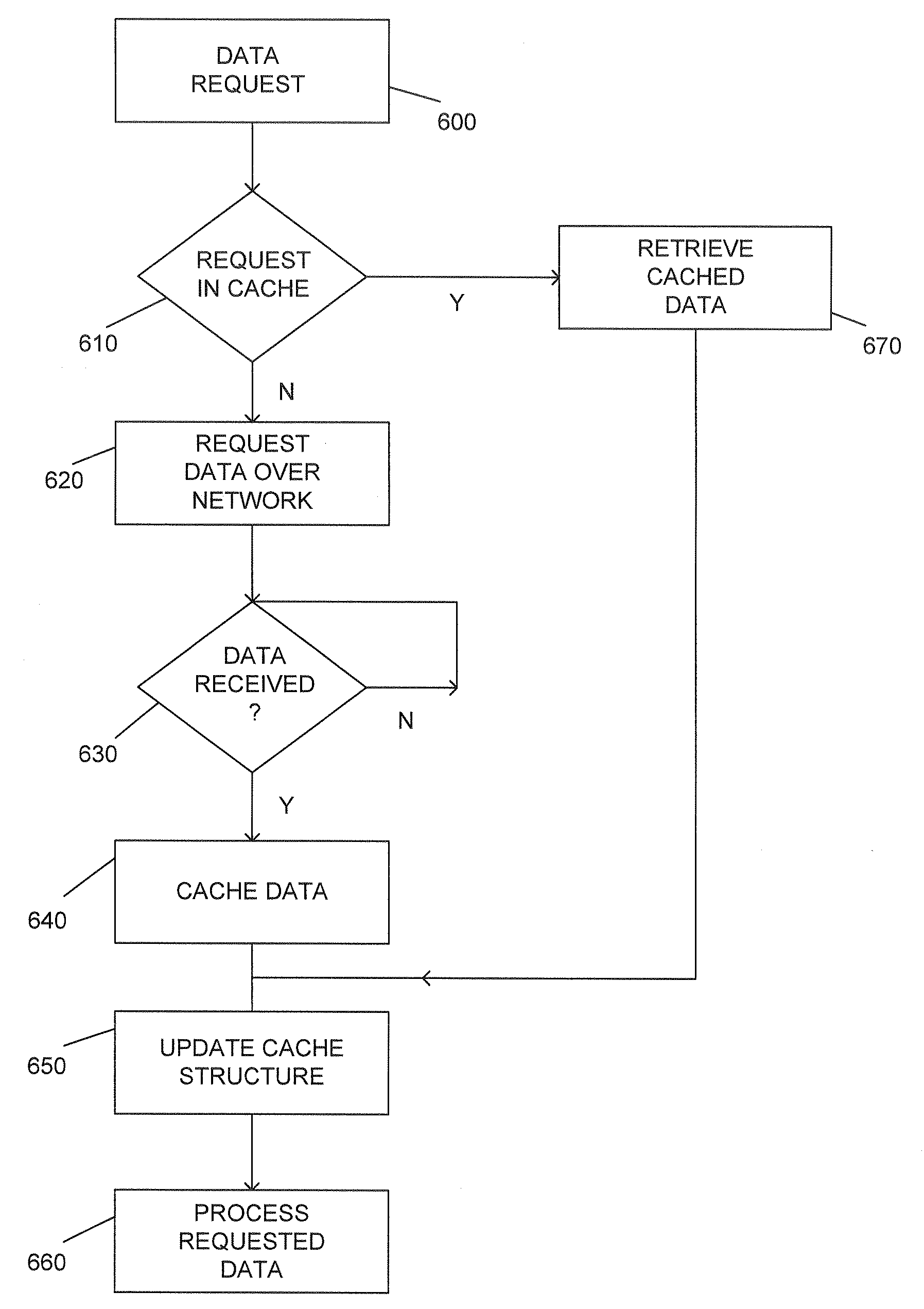
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
503results about How to "Network degradation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
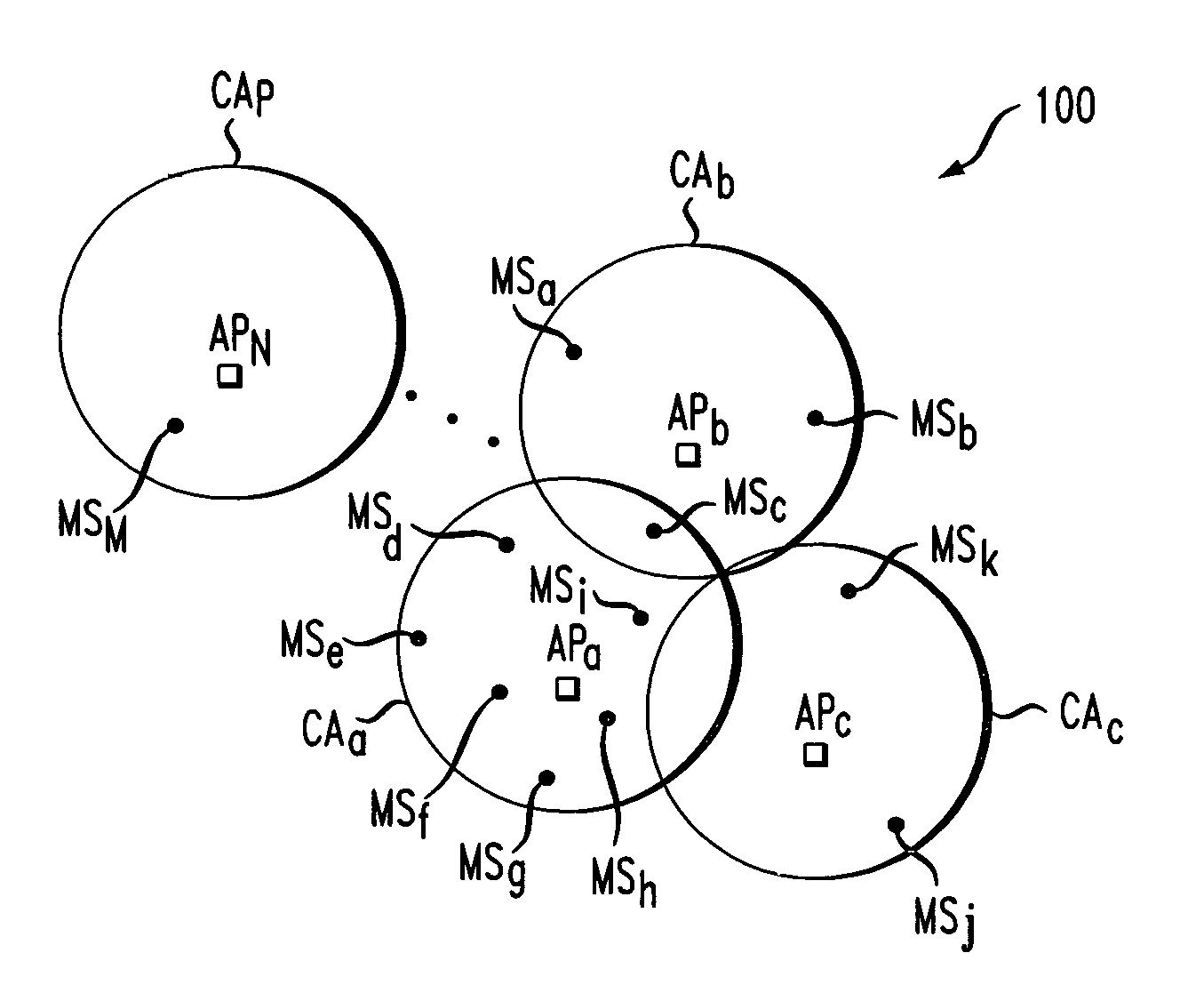
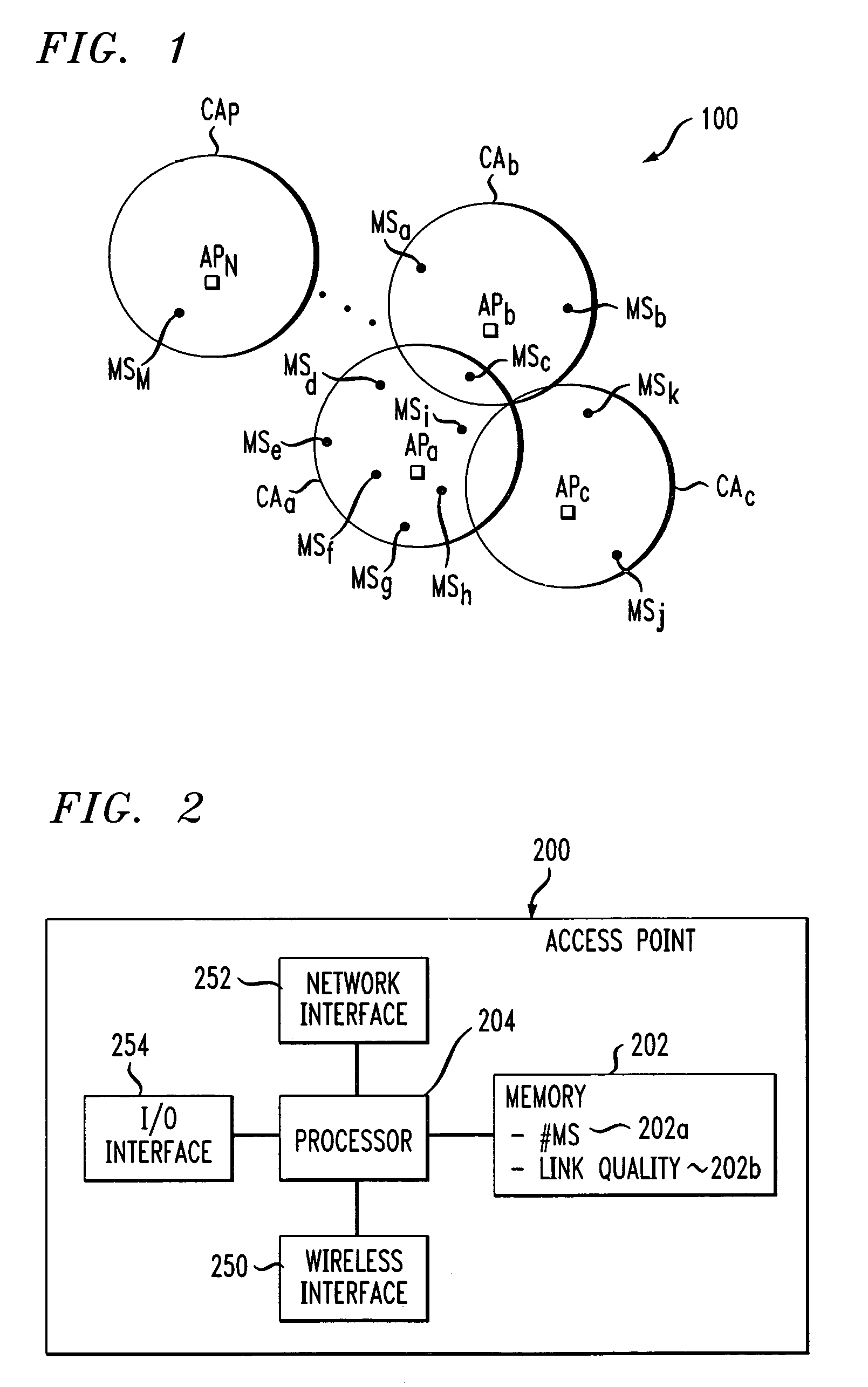
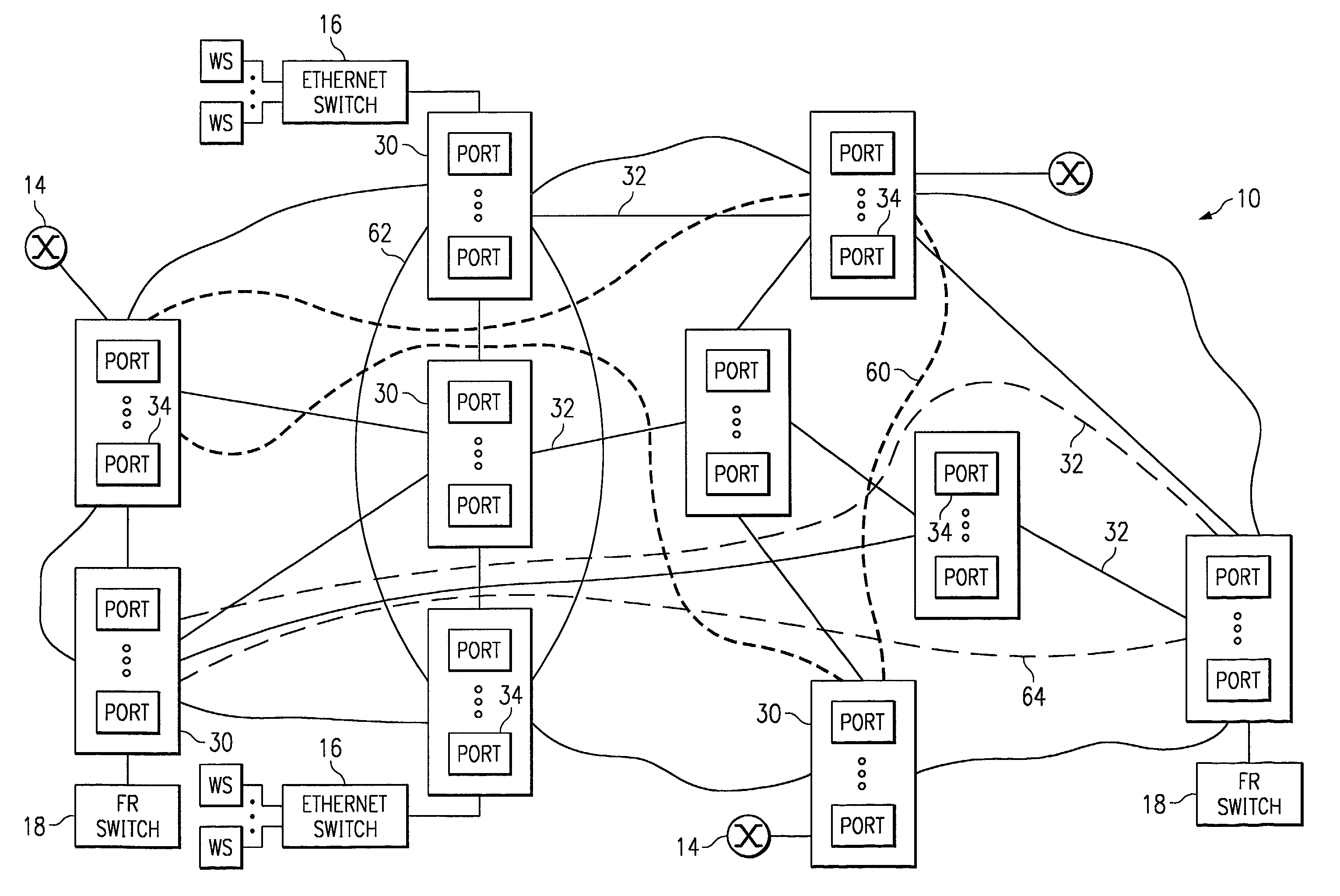
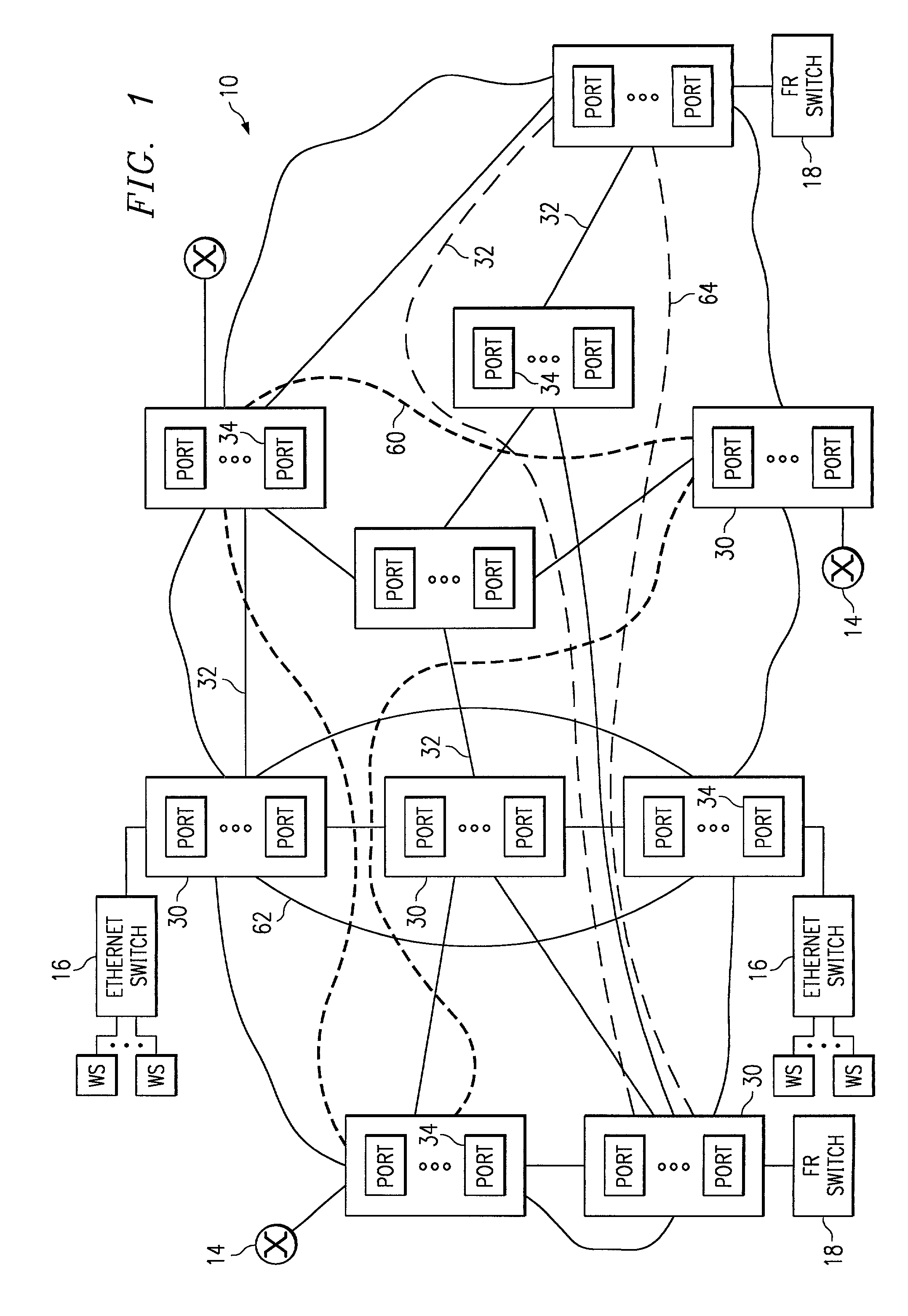
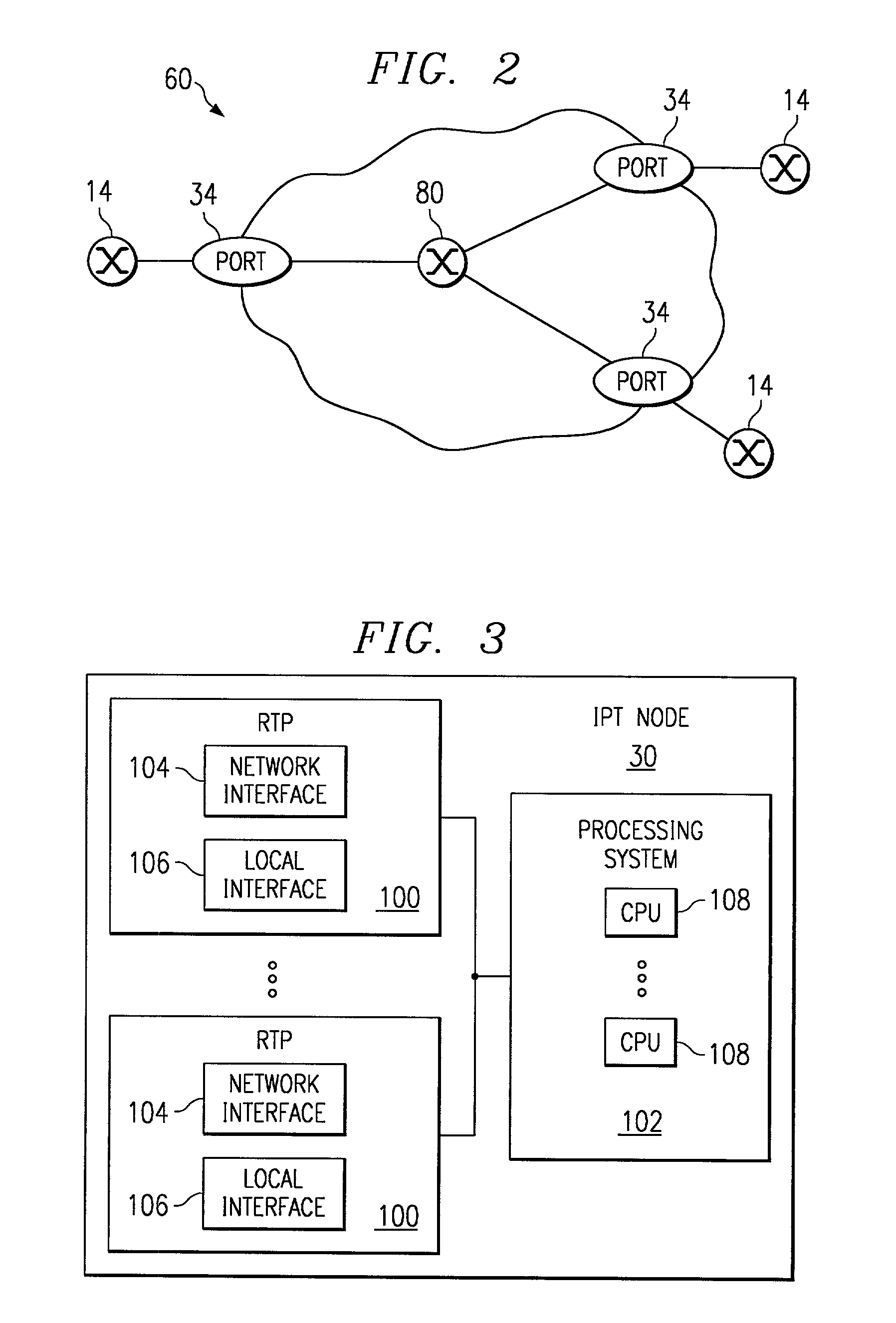
Intrusion detection in a data center environment
ActiveUS20060095968A1Reduce false-positivesGreat granularityError preventionTransmission systemsTraffic volumeIntrusion detection system
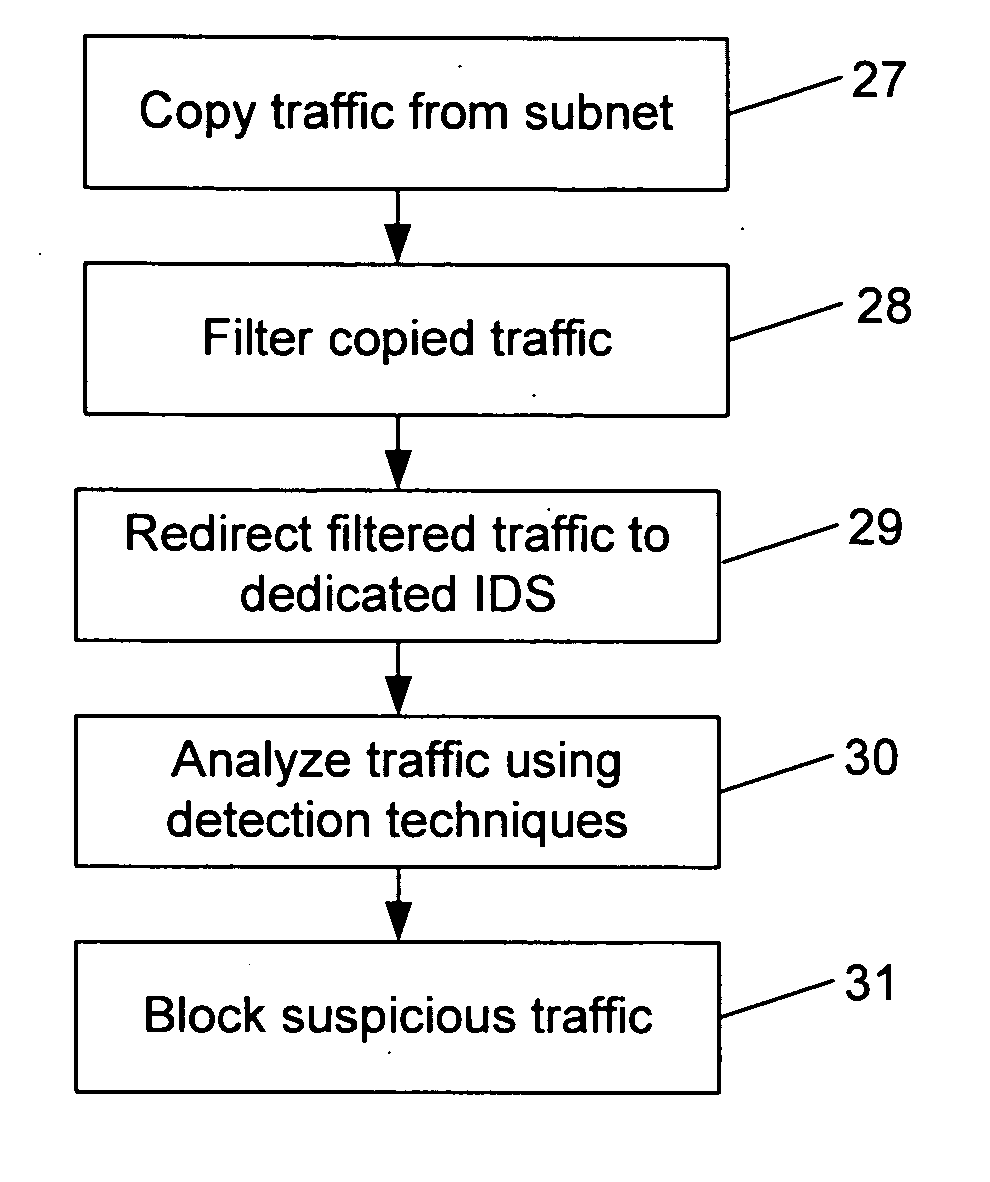
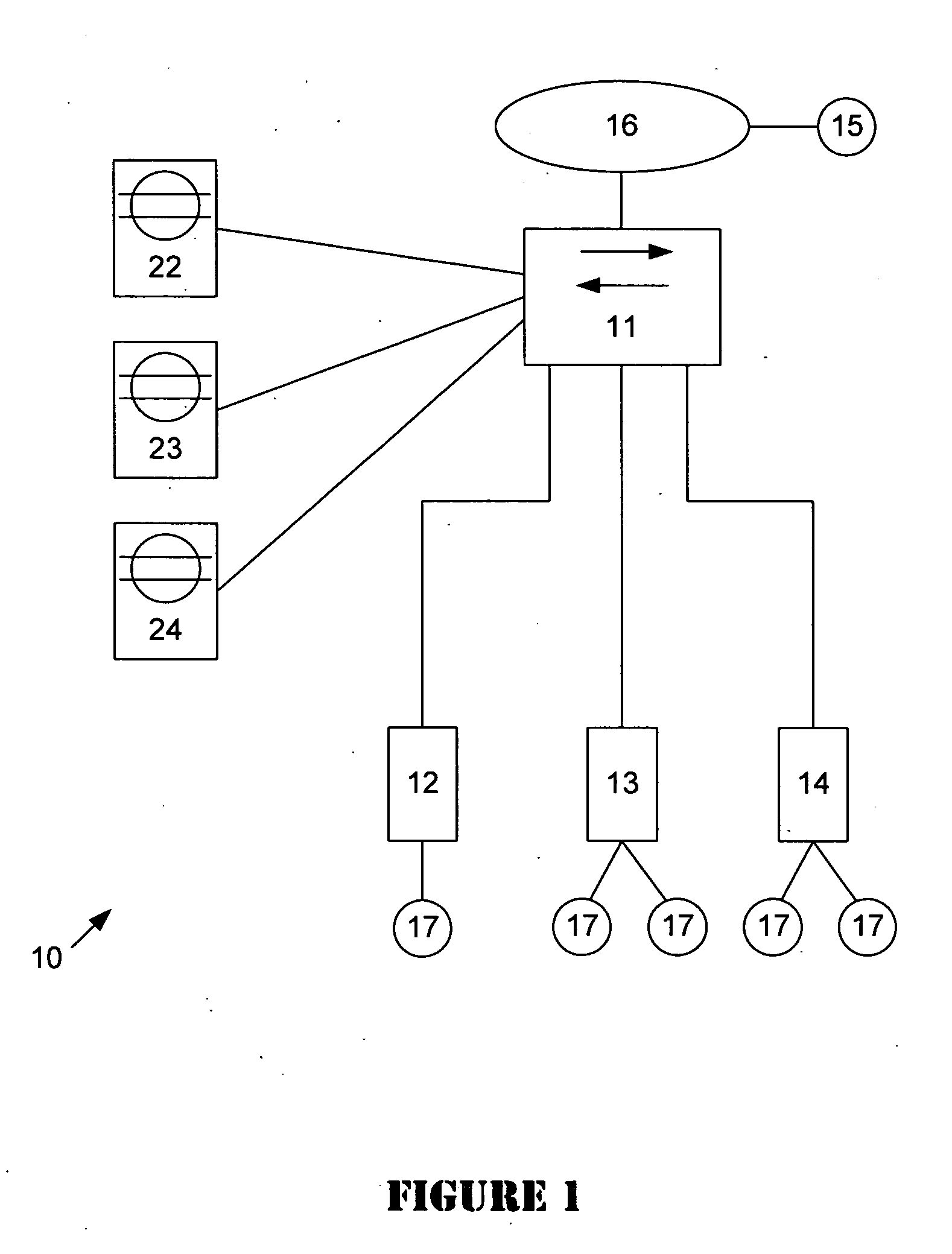
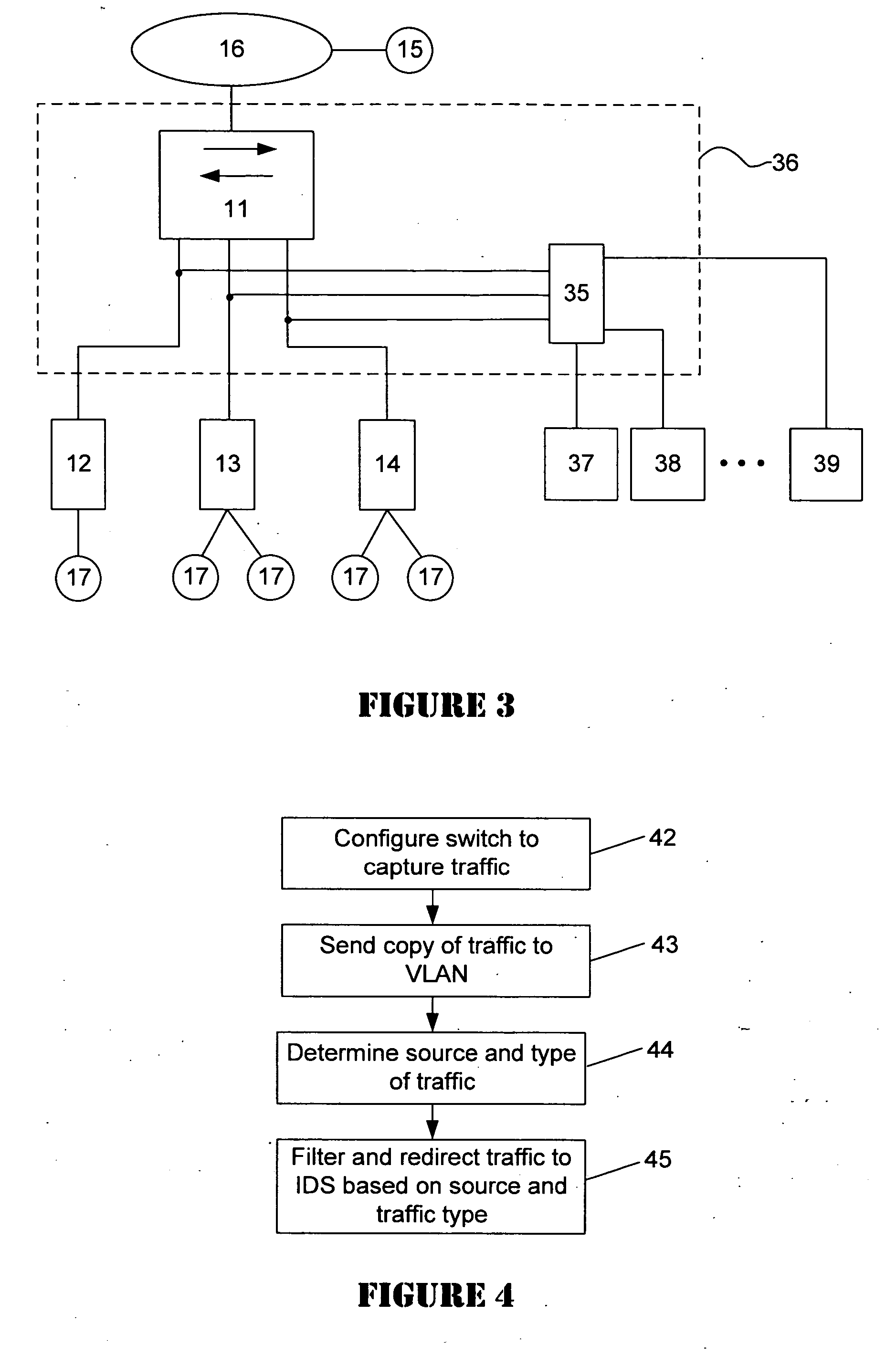
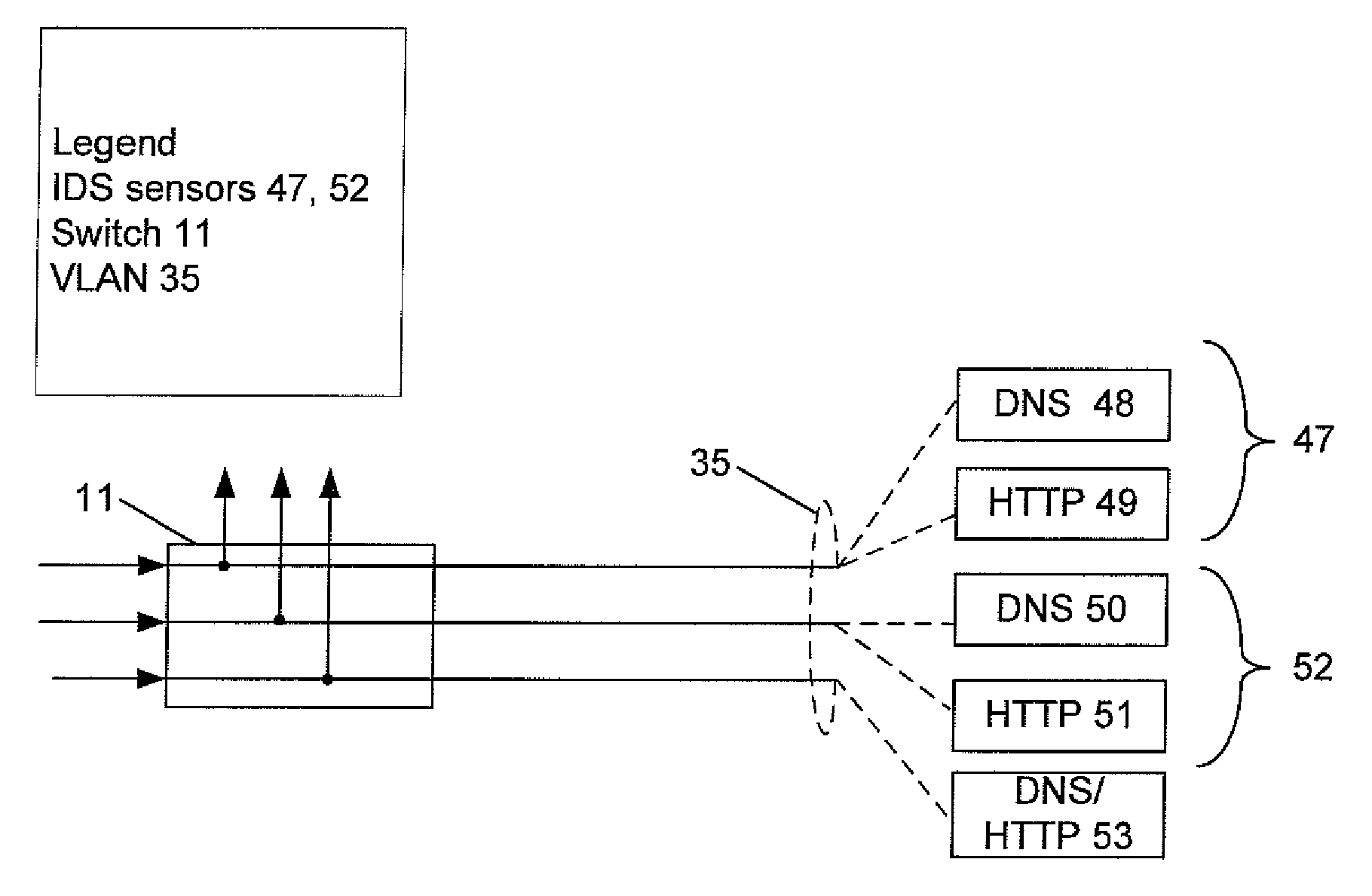
An intrusion detection system (IDS) is capable of identifying the source of traffic, filtering the traffic to classify it as either safe or suspect and then applying sophisticated detection techniques such as stateful pattern recognition, protocol parsing, heuristic detection or anomaly detection either singularly or in combination based on the traffic type. In a network environment, each traffic source is provided with at least one IDS sensor that is dedicated to monitoring a specific type of traffic such as RPC, HTTP, SMTP, DNS, or others. Traffic from each traffic source is filtered to remove known safe traffic to improve efficiency and increase accuracy by keeping each IDS sensor focused on a specific traffic type.
Owner:CISCO TECH INC
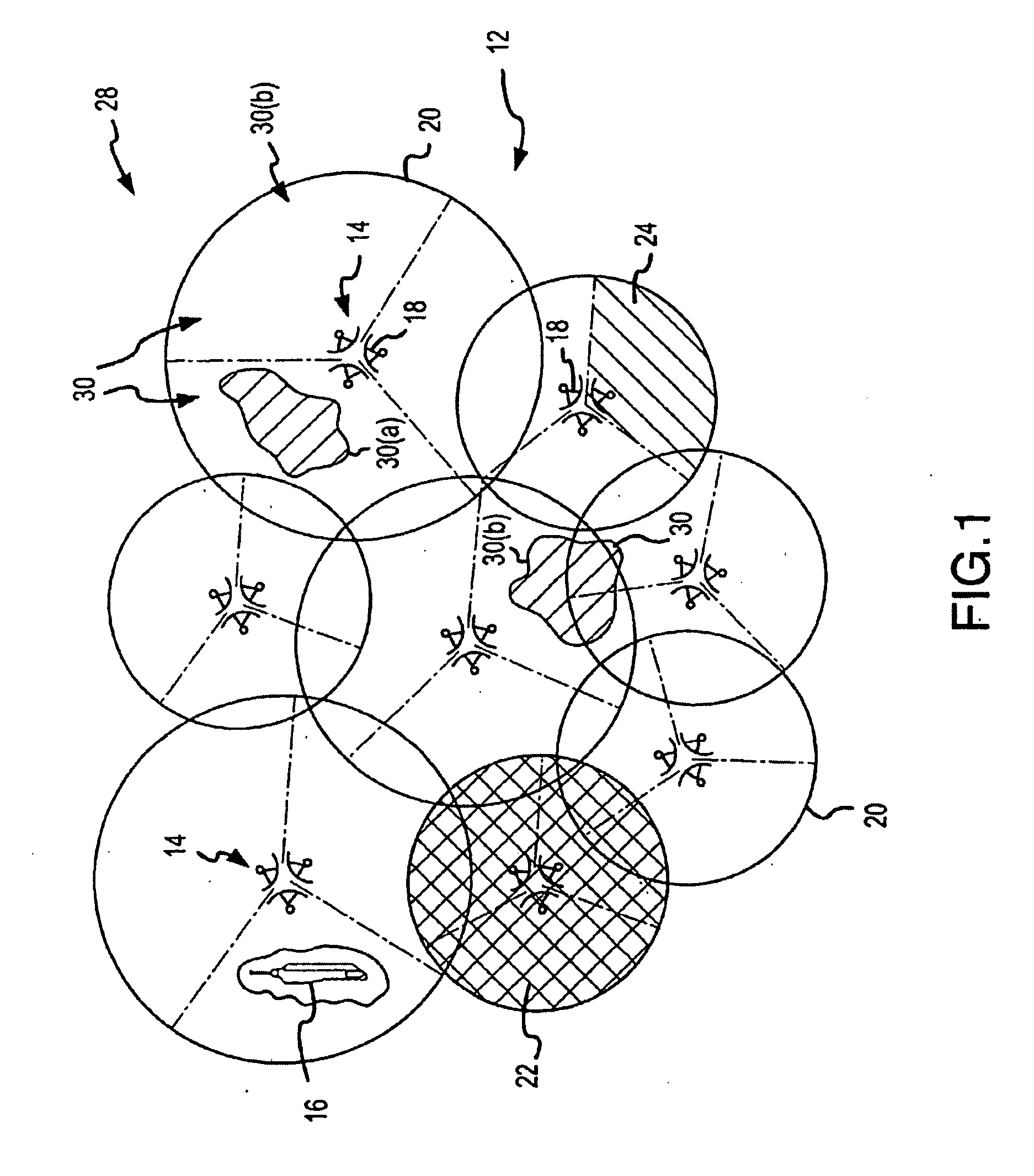
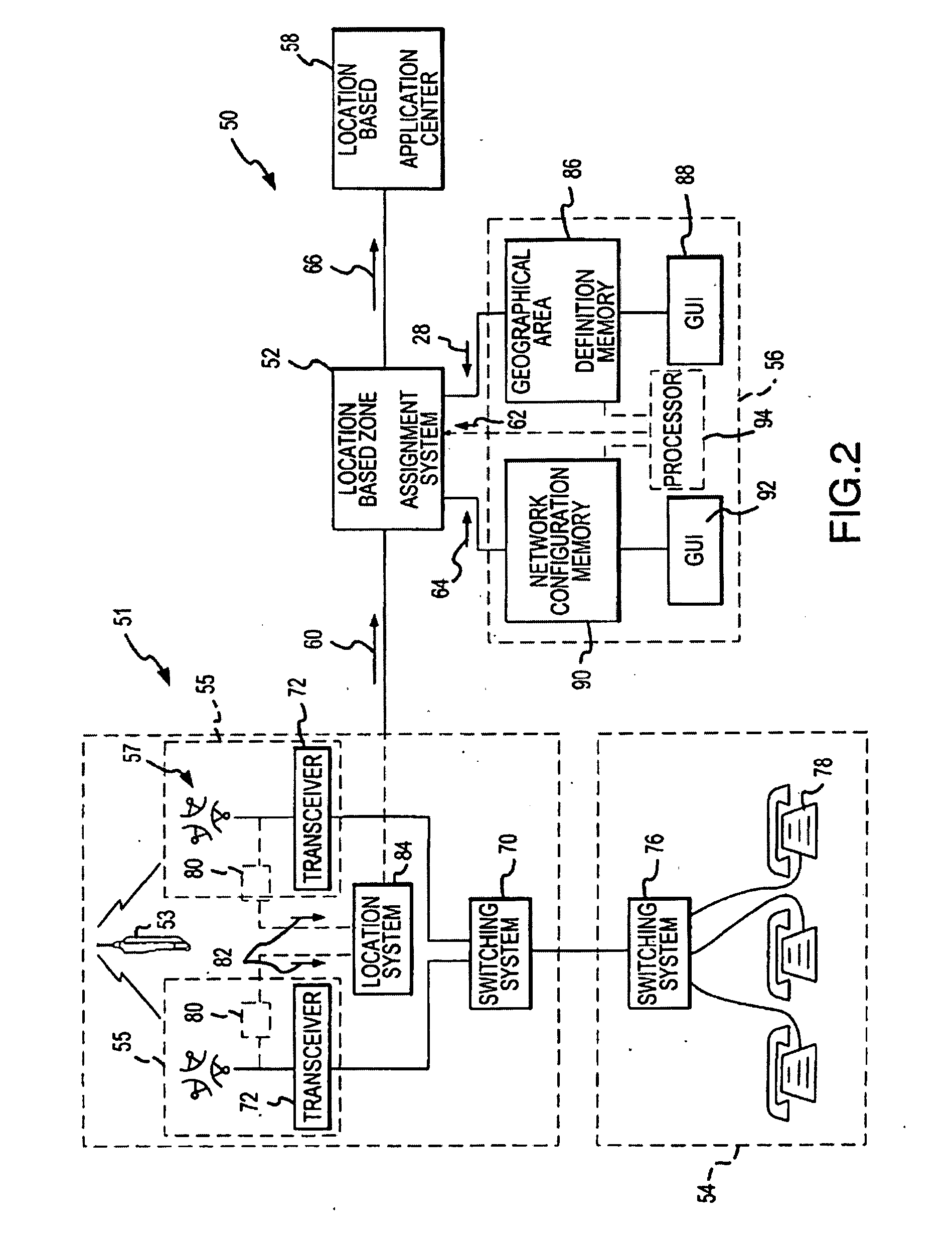
Wireless network with adaptive autonomous location push
InactiveUS20070026871A1Add supportReduce network loadRadio/inductive link selection arrangementsLocation information based serviceSelf adaptiveWireless network
A method of providing location-based services includes transmitting a first location criterion from a wireless network server to a wireless device. The method also includes evaluating whether a physical location of the wireless device satisfies the first location criterion. The process of evaluating is performed in part using the wireless device. When the first location criteria is satisfied, the method further includes transmitting an indication from the wireless device to the server that the first location criterion has been satisfied.
Owner:UNWIRED PLANET
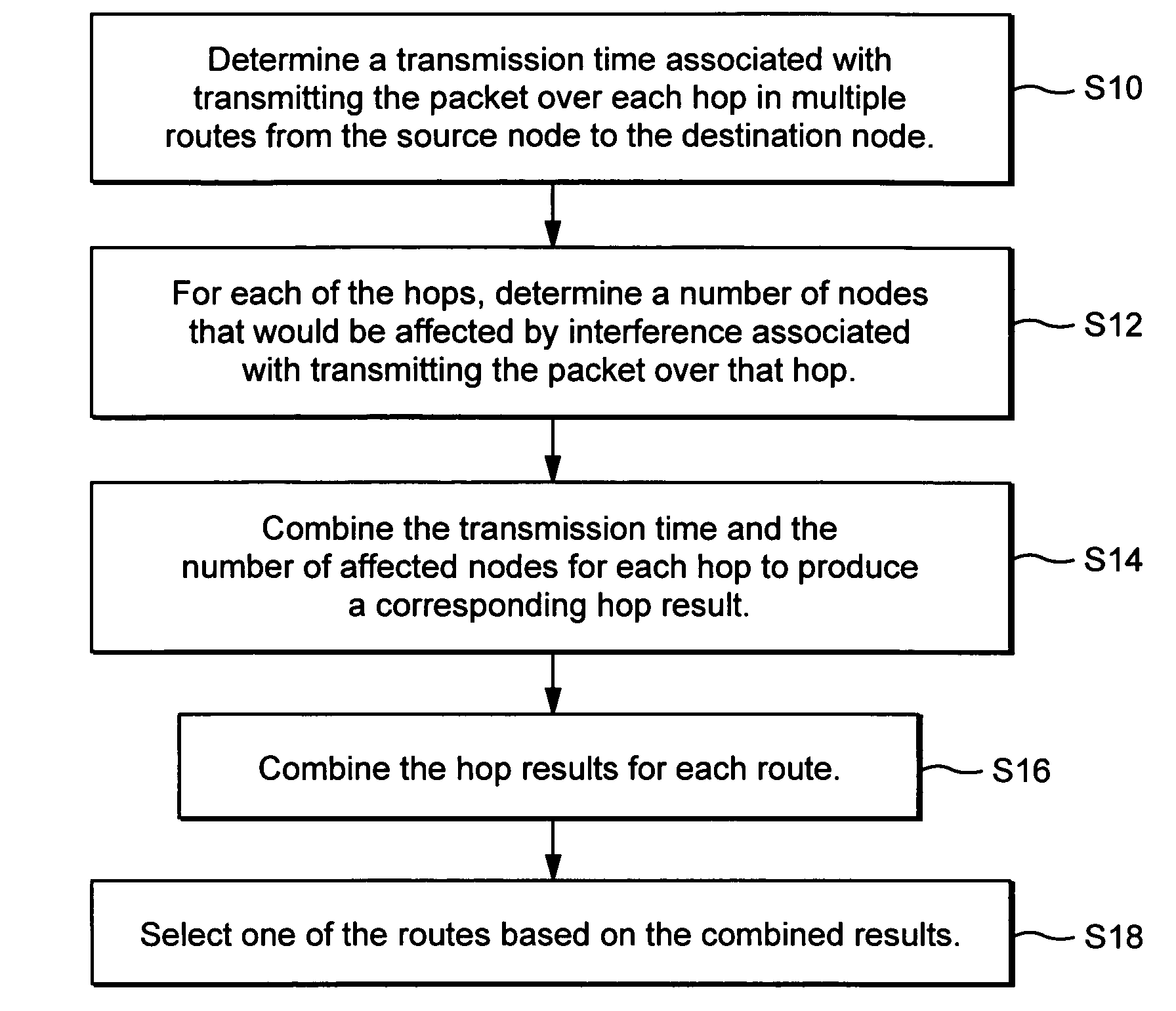
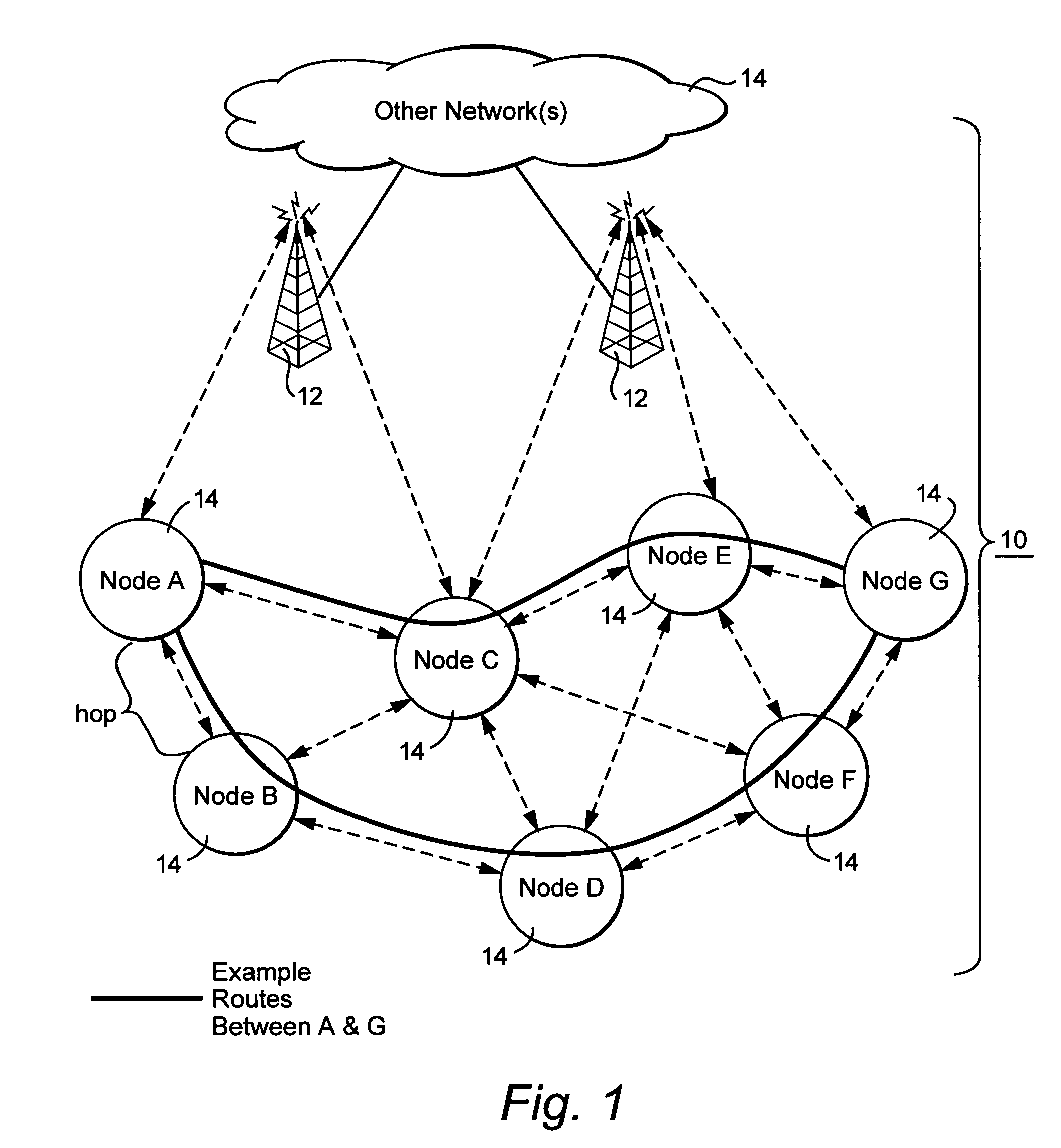
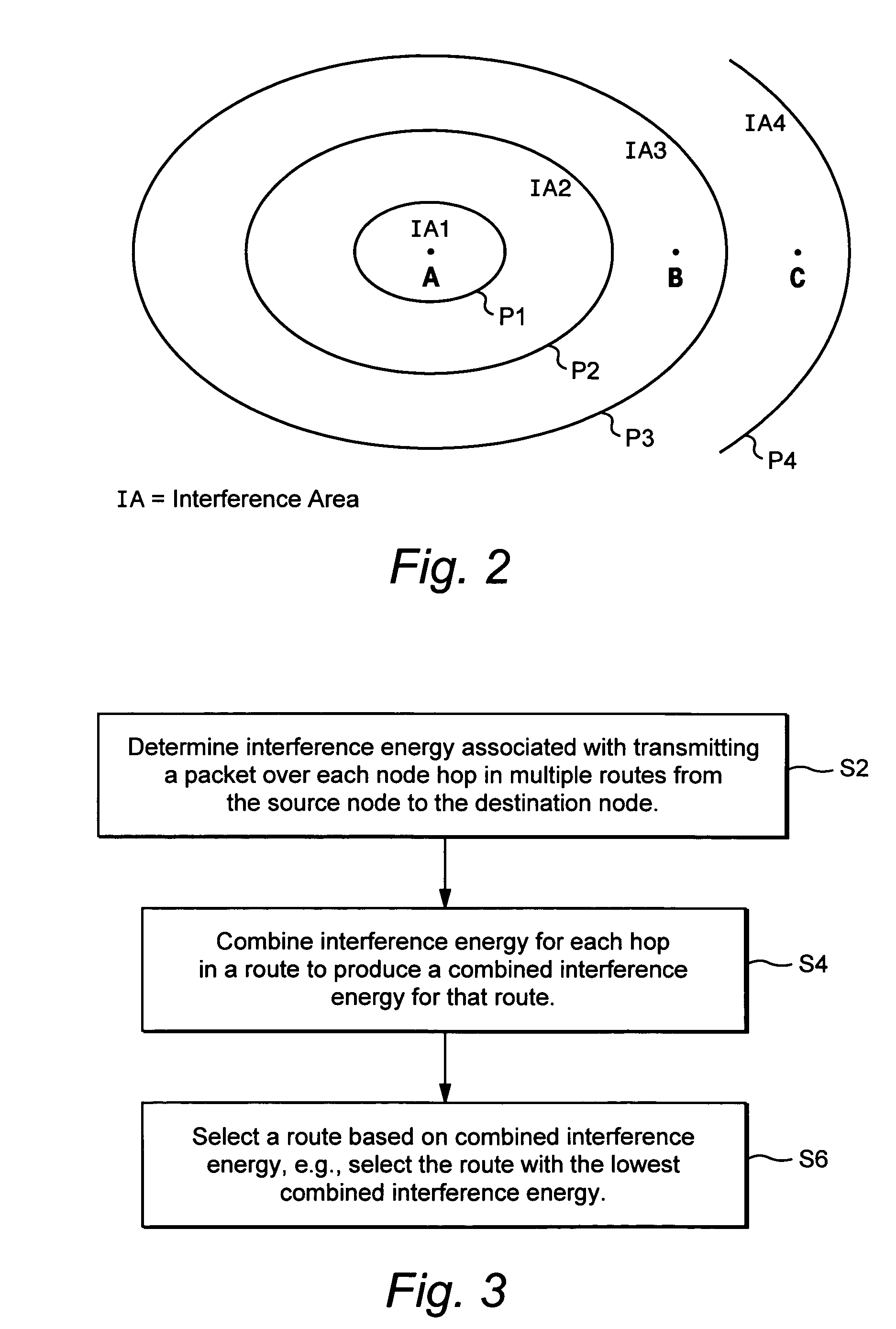
Interference-based routing in a wireless mesh network
ActiveUS7554998B2Low costReduce data rateEnergy efficient ICTError preventionComputer networkWireless mesh network
Route selection through a wireless mesh network between a source node and a destination node is based on minimizing generated interference in order to increase the capacity of the network. An interference energy associated with transmitting a packet over each hop in multiple routes from the source node to the destination node is determined. The interference energy for each hop is combined to generate a combined interference energy for each route. One of the routes is selected based on the combined interference energy determined for each route.
Owner:TELEFON AB LM ERICSSON (PUBL)
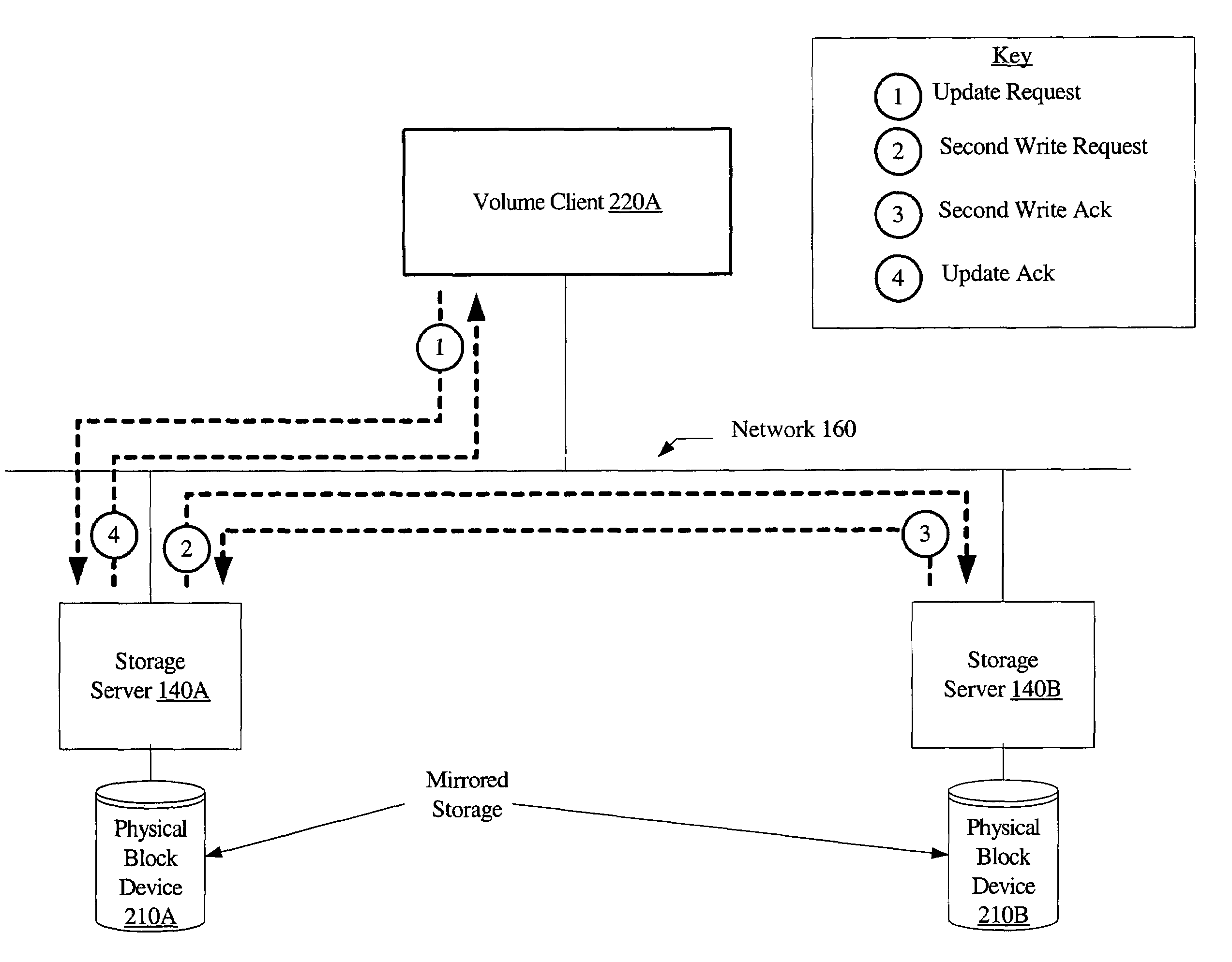
System and method for write forwarding in a storage environment employing distributed virtualization
ActiveUS7389393B1Reduce network congestionNetwork degradationError detection/correctionMemory systemsVirtualizationClient-side
A system for write forwarding in a storage environment employing distributed virtualization includes a first and a second storage server providing access to a first and a second physical storage device, respectively, a virtual device server and a virtual device client. The virtual device server may be configured to aggregate storage in the first and second physical storage device into a virtual storage device and make the virtual storage device accessible to the virtual device client for I / O operations. An update requested by the virtual device client may require a first physical write operation at the first physical storage device and a second physical write operation at the second physical device. The virtual device client may be configured to send an update request to the first storage server, rather than to both the first and the second storage servers. The first storage server may respond to the update request by starting the first physical write operation, and forwarding a request for the second physical write operation to the second storage server.
Owner:SYMANTEC OPERATING CORP
Peer-to-peer network content object information caching
InactiveUS20090271577A1Network degradationShort response timeData processing applicationsDigital data information retrievalDistributed computingPeer-to-peer
In a peer-to-peer network system, a local node communicates with a remote node on which detailed information about content objects resides and optionally, the content objects reside. The local node uses caching, message request resizing and predictive message requesting to speed response time to user requests and internal control node requests.
Owner:LEE CAPITAL
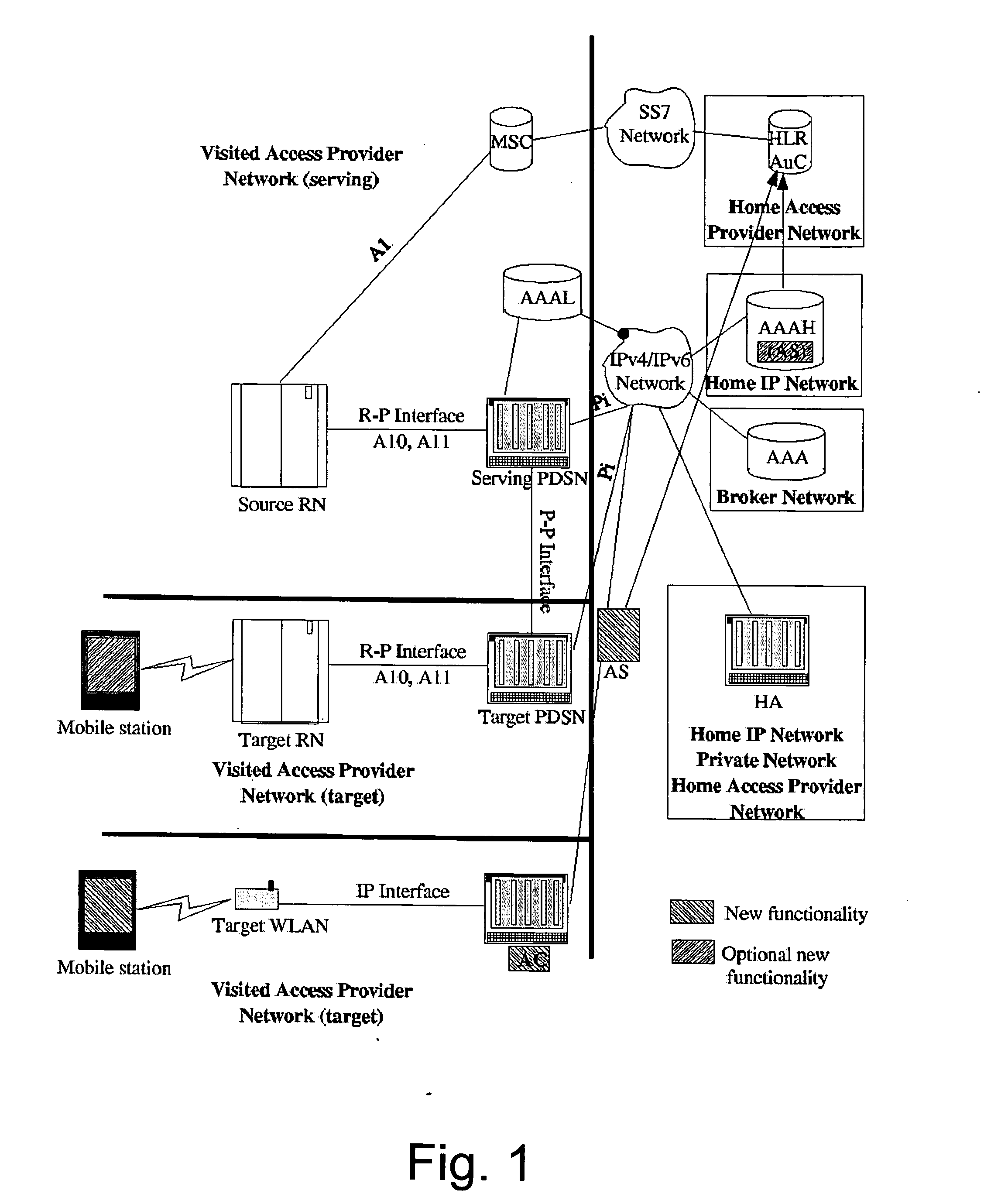
Method and apparatus for performing handover
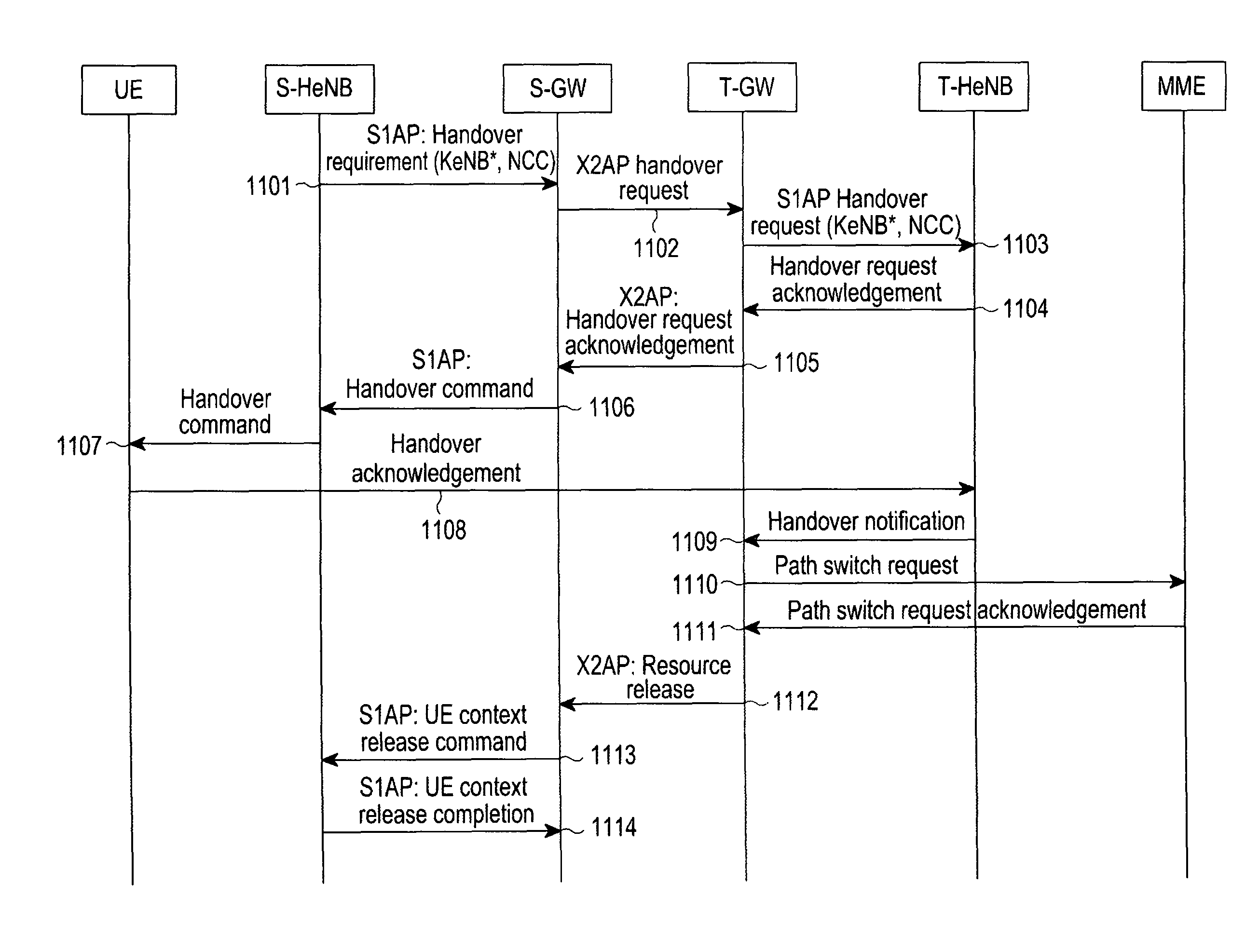
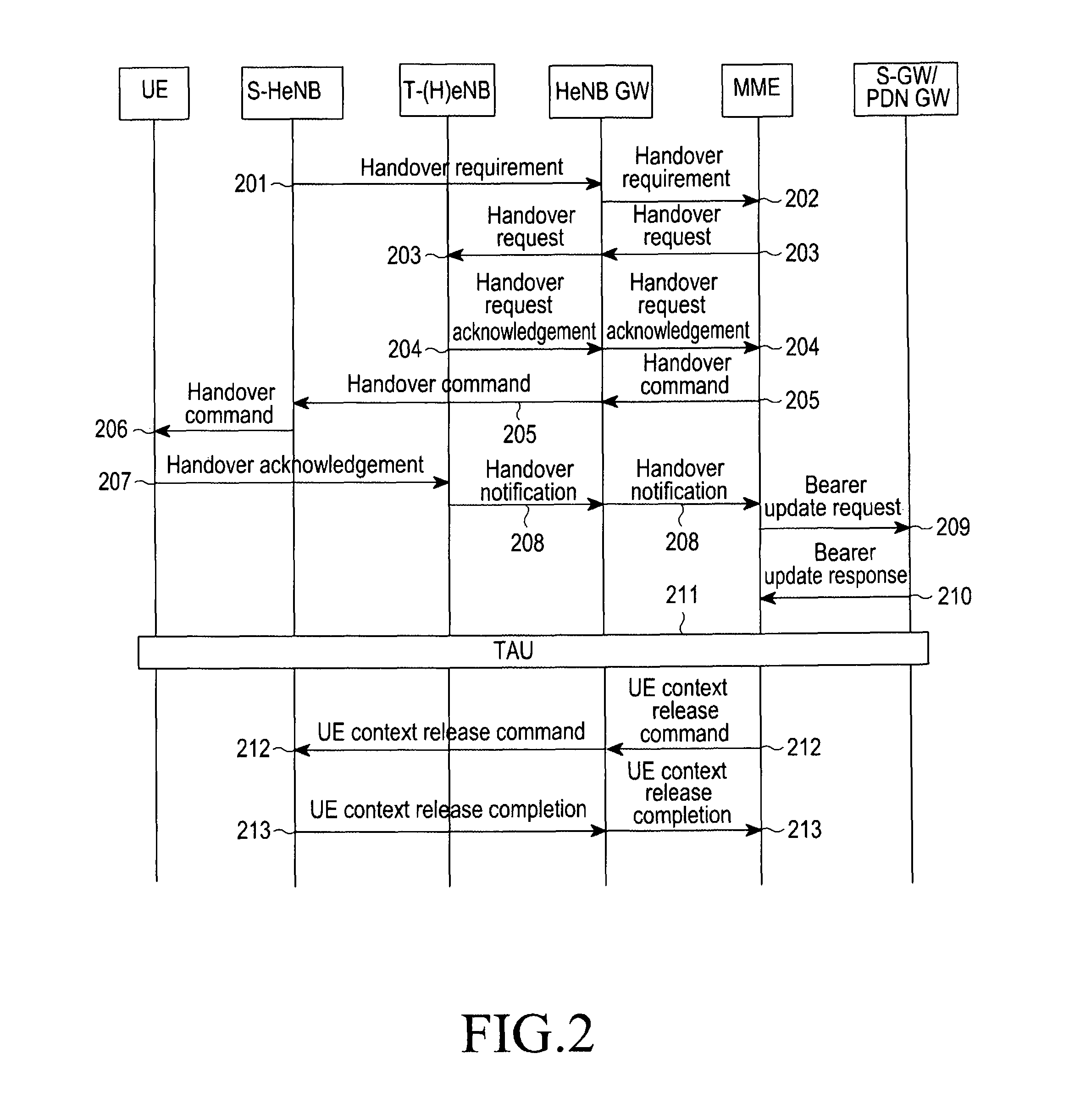
ActiveUS8520636B2Network degradationLow costNetwork topologiesWireless commuication servicesUser equipmentHandover
A method and an apparatus perform a handover using the X2 interface. A source base station transmits a handover requirement message, for a handover to a destination base station of a user equipment (UE), to a source base station gateway. When a handover command message indicating performing of the handover to a destination base station of the UE is received from the source base station gateway, the handover command message is transmitted to the UE. When a UE context release command message is received from the source base station gateway, a context of the UE is released. And a UE context release completion message, representing that the context of the UE is released, is transmitted to the source base station gateway. The handover requirement message includes a Next-hop Chaining Counter (NCC) and an encryption key for a communication between the UE and the destination base station.
Owner:SAMSUNG ELECTRONICS CO LTD
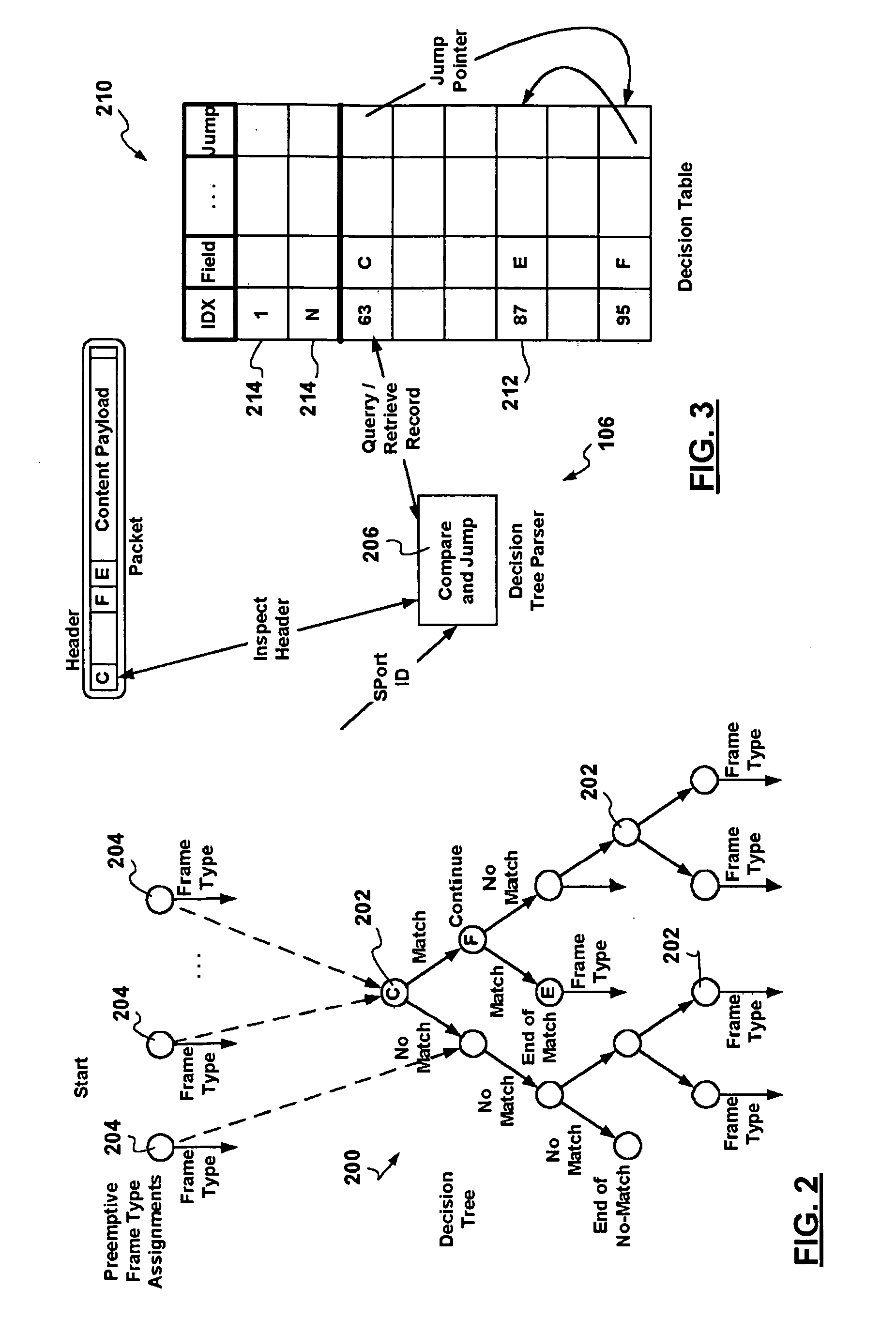
Combined pipelined classification and address search method and apparatus for switching environments
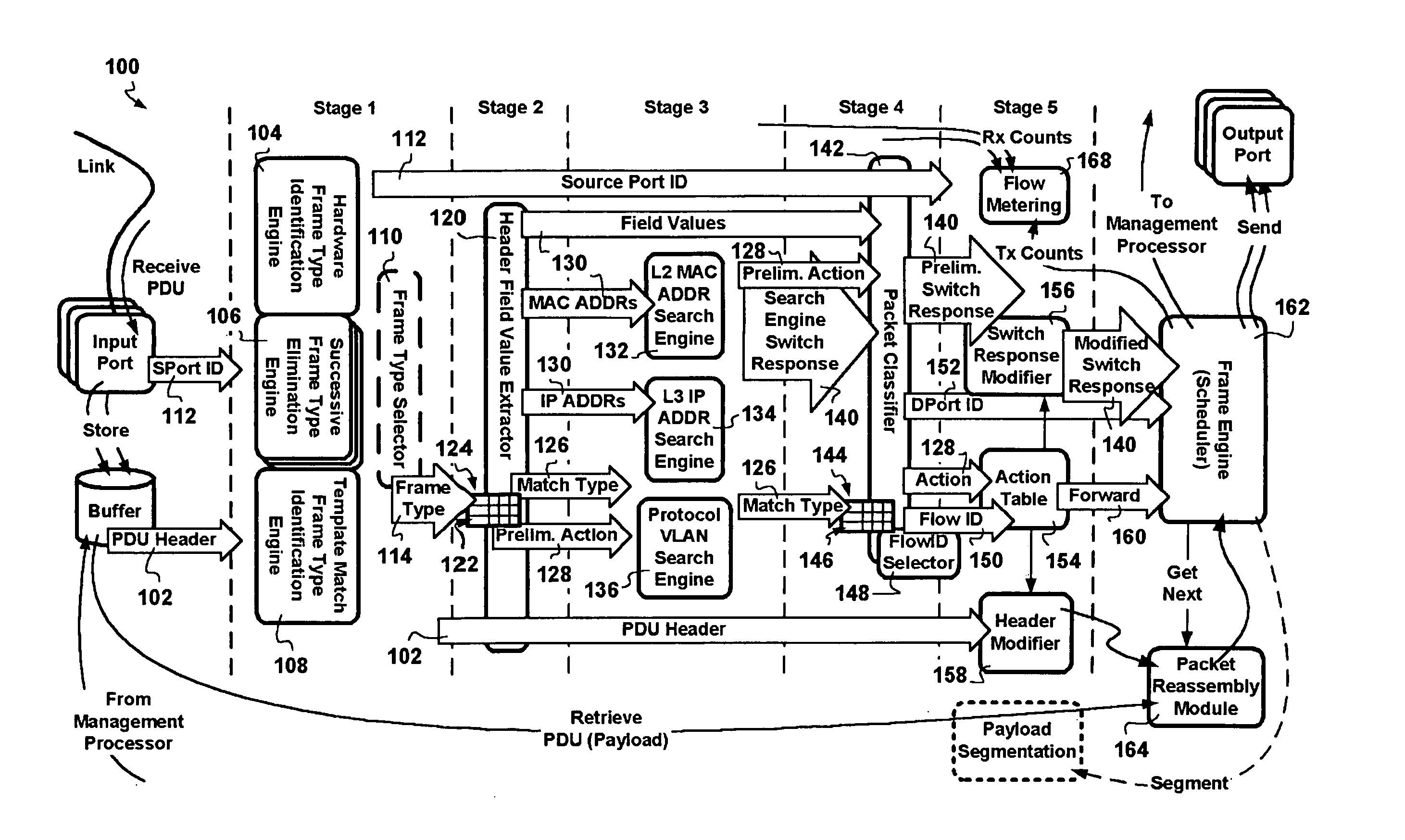
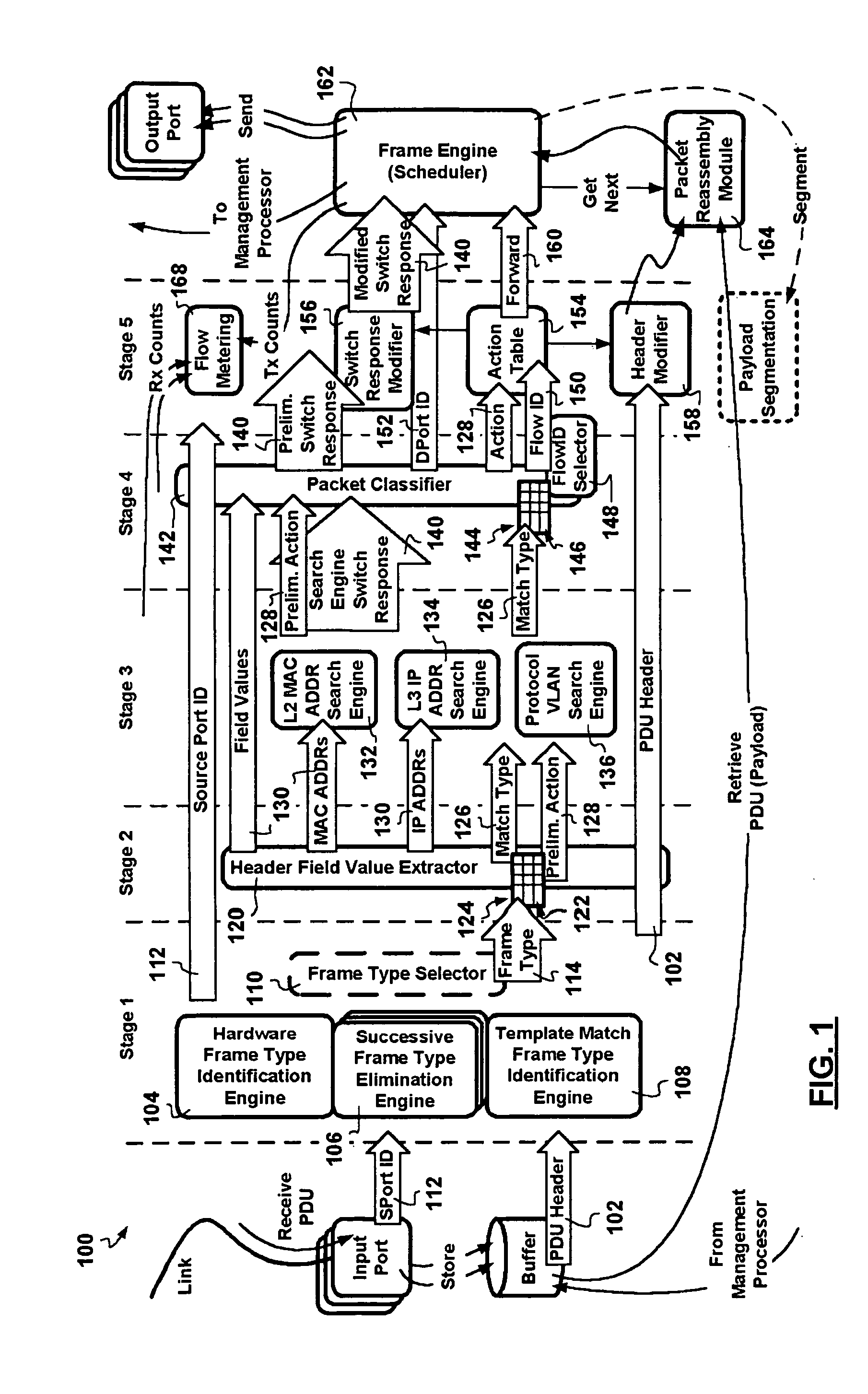
InactiveUS20060002386A1Network degradationReduce data transfer bandwidthTime-division multiplexData switching by path configurationNetwork addressingObsolescence
A packet switching node having a pipelined packet processing architecture processing packets received via an input port associated with the packet switching node is presented. The method performed by the apparatus includes: determining a packet frame type of the packet received; selectively extracting packet header field values specific to a packet frame type, the extracted packet header field value including packet addressing information; ascribing to the packet a preliminary action to be performed in respect of the packet; searching packet switching information tracked by the packet switching node based on extracted packet addressing information; formulating a preliminary switch response for the packet; classifying the packet into one of a plurality of packet flows; modifying the preliminary switch response in accordance with one of the preliminary action, the packet flow into which the packet was classified, and a default port action corresponding to the input port; modifying the packet header in accordance with one of the preliminary action, the packet flow, and the default port action; and processing the packet in accordance with the switch response. Advantages are derived from: pipelined processing of packets which enables short-cutting the rest of the processing for improper packets; a flexible frame type determination which is fast for well know frame types yet flexible in support of new frame types delaying obsolescence of a particular implementation; an early determination of a processing action which is successively refined by subsequent stages; a combined Layer-2 and Layer-3 network addressing search engine operating on short bit length indexed Layer-2 and Layer-3 network addresses reducing network address table storage requirements, requiring a reduced data transfer bandwidth for network address table access, a large external hashed primary network address table, and a small internal secondary network address table; an early determination of a switch response; and packet-classification-based switch response and packet header modification.
Owner:SYNAPTICS INC
Network appliance for dynamic protection from risky network activities
InactiveUS20160044054A1Efficient solutionLighten the taskMemory loss protectionError detection/correctionNetwork activityDistributed computing
Electronic appliances, computer-implemented systems, non-transitory media, and methods are provided to identify risky network activities using intelligent algorithms. The appliances, systems, media, and methods enable rapid detection of risky activities.
Owner:NORSE NETWORKS INC
Automated containment of network intruder
InactiveUS20070192862A1Network degradationLow costMemory loss protectionError detection/correctionAutomatic controlVirtual LAN
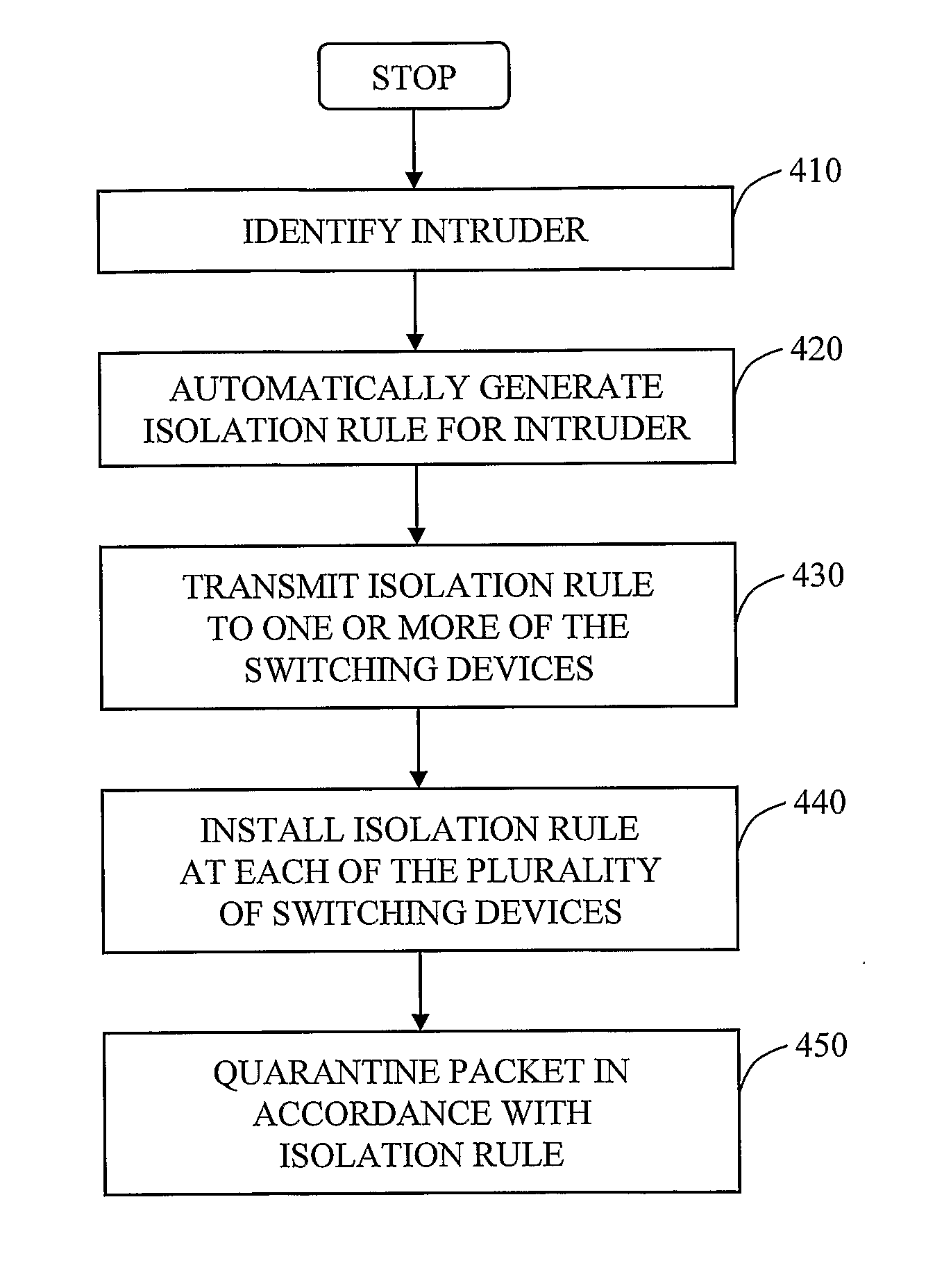
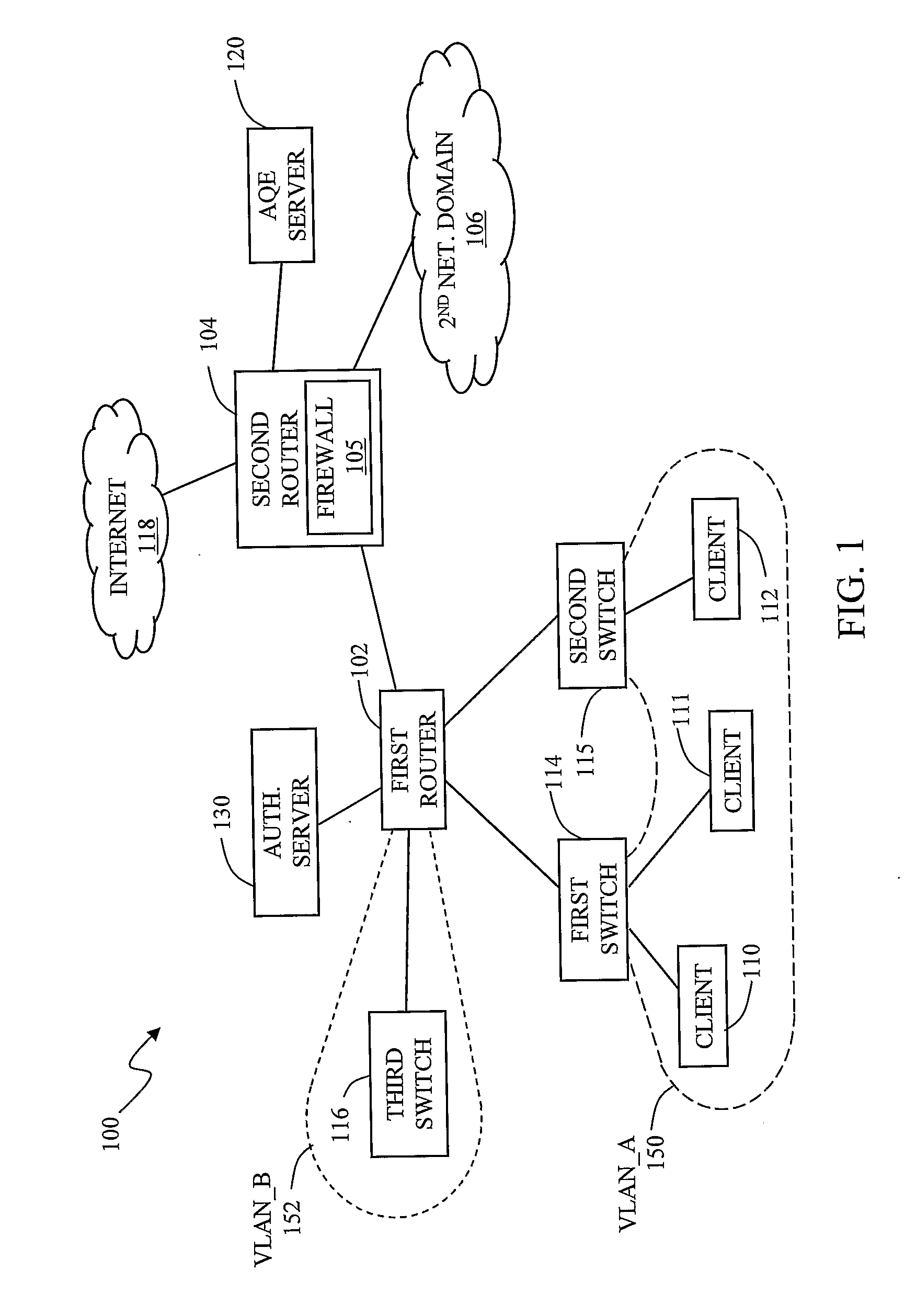
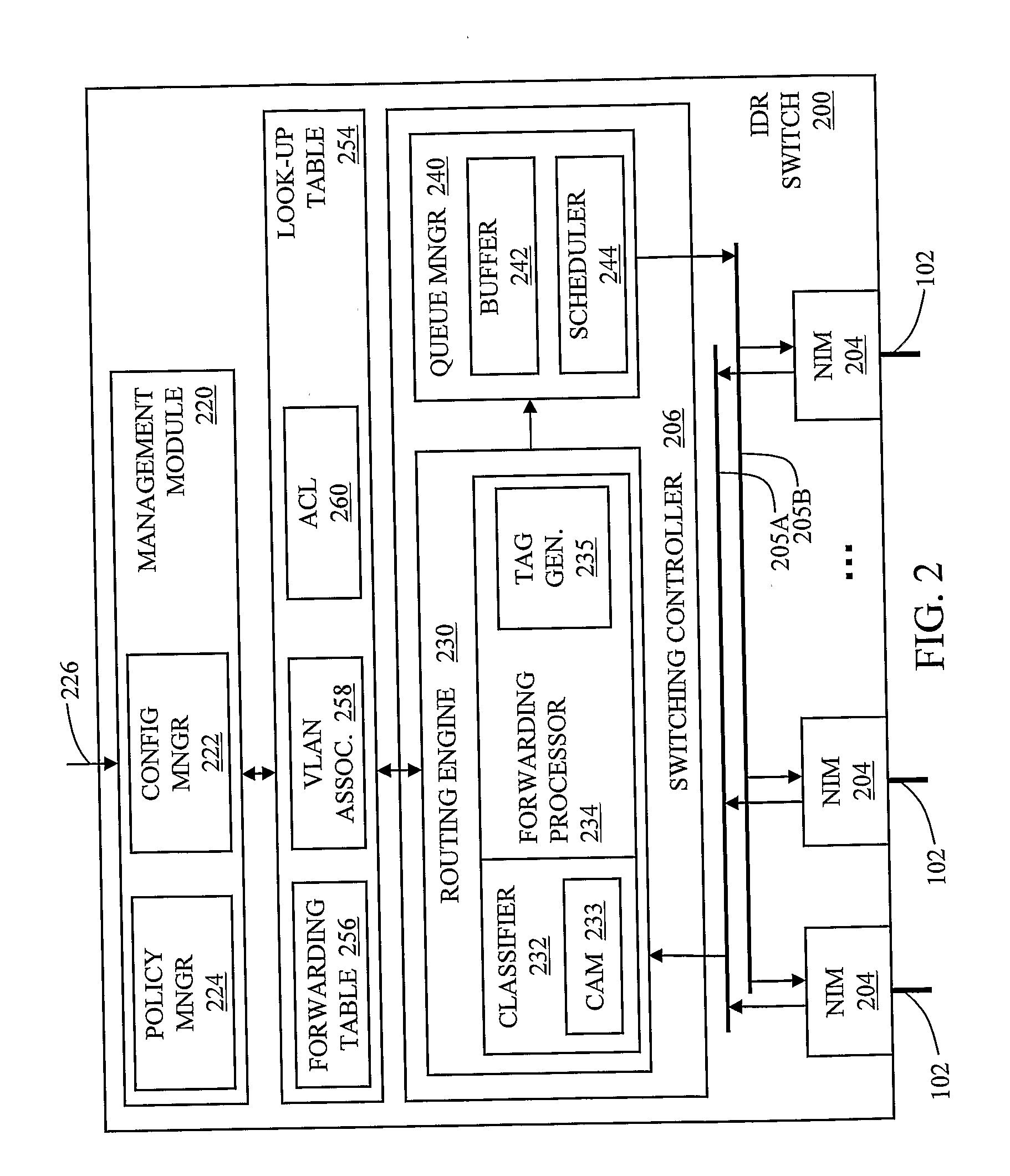
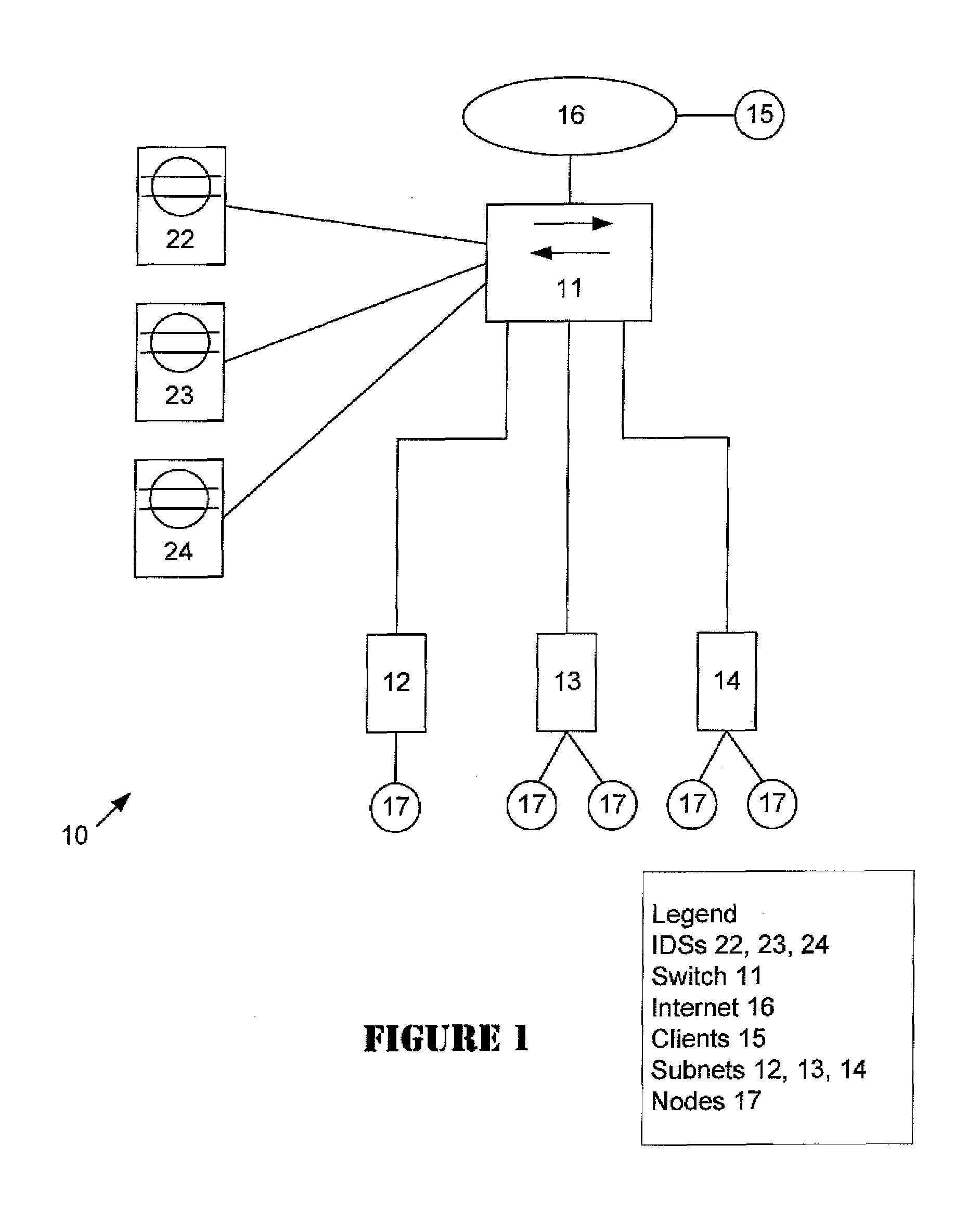
The invention in the preferred embodiment features a system (200) and method for automatically segregating harmful traffic from other traffic at a plurality of network nodes including switches and routers. In the preferred embodiment, the system (200) comprises an intrusion detection system (105) to determine the identity of an intruder and a server (130) adapted to automatically install an isolation rule on the one or more network nodes (114, 115, 116) to quarantine packets from the intruder. The isolation rule in the preferred embodiment is a virtual local area network (VLAN) rule or access control list (ACL) rule that causes the network node to route any packets from the intruder into a quarantine VLAN or otherwise isolate the traffic from other network traffic. In large networks, the isolation rule may be installed on a select plurality of network nodes under the gateway router (104) associated with the node at which the intruder first entered the network (100).
Owner:VERMEULEN VINCENT +1
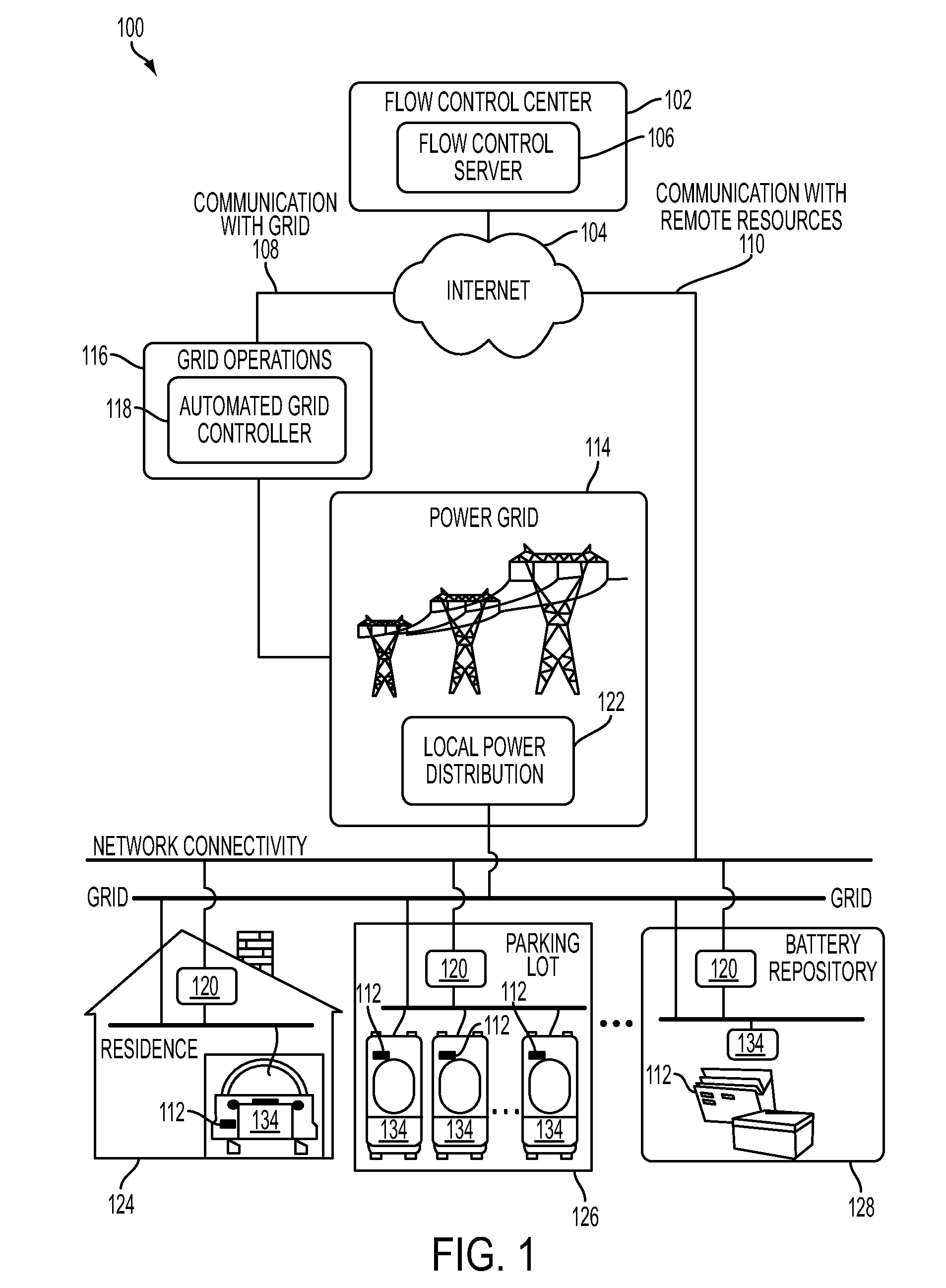
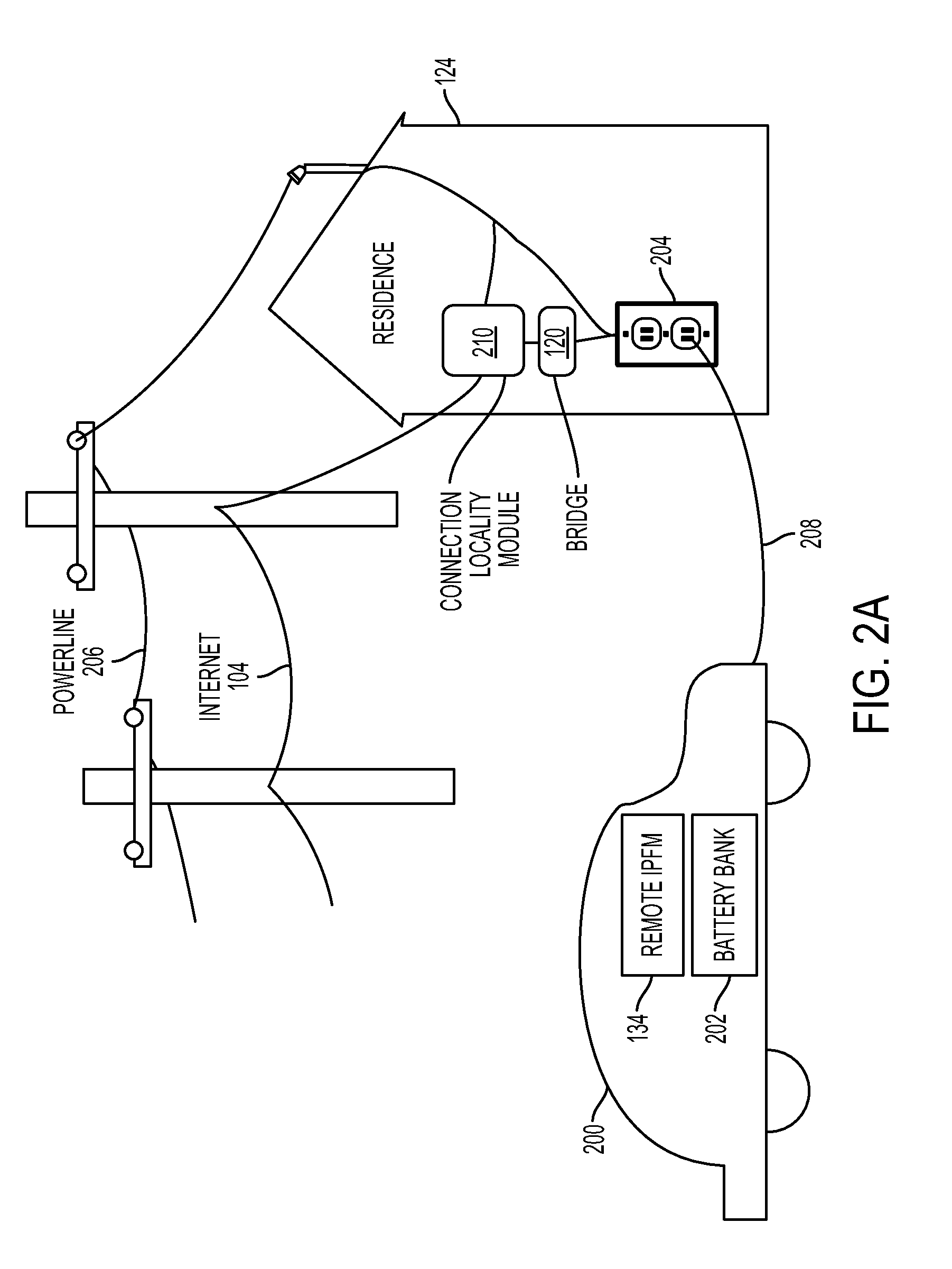
System and methods for smart charging techniques
InactiveUS20110016063A1Reduce electricity costsNetwork degradationLevel controlVehicular energy storageElectric powerLoad management
A system and methods that enables smart charging techniques. A smart charging method may include periodically updated schedules. In addition, a smart charging method may include schedules with overrides. Further, a smart charging may involve a method for local load management in the presence of uncontrolled loads. A smart charging method for managing electric resources may also provide direct control over prices-to-devices enabled devices.
Owner:GRIDPOINT
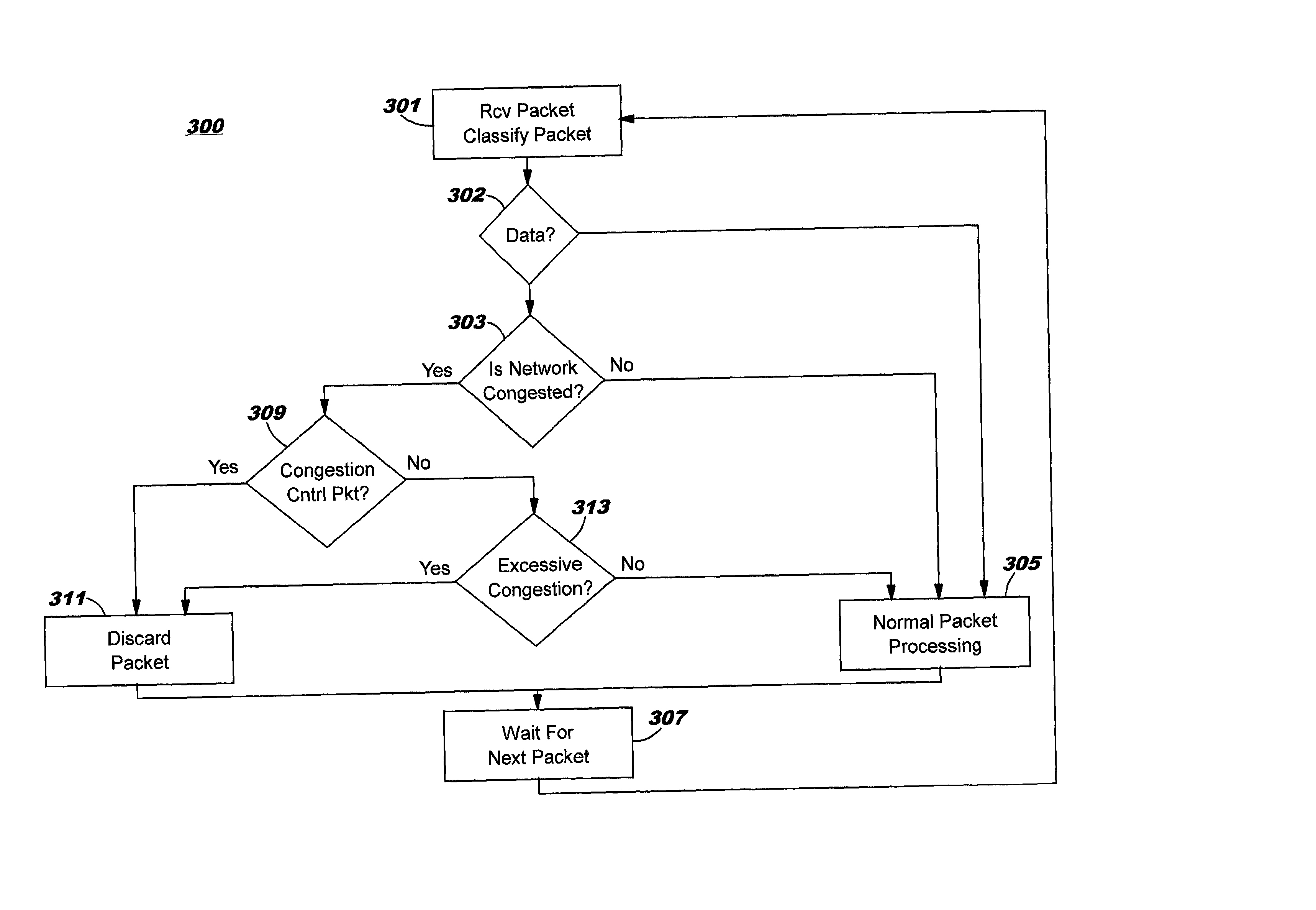
Controlling network congestion using a biased packet discard policy for congestion control and encoded session packets: methods, systems, and program products
ActiveUS7042841B2Increase bitrateNetwork degradationError preventionTransmission systemsControl systemNetwork congestion control
Owner:IBM CORP +1
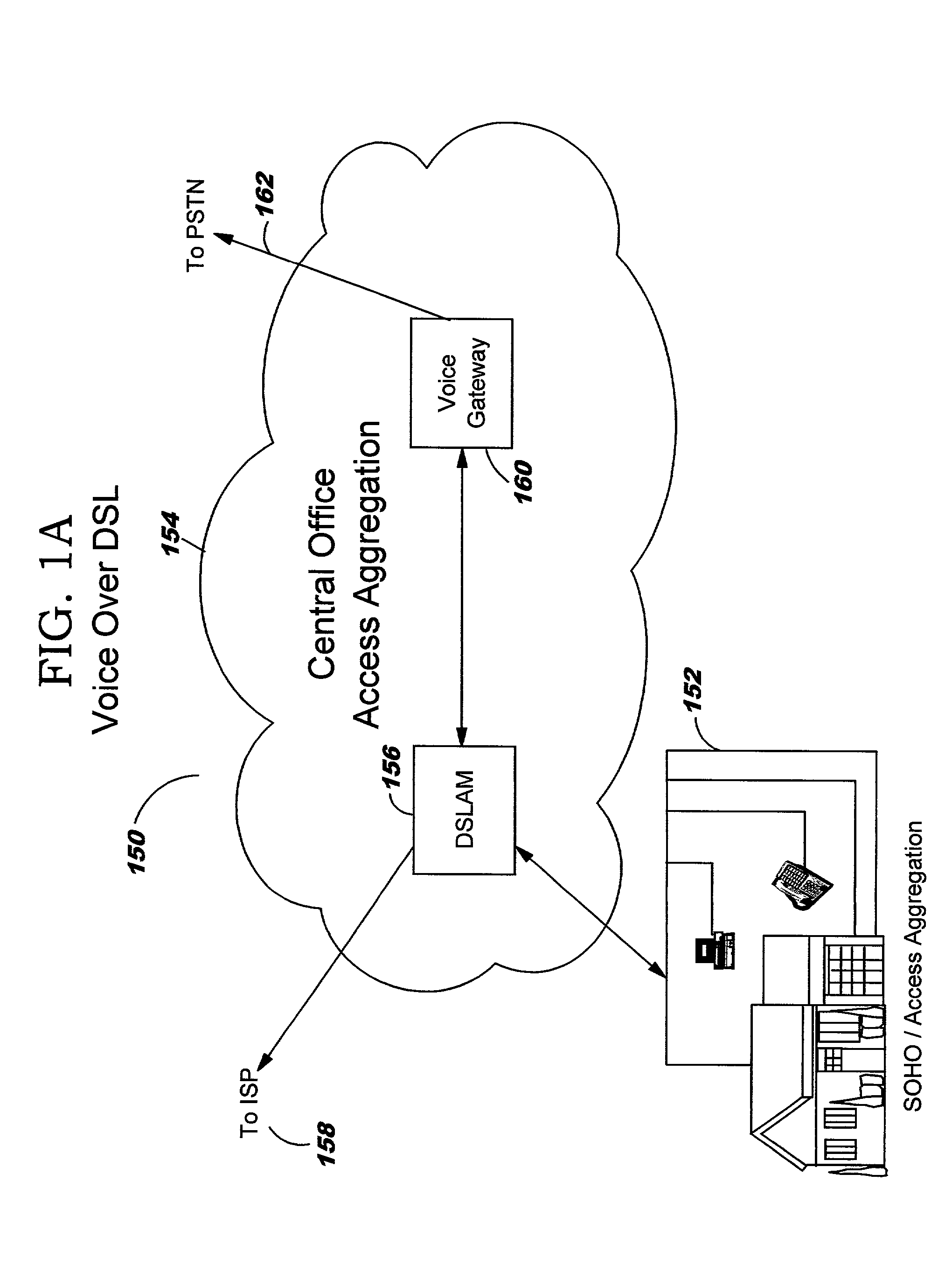
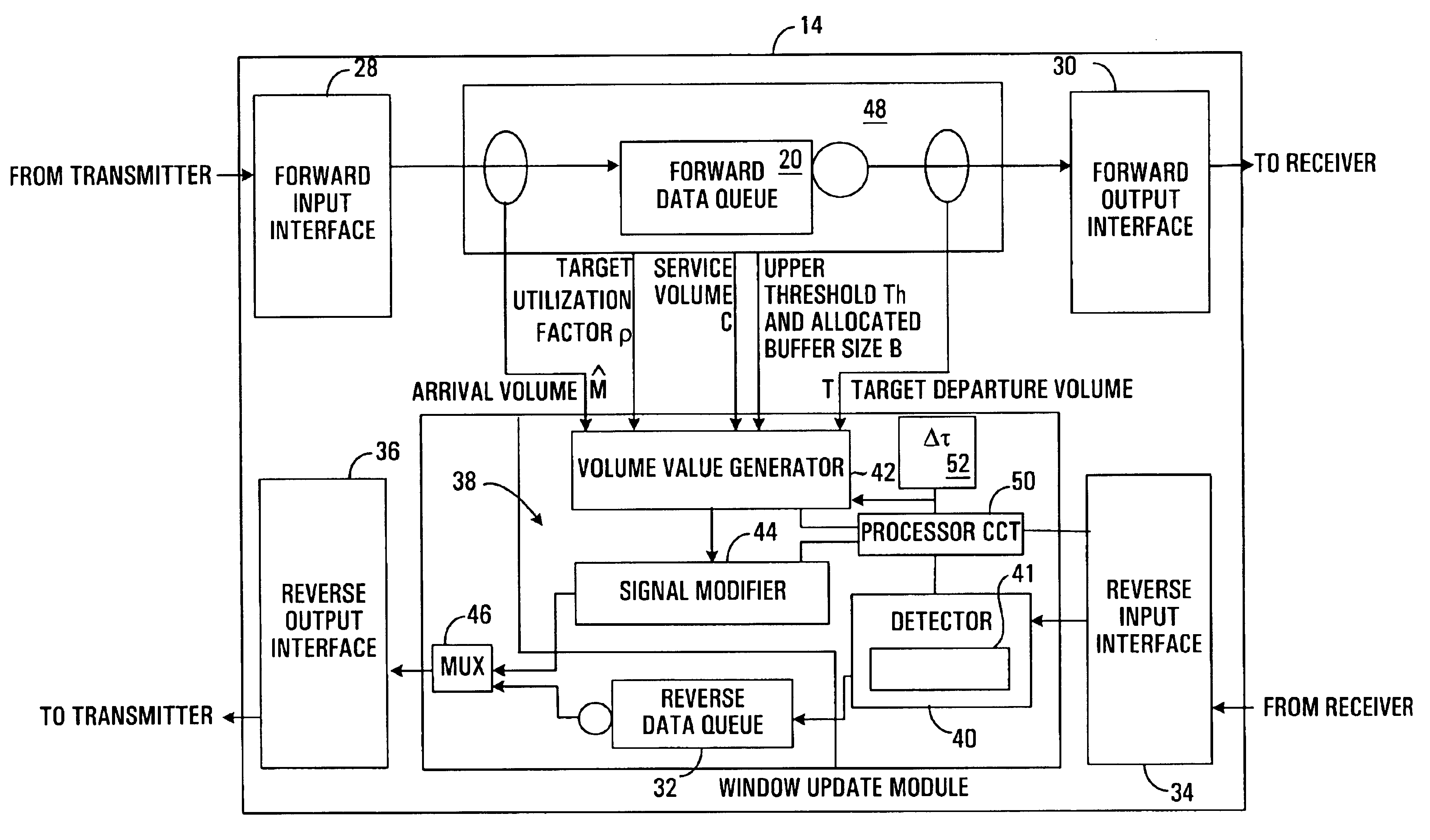
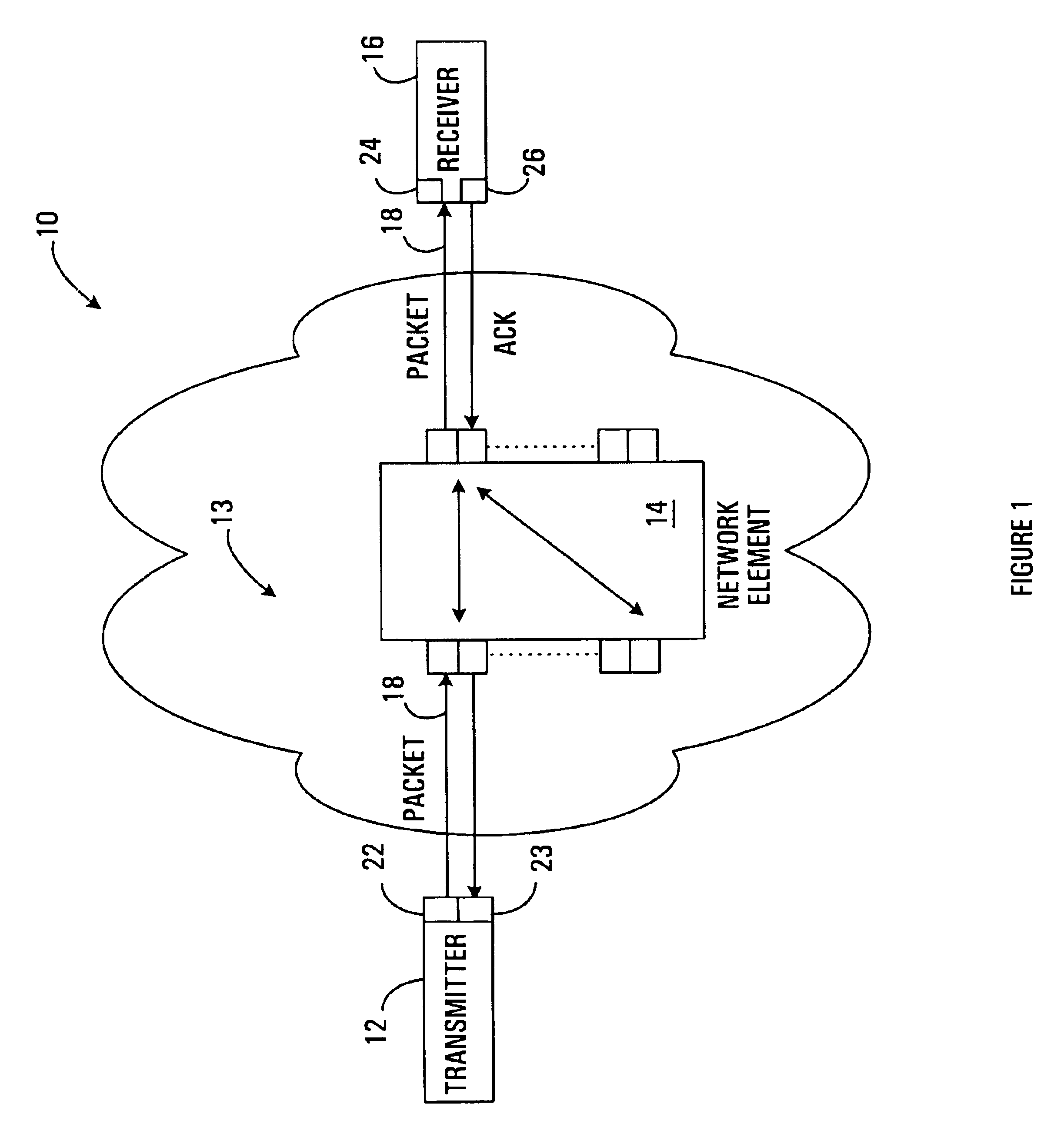
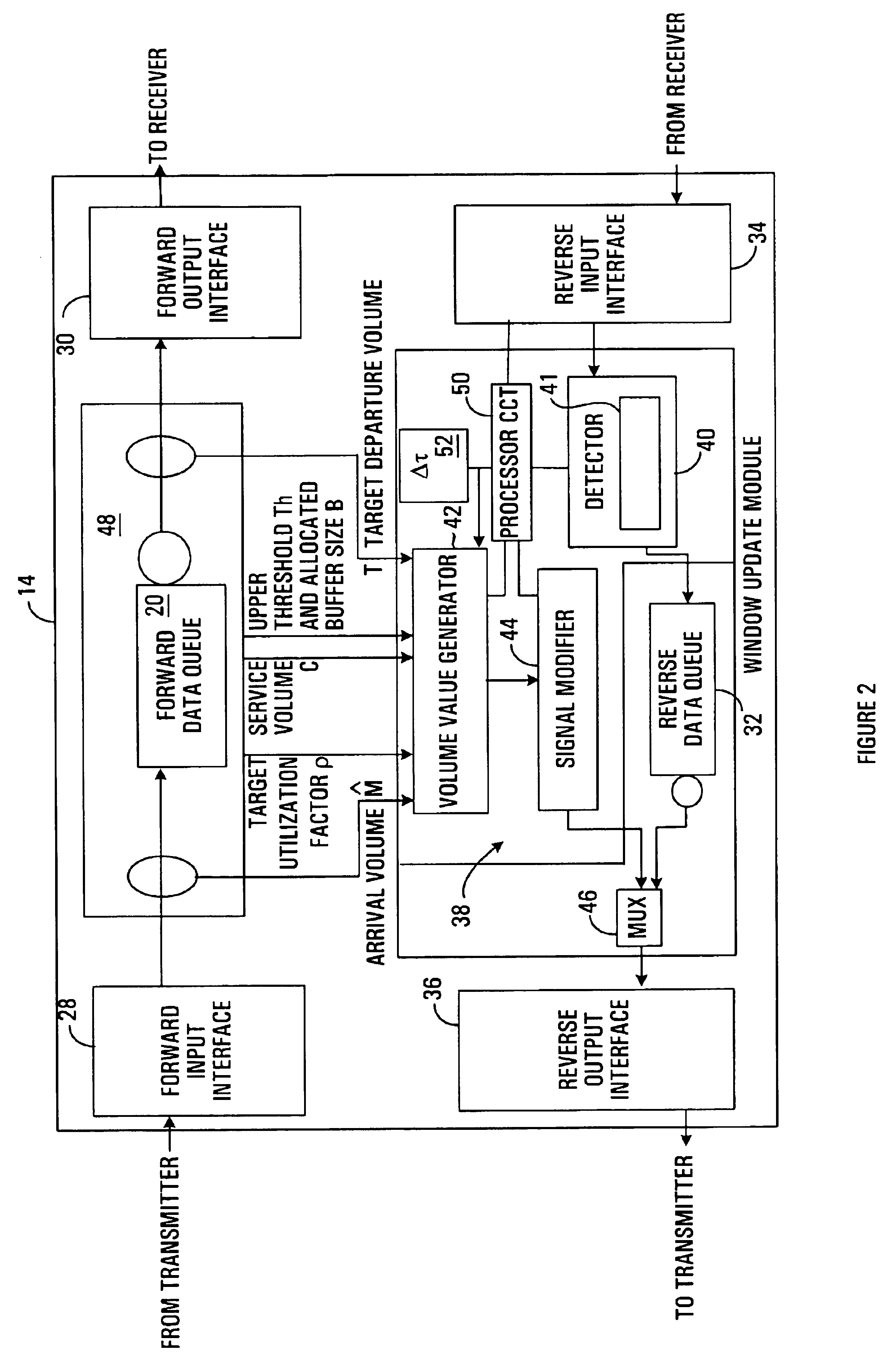
Method and apparatus for adjusting packet transmission volume from a source
InactiveUS6990070B1Improve overall utilizationReduce transmissionError preventionTransmission systemsComputer scienceTransmitter
A method and apparatus are provided for adjusting the volume of data communicated between a transmitter and a receiver on a network, in a time interval. The method involves producing a desired volume value in response to a volume value specified by the receiver and a difference between a target departure volume and an estimate of arrival volume of data at a queue through which data passes from the transmitter to the receiver, and communicating the desired volume value to the transmitter in response to an acknowledgement signal produced by the receiver.
Owner:RPX CLEARINGHOUSE
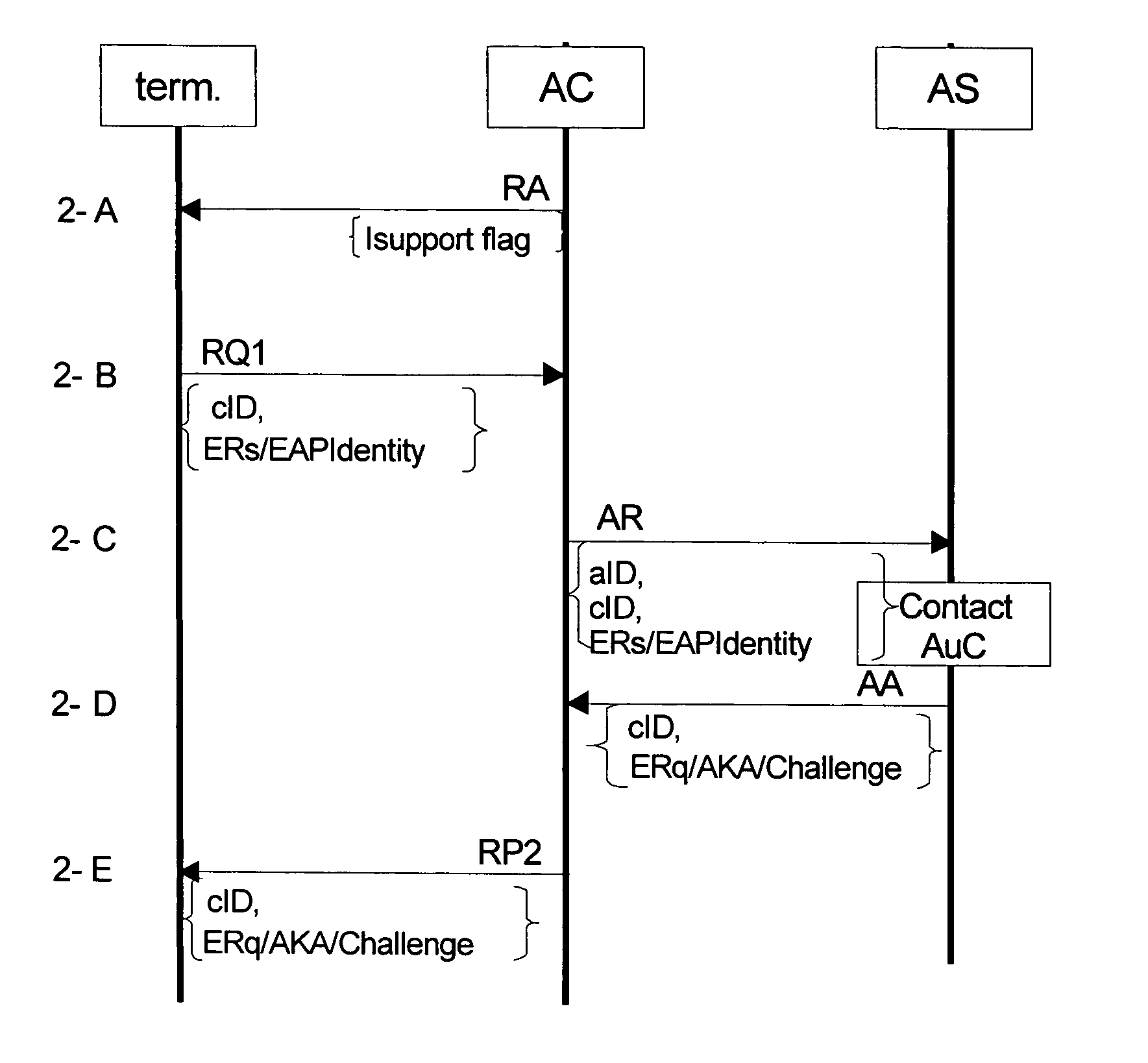
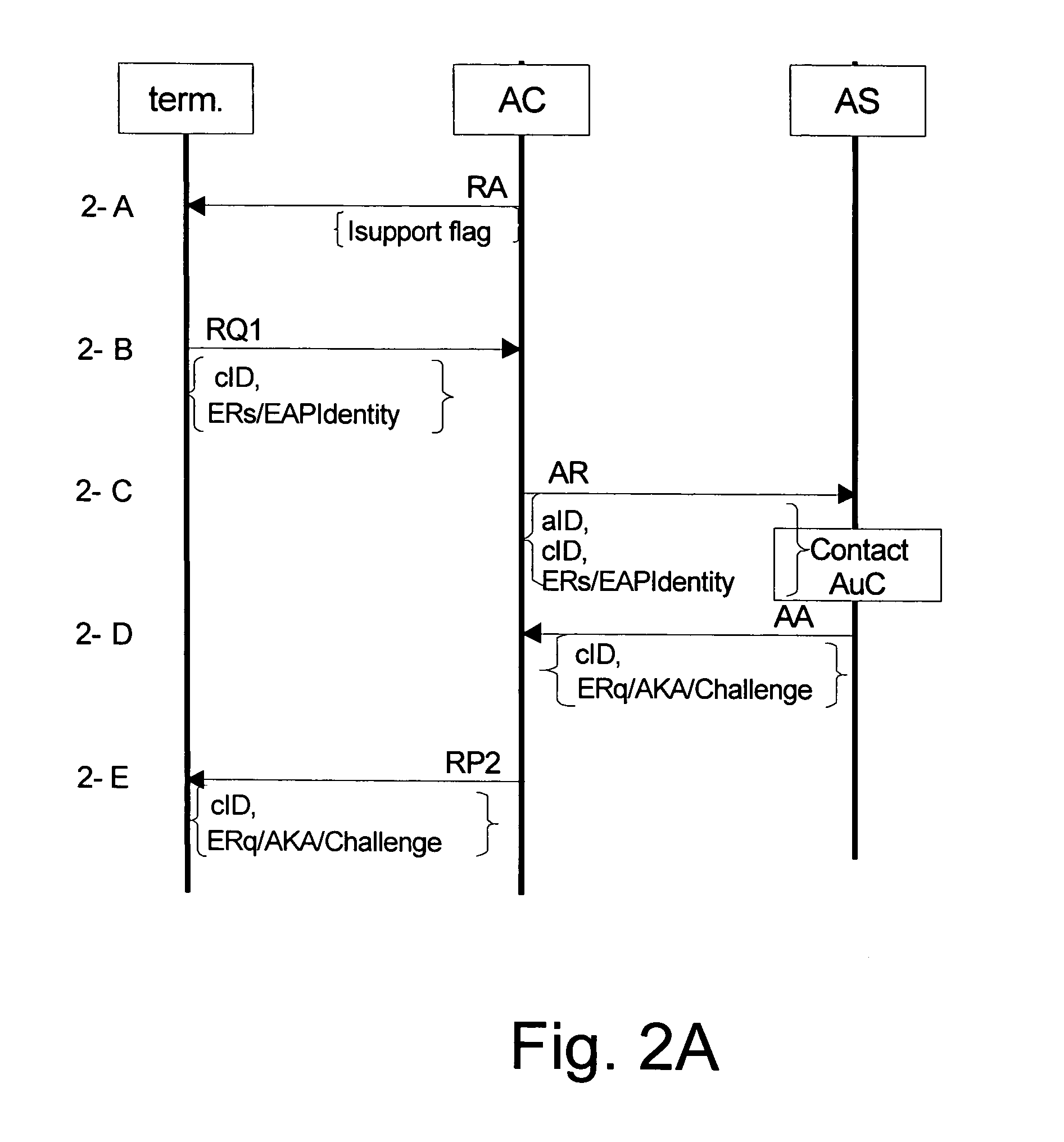
Authentication in heterogeneous IP networks
ActiveUS20050078824A1Authentication procedure is simplifiedNetwork degradationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsAccess networkAuthentication server
The invention proposes a system for authenticating and authorizing network services comprising: a mobile device being adapted to, upon receipt of an information message indicating at least one network access type, determine the network access type, to create a start message containing at least a user identity, and to encapsulate the start message in an authentication message compatible with the access network identified in the information message, and an access controller for reading the encapsulated message from the mobile and forwarding the encapsulated message to an authentication server identified in the encapsulated message. The invention also proposes a corresponding method for authenticating and authorizing network services, and an access control device, a subscriber device and a router device.
Owner:NOKIA TECHNOLOGLES OY
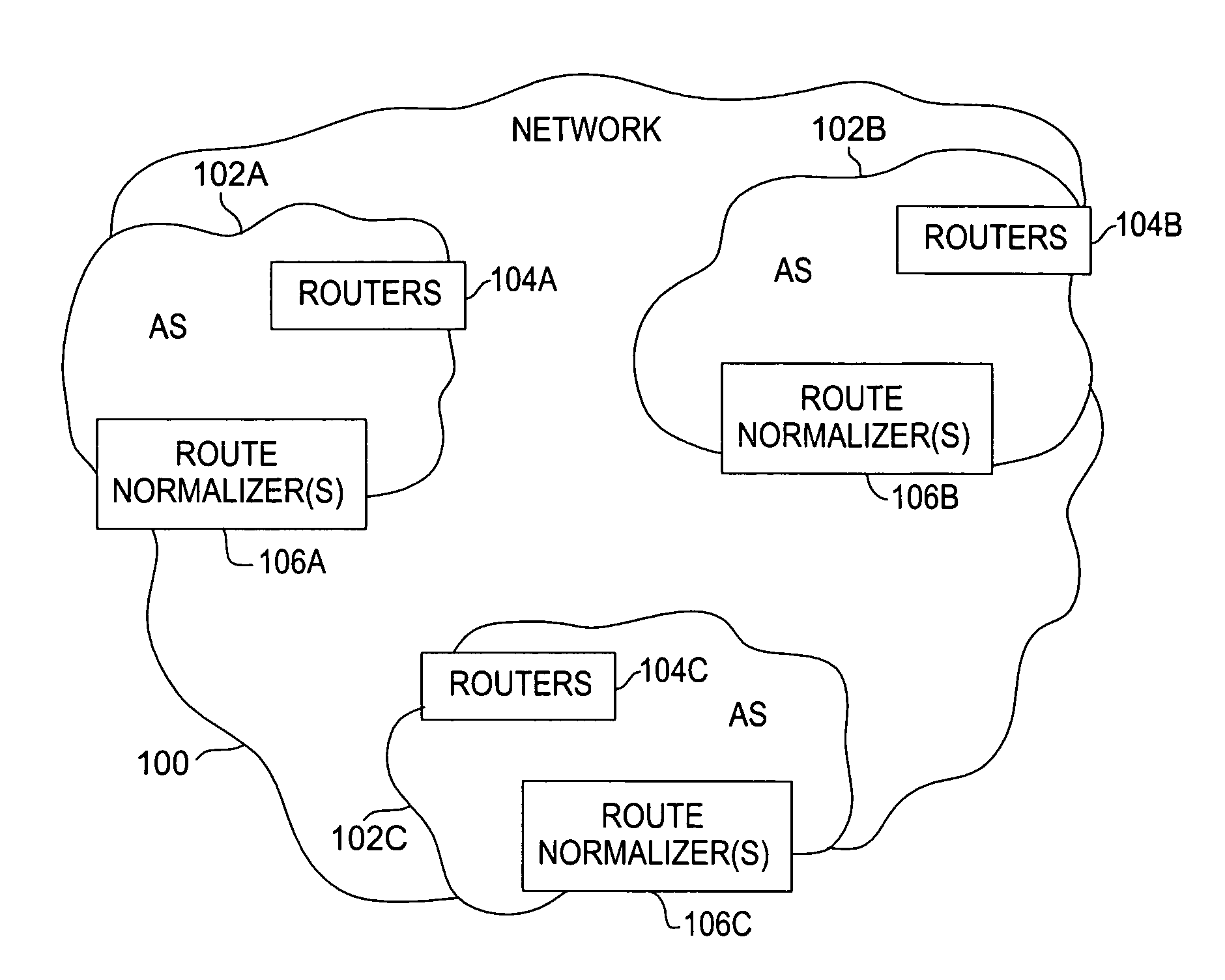
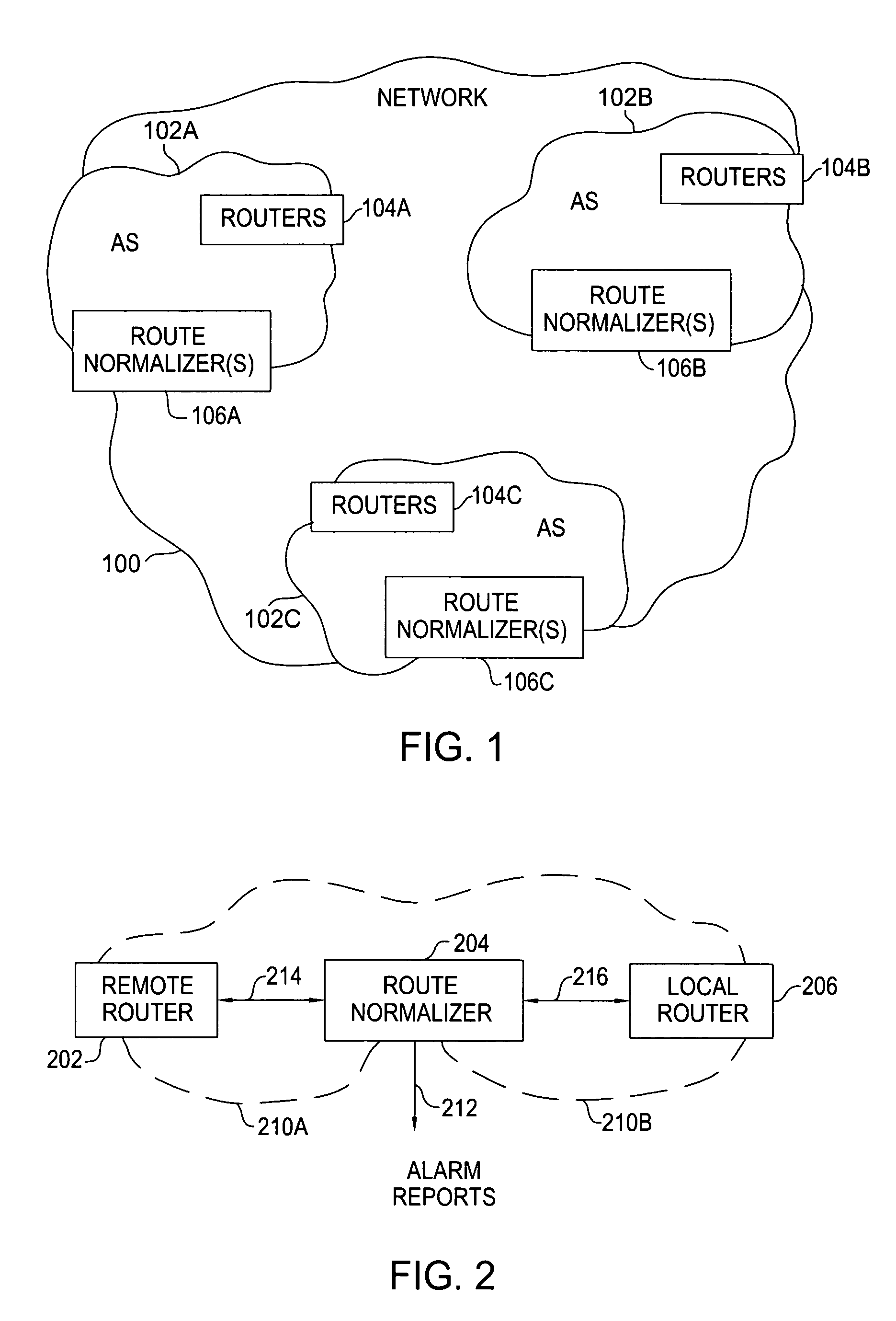
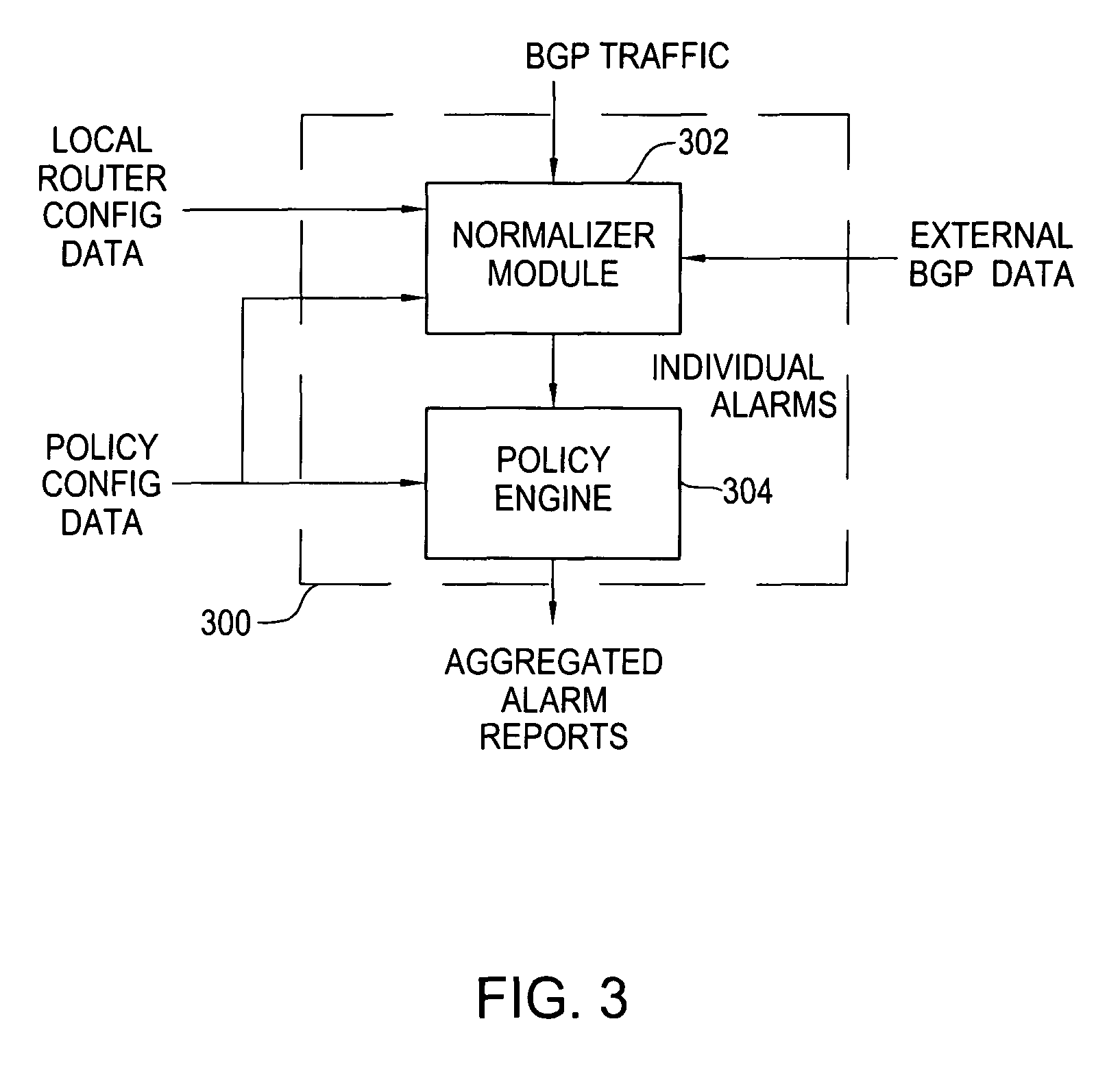
Method and apparatus for mitigating routing misbehavior in a network
ActiveUS8141156B1Network degradationReduce instabilityMemory loss protectionError detection/correctionProtocol for Carrying Authentication for Network AccessNetwork method
Method and apparatus for mitigating routing misbehavior in a network is described. In one example, routing protocol traffic is received from a remote router destined for a local router. The routing protocol traffic is parsed to identify a subset of traffic. The subset of traffic is normalized to identify and correct misconfigured routing updates. The routing protocol traffic is provided to the local router. In one embodiment, the subset of traffic is normalized by at least one of detecting and correcting routing protocol semantics, detecting and correcting violations in routing policies, detecting and correcting routing anomalies, or mitigating routing instability.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO +1
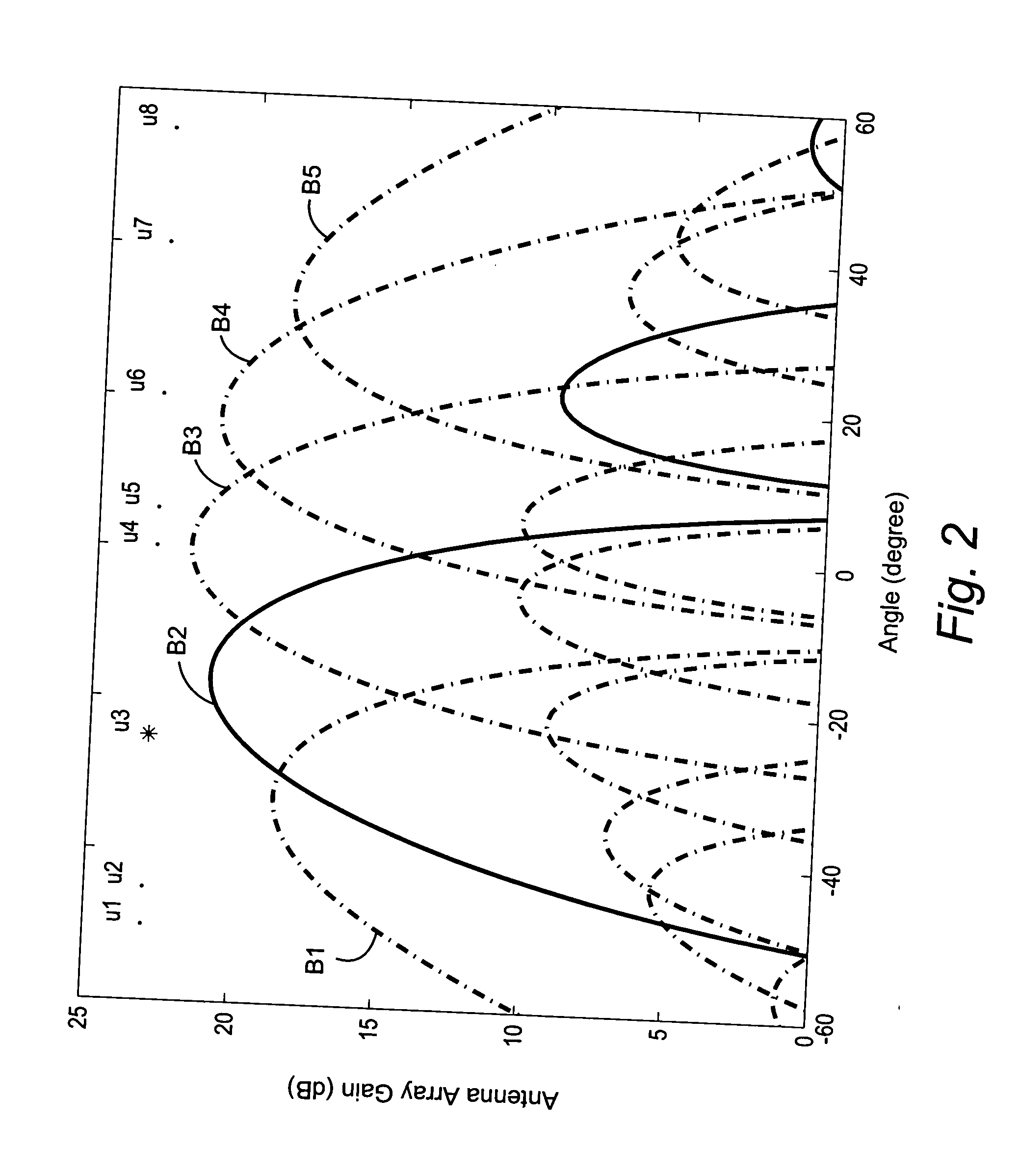
Reducing shared downlink radio channel interference by transmitting to multiple mobiles using multiple antenna beams
ActiveUS20050064872A1Inhibition effectImprove data transfer rateSpatial transmit diversityRadio/inductive link selection arrangementsRadio channelMobile radio
A radio base station includes multiple antennas associated with a cell. Multiple mobile radios are selected to receive transmissions over a shared radio channel during a predetermined time interval. Information is transmitted over the shared radio channel to multiple mobile radios in the cell during the predetermined time interval using multiple antenna beams. As a result, interference from the transmission appears as white additive Gaussian noise in time and in space in the cell. A “flashlight effect” caused by a single beam transmission over the shared channel during a predetermined time interval that would normally detrimentally impact mobile channel quality detection is avoided. Other methods for avoiding the flashlight effect are described.
Owner:TELEFON AB LM ERICSSON (PUBL)
WLAN having load balancing based on access point loading
ActiveUS7400901B2Improve network performanceEfficient loadingError preventionFrequency-division multiplex detailsMobile stationSignal intensity
A network having distribution of access point loading includes access points to which mobile stations can associate themselves based upon access point beacon signal levels and loading levels for the various access points. A mobile station receives beacon signals from various access points and determines a signal strength for the received beacon signals. The mobile station also receives access point loading information from the access points. The mobile station associates with an access point based upon the access point beacon signal strengths and the access point loading information.
Owner:AT&T INTPROP II L P
Intrusion detection in a data center environment
ActiveUS7610375B2Network degradationRemove noiseError preventionTransmission systemsTraffic capacityData center
Owner:CISCO TECH INC
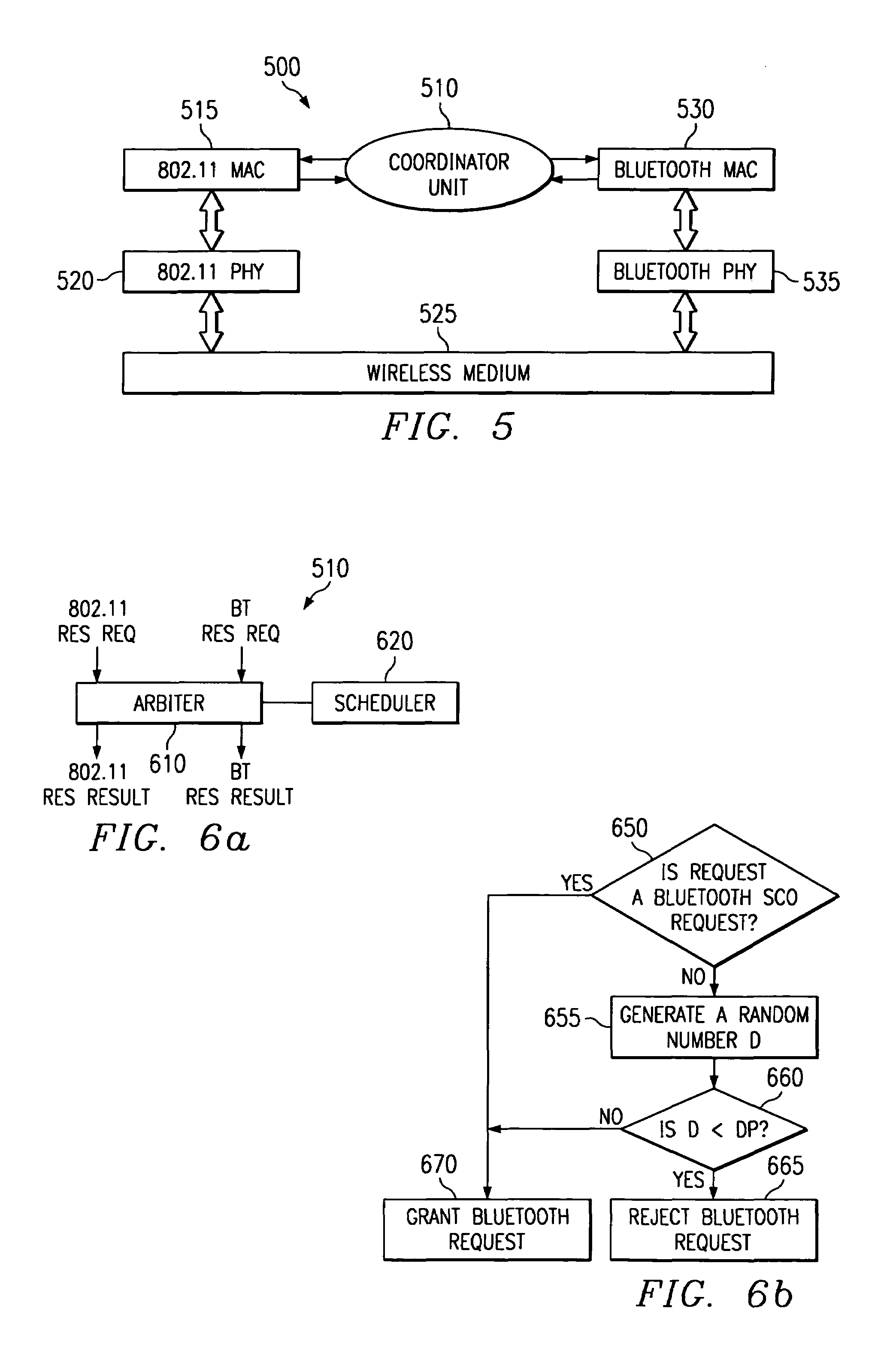
Collaborative mechanism of enhanced coexistence of collocated wireless networks
InactiveUS7099671B2Network degradationReduce collisionNetwork traffic/resource managementData switching by path configurationWireless mesh networkOperating frequency
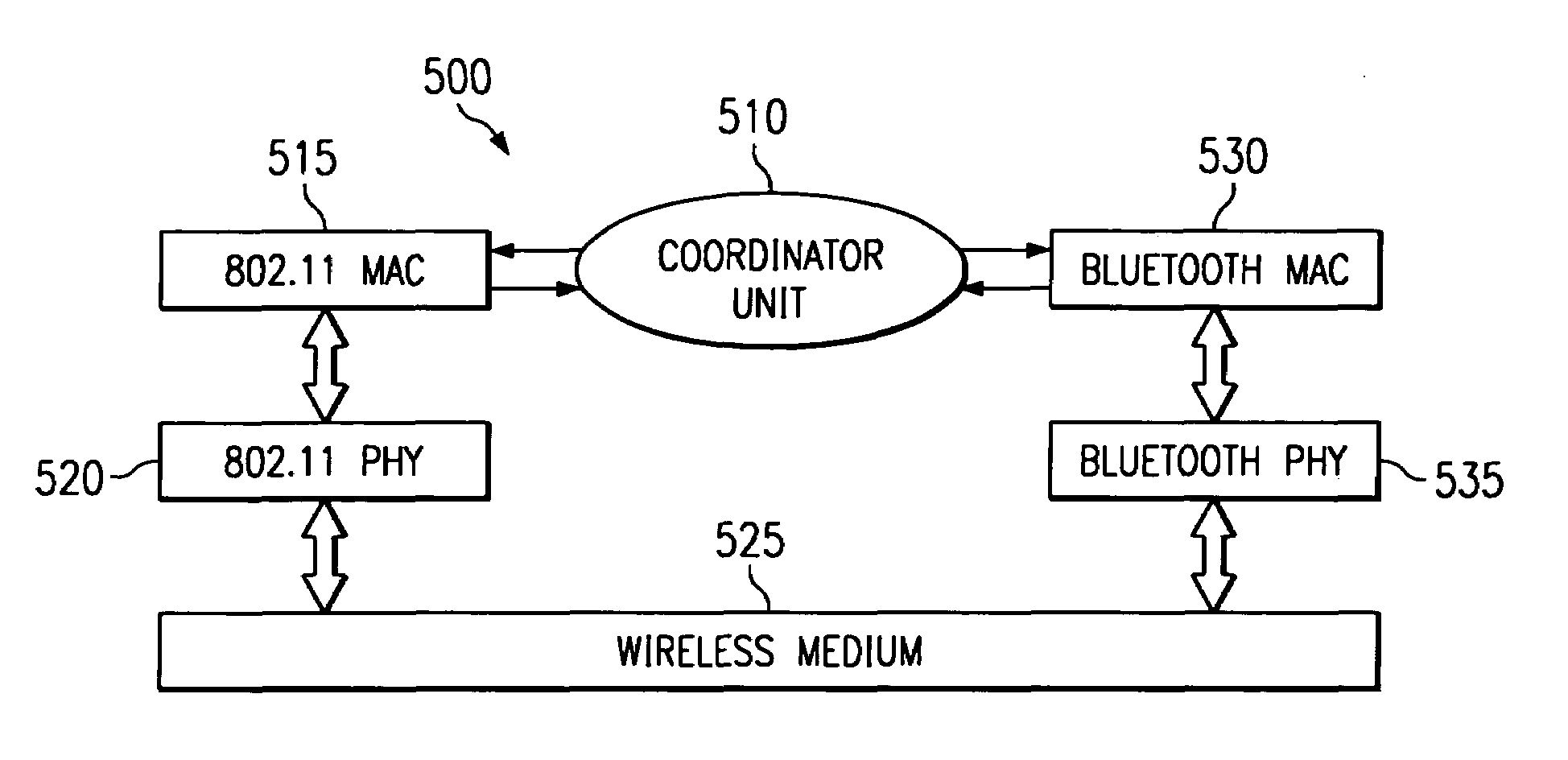
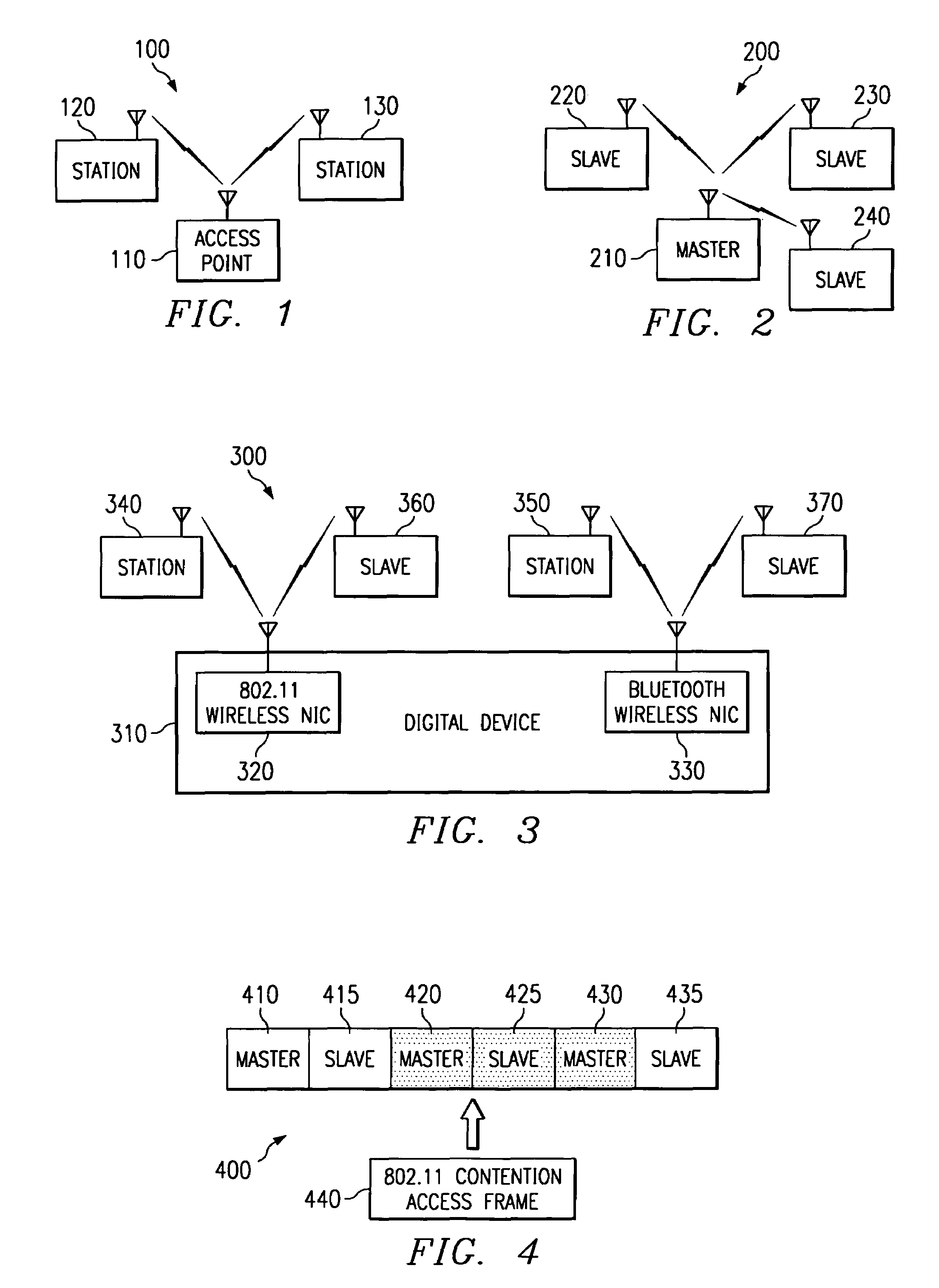
A digital device 310 with a plurality of collocated wireless networks encounters inter-network interference if the collocated wireless networks operate in a common operating frequency. A coordinator unit 510, coupled to the plurality of wireless networks, provides a transmission reservation system wherein a wireless network with a need to transmit can request and receive a reservation for time to transmit. The coordinator unit 510 provides a way to schedule transmissions from the plurality of wireless networks and to reduce the probability of collisions.
Owner:TEXAS INSTR INC
Partitioning social networks
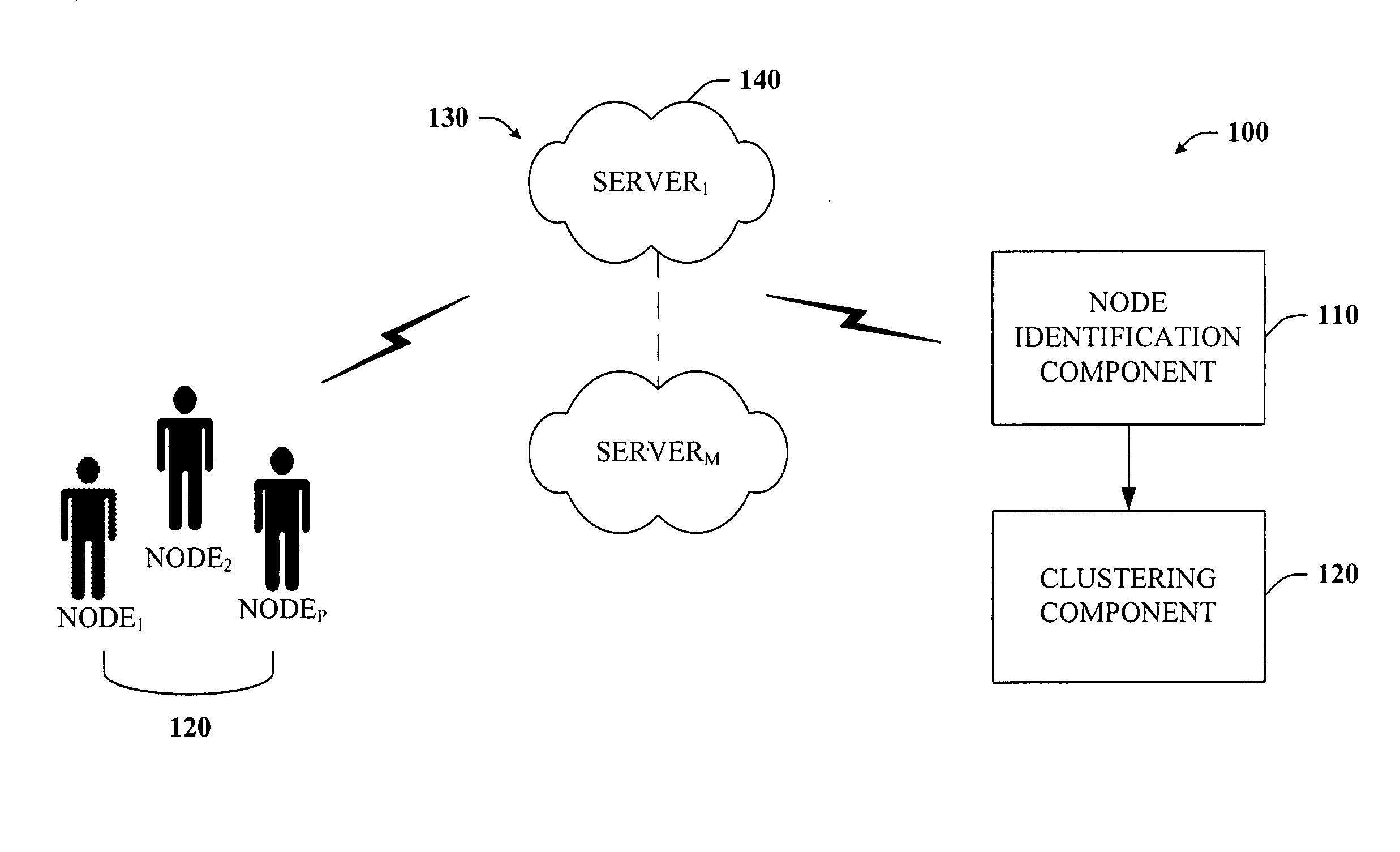
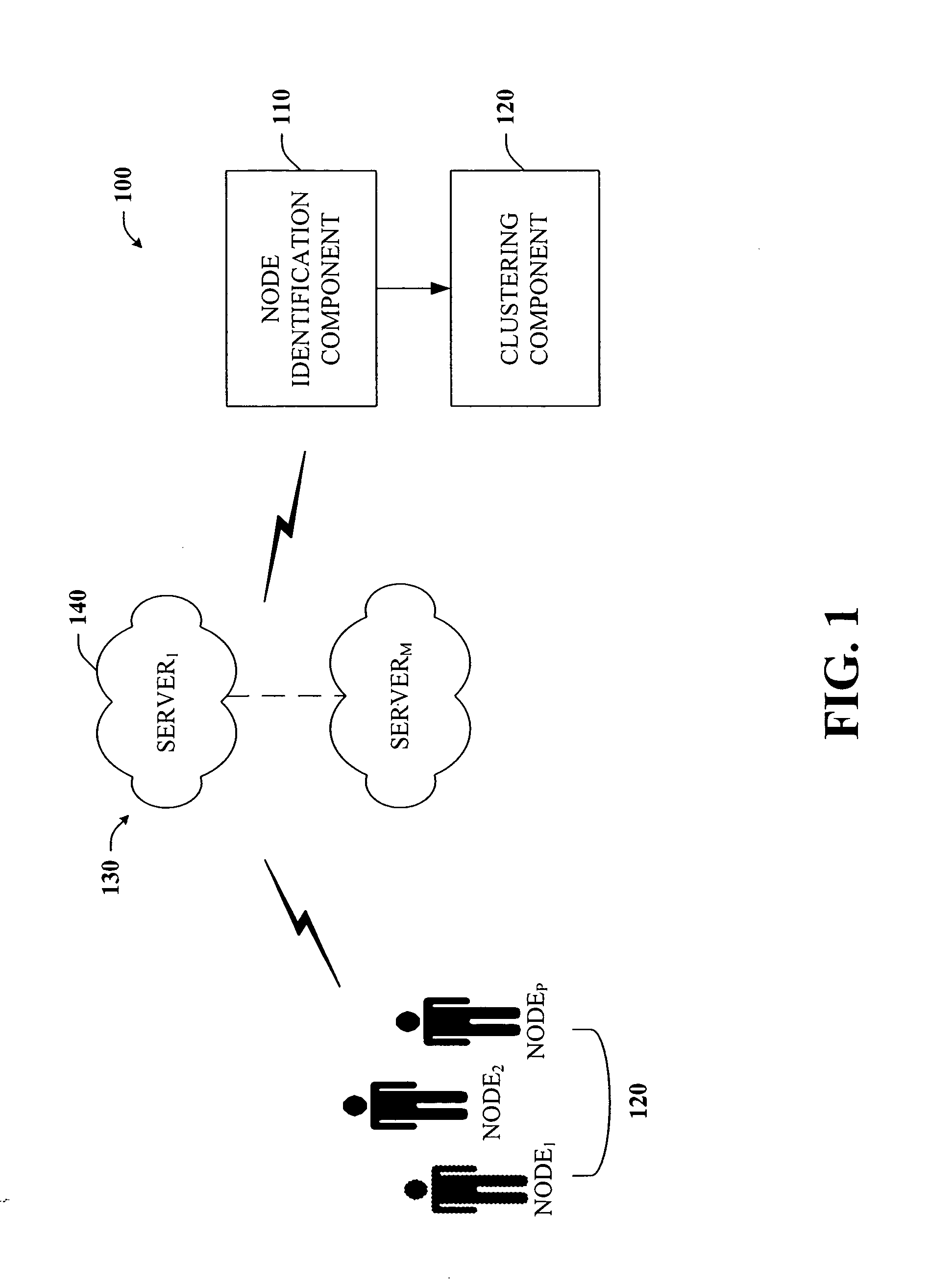
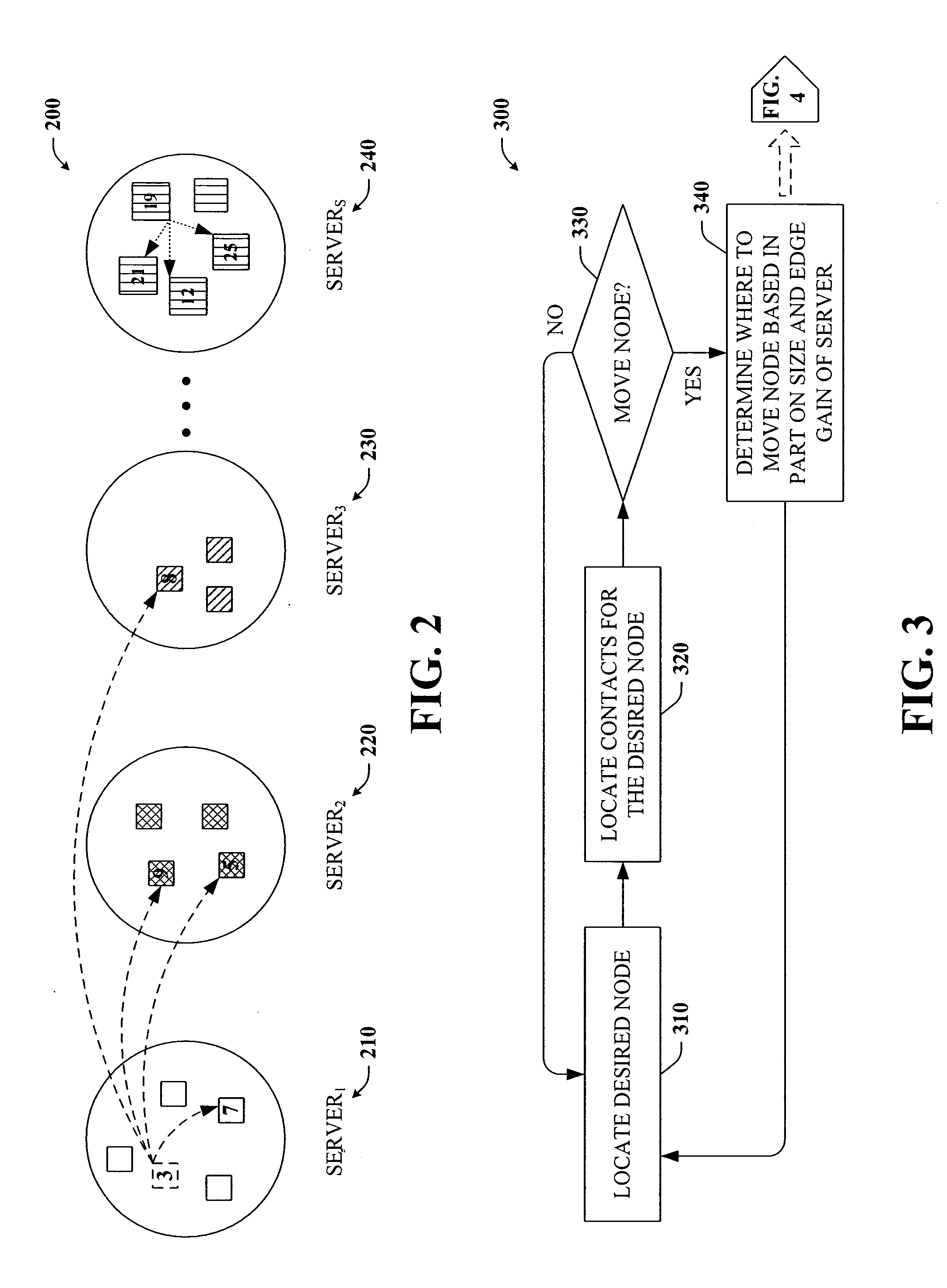
ActiveUS20060015588A1Communication be reduceEasy to placeDigital computer detailsMarketingTraffic volumeTraffic capacity
The present invention provides a unique system and method that facilitates reducing network traffic between a plurality of servers located on a social-based network. The system and method involve identifying a plurality of vertices or service users on the network with respect to their server or network locations. The vertices' contacts or connections can be located or determined as well. In order to minimize communication traffic, the vertices and their connections with respect to their respective server locations can be analyzed to determine whether at least a subset of nodes should be moved or relocated to another server to facilitate mitigating network traffic while balancing user load among the various servers or parts of the network. Thus, an underlying social network can be effectively partitioned. In addition, the network can be parsed into a collection of nested layers, whereby each successively less dense layer can be partitioned with respect to the previous (partitioned) more dense layer.
Owner:MICROSOFT TECH LICENSING LLC
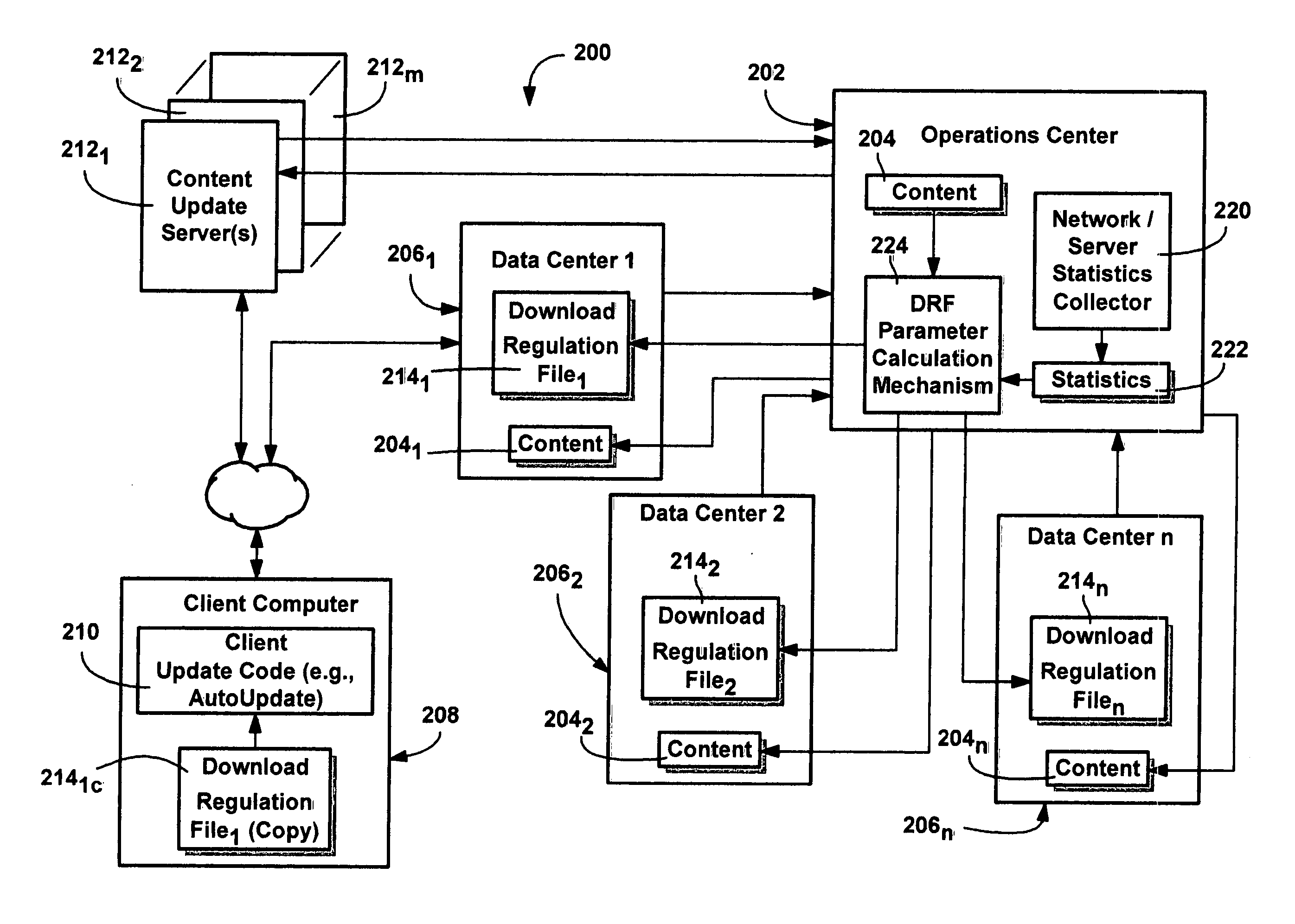
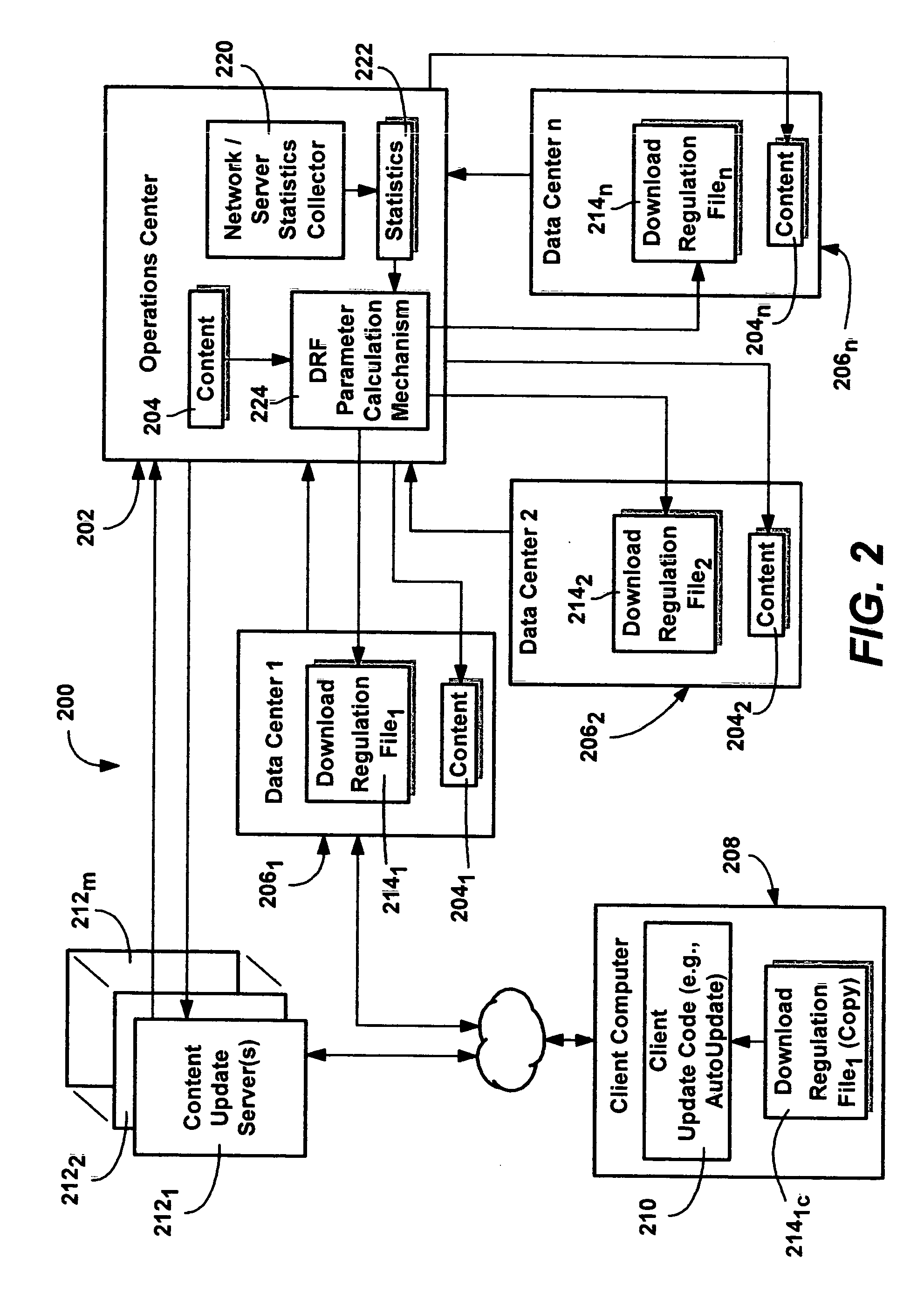
Network download regulation method and system
InactiveUS20050120040A1Reduce decreaseEfficient and cost-effectiveMultiple digital computer combinationsTransmissionControl mannerSoftware update
A system and method by which content, such as a software update, is downloaded in a controlled manner to clients so as to reduce peak demands, by modulating the number of clients that can request (e.g., automatically) to download content. To this end, before any download is requested, each client receives information that the client uses to determine whether to request the content now, or back off and retry the download process later. In one implementation, the information is provided via a download regulation file, comprising acceptance percentage and time window parameters that are occasionally varied based on current network load-related statistics. Clients generate a random number that is evaluated against the acceptance percentage (probability threshold) to determine whether to download or back off. The time window specifies how long downloading clients are allowed to download, or how long backed-off clients need to wait before restarting the regulated download process.
Owner:MICROSOFT TECH LICENSING LLC
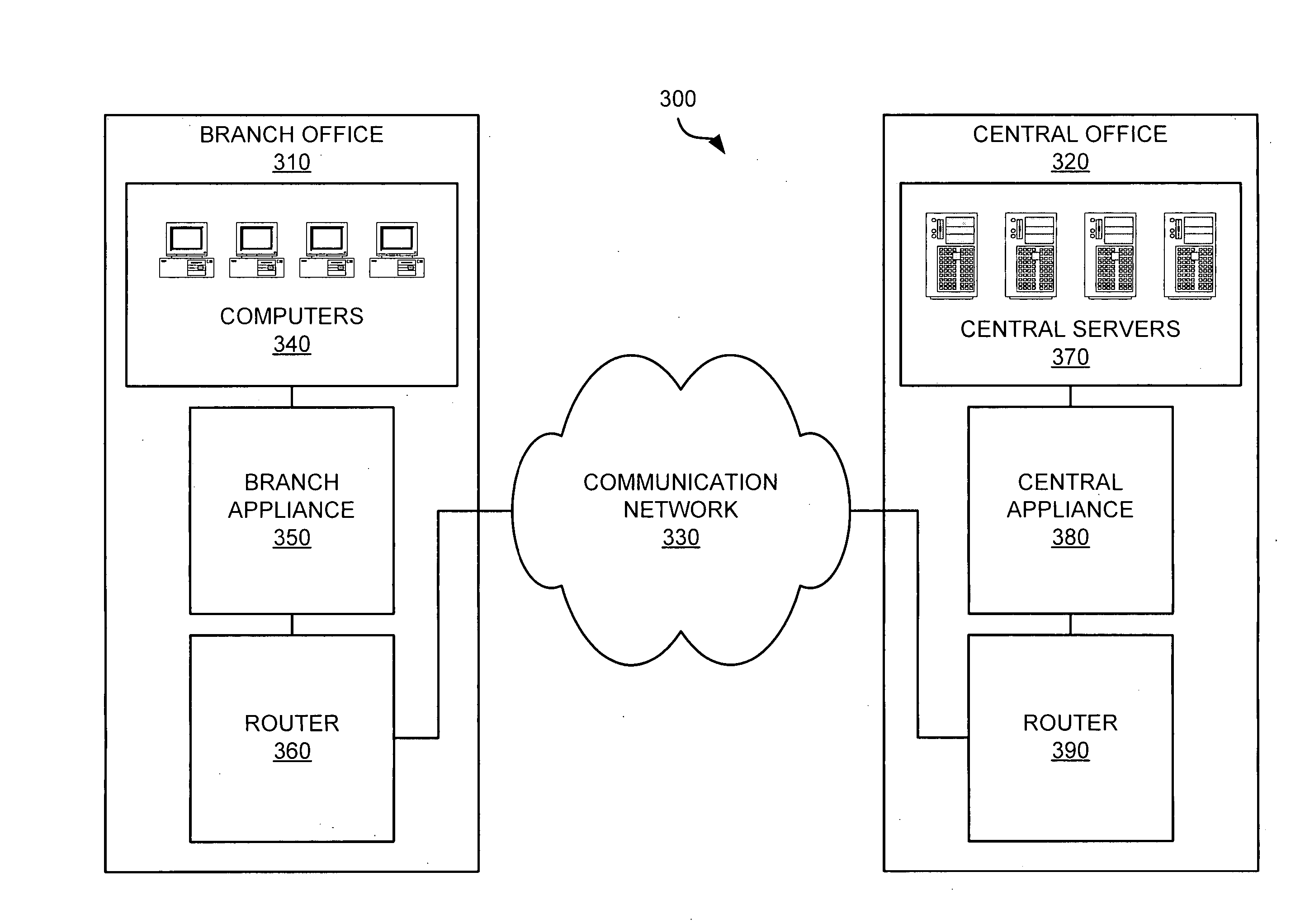
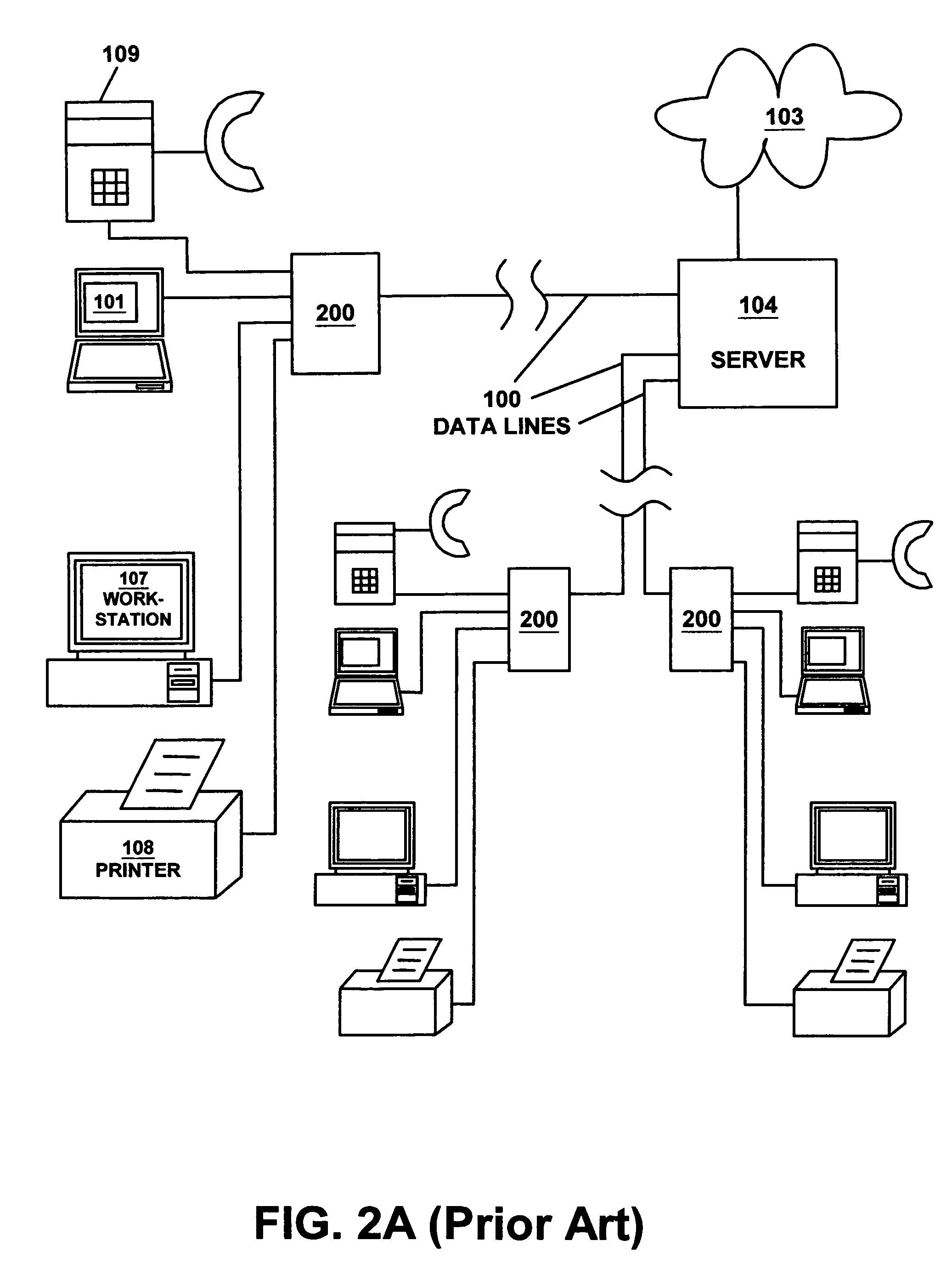
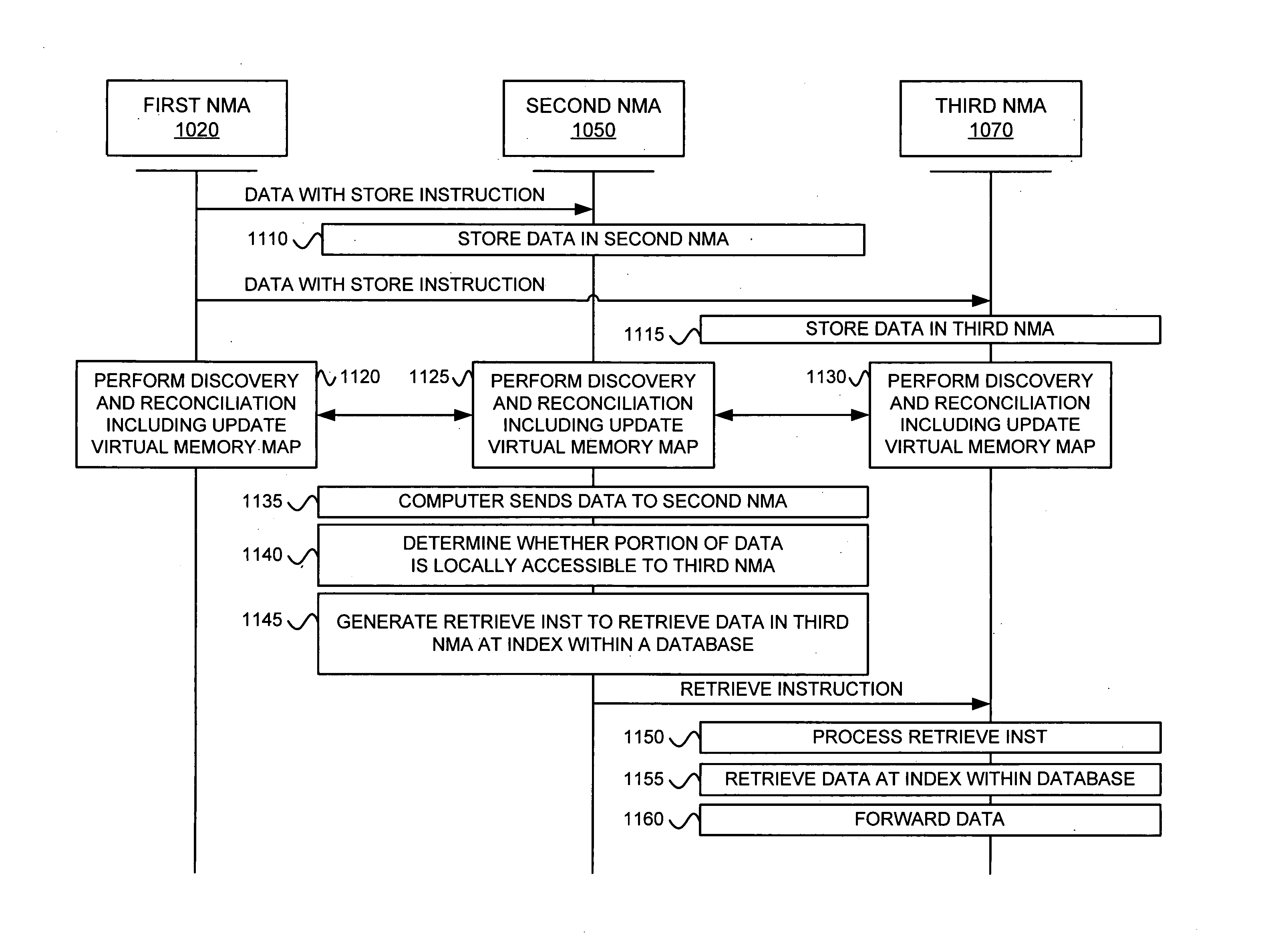
Network memory architecture
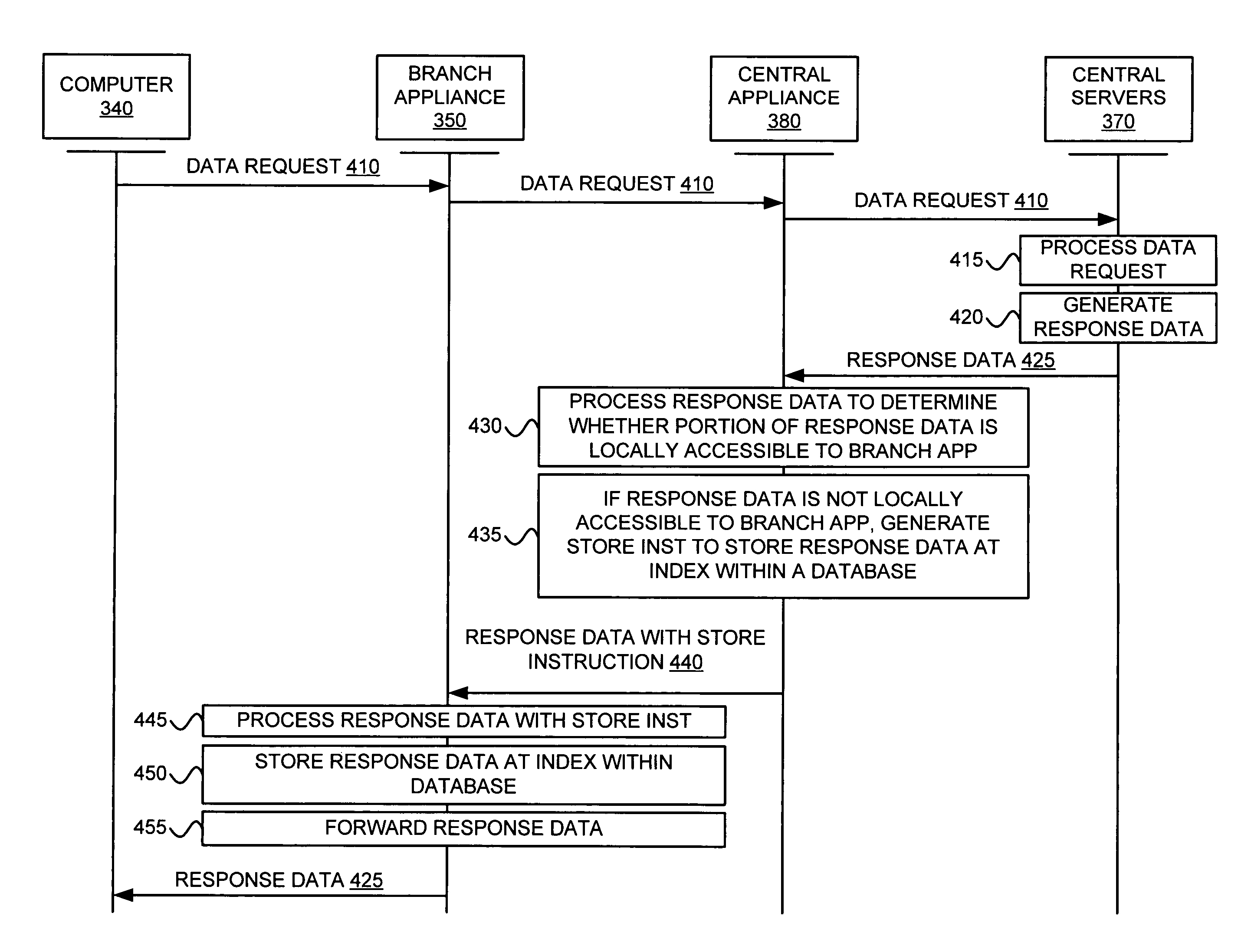
ActiveUS20070050475A1Reduce latencyReduce trafficMultiple digital computer combinationsNetwork connectionsTerm memoryMemory architecture
A network memory system comprises a first appliance and a second appliance. The first appliance receives data and determines whether a portion of the data is locally accessible to the second appliance. The first appliance generates an instruction based on the determination and transfers the instruction to the second appliance over a communication network. The second appliance receives the instruction from the first appliance over the communication network and processes the instruction to obtain the data. The second appliance then transfers the data to a computer.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Controlling network congestion using a biased packet discard policy for congestion control and encoded session packets: methods, systems, and program products
ActiveUS20030012137A1Increase bitrateImprove voice qualityError preventionFrequency-division multiplex detailsControl systemNetwork congestion control
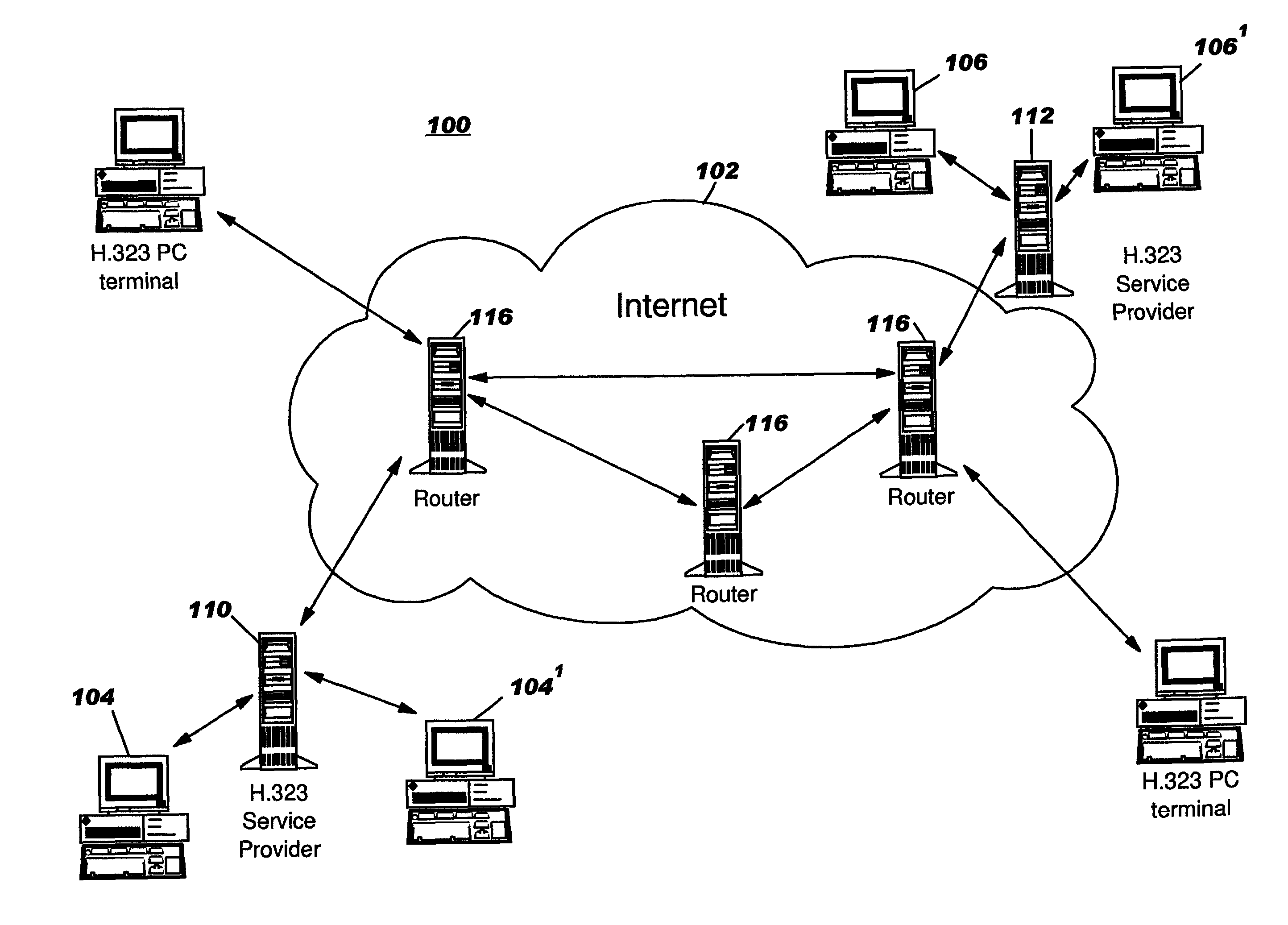
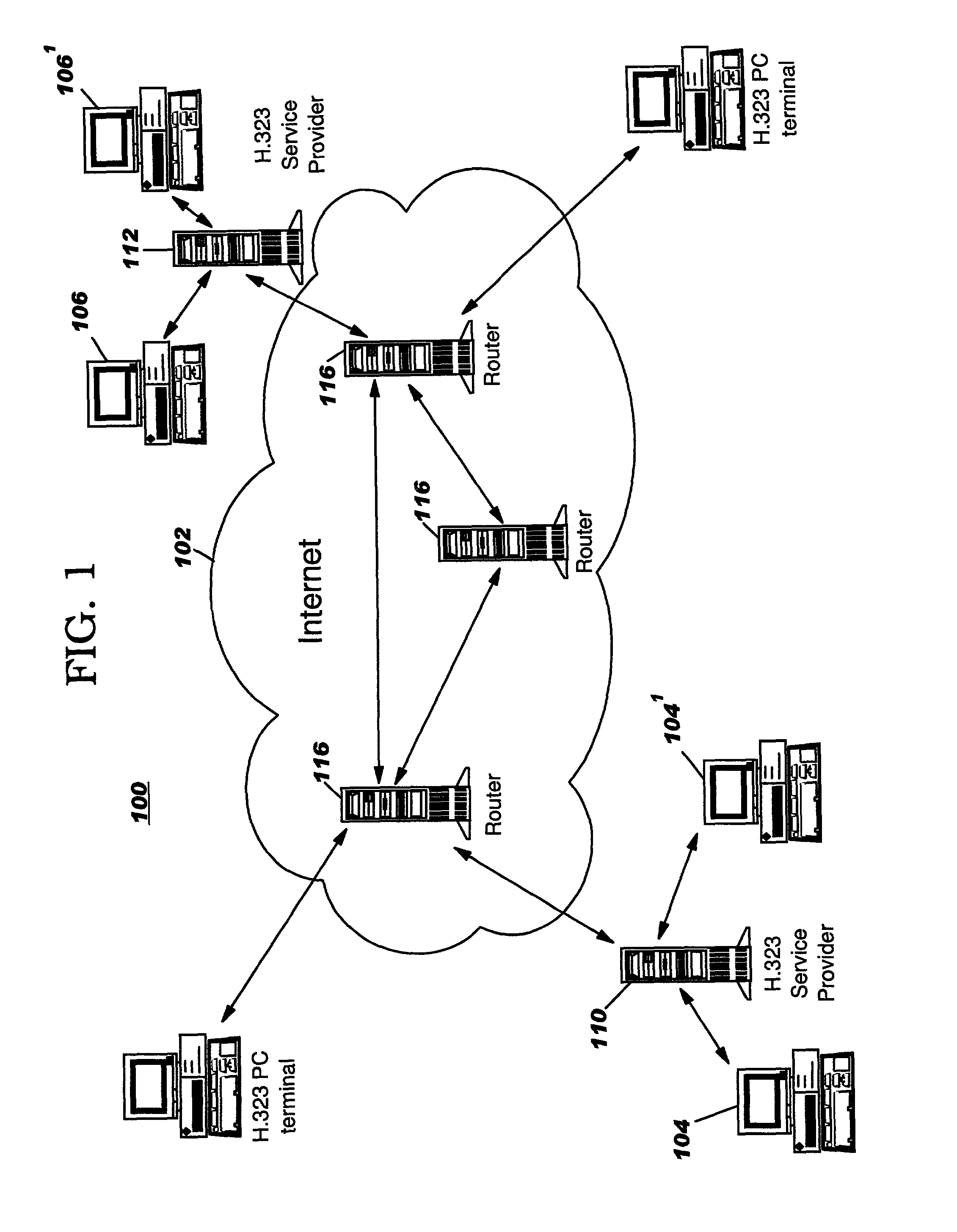
A packet network congestion control system using a biased packet discard policy includes a plurality of end points having codecs operating in a framework, e.g. ITU-T H.323 protocol to establish a communication session. The protocol enables the codecs to negotiate codec type and associated parameters. Once a connection and session are established, compressed voice and data packets start flowing between the two end points. A control entity supplies congestion control packets periodically. The control packets provide a "heartbeat" signal to the codec at the other end of the session. Each codec receiver uses the "heartbeat" signal as an indication of network congestion. As network congestion increases, routers within the network discard excess packets to prevent network failure. The network discards all packets classified as congestion control packets whenever a flow control mechanism detects congestion or a trend toward congestion. As packets are discarded, the end points renegotiate codec type and / or parameters to realize lower bit rates.
Owner:IBM CORP +1
Systems, Methods, and Apparatuses for Managing the Flow of Traffic in Data Networks
InactiveUS20120182865A1Network degradationIncrease profitError preventionFrequency-division multiplex detailsTraffic volumeNetwork method
Methods or systems for management and / or optimization of at least a portion of a data network by generating a set of paths between each origin and destination pair, pruning the set of paths to generate a pruned set of paths; and computing an optimum path between each origin and destination pair. Methods and systems for generating a diverse set of path options for the routing of traffic within at least a portion of a network comprising: generating a set of paths between each origin and destination pair; and pruning the set of paths to generate a pruned set of diverse path options within at least a portion of a network.
Owner:VPISYST
Method and system for quality of service (QoS) support in a packet-switched network
InactiveUS7075927B2Reduce in quantityNetwork degradationError preventionTransmission systemsQuality of serviceDelayed binding
A method and system for transporting traffic having disparate qualities of service classes across a packet-switched network includes receiving at an ingress node of a network a plurality of packets each comprising a quality of service (QoS) class defined externally to the network. Packets having a QoS class comprising delay bound guarantees and a low drop priority are combined into a first internal QoS class. Packets having a QoS class comprising a flexible drop priority and no delay bound guarantees are combined into a second internal QoS class. Packets having a QoS class including no delivery guarantees are combined into a third internal QoS class. The packets are transmitted in the network based on their internal QoS class.
Owner:FUJITSU LTD
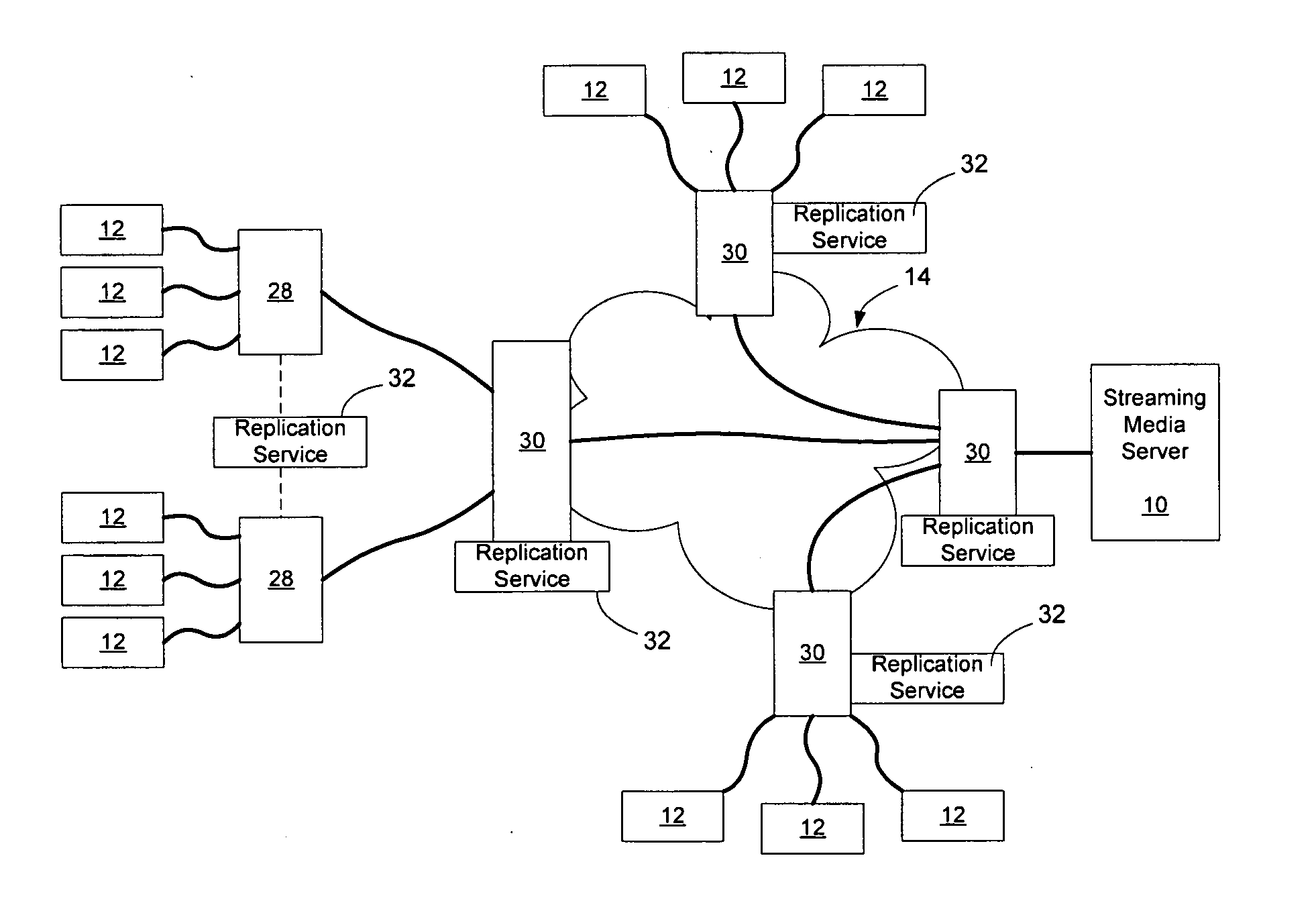
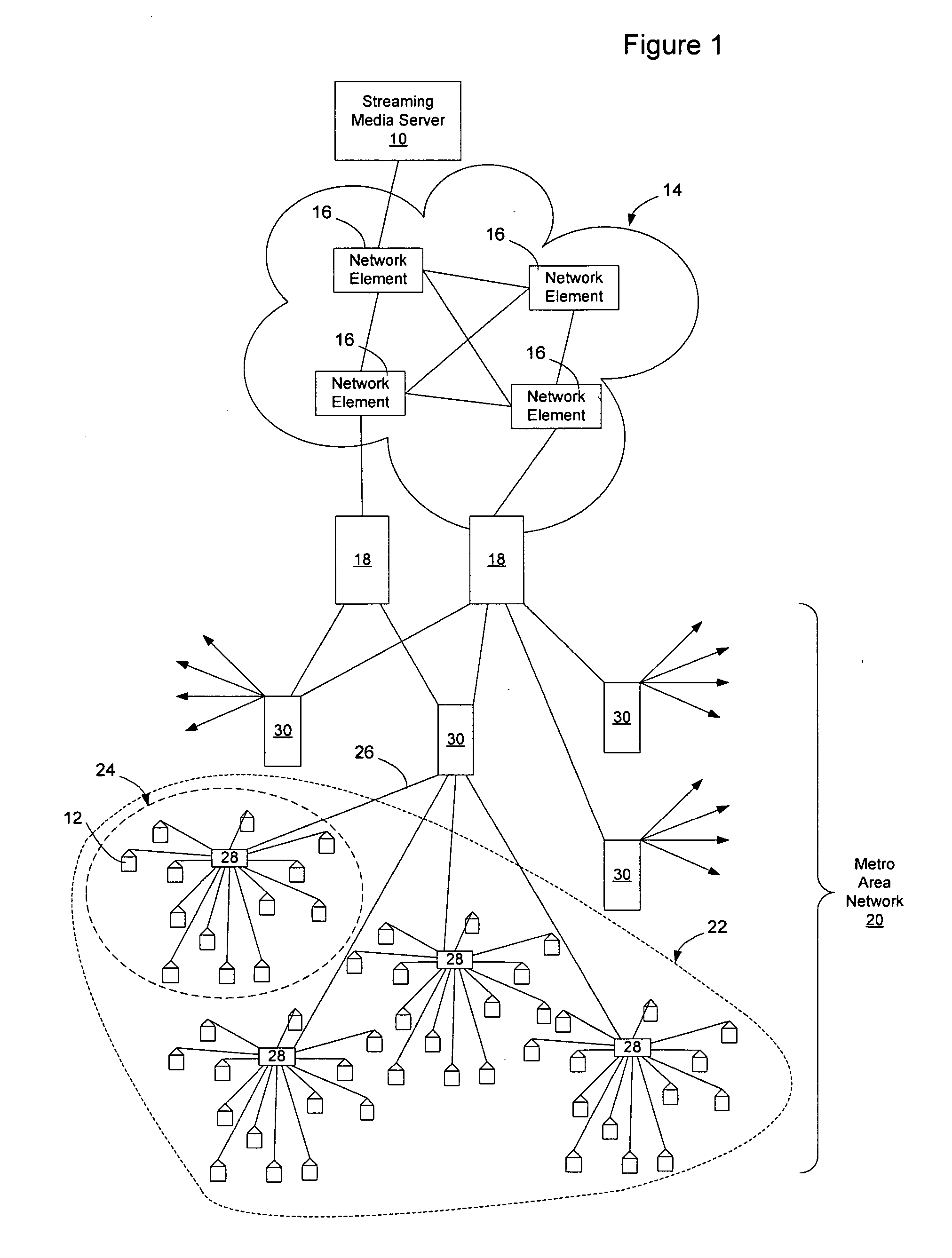
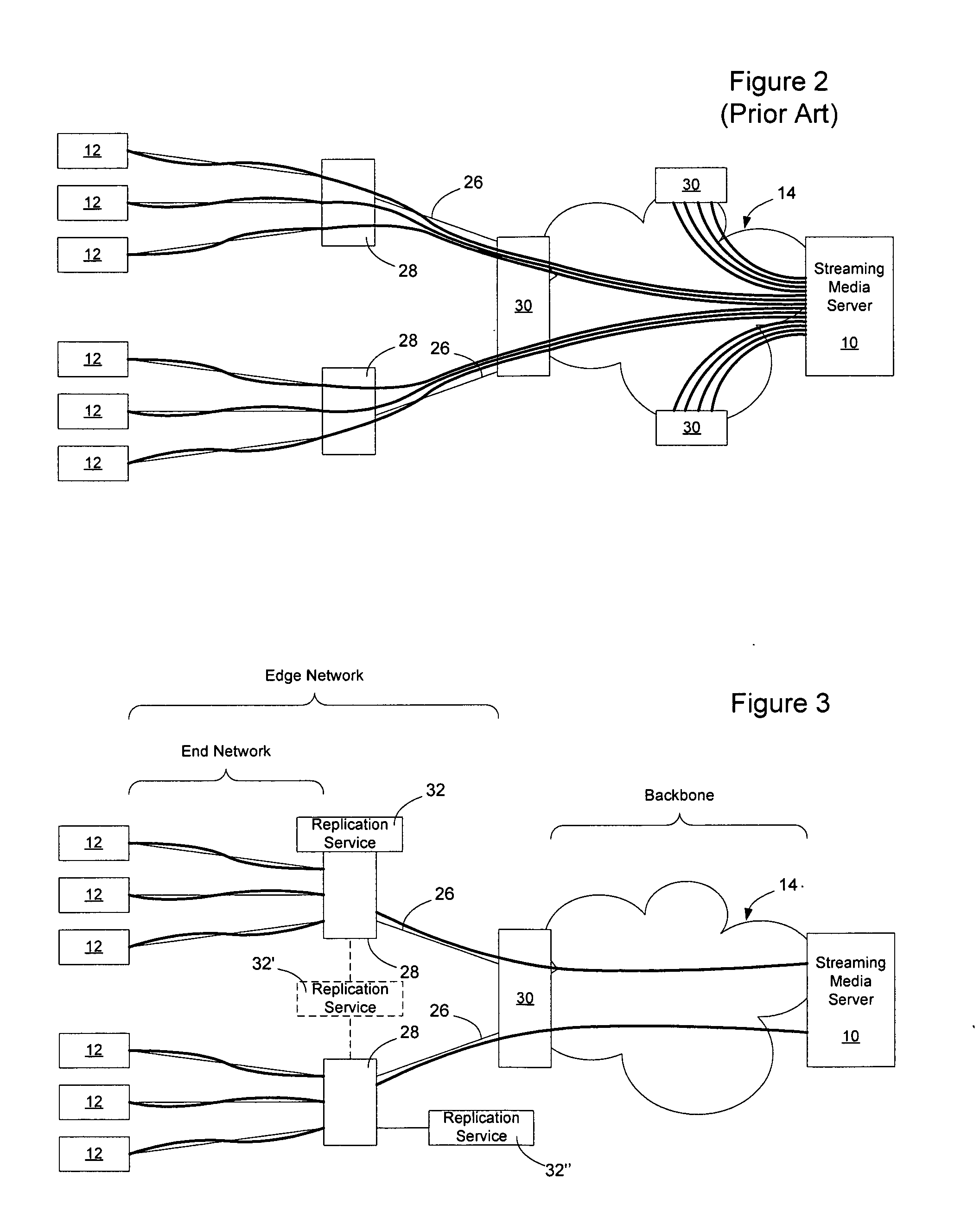
Method and apparatus for live streaming media replication in a communication network
InactiveUS20050076099A1Network degradationReduce in quantityMultiple digital computer combinationsTransmissionMedia serverClient-side
Replication of live streaming media services (SMS) in a communication network may be enabled by introducing the streaming media-savvy replication service on a network element, through a number of functions such as client / service registration and classification, packet interception and forwarding, media replication, status monitoring and configuration management. In an embodiment, client requests and server replies of an SMS are intercepted and evaluated by the network element. If the SMS is not streaming through the network element, the replication service registers the SMS and establishes a unique SMS session for the requesting clients. If the SMS is already streaming through the network element, the replication service replicates the streaming media and forwards it to the requesting clients. This reduces bandwidth usage on the links connecting the streaming media server with the network element and reduces the number of client connections to the streaming media provider's servers.
Owner:NORTEL NETWORKS LTD
Intelligent concentrator usage
InactiveUS7023809B1Low costEasy to manageMultiplex system selection arrangementsError preventionNetwork connectionPower over
The present invention relates to a computer network and a method for using the network The network and method employ powered multiplexing connection devices which electronically couple two or more network devices to the network. The signals from the network devices to the network are multiplexed at the powered multiplexing connection devices and the signals from the network to the network devices are demultiplexed at the powered multiplexing connection devices. The multiplexing enables the various work-center devices to communicate with the network and, in some cases, to receive power over the network connection. The intelligent electronic circuitry is also capable of aiding in network security and management and in monitoring the status of the network infrastructure. A primary advantage of the disclosed invention is an enormous reduction in the network administrator's workload in that a significant portion of the labor involved in managing and modifying a network is alleviated or obviated by the powered, intelligent, multiplexing connection devices.
Owner:VALTRUS INNOVATIONS LTD
Network memory appliance
ActiveUS20070038815A1Network degradationQuick searchMultiple digital computer combinationsNetwork connectionsNetwork storageData processing
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
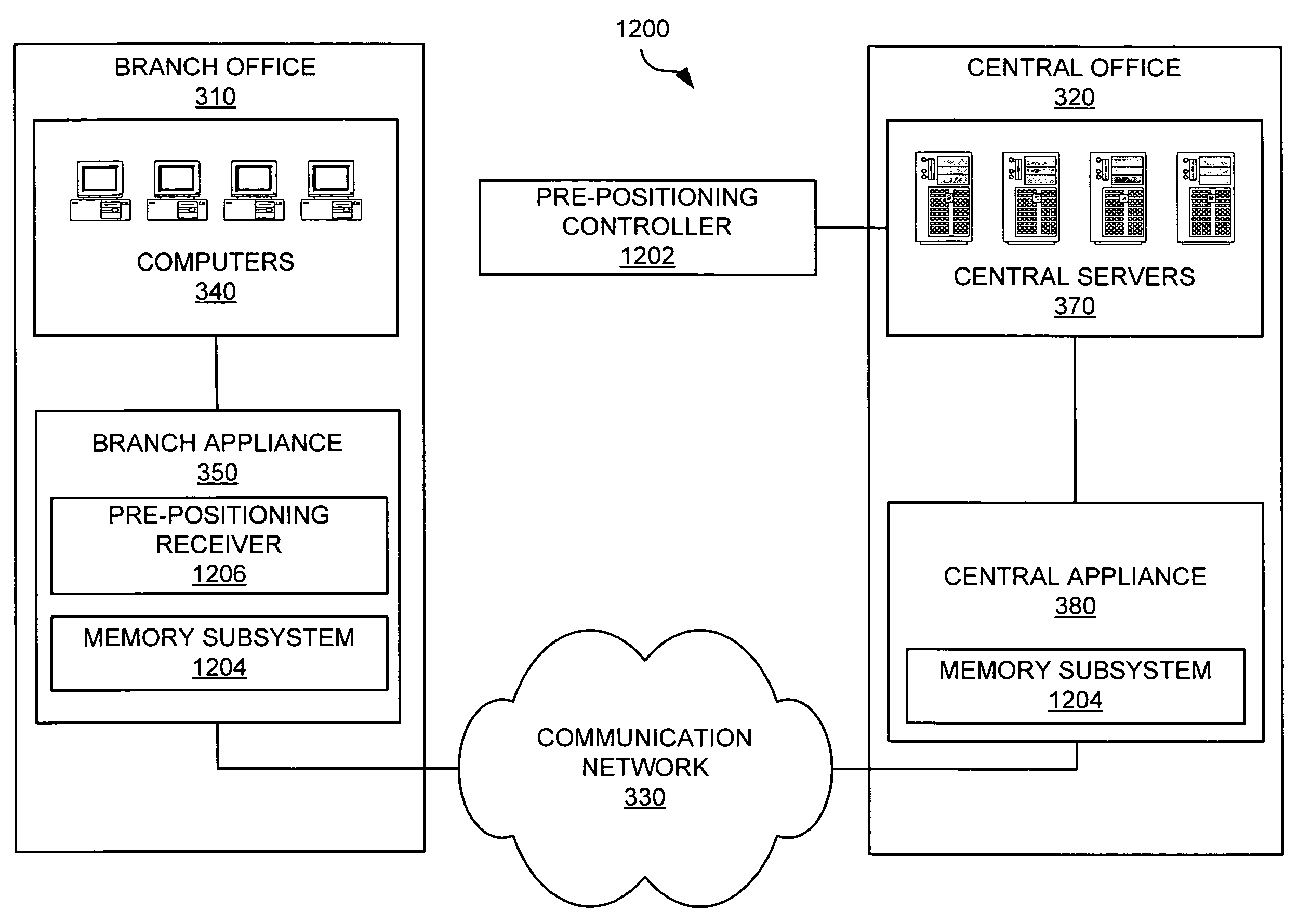
Pre-positioning data in a network memory appliance
InactiveUS7698431B1Quick searchWithout license feeDigital computer detailsNetwork connectionsFile systemSoftware update
Systems and methods for pre-positioning data in a network memory are described. A pre-positioning command may be executed to position specific data at one or more network memory appliances before the data is requested at a branch office. For example, the first download of a software update over the communication network at a branch office may require several minutes. To make the first download of the software update faster, the software update may be downloaded previously to the branch appliance. According to various embodiments, the pre-positioning command may comprise a time of transfer and / or a schedule. The data may be received by a pre-positioning receiver such as a file system server, a hypertext transfer protocol server, a file transfer protocol server, or a virtual client.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
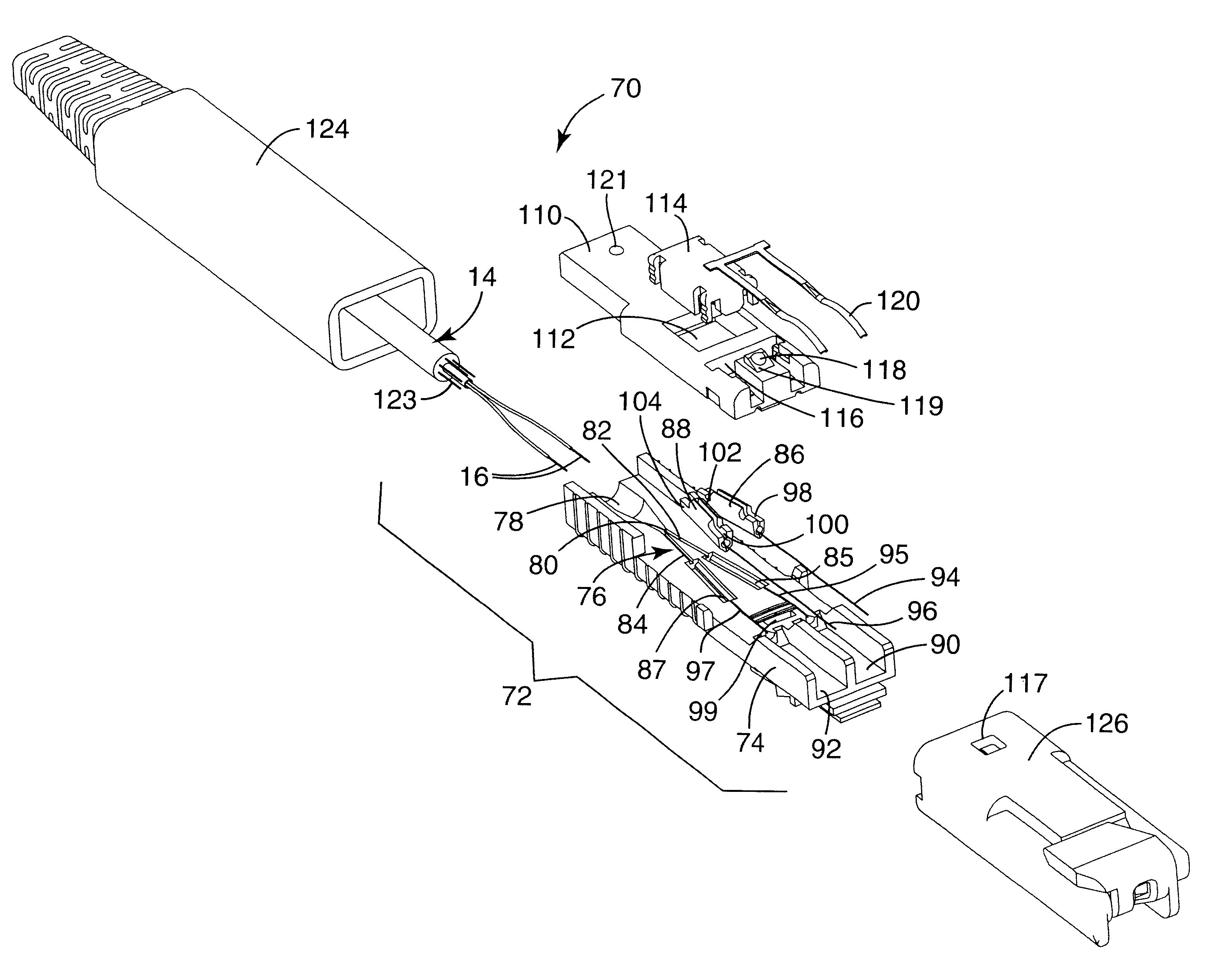
Optical fiber plug
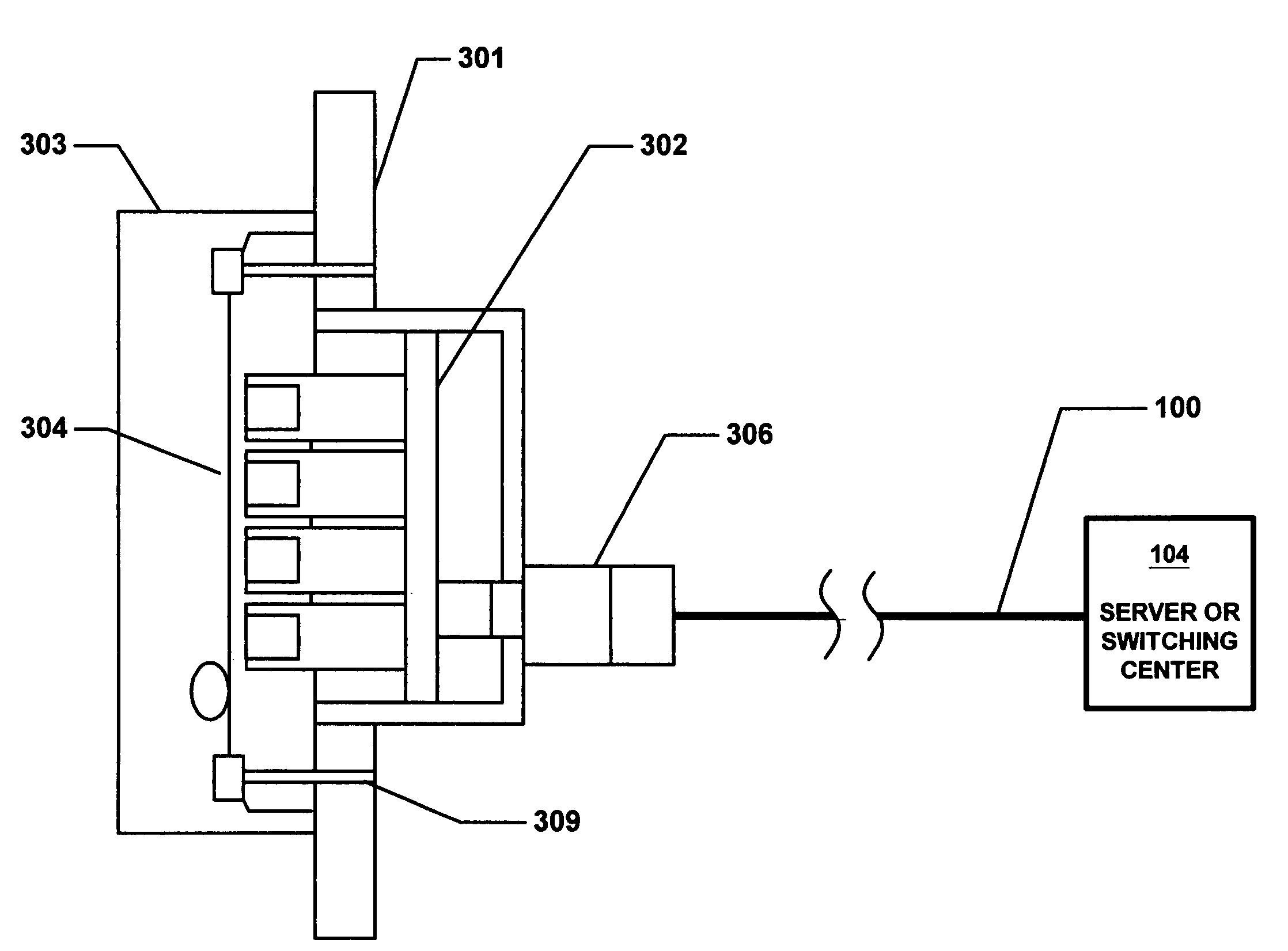
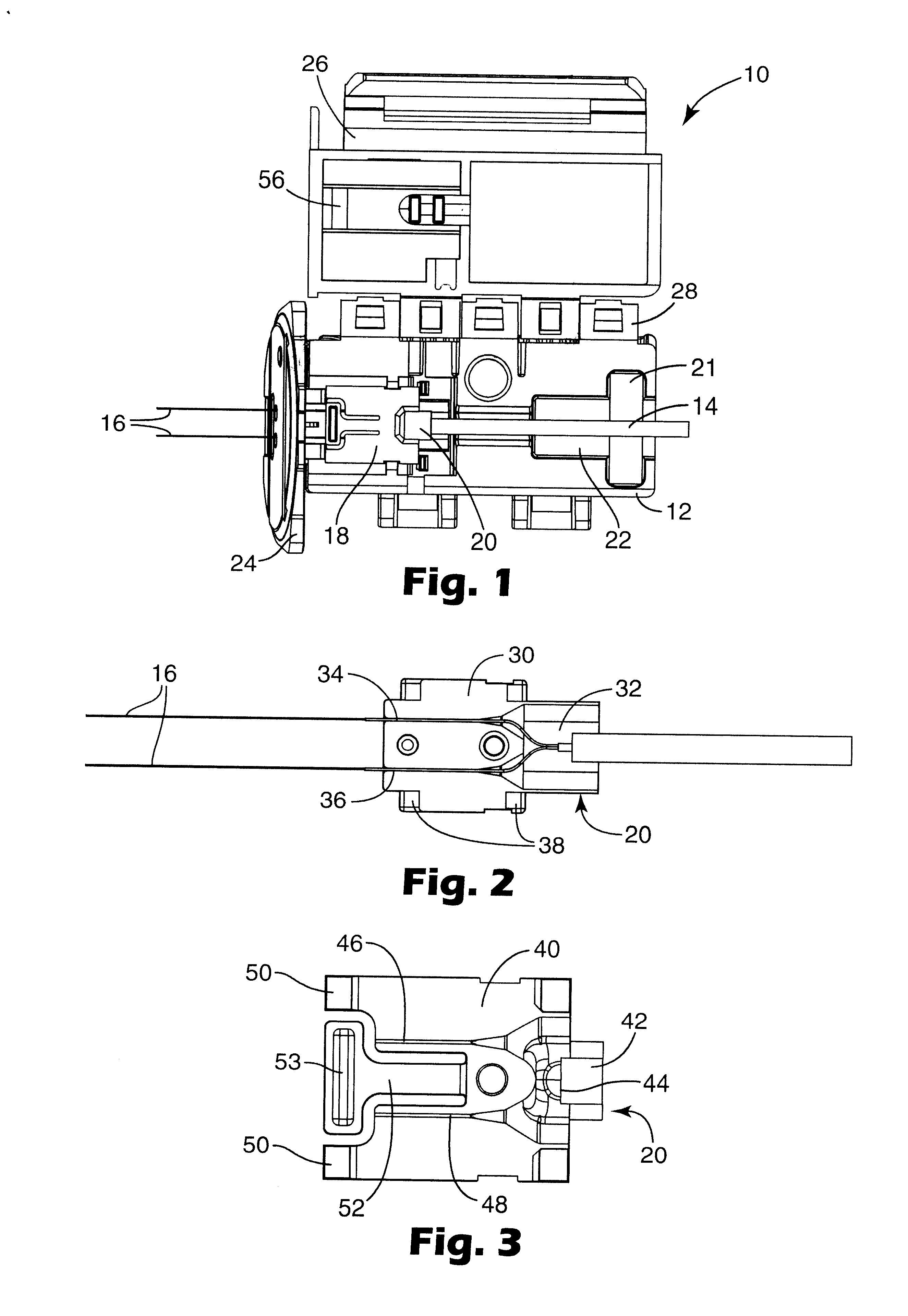
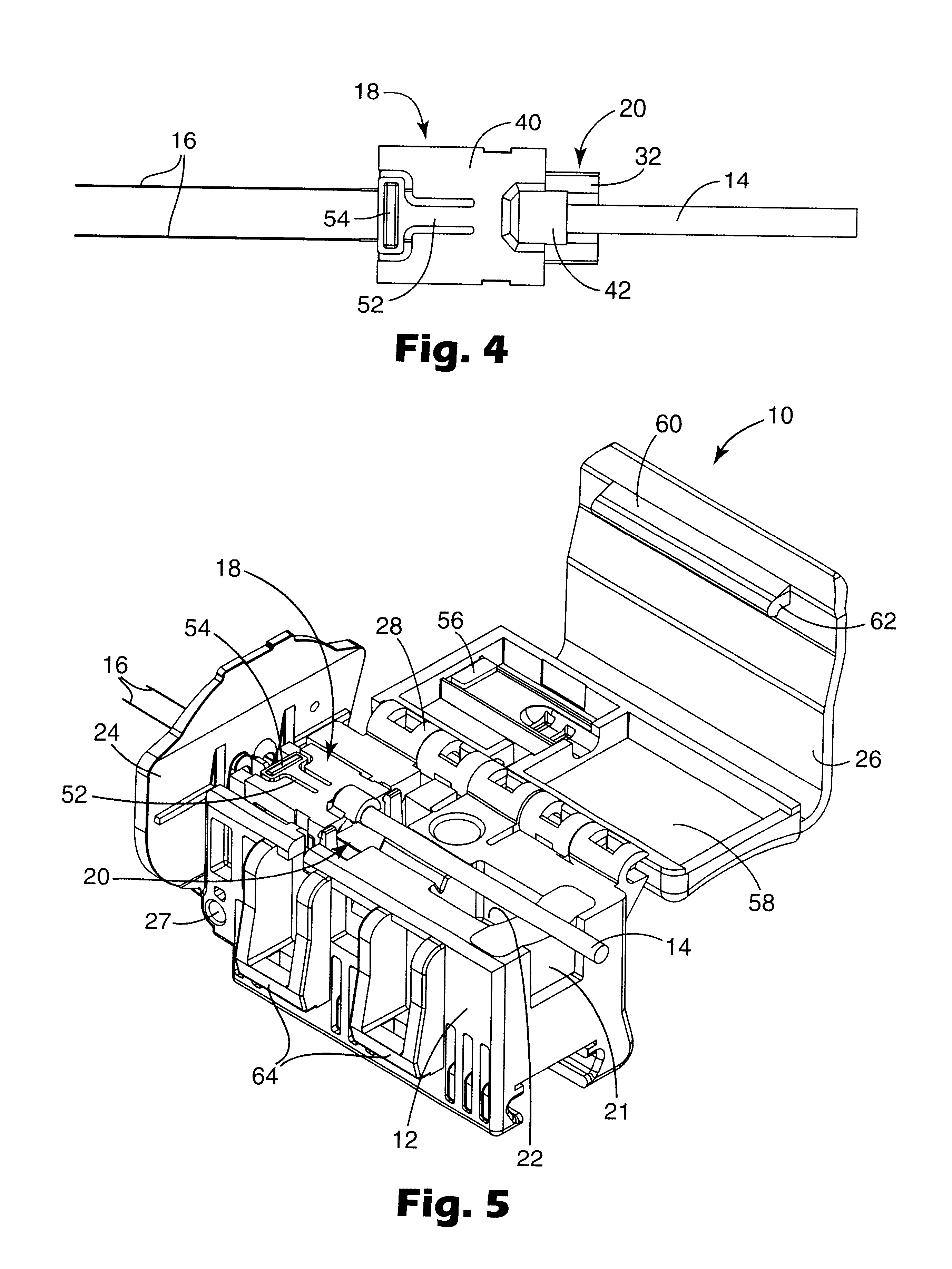
InactiveUS6848838B2Precise alignmentAccurate orientationCoupling light guidesFiberOptical fiber connector
An optical fiber connector plug for an optical fiber connection comprises a connecting portion including a rear entry at a first end and a first fiber stub exit opening to a first fiber stub channel. The first fiber stub exit is parallel to a second fiber stub exit opening to a second fiber stub channel. The first and second fiber stub exits are formed opposite the first end. The rear entry divides at a junction into a first fiber groove and a second, diverging fiber groove. The connecting portion includes crimp elements each having an open-ended bore. Each crimp element contains an optical fiber stub. A molded top attached to the connecting portion includes a substantially rectangular opening. The opening contains a compression element that moves to form splices by capturing a stripped optical fiber and an optical fiber stub in each of the crimp elements. A bend relief boot encloses the connecting portion at one end, while a shroud releasably engages it at the other end.
Owner:3M INNOVATIVE PROPERTIES CO
Network memory appliance for providing data based on local accessibility
ActiveUS8312226B2Quick searchNetwork degradationMultiple digital computer combinationsNetwork connectionsProcessing InstructionAccessibility
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com