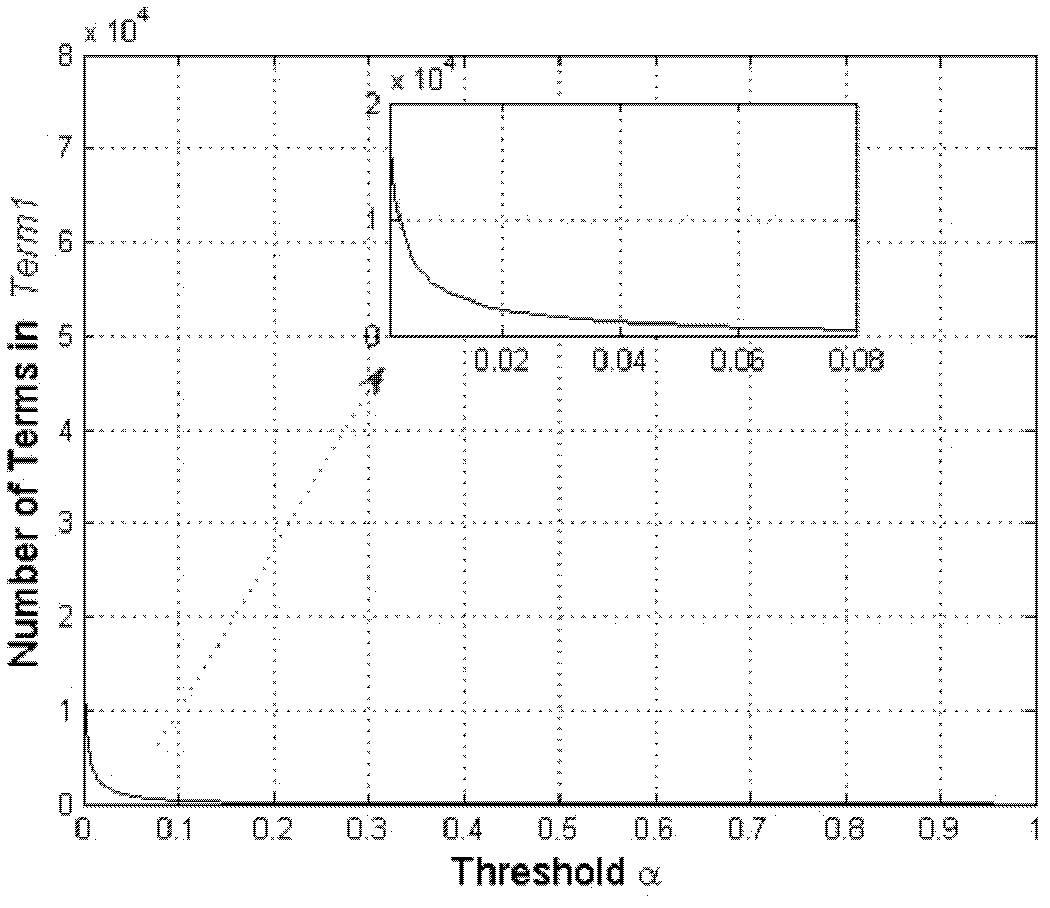
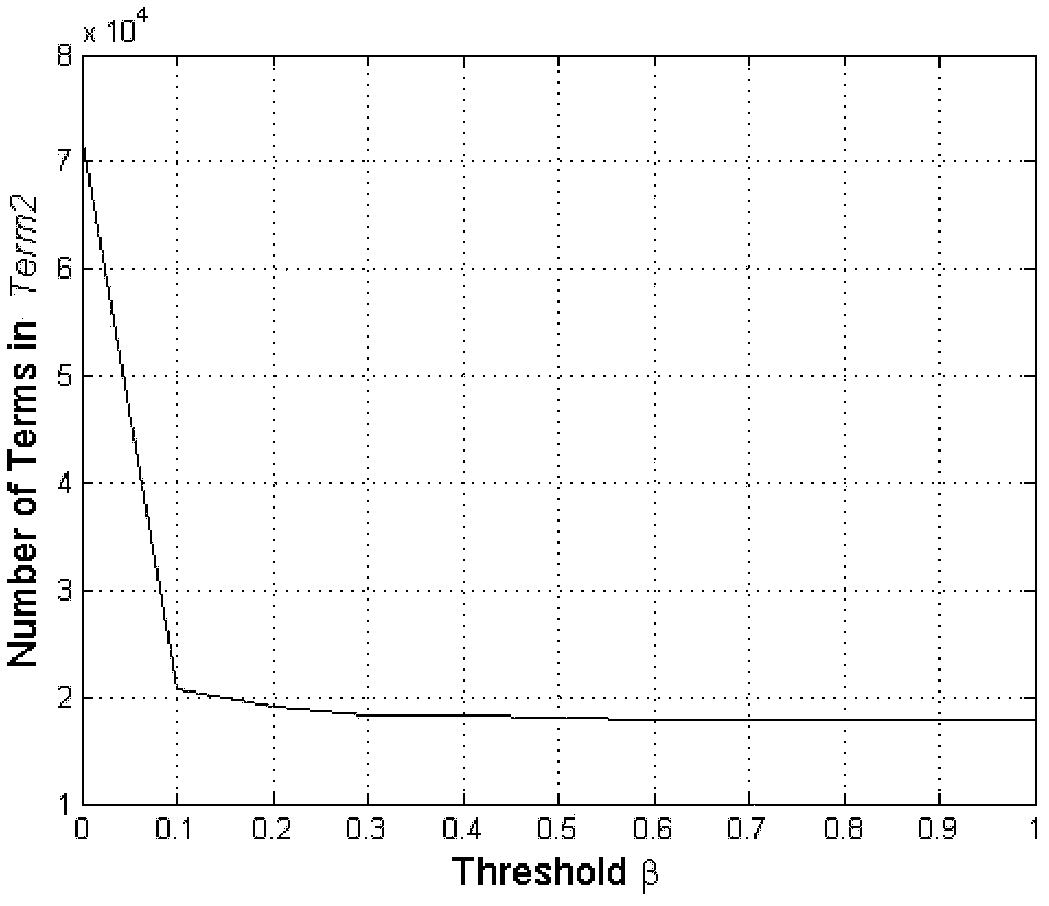
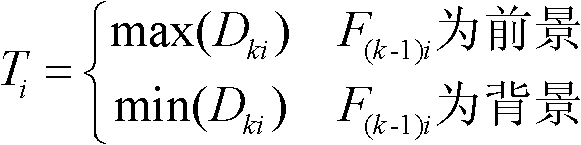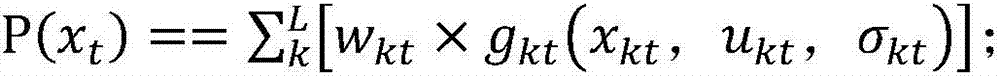Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2062results about How to "Reduce false positives" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
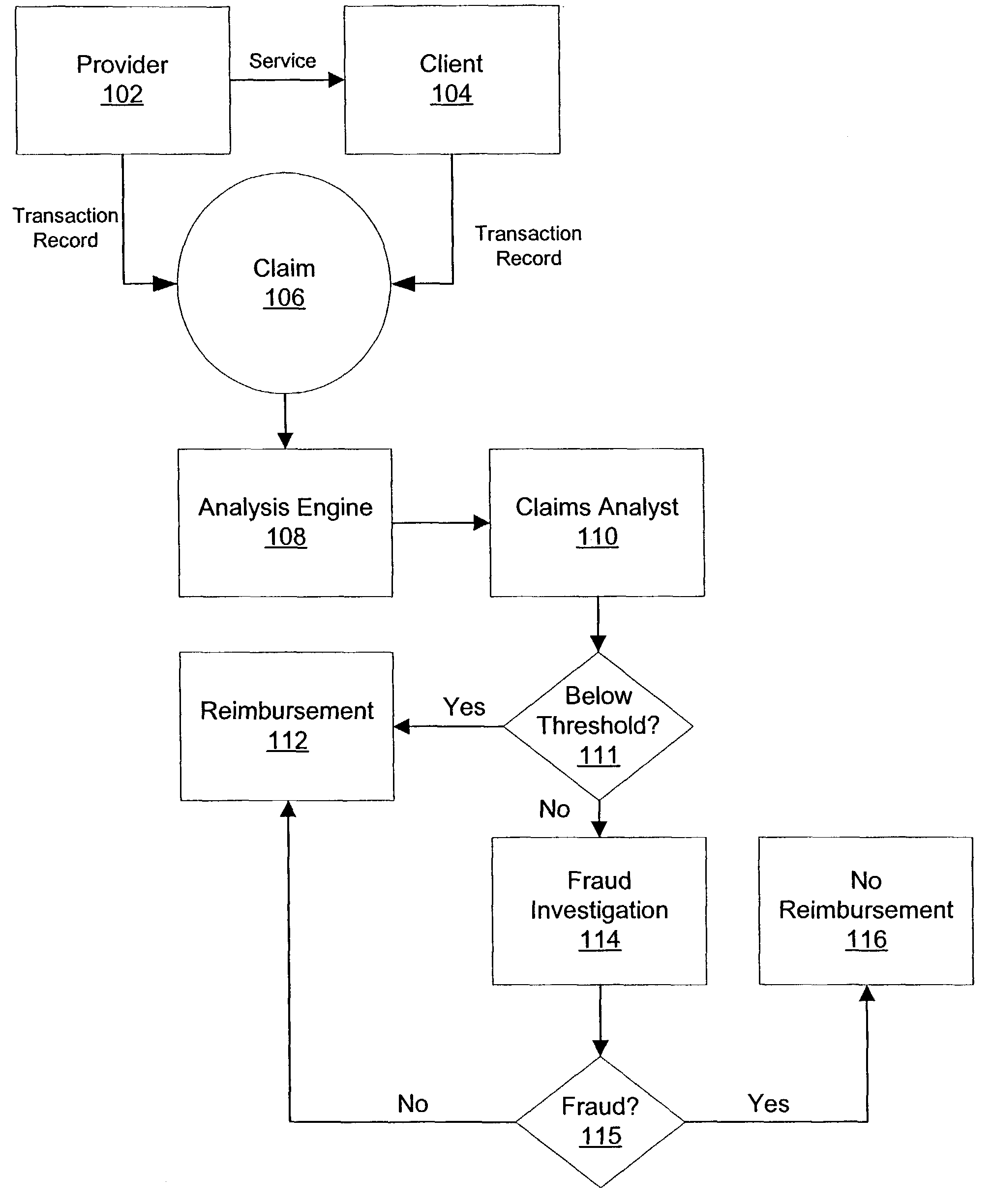
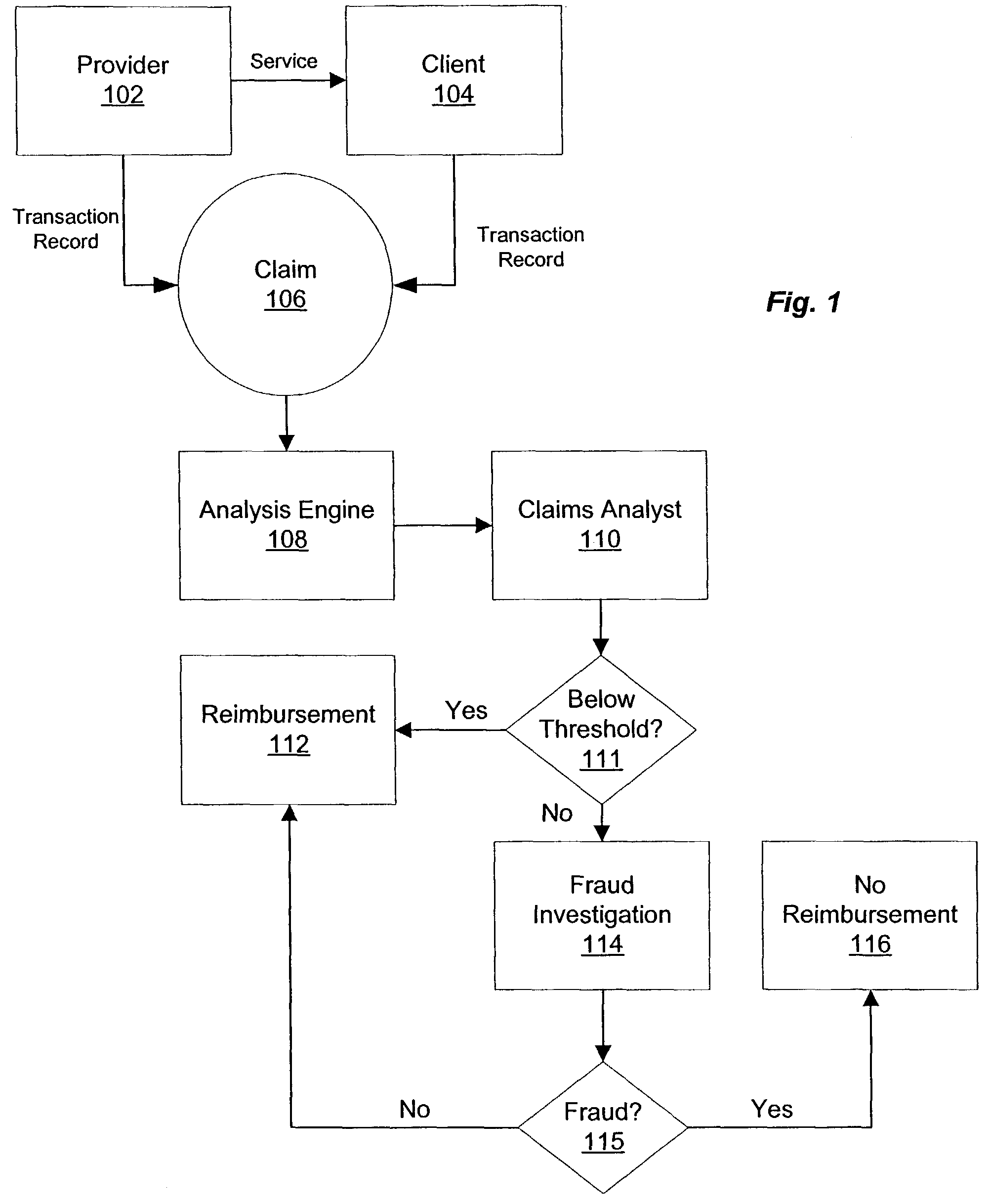
Intrusion detection in a data center environment
ActiveUS20060095968A1Reduce false-positivesGreat granularityError preventionTransmission systemsTraffic volumeIntrusion detection system
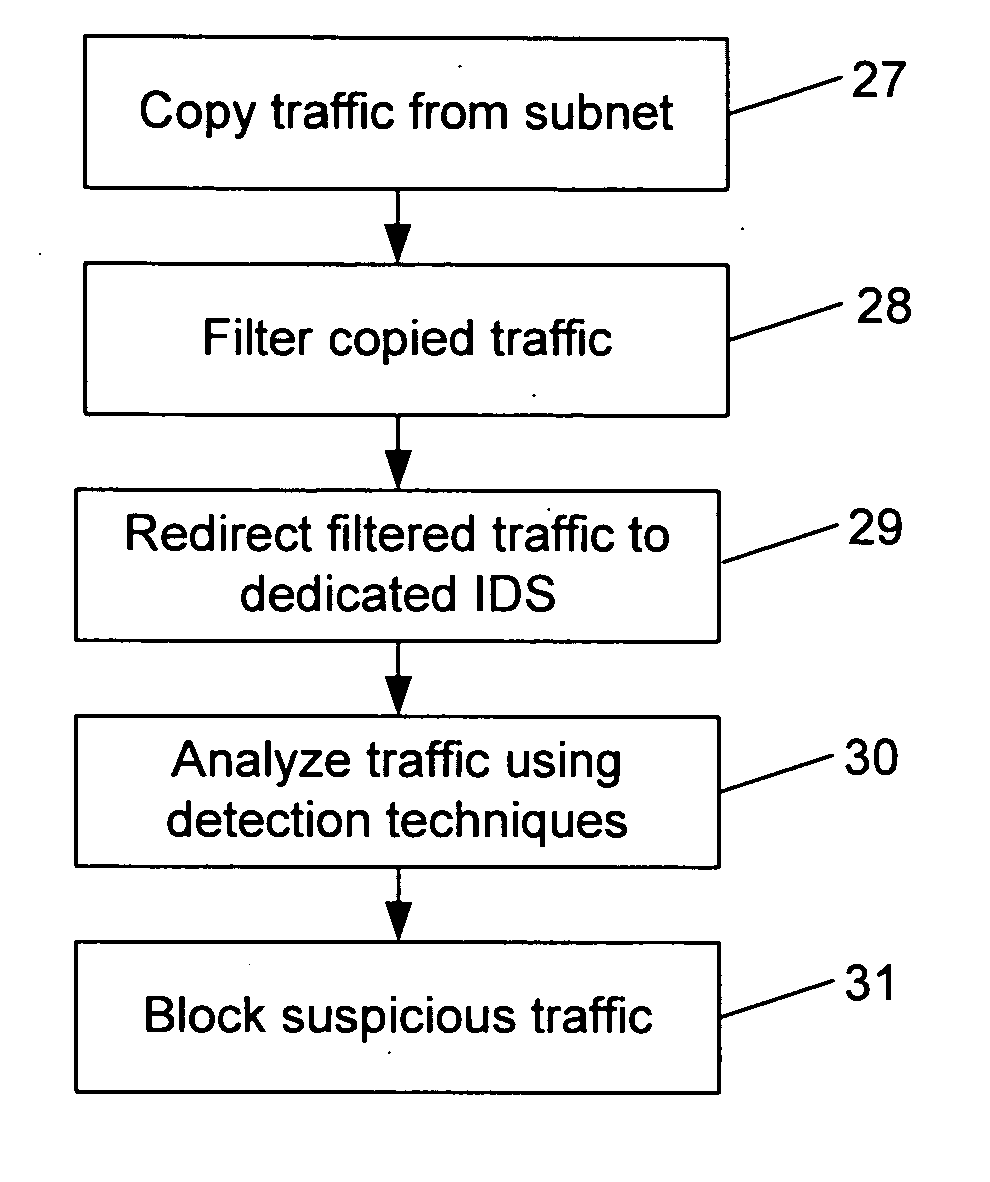
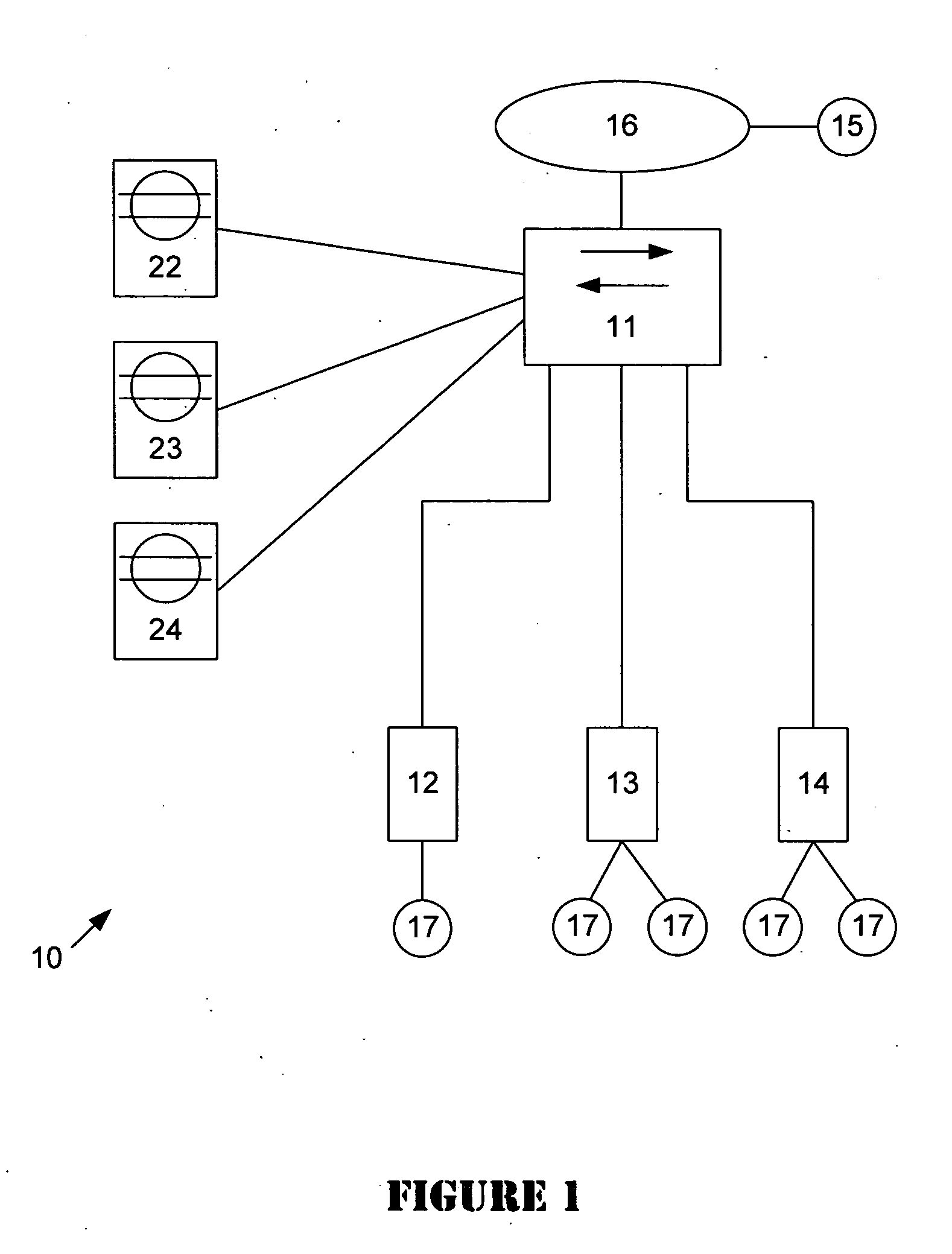
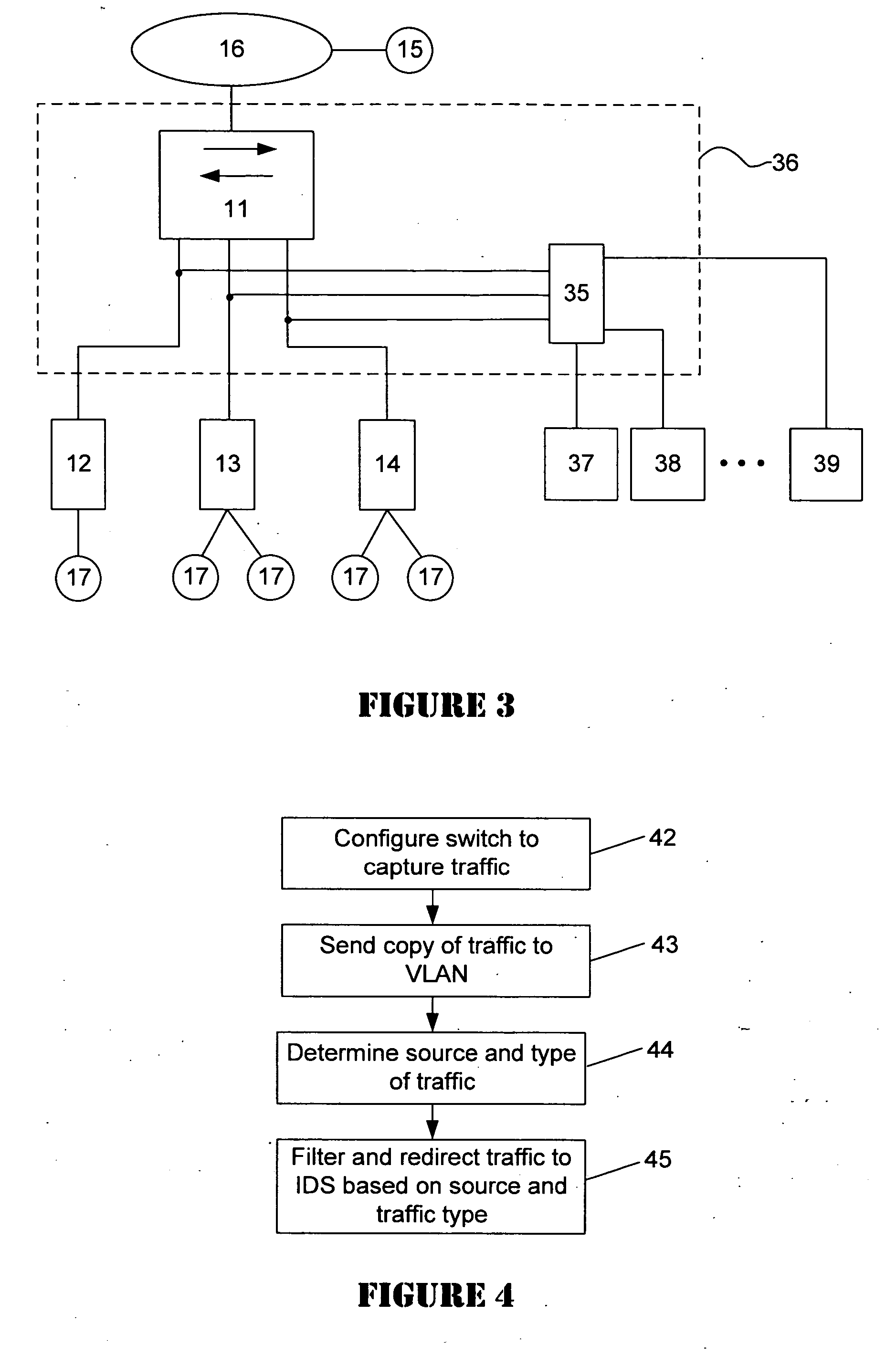
An intrusion detection system (IDS) is capable of identifying the source of traffic, filtering the traffic to classify it as either safe or suspect and then applying sophisticated detection techniques such as stateful pattern recognition, protocol parsing, heuristic detection or anomaly detection either singularly or in combination based on the traffic type. In a network environment, each traffic source is provided with at least one IDS sensor that is dedicated to monitoring a specific type of traffic such as RPC, HTTP, SMTP, DNS, or others. Traffic from each traffic source is filtered to remove known safe traffic to improve efficiency and increase accuracy by keeping each IDS sensor focused on a specific traffic type.
Owner:CISCO TECH INC
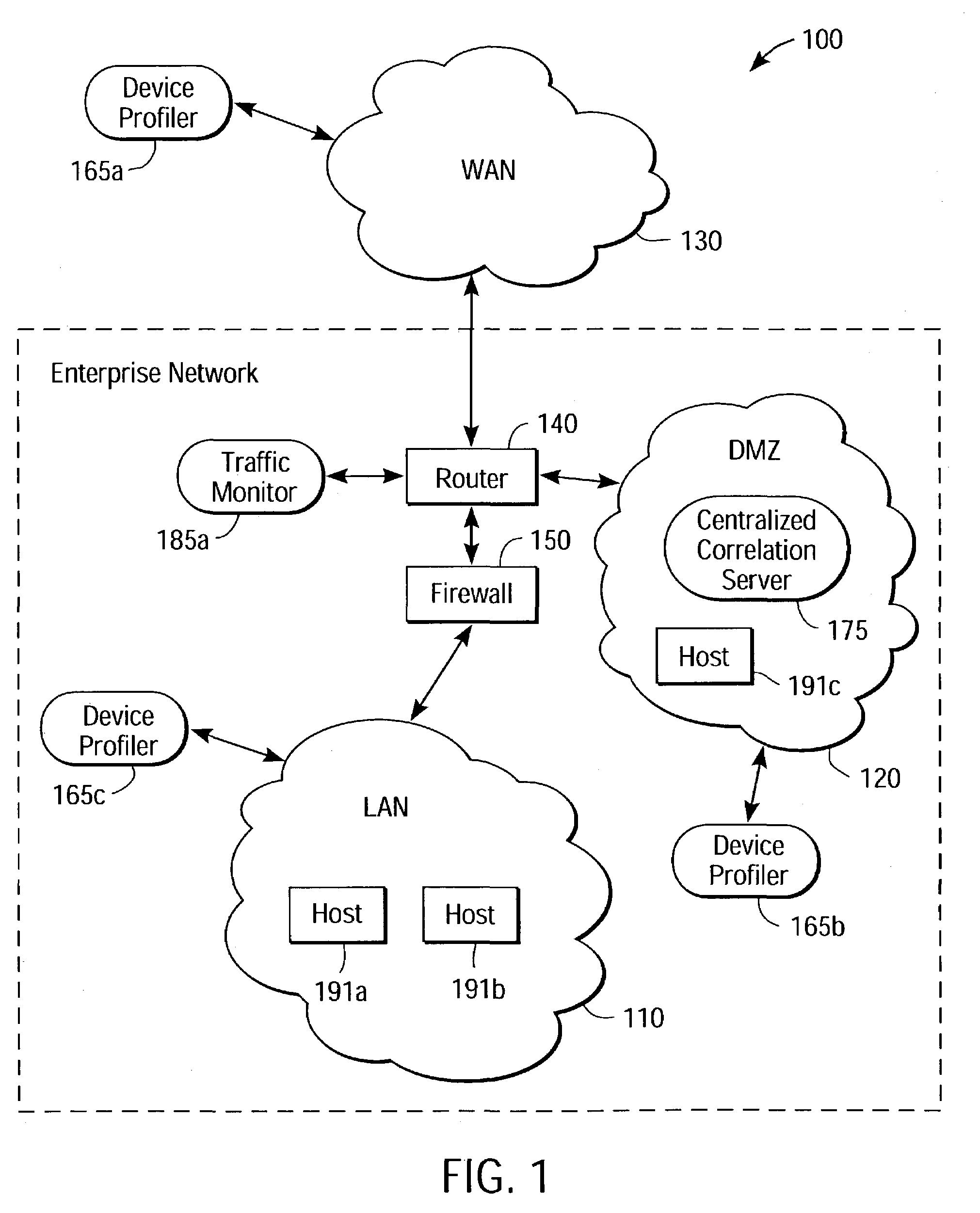
Network security system having a device profiler communicatively coupled to a traffic monitor
InactiveUS7181769B1Effective monitoringReduce false-positivesMemory loss protectionError detection/correctionNetwork security policyTraffic volume
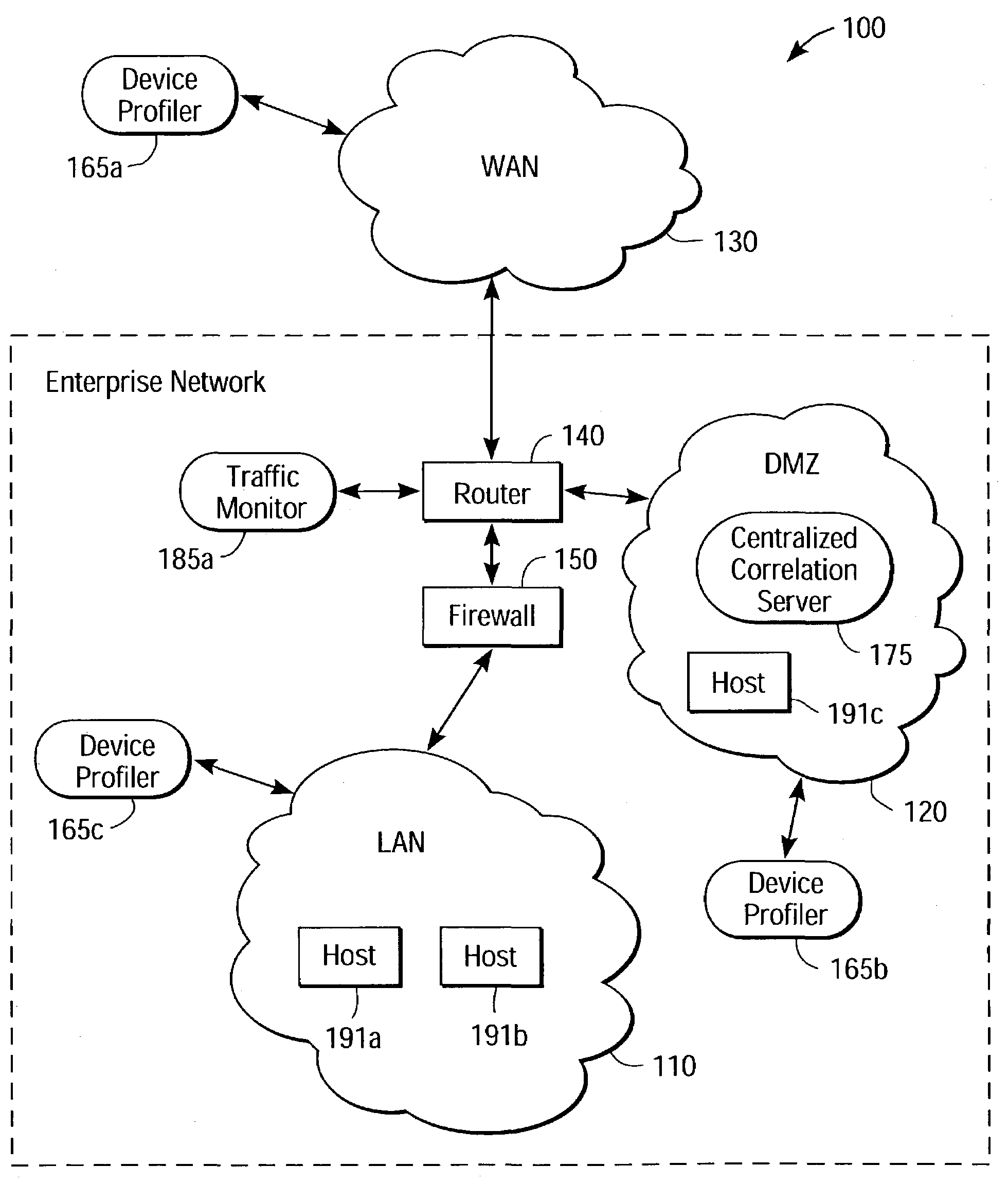
A system and method for providing distributed security of a network. Several device profilers are placed at different locations of a network to assess vulnerabilities from different perspectives. The device profiler identifies the hosts on the network, and characteristics such as operating system and applications running on the hosts. The device profiler traverses a vulnerability tree having nodes representative of characteristics of the hosts, each node having an associated set of potential vulnerabilities. Verification rules can verify the potential vulnerabilities. A centralized correlation server, at a centrally accessible location in the network, stores the determined vulnerabilities of the network and associates the determined vulnerabilities with attach signatures. Traffic monitors access the attack signatures and monitor network traffic for attacks against the determined vulnerabilities.
Owner:TRIPWIRE
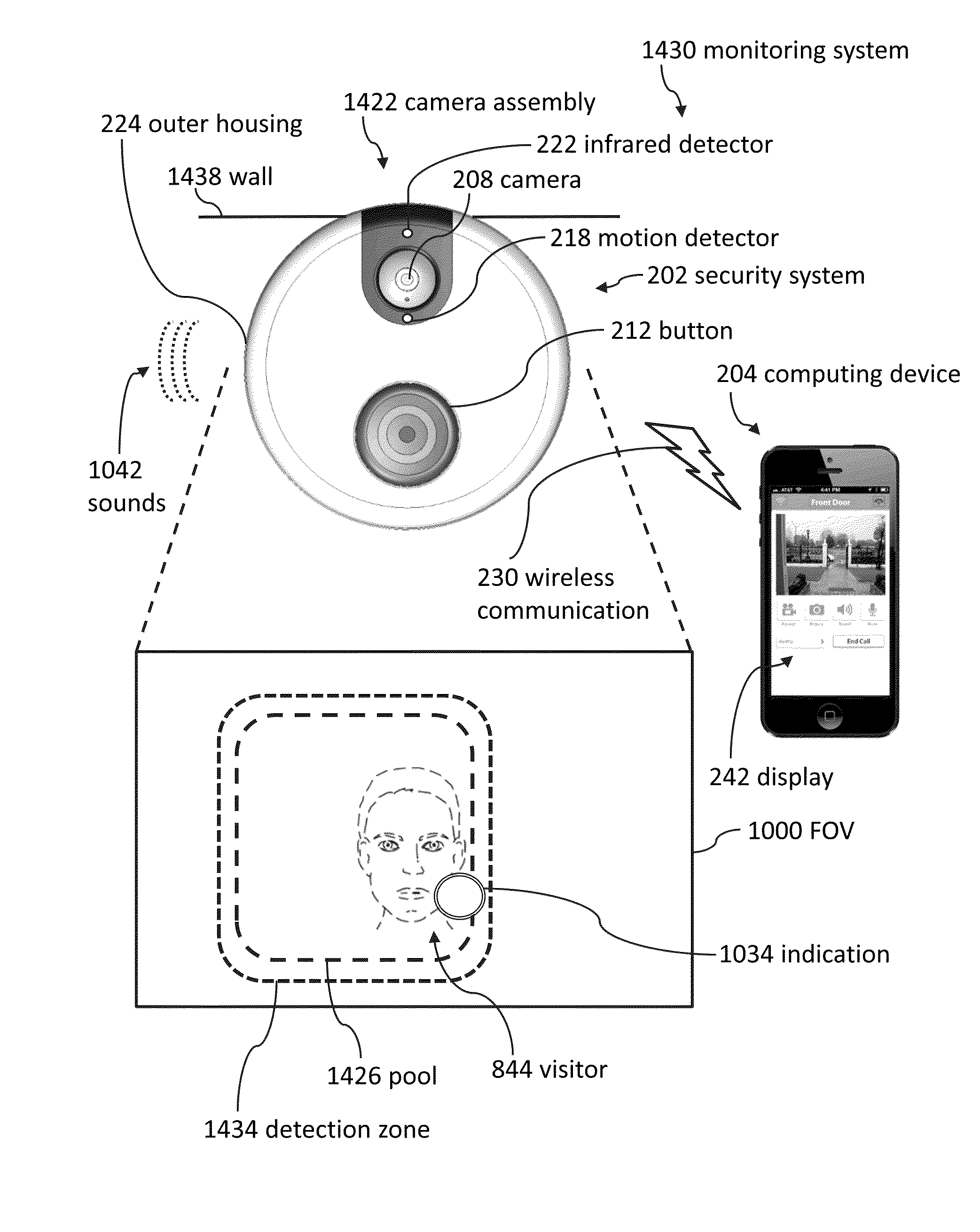
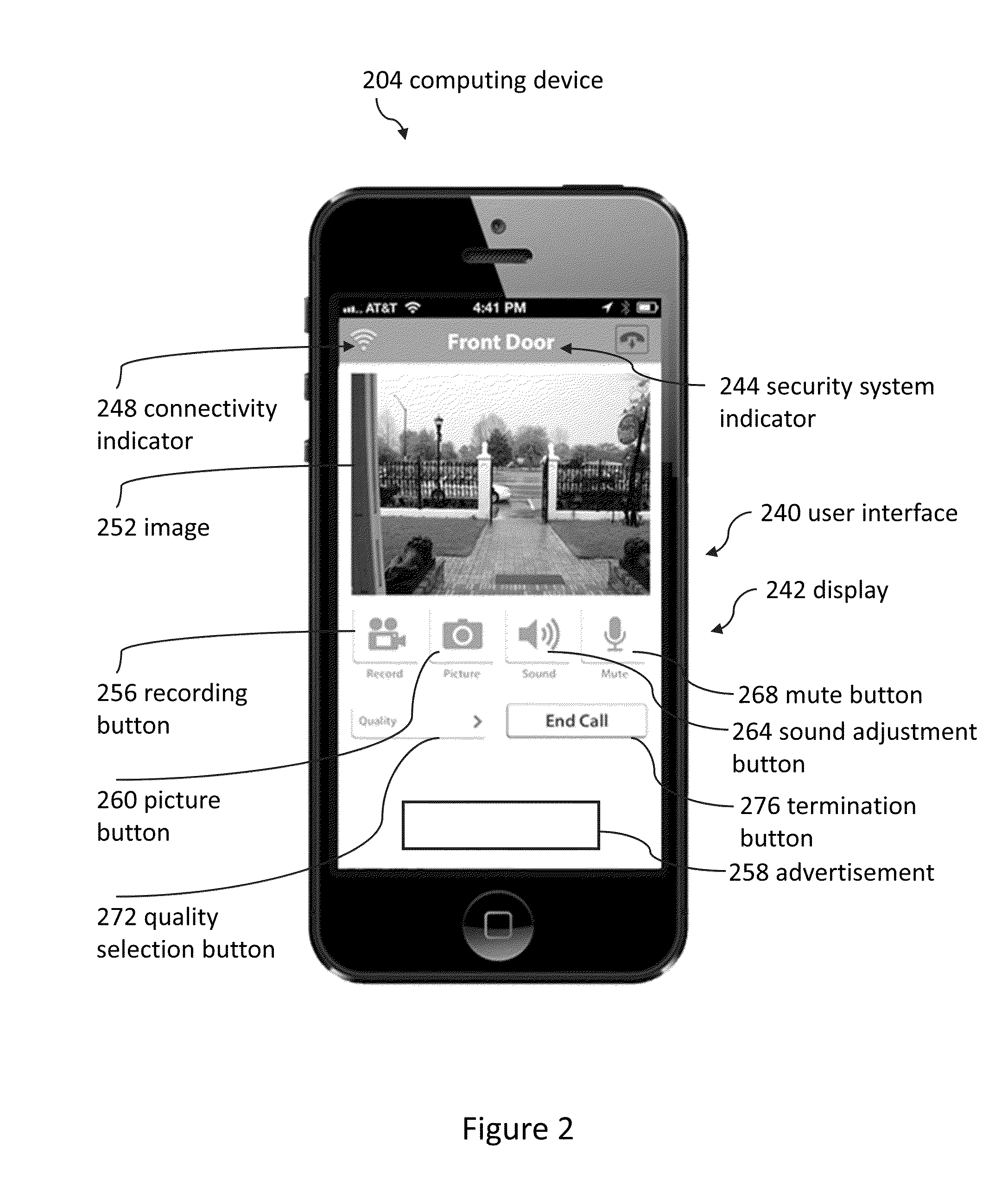
Pool monitor systems and methods
ActiveUS9049352B2Reduce false positivesTelephonic communicationColor television detailsRemote computingField of view
Cameras can be used to detect if unauthorized visitors enter pool areas. Cameras can send alerts to remote computing devices regarding unauthorized pool entry. Several embodiments include using a camera to take an image of a pool area, sending the image from the camera to a remote computing device, displaying the image on the remote computing device, and using the remote computing device to select a detection zone. Some embodiments include ignoring certain portions of the camera's field of view in response to detection zone selections.
Owner:SKYBELL TECH IP LLC
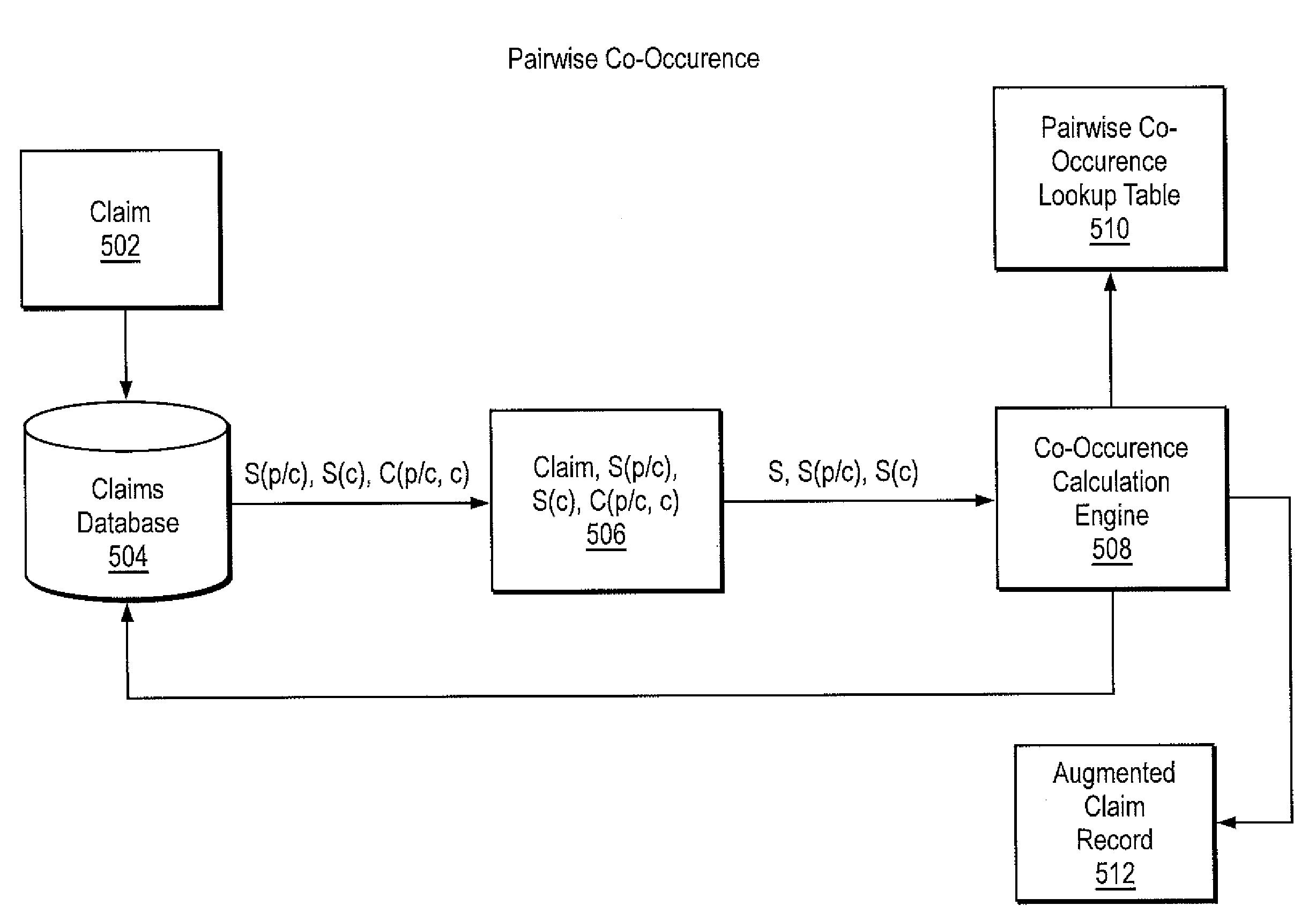
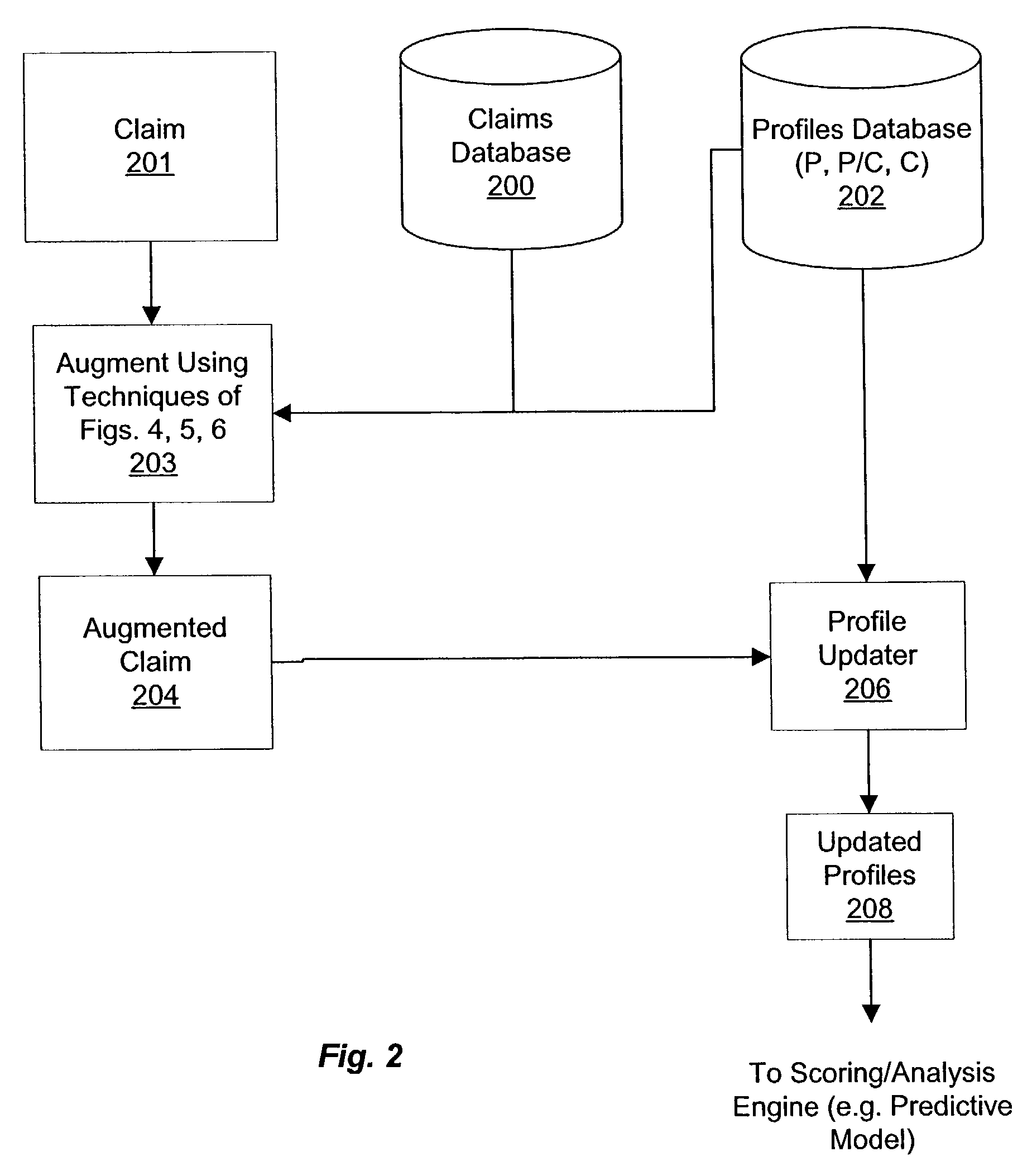
Consistency modeling of healthcare claims to detect fraud and abuse
InactiveUS20080249820A1Accurate pictureEasy to detectComplete banking machinesMedical data miningData dredgingPredictive modelling
Transaction-based behavioral profiling, whereby the entity to be profiled is represented by a stream of transactions, is required in a variety of data mining and predictive modeling applications. An approach is described for assessing inconsistency in the activity of an entity, as a way of detecting fraud and abuse, using service-code information available on each transaction. Inconsistency is based on the concept that certain service-codes naturally co-occur more than do others. An assessment is made of activity consistency looking at the overall activity of an individual entity, as well as looking at the interaction of entities. Several approaches for measuring consistency are provided, including one inspired by latent semantic analysis as used in text analysis. While the description is in the context of fraud detection in healthcare, the techniques are relevant to application in other industries and for purposes other than fraud detection.
Owner:FAIR ISAAC & CO INC
System for detecting, analyzing, and controlling infiltration of computer and network systems
ActiveUS20140298469A1Reduce false positiveEliminate false negativesMemory loss protectionError detection/correctionNetworked systemComputerized system
A method for detecting and manipulating a malicious actor / communication on a computer network or system. The method includes the steps of incorporating one or more synthetic vulnerabilities into the computer system at distinct locations, where each synthetic vulnerability presents an opportunity for exploitation by a malicious actor / communication, detecting an exploitation of one of the vulnerabilities by an actor, analyzing the actor to determine if the actor is a malicious actor / communication; and manipulating the malicious actor / communication. A computer program on a storage medium is also disclosed.
Owner:LOGOS TECH HOLDCO INC
Movement human abnormal behavior identification method based on template matching
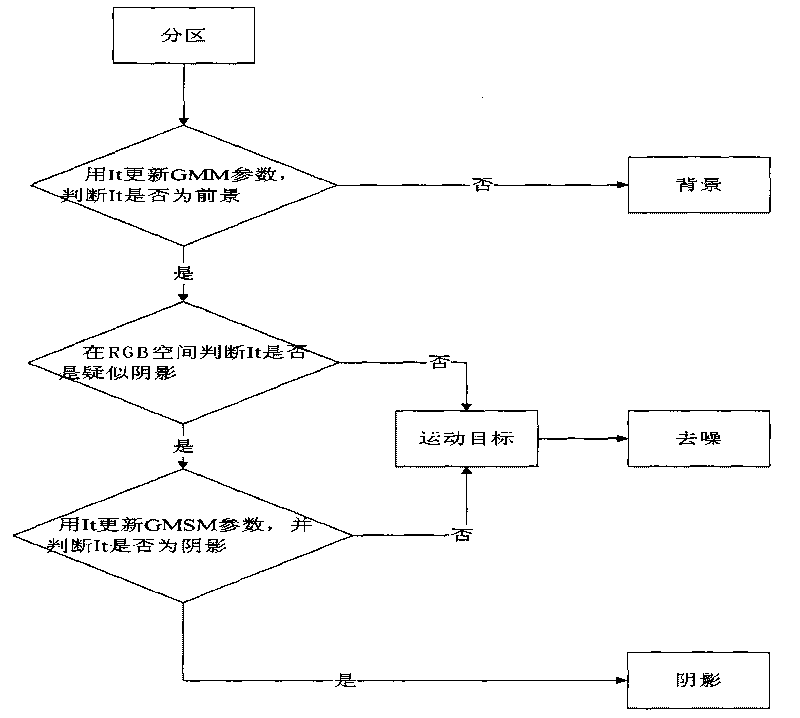
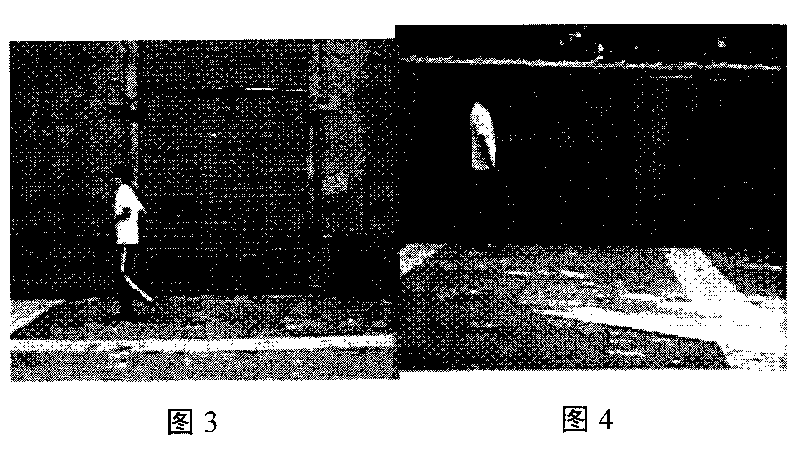
InactiveCN101719216AGood effectThe effect is accurateCharacter and pattern recognitionVisual technologyAnomalous behavior
The invention relates to a movement human abnormal behavior identification method based on template matching, which mainly comprises the steps of: video image acquisition and behavior characteristic extraction. The movement human abnormal behavior identification method is a mode identification technology based on statistical learning of samples. The movement of a human is analyzed and comprehended by using a computer vision technology, the behavior identification is directly carried out based on geometric calculation of a movement region and recording and alarming are carried out; the Gaussian filtering denoising and the neighborhood denoising are combined for realizing the denoising, thereby improving the independent analysis property and the intelligent monitoring capacity of an intelligent monitoring system, achieving higher identification accuracy for abnormal behaviors, effectively removing the complex background and the noise of a vision acquired image, and improving the efficiency and the robustness of the detection algorithm. The invention has simple modeling, simple algorithm and accurate detection, can be widely applied to occasions of banks, museums and the like, and is also helpful to improve the safety monitoring level of public occasions.
Owner:XIDIAN UNIV
Electric vehicle battery monitoring and management system and monitoring method of batteries
ActiveCN105904992AEasy to operate and controlImprove accuracyElectric devicesVehicular energy storageElectrical batteryControl system
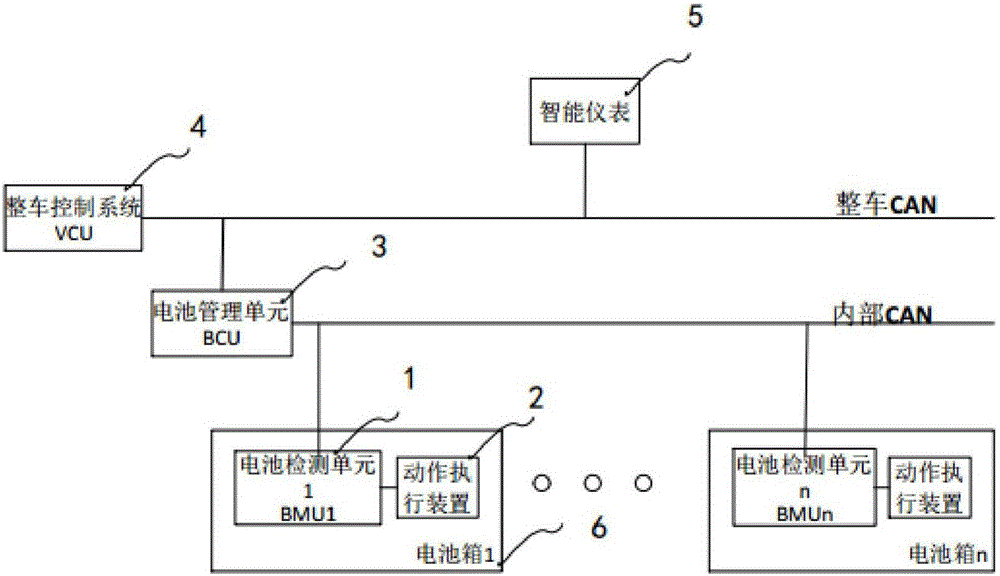
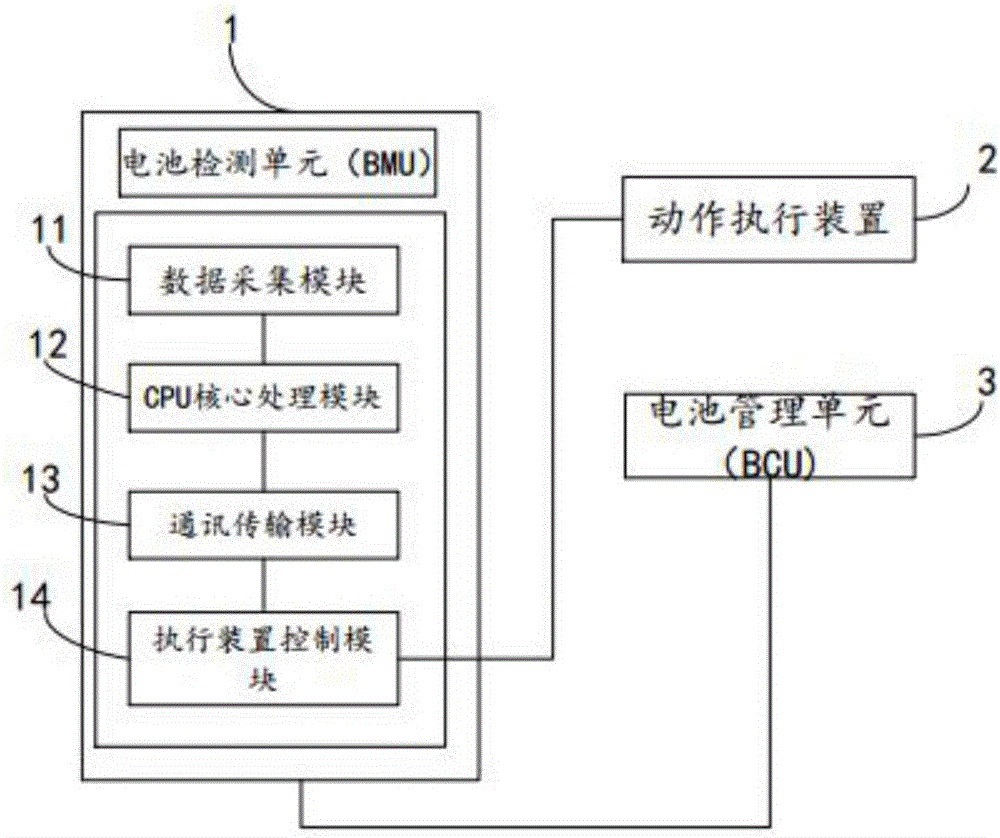
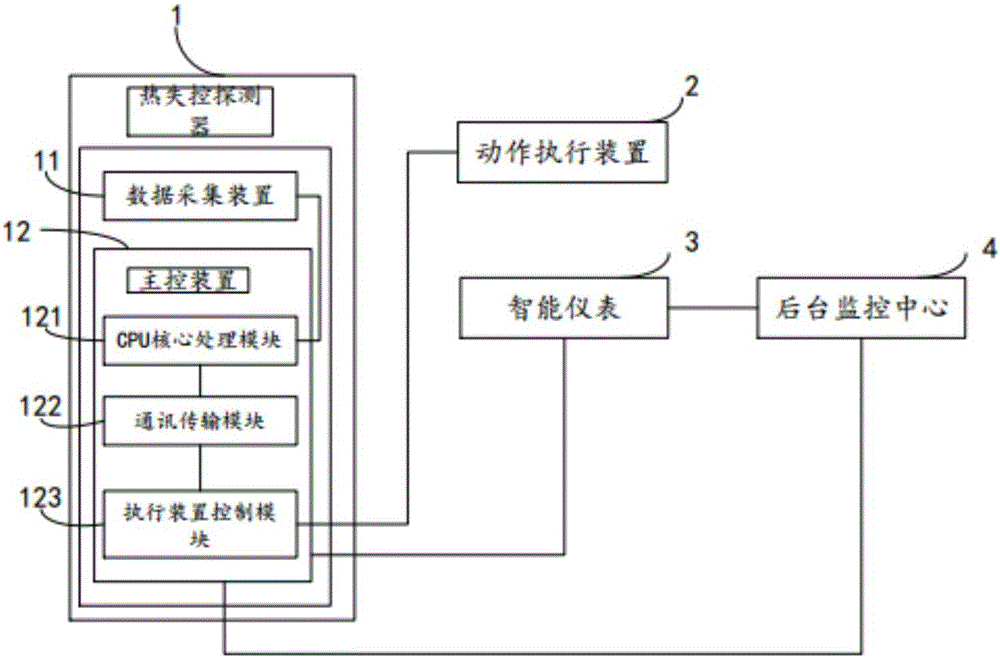
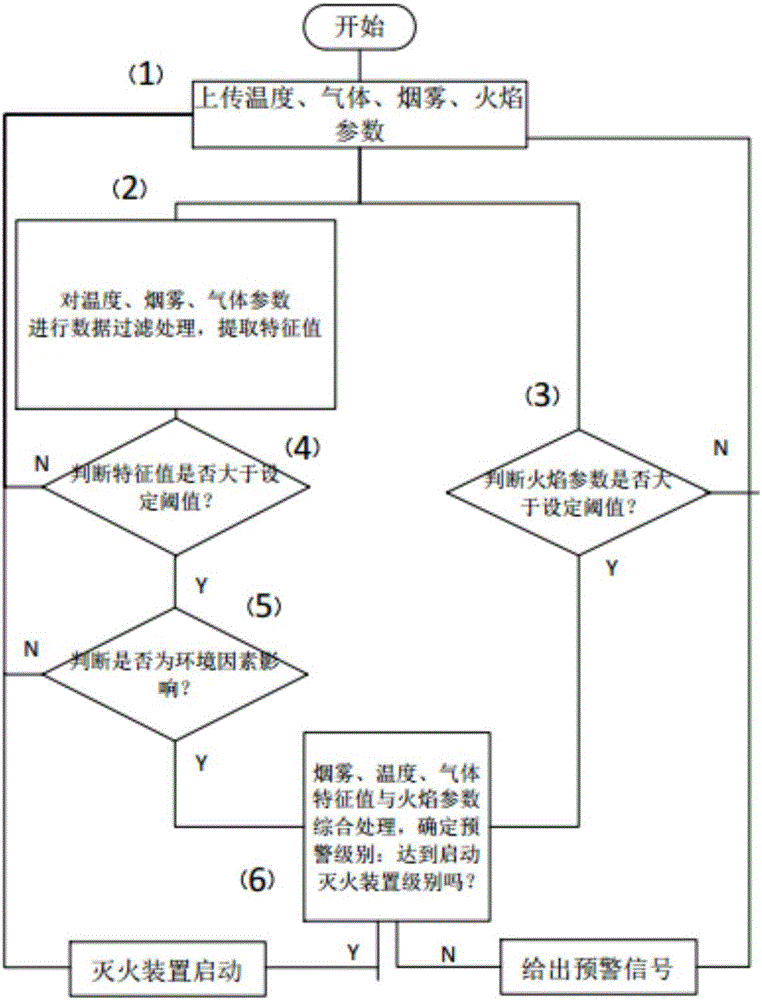
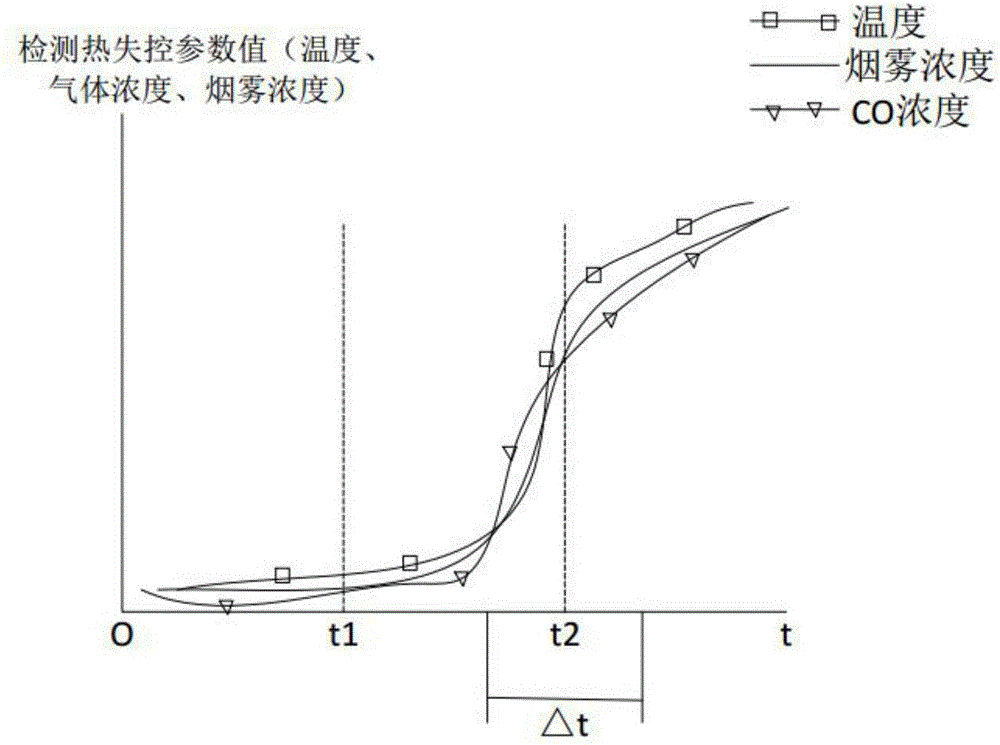
The invention relates to the technical field of electric vehicle safe operation, in particular to an electric vehicle battery monitoring and management system. The electric vehicle battery monitoring and management system comprises a vehicle control system body and at least one battery box. Each battery box is internally provided with multiple sets of batteries. The electric vehicle battery monitoring and management system is characterized in that each battery box is internally further provided with a battery detection unit and an action executing device; each battery detection unit comprises a data acquisition module, a CPU core processing module, a communication transmission module and an executing device control module; and each data acquisition module comprises an acquisition device for acquiring the battery module temperature, the battery voltage and current and battery module environment parameters. The invention further discloses a monitoring method of the batteries. The monitoring method of the batteries comprises the steps that the temperature, the voltage and the current of the module as well as the temperature, smoke, gas, flame and other parameters in the battery boxes are monitored; and an early warning or fire fighting signal is sent out when the performance of the batteries is suddenly changed or thermal runaway occurs. According to the electric vehicle battery monitoring and management system and the monitoring method of the batteries, the development stage of thermal runaway can be accurately judged by comprehensively analyzing and processing the various parameters inside and outside battery modules, so that the thermal runaway detection accuracy is improved.
Owner:YANTAI INNOVATIVE NEW ENERGY TECH CO LTD
Consistency modeling of healthcare claims to detect fraud and abuse
InactiveUS7813937B1Accurate pictureEasy to detectMedical data miningFinanceData dredgingPredictive modelling
Transaction-based behavioral profiling, whereby the entity to be profiled is represented by a stream of transactions, is required in a variety of data mining and predictive modeling applications. An approach is described for assessing inconsistency in the activity of an entity, as a way of detecting fraud and abuse, using service-code information available on each transaction. Inconsistency is based on the concept that certain service-codes naturally co-occur more than do others. An assessment is made of activity consistency looking at the overall activity of an individual entity, as well as looking at the interaction of entities. Several approaches for measuring consistency are provided, including one inspired by latent semantic analysis as used in text analysis. While the description is in the context of fraud detection in healthcare, the techniques are relevant to application in other industries and for purposes other than fraud detection.
Owner:FAIR ISAAC & CO INC
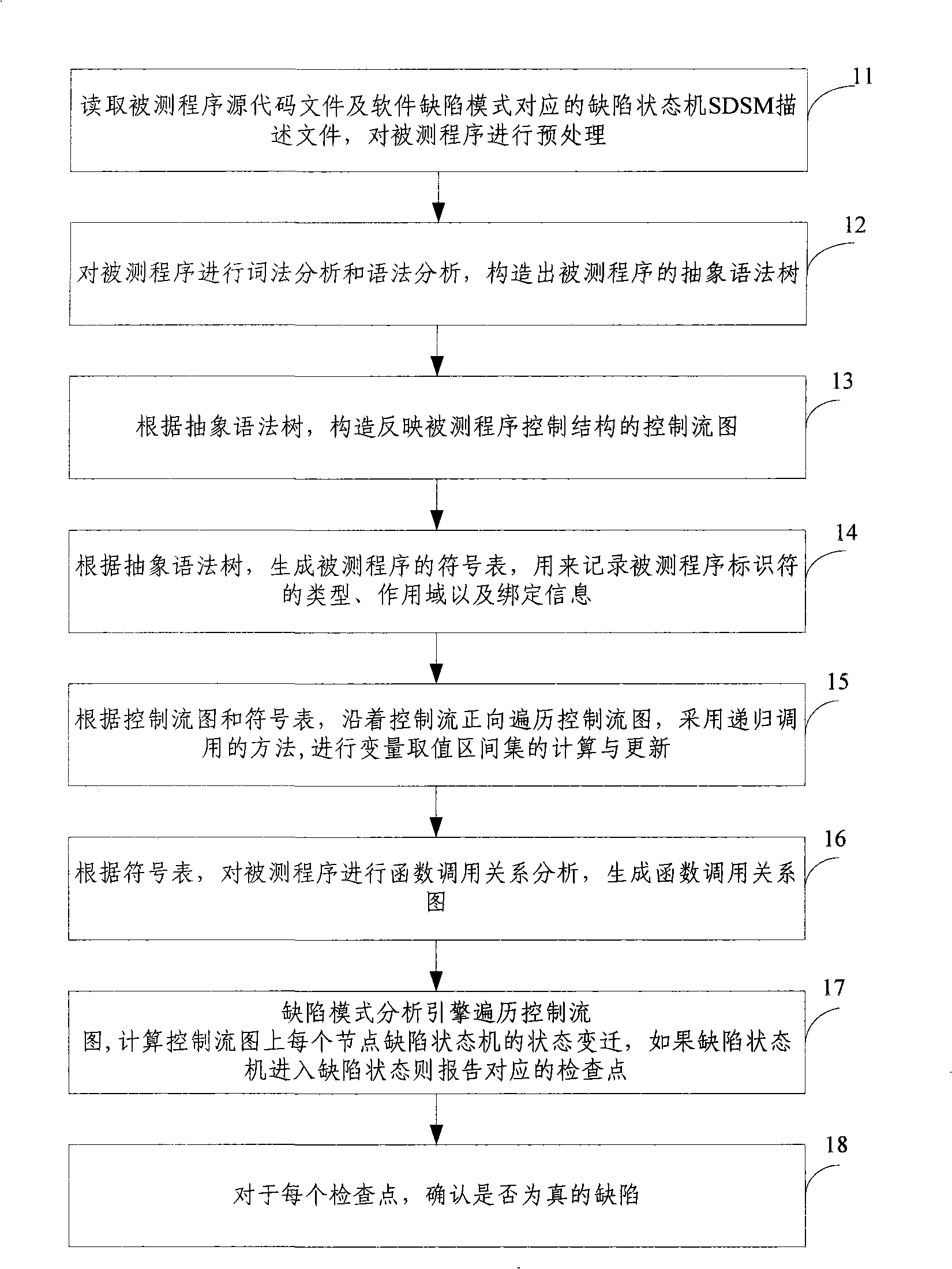
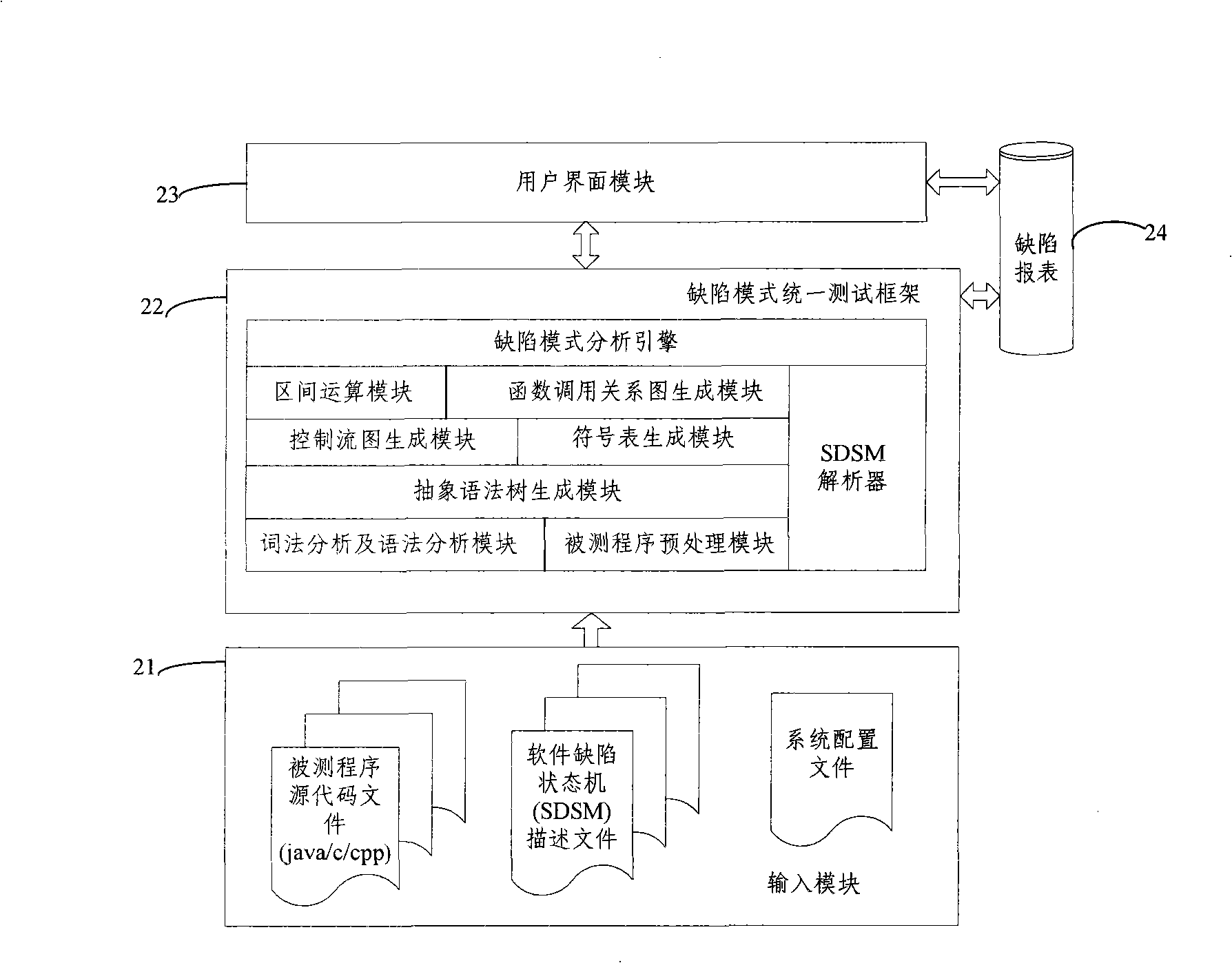
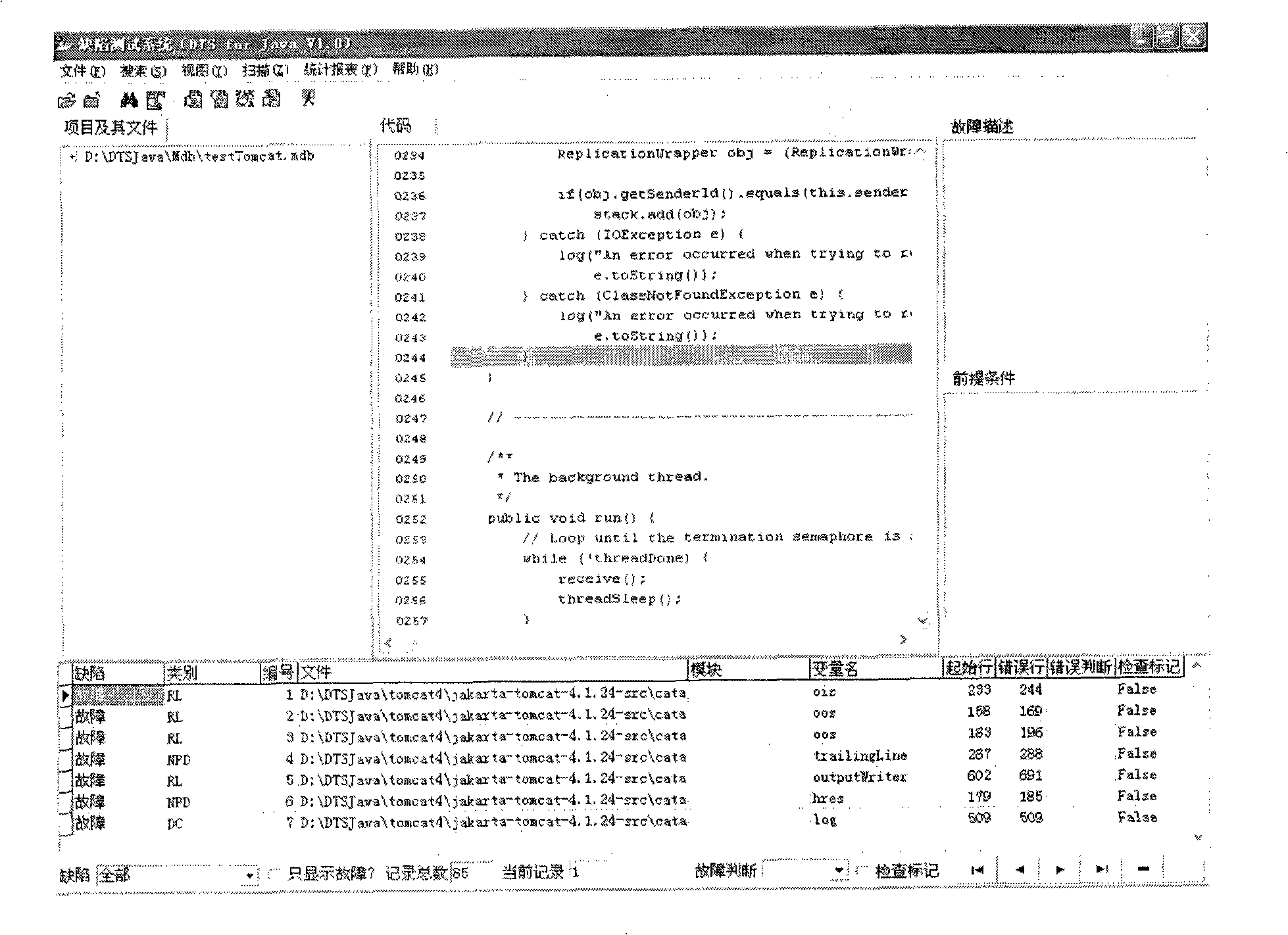
Test method and system based on software defect mode
InactiveCN101286132AReduce false positivesImprove test accuracySoftware testing/debuggingControl flowPresent method
The invention discloses a testing method based on software defect mode, comprising the steps of: reading source code files of programs to be tested and SDSM description file of a defect state machine, carrying out pre-processing of the programs to be tested, analyzing the SDSM description file; carrying out lexical analysis and grammar analysis of the programs to be tested and constructing abstract syntax tree; generating a control flow graph and a symbol table according to the abstract syntax tree and carrying out the calculating and updating of variable value interval sets according to the control flow graph and the symbol table; carrying out function invoking relation analysis of the programs to be tested and generating a function invoking relation graph; searching the control flow graph by taking the function as unit according to the function invoking relation graph, calculating the state migration of each node defect state machine on the control flow graph, and reporting corresponding checking point when the defect state machine enters the defect state. The invention also discloses a testing system based on software defect mode, which comprises an input module, a defect mode uniformity testing frame and a user interface module and completes the uniform test on the programs to be tested.
Owner:BEIJING UNIV OF POSTS & TELECOMM
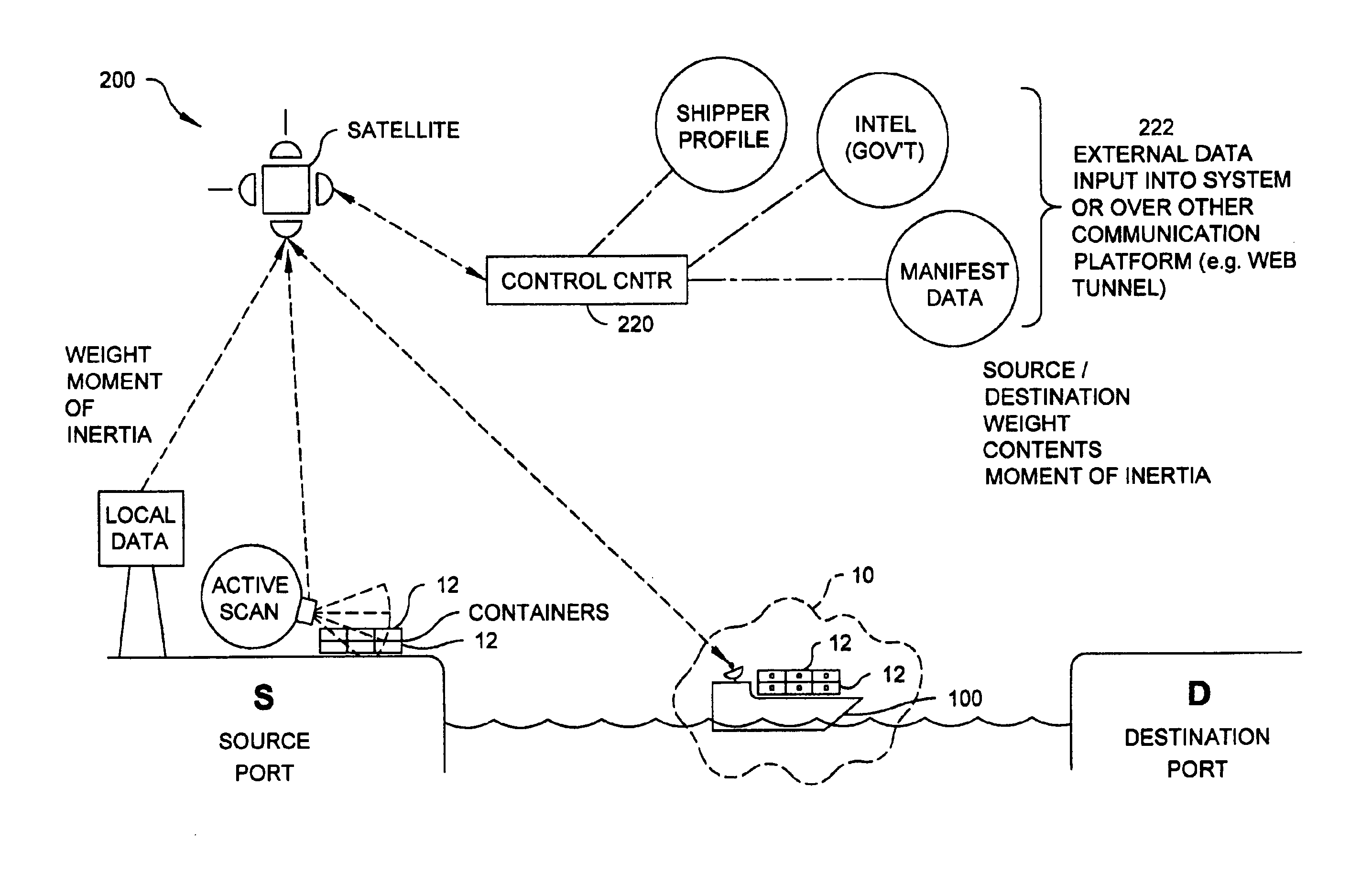
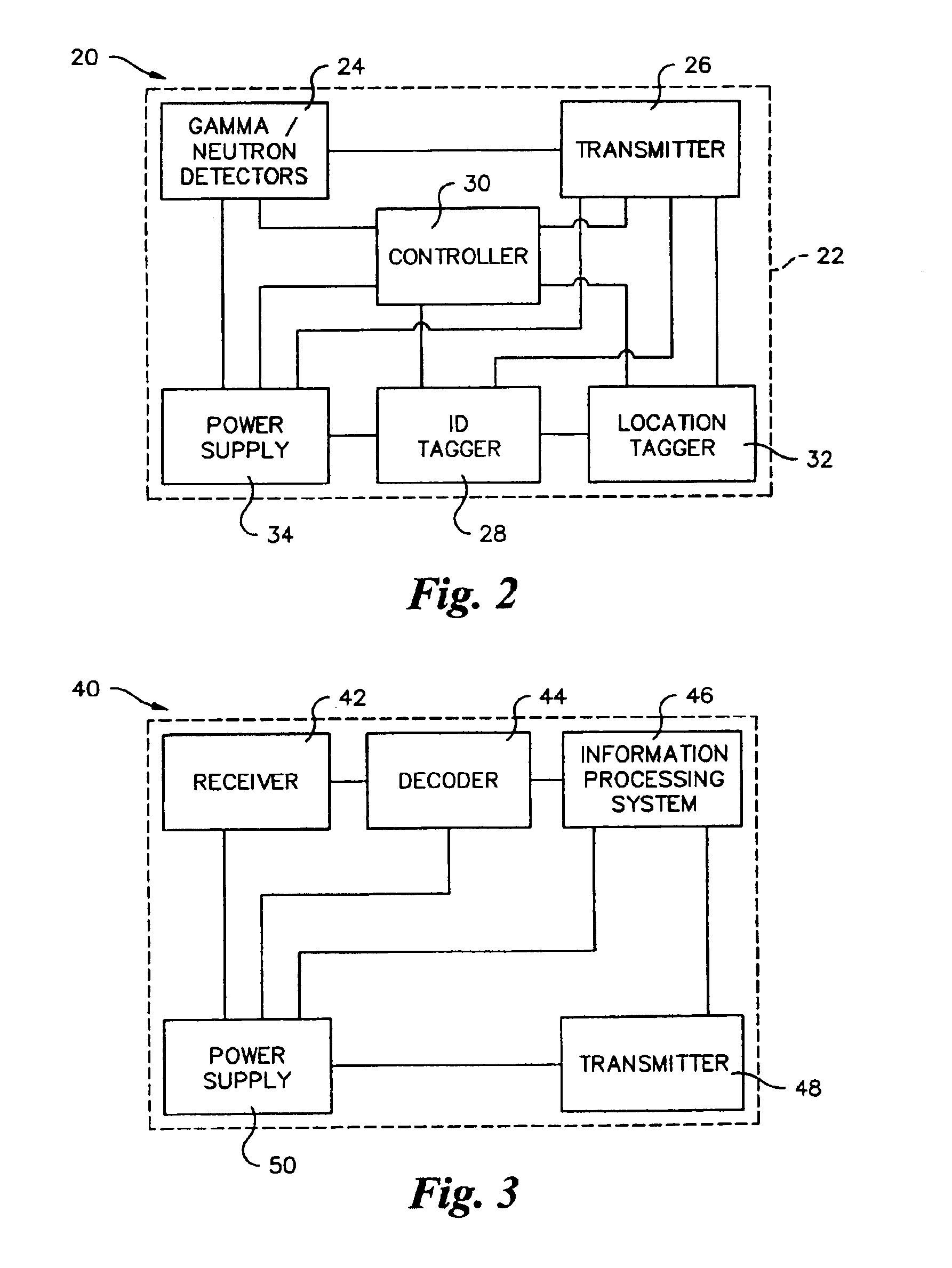
Apparatus and method for asynchronously analyzing data to detect radioactive material
InactiveUS6965314B2High sensitivityEasy to identifyElectric testing/monitoringRadio/inductive link selection arrangementsTransceiverRadioactive agent
A radioactive material detection system includes a cargo container monitoring system and a control center. The cargo container monitoring system has a radiation sensor configured to detect radiation over a predetermined or commanded period of time and a transceiver configured to send the information received from the radiation sensor. The control center is in communication with the transceiver of the cargo container monitoring system. The control center is configured to receive data from at least one additional source other than the cargo container monitoring system and to asynchronously analyze the data from the at least one additional source and the information from the radiation sensor, during transit, so as to detect radioactive material in a cargo container.
Owner:QUINTELL OF OHIO
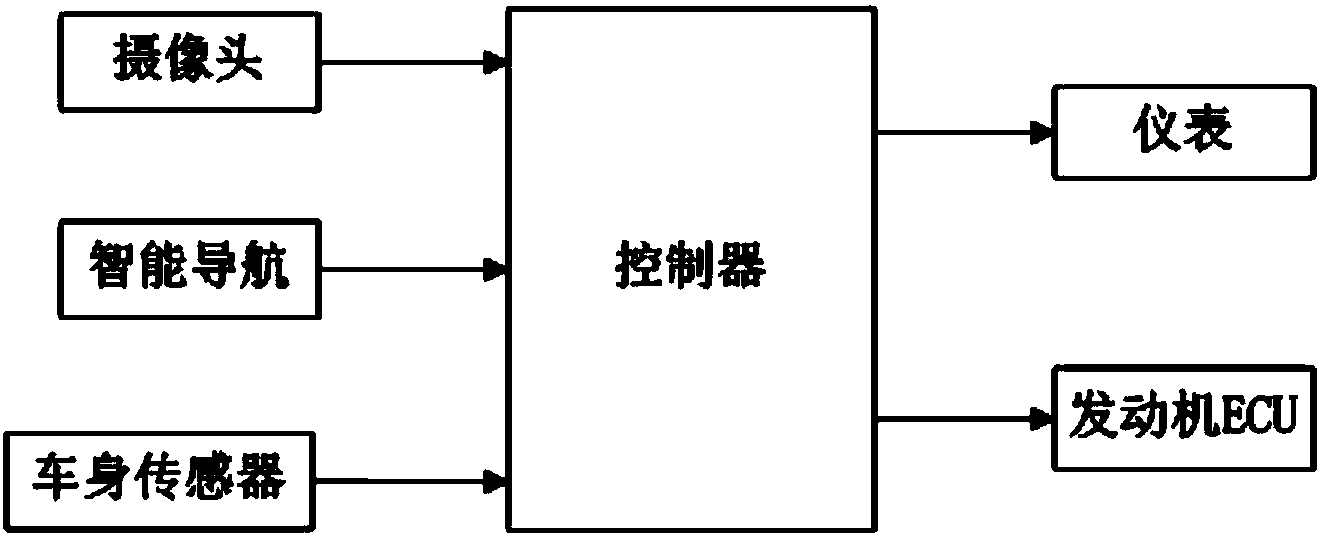
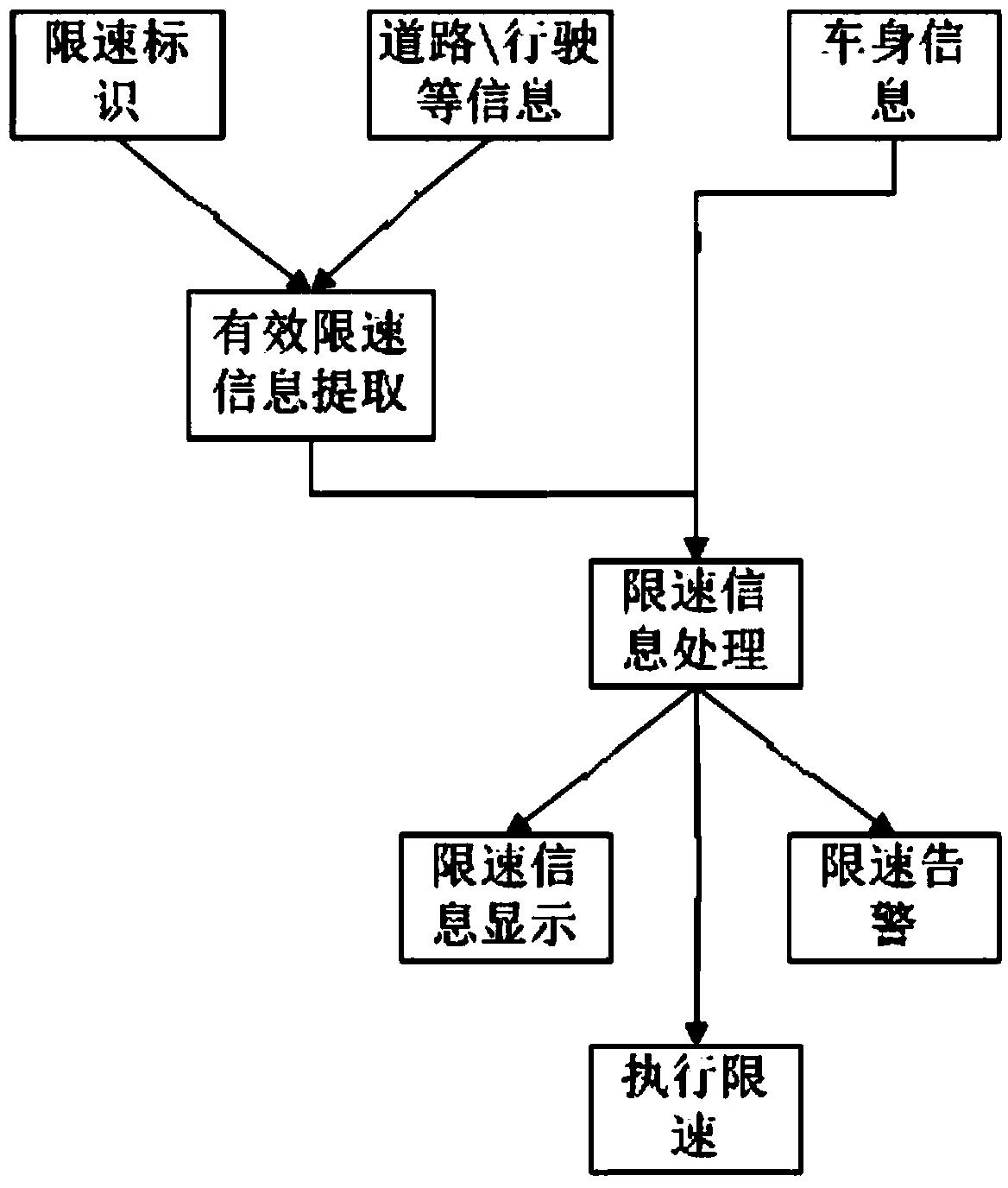
Automobile intelligent speed limiting system and automobile speed limiting method
ActiveCN103832282AImprove accuracyImprove recognition accuracyVehicle fittingsSpeed/accelaration controlImaging processingBody sensors
The invention discloses an automobile intelligent speed limiting system and an automobile speed limiting method, and relates to the technical field of automobile safety driving assistance. The automobile intelligent speed limiting system and the automobile speed limiting method can improve accuracy of speed limiting identification recognition and improve driving safety of a driver. The automobile intelligent speed limiting system comprises a camera, an intelligent navigation device, an automobile body sensor and a controller, wherein the camera can recognize road traffic identification boards and extract road traffic identification information through the image processing technology, the intelligent navigation device can provide current road information, navigation route information and national or regional traffic road speed limiting law related information in real time, the automobile body sensor can provide automobile body information in real time, a traffic speed limiting identification database is set up in the controller, the input end of the controller is connected with the camera, the intelligent navigation device and the automobile body sensor, and the output end of the controller is connected with an automobile instrument and an engine ECU. The automobile intelligent speed limiting system is used for assisting in limiting the speed of the automobile.
Owner:GREAT WALL MOTOR CO LTD
Pool monitor systems and methods
ActiveUS20150092055A1Reduce false positivesTelephonic communicationColor television detailsField of viewRemote computing
Cameras can be used to detect if unauthorized visitors enter pool areas. Cameras can send alerts to remote computing devices regarding unauthorized pool entry. Several embodiments include using a camera to take an image of a pool area, sending the image from the camera to a remote computing device, displaying the image on the remote computing device, and using the remote computing device to select a detection zone. Some embodiments include ignoring certain portions of the camera's field of view in response to detection zone selections.
Owner:SKYBELL TECH IP LLC
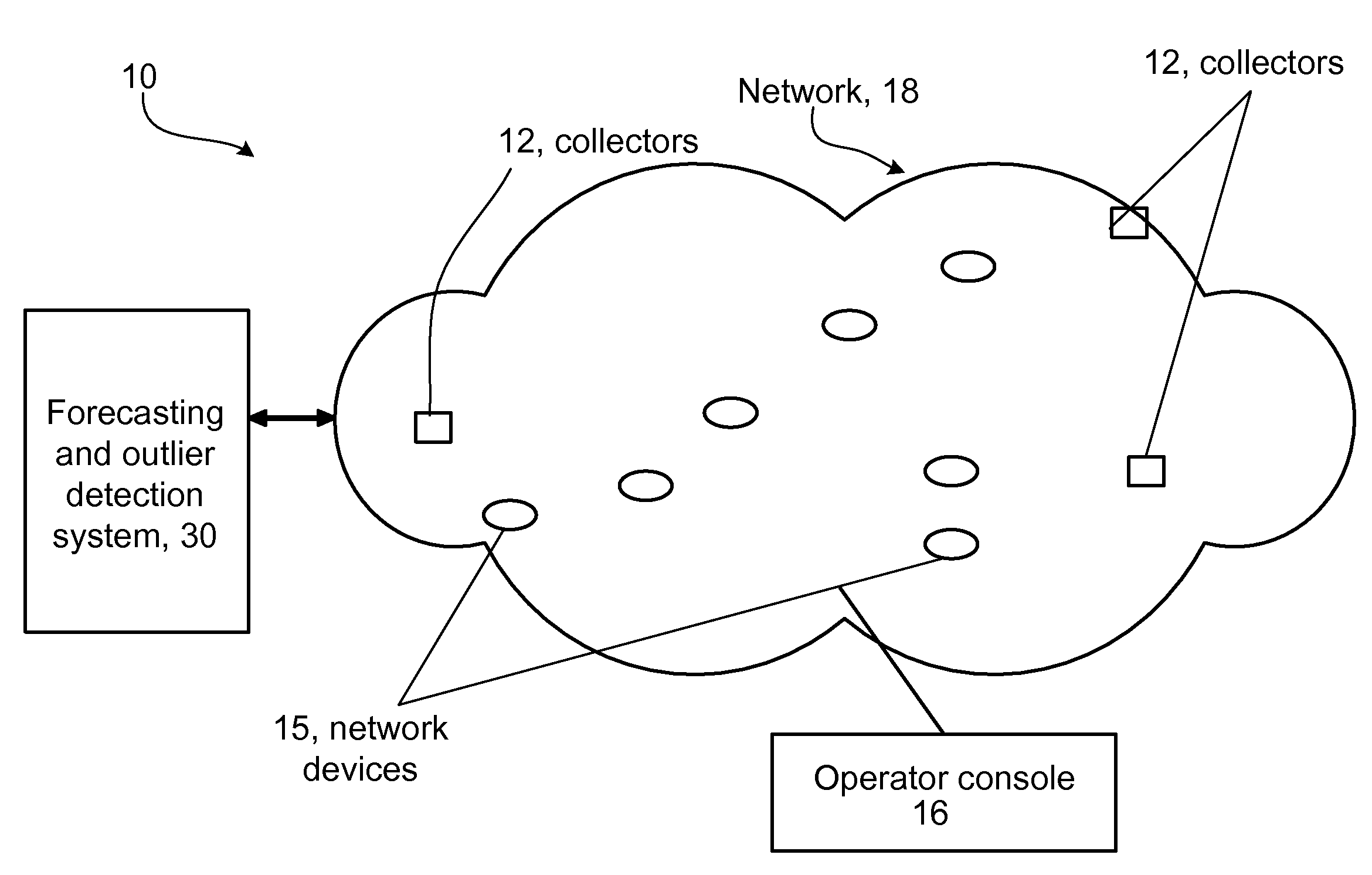
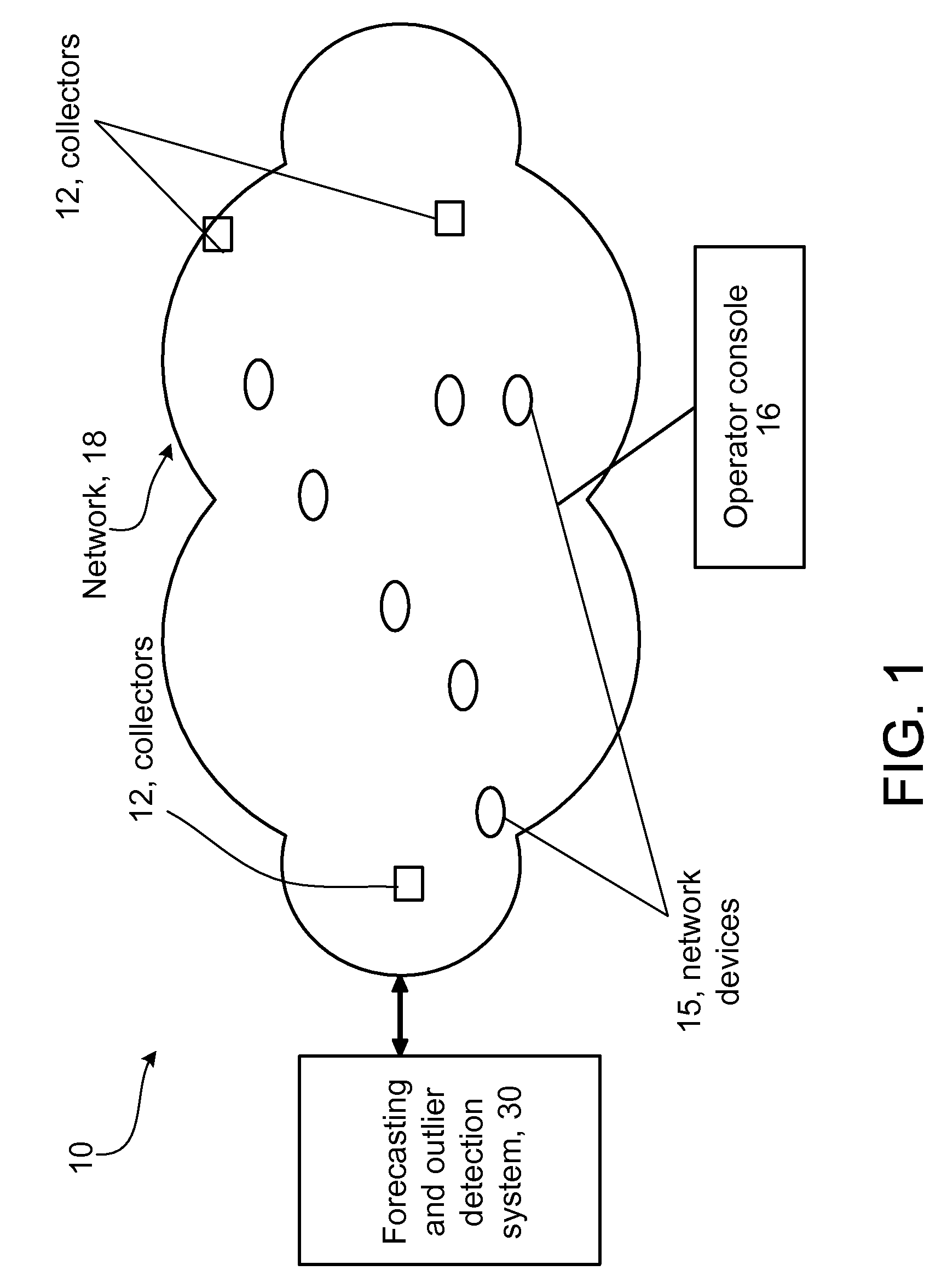
Detecting Outliers in Network Traffic Time Series
ActiveUS20100030544A1Reduce false alarm rateComputationally efficientAnalogue computers for electric apparatusTransmissionTraffic capacityOutlier
According to an aspect of the invention, a system and method is configured to detect time series outliers in network traffic.
Owner:RIVERBED TECH LLC
Systems and Methods for Spam Filtering
ActiveUS20110035451A1Reduce false-positivesMultiple digital computer combinationsFuzzy logic based systemsData miningElectronic mail
Owner:YAHOO ASSETS LLC
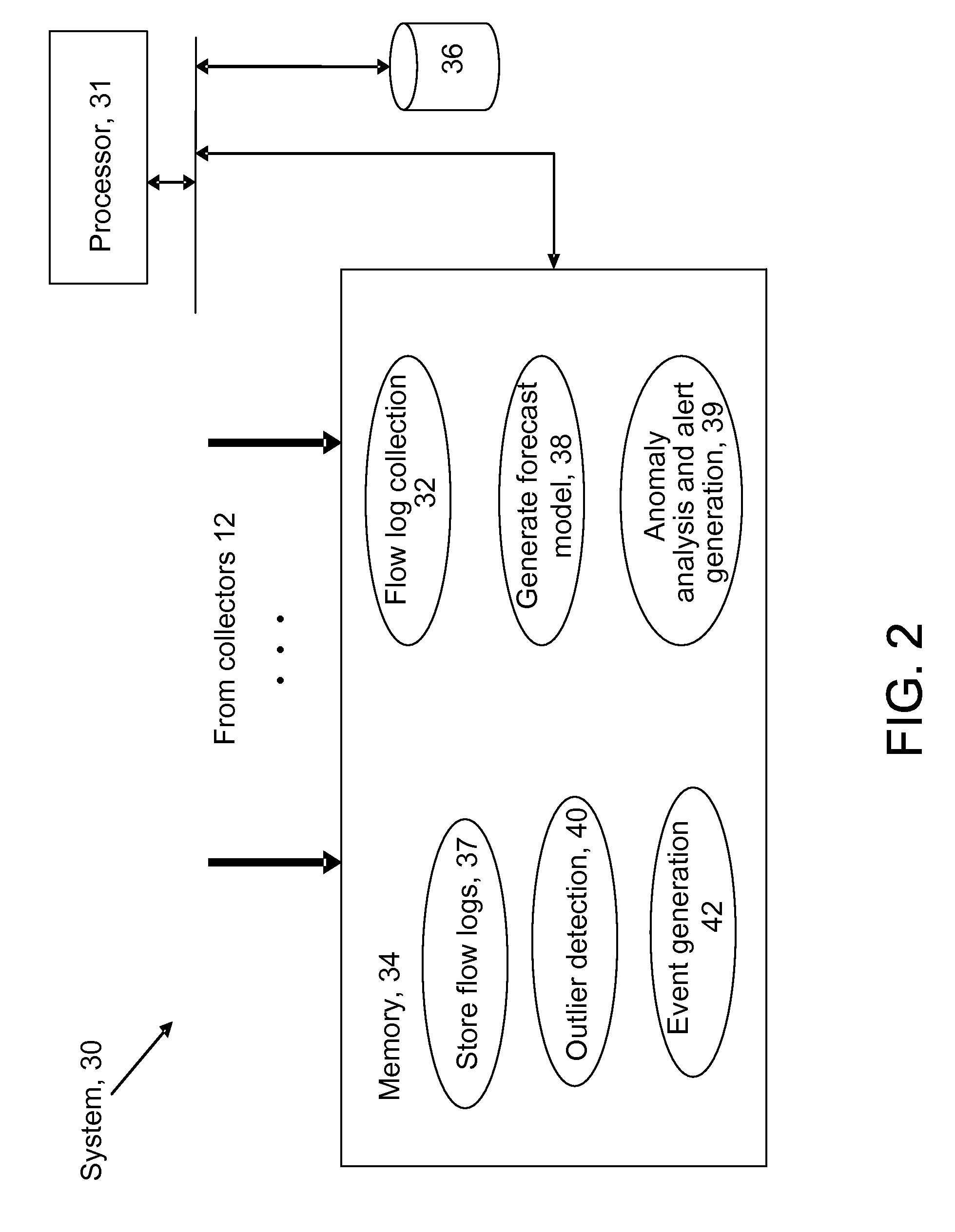
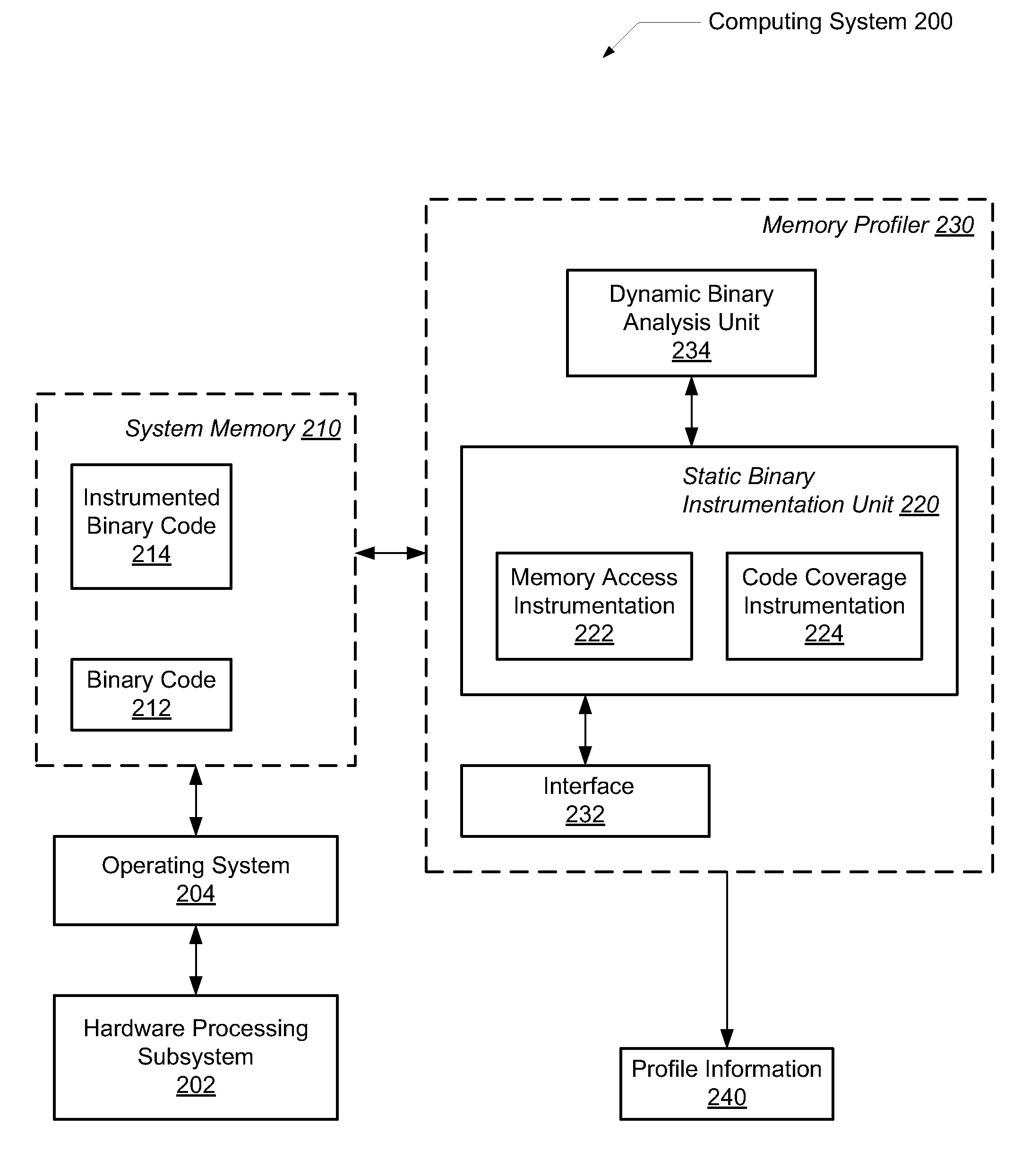
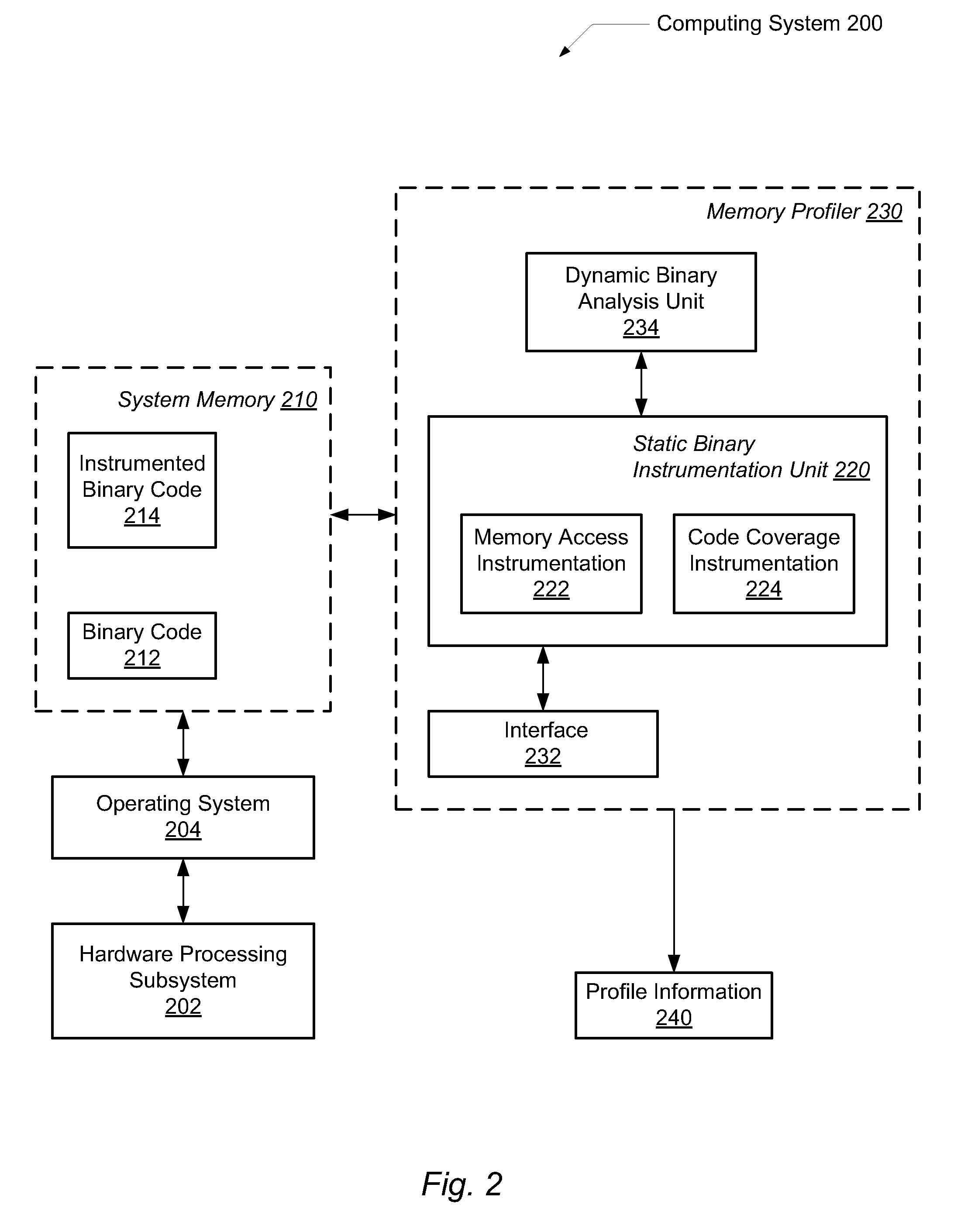
Efficient program instrumentation for memory profiling
ActiveUS20100146220A1Improve system performanceReduce false positiveError detection/correctionSpecific program execution arrangementsMemory profilingLoad instruction
A system and method for performing efficient program instrumentation for memory profiling. A computing system comprises a memory profiler comprising a static binary instrumentation (SBI) tool and a dynamic binary analysis (DBA) tool. The profiler is configured to selectively instrument memory access operations of a software application. Instrumentation may be bypassed completely for an instruction if the instruction satisfies some predetermined conditions. Some sample conditions include the instruction accesses an address within a predetermined read-only area, the instruction accesses an address within a user-specified address range, and / or the instruction is a load instruction accessing a memory location determined from a data flow graph to store an initialized value. An instrumented memory access instruction may have memory checking analysis performed only upon an initial execution of the instruction in response to determining during initial execution that a read data value of the instruction is initialized. Both unnecessary instrumentation and memory checking analysis may be reduced.
Owner:ORACLE INT CORP
Battery thermal runaway detection system and detection method thereof
The invention relates to the technical field of new energy automobile battery safety monitoring, and particularly relates to a battery thermal runaway detection system. The battery thermal runaway detection system comprises an intelligent instrument, a background monitoring center and a thermal runaway detector arranged in a battery box. The battery thermal runaway detection system is characterized in that the thermal runaway detector comprises a data acquisition device and a master control device. The data acquisition device is used for acquiring the current thermal runaway parameters of all the detection nodes in the battery box and transmitting the current thermal runaway parameters to the master control device. The master control device comprises a CPU core processing module, a communication transmission module and a performing device control module. The invention also relates to a battery thermal runaway detection method comprising the steps that whether a flame value is greater than or equal to the preset flame threshold is judged; data filtering is performed on temperature, gas and smoke parameters so that characteristic values are extracted; and the parameters are comprehensively processed so that starting a fire-extinguishing device or giving a warning signal is determined. The beneficial effects are that the detection system is enabled to accurately grasp the fire extinguishing time so that the hidden trouble can be timely disposed.
Owner:YANTAI INNOVATIVE NEW ENERGY TECH CO LTD
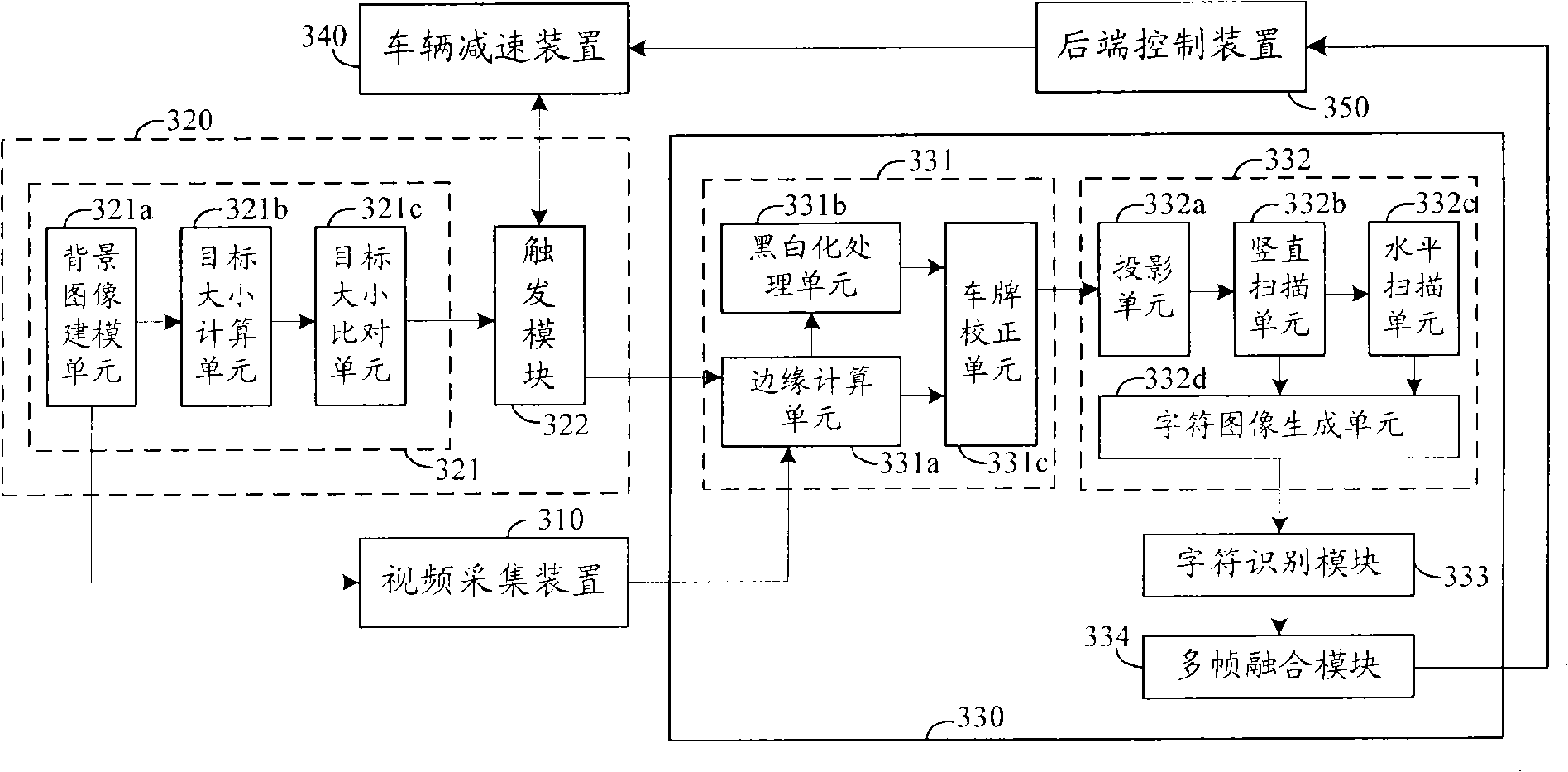
Method and system for discriminating license plate
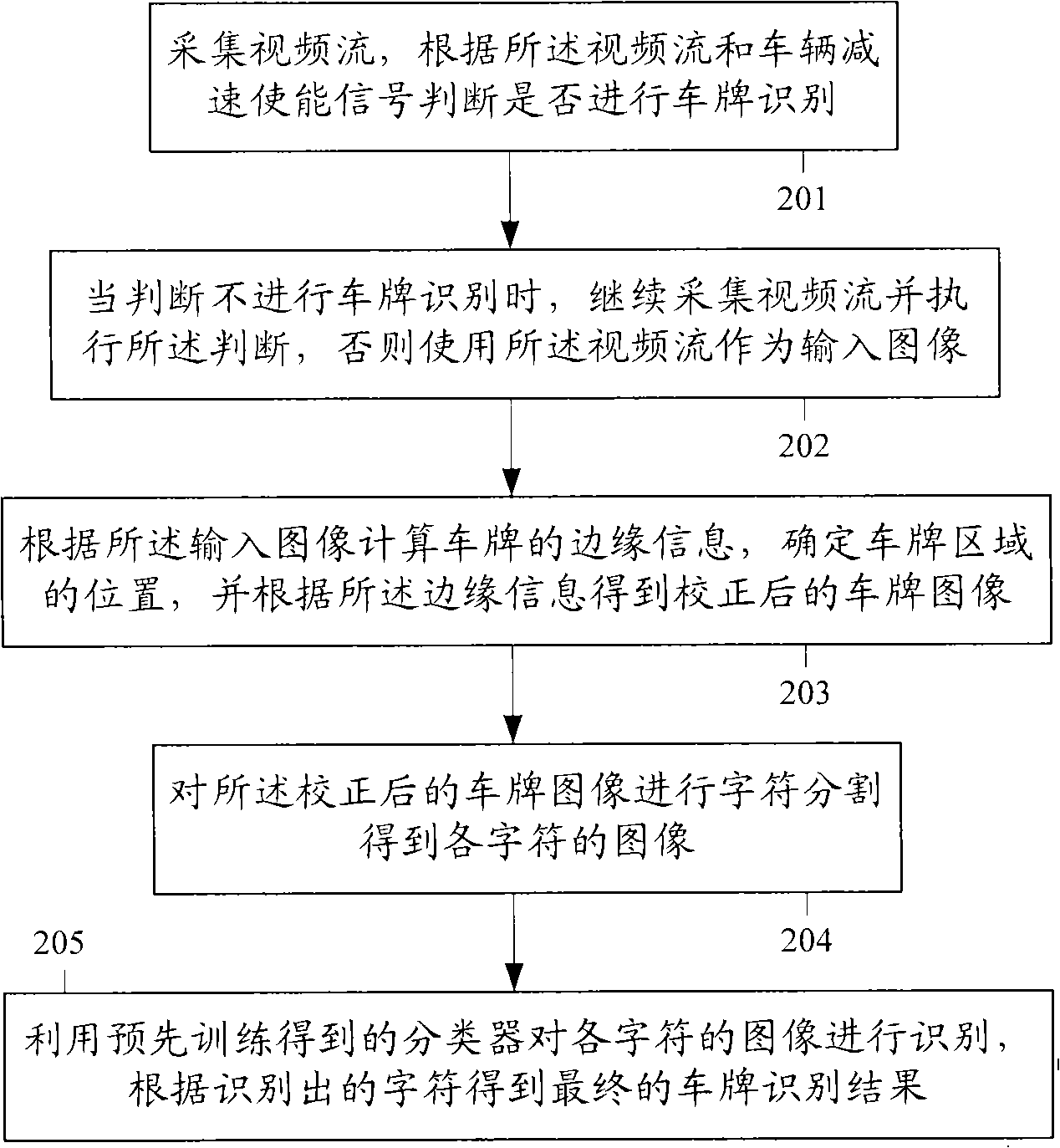
InactiveCN101303803AReduce false positivesLow costRoad vehicles traffic controlCharacter and pattern recognitionRoad surfaceLicense
The invention discloses a license plate recognition method, which comprises collecting video stream; whether the license plate recognition is to be triggered or not is judged according to the video stream and a vehicle deceleration enabling signal; when the license plate recognition is judged to be carried out, the video stream is taken as an input image; according to the input image, the edge information of the license plate is calculated and the position of a license plate region is determined, furthermore, a license plate image after correction is obtained according to the edge information; character segmentation is carried out on the license plate image after correction so as to obtain the image of each character; a classifier obtained by pre-training is utilized for recognizing the image of each character, and a final license plate recognition result is obtained according to the recognized character. Meanwhile, the invention also discloses a license plate recognition system. The license plate recognition method and the system disclosed by the invention determines whether the license plate recognition is to be triggered or not according to the video stream and the vehicle deceleration enabling signal, reduces erroneous inspection caused by interferent, carries out installation and debugging without damaging roads, and has lower installation and maintenance cost.
Owner:VIMICRO CORP
Surveillance network for unattended ground sensors
InactiveUS20070236343A1Reduce false positiveReduce false positivesBurglar alarmElectric signalling detailsEvent dataUnattended ground sensor
A method for responding to a sensor event is provided, comprising the steps of: (a) recognizing and analyzing a sensor event, and declaring an alarm condition; (b) taking a picture, storing the picture, and transmitting the picture to a central server; (c) notifying subscribers with a message that can contain visual confirmation and other data describing the alarm event; and (d) interrogating a module, downloading event data and images.
Owner:BECKSTED ALBERT MICHAEL +1
Malicious code detection method and system based on plurality of URLs (Uniform Resource Locator)
ActiveCN102801697AImprove the detection effectAvoid variable problemsComputer security arrangementsTransmissionAnti virusNetwork packet
The invention discloses a malicious code detection method based on a plurality of URLs (Uniform Resource Locator), comprising the following steps of: capturing all network communication data packets within appointed time intervals; sequentially analyzing all the network communication data packets and extracting the URL in each data packet; carrying out formalization treatment on all the extracted URLs; matching the URLs (which are subjected to the formalization treatment) as URLs to be detected with a characteristic database; and if the matching is successful, carrying out matching with a data model base, determining threat types and outputting corresponding detection results. The invention further discloses a malicious code detection device based on the plurality of URLs. According to the malicious code detection method and system disclosed by the invention, the disadvantages and the limitation of current anti-virus software characteristic code matching and URL filtering are solved; and the detectable rate of a malicious Trojan program is greatly improved.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
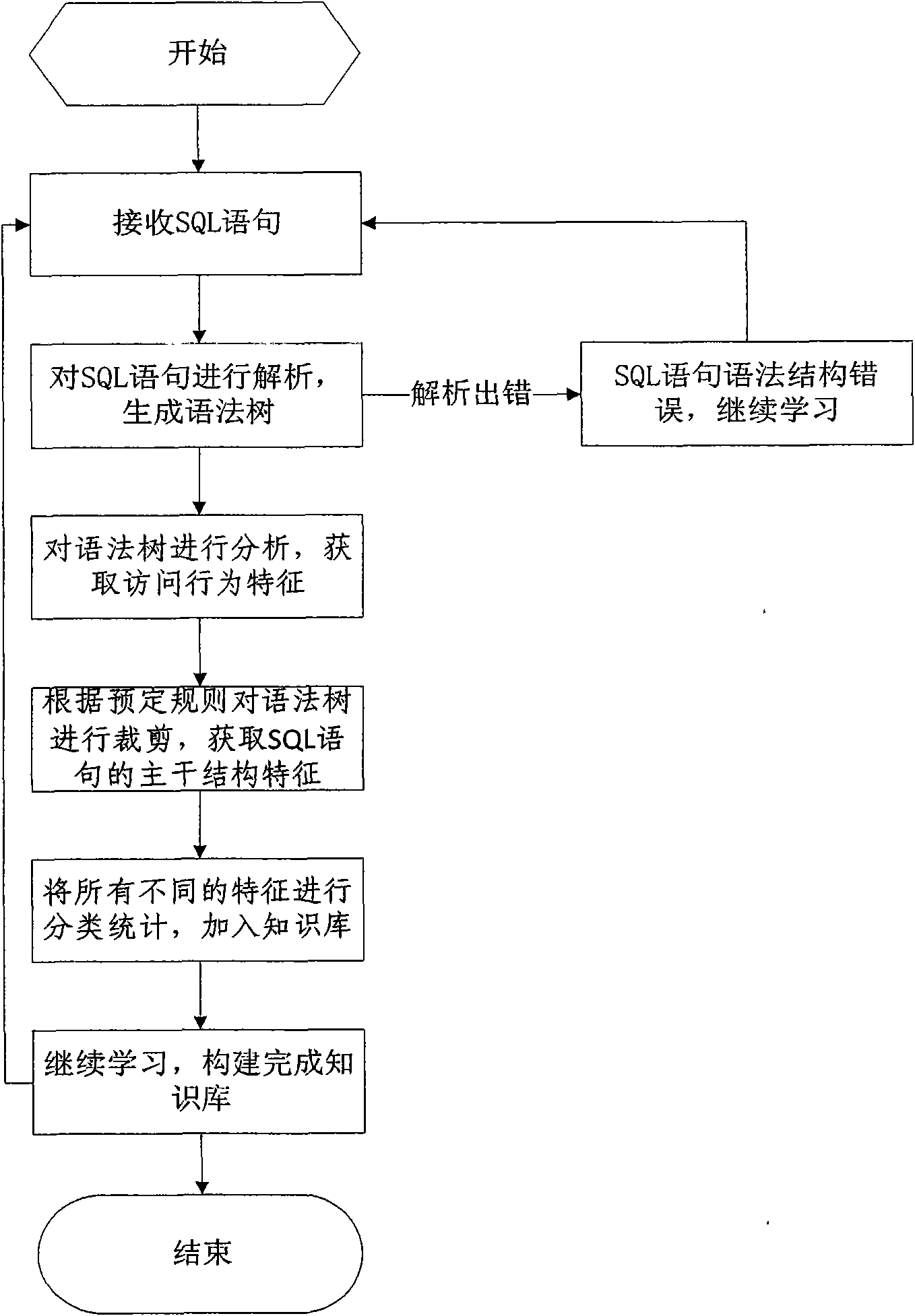
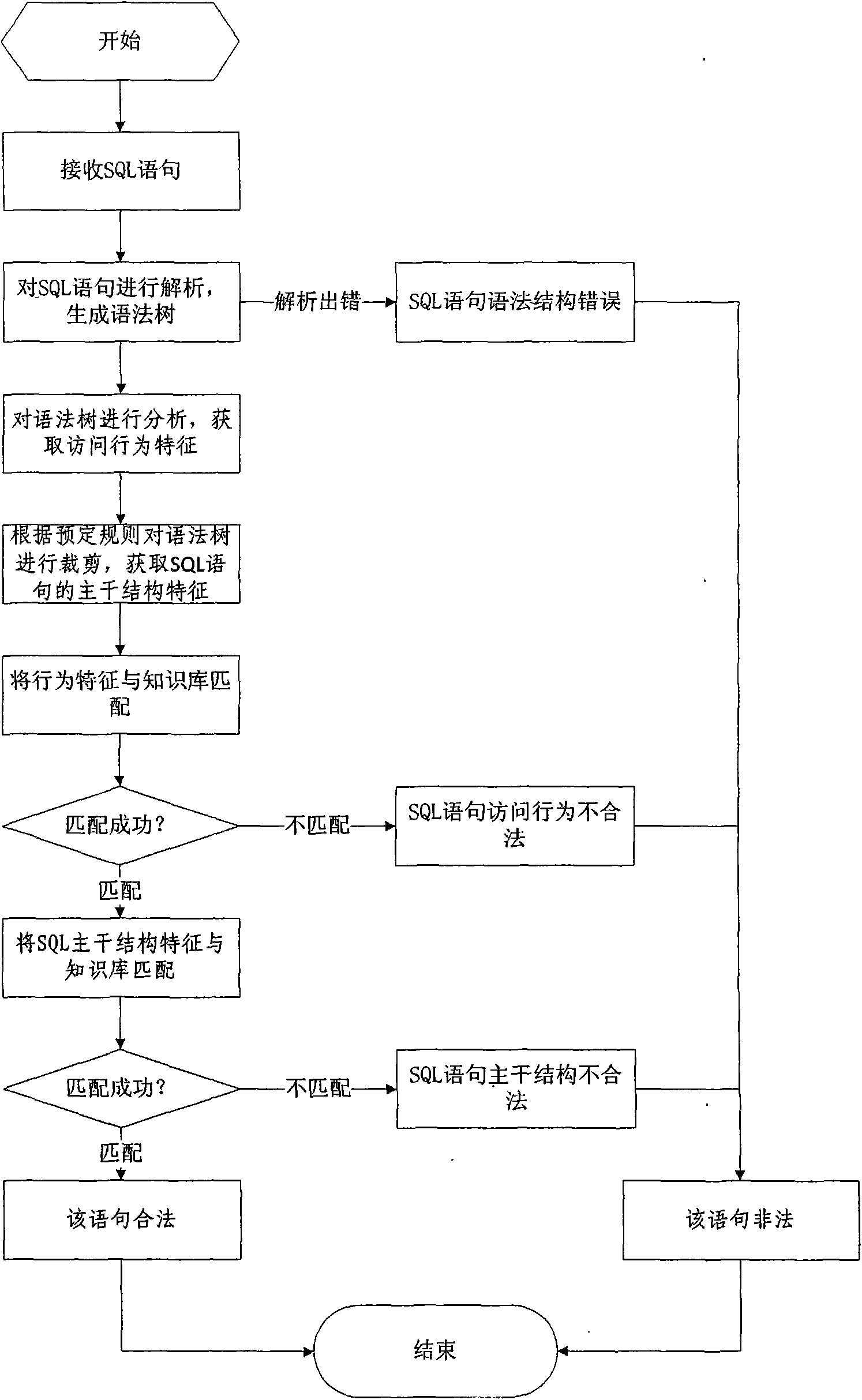
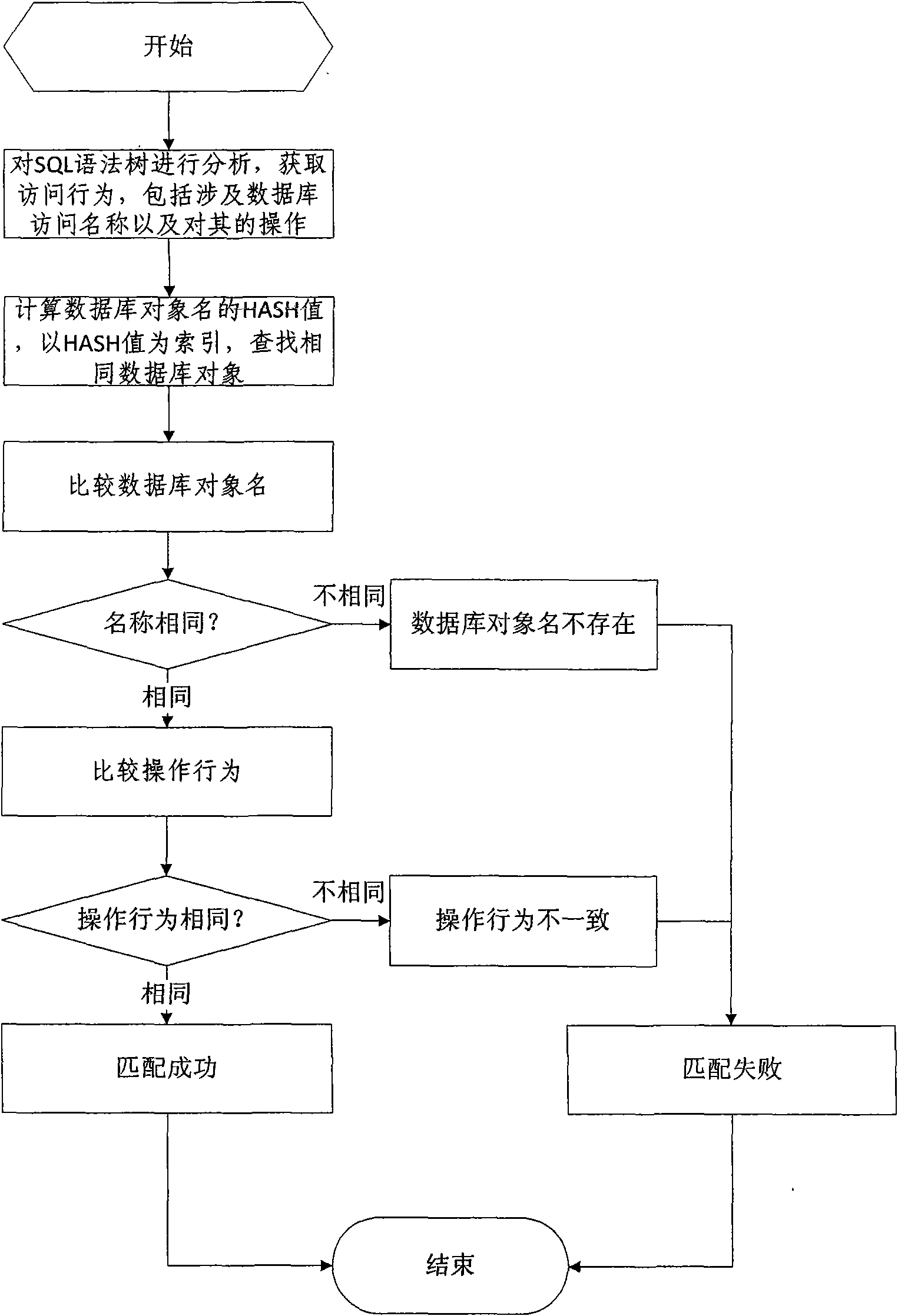
Database SQL infusion protecting method based on self-learning
InactiveCN101609493AOvercome false negativesOvercome the False Positive FlawComputing modelsDigital data protectionLearning basedSQL injection
The invention discloses a database SQL infusion protecting method based on self-learning, comprising a learning phase and a filtering phase. The learning phase works in safe environment. At the moment, all SQL sentences are legitimate SQL sentences generated by an application system. A knowledge model (knowledge base) of the legitimate SQL sentences can be constituted by analyzing the sentences as well as analyzing and summarizing the characteristics of the sentences on the basis of sentence analysis results. The filtering phase works in real environment. At the moment, all SQL sentences are assumed to be possibly illegitimate SQL sentences. The sentences undergo pattern matching with the knowledge base established in the safe environment. If the matching is successful, the sentences are legitimate SQL sentences, otherwise, the sentences are illegitimate SQL sentences. The database SQL infusion protecting method has the advantage that an SQL infusion protecting system based on learning the legitimate SQL sentences can greatly reduce the false report rate and missing report rate which are caused by traditional SQL infusion protection, and the defending capability of the whole system can be improved.
Owner:STATE GRID ELECTRIC POWER RES INST +1
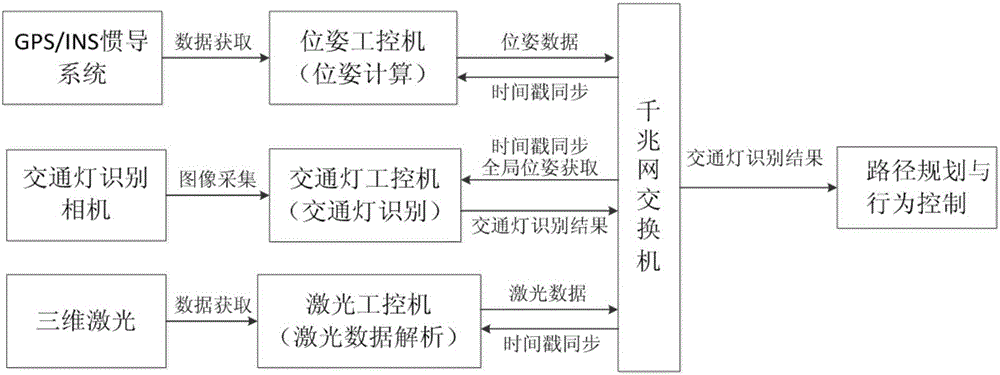
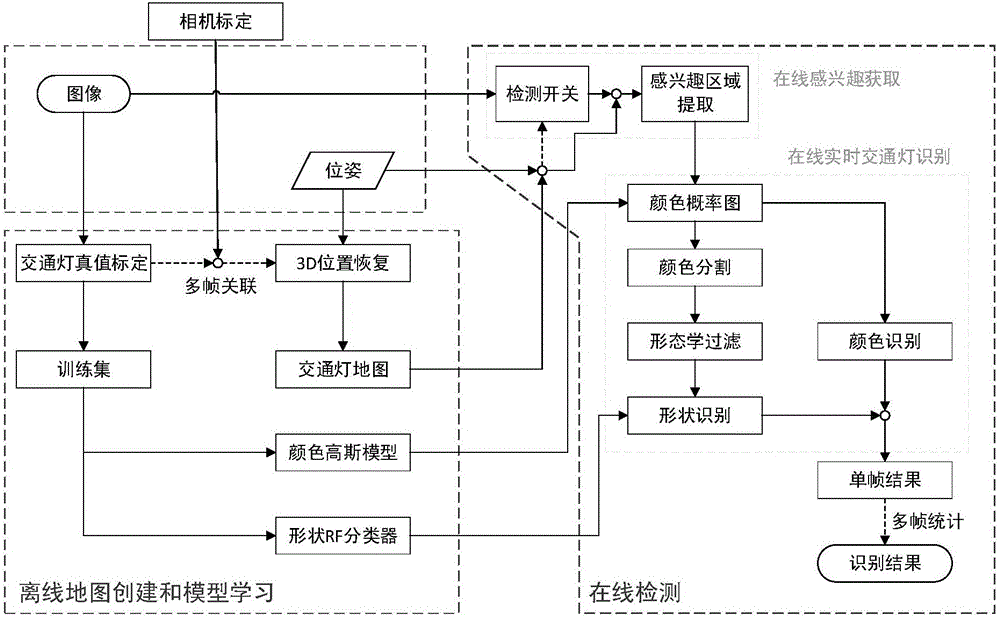
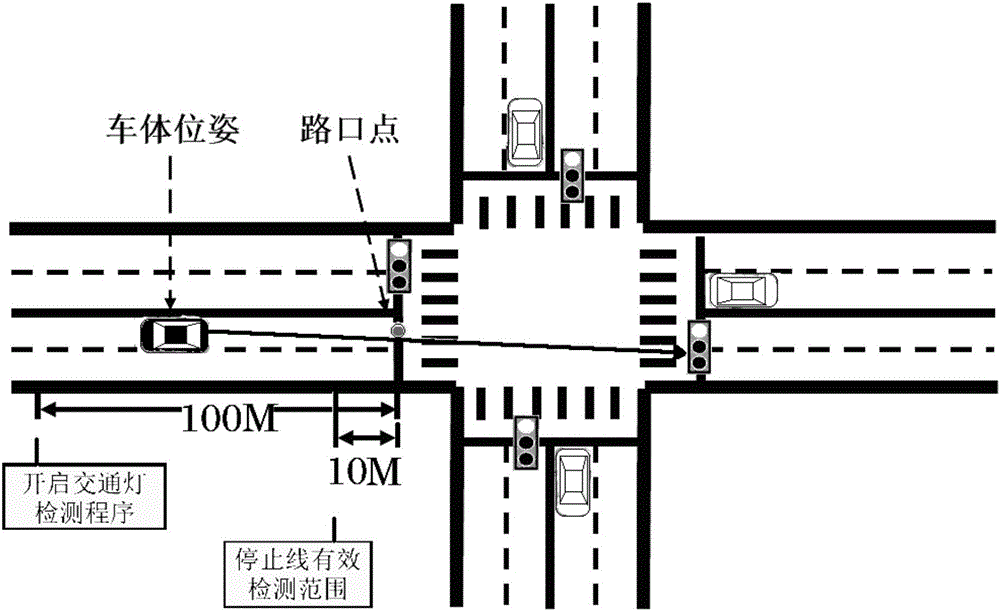
System for real-time identifying urban traffic lights based on single eye vision and GPS integrated navigation system
ActiveCN105930819ARealize identificationRecognition is stable and continuousCharacter and pattern recognitionDistance detectionNavigation system
The invention discloses a system for real-time identifying urban traffic lights based on single eye vision and a GPS integrated navigation system. The system establishes a map of traffic lights in an off-line manner through the methods of interactive image annotation, camera calibration, 3D position recovery, etc., and provides position coordinates and semantic attributes of the traffic lights under the globally positioned GPS coordinate system. Upon online detection, with the established offline map of traffic lights as a prior, an area of interest is determined by solving the substantial scope of the traffic lights in images in combination with the pose position, and the identification of the color segmentation and shapes of the traffic lights are carried out by using form information of the traffic lights in the area of interest. The system is applicable to road conditions and scenarios of different kinds, implements stable and long-distance detection sensing of the traffic lights under various environments. Since the system adopts a low-cost and low-power consumption navigation device, an image acquisition device and a computer platform, the system can be widely applied to the fields of vision navigation of driverless vehicles, vision auxiliary driving of intelligent vehicles, etc.
Owner:XI AN JIAOTONG UNIV
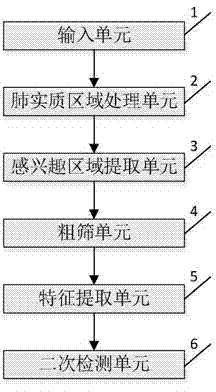
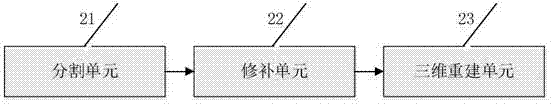
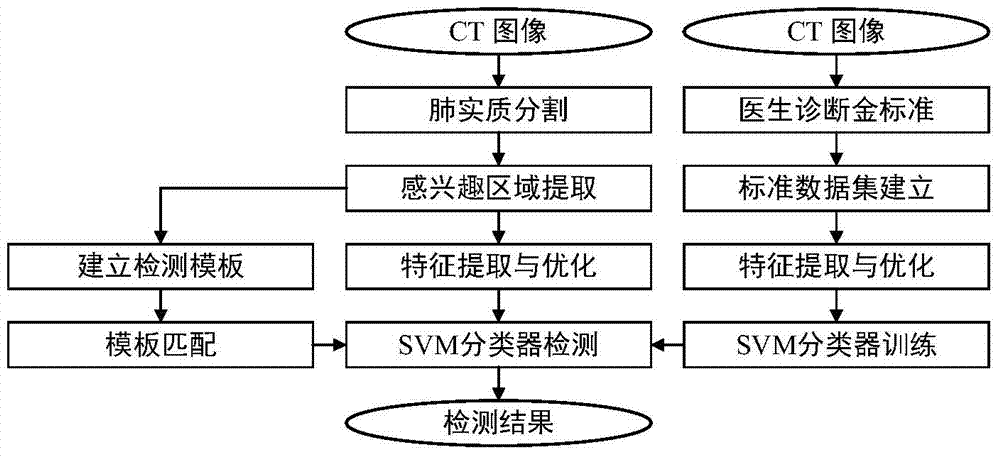
Pulmonary nodule detection device and method based on shape template matching and combining classifier
ActiveCN104751178AIncreased sensitivityEasy to detectImage analysisCharacter and pattern recognitionPulmonary parenchymaPulmonary nodule
A pulmonary nodule detection device and method based on a shape template matching and combining classifier comprises an input unit, a pulmonary parenchyma region processing unit, a ROI (region of interest) extraction unit, a coarse screening unit, a feature extraction unit and a secondary detection unit. The input unit is used for inputting pulmonary CT sectional sequence images in format DICOM; the pulmonary parenchyma region processing unit is used for segmenting pulmonary parenchyma regions from the CT sectional sequence images, repairing the segmented pulmonary parenchyma regions by the boundary encoding algorithm and reconstructing the pulmonary parenchyma regions by the surface rendering algorithm after the three-dimensional observation and repairing; the ROI extraction unit is used for setting a gray level threshold and extracting the ROI according to the repaired pulmonary parenchyma regions; the coarse screening unit is used for performing coarse screening on the ROI by the pulmonary nodule morphological feature design template matching algorithm and acquiring selective pulmonary nodule regions; the feature extraction unit is used for extracting various feature parameters as sample sets for the post detection according to selective nodule gray levels and morphological features; the secondary detection unit is used for performing secondary detection on the selective nodule regions through a vector machine classifier and acquiring the final detection result.
Owner:KANGDA INTERCONTINENTAL MEDICAL EQUIP CO LTD
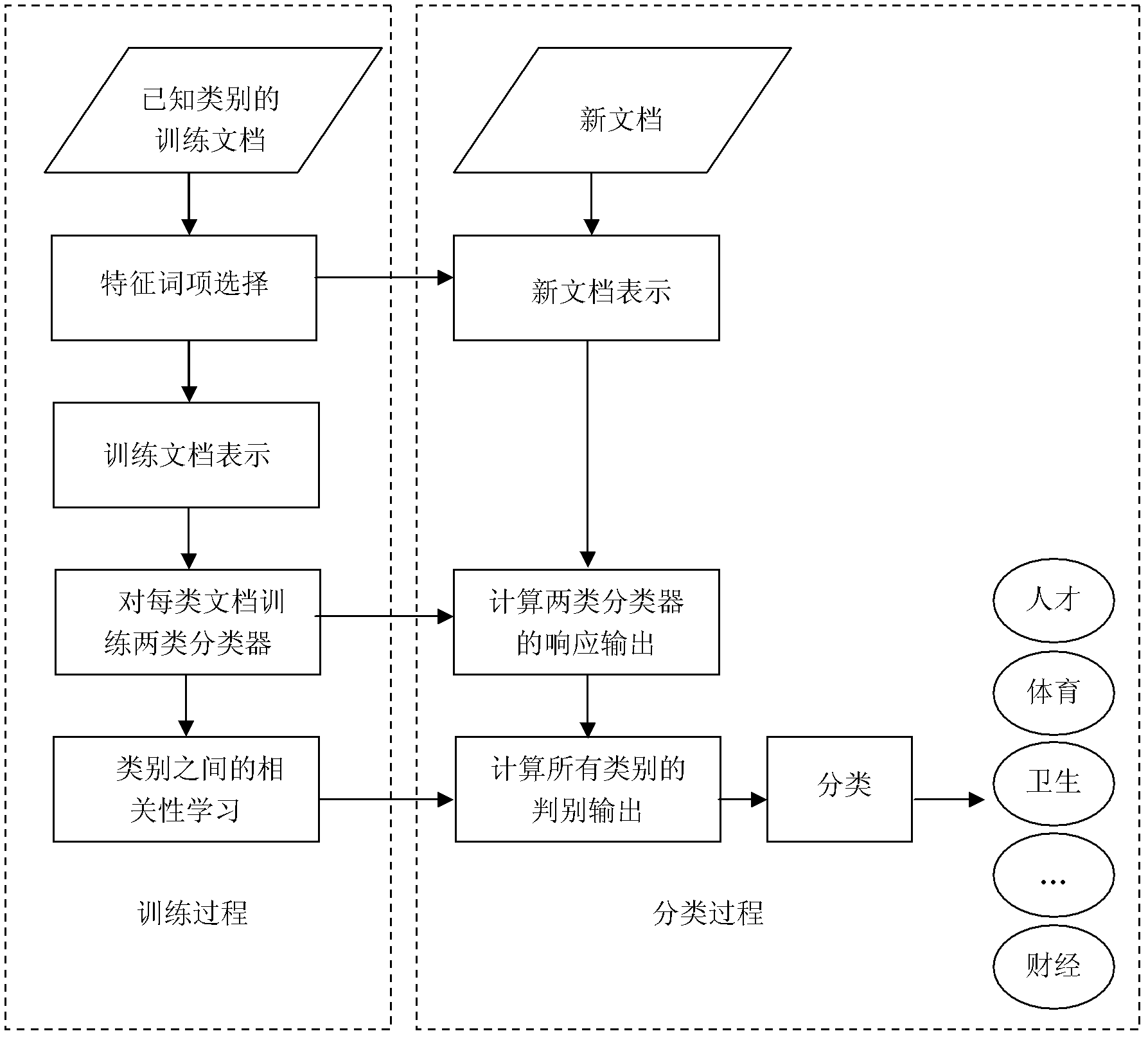
Chinese text sorting method based on correlation study between sorts
InactiveCN102332012AStrong dependenceTo solve the classification accuracy is not highSpecial data processing applicationsDocument preparationLexical frequency
The invention discloses a Chinese text sorting method based on correlation study between sorts. The method comprises the following steps of: firstly, dividing words of a document and performing rough selection on characteristics by computing word frequencies; secondly, further determining representative word items according to discrimination indexes between the word items and sorts so as to form characteristic word items which are finely selected; thirdly, training the document to be expressed by a tfidf weight and a discrimination index weight according to an index of the characteristic word items; fourthly, establishing a group of two-sort sorters corresponding to different projection vectors and training to obtain a code array expressing the correlation between two-sort sorters; and finally, projecting a multi-vector expression of a new document to all the two-sort sorters, introducing the code array, computing the similarity between each sort and the document, and outputting the maximum of the similarity as a sort judging result of the new document. The new document is sorted based on a correlation studying result between the sorts, and the running efficiency of an algorithm is improved on the premise of ensuring the sorting performance.
Owner:南方报业传媒集团
Video monitoring method and system
InactiveCN102547244AReduce false positivesImprove accuracyImage analysisClosed circuit television systemsKalman filterBehavior recognition
The invention discloses a video monitoring method and a video monitoring system. The method comprises the following steps: S100, acquiring a video stream to be analyzed currently; S200, detecting whether a motion object exists in the video stream, if yes, carrying out background modeling, morphological process and eliminating shadow, if no, carrying out circular detection; S300, using a particle filtering or a Kalman filtering tracking method to track the motion object; S400, analyzing the shape information and motion characteristics of the motion object, analyzing abnormal situations by utilizing dispersion degree and area information, classifying the motion object and accomplishing abnormal action identification process analysis; and S500, making an emergency alarm when abnormal situation happens to the video stream. With the method in the invention, the motion object can be analyzed intelligently, multiple bottom layer calculation for one same video stream is carried out only once, and miss report and false report rate of abnormal action in monitoring can be reduced; and with the method. Besides, the method also can be linkaged with security, so that monitoring personnel can make response in time.
Owner:深圳辉锐天眼科技有限公司
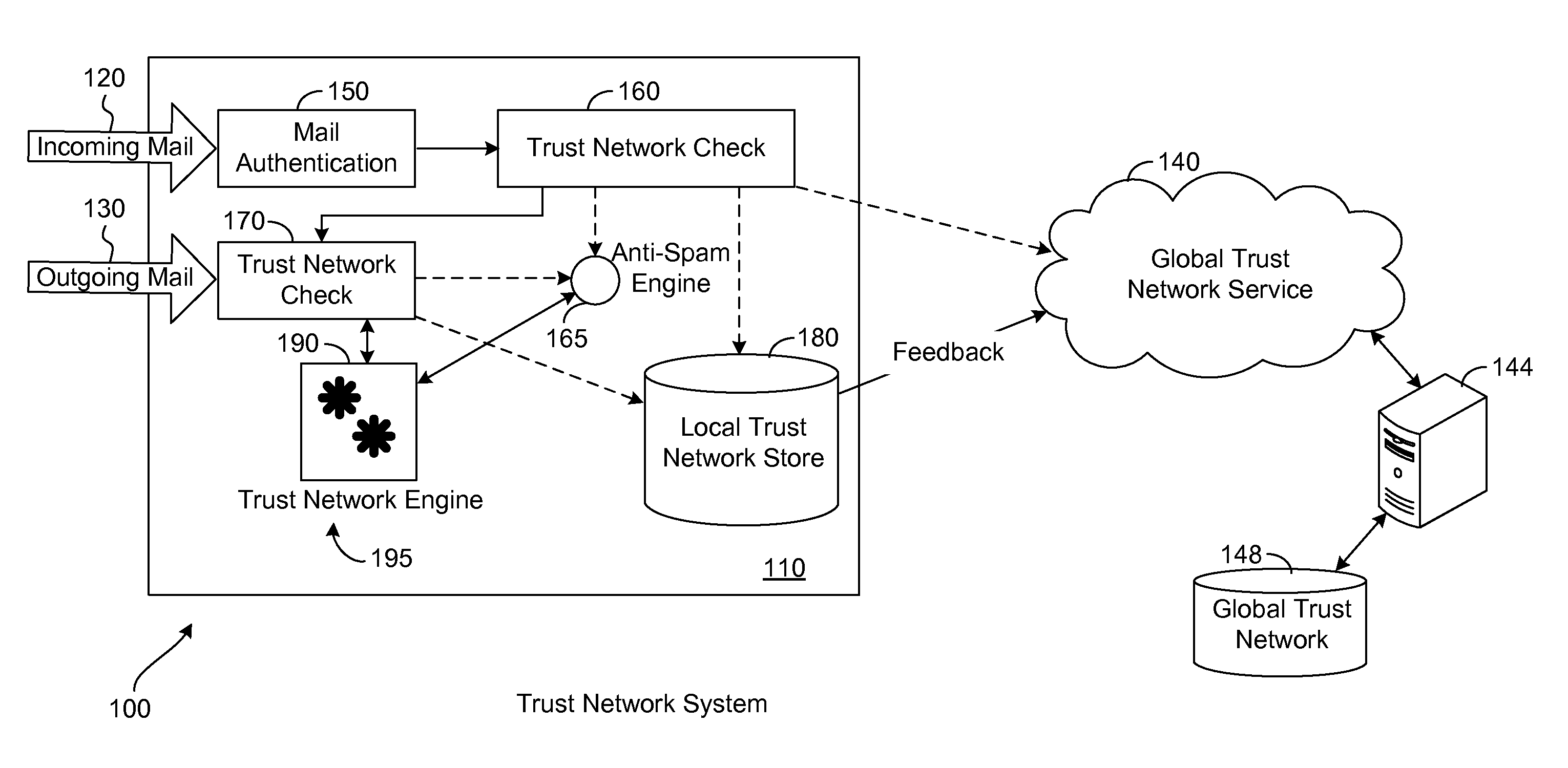
Trust network to reduce e-mail spam
ActiveUS8392357B1Reduce spamEasy to processDigital data processing detailsTransmissionEmail addressInternet privacy
A trust network database has any number of nodes, each node representing a user e-mail address. Links between nodes represent whether one user trusts another. Trust (that the recipient is trusted) is established when a sender sends an e-mail message to a recipient. The recipient is effectively placed on the white list for the sender. A legitimate e-mail address creates a strong trust link, otherwise it is weak. A spam count tracks by an amount of spam sent by each node. Outgoing e-mail messages are screened to make a determination that the sender trusts the recipient and that information is added to a local or remote trust network. Incoming e-mail messages are first screened to determine that the sender is legitimate. Then, the sender and recipient e-mail addresses are forwarded to the trust network to make a determination as to whether the recipient trusts the sender. A score (based upon number and type of links into or out of a node, the spam count for the node, etc.) for the sender is returned indicating whether or not the e-mail message is likely to be spam. An anti-spam engine is bypassed, used normally, or used aggressively based upon the score.
Owner:TREND MICRO INC
Brand notification systems and methods
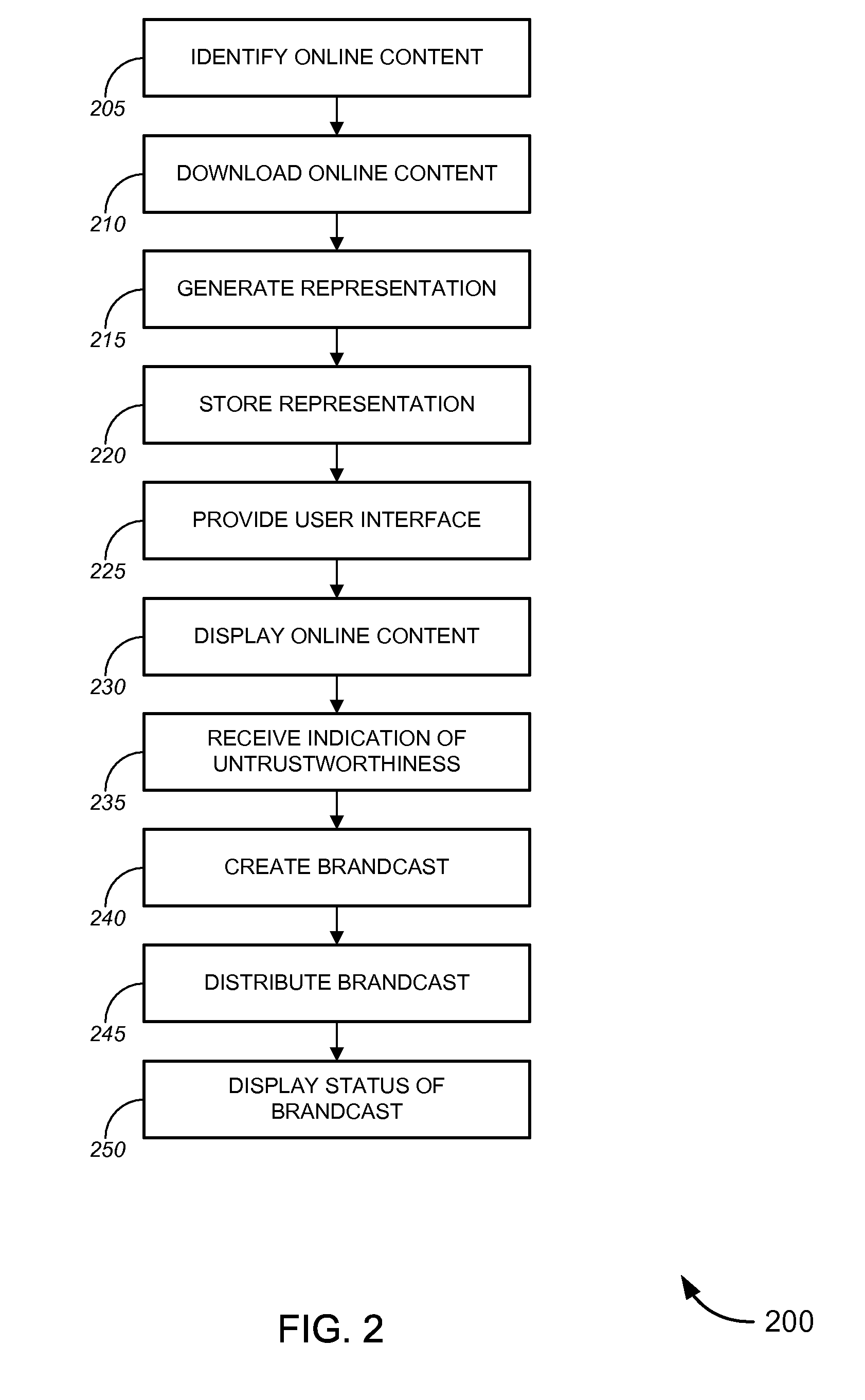
InactiveUS20090119143A1Reduce false positiveImprove securityComputer security arrangementsMarketingWeb siteWeb page
Tools and techniques for identifying brand misuse and / or for distributing information about such misuse. Certain of the tools and techniques can be used to determine that a set of online content (e.g., a web site, web page, or portion thereof) is untrustworthy (for example, because that set of online content misuses a brand) and generate a brand notification feed indicating the untrustworthiness of the set of online content. This brand notification feed might be distributed to a security vendor, who can incorporate information from the brand notification feed into the information it provides to clients.
Owner:CAMELOT UK BIDCO LTD
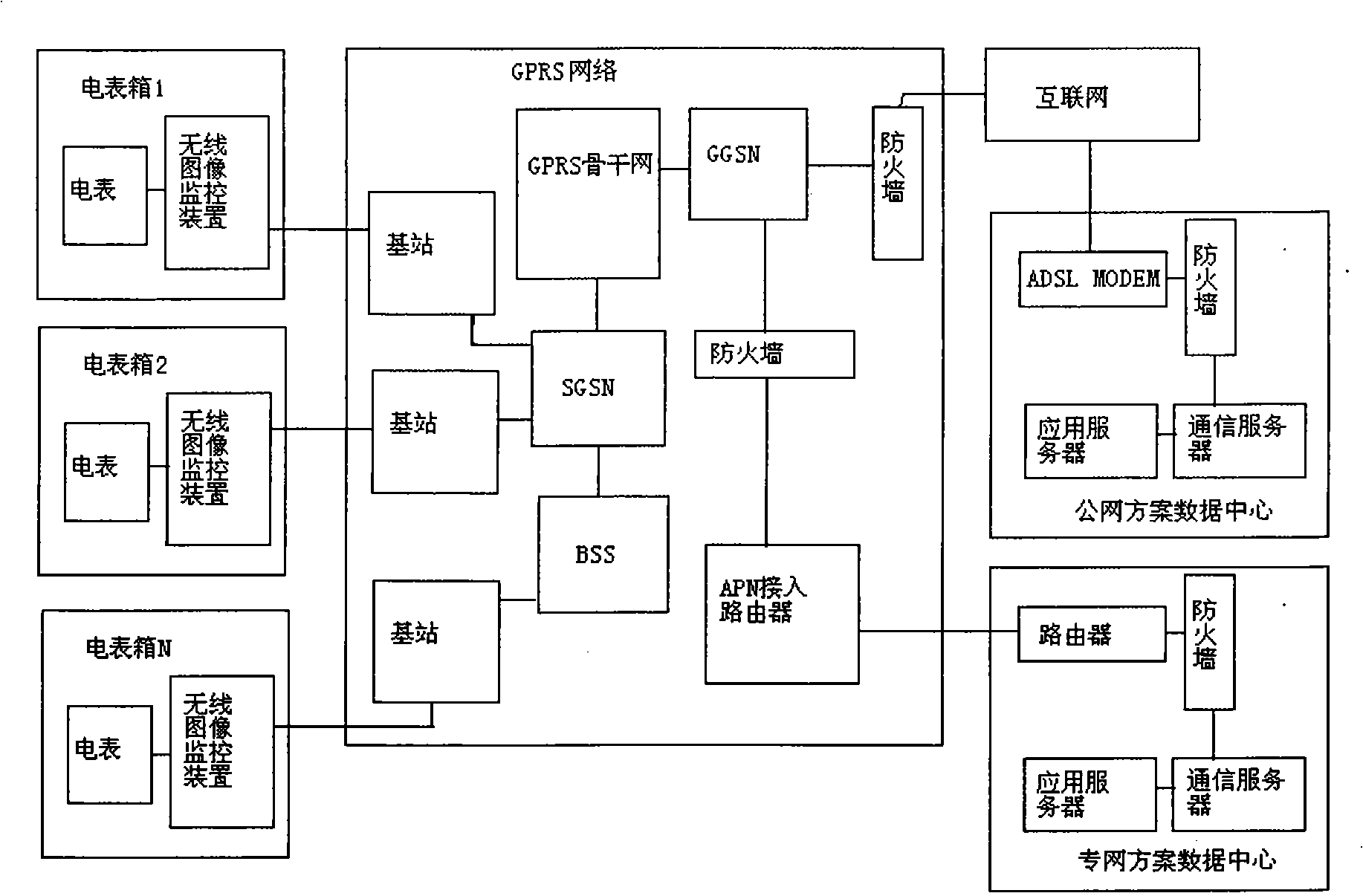
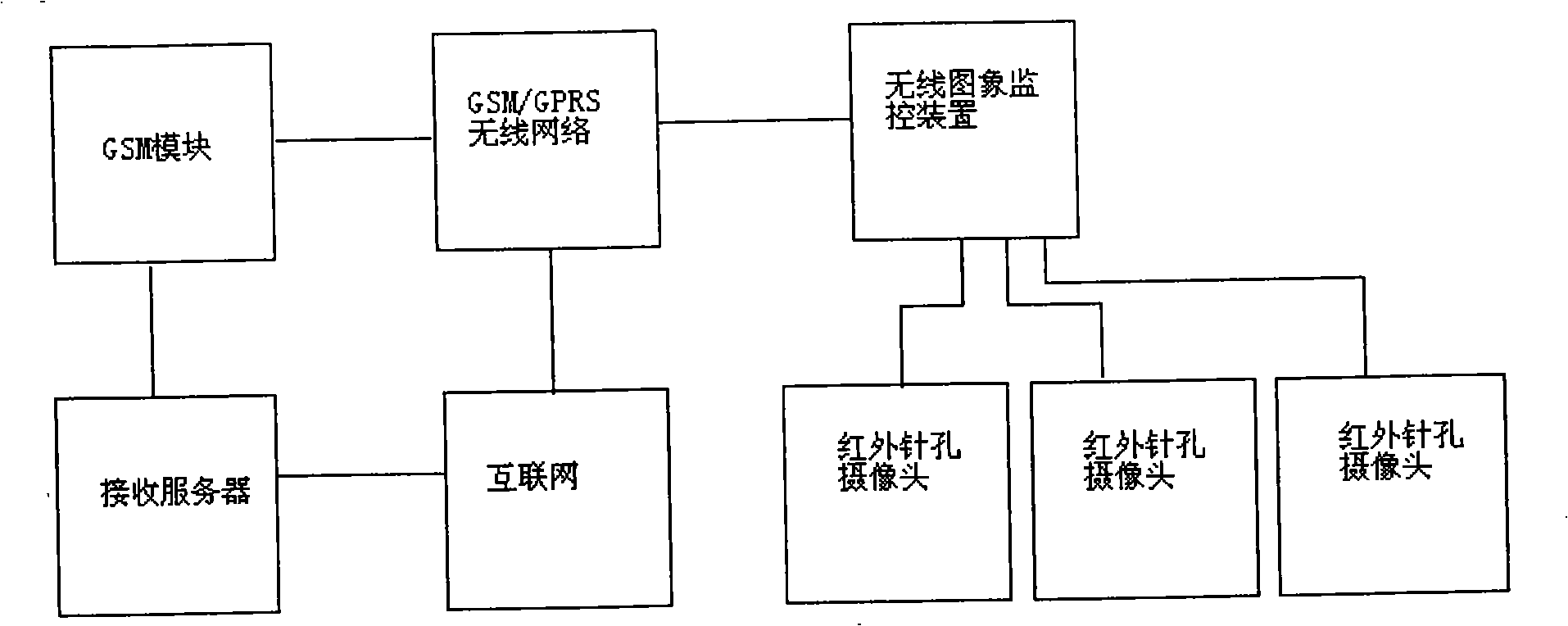
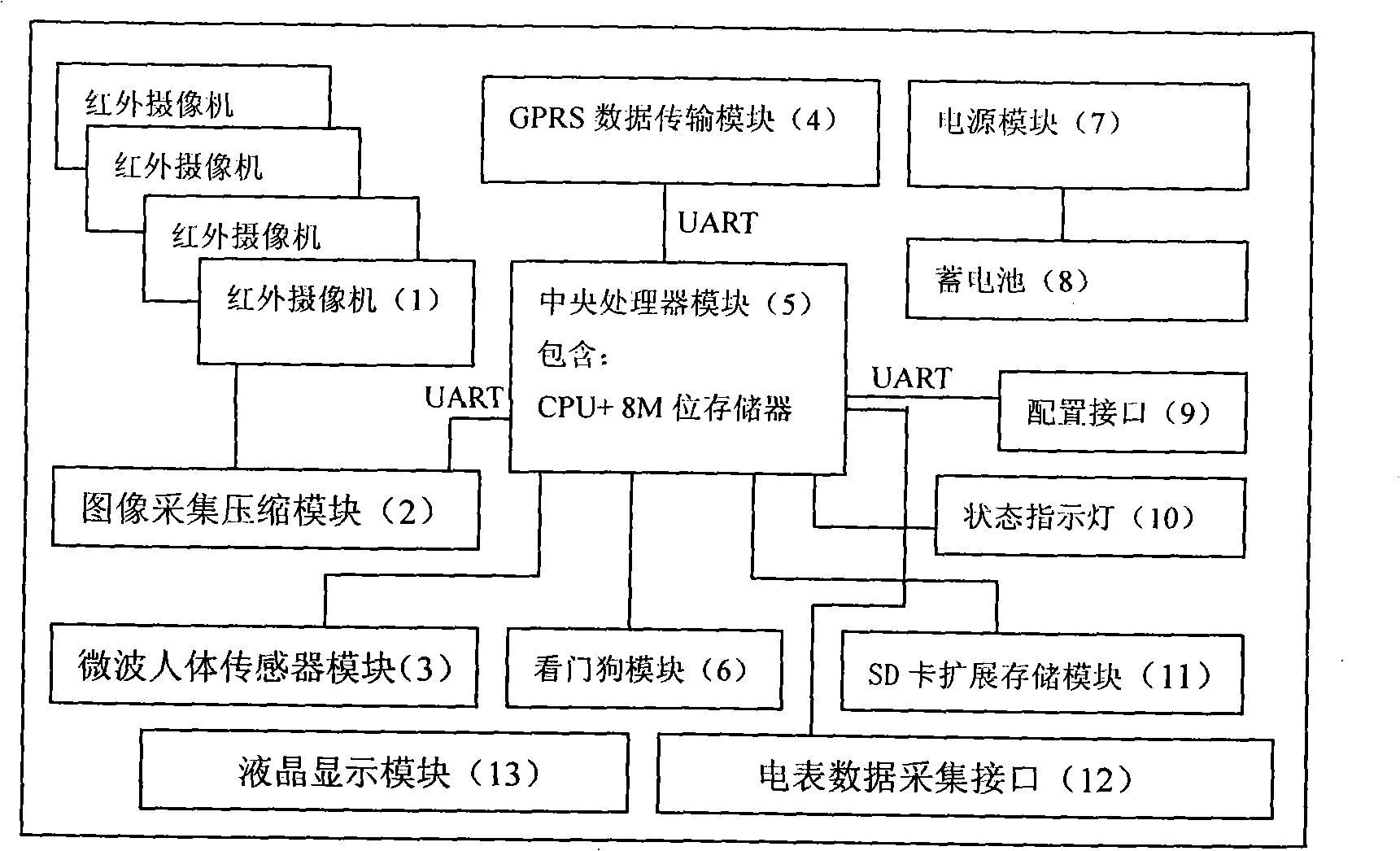
Wireless data and image double-acquisition anti-electricity theft monitoring system and method thereof
InactiveCN101320053AAcquisition timingReal-time acquisitionTransmissionBurglar alarmElectricityMicrowave
The invention discloses a wireless data-image dual acquirement anti-electricity-theft monitoring system and method which uses a microwave body sensor to conduct the real time detection to activities of people around an electricity meter box. Based on the method of the image shooting of a camera, the monitoring system provided by the invention uses a camera to continuously shoot and store the images of the activities of people around the electricity meter box and can real time transmit alarming information, electricity meter data and image information to a motoring server through GPRS network; and then, the motoring server can send the received alarming information to the mobile phones or computers of users in time, and users can read the alarming information from the mobile phones or computers of users in distance. Besides the functions of remote electricity meter data acquiring, the anti-electricity-theft monitoring and real-time alarming, the monitoring system also can transmit field images in time and obtain images stored by field equipment later for providing convincible proofs during handling the electricity theft of illegal users.
Owner:STATE GRID SHANDONG ELECTRIC POWER
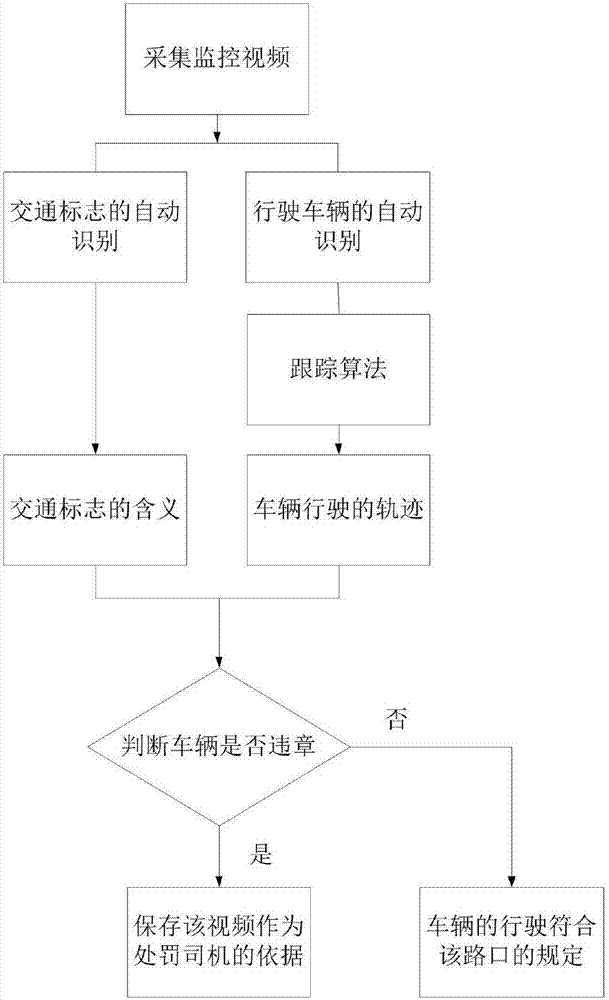
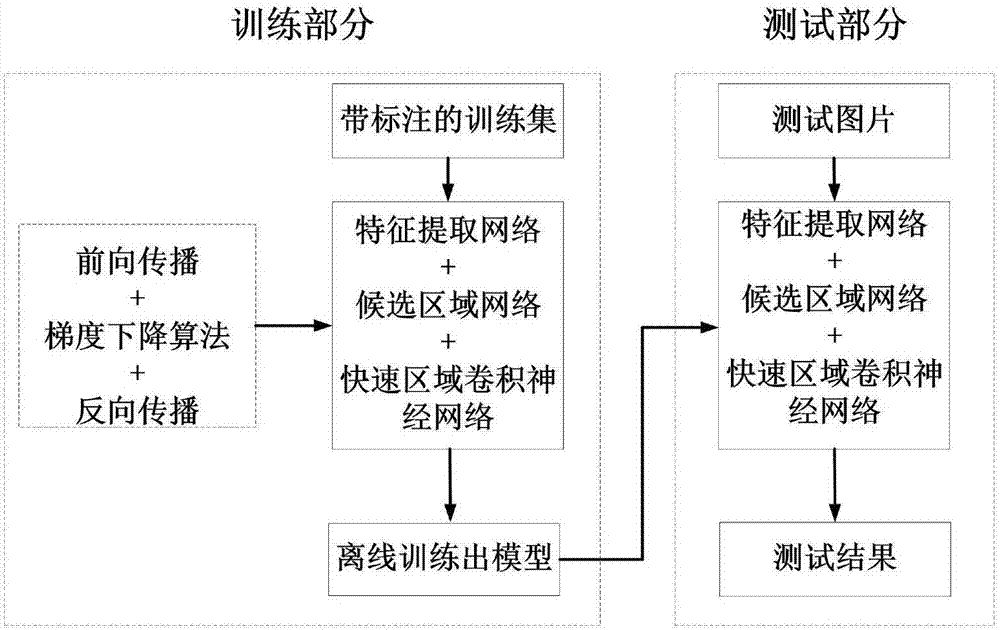
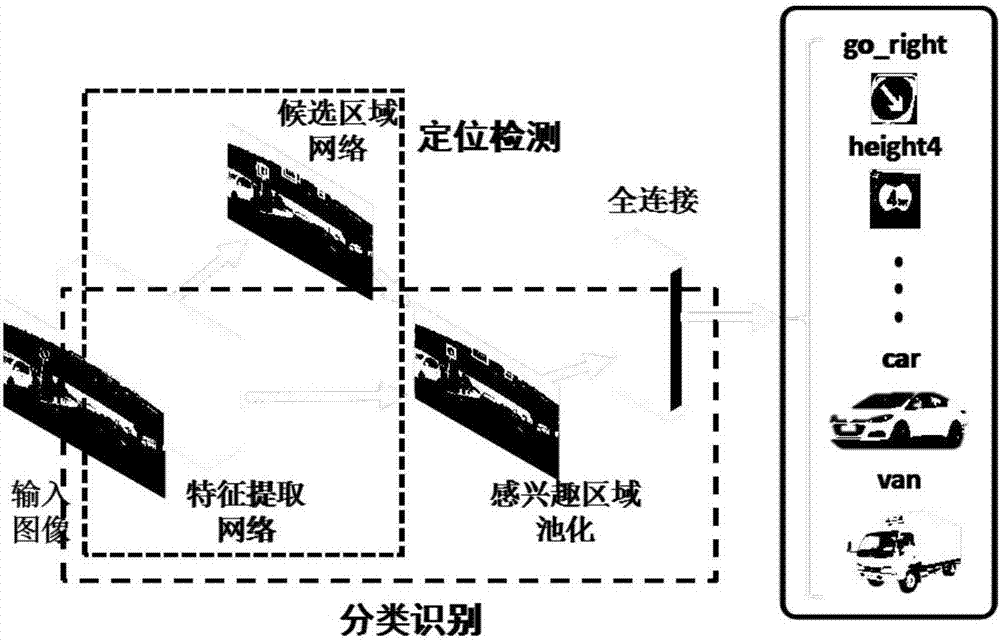
Intersection vehicle violation detection system based on traffic sign identification
InactiveCN106886755AReduce false positivesImprove efficiencyRoad vehicles traffic controlCharacter and pattern recognitionFalse detectionDeep learning
The patent discloses an intersection vehicle violation detection and identification method based on deep learning. The method comprises the following steps of 1, collecting intersection video detection images; 2, identifying traffic signs and vehicles; 3, tracking the vehicles; and 4, performing vehicle violation detection and identification. Based on automatic identification and tracking of the traffic signs and the vehicles in the intersection monitoring videos, the violation conditions of vehicles at the intersection can be automatically identified, and the system has few false detection and high efficiency.
Owner:BEIHANG UNIV
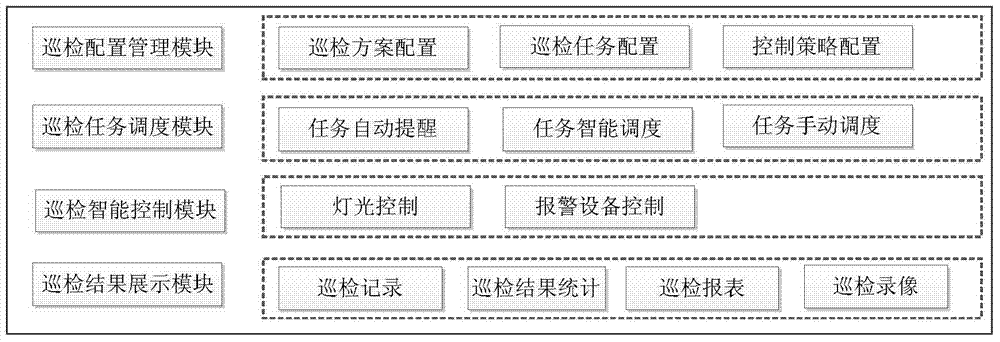
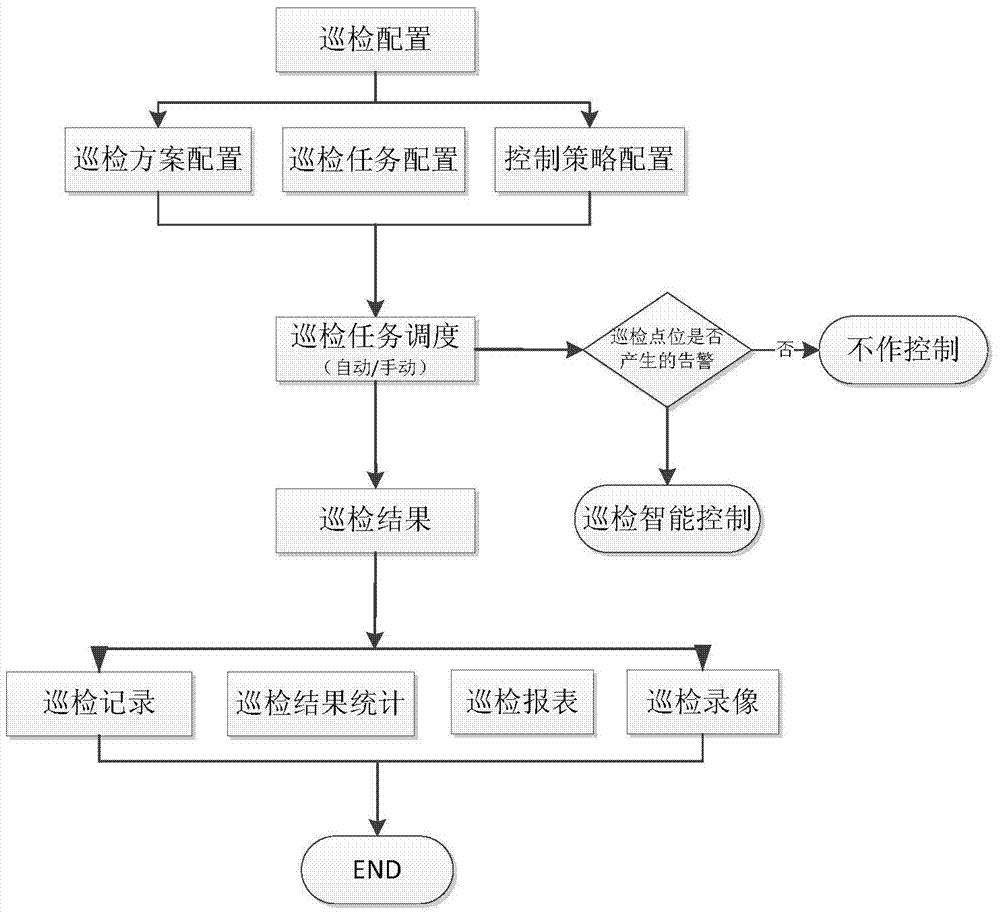
Video-monitoring-based transformer substation tour-inspection intelligent-scheduling and control system
ActiveCN103699075ARealize intelligent schedulingRealize intelligent controlClosed circuit television systemsProgramme total factory controlVideo monitoringControl system
The invention discloses a video-monitoring-based transformer substation tour-inspection intelligent-scheduling and control system, which comprises a tour-inspection configuration management module, a tour-inspection task scheduling module, a tour-inspection intelligent-control module and a tour-inspection result display module, wherein the tour-inspection configuration management module is used for generating tour-inspection schemes, tour-inspection tasks associated with the tour-inspection schemes and tour-inspection control strategies by configuration data; the tour-inspection task scheduling module can be used for manually or automatically scheduling the tour-inspection tasks; the tour-inspection intelligent-control module is used for intelligently controlling a tour-inspection process; the tour-inspection result display module is used for displaying tour-inspection results in diversified forms of list, statistics, report forms and the like. According to the system, a complete set of flow scheme with intelligent scheduling and control functions is formed by video tour-inspection route setting, task scheduling, control linkage and the tour-inspection results, and report forms and reports can be automatically generated, so that the working efficiency, accuracy and timeliness are improved; the system is used for the video-monitoring remote intelligent tour-inspection of a transformer substation.
Owner:STATE GRID CORP OF CHINA +2
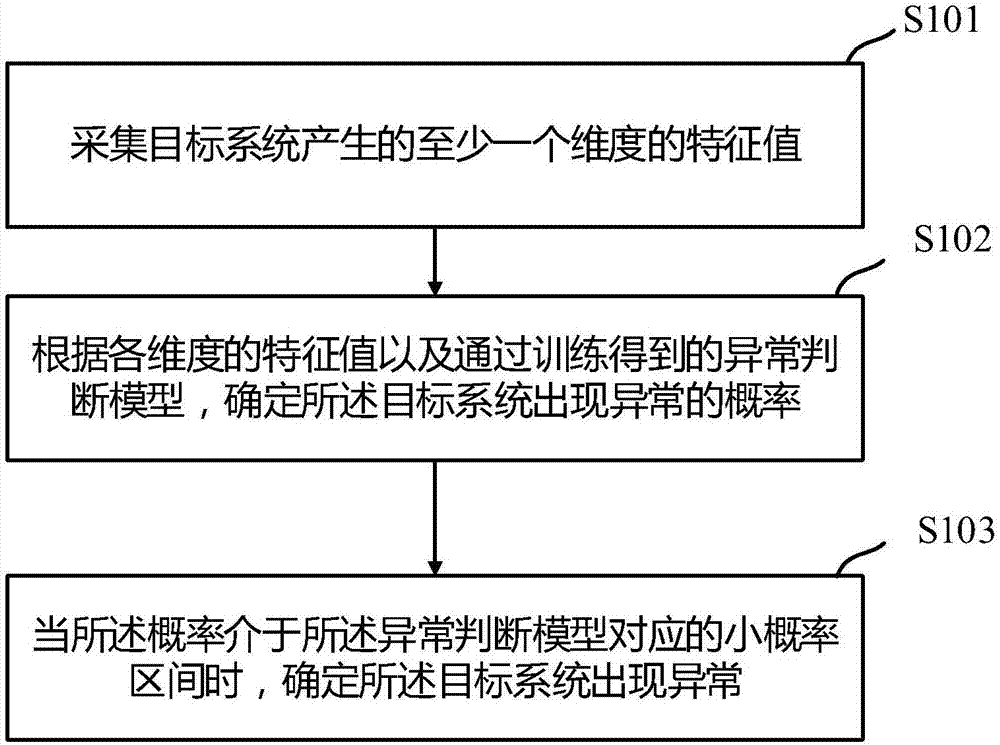
System exception monitoring method and apparatus
ActiveCN107066365AReduce false positivesReduce false negative rateHardware monitoringSmall probabilityGoal system
The invention discloses a system exception monitoring method and apparatus. The method comprises the steps of firstly, determining an eigenvalue of each dimension generated by a target system; then according to a pre-trained exception judgment model, determining a probability of generating an exception in the target system; and when the probability is in a small probability interval corresponding to the exception judgment model, determining that the exception is generated in the target system. Through the method provided by the invention, the running condition of the target system is determined according to the trained exception judgment model, and corresponding processing can be performed according to the actual running condition of the target system; and compared with the prior art, the false reporting and missing reporting probabilities of target system exception are reduced and the monitoring accuracy and efficiency are improved.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com