Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4287 results about "Secure communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Secure communication is when two entities are communicating and do not want a third party to listen in. For that they need to communicate in a way not susceptible to eavesdropping or interception. Secure communication includes means by which people can share information with varying degrees of certainty that third parties cannot intercept what was said. Other than spoken face-to-face communication with no possible eavesdropper, it is probably safe to say that no communication is guaranteed secure in this sense, although practical obstacles such as legislation, resources, technical issues (interception and encryption), and the sheer volume of communication serve to limit surveillance.
Wireless media system and player and method of operation
ActiveUS20060258289A1Easy to useMultimedia data browsing/visualisationPayment architectureUltra-widebandSecure communication
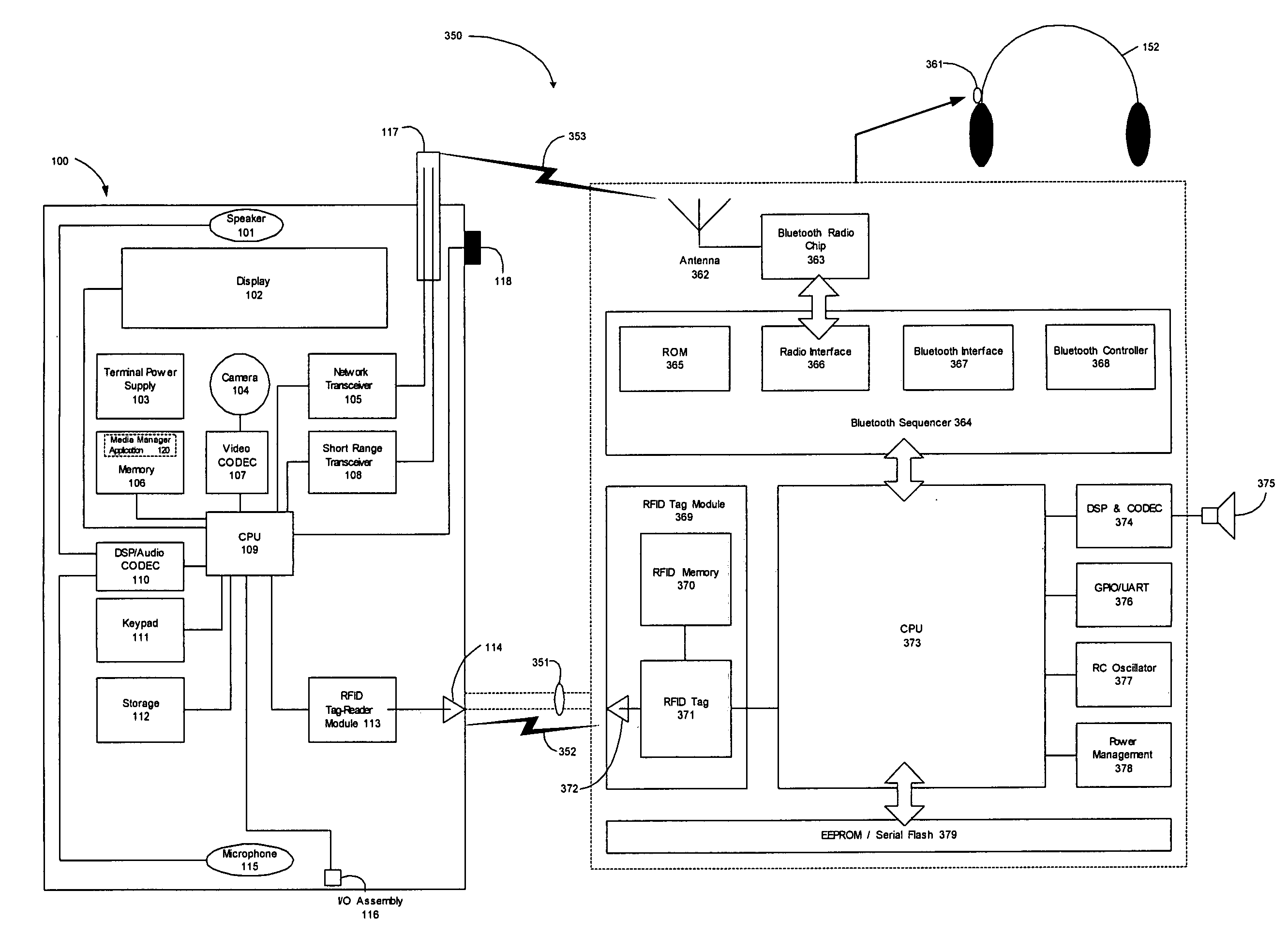
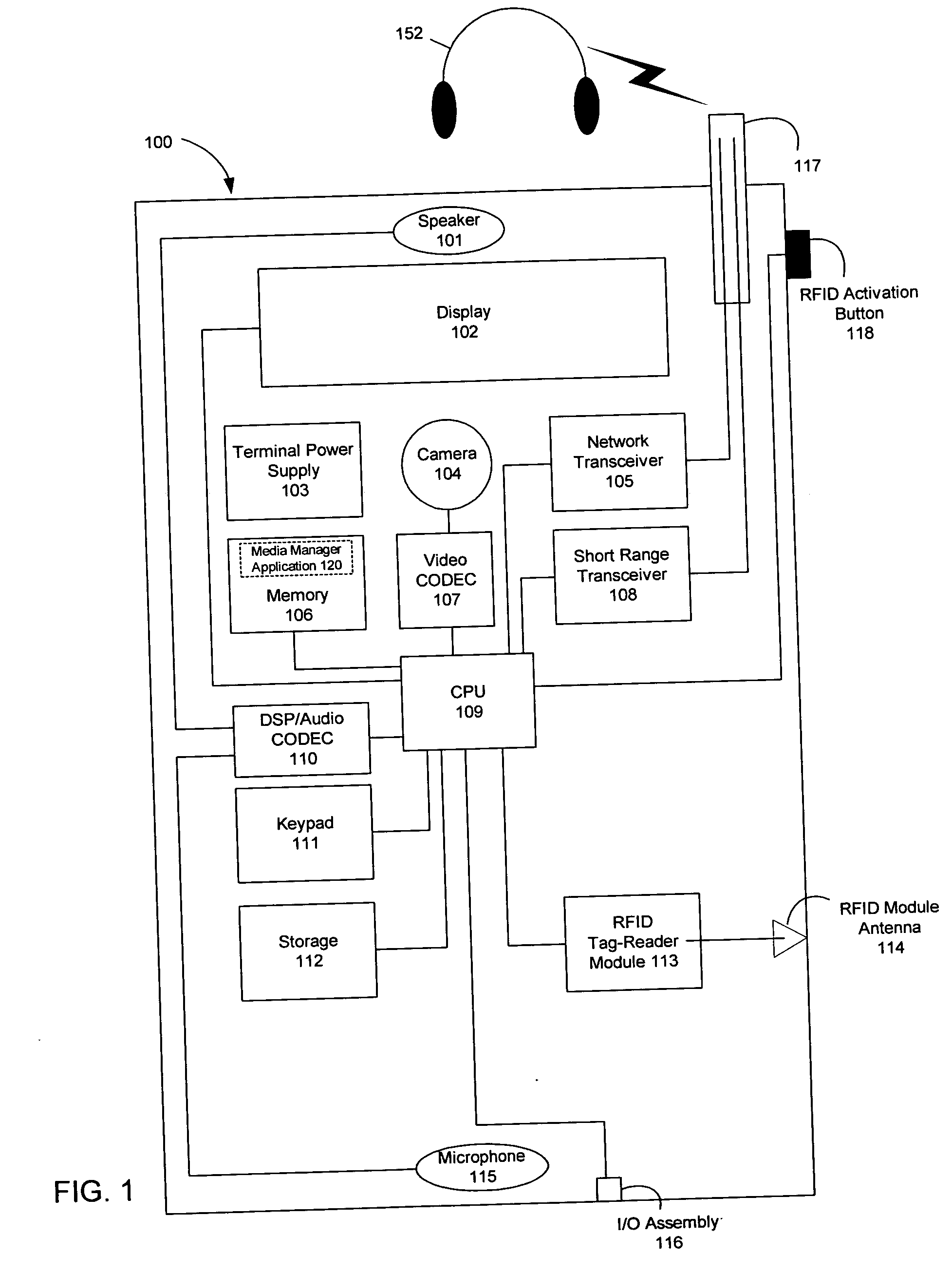
A wireless media player and a related system and methodology are disclosed. One aspect of the wireless media player system pertains to a virtual connector system, apparatus, and method for the automatic establishment of wireless connectivity with other electronic devices. In one embodiment, the media player device employs the use of integrated Radio Frequency Identification (RFID) technology to exchange communication settings, media capability, and other parameters with an external device that also has integrated RFID technology. The automatic exchange of settings and other information via a proximity-based RFID data exchange allows a media player to quickly establish a secure communication link with another device via a commonly supported wireless protocol such as Ultra Wideband (UWB) or Bluetooth. Another aspect of the media player system pertains to a method of using the captured media capability of the connecting device to customize certain menu options and software parameters in the media player.
Owner:SYNDEFENSE
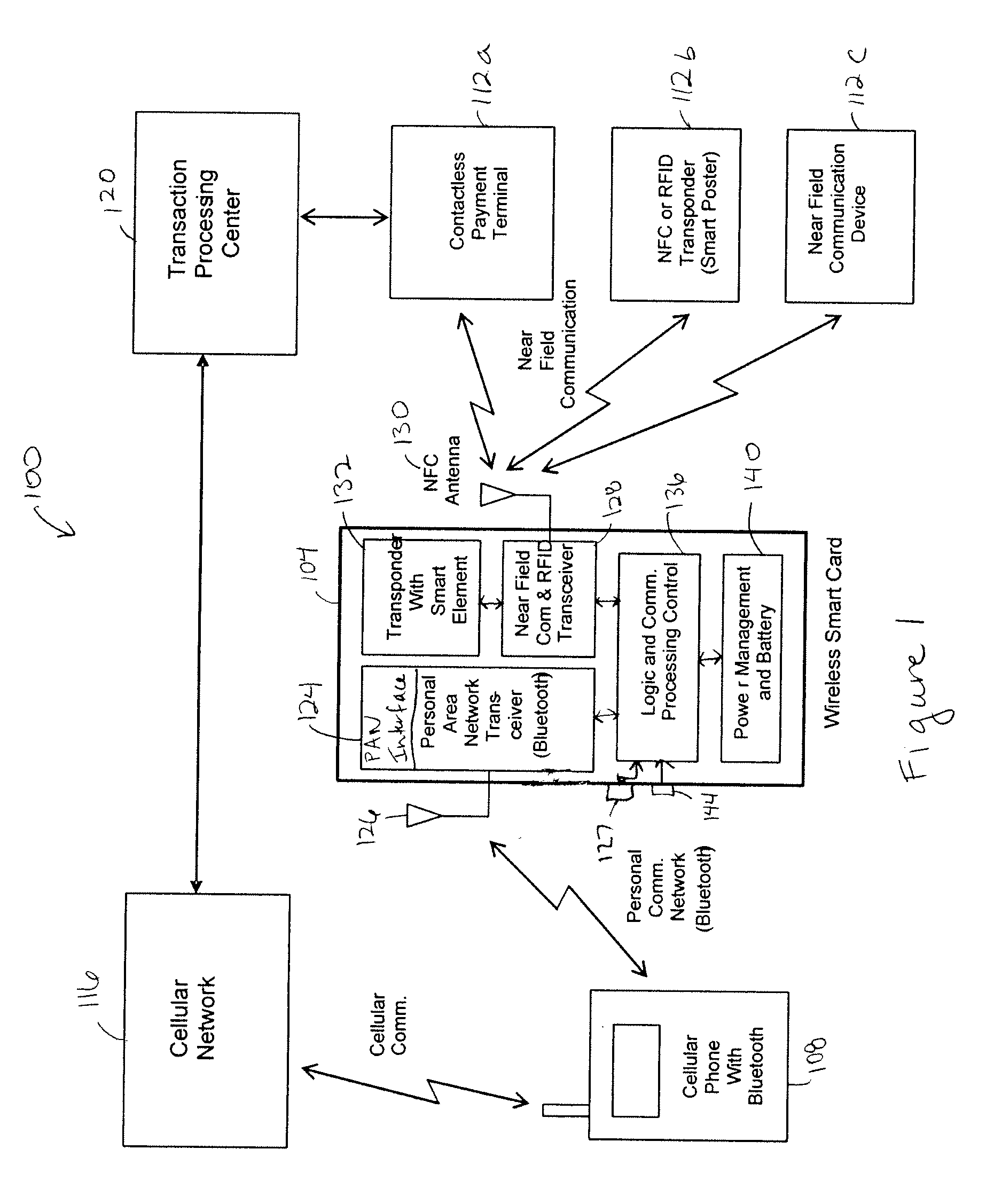
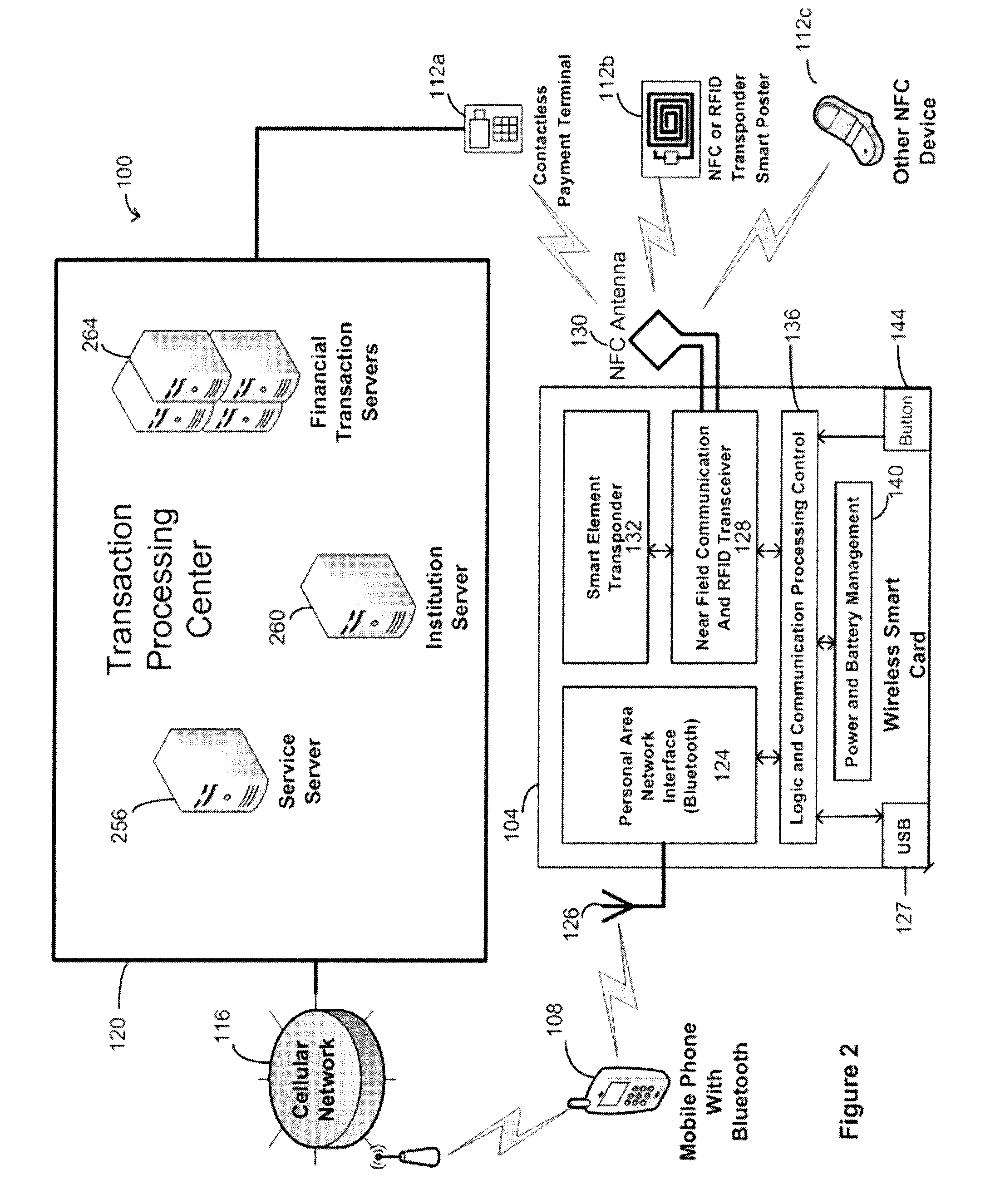
Wireless smart card and integrated personal area network, near field communication and contactless payment system
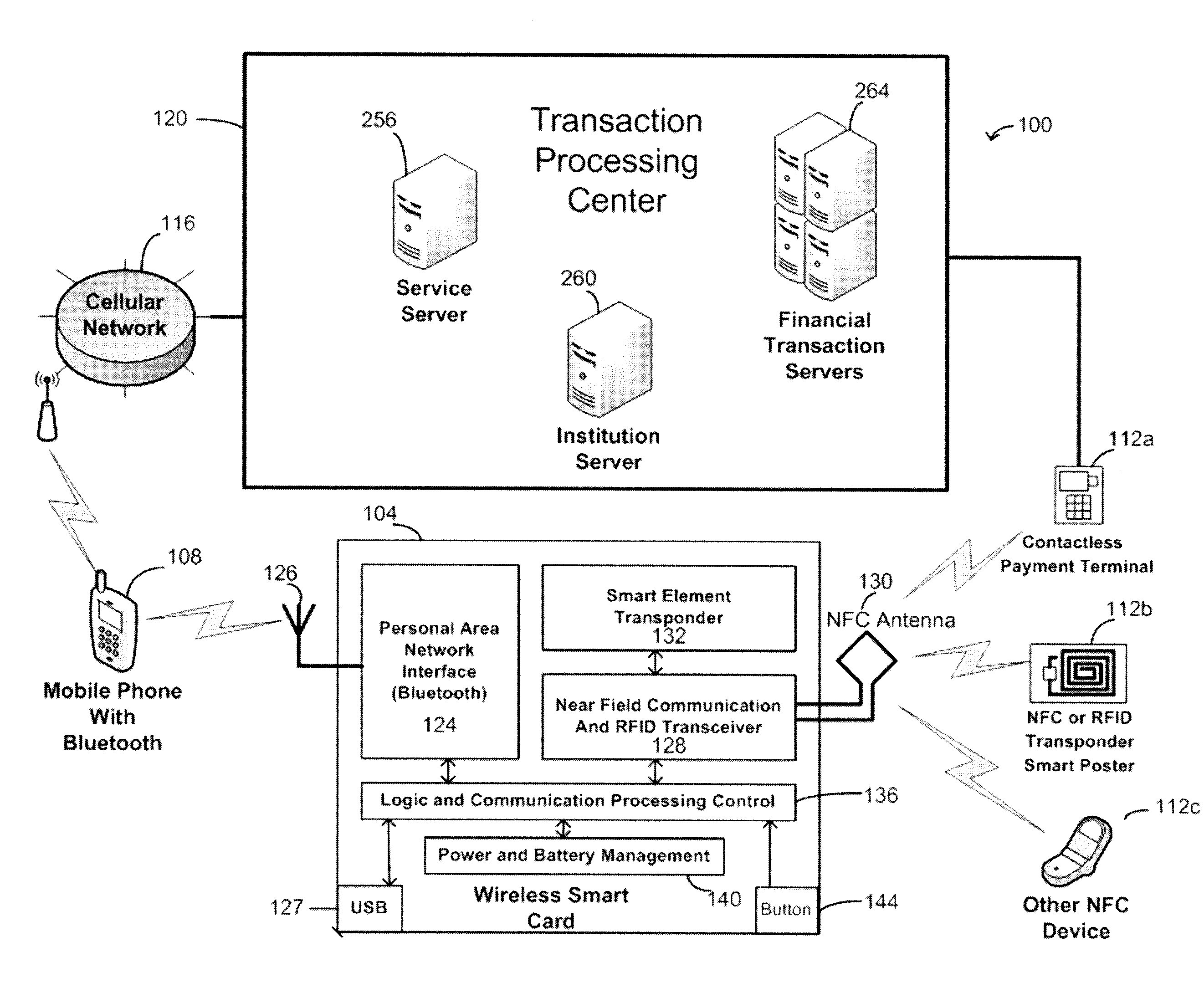
A wireless smart card having a personal area network transceiver, such as a Bluetooth transceiver, to couple the wireless smart card with a mobile communication device, and a near field communication (NFC) and radio-frequency identification (RFID) transceiver to couple the wireless smart card to a wireless transaction device, and a transponder with a secure element to allow secure communications between the mobile communication device with the wireless smart card and the wireless smart card and the wireless transaction device is described. The wireless smart card allows, for example, contactless payment through a Bluetooth-enabled mobile communication device without modification to the mobile communication device.
Owner:WIRELESS DYNAMICS
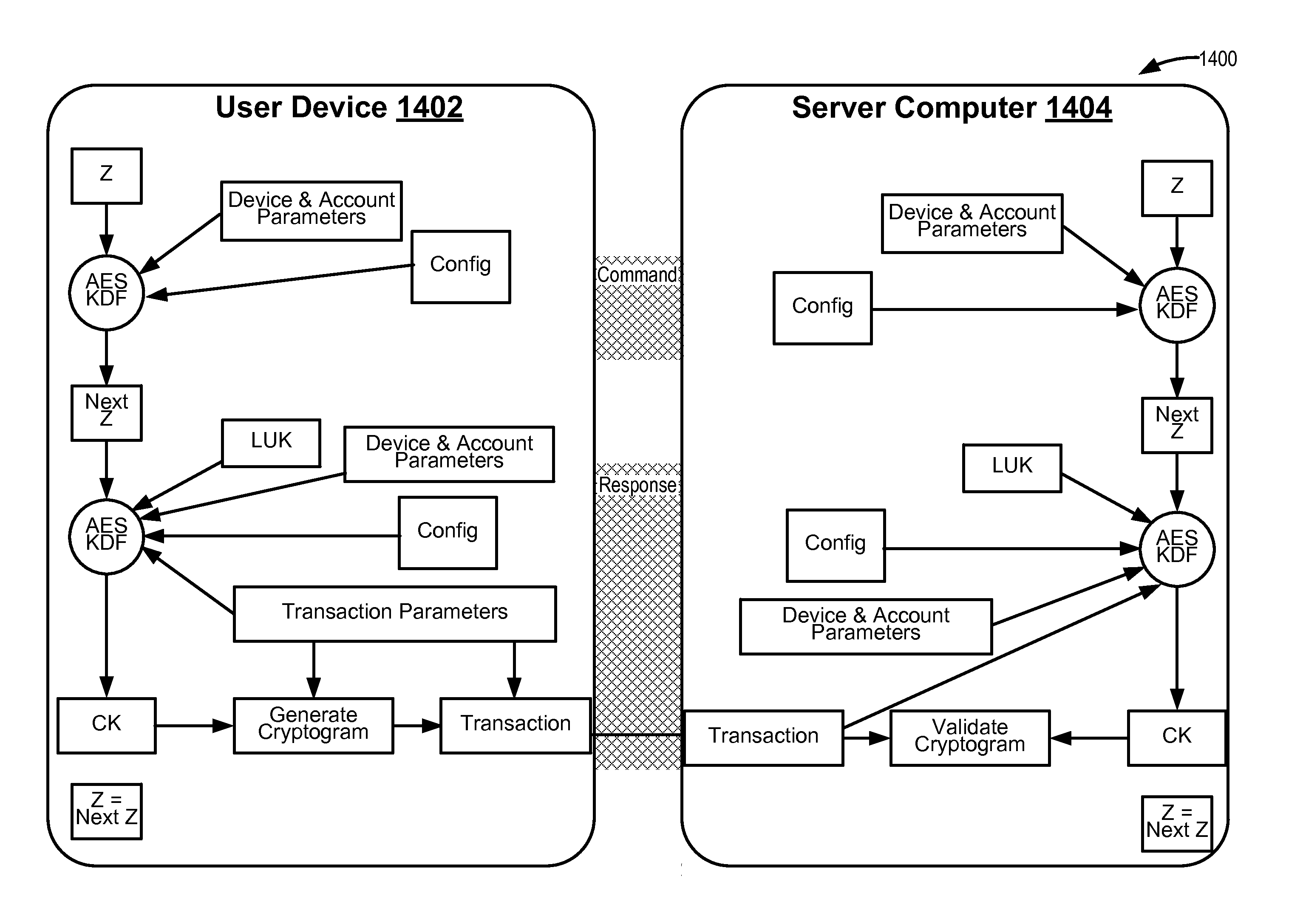
Methods for secure cryptogram generation
ActiveUS20160065370A1Avoid attackKey distribution for secure communicationMultiple keys/algorithms usageSecure communicationUser device
Embodiments of the invention introduce efficient methods for securely generating a cryptogram by a user device, and validating the cryptogram by a server computer. In some embodiments, a secure communication can be conducted whereby a user device provides a cryptogram without requiring the user device to persistently store an encryption key or other sensitive data used to generate the cryptogram. For example, the user device and server computer can mutually authenticate and establish a shared secret. Using the shared secret, the server computer can derive a session key and transmit key derivation parameters encrypted using the session key to the user device. The user device can also derive the session key using the shared secret, decrypt the encrypted key derivation parameters, and store the key derivation parameters. Key derivation parameters and the shared secret can be used to generate a single use cryptogram key. The cryptogram key can be used to generate a cryptogram for conducting secure communications.
Owner:VISA INT SERVICE ASSOC
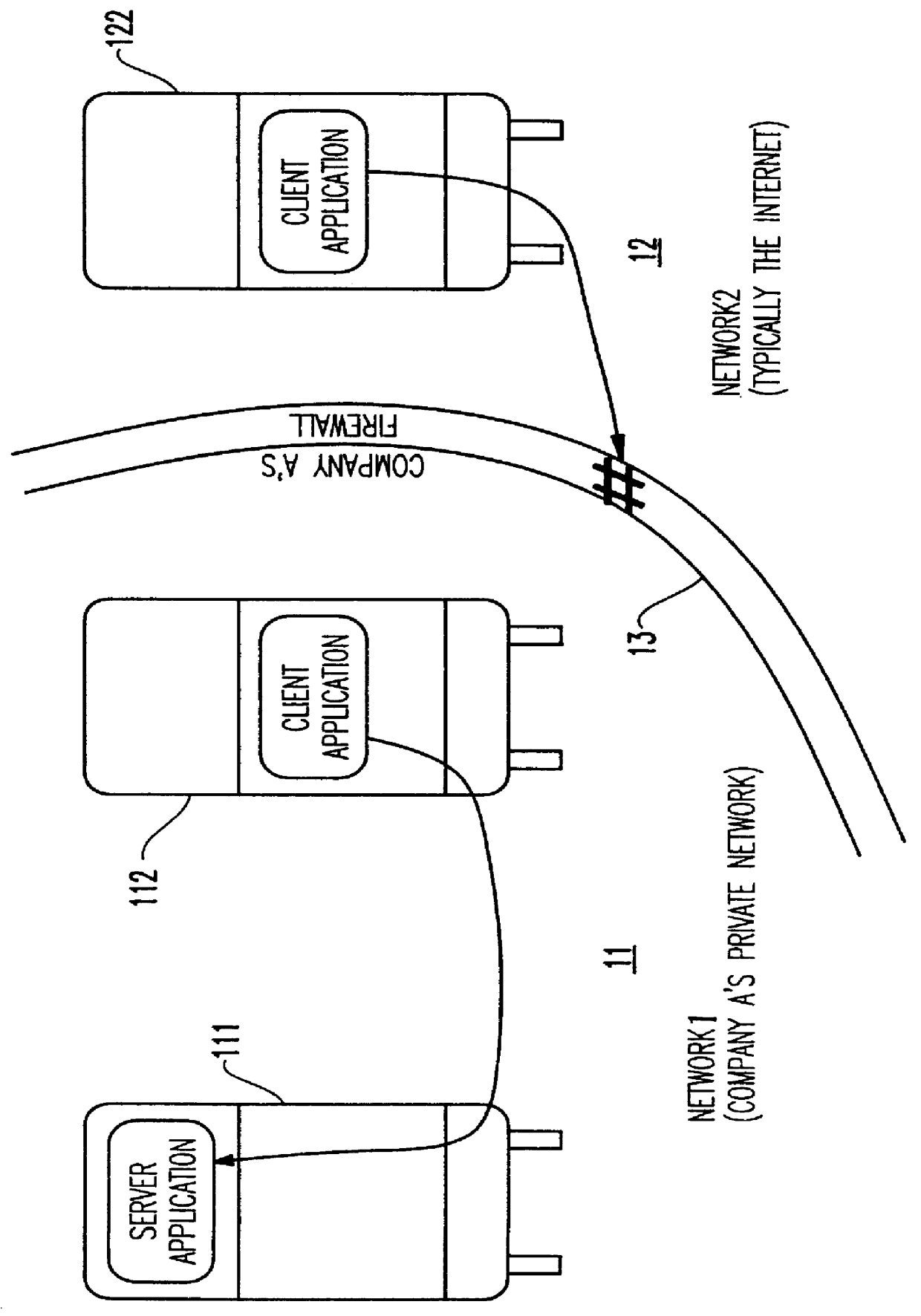
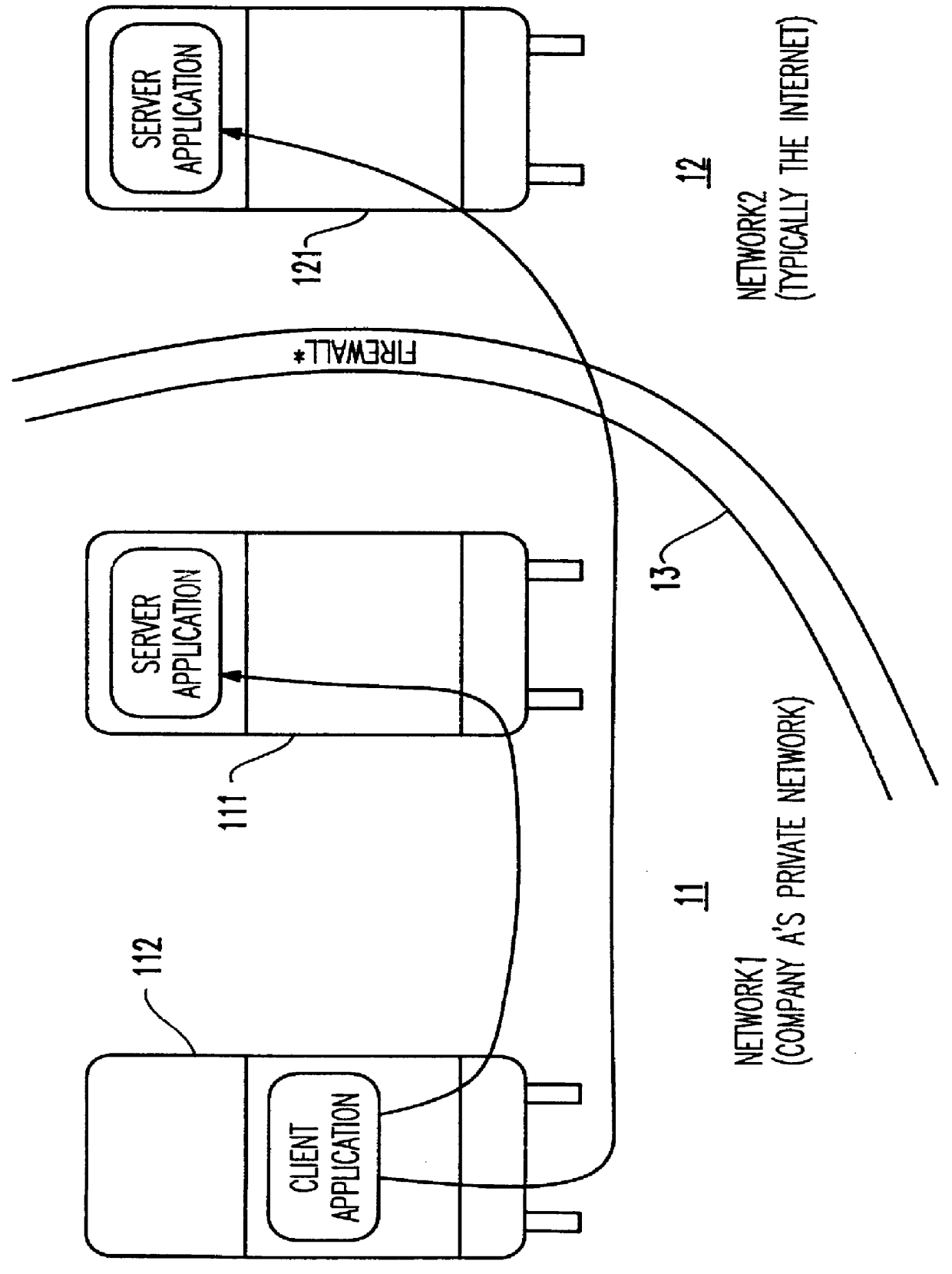
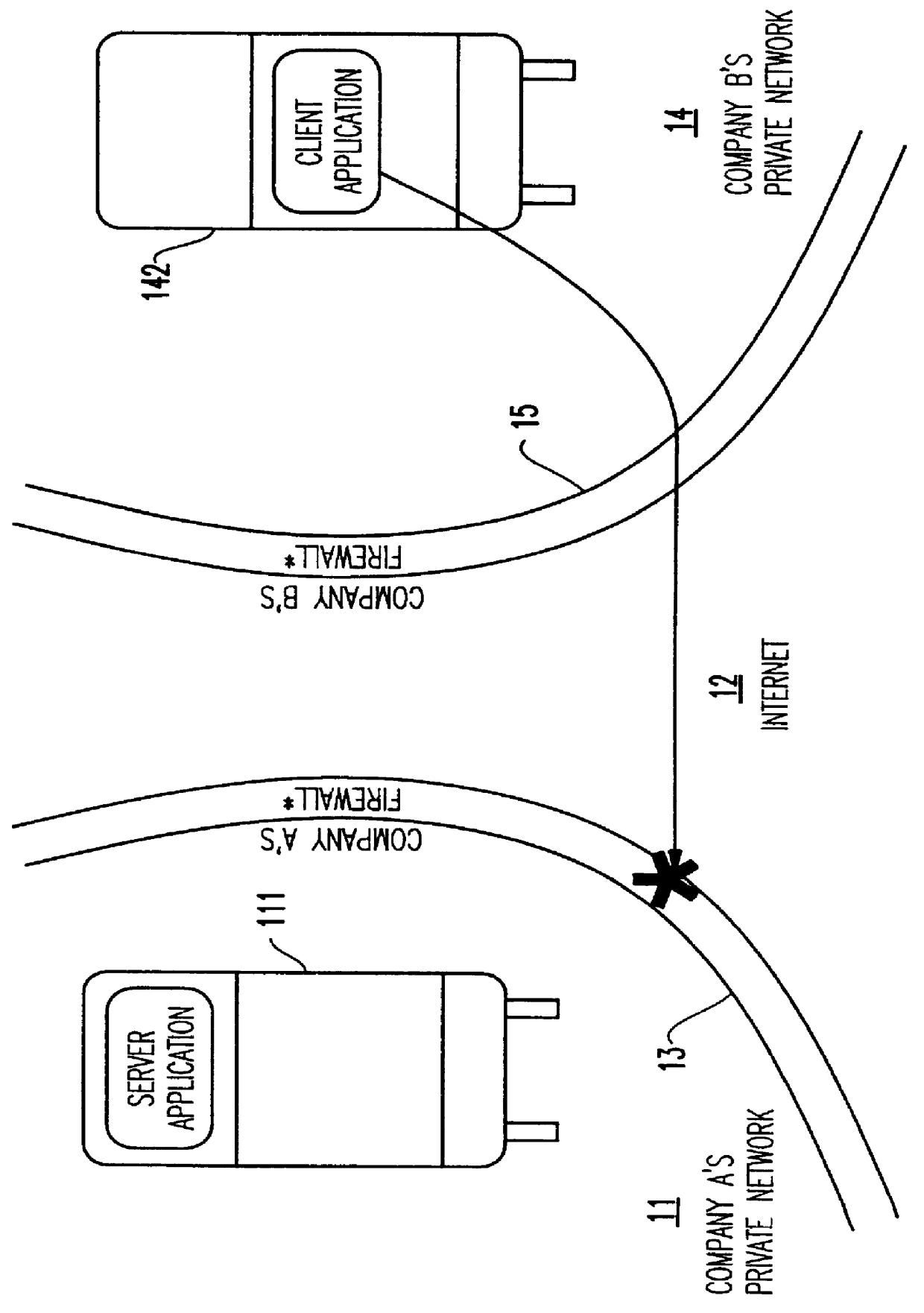
Method and apparatus for lightweight secure communication tunneling over the internet
InactiveUS6104716AData switching by path configurationMultiple digital computer combinationsSOCKSSecure communication
A lightweight secure tunneling protocol or LSTP permits communicating across one or more firewalls by using a middle server or proxy. Three proxies are used to establish an end-to-end connection that navigates through the firewalls. In a typical configuration, a server is behind a first firewall and a client behind a second firewall are interconnected by an untrusted network (e.g., the Internet) between the firewalls. A first inside firewall SOCKS-aware server-side end proxy connects to the server inside the first firewall. A second inside firewall SOCKS-aware client-side end proxy is connected to by the client inside the second firewall. Both server-side and client-side end proxies can address a third proxy (called a middle proxy) outside the two firewalls. The middle proxy is usually started first, as the other two end proxies (server and client) will initiate the connection to the middle proxy some time after they are started. Since the middle proxy is mutually addressable by both inside proxies, a complete end-to-end connection between the server and client is established. It is the use of one or more middle proxies together with the LSTP that establishes the secure communications link or tunnel across multiple firewalls.
Owner:IBM CORP
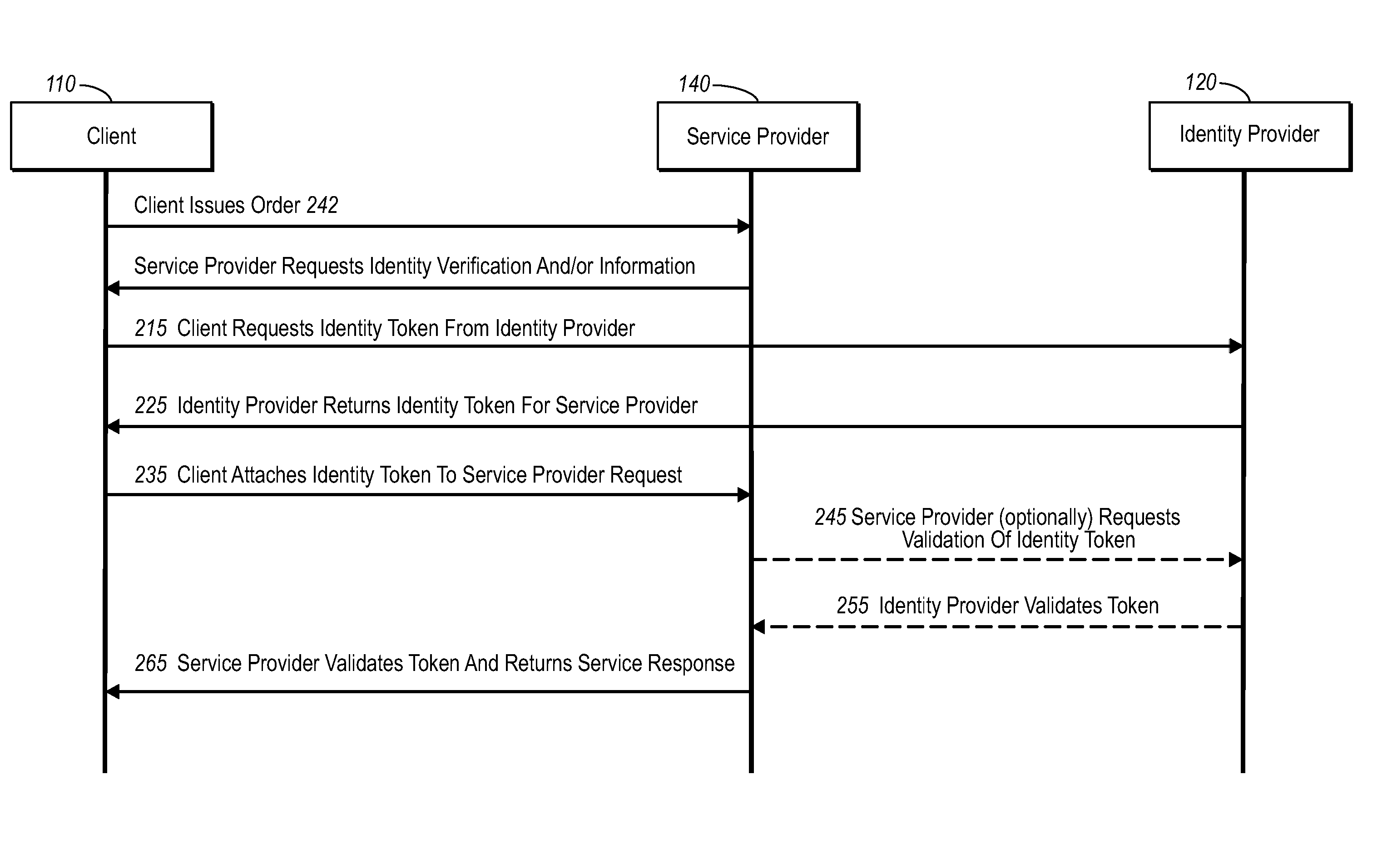
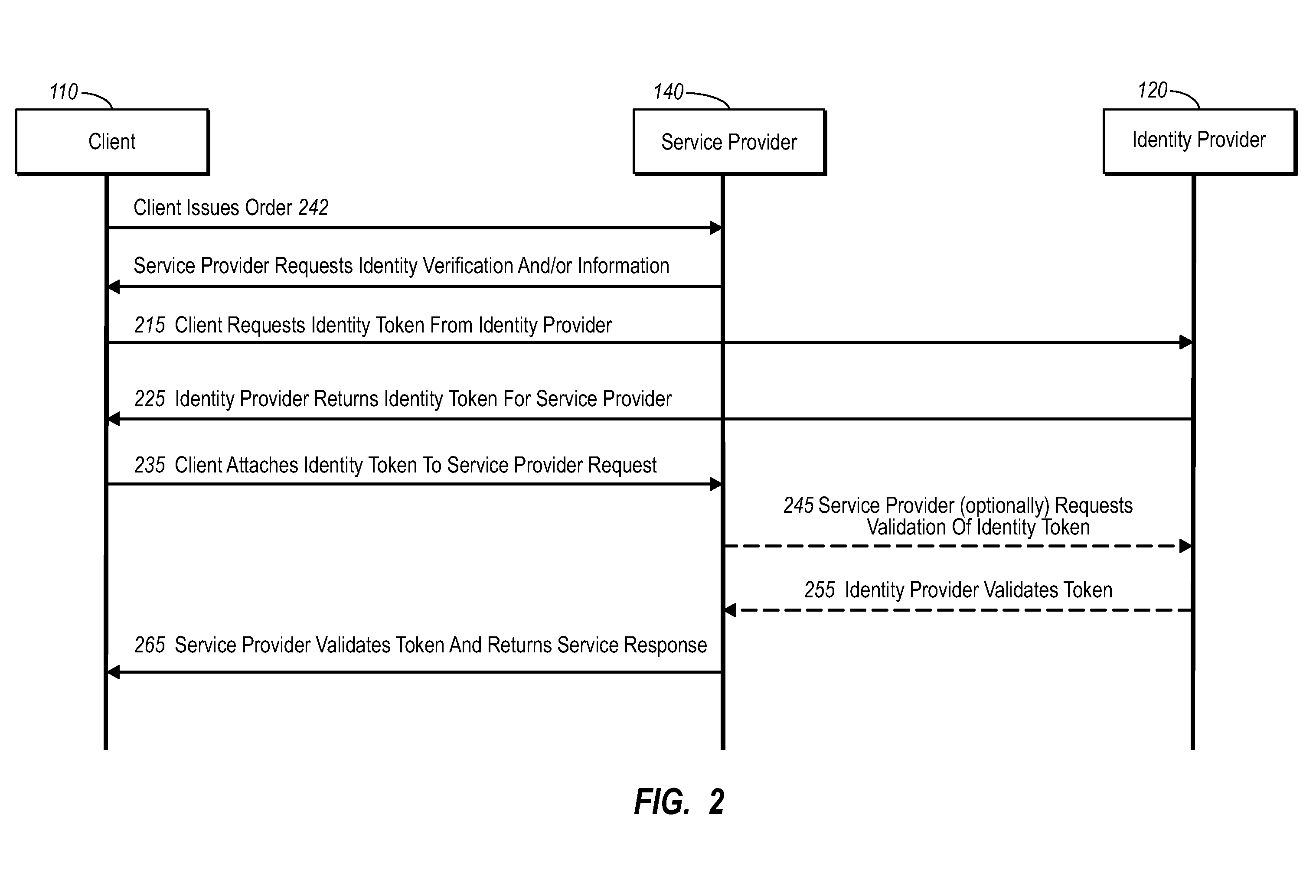
Secure network commercial transactions
InactiveUS20060235795A1Reduce the burden onSimpler and more secure online commercial transactions frameworkFinanceBuying/selling/leasing transactionsPaymentSecure communication
Current embodiments provide for authorization and payment of an online commercial transaction between a purchaser and a merchant including verification of an identity of the purchaser and verification of an ability of the purchaser to pay for the transaction, where the identity provider and the payment provider are often different network entities. Other embodiments also provide for protocols, computing systems, and other mechanisms that allow for identity and payment authentication using a mobile module, which establishes single or multilevel security over an untrusted network (e.g., the Internet). Still other embodiments also provide for a three-way secure communication between a merchant, consumer, and payment provider such that sensitive account information is opaque to the merchant, yet the merchant is sufficiently confident of the consumer's ability to pay for requested purchases. In yet another embodiment, electronic billing information is used for authorization, auditing, payment federation, and other purposes.
Owner:MICROSOFT TECH LICENSING LLC
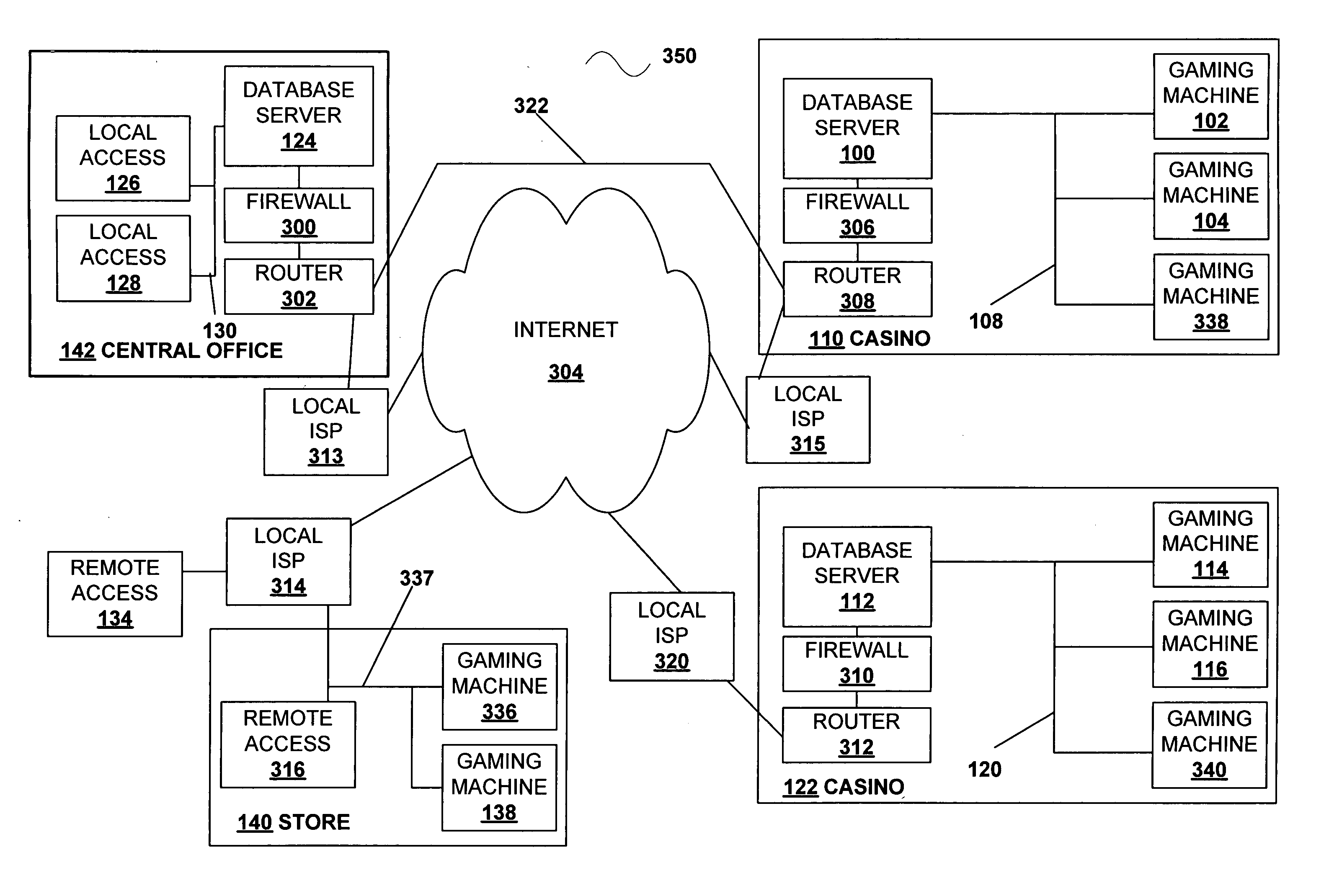
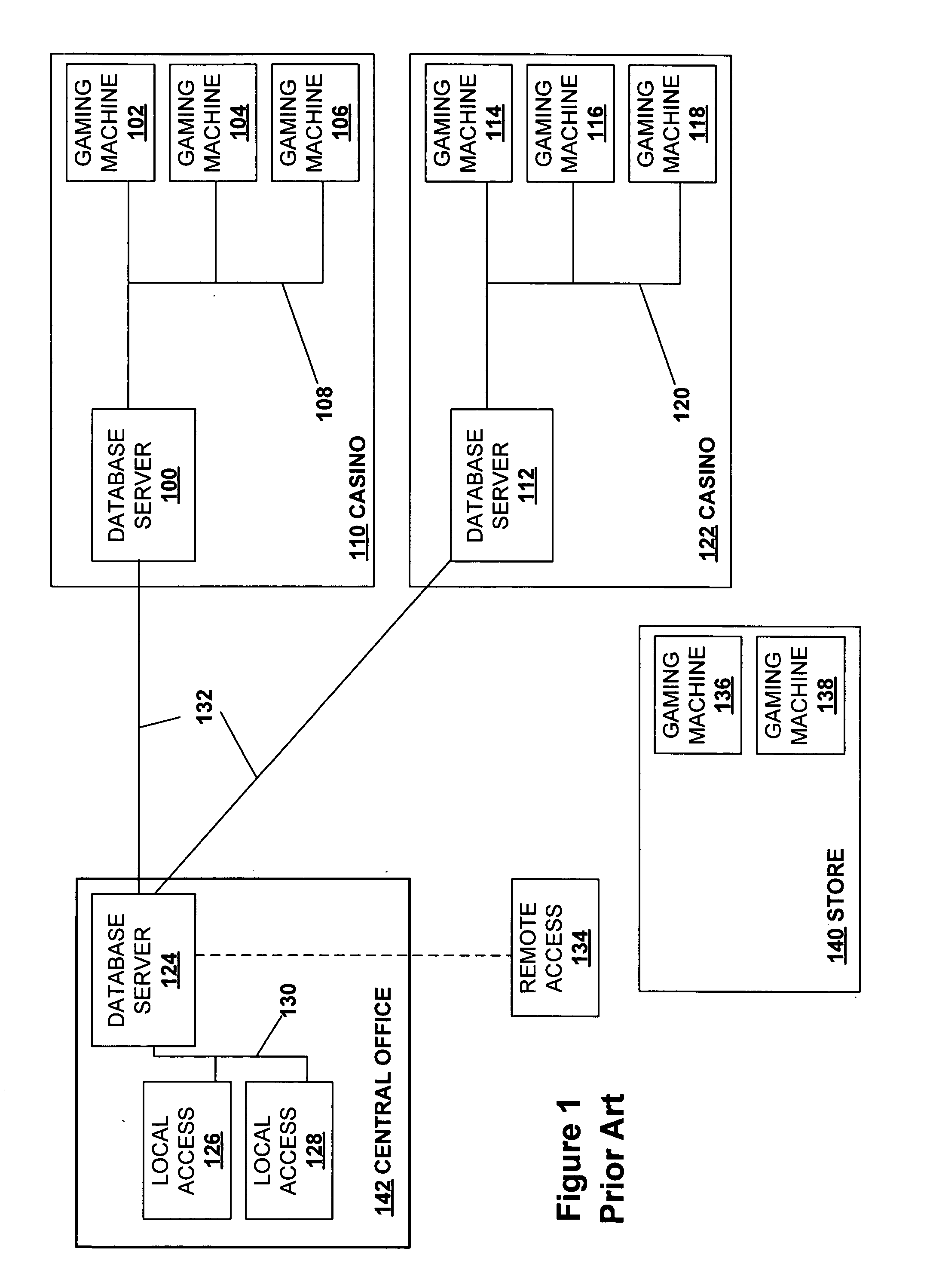
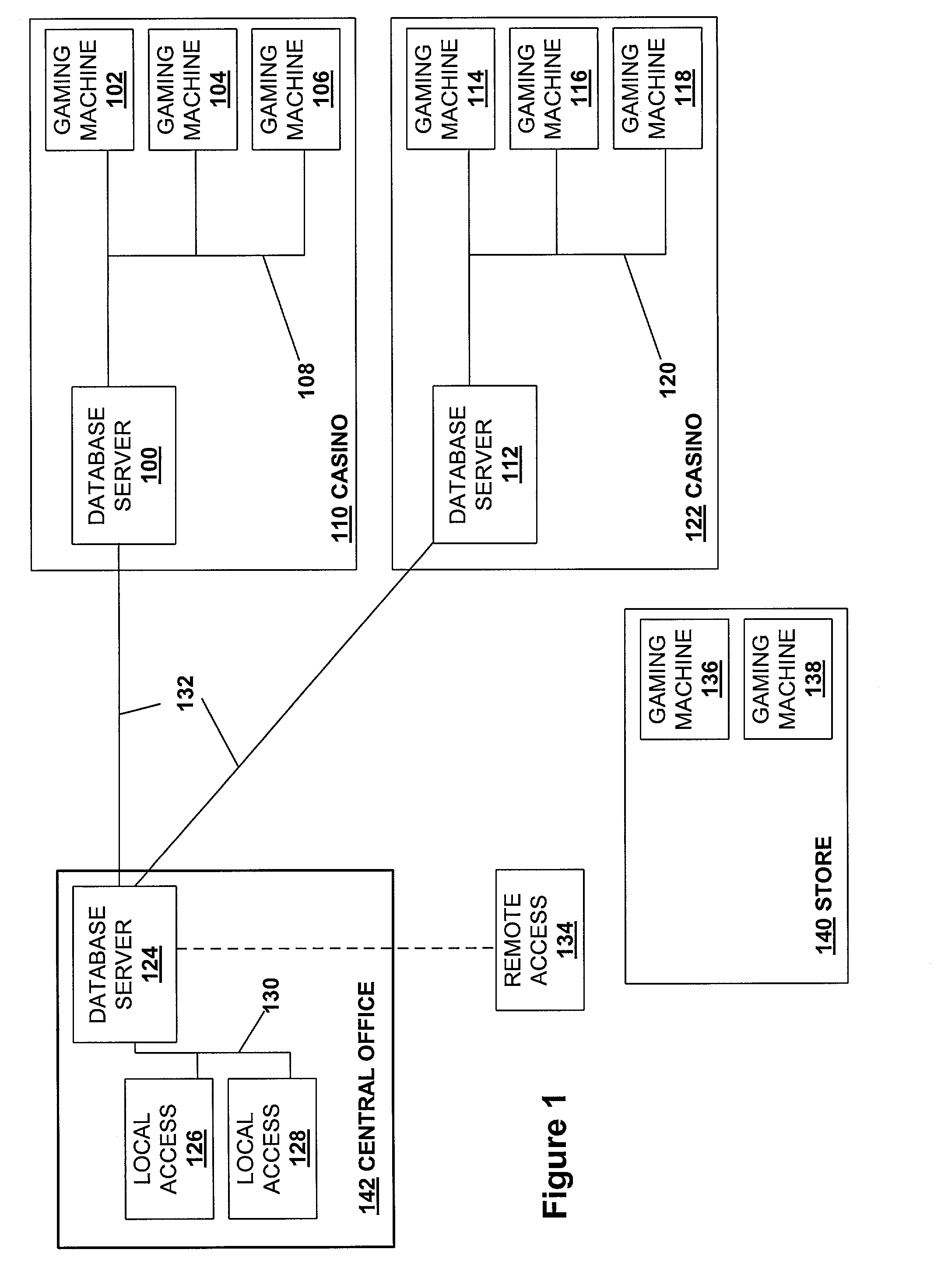
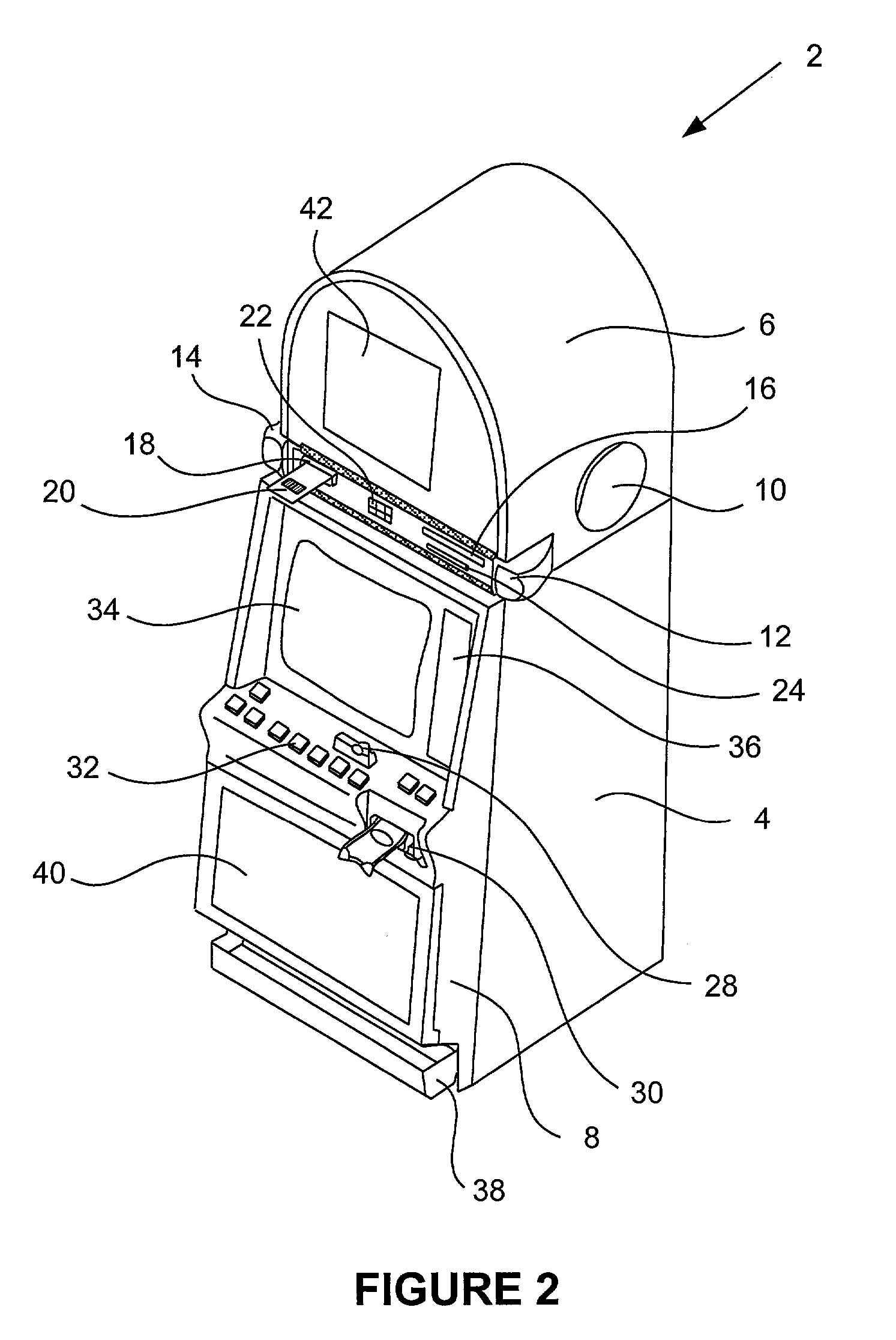
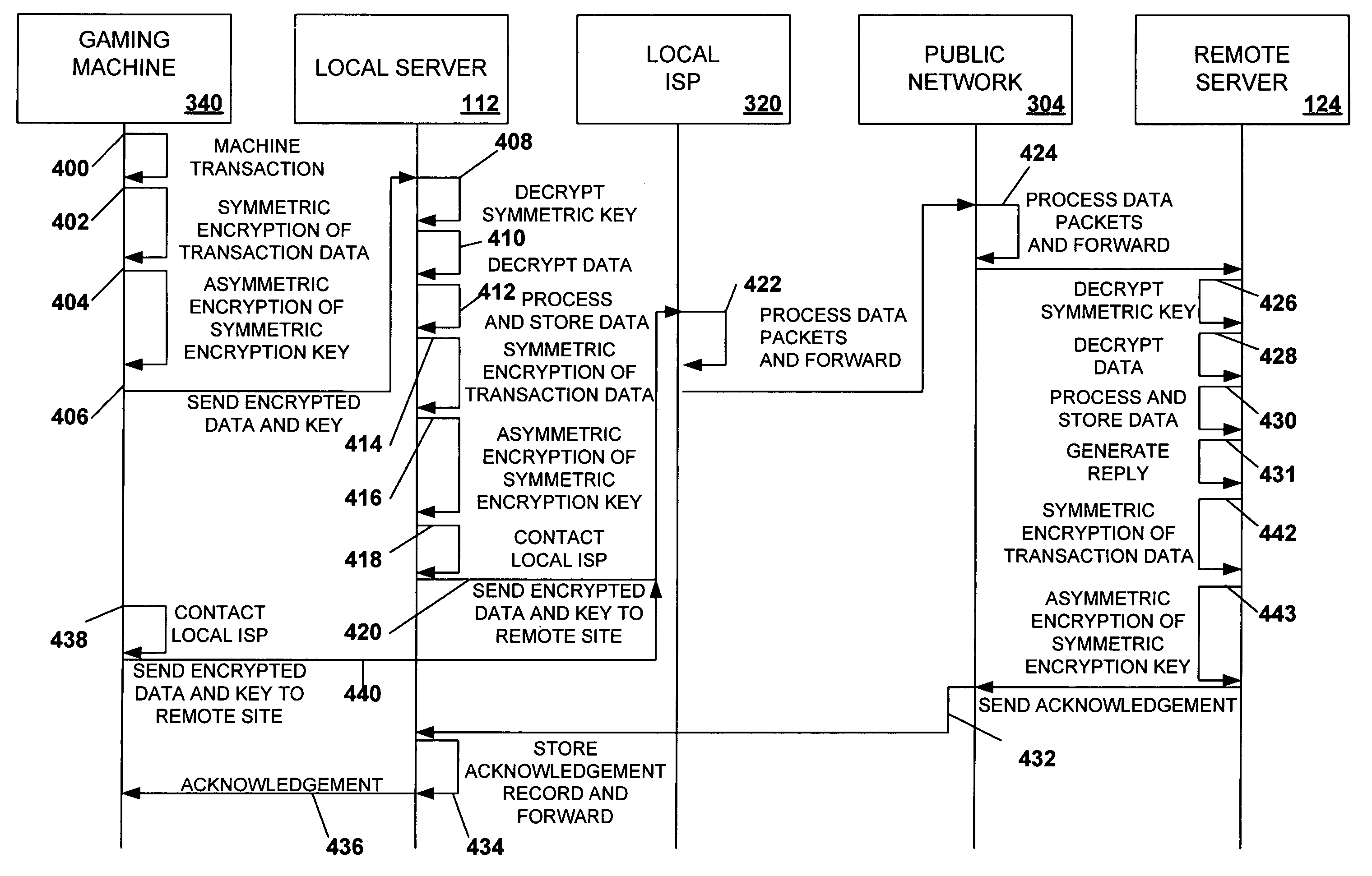
Secured virtual network in a gaming environment
InactiveUS20050192099A1Key distribution for secure communicationApparatus for meter-controlled dispensingSecure communicationThe Internet
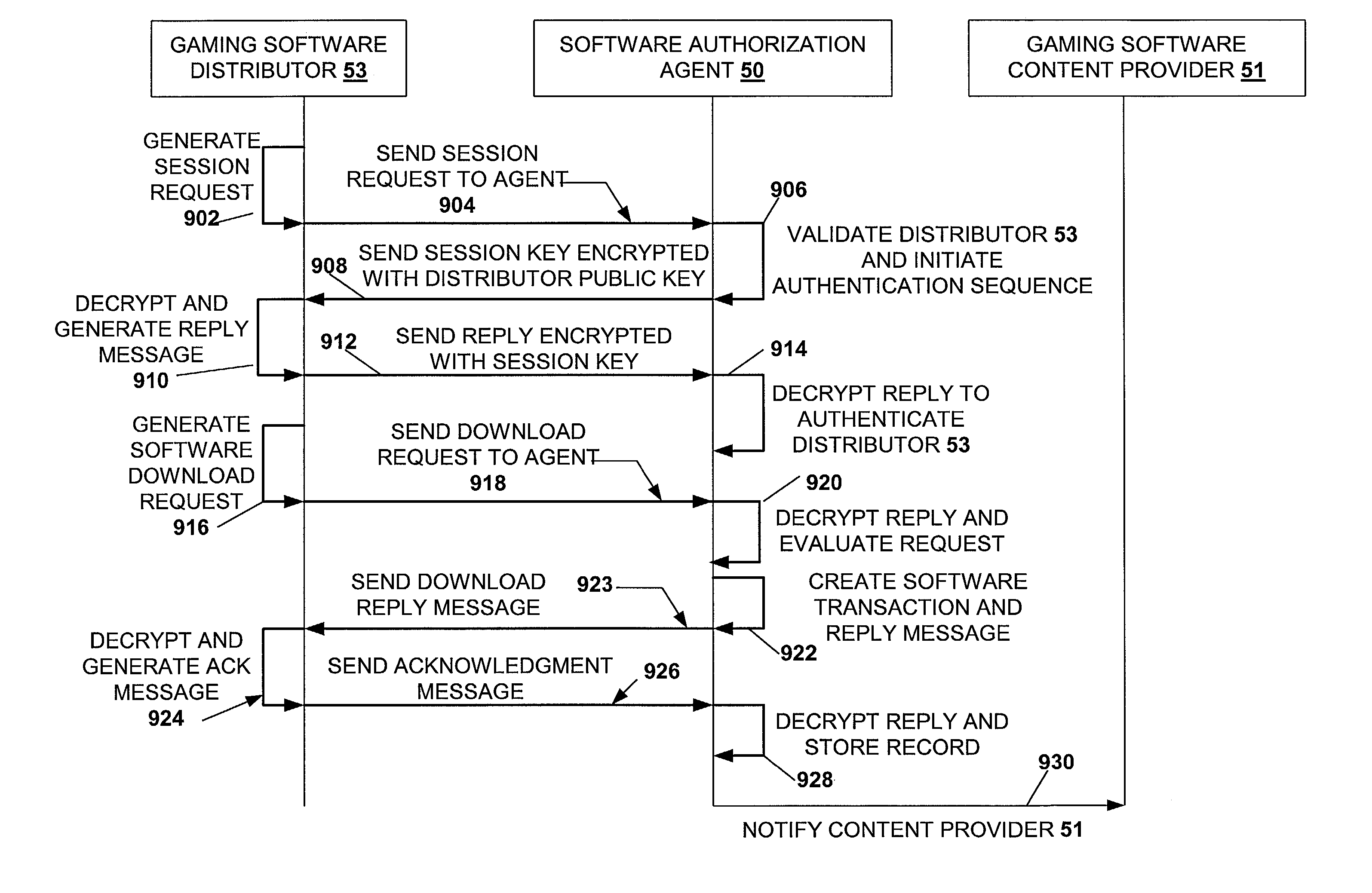
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
Secured virtual network in a gaming environment
InactiveUS7168089B2Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
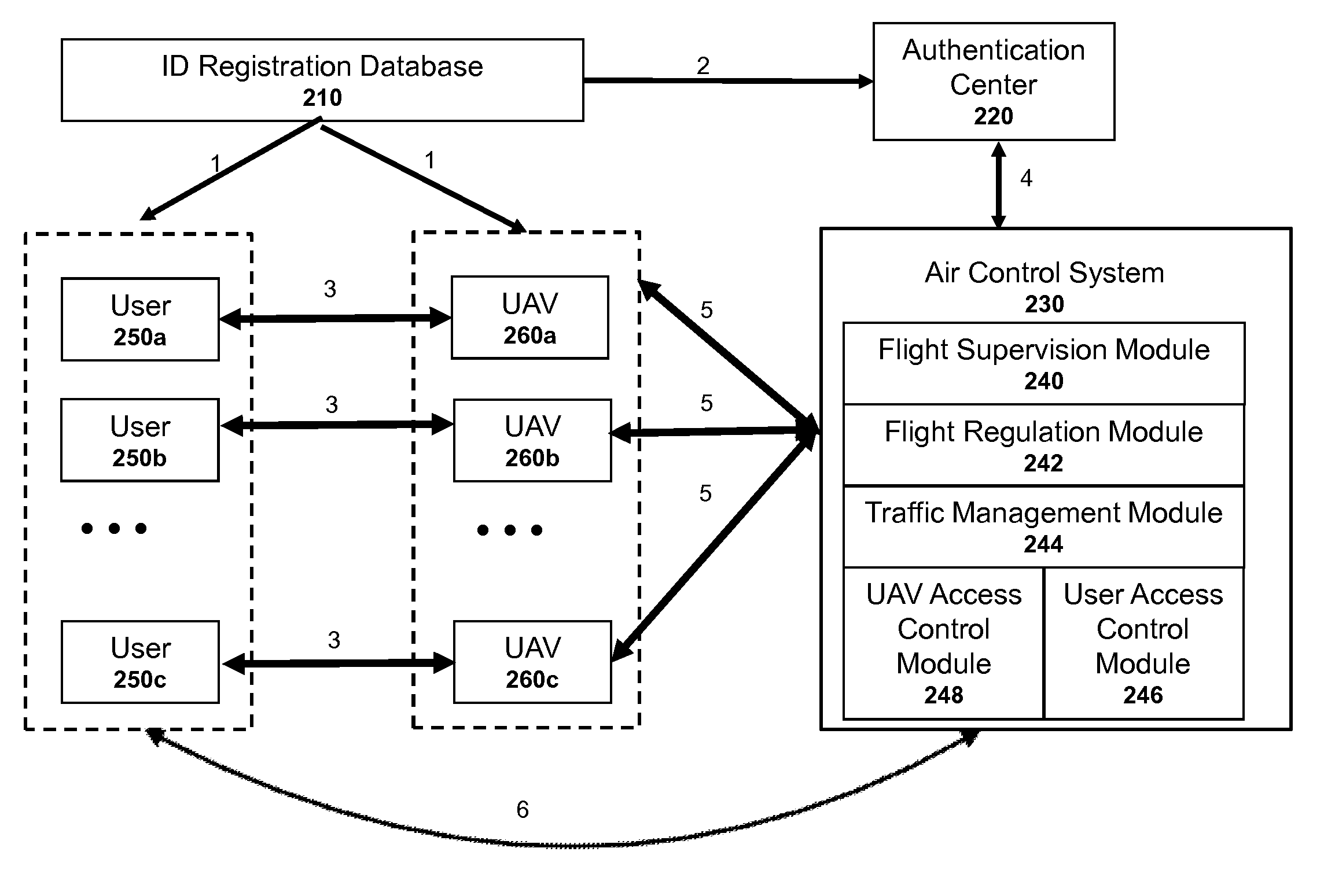
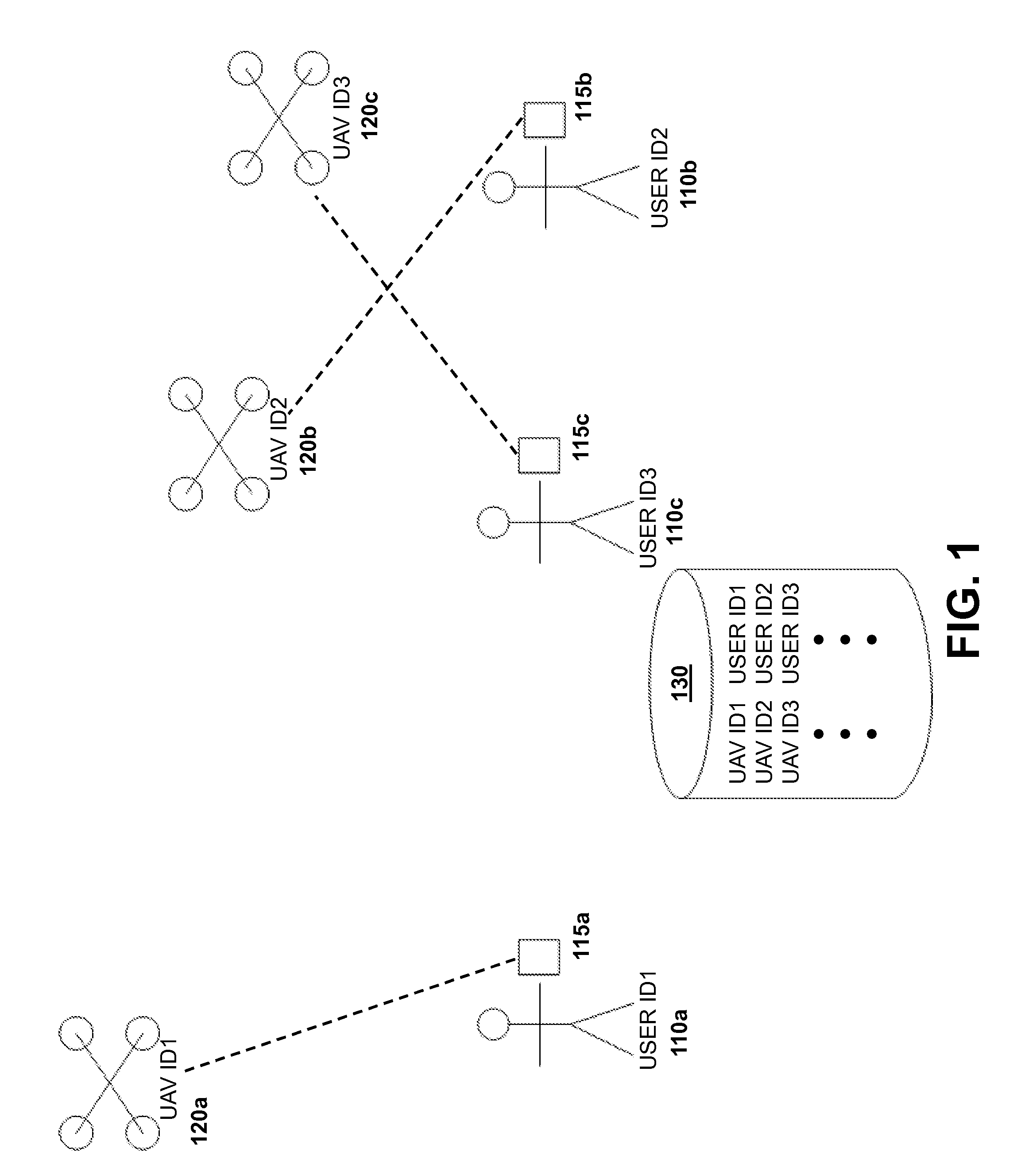
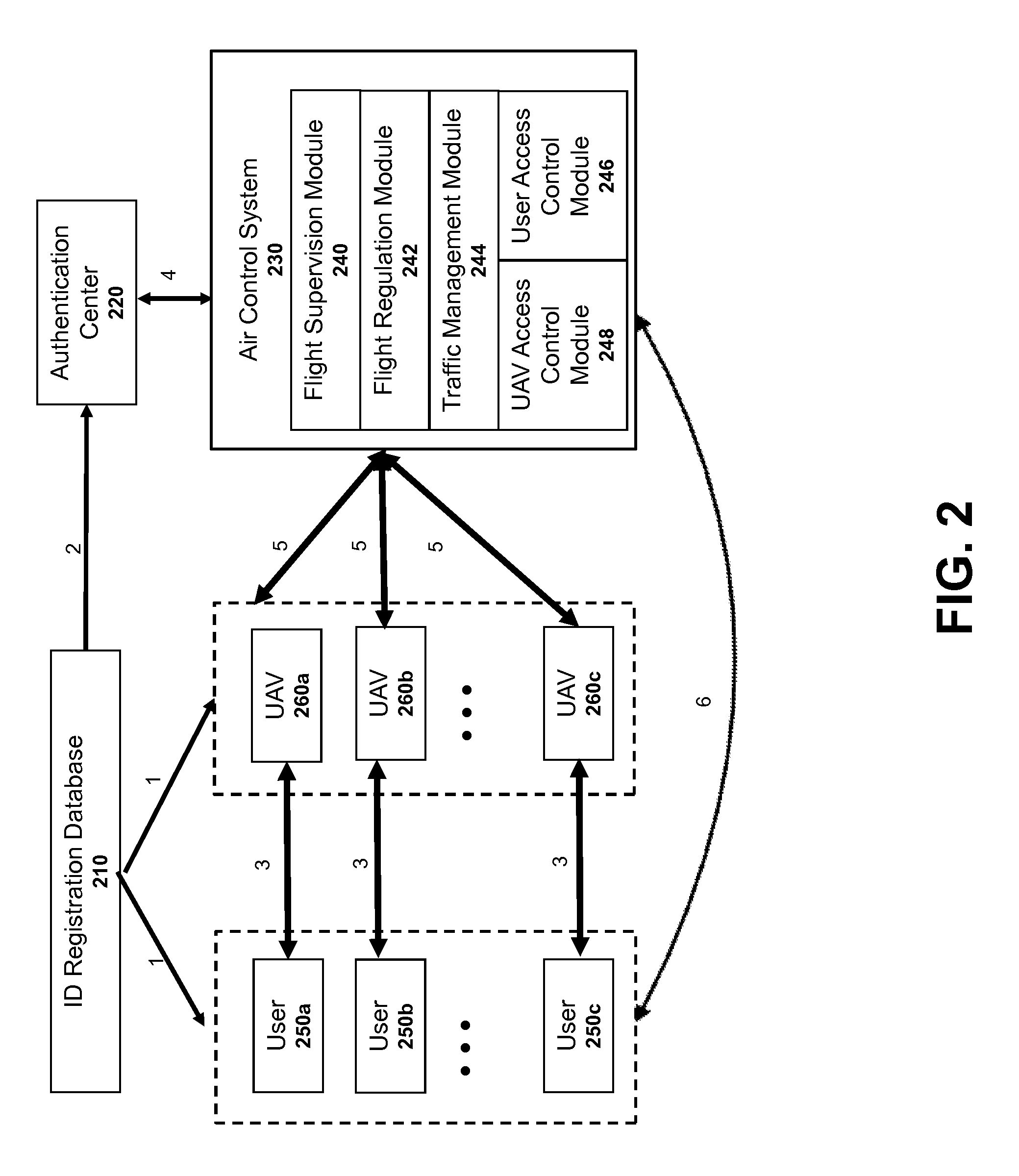
Authentication systems and methods for generating flight regulations
ActiveUS9412278B1Improve flight safetyRemote controlled aircraftDigital data authenticationAuthentication systemComputer science
Systems and methods for UAV safety are provided. An authentication system may be used to confirm UAV and / or user identity and provide secured communications between users and UAVs. The UAVs may operate in accordance with a set of flight regulations. The set of flight regulations may be associated with a geo-fencing device in the vicinity of the UAV.
Owner:SZ DJI TECH CO LTD
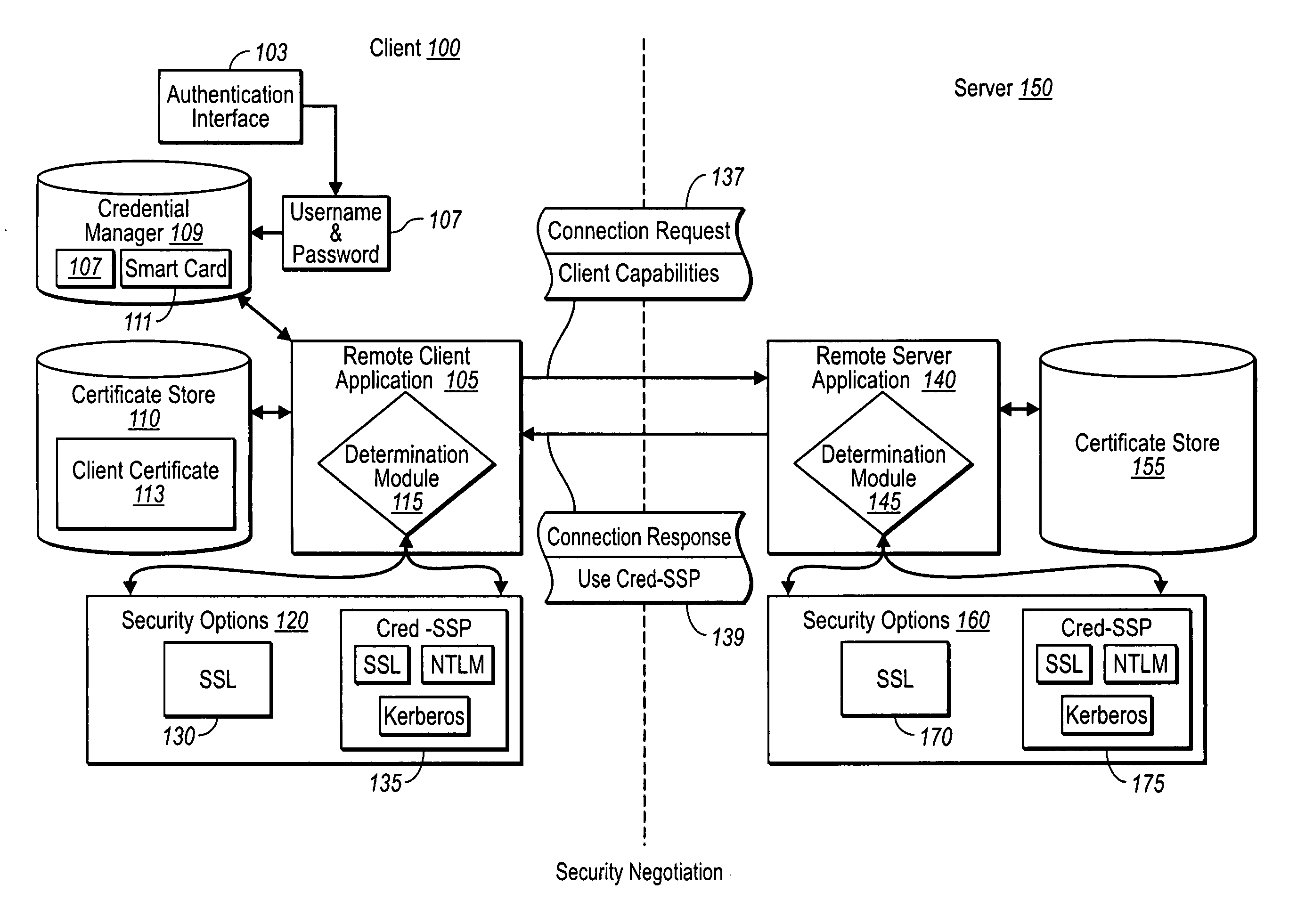
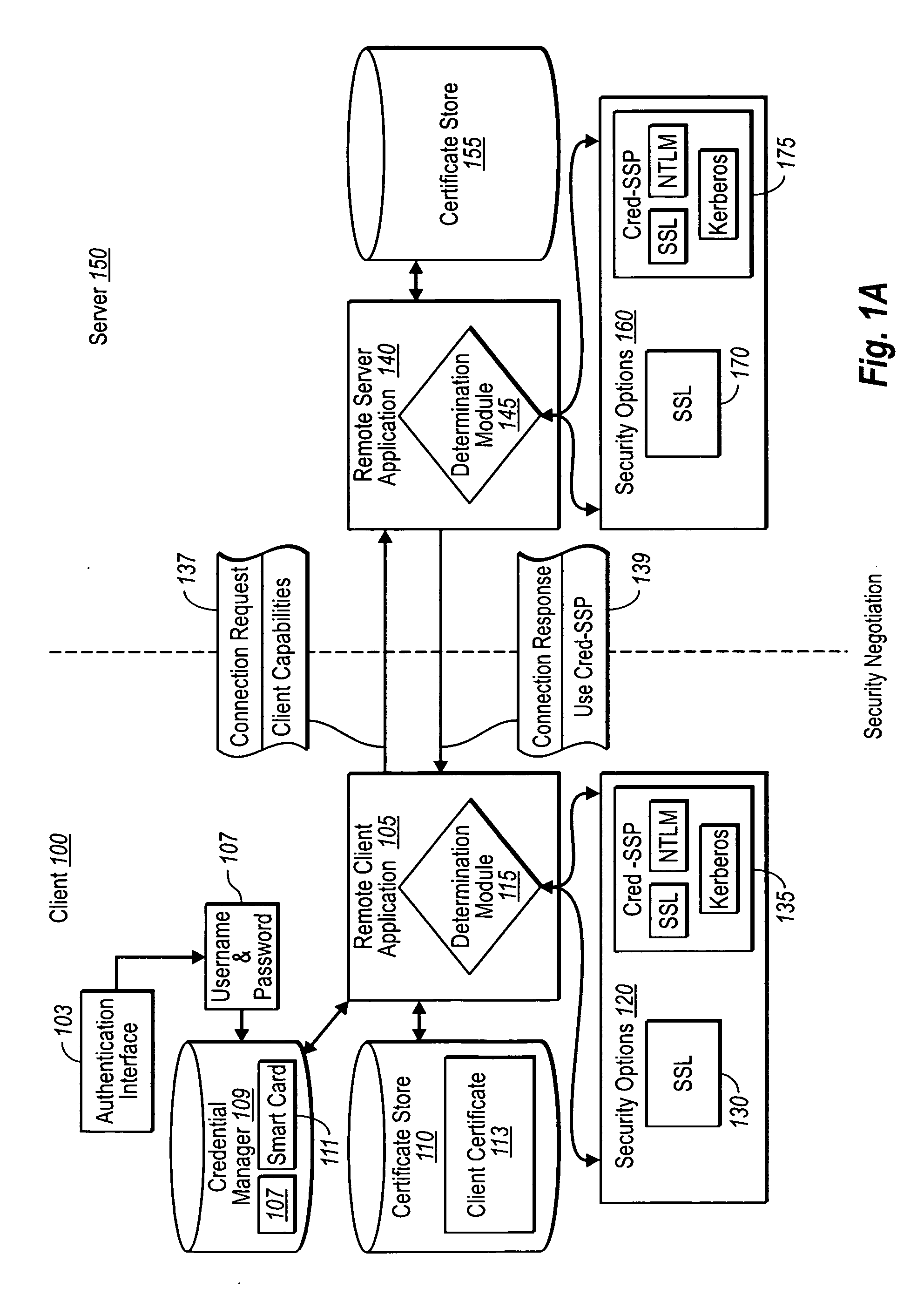
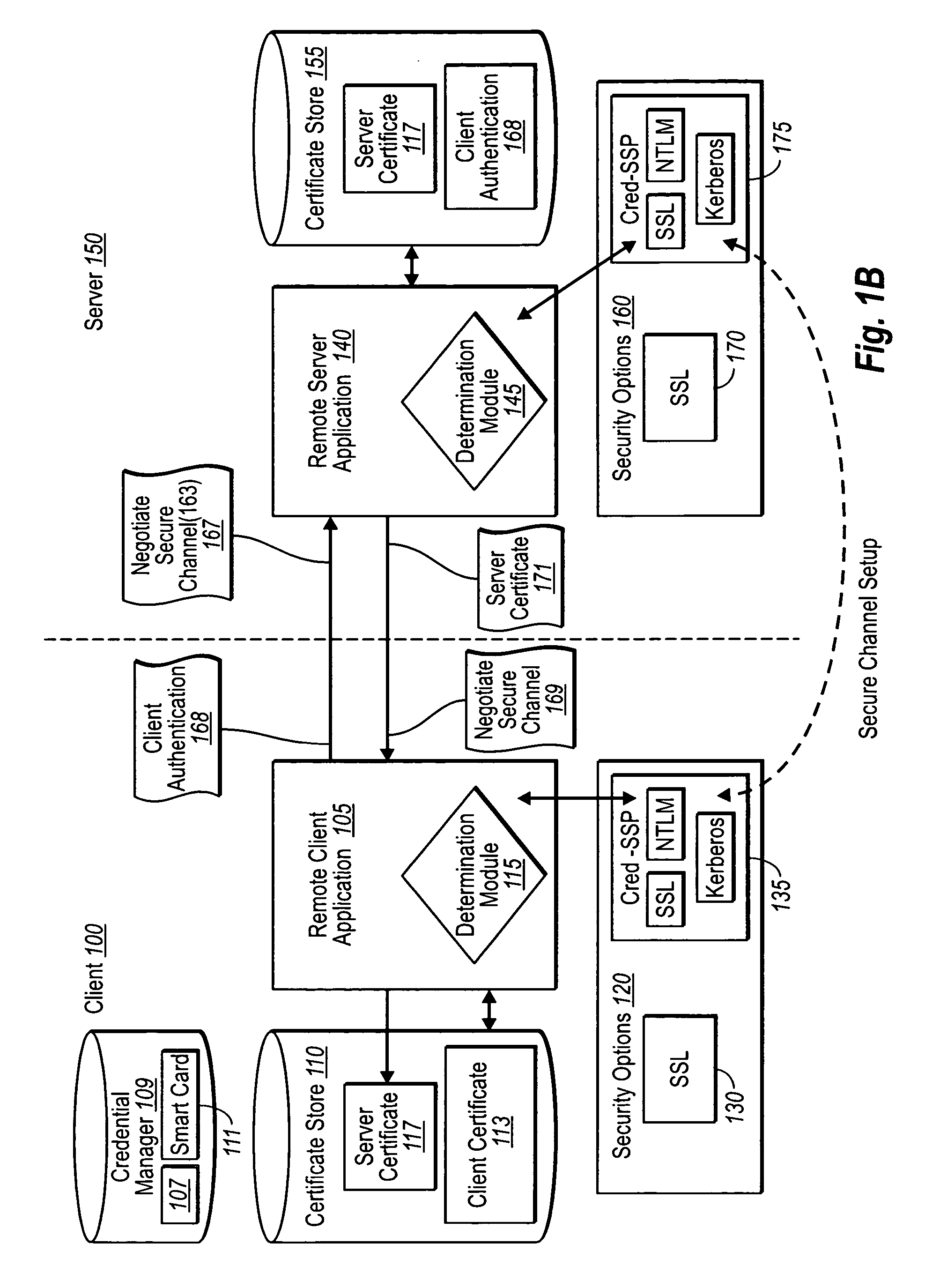
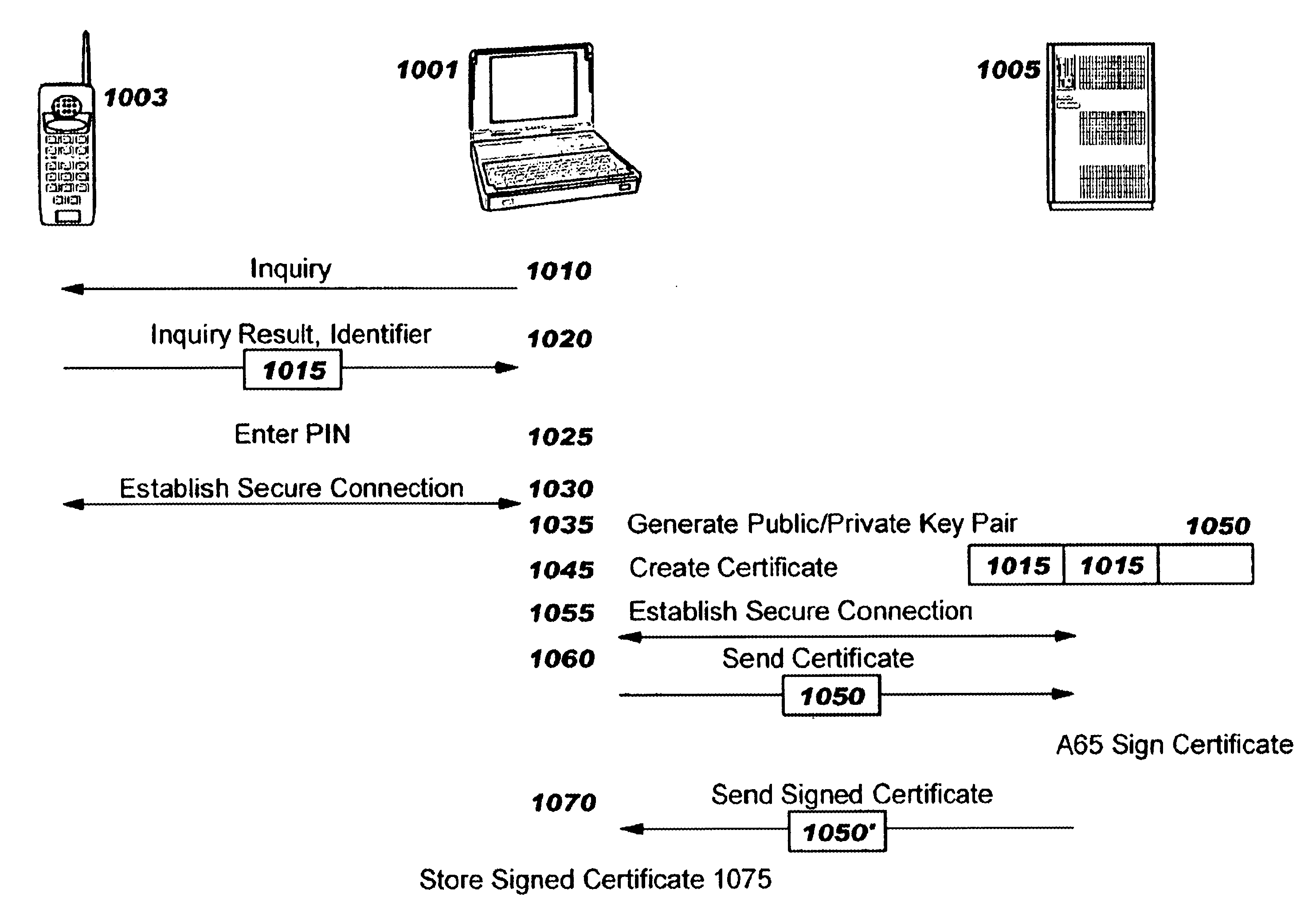
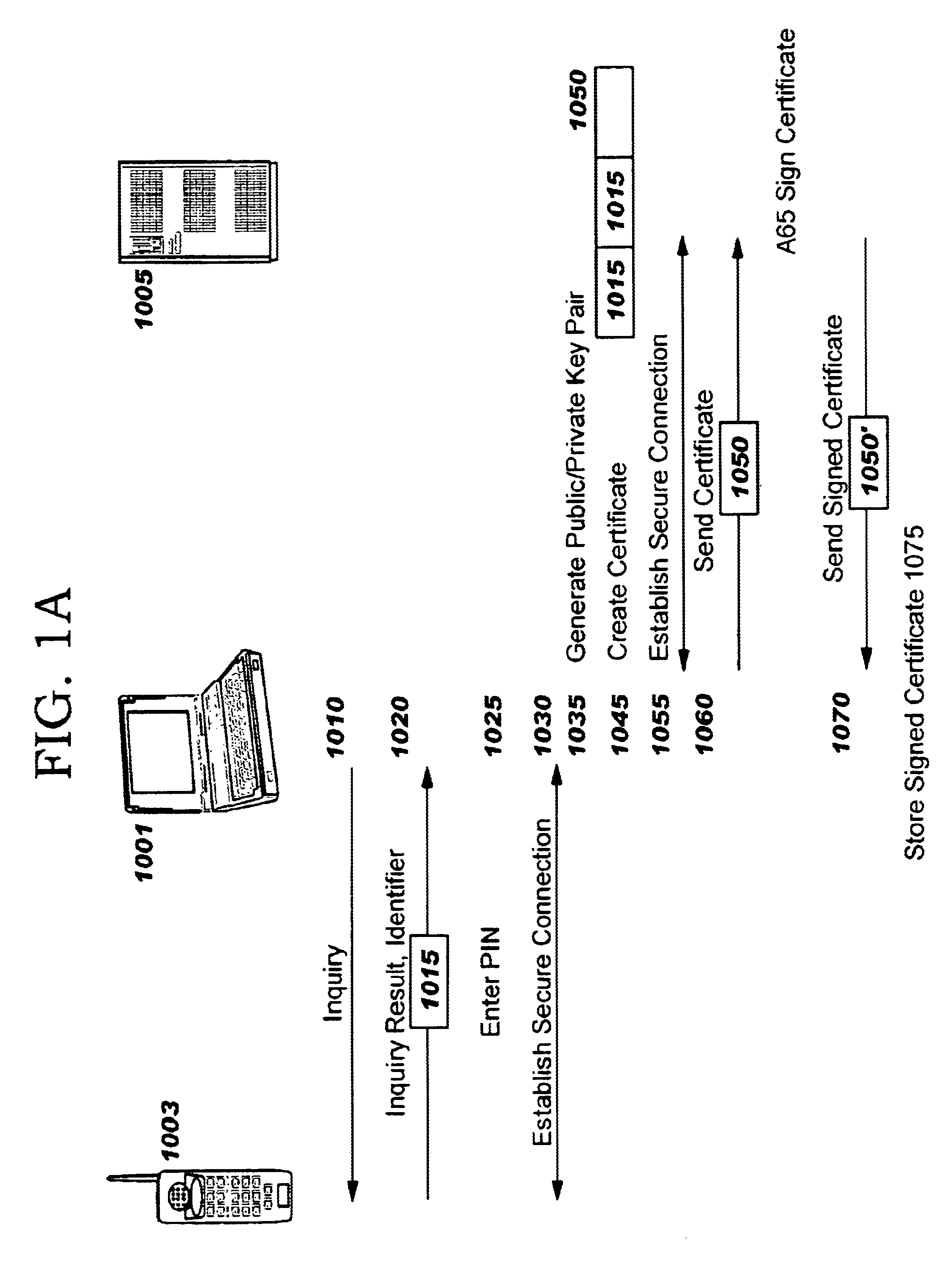
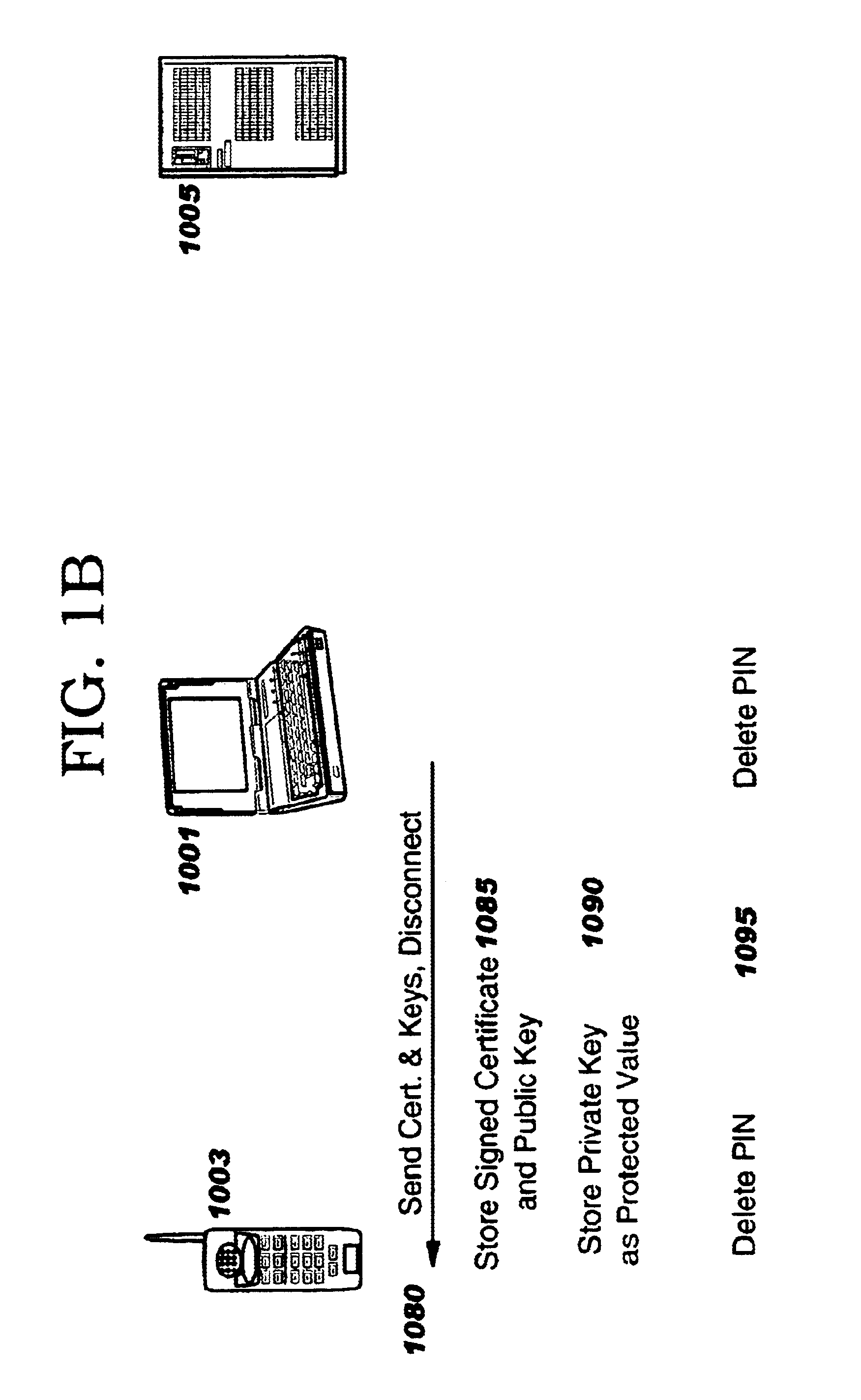
Creating secure interactive connections with remote resources
ActiveUS20070061878A1Easy to adaptDigital data processing detailsUser identity/authority verificationSecure communicationClient-side
Implementations of the present invention efficiently establish secure connections between a client and server, at least in part by authenticating the client and server early on in the connection setup phases. A client initiating a connection with a server identifies the secure communication protocols enabled at the client, and identifies these protocols in a connection request it sends to the server. The server processes the message and responds with a communication protocol it deems appropriate for the connection. The client and server then exchange appropriate authentication information, and then establish a connection session that implements the chosen communication protocol, and encrypts messages using the negotiated communication protocol. Additional implementations relate to reestablishing dropped connections behind virtual Internet Protocol addresses, without necessarily having to recommit much connection resource overhead.
Owner:MICROSOFT TECH LICENSING LLC
Electronic game system, method of managing and regulating said system
InactiveUS6117011AImprove securityAvoid possibilityComputer controlSimulator controlSecure communicationAutomatic control
PCT No. PCT / RU95 / 00241 Sec. 371 Date Jan. 27, 1998 Sec. 102(e) Date Jan. 27, 1998 PCT Filed Nov. 10, 1995 PCT Pub. No. WO97 / 05557 PCT Pub. Date Feb. 13, 1997An electronic gaming system is disclosed that includes a central computer station, a plurality of peripheral computer stations, and a data exchange network for coupling the peripheral computer stations to the central computer station. The central computer station includes an administrative subsystem, a player's registration subsystem, a game accounts managing subsystem, an information tabulating, storing and searching subsystem, a game recording subsystem, a scoring subsystem, a wagering and betting subsystem, an executive gaming subsystem, an electronic payment subsystem, an information protection subsystem, a secure communications subsystem, and a game selection subsystem. Each of the peripheral computer stations include a subsystem for admitting and registering players with the central computer station and a gaming interface subsystem. To ensure security of the electronic gaming system, a player seeking to enter the system transmits an encoded message from their peripheral computer station to the central computer station that includes a set of key attributes associated with the player. The central computer station decodes and compares the transmitted set of key attributes with individual information previously stored in the information protection subsystem in order to identify each player during registration based upon the set of key attributes transmitted by each player. The system may automatically control money transactions with each player's bank accounts based upon the player's scoring and wagers in each selected game.
Owner:LYDIA VLADIMIROVNA NESTERENKO
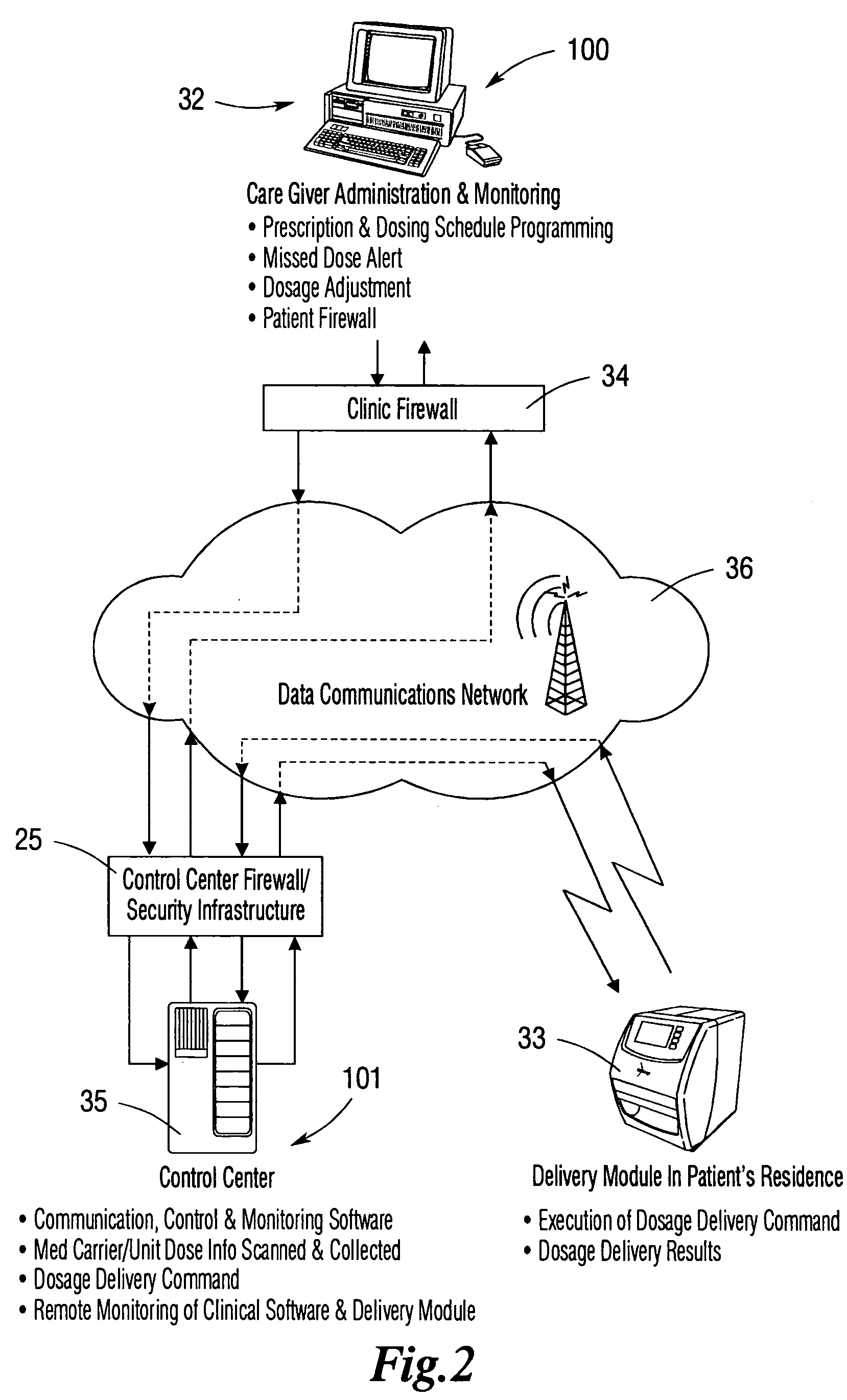
Integrated, non-sequential, remote medication management and compliance system
ActiveUS20050240305A1Precise deliveryMechanical clocksDrug and medicationsSecure communicationIndividual dose
An integrated medication management and compliance system for enabling a care provider to remotely manage and deliver individual doses of therapeutic products to a patient, in a non-sequential fashion. The system includes delivery apparatus remotely located from the care provider, wherein the apparatus stores a plurality of sealed unit dose packages that are delivered to a patient at a scheduled dosing time. The delivery apparatus is coupled to a control facility and to a computer terminal of the care provider by way of a secure communications network. The system enables the patient's medication regimen to be remotely tailored in real-time to accommodate fluid medical conditions.
Owner:EMMA HEALTH TECH INC
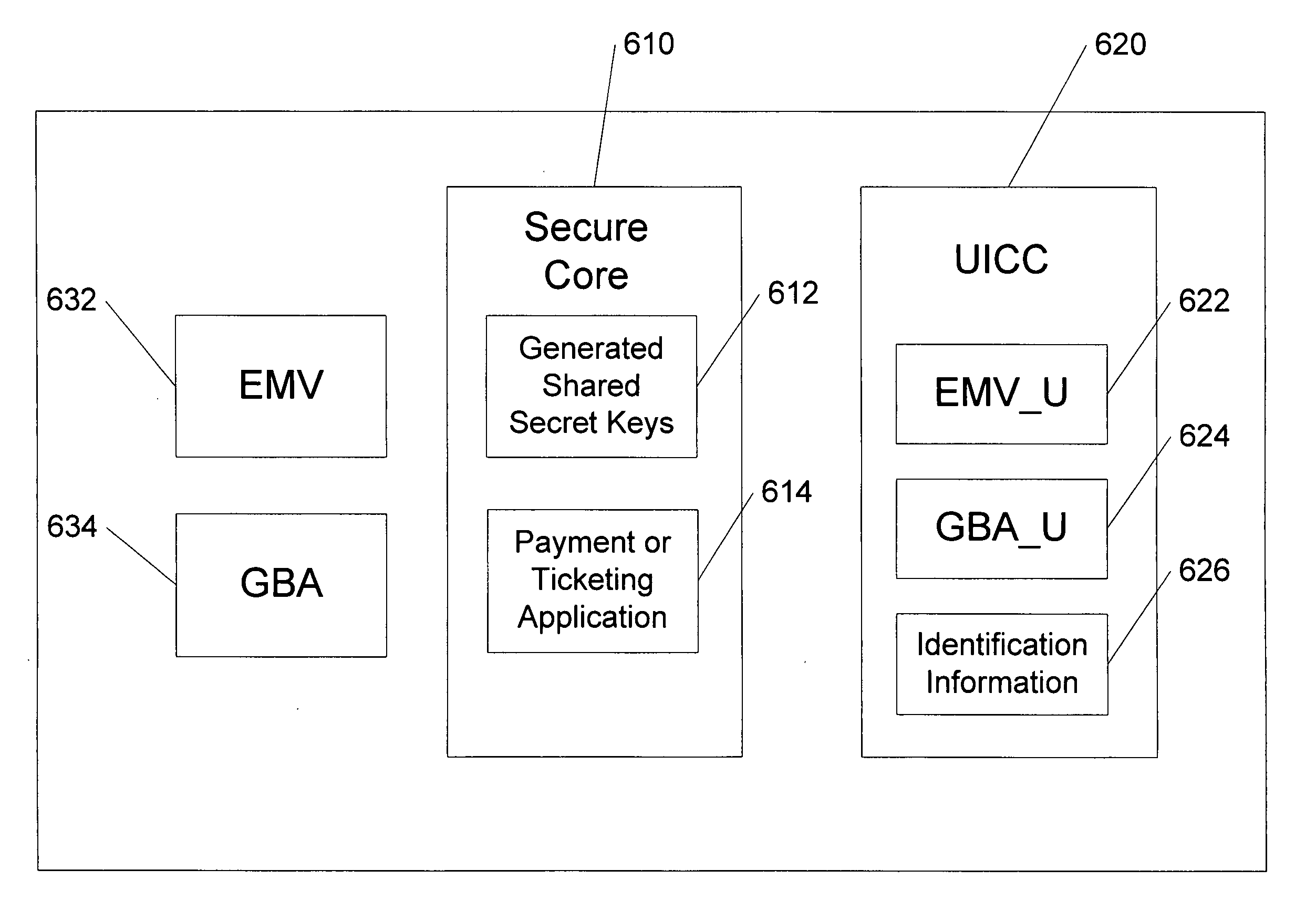
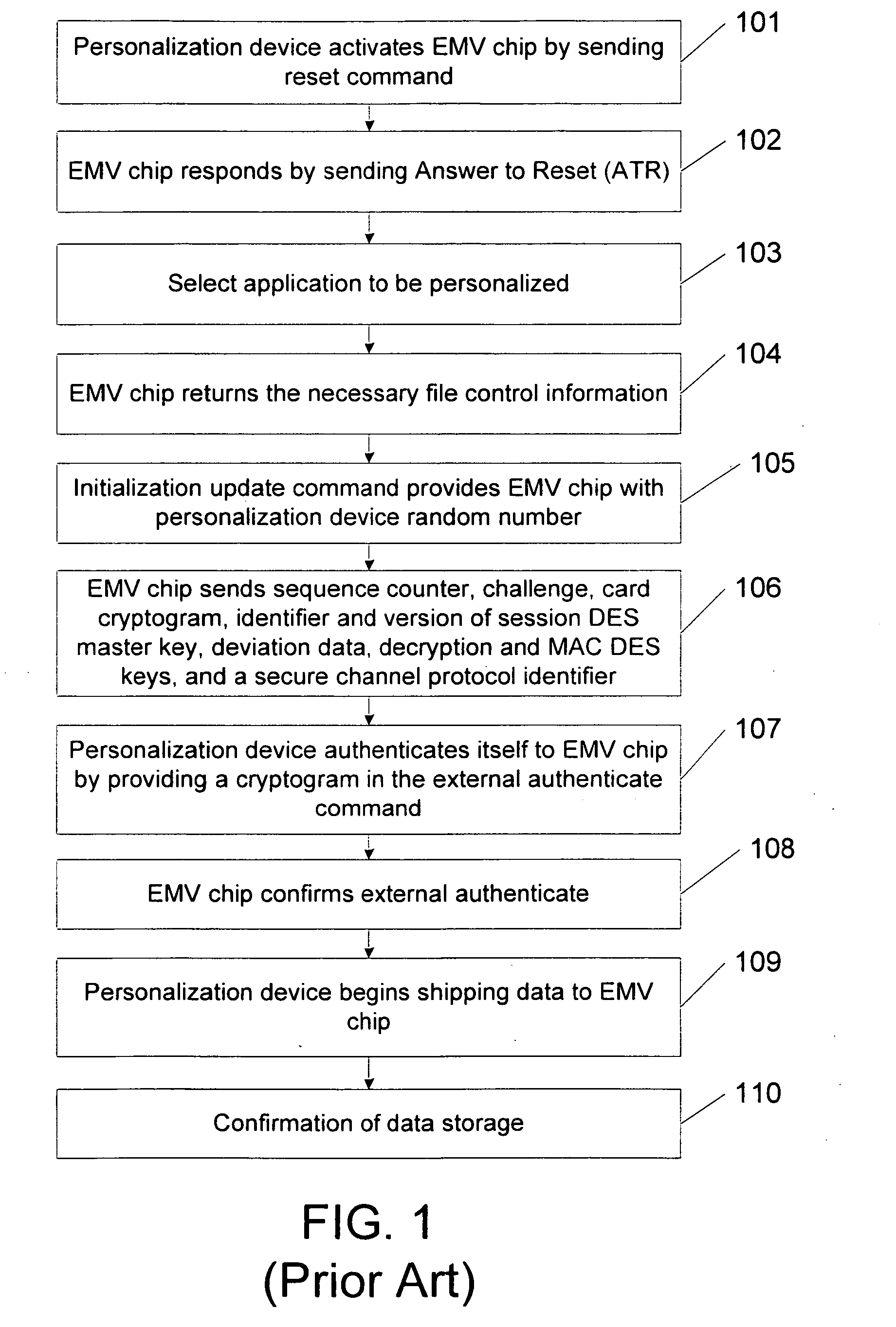
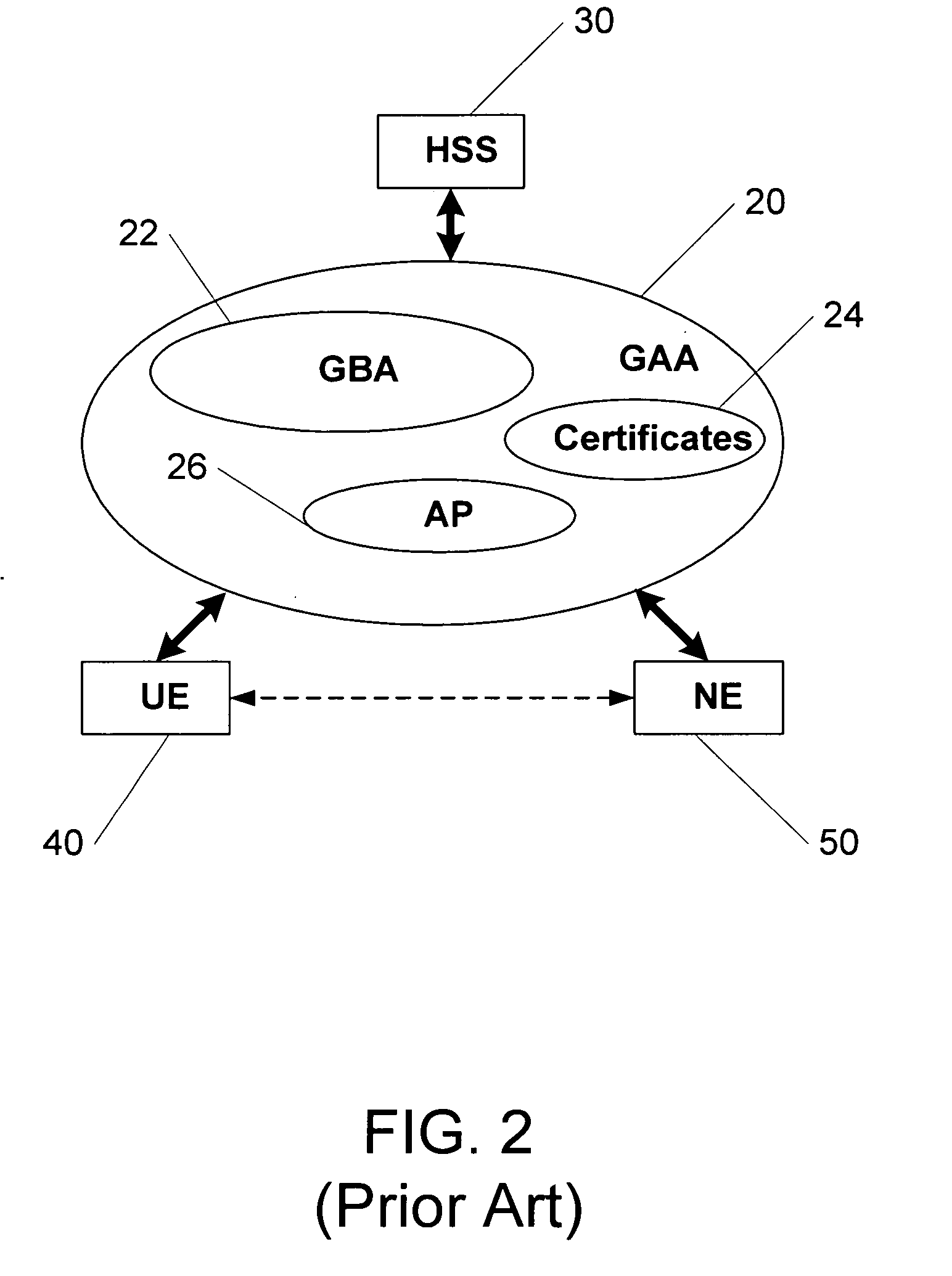
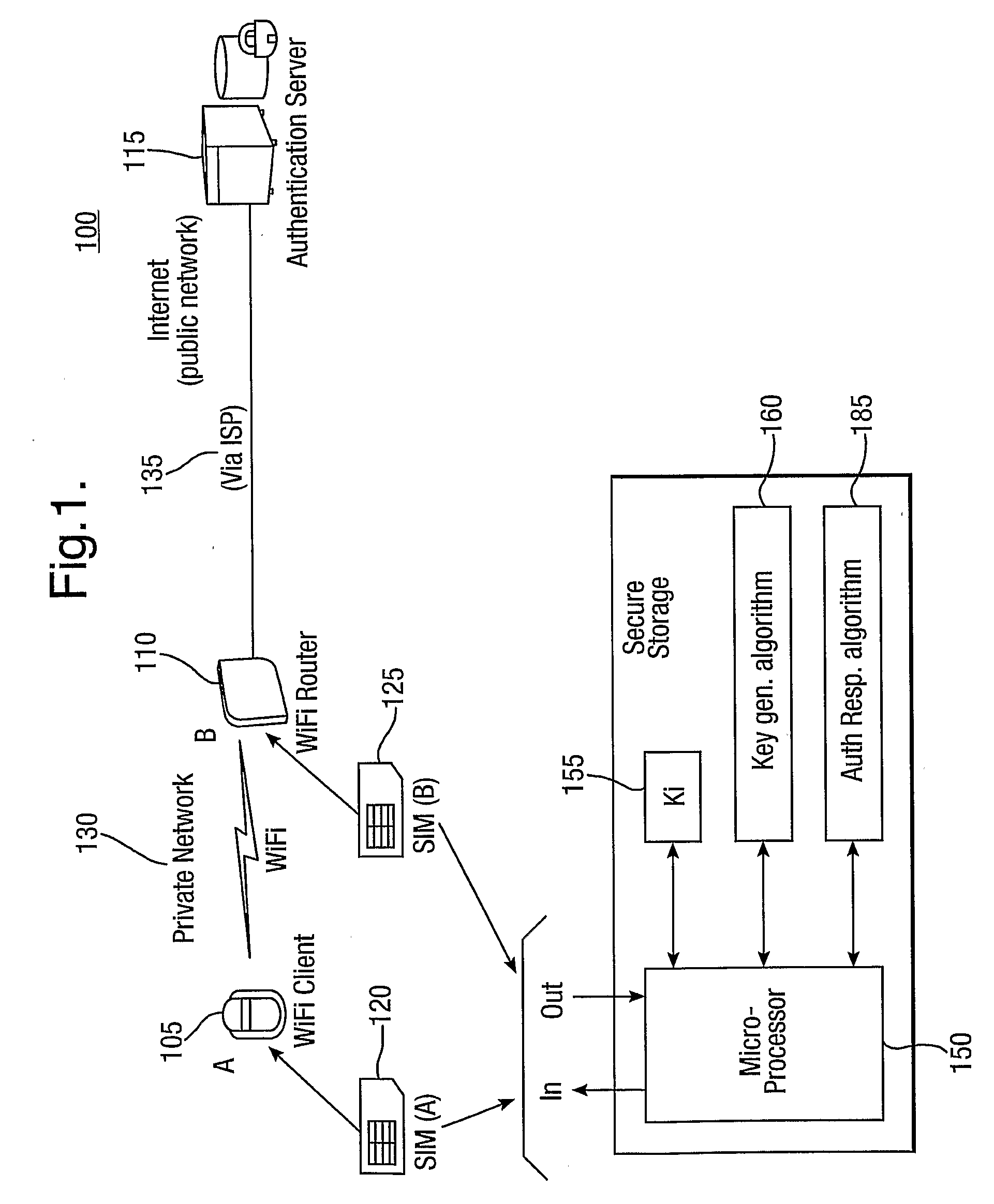
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECHNOLOGLES OY
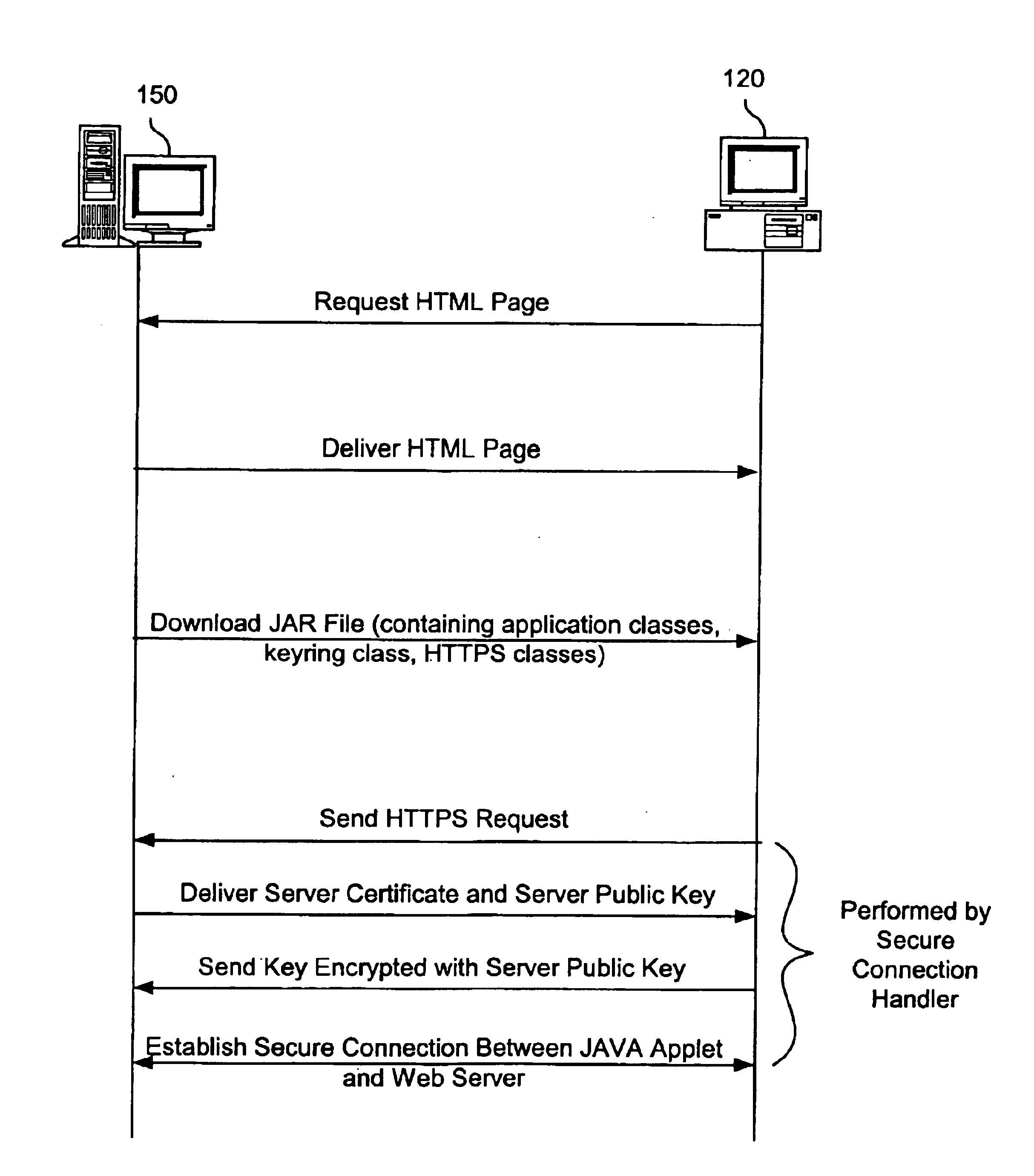
Method and apparatus for establishing a secure communication connection between a java application and secure server
InactiveUS6874084B1Improve portabilityIncrease flexibilityDigital computer detailsSecuring communicationSecure communicationWeb service
A method and apparatus for establishing a secure communication connection between a Java application or applet and a secure server is provided. An HTTPS handler is provided that may be used by Java applications or applets to establish secure communication connections with secure Web servers.
Owner:IBM CORP
Method and apparatus for creating a secure communication channel among multiple event service nodes
InactiveUS7013389B1Easy to scaleUser identity/authority verificationSecure communicationGroup session
An approach for establishing secure multicast communication among multiple event service nodes is disclosed. The event service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the event service nodes include the group session key and the private keys of the event service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the event service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can readily be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Event service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
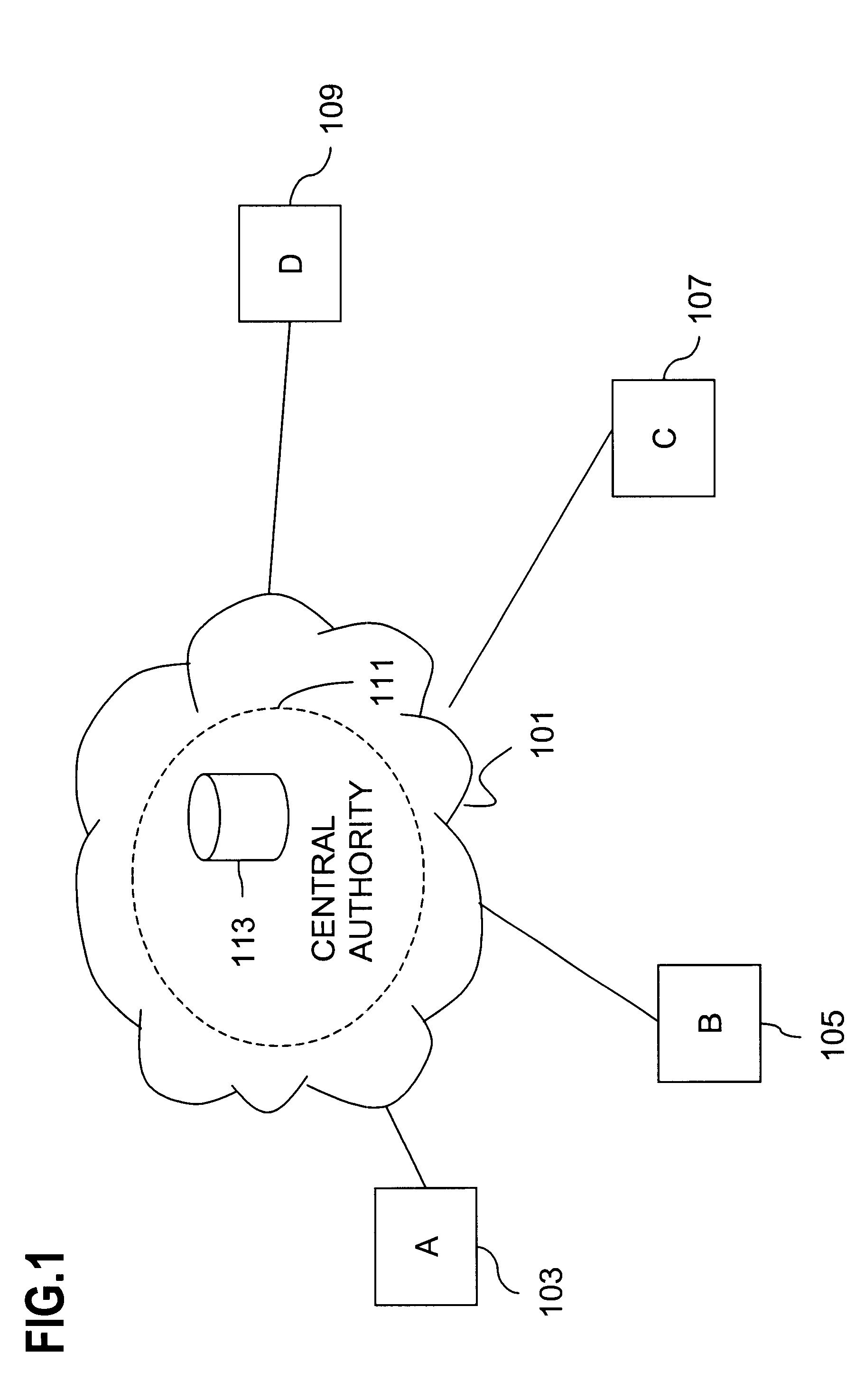
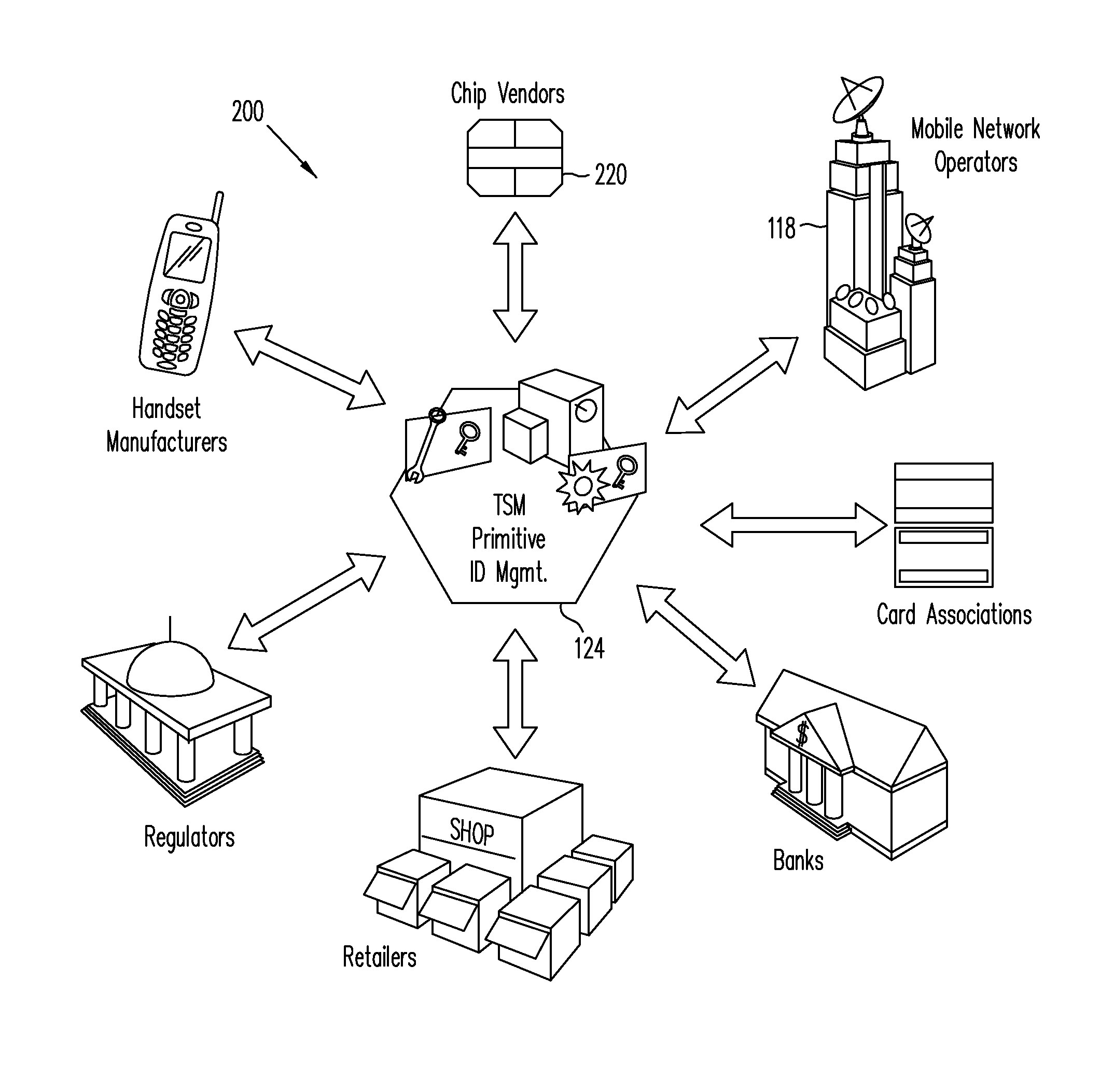
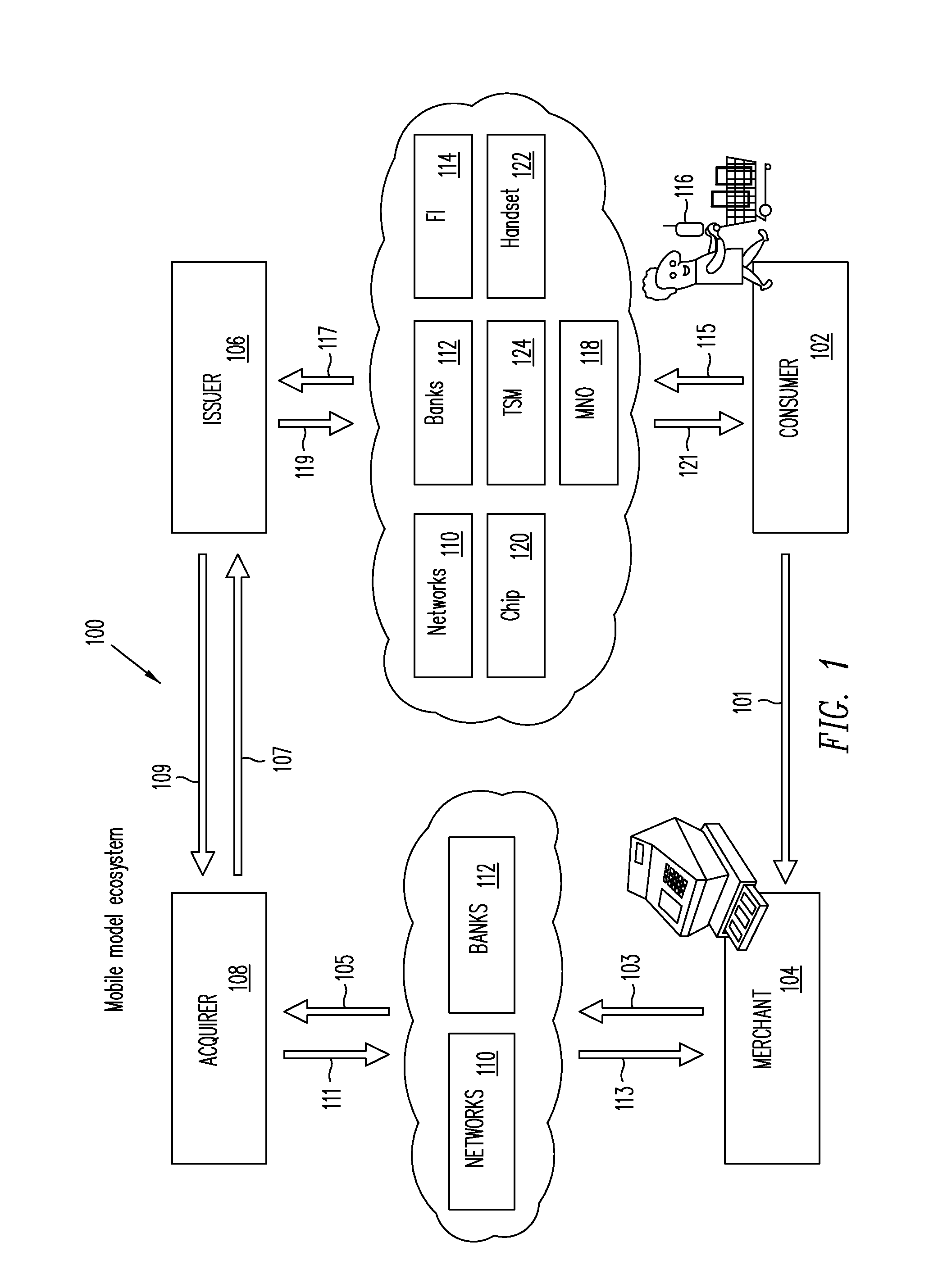
Trusted Integrity Manager (TIM)
A system for use with a trusted service manager (TSM) and a mobile device having a subscriber unique identifying data, according to one embodiment, includes: a server in which the server validates an application against the unique and identifying data of the mobile device and provides the validated application for the mobile device; and a secure element (SE) acting as a client in which the SE is present in the mobile device as client; the validated application from the server is installed in the SE; and the SE is adapted to execute the validated application to perform a service process. The service process includes enablement of payment functions on the mobile device, in which enablement of payment functions includes: providing secure communication between the mobile device and the server; secure provisioning of a payment instrument on the mobile device, wherein authentication and verification for the payment instrument on the mobile device is provided by the server; and binding the payment instruments and the validated application to the mobile device to provide a strong ID management for enhanced user protection and system security and integrity.
Owner:PAYPAL INC
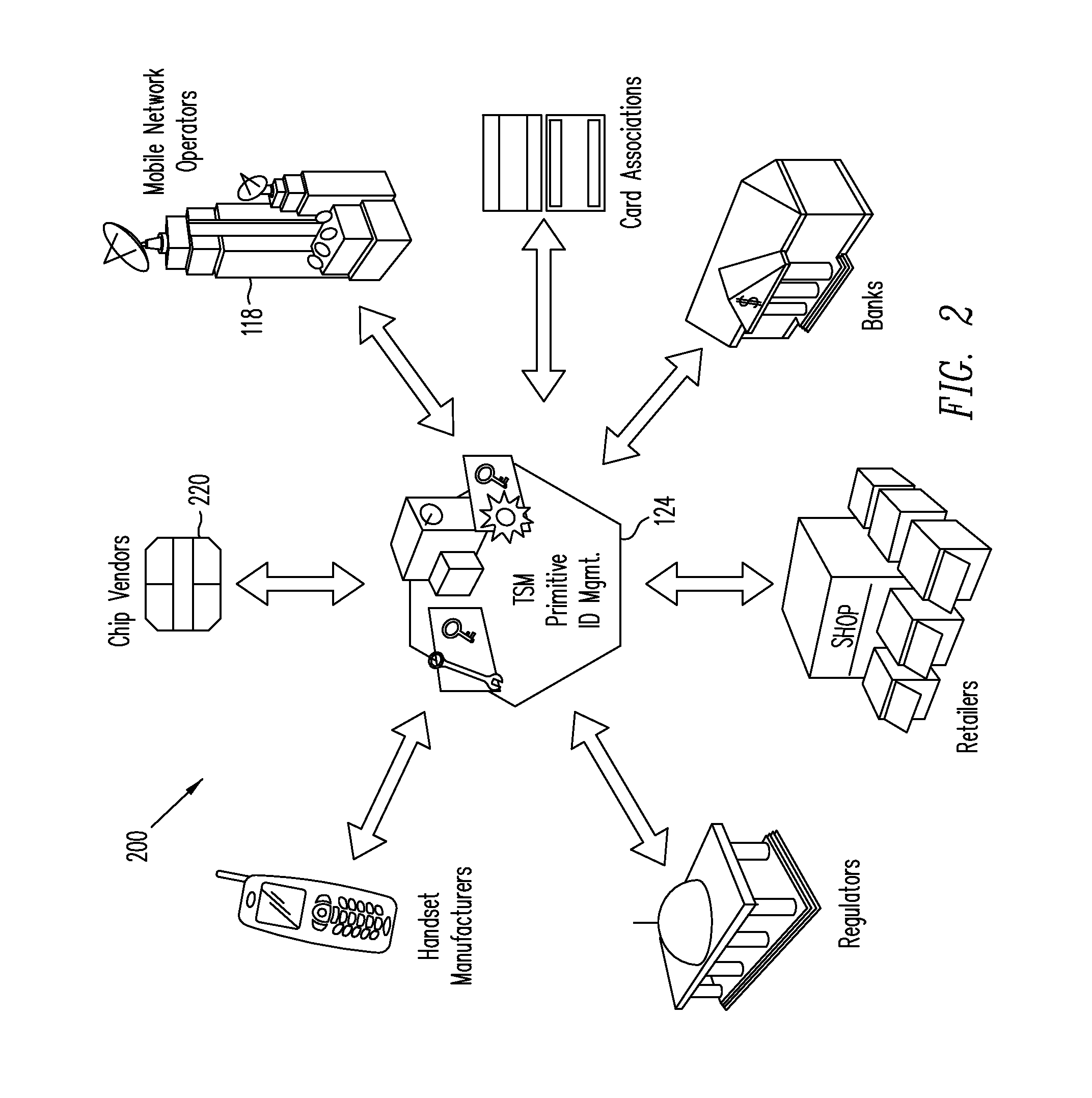
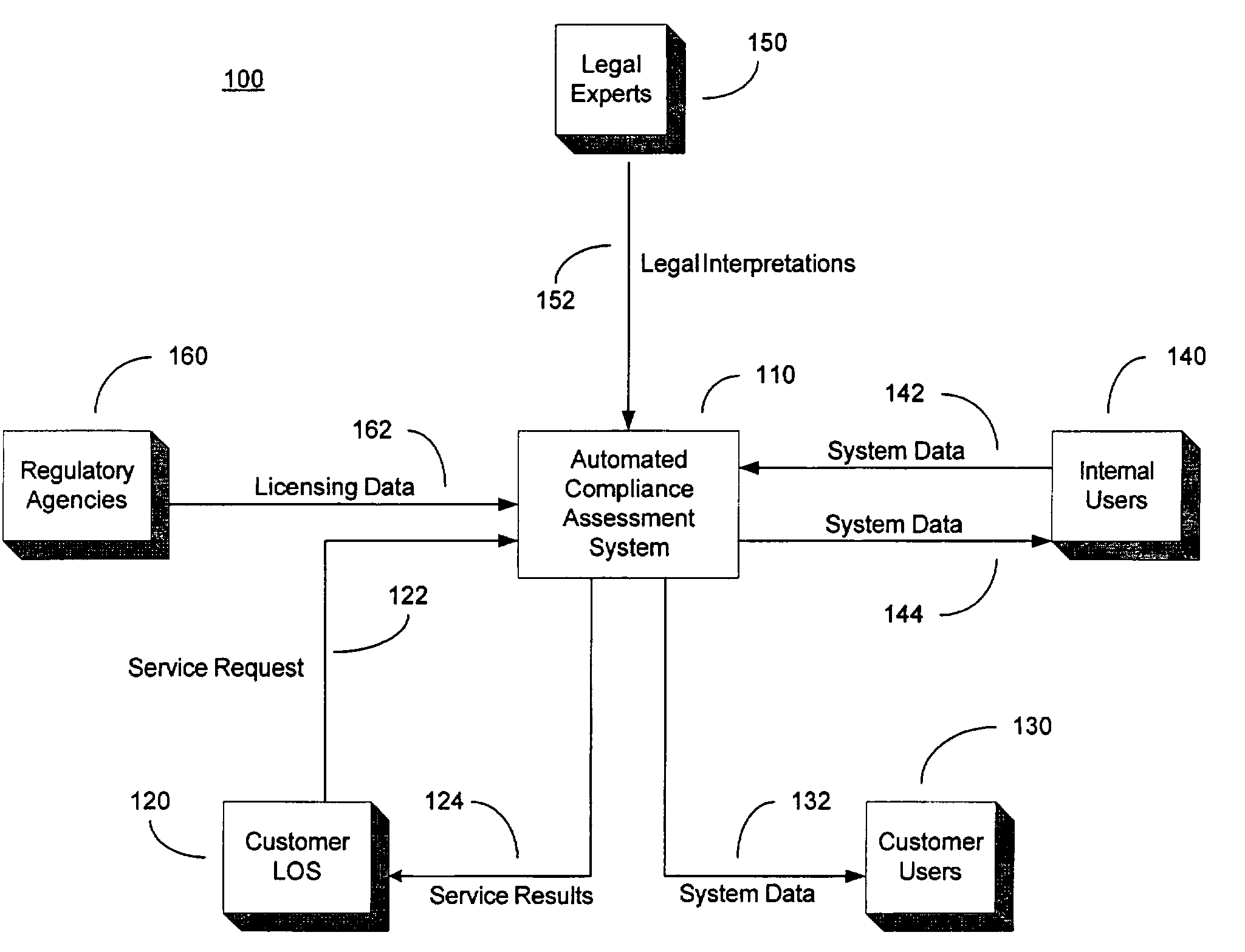
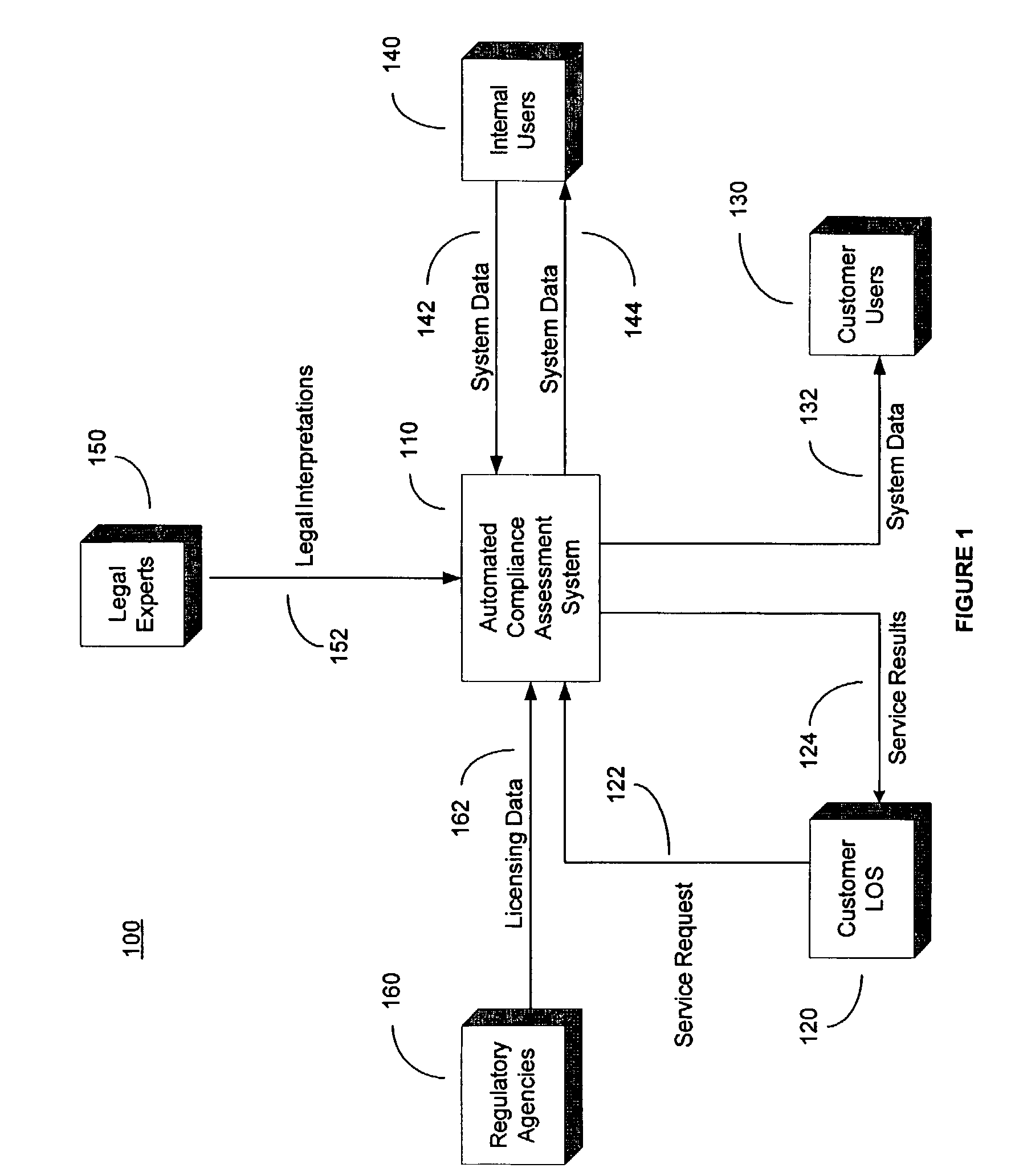
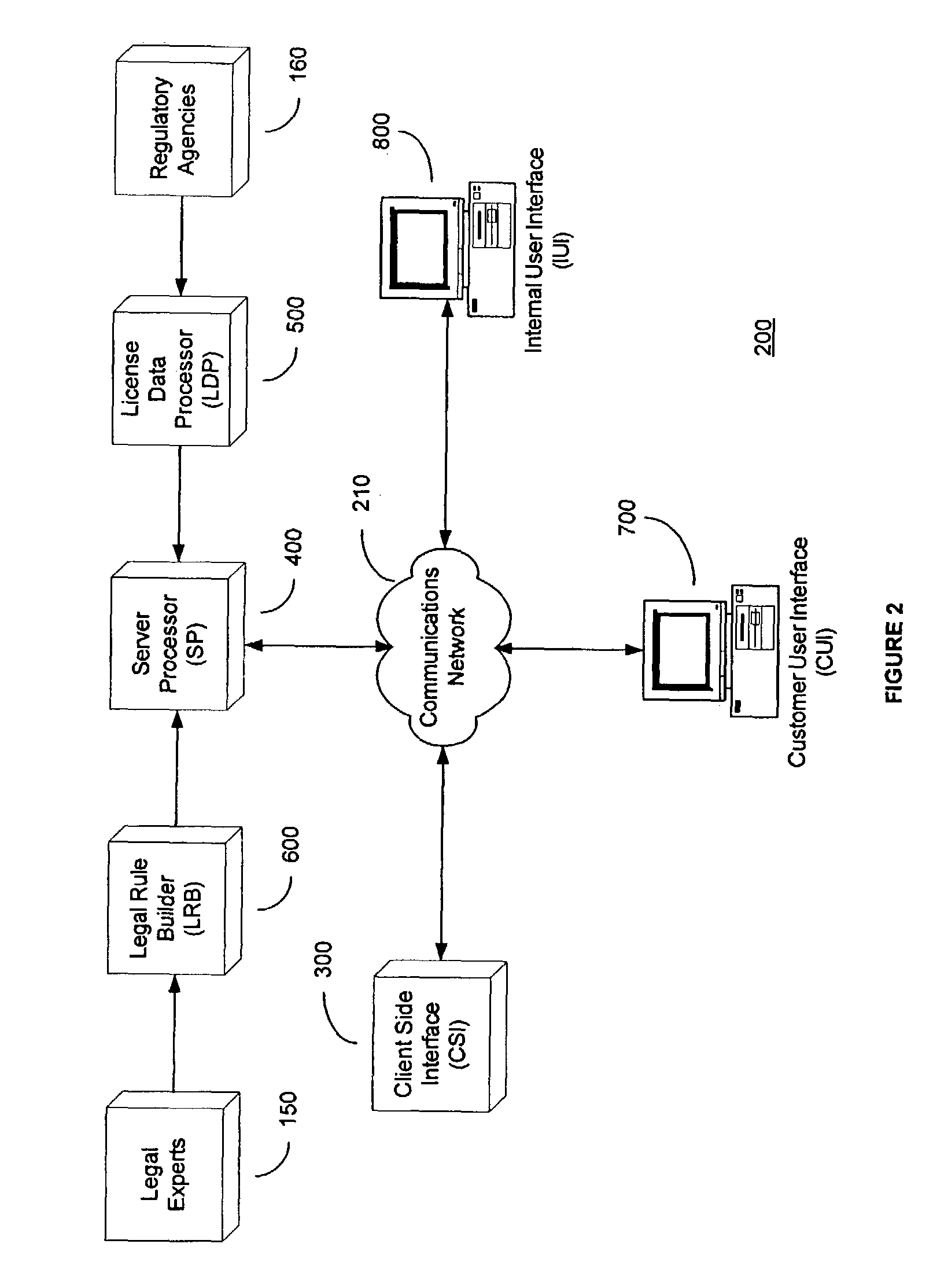
System and method for automated loan compliance assessment
An automated system and method for reviewing and assessing compliance with legal compliance requirements for loan applications. Loan application data is extracted from client loan origination systems and transmitted as a loan information file over a secure communication network to an automated compliance assessment system server where the loan information file is audited for compliance with Federal, state, and local legal compliance requirements. The loan information file is reviewed for legal compliance requirements imposed by Federal, State, and local jurisdictions, as well as licensing requirements that the client loan company and related personnel must satisfy. The results of the audit process are transmitted over a secure communication network to the client loan company, with areas of noncompliance indicated. The automated compliance assessment system server also stores rules data derived from legal compliance requirements, license data derived from regulatory requirements, system setup data and supplemental system application data.
Owner:ICE MORTGAGE TECH INC
System and method for secure electronic communication services
InactiveUS20090198997A1Easy accessSecure transmissionKey distribution for secure communicationMultiple keys/algorithms usageScalable systemEmail address
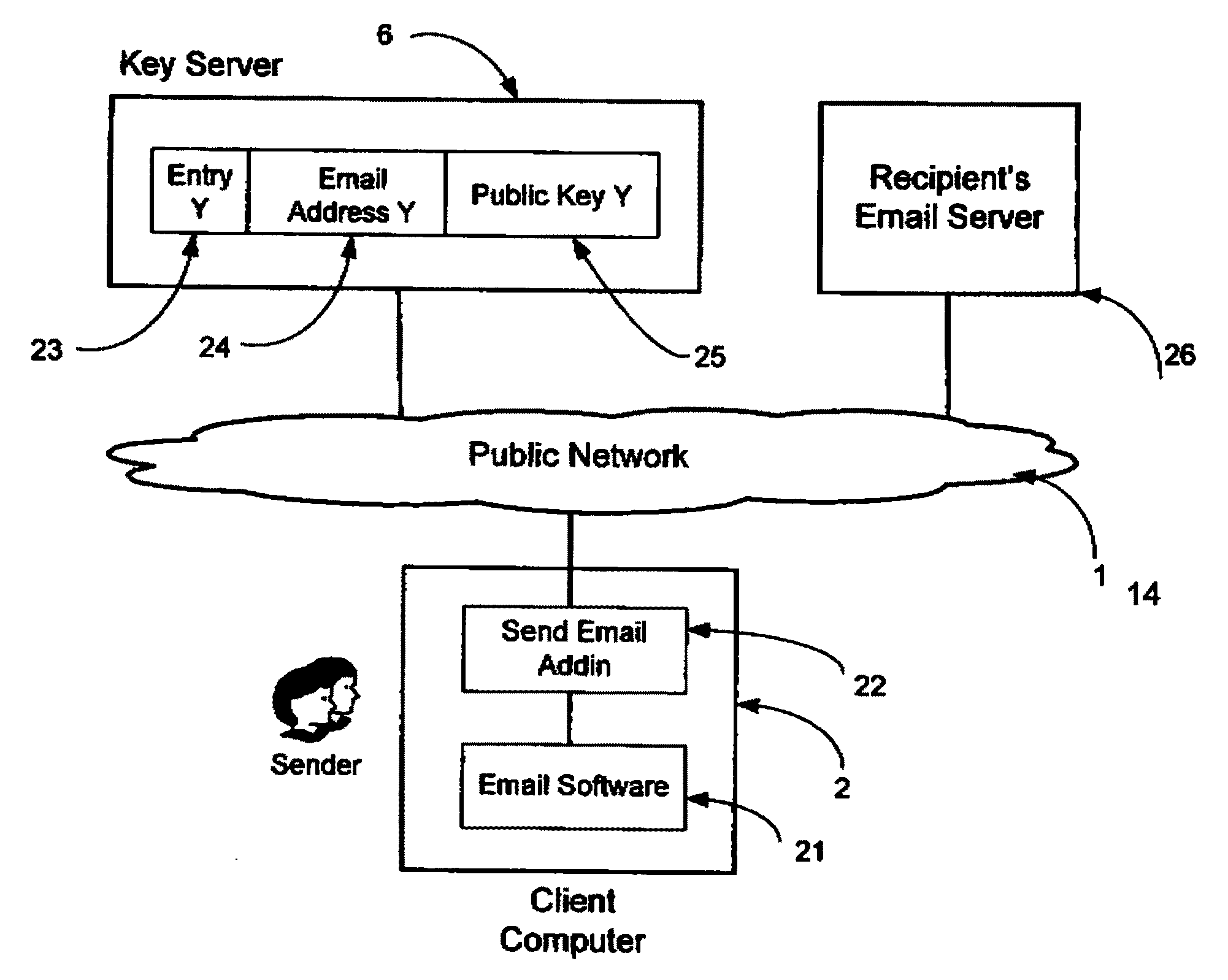
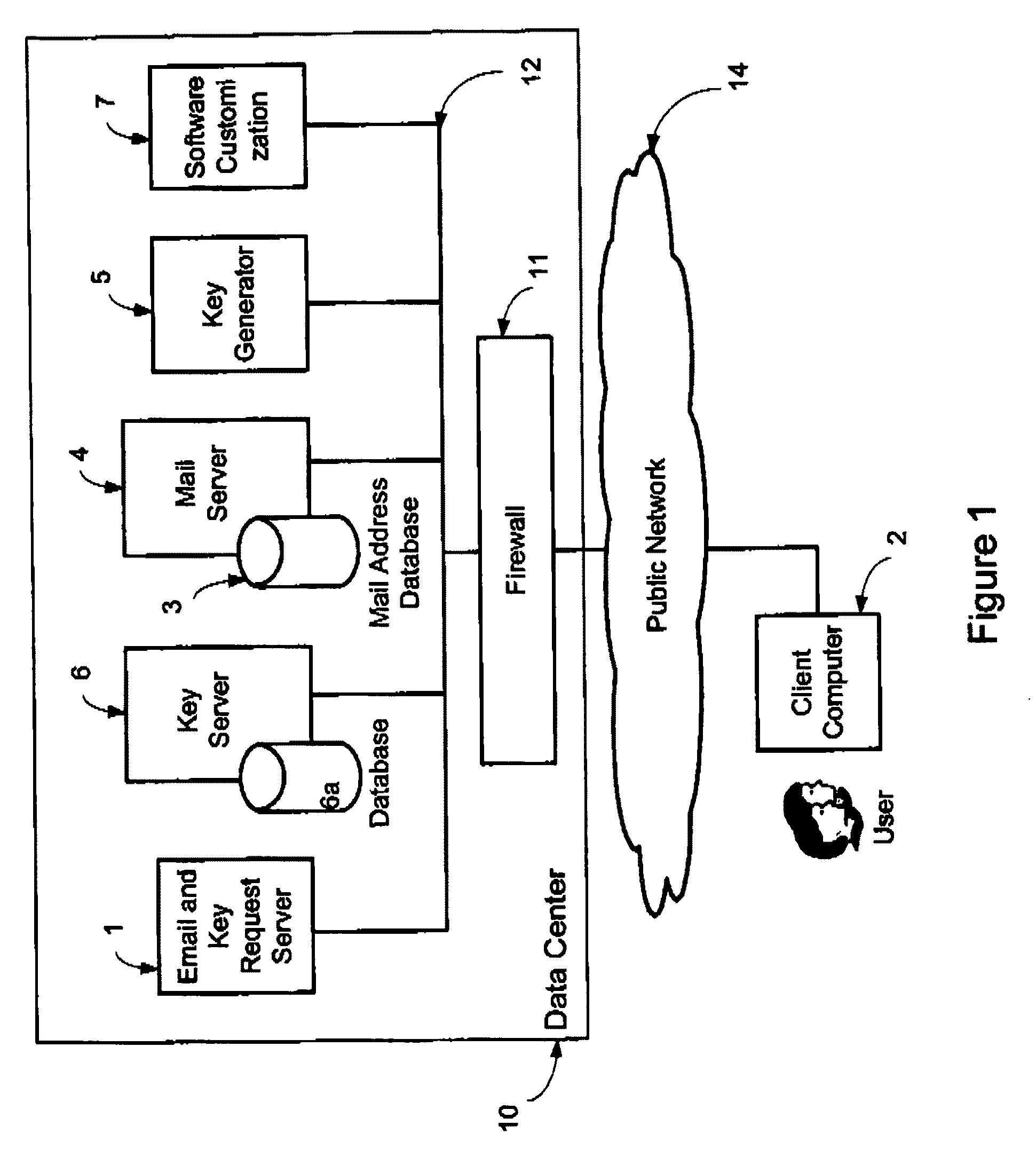
A system, method and software module for secure electronic communication services, wherein a public key (25) of private-public-key pair (30,25) is associated with an email address (24), internet name or other registered unique identifier; the registered user of the unique identifier holds the private-key (30) securely, and the respective public-key (25) is made accessible on a key server (6) for look-up and retrieval by other users, for encryption of communications to be sent to the holder of the private-key, and optionally for message confidentiality, message integrity and authentication of sender and recipient, without requiring certificates. A distributed and scalable system is provided by a server network (600; 401, 501) for registration, key distribution and management preferably using a kDNS server hierarchy (601,602,603) or a key-DNS server hierarchy (701,702,) and associated protocols so that public-keys of recipients can be searched and retrieved over the internet based on the recipients email address or other unique identifier, thus facilitating secure communication between users in different network domains and organizations.
Owner:TOPOSIS CORP
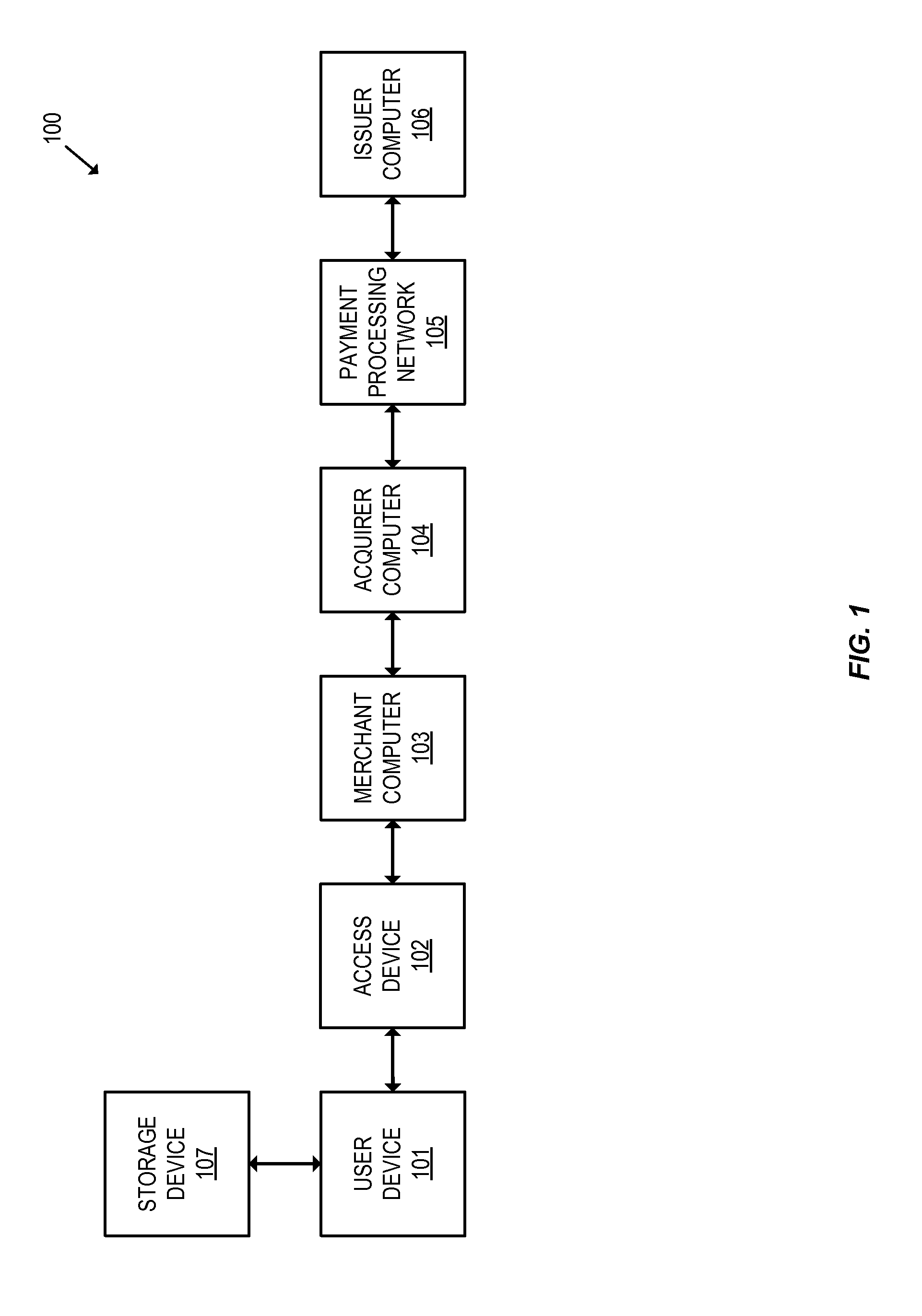
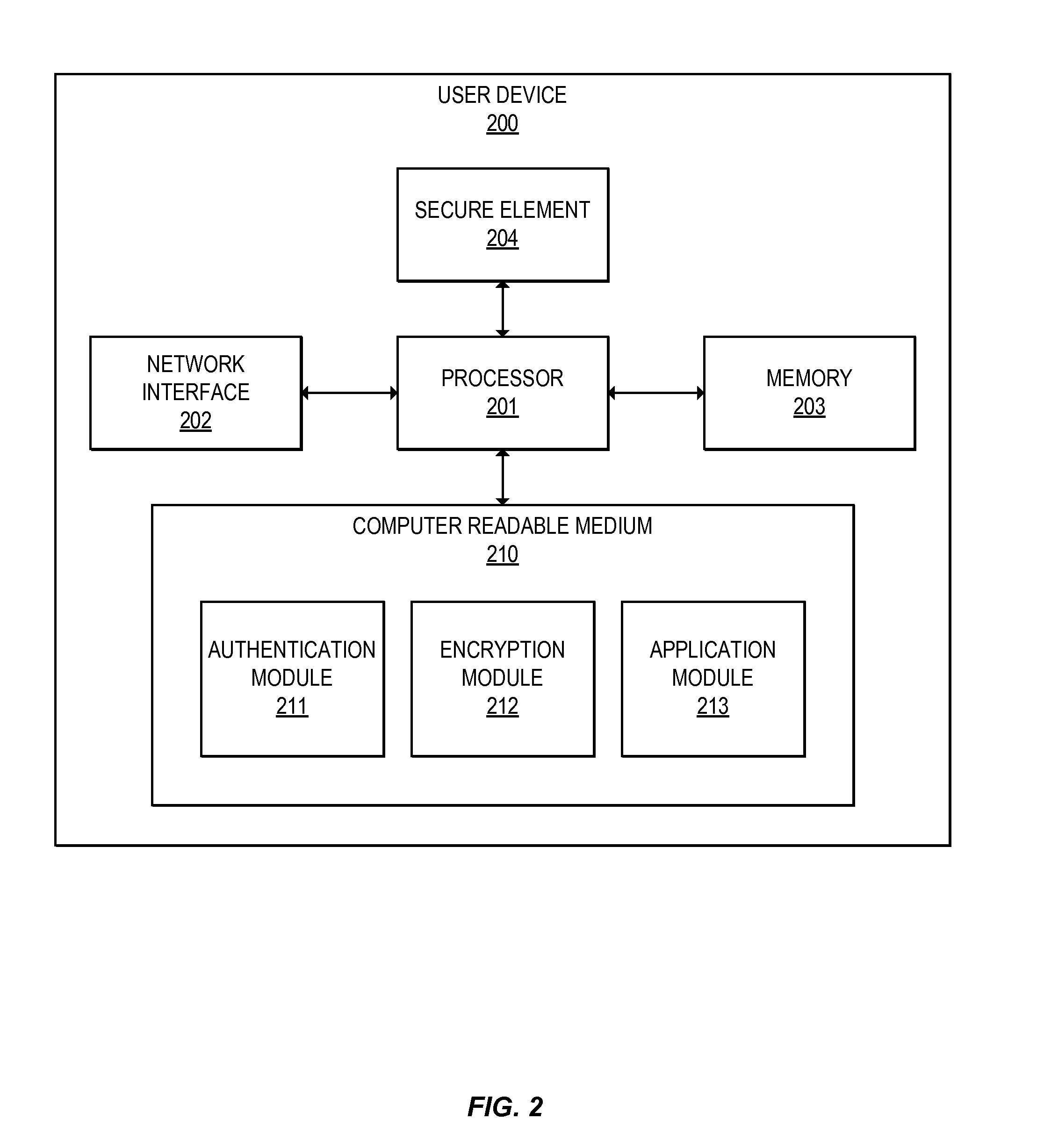
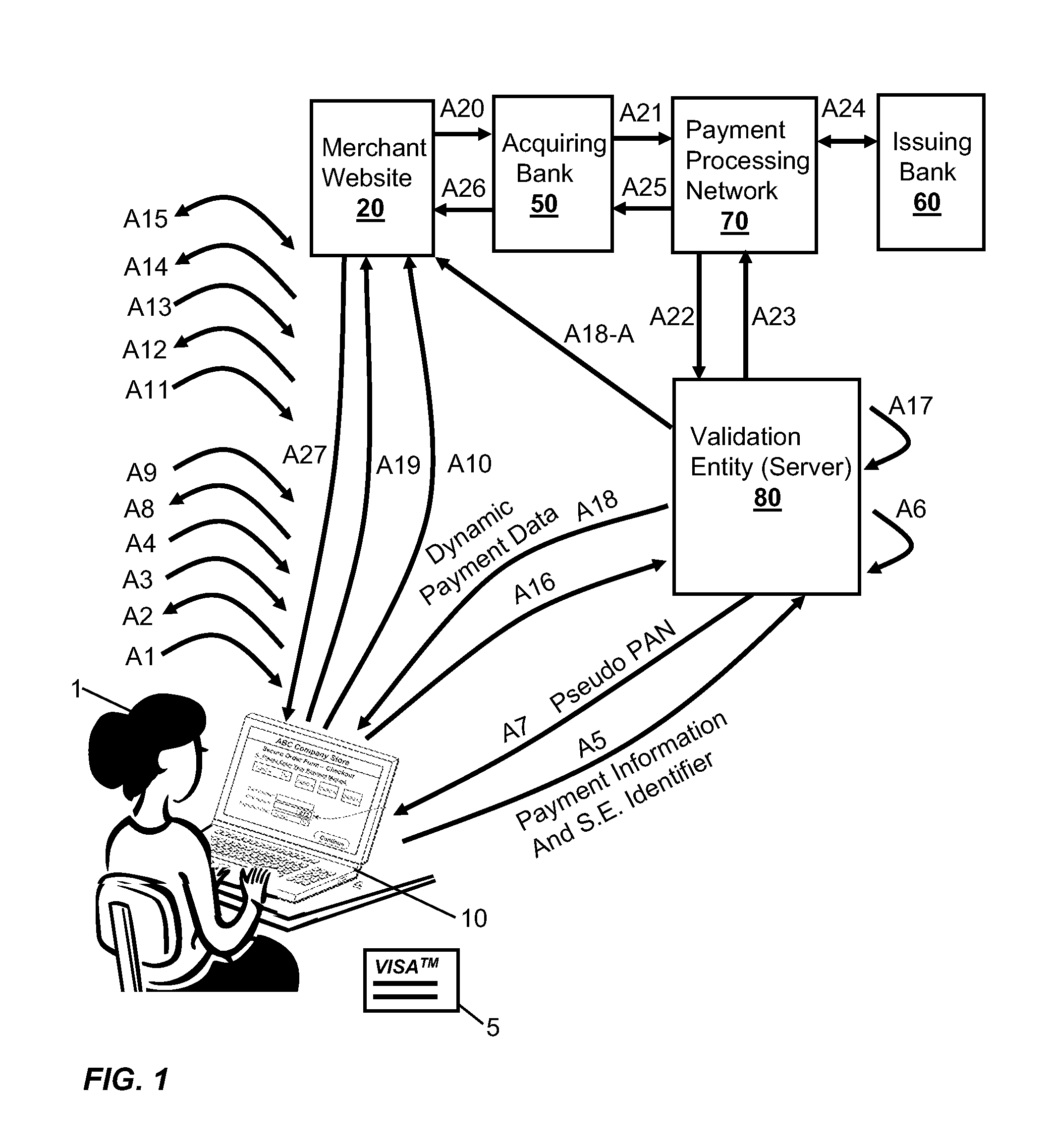
Integration of Payment Capability into Secure Elements of Computers
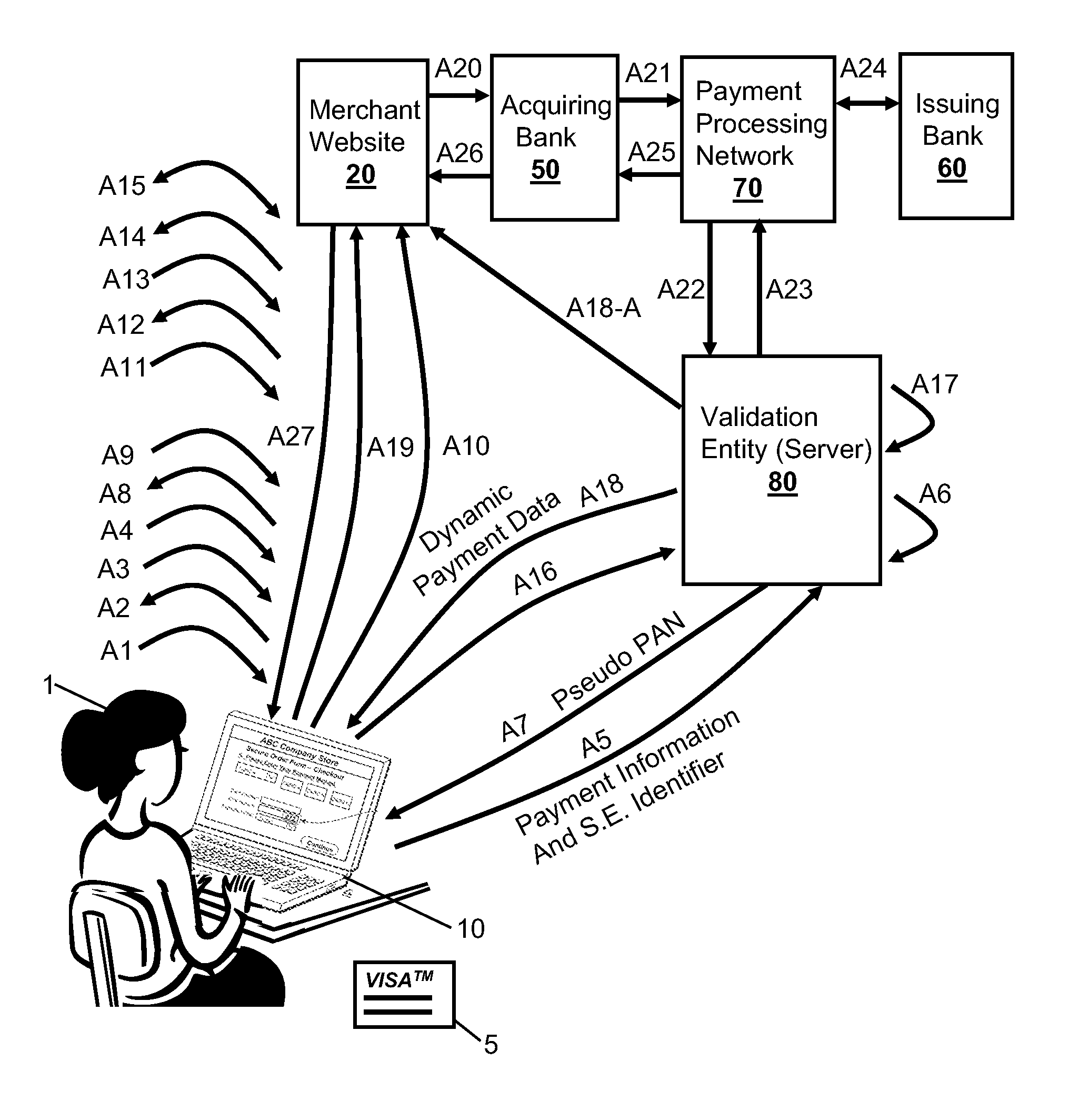
Methods, secure elements, validation entities, and computer program products for effecting secure communication of payment information to merchants for Internet-based purchases. Payment information for a user's real payment information is installed in a secure element of a computer, the payment information may comprise a pseudo PAN number for the portable consumer device provided by a validation entity. The secure element is shielded from the computer's operating system to thwart hacker attacks. The user accesses the secure element to make a purchase. In response, the secure element contacts the validation entity with the pseudo account number, and in response obtains dynamic payment information that the secure element can used to effect the payment. The dynamic payment information comprises an account number that is different from the pseudo PAN, and which has at least one difference which respect to the user's real payment information.
Owner:VISA INT SERVICE ASSOC
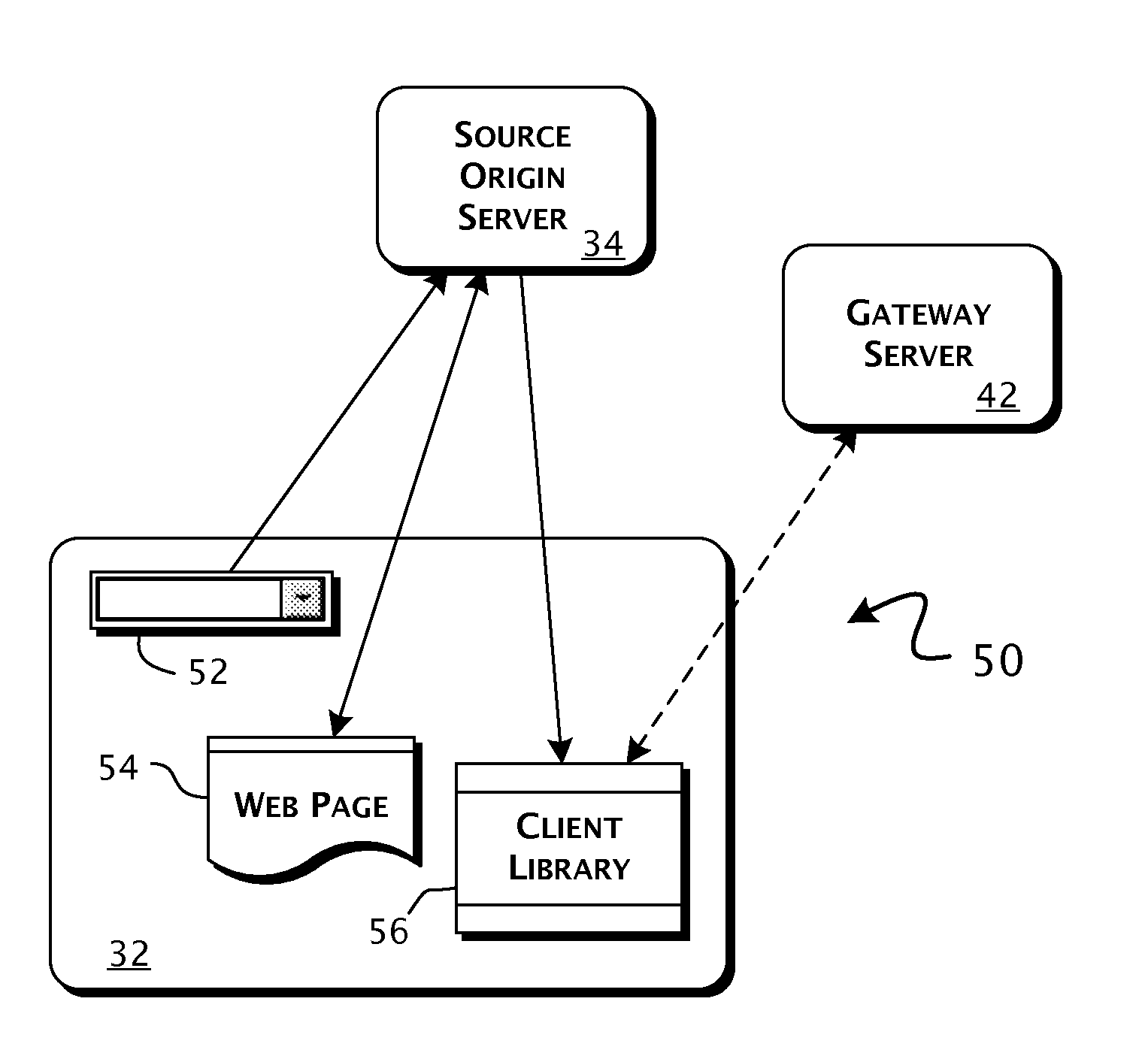
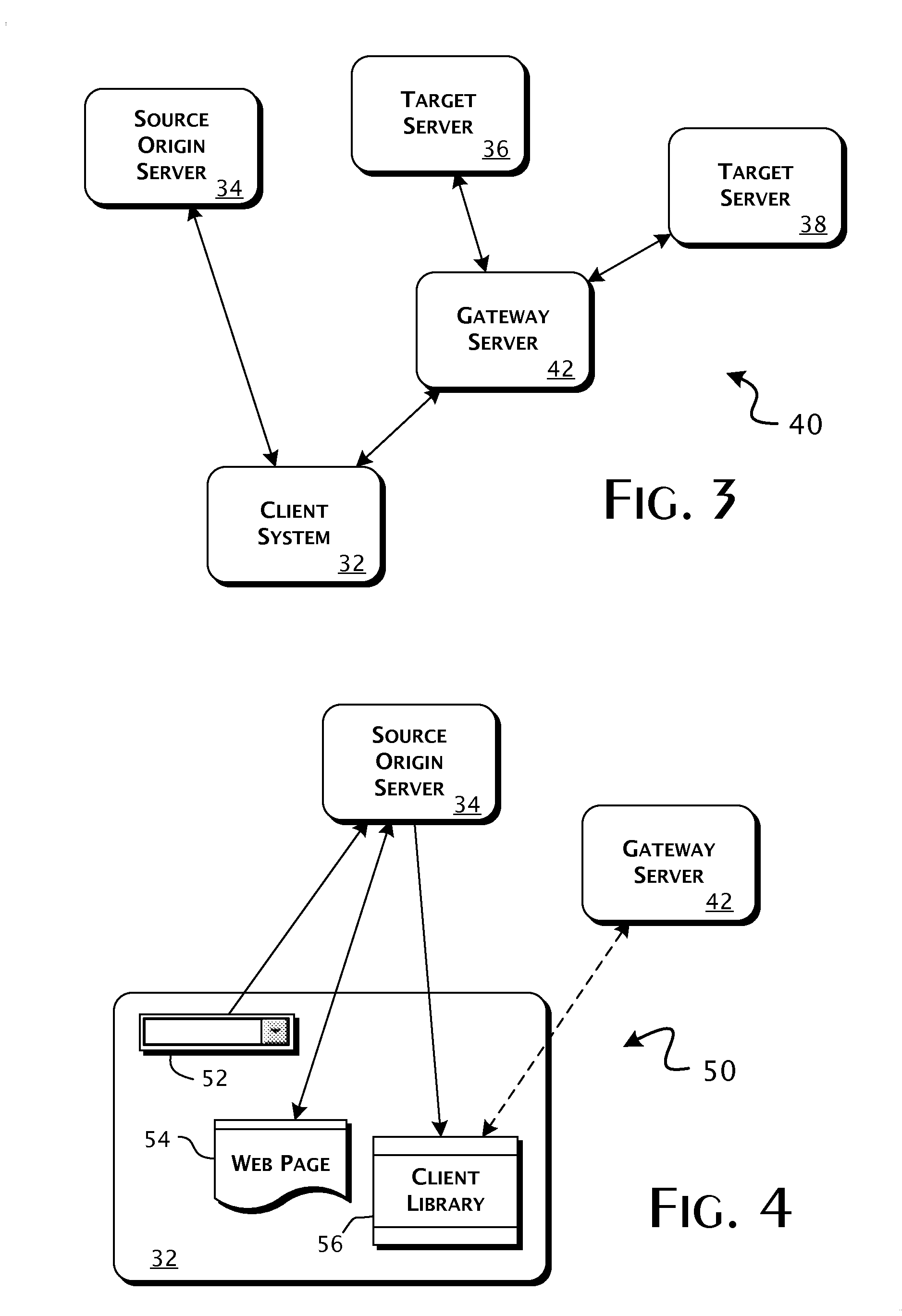
Enterprise client-server system and methods of providing web application support through distributed emulation of websocket communications
ActiveUS20100281107A1Appropriate deliveryEffective supportInterprogram communicationMultiple digital computer combinationsSecure communicationClient-side
A system enabling service communications in distributed Web applications between servers otherwise inaccessible due to cross-origin security restrictions in pre-HTML5 compliant Web-browser clients. A Web-browser client executes a client-side Web application received from a source origin server having a defined source origin and requests connections to request identified Web-application services. Execution of an emulation client library establishes a bidirectional capable HTTP-based communications connection between the Web-browser client and a gateway server, having a target origin outside the scope of the source origin, providing access to the request identified Web-application service. The bidirectional capable HTTP-based communications connection includes a cross-origin communications bridge providing a secure communications path between the source and target origins. The gateway server can establish an HTML5 compliant connection to a target defined service, provided by a target server, having a predefined relation to the request identified Web-application service.
Owner:KAAZING CORP
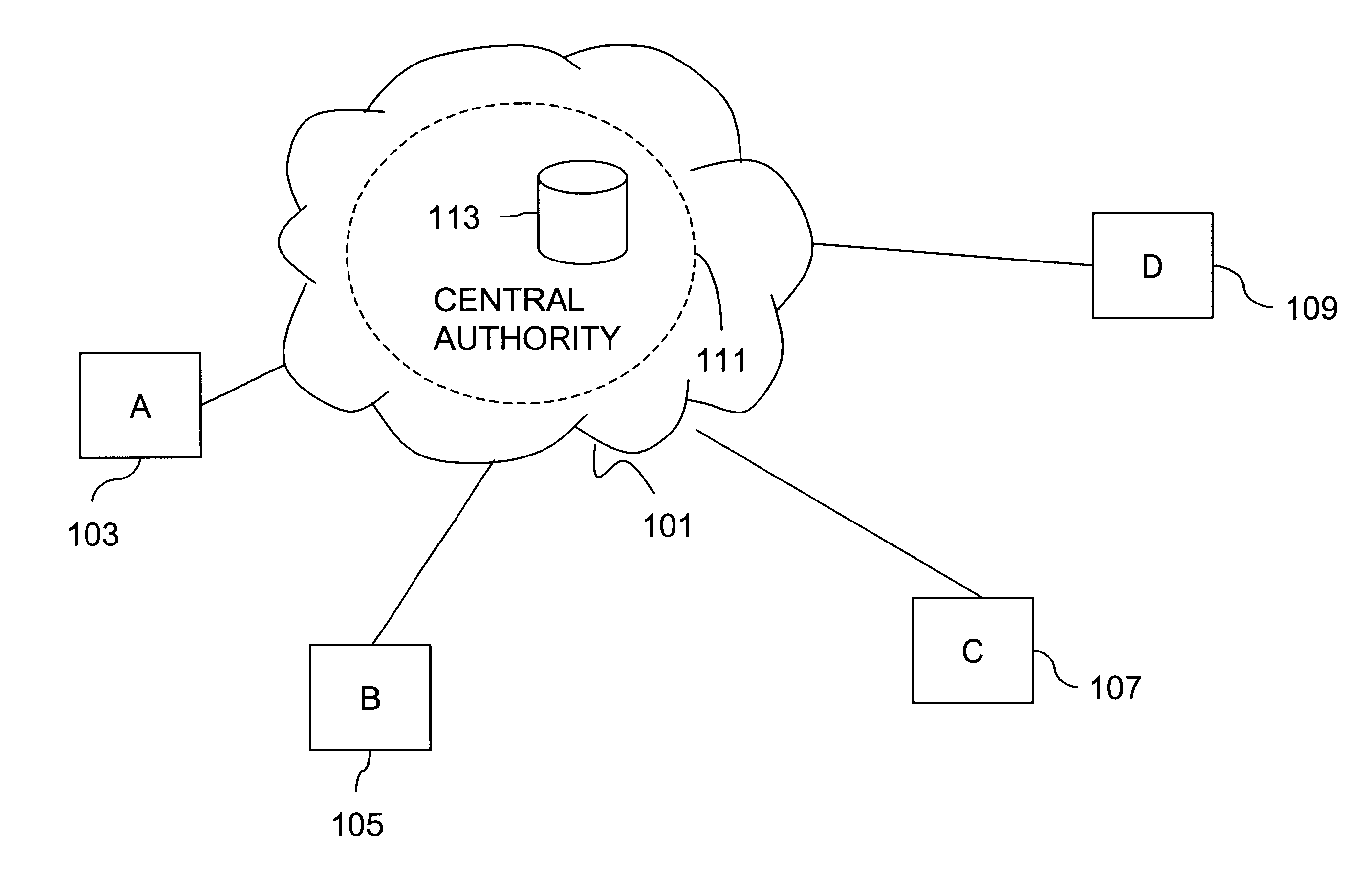
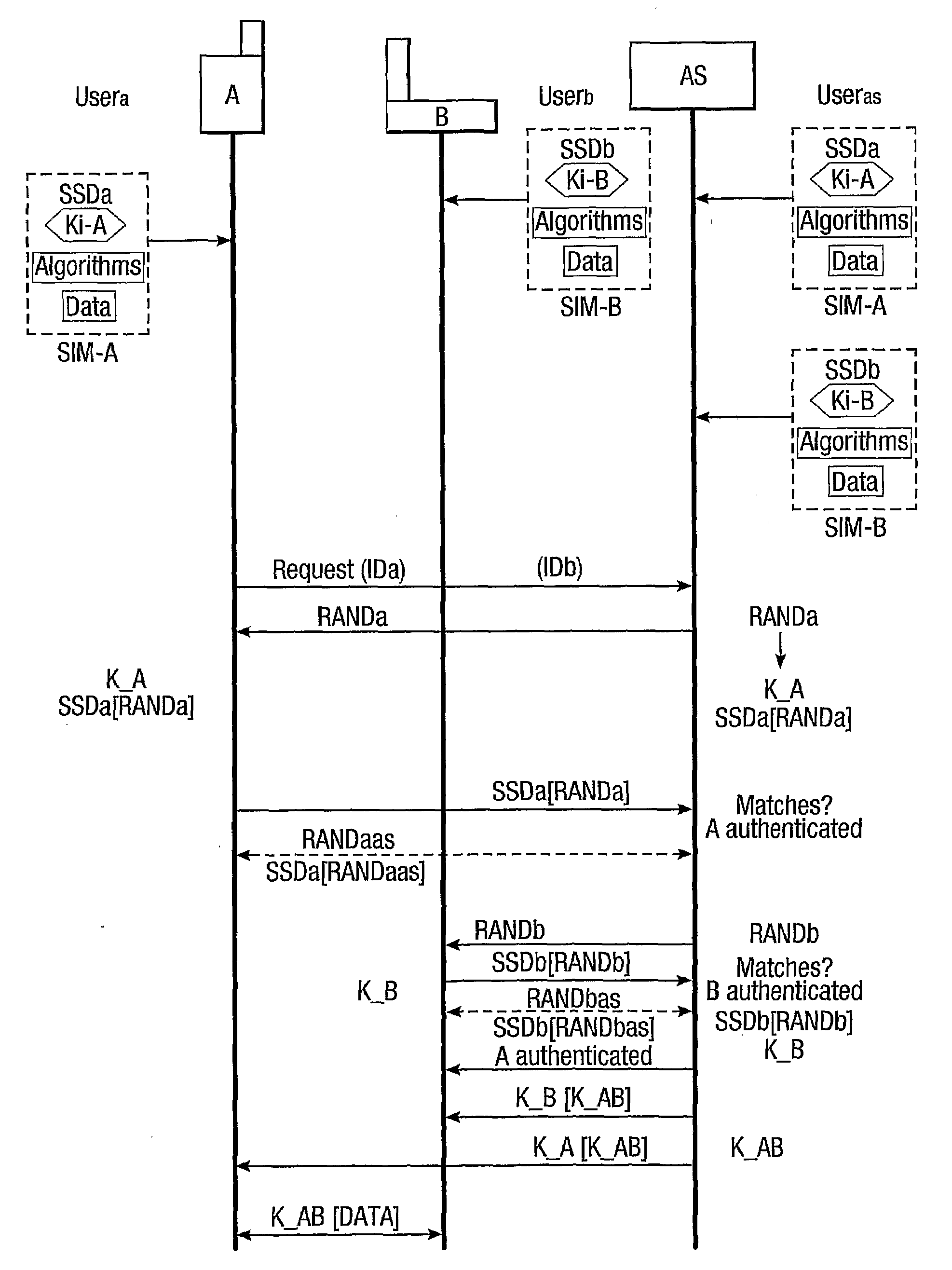
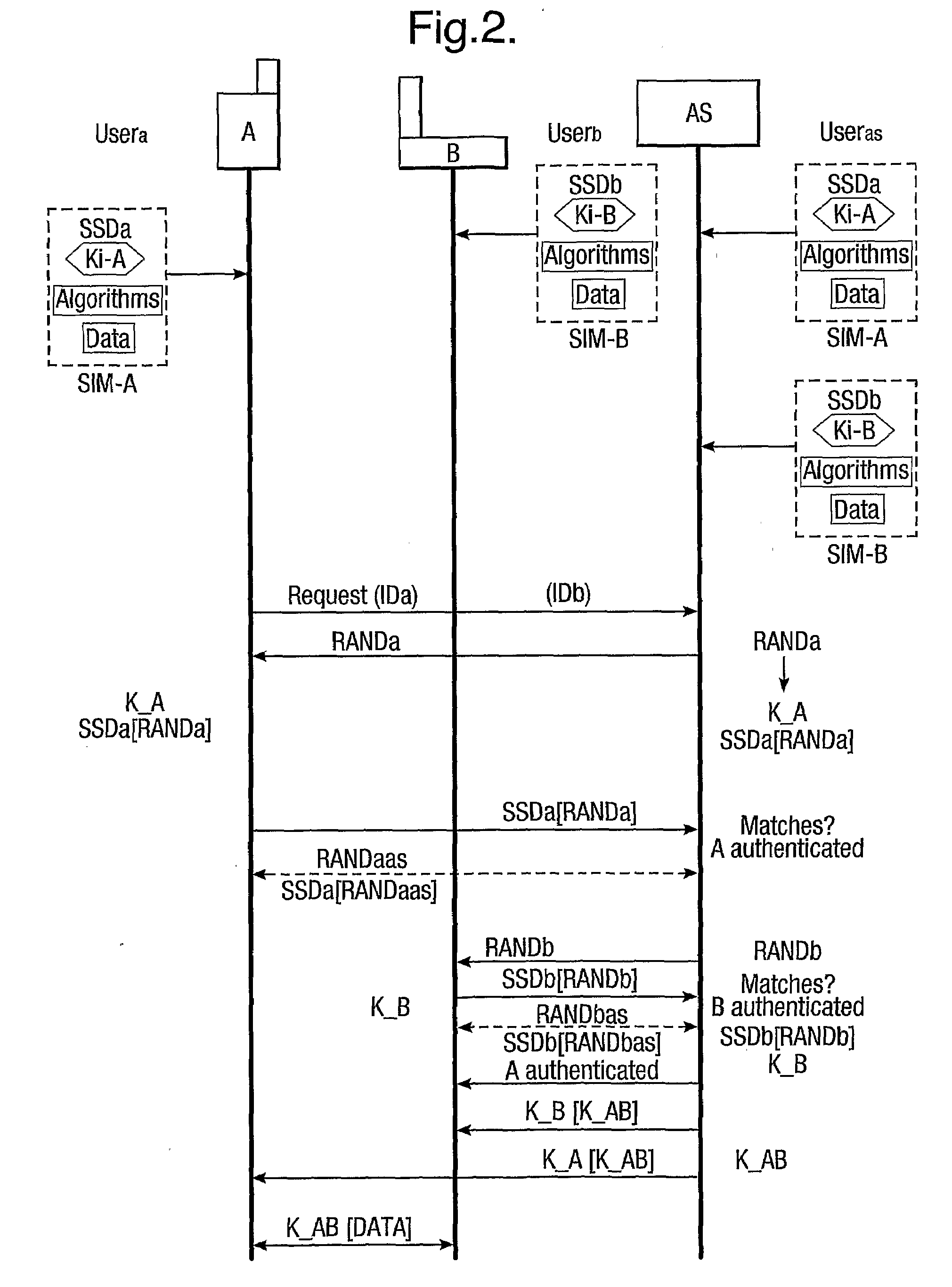
Provision of secure communications connection using third party authentication
ActiveUS20090287922A1Connection securityCommunication securityKey distribution for secure communicationUser identity/authority verificationThird partySecure communication
The present invention relates to communications, and in particular though not exclusively to forming a secure connection between two untrusted devices. The present invention provides a method of securely connecting a first device (A) to a second device (B) using a third party authentication server (AS) coupled to the second device, the first device and the authentication server both having first device shared secret data (SSDa) and the second device and the authentication server both having second device shared secret data (SSDb). The method comprises receiving a request from the first device at the authentication server; the authentication server and the first device both generating a first device key (K_A) using the first device shared secret data in response to a first device random number (RANDa) sent from the authentication server to the first device; the authentication server and the second device both generating a second device key (K_B) using the second device shared secret data in response to a second device random number (RANDb) sent from the authentication server to the second device; and the authentication server securely forwarding to the second device (B) and the first device (A) a common key (K_AB) using the second and first device keys (K_B, K_A).
Owner:BRITISH TELECOMM PLC
Secured virtual network in a gaming environment
InactiveUS7515718B2Mosaic printer telegraph systemKey distribution for secure communicationSecure communicationThe Internet
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
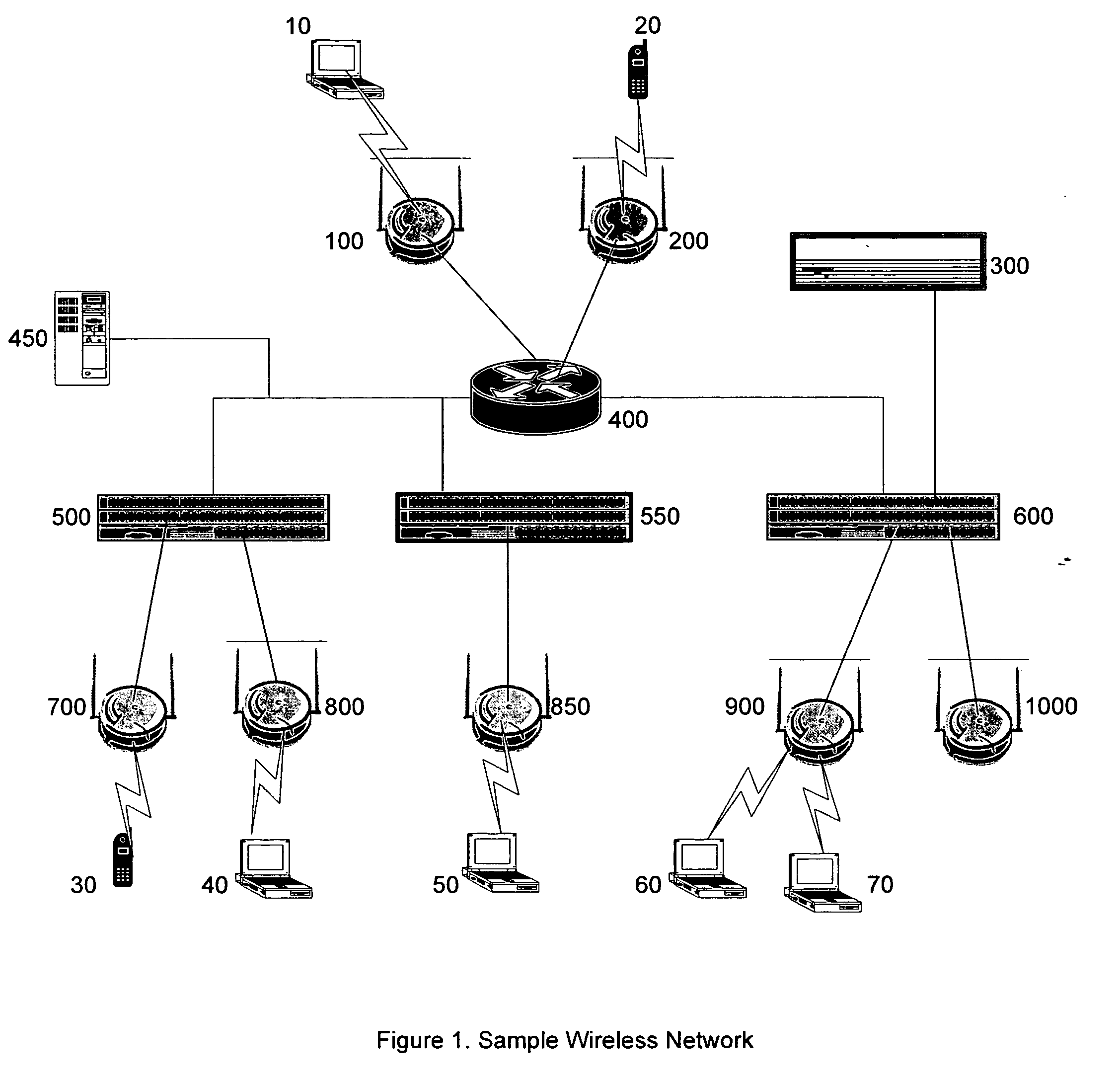
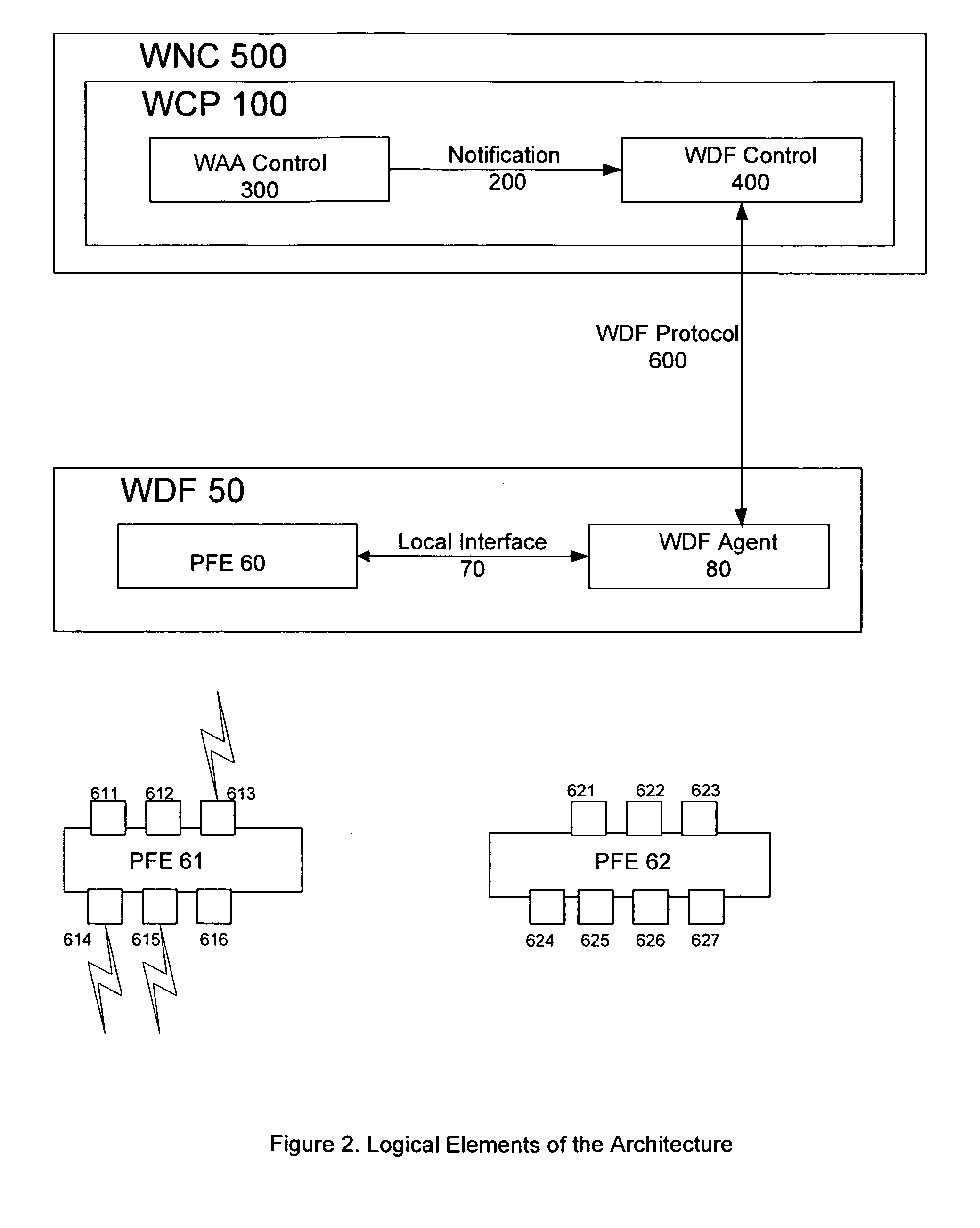
Flexible, scalable, wireless data forwarding and mobility for secure wireless networks
InactiveUS20070064673A1Facilitate message passingFacilitate other communicationData switching by path configurationSecurity arrangementSecure communicationWireless data
Systems and methods are described to allow secure undisrupted communication from wireless clients that roam a wide area network. System architectures and communication protocols are provided to ensure that wireless clients can seamlessly associate and reassociate with controllers on the network, without disruption to ongoing secure communications.
Owner:BHANDARU NEHRU +7
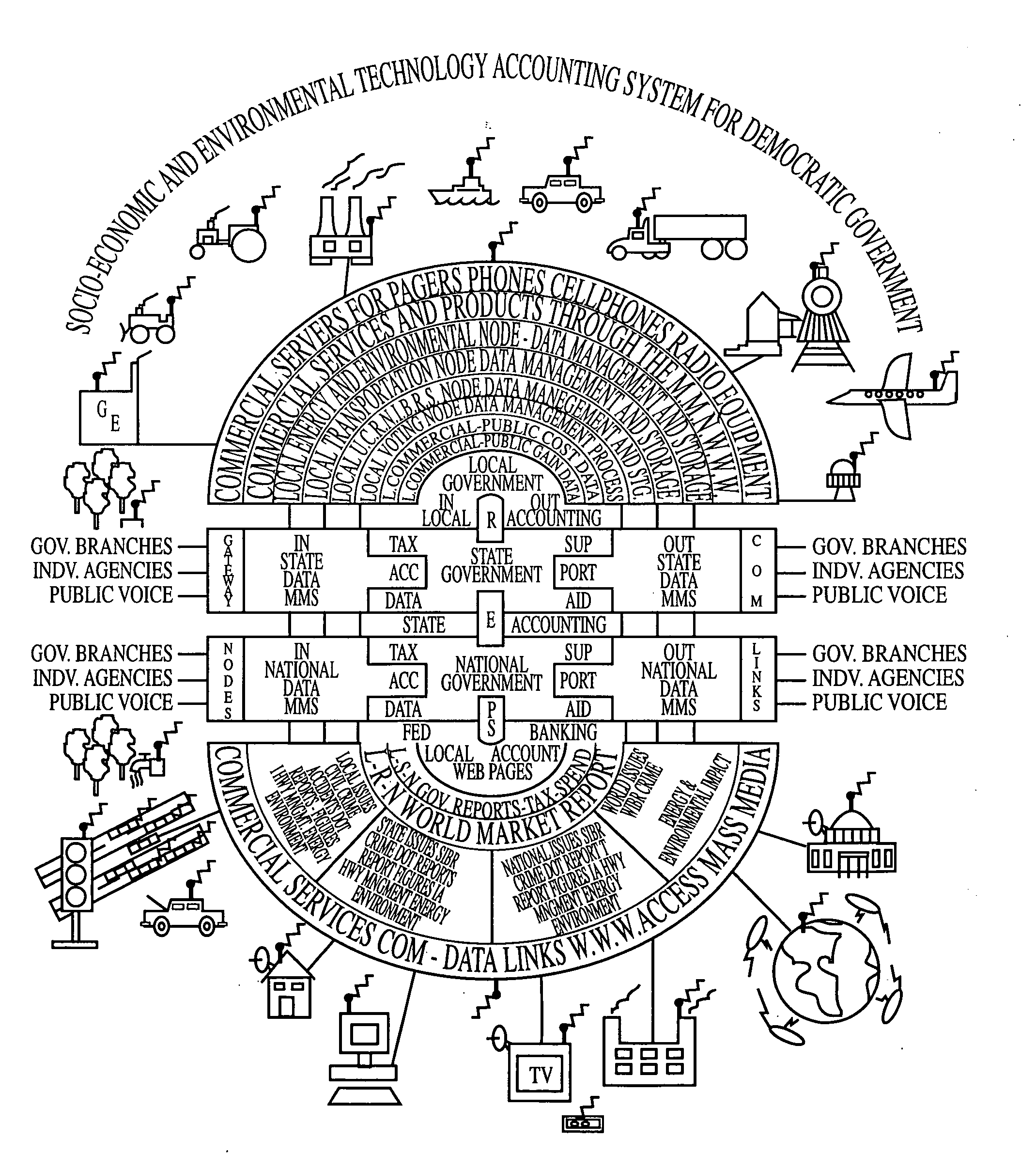
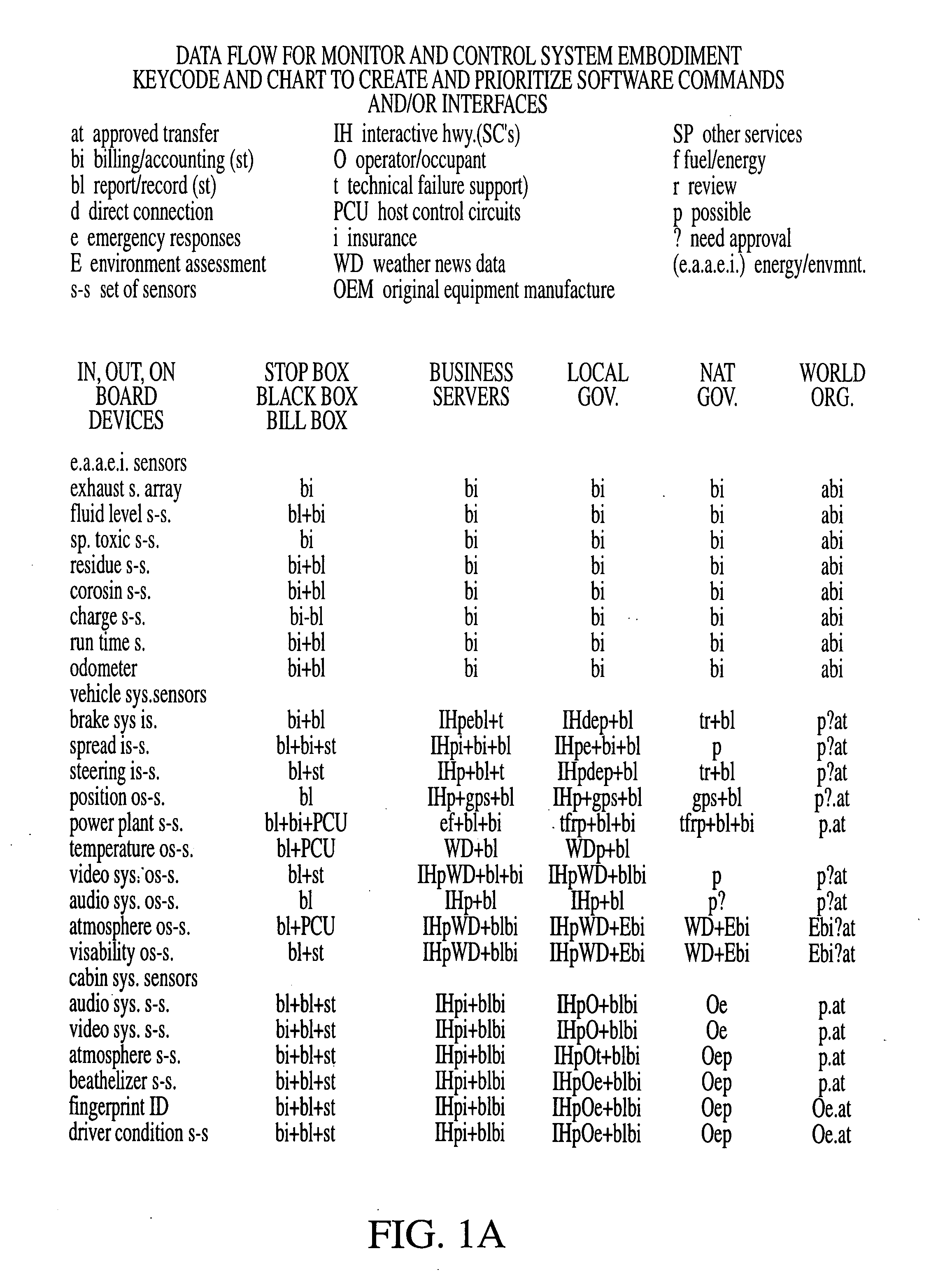
Automated accounting system that values, controls, records and bills the uses of equipment/vehicles for society
InactiveUS20060287783A1Fairly and accurately monitor and control the impact of equipment use on the world's environment andVehicle testingTelemetry/telecontrol selection arrangementsSecure communicationEnvironment effect
This invention addresses environmental social and commercial uses and includes a monitoring system which is a network of on, in, out and off-board devices working together with people through software and interfaces to provide services and make accountable humanity's machines and their actions through safe secure communication. Control devices are used to provide accountability for their socio-economic and environmental impact. Along with these systems networked together, additional devices and variations needed to complete these operations nationally and world wide are also provided. Unique ways interface a network of separate devices or IC circuits to create an interactive secure control system or center that can be remotely controlled. A control device for society to fairly and accurately monitor and control the impact of equipment use on the world environment, and a nation's infrastructure while developing commercial companies to fulfill these needs and services for the equipment and the people who own and operate them for today and into the future are also provided. A set of secure devices and systems are also included to analyze society and machine interaction.
Owner:KLINE & WALKER
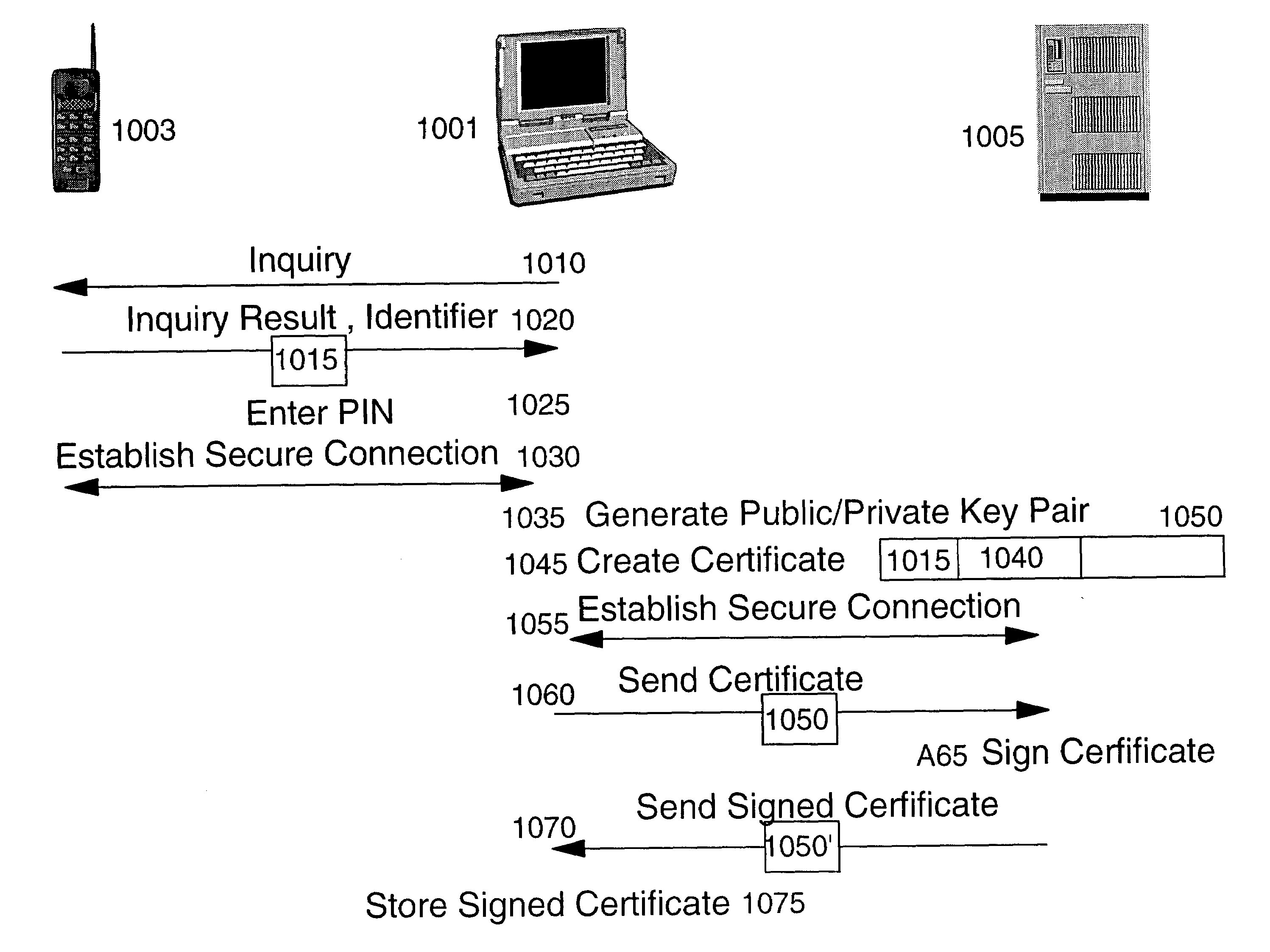
Method and apparatus for efficiently initializing secure communications among wireless devices
InactiveUS6886095B1Efficient administrationEliminating inflexibilityUser identity/authority verificationRadio/inductive link selection arrangementsSecure communicationRadio networks
A method and system for efficiently establishing secure communications between mobile devices in a radio network. The present invention utilizes public key cryptography and unique hardware identifiers to enable authorizations for access to wireless networks, such as picocells. The present invention prevents the mobile user from maintaining a plurality of secrets such as user identifier / password pairs, PINs, or encryption keys, for access to each device to which he might require access.
Owner:IBM CORP
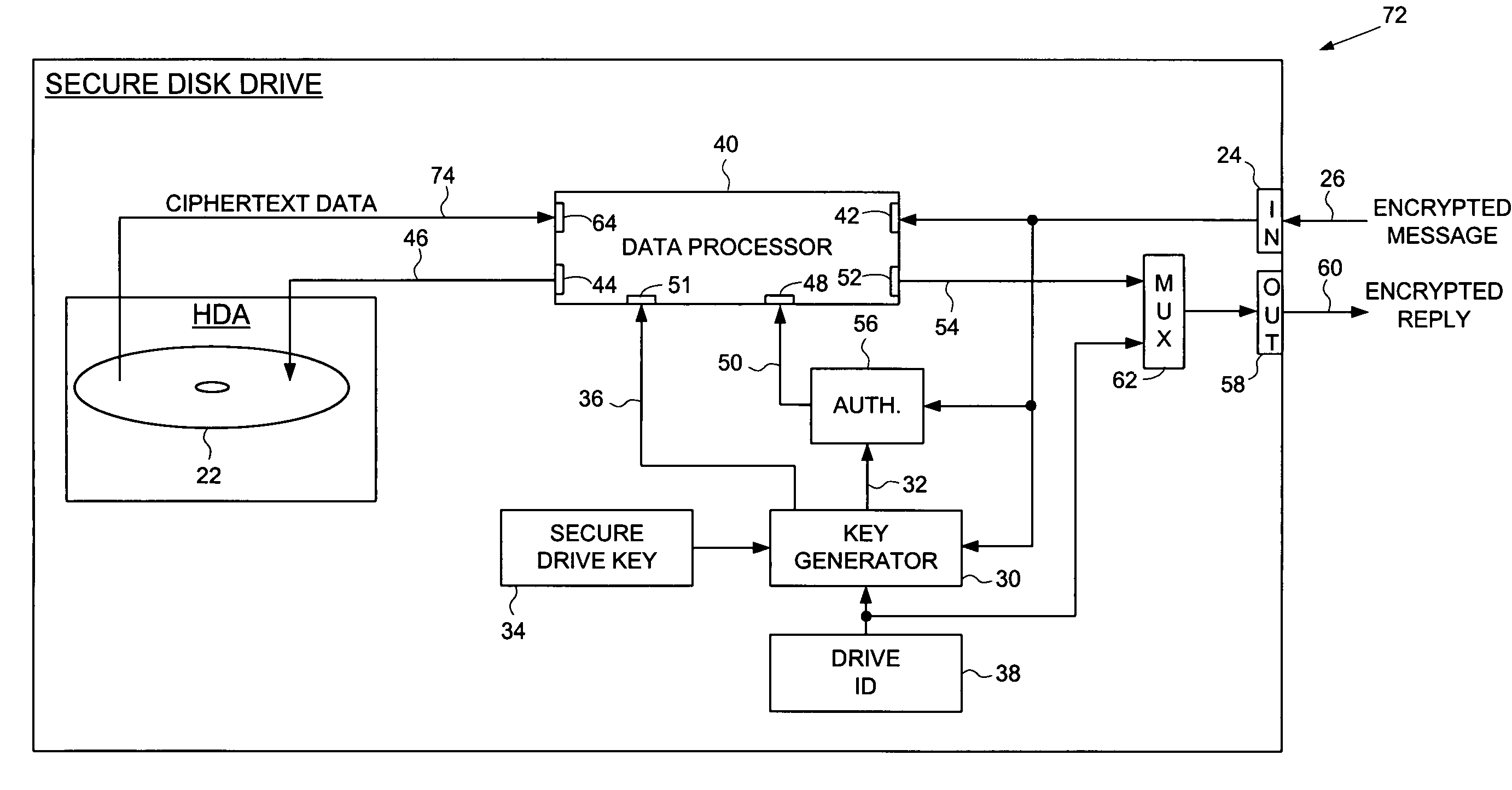
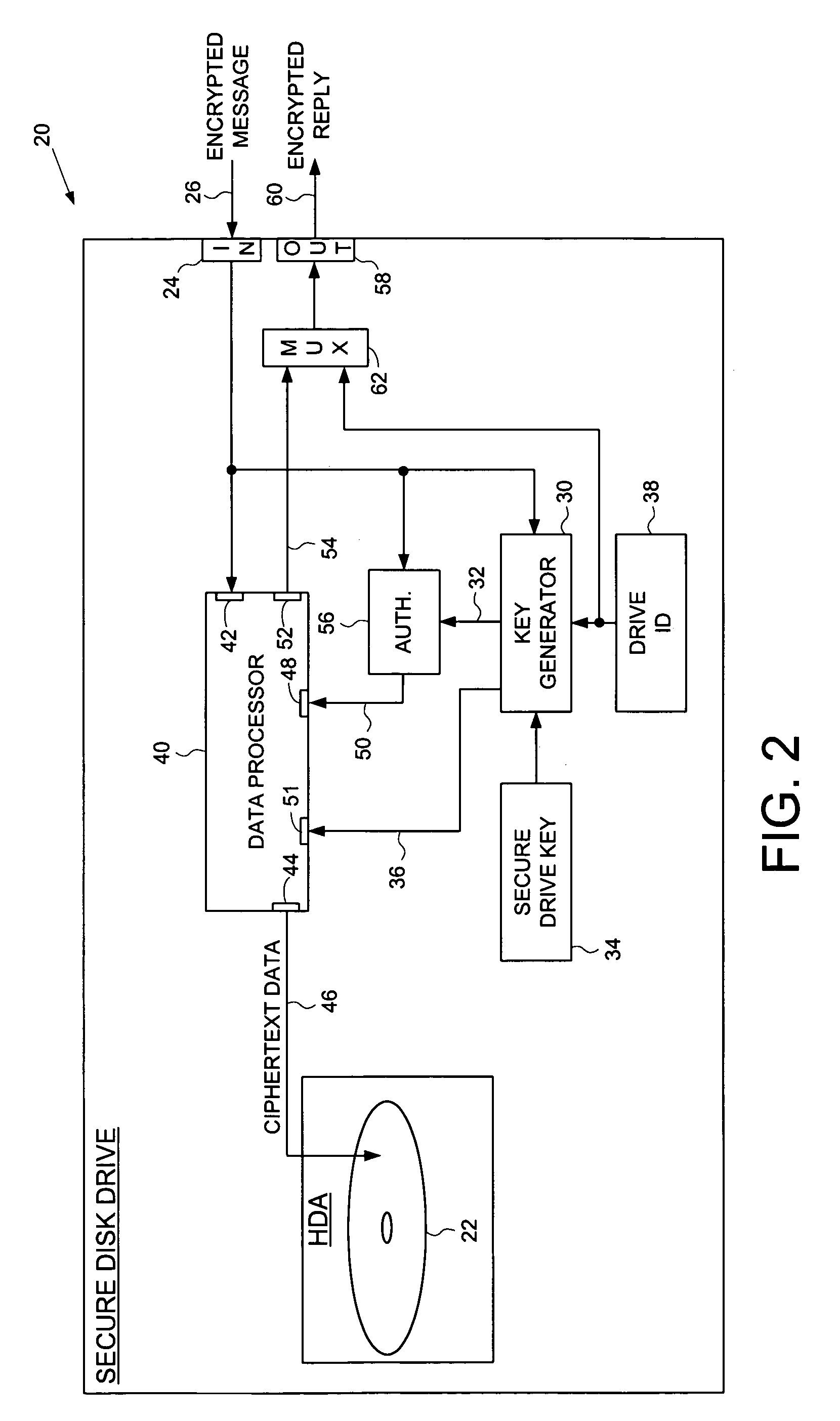
Secure disk drive comprising a secure drive key and a drive ID for implementing secure communication over a public network
InactiveUS7215771B1Volume/mass flow measurementUser identity/authority verificationSecure communicationCiphertext
A secure disk drive is disclosed comprising a disk for storing data, and an input for receiving an encrypted message from a client disk drive, the encrypted message comprising ciphertext data and a client drive ID identifying the client disk drive. The secure disk drive comprises a secure drive key and an internal drive ID. A key generator within the secure disk drive generates a client drive key based on the client drive ID and the secure drive key, and an internal drive key based on the internal drive ID and the secure drive key. The secure disk drive further comprises an authenticator for verifying the authenticity of the encrypted message and generating an enable signal, the authenticator is responsive to the encrypted message and the client drive key. The secure disk drive further comprises a data processor comprising a message input for receiving the encrypted message from the client disk drive, and a data output for outputting the ciphertext data to be written to the disk. The data processor further comprises an enable input for receiving the enable signal for enabling the data processor, and a key input for receiving the internal drive key, the internal drive key for use in generating a message authentication code. The data processor outputs reply data comprising the message authentication code. The secure disk drive outputs a reply to the client disk drive, the reply comprising the reply data and the internal drive ID.
Owner:WESTERN DIGITAL TECH INC
Secure sockets layer proxy architecture
ActiveUS20030014628A1Low hardware requirementsLower latencyError detection/correctionMultiple digital computer combinationsSecure communicationChannel coupling
A method for secure communications between a client and one of a plurality of servers performed on an intermediary device coupled to the client and said plurality of servers. In one aspect, the method comprises: establishing an open communications session between the intermediary device and the client via an open network; negotiating a secure communications session with the client; establishing an open communications session with said one of said plurality of servers via a secure network; receiving encrypted data from the client via the secure communications session; decrypting encrypted application data; forwarding decrypted application data to the server via the secure network; receiving application data from the server via the secure network; encrypting the application data; and sending encrypted application data to the client. In a further aspect, an apparatus including a network interface communicating with the public network and the secure network at least one processor, programmable dynamic memory addressable by the processor, and a communications channel coupling the processor, memory and the network communications interface is provided. The apparatus further includes a proxy TCP communications engine, a proxy SSL communications engine, a server TCP communications engine; and a packet data encryption and decryption engine.
Owner:NEXSI SYST
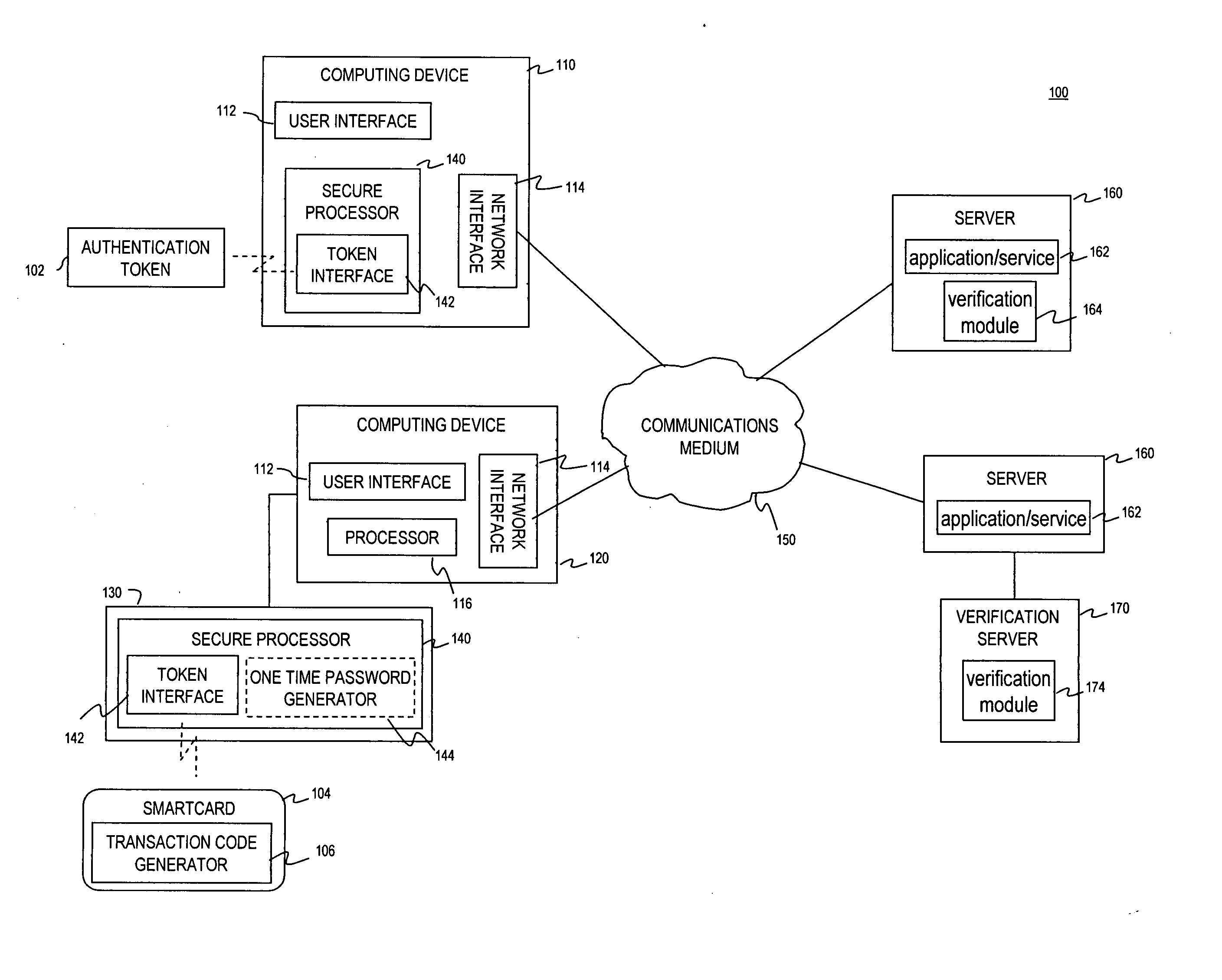
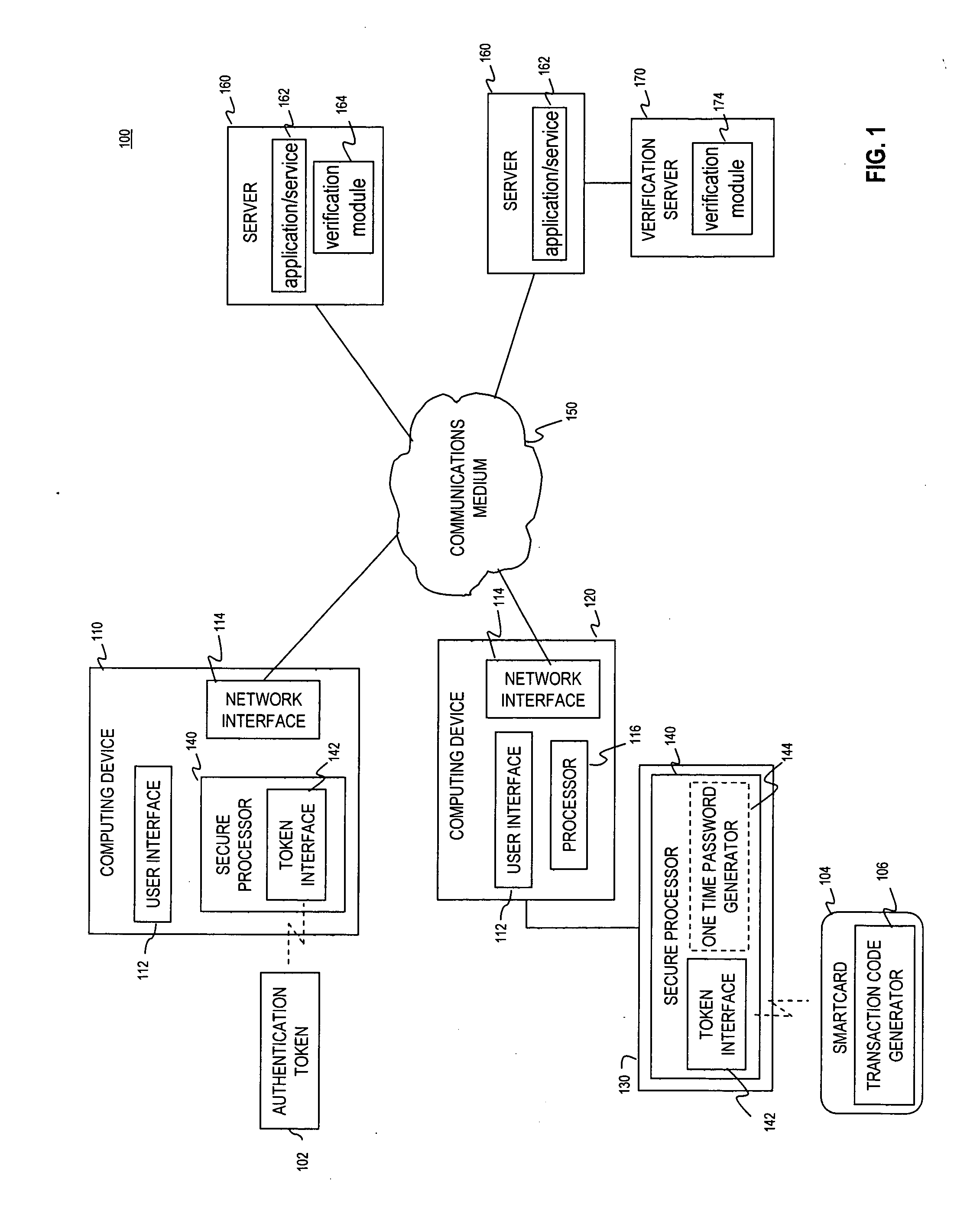
Multi-factor authentication using a smartcard
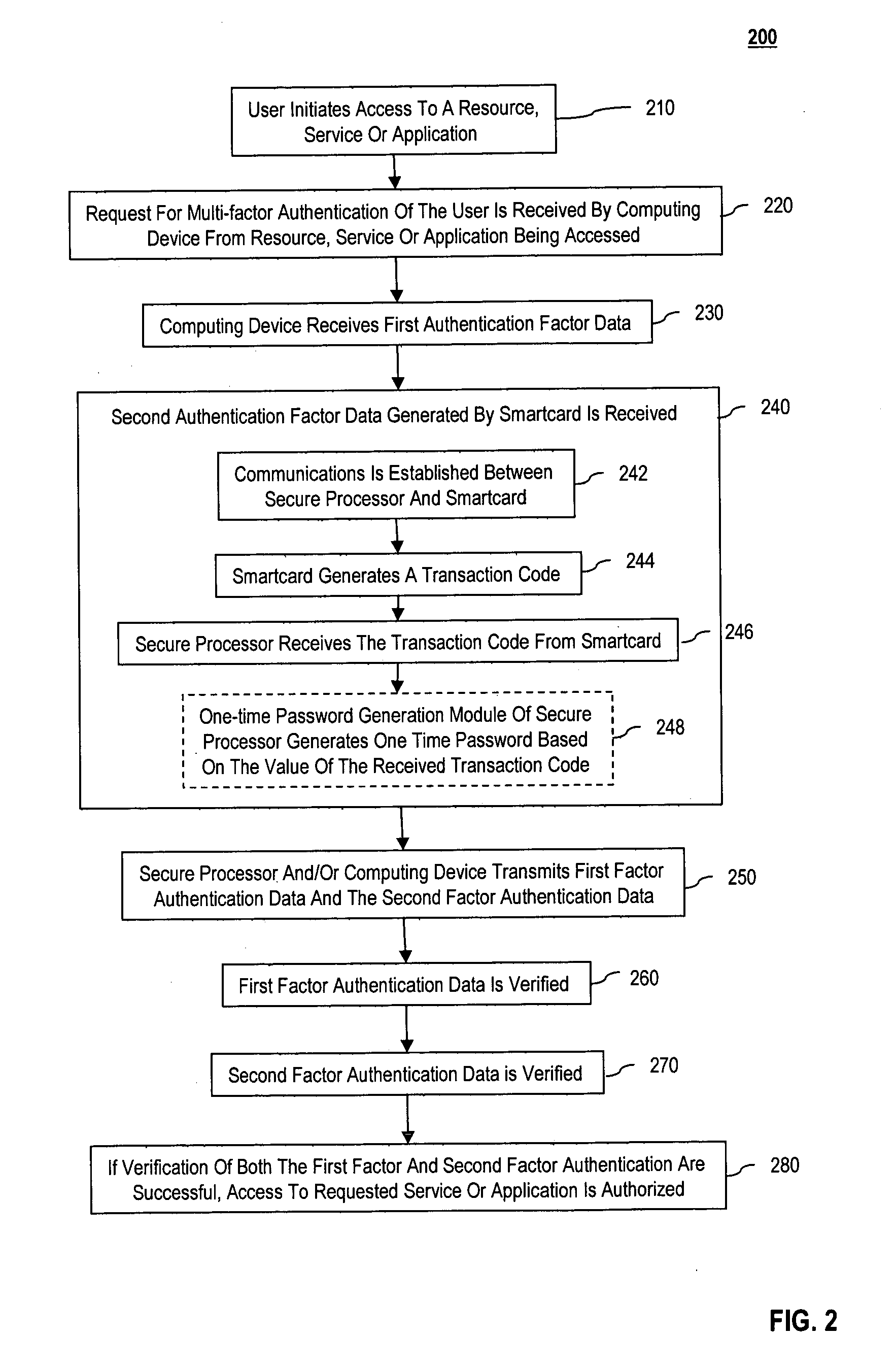
ActiveUS20070118745A1Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
Methods and systems are provided for non-cryptographic capabilities of a token such as a smartcard to be used as an additional authentication factor when multi-factor authentication is required. Smartcards are configured to generate a transaction code each time a transaction is attempted by the smartcard. The transaction code is dynamic, changing with each transaction, and therefore is used as a one-time password. When a user attempts to access a service or application requiring at least two authentication factors, a secure processor is used to read transaction code from the smartcard. The secure processor establishes a secure communication with the remote computer hosting the service or application. The transaction code can then be encrypted prior to transmission over the public Internet, providing an additional layer of security.
Owner:AVAGO TECH INT SALES PTE LTD
Method for mapping at least two authentication devices to a user account using an authentication server
ActiveUS20180198614A1Improve securityReduce security risksSynchronising transmission/receiving encryption devicesUser identity/authority verificationSecure communicationAuthentication server
The invention provides a method for mapping at least two authentication devices to a user account using an authentication server, where each authentication device connects to the authentication server using a secured communication channel; their mapping to the user account is recorded on the authentication server, and, when a transfer of data between the authentication devices mapped to the user account occurs, the data is passed over from the first authentication device to the authentication server using a secured communication channel and from the authentication server to another authentication device mapped to the account of said user using a secured communication channel, where the aforesaid secured communication channel is created by the second authentication device. This procedure allows the use of a single personal local authentication factor for multiple authentication devices and increases the security of authentication of devices with authentication servers.
Owner:ADUCID
Method and apparatus for providing secure wireless communication
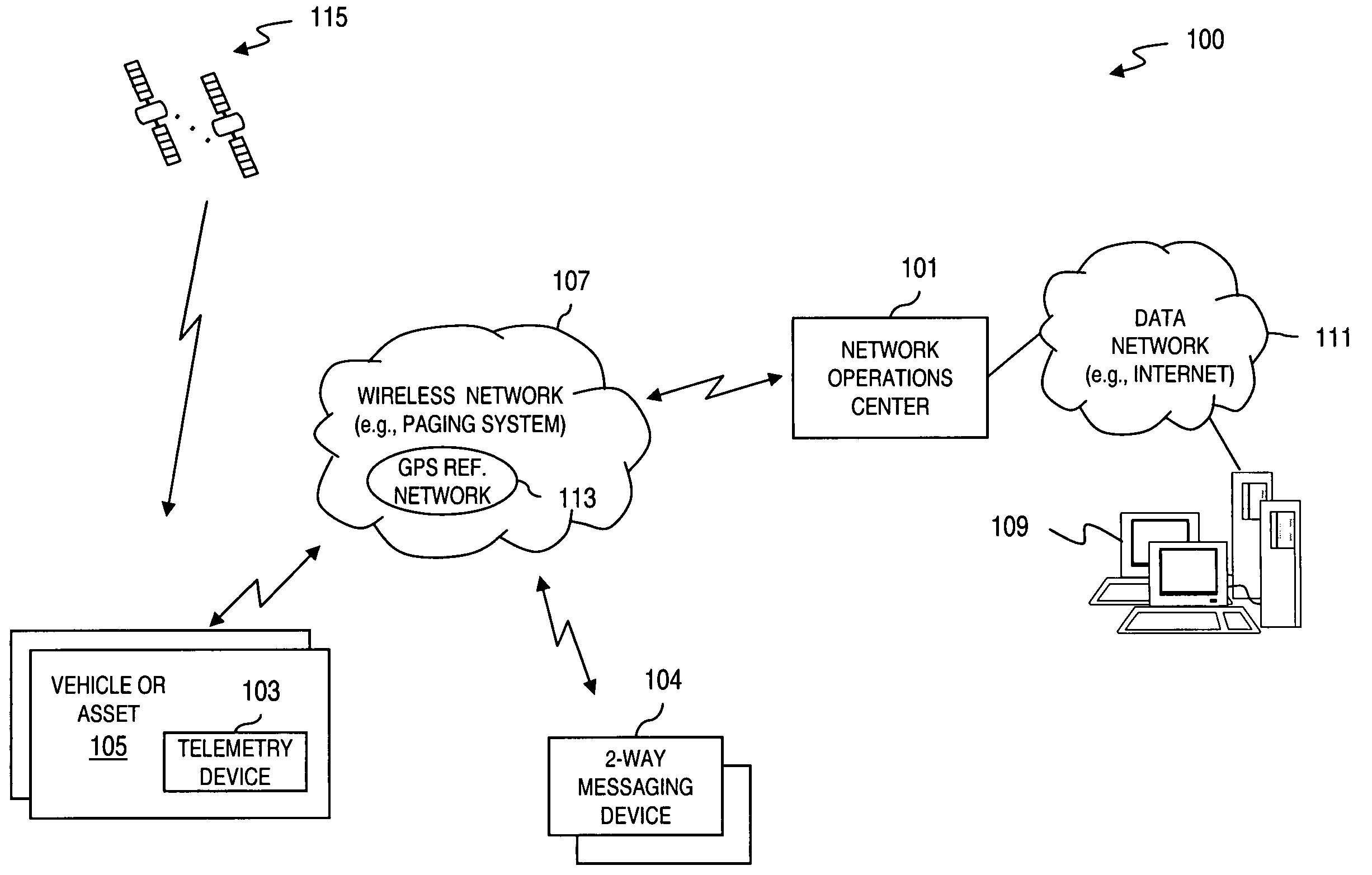
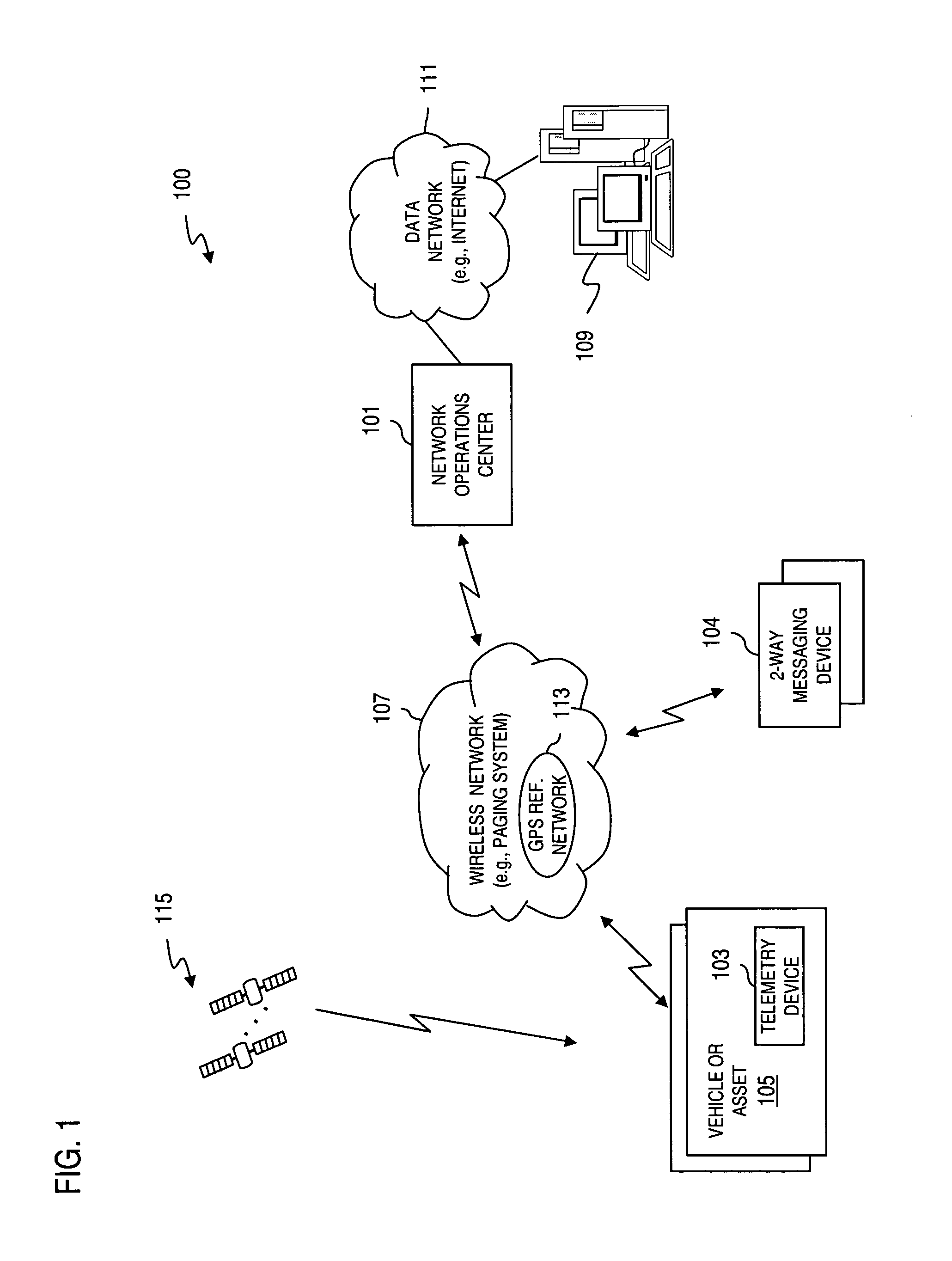
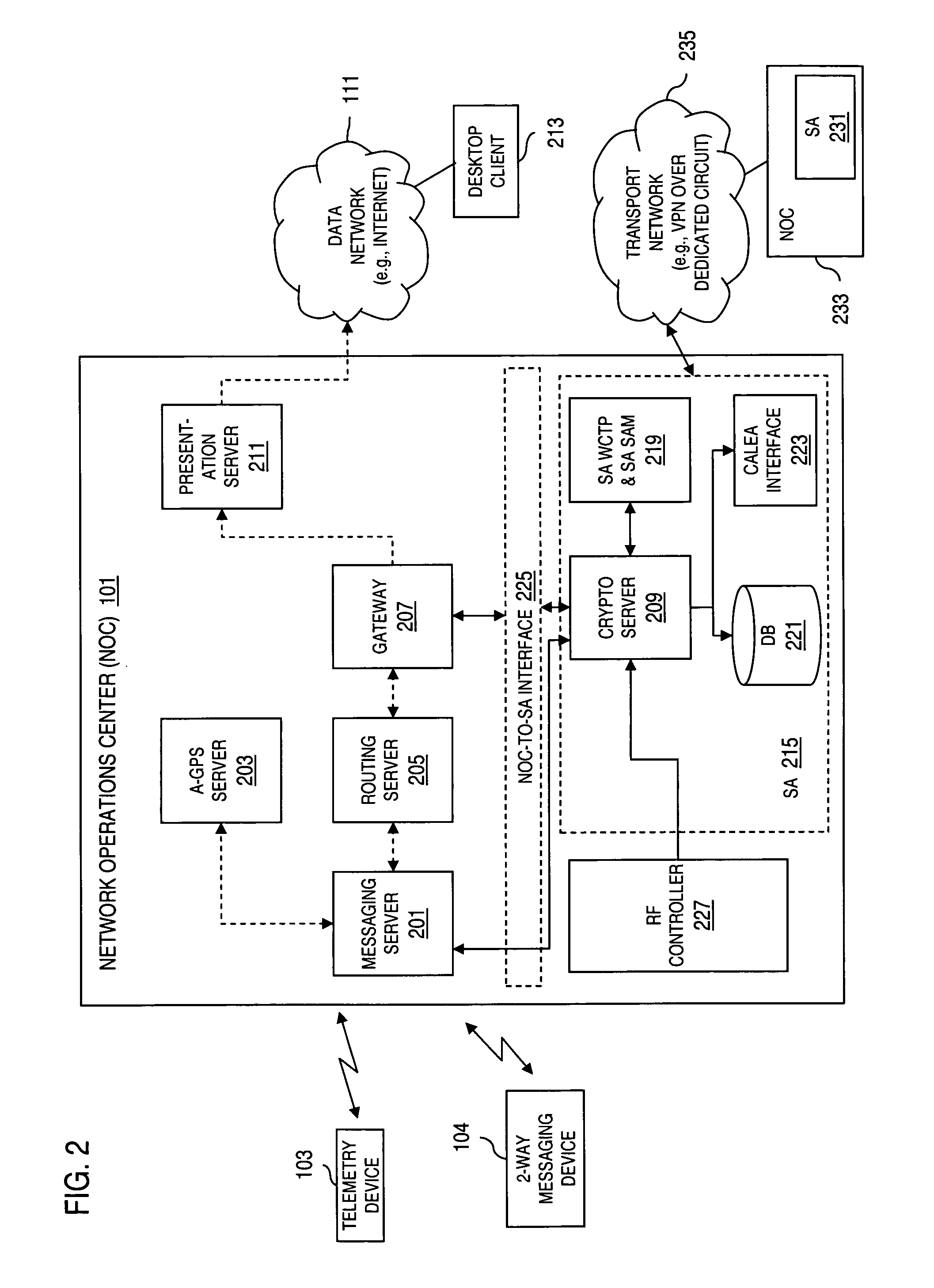
InactiveUS7496347B2Key distribution for secure communicationUnauthorised/fraudulent call preventionSecure communicationComputer network
An approach is provided for securely communicating in a wireless network. A cryptographic server generates a command to enable a secure mode of operation for a wireless device, wherein the wireless device can operate in a secure mode and an unsecure mode in support of two-way messaging. The cryptographic server sends the command to the wireless device to activate the secure mode of operation. The secure mode of operation provides transmission of an encrypted message by the wireless device over the wireless network.
Owner:VELOCITA WIRELESS
Method and apparatus for efficiently initializing mobile wireless devices
InactiveUS6980660B1Efficient administrationEliminating inflexibilityKey distribution for secure communicationDigital data processing detailsSecure communicationUnique identifier
A method and system for enabling wireless devices distributed throughout an enterprise to be efficiently initialized for secure communications. The method and system utilize well known public key cryptography and machine unique identifiers to establish a secure channel and initialize the wireless devices.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com