Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3192results about How to "Improve security level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
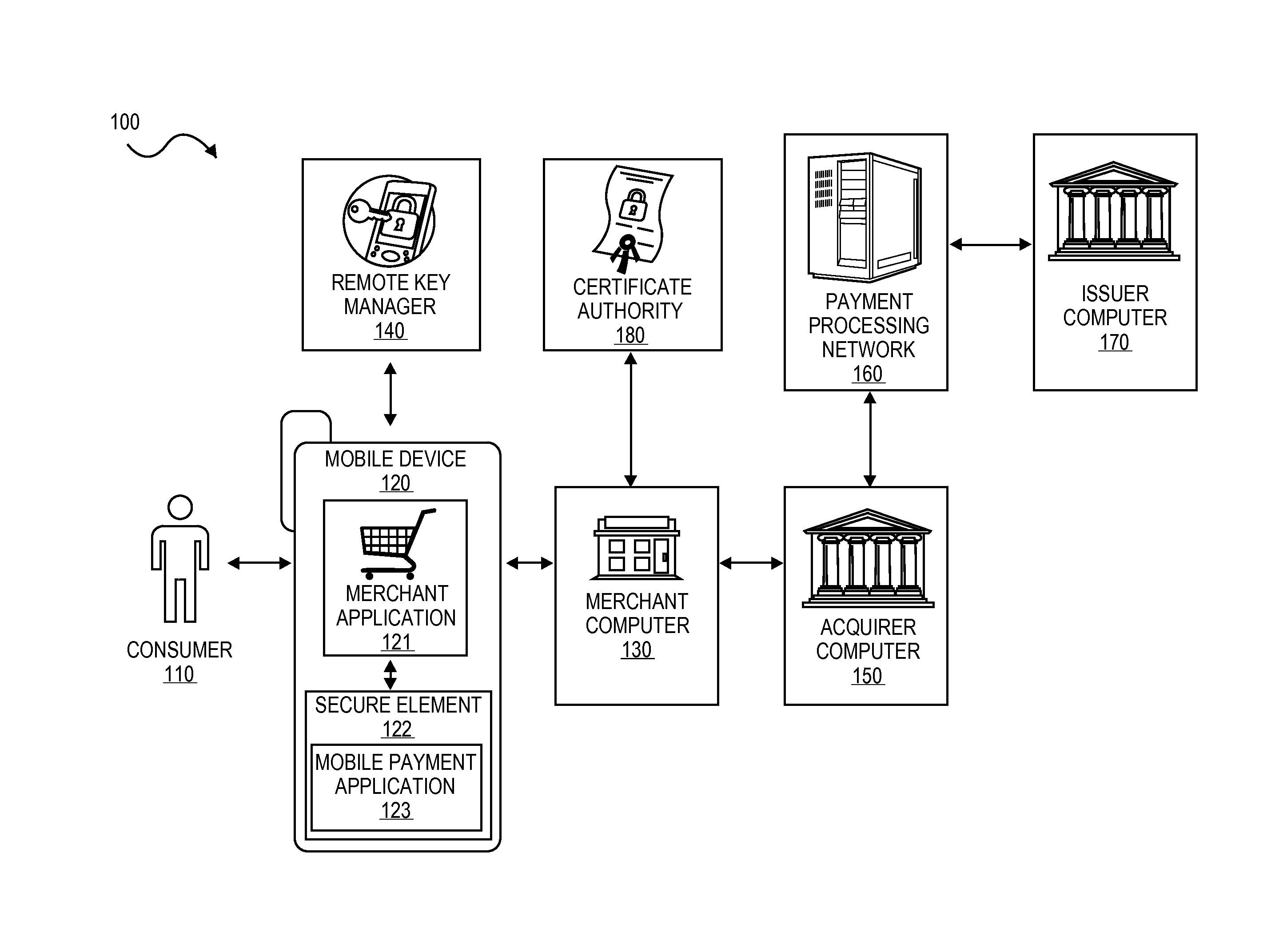
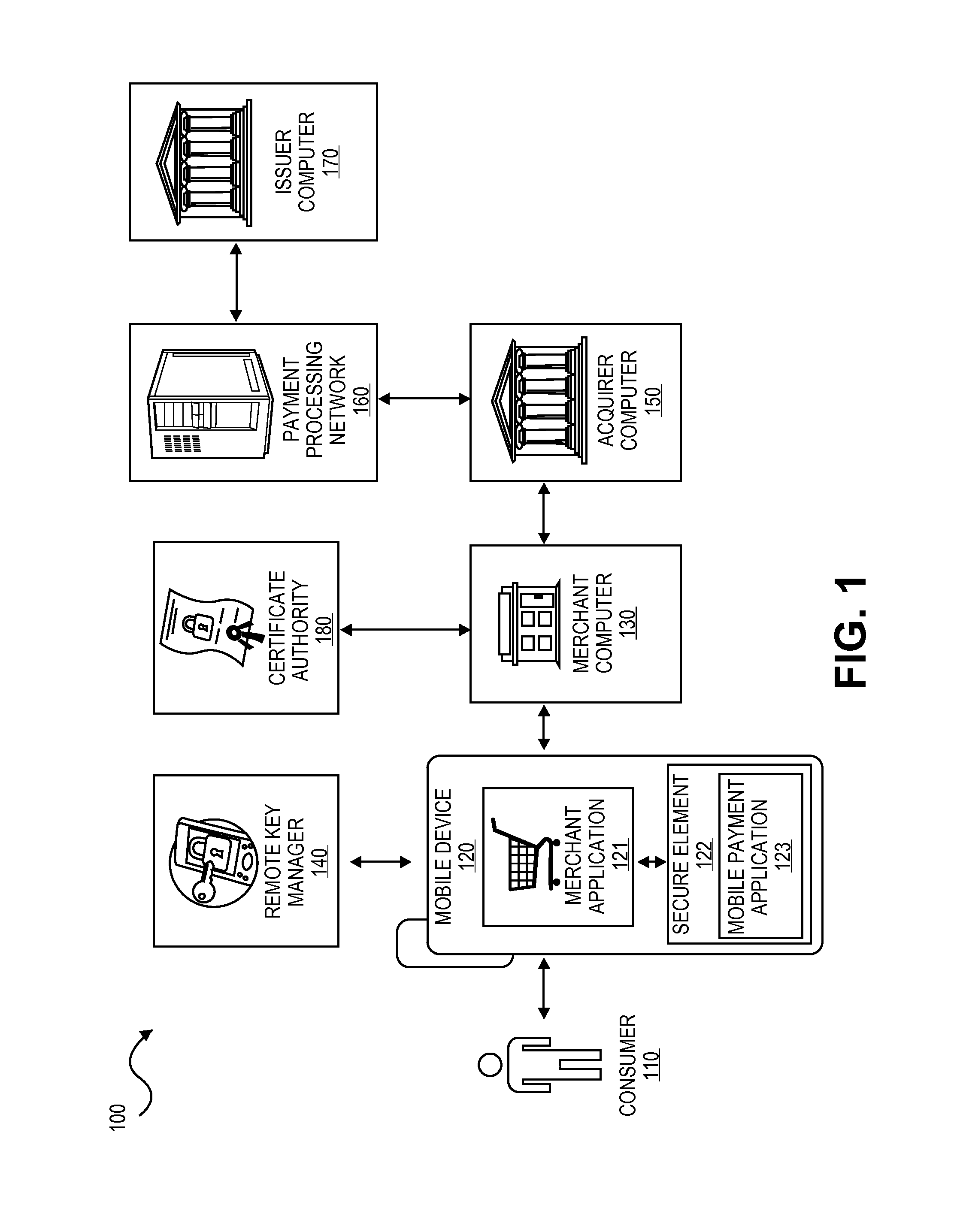
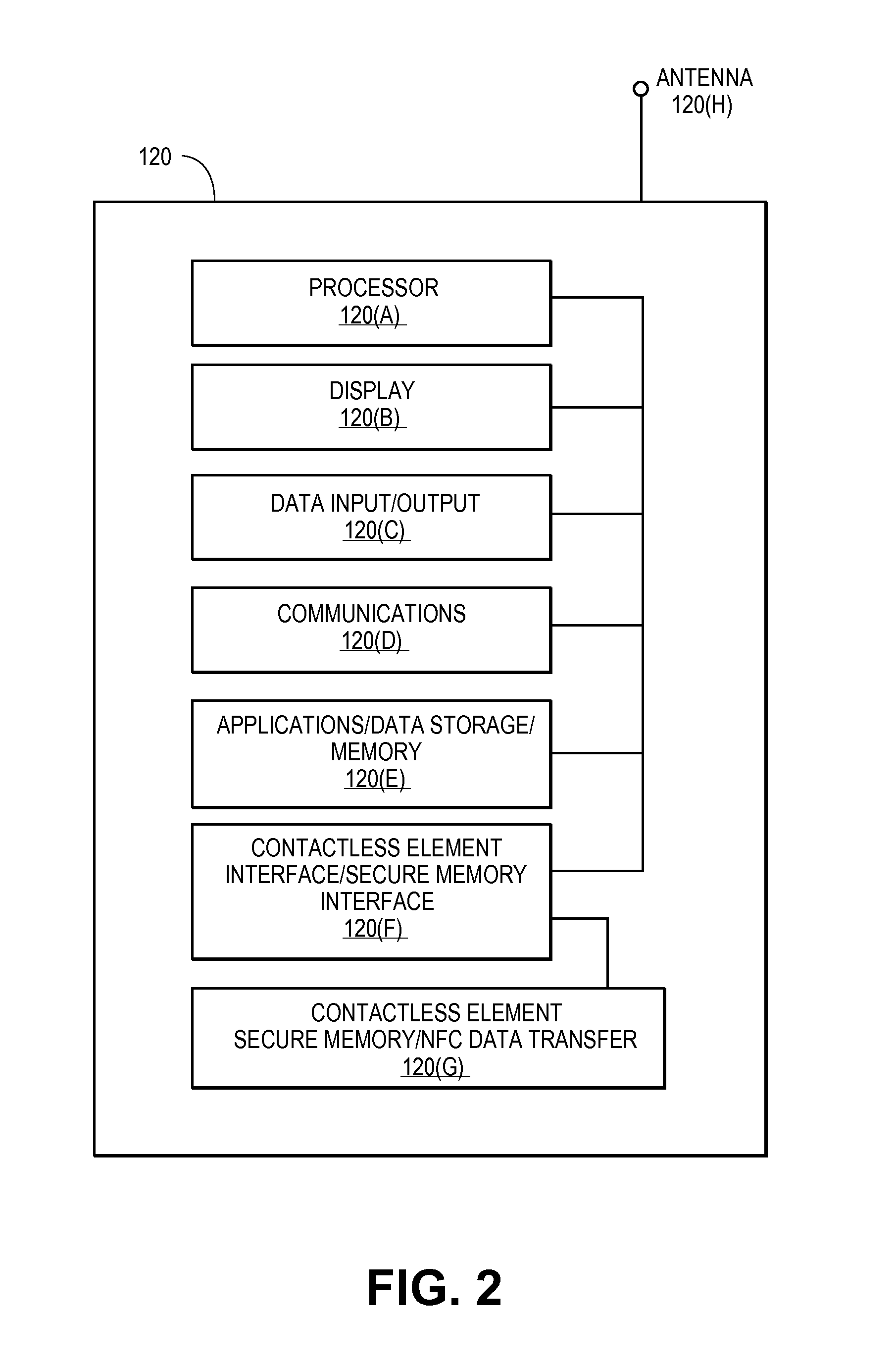
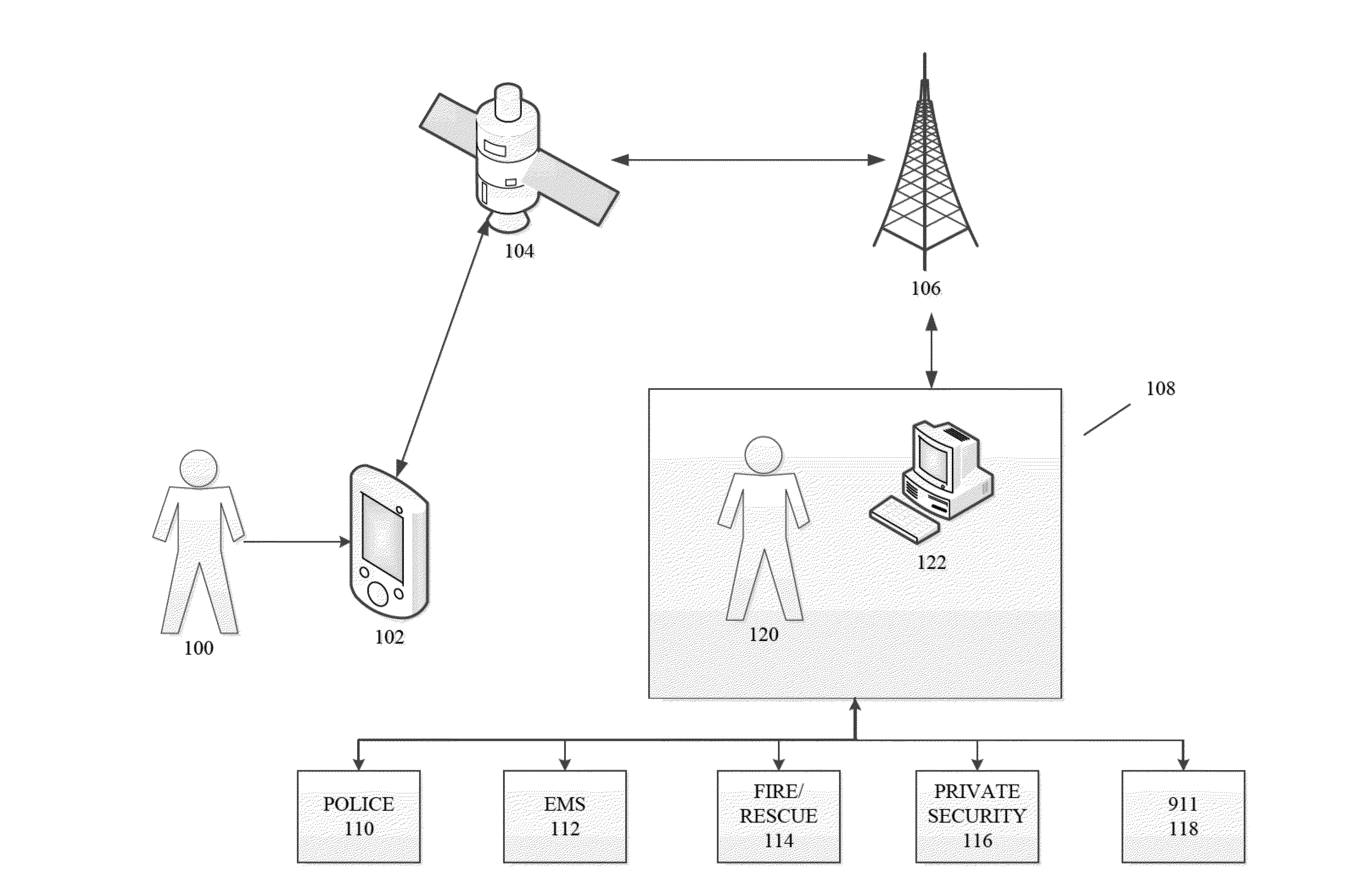
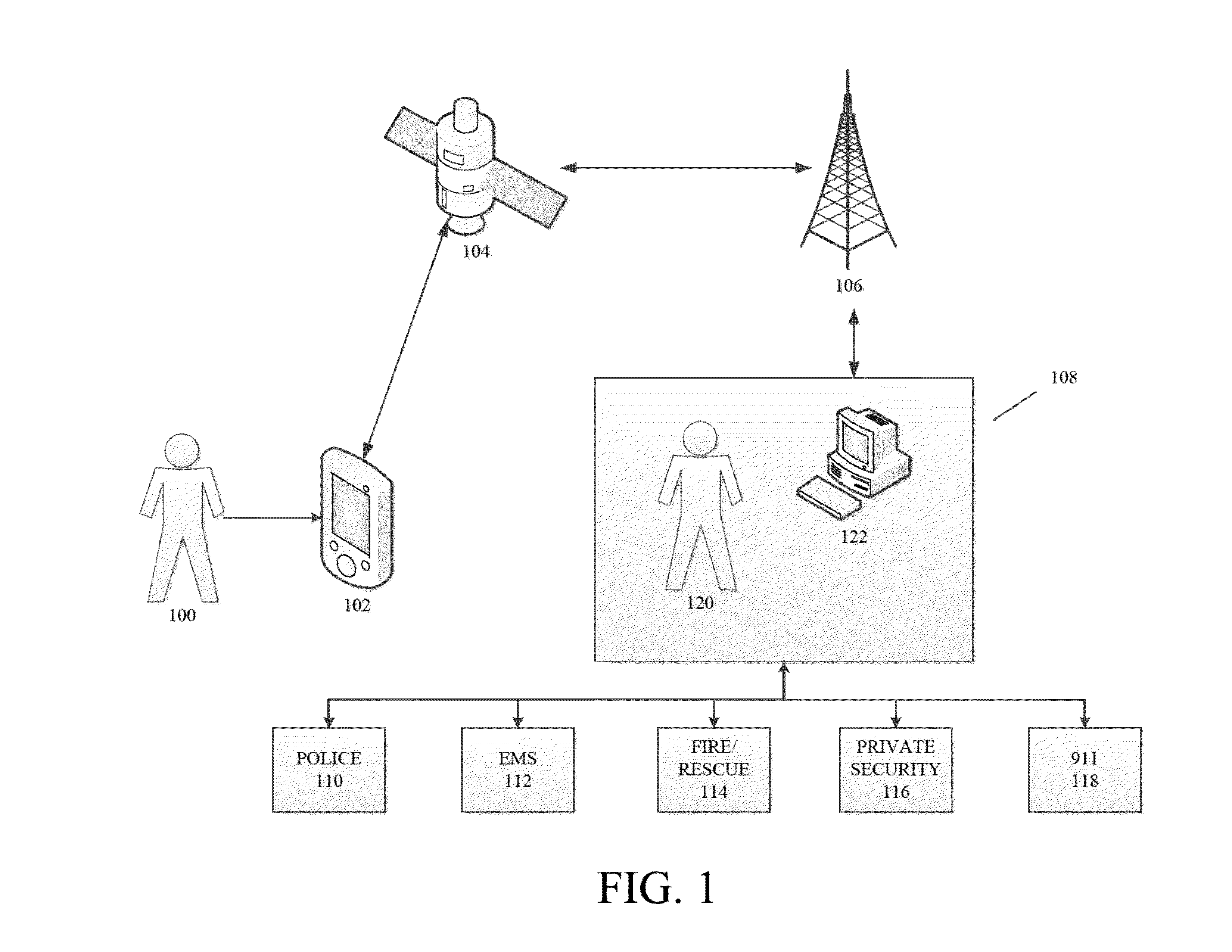
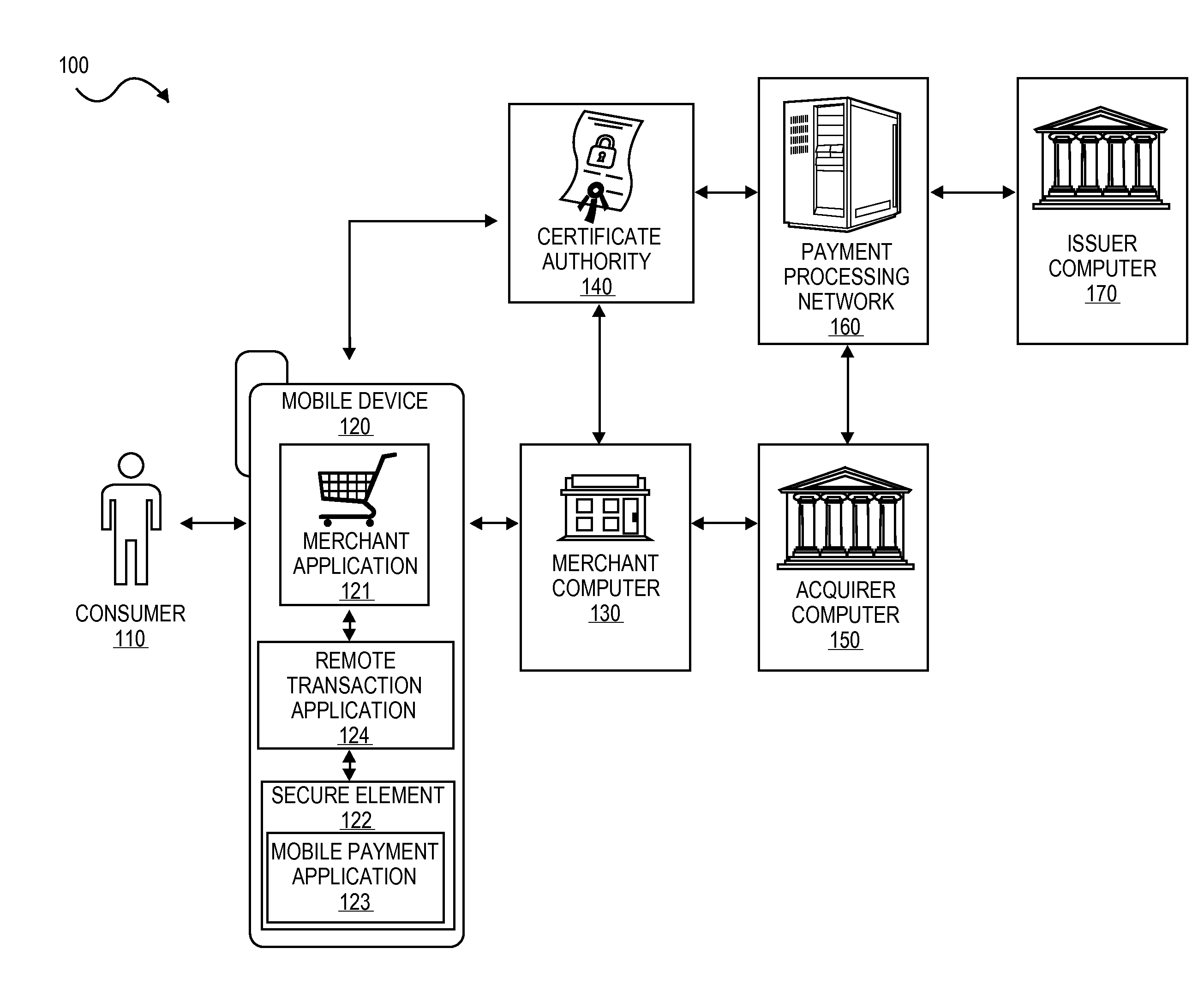
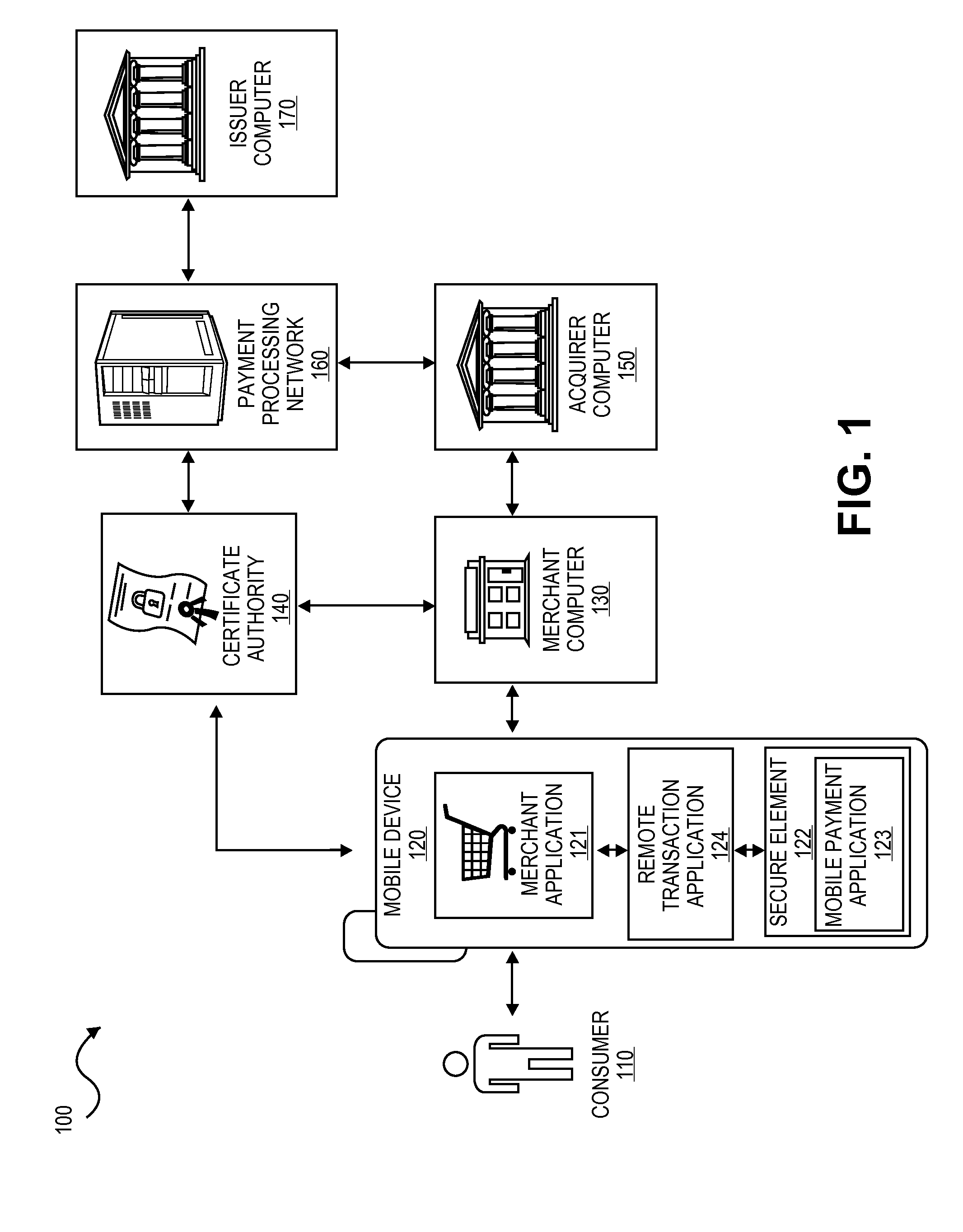
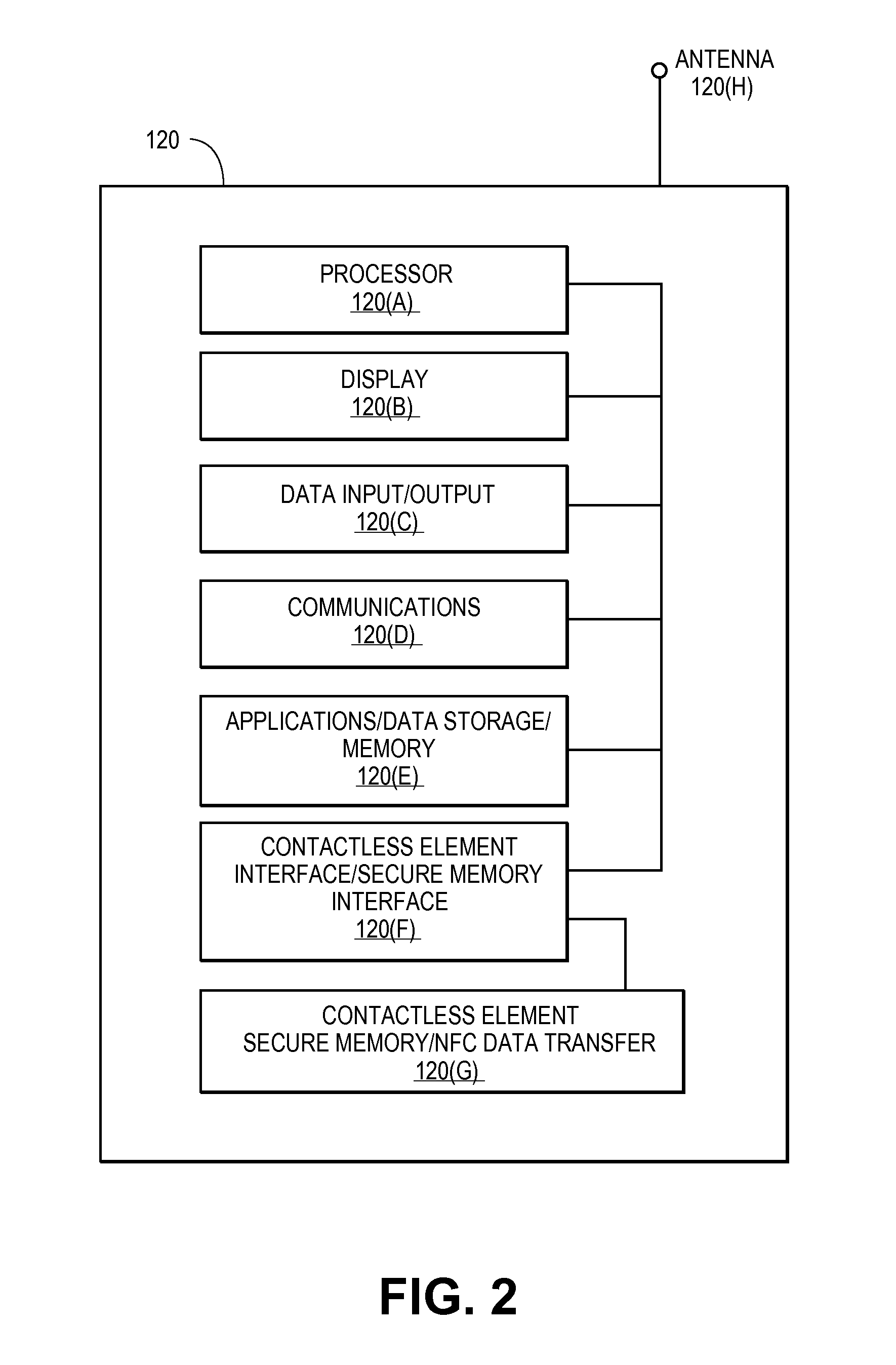
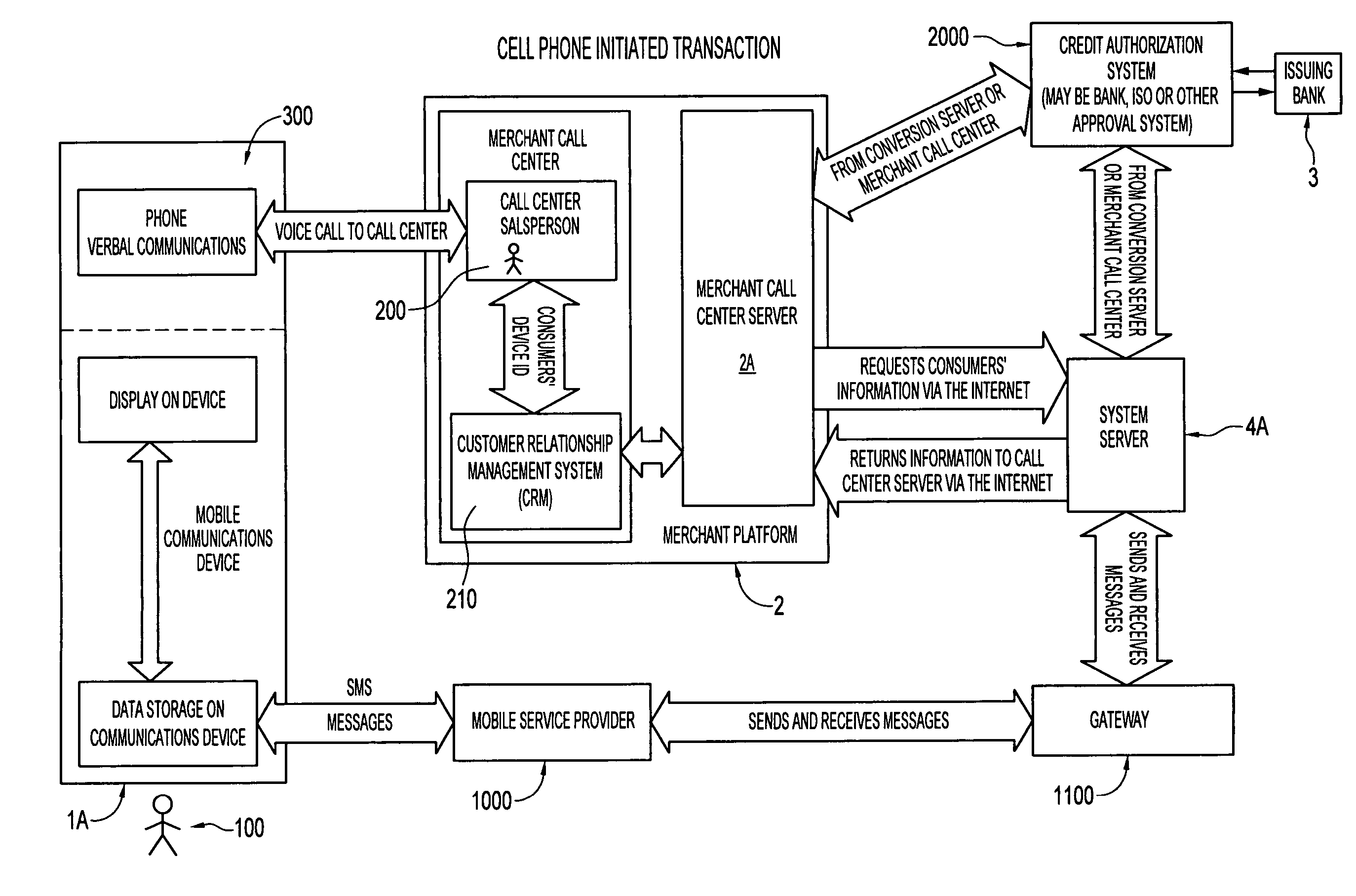
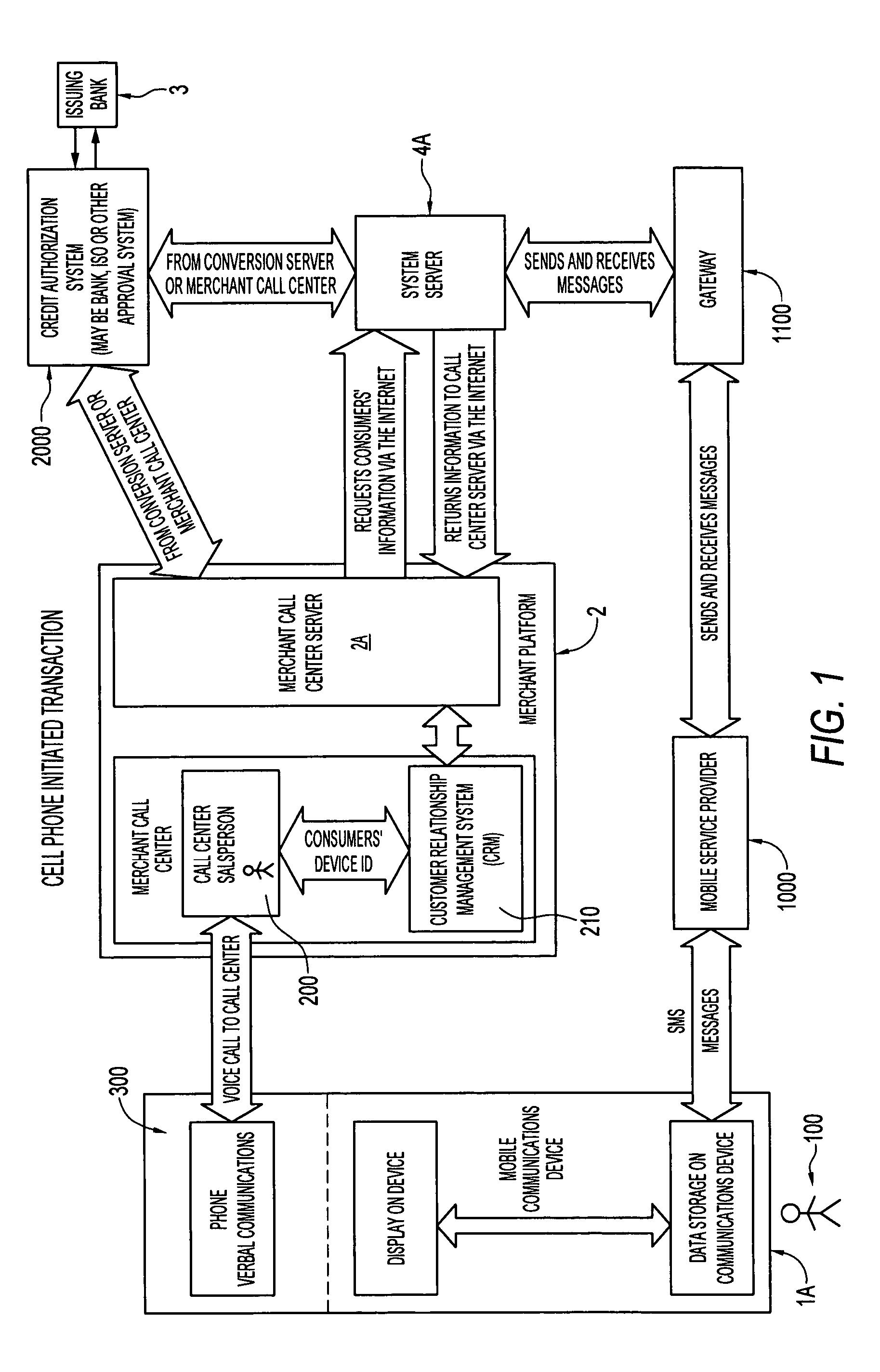
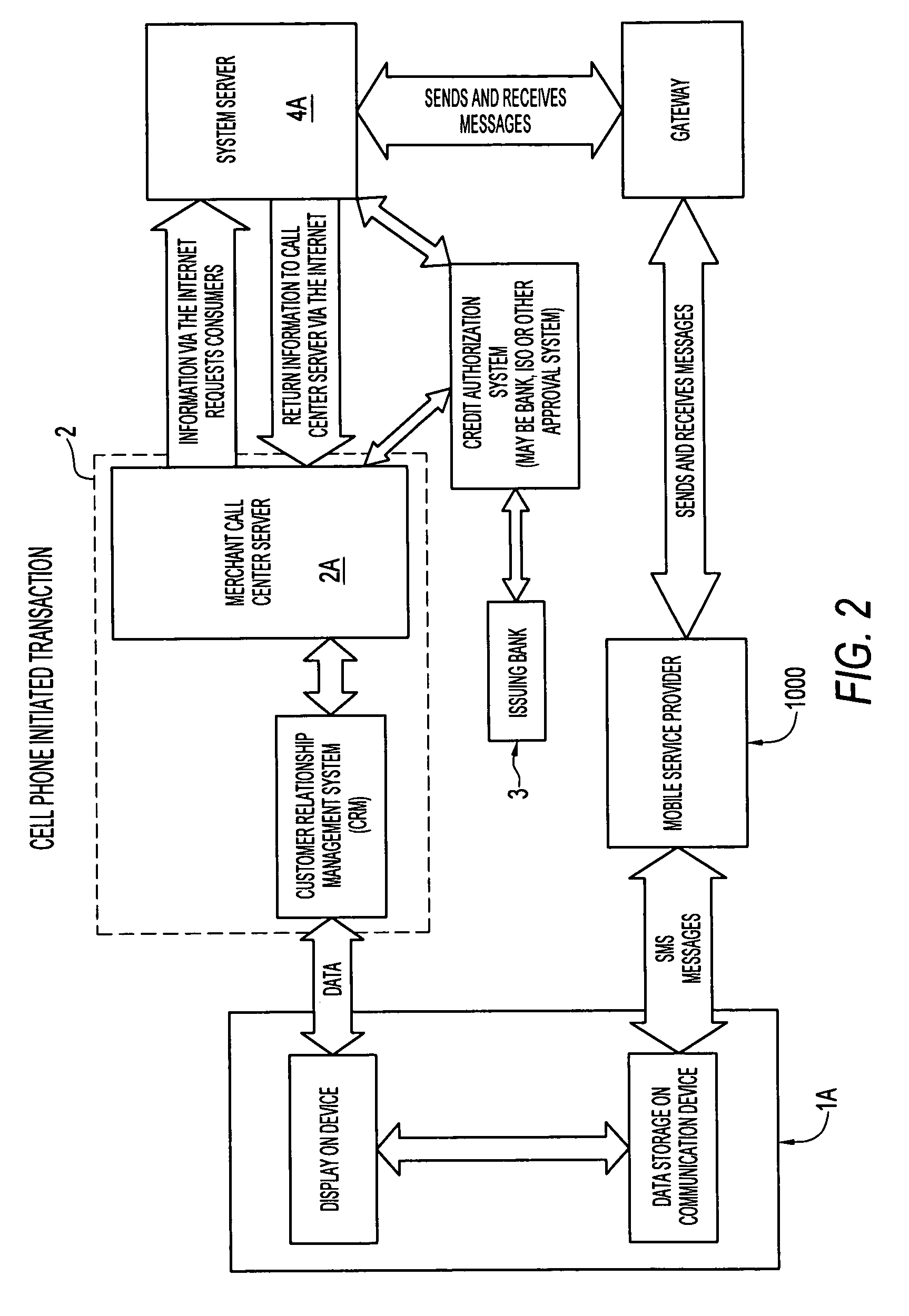
Secure remote payment transaction processing
ActiveUS20150019443A1Improve security levelImprove securityProtocol authorisationThird partyPayment transaction
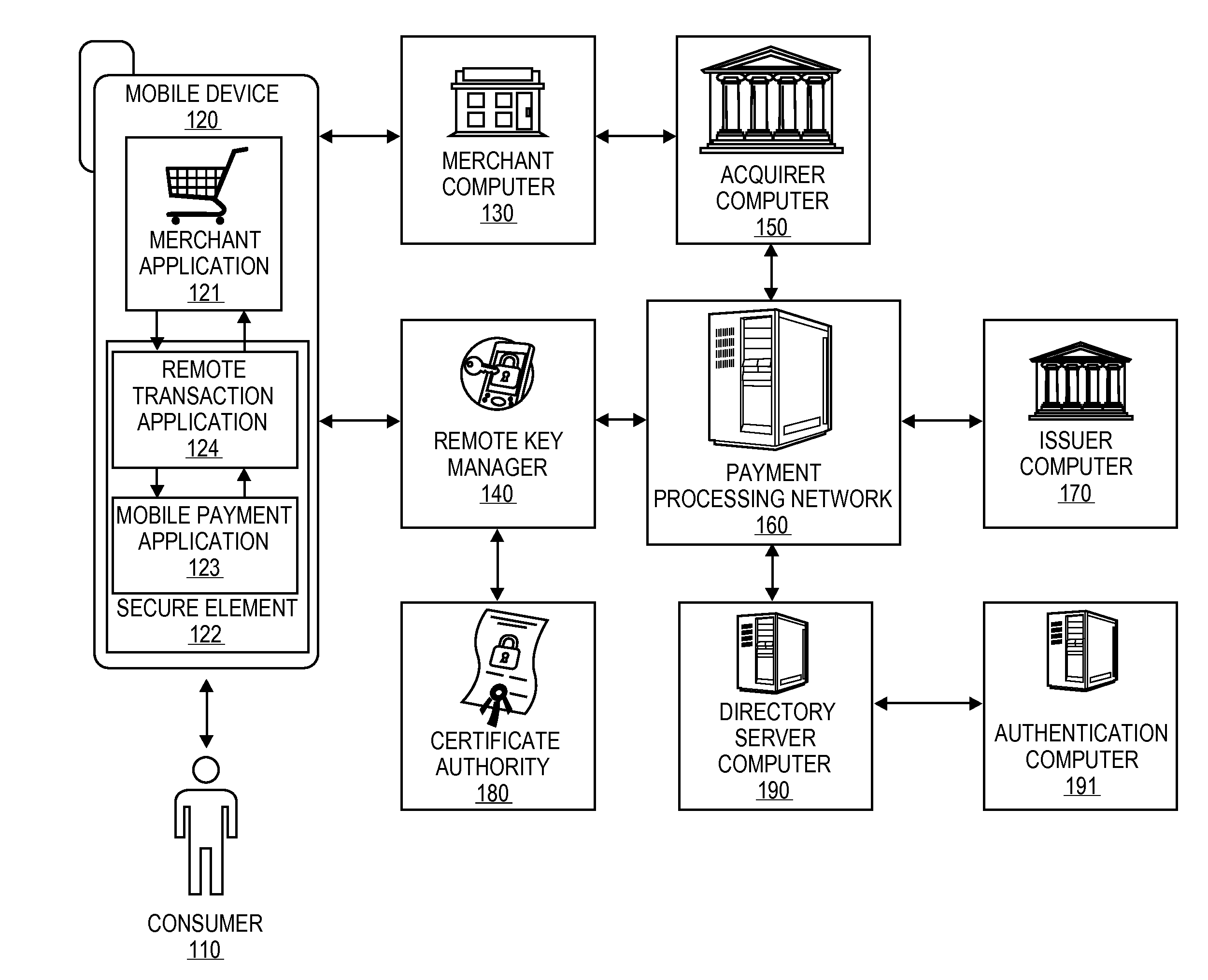
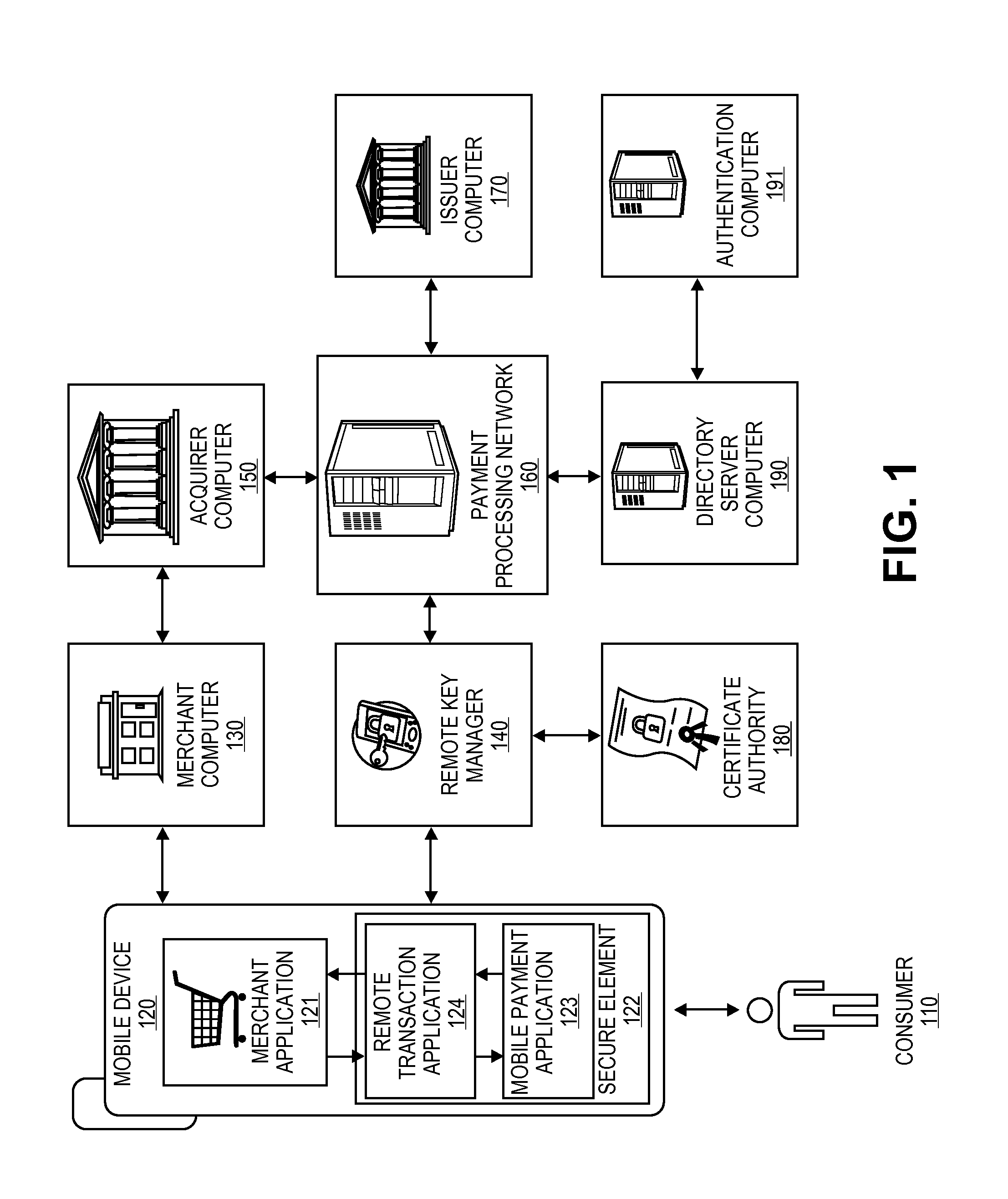
Embodiments of the present invention are directed to methods, apparatuses, computer readable media and systems for securely processing remote transactions. One embodiment of the invention is directed to a method of processing a remote transaction initiated by a mobile device comprising a server computer receiving a payment request including encrypted payment information. The encrypted payment information being generated by a mobile payment application of the mobile device and being encrypted using a third party key. The method further comprises decrypting the encrypted payment information using the third party key, determining a transaction processor public key associated with the payment information, and re-encrypting the payment information using the transaction processor public key. The method further comprises sending a payment response including the re-encrypted payment information to a transaction processor. The transaction processor decrypts the re-encrypted payment information using a transaction processor private key and initiates a payment transaction.
Owner:VISA INT SERVICE ASSOC
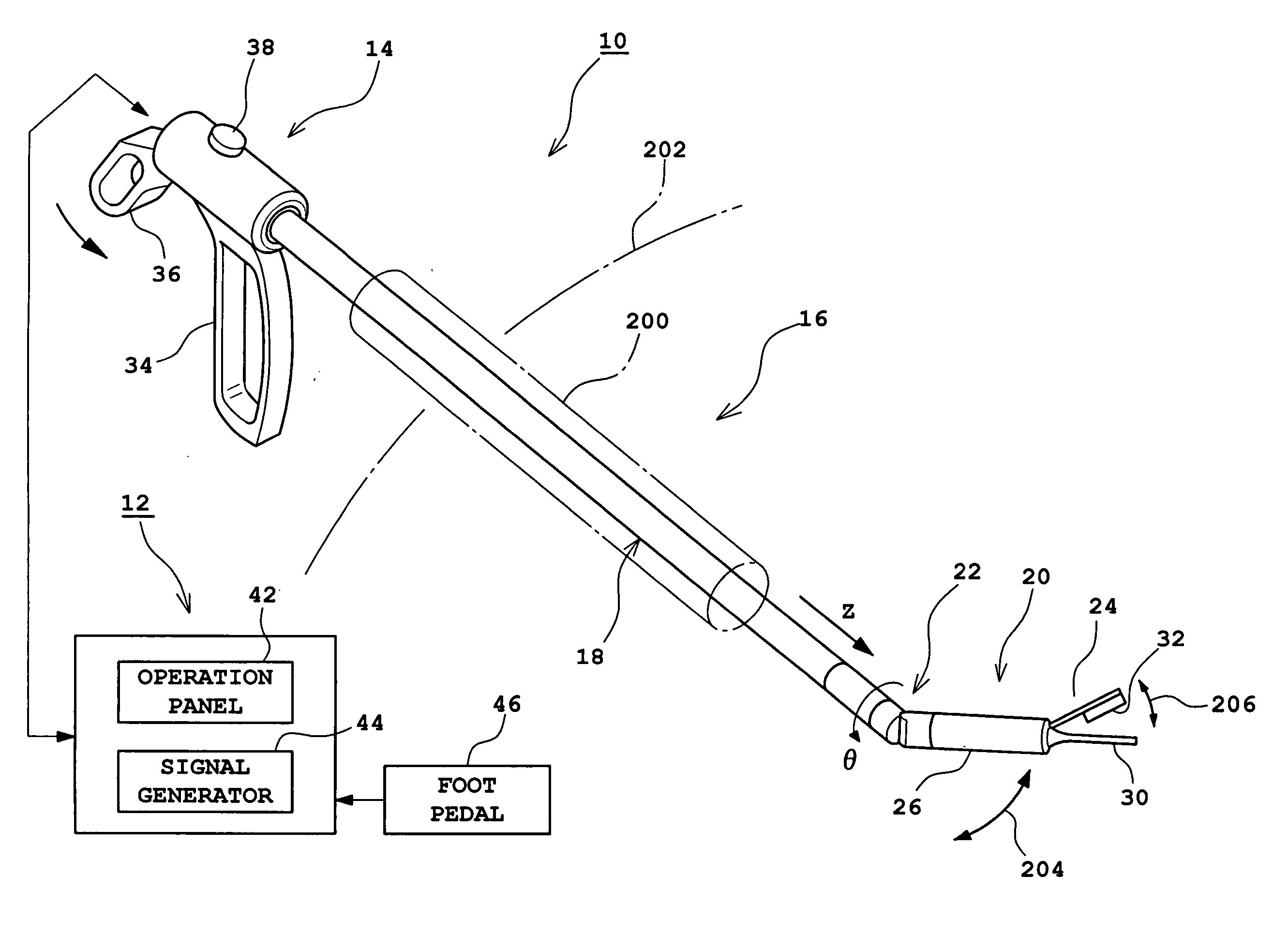
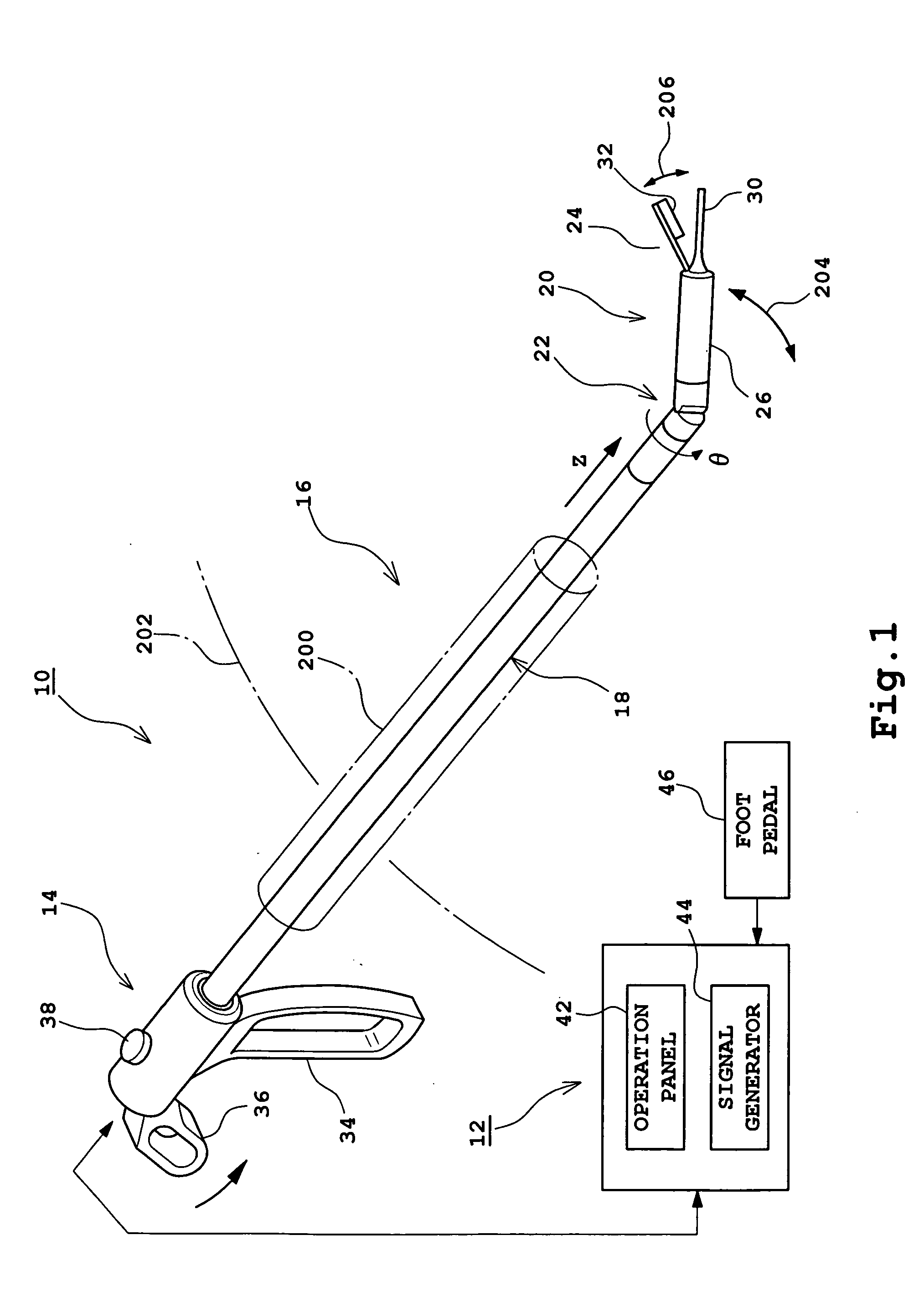
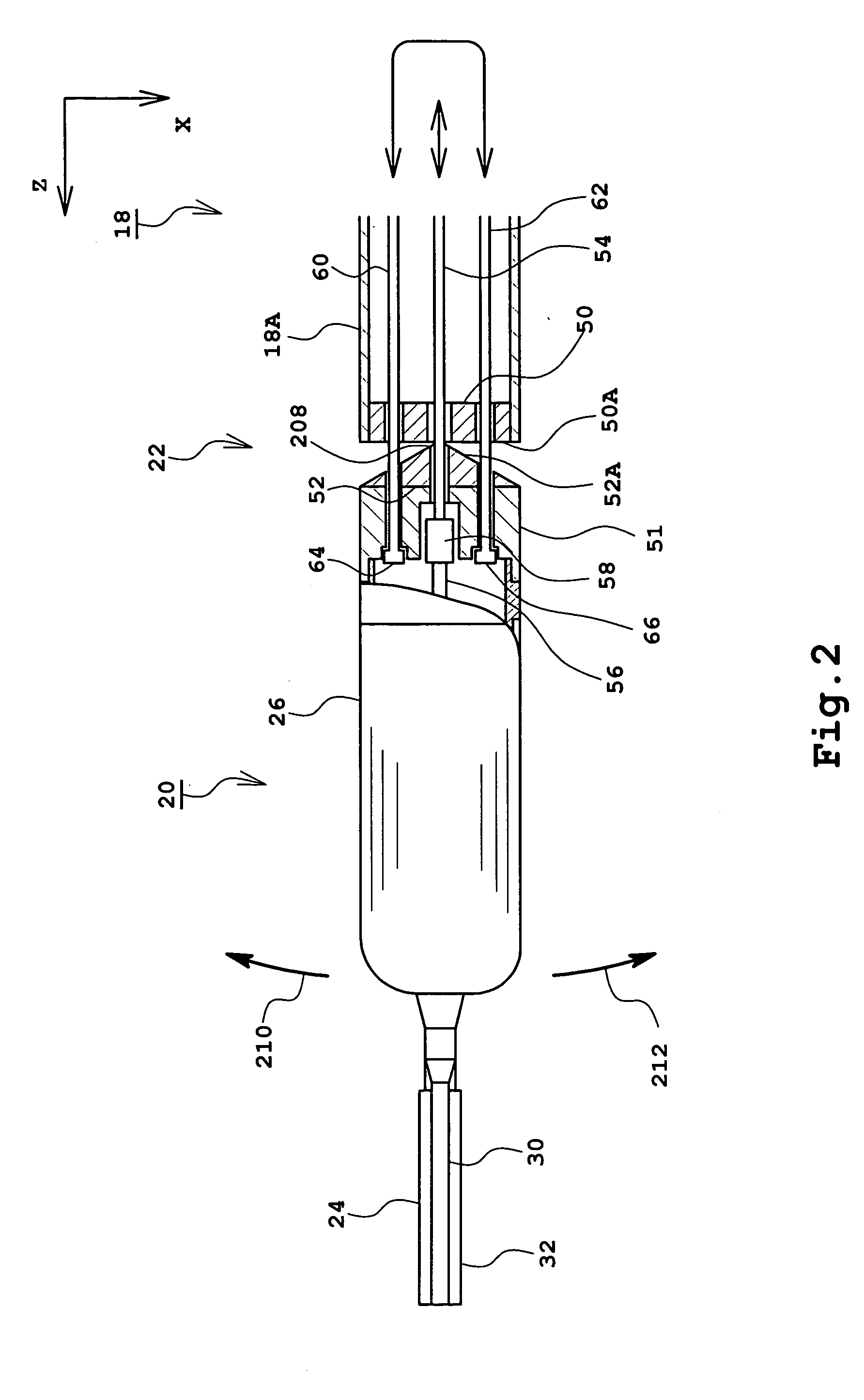
Ultrasonic surgical apparatus
InactiveUS20060058825A1Easy to operateImprove security levelEndoscopic cutting instrumentsSurgical forcepsTransducerExtremity Part
An ultrasonic surgical apparatus which can be used in laparoscopic surgery. The ultrasonic surgical apparatus includes an inserting unit and an operation unit. The inserting unit is inserted into a guide member called a trocar. The inserting unit includes an elongated member, a tip portion, and also a joint section provided between the elongated member and the tip portion. The tip portion includes a transducer unit and an oscillation member, and preferably further includes a clamp member and an open / close mechanism. The joint section enables the tip portion to be slanted with respect to the elongated member. The operation unit includes a mechanism for operating the joint section, and preferably further includes a mechanism for operating the clamp member. The direction of the oscillation member can be varied by the joint section. Because ultrasonic oscillation is generated in the tip portion, effective transmission of the ultrasonic oscillation to the oscillation member can be achieved.
Owner:ALOKA CO LTD
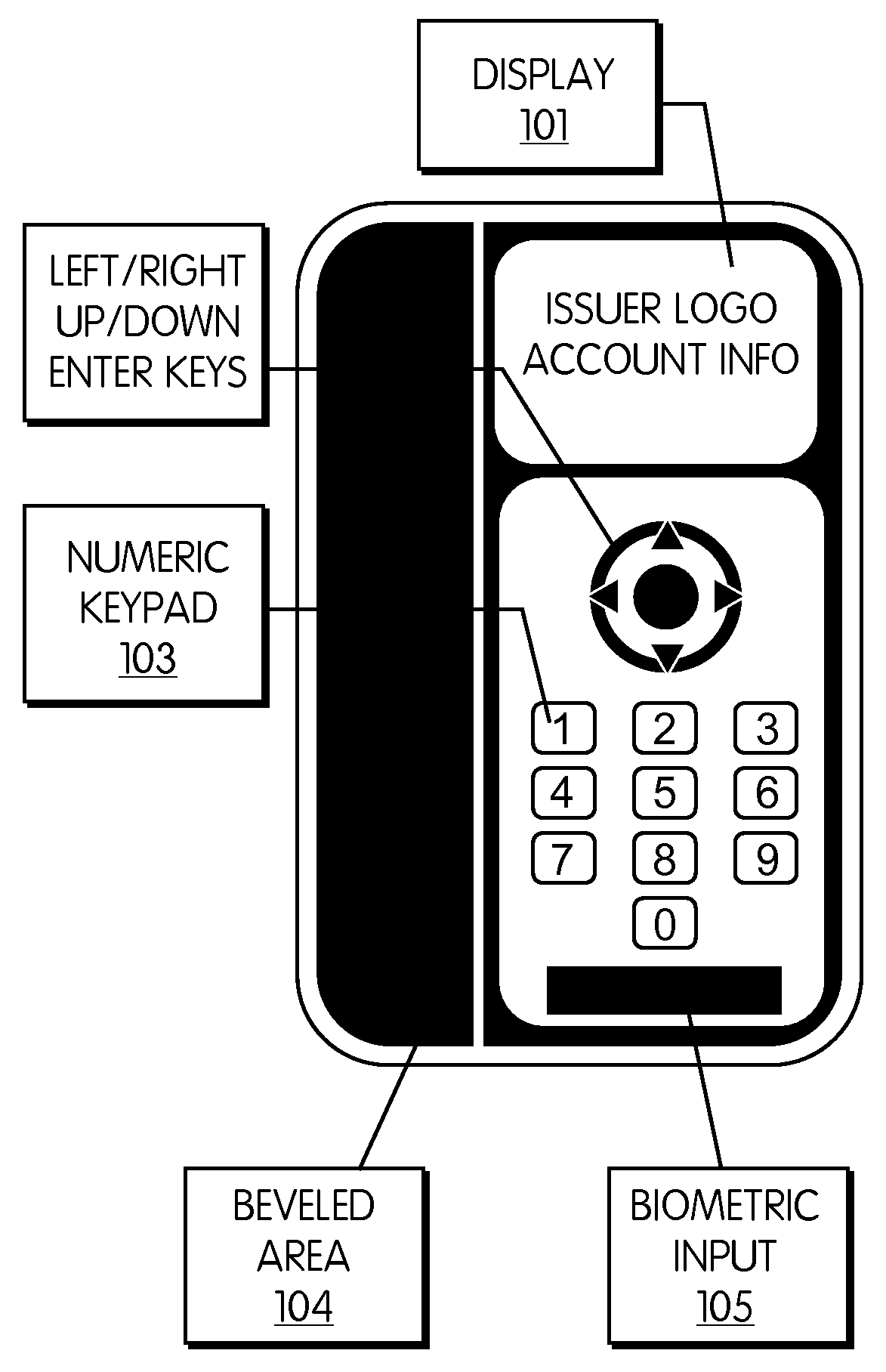
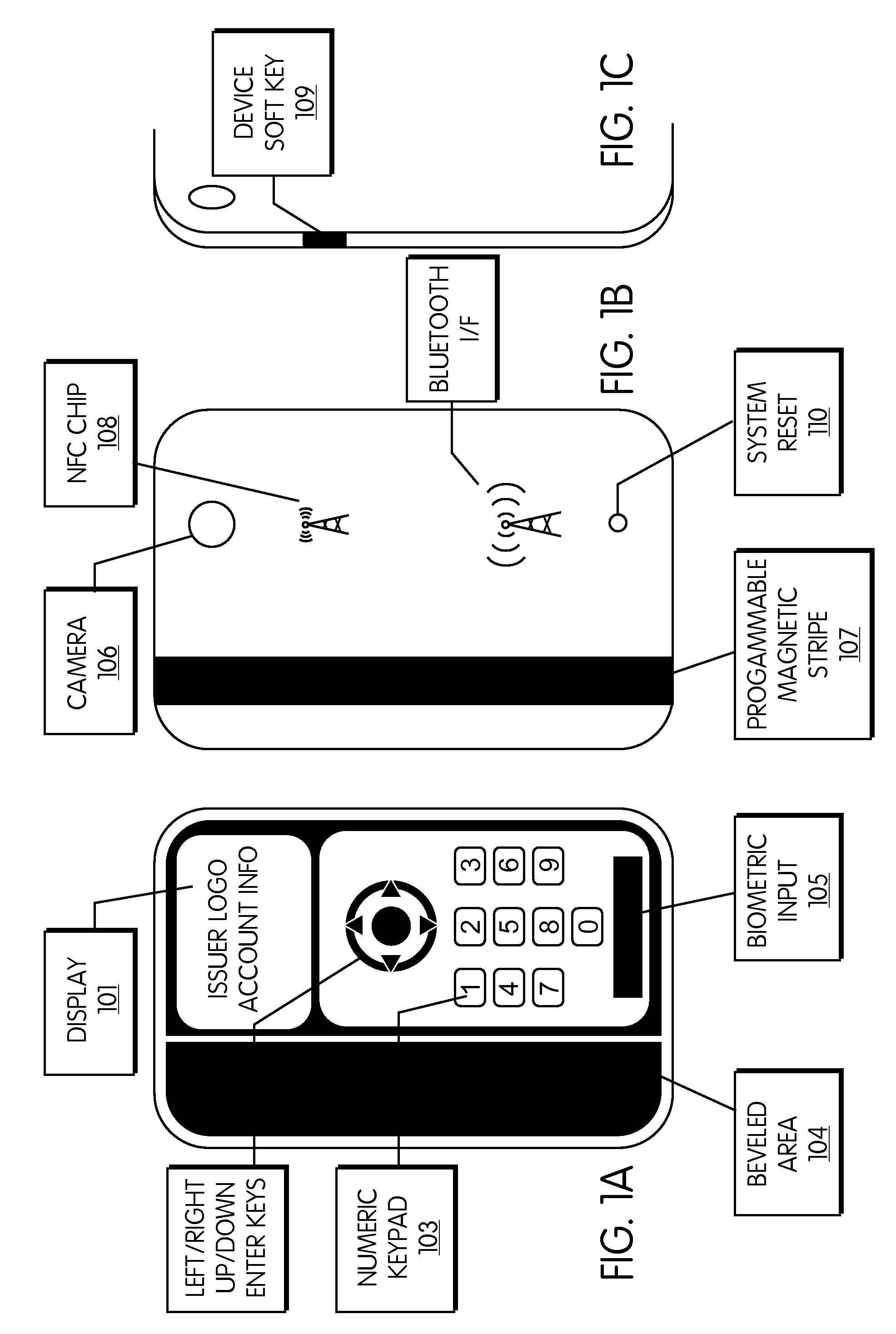
Point Of Sale Transaction Device With Magnetic Stripe Emulator And Biometric Authentication
InactiveUS20080126260A1Cost effectiveImprove security levelAcutation objectsPoint-of-sale network systemsData setComputer science
A handheld unit which is capable of emulating a plurality of smartcards or magnetic stripe cards. The unit has the capability of storing a plurality of data sets representing a plurality of accounts. The unit is equipped with an RF interface that can emulate a smartcard interface that is capable of communicating with smartcard readers at POS or ATM terminals, or anywhere else a smartcard may be utilized. The unit is also equipped with a programmable magnetic strip such that it can be used anywhere a magnetic stripe card can be swiped or inserted. The unit is equipped with a biometric sensor to positively verify an authenticated user.
Owner:X CARD HLDG
Secure Remote Payment Transaction Processing Including Consumer Authentication
ActiveUS20150088756A1Improve security levelProtocol authorisationPayment transactionEncryption decryption
Embodiments of the invention are directed to methods, apparatuses, computer-readable media, and systems for securely processing remote transactions. One embodiment is directed to a method of processing a remote transaction initiated by a communication device. The method comprising a server computer receiving a payment request including encrypted payment information that is encrypted using a first key. The encrypted payment information including security information. The method further comprises decrypting the encrypted payment information using a second key, obtaining an authentication response value for the remote transaction from an authentication computer associated with an issuer, updating the decrypted payment information to include the authentication response value, re-encrypting the decrypted payment information using a third key, and sending a payment response including the re-encrypted payment information to a transaction processor. The transaction processor decrypting the re-encrypted payment information using a fourth key and initiating a payment transaction using the decrypted payment information.
Owner:VISA INT SERVICE ASSOC
Methods and systems for requesting the aid of security volunteers using a security network
InactiveUS20140118140A1Reduce morbidityMaintain awarenessAlarmsElectric signalling detailsDividing attentionMobile device
The disclosure generally relates to providing a network of security volunteers who can opt-in to provide security services and / or a physical presence to deter, distract, delay, or prevent a potentially threatening situation. Security volunteers can receive alerts from a central monitoring center regarding nearby distress signals sent from a victim's device, and can then proceed to the location of the victim. Security volunteers can view their location and the location of the victim on a map on their mobile devices, as well as communicate with a victim's device, the central monitoring center, and other security volunteers who are responding to the scene.
Owner:AMIS DAVID
Secure Remote Payment Transaction Processing Using a Secure Element
ActiveUS20150052064A1Improve security levelImprove securityPayment protocolsSecuring communicationPayment transactionTransaction data
Embodiments of the present invention are directed to methods, apparatuses, computer readable media and systems for securely processing remote transactions. One embodiment of the invention is directed to a method of processing a remote transaction initiated by a mobile device. The method comprises receiving, by a mobile payment application on a secure memory of the mobile device, transaction data from a transaction processor application on the mobile device. The method further comprises validating that the transaction processor application is authentic and in response to validating the transaction processor application, providing encrypted payment credentials to the transaction processor application. The transaction processor application further initiates a payment transaction with a transaction processor server computer using the encrypted payment credentials.
Owner:VISA INT SERVICE ASSOC
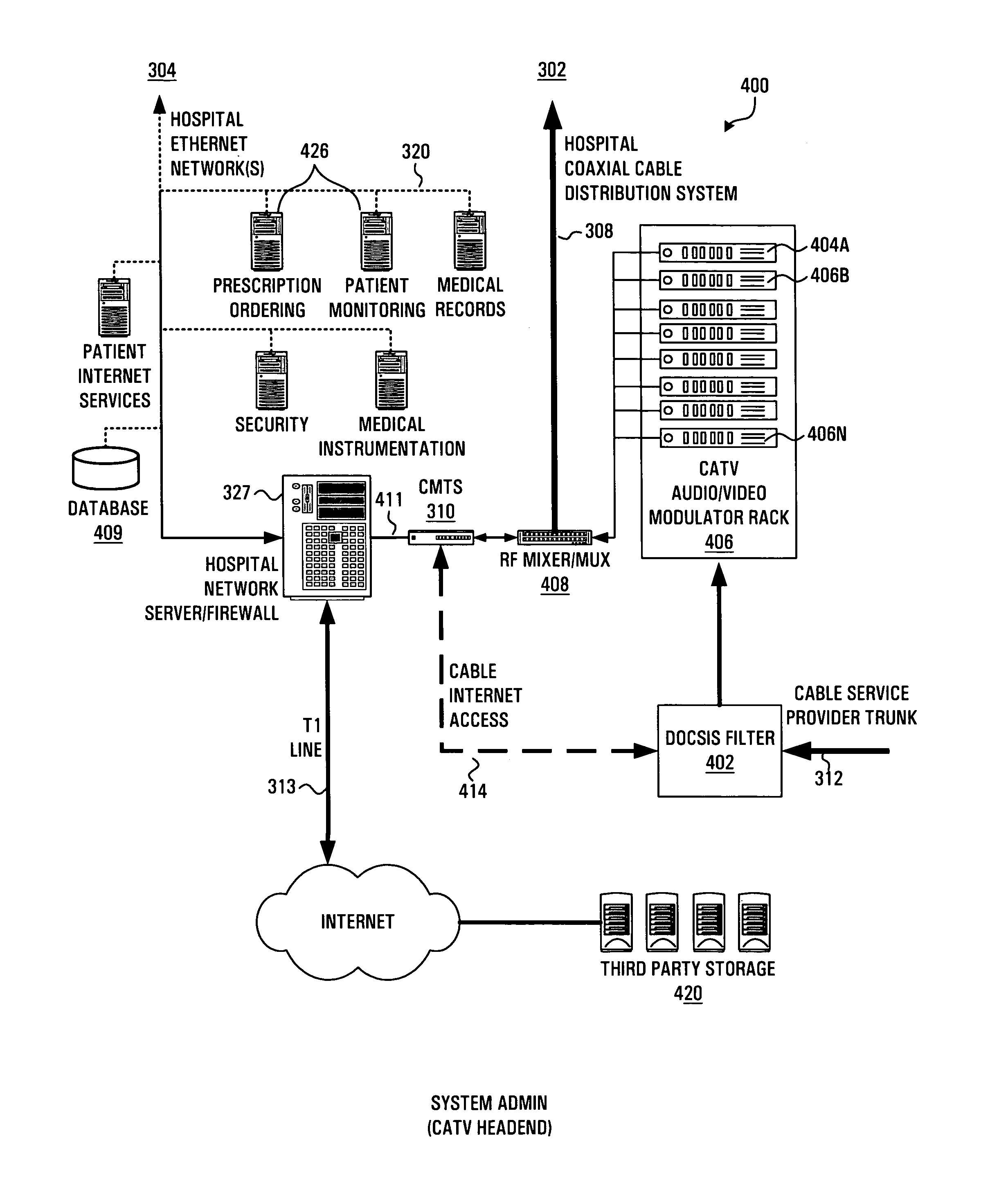
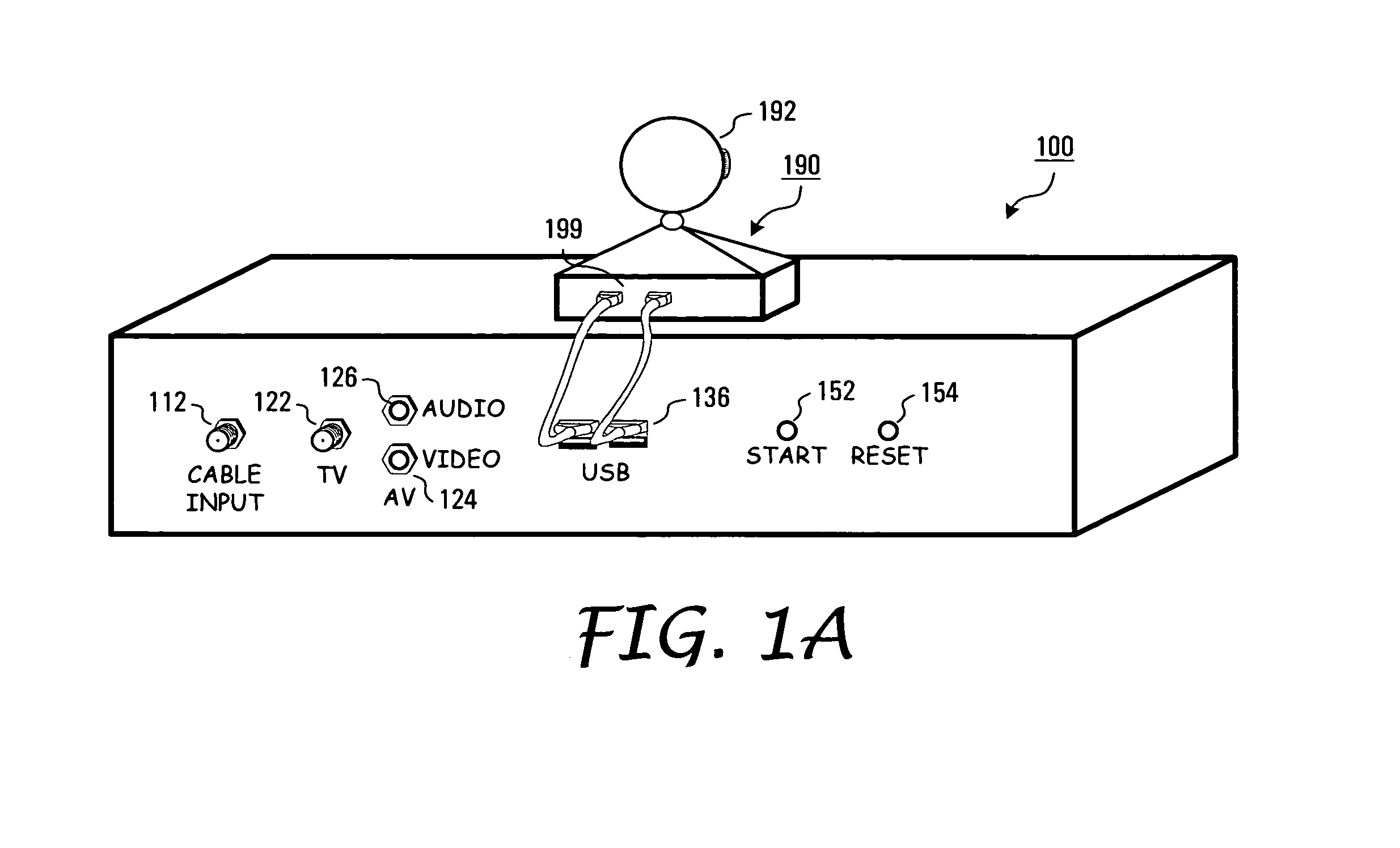
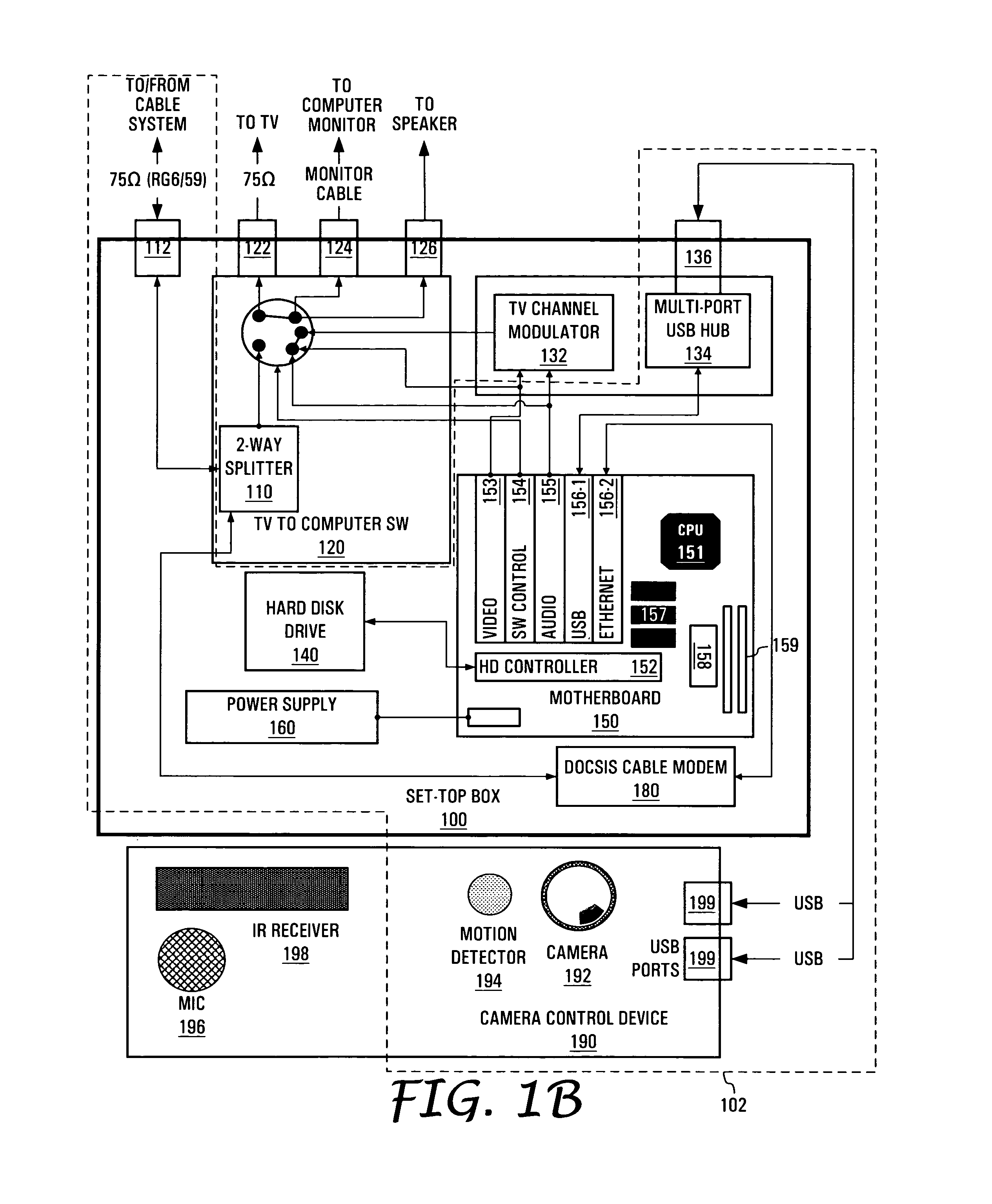
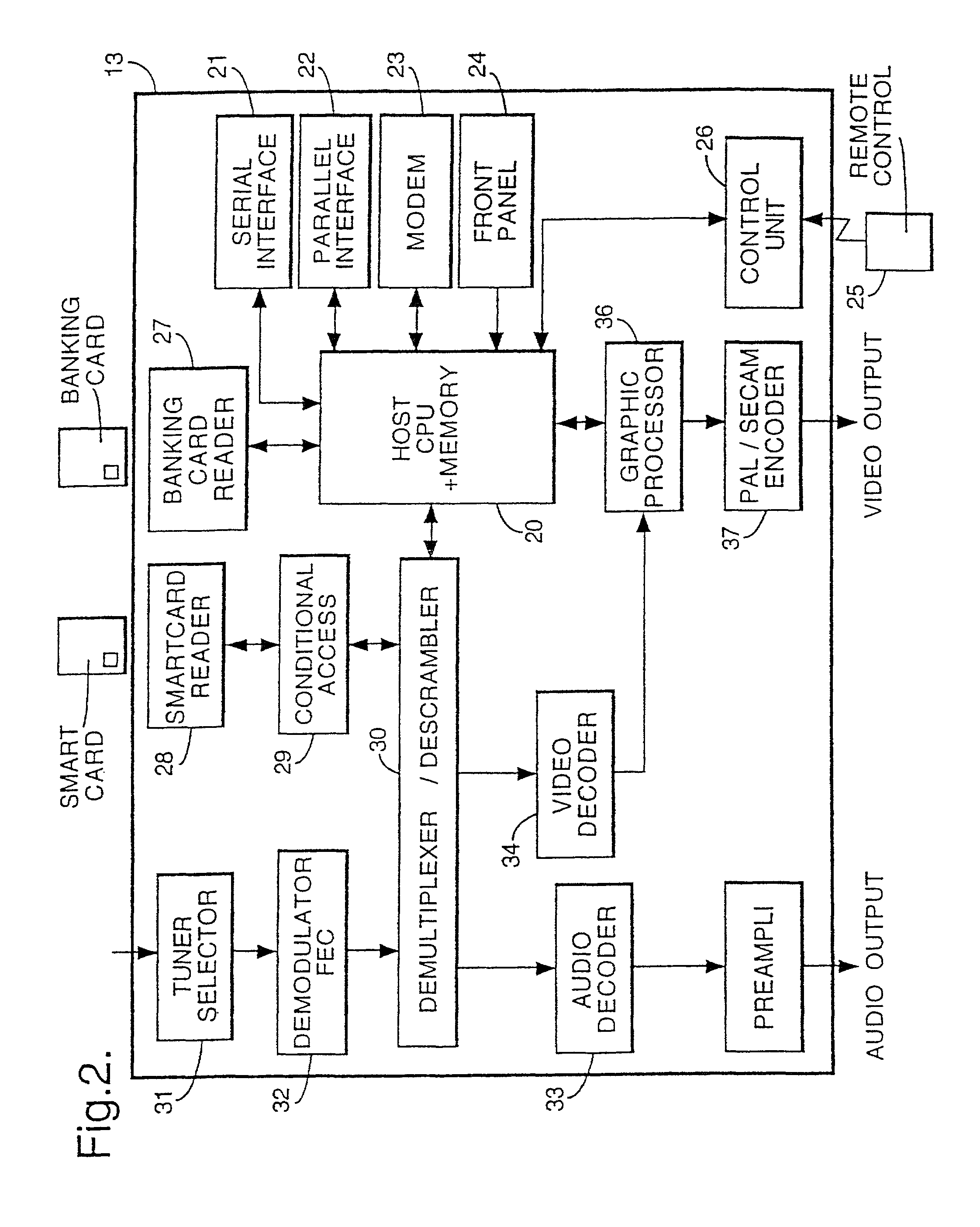
Non-intrusive data transmission network for use in an enterprise facility and method for implementing
ActiveUS7477285B1Improve security levelTelevision system detailsColor television detailsCamera controlInformation access
The present invention is directed to a non-intrusive data transmission network for use in a healthcare facility and method for implementing such network. Each individual patient's room is equipped with a set-top control device, a separate camera, microphone, control module camera control device. The SCD allows for a non-intrusive installation within a minimum amount of time. By utilizing the existing cable television infrastructure, the device creates a high-speed data network throughout the facility. The interface between the SCD and the CCD is accomplished through a standard interface for universally connecting auxiliary devices, such as USB, for enabling expandable, hot-pluggable Plug and Play serial device interfaces. These ports allow external devices such as the camera, microphone, infrared keyboard and privacy control unit to communicate with the SCD. Additional USB ports on the SCD allow for other devices to be connected to the network at a future time. Such devices include those for instrument monitoring, doctor information access or pharmaceutical prescription ordering. Visual information such as e-mail, web browsing, video and audio communications via web camera applications from family members, friends or other parties may be viewed by the patient from the in-room TV set by way of the internal RF modulator (and connecting to the Internet via the patient Internet server). The SCD switches from the standard cable TV channels to the SCD by way of an internal switch controlled by the patient from an infrared control. This control also enables or disables the camera to allow for privacy at times when such privacy is required from external Internet access. The system is configurable to offer this privacy to be layered from specific Internet or external users to the nurses, doctors or security department as the hospital desires.
Owner:CAREVIEW COMM INC
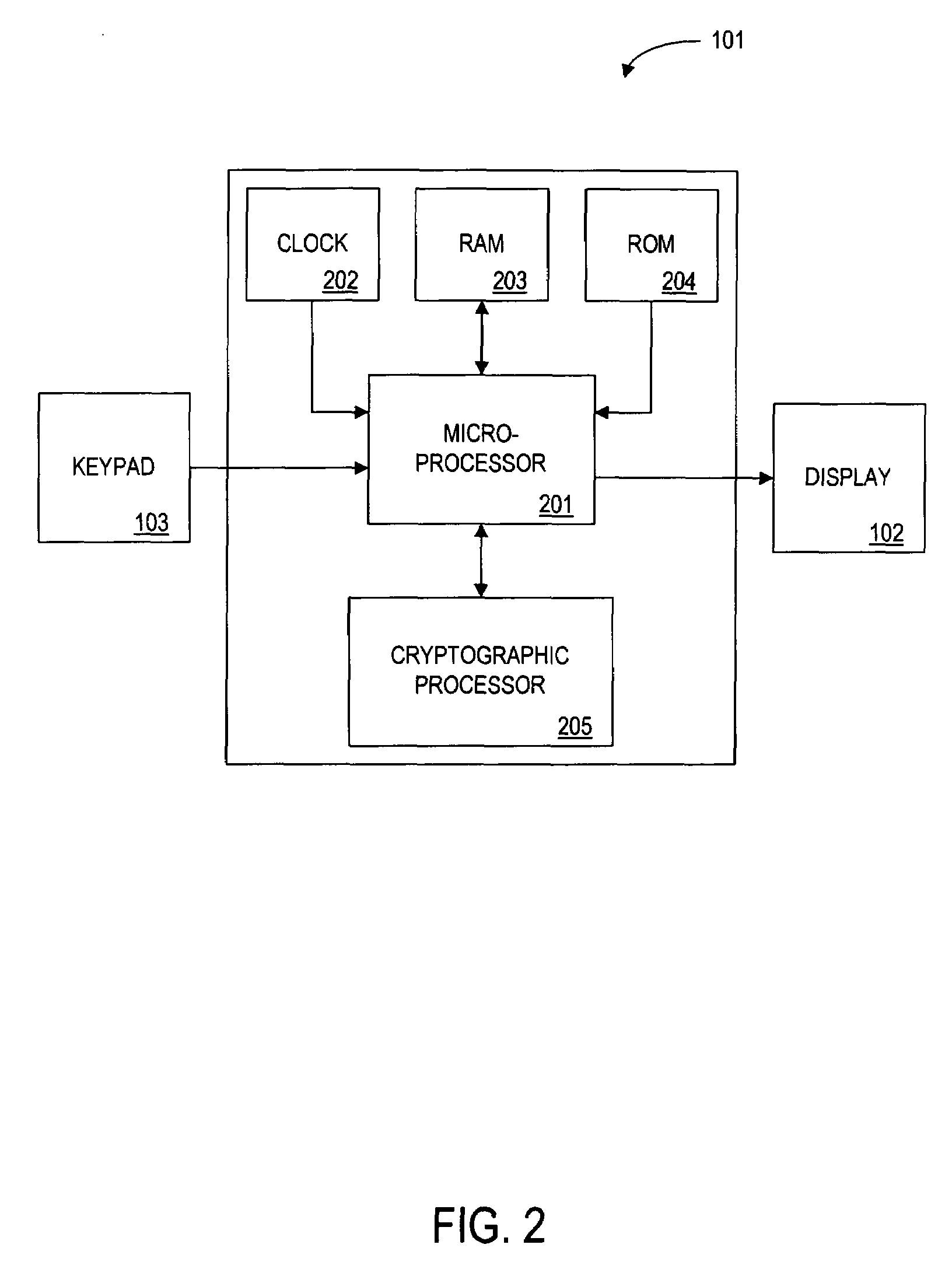
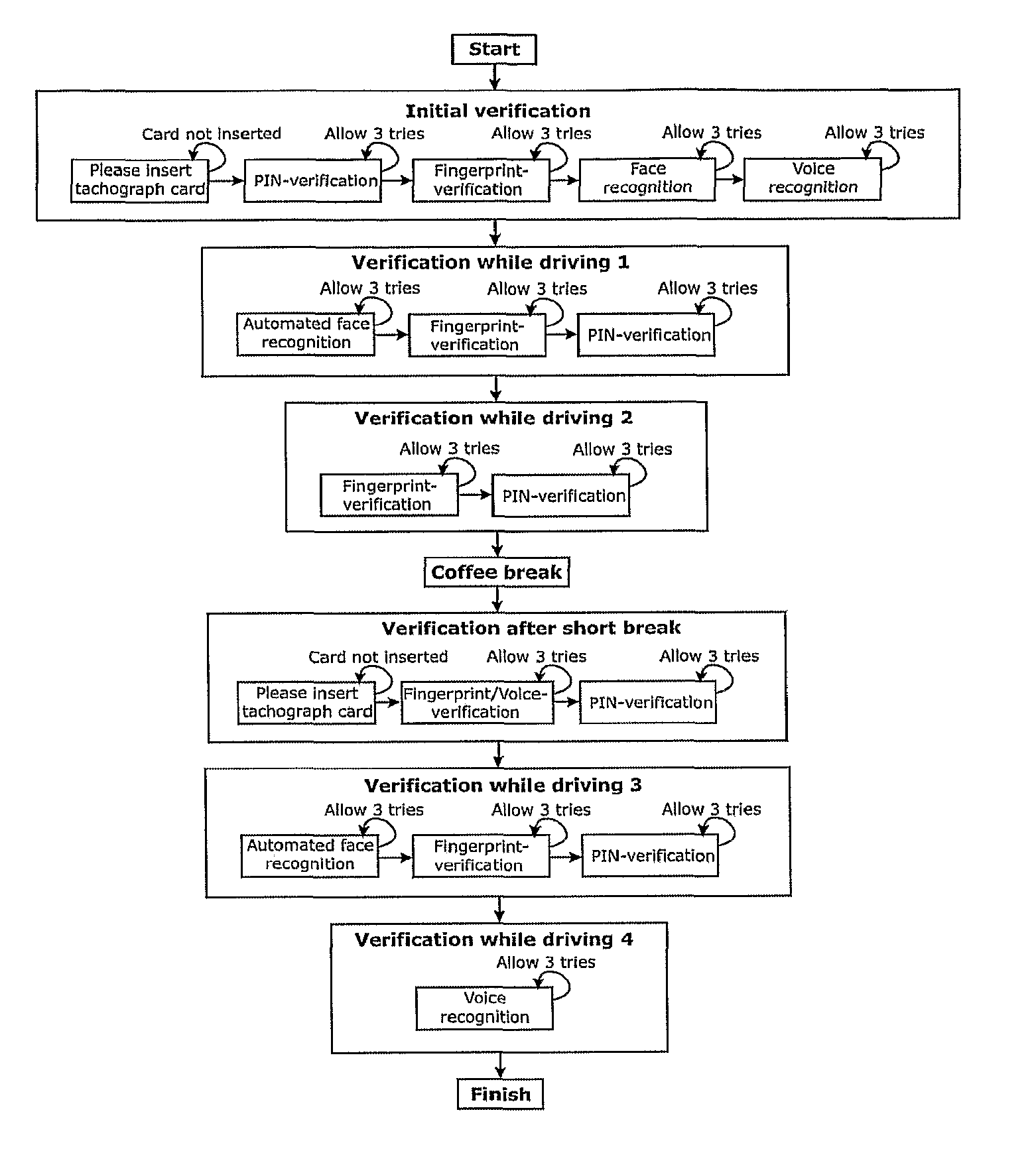
Method for Performing Driver Identity Verification
InactiveUS20080252412A1Improve security levelElectric signal transmission systemsMultiple keys/algorithms usageDriver/operatorRemedial action
Method for assuring that the operator of a vehicle is an authorized driver, the method including utilizing an onboard, multi-mode driver identification system to ascertain whether an operator is an authorized driver. A first driver identification procedure is performed on a present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle. A second driver identification procedure is performed on the present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle, wherein the first and second driver identification procedures are performed with a time interval therebetween, the time interval being dependent upon the nature of the work being performed by the operator. A remedial measure is exercised to avert potentially negative impact when the present operator of the vehicle is determined to be an unauthorized driver based upon at least one of the performed identification procedures.
Owner:VOLVO TECH
Private data entry
InactiveUS20110006996A1Easy to useImprove security levelInput/output for user-computer interactionAcutation objectsGraphicsGraphical user interface
A device and method for creating a private entry display on a touchscreen is provided, wherein the touchscreen includes a plurality of touch cells corresponding to spatial locations on the touchscreen. A graphical user interface is generated for display on the touchscreen for a predefined operation, the graphical user interface including a plurality of input zones. A characteristic of the graphical user interface as displayed on the touchscreen for the predefined operation is alter in order to change the touch cells associated with the graphical user interface. The altered user interface then is displayed on the touchscreen.
Owner:SHARP KK
Proactive Security for Mobile Devices
ActiveUS20110141276A1Improve security levelPrivacy protectionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsActive safetyPassword
Methods, program products, and systems for proactively securing mobile devices are described. A mobile device can proactively determine whether the mobile device is associated with a security risk and the level of the security risk. Upon determining a security risk, the mobile device can transmit coordinates of its current geographic location to a server. To protect privacy of authorized users, the transmission can be disabled by entering a password. If multiple failed password attempts are detected, the mobile device can proactively increase a security level of the device, and selectively protect files or other content stored on the mobile device. In some implementations, the mobile device can be transitioned into a surveillance mode where the mobile device records or captures information associated with one or more of user actions, ambient sound, images, a trajectory of the device, and transmits the recorded or captured information to the network resource.
Owner:APPLE INC
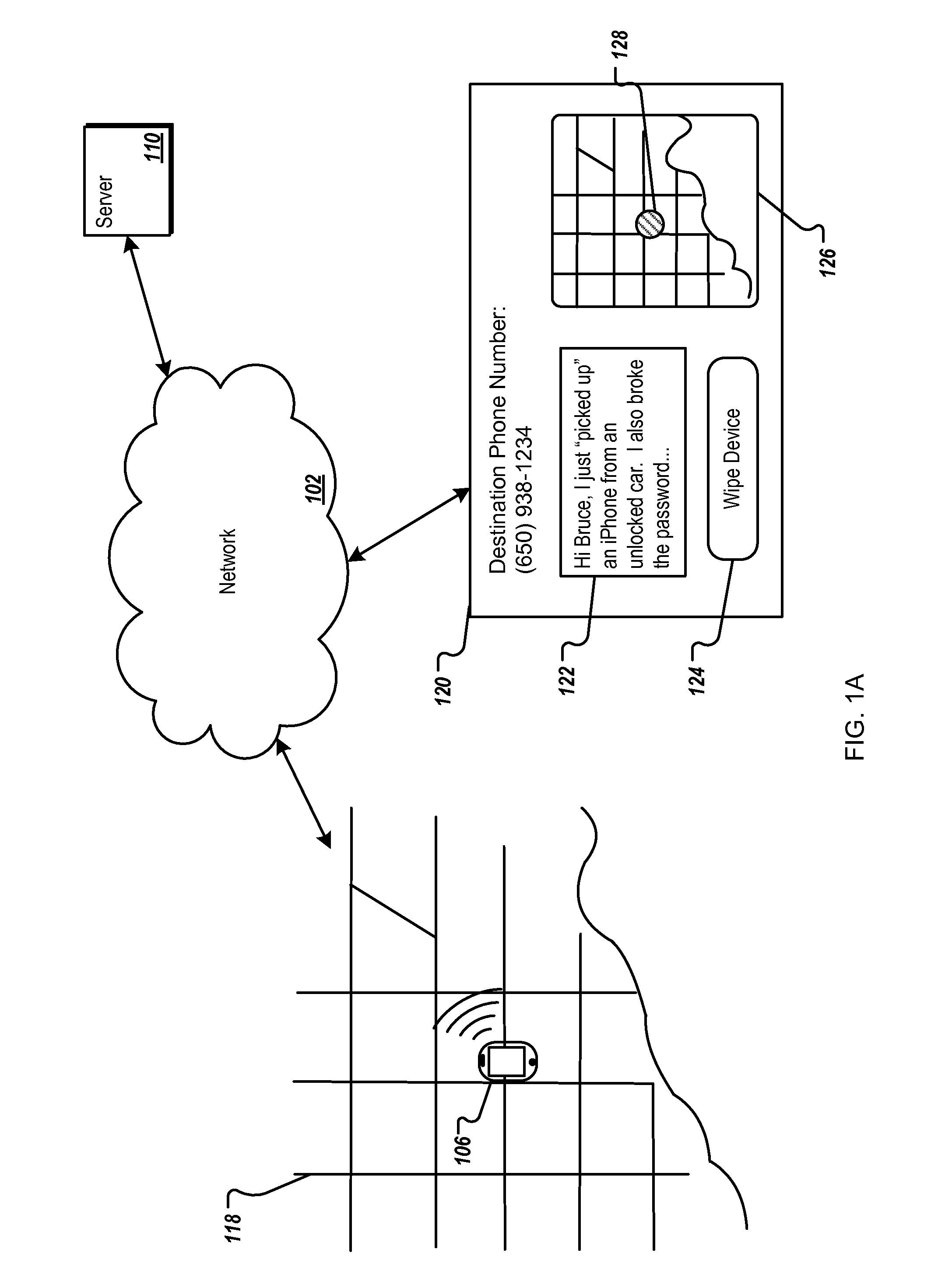
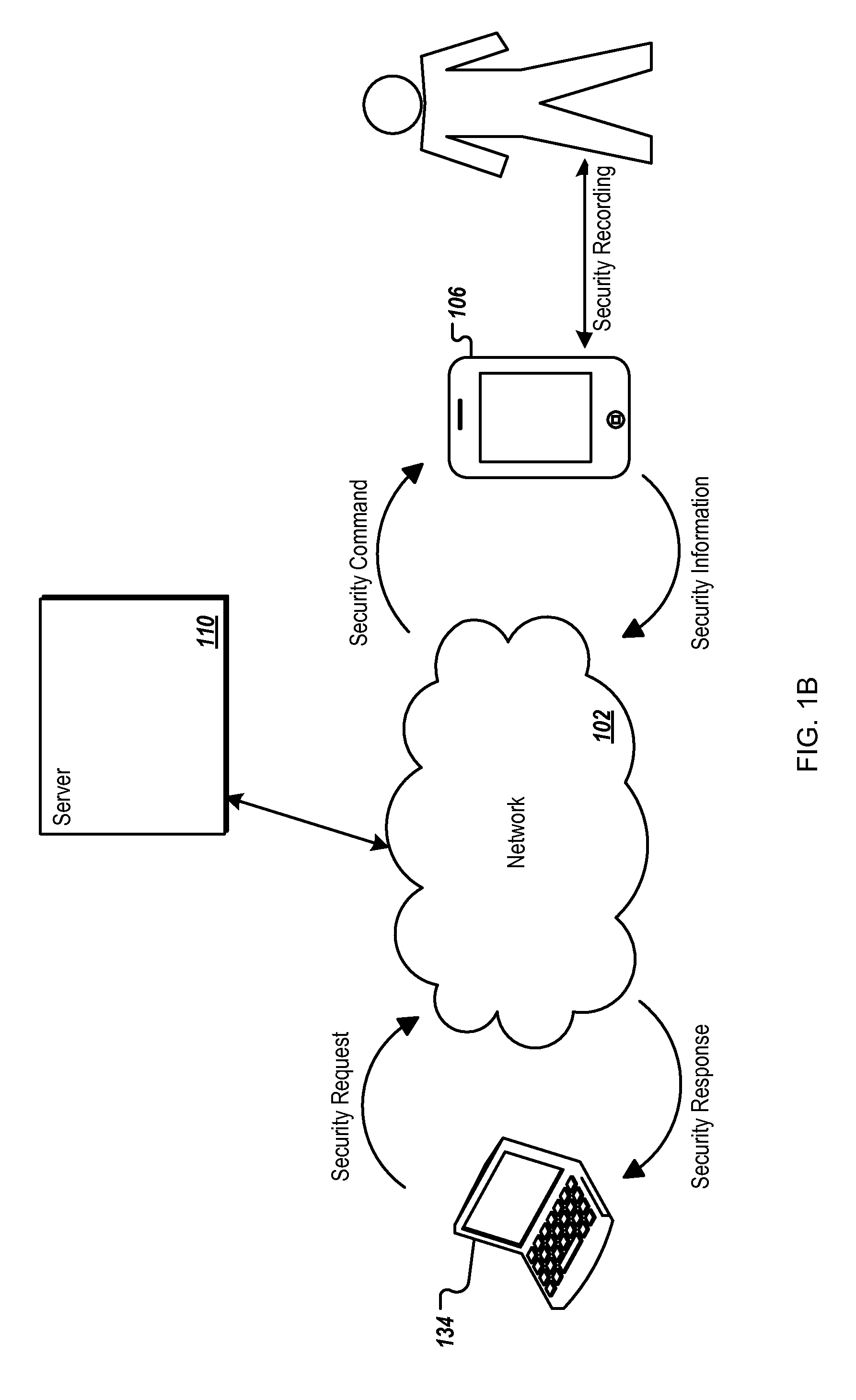
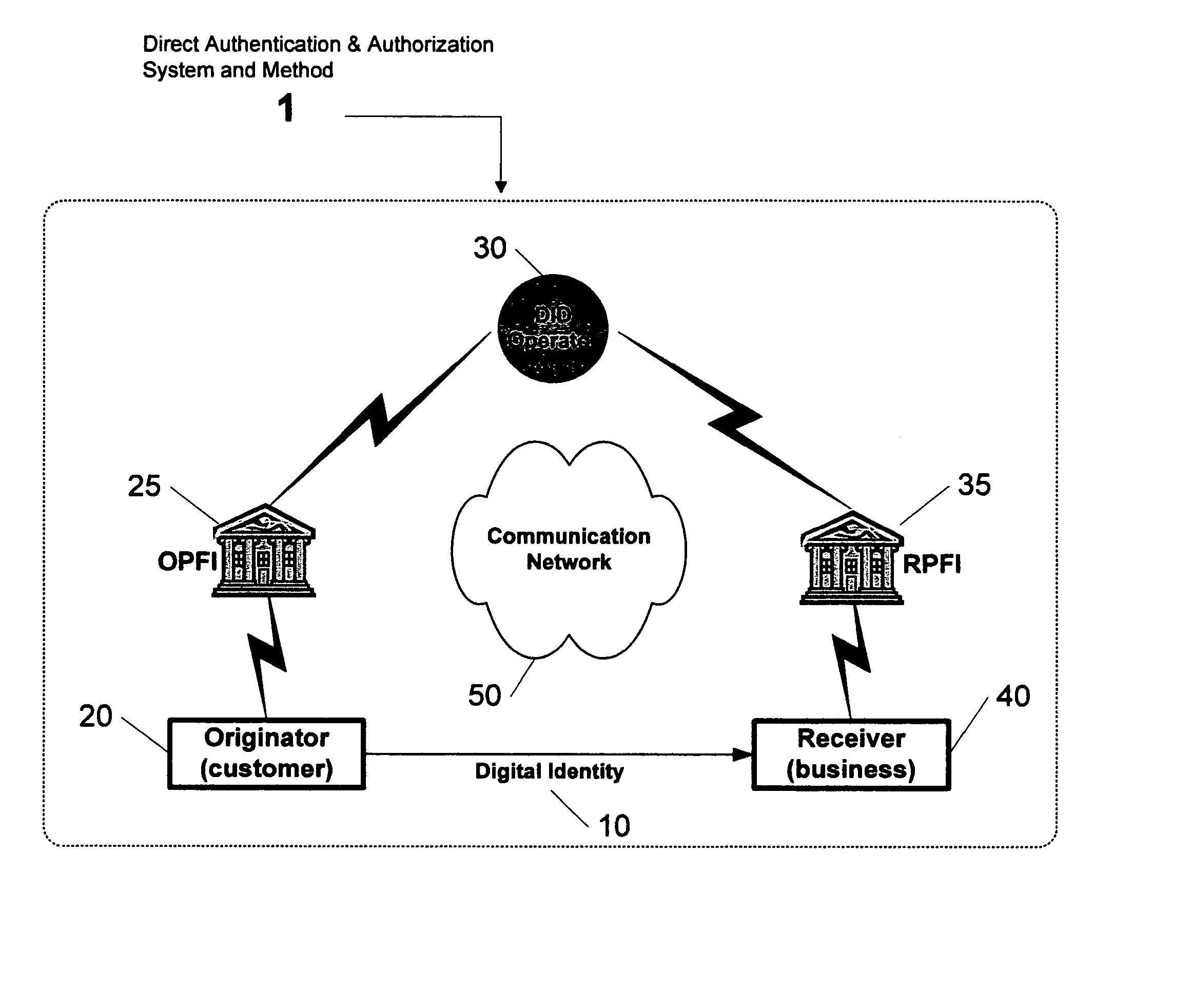
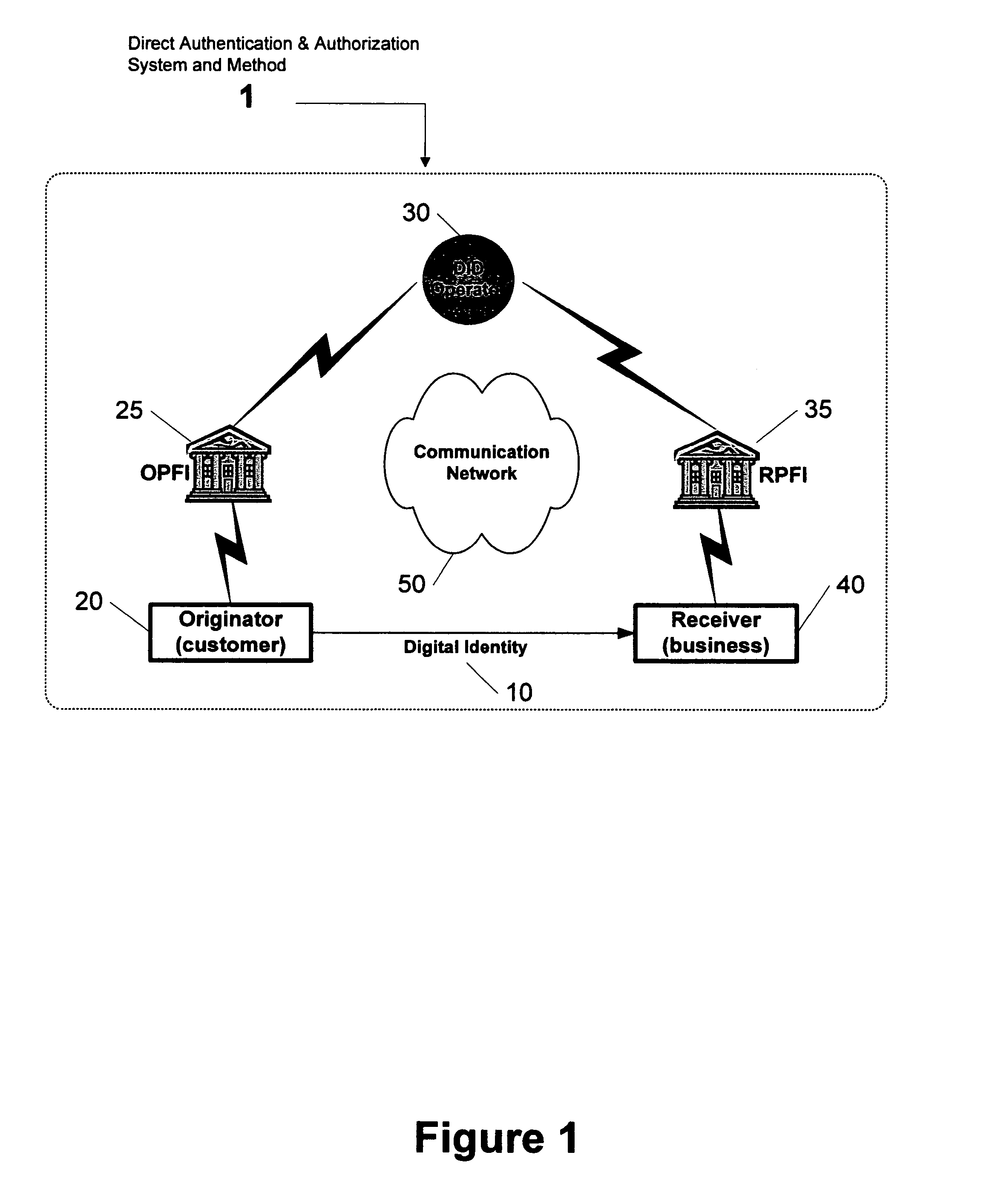
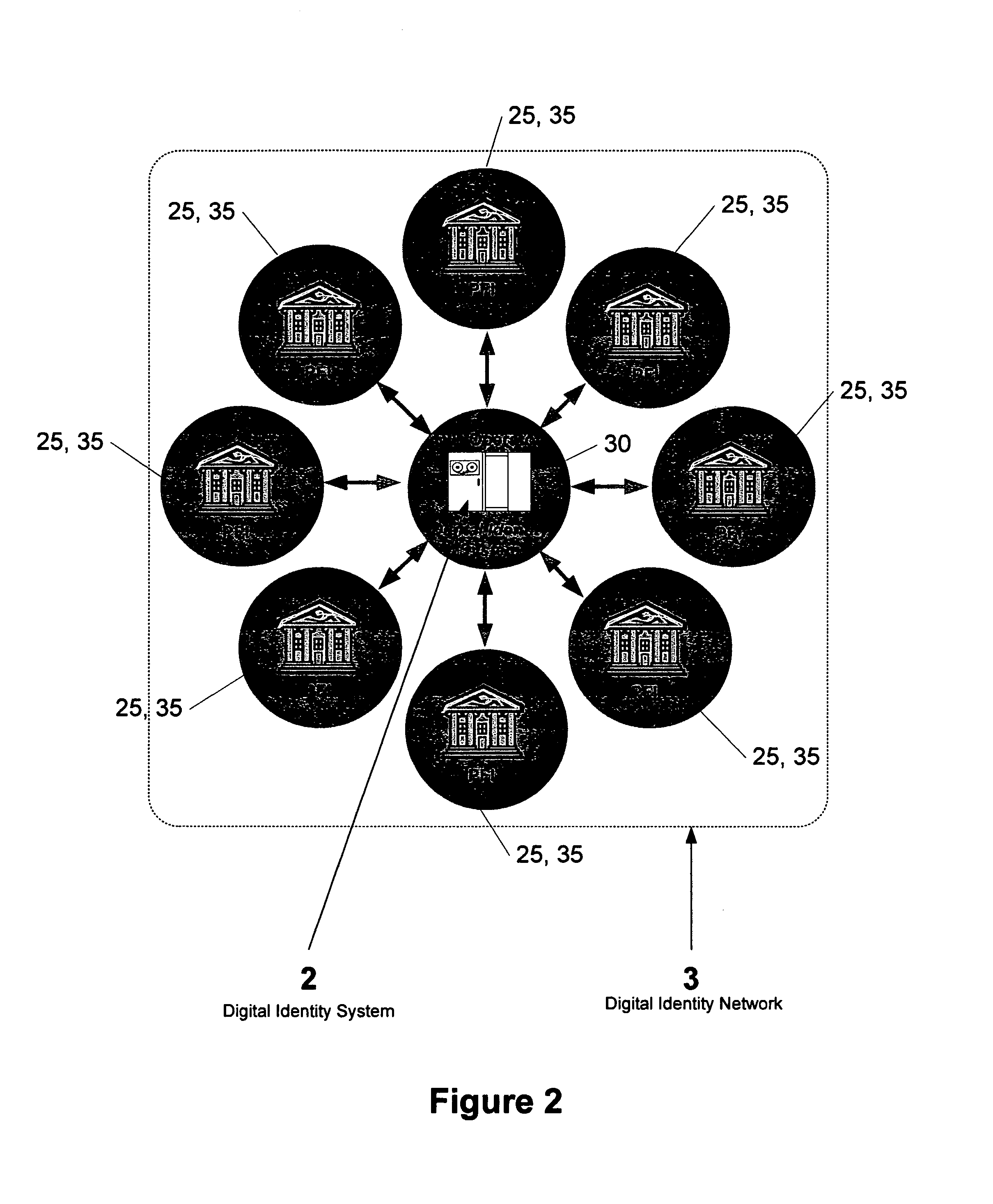
Direct authentication and authorization system and method for trusted network of financial institutions
A system and method for direct authentication and / or authorization of transactions. The system includes a trusted Digital Identity (DID) Network connecting an Originating Participating Financial Institution (OPFI) and a Receiving Participating Financial Institution (RPFI) through a DID Operator. The DID Operator may further be coupled to a DID System that calculates digital identities for Originators. According to the method, direct authentication of the Originator and / or authorization of the transaction is initiated upon the Originator communicating its digital identity to the Receiver. The Receiver subsequently provides the digital identity to the RPFI. The RPFI is then able to communicate with the OPFI for authentication of the Originator and / or authorization of the transaction through the DID Operator based on Originator's digital identity. The transaction between the Originator and Receiver can be financial or non-financial and may include, for example, account-to-account transfers, identity authentication or express agreements. In another embodiment, authentication and / or authorization may be performed in real time.
Owner:ASGHARI KAMRANI NADER +1
Financial transaction system and method using electronic messaging
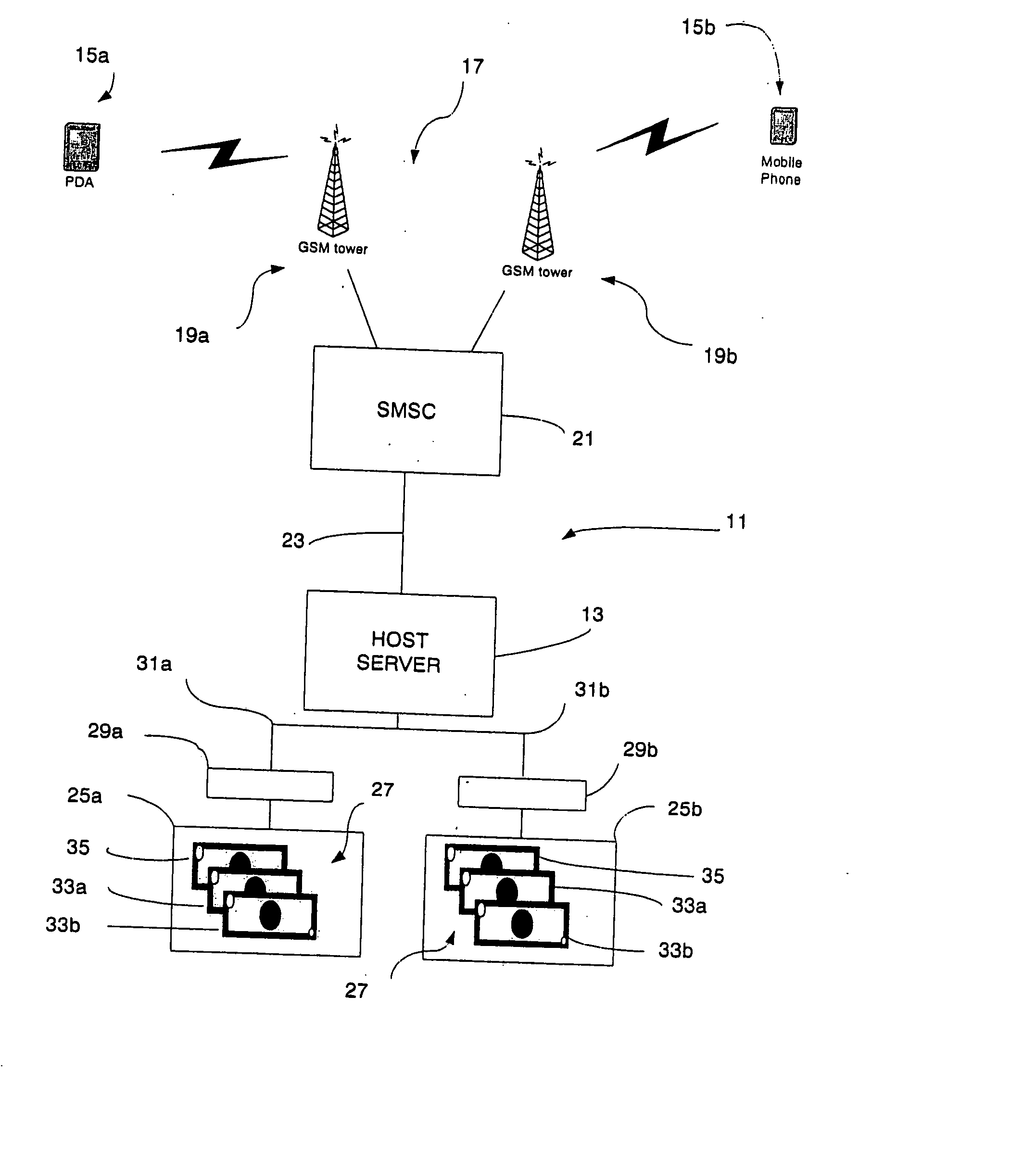
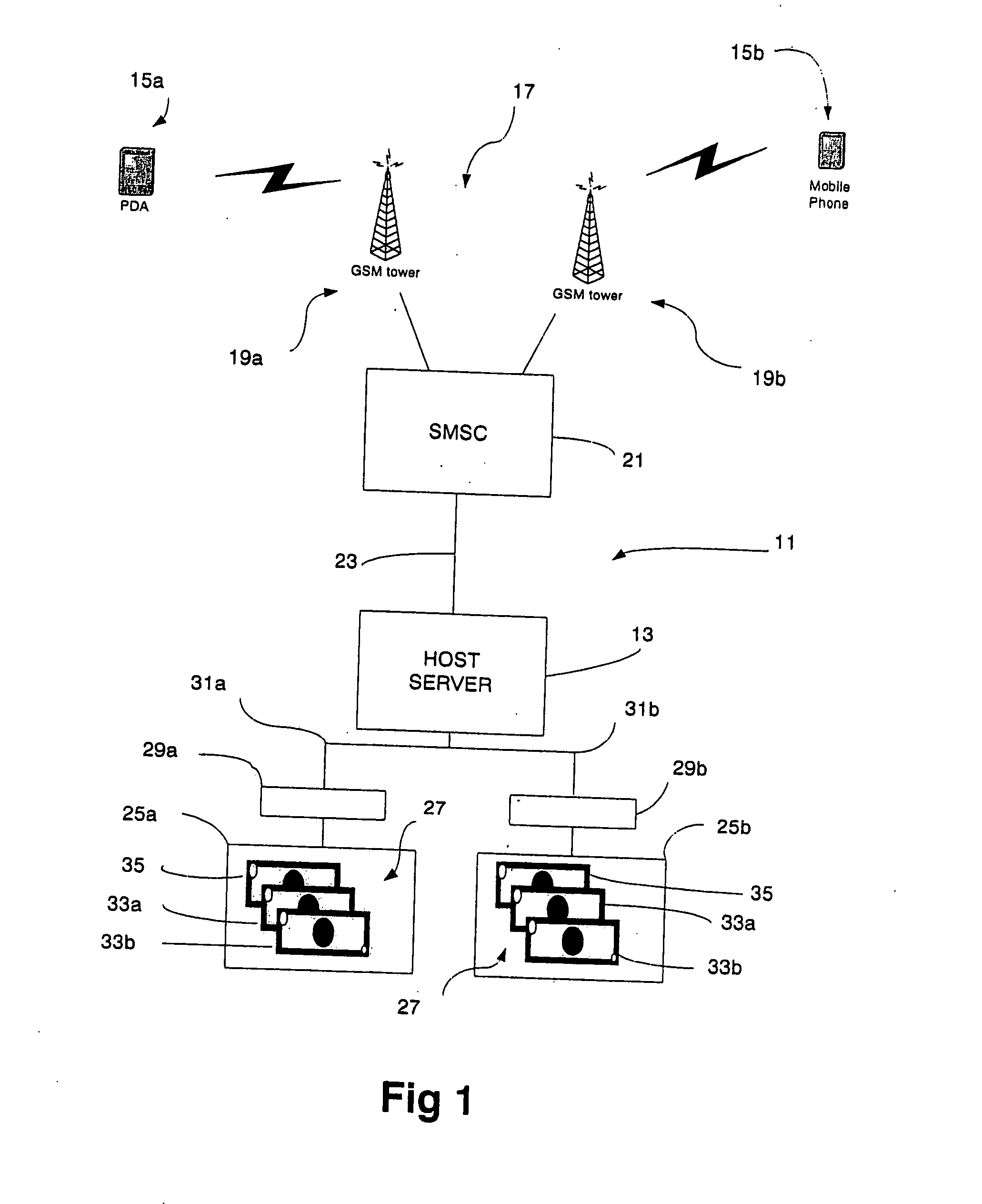
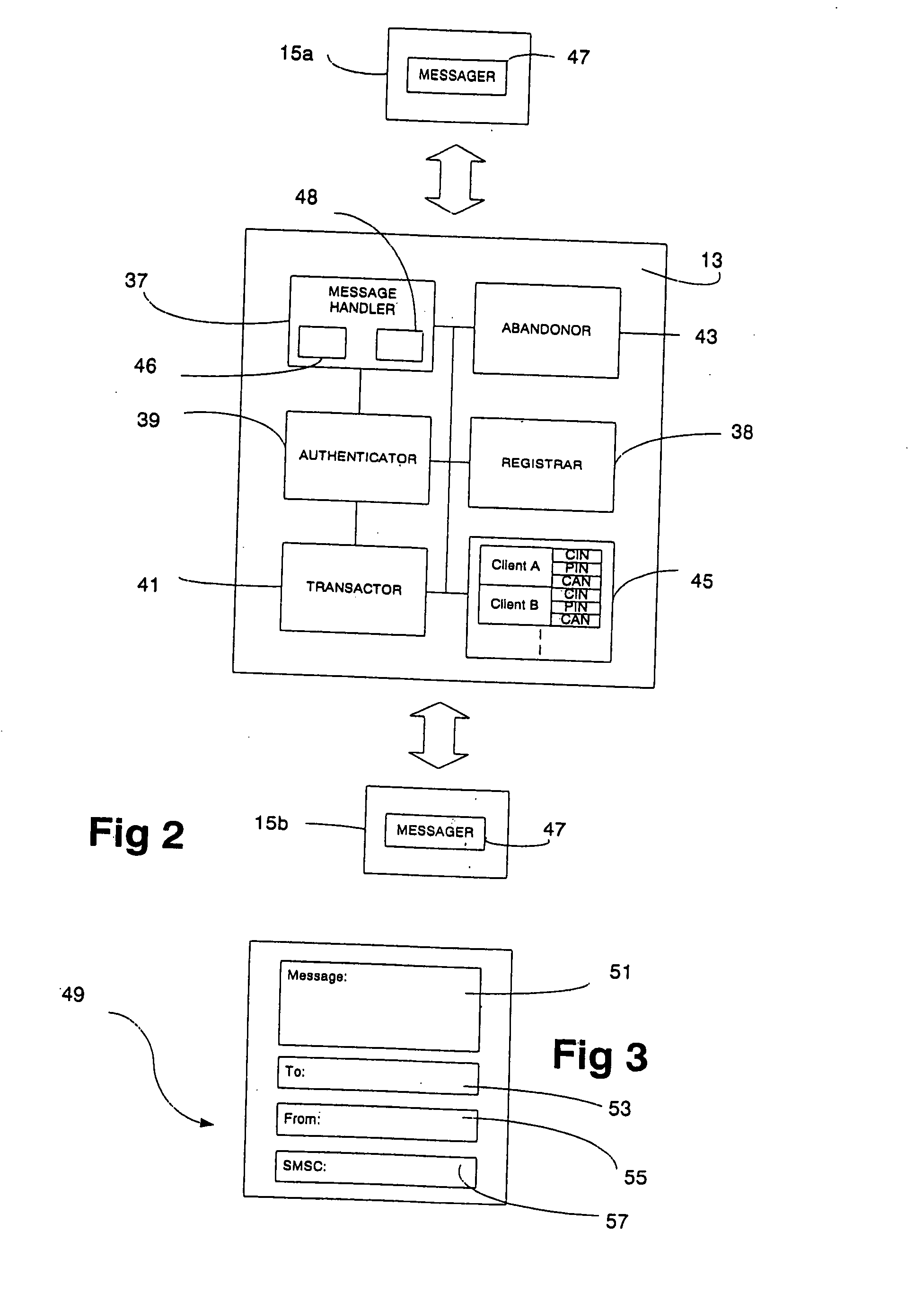
InactiveUS20050044042A1Efficient and flexibleImprove security levelFinanceDigital data processing detailsService provisionFinancial transaction
A method and a system for performing financial transactions between parties having clients (15a, 15b) with an electronic messaging facility and a banking account facility with a financial institution. Each party has an electronic messaging address (CIN) associated with the electronic messaging facility and a banking account number (CAN) associated with the banking account facility (27) thereof. A financial service provider server (13) is interfaced with the electronic messaging facility to handle communications between the clients (15a, 15b) of the parties and is also interfaced with the banking account facilities (27) of the parties to perform the financial transaction. The electronic messaging address (CIN) of each party is linked with the banking account facility therefor, and thus the banking account number(s) (CAN) thereof, within a database (45) associated with the server (13) to facilitate the financial transaction. The server (13) undertakes an authentication process within one and / or the other party using the electronic messaging facility requiring confirmation of a PIN also stored in the database (45). The authentication process is characterised by the server (13) providing the client (15a) of the one party instigating the financial transaction with a different electronic messaging address to “reply to” when requesting the PIN, from the original electronic messaging address of the server (13) used by that same party to initiate the financial transaction, to enhance the security of the transaction.
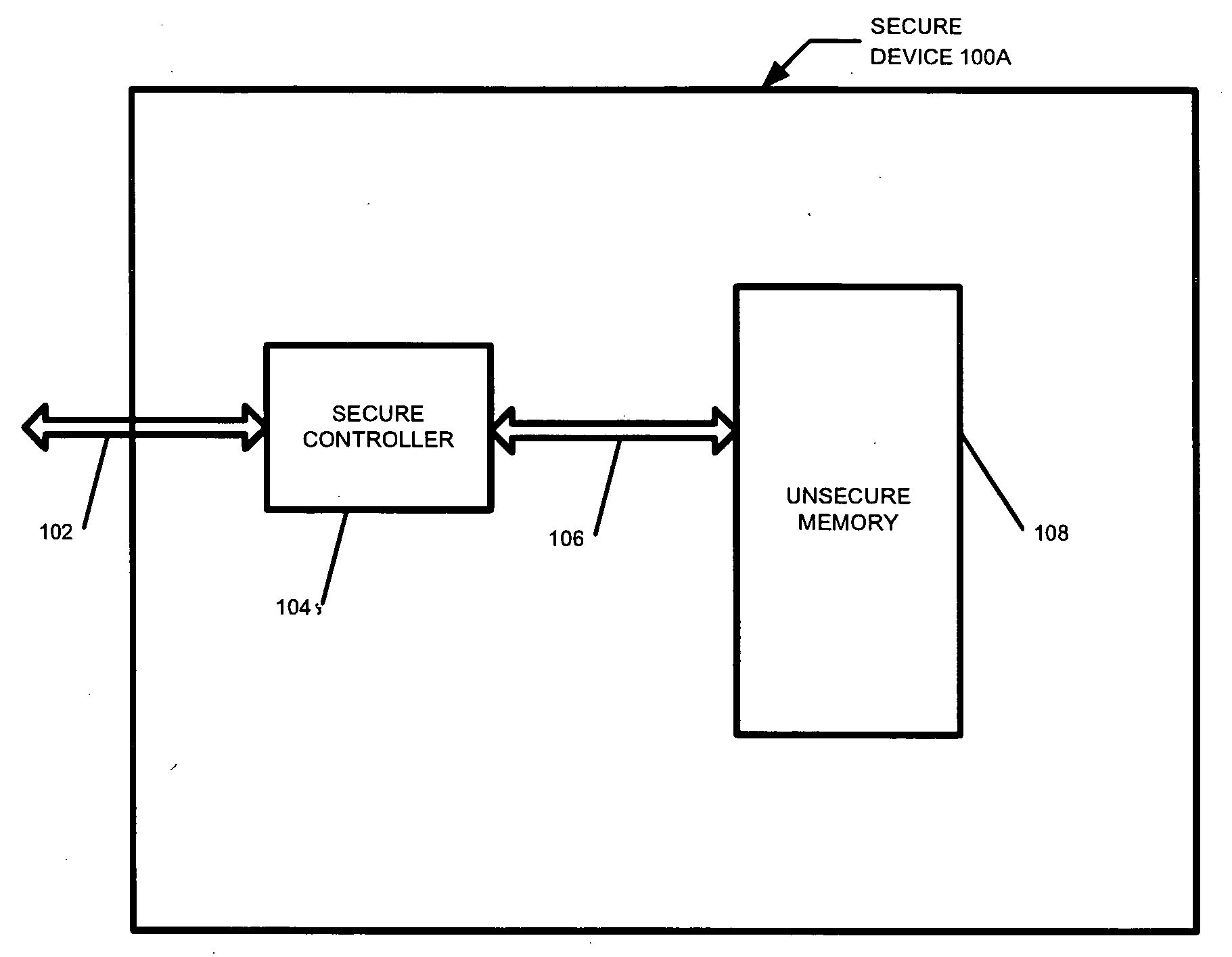
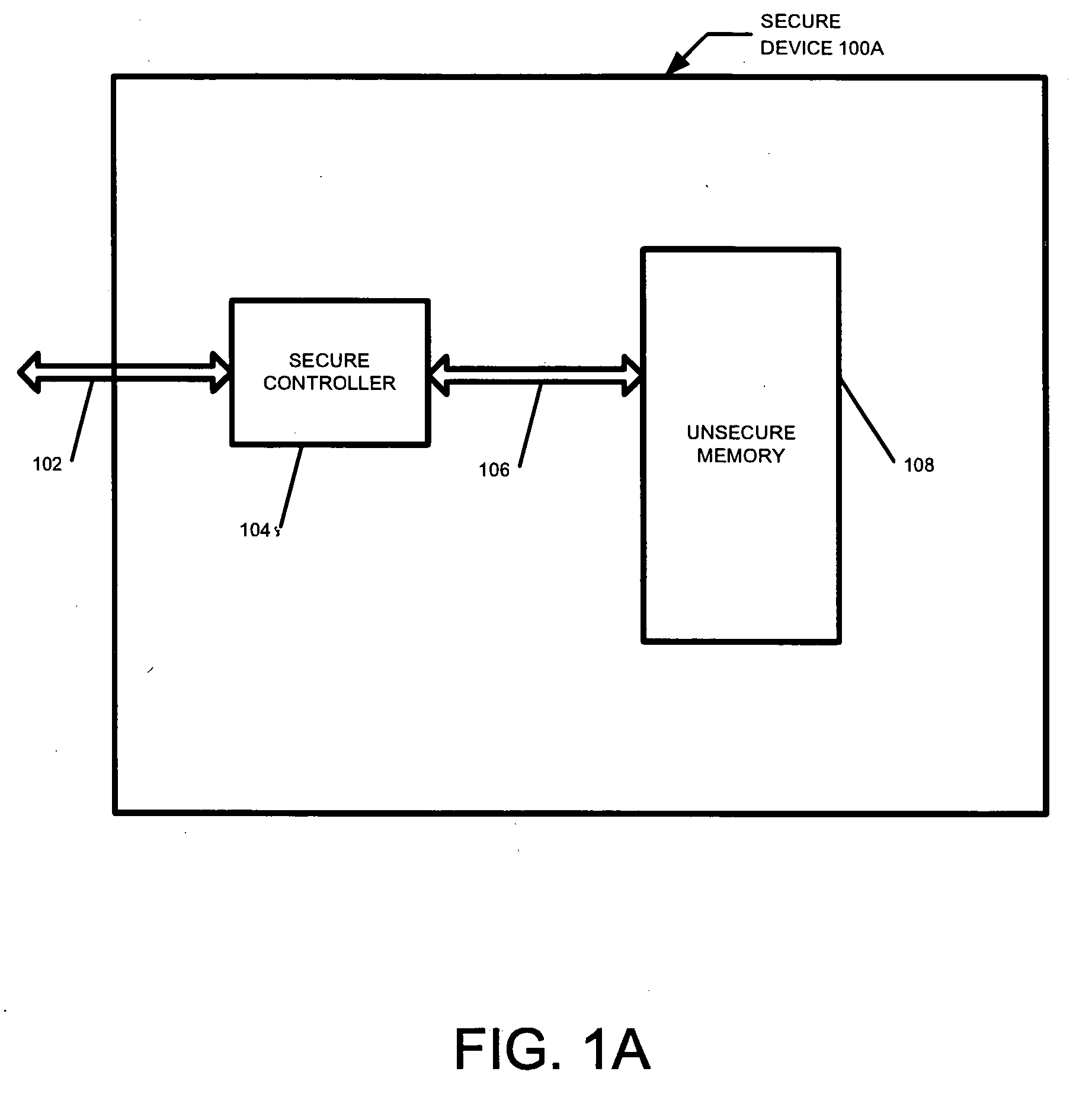
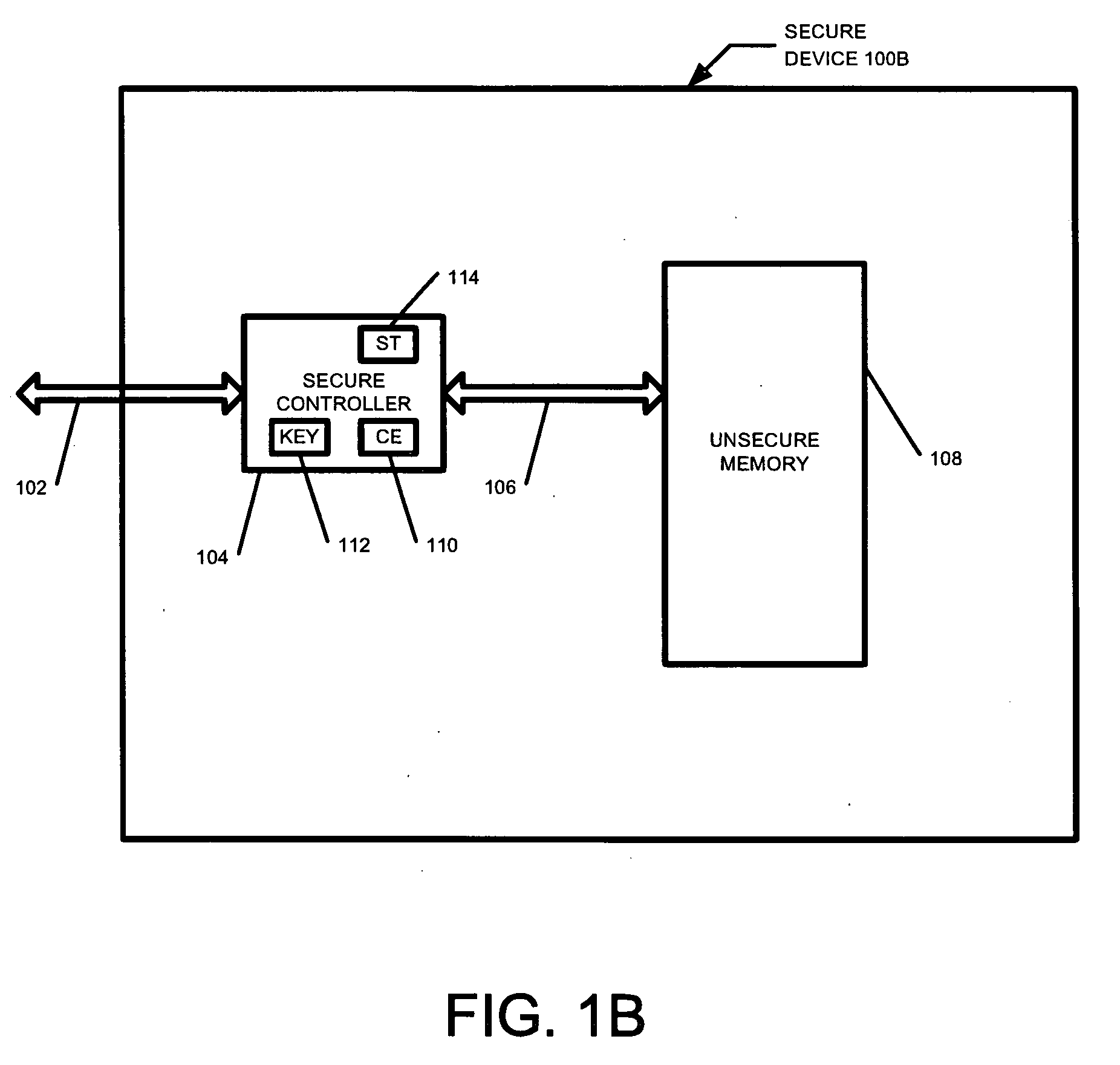
Secure yet flexible system architecture for secure devices with flash mass storage memory
InactiveUS20070061597A1Operational securityImprove security levelMemory architecture accessing/allocationUser identity/authority verificationLarge capacitySafety Equipment
A device with mass storage capability that uses a readily available non secure memory for the mass storage but has firmware (and hardware) that provides security against unauthorized copying of data. This is true even though the firmware itself is stored in the non secure mass storage memory, and therefore potentially vulnerable to hacking. An indication of the authenticity of the firmware must be present before it will be executed by the device. This protects the device contents from unauthorized duplication or tampering. Additional functionality can be added to the device with additional firmware applications, and the authenticity of those additional applications will also be verified before they will be executed. This further prevents unauthorized copying or tampering of secure content through any mechanisms that may be unscrupulously introduced. Any data within the mass storage memory may also be encrypted.
Owner:SANDISK TECH LLC +1
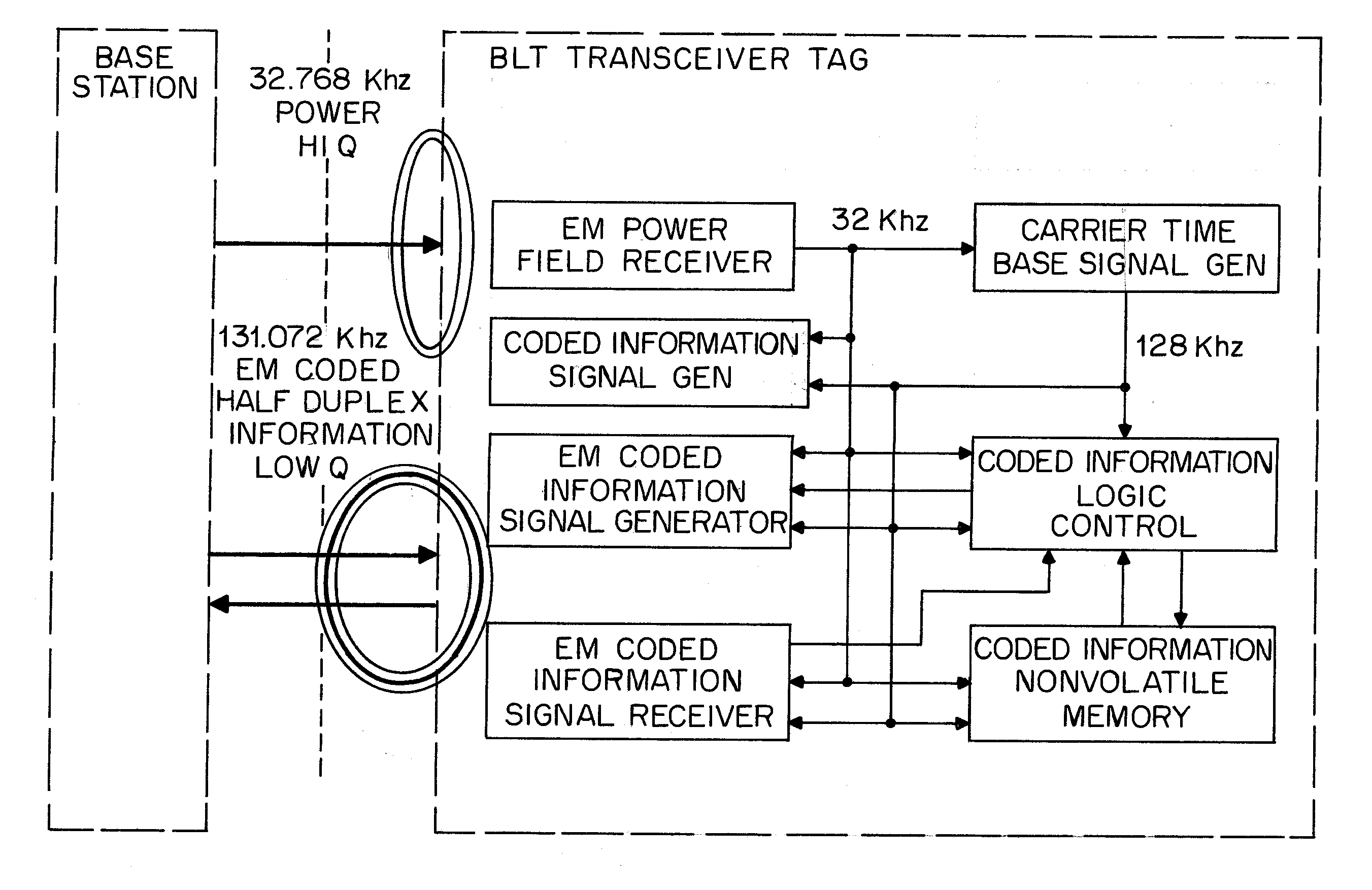
Radio tag and system
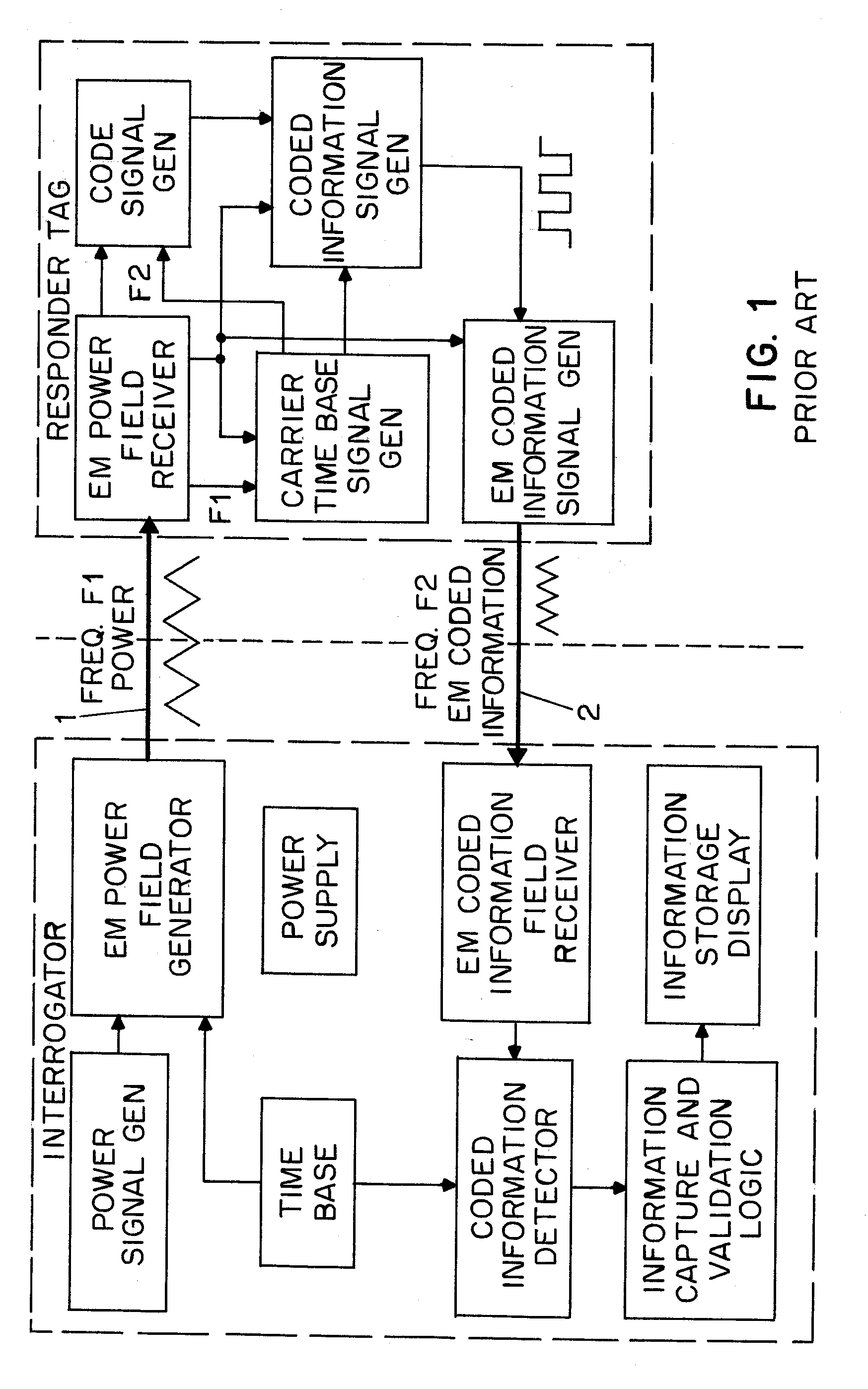
InactiveUS20070096875A1Double communication speedIncrease rangeSubscribers indirect connectionRecord carriers used with machinesCouplingData signal
Passive tags use two antennas with only limited mutual coupling, one of which receives a power / clock field and the other of which receives a data signal. An area-reading antenna, or two or more antennas, are deployed to generate the power / clock field, from a base station. The base station, or active tags, or both, generate the data signals from time to time. This topology together with the use of low frequencies permits area reads, and permits small and economical passive tags, and further permits localization of a particular passive tag as being nearby to a particular active tag.
Owner:VISIBLE ASSET INC
Method and device for generating a single-use financial account number
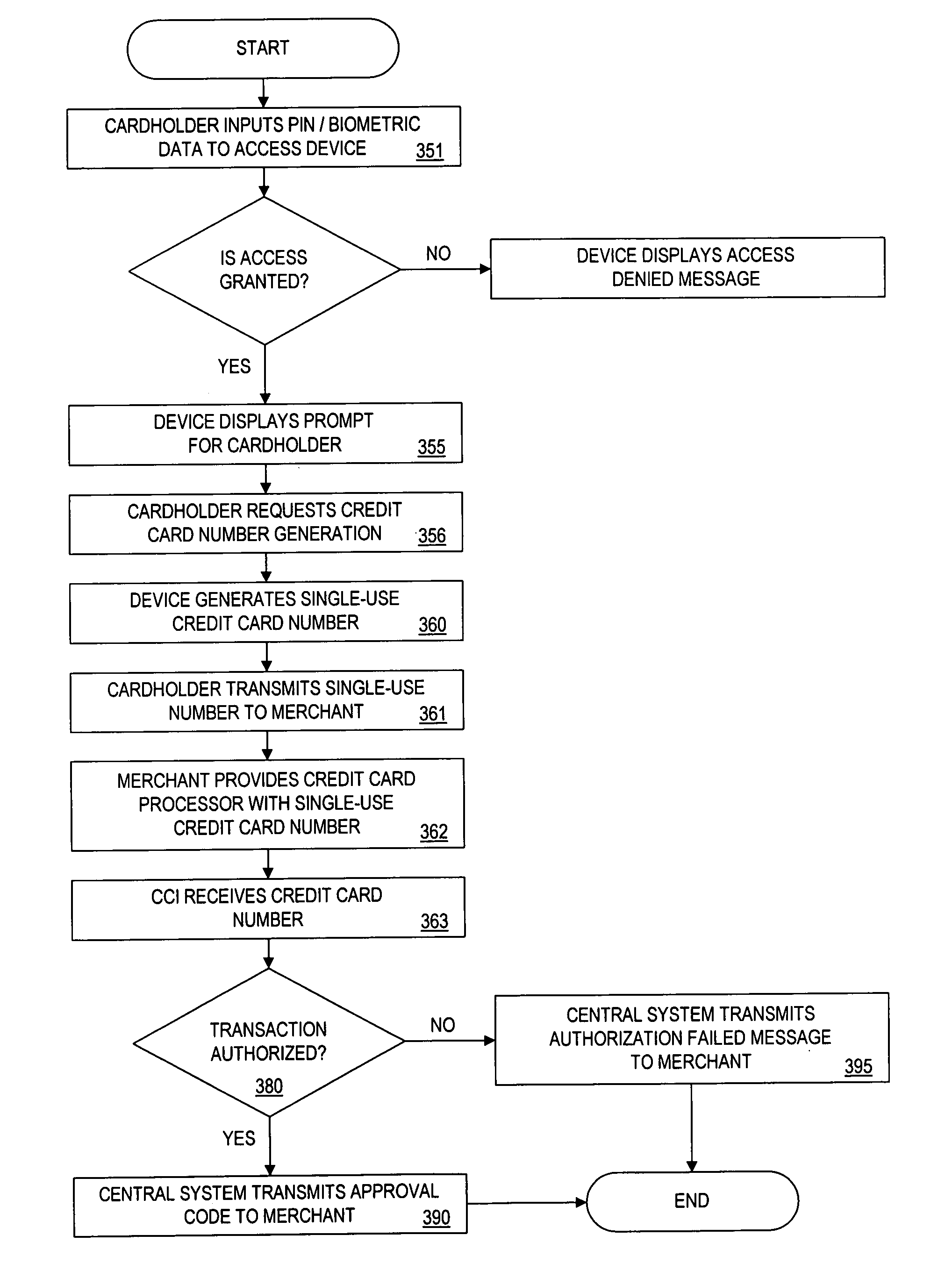
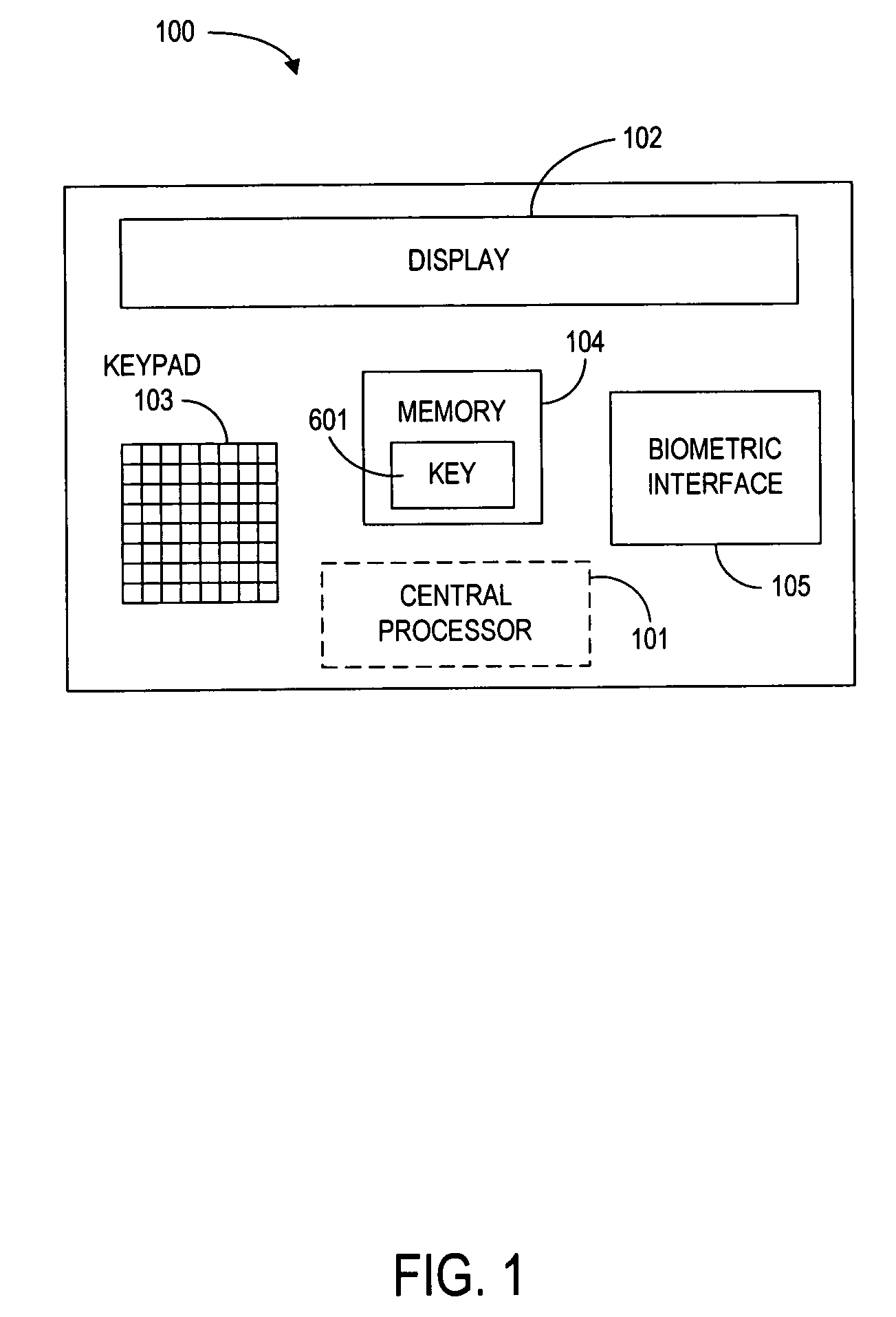
InactiveUS7177835B1Improve security levelReduce riskFinanceCredit schemesFinancial transactionData element
Owner:PAYPAL INC +1
Method for performing driver identity verification
InactiveUS8344849B2Improve security levelElectric signal transmission systemsImage analysisRemedial actionEngineering
Method for assuring that the operator of a vehicle is an authorized driver, the method including utilizing an onboard, multi-mode driver identification system to ascertain whether an operator is an authorized driver. A first driver identification procedure is performed on a present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle. A second driver identification procedure is performed on the present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle, wherein the first and second driver identification procedures are performed with a time interval therebetween, the time interval being dependent upon the nature of the work being performed by the operator. A remedial measure is exercised to avert potentially negative impact when the present operator of the vehicle is determined to be an unauthorized driver based upon at least one of the performed identification procedures.
Owner:VOLVO TECH
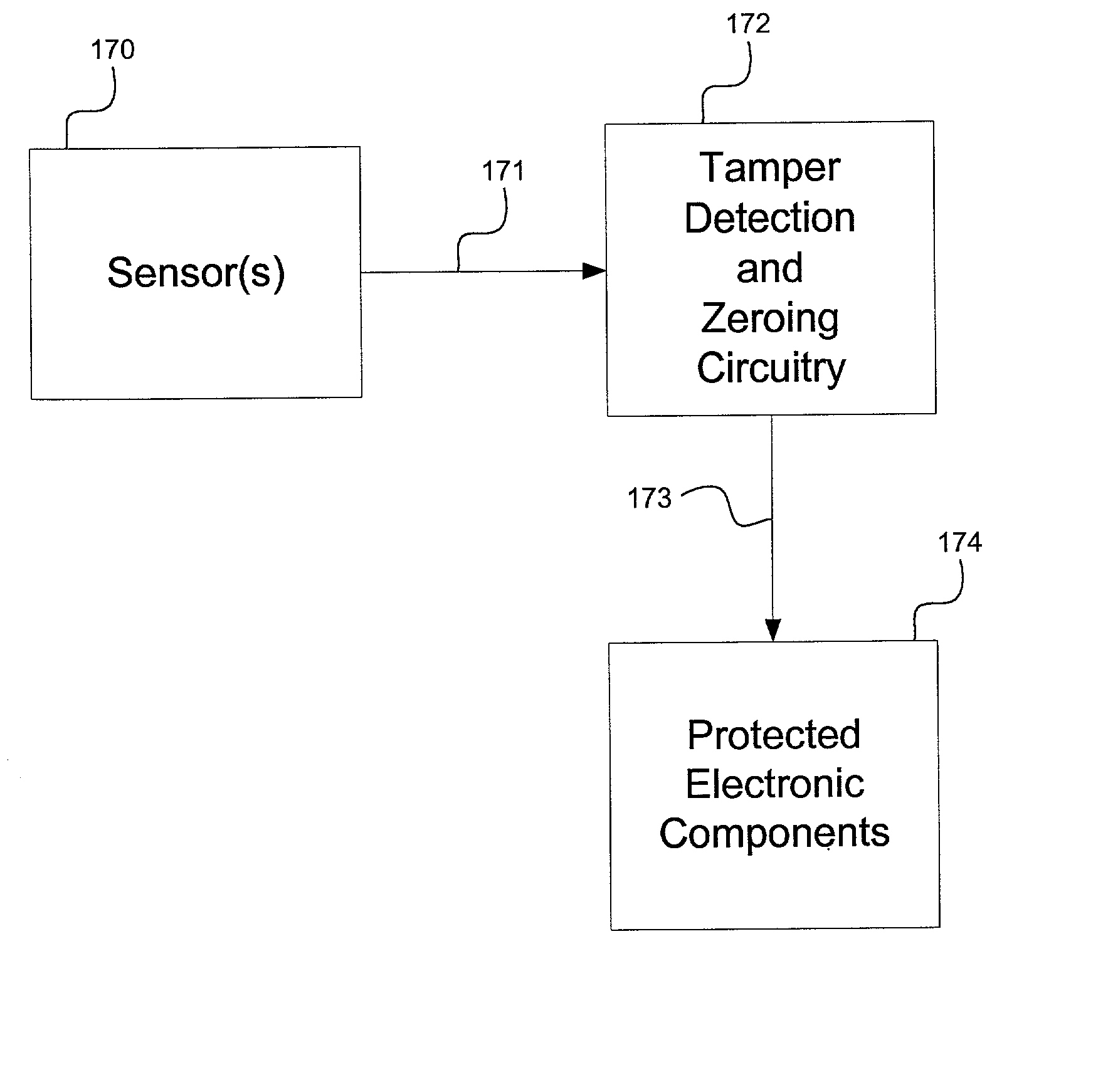
Security module system, apparatus and process
InactiveUS20020002683A1Easy to changeImprove protectionPrinted circuit assemblingSemiconductor/solid-state device detailsEngineeringShort circuit
A system, method and apparatus for protecting circuit components from unauthorized access. The circuit components to be protected are disposed on a first layer of a substrate with a plurality of layers. A cover member composed of a plurality of layers is abutted to the substrate, defining an enclosure space for enclosing the circuit components to be protected. A three-dimensional resistive network sensor surrounds the protected circuit components. The sensor comprises at least one conduction path in at least one of the layers below the first layer of the substrate and at least one conduction path in at least one of the layers of the cover member and also comprises a plurality of vias transverse to and electrically connecting the conduction paths. A short or open in the sensor will be detected by a tamper detection circuit that is disposed on the first layer of a substrate.
Owner:SAFENET
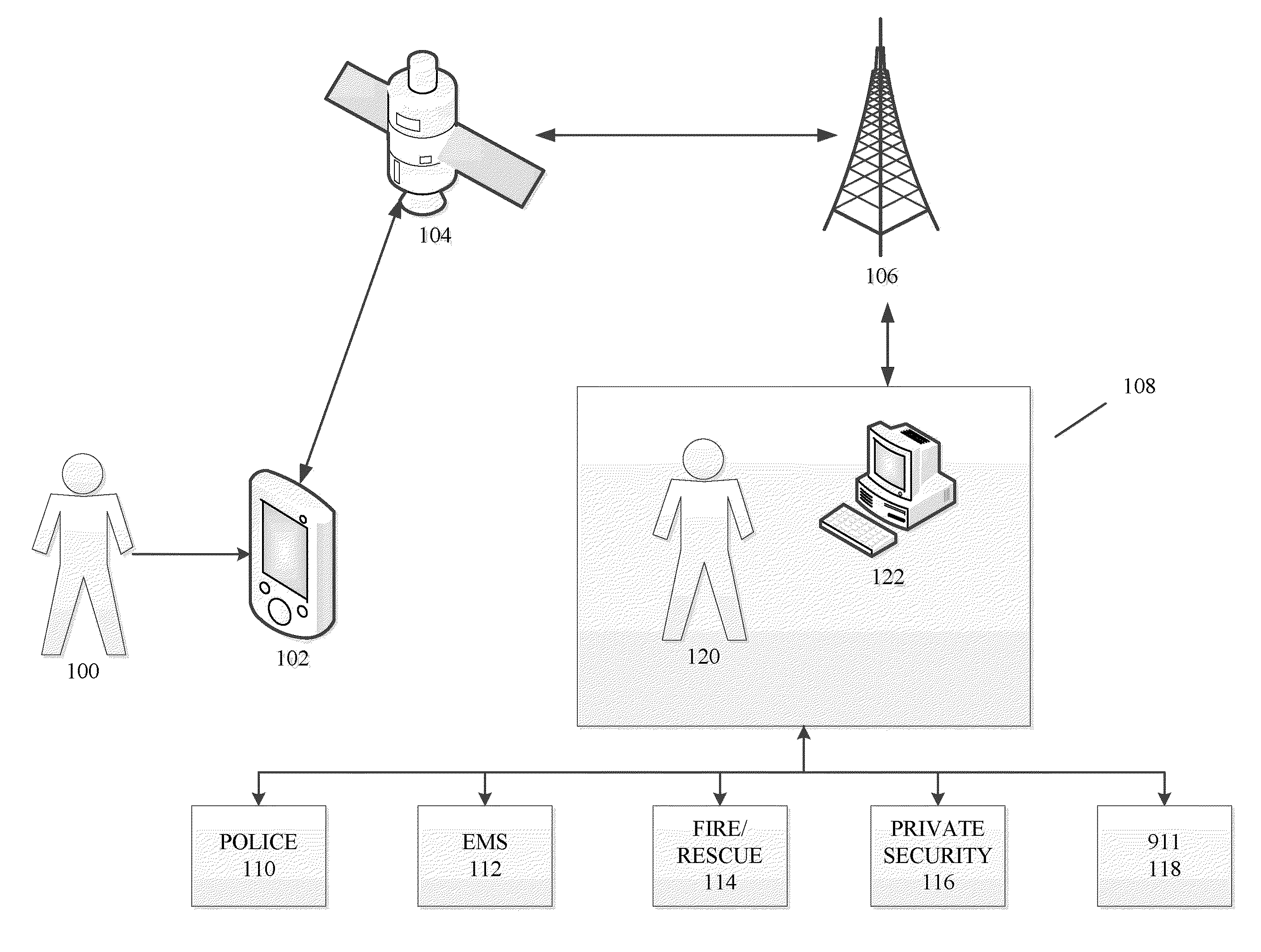
Methods and systems for threat assessment, safety management, and monitoring of individuals and groups
InactiveUS20110046920A1Improve security levelReduce morbidityError detection/correctionMultiple digital computer combinationsComputer scienceSecurity management
The disclosure generally relates to methods and systems anticipating a potentially threatening or dangerous incident, and providing varying levels of response to a user. In an exemplary embodiment, the present invention provides varying levels of assistance to a user prior to, during, and after a threatening incident occurs. By providing assistance prior to a threatening incident occurring, the system may be able to thwart potential attacks, bodily harm, robberies, break-ins, and other criminal or dangerous activity. The assistance can be, for example, in the form of deterrents, alerting first responders to go to the scene, sending security personnel to the scene, remotely monitoring the scene, remotely interacting with the scene, providing information and advice to the user.
Owner:STRIDER
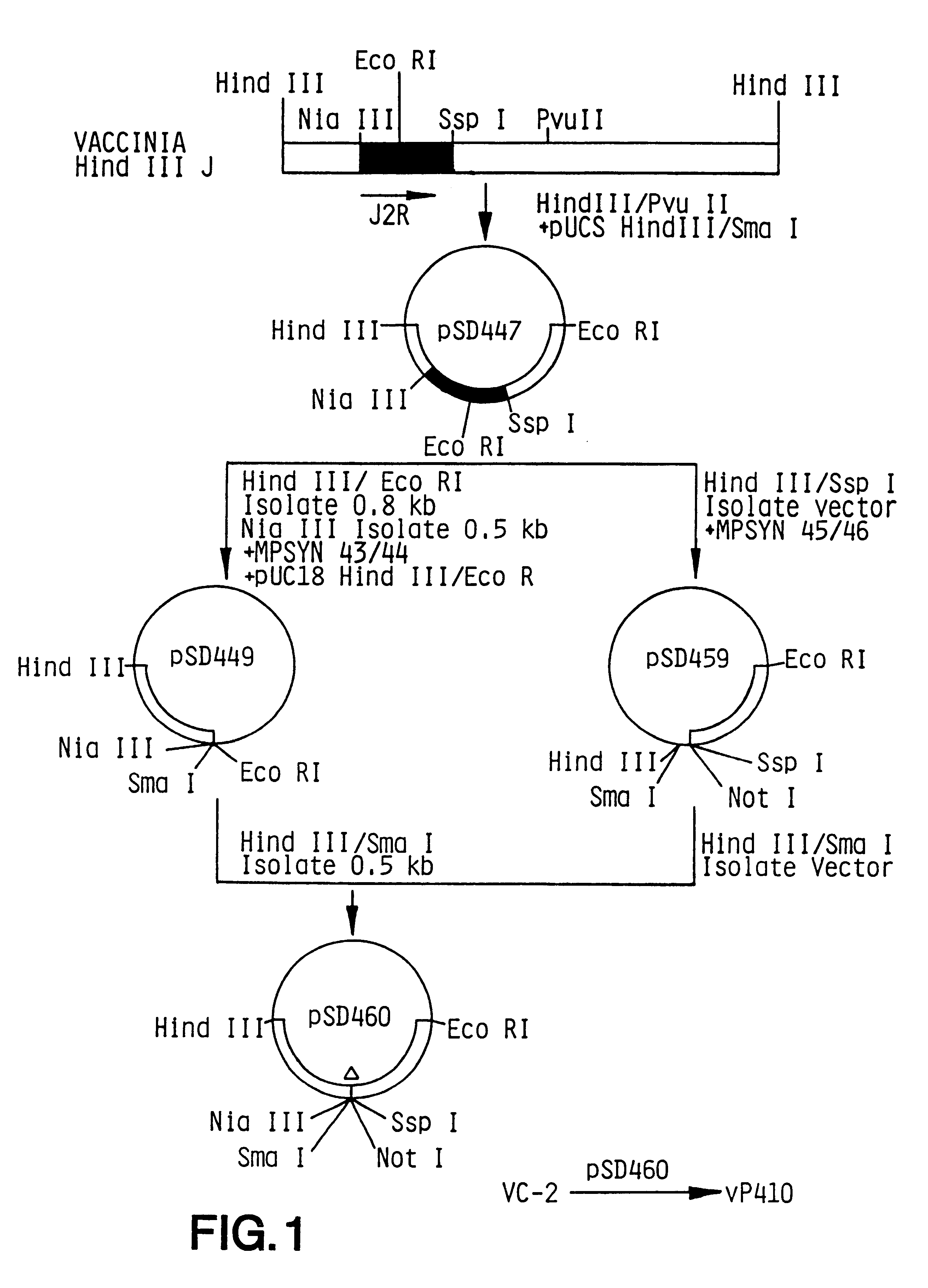
Pox virus containing DNA encoding a cytokine and/or a tumor associated antigen
InactiveUS6265189B1Improve securityImprove security levelVirusesPeptide/protein ingredientsHuman tumorWild type
Attenuated recombinant viruses containing DNA coding for a cytokine and / or a tumor associated antigen, as well as methods and compositions employing the viruses, are disclosed and claimed. The recombinant viruses can be NYVAC or ALVAC recombinant viruses. The DNA can code for at least on of: human tumor necrosis factor; nuclear phosphoprotein p53, wildtype or mutant; human melanoma-associated antigen; IL-2; IFNgamma; IL-4; GNCSF; IL-12; B7; erb-B-2 and carcinoembryonic antigen. The recombinant viruses and gene products therefrom are useful for cancer therapy.
Owner:VIROGENETICS
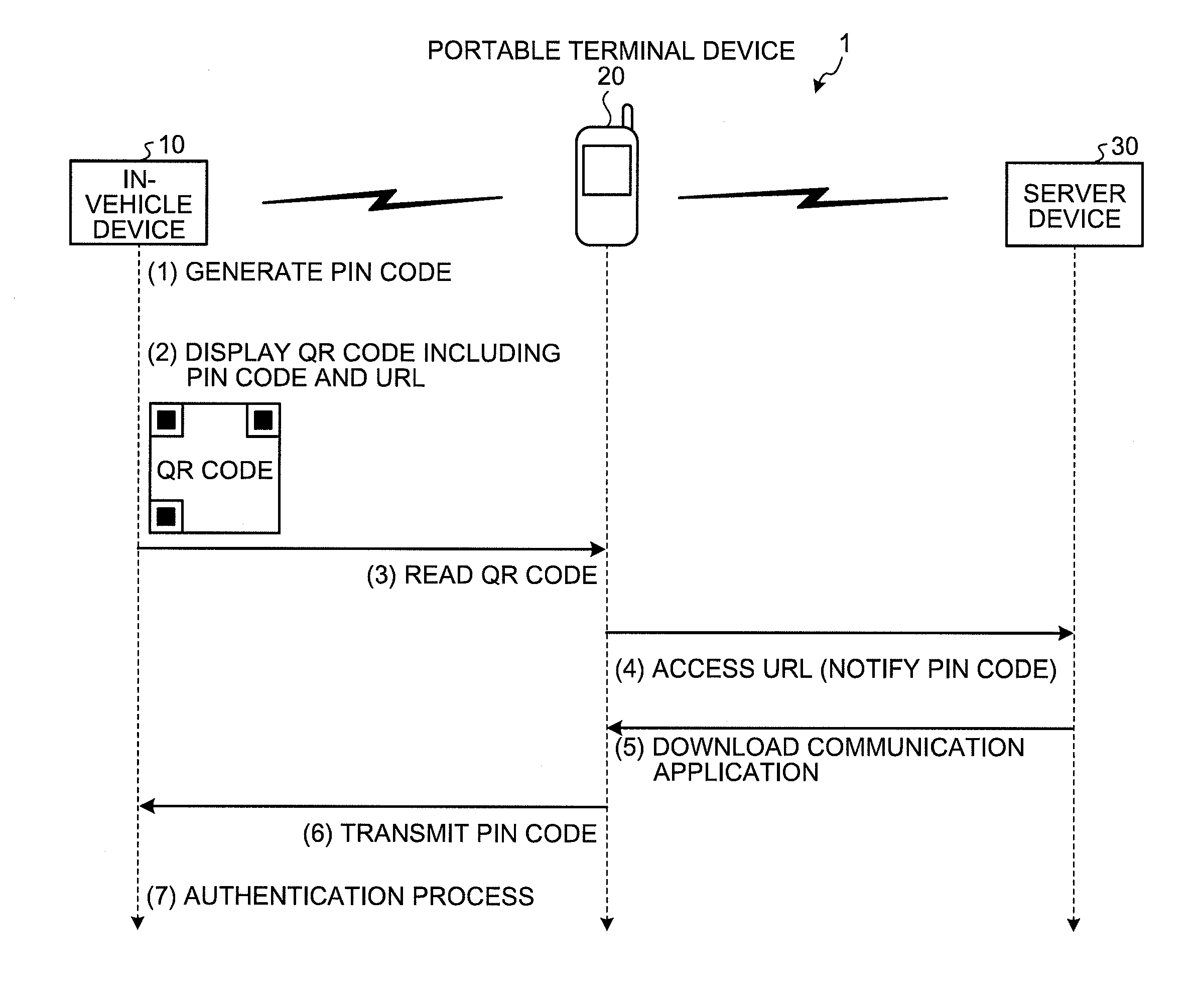
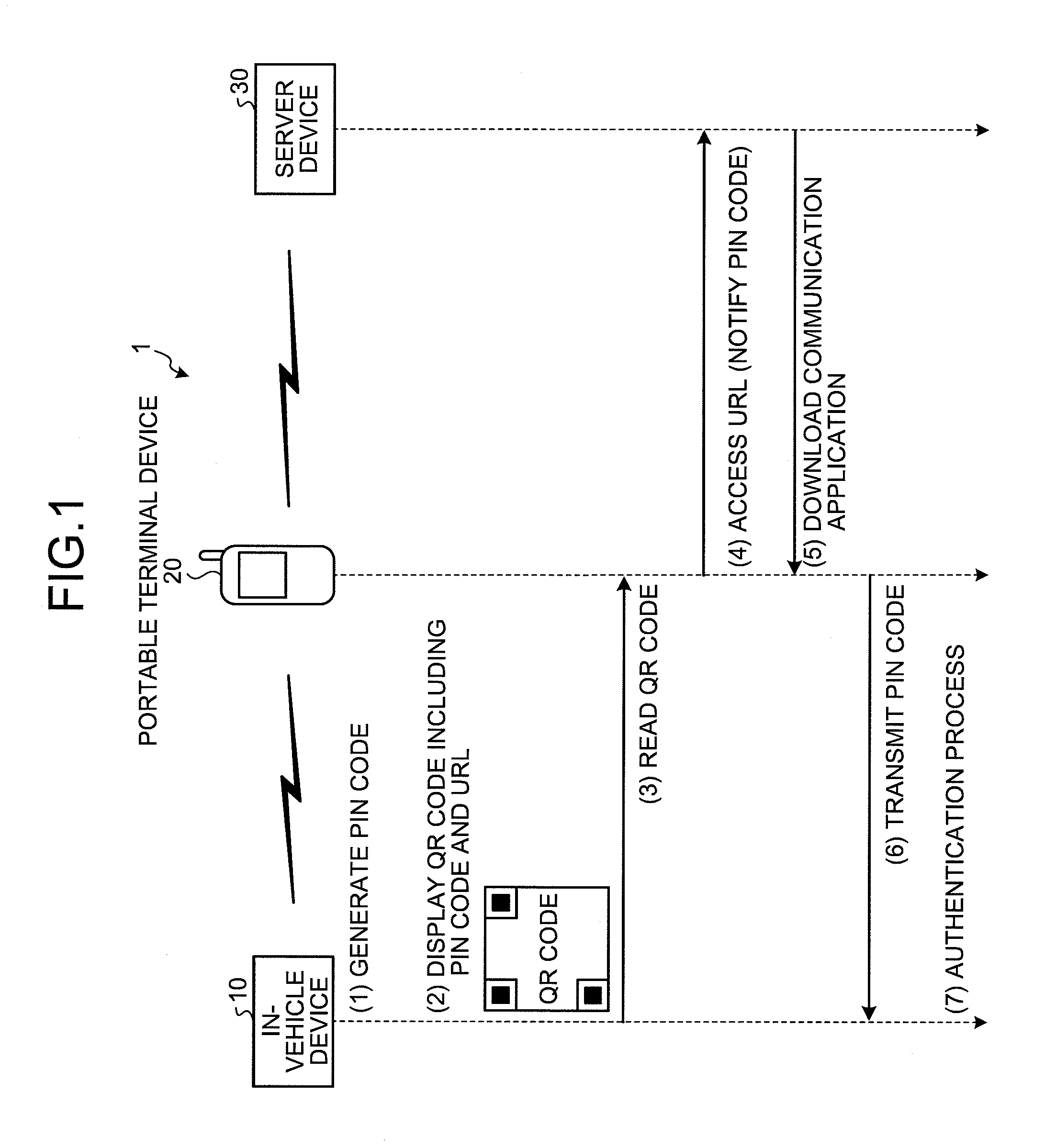
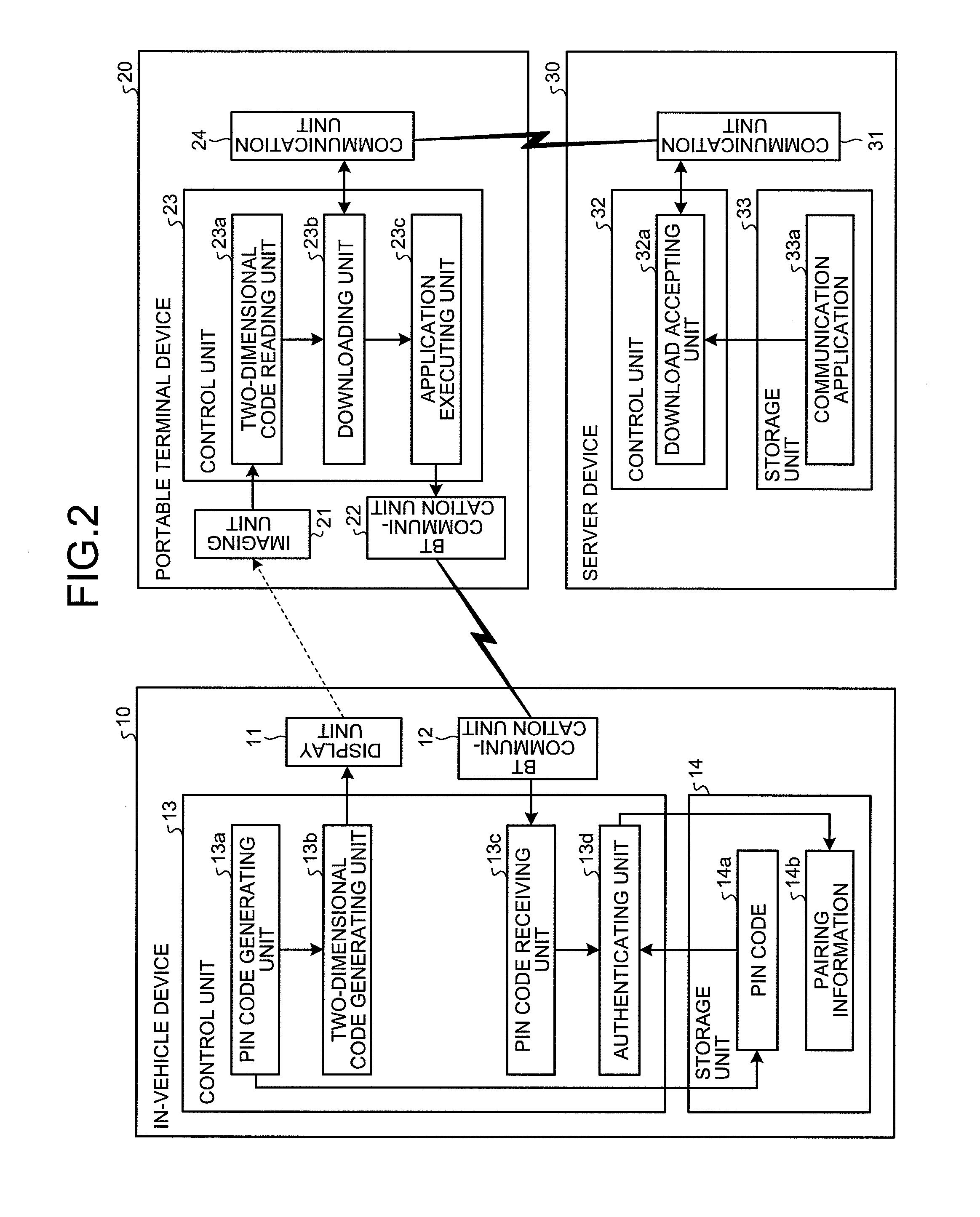
Authentication method, authentication system, in-vehicle device, and authentication apparatus
InactiveUS20100241857A1Prevent unauthorized accessSimple wayKey distribution for secure communicationAnti-theft devicesIn vehicleTerminal equipment
An authentication system is configured such that: an in-vehicle device generates an authentication key, and displays on a display unit, a two-dimensional code including the generated authentication key and a URL indicating a predetermined WEB page on a network; and a portable terminal device acquires the authentication key and the URL from the two-dimensional code by reading the two-dimensional code via an imaging unit, downloads a communication program for communicating with the in-vehicle device from the WEB page indicated by the URL, and transmits the authentication key to the in-vehicle device by causing the downloaded communication program to operate.
Owner:FUJITSU GENERAL LTD
Electronic bankbook and processing system for financial transaction information using electronic bankbook
InactiveUS6029887AImprove security levelImprove securityComplete banking machinesFinanceReceiptSemiconductor memory
PCT No. PCT / JP95 / 01427 Sec. 371 Date Mar. 18, 1996 Sec. 102(e) Date Mar. 18, 1996 PCT Filed Jul. 18, 1995 PCT Pub. No. WO96 / 02890 PCT Pub. Date Feb. 1, 1996The object of the present invention is to propose an account bankbook, a money transfer card, a receipt file, and a checkbook utilizing an optical card, an IC card, or a hybrid optical / IC card. On the surface of a resin card base board 1 are formed an IC chip 11, an optical recording sheet 13, a magnetic stripe 14, and an embossment 12. In a semiconductor memory within the IC chip 11 are written validation keys, search keys, payee information, the upper limit amount of a check, and a program for processing transaction data. Access restrictions corresponding to various applications are imposed upon these data. The history of various cash transactions is recorded in the optical recording sheet 13. These records are of write-once type and rewriting or deletion thereof is impossible.
Owner:N T T DATA TSUSHIN KK
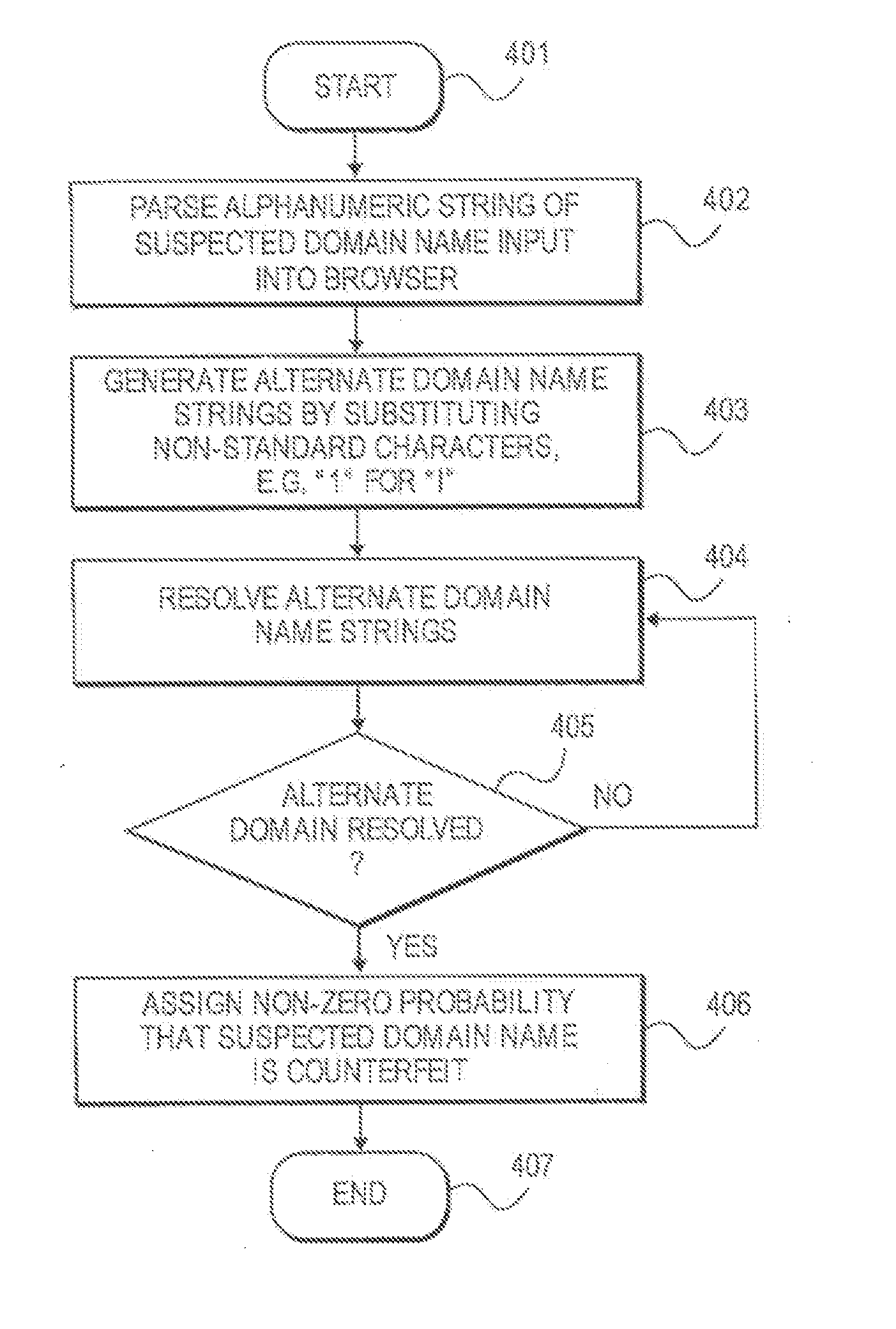
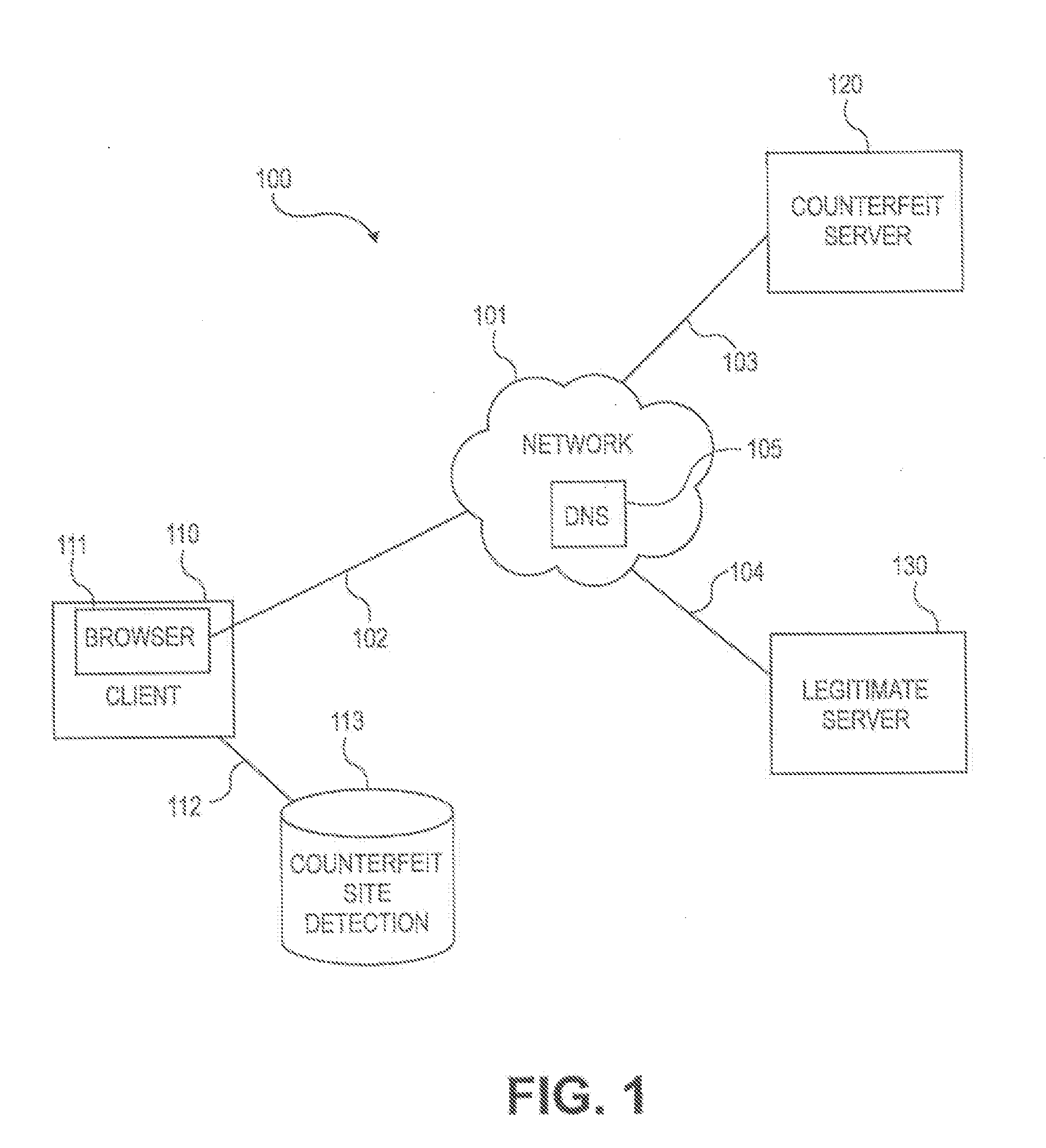
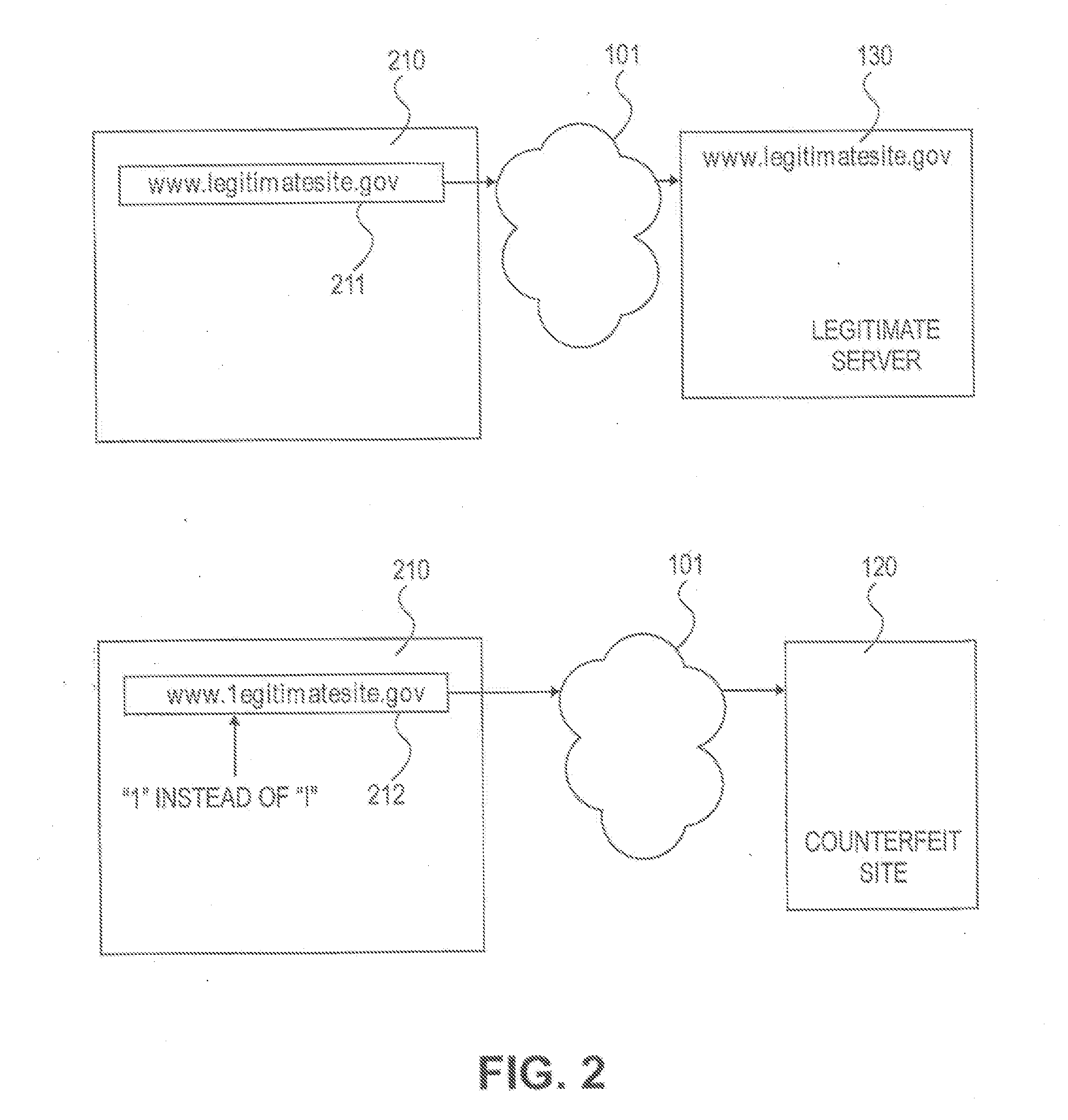
Method and system for determining a probability of entry of a counterfeit domain in a browser
ActiveUS20080092242A1Easy to useImprove security levelMemory loss protectionDigital data processing detailsDomain nameUniform resource locator
Embodiments of the present invention provide a method and system for determining a probability that a suspected domain name of a domain accessed using a universal resource locator (URL), which can be entered as a character string into a browser associated with a client in a net environment, is a counterfeit of a legitimate domain name. Characters in the suspected domain name can be identified as known as likely to be deceptively substituted for corresponding legitimate characters of a legitimate domain name. An alternate domain name is generated by substituting predetermined characters with the corresponding legitimate characters. An attempt can be made to resolve alternate domains of the alternate domain names. If the names are successfully resolved, a non-zero probability is assigned to the suspected domain name as being counterfeit.
Owner:RED HAT
Method for repairing intervertebral discs
ActiveUS20080103564A1Increase pressureHalt leakageDiagnosticsPharmaceutical delivery mechanismIntervertebral discBiomedical engineering
A method of repairing a defect in an annulus fibrosus of an intervertebral disc, without excising the entire nucleus pulposus of the disc. The method includes inserting an introducer needle through the annulus fibrosus by puncturing the annulus fibrosus with the introducer needle, injecting an in situ curable, bio-compatible polymerizable or polymeric material composition into the disc through the introducer needle directly or indirectly so that the in situ curable composition contacts a defect in the annulus fibrosus; and curing said material in situ.
Owner:PAUZA KEVIN
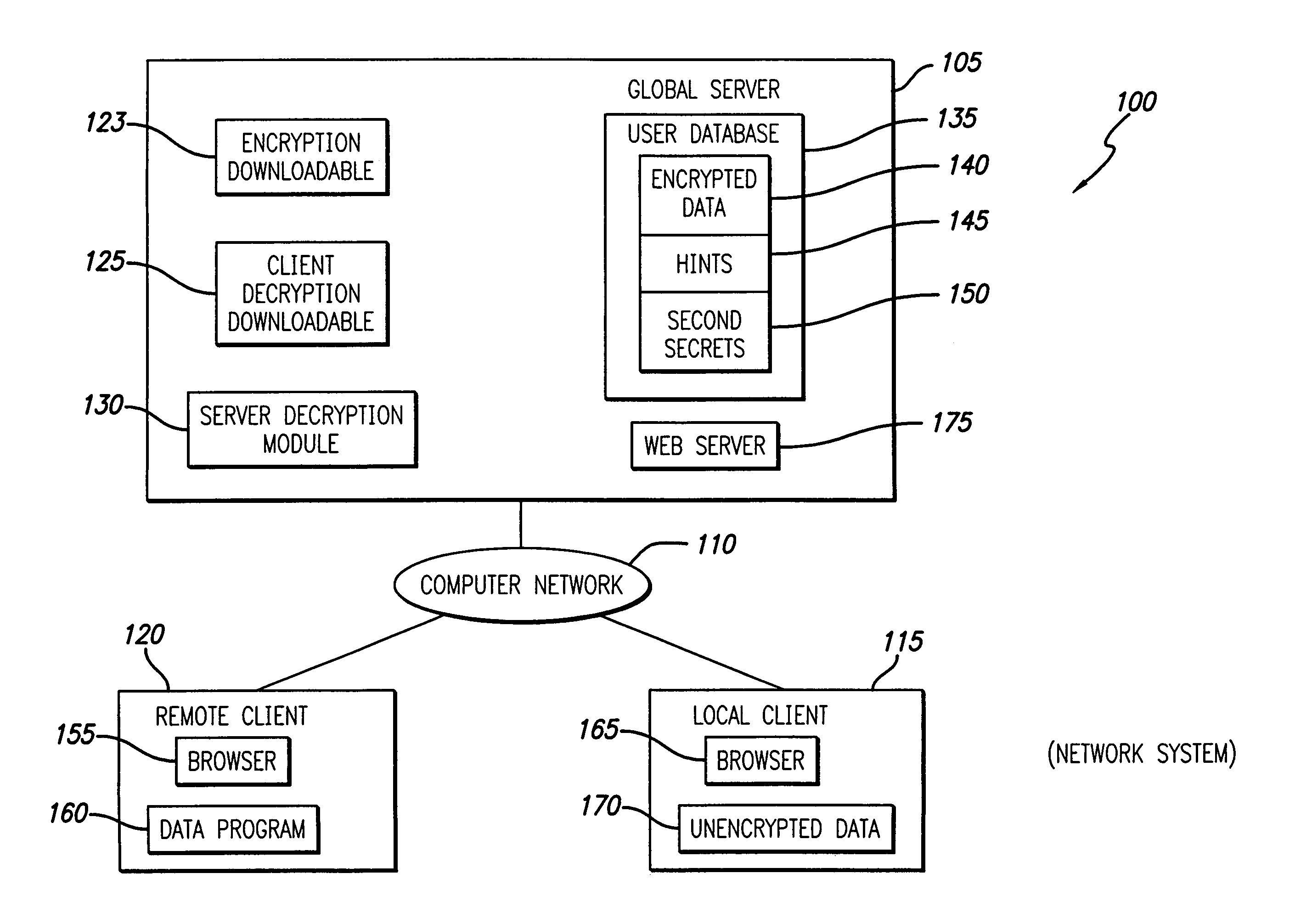
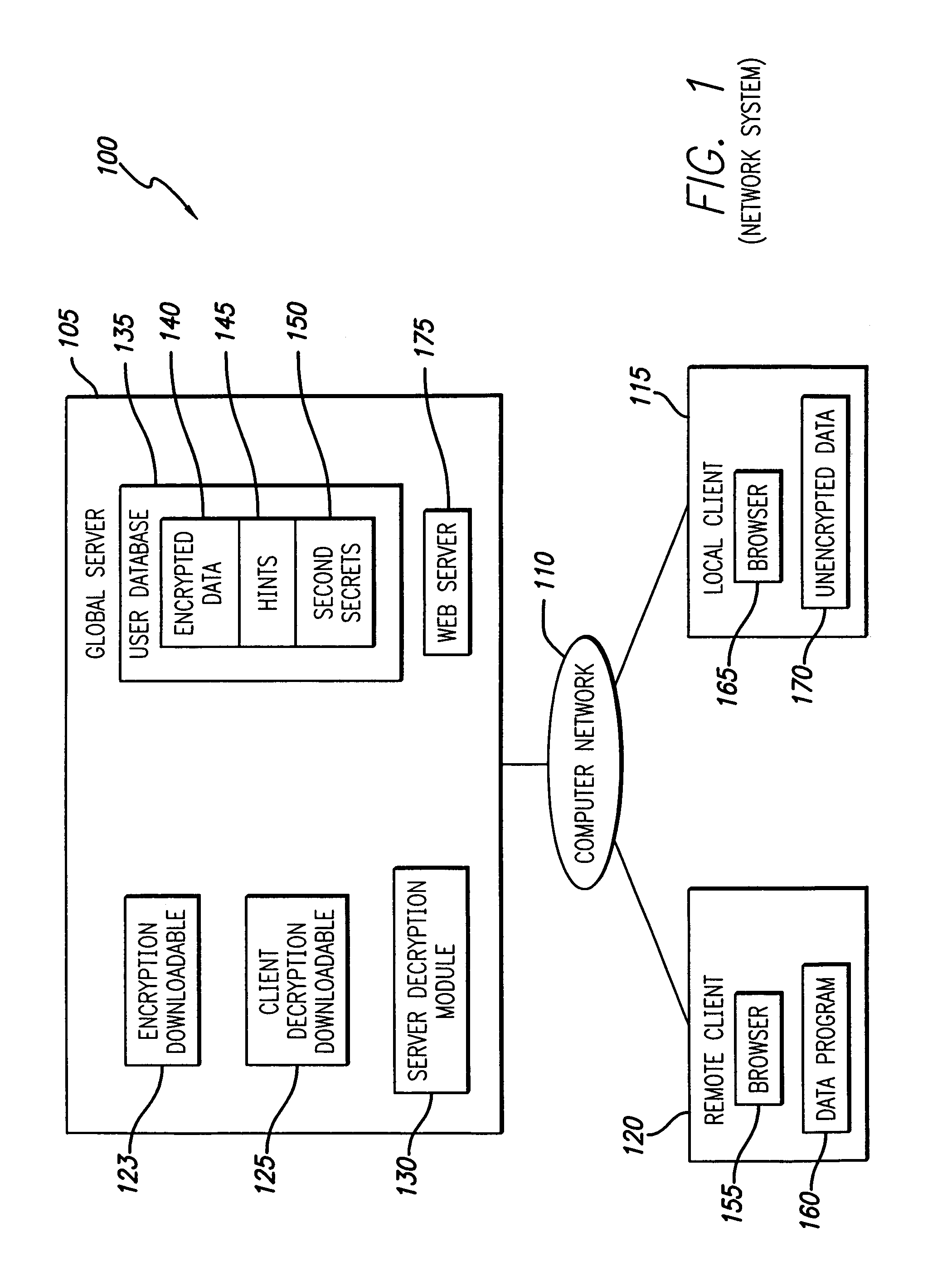
System and method for encrypting and decrypting files
InactiveUS7373517B1Improve the level ofEasy accessKey distribution for secure communicationDigital data processing detailsPasswordClient-side
A system and method distribute the task of decryption between a server and a client. To encrypt data, the client generates an encryption / decryption key. Namely, a user interface obtains a password, generally from a user. A hint generator generates a hint. A key generator generates the key based on the password and the hint. In one embodiment, the key generator hashes the password to generate a first secret, hashes the first secret to generate a second secret, hashes the first secret with the hint to generate an intermediate index, and hashes the second secret and the intermediate index to generate the key. An encryption engine can then use the key to encrypt data. The client then sends the encrypted data and possibly the hint for storage on the server. To decrypt the data, the key must be determined. Accordingly, the server knows some information and the user knows some information for decrypting the data. To generate the key, the decrypting client must first obtain rights to retrieve the hint from the server and must obtain the password from the user. Increased level of security is achieved.
Owner:TACTICA INT +2
Method for electronic payment
ActiveUS7275685B2Improve security levelReduce the possibilityFinanceCredit schemesCredit cardVoice communication
Owner:ADVANCED TRANSACTIONS LLC
Cash dispensing automated banking machine system and communication method
InactiveUS7606767B1Easy to operateMaintain securityFinancePayment architectureApplication serverMachining system
A method of operating an automated banking machine is provided. The method comprises sending a configuration XML message to an ATM from an application server, wherein the configuration XML data includes configuration data targeted to the ATM. The method also includes sending with the application server an application XML message to the ATM, wherein the application XML message includes application data. In addition, the method includes mapping the application data to at least one corresponding resource on the ATM responsive to the configuration data. In addition, the method includes performing a banking transaction using the at least one resource on the ATM responsive to the application XML message.
Owner:DIEBOLD NIXDORF
Aerosolization device
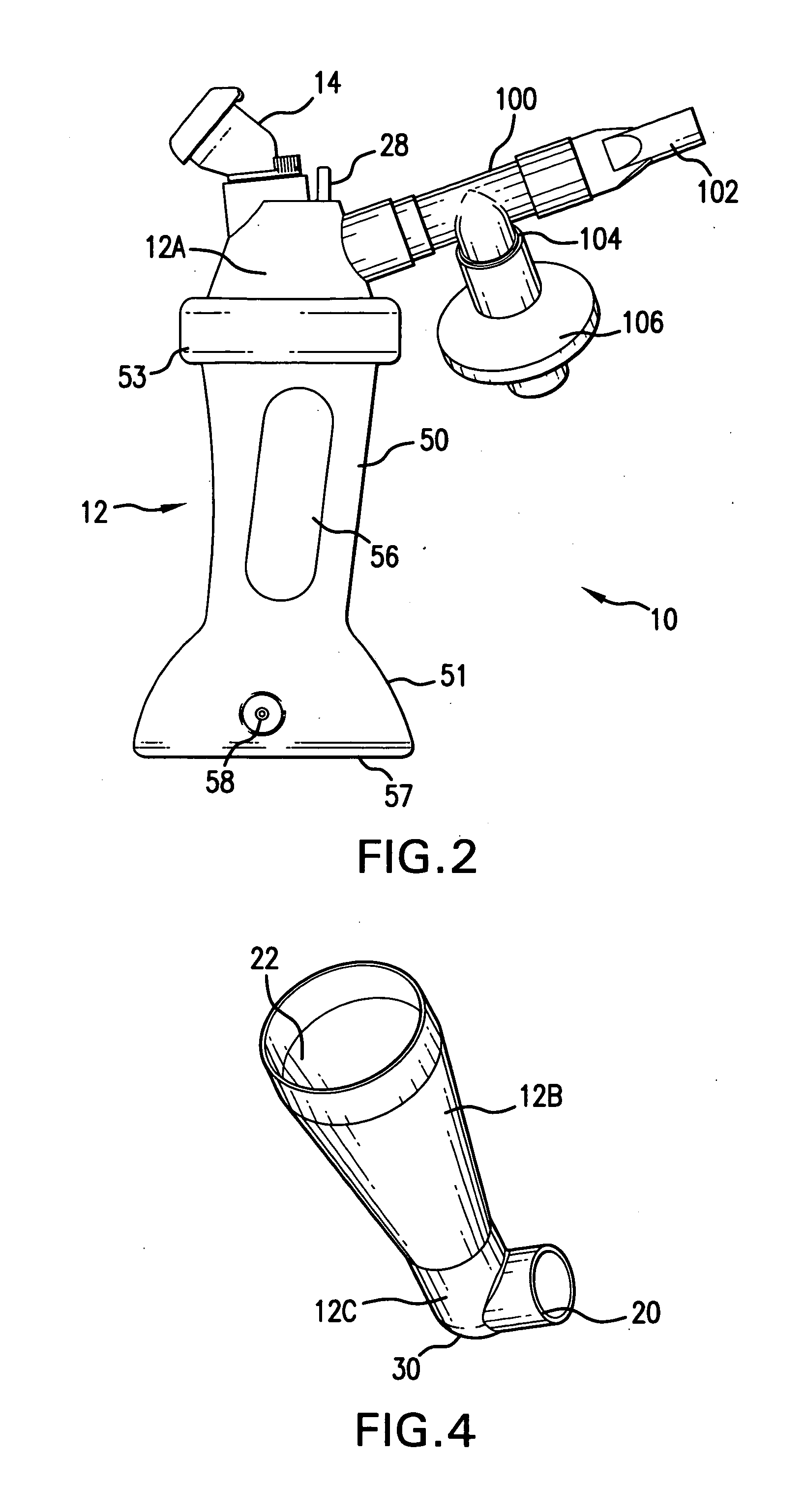
InactiveUS20110108025A1Reduce needImprove security levelTracheal tubesRespiratory masksNebulizerAerosol deposition
An aerosol transfer device (10) for medical aerosol generators comprises a body (12), fluidically coupled to a nebulizer (14) and to a patient interface (16). An ambient air intake (20) is formed into a lower body (12C). The body is shaped and configured to optimize mixing of ambient air from the ambient air intake and the aerosol generated by the nebulizer, resulting in the formation of an aerosol plume having optimum characteristics for delivery of the aerosol to the patient's pulmonary system, such as the central or deep lung regions. The shape and dimensions of the body are further designed to minimize aerosol deposition, thus improving delivery efficiency.
Owner:NEKTAR THERAPEUTICS INC
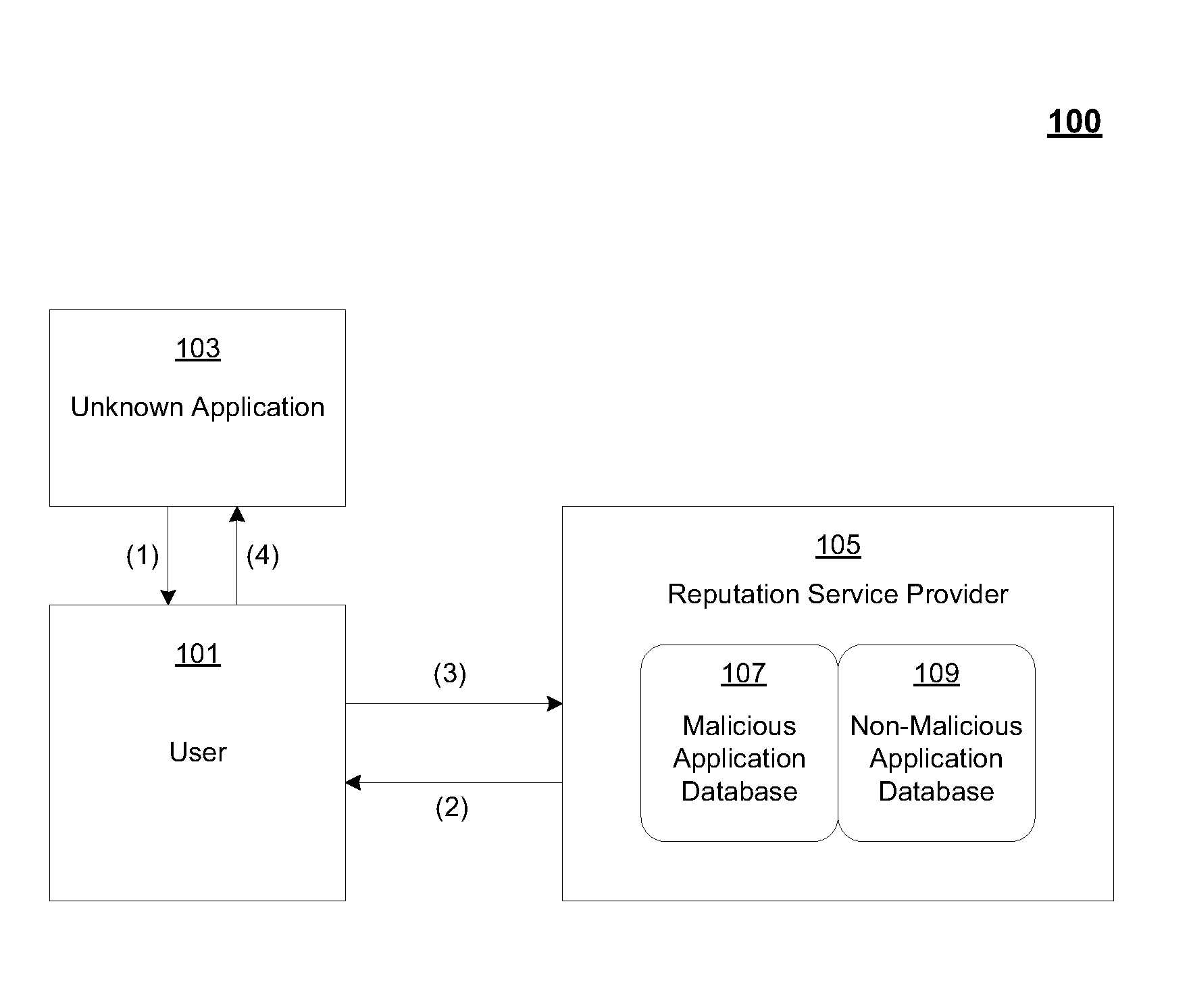
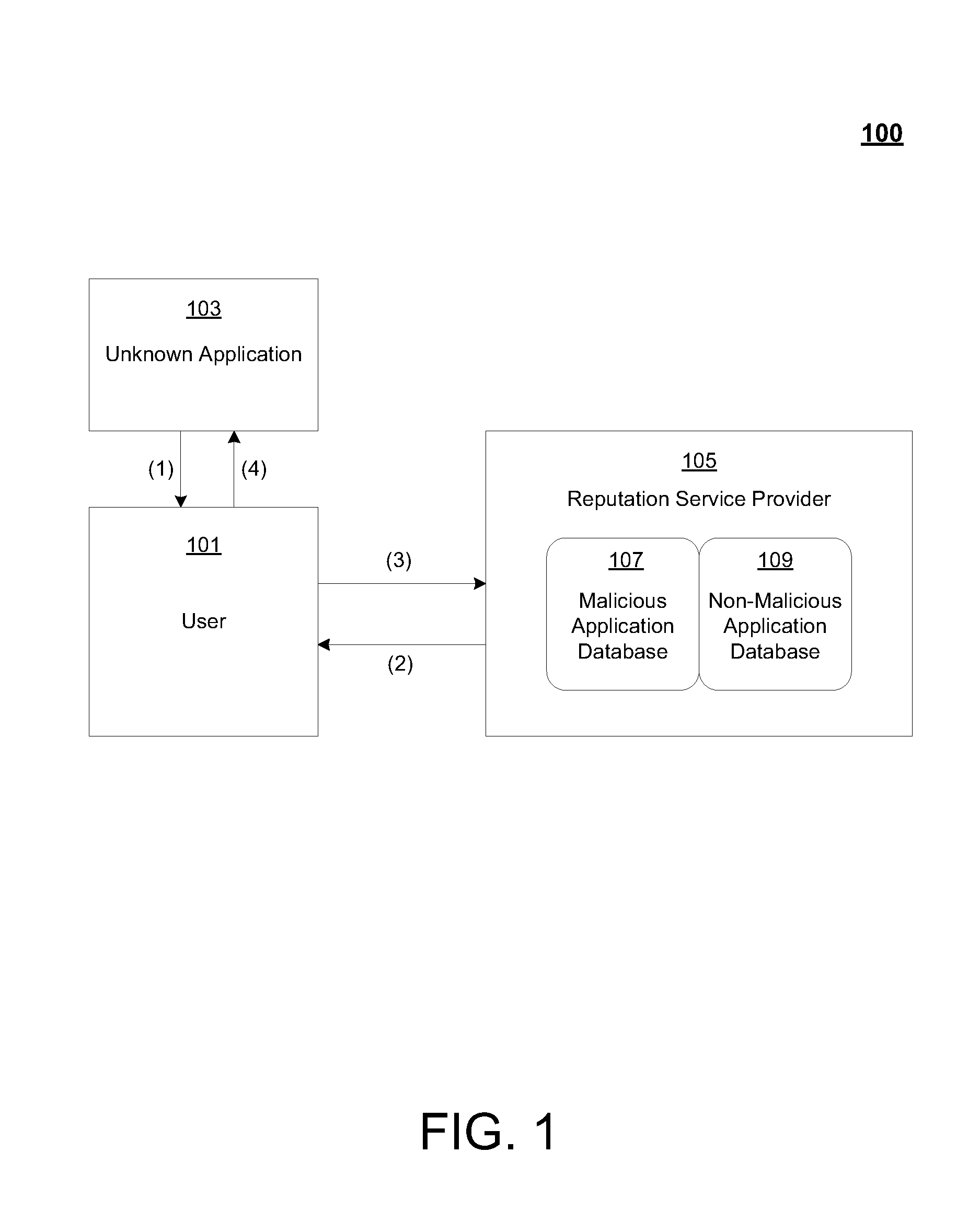
Application reputation service
ActiveUS20100005291A1Reduce riskImprove security levelMemory loss protectionUnauthorized memory use protectionInternet privacySubject matter
The claimed subject matter is directed to the use of an application reputation service to assist users with minimizing their computerized machines' exposure to and infection from malware. Specifically, the claimed subject matter provides a method and system of an application reputation service that contains the reputations for elements that are known to be non-malicious as well as those known to be malicious.One embodiment of the claimed subject matter is implemented as a method to determine the reputation of an element (e.g., an application). When a user attempts to install or execute a new application, the Application Reputation Service is queried by the user's machine with a set of identities for the element. The Application Reputation Service determines the reputation of the application by referencing a knowledge base of known reputations and returns an indication (e.g., an overall rating, or a flag) of how safe that application would be to install and run on the user's computer.
Owner:MICROSOFT TECH LICENSING LLC
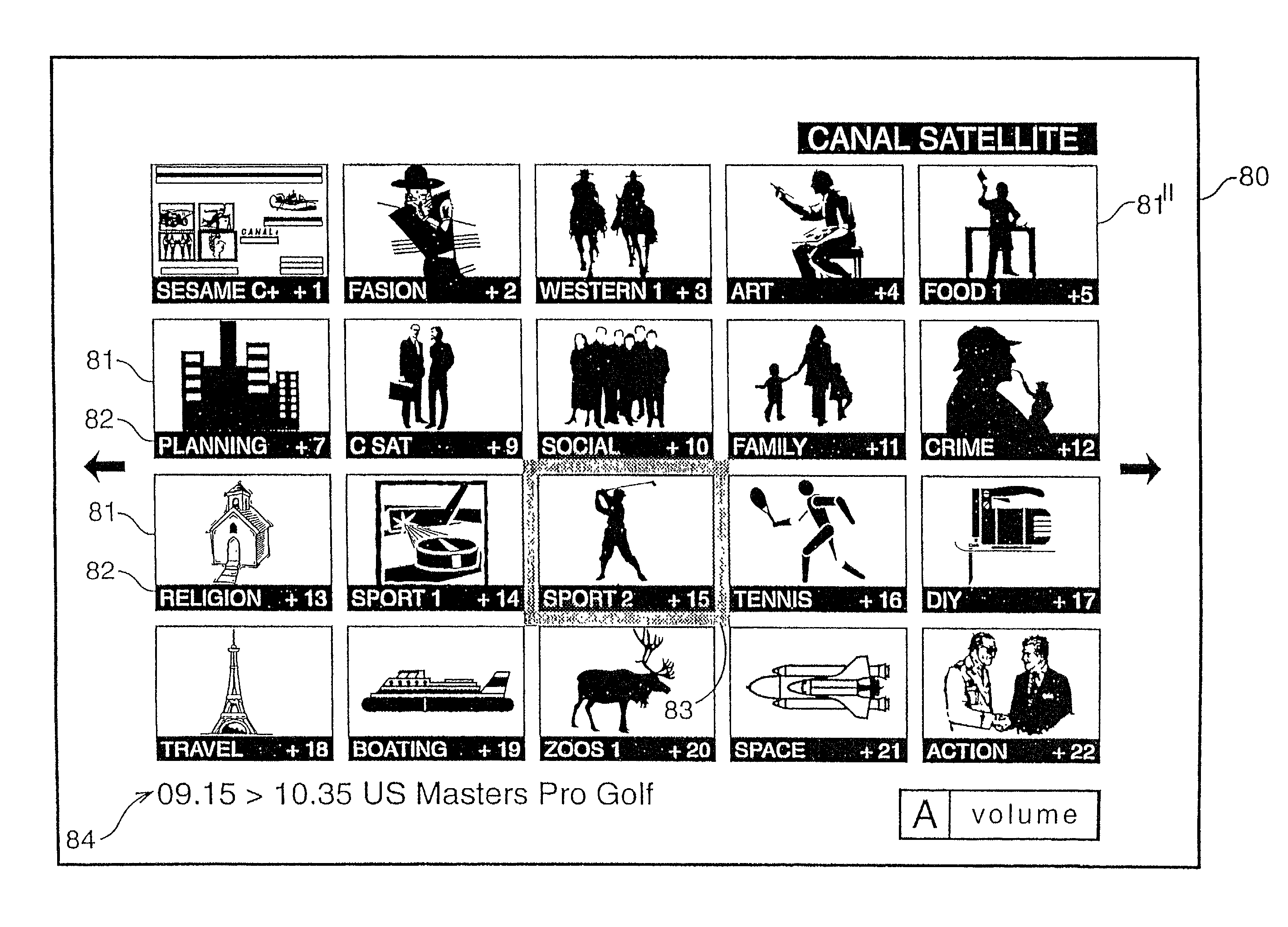
Navigation system for a multichannel digital television system
InactiveUS7757252B1Prevent videoPrevent audio accessTelevision system detailsAnalogue secracy/subscription systemsTelecommunicationsNavigation system
The present invention provides a digital television system where access rights to a programme or channel are received analyzed by the decoder in determining whether to permit or prohibit full audio and visual access by the user to that programme or channel when displayed in respective windows of a mosaic formation.
Owner:INTERDIGITAL CE PATENT HLDG
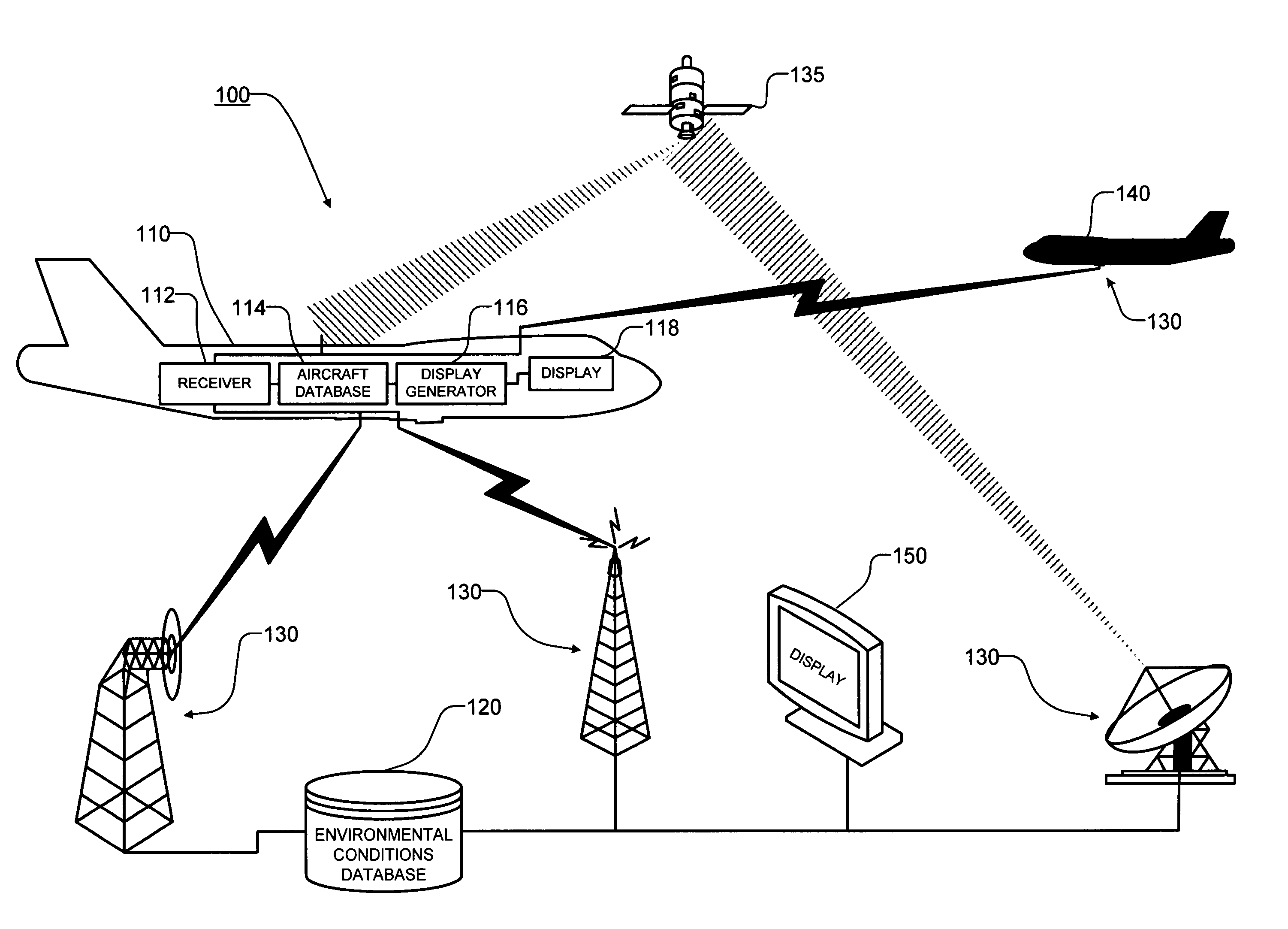
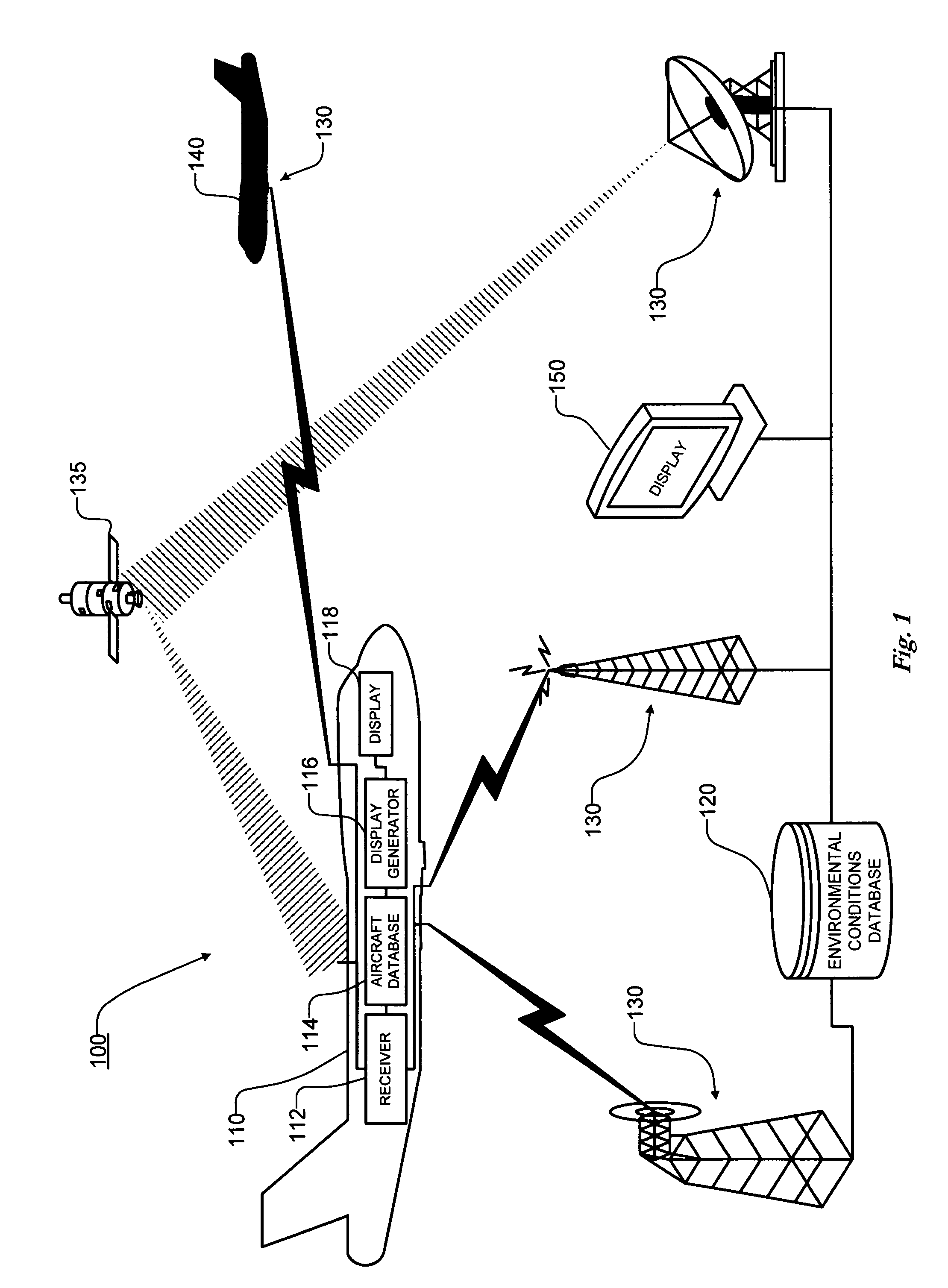
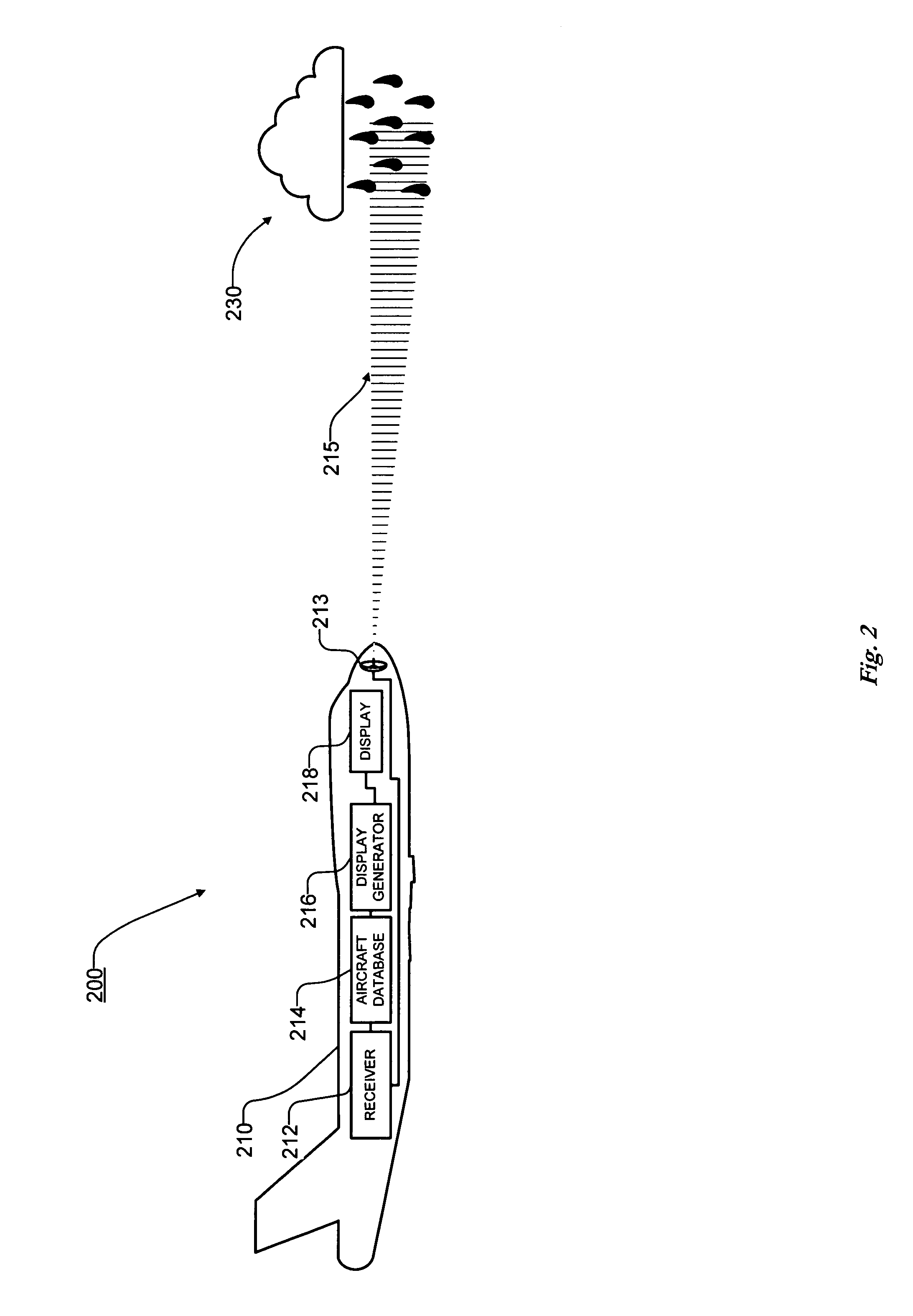
Transmission, receipt, combination, sorting, and presentation of vehicle specific environmental conditions and hazards information
InactiveUS7471995B1Improve situational awarenessImprove safetyInstruments for road network navigationEnergy saving arrangementsReceiptEngineering
A method for planning or updating a travel route for a vehicle based on a potential affect of environmental conditions on a particular vehicle and displaying environmental conditions information on a display.
Owner:DTN LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com