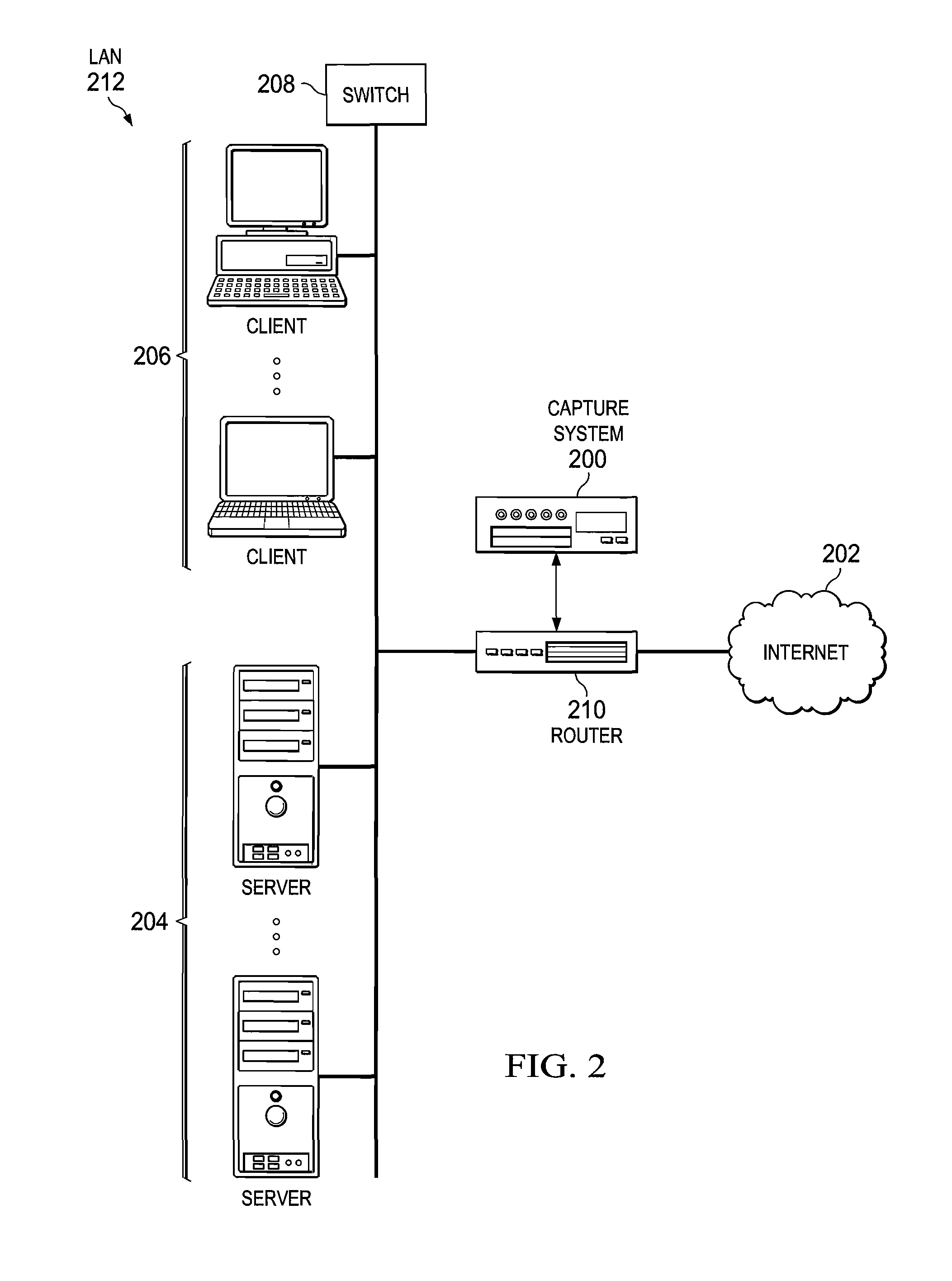
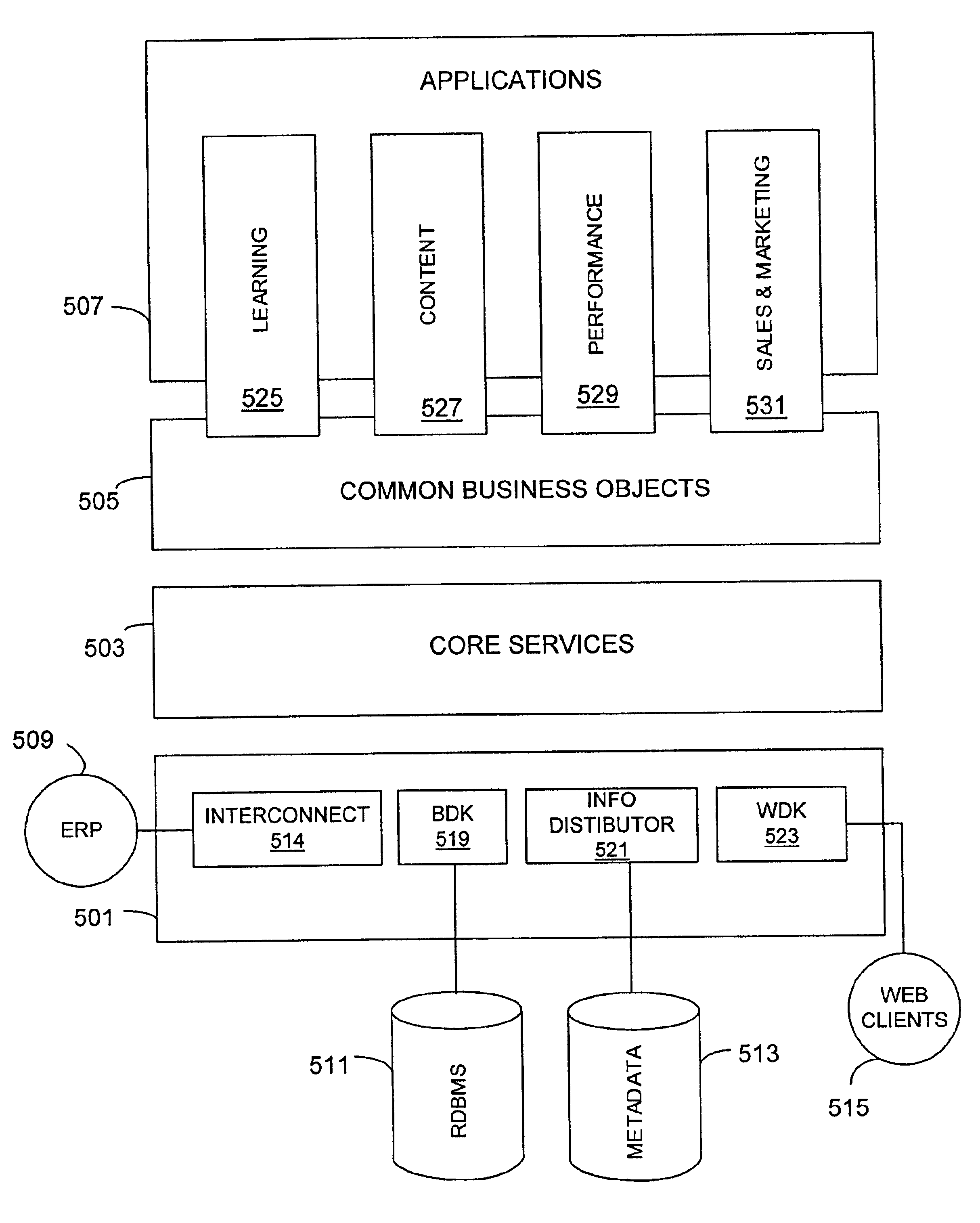
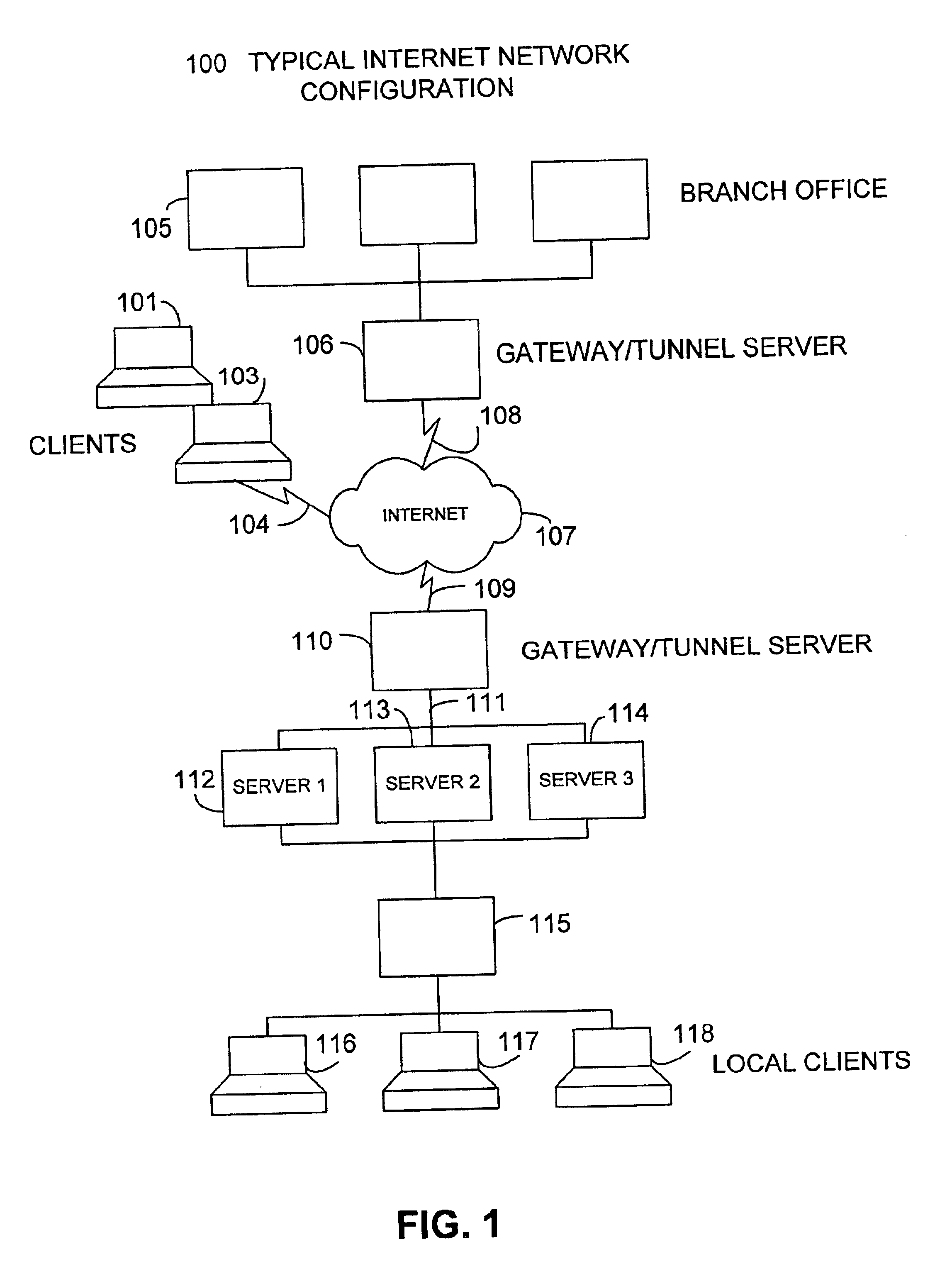
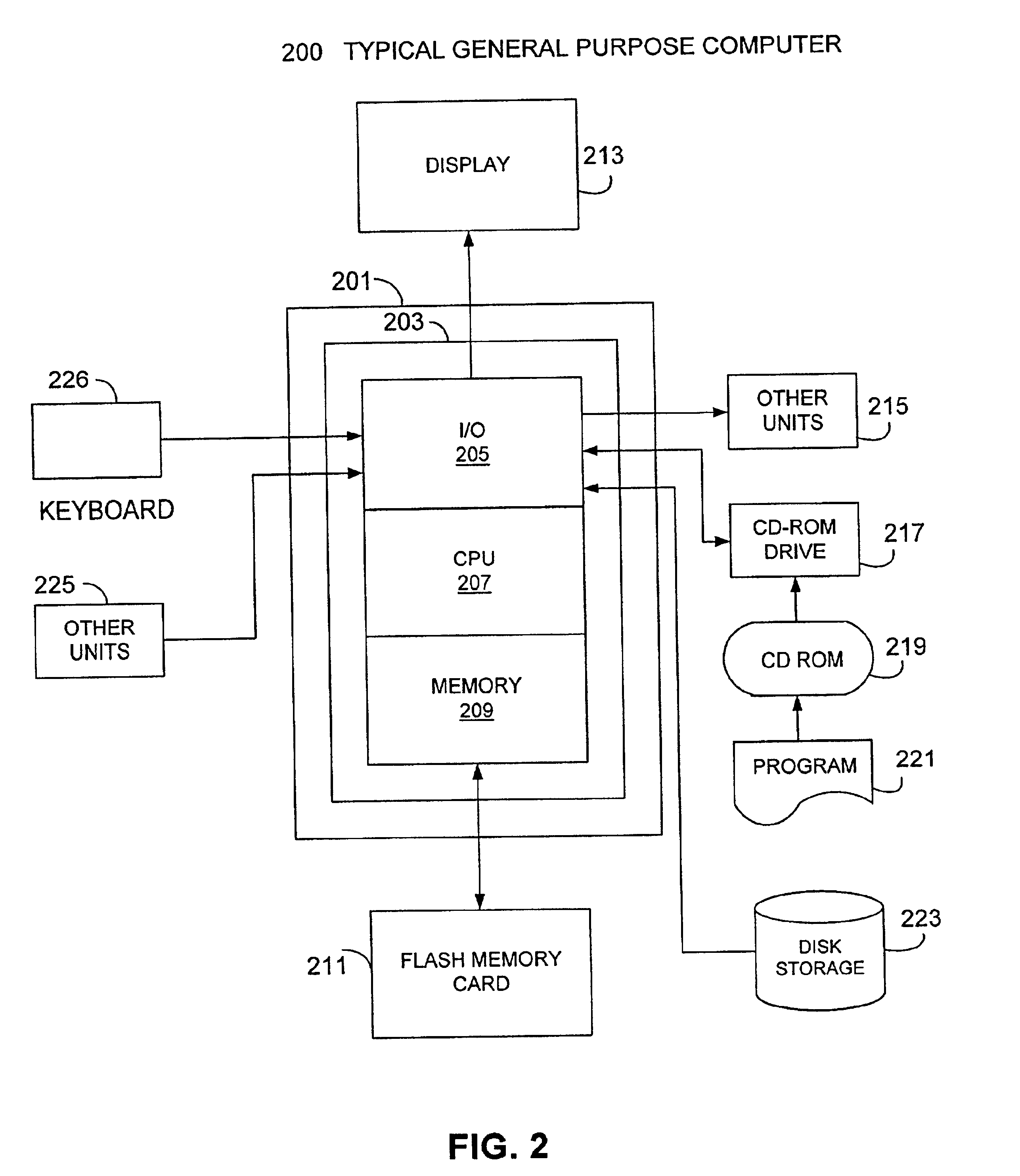
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4609 results about "Security management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security management is the identification of an organization's assets (including people, buildings, machines, systems and information assets), followed by the development, documentation, and implementation of policies and procedures for protecting these assets.
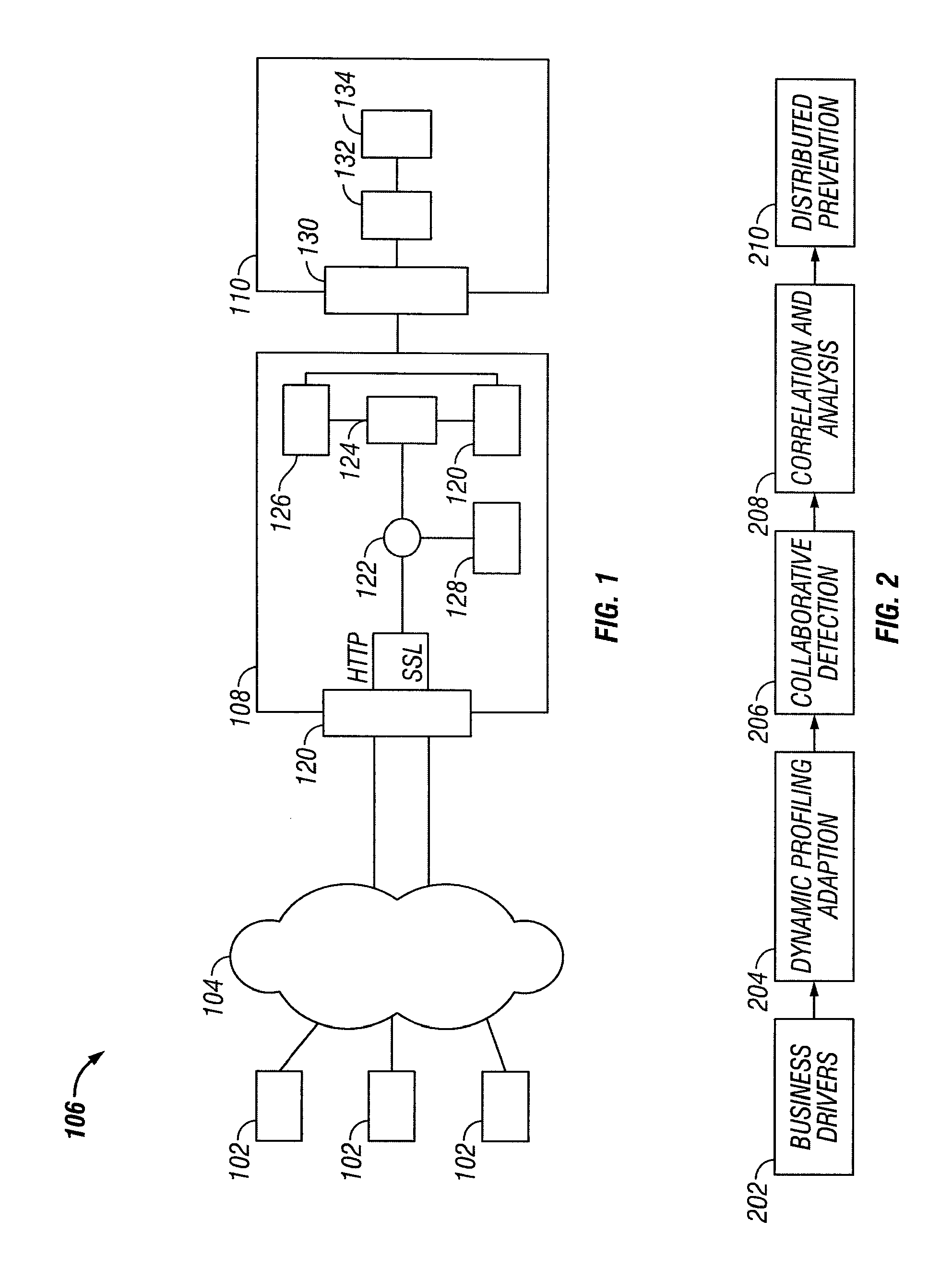
Method and apparatus for a web-based application service model for security management
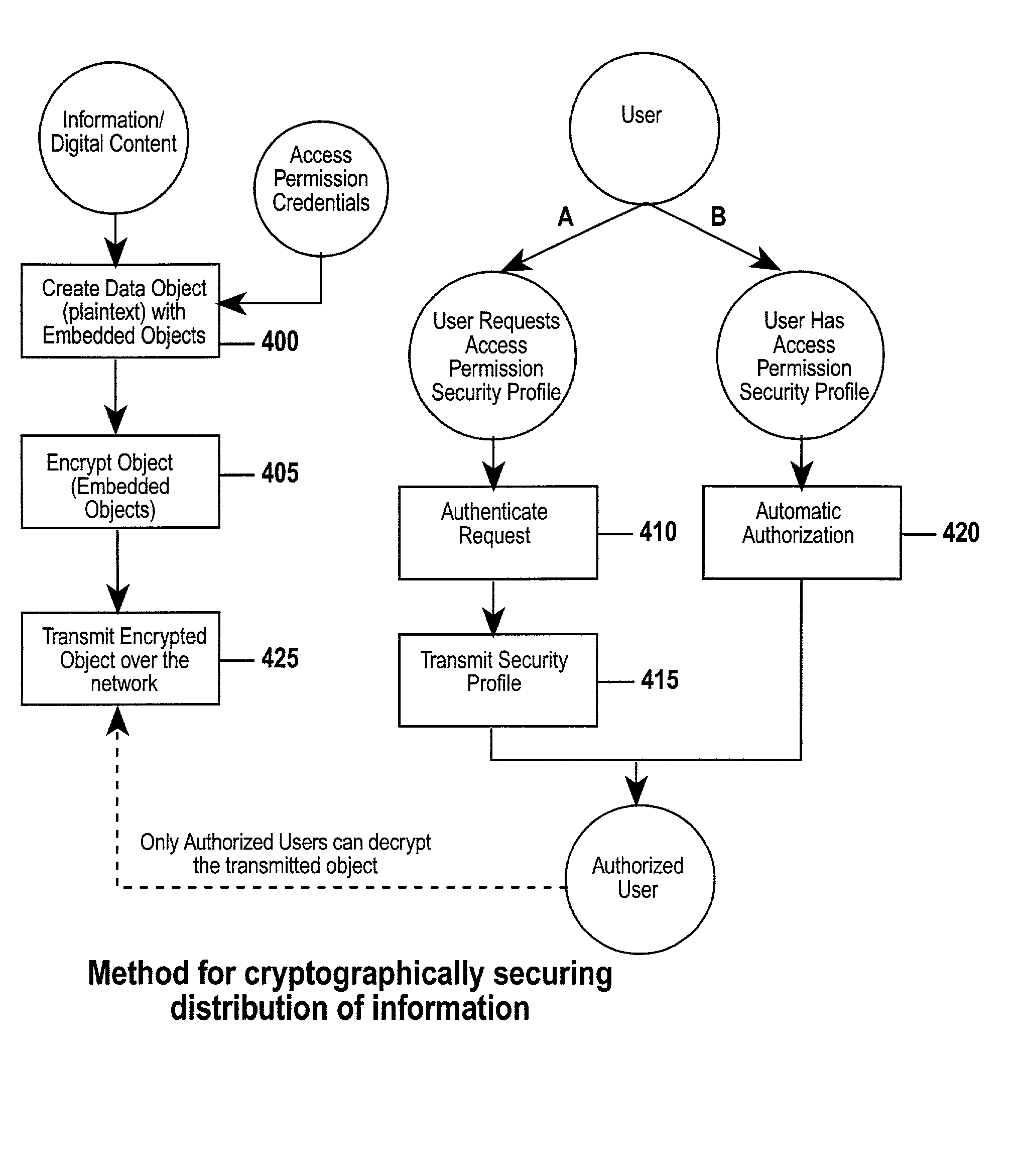
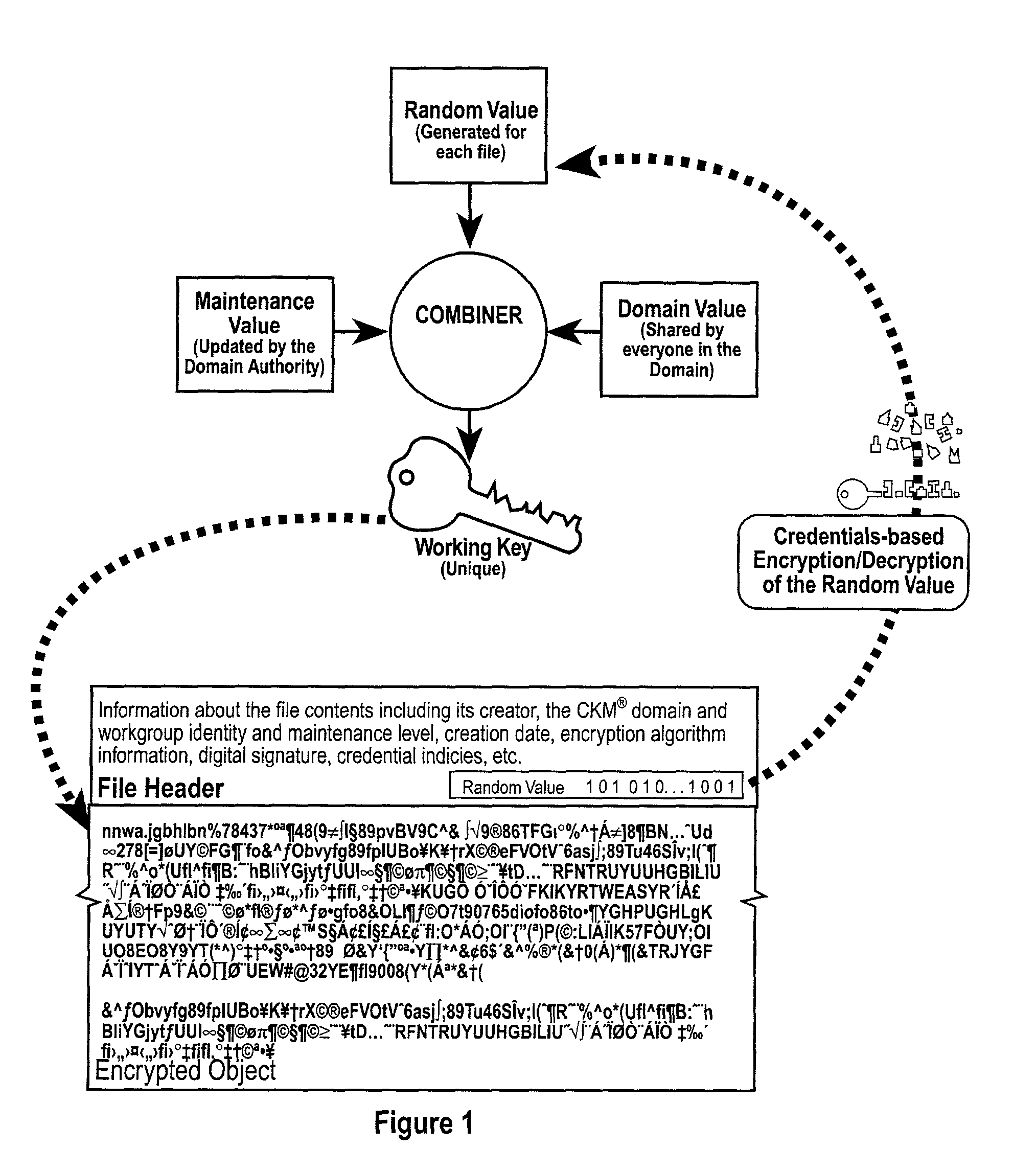
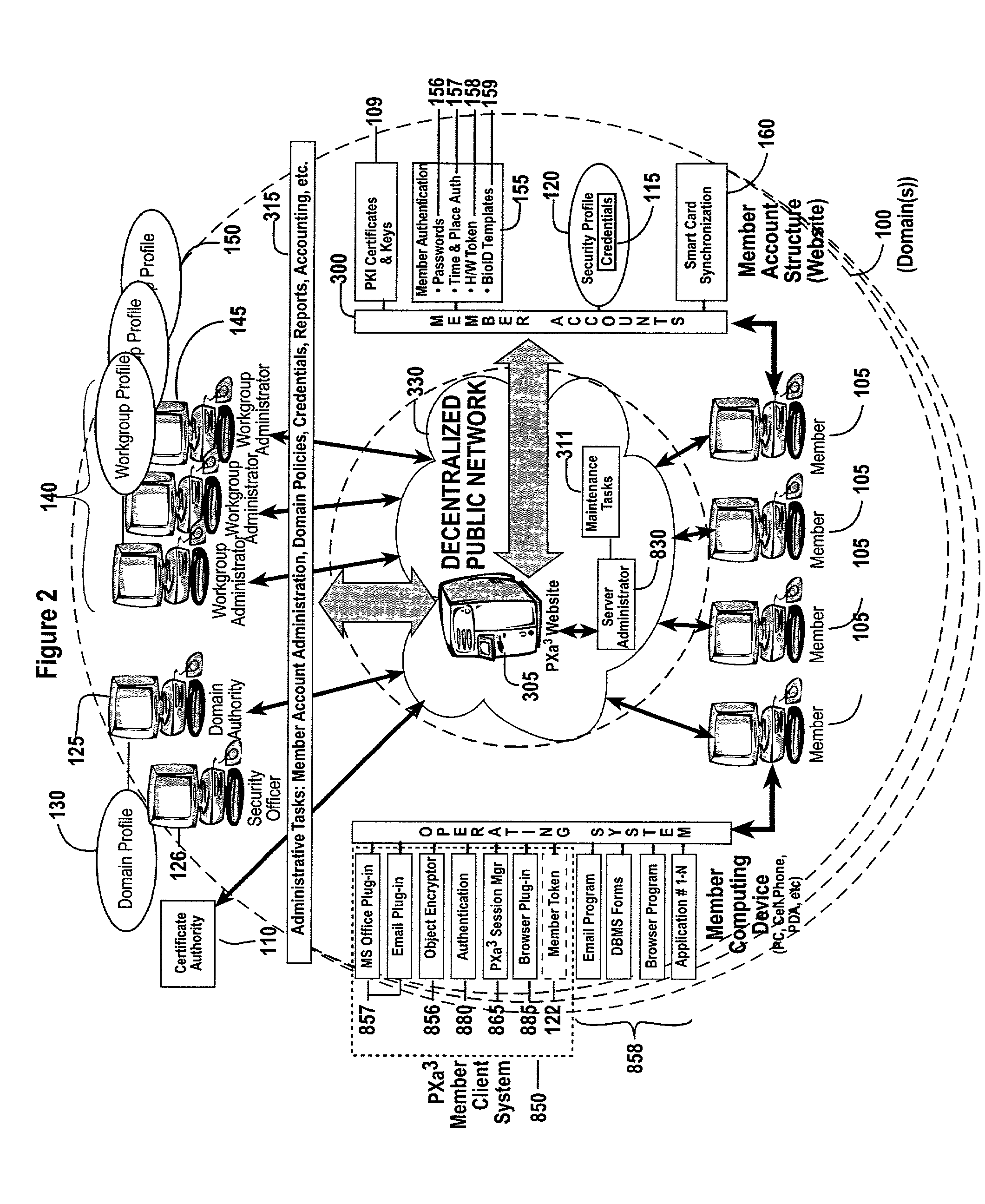
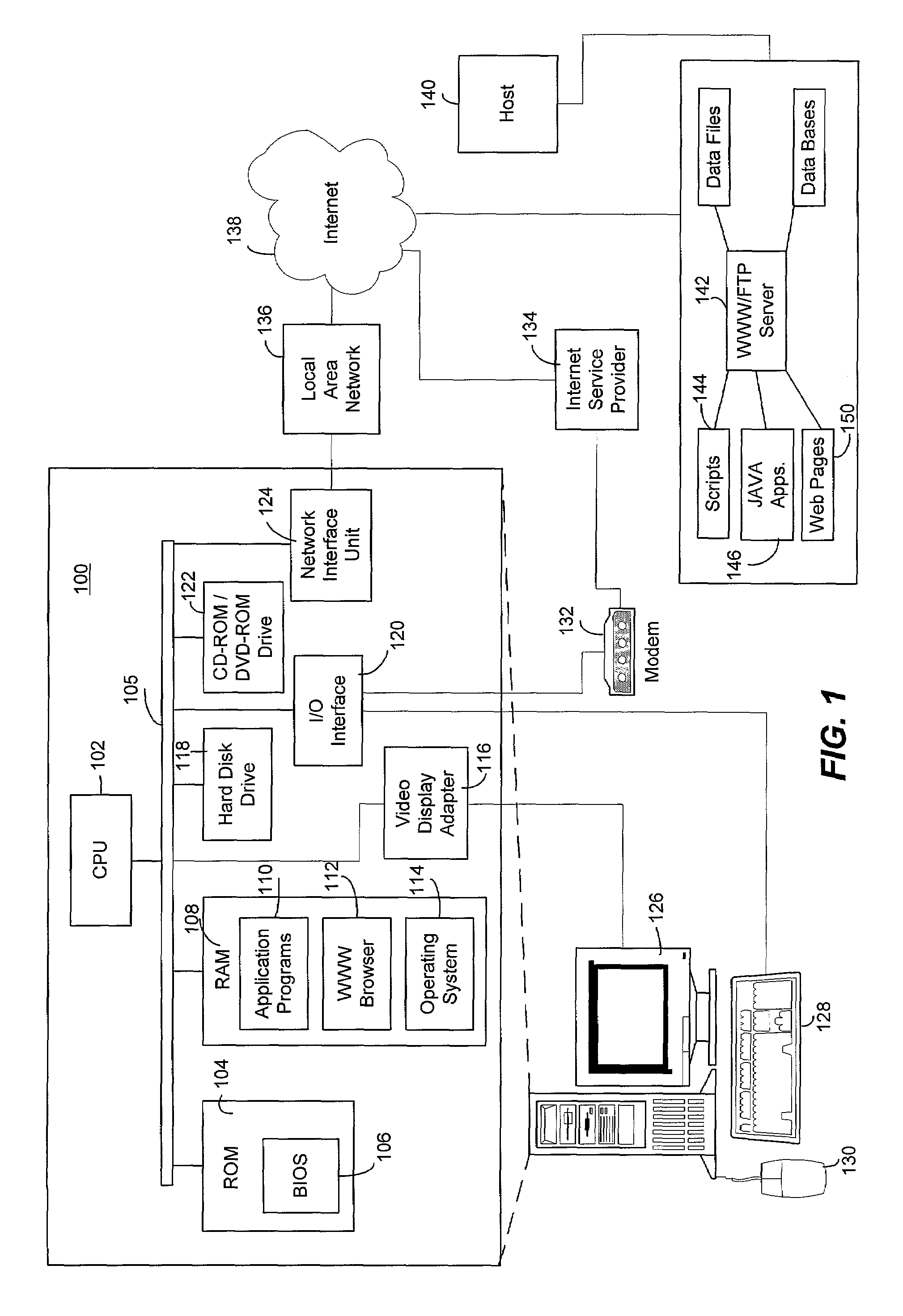
The invention combines cryptographic key management technology with various authentication options and the use of a companion PKI system in a web-centric cryptographic key management security method and apparatus called PXa3(TM) (Precise eXtensible Authentication, Authorization and Administration). The PXa3 model uses a security profile unique to a network user and the member domain(s) he / she belongs to. A PXa3 server holds all private keys and certificates, the user's security profile, including credentials and the optional authentication enrollment data. The server maintains a security profile for each user, and administrators simply transmitted credential updates and other periodic maintenance updates to users via their PXa3 server-based member accounts. Domain and workgroup administrators also perform administrative chores via a connection to the PXa3 web site, rather than on a local workstation. A member's security profile, containing algorithm access permissions, credentials, domain and maintenance values, a file header encrypting key, optional biometric templates, and domain-specific policies is contained in one of two places: either on a removable cryptographic token (e.g., a smart card), or on a central server-based profile maintained for each member and available as a downloadable "soft token" over any Internet connection.
Owner:SIVAULT INC
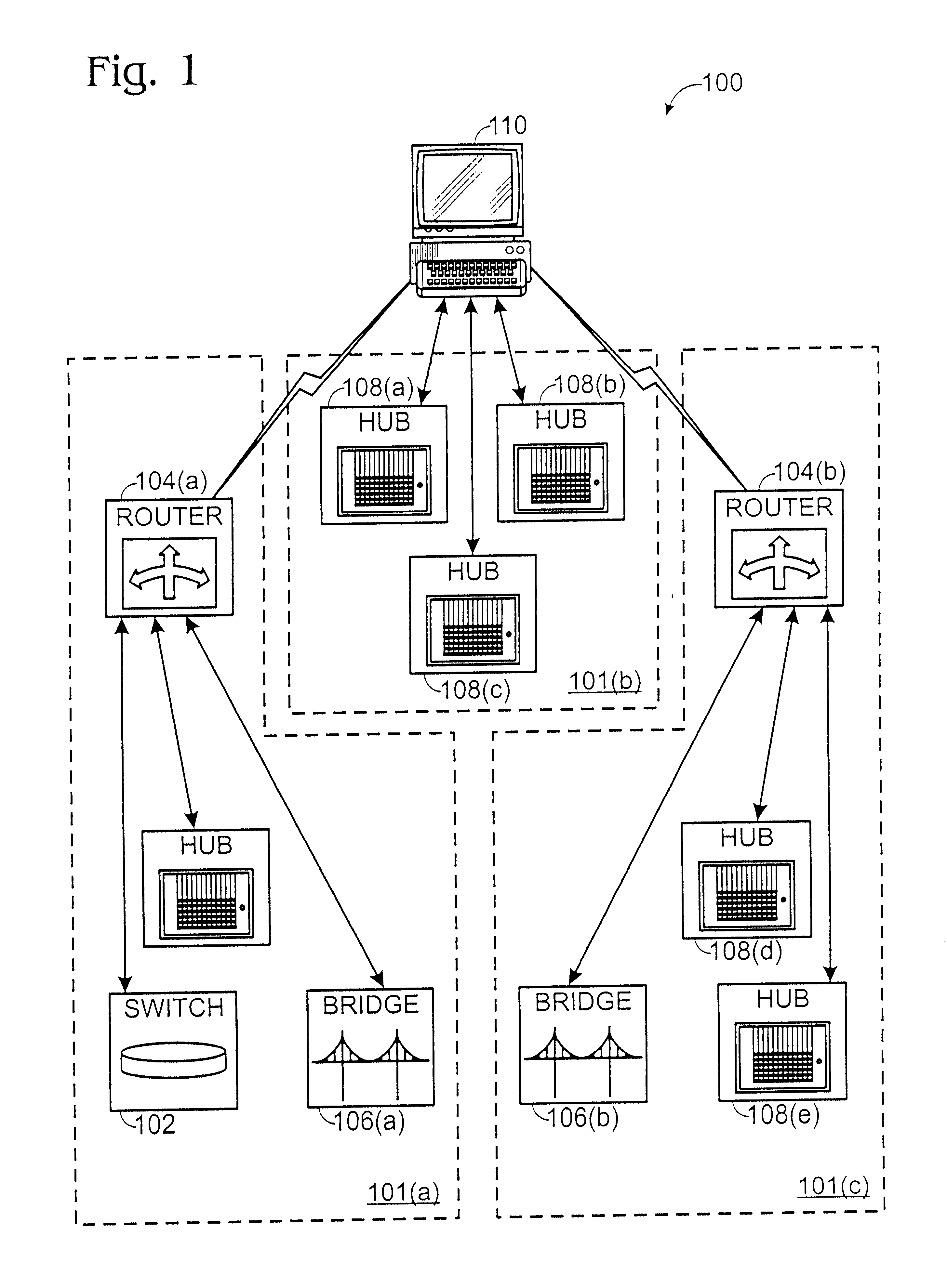
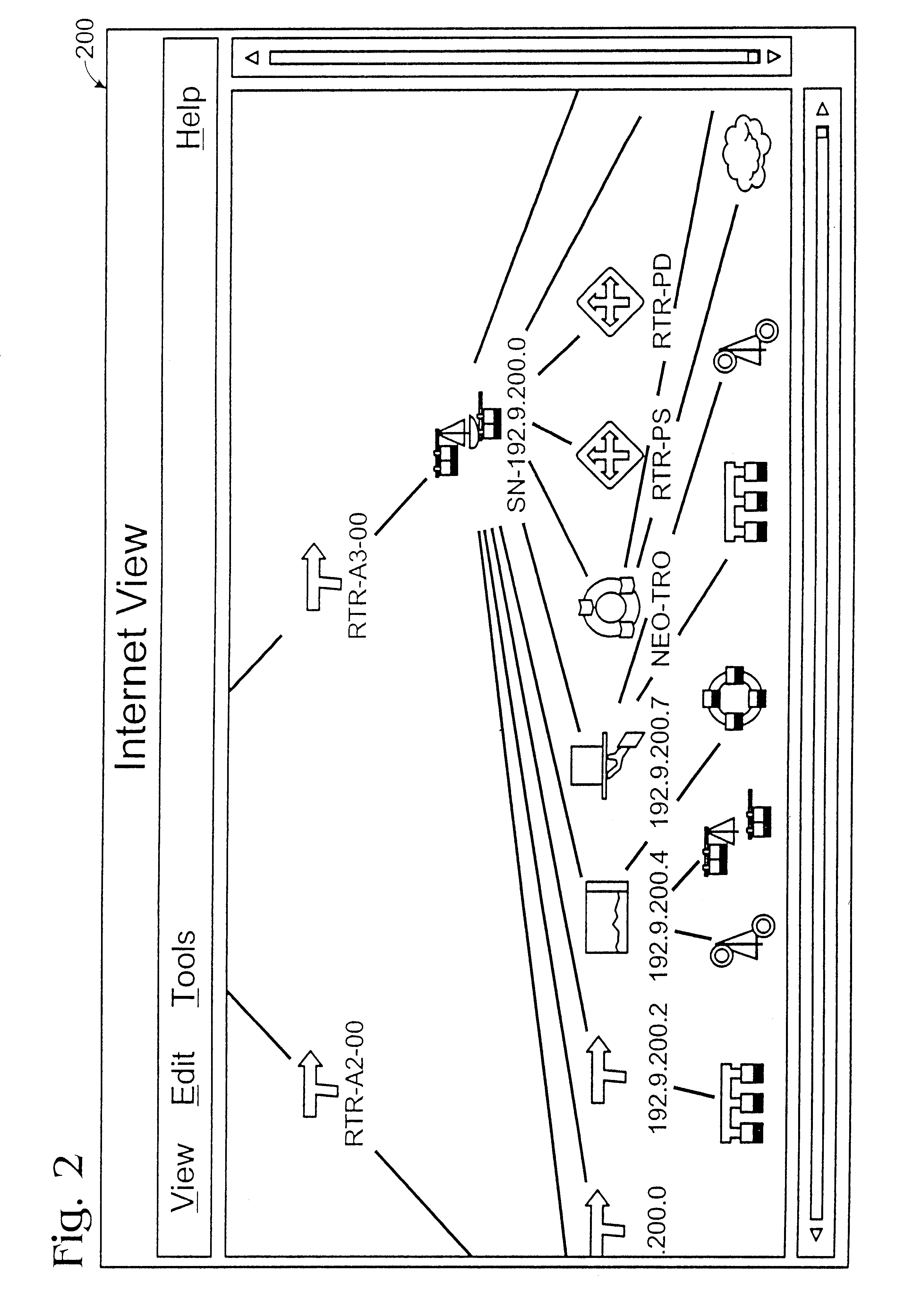
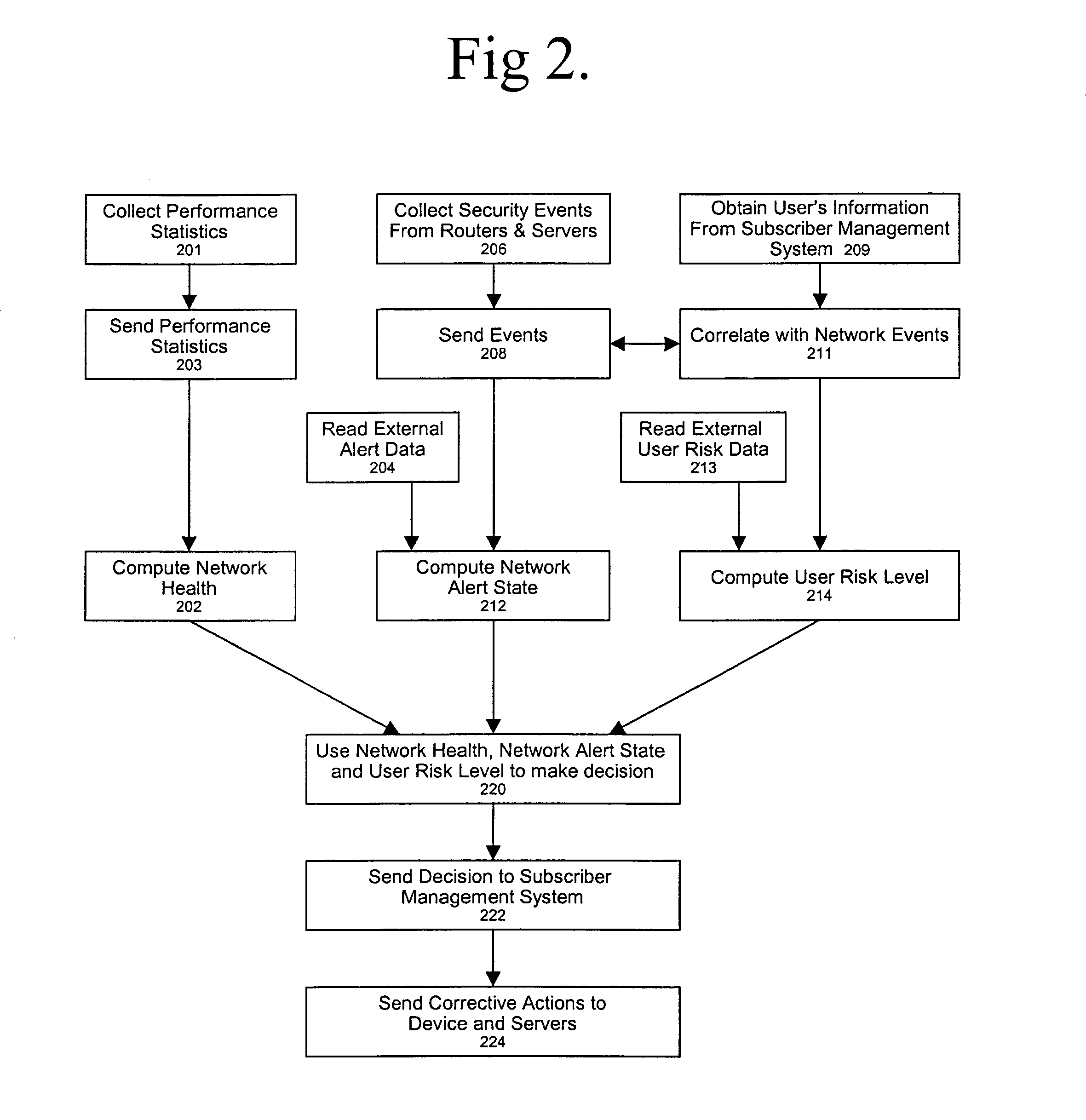
Method and apparatus for displaying health status of network devices
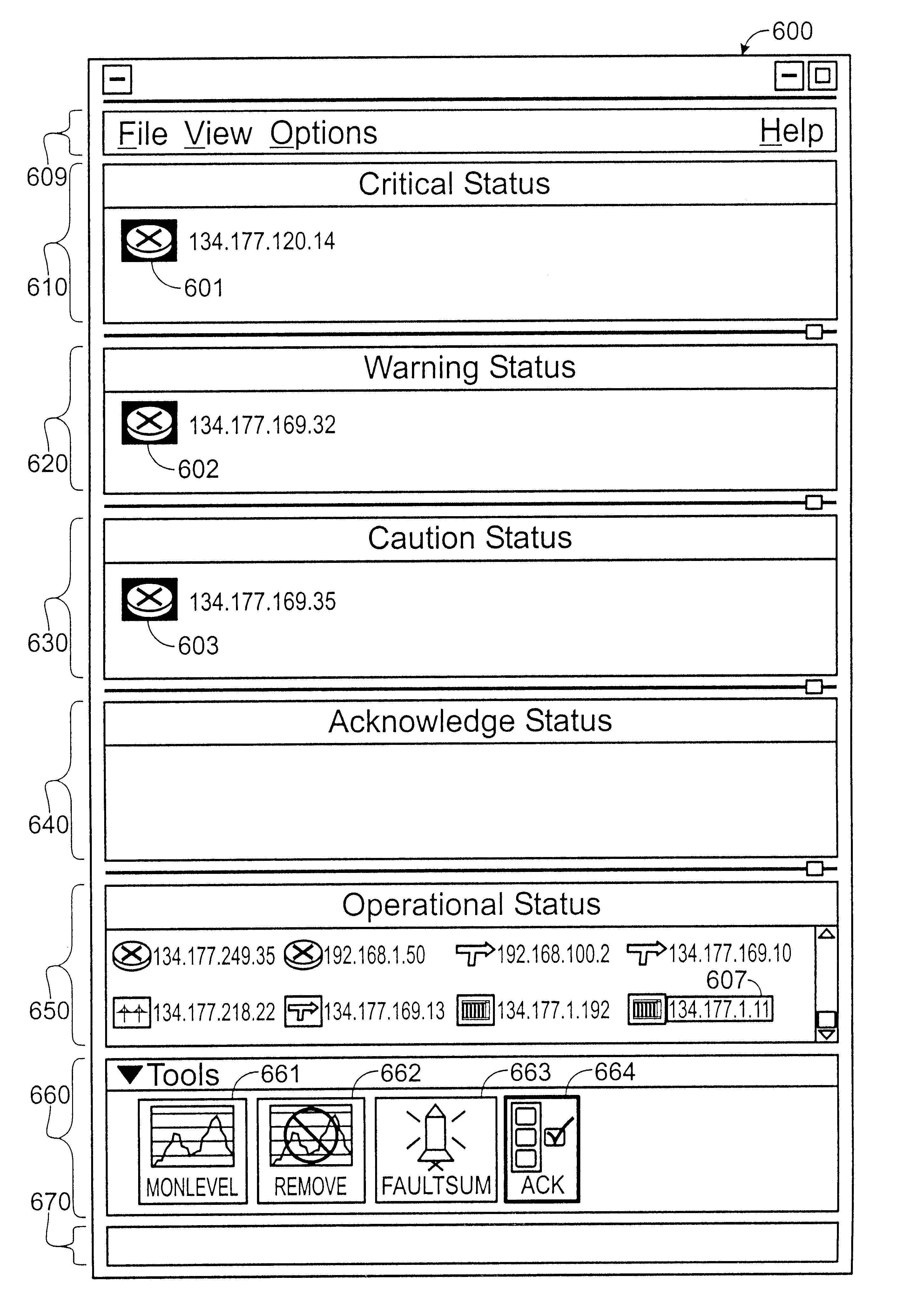
A method and apparatus for concurrently displaying from a single window on a network management station the health status of all network devices and objects of a computer network. The network devices may be categorized according to state or device type, as determined by the network manager. The method and apparatus provides a network manager with the ability to determine the current state of network devices and objects within an enterprise network and invoke further actions such as configuration, performance, fault, and security management tasks. The network manager can drag and drop icons from one network management system application window to another network management system application window to obtain fault information about network devices and objects, thus allowing multiple network management system applications to run concurrently on the same network management station. The network manager is further able to add new network devices and objects by dragging site, folder or device icons from one network management system application window to a second network management system application window for displaying the health status of the new devices. The dragged-in devices are added to the appropriate status panes within the second window according to the method of the present invention.
Owner:NORTEL NETWORKS LTD
Policy-based network security management
ActiveUS7237267B2Memory loss protectionError detection/correctionNetwork resource managementCourse of action
A policy-based network security management system is disclosed. In one embodiment, the system comprises a security management controller comprising one or more processors; a computer-readable medium carrying one or more sequences of instructions for policy-based network security management, wherein execution of the one or more sequences of instructions by the one or more processors causes the one or more processors to perform the steps of receiving a set of data regarding a user of a computer network; automatically deciding on a course of action based on the set of data, wherein the course of action may be adverse to the user although the set of data is insufficient to establish whether the user is performing a malicious action; and sending signals to one or more network elements in the computer network to implement the decision.
Owner:CISCO TECH INC
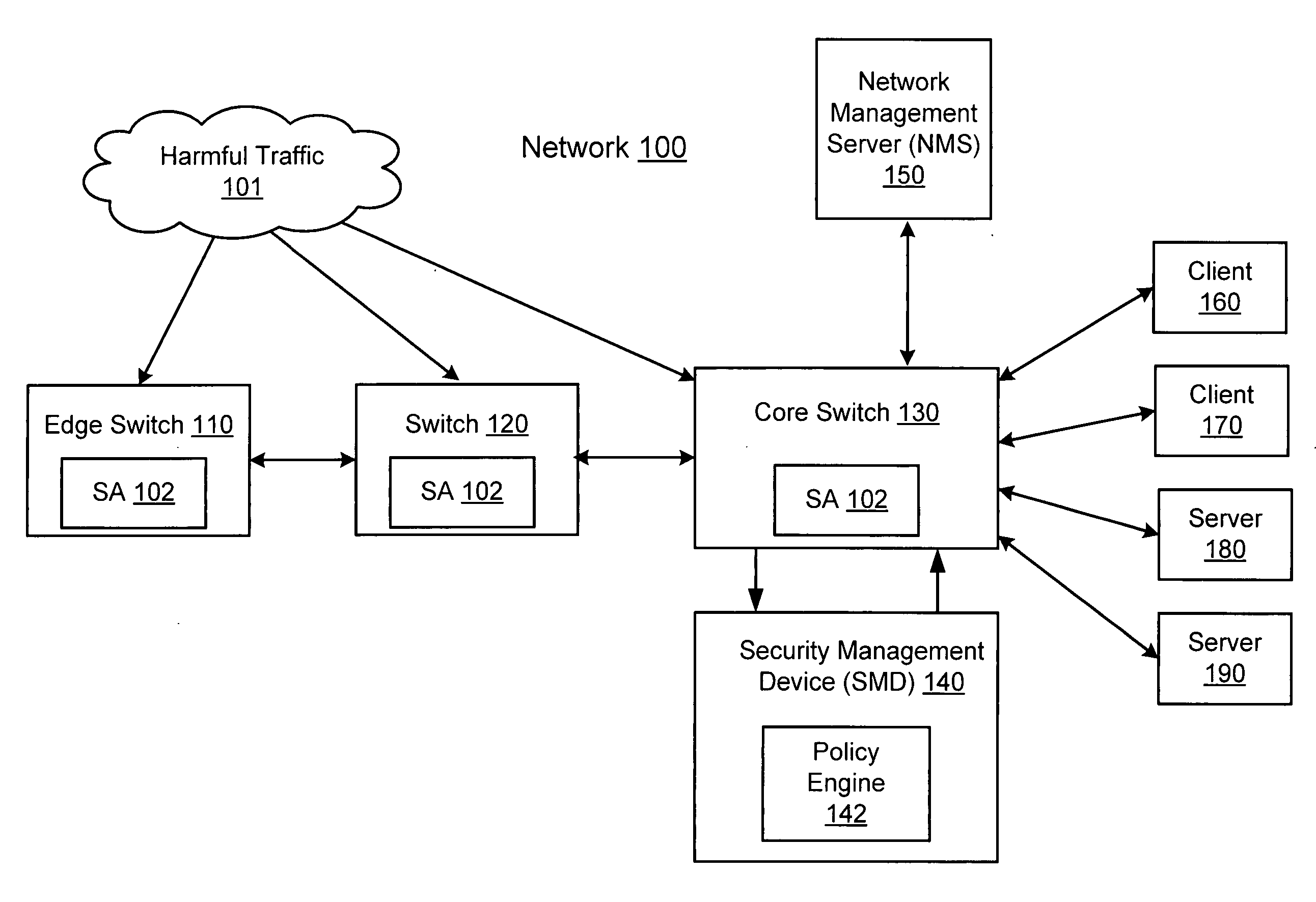
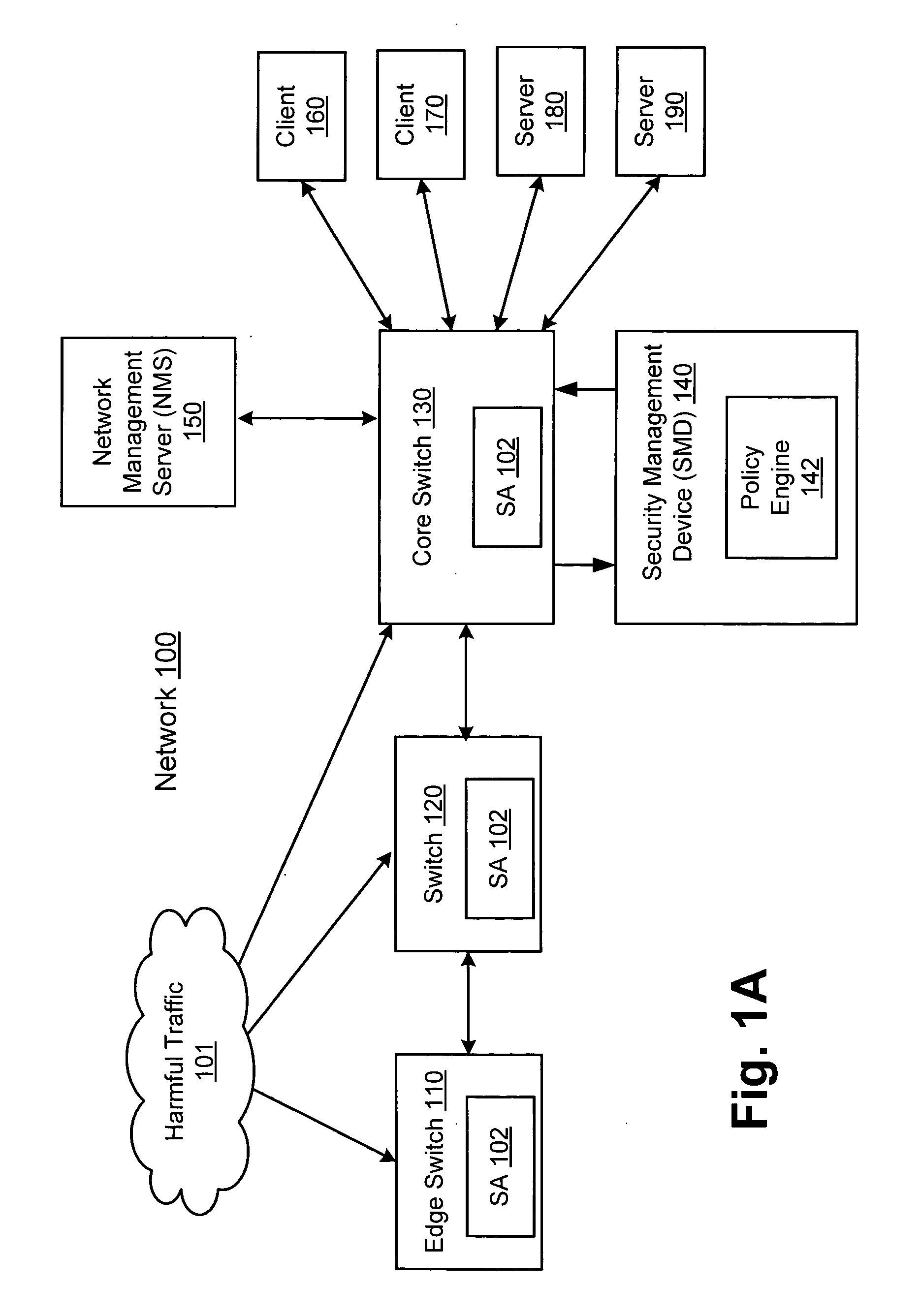
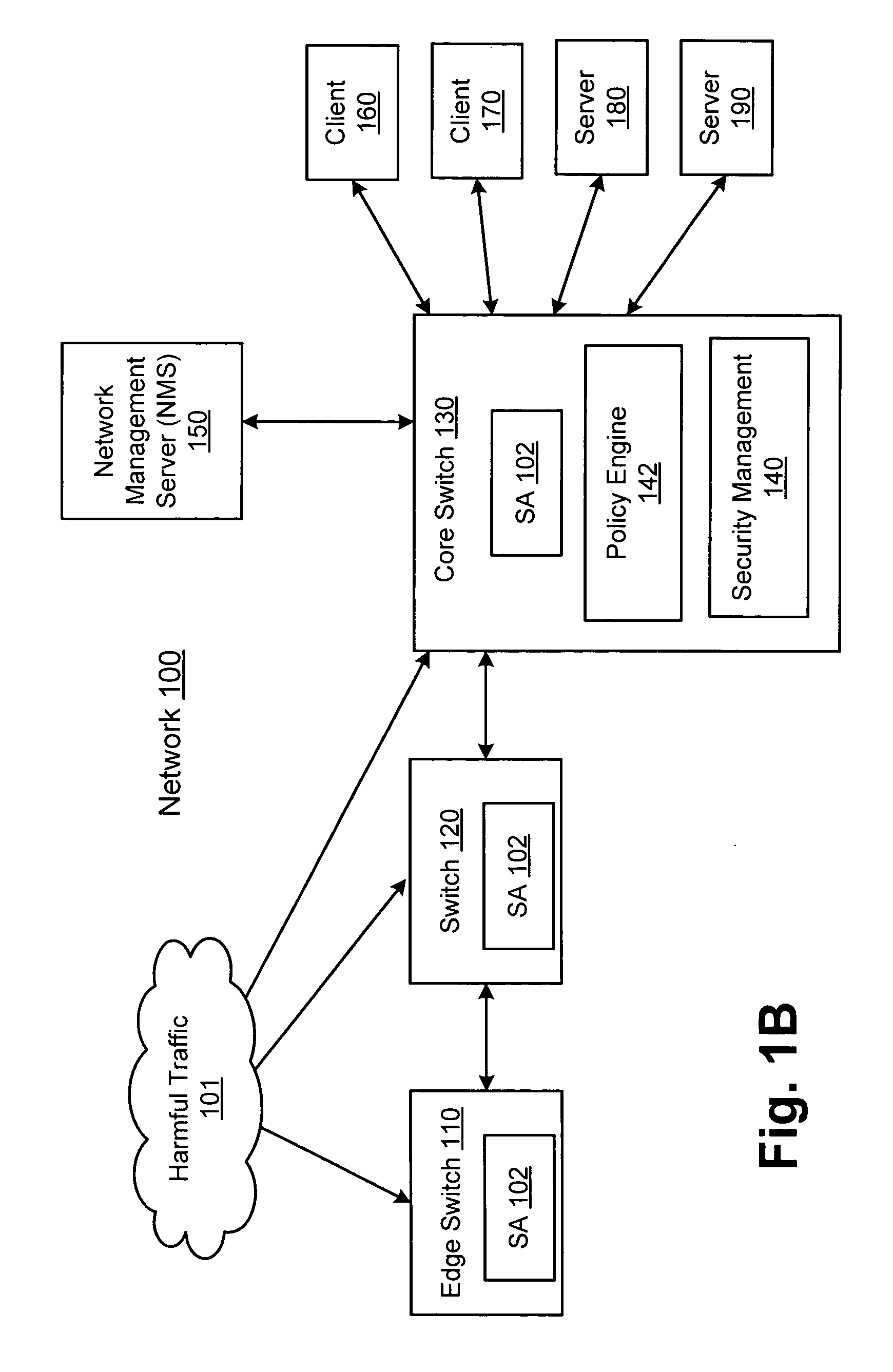
Network threat detection and mitigation
ActiveUS20070157306A1Error preventionFrequency-division multiplex detailsInternet trafficNetwork switch
A network switch automatically detects undesired network traffic and mirrors the undesired traffic to a security management device. The security management device determines the source of the undesired traffic and redirects traffic from the source to itself. The security management device also automatically sends a policy to a switch to block traffic from the source.
Owner:EXTREME NETWORKS INC
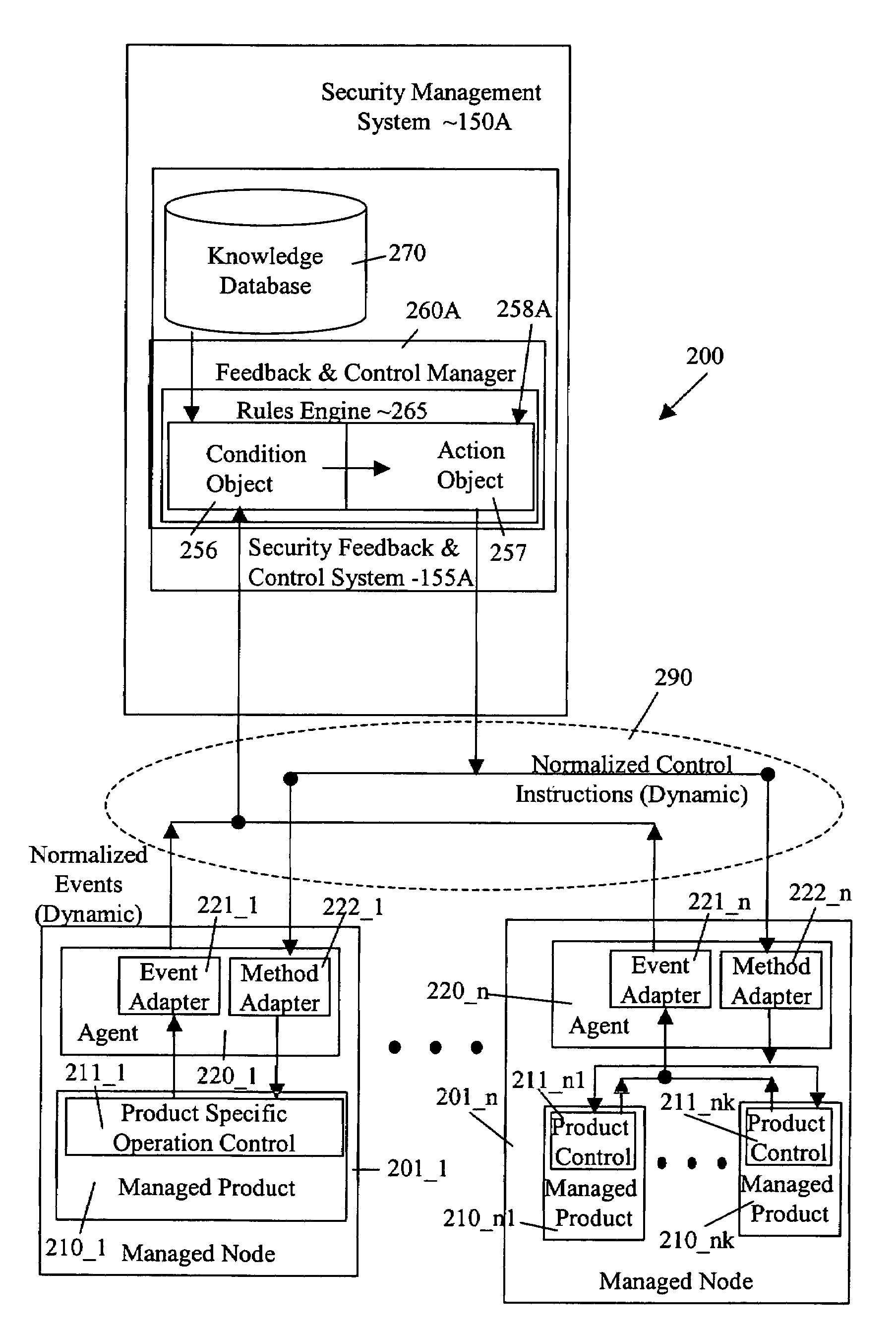
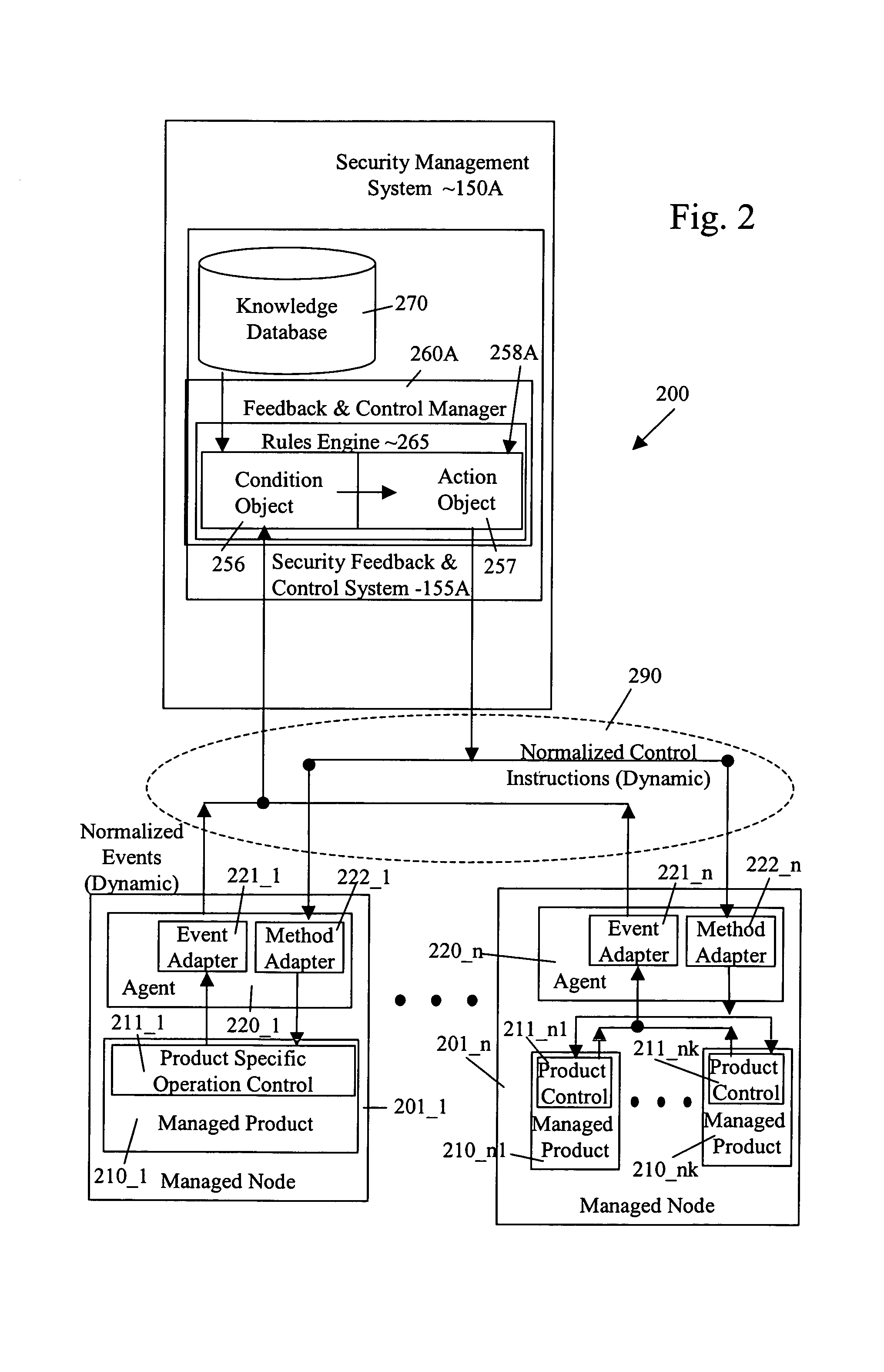
Security management system including feedback and control
InactiveUS7472422B1Memory loss protectionError detection/correctionPolicy decisionSafety management systems
A system uses automatic feedback and control to secure a network infrastructure by iterative convergence of the network's security structure to meet a security policy. Following initialization, a security feedback control system of the security management system makes dynamic adjustments to the system using bi-directional services that are controlled via policy decision components, without user intervention.
Owner:SYMANTEC CORP
System and method of securing web applications across an enterprise
ActiveUS20080034425A1Avoid attackMemory loss protectionError detection/correctionTraffic capacityWeb application
A system and method for protection of Web based applications are described. The techniques described provide an enterprise wide approach to preventing attacks of Web based applications. Individual computer networks within the enterprise monitor network traffic to identify anomalous traffic. The anomalous traffic can be identified by comparing the traffic to a profile of acceptable user traffic when interacting with the application. The anomalous traffic, or security events, identified at the individual computer networks are communicated to a central security manager. The central security manager correlates the security events at the individual computer networks to determine if there is an enterprise wide security threat. The central security manager can then communicate instructions to the individual computer networks so as to provide an enterprise wide solution to the threat
Owner:TRUSTWAVE HOLDINGS
System and method to provide secure navigation to resources on the internet
InactiveUS6381579B1Quick changeBuying/selling/leasing transactionsResourcesWeb browserManagement tool
Provide an electronic-business-to-electronic-business portal that organizes the access to extended business applications. A method allows end users to access a server using standard Web browsers, and then view their own customized menu of applications. Enhanced security and administrative tools allow this portal to be shared throughout enterprises and across supply chains, providing secure access to collaborative applications by business partners and suppliers. Access to specific applications is granted to authorized users and teams, within and outside of a company. Real-time, on-line registration of users allows for rapid changes in teams and projects. Users can be added, deleted, or have access levels altered to reflect changes in the makeup of teams. Provide a common infrastructure for application administration, security management, and directory use, which can help reduce information technology (IT) costs and speed solution deployment.
Owner:TWITTER INC
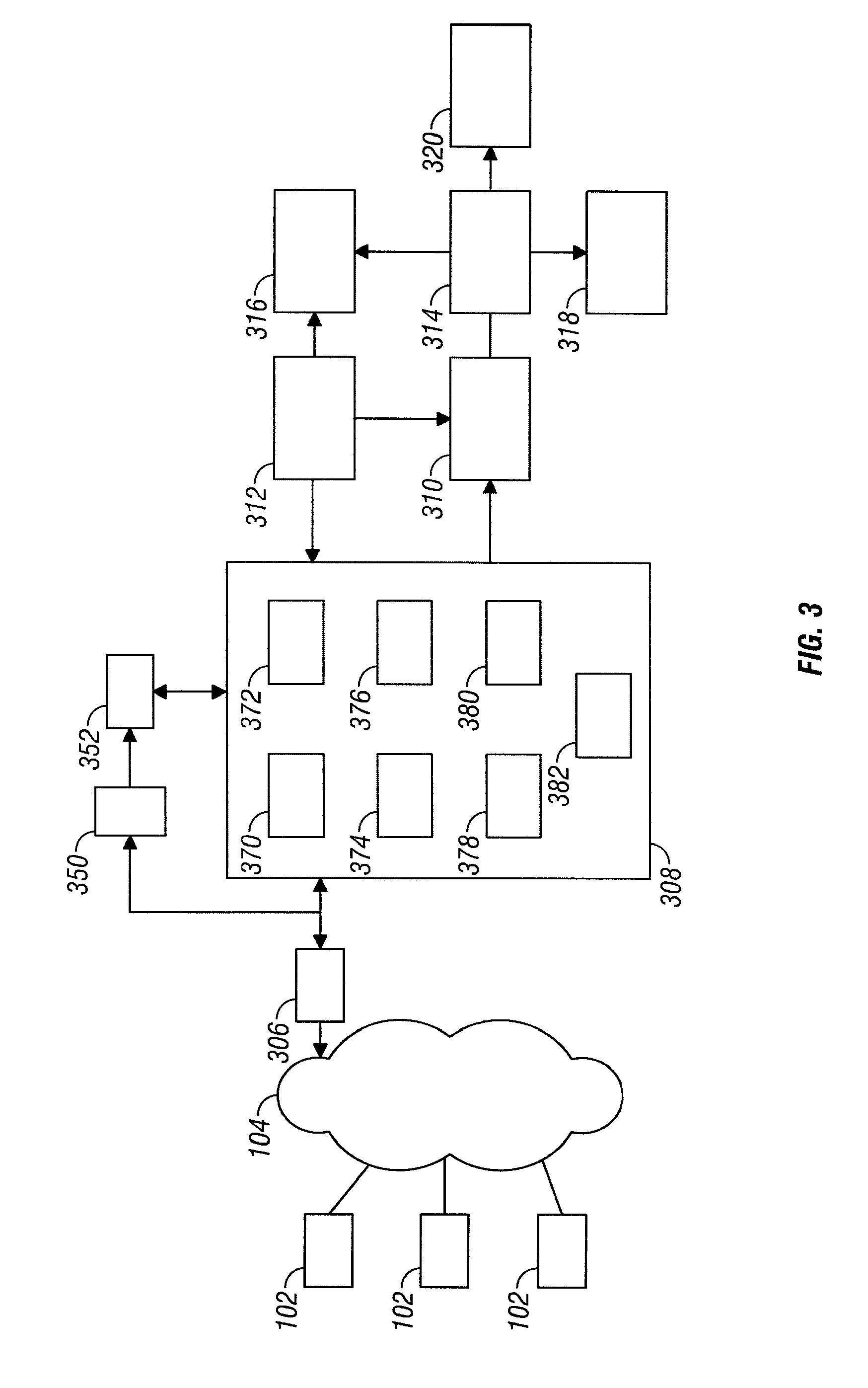
Method and System for Managing Computer Security Information
InactiveUS20020078381A1Efficient managementReduce processing speedMemory loss protectionDigital data processing detailsTraffic capacitySafety management systems
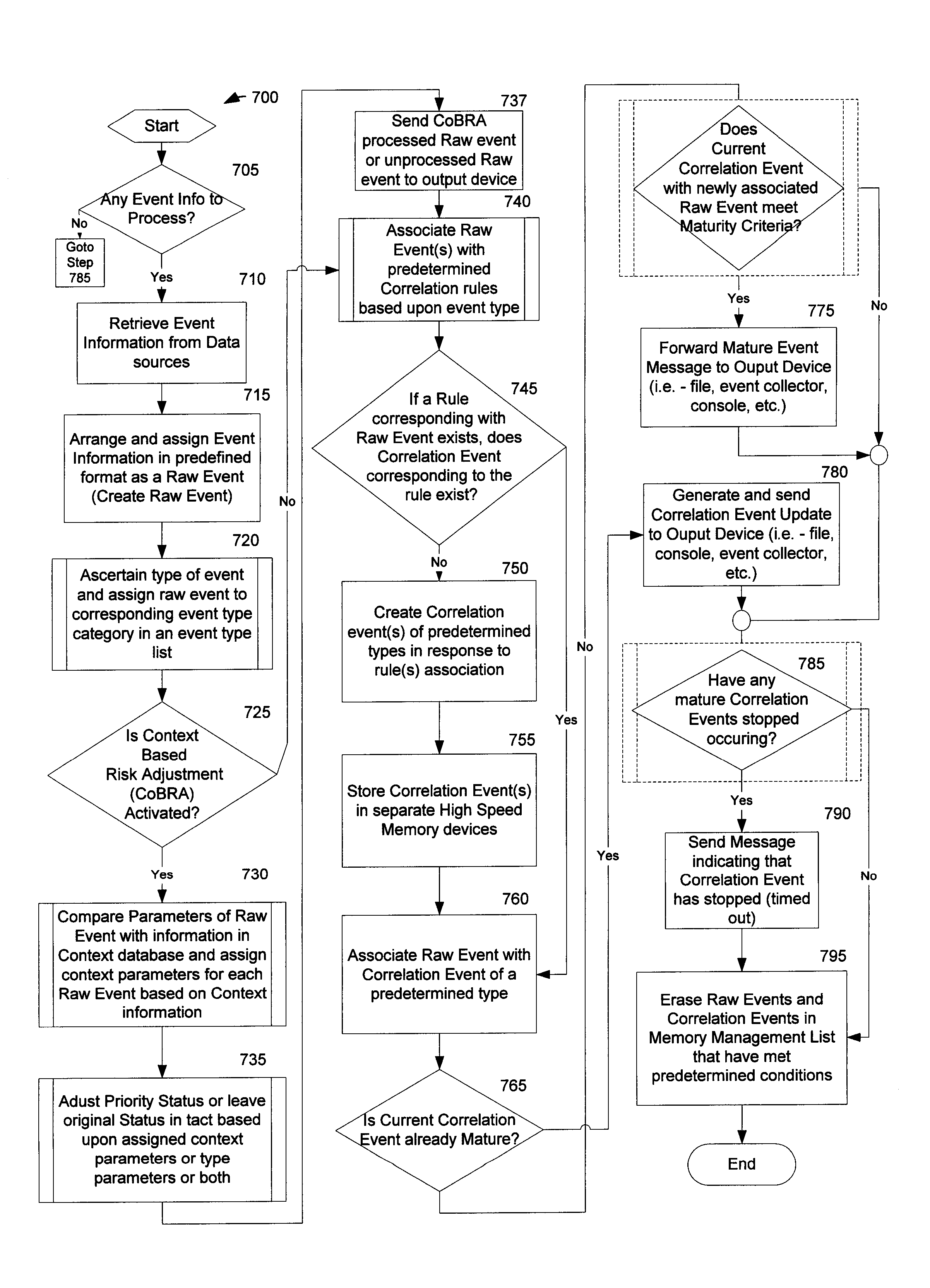
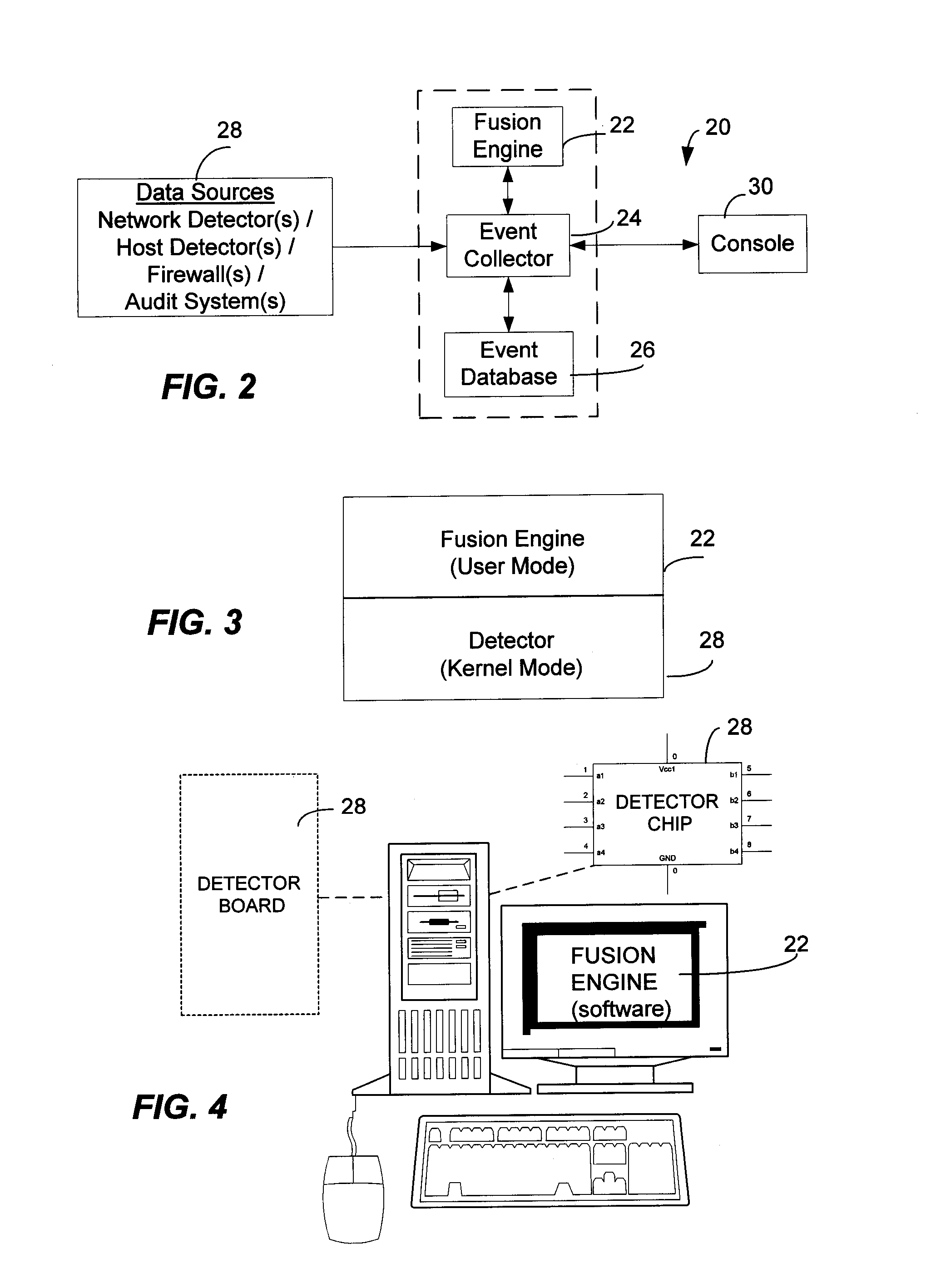
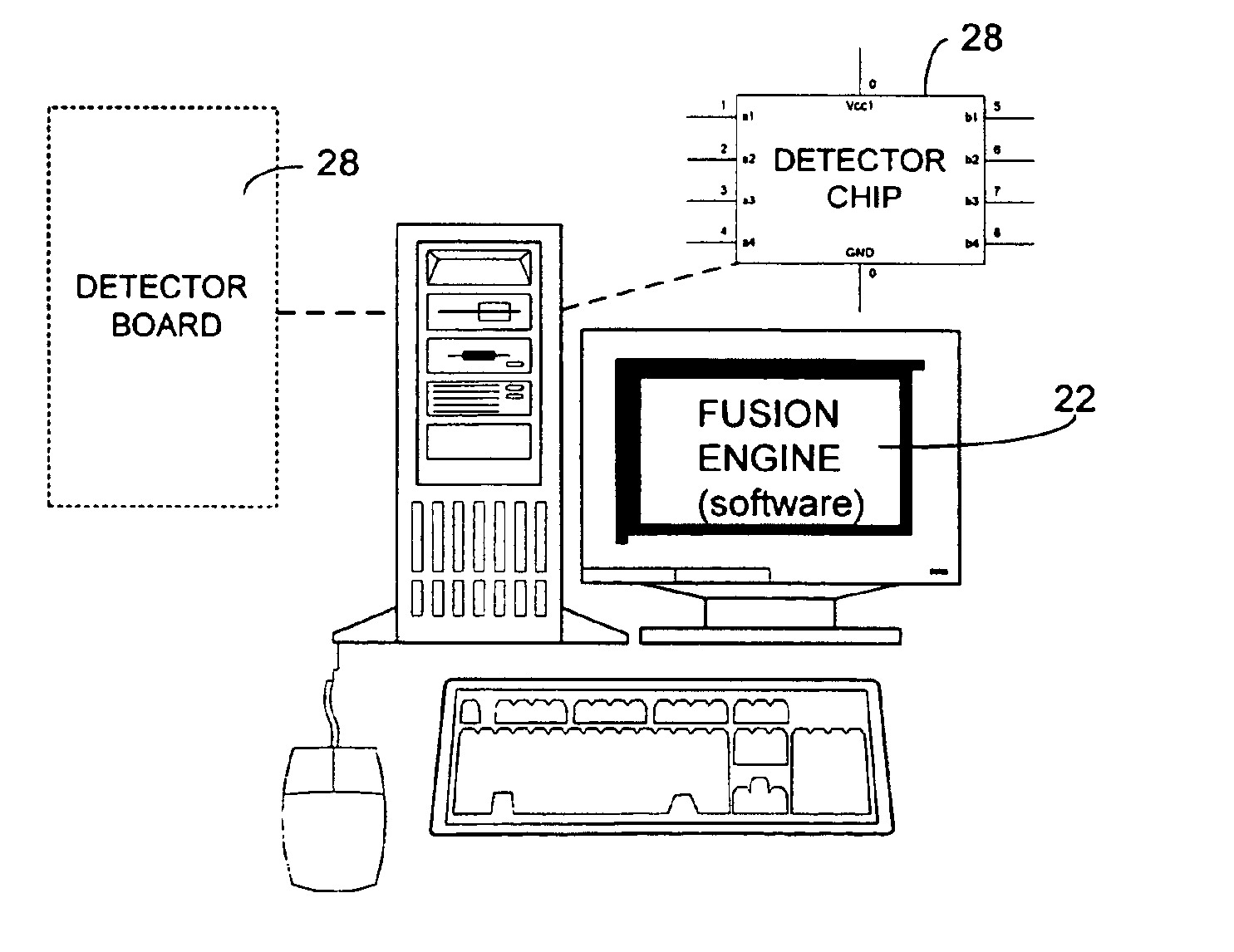
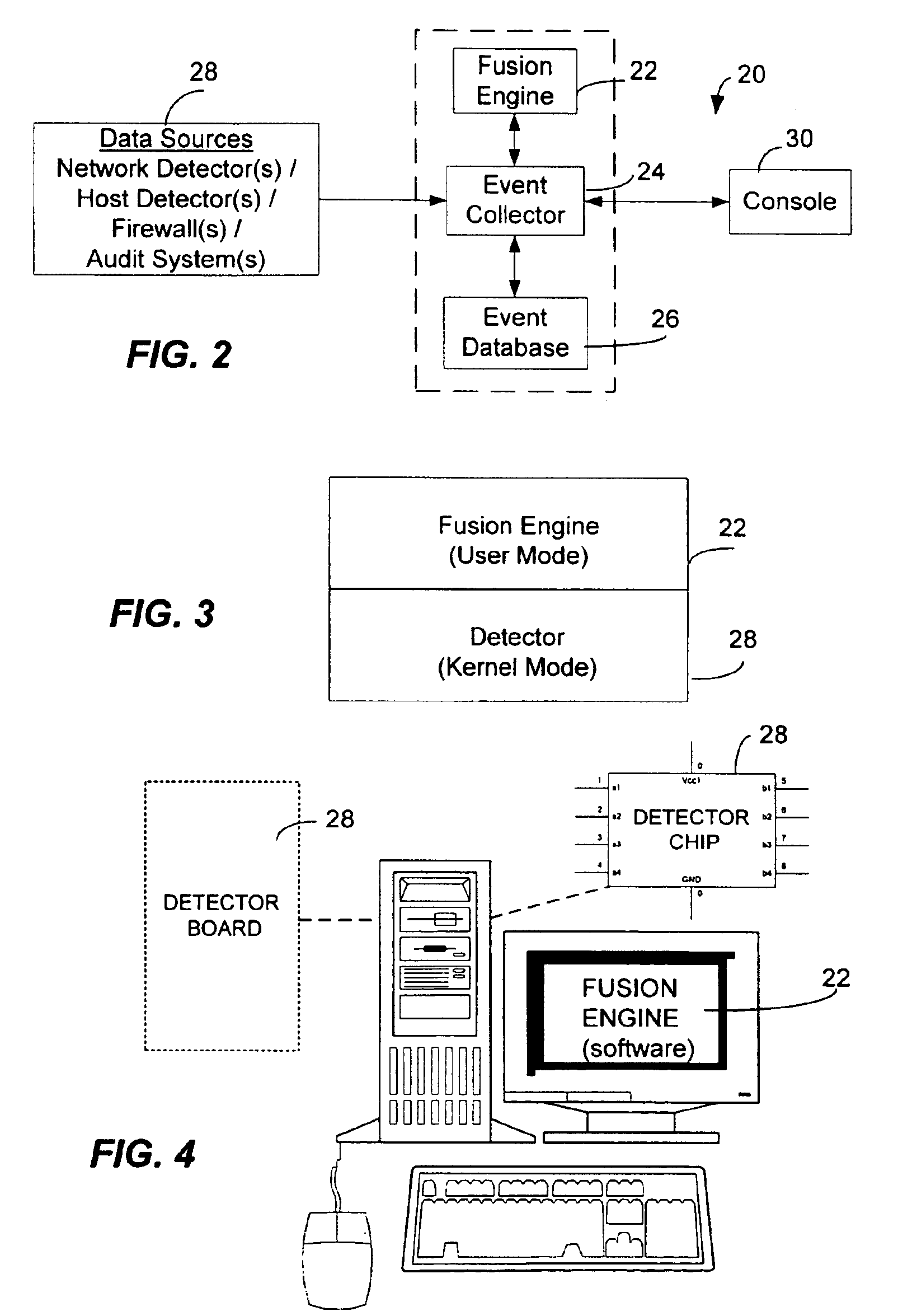
<heading lvl="0">Abstract of Disclosure< / heading> A security management system includes a fusion engine which "fuses" or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:IBM CORP
Information targeting systems and methods
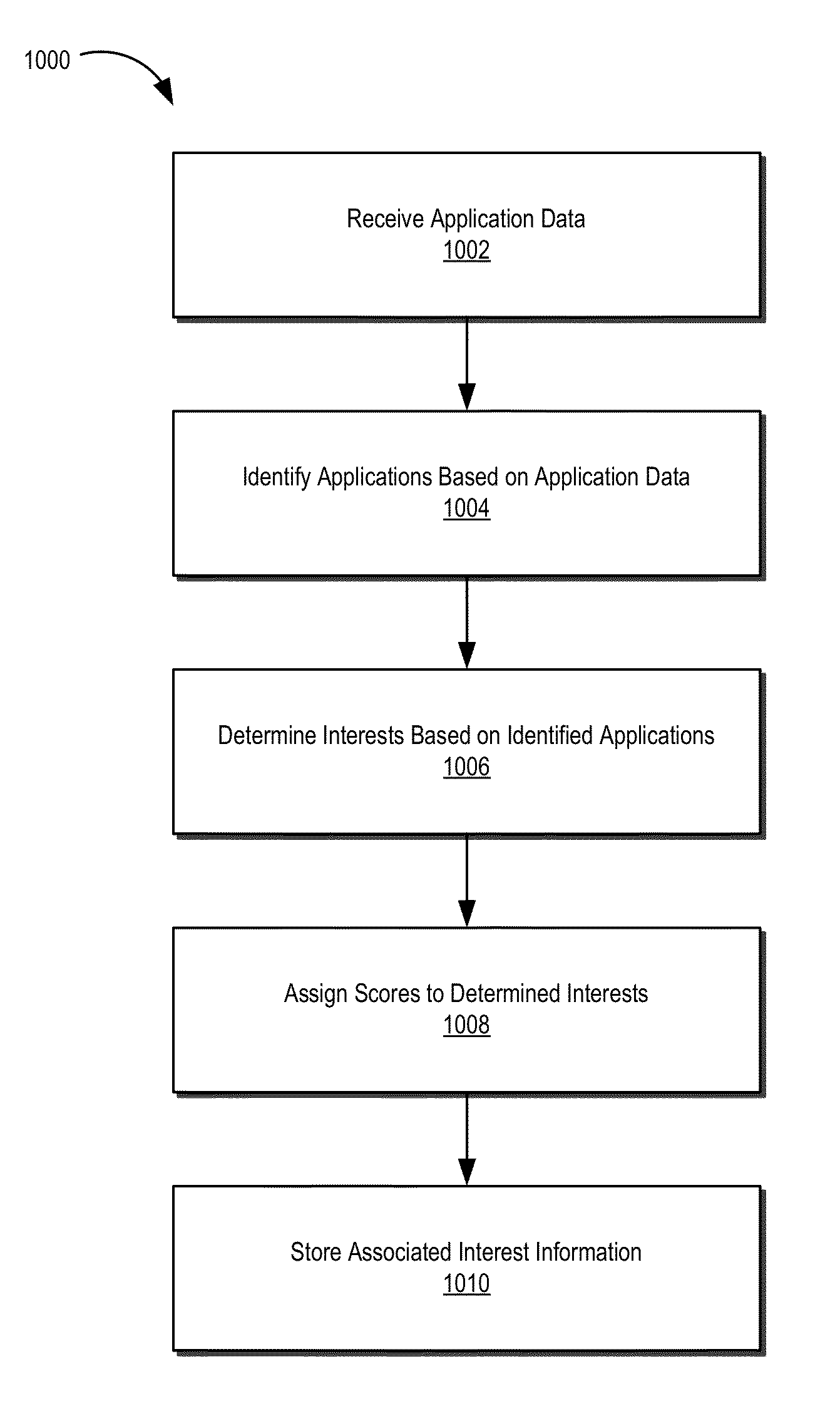
ActiveUS9355157B2Facilitate secure collection and use and management and distributionConvenient and effective positioningDigital data information retrievalSpecial data processing applicationsInternet privacyElectronic information
The present disclosure relates generally to systems and methods for the secure management of electronic information relating to a user. In certain embodiments, systems and methods disclosed herein may allow for personal information related to a user to be used in connection with information targeting systems and methods configured to match and / or target information for delivery to a user based on the user's interests. In some embodiments, personal information relating to a user may be stored and / or managed in a personal ontology graph or other data structure including, among other things, various inferred interests of the user derived from available personal information.
Owner:INTERTRUST TECH CORP
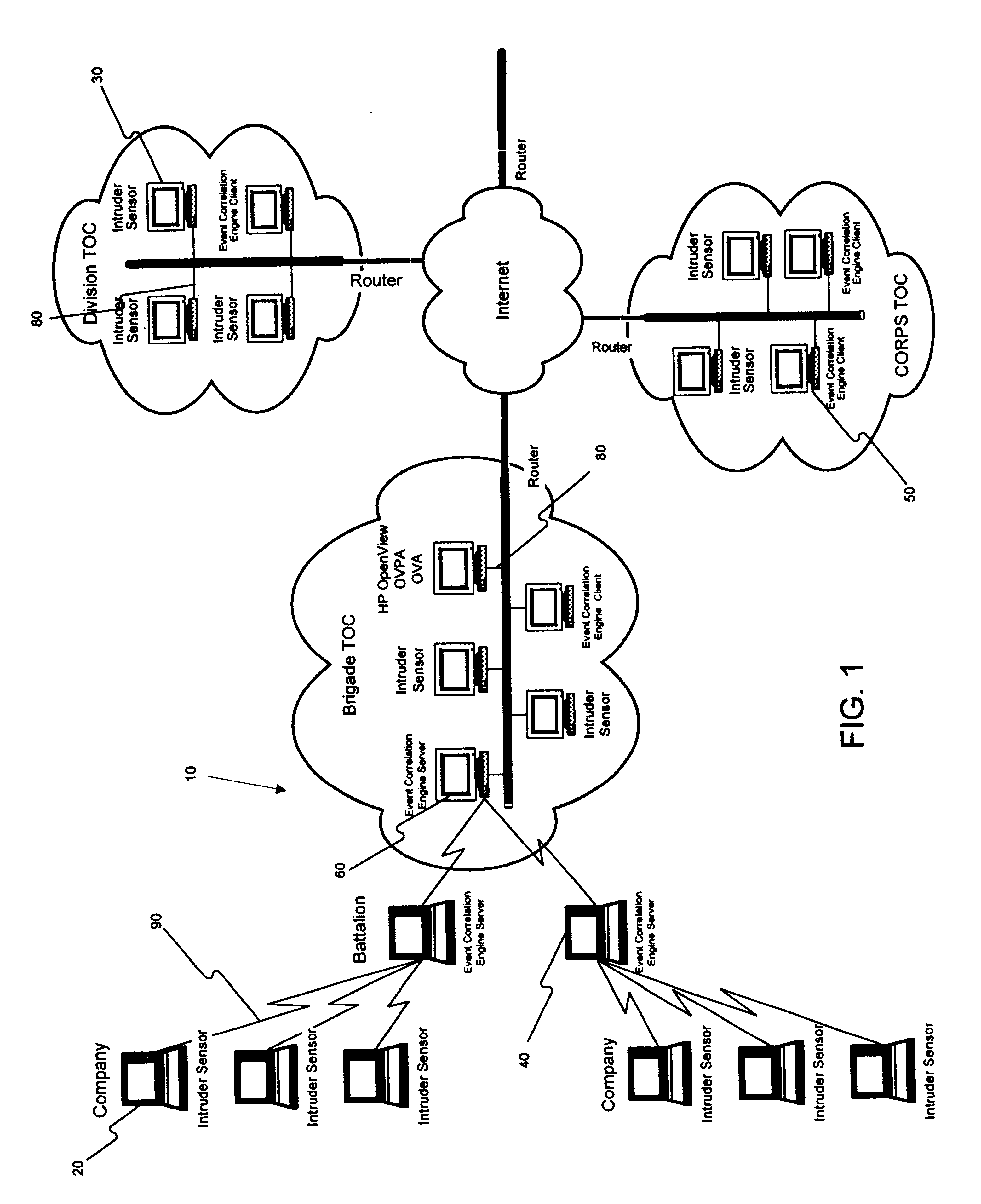
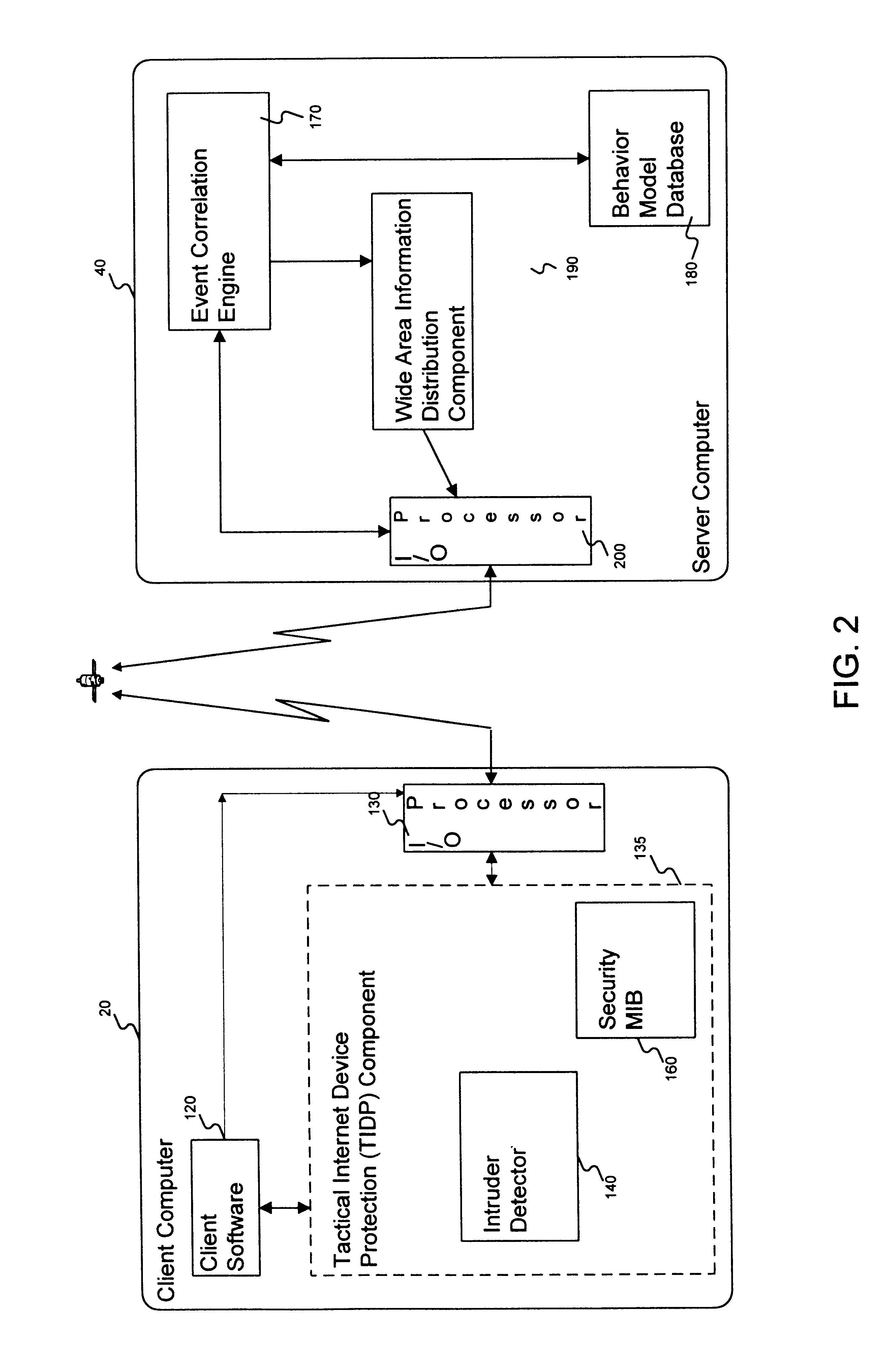
Method and apparatus for an intruder detection reporting and response system
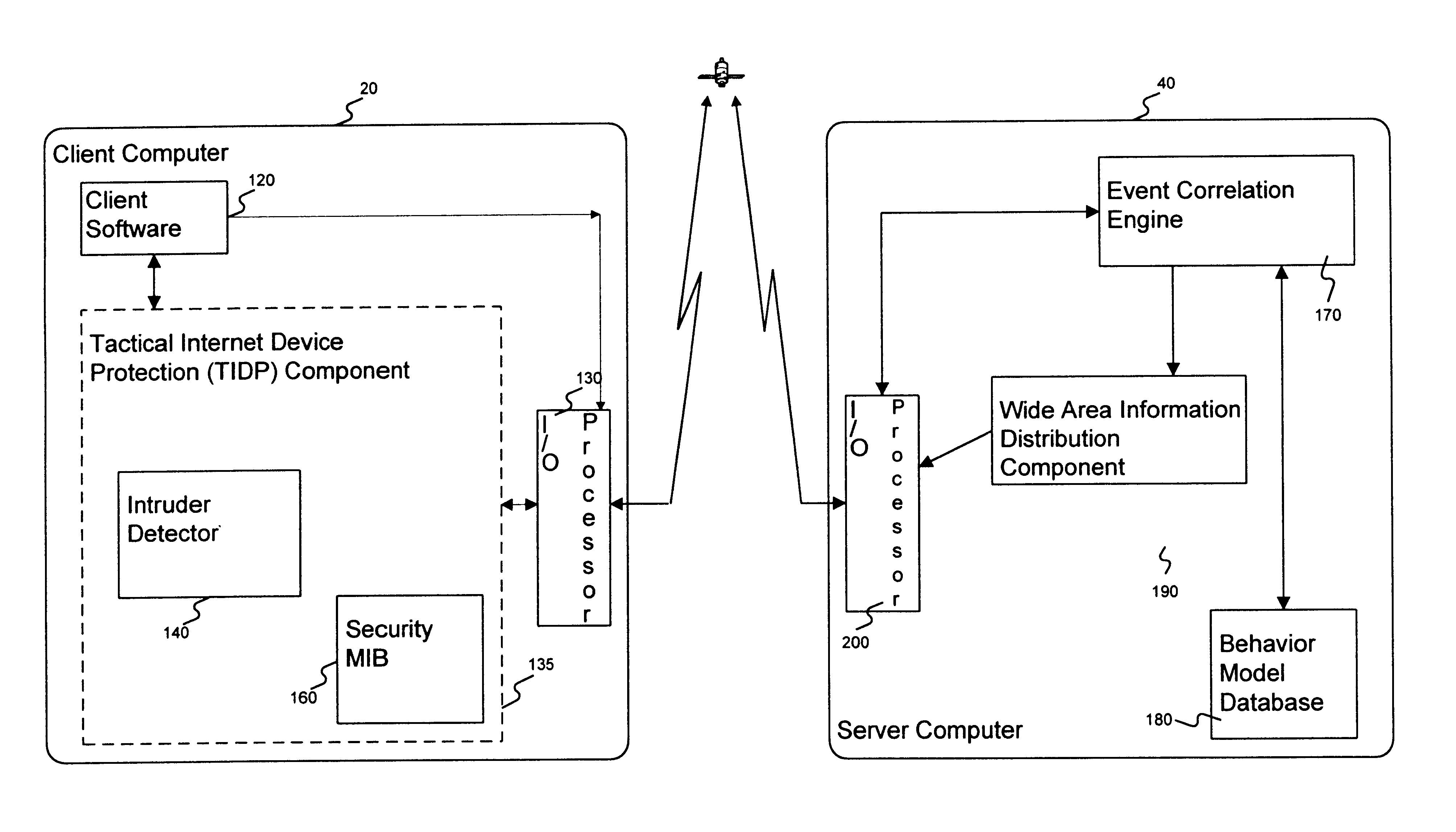
InactiveUS6910135B1Improve securityWide rangeMemory loss protectionError detection/correctionThe InternetWorkstation
A method and apparatus is disclosed for improving the security of computer networks by providing a means operating passively on the network for detecting, reporting and responding to intruders. The system is comprised of a plurality of intruder sensor client computers and associated event correlation engines. Resident in the memory of the client computer and operating in the background is a Tactical Internet Device Protection (TIDP) component consisting of a passive intruder detector and a security Management Information Base (MIB). The passive intruder detector component of the TIDP passively monitors operations performed on the client computer and emits a Simple Network Management Protocol (SNMP) trap to an event correlation engine when it identifies a suspected intruder. The event correlation engine, through the use of a behavior model loaded in its memory, determines whether the user's activities are innocent or those of a perspective intruder. When the event correlation engine is unable to classify a user based on a single trap message, it can request historical information from the security MIB, a database of the operating history of the client computer including a chronology of the illegal operations performed on the client. Once the event correlation engine determines that an intruder is located at an associated client workstation, it generates a status message and transmits the message to all of its subscribers, informing them of the presence and location of a suspected intruder.
Owner:LEVEL 3 COMM LLC +2
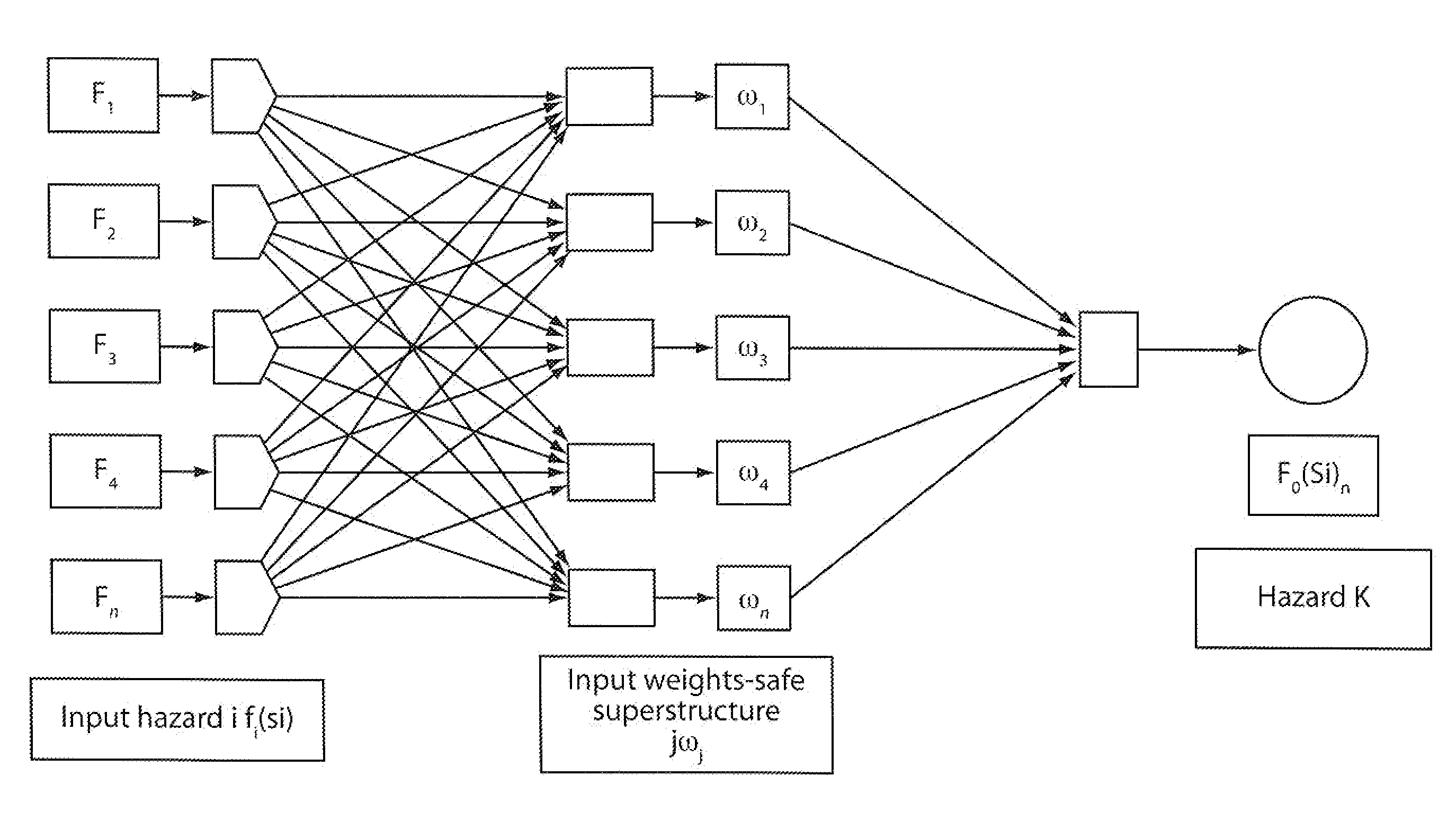
Design of computer based risk and safety management system of complex production and multifunctional process facilities-application to fpso's
InactiveUS20120317058A1Strong robust attributeStrong robust attributesDigital computer detailsFuzzy logic based systemsProcess systemsNerve network
A method for predicting risk and designing safety management systems of complex production and process systems which has been applied to an FPSO System operating in deep waters. The methods for the design were derived from the inclusion of a weight index in a fuzzy class belief variable in the risk model to assign the relative numerical value or importance a safety device or system has contain a risk hazards within the barrier. The weights index distributes the relative importance of risk events in series or parallel in several interactive risk and safety device systems. The fault tree, the FMECA and the Bow Tie now contains weights in fizzy belief class for implementing safety management programs critical to the process systems. The techniques uses the results of neural networks derived from fuzzy belief systems of weight index to implement the safety design systems thereby limiting use of experienced procedures and benchmarks. The weight index incorporate Safety Factors sets SFri {0, 0.1, 0.2 . . . 1}, and Markov Chain Network to allow the possibility of evaluating the impact of different risks or reliability of multifunctional systems in transient state process. The application of this technique and results of simulation to typical FPSO / Riser systems has been discussed in this invention.
Owner:ABHULIMEN KINGSLEY E
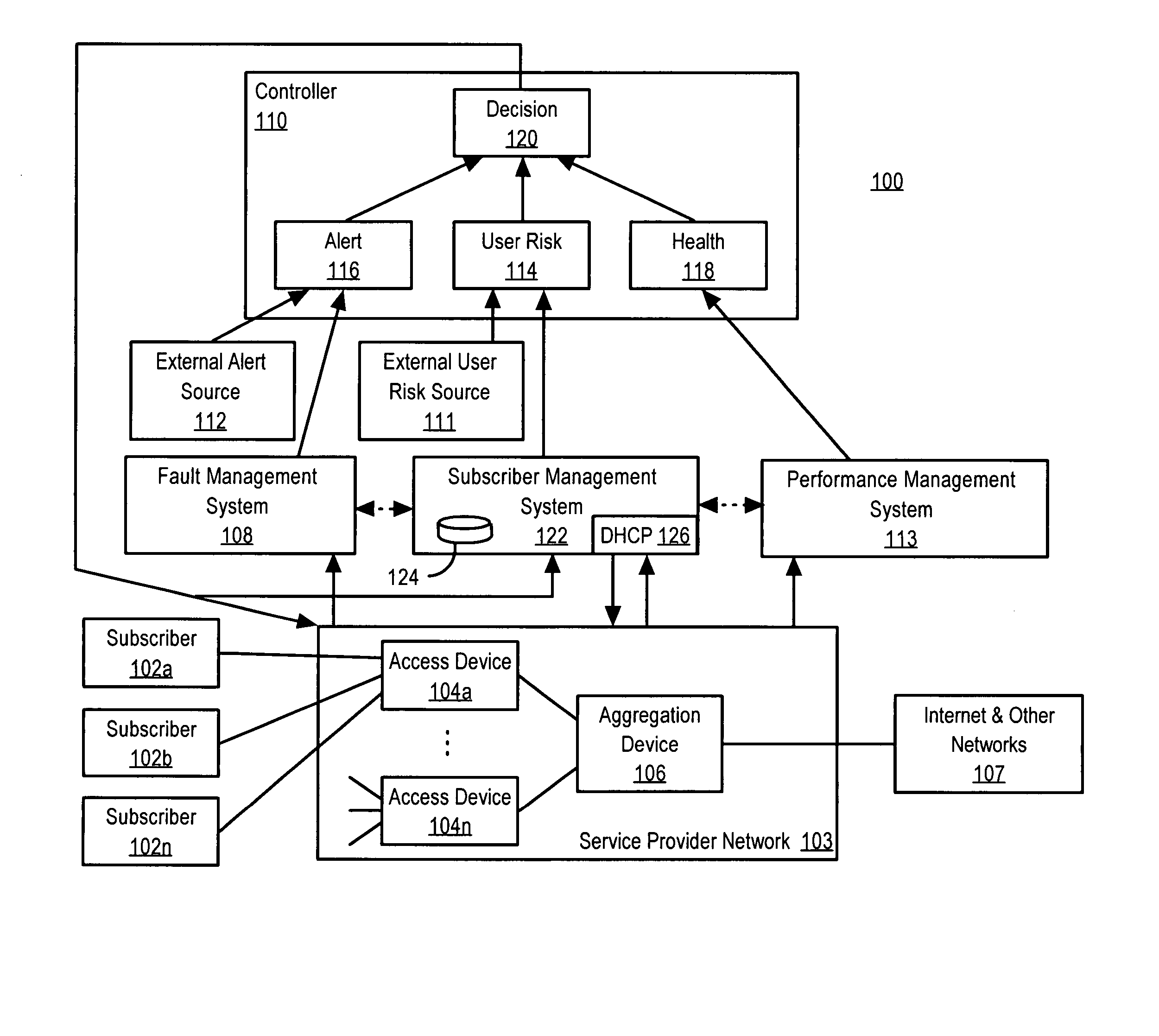
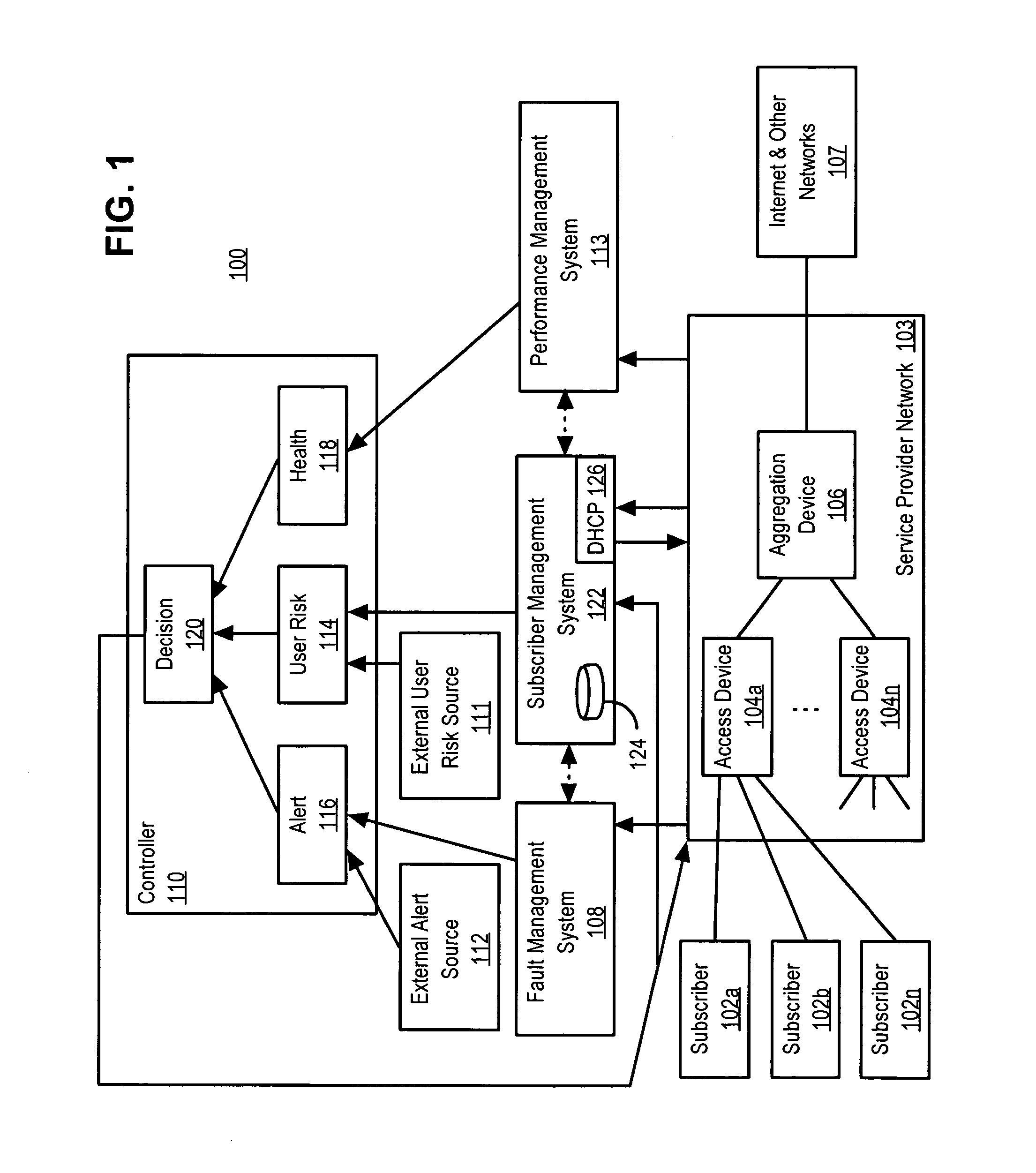
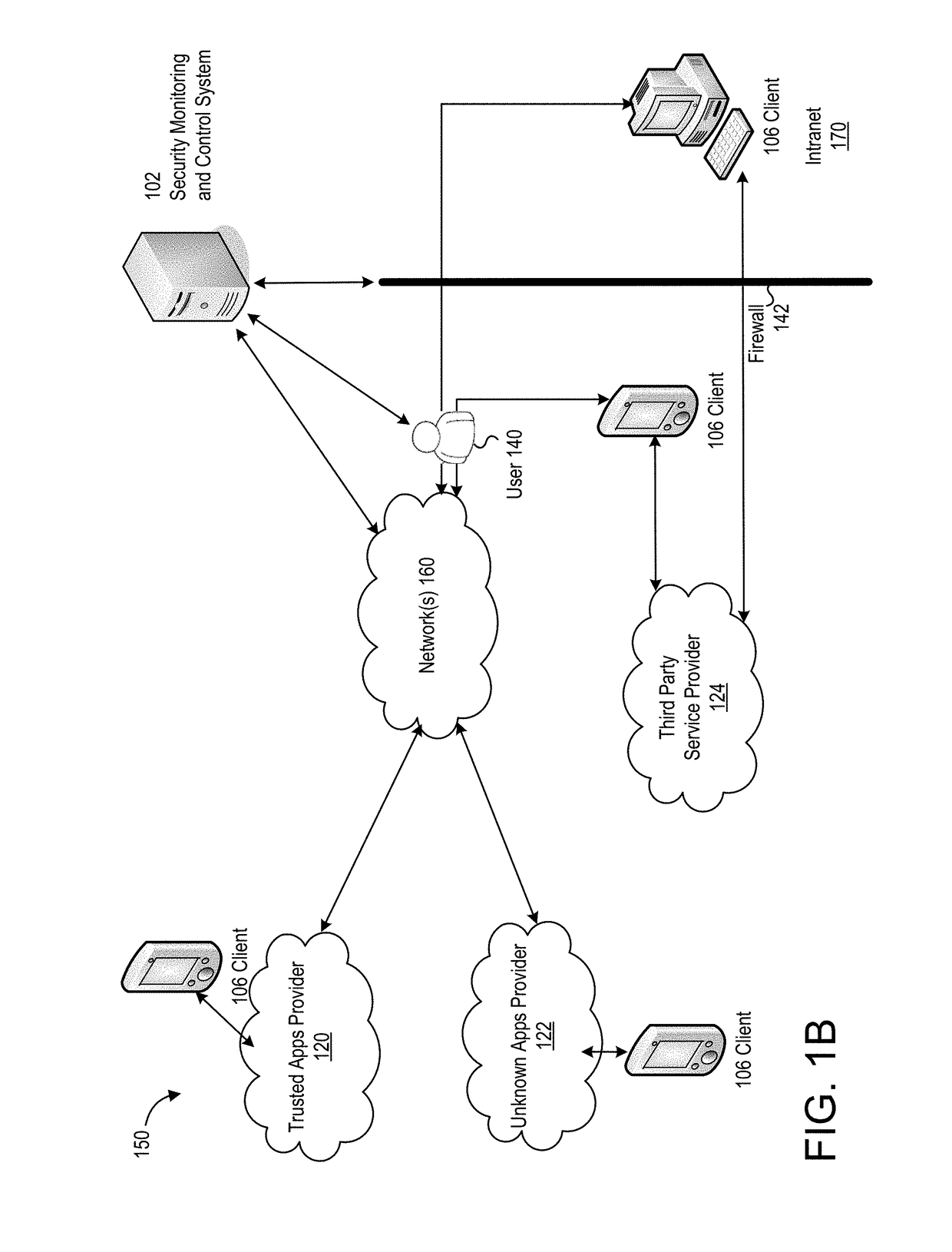
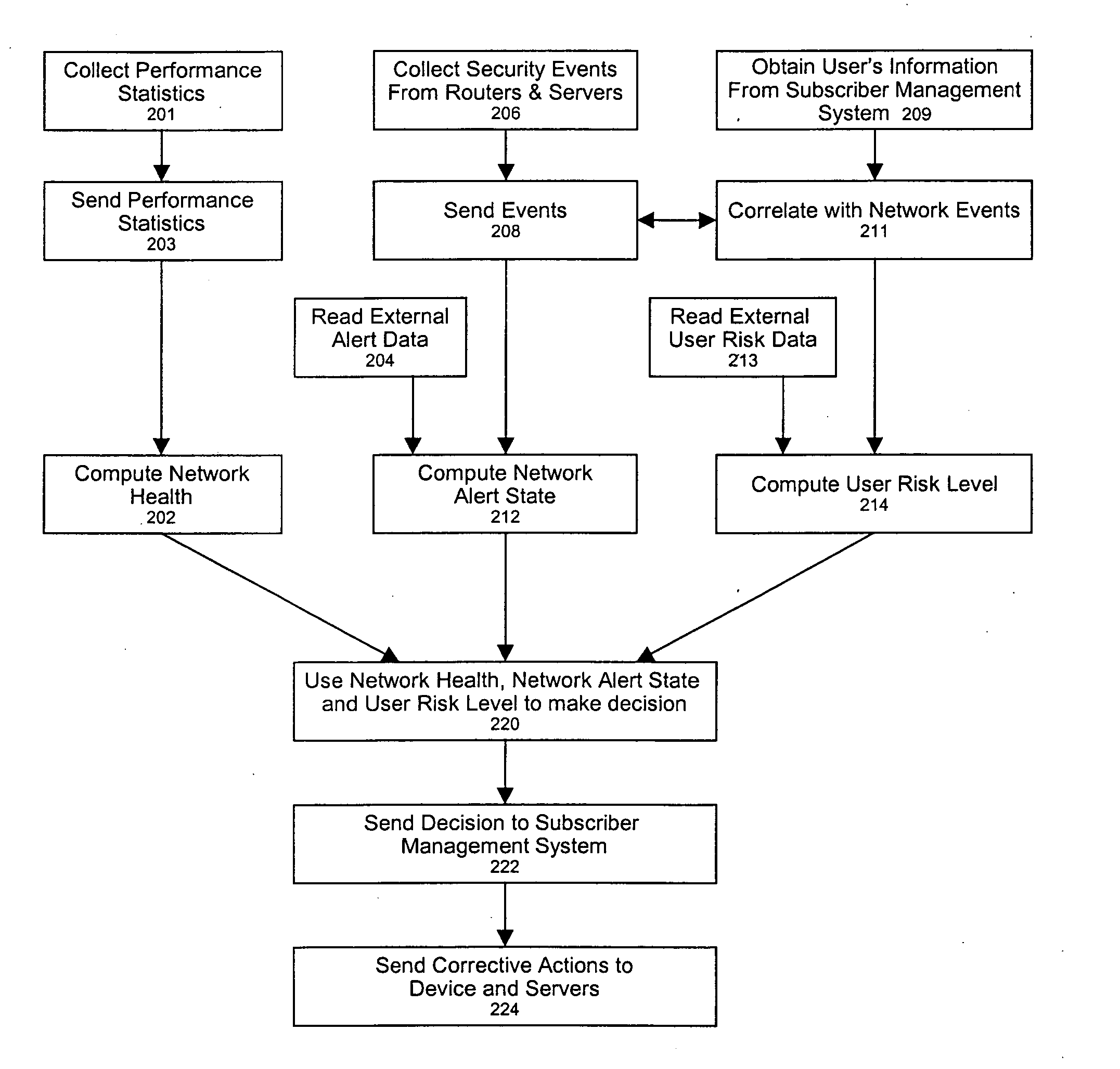
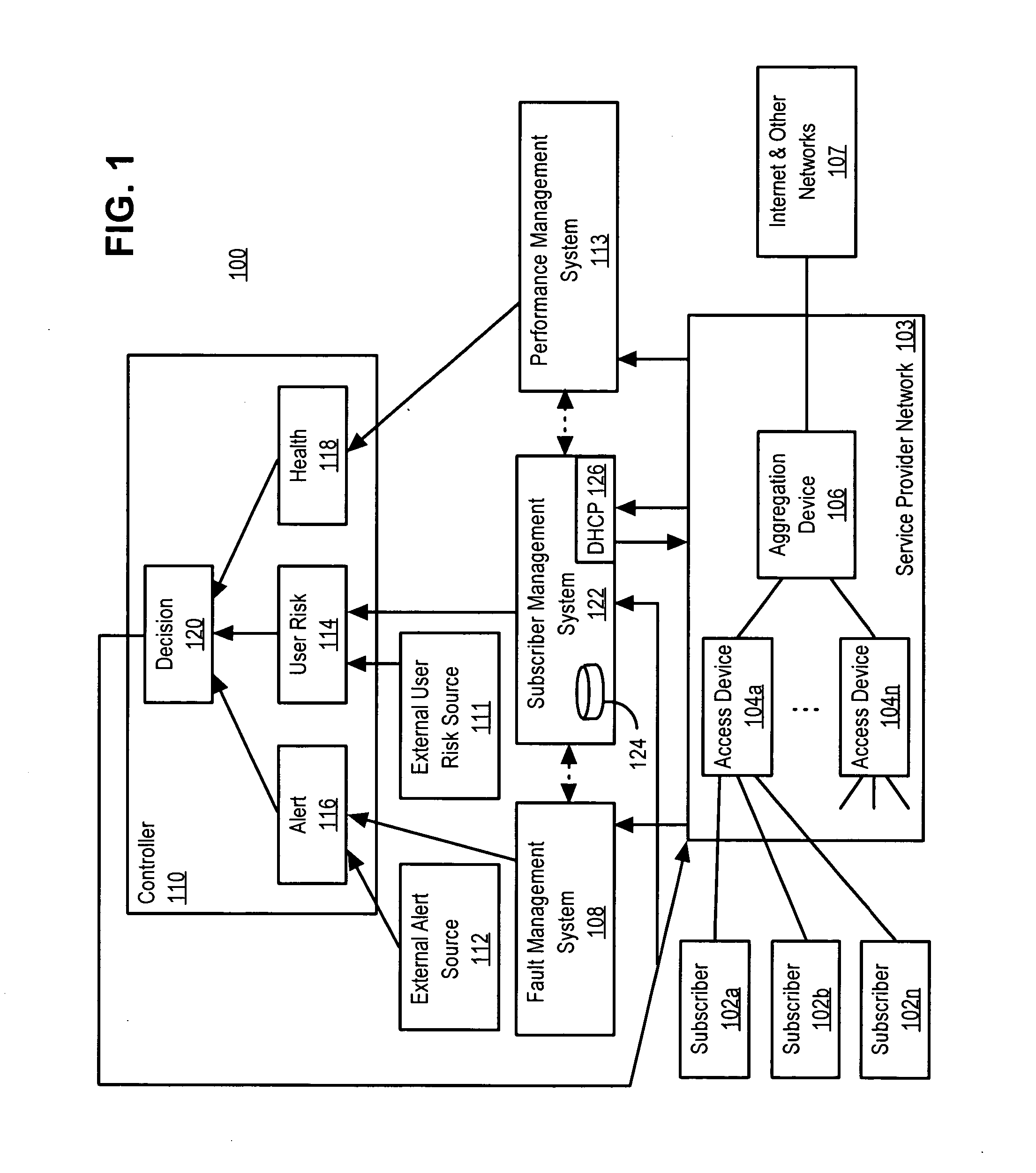
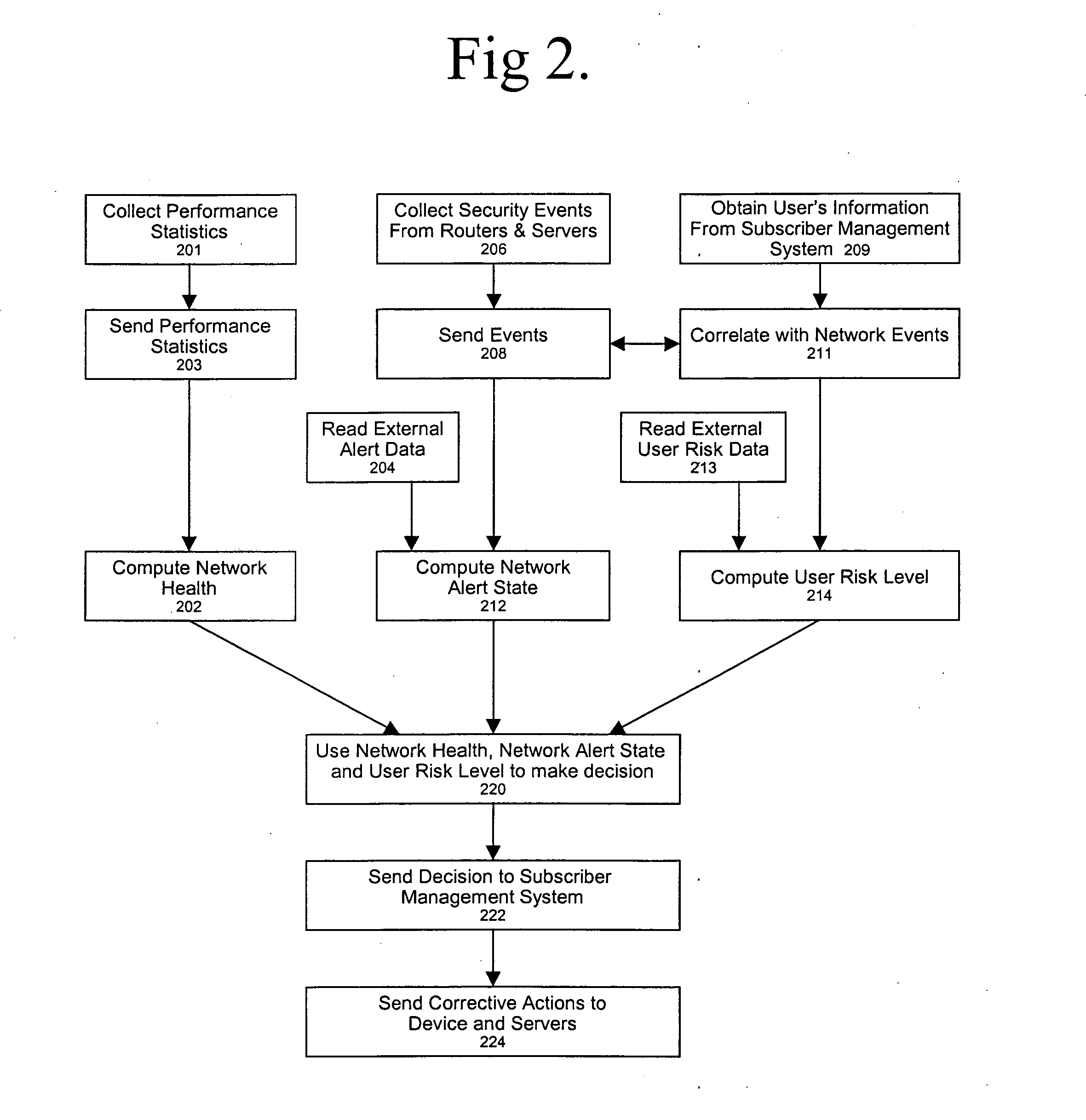
End user risk management
ActiveUS7490356B2Respond effectivelyMemory loss protectionDigital data processing detailsReal time analysisSafety management systems
A flexible, efficient and easy-to-use computer security management system effectively evaluates and responds to informational risks on a wide variety of computing platforms and in a rapidly changing network environment. An individual computer system dynamically monitors its end user, without regard to network connectivity, in order to calculate a risk score and to ensure that the end user's behavior does not put corporate information or other assets at risk. Data regarding such risks and responses are analyzed and stored in real-time.
Owner:CITRIX SYST INC
End user risk management
ActiveUS20060020814A1Respond effectivelyMemory loss protectionDigital data processing detailsReal time analysisComputer science
A flexible, efficient and easy-to-use computer security management system effectively evaluates and responds to informational risks on a wide variety of computing platforms and in a rapidly changing network environment. An individual computer system dynamically monitors its end user, without regard to network connectivity, in order to calculate a risk score and to ensure that the end user's behavior does not put corporate information or other assets at risk. Data regarding such risks and responses are analyzed and stored in real-time.
Owner:CITRIX SYST INC
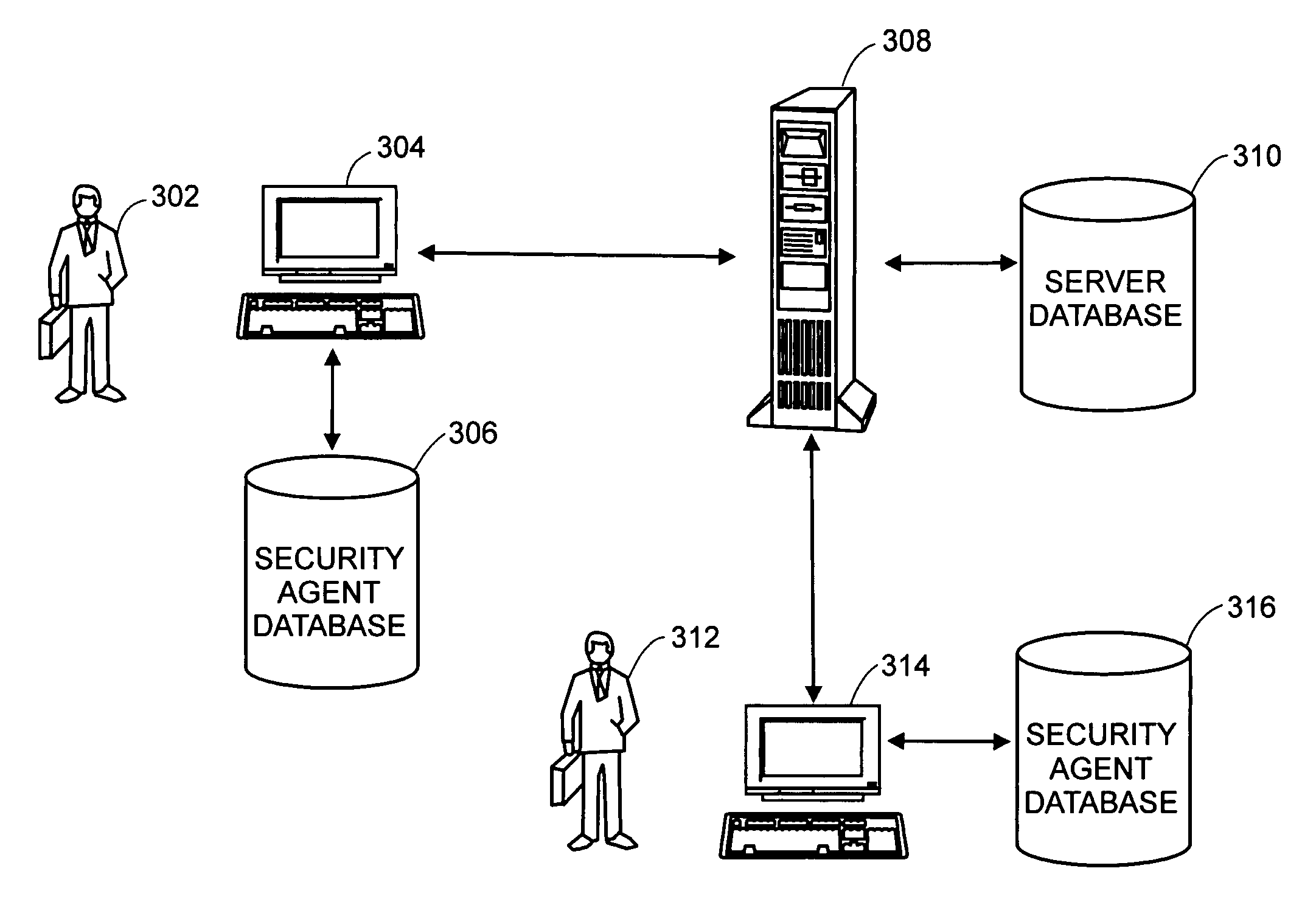
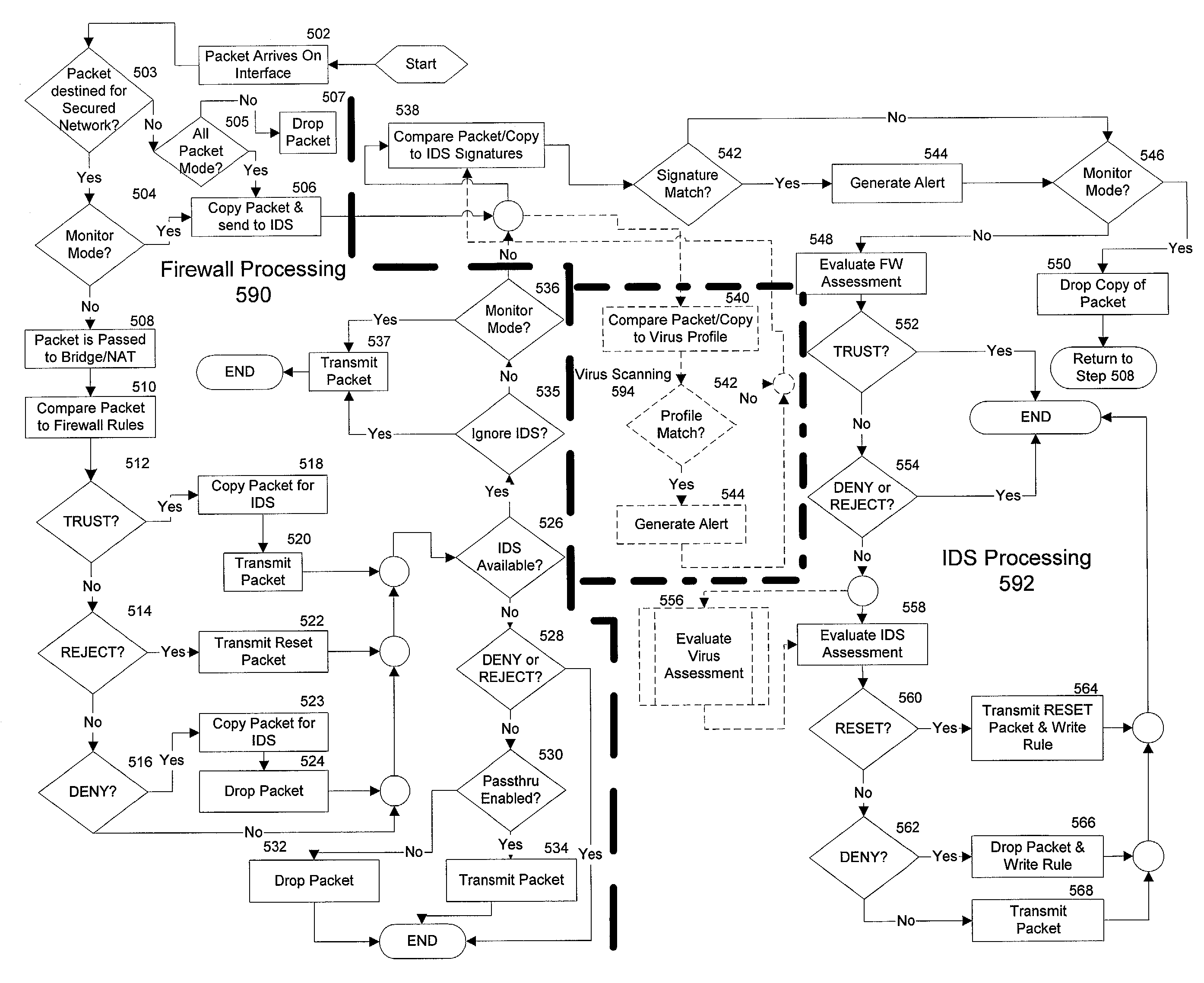
Integrated computer security management system and method
InactiveUS7331061B1Centralized controlIncrease speedMemory loss protectionError detection/correctionSafety management systemsSecurity management
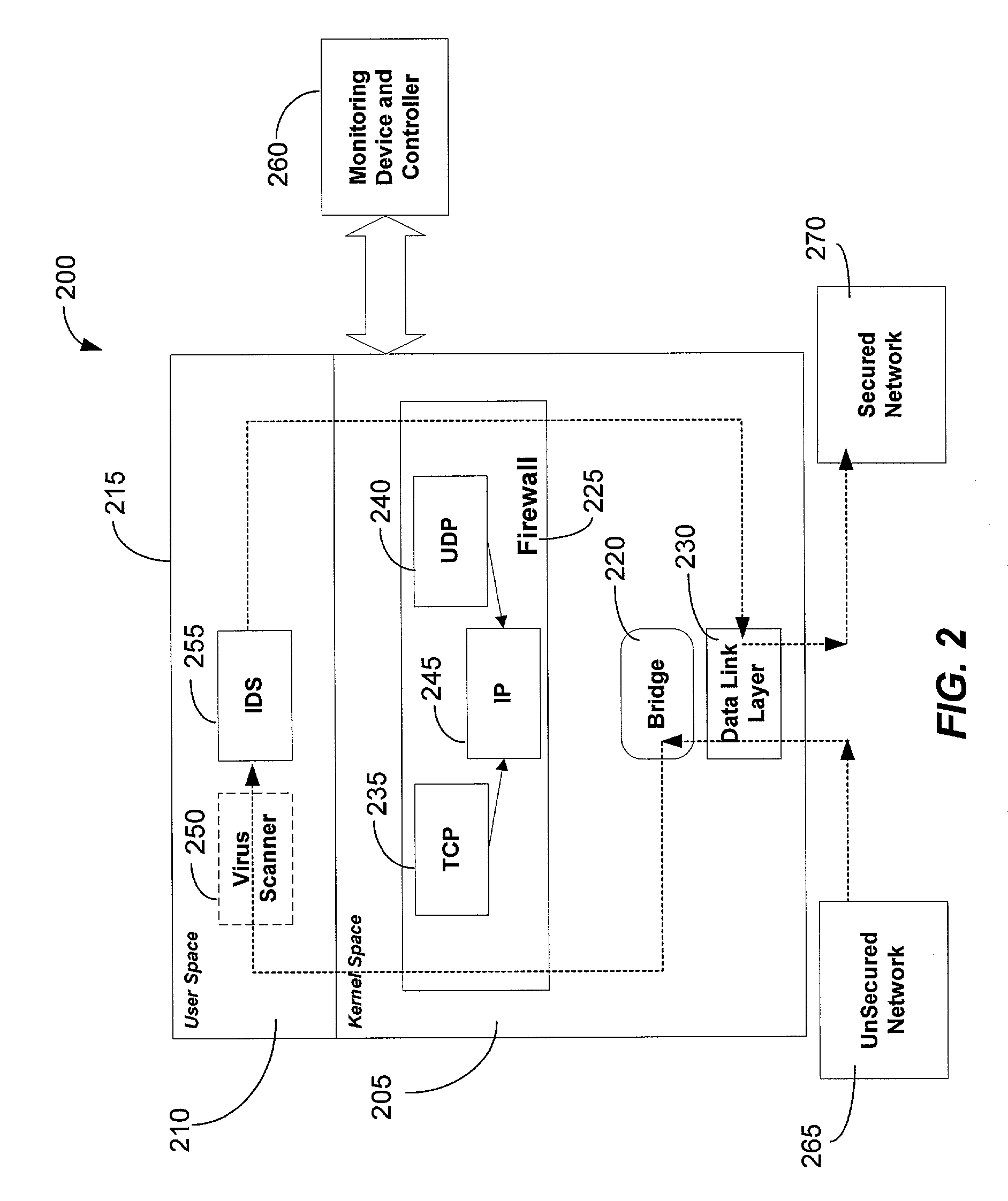
The present invention is generally directed to a computer security management system that integrates a firewall with an intrusion detection system (IDS). In other words, the firewall and IDS of the present invention can be designed to communicate process or status information and packets with one another. The present invention can facilitate centralized control of the firewall and the IDS and can increase the speed at which packets are passed between a secured computer network and an external network. Increased packet processing speed can be achieved in several ways. For example, the firewall and IDS can process packets in series, in parallel, and sometimes singularly when one of the components is not permitted to process a packet. Alternatively, singular processing can also be performed when one component is permitted to pass a packet to the secured computer network without checking with the other component.
Owner:SECUREWORKS
System and method for data mining and security policy management
ActiveUS8447722B1Digital data processing detailsComputer security arrangementsData managementSecurity policy management
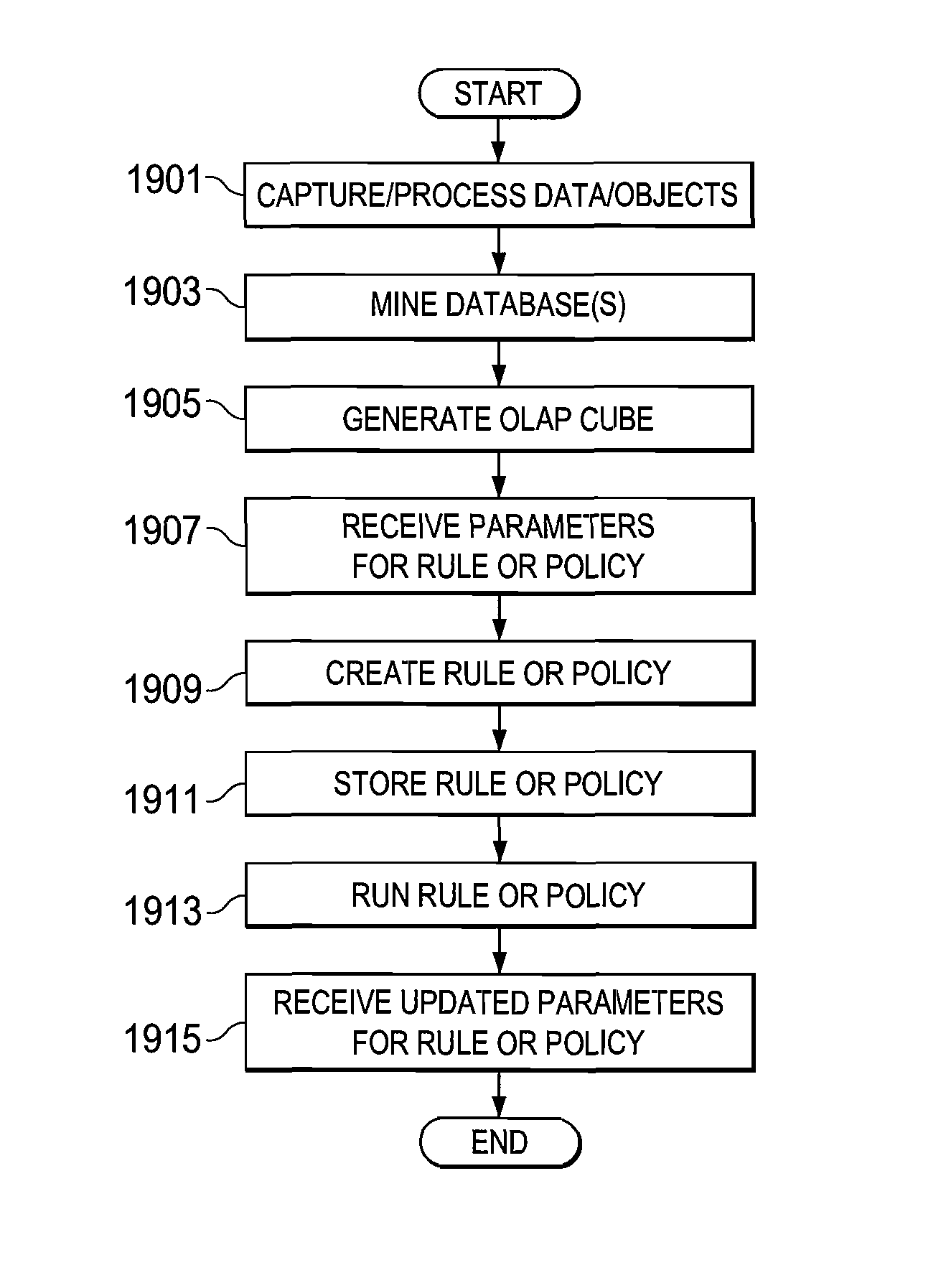
A method is provided in one example and includes generating a query for a database for information stored in the database. The information relates to data discovered through a capture system. The method further includes generating an Online Analytical Processing (OLAP) element to represent information received from the query. A rule based on the OLAP element is generated and the rule affects data management for one or more documents that satisfy the rule. In more specific embodiments, the method further includes generating a capture rule that defines items the capture system should capture. The method also includes generating a discovery rule that defines objects the capture system should register. In still other embodiments, the method includes developing a policy based on the rule, where the policy identifies how one or more documents are permitted to traverse a network.
Owner:MCAFEE LLC
Method and apparatus for an improved security system mechanism in a business applications management system platform
InactiveUS6850893B2Minimizing user input effortMinimize effortSpecific access rightsDigital data processing detailsSafety management systemsImproved method
The present invention provides a solution to the needs described above through an improved method and apparatus for an improved security system mechanism in a business applications management system platform. The security management system partitions a number of business objects into a number of hierarchical domains. A security list is then created and configured to grant a member the right to perform a security operation on the business object located within the hierarchical domain. The security list is created by adding the security operation to the security list, applying the security operation to one of the multiple domains, and adding members to the security list.
Owner:SABA SOFTWARE
Methods and systems for threat assessment, safety management, and monitoring of individuals and groups
InactiveUS20110046920A1Improve security levelReduce morbidityError detection/correctionMultiple digital computer combinationsComputer scienceSecurity management
The disclosure generally relates to methods and systems anticipating a potentially threatening or dangerous incident, and providing varying levels of response to a user. In an exemplary embodiment, the present invention provides varying levels of assistance to a user prior to, during, and after a threatening incident occurs. By providing assistance prior to a threatening incident occurring, the system may be able to thwart potential attacks, bodily harm, robberies, break-ins, and other criminal or dangerous activity. The assistance can be, for example, in the form of deterrents, alerting first responders to go to the scene, sending security personnel to the scene, remotely monitoring the scene, remotely interacting with the scene, providing information and advice to the user.
Owner:STRIDER
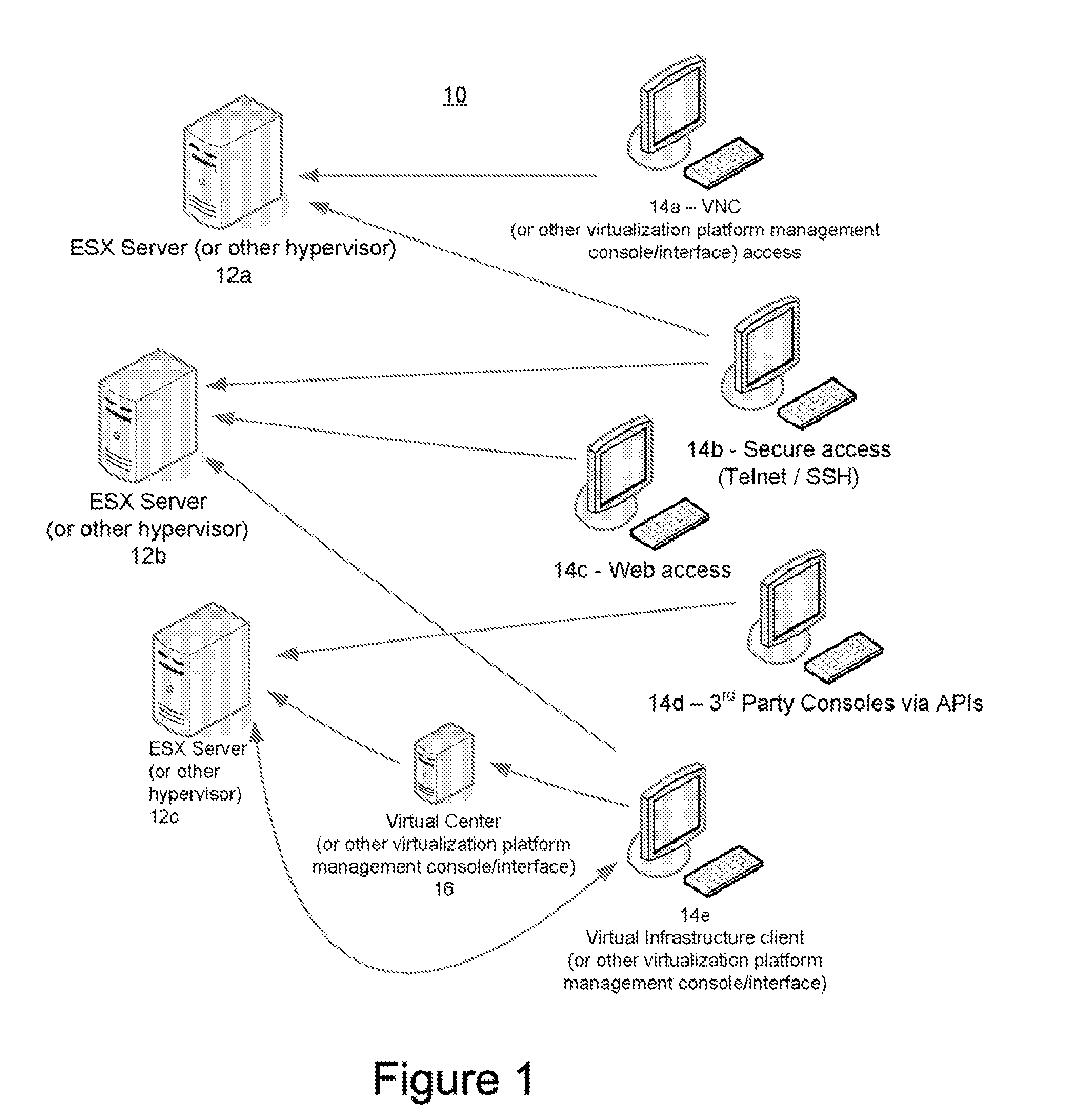
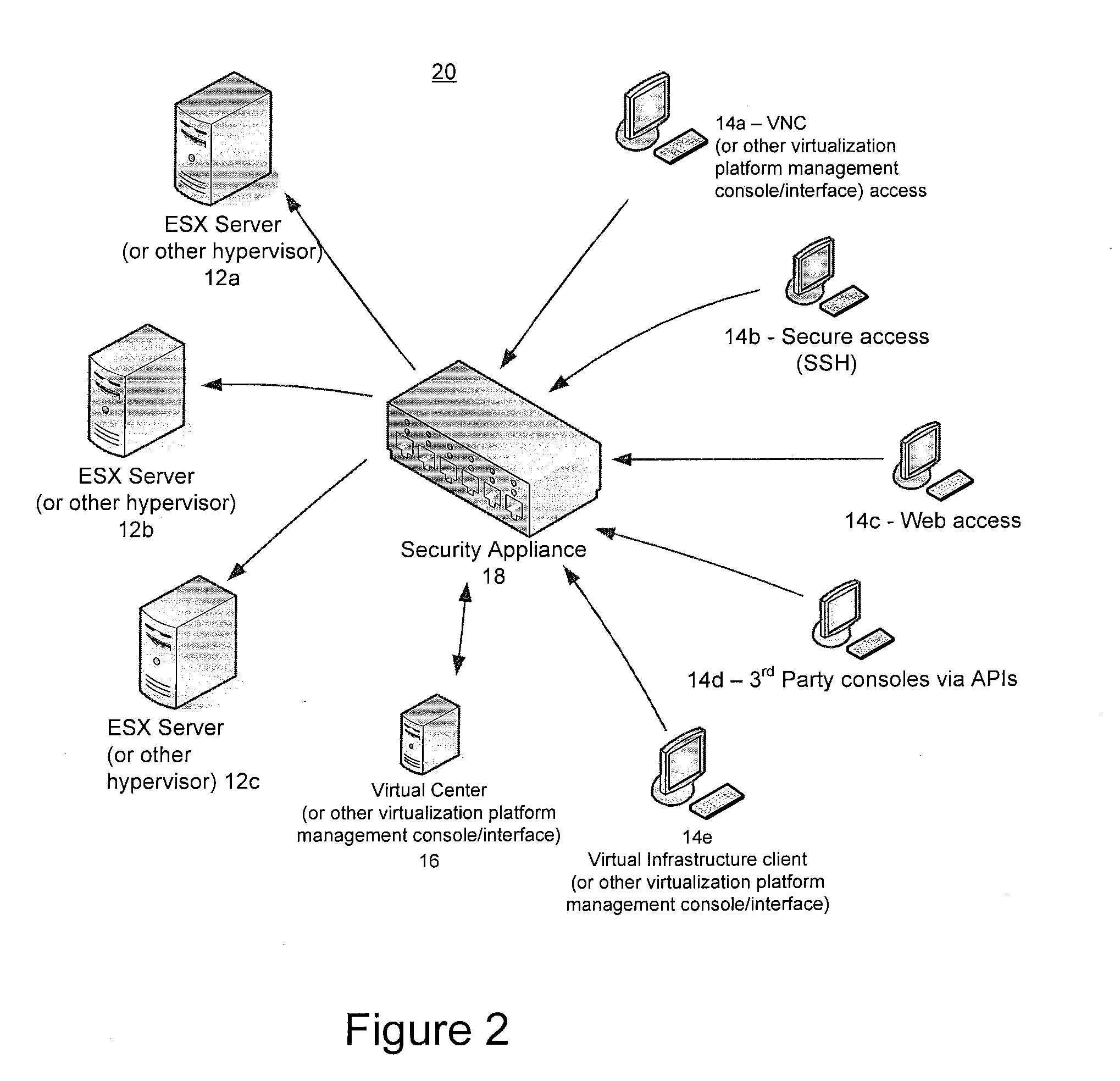
Methods and systems for securely managing virtualization platform
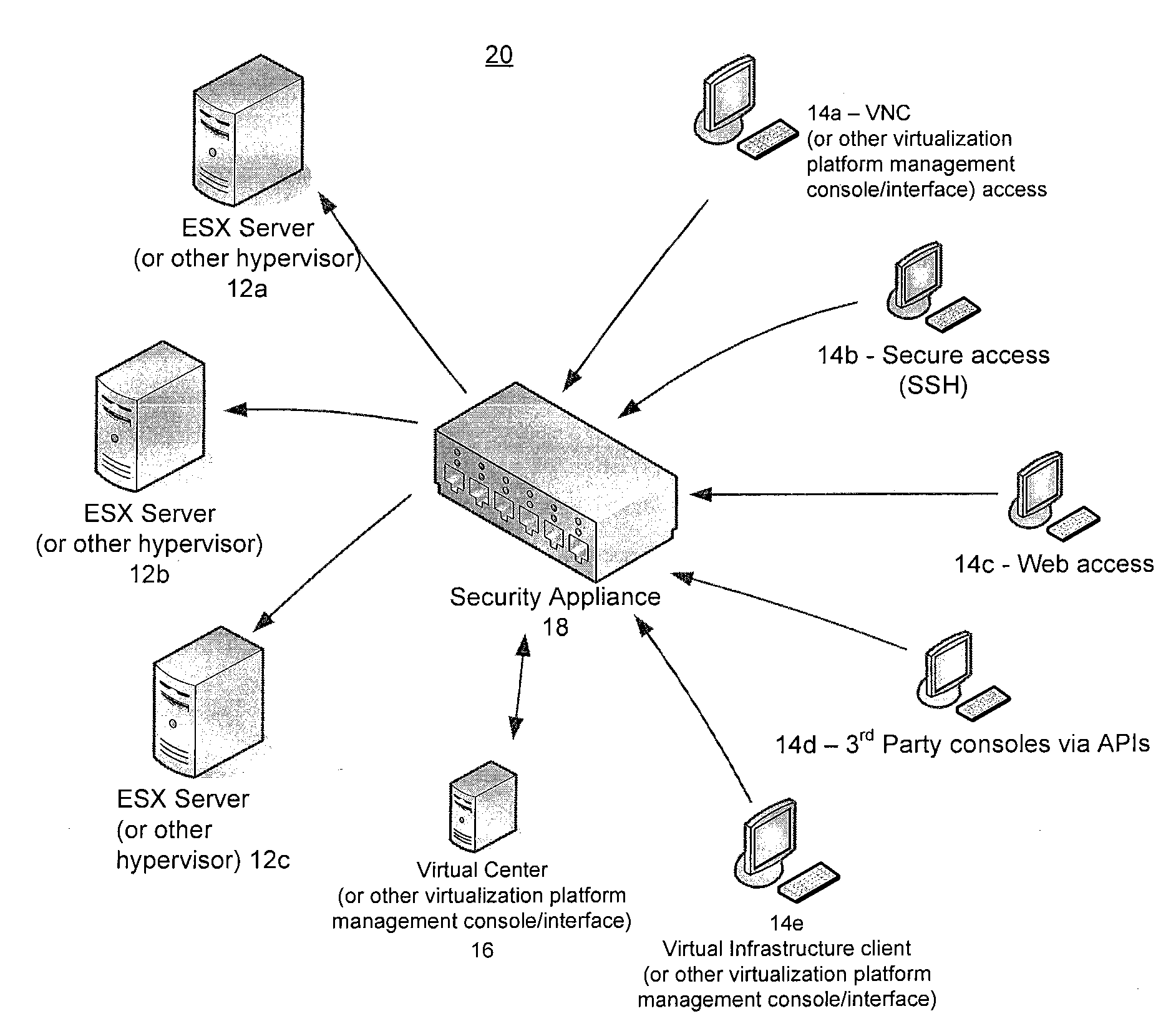
ActiveUS20100071035A1Avoid lostPotential problemDigital data processing detailsUser identity/authority verificationVirtualizationControl layer
Virtualization platforms and management clients therefor are communicatively coupled to one another via a control layer logically disposed therebetween. The control layer is configured to proxy virtualization management commands from the management clients to the virtualization platforms, but only after successful authentication of users (which may include automated agents and processes) issuing those commands and privileges of those users as defined by access control information accessible to the control layer. The control layer may be instantiated as an application running on a physical appliance logically interposed between the virtualization platforms and management clients, or a software package running on dedicated hardware logically interposed between the virtualization platforms and management clients, or as an application encapsulated in a virtual machine running on a compatible virtualization platform logically interposed between the virtualization platforms and management clients.
Owner:HYTRUST
Techniques for discovering and managing security of applications
ActiveUS20170251013A1Minimizing security threatMinimizing riskTransmissionSafety management systemsData source
Techniques for discovery and management of applications in a computing environment of an organization are disclosed. A security management system discovers use of applications within a computing environment to manage access to applications for minimizing security threats and risks in a computing environment of the organization. The security management system can obtain network data about network traffic to identify unique applications. The security management system can perform analysis and correlation, including use of one or more data sources, to determine information about an application. The system can compute a measure of security for an application (“an application risk score”) and a user (“a user risk score”). The score may be analyzed to determine a threat of security posed by the application based on use of the application. The security system can perform one or more instructions to configure access permitted by an application, whether access is denied or restricted.
Owner:ORACLE INT CORP
Policy-based network security management
ActiveUS20050086502A1Potential economic damageReduce riskMemory loss protectionUser identity/authority verificationCourse of actionSecurity management
A policy-based network security management system is disclosed. In one embodiment, the system comprises a security management controller comprising one or more processors; a computer-readable medium carrying one or more sequences of instructions for policy-based network security management, wherein execution of the one or more sequences of instructions by the one or more processors causes the one or more processors to perform the steps of receiving a set of data regarding a user of a computer network; automatically deciding on a course of action based on the set of data, wherein the course of action may be adverse to the user although the set of data is insufficient to establish whether the user is performing a malicious action; and sending signals to one or more network elements in the computer network to implement the decision.
Owner:CISCO TECH INC
Method and system for managing computer security information
InactiveUS7089428B2Efficient managementMemory loss protectionDigital data processing detailsInternet trafficSafety management systems
A security management system includes a fusion engine which “fuses” or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:INT BUSINESS MASCH CORP
Secure management of authentication information
InactiveUS7490242B2Key distribution for secure communicationDigital data processing detailsInternet privacyApplication software
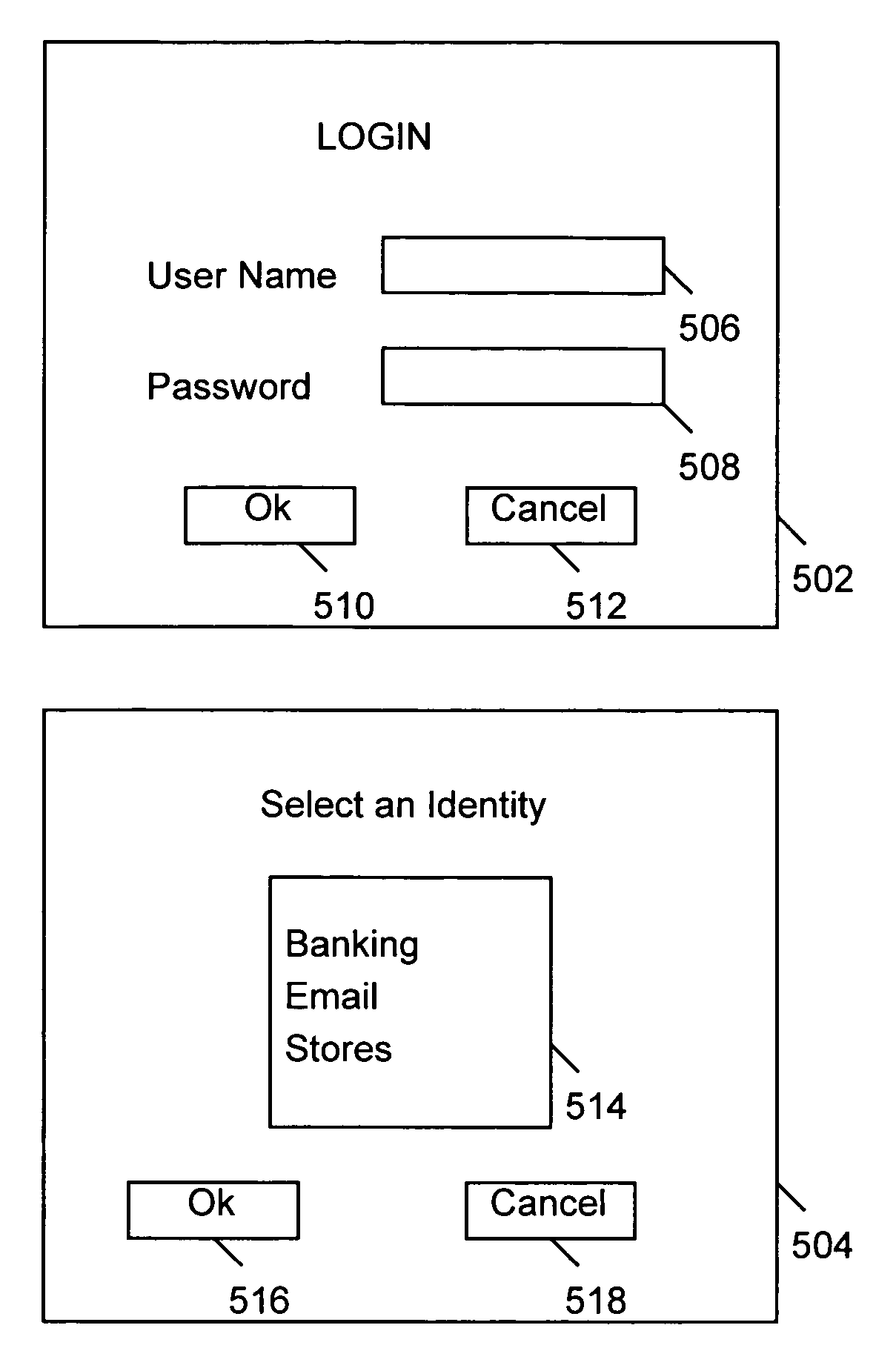
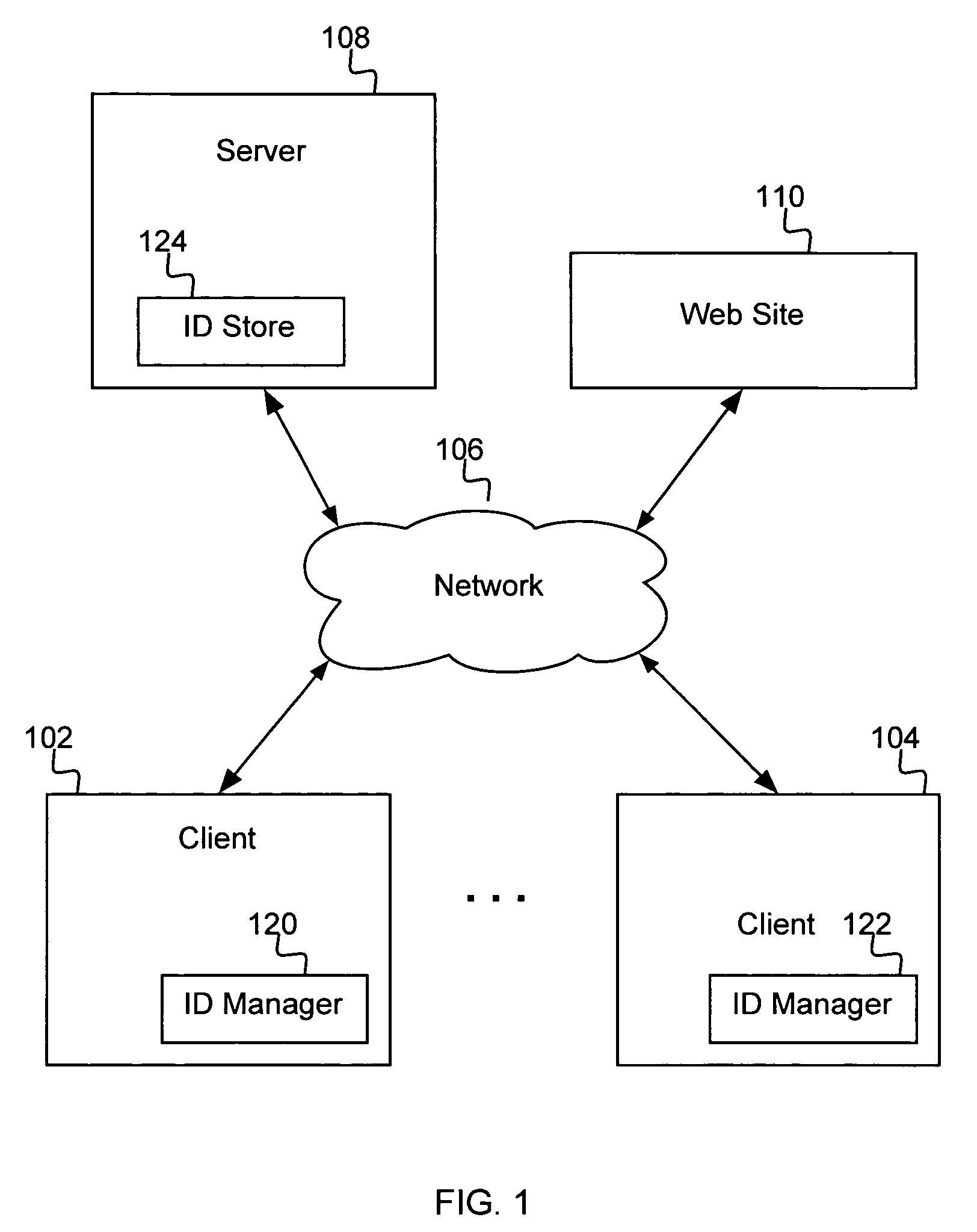
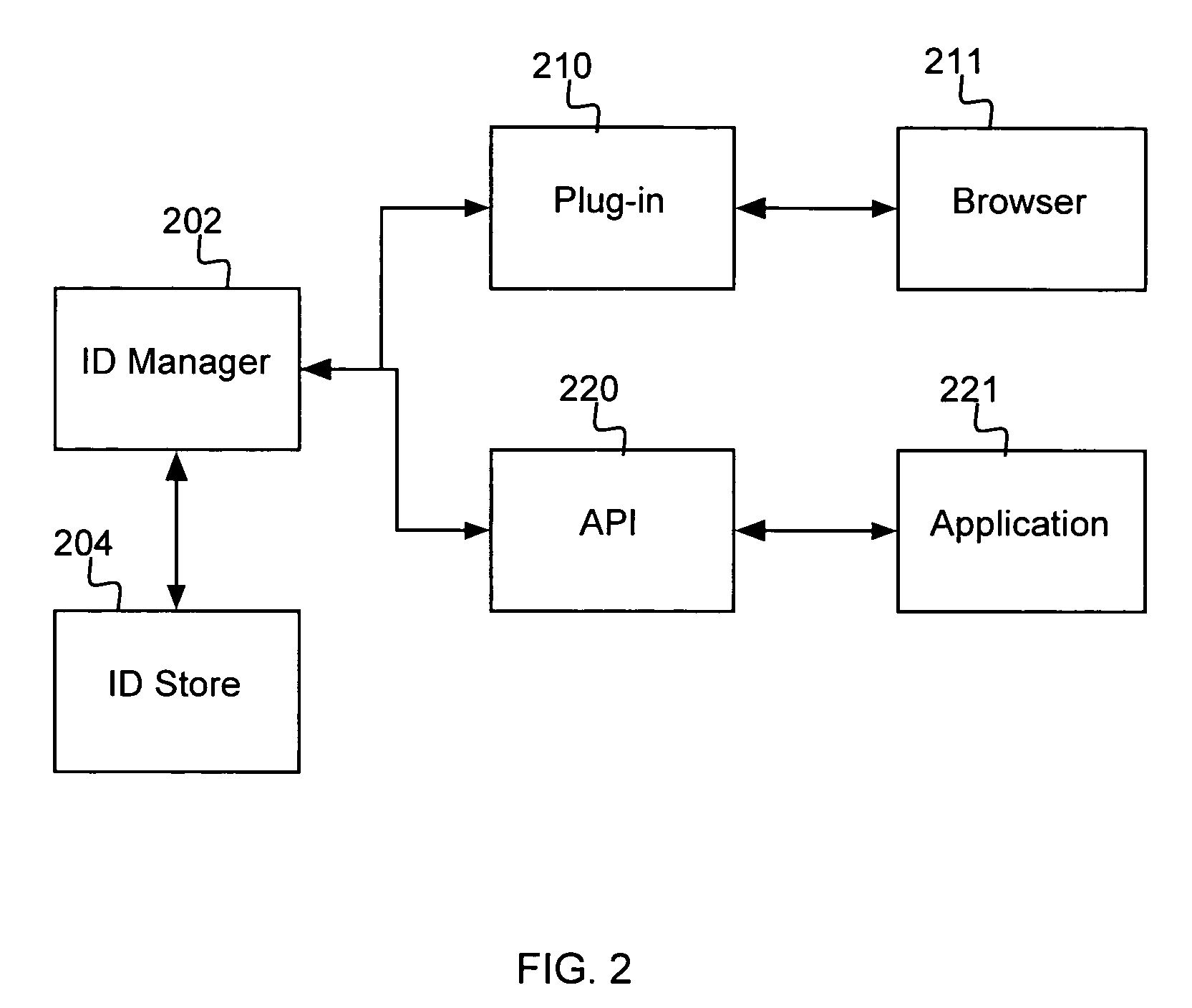
A system, method and computer program product are provided for managing authentication information for a user. According to the method, a master digital key is received from the user, and authentication of the user is obtained based on the master digital key. There is received from the user a selection of one identity from among a plurality of identities that are stored for the user. Authentication information for the user is provided into an application or web page based on the one identity selected by the user. In one embodiment, the authentication information is provided by recognizing a web page for which authentication information is stored, and automatically filling the authentication information for the user into appropriate elements of the web page.
Owner:IBM CORP
Method and system for wireless intrusion detection prevention and security management
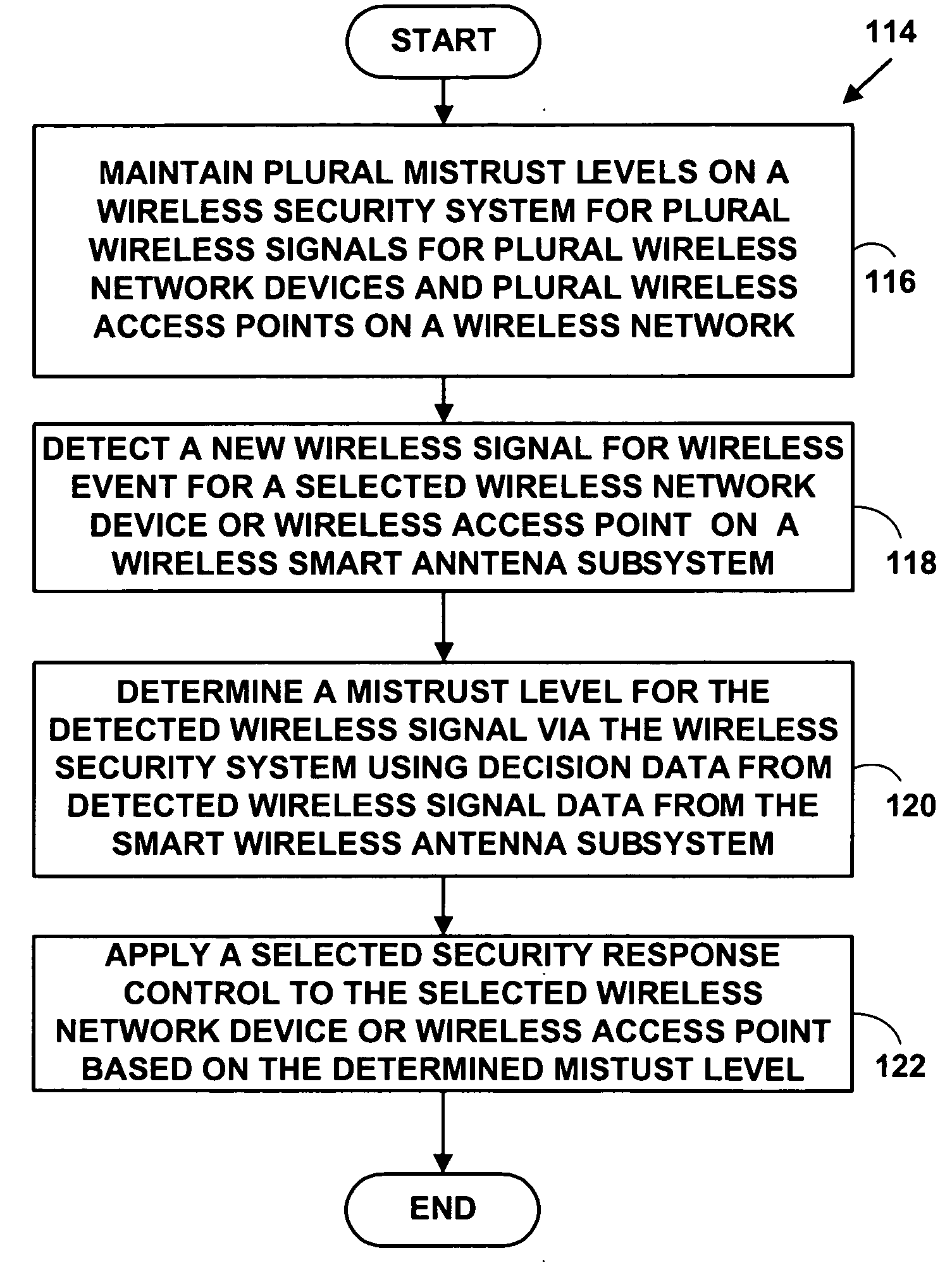
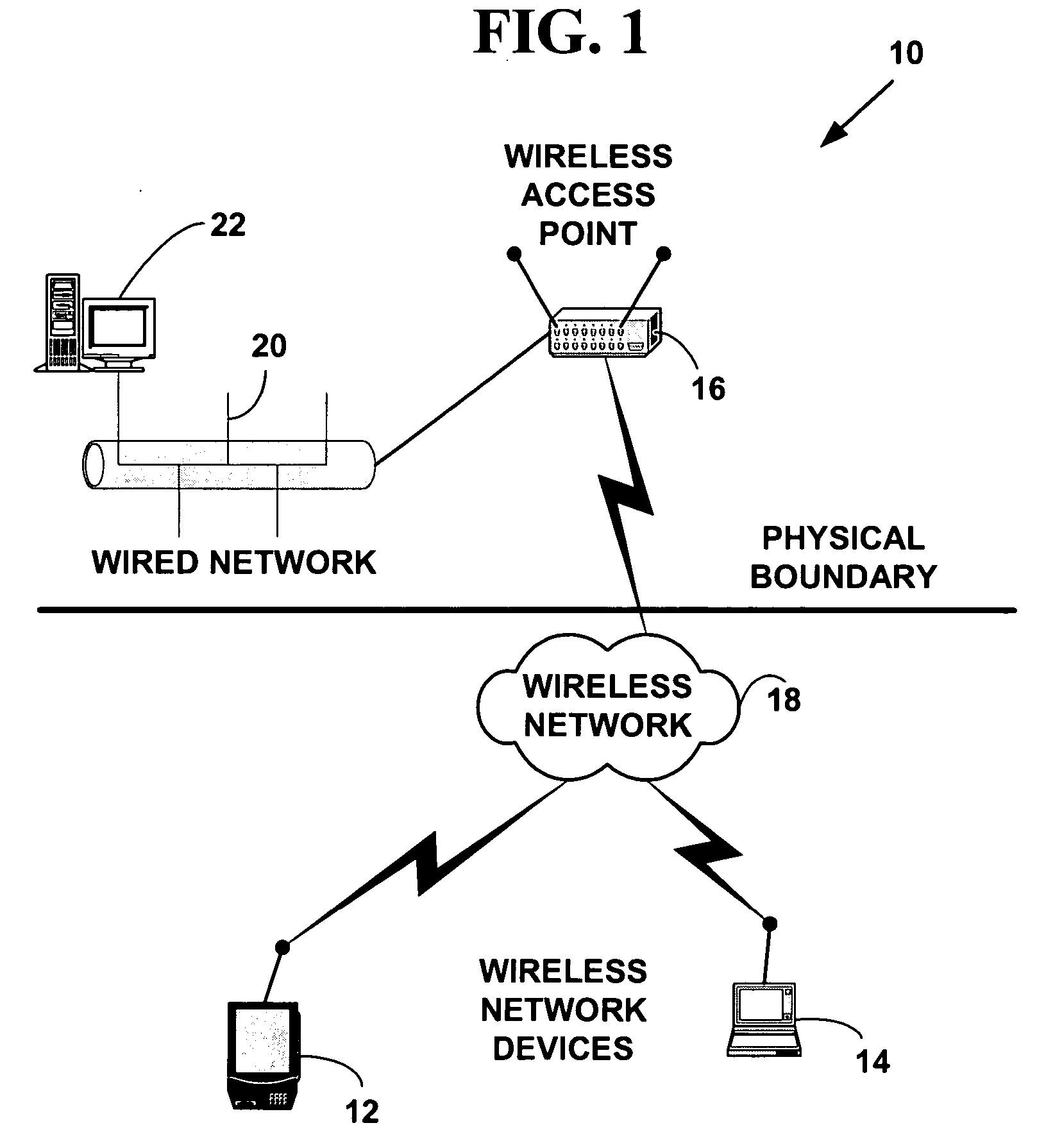
ActiveUS20050037733A1Spatial transmit diversityUnauthorised/fraudulent call preventionSystems managementIntrusion detection and prevention
A method and system for wireless intrusion detection, prevention and security management. The method and system provides autonomous wireless intrusion detection and prevention, with minimal or no operator intervention. The method and system integrates a physical layer (e.g., OSI layer 1) a smart wireless radio frequency (RF) antenna subsystem with a data-link layer (e.g., OSI layer 2) wireless security system management platform.
Owner:3E TECH INT
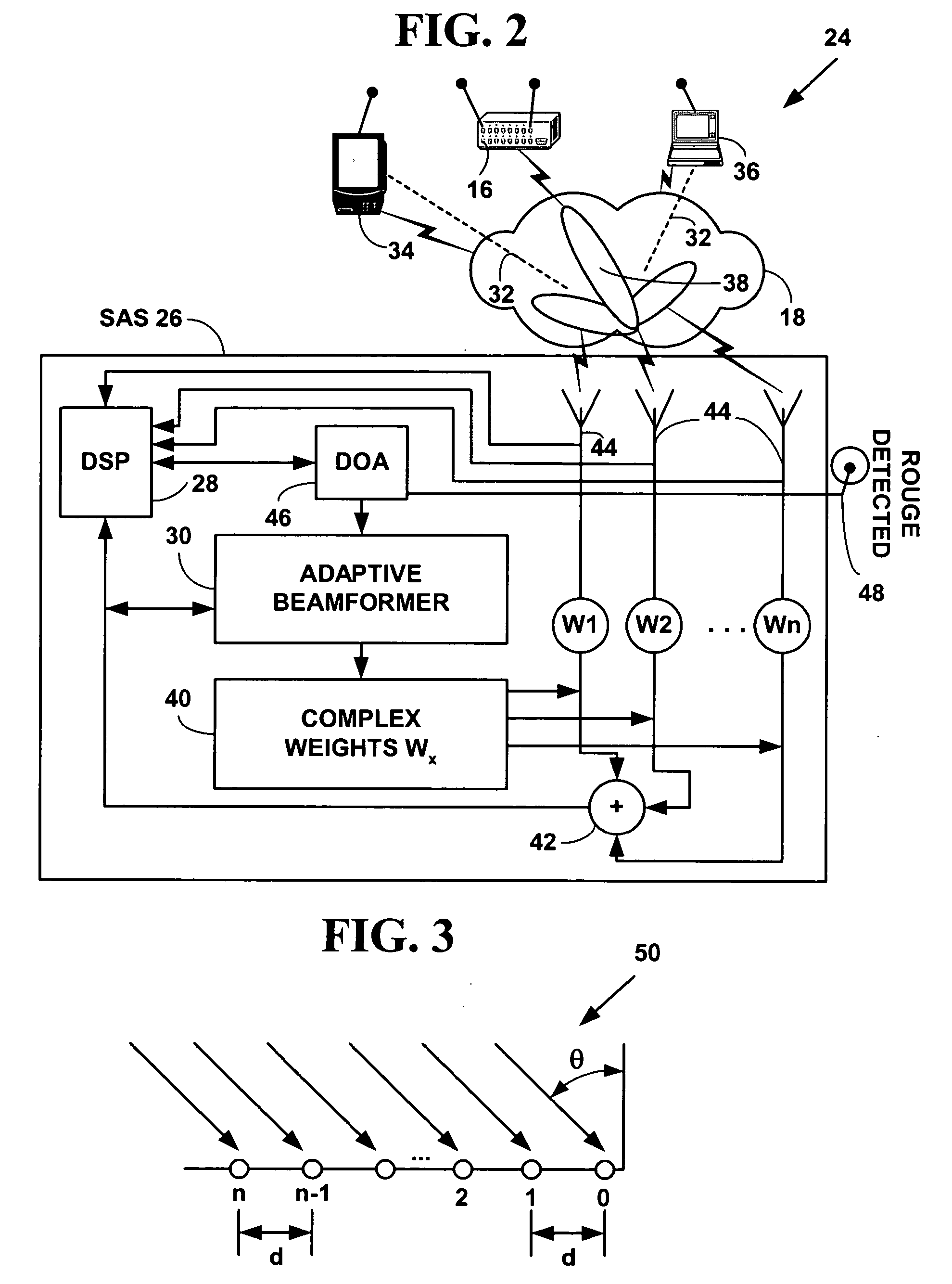
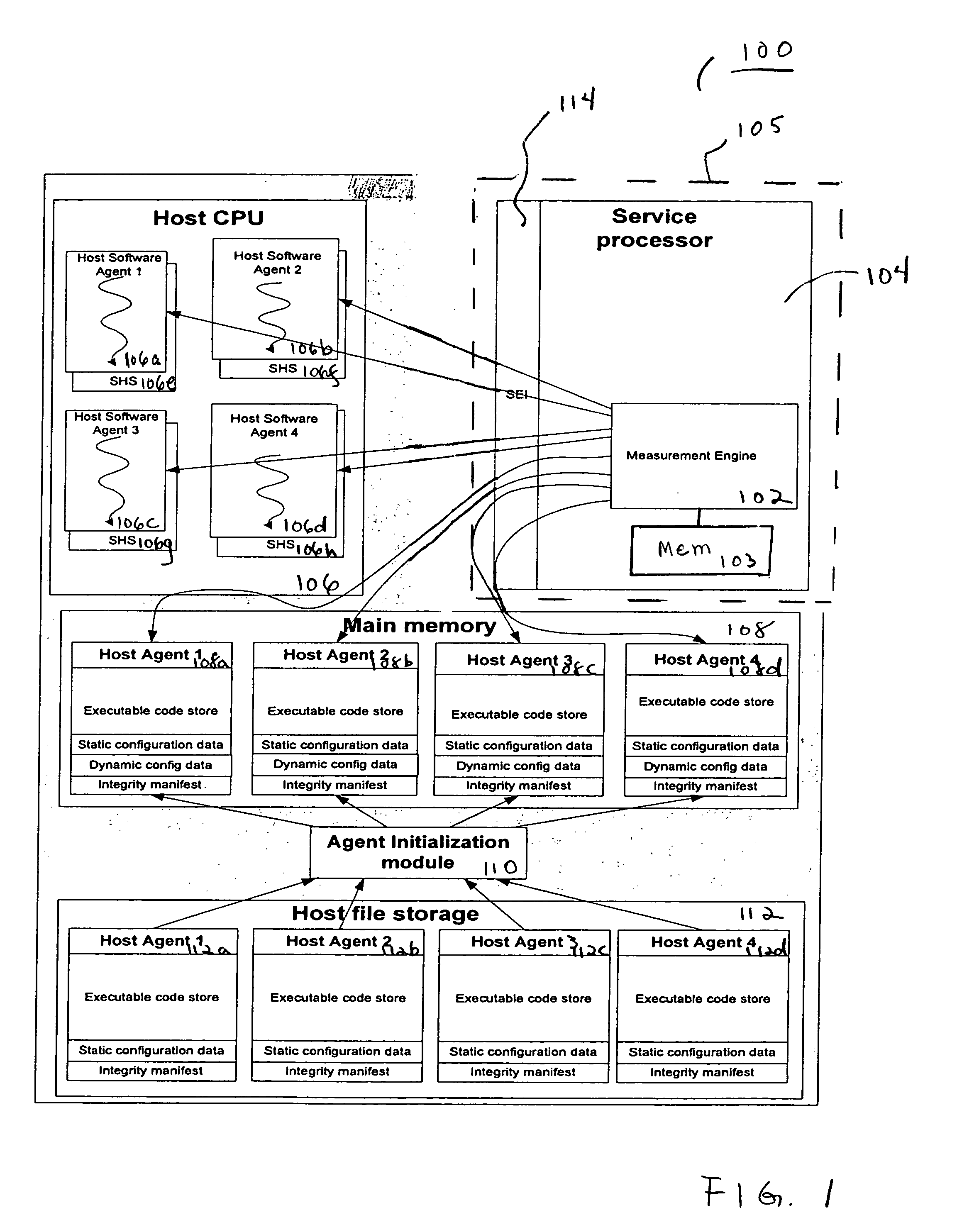
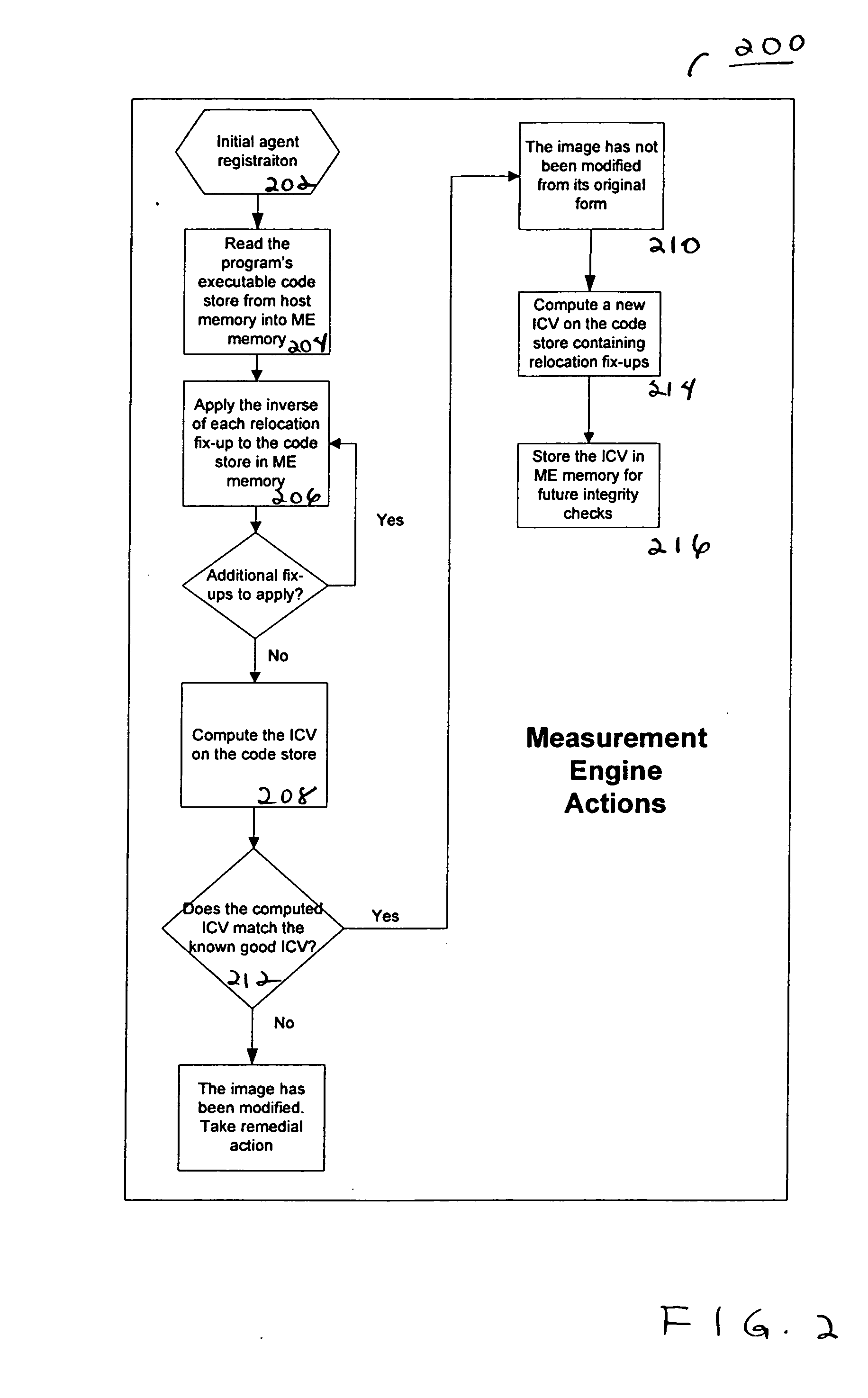
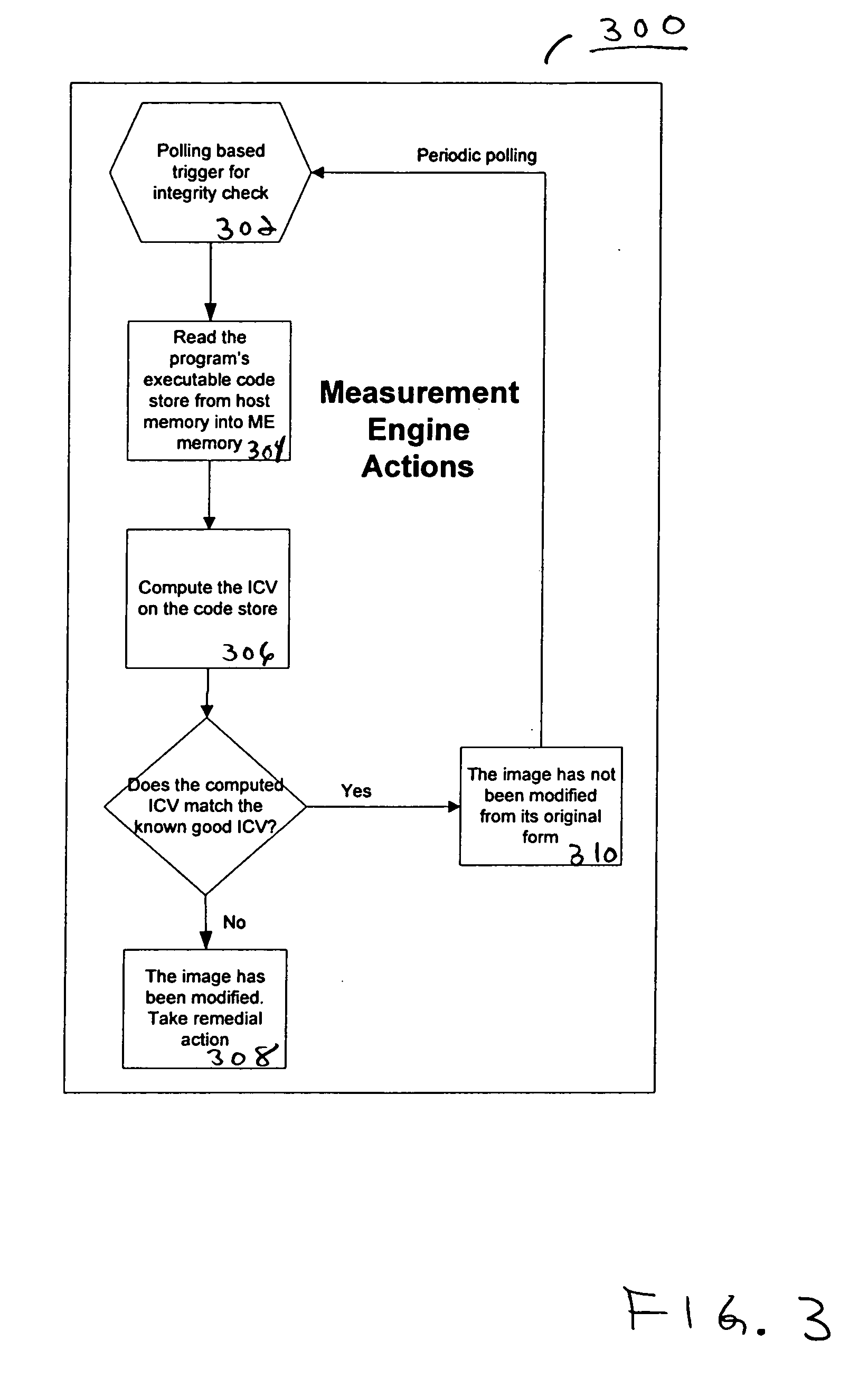
Agent presence monitor configured to execute in a secure environment
InactiveUS20070005957A1Memory loss protectionError detection/correctionSecurity managementRemote administration
Embodiments of a method and system for detecting and confirming an agent presence are disclosed herein. The agent presence can be confirmed by a secure management engine configured to execute in a secure execution environment. In various embodiments, a secure execution environment includes a service processor, a virtual partition, and an embedded microcontroller. The management engine is configured to monitor a signal communicated from the agent. Based on the monitored signal, an analysis determines an operational state of the agent. Embodiments include remote management applicability for monitoring a host agent.
Owner:INTEL CORP
Secure machine platform that interfaces to operating systems and customized control programs
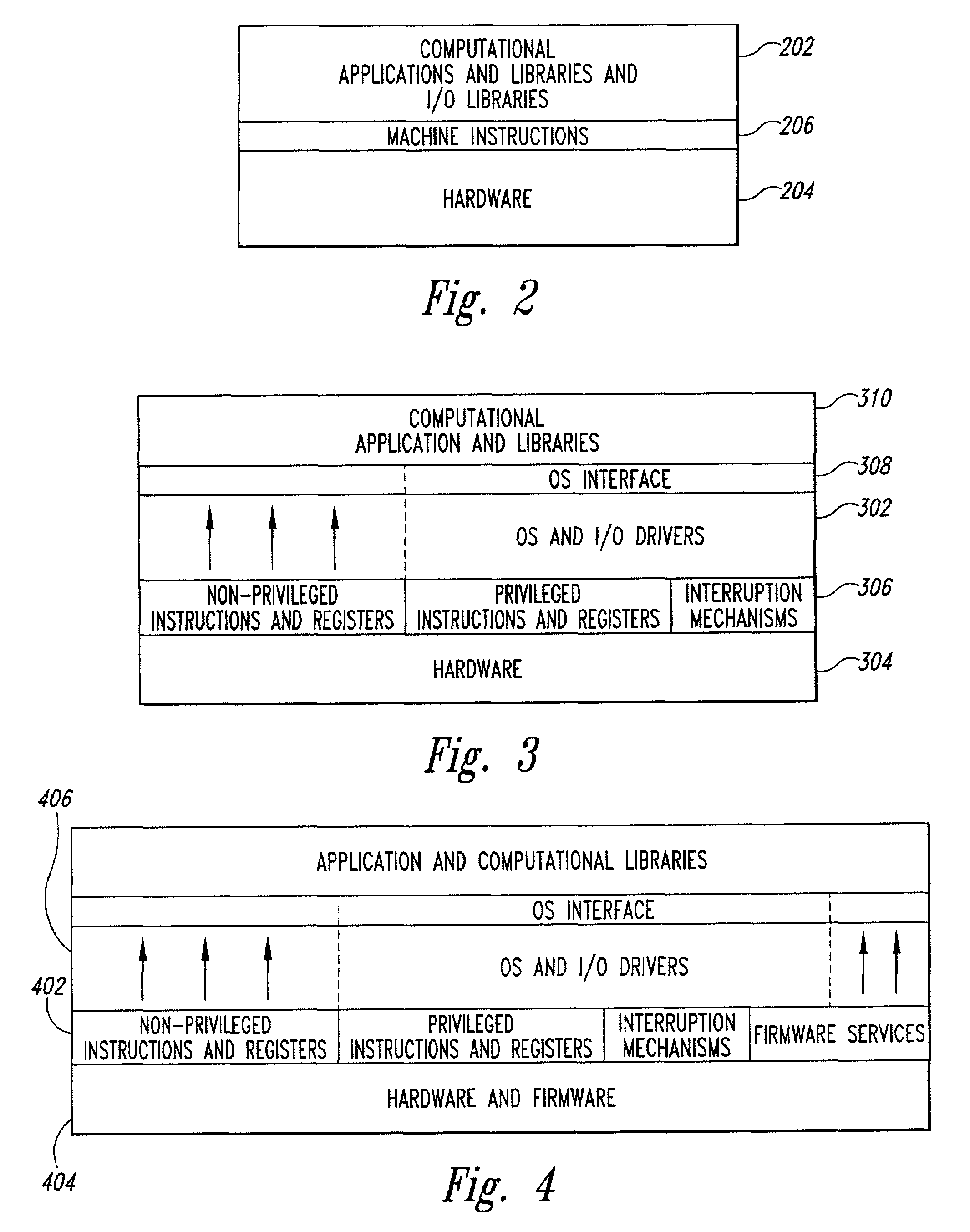
ActiveUS7073059B2Program initiation/switchingError detection/correctionOperational systemService provision
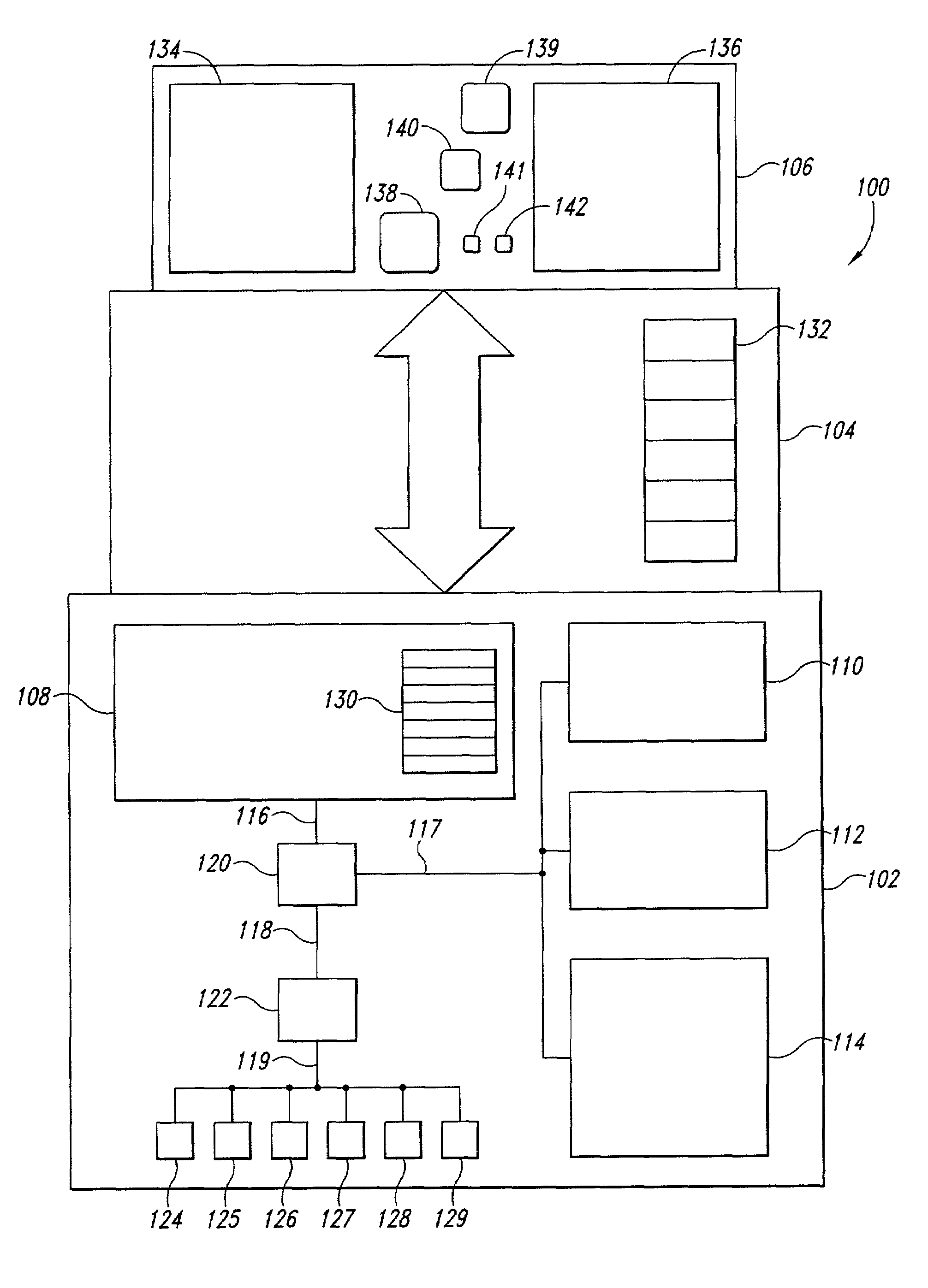
A combined-hardware-and-software secure-platform interface to which operating systems and customized control programs interface within a computer system. The combined-hardware-and-software secure-platform interface employs a hardware platform that provides at least four privilege levels, non-privileged instructions, non-privileged registers, privileged instructions, privileged registers, and firmware interfaces. The combined-hardware-and-software secure-platform interface conceals all privileged instructions, privileged registers, and firmware interfaces and privileged registers from direct access by operating systems and custom control programs, providing to the operating systems and custom control programs the non-privileged instructions and non-privileged registers provided by the hardware platform as well as a set of callable software services. The callable services provide a set of secure-platform management services for operational control of hardware resources that neither exposes privileged instructions, privileged registers, nor firmware interfaces of the hardware nor simulates privileged instructions and privileged registers. The callable services also provide a set of security-management services that employ internally generated secret data, each compartmentalized security-management service managing internal secret data without exposing the internal secret data to computational entities other than the security-management service itself.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
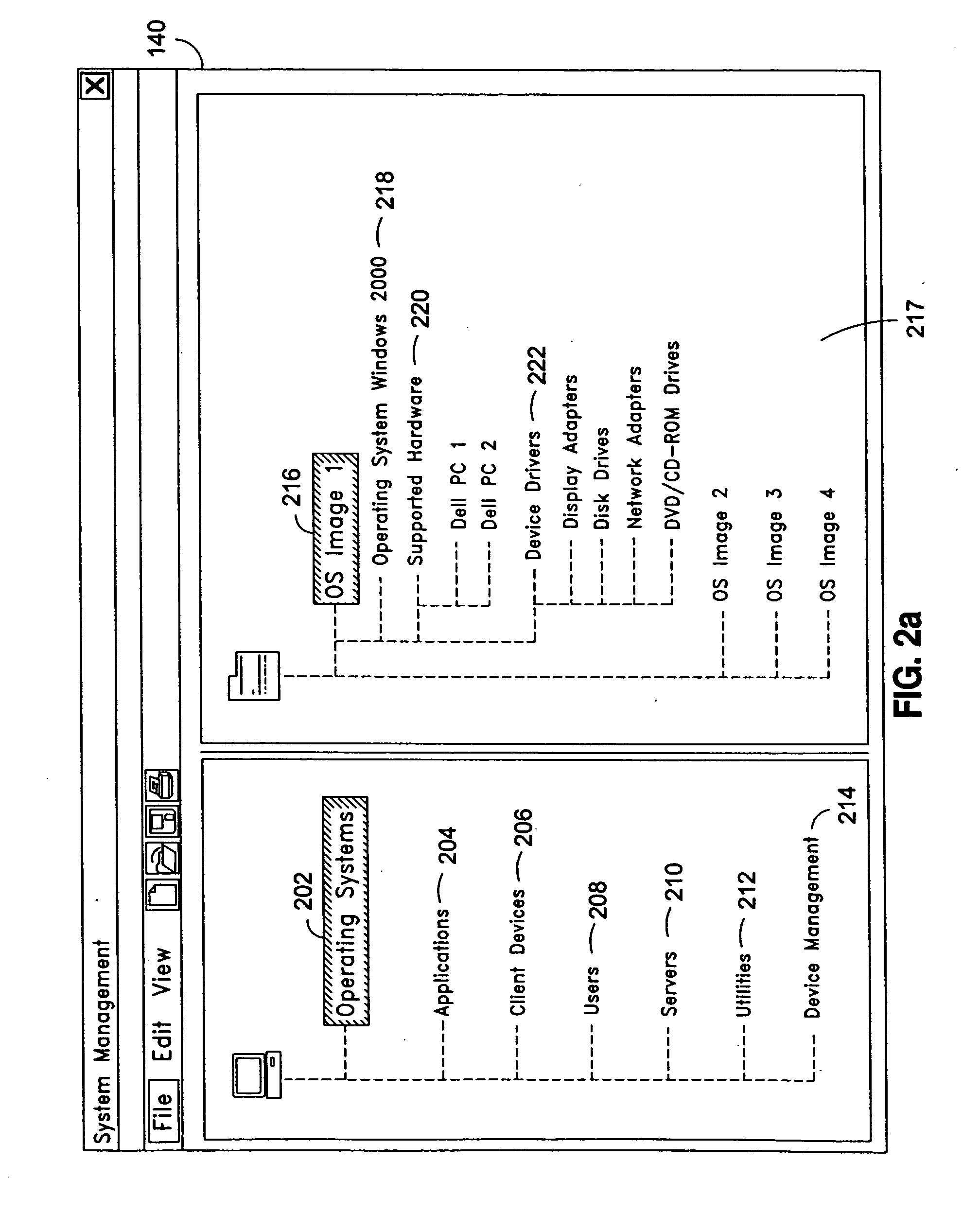
System and method for integrated on-demand delivery of operating system and applications
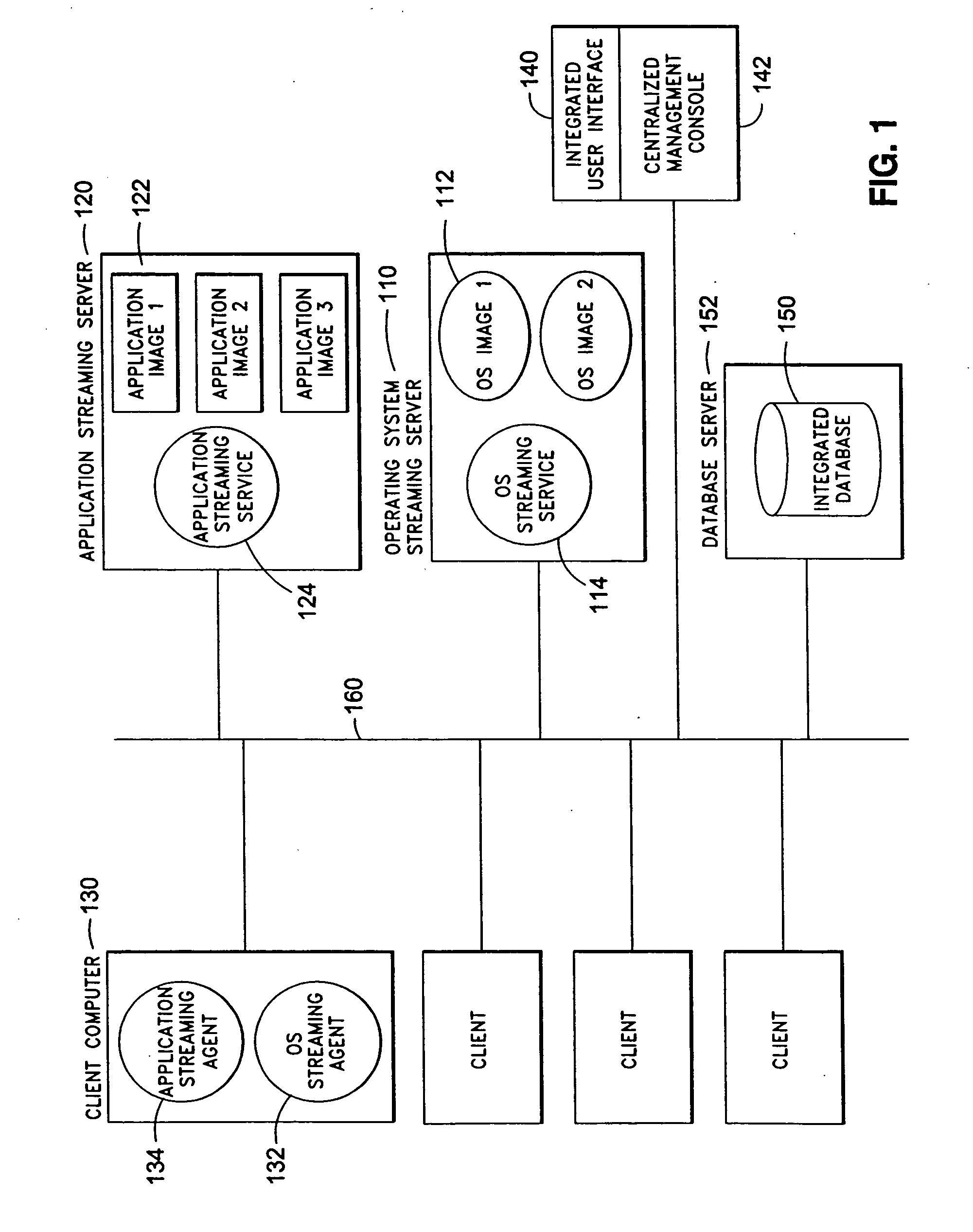
ActiveUS20060031547A1Accurate scaleMultiple digital computer combinationsProgram controlOperational systemSystems management
The present invention discloses a system and a method for integrated on-demand delivery of operating system and applications, where operating system images are separate and distinct from application images. Integration of operating system streaming and application streaming services makes streaming delivery possible to a wide range of client devices, including those without any local disk space such as thin-clients and diskless workstations. In addition, by integrating the centralized management of operating system delivery and application delivery, the present invention provides a complete solution to server-centric application management, thereby further reducing the total cost of ownership of network-based computing approach. Implementing the operating management functions at the client machine level of specificity and application management functions at the user level of specificity combined with providing separate and distinct operating system images and application images provides an inherently canonical architecture that allows proper scaling and affords appropriate security management functions. The result is a complete, scalable, robust, and reliable server-centric application and operating system management system with a lower total cost of ownership than existing products.
Owner:DELL MARKETING CORP
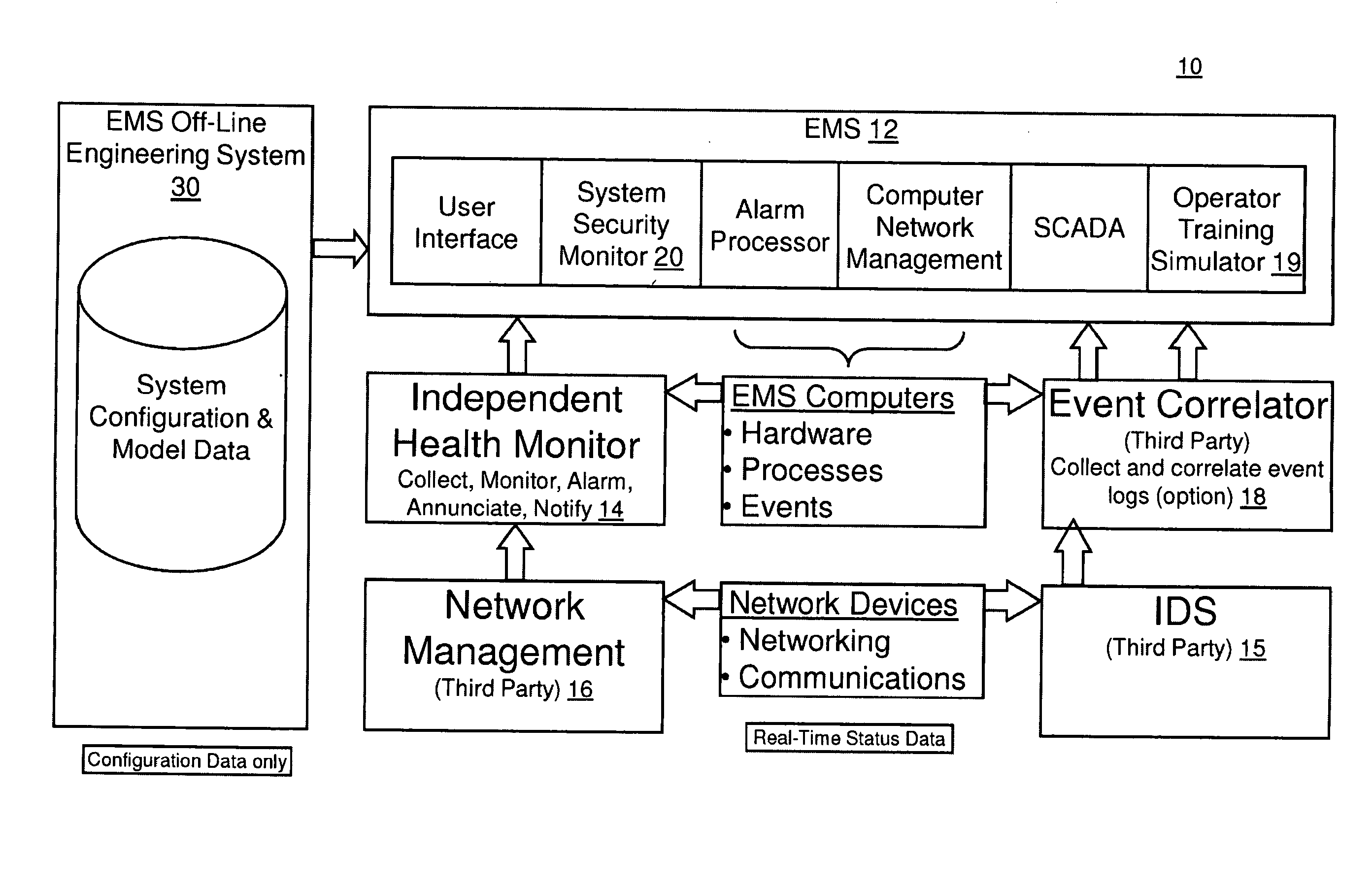
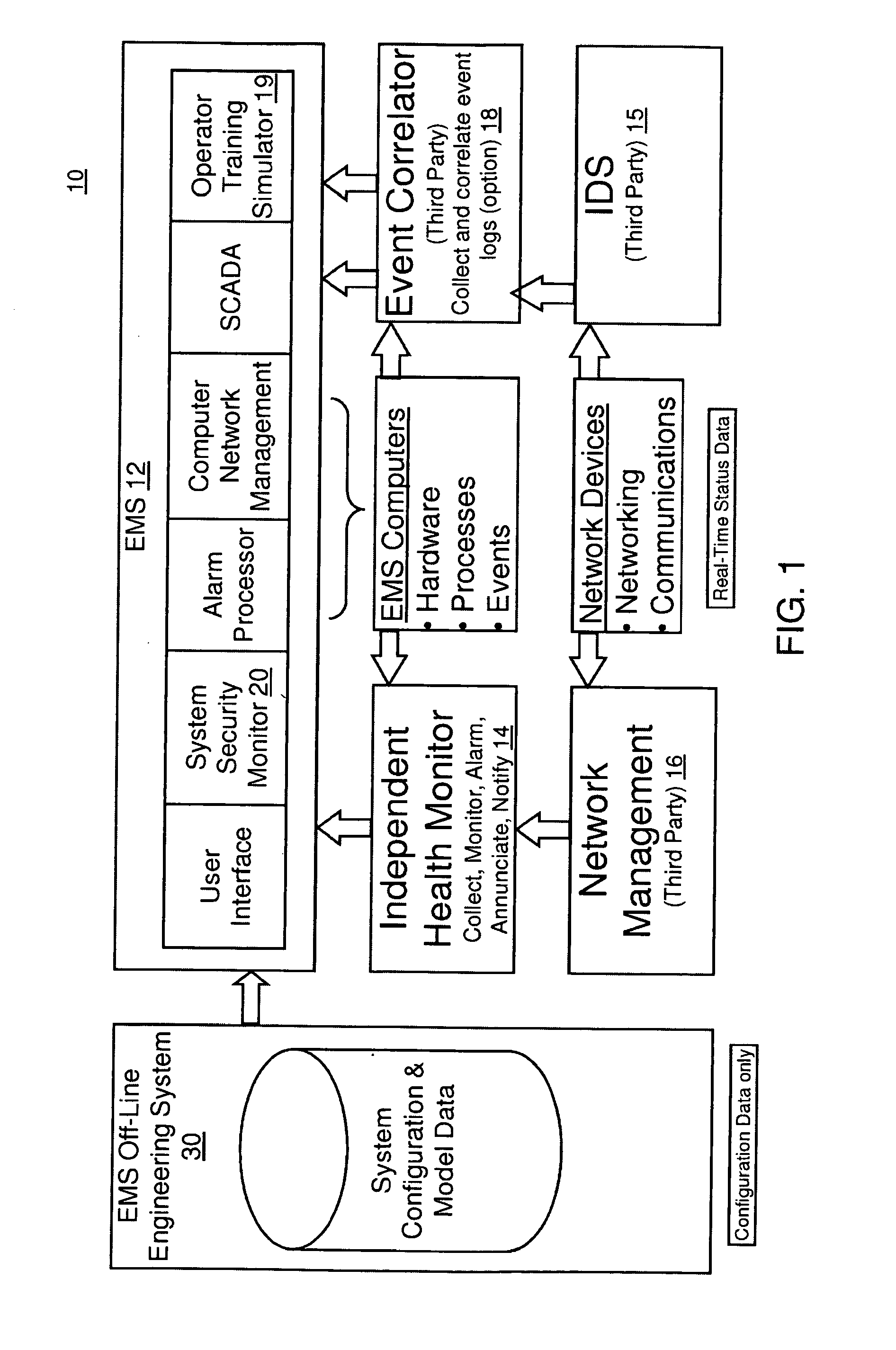
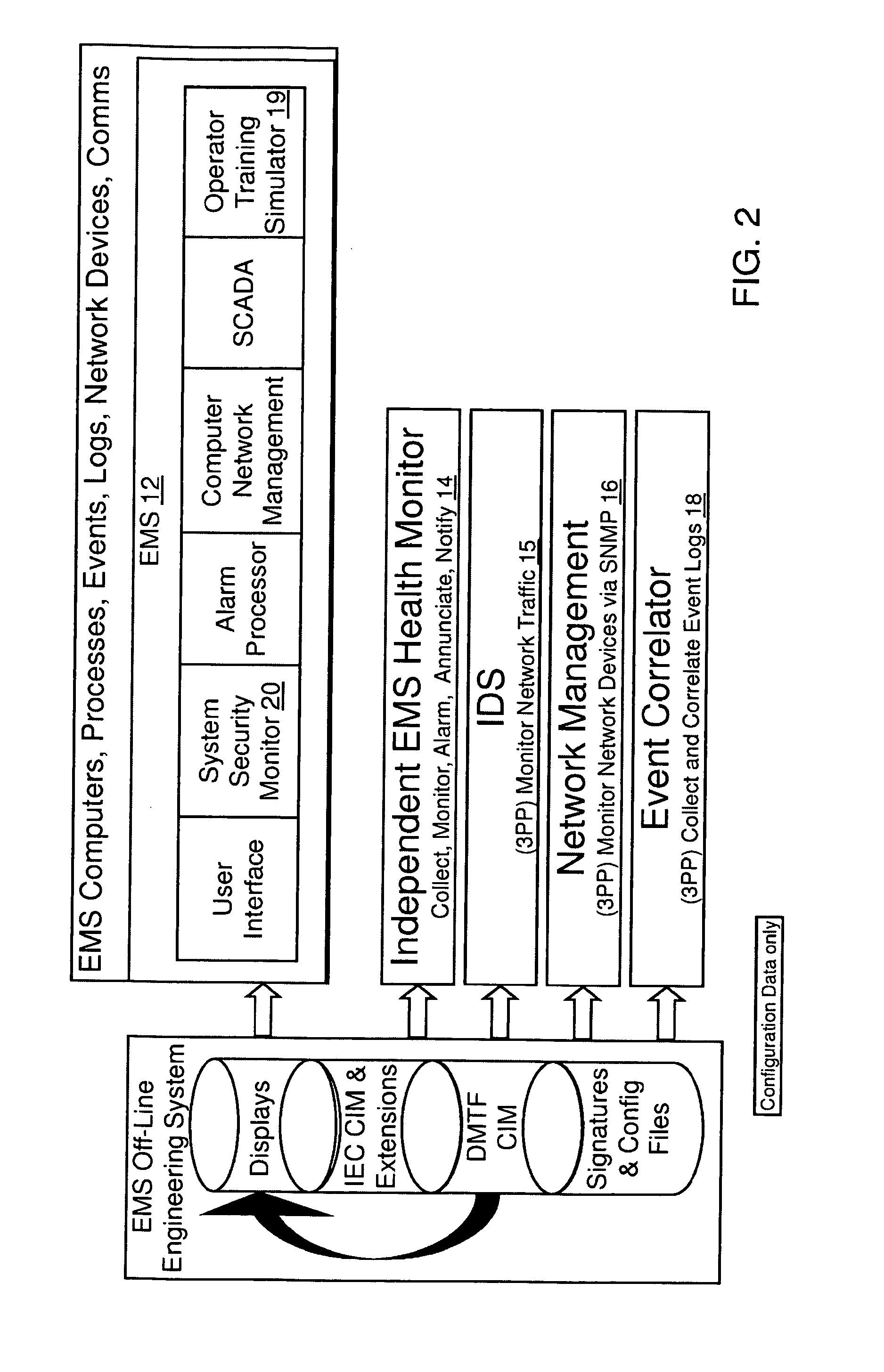
Method and system for cyber security management of industrial control systems
ActiveUS20110039237A1Low chanceFull accessMemory loss protectionError detection/correctionCommand and controlData acquisition
A method and system for cyber security management of Supervisory Control And Data Acquisition (SCADA) systems is provided to enhance situational awareness and cyber security management for industrial control systems. A centralized System Security Manager (SSM) is integrated into a SCADA to collect security related data for the industrial control system and an integrated command and control user interface displays security related data, a system security level, and interfaces with a user to allows for changing of system security settings for the industrial control system based on the security related data collected and manages changes in operational state of the SCADA based on the security level to restrict use of system interfaces and system accesses.
Owner:SIEMENS AG
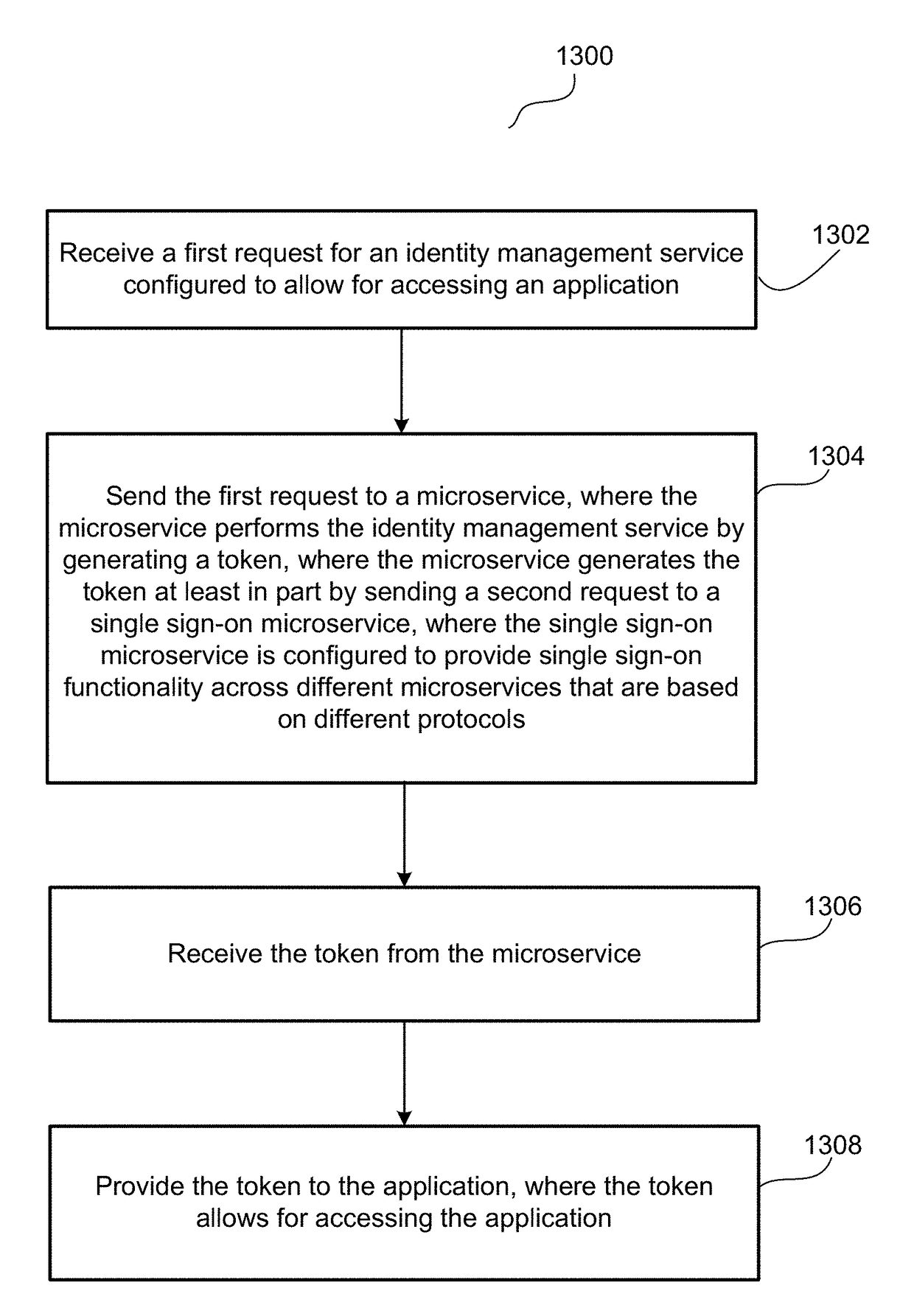
Single sign-on functionality for a multi-tenant identity and data security management cloud service
ActiveUS20180075231A1Digital data information retrievalDigital data authenticationInternet privacyCloud base
A cloud-based identity and access management system that implements single sign-on (“SSO”) receives a first request for an identity management service configured to allow for accessing an application. Embodiments send the first request to a first microservice which performs the identity management service by generating a token. The first microservice generates the token at least in part by sending a second request to a SSO microservice that is configured to provide SSO functionality across different microservices that are based on different protocols. Embodiments then receive the token from the first microservice and provide the token to the application, where the token allows for accessing the application.
Owner:ORACLE INT CORP
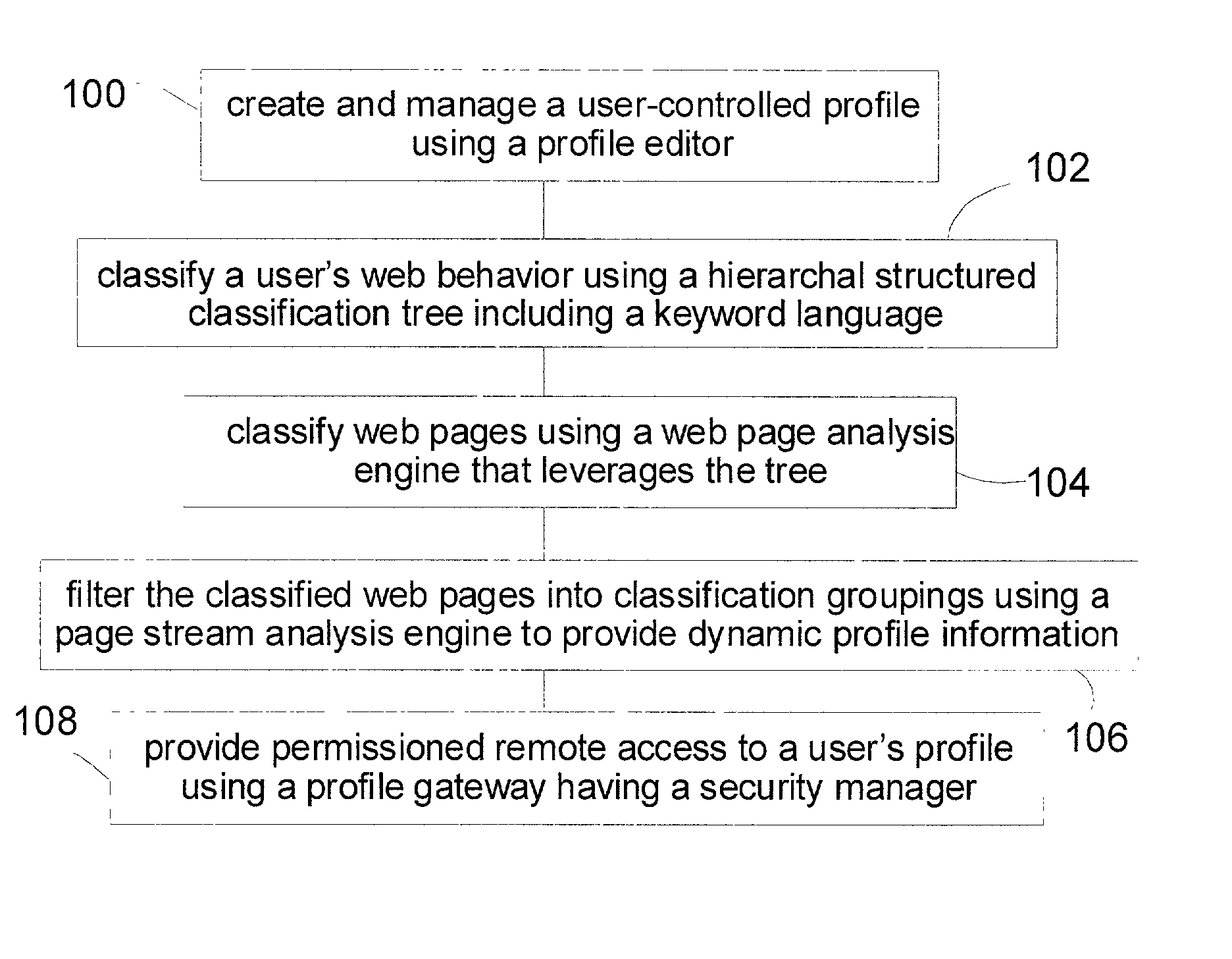
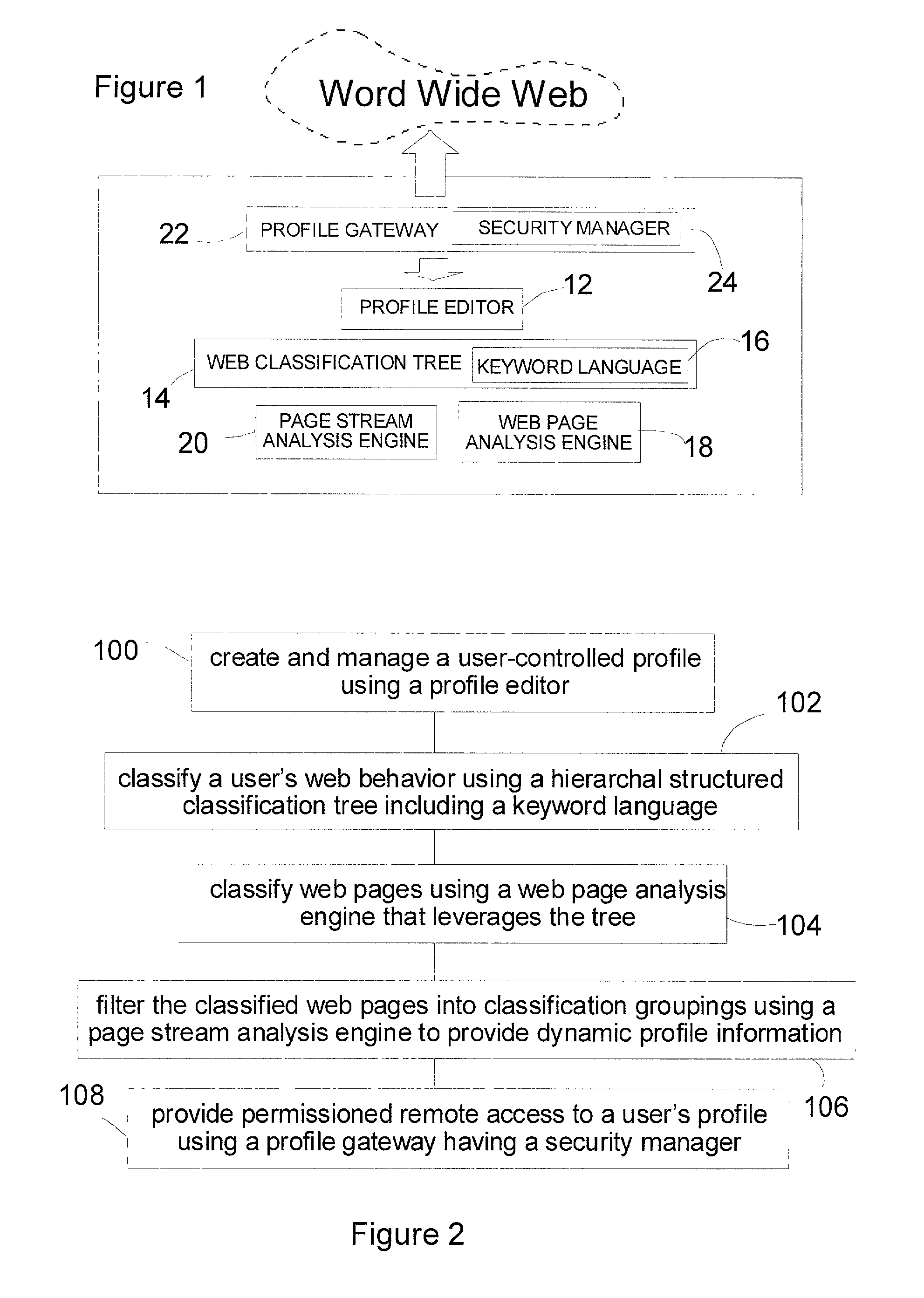
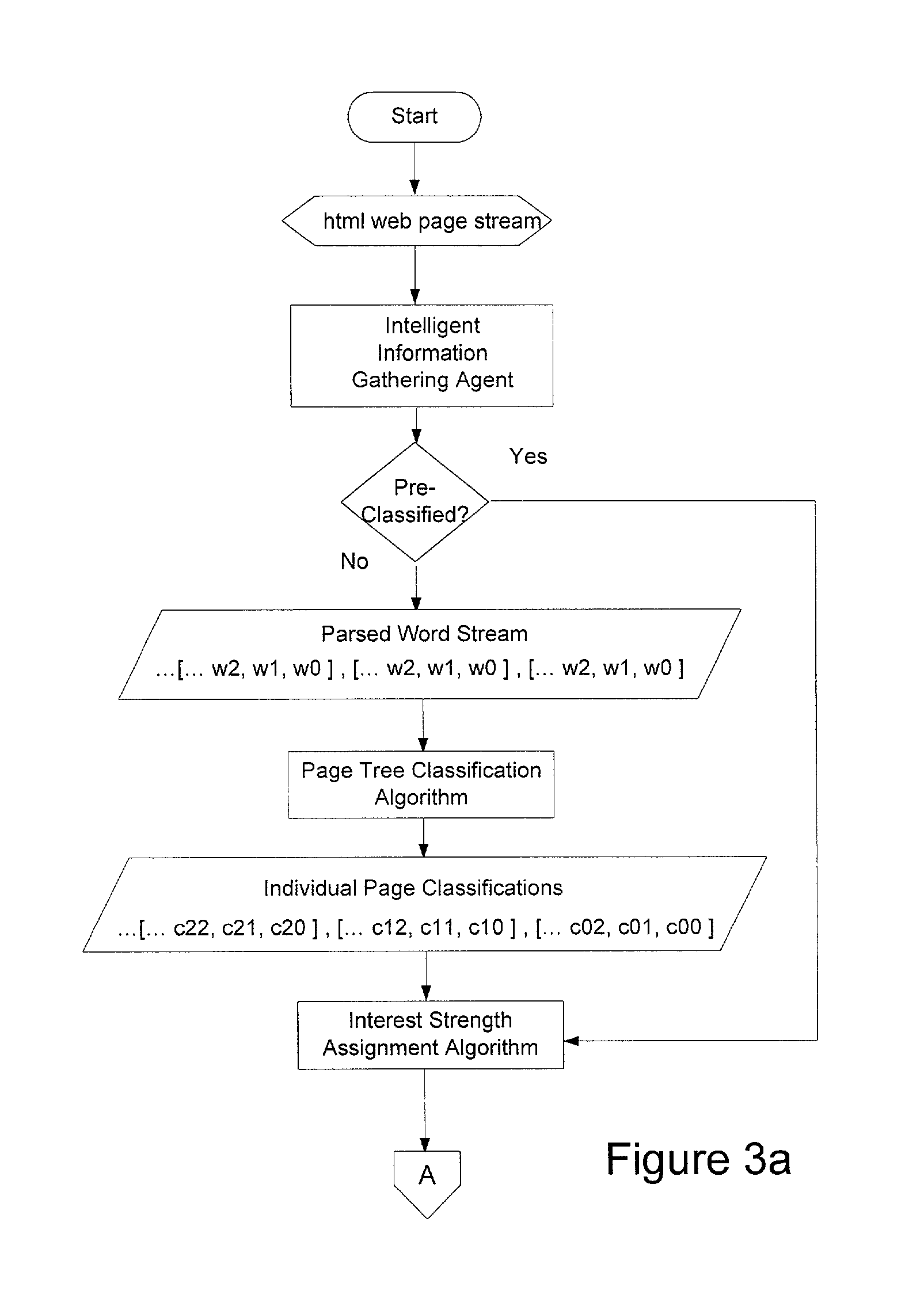
Web user profiling system and method
InactiveUS20030074400A1Less computing timeLess resourcesDigital data information retrievalMultiple digital computer combinationsEngineeringNetizen
A web user profiling system and method. The method includes a profile editor for user-controlled profile creation and management, a web classification tree including a keyword language, the tree providing a hierarchal structure for classifying a user's web behavior, and a web page analysis engine for classifying web pages viewed leveraging the tree. The system further includes a page stream analysis engine for filtering the classified web pages into classification groupings to provide dynamic user profile information, and a profile gateway having a security manager, the gateway providing permissioned remote access to a user's profile.
Owner:PATTERN DISCOVERY SOFTWARE SYST
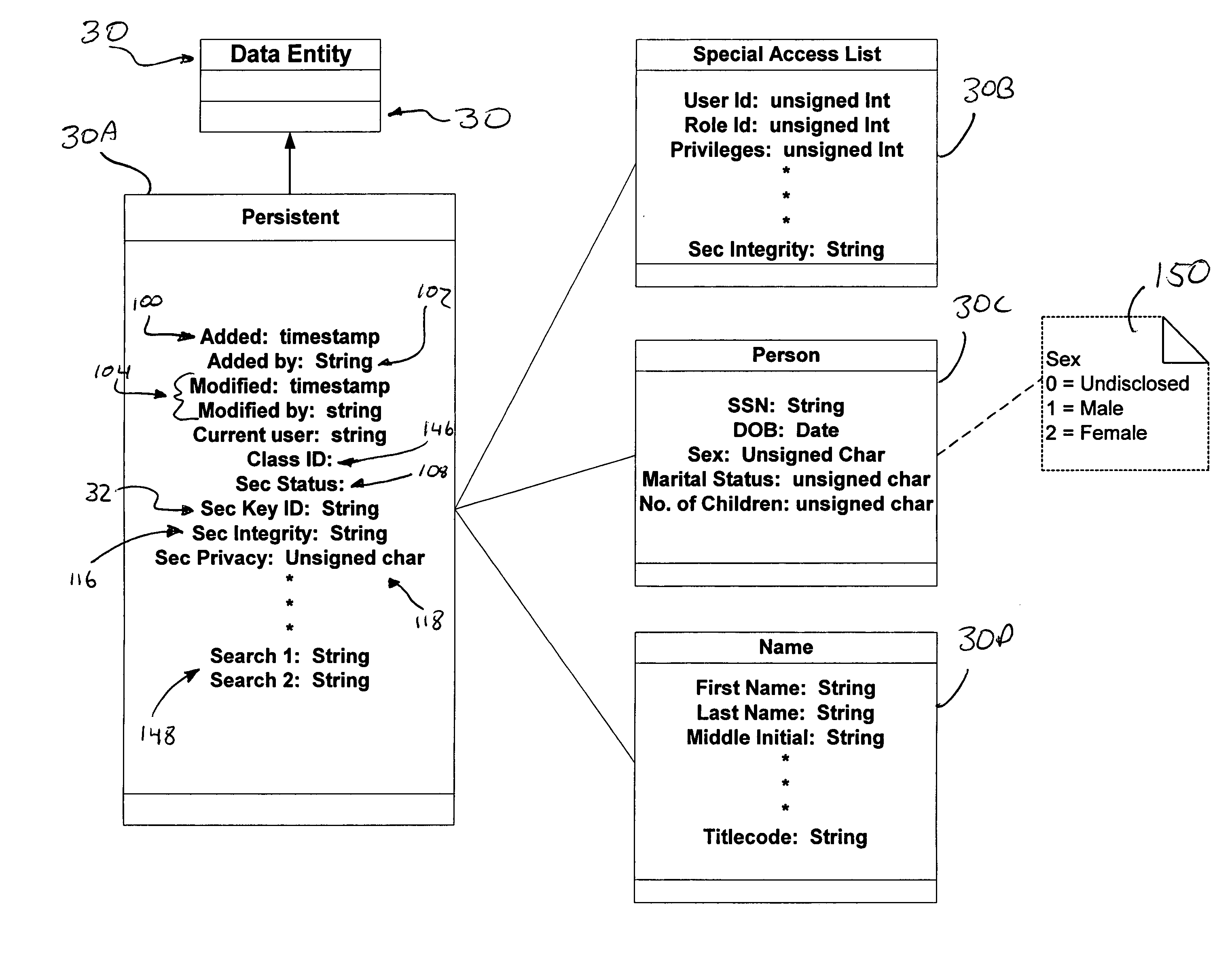
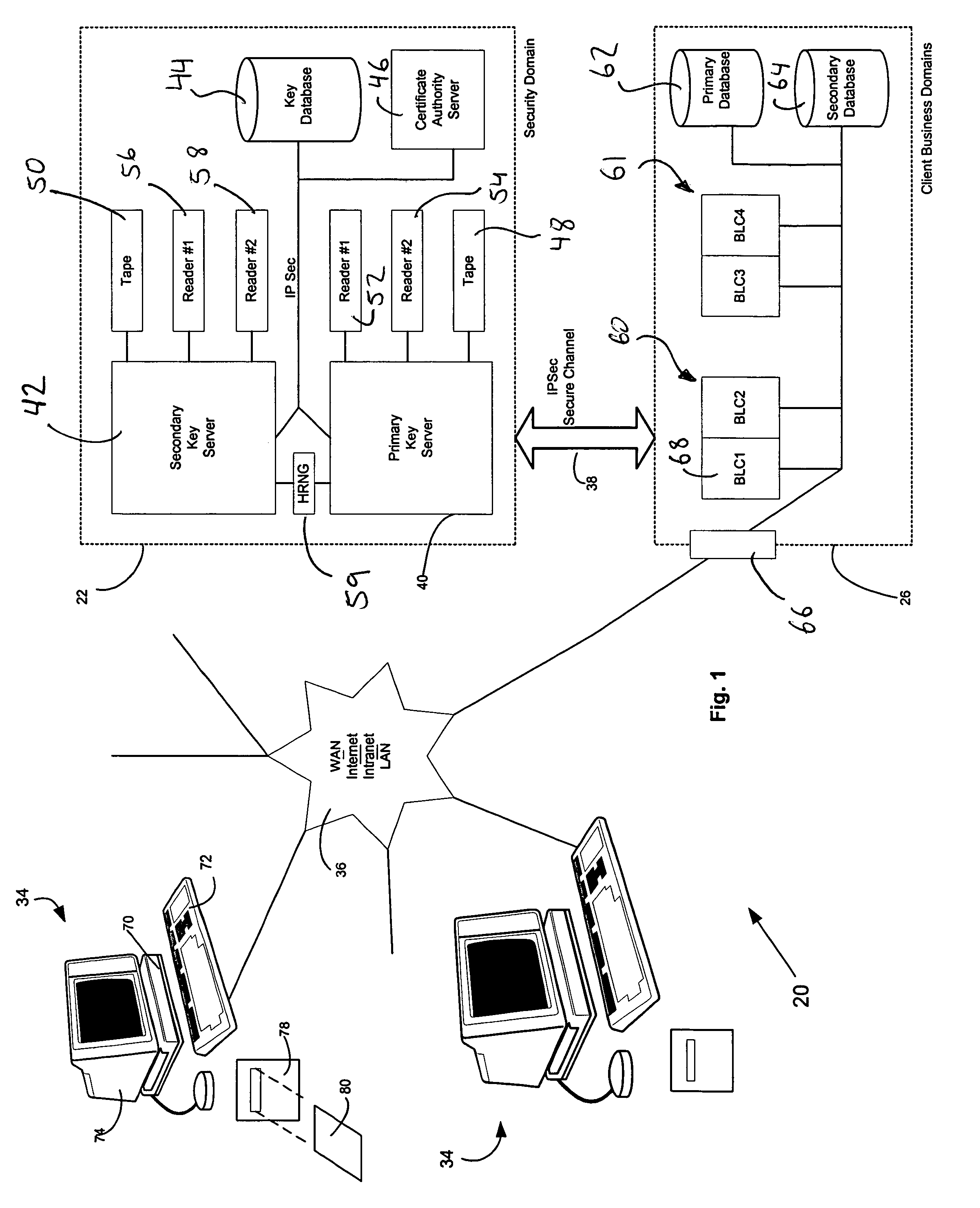
Hidden link dynamic key manager for use in computer systems with database structure for storage of encrypted data and method for storage and retrieval of encrypted data
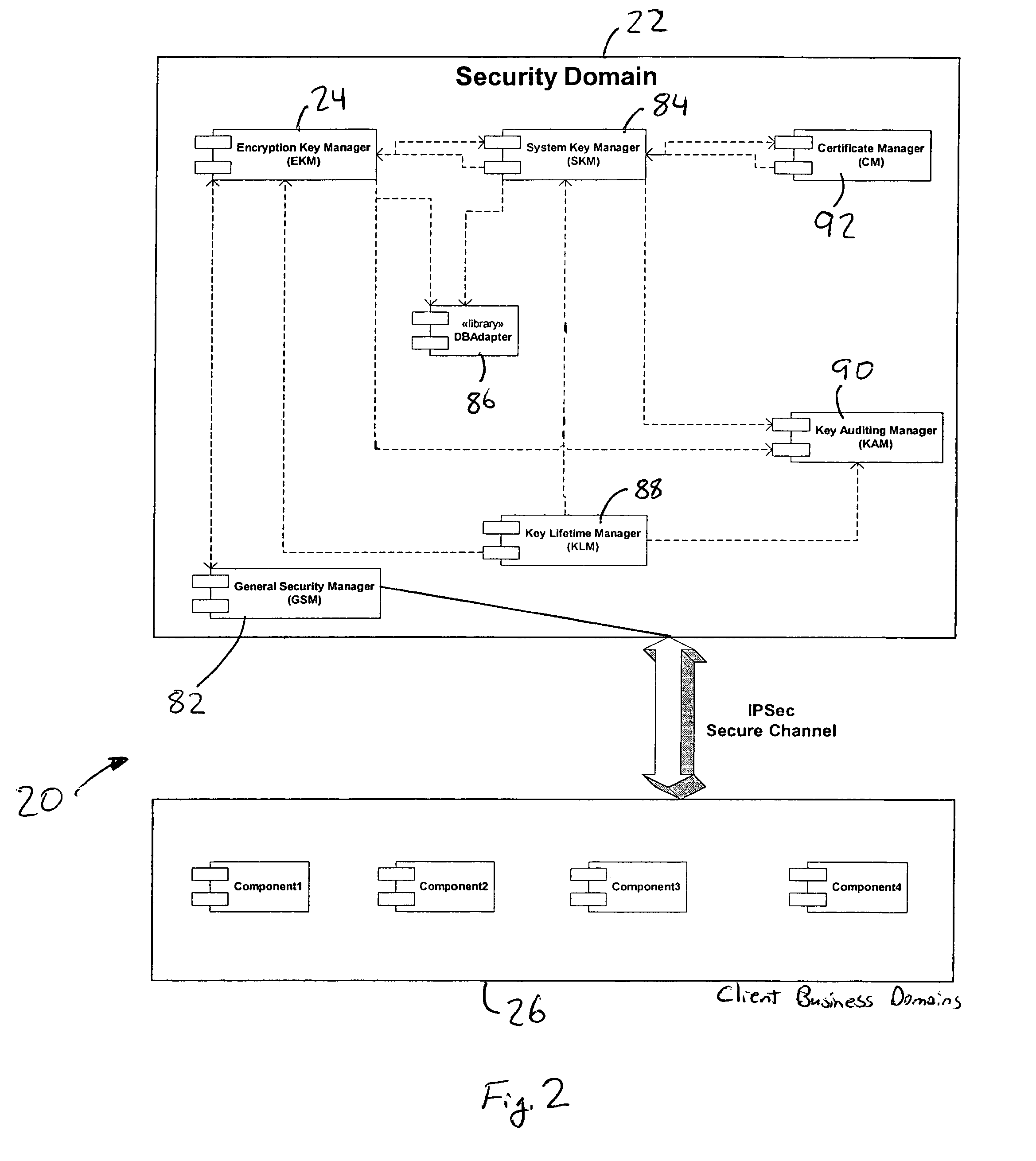
InactiveUS7362868B2Improve securityOpportunities decreaseMultiple keys/algorithms usageComputer security arrangementsCommon nameSecurity domain
A computer system (20) having a security domain (22), at least one client business domain (26), and a plurality of client terminals (34) utilizes a hidden link dynamic key manager (24, 84) and a database structure that includes encrypted data entities (30C, 30D) and a security identification attribute (32) for storage of encrypted data. Methods for encrypting data and for storing, decrypting, and retrieving encrypted data operate on the computer system (20), which also includes an information database (62) and a key database (44). The key database (44) is isolated from the information database (62). The hidden link key manager is stored in the security domain (22) and includes a system key manager (84) operable to generate system keys with system key common names and an encryption key manager (24) operable to generate encryption keys having encryption key identifications. The key managers (24, 84) operate on a key server (40), which is mirrored by a secondary key server (42). A general security manager (82) also operates on the key server (40) to control access to the security domain (22). The security information attribute (32) is stored with a persistent data entity (30A) that is associated with the other encrypted data entities (30C, 30D) by a database schema. The encryption key identification (112) for the encryption key used to encrypt the data entities (30C, 30D) is encrypted by a system key and then stored as part of the security information attribute (32). The system key common name hash value (114) is also stored in the security information attribute (32). The information data entities (30) are stored on the information database (62), but the encryption key identification (153), encryption key (154), system key common name hash value (156, 157), and system key common name (158) are stored in the key database (44) inside the security domain (22). The system key itself is stored on a Smart Card reader (56) inside the security domain.
Owner:FARRUKH ABDALLAH DR +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com