Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
436 results about "Directory entry" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
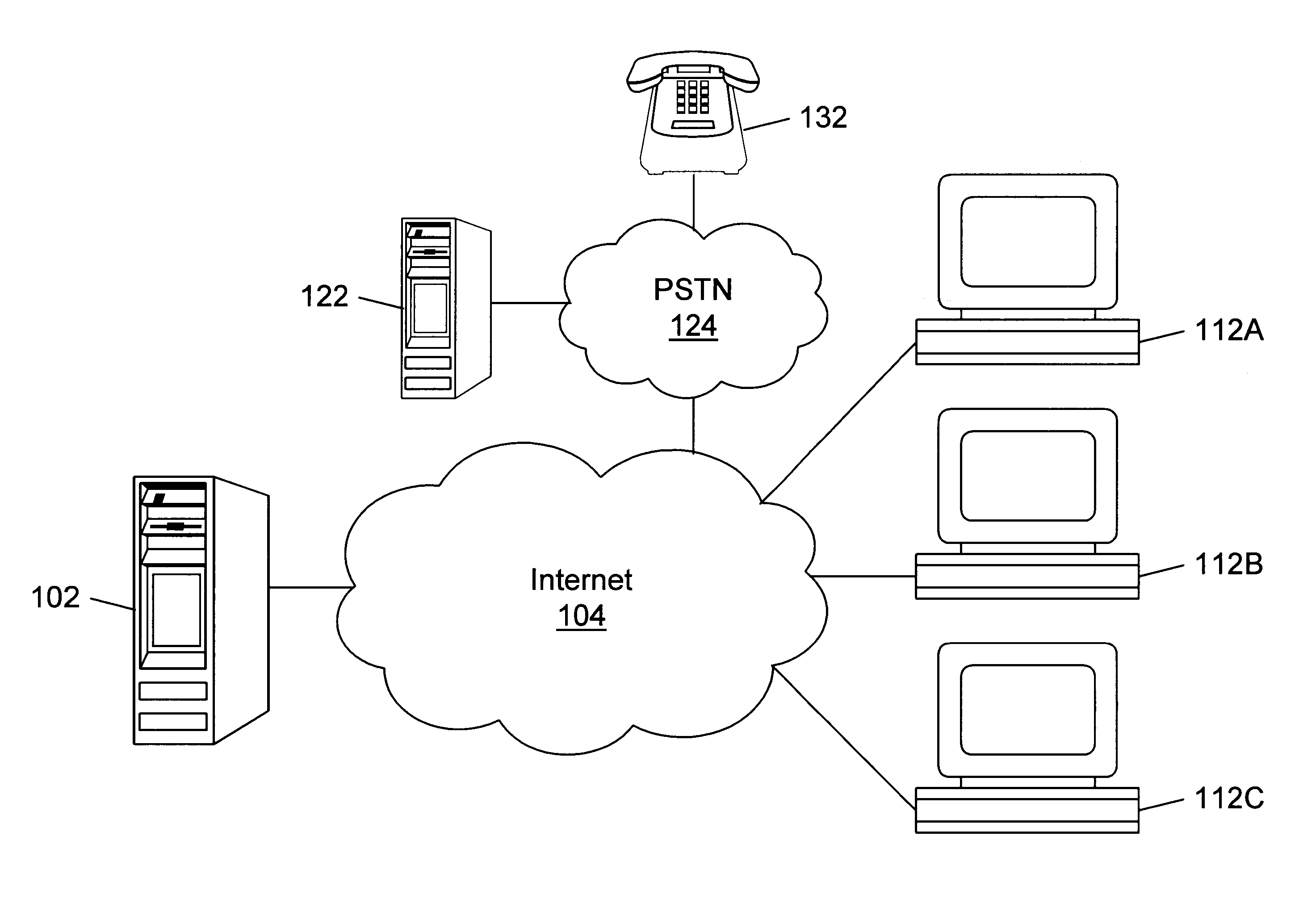
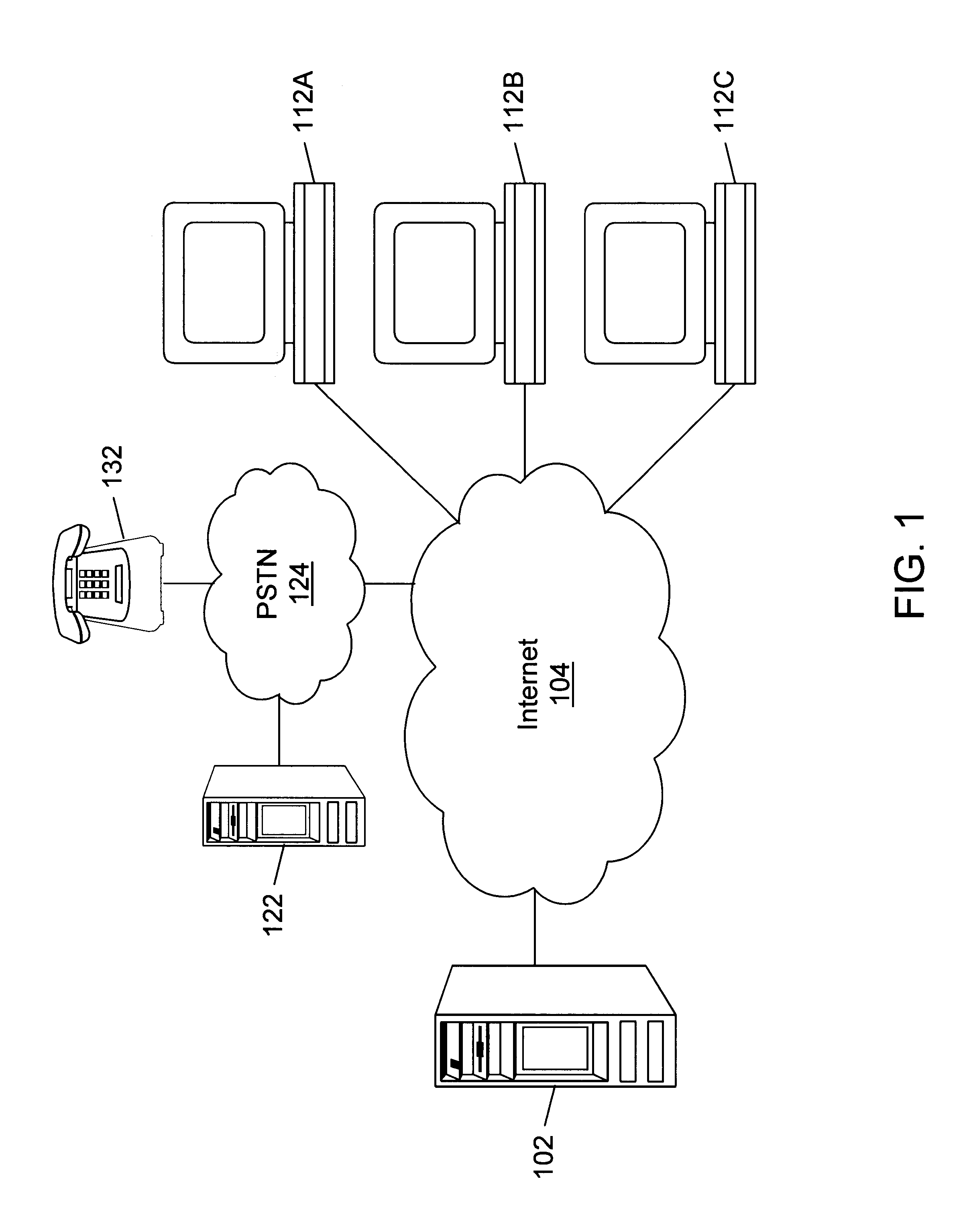
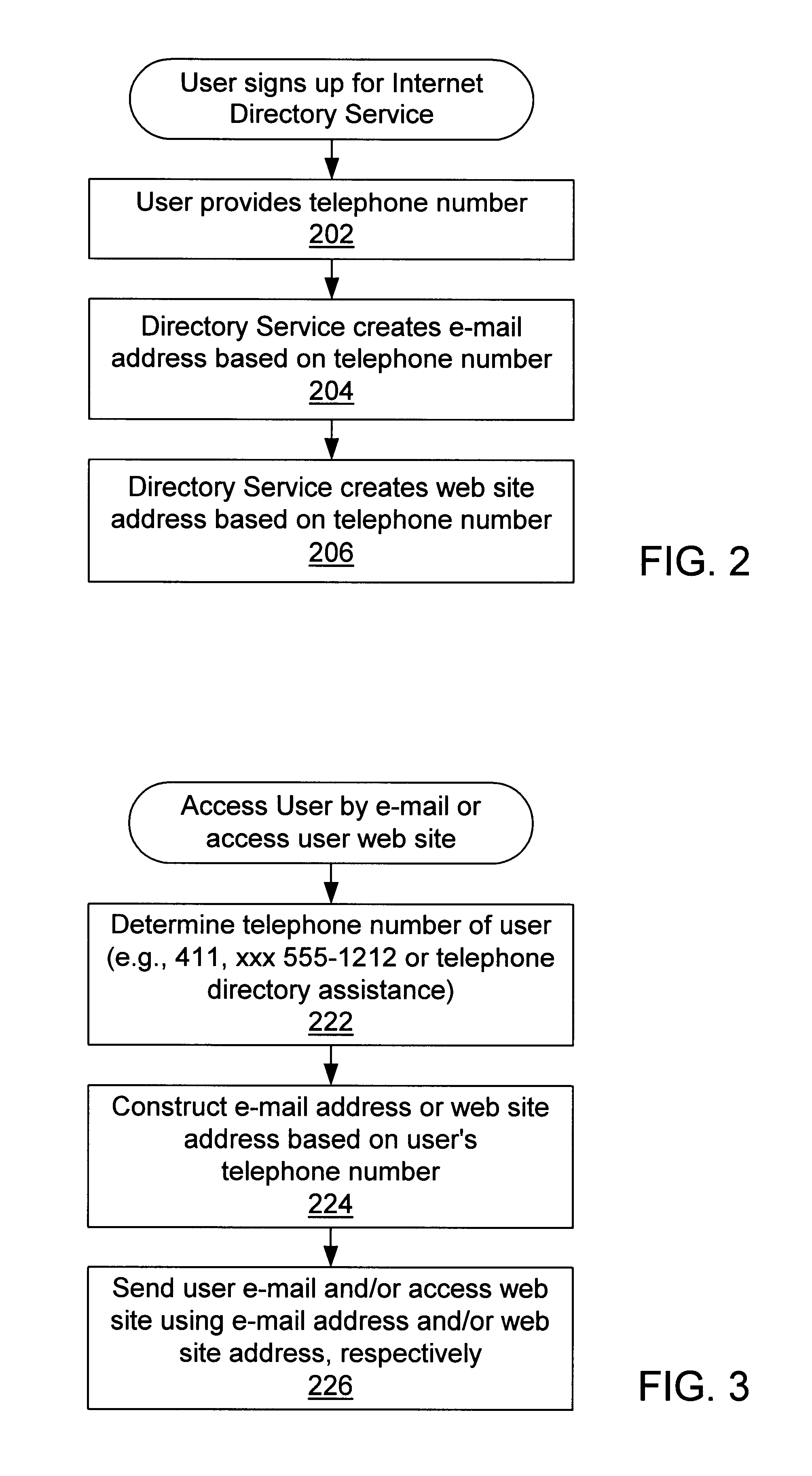
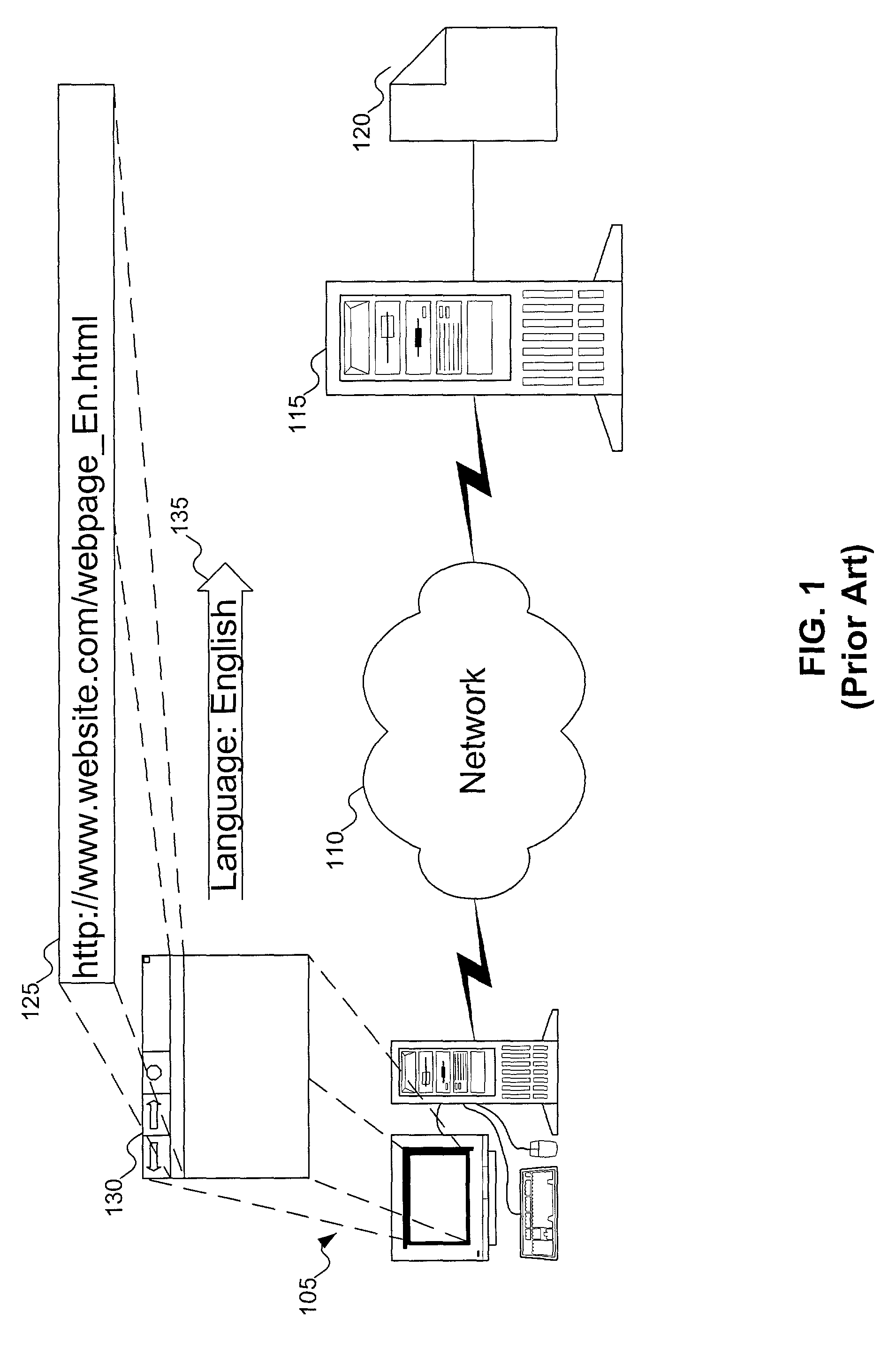
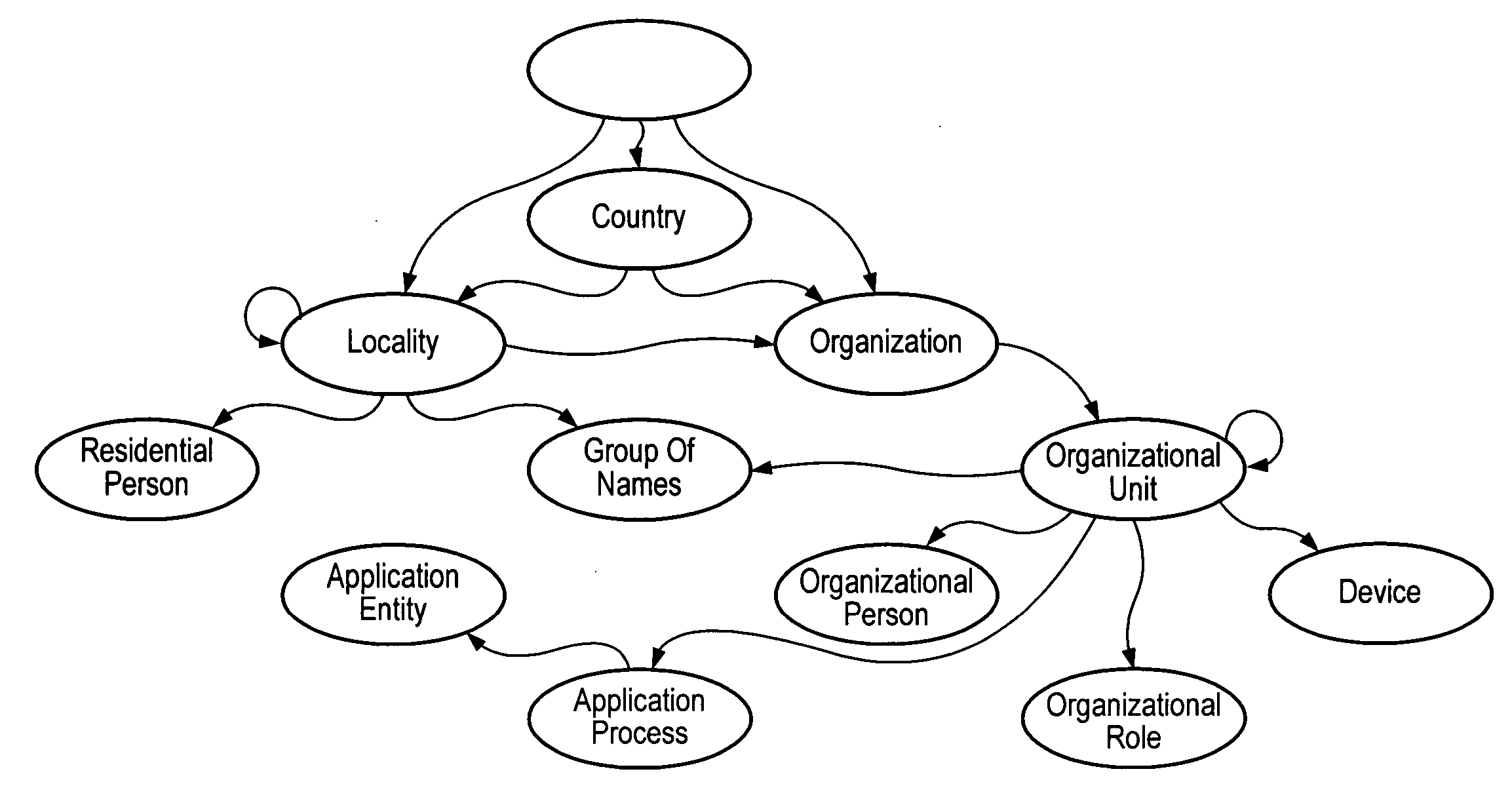
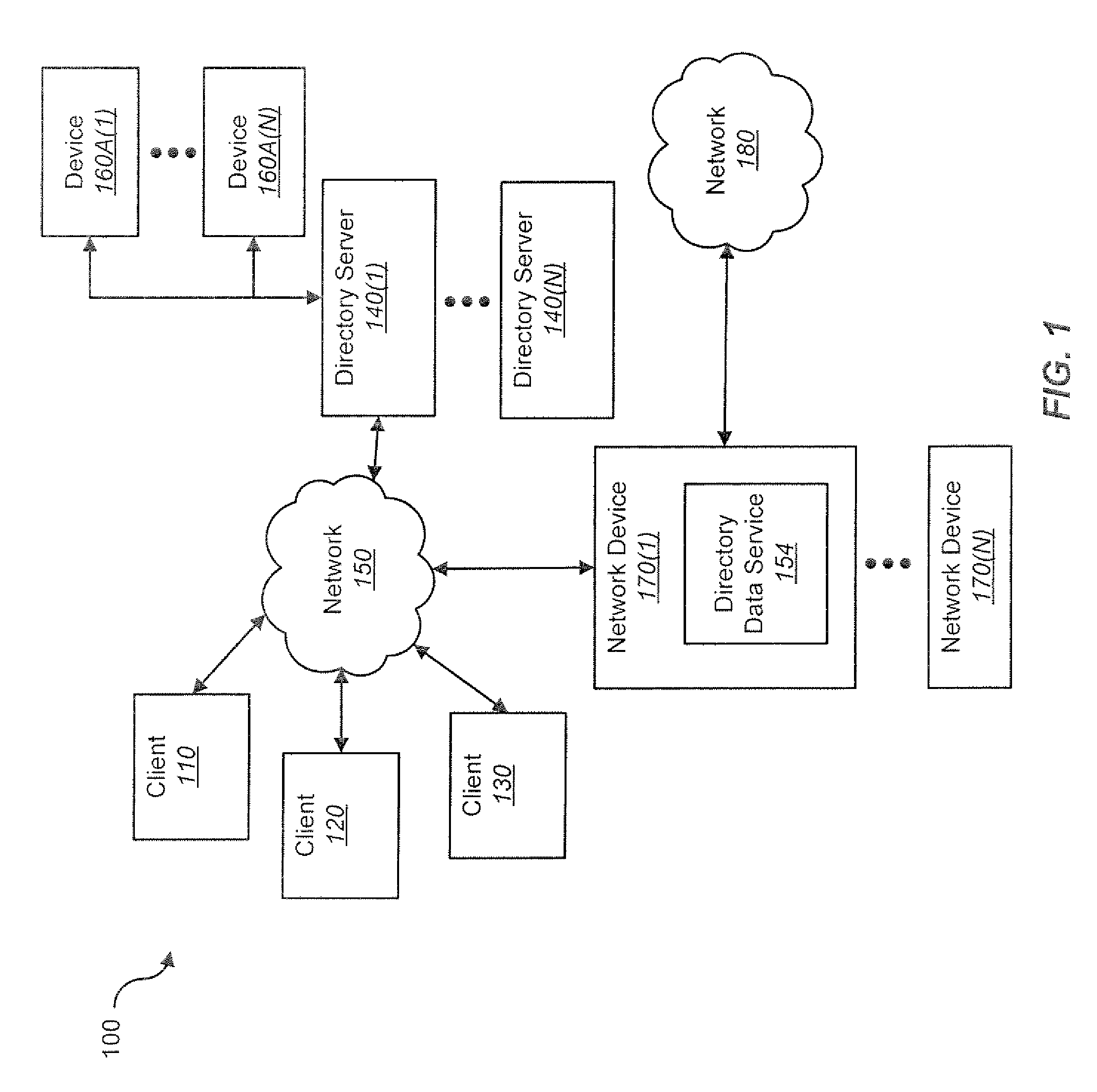
Internet directory system and method using telephone number based addressing
InactiveUS6788769B1Searches may be more readilyEasy to implementTelephone data network interconnectionsSpecial service for subscribersDomain nameEmail address
An Internet directory system and method that is based on user telephone number addressing. The system includes an interactive white and yellow pages directory that is based on telephone numbers. Thus, a user's telephone number is a unique identifier used to key other information within the directory. The telephone number may also be used as the primary component of an email address, domain name, or web site URL for the user. The use of a telephone number as the primary component of an e-mail address or domain name greatly simplifies the process of locating a user. E-mail addresses and domain names may be readily found using standard telephone information services, such as "411", as well as other telephone-based methods for obtaining telephone directory information. This Internet directory system and method brings all communication methods and directory services together using one searchable key, a user's telephone number. The directory entry page may be created, edited and updated by the subscriber using simple html editing or using a voice telephone call or via fax, without the use of a personal computer. Thus, the present invention provides an open directory model wherein the end users construct the directory, and the directory is "living", i.e., dynamically changeable and updateable. The power of the directory is thus placed in the users' hands. The telephone based Internet directory system of the present invention also provides addressing for unified messaging as well as locality in addressing.
Owner:WEISMAN SANFORD P
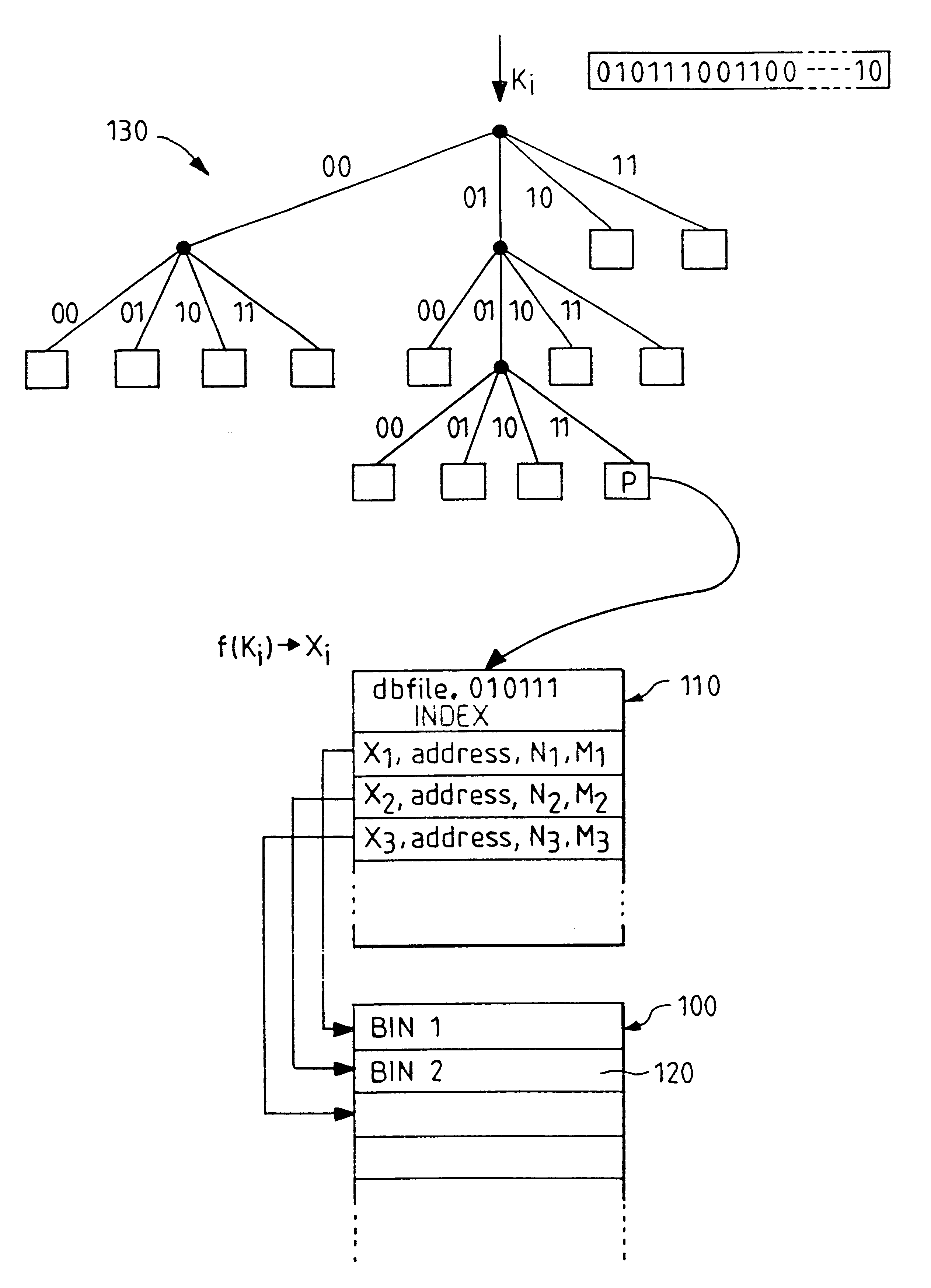
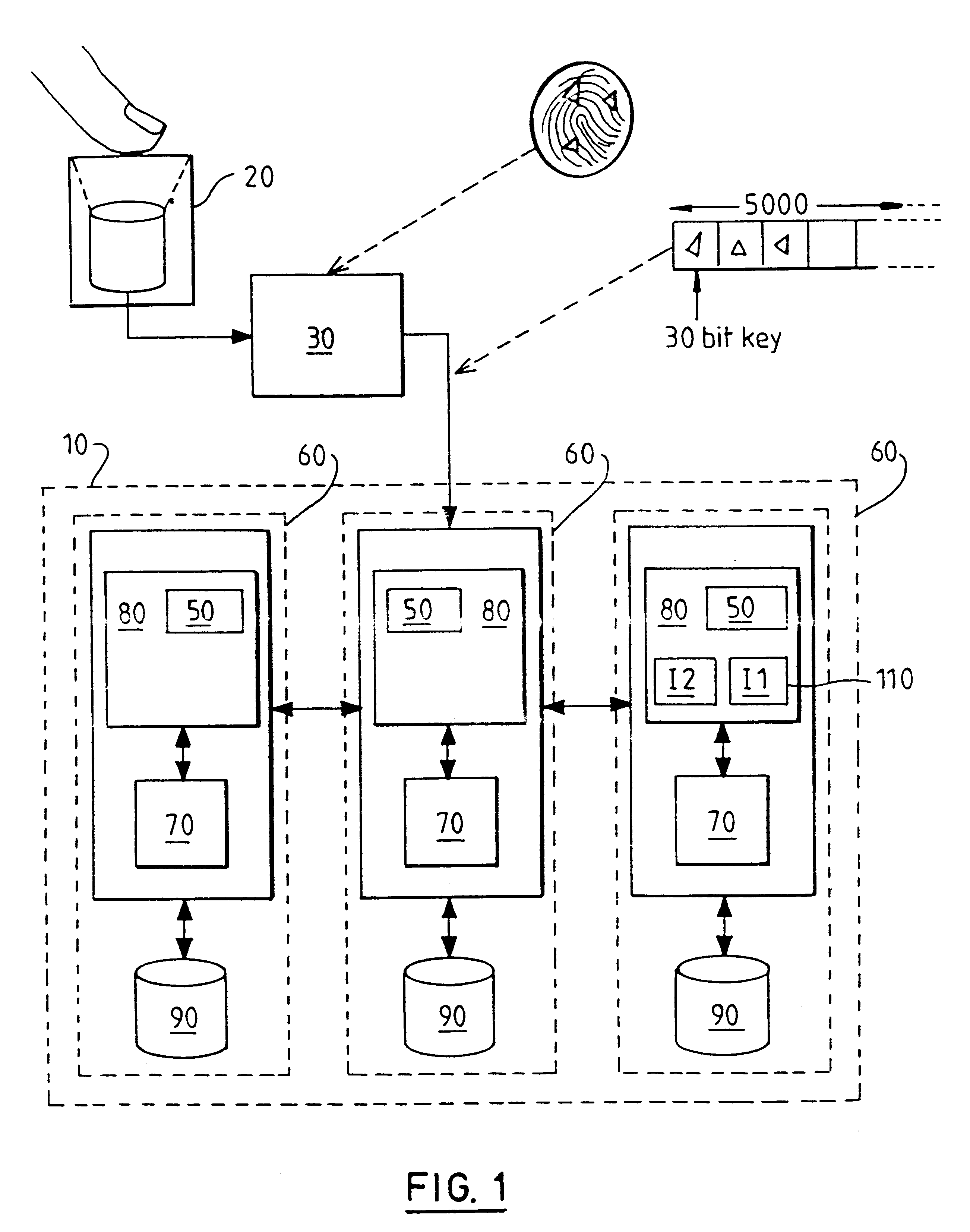
Indexed file system and a method and a mechanism for accessing data records from such a system
InactiveUS6292795B1Efficient access to dataWastefulData processing applicationsDigital data information retrievalExtensibilityCollision detection
A computer filing system includes a data access and allocation mechanism including a directory and a plurality of indexed data files or hash tables. The directory is preferably a radix tree including directory entries which contain pointers to respective ones of the hash tables. Using a plurality of hash tables avoids the whole database ever having to be re-hashed all at once. If a hash table exceeds a preset maximum size as data is added, it is replaced by two hash tables and the directory is updated to include two separate directory entries each containing a pointer to one of the new hash tables. The directory is locally extensible such that new levels are added to the directory only where necessary to distinguish between the hash tables. Local extensibility prevents unnecessary expansion of the size of the directory while also allowing the size of the hash tables to be controlled. This allows optimisation of the data access mechanism such that an optimal combination of directory-look-up and hashing processes is used. Additionally, if the number of keys mapped to an indexed data file is less than a threshold number (corresponding to the number of entries which can be held in a reasonable index), the index for the data file is built with a one-to-one relationship between keys and index entries such that each index entry identifies a data block holding data for only one key. This avoids the overhead of the collision detection of hashing when it ceases to be useful.
Owner:IBM CORP
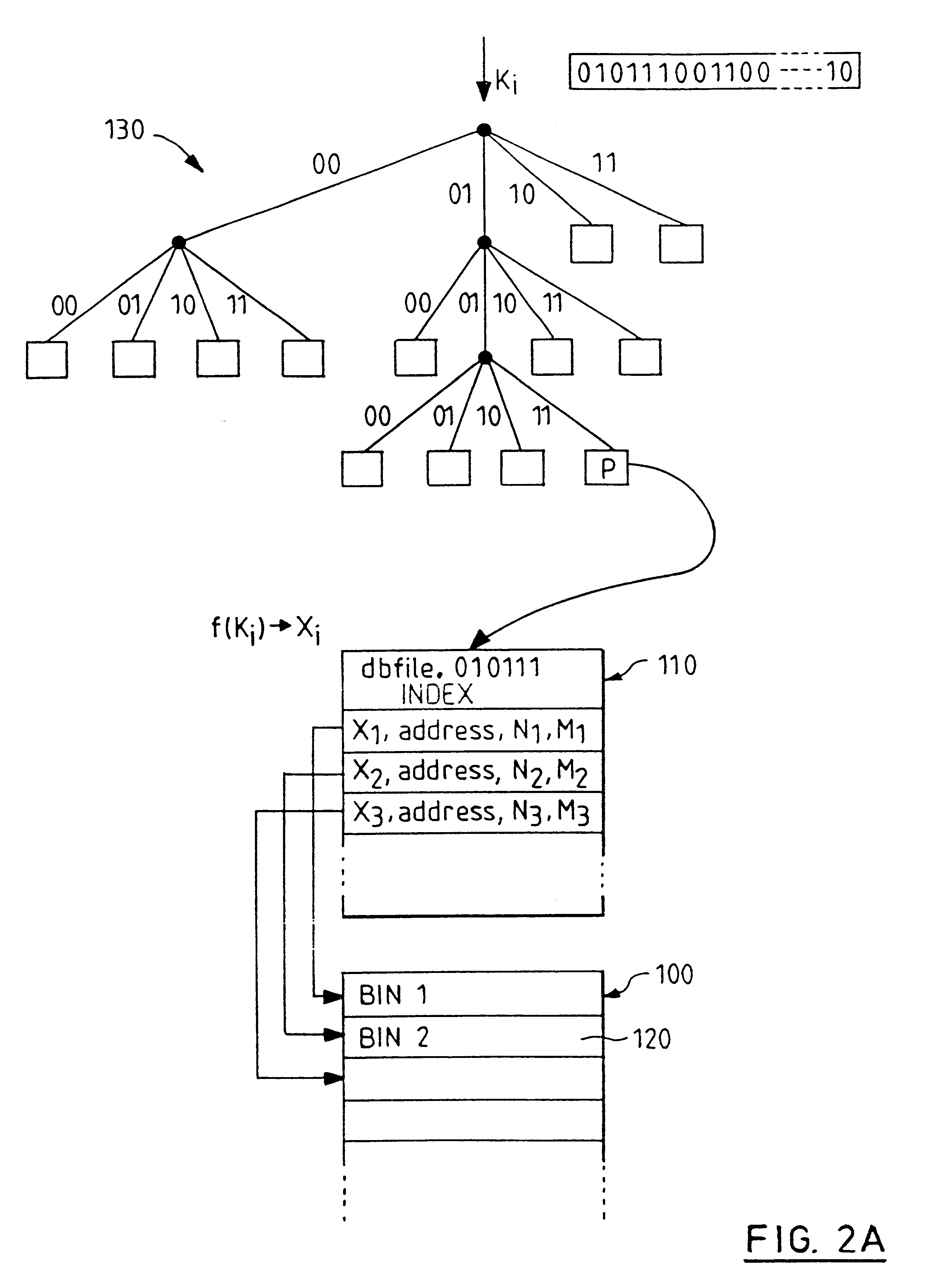
Method for organizing directories
InactiveUS6208993B1Improve performanceEasy retrievalData processing applicationsUnstructured textual data retrievalDatabase fileTrie
In a database file management system for accessing data records that correspond to items in a directory. The directory items are linked to a trie index that is arranged in blocks and being stored in a storage medium. The trie index enables accessing or updating the directory items data records by key or keys and being susceptible to an unbalanced structure of blocks. There is provided a method for constructing a layered index arranged in blocks, which includes the steps of providing the trie index and constructing a representative index over the representative keys of the trie index. The layered index enables accessing or updating the directory items by key or keys and it constitutes a balanced structure of blocks.
Owner:DB SOFTWARE INC
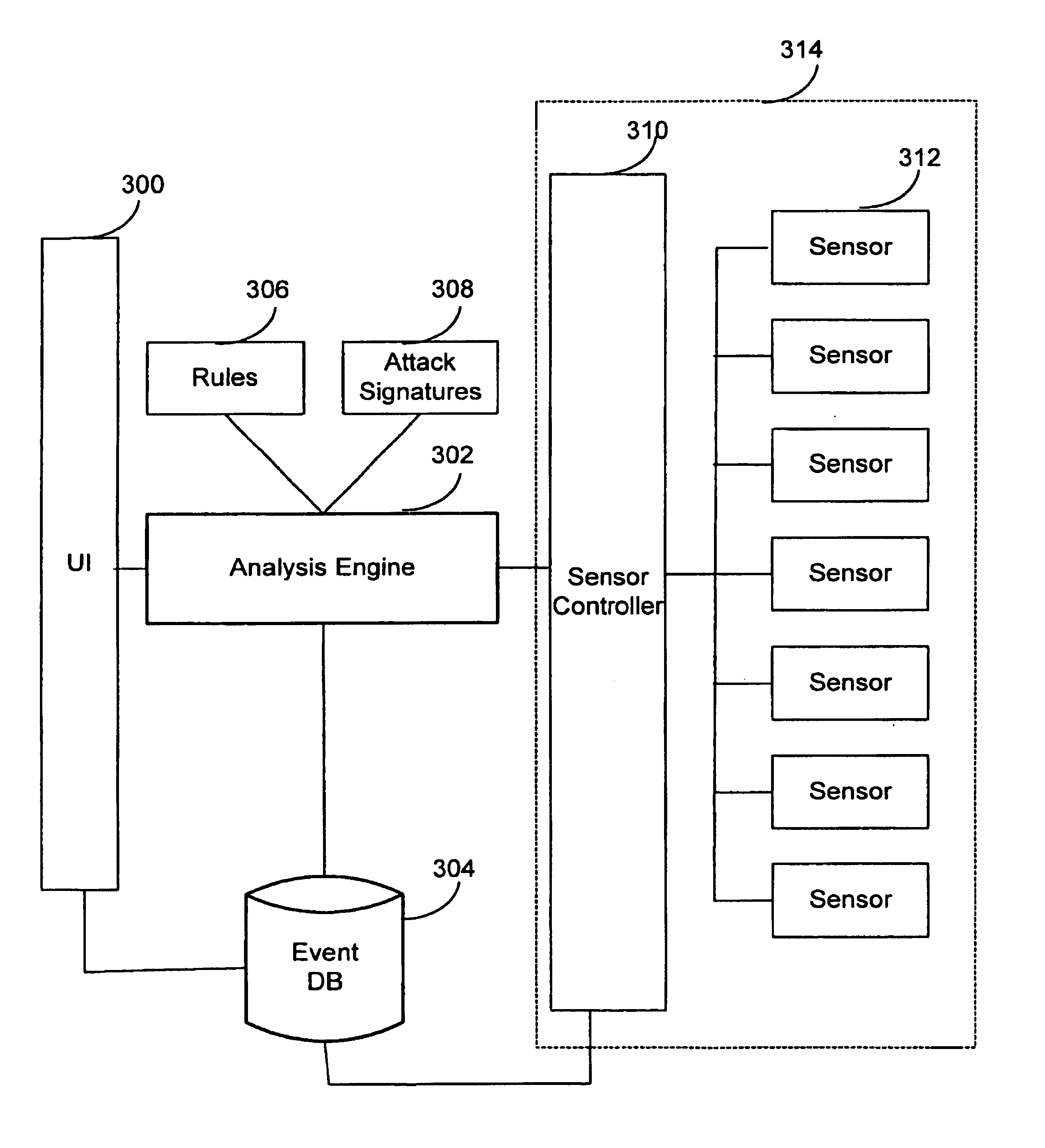
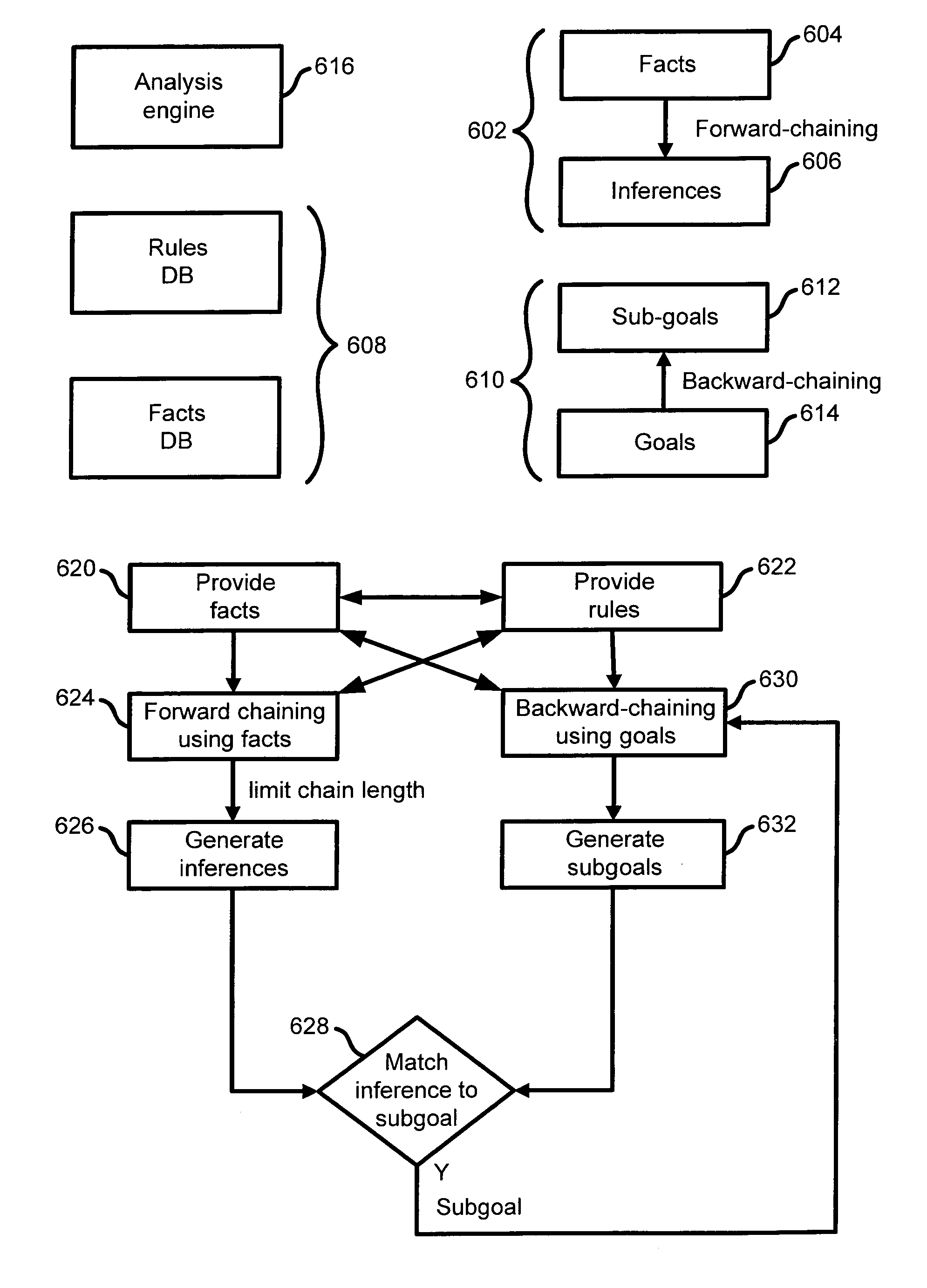
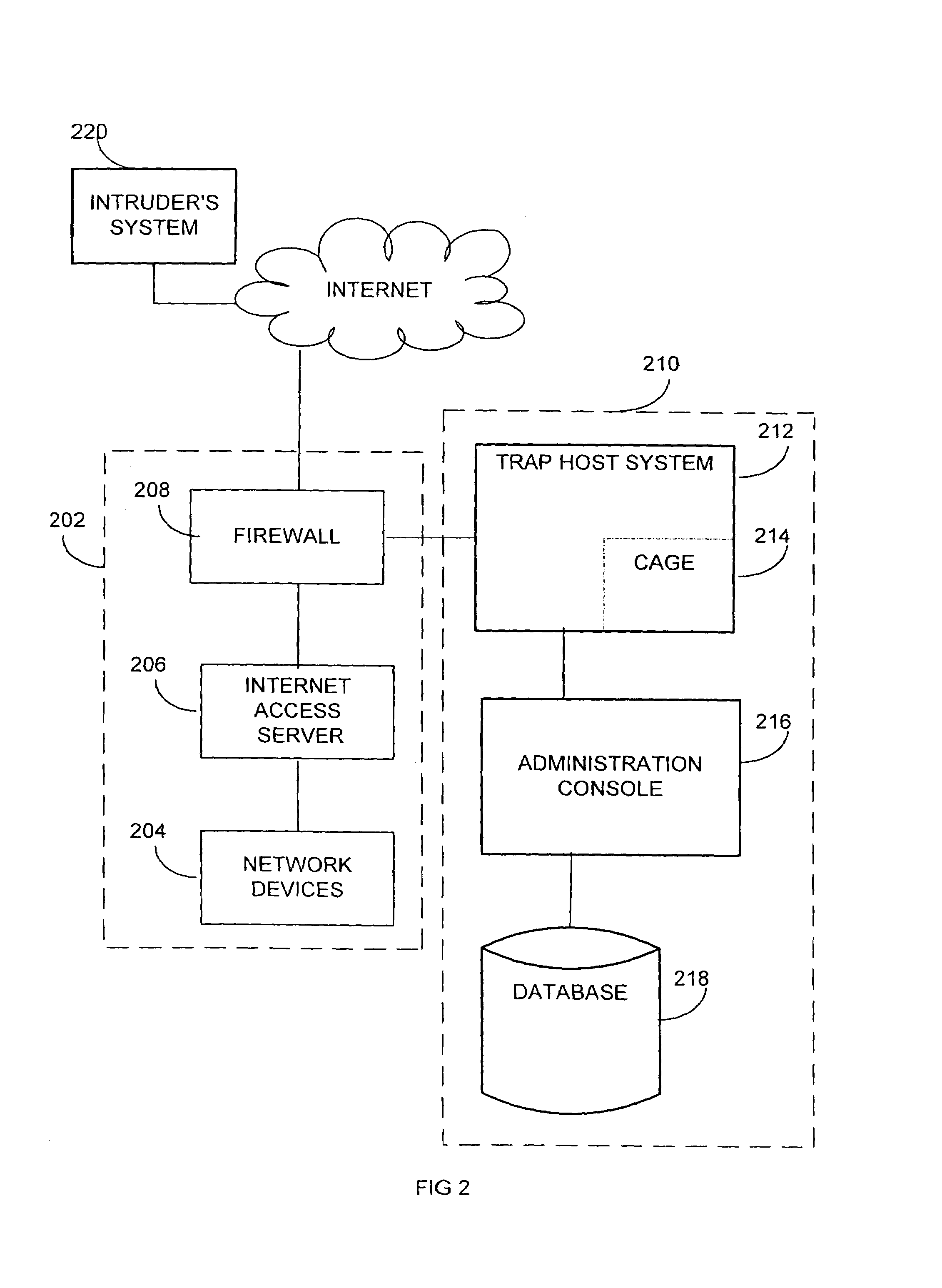
Extensible intrusion detection system
InactiveUS7065657B1Overcome problemsEnabling detectionDigital data processing detailsHardware monitoringTimestampAccess time
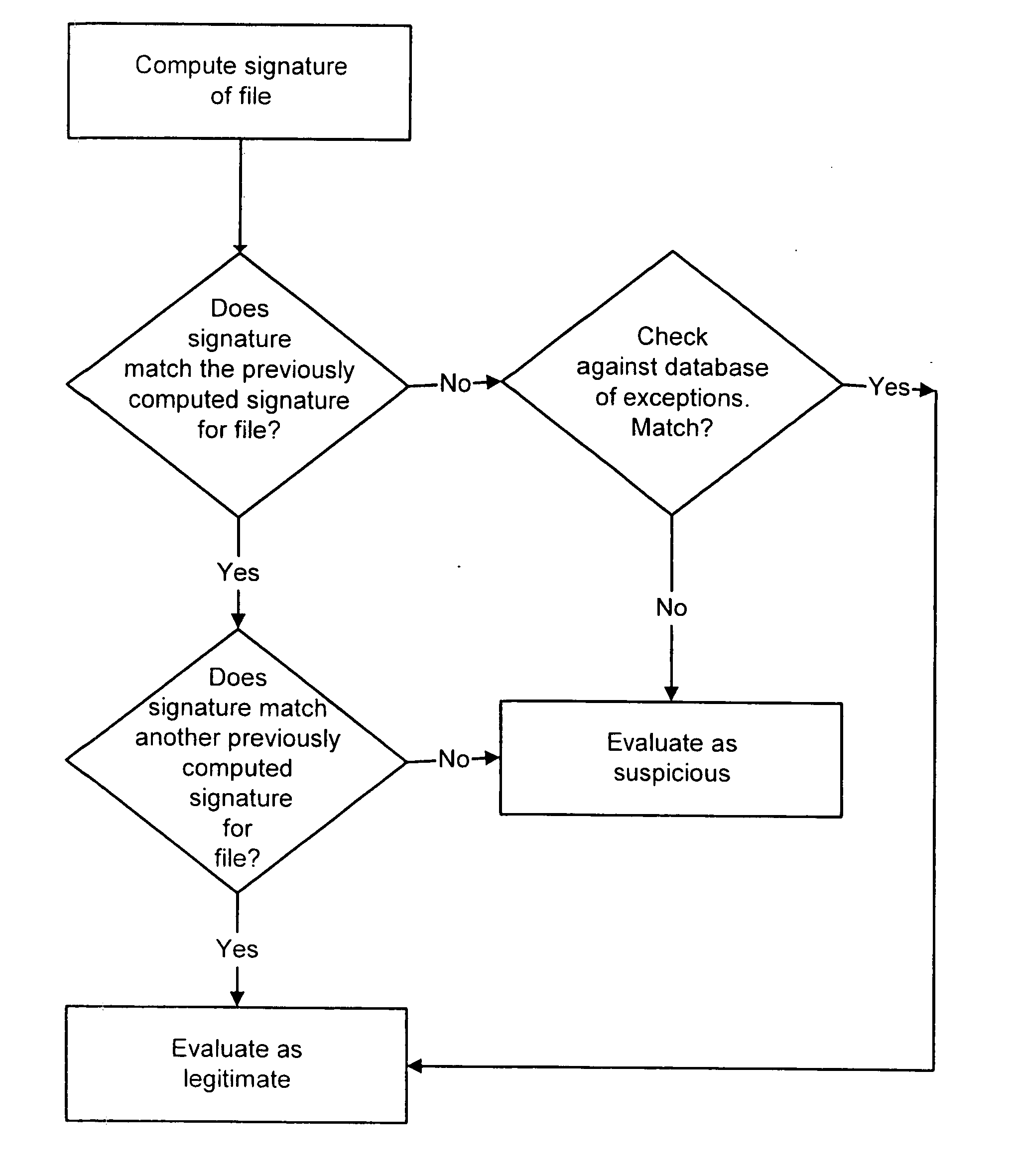
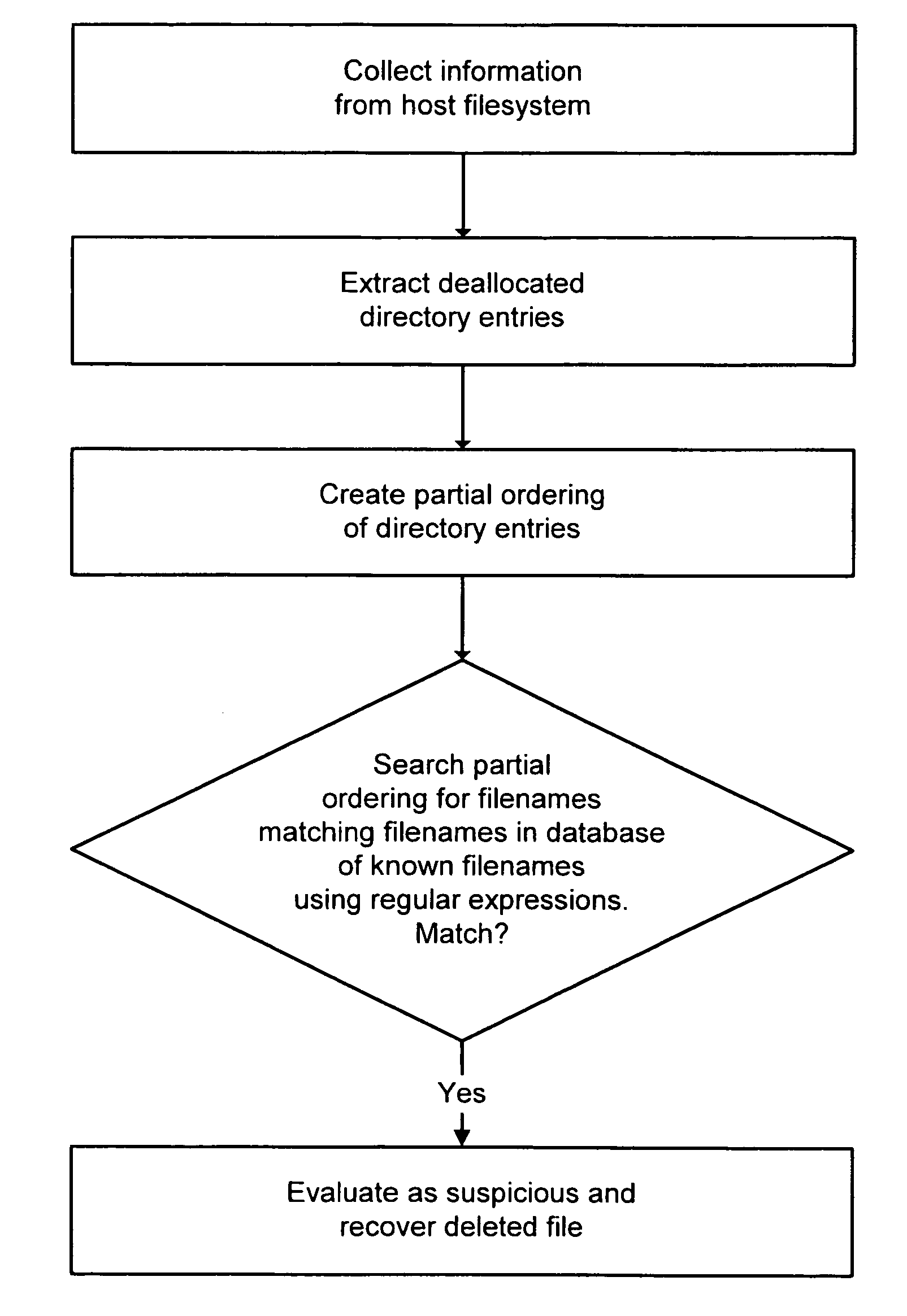
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
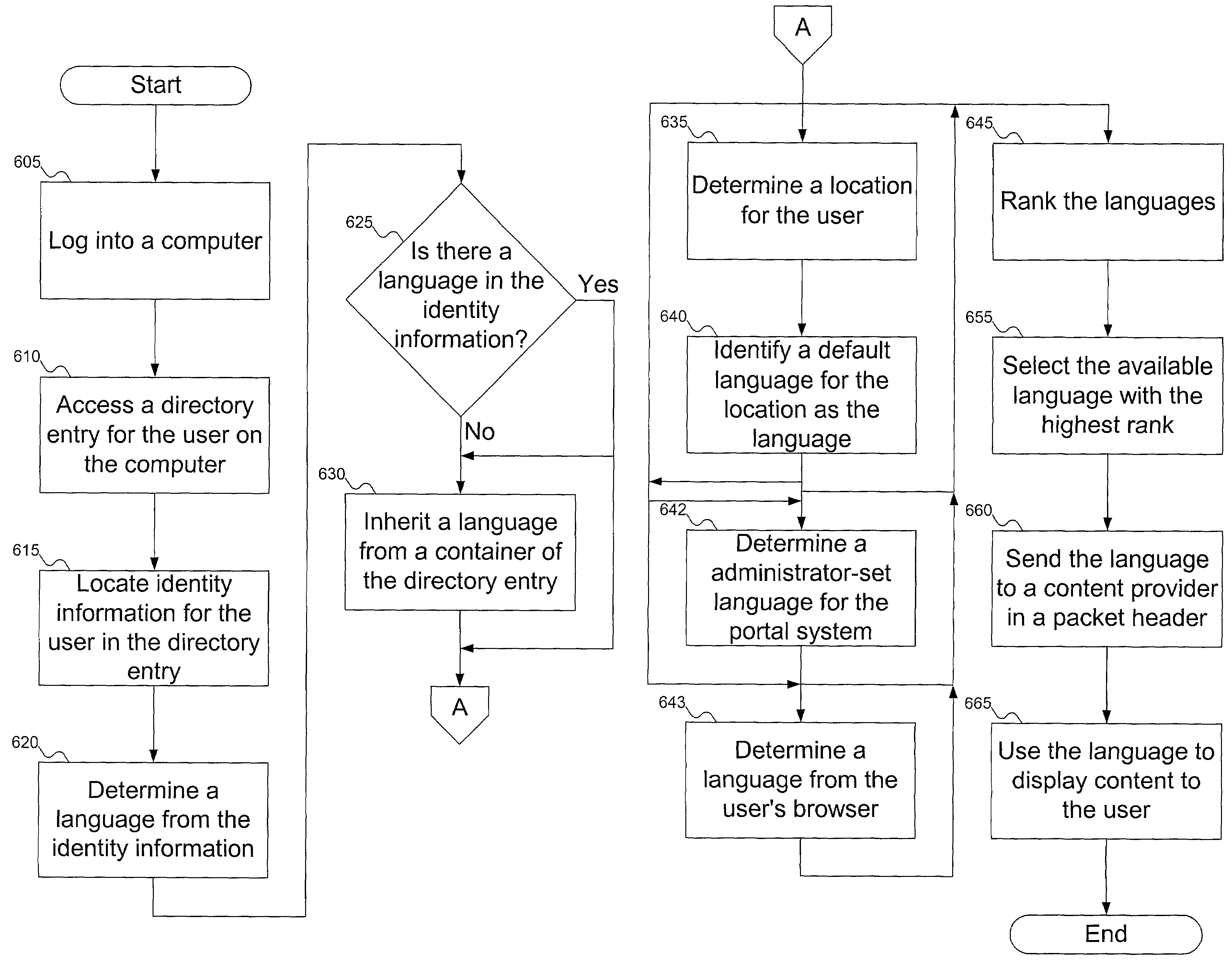
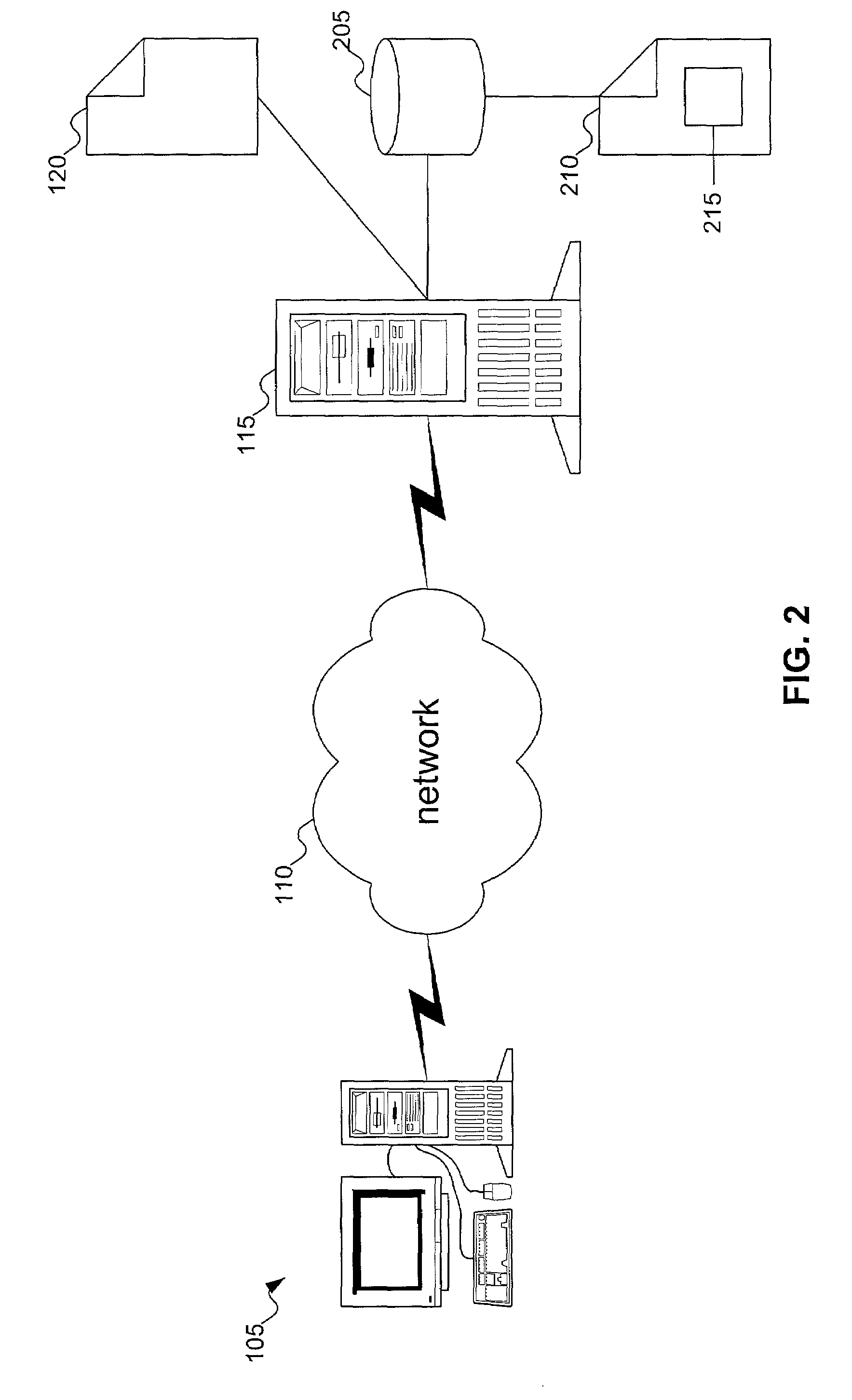
Method to dynamically determine a user's language for a network
InactiveUS7412374B1Natural language data processingSpecial data processing applicationsSystem identificationWorld Wide Web
A portal system identifies a language in which content can be displayed to the user. Possible languages can be determined from one or more of identity information for the user, a container for the user's directory entry, and the user's location. The determined languages can be ranked, and the highest-ranked available language can be selected for content display to the user.
Owner:RPX CORP
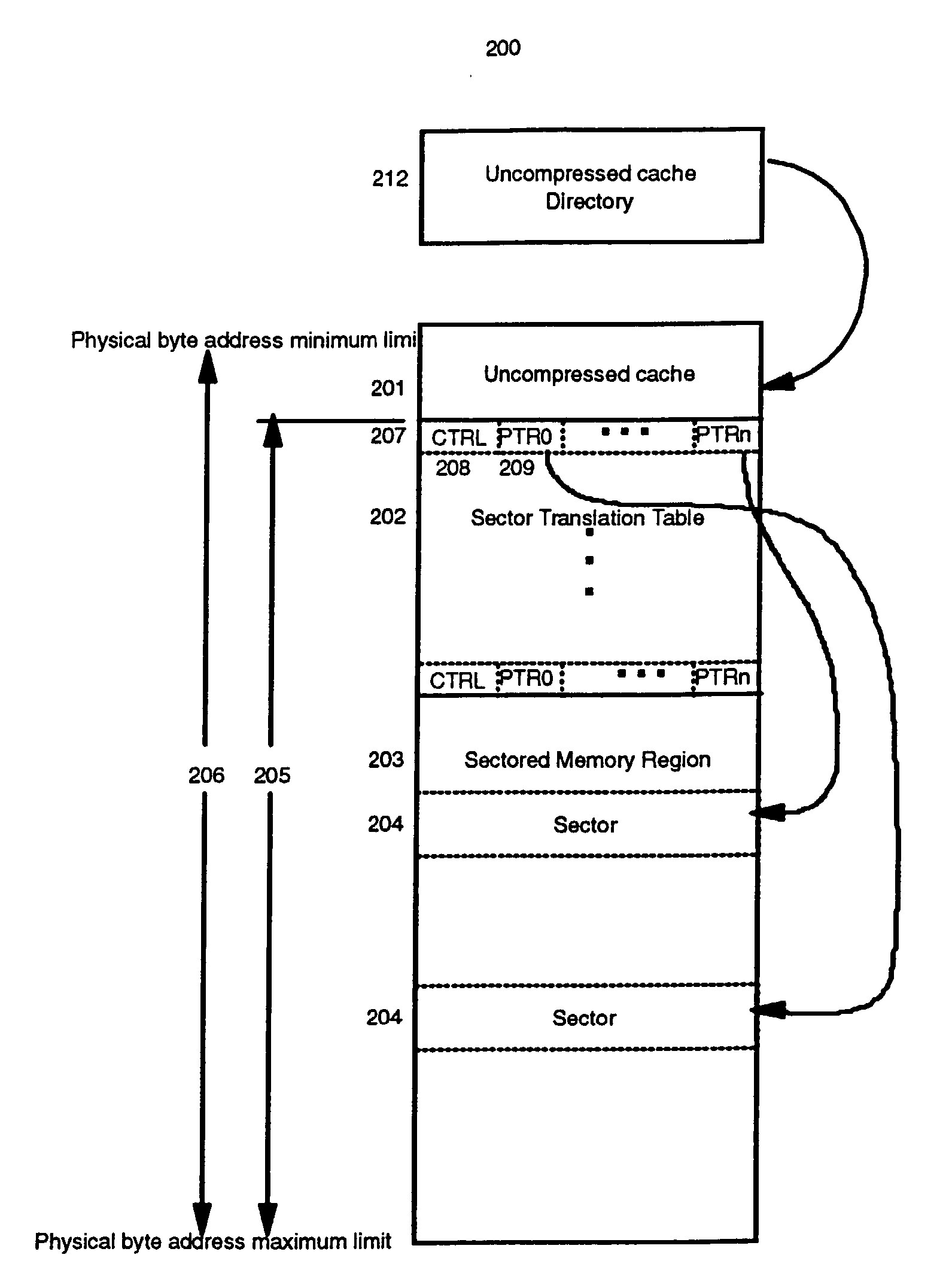
System and method for using a compressed main memory based on degree of compressibility
InactiveUS20040030847A1Low compressibilityAvoid compressionMemory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingCompressibility
A method and structure for reducing access latency and contention in a processing system is disclosed. The invention detects when the amount of available memory is outside a prescribed range, and responsively selects data blocks for compression (to add to the available memory,) or decompression (to use surplus available memory for uncompressed data,) until the amount of available memory is within the prescribed range. When data blocks are compressed, a DOC is determined and stored as an attribute in the directory entry associated with the data block. A most recently used list of recent data block addresses prevents those, as well those data blocks with poor DOC attributes, from being selected for recompression. All zero data blocks are detected to avoid standard compression / decompression overhead.
Owner:IBM CORP
System and method for detecting computer intrusions
InactiveUS6996843B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampAccess time
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
System and method for using timestamps to detect attacks
InactiveUS7203962B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampContinuation
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
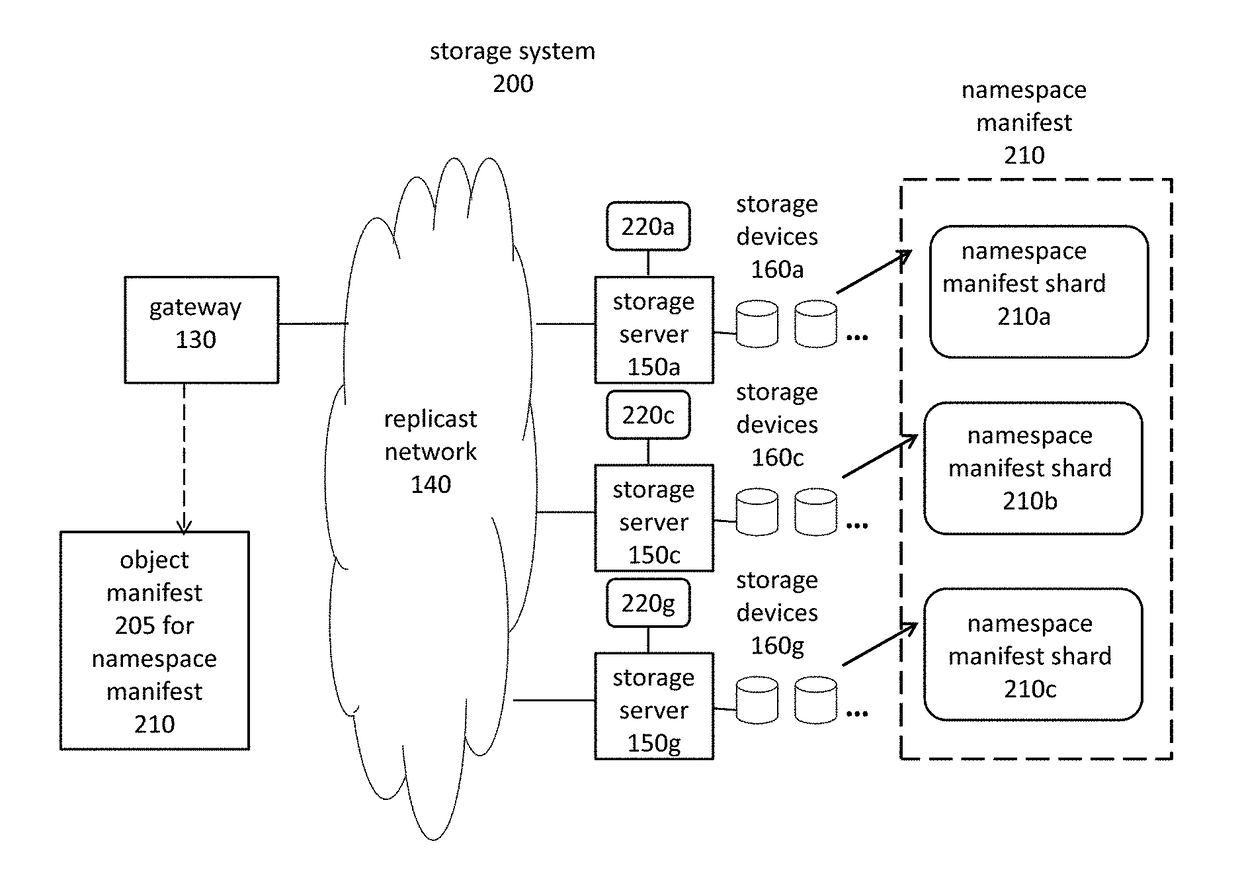
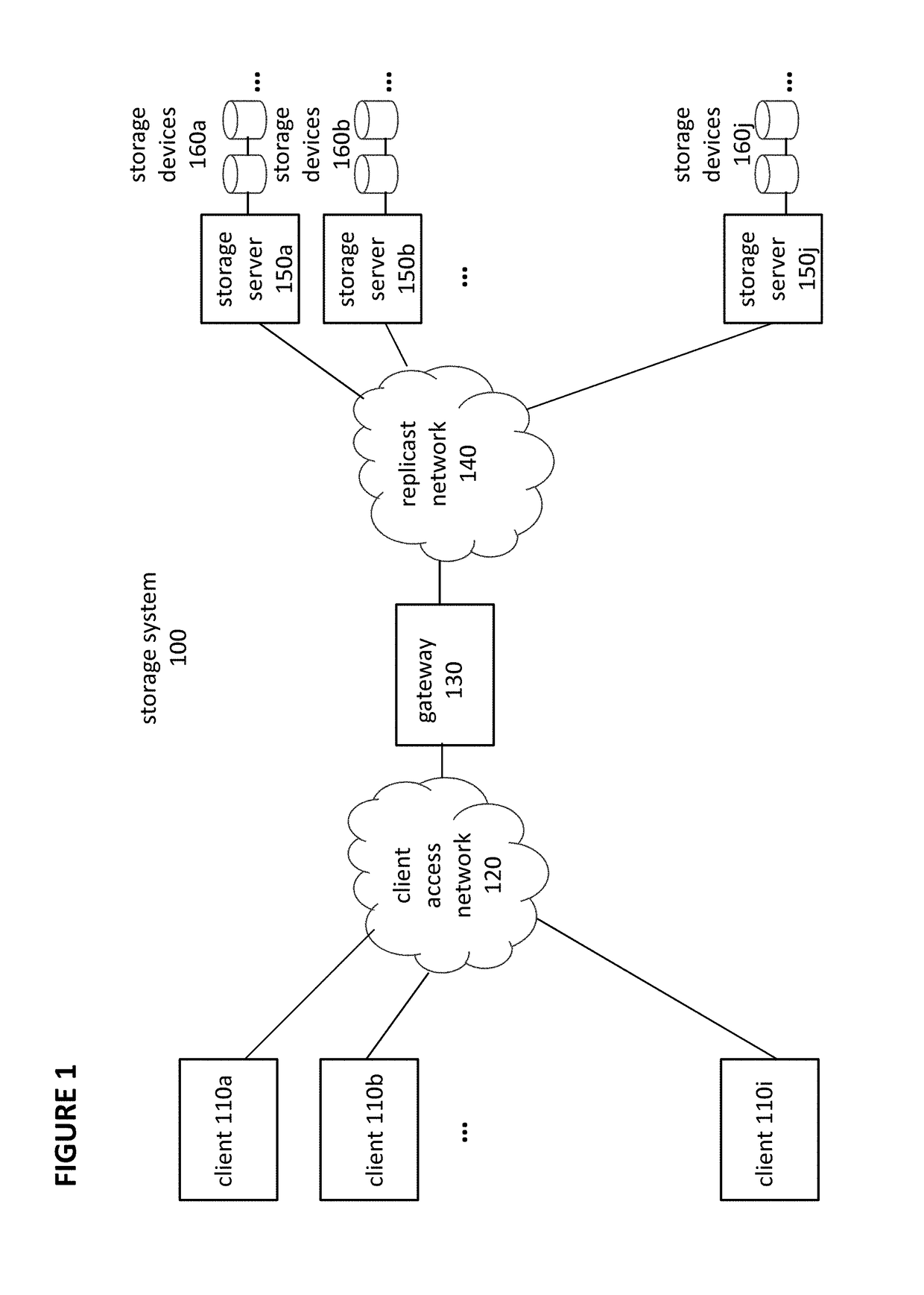
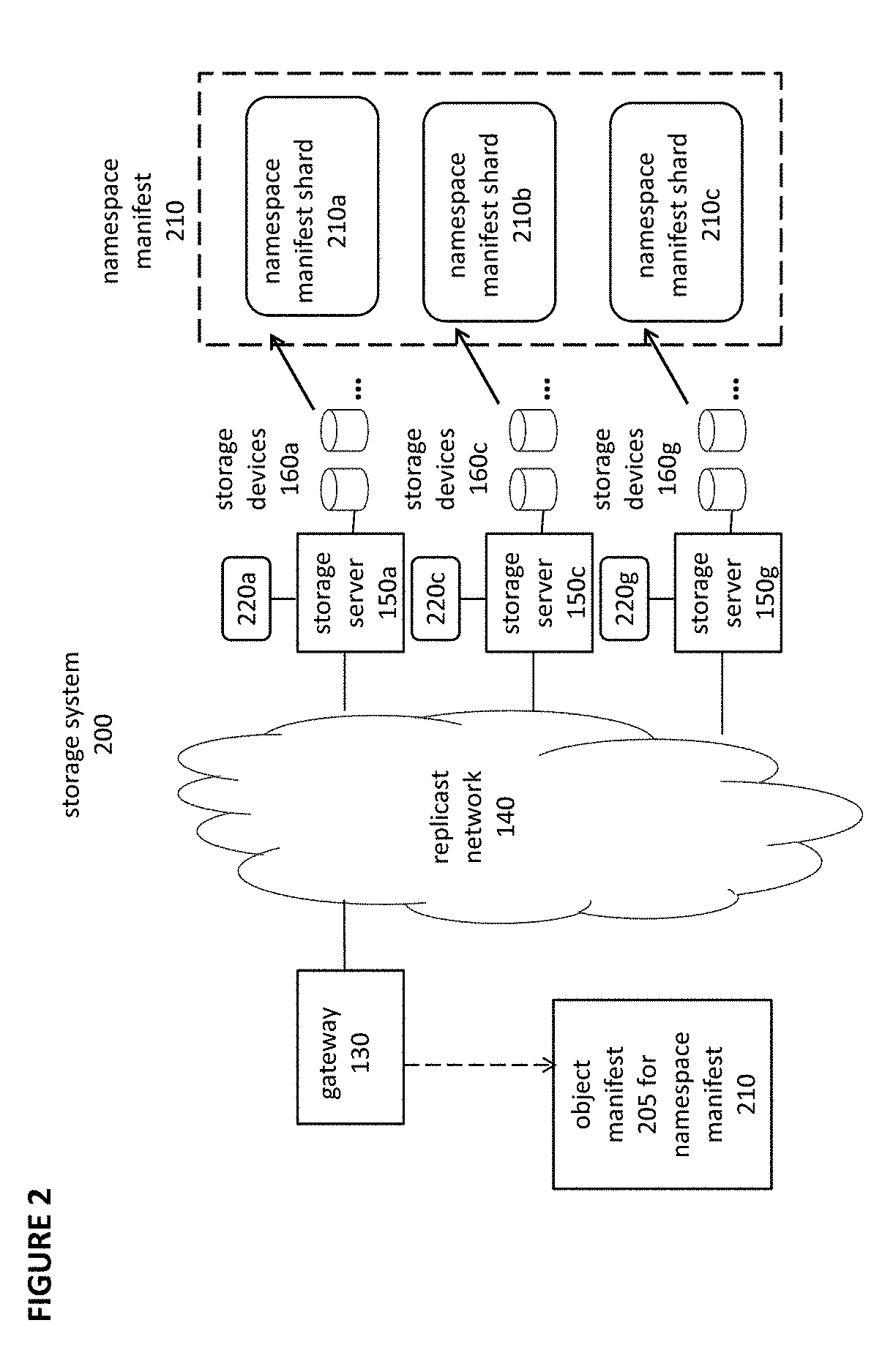
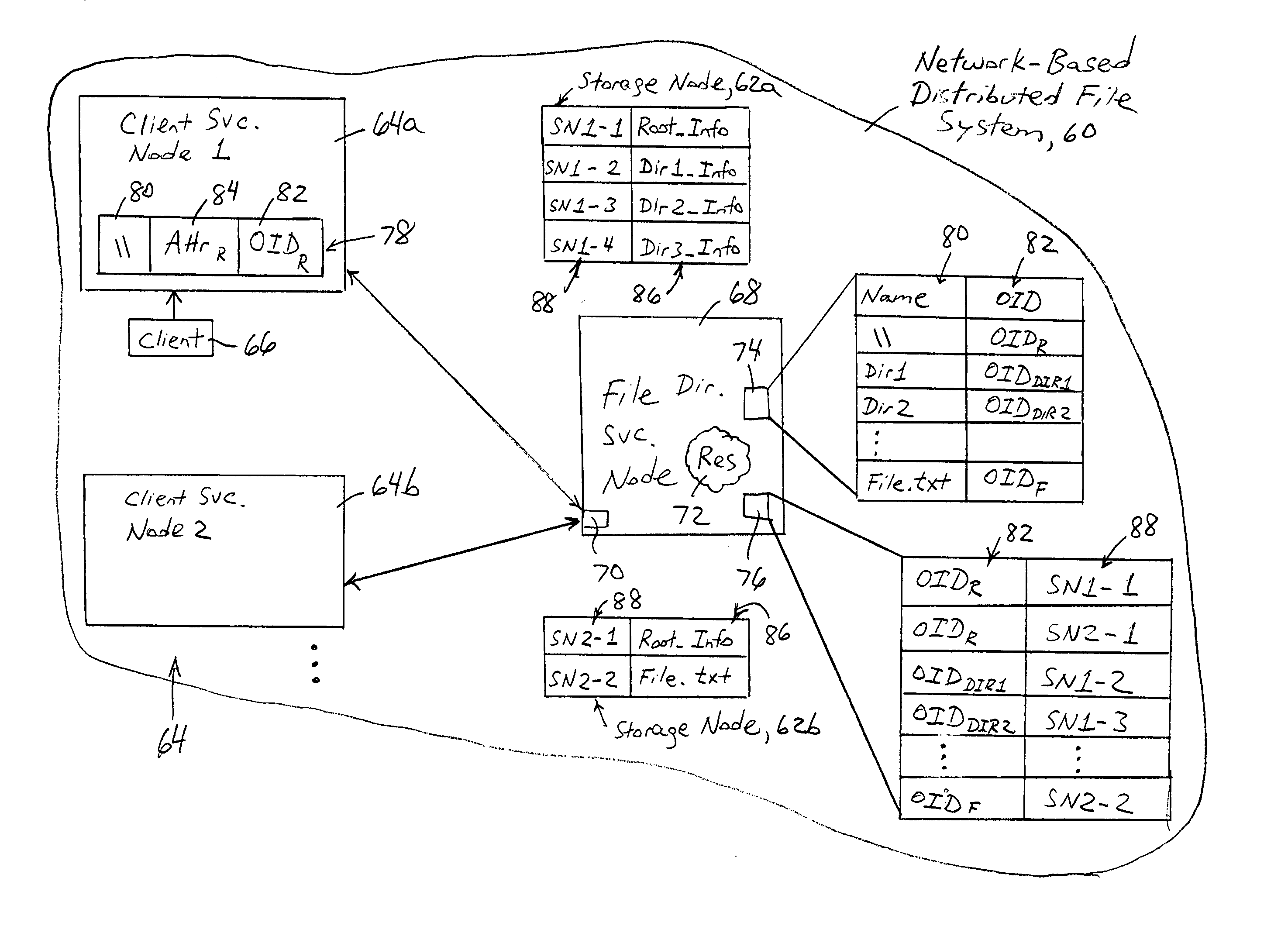
Object storage system with local transaction logs, a distributed namespace, and optimized support for user directories
ActiveUS9710535B2Maintain efficiencyProvide benefitsDigital data information retrievalUser identity/authority verificationTransaction logObject storage
The present invention relates to object storage systems that support hierarchical directories within a namespace manifest stored as an object. The namespace manifest is stored as namespace manifest shards that are determined based on a partial key derived from the full name of the referenced version manifest in each directory entry. Each storage server maintains a local transaction log that keeps track of changes to the namespace manifest in response to put transactions. The namespace manifest can be updated after each put transaction is acknowledged, which minimizes the number of write operations required for a put transaction. Updates to the namespace manifest are batched, distributed, and processed concurrently and in parallel by the storage servers that store the corresponding shards. This reduces the latency that would otherwise exist in the object storage cluster as a result of a put transaction. Updates to namespace manifest shards optionally occur in a batch process using MapReduce techniques.
Owner:NEXENTA BY DDN INC
Virtual file system
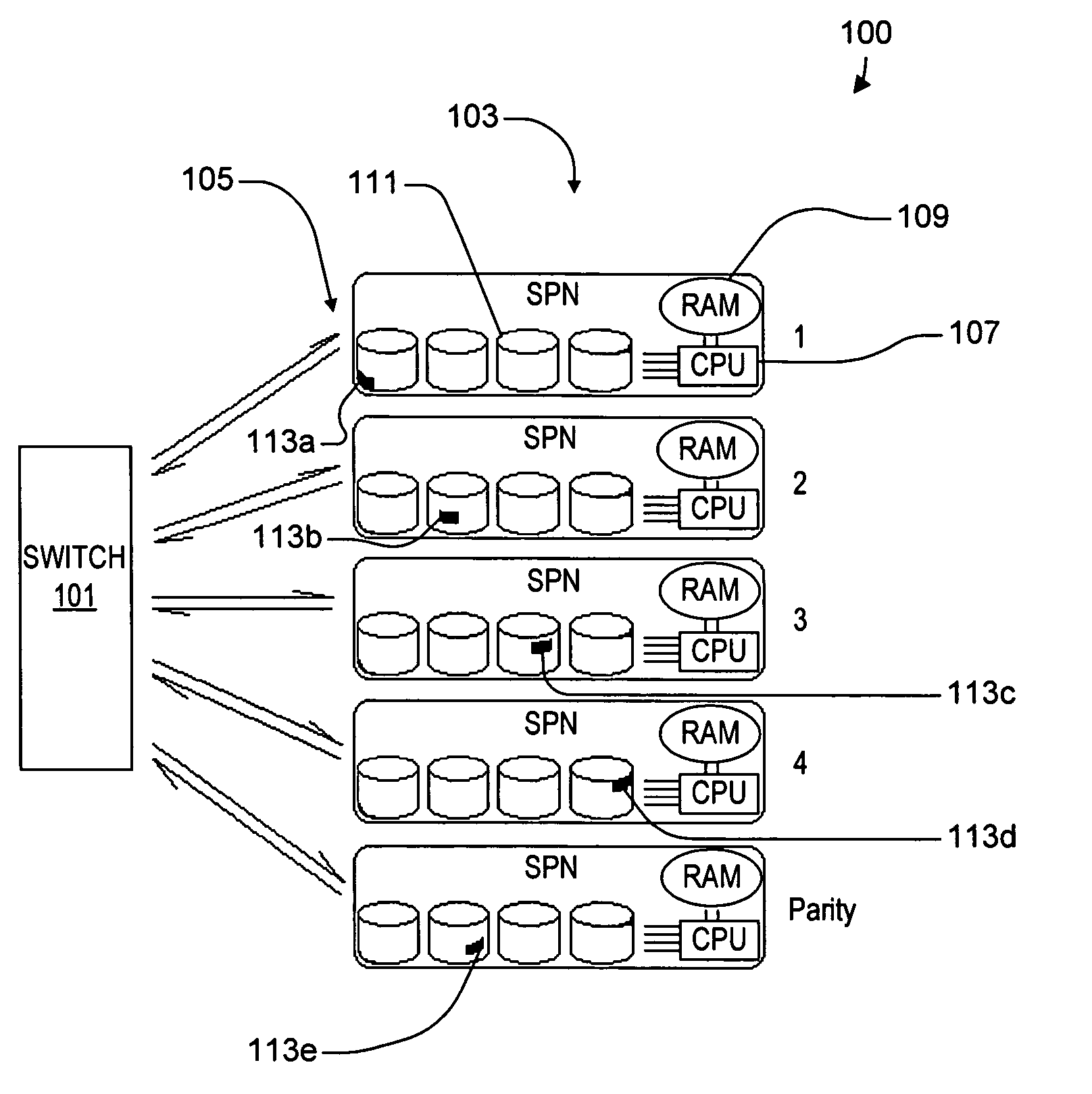
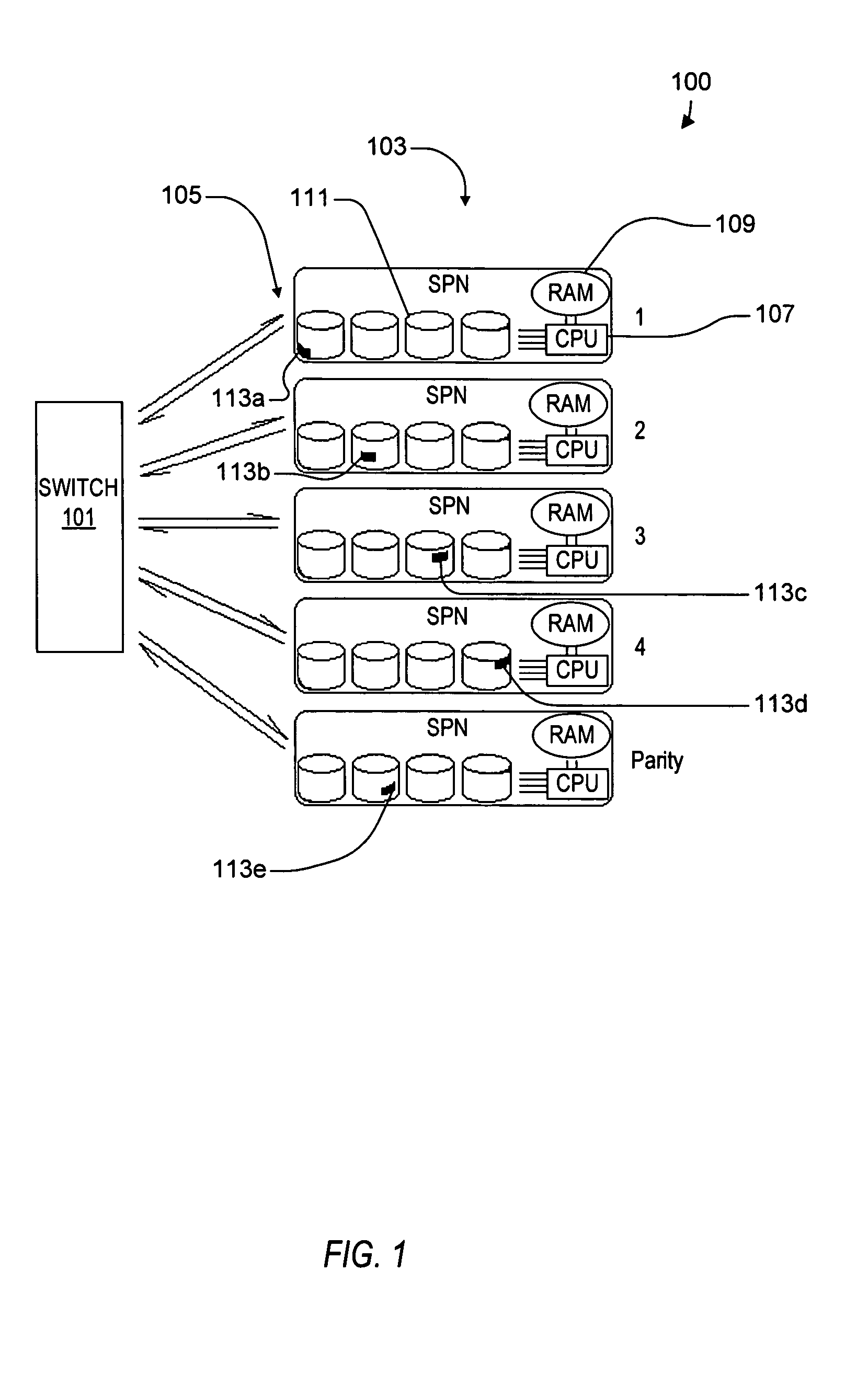
ActiveUS20050114350A1Input/output to record carriersRecording by optical meansVirtual file systemProcessor node
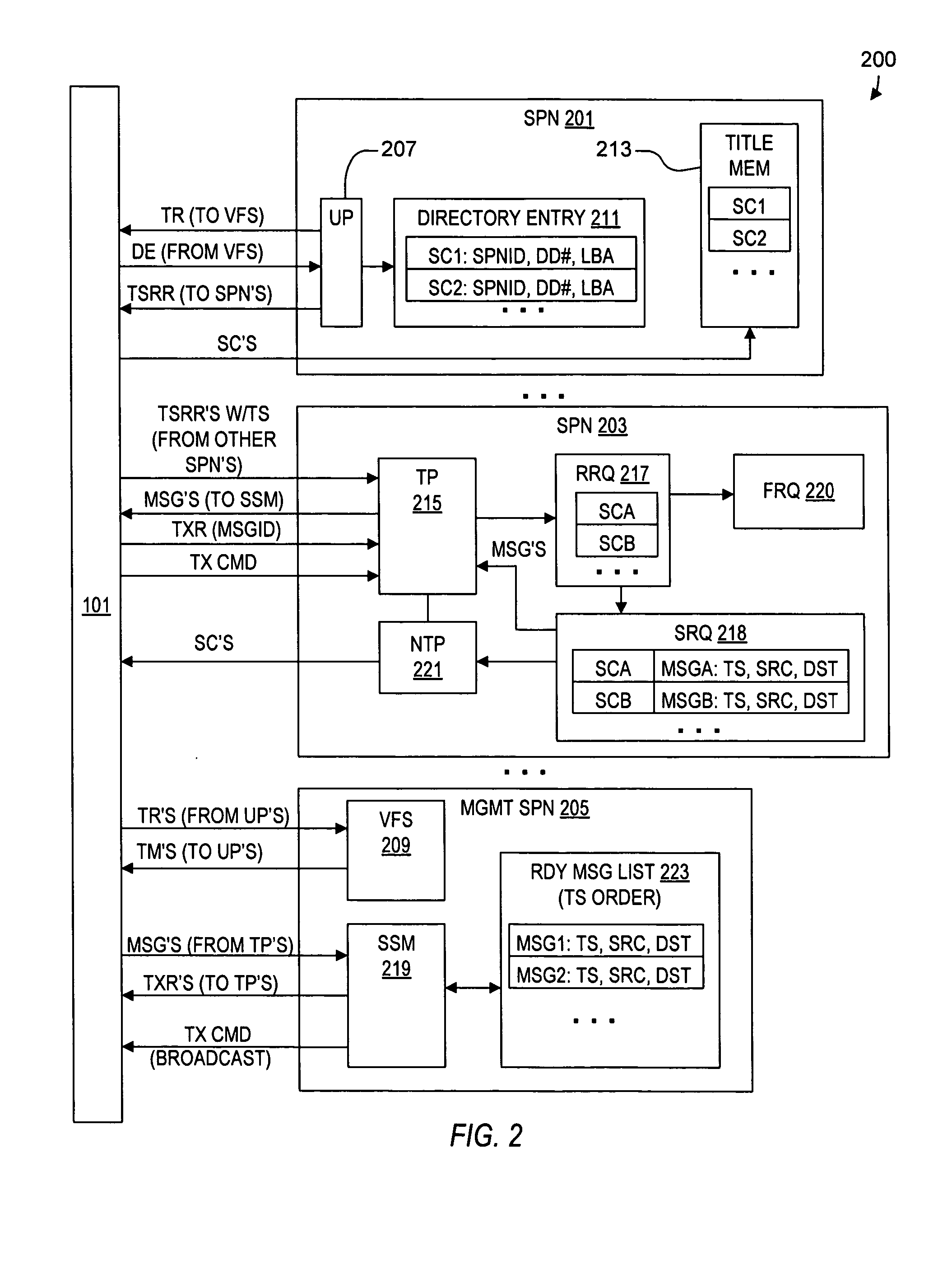
A virtual file system including multiple storage processor nodes including a management node, a backbone switch, a disk drive array, and a virtual file manager executing on the management node. The backbone switch enables communication between the storage processor nodes. The disk drive array is coupled to and distributed across the storage processor nodes and stores multiple titles. Each title is divided into data subchunks which are distributed across the disk drive array in which each subchunk is stored on a disk drive of the disk drive array. The virtual file manager manages storage and access of each subchunk, and manages multiple directory entries including a directory entry for each title. Each directory entry is a list of subchunk location entries in which each subchunk location entry includes a storage processor node identifier, a disk drive identifier, and a logical address for locating and accessing each subchunk of each title.
Owner:INTERACTIVE CONTENT ENGINES LLC
Building a meta file system from file system cells
InactiveUS6775679B2Data processing applicationsMemory adressing/allocation/relocationFile systemApplication software
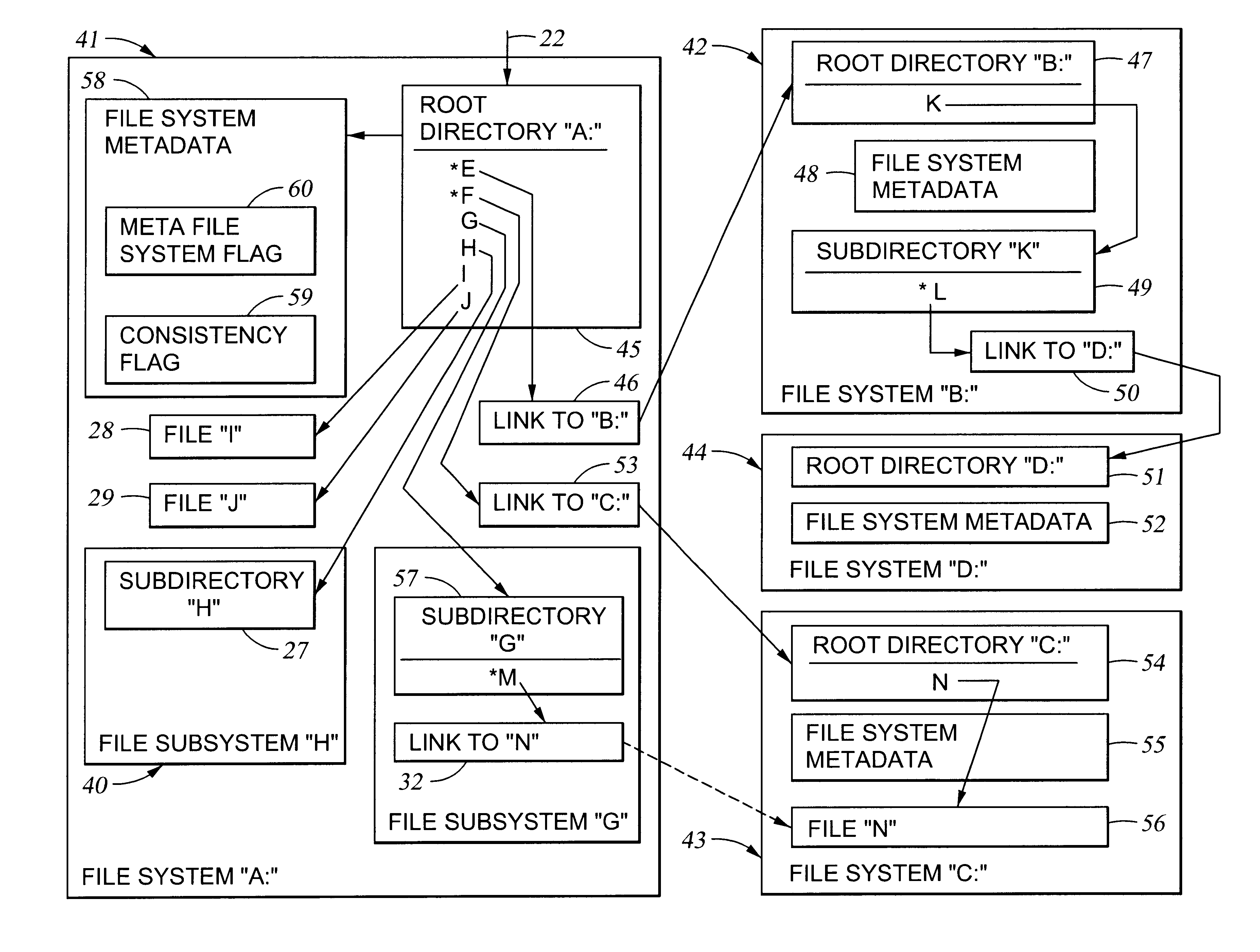
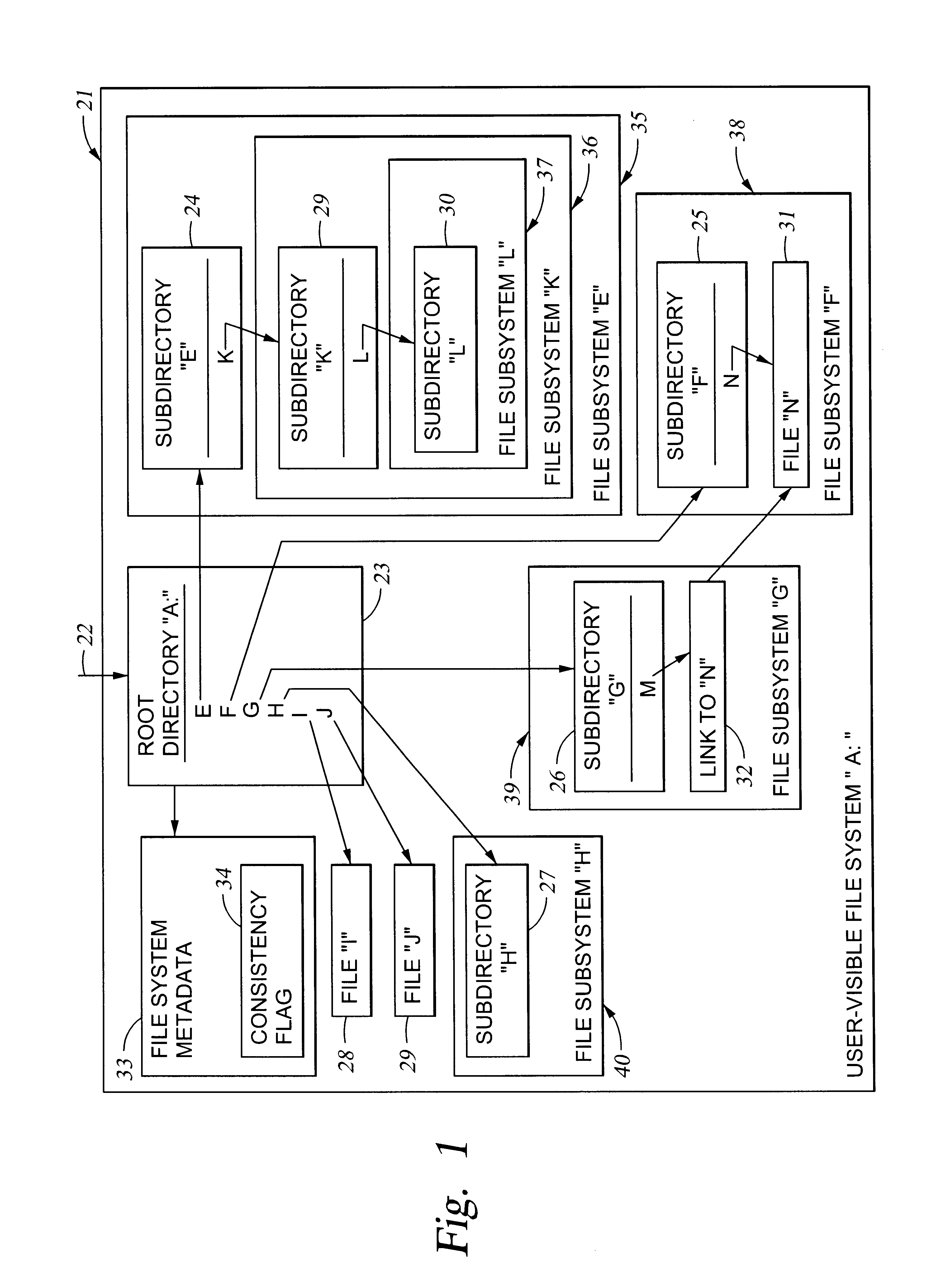
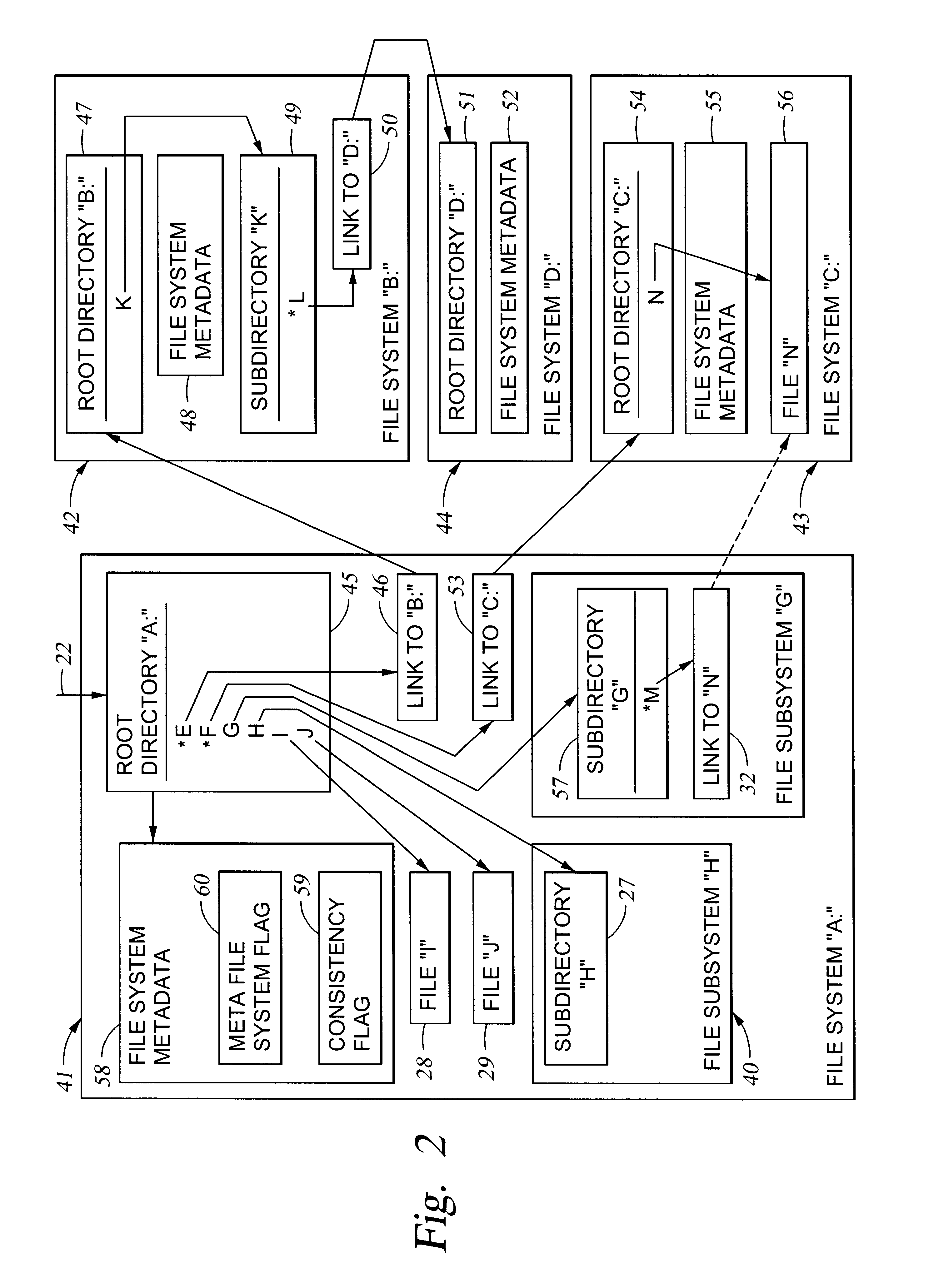
File system cells are linked together to form a meta file system that appears to a user or application program to be a single file system. Each file system cell may have a conventional file system format, and can be indistinguishable from a conventional file system except for information, such as directory entry attributes, indicating one or more links to other file system cells. These external links may include direct links that are hidden from the user or application program and define a hierarchy of the meta file system cells, and indirect links that appear in the user-visible file system. The meta file system substantially reduces crash recovery time because each file system cell functions as a consistency unit that can be repaired only if needed. The meta file system also permits the file system cells to be accessed concurrently by multiple processors in a file server.
Owner:EMC IP HLDG CO LLC
System and method for using timestamps to detect attacks
InactiveUS20070157315A1Overcome problemsEnabling detectionMemory loss protectionError detection/correctionData packProcess mechanism
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
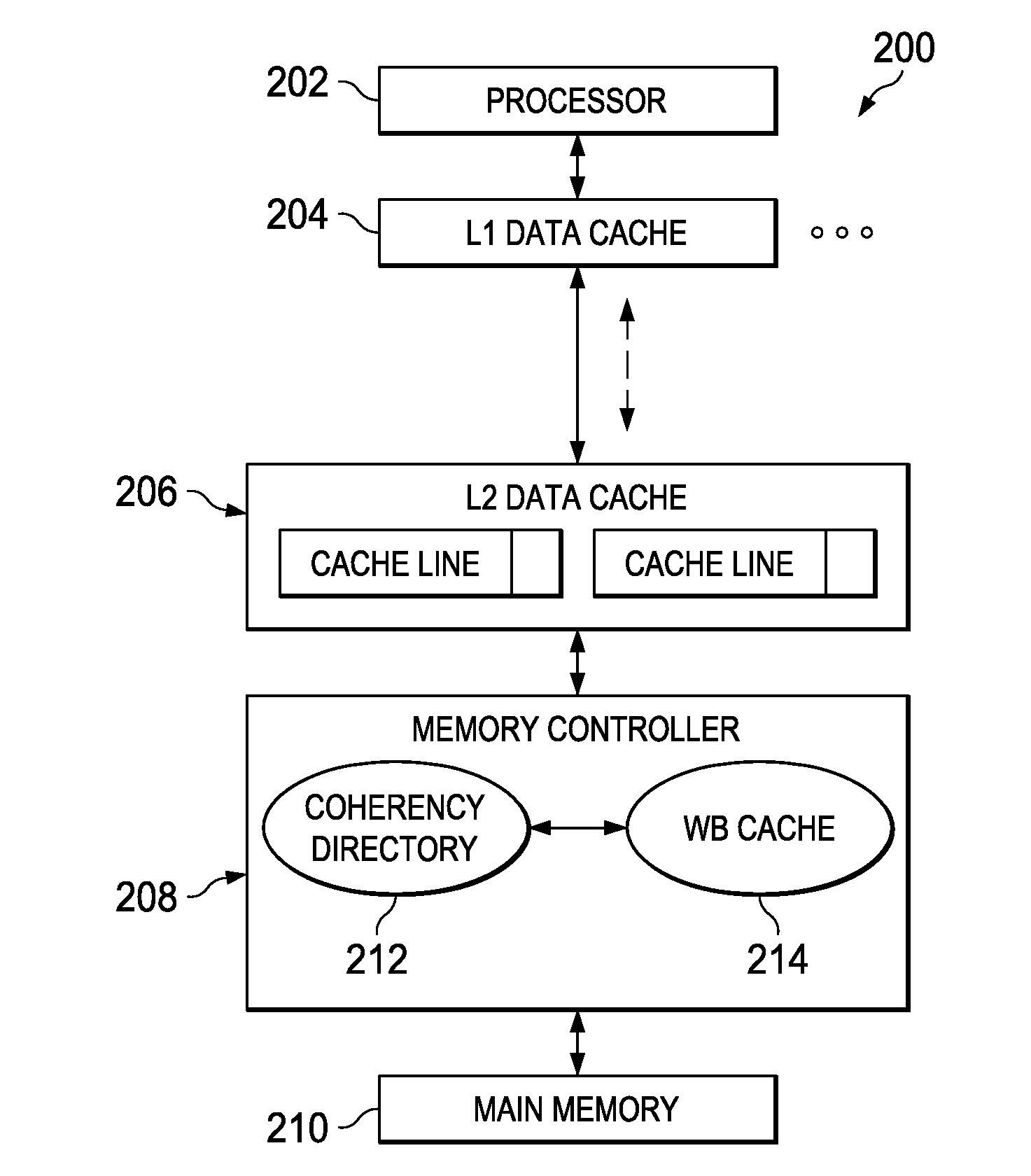
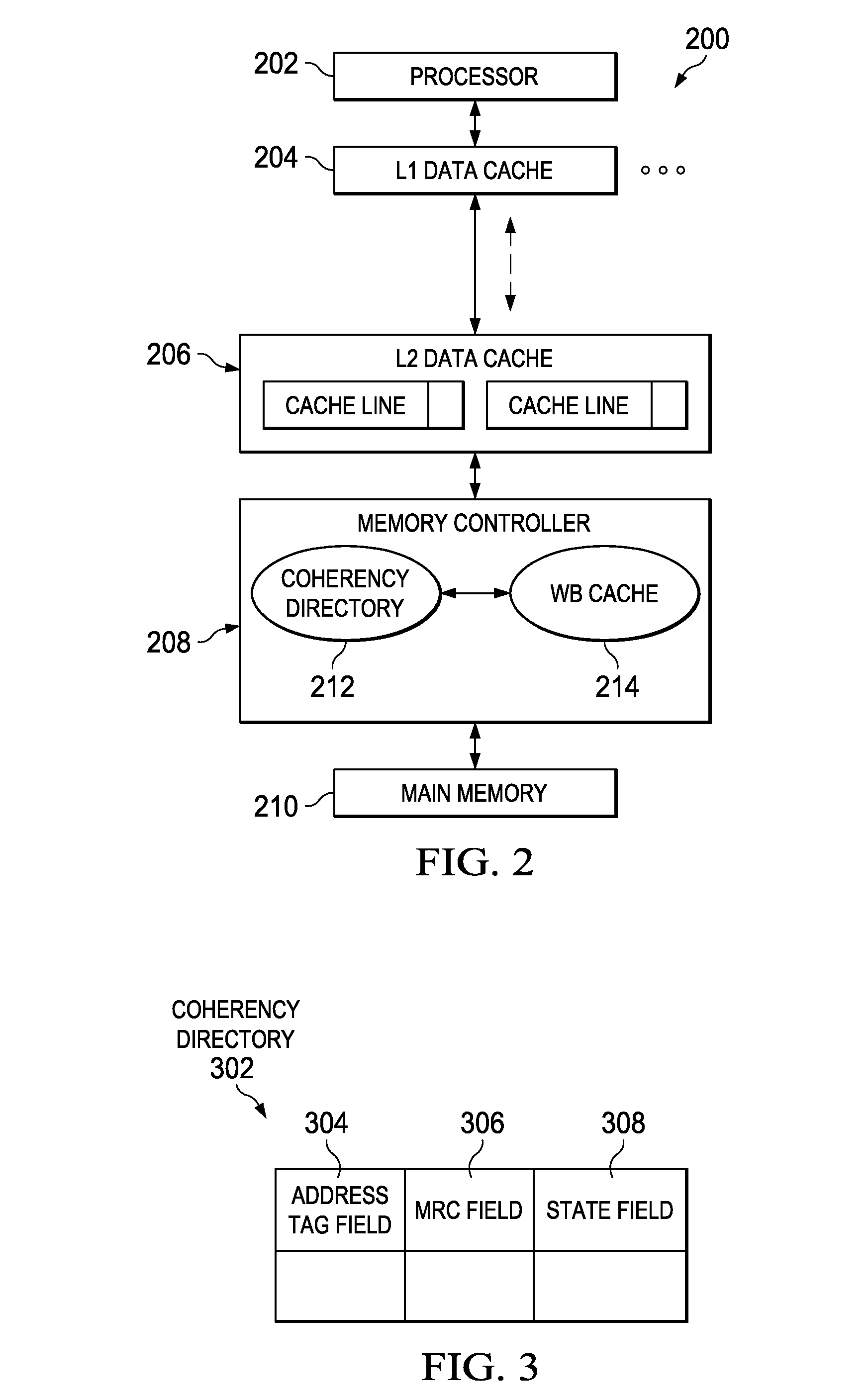
Write-Back Coherency Data Cache for Resolving Read/Write Conflicts
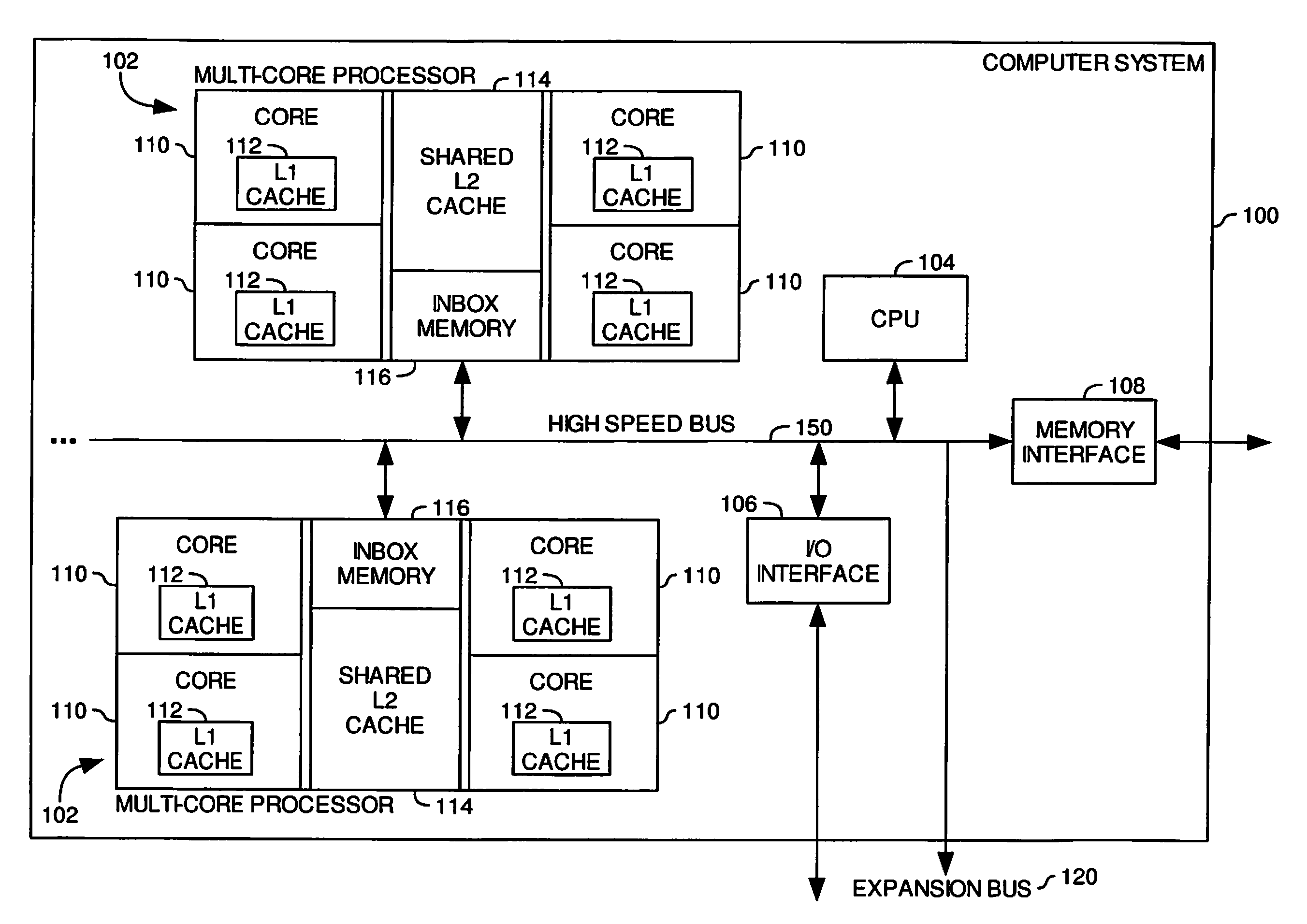
ActiveUS20100325367A1Improve system performanceMemory adressing/allocation/relocationParallel computingMemory controller
A write-back coherency data cache for temporarily holding cache lines. Upon receiving a processor request for data, a determination is made from a coherency directory whether a copy of the data is cached in a write-back cache located in a memory controller hardware. The write-back cache holds data being written back to main memory for a period of time prior to writing the data to main memory. If the data is cached in the write-back cache, the data is removed from the write-back cache and forwarded to the requesting processor. The cache coherency state in the coherency directory entry for the data is updated to reflect the current cache coherency state of the data based on the requesting processor's intended use of the data.
Owner:IBM CORP
Systems and methods for providing distributed cache coherence
ActiveUS20060031450A1Reduce bandwidth requirementsMaintain traffic scalabilityDigital computer detailsTransmissionDistributed cacheBandwidth requirement
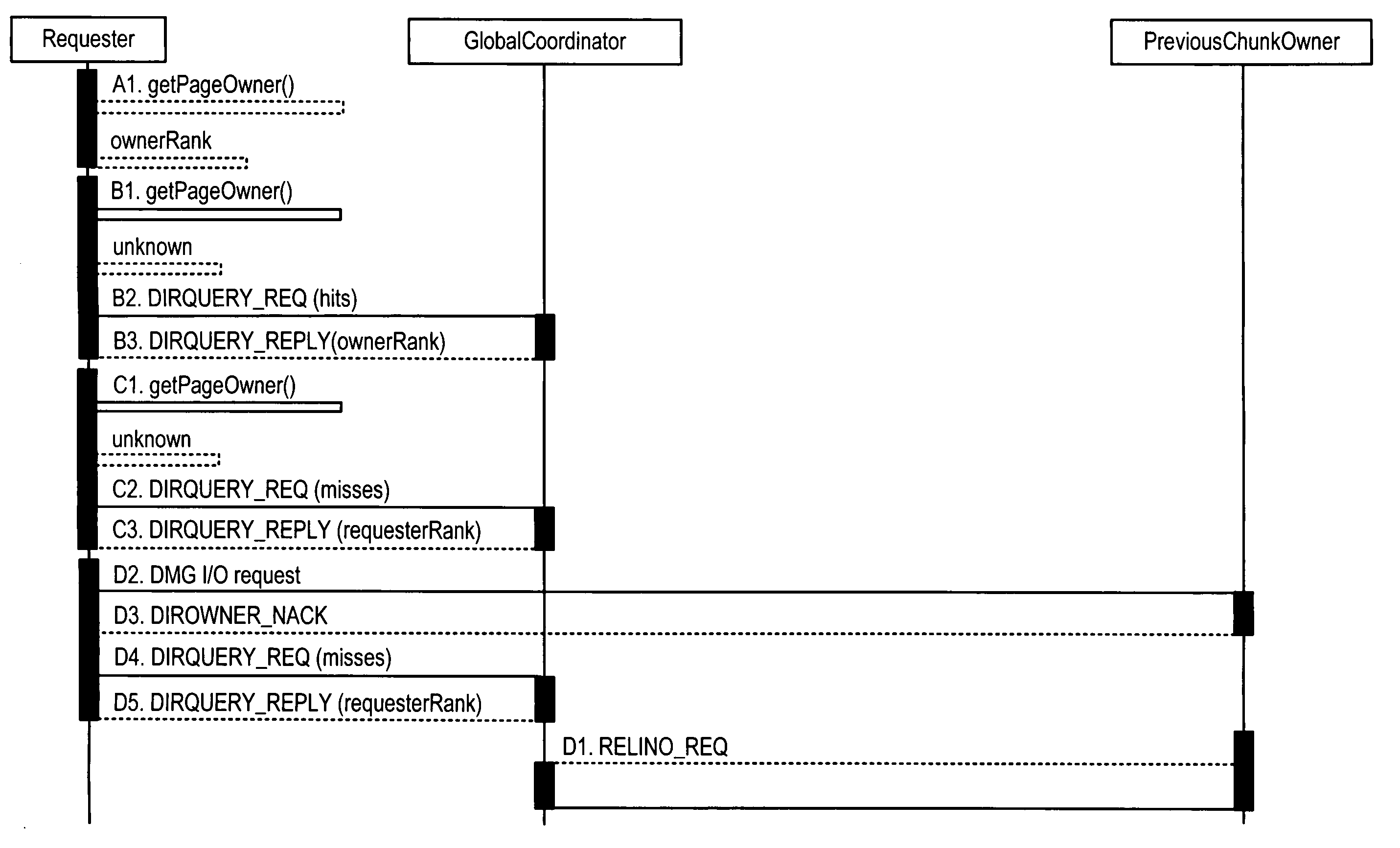
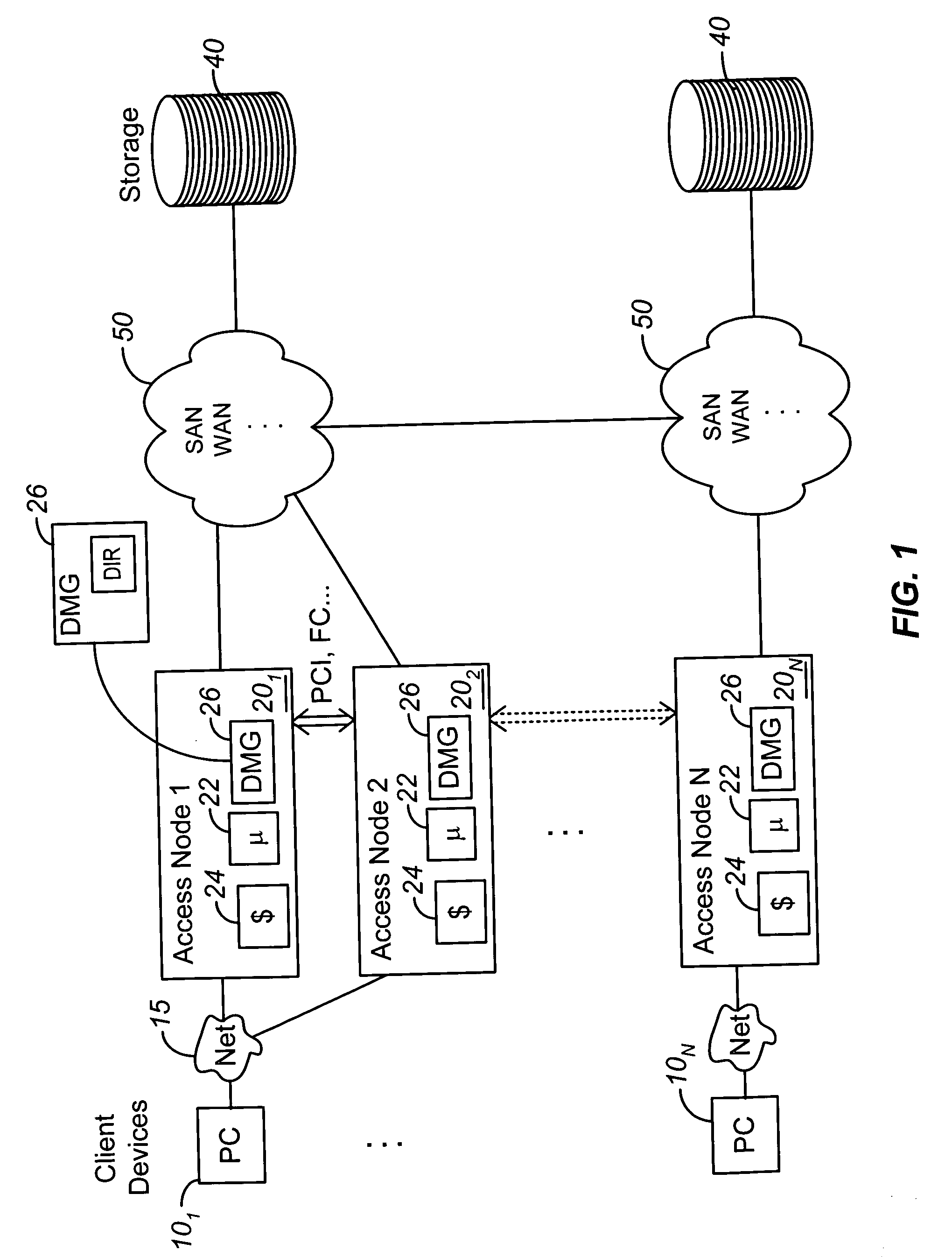
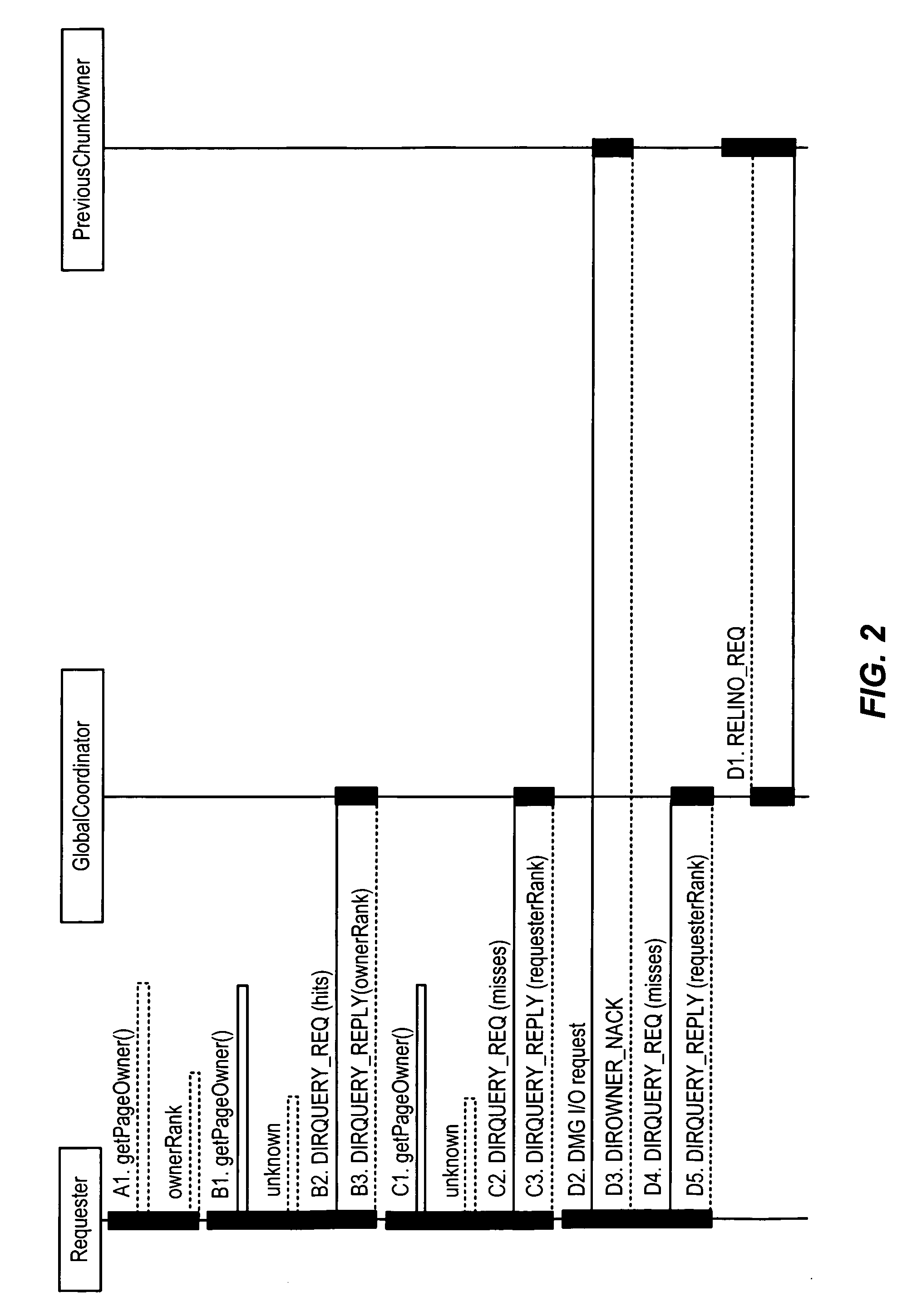
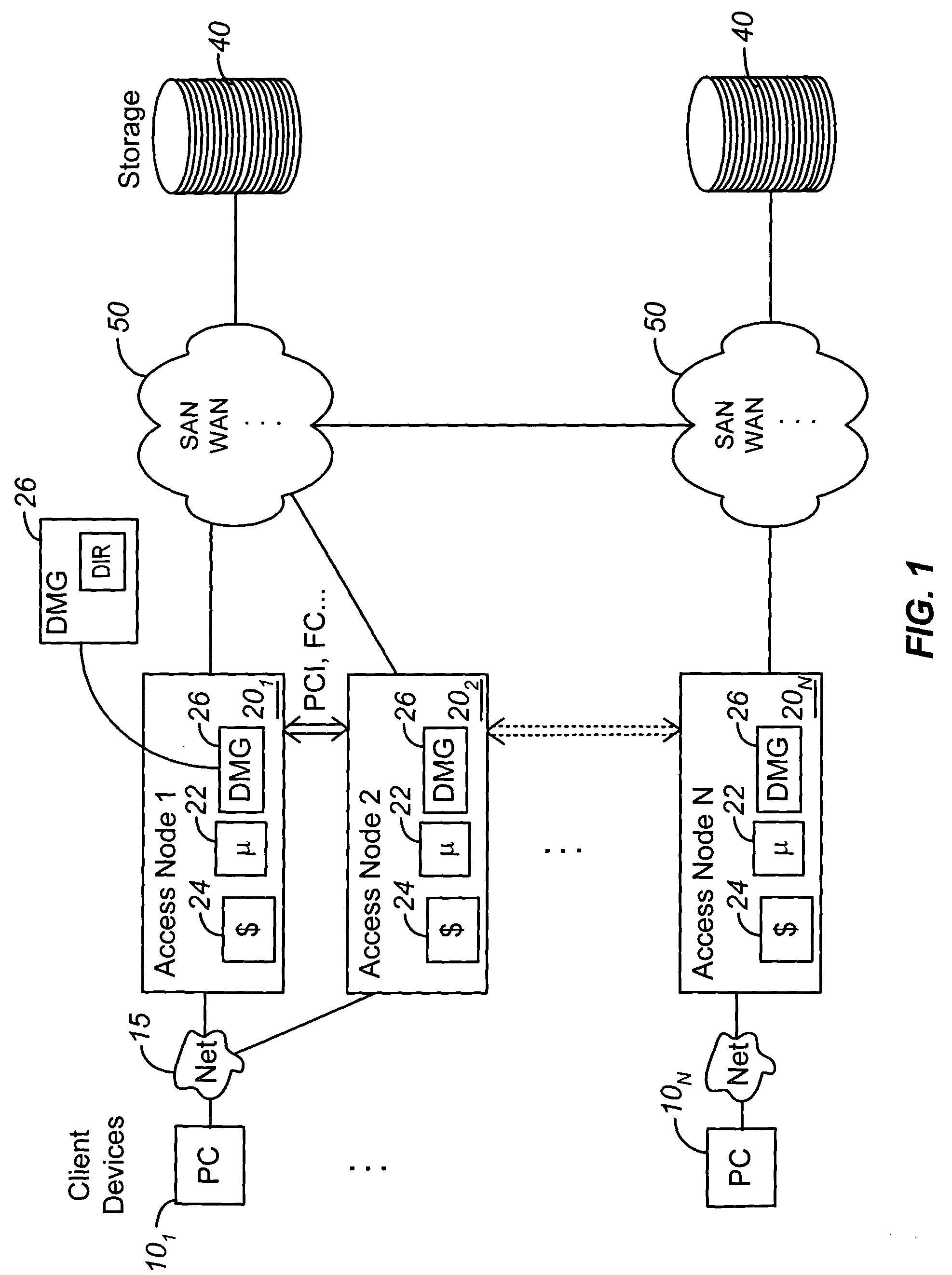
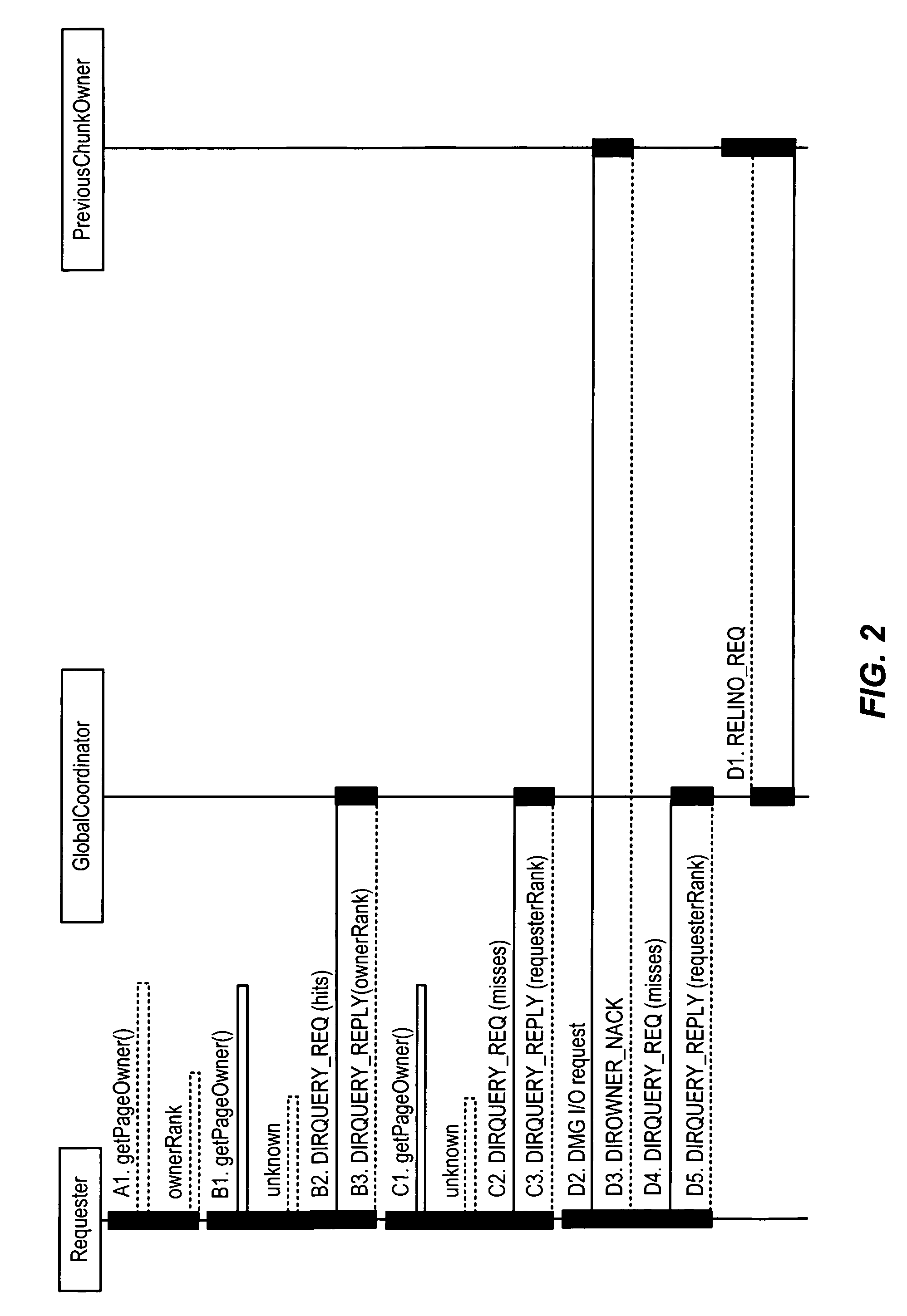
A plurality of access nodes sharing access to data on a storage network implement a directory based cache ownership scheme. One node, designated as a global coordinator, maintains a directory (e.g., table or other data structure) storing information about I / O operations by the access nodes. The other nodes send requests to the global coordinator when an I / O operation is to be performed on identified data. Ownership of that data in the directory is given to the first requesting node. Ownership may transfer to another node if the directory entry is unused or quiescent. The distributed directory-based cache coherency allows for reducing bandwidth requirements between geographically separated access nodes by allowing localized (cached) access to remote data.
Owner:EMC IP HLDG CO LLC
Data Cache Invalidate with Data Dependent Expiration Using a Step Value
InactiveUS20090019228A1Energy efficient ICTMemory adressing/allocation/relocationParallel computingData storing
According to embodiments of the invention, a step value and a step-interval cache coherency protocol may be used to update and invalidate data stored within cache memory. A step value may be an integer value and may be stored within a cache directory entry associated with data in the memory cache. Upon reception of a cache read request, along with the normal address comparison to determine if the data is located within the cache a current step value may be compared with the stored step value to determine if the data is current. If the step values match, the data may be current and a cache hit may occur. However, if the step values do not match, the requested data may be provided from another source. Furthermore, an application may update the current step value to invalidate old data stored within the cache and associated with a different step value.
Owner:IBM CORP
Computer system with processor cache that stores remote cache presence information
ActiveUS7096323B1Low costAvoid wastingMemory architecture accessing/allocationEnergy efficient ICTTraffic capacityComputerized system
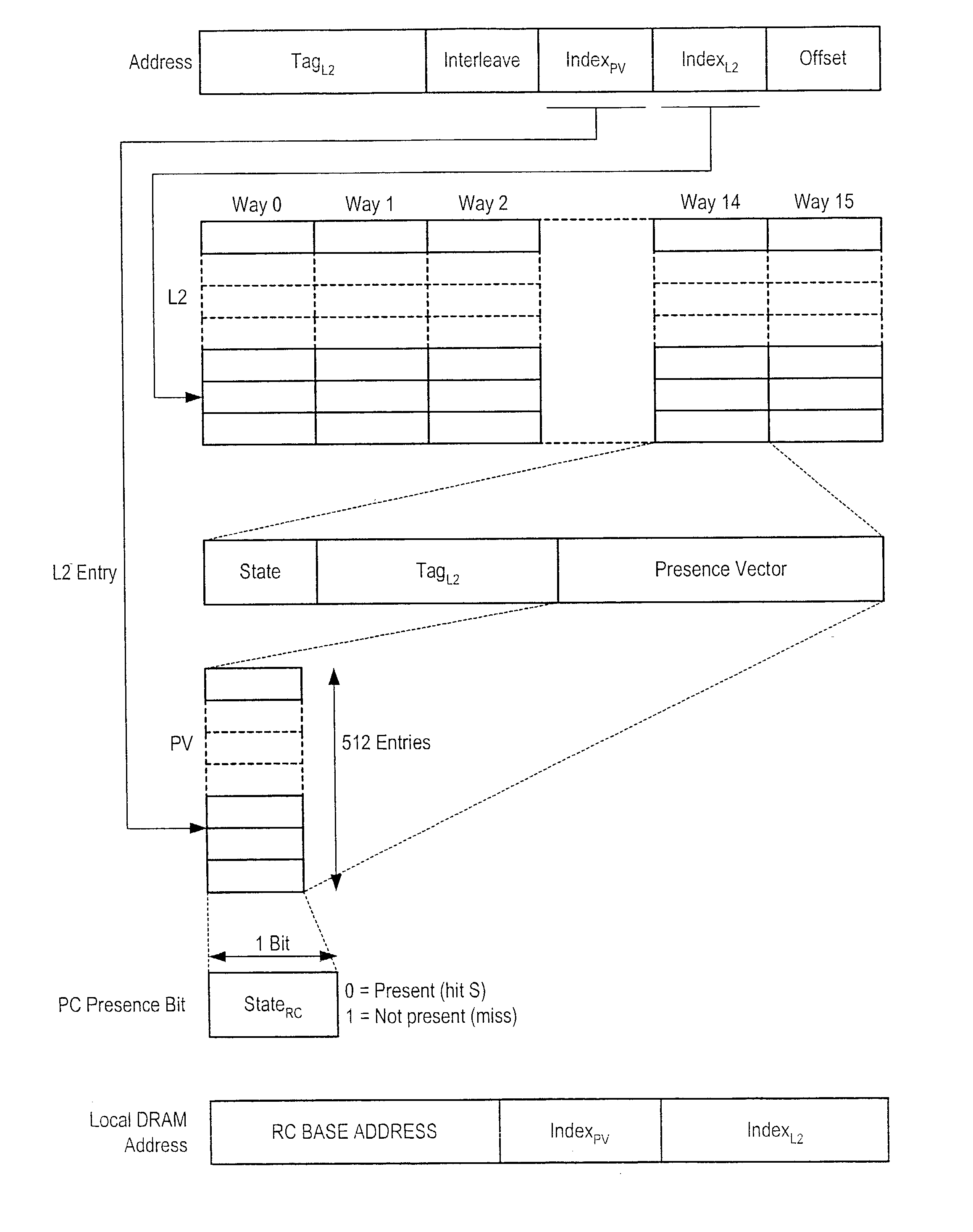
A computer system with a processor cache that stores remote cache presence information. In one embodiment, a plurality of presence vectors are stored to indicate whether particular blocks of data mapped to another node are being remotely cached. Rather than storing the presence vectors in a dedicated storage, the remote cache presence vectors may be stored in designated locations of a cache memory subsystem, such as an L2 cache, associated with a processor core. For example, a designated way of the cache memory subsystem may be allocated for storing remote cache presence vectors, while the remaining ways of the cache are used to store normal processor data. New data blocks may be remotely cached in response to evictions from the cache memory subsystem. In yet a further embodiment, additional entries of the cache memory subsystem may be used for storing directory entries to filter probe command and response traffic.
Owner:MEDIATEK INC
Arrangement for a distributed file system having data objects mapped independent of any data object attribute
ActiveUS20060179037A1Reduce necessityData processing applicationsDigital data processing detailsDistributed File SystemImage resolution
Each data file of a distributed file system is identified by a corresponding globally-unique object identifier that is independent of any attribute of the data file. A node in the distributed file system has a file system that includes a plurality of directory entries, where each directory entry has a file name field, an attributes field, and an object identifier field configured for specifying a globally-unique object identifier. The globally-unique object identifier is universally reachable by any node of the distributed file system and uniquely identifies the data file, enabling the data file to be universally identifiable by any node based on the corresponding object identifier. The data file can be stored independently of a device file system based on providing a resolution between the data file name and its object identifier, followed by a resolution between the object identifier and a selected location for the data file.
Owner:CISCO TECH INC
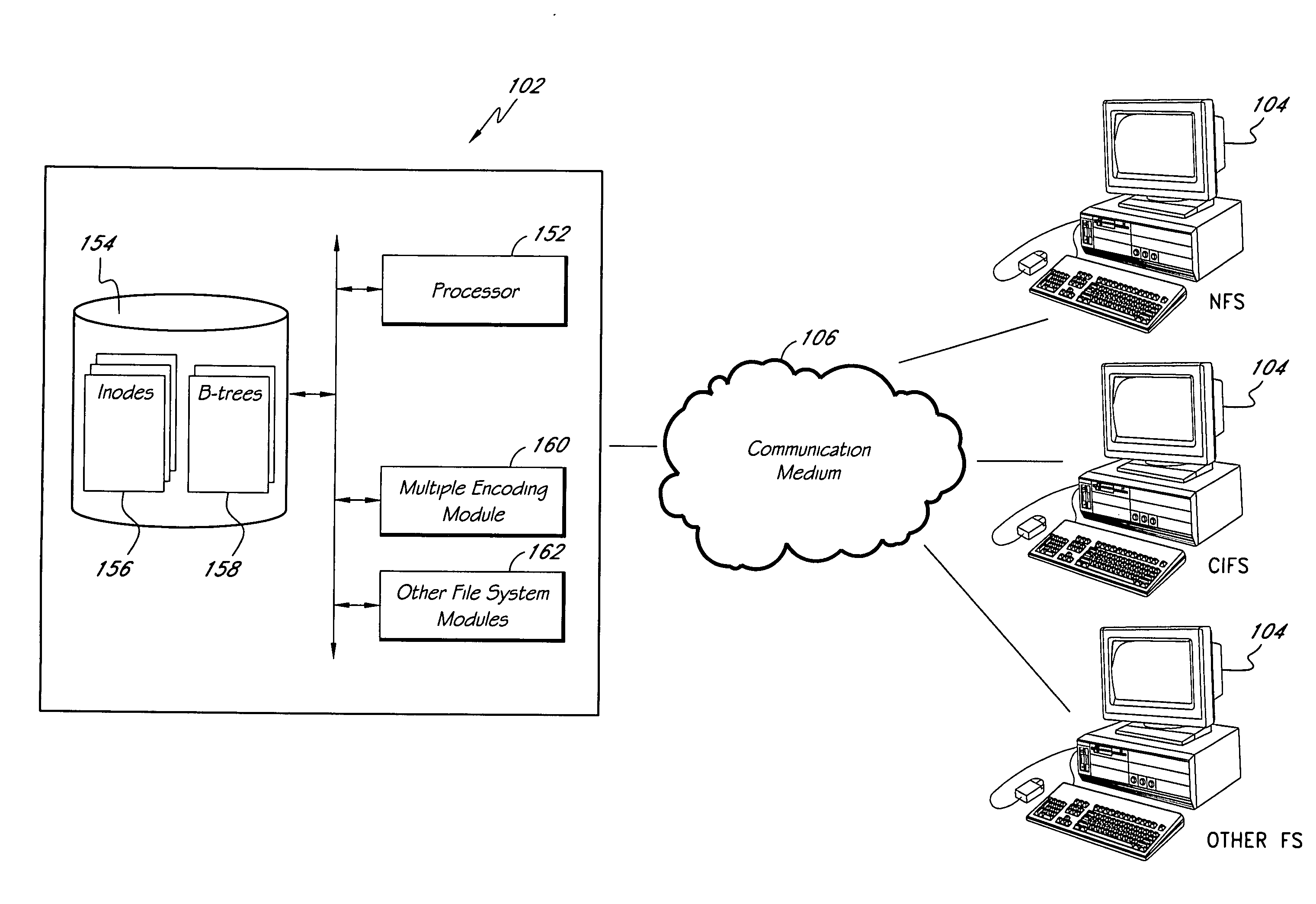
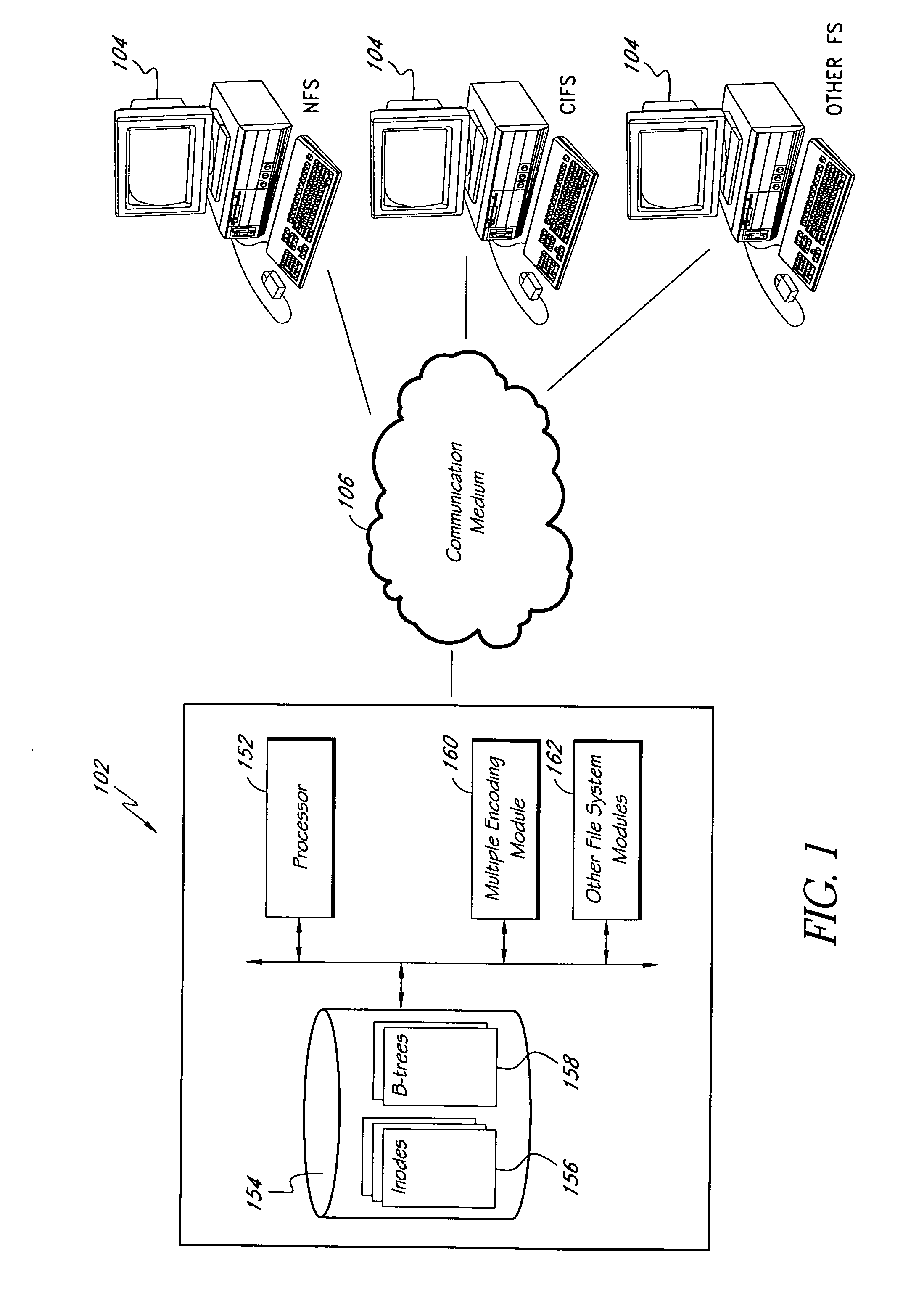
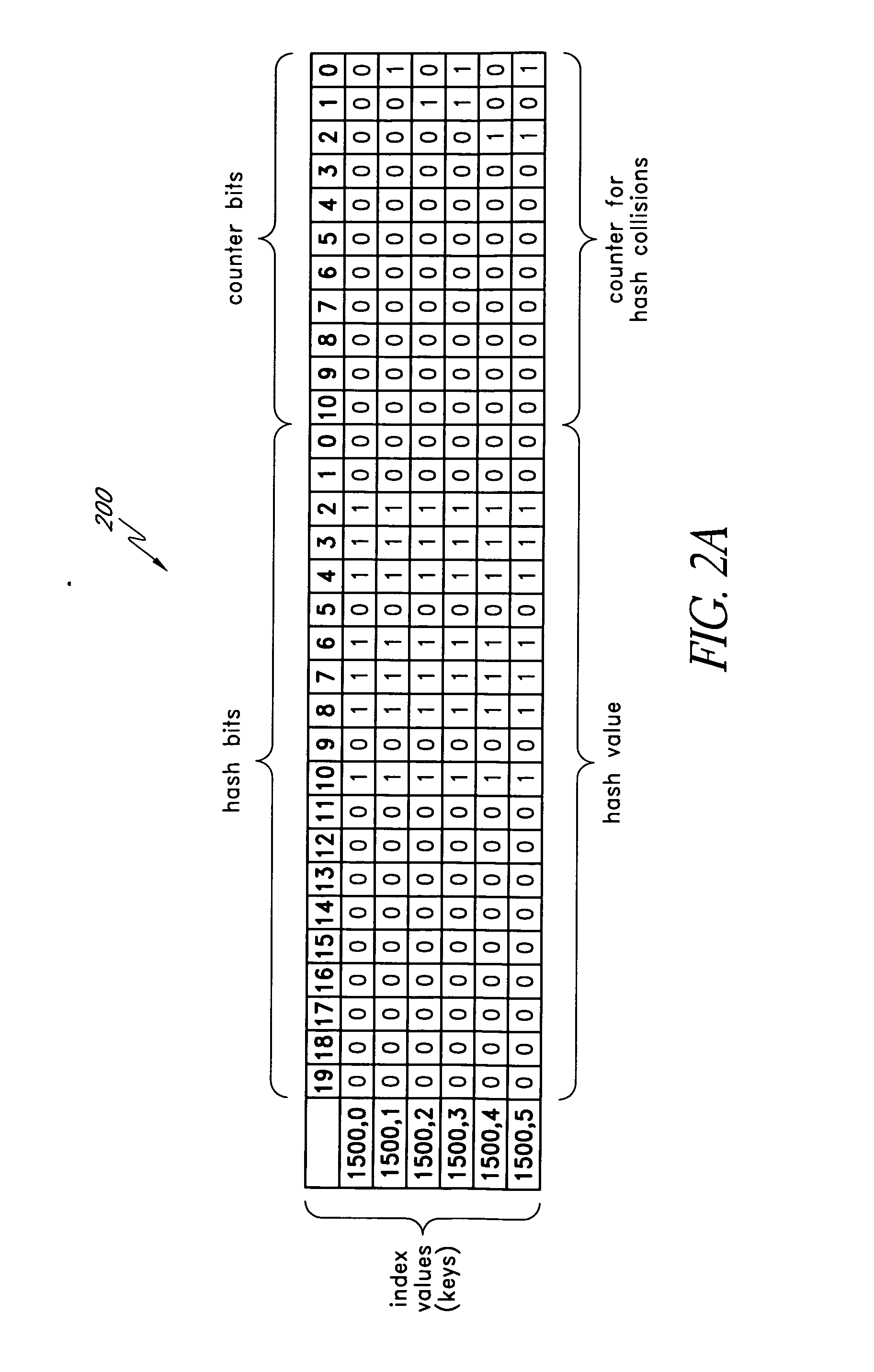
Systems and methods of directory entry encodings
ActiveUS20080154978A1Data processing applicationsDigital data information retrievalFile systemData store
In general, the invention relates to supporting multiple different character encodings in the same file system. In one embodiment, a method is provided for filename lookup that supports multiple character encodings. The method comprises storing filename data in a first character encoding into an indexed data structure. The method further comprises receiving filename data in a second encoding. The method also comprises looking up filename data in the indexed data structure using the second encoding.
Owner:EMC IP HLDG CO LLC
Methods and systems for providing a unified namespace for multiple network protocols
InactiveUS20110137966A1Easy data migrationEasy to navigateTransmissionSpecial data processing applicationsObject handlingObject store
A network storage server system includes a presentation layer that presents multiple namespaces over the same data stored in an object store, allowing users to simultaneously access data over multiple protocols. The system supports object location independence of the stored data objects by introducing a layer of indirection between directory entries and storage locations of stored data objects. In one embodiment, the directory entry of a data object points to a redirector file that includes an object locator (e.g., an object handle or a global object ID) of the data object. The directory entries of data objects are stored in a directory namespace (e.g., NAS path namespace). In another embodiment, a global object ID of the data object is directly encoded within the directory entry of the data object.
Owner:NETWORK APPLIANCE INC
Identity-based encryption system
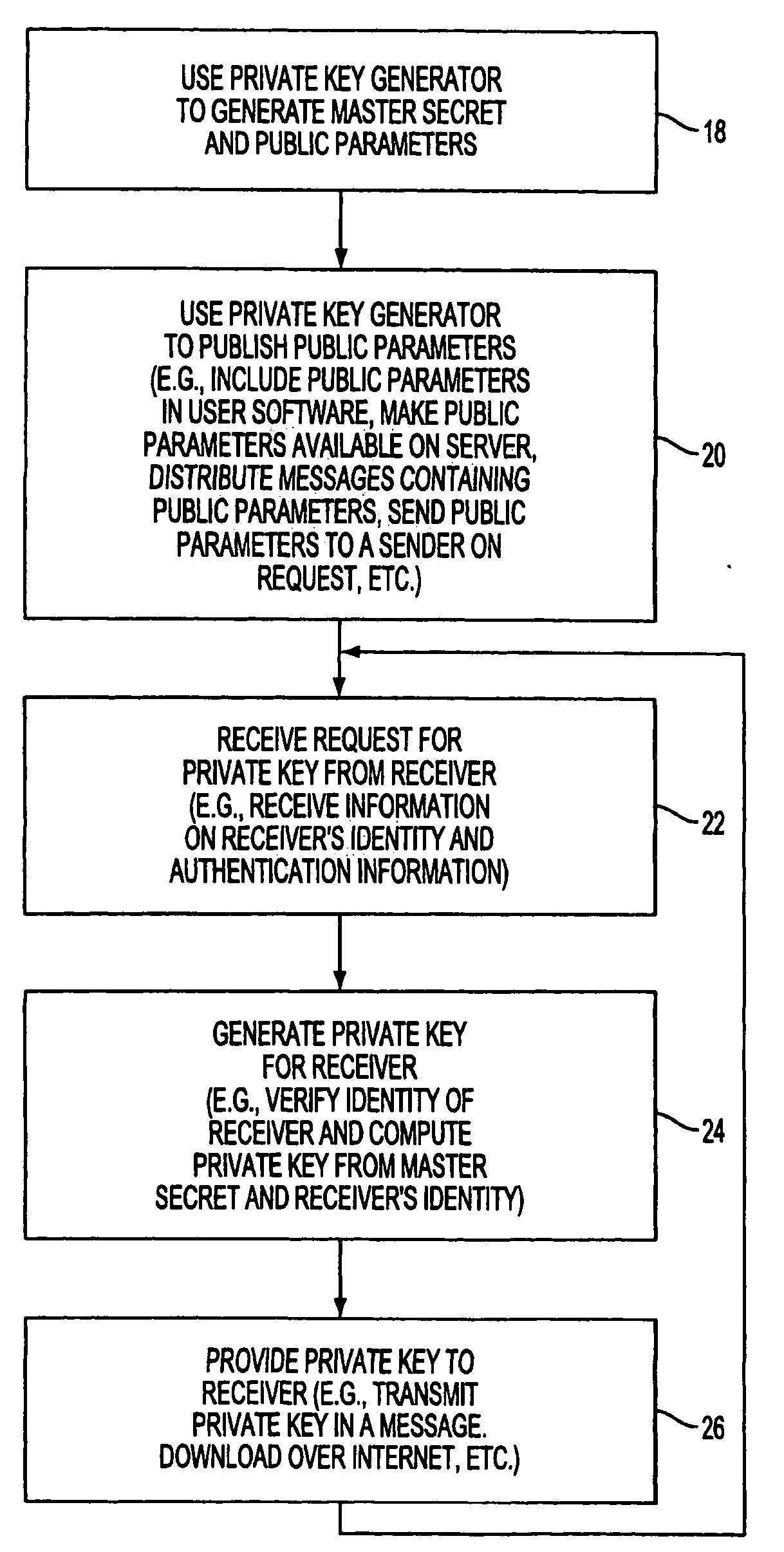
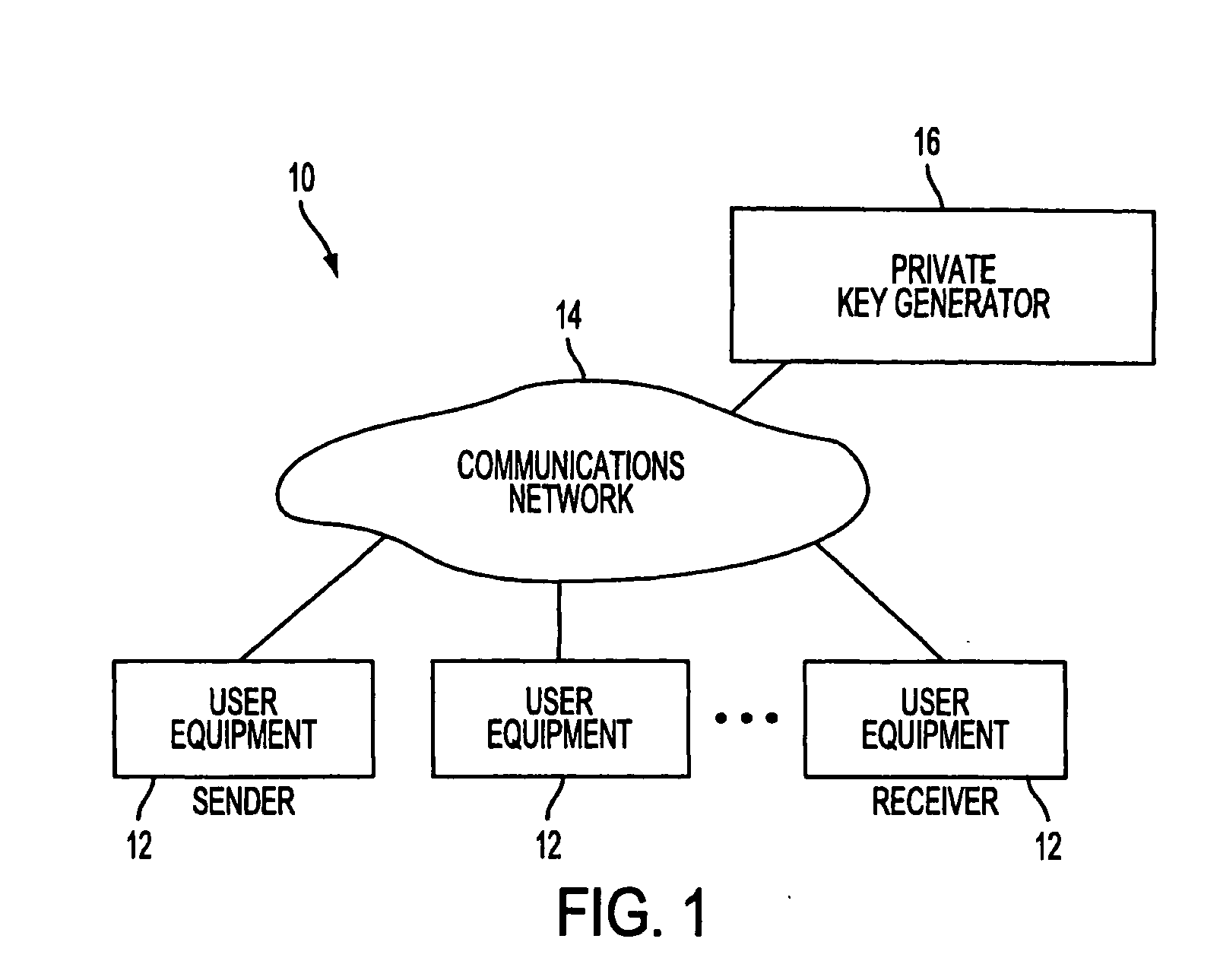
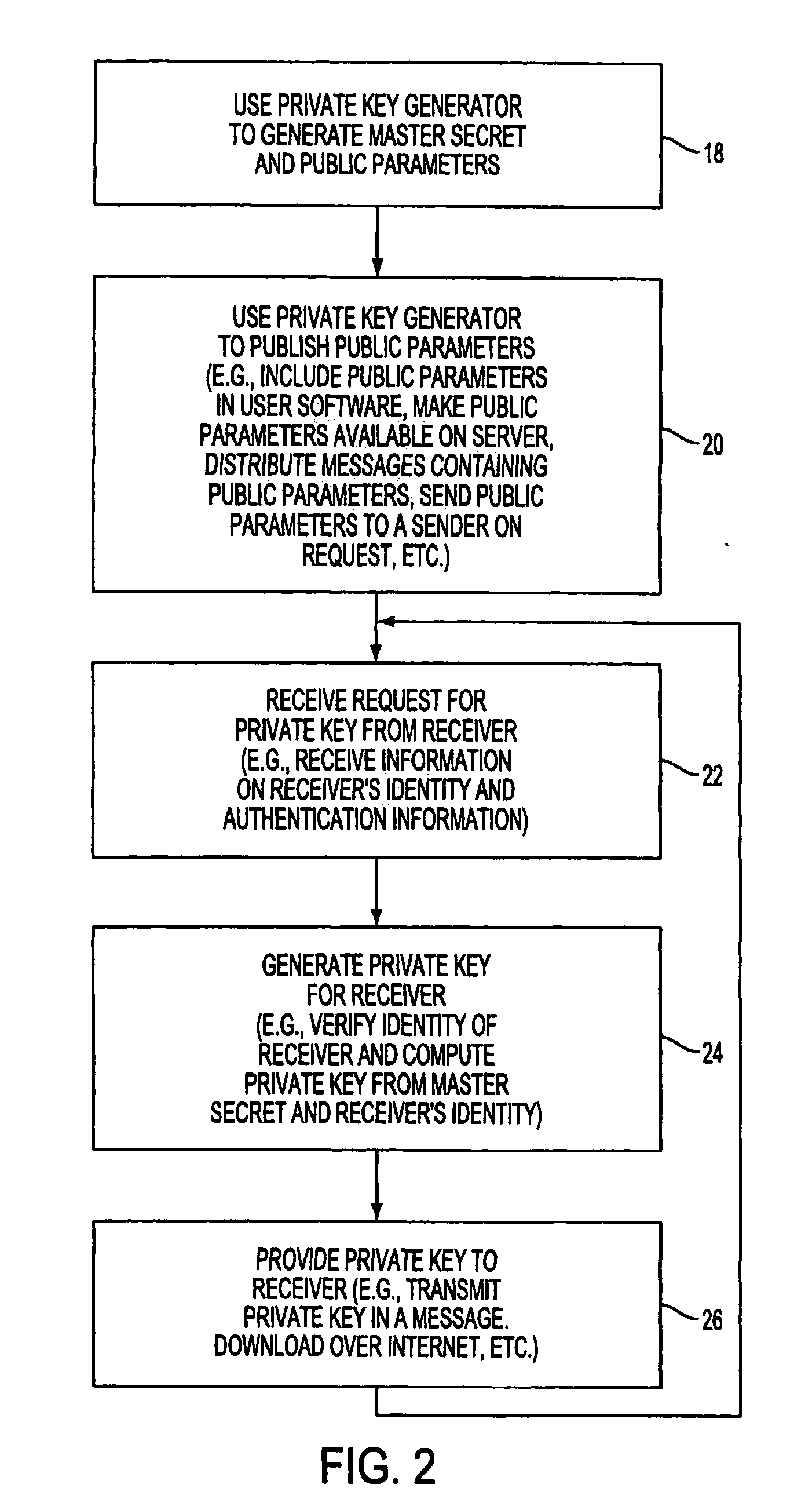
ActiveUS20080148047A1Avoid repetitionPublic key for secure communicationUser identity/authority verificationSecure communicationKey generator
A system is provided that uses identity-based encryption to support secure communications. Messages from a sender to a receiver may be encrypted using the receiver's identity and public parameters that have been generated by a private key generator associated with the receiver. The private key generator associated with the receiver generates a private key for the receiver. The encrypted message may be decrypted by the receiver using the receiver's private key. The system may have multiple private key generators, each with a separate set of public parameters. Directory services may be used to provide a sender that is associated with one private key generator with appropriate public parameters to use when encrypting messages for a receiver that is associated with a different private key generator. A certification authority may be used to sign directory entries for the directory service. A clearinghouse may be used to avoid duplicative directory entries.
Owner:MICRO FOCUS LLC
System and method for using login correlations to detect intrusions
InactiveUS7085936B1Overcome problemsEnabling detectionDigital data processing detailsUnauthorized memory use protectionContinuationTimestamp
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
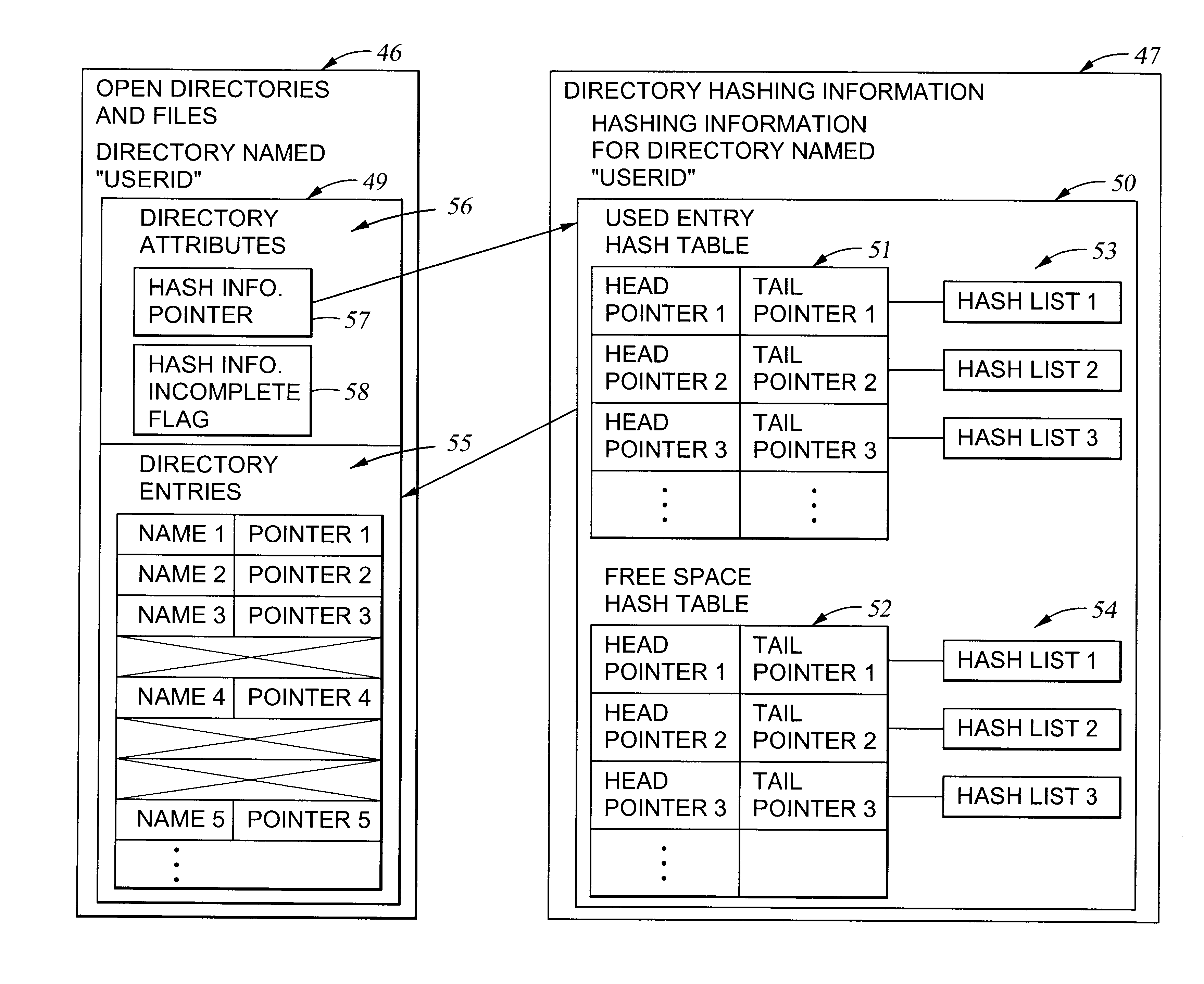
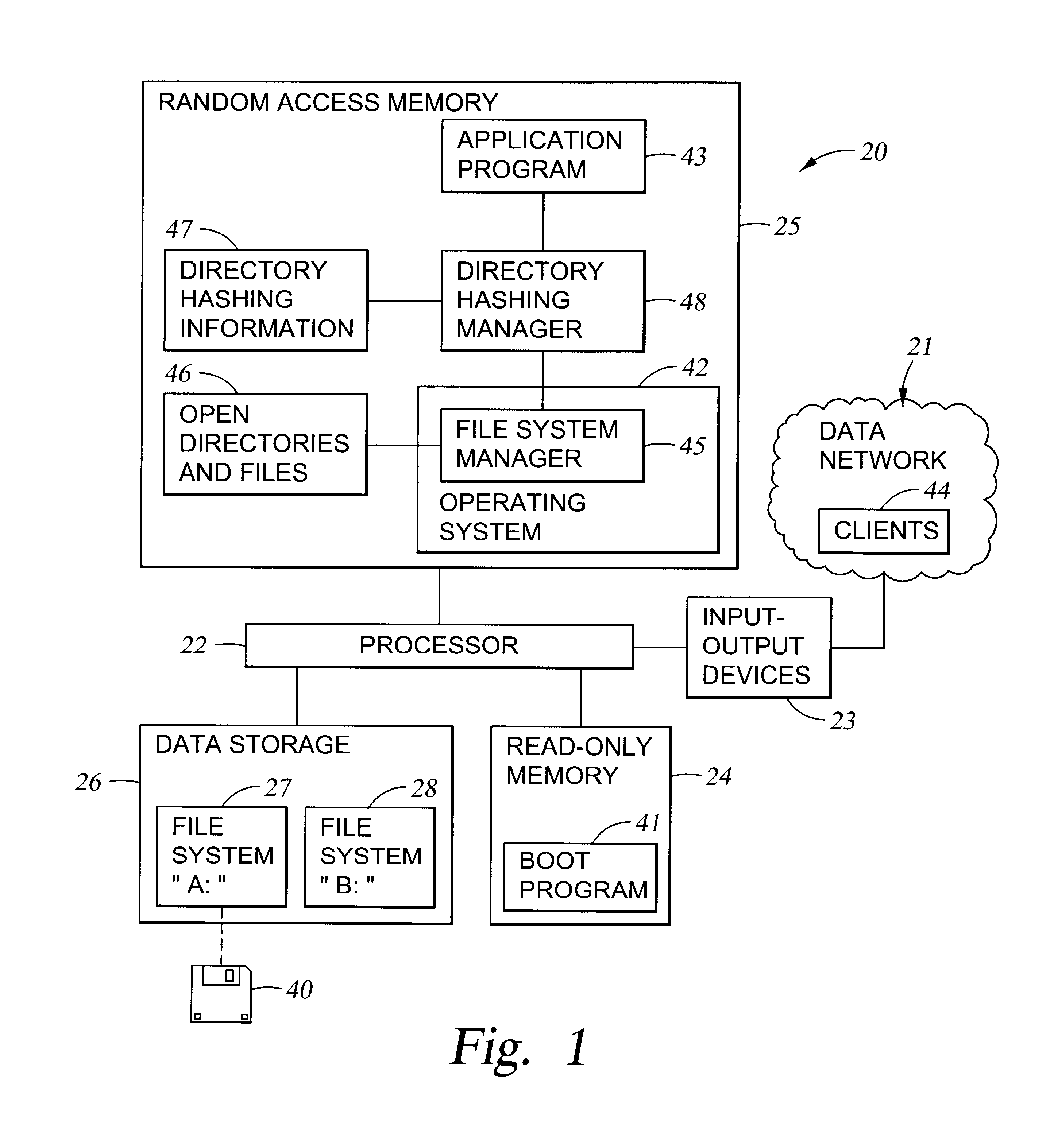
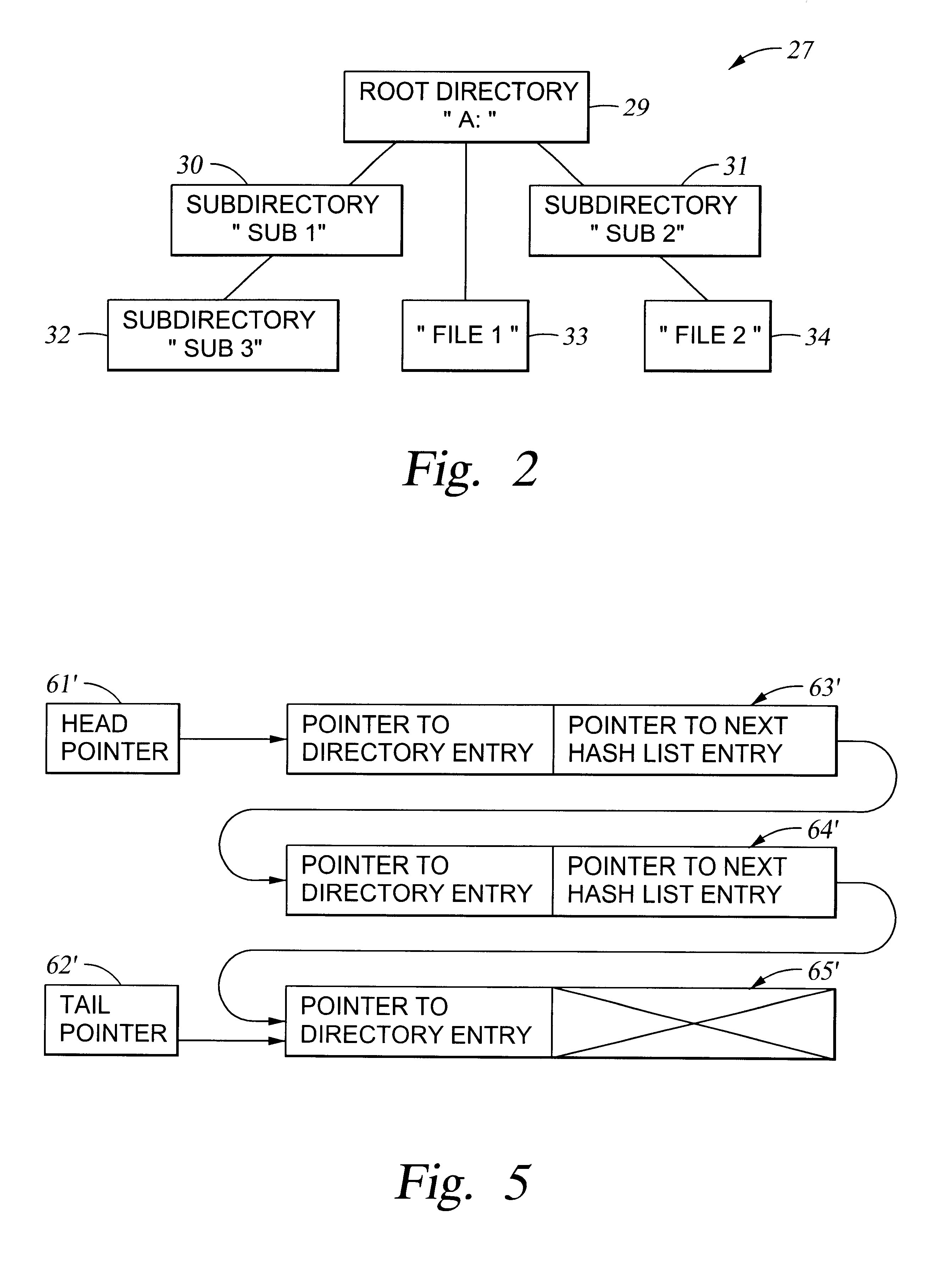
Very efficient in-memory representation of large file system directories
InactiveUS6625591B1Data processing applicationsDigital data information retrievalFile systemOut of memory
To accelerate searching of large file system directories, hashing information for a selected directory is compiled and retained in random access memory prior to a need for access to the directory to satisfy a file access request from an application. No change in the on-disk file system representation is required, nor is there any need for nonvolatile storage of the hashing information. If memory is scarce, the hashing information can be incomplete yet give hints for searching the most-recently-accessed directory entries. In a preferred implementation, the hashing information for a directory includes a hash table for searching for names of objects such as files, subdirectories or links in the directory, and a hash table for searching for free space in the directory.
Owner:EMC IP HLDG CO LLC
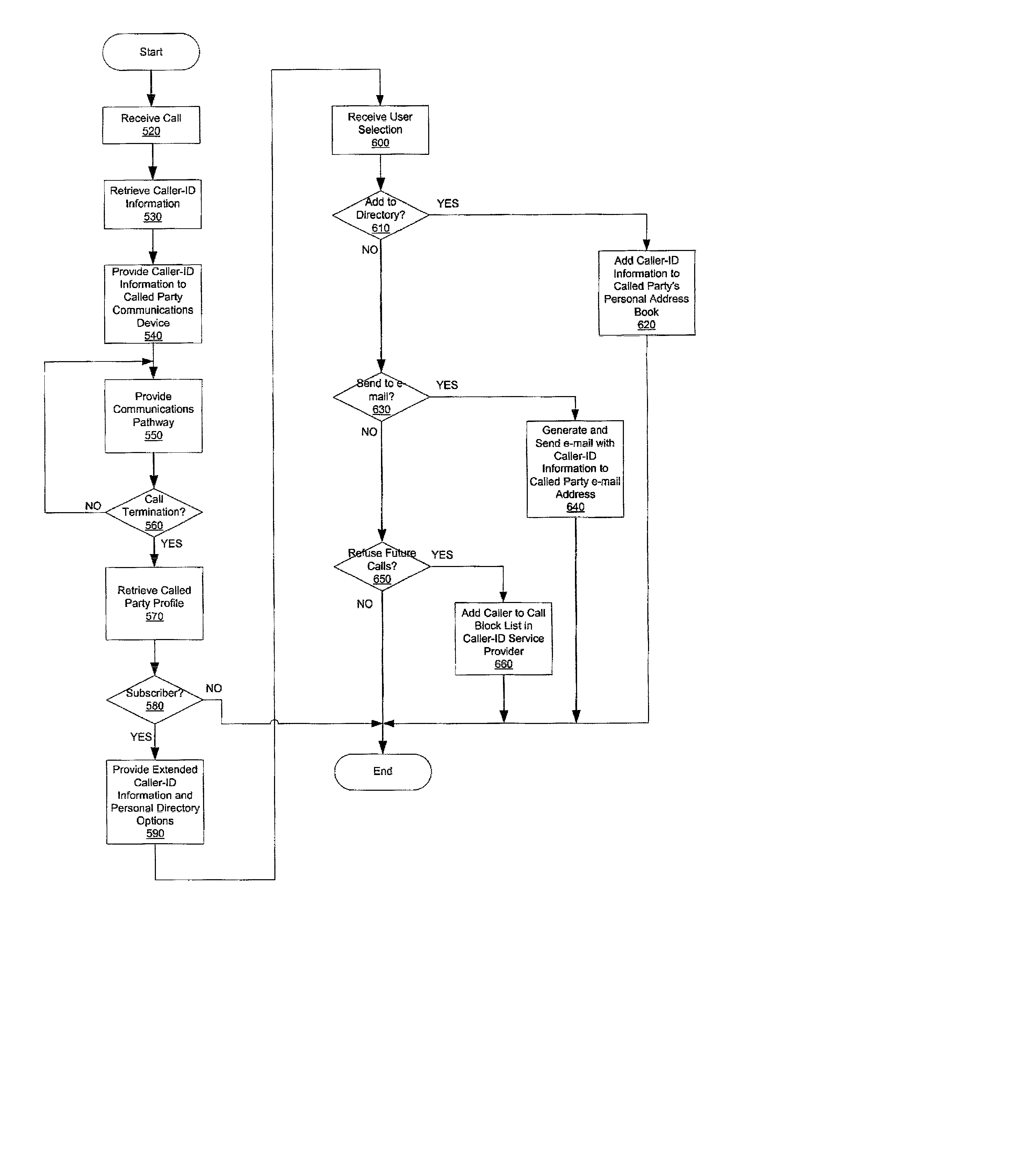
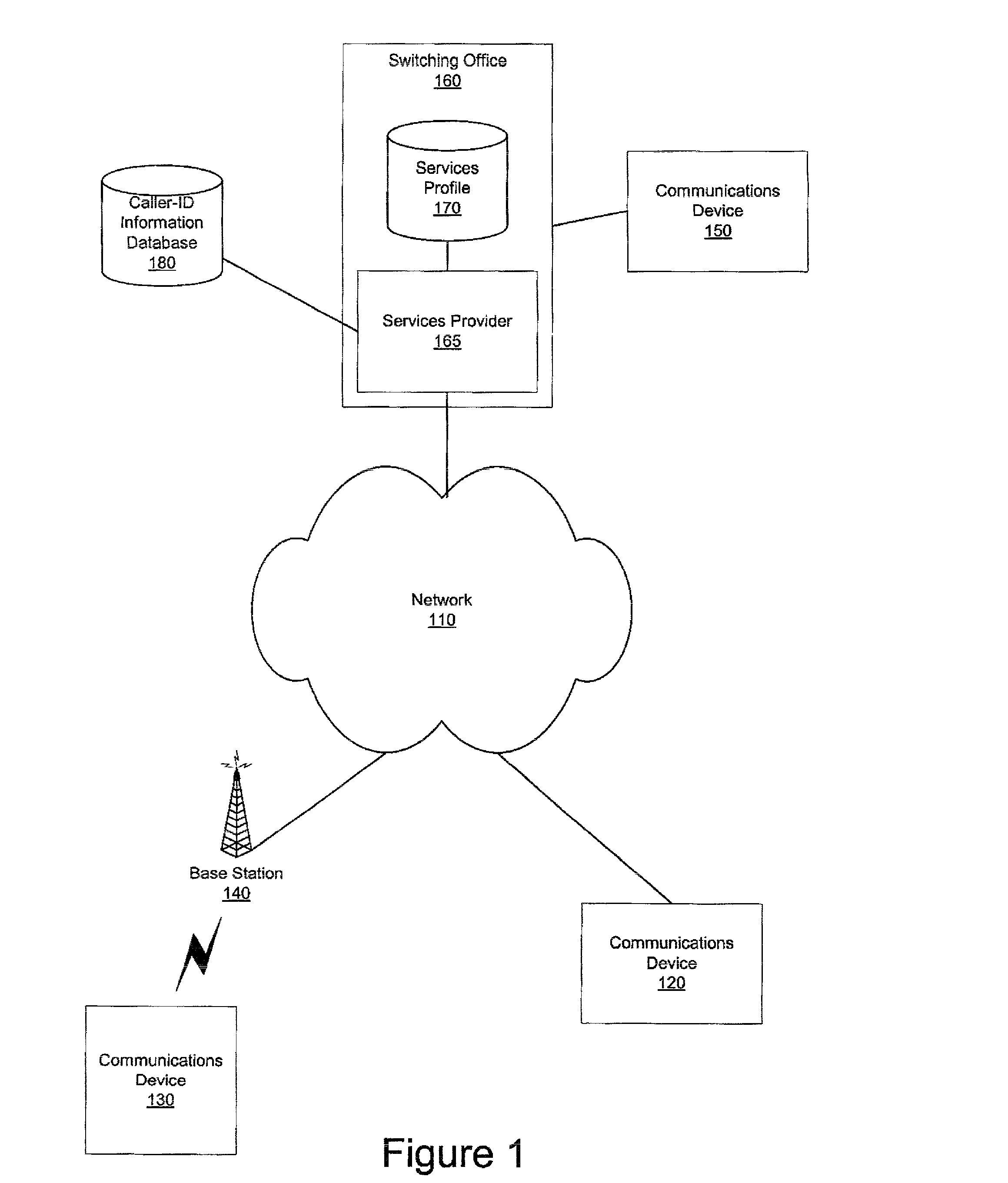
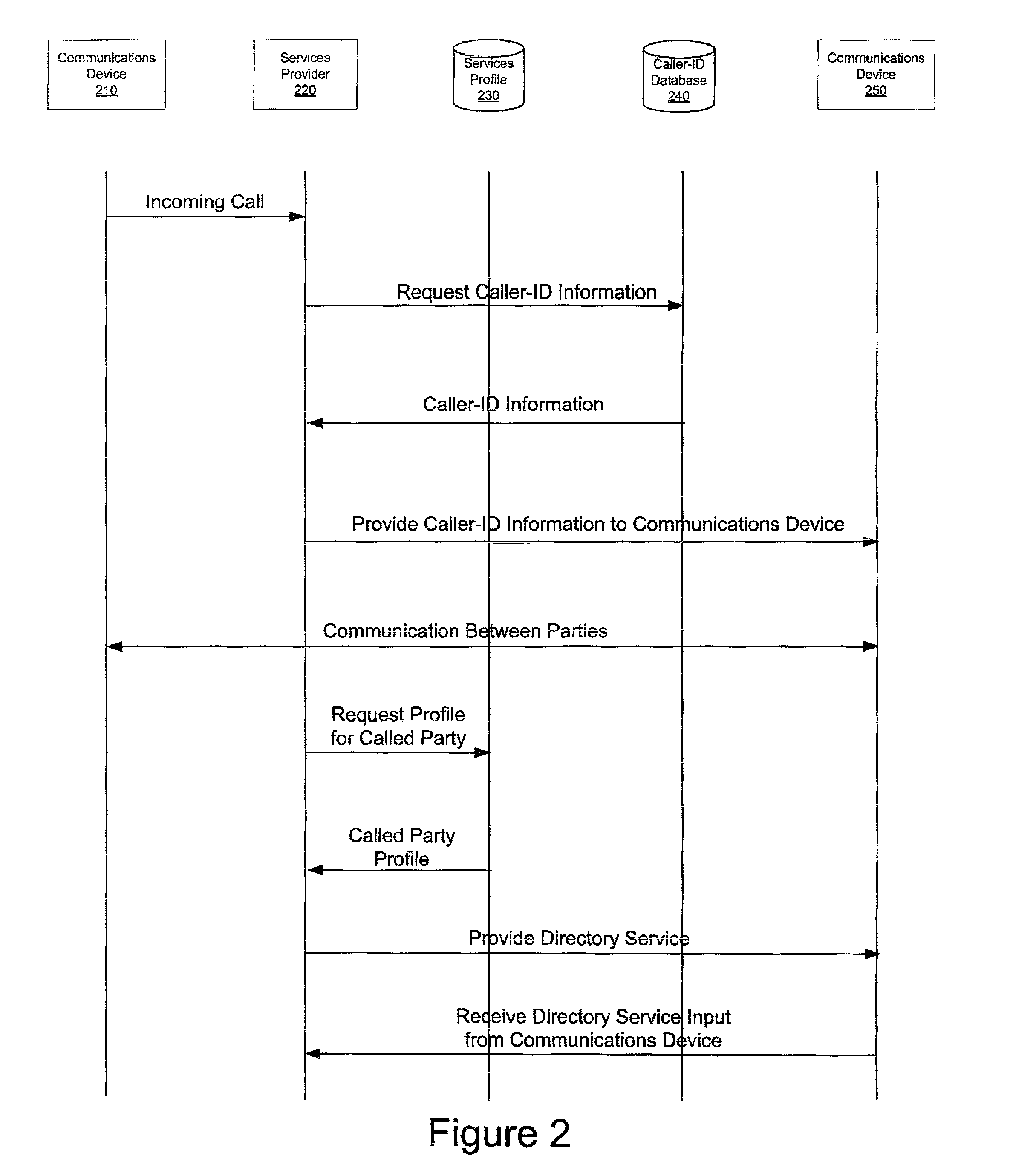
Apparatus, method and computer program product for automatic directory entry generation via caller-id
InactiveUS20020126814A1Automatic call-answering/message-recording/conversation-recordingCalling susbscriber number recording/indicationDisplay deviceCommunication device
An apparatus, method and computer program product for automatically generating directory entries based on caller-id information are provided. When a call is received from a calling party, the caller-id information is obtained from a caller-id database. Either before, during or after the communication connection is established between the calling party's communication device and the called party's communication device, the called party is given the option to store and / or update the caller-id information as a directory entry in a local directory of the called party's communication device. If the called party elects to have the calling party's caller-id information stored in the called party's directory, the caller-id information is transmitted to the called party's communication device and stored as an entry in the called party's local directory and is used for further processing such as call block and the like. The caller-id information stored in the party's local directory may be more than the caller-id information displayed on the communication device display.
Owner:IBM CORP
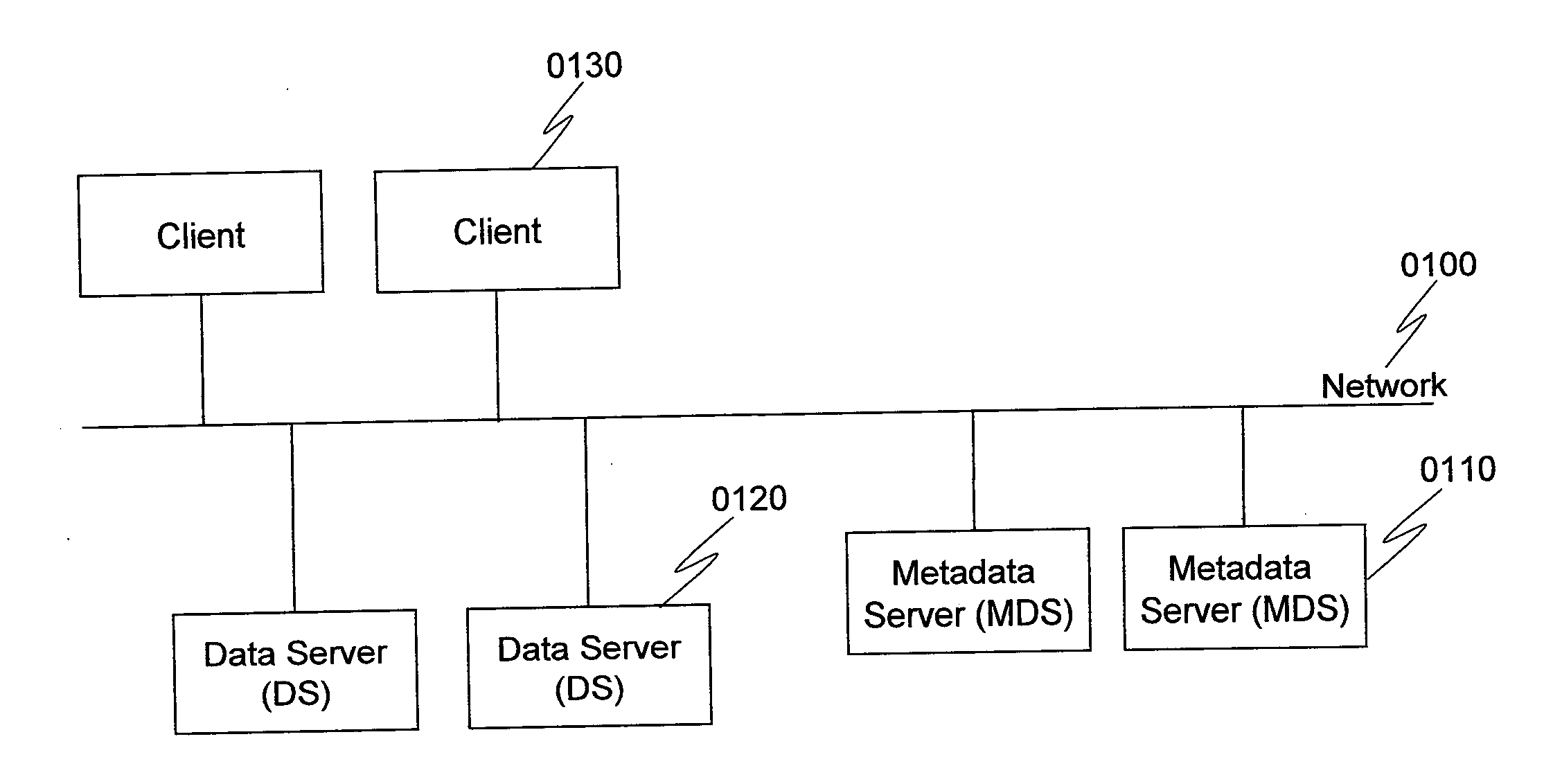
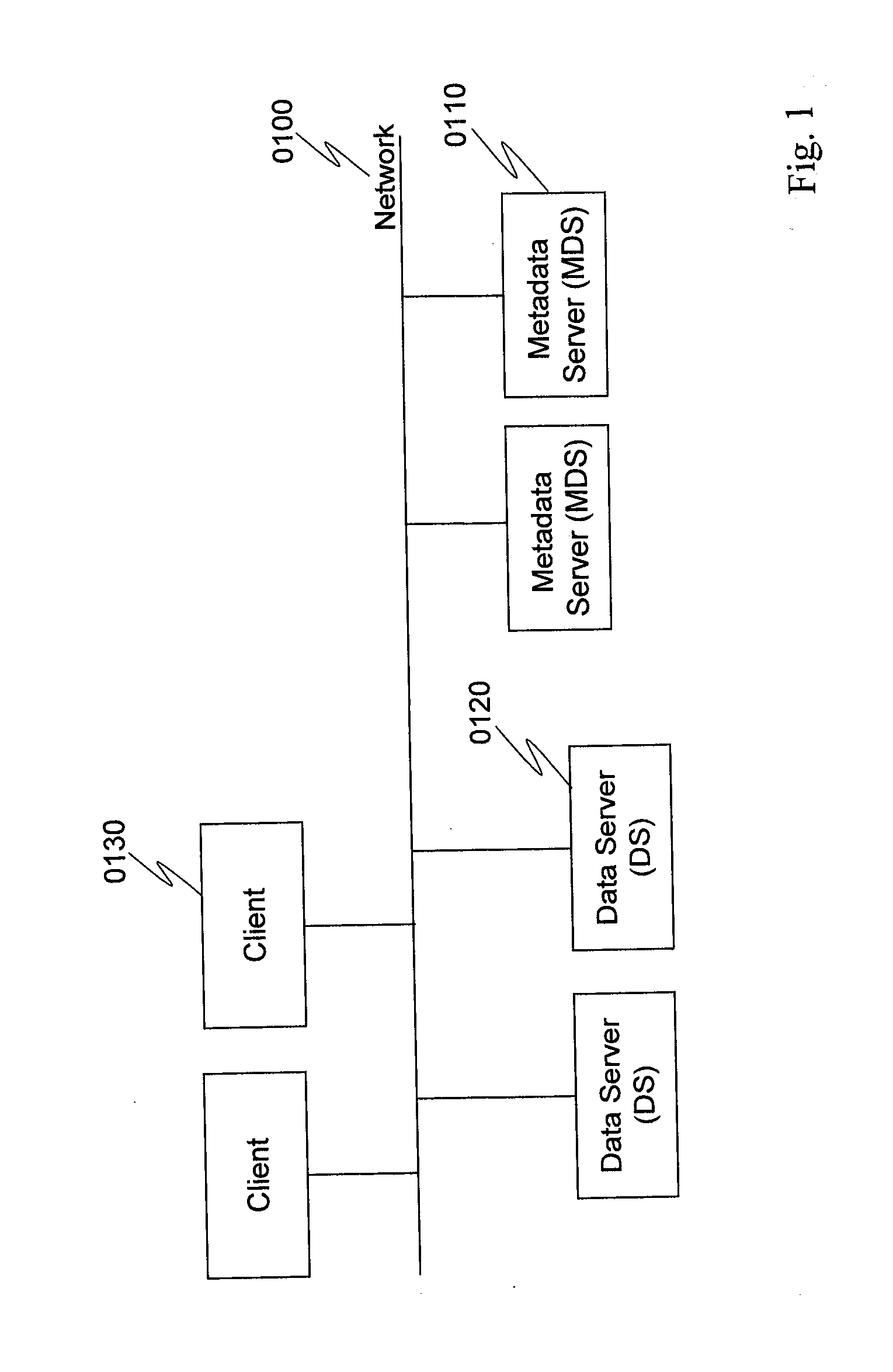
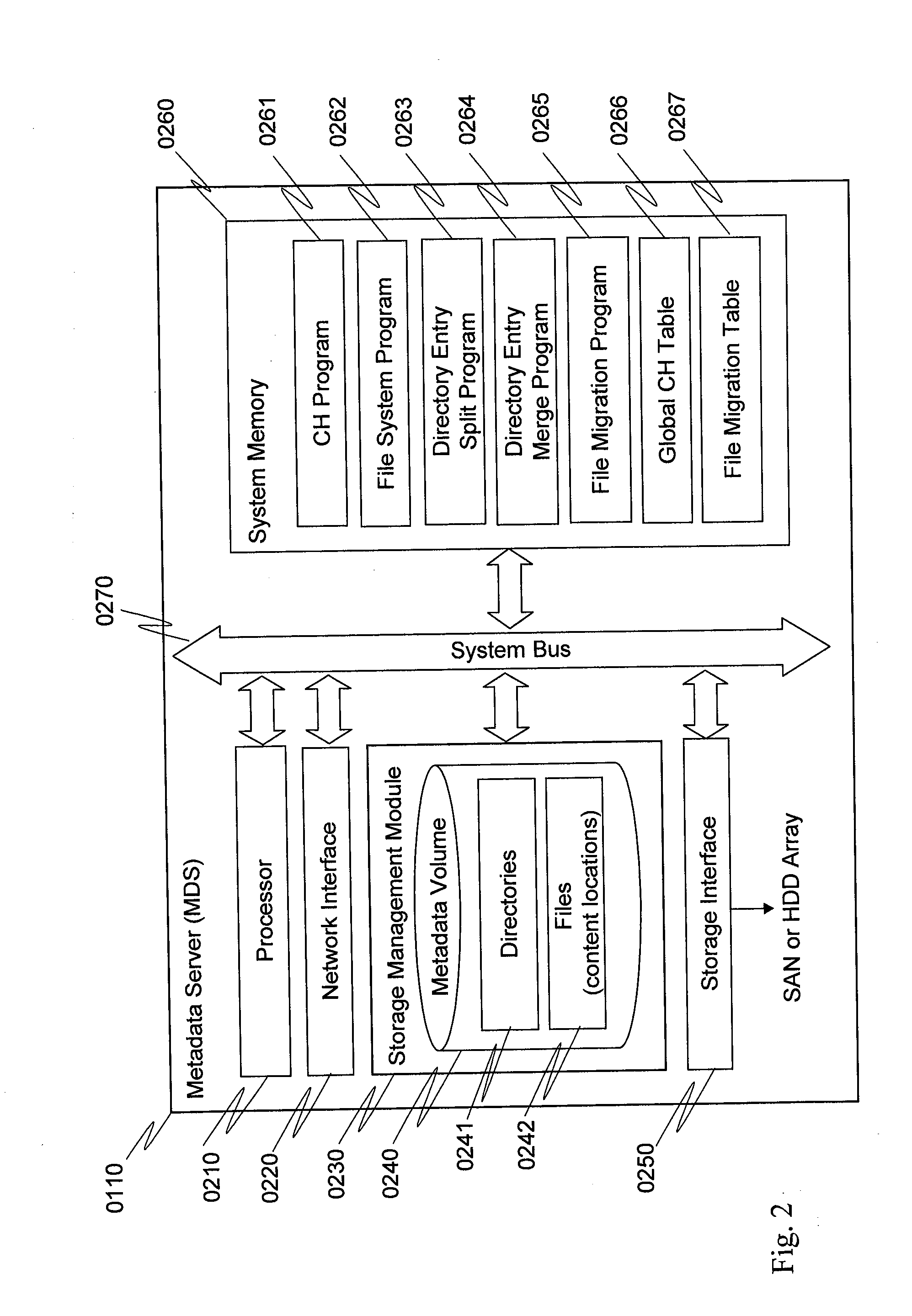
Method for directory entries split and merge in distributed file system
InactiveUS20130218934A1Improve performanceMinimize impactDigital data information retrievalSpecial data processing applicationsDistributed File SystemFile system
A distributed storage system has MDSs (metadata servers). Directories of file system namespace are distributed to the MDSs based on hash value of inode number of each directory. Each directory is managed by a master MDS. When a directory grows with a file creation rate greater than a preset split threshold, the master MDS constructs a consistent hashing overlay with one or more slave MDSs and splits directory entries of the directory to the consistent hashing overlay based on hash values of file names under the directory. The number of MDSs in the consistent hashing overlay is calculated based on the file creation rate. When the directory continues growing with a file creation rate that is greater than the preset split threshold, the master MDS adds a slave MDS into the consistent hashing overlay and splits directory entries to the consistent hashing overlay based on hash values of file names.
Owner:HITACHI LTD
Method and system for creating and utilizing managed roles in a directory system
ActiveUS20050021498A1Slow changeData processing applicationsDigital data processing detailsClient-sideDirectory system
Role is a comprehensive grouping mechanism. In a client-server directory system, roles transfer some of the complexity to the directory server. A role is defined by its role definition entry. Any client with appropriate access privileges can discover, identify and examine any role definition. A “managed” role is one that can be configured to provide search results similar to those available with a static grouping mechanism, i.e., to create a group entry that contains a list of members. Managed roles allow a user to create an explicit enumerated list of members. A managed role is a label stored with a directory entry.
Owner:ORACLE INT CORP
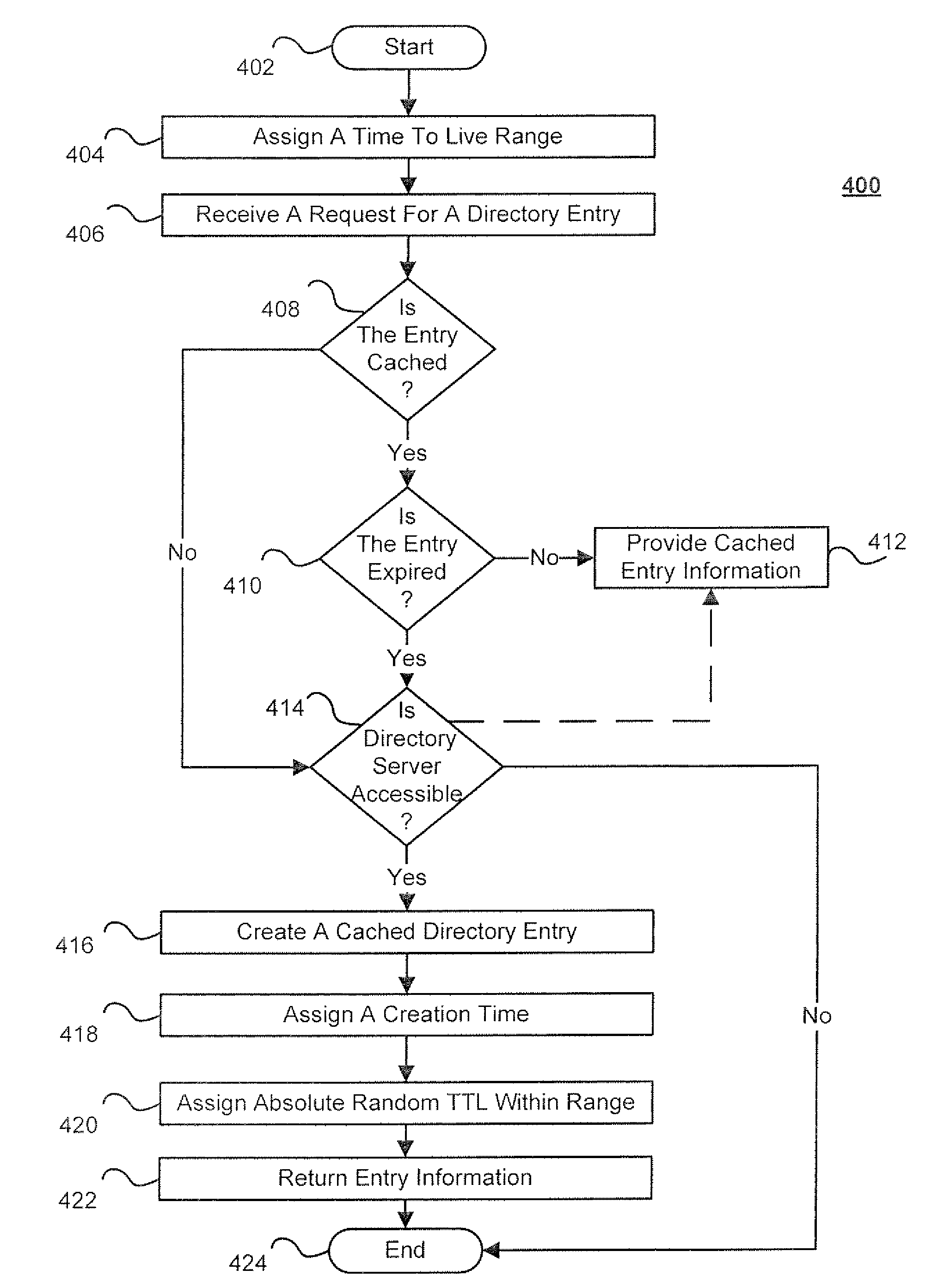
Techniques for directory server integration
ActiveUS8209491B2Reduce the amount requiredSpecial data processing applicationsMemory systemsExpiration TimeTime range
Techniques for directory server integration are disclosed. In one particular exemplary embodiment, the techniques may be realized as a method for directory server integration comprising setting one or more parameters determining a range of permissible expiration times for a plurality of cached directory entries, creating, in electronic storage, a cached directory entry from a directory server, assigning a creation time to the cached directory entry, and assigning at least one random value to the cached directory entry, the random value determining an expiration time for the cached directory entry within the range of permissible expiration times, wherein randomizing the expiration time for the cached directory entry among the range of permissible expiration times for a plurality of cached directory entries reduces an amount of synchronization required between cache memory and the directory server at a point in time.
Owner:CA TECH INC
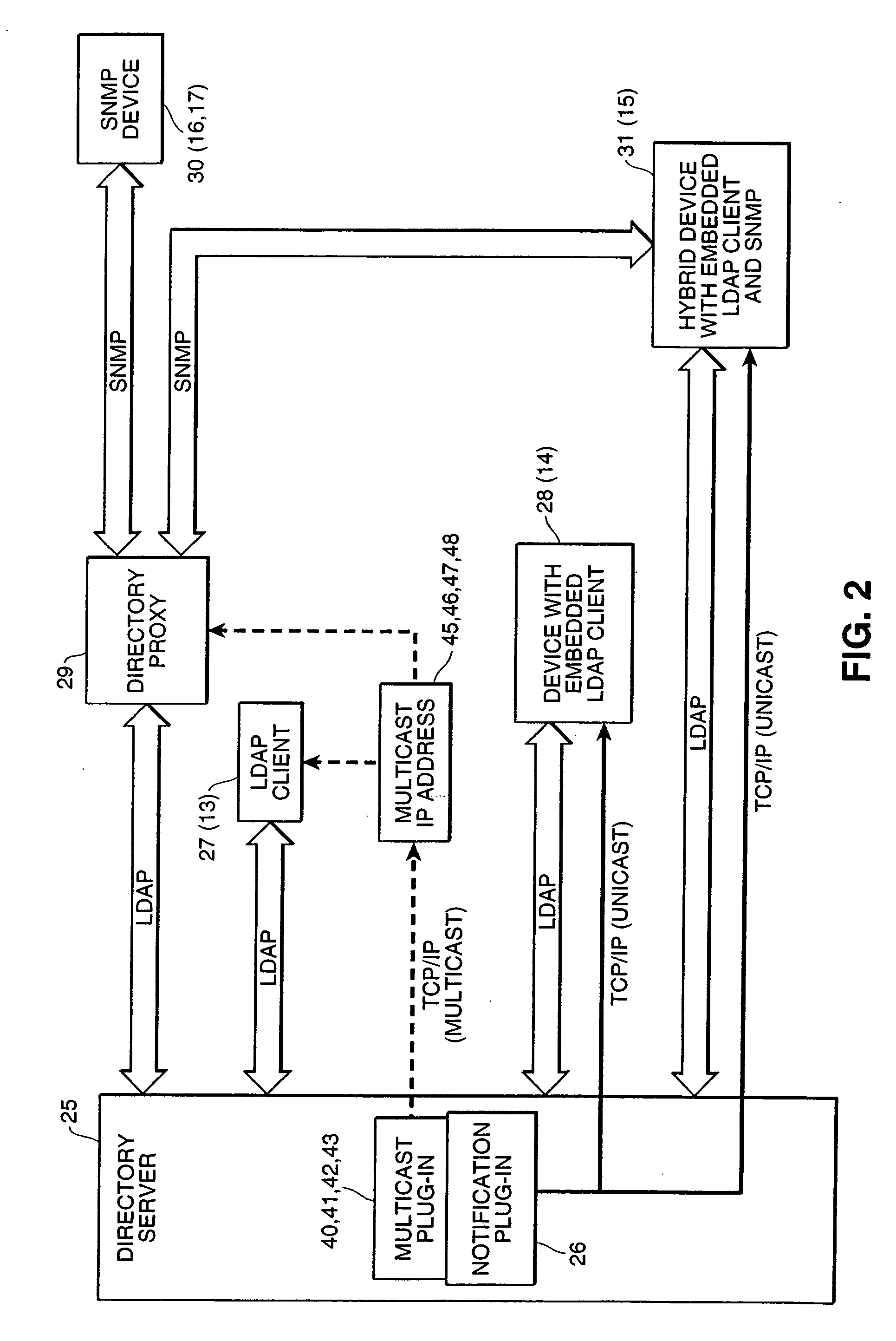
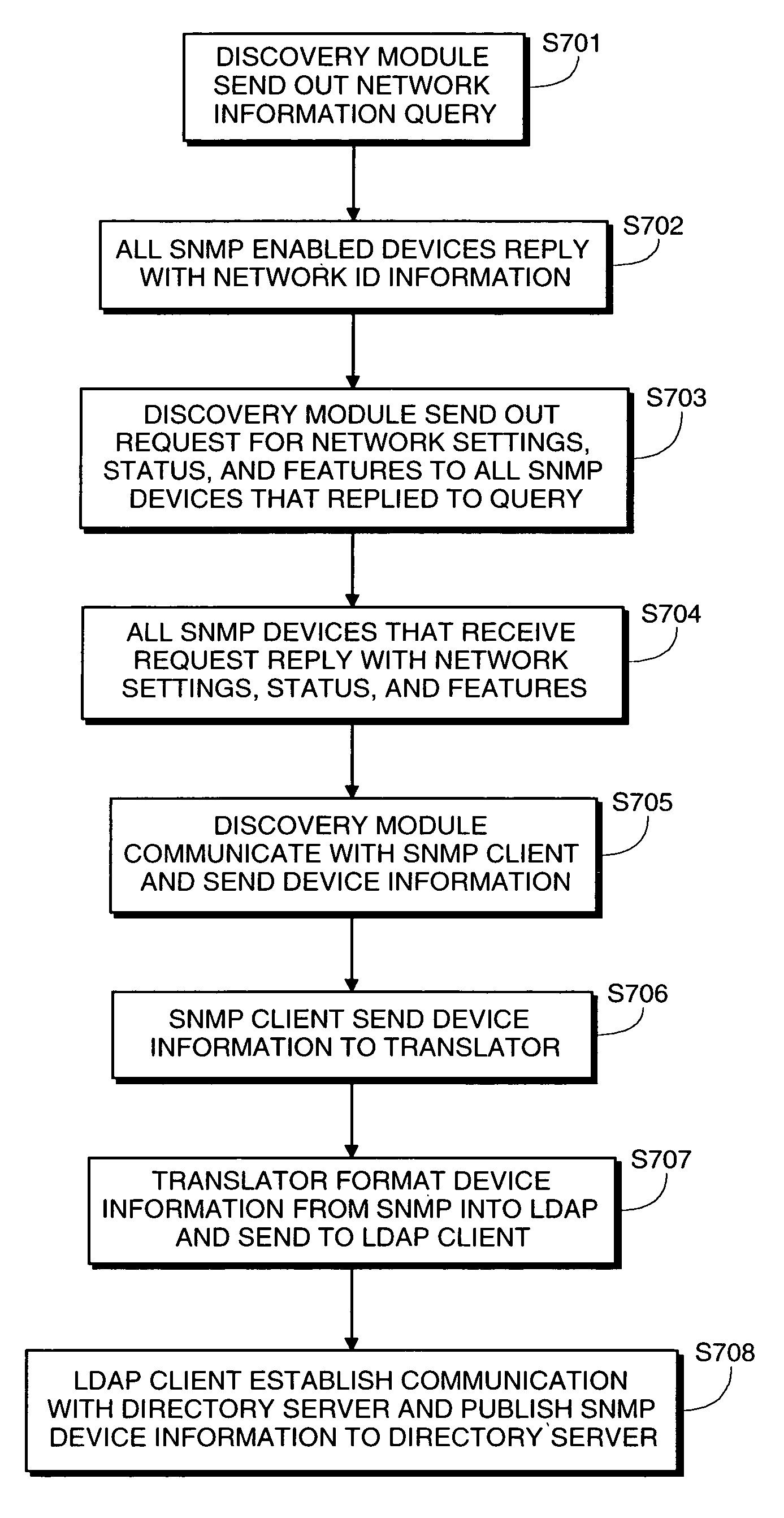
Directory-enabled device management
InactiveUS20060010232A1Reduce effortAdd supportMultiple digital computer combinationsData switching networksDirectory entryComputer security
Managing a plurality of network devices on a network by detecting the presence of at least one of the plurality of network devices on the network by using a first communication protocol, obtaining, by using the first communication protocol, an information block from each of the detected network devices, wherein the information block contains information related to the corresponding network device, formatting each information block into a directory entry, and sending each directory entry to a directory server via a second communication protocol.
Owner:CANON KK
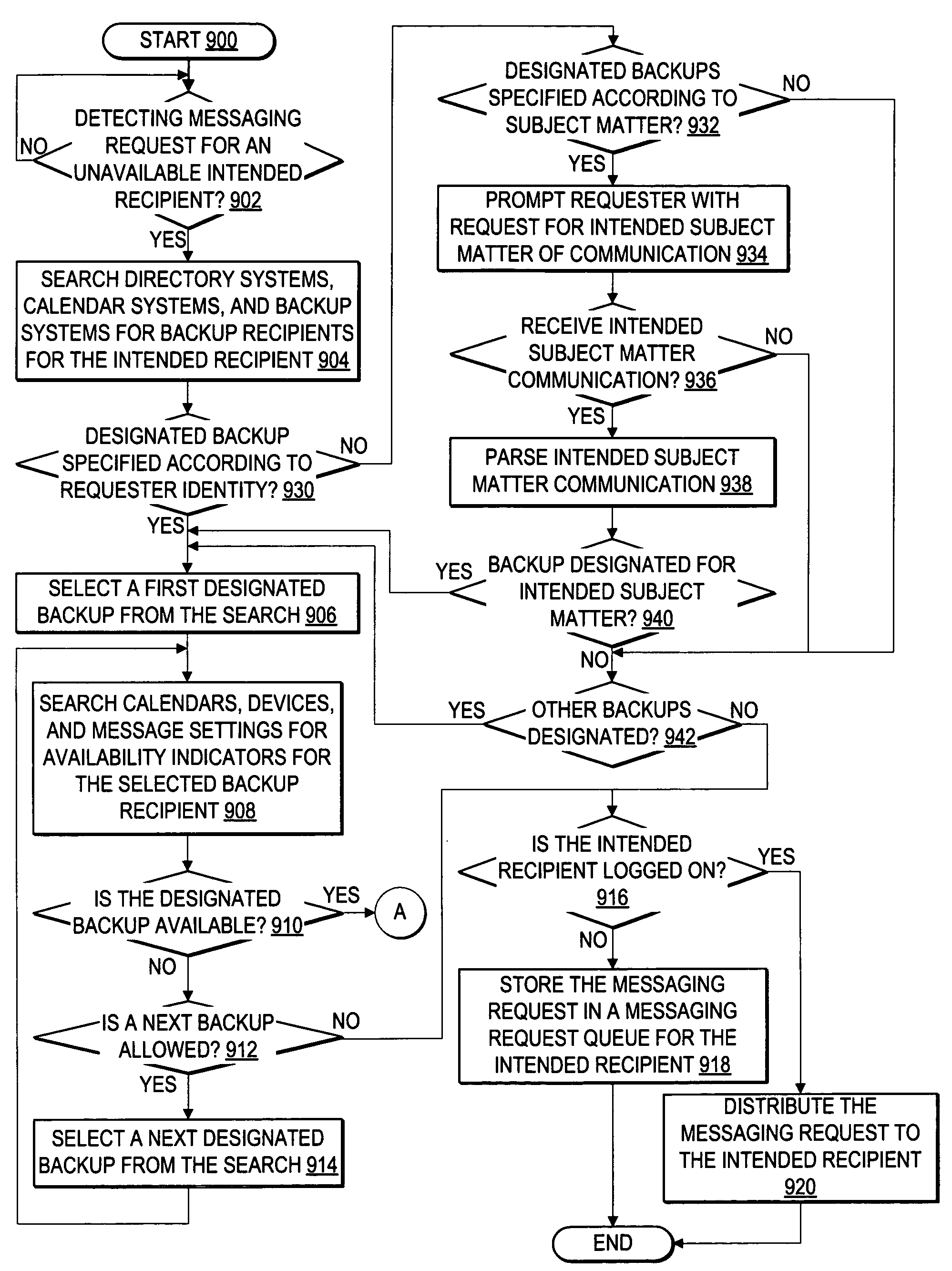
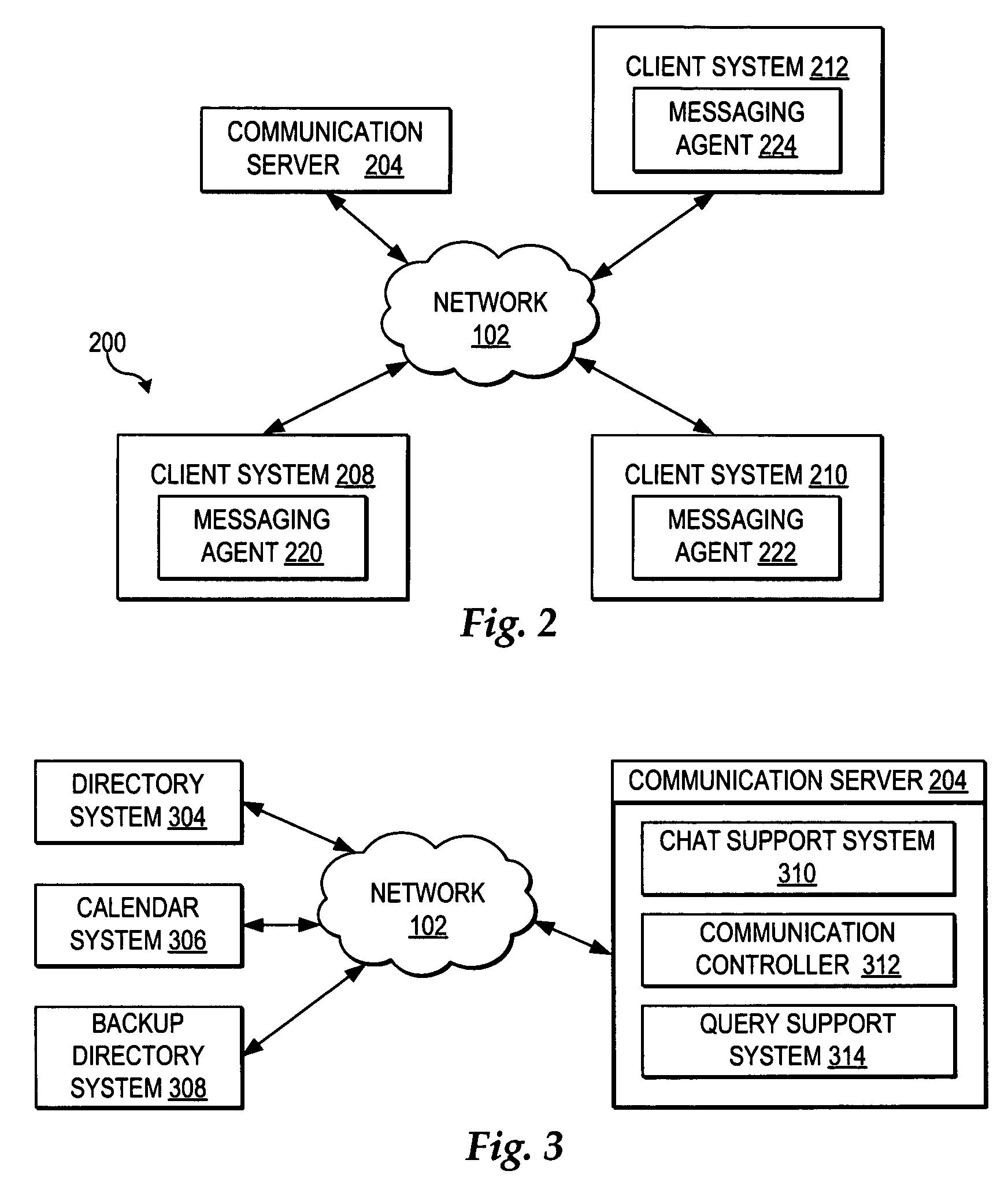
Automated selection of a backup recipient and distribution of an instant messaging request to the backup recipient
ActiveUS7295657B1Improving automated responseSpecial service for subscribersAutomatic call-answering/message-recording/conversation-recordingSupporting systemCommunications system
A method, system, and program for automated selection of a backup recipient and distribution of an instant messaging request to the backup recipient are provided. A communication support system detects a messaging request initiated by a requester for an intended recipient. The communication support system determines whether the intended recipient is available to respond to the messaging request from the requester. If the intended recipient is unavailable to respond to the messaging request from the requester, the communication support system searches at least one of a directory entry, a backup directory entry, and a schedule entry for the intended recipient to identify a designated backup for the messaging request. In particular, the designated backup recipient is selected from among multiple available backups where at least one characteristic of the messaging request matches at least one from among a current time period, a requester identity, and an intended subject matter specified in association with the designated backup recipient. Once the communication system selects a backup recipient, then the messaging request is distributed to the selected backup recipient, wherein the selected backup recipient is enabled then to respond to the messaging request.
Owner:SNAP INC
Directory-enabled device management
InactiveUS7024476B1Reduce effortAdd supportDigital computer detailsData switching networksComputer networkComputer science
Managing a plurality of network devices on a network by detecting the presence of at least one of the plurality of network devices on the network by using a first communication protocol, obtaining, by using the first communication protocol, an information block from each of the detected network devices, wherein the information block contains information related to the corresponding network device, formatting each information block into a directory entry, and sending each directory entry to a directory server via a second communication protocol.
Owner:CANON KK
Systems and methods for providing distributed cache coherence
ActiveUS7975018B2Reduce bandwidth requirementsReduce in quantityDigital computer detailsTransmissionComputer networkCache access
A plurality of access nodes sharing access to data on a storage network implement a directory based cache ownership scheme. One node, designated as a global coordinator, maintains a directory (e.g., table or other data structure) storing information about I / O operations by the access nodes. The other nodes send requests to the global coordinator when an I / O operation is to be performed on identified data. Ownership of that data in the directory is given to the first requesting node. Ownership may transfer to another node if the directory entry is unused or quiescent. The distributed directory-based cache coherency allows for reducing bandwidth requirements between geographically separated access nodes by allowing localized (cached) access to remote data.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com