Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1750 results about "Email address" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
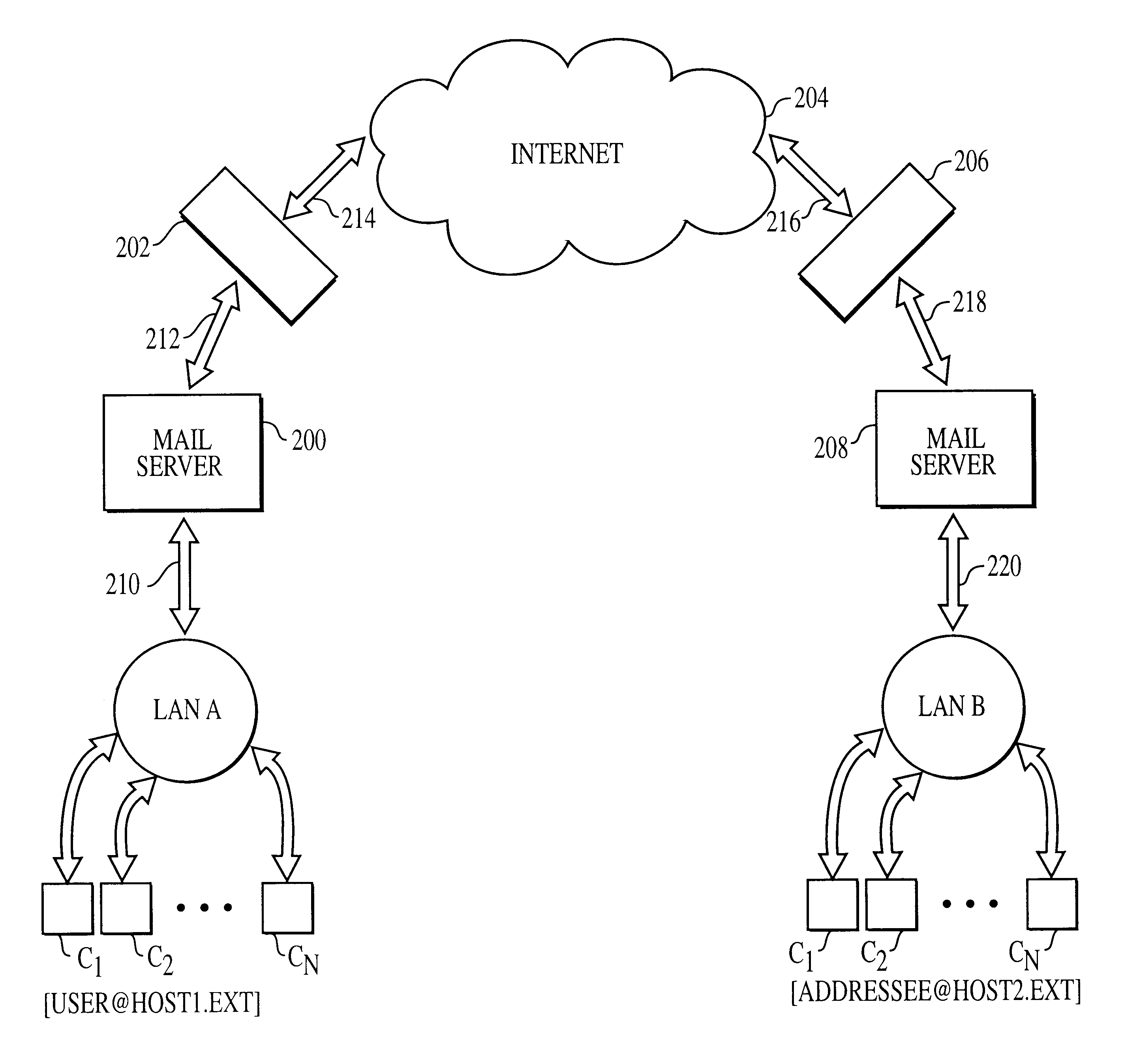
An email address identifies an email box to which email messages are delivered. A wide variety of formats were used in early email systems, but only a single format is used today, following the specifications developed for Internet mail systems since the 1980s. This article uses the term email address to refer to the addr-spec defined in RFC 5322, not to the address that is commonly used; the difference is that an address may contain a display name, a comment, or both.
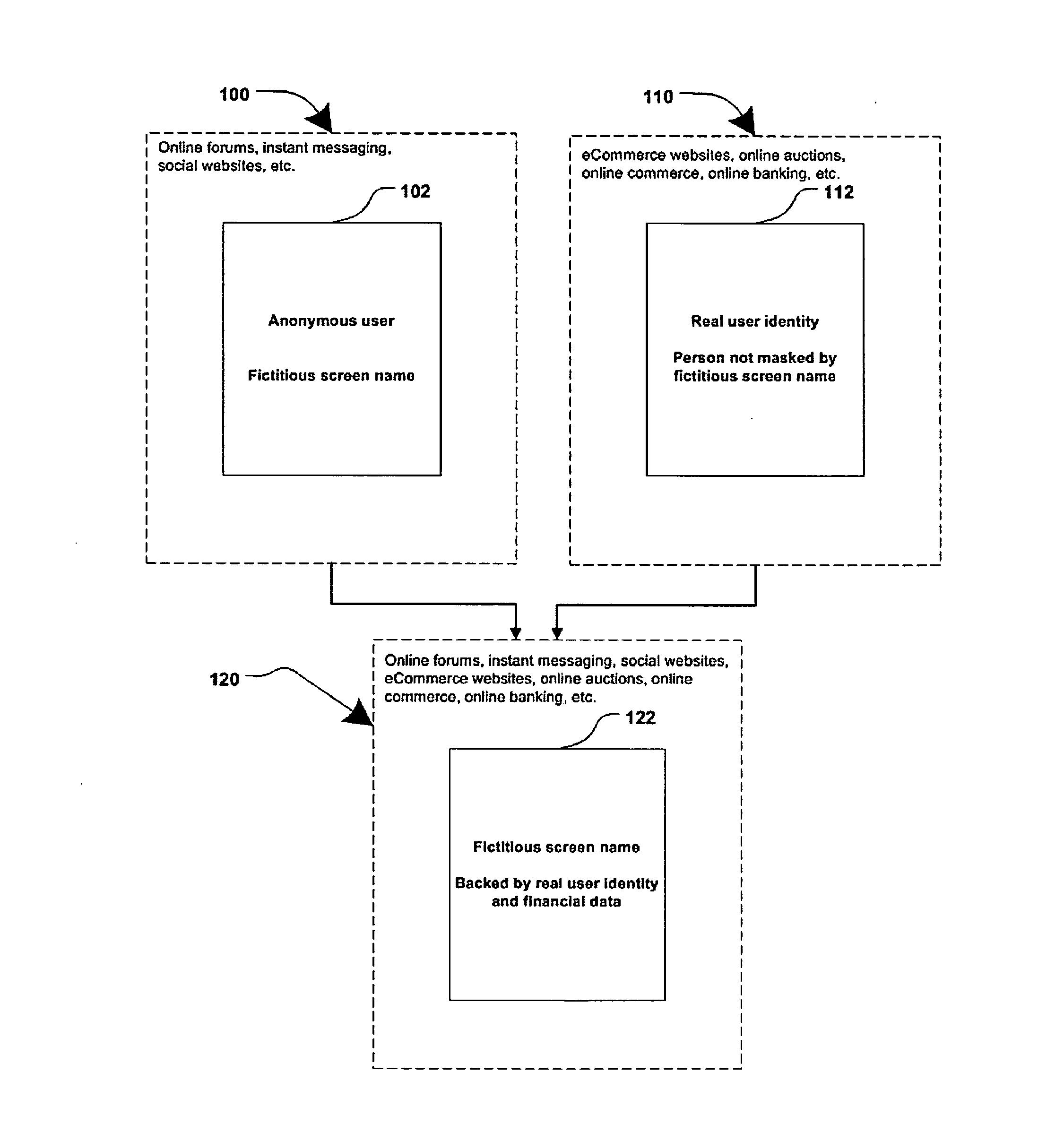
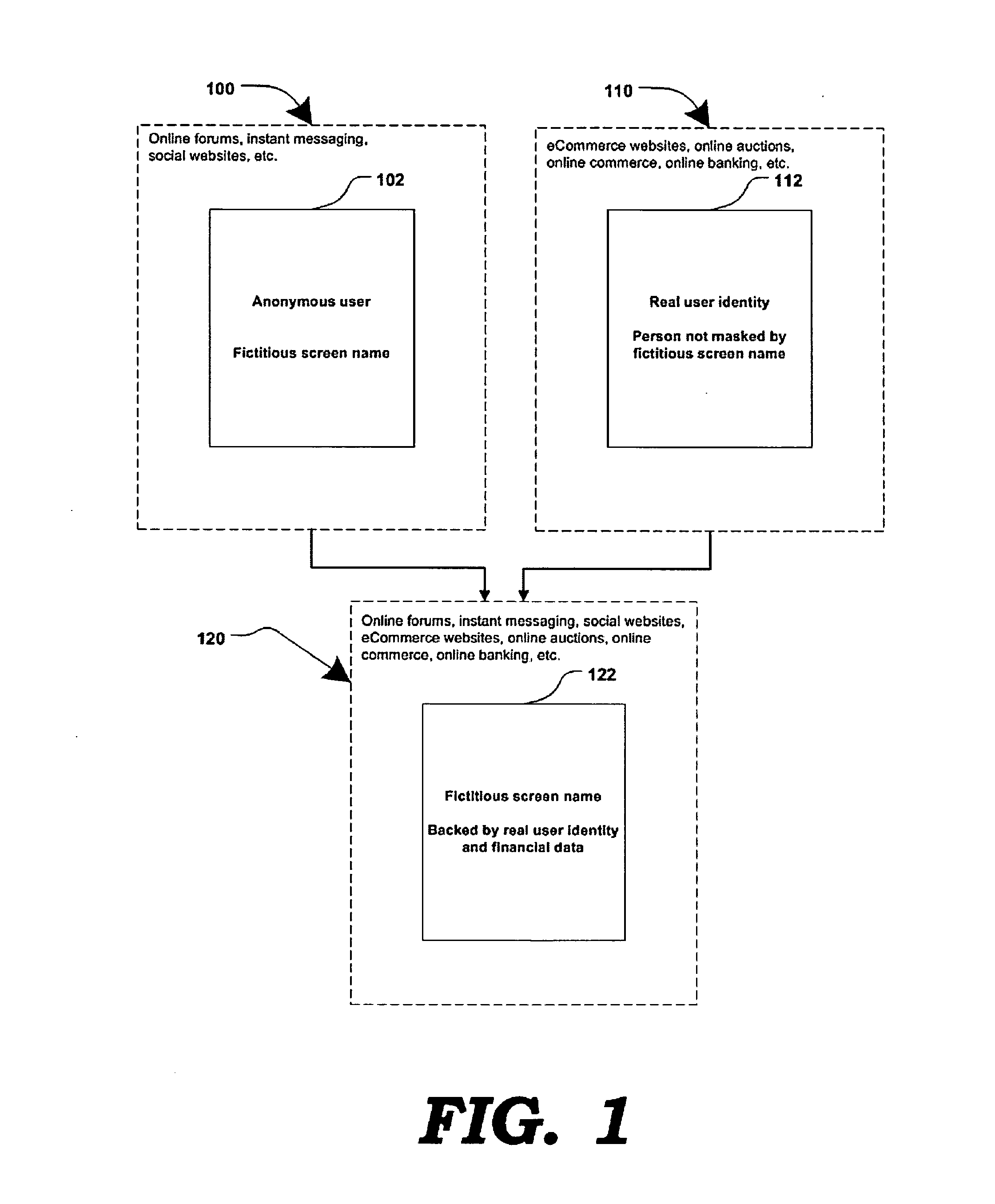
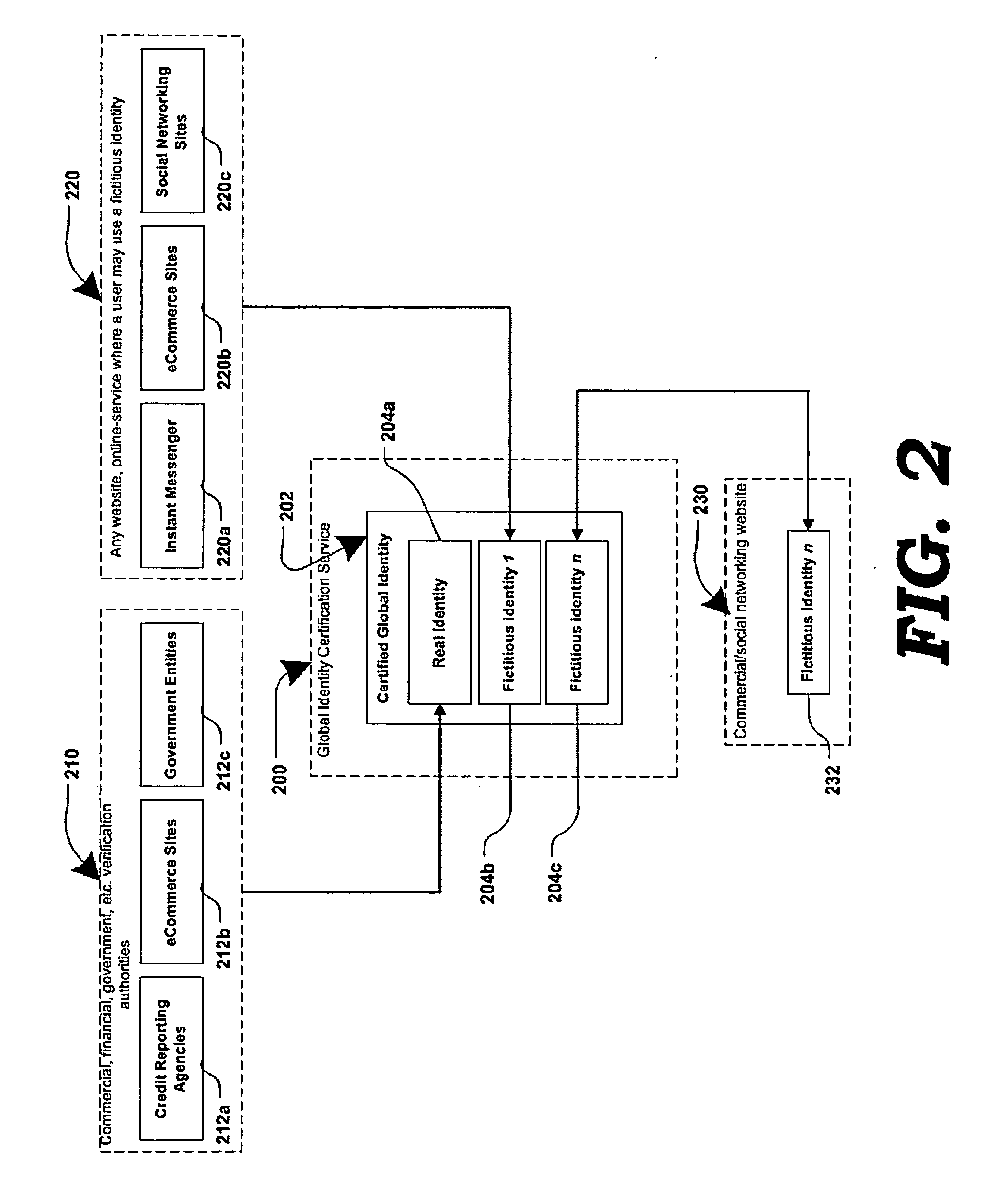
Method and systems for online advertising to users using fictitious user idetities
Various methods, systems and apparatus for associating fictitious user identities (e.g. screen names, user names, email addresses, handles, etc.) used in electronic communications (e.g. over the internet or mobile network via instant messenger, e-mail, social networks, ecommerce, auction websites, etc.) with real personal information (e.g. the true identity of an individual such as their name, address, credit score, driving record, mobile number, etc.) are disclosed. One such method may include discovering, verifying and storing real personal information, associated with fictitious user identities and email addresses. The method may further include allowing a remote user or service to submit a fictitious user identity and a query requesting real-user information associated with the submitted fictitious user identity. In one possible embodiment, a targeted-advertising service may utilize real user information, associated with a fictitious user name, to target advertisements at the user of the fictitious user name.
Owner:JAKOBSON GABRIEL +1
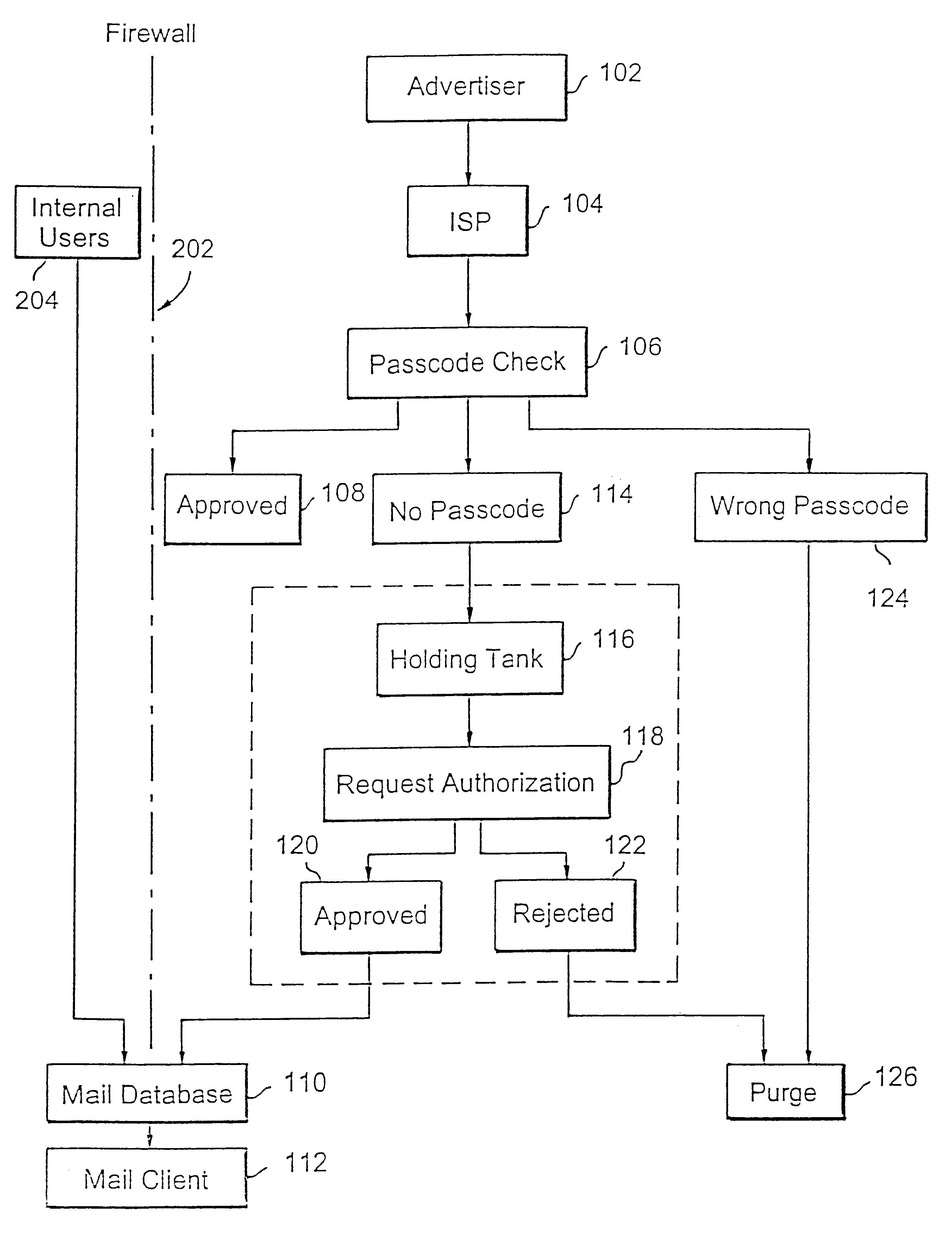
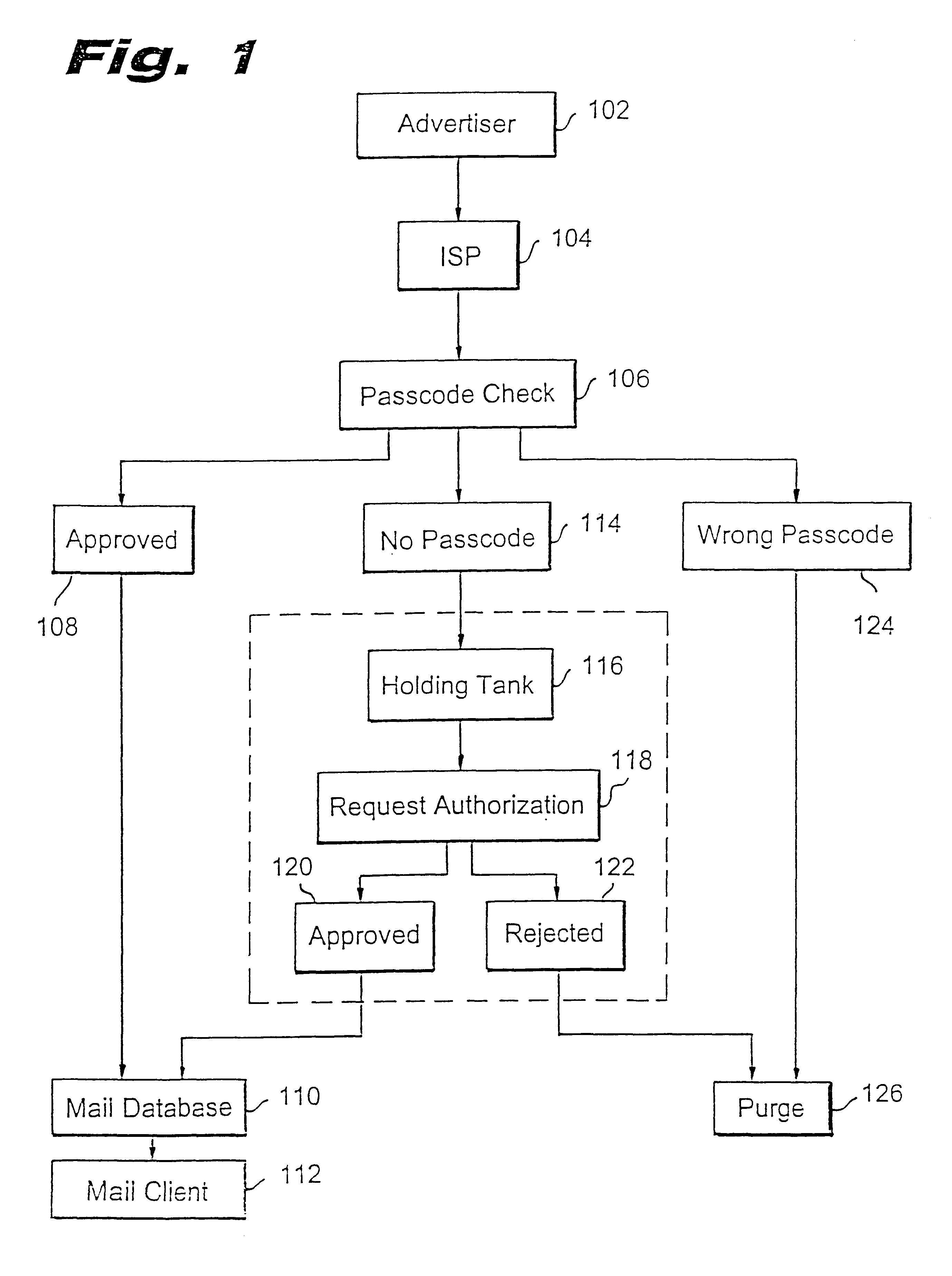
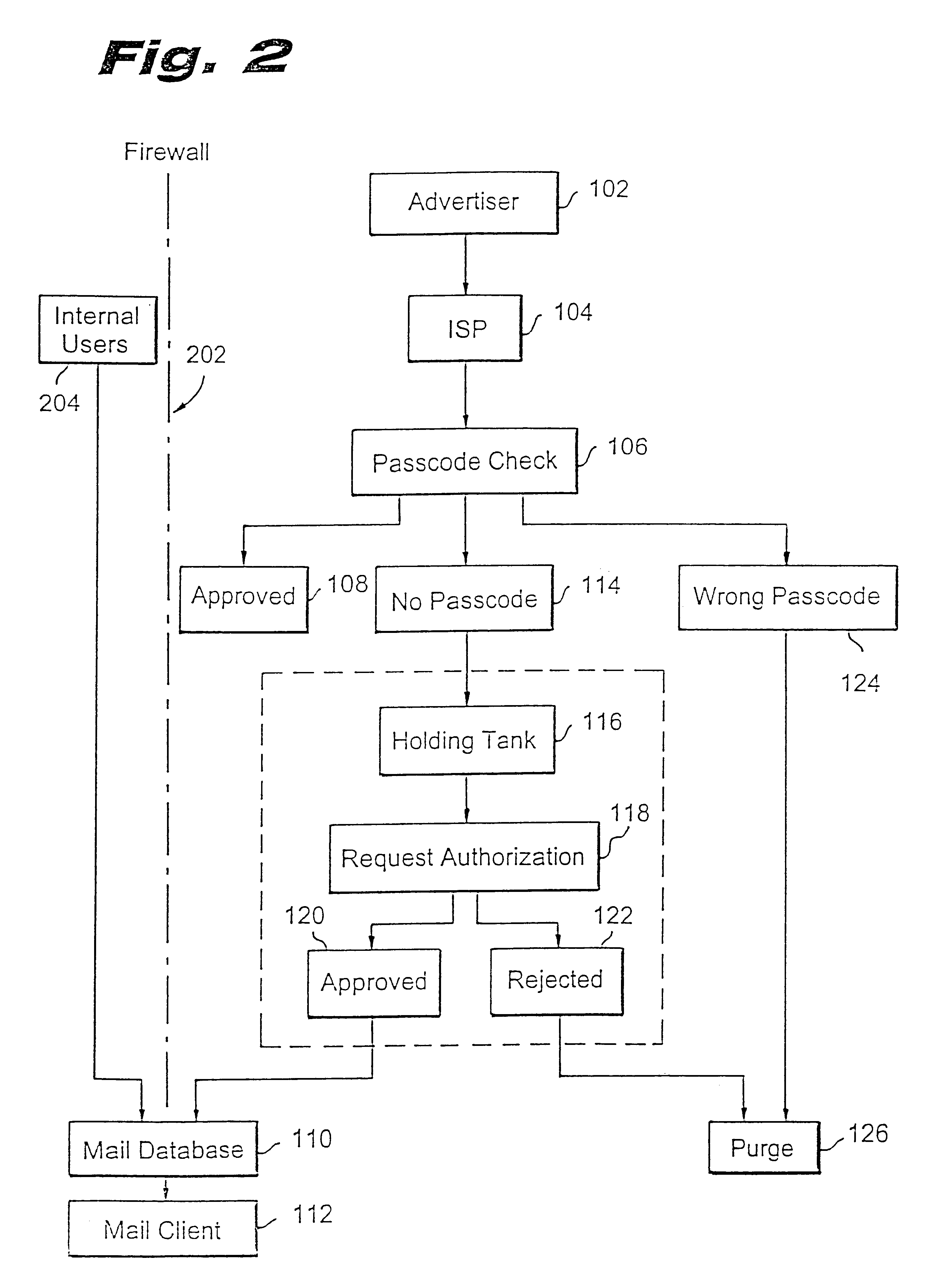
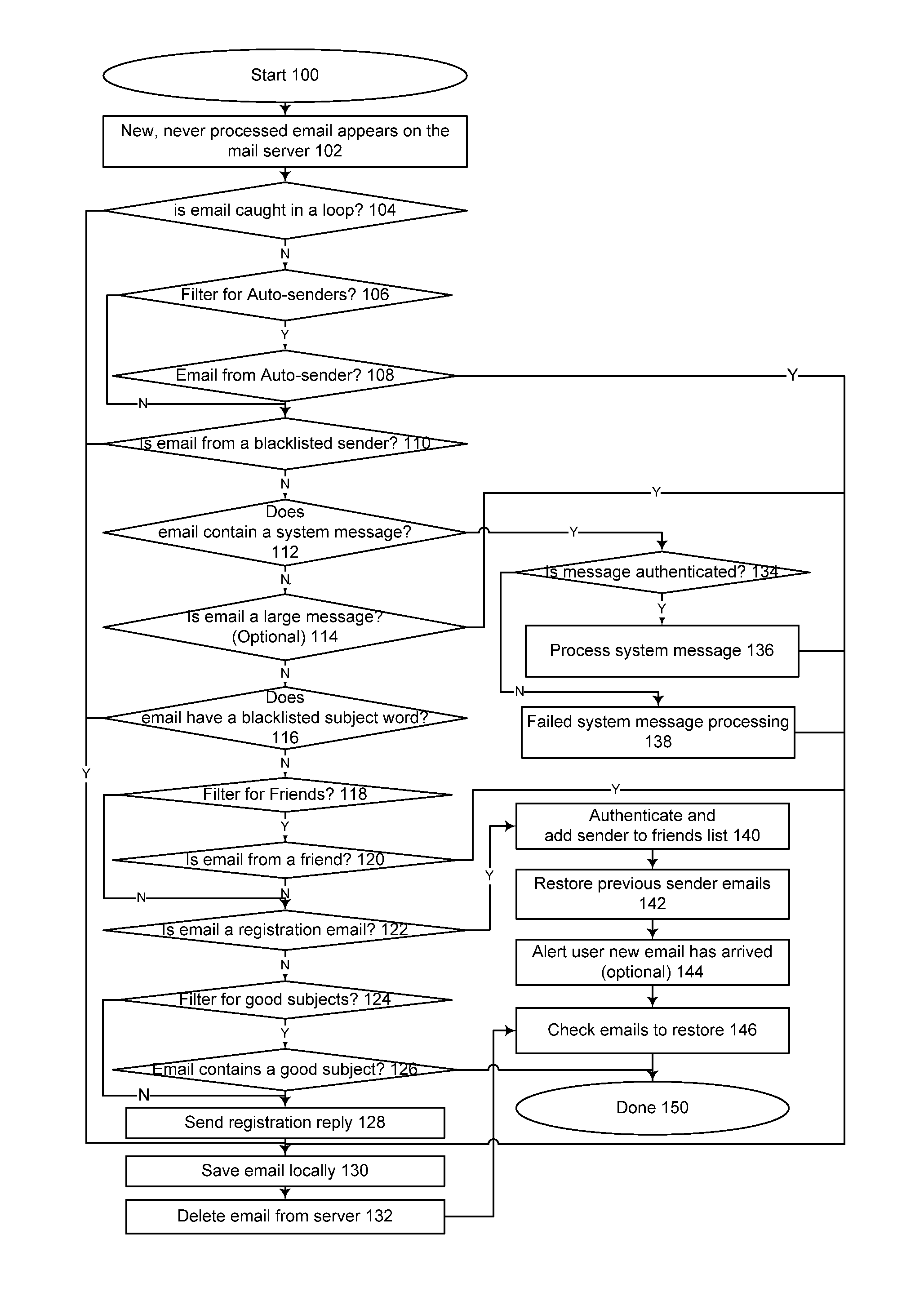
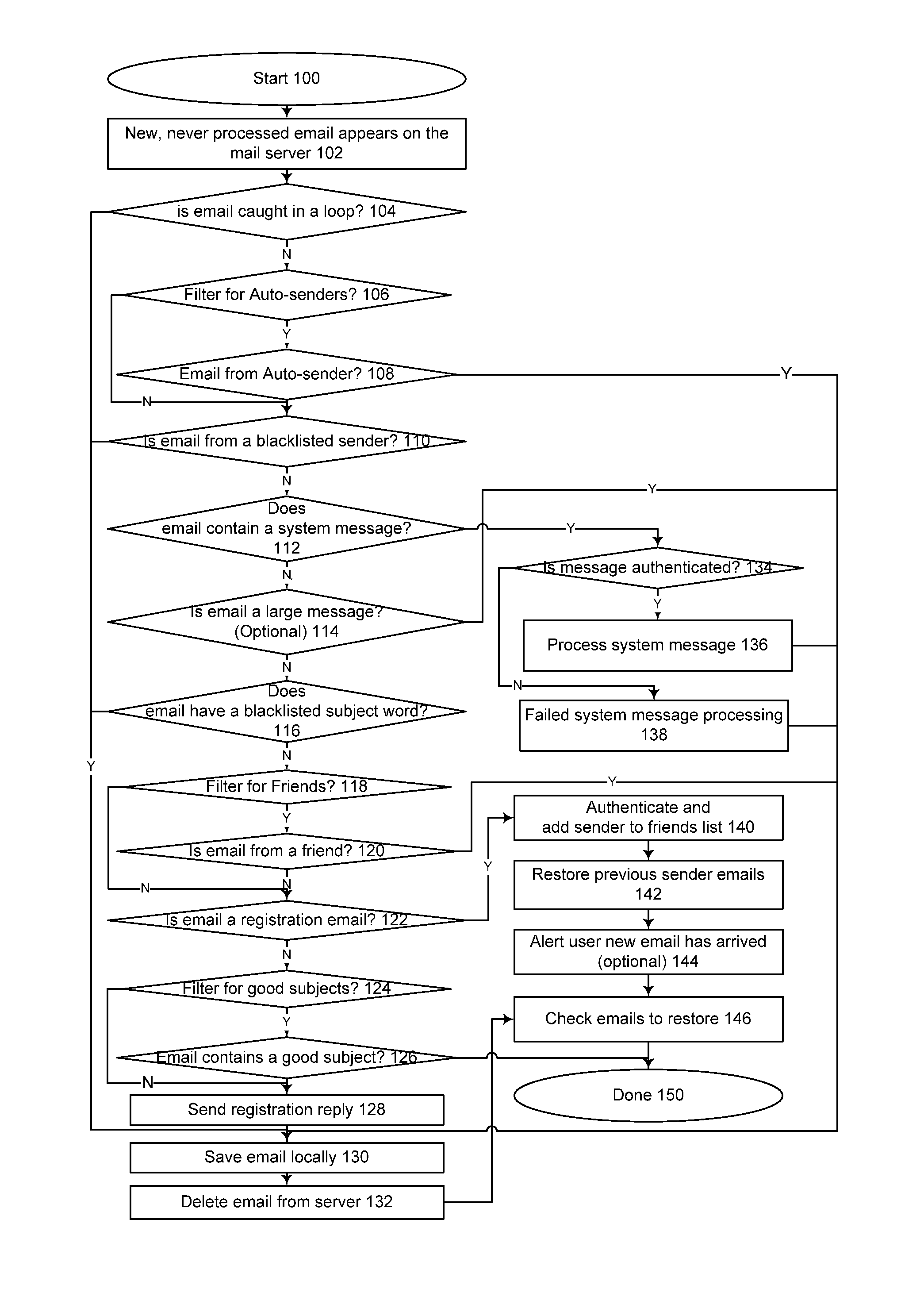
Method for blocking all unwanted e-mail (SPAM) using a header-based password
InactiveUS6266692B1Easy to sendEasy to solveOffice automationData switching networksEmail addressPassword
A method for blocking and / or filtering electronic mail. Selected senders are provided with a valid passcode associated with an e-mail address. When an e-mail is received at a mail server node, a field in a header of the e-mail is checked for a valid passcode associated with the destination e-mail address. If a valid passcode is detected, the e-mail is automatically sent to a receiver at the e-mail address. If an incorrect passcode is detected, the e-mail is automatically deleted at the server node and does not reach the receiver. If there is no passcode in the e-mail header, the e-mail is held temporarily, until the receiver approves to receive the e-mail. If the receiver rejects the e-mail, the e-mail is deleted. The present invention includes an additional capability for the senders of e-mails to request a passcode associated with a specific e-mail address in a lookup directory, before sending an e-mail to that address. Furthermore, the present invention enables firewall servers to block incoming e-mails only if they are received from the public Internet, thereby allowing all internal e-mails to reach the receiver without having to include valid passcodes.
Owner:TREND MICRO INC
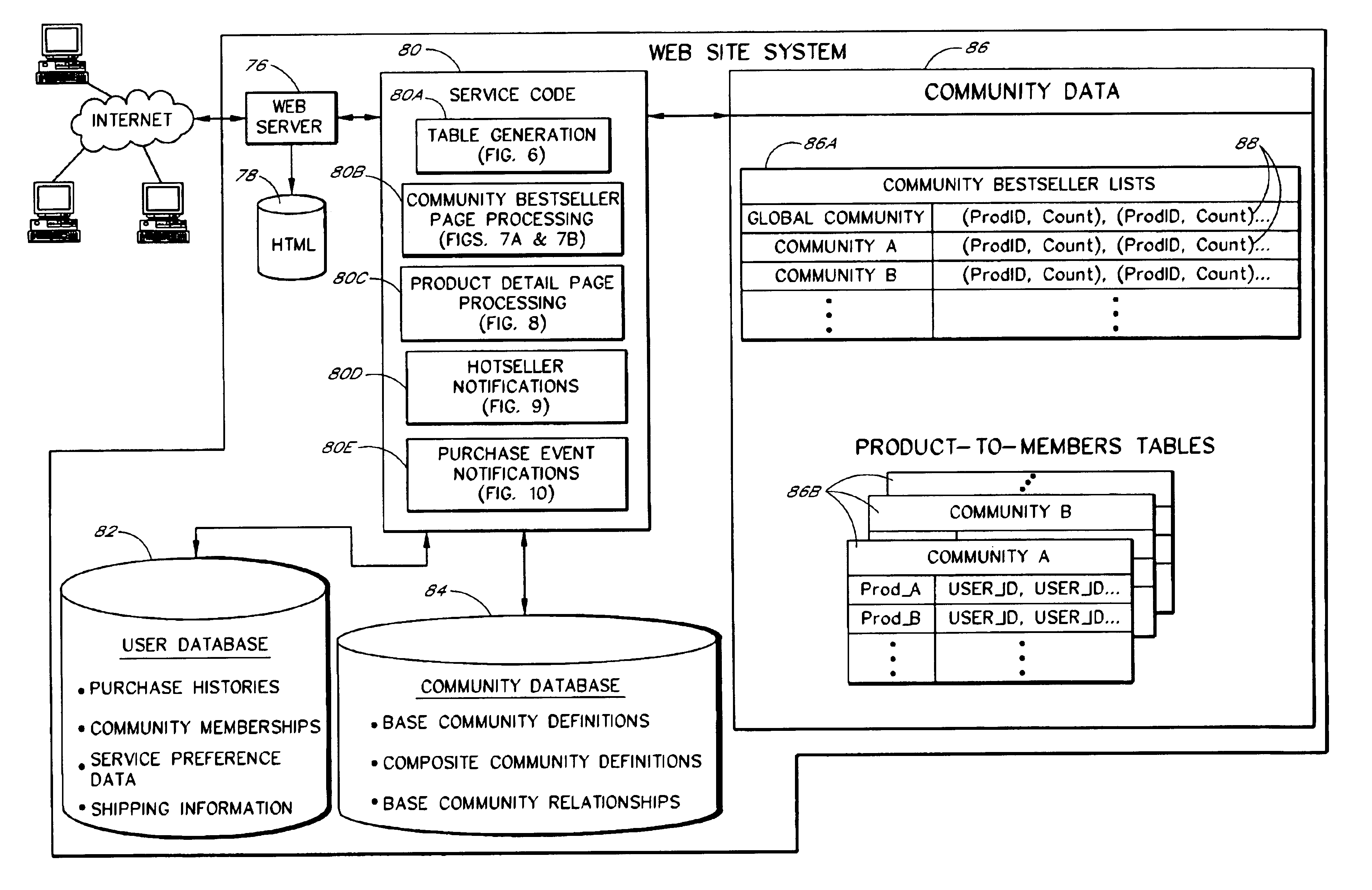
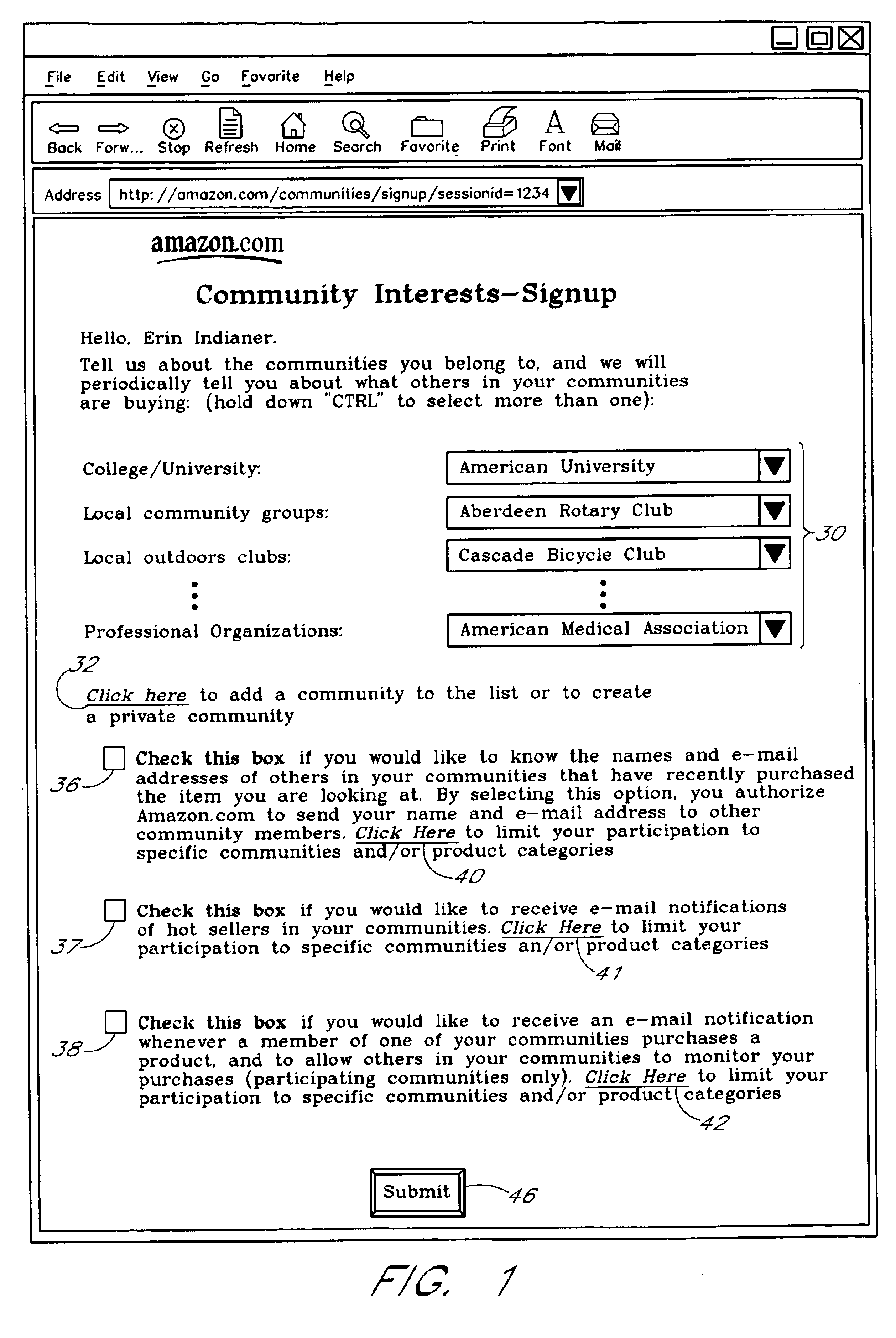
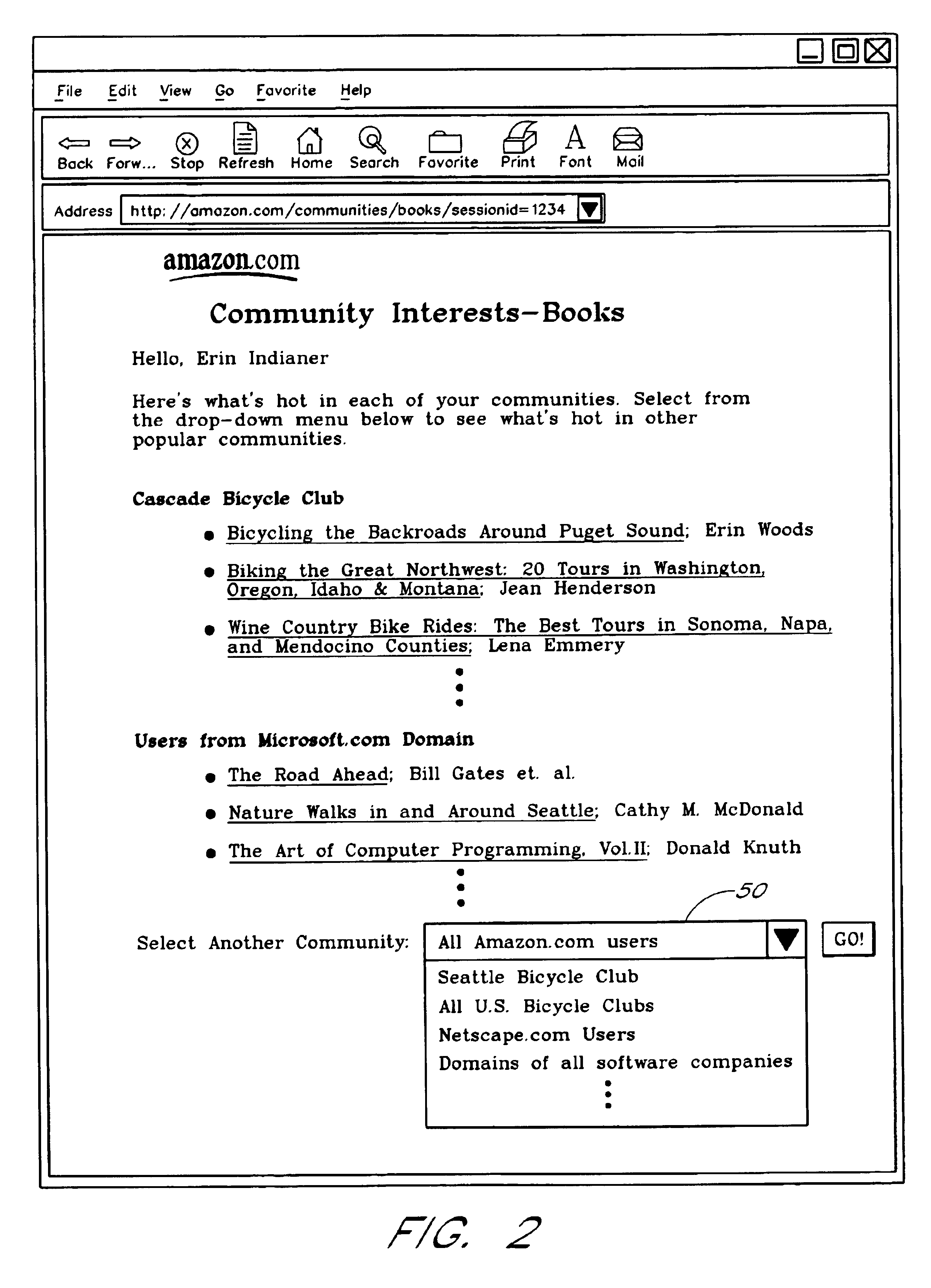
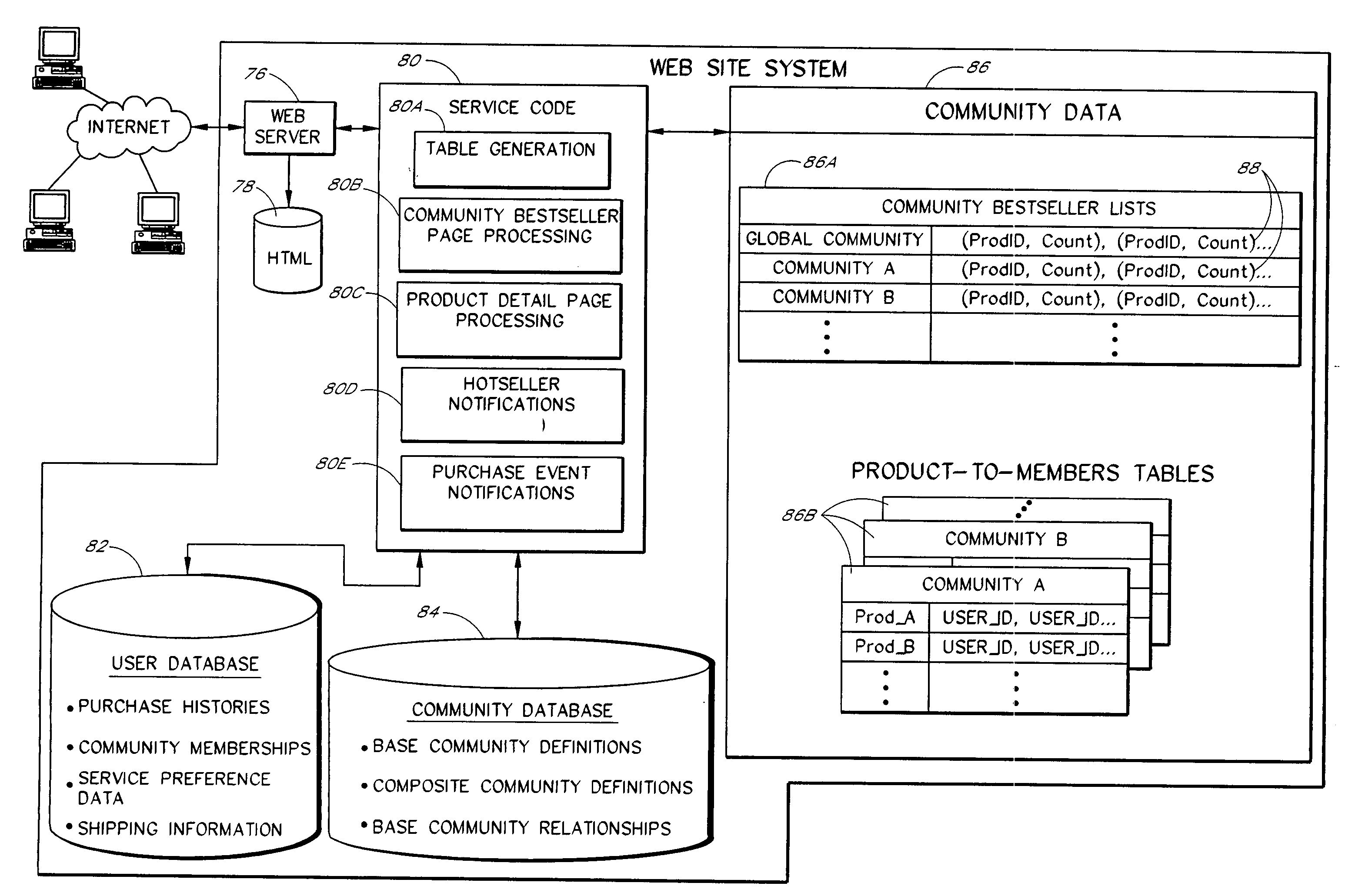
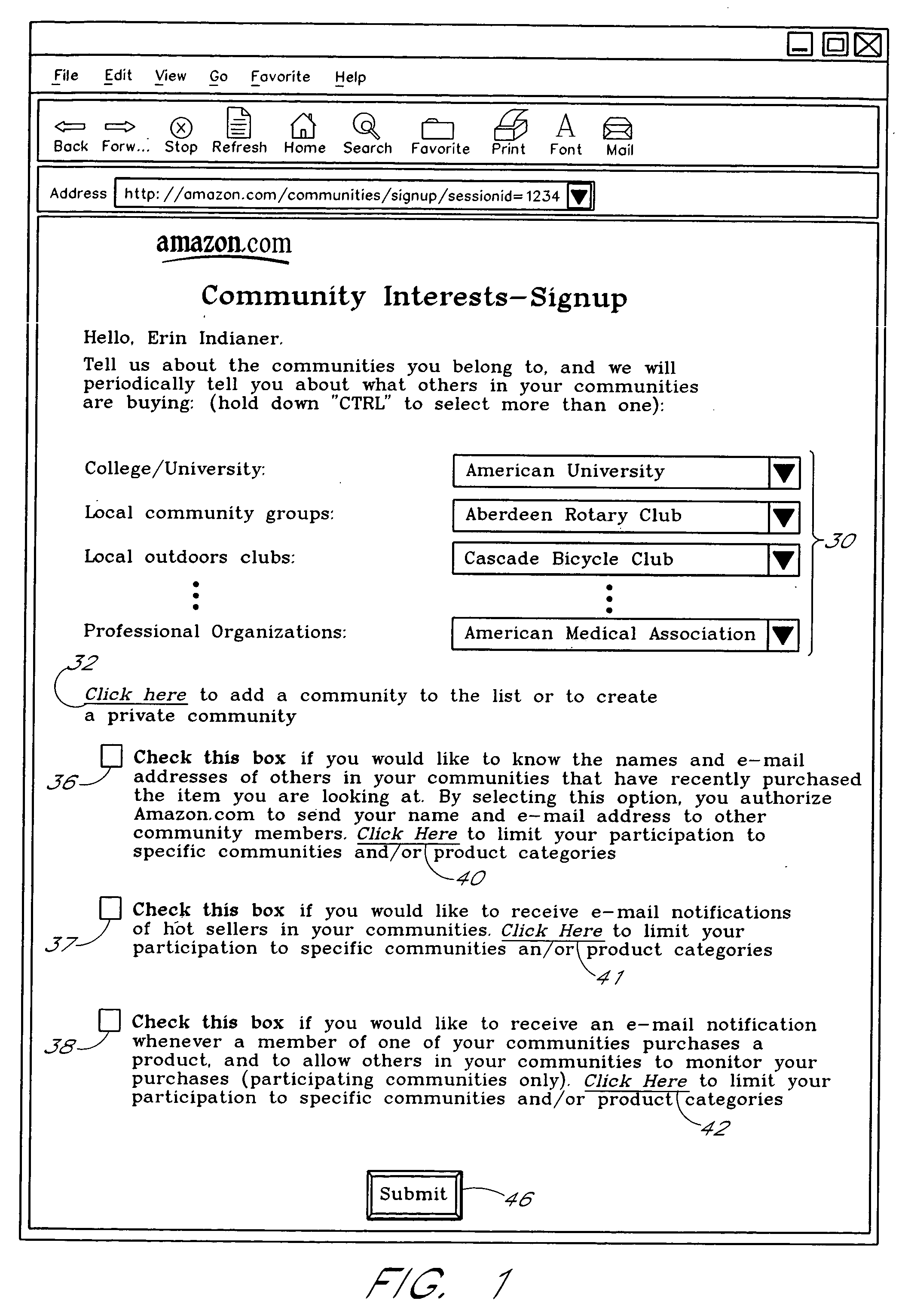
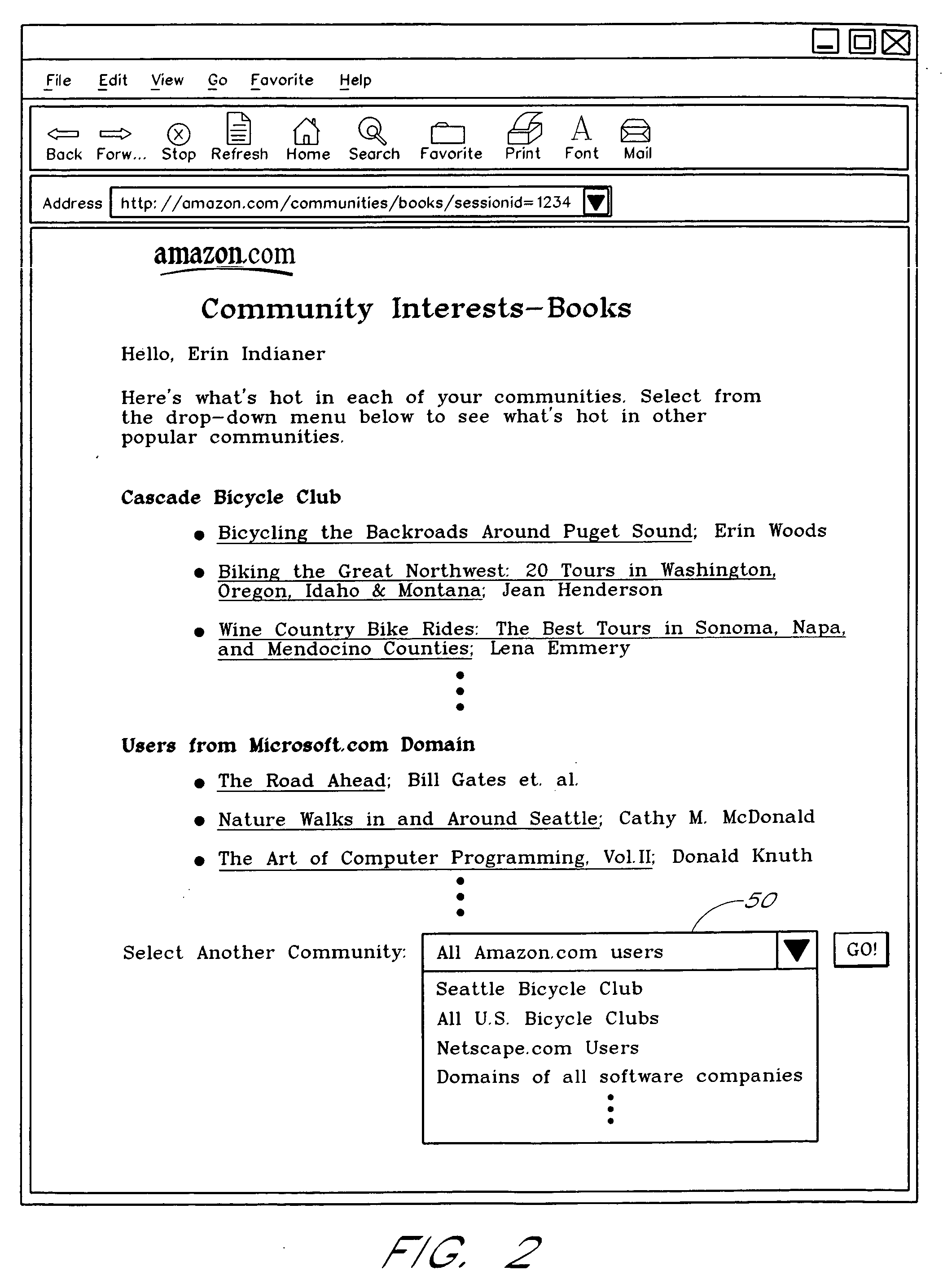
Computer services for assisting users in locating and evaluating items in an electronic catalog based on actions performed by members of specific user communities
A Web based system provides informational services for assisting customers in selecting products or other types of items from an electronic catalog of a merchant. Users of the system can create and join user communities, such as communities based on user hobbies, localities, professions, and organizations. The system also supports implicit membership communities that are based on email addresses (e.g., all users having a “nasa.com” email address), shipping / billing addresses, and other known user information. Using purchase history data collected for online users, the system automatically identifies and generates lists of the most popular items (and / or items that are becoming popular) within particular communities, and makes such information available to users for viewing. For example, in the context of an online book store users of the nasa.com community may automatically be presented a Web page which lists the bestselling book titles among nasa.com users, or may be sent email notifications of purchase events or hotselling books within the community. Another feature involves automatically notifying users interested in particular products of other users (preferably other members of the same community) that have purchased the same or similar products. For example, in one embodiment, when a user accesses a book detail page, the detail page is customized to include the names and email addresses of other members of the user's community that recently purchased the same book.
Owner:AMAZON TECH INC
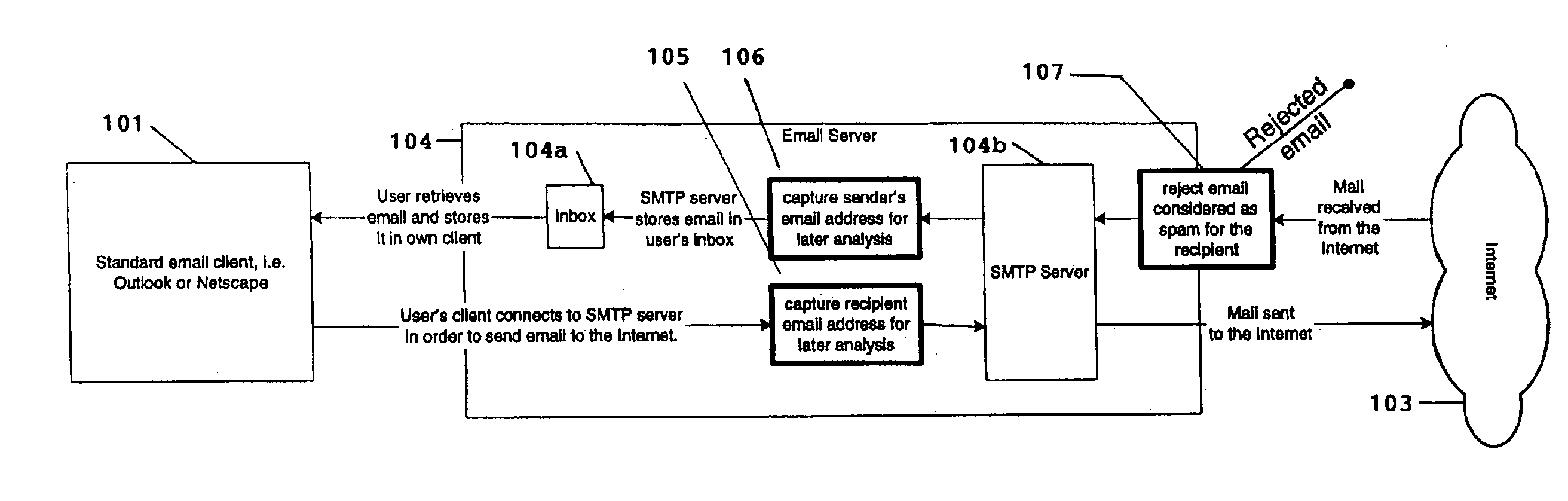
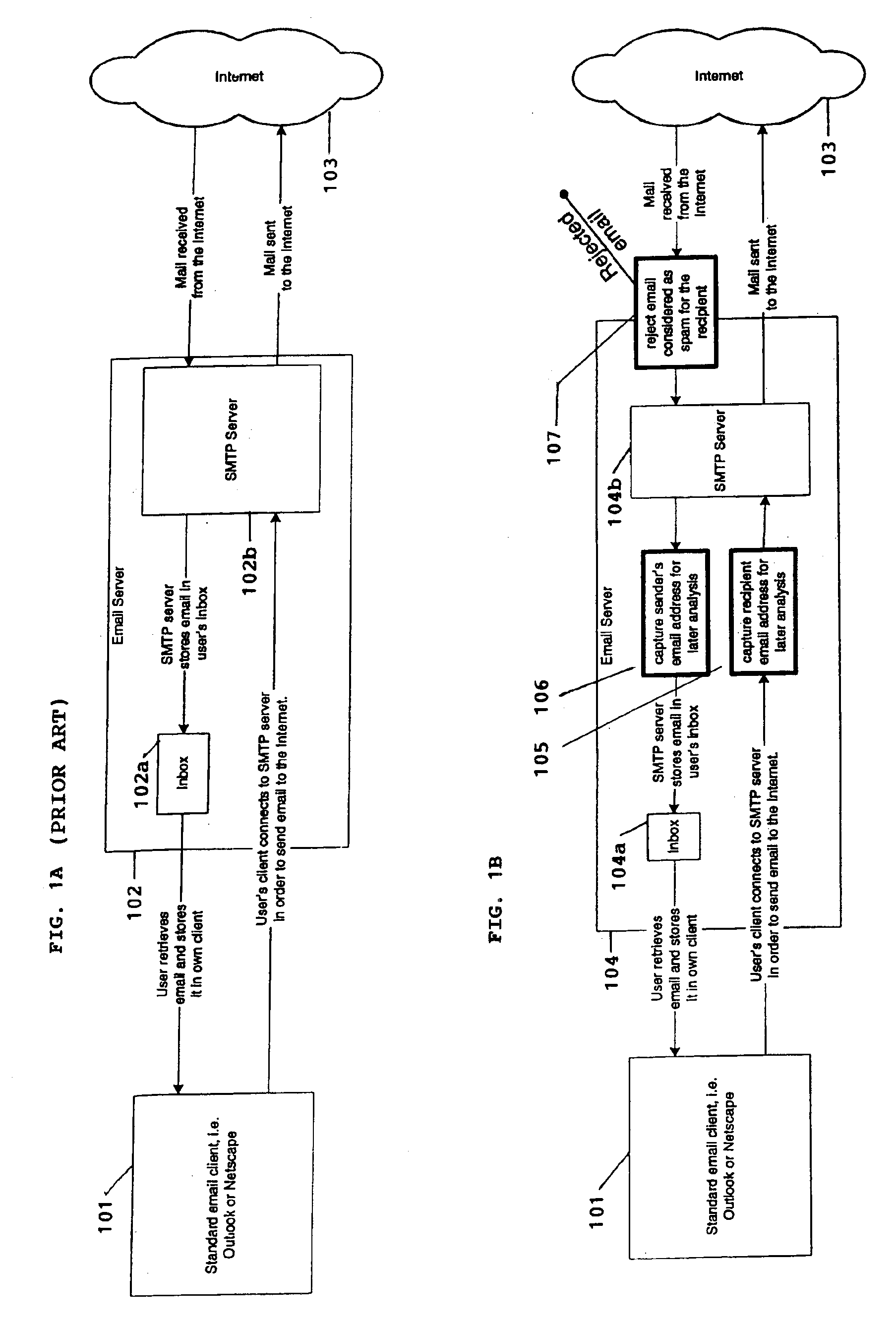
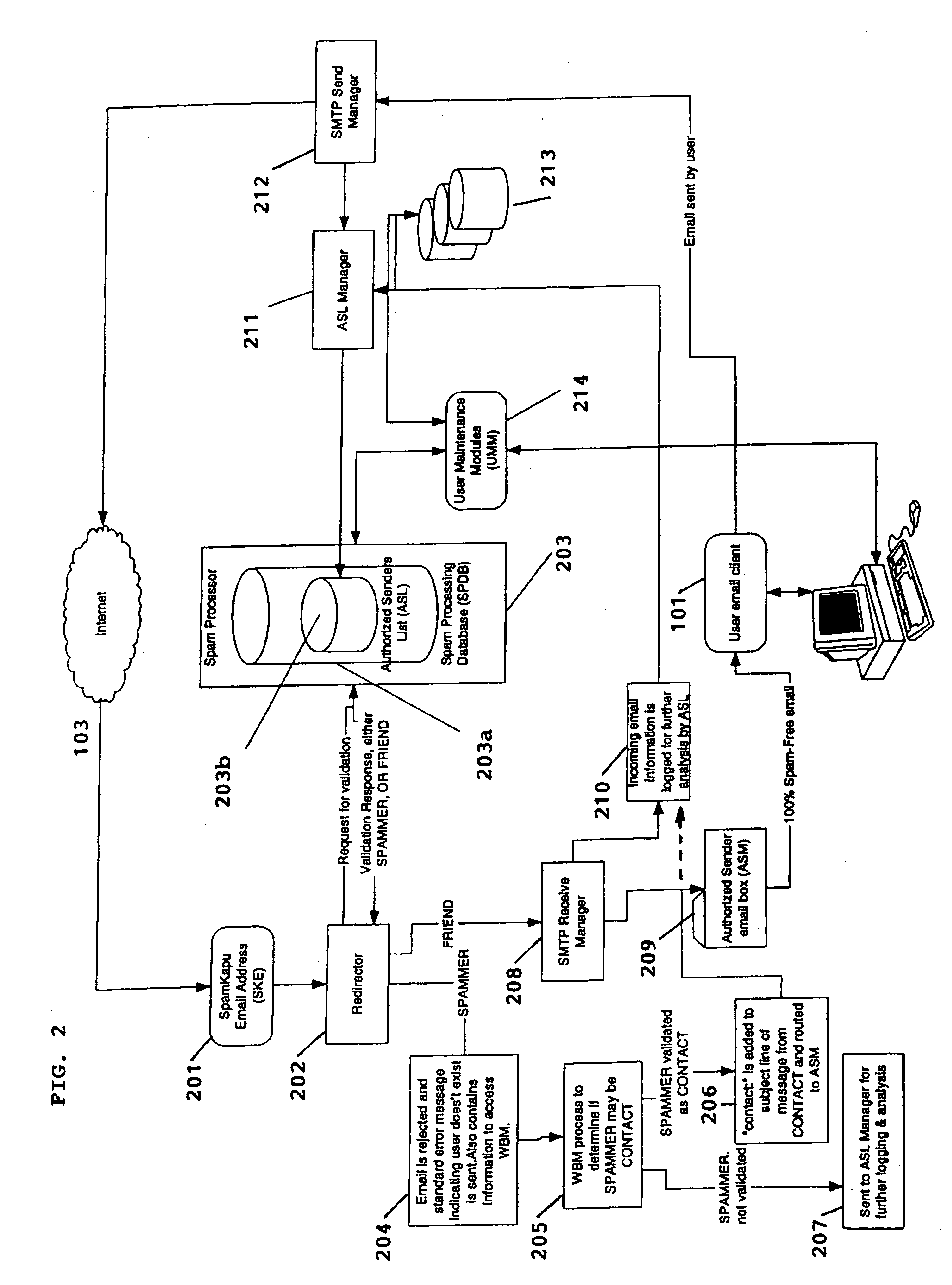
System for eliminating unauthorized electronic mail
InactiveUS6868498B1Hardware monitoringMultiple digital computer combinationsThird partyEmail address
A system for eliminating unauthorized email sent to a user on a network employs an email-receiving server connected between the network and the user's email client for receiving email addressed to the user and rejecting those in which the sender address does not match any of sender addresses maintained on an “authorized senders” list (ASL list). The ASL lists are maintained by an ASL manager in an ASL database operable with a spam processor module. A redirector module rejects the email if, upon sending a request for validation to the spam processor module, the sender's address does not match any authorized sender address on the ASL list. Email rejected by the redirector module is redirected to a web-based messaging (WBM) module which sends a message to the sender to confirm that the sender is a legitimate sender of email to the intended recipient. If the sender logs on to confirm their status, the WBM module executes an interaction procedure which can only be performed by a human, in order to ensure that the confirmation procedure is not performed by a mechanical program. The ASL manager maintains the ASL lists based upon sender address data collected from various sources and analyses of various email usage factors, including sent email, received email, contact lists maintained by the user, user preference inputs, third party programs, etc.
Owner:CUFER ASSET LTD LLC
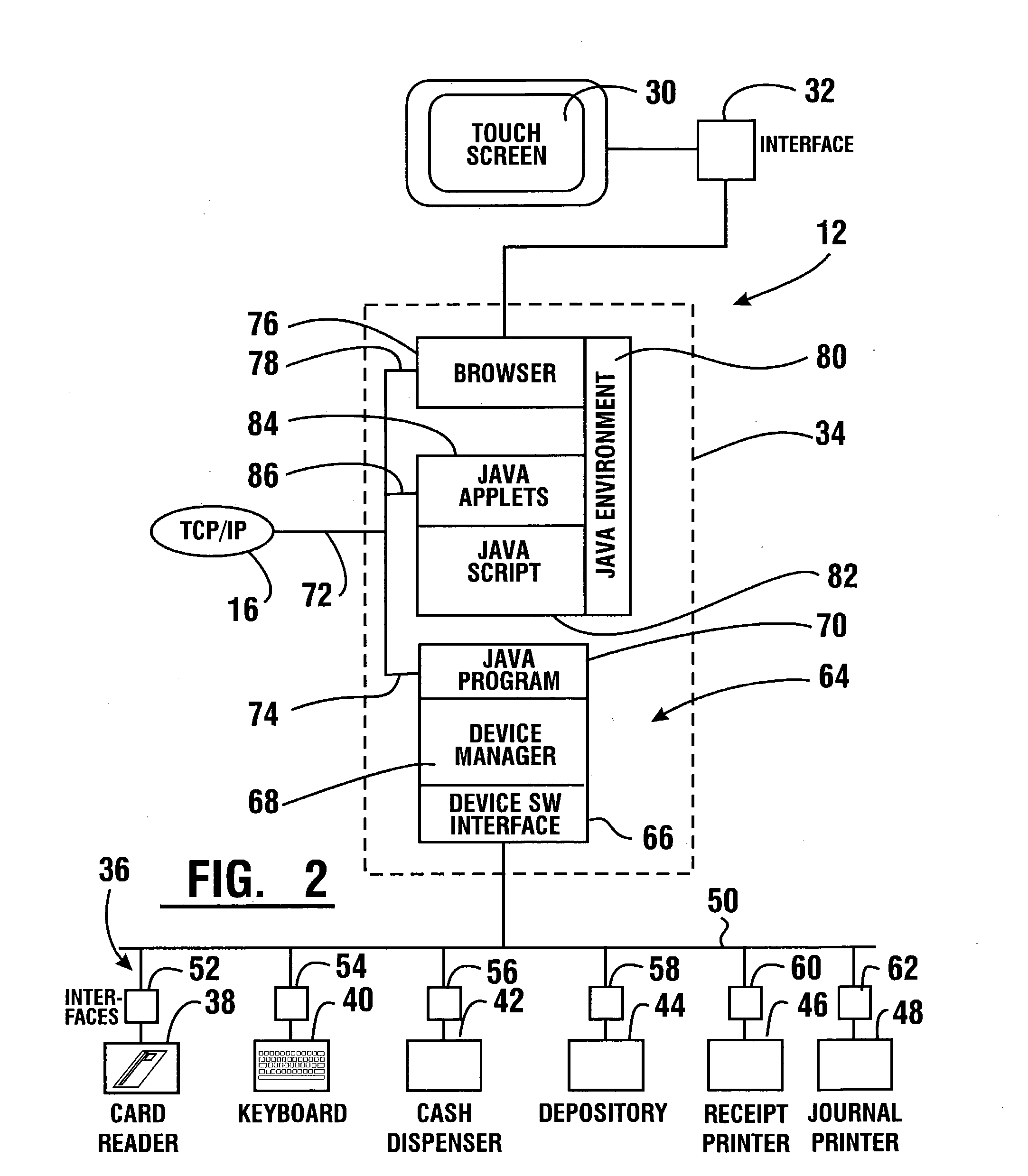
Automated banking machine system and method
InactiveUS20030217005A1Good user interfaceFunction increaseBuying/selling/leasing transactionsSpecific program execution arrangementsEmail addressCheque
A system and method of providing an electronic transaction receipt from a cash dispensing ATM. A bank host computer is operable to submit the receipt to a system address of record with the bank. The address of record corresponds to an e-mail address, phone number or other address associated with an account involved in the transaction. The receipt may include an image or images associated with the transaction. Thus, a user of an ATM is able to receive an electronic receipt corresponding to the ATM transaction. The system may also operate to image deposited checks deposited at an ATM. Copies of the imaged checks and other information can be electronically sent to a maker, payee, a clearinghouse or banks involved with the transaction. The system may also operate to provide the user with blank checks in hard copy or virtual checks for transactions.
Owner:DIEBOLD NIXDORF
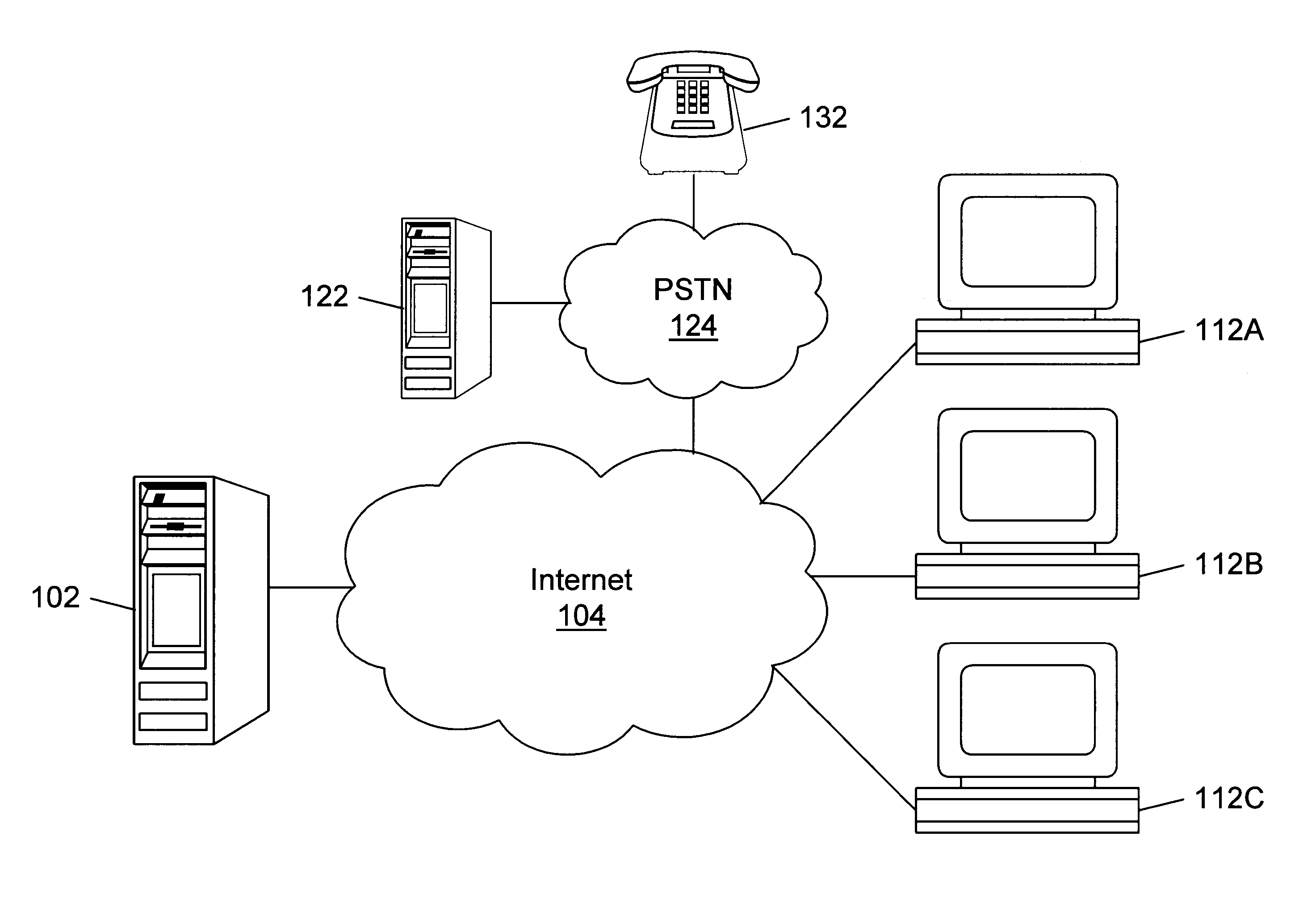
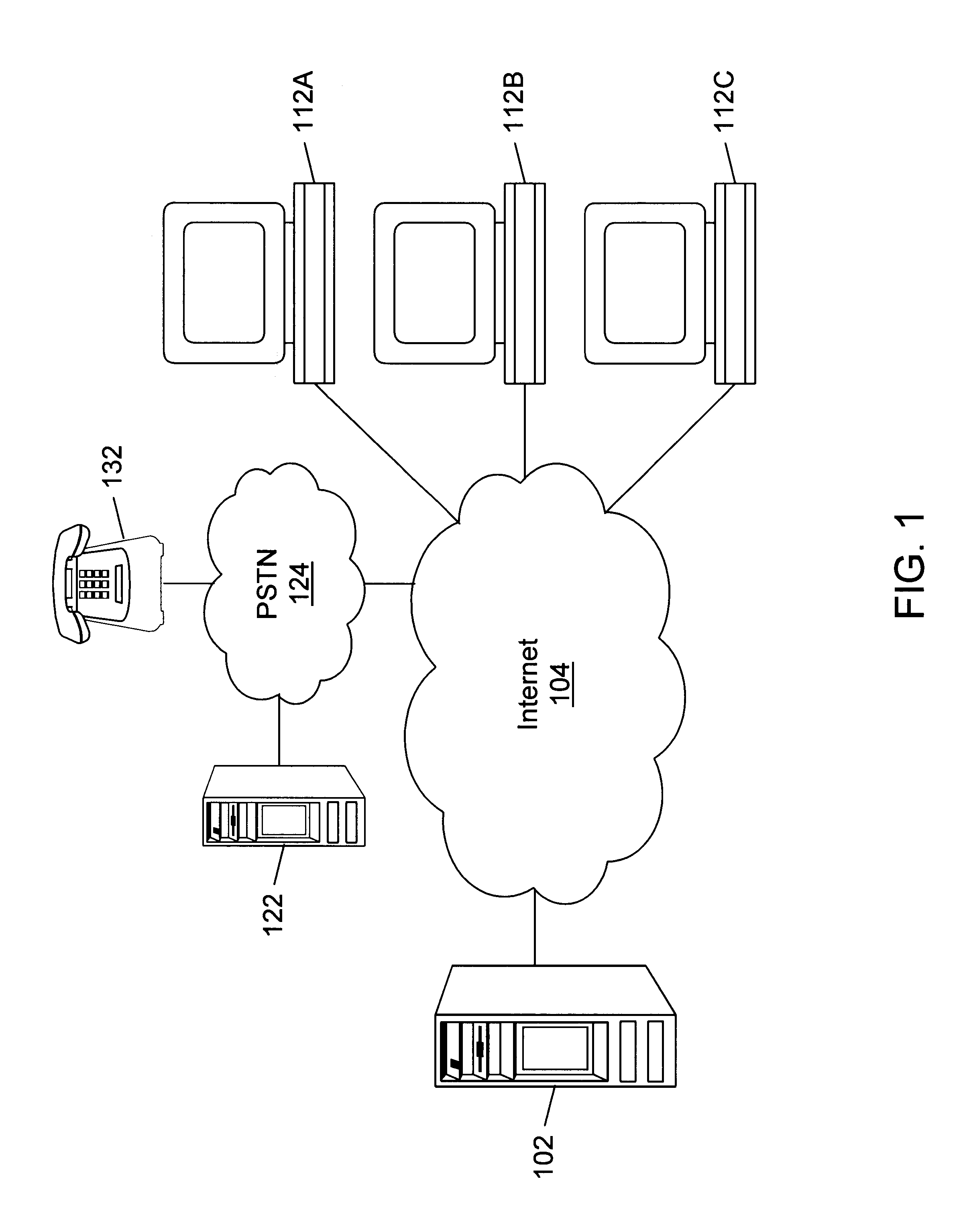
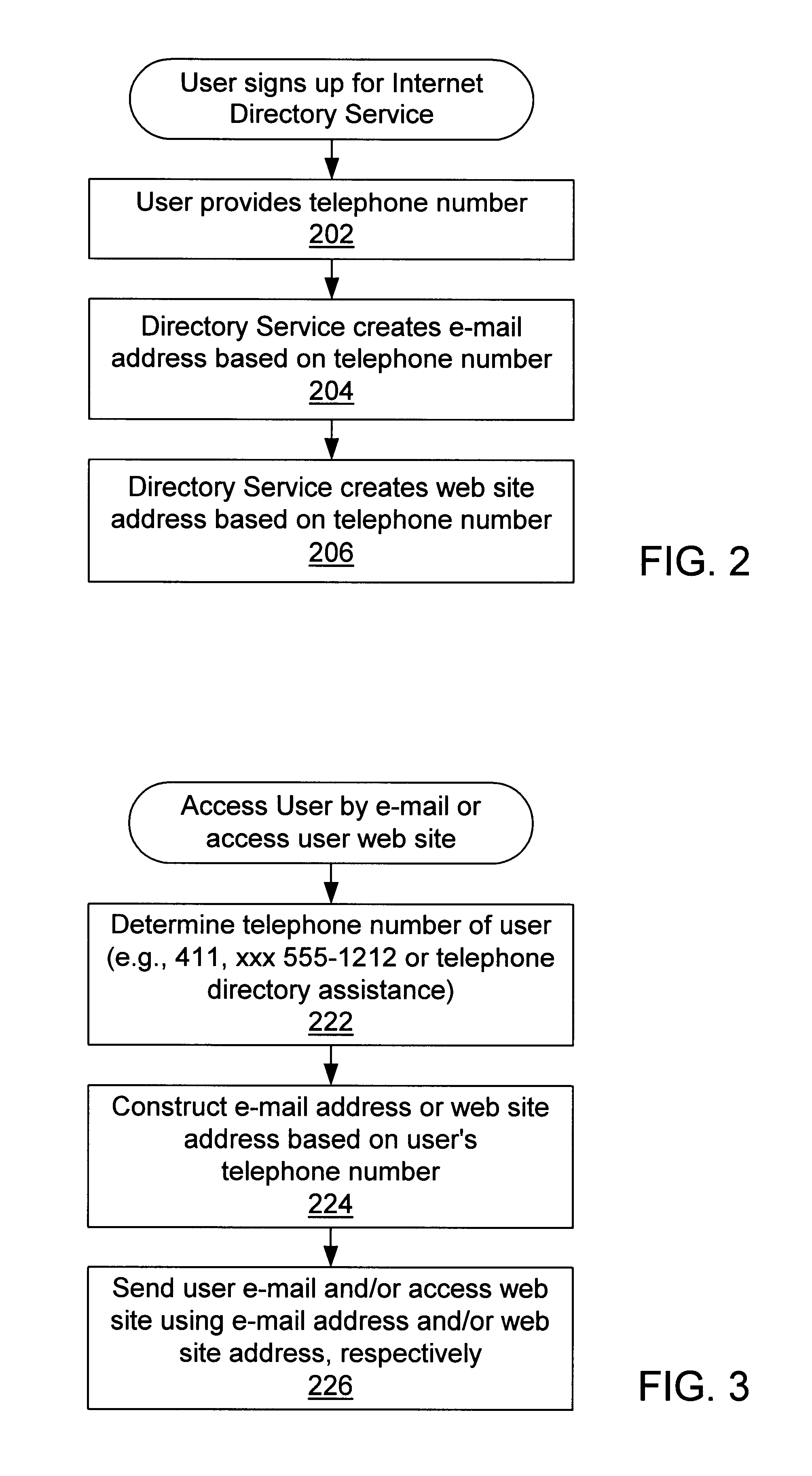
Internet directory system and method using telephone number based addressing
InactiveUS6788769B1Searches may be more readilyEasy to implementTelephone data network interconnectionsSpecial service for subscribersDomain nameEmail address
An Internet directory system and method that is based on user telephone number addressing. The system includes an interactive white and yellow pages directory that is based on telephone numbers. Thus, a user's telephone number is a unique identifier used to key other information within the directory. The telephone number may also be used as the primary component of an email address, domain name, or web site URL for the user. The use of a telephone number as the primary component of an e-mail address or domain name greatly simplifies the process of locating a user. E-mail addresses and domain names may be readily found using standard telephone information services, such as "411", as well as other telephone-based methods for obtaining telephone directory information. This Internet directory system and method brings all communication methods and directory services together using one searchable key, a user's telephone number. The directory entry page may be created, edited and updated by the subscriber using simple html editing or using a voice telephone call or via fax, without the use of a personal computer. Thus, the present invention provides an open directory model wherein the end users construct the directory, and the directory is "living", i.e., dynamically changeable and updateable. The power of the directory is thus placed in the users' hands. The telephone based Internet directory system of the present invention also provides addressing for unified messaging as well as locality in addressing.
Owner:WEISMAN SANFORD P
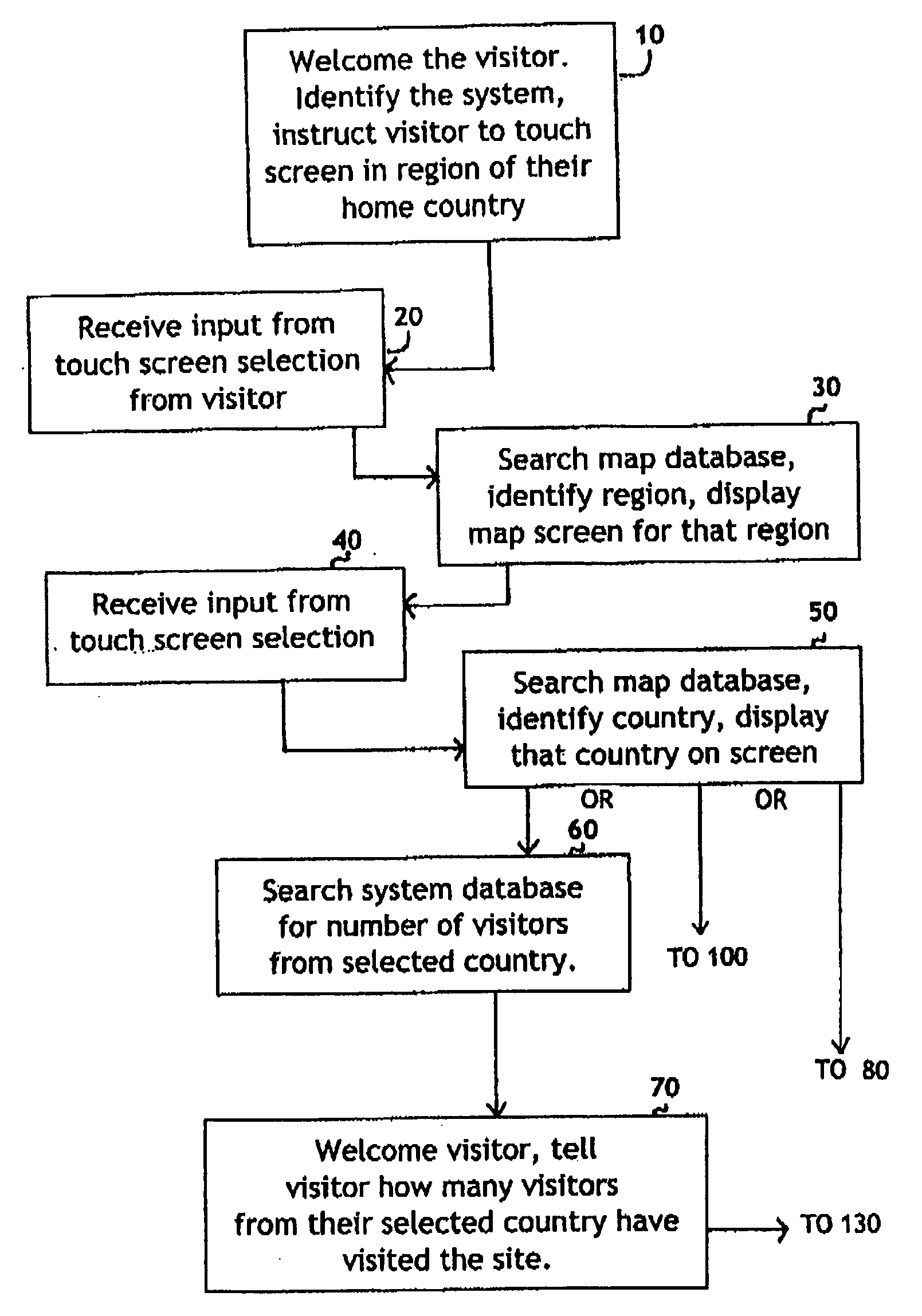
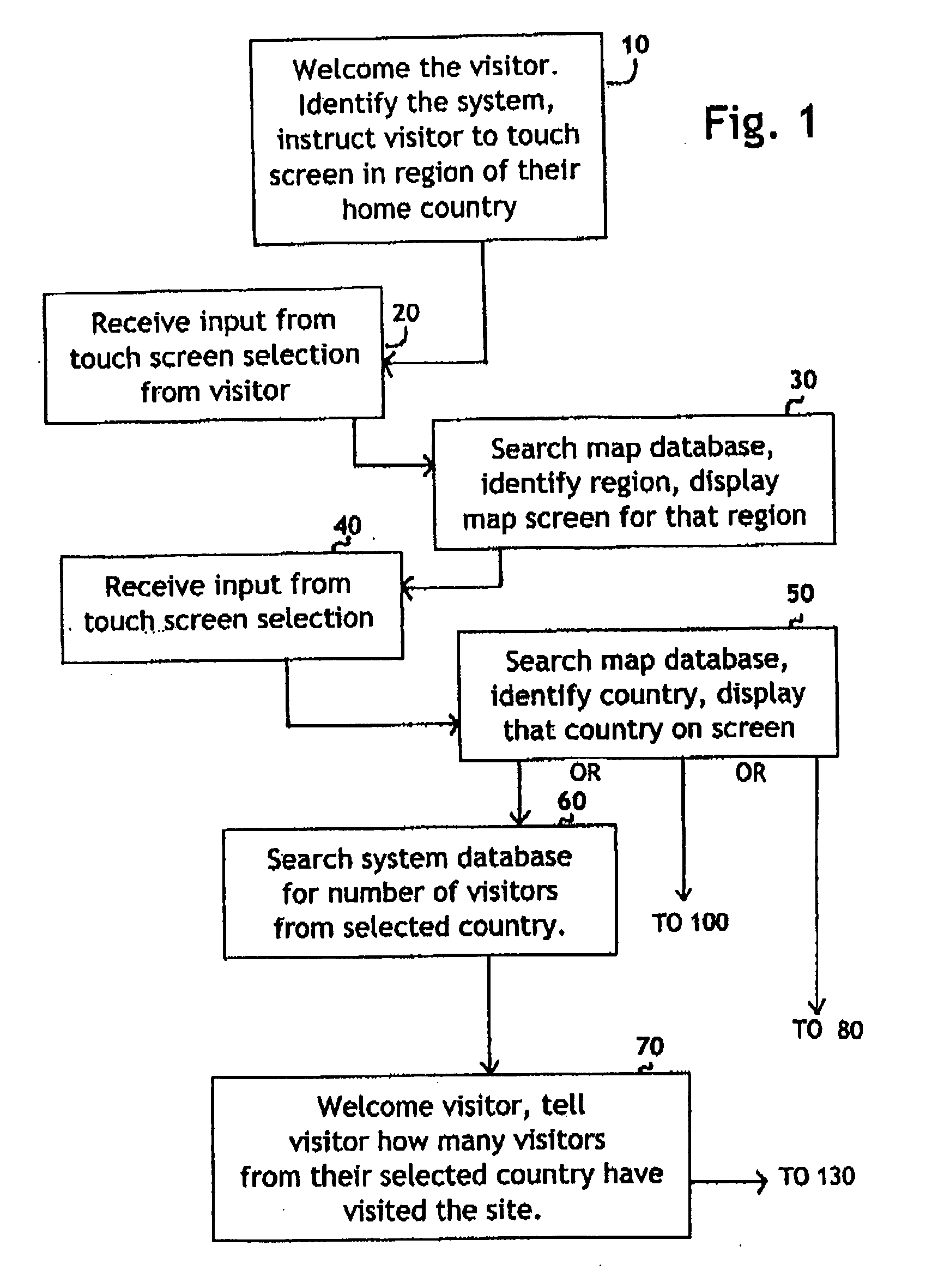
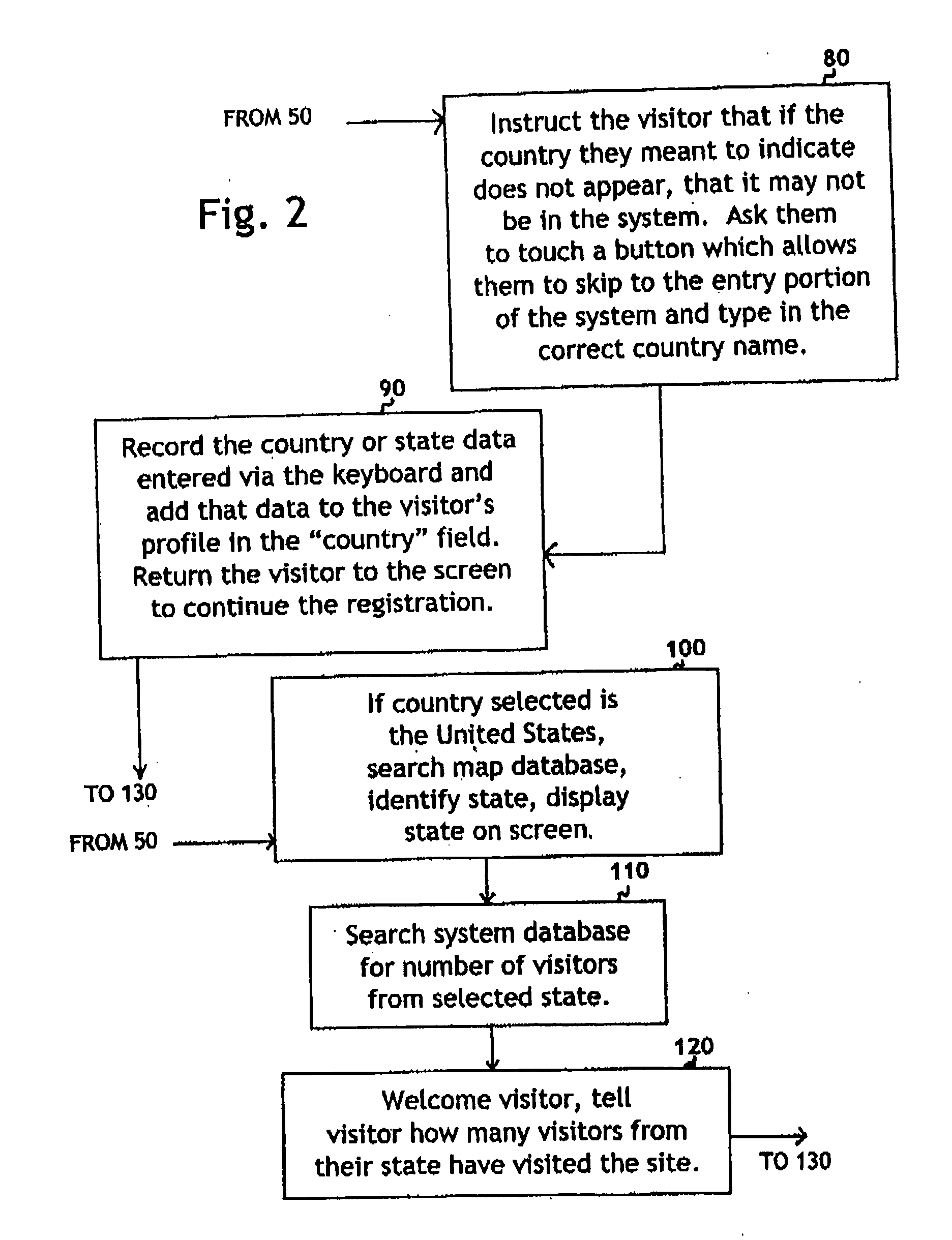
System for self-registering visitor information with geographic specificity and searchable fields
InactiveUS20080270938A1Easy retrievalBetter servedOffice automationGeographical information databasesEmail addressGeographic feature
An interactive visitor self-registration system for visitors to museums or other public sites using a digital computer or internet appliance device and a touchscreen monitor, which accesses a dedicated website, through a global computer network such as the Internet. It focuses on gathering information regarding residence of visitors as well as the information gathered by a traditional paper guest book. The system is searchable by visitors and by site staff. The information gathered by the system is stored on a dedicated website. A second, administration website, also password protected with an unpublished web address can be used by Site Administrators to customize the looks and options of their specific visitor self-registration system. Additionally, there is a public website which is accessible via the Internet which stores travel information for every signer to the system who logs on with his or her email address. These visitors can track their own travel via a map displayed on the website and be linked to the website for the sites they visit.
Owner:CARLSON ELIZABETH MARIE
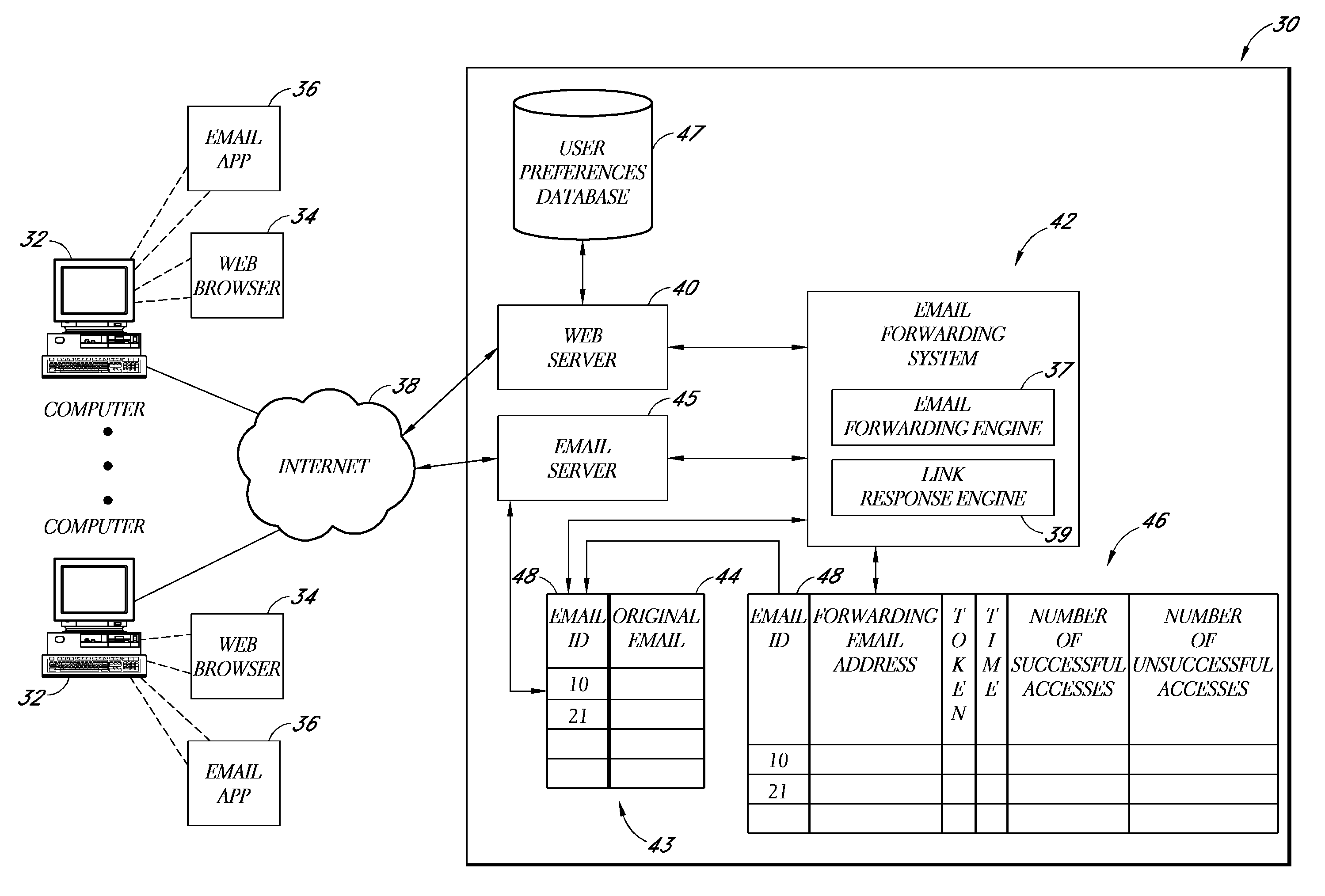
Electronic mail forwarding service
ActiveUS8214443B2Digital data processing detailsAnalogue secracy/subscription systemsEmail addressElectronic mail
A system and method are disclosed that enable an email service provider to implement an email forwarding service without losing associated page views. In one embodiment, rather than forwarding the entire email message, the email forwarding service generates a summary email message, and sends this summary email message to the forwarding email address pre-specified by the subscriber. This summary email message includes a link that is selectable by the user to view the original email message on a web site of the email service provider. Thus, even if the forwarding email address is hosted externally, the subscriber still views the full email message on a web site of the provider of the email forwarding service.
Owner:YAHOO ASSETS LLC
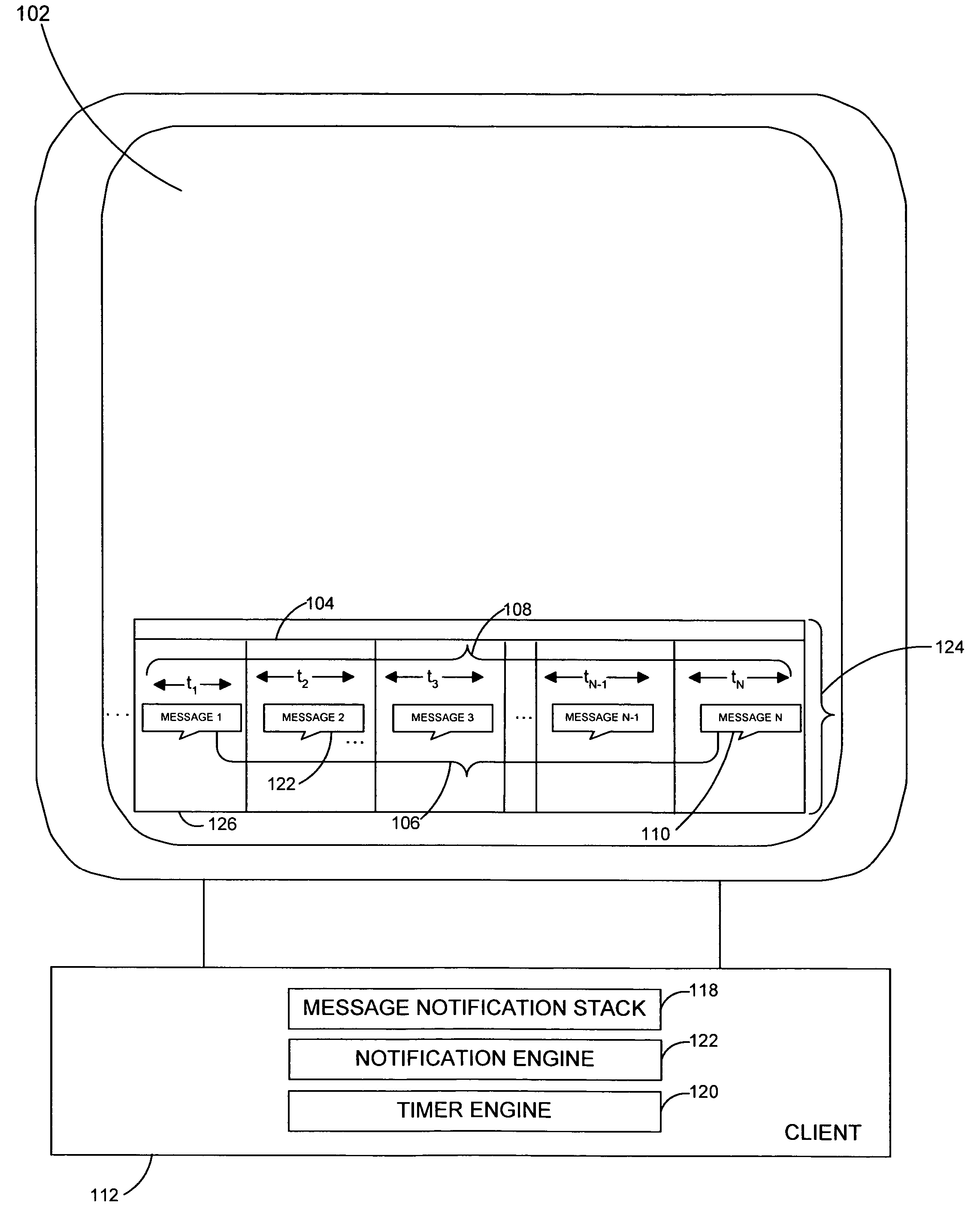
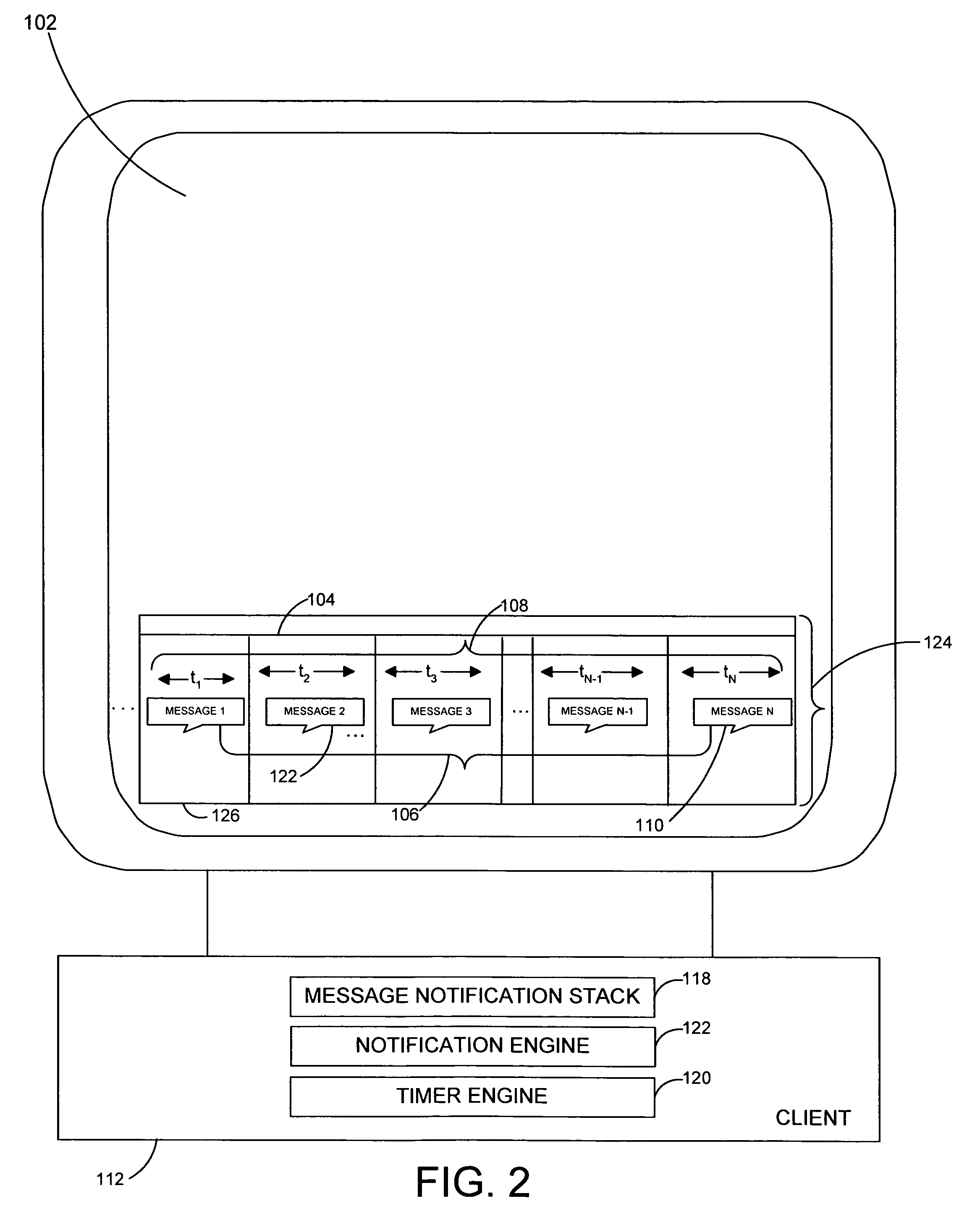
System and method for generating message notification objects on dynamically scaled timeline
InactiveUS20050268237A1Preserving spaceData processing applicationsMultiple digital computer combinationsEmail addressPassword
A system and related techniques to collect and manage a set of incoming message notification objects, such as instant message notifications, email notifications, download notifications, transaction notifications and others and present those objects to the user an icon, tile or other representation on a dynamically scaled timeline. According to embodiments, the dynamically scaled timeline may present the most recently received object farthest to the right on a notifications bar or facility, and slide objects to the left to represent that passage of time as those objects age. Instead of presenting those objects on a linear scale, according to the invention the time intervals in which the objects may be presented may be scaled to cause the oldest message objects to be presented on a relatively compressed dimension. The most recently received messages in contrast may be presented on wider intervals, to permit the user to perceive the differences in arrival of those items more clearly. According to embodiments, when more than one message object slides to an overlapping point with another, those objects may be stacked into a cascading message stack. When two or more stacks touch, they may be merged into a single stack. According to embodiments of the invention in another regard, when the user hovers over a given message object a popup box may appear which displays attributes of that object, such as message or other notification type, the date and time which the object was received, the source of the underlying message or other data. In further embodiments, one or more of the message notification objects may be clickable or otherwise reactivatable to reveal actions, dialogs, inputs or other interactions which were presented at the time the message was originally received, such as a query box to input a password or a selection for an email address.
Owner:MICROSOFT TECH LICENSING LLC
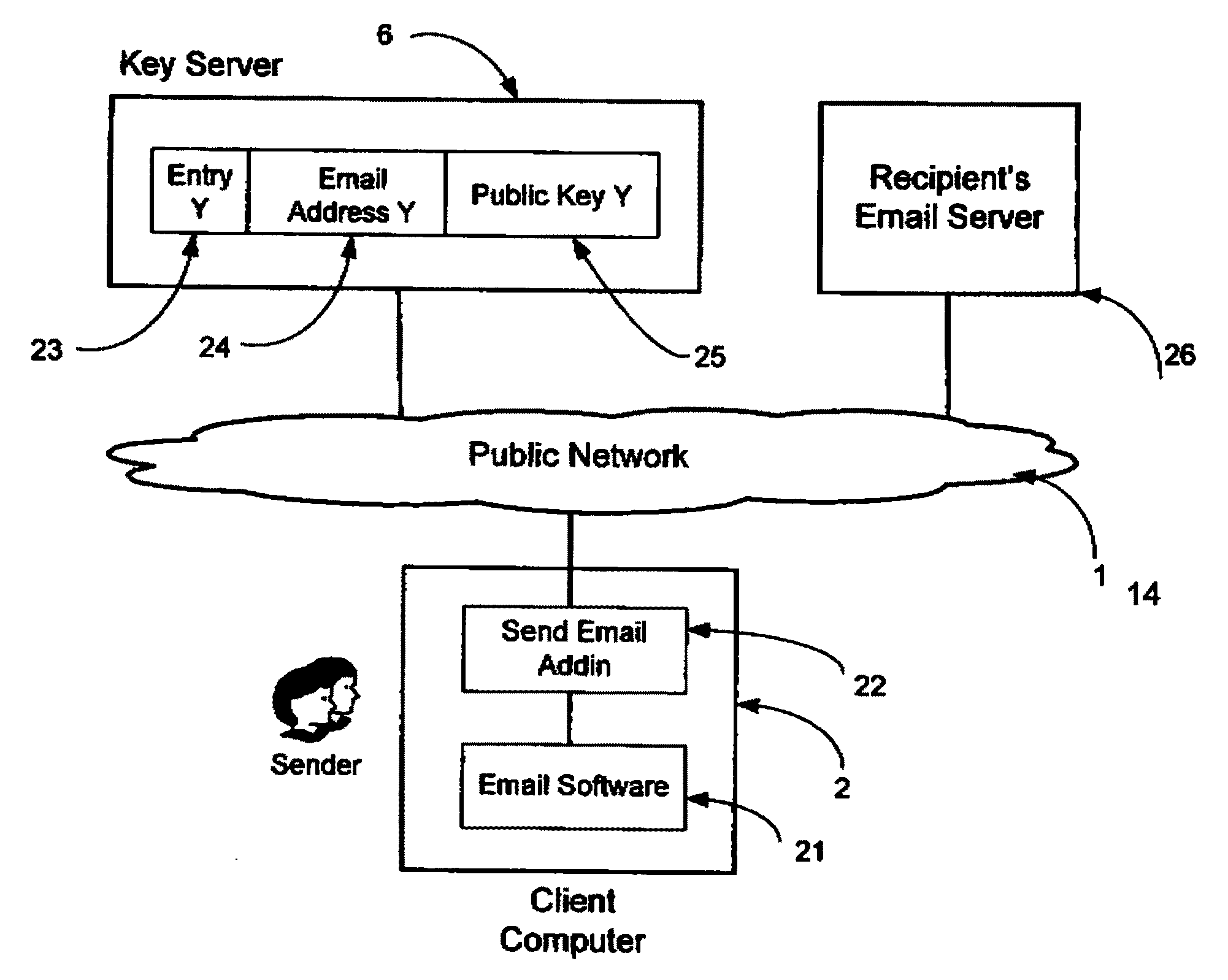
System and method for secure electronic communication services
InactiveUS20090198997A1Easy accessSecure transmissionKey distribution for secure communicationMultiple keys/algorithms usageScalable systemEmail address
A system, method and software module for secure electronic communication services, wherein a public key (25) of private-public-key pair (30,25) is associated with an email address (24), internet name or other registered unique identifier; the registered user of the unique identifier holds the private-key (30) securely, and the respective public-key (25) is made accessible on a key server (6) for look-up and retrieval by other users, for encryption of communications to be sent to the holder of the private-key, and optionally for message confidentiality, message integrity and authentication of sender and recipient, without requiring certificates. A distributed and scalable system is provided by a server network (600; 401, 501) for registration, key distribution and management preferably using a kDNS server hierarchy (601,602,603) or a key-DNS server hierarchy (701,702,) and associated protocols so that public-keys of recipients can be searched and retrieved over the internet based on the recipients email address or other unique identifier, thus facilitating secure communication between users in different network domains and organizations.
Owner:TOPOSIS CORP
Method and system for protecting a computer using a remote e-mail scanning device
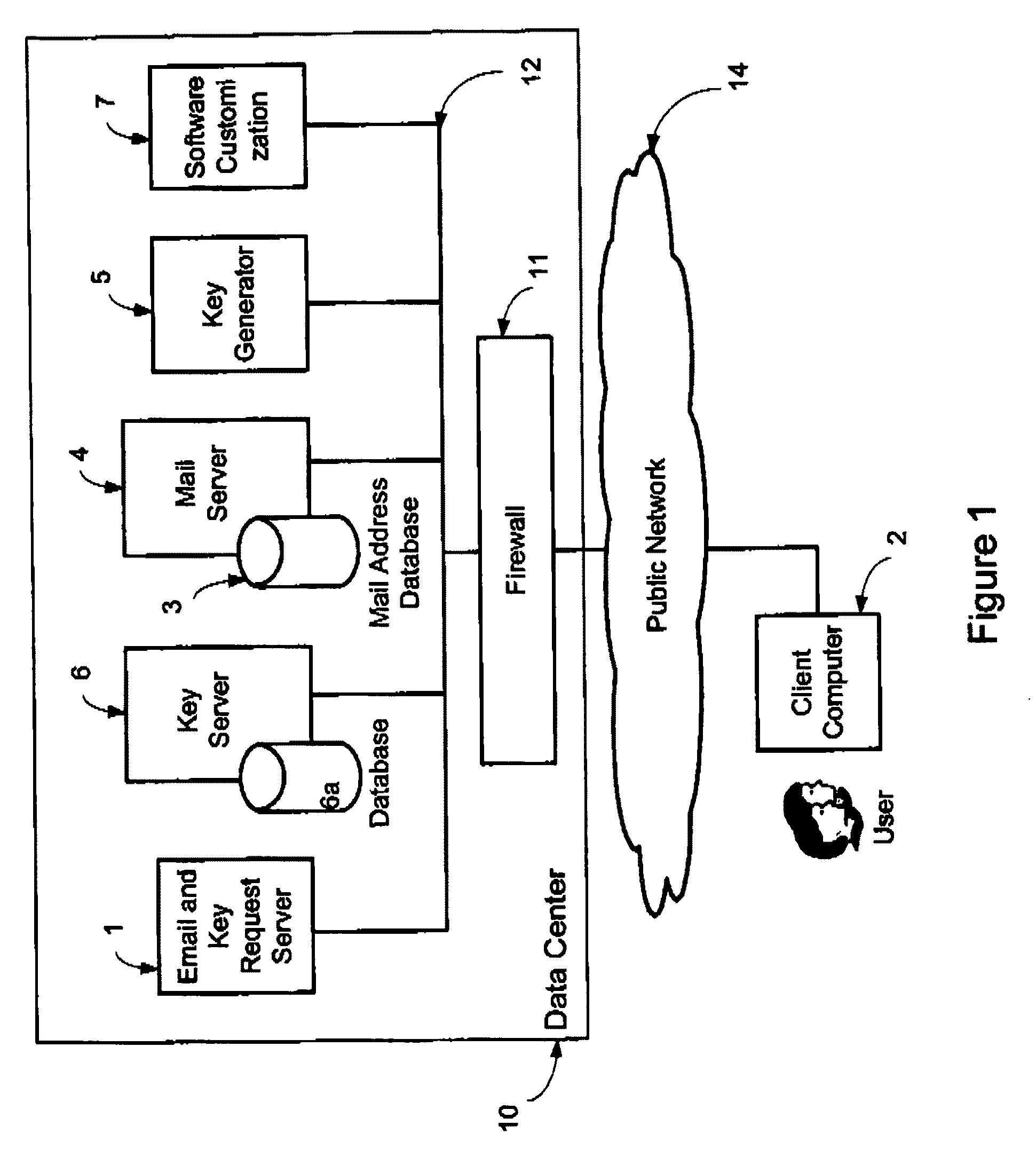
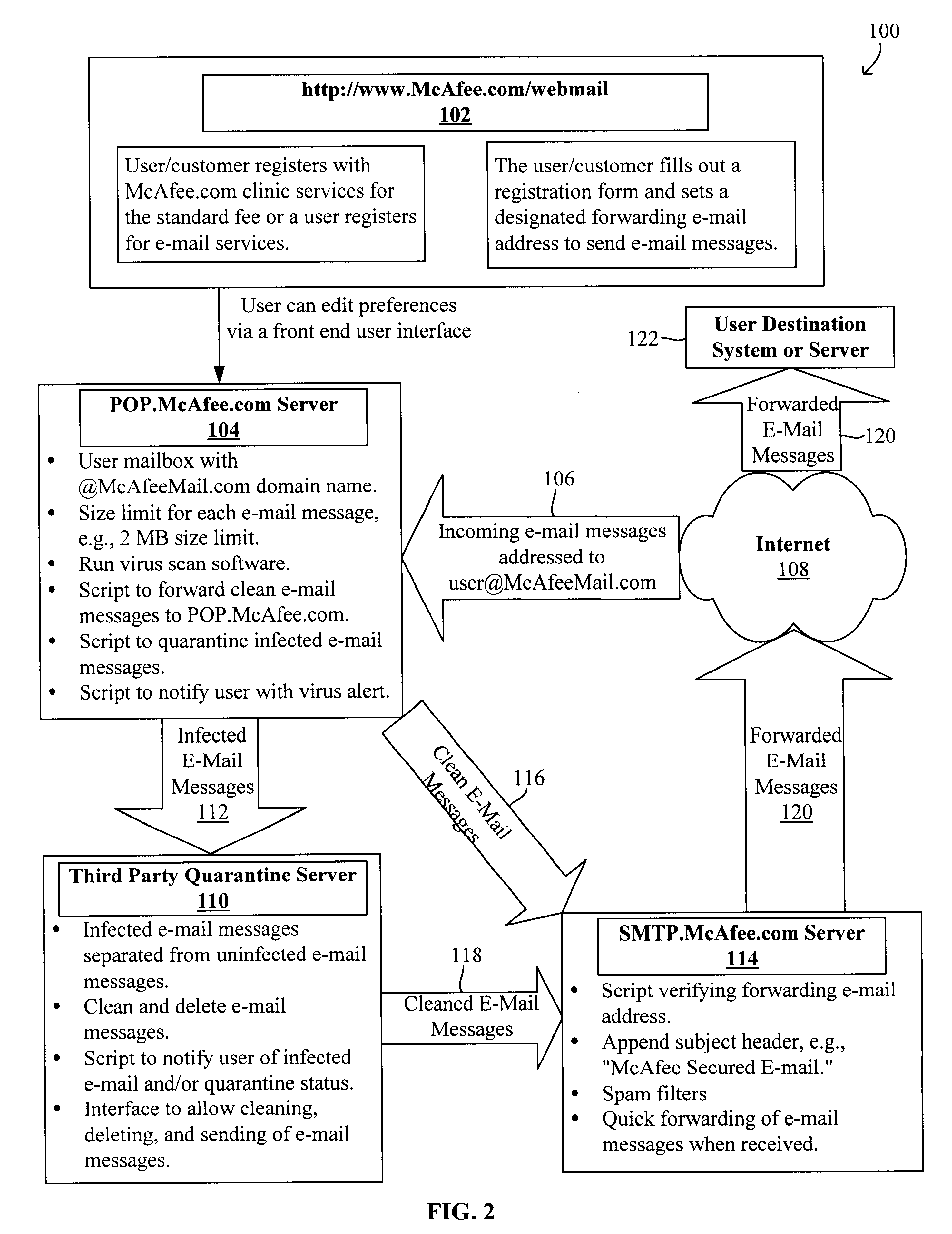
InactiveUS6701440B1Memory loss protectionUnauthorized memory use protectionEmail addressComputerized system
A system and method for a remote or network-based application service offering virus scanning, sniffing, or detecting of e-mail viruses prior to the e-mail messages arriving at the destination system or server are disclosed. The method protects a computer system that is configured to receive an e-mail message addressed to a destination e-mail address from viruses in an incoming e-mail message. The method generally includes receiving the incoming e-mail message at a remote e-mail receiving server, scanning the e-mail message for virus, forwarding the e-mail message if it is clean to a remote e-mail sending server, attempting to clean the e-mail message if it is infected to generate a cleaned e-mail message, forwarding the cleaned e-mail message, if any, to the remote e-mail sending server, and forwarding the clean or cleaned e-mail message, if any, to the destination e-mail address from the remote e-mail sending server. The system generally includes a remote e-mail receiving server for receiving the incoming e-mail message, a virus-detection program for scanning the e-mail message for virus, a remote e-mail virus processing server for attempting to clean the infected e-mail message, and a remote e-mail sending server forwarding the clean or cleaned e-mail message, if any, to the destination e-mail address.
Owner:MCAFEE LLC
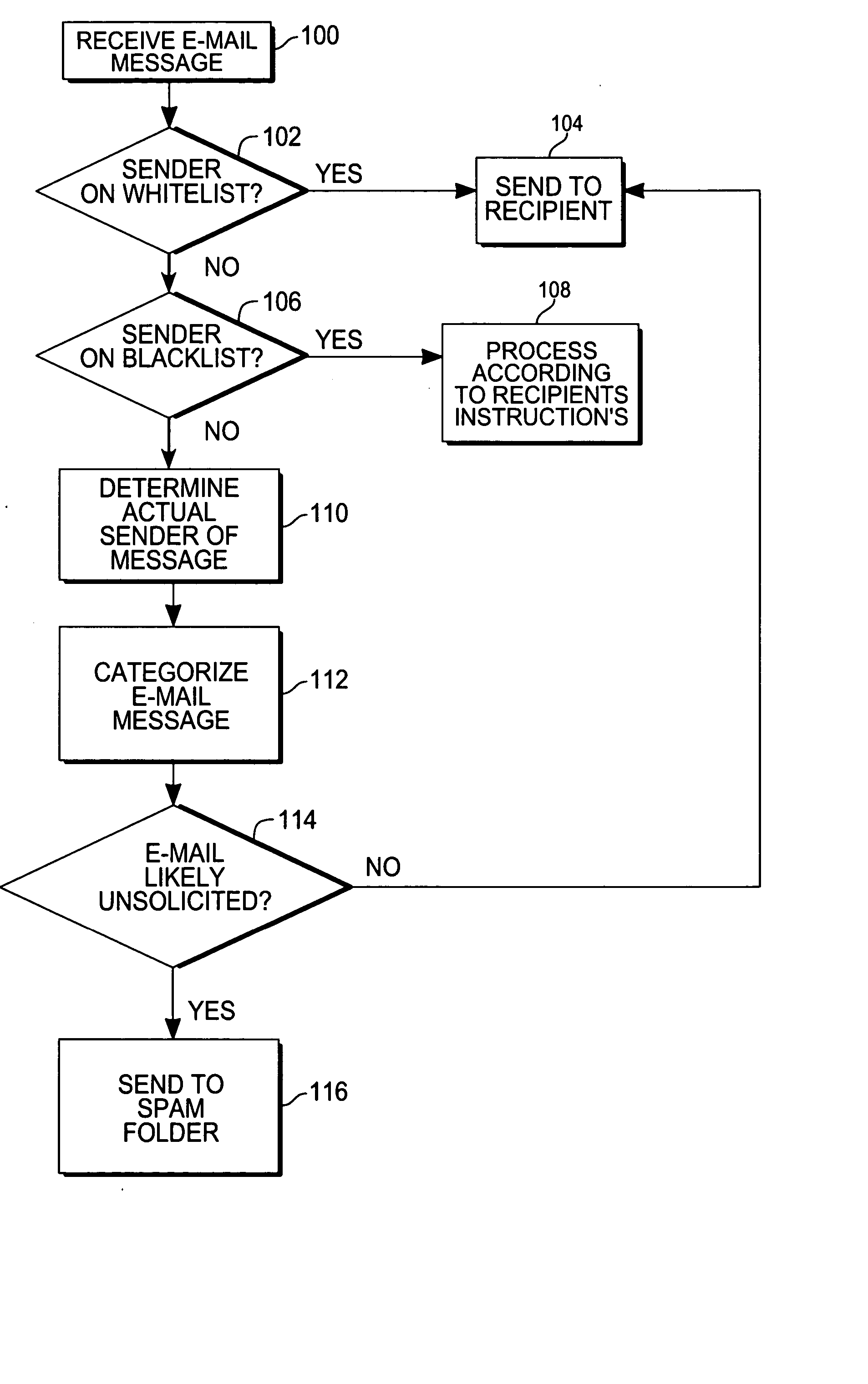
Spam filtering system and method
InactiveUS9177293B1Multiple digital computer combinationsOffice automationEmail addressFilter system
A spam filter system and method, for maintaining at least one database of permitted email addresses; automatically communicating with an email server, and selectively downloading and storing email not corresponding to entries in the database; automatically sending a challenge message in response to messages from non-permitted email addresses; if an appropriate response is received to the challenge message, adding the non-permitted email address to the database of permitted email addresses; and automatically restoring downloaded email messages from email addresses which become permitted.
Owner:COUSINS INTPROP
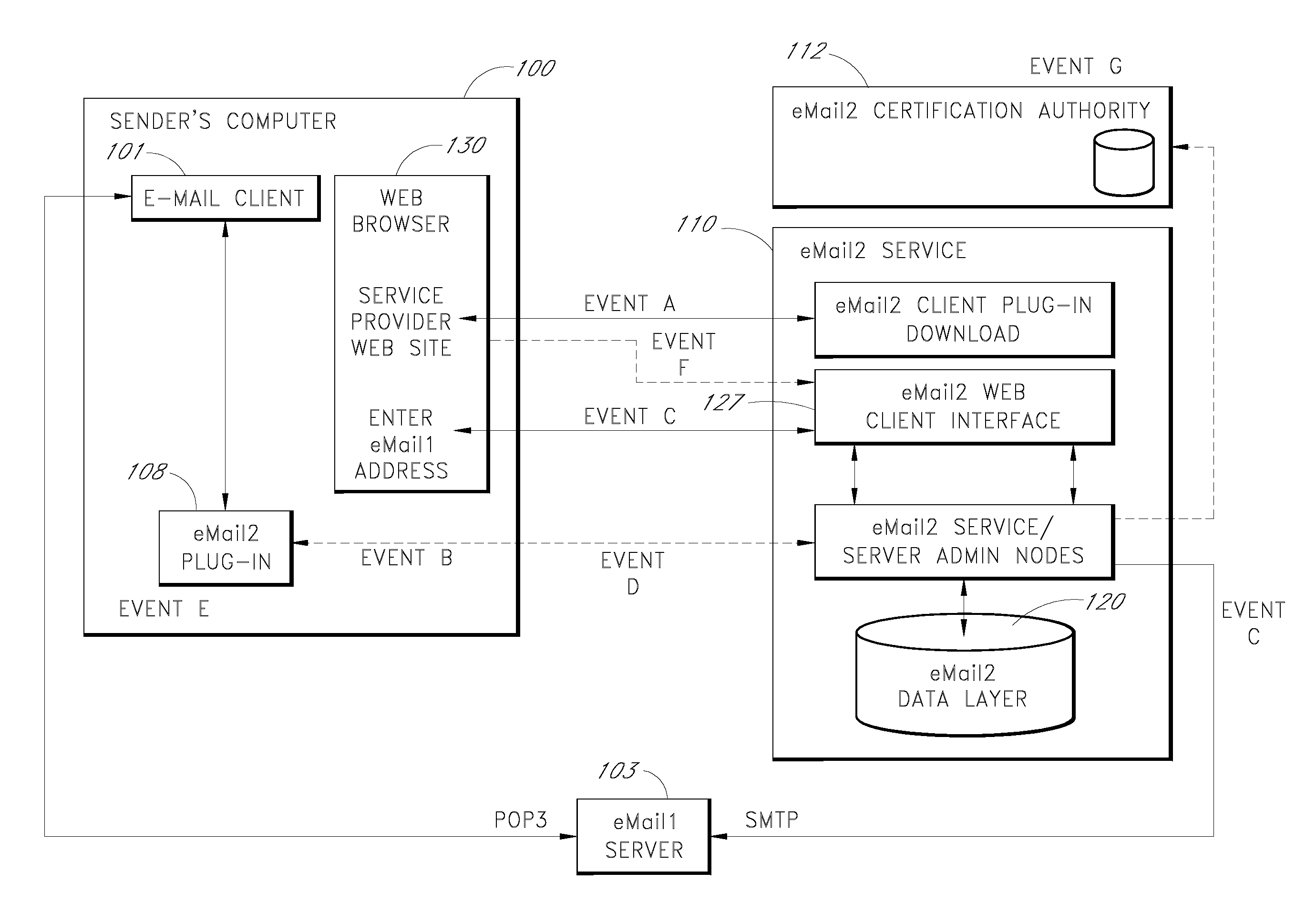
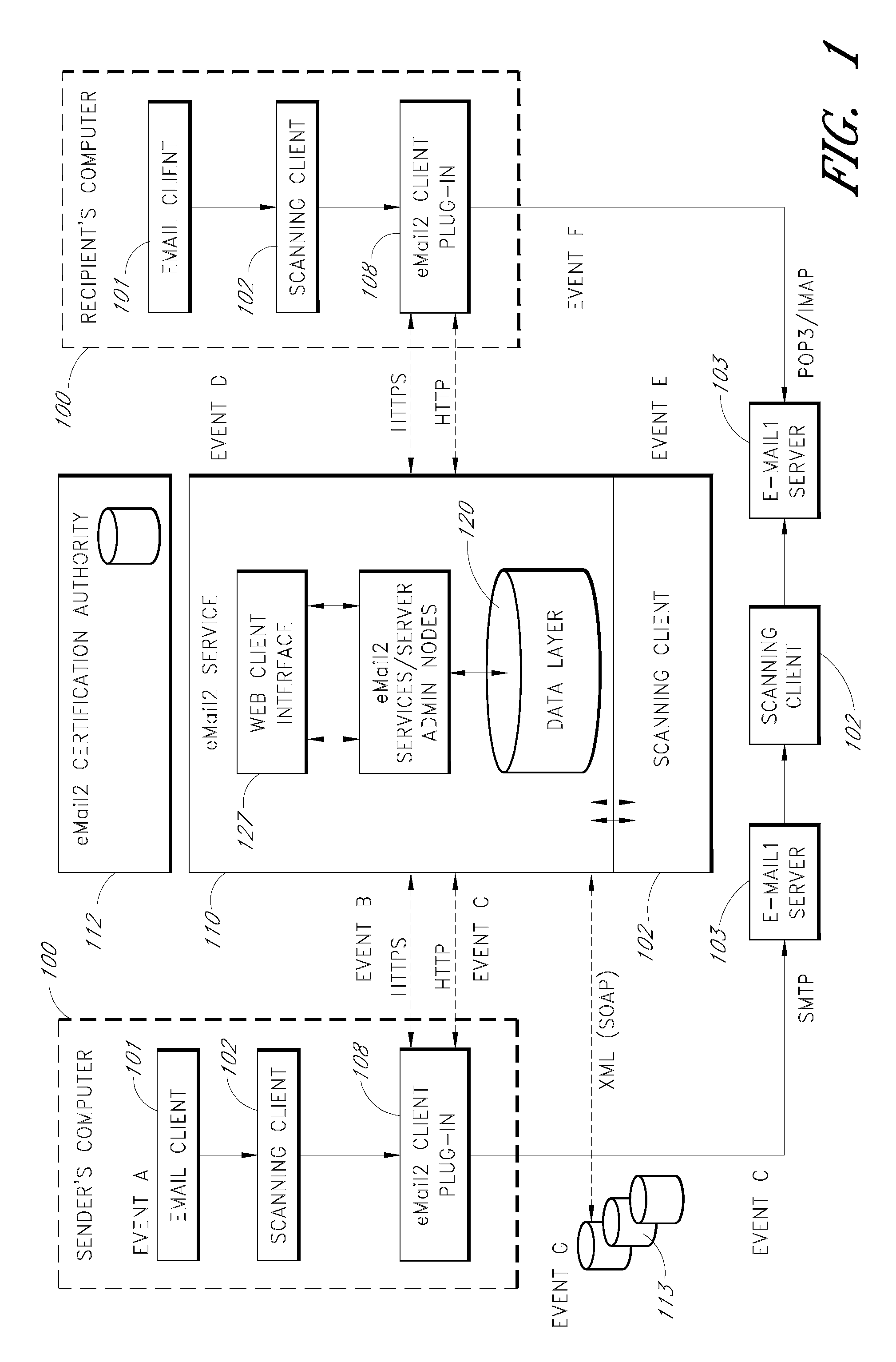
Secure electronic mail system
ActiveUS20070005713A1Easy to watchDigital data protectionMultiple digital computer combinationsEmail addressSecure transmission
An e-mail system is disclosed that overcomes many deficiencies of, but is backward compatible with, existing e-mail systems. Embodiments of the system may include various features, including but not limited to: (1) secure transfer of e-mail messages, without the need for users to replace existing e-mail clients or to change e-mail addresses; (2) tracking of all actions performed in connection with an e-mail transmission; (3) the ability for a recipient to view information about an e-mail message, optionally including information about how other addressees have responded to it, before deciding whether to retrieve the e-mail message; (4) the aggregation of entire e-mail conversations into a single threaded view; (5) the ability to include both private and public messages in a single e-mail communication; (6) sender control over downstream actions performed in connection with an e-mail message; (7) flexible control over cryptographic methods used to encrypt emails messages for storage.
Owner:APPRIVER CANADA ULC
Internet-enabled lead generation
InactiveUS6868389B1Special data processing applicationsMarket data gatheringEmail addressThe Internet
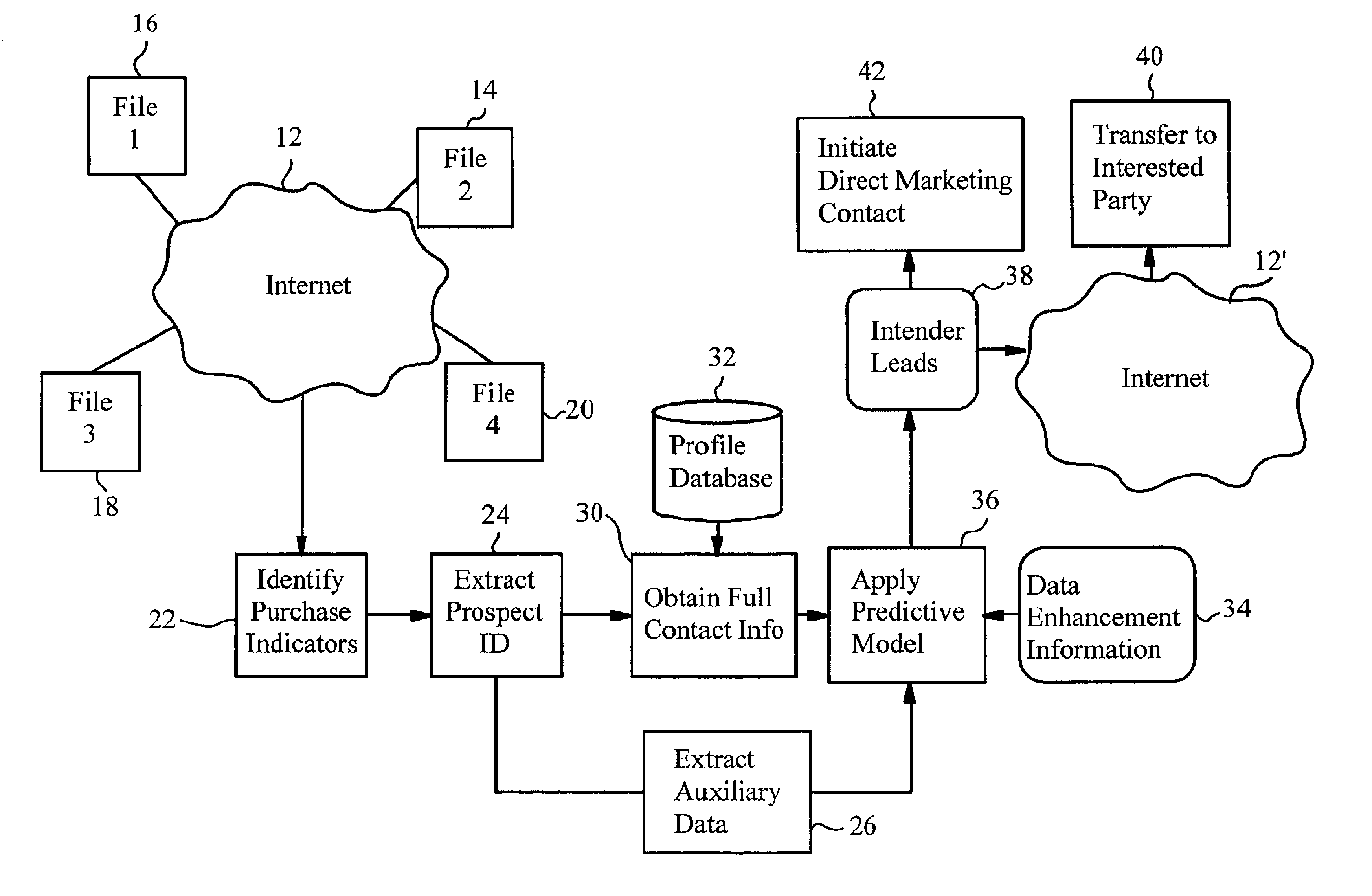
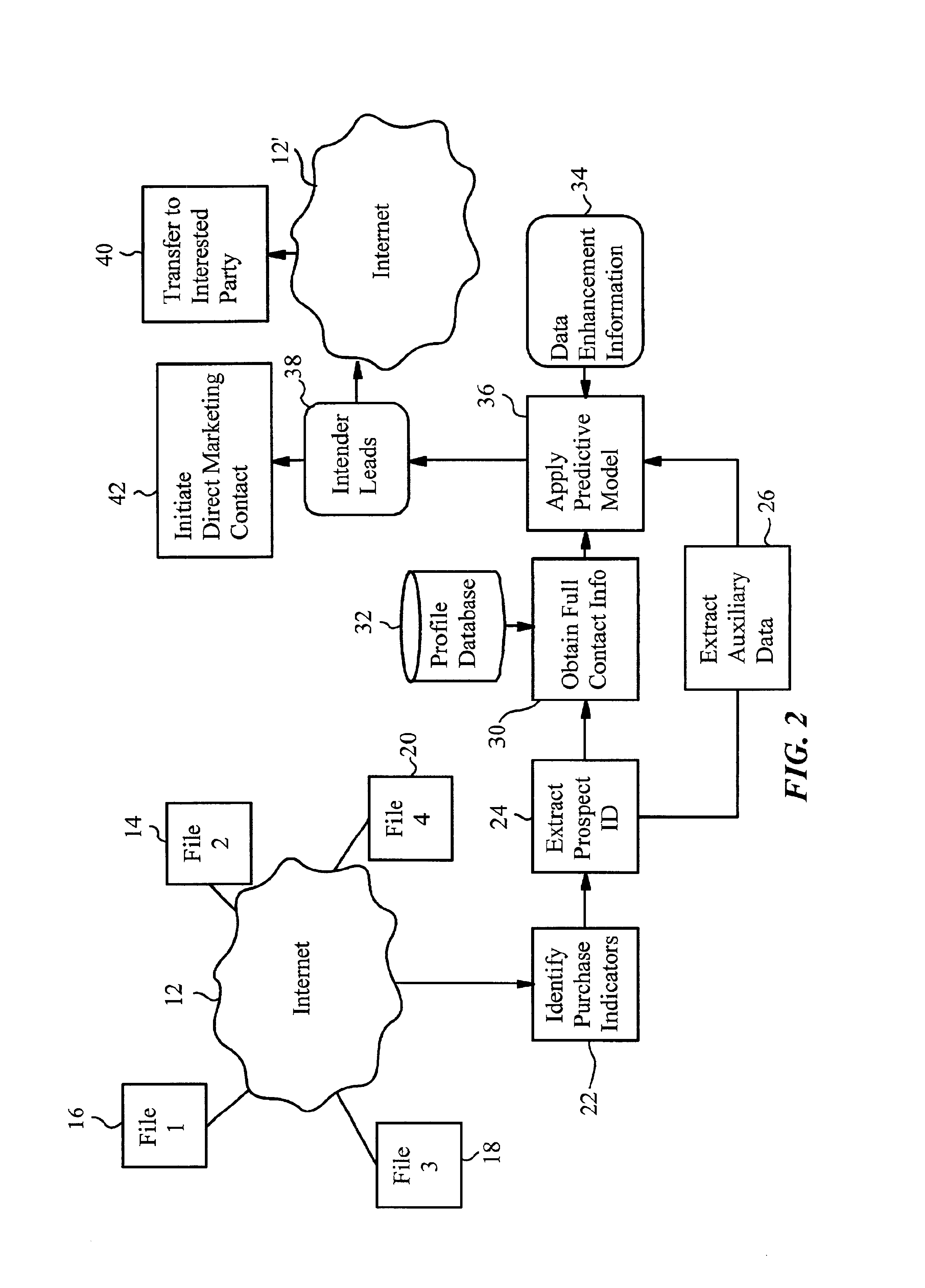
A method of generating intender leads in a distributed computer system includes the steps of identifying purchase indicators and extracting prospect identifiers from the purchase indicators. Purchase indicators are pieces of data that represent a potential future purchase by a prospect. For example, an online classified advertisement selling an automobile is a purchase indicator for a potential future purchase of a new car by the old car seller. The prospect identifier, such as a telephone number or email address, uniquely identifies the prospect likely to make the future purchase. Preferably, the method also contains the steps of obtaining full contact information for the prospect from a profile database, applying a predictive model to the prospects to select intender leads, and transferring the intender leads to an interested party, such as a direct marketing service or sales force. An intender lead is a lead for a person intending to make a purchase of a particular product or service within a given time period. Only some of the prospects are actual intenders. Preferably, the method also includes the steps of extracting auxiliary data that is independent of the prospect from the purchase indicator, and obtaining data enhancement information about the prospect from data enhancement databases. The predictive model is preferably also applied to the data enhancement information and auxiliary data. The method is particularly well-suited for the Internet, which is a large source of publicly-available purchase indicators that is constantly updated. The intender leads are preferably transferred over the Internet, e.g. by email, so that they arrive at the sales force when they are still “hot.”
Owner:MEDIA DIRECT
Method and system for enhancing reliability of communication with electronic messages
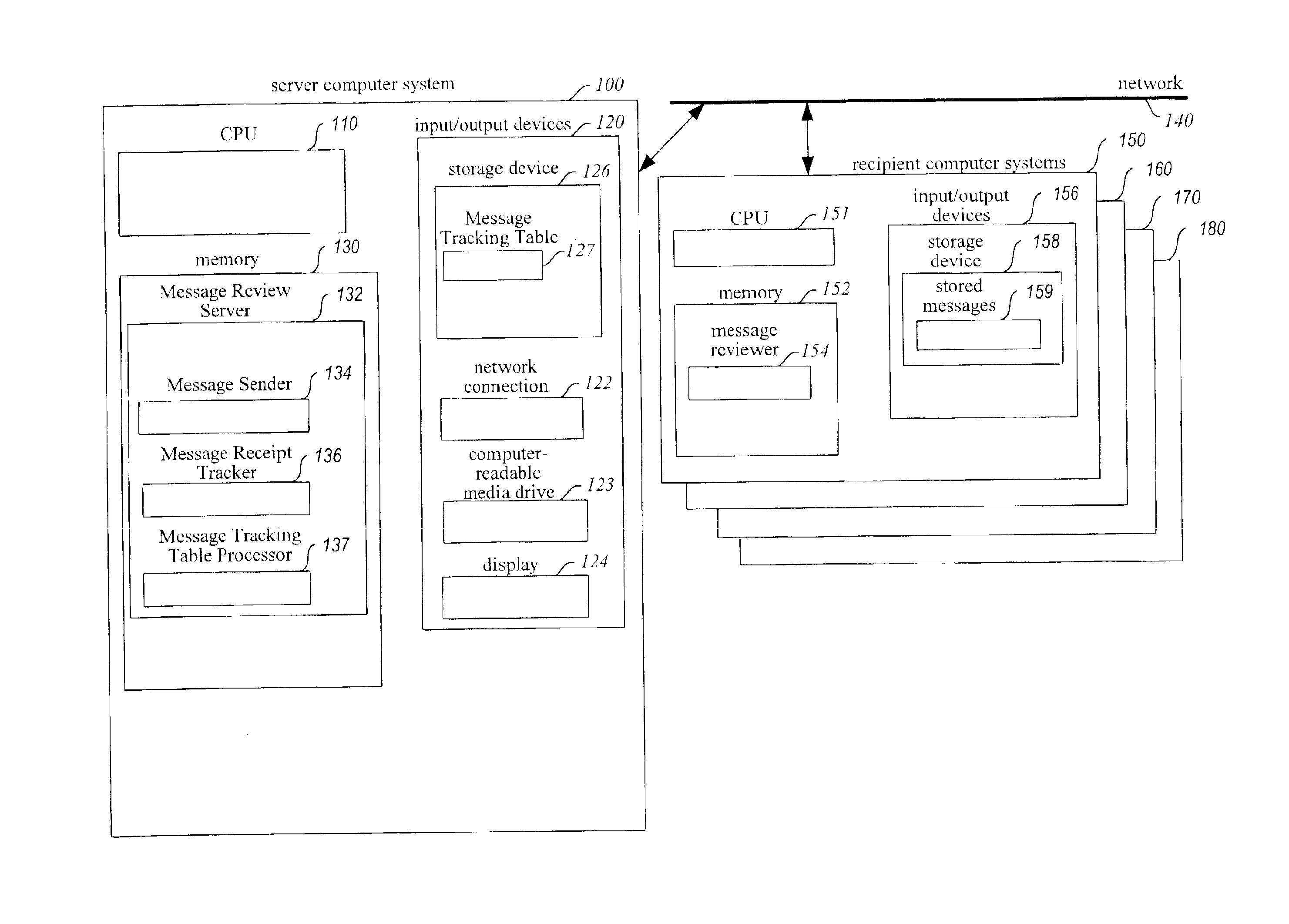
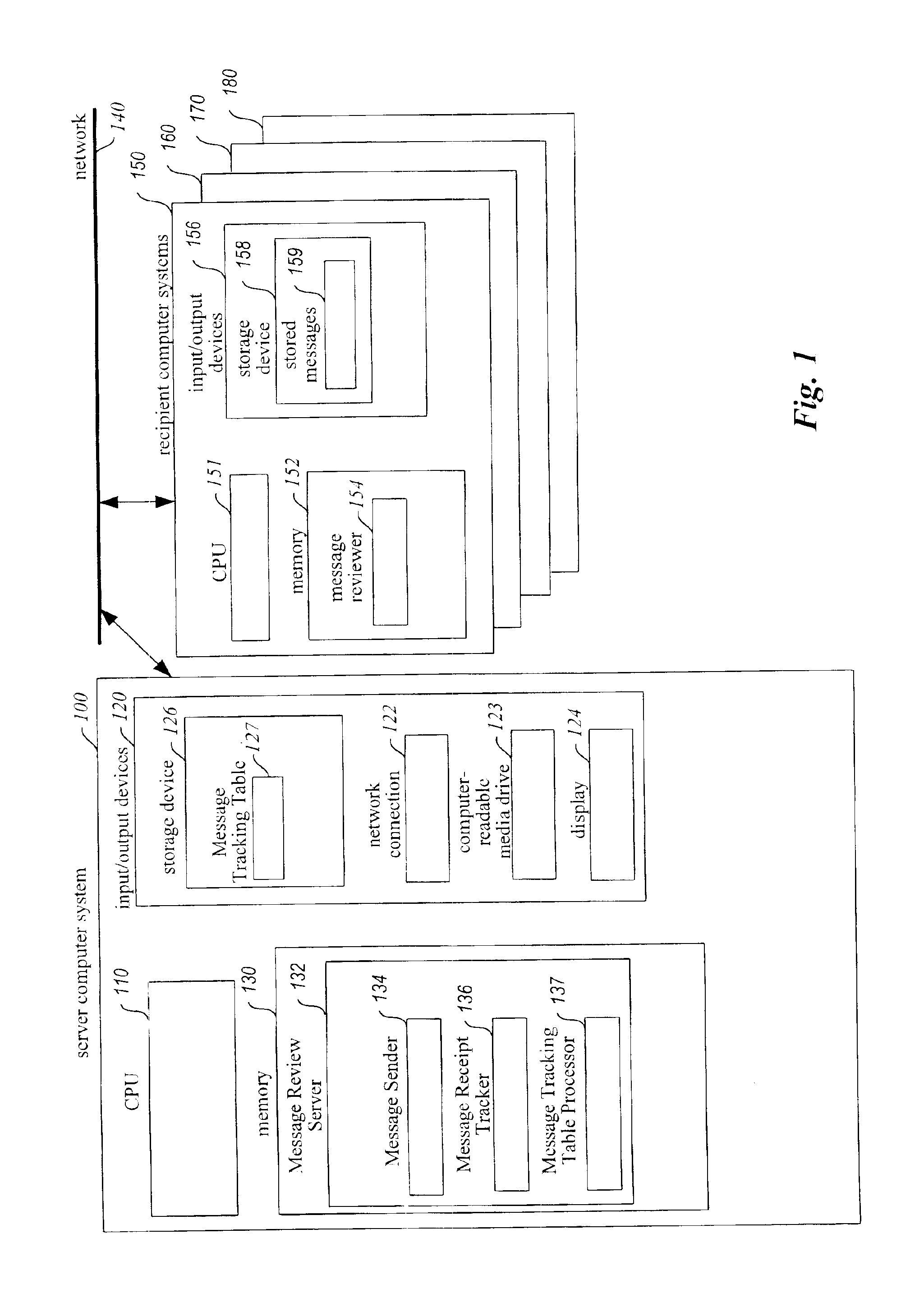
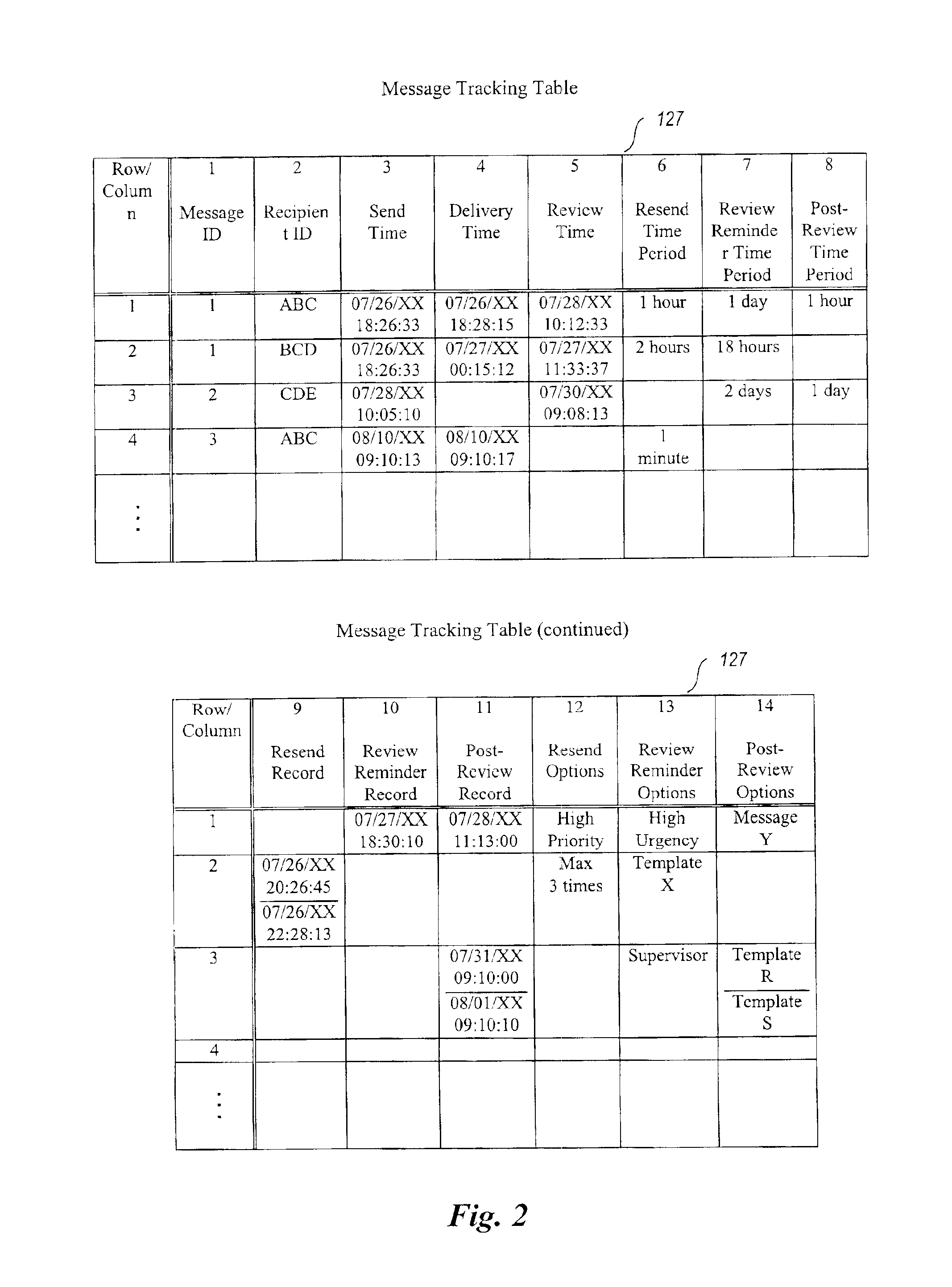
InactiveUS6854007B1Improve reliabilitySpecific activityMultiple digital computer combinationsPersonalizationComputer hardware
A system for enhancing the reliability of communicating with electronic messages. The system sends an electronic message to designated recipients, and then automatically helps ensure that each message has been successfully delivered within a specified period of time and that each message has been reviewed within a specified period of time. In addition, the system automatically performs specified activities after review of a message takes place. The sender of an electronic message initiates reliability-enhanced messaging by specifying message delivery information and message review information. The sender can specify that if delivery or review notifications are not received within specified periods of time, the message will be resent to the recipient or a reminder message will be sent to the recipient or to another user. The message information can include various frequency and duration options, such as resending a message only once or resending it every 2 hours for a week. Message information can also specify to resend the message with a higher transmission priority or review urgency so that its delivery and review is more likely, or could specify to use a different recipient system for the recipient (e.g., to a second email address if a first address fails, or to a pager if a cellular phone is not available). Each recipient of a message can have individualized message delivery information. The system tracks whether each message has been delivered to each recipient, and uses the message delivery information to resend the messages whose delivery and review was not confirmed.
Owner:MEI CALIFORNIA
Computer services for identifying and exposing associations between user communities and items in a catalog
A computer-implemented service associated with an electronic catalog analyzes purchase histories of users, and / or other types of activity data reflective of user affinities for specific items, to identify items that are significantly more popular in specific user communities than in a general user population. The communities may, for example, include email-based communities (e.g., all users with email addresses associated with a particular company), shipping address based communities (e.g., all users with shipping addresses in Seattle), and / or communities based on other types of user attributes. In one embodiment, a user of the service can select a particular community, such as by selecting the name of a corresponding organization or geographic region, to view a list of items having relatively high popularity levels therein. The results of the analysis may additionally or alternatively be used to affirmatively notify users of associations between particular items and communities, and / or to recommend items to users.
Owner:AMAZON TECH INC
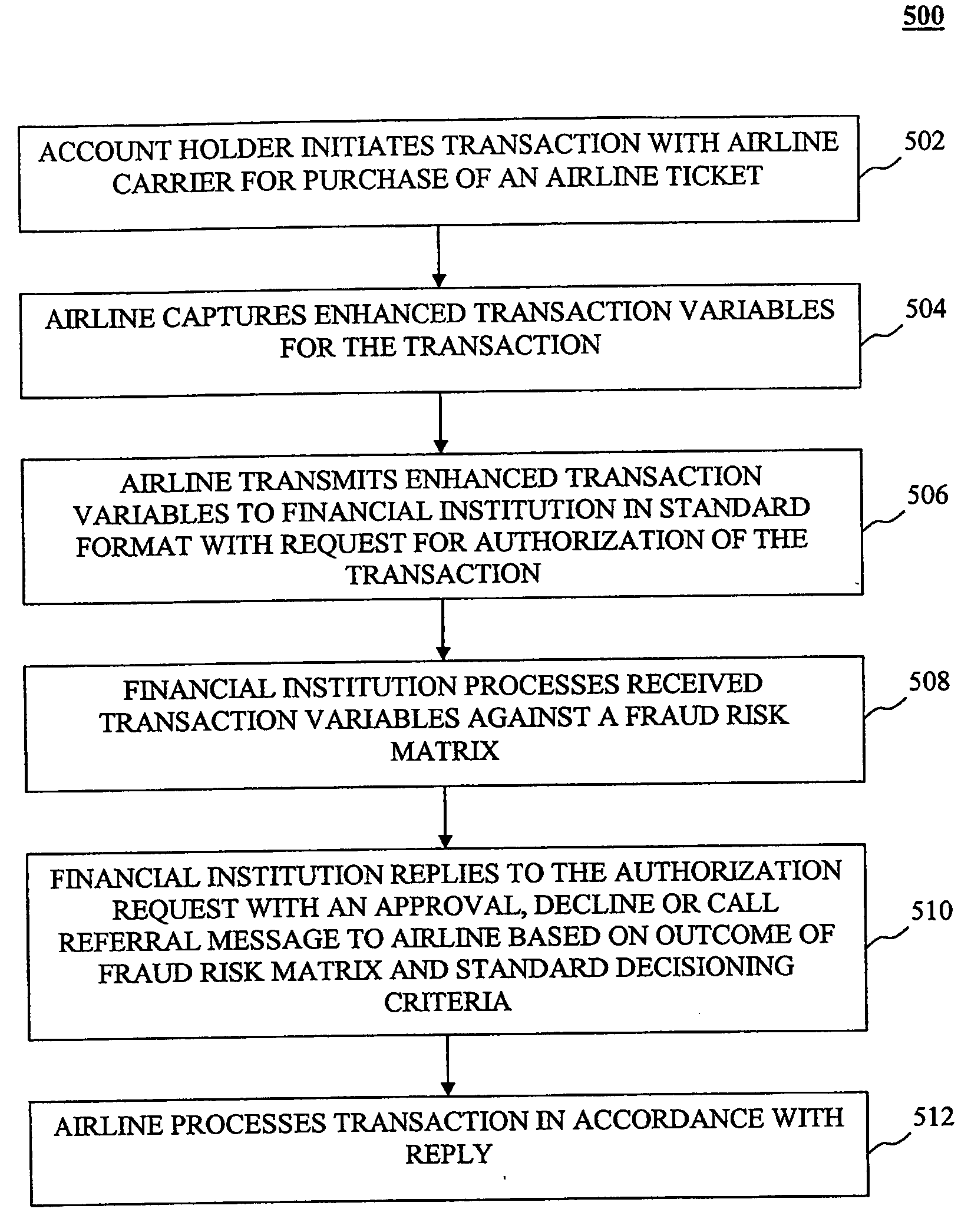
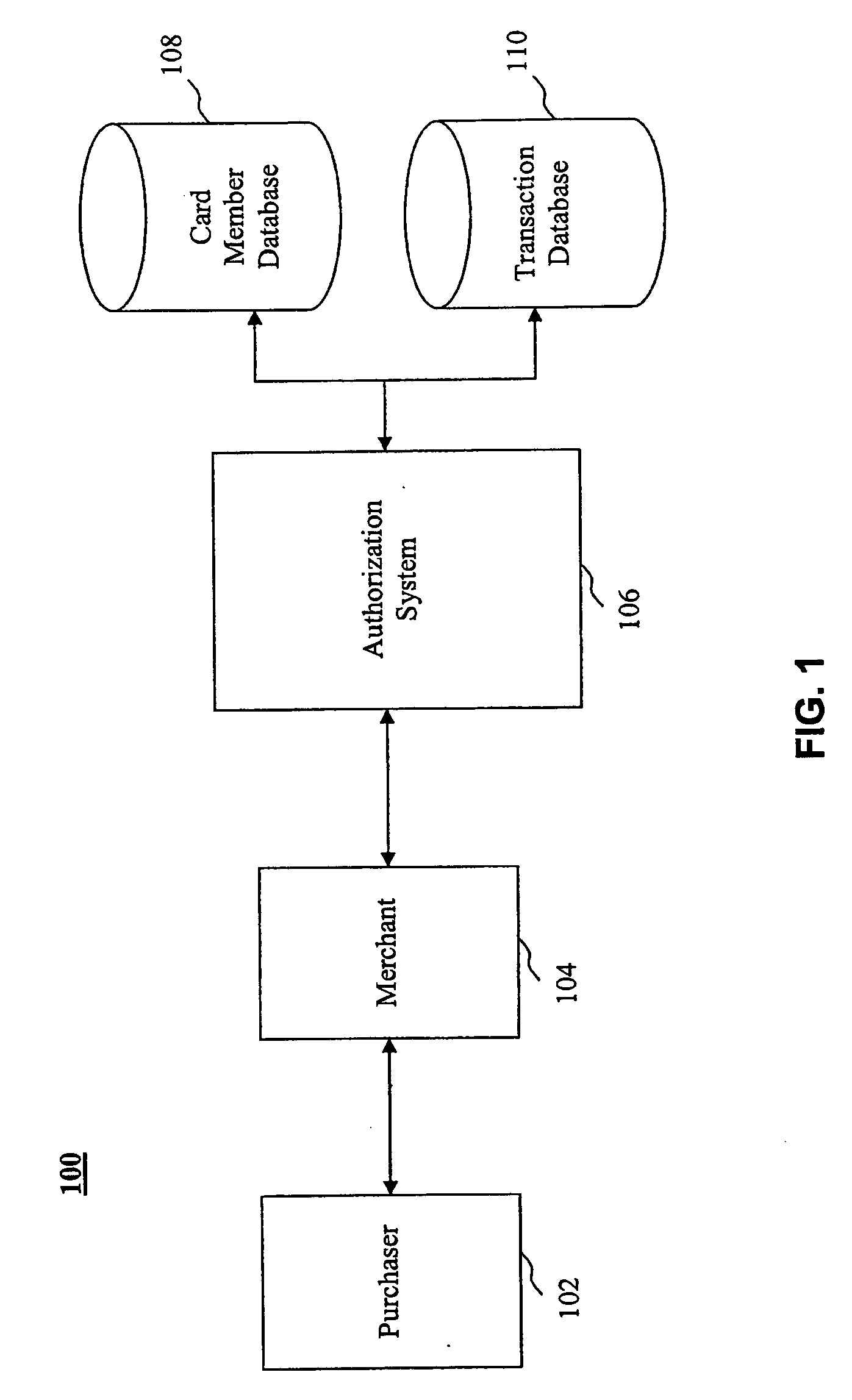
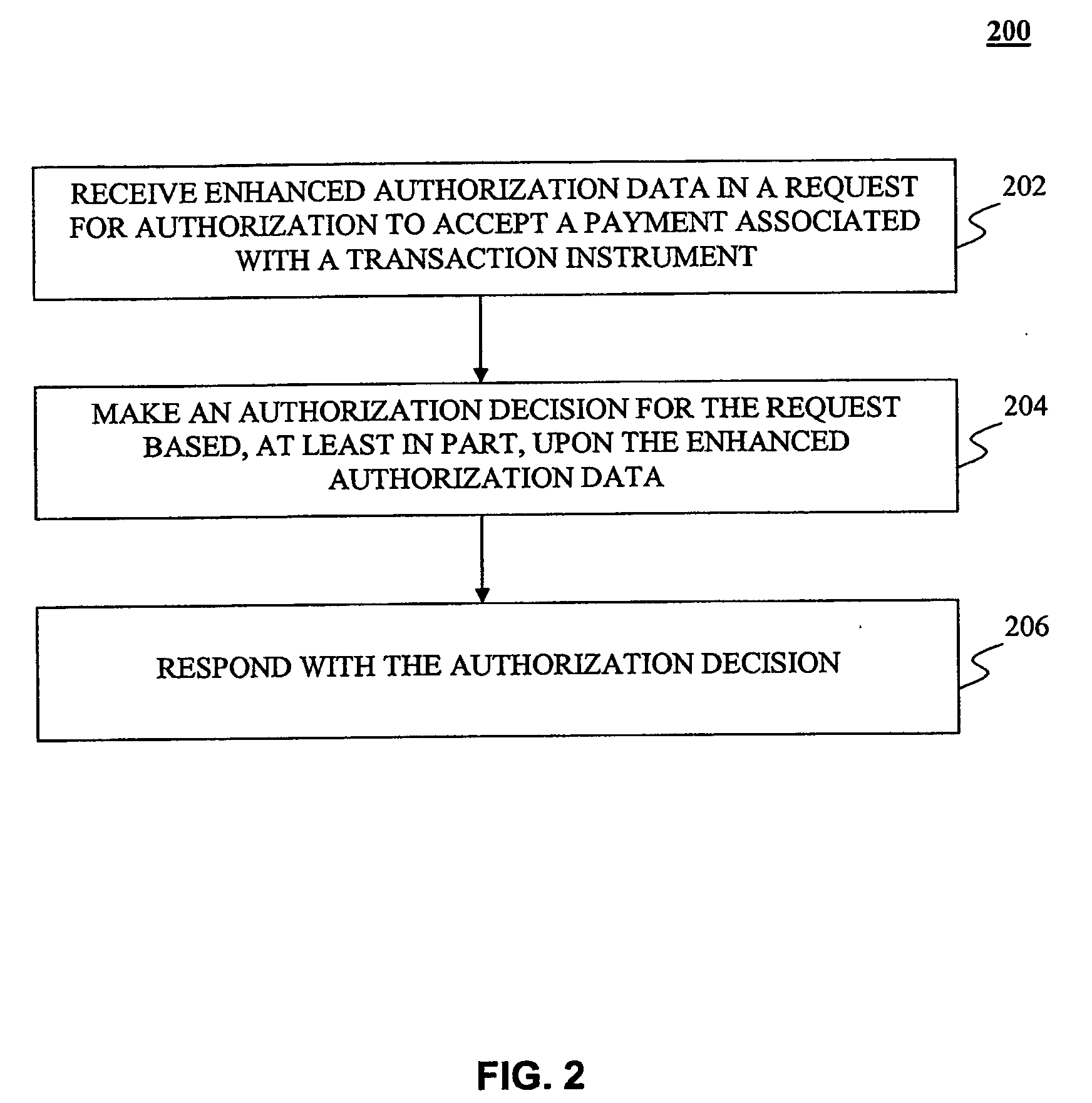
System, method and computer program product for authorizing transactions using enhanced authorization data
The present invention provides systems, methods and computer program products for authorizing transactions based on, at least in part on, enhanced authorization data. In one embodiment, enhanced authorization data is received in a request for authorization to accept a transaction instrument as payment. Examples of enhanced authorization data include an automatic number identification, an information identifier, an email address, a contact telephone number, a ship-to-name, ship-to-address, an Internet Protocol address, and a seller identification. A risk analysis is performed based, at least in part, on the enhanced authorization data to determine the risk of the request being associated with a fraudulent purchase. The risk may be calculated by comparing the enhanced authorization data with information stored about the transaction instrument or with historical transaction information. Furthermore, the velocity of transactions associated with the enhanced authorization data may be measured in calculating the risk.
Owner:LIBERTY PEAK VENTURES LLC
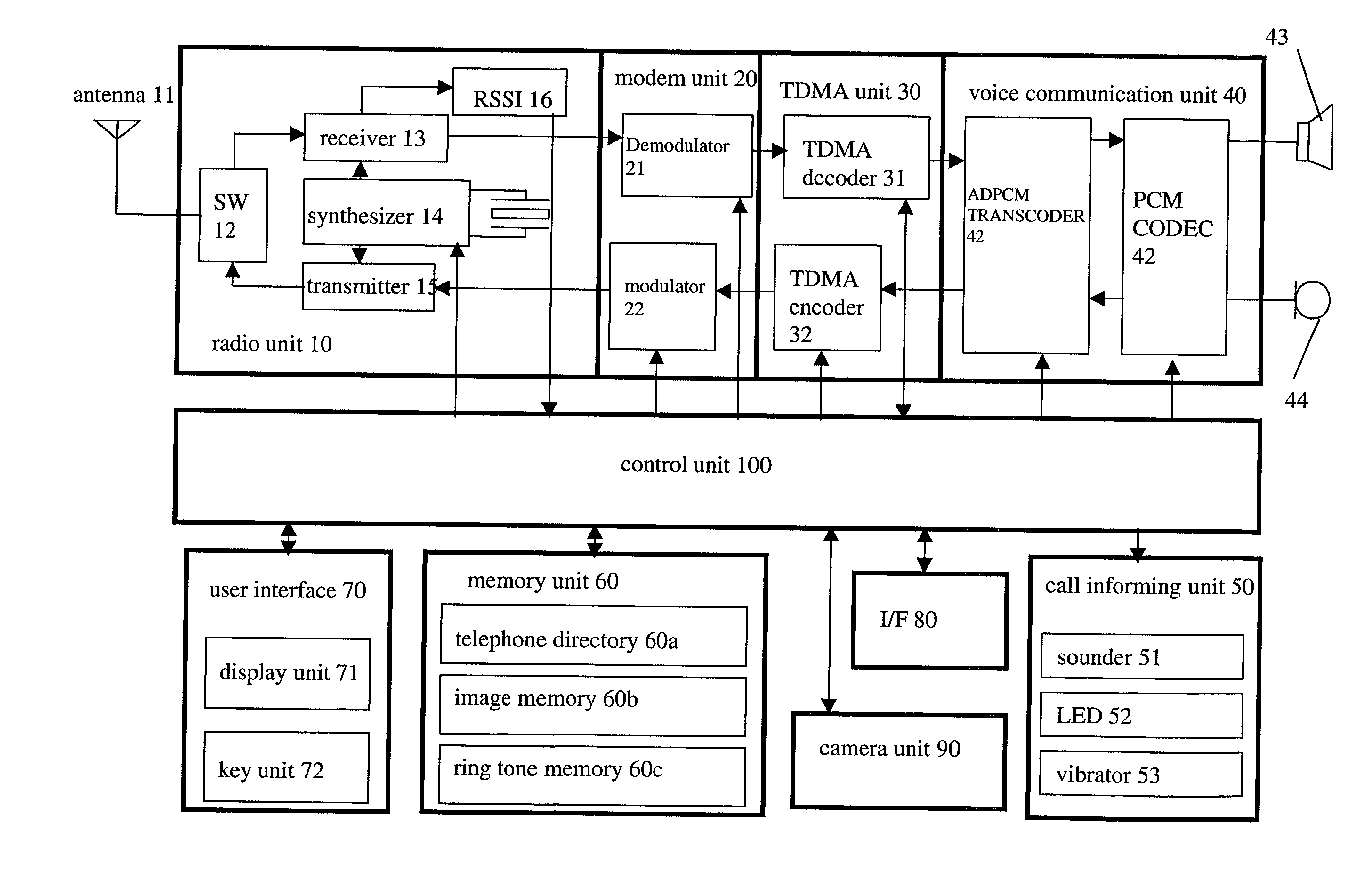
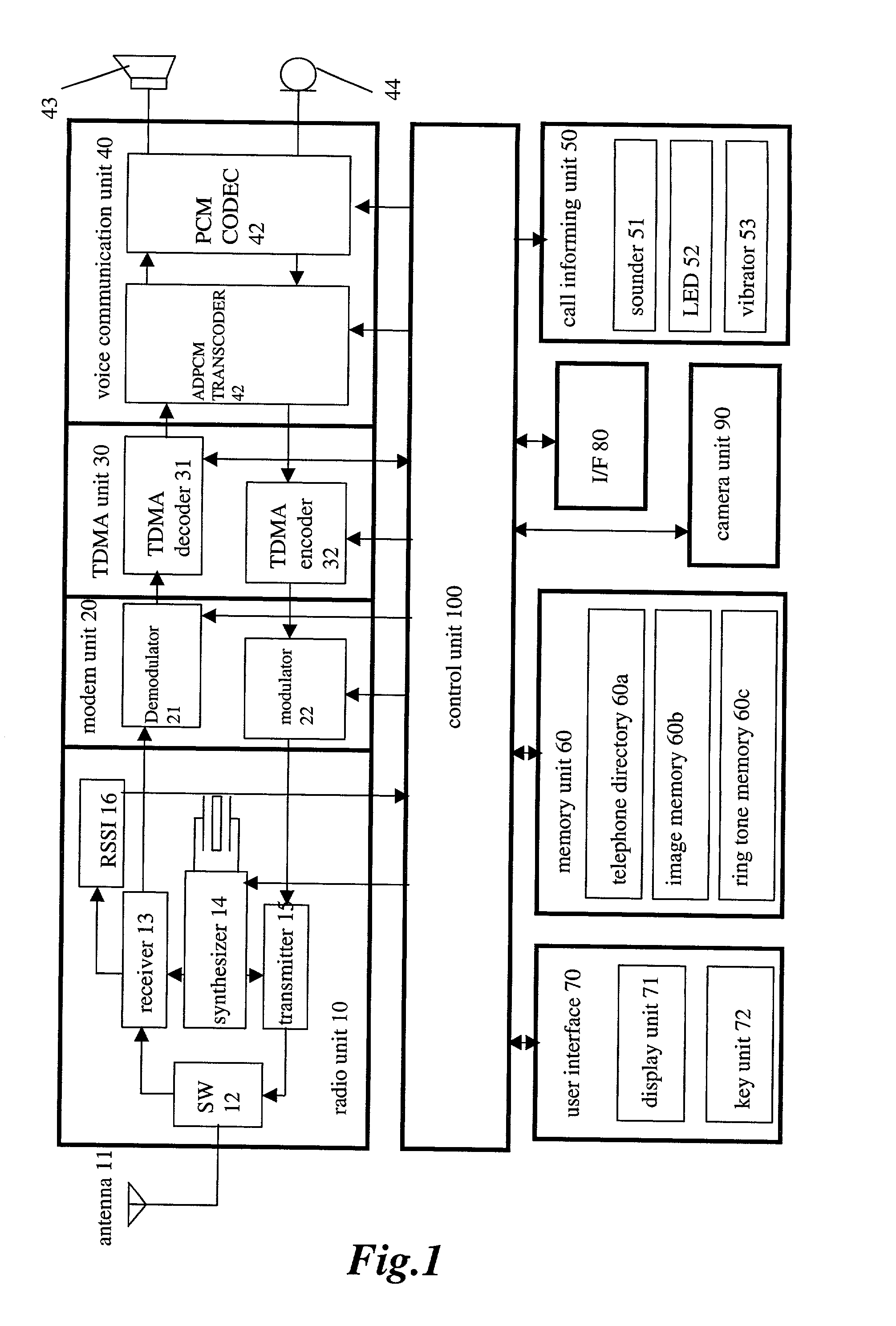
Communication apparatus for use in a communication system providing caller ID functionality
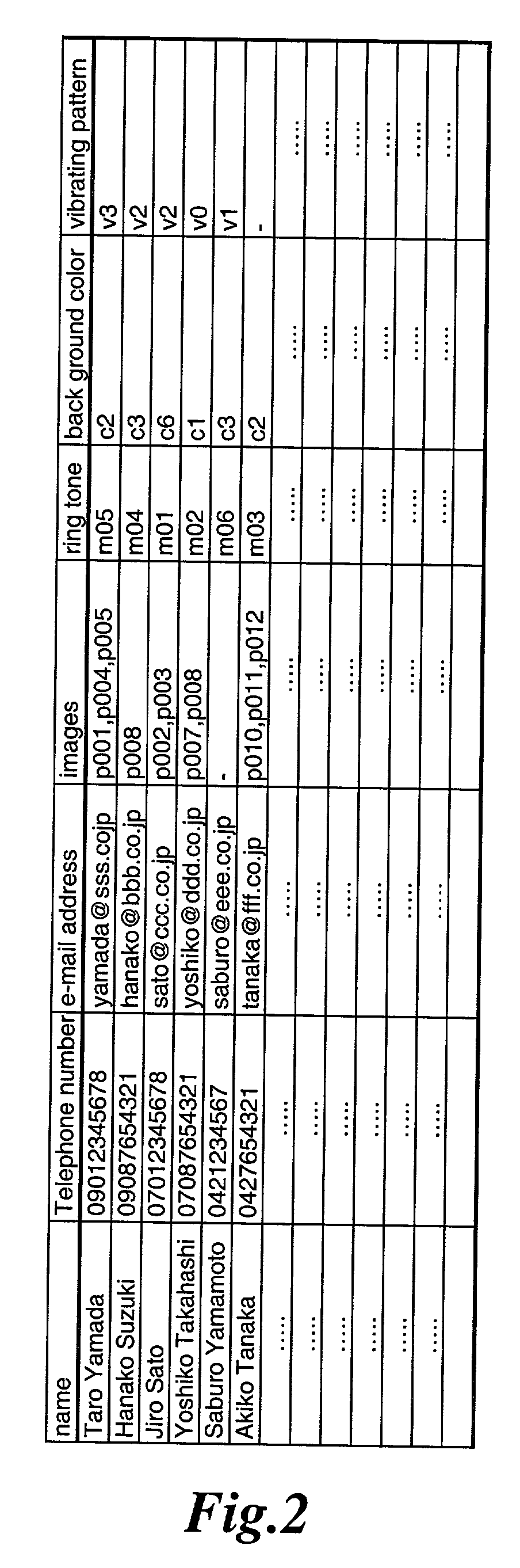
InactiveUS20020094806A1Special service for subscribersCalling susbscriber number recording/indicationData setEmail address
A telephone directory stores a plurality of data sets including a name, a telephone number, e-mail address, image pattern numbers, a ring tone number, a background color number, and a vibrating pattern. An image memory stores images corresponding to each image pattern number. A ring tone memory stores ring tone data corresponding to each ring tone pattern. When a radio communication apparatus receives an incoming call signal, the control unit informs of an incoming voice or message call by repeatedly displaying the images on a display unit.
Owner:KK TOSHIBA
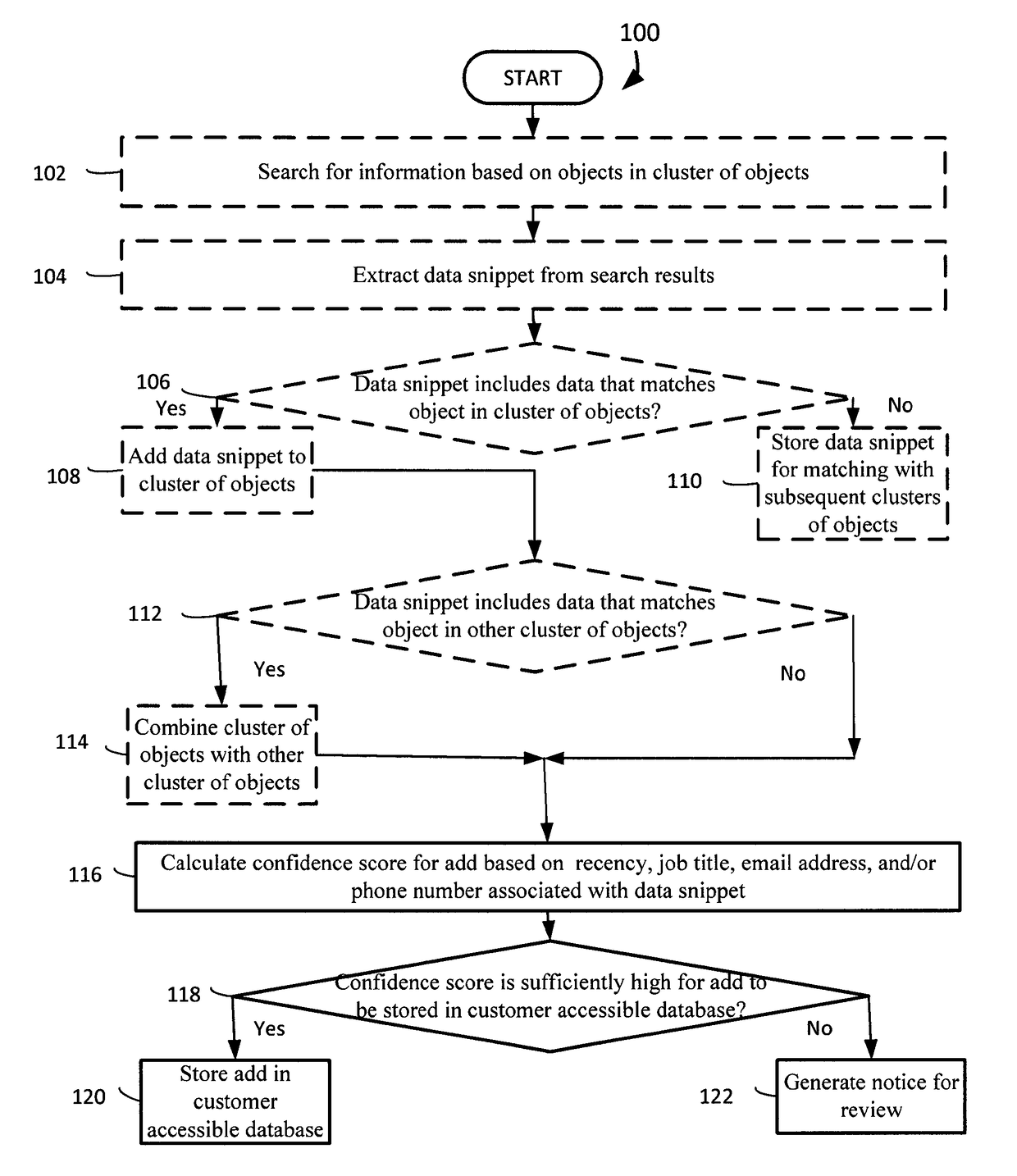
Confidently adding snippets of search results to clusters of objects
ActiveUS9760620B2Quality improvementMetadata text retrievalRelational databasesEmail addressData mining
Systems and methods are provided for matching snippets of search results to clusters of objects. A system adds a data snippet of a search result to a cluster of objects. The system calculates a confidence score for the add based on the recency, a job title, an email address, and / or a phone number associated with the data snippet. The system stores the add in the customer accessible database if the confidence score is sufficiently high for the add to be stored in the customer accessible database. The system generates a notice for review if the confidence score is not sufficiently high for the add to be stored in the customer accessible database.
Owner:SALESFORCE COM INC
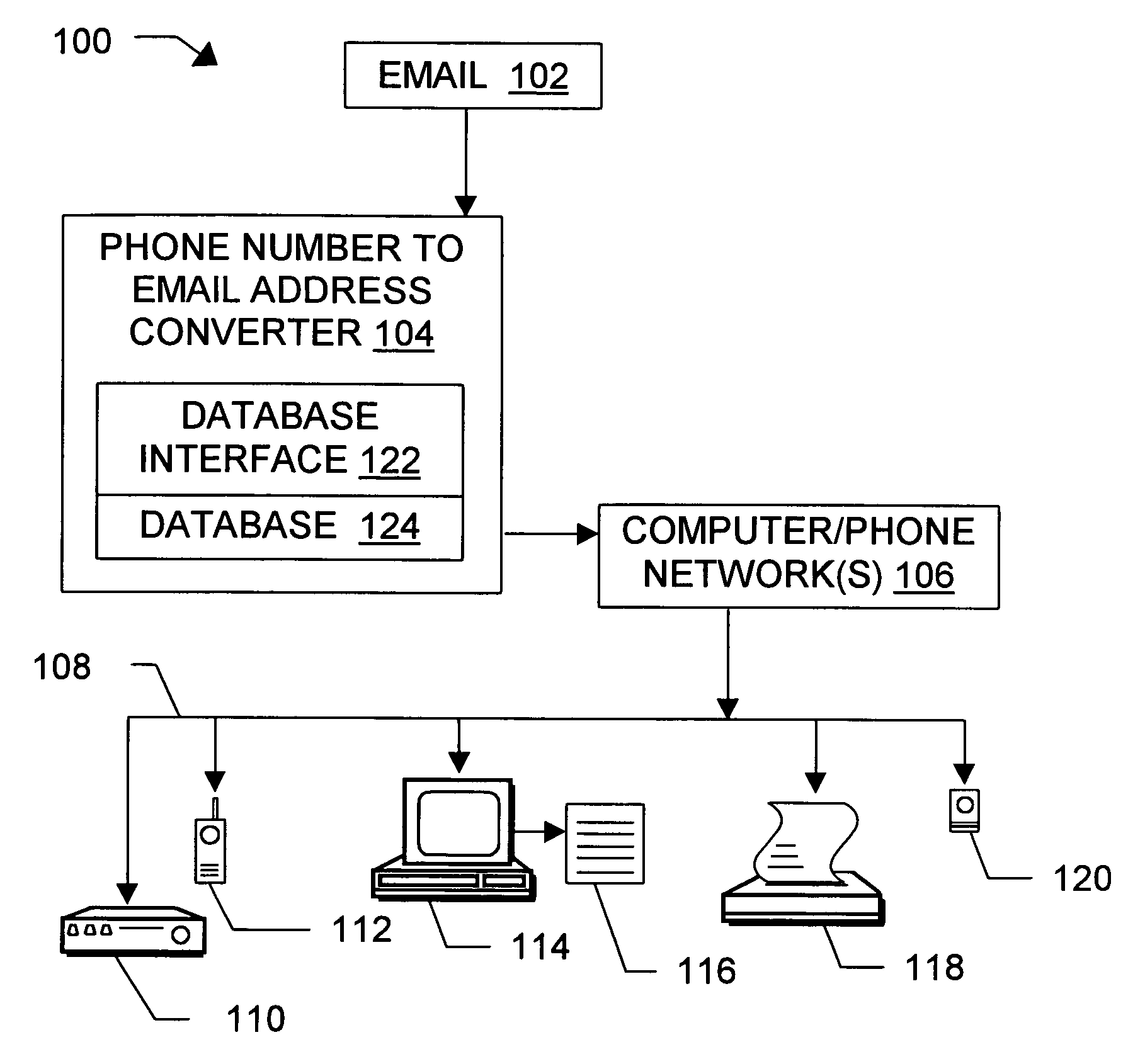
Message routing
InactiveUS6981023B1Easy to getRemove the burdenInterconnection arrangementsPublic key for secure communicationEmail addressSelective calling
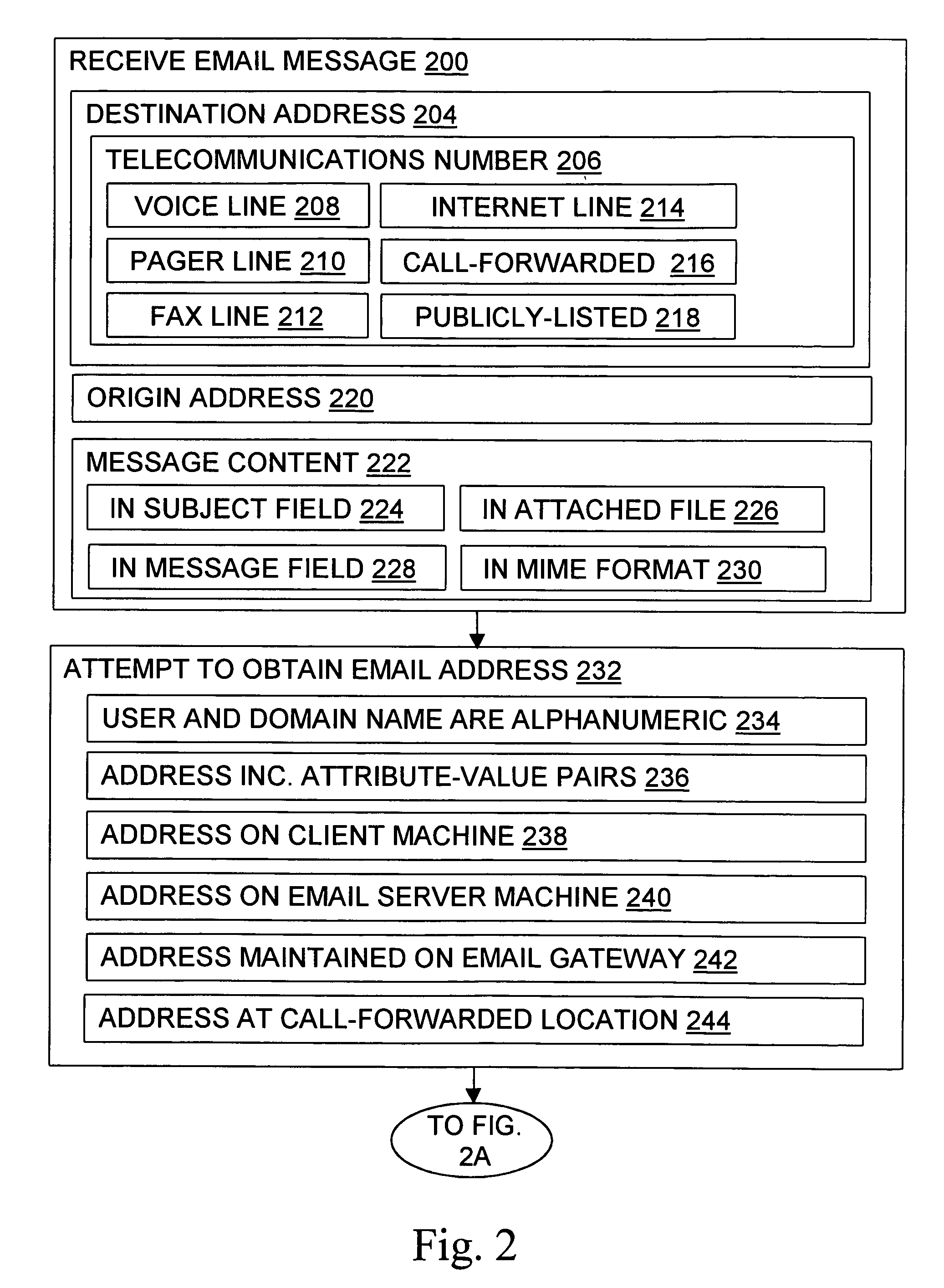
Methods, devices, signals, and systems are provided in a message routing architecture which provides improved capabilities for integrating “digital” communication through email messages with “analog” communication through voice and / or fax or pager messages. Email can be addressed using nothing more than a standard telephone or fax number. If the registered owner of the telephone or fax number has a corresponding email address, then the invention converts the telephone or fax number to the email address for delivery and uses standard email delivery systems to deliver the message. If no conventional delivery email address is known, or if the message sender or recipient specify multiple delivery modes, then the email message content is transformed into voice, pager and / or fax content and delivered to the recipient using the telephone or fax number which was specified as the email address. Familiar telecommunications services such as call forwarding and selective call blocking can also be used with messages that originate as email. The invention also supports use of telecommunications numbers as indexes into databases which contain public key certificates, to make it unnecessary for a proposed message recipient to provide its public key expressly in advance to each particular proposed message originator.
Owner:HAMILTON MICHAEL +1
Electronic calendar with group scheduling and storage of user and resource profiles
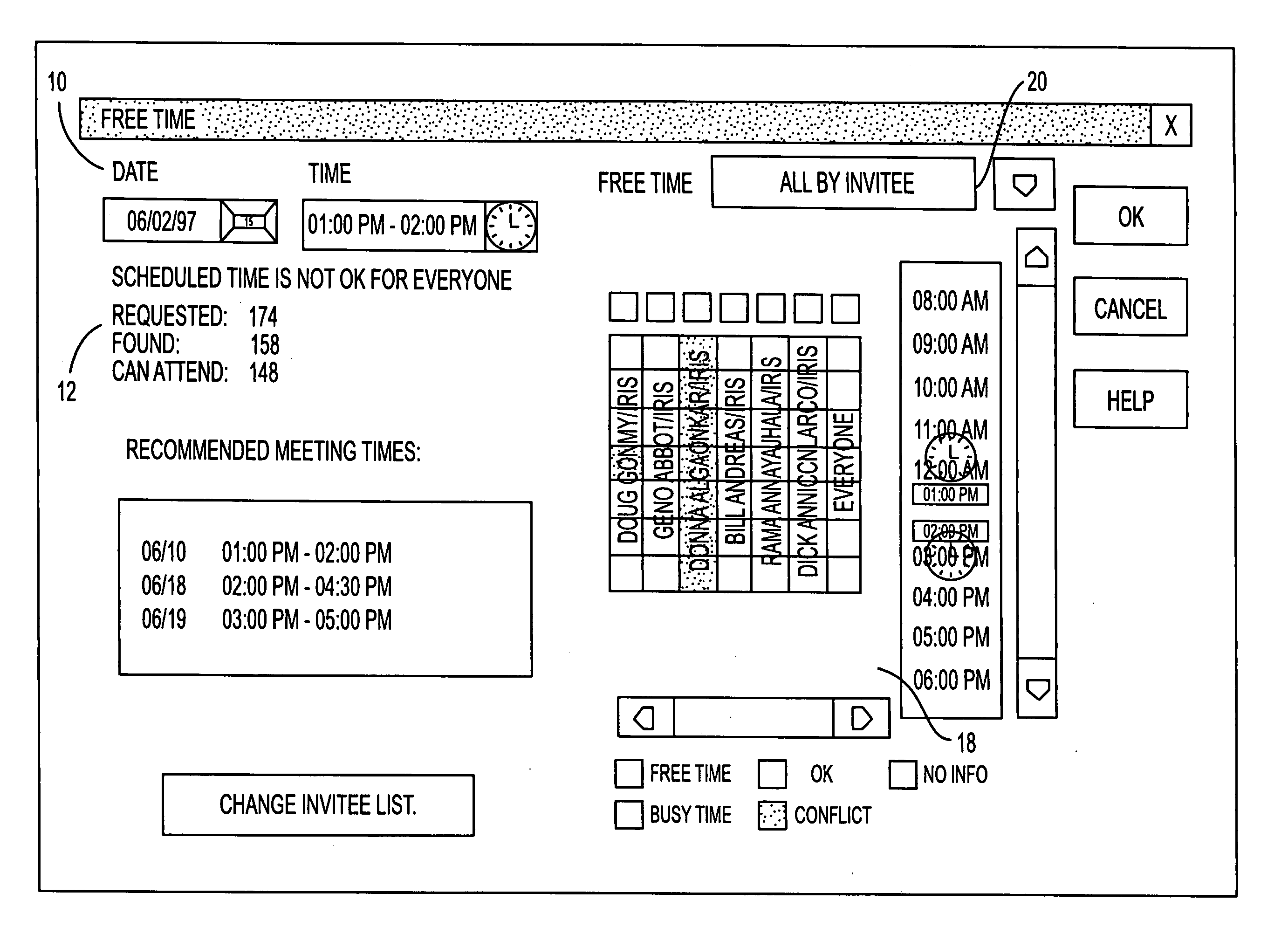
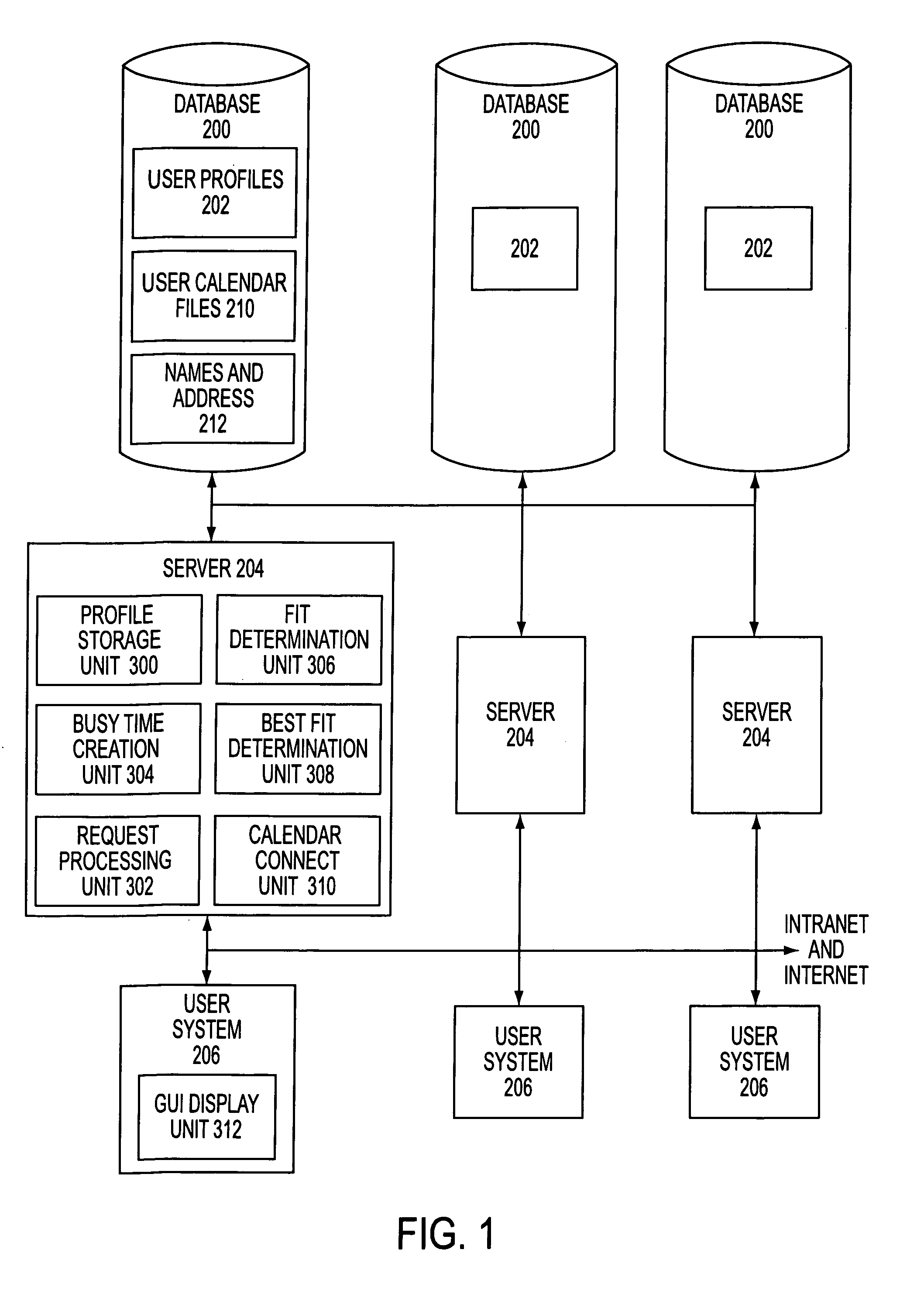
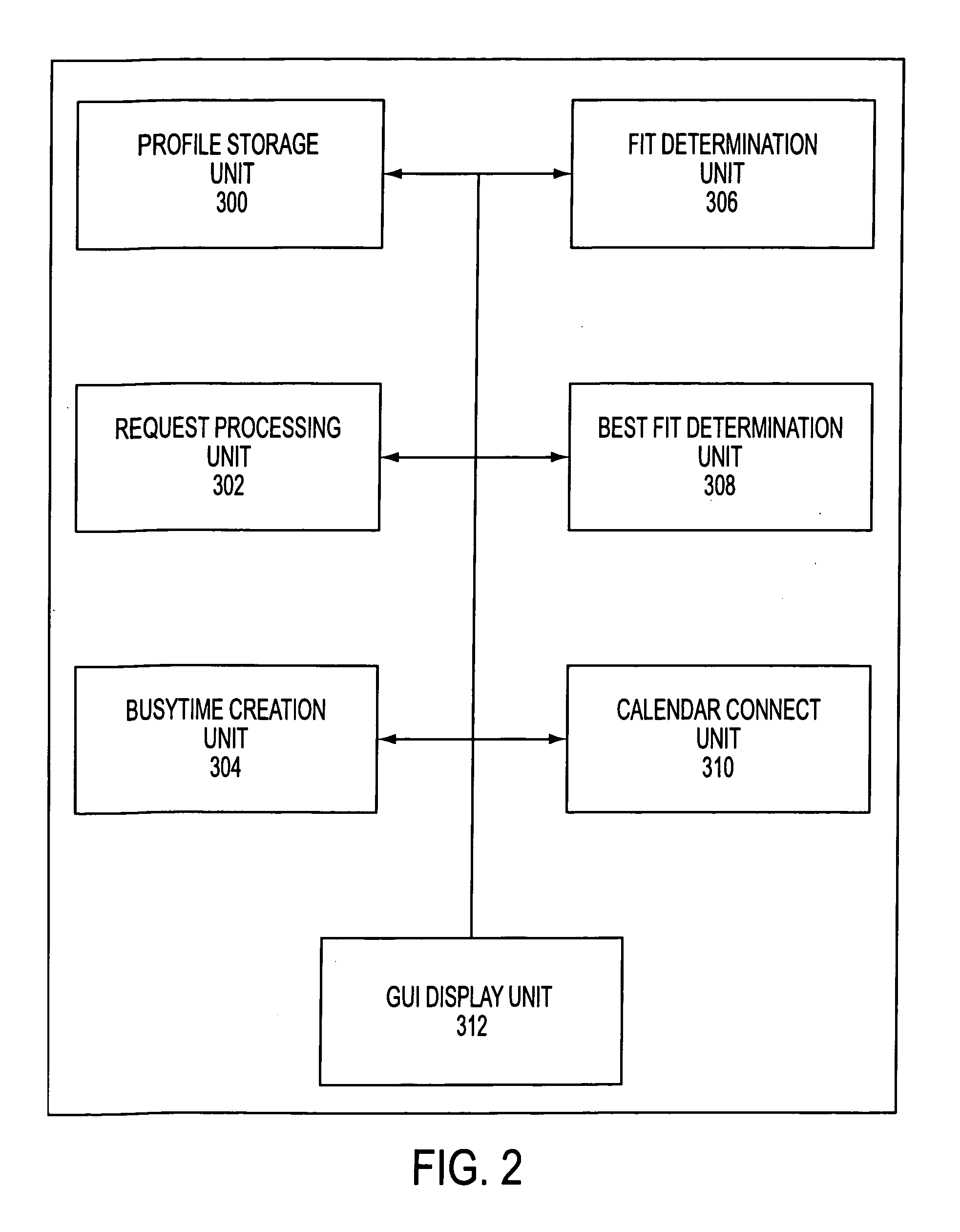
InactiveUS7082402B2Convenient treatmentEnhanced information management capabilityText processingOffice automationBusy timeEmail address
A system for scheduling time intervals for a plurality of users comprises a database associated with one or more server means for storing a profile for each potential invitee of the system. Each invitee profile comprises user profiles that have information regarding available and unavailable times for that user and the electronic mail address for the user and resource profiles having information about the available times for a particular resource such as a room or equipment. A request generator connected over a network to the one or more server generates a request for allocation of a time interval for one or more of the plurality of invitees. The system then provides a busy time determination device that gathers the profiles for the plurality of invitees that were requested by the request generating means and that are available in the databases and determines whether those invitees are available during the time interval requested by the request generating means. For all available invitees, the electronic mail address in the profile is used to send each available requested invitee an invitation to attend at the requested time interval.
Owner:IBM CORP
Method and apparatus for adding data attributes to e-mail messages to enhance the analysis of delivery failures
InactiveUS6959324B1Multiple digital computer combinationsData switching networksEmail addressMessage delivery
A dead e-mail identification locator discovers dead e-mail addresses without forwarding messages to valid recipients. Existing headers in the mail protocol are extended to include a test header. A mail server that supports the protocol extension of the present invention may send a reply if the address does not exist and may discard the message if the address does exist. The test header allows a sender to test an e-mail address for validity without the message being forwarded to the user, as will be described below. The sender may be a dead e-mail locator program, which tests a plurality of e-mail addresses. The sender and recipient mail servers may include attributes in the test header to enhance the analysis of delivery failures. Using these attributes, the dead e-mail address locator can pinpoint the location of e-mail message delivery failure and profile the performance of routing of messages and other details hidden from users.
Owner:SNAP INC
Identity theft and fraud protection system and method
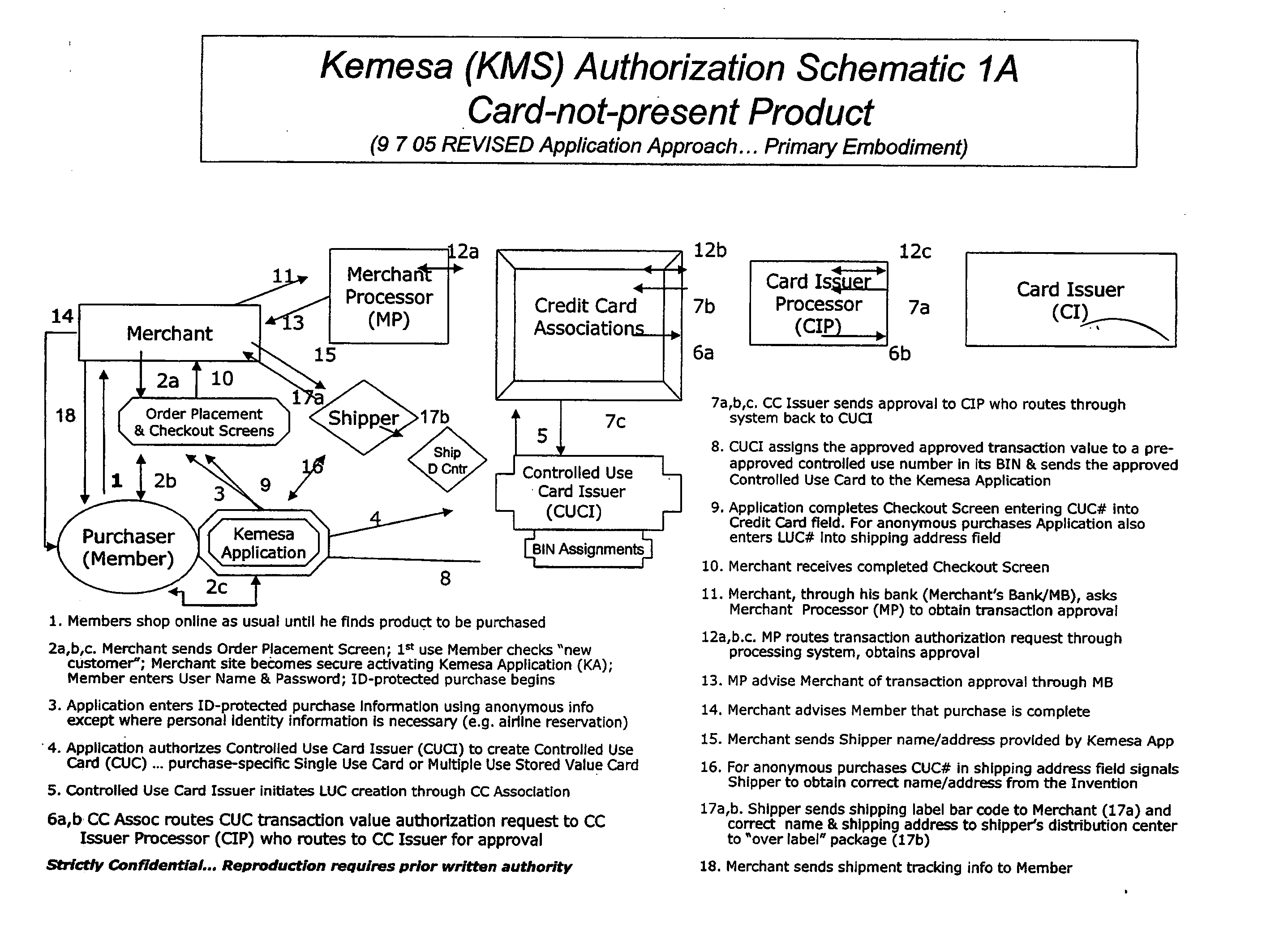
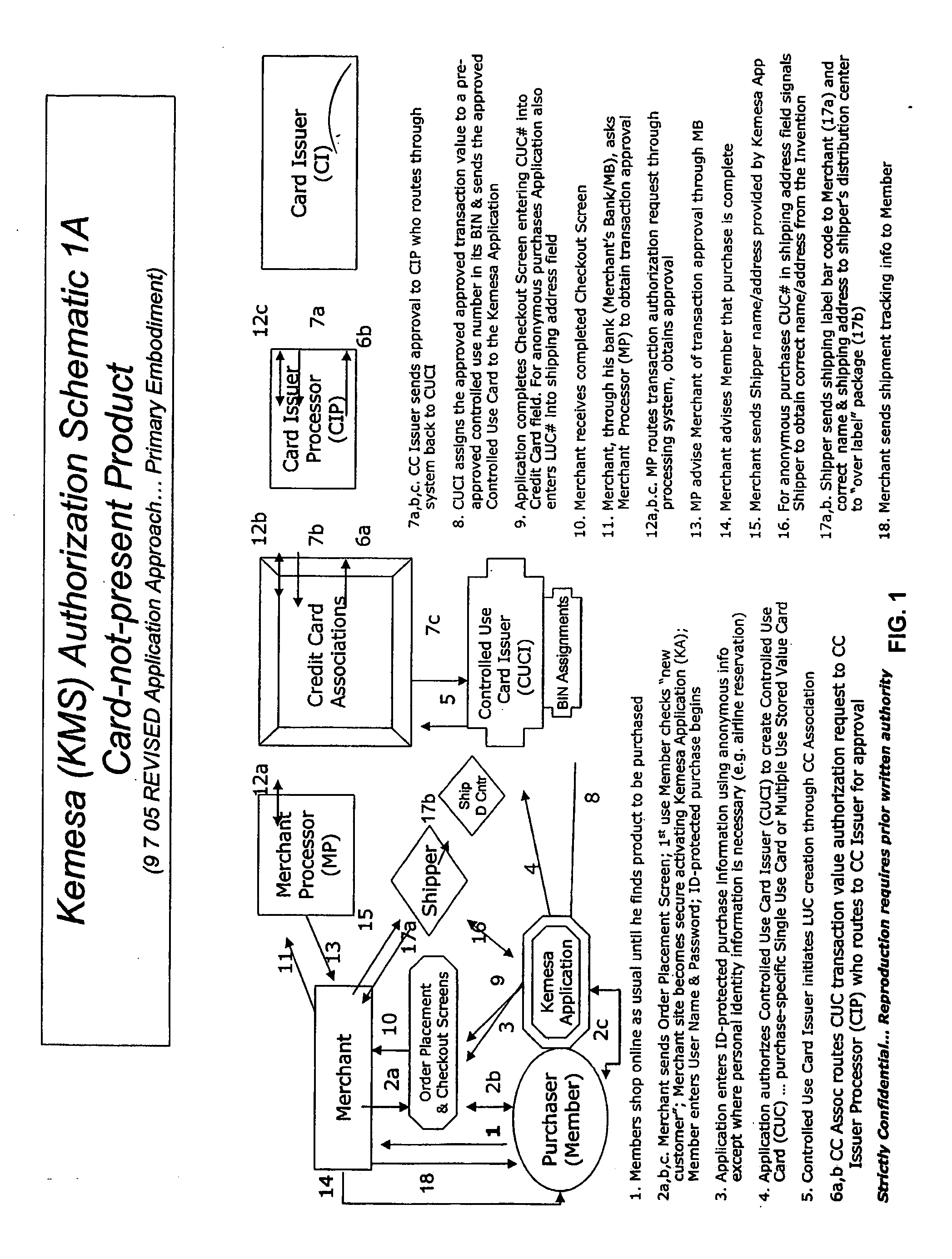
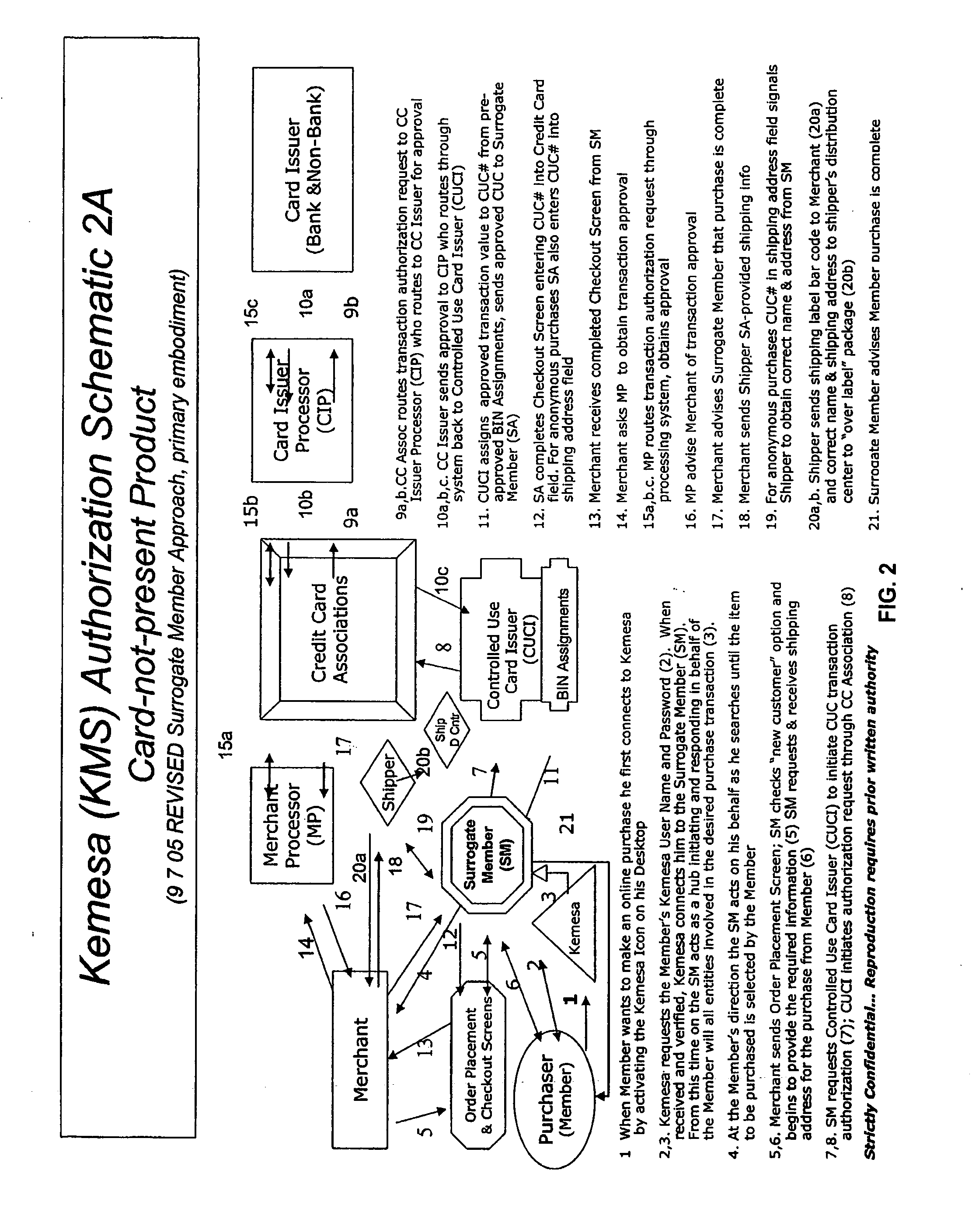
ActiveUS20070083460A1Prevent theftMaximum anonymityFinanceDigital data protectionCredit cardEmail address
A system and method for preventing personal identity theft when making online and offline purchases requires a purchaser to first subscribe and become a member user by registering and providing relevant personal identity information. Once registered, the member is assigned a user name and a password. The subscribing member's personal identity information is then encrypted and stored at one or more highly secure locations. The ID protection system obtains a controlled use card (CUC) through a CUC issuer on behalf of the member for use to make each purchase transaction. The CUC is anonymous with respect to user (member) identity and may be a purchase-specific single-use card or a multiple-use stored value card with no traceable connection to any other financial account. When the member makes a secure online purchase, the system software enters anonymous information (i.e. not revealing the member's real name, email address, billing information, etc.) on the merchant's order placement screen, except in instances where the member's real identity information is required (e.g. airline tickets). The merchant receives the completed checkout screen, obtains credit approval through a credit card association, and sends the shipping information to a shipper which independently obtains the correct shipping name and address from the ID protection system prior to shipping the purchased product(s).
Owner:VIPR SYST +1
System and method for facilitating user input by providing dynamically generated completion information
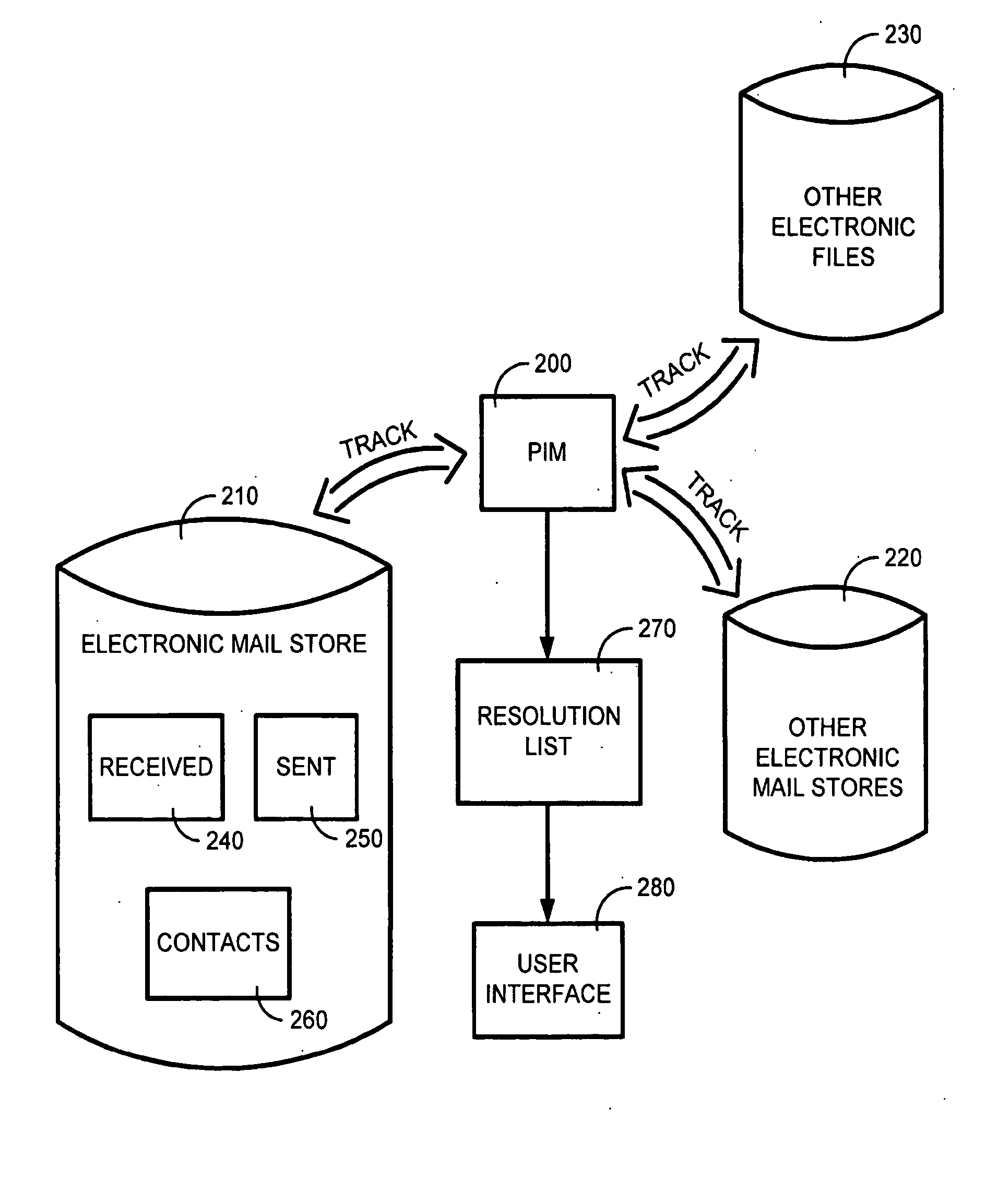
InactiveUS20050108344A1Facilitate user inputText processingMultiple digital computer combinationsEmail addressUser input
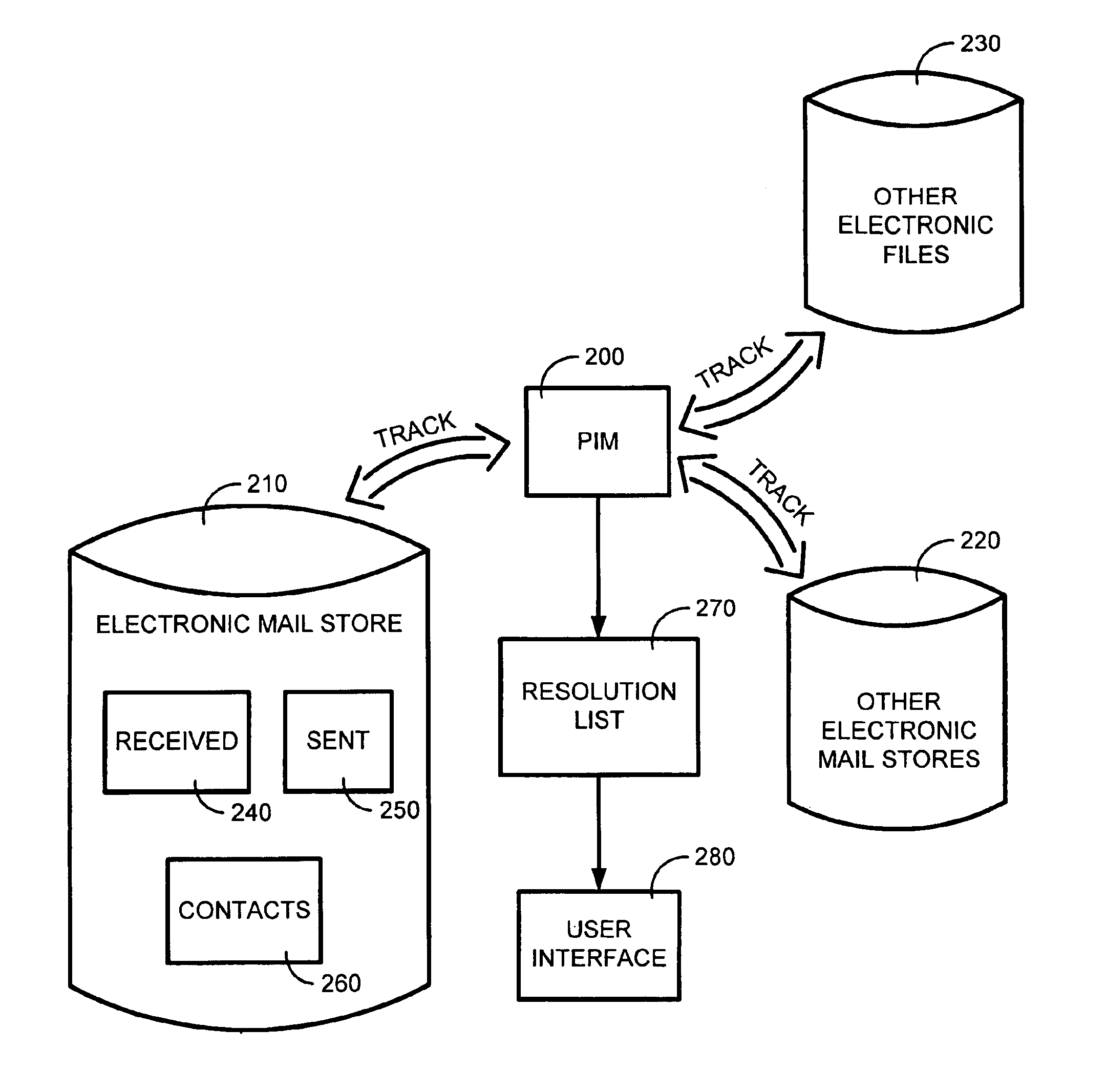
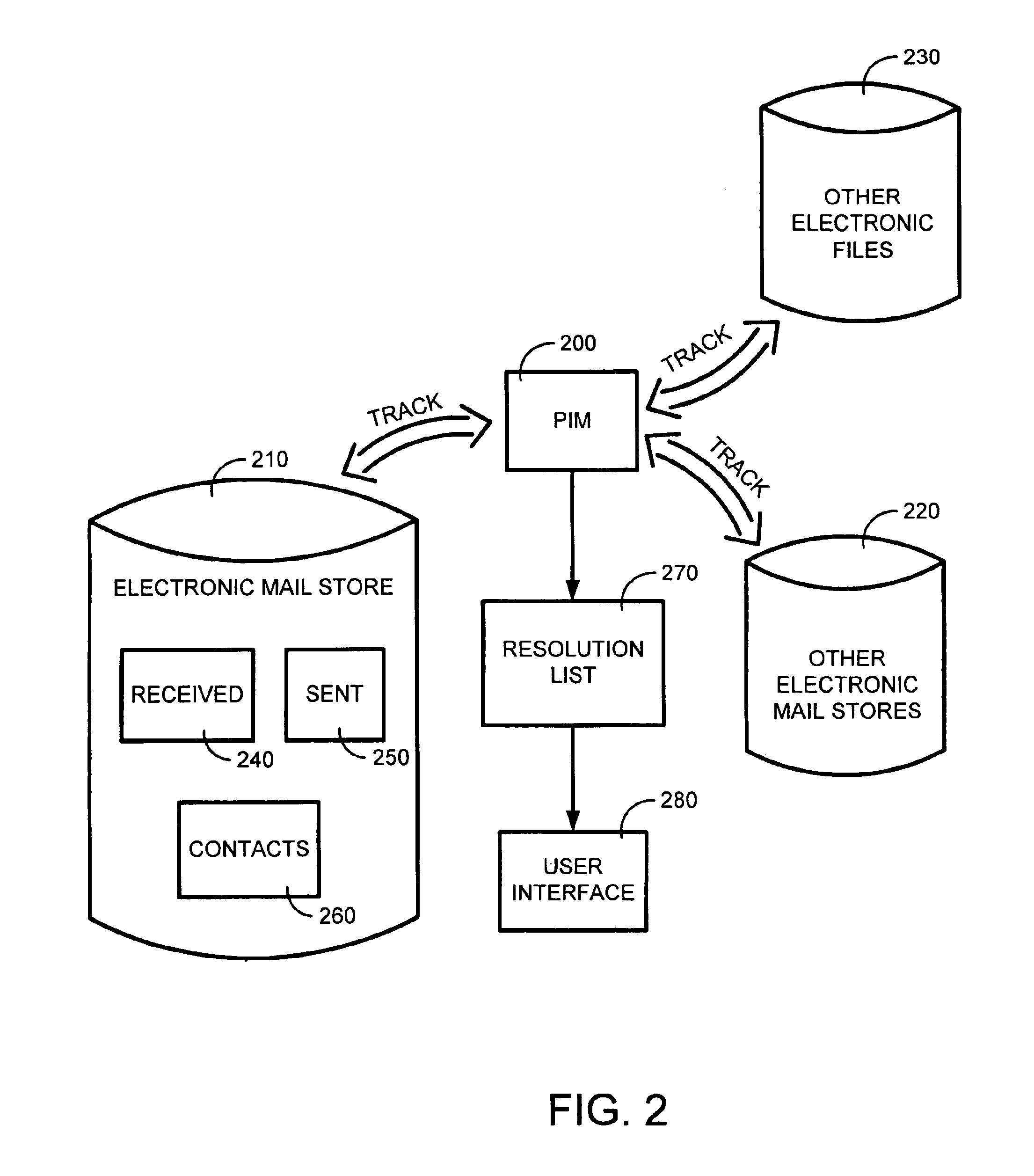
The system and method of the present invention automatically provides dynamically generated completion information for facilitating user input of email addresses or contact information. This completion information is developed from a “data store” comprised of multiple data sources such as previously sent or received email, and other types of electronic files such as word processor or spreadsheet files. The present invention monitors and uses the information in the data store to automatically store, track, maintain, and organize data entries in a dynamic “resolution list”. As a user begins to input an email address or contact, the present invention can either automatically complete the entry using a most probable result from the resolution list, or can display a list of likely matches from which the user may select the desired email address or contact.
Owner:MICROSOFT TECH LICENSING LLC
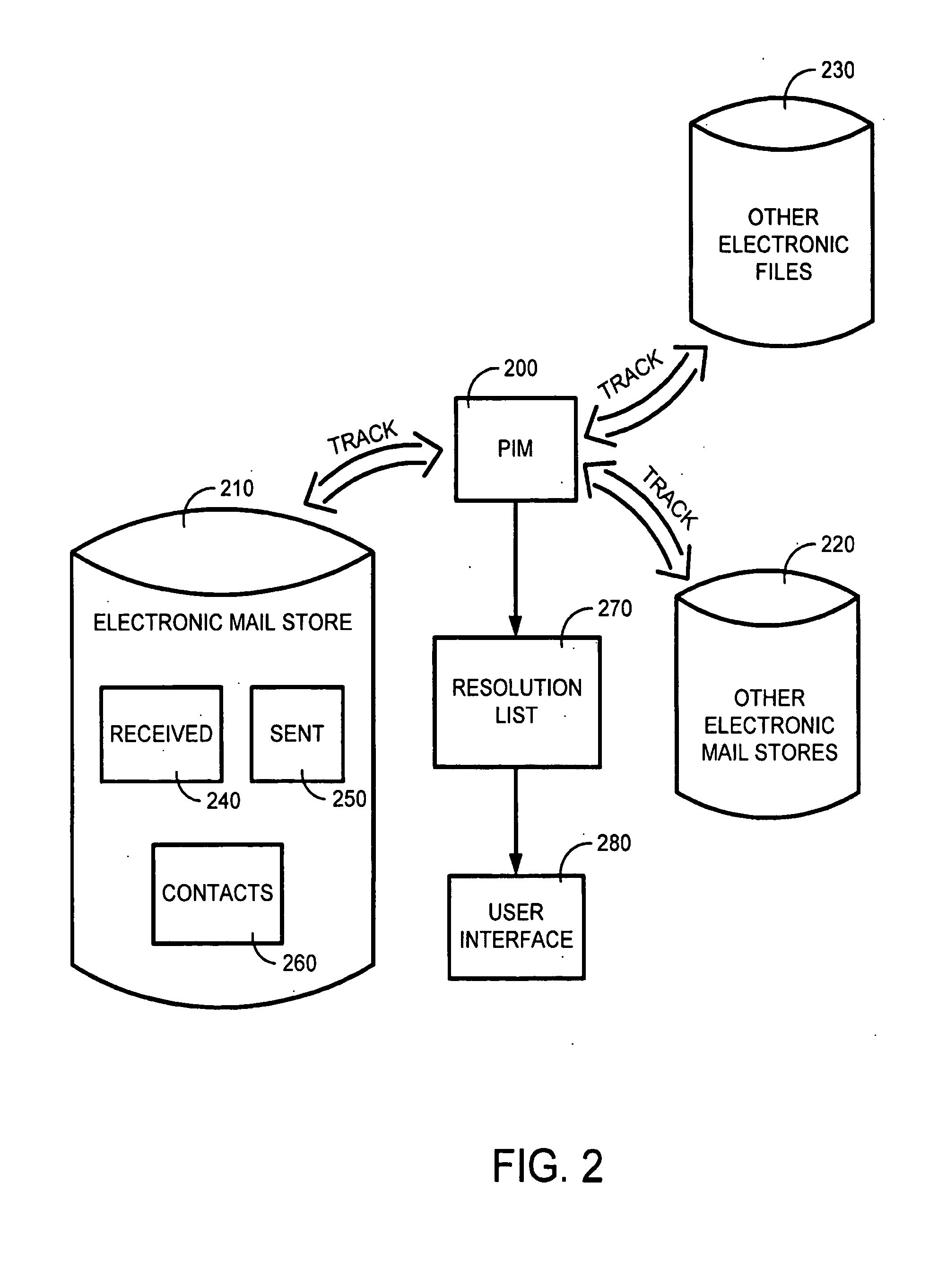
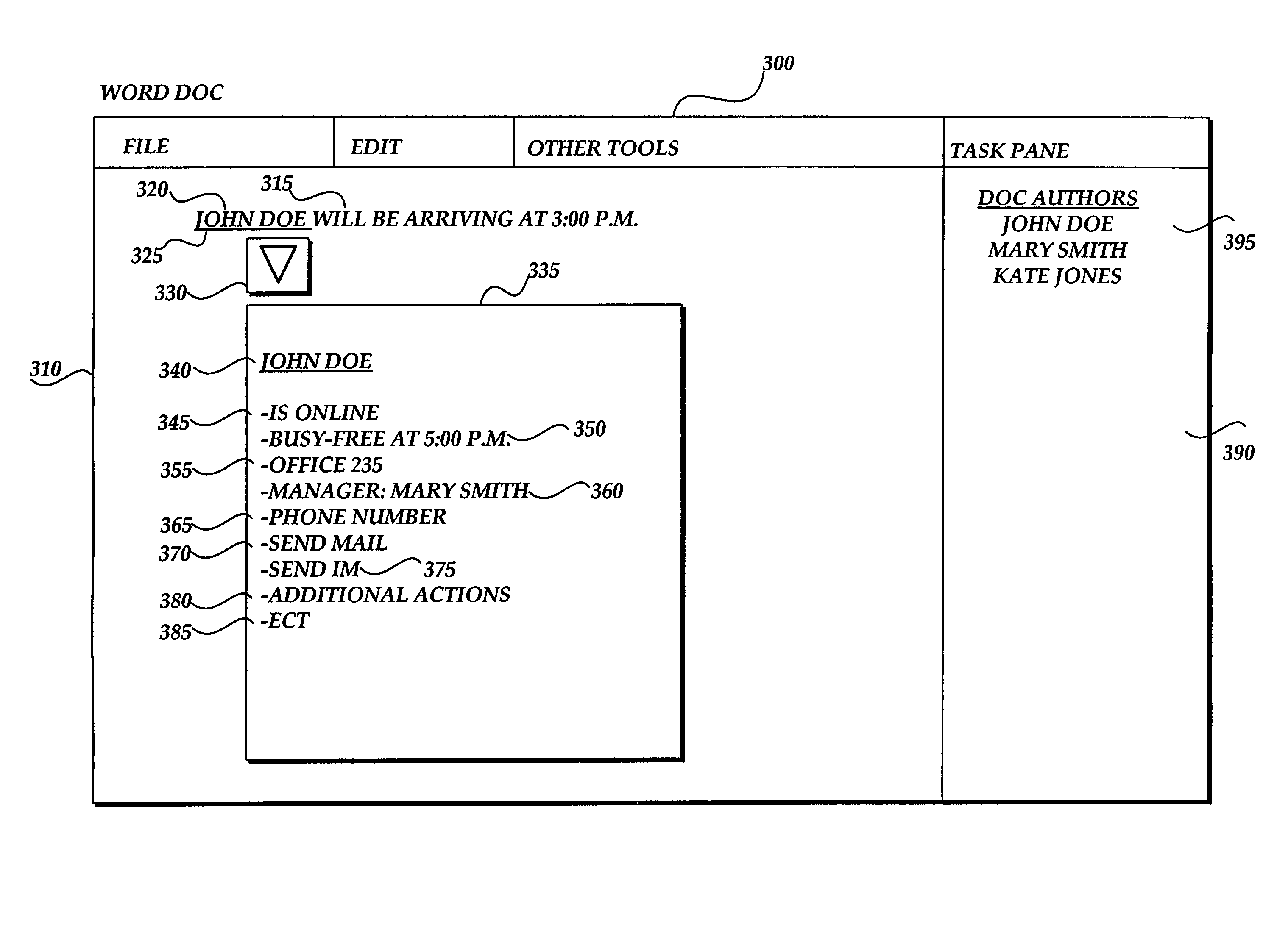
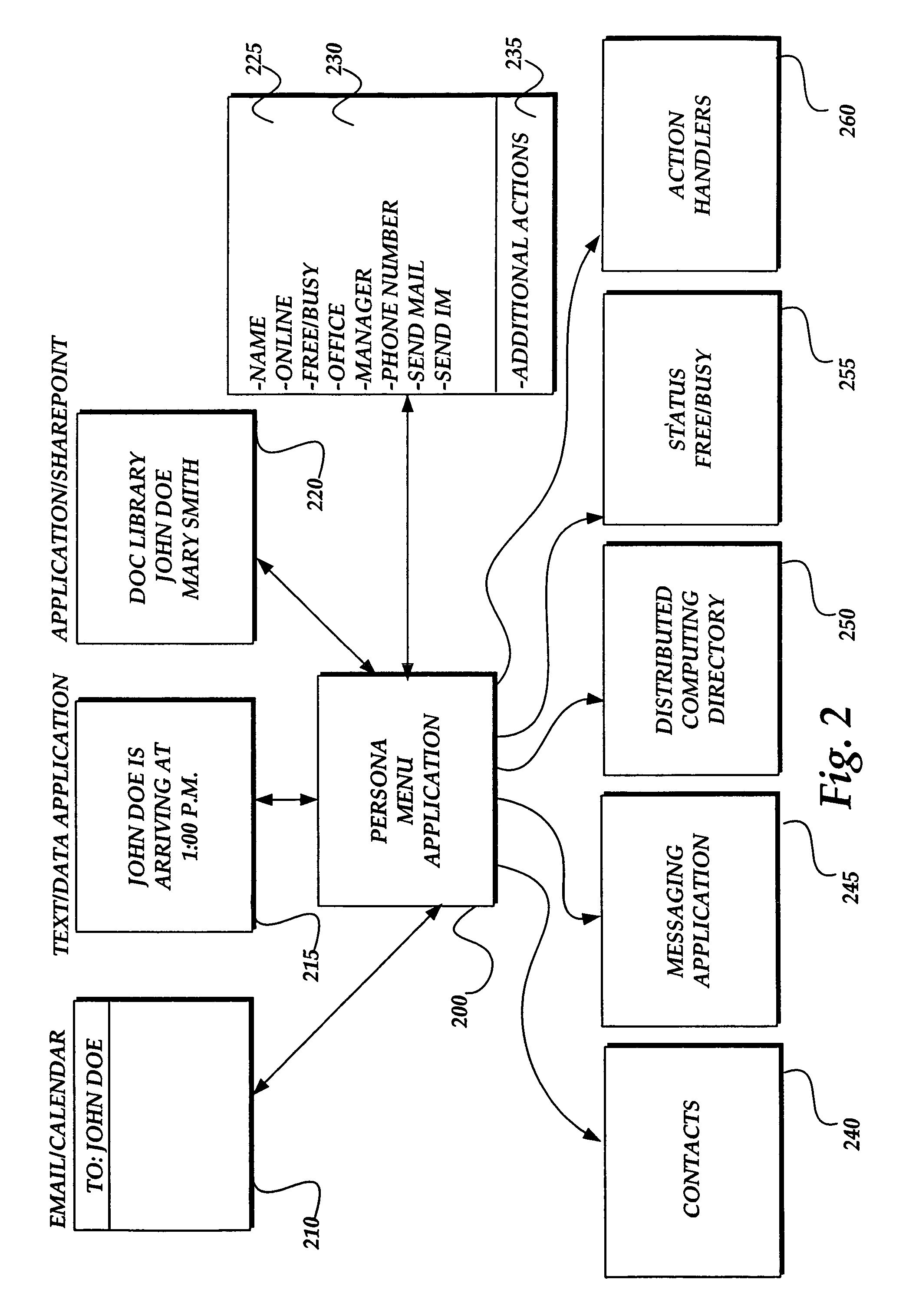
Persona menu
InactiveUS7634732B1Quickly and efficiently viewOffice automationInput/output processes for data processingElectronic documentEmail address
Methods and systems provide for aggregating person-centric data from one or more data sources and for providing the aggregated data to a user via a computer-displayed user interface that is keyed on or otherwise associated with an identified name in electronically presented text or data. A name in the text or data of an electronic document is identified and is associated with a unique identification, such as an electronic mail address. The unique identification is used by a persona menu application to obtain person-centric data from a variety of data sources. Example data sources include electronic mail contact files, electronic mail and calendaring system free / busy status files, directories of person-centric data related to persons associated with a distributed computing network, and instant messaging files. A data structure is populated with the returned data. Upon user selection, a user interface containing aggregated data associated with the identified name is displayed to the user to provide the user helpful information and actions associated with the identified name.
Owner:MICROSOFT TECH LICENSING LLC
System and method for automatically populating a dynamic resolution list
The system and method of the present invention automatically provides dynamically generated completion information for facilitating user input of email addresses or contact information. This completion information is developed from a “data store” comprised of multiple data sources such as previously sent or received email, and other types of electronic files such as word processor or spreadsheet files. The present invention monitors and uses the information in the data store to automatically store, track, maintain, and organize data entries in a dynamic “resolution list”. As a user begins to input an email address or contact, the present invention can either automatically complete the entry using a most probable result from the resolution list, or can display a list of likely matches from which the user may select the desired email address or contact.
Owner:MICROSOFT TECH LICENSING LLC
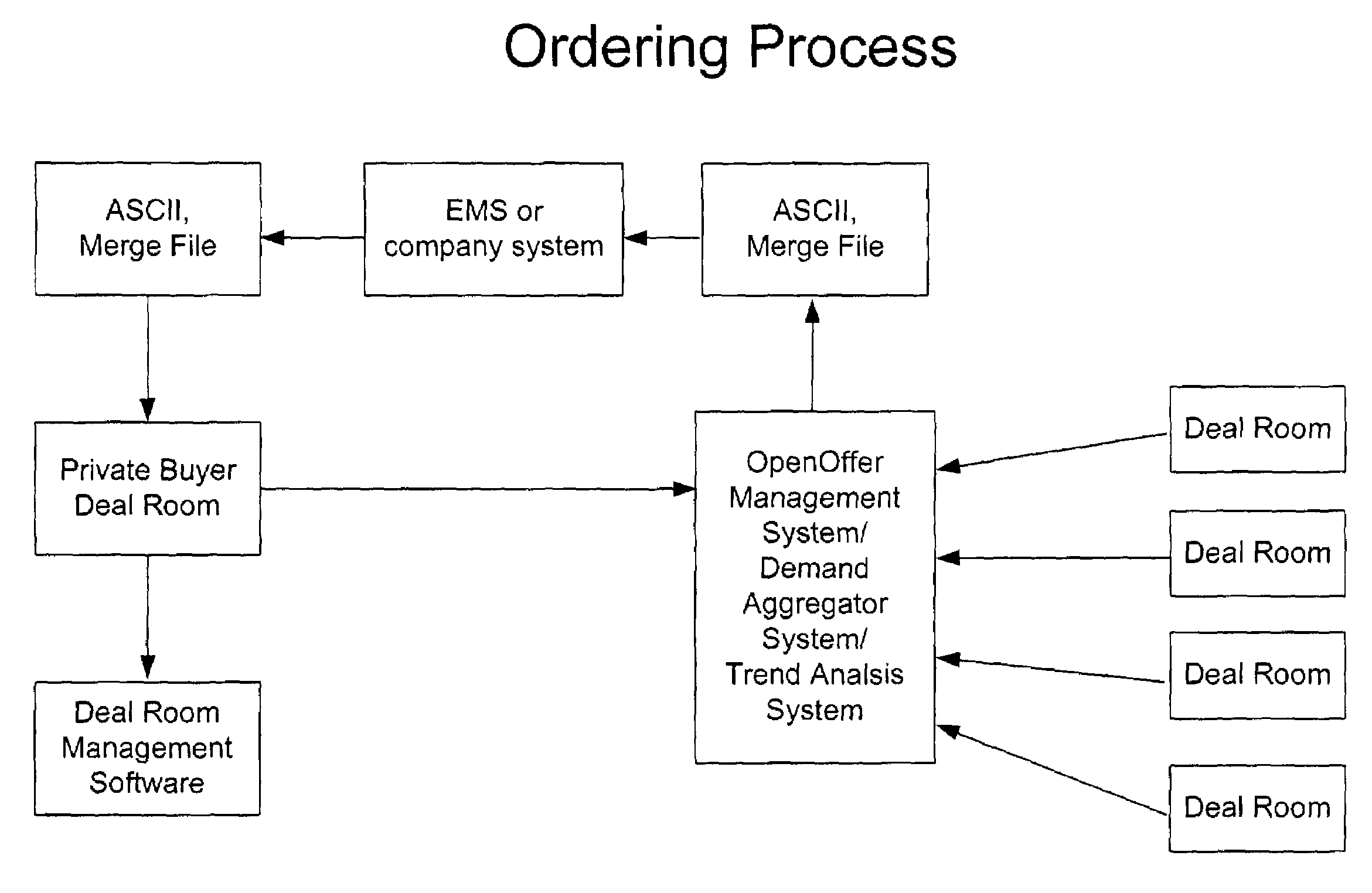
Demand aggregation system
The demand aggregation system includes buyer sponsored DealRooms, seller sponsored DealRooms, and multiple buyer and multiple seller sponsored DealRooms. Moreover, the demand aggregation system includes a customer relations management (CRM) package. In the CRM package, information on buyer and prospective buyers are loaded into a database that can include information such as: individual name; company name and address; email address; phone number; cell number; products purchased; volumes; time of purchase. Further the CRM package can be integrated with the demand aggregation system as well as a customer resource planning system (e.g., MRP, ERP).
Owner:EWIN WIN +1
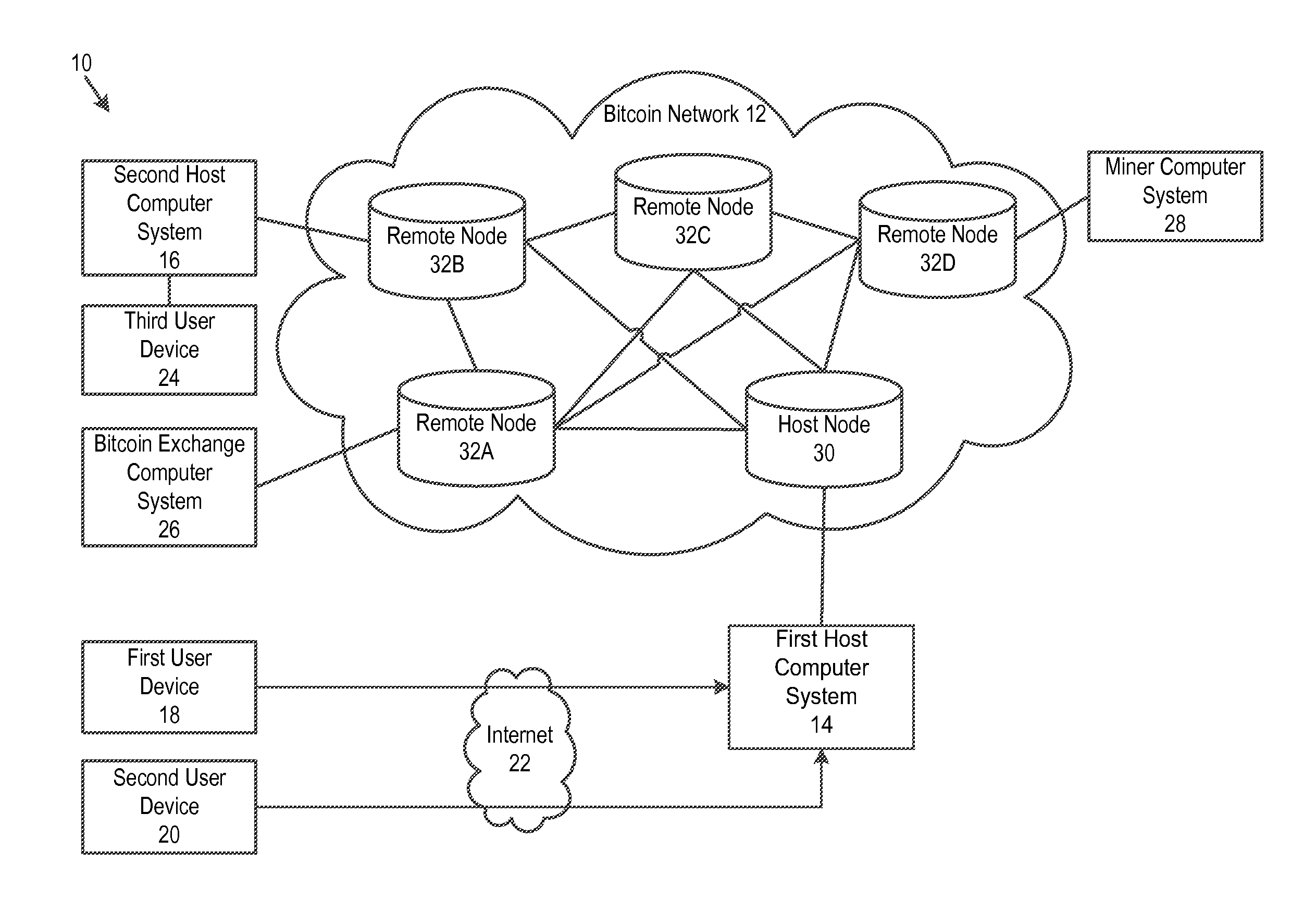
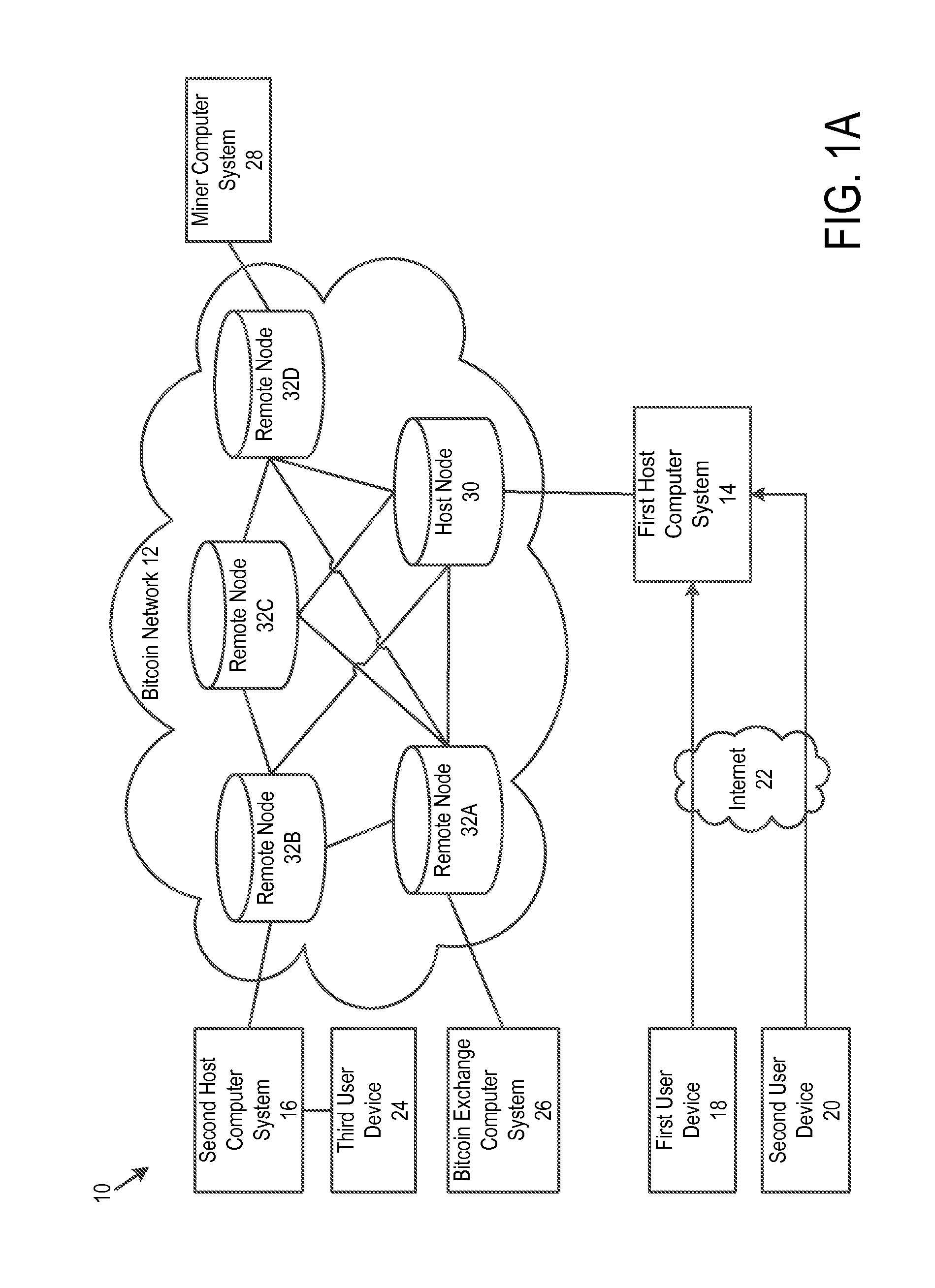
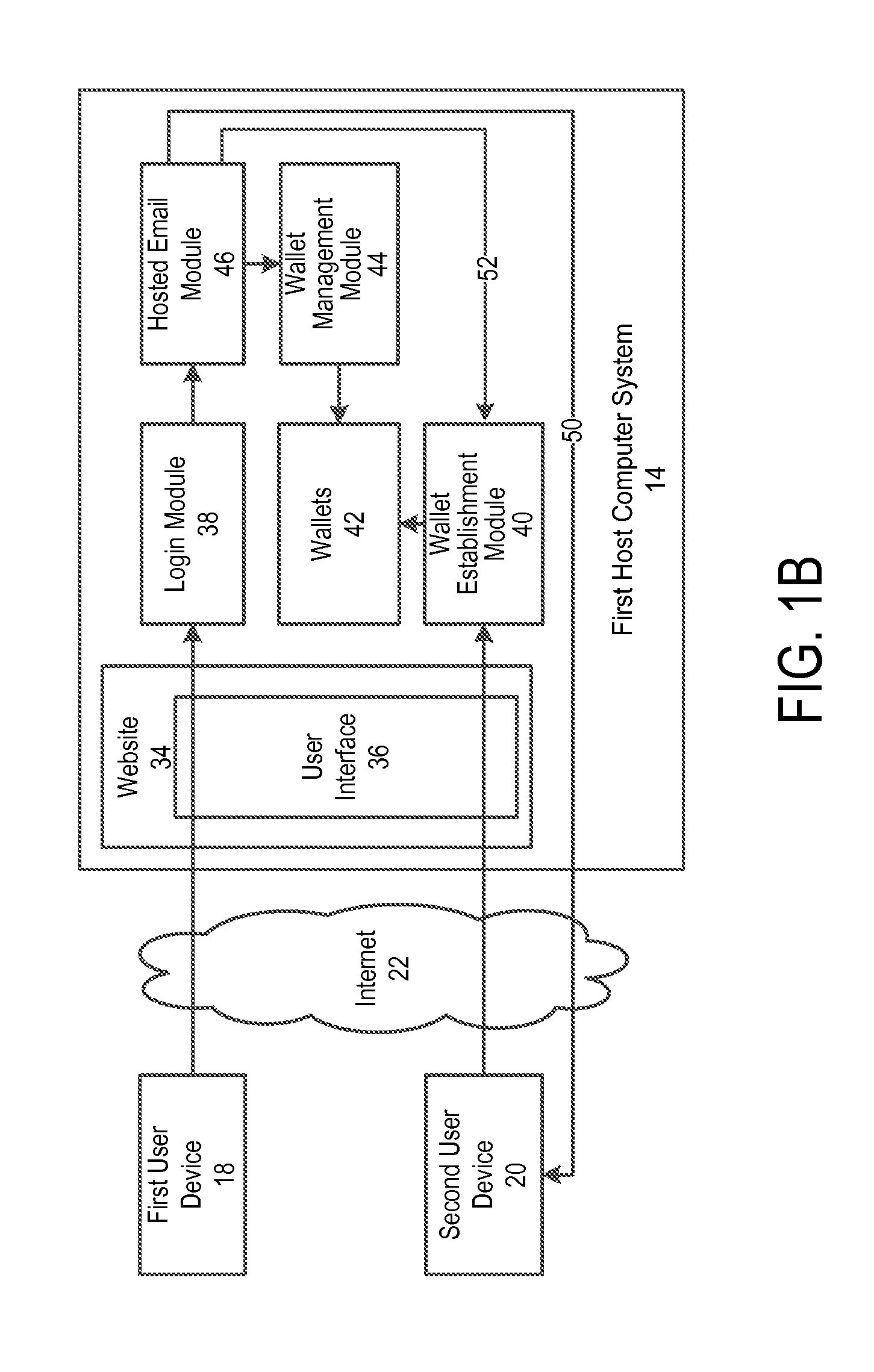
Off-block chain transactions in combination with on-block chain transactions
A system and method for transaction bitcoin is described. Bitcoin can be sent to an email address. No miner's fee is paid by a host computer system. Hot wallet functionality is provided that transfers values of some Bitcoin addresses to a vault for purposes of security. A private key of a Bitcoin address of the vault is split and distributed to keep the vault secure. Instant exchange allows for merchants and customers to lock in a local currency price. A vault has multiple email addresses to authorize a transfer of bitcoin out of the vault. User can opt to have private keys stored in locations that are under their control. A tip button rewards content creators for their efforts. A bitcoin exchange allows for users to set prices that they are willing to sell or buy bitcoin and execute such trades.
Owner:COINBASE
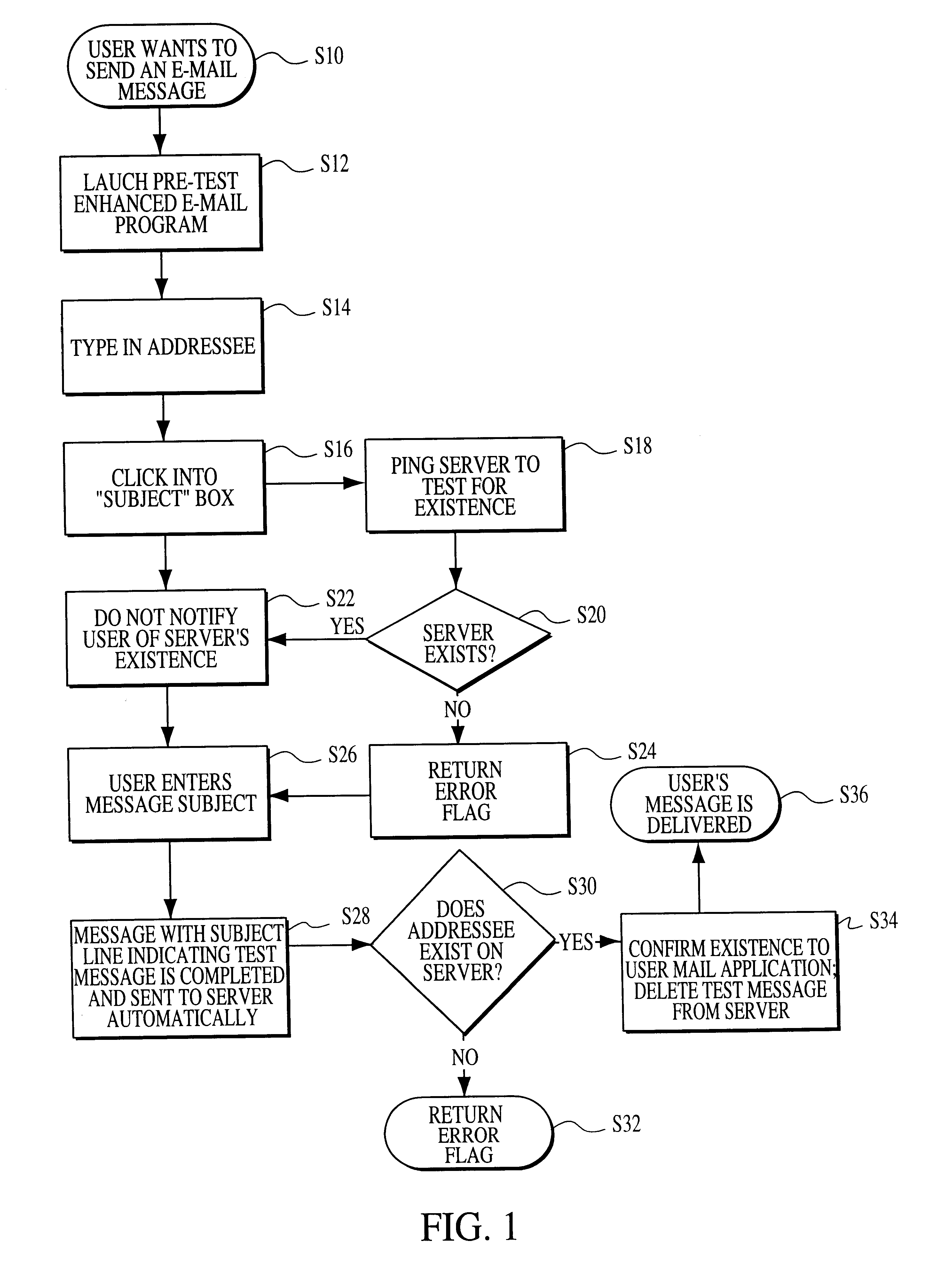
Pre test electronic mail process
InactiveUS6434601B1Easy to mergeEliminating the potential of losingMultiple digital computer combinationsData switching networksEmail addressInternet privacy
The present invention provides a method and apparatus which operates completely in the background (i.e., transparent to the user) to verify the validity of an addressee's Internet e-mail address. The invention seeks to prevent the delivery of an e-mail message having an incorrect user name, server name, or a misspelling in either or both in the addressee's Internet e-mail address. If an error is detected, it is called to the sender's attention, where it may be corrected before the message is sent.
Owner:ROUND ROCK RES LLC +1
Method for creating a whitelist for processing e-mails
ActiveUS20050080855A1Multiple digital computer combinationsData switching networksEmail addressAddress book
A method of creating a whitelist for processing received e-mail messages. A whitelist is created by software running at an e-mail recipient's computer. The whitelist is constructed using e-mail addresses stored by the recipient (for instance, in an “address book”) as well as using the To:, Cc:, and Bcc: information of e-mails sent by the recipient. The subject line of a received message is also checked to see if it matches the subject line of a message recently sent by the user. If so, the sender is added to the whitelist.
Owner:PROOFPOINT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com