Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4454 results about "Centralized management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Centralized management. Management practice in which all or most decision makers (who have the authority, control, and responsibility for the entire organization) are located in one central office (the headquarters).
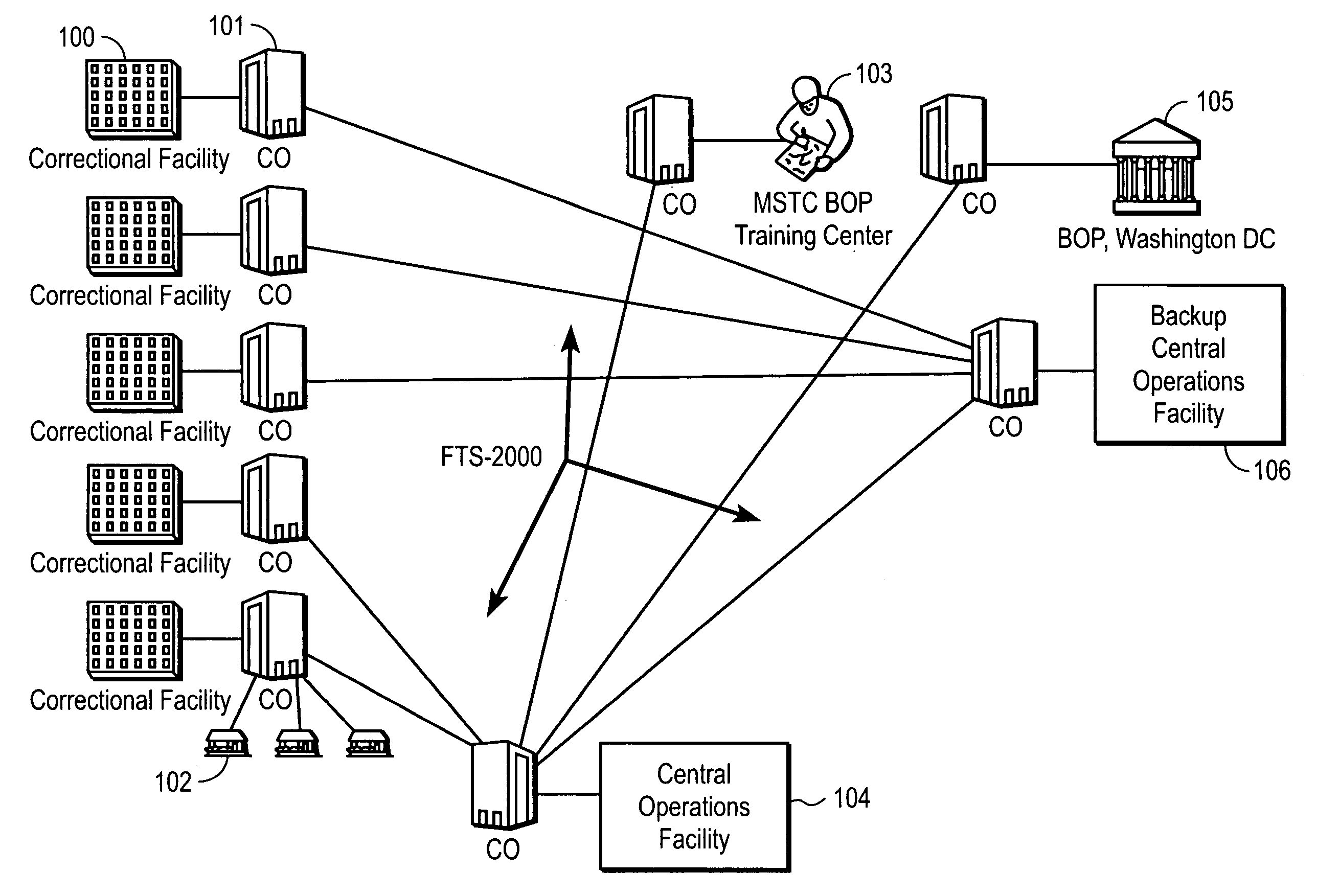
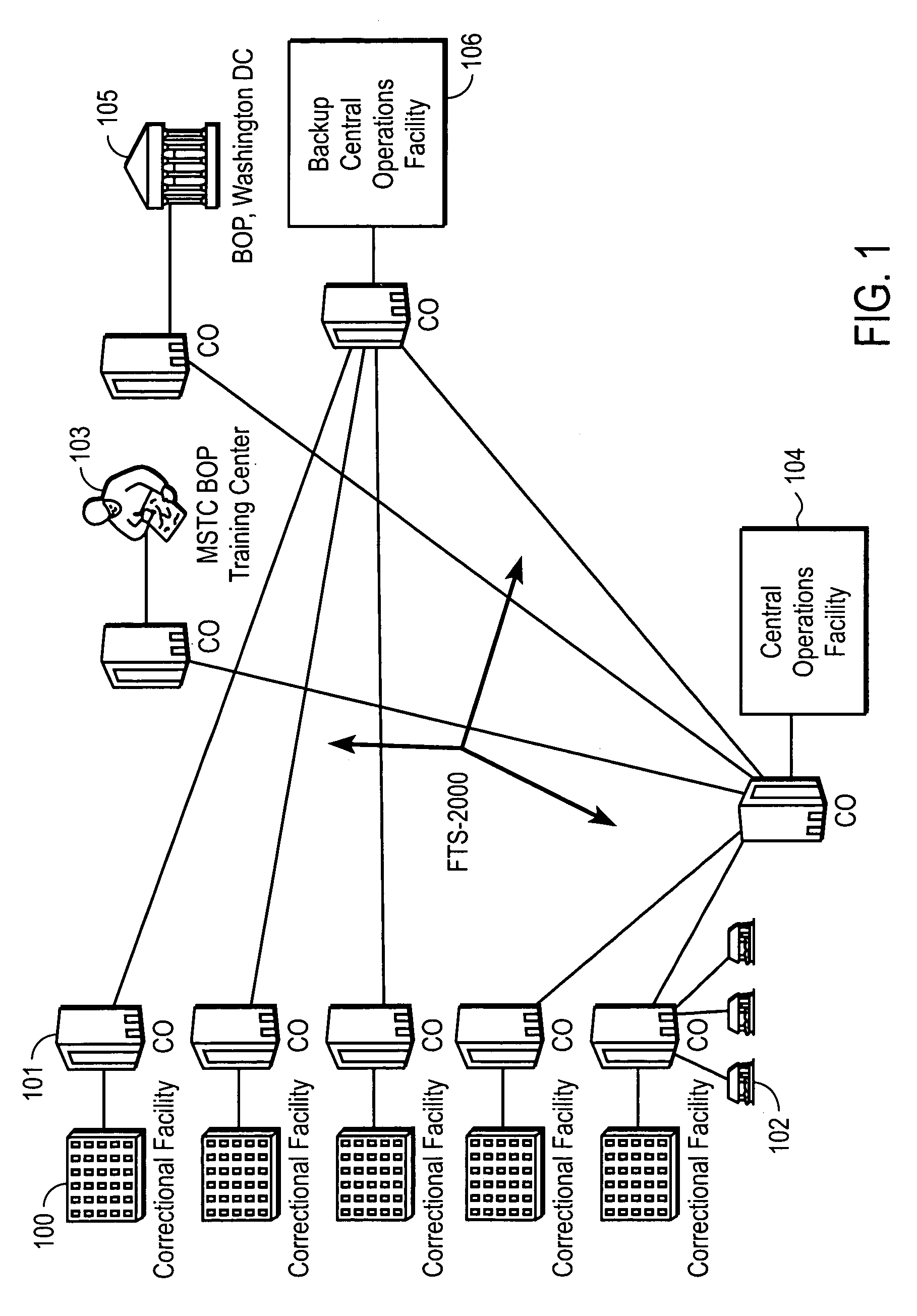
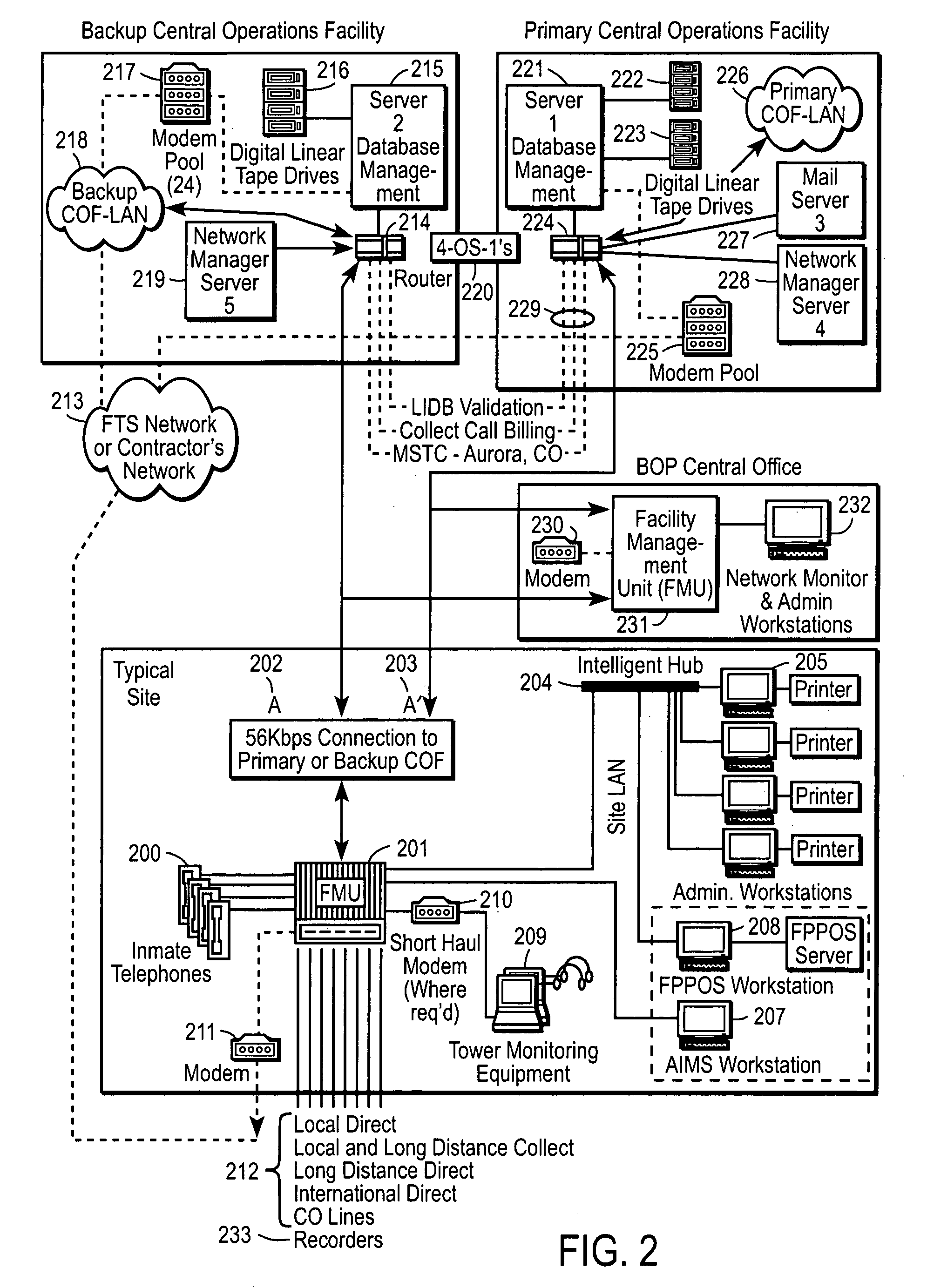
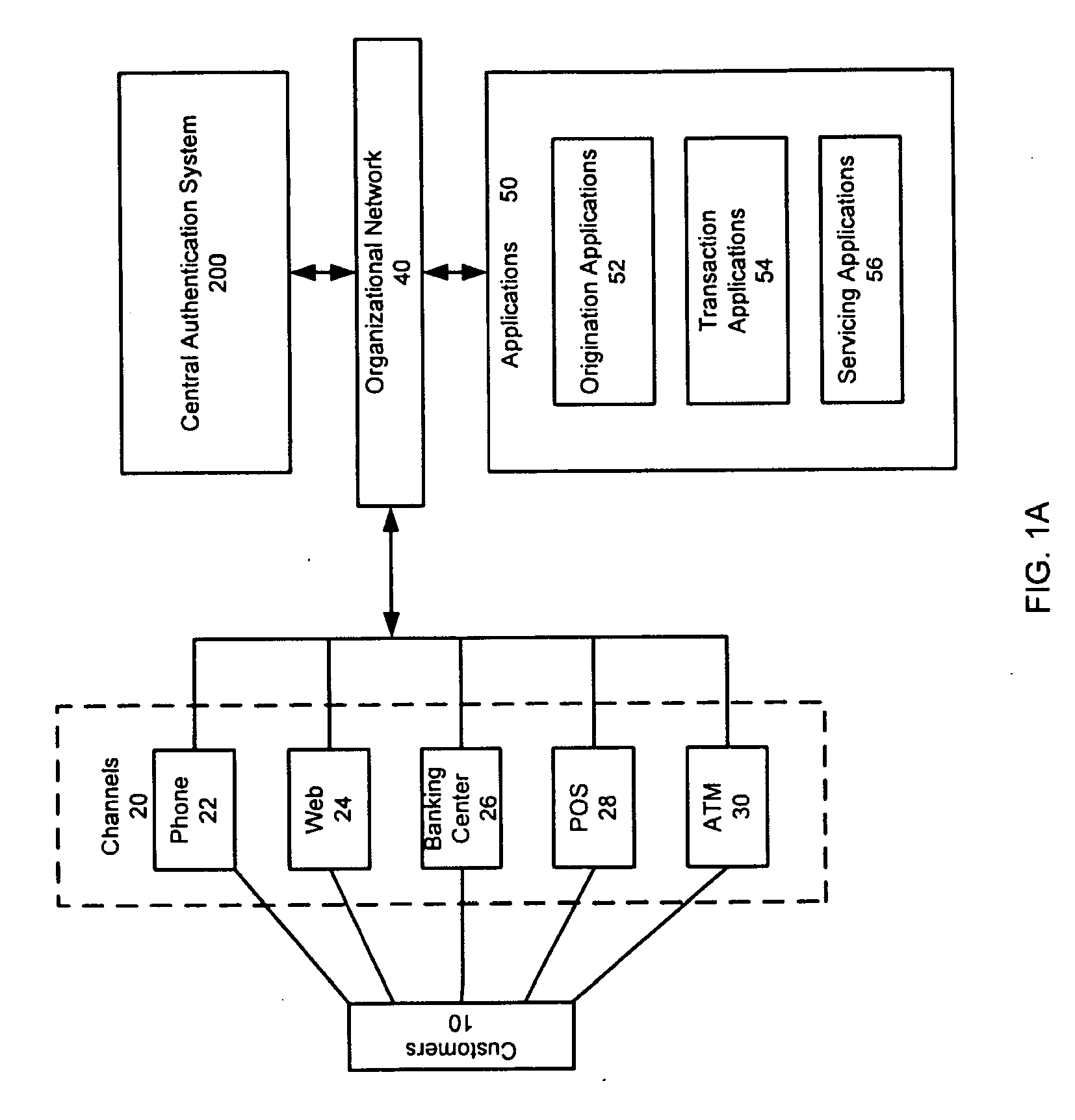
Computer-based method and apparatus for controlling, monitoring, recording and reporting telephone access
InactiveUS7106843B1Improve securityLow costUnauthorised/fraudulent call preventionEavesdropping prevention circuitsManagement unitCentralized management
A method and apparatus for managing institutional telephone activity utilizing a computer-based telephony management unit to connect institutional telephones with outside telephone lines. The unit provides institutional users with fully automated, direct dial and collect calling privileges for local, long distance, and international calls. The unit contains a database for storing the calling privileges and restrictions of institutional users, for recording calling transactions made by the users, and for managing user monetary accounts. The unit can record up to 400 hours of conversation in a digital format. The unit provides various administrative capabilities, including user account management, audit trails, transaction reports, centralized management and report capabilities, and detection of fraudulent calling.
Owner:AMERICAN CAPITAL FINANCIAL SERVICES +1
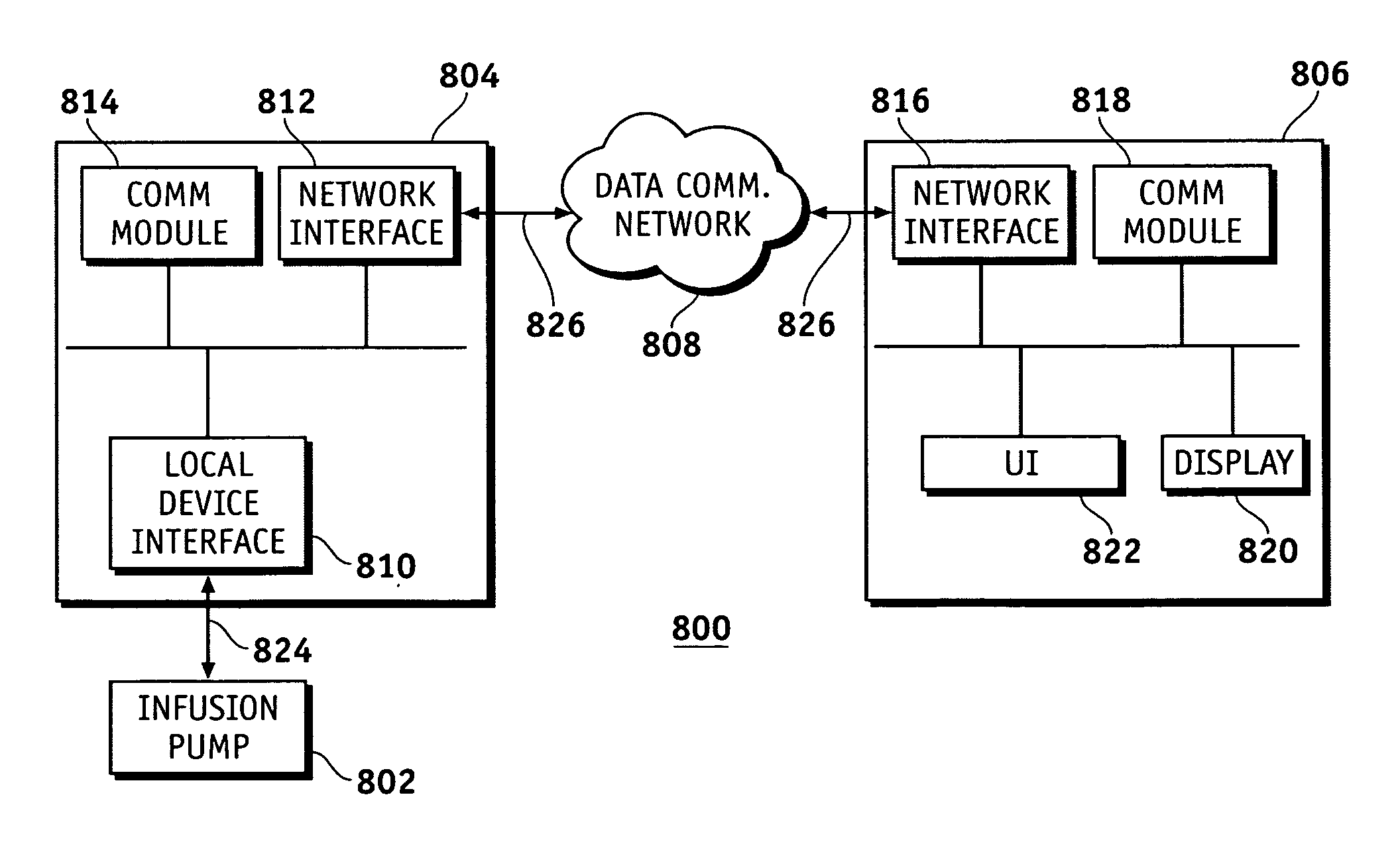
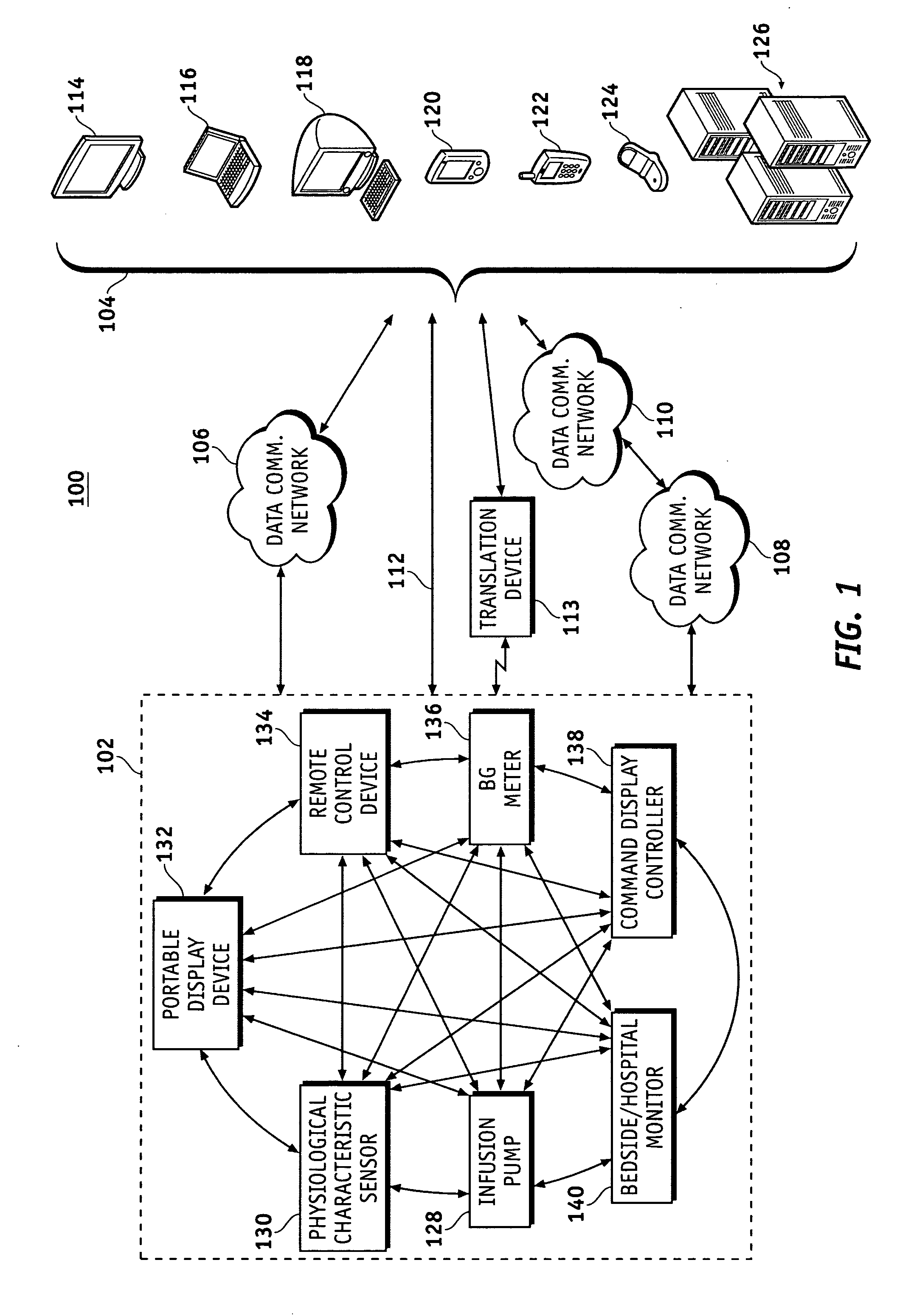
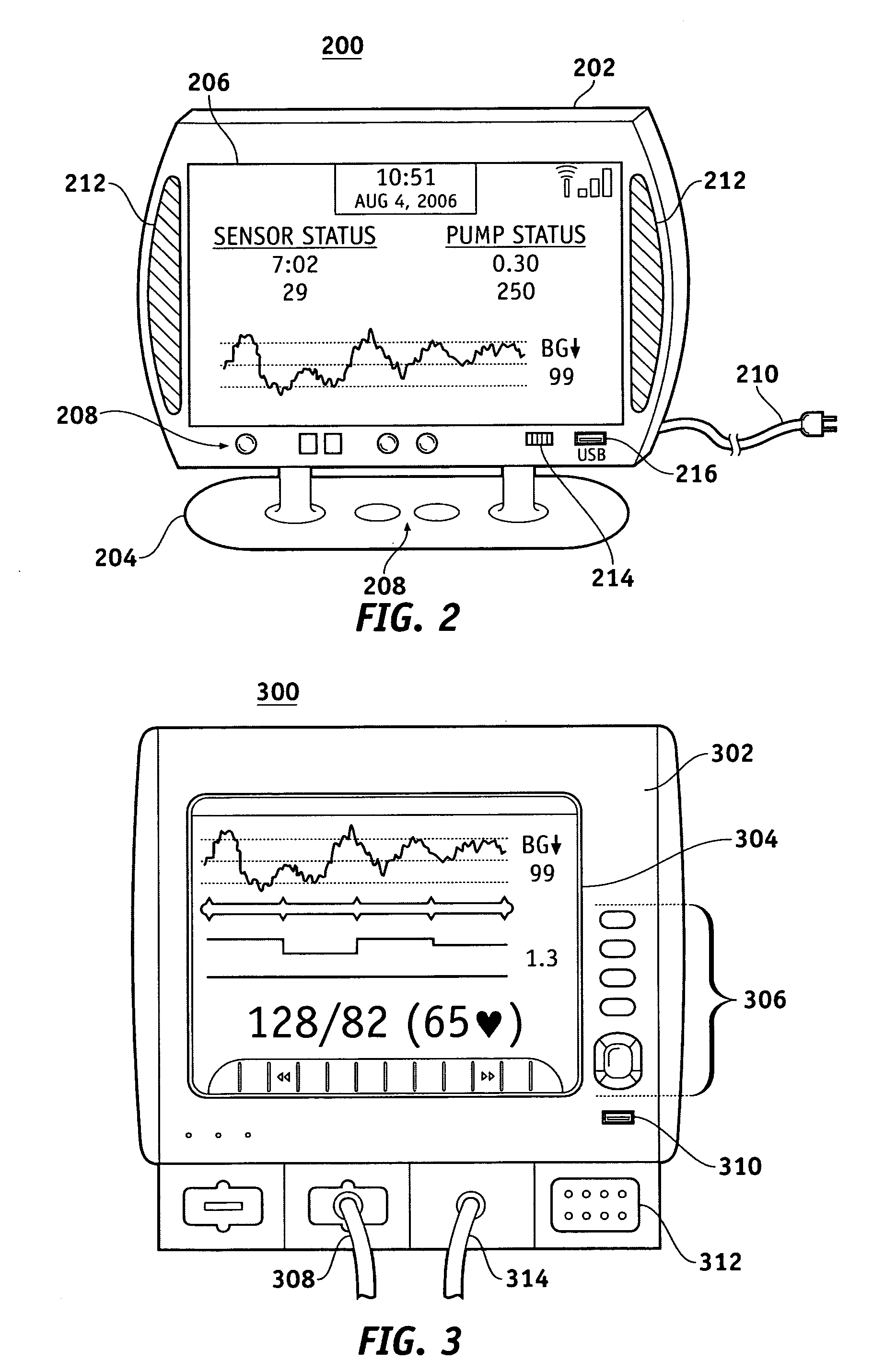
Router device for centralized management of medical device data
InactiveUS20070255348A1Facilitates centralized gatheringEasy to processElectrotherapyDrug and medicationsControl signalFluid infusion
A fluid infusion system as described herein includes a number of local “body network” devices, such as an infusion pump, a handheld monitor or controller, a physiological sensor, and a bedside or hospital monitor. The body network devices can be configured to support communication of status data, physiological information, alerts, control signals, and other information between one another. In addition, the body network devices can be configured to support networked communication of status data, physiological information, alerts, control signals, and other information between the body network devices and “external” devices, systems, or communication networks. Such external communication allows the infusion system to be extended beyond the traditional short-range user environment. One particular system embodiment includes a network router device that functions as a centralized storage, processing, and routing unit for data received from the body network devices. The network router device is configured to generate HTML documents (web pages) to facilitate Internet-based setup, management, and control.
Owner:MEDTRONIC MIMIMED INC
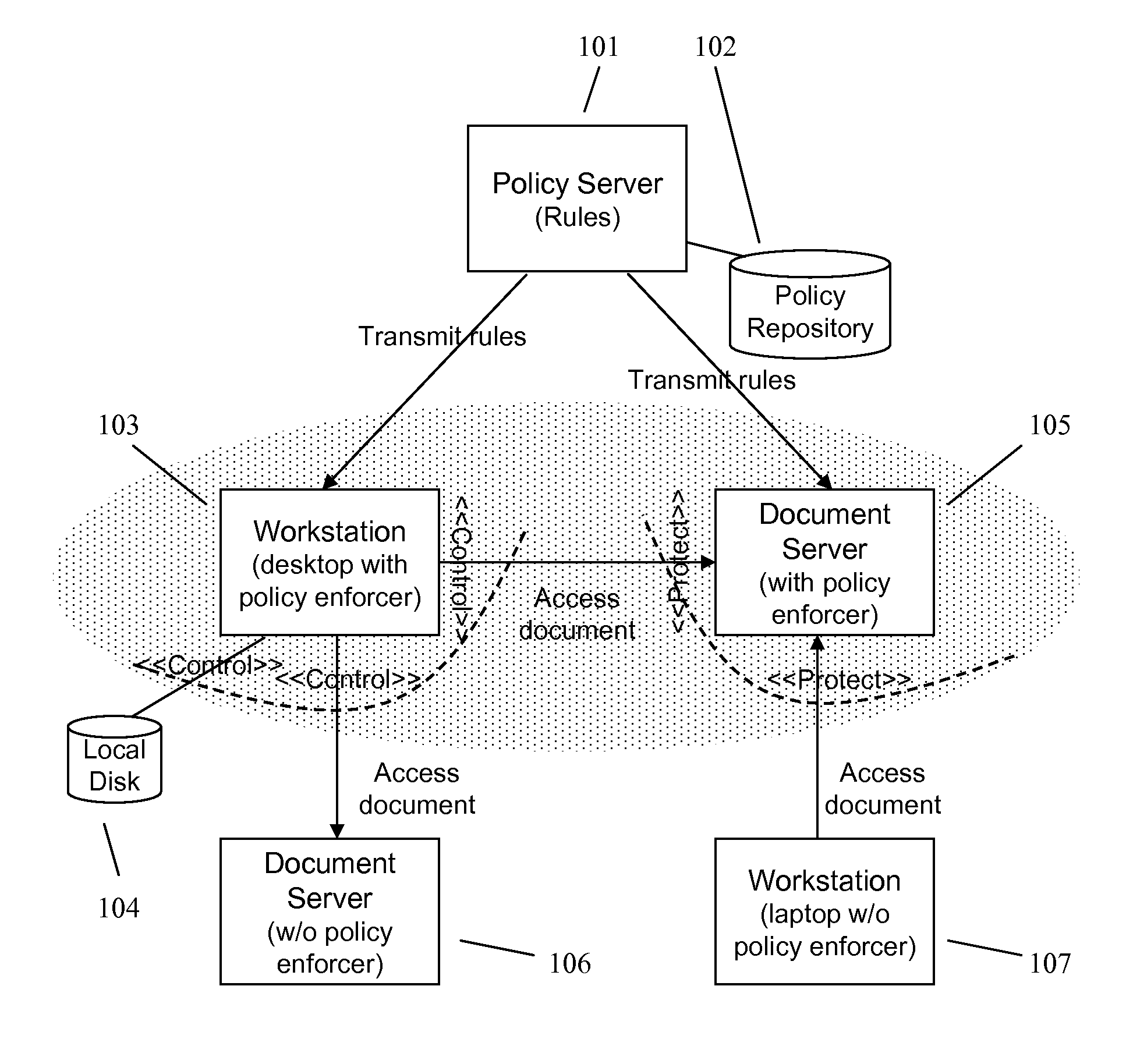
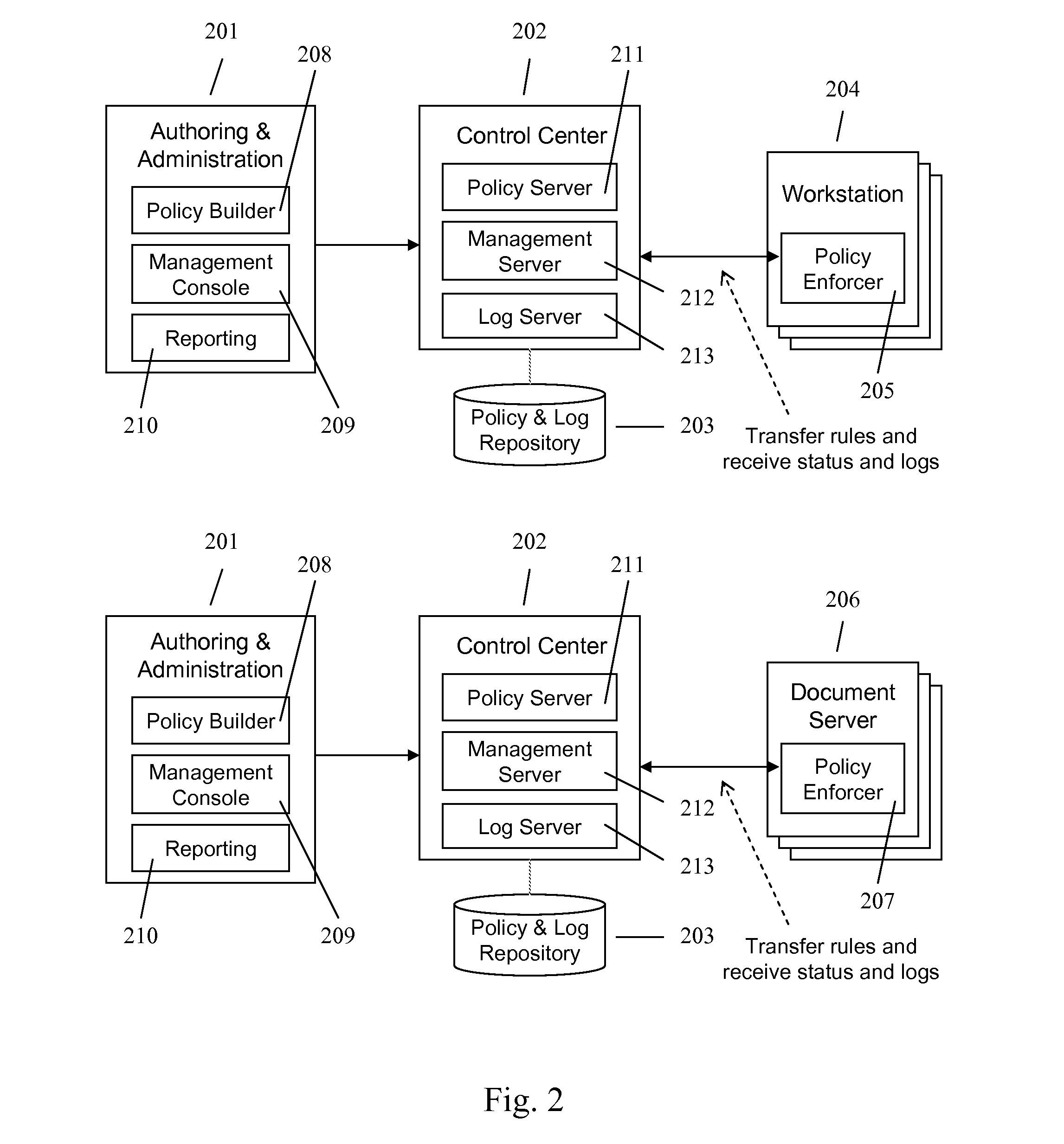
Enforcing Control Policies in an Information Management System
ActiveUS20070156897A1Digital data processing detailsDigital computer detailsClient-sideCentralized management
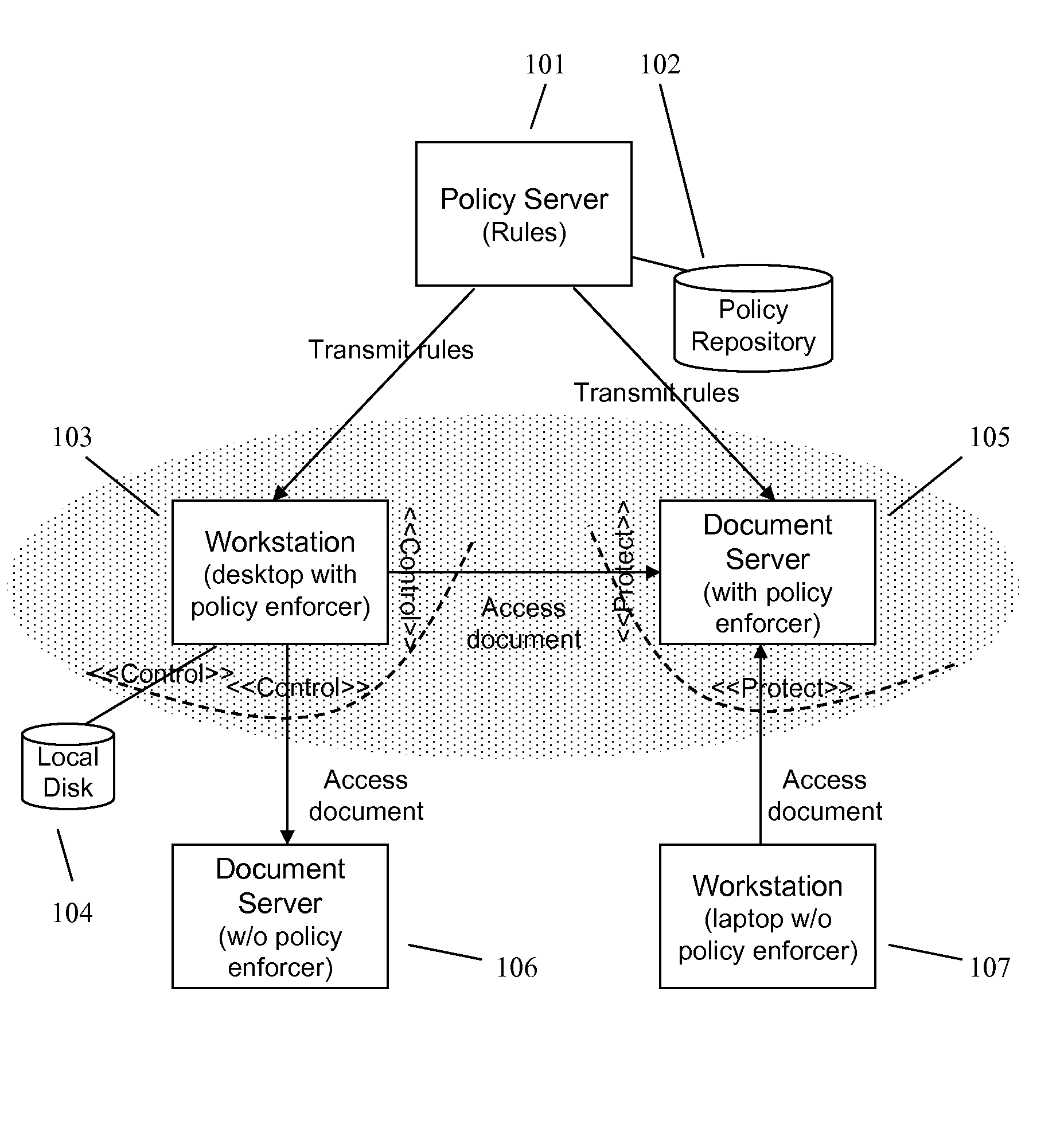
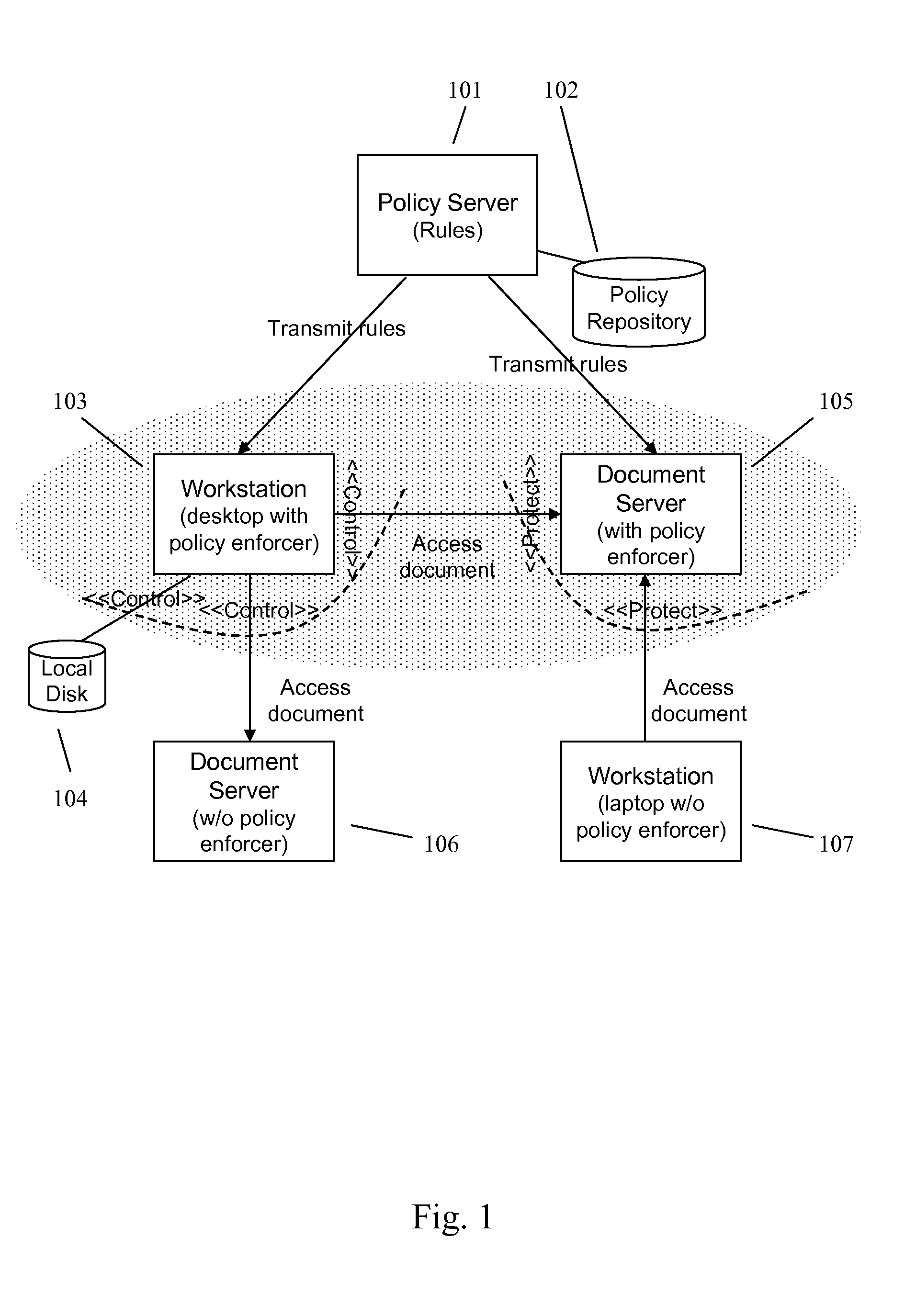
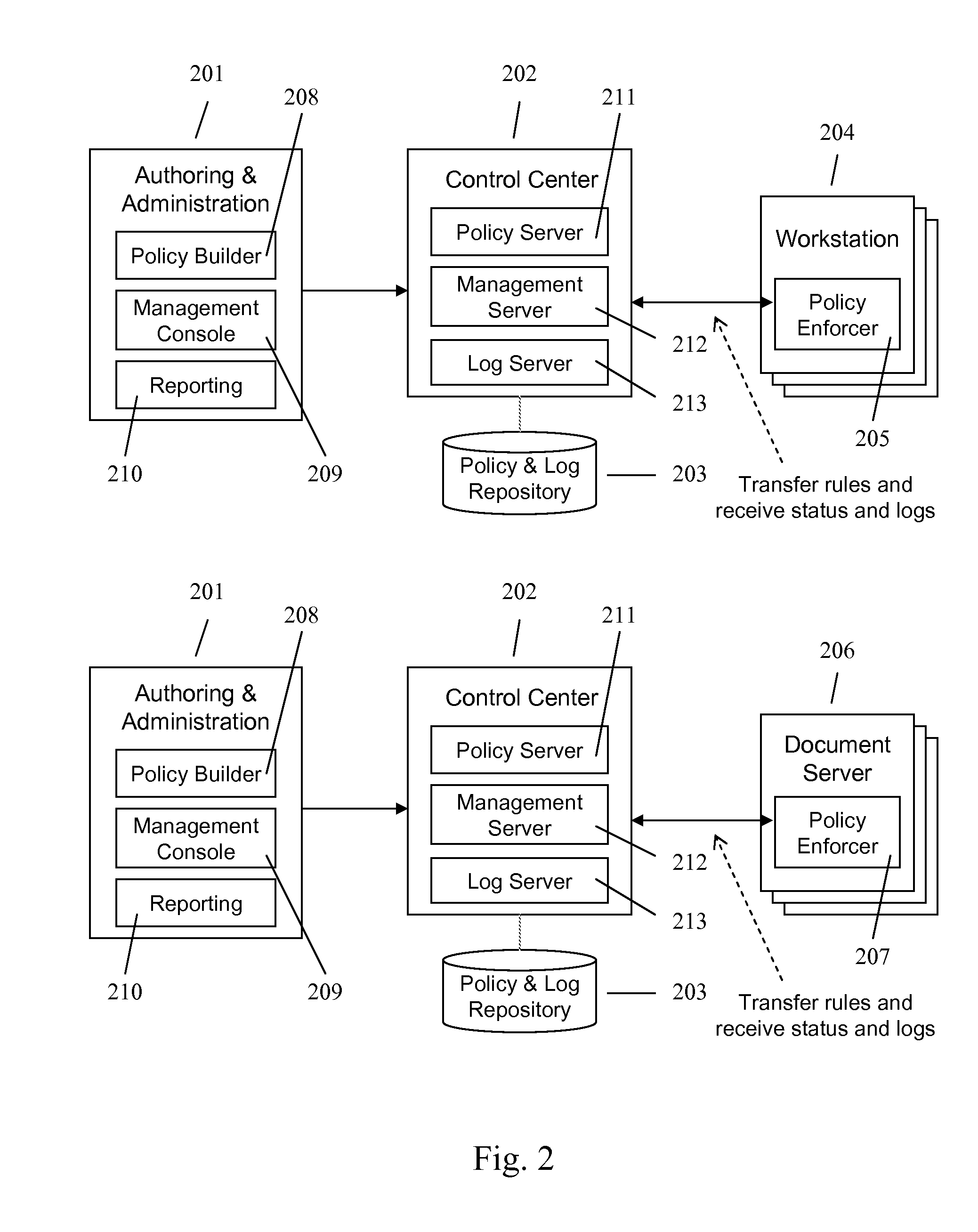
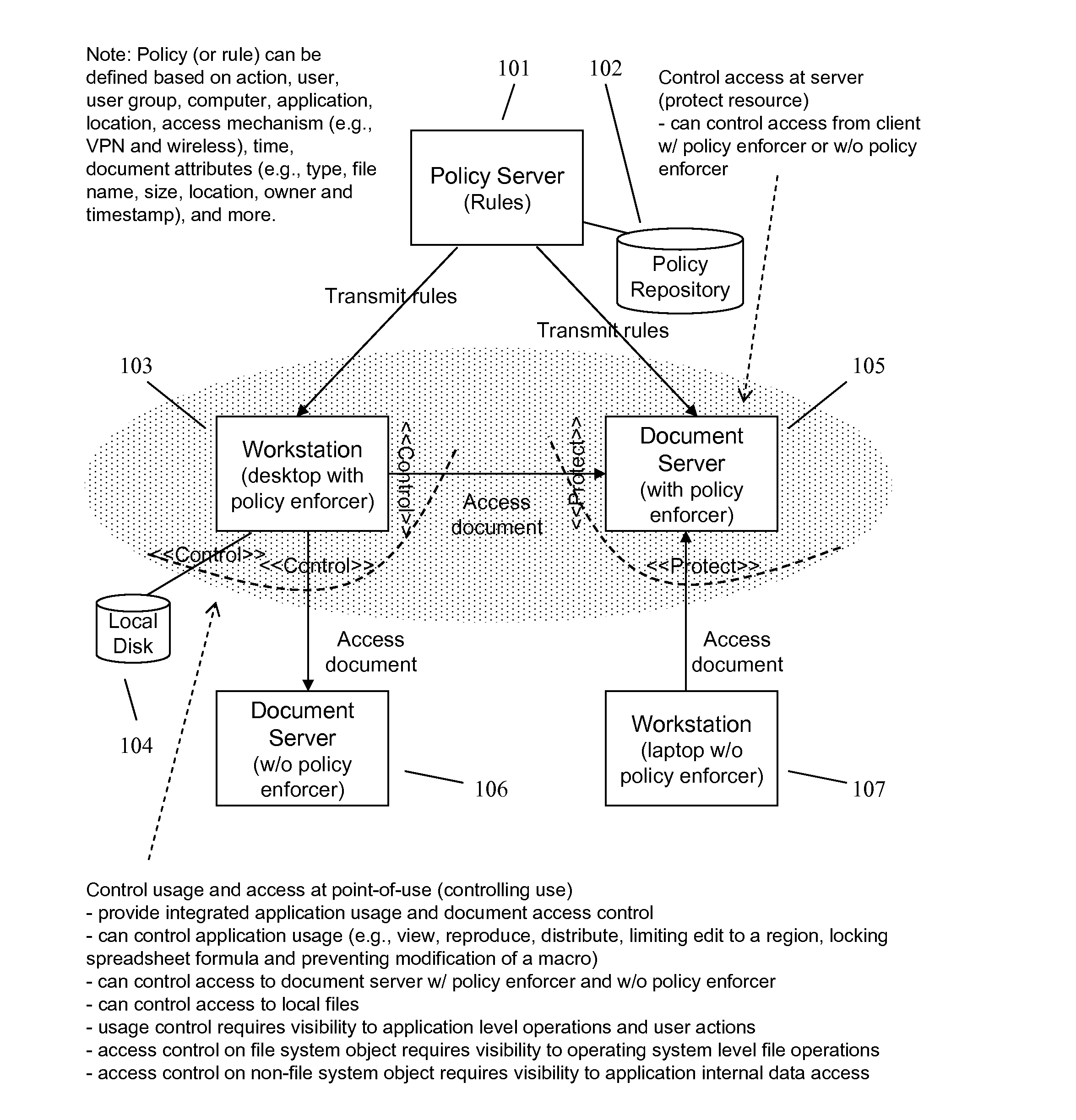
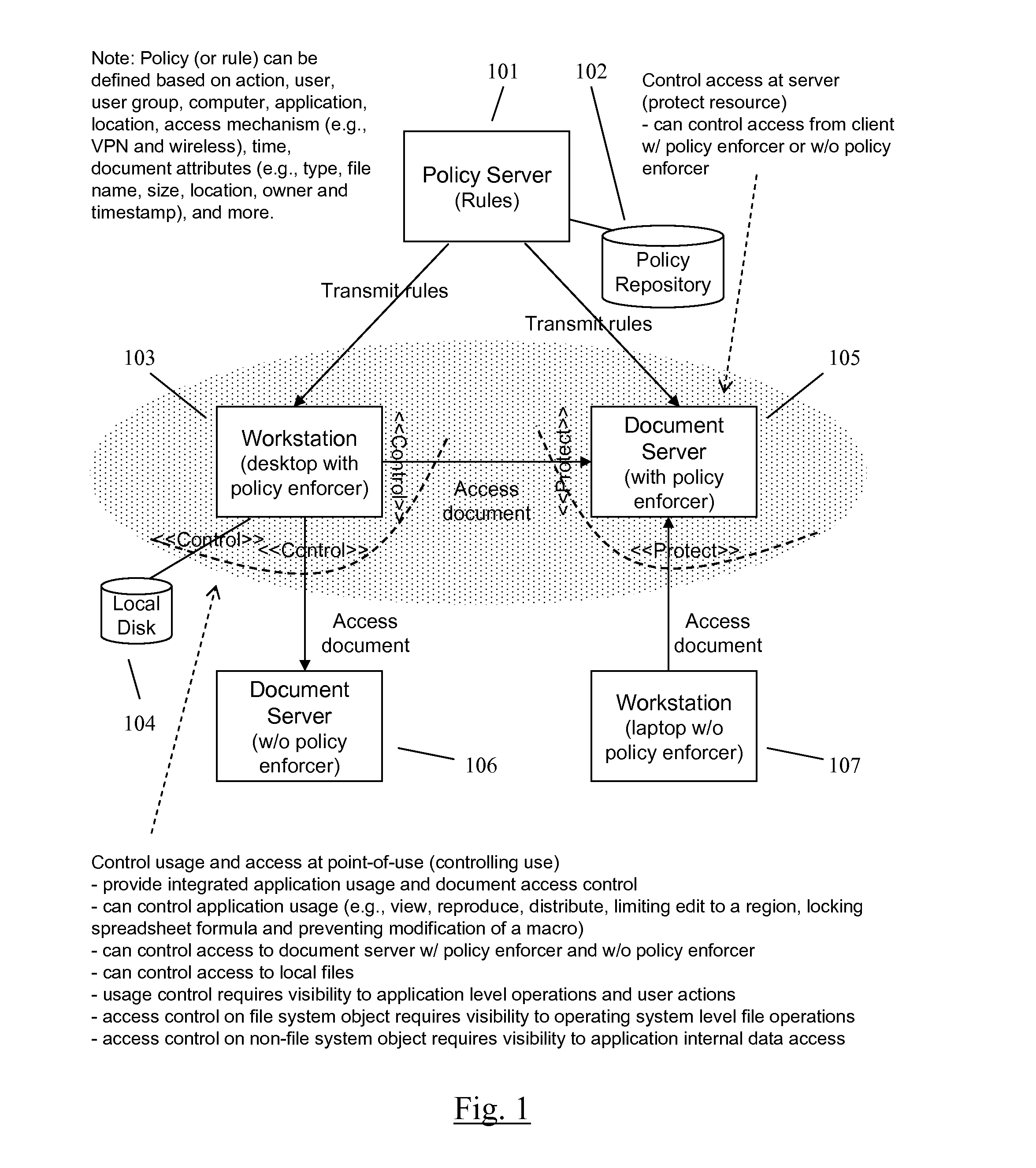
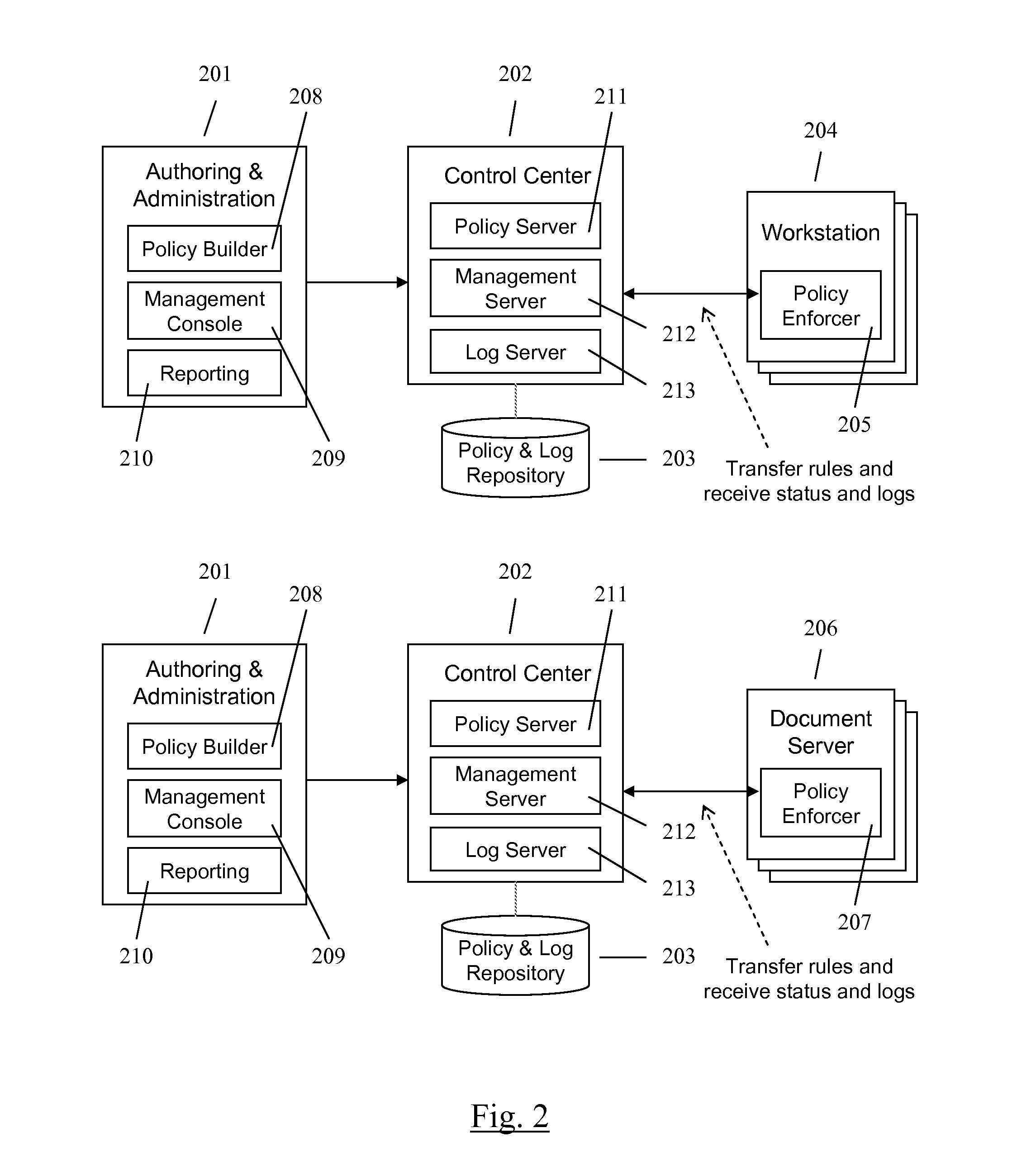
A method and apparatus for controlling document access and application usage using centrally managed rules. The rules are stored and manipulated in a central rule database via a rule server. Policy enforcers are installed on client systems and / or on servers and perform document access and application usage control for both direct user document accesses and application usage, and application program document accesses by evaluating the rules sent to the policy enforcer. The rule server decides which rules are required by each policy enforcer. A policy enforcer can also perform obligation and remediation operations as a part of rule evaluation. Policy enforcers on client systems and servers can operate autonomously, evaluating policies that have been received, when communications have been discontinued with the rule server.
Owner:BLUE JUNGLE
Apparatus and method for providing secure network communication
InactiveUS20020162026A1Eliminate attackEliminate needData taking preventionDigital data processing detailsFault toleranceIntelligent Network
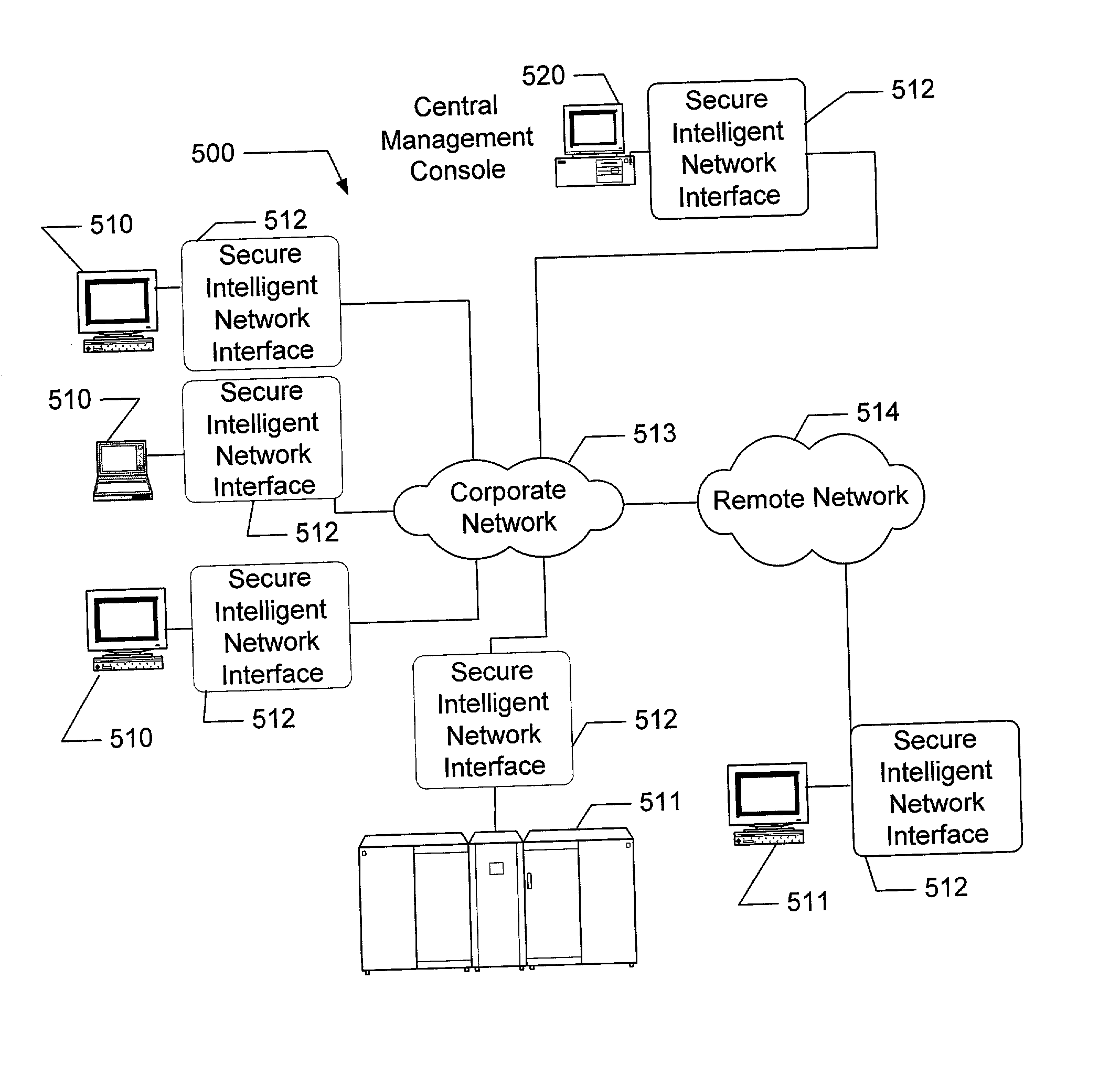
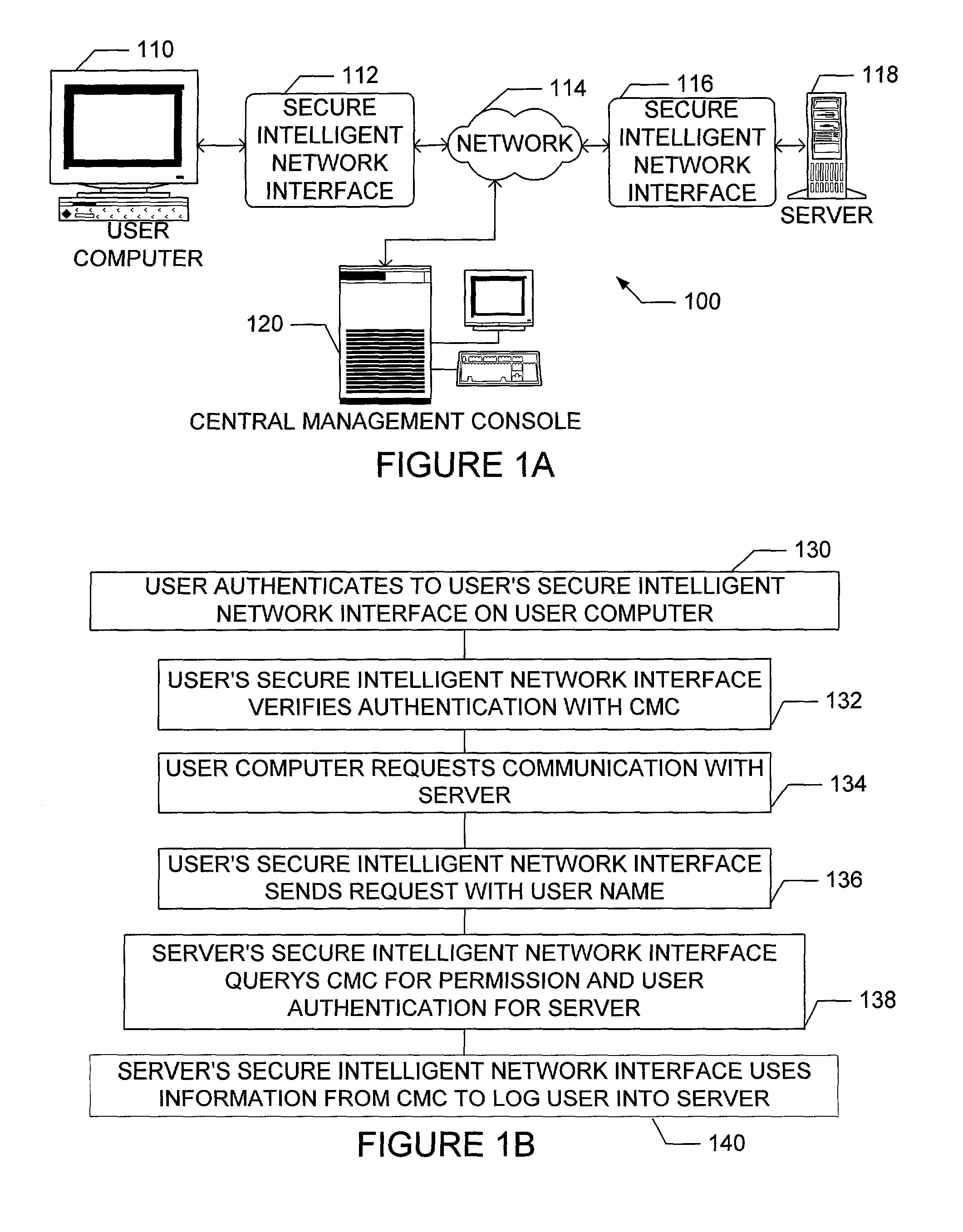
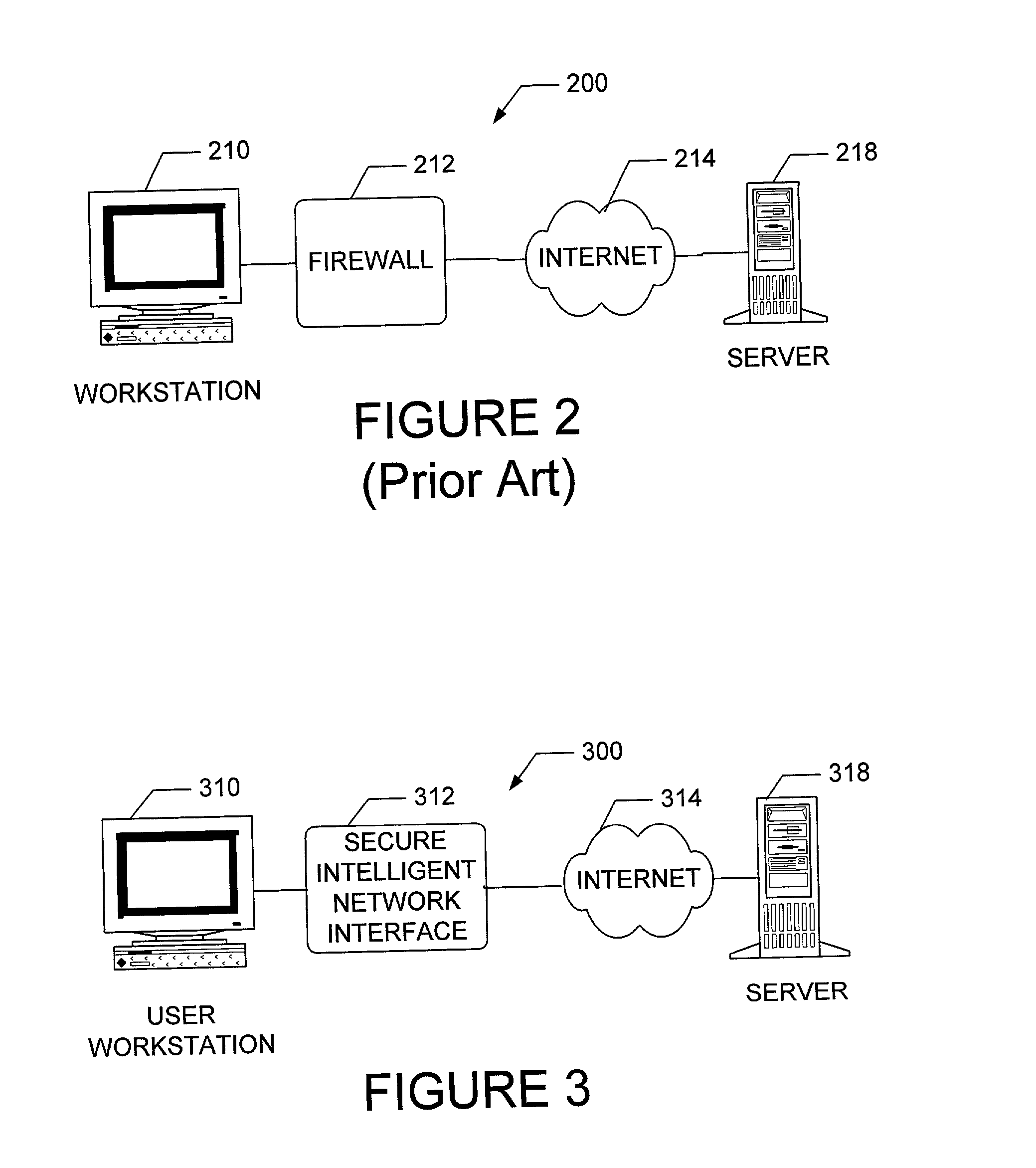
The present invention is drawn to an apparatus and method for providing secure network communication. Each node or computer on the network has a secure, intelligent network interface with a coprocessor that handles all network communication. The intelligent network interface can be built into a network interface card (NIC) or be a separate box between each machine and the network. The intelligent network interface encrypts outgoing packets and decrypts incoming packets from the network based on a key and algorithm managed by a centralized management console (CMC) on the network. The intelligent network interface can also be configured by the CMC with dynamically distributed code to perform authentication functions, protocol translations, single sign-on functions, multi-level firewall functions, distinguished-name based firewall functions, centralized user management functions, machine diagnostics, proxy functions, fault tolerance functions, centralized patching functions, Web-filtering functions, virus-scanning functions, auditing functions, and gateway intrusion detection functions.
Owner:NEUMAN MICHAEL +1
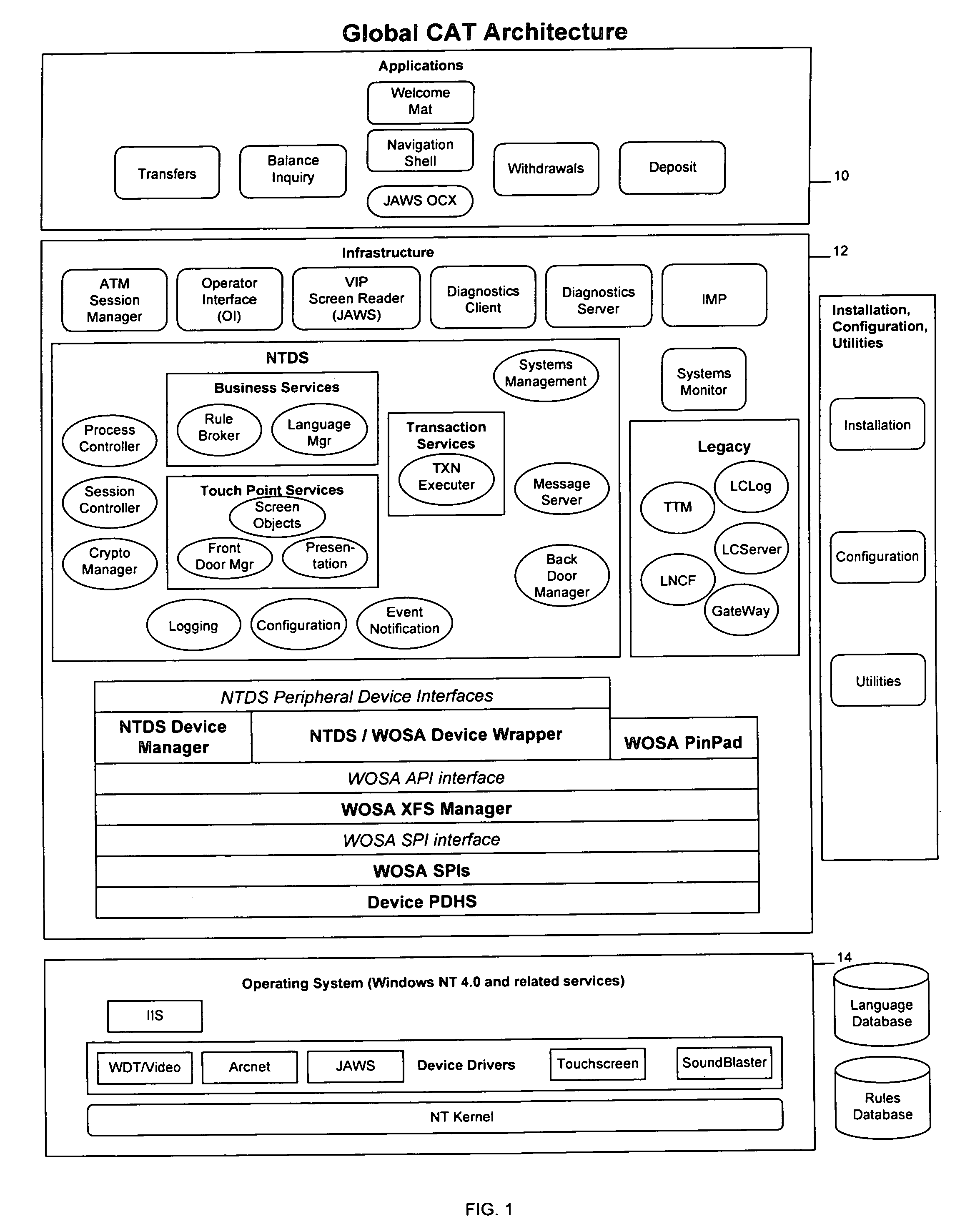
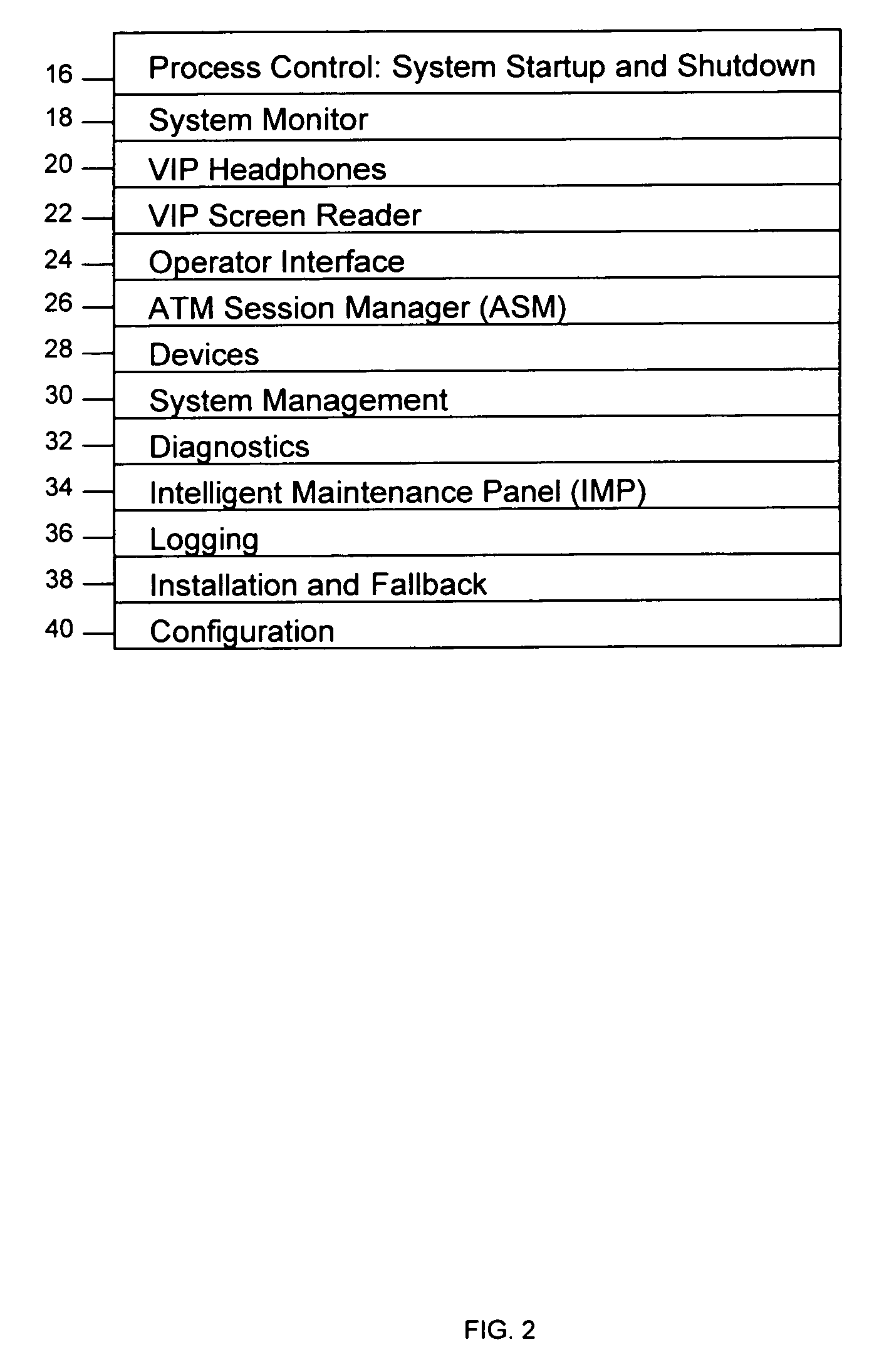
System and method for providing global self-service financial transaction terminals with worldwide web content, centralized management, and local and remote administration
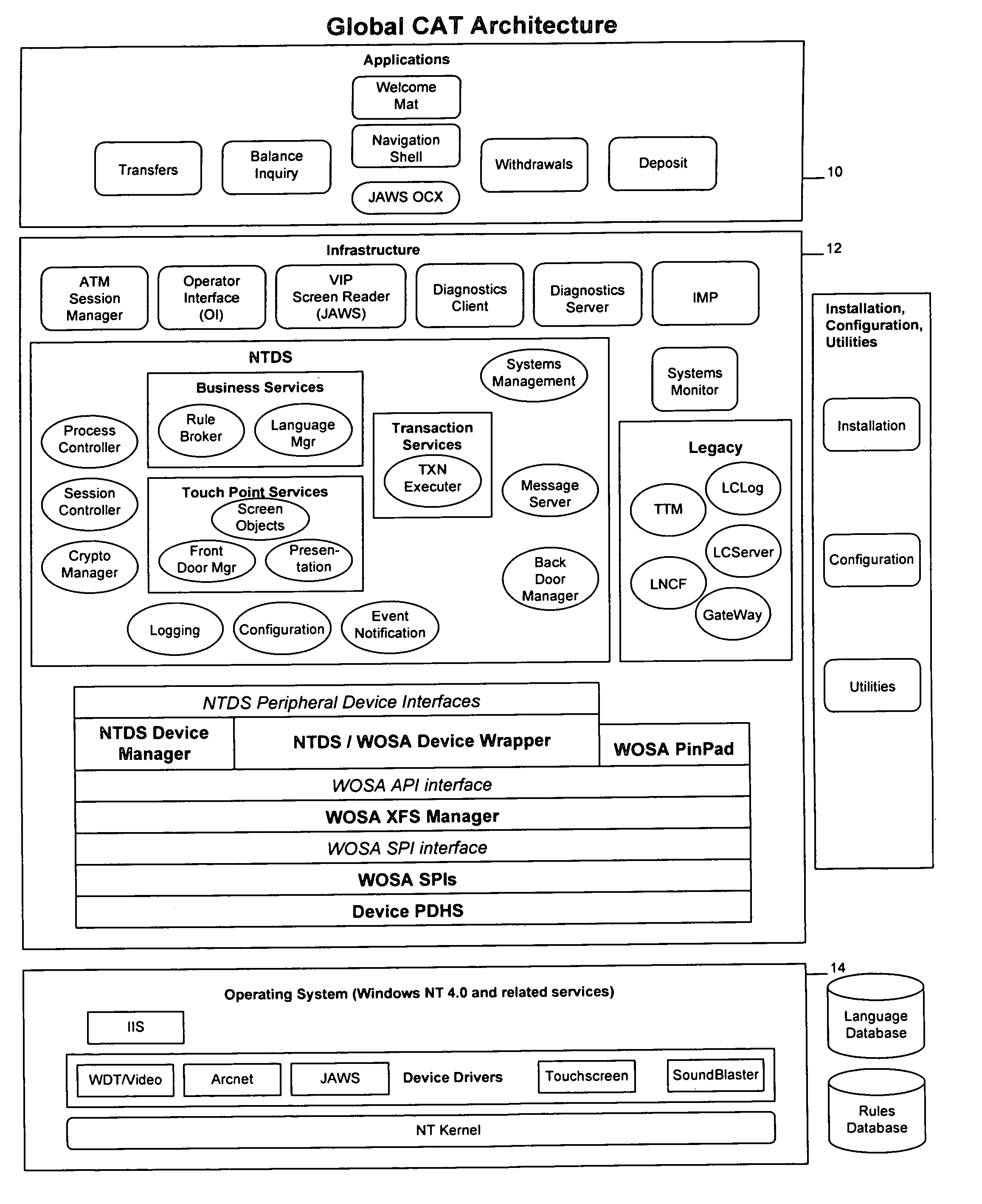
A method and system for providing global self-service transaction terminals or automatic teller machines (ATMs) affords worldwide web content to ATM customers, centralized management for ATM operators, and supports local and remote administration for ATM field service personnel. The system includes multiple ATMs coupled over a network to a host, and the ATMs are provided with a touch screen interface and an interface for visually impaired persons. The ATMs enable both local and remote administration of ATM operations by bank personnel and an integrated network control. The ATMs are web-enabled, and ATM communications are performed over a communications network.
Owner:CITICORP CREDIT SERVICES INC (USA)
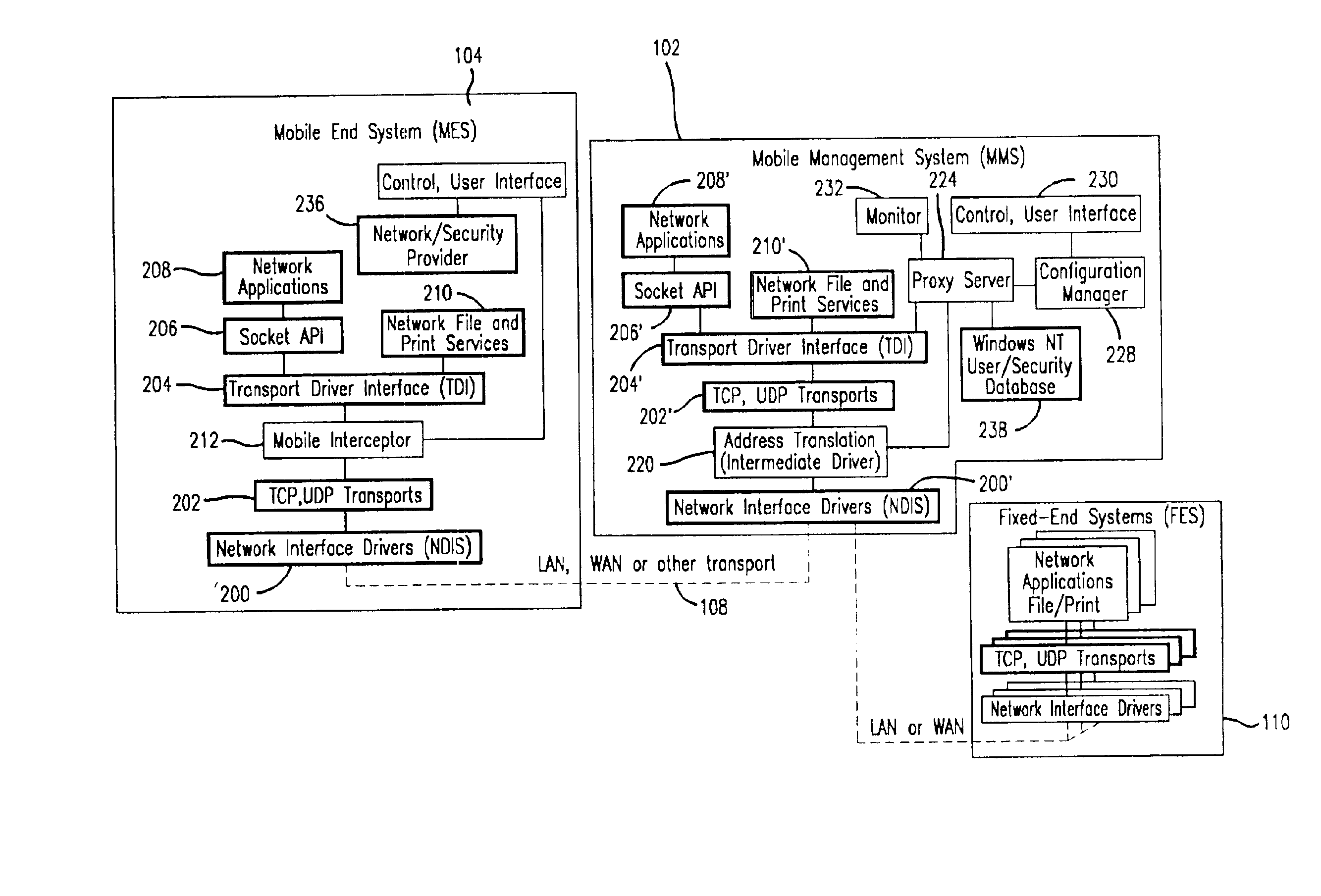
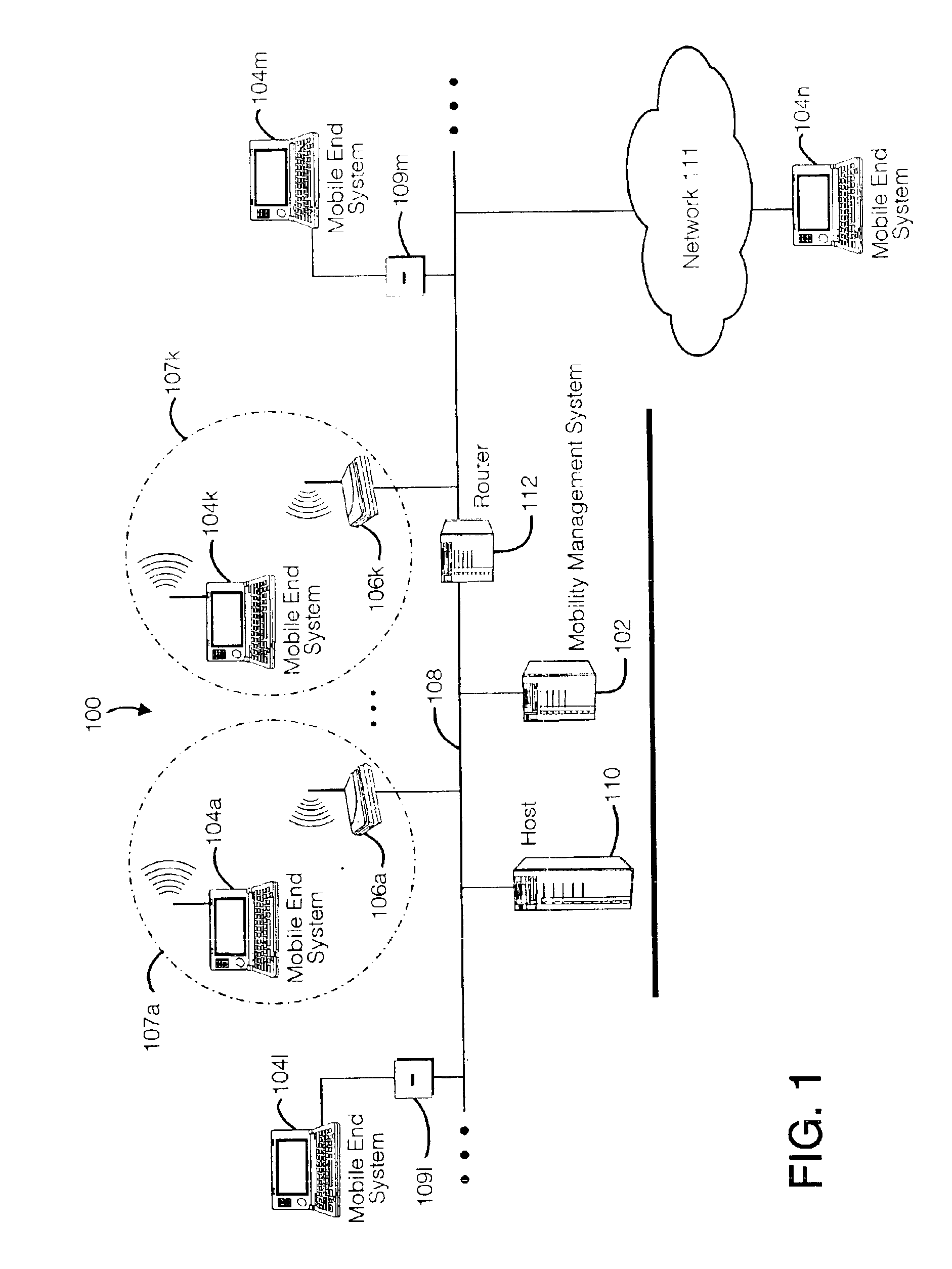
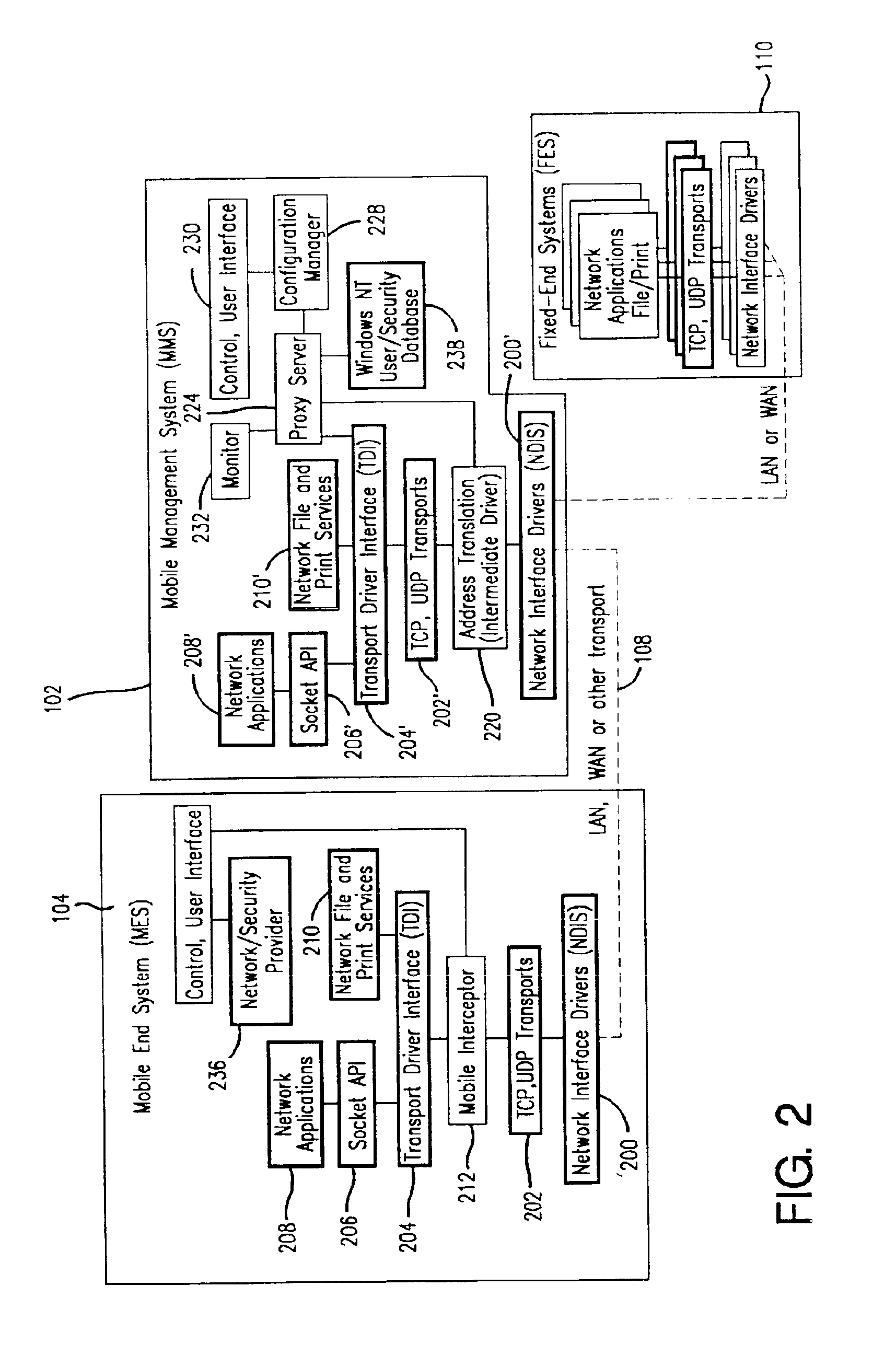
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS6981047B2Error prevention/detection by using return channelData switching by path configurationMobile endNetwork address
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. The solution extends the enterprise network, letting network managers provide mobile users with easy access to the same applications as stationary users without sacrificing reliability or centralized management. The solution combines advantages of existing wire-line network standards with emerging mobile standards to create a solution that works with existing network applications. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. In one example, Mobility Management Server communicates with Mobile End Systems using Remote Procedure Call and Internet Mobility Protocols.
Owner:MOBILE SONIC INC
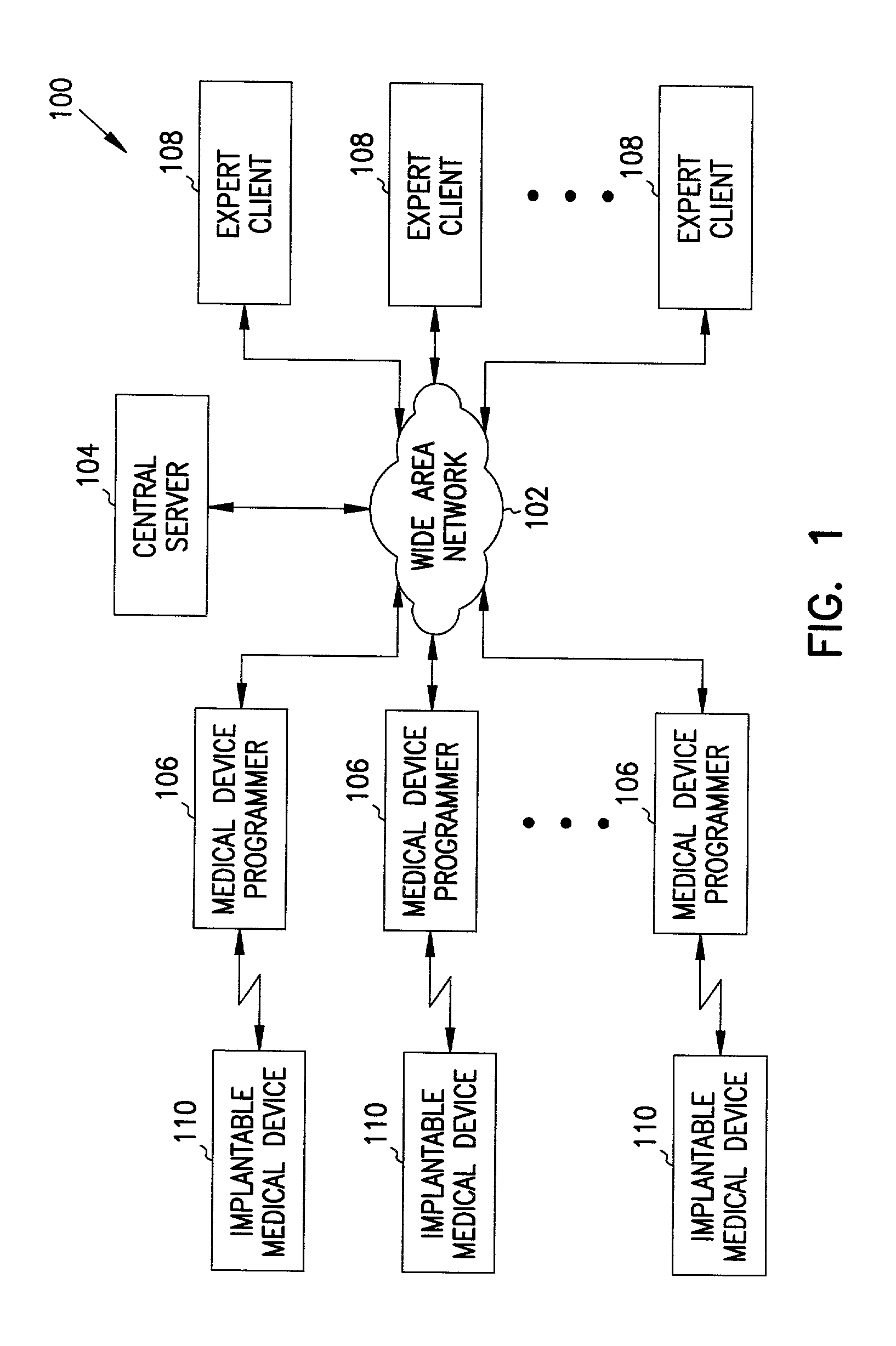
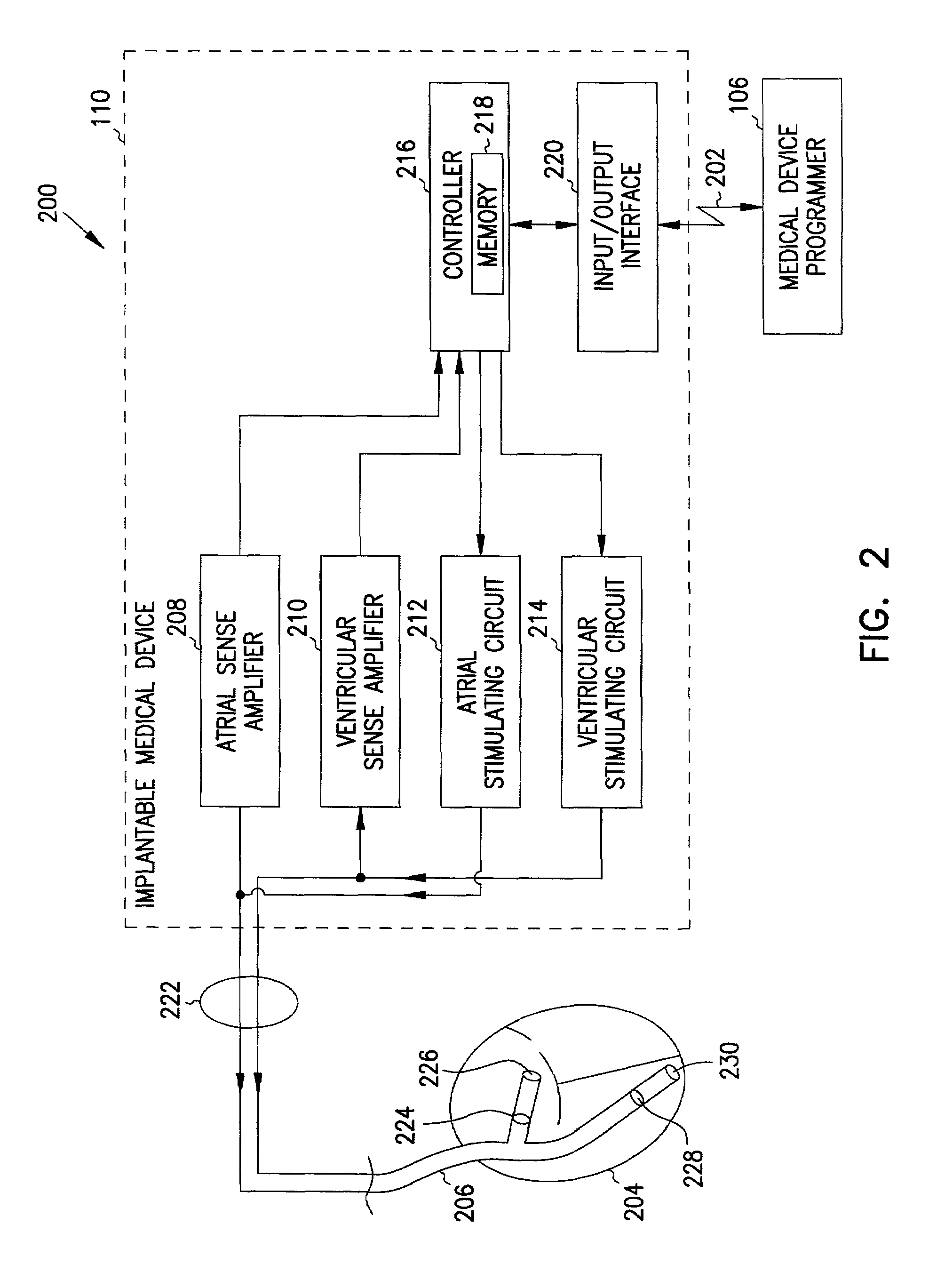
Centralized management system for programmable medical devices
InactiveUS7383088B2Physical therapies and activitiesData processing applicationsCentralized managementMedical prescription
A centralized management system for medical devices includes a network, a central server coupled to the network, and a medical device programmer coupled to the network. The central server includes at least one prescription system for prescribing at least one programmable parameter of a medical device based on at least one characteristic of a patient. The medical device programmer communicates at least one characteristic of a patient to the central server via the network, receives at least one parameter from the central server via the network, and programs the medical device using the at least one parameter. In one embodiment, the central server hosts expert prescription systems defined by multiple experts, and a user selects one of the expert prescription systems. In another embodiment, the central server hosts a custom prescription system defined by the user.
Owner:CARDIAC PACEMAKERS INC
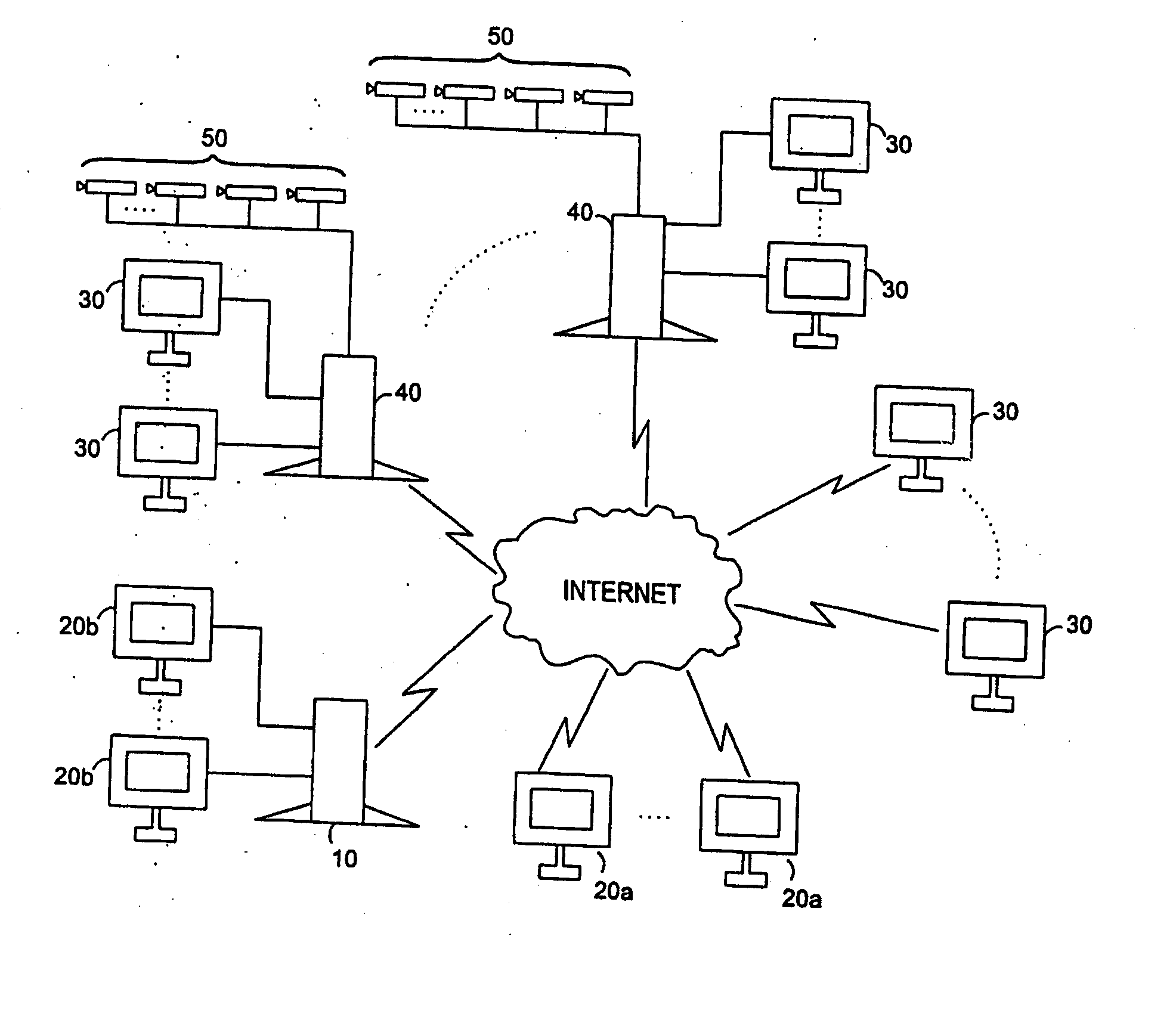
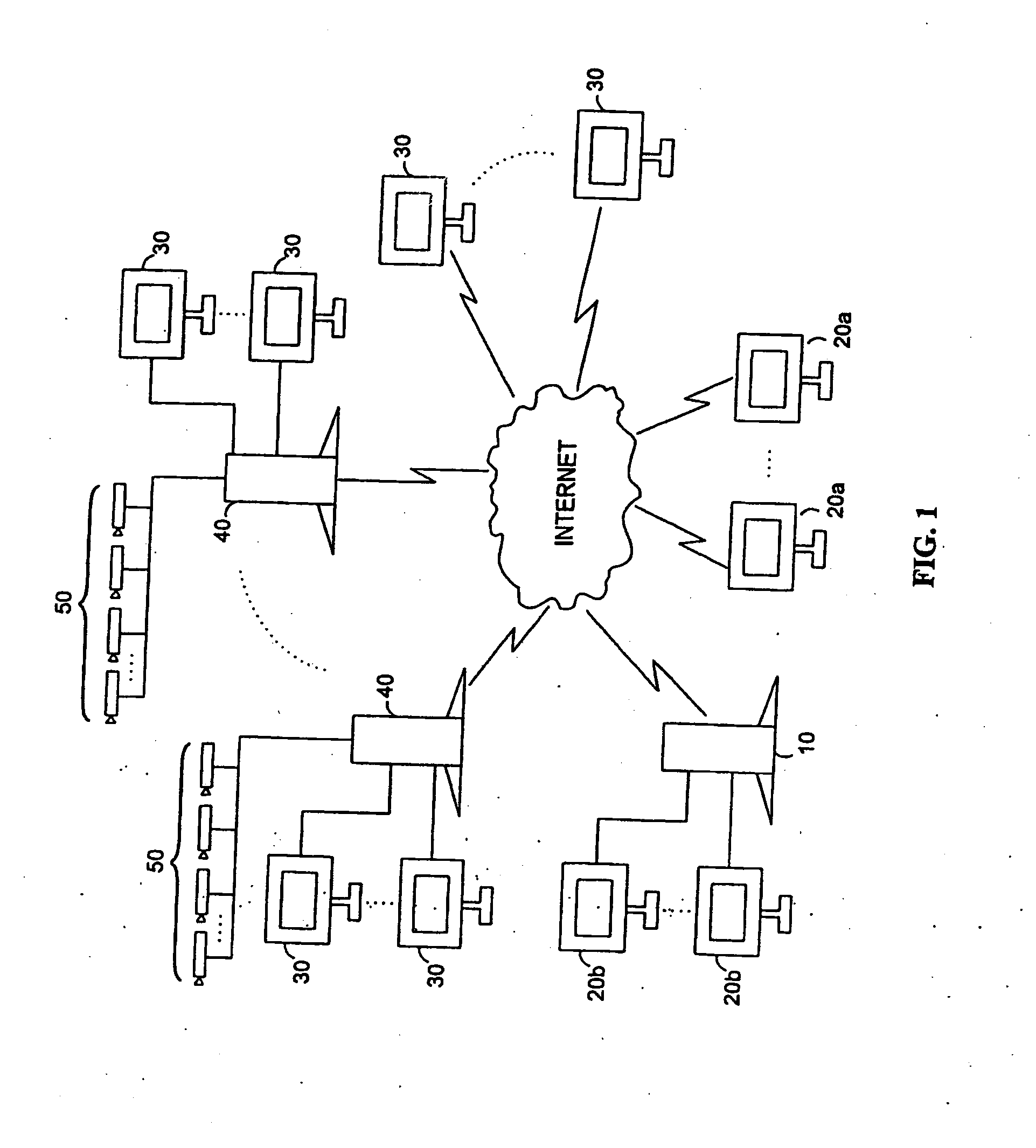
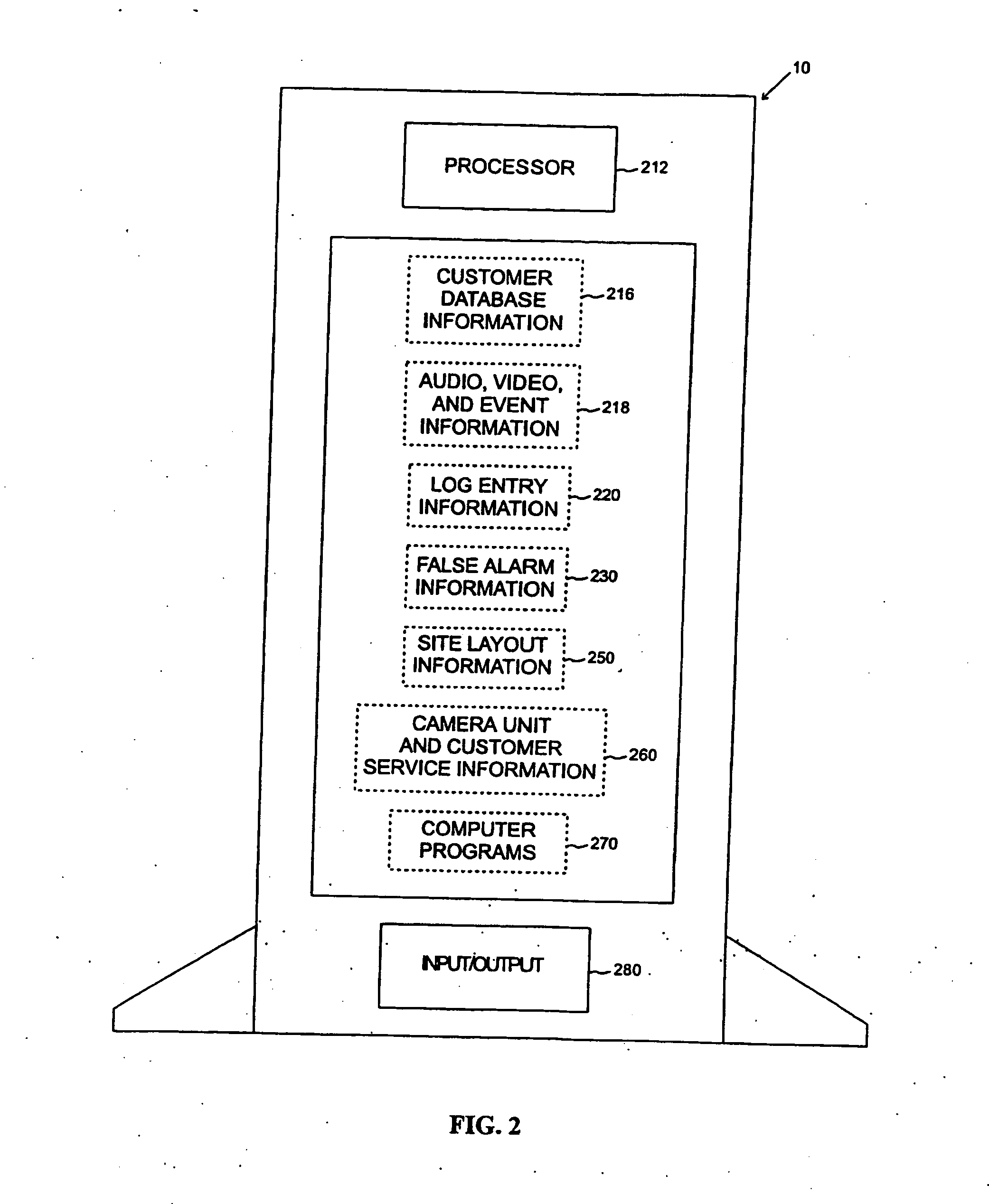
Networked digital security system and methods
InactiveUS20060053459A1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningWeb serviceWorkstation
A networked digital security system is disclosed that preferably includes a centralized administrator web server coupled via a communication network such as the Internet to a plurality of customer servers and-a plurality of customer work stations. The centralized web server advantageously provides a point of control and management of the networked digital security system. The customer servers and customer work stations are preferably located at the customer's monitored sites. The customer servers are coupled to one or more intelligent camera units, which are preferably fully integrated intelligent units that gather, analyze, and transmit video, audio, and associated detected alarm event information to their associated customer server and the administrator web server. The camera units also include an intelligent automatic gain controller, an encoder buffer controller, and a network bandwidth priority controller. The system supports several compression algorithm standards.
Owner:AXCESS INT INC
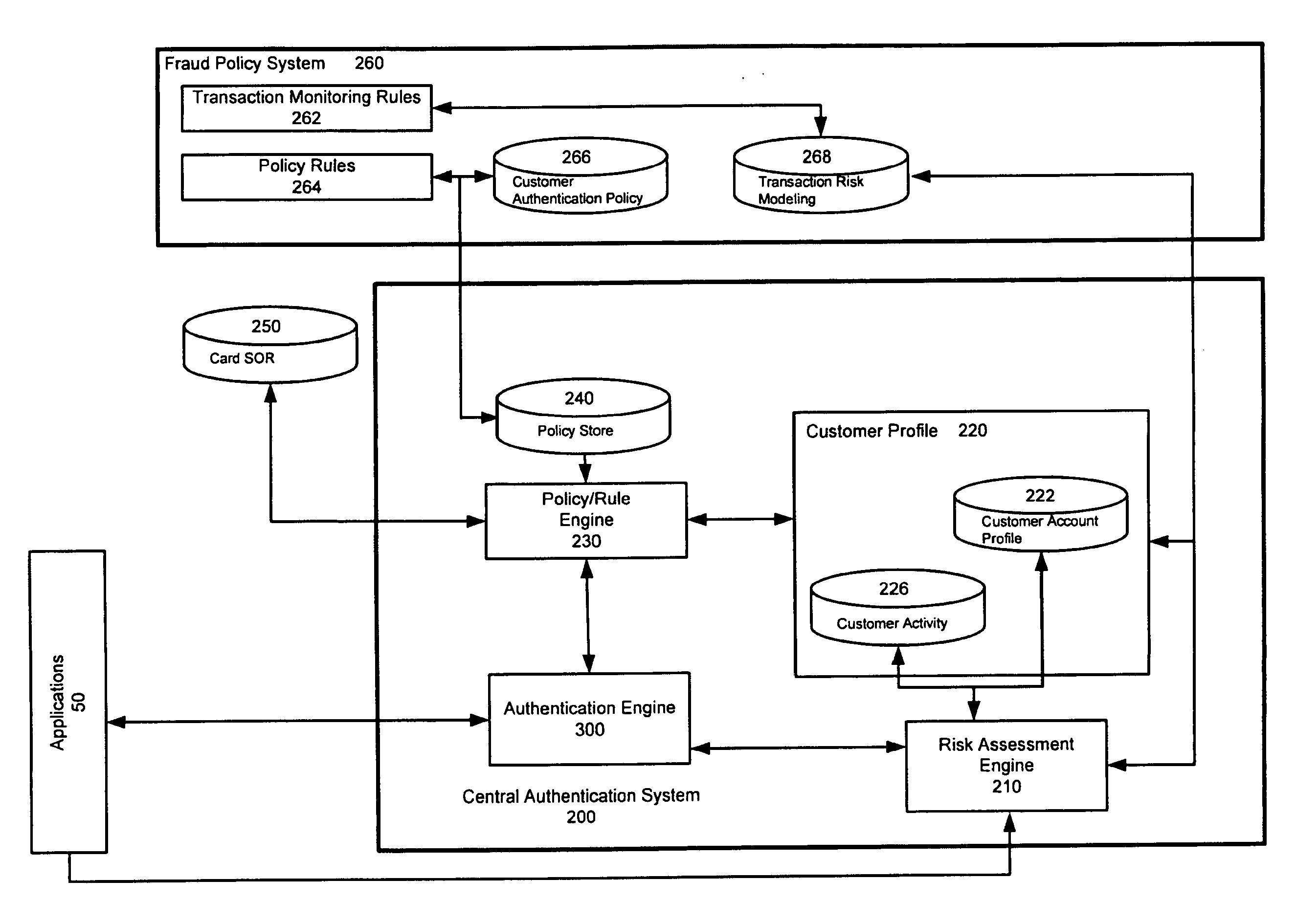
Authentication System and Method
ActiveUS20120297446A1Payment architectureDigital data authenticationInternet privacyCentralized management
Owner:JPMORGAN CHASE BANK NA
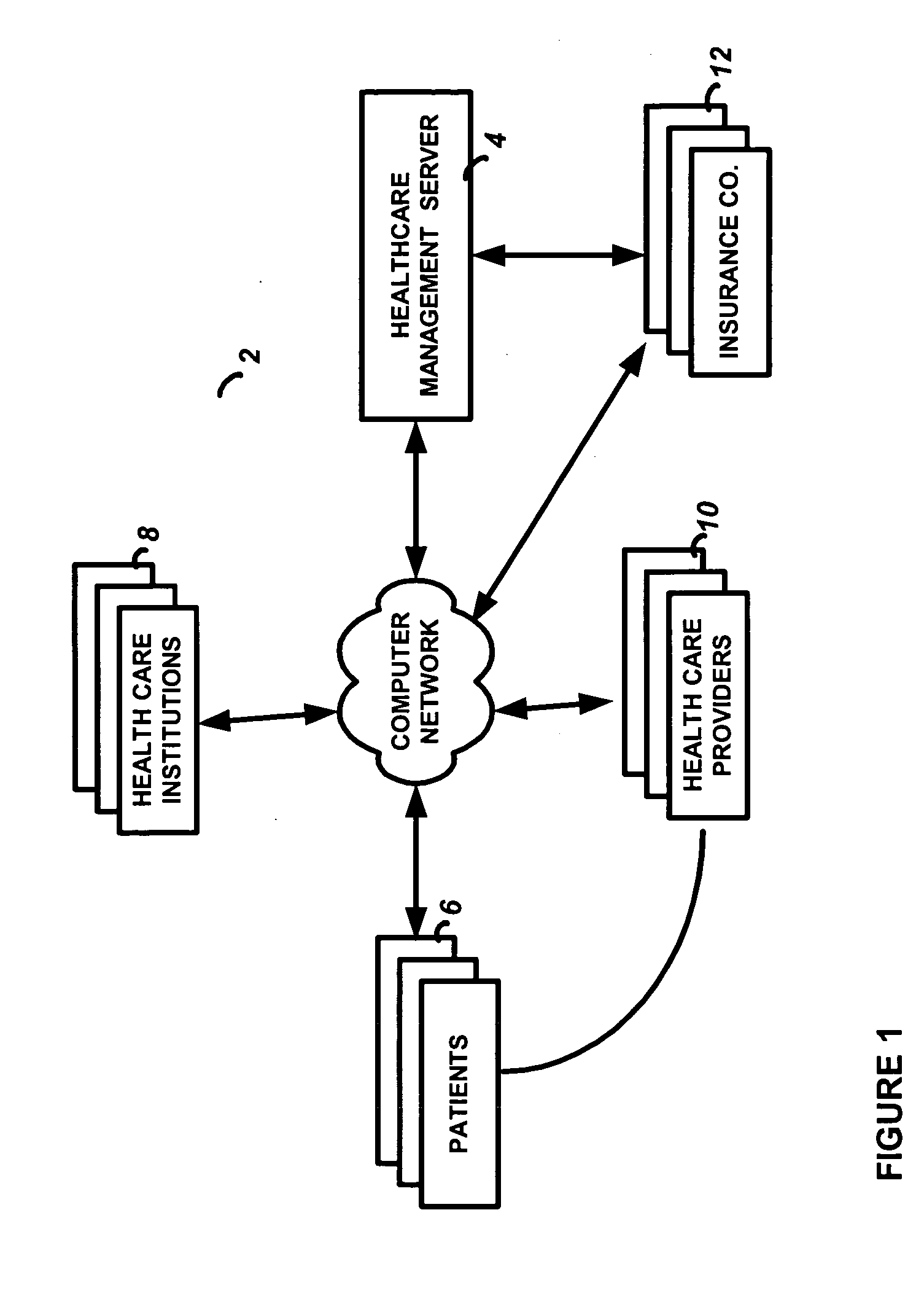
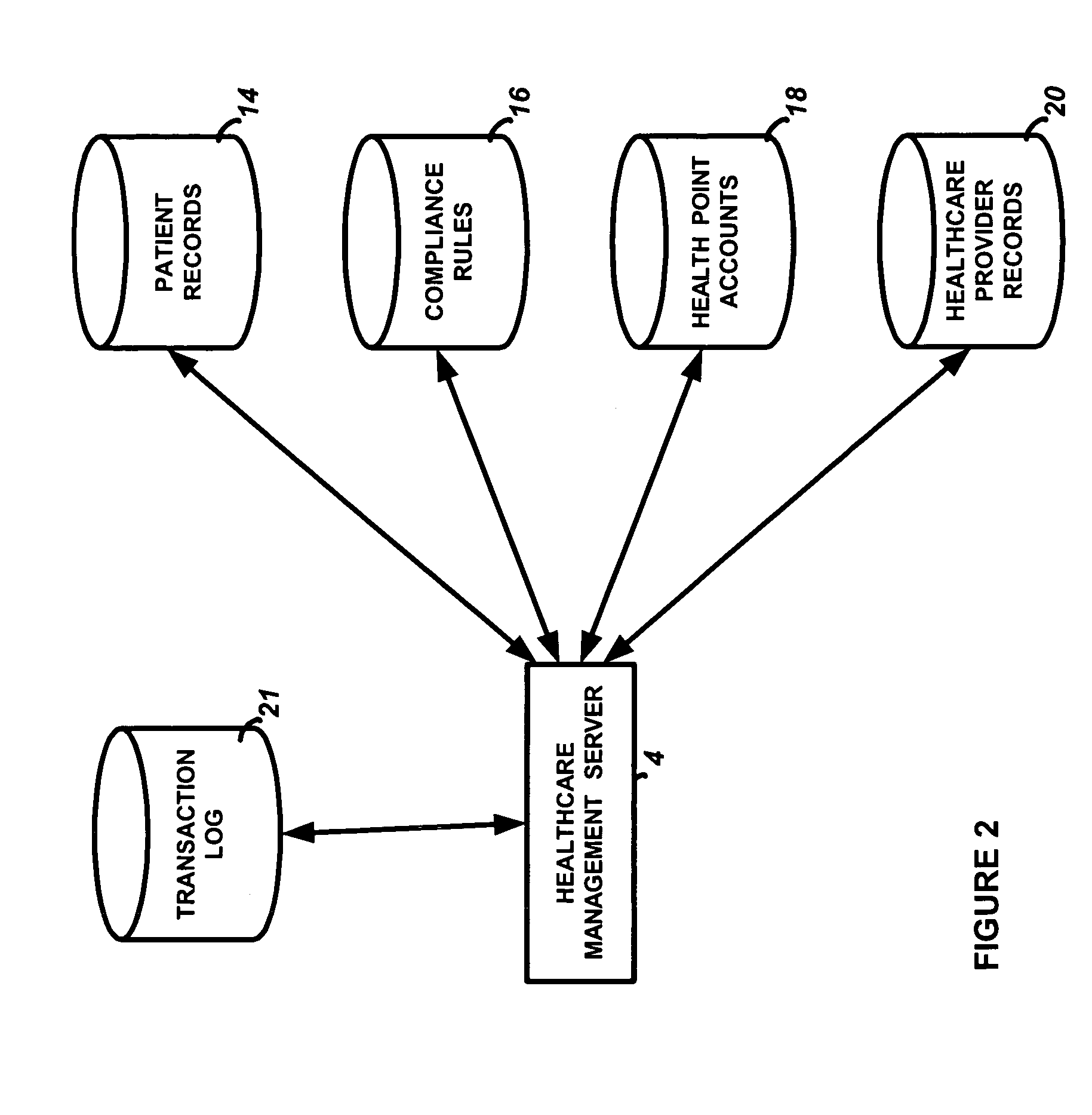
System and method for centralized management and monitoring of healthcare services
InactiveUS20060064320A1Reduced insurance premiumReduced insurance premiumsData processing applicationsMedical equipmentMonitoring systemCentralized management
A centralized healthcare management and monitoring system and service including a healthcare management server computer interconnected to a computer network, having a first repository of records with patient healthcare information and a second repository with predetermined compliance rules with information regarding an interaction between multiple entities associated with the healthcare management server computer. Multiple healthcare provider computers, associated with a healthcare provider, allow input of patient identification indicia identification indicia presented by a patient and communicating with the healthcare management server computer over the computer network. A query is sent to the healthcare management server computer that includes the patient identification indicia; an identification of the healthcare services performed or proposed to be performed by the associated healthcare provider; and an identification of the healthcare provider performing the healthcare services. The healthcare management server computer then utilizes the query to access the first and second repositories to determine if the parameters of the query are in compliance with one or more of the predetermined compliance rules.
Owner:POSTREL RICHARD
Clustered computer system with centralized administration
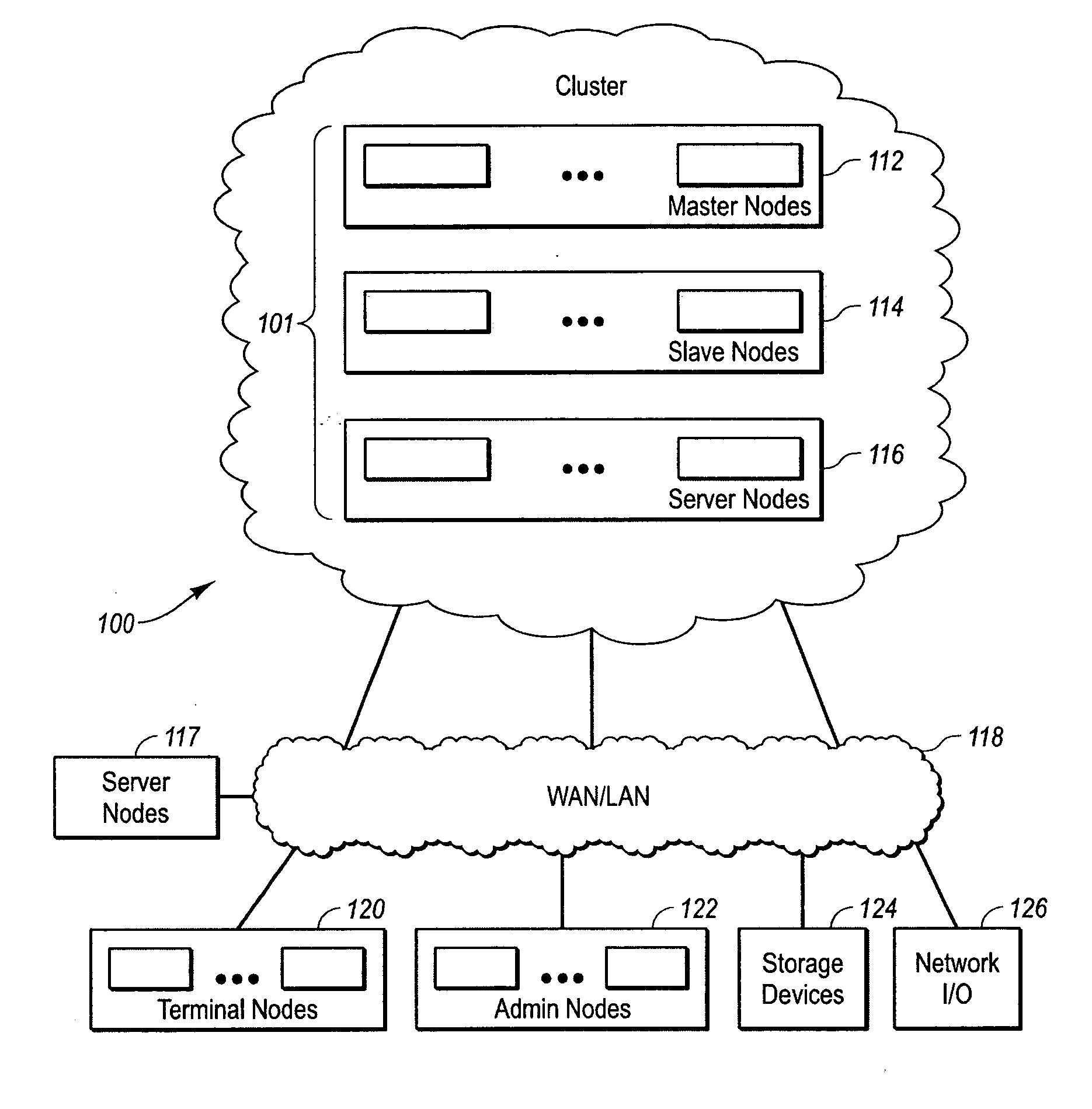
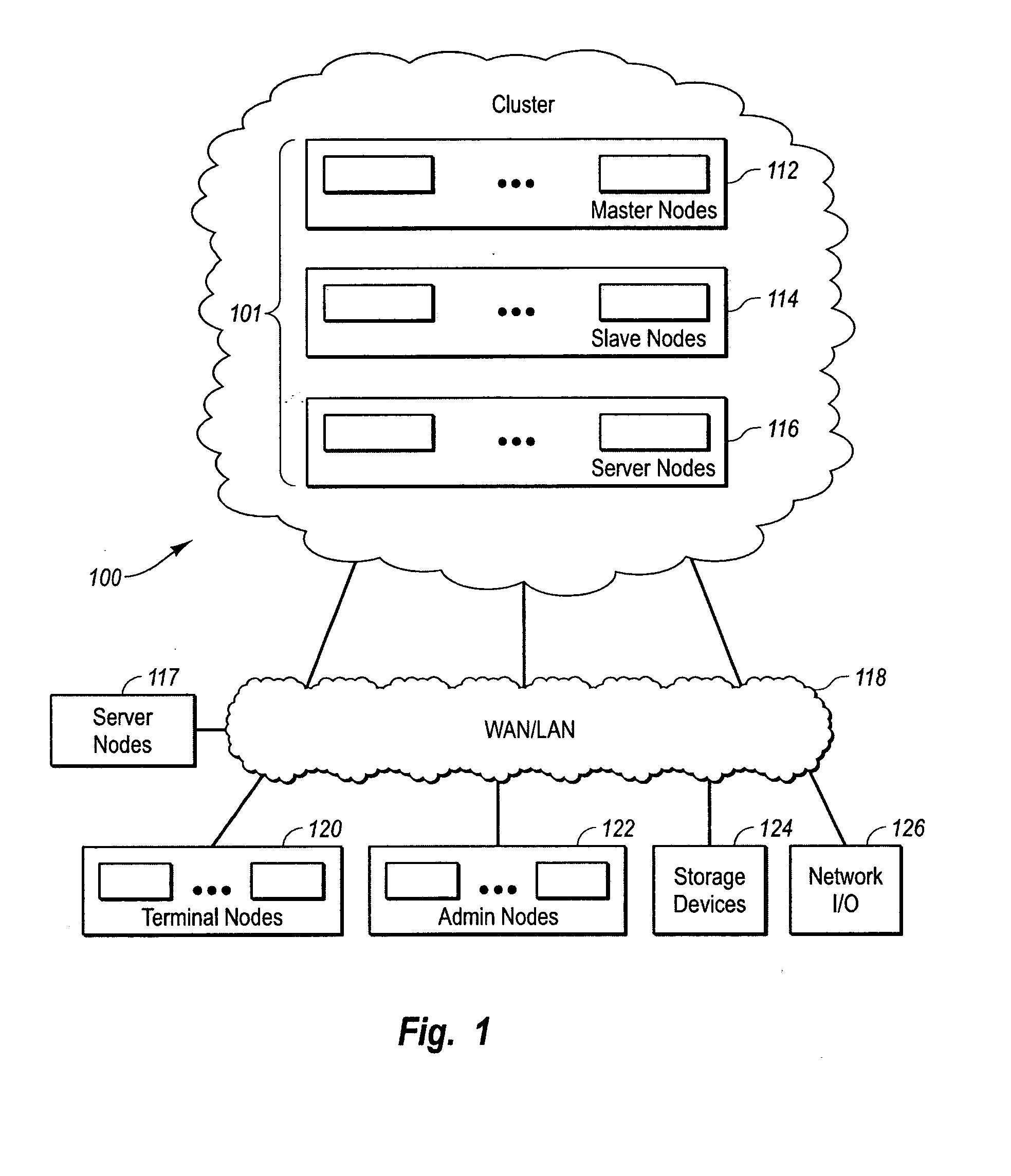
InactiveUS20060053216A1Digital computer detailsComputer security arrangementsOperational systemComputer cluster
Systems and methods for a computer cluster and for conducting user sessions in a managed enterprise computer network. A cluster includes multiple inter-connected nodes with specific roles. Master nodes administer and monitor slave nodes and the slave nodes are used to conduct user sessions with users through terminal nodes that provide an interface to the cluster. The cluster also may include server nodes that provide network services. Master nodes also control admittance to the cluster of external nodes and sub-clusters. Admin nodes form a control plane used to control and administer the cluster through the master nodes. The cluster provides a virtual environment for the user session that is built from at least an operating system image, an application image and other data needed for the user session.
Owner:METAMACHINIX
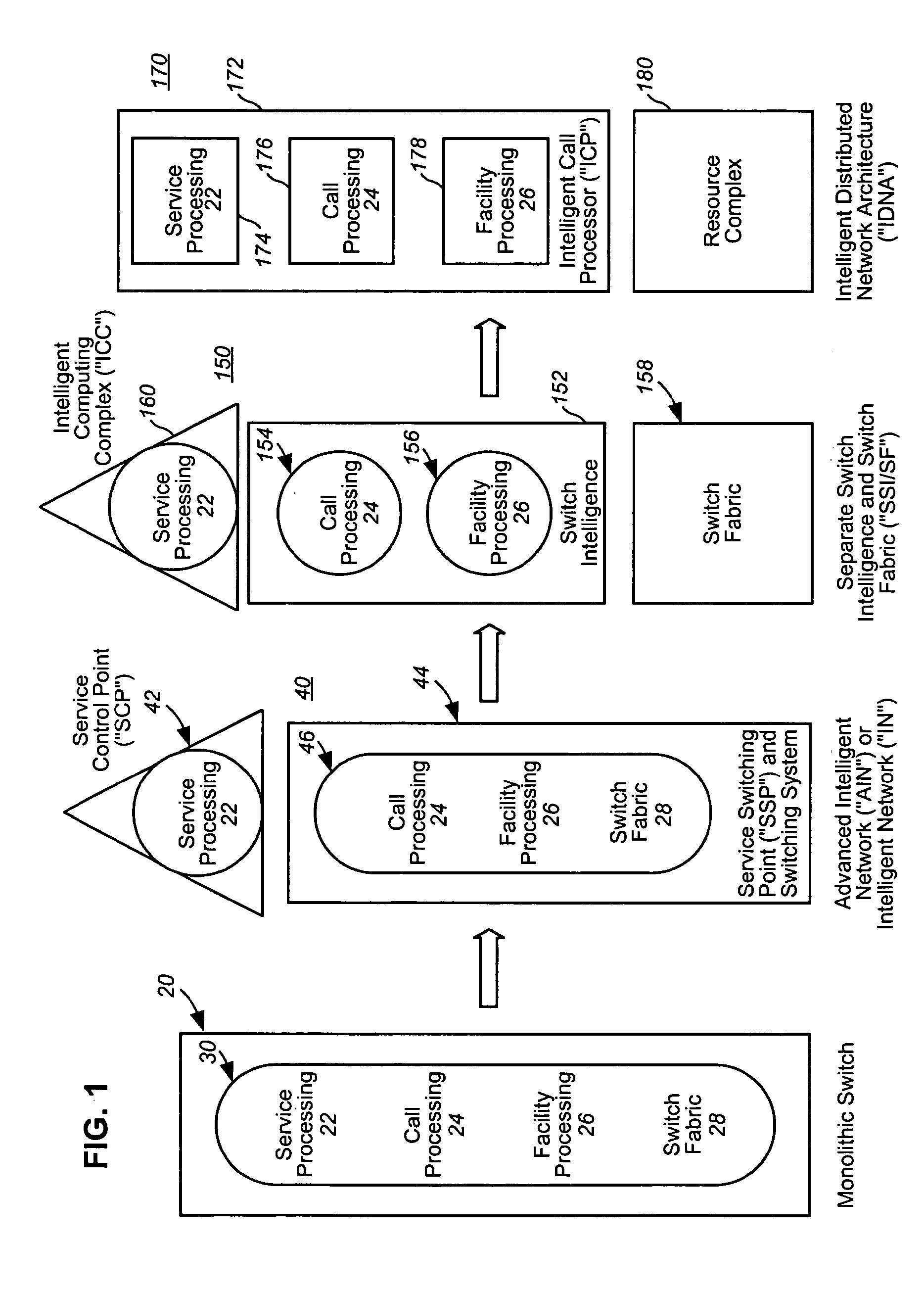
Intelligent network
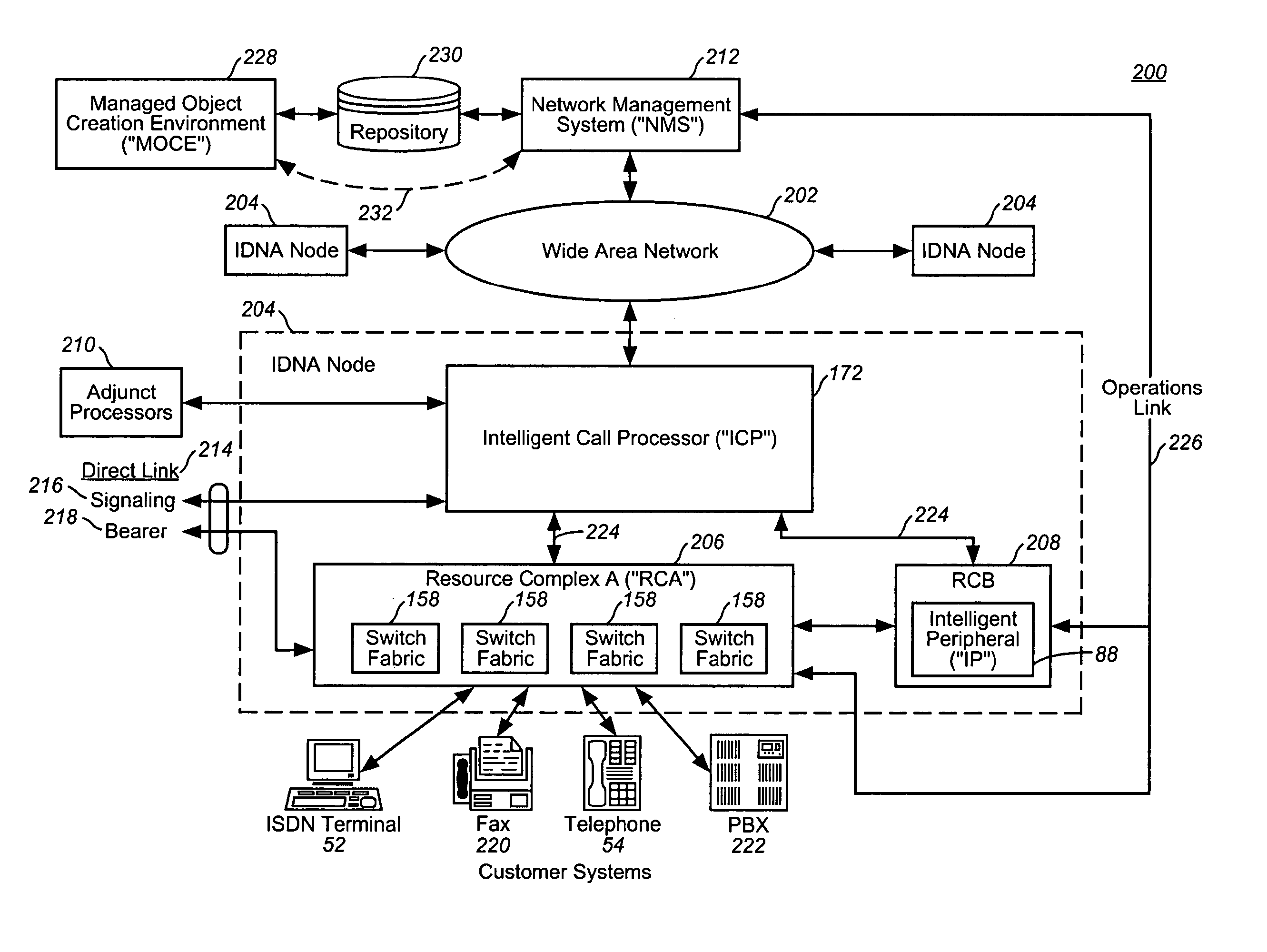
InactiveUS7209964B2Easy to handleEliminate dependenciesInterconnection arrangementsSpecial service for subscribersExchange networkBusiness object
In a telecommunications switching network having a resource complex including network switches, an intelligent service platform for providing intelligent call processing and service execution for call events received at the switches and requiring call processing services. A centralized administration system is provided that comprises a system for storing one or more reusable business objects that each encapsulate a distinct call-processing function, and any associated data required by the business object; a system for distributing selected business objects and associated data to selected nodes in the switching network based on pre-determined node configuration criteria; and, a system for activating the business objects in preparation for real-time use. A computing platform is provided within each node for executing those business objects required to perform a service in accordance with an event received at the network switch. Also within a node is a storage and retrieval system for sorting and retrieving selected objects and any associated data distributed by the administration system, and making them locally available to the computing platform when required to perform a service. An underlying location-independent communication system is provided to coordinate interaction of one or more business objects to perform the service in response to needs of the received event.
Owner:VERIZON PATENT & LICENSING INC
Hierarchical system and method for centralized management of thin clients
InactiveUS20030061323A1Digital computer detailsData switching networksInformation dispersalInformation transmission
A system and method for managing a network of thin clients is disclosed. The thin clients may be organized into a hierarchy with multiple administrative servers in a hierarchy, each managing one or more thin clients. Updates to thin client configurations may be performed by propagating update information to a top-level master administrative server, which in turn conveys the update information to one or more lower-level remote administrative servers, which in turn convey the update information to their managed thin clients. To simplify network management, the thin clients may be organized into arbitrary clusters, regardless of their position within the hierarchy structure. The hierarchy may also be used to control the propagation of error messages from thin clients. The hierarchy may be implemented using a thin client management program that configures thin clients according to their position within the hierarchy.
Owner:EAST KENNETH H +4
Distributed TDMA for wireless mesh network
InactiveUS20050201340A1Optimizing bandwidth usageFree communicationSynchronisation arrangementNetwork traffic/resource managementQuality of serviceWireless mesh network
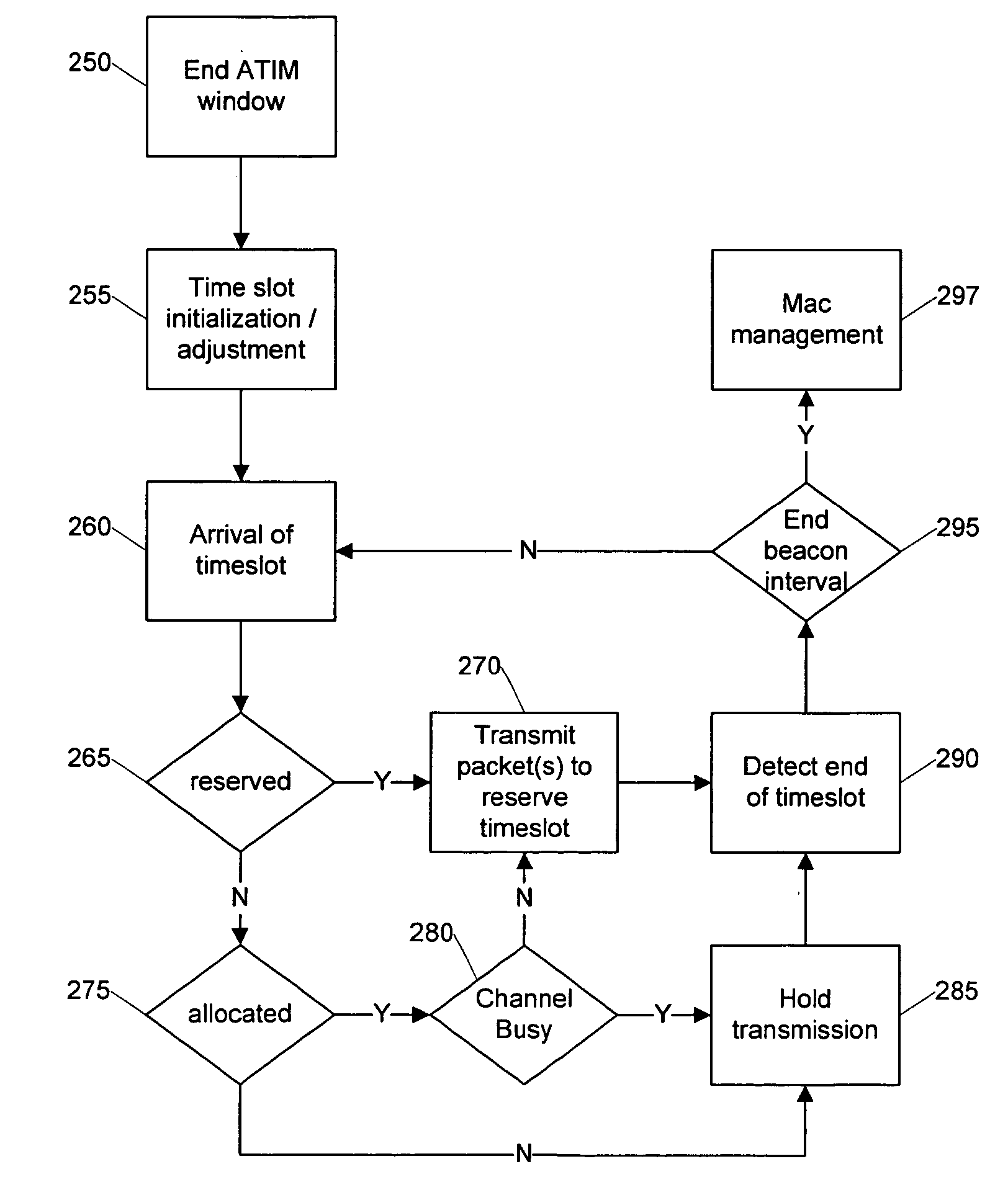
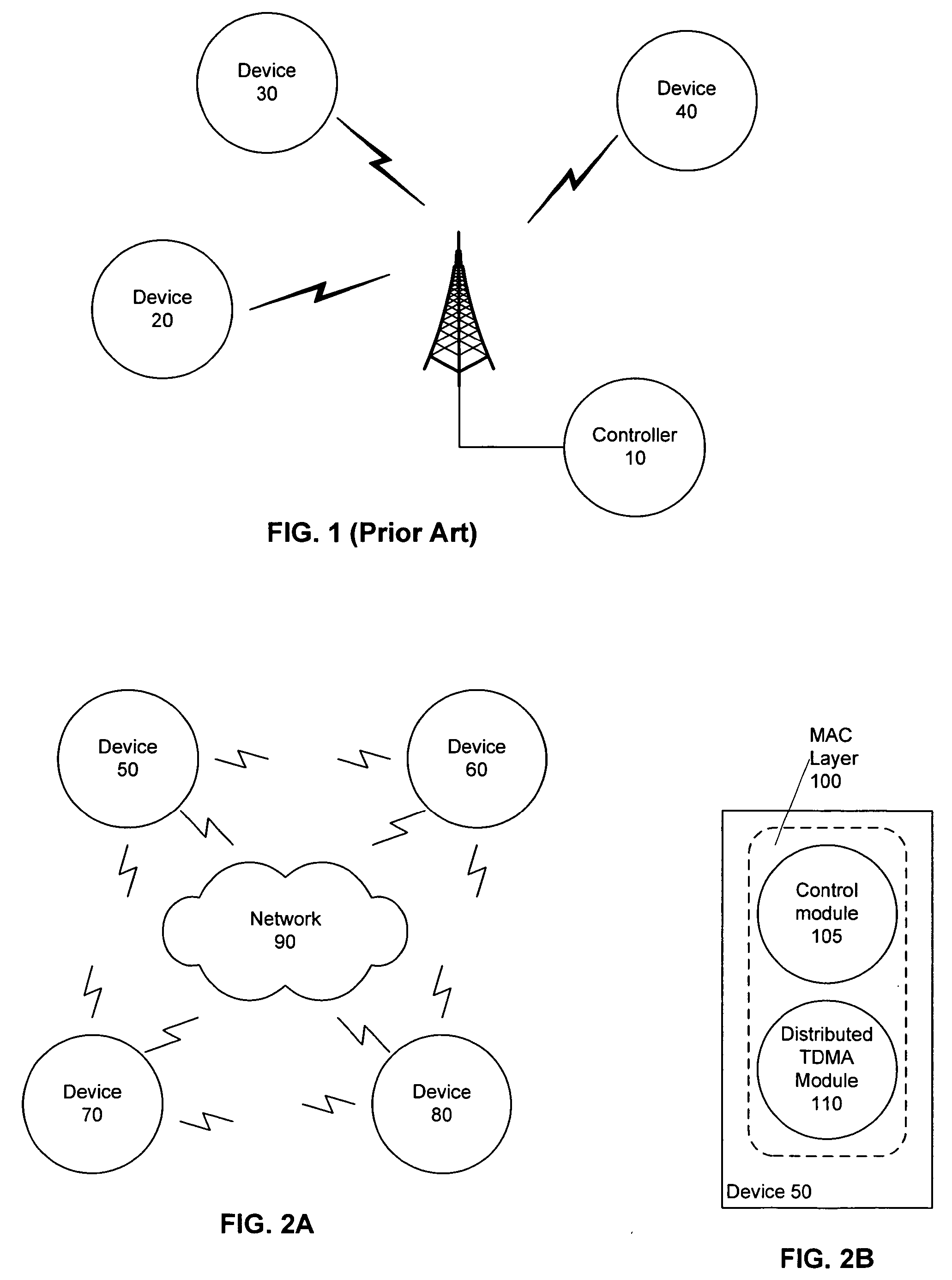
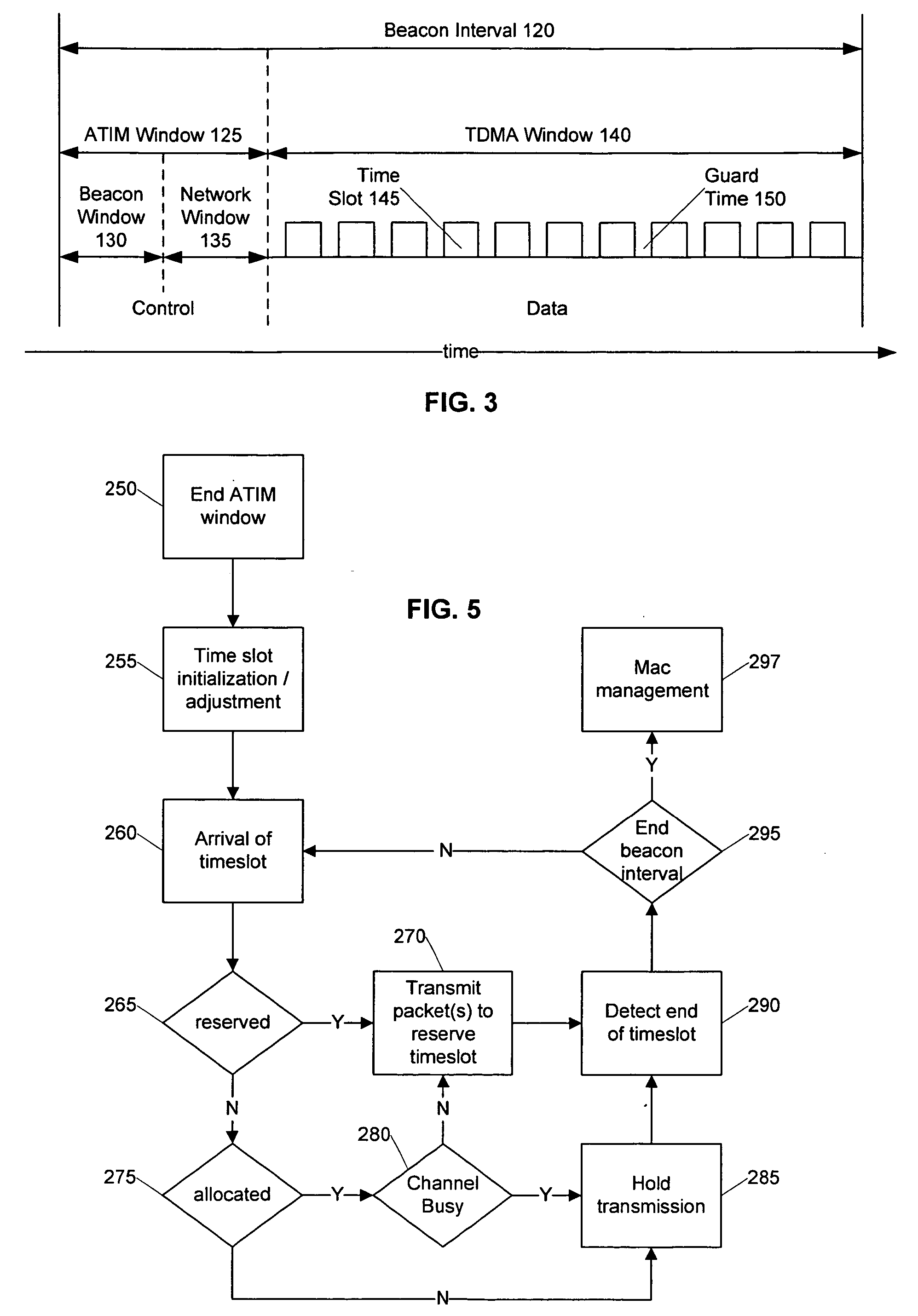
Systems and methods are provided that facilitate distributed TDMA communication amongst nodes in an ad hoc wireless network without the need for centralized management and control. A wireless communication device includes a MAC layer that is configured to synchronize its local clock from a beacon frame that is sent by another node in the ad hoc network. After synchronizing its clock to the ad hoc network, the device identifies a timeslot for transmission. When the timeslot arrives, the device senses the channel to determine if there is traffic and if there is no traffic, the device reserves the timeslot by transmitting. In this fashion, a plurality of timeslots can be divided amongst the devices in the ad hoc wireless network for optimized collision free communication using distributed TDMA. This distributed TDMA communication can also be applied across multiple channels in a wireless network to significantly increase bandwidth and quality-of-service.
Owner:COMMWORKS SOLUTIONS LLC +1
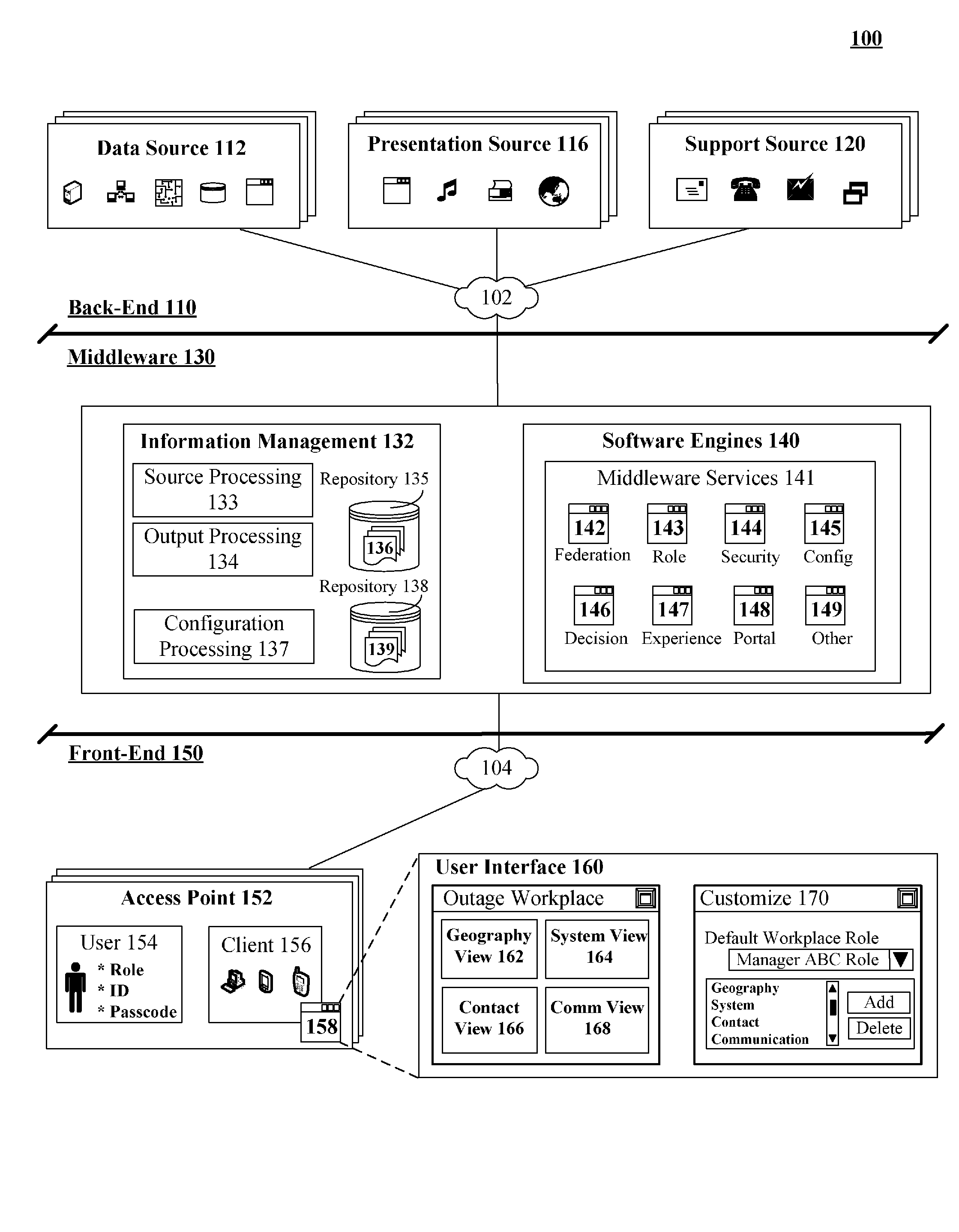
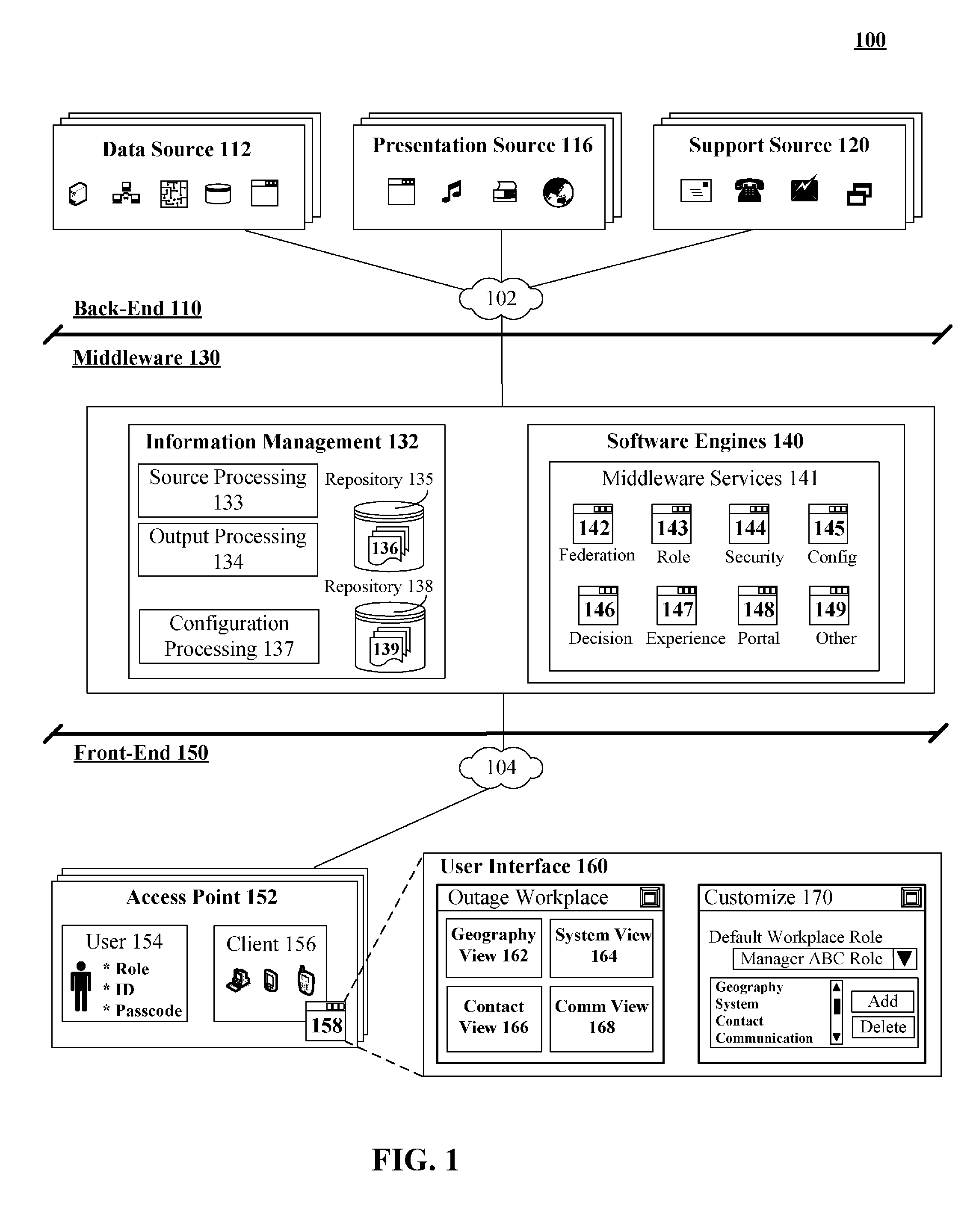
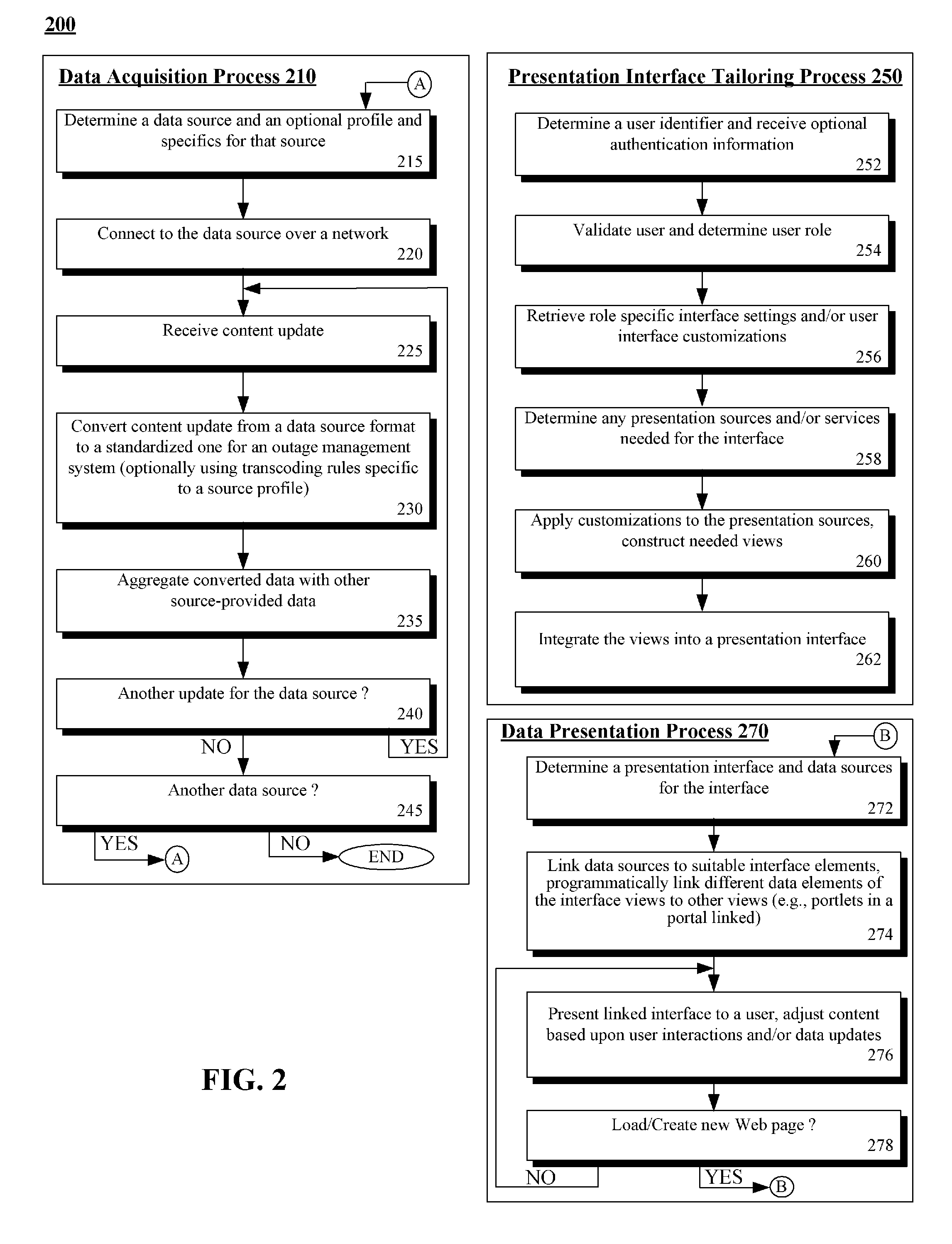
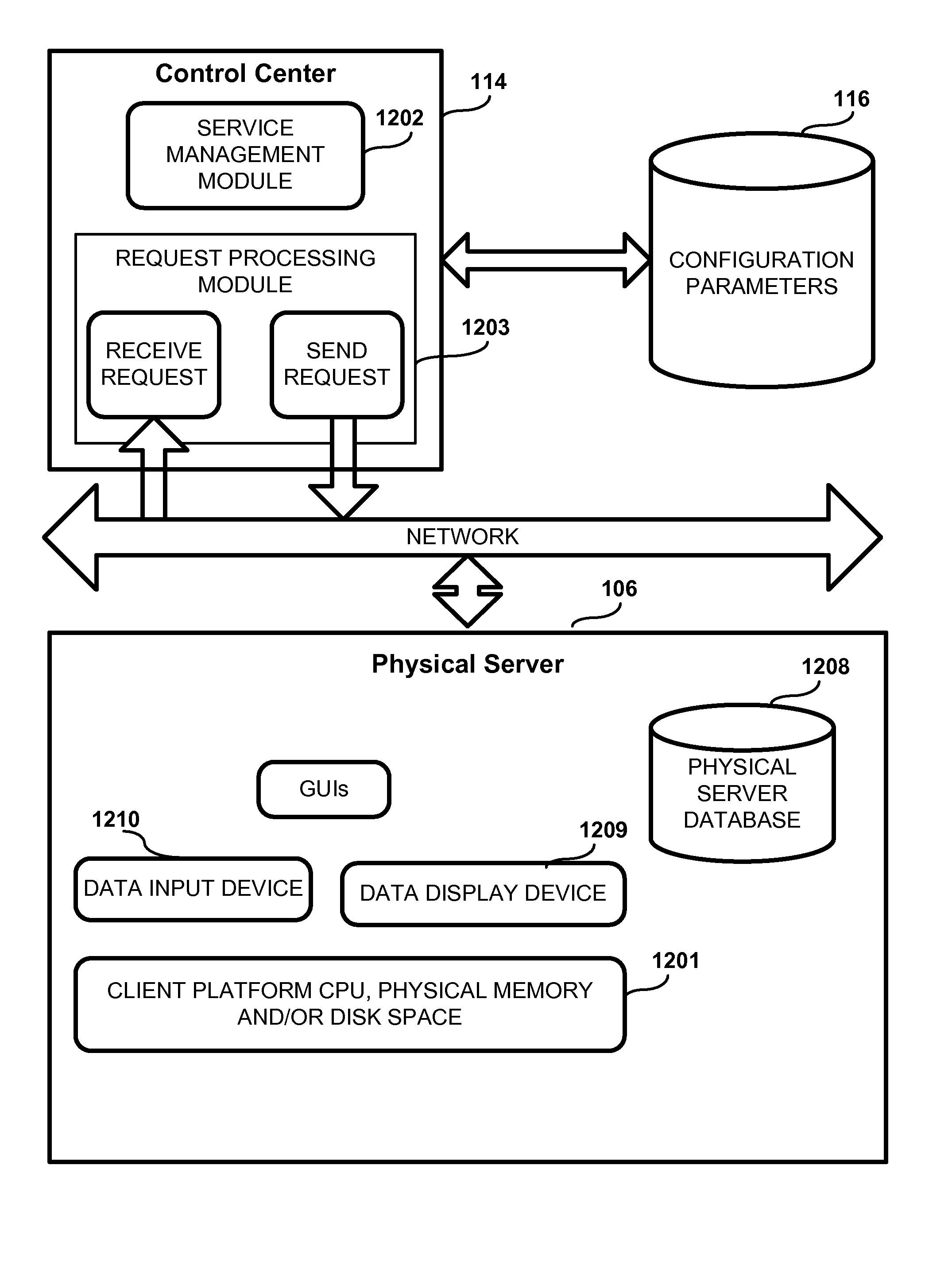
Outage management portal leveraging back-end resources to create a role and user tailored front-end interface for coordinating outage responses
A solution for centrally managing and federating outage specific information and for rapidly providing controlled access to this information in a role tailored fashion. The information can be gathered and provided in real-time along with programmatically determined proposed actions. An information recipient can configure and dynamically change the manner in which the information is presented, so that relevant information for that recipient can be rapidly digested. For example, a manager with a moderate level of technical knowledge may want information to be presented pictorially and in summary fashion, while a highly technical troubleshooter may want to configure information presentation to show key network statistics and values. In one embodiment, outage information can be presented in a Web portal having multiple discrete and customizable portlets, which include a geography portlet and a system portlet.
Owner:DAEDALUS BLUE LLC
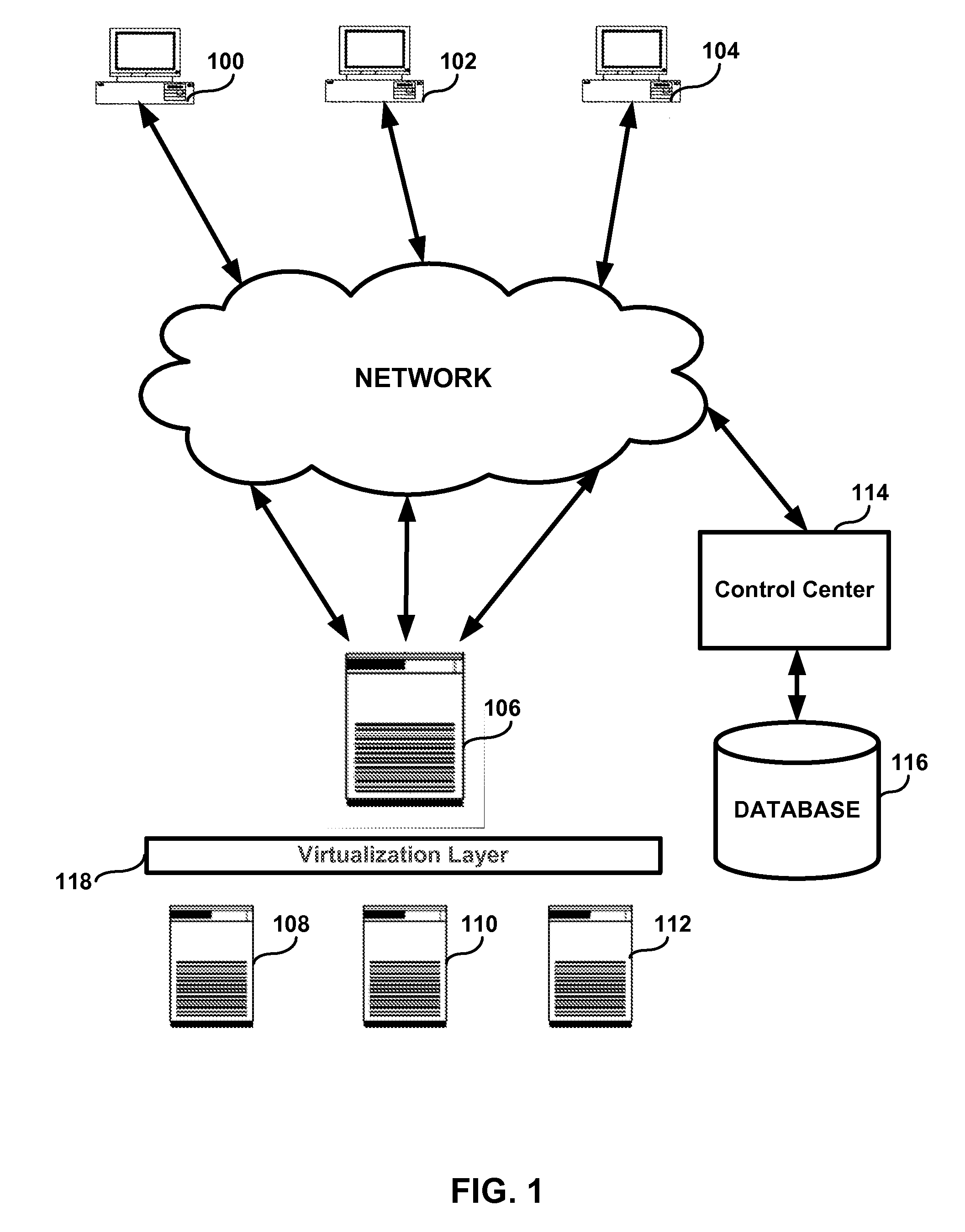
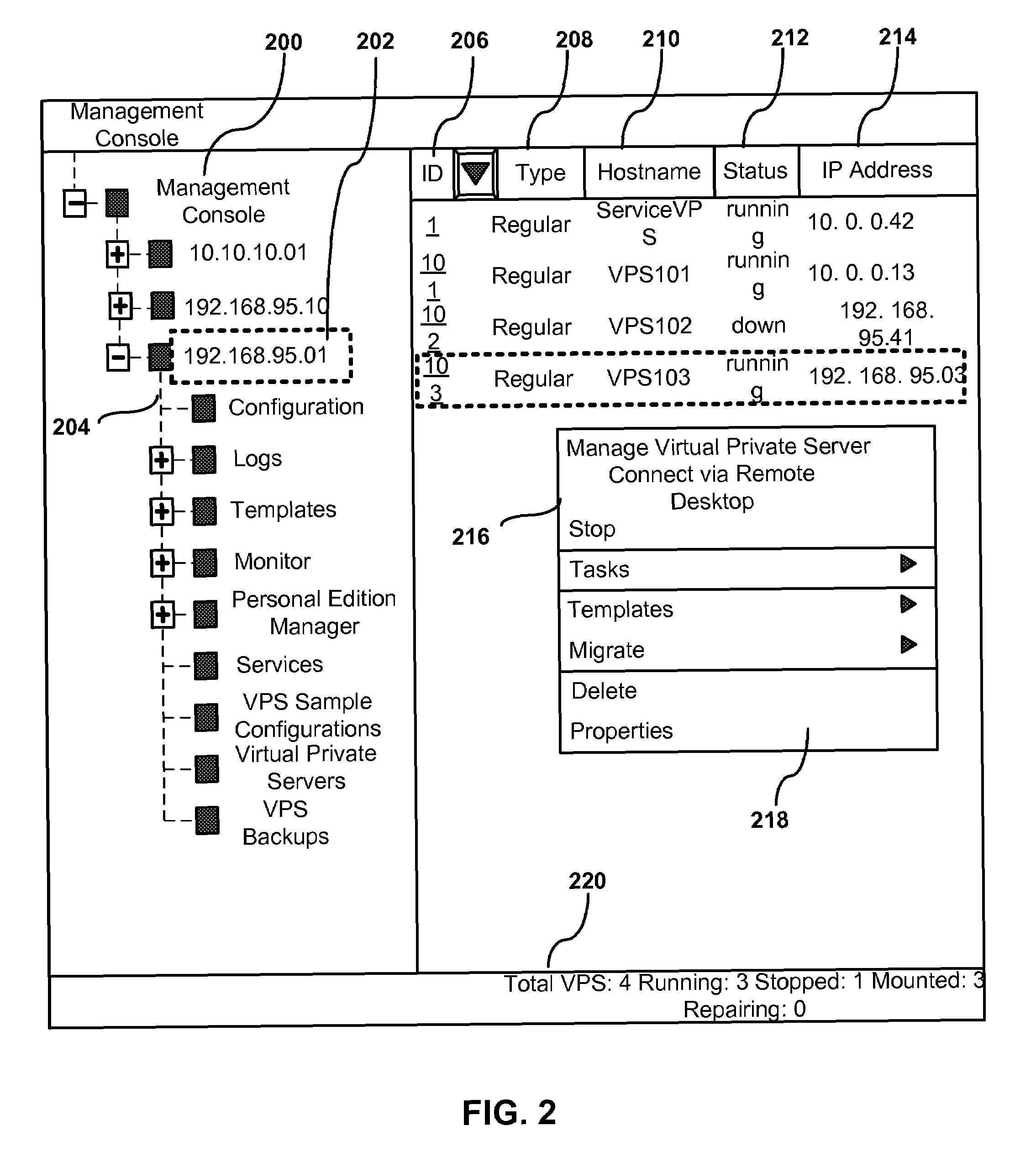
Management of virtual and physical servers using graphic control panels
A system, method and computer program product for providing centralized management of multiple Virtual Execution Environments (VEEs) implemented on multiple physical servers. Each VEE is a virtual server. Multiple virtual servers of various types and formats are implemented on multiple physical servers. The physical servers are connected into a network. An intuitive graphical user interface (GUI) of a central console for remote management and administration of a plurality of virtual servers and multiple physical servers is provided. The system includes server managers controlled from a common control center. The system also includes a database containing configuration data and data related to operation formats of the physical and virtual servers. A server system can be a plurality of physical servers and VEEs implemented on them or it can be a plurality of VEEs executed on one physical server.
Owner:MIDCAP FINANCIAL TRUST
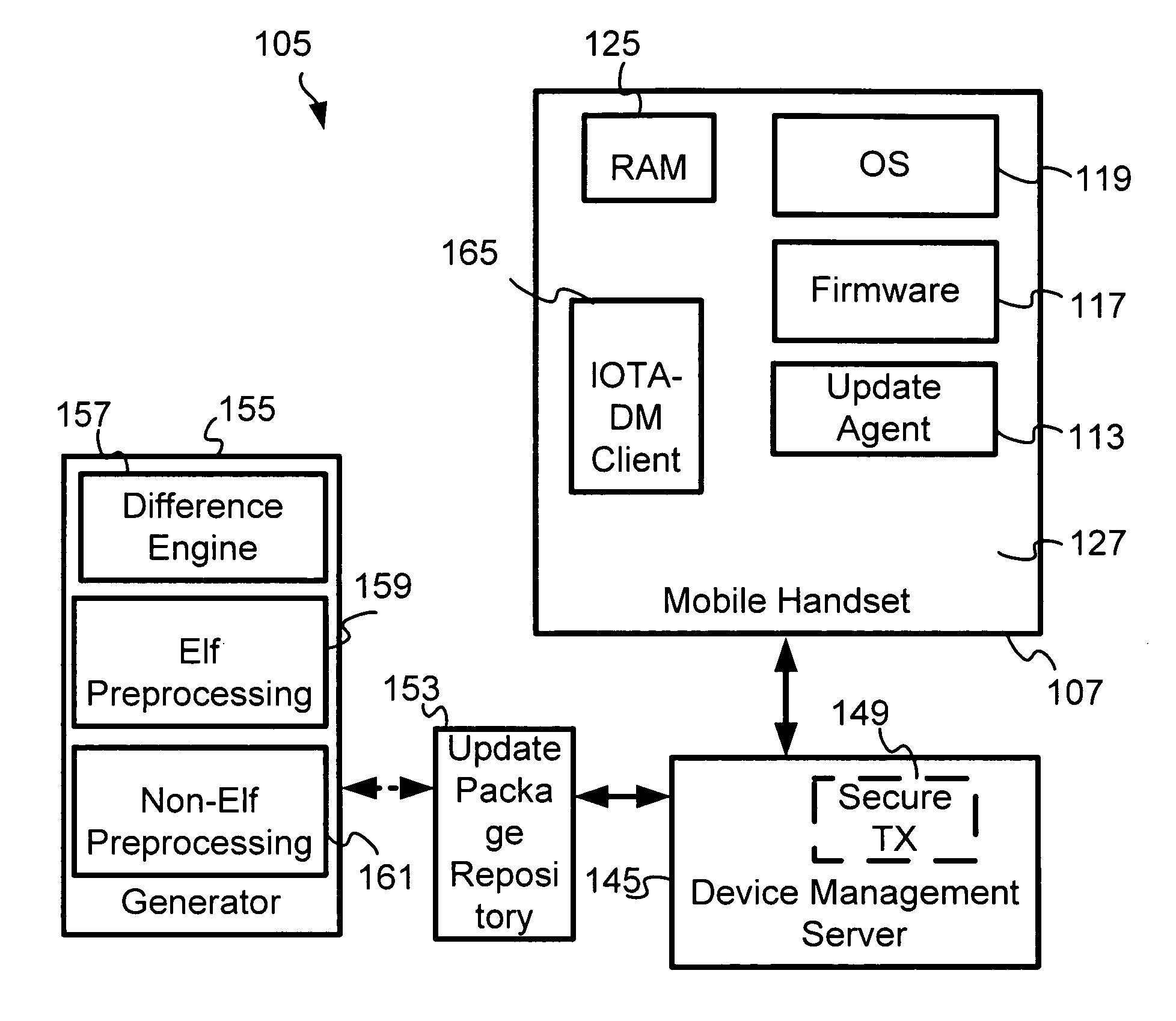
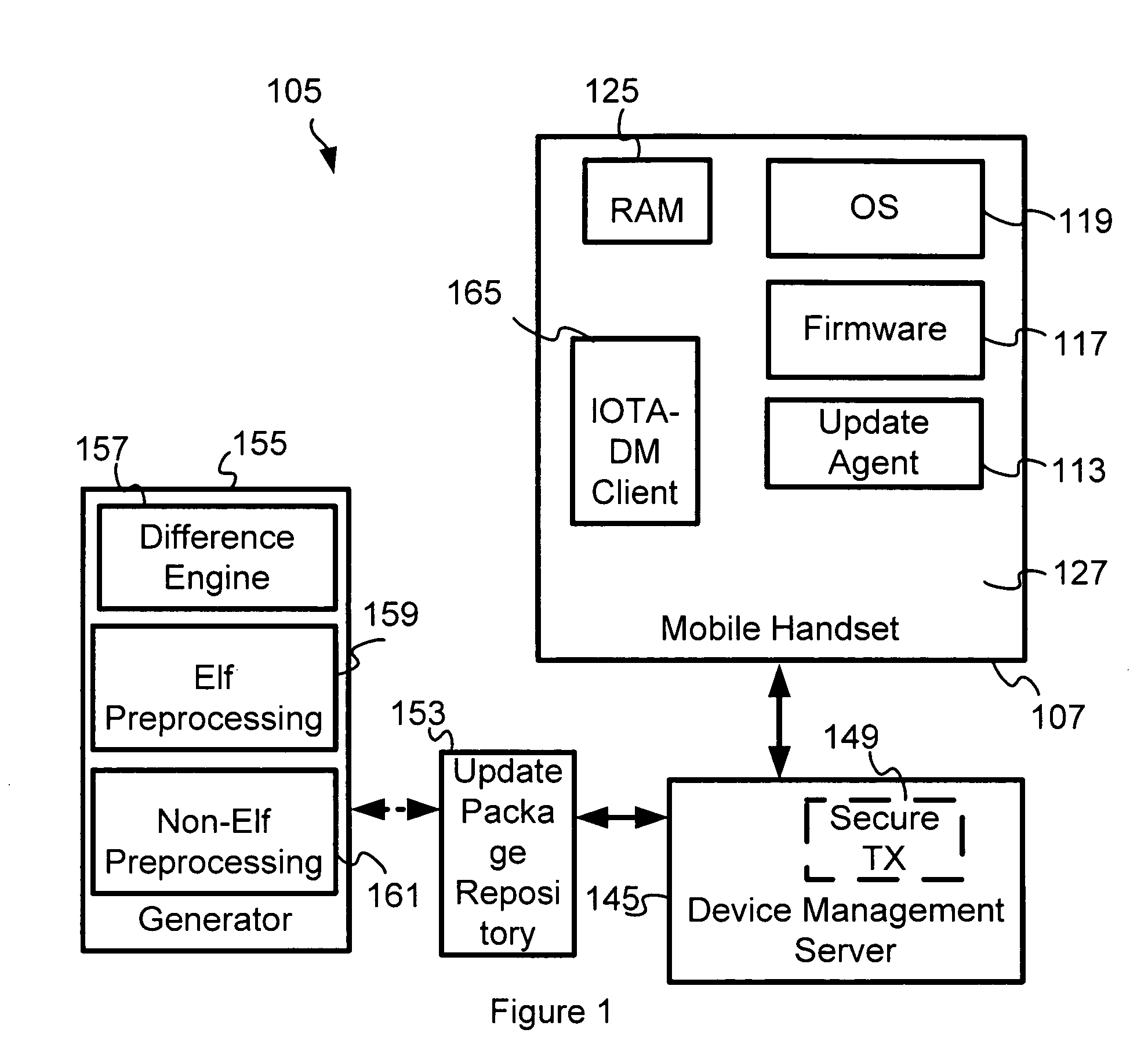
Centrally managed solution for all device management activities
ActiveUS20070169093A1Security arrangementSpecific program execution arrangementsCentralized managementClient-side
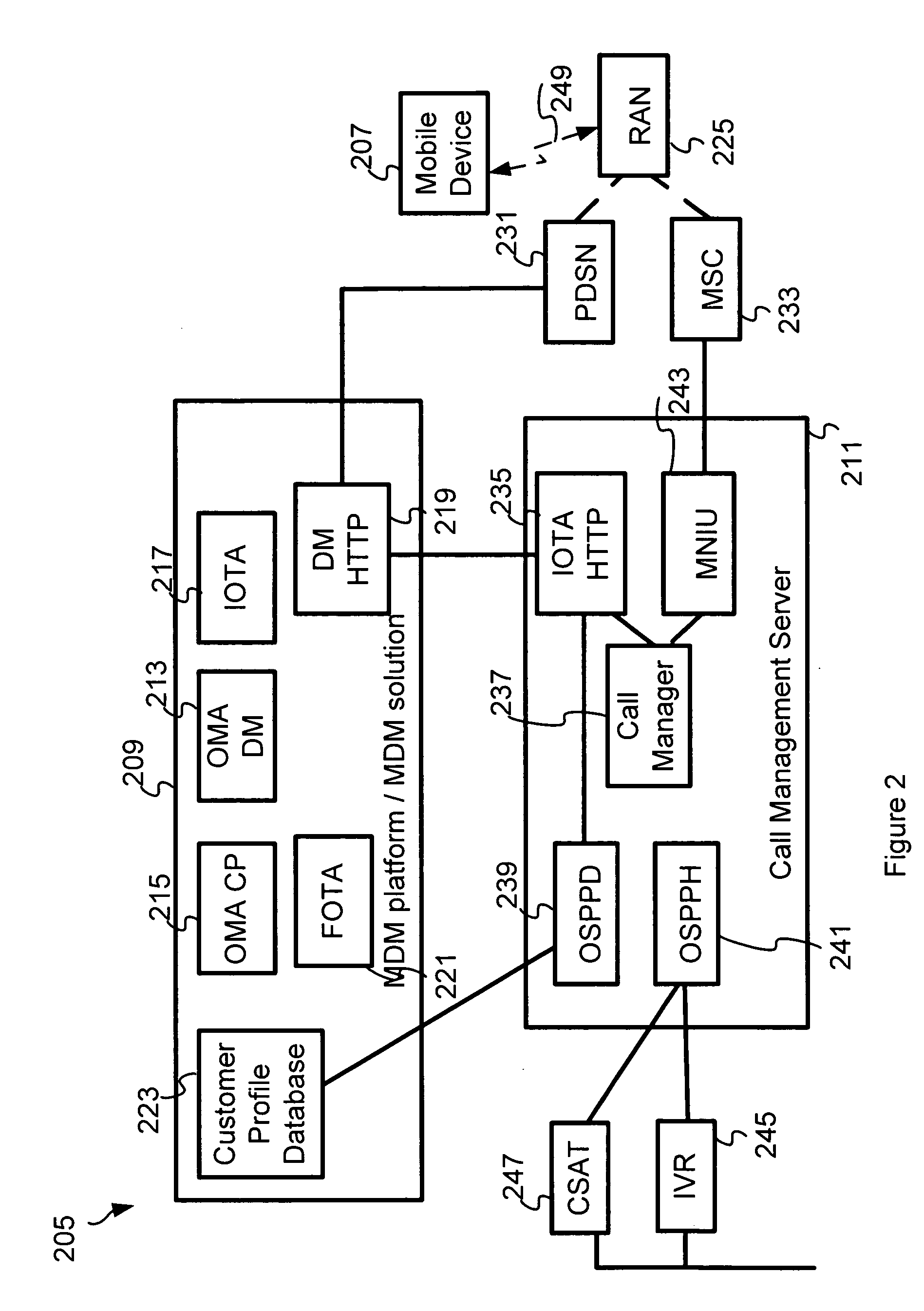
A centrally managed solution for all device management activities. This includes a set of device and subscriber registries, which are being constantly updated as new terminals, and subscribers are added to the system. It also includes support for legacy CDMA specific device management standards such as OTASP and OTAPA and support for remote handset configuration via SMS, using the latest standards from the Open Mobile Alliance Client Provisioning. In one embodiment, it includes support for remote handset configuration over IP, using the latest Open Mobile Alliance Client Provisioning and IOTA device management standards.
Owner:QUALCOMM INC
Virtual knowledge management system
InactiveUS20060111953A1Multiprogramming arrangementsOffice automationAutomatic controlDocument preparation
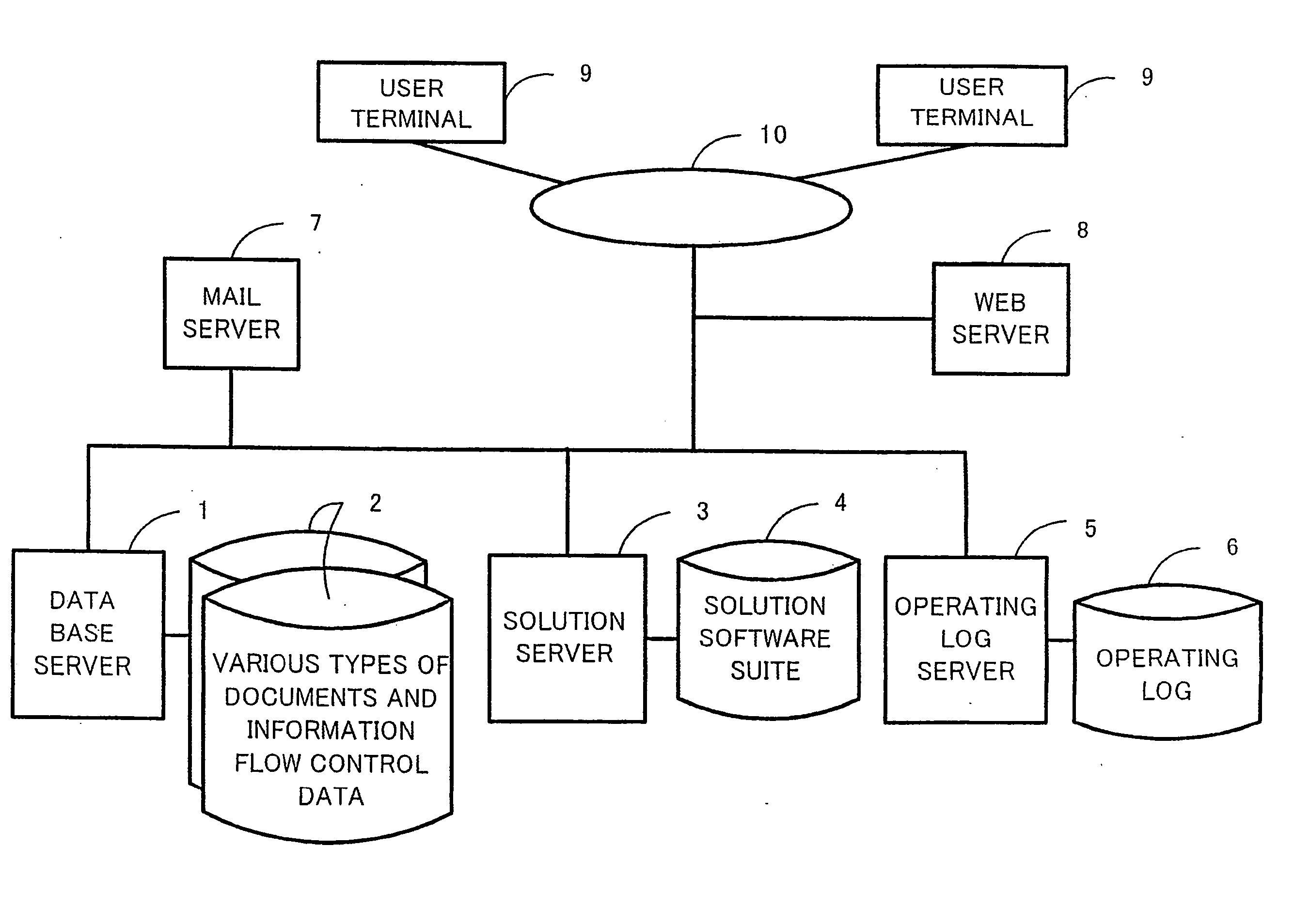
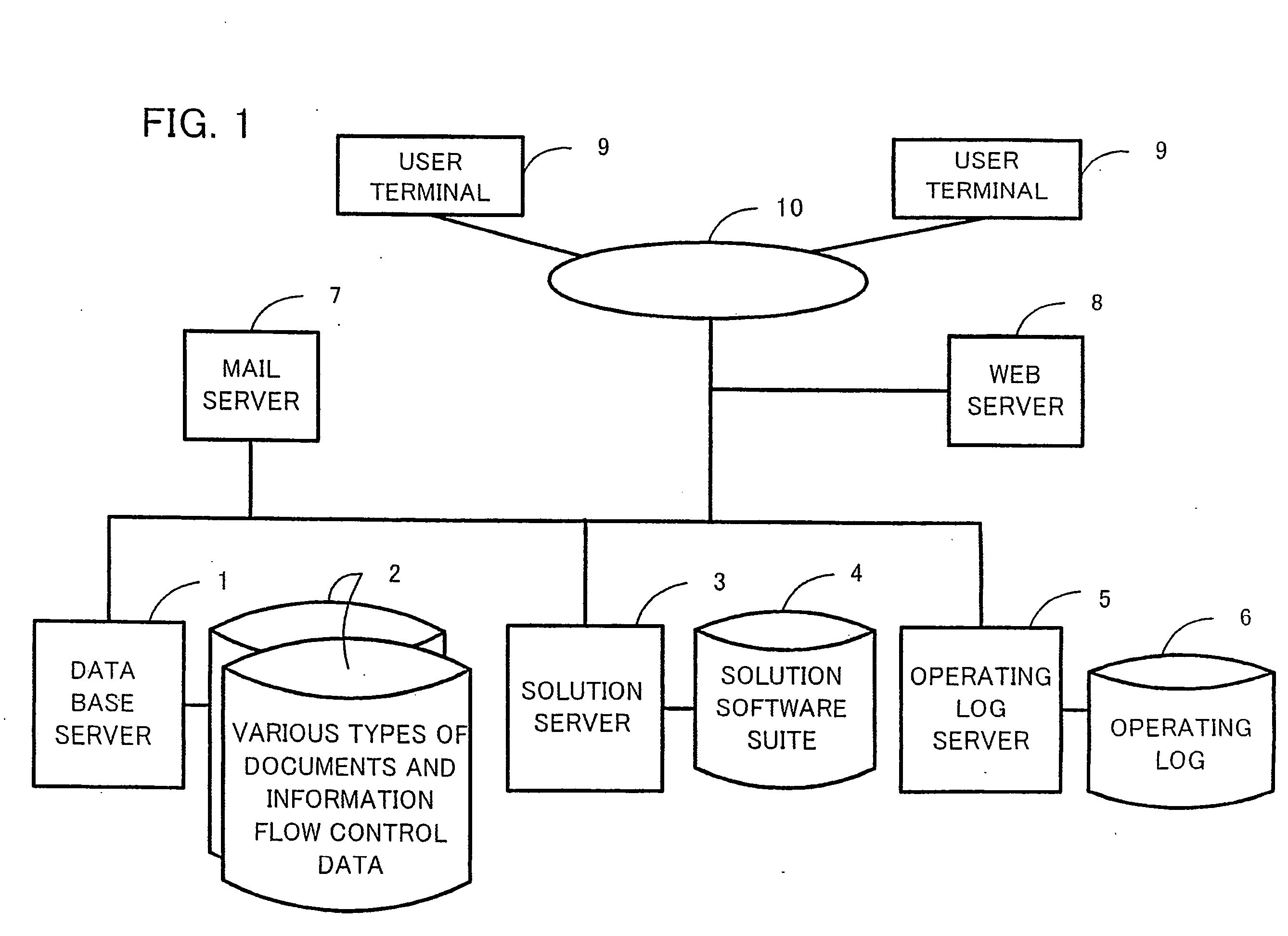
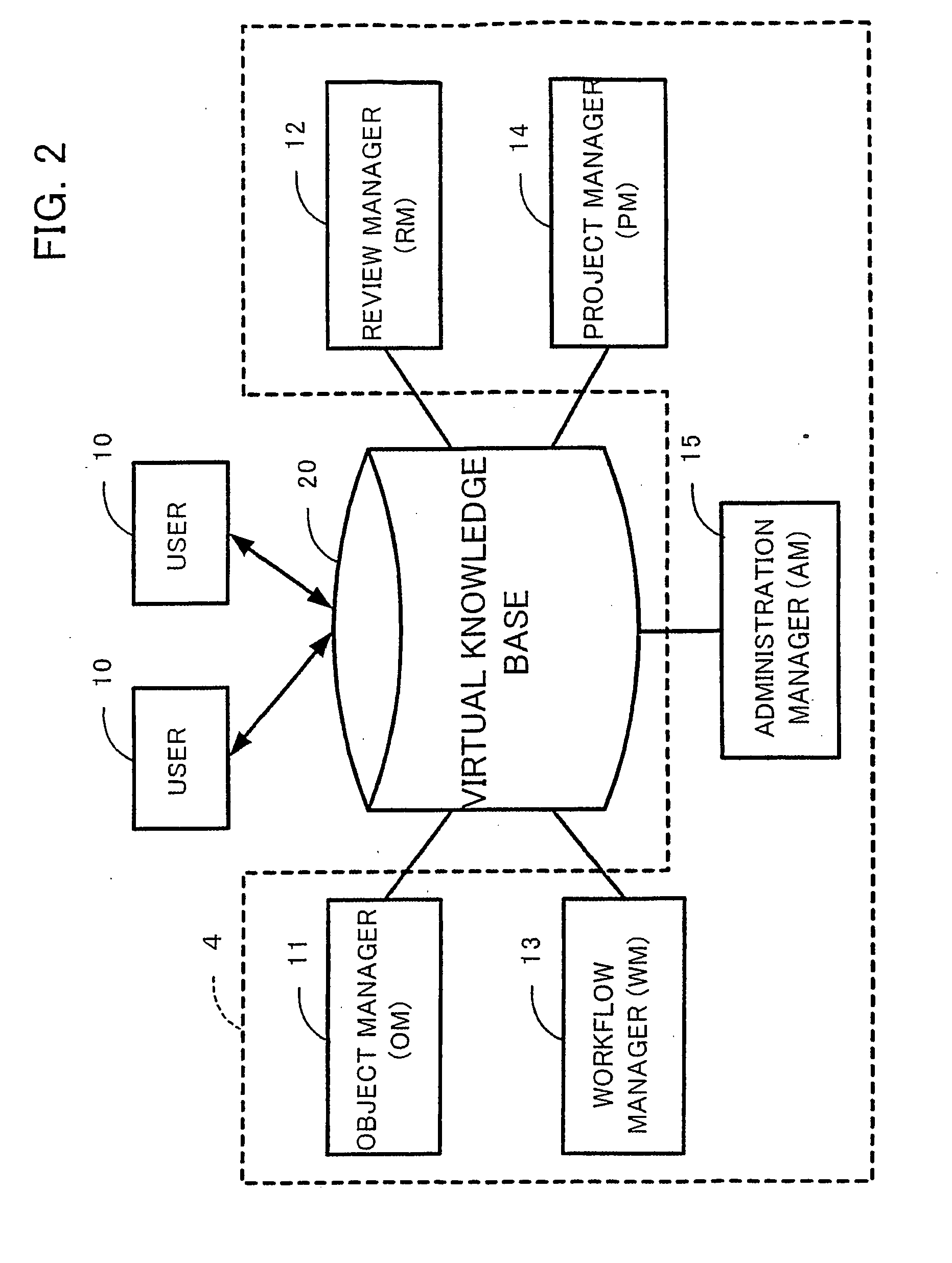
It is an object of the present invention to provide a virtual knowledge management system which controls the flow of information relating to the performance of business in an enterprise. The flow of information that is intensively administered by a virtual knowledge base 20 is automatically controlled on the basis of information flow control data 40 including document utilization authorization data, mail communications control data, workflow model data, project data and the like. The utilization of document objects by users is controlled in accordance with the document utilization authorization data. The forwarding of and reply to email messages among users is controlled in accordance with the mail communications control data. The order of work among a plurality of users involved in a certain business process is controlled in accordance with the workflow model data. The flow of information among a plurality of users involved in a certain project is controlled in accordance with the project data. The information flow control data 40 is configurable.
Owner:KNOWLEDGE IT CORP
Enforcing Universal Access Control in an Information Management System
ActiveUS20080301760A1Digital data processing detailsAnalogue secracy/subscription systemsApplication softwareCentralized management
A method and apparatus for controlling document access and application usage using centrally managed rules. The rules are stored and manipulated in a central rule database via a rule server. Policy enforcers are installed on client systems and / or on servers and perform document access and application usage control for both direct user document accesses and application usage, and application program document accesses by evaluating the rules sent to the policy enforcer. The rule server decides which rules are required by each policy enforcer. A policy enforcer can also perform obligation and remediation operations as a part of rule evaluation. Policy enforcers on client systems and servers can operate autonomously, evaluating policies that have been received, when communications have been discontinued with the rule server.
Owner:NEXTLABS
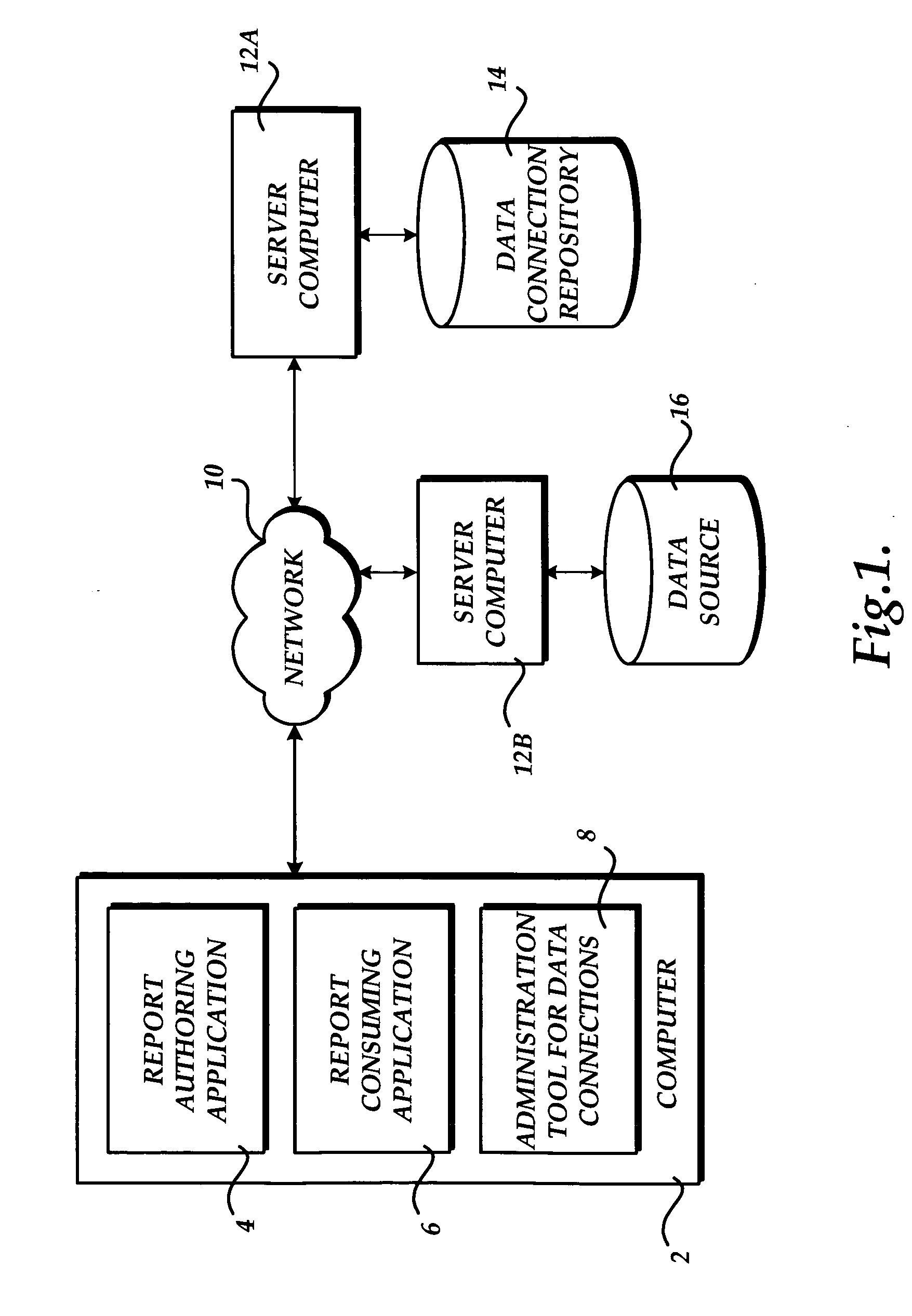
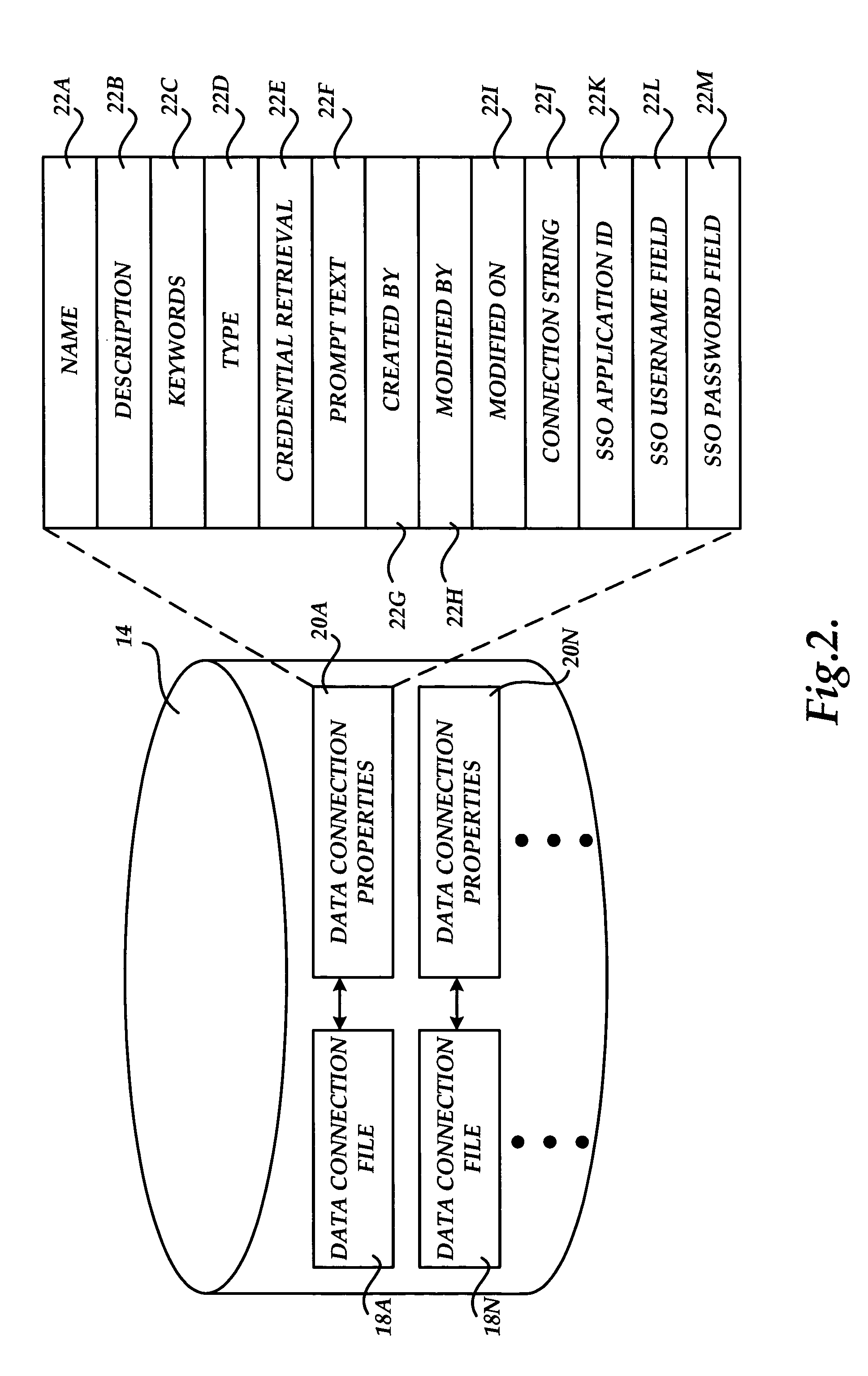
Method, system, and apparatus for discovering and connecting to data sources
InactiveUS20050278307A1Easy to publishEasy to shareSpecial service provision for substationData processing applicationsData connectionSoftware engineering
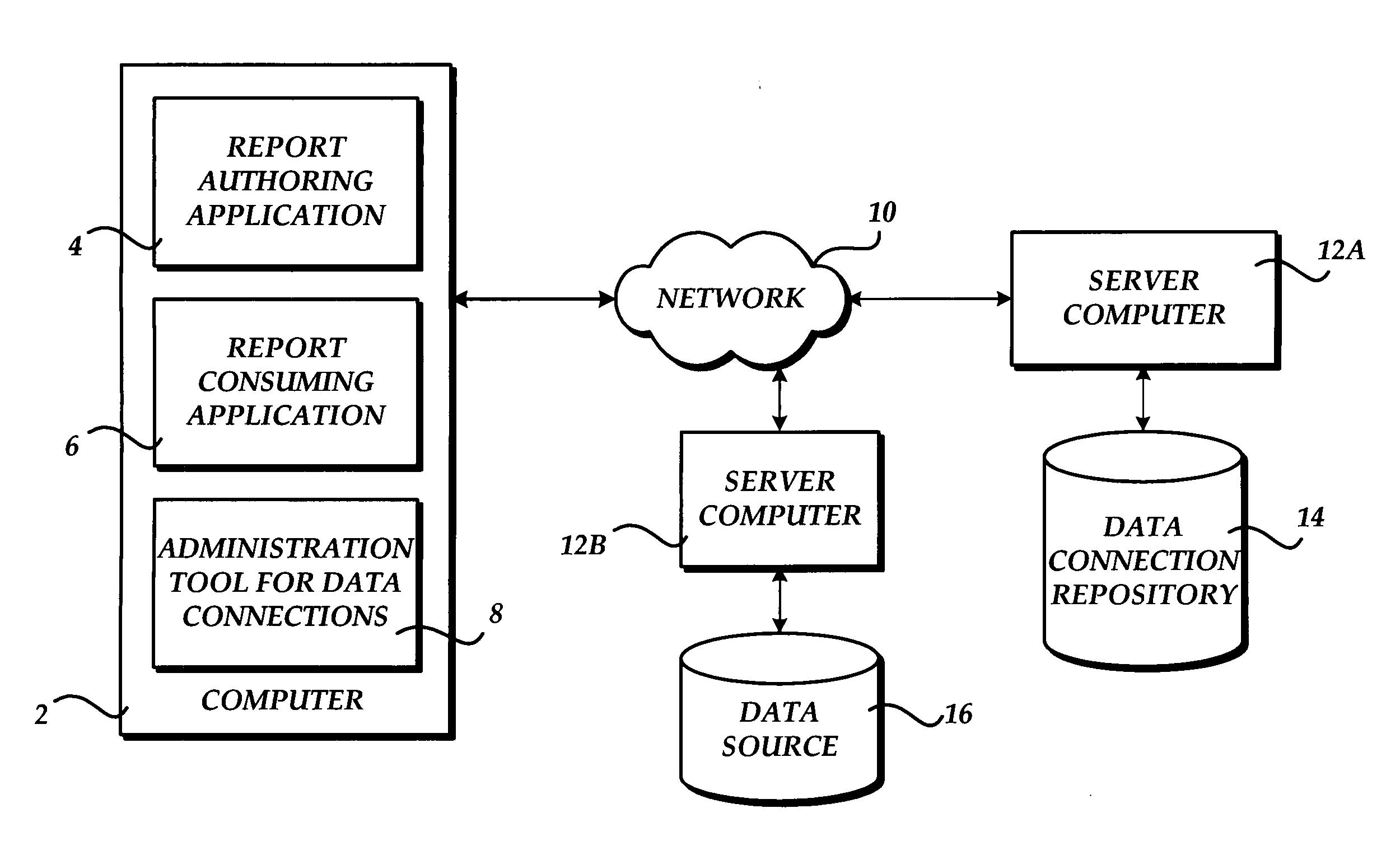
A method, system, and apparatus for discovering and connecting to data sources are provided. A system is provided that includes a server computer operative to maintain a centrally managed repository of data connection definitions. A client computer is also provided including an application program capable of consuming data from a data source. When a request is received by the application to connect to a data source, a list of available sources is retrieved from the server computer. If one of the data sources in the list is selected, a data connection file is retrieved and utilized to connect to the data source. If a report is opened by the application that includes a reference to a data source, the repository is utilized to confirm the connection to the data source.
Owner:MICROSOFT TECH LICENSING LLC
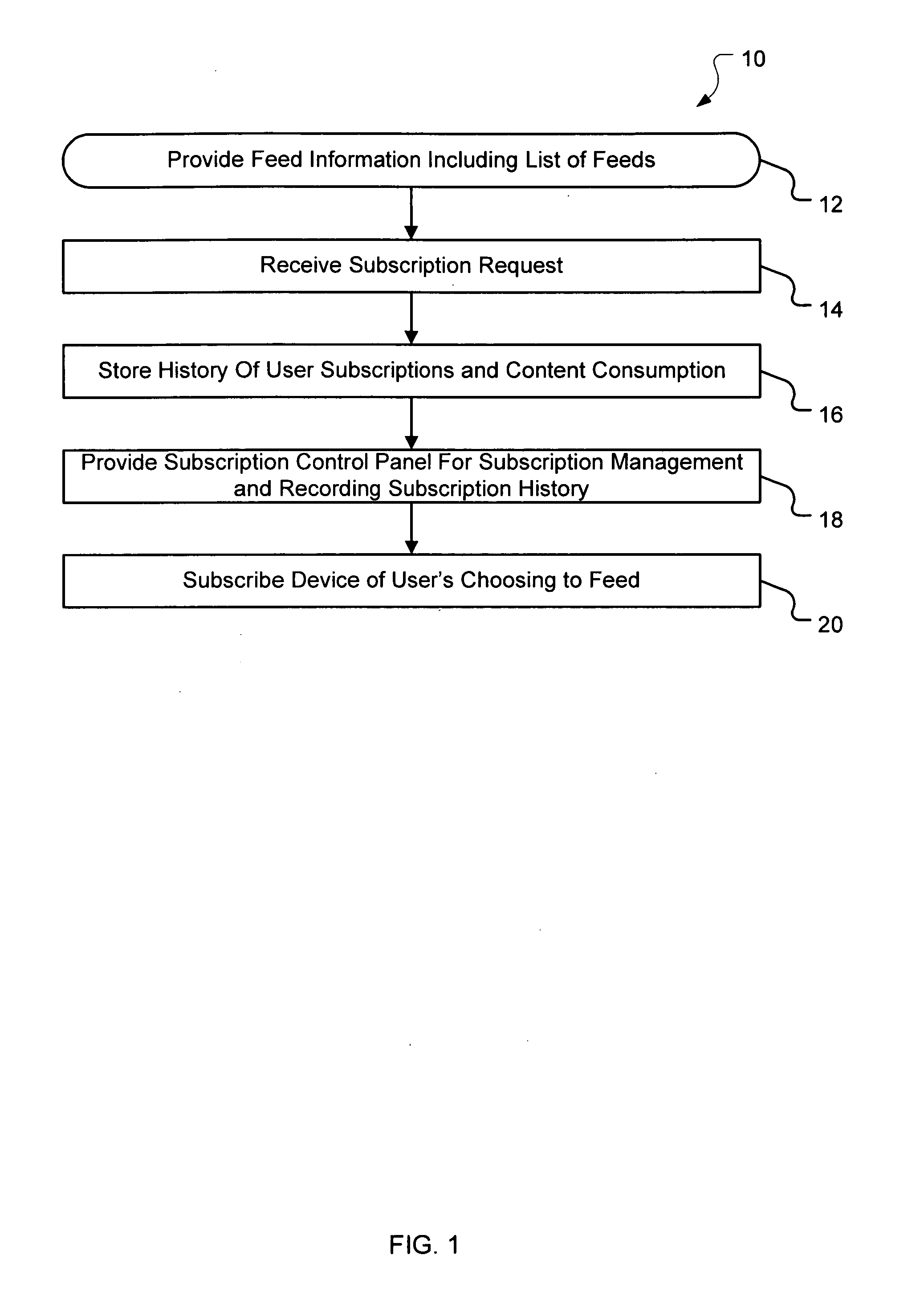
Subscription control panel
ActiveUS20070088832A1Simple methodMultiple digital computer combinationsElectric digital data processingCentralized managementWorld Wide Web
Systems and methods are provided for centrally managing subscriptions to feeds accessible at different locations on a network. A subscription server is provided that a user can log in to from any of the user's rendering devices and use to manage subscriptions to feeds, including subscribing to feeds, listening to episodes of feeds, downloading episodes to a rendering device, and rating and reviewing episodes. The user's history of actions with respect to feeds is tracked and stored on the subscription server. The user can then access this history via user interfaces generated by the subscription server to determine what actions the user has performed in the past.
Owner:GOOGLE LLC
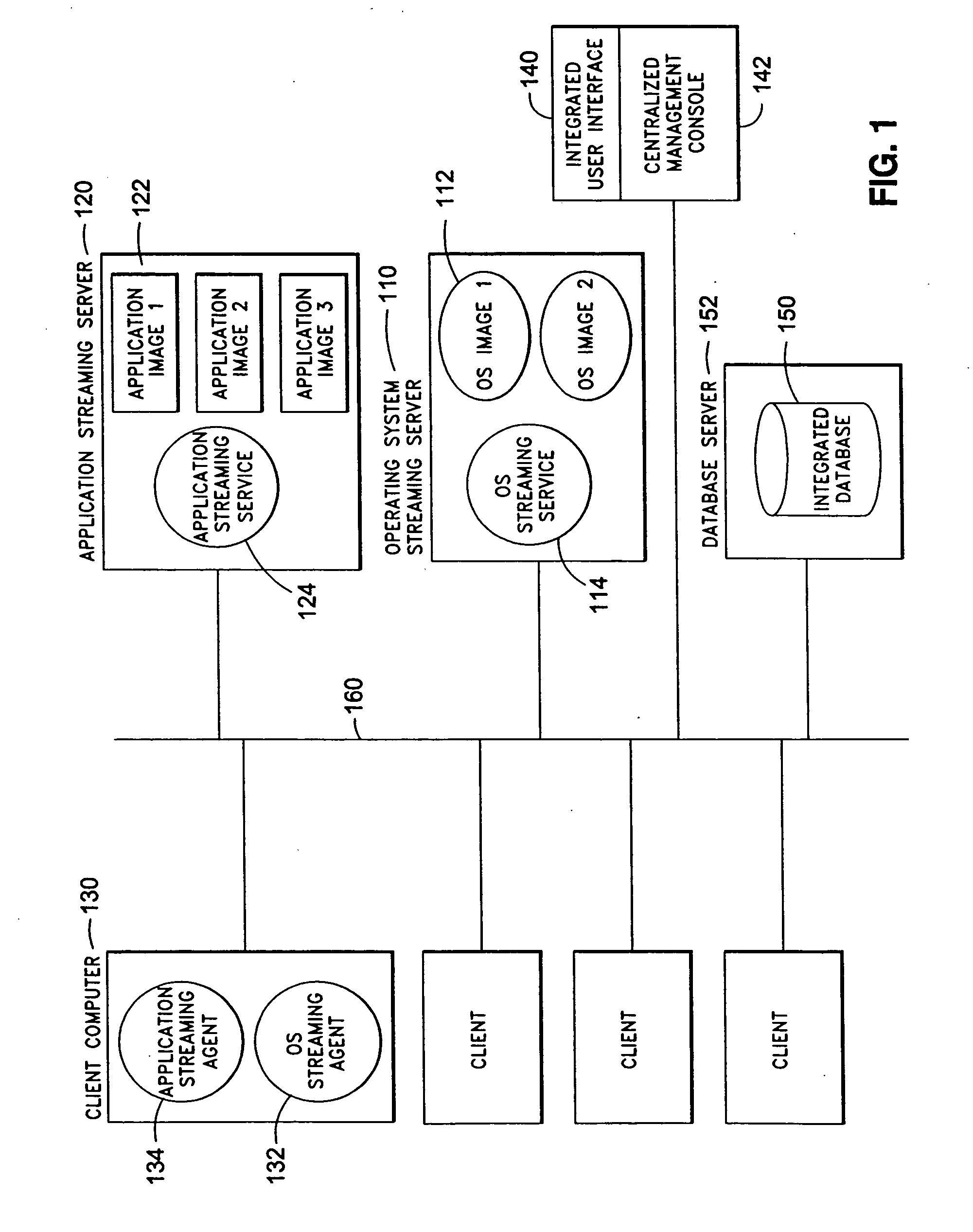
System and method for integrated on-demand delivery of operating system and applications
ActiveUS20060031547A1Accurate scaleMultiple digital computer combinationsProgram controlOperational systemSystems management
The present invention discloses a system and a method for integrated on-demand delivery of operating system and applications, where operating system images are separate and distinct from application images. Integration of operating system streaming and application streaming services makes streaming delivery possible to a wide range of client devices, including those without any local disk space such as thin-clients and diskless workstations. In addition, by integrating the centralized management of operating system delivery and application delivery, the present invention provides a complete solution to server-centric application management, thereby further reducing the total cost of ownership of network-based computing approach. Implementing the operating management functions at the client machine level of specificity and application management functions at the user level of specificity combined with providing separate and distinct operating system images and application images provides an inherently canonical architecture that allows proper scaling and affords appropriate security management functions. The result is a complete, scalable, robust, and reliable server-centric application and operating system management system with a lower total cost of ownership than existing products.
Owner:DELL MARKETING CORP
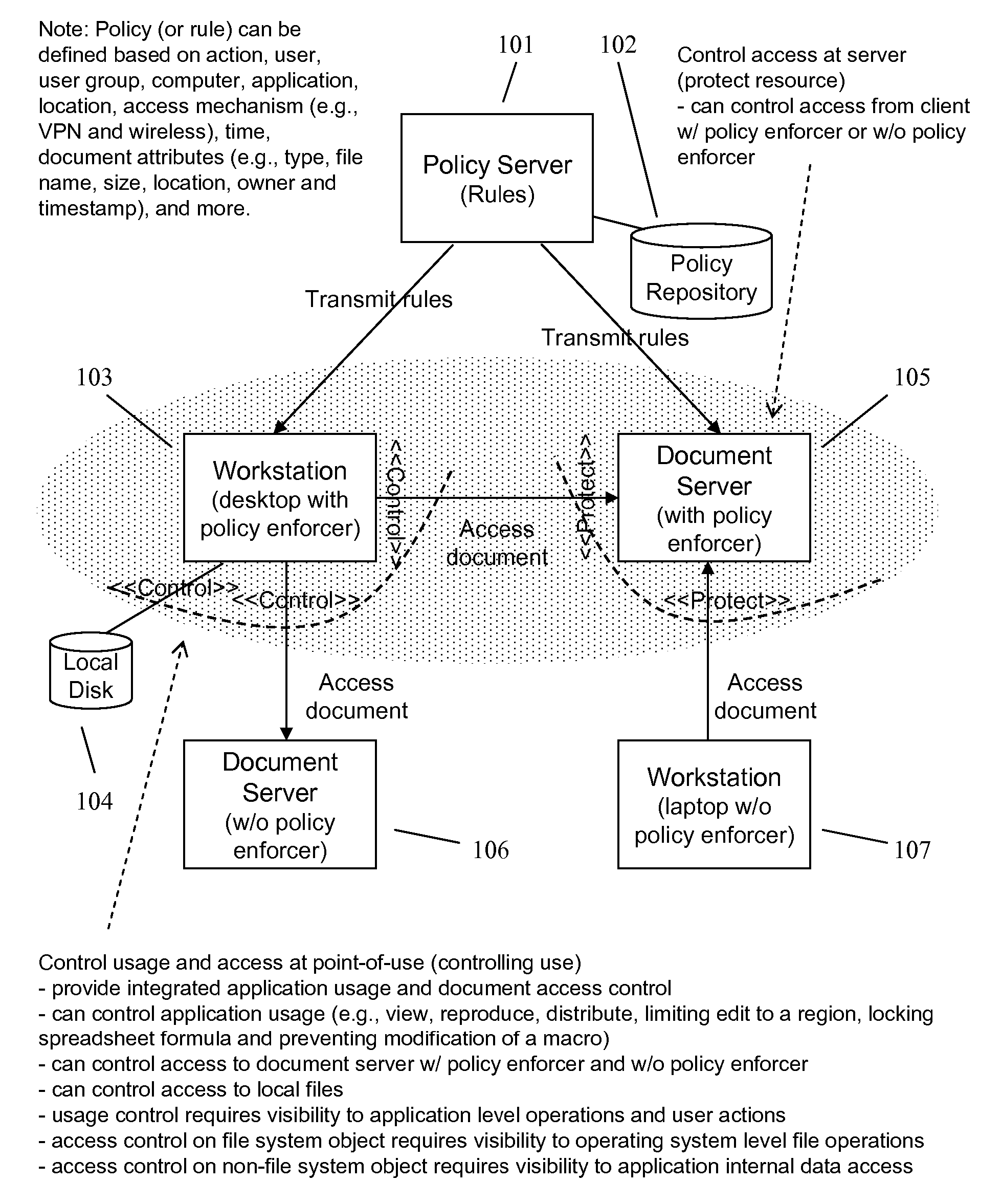
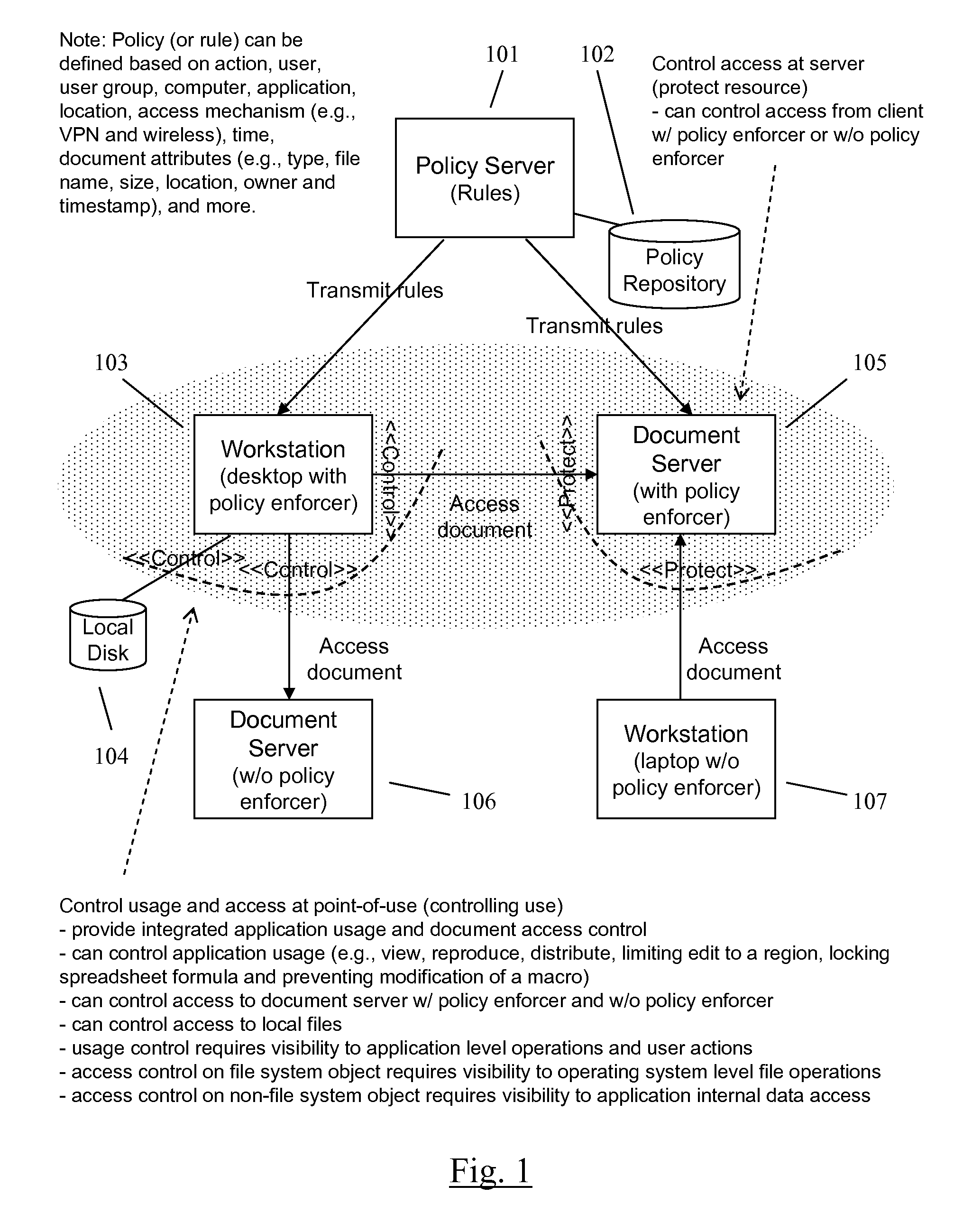
Enforcing Access Control Policies on Servers in an Information Management System
ActiveUS20080060080A1Digital data processing detailsAnalogue secracy/subscription systemsPaper documentDocument preparation
A method and apparatus for controlling document access and application usage using centrally managed rules. The rules are stored and manipulated in a central rule database via a rule server. Policy enforcers are installed on client systems and / or on servers and perform document access and application usage control for both direct user document accesses and application usage, and application program document accesses by evaluating the rules sent to the policy enforcer. The rule server decides which rules are required by each policy enforcer. A policy enforcer can also perform obligation and remediation operations as a part of rule evaluation. Policy enforcers on client systems and servers can operate autonomously, evaluating policies that have been received, when communications have been discontinued with the rule server.
Owner:NEXTLABS
Enforcing Policy-based Application and Access Control in an Information Management System
ActiveUS20080066148A1Digital data processing detailsAnalogue secracy/subscription systemsCentralized managementClient-side
Owner:NEXTLABS INC
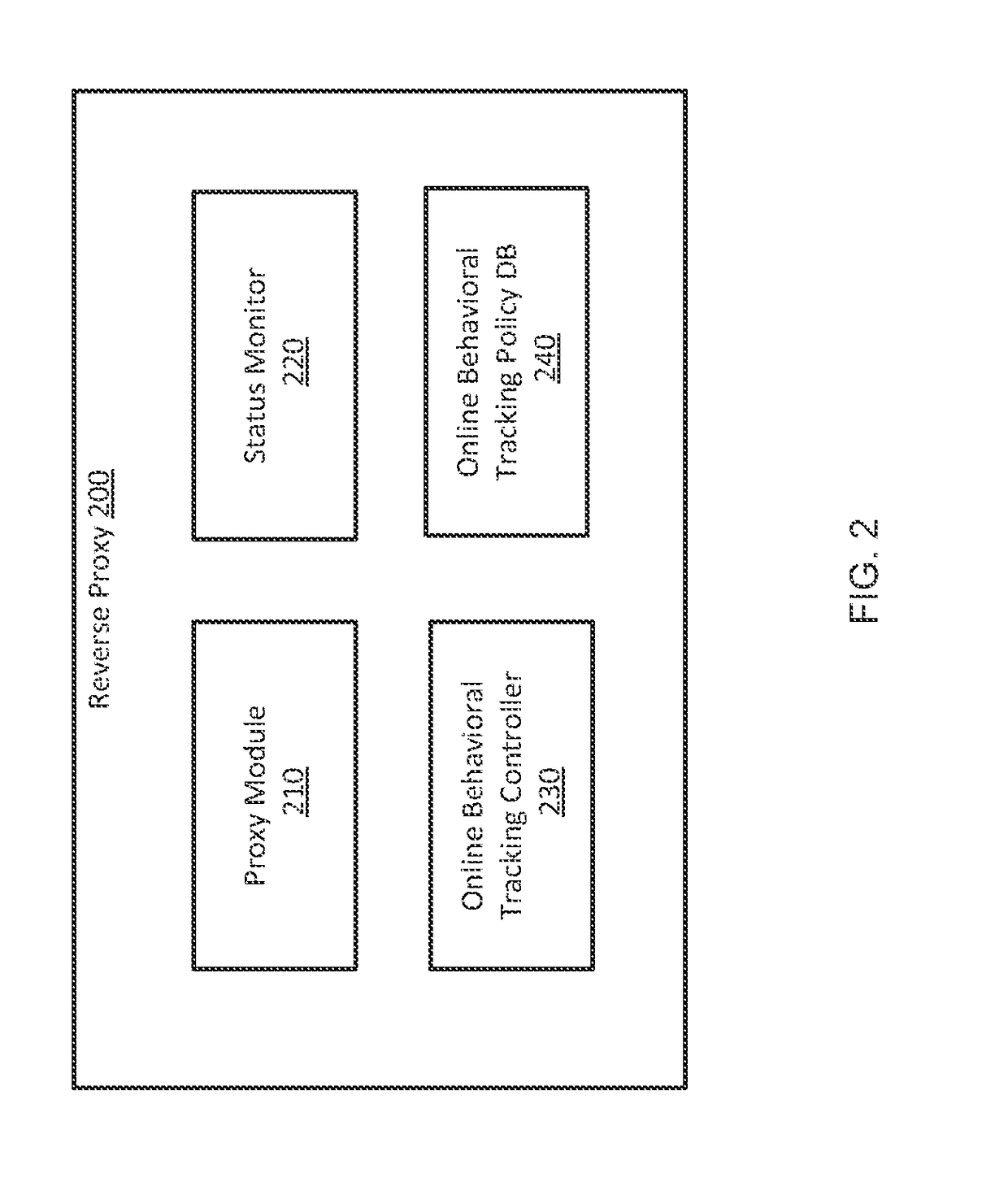
Centralized management and enforcement of online behavioral tracking policies
Systems and methods for manipulating online behavioral tracking policies are provided. According to one embodiment, a hypertext transfer protocol (HTTP) response transmitted from a web server to a client is captured by a network security device. A status of the client is determined by the network security device. An online behavioral tracking policy associated with the client is identified by the network security device based on the determined status. The identified online behavioral tracking policy is enforced by the network security device by modifying the HTTP response. The modified HTTP response is transmitted by the network security device to the client.
Owner:FORTINET
Method, system, and apparatus for the management of the electronic files
InactiveUS20070150299A1Easily correspondLot of disk spaceComputer security arrangementsOffice automationNon-disclosure agreementCentralized management
The primary design goals of the current system are (as a matter of example, but not limited to the following, by any means): to enable Organizations to send documents to Readers ensuring that only those authorized Readers can “read” the contents; to be a low cost, easy to use system, with zero to minimum installation requirements at the Companies and Readers end; to provide the service primarily as an ASP service with the ability to be easily deployed and maintained into an Enterprise environment; to enable Companies to send documents anywhere in the world and receive the same level of protection and comfort regardless of location of Reader; to provide a centrally managed, but distributed, Reader authentication and authorization method / process for all Companies to use in any country; to provide a central NDA (Non Disclosure Agreement) Registry for any size company; and to provide a secure guaranteed on-line signing process for business contracts and agreements.
Owner:FLORY CLIVE F
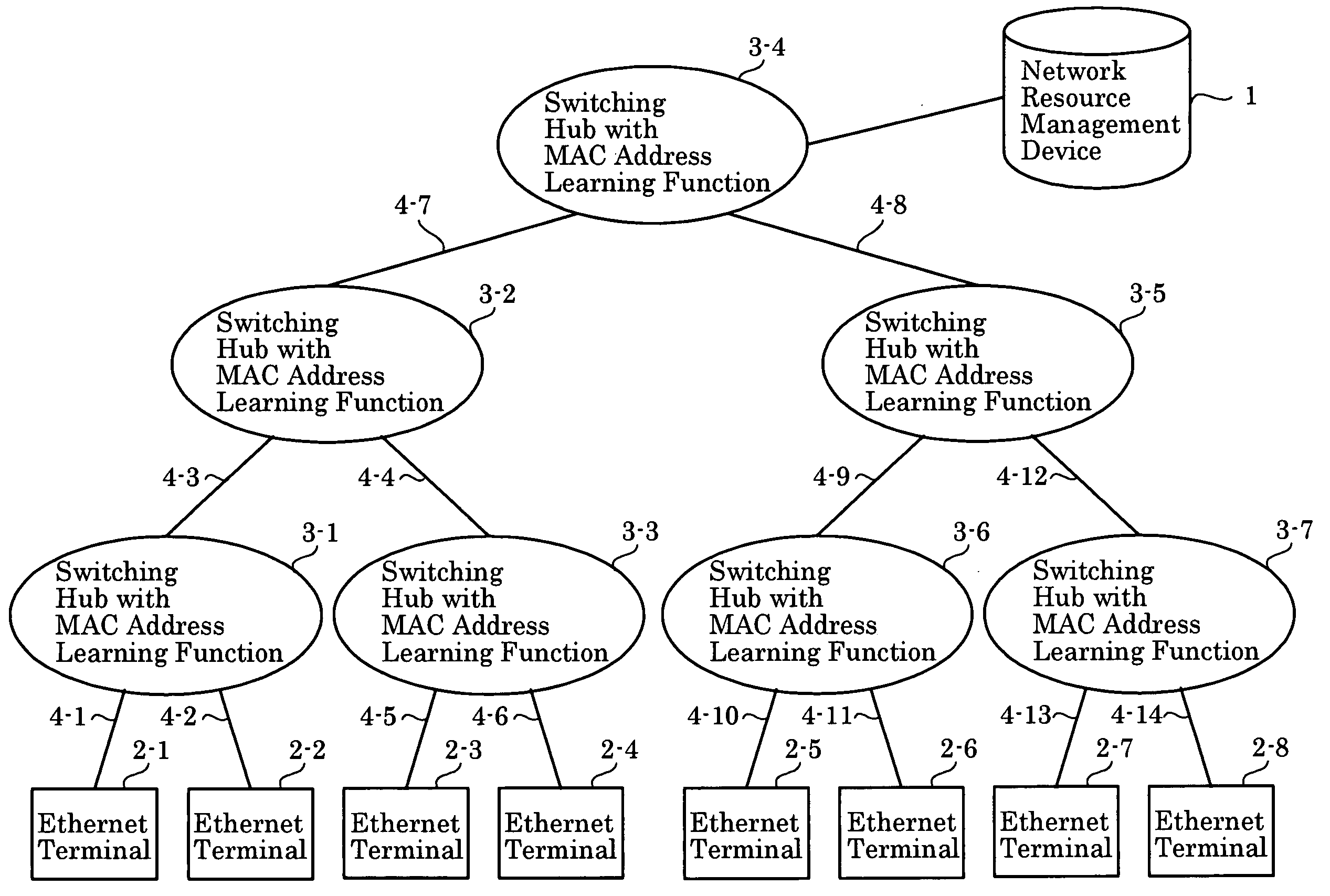
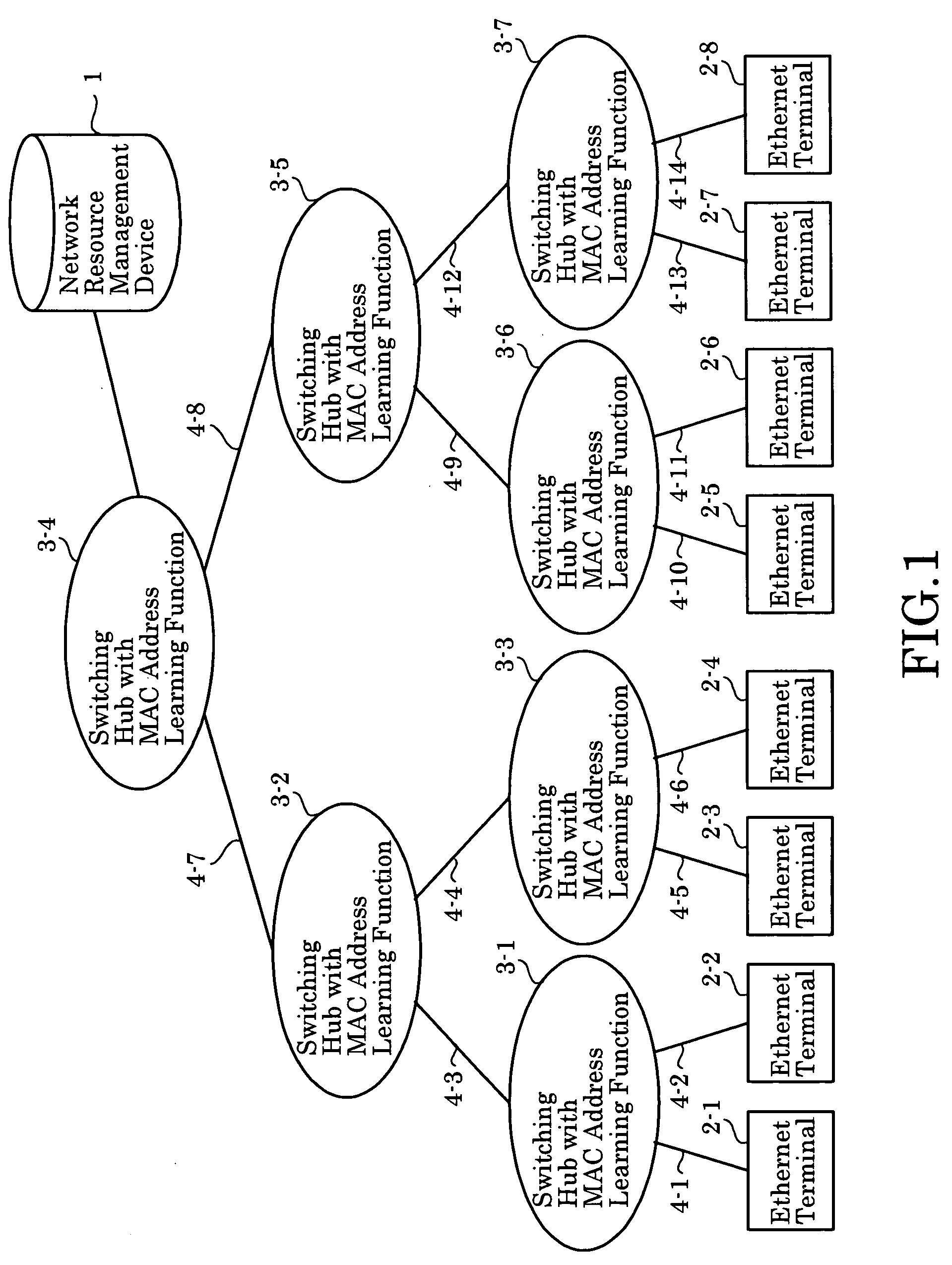
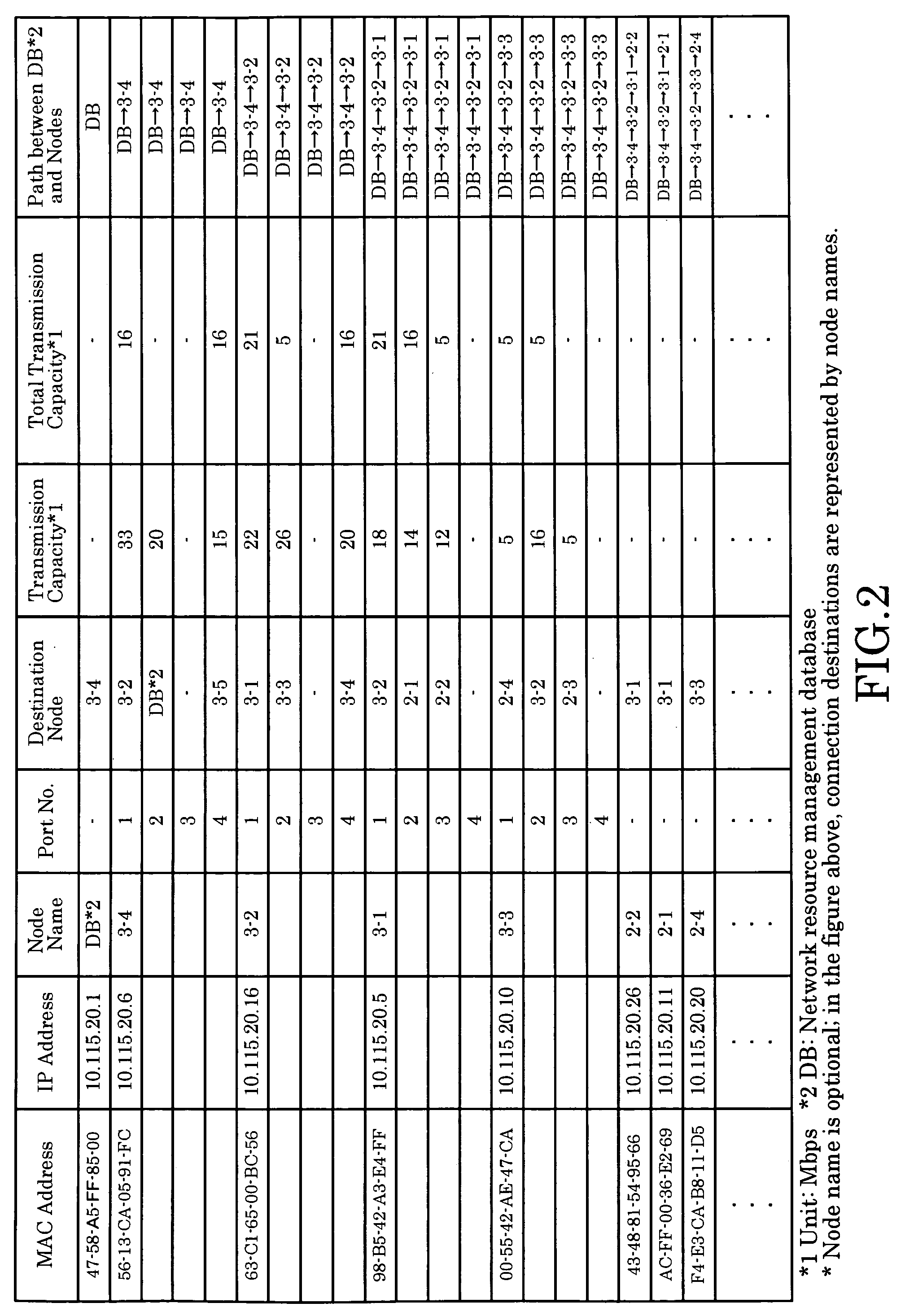
Ransmission Capacity Allocation Method, Communications Network, and Network Resource Management Device
InactiveUS20080239957A1Wasting network resourceError preventionTransmission systemsNetwork resource managementComputer terminal
The invention implements inter-terminal transmission with guaranteed capacity based on the single-path configuration function of networks composed of switching hubs with an MAC address learning function and centralized management of transmission capacity, without control over hubs. The capacity to be used by transmission links on a network is stored in advance and transmission capacity along the path to be used is allocated based on requests from terminals, with the allocation removed using a Terminate Request. At such time, by using transmission links and switching hubs with an MAC address learning function, transmission is limited to single-path transmission.
Owner:YAZAKI CORP
Plant-level comprehensive supervision platform
InactiveCN105187771ARealize centralized managementQuality improvementClosed circuit television systemsTransmissionVideo monitoringIntelligent lighting
The invention relates to a monitoring system and specifically relates to a plant-level comprehensive supervision platform. The plant-level comprehensive supervision platform comprises a front-end system, a transmission network and a master station system, wherein the front-end system is integrated with subsystems of video monitoring, environmental monitoring, security guard, fire alarm, one-card-through, entrance and exit control, maloperation prevention, gps positioning, intelligent lighting, intelligent control and the like in a thermal power plant; the transmission network functions as a bridge for connecting the front end and the platform; the master station system comprises a local monitoring center, a cloud computing system, an application platform and a whole network operation and maintenance platform. The comprehensive supervision platform is a large online monitoring system integrated with hardware, software and network; the platform software is taken as the core to realize centralized management on all zones; besides, centralized monitoring and uniformed management on the front-end system can be realized at a regulation and control center; in short, the plant-level comprehensive supervision platform escorts the smart grid.
Owner:SHANDONG CHUANGDE SOFTWARE TECH
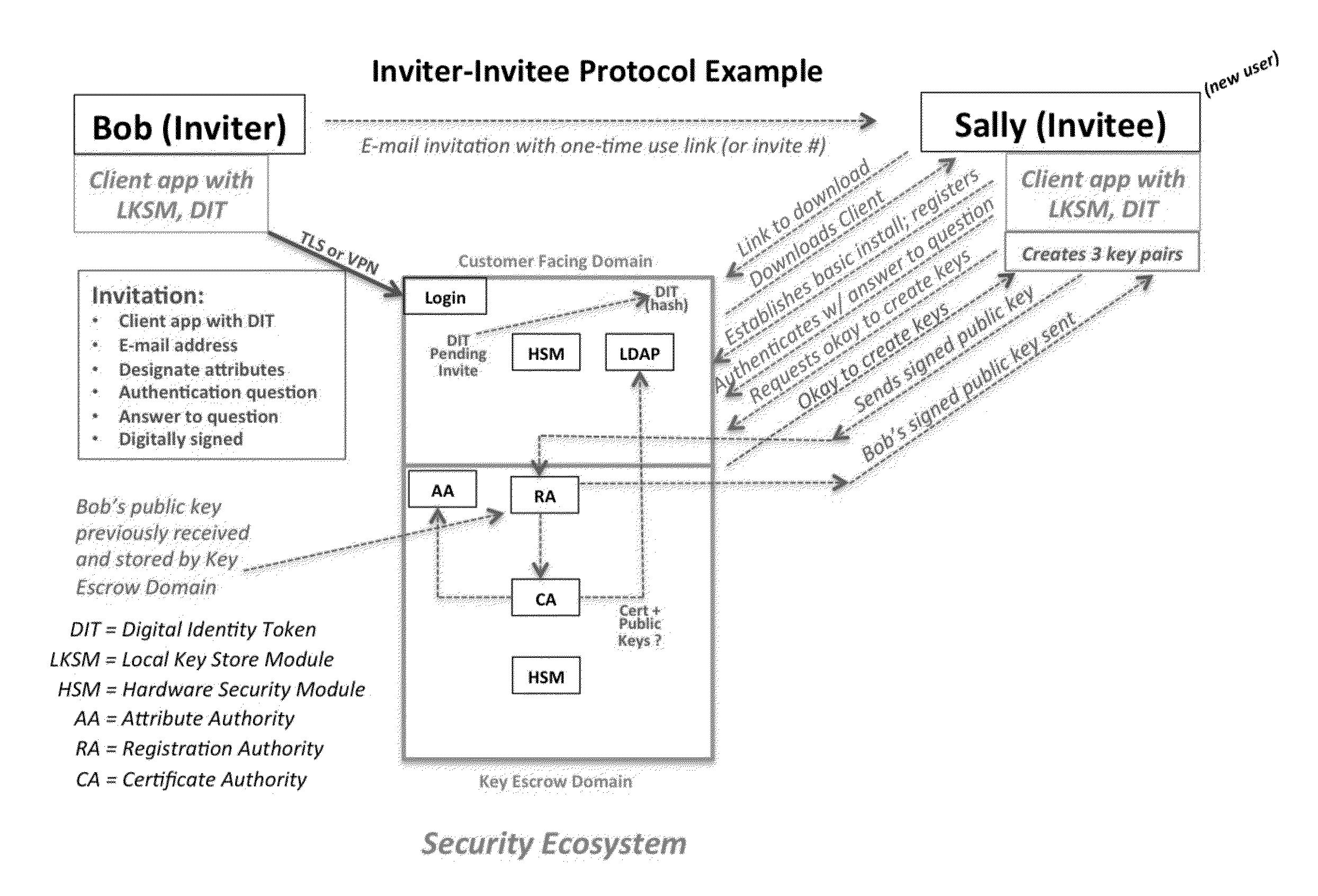
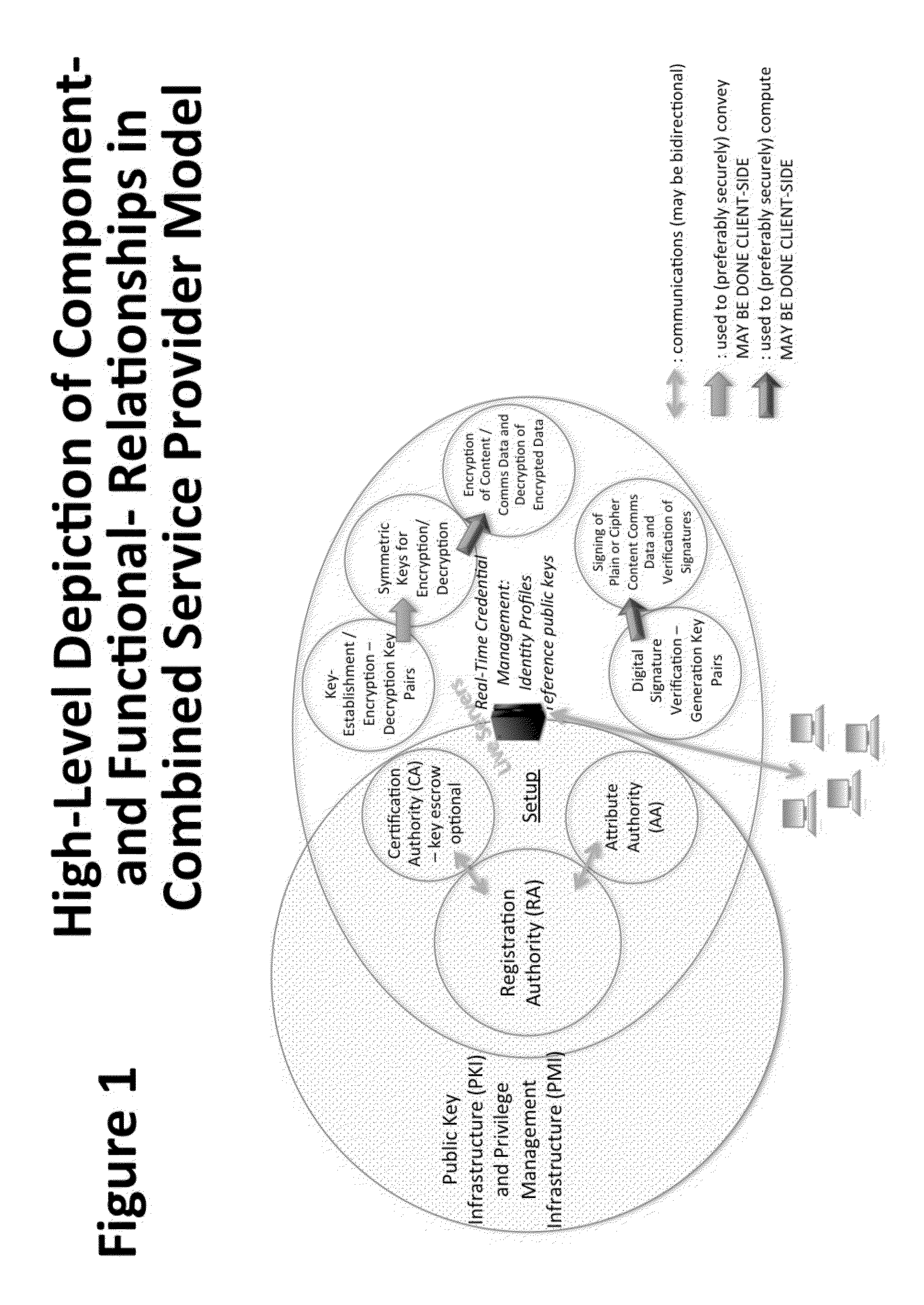
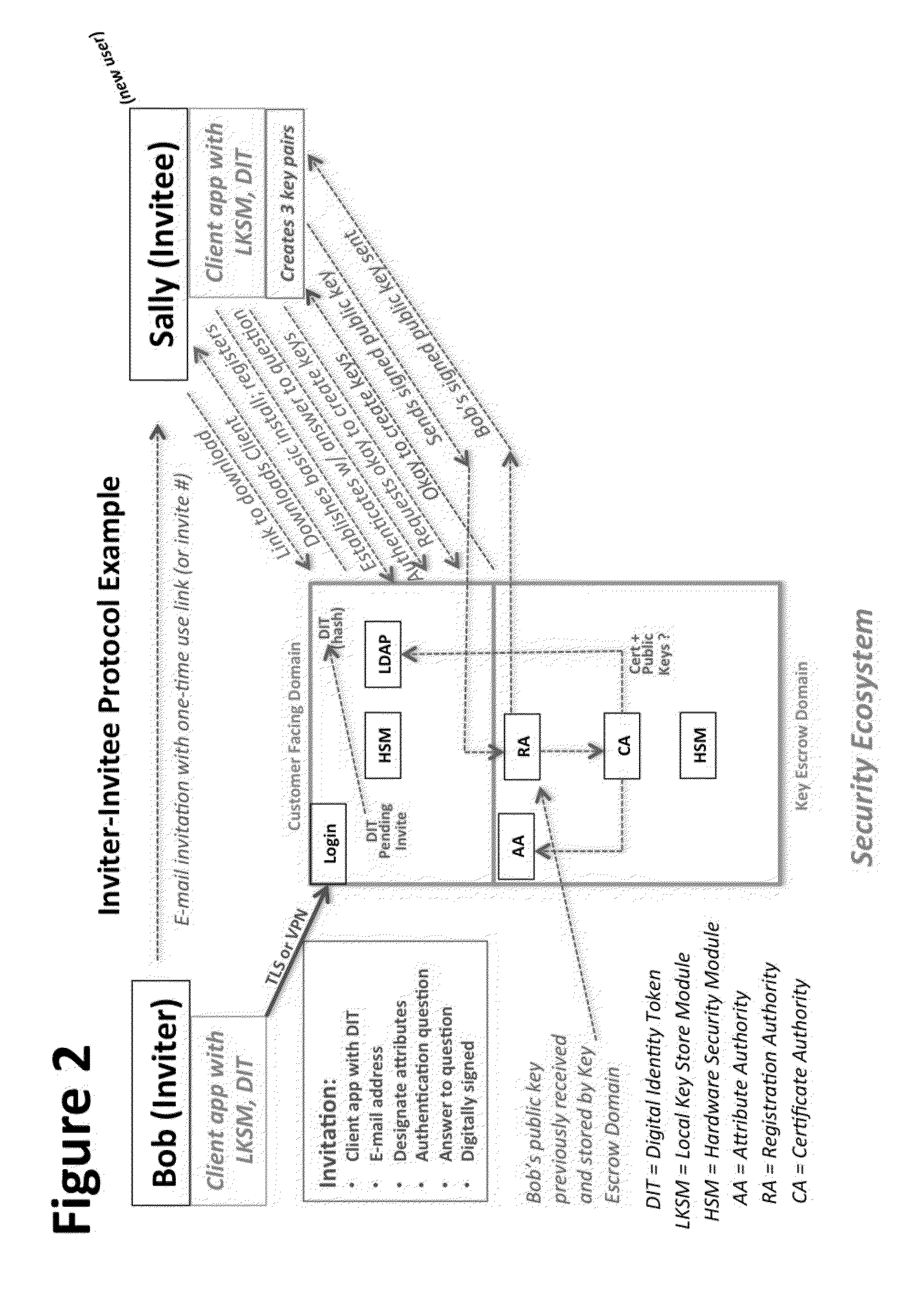
System and Method to Enable PKI- and PMI- Based Distributed Locking of Content and Distributed Unlocking of Protected Content and/or Scoring of Users and/or Scoring of End-Entity Access Means - Added
ActiveUS20150312233A1Key distribution for secure communicationUser identity/authority verificationTrust relationshipThin client
A central server configured with an Attribute Authority (“AA”) acting as a Trusted Third Party mediating service provider and using X.509-compatible PKI and PMI, VPN technology, device-side thin client applications, security hardware (HSM, Network), cloud hosting, authentication, Active Directory and other solutions. This ecosystem results in real time management of credentials, identity profiles, communication lines, and keys. It is not centrally managed, rather distributes rights to users. Using its Inviter-Invitee protocol suite, Inviters vouch for the identity of Invitees who successfully complete the protocol establishing communication lines. Users establish and respond to authorization requests and other real-time verifications pertaining to accessing each communication line (not end point) and sharing encrypted digital files. These are auditable, brokered, trusted-relationships where such relationships / digital agreements can each stand-alone (for privacy) or can leverage build-up of identity confidence levels across relationships. The service is agnostic to how encrypted user content is transported or stored.
Owner:T CENT
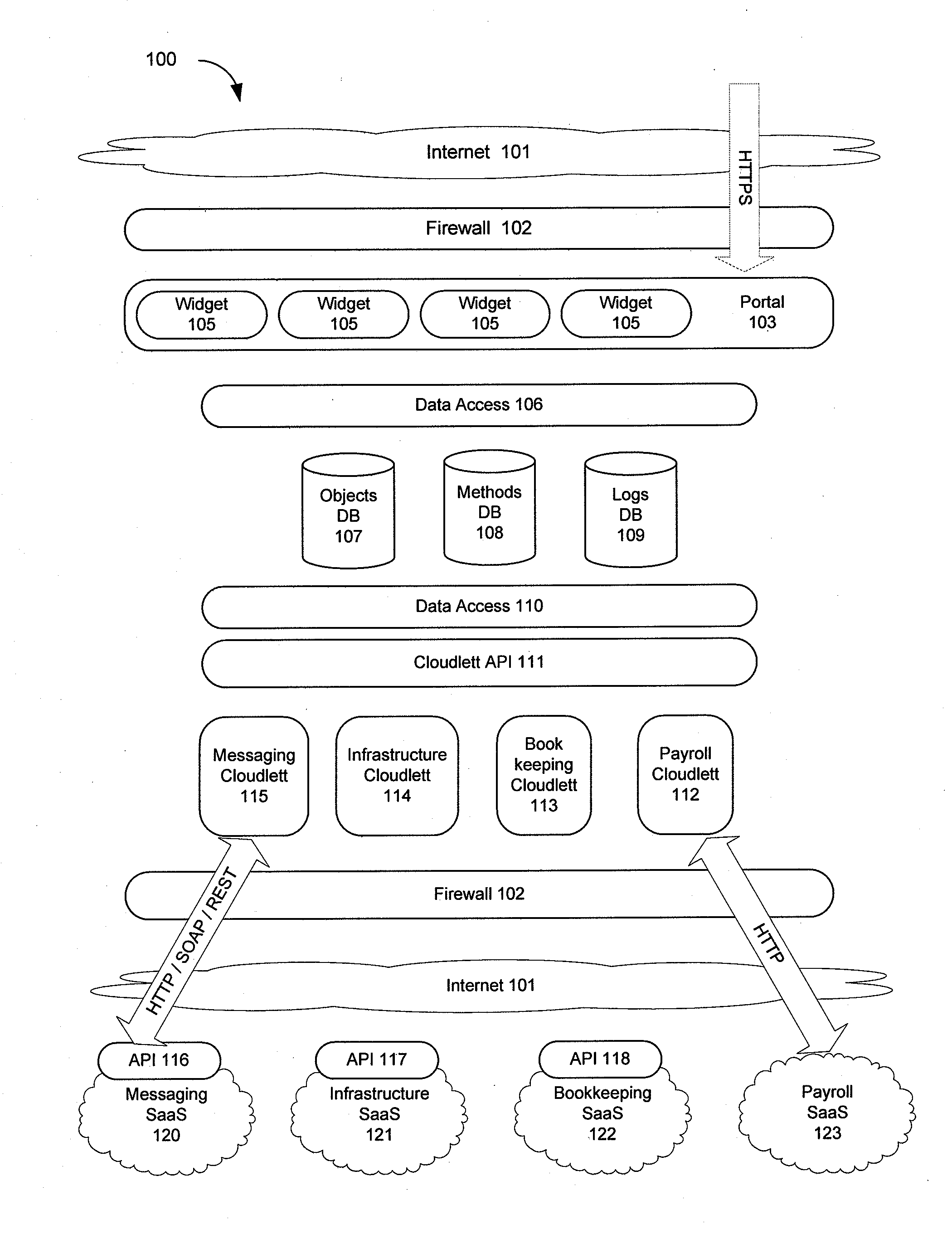
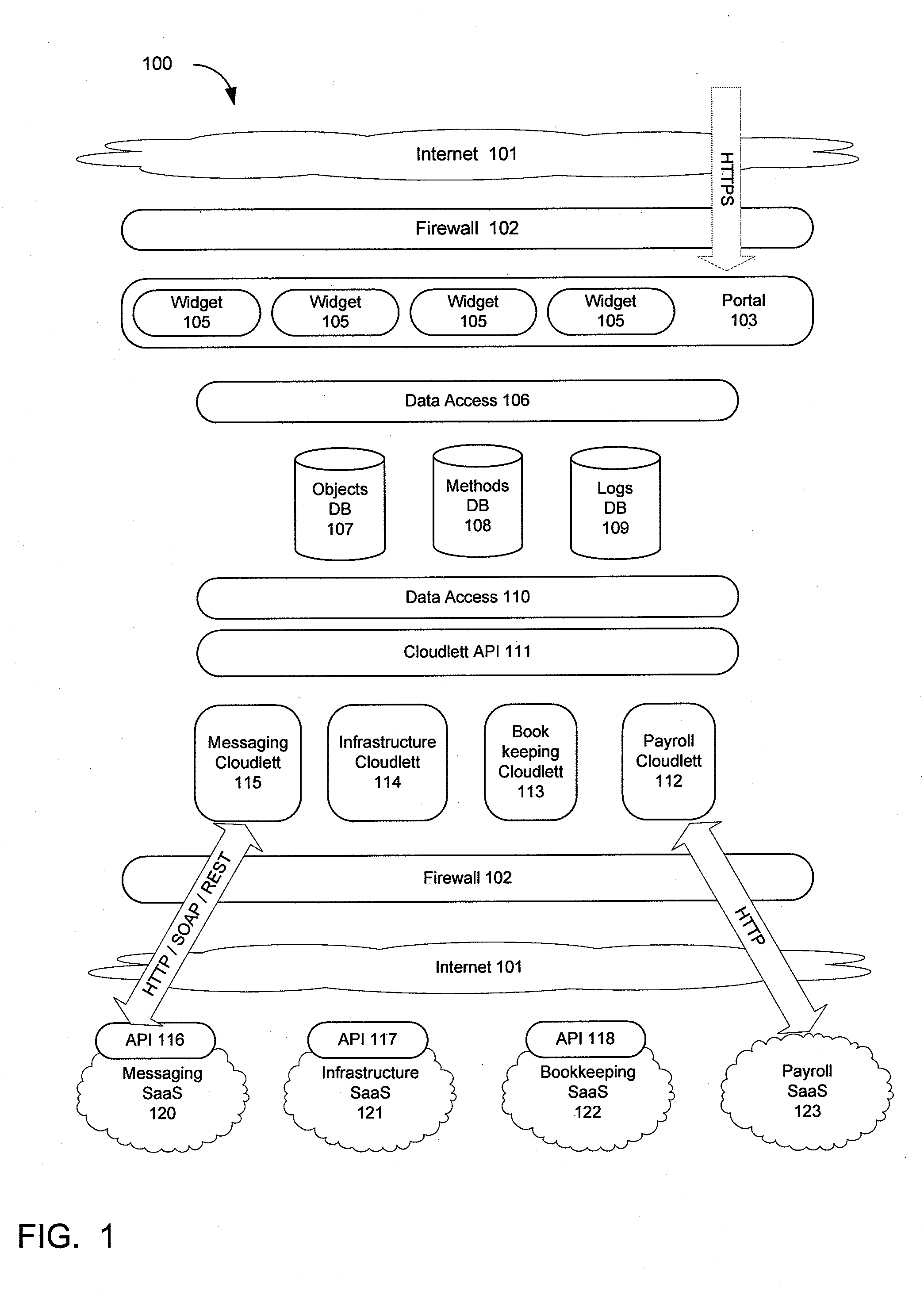
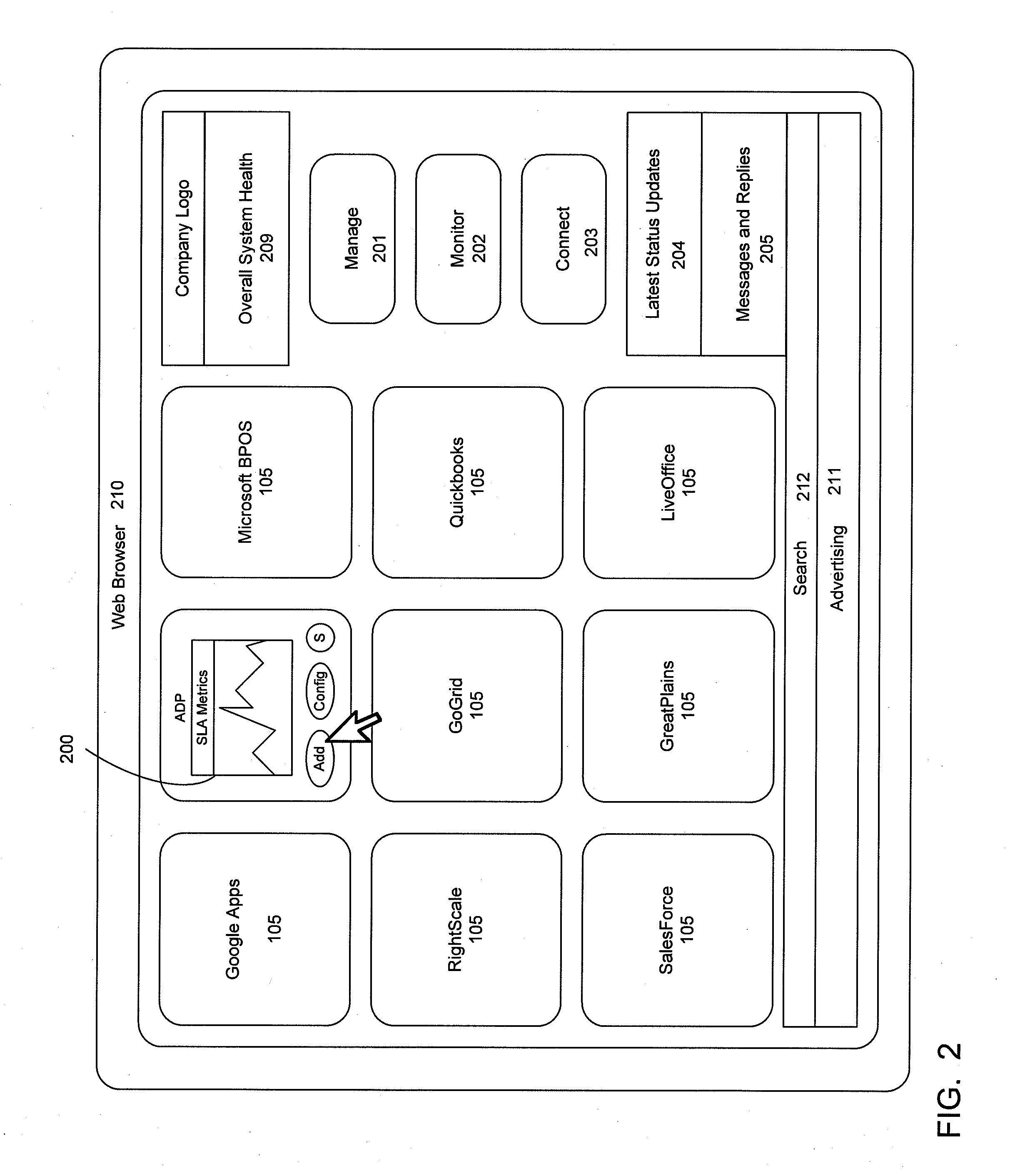
Centrally managing and monitoring software as a service (SAAS) applications
ActiveUS20100250712A1Data processing applicationsMultiple digital computer combinationsApplication softwareCentralized management
An apparatus, system, method and program providing a multi-tenant software as a service (SaaS) application that manages and monitors the use of other SaaS applications via a common connection and database framework. An Internet-based interface is provided as a single portal for monitoring and managing the use of SaaS applications. Objects and the state of these objects including all associated attributes related to the SaaS applications are stored in databases associated with the Internet-based interface. The Internet-based interface also provides a social networking infrastructure and an application exchange infrastructure that allows sharing of information related to the SaaS applications.
Owner:III HLDG 1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com