized news, in which a third party server customized its interaction with the user. The User Model includes continually-updated measures of user interest in words or phrases, web sites, topics, products, and product features. The measures are updated based on both positive examples, such as documents the user bookmarks, and negative examples, such as search results that the user does not follow. Users are clustered into groups of similar users by calculating the distance between User Models.
Owner:PERSONALIZED USER MODEL PUM
Interactive music playlist sharing system and methods
InactiveUS20060143236A1Limited accessDigital data information retrievalElectronic editing digitised analogue information signalsWeb siteThird party
A community media playlist sharing system is disclosed, wherein system users can upload media playlists which are automatically converted to a standardized format, media playlists can be shared with other users of the community media playlist sharing system, users can link to other playlists and obtain media from playlists automatically from third party points of purchase, users can provide recommendations, ratings and rankings relative to other playlists by system users and receive recommendations from other users and an editorial staff, participate in social networking functions including forums, discussions, weblogs, playlist topic groups and inter-user communications based on affinity for similar playlists, create playlists manually, automatically, or in real time, and wherein system users can obtain points for participation and popularity in the system and obtain profit by meta-affiliate sharing of profit for purchases of music made through playlists submitted by that user as well as through playlist toolbars distributed to third party websites.
Owner:CONCERT TECH
System and method for fraud monitoring, detection, and tiered user authentication
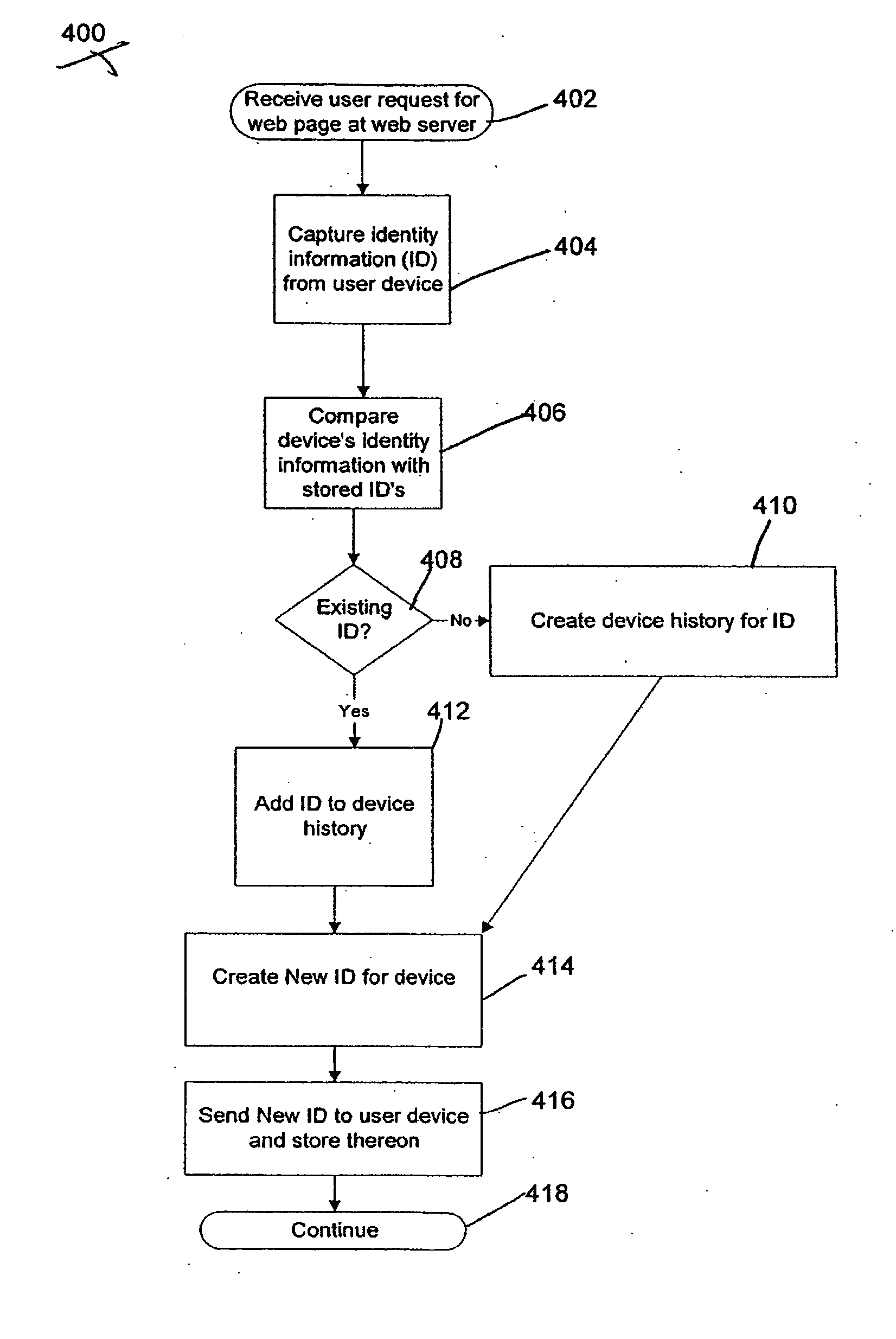
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
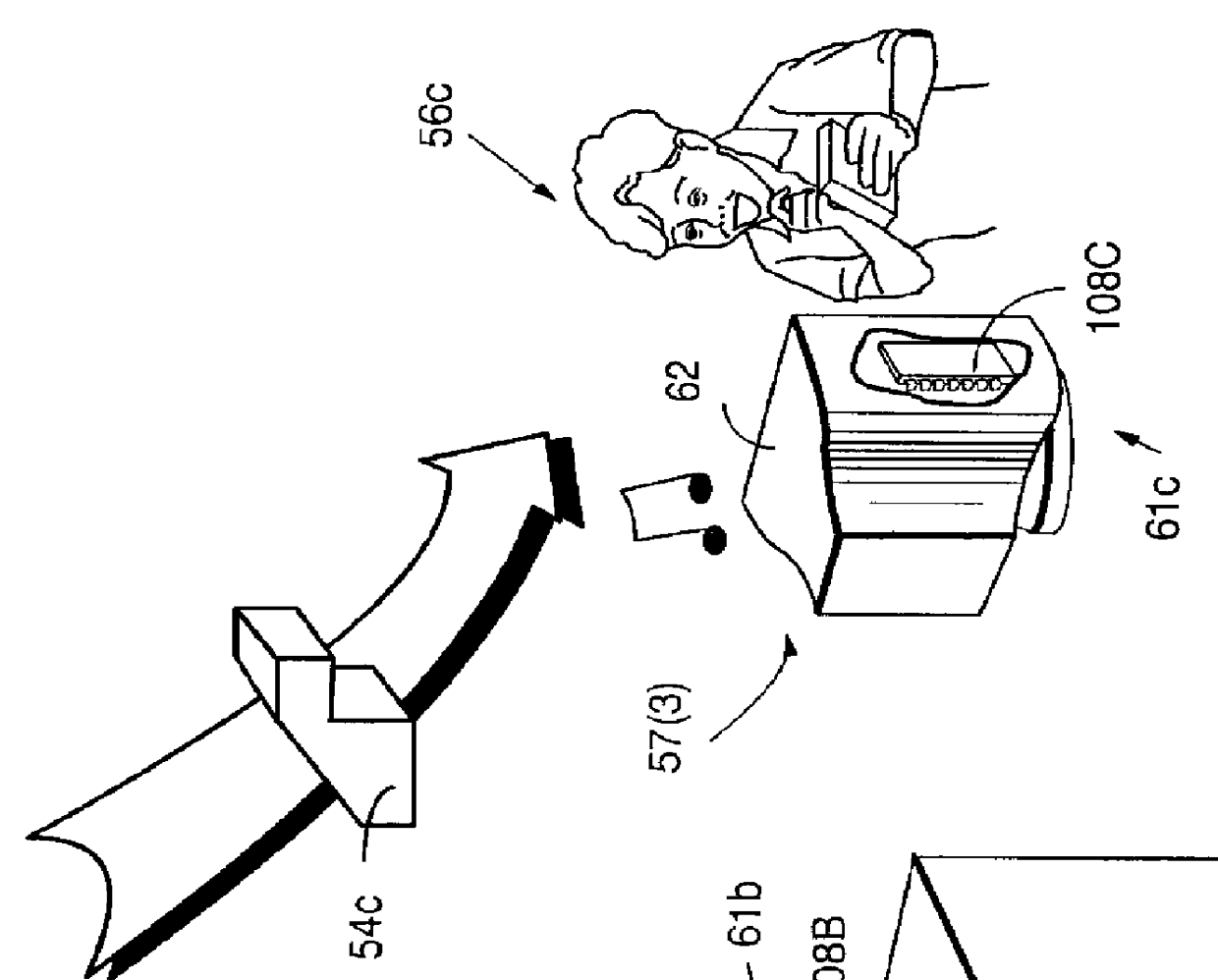
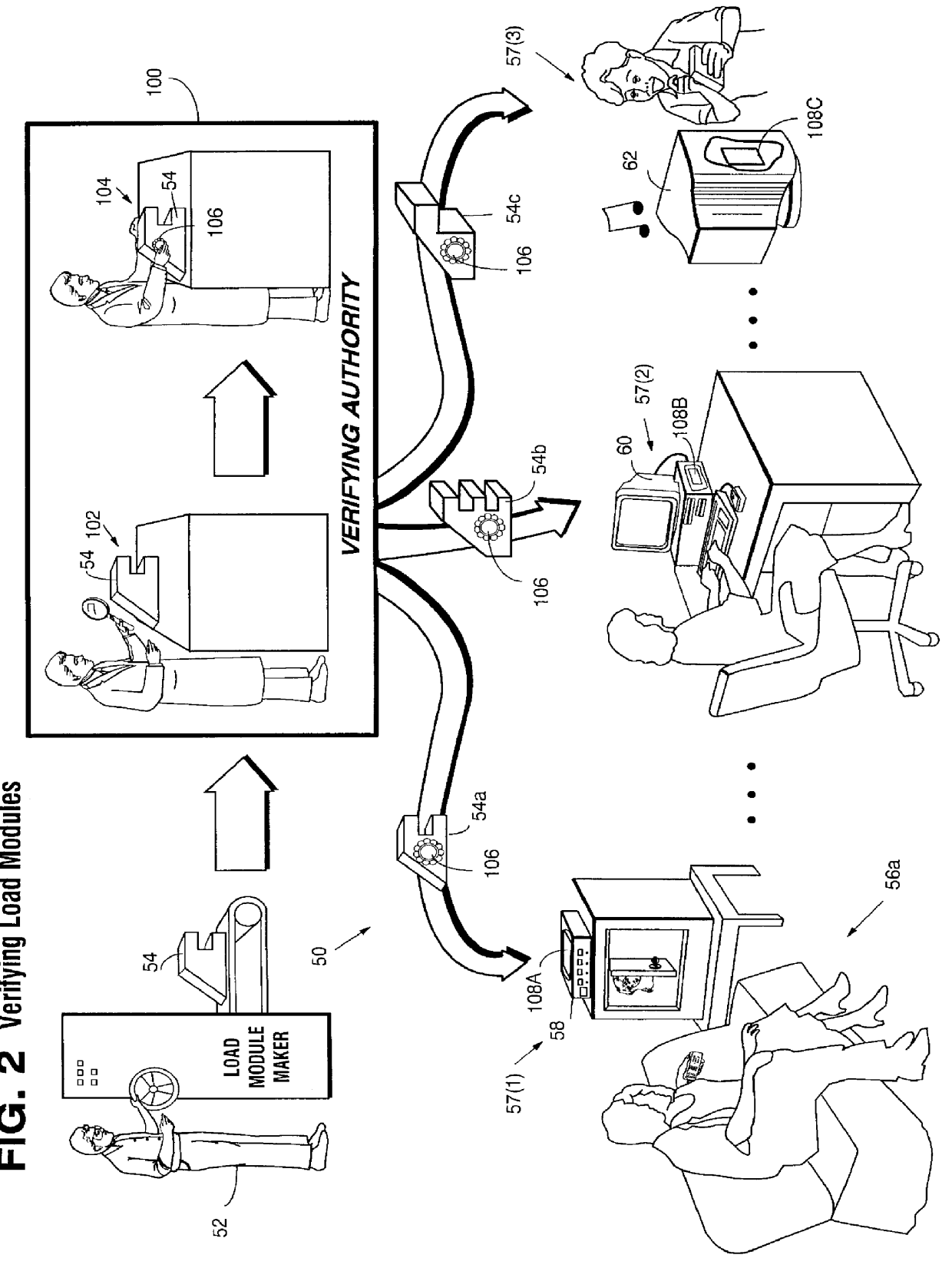
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
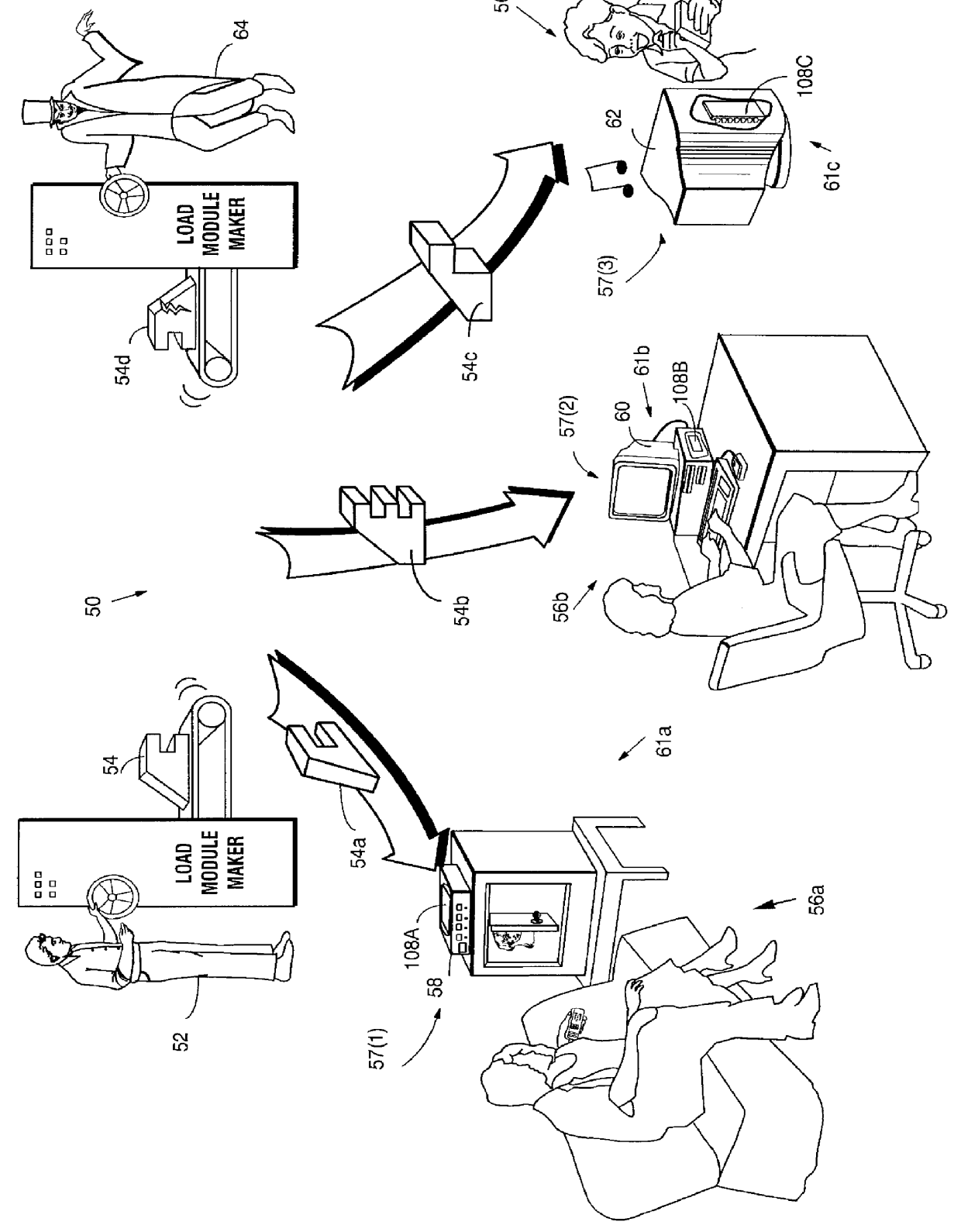
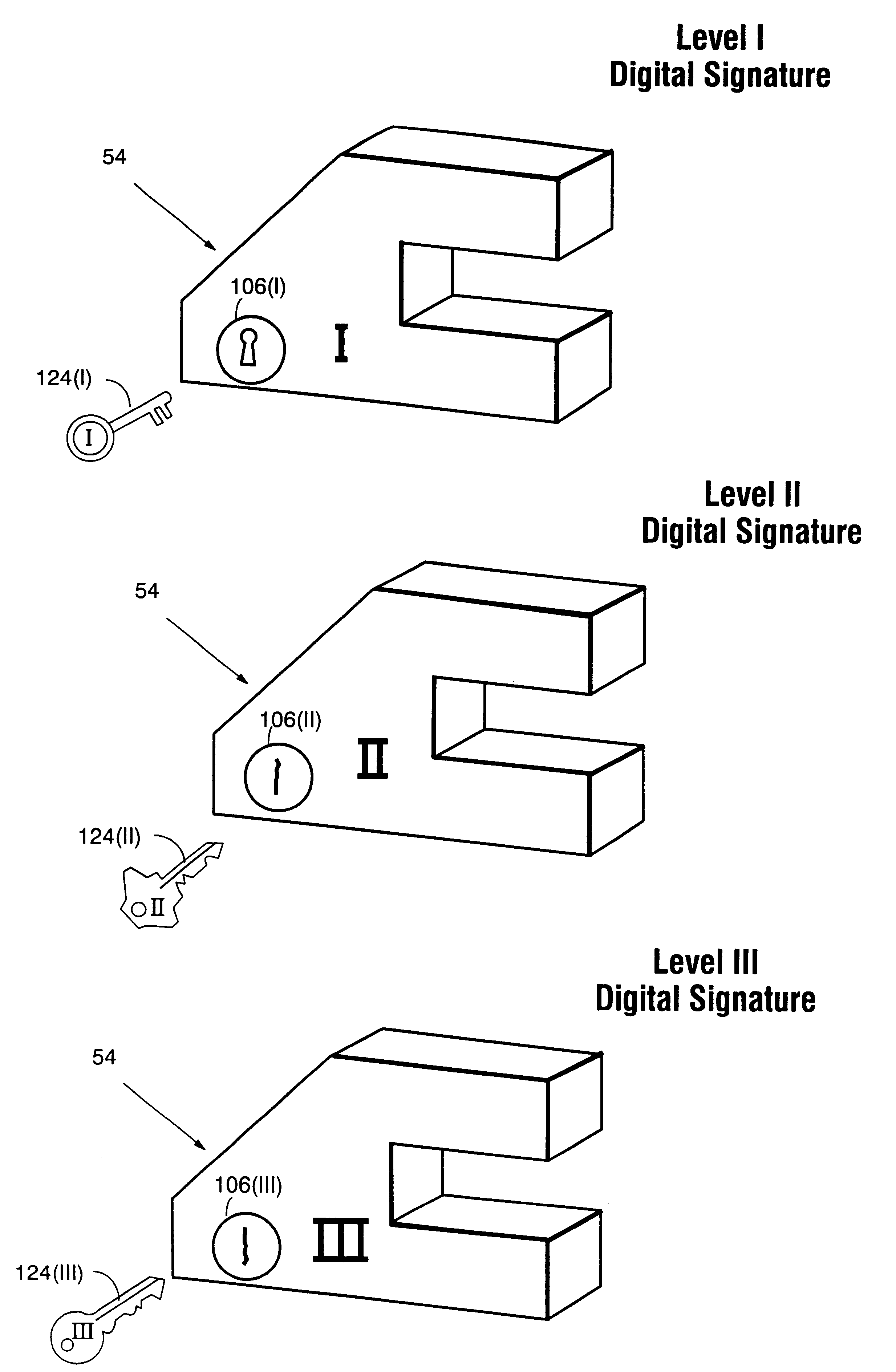
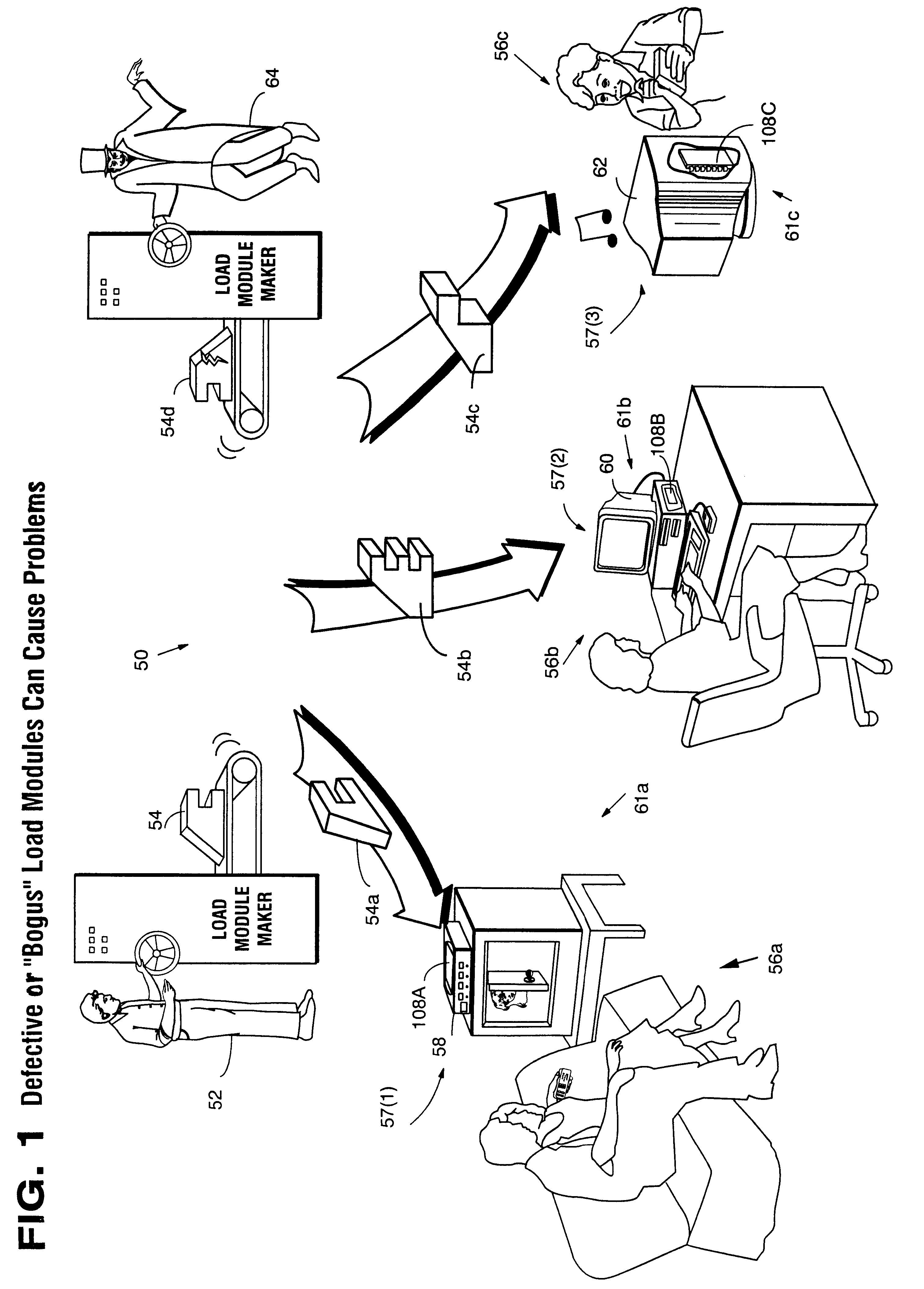
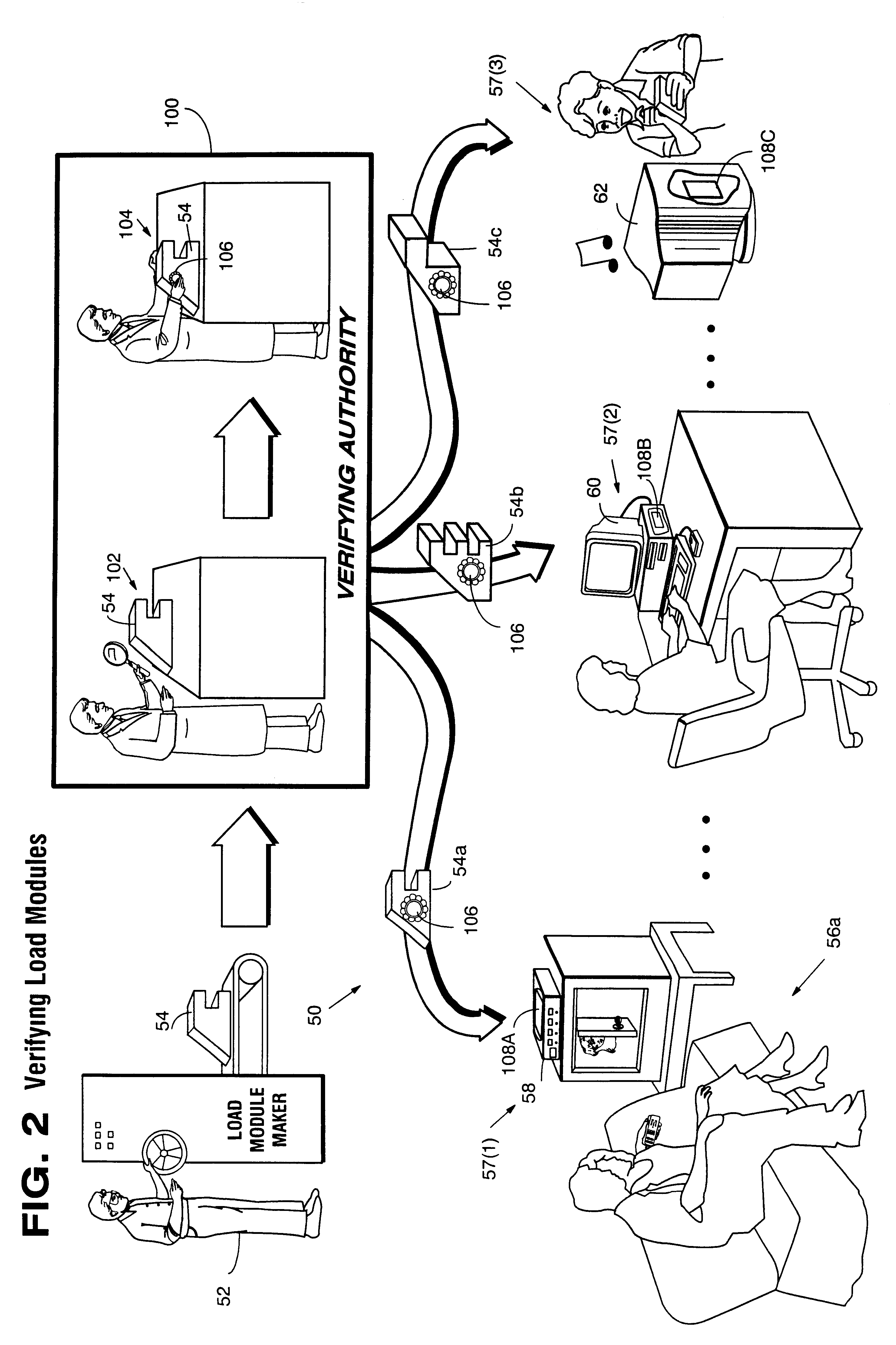
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
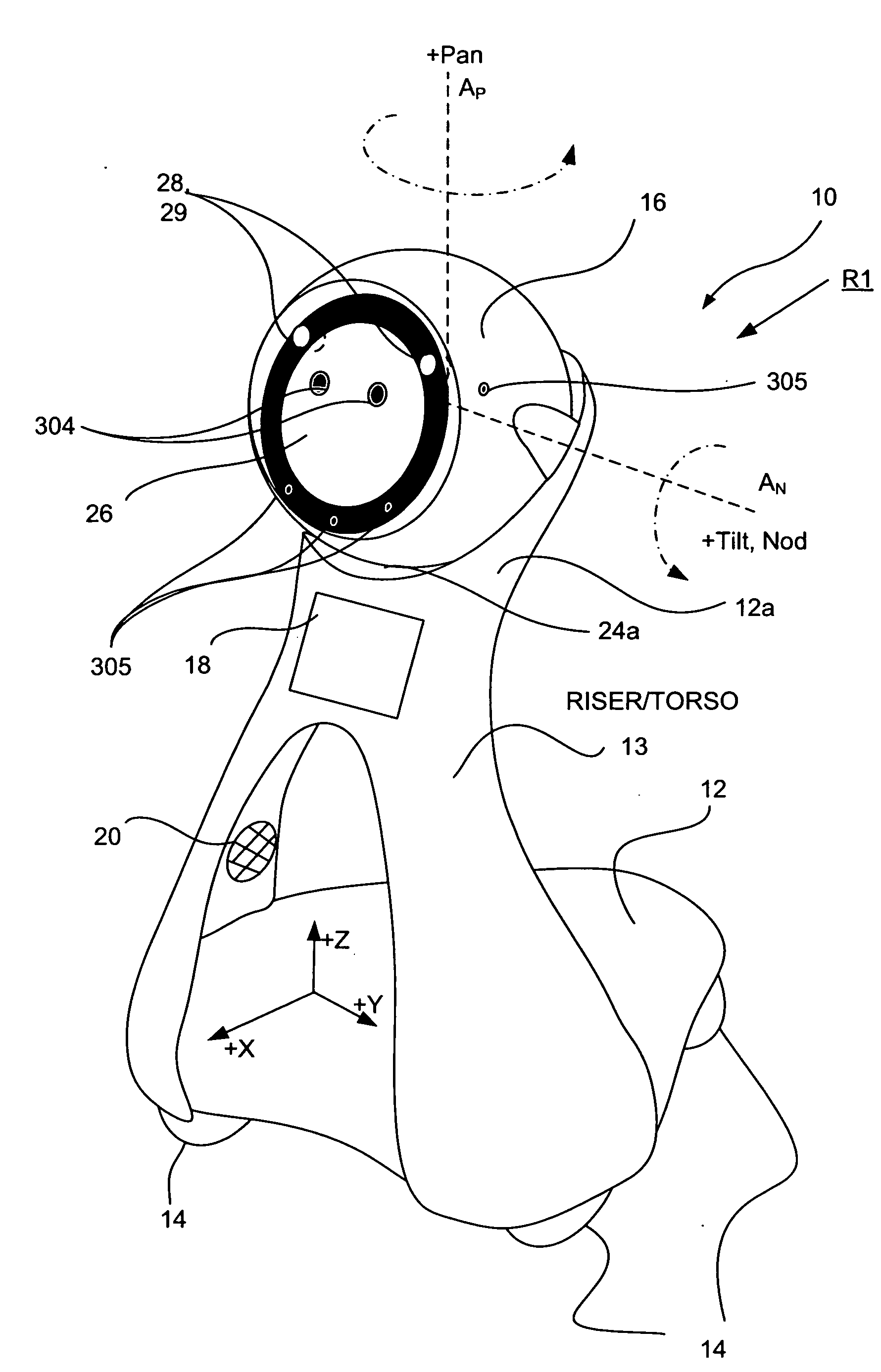
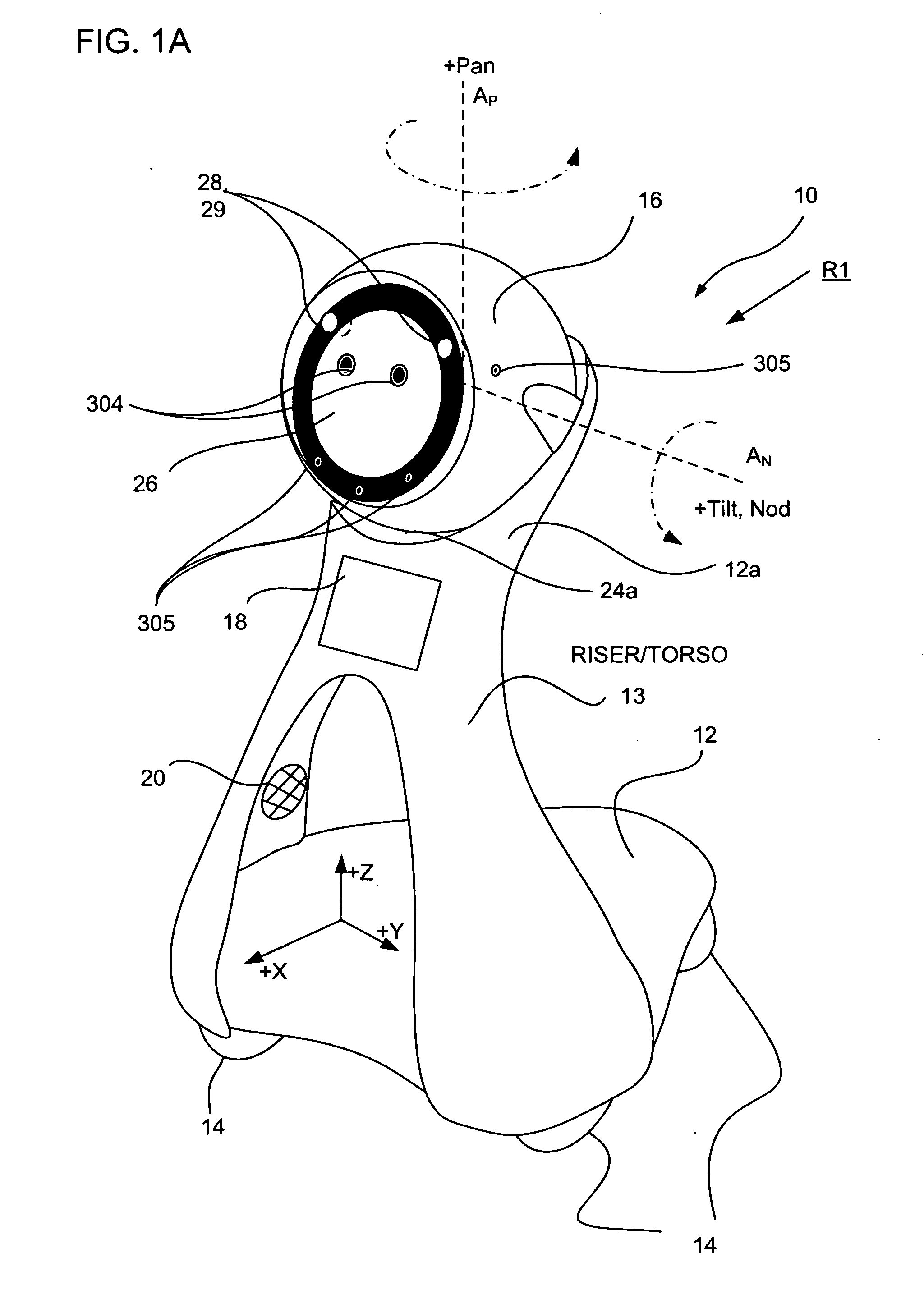
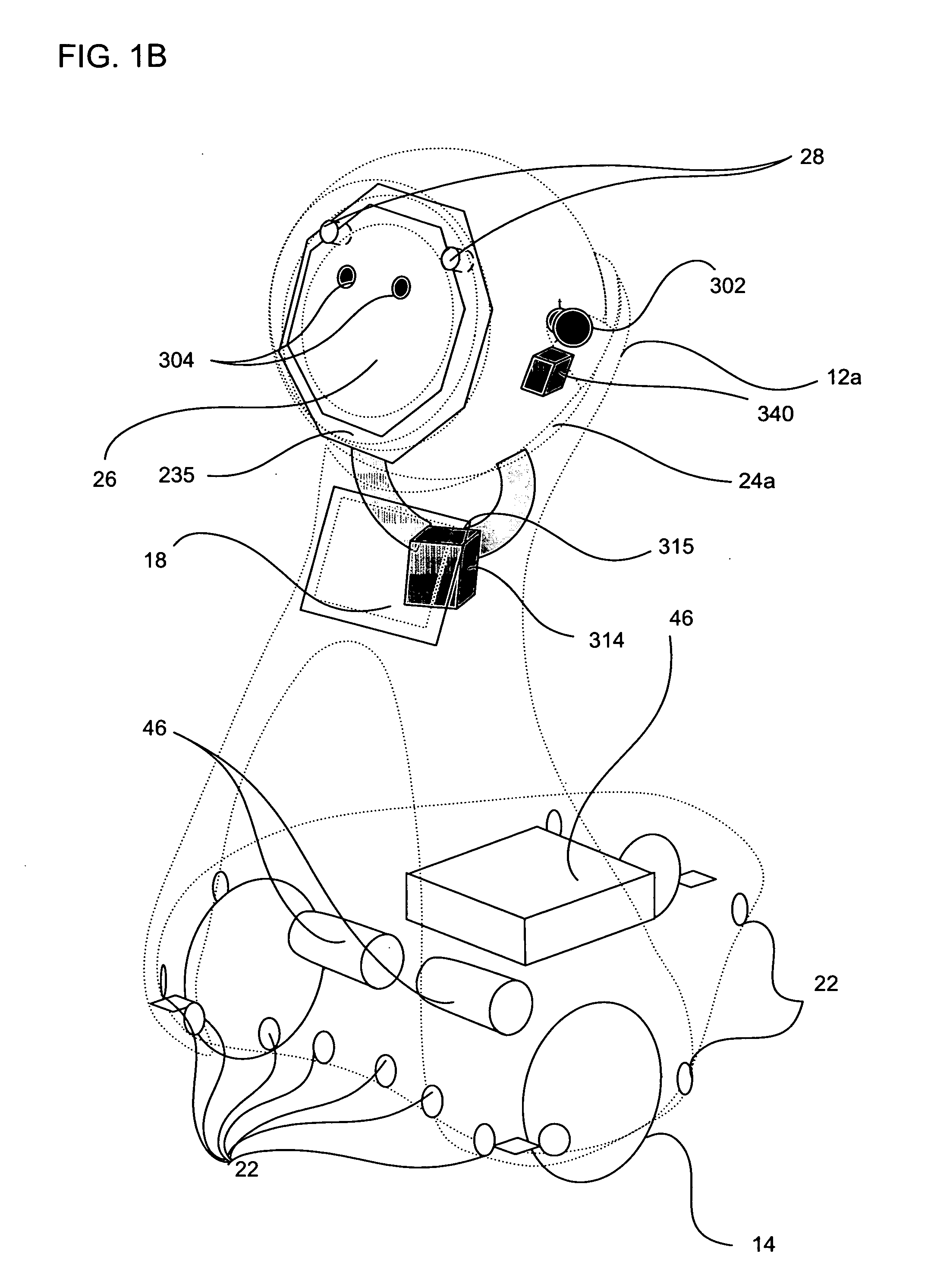
Companion robot for personal interaction
ActiveUS20070192910A1Improving presence scoreEnhanced presenceProgramme-controlled manipulatorLocal control/monitoringThird partyTeleconference
A mobile robot guest for interacting with a human resident performs a room-traversing search procedure prior to interacting with the resident, and may verbally query whether the resident being sought is present. Upon finding the resident, the mobile robot may facilitate a teleconferencing session with a remote third party, or interact with the resident in a number of ways. For example, the robot may carry on a dialogue with the resident, reinforce compliance with medication or other schedules, etc. In addition, the robot incorporates safety features for preventing collisions with the resident; and the robot may audibly announce and / or visibly indicate its presence in order to avoid becoming a dangerous obstacle. Furthermore, the mobile robot behaves in accordance with an integral privacy policy, such that any sensor recording or transmission must be approved by the resident.
Owner:IROBOT CORP
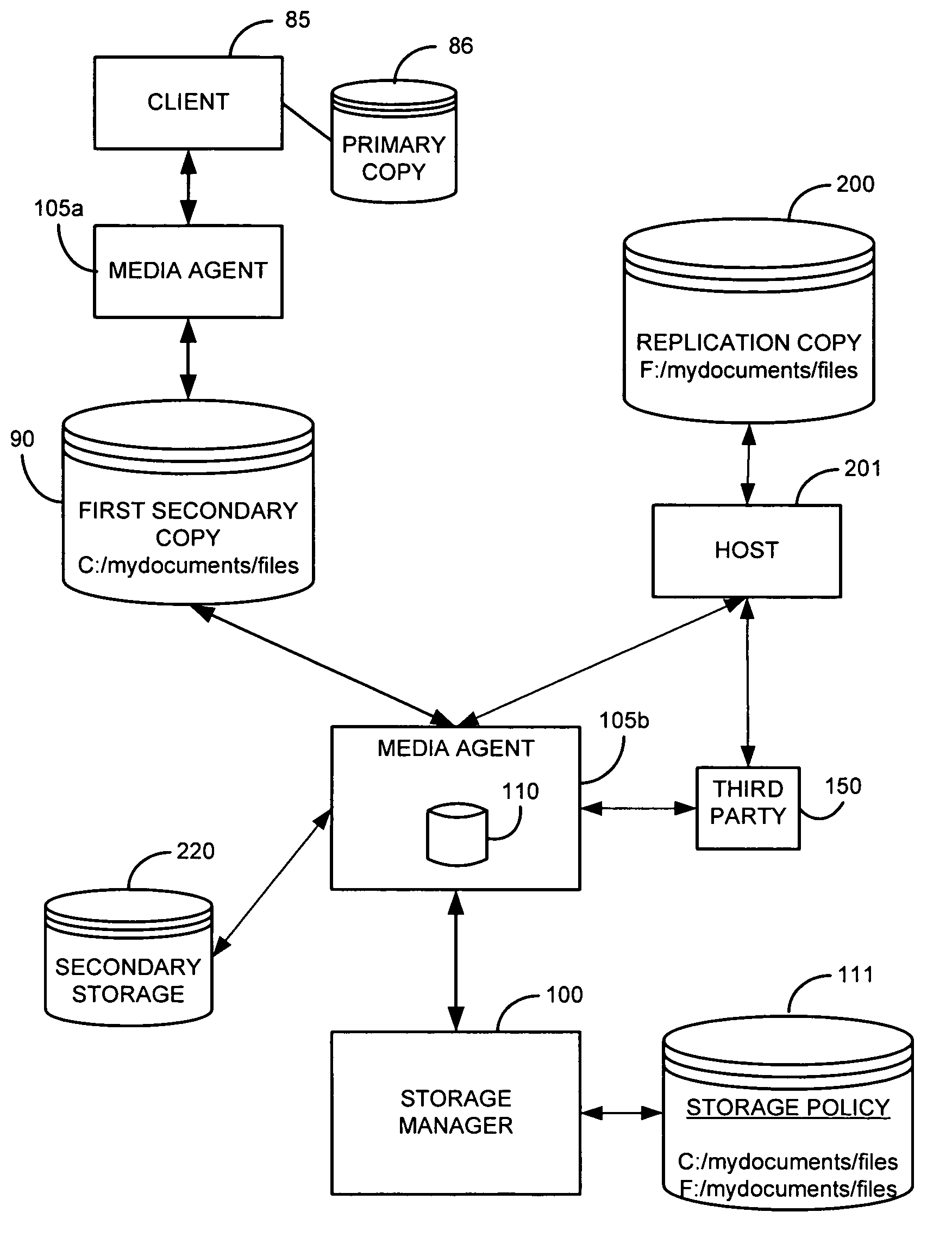
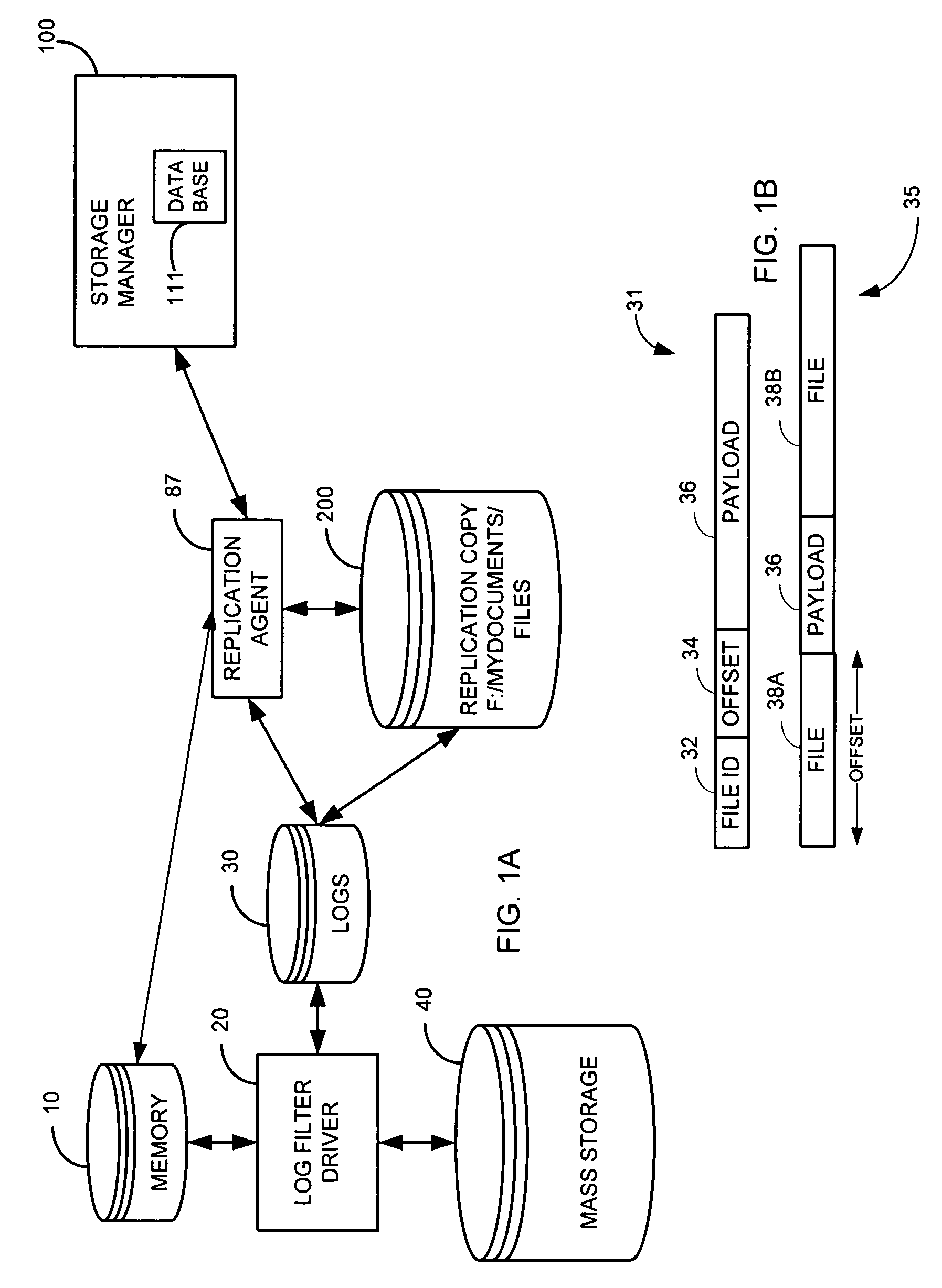
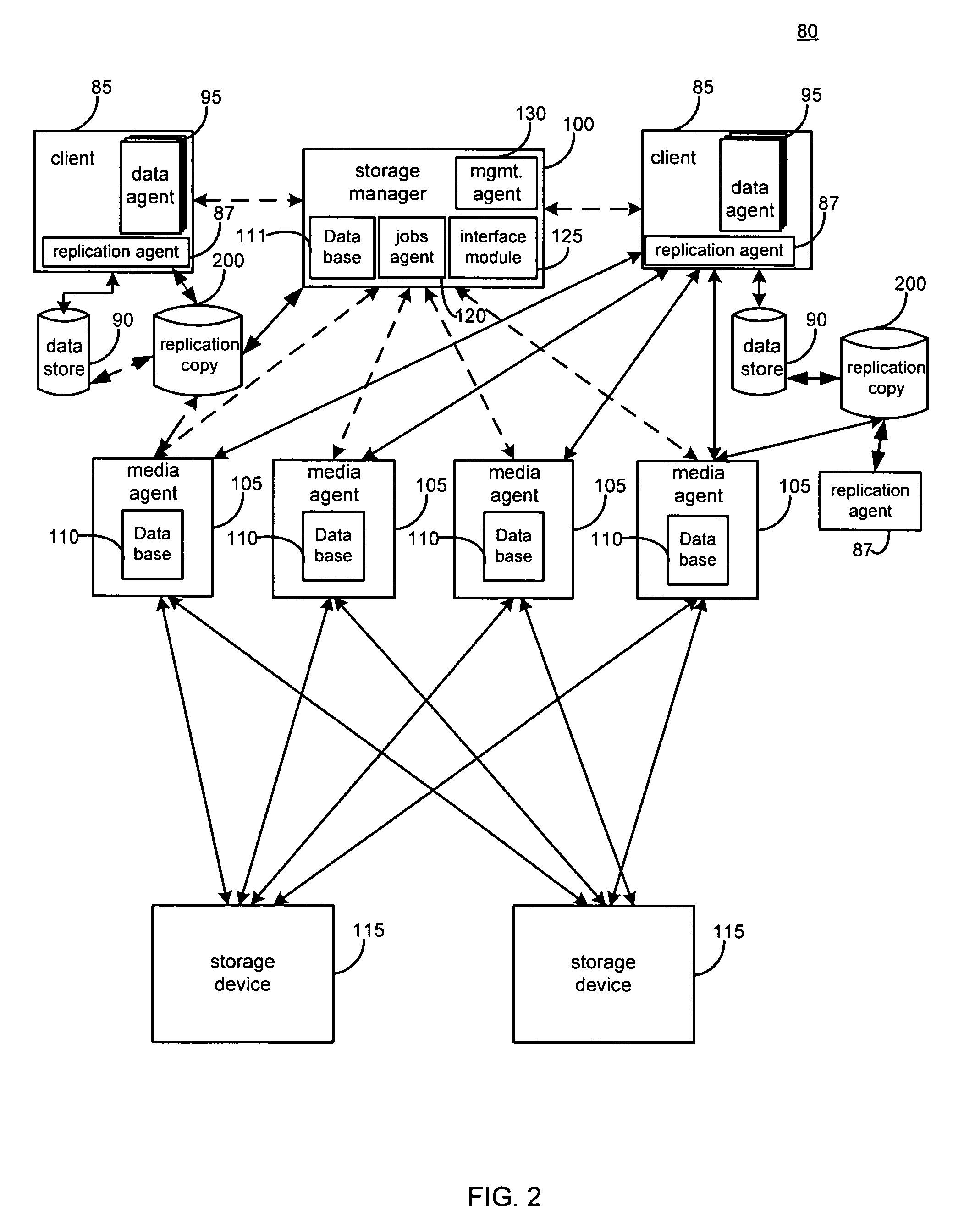
System and method for performing replication copy storage operations
InactiveUS7606844B2Data processing applicationsDatabase distribution/replicationThird partyEngineering
A system and method are provided for performing storage operations relating to a first secondary copy of electronic data. A storage policy or storage preferences may dictate that a replication copy should be used in storage operations performed to a particular client, sub-client, data, media or other item. Based on the storage policy, when a new client, sub-client, data, media or other item is received, a media agent determines whether there is a replication copy of the item. In the absence of a replication copy, one may be created. The replication copy may be provided by a third party application, or created by the client or a storage management system component. Information regarding the replication copy and its corresponding first secondary copy may be stored in a database. To optimize use of system resources, storage operations relating to the first secondary copy may be performed using the replication copy instead of the first secondary copy.
Owner:COMMVAULT SYST INC
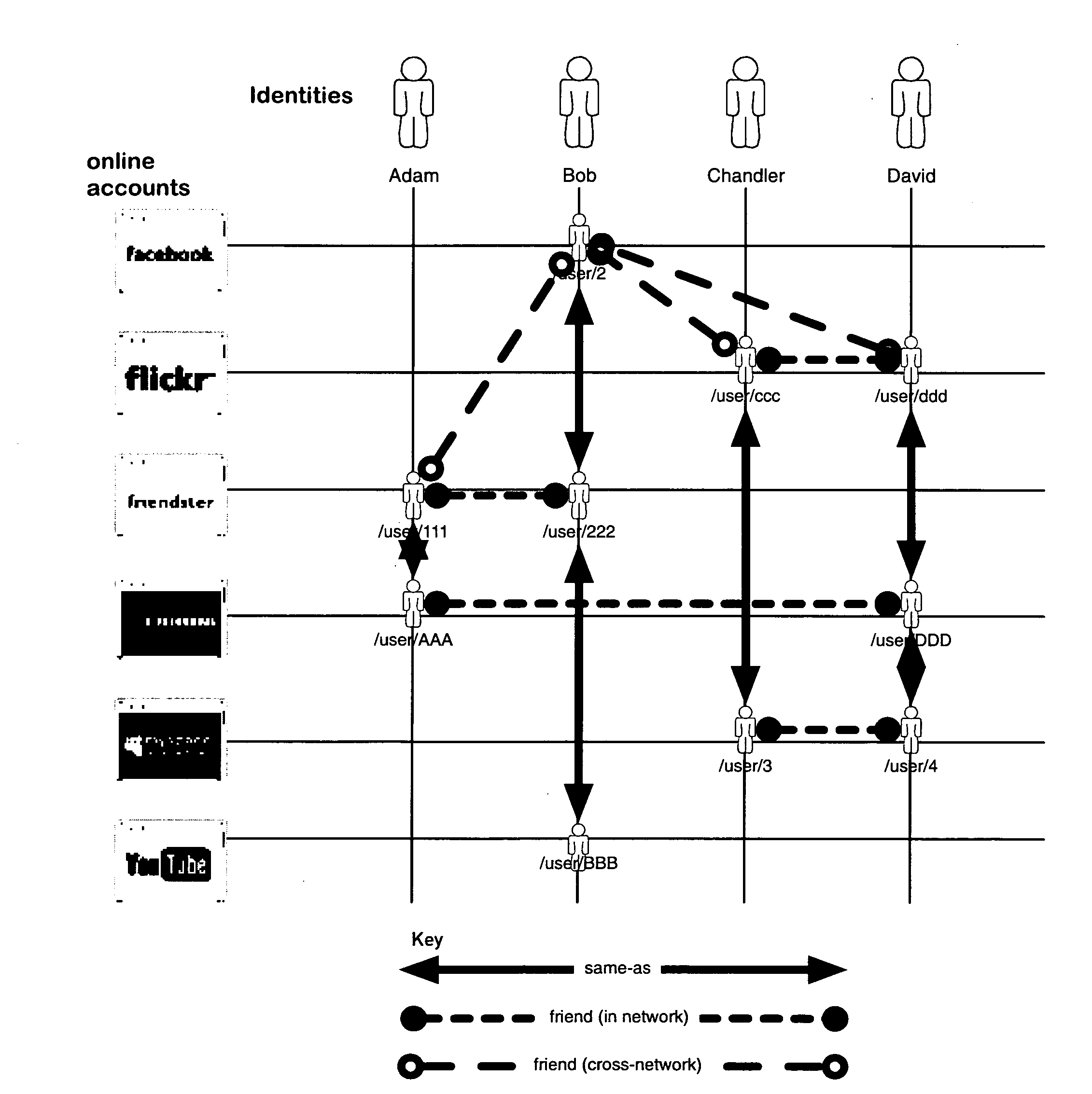
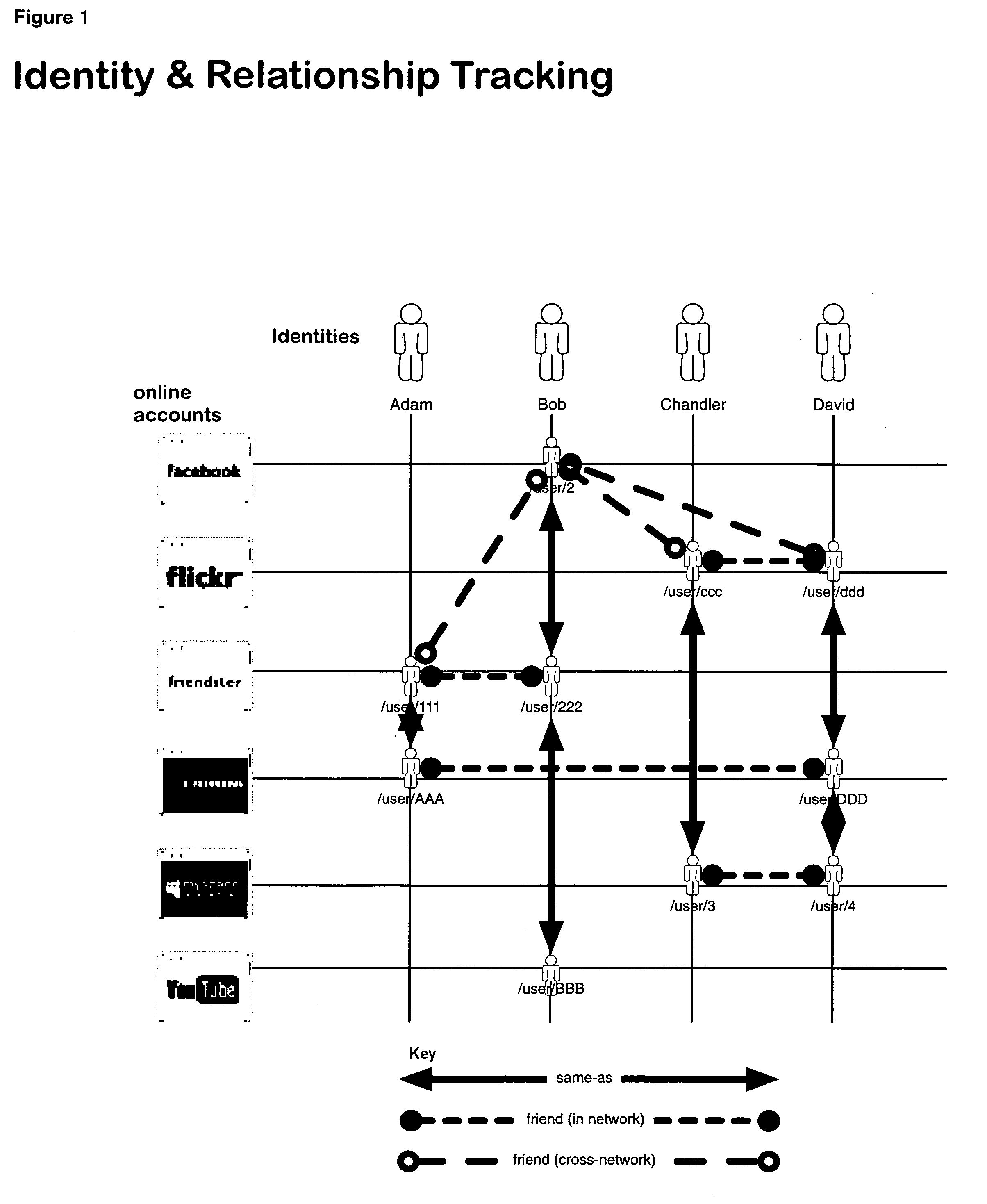
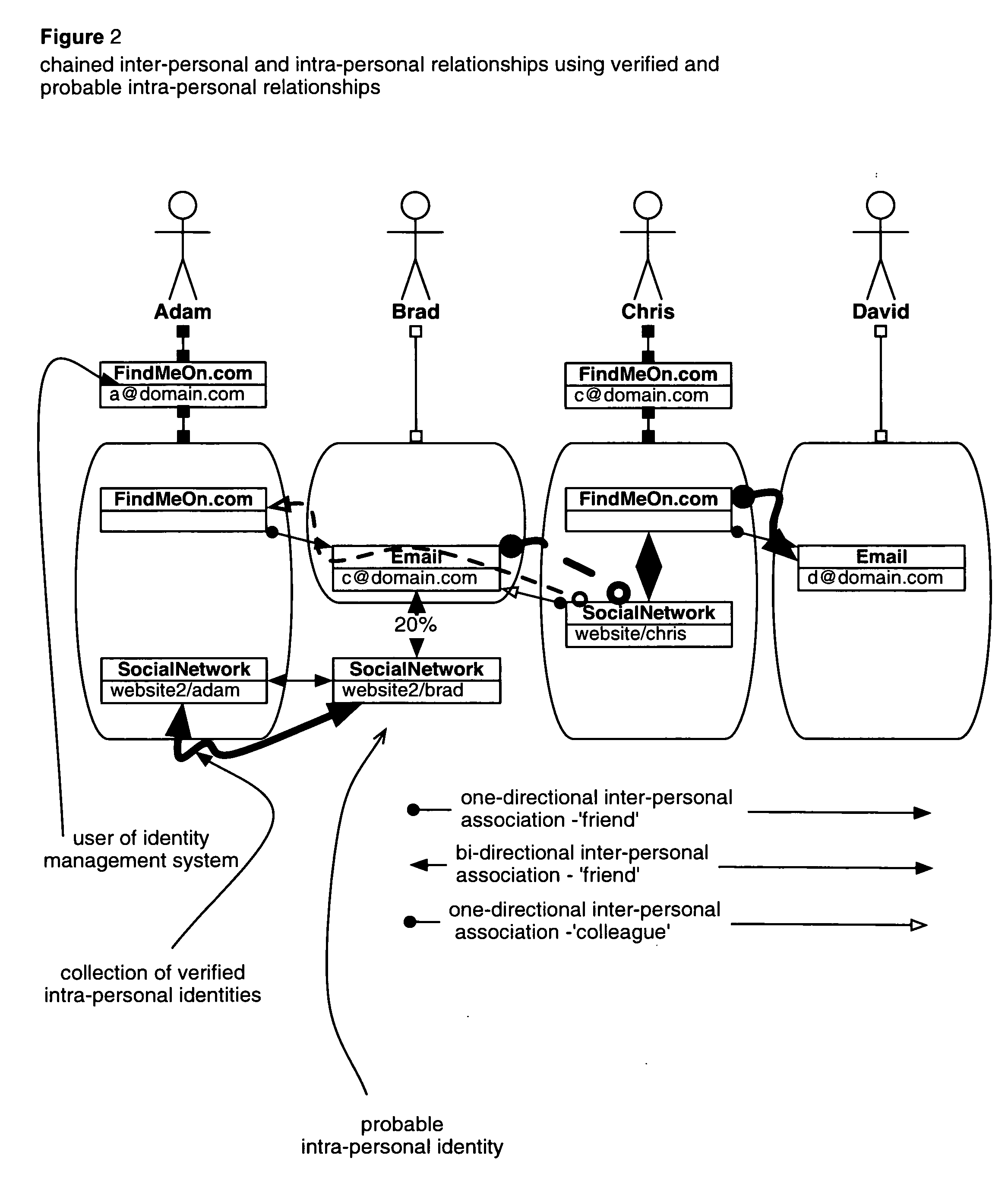
System and method for indexing, correlating, managing, referencing and syndicating identities and relationships across systems
ActiveUS20100274815A1Rich and more detailed and more completeRaise the possibilityDigital data information retrievalDigital data processing detailsThird partyFederated identity
A networking database containing a plurality of records for different identities in which identities are connected to one another by defined or interpreted Inter-Personal and Intra-Personal relationships. Individuals using the system may define, group and categorize specific identities and relationships; the system may also define, categorize and group both identities and relationships belonging to individuals registered with the system and unregistered users through computational analysis. Identities and relationships may be discovered by the system via an opt-in user-provided mechanism, via a third-party providing information, or through the system's own discovery. Identity and Relationship data can then be used to customize content.
Owner:VANASCO JONATHAN BRIAN
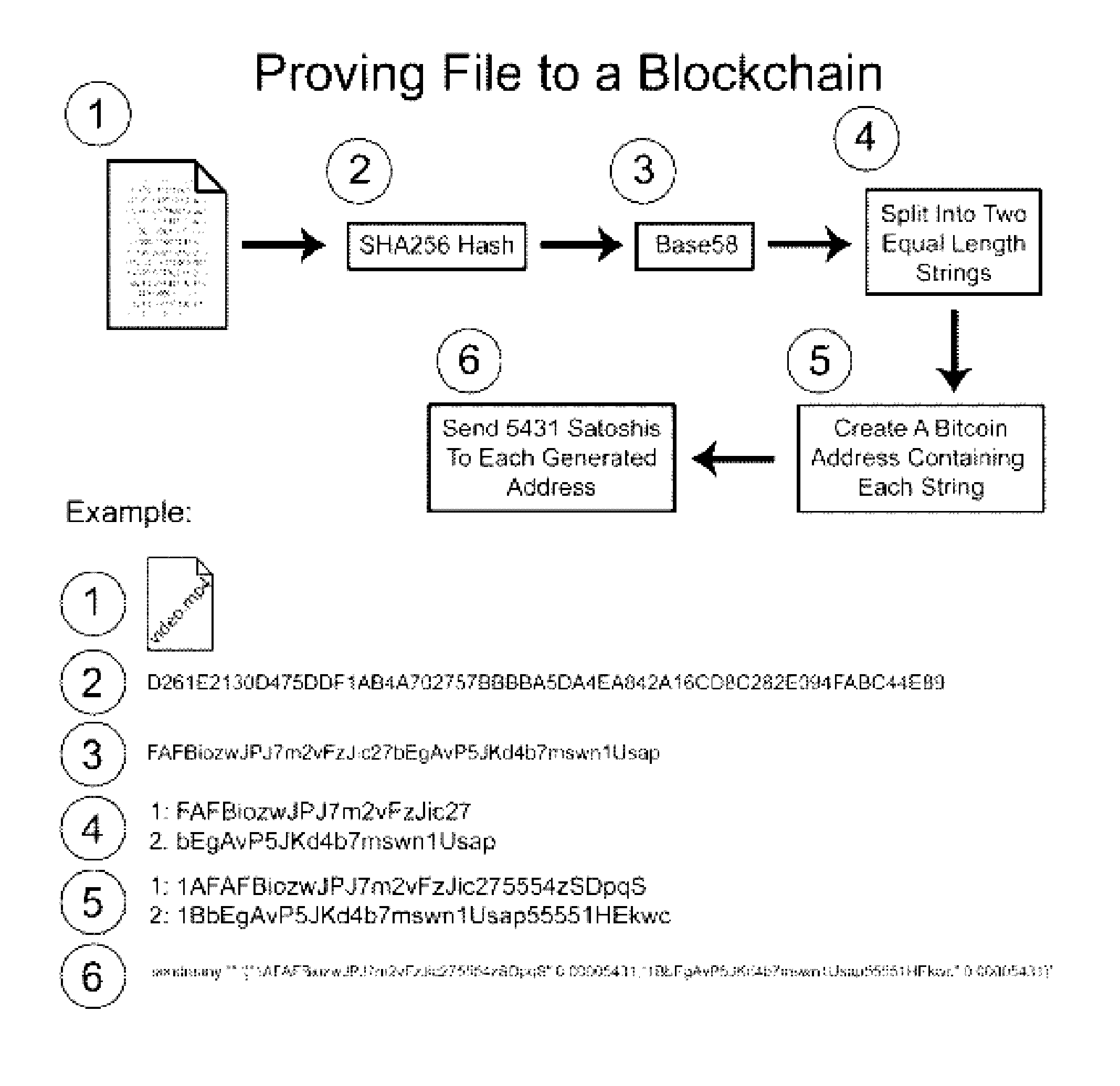
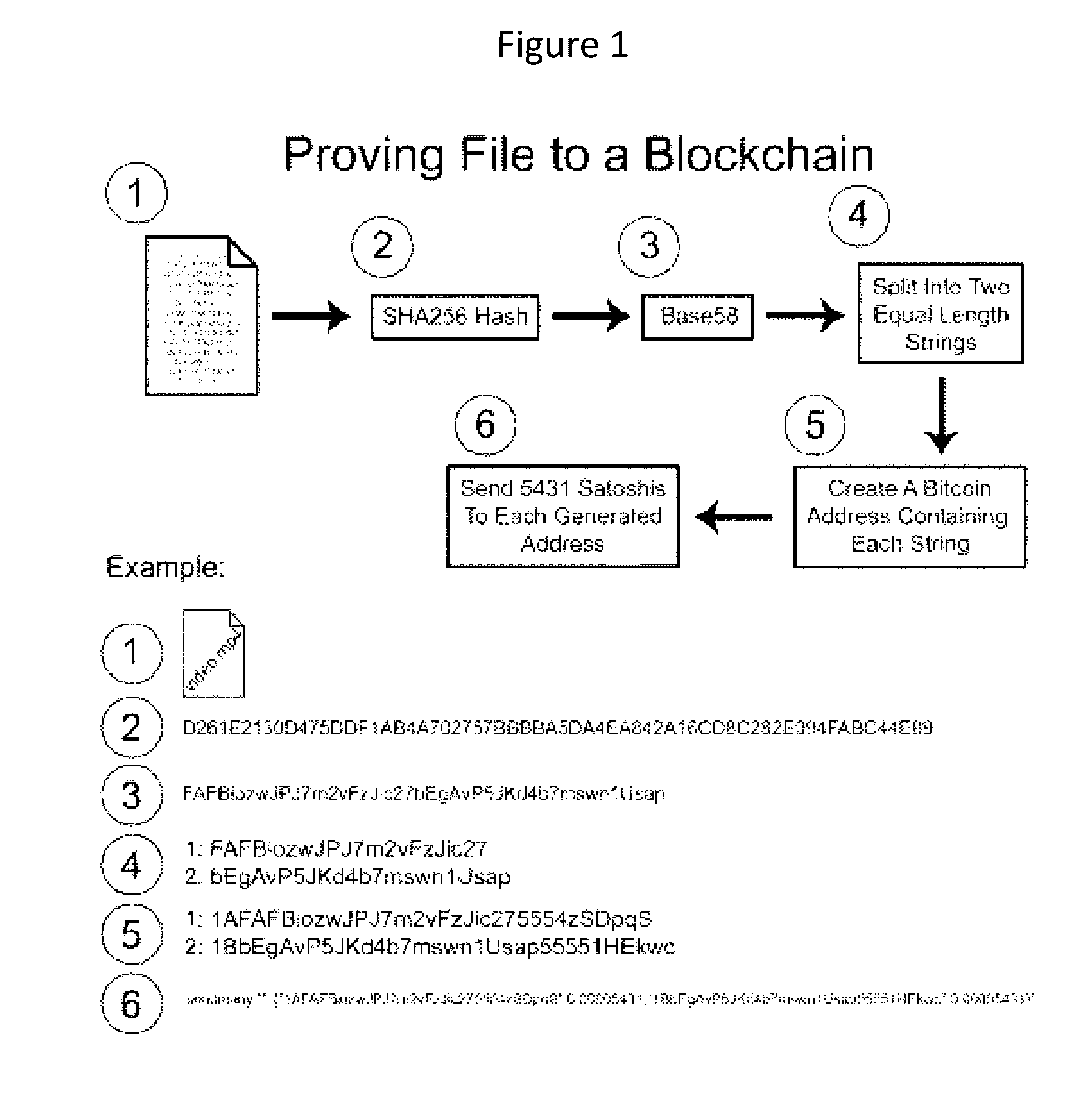
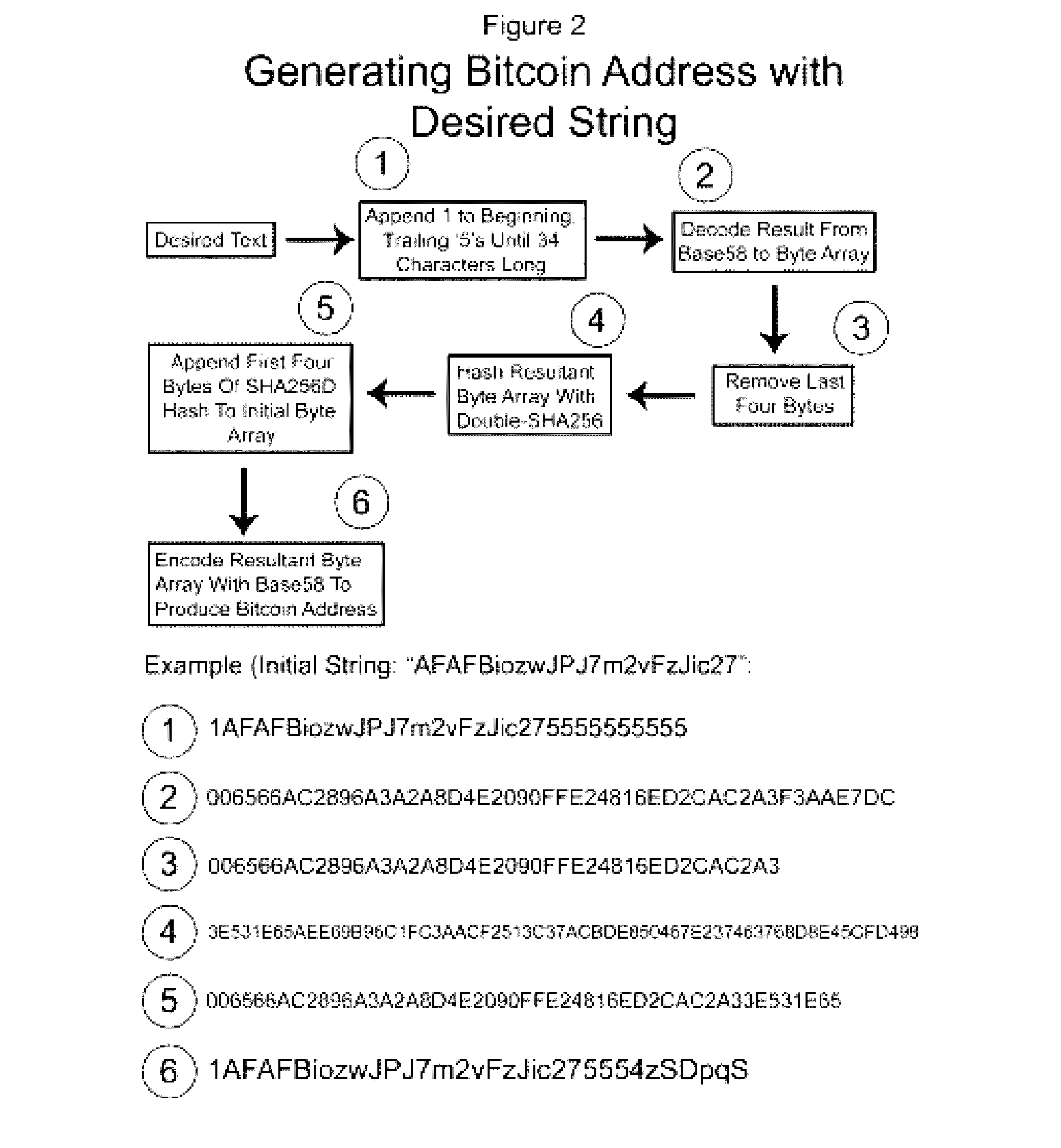
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
Methods and systems for interfacing with a third-party application
ActiveUS20100105454A1Increase excitementAdvertisementsApparatus for meter-controlled dispensingThird partyApplication software
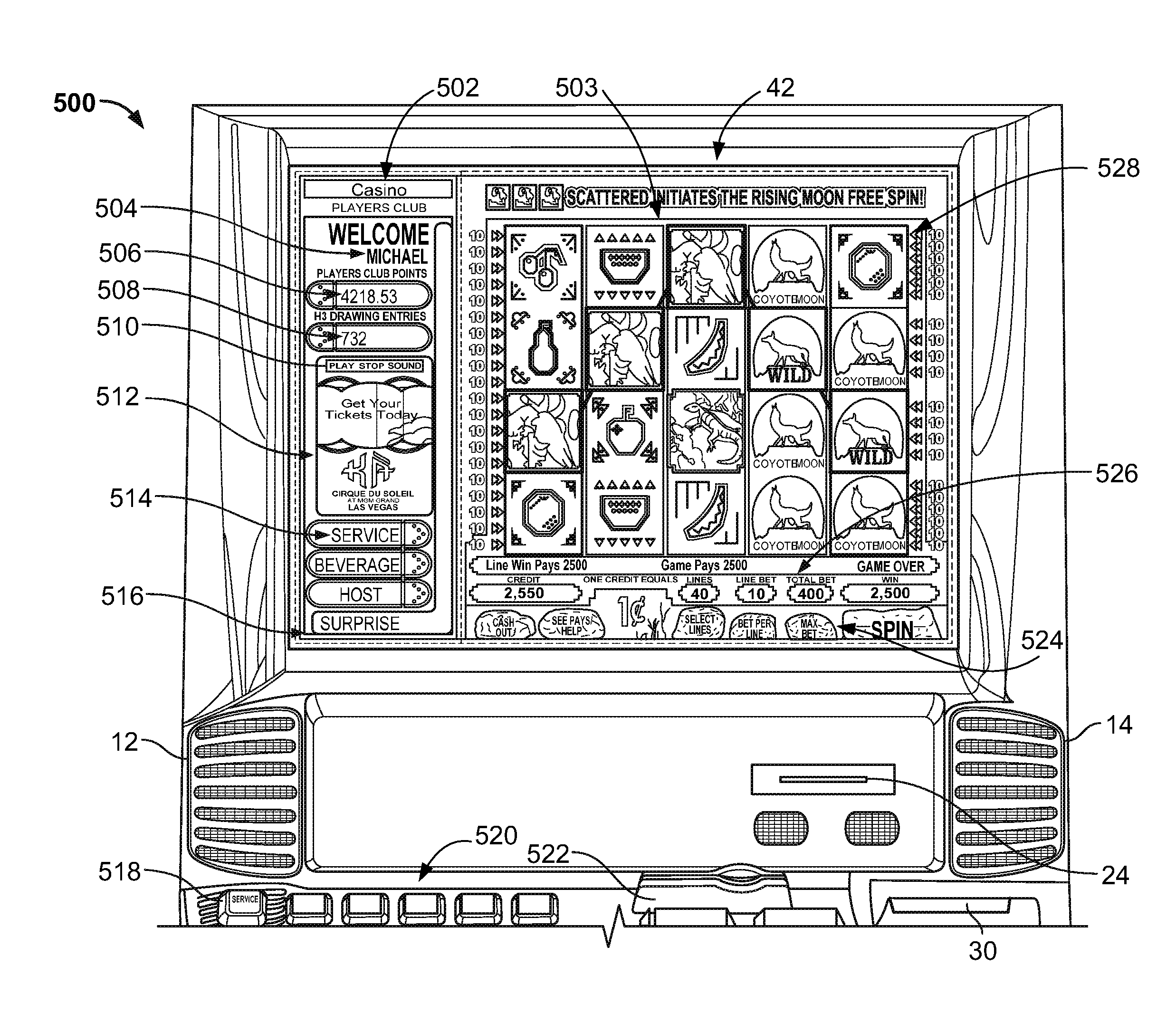
A system for interfacing with a third-party application is described. The system includes a third-party device, a server-based system configured to communicate with the third-party device, and a gaming device configured to communicate with the server-based system to display content of the product or service. The gaming device is configured to generate an outcome of a wager-based game independent of the content that is displayed.
Owner:IGT
Authentication and authorization methods for cloud computing security
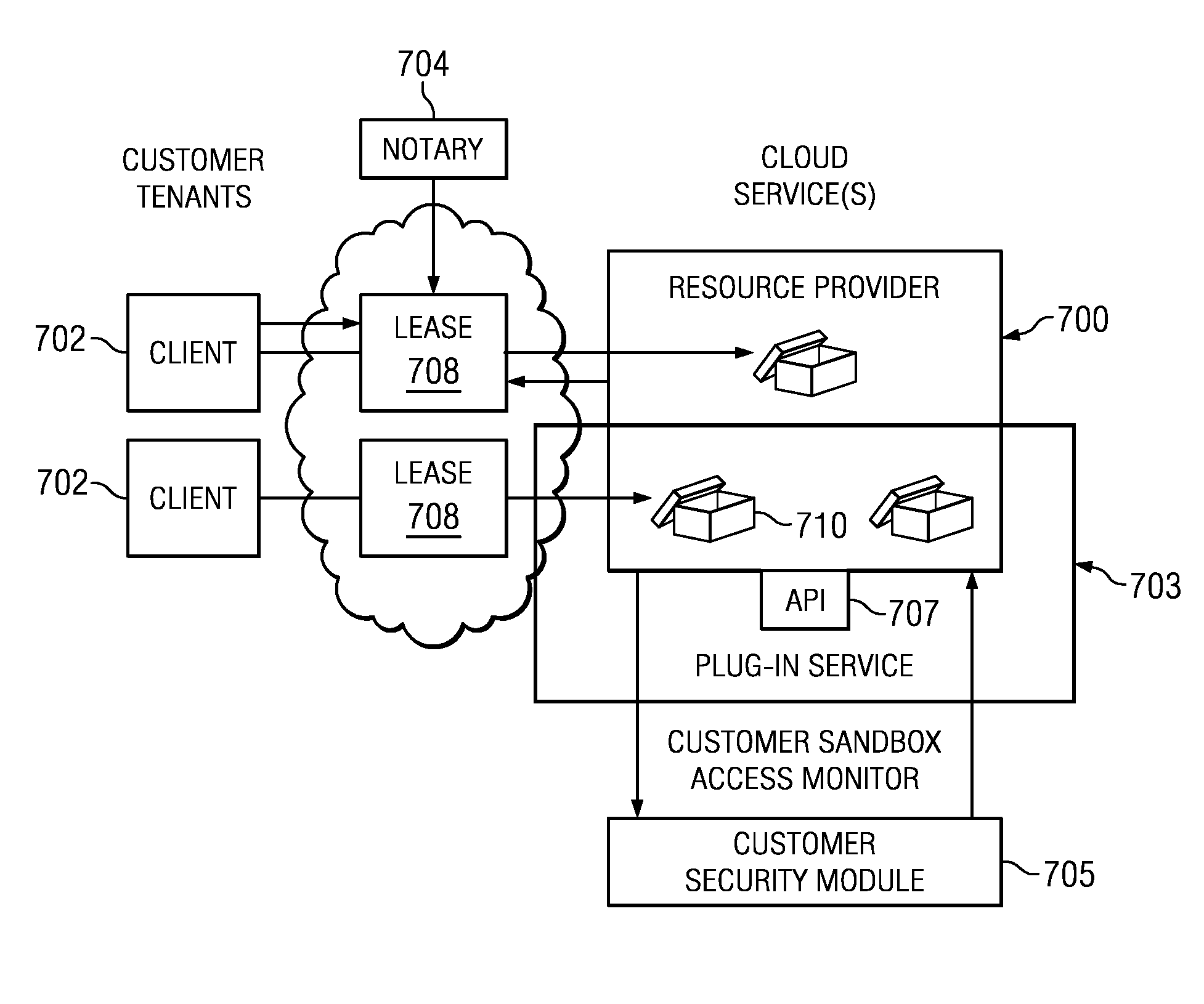
ActiveUS8769622B2Retain controlKey distribution for secure communicationDigital data processing detailsResource poolThird party
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
Secure interactive electronic account statement delivery system
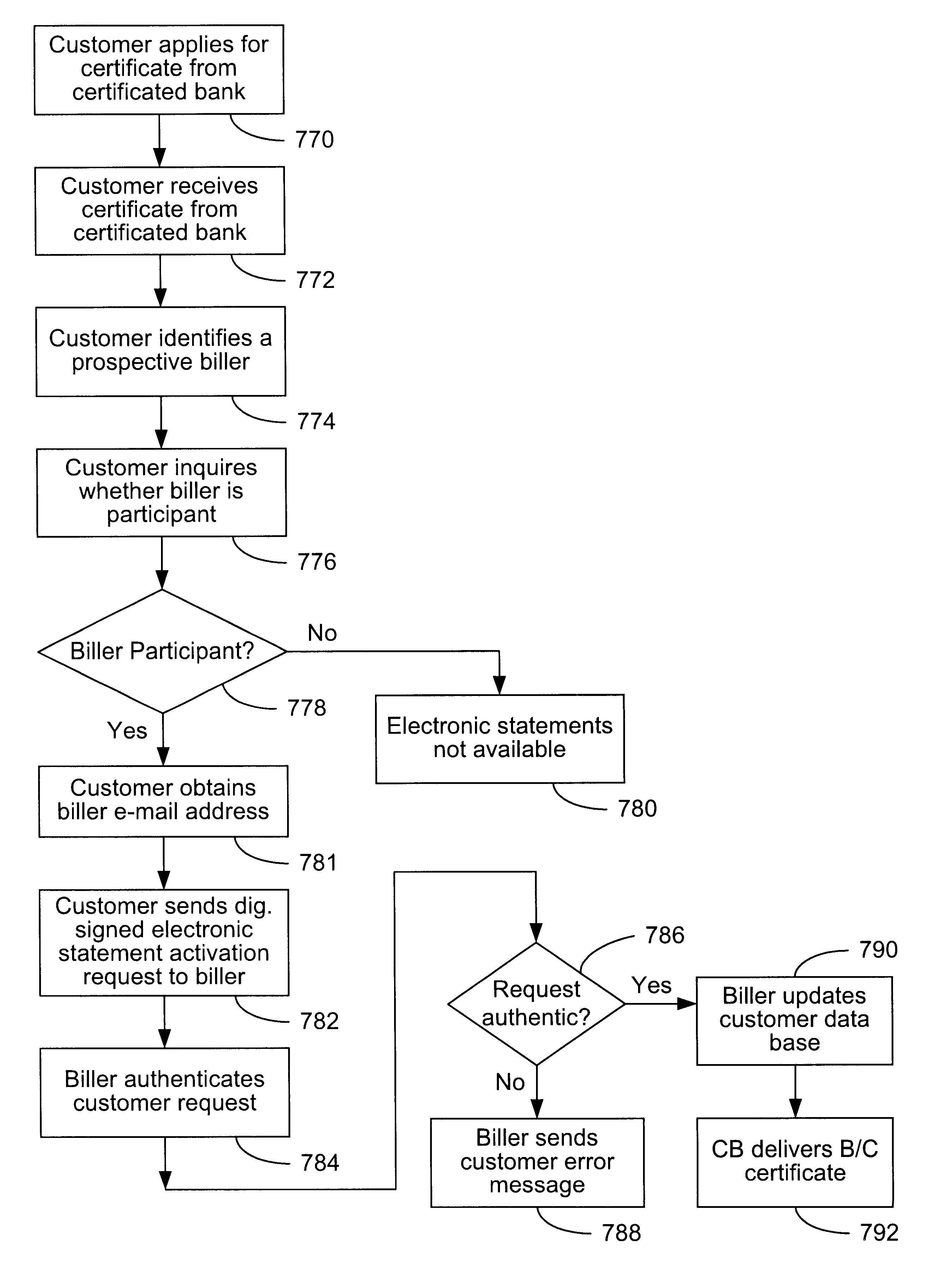
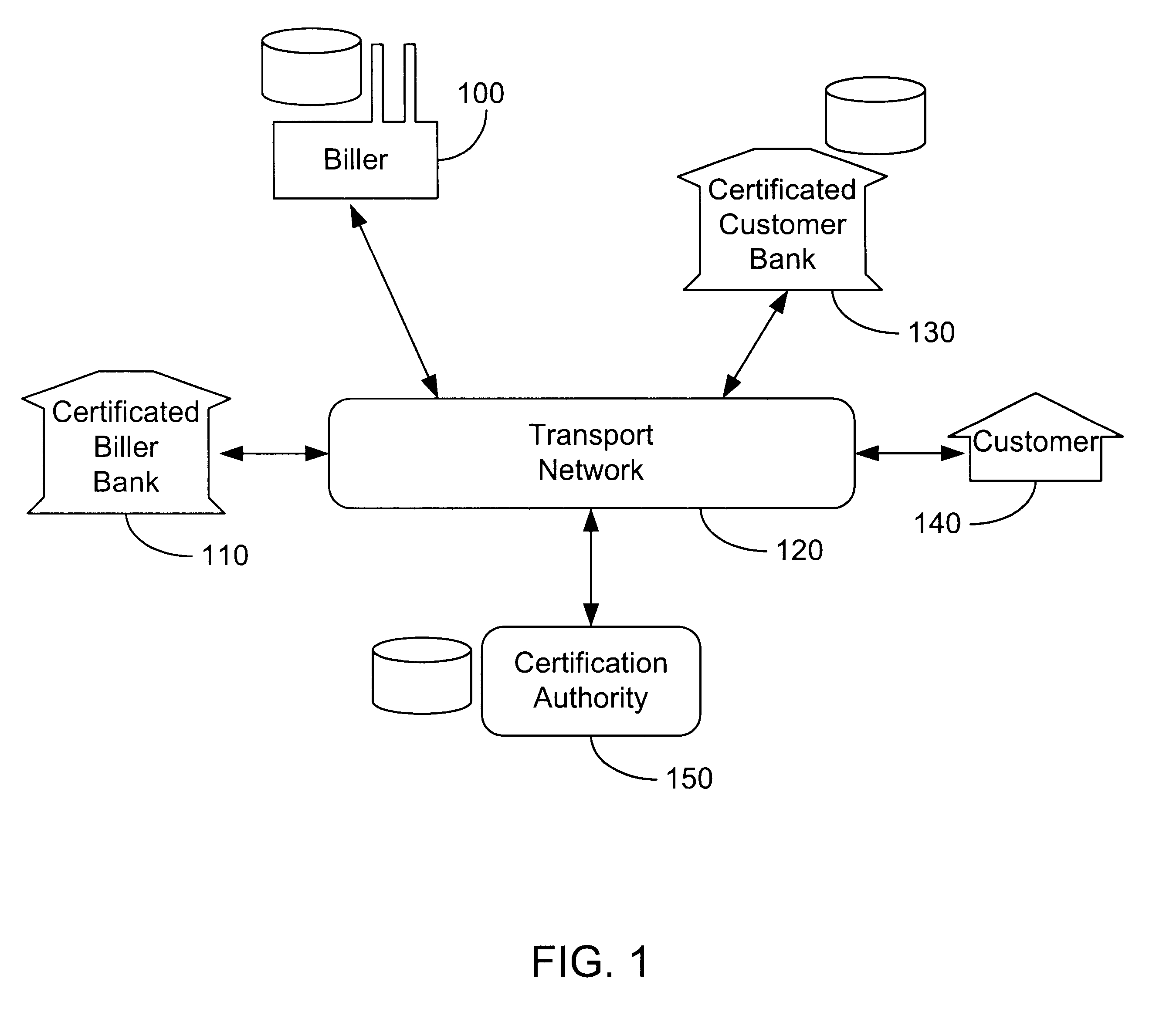
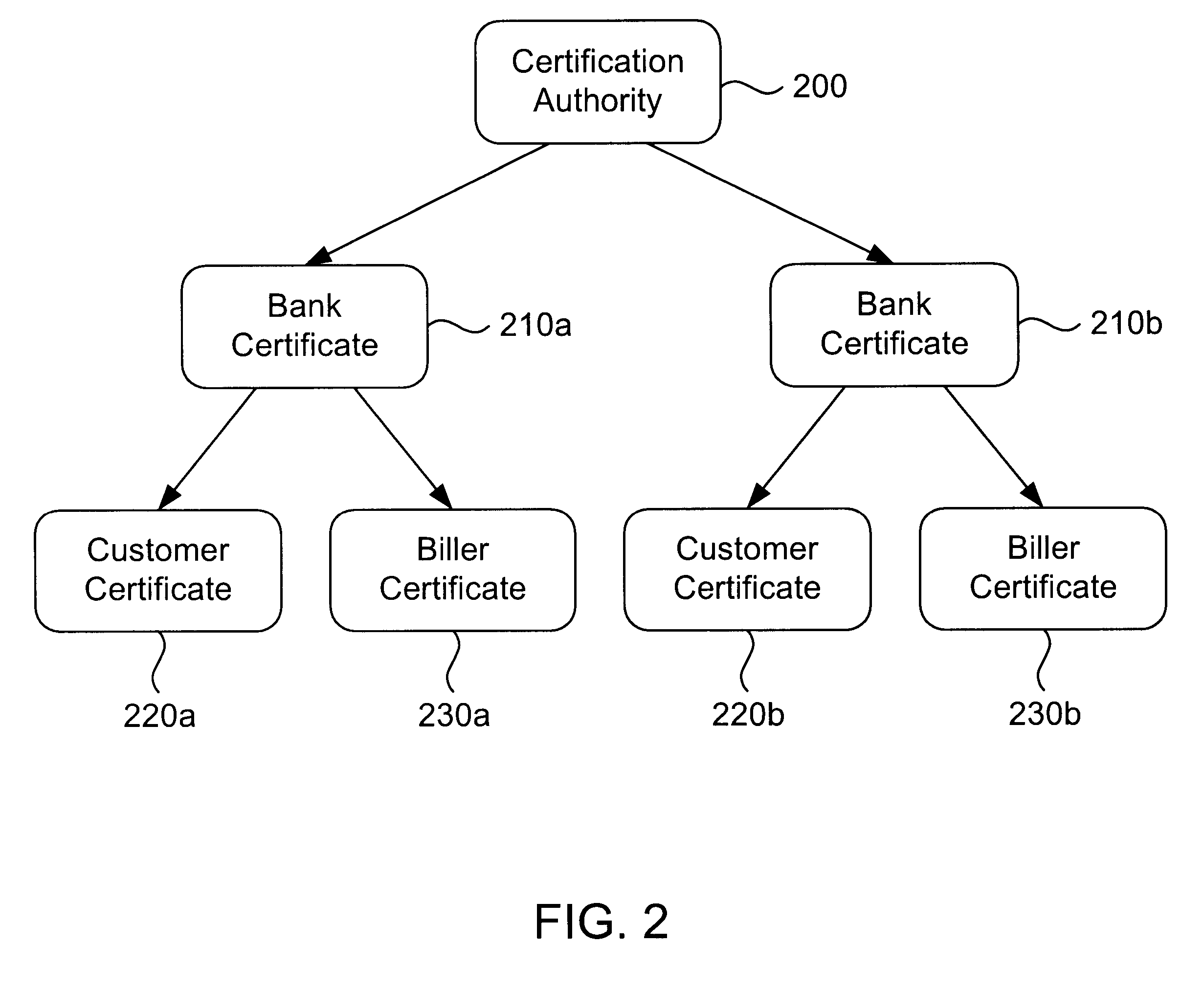
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
Methods for purchasing of goods and services
InactiveUS7349871B2Risk minimizationReducing credit card fraudPayment circuitsElectronic credentialsThird partyPurchasing
Owner:PCMS HOLDINGS INC
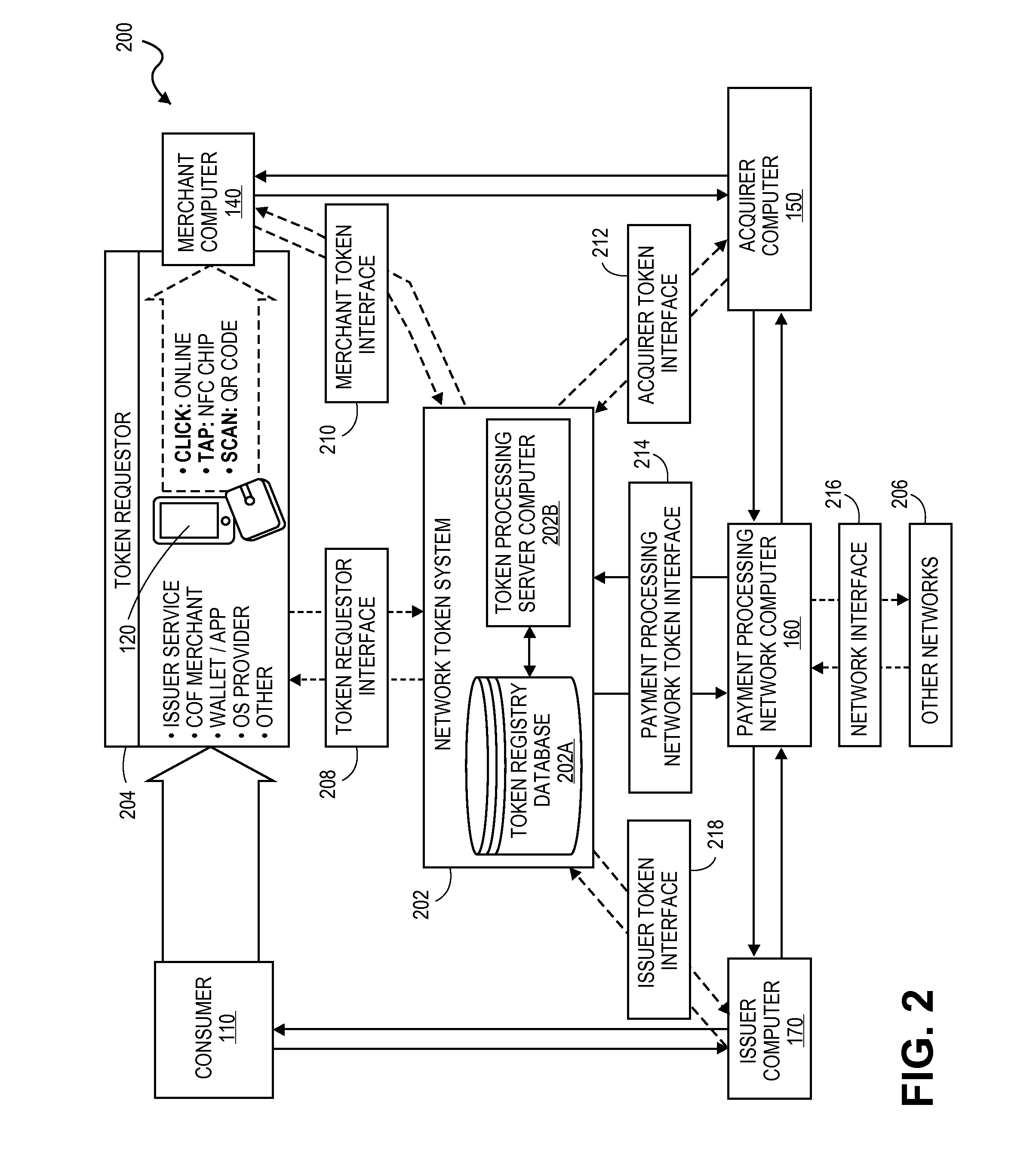
Systems and methods for communicating token attributes associated with a token vault
ActiveUS20150032627A1Convenient transactionSupported interoperabilityFinanceUser identity/authority verificationThird partyPayment transaction
Systems and methods for interoperable network token processing are provided. A network token system provides a platform that can be leveraged by external entities (e.g., third party wallets, e-commerce merchants, payment enablers / payment service providers, etc.) or internal payment processing network systems that have the need to use the tokens to facilitate payment transactions. A token registry vault can provide interfaces for various token requestors (e.g., mobile device, issuers, merchants, mobile wallet providers, etc.), merchants, acquirers, issuers, and payment processing network systems to request generation, use and management of tokens. The network token system further provides services such as card registration, token generation, token issuance, token authentication and activation, token exchange, and token life-cycle management.
Owner:VISA INT SERVICE ASSOC
Authentication and authorization methods for cloud computing security platform
ActiveUS20130007845A1Retain controlDigital data processing detailsUser identity/authority verificationThird partyResource pool
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
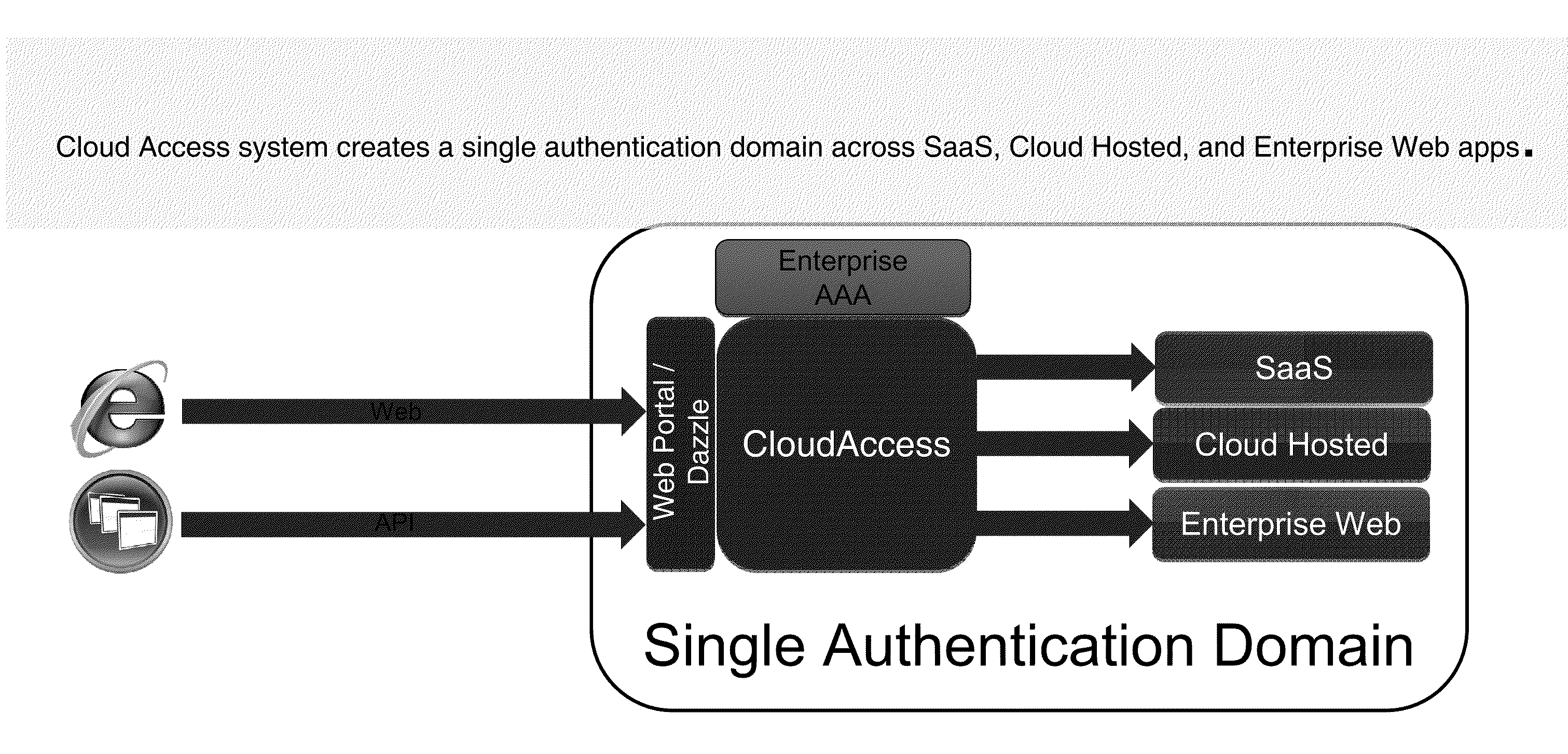
Systems and Methods for Providing a Single Click Access to Enterprise, SAAS and Cloud Hosted Application
ActiveUS20110277027A1Input/output for user-computer interactionDigital data processing detailsThird partyGraphics
The present disclosure is directed to methods and systems of providing a user-selectable list of disparately hosted applications. A device intermediary to a client and one or more servers may receive a user request to access a list of applications published to the user. The device may communicate to the client the list of published applications available to the user, the list comprising graphical icons corresponding to disparately hosted applications, at least one graphical icon corresponding to a third-party hosted application of the disparately hosted applications, the third party hosted application served by a remote third-party server. The device may receive a selection from the user of the at least one graphical icon. The device may communicate, from the remote third party server to the client of the user, execution of the third party hosted application responsive to the selection by the user.
Owner:CITRIX SYST INC
Systems and methods using cryptography to protect secure computing environments
InactiveUS6292569B1Improve connectivityComputationally orRecording carrier detailsError detection/correctionThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm.
Owner:INTERTRUST TECH CORP
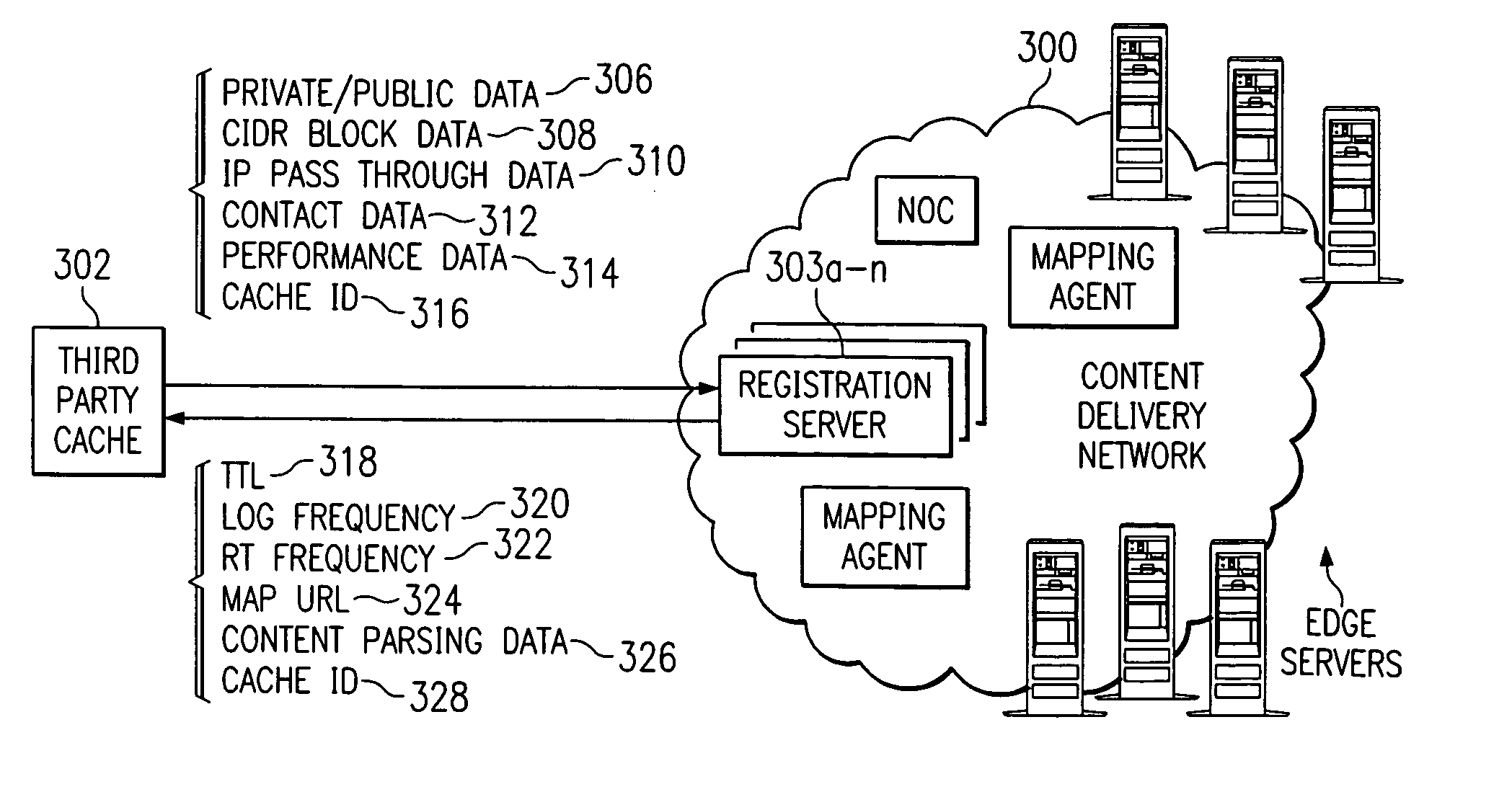
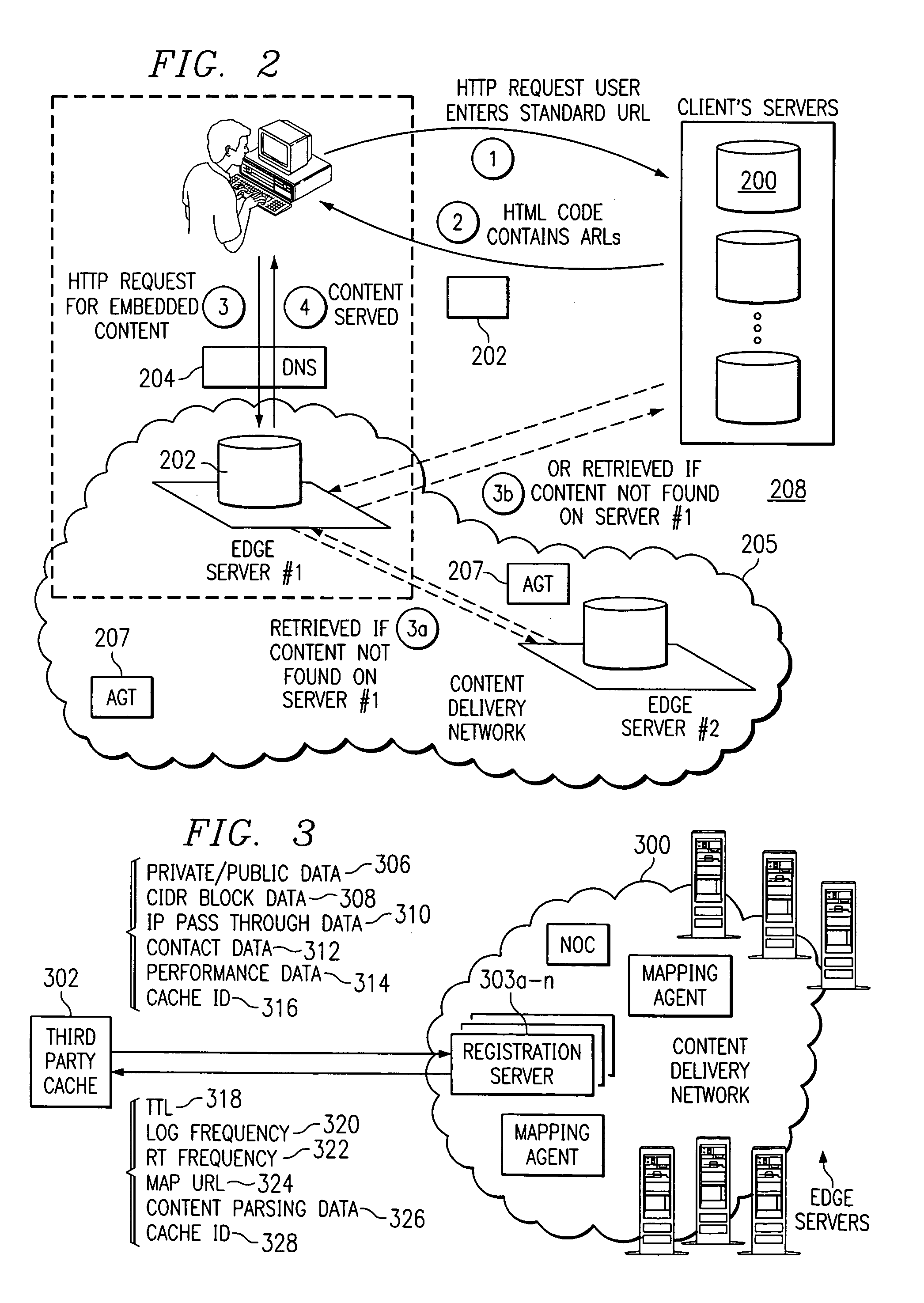
Internet content delivery service with third party cache interface support
InactiveUS7010578B1Increase reachImprove performanceDigital data information retrievalMultiple digital computer combinationsThird partyOff the shelf
Third party cache appliances are configured into a content delivery service to enable such devices to cache and serve content that has been tagged for delivery by the service. The invention enables the content delivery service to extend the reach of its network while taking advantage of high performance, off-the-shelf cache appliances. If the third party caches comprise part of a third party content delivery network, the interconnection of caches to the CDS according to the present invention enables the CDS and the third party network to share responsibility for delivering the content. To facilitate such “content peering,” the CDS may also include a traffic analysis mechanism to provide the third party network with preferably real-time data identifying the content delivered by the CDS from the third party caches. The CDS may also include a logging mechanism to generate appropriate billing and reporting of the third party content that is delivered from the cache appliances that have been joined into the CDS.
Owner:AKAMAI TECH INC
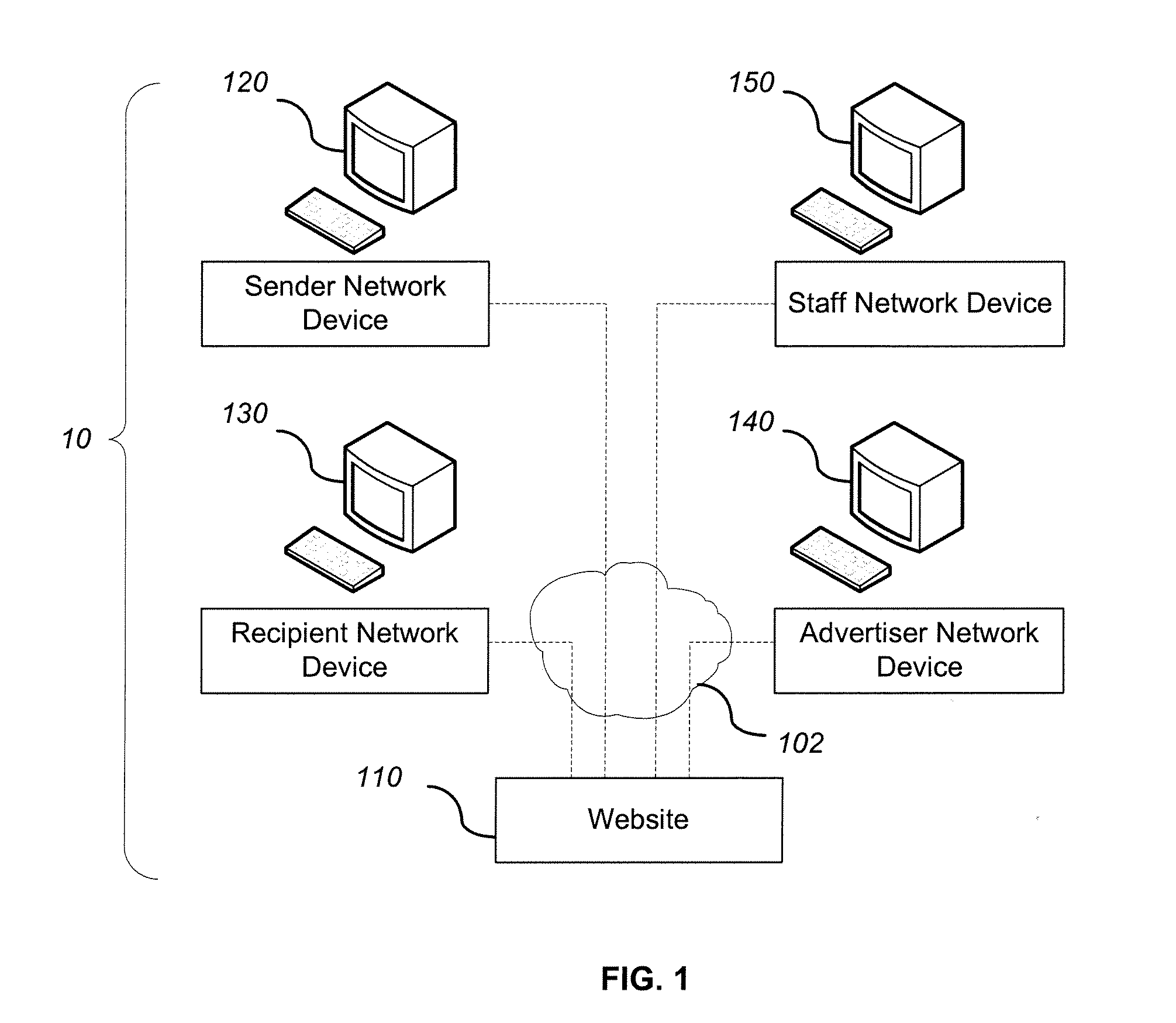
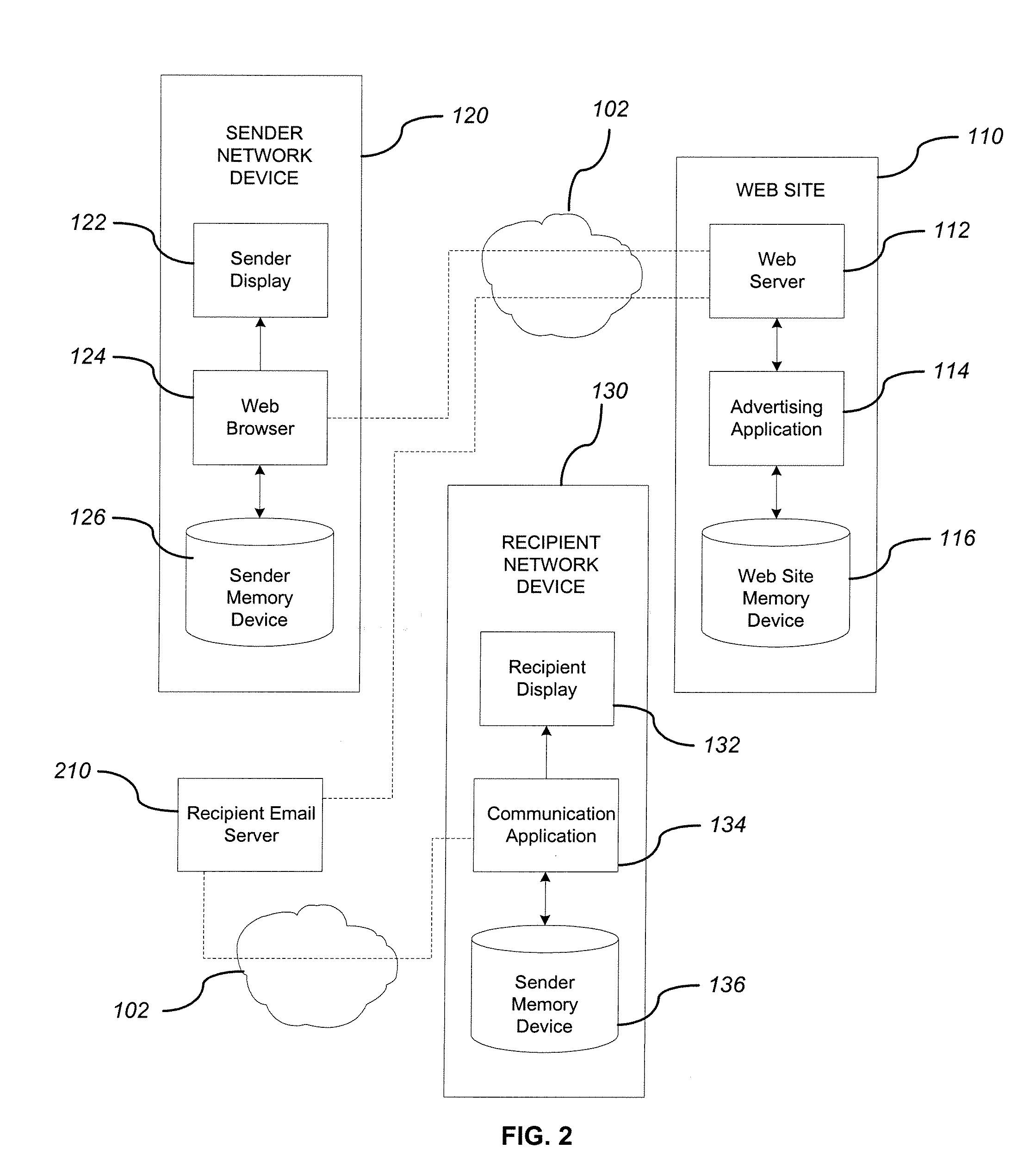
System and method for adding an advertisement to a personal communication
ActiveUS20090030774A1Accurate predictionIncrease probabilityDiscounts/incentivesAdvertisementsWeb siteThird party
A system and method is provided for adding an advertisement to a digital message and providing additional communication data to a recipient that interacts with the advertisement regardless of the network device the recipient is utilizing. An advertisement generator residing on a network host accepts digital messages from contributors and allows the contributors to select an advertisement to be displayed with their contributed messages. These digital messages may be sent to specified recipients or published on a Web site. Using stored personal data associated with the contributor and with the recipient of a digital message, in addition to the content of the message itself, the advertisement generator suggests advertisements to be included with the digital messages based on their contextual relevance. In exchange for including an advertisement with a digital message, a contributor is compensated. If the contributor-selected advertisement is provided by a third party advertiser, the message, contributor, and advertisement data is utilized to compensate the contributor of that message for sending it to at least one recipient or posting it on a Web site. If the advertisement is interactive, and the advertisement is interacted with, the advertisement generator will provide the recipient with additional communication data in a format that can be understood by the recipient network device.
Owner:ROTHSCHILD RICHARD ANTHONY
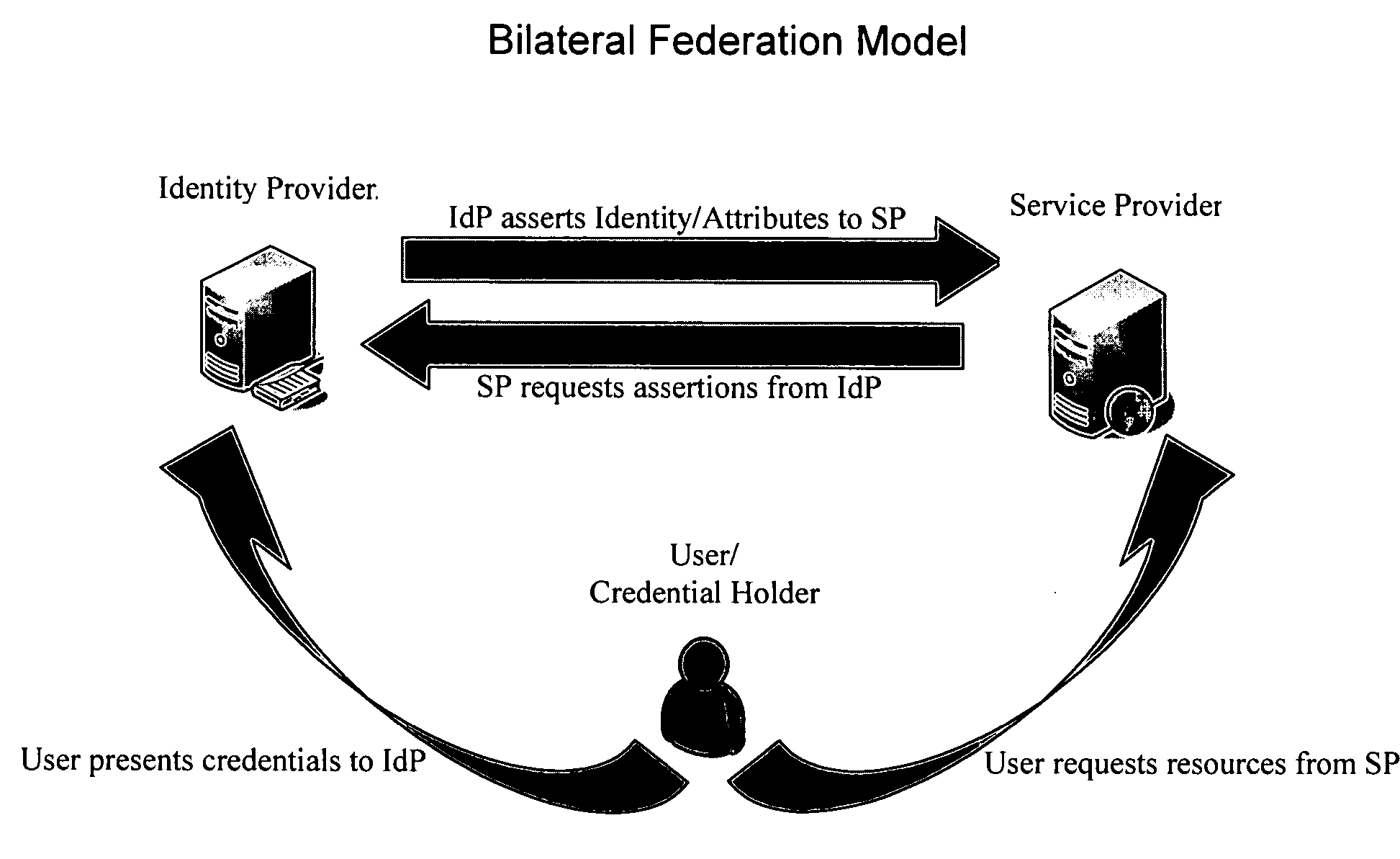
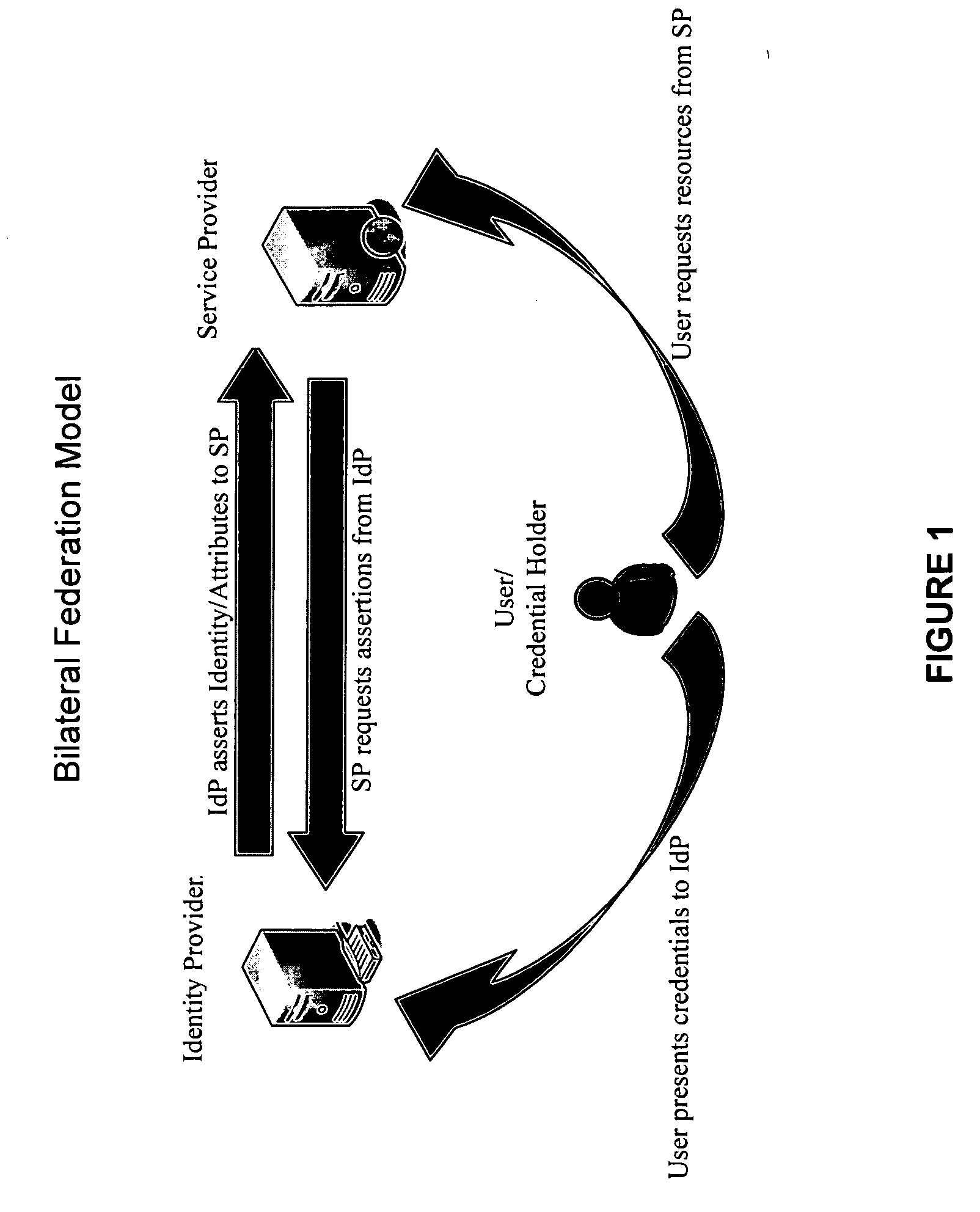
Systems and methods for enabling trust in a federated collaboration
ActiveUS20060129817A1Ensure complianceDigital data processing detailsUser identity/authority verificationThird partySuccessful completion
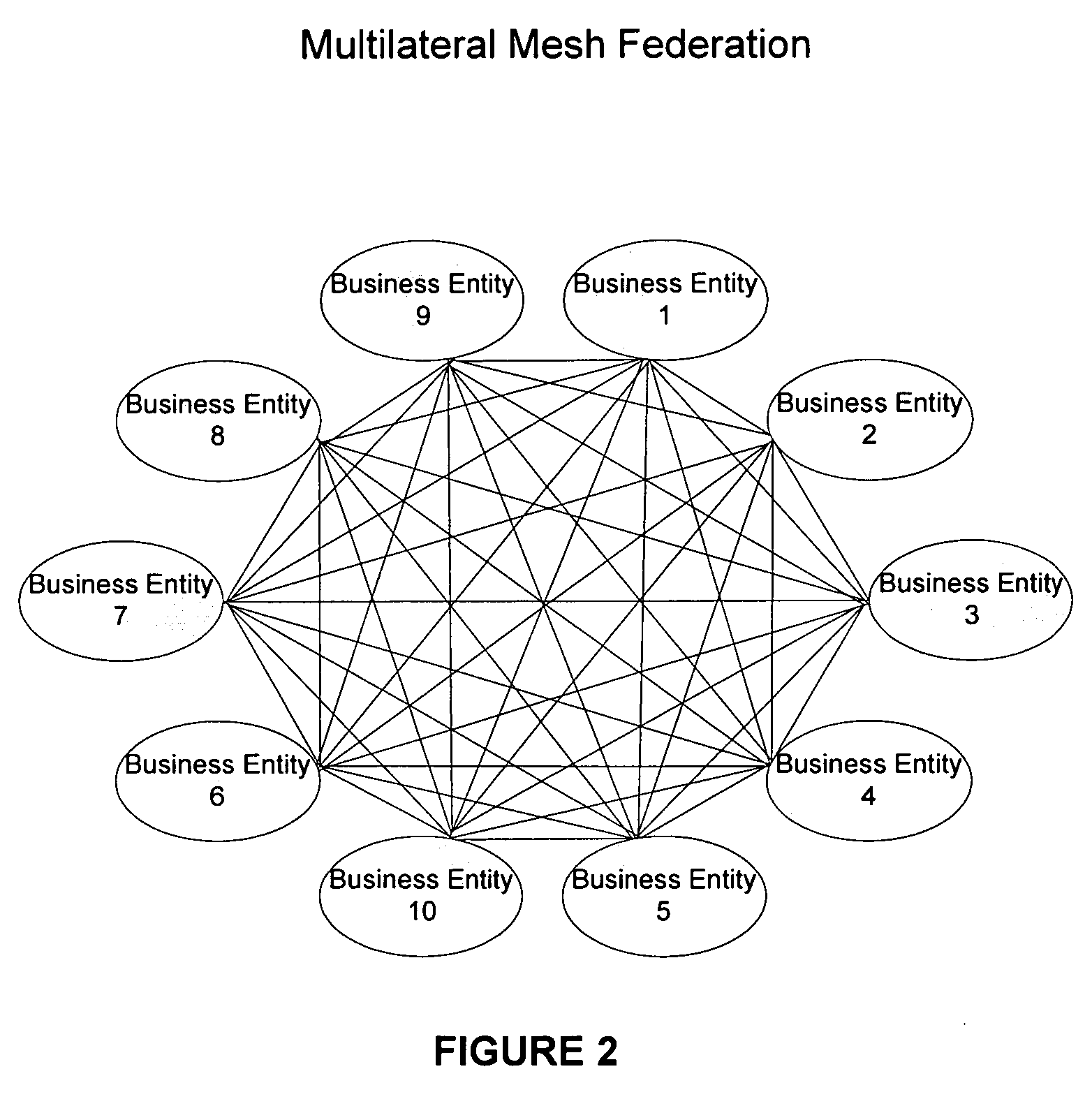
Systems and methods consistent with the present invention enable explicit and multilateral trust across a community of federated servers via a network. A trusted third party establishes a framework of policies and procedures governing a federation. Organizations joining the federation submit to an audit process of internal policies and procedures to ensure compliance with the policies and procedures of the federation. Upon successful completion of an audit, an organization may receive a digital certificate containing the digital public key of the organization and indicating approval of the trusted third party. The organization may then use the associated digital private key for signing security assertions associated with a request for resources from another federation service provider. The service provider may trust the assertion from the organization based on trust placed in trusted third party by the service provider and the trust placed in the organization by the trusted third party.
Owner:EXOSTAR CORP
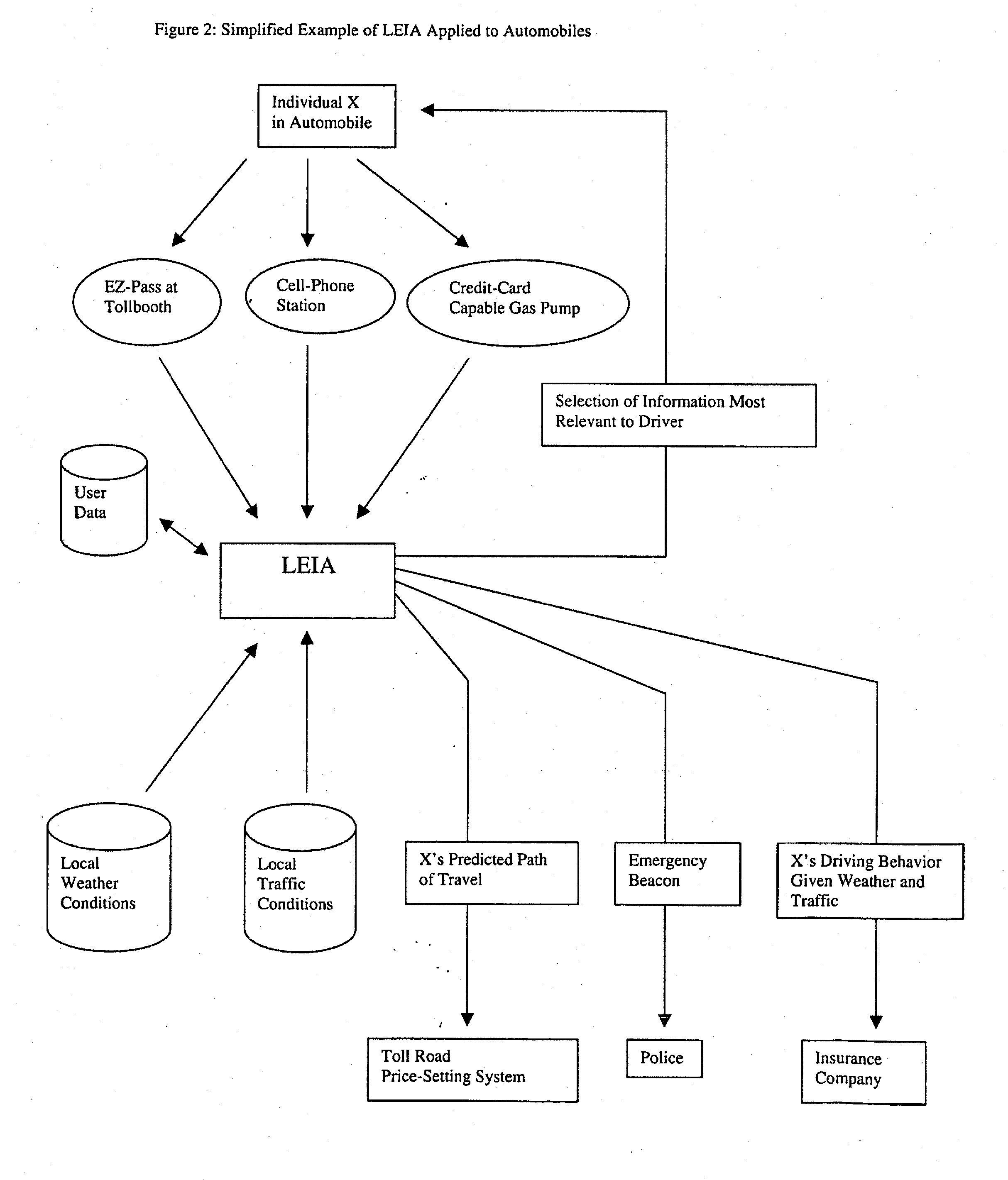
System and Method for Monitoring and Improving Driver Behavior
ActiveUS20080319602A1Reduce actionImprove securityVehicle testingRegistering/indicating working of vehiclesThird partyDriver/operator
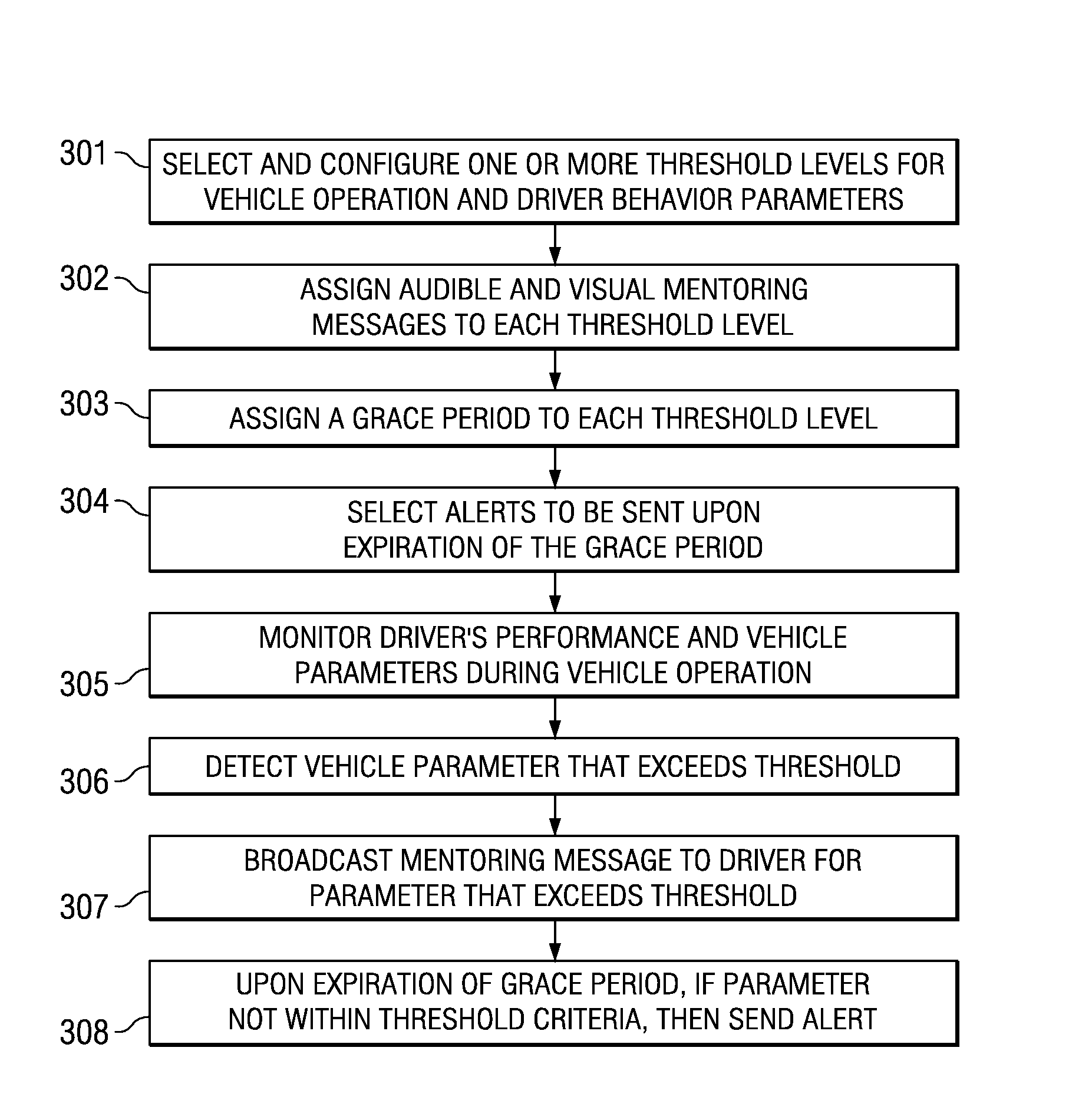
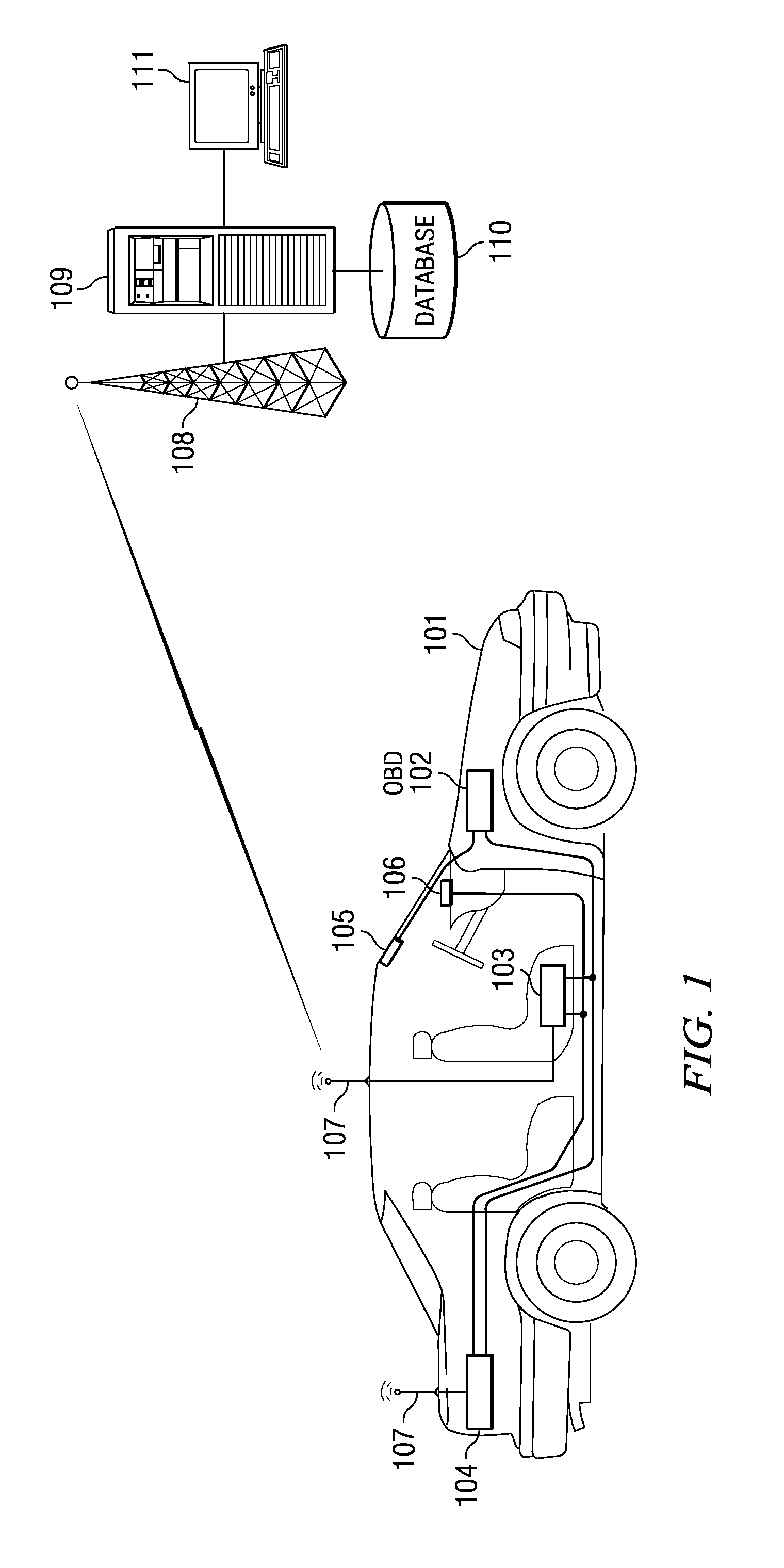
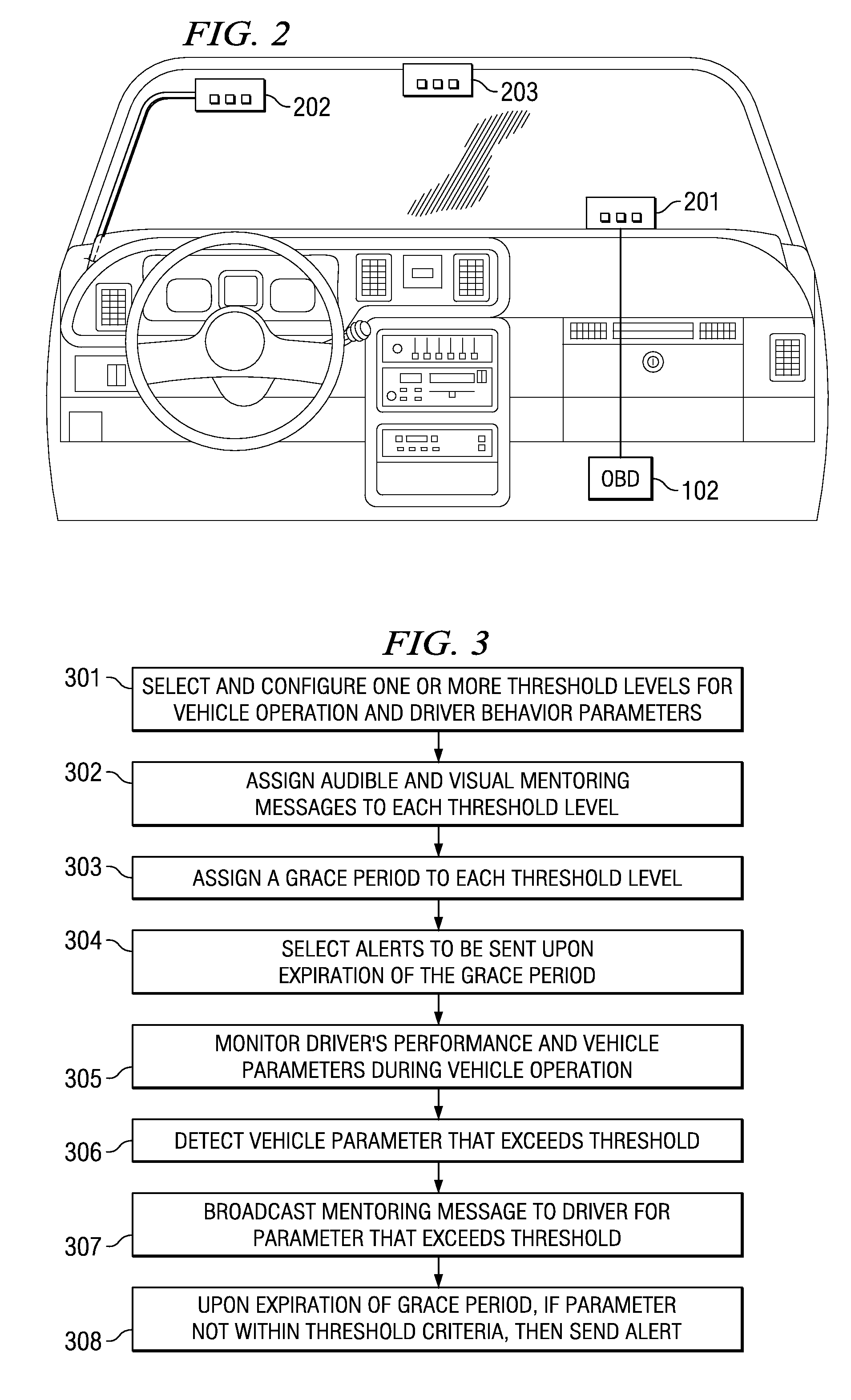
System and method for providing feedback to drivers. The system monitors selected vehicle parameters while a vehicle is being driven, and detects one or more vehicle operation violations by comparing the selected vehicle parameters to predetermined thresholds. A mentoring message is provided to the driver if the threshold is exceeded. If a vehicle operation violation has not been corrected within a preselected time period, then a violation report may be sent to a third party or a central server and / or a different mentoring message may be provided to the driver. Vehicle parameter data may be monitored from an on-board vehicle diagnostic system. The mentoring message may be an audible warning, such as a spoken message, or a visual warning, such as a text message. The selected vehicle parameters may be a vehicle speed, a vehicle acceleration, or a vehicle seatbelt use.
Owner:IWI
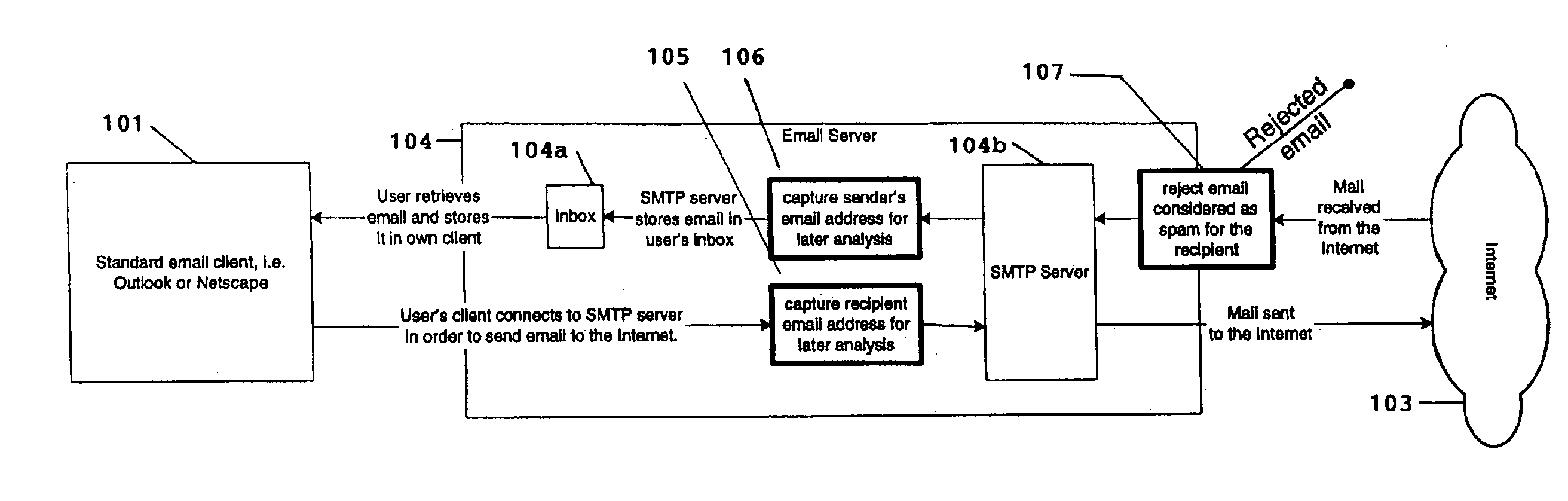
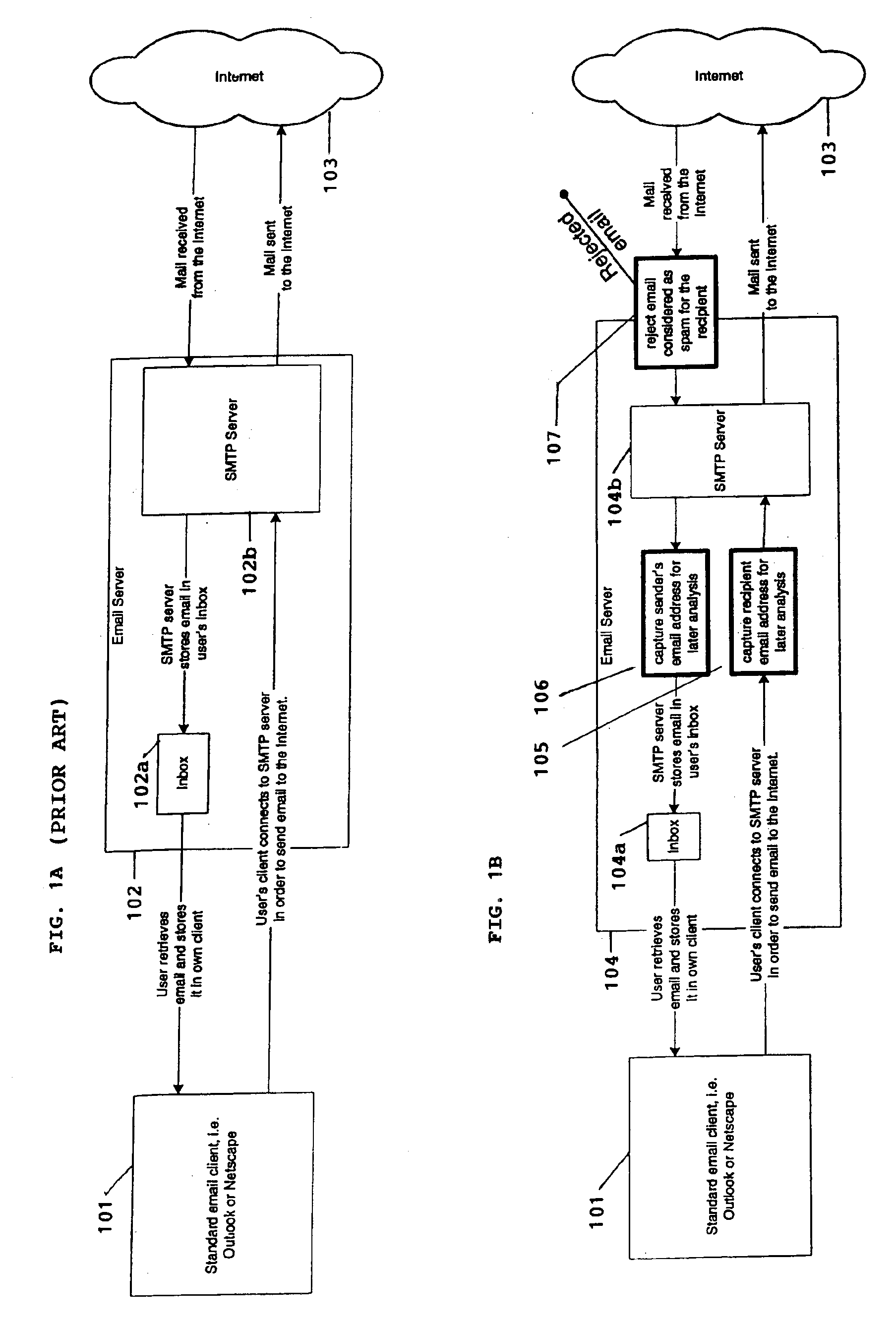
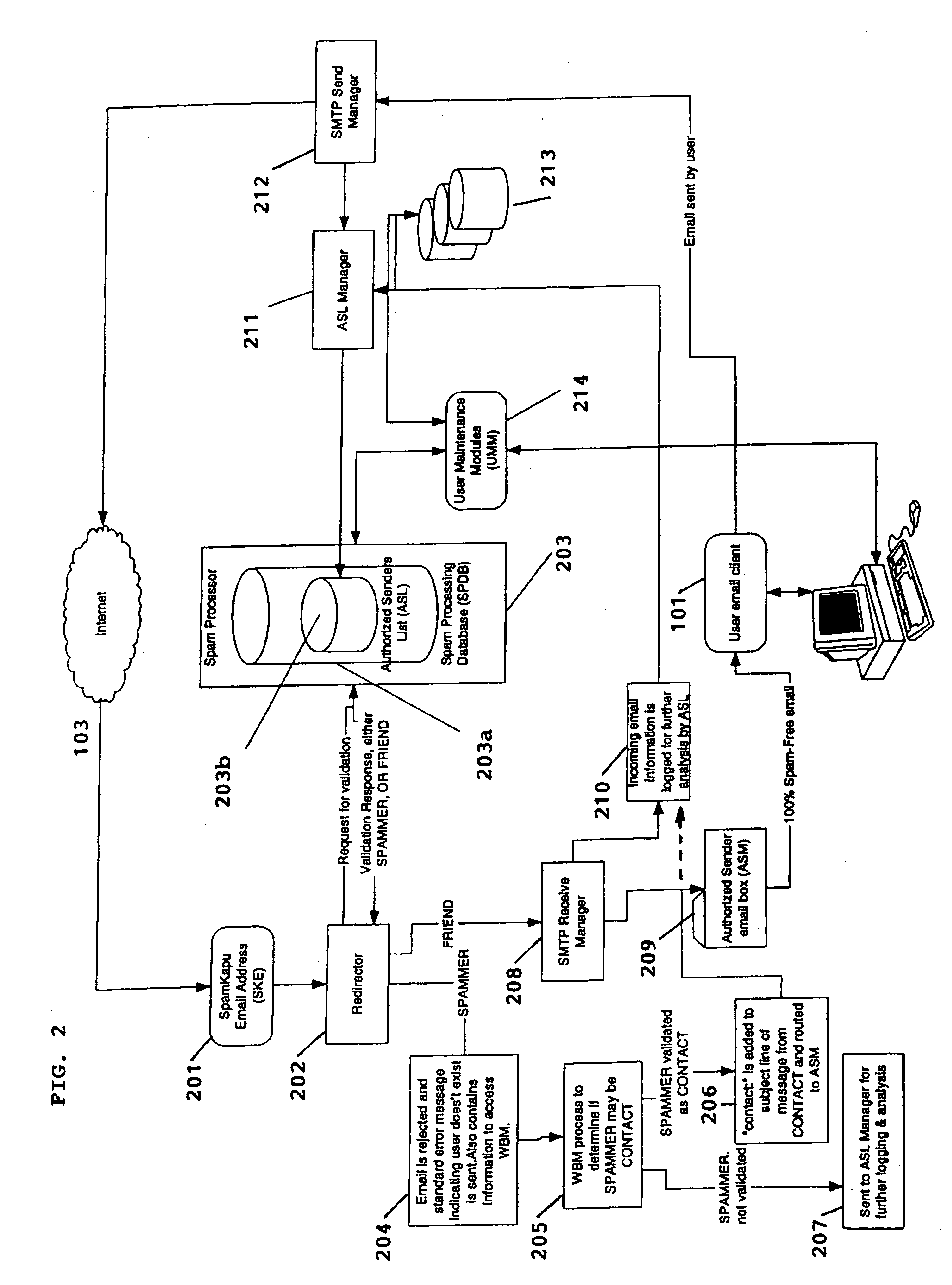
System for eliminating unauthorized electronic mail
InactiveUS6868498B1Hardware monitoringMultiple digital computer combinationsThird partyEmail address
A system for eliminating unauthorized email sent to a user on a network employs an email-receiving server connected between the network and the user's email client for receiving email addressed to the user and rejecting those in which the sender address does not match any of sender addresses maintained on an “authorized senders” list (ASL list). The ASL lists are maintained by an ASL manager in an ASL database operable with a spam processor module. A redirector module rejects the email if, upon sending a request for validation to the spam processor module, the sender's address does not match any authorized sender address on the ASL list. Email rejected by the redirector module is redirected to a web-based messaging (WBM) module which sends a message to the sender to confirm that the sender is a legitimate sender of email to the intended recipient. If the sender logs on to confirm their status, the WBM module executes an interaction procedure which can only be performed by a human, in order to ensure that the confirmation procedure is not performed by a mechanical program. The ASL manager maintains the ASL lists based upon sender address data collected from various sources and analyses of various email usage factors, including sent email, received email, contact lists maintained by the user, user preference inputs, third party programs, etc.
Owner:CUFER ASSET LTD LLC
Media content device and system
A device for obtaining media content from a source and storing the media content for subsequent playback. A response mechanism enables a listener to generate response information associated with particular media content that is being rendered by the device. This response information can be delivered to a third party system for triggering the performance of specific actions related to the media content. A content system interfaces to the device and to the Internet. The content system obtains media content from one or more sources via the Internet and delivers the content to the device.
Owner:RPX CORP
System for collecting, analyzing, and transmitting information relevant to transportation networks
InactiveUS20130059607A1Accurate predictionEmergency connection handlingFinanceThird partyPosition dependent
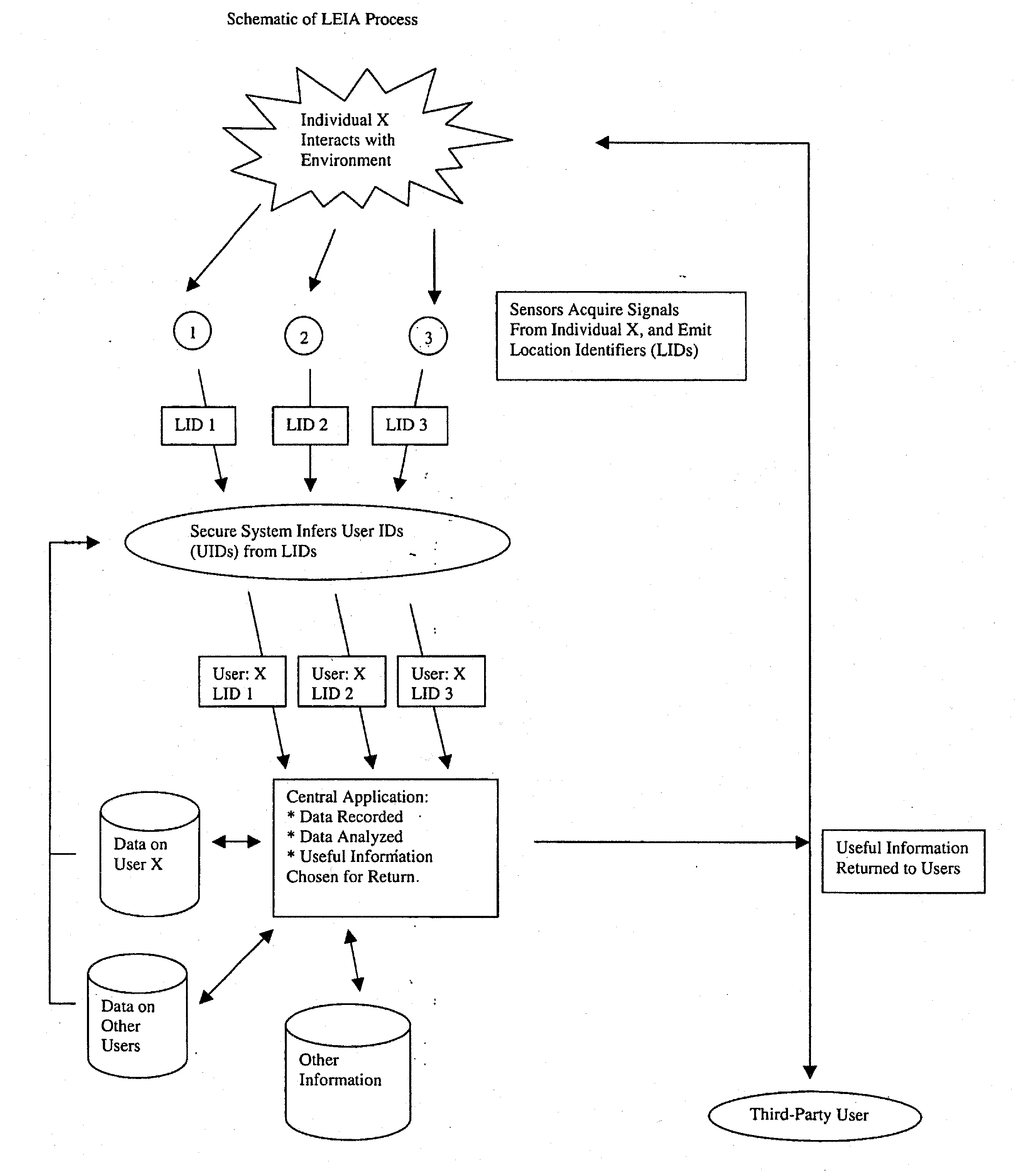
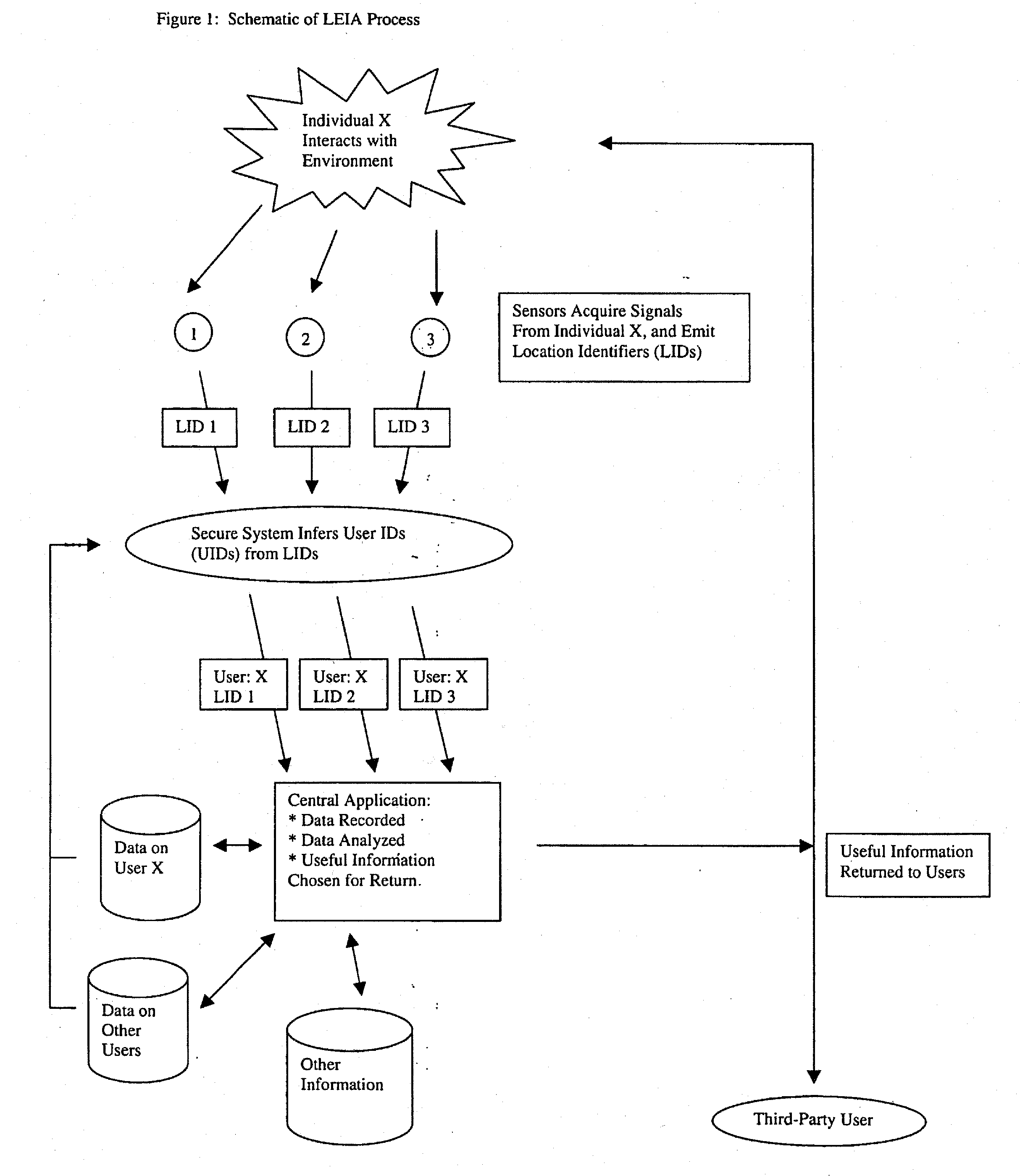
When individual persons or vehicles move through a transportation network, they are likely to be both actively and passively creating information that reflects their location and current behavior. In this patent, we propose a system that makes complete use of this information. First, through a broad web of sensors, our system collects and stores the full range of information generated by travelers. Next, through the use of previously-stored data and active computational analysis, our system deduces the identity of individual travelers. Finally, using advanced data-mining technology, our system selects useful information and transmits it back to the individual, as well as to third-party users; in short, it forms the backbone for a variety of useful location-related end-user applications.
Owner:APPLE INC
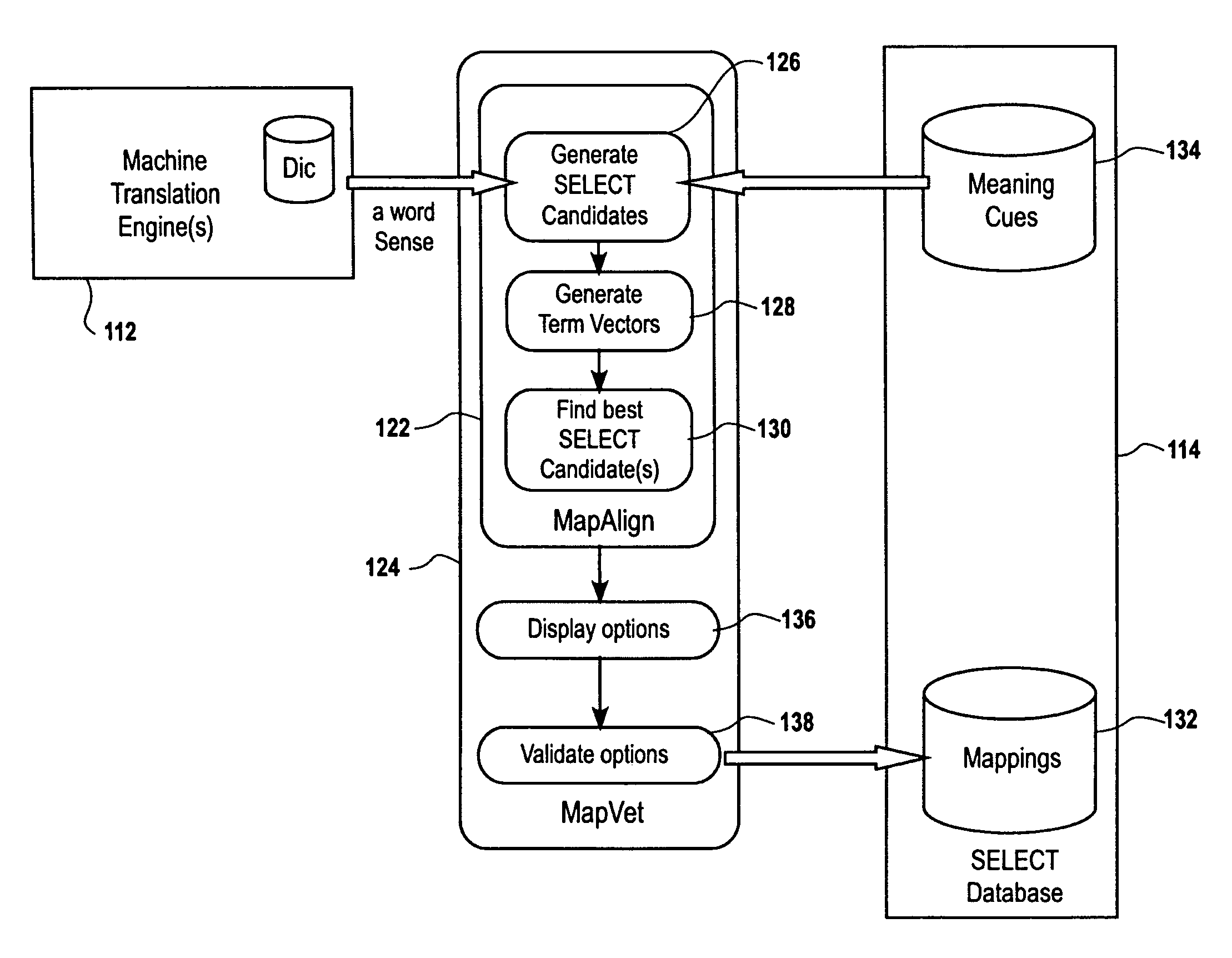
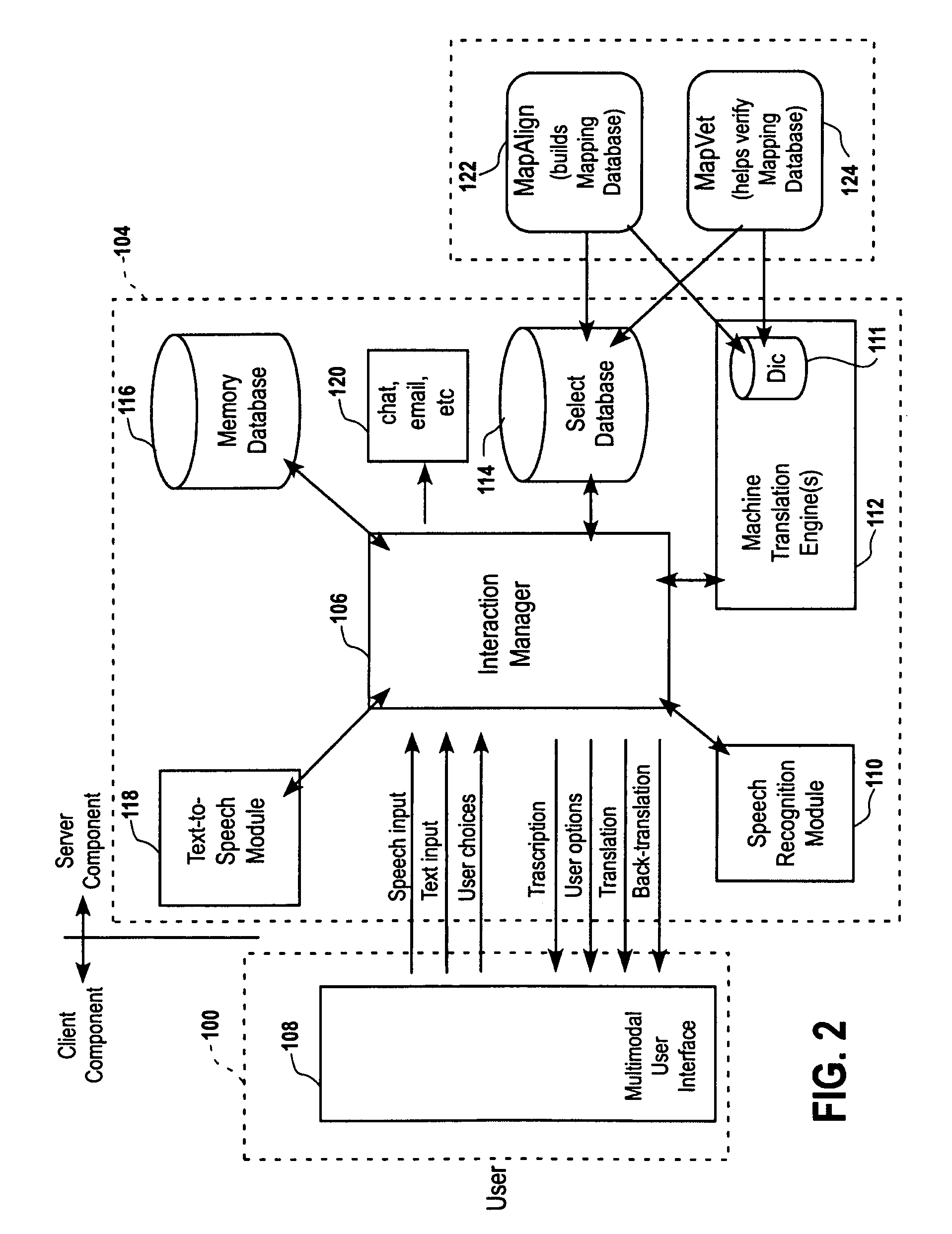
Speech-enabled language translation system and method enabling interactive user supervision of translation and speech recognition accuracy
ActiveUS7539619B1Natural language translationSpeech recognitionSpeech to speech translationAmbiguity
A system and method for a highly interactive style of speech-to-speech translation is provided. The interactive procedures enable a user to recognize, and if necessary correct, errors in both speech recognition and translation, thus providing robust translation output than would otherwise be possible. The interactive techniques for monitoring and correcting word ambiguity errors during automatic translation, search, or other natural language processing tasks depend upon the correlation of Meaning Cues and their alignment with, or mapping into, the word senses of third party lexical resources, such as those of a machine translation or search lexicon. This correlation and mapping can be carried out through the creation and use of a database of Meaning Cues, i.e., SELECT. Embodiments described above permit the intelligent building and application of this database, which can be viewed as an interlingua, or language-neutral set of meaning symbols, applicable for many purposes. Innovative techniques for interactive correction of server-based speech recognition are also described.
Owner:ZAMA INNOVATIONS LLC
Determining website reputations using automatic testing
ActiveUS20060253458A1Digital data information retrievalComputer security arrangementsThird partyWeb site
An aspect of the present invention relates to methods and systems involving automatically generating a third party assessment of a website's reputation, and storing an indicia of the assessment in a format and location that may be accessible by a client computing facility attempting to interact with the website.
Owner:MCAFEE LLC
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
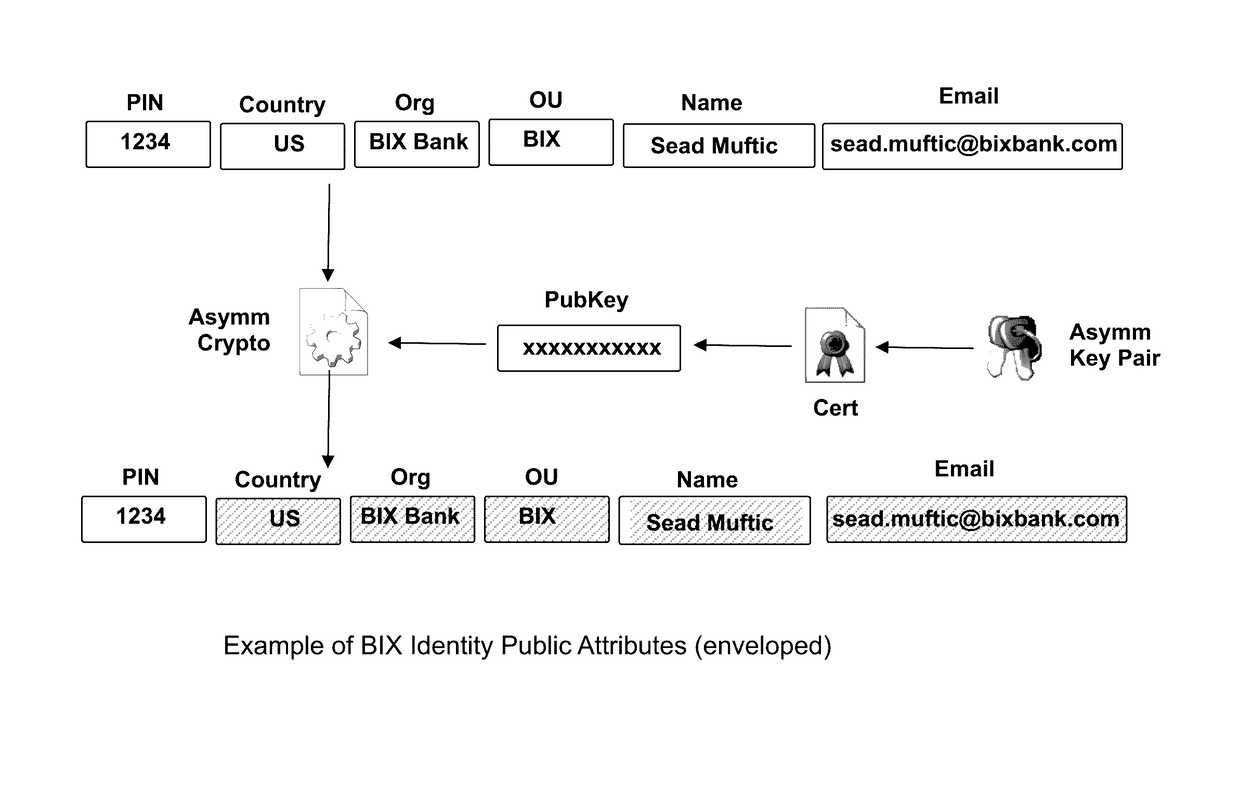
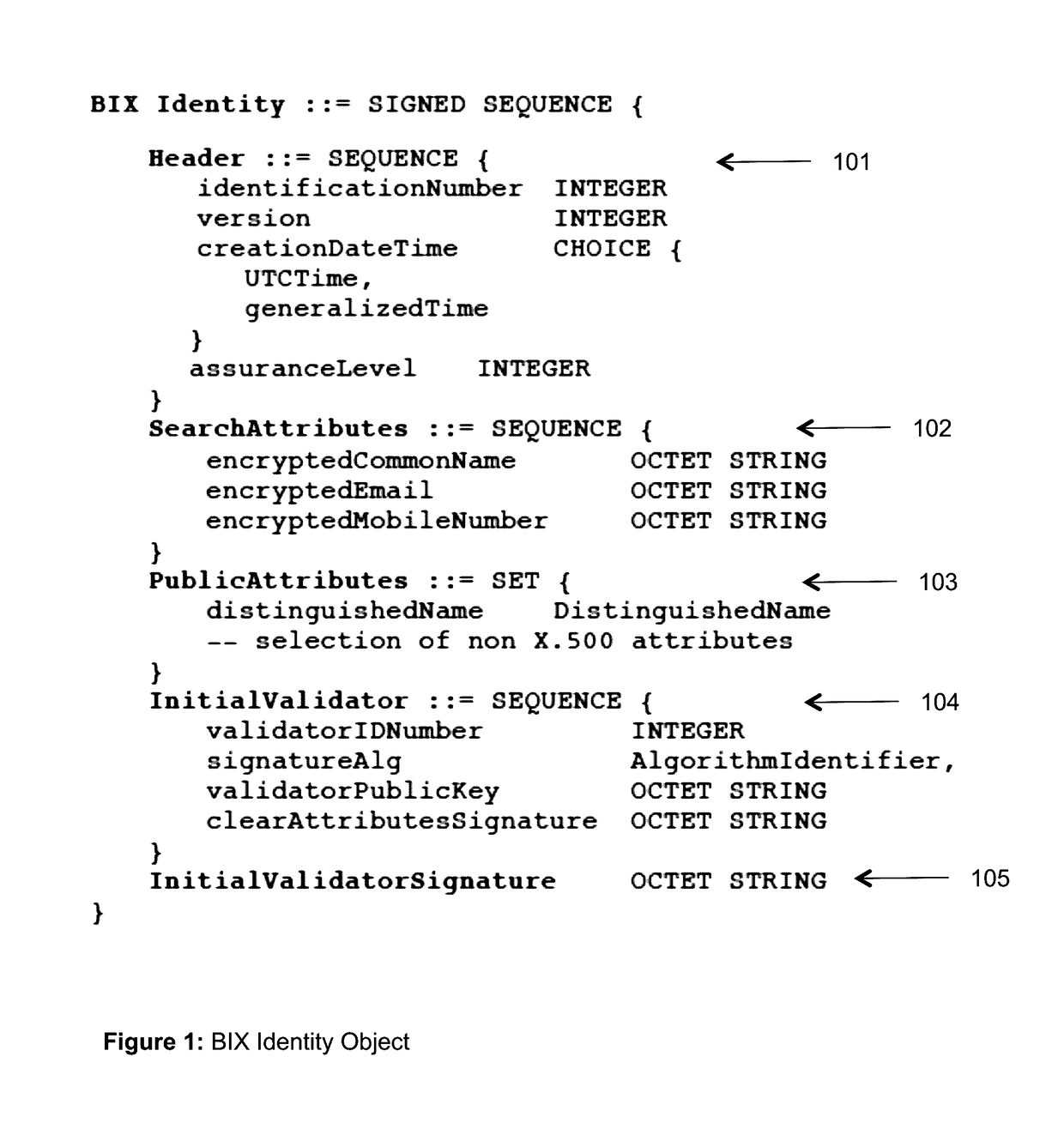
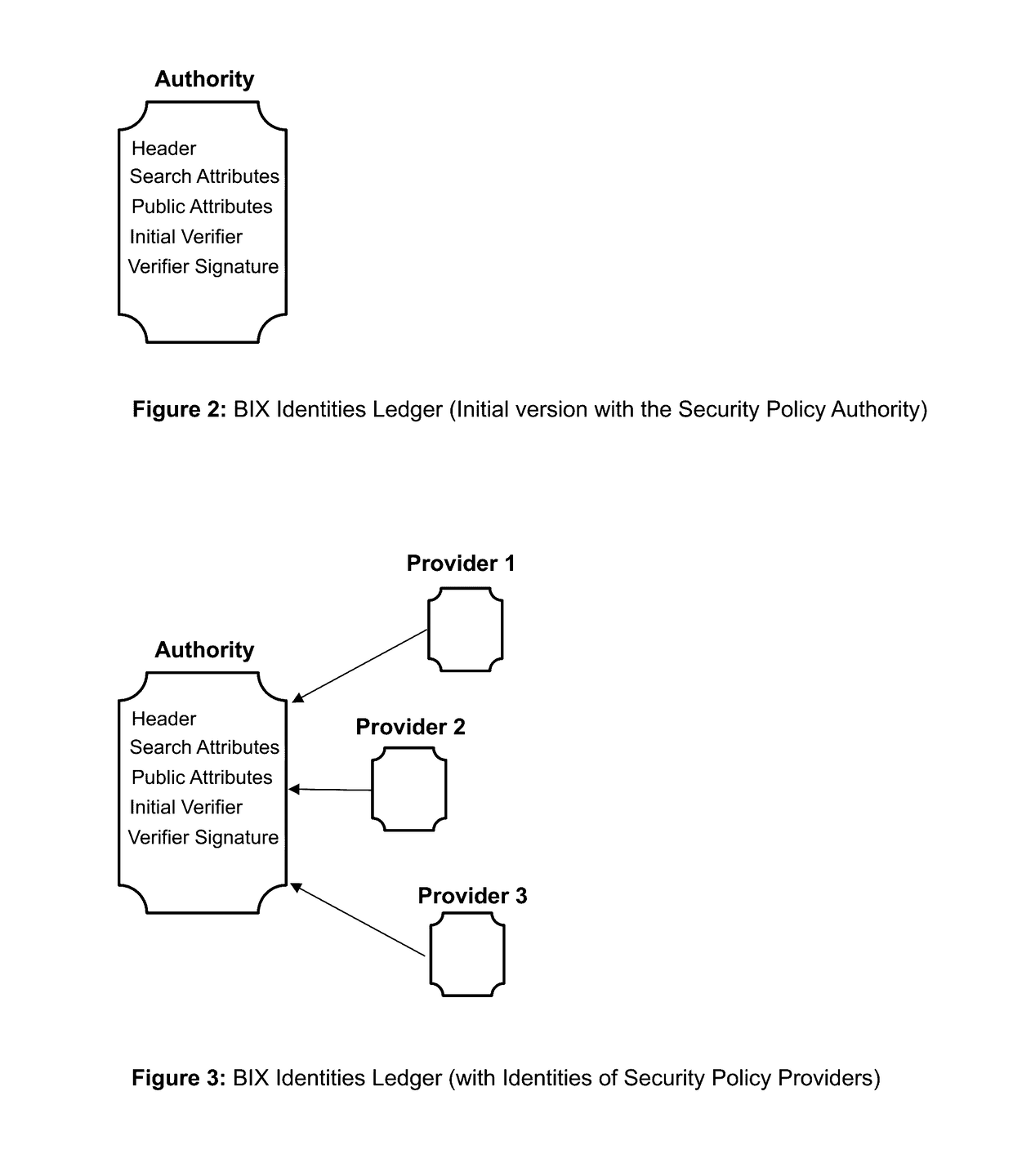
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
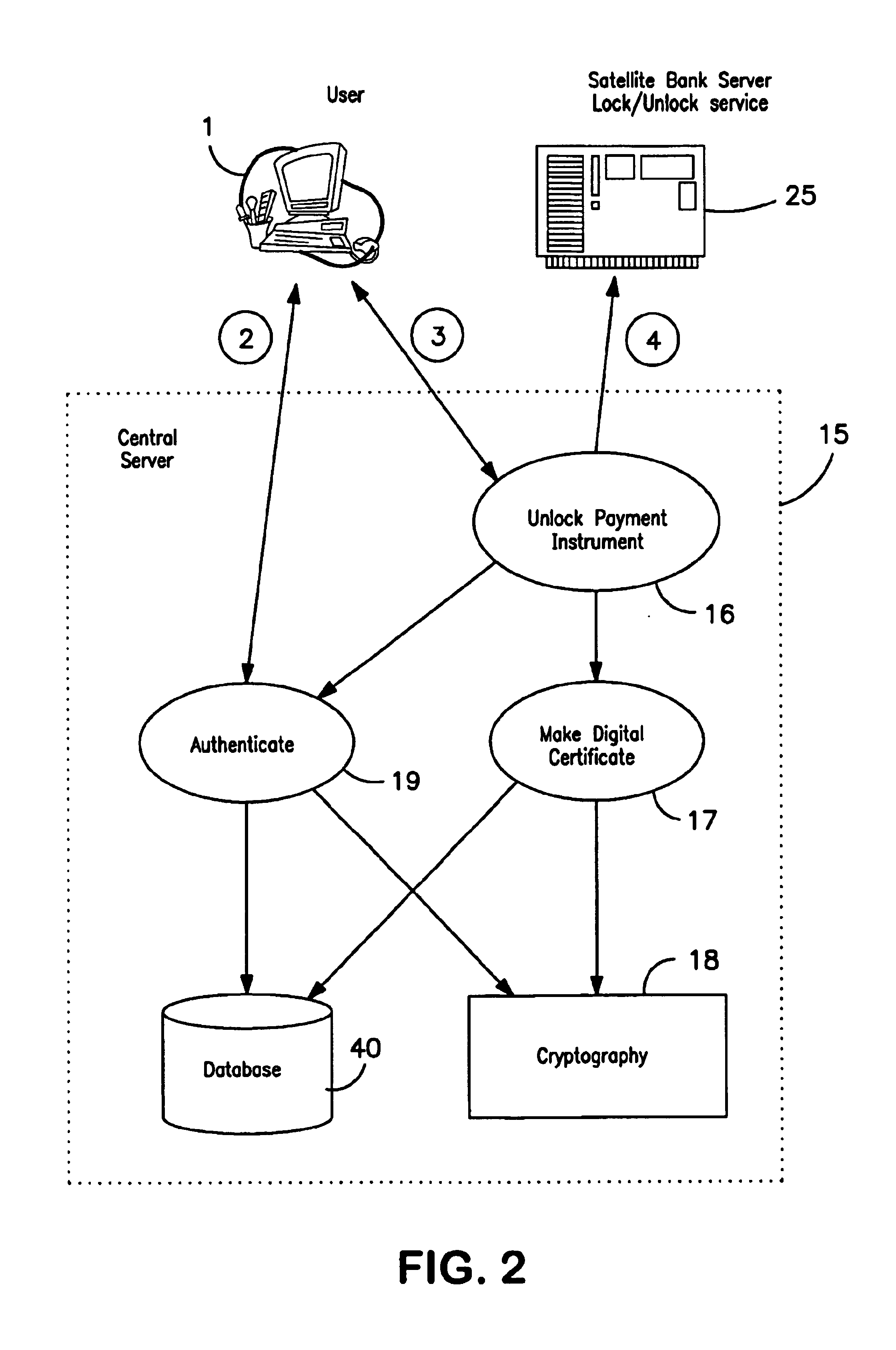
Payment instrument authorization technique
InactiveUS6931382B2Strong authenticationPayment circuitsSpecial data processing applicationsThird partyAuthorization
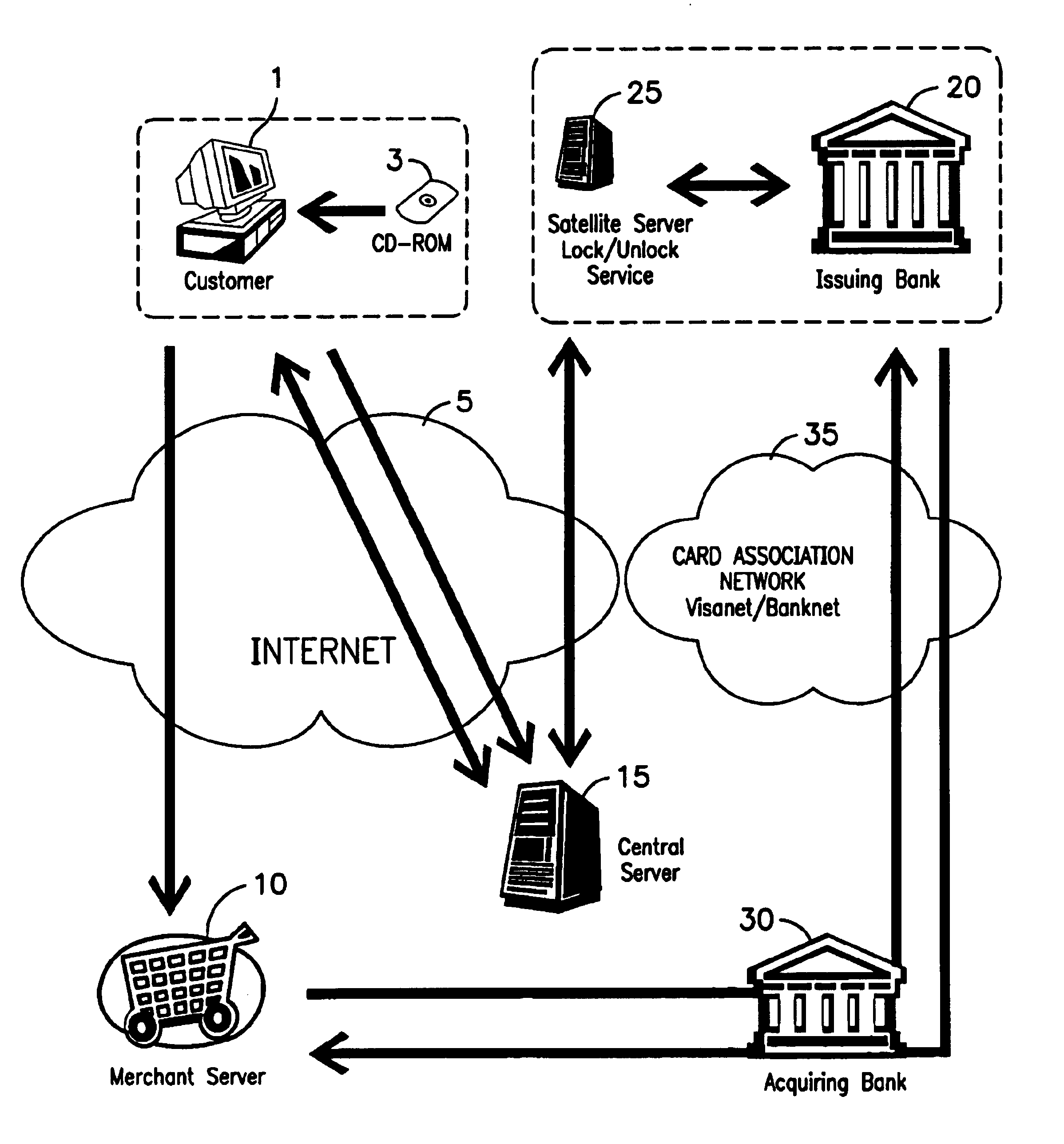
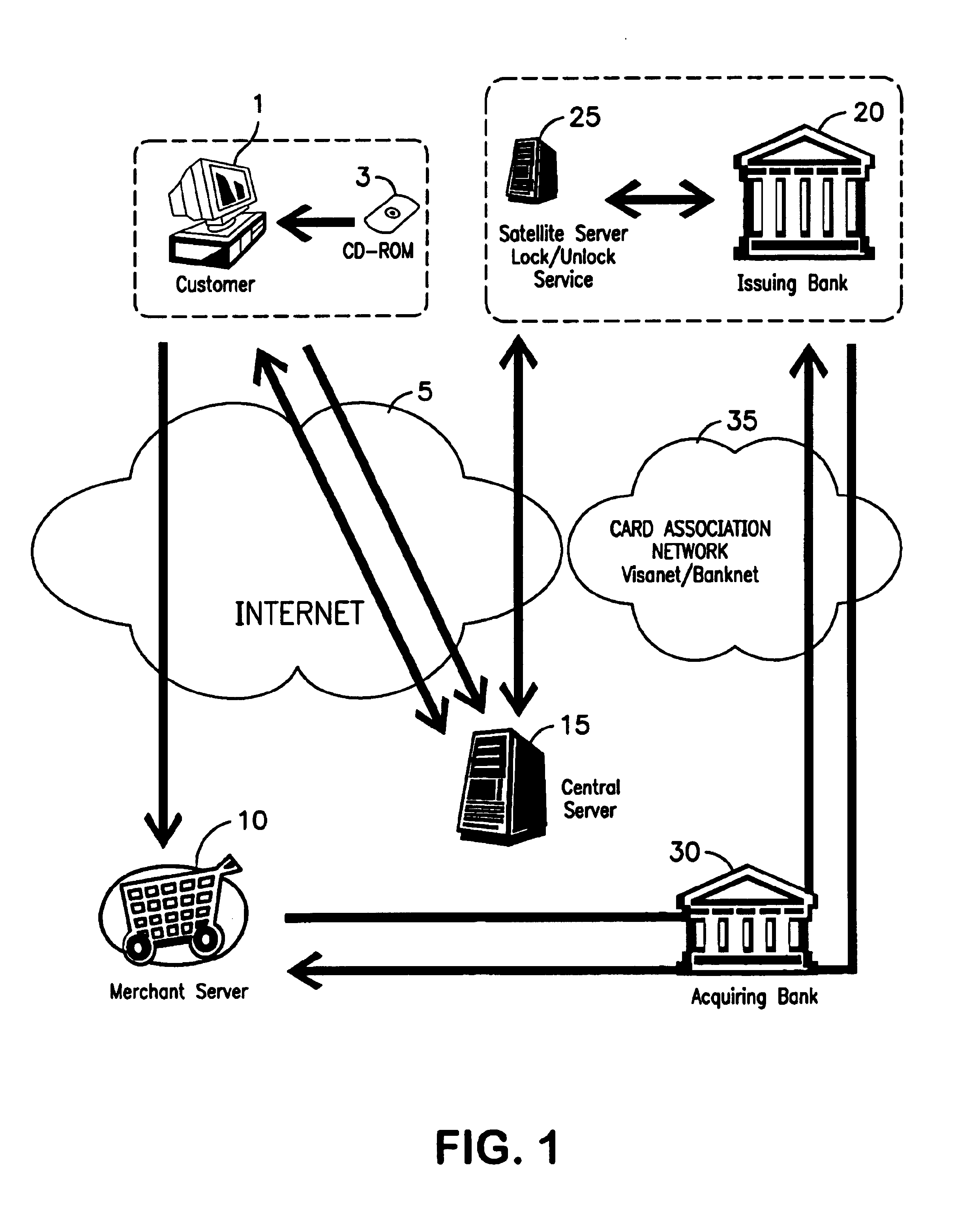
A method is provided for protecting a payment instrument in non-face-to-face transactions. The payment instrument is issued by an issuing entity and associated with an authorized instrument holder. The authorized instrument holder is subject to authentication by a trusted third party with whom the payment instrument holder has previously registered. The method includes: the authorized instrument holder communicating with the issuing entity to block, on a default basis, authorization of the payment instrument for non-face-to-face transactions unless authorized to unblock the payment instrument by the trusted third party; prior to a non-face-to-face transaction, the authorized instrument holder communicating with the trusted third party to subject him or herself to authentication and to request that the payment instrument be unblocked; and the trusted third party authenticating the authorized instrument holder, and if the authentication result is positive, communicating with the issuing entity to request unblocking of the payment instrument.
Owner:KIOBA PROCESSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com