Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
54 results about "Secure multicast" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
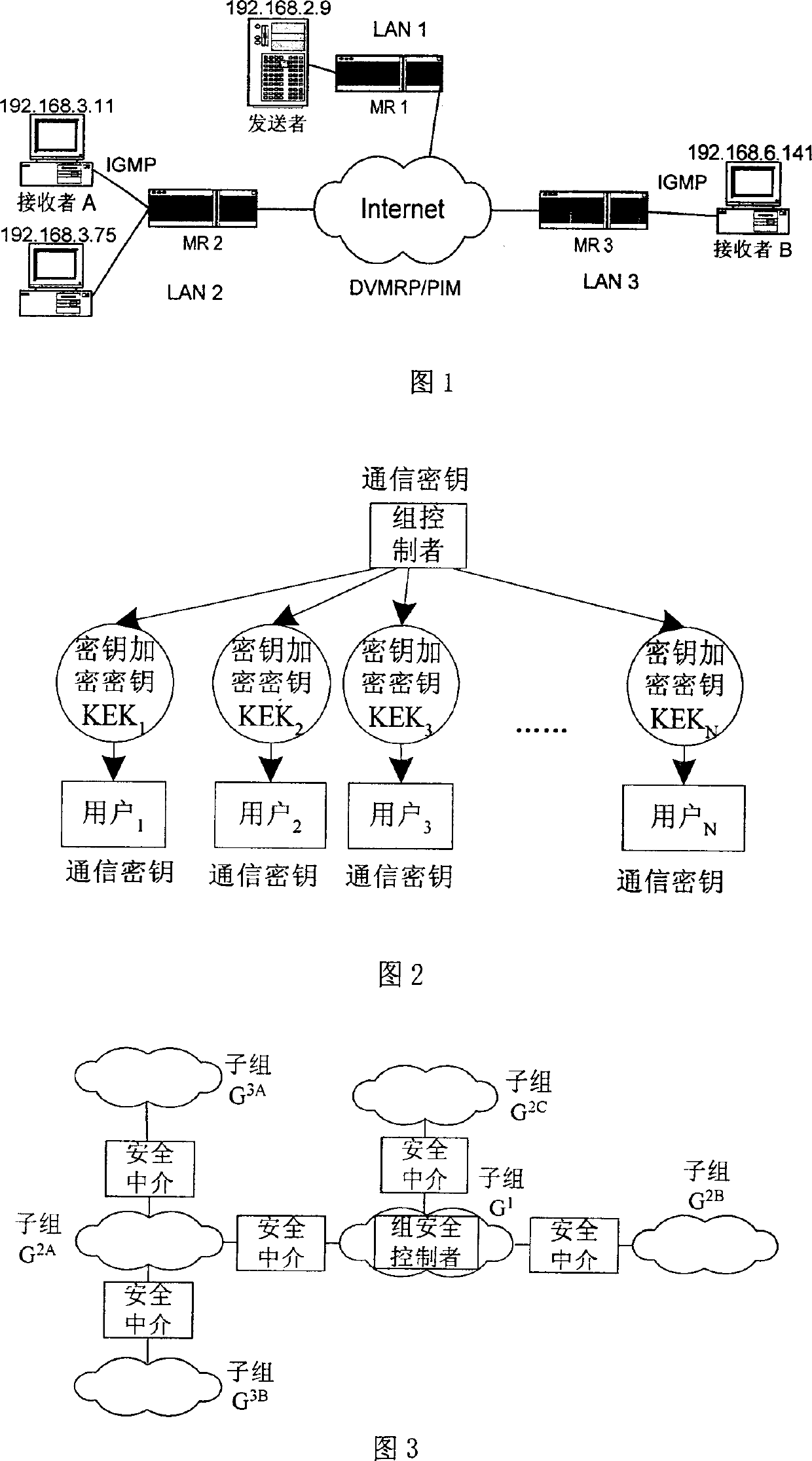
IP Multicast is an internet communication method where a single data packet can be transmitted from a sender and replicated to a set of receivers. The replication techniques are somewhat dependent upon the media used to transmit the data. Transmission of multicast on an inherent broadcast media such as Ethernet or a satellite link automatically allows the data packet to be received by all the receivers directly attached to the media. In contrast, transmission of multicast on media that is point-to-point or point-to-multipoint requires the packet to be replicated for each link. The replication process should occur in an optimal manner where a distribution tree is built within the network. The packet can be replicated at each of the branches in the tree. This mitigates the requirement for the sender to replicate the packet once for each recipient. The use of IPsec as a communication link requires a point-to-point connection establishment. Usually, the security is required from sender to receiver which implies the sender must replicate the packet on each of the secure connections - one for each receiver.
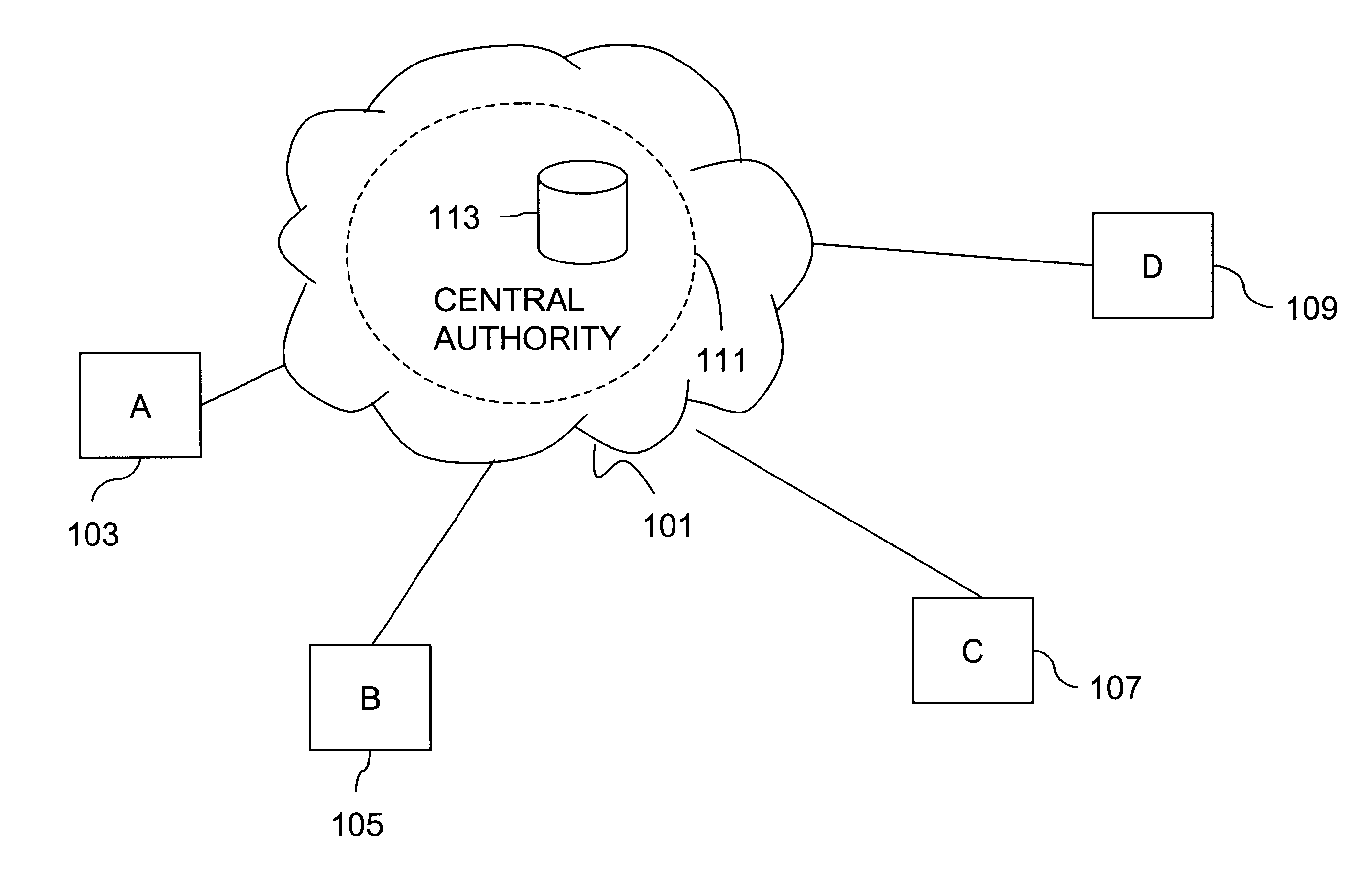
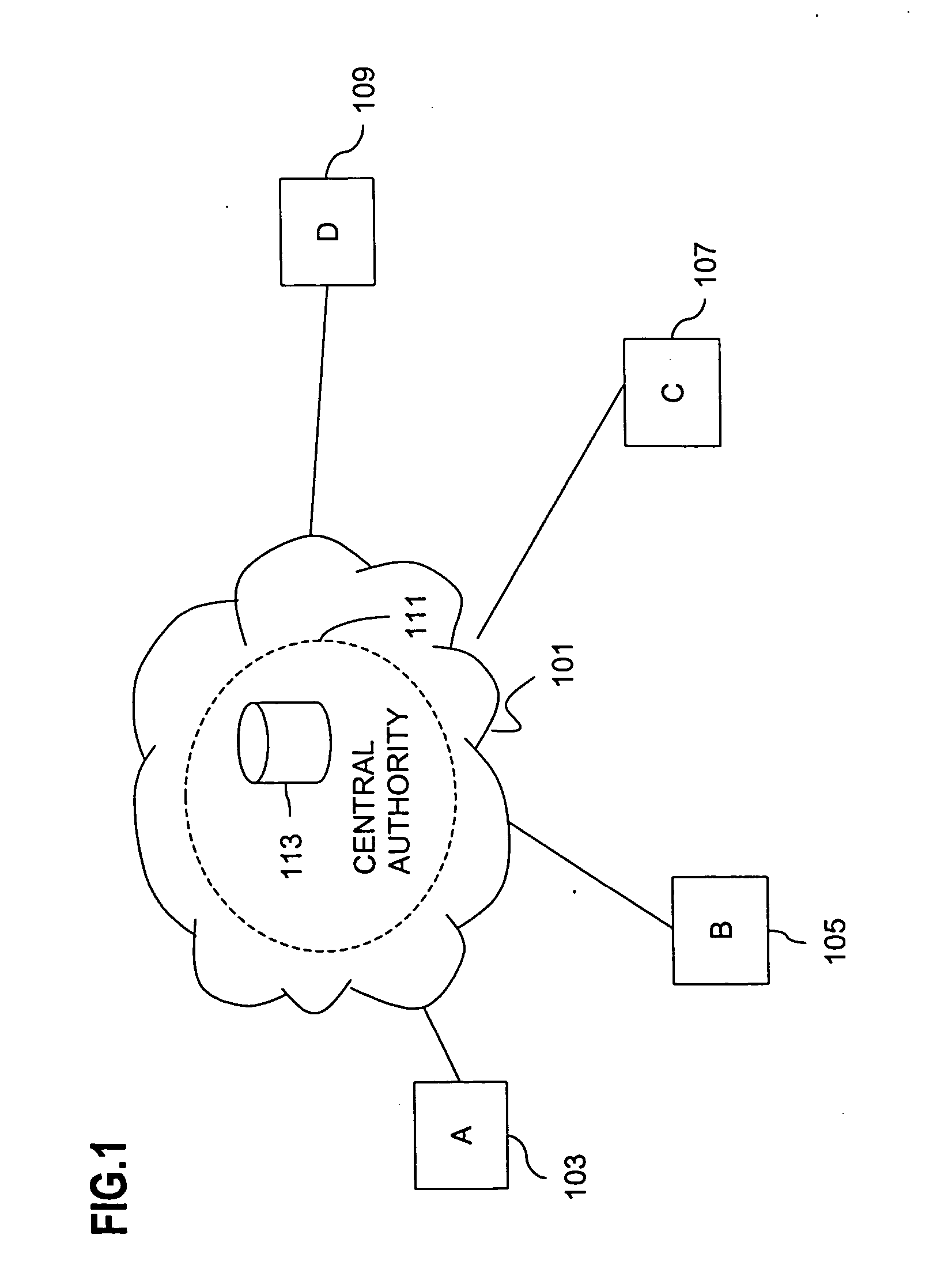
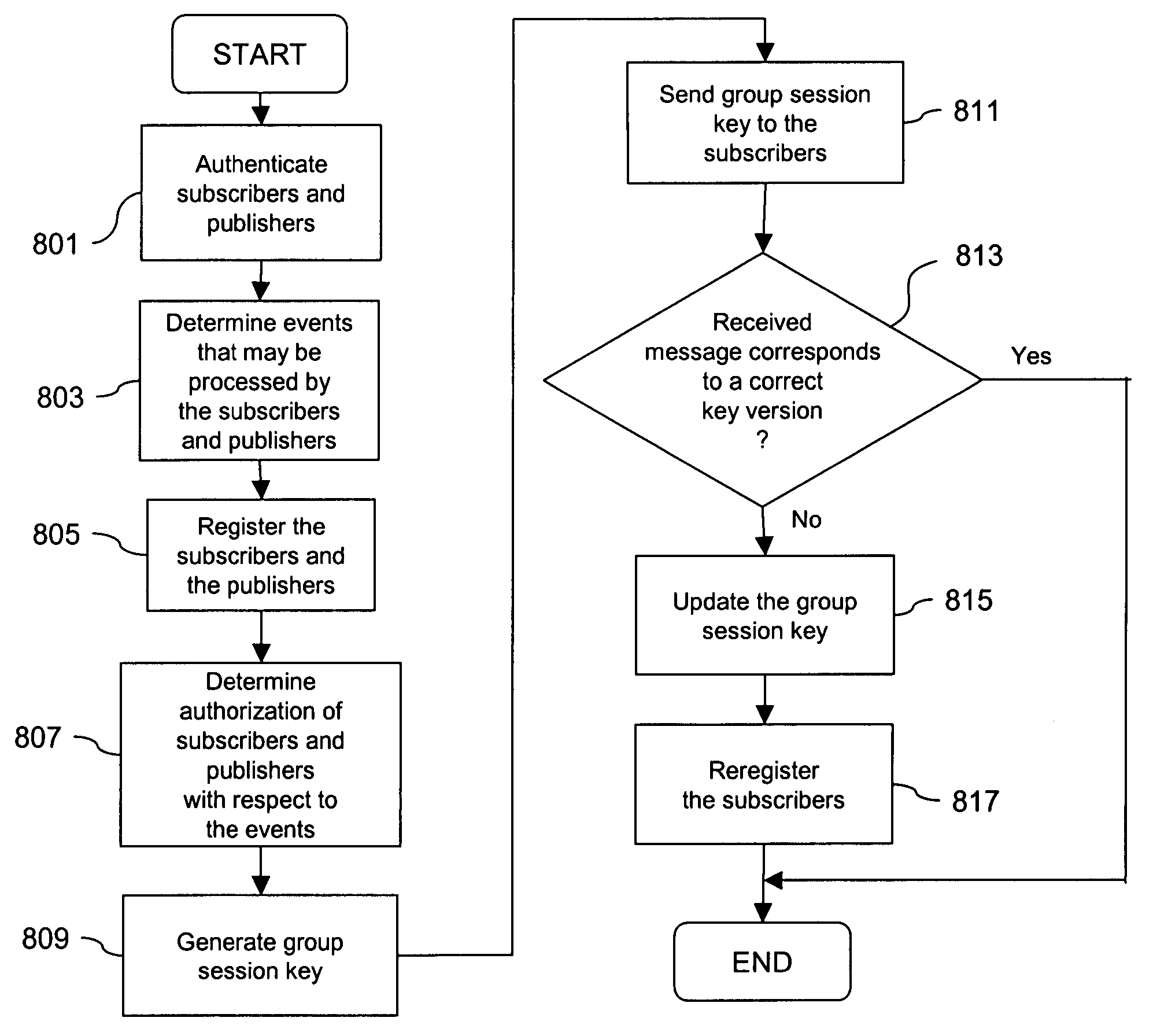
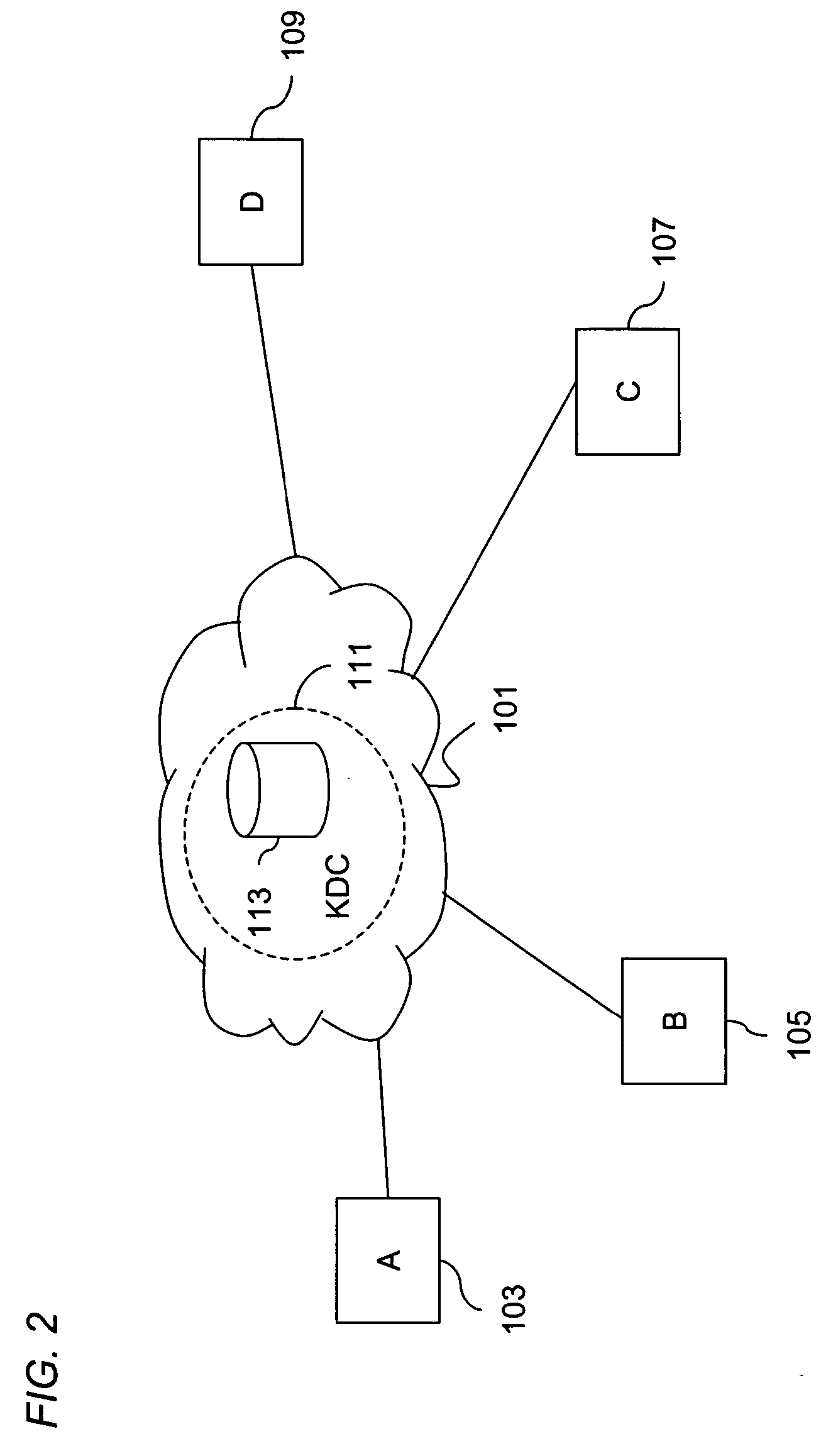
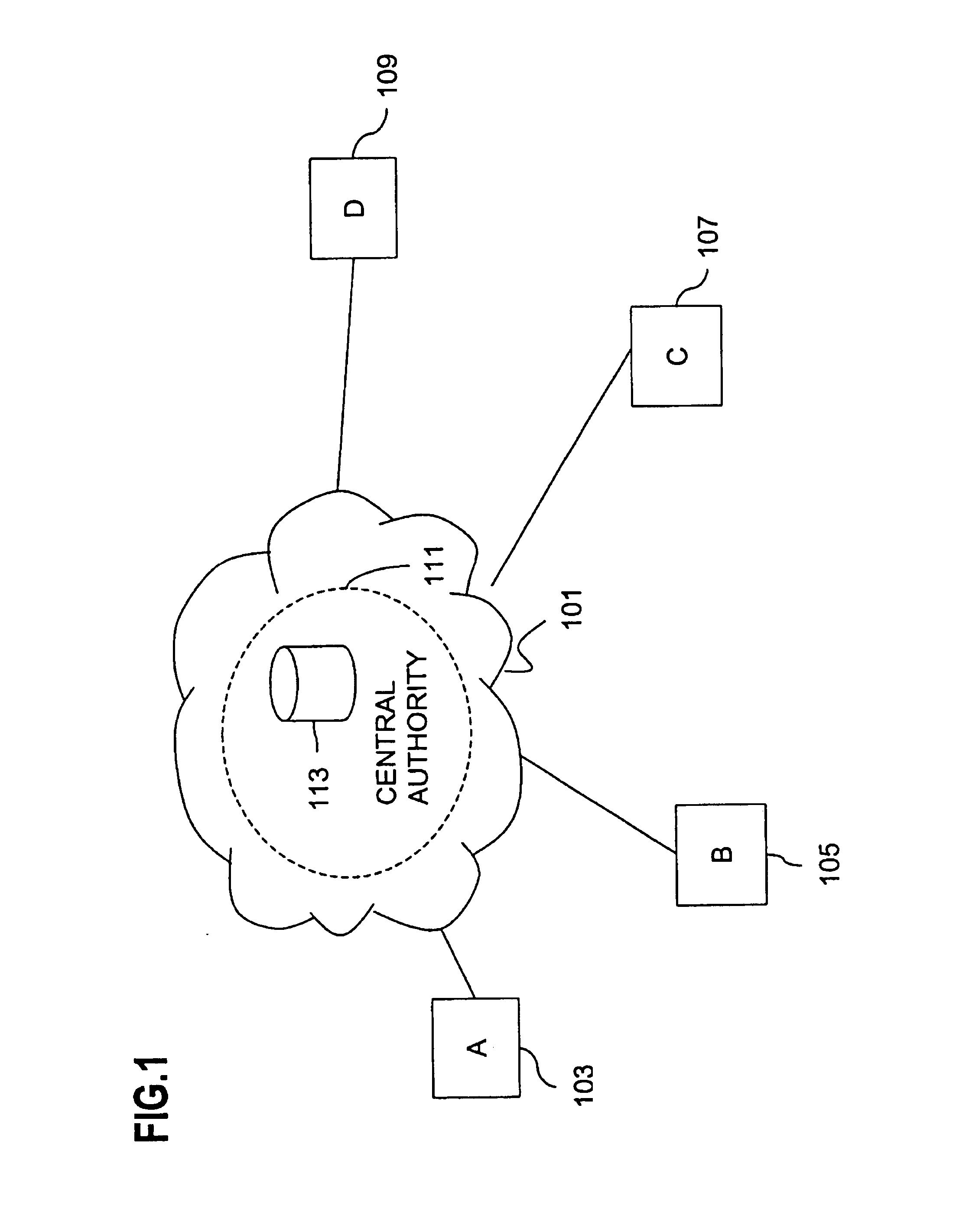
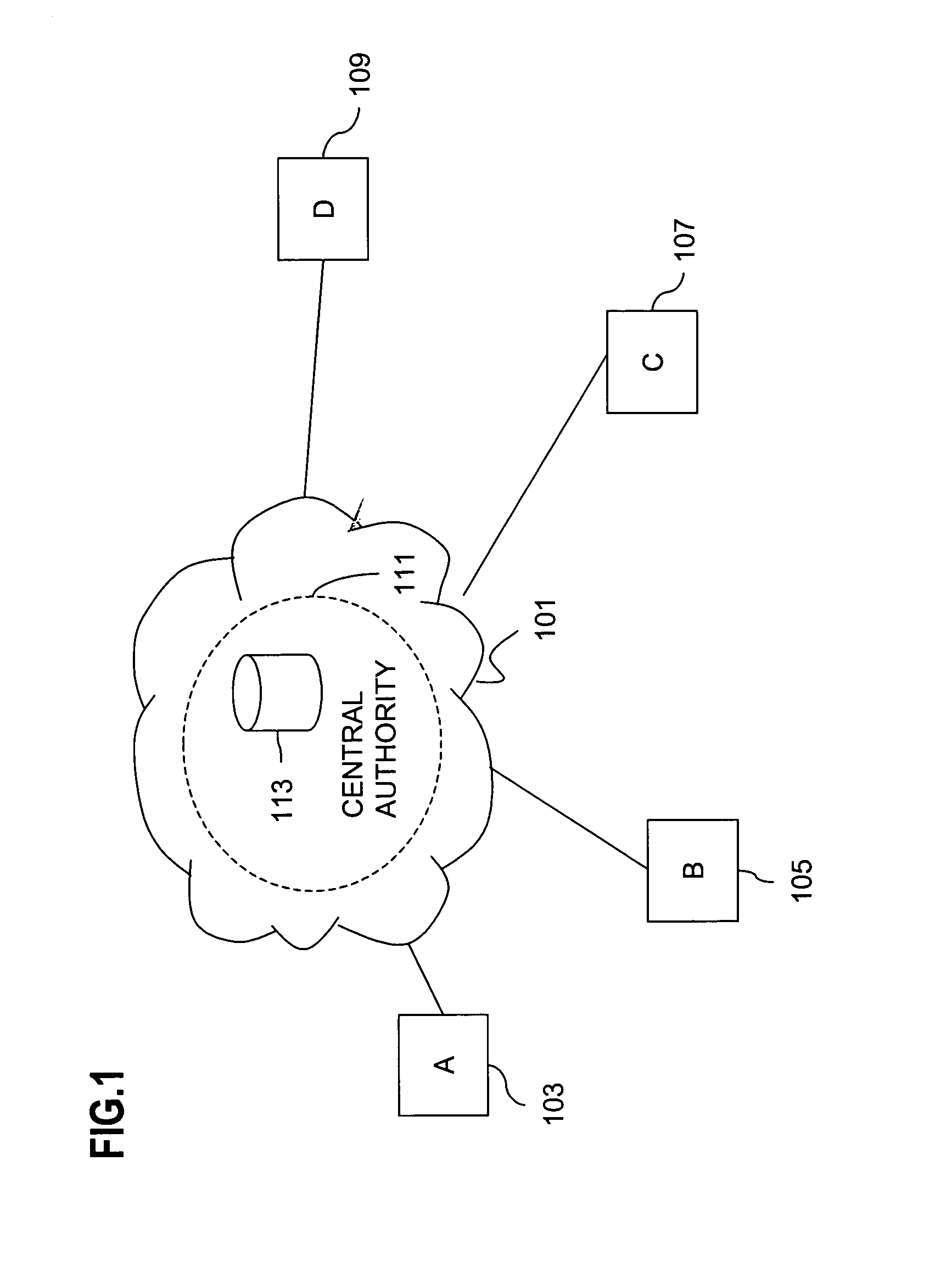
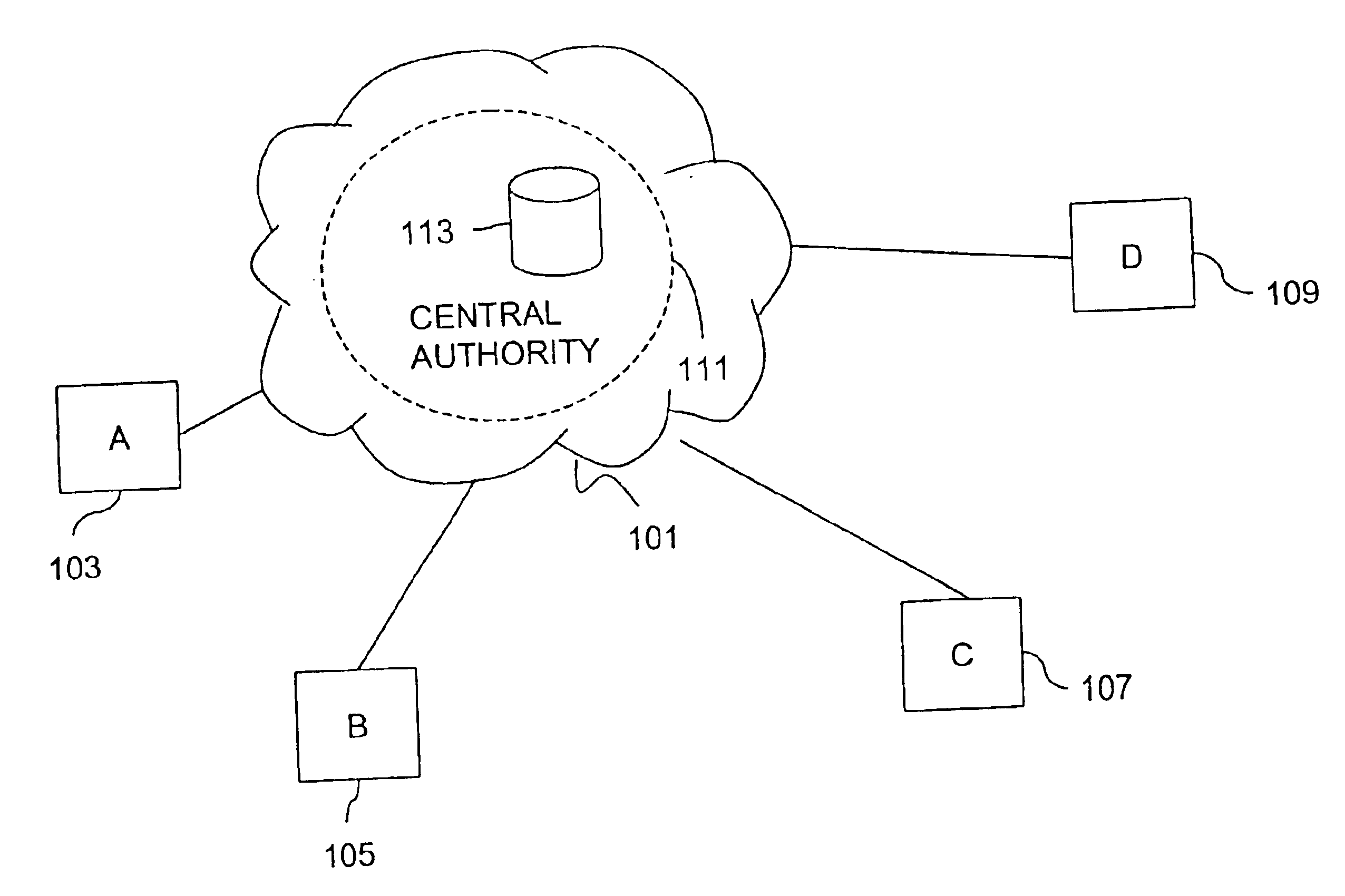
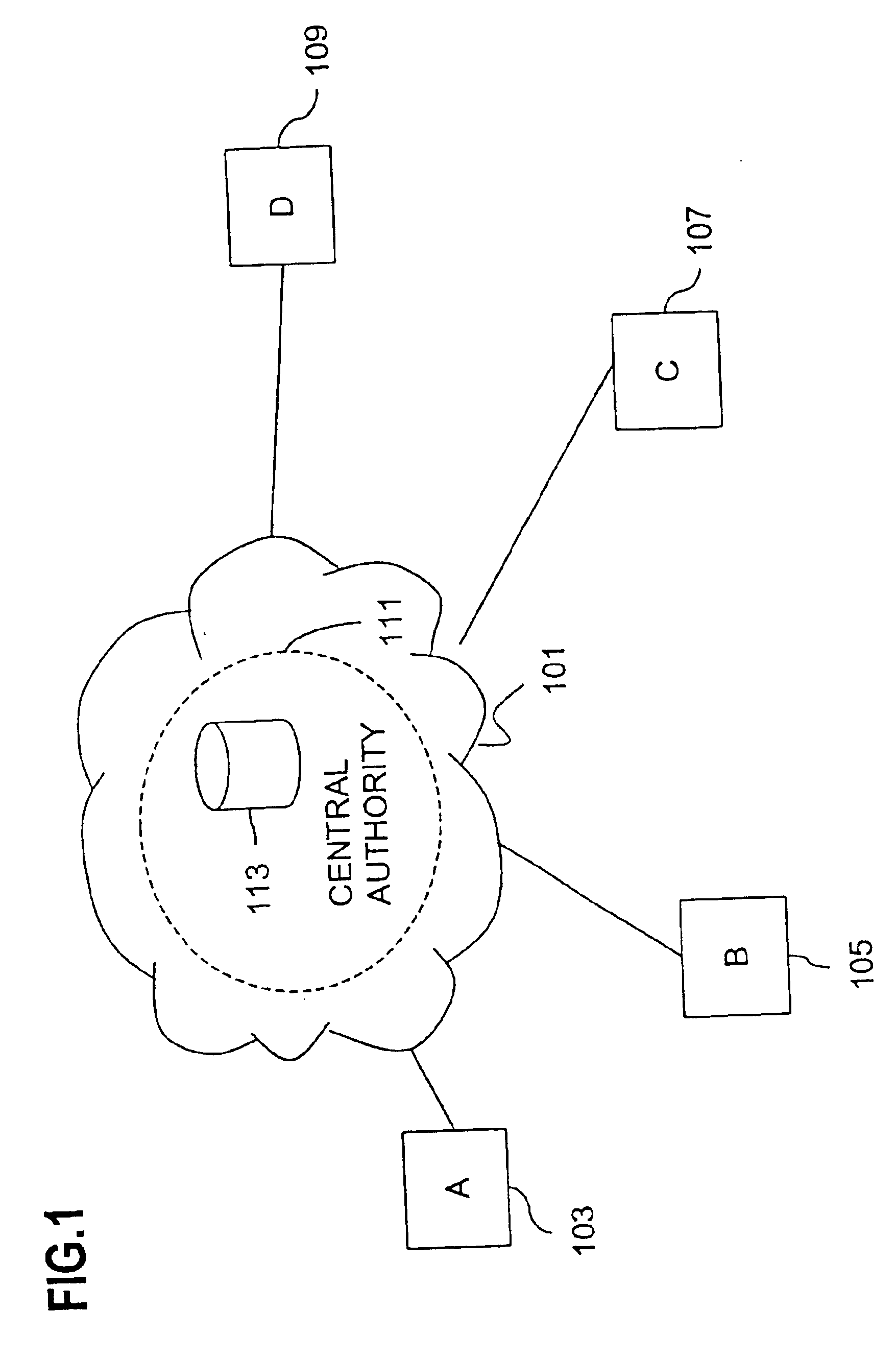
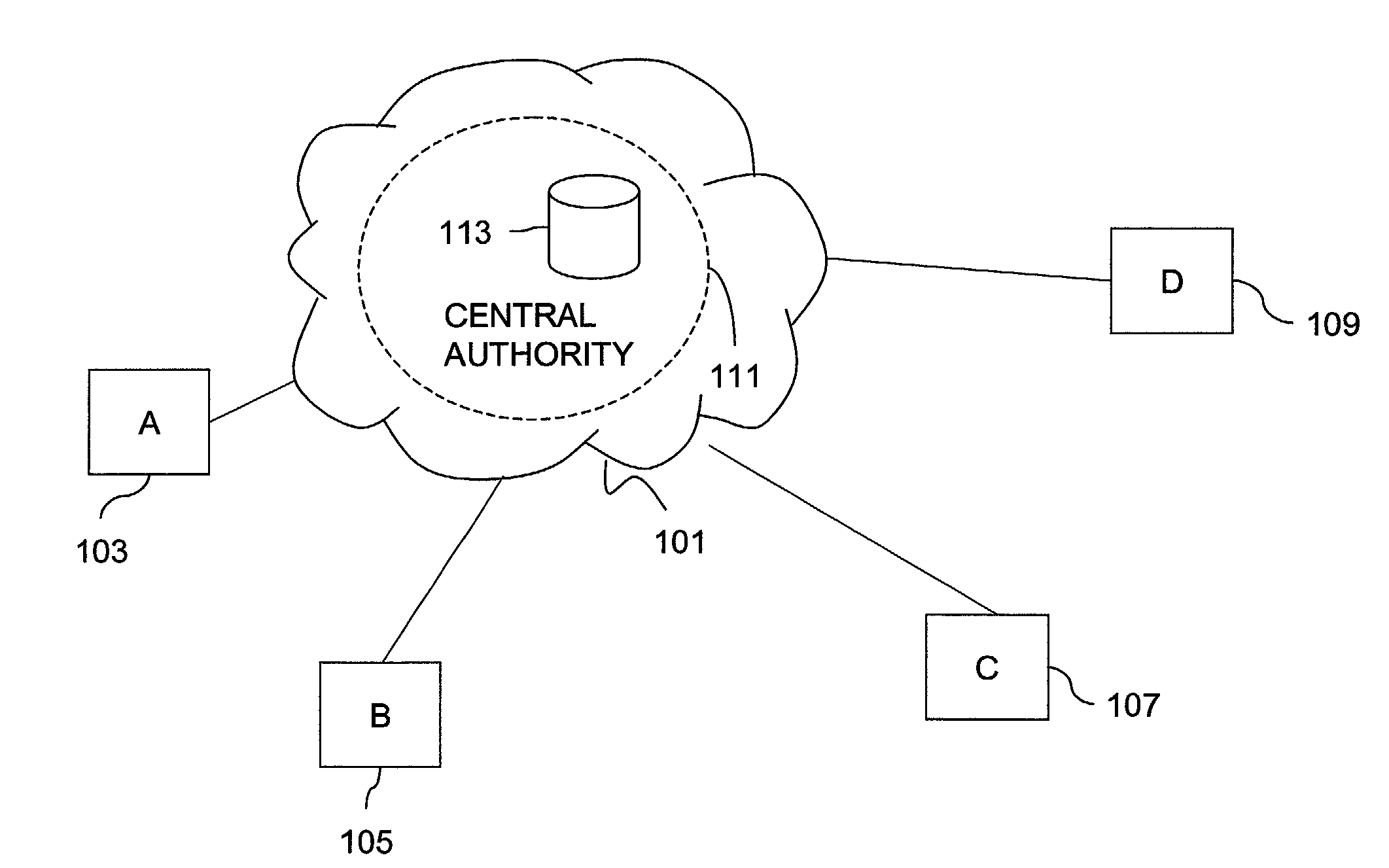
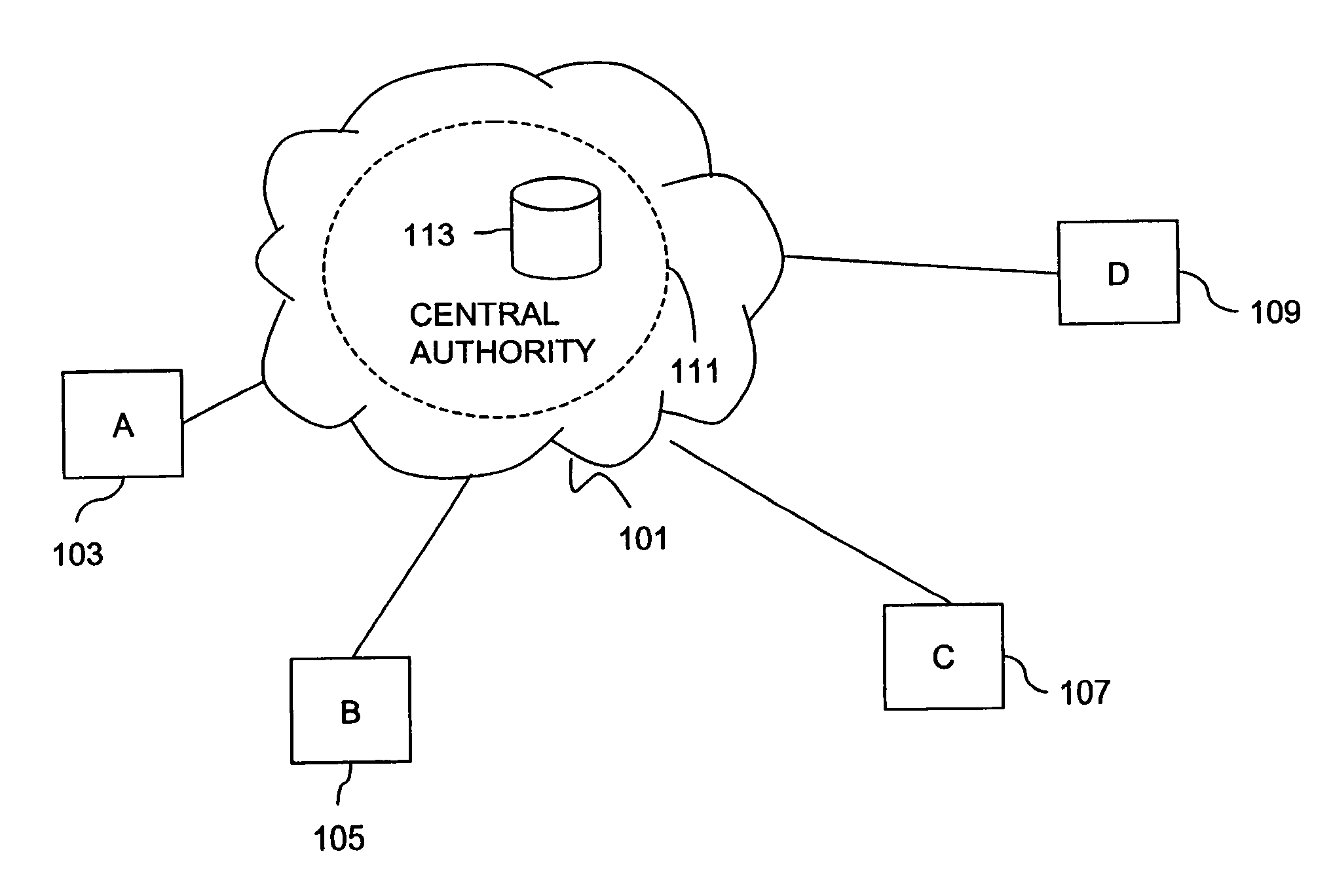
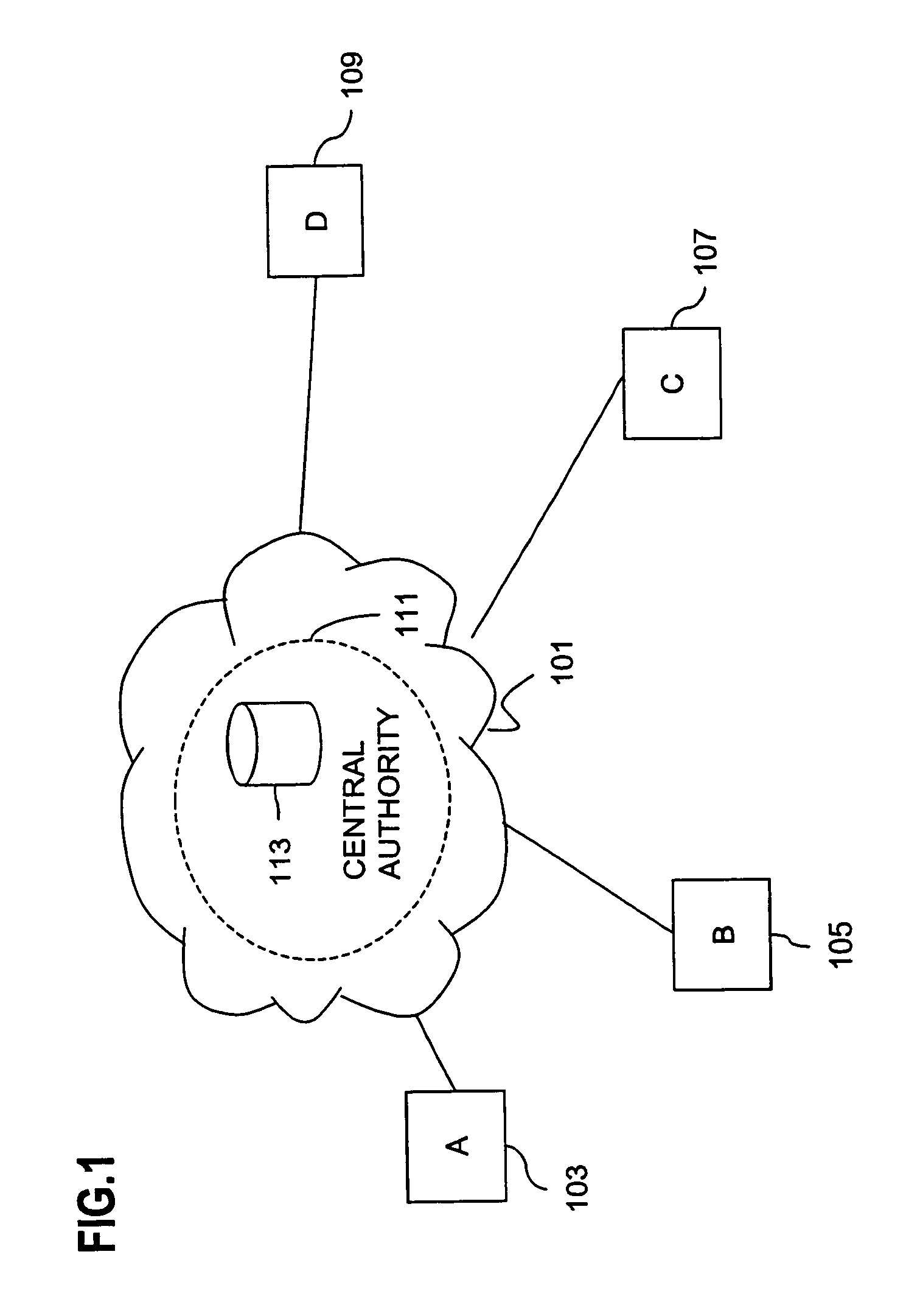
Method and apparatus for creating a secure communication channel among multiple event service nodes
InactiveUS7013389B1Easy to scaleUser identity/authority verificationSecure communicationGroup session
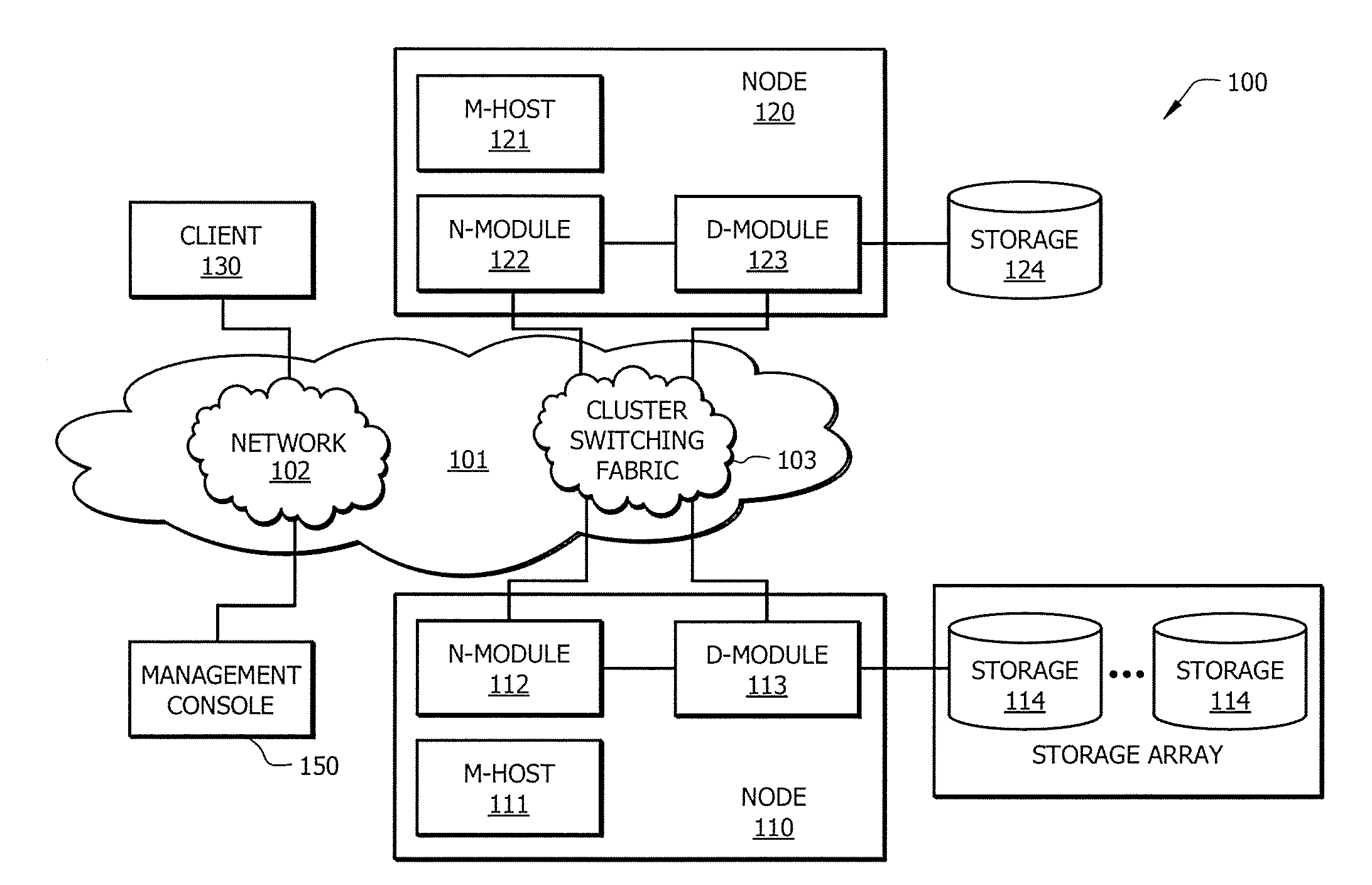
An approach for establishing secure multicast communication among multiple event service nodes is disclosed. The event service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the event service nodes include the group session key and the private keys of the event service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the event service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can readily be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Event service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
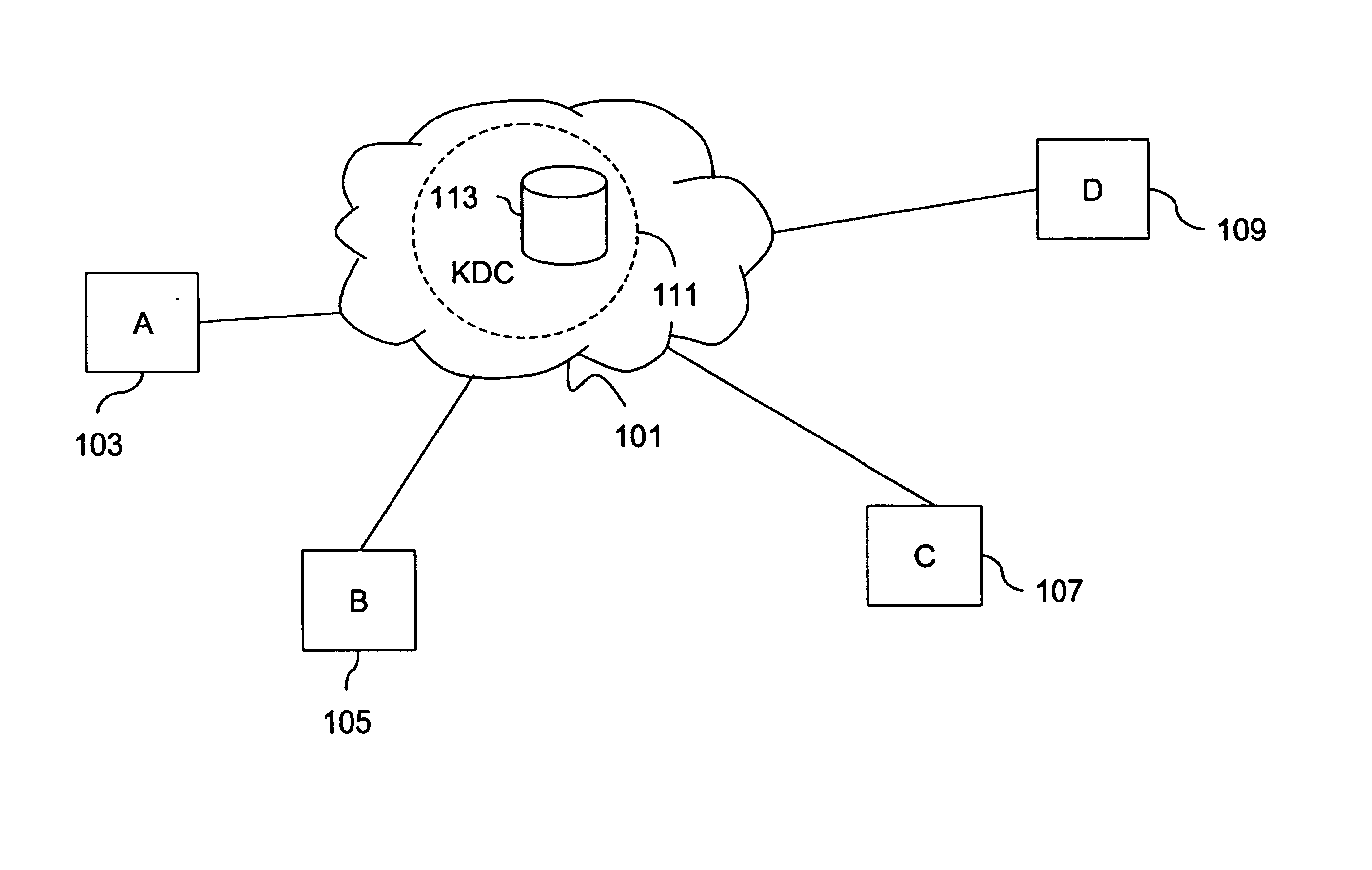
Method and apparatus for distributing and updating private keys of multicast group managers using directory replication
InactiveUS20050044356A1Optimize allocationKey distribution for secure communicationGroup sessionSecure multicast
An approach for establishing secure multicast communication among multiple multicast proxy service nodes is disclosed. The multicast proxy service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the multicast proxy service nodes include the group session keys that are members of the secure multicast or broadcast groups. Because keys as well as key version information are housed in the directory, multicast security can be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Multicast proxy service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
Directory enabled secure multicast group communications
InactiveUS20050097317A1Provide scalabilityImprove scalabilityKey distribution for secure communicationUser identity/authority verificationSecure communicationGroup session
An approach for establishing secure communication among multiple multicast groups using a multi-master directory is disclosed. The multi-master directory is on a per object and per attribute access controls basis. The event service nodes, which can implemented as event servers, are distributed throughout an enterprise domain. The attributes of the event service nodes include the group session key and the private keys of the event service nodes. A standardized authentication service is used to register publishers and subscribers. These publishers and subscribers can individually belong to multiple multicast groups under a readily scalable, secure network architecture.
Owner:CISCO TECH INC
Secure multicast transmission
InactiveUS20070028099A1Reduce amountReduce loadSpecial service provision for substationKey distribution for secure communicationComputer hardwareSecure multicast
A method of multicasting data. The method includes providing a data block for multicasting, generating a plurality of segments that represent the data block, such that a receiver needs to receive fewer than all the generated segments in order to reconstruct the data block, encrypting at least a portion of the generated segments, so as to generate encrypted data units encrypted with a plurality of different keys or encryption methods and transmitting the encrypted data units over one or more multicast channels.
Owner:BAMBOO MEDIACASTING
Method and apparatus for distributing and updating private keys of multicast group managers using directory replication
InactiveUS7103185B1Optimize allocationKey distribution for secure communicationSynchronising transmission/receiving encryption devicesGroup sessionSecure multicast
An approach for establishing secure multicast communication among multiple multicast proxy service nodes is disclosed. The multicast proxy service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the multicast proxy service nodes include the group session key and the private keys of the multicast proxy service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the multicast proxy service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Multicast proxy service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
Directory enabled secure multicast group communications
InactiveUS7089211B1Improve scalabilitySpecial service provision for substationKey distribution for secure communicationSecure communicationGroup session
An approach for establishing secure communication among multiple multicast groups using a multi-master directory is disclosed. The multi-master directory is on a per object and per attribute access controls basis. The event service nodes, which can implemented as event servers, are distributed throughout an enterprise domain. The attributes of the event service nodes include the group session key and the private keys of the event service nodes. A standardized authentication service is used to register publishers and subscribers. These publishers and subscribers can individually belong to multiple multicast groups under a readily scalable, secure network architecture.
Owner:CISCO TECH INC
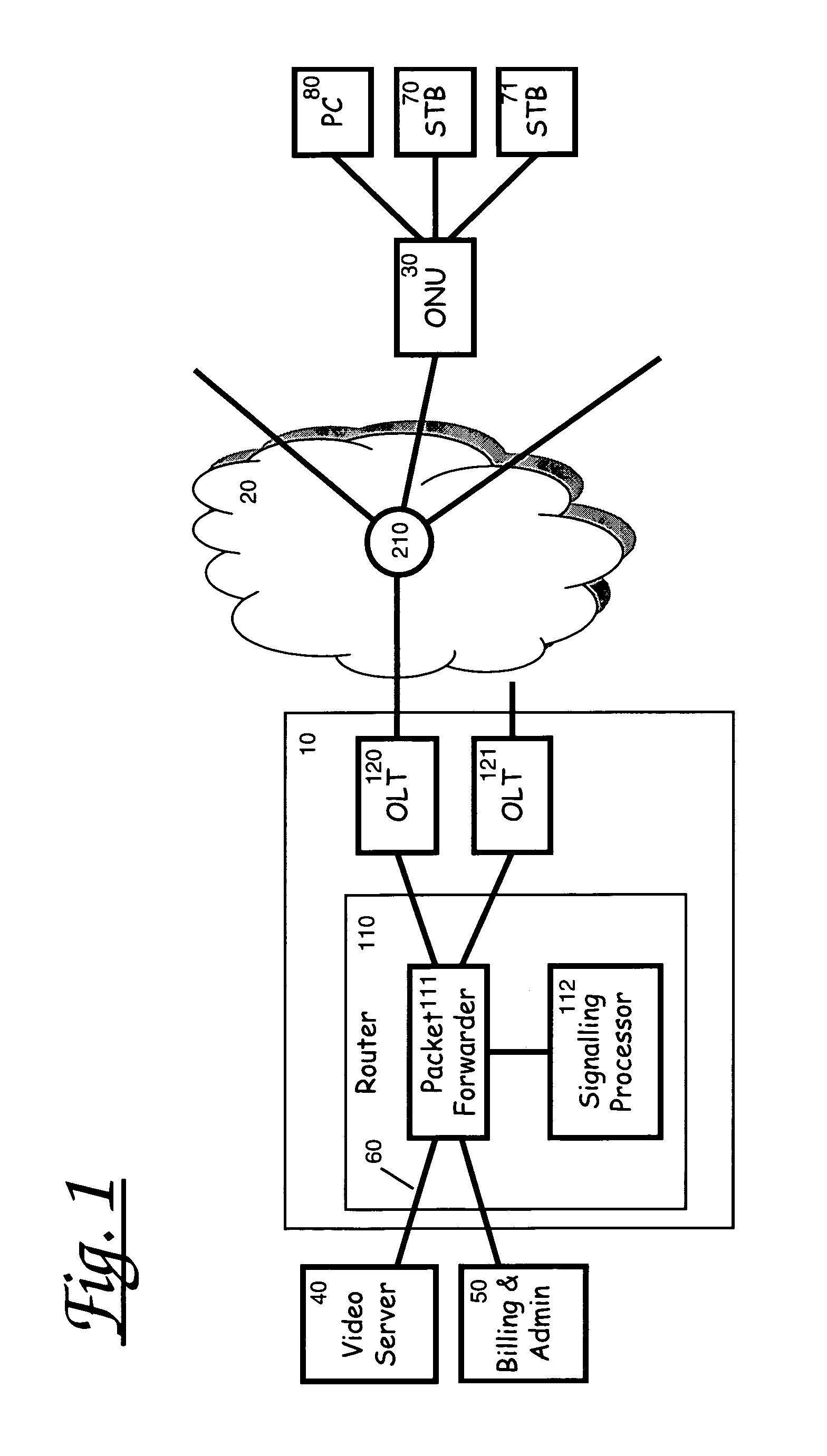
Access control enhancements for delivery of video and other services
InactiveUS6970461B2Improve securityIncreased complexitySpecial service provision for substationAnalogue secracy/subscription systemsAccess networkSecure multicast
A method of providing secure multicast over a local access network by means of a network access unit having a channel request vetting function and a permitted channel list. Channel requests from a subscriber are vetted with respect to the permitted channel list and forwarded only if permitted. The permitted list may be dynamically updated under headend control to allow users to subscribe to, and unsubscribe from, services upon request.
Owner:INT LICENSE EXCHANGE OF AMERICA LLC
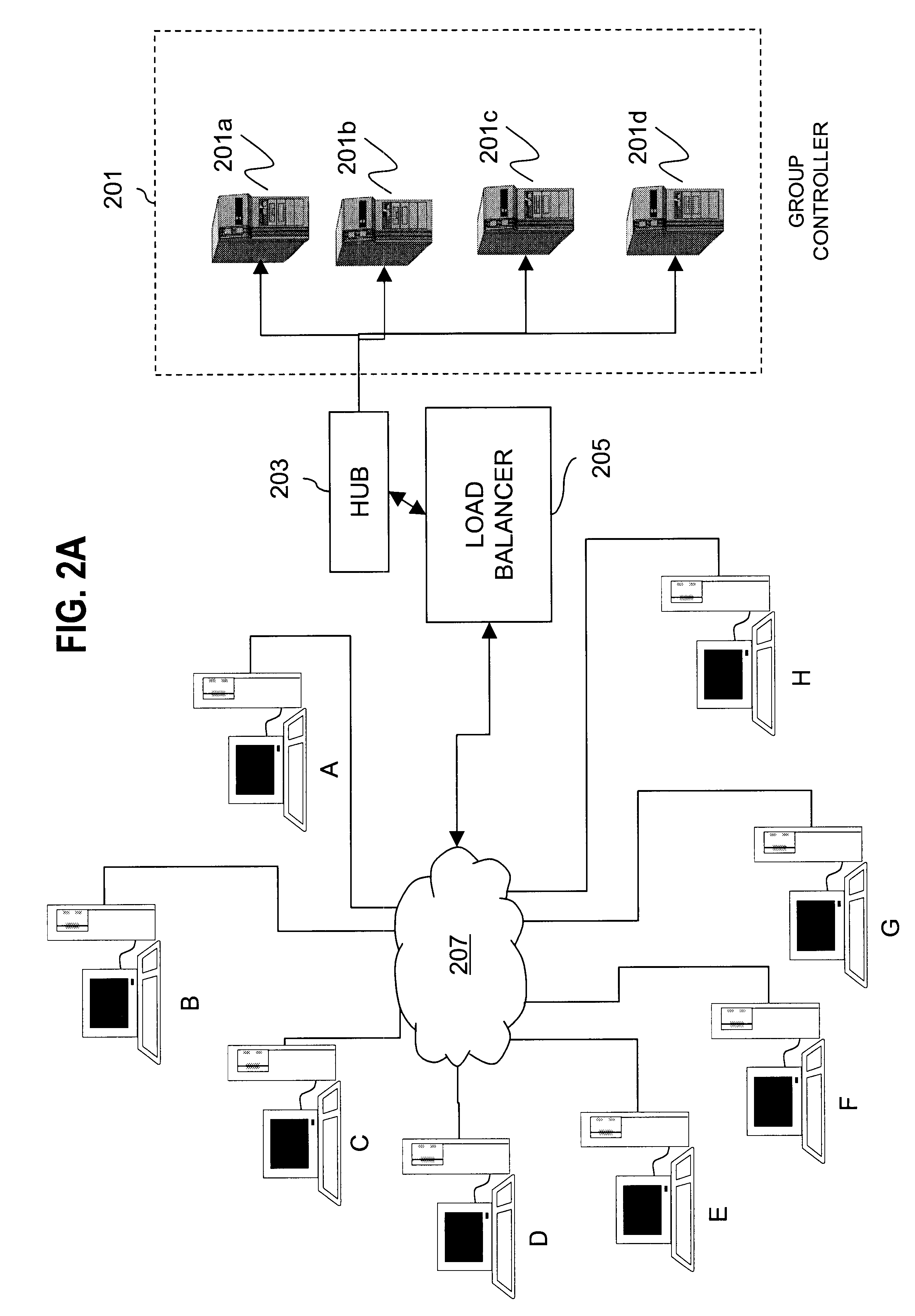
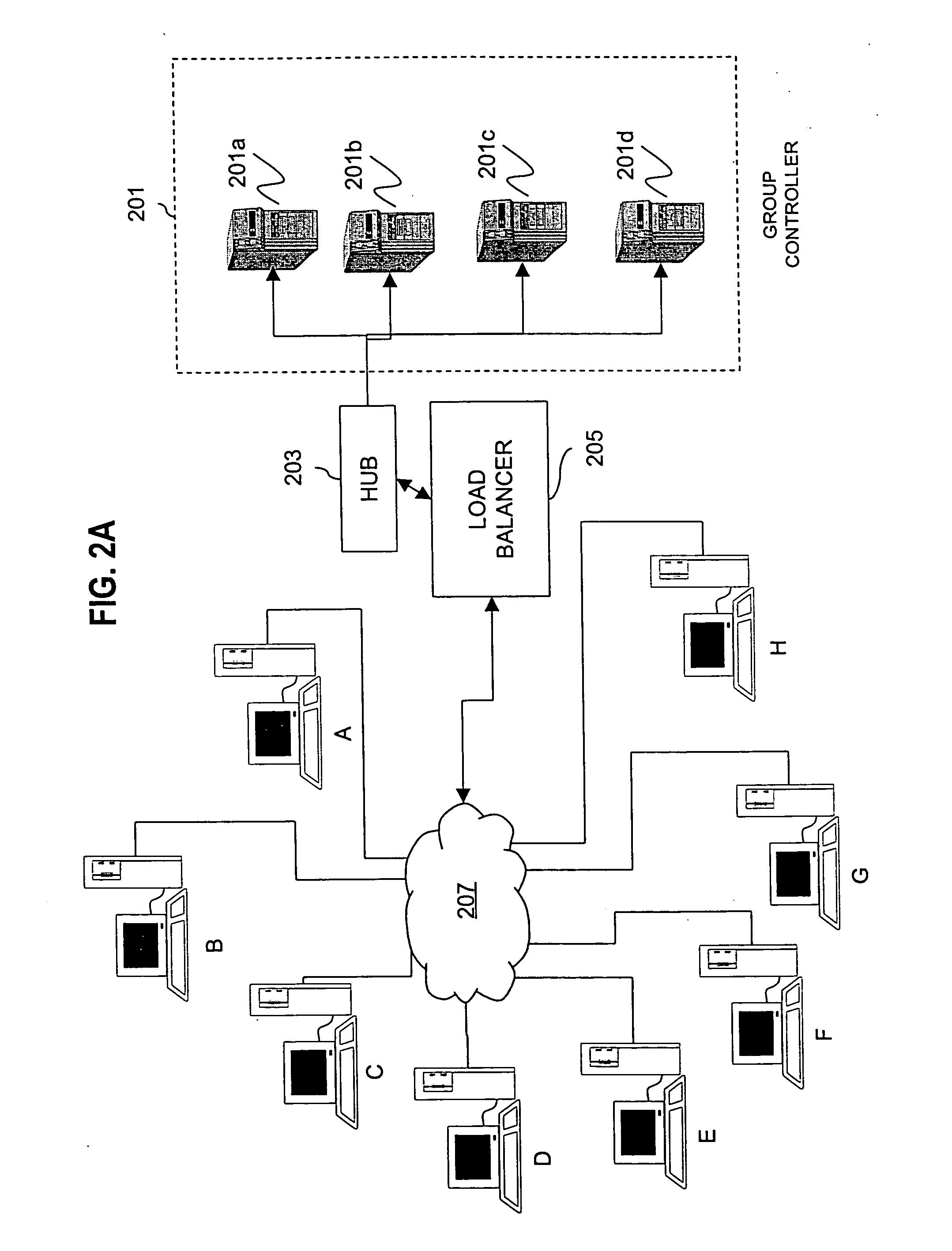
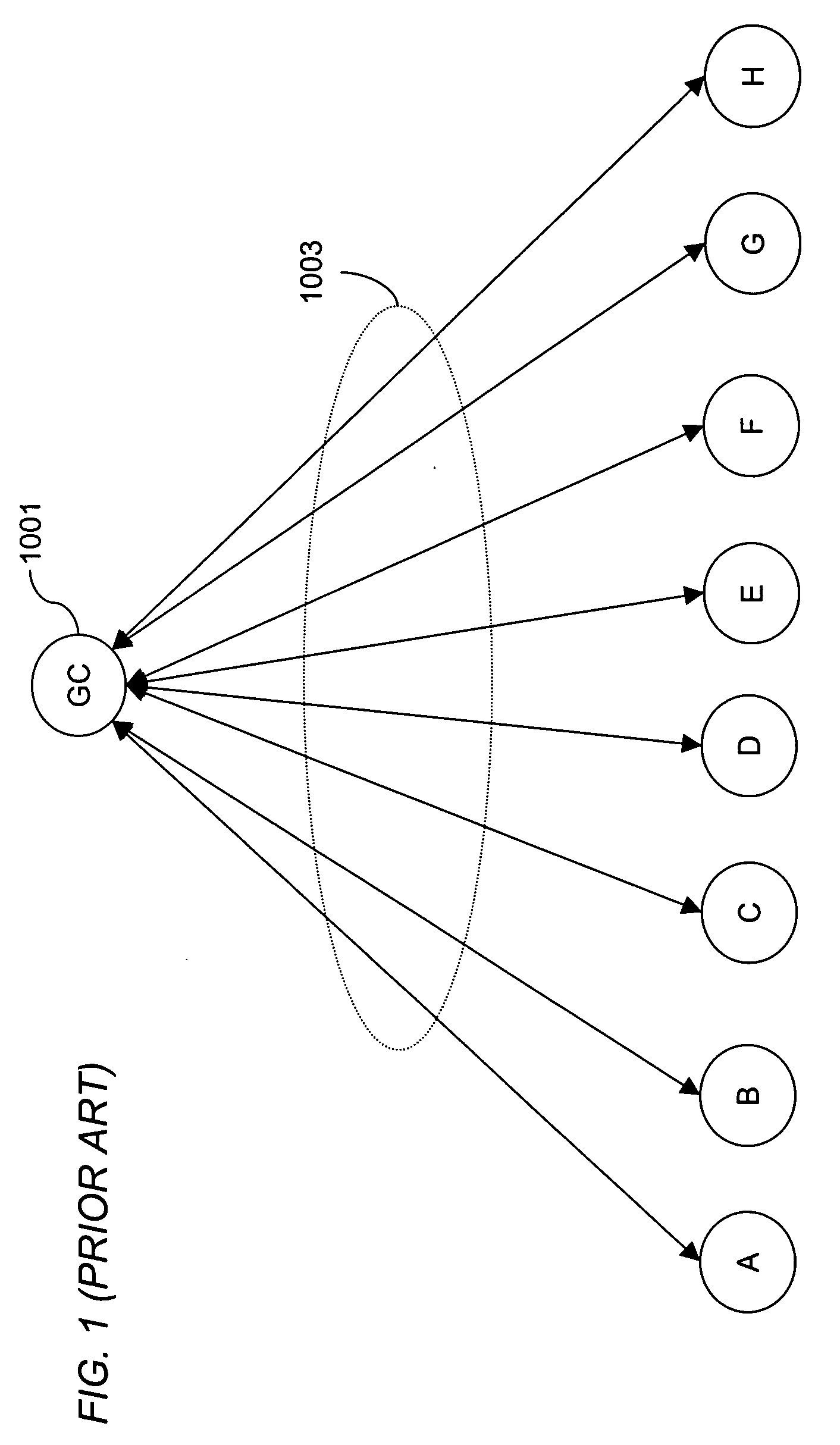
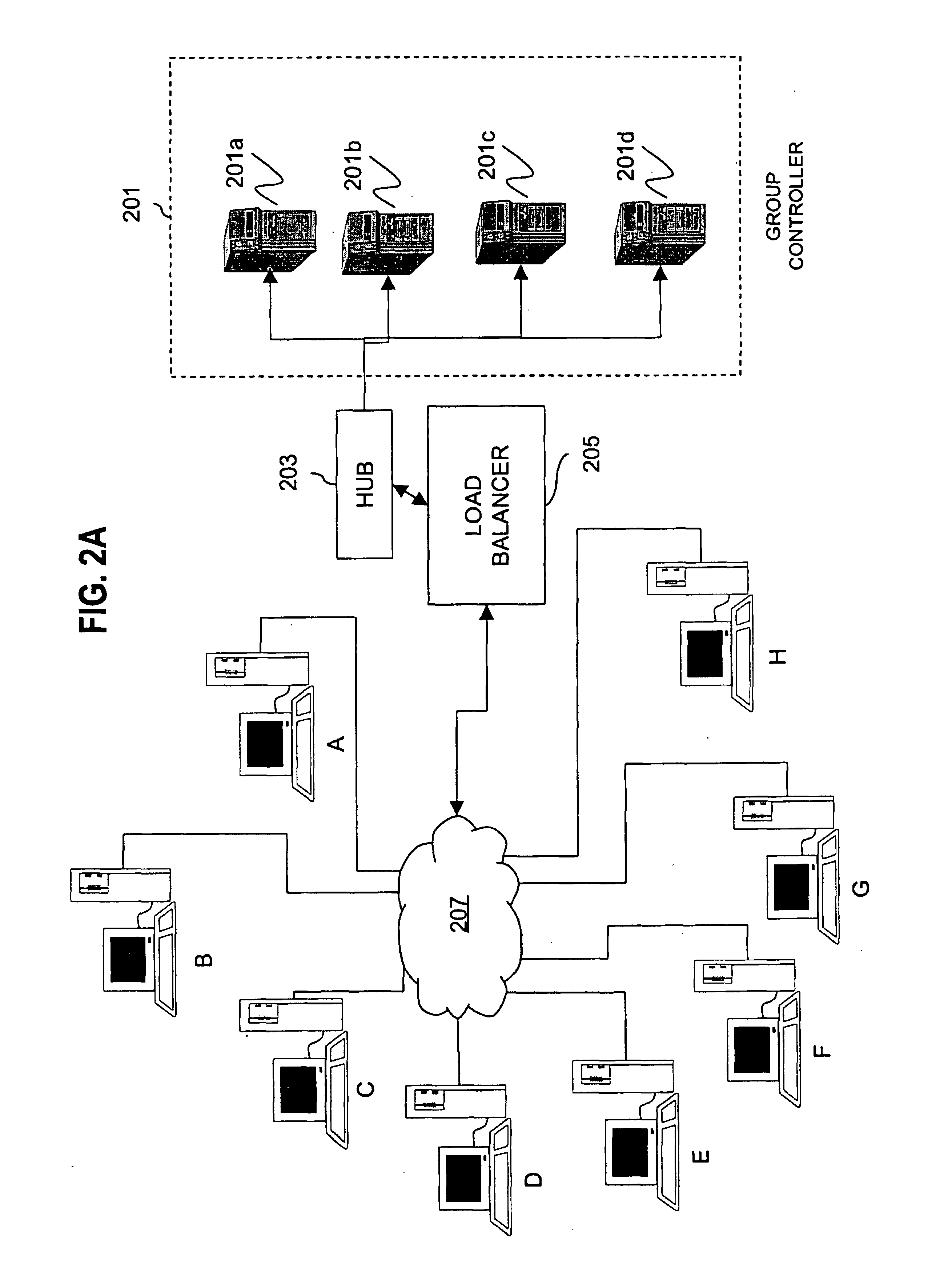
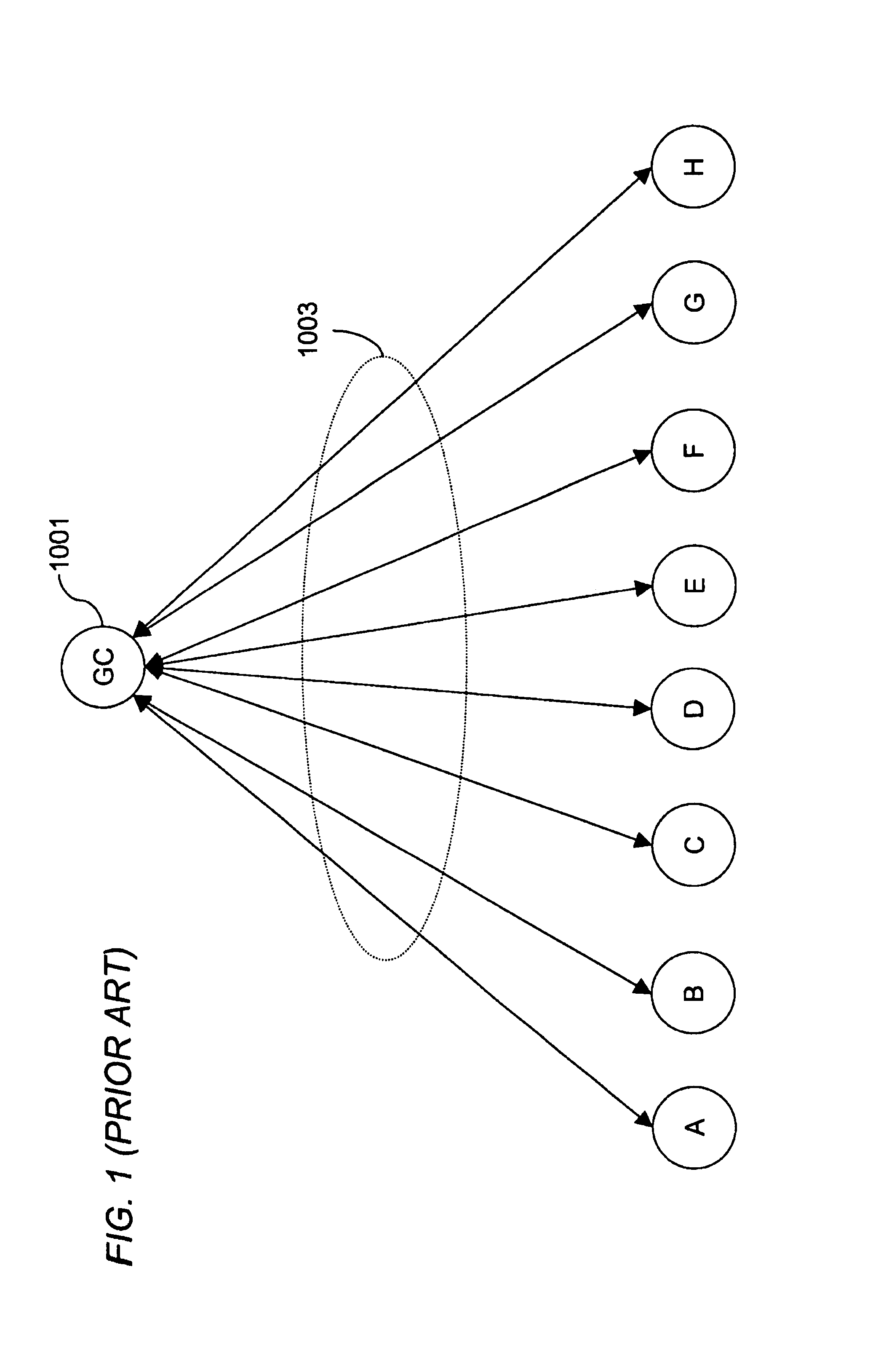
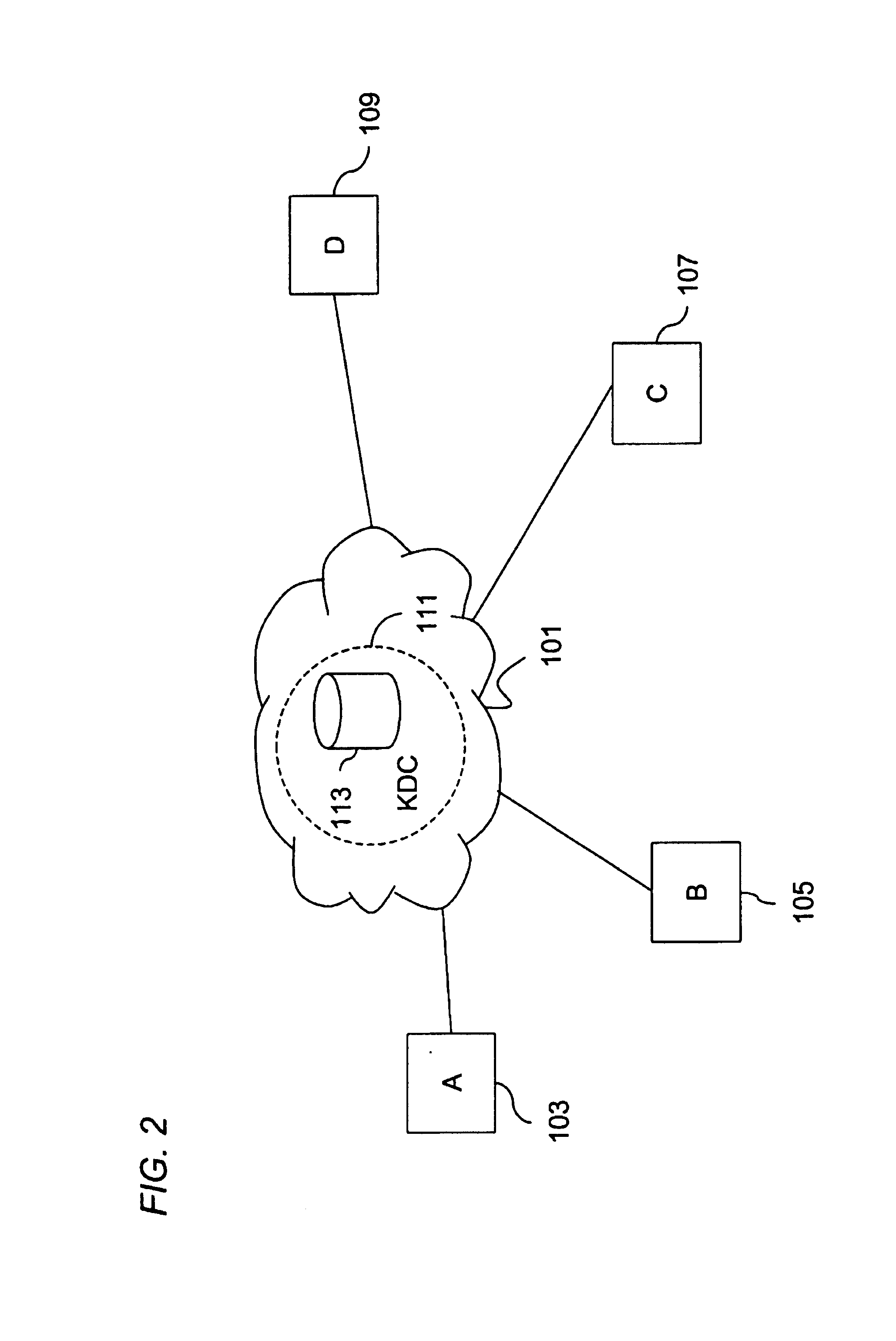
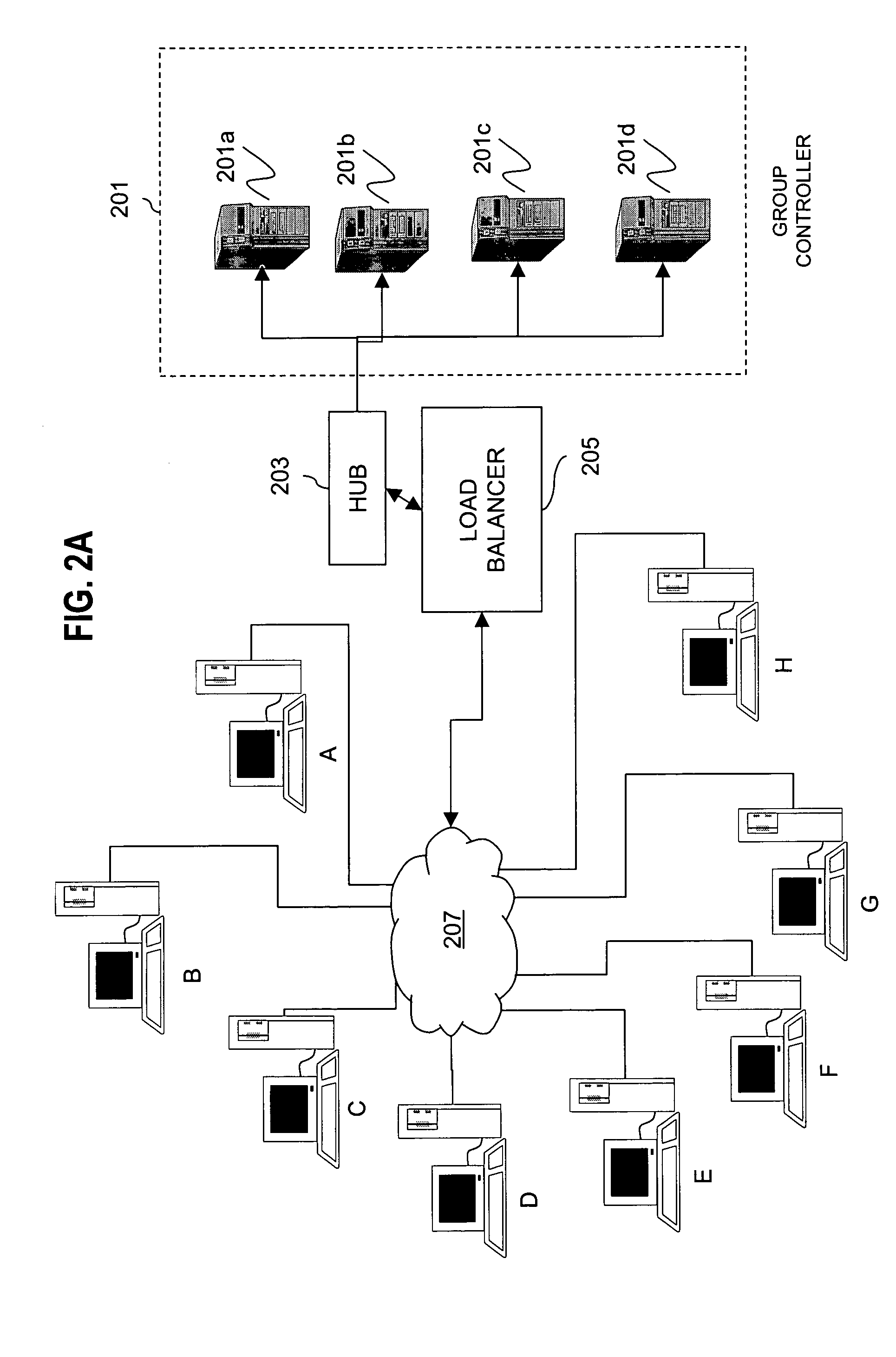
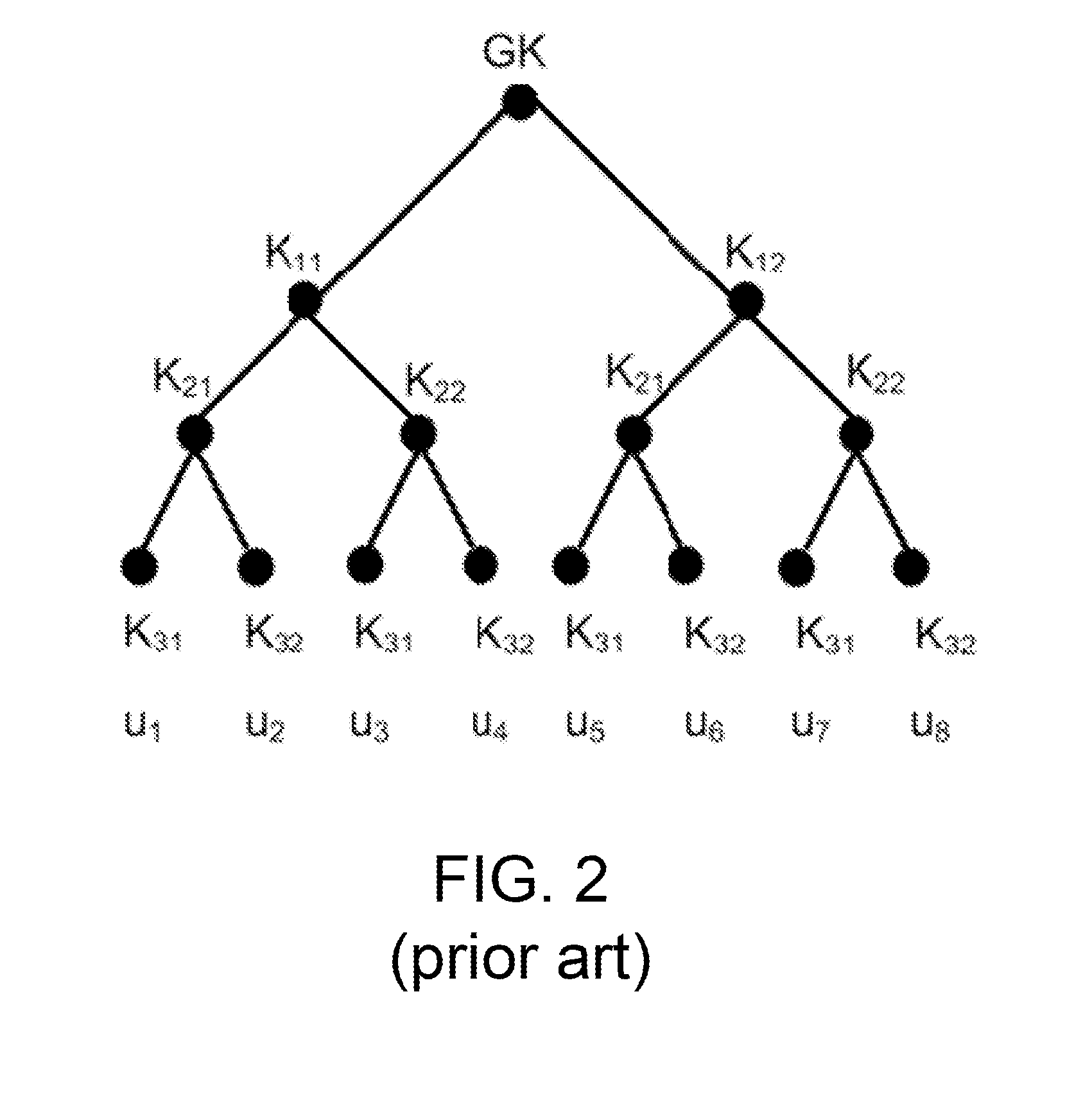
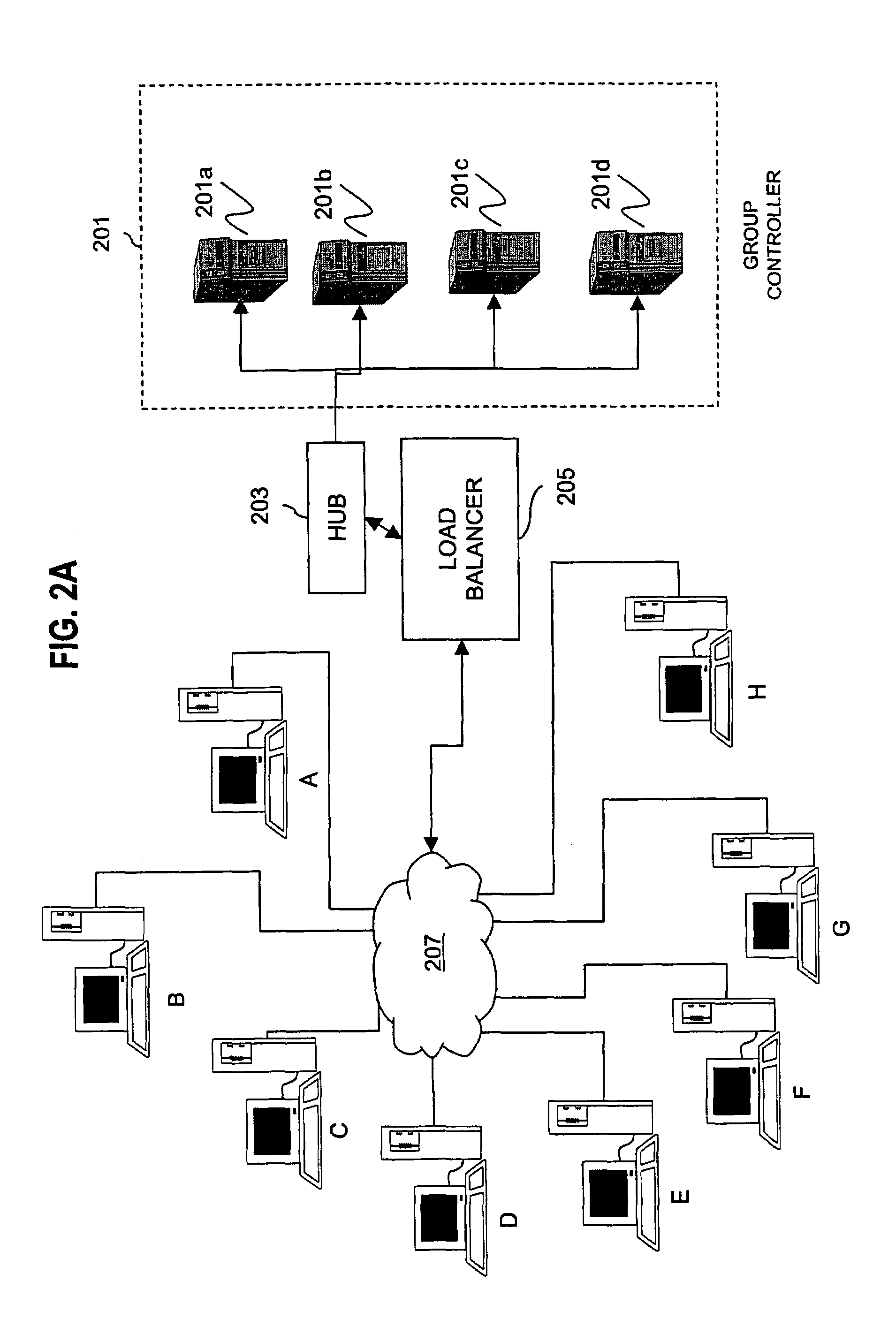
Method for overcoming the single point of failure of the central group controller in a binary tree group key exchange approach
InactiveUS7260716B1Improve scalabilityLess attentionKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer networkStructure of Management Information
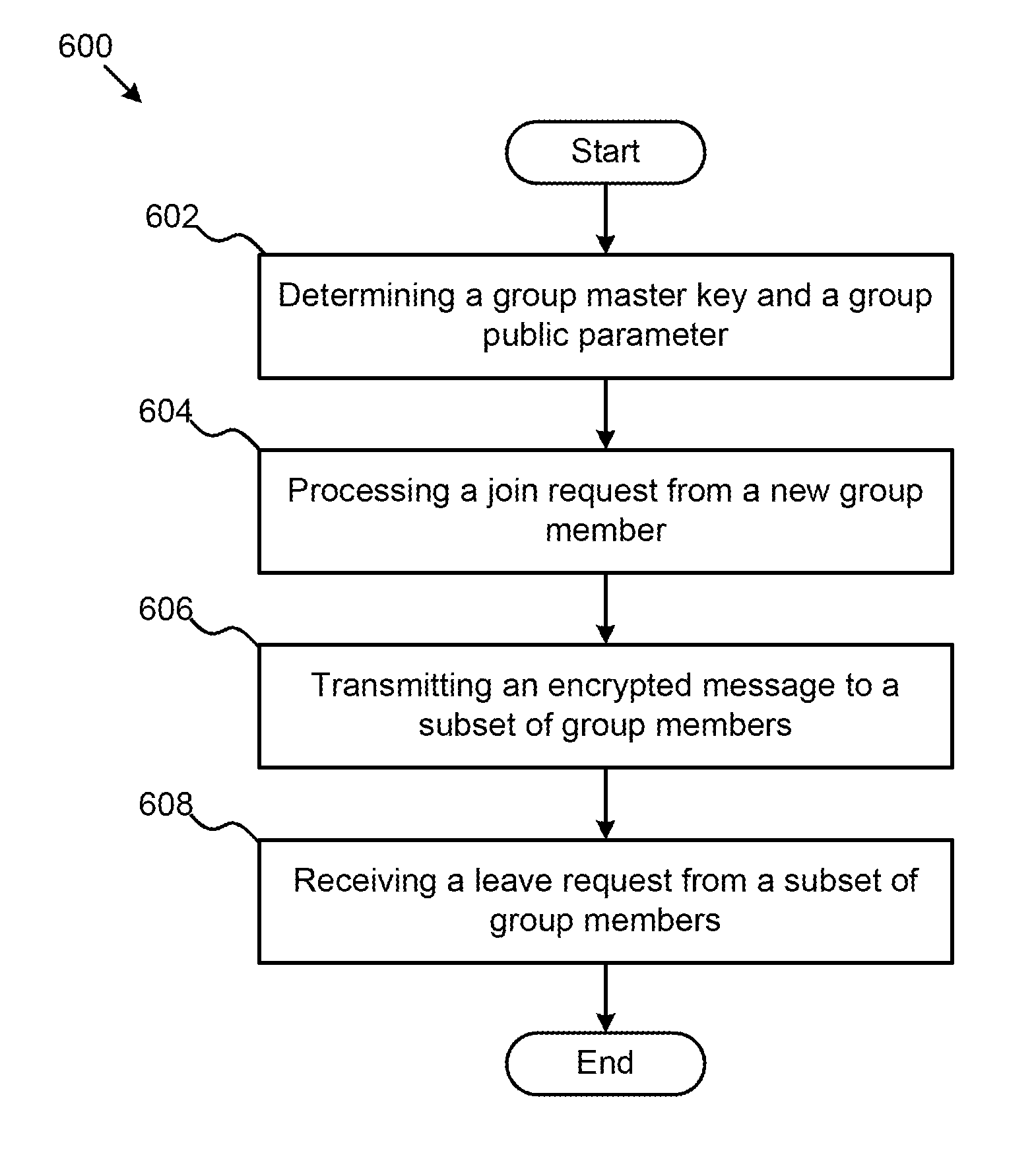
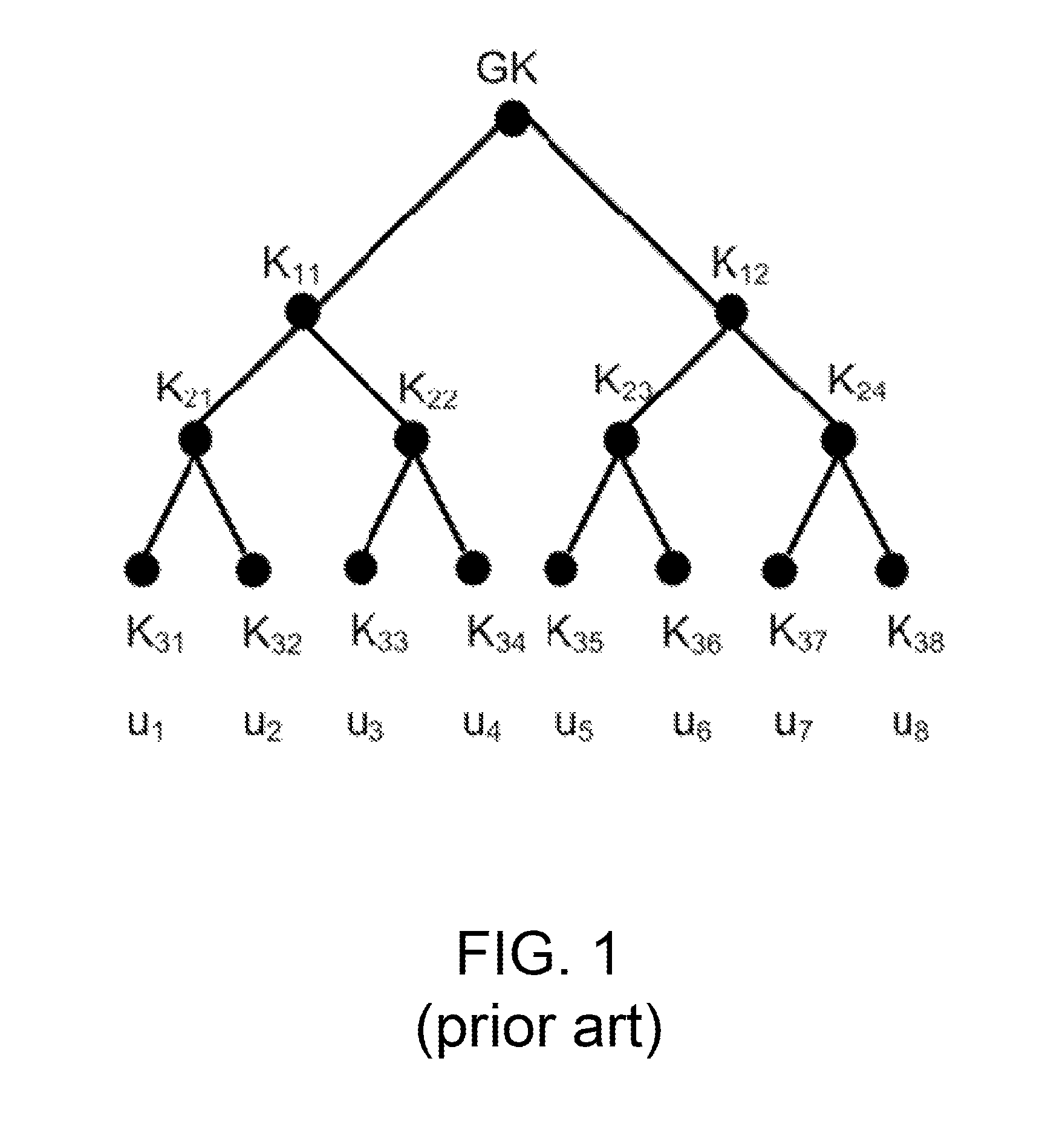
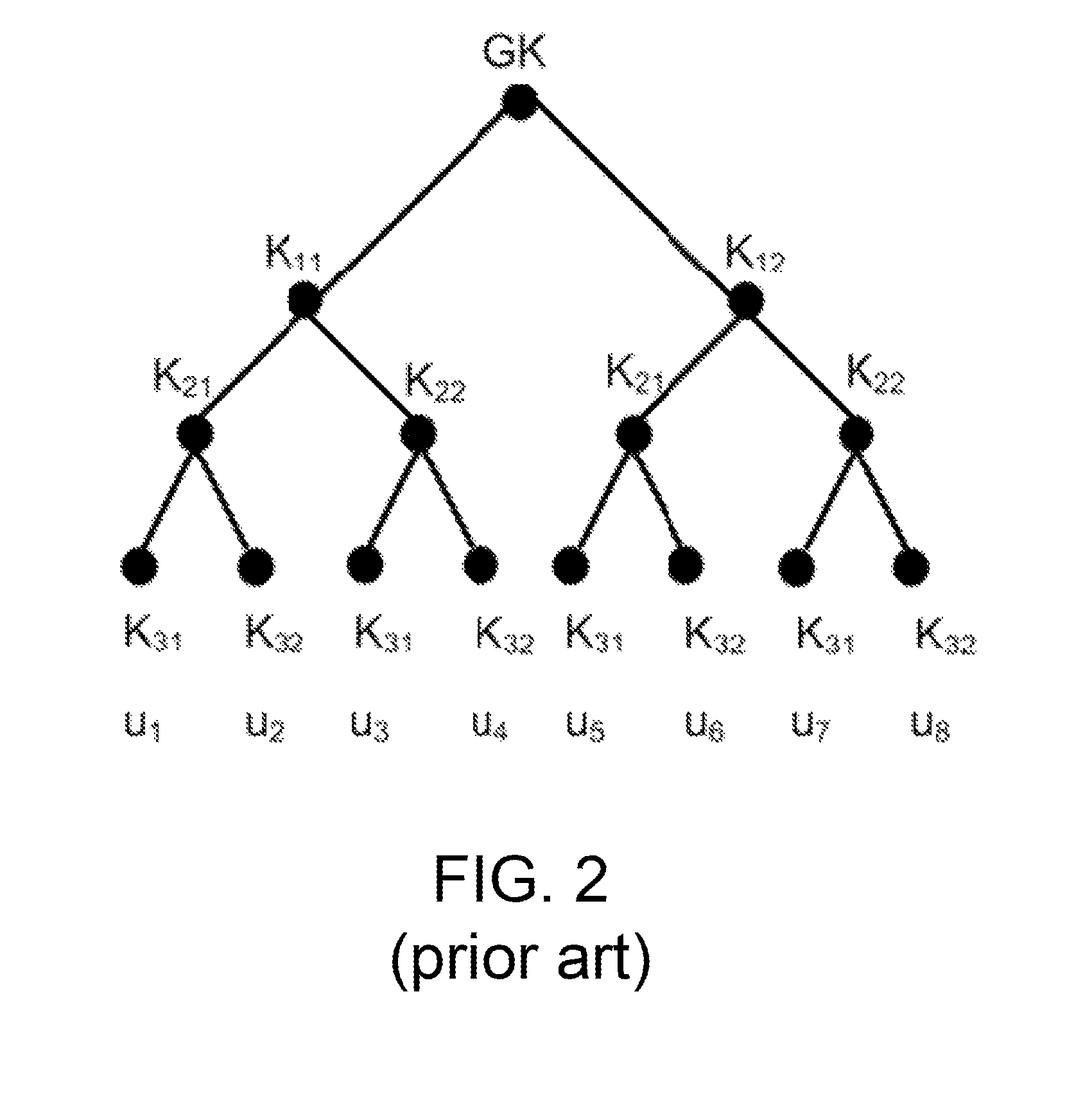
An approach for managing addition or deletion of nodes in a multicast or broadcast group, which avoids introducing a single point of failure at a group controller, certificate authority, or key distribution center, is disclosed. A central group controller utilizes a binary tree structure to generate and distribute session keys for the establishment of a secure multicast group among multiple user nodes. The central group controller is replicated in a plurality of other group controllers, interconnected in a network having a secure communication channel and connected to a load balancer. The secure communication channel is established using a public key exchange protocol. The load balancer distributes incoming join / leave requests to a master group controller. The master group controller processes the join or leave, generates a new group session key, and distributes the new group session key to all other group controller replicas. Each group controller is successively designated as master group controller in real time when a former master group controller crashes or relinquishes its master authority.
Owner:CISCO TECH INC
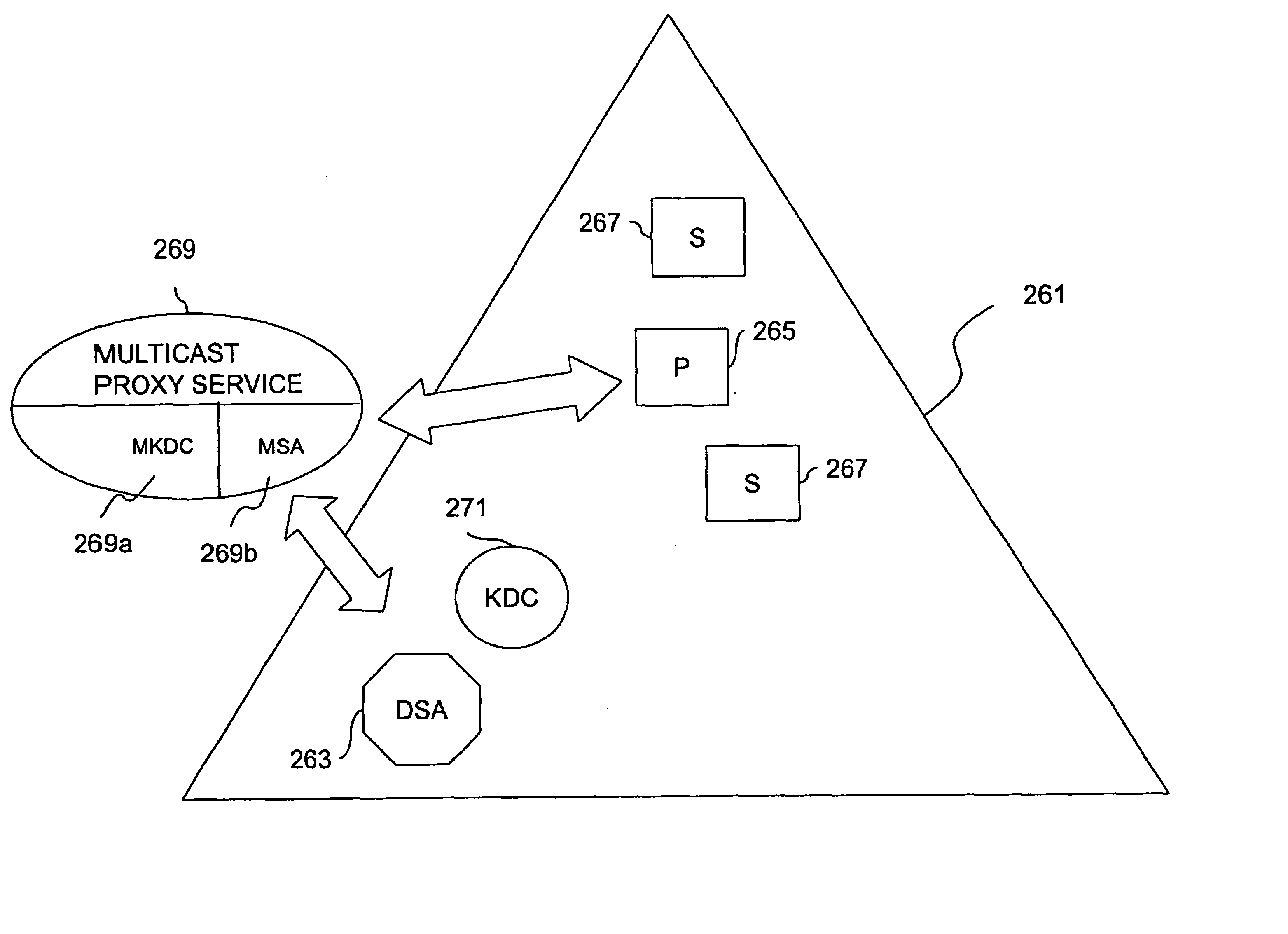
Method and apparatus for distributing and updating group controllers over a wide area network using a tree structure
InactiveUS6901510B1Reduces the workload on the group controllerSpecial service provision for substationKey distribution for secure communicationBinary treeWide area network
Apparatus and computer-readable media are disclosed for establishing secure multicast communication among multiple multicast proxy service nodes of domains of a replicated directory service that spans a wide area network. Domains are organized in a logical tree. Each domain has a logical tree that organizes the multicast proxy service nodes, a group manager at the root node, a multicast key distribution center, multicast service agent, directory service agent and key distribution center. Multicast proxy service nodes store a group session key and a private key. Replication of the directory performs key distribution. A multicast group member joins or leaves the group by publishing message. The local key distribution center and multicast service agent obtain the publisher's identity from a local directory service agent. Based on the identity, a secure channel is established with the directory service agent in the group member's domain. Keys of the binary tree branch that contains the joining or leaving node are updated, and an updated group session key and a new private key are received.
Owner:CISCO TECH INC
Method and apparatus providing secure multicast group communication
InactiveUS7434046B1Eliminating single point of failureReduce in quantityKey distribution for secure communicationMultiple keys/algorithms usageComputer networkGroup session
An approach for establishing secure multicast communication among multiple members that participate in a multicast group is disclosed. In one feature, multiple multicast proxy service nodes (MPSNs) are defined and control when members join or leave the multicast group. The MPSNs are logically represented by a first binary tree in which each node of the first binary tree is associated with a domain of a directory service and one or more of the MPSNs. A second binary tree is created that has leaf nodes representing each member. The second binary tree is stored in a domain of the directory service with a root node that represents one or more of the MPSNs. The members can each establish multicast communication and serve as a key distribution center. When a member joins the multicast group, a new group session key is determined by replicating a branch of the second binary tree.
Owner:CISCO TECH INC
Access control enhancements for delivery of video and other services
InactiveUS20040240466A1Improve securityMinimum increase in ONU complexitySpecial service provision for substationFrequency-division multiplexAccess networkSecure multicast
A method of providing secure multicast over a local access network by means of a network access unit having a channel request vetting function and a permitted channel list. Channel requests from a subscriber are vetted with respect to the permitted channel list and forwarded only if permitted. The permitted list may be dynamically updated under headend control to allow users to subscribe to, and unsubscribe from, services upon request.
Owner:INT LICENSE EXCHANGE OF AMERICA LLC
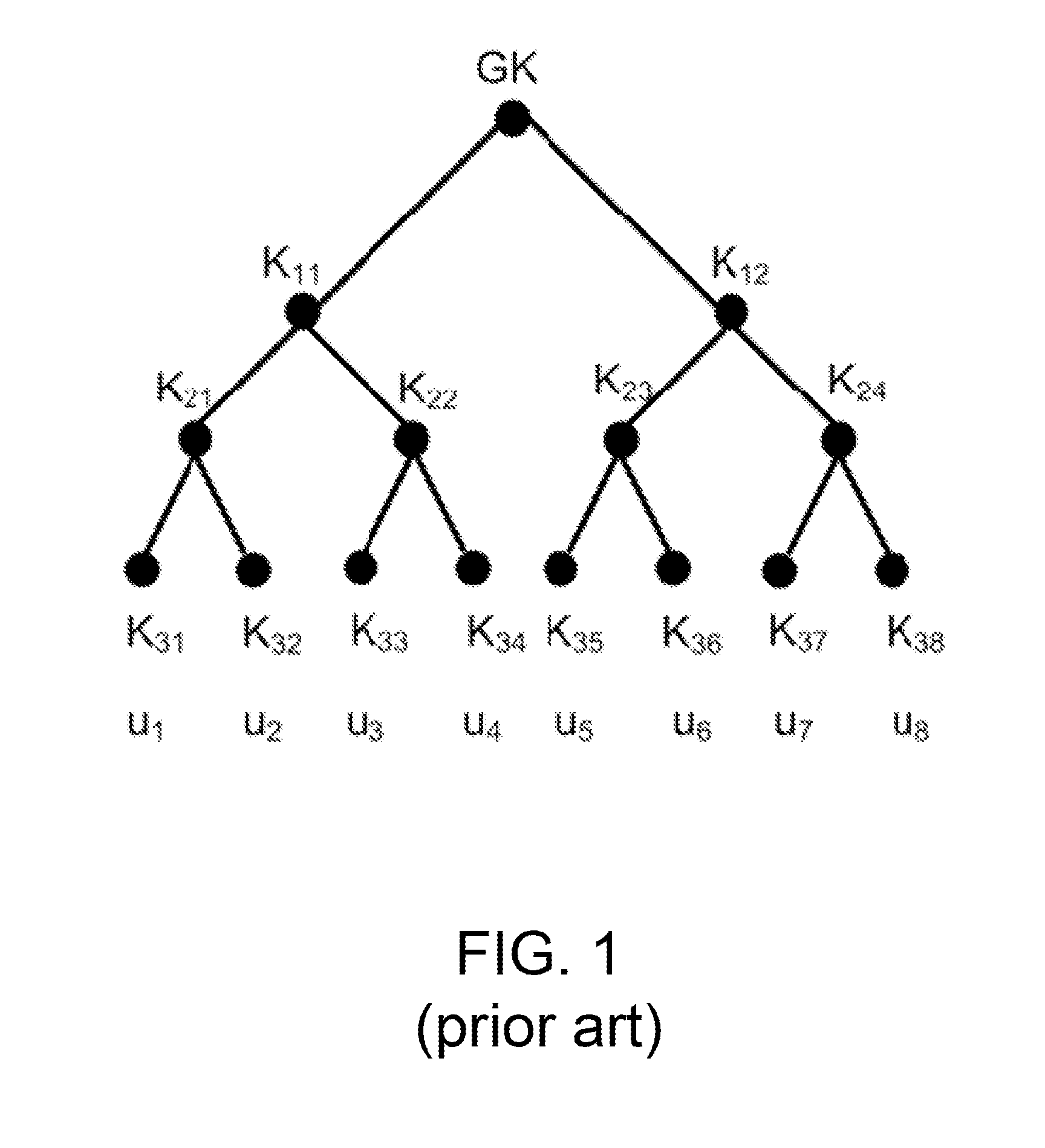
Methods, Systems, and Apparatuses for Optimal Group Key Management for Secure Multicast Communication
InactiveUS20120257756A1Constant message sizeImmune to collusion attackKey distribution for secure communicationGroup controllerSecure multicast
Apparatuses, systems, and methods for optimal group key (OGK) management that may achieve non-colluding and / or the storage-communication optimality are disclosed. In some embodiments, a group controller (GC) is responsible for key generation and distribution and the group data are encrypted by a group key. When joining the group, in some embodiments, each group member (GM) is assigned a unique n-bit ID and a set of secrets, in which each bit is one-to-one mapped to a unique secret. Whenever GMs are revoked from the group, in some embodiments, the GC will multicast an encrypted key-update message. Only the remaining GMs may be able to recover the message and update GK as well as their private keys. The disclosed OGK scheme can achieve storage-communication optimality with constant message size and immune to collusion attack and also may outperform existing group key management schemes in terms of communication and storage efficiency.
Owner:ARIZONA STATE UNIVERSITY
Method and apparatus for creating a secure communication channel among multiple event service nodes
An approach for establishing secure multicast communication among multiple event service nodes is disclosed. The event service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the event service nodes include the group session key and the private keys of the event service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the event service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can readily be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service.
Owner:CISCO TECH INC
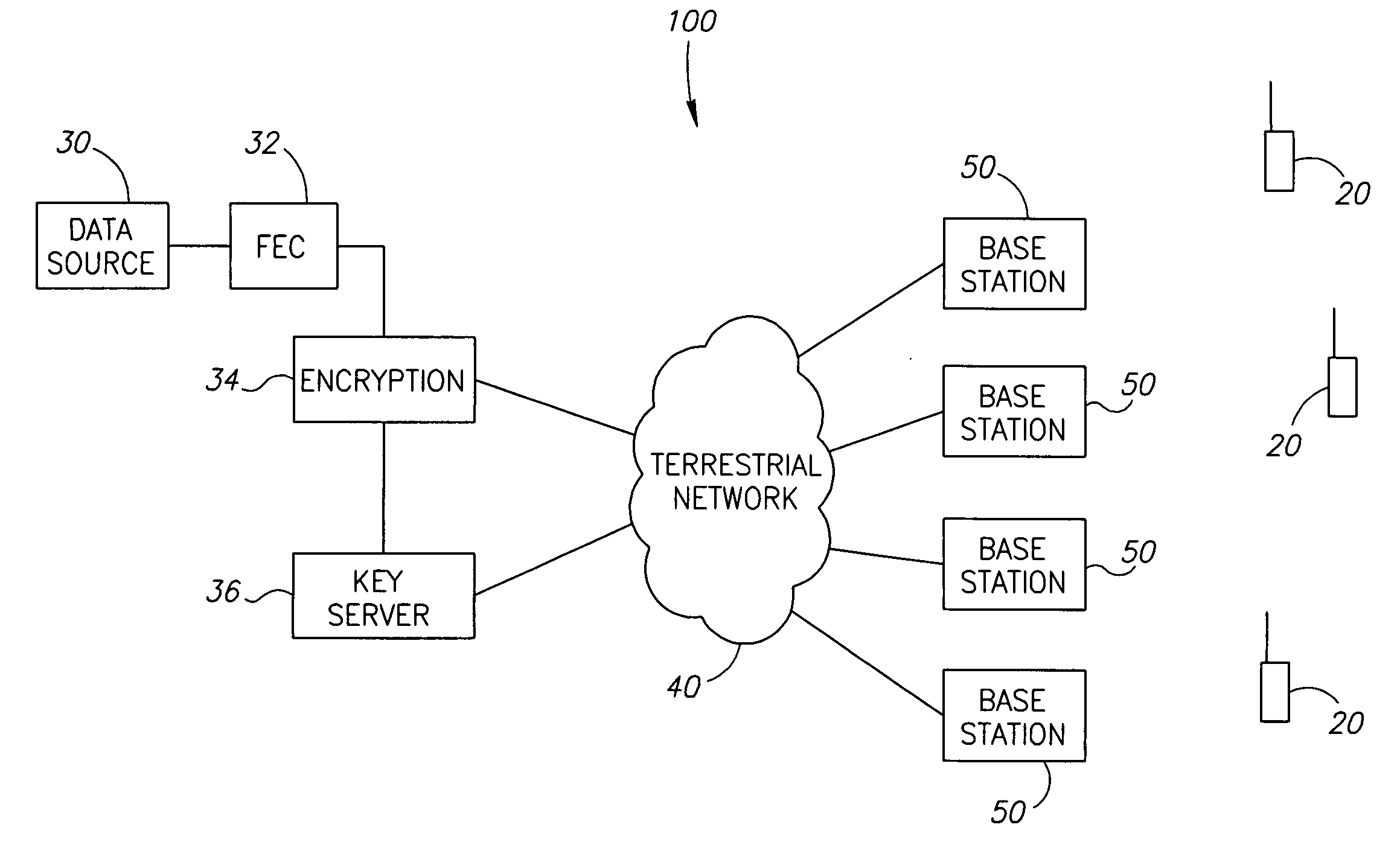
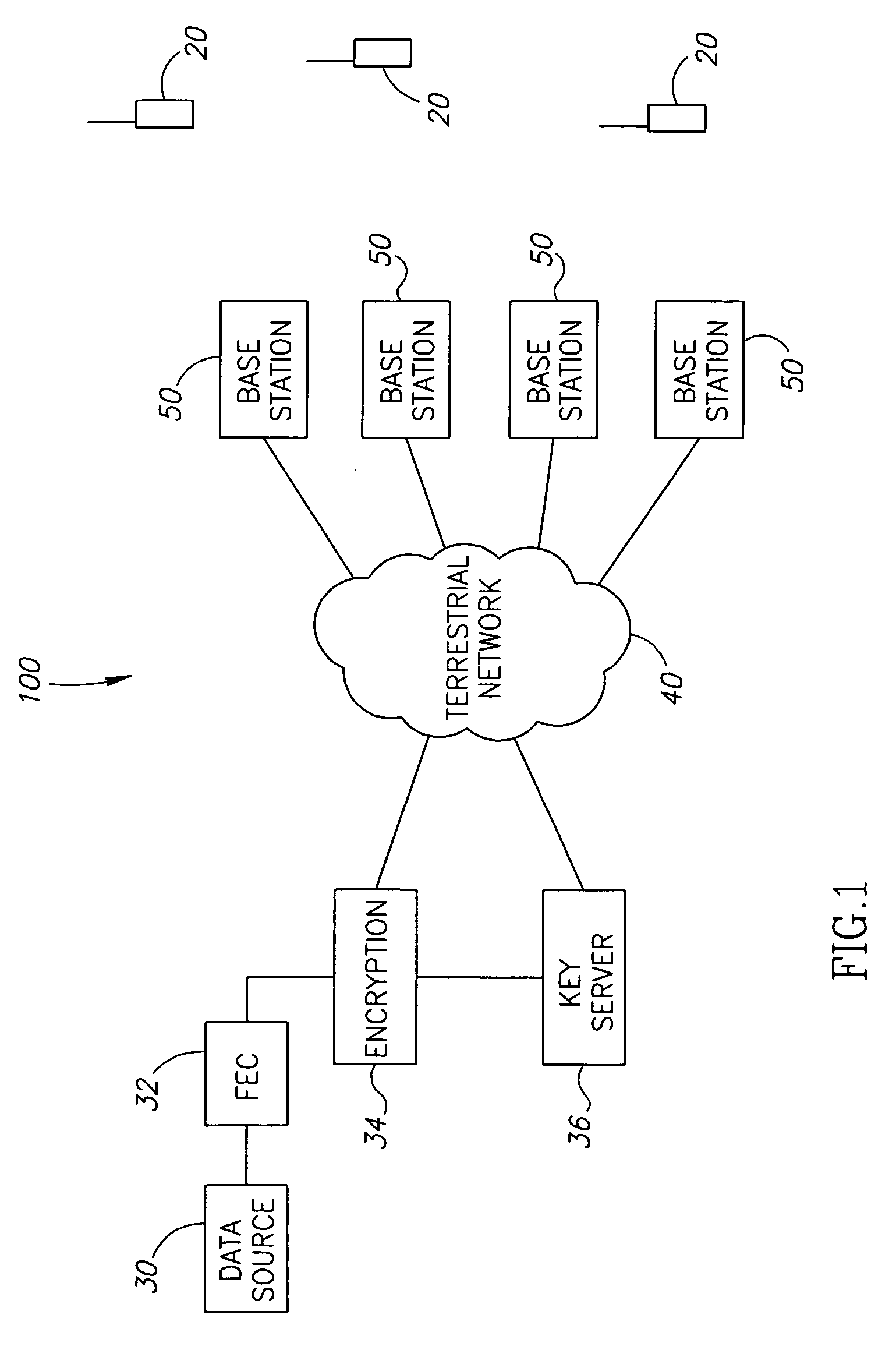
Method and apparatus for establishing a secure multicast communication session
ActiveUS20100278336A1Network degradationLift restrictionsKey distribution for secure communicationMultiple keys/algorithms usageClient-sideSecure multicast
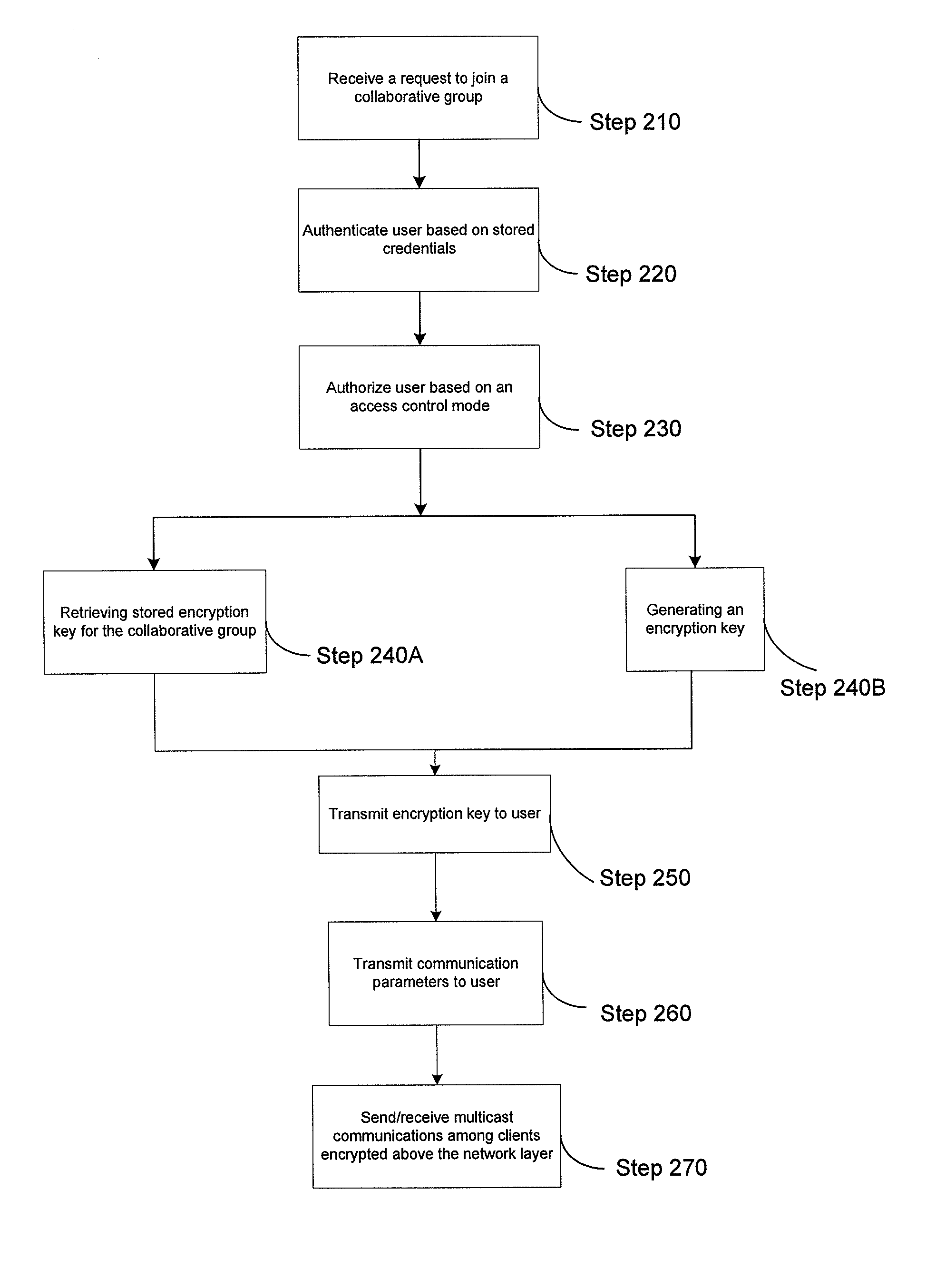
A system for establishing an encrypted multicast communication session over a communications network can include a client means (e.g., a radio, laptop, workstation, phone, PDA) and a server means. The client means can transmit a request for a first user to join a pre-defined collaborative group, including at least the first user and a second user. The client means can transmit a request for a first user to create or select a collaborative group based on specified criteria. The system can also include a server means that can retrieve, select or generate an encryption key for the collaborative group and transmit the encryption key to the first user via the client means. The server can transmit the encryption key to the second user via a second client means. The client means can communicate via multicast, encrypting end-to-end above the network layer using the encryption key received from the server means.
Owner:MITRE SPORTS INT LTD
Apparatus and method for distributing management keys in a multicast domain
InactiveUS7269728B1Special service provision for substationSecuring communicationSecure multicastComputer science
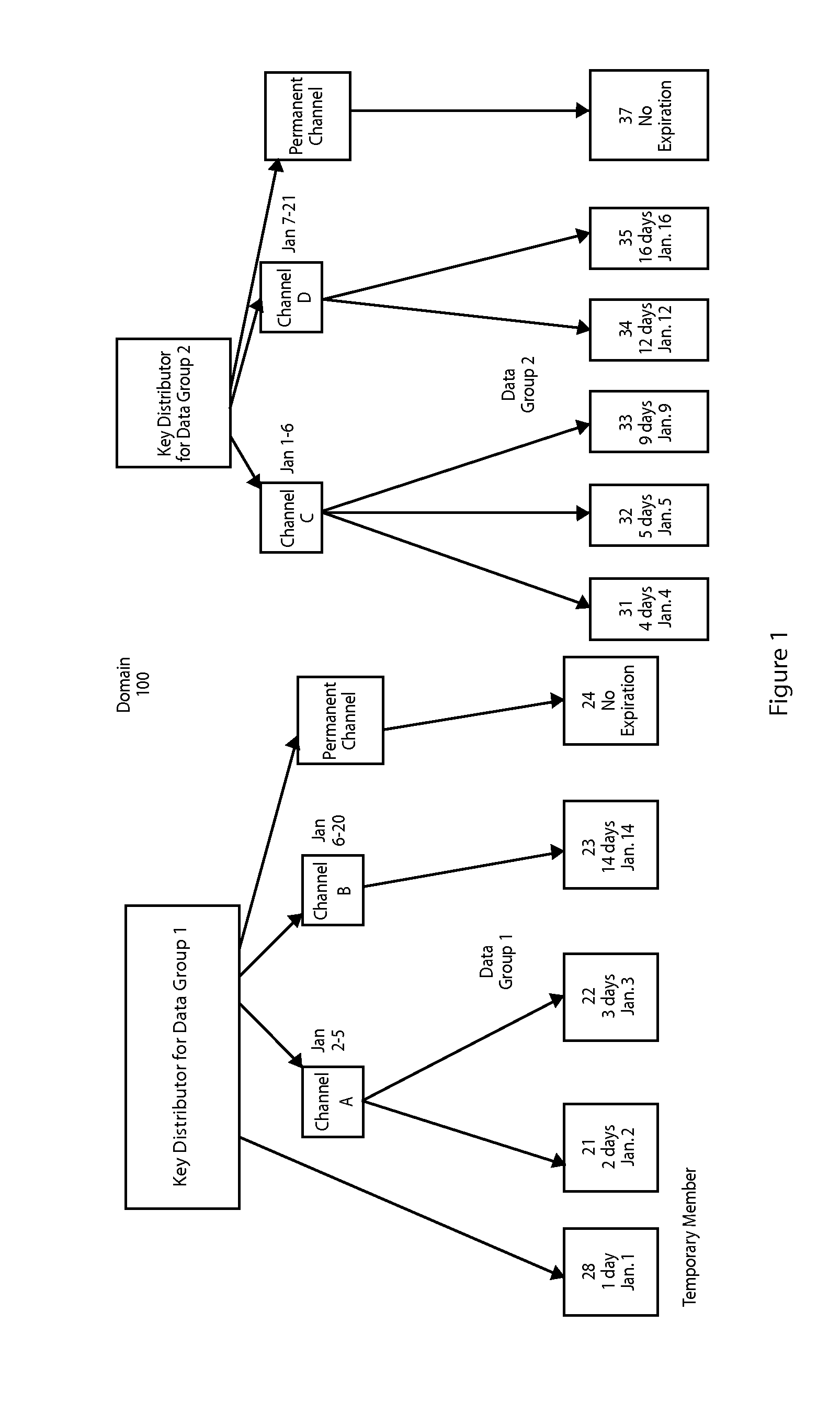
A method and apparatus for distributing keys in a multicast domain is provided. In a secure multicast domain, a request to join a multicast group for a time period occurs. A key distributor which controls access to the multicast data group determines if the request will be accepted. If the request is accepted the key distributor assigns the member to a virtual channel, wherein each virtual channel is defined by a time period. A data group key is forwarded to the member as is a virtual channel key. The member can then receive and decode events from the data group on the assigned virtual channel.
Owner:RPX CLEARINGHOUSE
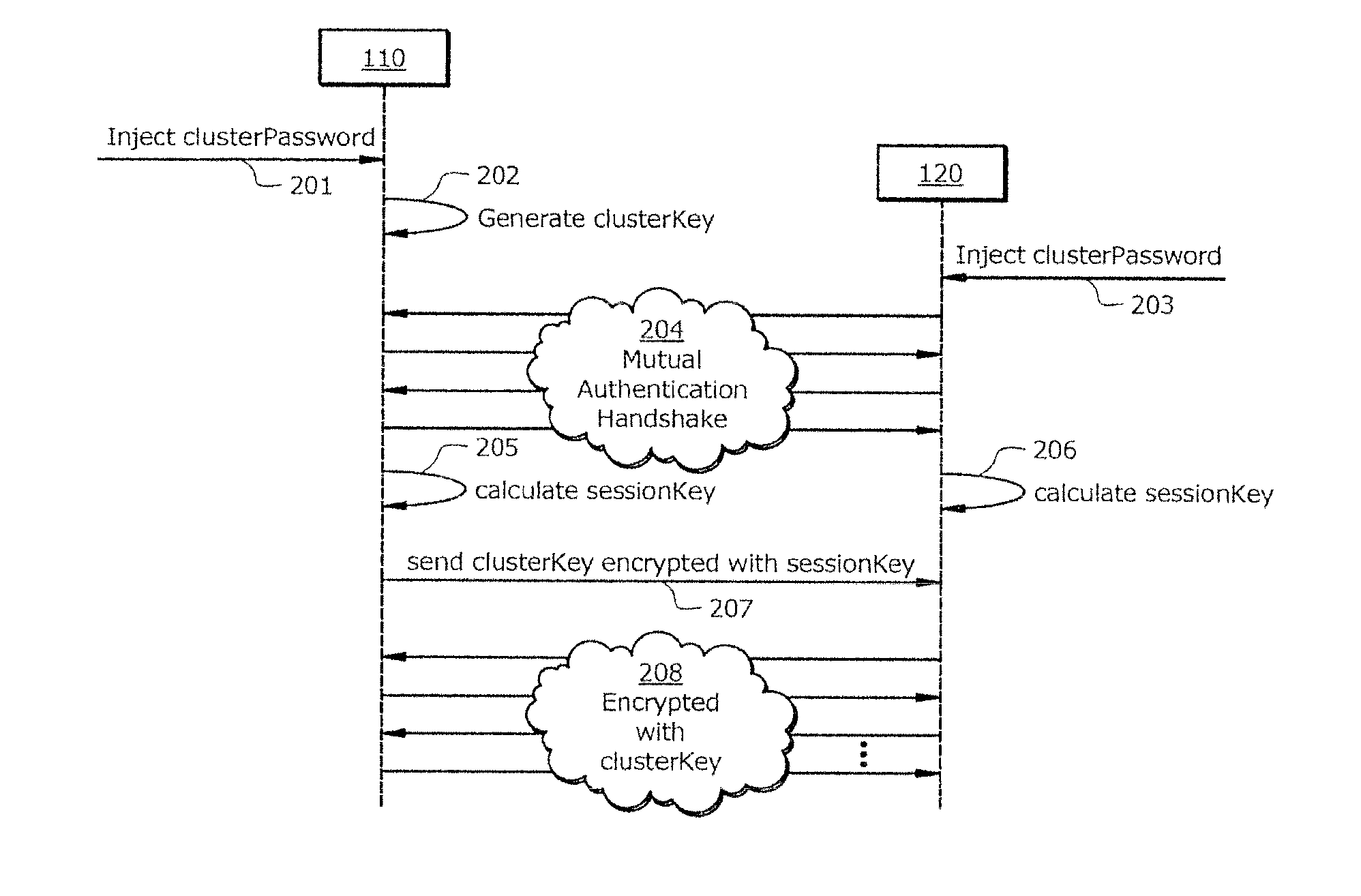
Systems and methods for providing secure multicast intra-cluster communication
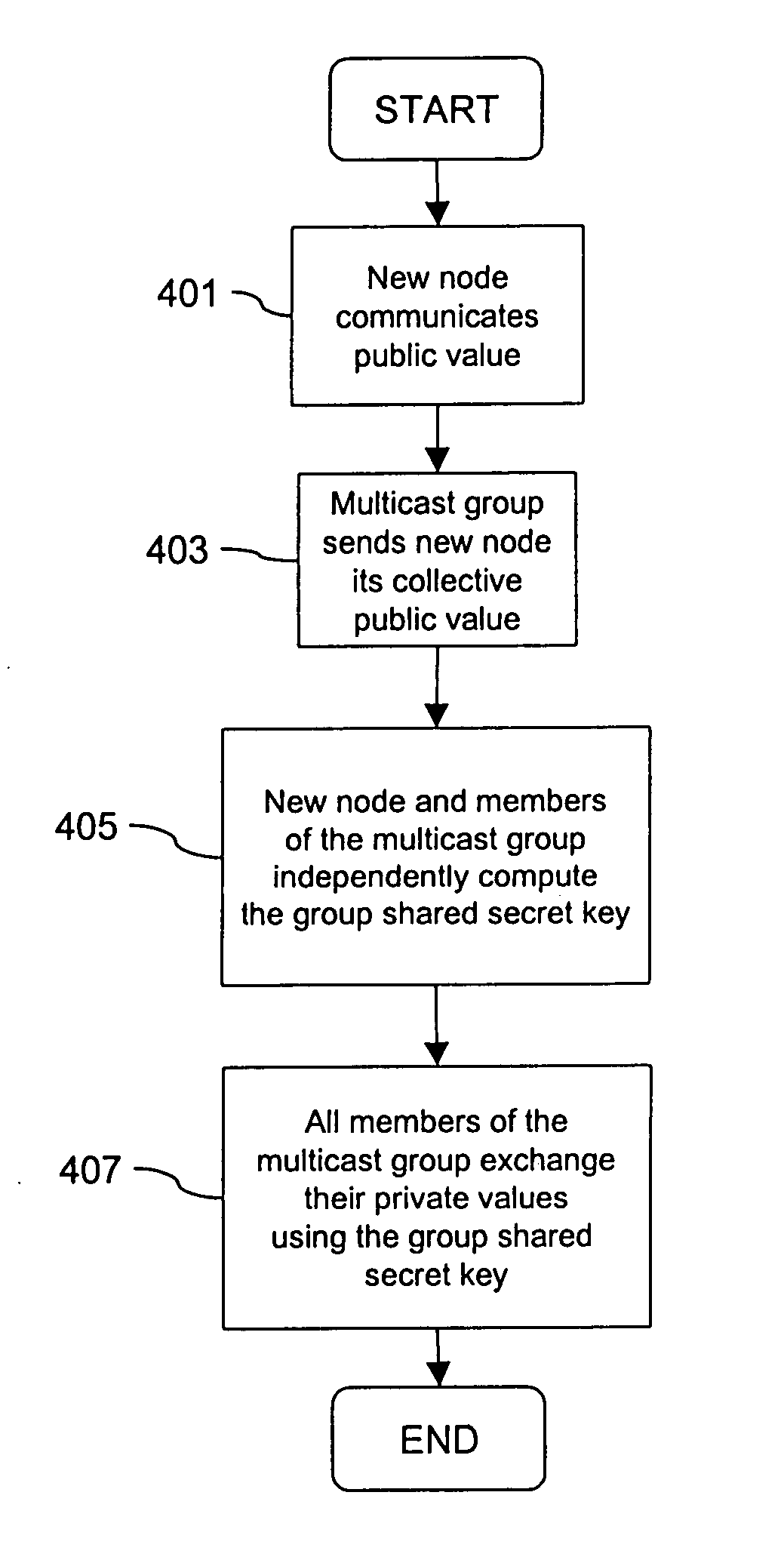
ActiveUS20130054966A1Easy to optimizeAvoid configurationDigital data processing detailsUser identity/authority verificationCommunications systemSecure multicast
Systems and methods which facilitate secure multicast communications between any valid node of a cluster using authentication between a node joining the cluster and any single node which is validly part of the cluster are disclosed. In accordance with embodiments, a cluster key is utilized to provide security with respect to intra-cluster communications. The cluster key of embodiments is shared by a node which is already part of the cluster with a node joining the cluster only after these two nodes mutually authenticate one another. The mutual authentication handshake of embodiments implements a protocol in which a session key is calculated by both nodes, thereby providing a secure means by which a cluster key may be shared. Having the cluster key, each node of the cluster is enabled to securely communicate with any other node of the cluster, whether individually (e.g., unicast) or collectively (e.g., multicast), according to embodiments.
Owner:NETWORK APPLIANCE INC
Methods, systems, and apparatuses for optimal group key management for secure multicast communication
InactiveUS8837738B2Storage-communication optimalityConstant sizeKey distribution for secure communicationGroup controllerSecure multicast
Apparatuses, systems, and methods for optimal group key (OGK) management that may achieve non-colluding and / or the storage-communication optimality are disclosed. In some embodiments, a group controller (GC) is responsible for key generation and distribution and the group data are encrypted by a group key. When joining the group, in some embodiments, each group member (GM) is assigned a unique n-bit ID and a set of secrets, in which each bit is one-to-one mapped to a unique secret. Whenever GMs are revoked from the group, in some embodiments, the GC will multicast an encrypted key-update message. Only the remaining GMs may be able to recover the message and update GK as well as their private keys. The disclosed OGK scheme can achieve storage-communication optimality with constant message size and immune to collusion attack and also may outperform existing group key management schemes in terms of communication and storage efficiency.
Owner:ARIZONA STATE UNIVERSITY
Safety multicast method based on protocol of conversation initialization
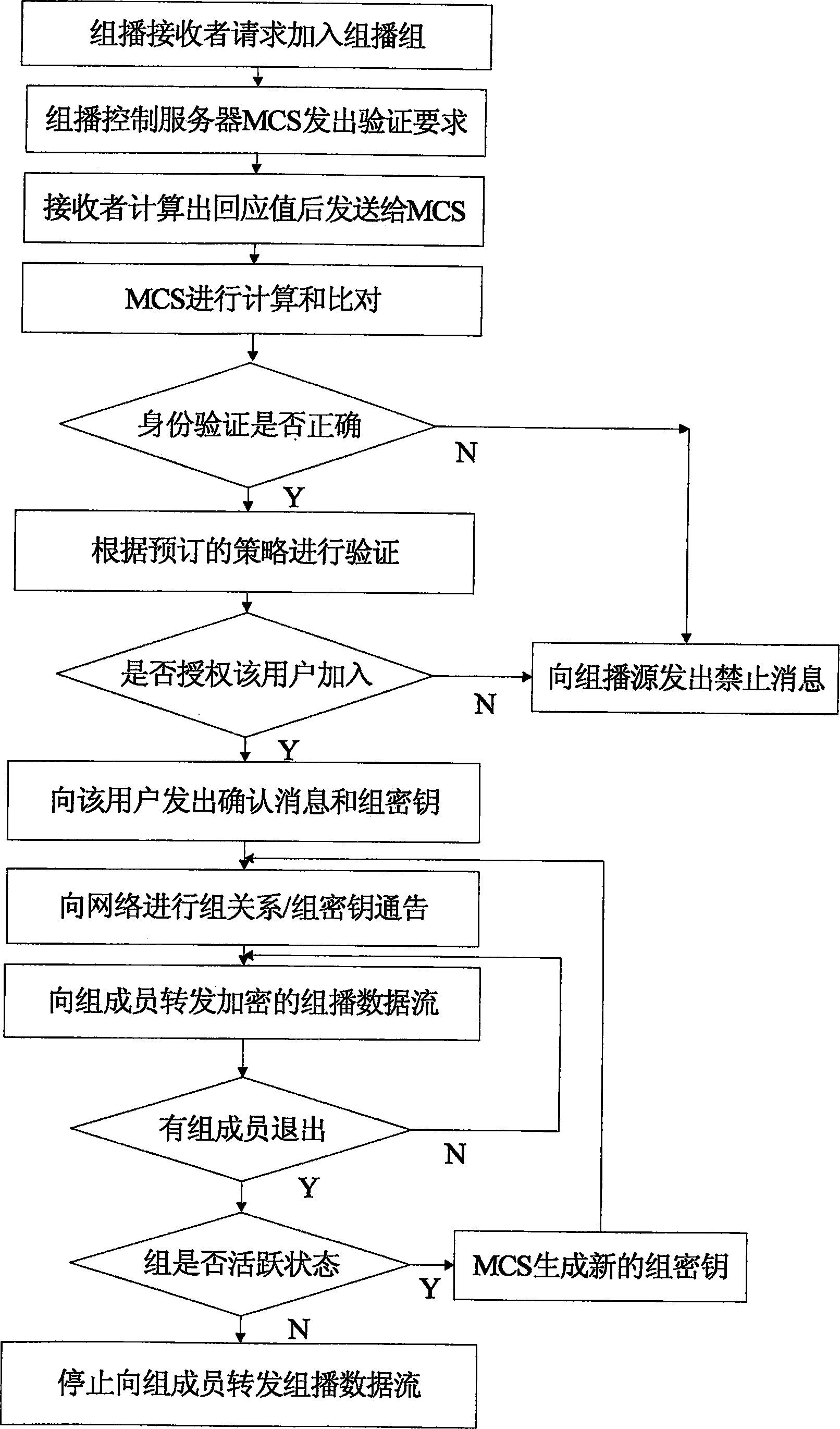
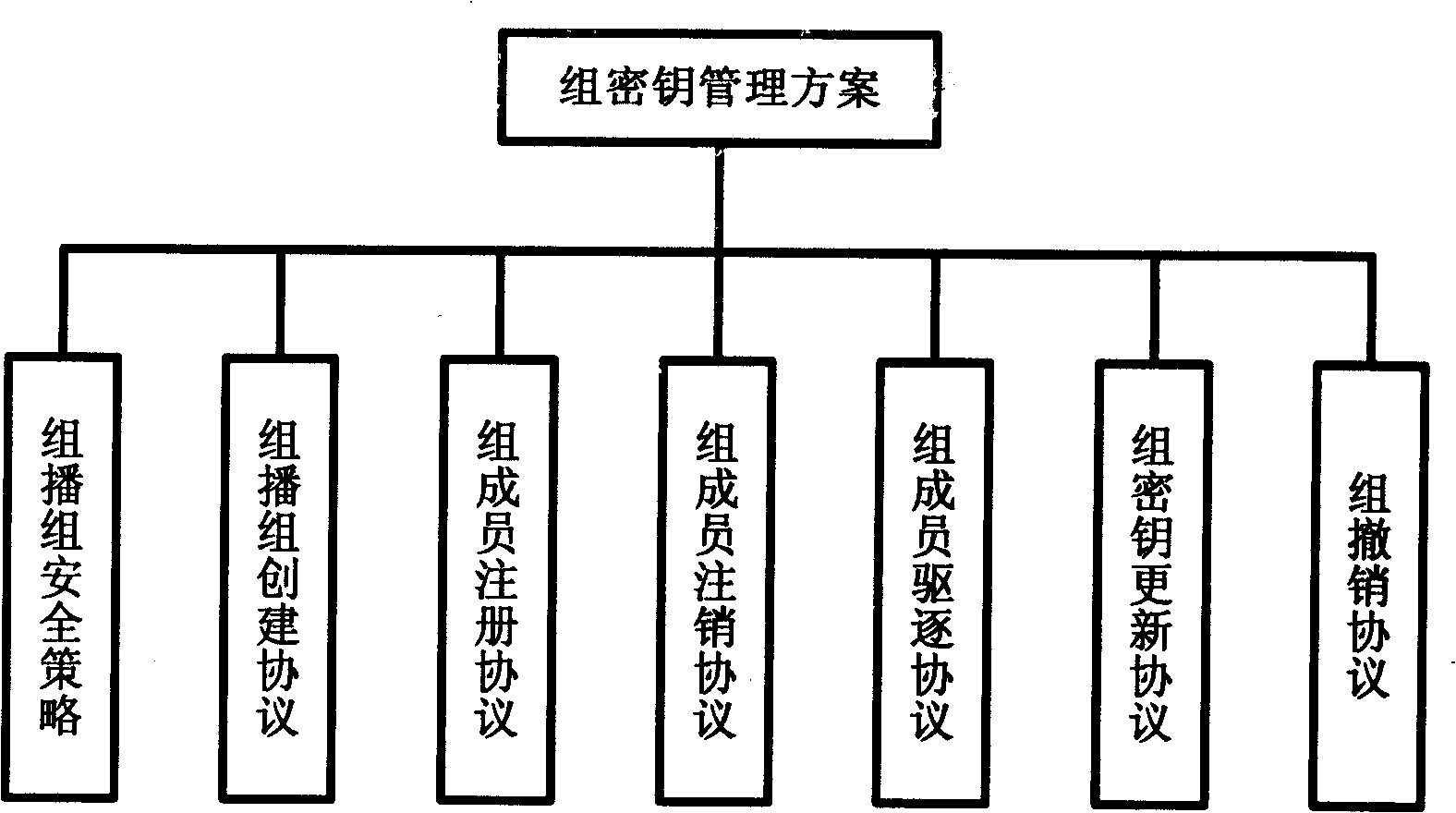
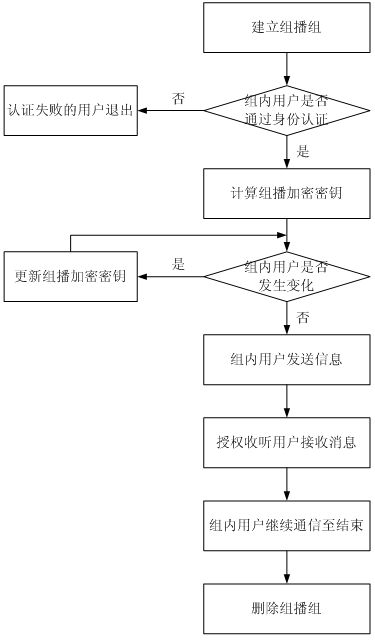
InactiveCN1874224ASolve the requestSolve the statistical billing abilityUser identity/authority verificationSecure communicationMethod selection
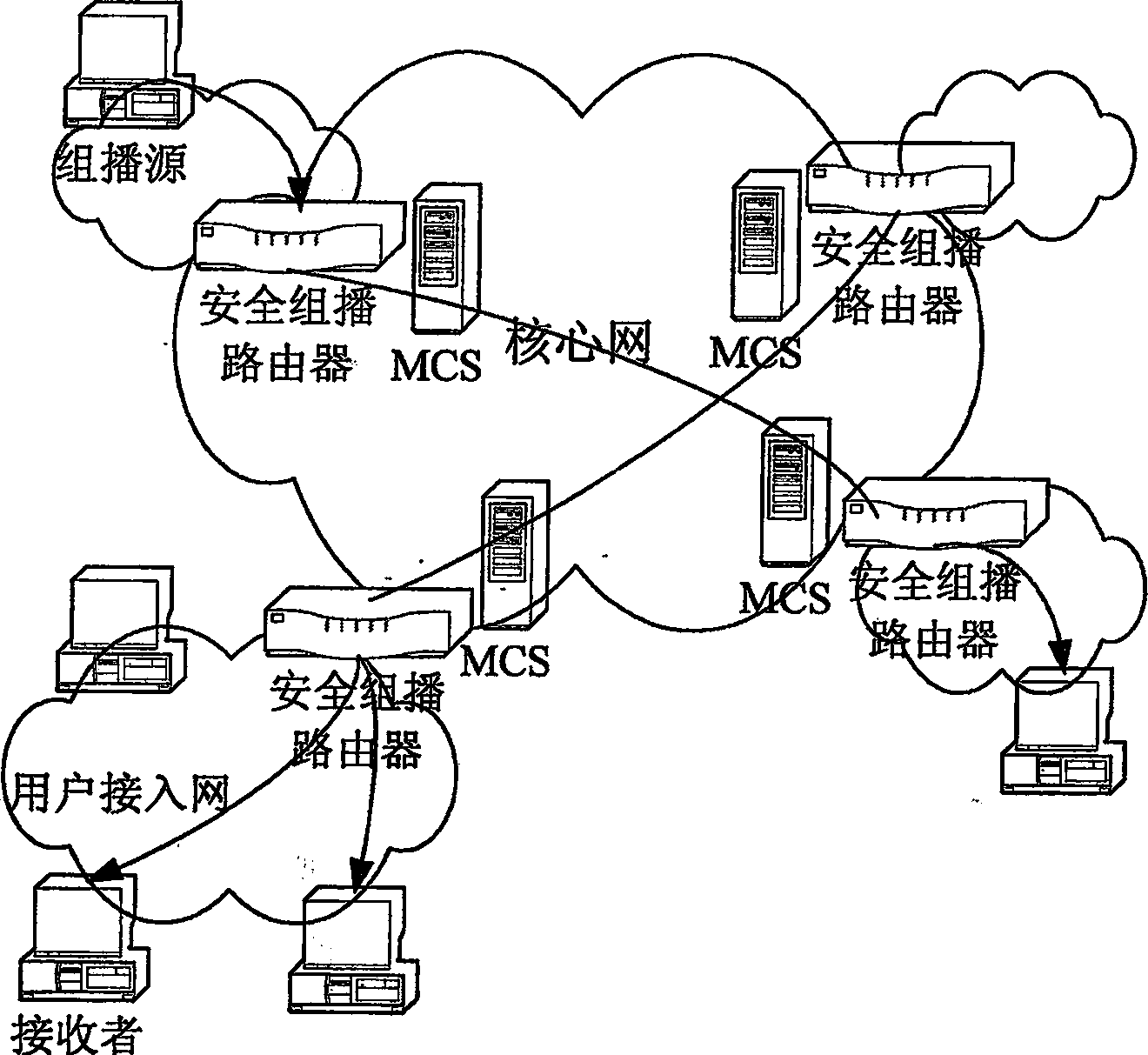
The safe multicast method is a first method of using the protocol of conversation initialization to implement operation of safe multicast. The method presents a set of scheme for solving issue of safe multicast including access control of multicast source, access control for receiver, management of group key, authentication of multicast source, service statistics, and charging capability. The method includes procedures: using route in network to encrypt data of multicast to guarantee access control of service, and safe comm.; method for authenticating multicast source in two stages is adopted; when IGMP / MLD adapter layer implements the method, working mode of traditional multicast route system does not need to be changed; three expansion techniques including cluster of regional multicast control server, regional physical and logical segmentations. The expansibility is suitable to large-scale network environment, and concurrent use. The invention does not change core network.
Owner:SOUTHEAST UNIV
MIPv6 based security multicast method and steps
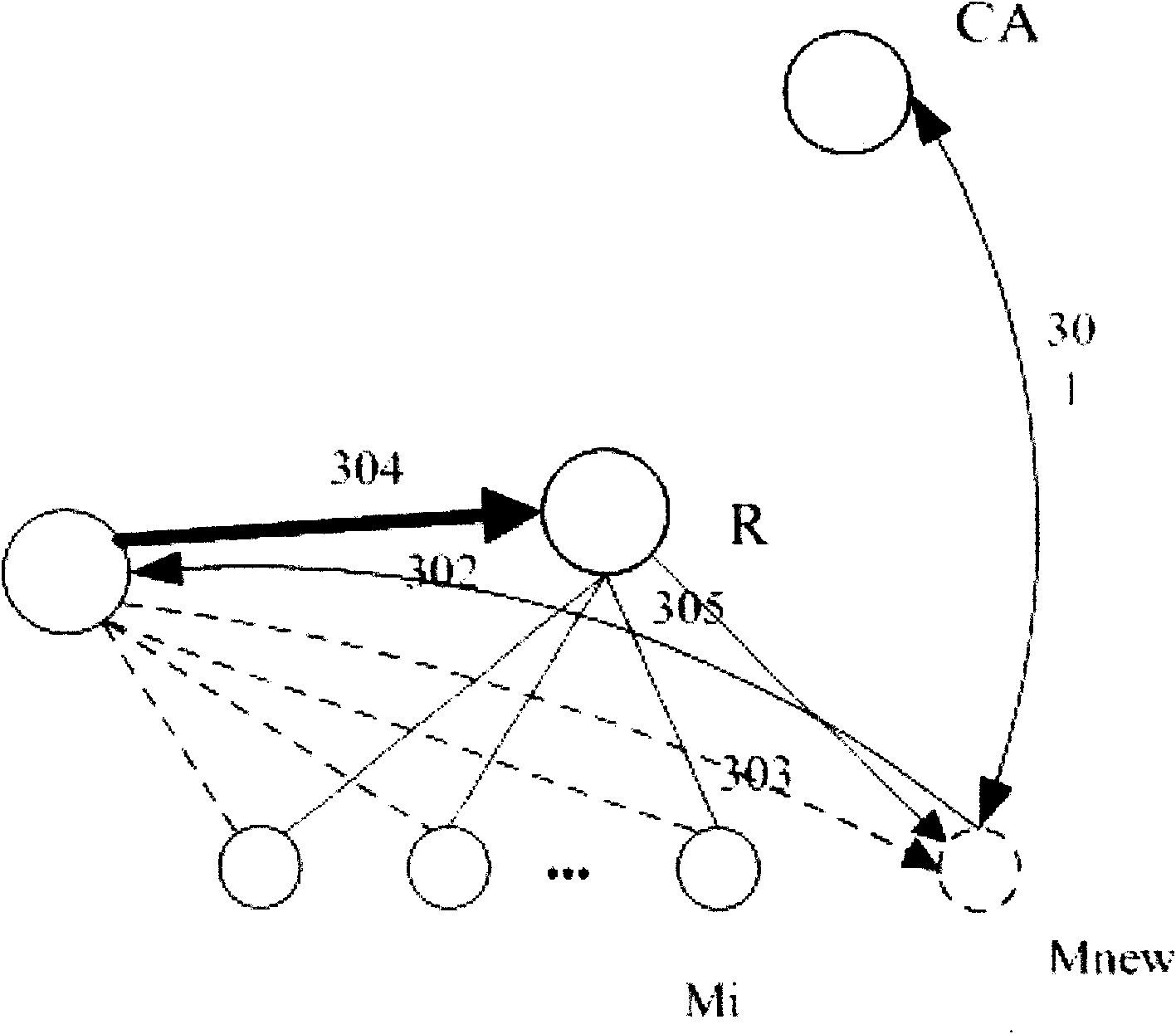
ActiveCN101588235AImprove securityReduce attackSpecial service provision for substationKey distribution for secure communicationSecurity associationNetwork packet
The invention belongs to the field of communication network security, and relates to an MIPv6 based security multicast method applied to a mobile communication network, which is characterized in that: the method comprises an authentication center 1, a group member 2, a multicast source 3 and GCKS 4, wherein the authentication center is used for authenticating the group member, the multicast source and the GCSK and distributing certificates; the GCKS is used for authenticating access registration and distributing key update messages for the group member to forward an information list of the group member 2 to an access router, is used for performing security association negotiation with the multicast source, and is used for negotiating and constructing a group key among GCKS; the multicast source 3 is used for sending a multicast data packet to the group member 2 through an intermediate router; and the group member 2 is used for acquiring the multicast data packet. The method makes that the security multicast technology can be used for actual multicast application become possible, improves the security of multicast communication, separates functions of the GCKS and the router, and can well avoid the problem of single point of failure to improve the multicast management efficiency obviously.
Owner:XIDIAN UNIV
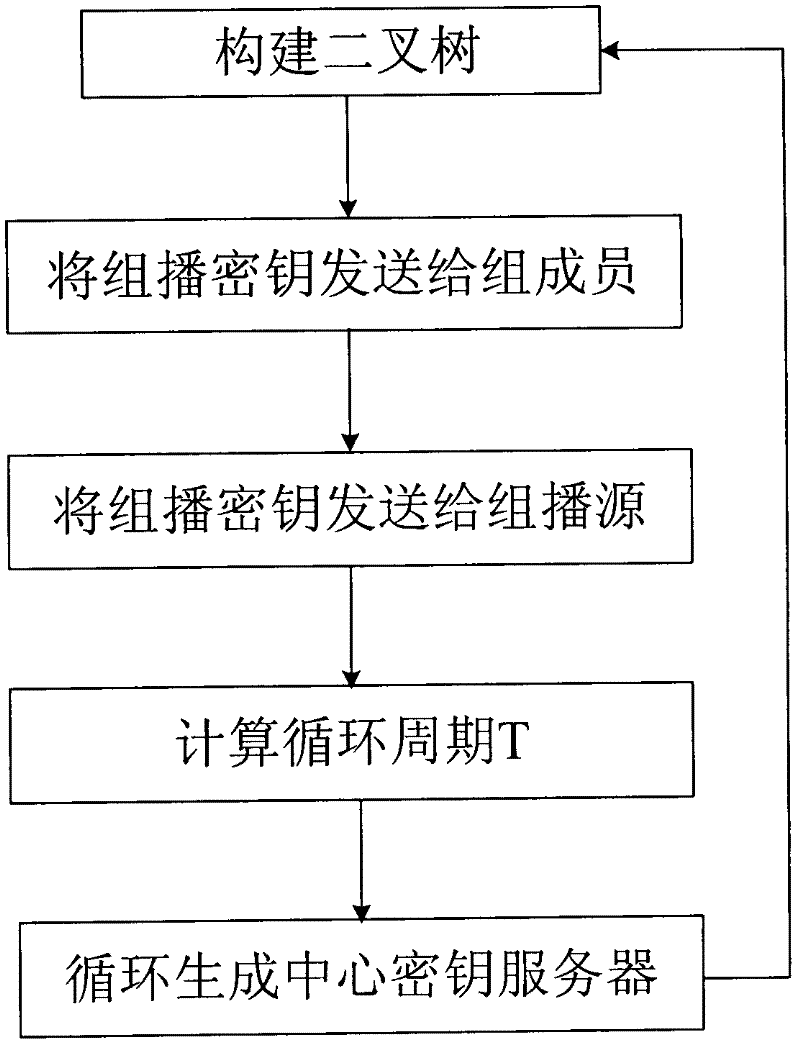
Safe multicast key management method based on MIPv6 (Mobile Internet Protocol version 6)
InactiveCN102413465AImprove update efficiencyAvoid single point of failureSecurity arrangementSecure multicastMobile context
The invention discloses a safe multicast key management method based on MIPv6 (Mobile Internet Protocol version 6), which overcomes the problem that the prior art cannot process a frequent change of members under a mobile environment. In the method provided by the invention, a distribution type multicast key management method is adopted and a binary tree is periodically constructed by a key server to generate a center key server; the center key server is responsible for generating group keys and safely distributing the group keys to other key servers; and the group keys are distributed to the members in the group by the other key servers, so that the updating efficiency of the group keys is improved and the communication traffic and the calculation amount are reduced.
Owner:XIDIAN UNIV
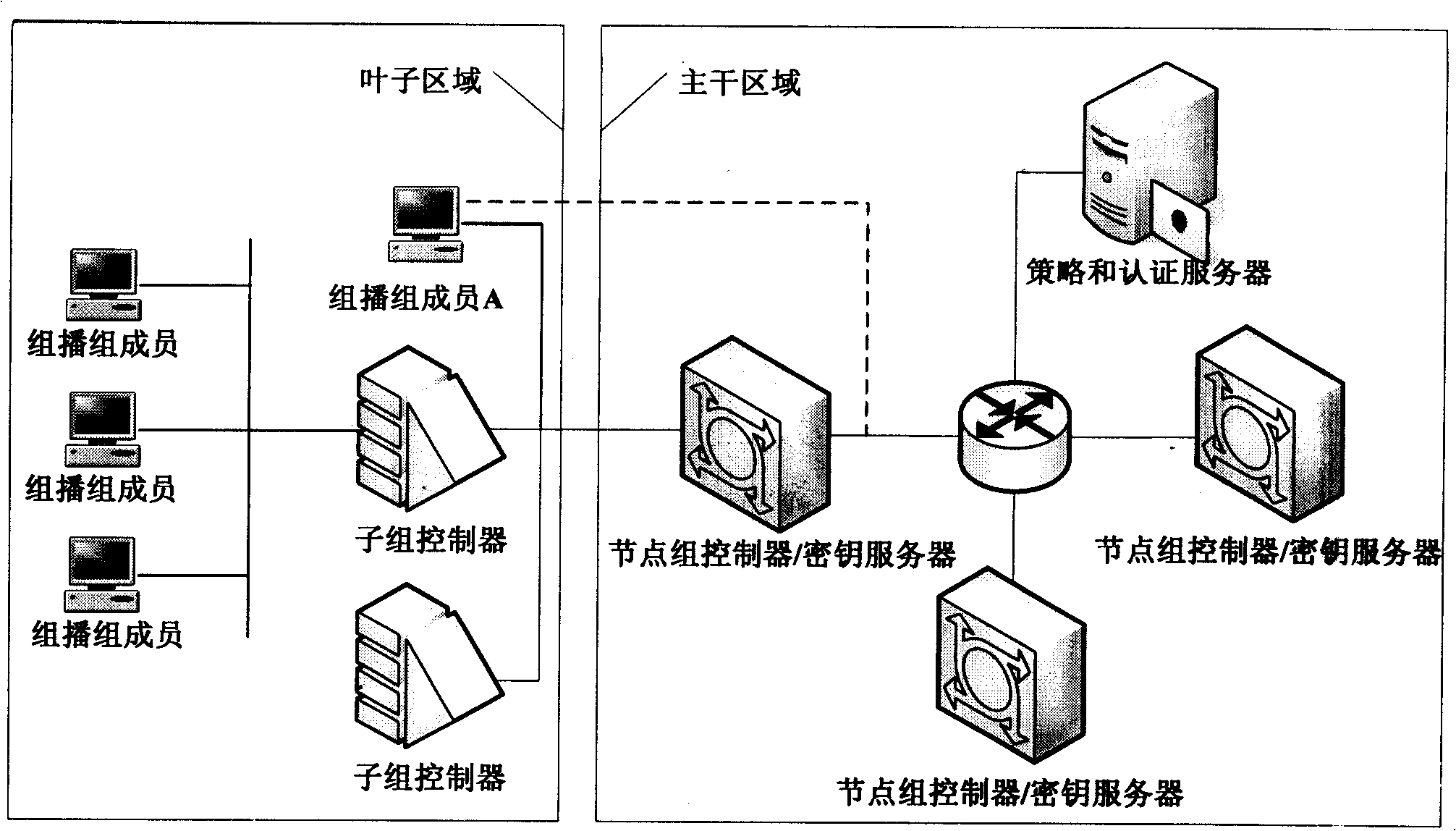
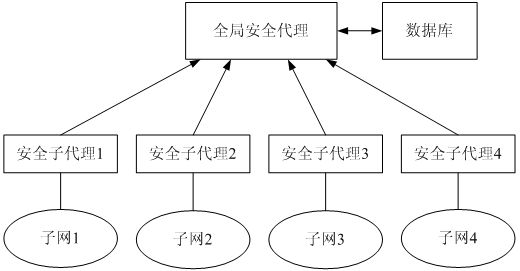
Design of large-scale dynamic multicasting security system framework
InactiveCN101286838AMeet performance requirementsMeet application requirementsSpecial service provision for substationKey distribution for secure communicationViewpointsSecure multicast
The invention relates to a dynamic secure multicast system architecture in large-scale network environment, which is characterized in that a new set of dynamic secure multicast system architecture is designed; the dynamic secure multicast system architecture divides whole multicast into different areas, only updates the encryption key of a group after the members of each group are changed, avoids system expense brought by the update of the encryption key of whole group caused by frequent changes of group members, realizes the flexible extension mechanism with respect to the encryption key management and data distribution of each subarea, realizes the safe certification mechanism based on Kerberos, so as to carry out management of multicast from the viewpoints of controlling safety and data safety. According to the characteristics and requirements of IPv6 protocol, a set of relatively complete group encryption key management mechanism is realized to be applicable to the requirement for safety and practicability of most multicasts in China Education and Research NET of second generation (CERNET2) and similar network environments.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Group broadcast cipher key managing method based on physical layer
InactiveCN1716853AReduce overheadEfficient managementSpecial service provision for substationMultiple keys/algorithms usageExtensibilityMulticast network
The present invention discloses a kind of managing method for group transmission key secret code based on the physical levels of group transmission network. It relates to internet safety group transmission field, which is used as a means for graduating subgroup, group transmission key secret code administration and group transmission communication in the group transmission service, thus reducing the expenses for the renewal of the group key secret code. The source of group transmission uses the local subgroup communication key secret code with the SEK data, transmit it to the physical subgroup; and after the local physical subgroup of the group safety agent has received, deciphered it, then it uses the communication key secret code with enciphered data of the logical subgroup to transmit it to other physical subgroups, and the other physical subgroups of the group safety agents, having received it, use the logical subgroup communication key secret code with encryption group to transmit it to the group transmitting receivers of the physical subgroup. The group transmitting receivers use the local transmission key secret code to obtain data through decryption. The invention can effectively divide the subgroups and resolve the problem of the key secret code administration of the safety group transmission, thus reducing the expenses for the renewal of the group transmission key secret code without limitation to scope and with favorable expansion.
Owner:UNIV OF SCI & TECH OF CHINA
Multicast service load sharing method and system and video live broadcast system
ActiveCN109962800AEasy to useAvoid influenceData switching networksStructure of Management InformationTranscoding
The invention provides a multicast service load sharing method, a multicast service load sharing system and a video live broadcast system. The method comprises the following steps of: respectively setting a first multicast transcoding server, a first convergence point RP, a second multicast transcoding server and a second convergence point RP in two areas; wherein the first RP synchronizes the multicast stream to the second RP, and the first multicast transcoding server and the second multicast transcoding server respectively transcode the multicast stream and respectively send the transcodedmulticast stream to the first RP and the second RP for registration for providing live broadcast service. The invention discloses a method, a system and a video live broadcast system. By setting a networking structure of the double RPs and the multicast transcoding server remotely and carrying out related data configuration, faults of the multicast transcoding server or the RPs can be prevented from influencing users of the whole network, and meanwhile, remote nodes can realize mutual hot standby, so that the effect of remote disaster recovery can be achieved, and the use experience of the users can be improved.
Owner:CHINA TELECOM CORP LTD
Multicast security agent assembly and multicast encryption management method
InactiveCN102684875AEnsure safetyMulticast Security GuaranteeSpecial service provision for substationKey distribution for secure communicationAttackEngineering
The invention relates to a multicast security agent assembly and a multicast encryption management method. File encryption and decryption submodules in a multicast module serve as specific execution modules for multicast users to encrypt / decrypt messages or files, an RSA (Rivest-Shamir-Adleman) algorithm is adopted as a multicast encryption / decryption algorithm, and private keys of the users are taken as decryption keys. After system authentication, if some users in an intranet need intra-group communication, a group key formed by a product of the private keys of all the members can ensure multicast security; and when new users participate in the intranet or the old users exit the intranet, the new users can not access communication contents before accessing and the exited users can not access the communication contents after exiting through updating the group key, therefore, the functions of encryption with one key and decryption with multiple keys in a multicast group are realized. When group members change, the keys (namely the private keys) of the other users in the group do not need to be updated, thereby realizing the encryption on the multicast information, and achieving important forward secrecy, backward secrecy, inner attack resistance and the like in security multicast.
Owner:HENAN UNIV OF SCI & TECH
Systems and methods for providing secure multicast intra-cluster communication
ActiveUS20140245390A1Easy to joinAvoid configurationDigital data processing detailsMultiple digital computer combinationsCommunications systemSecure multicast
Systems and methods which facilitate secure multicast communications between any valid node of a cluster using authentication between a node joining the cluster and any single node which is validly part of the cluster are disclosed. In accordance with embodiments, a cluster key is utilized to provide security with respect to intra-cluster communications. The cluster key of embodiments is shared by a node which is already part of the cluster with a node joining the cluster only after these two nodes mutually authenticate one another. The mutual authentication handshake of embodiments implements a protocol in which a session key is calculated by both nodes, thereby providing a secure means by which a cluster key may be shared. Having the cluster key, each node of the cluster is enabled to securely communicate with any other node of the cluster, whether individually (e.g., unicast) or collectively (e.g., multicast), according to embodiments.
Owner:NETWORK APPLIANCE INC
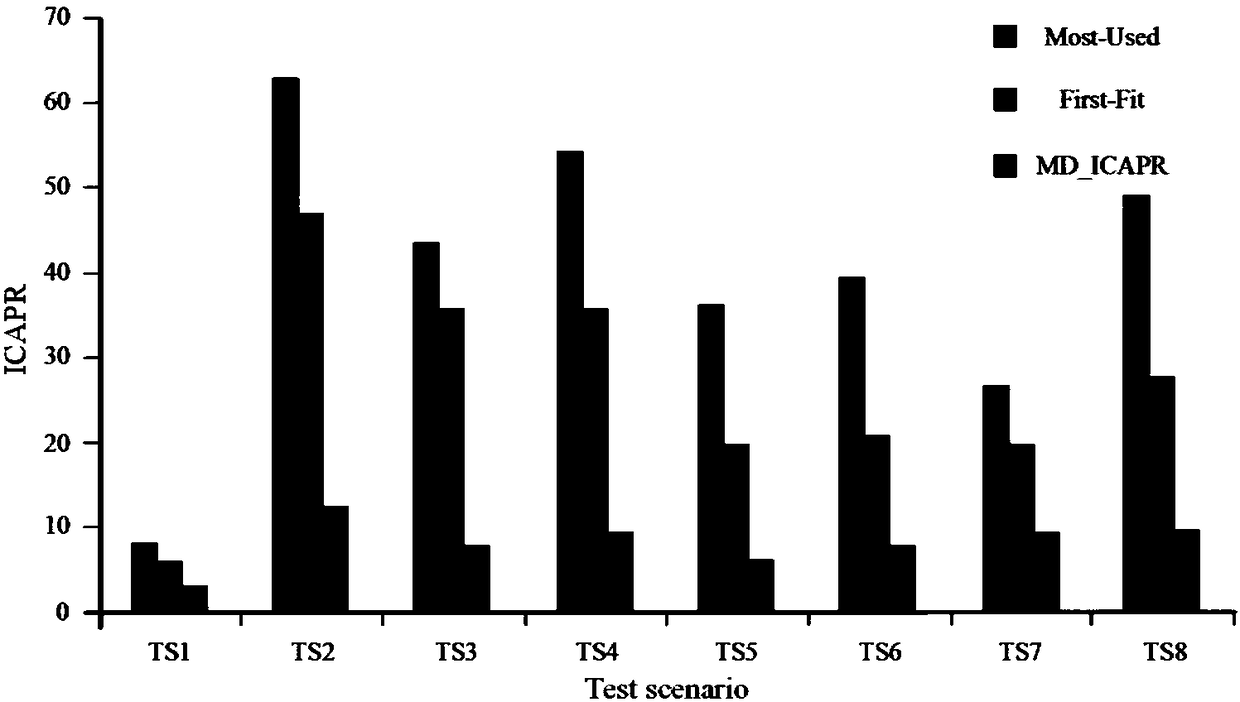
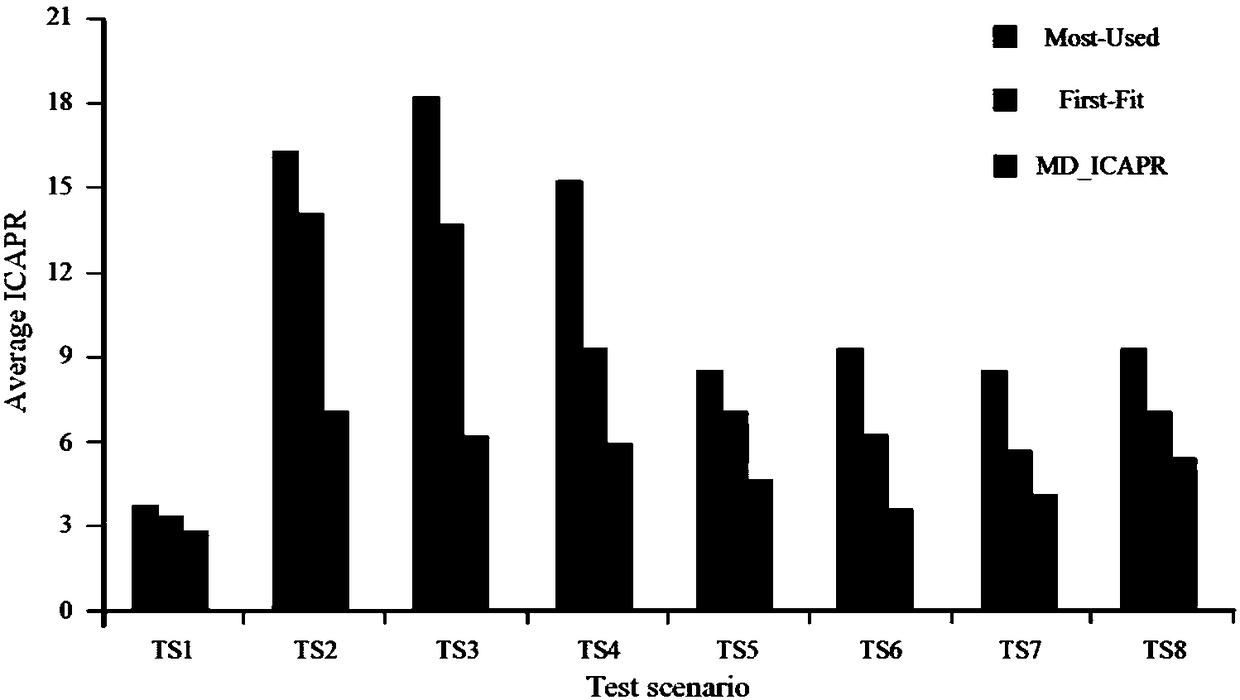
Multi-domain optical network secure multicast wavelength distribution method and system
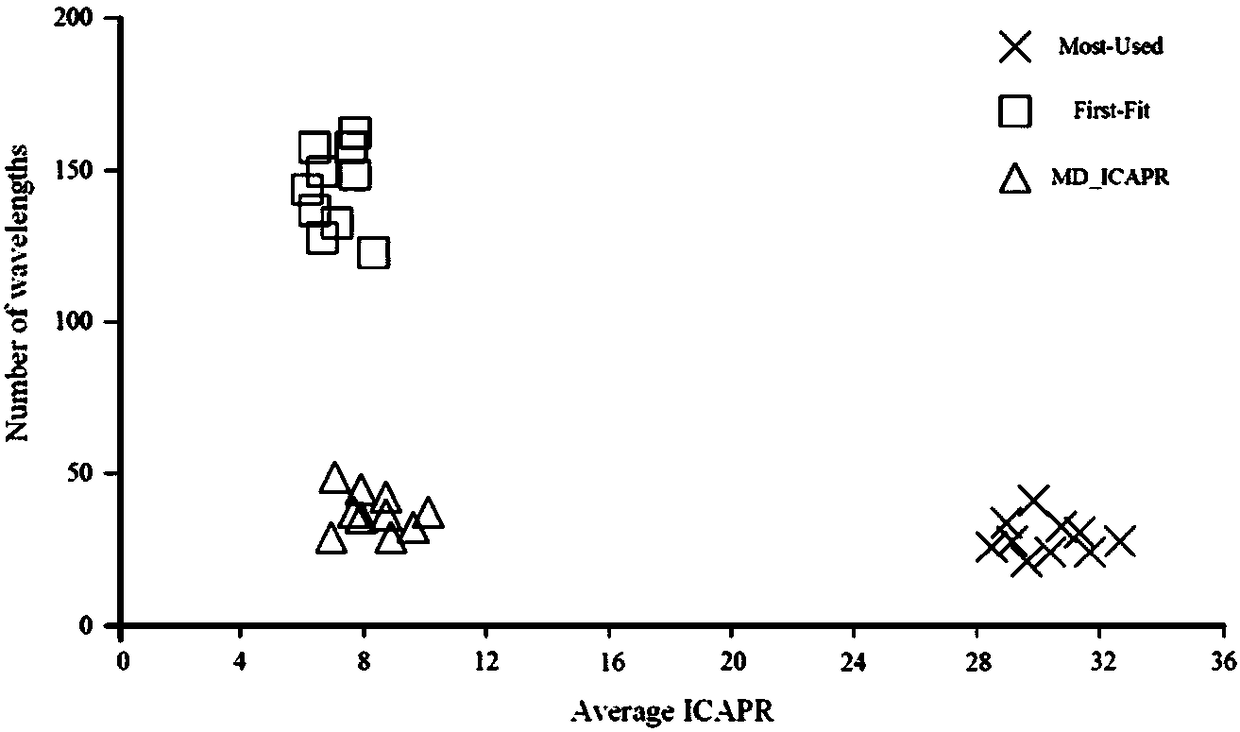
ActiveCN108260033AImprove securityReduce connection blocking rateMultiplex system selection arrangementsWavelength-division multiplex systemsDistribution methodLength wave
The invention discloses a multi-domain optical network secure multicast wavelength distribution method and system. The method comprises the following steps: introducing the concept of in-band crosstalk attack propagation radius ICAPR for quantitatively describing the degree of the worst case of the in-band crosstalk attack propagation of the optical network, and then translating a wavelength distribution problem requested by multiple multicasts into a classical assignment problem on this basis, and solving the problem through a Hungarian method. Through the distribution method disclosed by theinvention, the wavelength distribution scheme with high security can be acquired in the polynomial time, the connection blocking rate can be reduced, and the use ratio of the system wavelength resource is improved.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Systems and methods for providing secure multicast intra-cluster communication
ActiveUS8719571B2Easy to joinAvoid configurationDigital data processing detailsUser identity/authority verificationCommunications systemSecure multicast
Owner:NETWORK APPLIANCE INC
Secure multicast method for overlay network at low expenses
ActiveCN103997463AImprove distribution efficiencyImprove securityData switching networksRound complexitySystem stability
The invention discloses a secure multicast method for an overlay network at low expenses, and relates to the field of data communication technology, in particular to secure and efficient data transmission of the overlay network. A multicast tree is constructed by the adoption of a bottom-up hierarchical clustering strategy, the number of child nodes of a cluster head is reduced so that the complexity of a control algorithm for maintaining the topological relation through all nodes can be a constant, and it is ensured that node expenses cannot be increased along with increase of multicast scale; a self-balancing binary tree algorithm is adopted in a cluster to construct a multicast distribution path, system stability is guaranteed, and meanwhile the probability of data delay is reduced; a secret key distinguishing strategy is adopted during data distribution, different secret key strategies are adopted for the zeroth layer of nodes and the non-zeroth layer of nodes for encryption transmission of data, and data security is guaranteed.
Owner:PLA UNIV OF SCI & TECH
Safety multicast source authentication method based on group data packet coupling
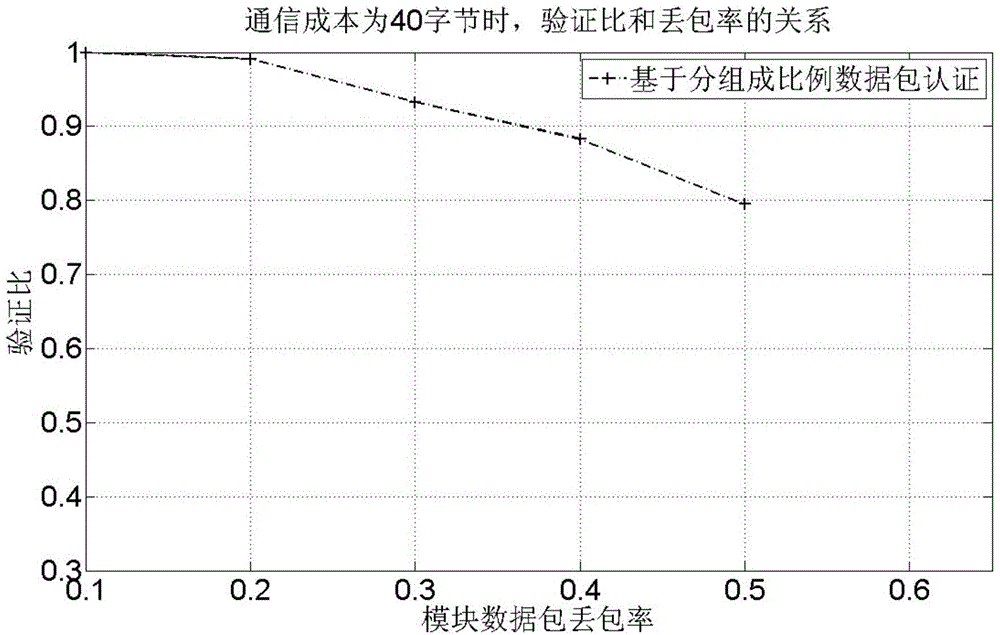
ActiveCN103957102AReduce communication costsReduce computing costUser identity/authority verificationData switching networksComputer hardwarePacket loss
The invention provides a safety multicast source authentication method based on group data packet coupling for solving the disadvantages of overlarge communication cost of a basic Merkle Hash tree source authentication mode. Through dividing a data packet into four groups, intergroup data packets are attached to Hash values, i.e., digest values, and bit packets are arranged. The method provided by the invention can effectively reduce the communication cost and calculation cost which are based on a tree chain source authentication method and ensures that a verification ratio is not greatly decreased. Though an authentication delay which changes correspondingly is generated at a receiving end, multiple threads and multiple data packet can be employed, and at the same time, transmission and authentication are carried out in an orderly mode. Generally speaking, under the condition that a transceiving end channel satisfies a corresponding actual environment and server configuration, the method provided by the invention has the advantages of quite good packet loss resistance robustness and quite low communication cost.
Owner:SOUTHWEAT UNIV OF SCI & TECH
Weak security multicast rate allocation method based on network coding for multimedia data streams
ActiveCN108234326AMaximize secure data transfer throughputMaximize data transfer throughputData switching networksMathematical modelMultimedia data streams
The invention discloses a weak security multicast rate allocation method based on network coding for multimedia data streams. The method comprises the following steps: obtaining a communication network where the multimedia data streams are located and parameters of the multimedia streams thereon, comprising a node set composed of a single server, all routers and a client receiving all data, a directed link set between the nodes in the node set, the capacity of each link, the number of data streams in the multimedia streams, a set of these data streams, and the weight of each data stream; expressing the communication network as a directed graph according to the obtained parameters; establishing a mathematical model of an optimal rate allocation method based on linear programming according to the directed graph; solving the mathematical model; and obtaining the maximum weighted data transmission throughput rate and a corresponding rate allocation scheme, that is, the transmission rate oneach link, of the multimedia stream transmission under a weak security condition. By adoption of the weak secure multicast rate allocation method, malicious intermediate routing nodes where the multimedia data stream transmission path in the multicast communication passes through met the weak security requirements, and the weighted throughput rate of the secure transmission is improved, thereby providing good security and improving the utilization rate of network resources.
Owner:SUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com