Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
199 results about "Indirection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer programming, indirection (also called dereferencing) is the ability to reference something using a name, reference, or container instead of the value itself. The most common form of indirection is the act of manipulating a value through its memory address. For example, accessing a variable through the use of a pointer. A stored pointer that exists to provide a reference to an object by double indirection is called an indirection node.
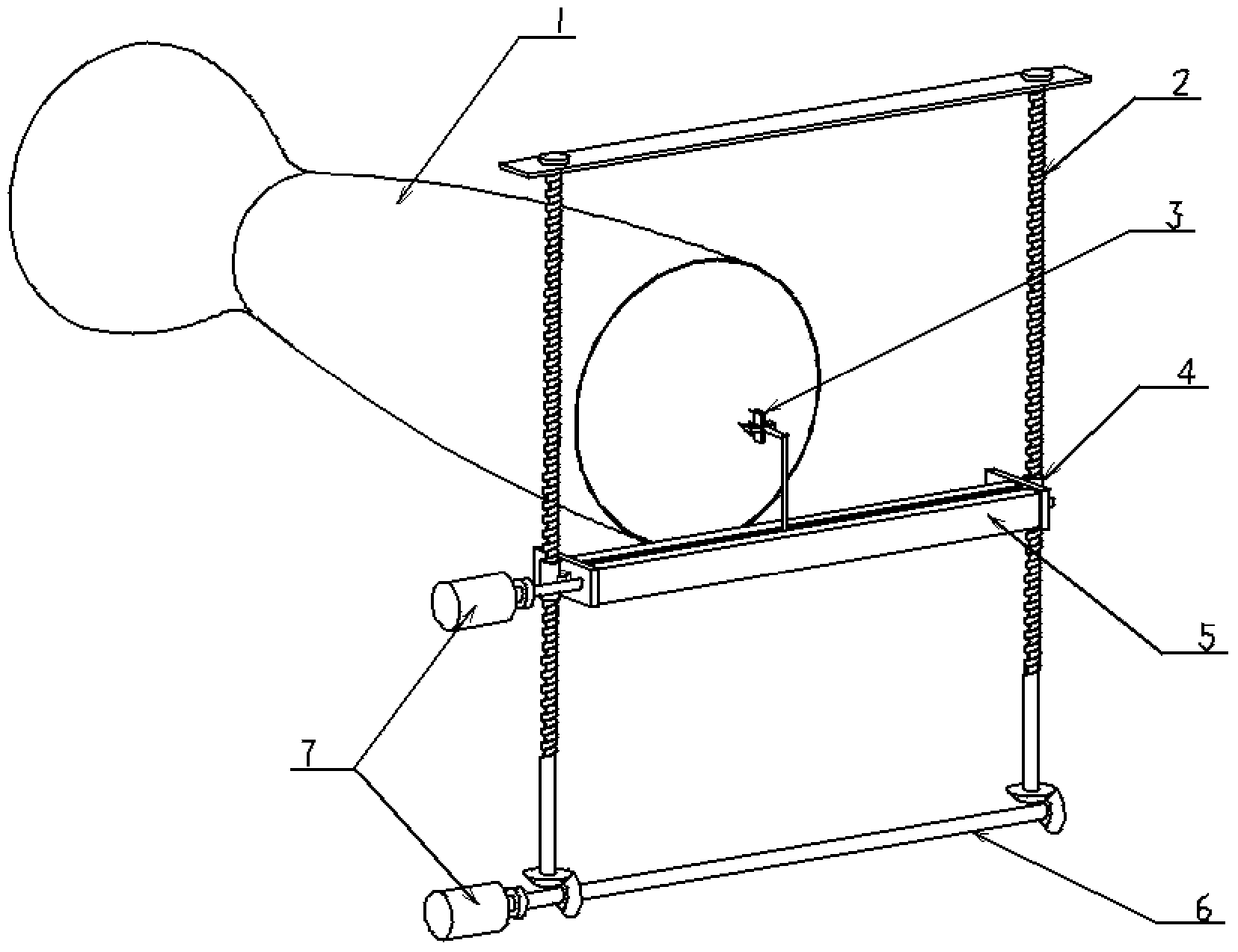
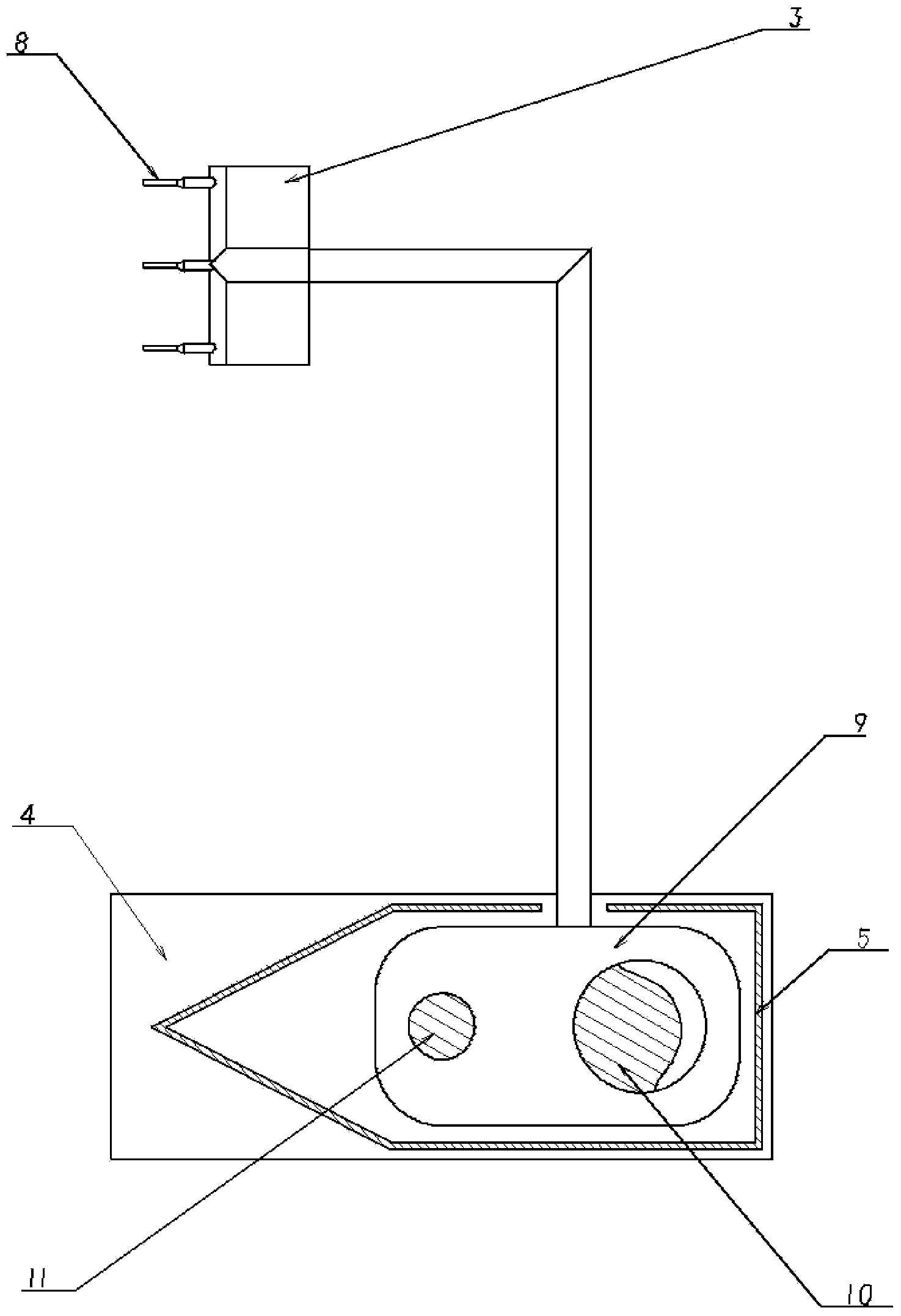
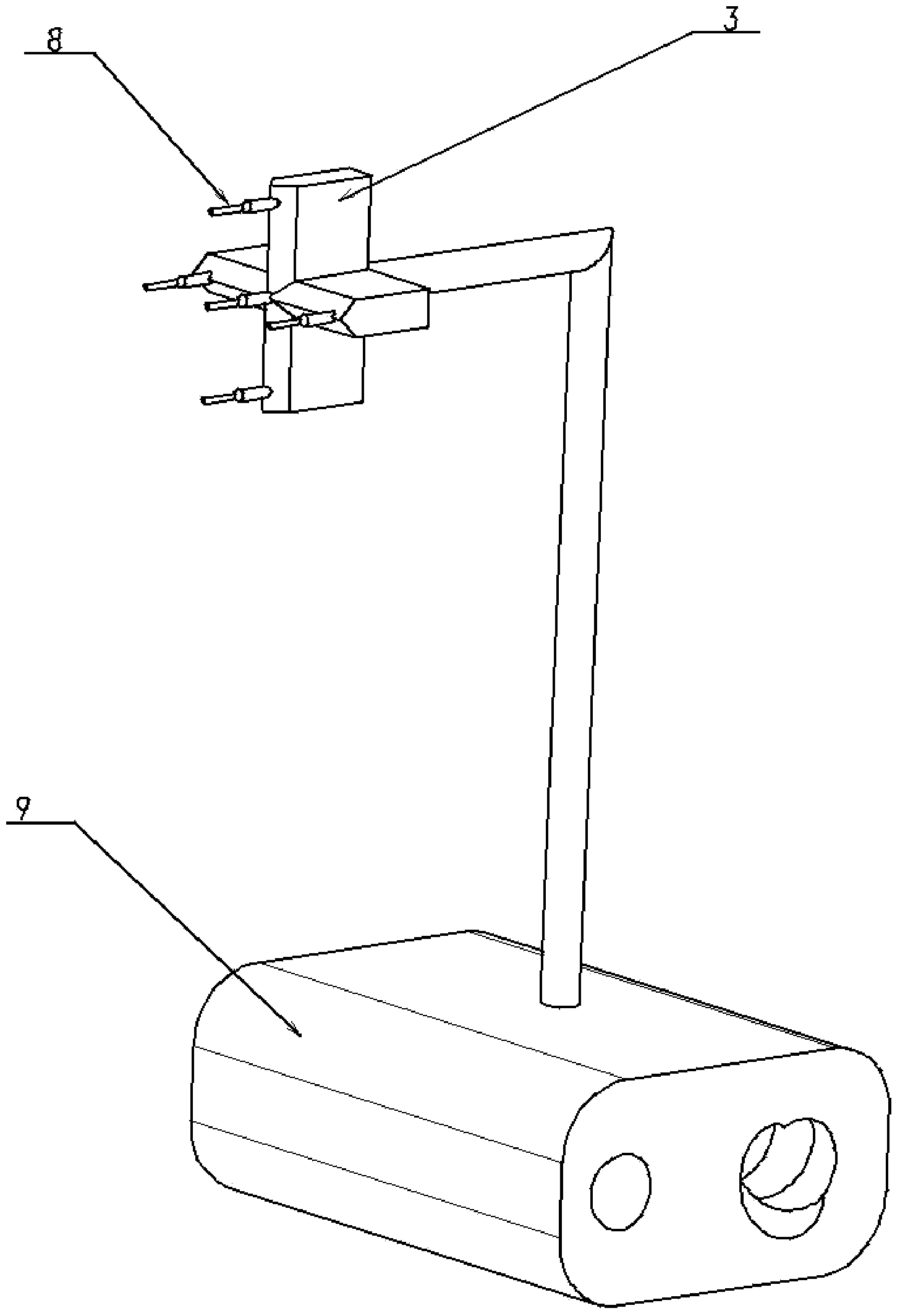
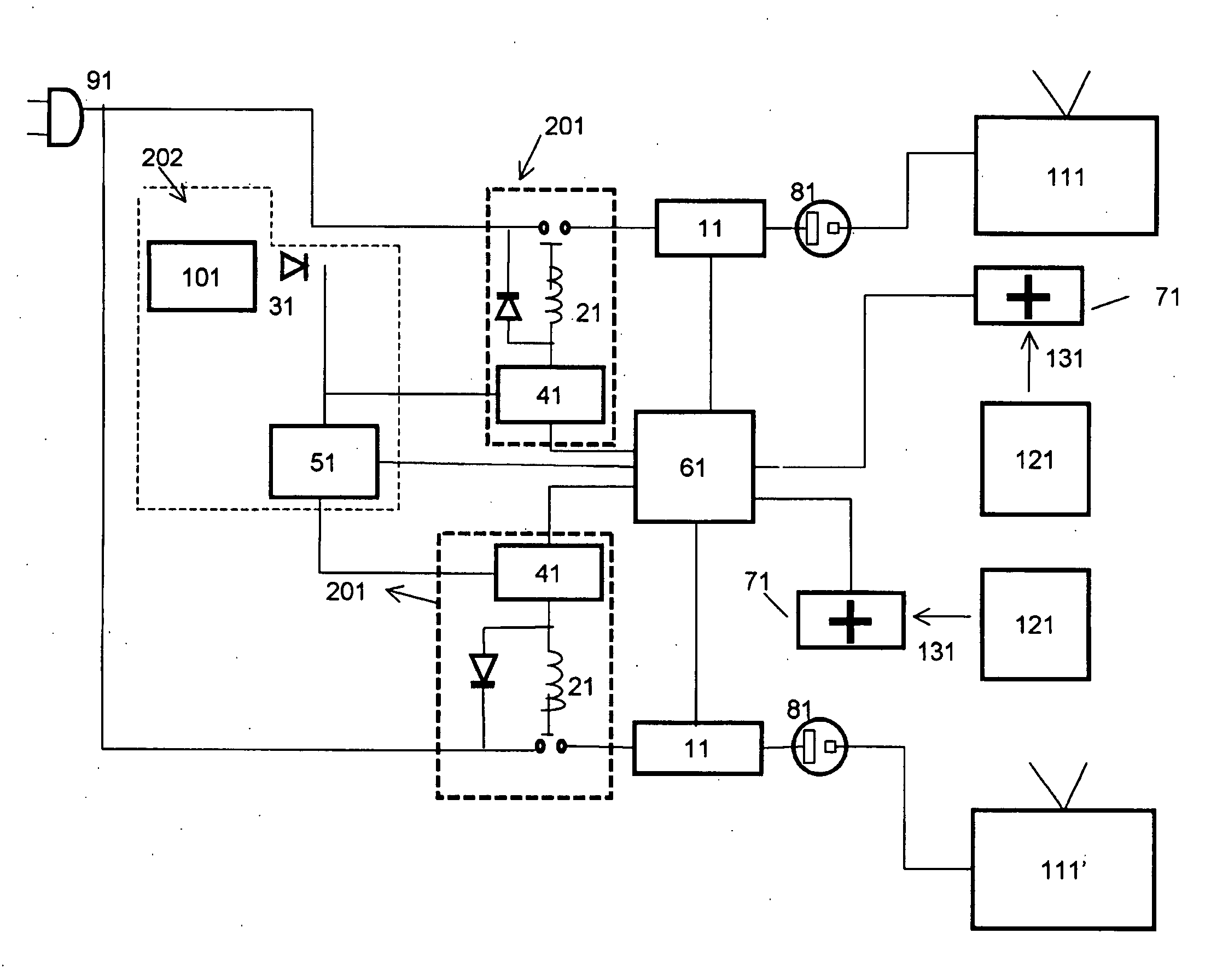
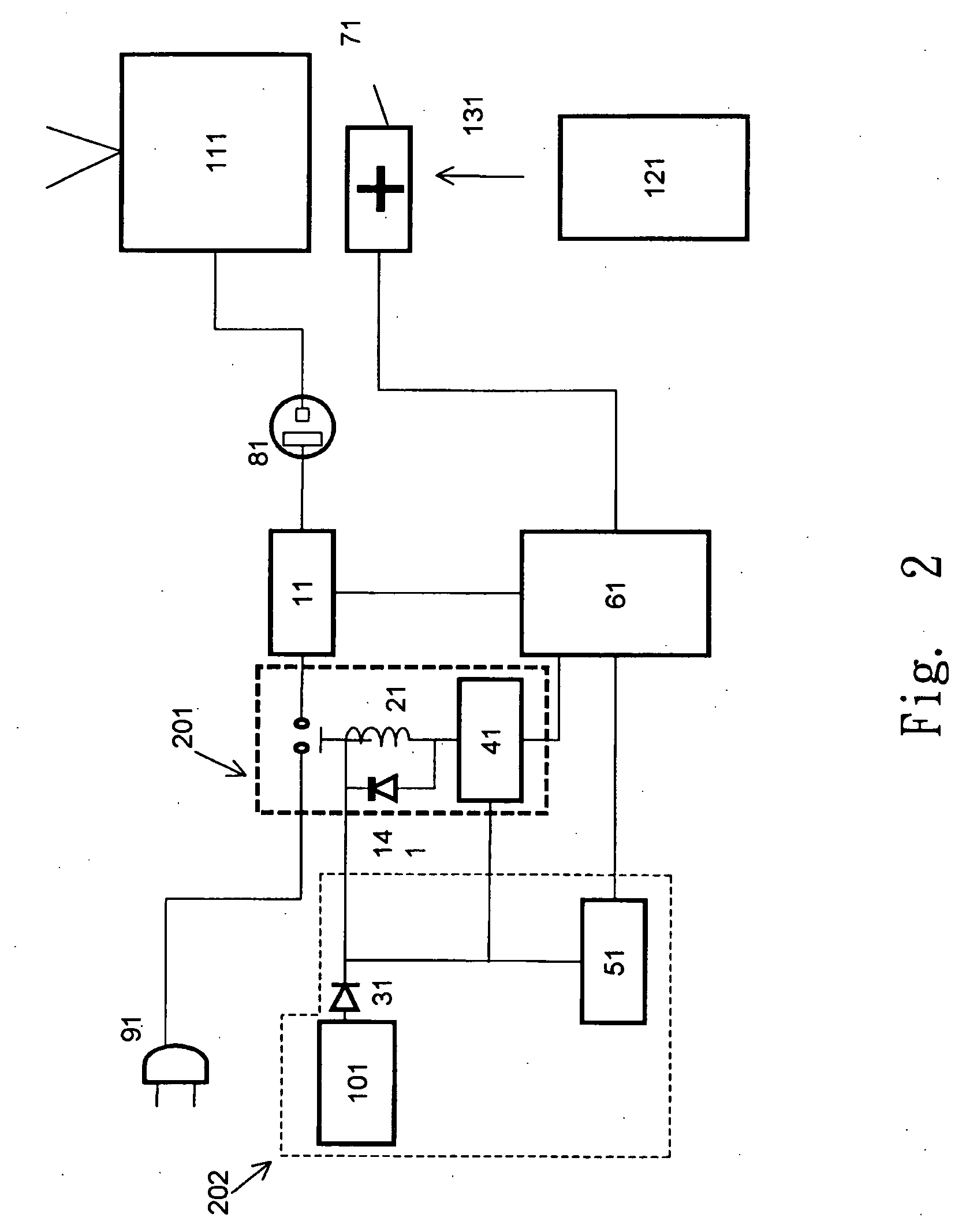
Active forceps
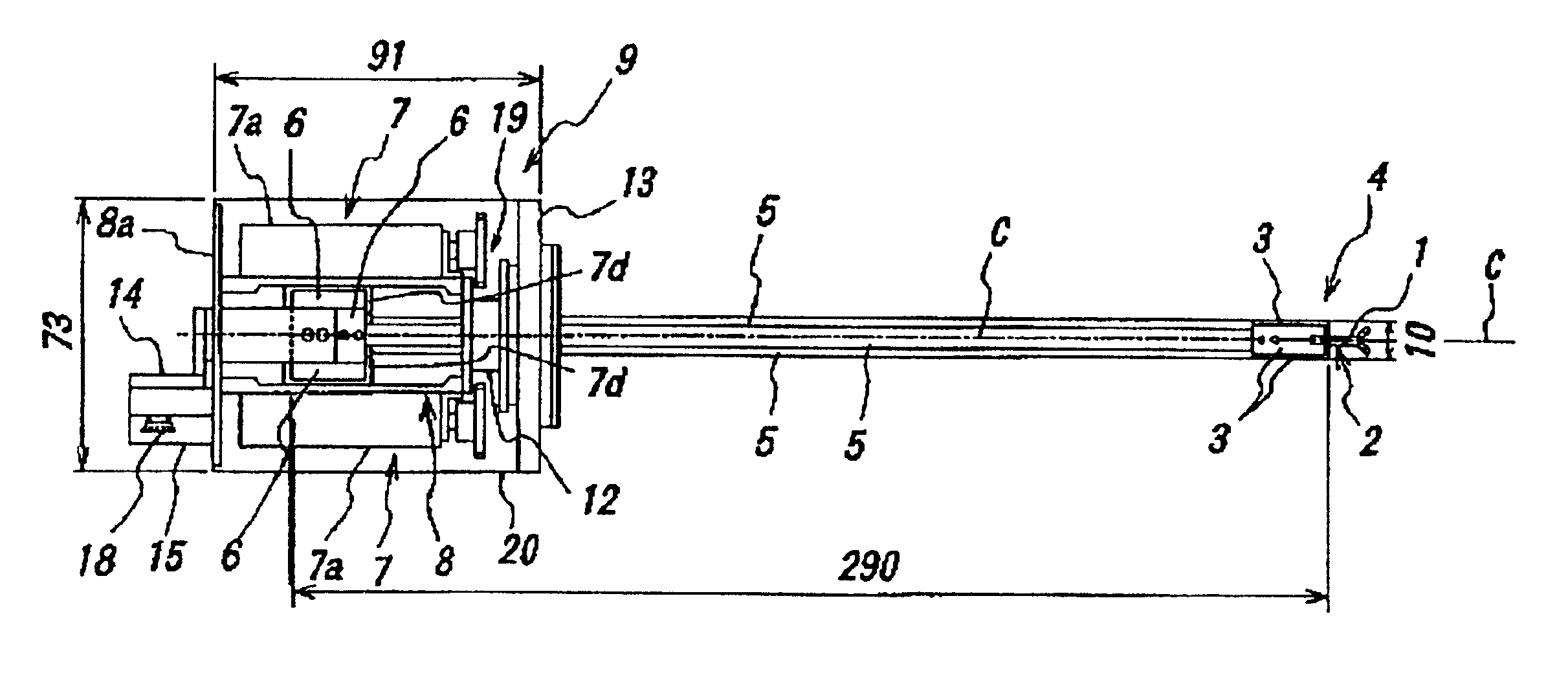
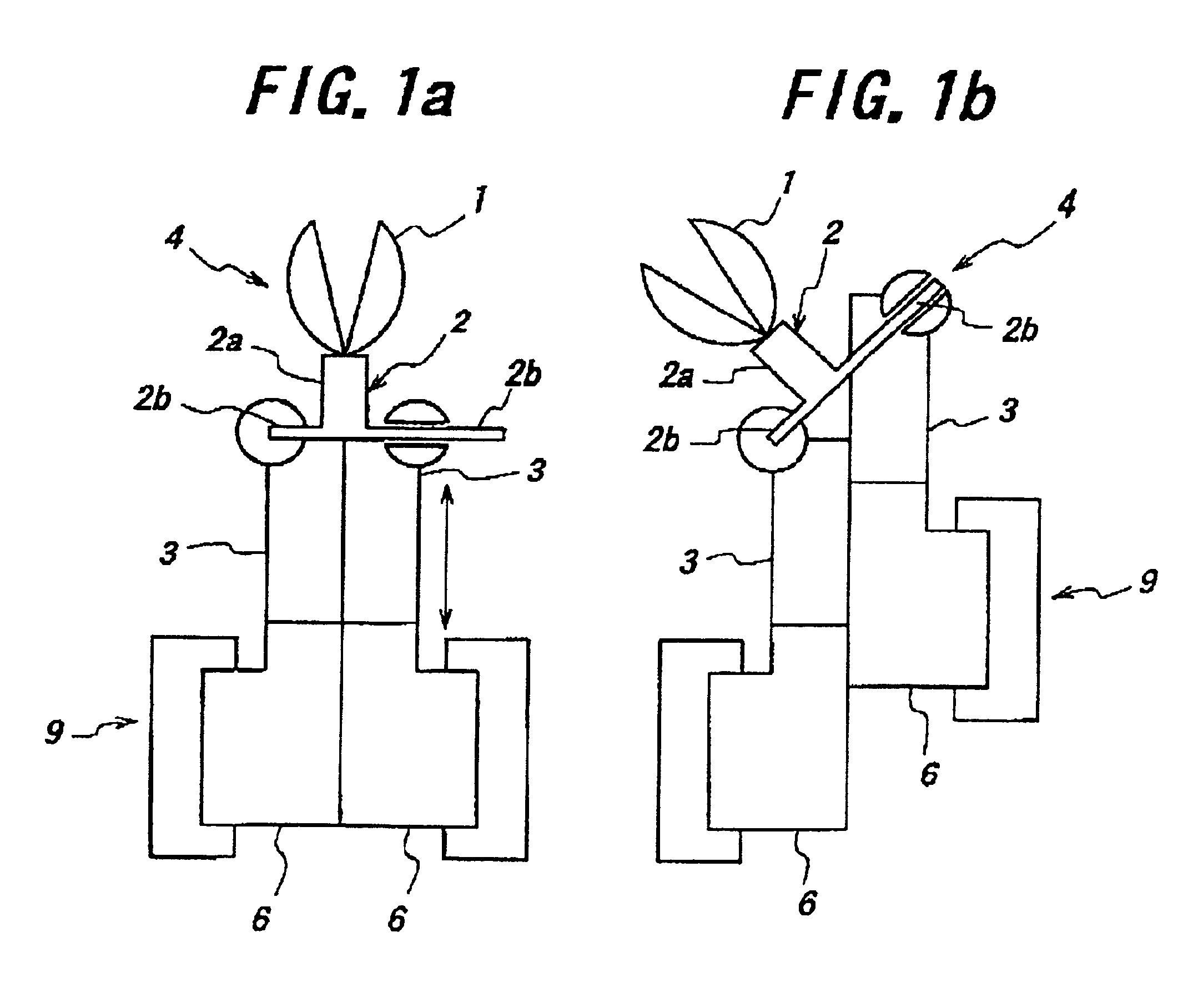
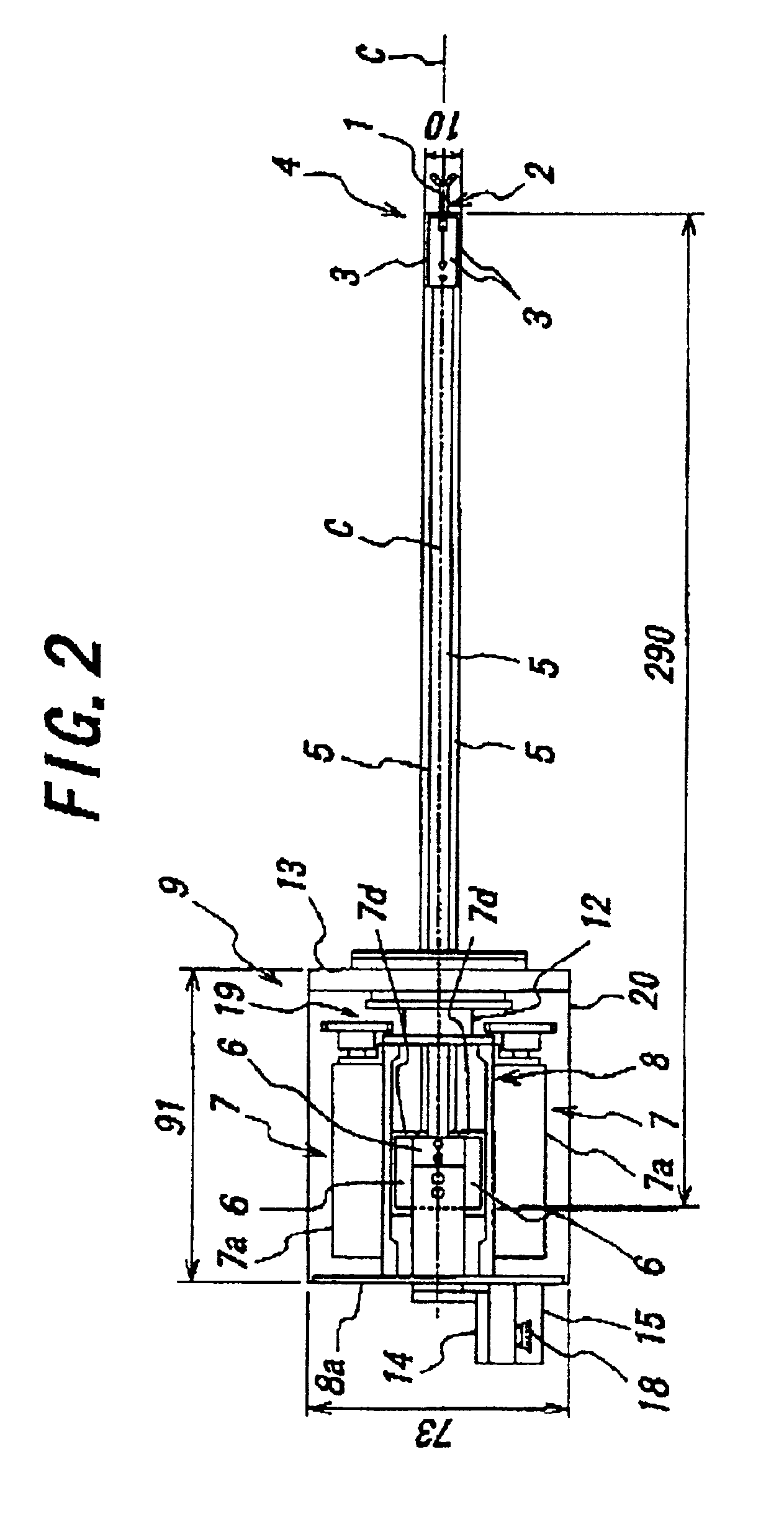
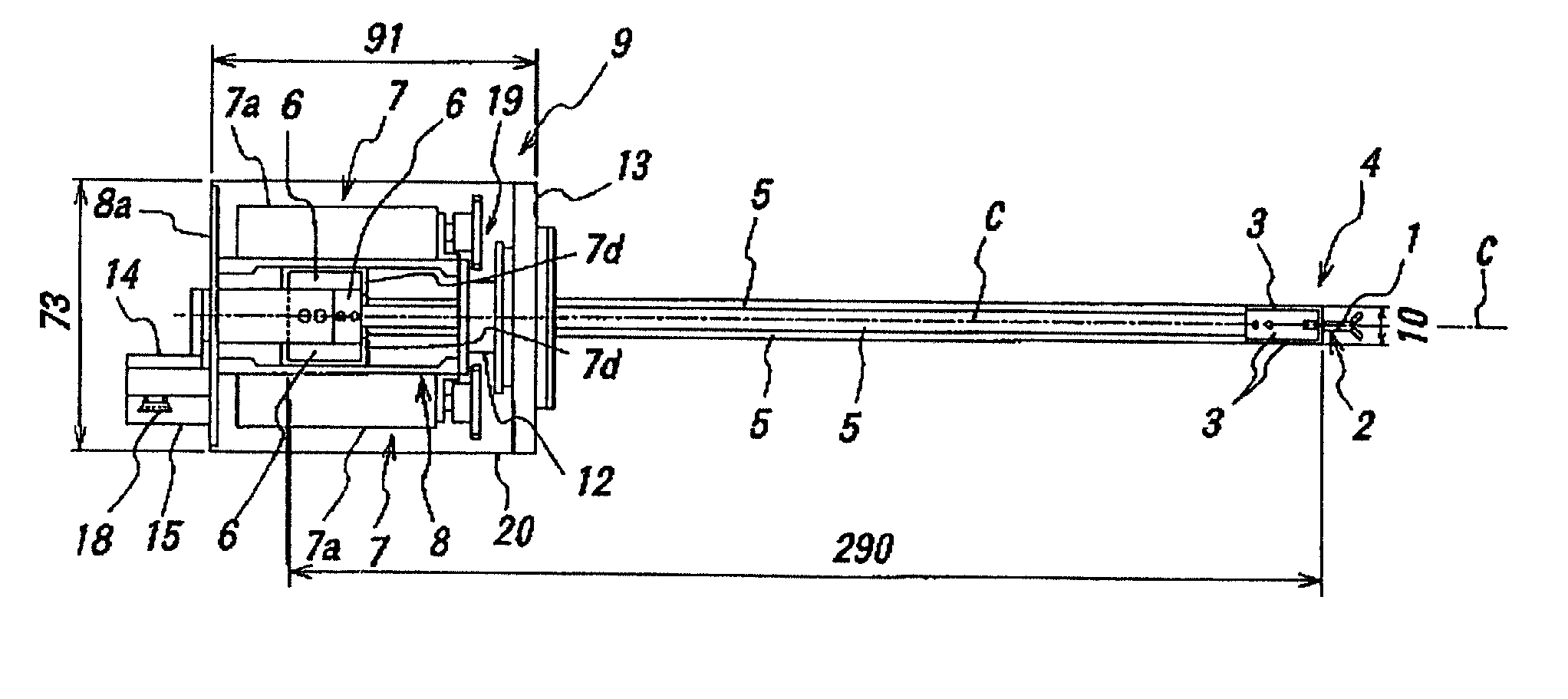
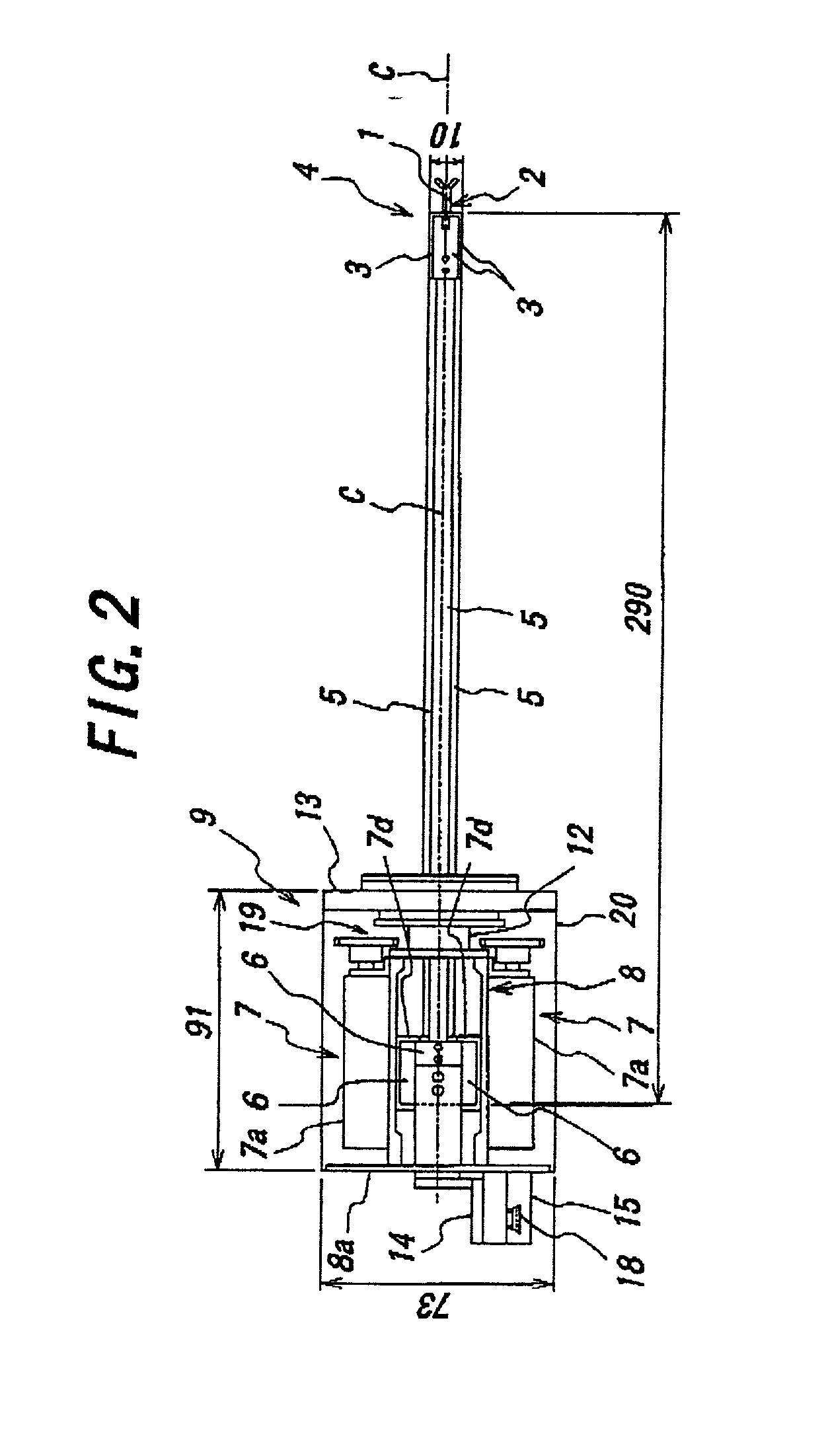
Endoscopic surgical operation such as evisceration has been so far hardly achieved by a medical robot, since it requires high power. The present invention provides a downsized high-flexibility active forceps to enable such an operation, without needing a large space for manipulation to target a limited operative area. An active forceps of the present invention comprises: a tip forceps part 4 having, a tip supporting member 2 to support a forceps tip 1 at a center section 2a with a plurality of arms 2b laterally projected therefrom, and a plurality of tip side advancing and retreating members 3 connected at a front end with the plurality of arms respectively oscillatable while connected to one another relatively movable in directions toward front and rear ends; and a forceps bottom part 9 having, a plurality of bottom side advancing and retreating members 6 each integrally coupled to the plurality of tip side advancing and retreating members 3, while connected to one another relatively movable indirections toward front and rear ends to constitute a link mechanism together with the tip side advancing and retreating members 3 and the tip supporting member 2, and a bottom frame 8 provided with forward and backward actuating means 7 for moving relatively to one another the bottom side advancing and retreating members 6 in directions toward front and rear ends.
Owner:TOKYO UNIV OF THE
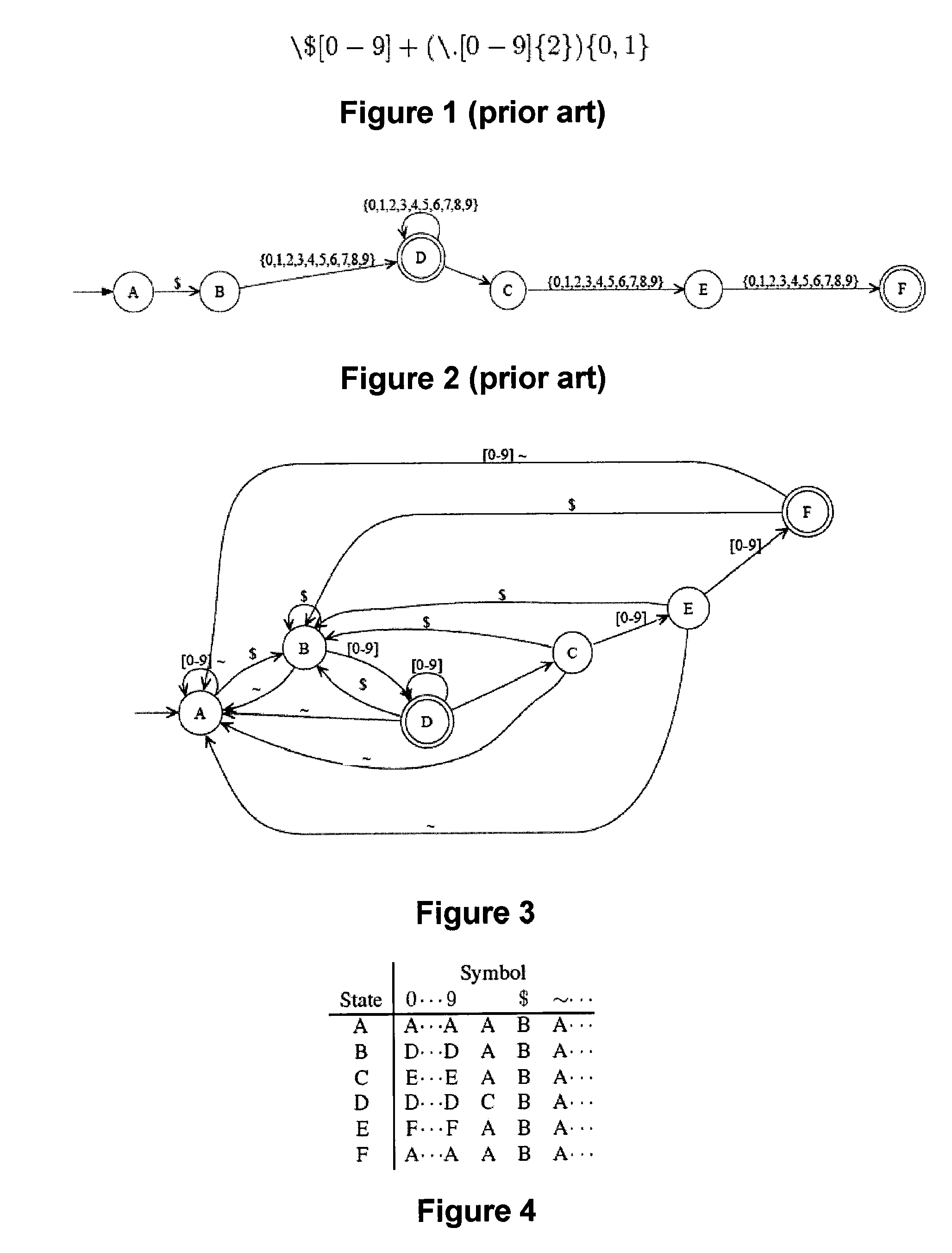
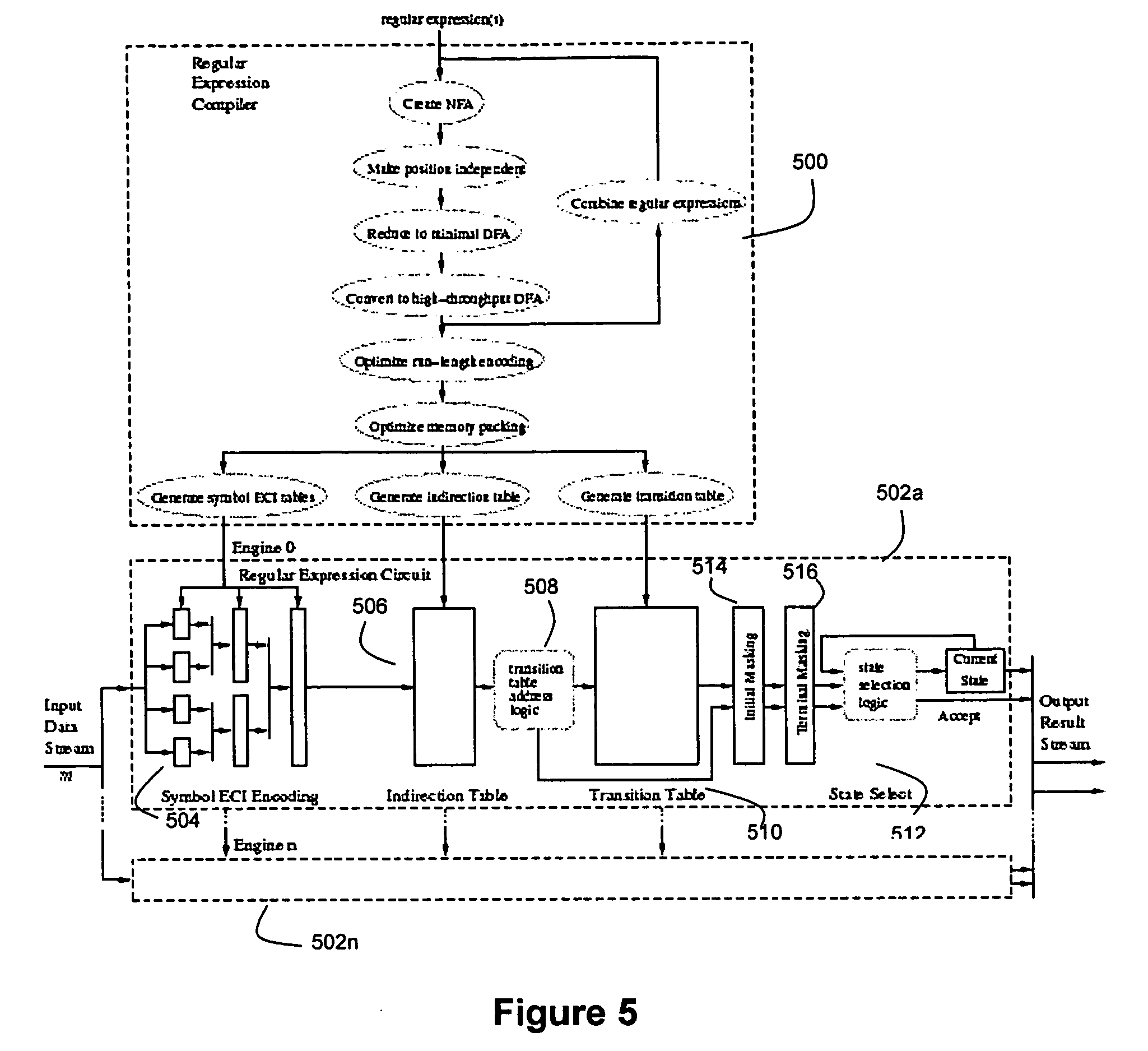
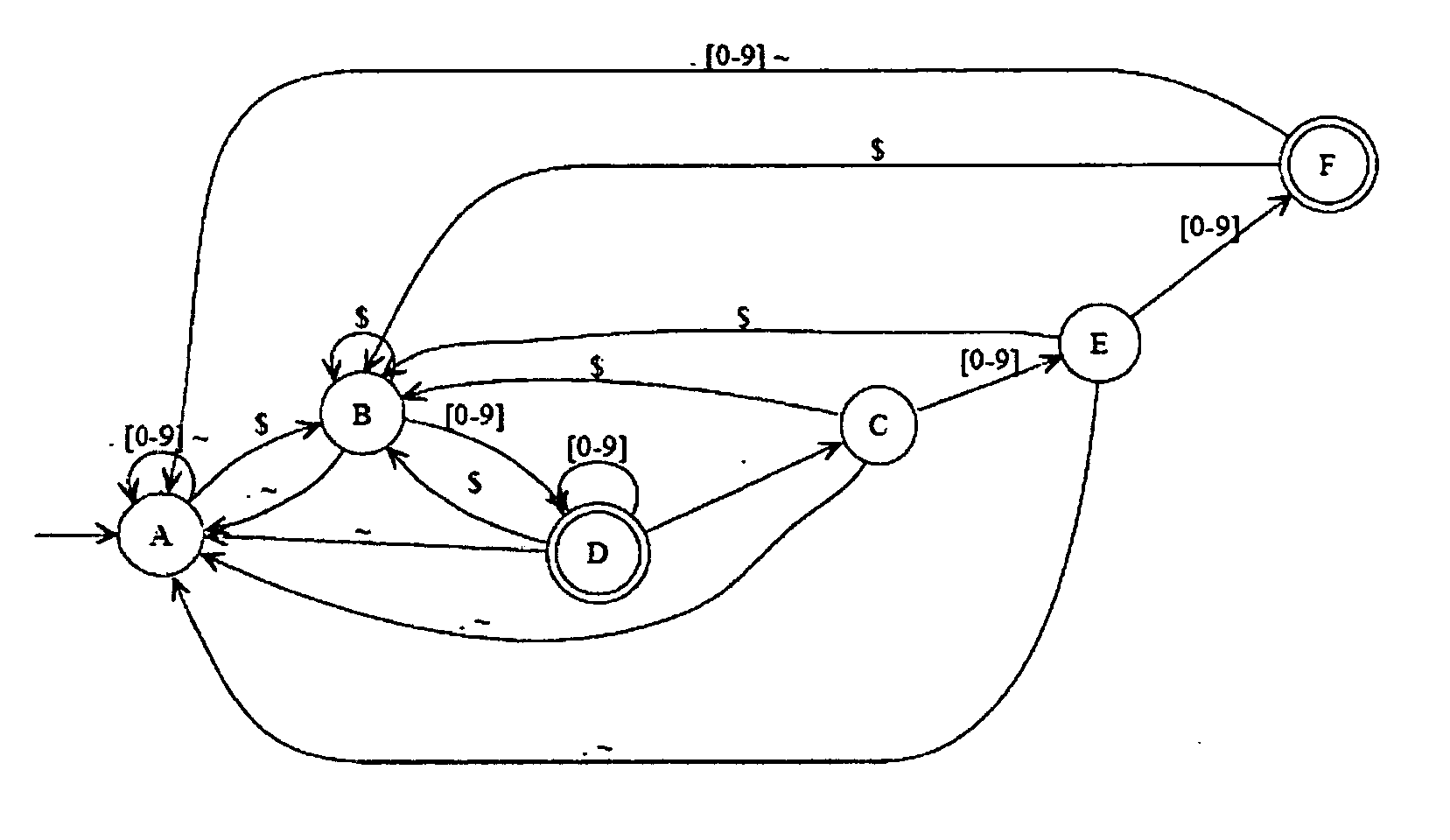
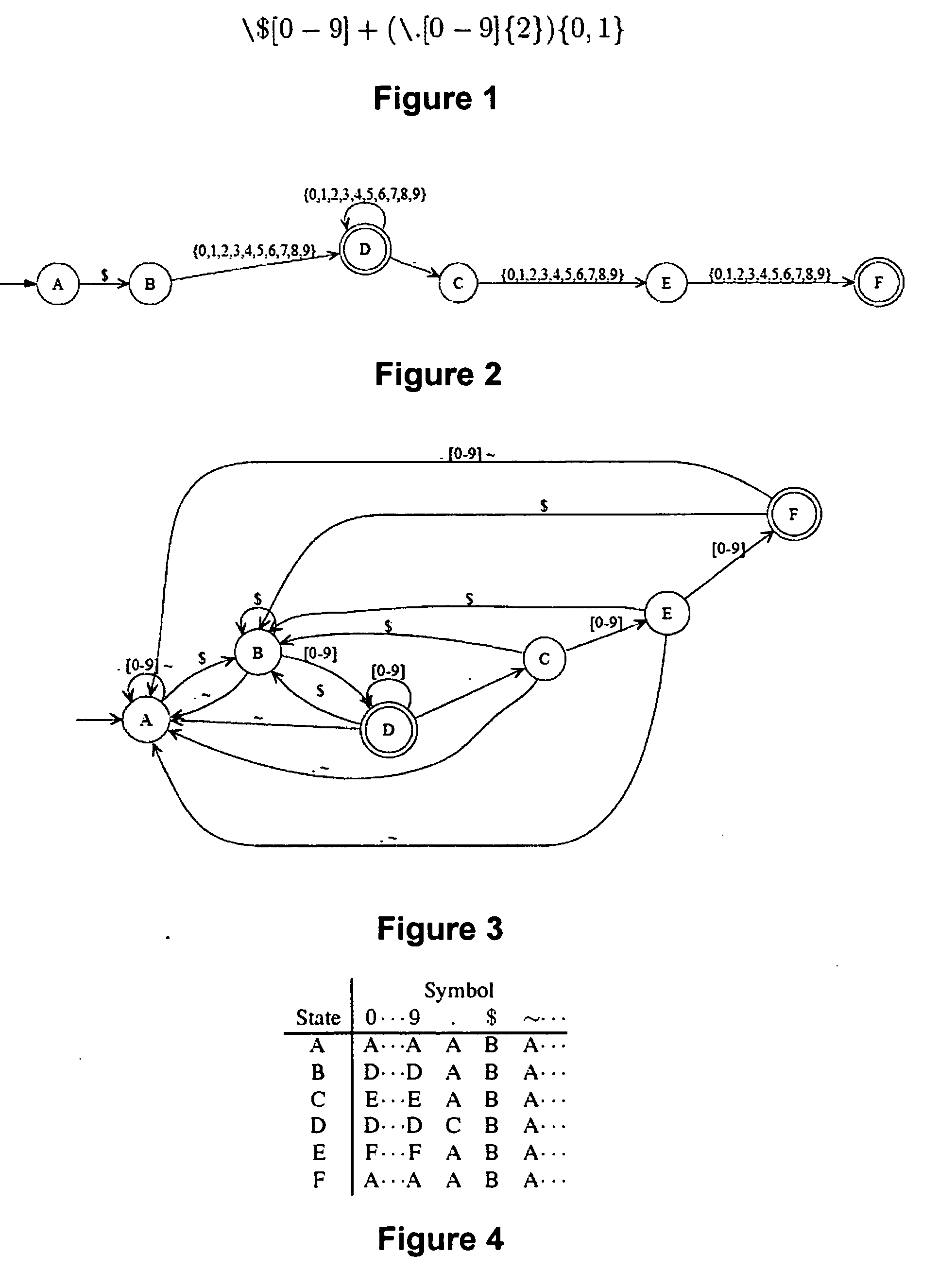
Method and device for high performance regular expression pattern matching
ActiveUS7702629B2Minimize the numberData processing applicationsDigital data information retrievalState dependentPattern matching
Disclosed herein is an improved architecture for regular expression pattern matching. Improvements to pattern matching deterministic finite automatons (DFAs) that are described by the inventors include a pipelining strategy that pushes state-dependent feedback to a final pipeline stage to thereby enhance parallelism and throughput, augmented state transitions that track whether a transition is indicative of a pattern match occurring thereby reducing the number of necessary states for the DFA, augmented state transition that track whether a transition is indicative of a restart to the matching process, compression of the DFA's transition table, alphabet encoding for input symbols to equivalence class identifiers, the use of an indirection table to allow for optimized transition table memory, and enhanced scalability to facilitate the ability of the improved DFA to process multiple input symbols per cycle.
Owner:IP RESERVOIR
Method and device for high performance regular expression pattern matching
ActiveUS20070130140A1Minimize the numberData processing applicationsDigital data information retrievalAlgorithmPattern matching
Disclosed herein is an improved architecture for regular expression pattern matching. Improvements to pattern matching deterministic finite automatons (DFAs) that are described by the inventors include a pipelining strategy that pushes state-dependent feedback to a final pipeline stage to thereby enhance parallelism and throughput, augmented state transitions that track whether a transition is indicative of a pattern match occurring thereby reducing the number of necessary states for the DFA, augmented state transition that track whether a transition is indicative of a restart to the matching process, compression of the DFA's transition table, alphabet encoding for input symbols to equivalence class identifiers, the use of an indirection table to allow for optimized transition table memory, and enhanced scalability to facilitate the ability of the improved DFA to process multiple input symbols per cycle.
Owner:IP RESERVOIR
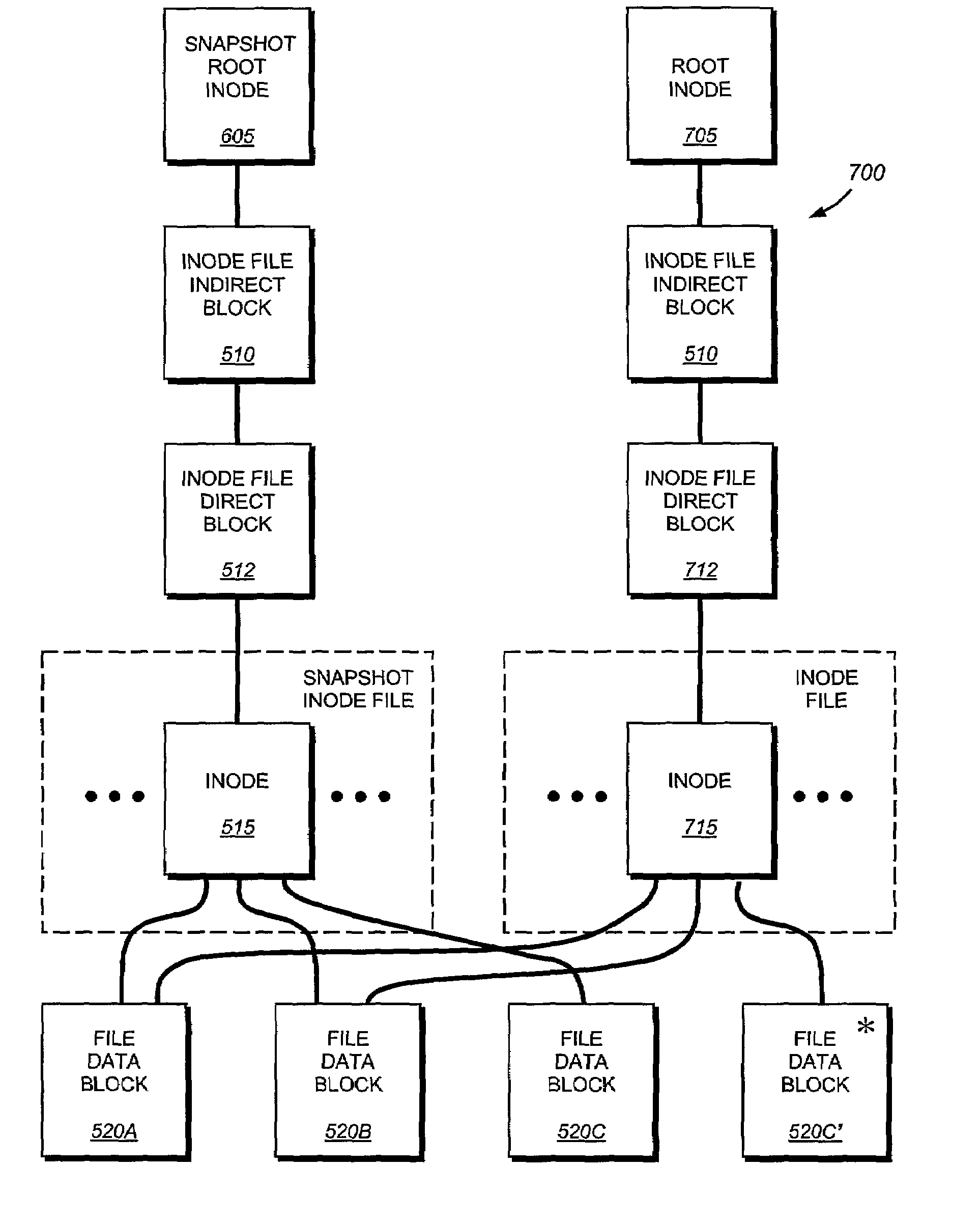
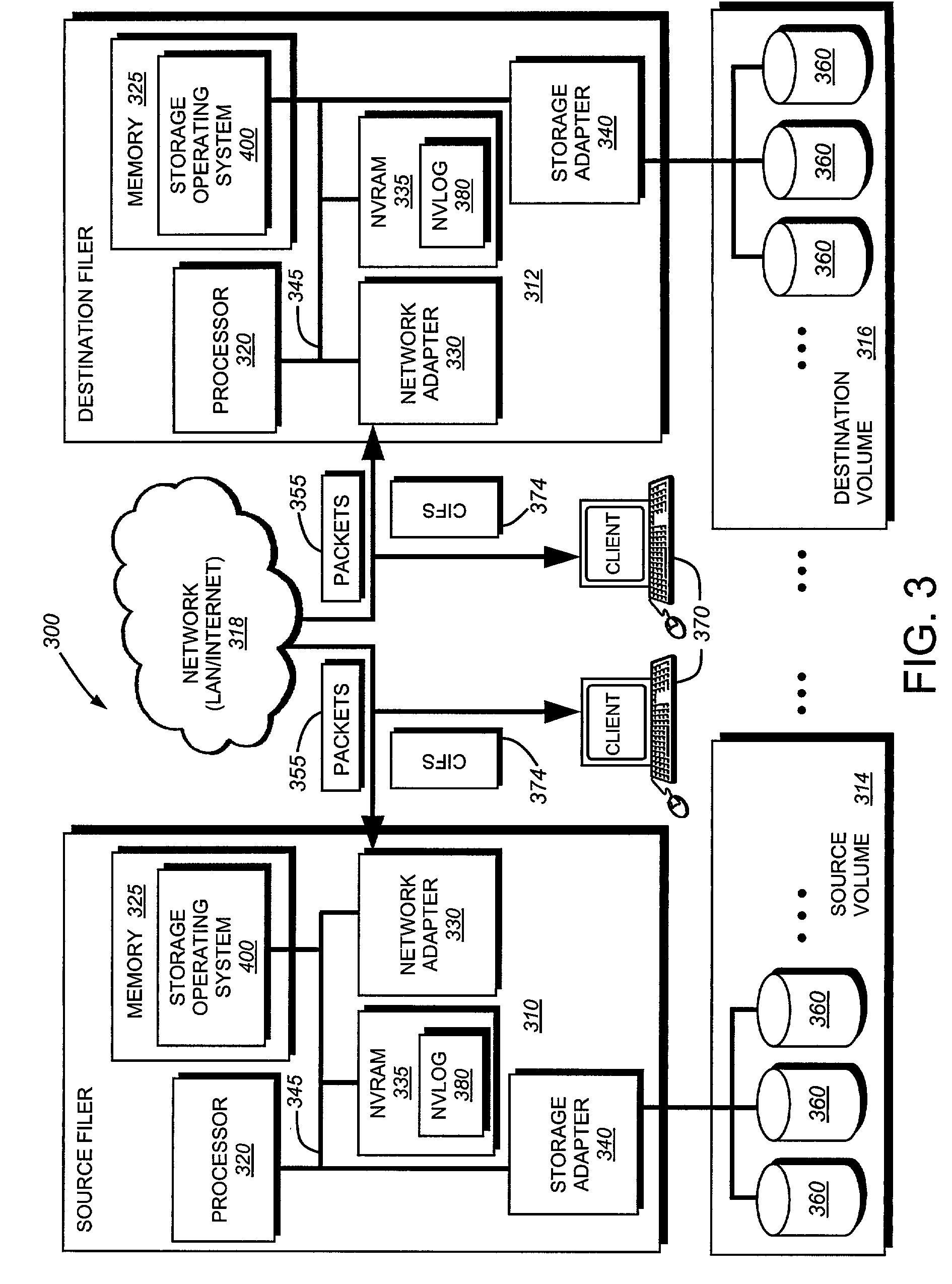
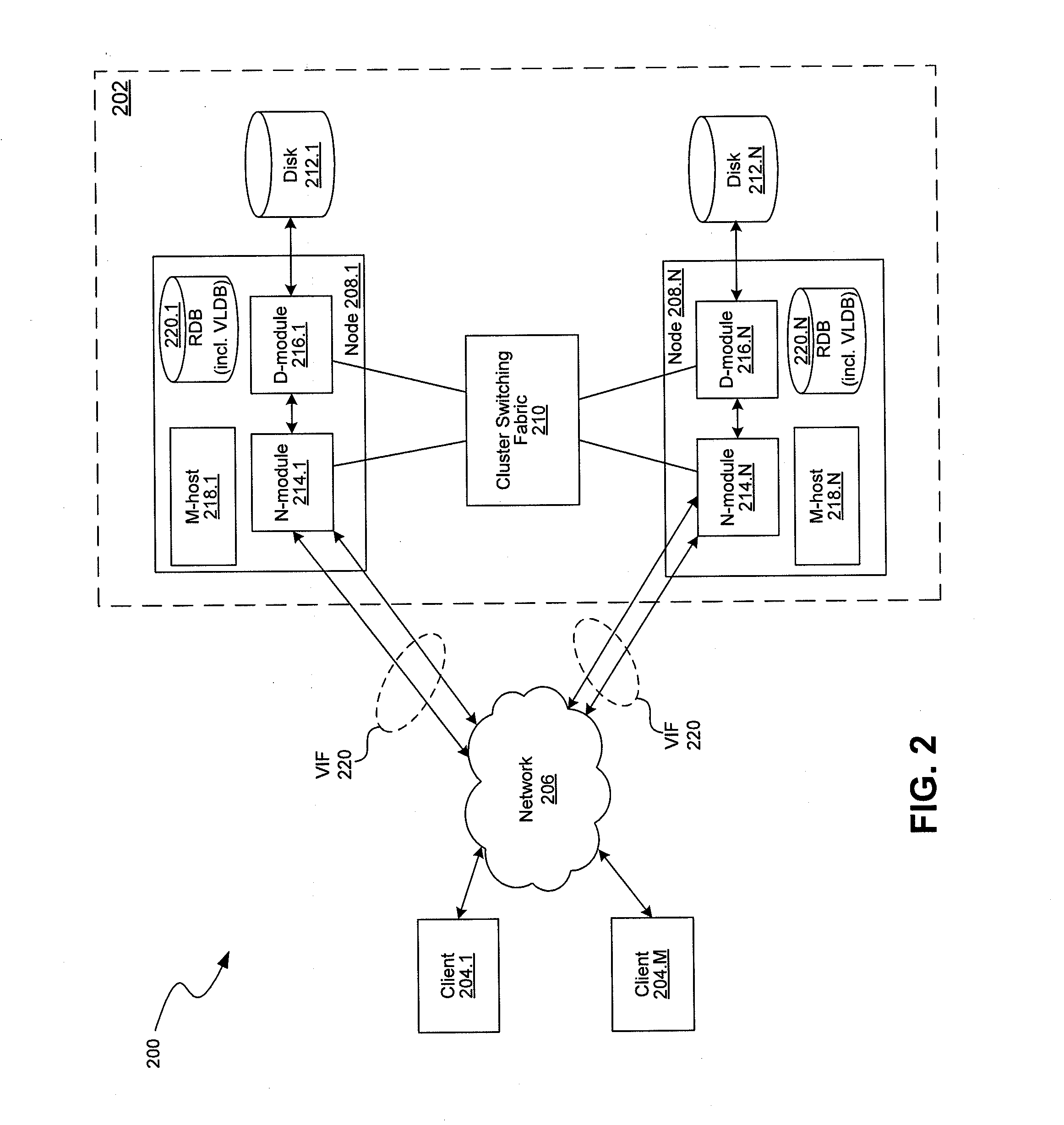
System and method for redirecting access to a remote mirrored snapshot
ActiveUS7010553B2Significant processing timeSignificant processor overheadDigital data information retrievalData processing applicationsInodeIndirection
In a system and method for updating a remote replicated destination file system snapshot with changes in a source file system snapshot, users and processes are redirected to a local exported snapshot of the replicated snapshot on the active file system on the destination before beginning the next update of the active file system's replicated snapshot. In this manner, an unstable replicated snapshot is not accessed. Indirection is introduced into inode lookup at the destination as the destination's active file system is being updated. The indirection can be based upon a snapshot ID that conforms to a latest exported snapshot ID.
Owner:NETWORK APPLIANCE INC
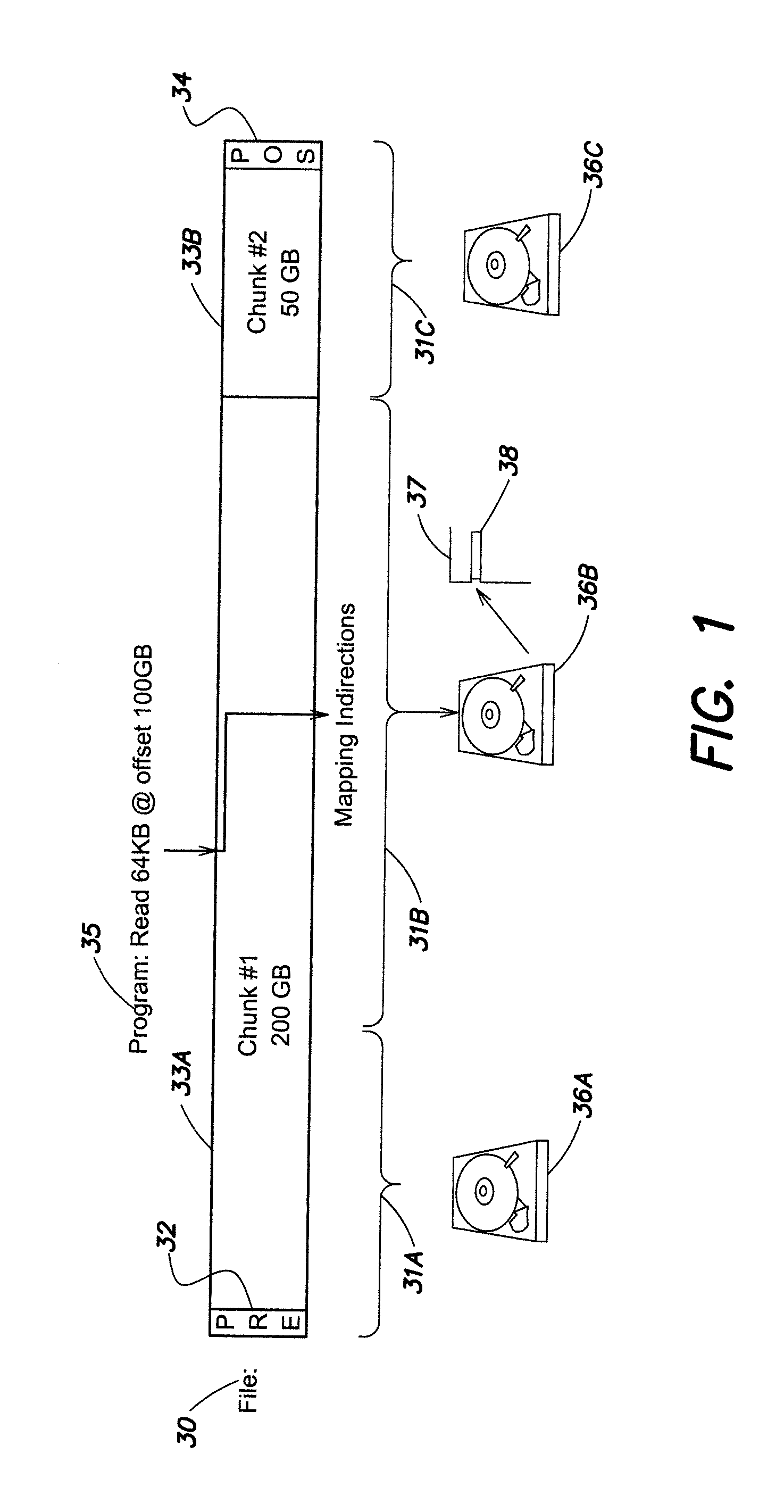
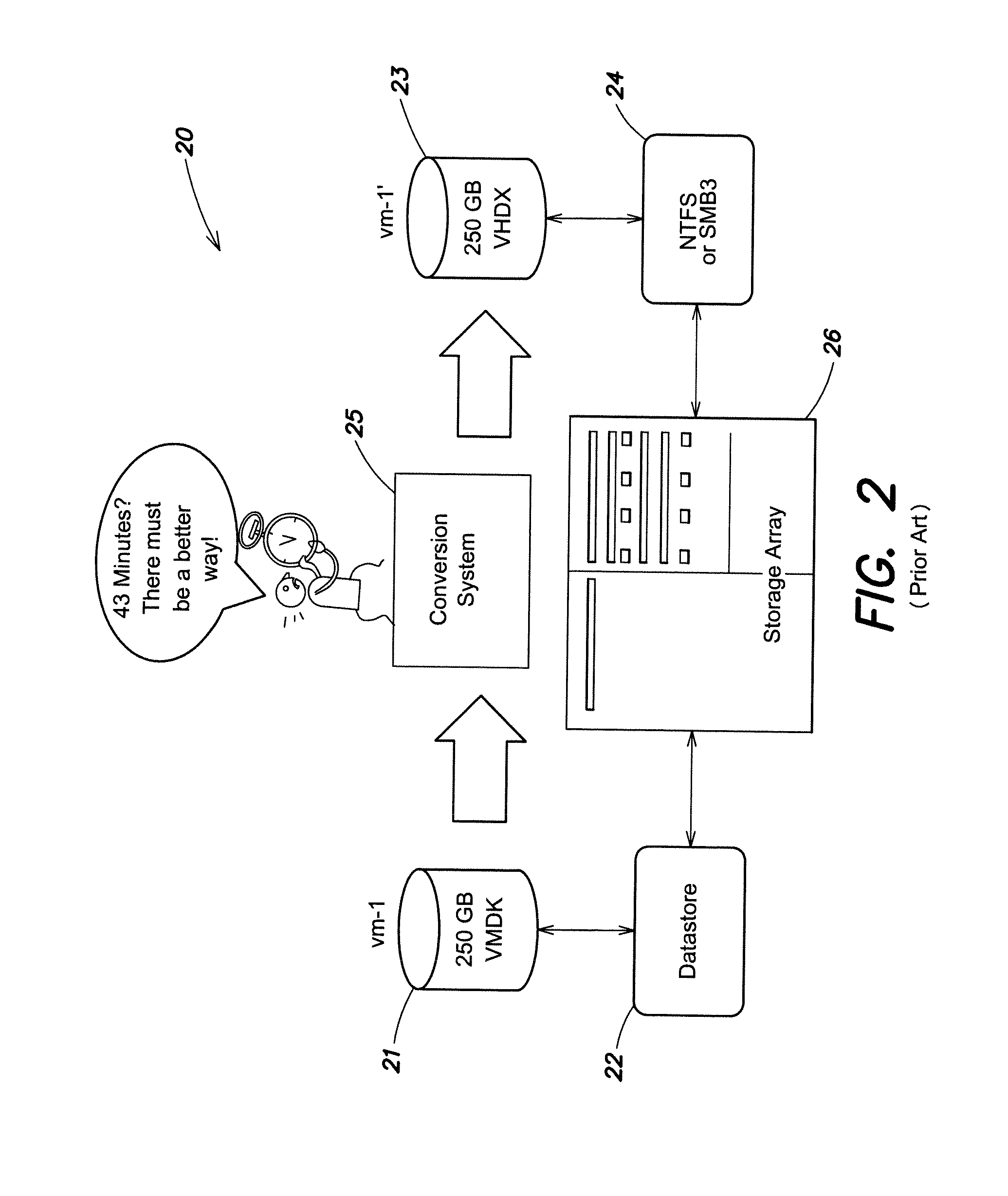
System and method for virtual machine conversion
ActiveUS20150058382A1Improve efficiencyDigital data information retrievalProgram controlFile systemData element
System and method for conversion of virtual machine files without requiring copying of the virtual machine payload (data) from one location to another location. By eliminating this step, applicant's invention significantly enhances the efficiency of the conversion process. In one embodiment, a file system or storage system provides indirections to locations of data elements stored on a persistent storage media. A source virtual machine file includes hypervisor metadata (HM) data elements in one hypervisor file format, and virtual machine payload (VMP) data elements. The source virtual machine file is converted by transforming the HM data elements of the source file to create destination HM data elements in a destination hypervisor format different from the source hypervisor format; maintaining the locations of the VMP data elements stored on the persistent storage media constant during the conversion from source to destination file formats without reading or writing the VMP data elements; and creating indirections to reference the destination HM data elements in the destination hypervisor format and the existing stored VMP data elements.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
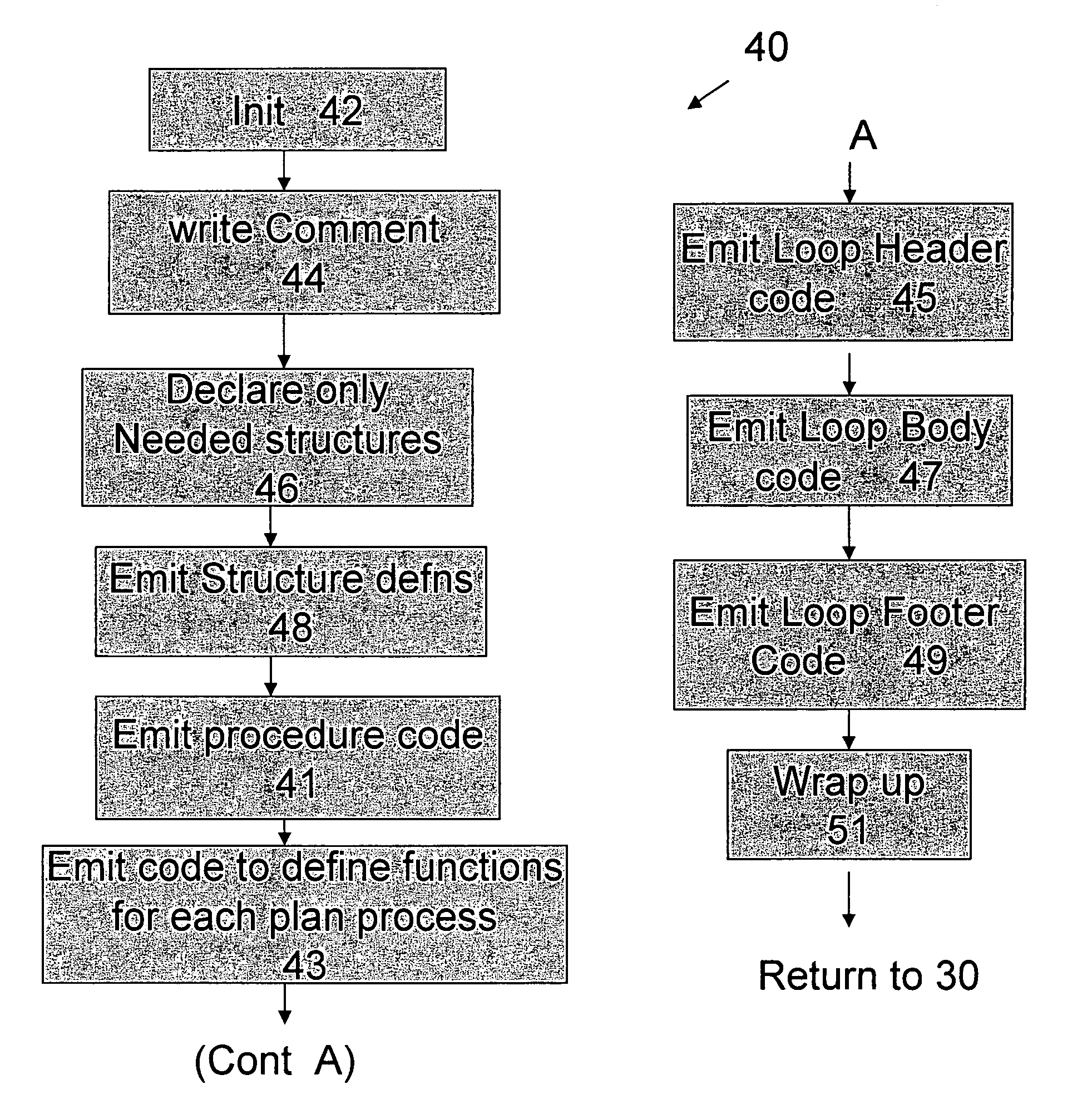
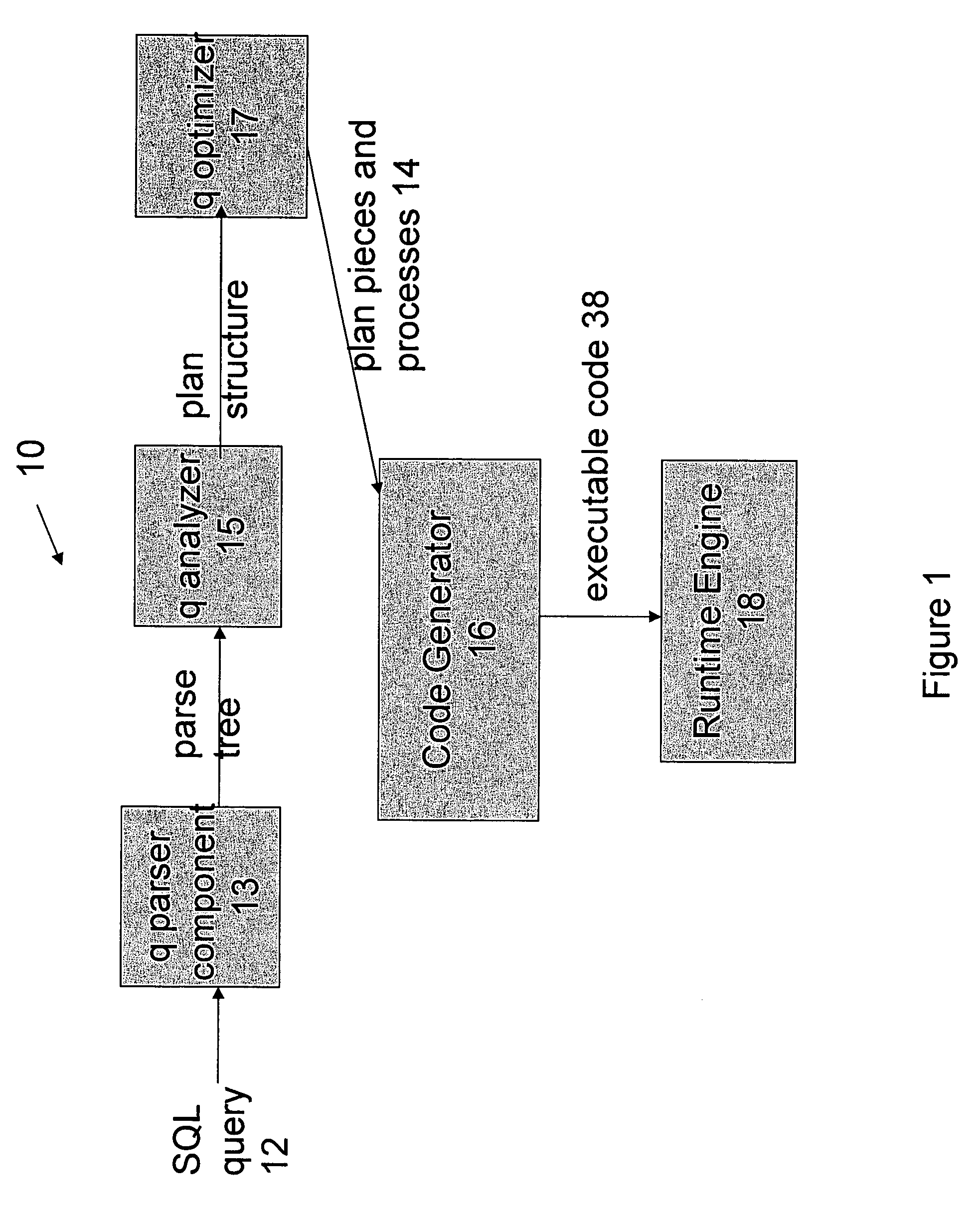
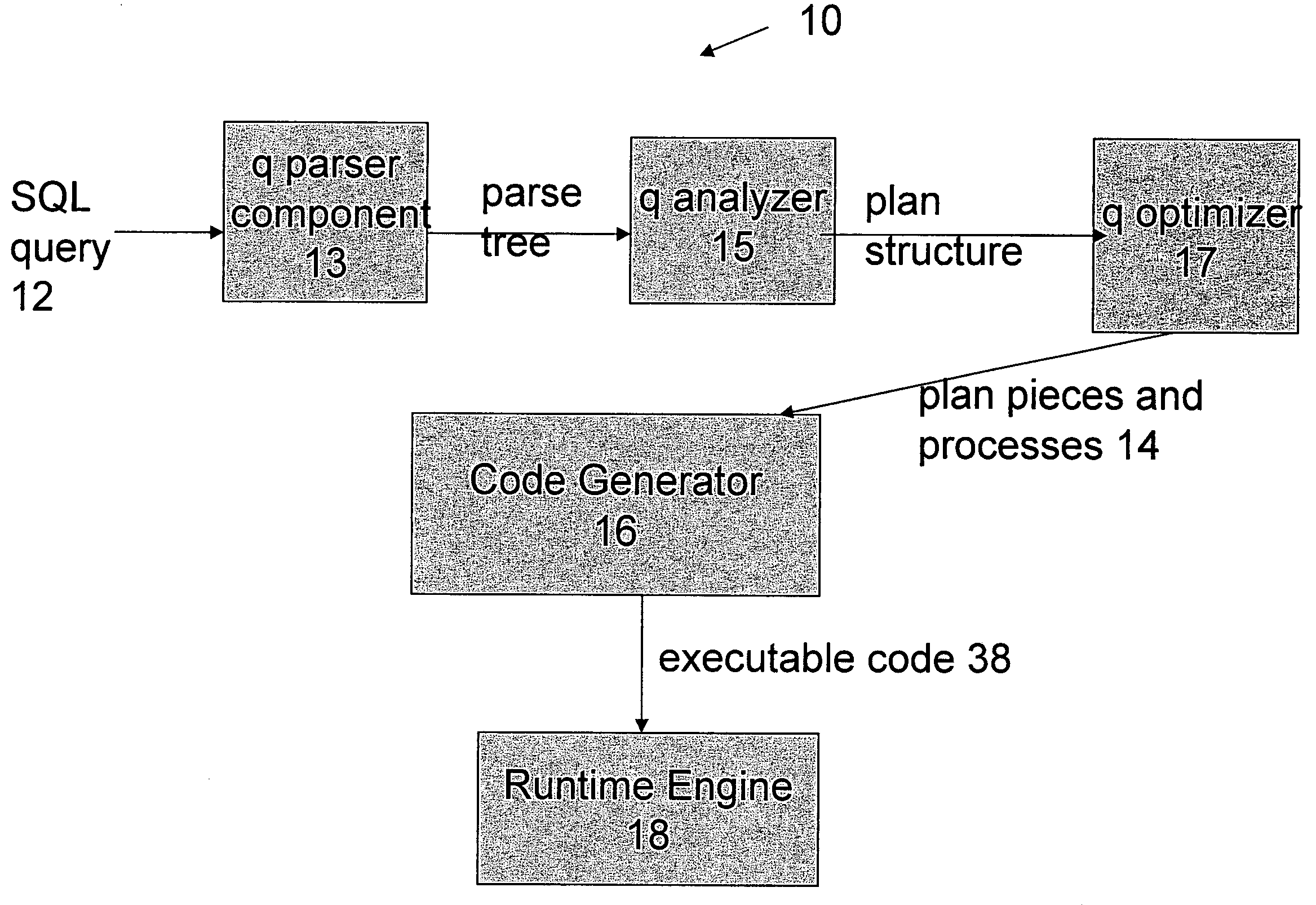
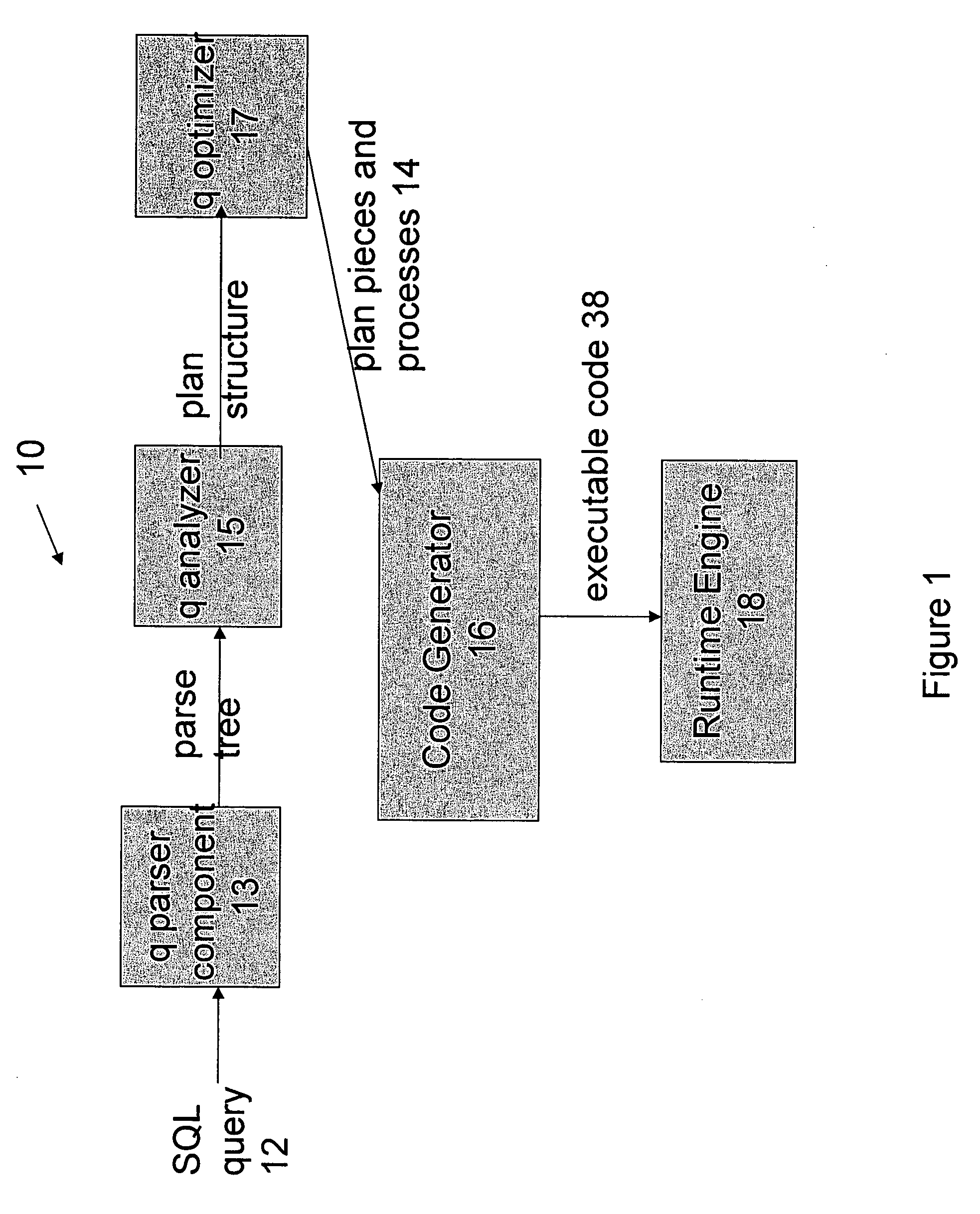
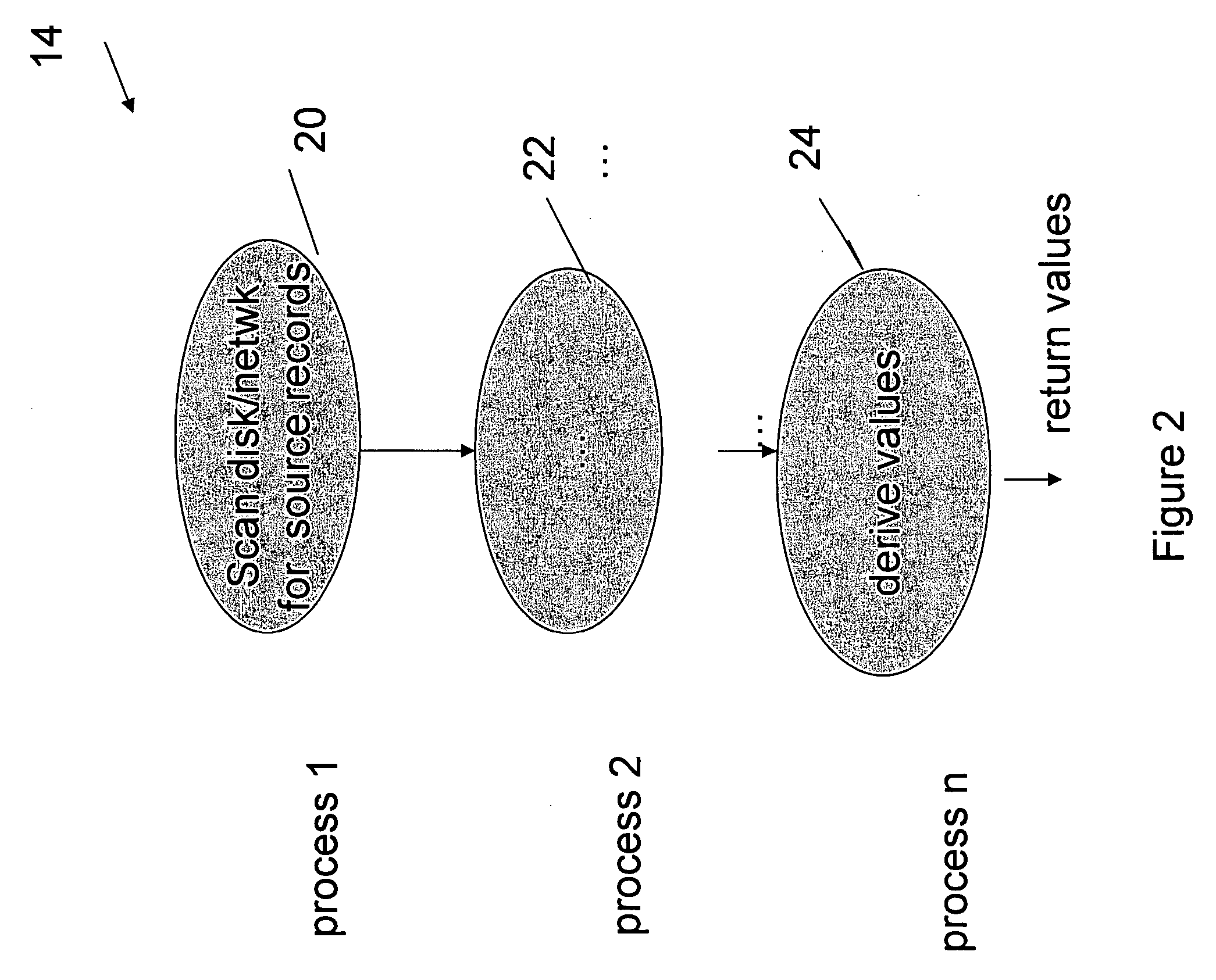
Optimized SQL code generation
ActiveUS7430549B2Reduce and minimize compilation timeReduce and minimize execution timeDigital data information retrievalData processing applicationsExecution planCode generation
This invention relates generally to a system for processing database queries, and more particularly to a method for generating high level language or machine code to implement query execution plans. The present invention provides a method for generating executable machine code for query execution plans, that is adaptive to dynamic runtime conditions, that is compiled just in time for execution and most importantly, that avoids the bounds checking, pointer indirection, materialization and other similar kinds of overhead that are typical in interpretive runtime execution engines.
Owner:INT BUSINESS MASCH CORP
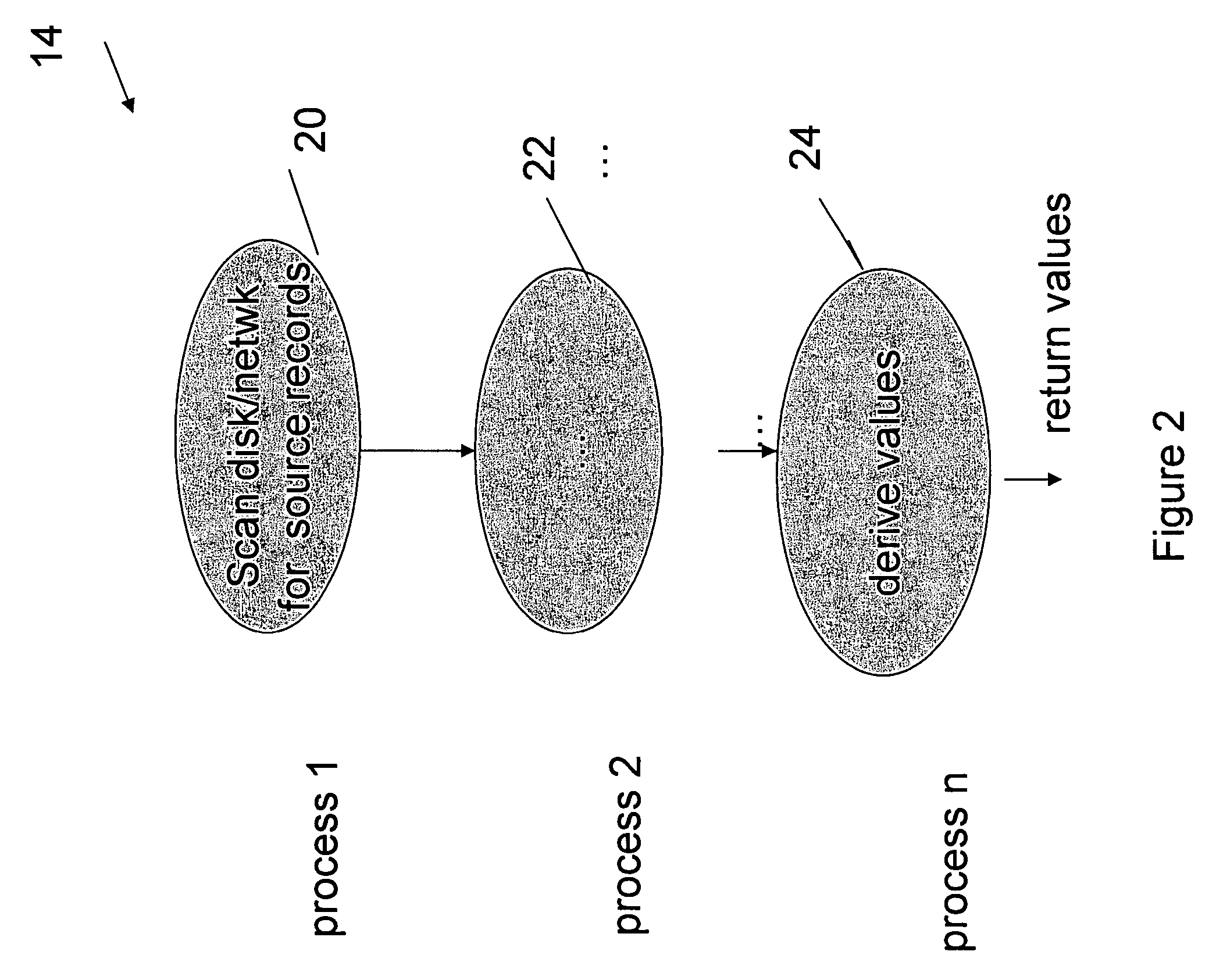
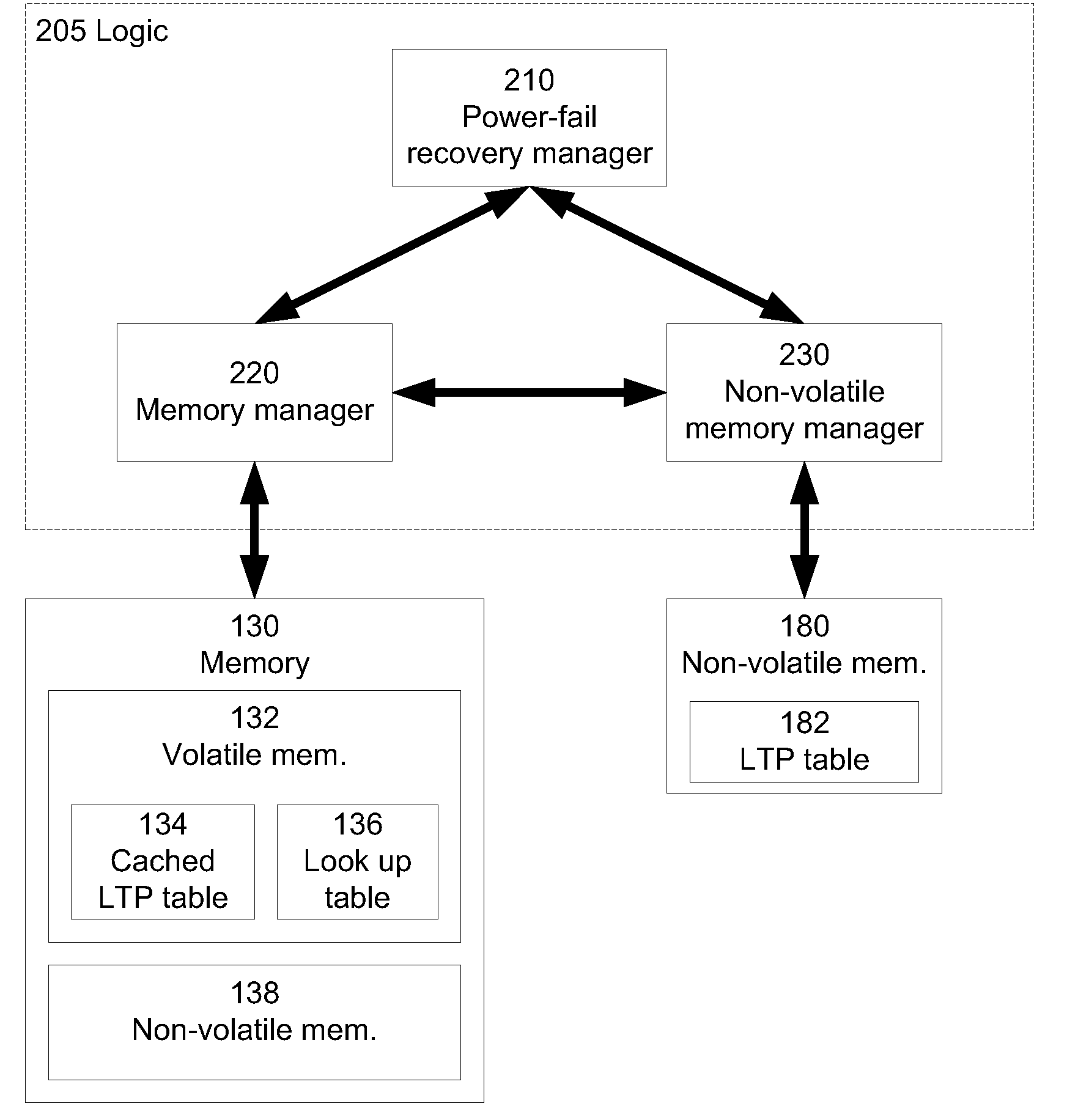
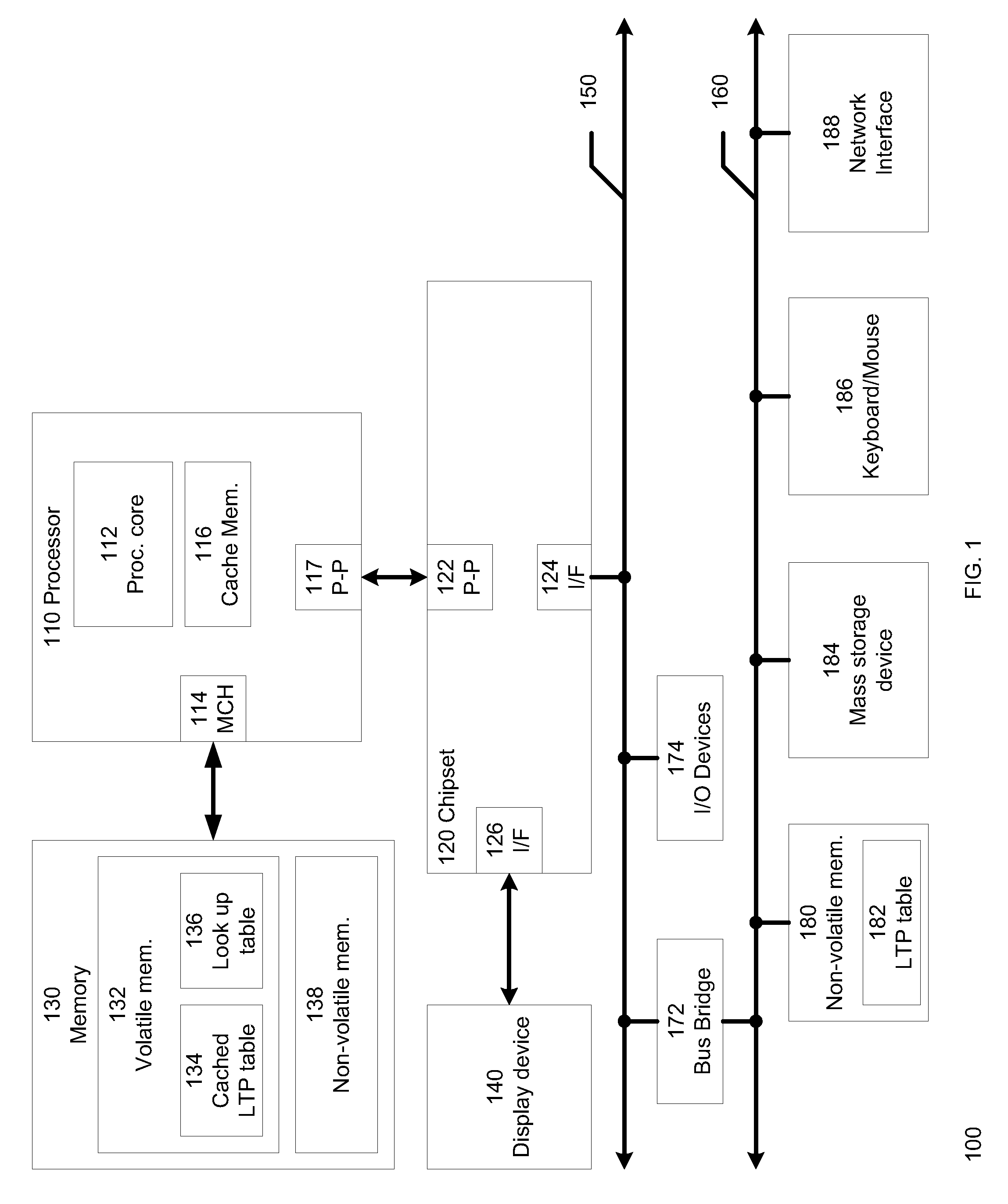
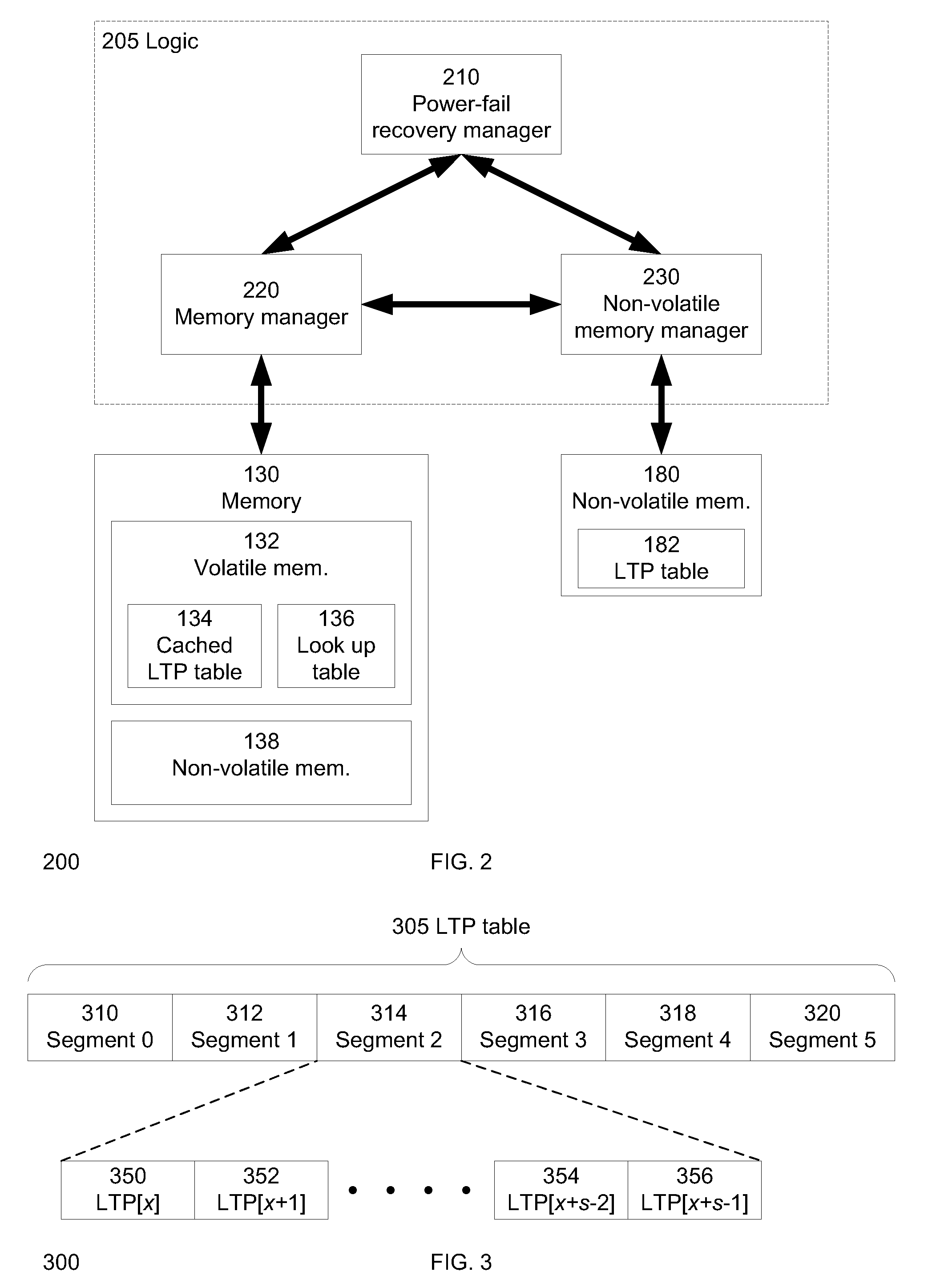
Method and system for managing a NAND flash memory
ActiveUS20100332730A1Memory architecture accessing/allocationMemory adressing/allocation/relocationPagingDatabase
A method and system to facilitate paging of one or more segments of a logical-to-physical (LTP) address mapping structure to a non-volatile memory. The LTP address mapping structure is part of an indirection system map associated with the non-volatile memory in one embodiment of the invention. By allowing one or more segments of the LTP address mapping structure to be paged to the non-volatile memory, the amount of volatile memory required to store the LTP address mapping structure is reduced while maintaining the benefits of the LTP address mapping structure in one embodiment of the invention.
Owner:SK HYNIX NAND PROD SOLUTIONS CORP
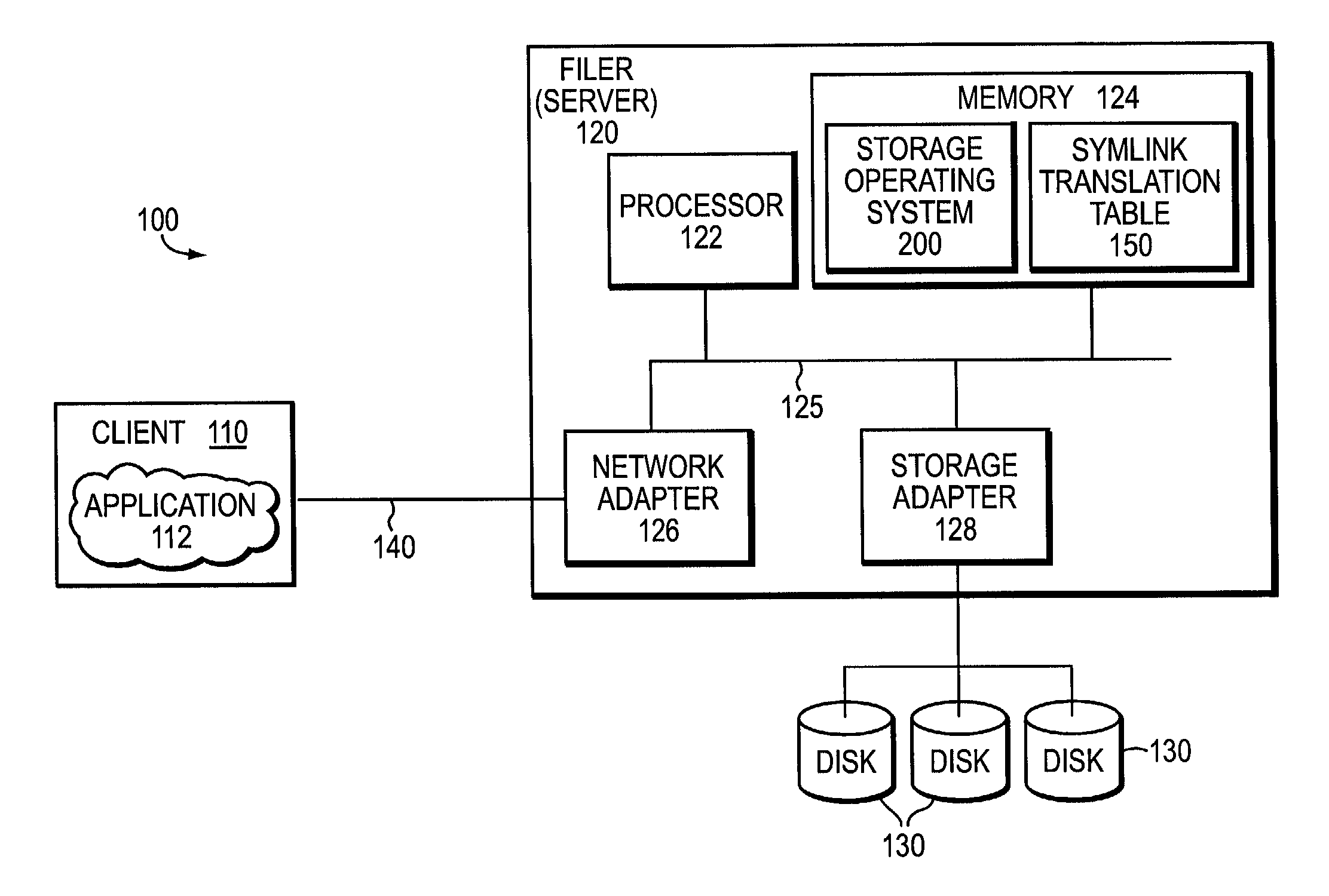
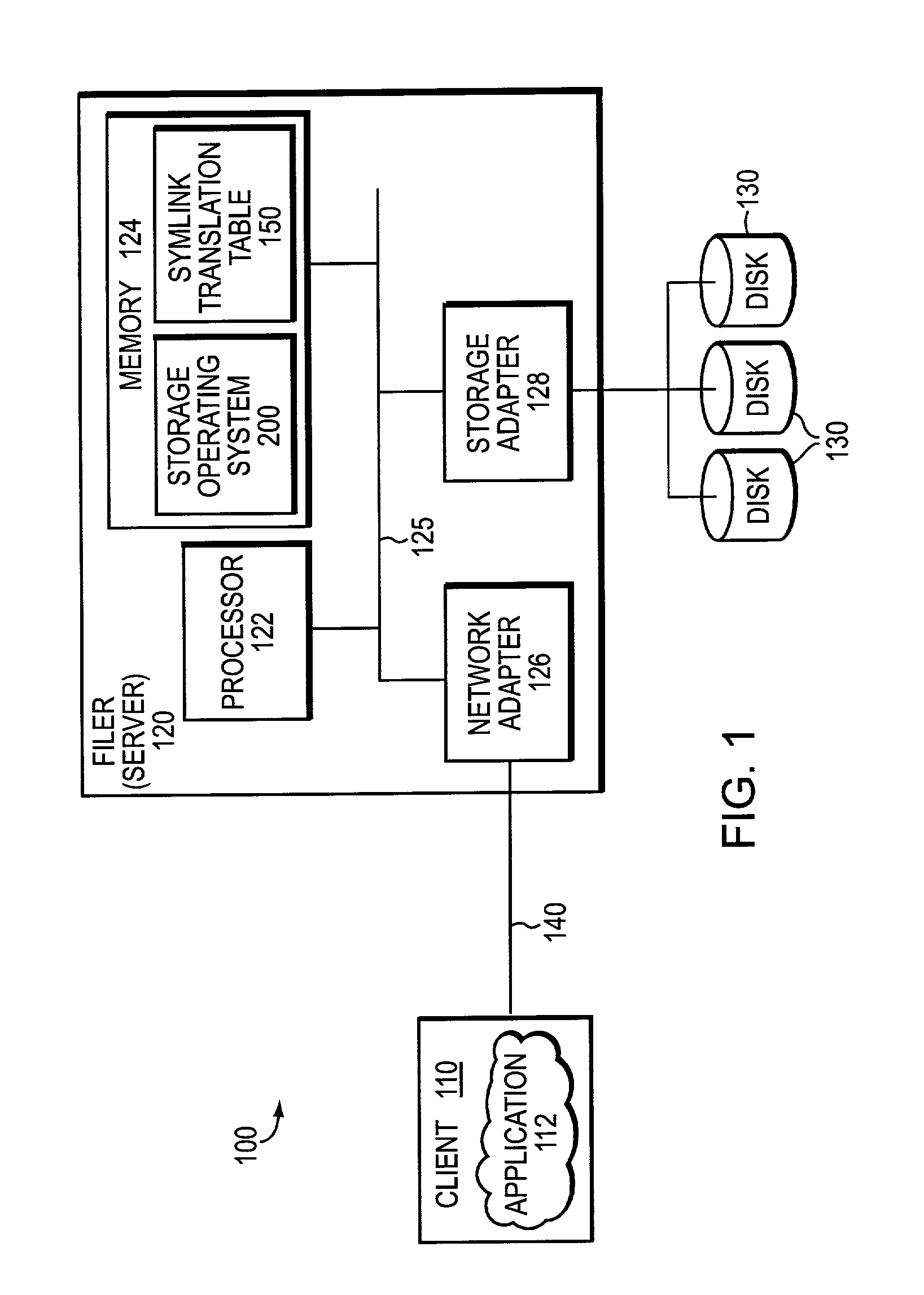
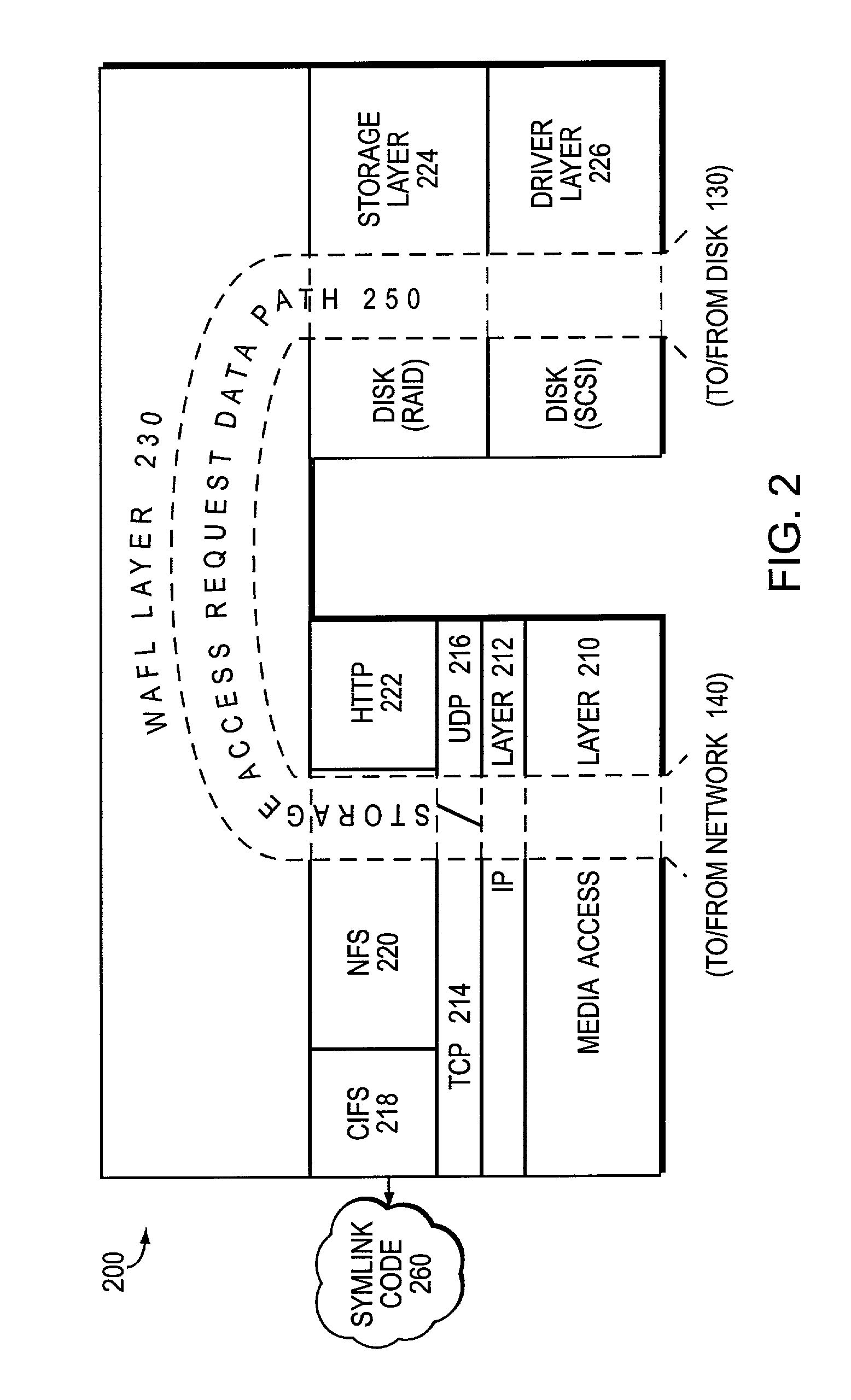
Technique to enable support for symbolic link access by windows clients
ActiveUS6968345B1Solve problemsEnhanced levelData processing applicationsMultiple digital computer combinationsDistributed File SystemSymbolic link
A widelink directive provides an enhanced level of indirection with respect to a resource, such as a unit of storage, attached to a destination, such as a storage system. The widelink has a scope of indirection that is “wider” than a conventional symbolic link (“symlink”). The novel widelink directive is similar to the distributed file system (DFS) facility that allows DFS-enabled common internet file system clients to resolve uniform naming convention paths to locations that may or may not be on an original storage system, such as a multi-protocol filer, or original protocol server of the filer. By taking advantage of clients that support the DFS facility, the widelink directive is quite flexible in that it can be used to resolve symlinks that “leave” a share.
Owner:NETWORK APPLIANCE INC
Methods and systems for providing a unified namespace for multiple network protocols
InactiveUS20110137966A1Easy data migrationEasy to navigateTransmissionSpecial data processing applicationsObject handlingObject store
A network storage server system includes a presentation layer that presents multiple namespaces over the same data stored in an object store, allowing users to simultaneously access data over multiple protocols. The system supports object location independence of the stored data objects by introducing a layer of indirection between directory entries and storage locations of stored data objects. In one embodiment, the directory entry of a data object points to a redirector file that includes an object locator (e.g., an object handle or a global object ID) of the data object. The directory entries of data objects are stored in a directory namespace (e.g., NAS path namespace). In another embodiment, a global object ID of the data object is directly encoded within the directory entry of the data object.
Owner:NETWORK APPLIANCE INC
Optimized SQL code generation
ActiveUS20050027701A1Reduce and minimize compilation timeReduce and minimize execution timeDigital data information retrievalData processing applicationsExecution planSQL
This invention relates generally to a system for processing database queries, and more particularly to a method for generating high level language or machine code to implement query execution plans. The present invention provides a method for generating executable machine code for query execution plans, that is adaptive to dynamic runtime conditions, that is compiled just in time for execution and most importantly, that avoids the bounds checking, pointer indirection, materialization and other similar kinds of overhead that are typical in interpretive runtime execution engines.
Owner:IBM CORP
System for storing distributed hashtables
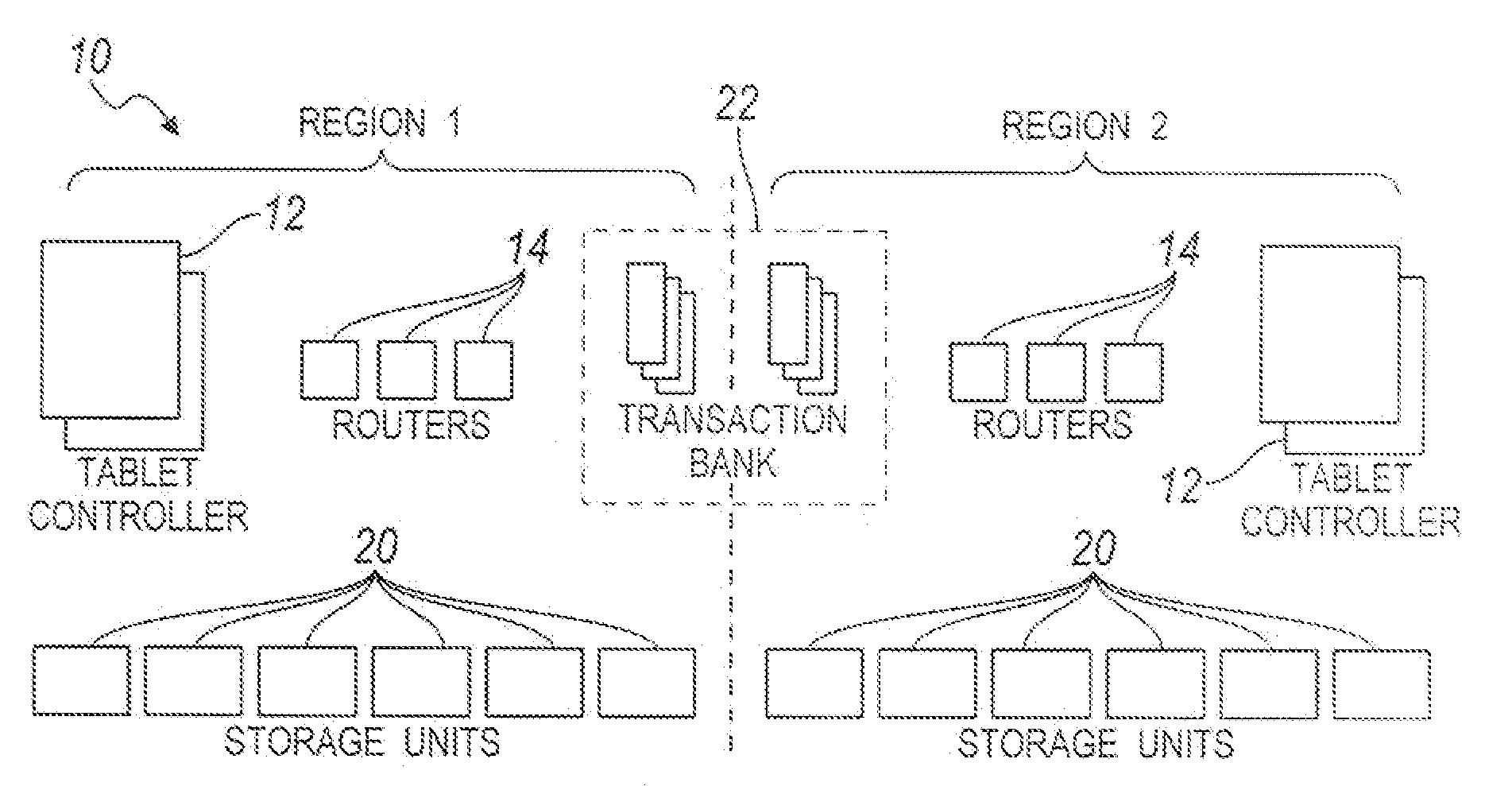
InactiveUS20090144220A1Easy accessImprove performanceDigital data information retrievalSpecial data processing applicationsTablet computerClient-side
A system for storing a distributed hash table. The system includes a storage unit, a tablet controller, a router, and a transaction bank. The storage unit has a plurality of tablets forming a hash table and each of the tablets includes multiple records. The tablet controller maintains a relationship between each tablet and the storage unit. The router hashes a record's key to determine the tablet associated with each record. Further, the router distributes messages from clients to the storage units based on the tablet-storage unit relationship thereby serving as a layer of indirection. The transaction bank propagates updates made in one record to all other replicas of the record.
Owner:OATH INC
Virtual resource ID mapping
InactiveUS20050010924A1Data processing applicationsProgram initiation/switchingS systemResource identifier
The present invention provides virtual mapping of system resource identifiers in use by a software application for the purpose of making the running state of an application node independent. By adding a layer of indirection between the application and the resource, new system resources are reallocated and then can be mapped to the application's existing resource requirements while it is running, without the application detecting a failure or change in resource handles. This layer of indirection makes the application's system resource identifier (system RID) transparent to the application. RID's are usually numeric in form, but can also be alphanumeric. RID's are unique to a machine, and can be reused once all claims to a specific RID have been given up.
Owner:SYMANTEC OPERATING CORP
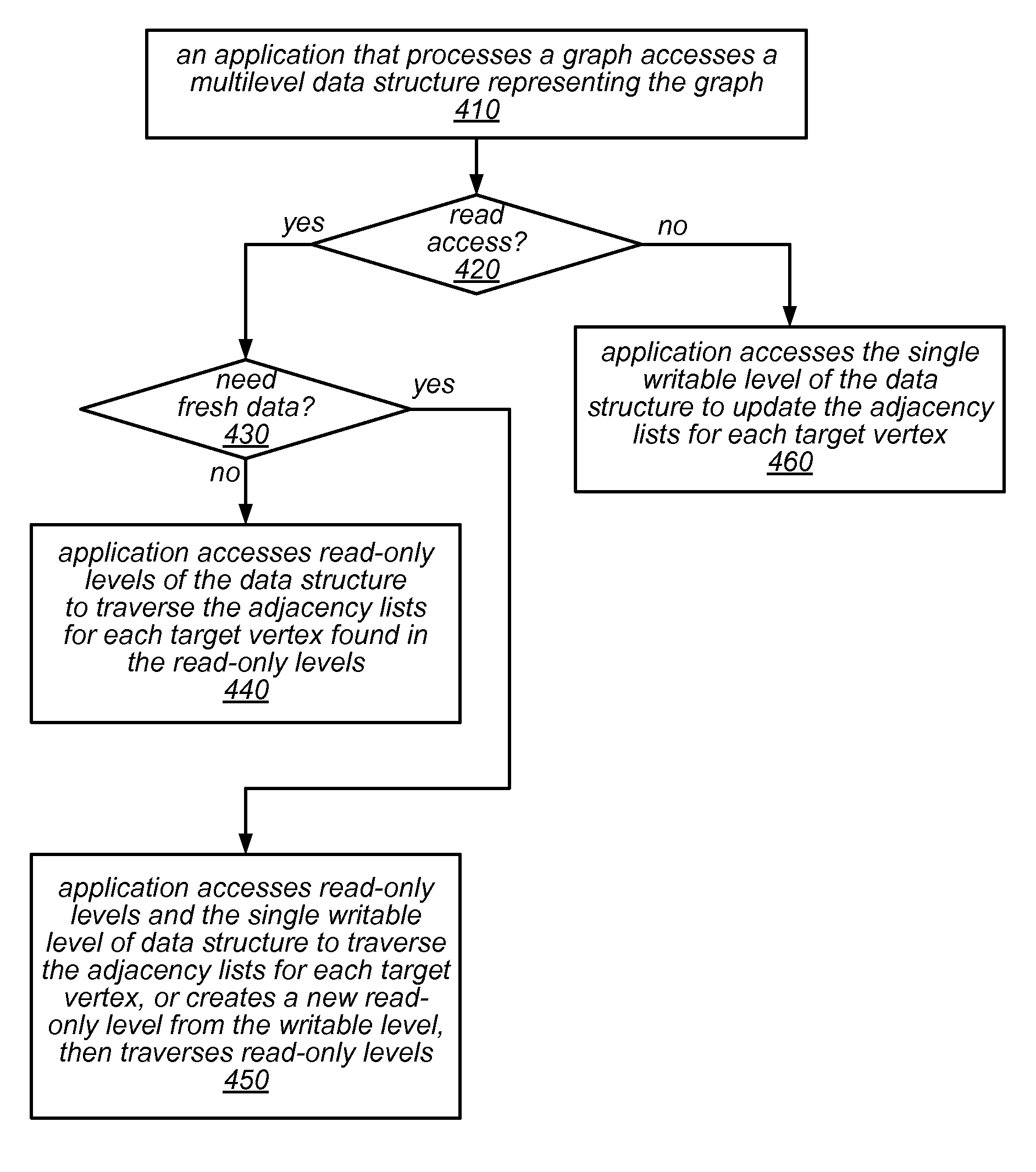
Graph Processing Using a Mutable Multilevel Graph Representation
ActiveUS20160071233A1Improve performanceIncrease spacingDrawing from basic elementsImage memory managementTheoretical computer scienceAdjacency list
A mutable multilevel data structure representing a graph structure may include multiple read-only levels and a single writable level. Each read-only level may include a vertex table (which includes references to edge tables on the same level or a different level containing elements of adjacency lists for some vertices) and an edge table (which includes elements of adjacency lists that changed since the previous read-only level). A hybrid variant may switch between a performance-optimized variant (whose edge tables include complete adjacency lists for vertices whose edge sets were modified) and a space-optimized variant (whose edge tables include only newly added adjacency list elements). The vertex tables and / or the writable level may be implemented using copy-on-write arrays, each including an indirection table and multiple fixed-sized data pages. Computations may be run on the read-only levels or on the writable level and read-only levels.
Owner:ORACLE INT CORP
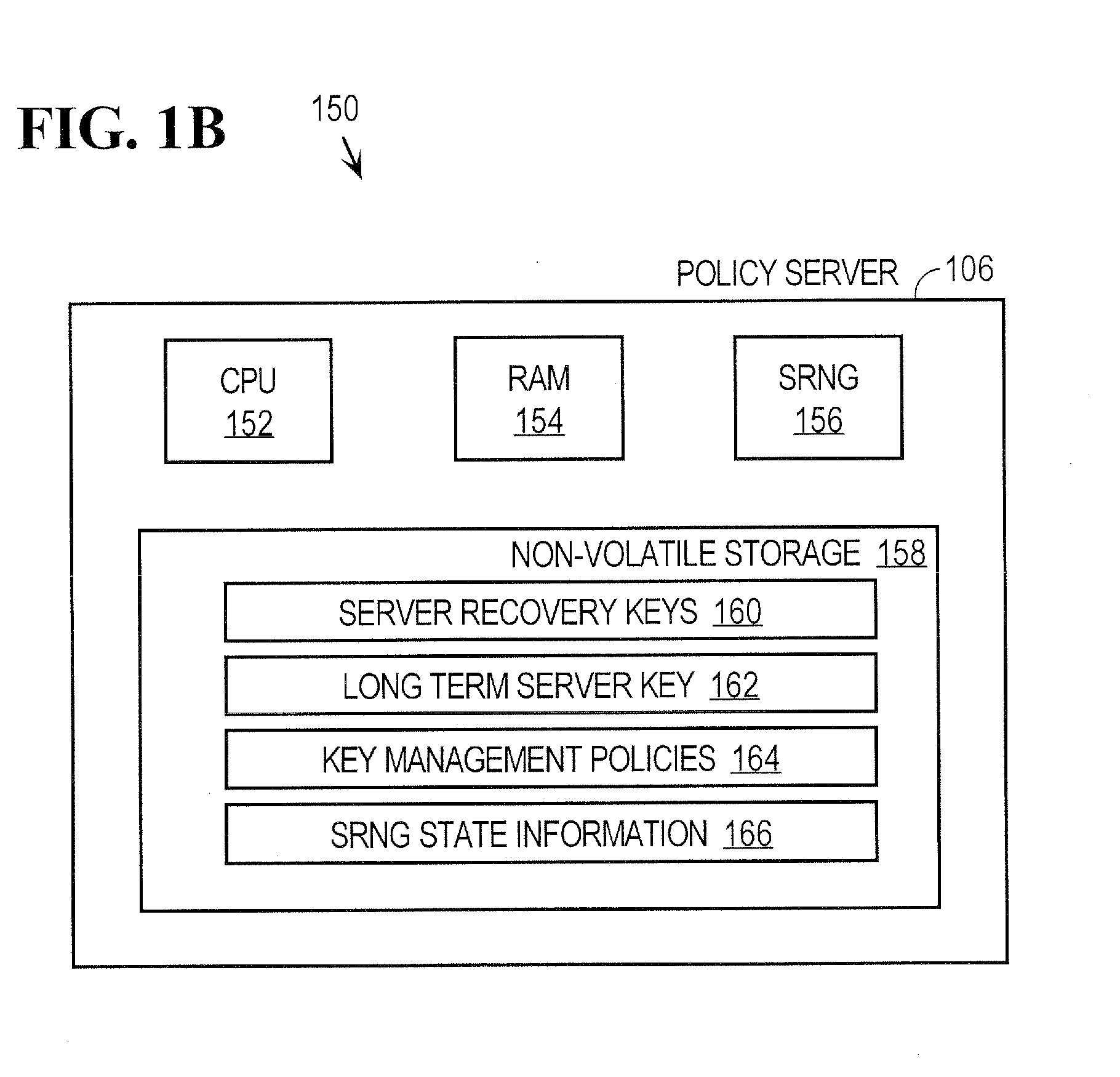
Approach for managing access to messages using encryption key management policies
ActiveUS7333616B1Key distribution for secure communicationUnauthorized memory use protectionGraphicsData format
Controlling access to disseminated messages includes implementing one or more key management policies that specify how various encryption keys are maintained and in particular, when encryption keys are made inaccessible. Deleting a particular key renders inaccessible all copies of messages, known or unknown, associated with the particular key, regardless of the location of the associated messages. A message may be directly associated with a deleted key. For example, a message may be directly associated with a deleted key by having been encrypted using the deleted key. A message may also be indirectly associated with a deleted key. For example, a message may be indirectly associated with a deleted key by being encrypted with a key that in turn was encrypted using the deleted key. Any number of levels are indirection are possible and either situation makes the message unrecoverable. The approach is applicable to any type of data in any format and the invention is not limited to any type of data or any type of data format. Examples of data include, but are not limited to, text data, voice data, graphics data and email. Although embodiments of the invention are described hereinafter in the context of controlling access to email, the invention is not limited to the email context and is applicable to controlling access to any type of messages or data.
Owner:CHECK POINT SOFTWARE TECH LTD
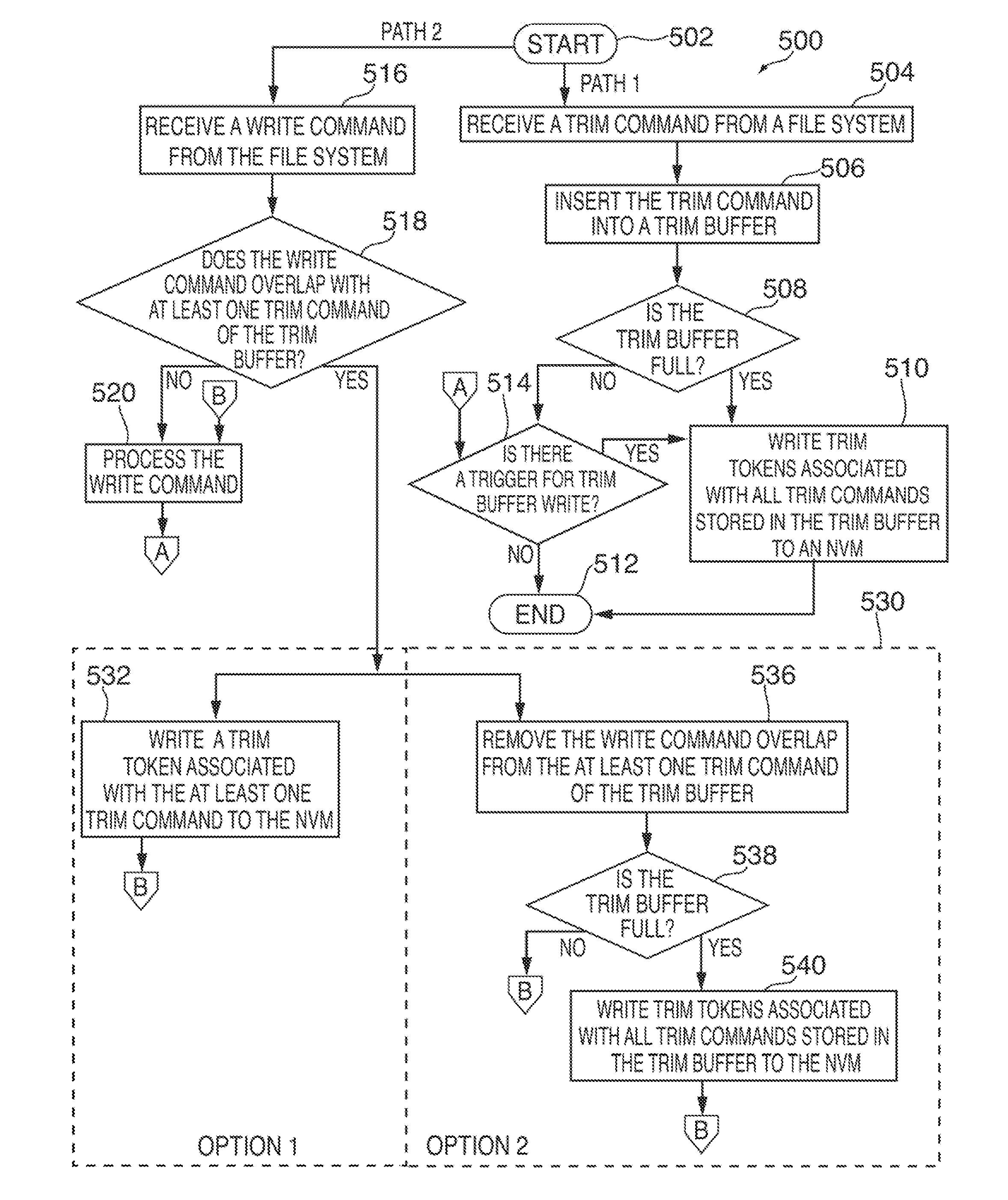
Trim token journaling
Systems and methods are disclosed for trim token journaling. A device can monitor the order in which trim commands and write commands are applied to an indirection system stored in a volatile memory of the device. In some embodiments, the device can directly write to a page of an NVM with a trim token that indicates that a LBA range stored in the page has been trimmed. In other embodiments, a device can add pending trim commands to a trim buffer stored in the volatile memory. Then, when the trim buffer reaches a pre-determined threshold or a particular trigger is detected, trim tokens associated with all of the trim commands stored in the trim buffer can be written to the NVM. Using these approaches, the same sequence of events that was applied to the indirection system during run-time can be applied during device boot-up.
Owner:APPLE INC
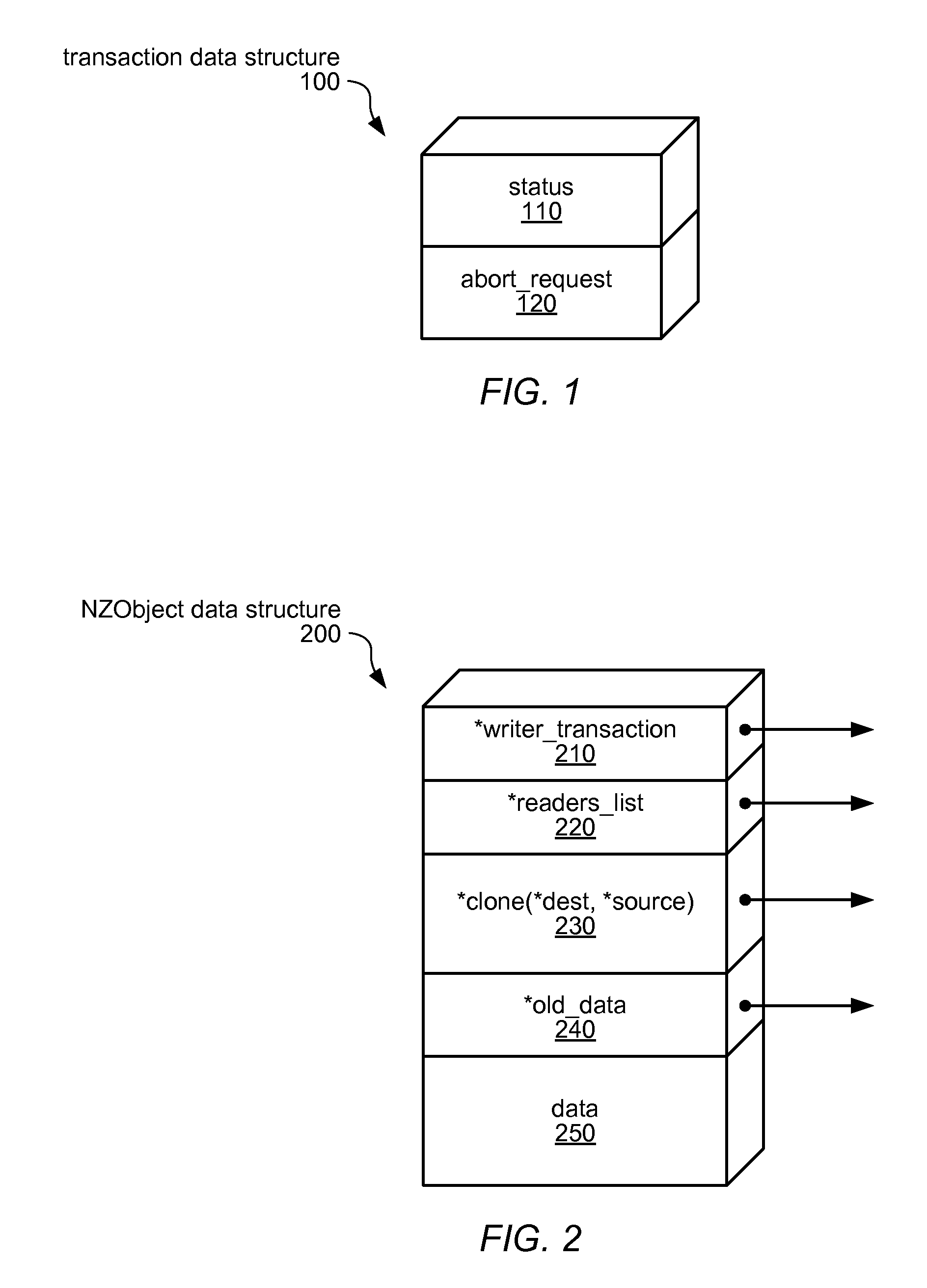
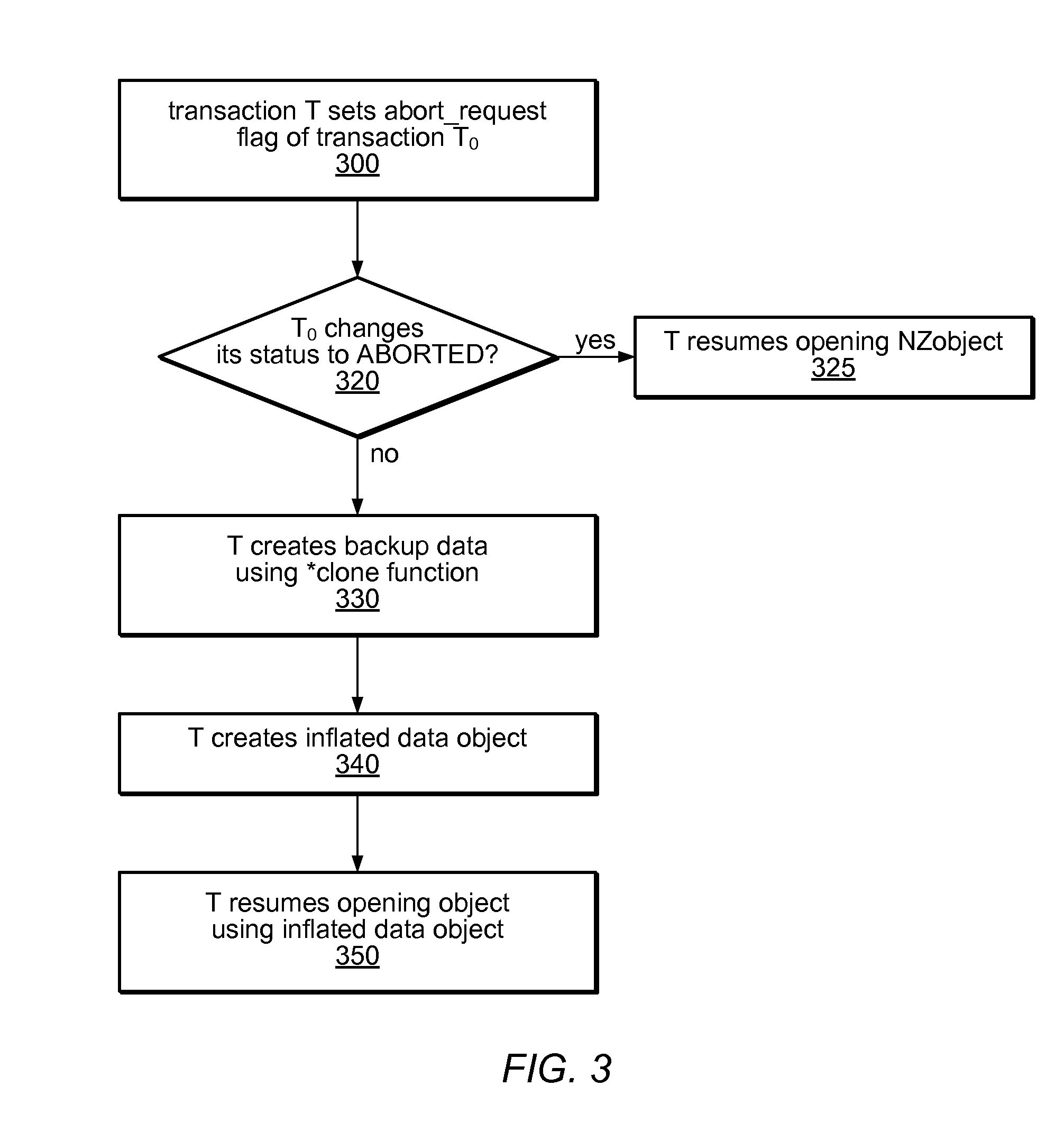
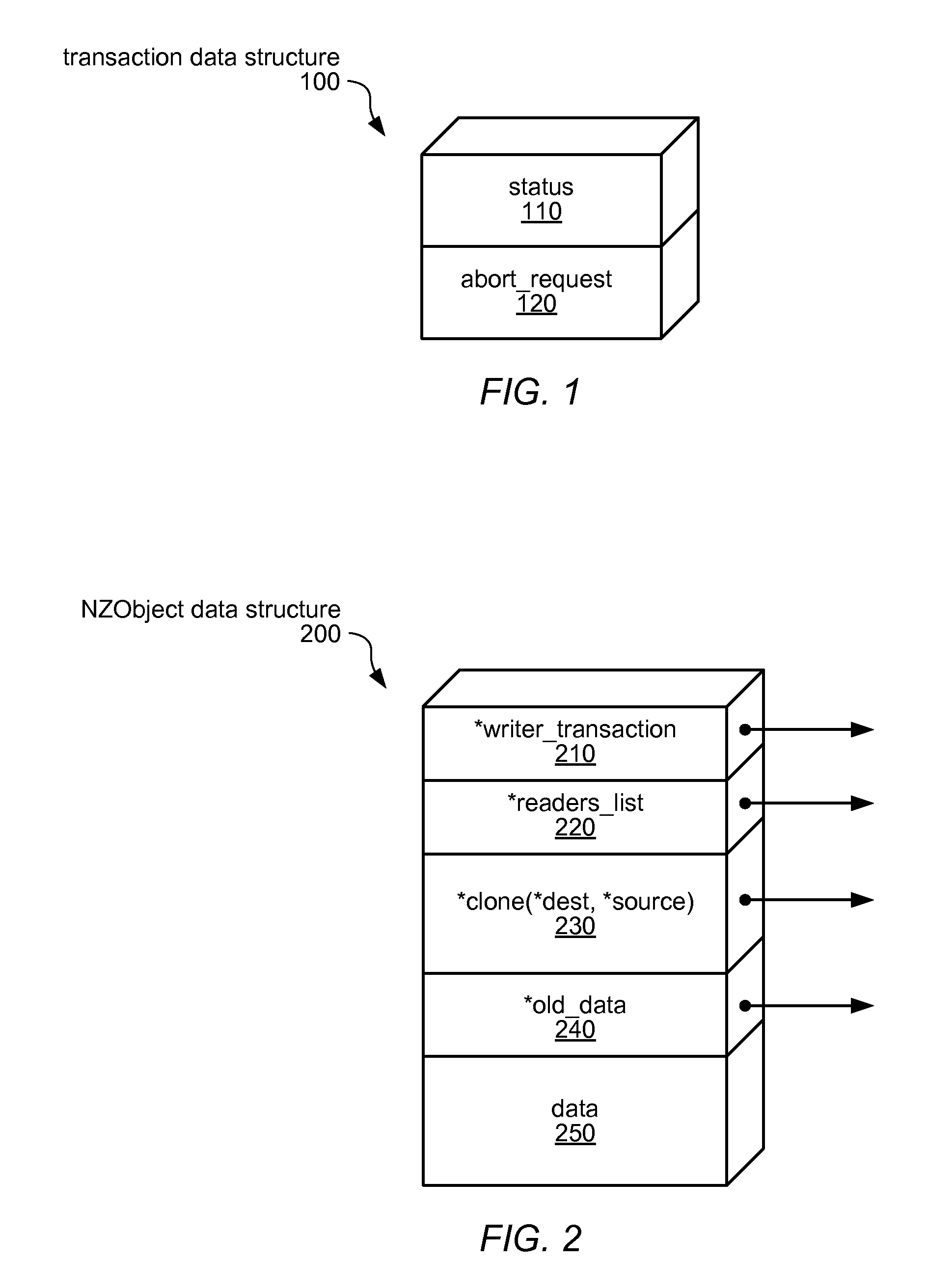
System and Method for Implementing Nonblocking Zero-Indirection Transactional Memory
ActiveUS20090171962A1Digital data processing detailsSpecial data processing applicationsObject basedSoftware
Systems and methods for implementing and using nonblocking zero-indirection software transactional memory (NZSTM) are disclosed. NZSTM systems implement object-based software transactional memory that eliminates all levels of indirection except in the uncommon case of a conflict with an unresponsive thread. Shared data is co-located with a header in an NZObject, and is addressable at a fixed offset from the header. Conflicting transactions are requested to abort themselves without being forced to abort. NZObjects are modified in place when there are no conflicts, and when a conflicting transaction acknowledges the abort request. In the uncommon case, NZObjects are inflated to introduce a locator and some levels of indirection, and are restored to their un-inflated form following resolution of the conflict. In some embodiments, transactions are executed using best effort hardware transactional memory if it is available and effective, and software transactional memory if not, yielding a hybrid transactional memory system, NZTM.
Owner:ORACLE INT CORP
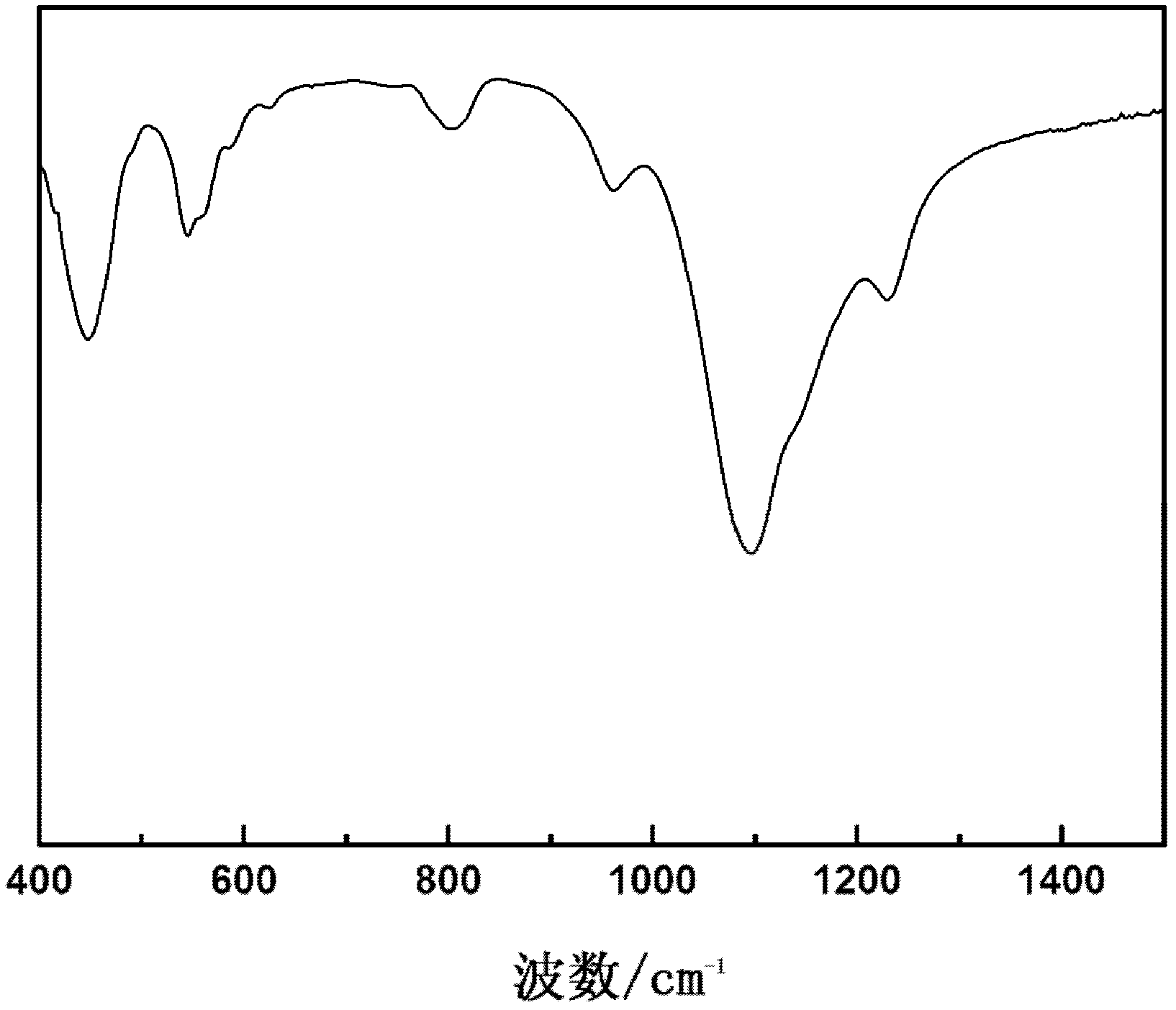
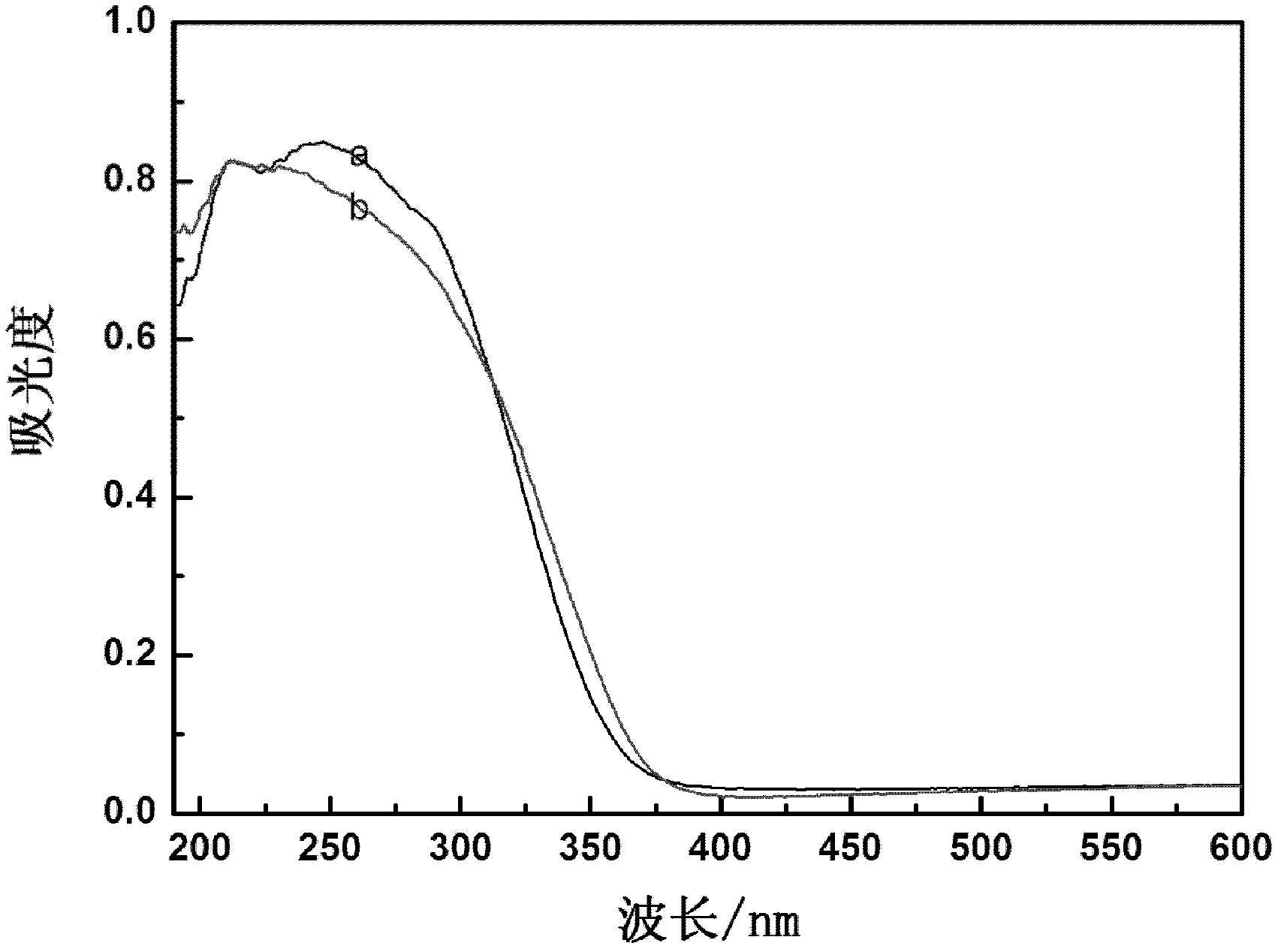
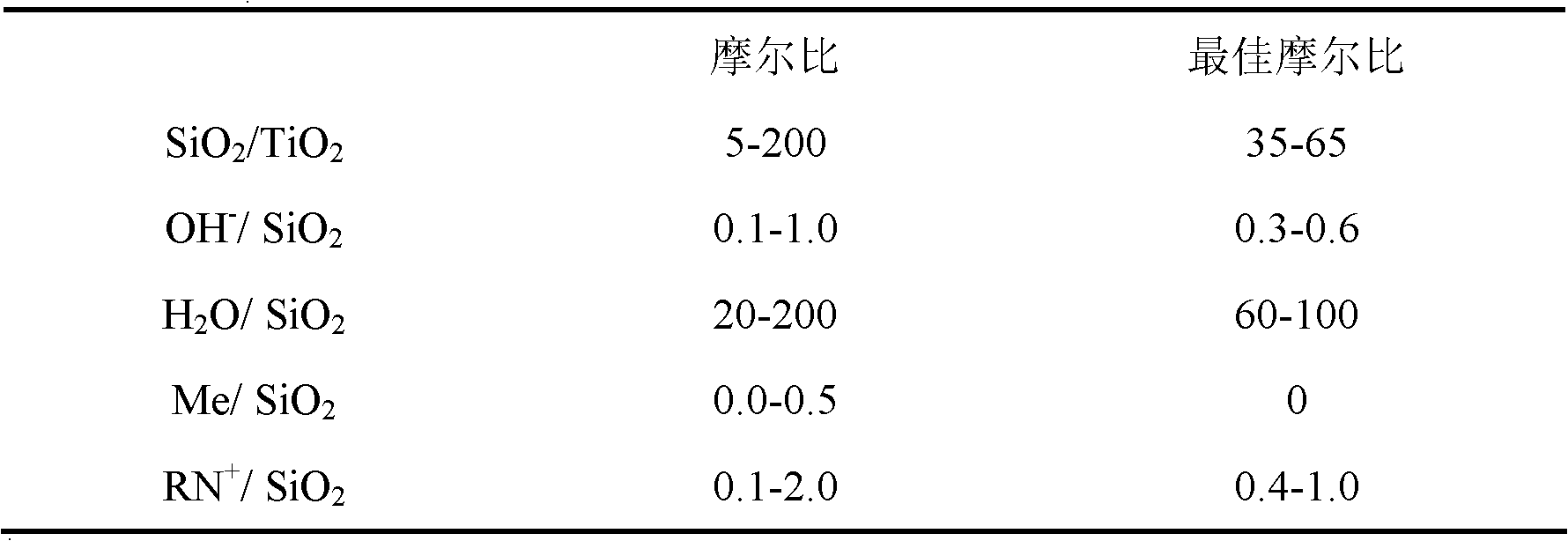
Synthesis method of titanium silicalite TS-1
ActiveCN102320619ASuppress generationLow costCrystalline aluminosilicate zeolitesMolecular sieveDepolymerization
The invention belongs to the field of preparation of molecular sieve material, and discloses a synthesis method of a titanium silicalite TS-1. The method is characterized by comprising the following steps of: preparing a titanium-silicon gel with a silicon source, a titanium source, a template agent, an alkaline mineralizing agent and water according to certain proportion, and introducing right amount of alkali metal salt in the gel preparation process through a direction method or an indirection method; then, executing hydrothermal crystallization at 160-180 DEG C; and obtaining the titanium silicalite TS-1 after filtering, washing, drying and roasting. With the synthesis method provided by the invention, depolymerization of the silicon source can be promoted in the gel preparation process, so that titanium can enter into a skeleton smoothly and generation of amorphous six-coordinate non-skeleton titanium can be restrained. Based on the action of alkaline metal ions and an acid site of the molecular sieve non-skeleton titanium, the acid site of the cheap titanium silicalite TS-1 is removed, and selectivity of propylene epoxide is greatly improved while taking the titanium silicalite TS-1 as the catalyst for the propylene epoxidation.
Owner:DALIAN UNIV OF TECH
System and method for implementing nonblocking zero-indirection transactional memory
ActiveUS8140497B2Digital data processing detailsSpecial data processing applicationsObject basedIndirection
Systems and methods for implementing and using nonblocking zero-indirection software transactional memory (NZSTM) are disclosed. NZSTM systems implement object-based software transactional memory that eliminates all levels of indirection except in the uncommon case of a conflict with an unresponsive thread. Shared data is co-located with a header in an NZObject, and is addressable at a fixed offset from the header. Conflicting transactions are requested to abort themselves without being forced to abort. NZObjects are modified in place when there are no conflicts, and when a conflicting transaction acknowledges the abort request. In the uncommon case, NZObjects are inflated to introduce a locator and some levels of indirection, and are restored to their un-inflated form following resolution of the conflict. In some embodiments, transactions are executed using best effort hardware transactional memory if it is available and effective, and software transactional memory if not, yielding a hybrid transactional memory system, NZTM.
Owner:ORACLE INT CORP
Adaption resource module and operating method therefor
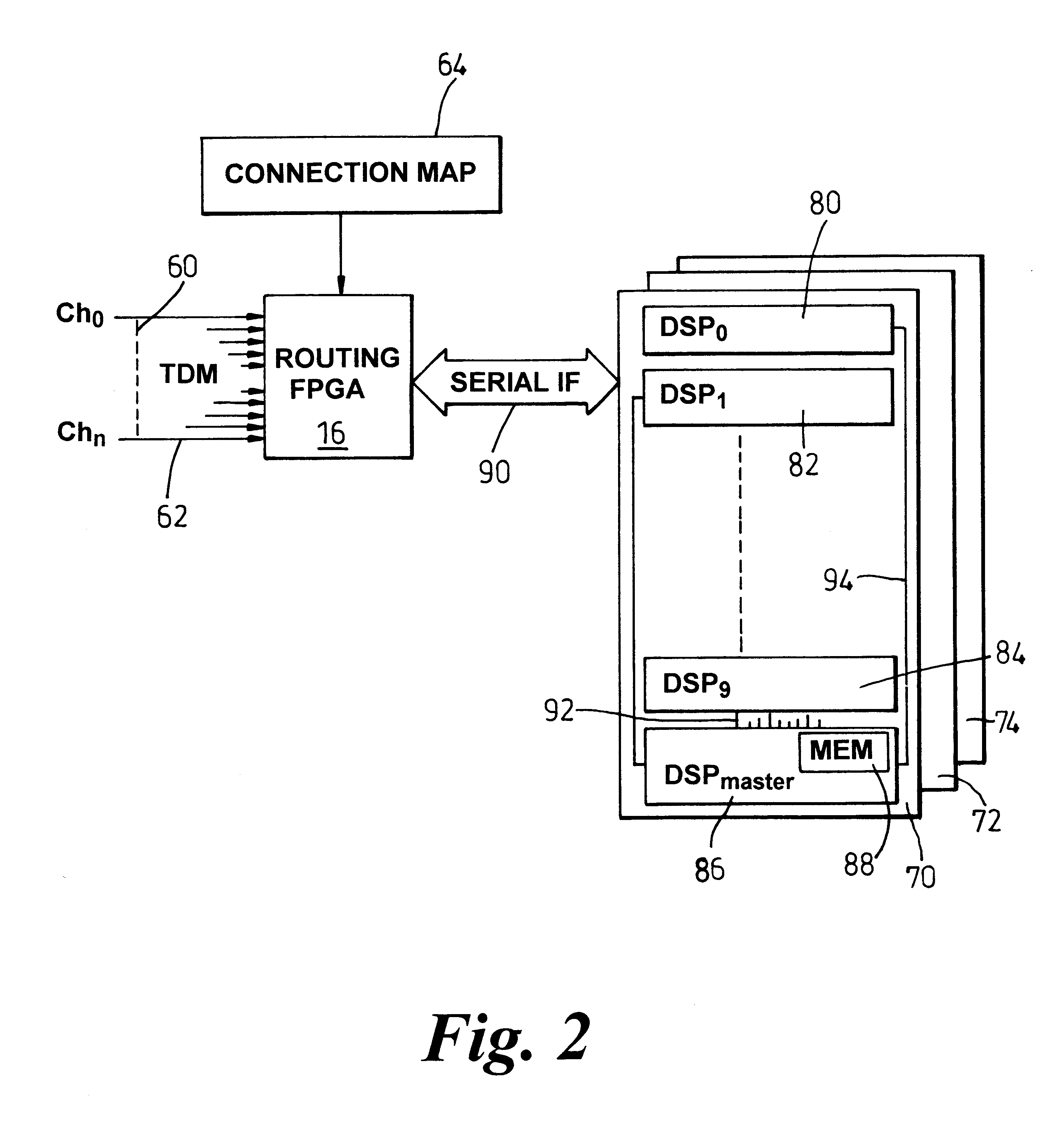
InactiveUS6266342B1Simple systemTime-division multiplexData switching by path configurationModularityParallel computing
In order to support both signalling processing on a per channel basis and multiple adaptation protocols, an interface (10) is modularised principally by function. Incident channels (60-62, Cho-Chn) are applied to a routing device (16) that consults a connection map (64) to determine an appropriate path, via an interface (90), for signal processing of each channel, as shown in FIG. 2. Modularised processing platforms (70-74) each contain a number of signal processors (80-86), with each processing platform providing an additional level of indirection with respect to channel handling. In this latter respect, one of the signal processors (86) on each platform is assigned to distribute channel processing to appropriately configured other ones of the signal processors and such that signal processing functions may be distributed between the other ones (80-84) of the signal processors. The present invention is particularly useful in relation to a narrowband-broadband interface to support differing adaptation protocols that require different signal processing functions and also to vary signal processing capabilities on a per call basis.
Owner:RPX CLEARINGHOUSE
Collection view objects for displaying data collection items in user interface elements
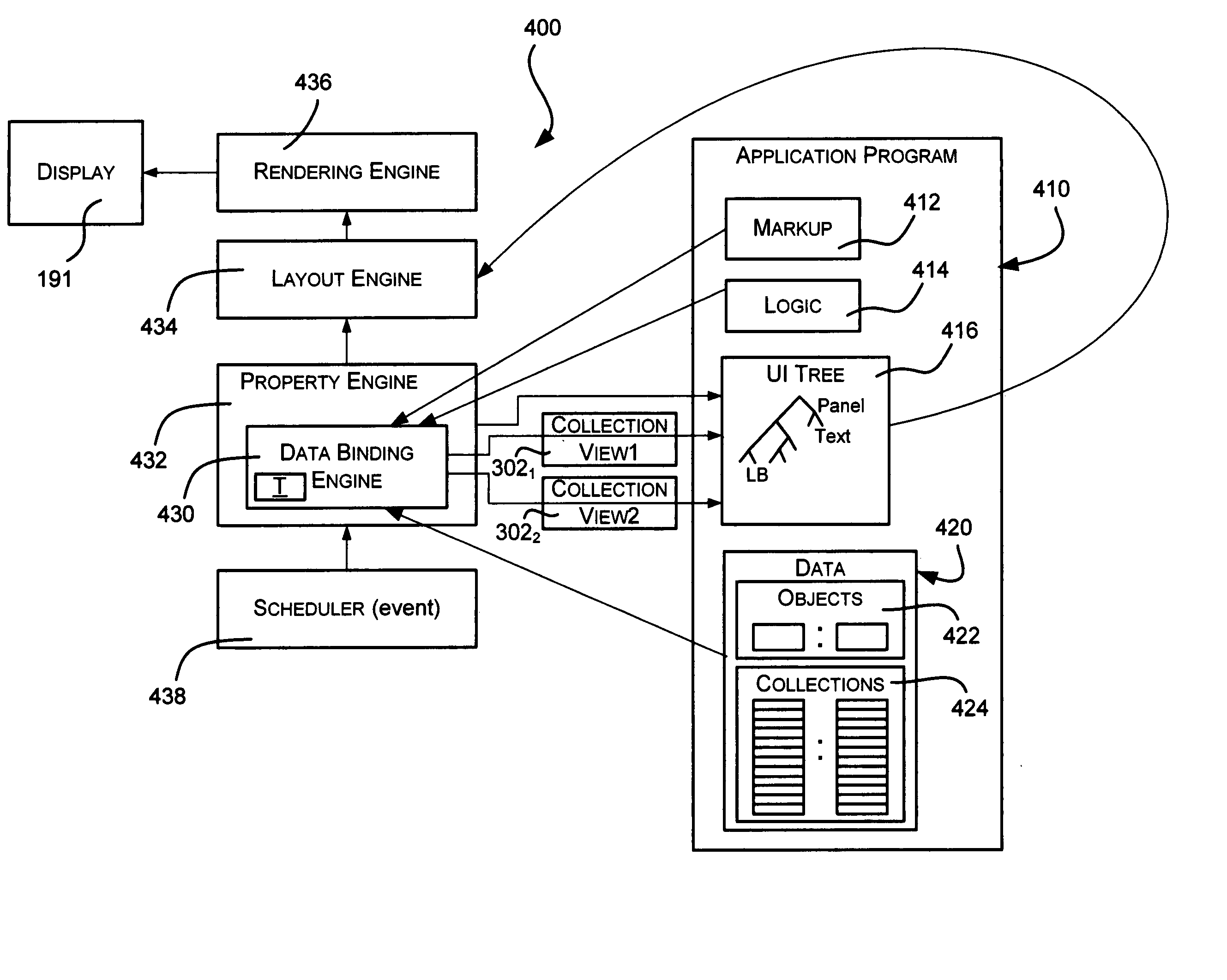
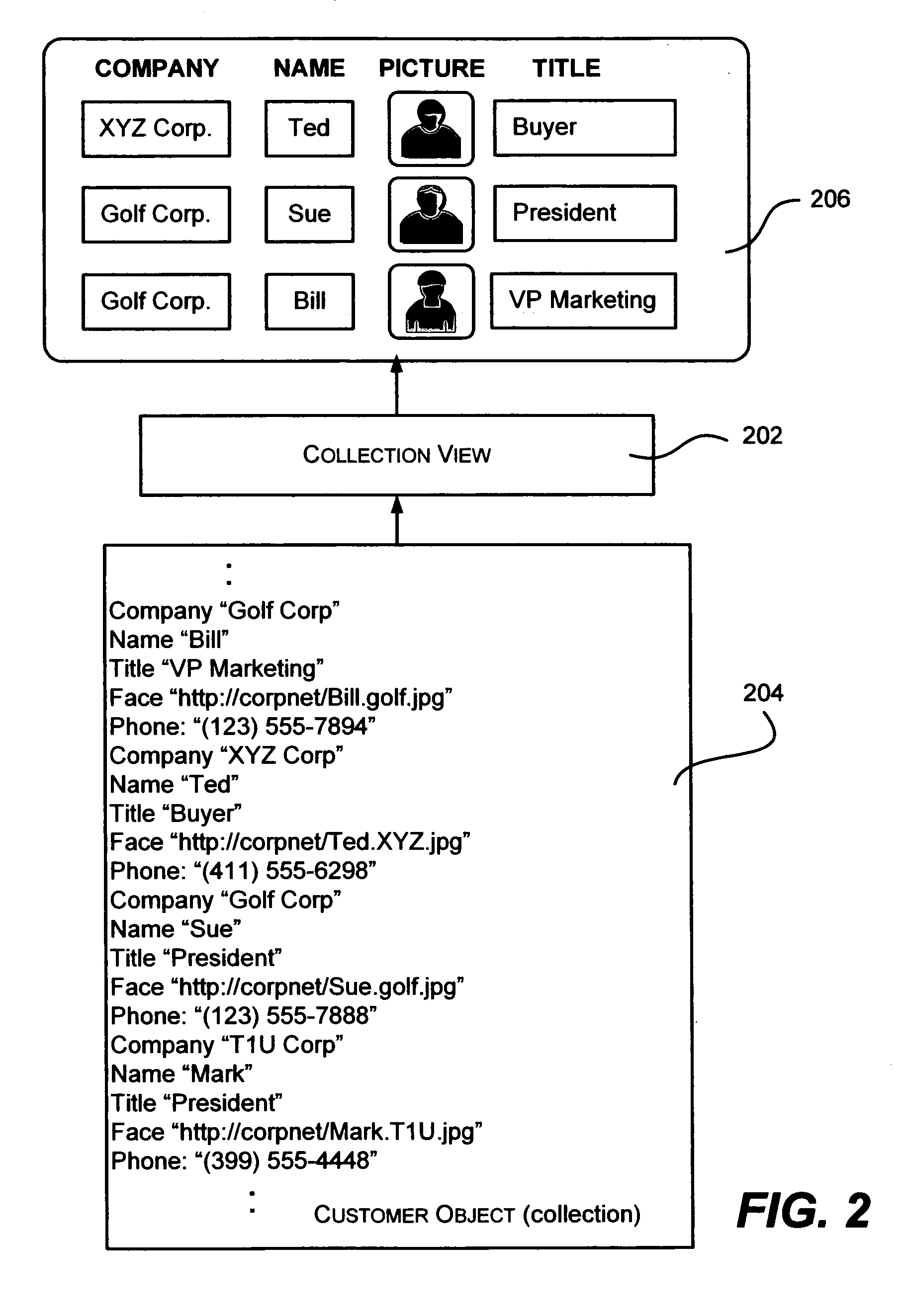
InactiveUS20060090139A1Good choiceEasy to watchDigital data processing detailsNatural language data processingEeg dataSemantics
Described are collection view objects, which provide a user interface view over a data collection, where each view may have its own sort order, filter and / or grouping criteria, as well as current item semantics. A user interface element is bound to a data collection, such as via markup language (e.g., XAML). At runtime, a collection view object is instantiated as an indirection between the data collection and the user interface element, whereby a collection of data items is viewed according to how each collection view object is currently configured with respect to sorting, filtering and / or grouping. Multiple collection views may be specified on the same data collection, whereby distinct simultaneous views of the data items may be presented in different user interface elements. The collection view object dynamically updates the displayed data as changes are made in the data collection. A current item may be selected within the collection view.
Owner:MICROSOFT TECH LICENSING LLC
System and method for topical document searching
ActiveUS20070255686A1Search is limitedDigital data information retrievalSpecial data processing applicationsSubject matterPaper document
Systems and methods are providing for searching for documents within topically-defined clusters. A search space is defined, starting with one or more source documents, by examining references from one documents to another and following the networks of references to some level of indirection. Depending on the embodiment, references may be followed from a document containing a reference to a referred-to document, or from a referred-to document to a document containing a reference, or both. Once a search space has been defined, a query is executed, and documents within the search space that satisfy the query parameters are identified. In certain embodiments of the invention, the documents primarily relate to legal materials, and one or more source documents are associated with one or more topics within a topic directory. In such embodiments, a search query may be limited to one or more selected topics by executing the search query within a search space defined using the associated document or documents as the source.
Owner:BLOOMBERG +2
Indirect measuring method for hypersonic speed wind tunnel turbulence scale
ActiveCN103969022AAccurate and reliable measurement resultsFunction relation simplificationAerodynamic testingEngineeringData collecting
The invention relates to wind tunnel turbulence scale measuring, in particular to an indirect measuring method for hypersonic speed wind tunnel turbulence scale. According to the indirection measuring method for hypersonic speed wind tunnel turbulence scale, a miniature airspeed head is used for measuring pressure pulsation in a hypersonic speed wind tunnel flow field, and then the turbulence scale is indirectly obtained according to relation conversion between pressure pulsation and speed pulsation. The method includes the steps of wind tunnel data collecting and data analyzing. According to wind tunnel data collection process, an adjustable device of the miniature airspeed tube is used for measuring pulsation pressure values at different positions of wind tunnel incoming flows, and other probes are used for measuring other wind tunnel data. According to the data analyzing process, the measured pressure pulsation values and other wind tunnel data are analyzed to obtain the function relation expression between pressure pulsation and speed pulsation in hypersonic speed airflows through deduction, and therefore the hypersonic speed wind tunnel turbulence scale is obtained through calculation. The function relation expression between pressure pulsation and speed pulsation is simple and clear, the hypersonic speed wind tunnel turbulence scale can be obtained only by pressure pulsation measurement and simple calculation, and the indirect measuring method is convenient and rapid to implement.
Owner:XIAMEN UNIV
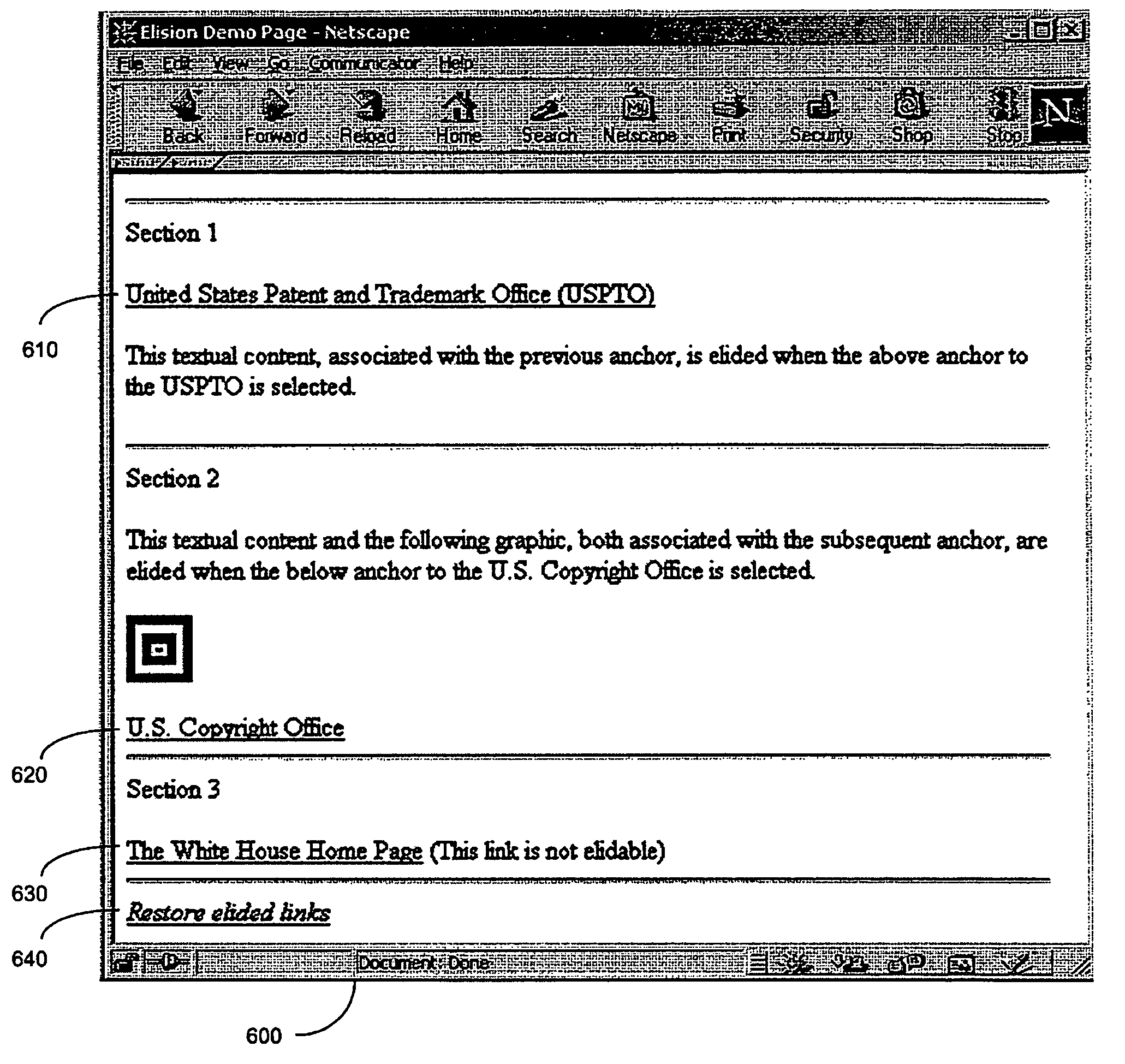
Eliding web page content
InactiveUS7216297B1Data processing applicationsDigital data processing detailsHyperlinkUniform resource locator
A method and system for providing click-once links is disclosed. Elision is used to automatically remove a URL and associated content from a web page as hyperlinks are selected, reducing previously visited material and providing visual feedback to a user. When a user selects an elision-enabled hyperlink, the hyperlink and its associated content are not displayed during subsequent displaying of the same web page. Web pages may be generated on the origin server and a browser client updates the content automatically. Click-once links may be flagged in an enclosing HTML source page through a combination of an indirection through a JavaScript function in an anchor and an additional HTML tag. Cookies may be used to record information about which links have been followed and to share such information with the origin server for use in subsequent page generation, or the browser may be adapted to perform elision without using cookies.
Owner:RPX CORP
Intellectual power saving switching assembly
InactiveUS20090289507A1Save powerBoards/switchyards circuit arrangementsPower network operation systems integrationTransceiverAC power
An intellectual power saving switching assembly connected between an external AC power input and a device to be monitored for automatically turning on or turning off power supplied to the device to be monitored. The assembly includes a power source; an AC power input; a switchable AC power switch device; at least one current detector for detecting current flowing into the device to be monitored by direct detection or indirection detection; at least one AC power output end for supplying power from the current detector to the device to be monitored; a signal detecting transceiver for detecting an actuation signal from a remote controller; and a logic electronic circuit capable of receiving standby signals from the current detector and a far end actuation signals so as to perform status determination for interrupting or transferring the current from the AC power input to the device to be monitored.
Owner:SHIU YING LIANG
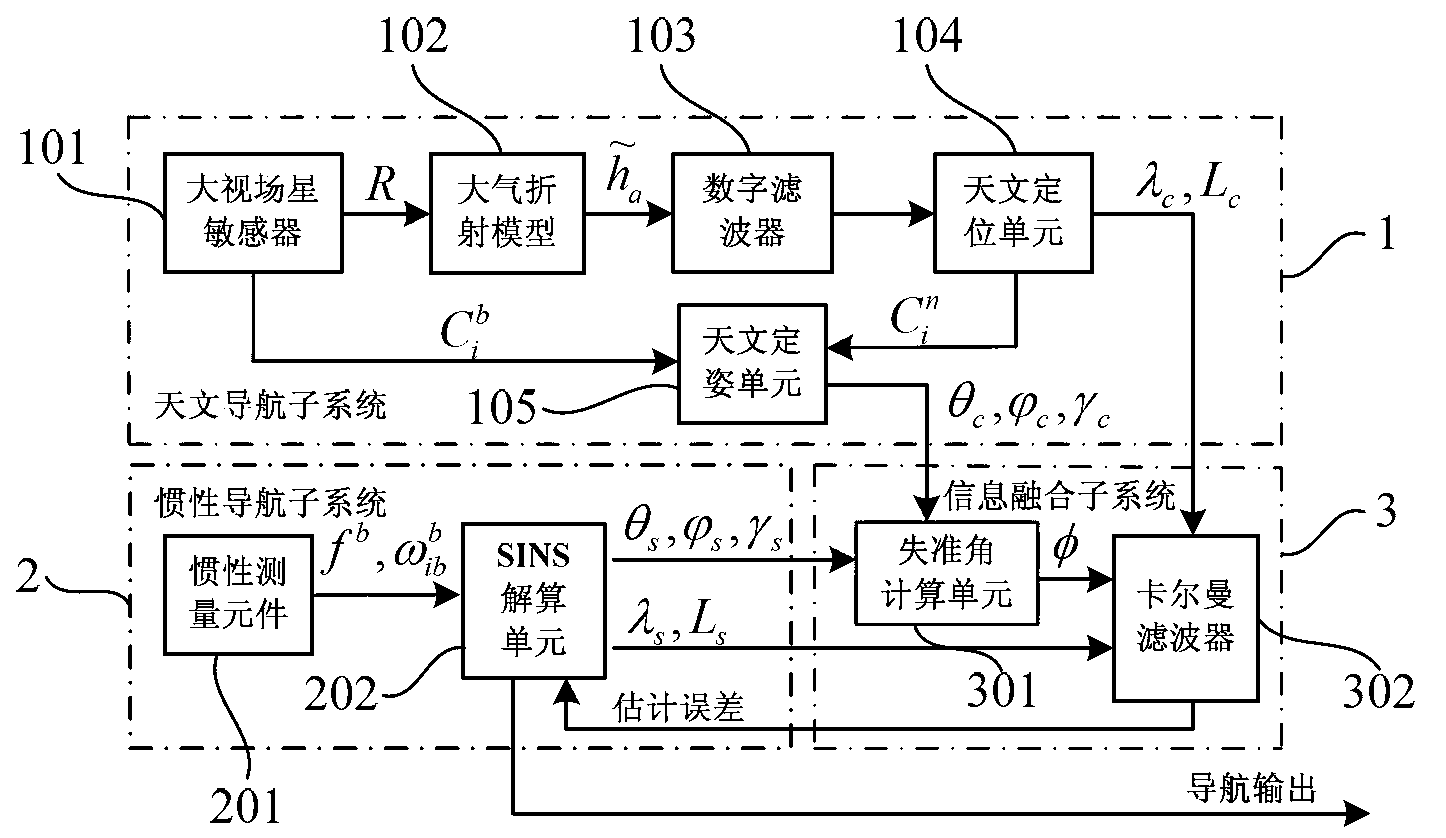
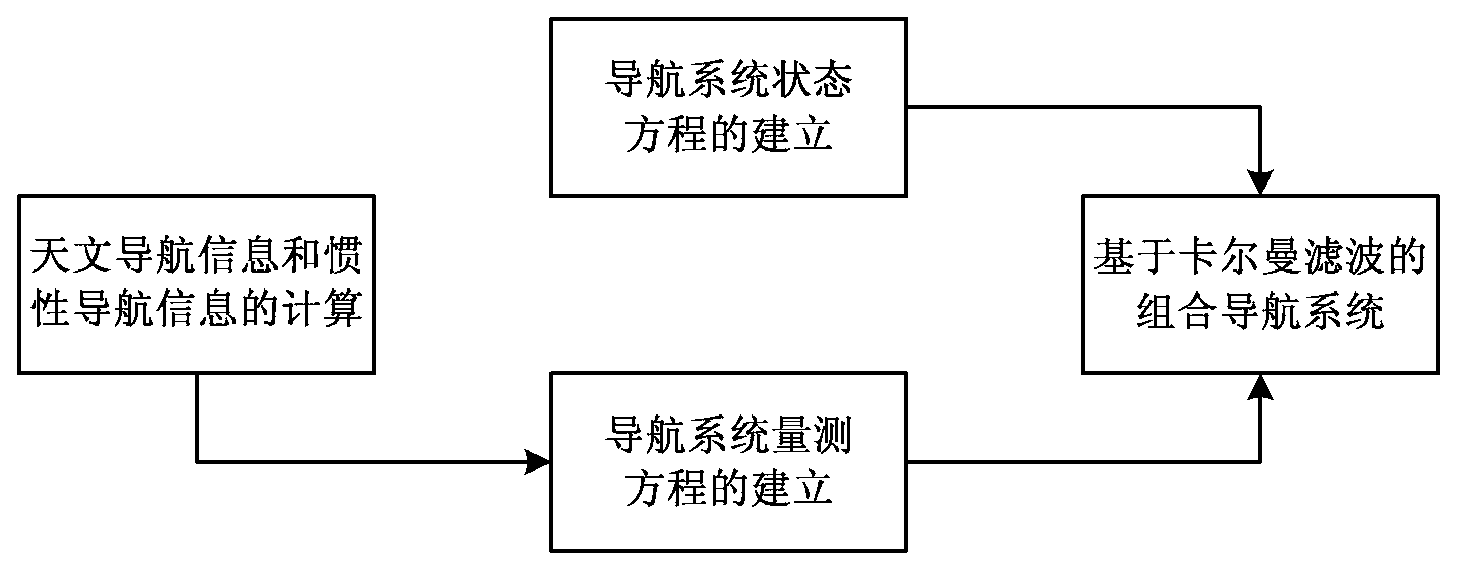
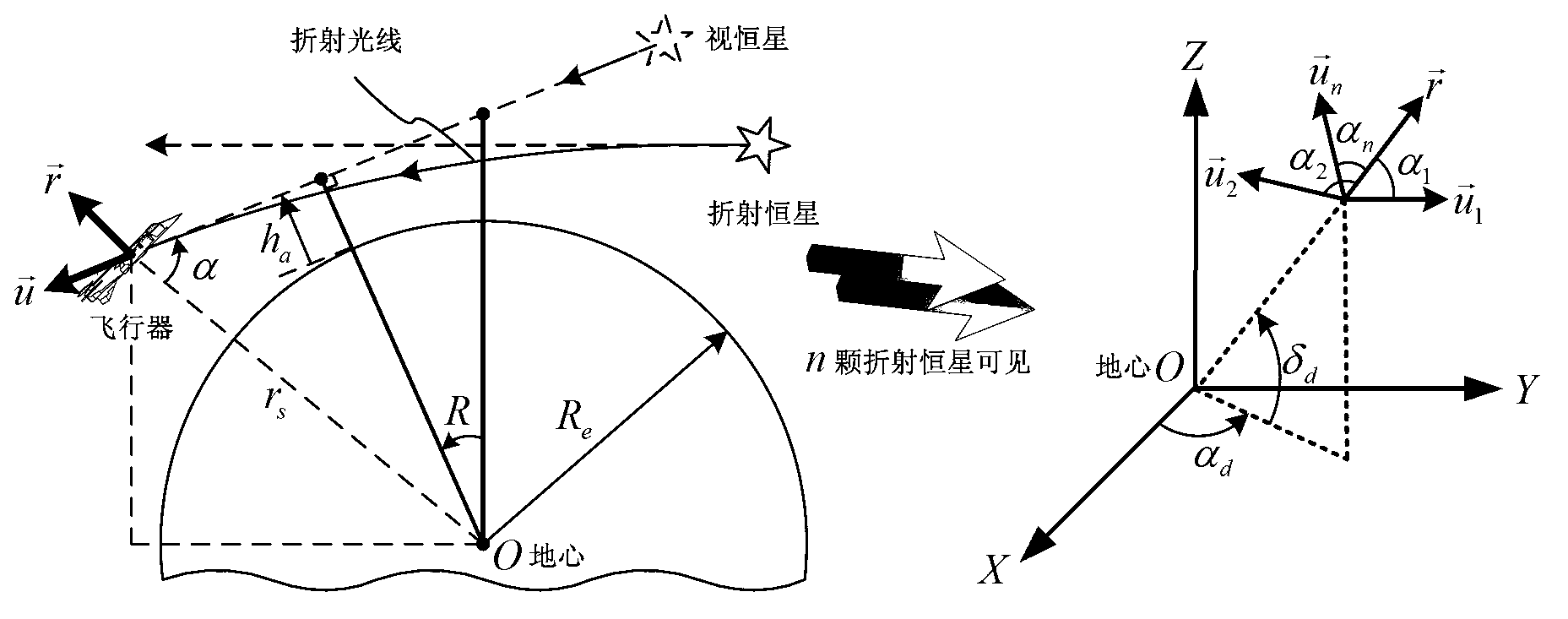
SINS/CNS integrated navigation system based on comprehensive optimal correction and navigation method thereof
InactiveCN103076015ARealize analytical astronomical positioningHigh precisionNavigation by speed/acceleration measurementsNavigation by astronomical meansFixed starsHorizon
The invention provides an SINS / CNS integrated navigation system based on comprehensive optimal correction and a navigation method thereof, and belongs to the technical field of integrated navigation. The integrated navigation system comprises an astronavigation subsystem, an inertia navigation subsystem and an information fusion subsystem. The navigation method comprises the following steps: analyzing celestial fix based on starlight refraction, building up navigation system state equations, building up navigation system measuring equations and performing information fusion of an integrated navigation system based on Kalman filtering. According to the invention, by utilizing the basic principle of starlight refraction indirection sensitive horizon and a large viewing field star sensor, the characteristics of a plurality of fixed stars can be observed at the same time, and the starlight refraction indirection sensitive horizon method is applied to aircrafts that do not fulfill track kinetics, so that the problem of high-precision autonomous horizon of the celestial navigation system is solved. According to the invention, position and posture information of the celestial navigation system are fully utilized to perform comprehensive optimal correction on the SINS deviation, so that the integrated navigation accuracy is significantly improved.
Owner:BEIHANG UNIV
Active forceps
Endoscopic surgical operation such as evisceration has been so far hardly achieved by a medical robot, since it requires high power. The present invention provides a downsized high-flexibility active forceps to enable such an operation, without needing a large space for manipulation to target a limited operative area. An active forceps of the present invention comprises: a tip forceps part 4 having, a tip supporting member 2 to support a forceps tip 1 at a center section 2a with a plurality of arms 2b laterally projected therefrom, and a plurality of tip side advancing and retreating members 3 connected at a front end with the plurality of arms respectively oscillatable while connected to one another relatively movable in directions toward front and rear ends; and a forceps bottom part 9 having, a plurality of bottom side advancing and retreating members 6 each integrally coupled to the plurality of tip side advancing and retreating members 3, while connected to one another relatively movable indirections toward front and rear ends to constitute a link mechanism together with the tip side advancing and retreating members 3 and the tip supporting member 2, and a bottom frame 8 provided with forward and backward actuating means 7 for moving relatively to one another the bottom side advancing and retreating members 6 in directions toward front and rear ends.
Owner:TOKYO UNIV OF THE
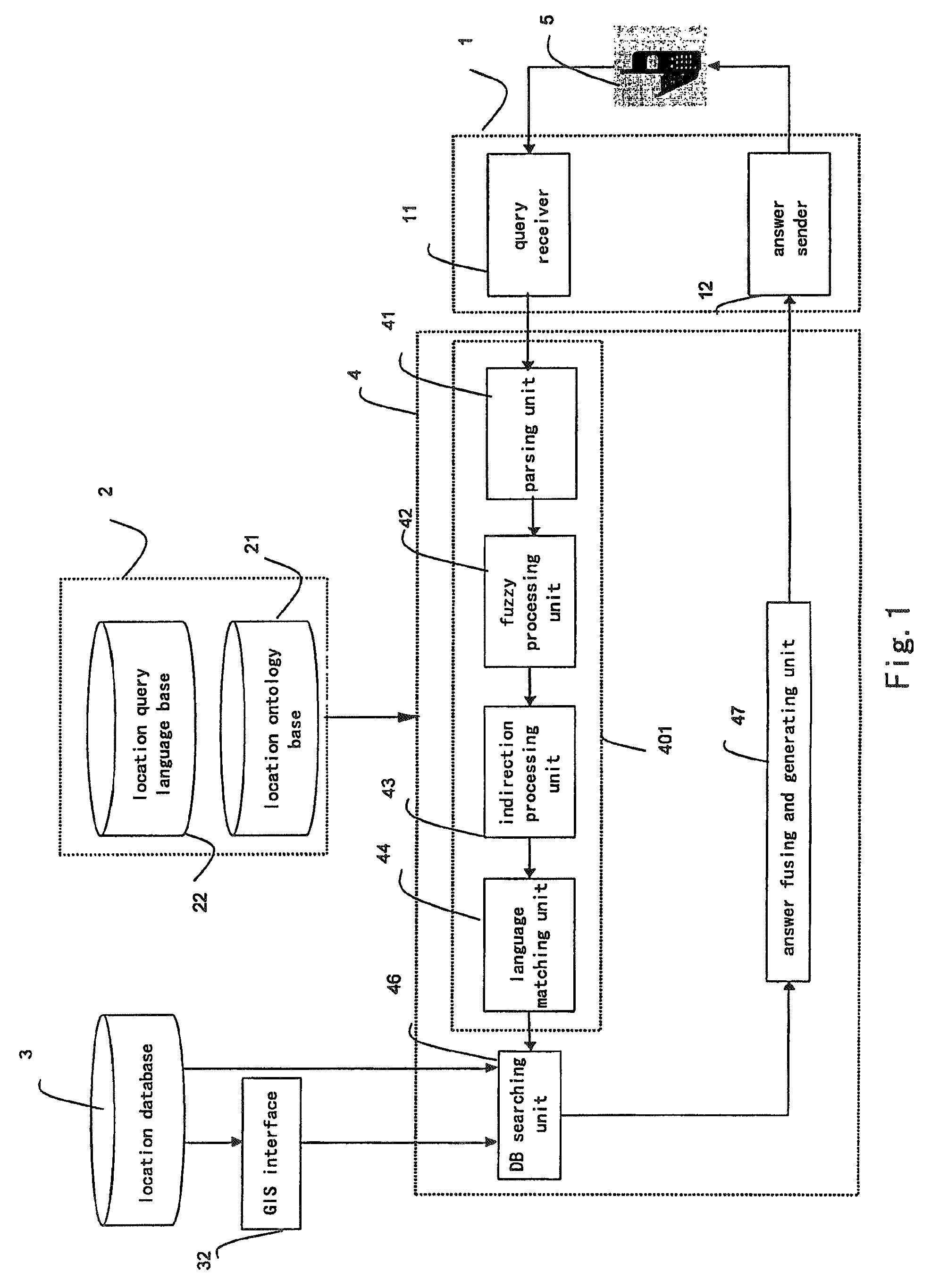
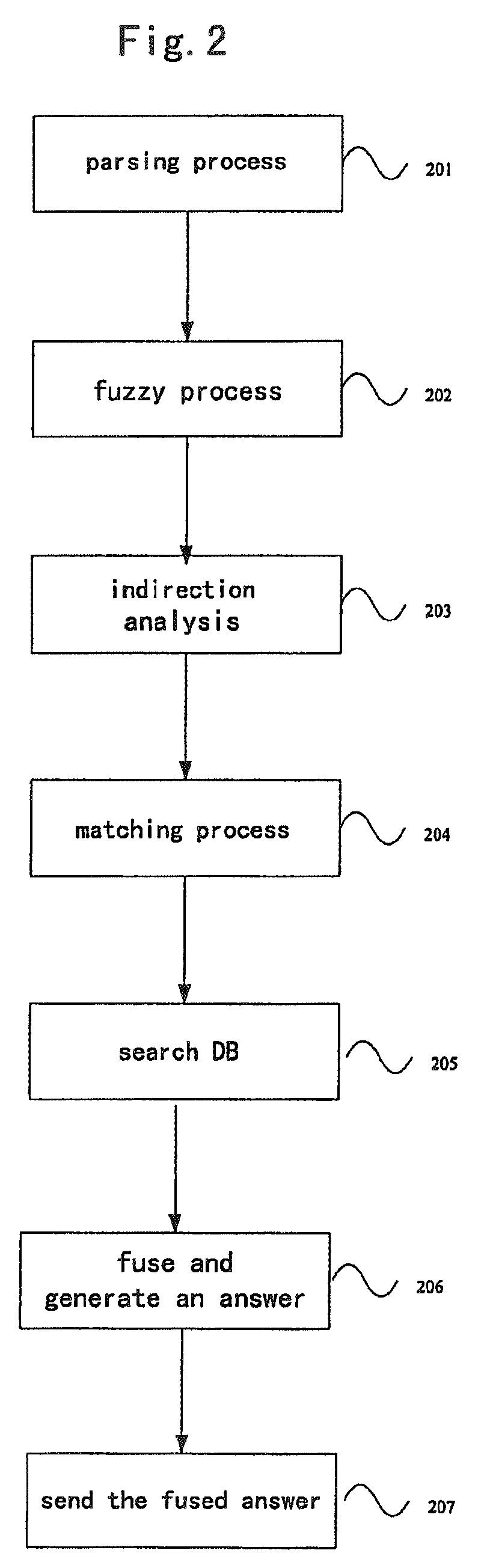
Natural language based location query system, keyword based location query system and a natural language and keyword based location query system
InactiveUS7937402B2Increase freedomOvercome defectsDigital data information retrievalDigital data processing detailsFuzzy queryDegrees of freedom
A natural language based location query system and a method thereof. The system comprises a receiving device which receives a request for natural language query from a user terminal; an access device which accesses a location ontology base and a location query language base that are external to the system or internal in the system, wherein the location ontology base comprising knowledge descriptions about the field of a location service, and the location query language base comprising a language model for the location service query; a natural language query processing device which performs at least one of a fuzzy processing and an indirection processing on the received request for natural language query by searching the location ontology base and the location query language base with the access device, retrieves location information corresponding to the request from a location database; and a sending device which sends the location information to the user terminal. This invention also provides a keyword based location query system and a method thereof, and a natural language based and keyword based location query system and a method thereof. This invention not only process user fuzzy query and indirect query, but also process compound sentence query and query having semantic error. Therefore, the degree of freedom of user query is enhanced and the location query is more flexible and accurate.
Owner:NEC (CHINA) CO LTD
Approach For Managing Access to Messages Using Encryption Key Management Policies
InactiveUS20080212782A1Key distribution for secure communicationComputer security arrangementsData formatIndirection
Controlling access to disseminated messages includes implementing one or more key management policies that specify how various encryption keys are maintained and in particular, when encryption keys are made inaccessible. Deleting a particular key renders inaccessible all copies of messages, known or unknown, associated with the particular key, regardless of the location of the associated messages. A message may be directly or indirectly associated with a deleted key. Any number of levels of indirection are possible and either situation makes the message unrecoverable. The approach is applicable to any type of data in any format and the invention is not limited to any type of data or any type of data format.
Owner:CHECK POINT SOFTWARE TECH LTD
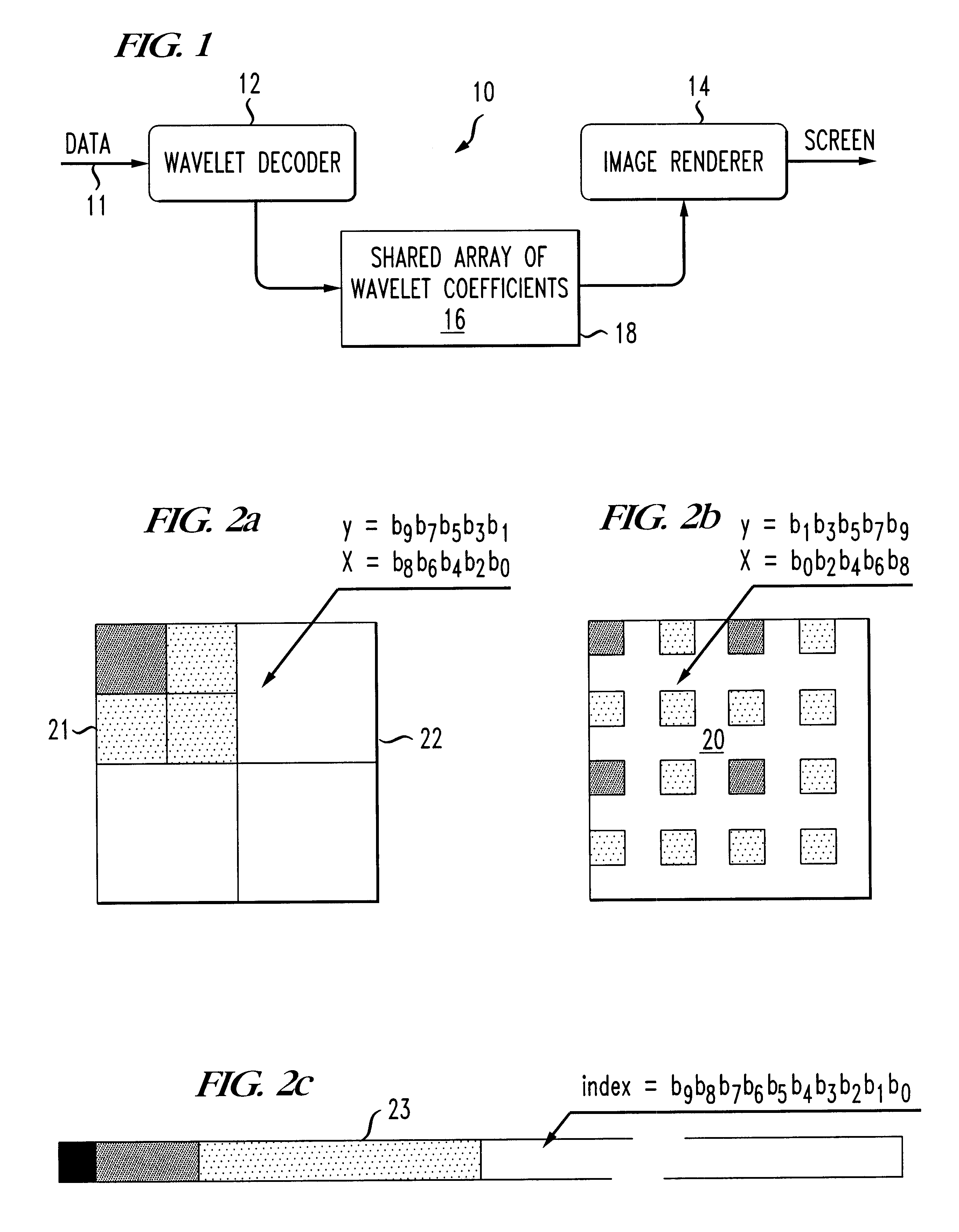
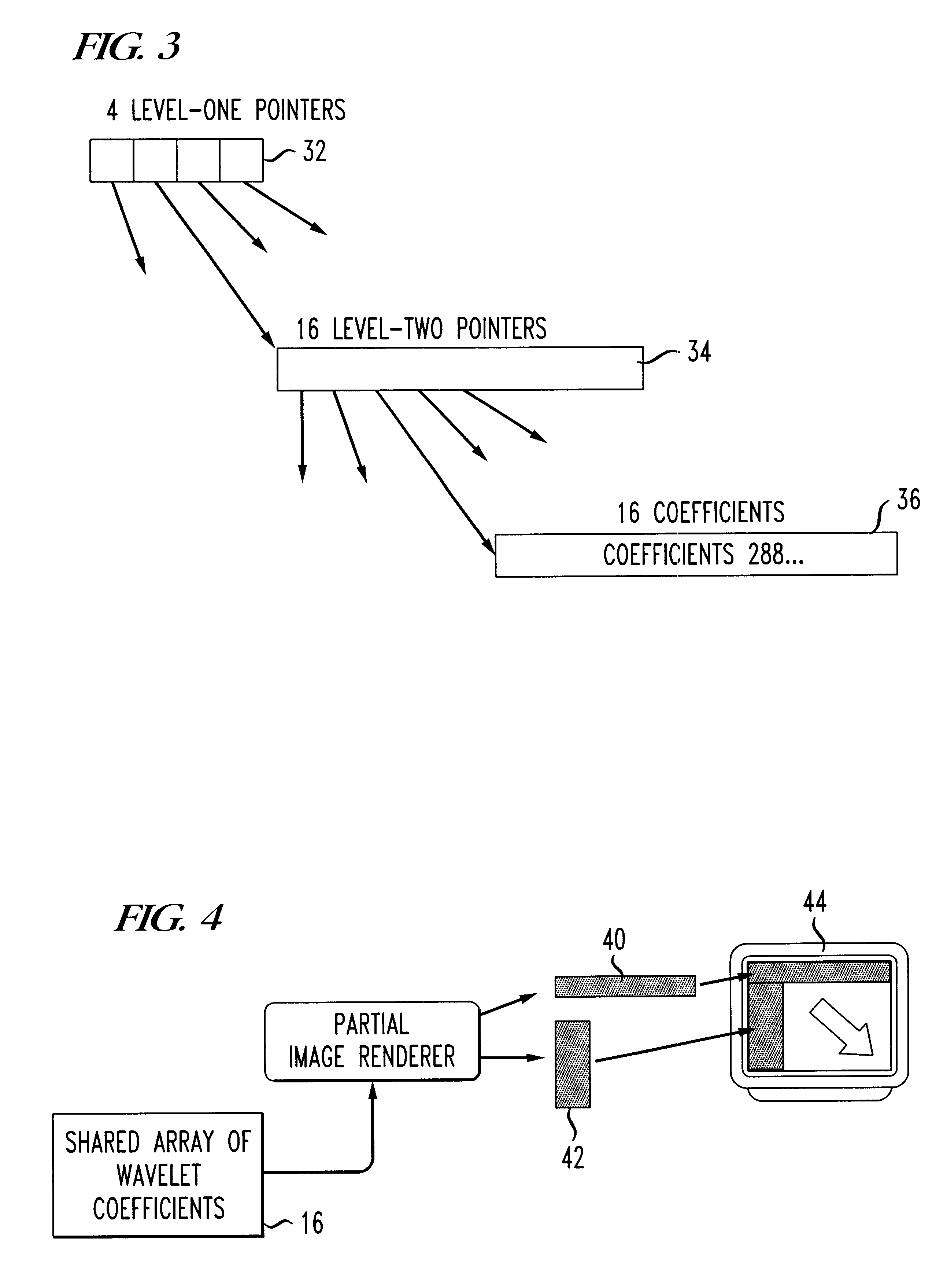
Progressive image decoder for wavelet encoded images in compressed files and method of operation
InactiveUS6587588B1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningArray data structureGray level
A progressive image display decoder and method of operation for wavelet encoded images achieves reduced memory storage requirements for wavelet transform coefficients and reduced execution time in displaying the image thereby overcoming the limitations of the prior art. Conveniently, a wavelet image format, typically DjVu IW44 facilitates progressive rendering and smooth scrolling of large color or gray level images with limited memory requirements. The progressive wavelet decoder is composed of two components. The first component decodes the incoming image data and updates an array of wavelet coefficients. The second component applies an inverse wavelet transform to the array of wavelet coefficients for the purpose of reconstructing the image. The operation of the first component (the decoder) is triggered by the incoming compressed image data. The received data is decoded and is used to apply updates to an array of wavelet coefficients. Each update improves the accuracy of the coefficients and therefore improves the fidelity of the reconstructed image. The coefficient array is composed of several two-dimensional arrays (one for each of the color components) having one entry corresponding to each 32x32 blocks in the image. Each entry contains 1024 wavelet coefficients organized as a sparse array with two levels of indirection. The operation of the second component (the renderer) is typically triggered when enough data has been received to display an updated version of the image, or when the user performs an action which requires displaying a new part of the image. In the latter case, the renderer only reconstructs the pixel values for the parts of the image, which are needed. A further reduction of the computation time is obtained by using "lifting" for implementing a fast inverse wavelet transform.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
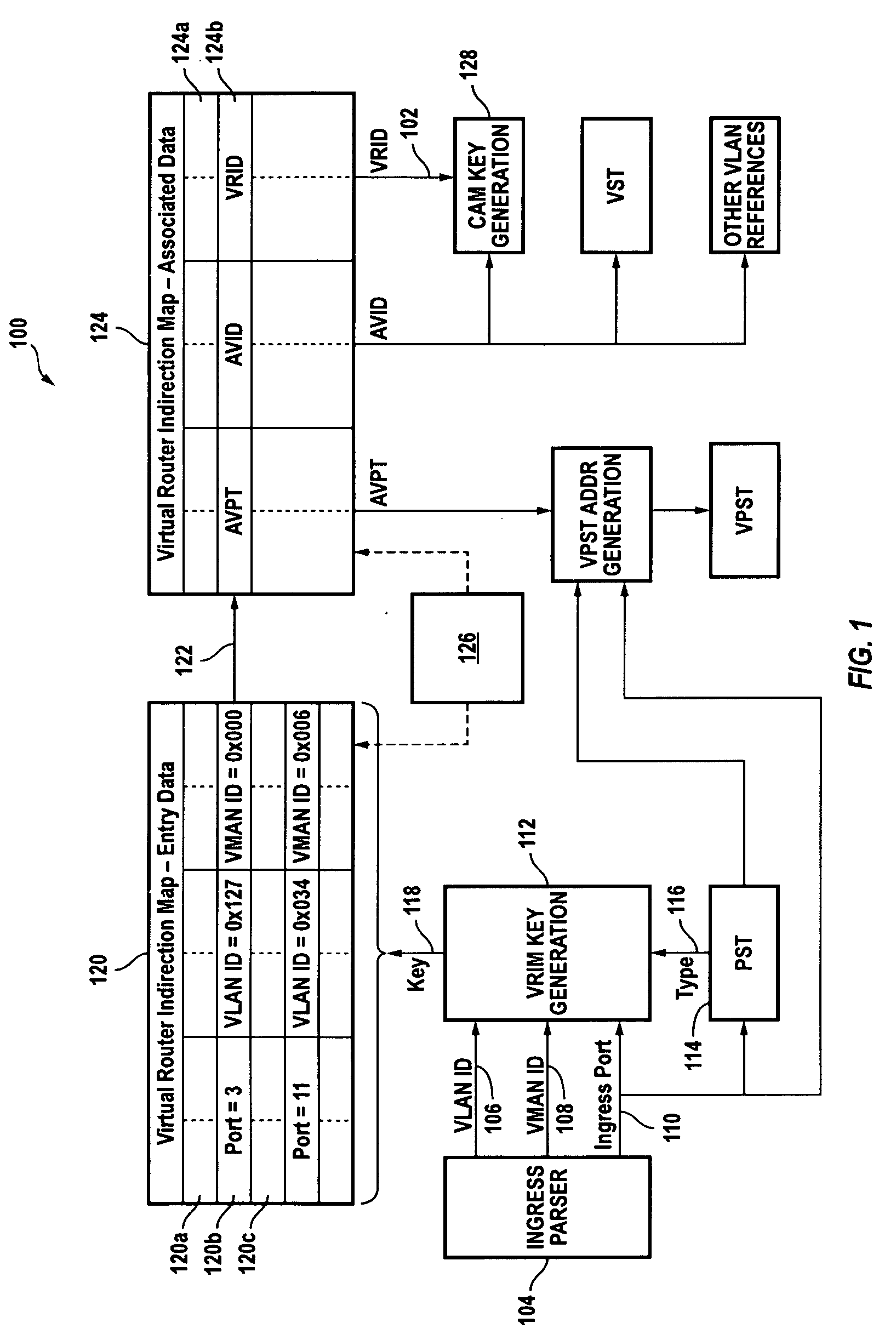
Method of providing virtual router functionality
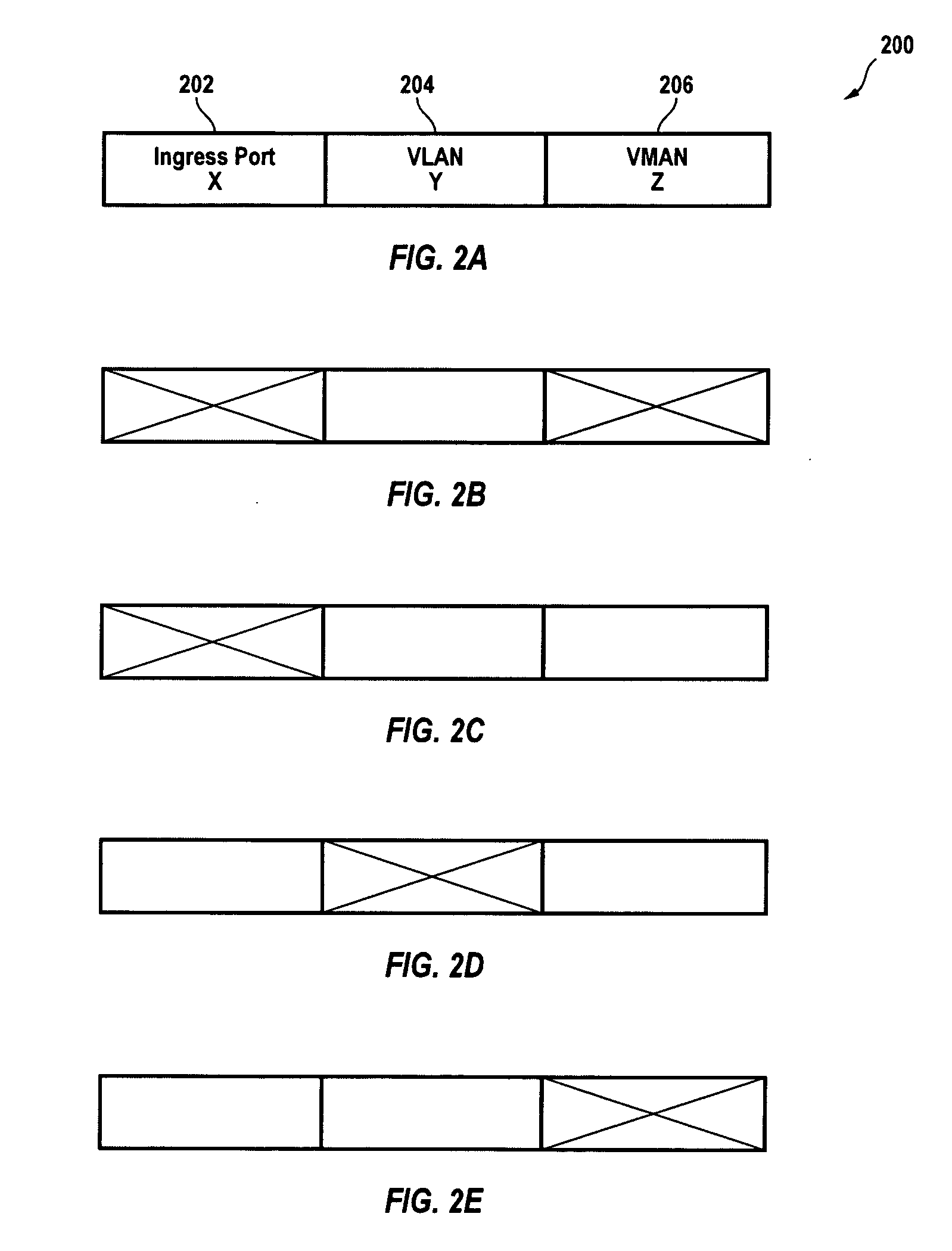
A method of presenting different virtual routers to different end users, classes of service, or packets is provided. An incoming packet is received having a VLAN field and at least one additional field. A key is formed from the VLAN field and at least one other packet field, and mapped into a virtual router identifier (VRID) using an indirection mapping process. The VRID identifies a particular virtual router configuration from a plurality of possible virtual router configurations. A networking device is configured to have the particular virtual router configuration identified by the VRID, and the packet is then forwarded by the configured device.
Owner:EXTREME NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com