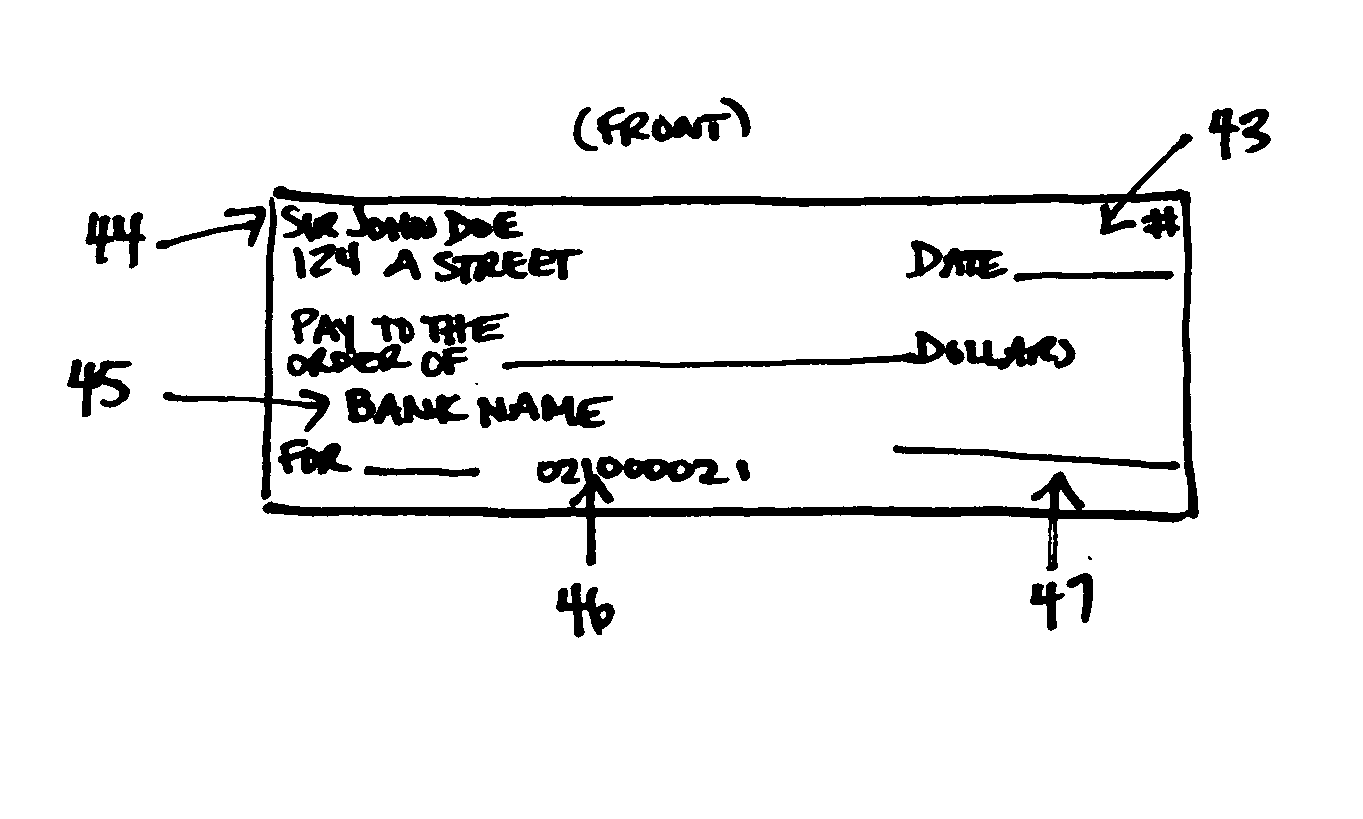Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
19930results about "Protocol authorisation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
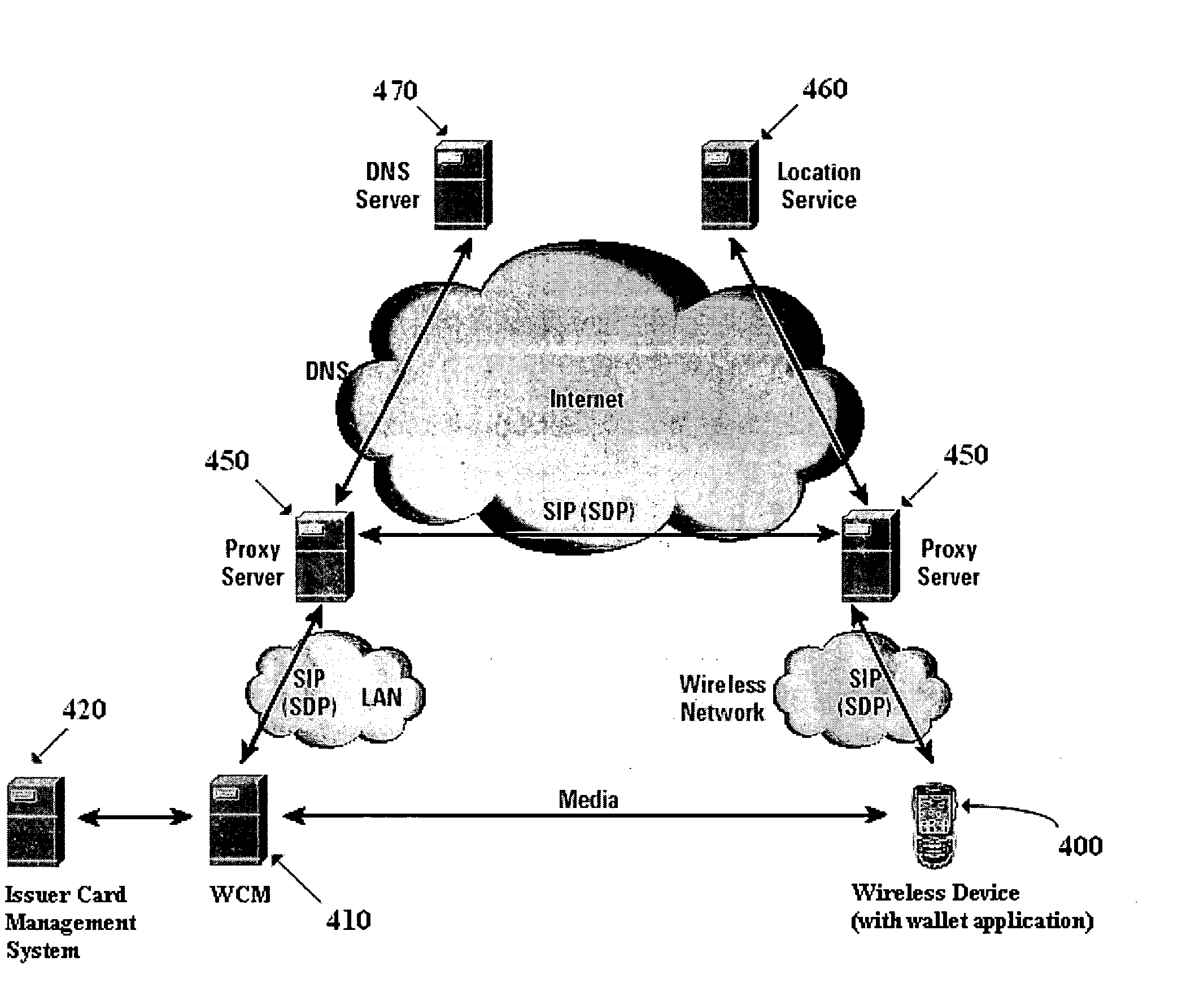
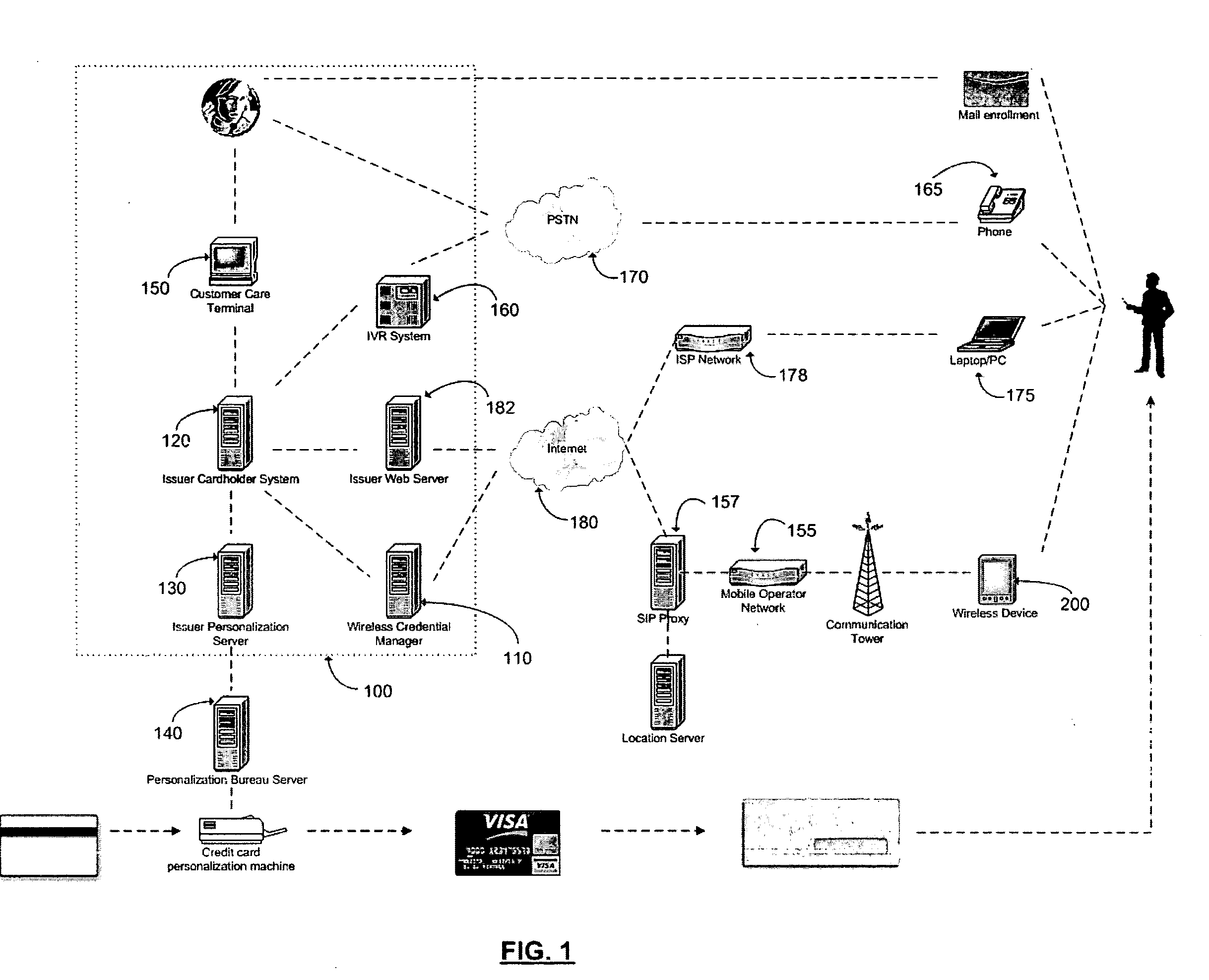
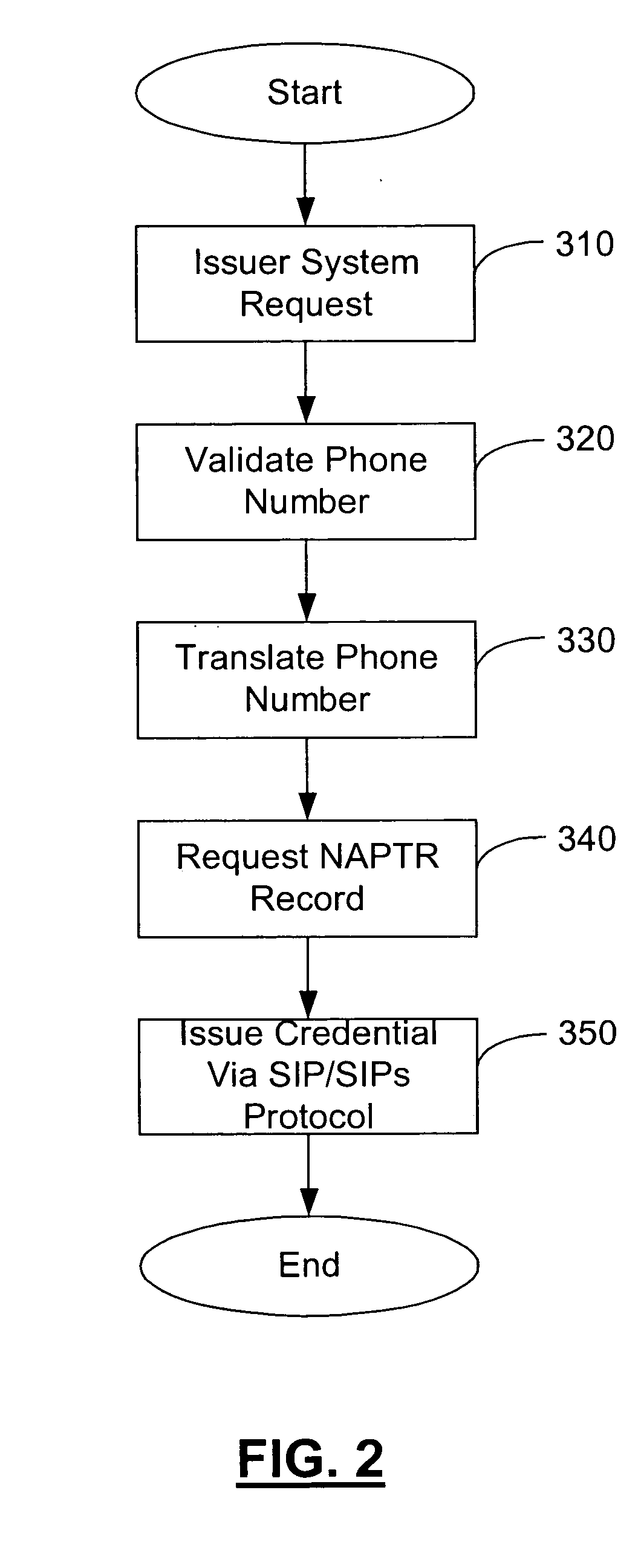
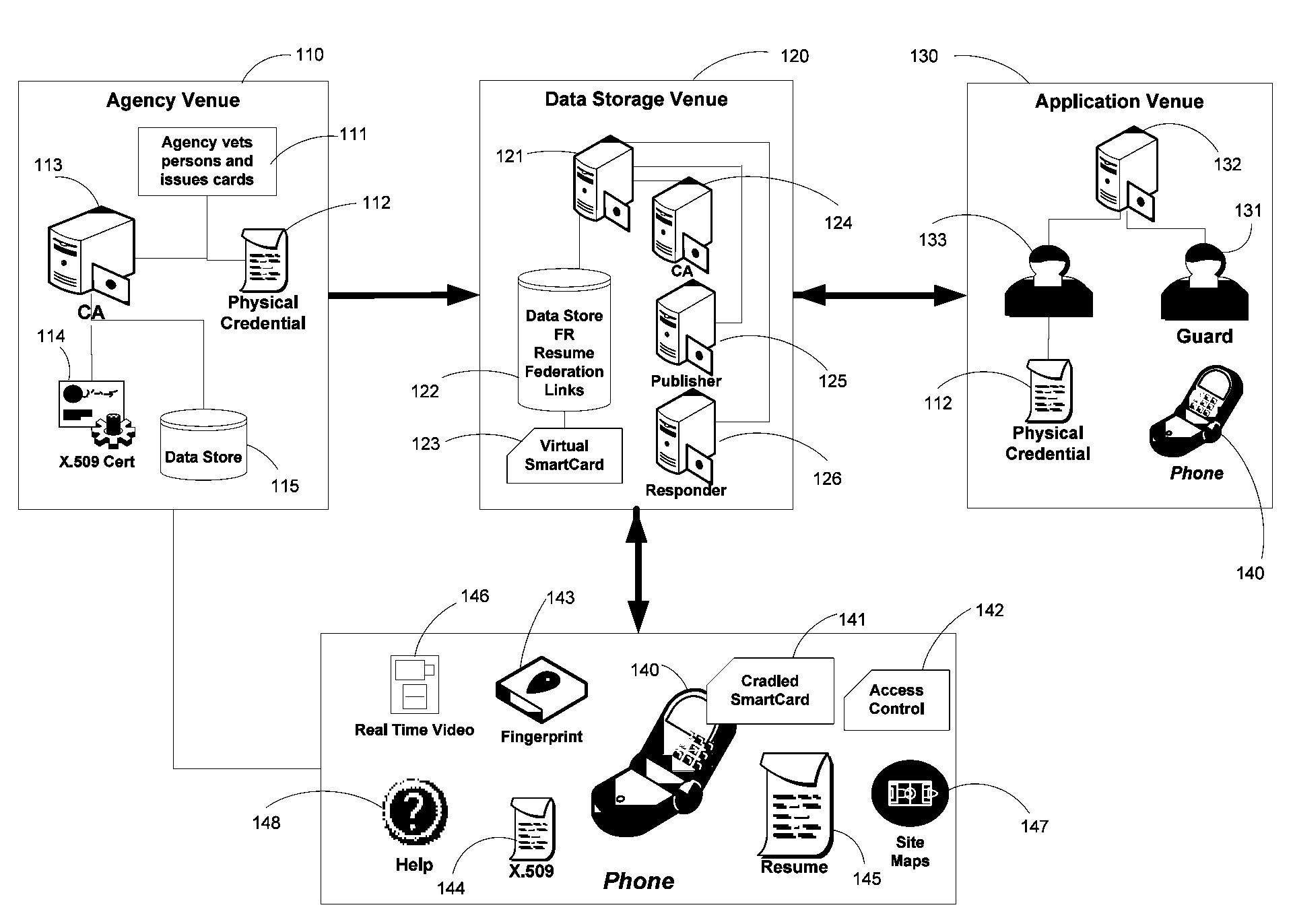
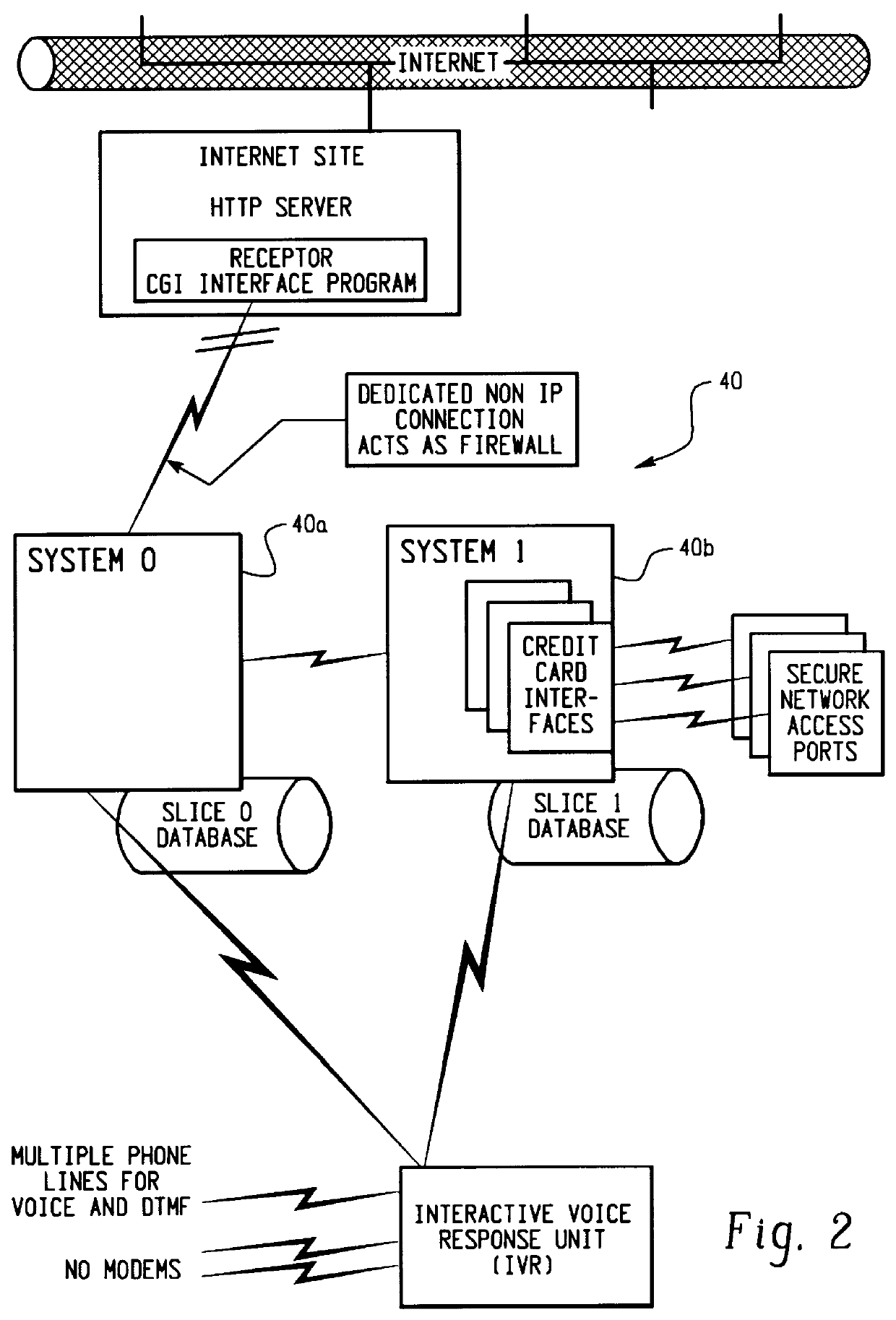
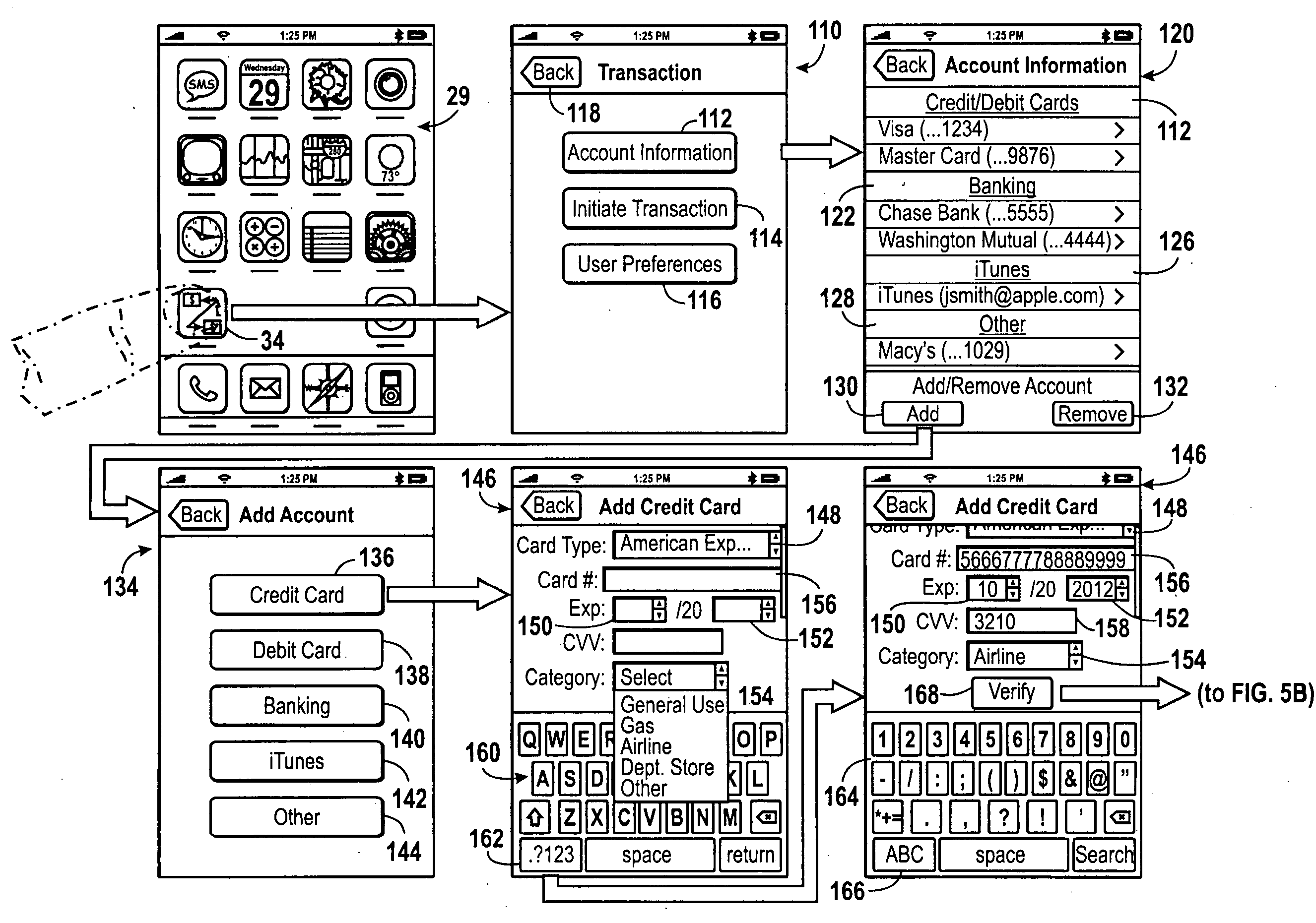
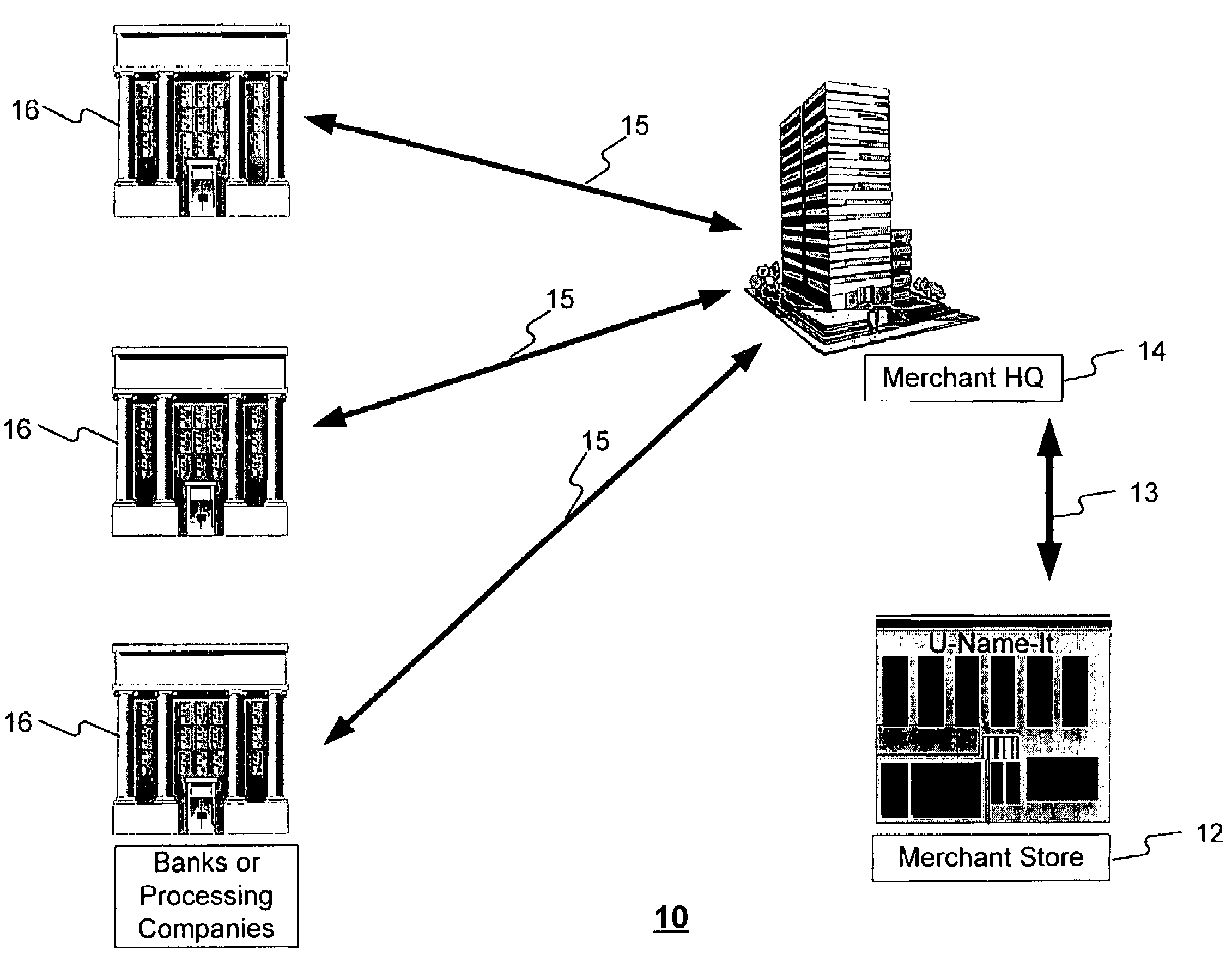
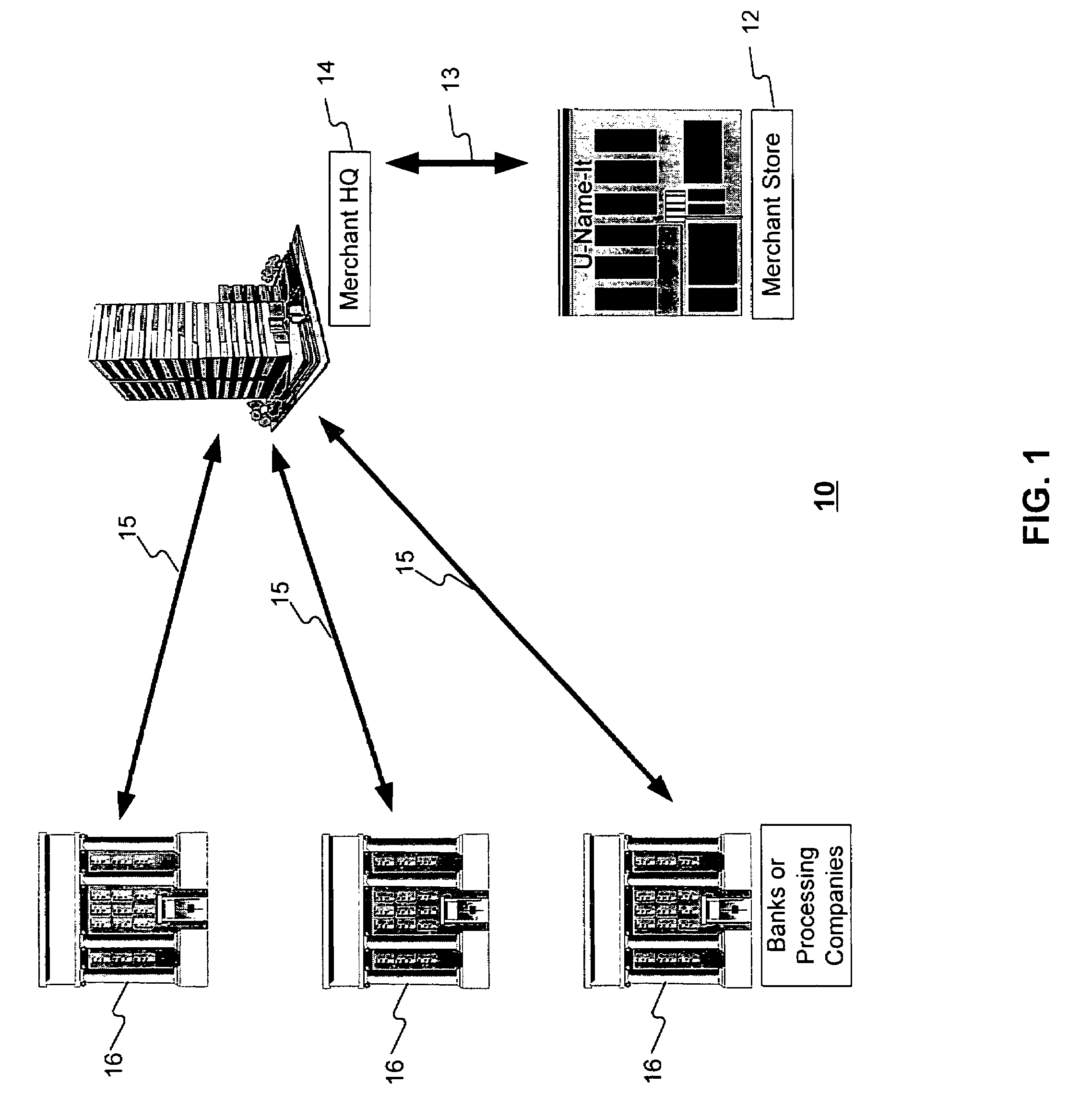
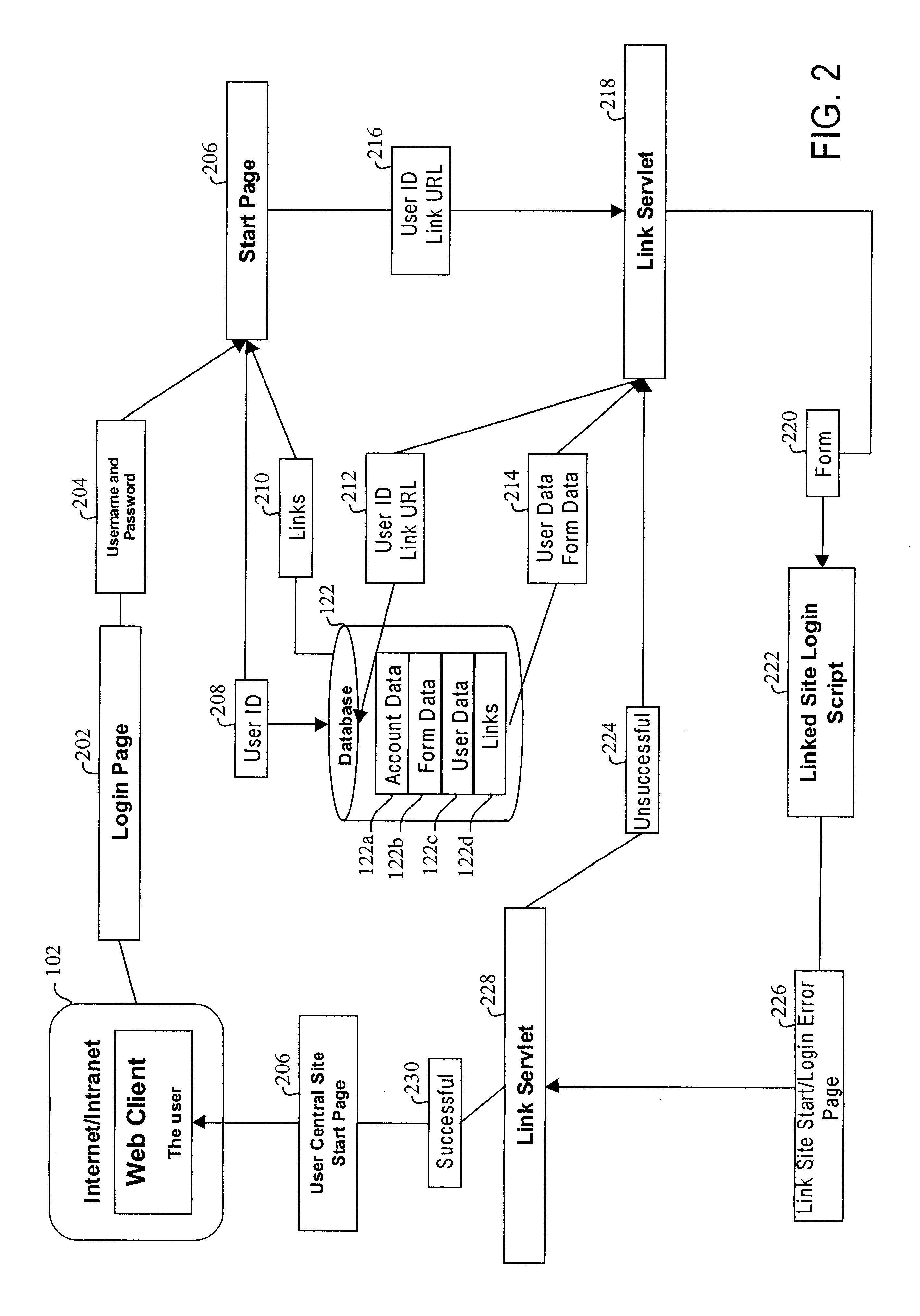
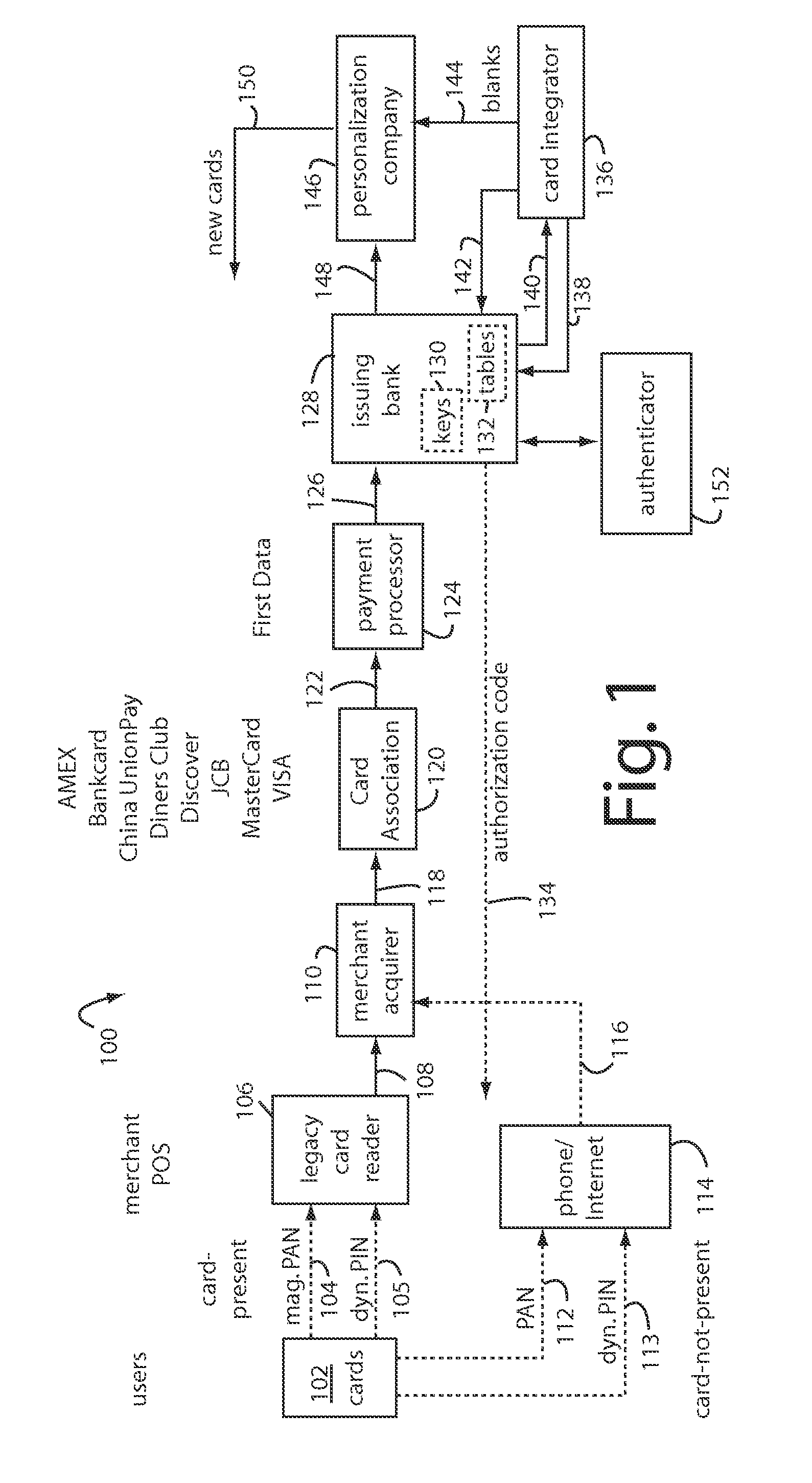
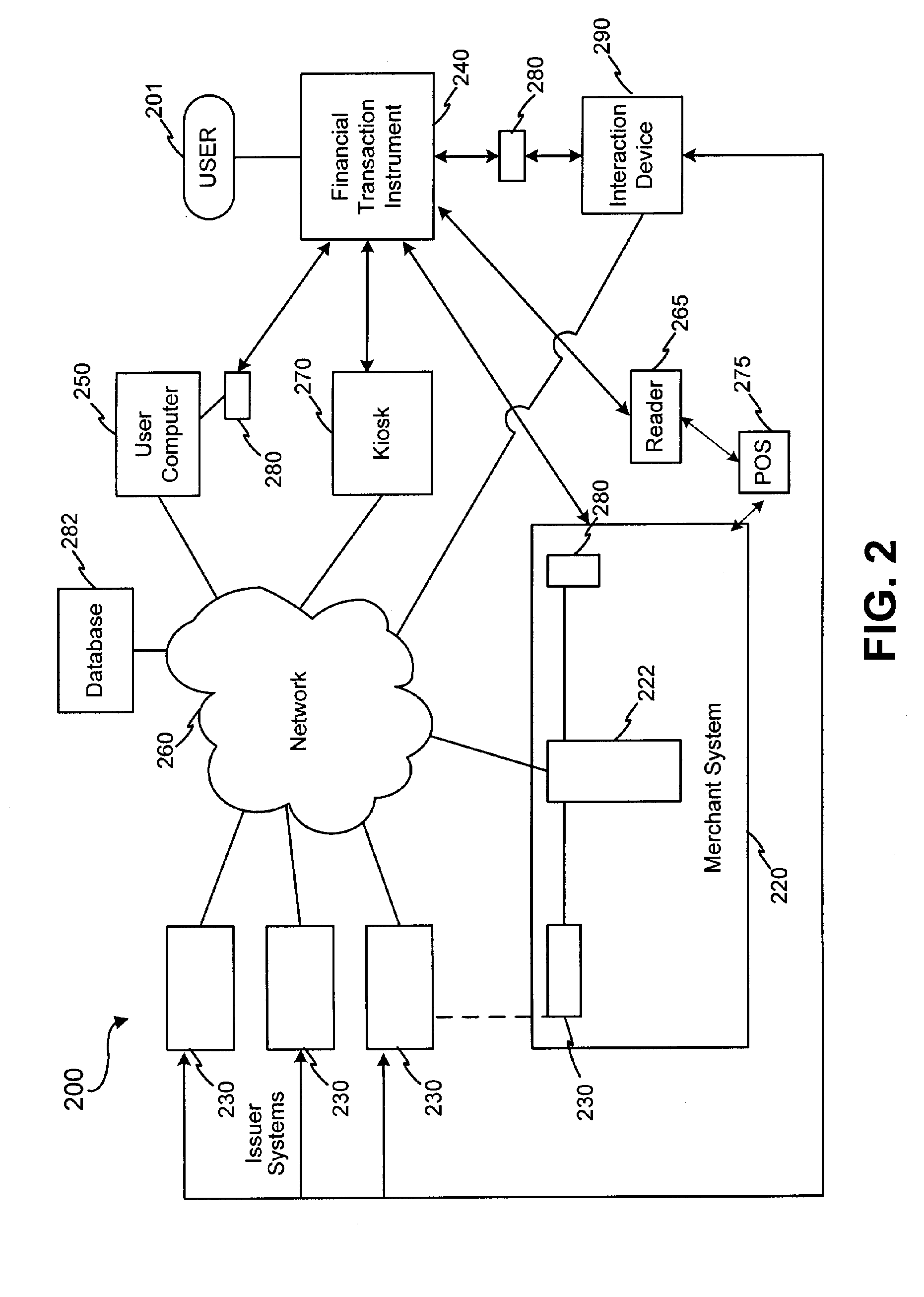
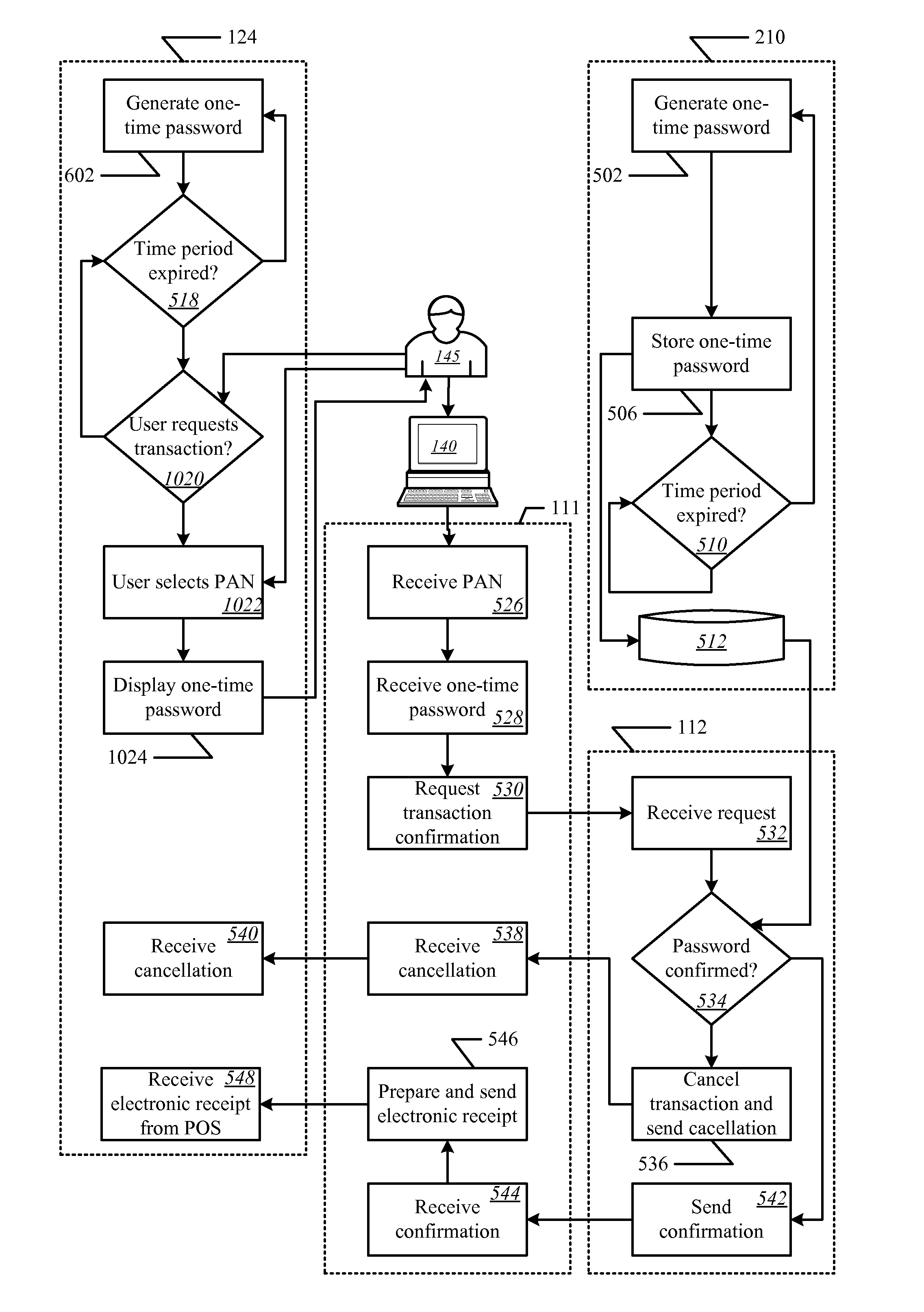
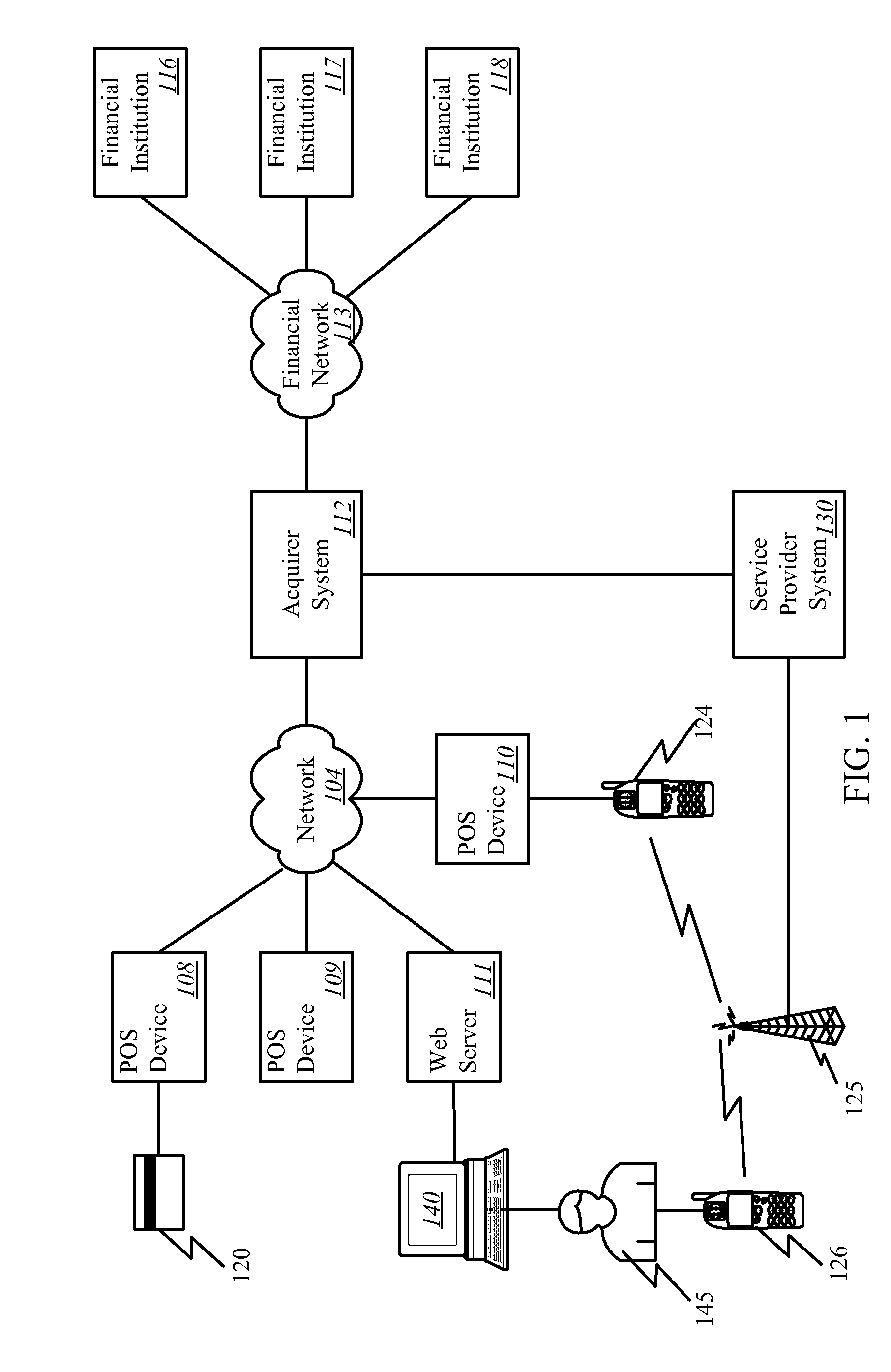
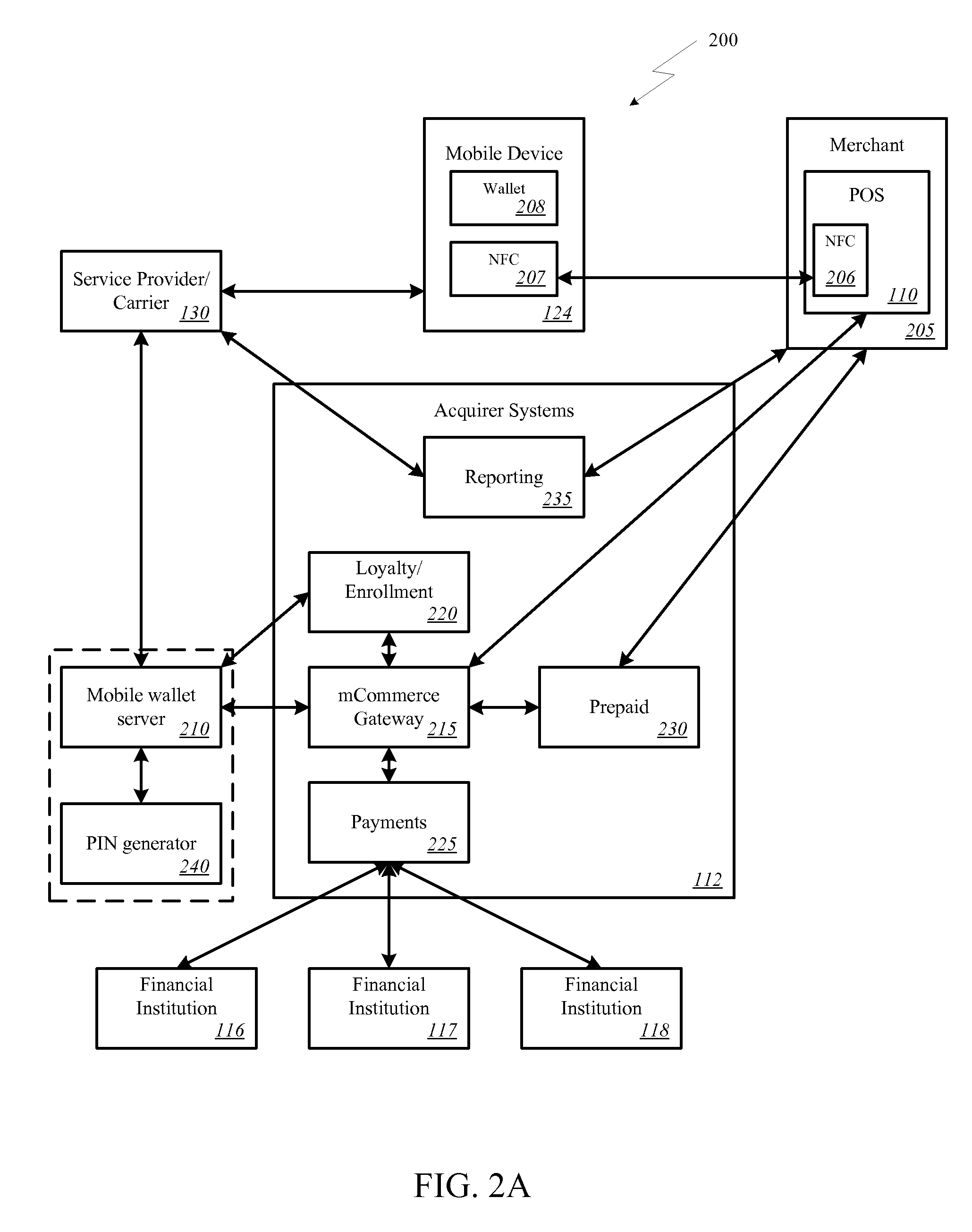
Method and apparatus for managing credentials through a wireless network
ActiveUS20060165060A1Convenient and efficient and secure distributionNear-field in RFIDData switching by path configurationCredit cardWireless mesh network
A novel system and methodology for conducting financial and other transactions using a wireless device. Credentials may be selectively issued by issuers such as credit card companies, banks, and merchants to consumers permitting the specific consumer to conduct a transaction according to the authorization given as reflected by the credential or set of credentials. The preferred mechanism for controlling and distributing credentials according to the present invention is through one or more publicly accessible networks such as the Internet wherein the system design and operating characteristics are in conformance with the standards and other specific requirements of the chosen network or set of networks. Credentials are ultimately supplied to a handheld device such as a mobile telephone via a wireless network. The user holding the credential may then use the handheld device to conduct the authorized transaction or set of transactions via, for example, a short range wireless link with a point-of-sale terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
Multifactorial optimization system and method
A method for providing unequal allocation of rights among agents while operating according to fair principles, comprising assigning a hierarchal rank to each agent; providing a synthetic economic value to a first set of agents at the a high level of the hierarchy; allocating portions of the synthetic economic value by the first set of agents to a second set of agents at respectively different hierarchal rank than the first set of agents; and conducting an auction amongst agents using the synthetic economic value as the currency. A method for allocation among agents, comprising assigning a wealth generation function for generating future wealth to each of a plurality of agents, communicating subjective market information between agents, and transferring wealth generated by the secure wealth generation function between agents in consideration of a market transaction. The method may further comprise the step of transferring at least a portion of the wealth generation function between agents.
Owner:MEADWESTVACO CORP
Transactional services
InactiveUS20070198432A1High level of throughputHigh level of efficiencyCryptography processingComputer security arrangementsTransaction serviceDatabase
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
Wireless wallet
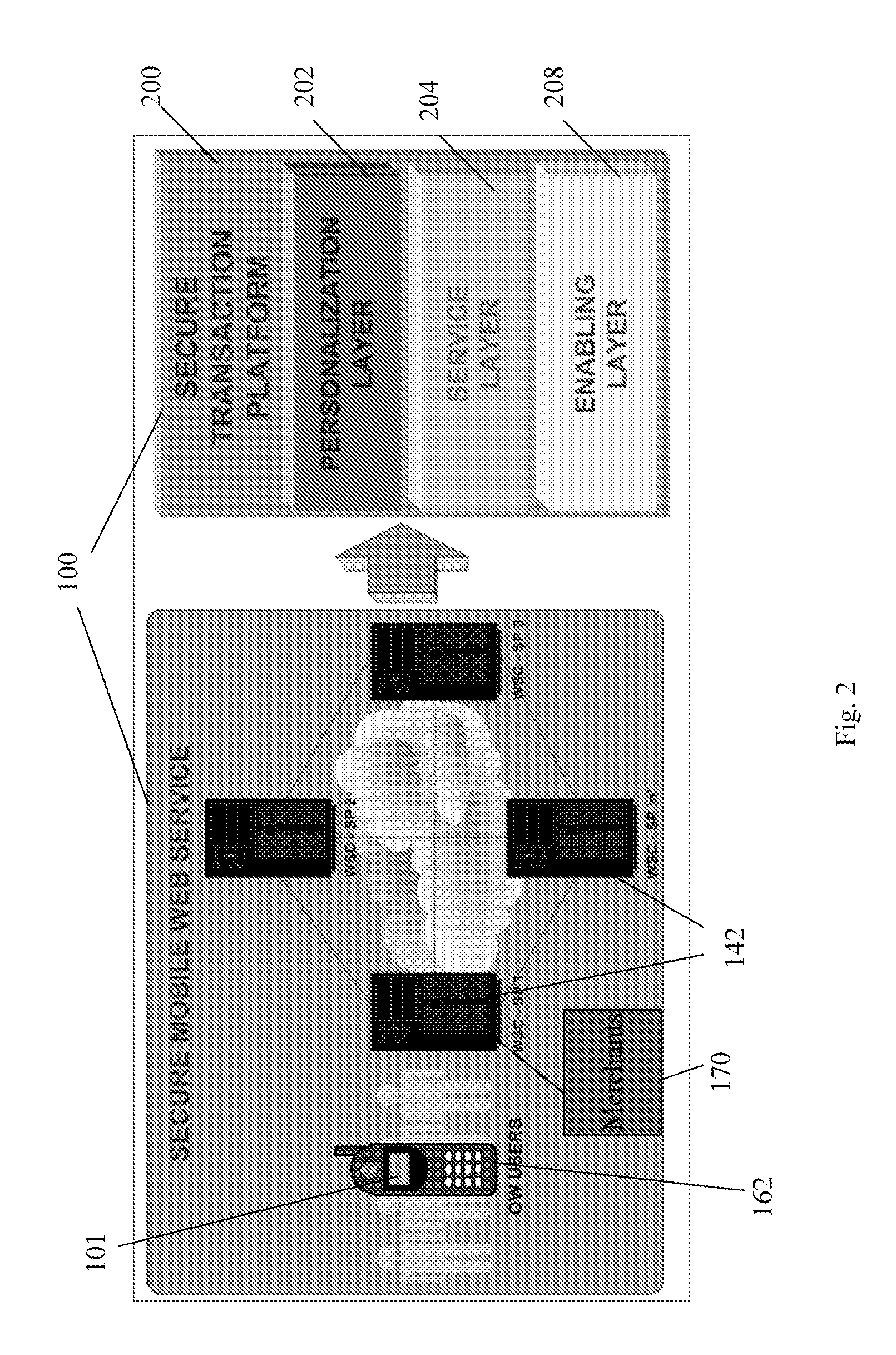
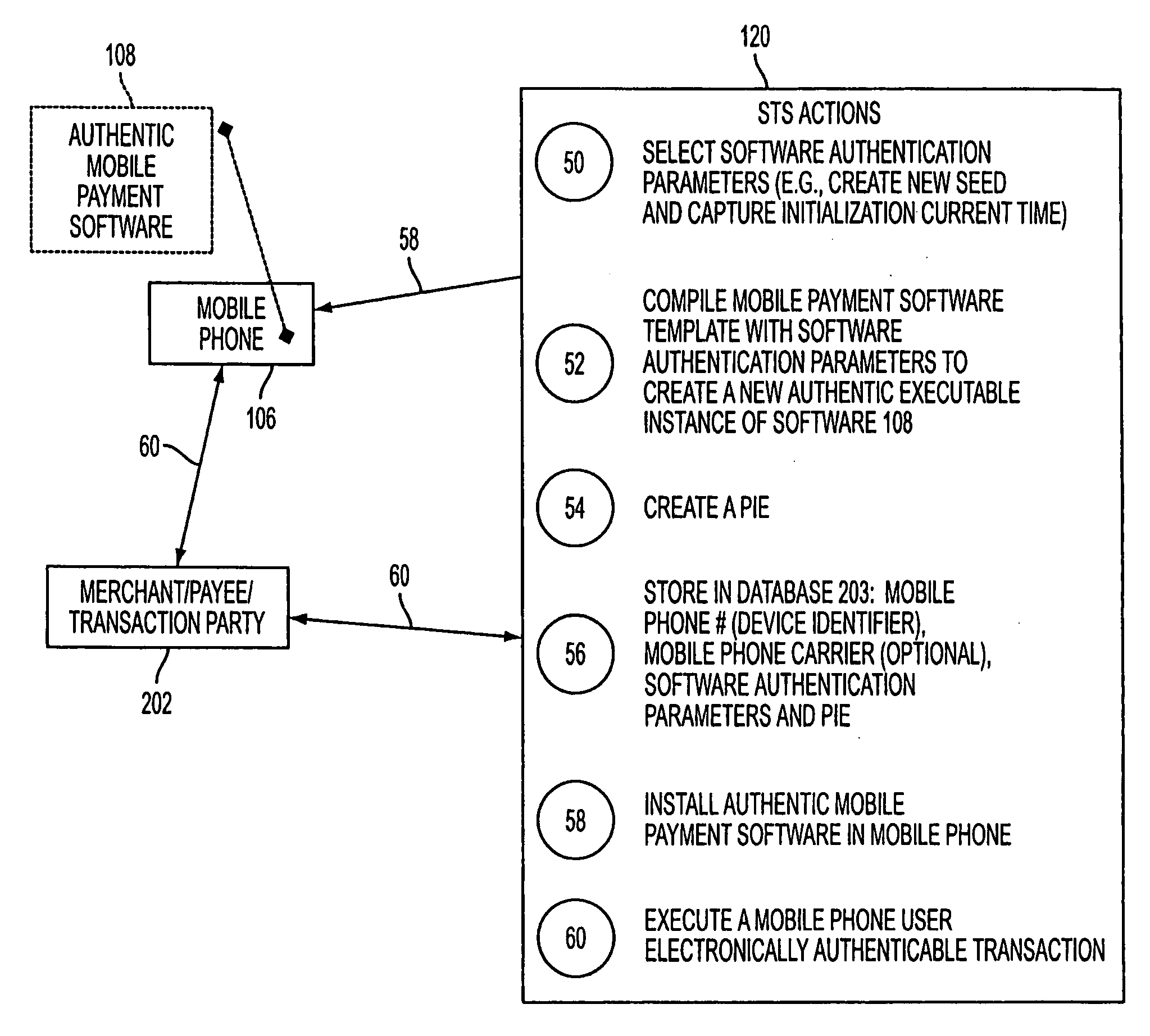
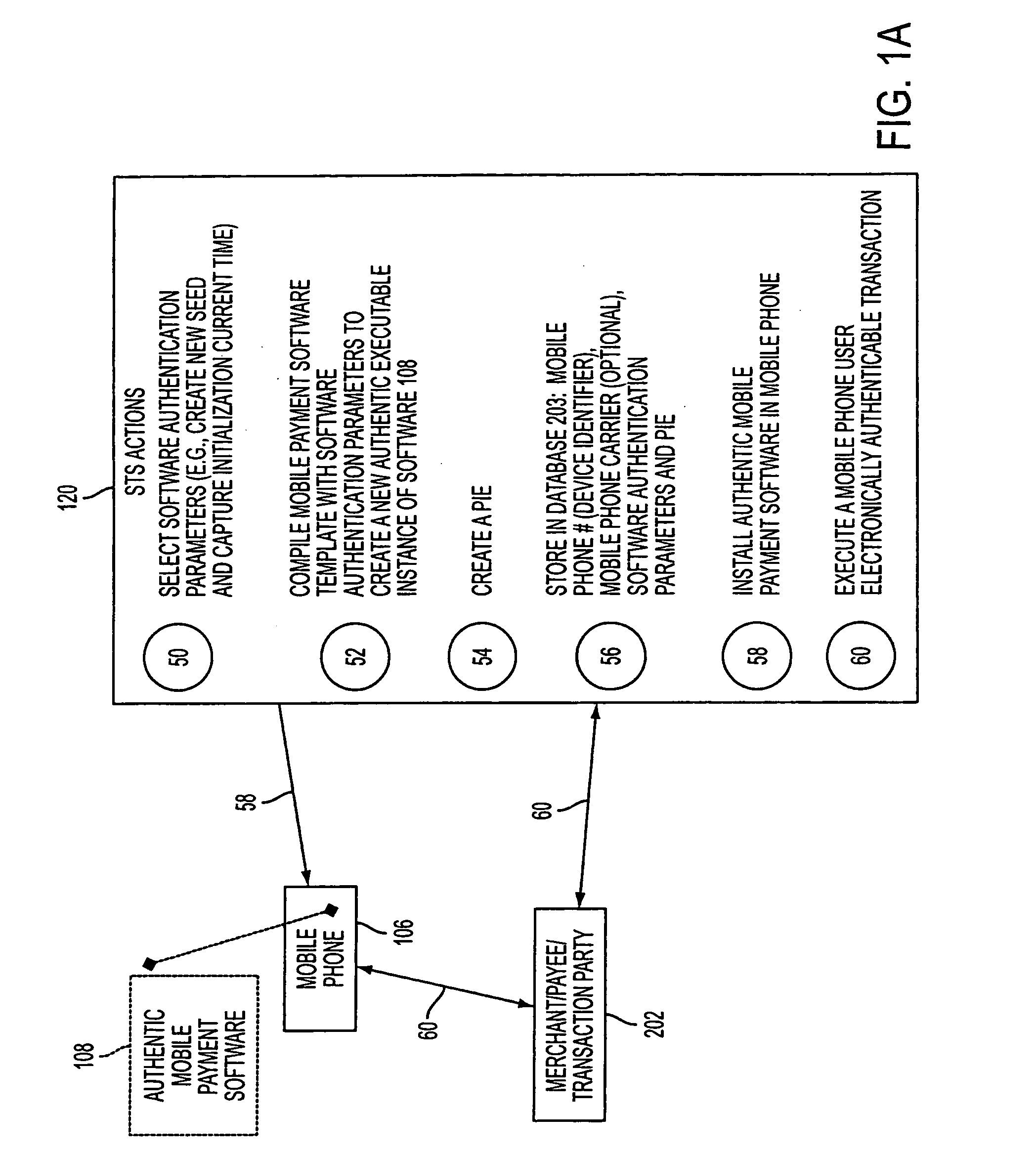
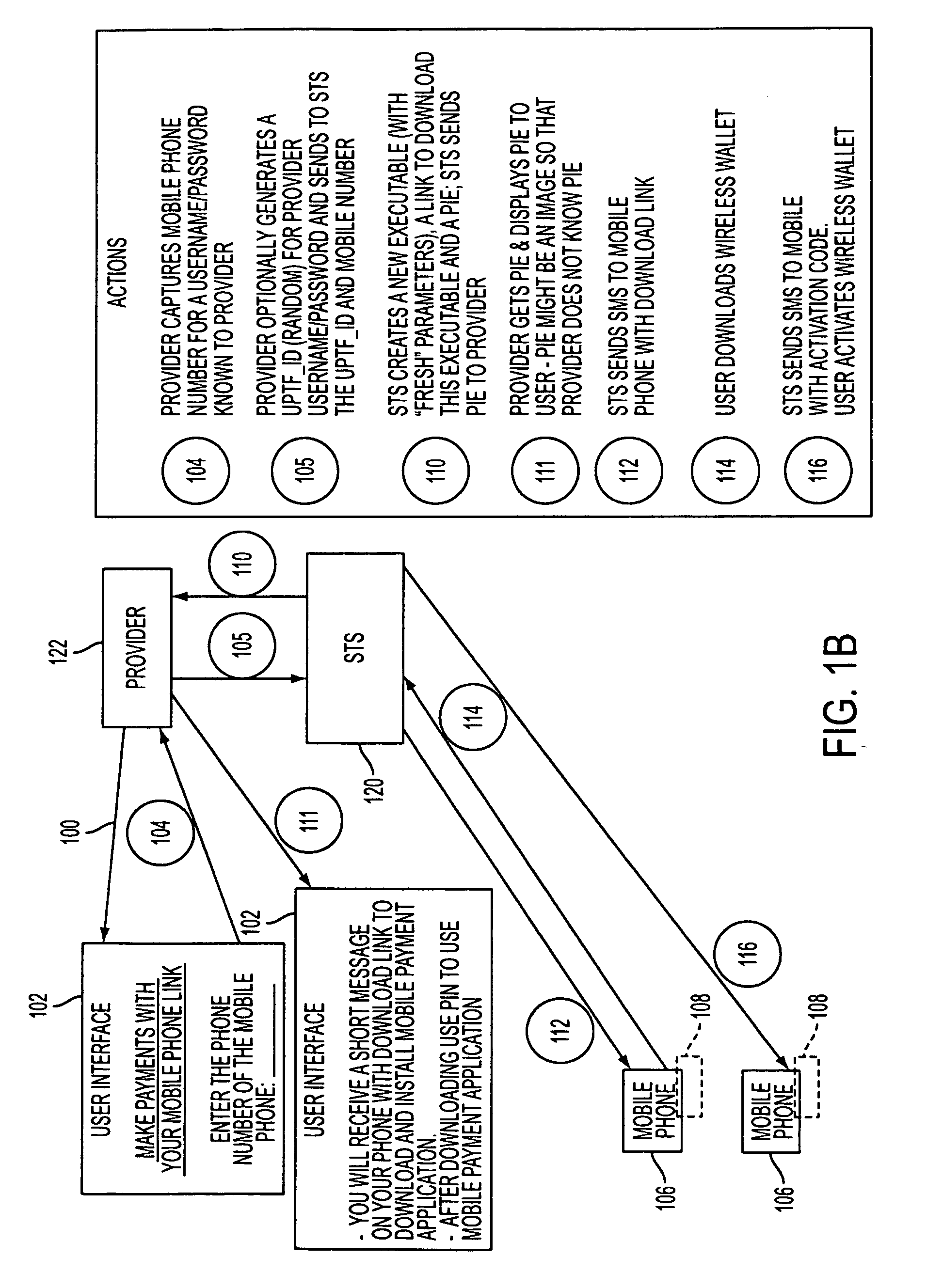
A mobile phone system and method of initializing, at a secure transaction server (STS), a mobile payment software with a software authentication parameter, as an authentic mobile payment software; providing an STS correlation between a personal identification entry (PIE) and the authentic mobile payment software; installing, in a mobile phone, the authentic mobile payment software; and inputting, by a user, the PIE to the installed authentic mobile payment software to generate according to the PIE and the software authentication parameter a transformed secure authenticable mobile phone cashless monetary transaction over the mobile phone network, as a mobile phone wireless wallet of the user of the mobile phone. The mobile phone authenticable cashless monetary transaction is performed according to an agreement view(s) protocol.
Owner:PCMS HOLDINGS INC
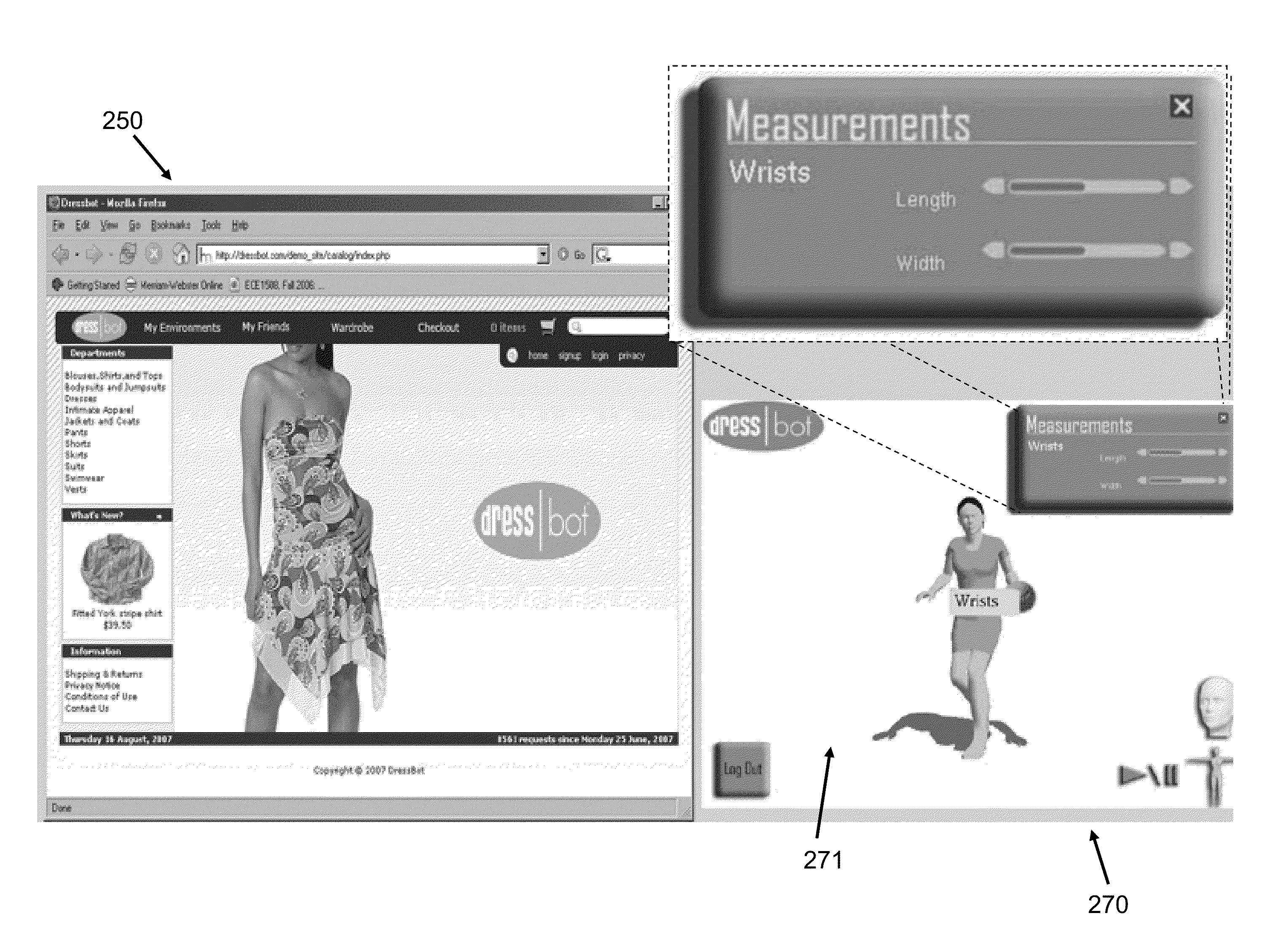
System and Method for Collaborative Shopping, Business and Entertainment
The methods and systems described herein relate to online methods of collaboration in community environments. The methods and systems are related to an online apparel modeling system that allows users to have three-dimensional models of their physical profile created. Users may purchase various goods and / or services and collaborate with other users in the online environment.
Owner:DRESSBOT
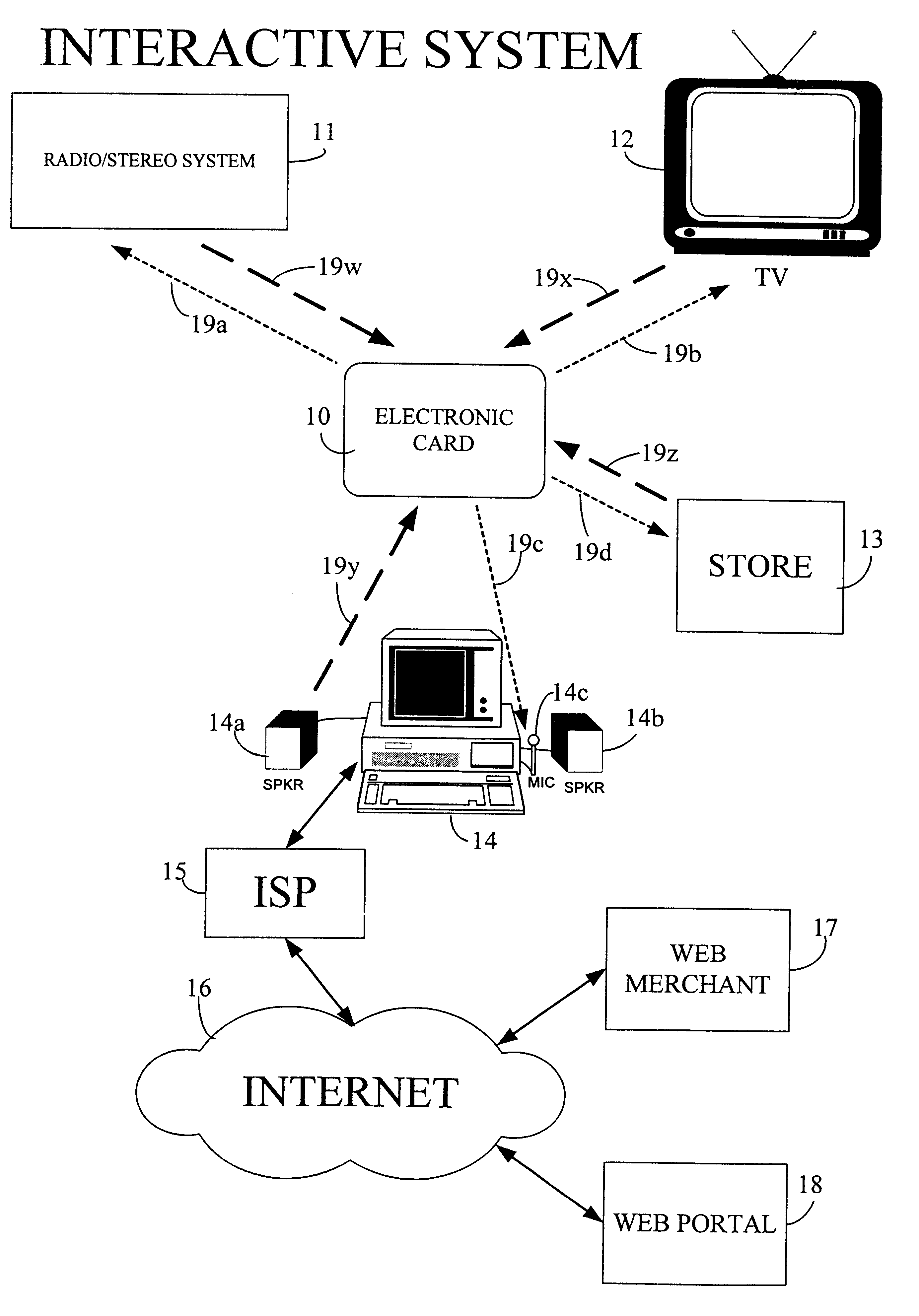
Physical presence digital authentication system
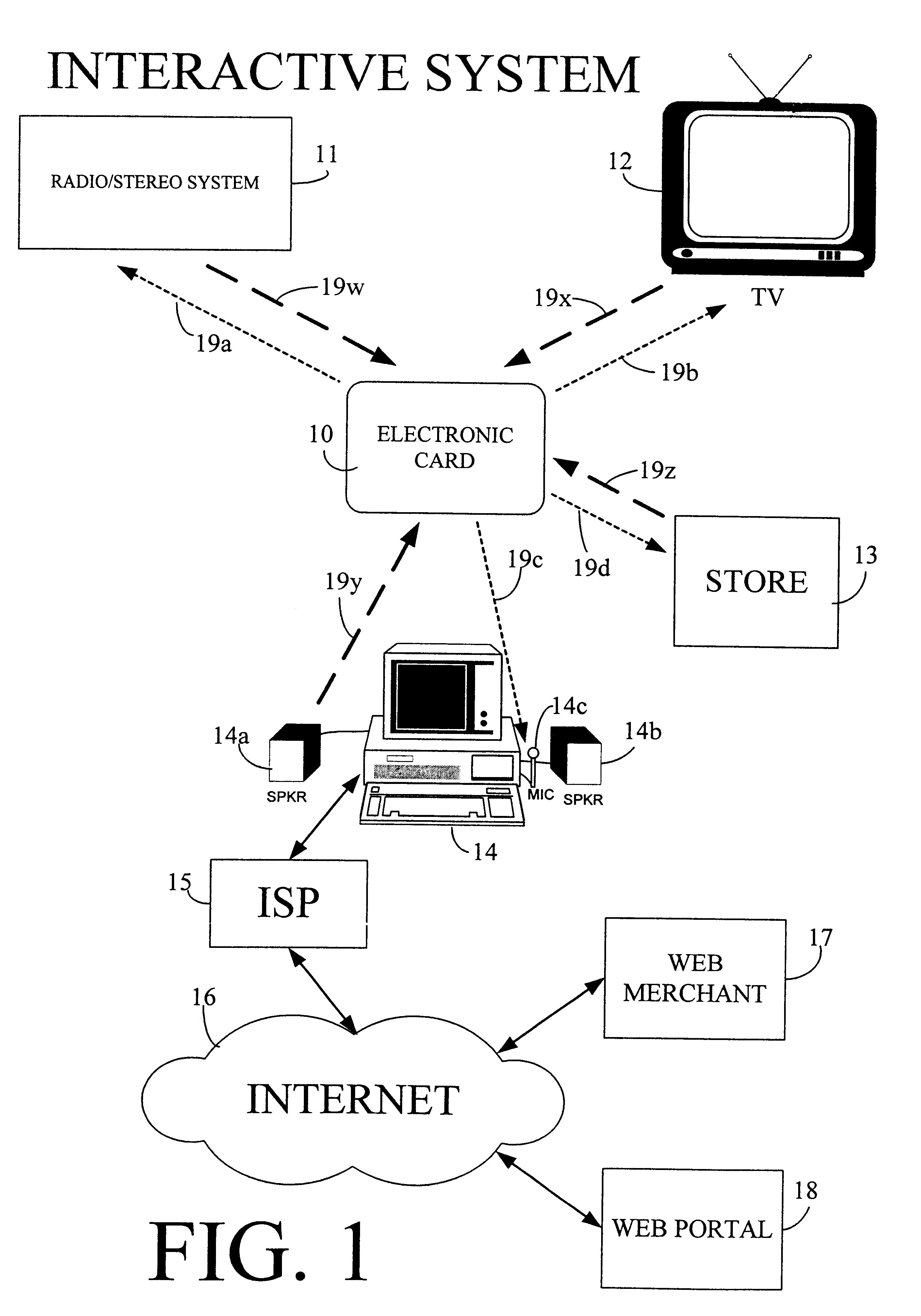
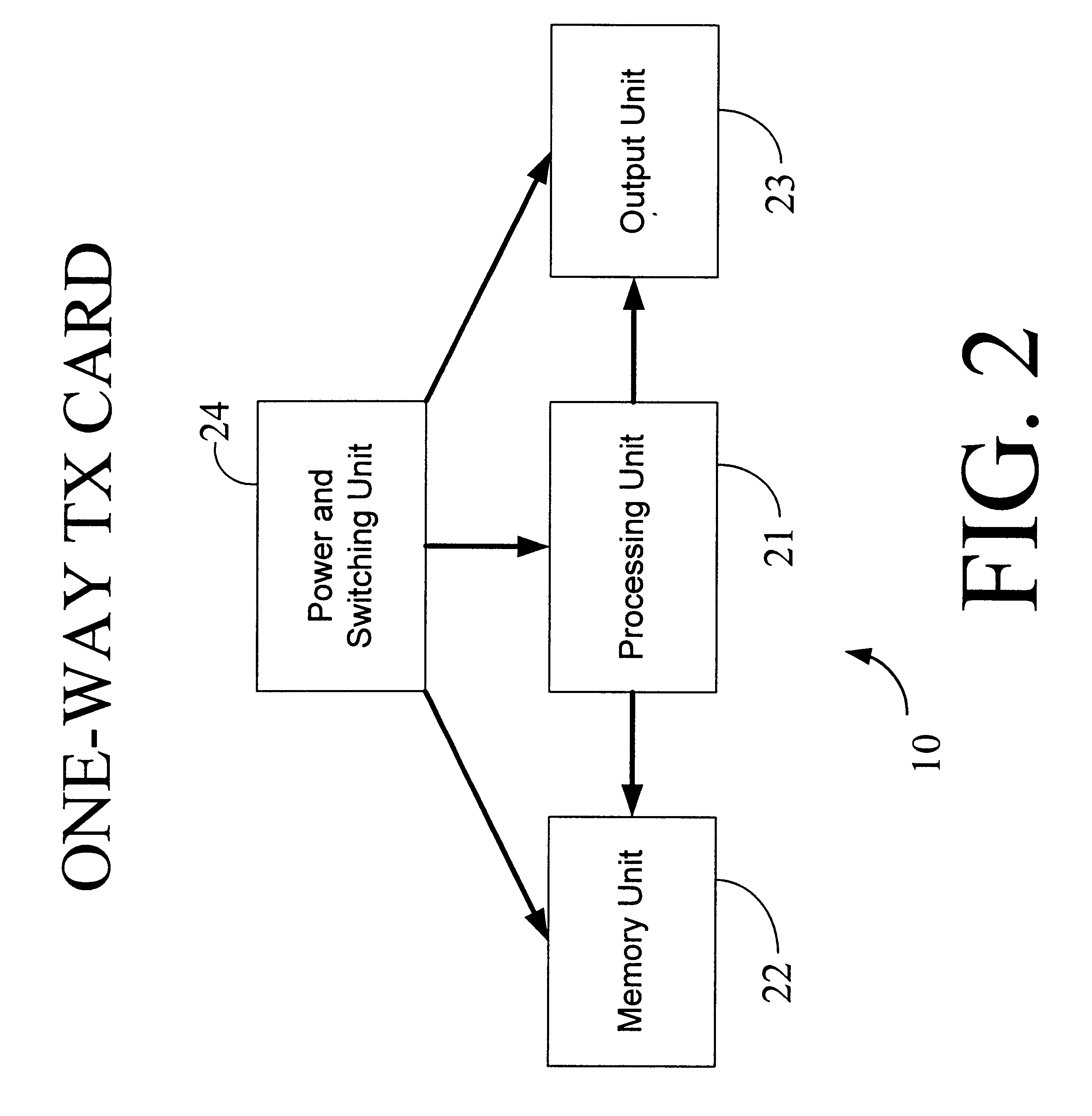
InactiveUS6607136B1Enhanced interactionMass scalableCredit registering devices actuationDiscounts/incentivesCrowdsAcoustic wave
The interactive authentication system allows a consumer to interact with a base station, such as broadcast media (e.g., television and radio) or PC, to receive coupons, special sales offers, and other information with an electronic card. The electronic card can also be used to transmit a signal that can be received by the base station to perform a wide variety of tasks. These tasks can include launching an application, authenticating a user at a website, and completing a sales transaction at a website (e.g., by filling out a form automatically). The interaction between the base station and the electronic card is accomplished by using the conventional sound system in the base station so that a special reader hardware need not be installed to interact with the electronic card. The user is equipped with an electronic card that can receive and transmit data via sound waves. In the various embodiments, the sound waves can be audible or ultrasonic (which can be slightly audible to some groups of people).
Owner:SONIXIO INC
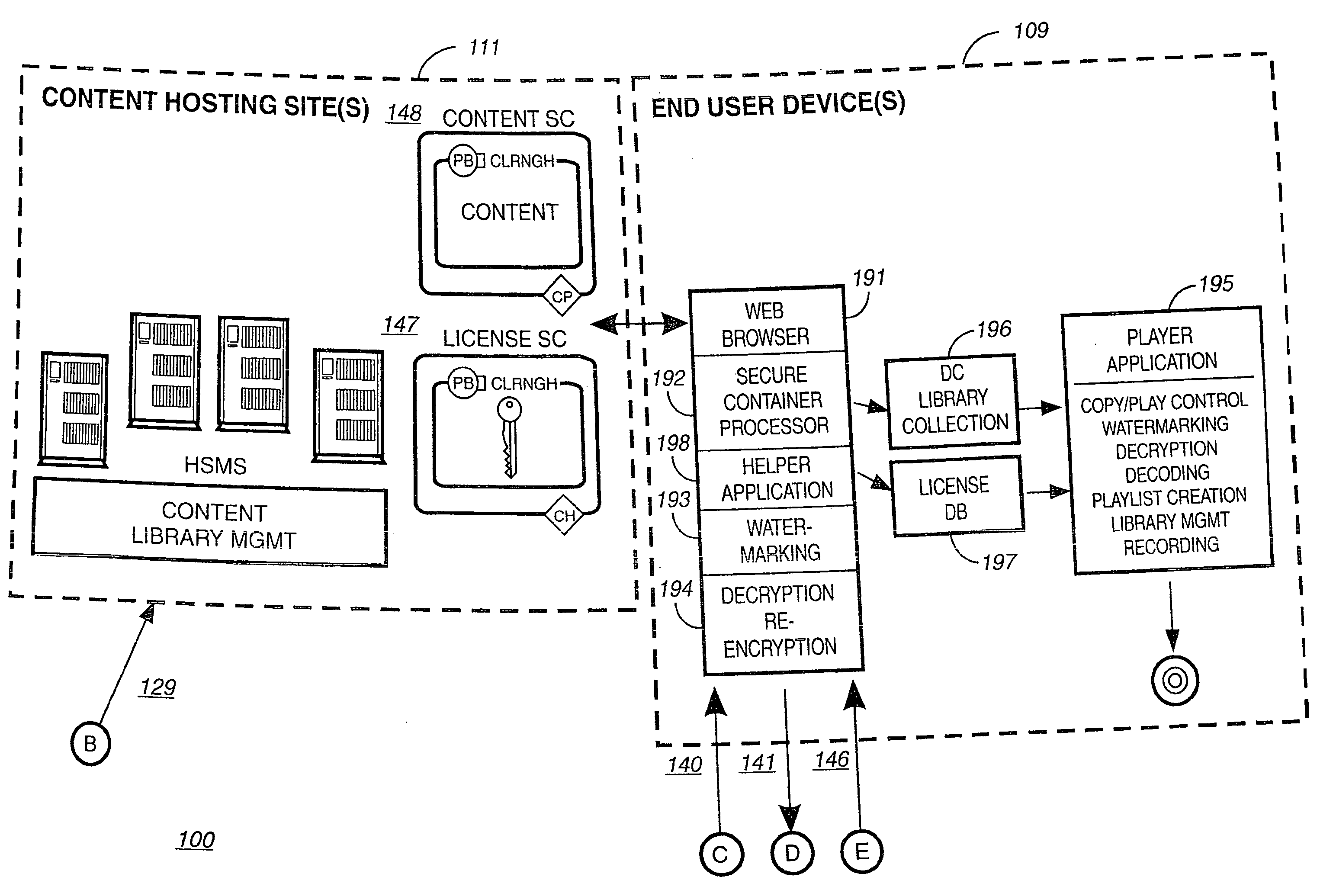
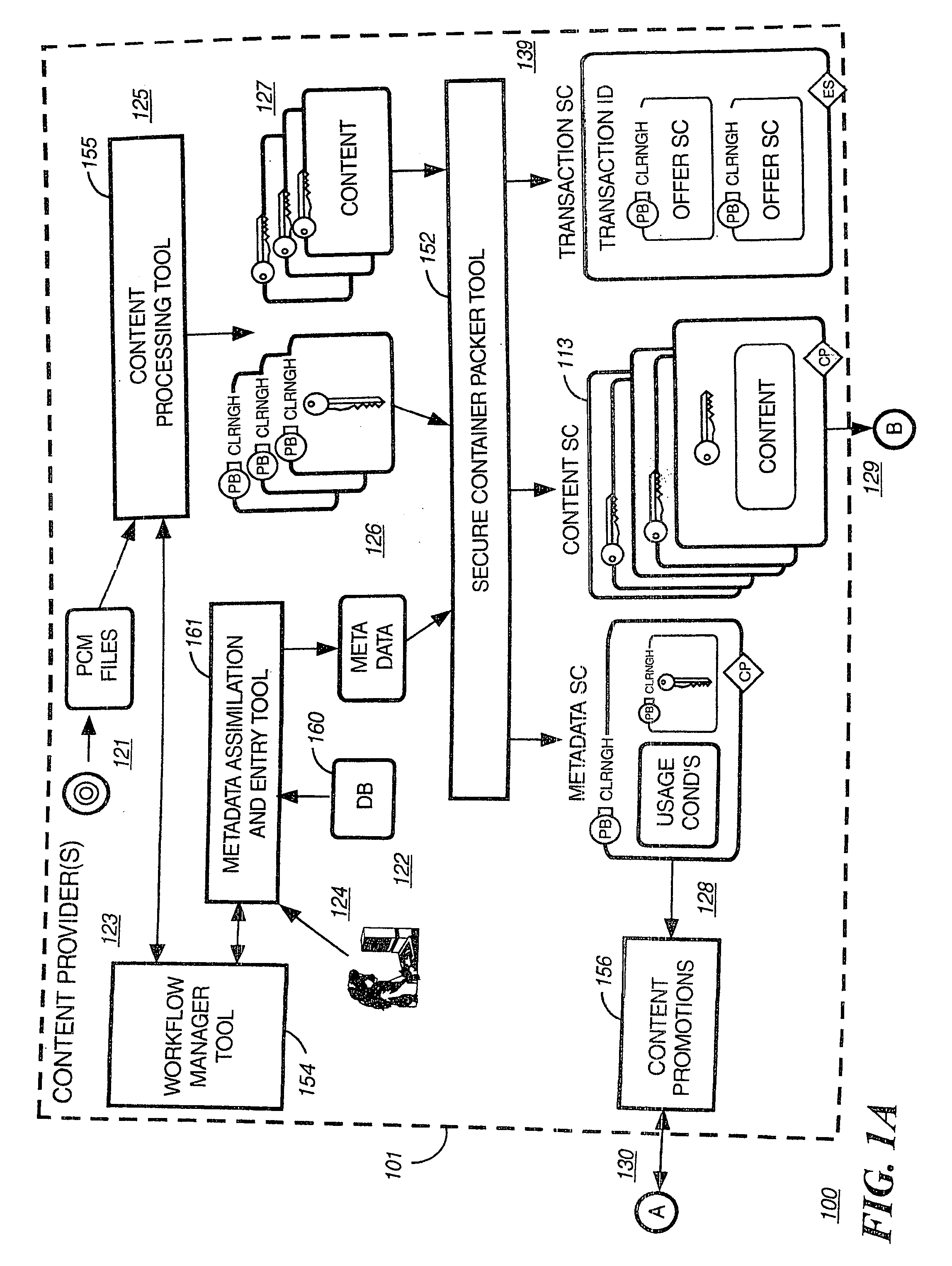
Secure electronic content distribution on CDS and DVDs
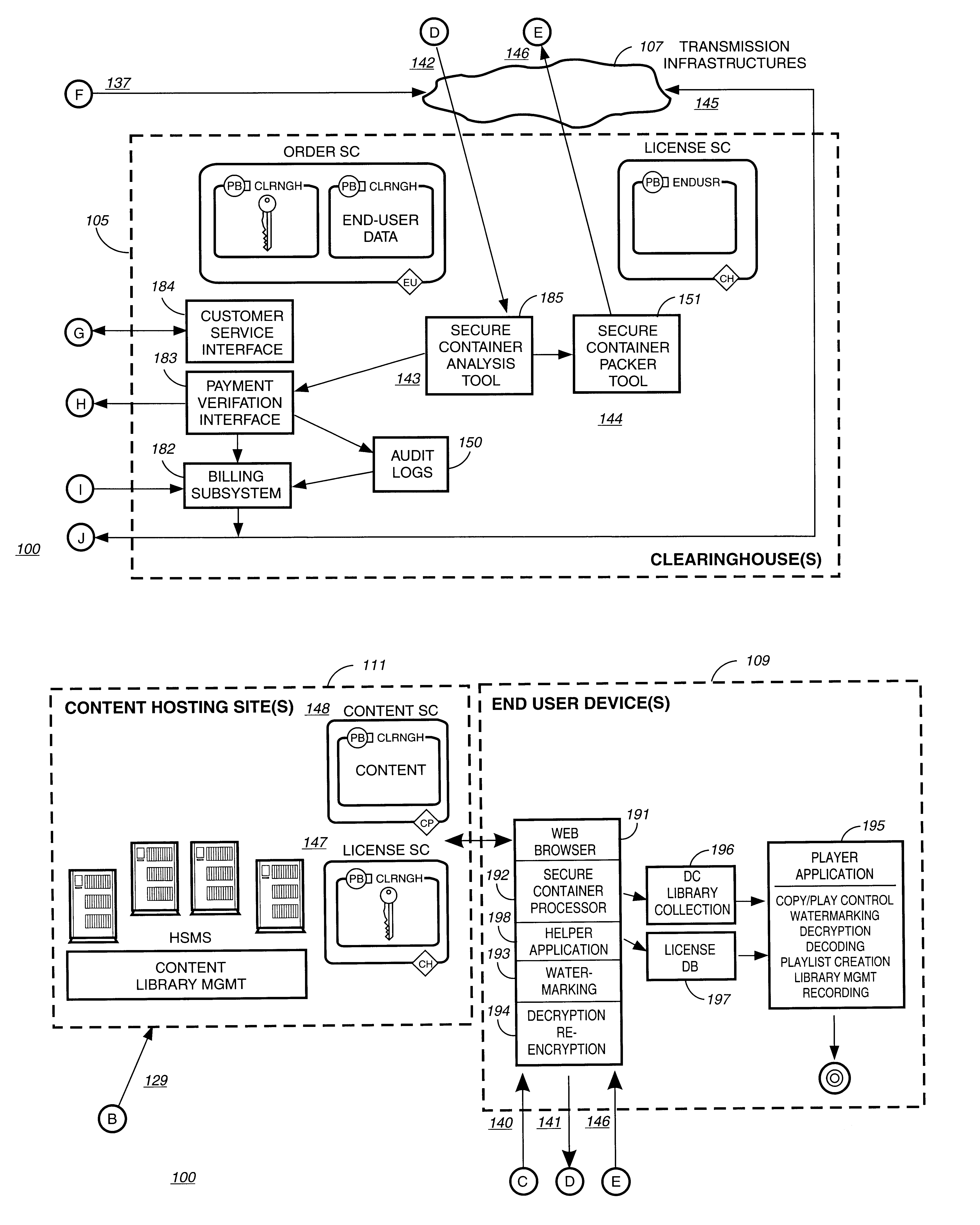
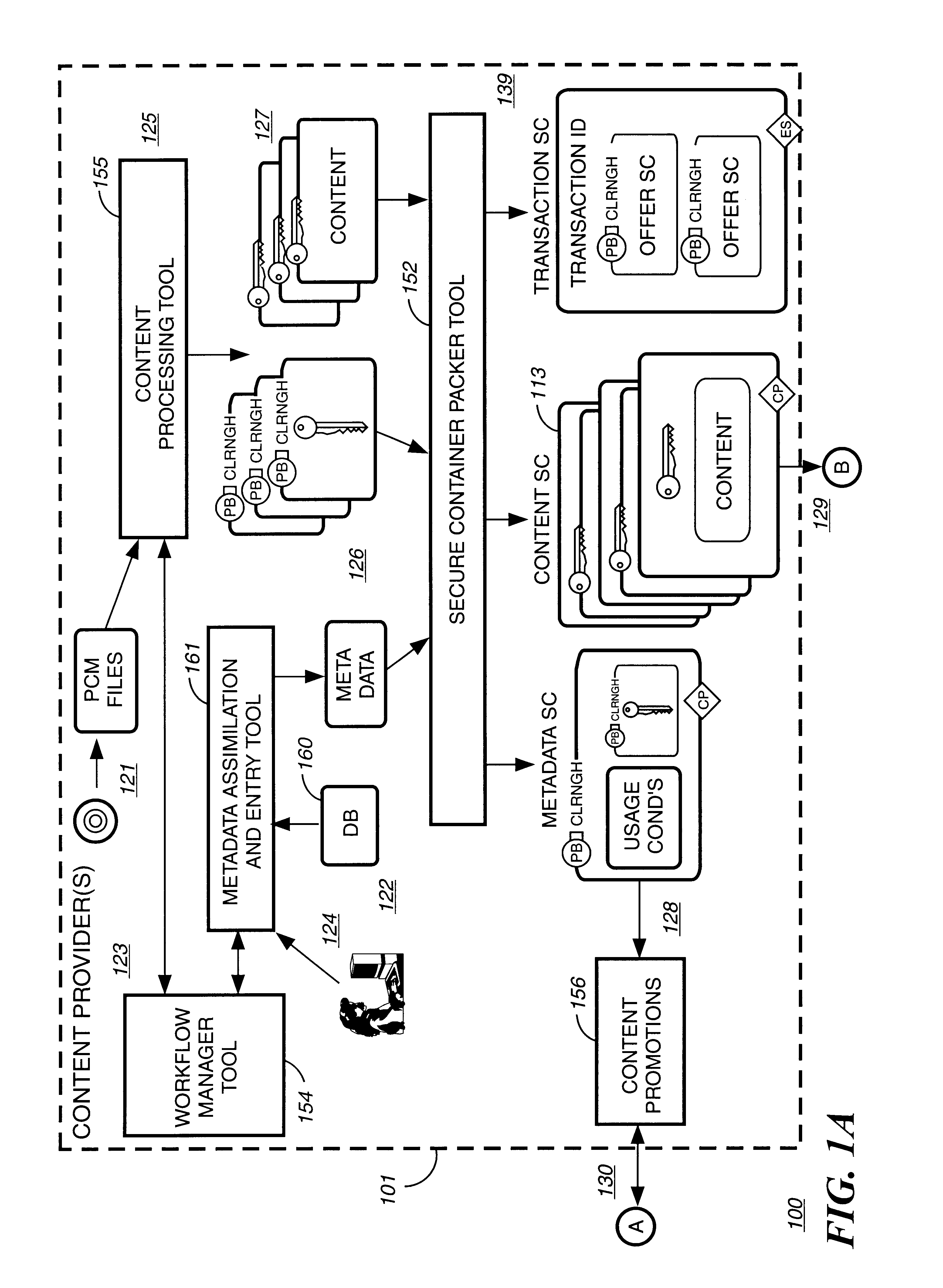
InactiveUS6611812B2Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
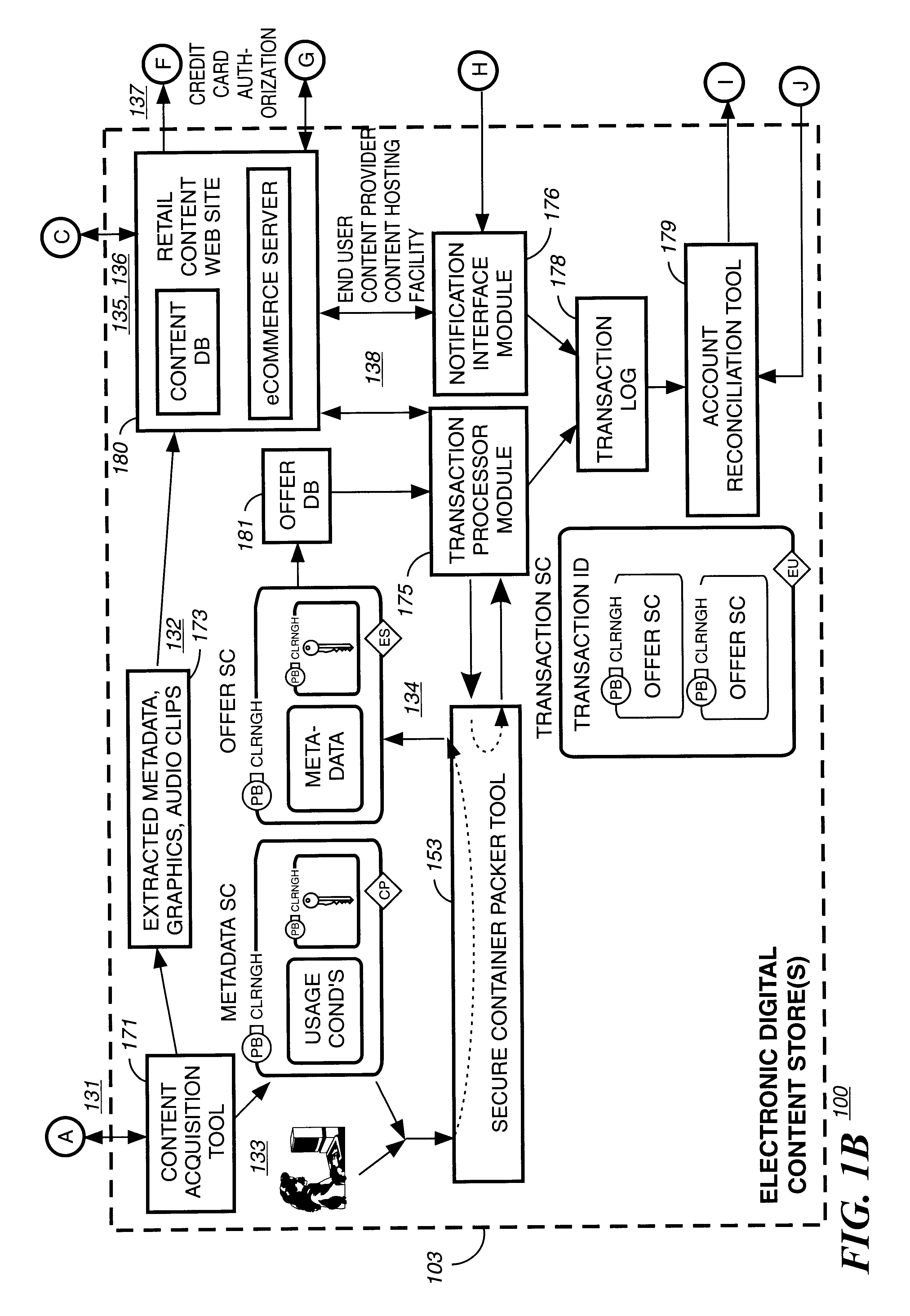
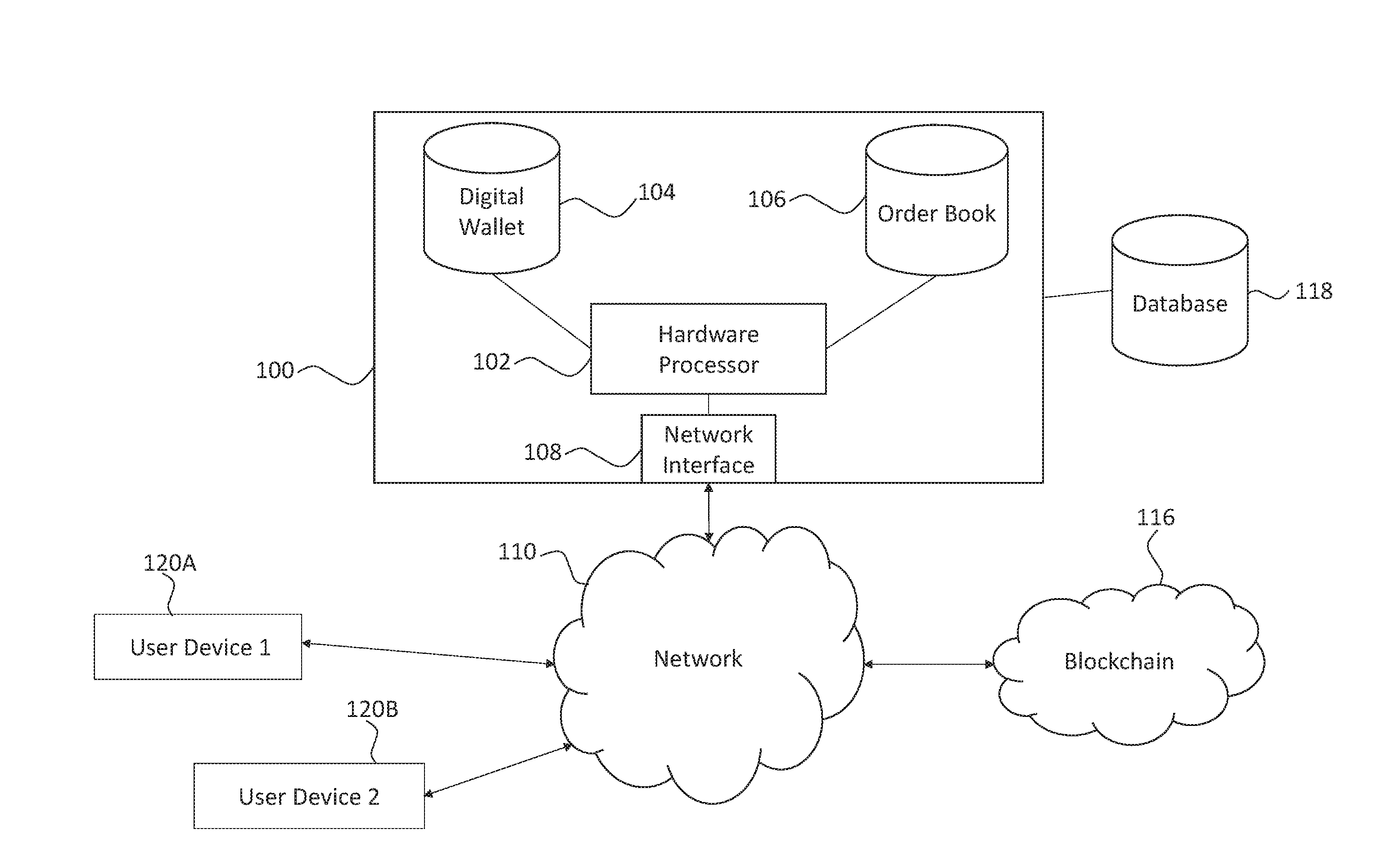
Systems and methods of blockchain transaction recordation
Owner:NASDAQ INC
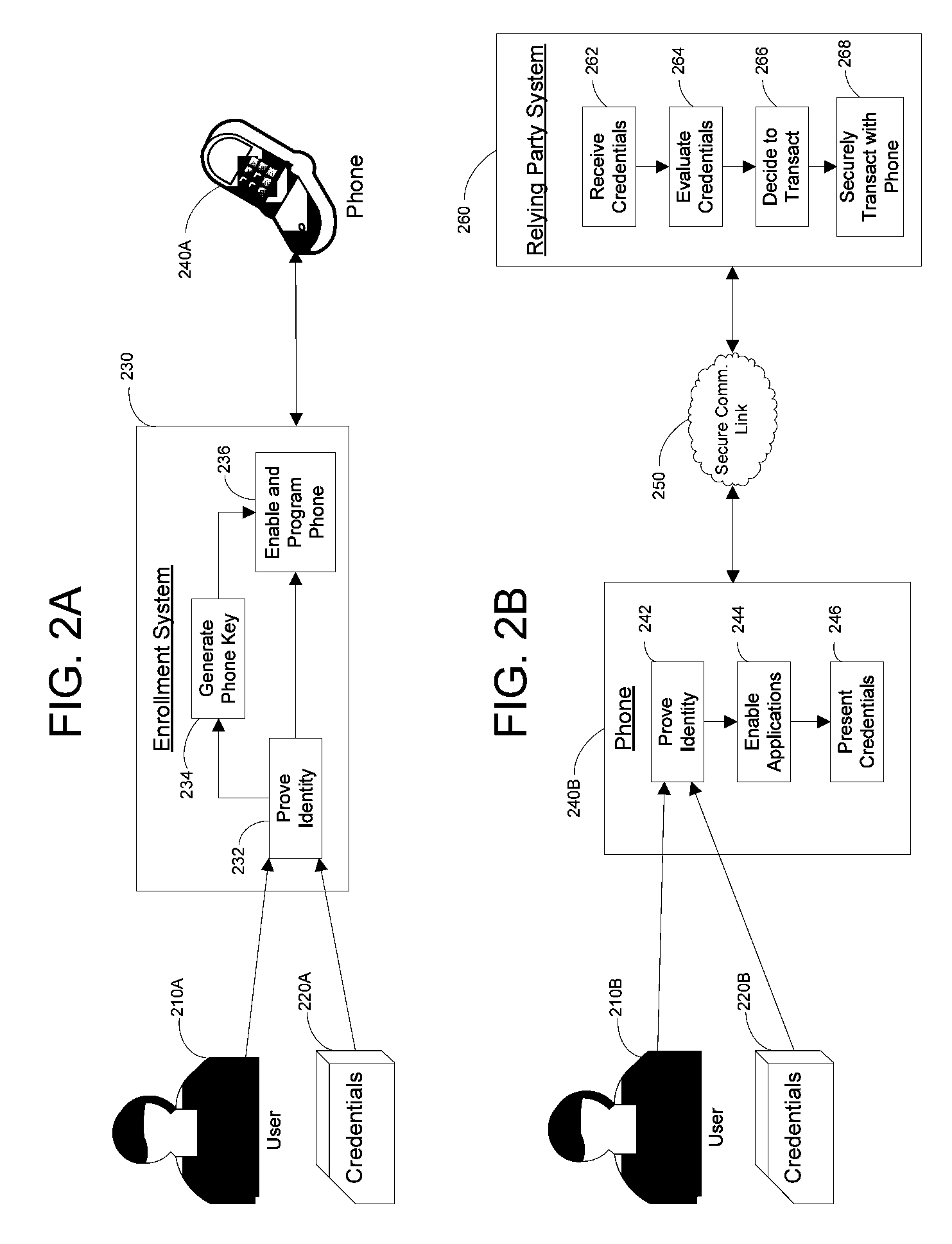
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20090132813A1Save bandwidthSaving response timeDigital data processing detailsUser identity/authority verificationElectronic systemsFinancial transaction
Apparatus and methods perform transactions in a secure environment between an individual and another party, such as a merchant, in various embodiments. The individual possesses a mobile electronic device, such as a smartphone, that can encrypt data according to a public key infrastructure. The individual authenticates the individual's identity to the device, thereby unlocking credentials that may be used in a secure transaction. The individual causes the device to communicate the credentials, in a secure fashion, to an electronic system of a relying party, in order to obtain the relying party's authorization to enter the transaction. The relying party system determines whether to grant the authorization, and communicates the grant and the outcome of the transaction to the device using encryption according to the public key infrastructure.
Owner:SURIDX
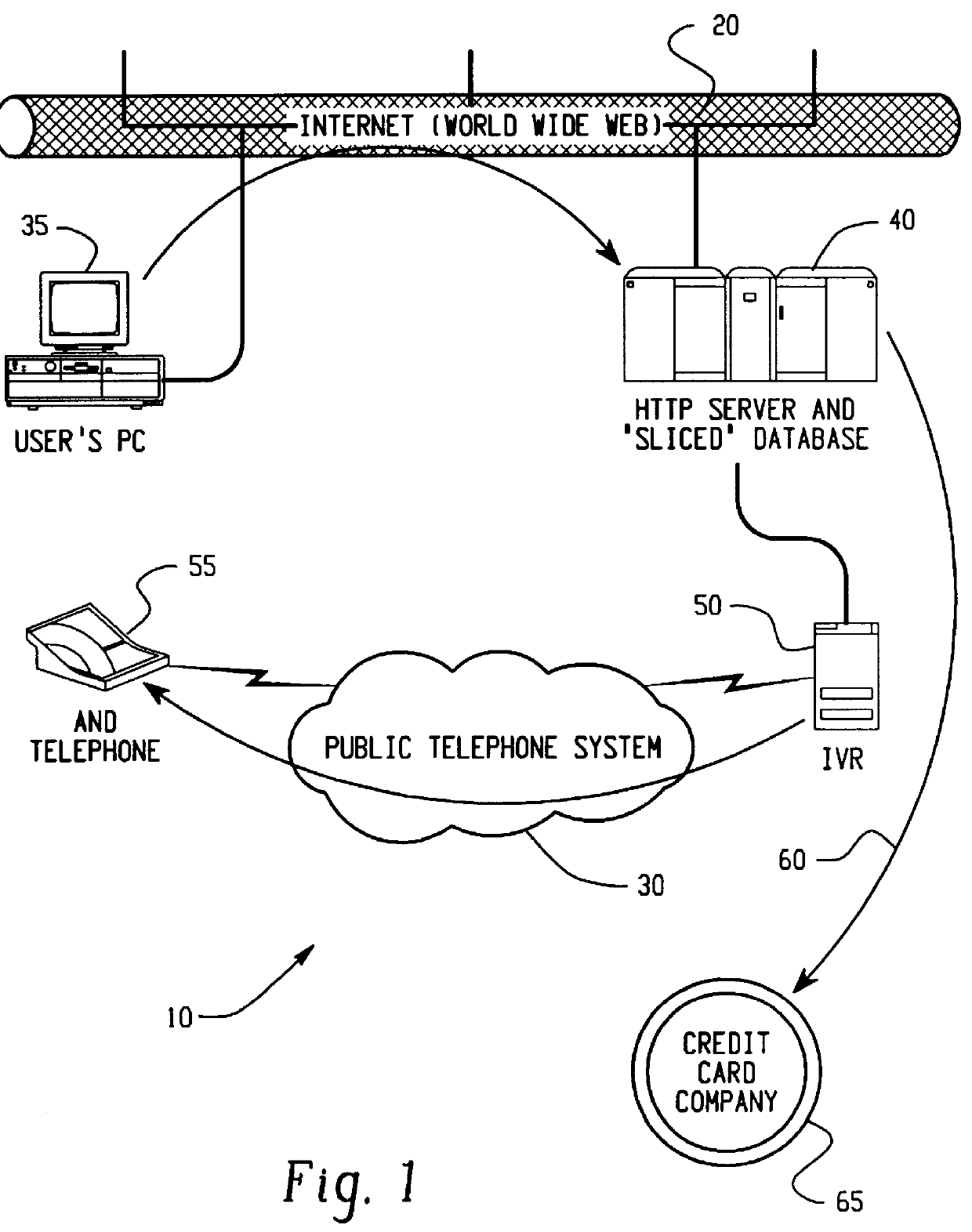
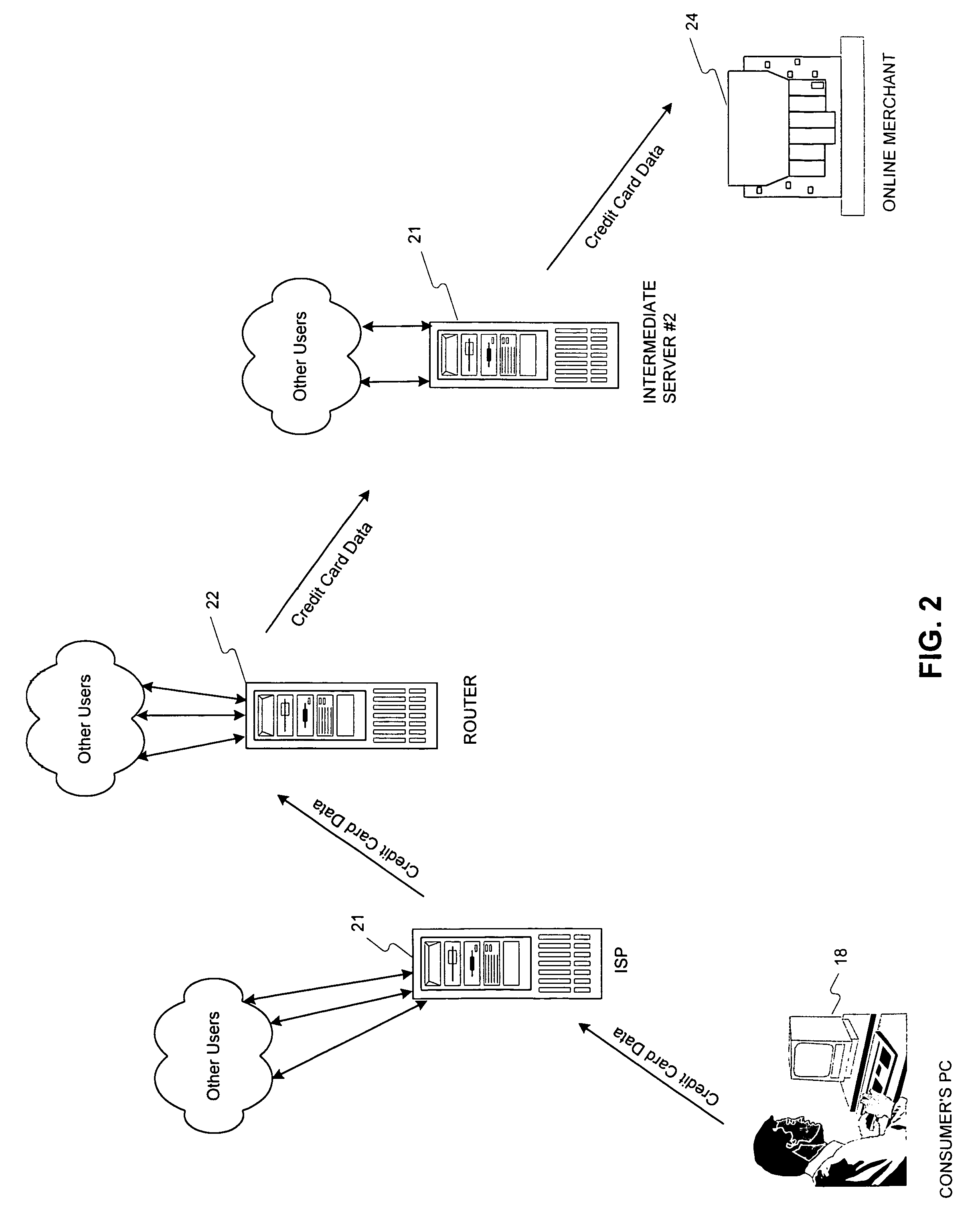
Transaction security method and apparatus
A method for performing secure transactions, such as credit card purchases, using two or more non-secure networks (such as the Internet and the public telephone system) in such a way that security is insured. A person wishing to initiate a secure transaction sends a message over one of the non-secure networks to a computer. That computer automatically uses the second non-secure network to contact the person back to verify the transaction. The call-back mechanism employs a method to authenticate the identity or authority of the person initiating the transaction. No single wire-tapping or network snooping device sees the entire transaction. No single database contains the entire set of information.
Owner:PICKETT THOMAS E
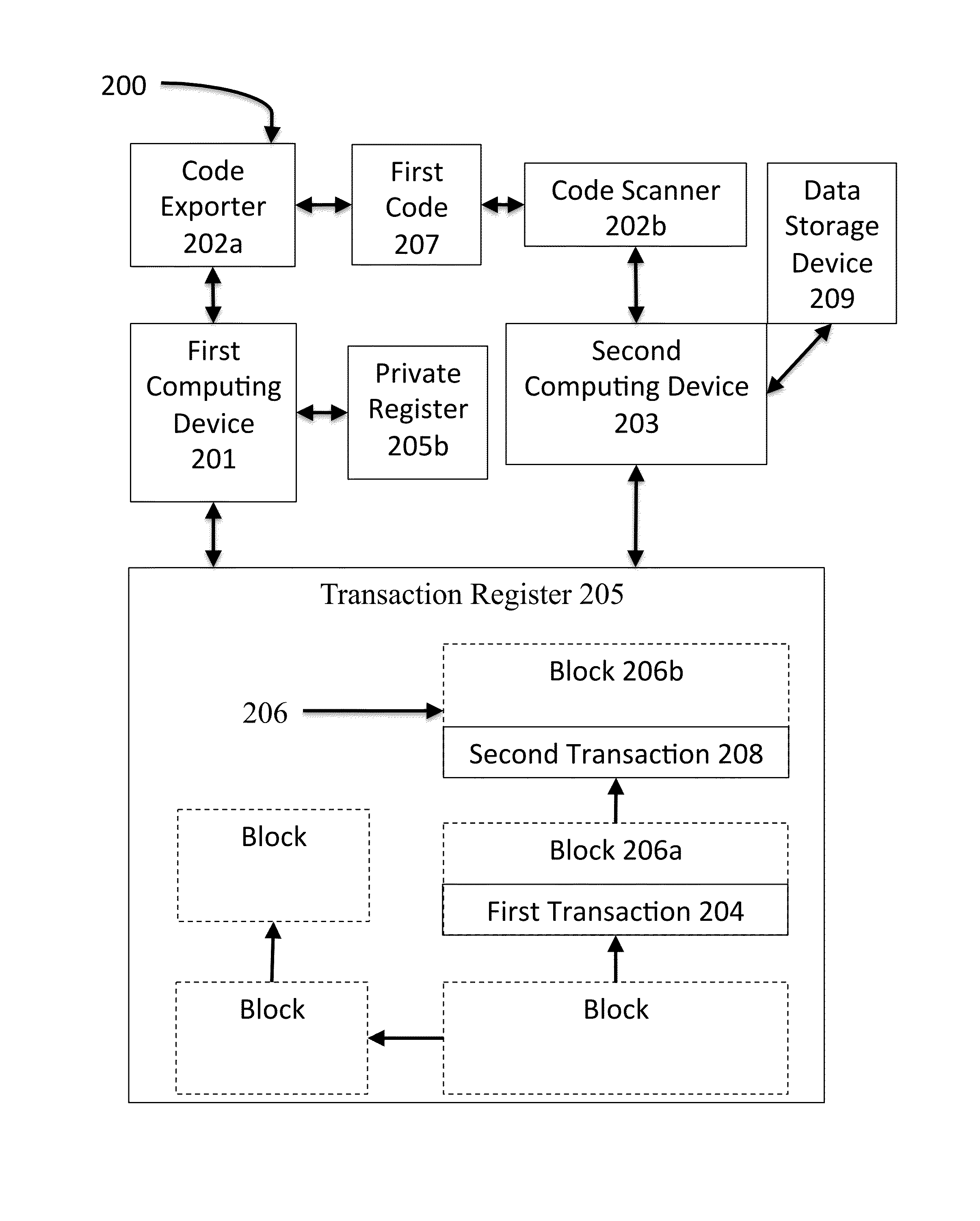
System and method for block-chain verification of goods
A method for block-chain verification of goods includes scanning, by a computing device, using a code scanner, an address from a code affixed to a product, verifying, by the computing device, that the address is associated with a crypto-currency transaction recorded at a transaction register, obtaining, by the computing device, at least one current transaction datum, and determining, based on the verification and the at least one current transaction datum, that the product is authentic.
Owner:THE FILING CABINET
Systems and methods for communicating token attributes associated with a token vault
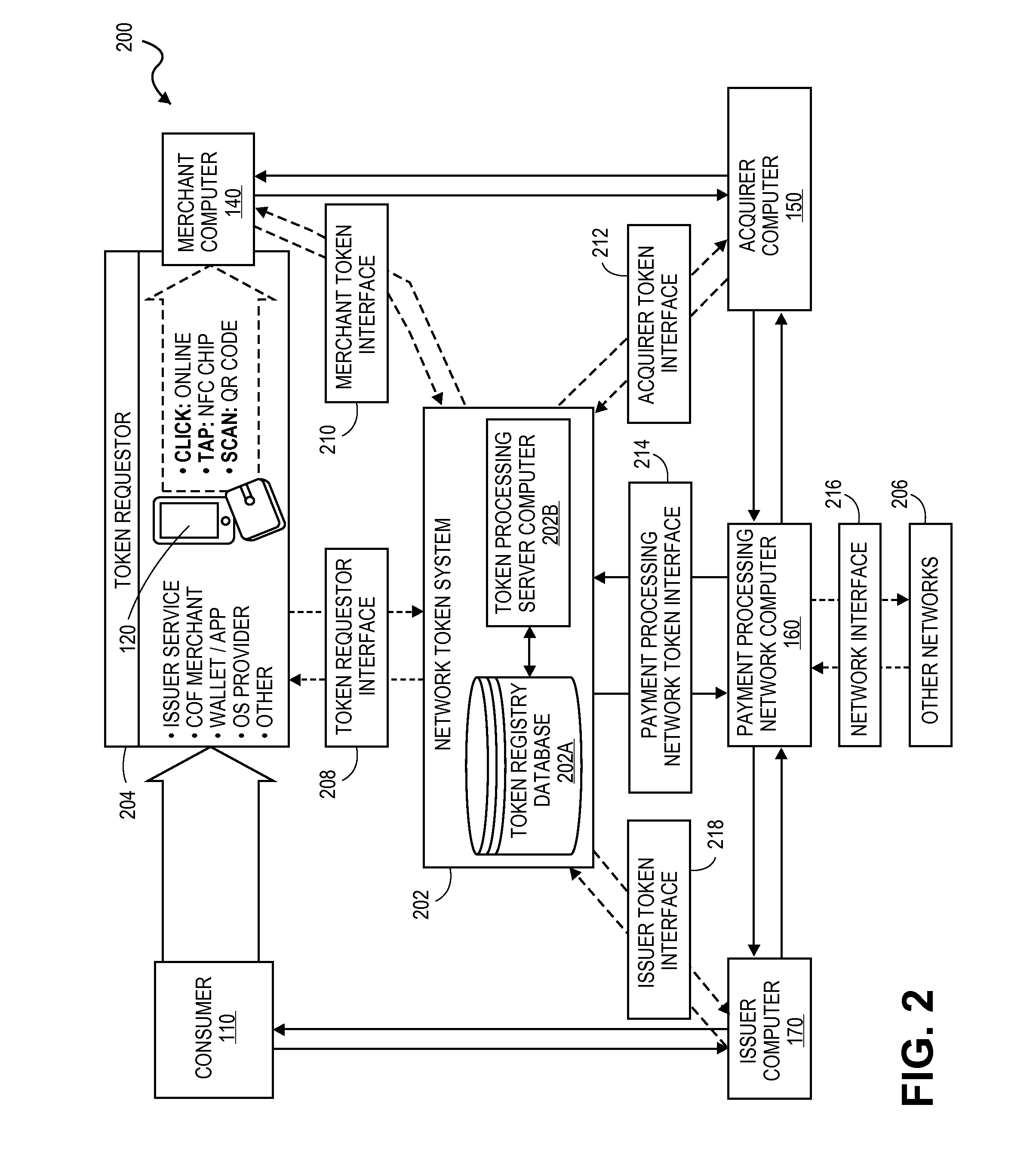
ActiveUS20150032627A1Convenient transactionSupported interoperabilityFinanceUser identity/authority verificationThird partyPayment transaction
Systems and methods for interoperable network token processing are provided. A network token system provides a platform that can be leveraged by external entities (e.g., third party wallets, e-commerce merchants, payment enablers / payment service providers, etc.) or internal payment processing network systems that have the need to use the tokens to facilitate payment transactions. A token registry vault can provide interfaces for various token requestors (e.g., mobile device, issuers, merchants, mobile wallet providers, etc.), merchants, acquirers, issuers, and payment processing network systems to request generation, use and management of tokens. The network token system further provides services such as card registration, token generation, token issuance, token authentication and activation, token exchange, and token life-cycle management.
Owner:VISA INT SERVICE ASSOC
Peer-to-peer financial transaction devices and methods
Various techniques are provided for carrying out peer-to-peer financial transactions using one or more electronic devices. In one embodiment, a request for payment is transmitted from a first device to a second device using a near field communication (NFC) interface. In response to the request, the second device may transmit payment information to the first device. The first device may select a crediting account and, using a suitable communication protocol, may communicate the received payment information and selected crediting account to one or more external financial servers configured to process and determine whether the payment may be authorized. If the payment is authorized, a payment may be credited to the selected crediting account. In a further embodiment, a device may include a camera configured to obtain an image of a payment instrument. The device may further include an application to extract payment information from the acquired image.
Owner:APPLE INC
System and method for processing financial transactions
InactiveUS7571139B1Improve securityGreat degree of convenienceFinanceCash registersPaymentFinancial transaction
A network for processing retail sales transactions includes a customer transceiver with a unique customer number, a reader receiving the customer number and sending it to a point-of-sale device where it is combined with transaction information to form a transaction entry. The transaction entry is sent through a merchant computer to a transaction processing system having a customer database. The transaction processing system references an entry in the customer database corresponding to the customer / transmitter ID number and routes the transaction entry to a payment processing system specified in the customer database entry.
Owner:EXXON RES & ENG CO +1
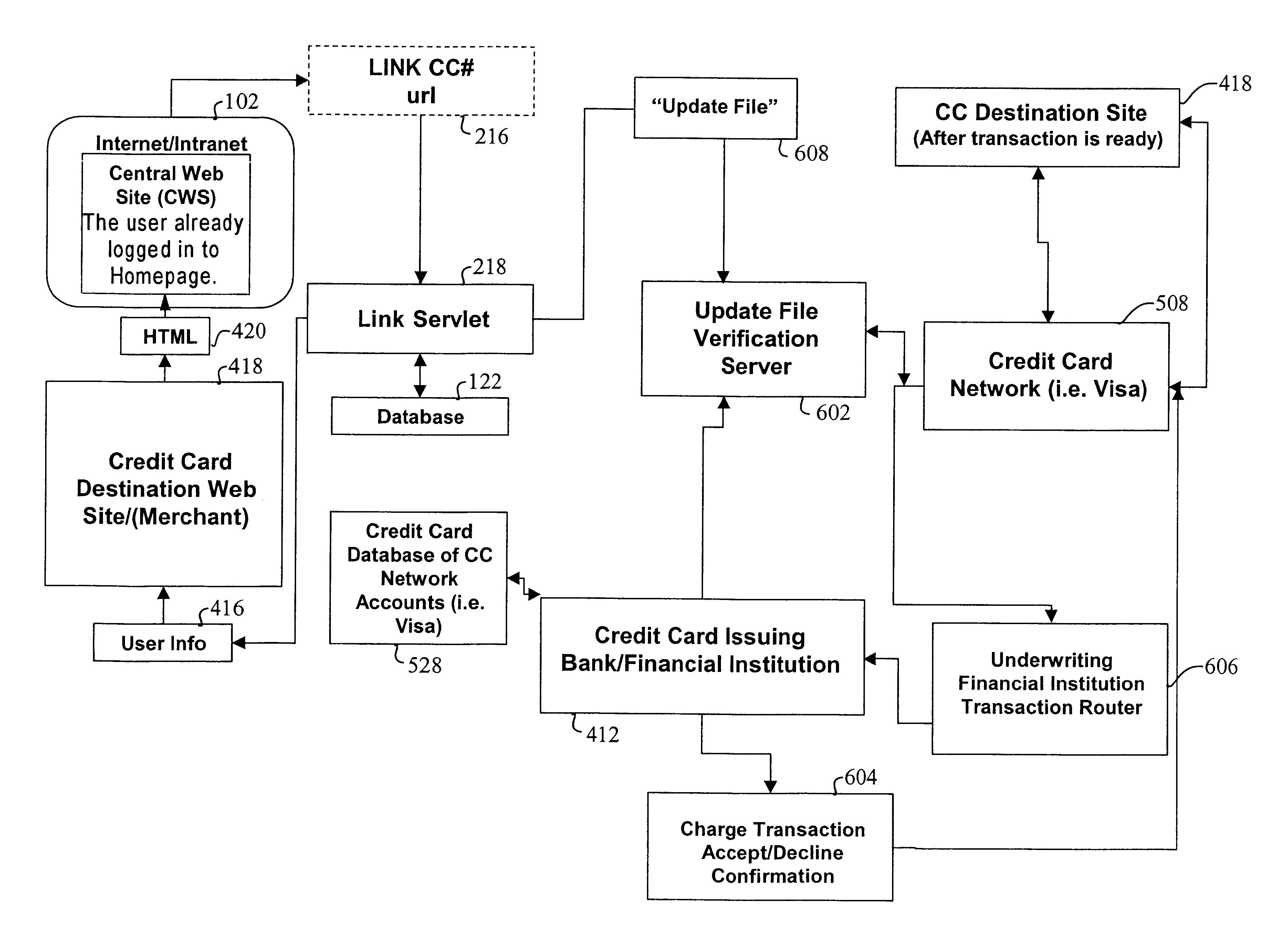
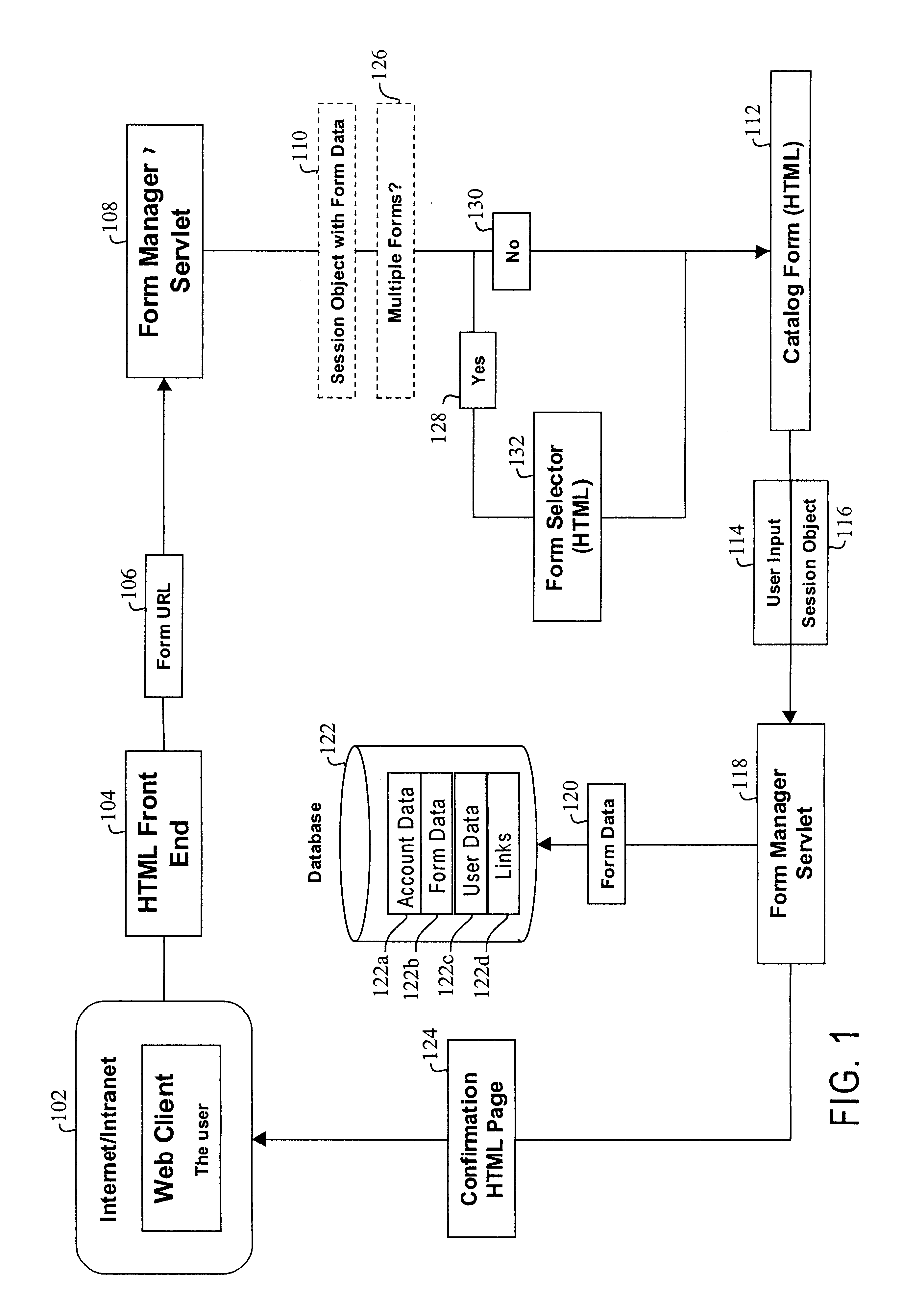
Method, system and computer readable medium for web site account and e-commerce management from a central location
InactiveUS6879965B2Minimizing activation timeMinimizing financial exposureComplete banking machinesAcutation objectsWeb siteData field
A method, system and computer readable medium for, from a central Web site, performing at least one of registering a user at a destination Web site, logging in a user at a destination Web site and managing an online financial transaction at a destination Web site, including parsing a form Web page of the destination Web site to extract form data fields therefrom; mapping form data fields of a central Web site form to corresponding extracted form data fields of the form Web page of the destination Web site; and using the mapped form data fields to perform at least one of registering a user at the destination Web site, logging in a user at the destination Web site and managing an online financial transaction of a user at the destination Web site. In another aspect, there is provided a method, system and computer readable medium for managing an online or offline financial transaction of a user, from a central Web site, including generating financial transaction account information for a user based on existing credit or debit card information; gathering from the user one or more limits that are applied to a financial transaction performed based on the financial transaction account information; receiving from a source information indicating that an online or offline financial transaction using the financial transaction account information is in progress; applying the one or more limits gathered from the user to approve or disapprove the online or offline or online financial transaction that is in progress; and transmitting an approval or disapproval signal to the source based on a result of the applying step.
Owner:SLINGSHOT TECH LLC
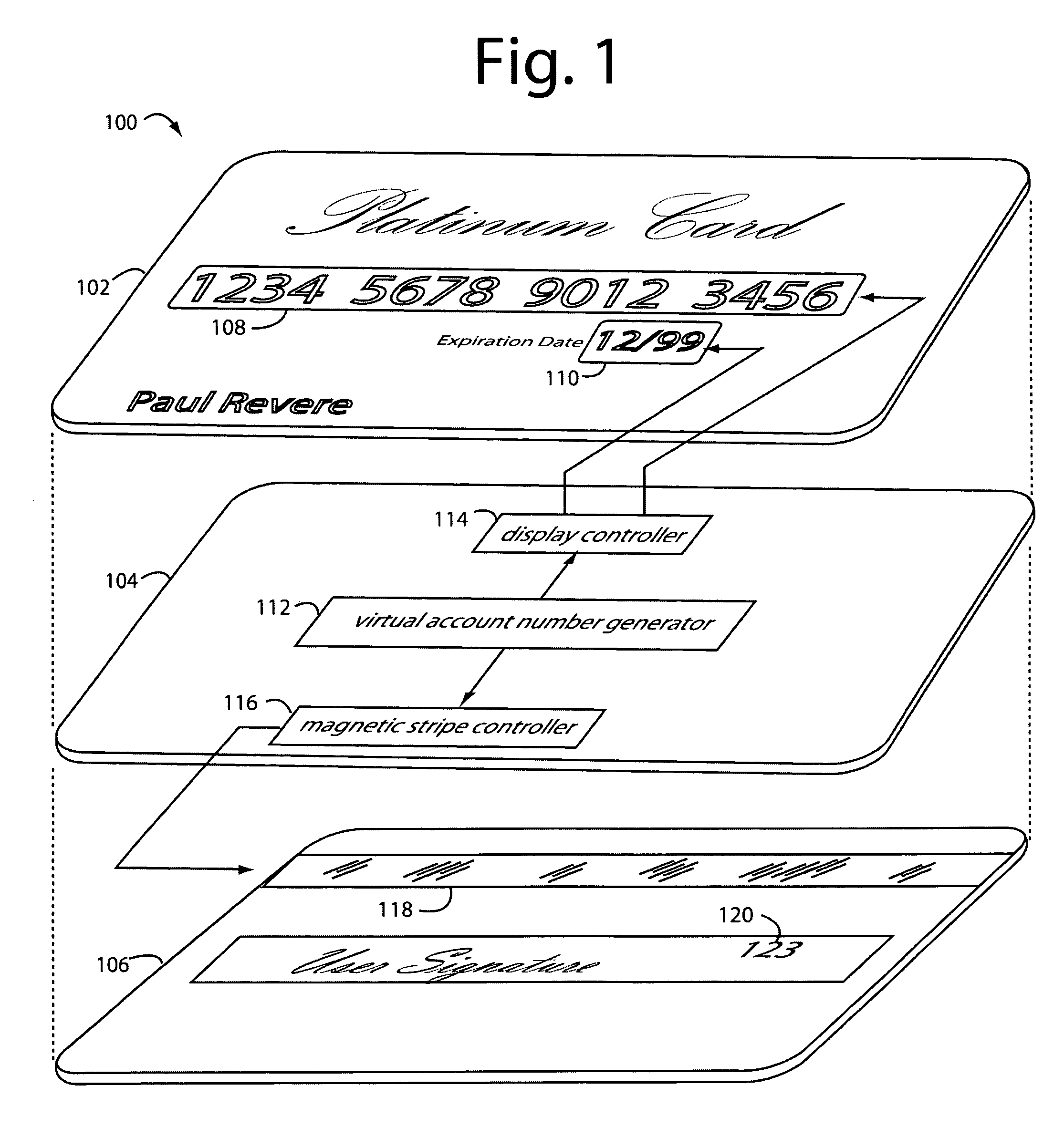
Payment card with internally generated virtual account numbers for its magnetic stripe encoder and user display
A payment card comprises an internal virtual account number generator and a user display for online transactions. Offline transactions with merchant card readers are enabled by a magnetic array positioned behind the card's magnetic stripe on the back. The internal virtual account number generator is able to program the magnetic bits encoded in the magnetic stripe to reflect the latest virtual account number. The internal virtual account number generator produces a sequence of virtual numbers that can be predicted and approved by the issuing bank. Once a number is used, it is discarded and put on an exclusion list.
Owner:FITBIT INC
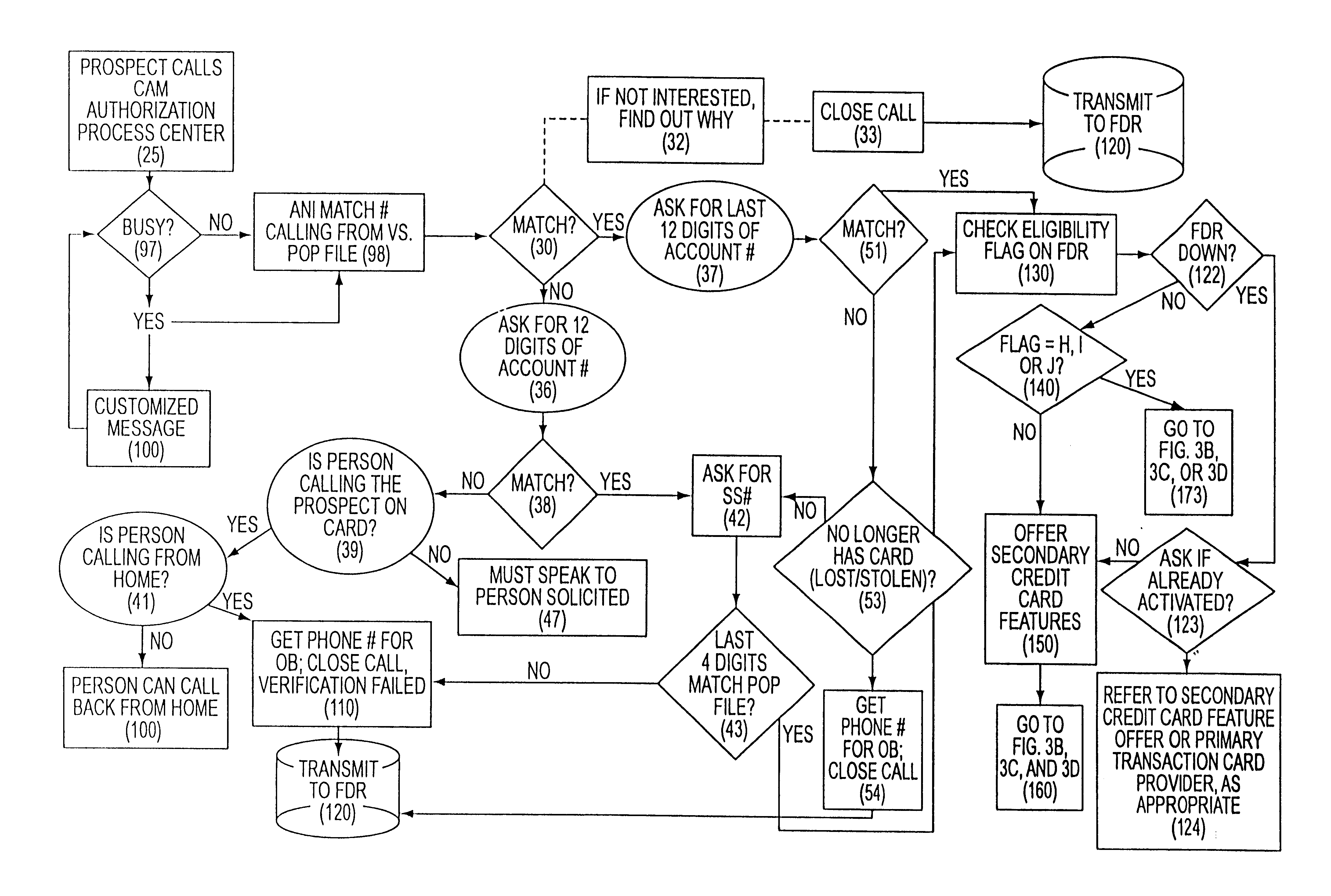
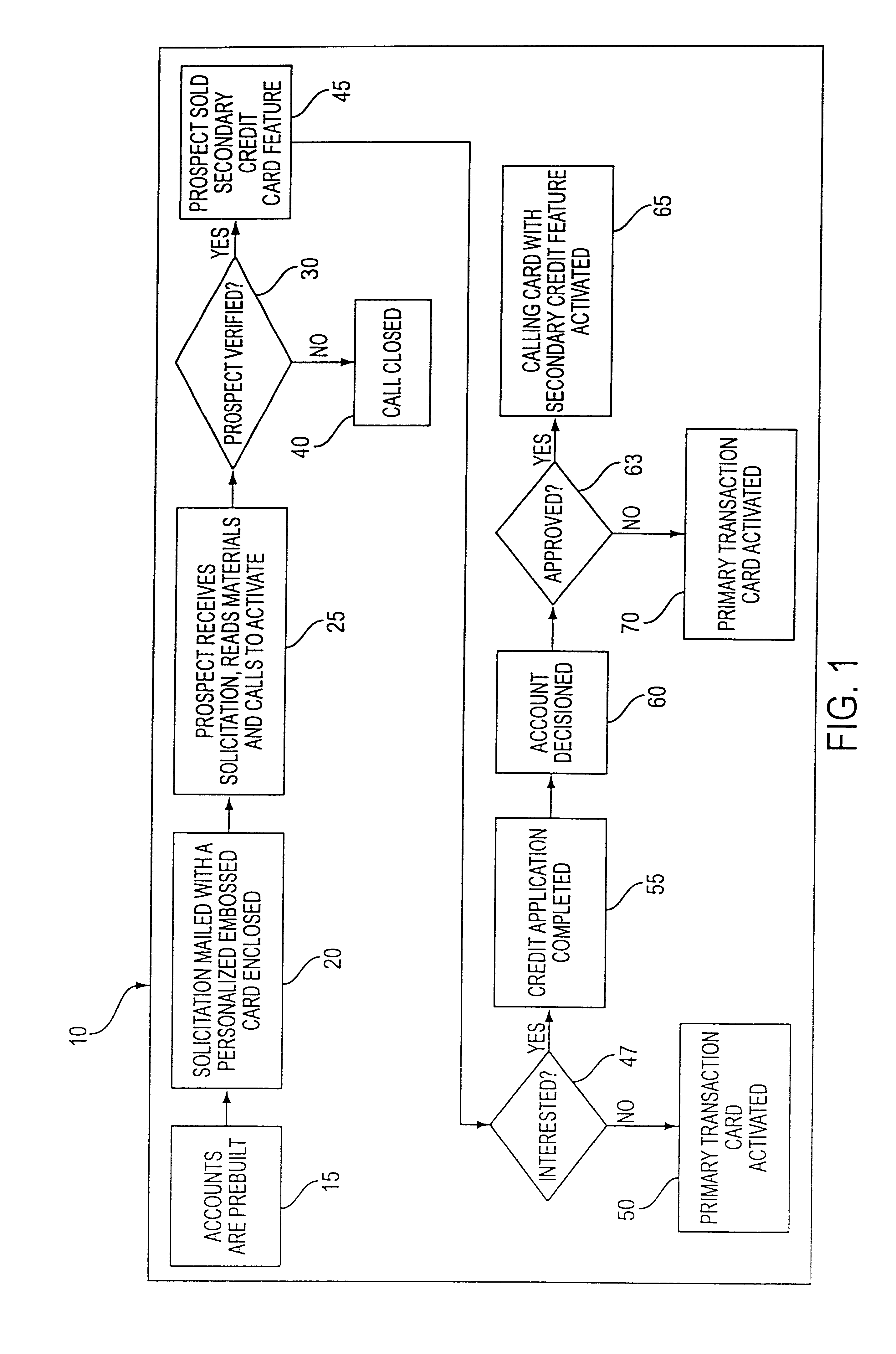
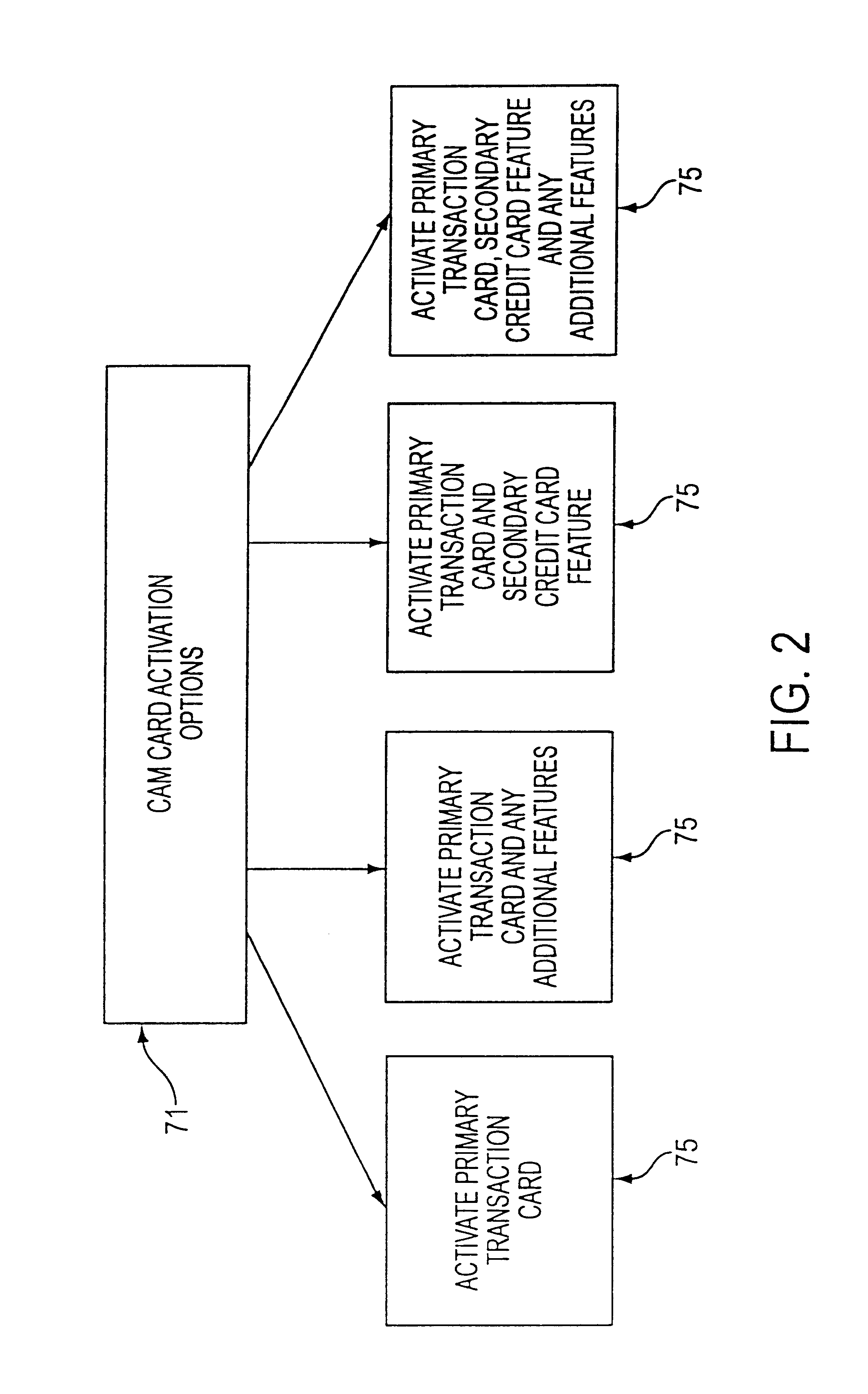
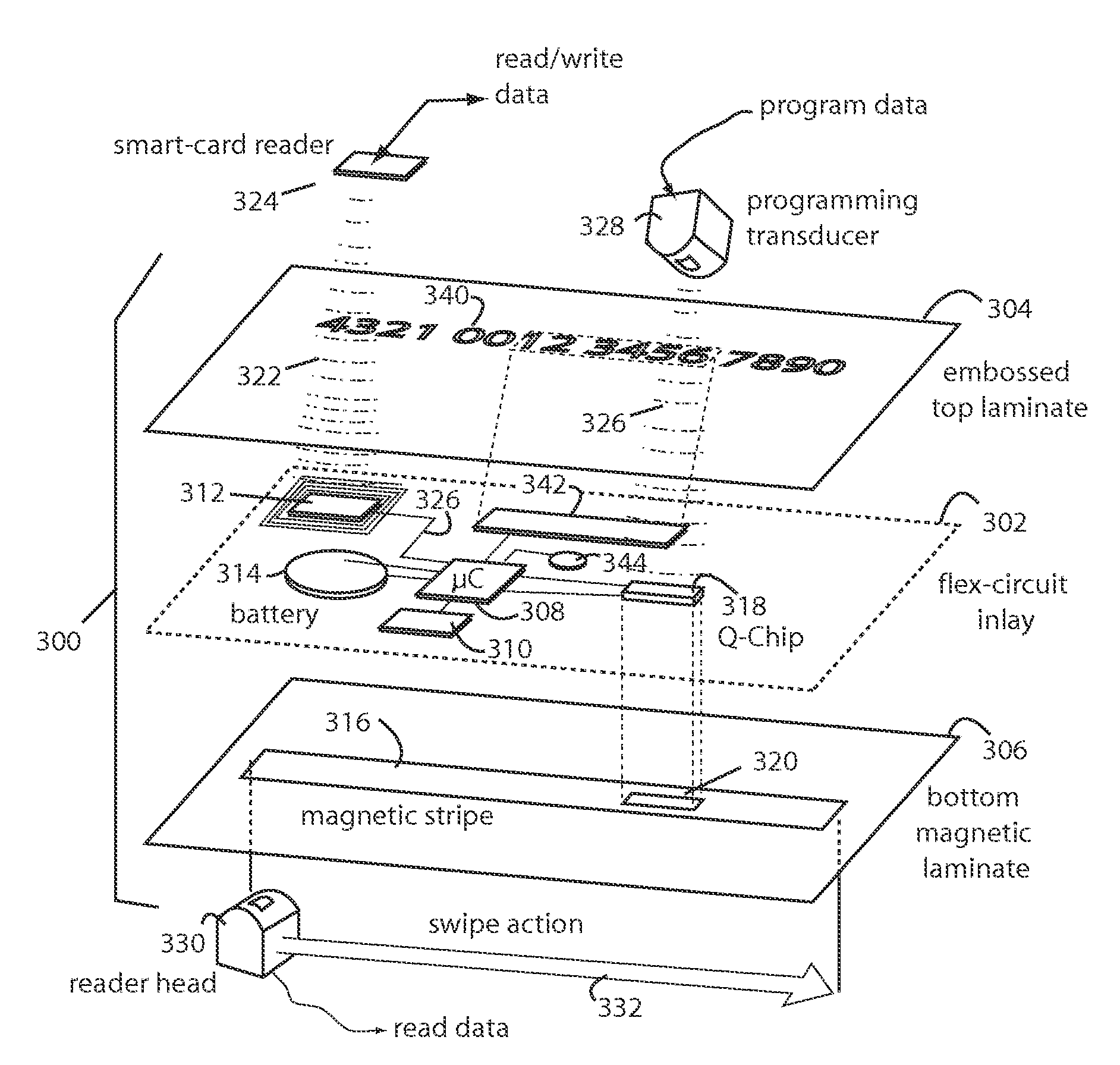
Customer activated multi-value (CAM) card
InactiveUS6865547B1Easy to useCredit registering devices actuationDiscounts/incentivesCredit cardGasoline
The Customer Activated Multi-Value (CAM) card provides a customer with a primary use as a transaction card which can be further activated to have a secondary use as a credit card. The CAM card can be activated as a transaction card or as a transaction card with a credit card feature. Activation of the CAM card as a transaction card allows the customer to purchase goods and services from one specific vendor and to establish a relationship with that vendor for the goods or services rendered (for example, telephone calling card or gasoline product purchasing card) while enjoying reward benefits based on those purchases. Activation of the credit feature of the card allows the customer to interact with any merchant that accepts traditional credit cards such as VISA®, MASTERCARD®, AMERICAN EXPRESS®, or DISCOVER®. The combination of features allows a customer to purchase various goods and services from several different merchants. If the customer chooses to activate the CAM card as both a transaction card and a credit card, the customer is given the benefit of using the card in both manners described above.
Owner:JPMORGAN CHASE BANK NA
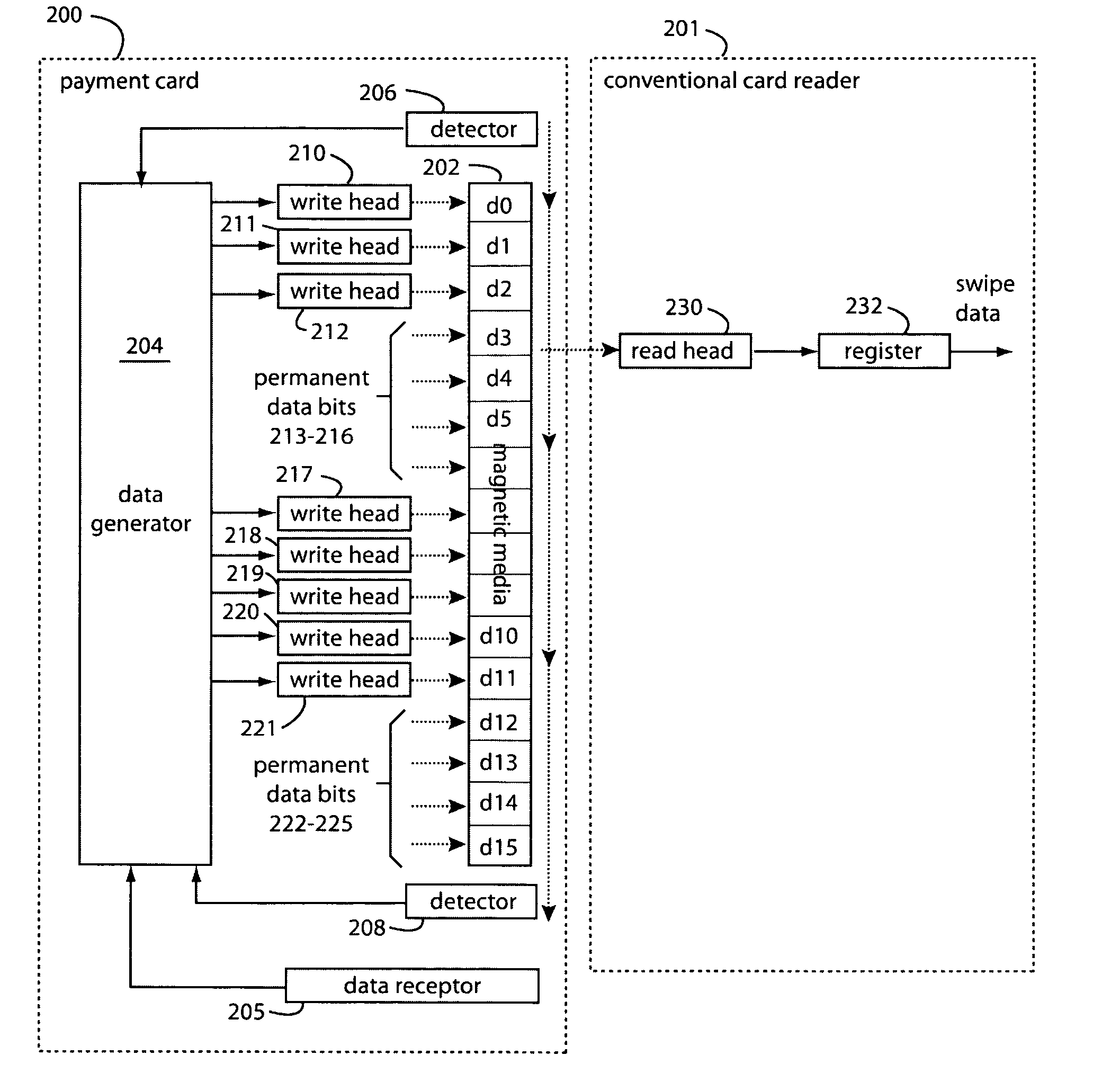
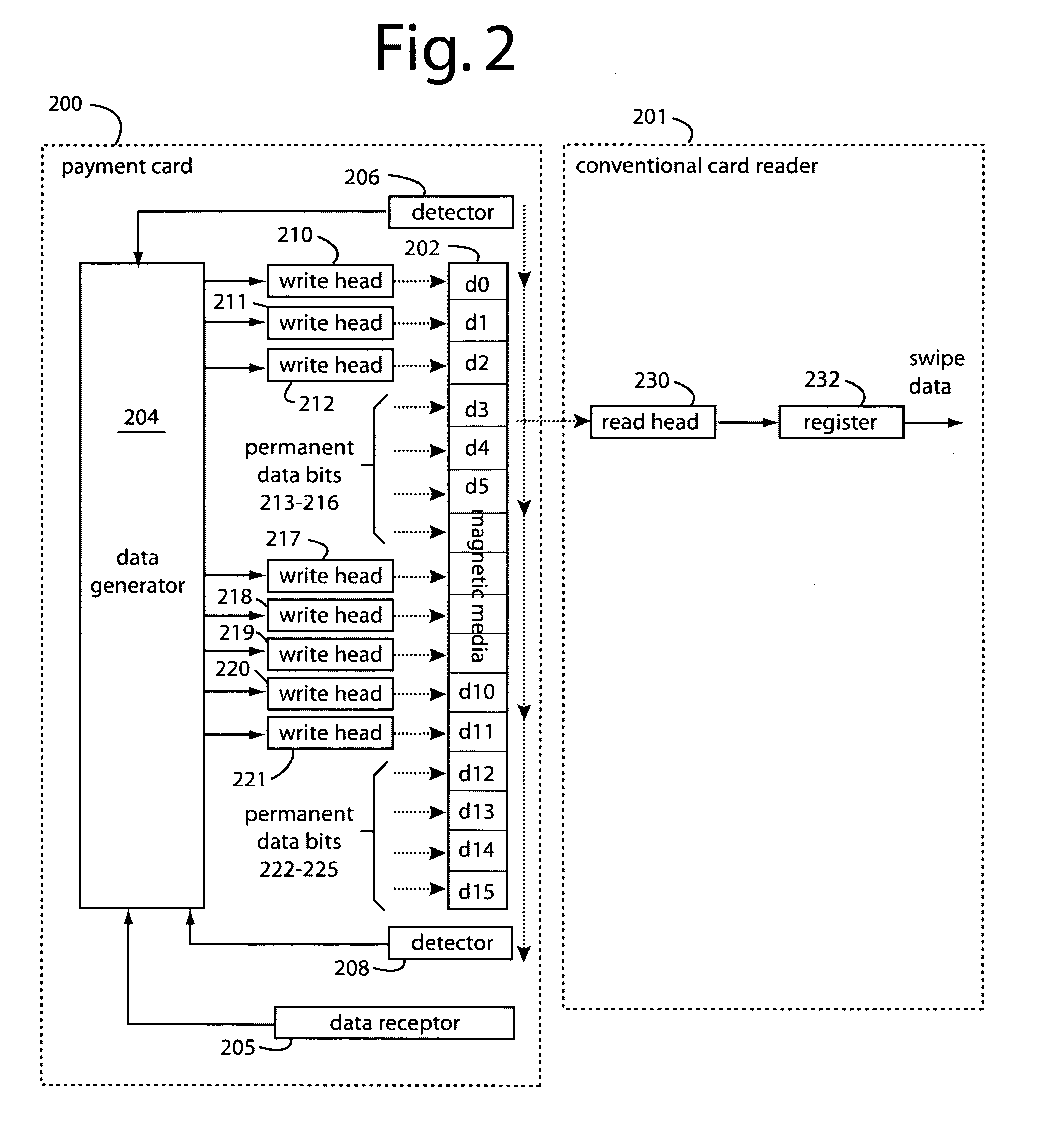
Payment card financial transaction authenticator
InactiveUS20080201264A1Sufficient dataAcutation objectsFinanceCryptographic nonceFinancial transaction
A payment card financial transaction authenticates for providing overall financial network security computes a number of results from a cryptographic key that match values that were selectively used to personalize individual payment cards with their individual user identification and account access codes. An account access code is later presented daring a financial transaction involving at least one of those individual payment cards. A dynamic portion is included in a merchant's magnetic reading of the payment card. Then authenication can proceed by matching it with values computed from the cryptographic key.
Owner:FITBIT INC
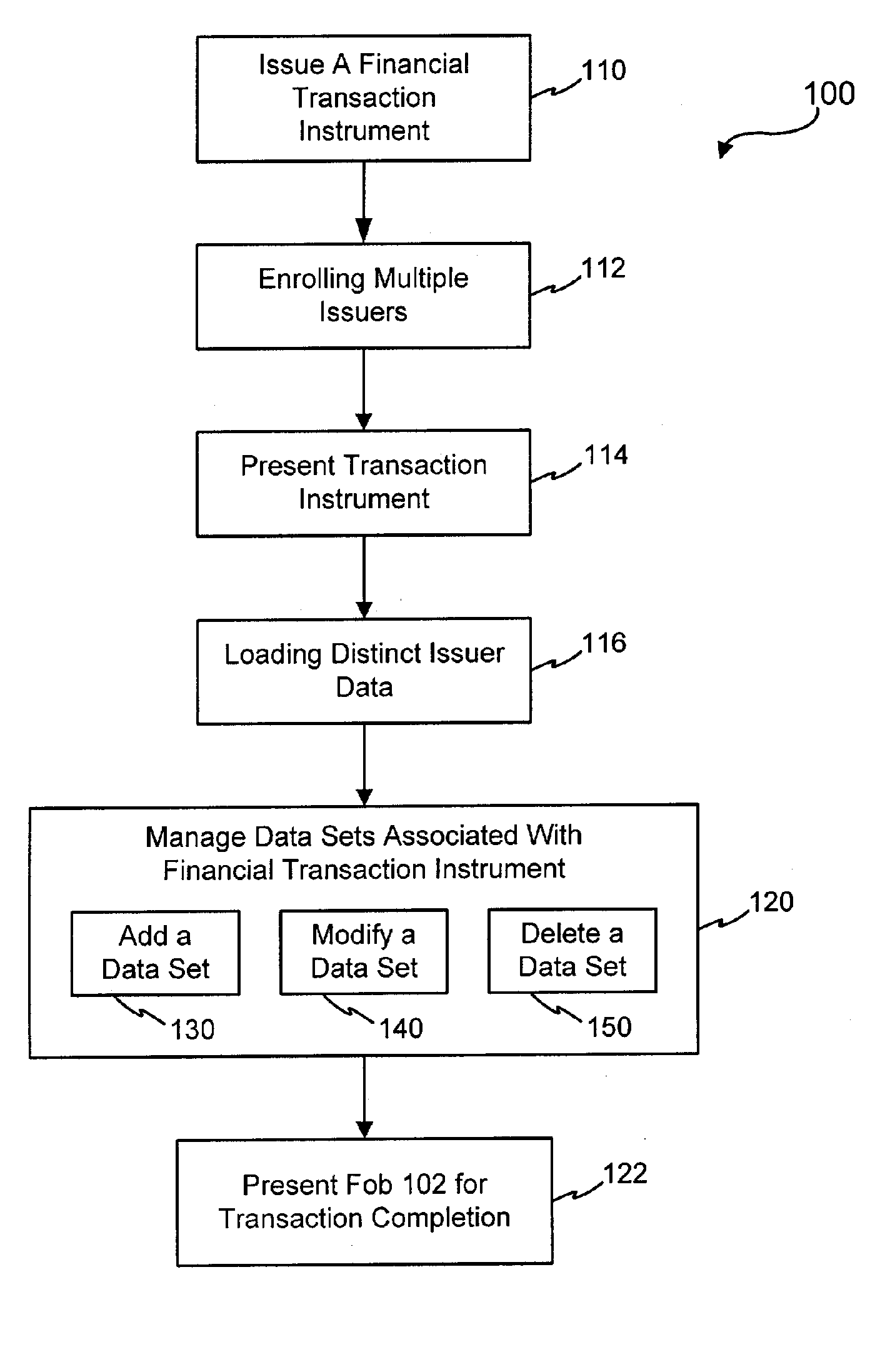
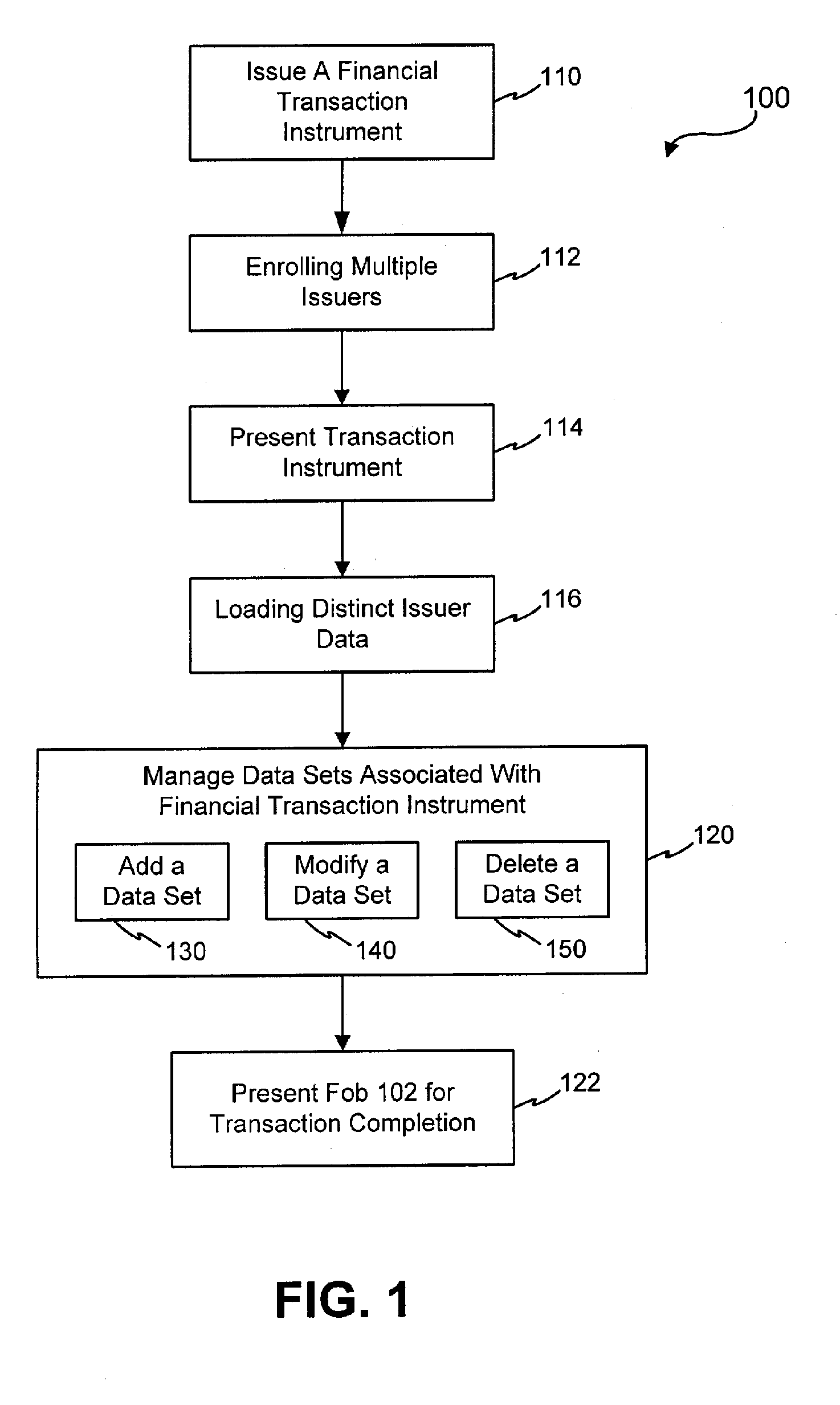
Systems and methods for managing multiple accounts on a RF transaction device using secondary identification indicia
InactiveUS20050171898A1Easy to manageEliminate needAcutation objectsFinanceData setFinancial transaction
Systems and methods are configured to manage data sets associated with a transaction device. For example, a method is provided for facilitating the management of distinct data sets on a transaction device that are provided by distinct data set owners, wherein the distinct data sets may include differing formats. The method includes the steps of: adding, by a read / write, a first data set to the financial transaction device, wherein the first data set is owned by a first owner; adding, by the read / write device, a second data set to the financial transaction device, wherein the second data set is owned by a second owner; and storing the first data set and the second data set on the financial transaction device in accordance with an owner defined format. The first and second data sets are associated with first and second owners, respectively, and are configured to be stored independent of each other The transaction device user may be permitted to select at least one of the multiple data sets for transaction completion using a secondary identifier indicia. Where the user selects multiple accounts for transaction completion, the user may be permitted to allocate portions of a transaction to the selected transaction accounts. The transaction request may be processed in accordance with the user's allocations.
Owner:LIBERTY PEAK VENTURES LLC
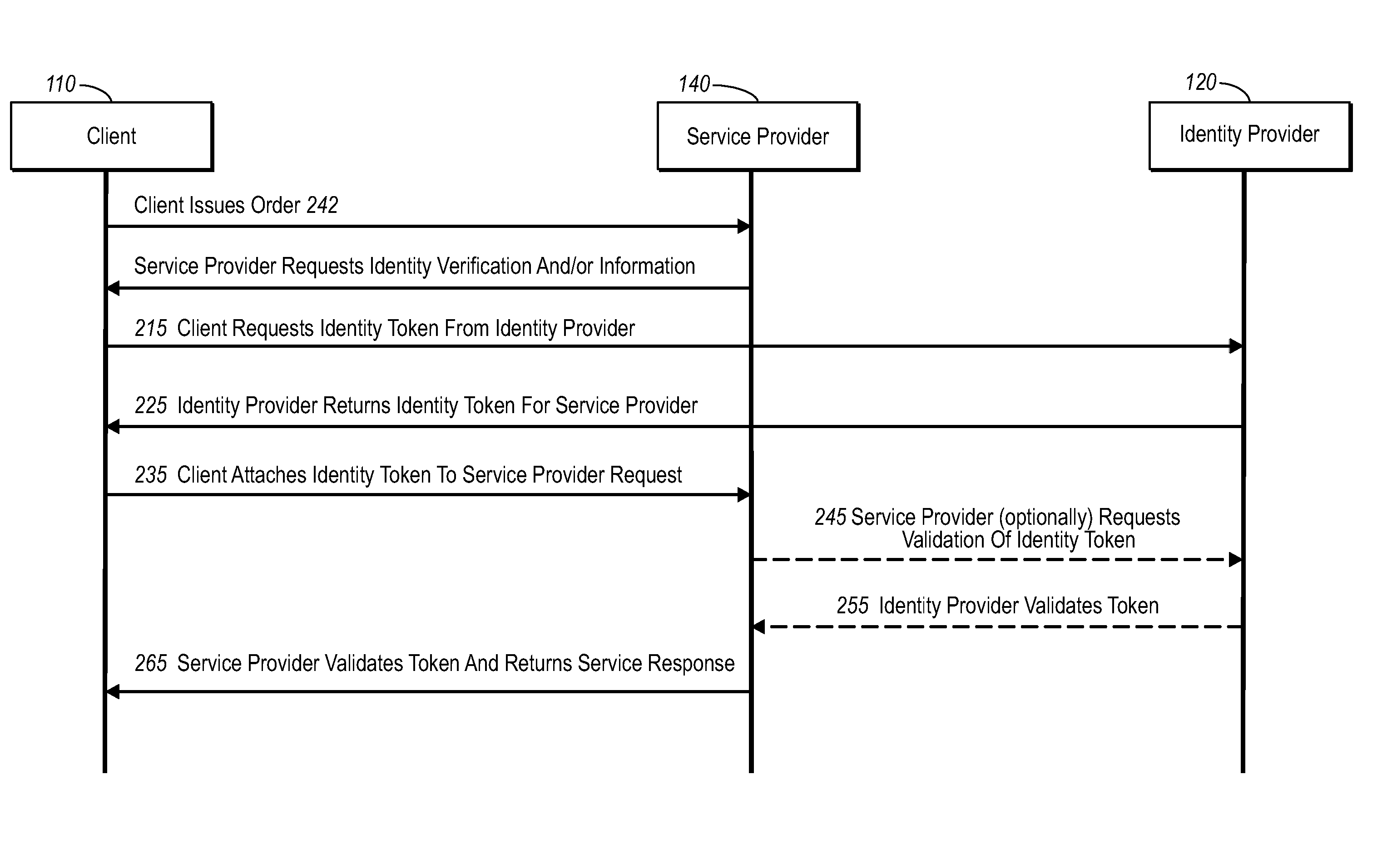
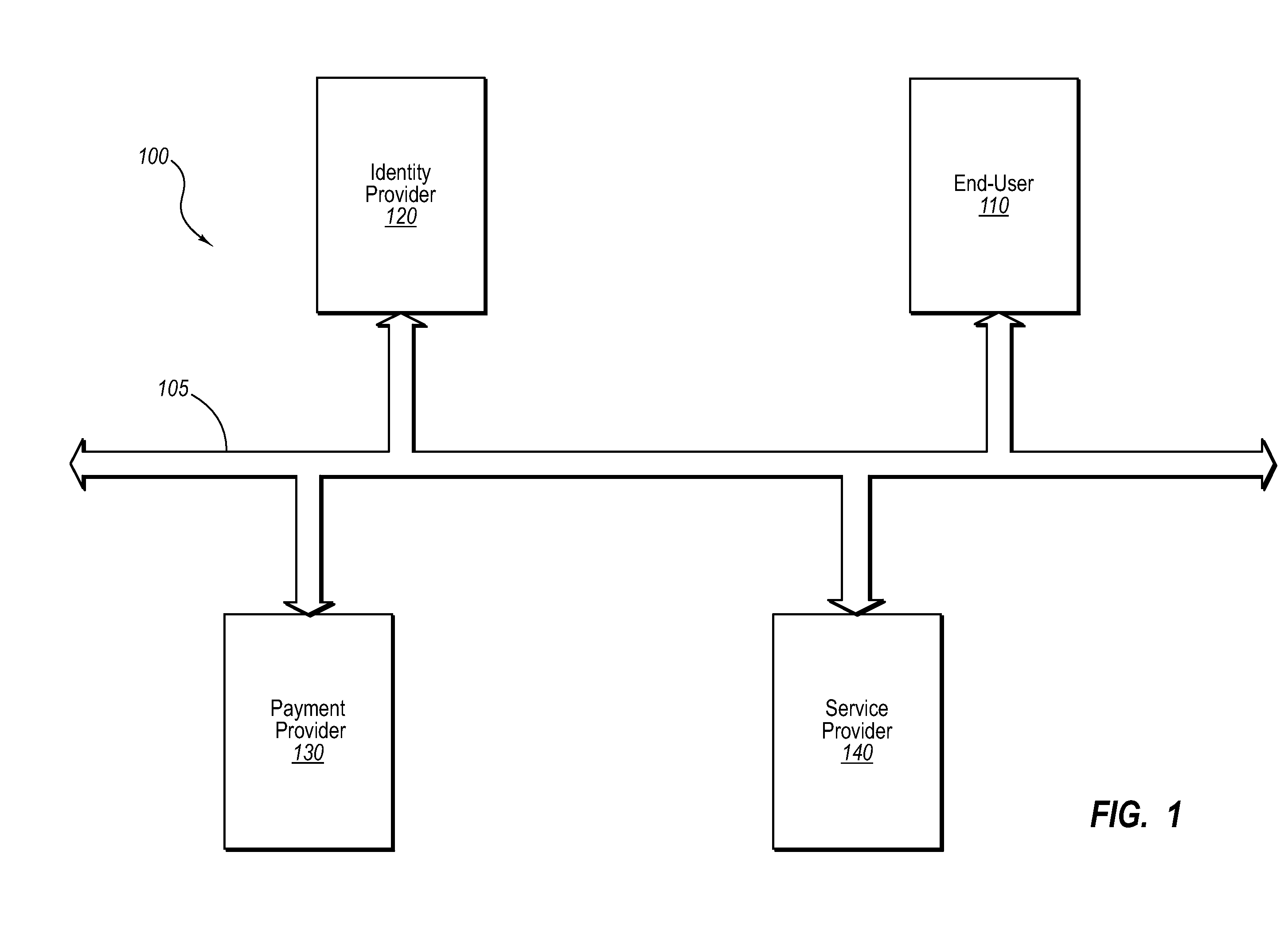
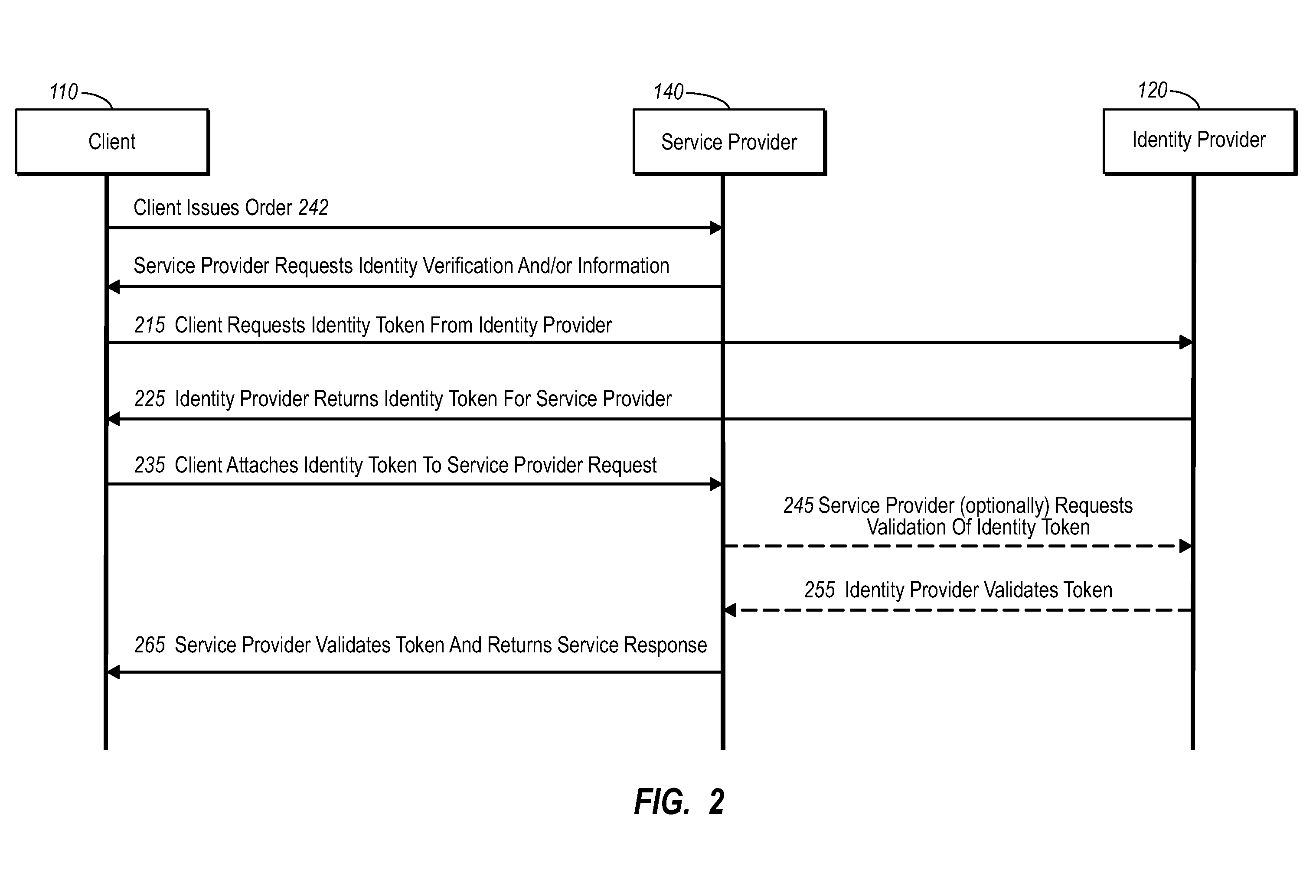
Secure network commercial transactions
InactiveUS20060235795A1Reduce the burden onSimpler and more secure online commercial transactions frameworkFinanceBuying/selling/leasing transactionsPaymentSecure communication
Current embodiments provide for authorization and payment of an online commercial transaction between a purchaser and a merchant including verification of an identity of the purchaser and verification of an ability of the purchaser to pay for the transaction, where the identity provider and the payment provider are often different network entities. Other embodiments also provide for protocols, computing systems, and other mechanisms that allow for identity and payment authentication using a mobile module, which establishes single or multilevel security over an untrusted network (e.g., the Internet). Still other embodiments also provide for a three-way secure communication between a merchant, consumer, and payment provider such that sensitive account information is opaque to the merchant, yet the merchant is sufficiently confident of the consumer's ability to pay for requested purchases. In yet another embodiment, electronic billing information is used for authorization, auditing, payment federation, and other purposes.
Owner:MICROSOFT TECH LICENSING LLC
Wireless electronic check deposit scanning and cashing machine with web-based online account cash management computer application system
Wireless Electronic Check Deposit Scanning and Cashing Machine (also known and referred to as WEDS) Web-based Online account cash Management computer application System (also known and referred to as OMS virtual / live teller)—collectively invented integrated as “WEDS.OMS” System. Method and Apparatus for Depositing and Cashing Ordinary paper and / or substitute checks and money orders online Wirelessly from home / office computer, laptop, Internet enabled mobile phone, pda (personal digital assistant) and / or any Internet enabled device. WEDS enables verification and transmittal of image, OMS is the navigation tool used to set commands and process requests, integrated with WEDS, working collectively as WEDS.OMS System.
Owner:USAA
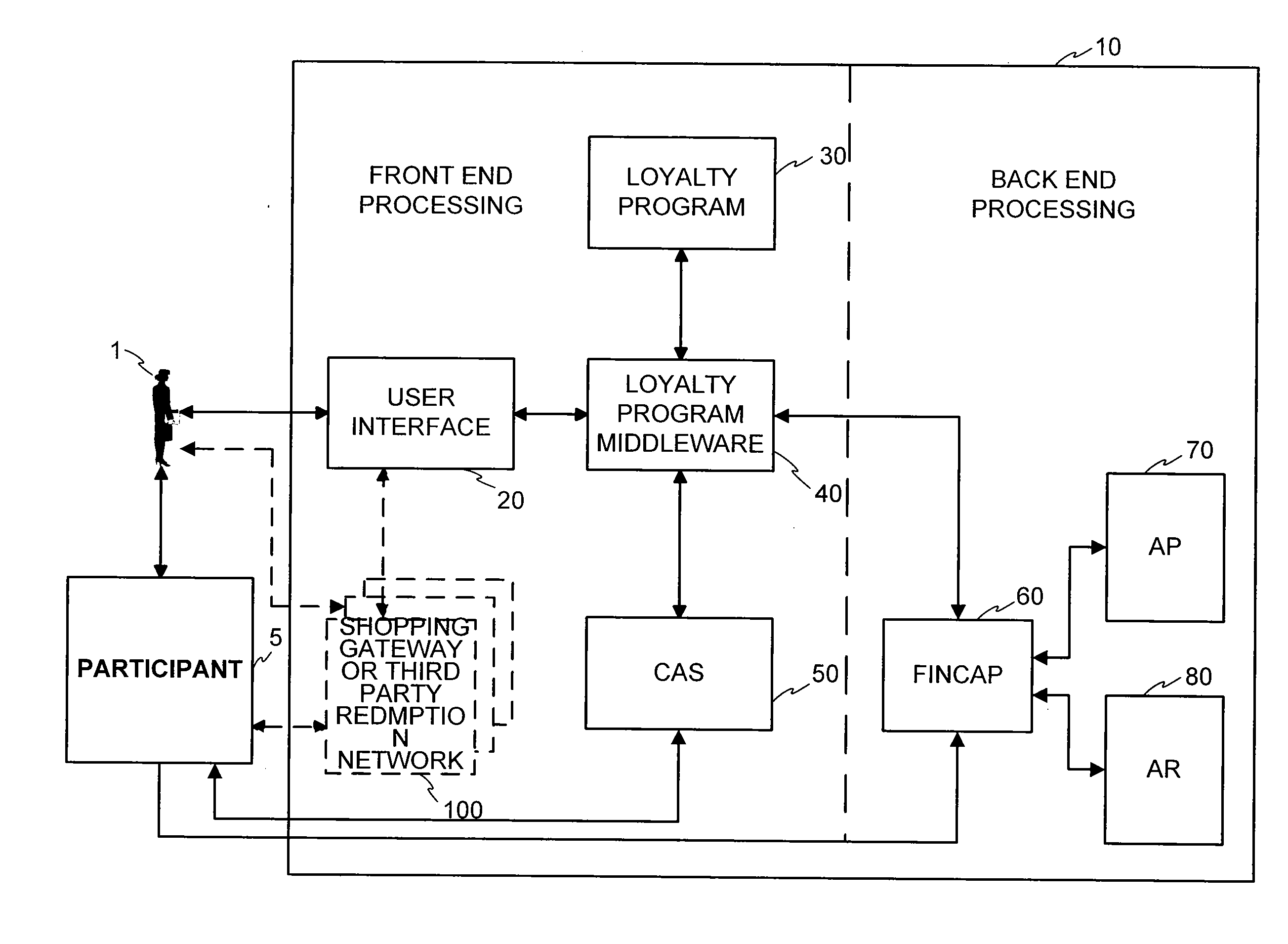
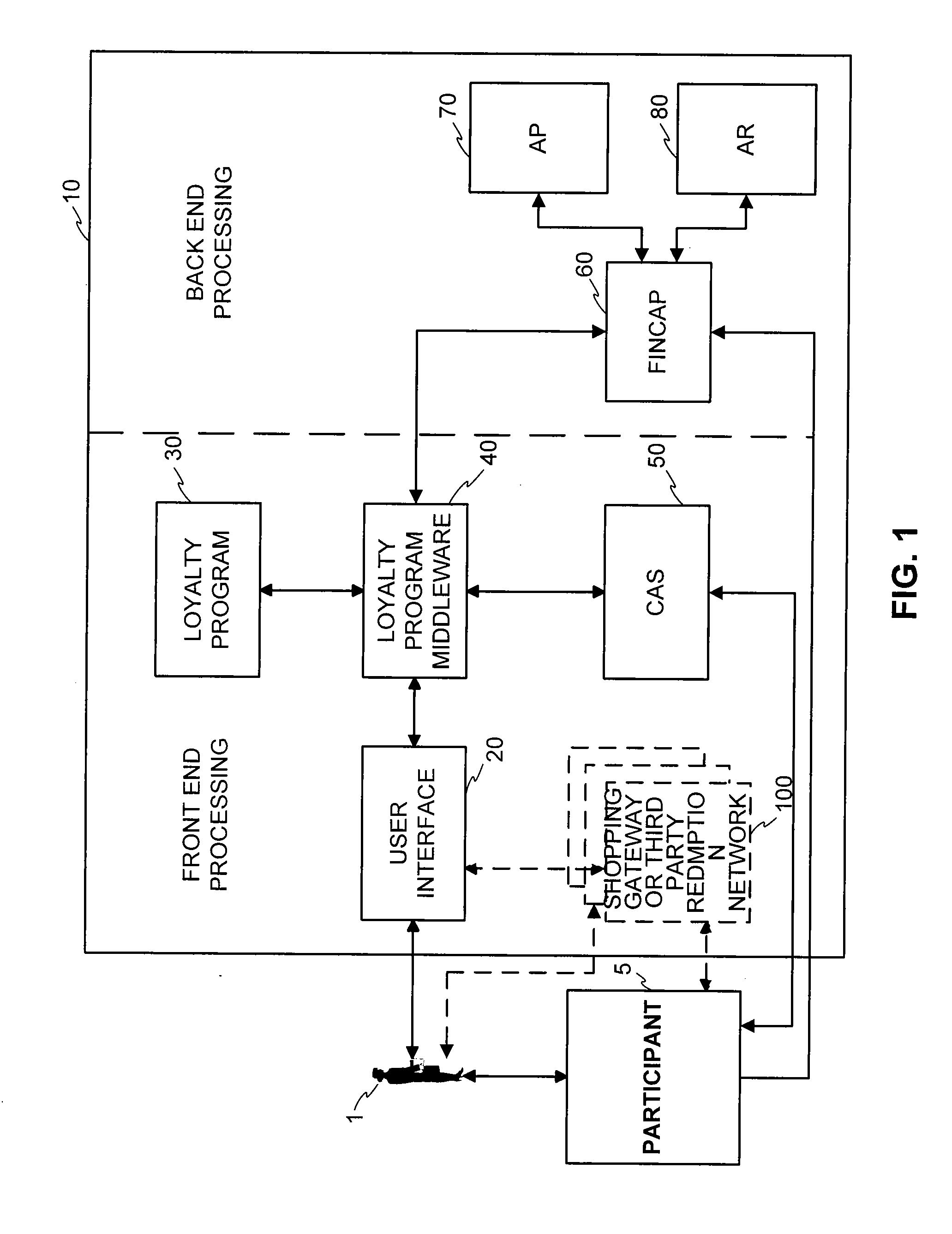
System and method for issuing and using a loyalty point advance
InactiveUS20070129955A1Convenient transactionFinanceBilling/invoicingLoyalty programComputer science
A system and method for spending loyalty points over a computerized network to facilitate a loyalty point transaction is disclosed. The system enables a participant of a loyalty program to accept an advance of loyalty point when a loyalty account balance is insufficient to make a desired purchase. An amount of loyalty points available as an advance to a participant is determined based on a number of criteria related to the participant, financial account activity, and loyalty account activity. The participant is allotted a predetermined length of time to earn or purchase enough loyalty points to repay the balance of advanced loyalty points. If, at the conclusion of such predetermined length of time, sufficient points have not been earned to offset the loyalty point advance, the participant is charged the currency value of each outstanding loyalty point. The participant may be assessed interest charges and / or fees at the time of the loyalty point advance, during reimbursement, or at the end of a time period for reimbursement.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC +1
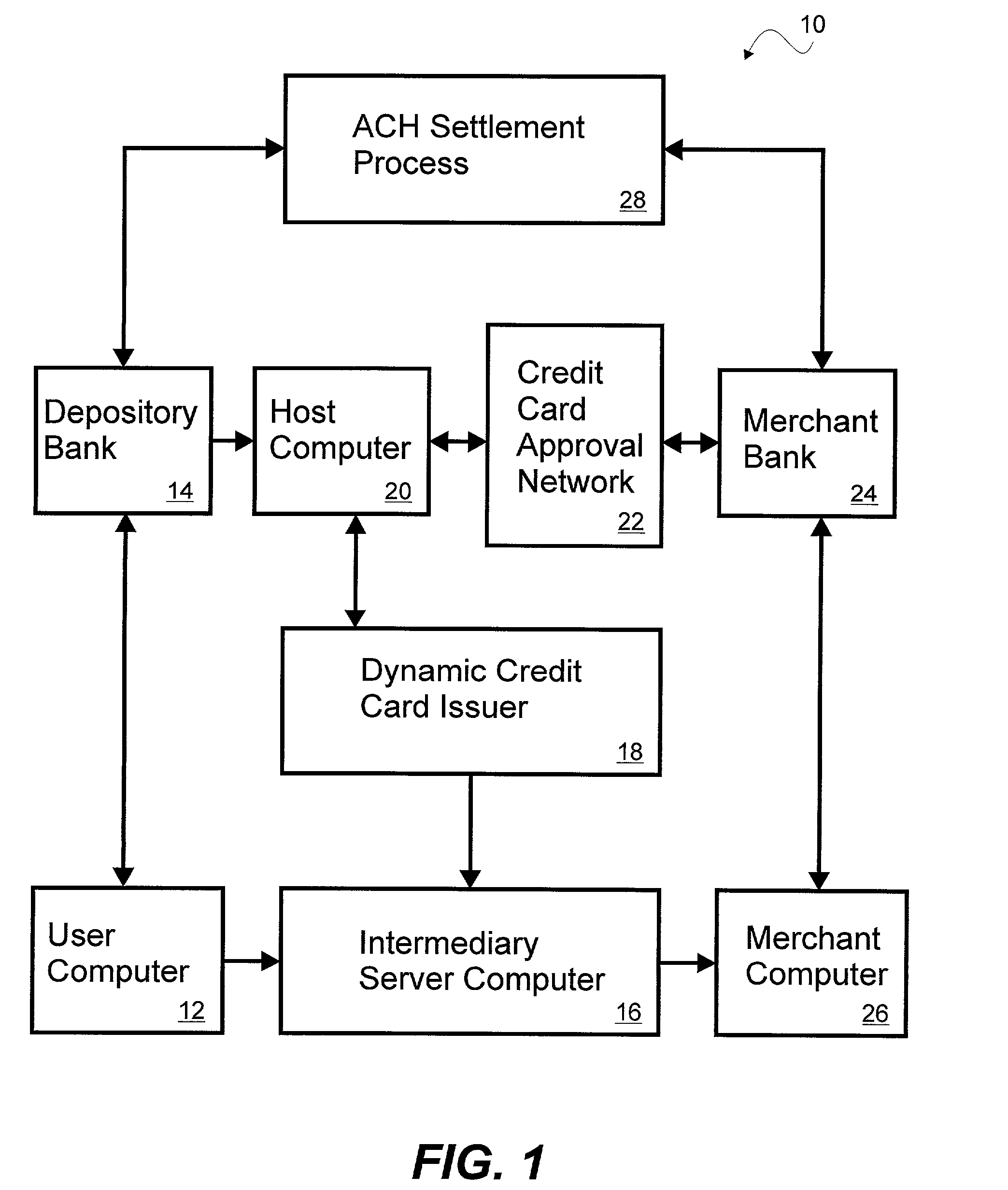
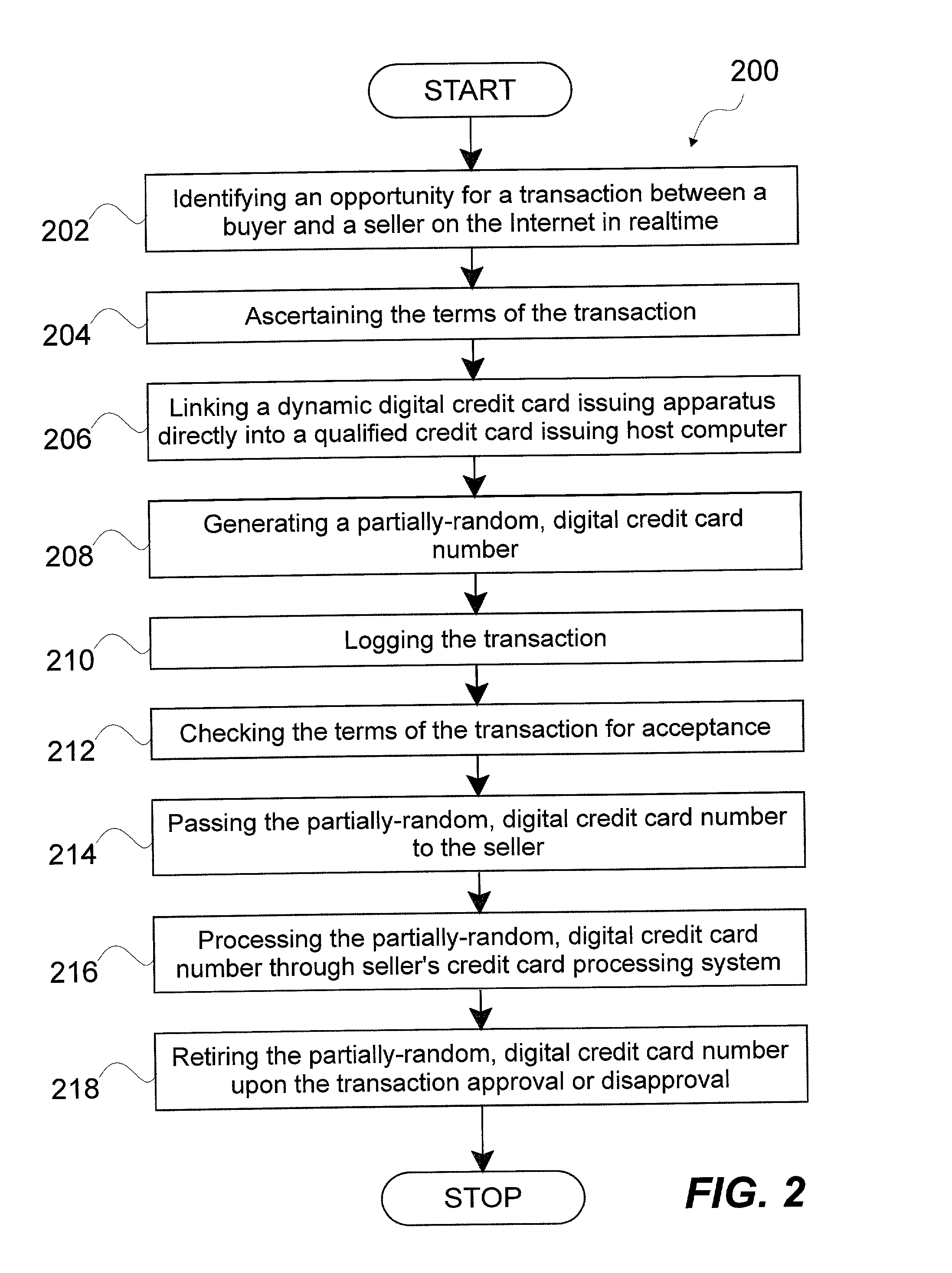
System and method for dynamically issuing and processing transaction specific digital credit or debit cards
A system and method of dynamically issuing credit card numbers and processing transactions using those credit card numbers is disclosed. A method according to the invention includes digitally recognizing a transaction opportunity on the Internet in real-time, recognizing the terms of the transaction, linking a dynamic digital credit card issuing apparatus directly into a qualified credit card issuing host, generating a partially random digital credit card number, logging the transaction, checking the terms of the transaction for acceptance, passing the dynamically issued digital credit card number to the merchant, processing the digital credit card number through the merchant's card processing system, receiving the transaction approval request, participating in credit card validity checking systems, processing the approval request in real-time, sending the requesting party a legitimate authorization code, and retiring the digital credit card number immediately upon transaction approval or disapproval. A system according to the invention implements the method of the invention.
Owner:ORANGATANGO
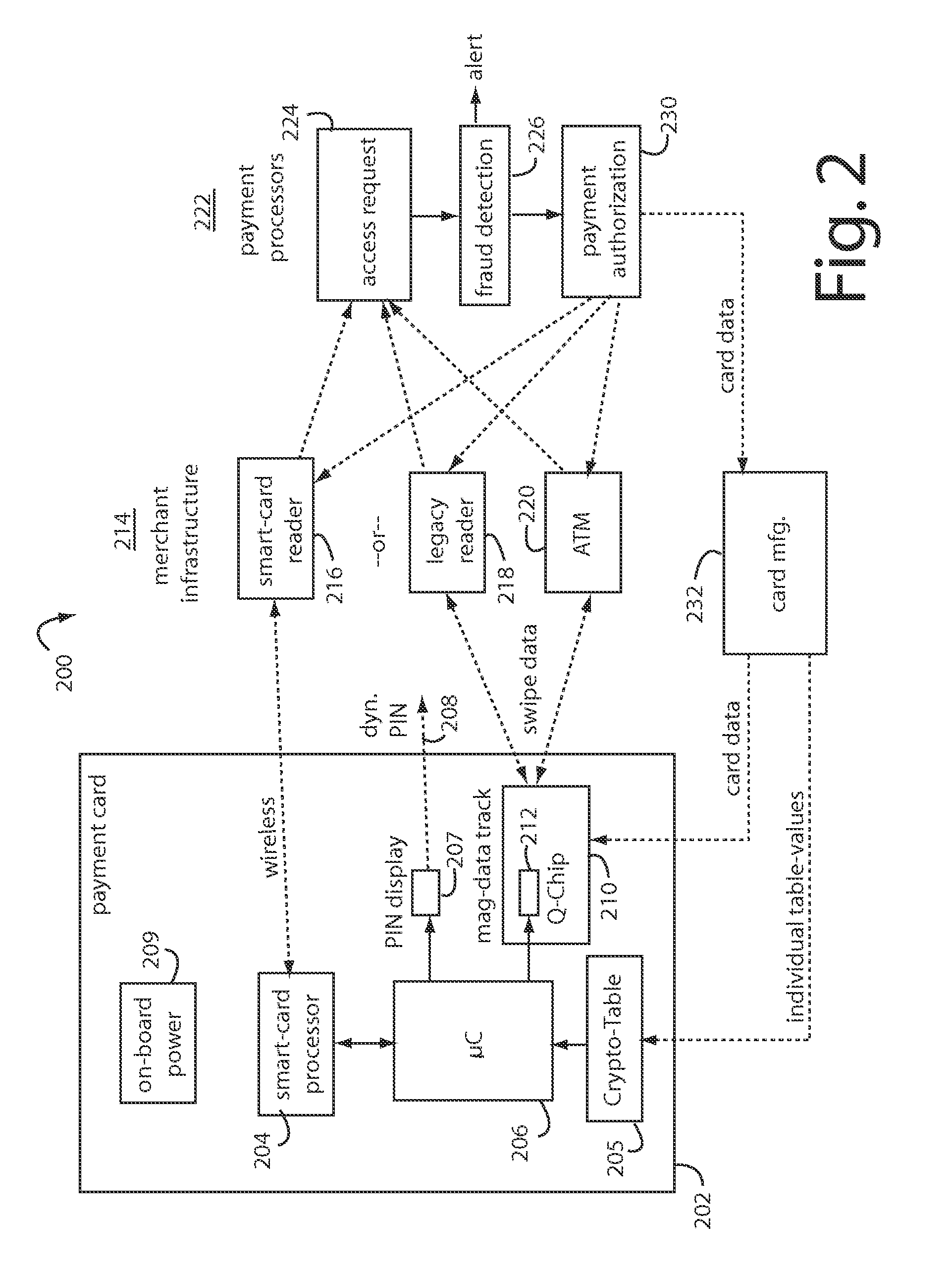
Onetime passwords for smart chip cards
ActiveUS8095113B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsDisplay deviceFinancial transaction
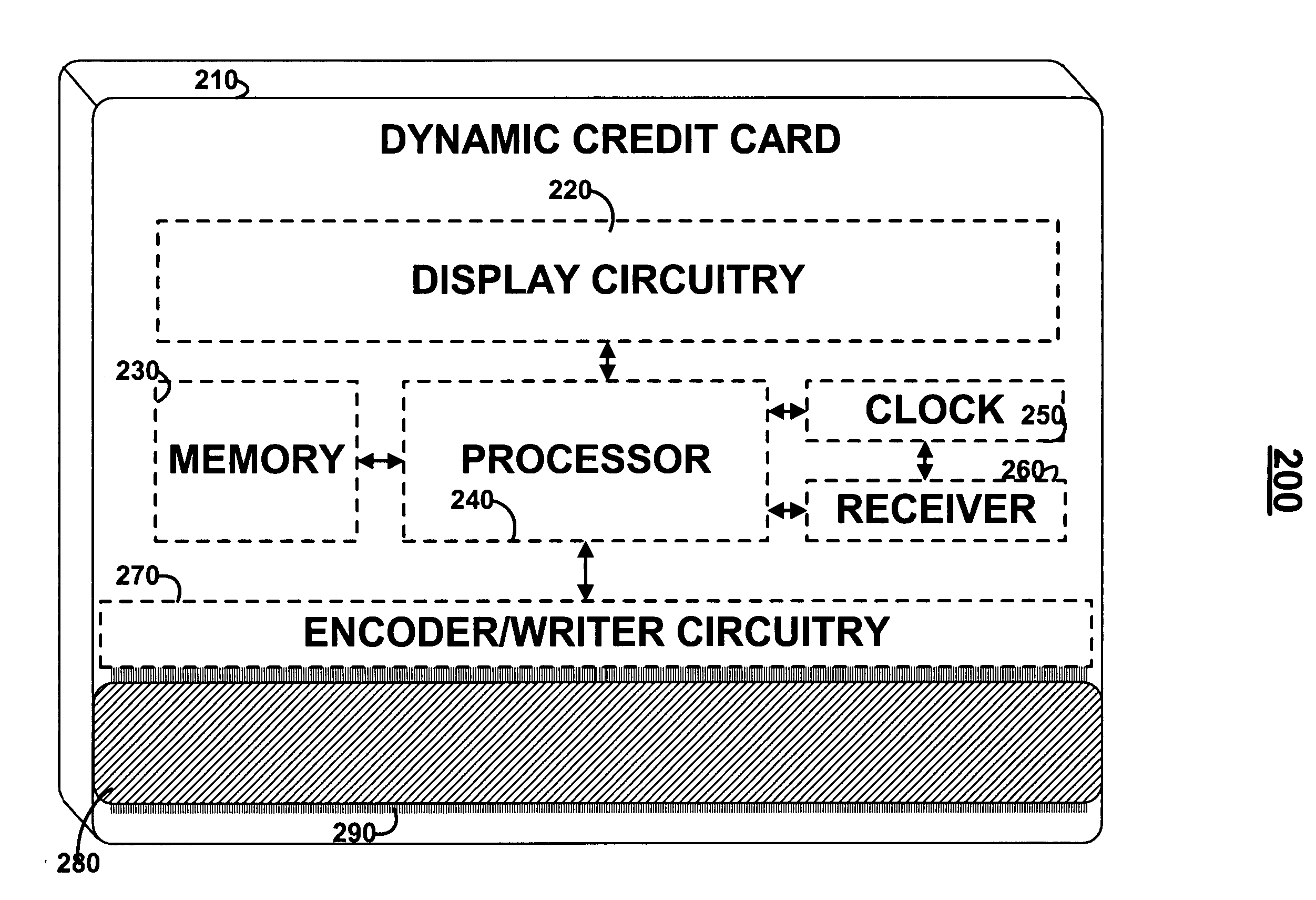
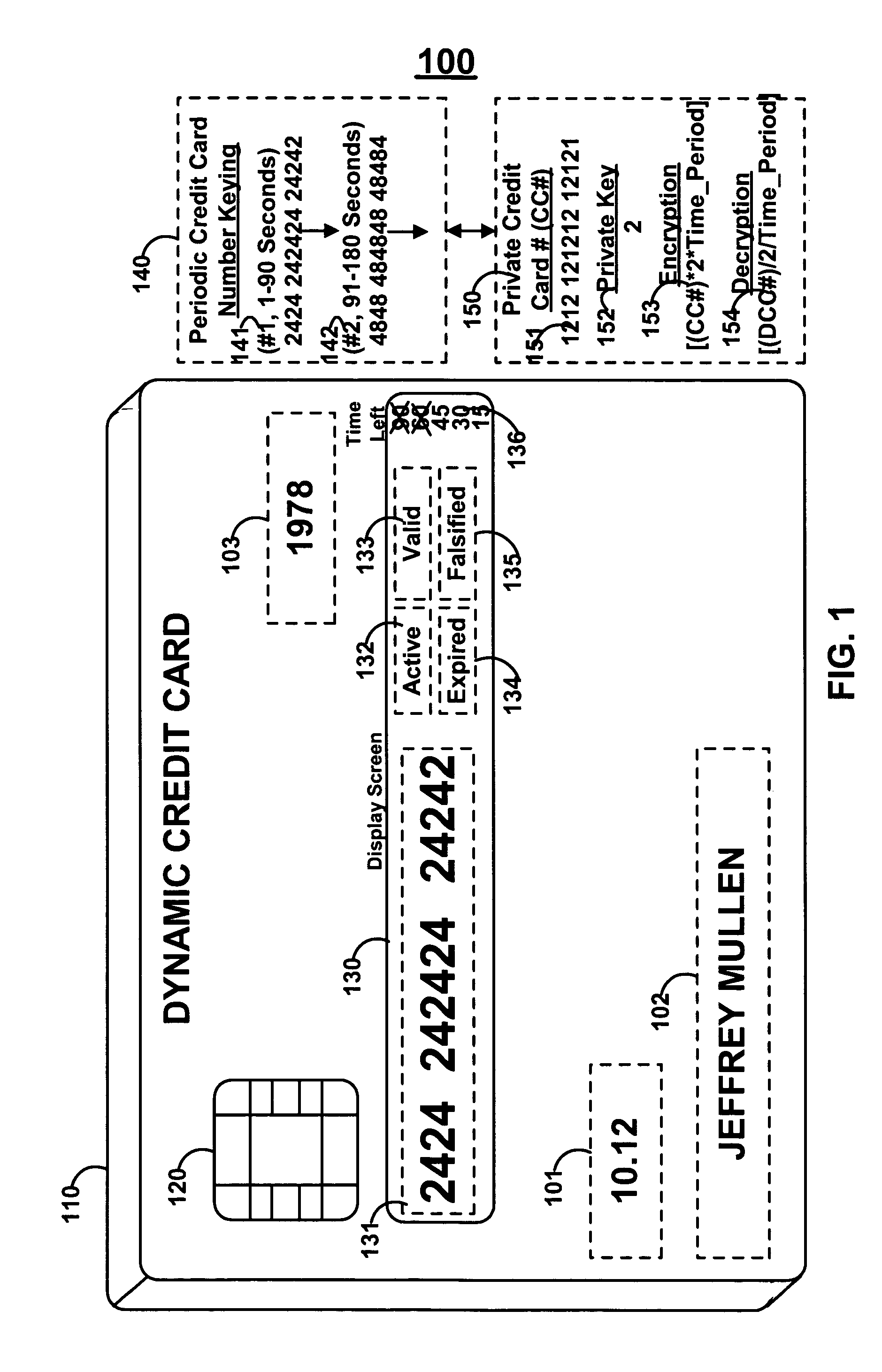
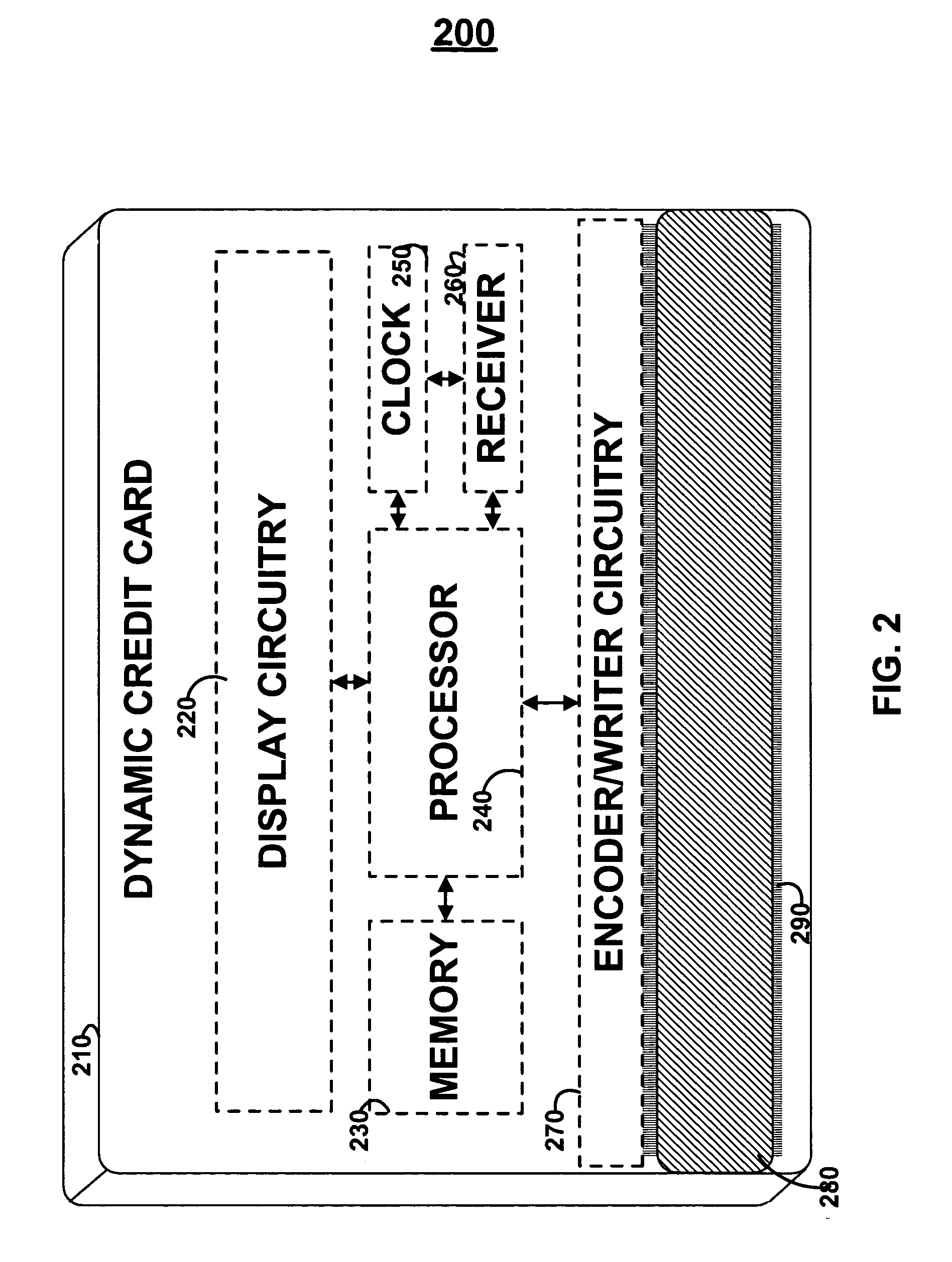
A financial transaction card is provided according to various embodiments described herein. The financial transaction card includes a card body with at least a front surface and a back surface. The financial transaction card may also include a near field communications transponder and / or a magnetic stripe, as well as a digital display configured to display alphanumeric characters on the front surface of the card body. The financial transaction card may also include a processor that is communicatively coupled with the near field communications transponder or magnetic stripe and the digital display. The processor may be configured to calculate one-time passwords and communicate the one-time passwords to both the near filed communications transponder or magnetic stripe and the digital display.
Owner:FIRST DATA
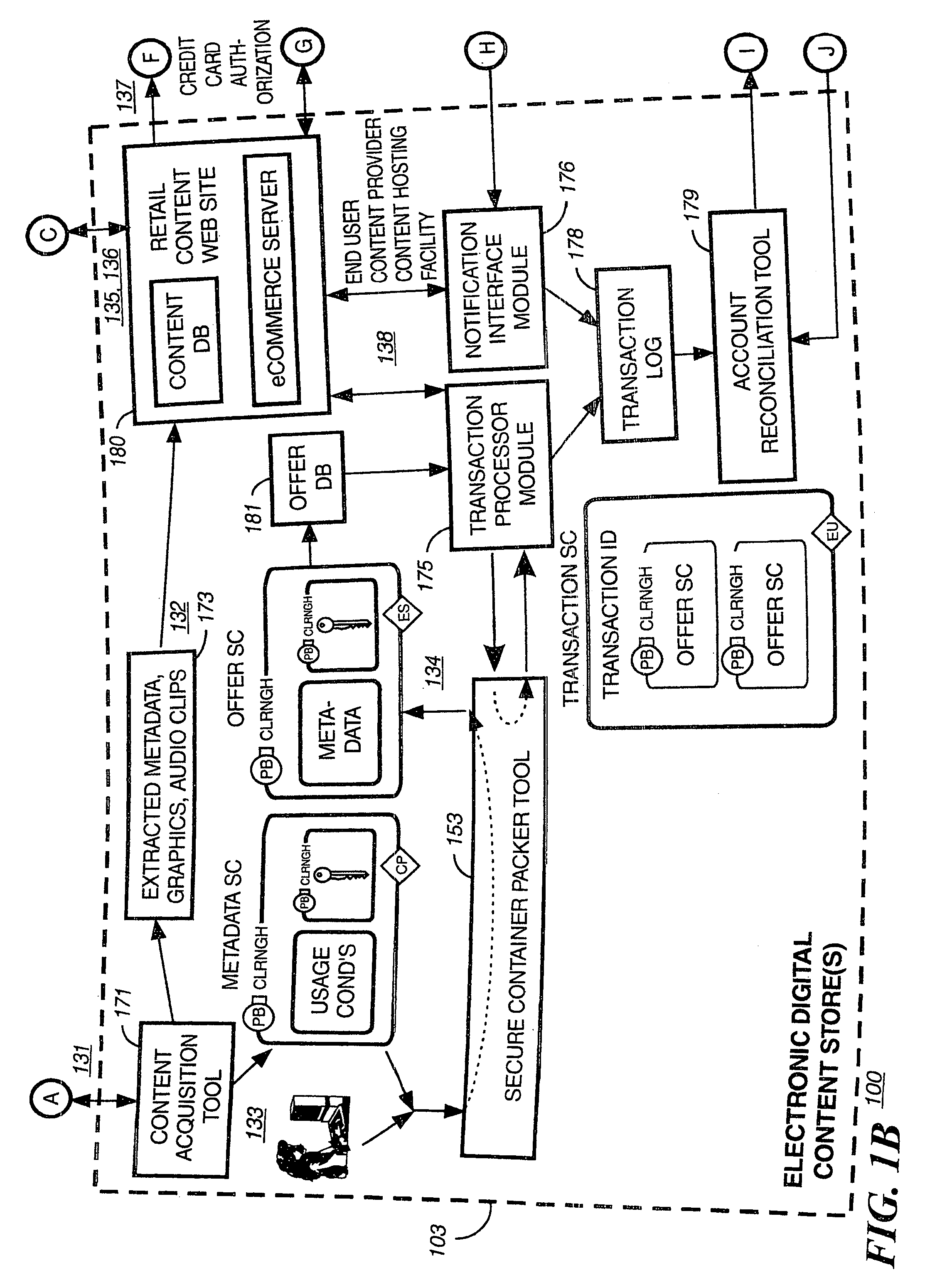
Super-distribution of protected digital content
Briefly according to the present invention, a system, computer readable medium and method to deliver encrypted digital content to from a first system for playing the content to a second system for playing the content. The method on the first user system comprising the steps of: reading from a computer readable medium metadata which has previously been associated with the content; selecting from the metadata associated content to decrypt; establishing a secure connection with an authorization authority, such as a clearinghouse, for decrypting the key used to encrypt the content; receiving a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted; decrypting the content and then encrypting the content with a new encryption key that is generated locally on the end user system.
Owner:WISTRON CORP
Electronic multiparty accounts receivable and accounts payable system
InactiveUS7206768B1Facilitating collection and trackingFacilitate communicationComplete banking machinesFinanceAccounts payableInvoice
The invention concerns a multiparty accounts receivable and accounts payable system that allows business trading partners to use a single, shared system for both accounts receivable and accounts payable management. The system of the invention forms an electronic “bridge” between a plurality of business trading partners for purposes of invoicing, dispute resolution, financing, and settlement of single and multiple currency debts. As the invoicing and settlement activities of the participants are funneled through a common system, the system allows a participant to aggregate all debts owed to other participants, aggregate all debts owed by the other participants, and net debts owed to other participants with debts owed by these participants. After aggregation and netting, the participant issues a single payment to settle numerous accounts payable items, and receives a single payment that settles numerous accounts receivable items. The system allows participants to use the substantial amount of financial and cash flow information captured by the system to borrow more efficiently by permitting lenders to view this information. Furthermore, the system provides a confirmation process to convert existing debt obligations into a new, independent payment obligation due on a date certain and free of any defenses to the underlying contract. The confirmed debt obligations provide a better source of working capital for the participants, or can be converted into electronic promissory notes. The system provides an electronic exchange for electronic promissory notes, allowing participants to raise working capital in various ways, for example, by selling them.
Owner:JPMORGAN CHASE BANK NA +1
Biometric authentication of mobile financial transactions by trusted service managers
ActiveUS20090307139A1Digital data processing detailsUser identity/authority verificationUser inputFinancial transaction
A method for authenticating a financial transaction at a point of sale (POS) includes storing an application program in a first secure element of a mobile phone. The application is configured to generate instruction codes to effect the financial transaction upon verification of a user's identity. The user's credentials are stored in a second SE of the phone, which is operable to verify the user's identity from a biometric trait of the user input to the phone and to generate data authenticating the financial transaction in response to the verification of the user's identity. At the POS, the user invokes the application and then inputs a biometric trait to the phone. The second SE verifies the user's identity, and upon verification, generates data authenticating the transaction. The financial transaction data, including the instruction codes and the authenticating data, are then transmitted from the phone to the POS.
Owner:PAYPAL INC
Method and system for providing transaction notification and mobile reply authorization
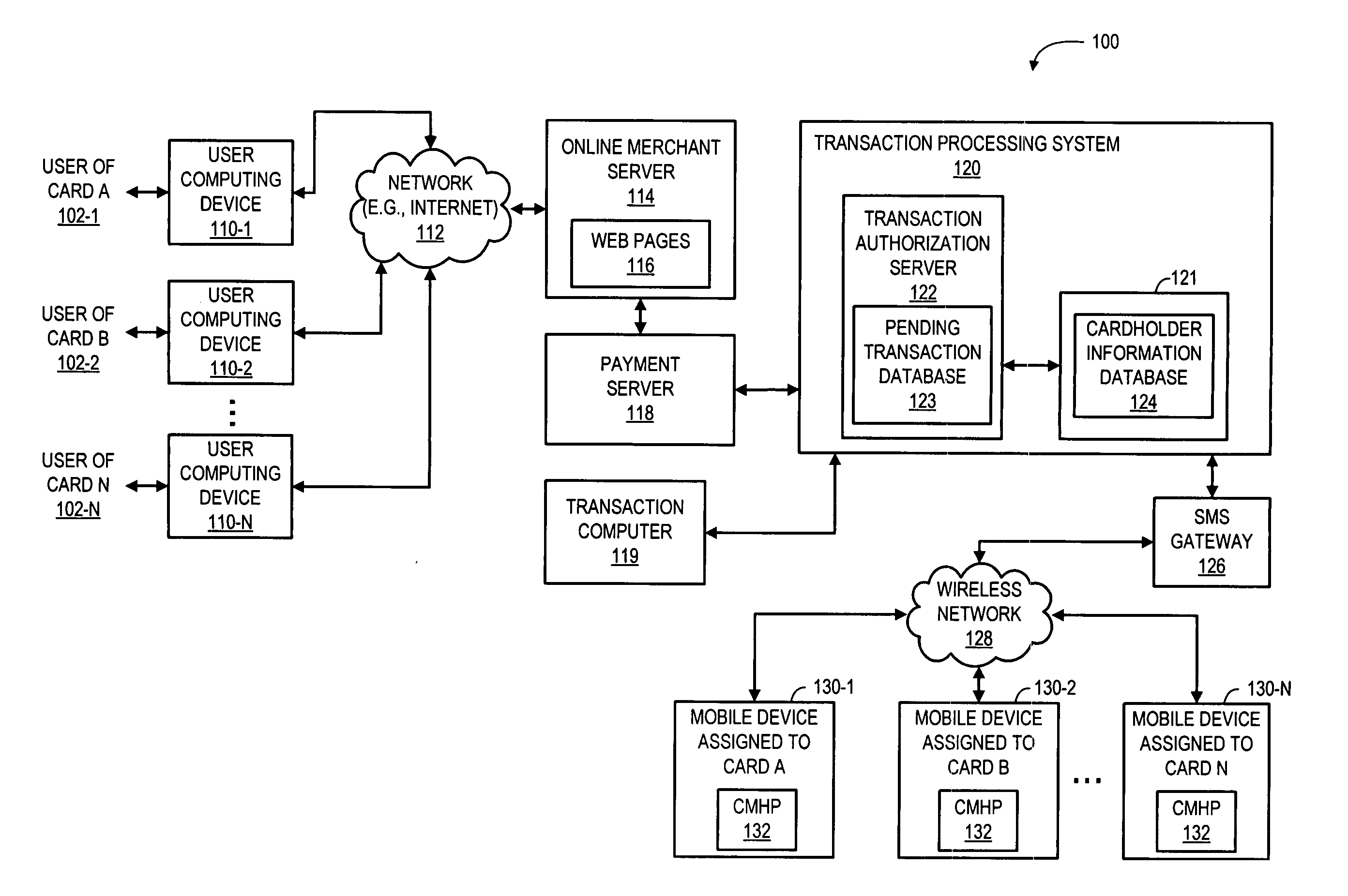
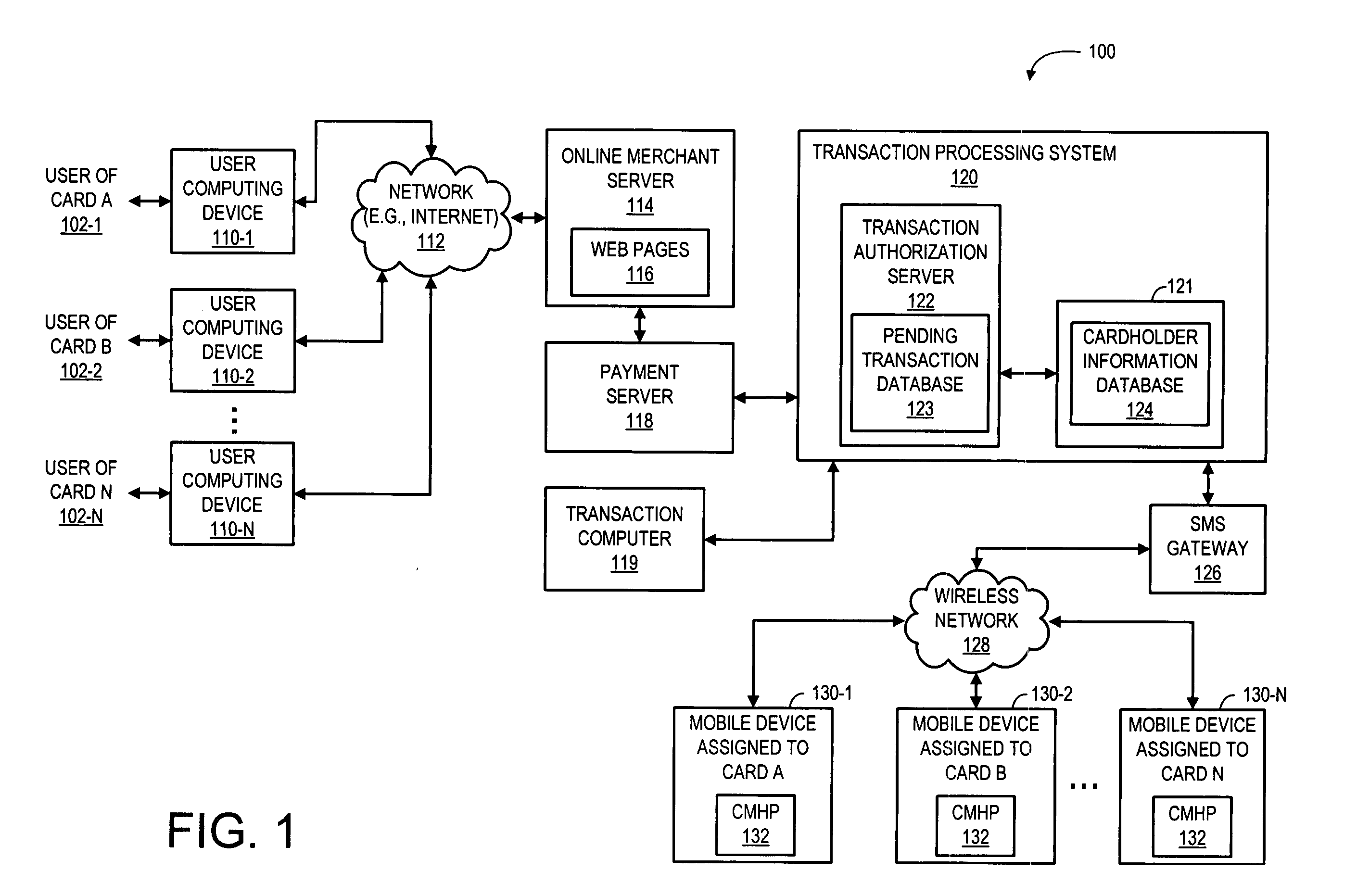
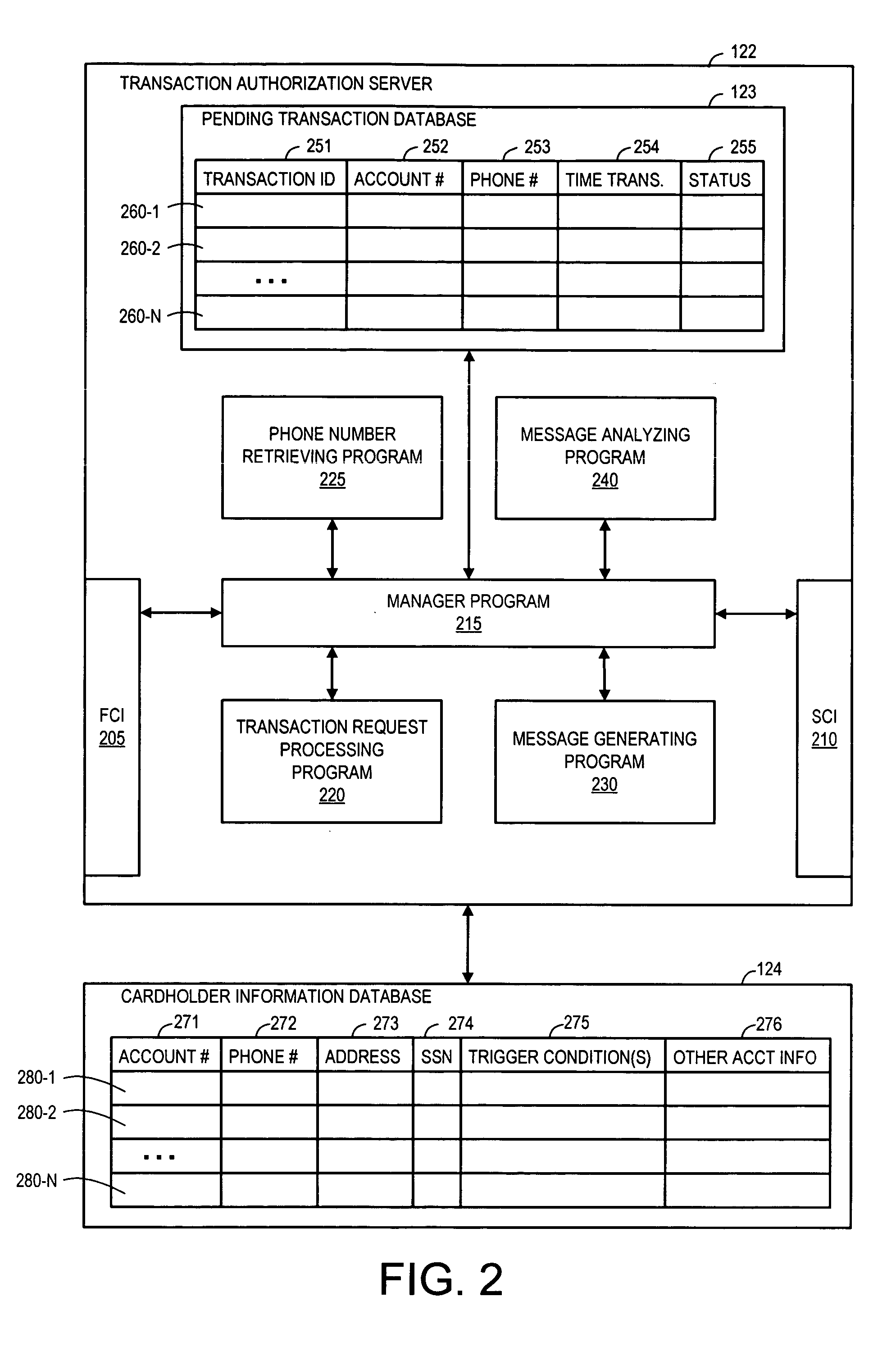
A system and a corresponding method are described for providing a notification of a pending transaction request and obtaining an authorization from a cardholder. The system maintains a database of account records, each of the account records including a phone number of a mobile device assigned to receive authorization request messages for the respective account. When a transaction request is received, the system determines a phone number of a mobile device assigned to receive authorization request messages for the account requesting the transaction by searching the database. The system generates and transmits an authorization request message to the phone number of the mobile device assigned to the account requesting the transaction. In response to the authorization request message, a reply message is returned from the mobile device, which explicitly indicates if a user of the mobile device approves or denies the transaction.
Owner:KIM MIKE
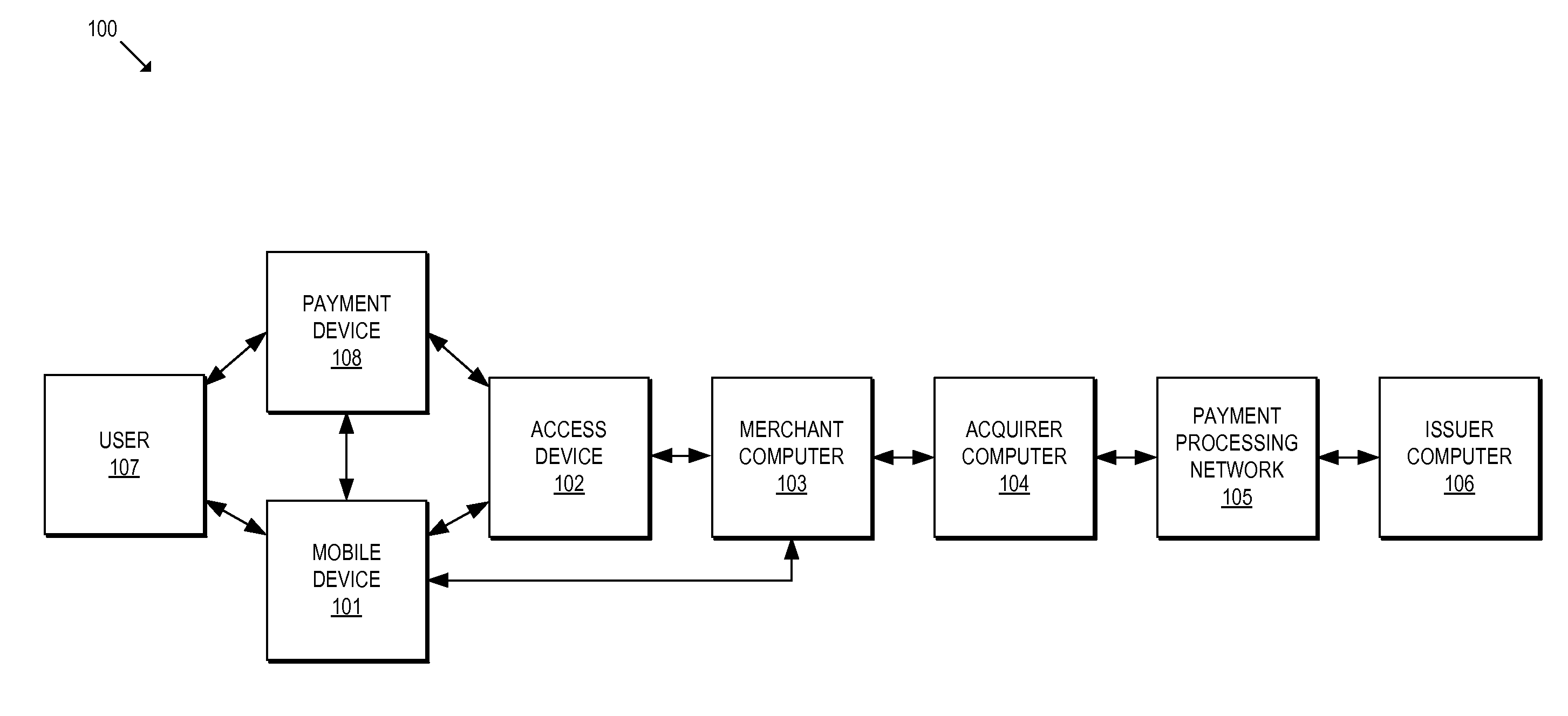
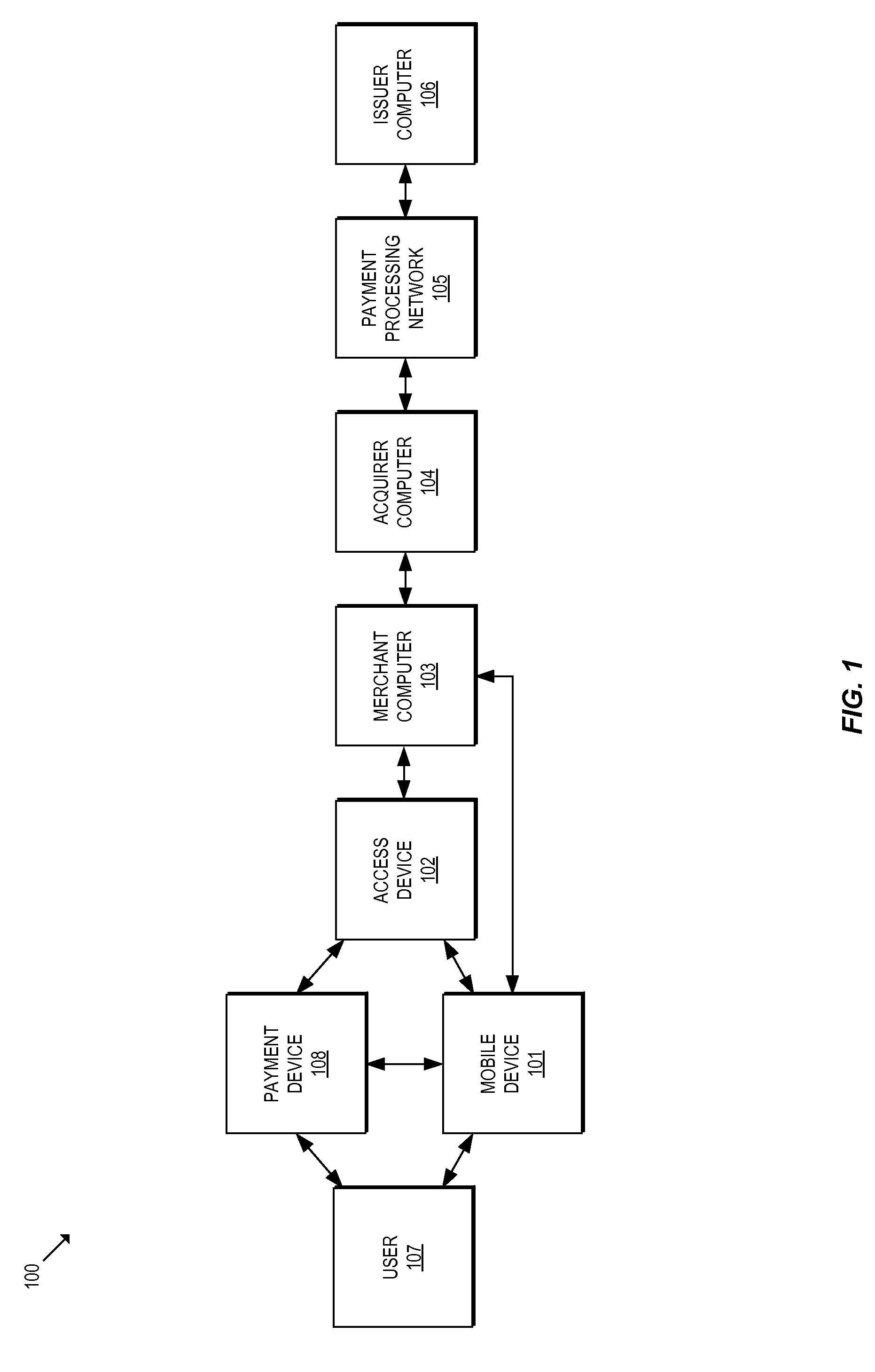
Methods and systems for provisioning mobile devices with payment credentials
ActiveUS20150046339A1Unnecessary delayProcessing speedFinanceElectronic credentialsPaymentMedium Risk
Embodiments are described that are directed to optimizing the provisioning of payment account credentials to mobile devices utilizing mobile wallets. In some embodiments, one of multiple provisioning schemes may be selectively chosen for payment account credential provisioning based upon a determined risk involved with a particular provisioning request. A low risk provisioning request leads to an immediate provisioning of a payment credential, whereas a provisioning request of high risk results in the provisioning request being denied. In some embodiments, medium risk provisioning requests will cause an additional user authentication to be performed before the payment account provisioning is finalized. The additional user authentication may occur using a separate communication channel than the channel in which the provisioning request was received.
Owner:VISA INT SERVICE ASSOC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com