Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
251 results about "Privacy policy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A privacy policy is a statement or a legal document (in privacy law) that discloses some or all of the ways a party gathers, uses, discloses, and manages a customer or client's data. It fulfills a legal requirement to protect a customer or client's privacy. Personal information can be anything that can be used to identify an individual, not limited to the person's name, address, date of birth, marital status, contact information, ID issue, and expiry date, financial records, credit information, medical history, where one travels, and intentions to acquire goods and services. In the case of a business it is often a statement that declares a party's policy on how it collects, stores, and releases personal information it collects. It informs the client what specific information is collected, and whether it is kept confidential, shared with partners, or sold to other firms or enterprises. Privacy policies typically represent a broader, more generalized treatment, as opposed to data use statements, which tend to be more detailed and specific.
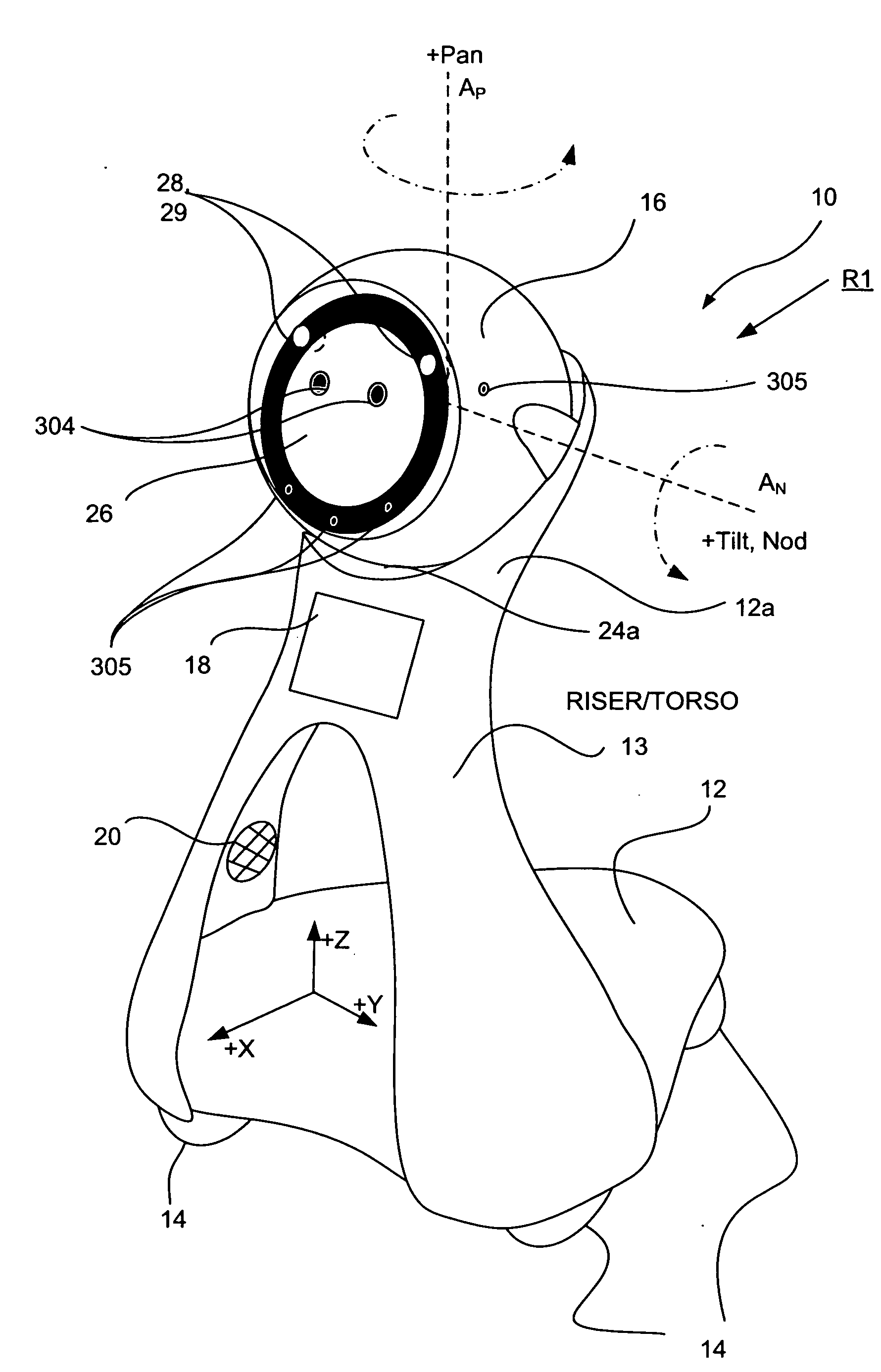
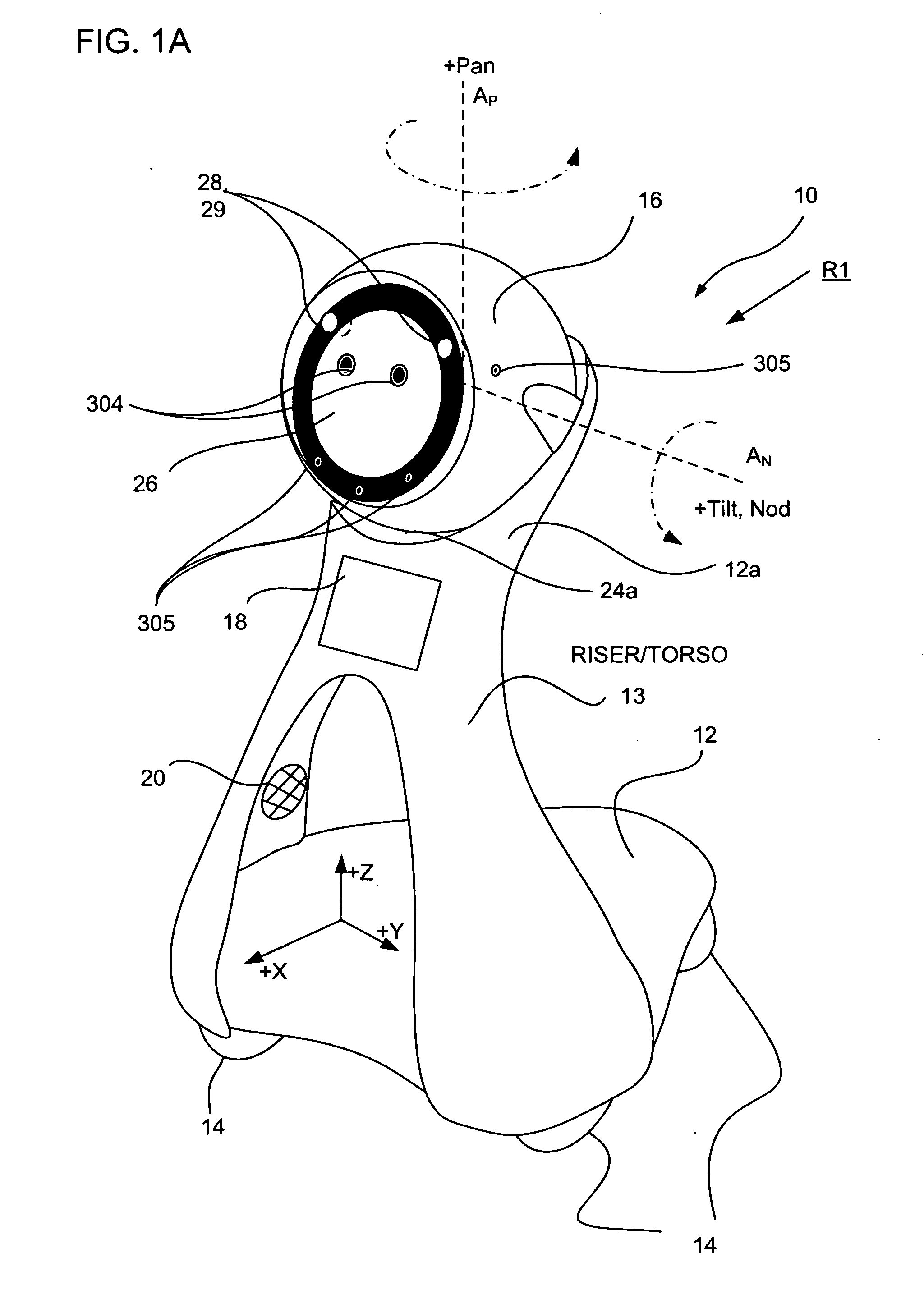
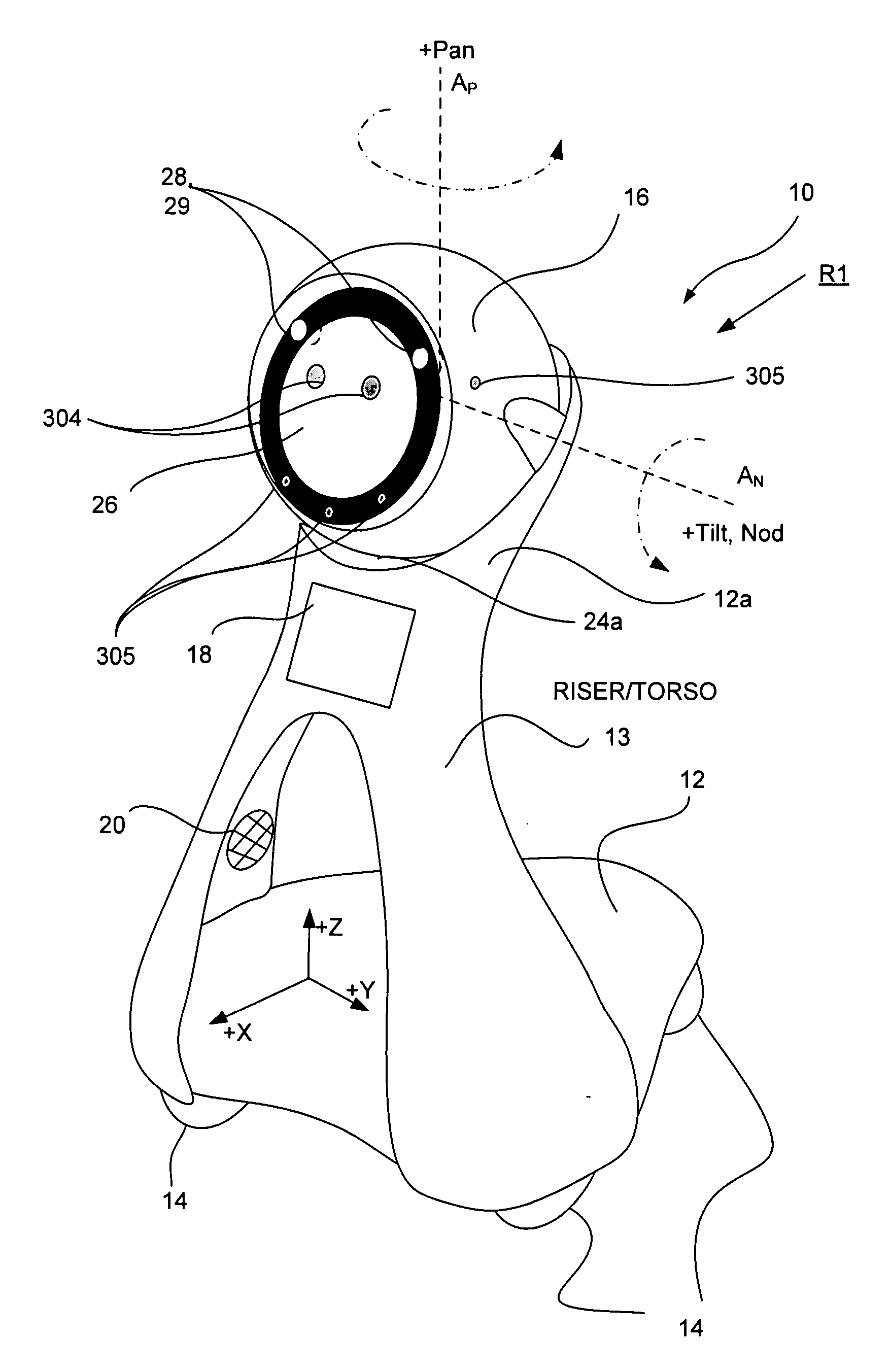
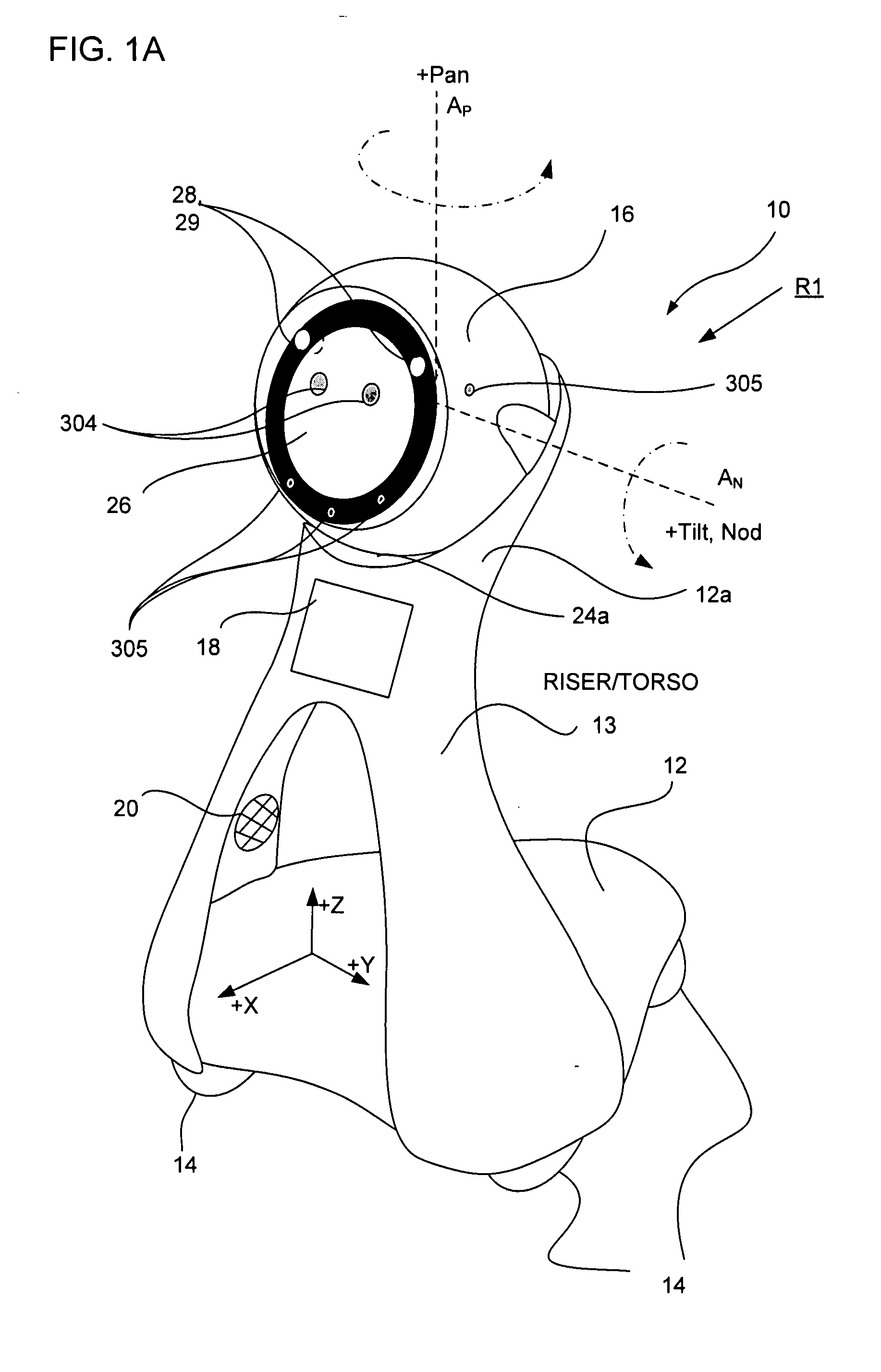
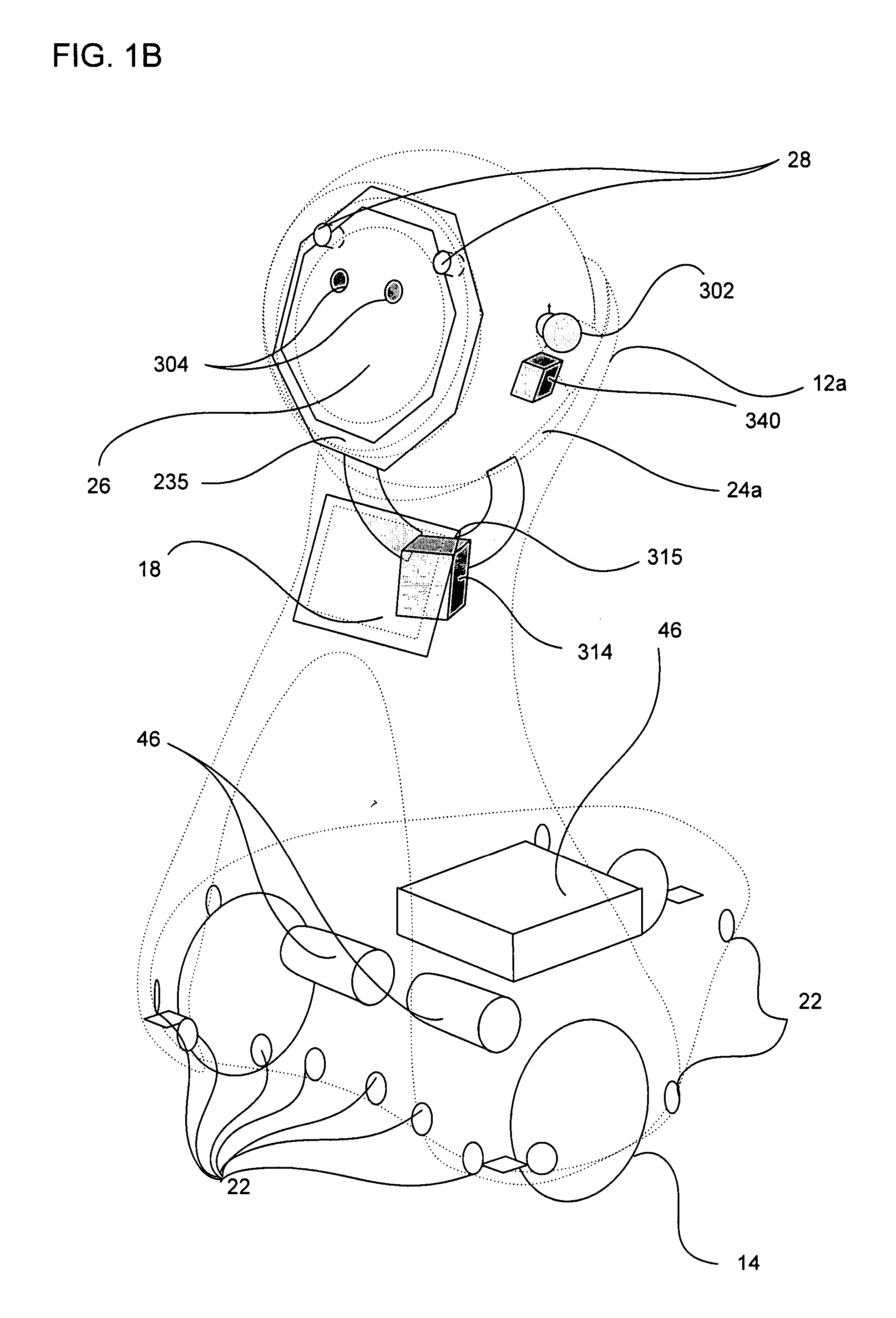
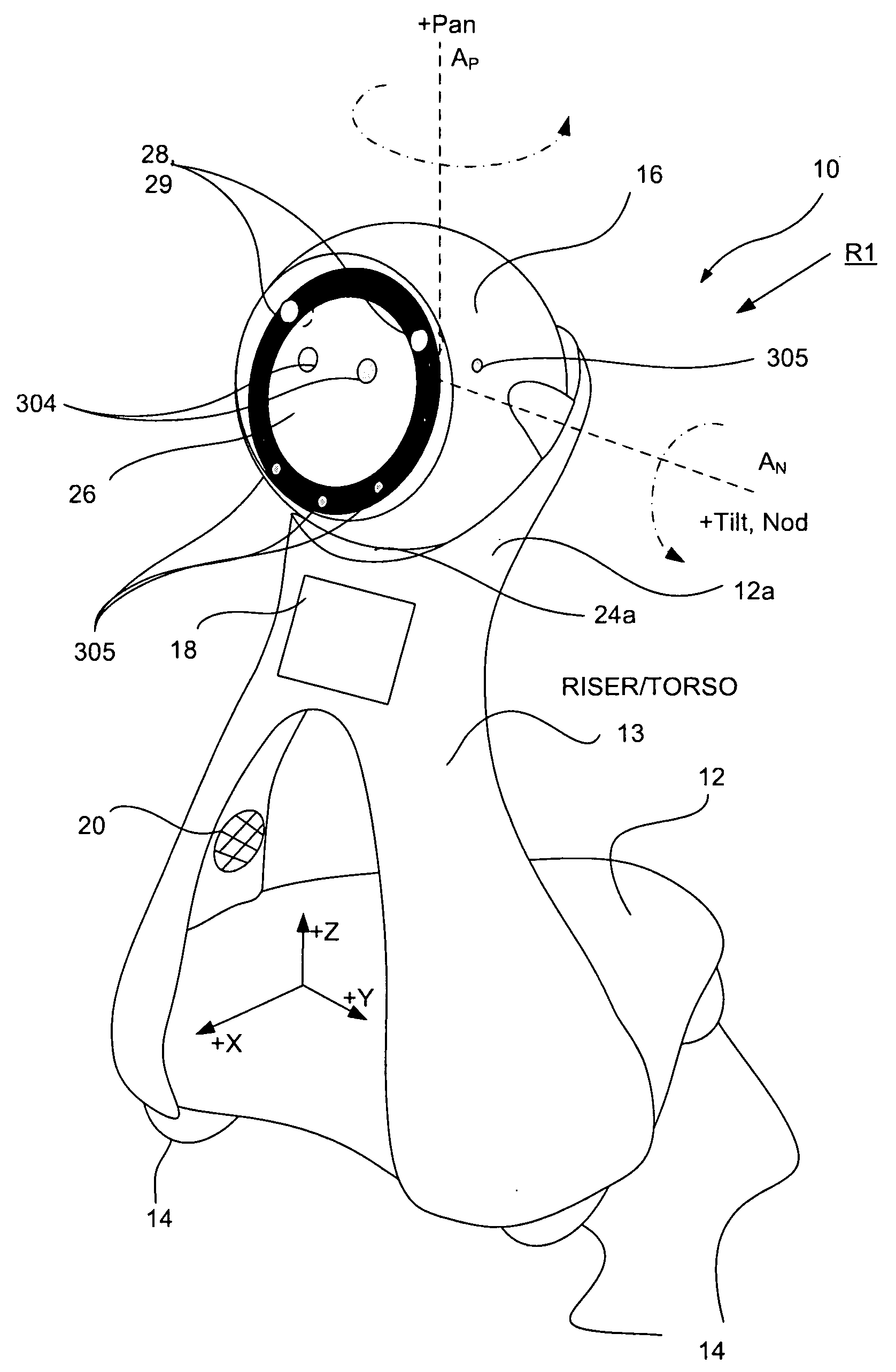
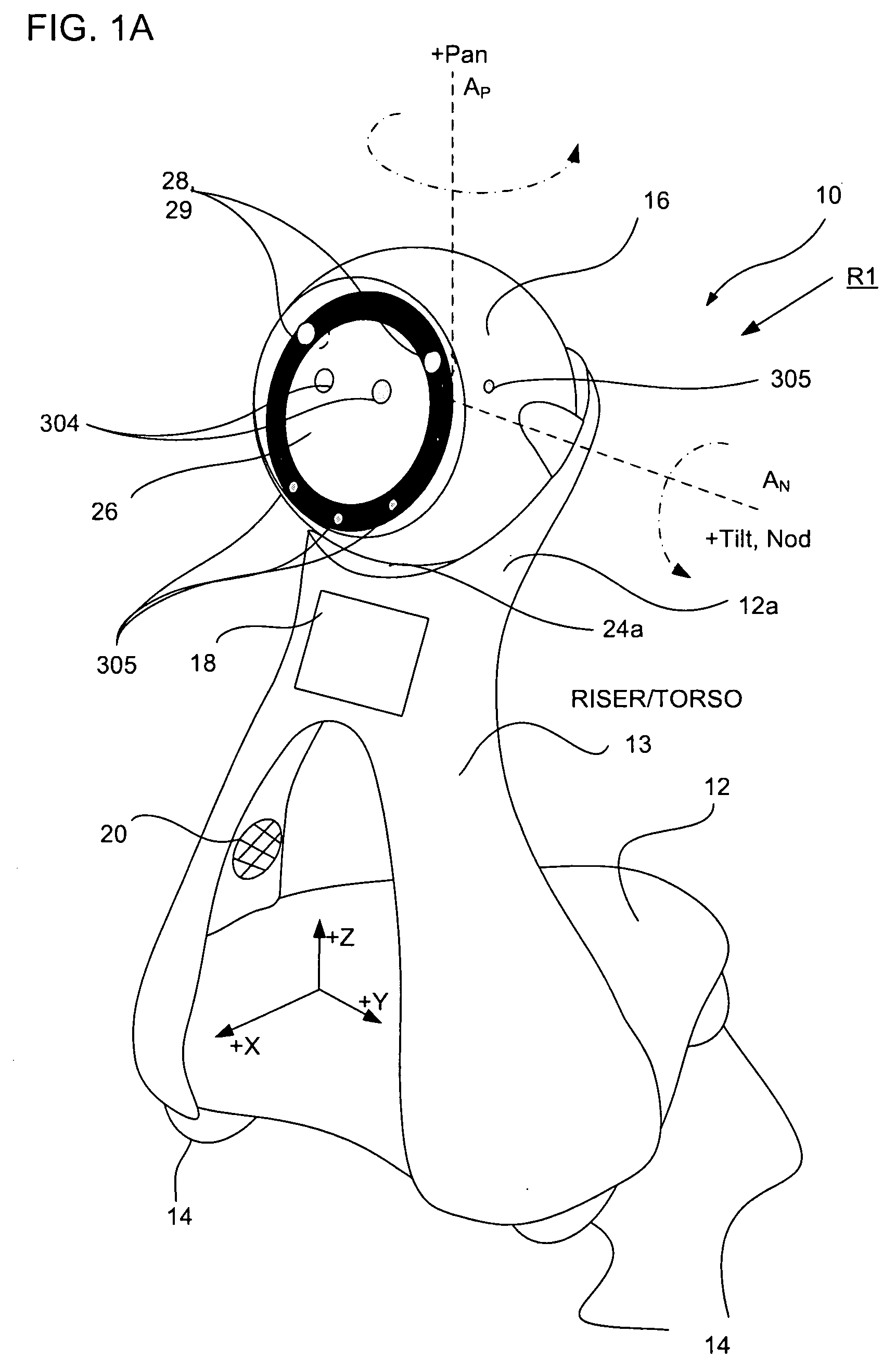
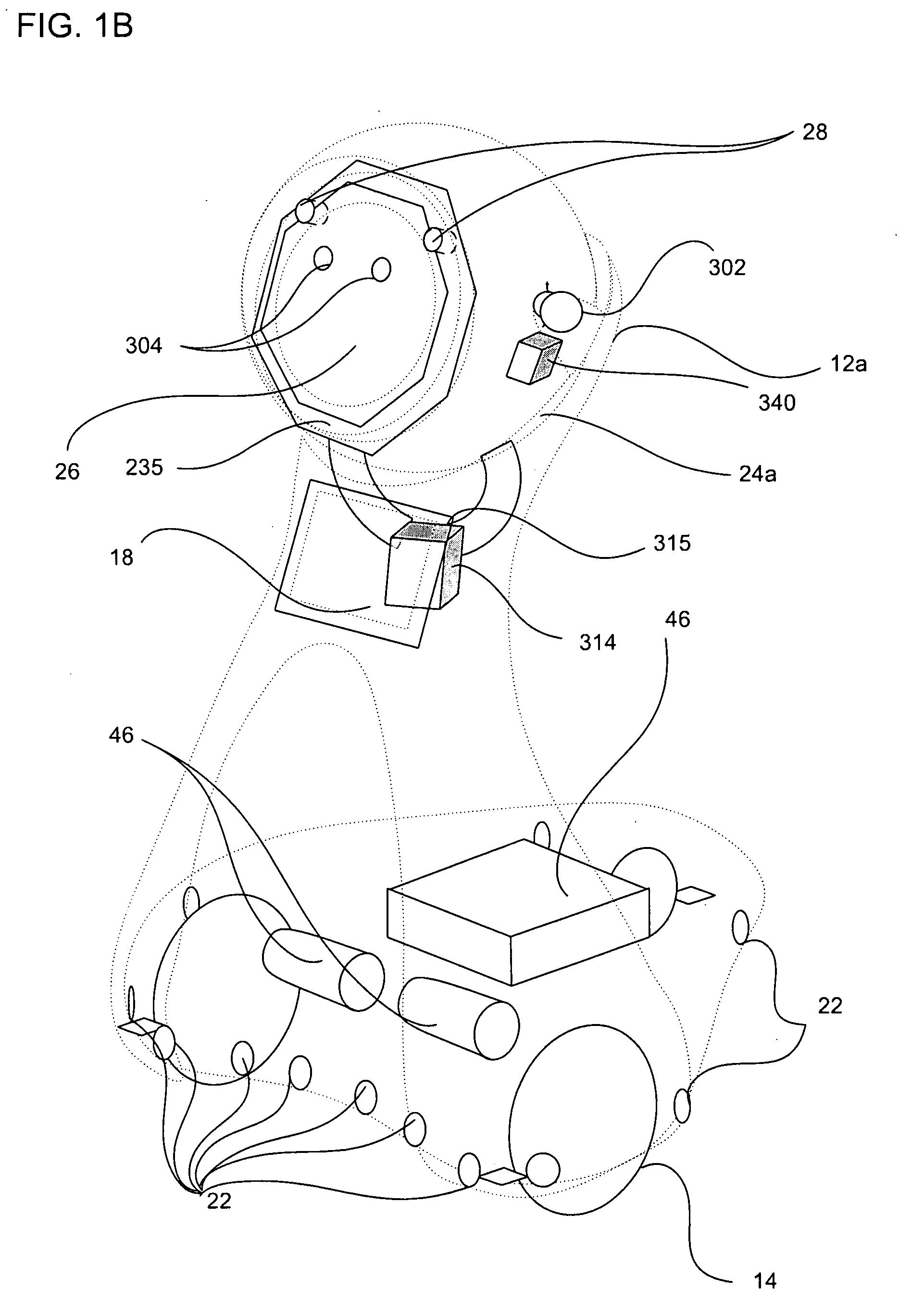
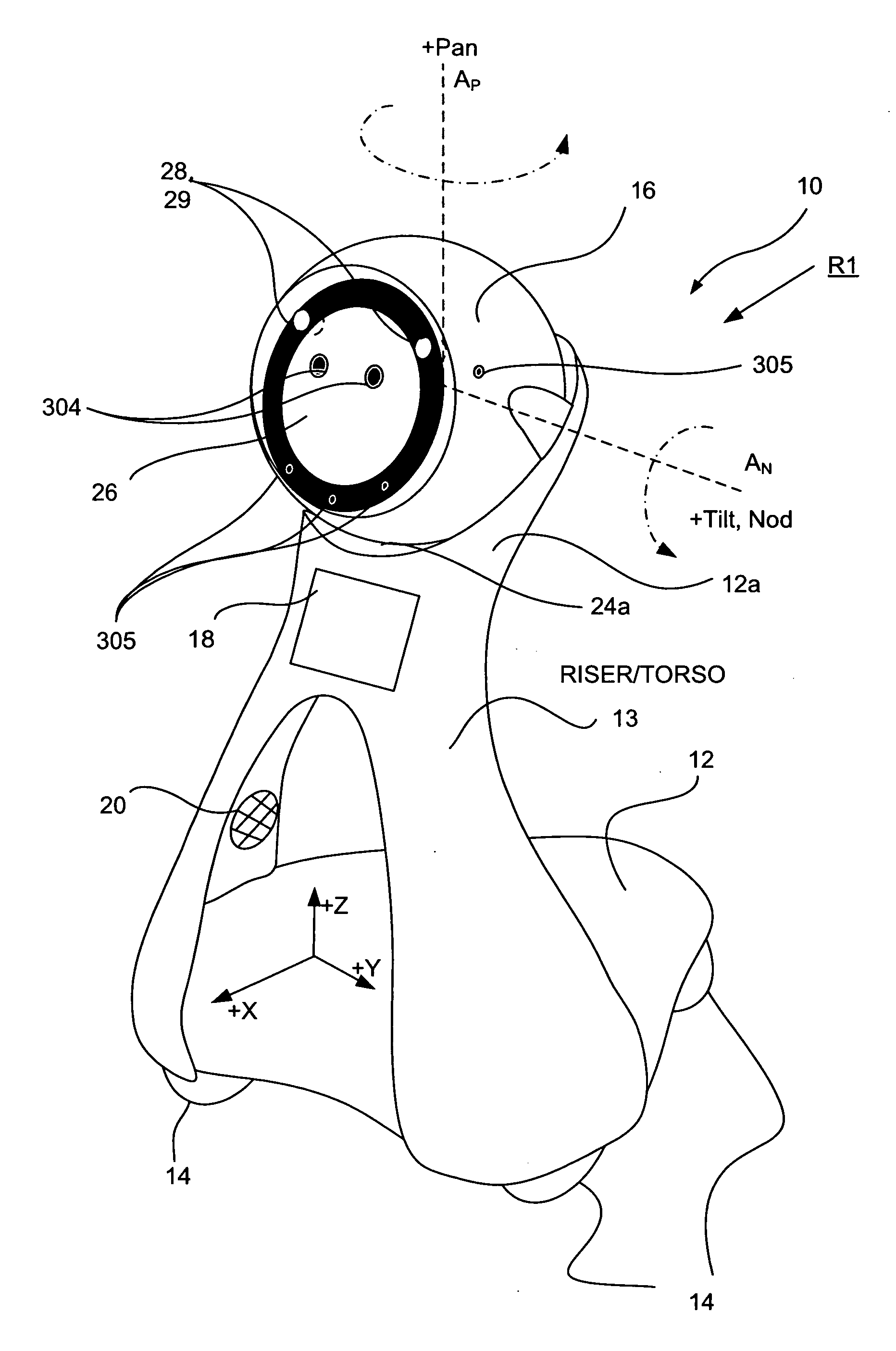
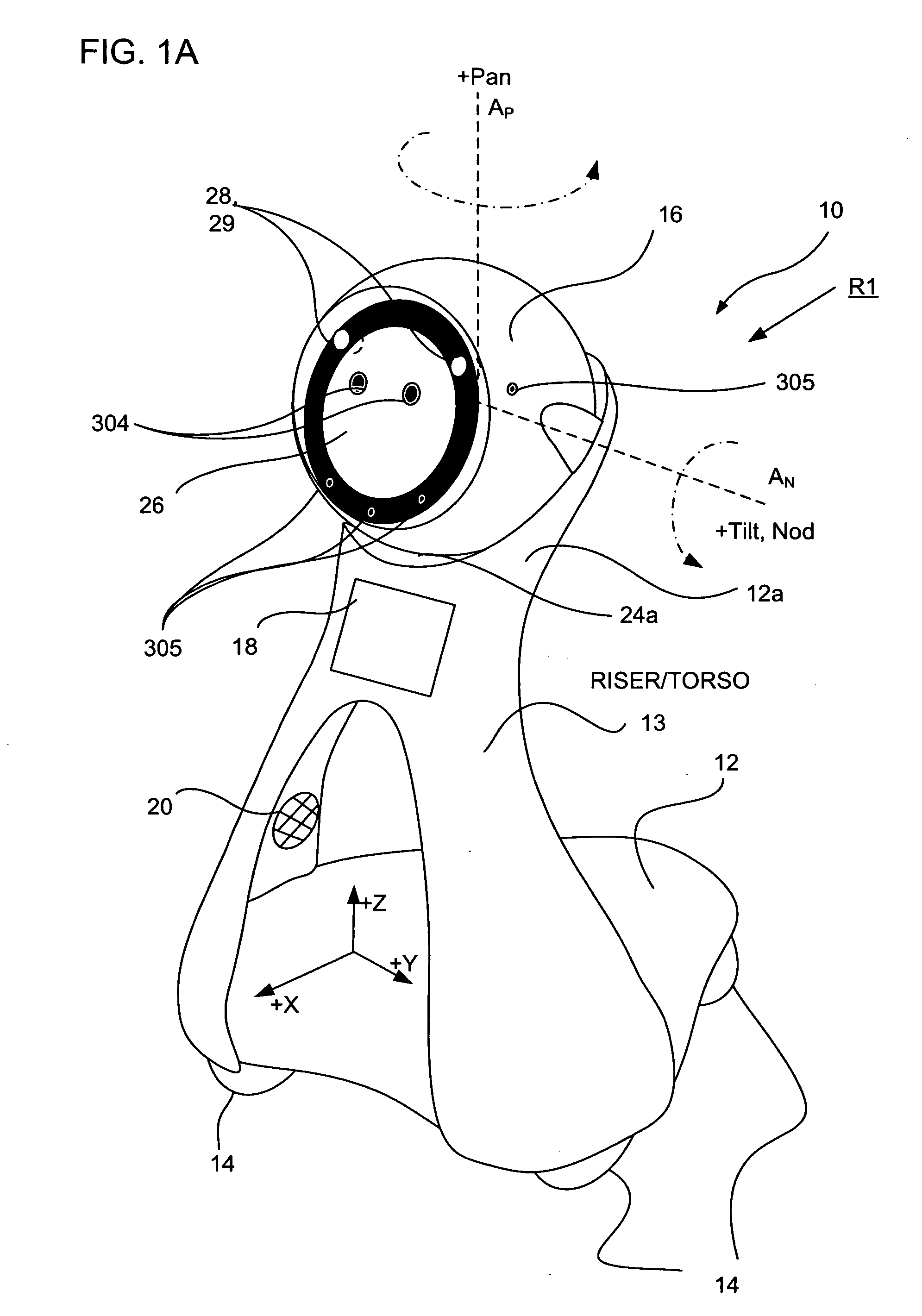
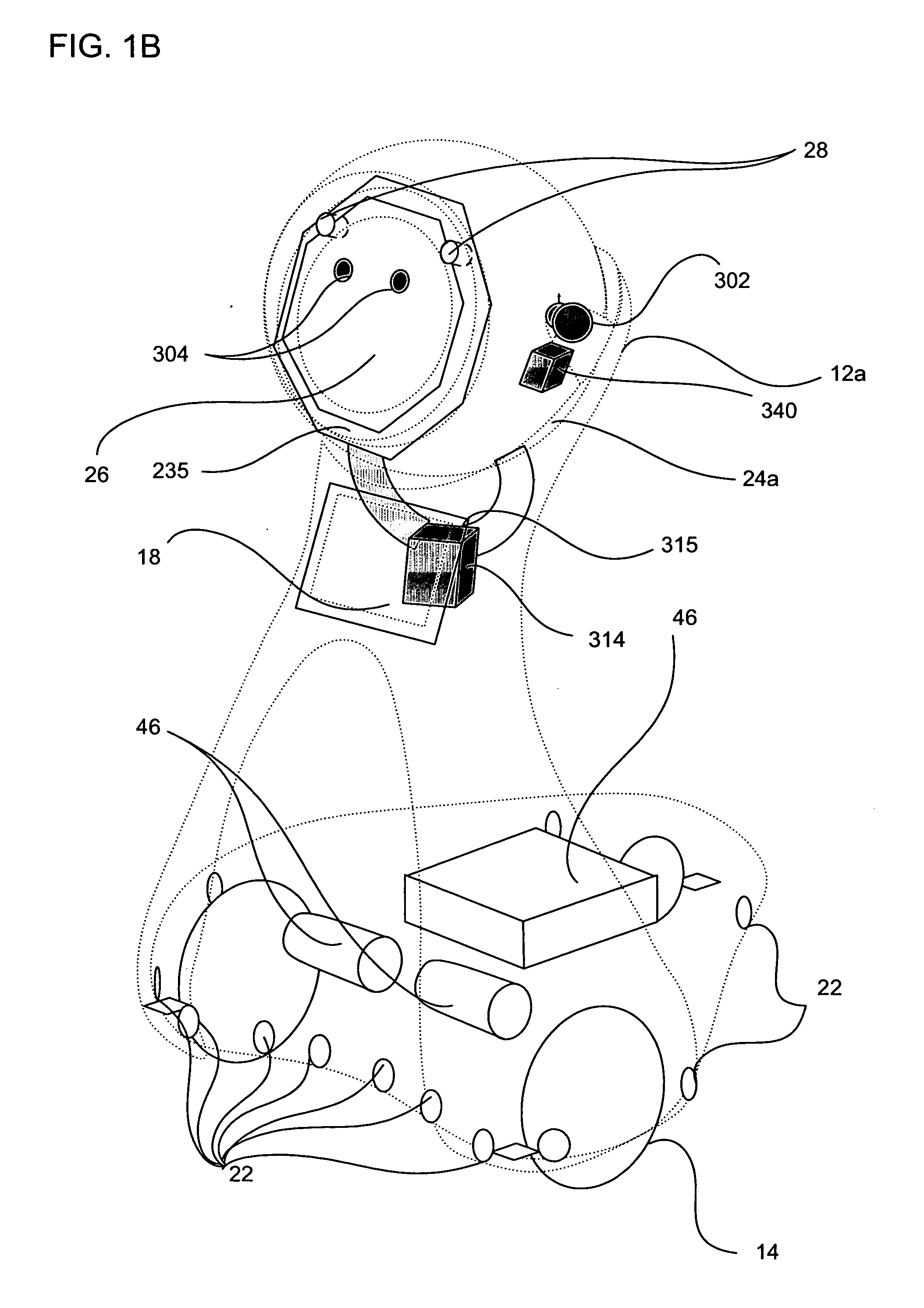
Companion robot for personal interaction
ActiveUS20070192910A1Improving presence scoreEnhanced presenceProgramme-controlled manipulatorLocal control/monitoringThird partyTeleconference
A mobile robot guest for interacting with a human resident performs a room-traversing search procedure prior to interacting with the resident, and may verbally query whether the resident being sought is present. Upon finding the resident, the mobile robot may facilitate a teleconferencing session with a remote third party, or interact with the resident in a number of ways. For example, the robot may carry on a dialogue with the resident, reinforce compliance with medication or other schedules, etc. In addition, the robot incorporates safety features for preventing collisions with the resident; and the robot may audibly announce and / or visibly indicate its presence in order to avoid becoming a dangerous obstacle. Furthermore, the mobile robot behaves in accordance with an integral privacy policy, such that any sensor recording or transmission must be approved by the resident.
Owner:IROBOT CORP
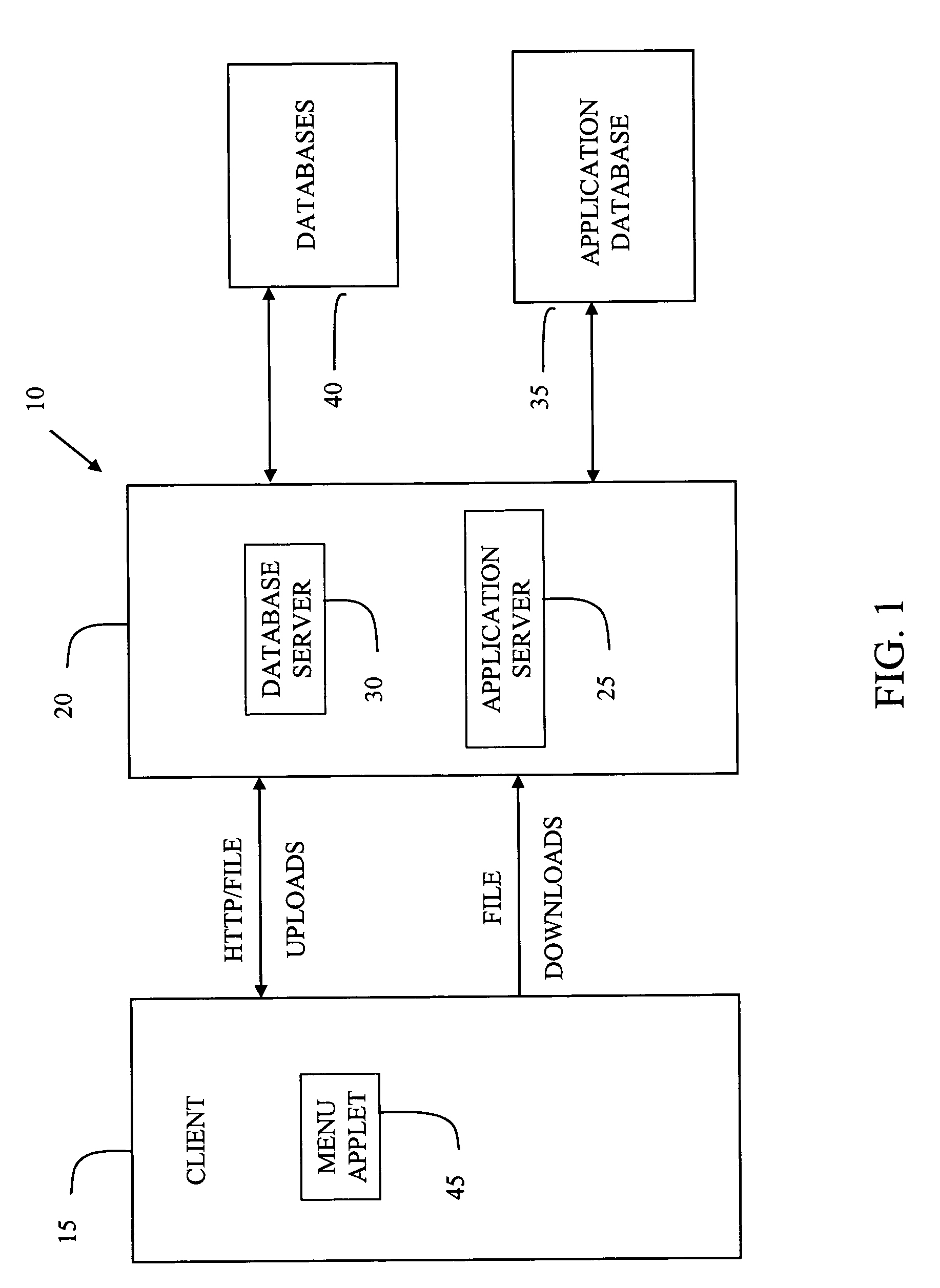
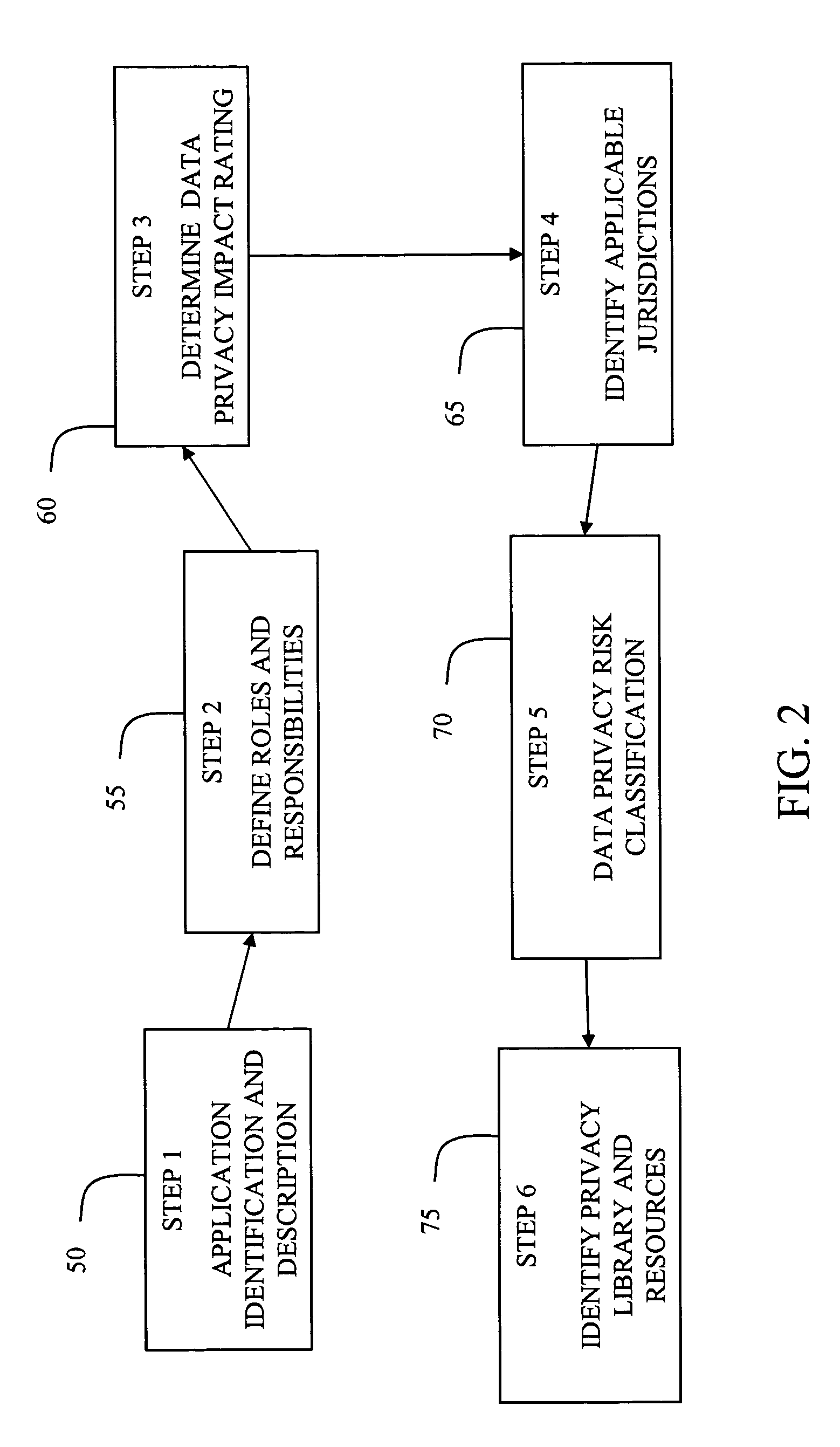
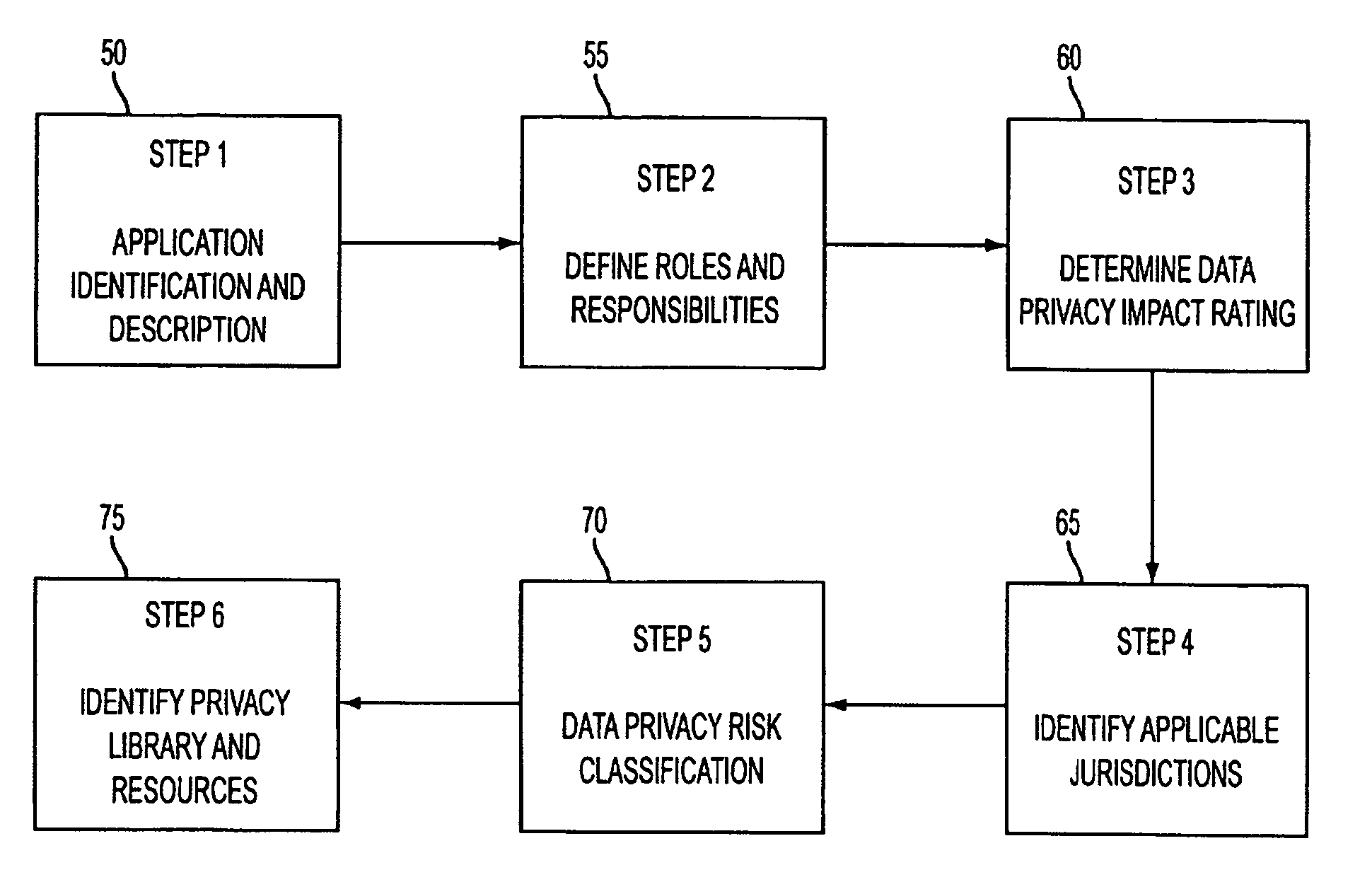
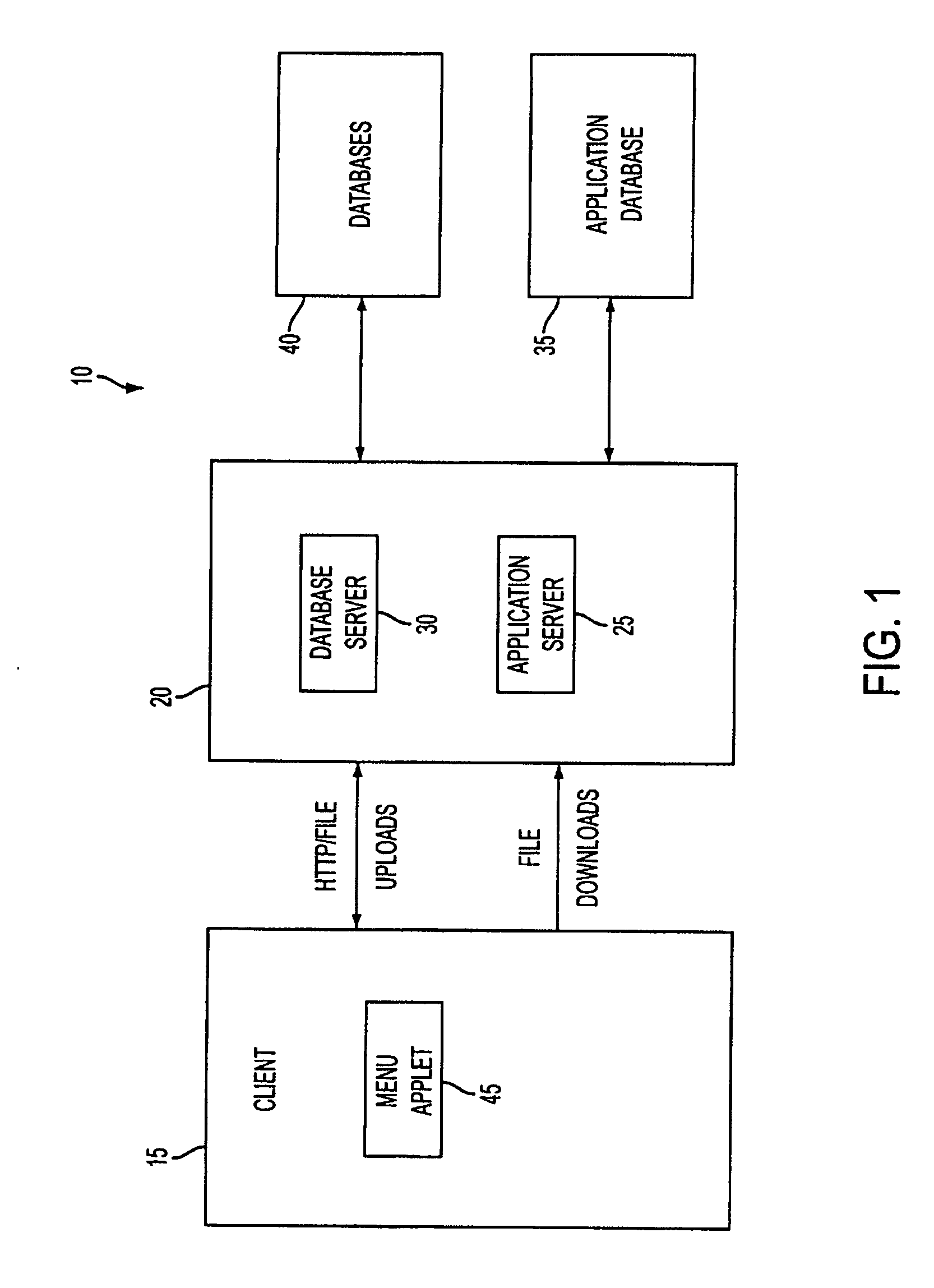
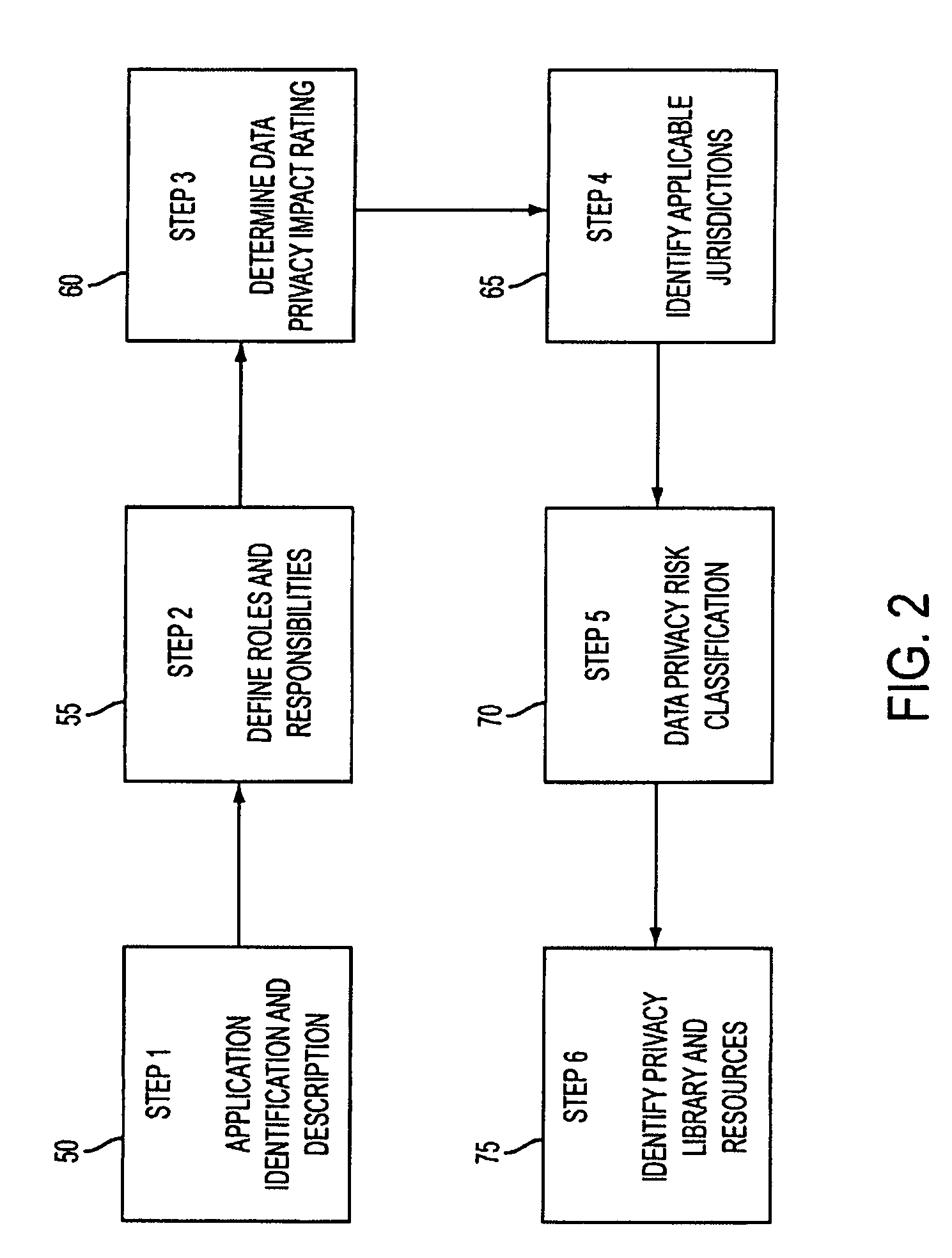
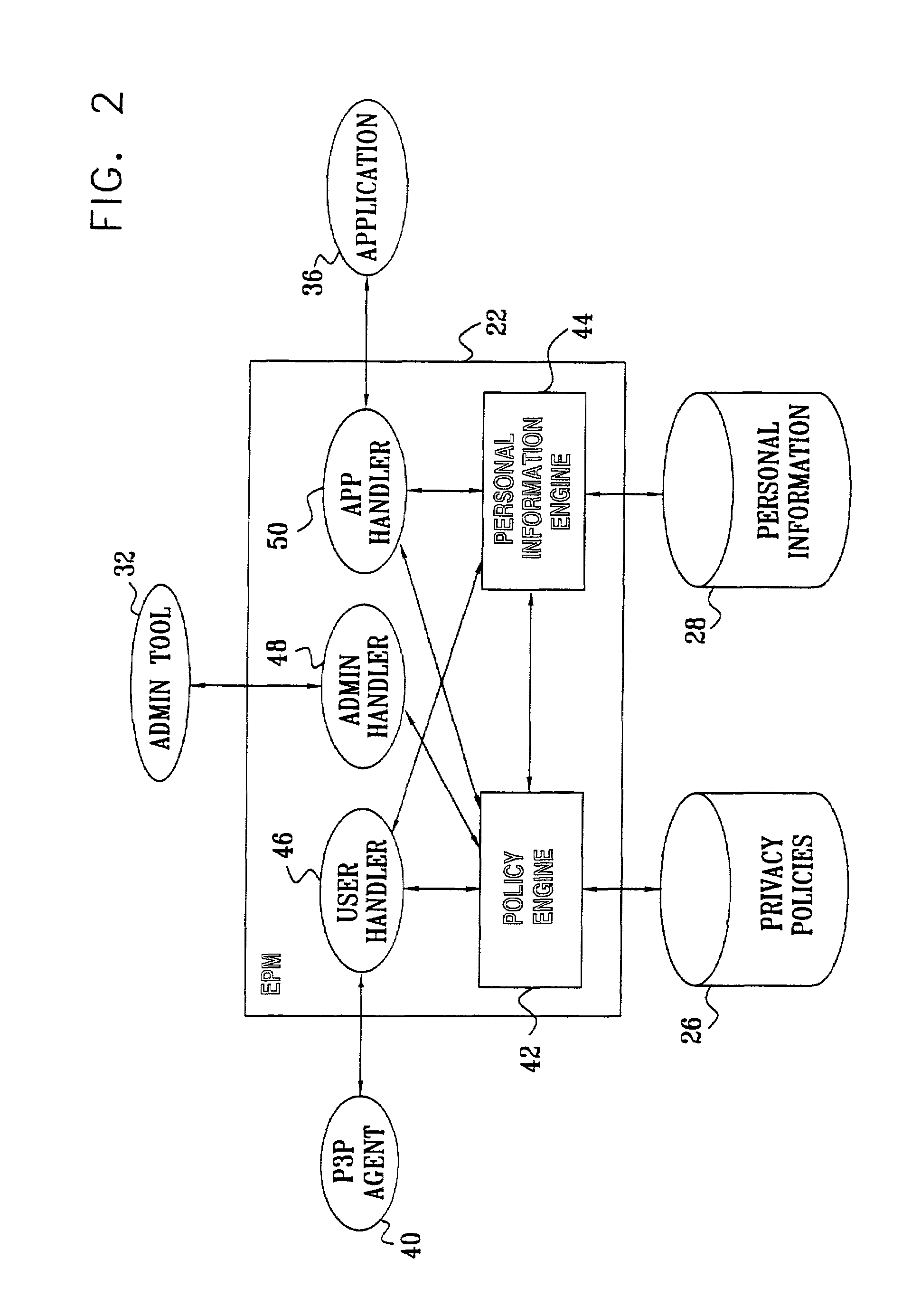
System and method for managing data privacy
ActiveUS7234065B2Easy to manageSpeed up the processUser identity/authority verificationUnauthorized memory use protectionInternet privacyKey issues
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
System and method for managing data privacy
InactiveUS20070283171A1Easy to manageSpeed up the processUnauthorized memory use protectionHardware monitoringInternet privacyKey issues
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
Internet privacy user interface
InactiveUS8166406B1Privacy protectionDigital computer detailsComputer security arrangementsWeb siteInternet privacy
Owner:MICROSOFT TECH LICENSING LLC
Personal information certification and management system
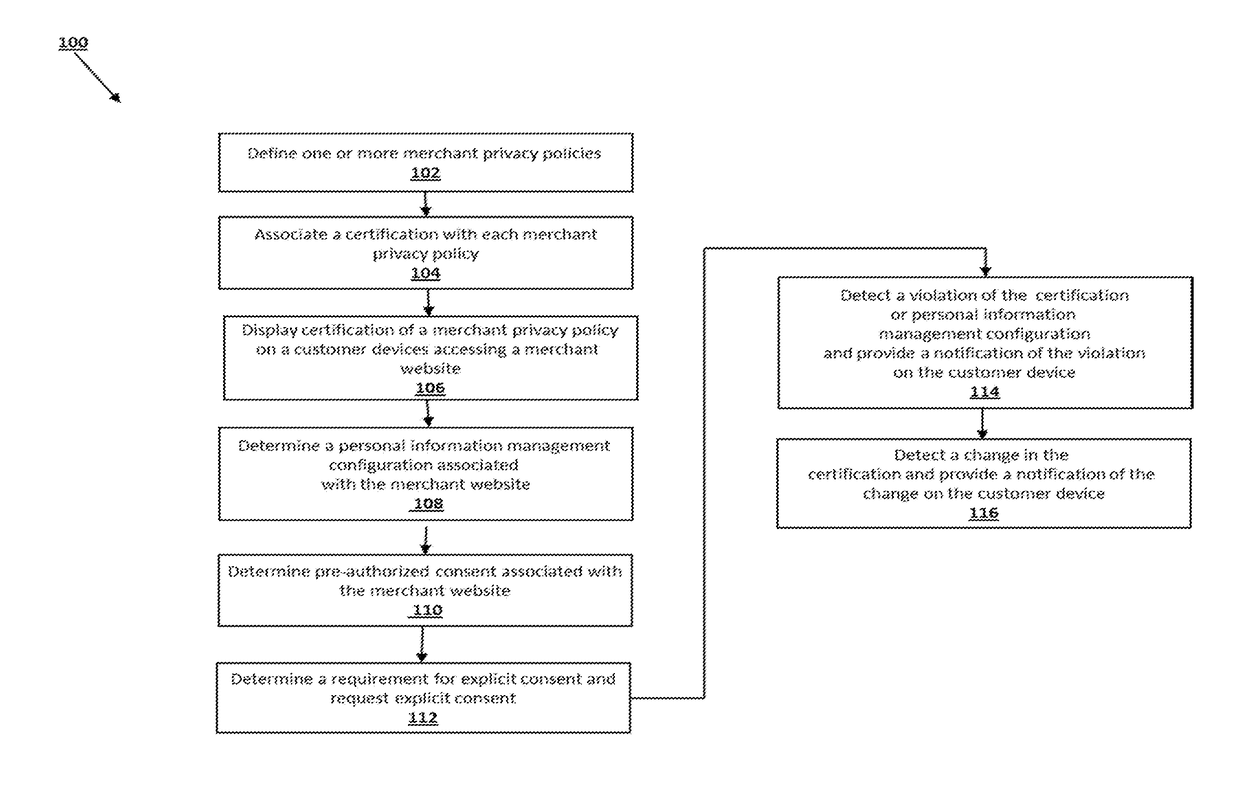
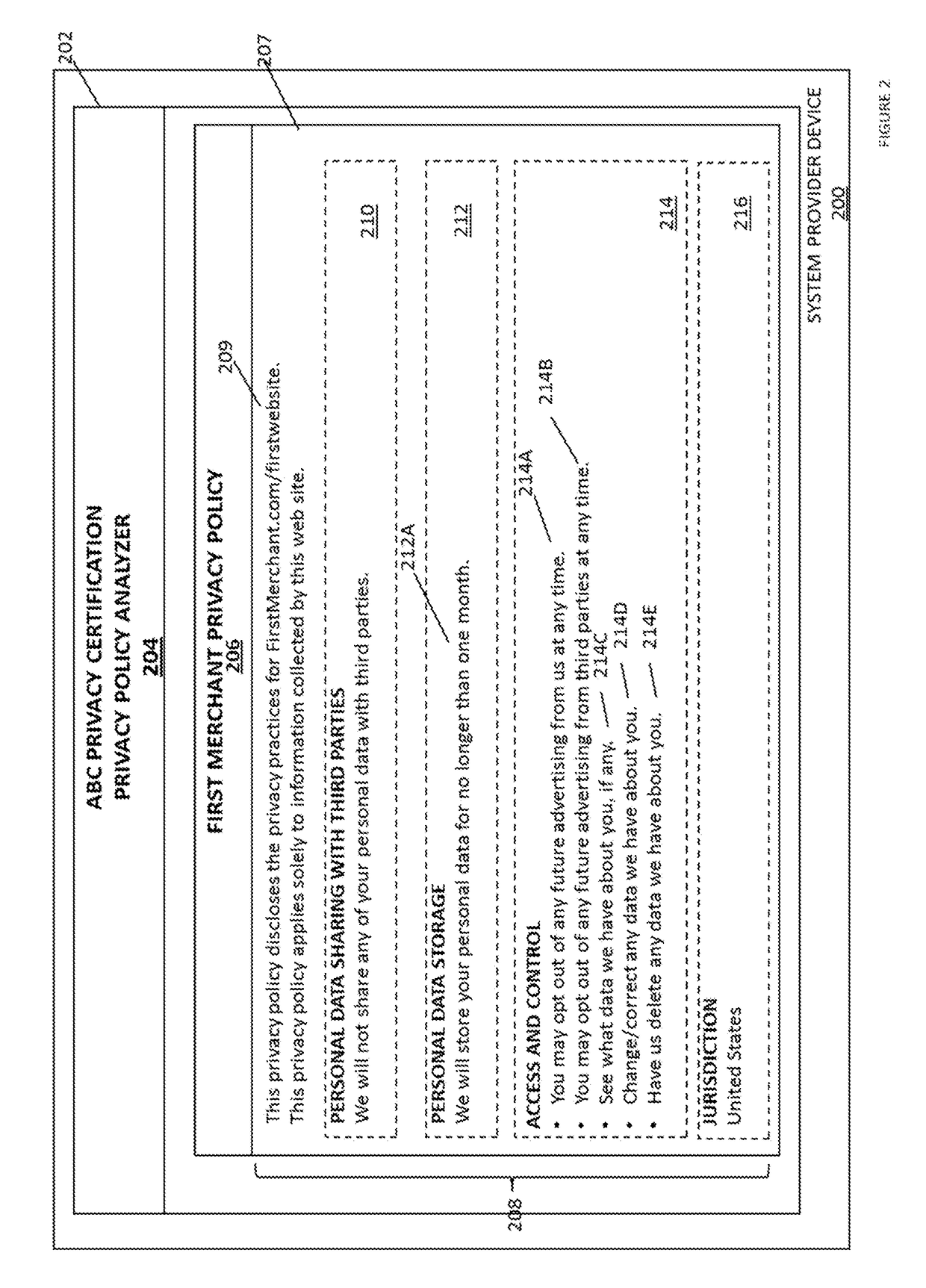
Systems and methods for providing personal information certification and management includes receiving, from a first device, a first privacy policy associated with a website, associating the first privacy policy with a first certification, and displaying, on a customer device in response to the determining that the customer device has accessed the website, the first certification. One or more pre-authorized consent configurations associated with the customer is retrieved, from a non-transitory memory. Pre-authorized consent associated with the website is determined according to the one or more pre-authorized consent configurations using the first certification. The pre-authorized consent is sent to the first device.
Owner:PAYPAL INC
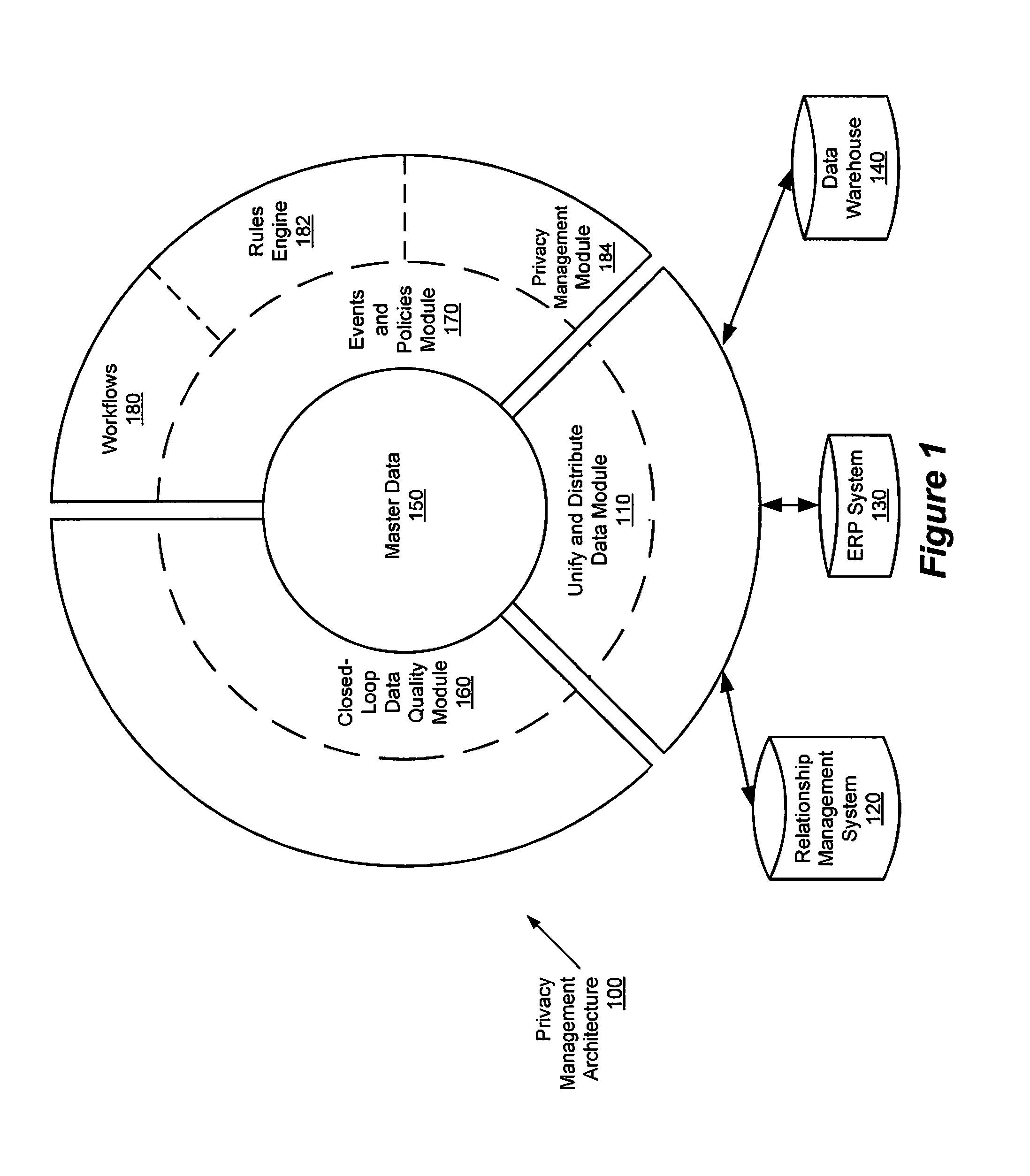
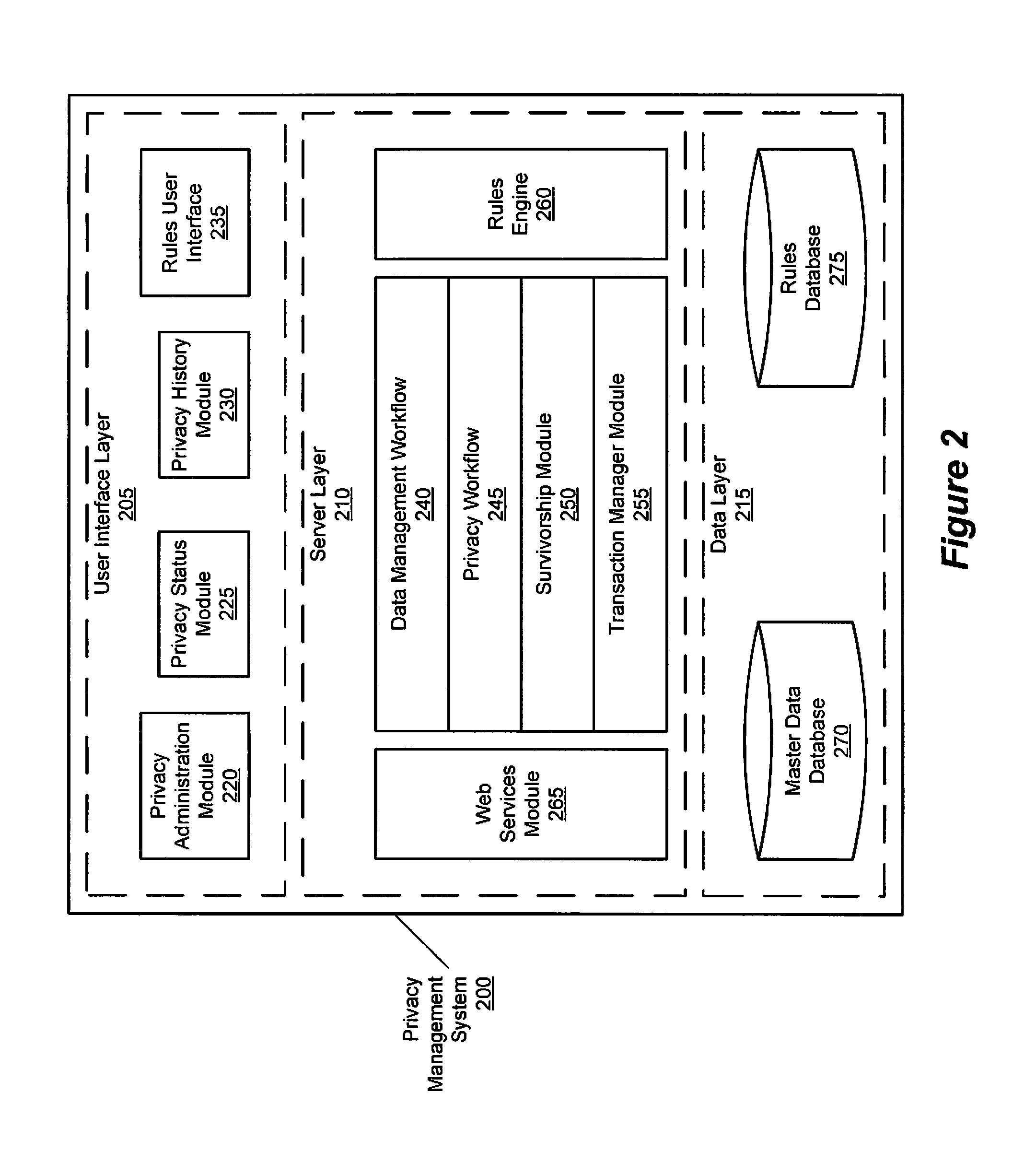
Privacy management policy hub
A system architecture is disclosed that includes a privacy management system. In particular, the privacy management system provides a policy hub for maintaining and managing customer privacy information. The privacy management system maintains a master data database for customer information and customer privacy preferences, and a rules database for privacy rules. The privacy management system captures, synchronizes, and stores customer privacy data. Privacy rules may be authored using a privacy management vocabulary, and can be customized for an enterprise's privacy policies.
Owner:ORACLE INT CORP
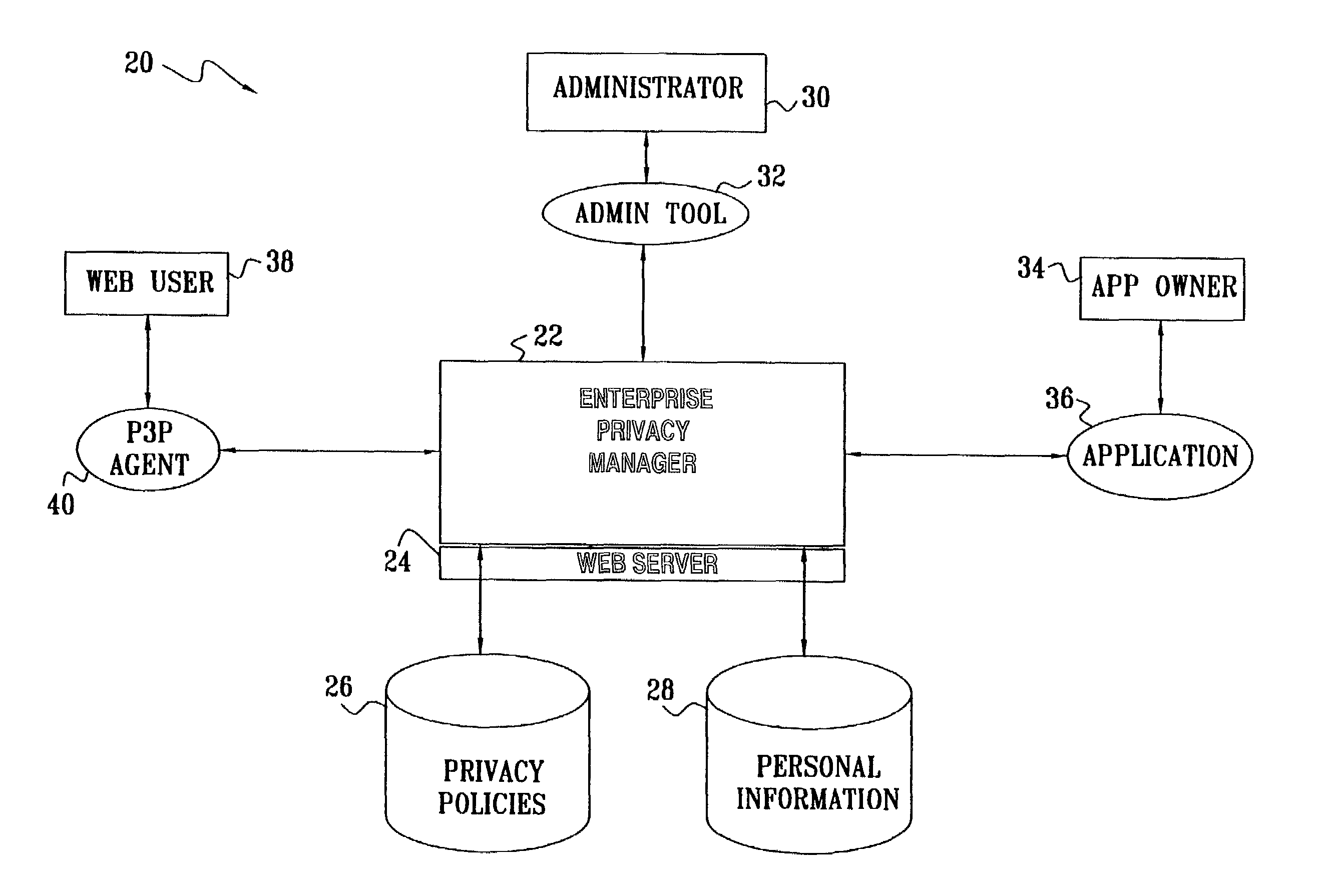
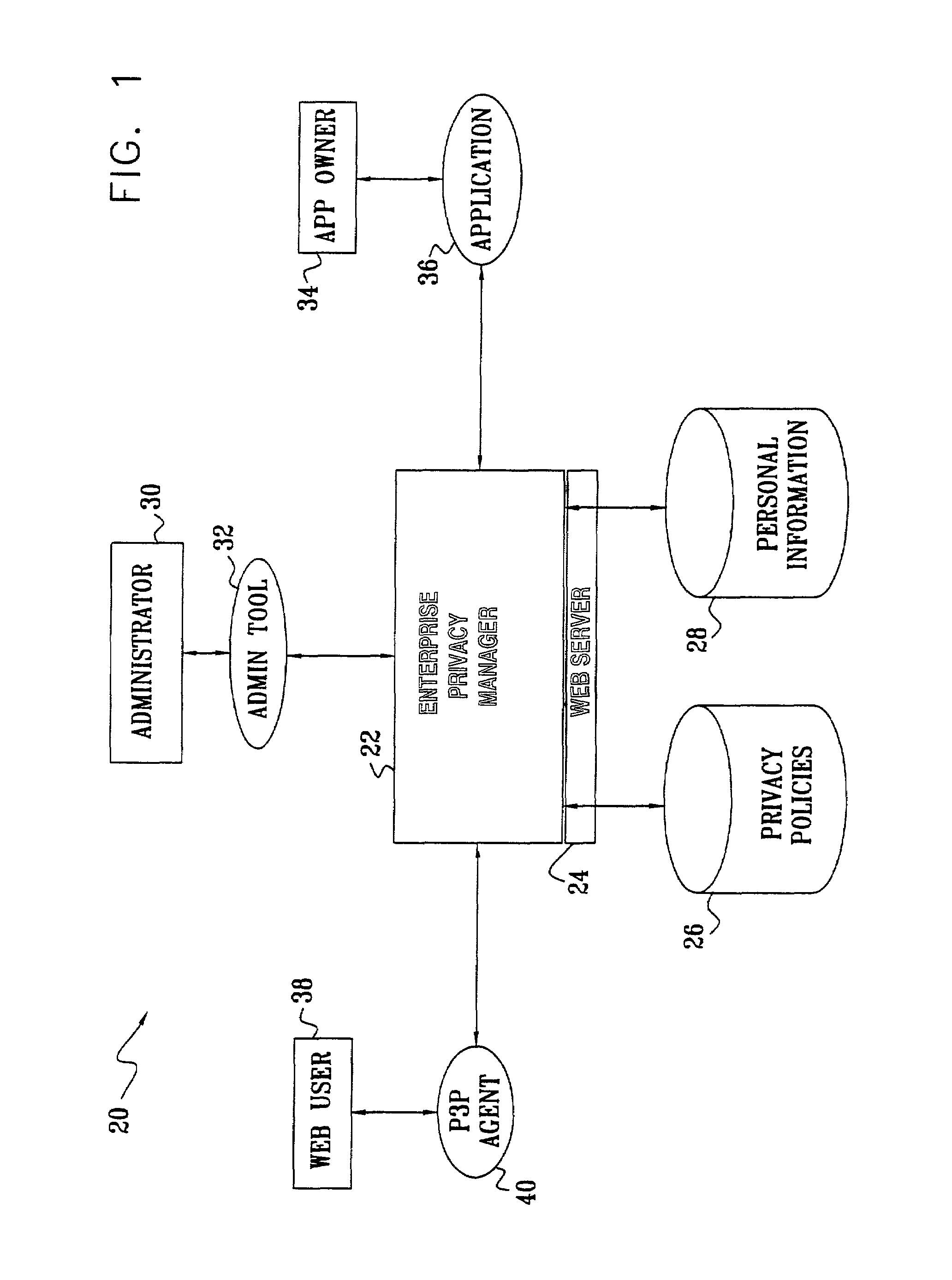
Enterprise privacy manager
InactiveUS7225460B2Remarkable effectEasy maintenanceUnauthorized memory use protectionComputer security arrangementsInternet privacyPrivacy policy
A method for privacy management includes providing a linked collection of interactive resources through which a user is able to exchange information with an enterprise that provides the resources, and assigning respective, non-uniform privacy policies to at least some of the resources regarding use of the information that is exchanged through the resources. The user, accessing a given one of the resources, is provided with the respective privacy policy for that resource. At least a portion of the information that is associated with the given one of the resources is exchanged with the user subject to the provided privacy policy.
Owner:IBM CORP
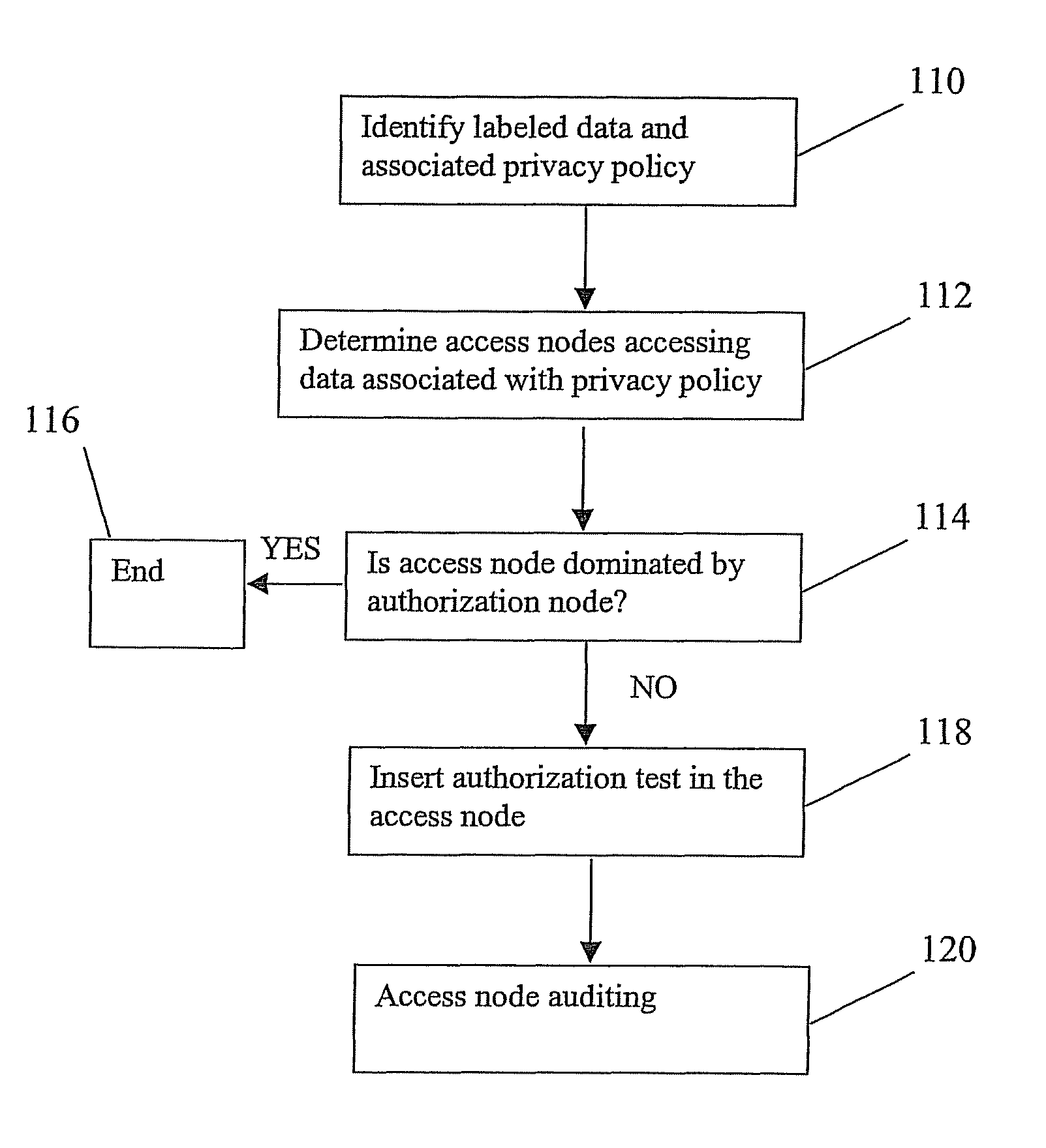
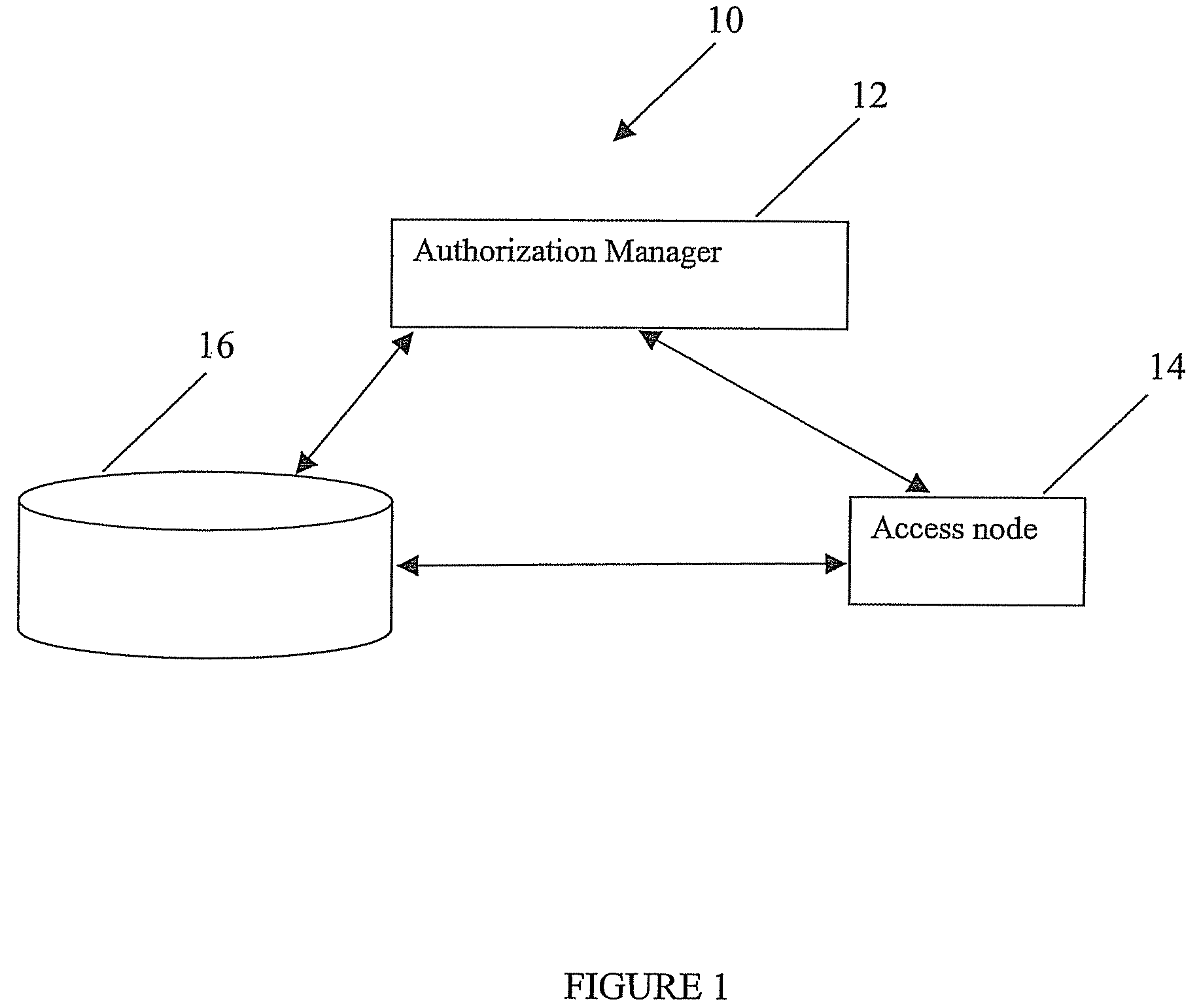
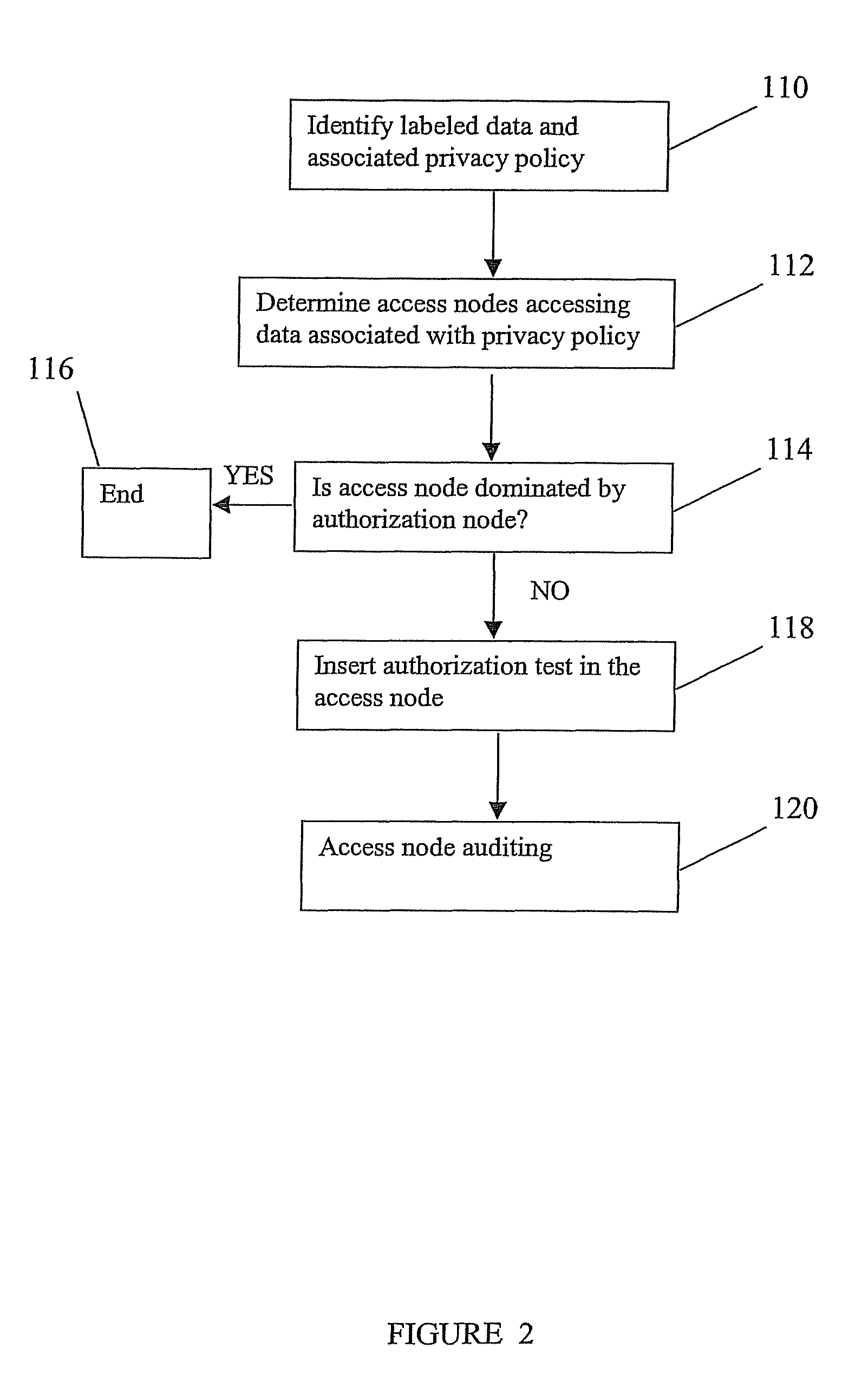
Method, system and computer program product for enforcing privacy policies
InactiveUS7877812B2Memory loss protectionDigital data processing detailsInternet privacyLabeled data
A method for enforcing privacy policies associated with data. The method includes accessing a database to identify labeled data in the database, the labeled data associated with a privacy policy. An access node accessing the label data is determined. For the access node accessing the labeled data, it is determined whether the access node applies an authorization test as indicated by the privacy policy. An authorization test is associated with the access node if the access node does not apply necessary authorization indicated by the privacy policy.
Owner:INT BUSINESS MASCH CORP
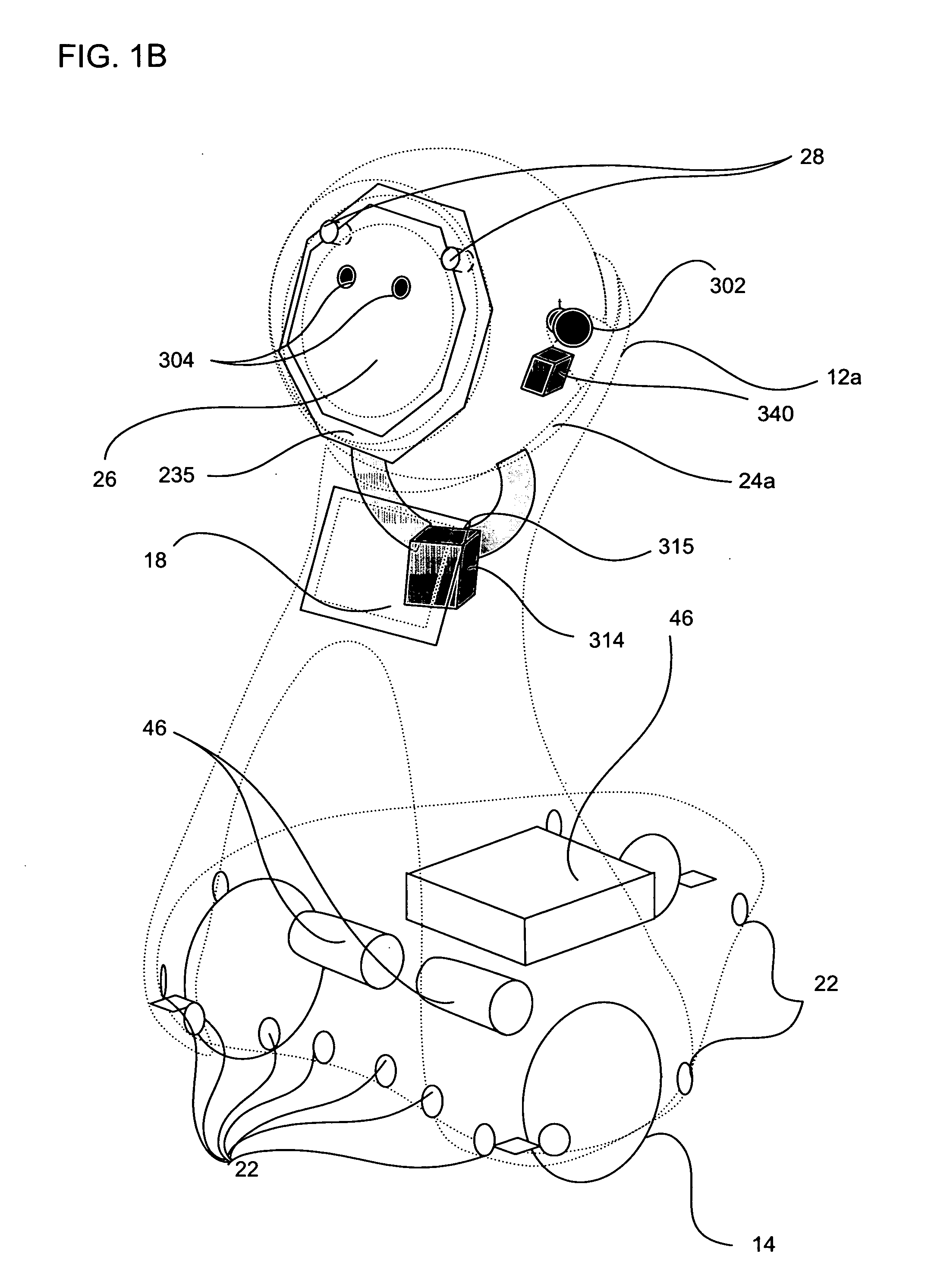
Companion robot for personal interaction
ActiveUS20070199108A1Enhanced presenceProgramme-controlled manipulatorLocal control/monitoringThird partyTeleconference
A mobile robot guest for interacting with a human resident performs a room-traversing search procedure prior to interacting with the resident, and may verbally query whether the resident being sought is present. Upon finding the resident, the mobile robot may facilitate a teleconferencing session with a remote third party, or interact with the resident in a number of ways. For example, the robot may carry on a dialogue with the resident, reinforce compliance with medication or other schedules, etc. In addition, the robot incorporates safety features for preventing collisions with the resident; and the robot may audibly announce and / or visibly indicate its presence in order to avoid becoming a dangerous obstacle. Furthermore, the mobile robot behaves in accordance with an integral privacy policy, such that any sensor recording or transmission must be approved by the resident.
Owner:IROBOT CORP
Companion robot for personal interaction
ActiveUS20090177323A1Enhanced presenceProgramme-controlled manipulatorDrug and medicationsThird partyRoomba
A mobile robot guest for interacting with a human resident performs a room-traversing search procedure prior to interacting with the resident, and may verbally query whether the resident being sought is present. Upon finding the resident, the mobile robot may facilitate a teleconferencing session with a remote third party, or interact with the resident in a number of ways. For example, the robot may carry on a dialogue with the resident, reinforce compliance with medication or other schedules, etc. In addition, the robot incorporates safety features for preventing collisions with the resident; and the robot may audibly announce and / or visibly indicate its presence in order to avoid becoming a dangerous obstacle. Furthermore, the mobile robot behaves in accordance with an integral privacy policy, such that any sensor recording or transmission must be approved by the resident.
Owner:AVA ROBOTICS INC
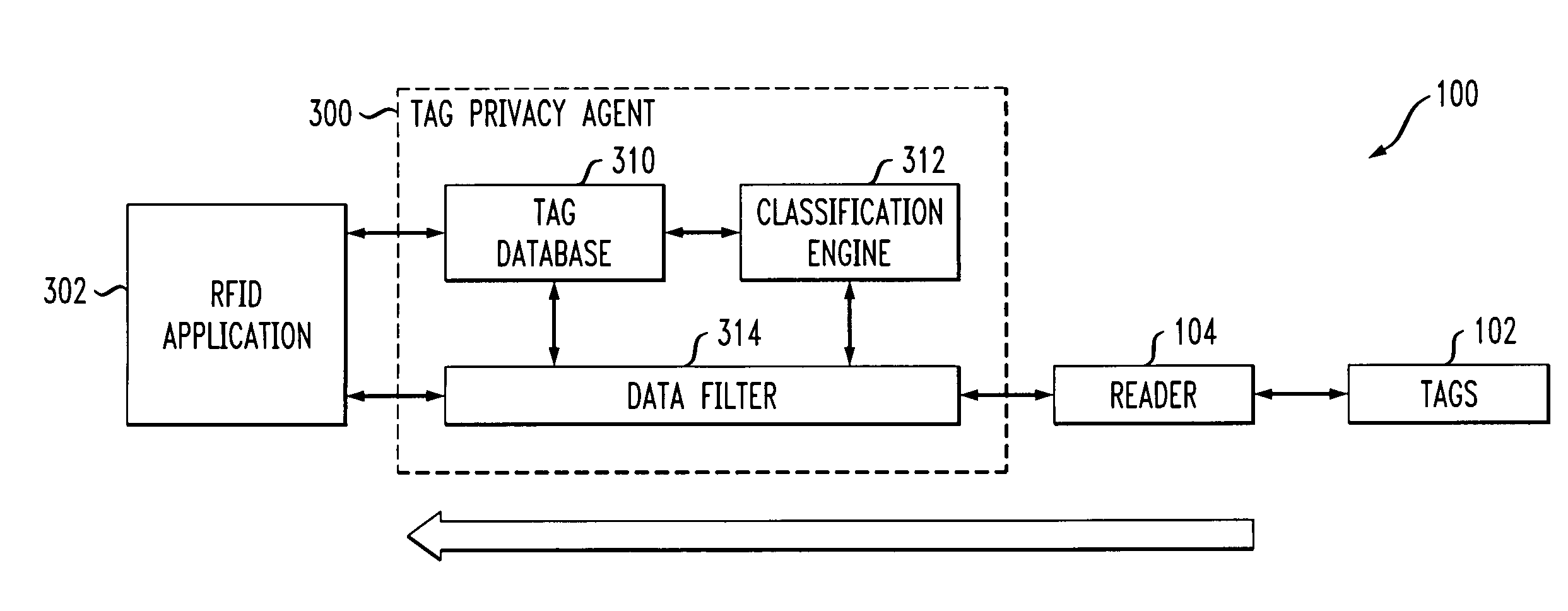
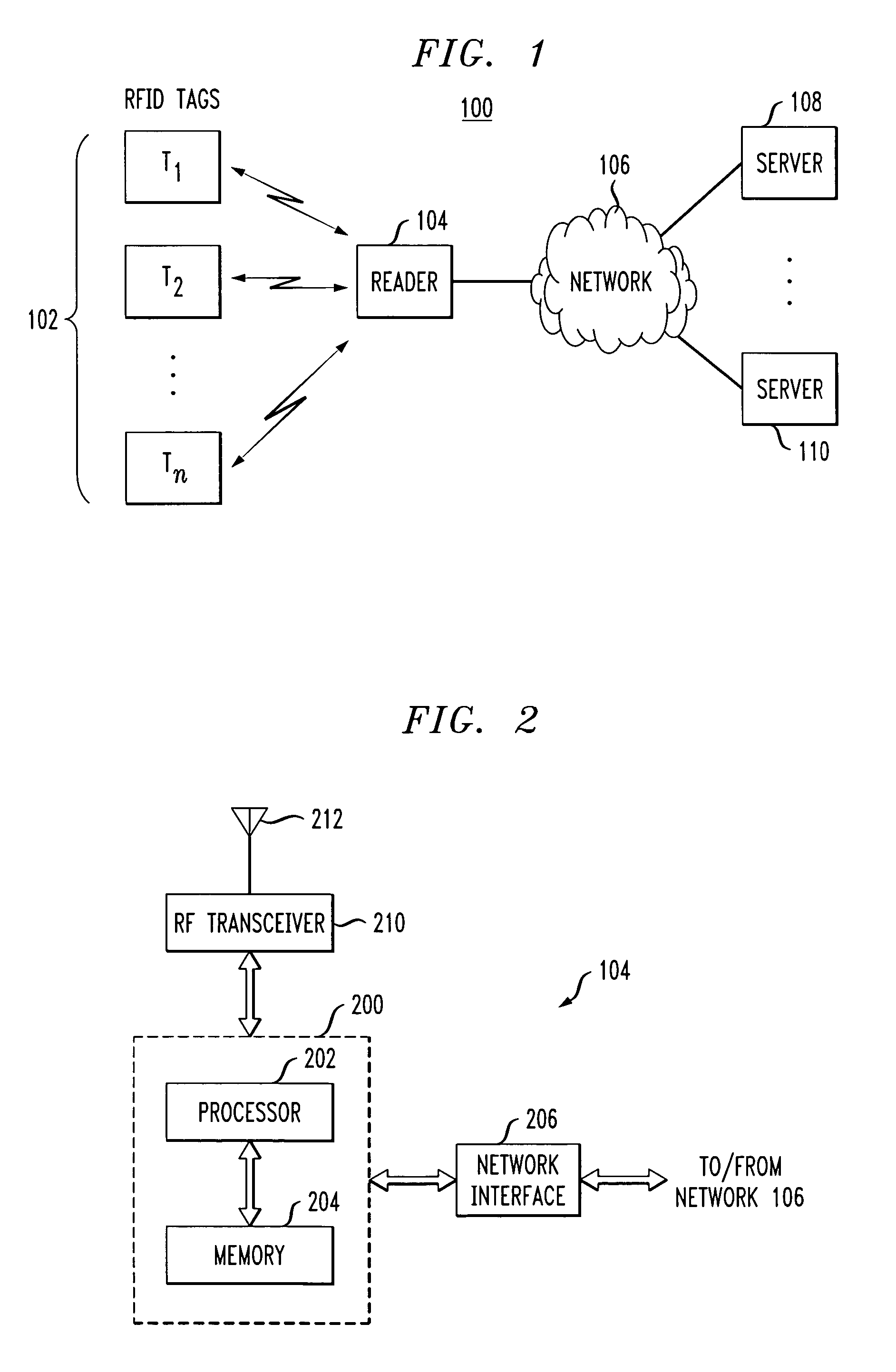
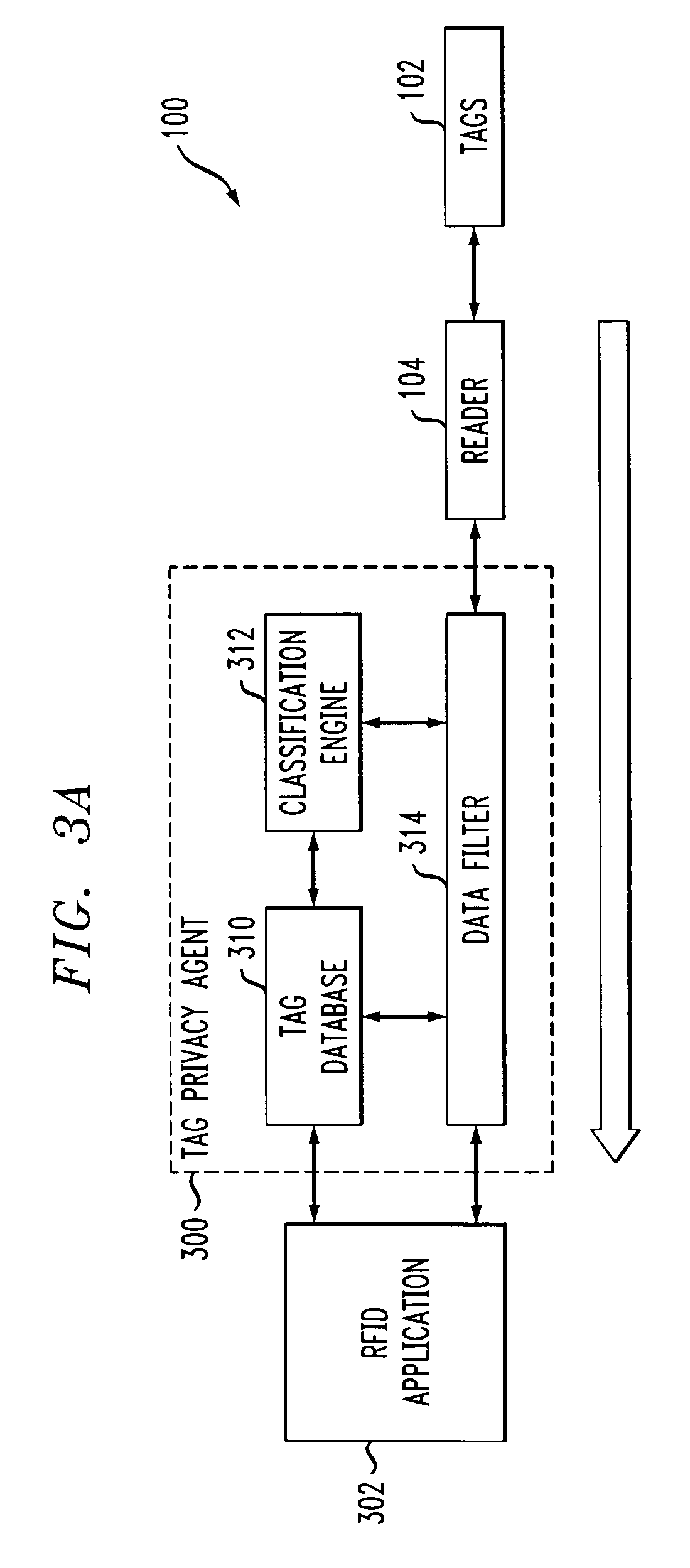
Radio frequency identification system with privacy policy implementation based on device classification
ActiveUS7298243B2Good flexibilityMemory record carrier reading problemsSubscribers indirect connectionClassification methodsComputer science
Methods and apparatus are disclosed for use in an RFID system comprising a plurality of RFID devices and at least one reader which communicates with one or more of the devices. In accordance with an aspect of the invention, identifiers transmitted by the RFID devices are received by the reader. The system determines a classification of at least one of the received identifiers, and implements a privacy policy for data associated with one or more of the received identifiers based at least in part on the determined classification. For example, the given RFID device may be configurable into at least a first state indicative of a first classification, such as a private classification, and a second state indicative of a second classification, such as a public classification. The reader may alter a type of query that it issues based at least in part on the determined classification. Alternatively or additionally, response by the given RFID device to a query received from the reader may be conditioned on the state of the RFID device. The reader may be configured, dynamically or otherwise, so as to issue queries causing such selective responses by the RFID devices.
Owner:EMC IP HLDG CO LLC
Companion robot for personal interaction
ActiveUS20070198128A1Enhanced presenceProgramme-controlled manipulatorLocal control/monitoringThird partyTeleconference
A mobile robot guest for interacting with a human resident performs a room-traversing search procedure prior to interacting with the resident, and may verbally query whether the resident being sought is present. Upon finding the resident, the mobile robot may facilitate a teleconferencing session with a remote third party, or interact with the resident in a number of ways. For example, the robot may carry on a dialogue with the resident, reinforce compliance with medication or other schedules, etc. In addition, the robot incorporates safety features for preventing collisions with the resident; and the robot may audibly announce and / or visibly indicate its presence in order to avoid becoming a dangerous obstacle. Furthermore, the mobile robot behaves in accordance with an integral privacy policy, such that any sensor recording or transmission must be approved by the resident.
Owner:AVA ROBOTICS INC
Sharing management system, sharing management method and program
In a policy-change input unit (10), a policy recalculation unit (133) compares, upon occurring of a change request of a privacy policy from a user, an existing policy against an updating policy, recalculates a transmission policy to be transmitted to other providers based on the result of comparison, and transmits the recalculated policy to the other policy. The policy recalculation unit (133) transmits a deletion request of personal information to another provider by using a deletion-request creation unit, upon judging that the another provider cannot use the personal information due to the change of privacy policy.
Owner:NEC CORP
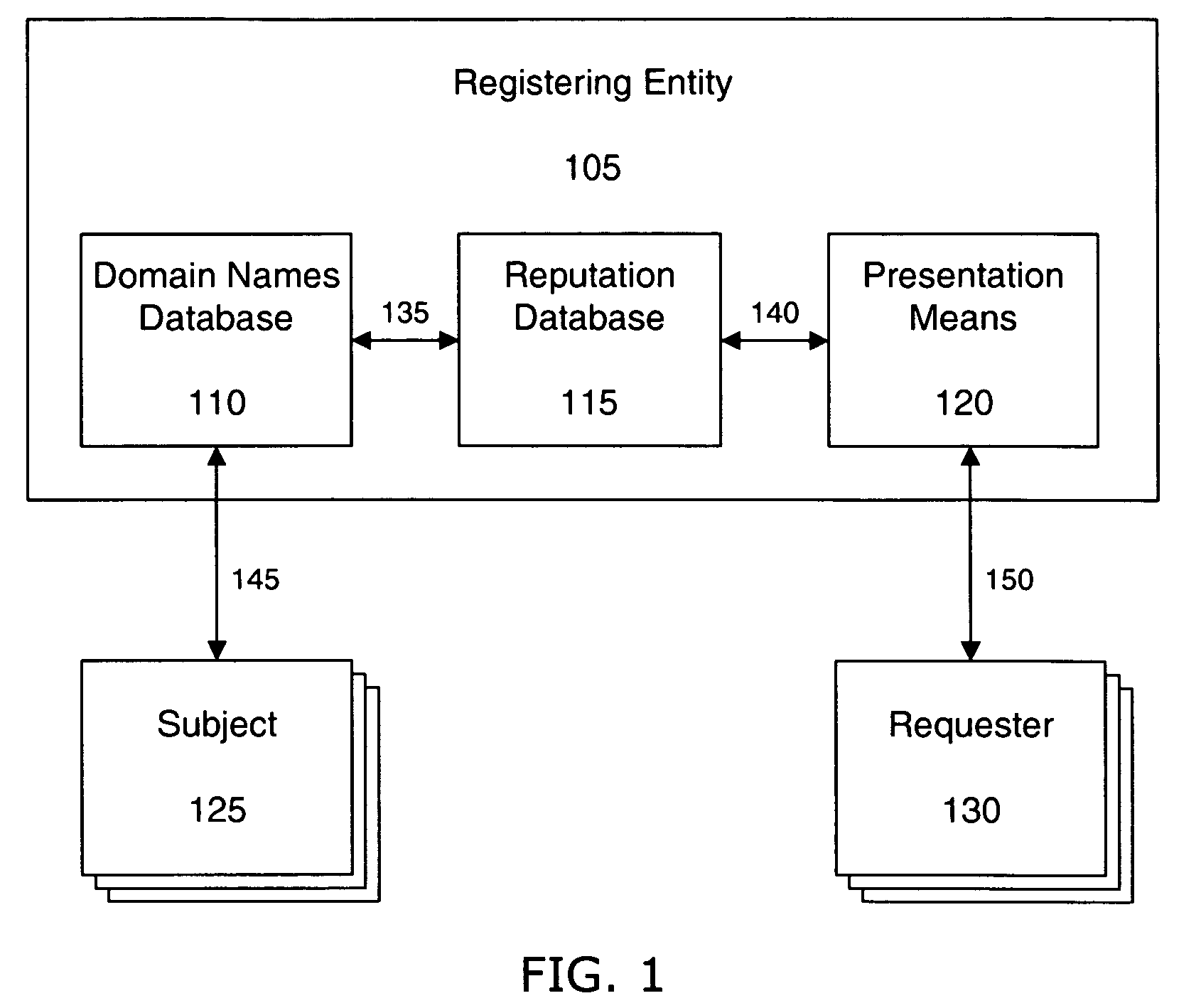
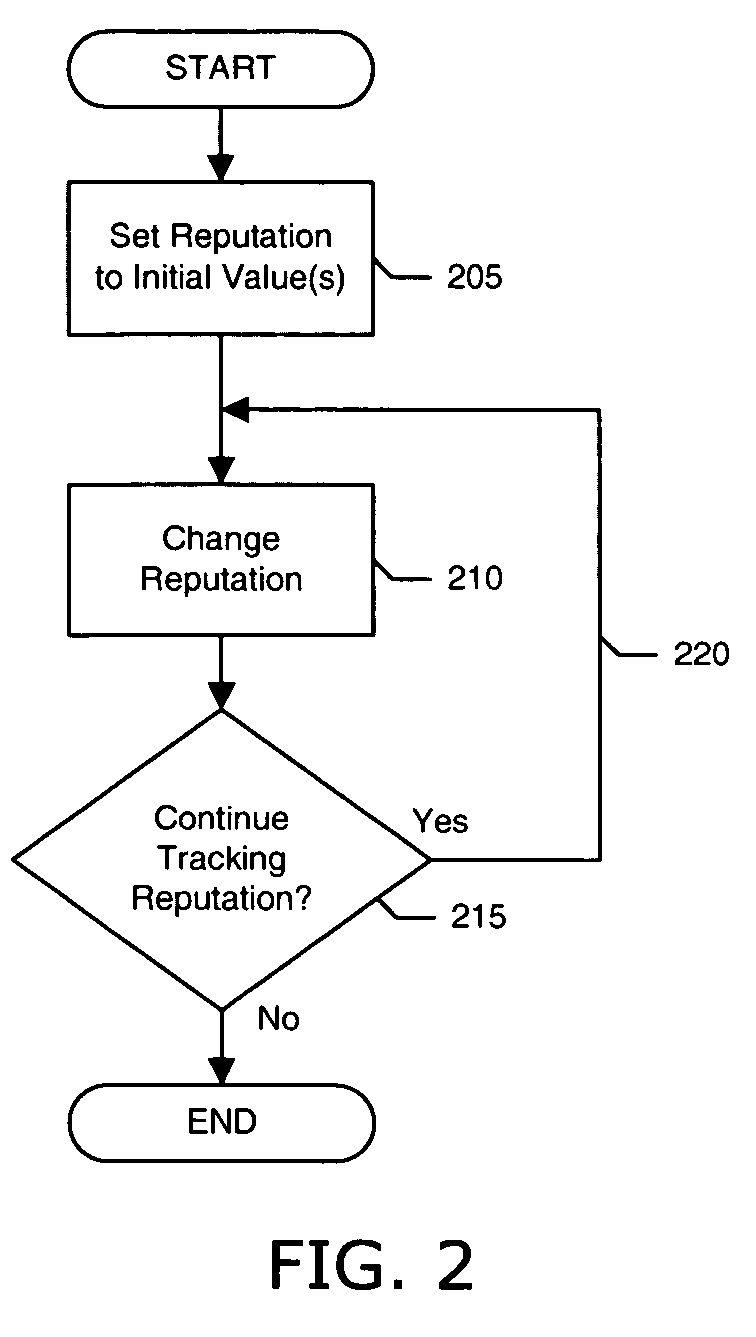
Presenting search engine results based on domain name related reputation
InactiveUS20060095404A1Effective trackingCombating various Internet abusesDigital data information retrievalSpecial data processing applicationsDomain nameWeb site
The invention describes a method for presenting search engine results based on domain name related reputation data. The search engine may sort or order search engine results based on domain name related reputation data. In some cases links connected to low reputation domain names may be excluded from search engine results. Alternatively, the search engine may show reputation ratings next to the links in the search engine results. Thus, allowing the Internet user to determine whether to visit the link or not. The reputation data may be tracked on the domain name itself, URLs, domain name purchaser or registrant, or email addresses associated with the domain name. The reputation data may include various categories, such as email practices, website content, privacy policies and practices, fraudulent activities, domain name related complaints, overall reputation, etc.
Owner:GO DADDY OPERATING
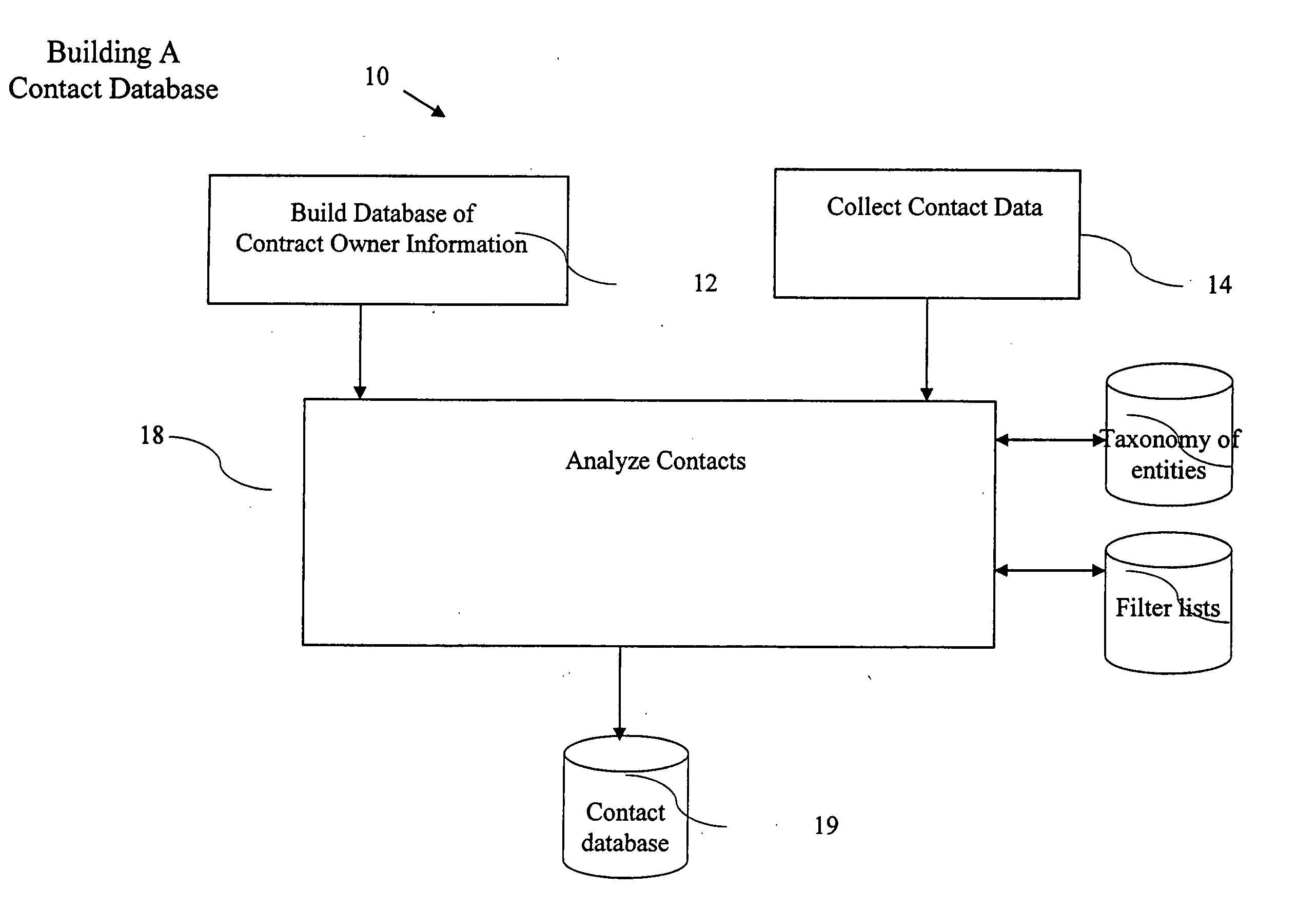
Relationship collaboration system
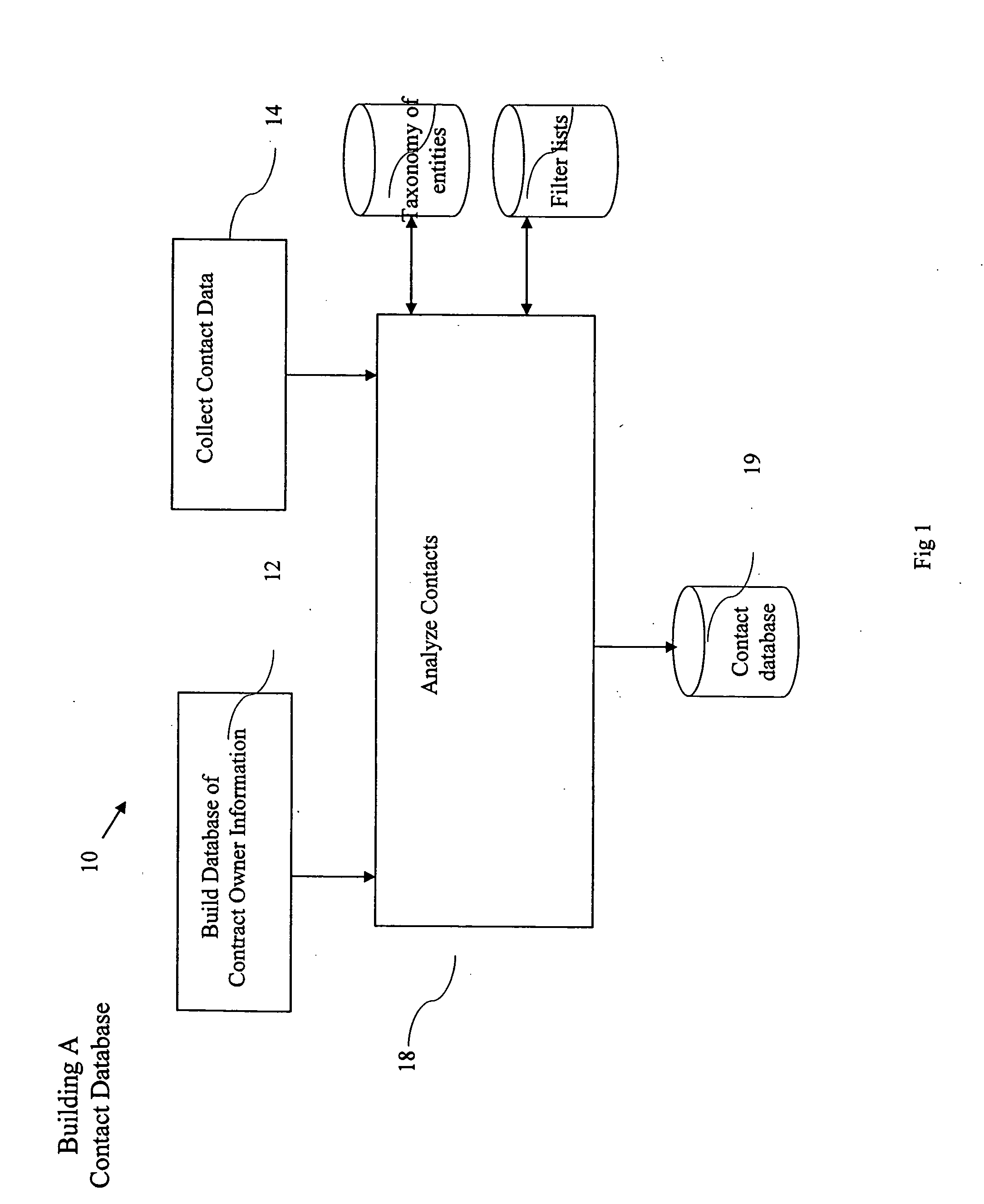
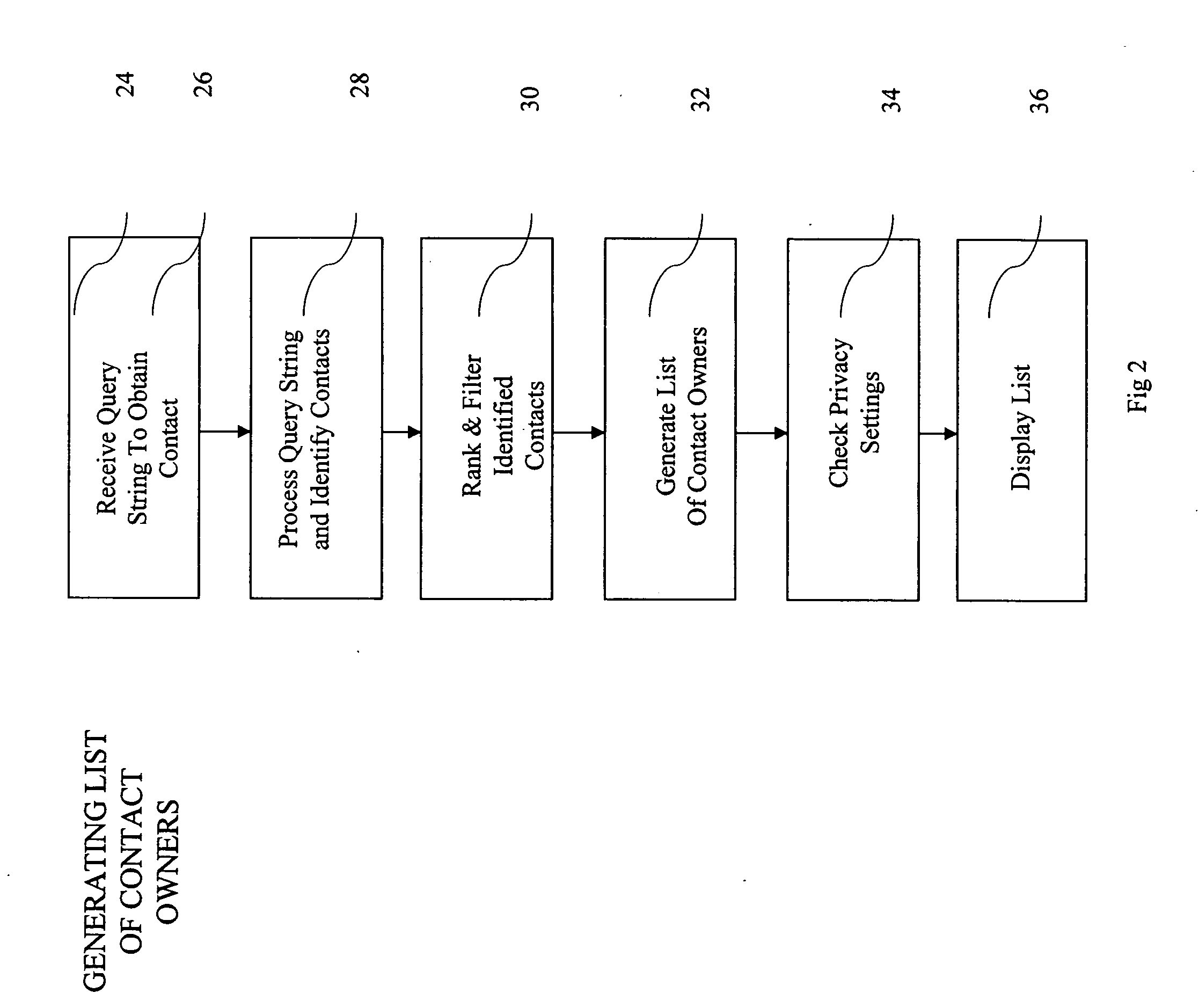
ActiveUS20050065980A1Improve identityData processing applicationsWeb data indexingDomain nameEmail address
A computer implemented method of processing data containing information about relationships between contacts and a community of contact owners, comprises: collecting data including contact information, contact owner information and one or more values related to strength of a relationship between the contact and the contact owner; evaluating the strength of the relationship based on the one or more values; and storing the collected data and evaluated strength in a computer database. A method of keying a database, comprises: building a database of records, each containing information about an entity, and each of which include a domain name field; and setting the domain name field as a key field; whereby a record for an entity is found by reference to a domain name. A method of keying a database, comprises: building a database of records, each containing information about an entity, and each of which include an email address field; and setting the email address field as a key field; whereby a record for an entity is found by reference to an email address. A method of keying a database, comprising: building a database of records, each containing information about an entity, and each of which includes a field holding an identifier uniquely associated with an entity by a convention of computer networking; and setting the field holding the identifier as a key field; whereby a record for an entity is found by reference to an identifier. A method of sharing relationship information, comprising: maintaining a database of relationship information records; selecting contact information according to a selection criterion; and returning selected relationship information also complying with restrictions set in a set of hierarchical privacy policies.
Owner:THOMSON REUTERS ENTERPRISE CENT GMBH
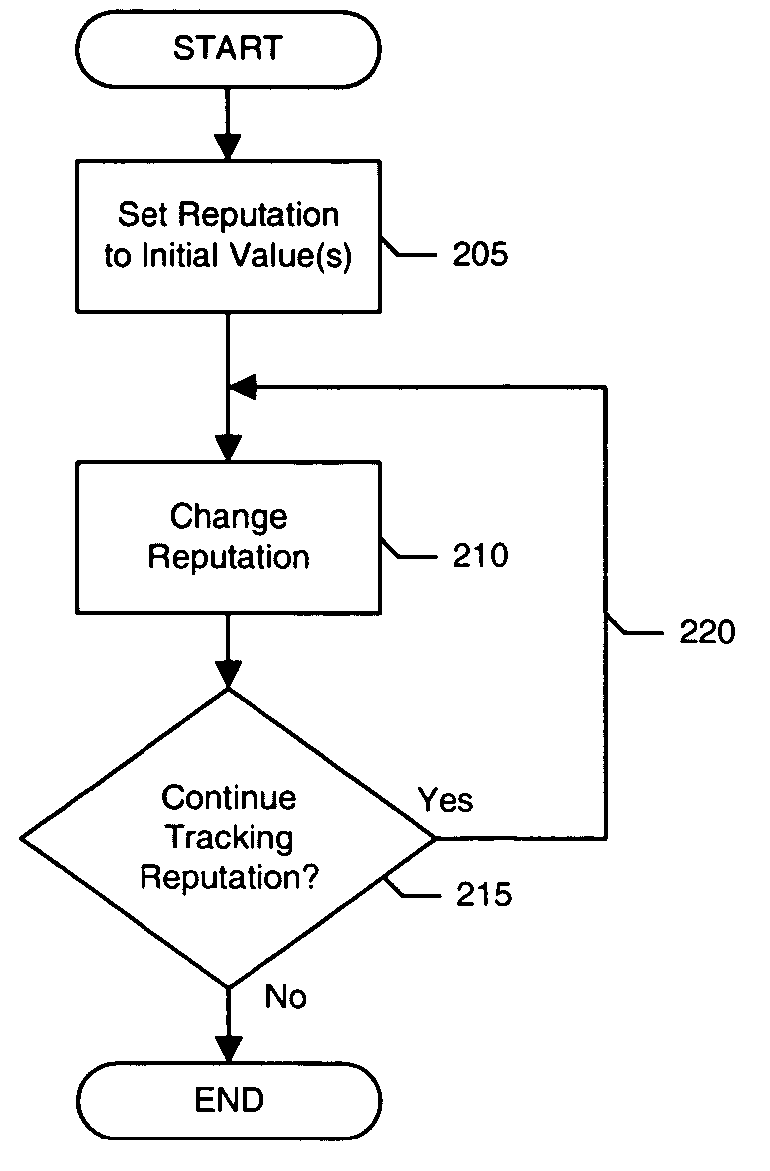
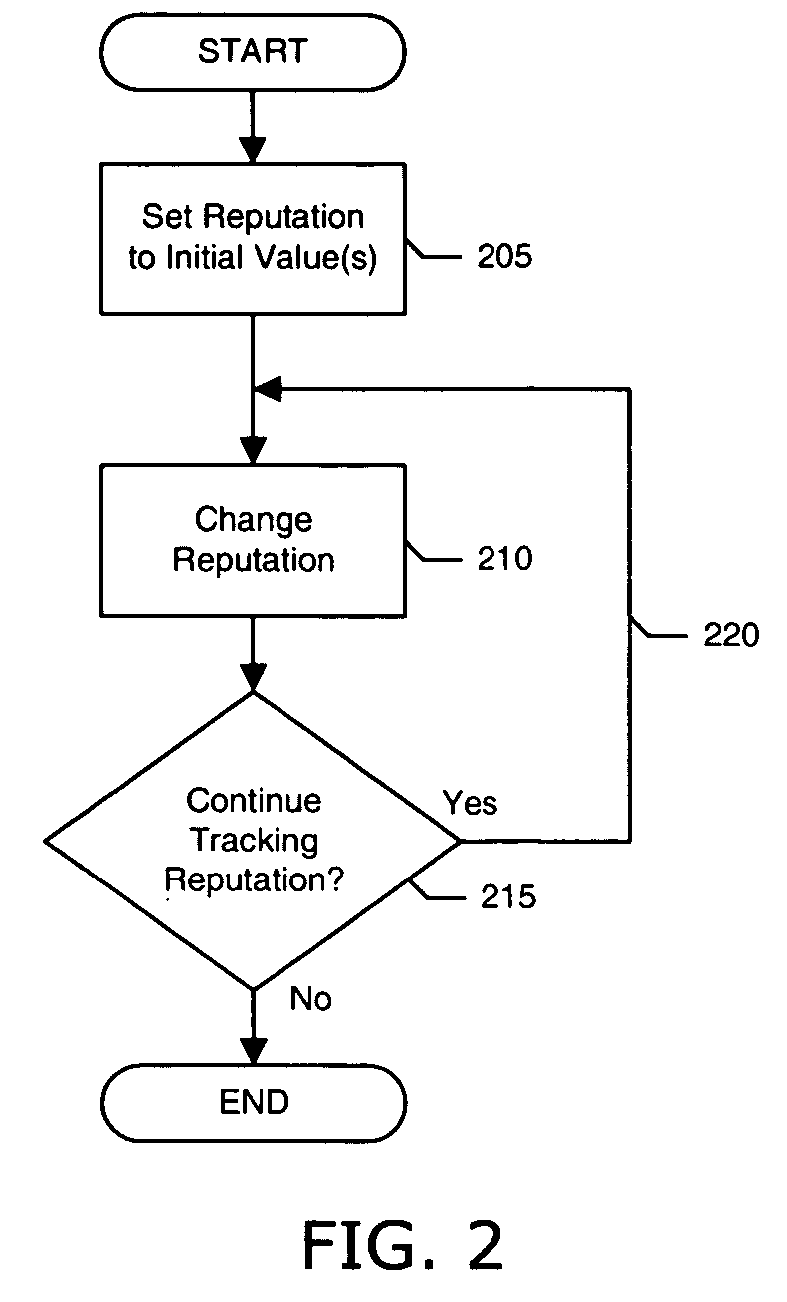
Tracking domain name related reputation
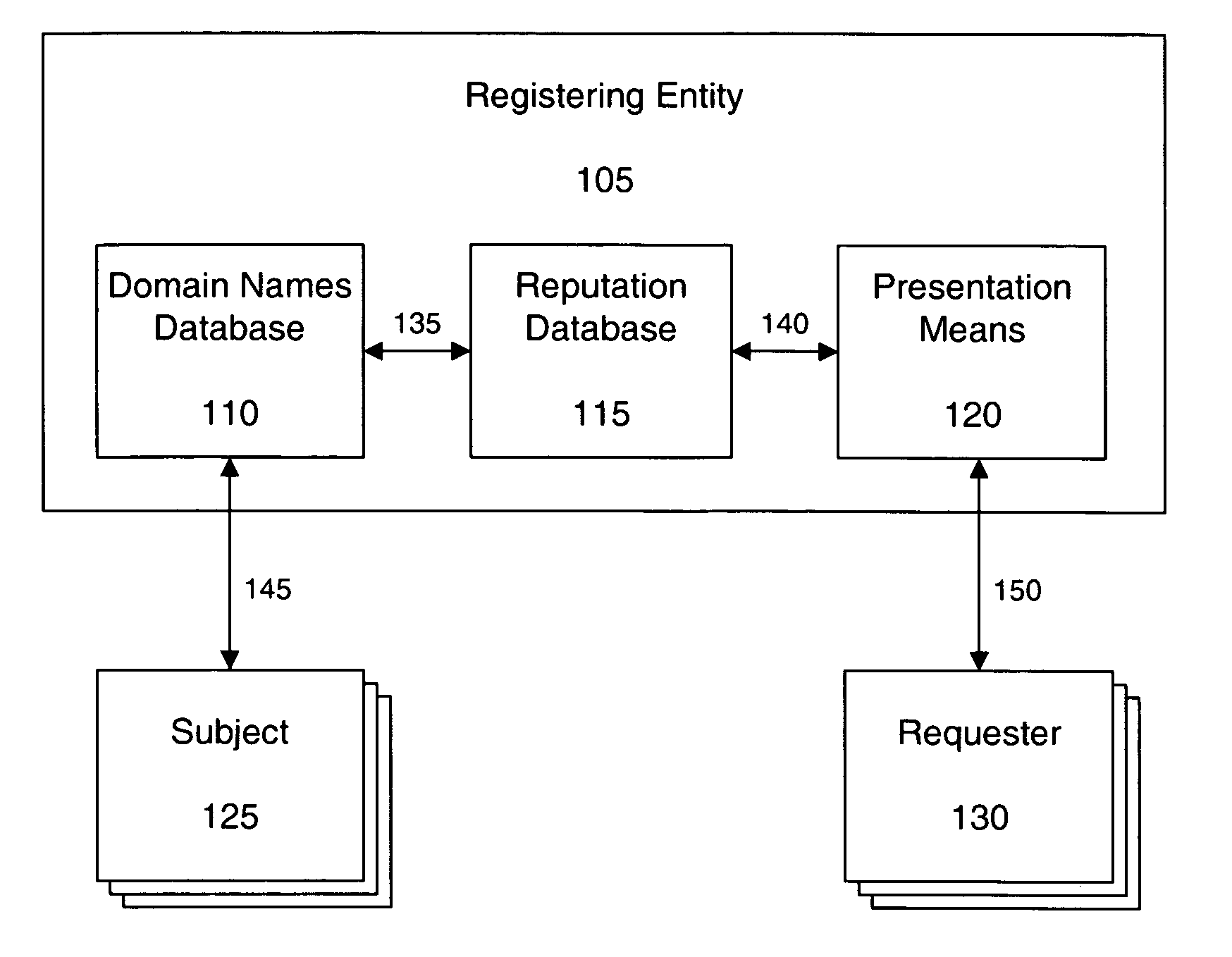
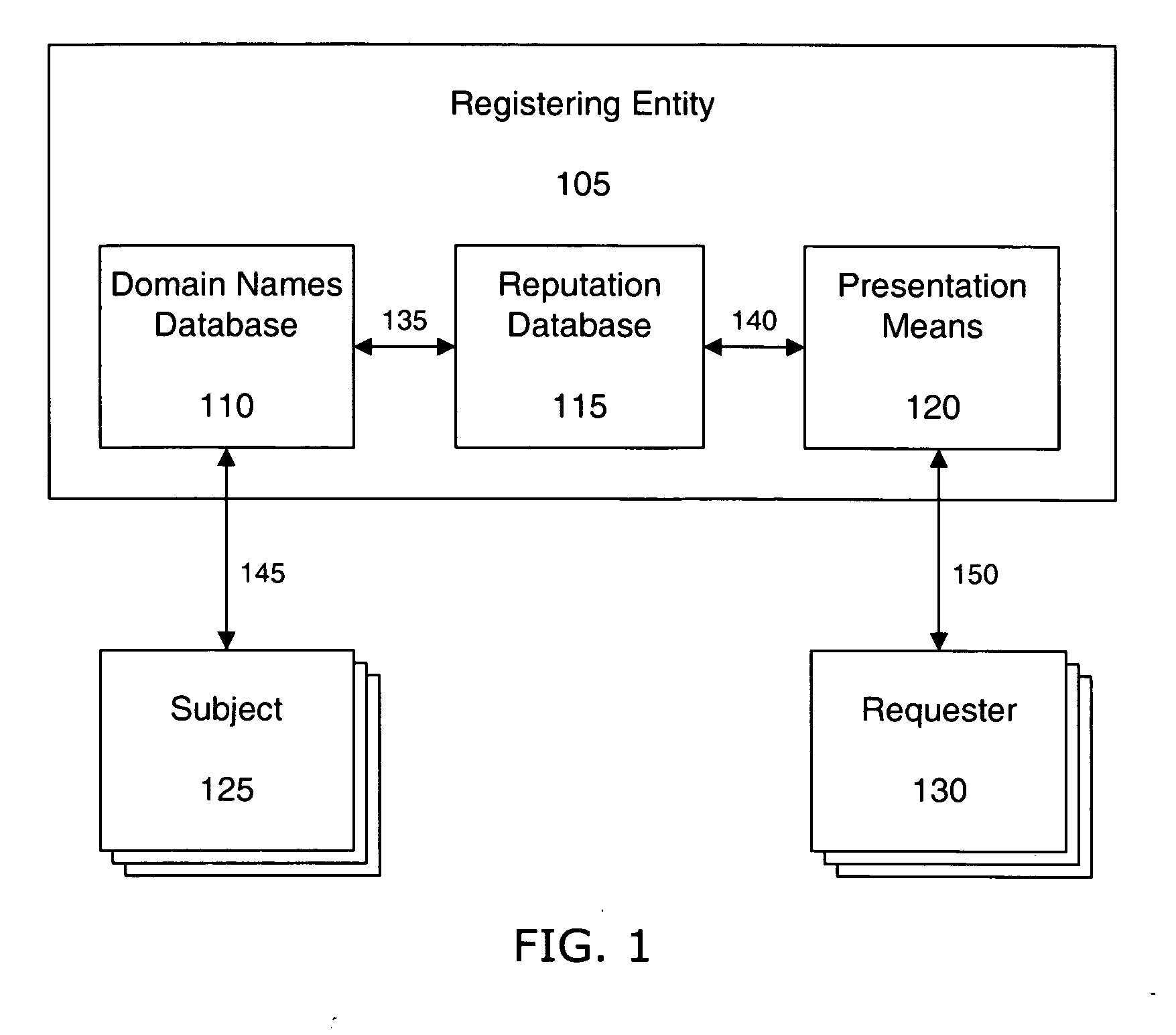
ActiveUS20060095586A1Effective trackingCombating various Internet abusesMultiple digital computer combinationsElectric digital data processingDomain nameWeb site
Systems and methods of the present invention allow for tracking of domain name related reputation by a domain name Registering Entity (e.g. Registry, Registrar, etc.). In a preferred embodiment, the Registering Entity maintains a database with reputation data that can be accessed by the requesters. The Registering Entity may update reputation data based on a variety of events related to the domain name. The reputation data may be tracked on the domain name itself, URLs, domain name purchaser or registrant, or email addresses associated with the domain name. The reputation data may include various categories, such as email practices, website content, privacy policies and practices, fraudulent activities, domain name related complaints, overall reputation, etc. The registrant may opt for a reputation service while registering domain name. The requester may decide whether to allow email messages or to visit URLs based on the domain name related reputation.
Owner:GO DADDY OPERATING
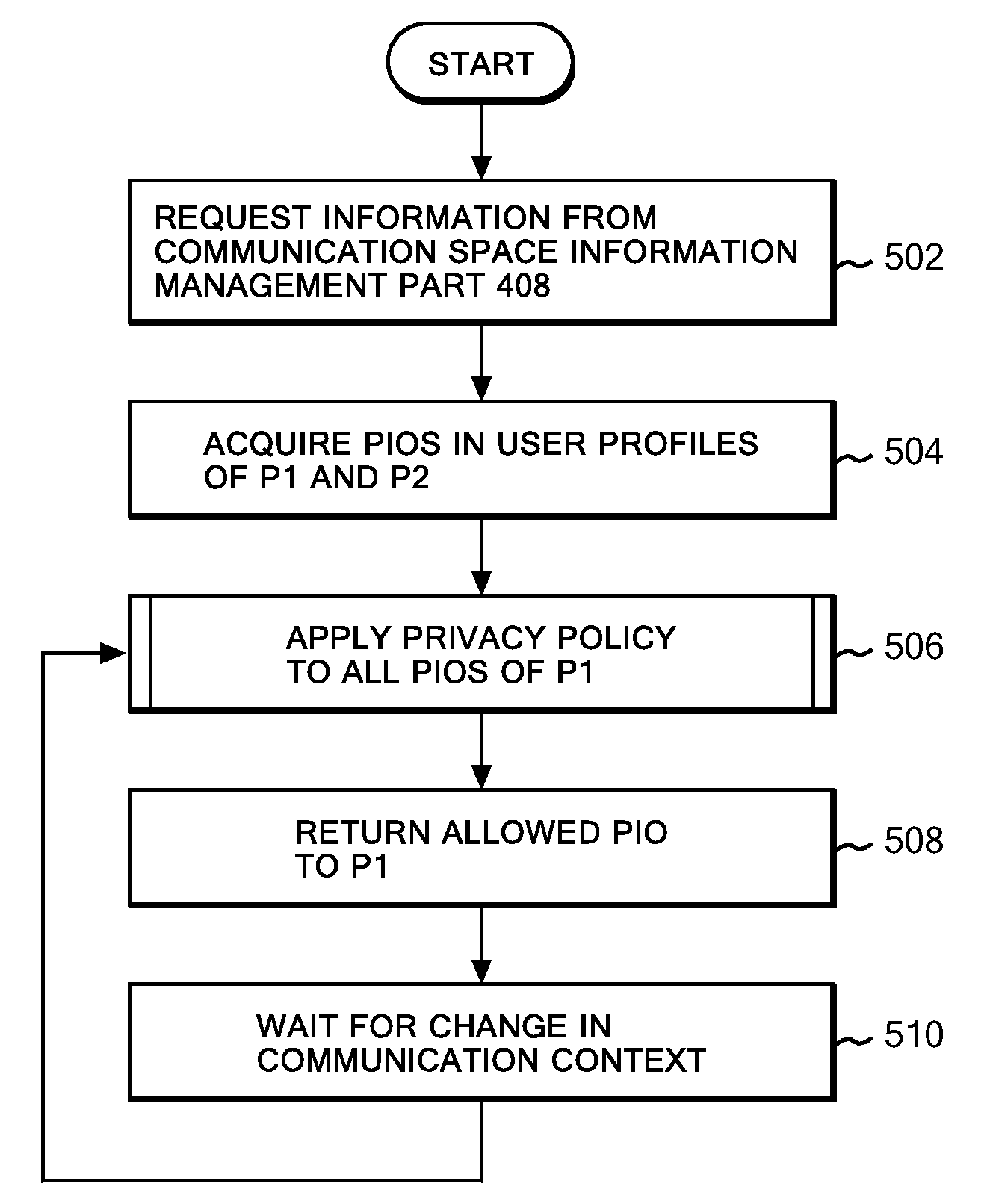
Privacy management system using user's policy and preference matching
By applying a privacy policy, which describes and manages a policy for disclosure of preference information, to the preference information, it is determined whether or not to disclose some or all of the information to a third party based on classification as a result of matching by a matching system. The description of a privacy policy makes it possible to achieve a meaningful communication by disclosing preference information to others within a detailed range while keeping the preference information undisclosed if the user does not wish disclosure thereof, such as disclosing only preference information including preferences matching those of the other user or disclosing only preference information including preferences shared in a certain user group.
Owner:IBM CORP
Personal information control and processing
InactiveUS20050105719A1Key distribution for secure communicationMultiple keys/algorithms usageInformation controlInternet privacy
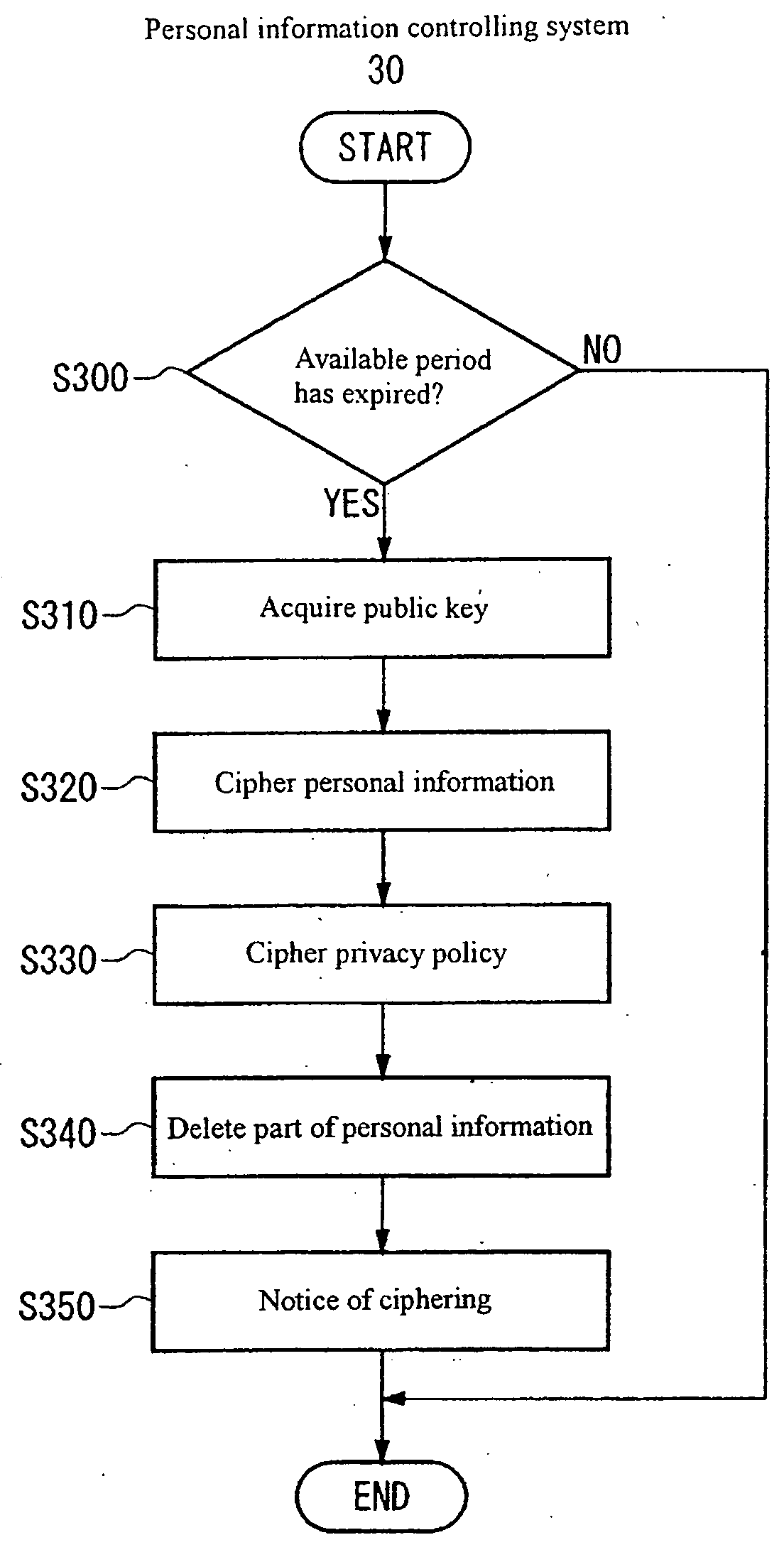
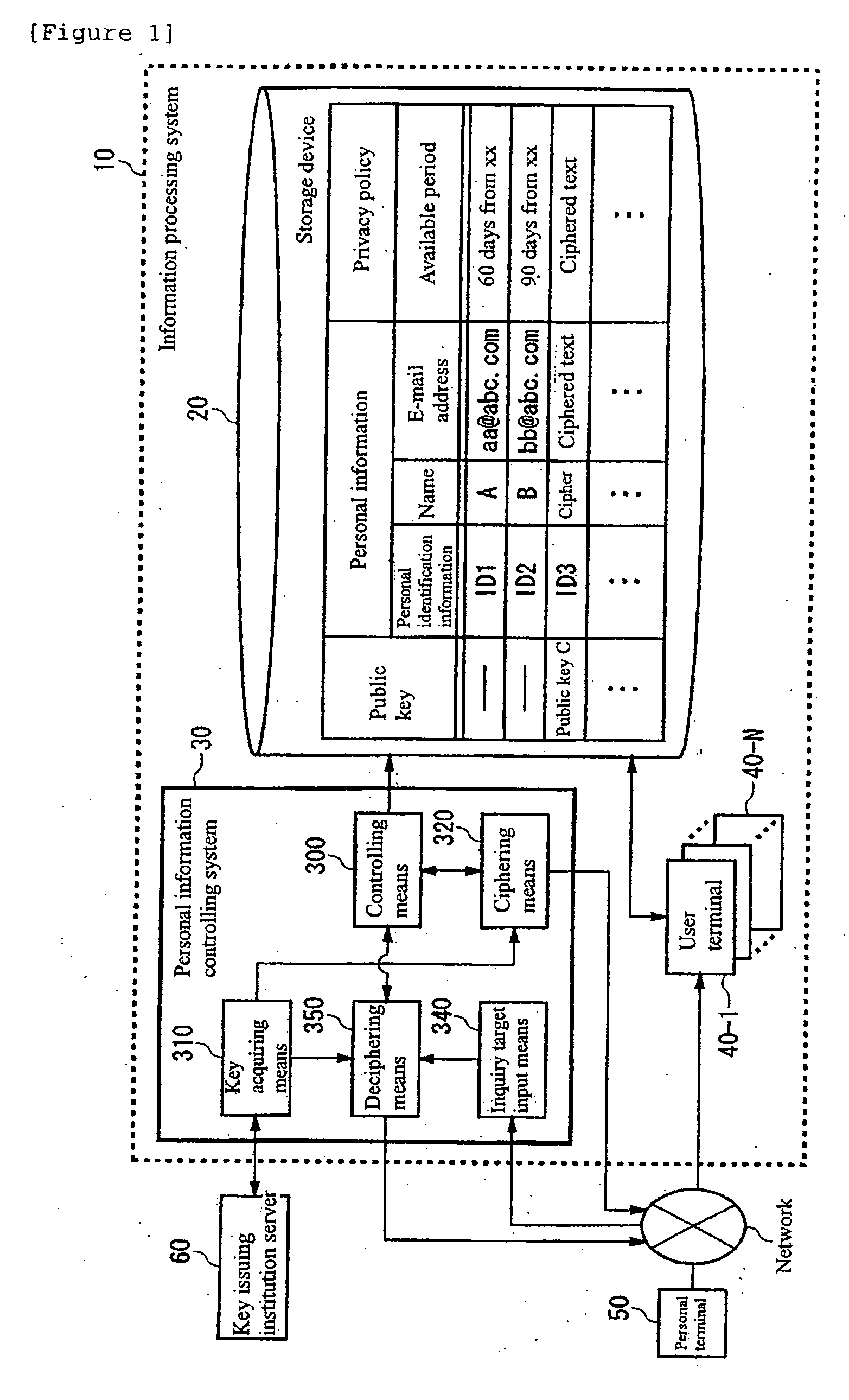
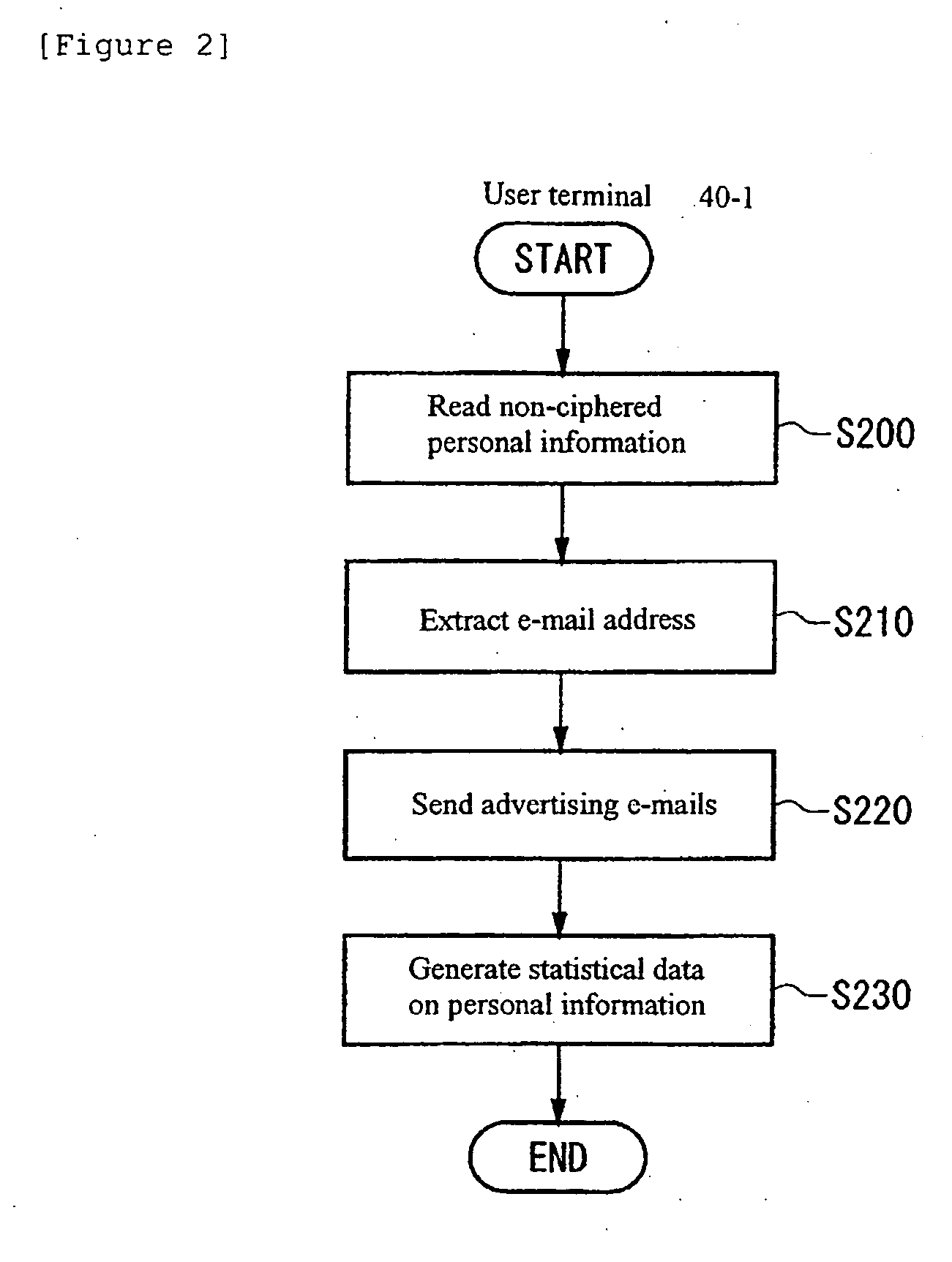
The present invention provides a personal information controlling system that limits use of personal information stored in a storage device. An example of a system comprises: controlling means for controlling a privacy policy for each piece of personal information in connection with a specified available period in which a user of the personal information is allowed to use the personal information, the privacy policy being information specifying the available period; key acquiring means for acquiring a cipher key for a cipher that can be deciphered by an administrator of the privacy policy and that cannot be deciphered by the user of the personal information; and ciphering means for using the cipher key acquired by the key acquiring means to cipher the personal information so that the user cannot use the personal information if the available period specified by the privacy policy has expired.
Owner:IBM CORP
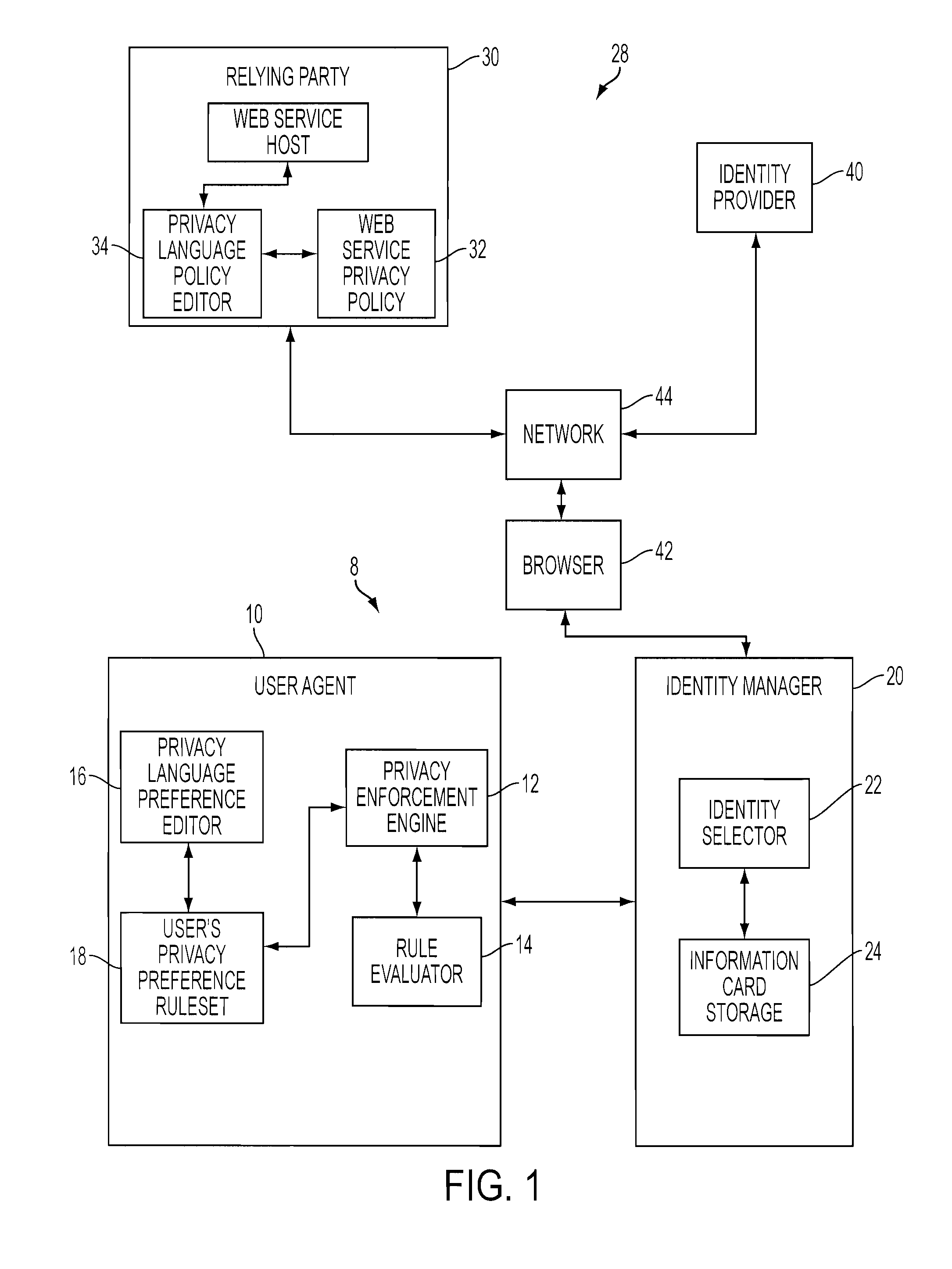
Preference editor to facilitate privacy controls over user identities
A privacy preference editor enables a user to institute privacy preferences relative to user identity information on a card-based and category-based basis. An identity selector furnishes information cards representative of user identities. The editor allows the user to set a privacy preference for each information card. Any proposed disclosure of an information card invokes its corresponding privacy preference. In turn, an agent engine evaluates the invoked privacy preference against the privacy policy of a relying party seeking the card information. The editor also permits the user to create information categories, populate the categories with a group of relevant user identity attributes, and set a privacy preference to the category. In this way, a category-specific privacy preference can be invoked by using the attribute required by the security policy as an index to the appropriate categorized group where the required attribute resides.
Owner:IBM CORP
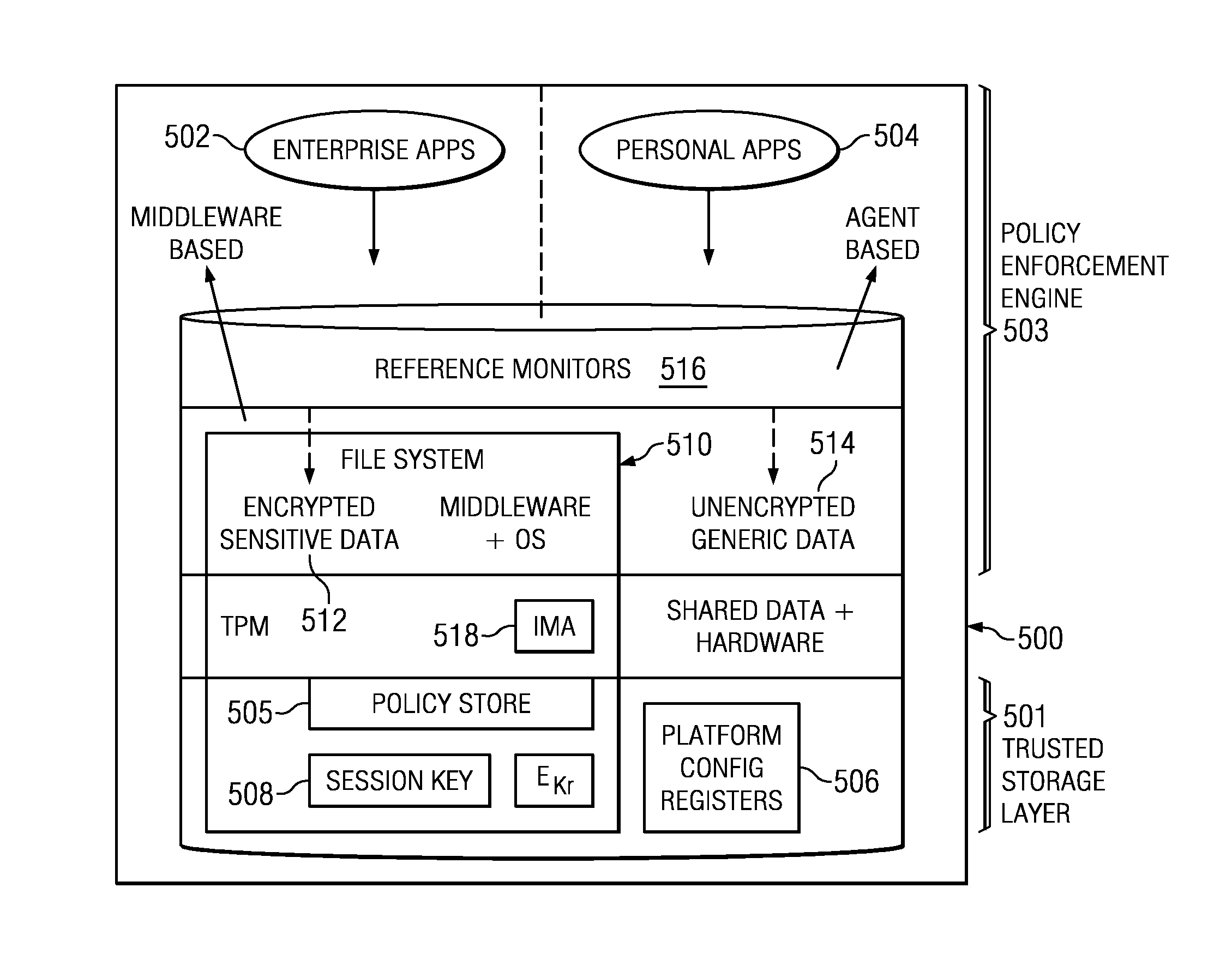
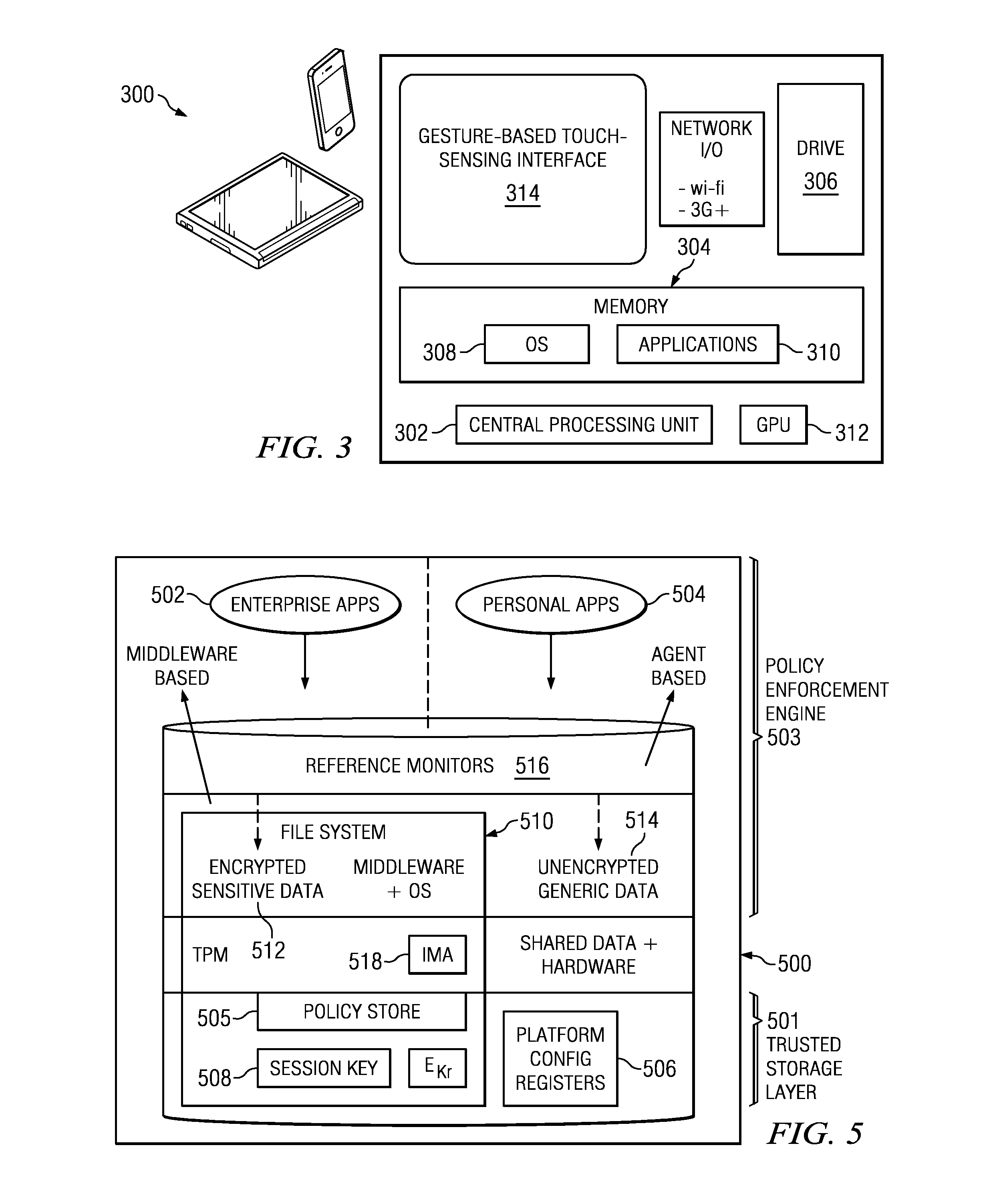
Policy-based dynamic information flow control on mobile devices
ActiveUS20130290709A1User identity/authority verificationComputer security arrangementsInternet privacyData access
A method and system are provided for securing data on a mobile device that supports both enterprise and personal applications. According to the method, information flows and data accesses are tracked on the device at run-time to enable access control decisions to be performed based on a policy, such as an enterprise privacy policy that has been distributed to the device from an enterprise server. The policy may be updated by events at the device as well as at the enterprise server.
Owner:IBM CORP
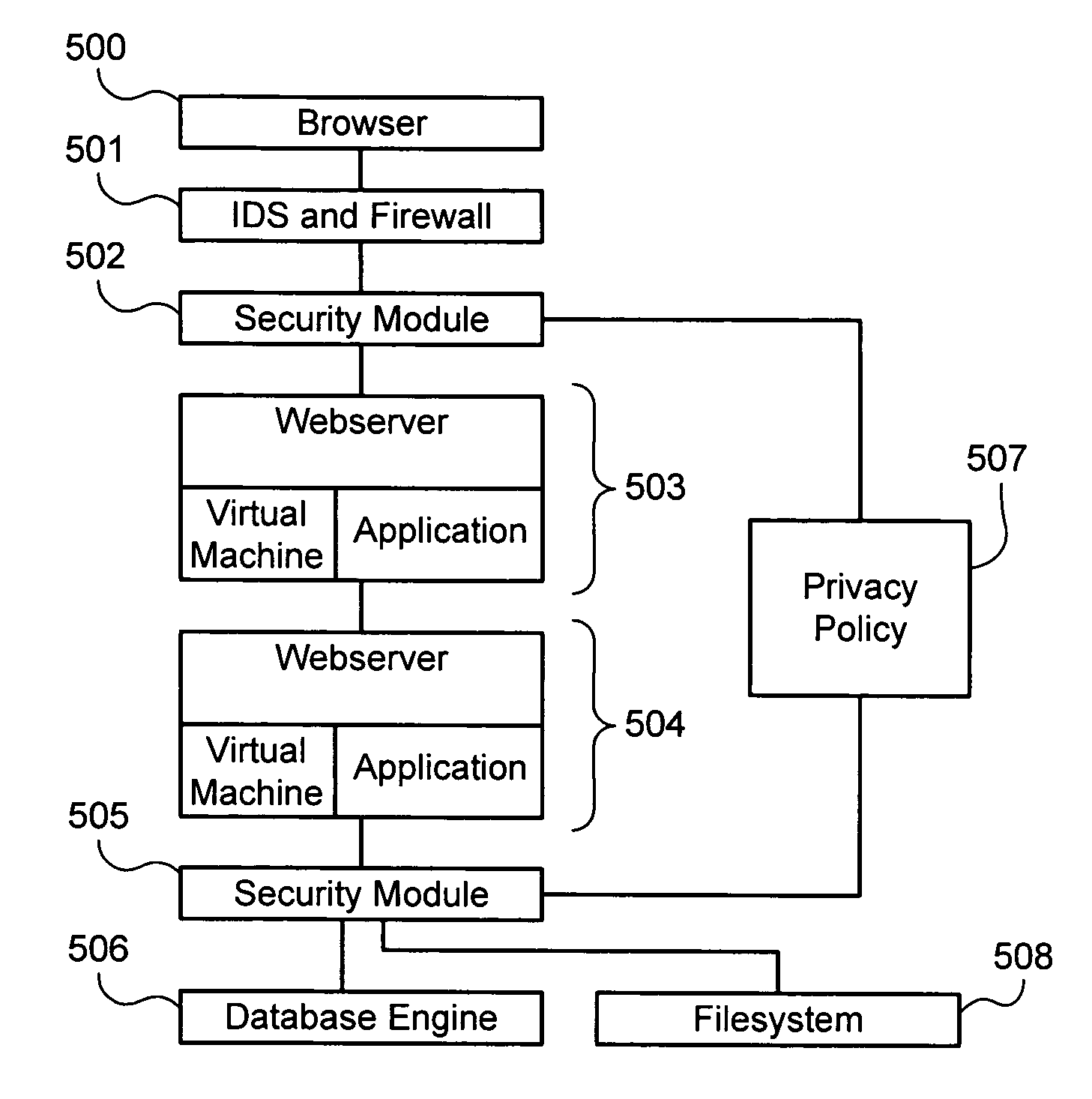
Establishing and enforcing security and privacy policies in web-based applications
ActiveUS20060143688A1Enhances security and privacyIncrease flexibilityMemory loss protectionUnauthorized memory use protectionObject handlingWeb application
Method, system, and computer code for implementing security and privacy policy in a web application having an execution environment in which a representation of each object handled by the execution environment accommodates data and an associated tag. An inbound tagging rule is established for tagging inbound objects according to a respective source of each of the inbound objects. A tag is assigned to an object being operated on by the execution environment based on the inbound tagging rule. A security / privacy rule is established for performing security / privacy actions on outbound objects according to a respective tag of each of the outbound objects. A security / privacy action is performed on the object being operated on by the execution environment based on the security / privacy rule.
Owner:FORTRA LLC
Auditable privacy policies in a distributed hierarchical identity management system
ActiveUS20050283443A1User identity/authority verificationPayment architectureThird partyInternet privacy
A set of methods, and systems, for enabling the audit tracking of user agreement with policies, such as privacy policies in an authenticated fashion is disclosed herein. The method and system make use of third party signatures of privacy policies to show user approval of the policy as it pertains to released data.
Owner:CALLAHAN CELLULAR L L C
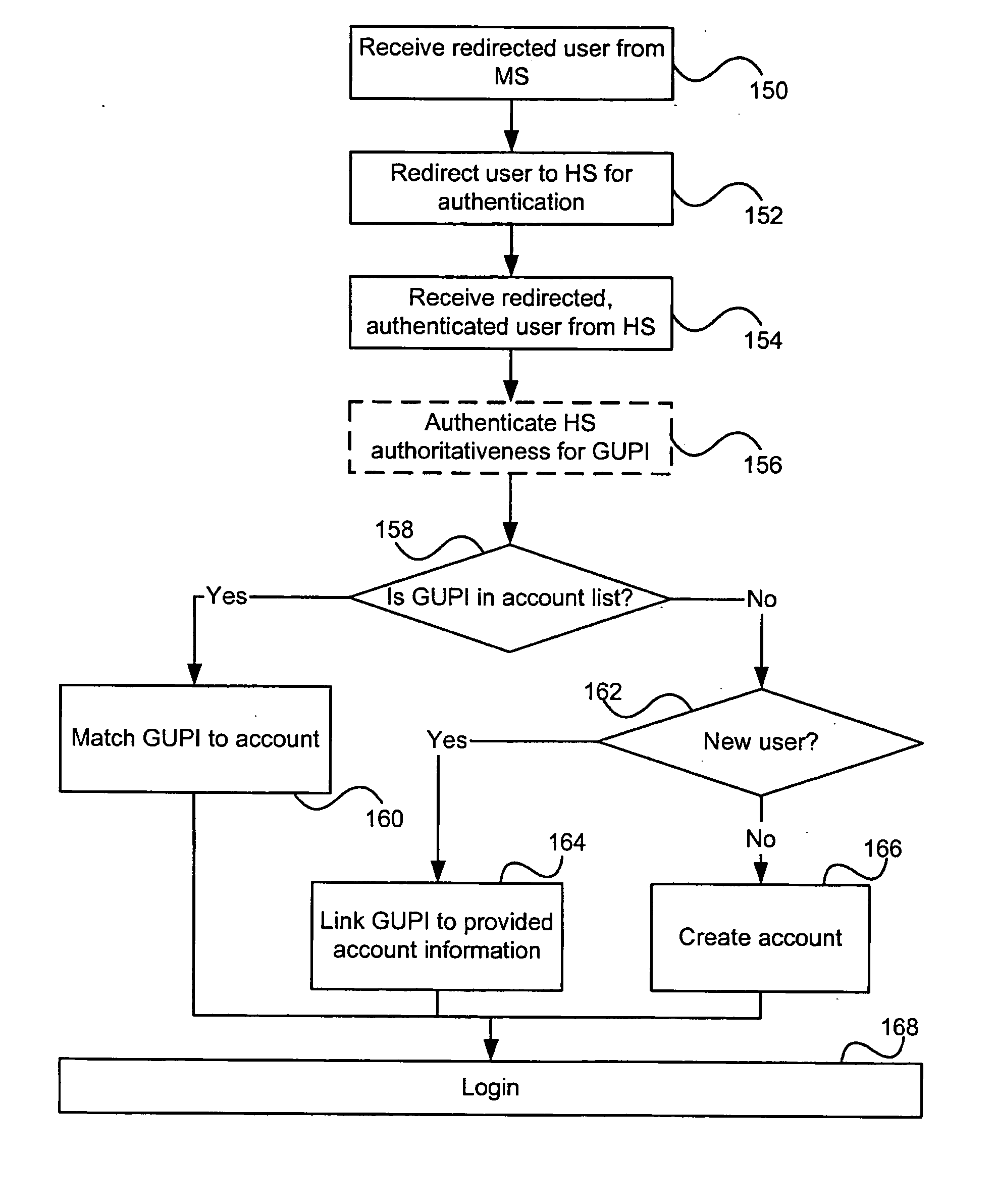
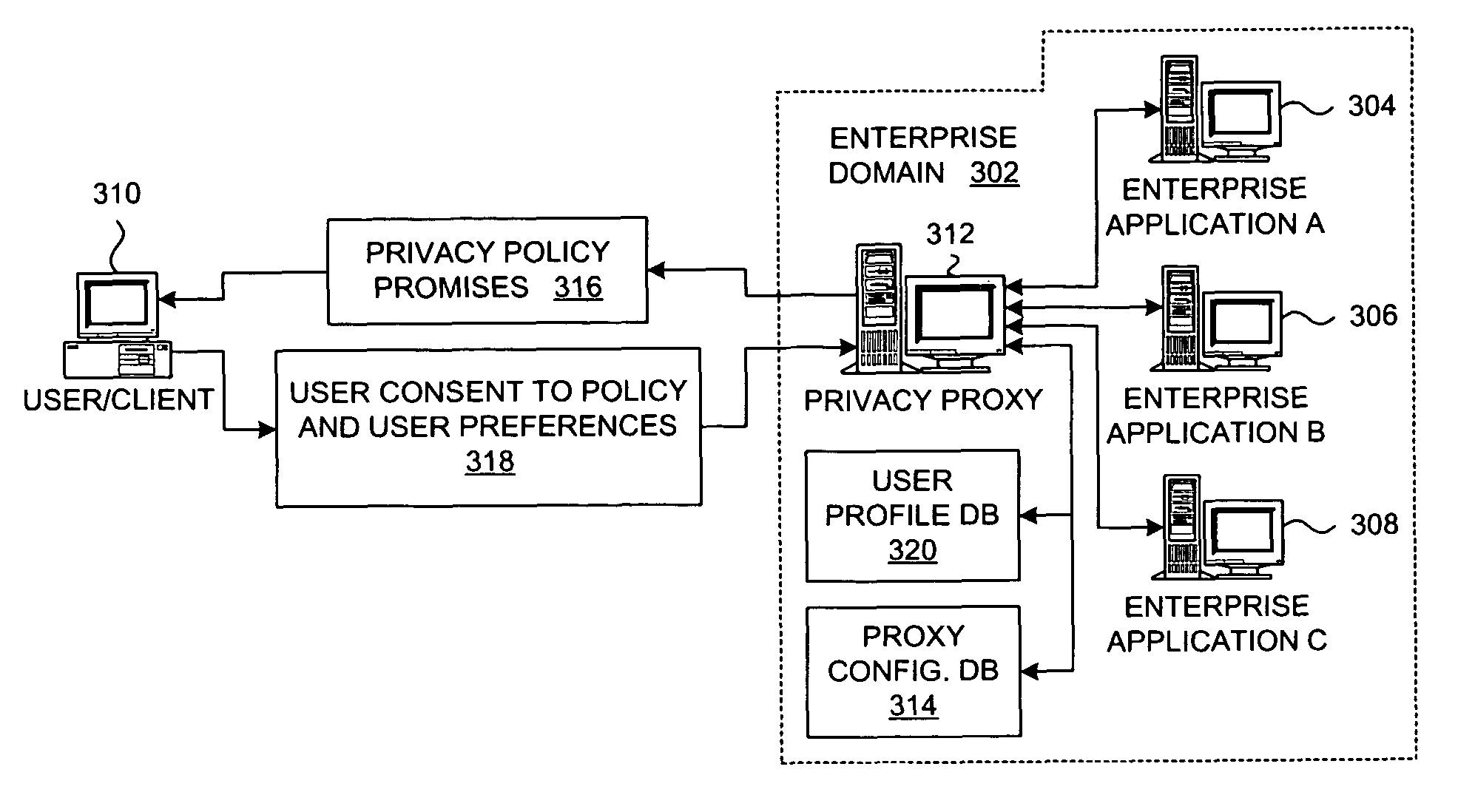
Method and system for implementing privacy notice, consent, and preference with a privacy proxy
ActiveUS8464311B2Digital data processing detailsUser identity/authority verificationData processing systemInternet privacy
A method is presented for processing data for a privacy policy concerning management of personally identifiable information. A proxy intercepts a first message from a server to a client and determines that the first message initiates collection of personally identifiable information from a user of the client. The proxy then sends a second message to the client that requests consent from the user to the privacy policy. If the user provides consent within a third message that is received by the proxy from the client, then the proxy sends the intercepted first message to the client. If the user does not provide consent, then the proxy sends a fourth message to the server that fails the collection of personally identifiable information from the client by the server. The proxy may also obtain user preferences for options concerning management of the personally identifiable information by a data processing system.
Owner:IBM CORP
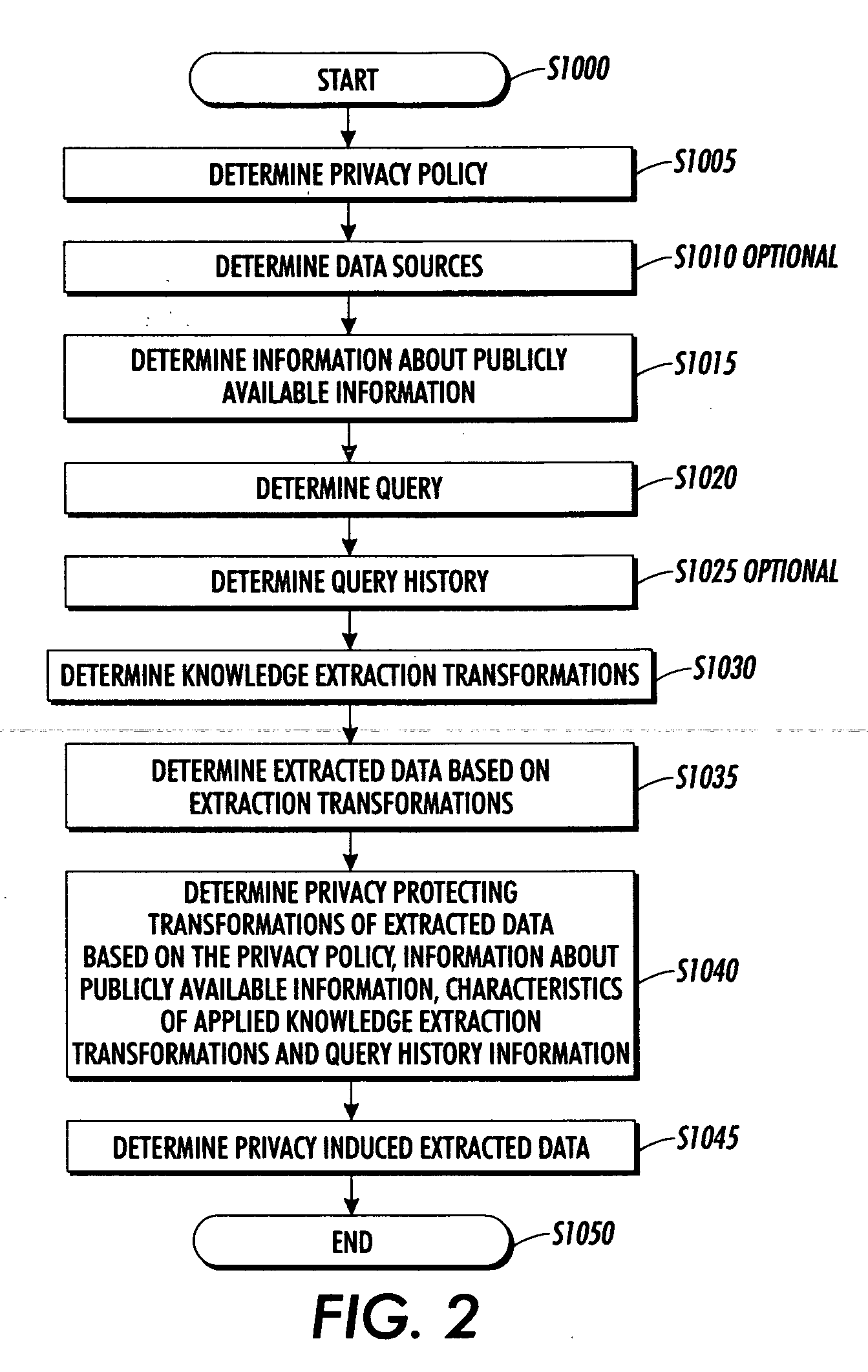
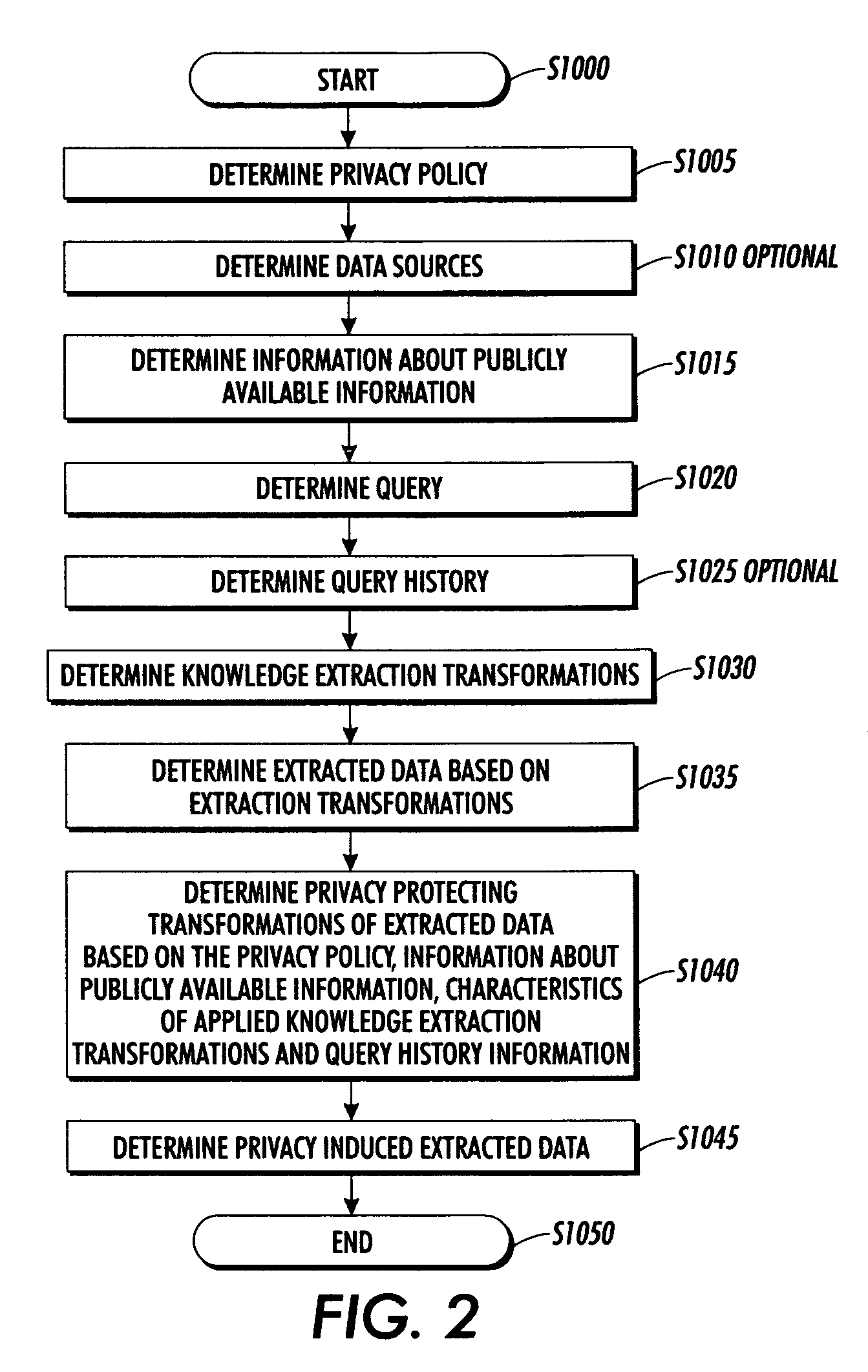
Systems and methods for protecting privacy
InactiveUS20060123461A1Digital data processing detailsComputer security arrangementsPrivacy protectionKnowledge extraction
Techniques for providing privacy protection are provided. A query is received. Privacy policy information, extracted knowledge and optional information about available public information are determined. Information about the knowledge extraction transformations applied to create the extracted knowledge and the source data is determined. Privacy protecting transformations are determined and applied to transform the extracted knowledge based on the selected privacy policy, optional information about available public information, the characteristics of the applied knowledge extractions transformations, the source data and optional previous user queries.
Owner:PALO ALTO RES CENT INC
Auditable privacy policies in a distributed hierarchical identity management system
Owner:CALLAHAN CELLULAR L L C
Data privacy management system and method
InactiveUS20050251865A1Minimize impactKey distribution for secure communicationPublic key for secure communicationObfuscationInternet privacy
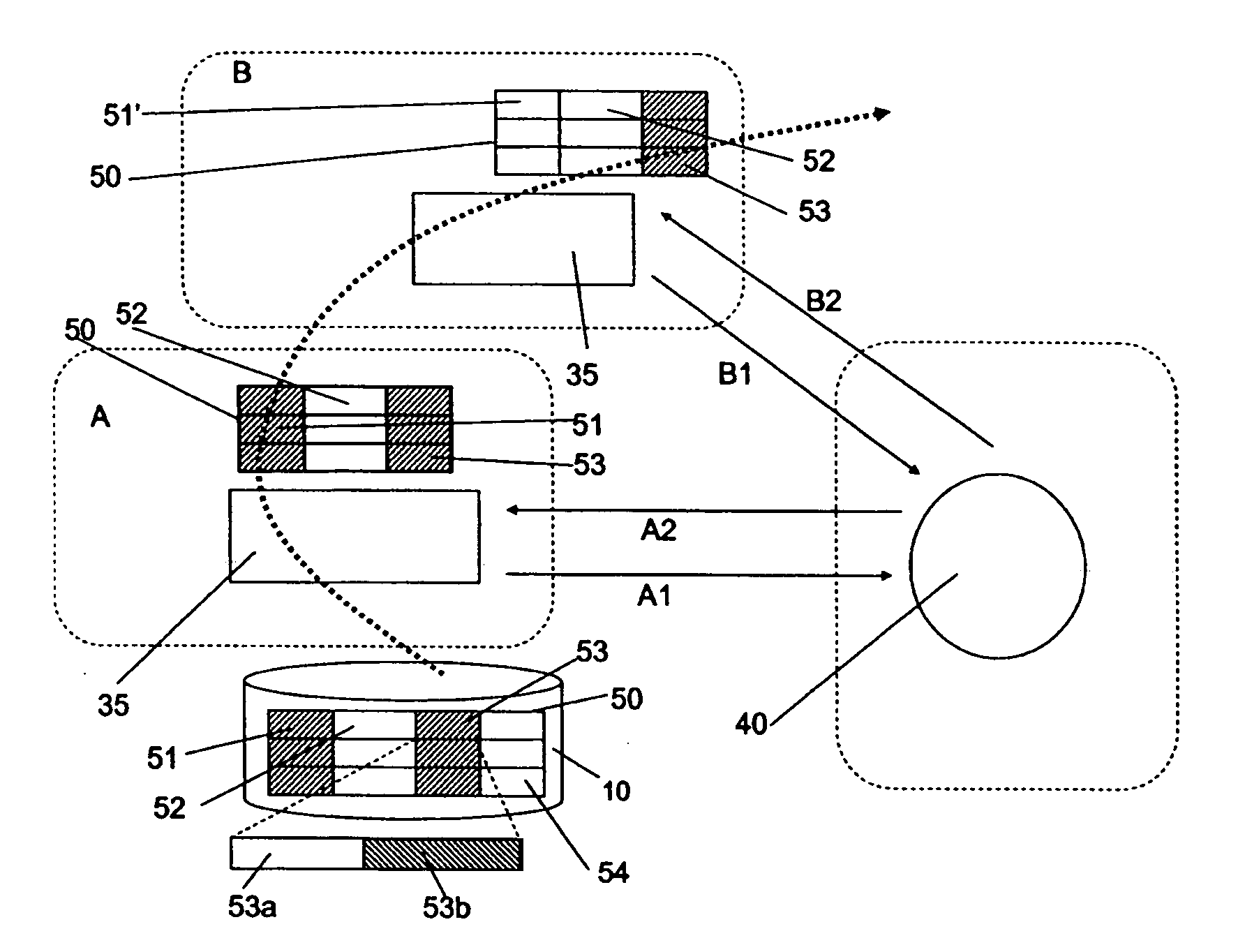
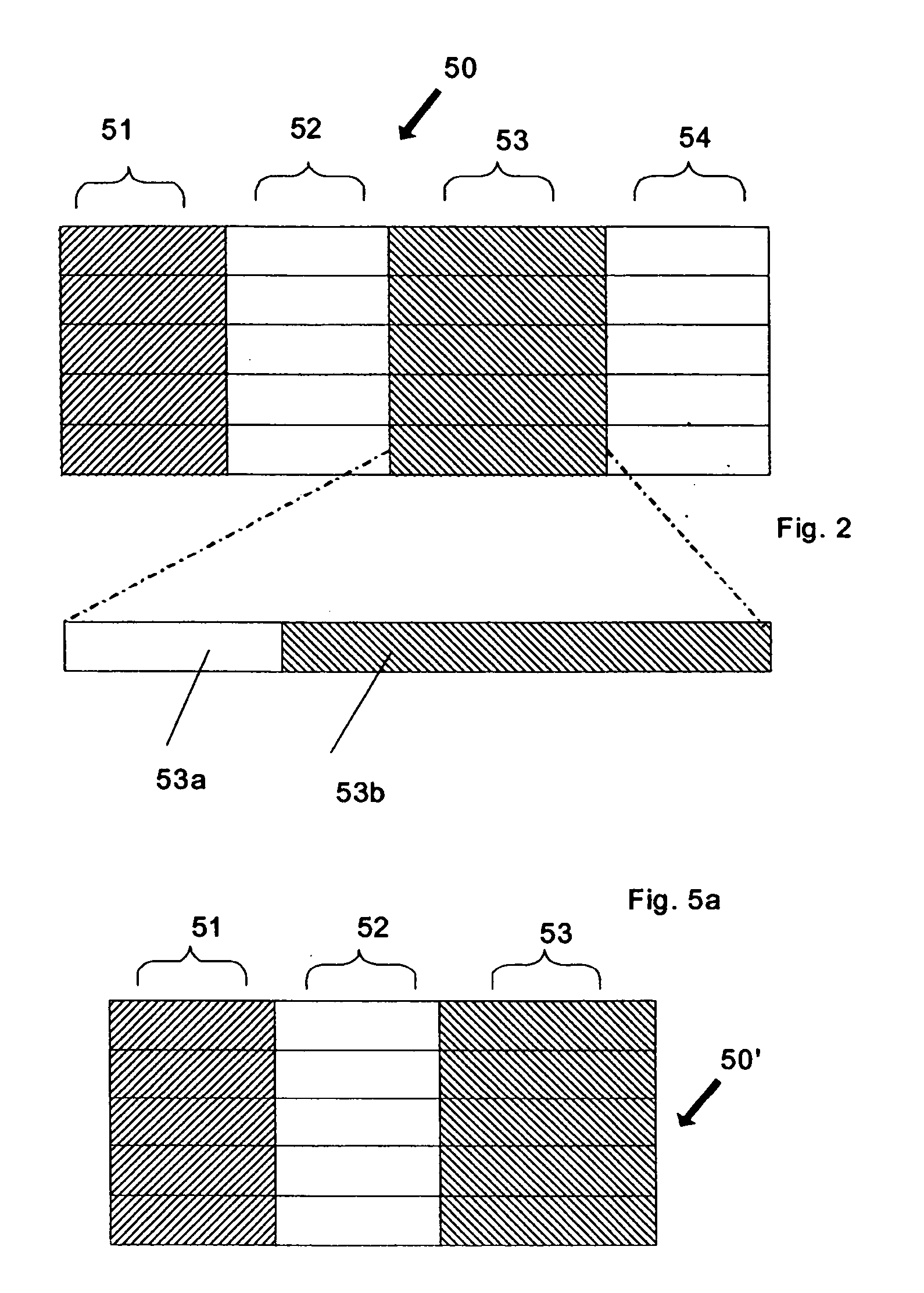
A data privacy management system includes a data repository, a private data mediating system and a privacy manager. The data repository stores private data items in an obfuscated form. Each private data item has associated privacy policy data a defining conditions to be met to ensure the privacy of the data item. A private data mediating system communicates with the privacy manager to obtain de-obfuscated private data items that are extracted from the data repository 10. De-obfuscation of the data 51, 53 is subject to satisfaction of the privacy manager that the respective conditions ensuring privacy of the data item are met.
Owner:HEWLETT PACKARD DEV CO LP
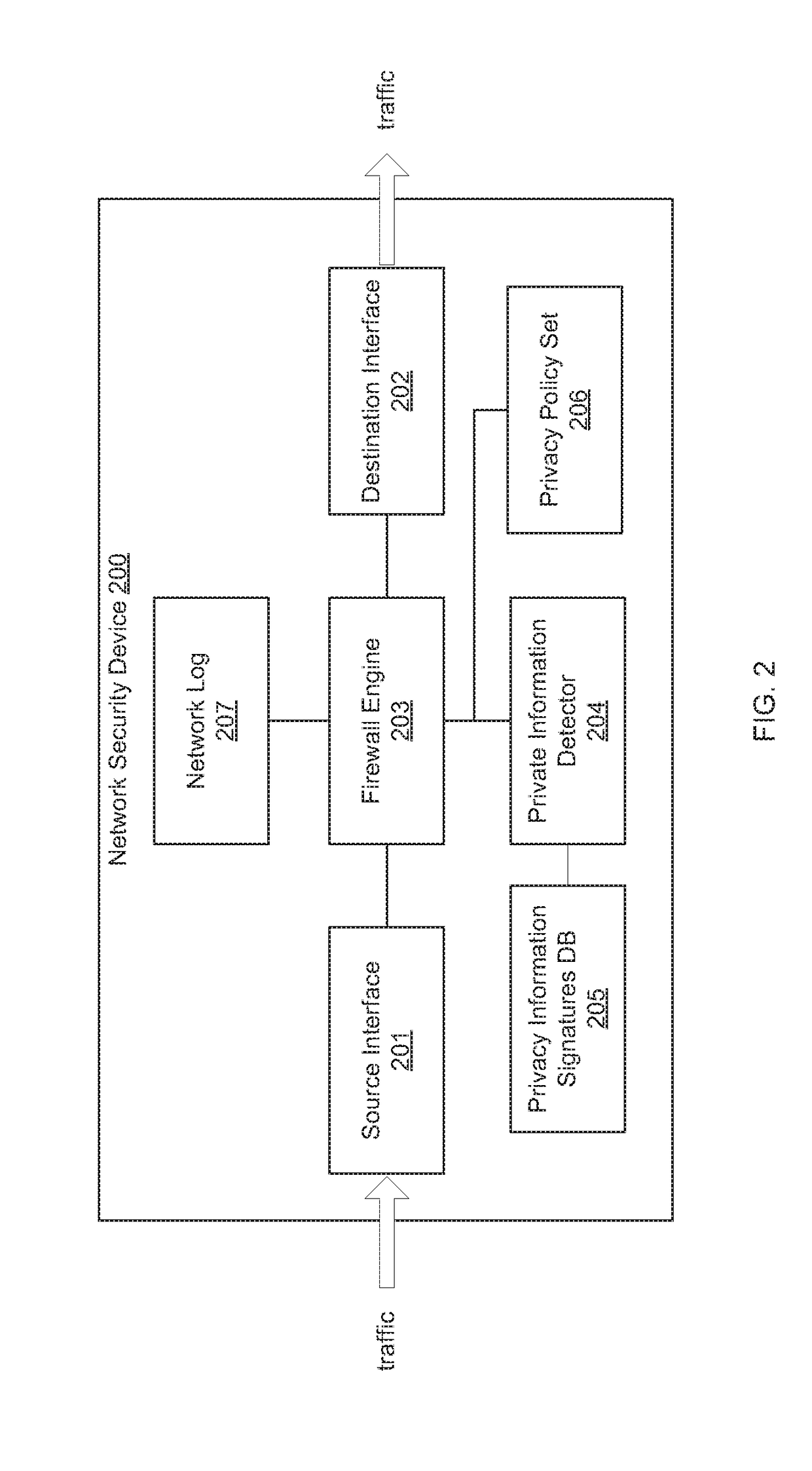
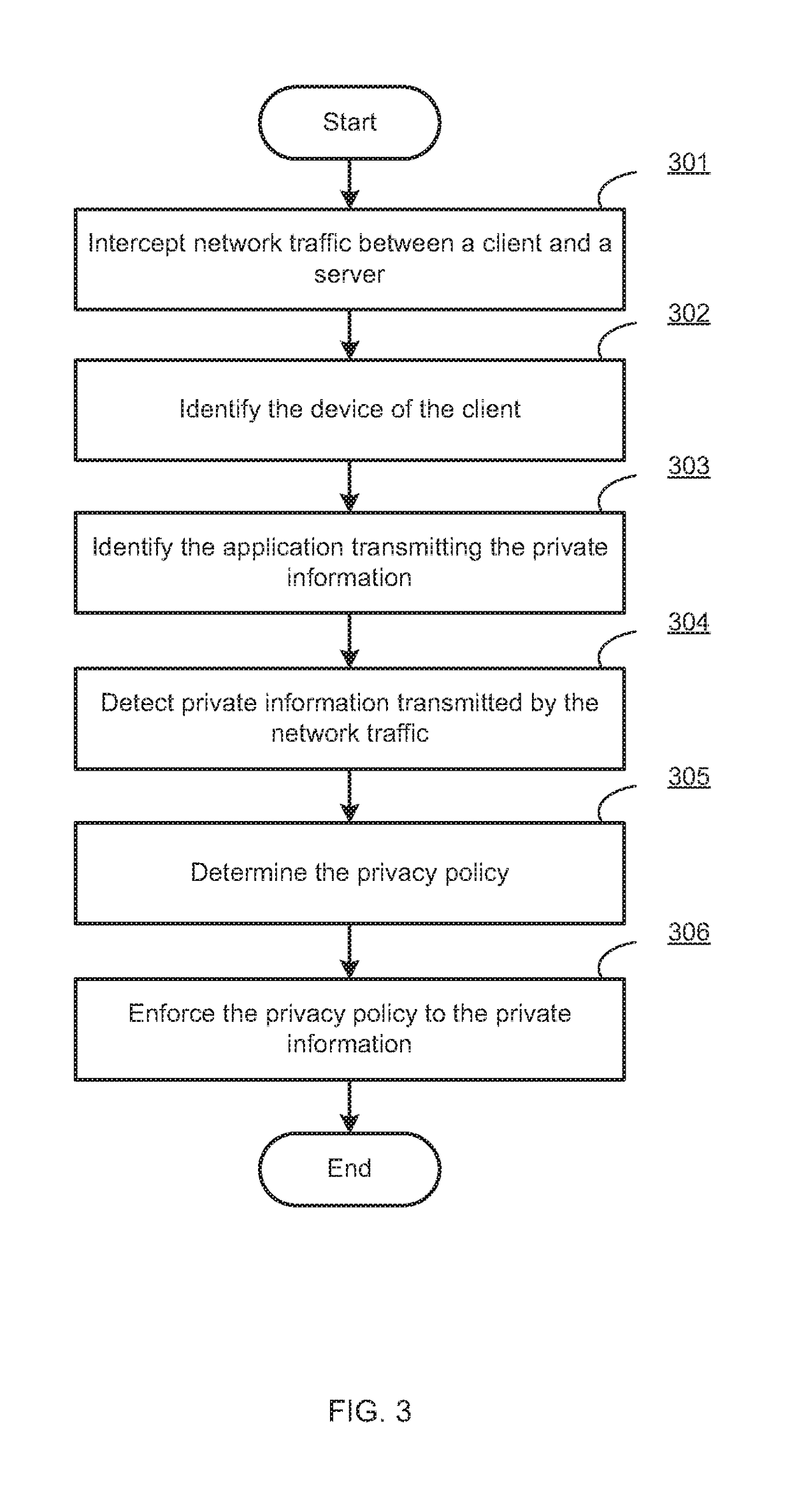
Centralized management and enforcement of online privacy policies
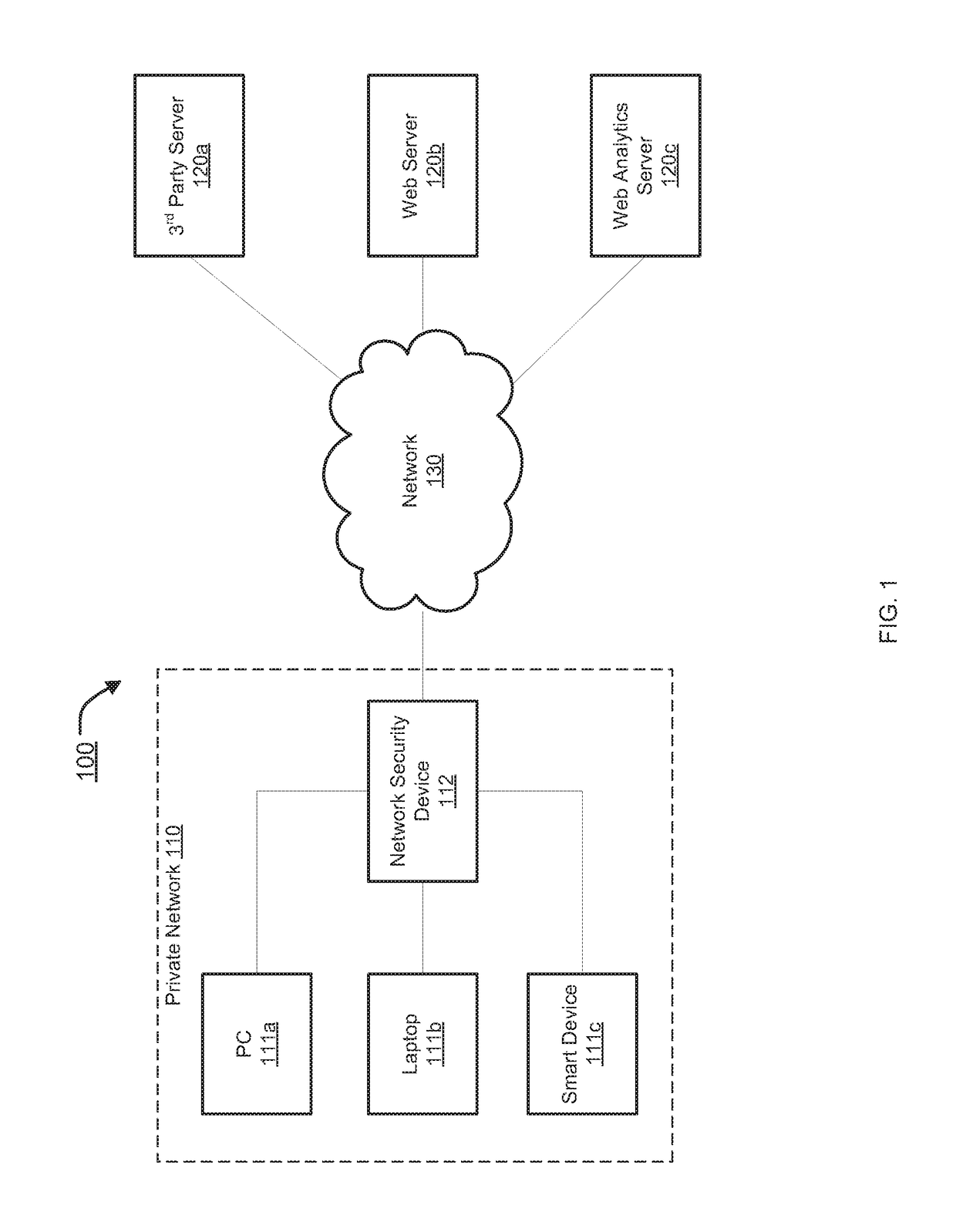
Systems and methods for centralized management and enforcement of online privacy policies of a private network are provided. According to one embodiment, existence of private information contained in a data packet originated by a client device of a private network and destined for a server device external to the private network is identified by a network security device protecting the private network by scanning the data packet for information matching a signature contained within a private information signature database. An online privacy policy of the private network is determined by the network security device that is applicable to the private information with reference to a privacy policy set defined by an administrator of the private network. The online privacy policy is enforced by the network security device on the data packet by performing one or more actions specified by the online privacy policy to the data packet.
Owner:FORTINET
Systems and methods for protecting privacy
InactiveUS7797725B2Digital data processing detailsComputer security arrangementsApplying knowledgePrivacy protection
Techniques for providing privacy protection are provided. A query is received. Privacy policy information, extracted knowledge and optional information about available public information are determined. Information about the knowledge extraction transformations applied to create the extracted knowledge and the source data is determined. Privacy protecting transformations are determined and applied to transform the extracted knowledge based on the selected privacy policy, optional information about available public information, the characteristics of the applied knowledge extractions transformations, the source data and optional previous user queries.
Owner:PALO ALTO RES CENT INC
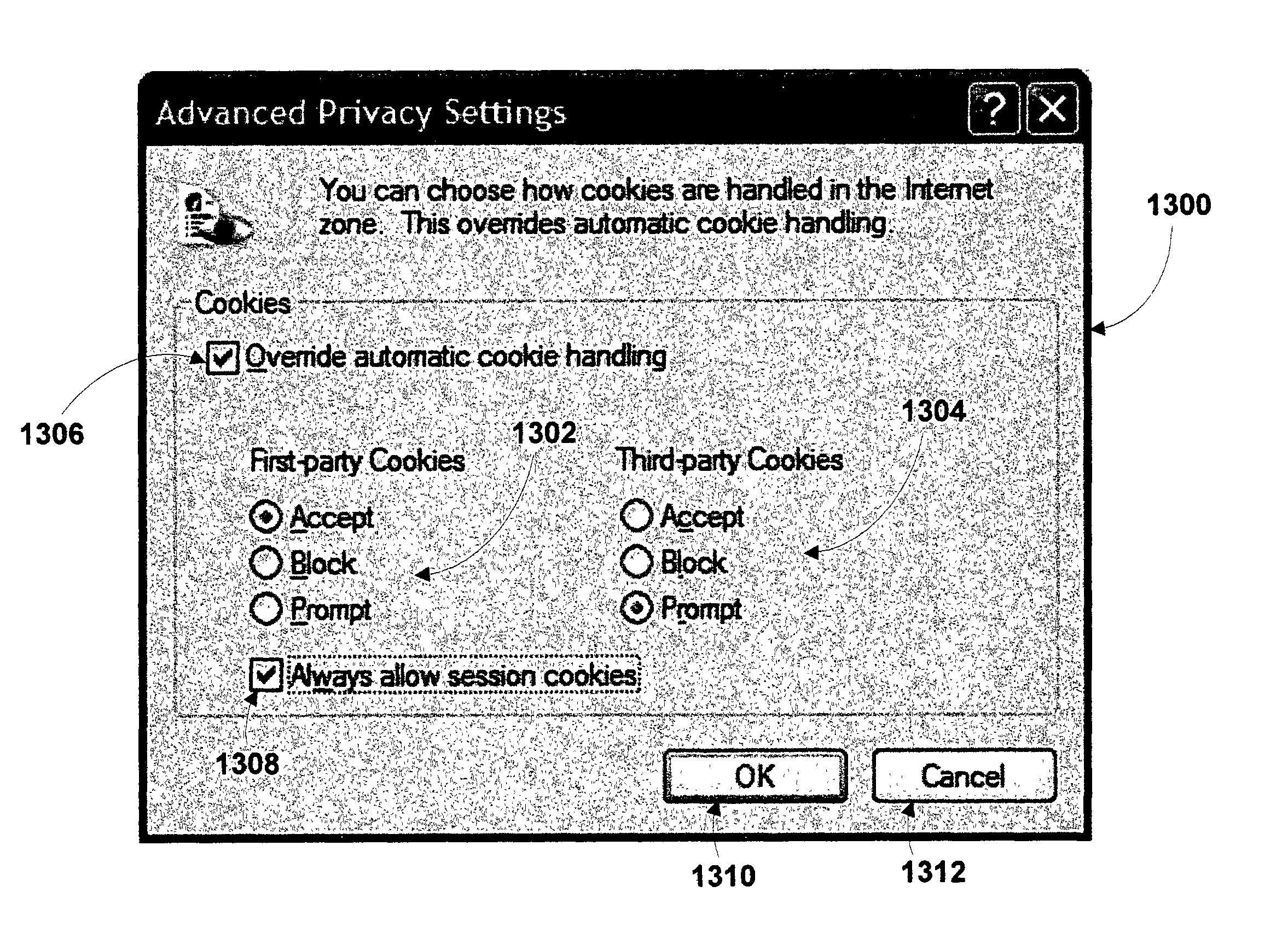
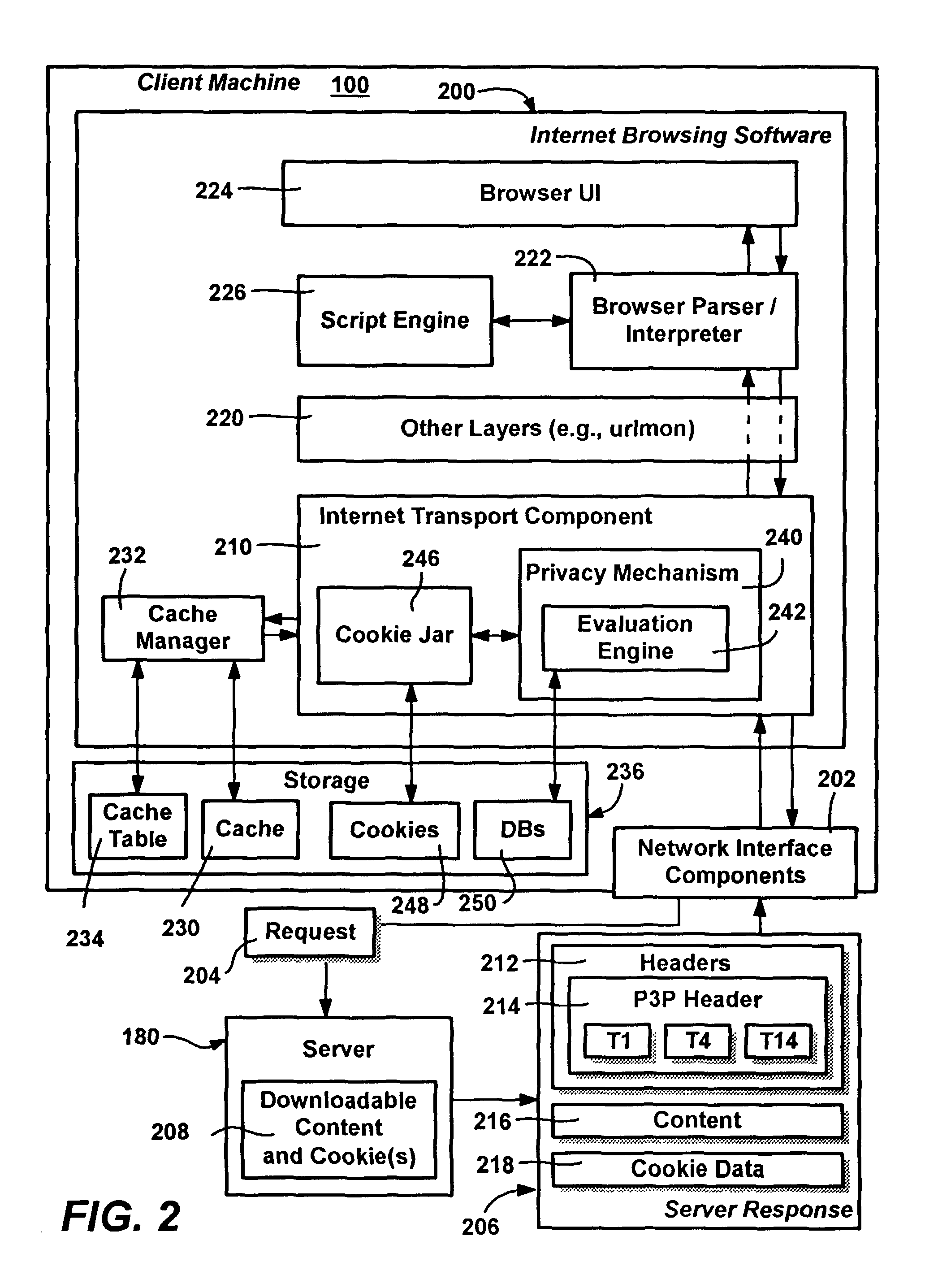
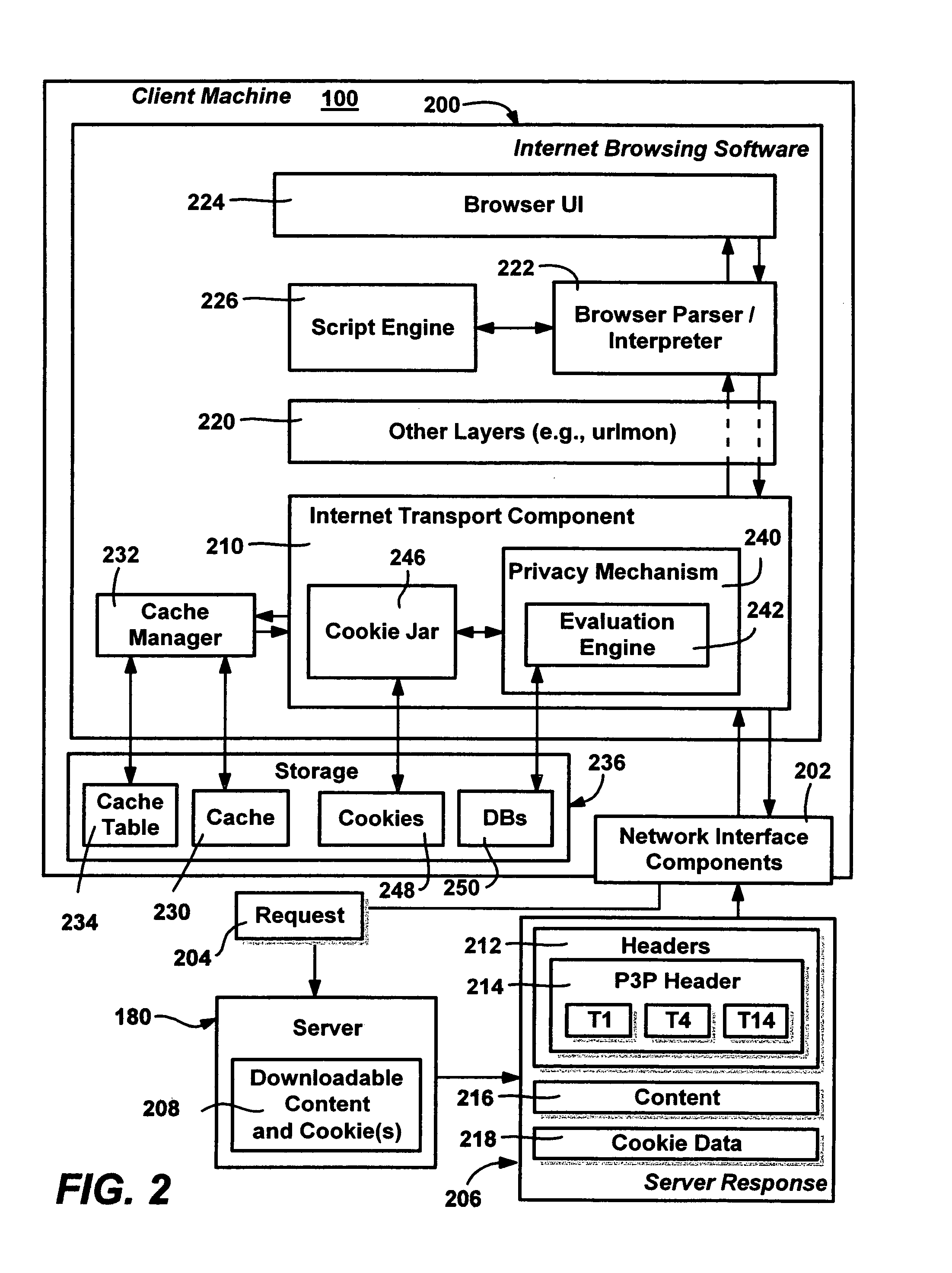
Method and system for protecting internet users' privacy by evaluating web site platform for privacy preferences policy
InactiveUS20050257250A1Digital data processing detailsUser identity/authority verificationThird partyWeb site
A system and method that evaluates privacy policies from web sites to determine whether each site is permitted to perform operations (e.g., store, retrieve or delete) directed to cookies on a user's computer. Various properties of each cookie and the context in which it is being used are evaluated against a user's privacy preference settings to make the determination. An evaluation engine accomplishes the evaluation and determination via a number of criteria and considerations, including the cookie properties, its current context, the site, the zone that contains the site, and any P3P data (compact policy) provided with the site's response. The user privacy preferences are evaluated against these criteria to determine whether a requested cookie operation is allowed, denied or modified. A formalized distinction between first-party cookies versus third-party cookies may be used in the determination, along with whether the cookie is a persistent cookie or a session cookie.
Owner:MICROSOFT TECH LICENSING LLC
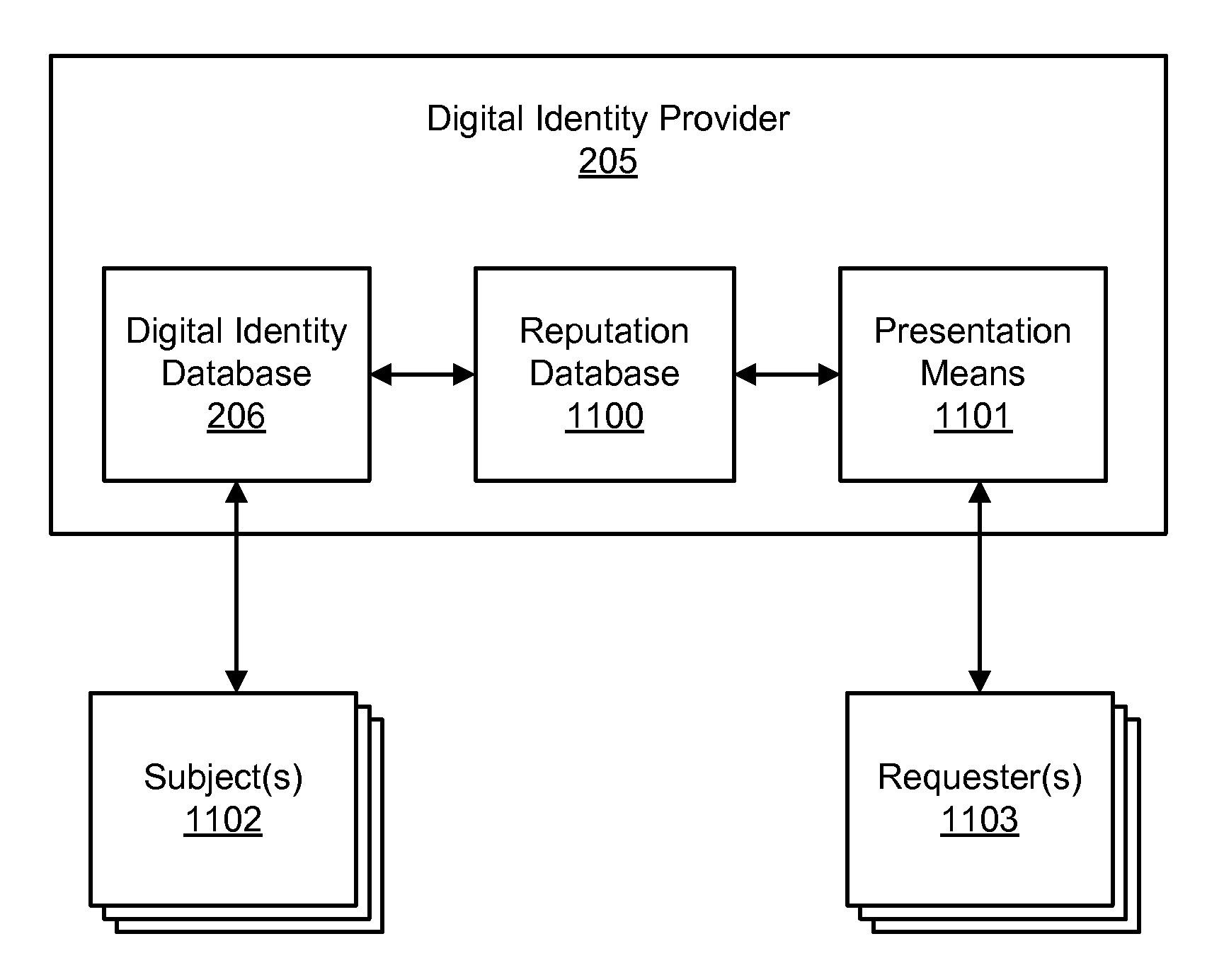
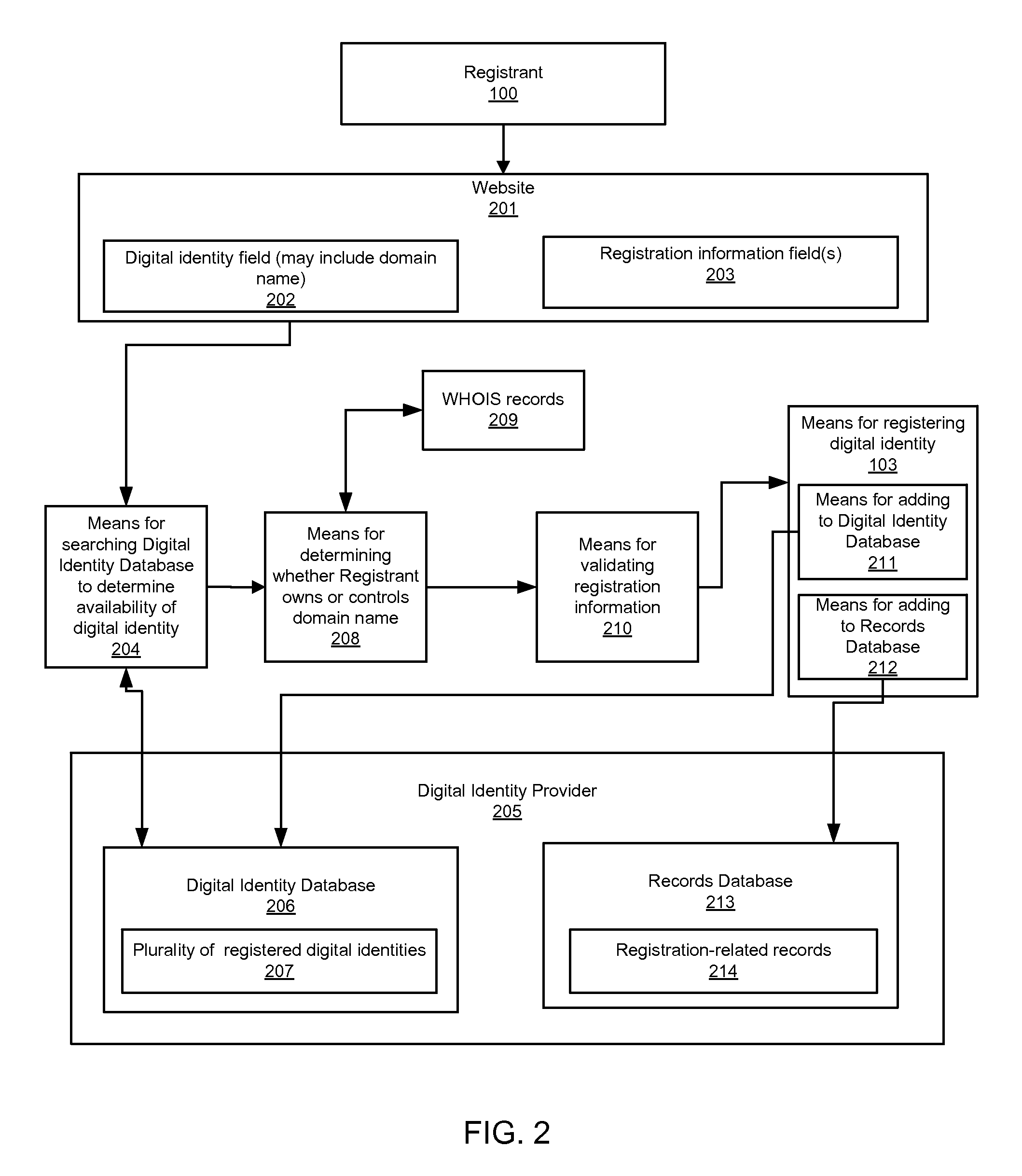
Accessing digital identity related reputation data
InactiveUS20090248623A1Effective registrationDigital data processing detailsData switching networksDigital identityDomain name
Systems and processes of the present invention allow for tracking and publishing digital identity related reputation. In an example embodiment, a Digital Identity Provider maintains a database with reputation data that can be accessed by Requesters. The Digital Identity Provider may update reputation data based on a variety of events related to a digital identity. The reputation data may be tracked regarding the digital identity itself, digital identity purchaser or registrant, or an email address, domain name, URL, or website associated with the digital identity. The reputation data may include various categories, such as email practices, website content, privacy policies and practices, fraudulent activities, domain name related complaints, overall reputation, etc. The reputation data may be published in a publicly-available database, a private database, or via other methods. The Registrant may opt for a reputation service while registering a digital identity. The Requester may decide whether to interact with a digital identity based on the digital identity related reputation.
Owner:GO DADDY OPERATING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com