Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
297 results about "Distributed hash table" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
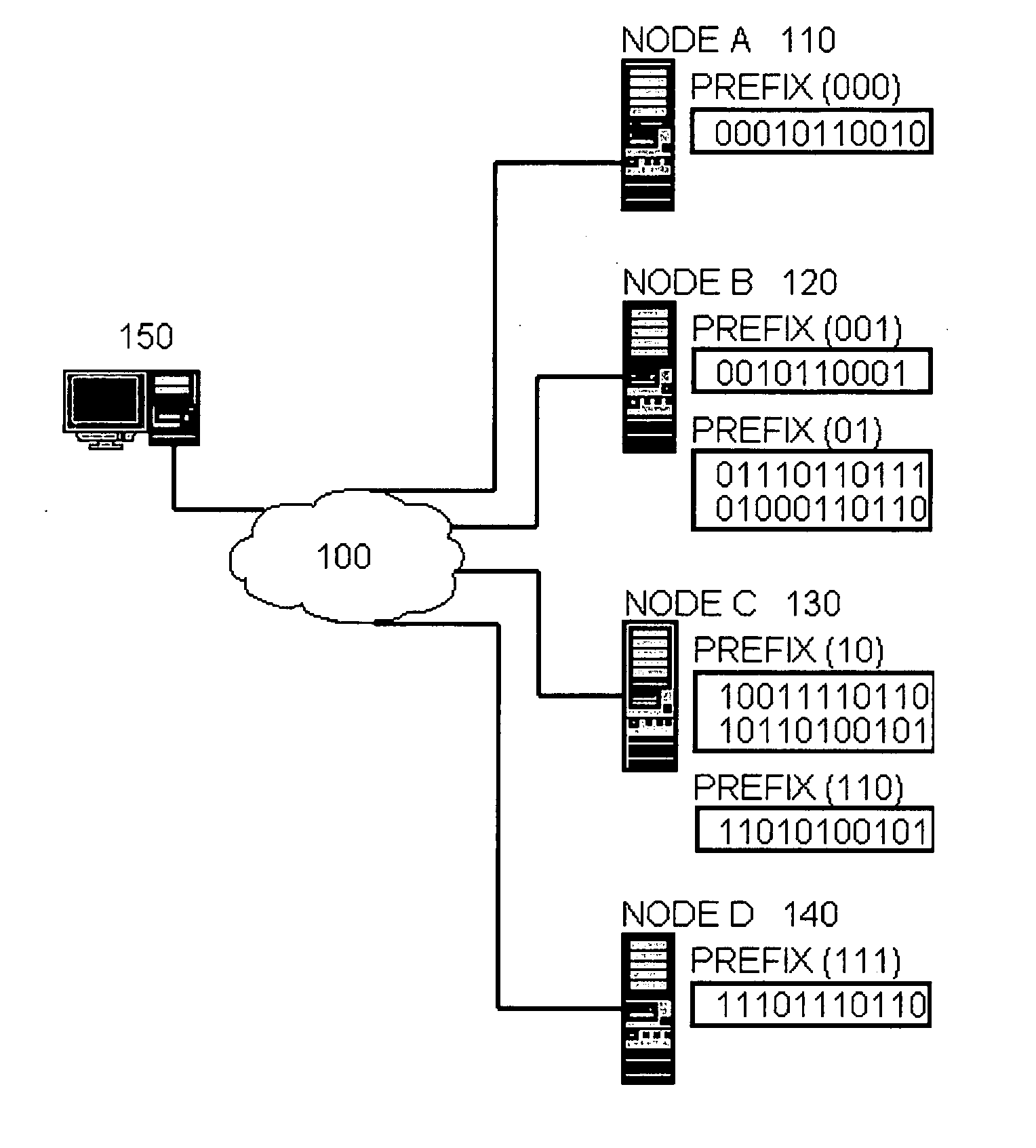
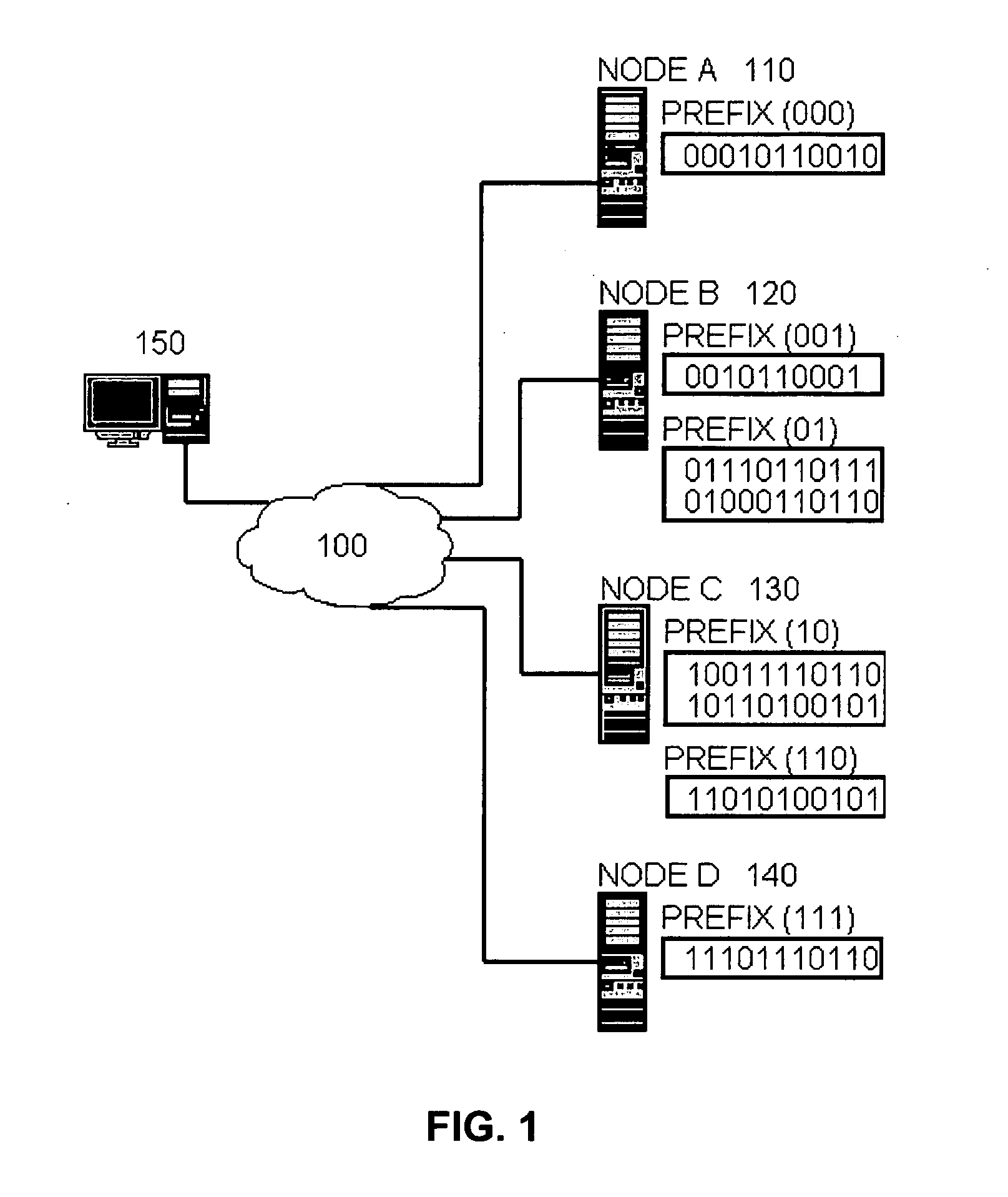
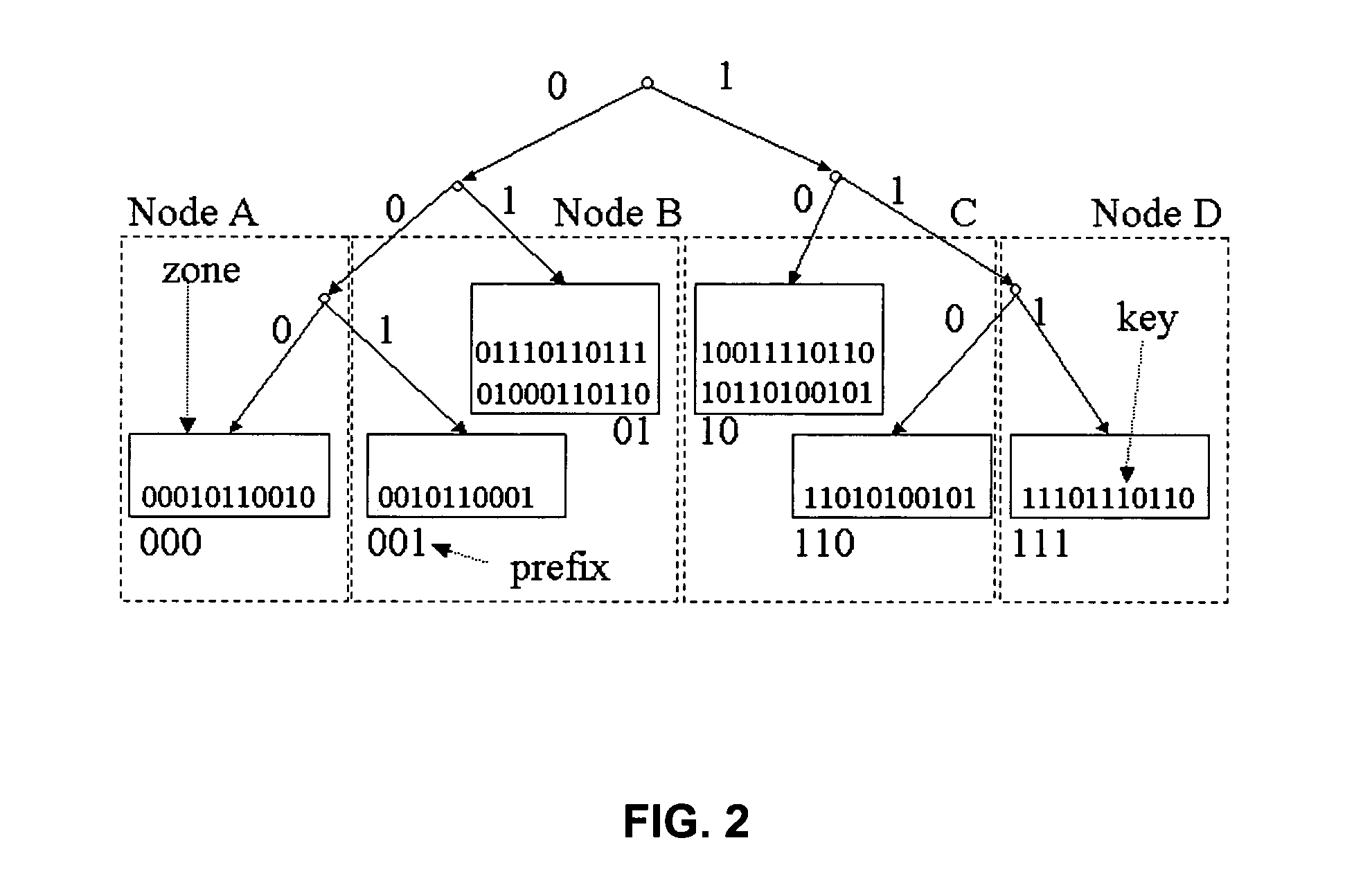
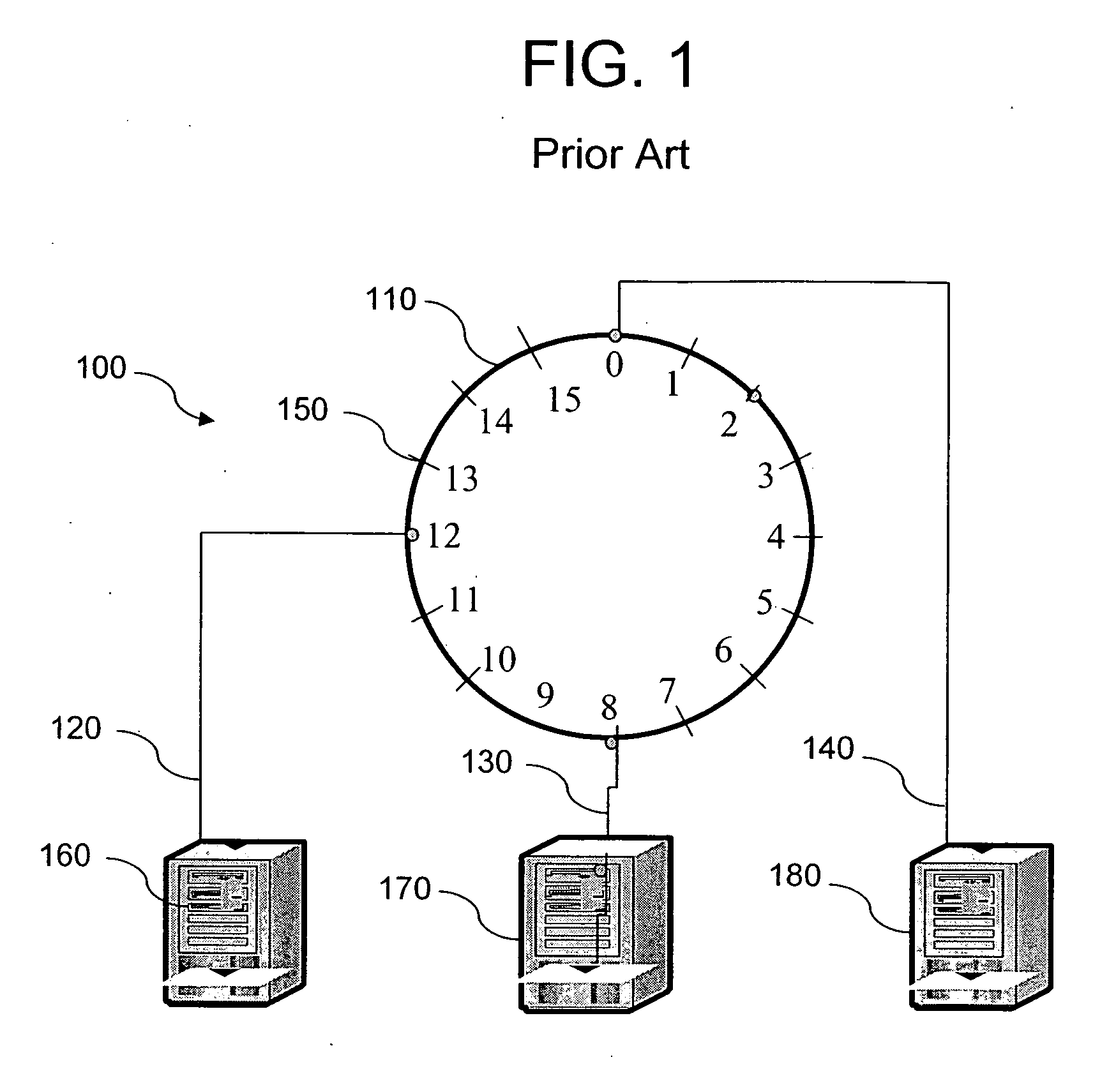
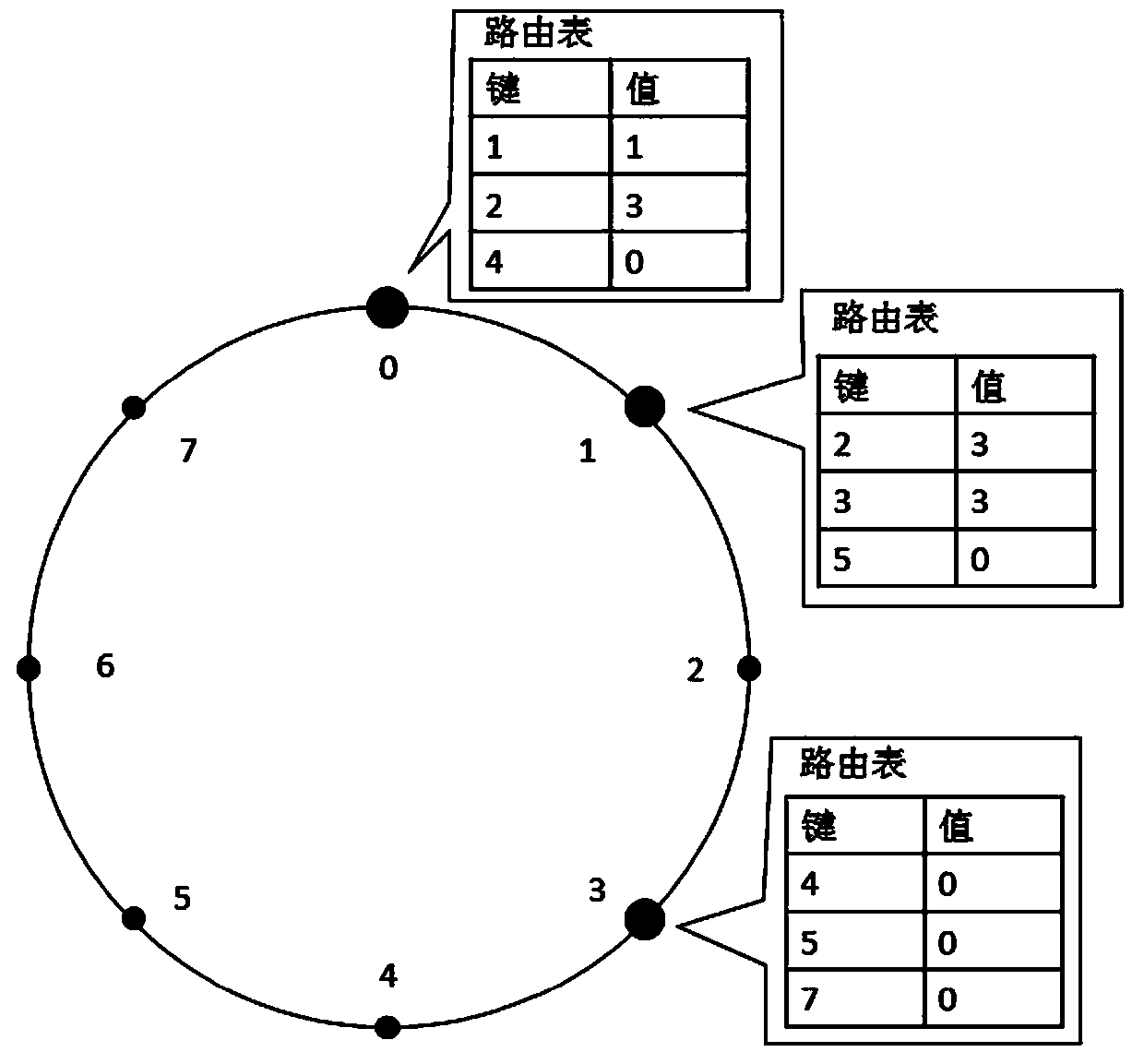
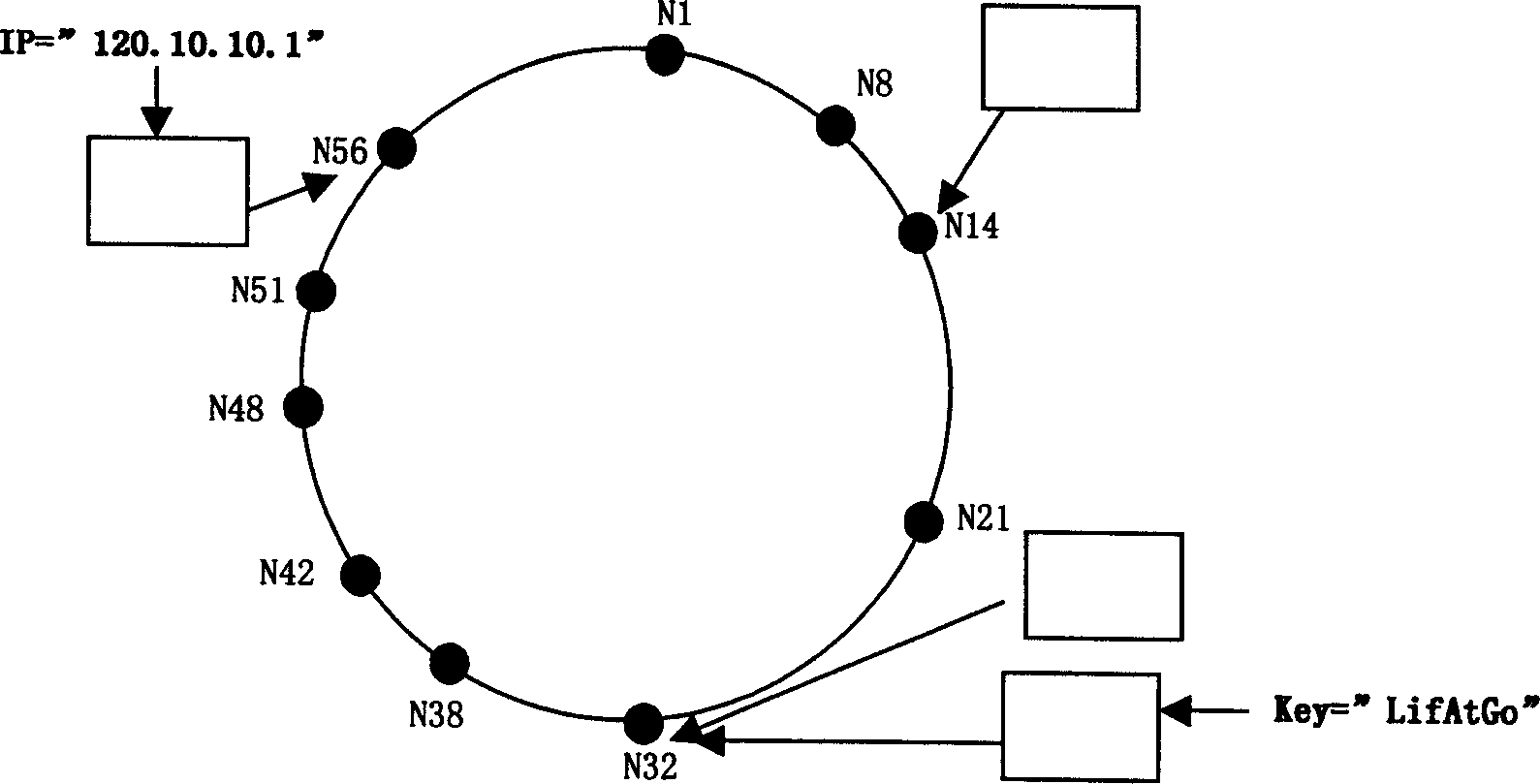
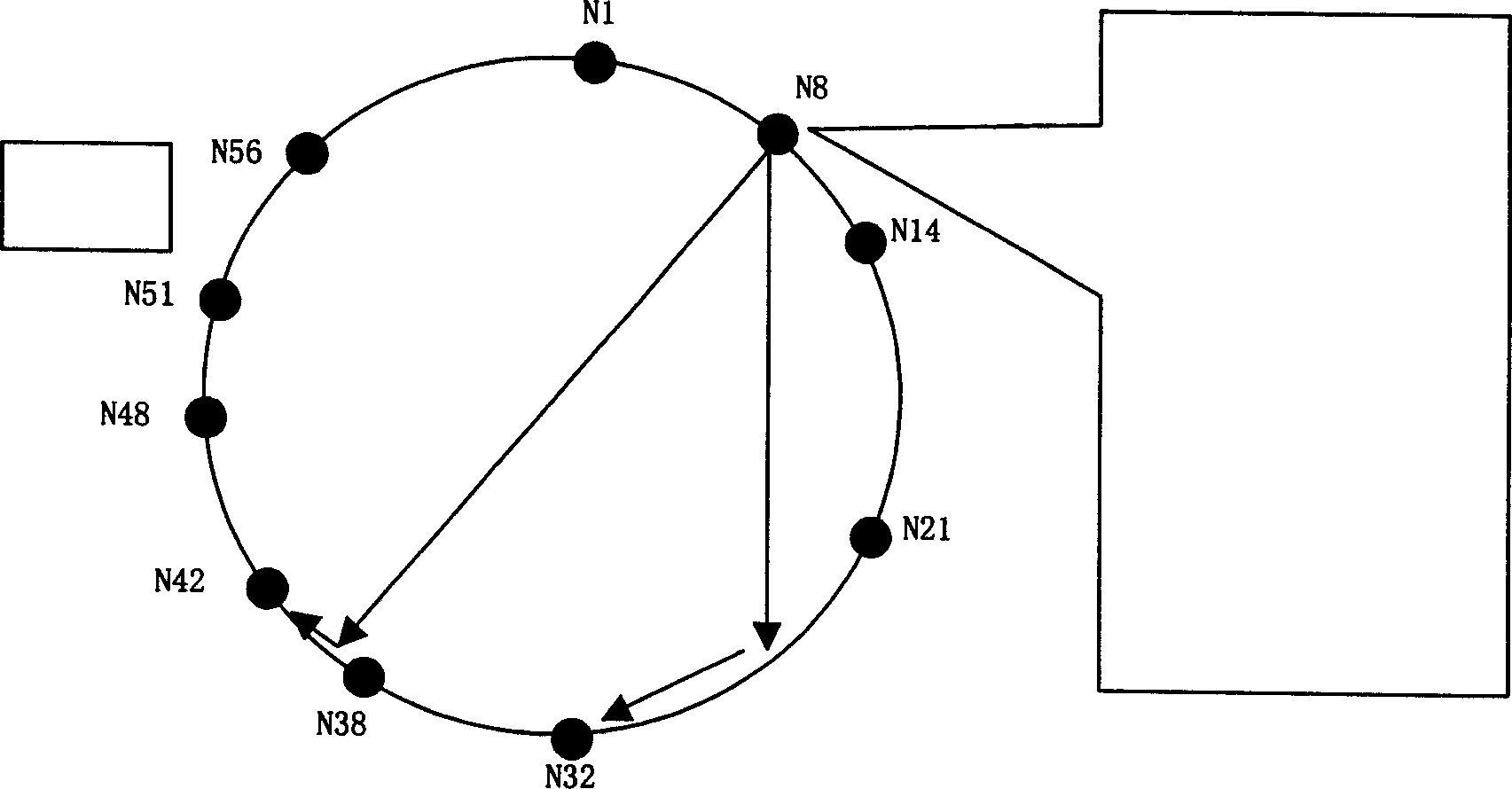
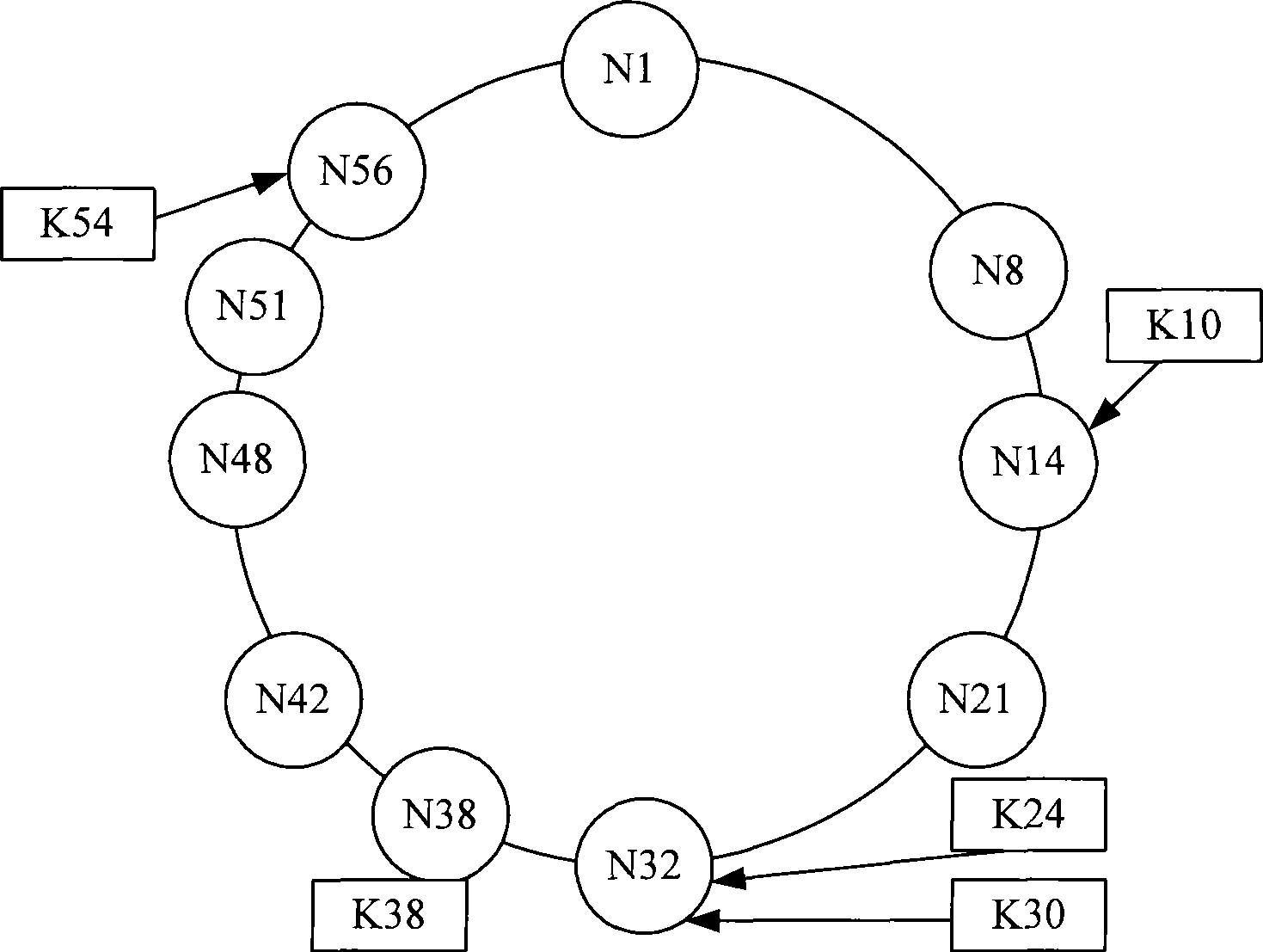
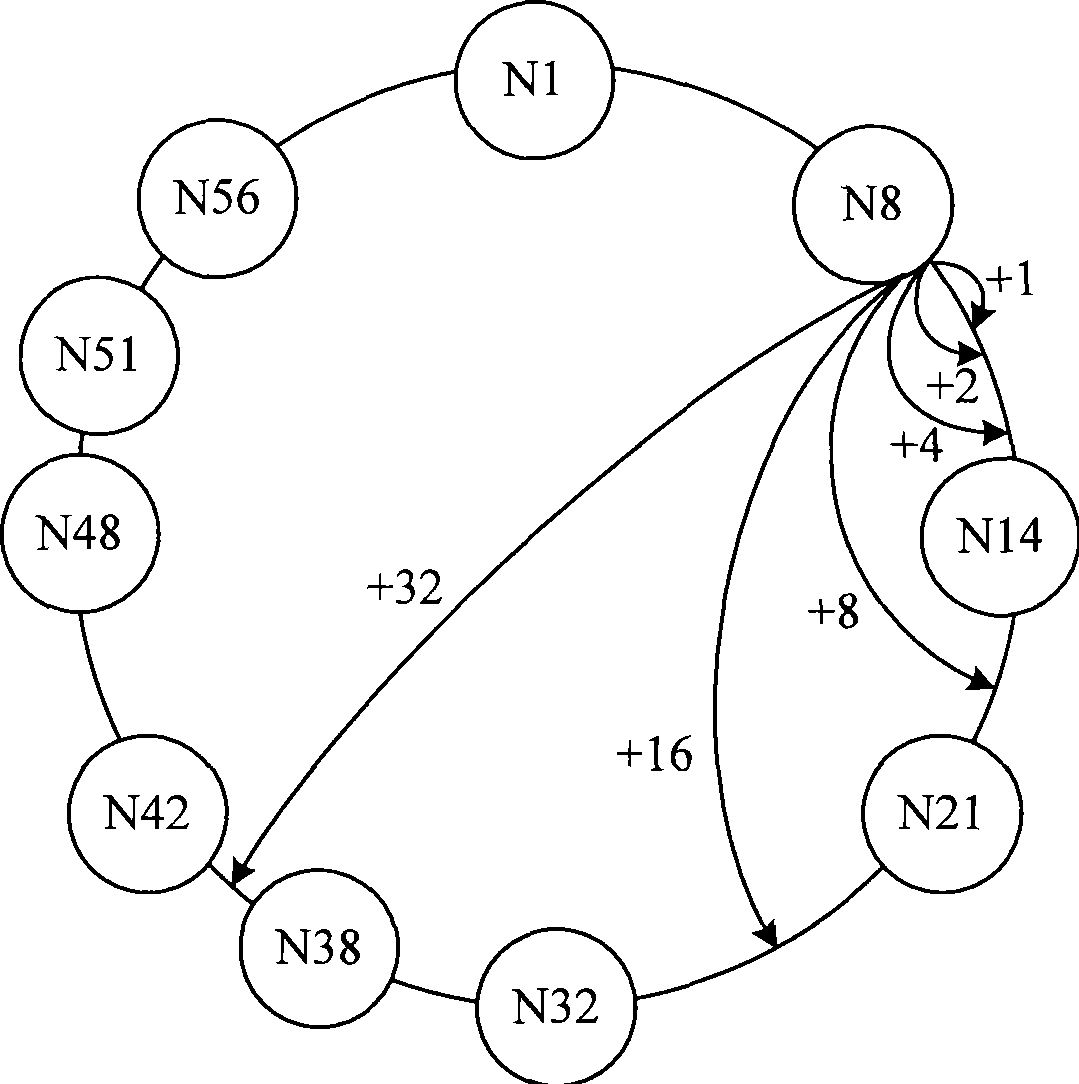
A distributed hash table (DHT) is a class of a decentralized distributed system that provides a lookup service similar to a hash table: (key, value) pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key. Keys are unique identifiers which map to particular values, which in turn can be anything from addresses, to documents, to arbitrary data. Responsibility for maintaining the mapping from keys to values is distributed among the nodes, in such a way that a change in the set of participants causes a minimal amount of disruption. This allows a DHT to scale to extremely large numbers of nodes and to handle continual node arrivals, departures, and failures.
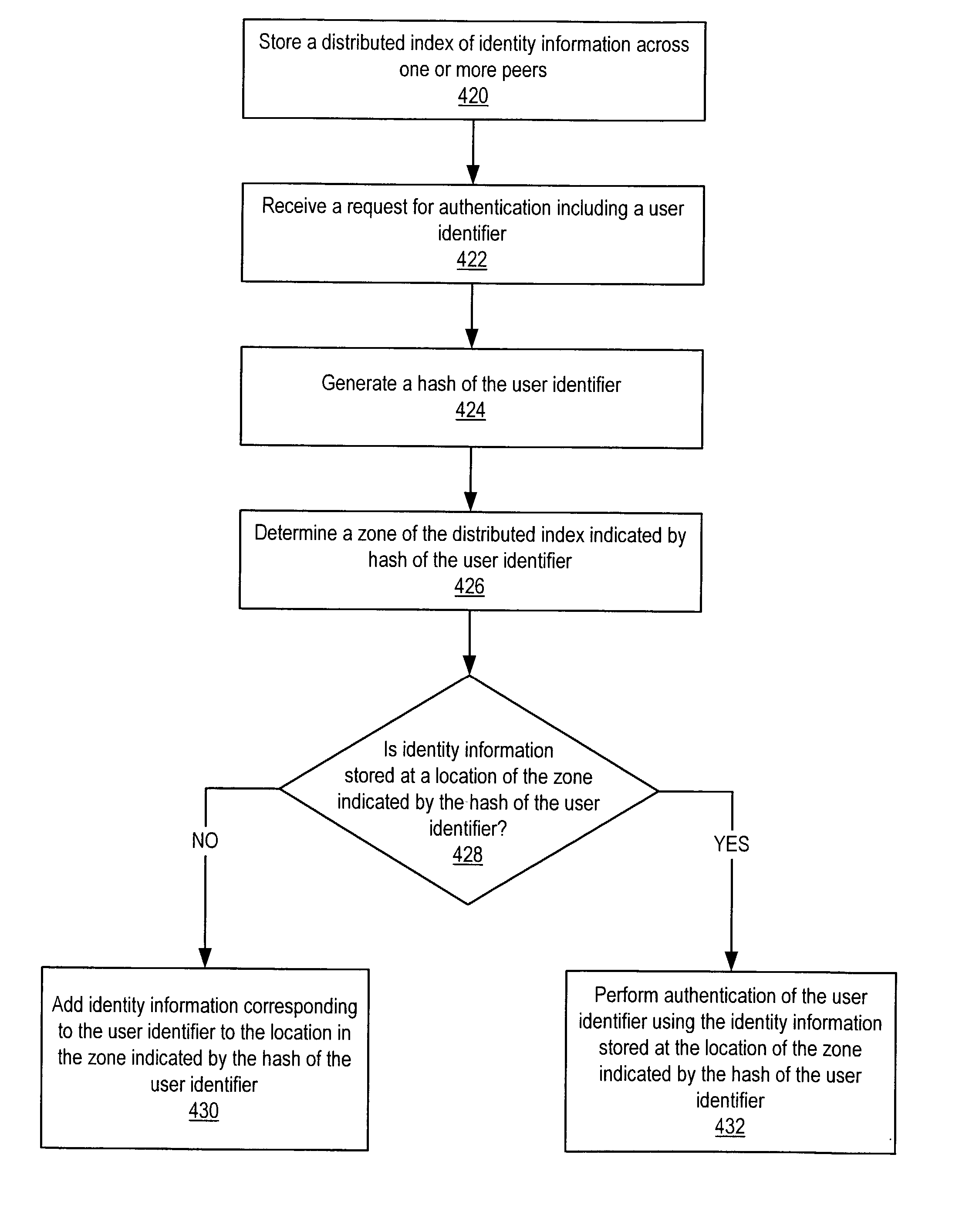
Distributed indexing of identity information in a peer-to-peer network
ActiveUS20040064693A1Digital data processing detailsUser identity/authority verificationDistributed indexDistributed hash table
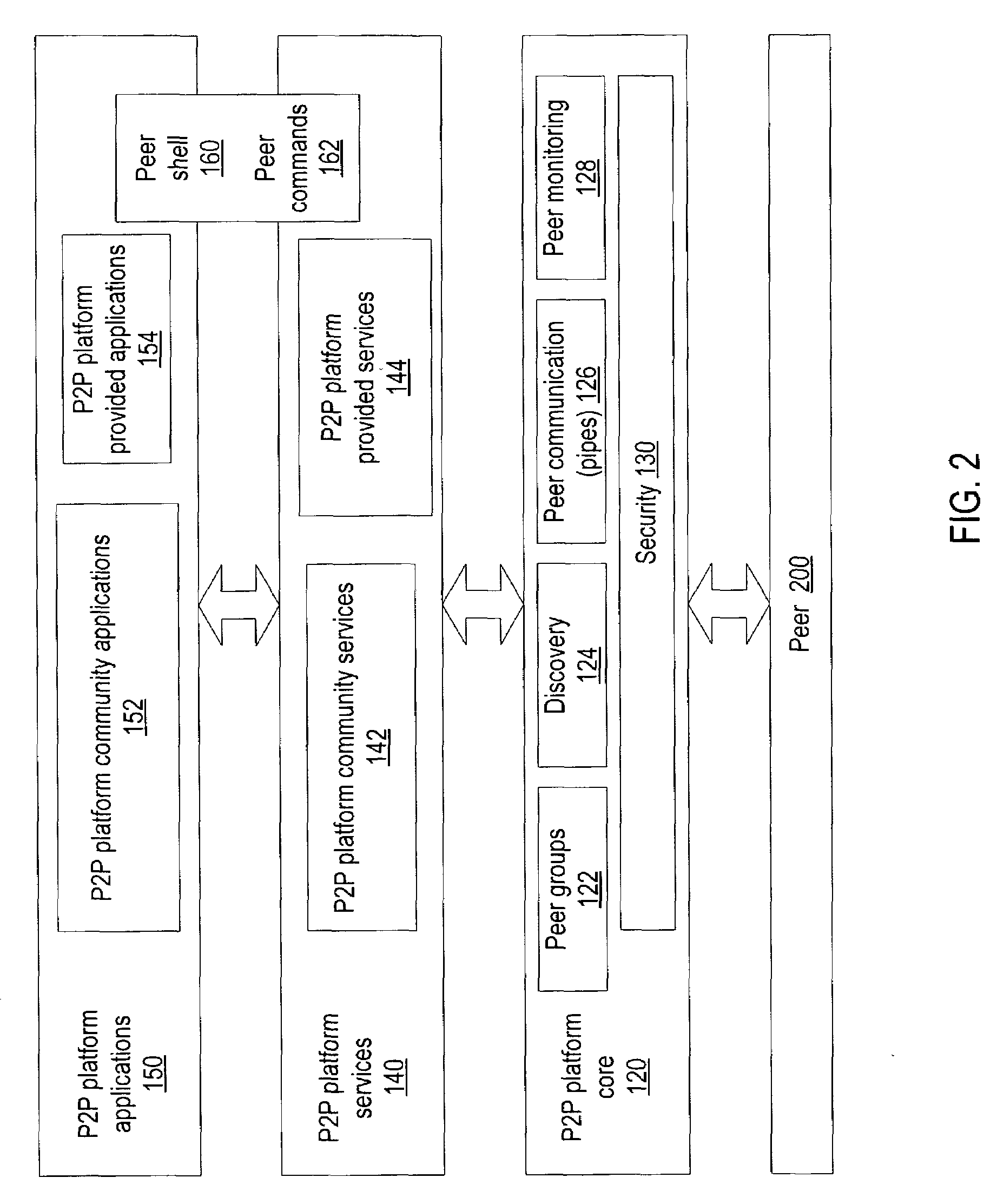
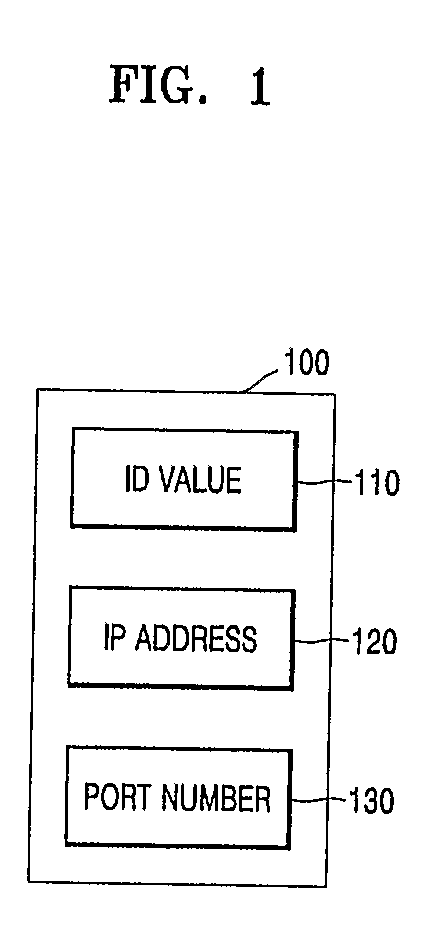
Embodiments of a distributed index mechanism for indexing and searching for identity information in peer-to-peer networks. In one embodiment, a distributed index may be used to store identity information in a decentralized manner on a plurality of peer nodes. The identity information may be used, for example, to authenticate users. Distributed indexes may allow identity information to be spread across multiple peer nodes so that the load is spread among the various peer nodes. In one embodiment, the distributed index may be a distributed hash table. One embodiment of a distributed index of identity information may be implemented in peer-to-peer networks implemented according to a peer-to-peer platform including one or more peer-to-peer platform protocols for enabling peer nodes to discover each other, communicate with each other, and cooperate with each other to form peer groups and share network resources.
Owner:ORACLE INT CORP
Distributed indexing of identity information in a peer-to-peer network
ActiveUS7206934B2User identity/authority verificationDigital computer detailsDistributed indexDistributed hash table
Embodiments of a distributed index mechanism for indexing and searching for identity information in peer-to-peer networks. In one embodiment, a distributed index may be used to store identity information in a decentralized manner on a plurality of peer nodes. The identity information may be used, for example, to authenticate users. Distributed indexes may allow identity information to be spread across multiple peer nodes so that the load is spread among the various peer nodes. In one embodiment, the distributed index may be a distributed hash table. One embodiment of a distributed index of identity information may be implemented in peer-to-peer networks implemented according to a peer-to-peer platform including one or more peer-to-peer platform protocols for enabling peer nodes to discover each other, communicate with each other, and cooperate with each other to form peer groups and share network resources.
Owner:ORACLE INT CORP
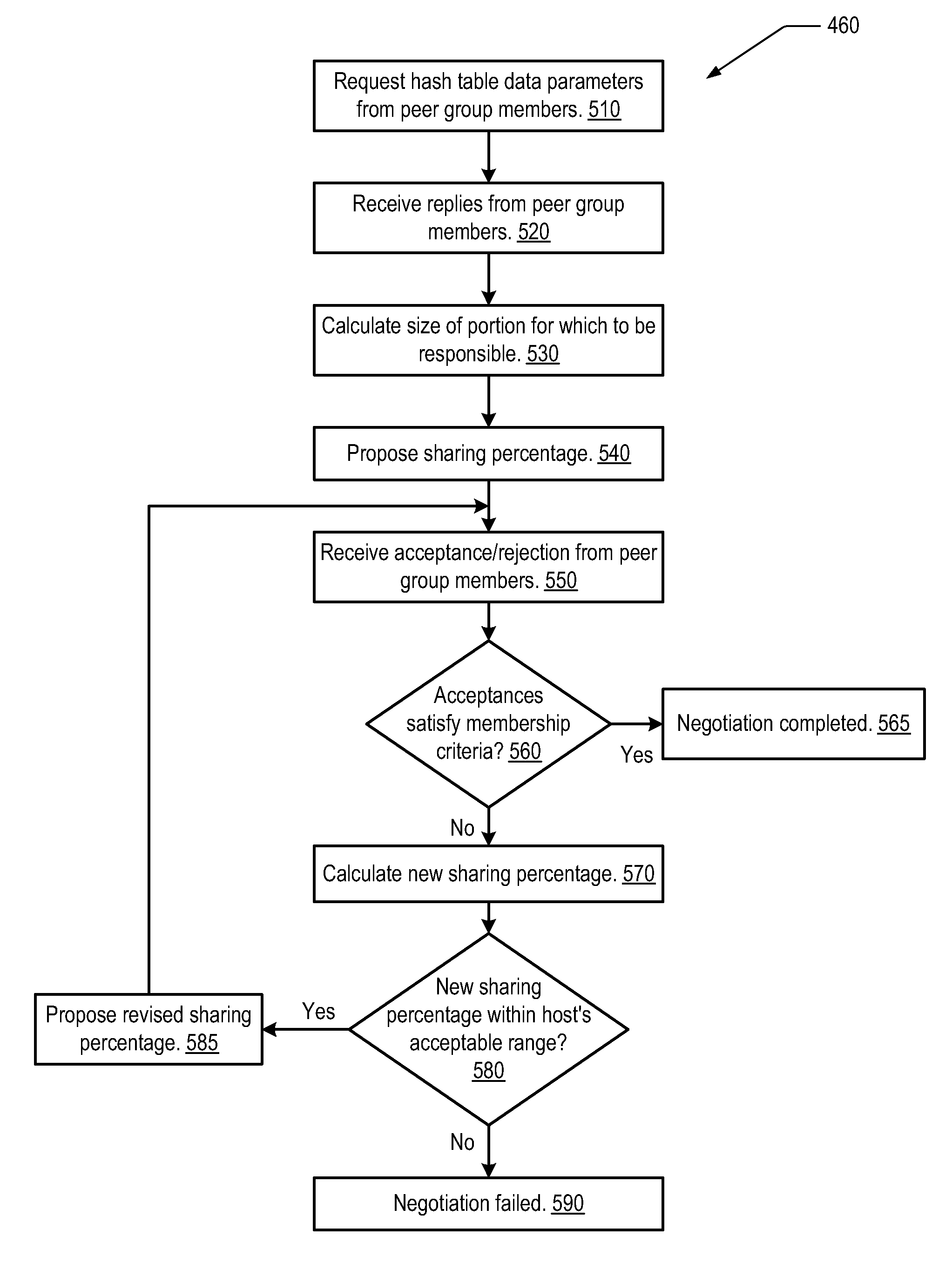
Use of distributed hashtables for wireless access mobility management
InactiveUS20080225780A1Simplifying and eliminatingSimplifying and eliminating centralized managementRadio/inductive link selection arrangementsWireless commuication servicesMobility managementMobile device
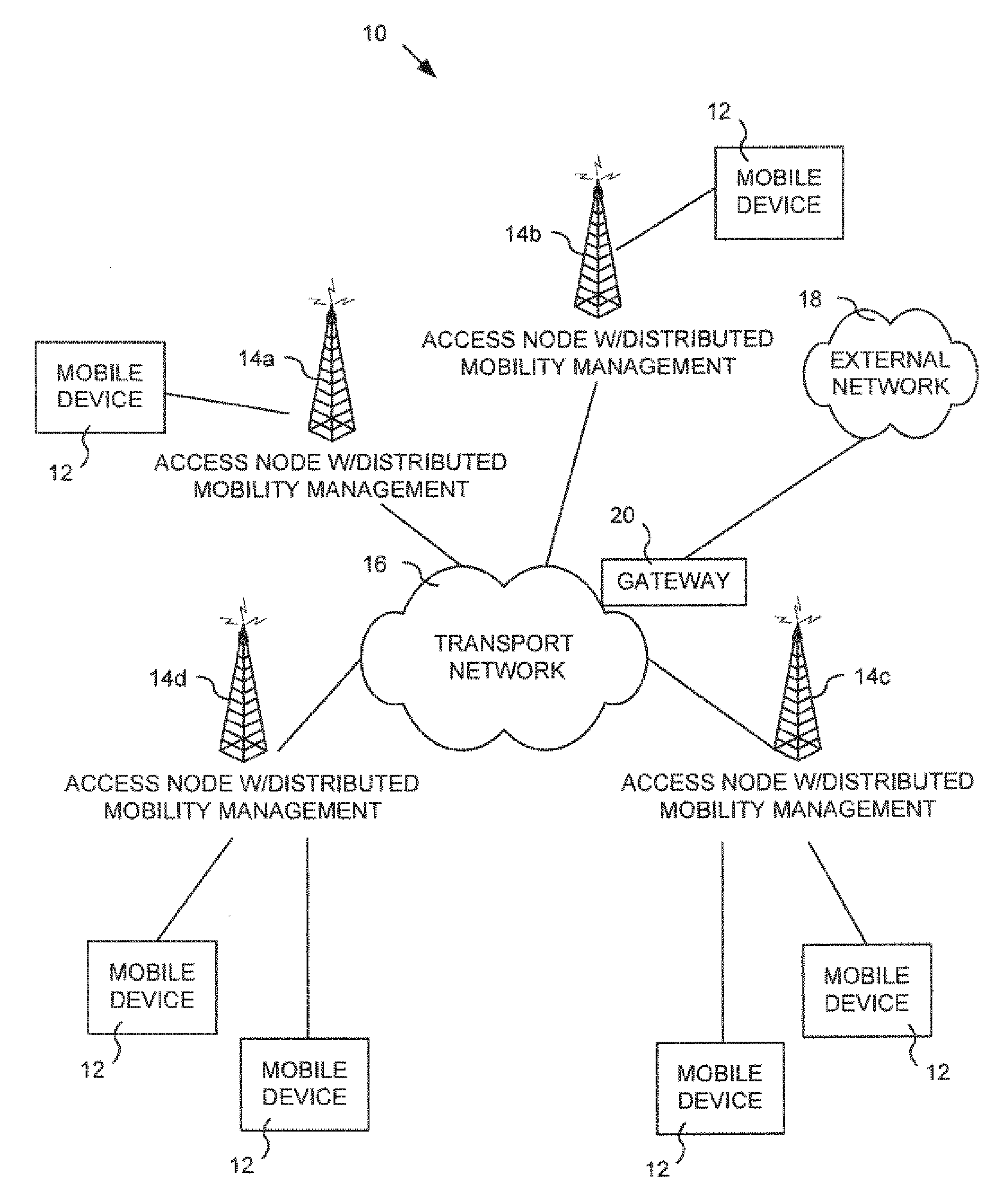
A method, apparatus and system for management of a wireless communication network in which the system has a plurality of access nodes. A distributed hash table (“DHT”) is created. The DHT contains mobility management data of mobile devices using the wireless communication network. The DHT is stored across at least a portion of the plurality of access nodes.
Owner:BLACKBERRY LTD
Content addressable storage systems and methods employing searchable blocks
ActiveUS20100070698A1Improve storage efficiencySimple for to recallSpecial data processing applicationsMemory systemsHash functionData content
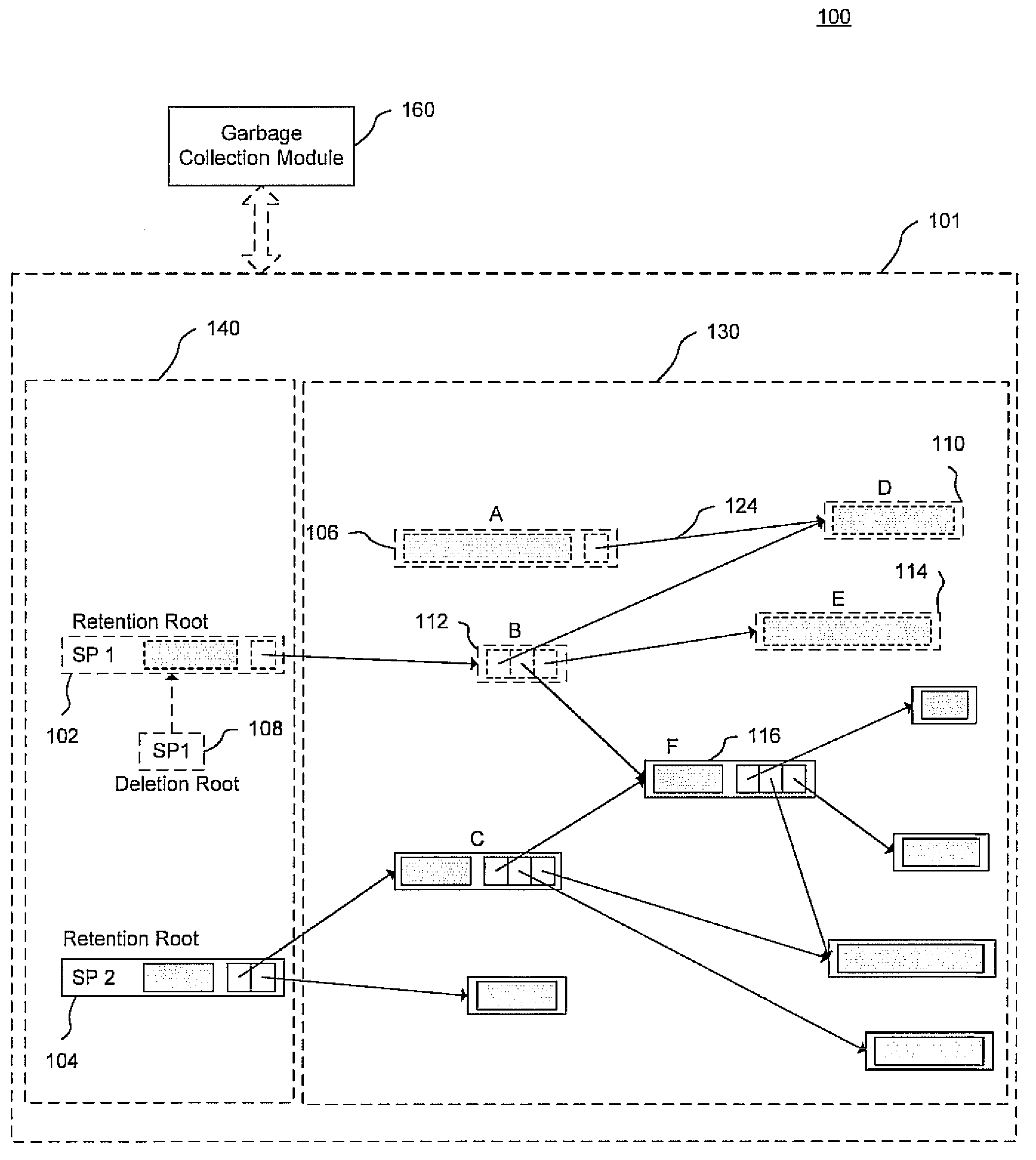
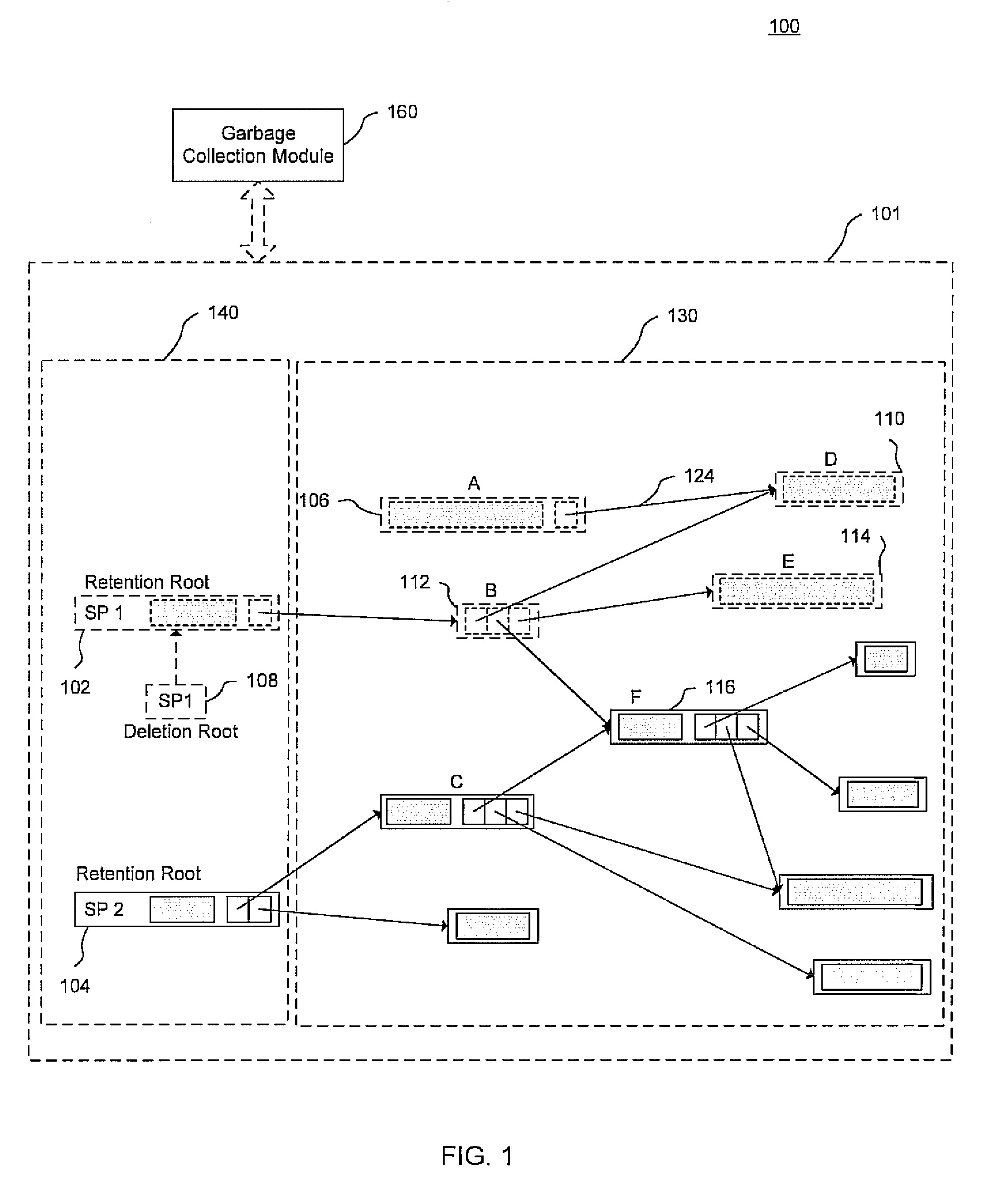
In accordance with exemplary embodiments of the present invention, a content addressable data structure system may include directed acyclic graphs (DAGs) of data content that are addressed using both a user-defined search key and content of data blocks. Internal keys of retention roots of the DAGs may be derived from the user-defined search key while the remaining blocks may be content addressed. As opposed to using a content address, the user may provide the search key when retrieving and deleting DAGs retaining the data content. In addition, the internal keys may be implemented using internal content addressable storage operations, such as applying a hash function and employing a distributed hash table.
Owner:NEC CORP
P2p Overplay Network Construction Method and Apparatus
InactiveUS20080130516A1Efficient searchEasy to operateData switching by path configurationNetwork constructionShared resource
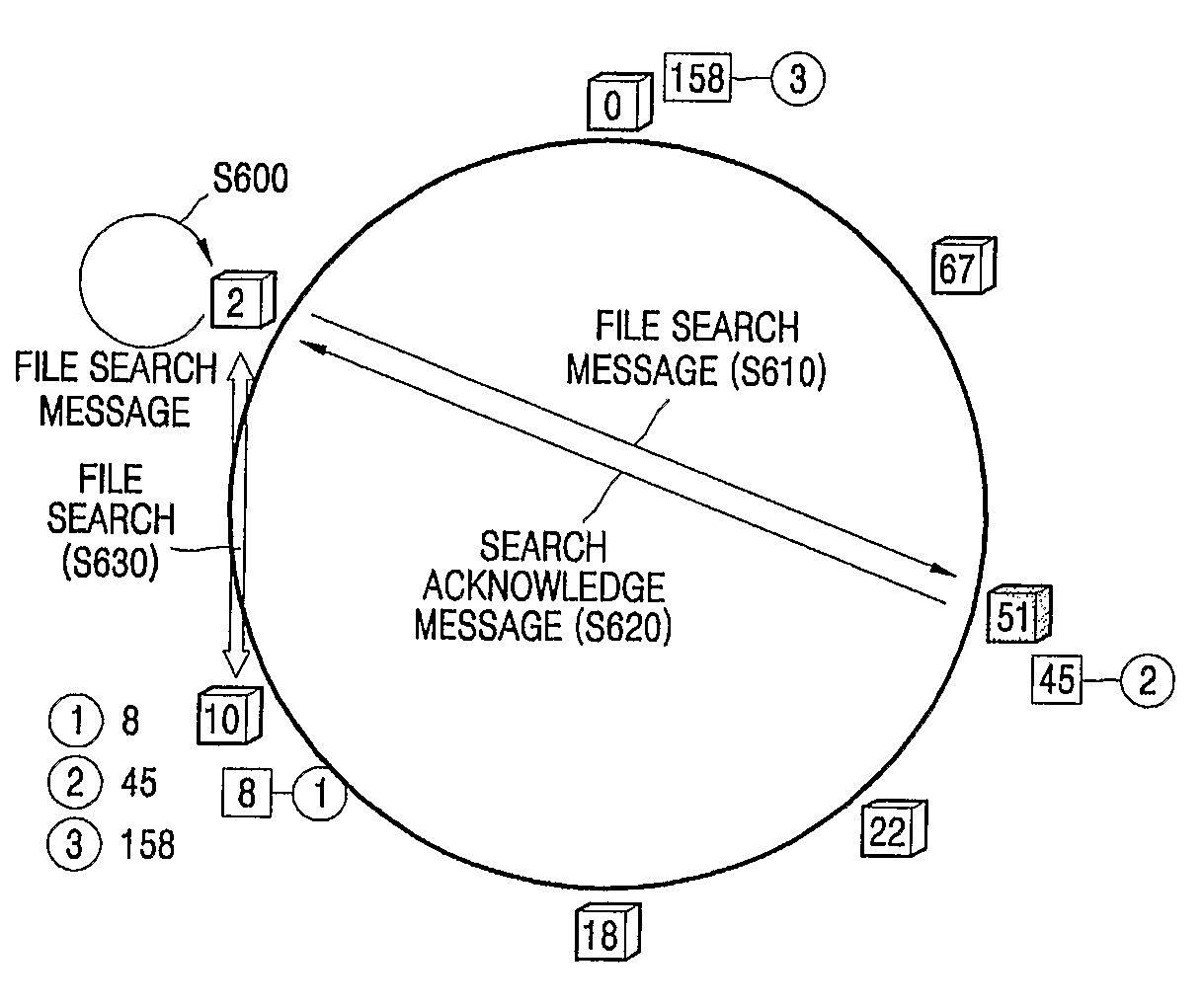
Provided are a method and apparatus for constructing a peer-to-peer (P2P) overlay network. The method of constructing a peer-to-peer (P2P) overlay network to obtain ID values of a plurality of nodes using a distributed hash table (DHT) and registering a node wishing to join the P2P overlay network where the plurality of nodes are sequentially located based on the obtained ID values, includes: (a) transmitting a join request message from the node wishing to join the P2P overlay network to a key node of the P2P overlay network; (b) a first node that received the join request message determining whether an ID value of the node wishing to join the P2P overlay network is a between value of an ID value of the first node and an ID value of a second node next to the first node, while sequentially transmitting the join request message to the plurality of nodes; and (c), if the first node determines that the ID value of the node wishing to join the P2P overlay network is the between value, registering the node wishing to join the P2P overlay network between the first and second nodes. Therefore, it is possible to more easily and efficiently search for sharing resources stored by each of the nodes.
Owner:ELECTRONICS & TELECOMM RES INST +1
System for storing distributed hashtables
InactiveUS20090144220A1Easy accessImprove performanceDigital data information retrievalSpecial data processing applicationsTablet computerClient-side
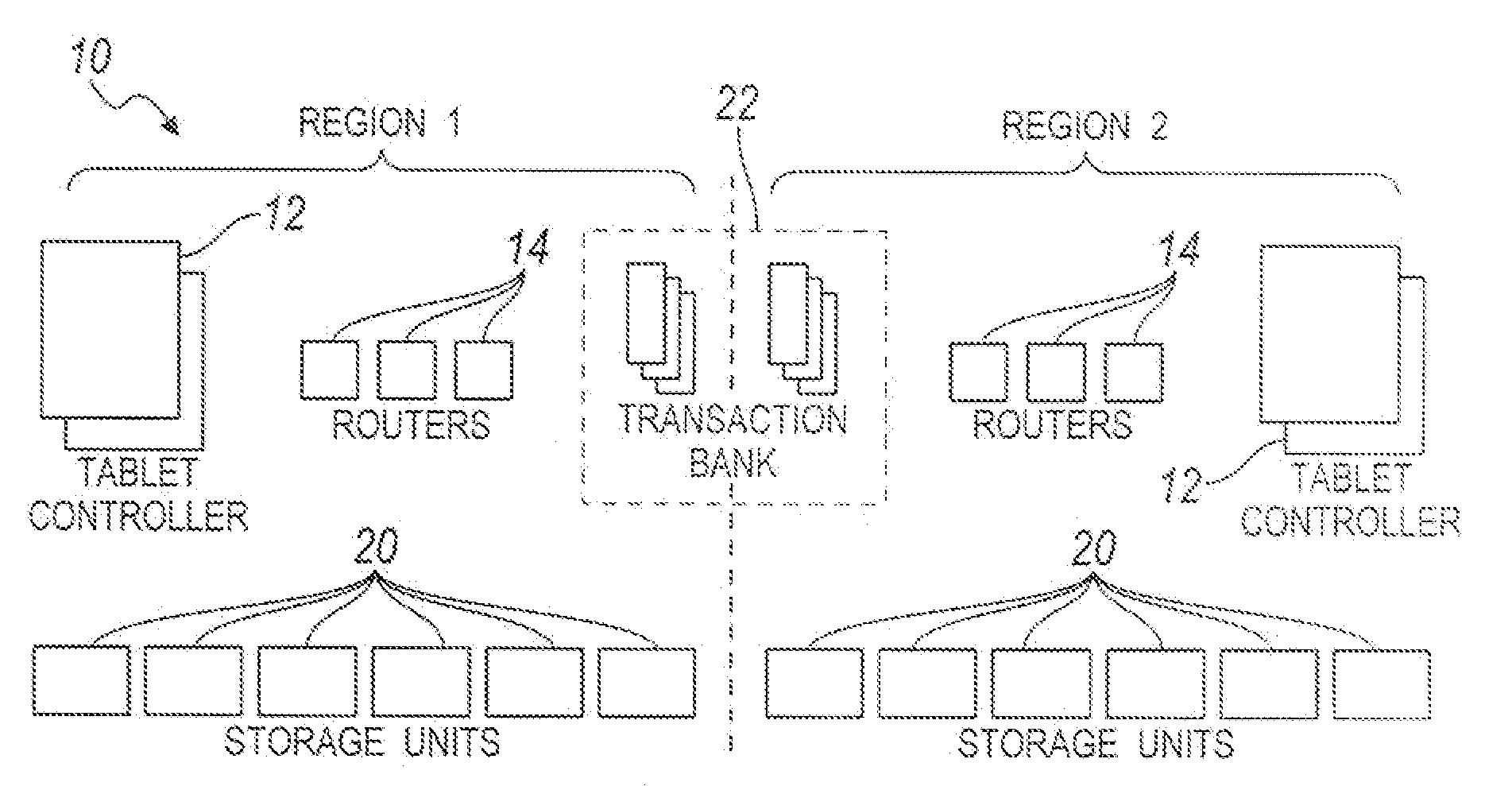
A system for storing a distributed hash table. The system includes a storage unit, a tablet controller, a router, and a transaction bank. The storage unit has a plurality of tablets forming a hash table and each of the tablets includes multiple records. The tablet controller maintains a relationship between each tablet and the storage unit. The router hashes a record's key to determine the tablet associated with each record. Further, the router distributes messages from clients to the storage units based on the tablet-storage unit relationship thereby serving as a layer of indirection. The transaction bank propagates updates made in one record to all other replicas of the record.
Owner:OATH INC
Systems and methods for distributed hash table in a multi-core system
ActiveUS20100322250A1Data switching by path configurationProgram controlResource informationDistributed hash table
The present invention is directed towards systems and methods for using a distributed hash table to maintain the same configuration and resource persistency across a plurality of cores in a multi-core system. The distributed hash table includes a plurality of partitions, each partition being owned by a respective core of the multi-core system. A core may establish resources in the partition it owns. A core may request other cores to establish resources in the partitions they own and send resource information to the core. The core may locally cache the resource information.
Owner:CITRIX SYST INC
Content acquisition method, node and content network
InactiveCN102143199AAvoid congestionAvoid paralysisTransmissionNetwork architectureDistributed hash table
Owner:HUAWEI TECH CO LTD
Method, System, and Devices for Network Sharing or Searching Of Resources
InactiveUS20100095009A1Improve and provide certain serviceResource searchingMultiple digital computer combinationsTransmissionCommunications systemContent sharing
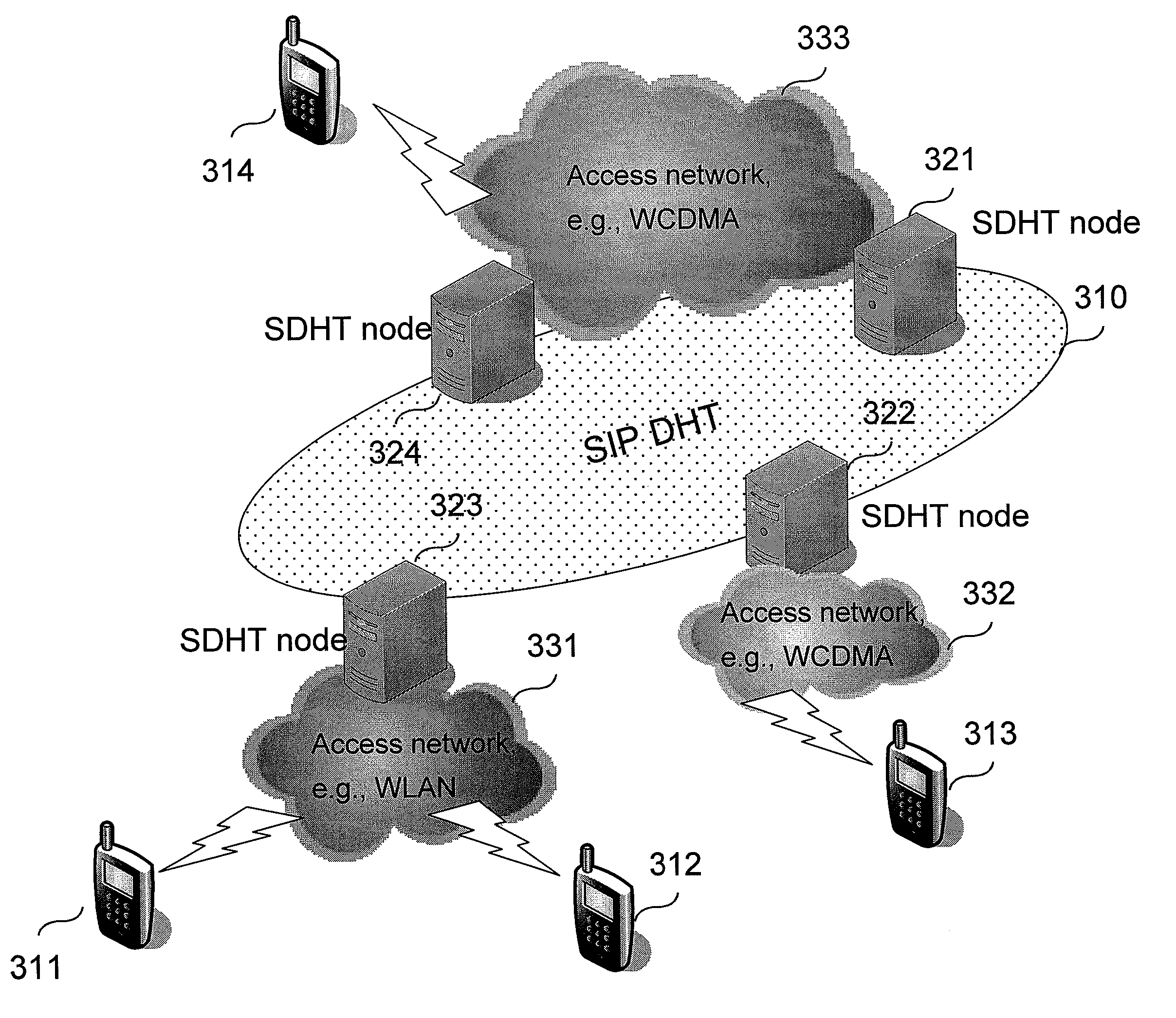
The invention presents an architecture of a distributed communication system that combines strengths of Distributed Hash Table (DHT) algorithms and social networks. The system forms a cost efficient platform for providing innovative mobile Services. Possible implementations of the proposed system in the IP Multimedia Subsystem and as a standalone SIP based system are presented. The architecture may also be deployed in other systems. Further, a content sharing inside community service is provided.
Owner:NOKIA CORP
Node, routing control method, and routing control program
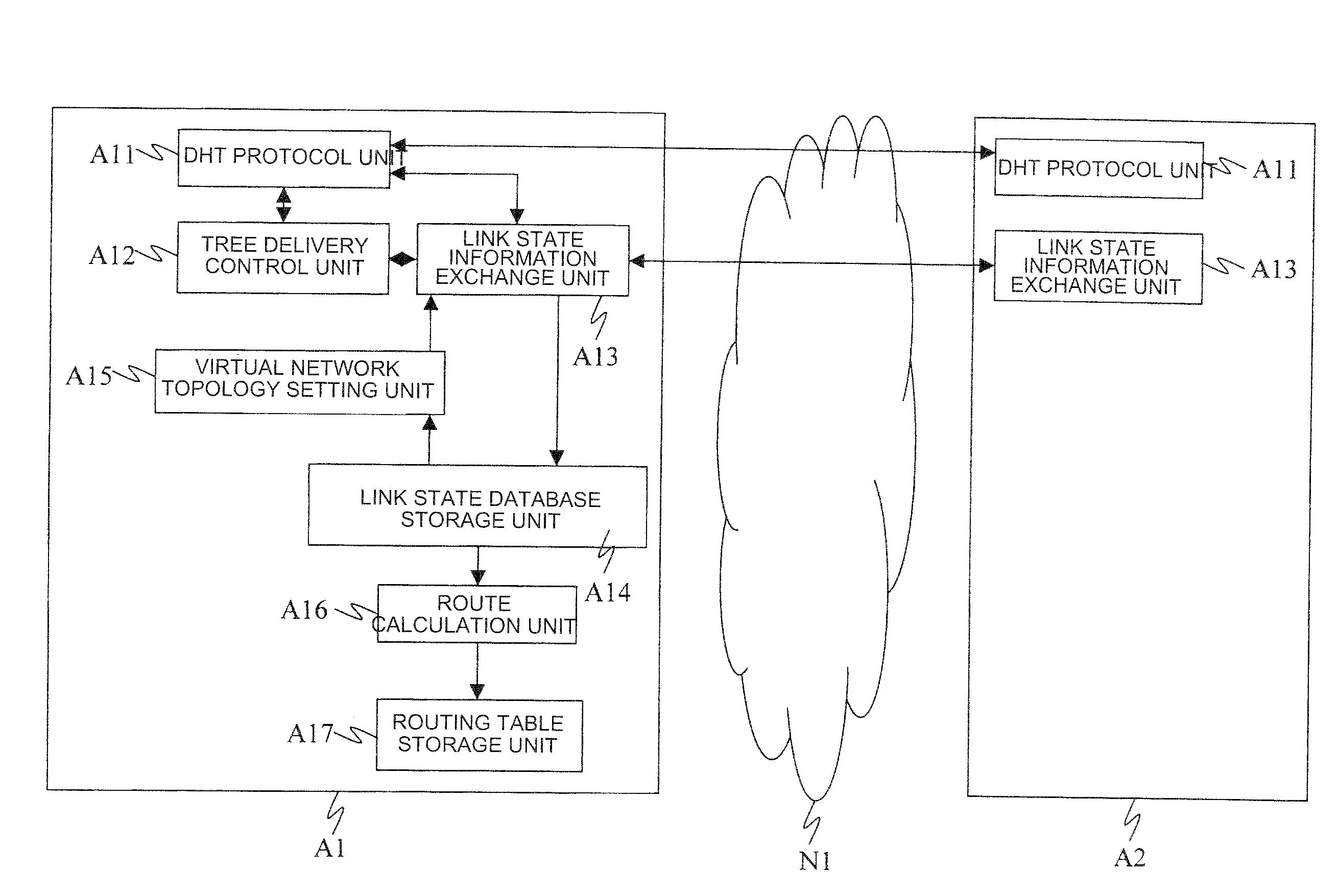
ActiveUS20090180489A1Reduce trafficData switching by path configurationNetwork connectionsOptimized Link State Routing ProtocolLink-state routing protocol
Disclosed is a node that includes a distributed hash table generation means that generates a distributed hash table which indicates the next node to which a message is to be transferred, using a link state routing protocol, a link state information that exchange unit sends and receives link state information, and a tree delivery control unit that determines the transfer destination of the link state information so that the link state information is delivered along a tree where the source node of the link state information is a root.
Owner:NEC CORP
Peer-to-peer system and method with prefix-based distributed hash table
InactiveUS20050135381A1Digital data processing detailsData switching by path configurationPath lengthDistributed hash table
Owner:NEC CORP
Method of distributed hash table node ID collision detection
InactiveUS20070233832A1Digital computer detailsTransmissionCollision detectionDistributed hash table
Owner:PANASONIC CORP
Layered controllable alliance block chain system
InactiveCN107786339AUser identity/authority verificationData switching networksChain systemDistributed hash table
The invention discloses a layered controllable alliance block chain system. The layered controllable alliance block chain system is characterized by comprising a core layer, a backbone layer and an application layer; through the adoption of a structured point-to-point transmission protocol, a node and a data object are mapped to a network by using a distributed hash table; the application layer reduces the selection determinacy by adopting the random routing and exchanges performance for routing security; the core layer and the backbone layer select an optimal or backup path to perform the security connection; the core layer nodes cooperate to generate a public digital credential; and each core layer node generates and maintains the private digital credential and an exchange relation between the private digital credential and the public digital credential; each node forms the workload certificate through one or more competitive computation in Hash, symmetric encryption, asymmetric encryption, random number and external dynamic exponential algorithm, and / or realizes consensus algorithm with the timestamp on the interest certificate of ownership through the node, and forms continuouspublic block chain and private block chain capable of being wedged in both way through the end-to-end connection of various blocks.
Owner:陈新
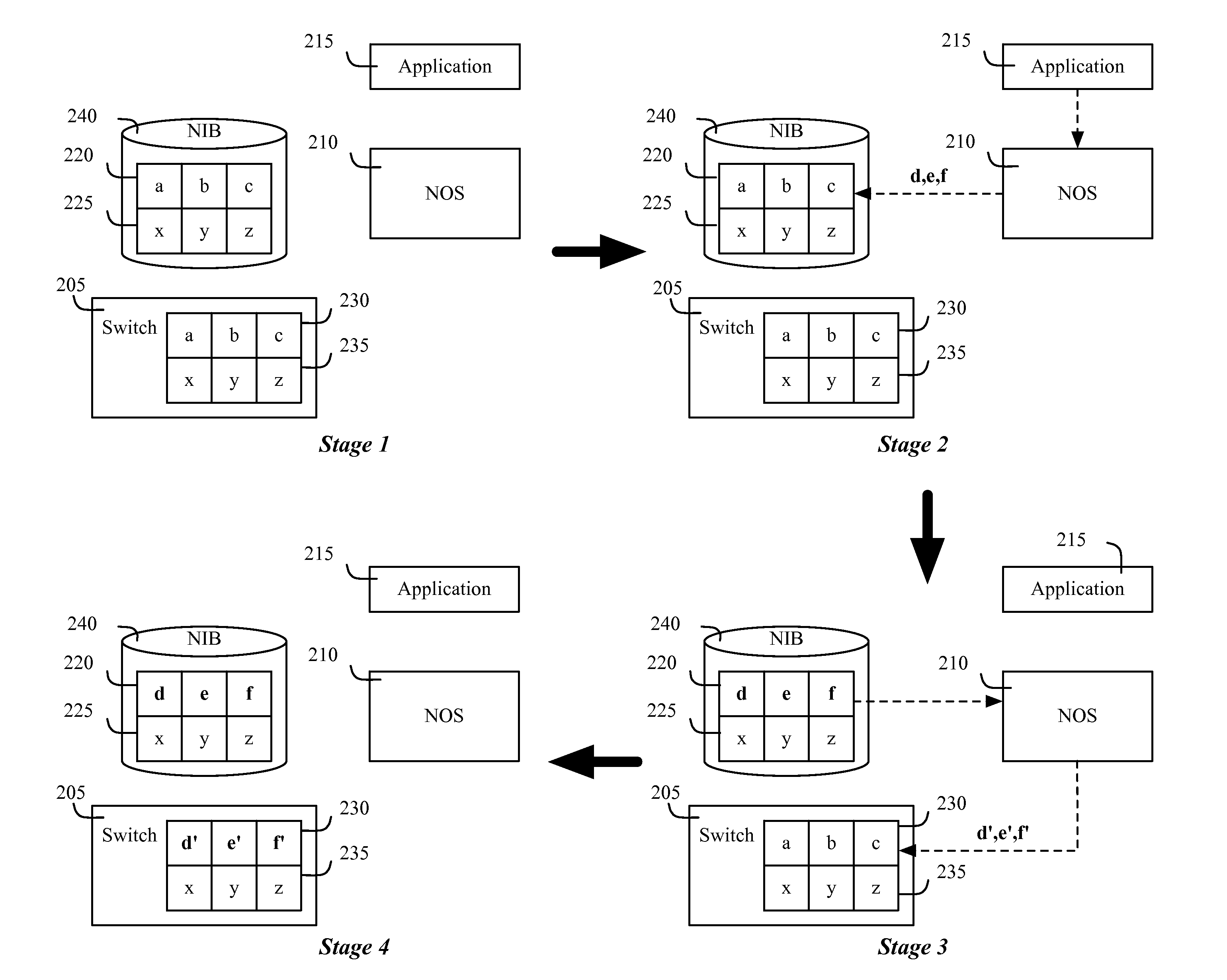
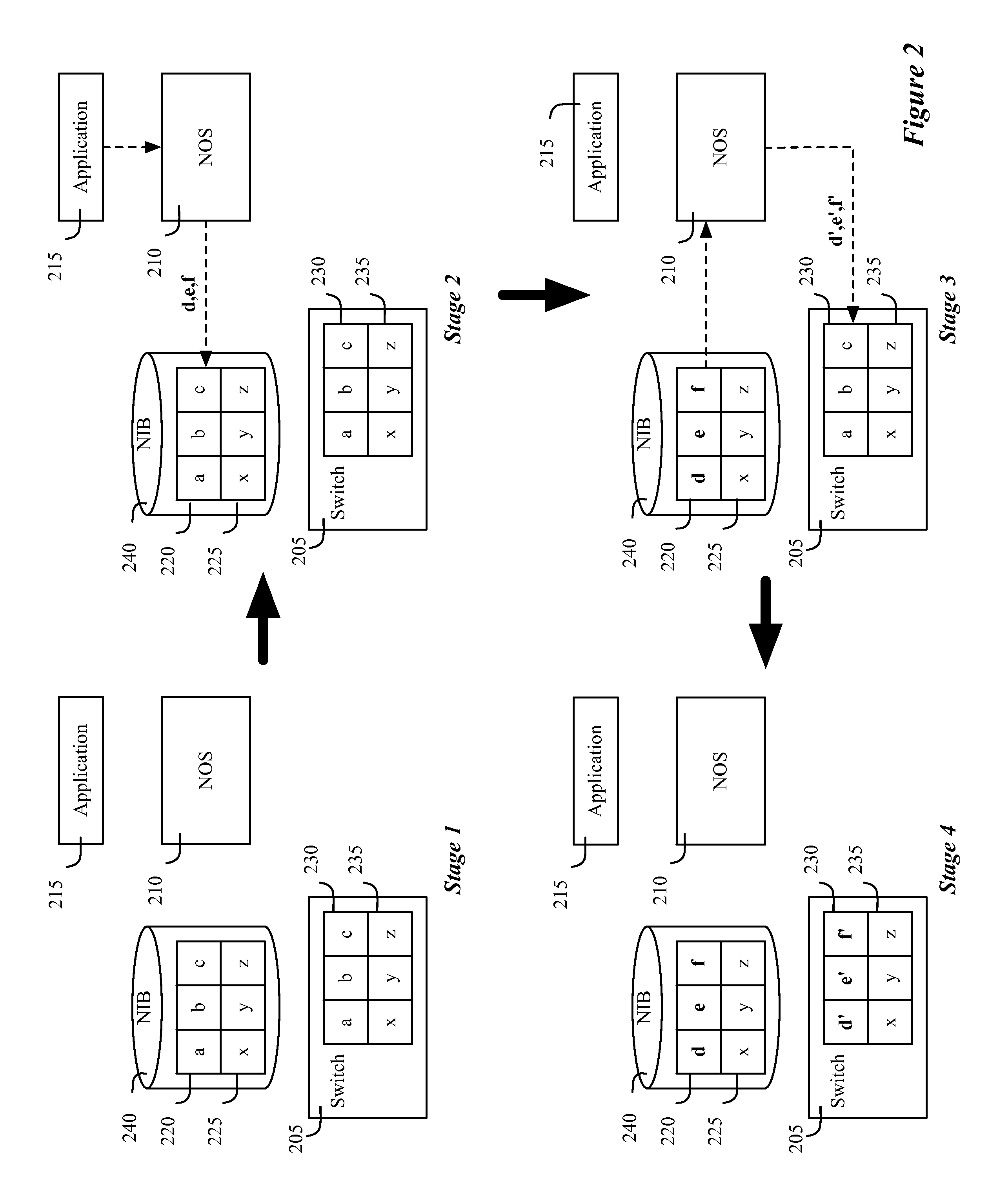
Distributed network control system with a distributed hash table
A network control system that includes several controllers for managing several switching elements and a distributed hash table (DHT) formed across the controllers for storing data regarding the switching elements that is accessible by the controllers. Each hash table serves as a DHT instance. In some embodiments, the DHT instances of all controller instances collectively store one set of records that is indexed based on hashed indices for quick access. These records are distributed across the different controller instances to minimize the size of the records within each instance and to allow for the size of the DHT to be increased by adding other DHT instances. According to this scheme, each DHT record is not stored in each controller instance. In fact, in some embodiments, each DHT record is stored in at most one controller instance.
Owner:NICIRA
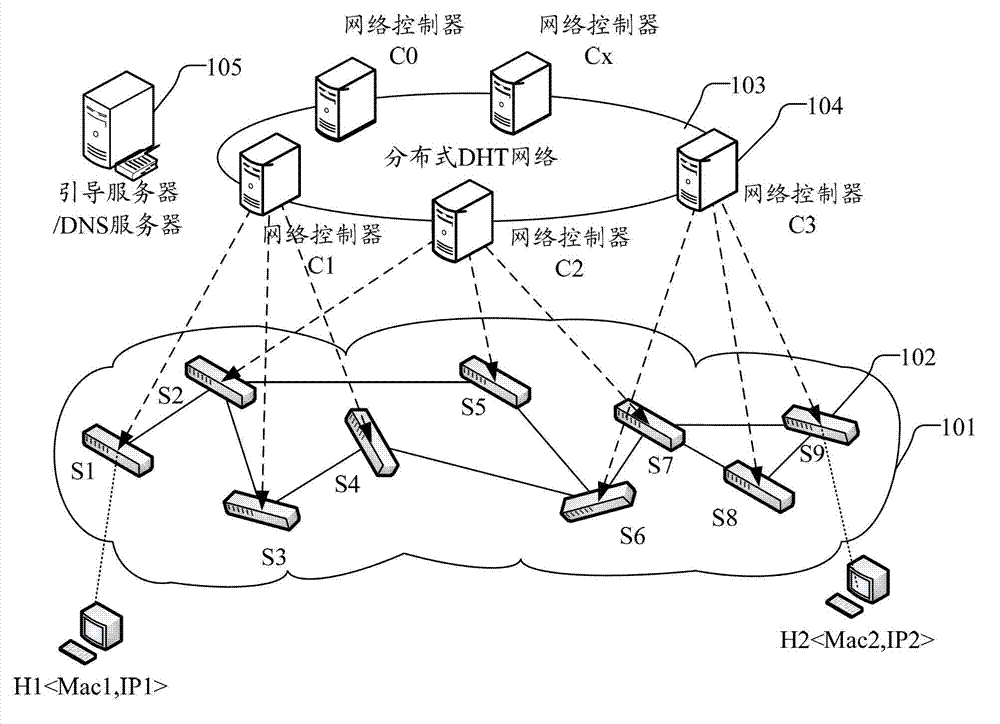
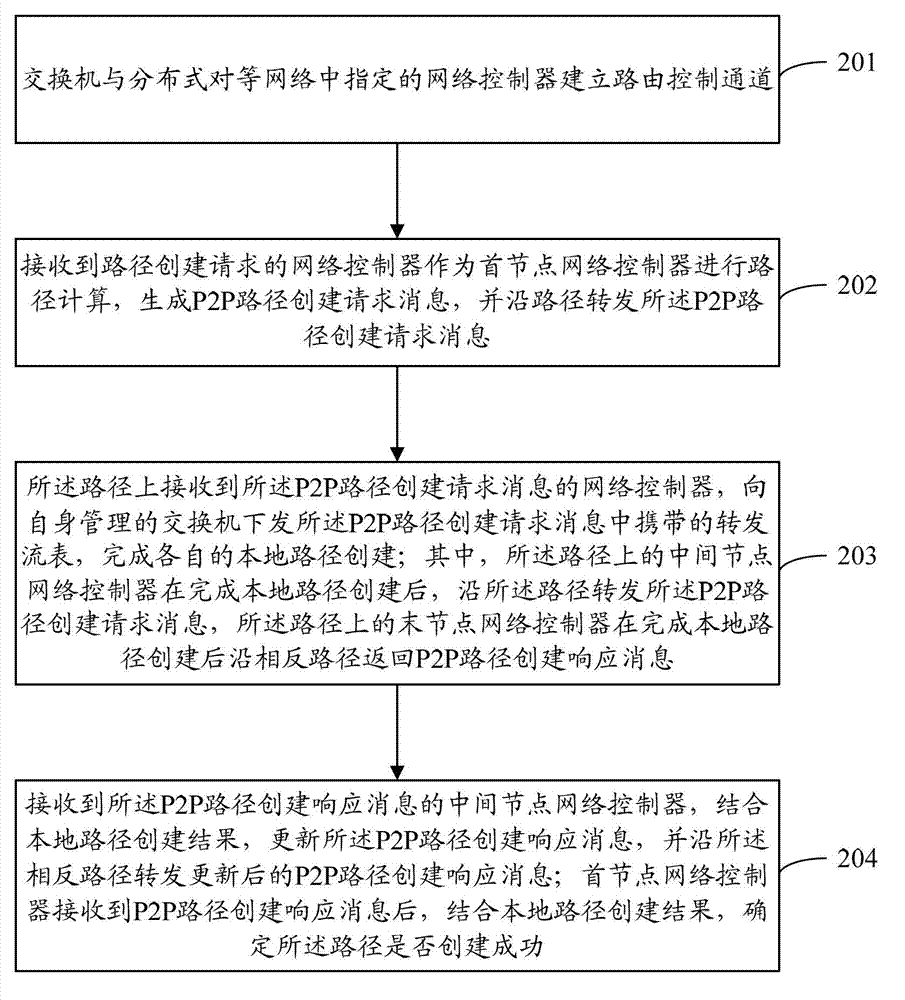
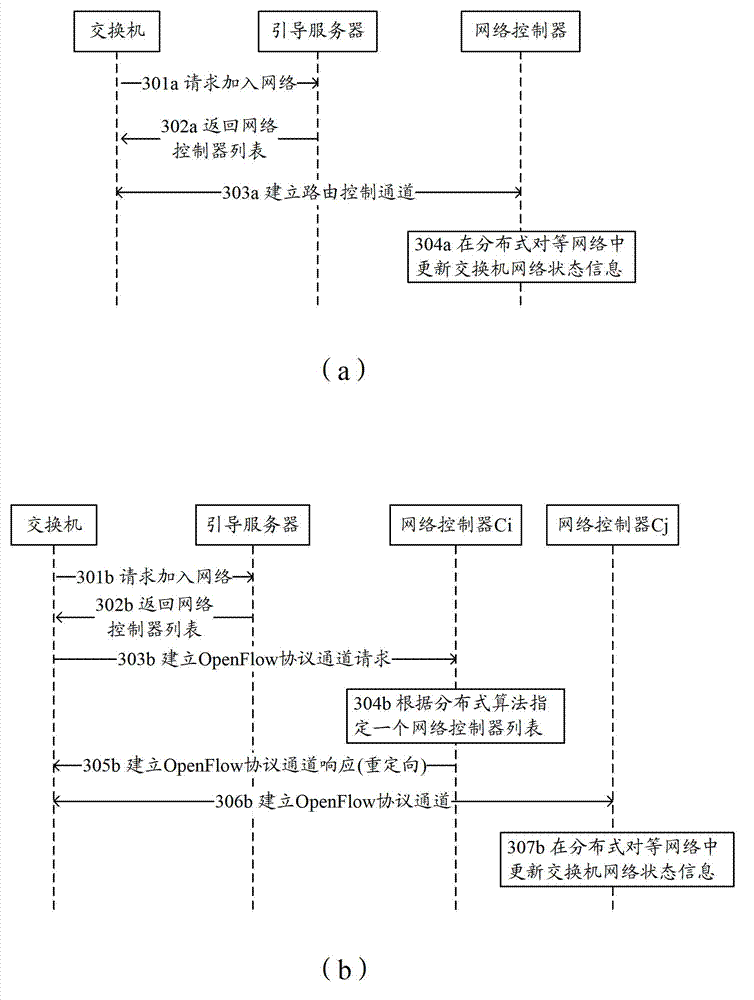
DHT-based (distributed hash table-based) control network implementation method, system and network controller
ActiveCN103051539ARealize automatic accessEasy to manageData switching networksNetwork controlControl channel
The invention discloses a DHT-based control network implementation method and a system. The DHT-based control network implementation method includes the following steps that switches establish control channels with specified network controllers in a distributed peer-to-peer network; the head node network controller generates a P2P (peer-to-peer) path creation request message, and the P2P path creation request message is forwarded along a path until reaching the tail node network controller; each network controller on the path issues a forwarding flow table carried by the P2P path creation request message to the switches managed by the network controller according to the P2P path creation request message, so that respective local paths are created; and according to received P2P path creation responses and local path creation results, the head node network controller determines whether paths are successfully created. The invention also discloses the network controller. According to the invention, the conditions that the network controller network can be self-organized and that the switches can automatically access the network can be ensured, and meanwhile, calculation and issue of network paths can be easily managed.
Owner:ZTE CORP
Method for storing data on a peer-to-peer network
InactiveUS20120311339A1Mitigate issueUser identity/authority verificationDigital signatureNetwork on
A method of storing data from a first node on a peer-to-peer network. The method includes creating a public and private key pair from a data item, determining a hash value for the public key, assigning the hash value as a user identifier for the user of the node, and storing the public key within a distributed hash table of the network. The user identifier corresponds to the key for the public key within the distributed hash table. The method includes the step of digitally signing the user identifier using the created private key.
Owner:UNIV OF CALIFORNIA IRVINE
Distributed storage of routing information in a link state protocol controlled network
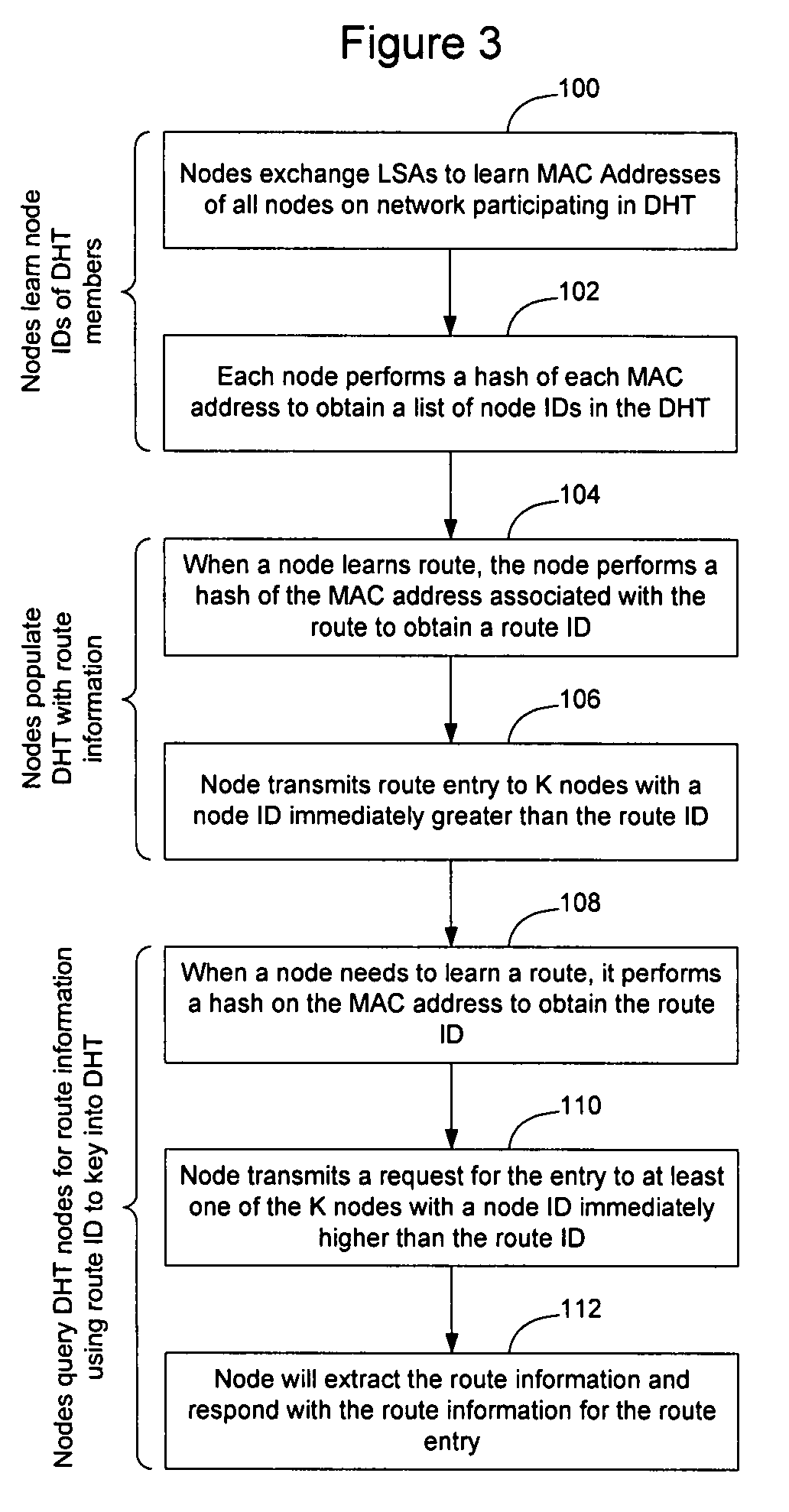
A distributed hash table is implemented to store routing information on a network. Node IDs exchanged in connection with implementation of a link state routing protocol are used as keys in the distributed hash table, and routes are stored at one or more nodes on the network. When a route is learned, the route is processed against the set of keys to determine which nodes should store the route. When a route is needed, the route is processed against the set of keys to determine which nodes should have the route information. The manner in which the route is processed against the set of keys is the same in both instances, so that the DHT may be used to store and retrieve route information on the network. The DHT may be implemented to store MAC addresses, IP addresses, MPLS labels, or other information of interest to enable routes to be stored and learned by network elements on the network.
Owner:RPX CLEARINGHOUSE
Decentralised multi-user online environment
InactiveUS20100146128A1Minimize the numberRaise the possibilityComputer security arrangementsMultiple digital computer combinationsSemantic filteringVirtual space
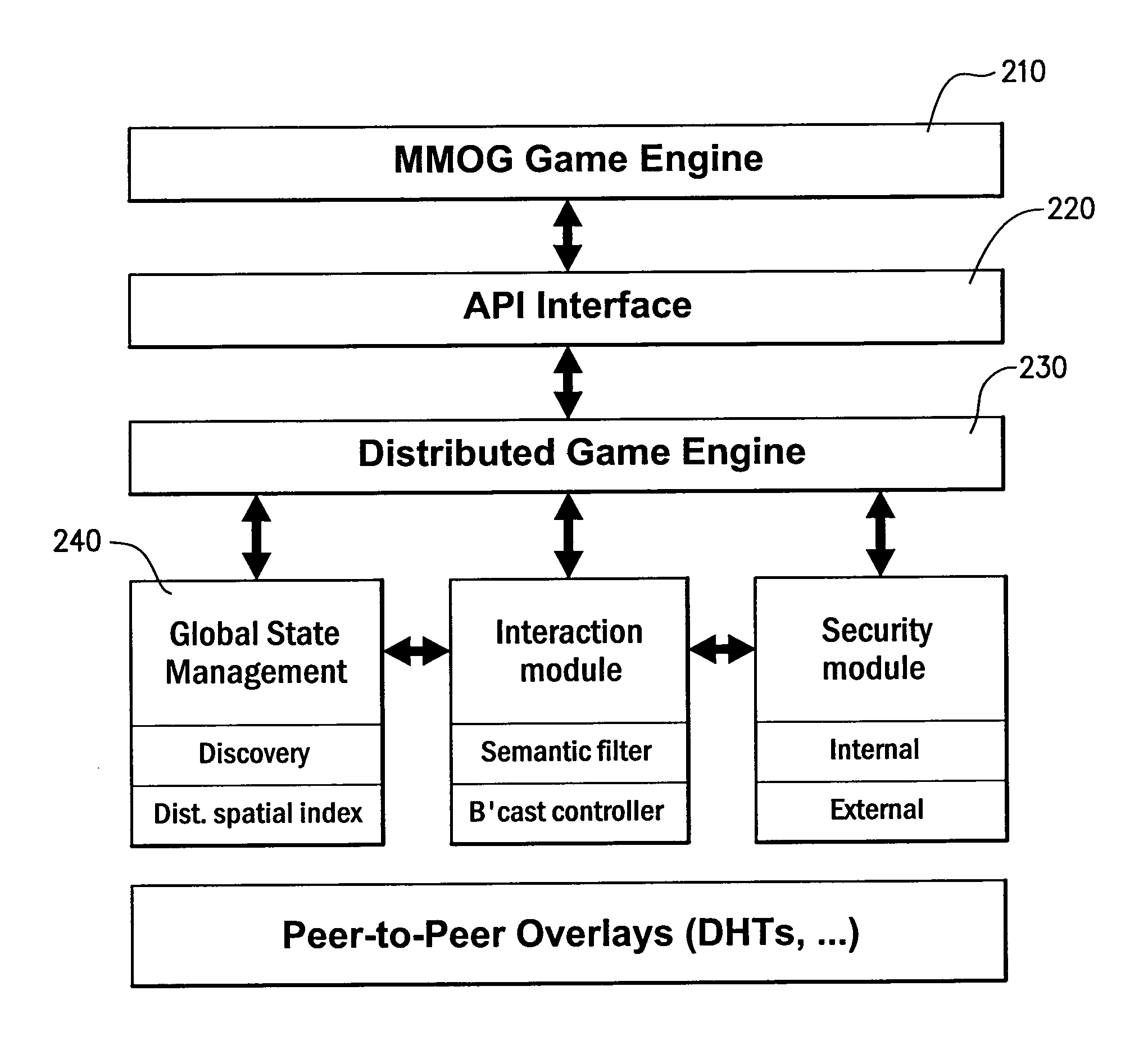
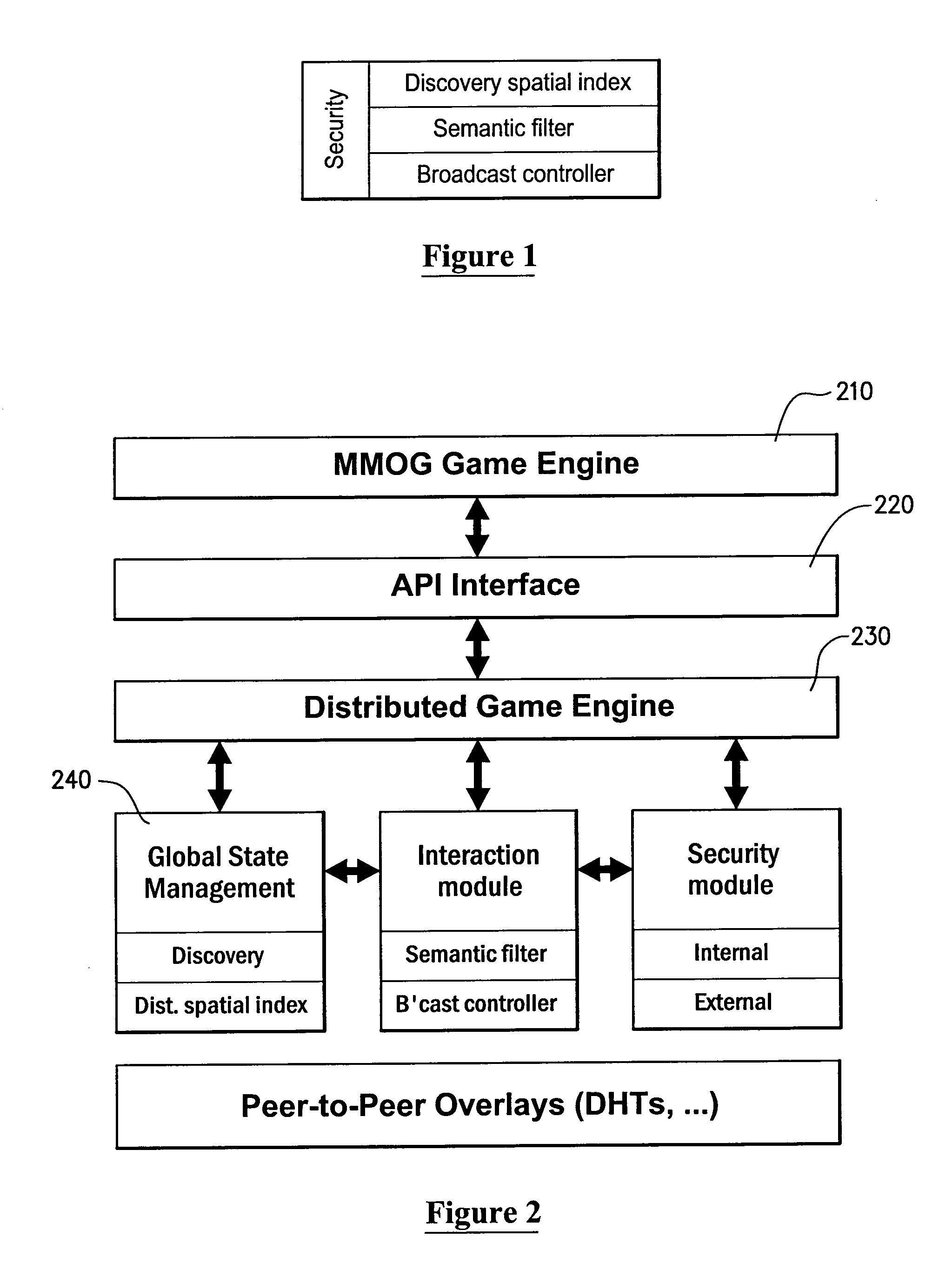
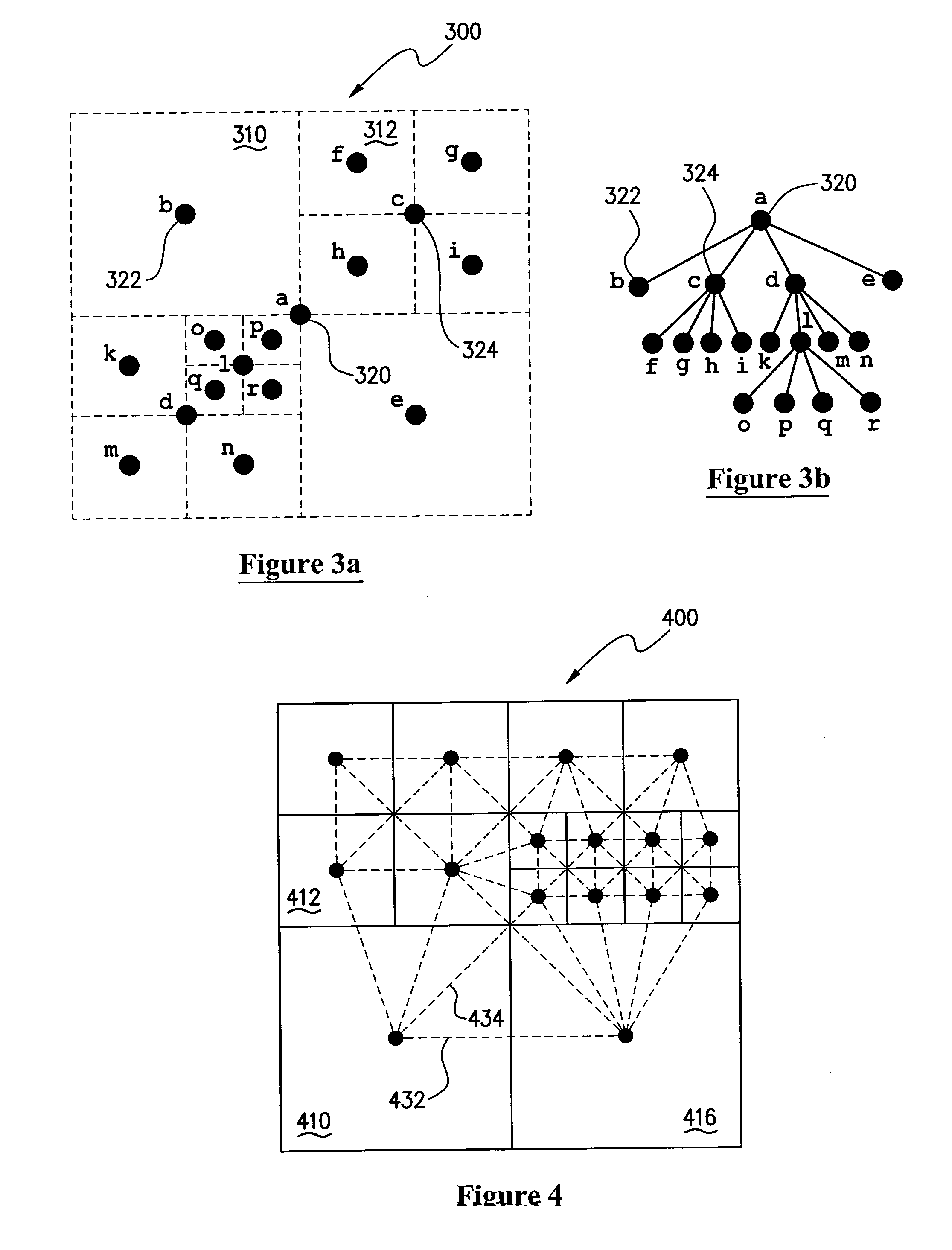
Protocols for facilitating a peer-to-peer real time network in which network state information and data processing is delegated to user nodes. A virtual space is recursively divided into a plurality of sub-regions represented by a logical tree, with responsibility for leaf nodes delegated to multiple user nodes. A distributed hash table can be used to store leaf node state and identity information. A discovery index protocol is provided for user nodes to effectively identify a user node responsible for a sub-region of interest. Further, a semantic filtering protocol limits communications primarily to other user nodes deemed relevant, so as to constrain bandwidth usage. A broadcast control protocol is provided to increase the number of simultaneous interactions for each user node. A security protocol is also provided to prevent any illegal activity by malicious nodes.
Owner:NAT ICT AUSTRALIA
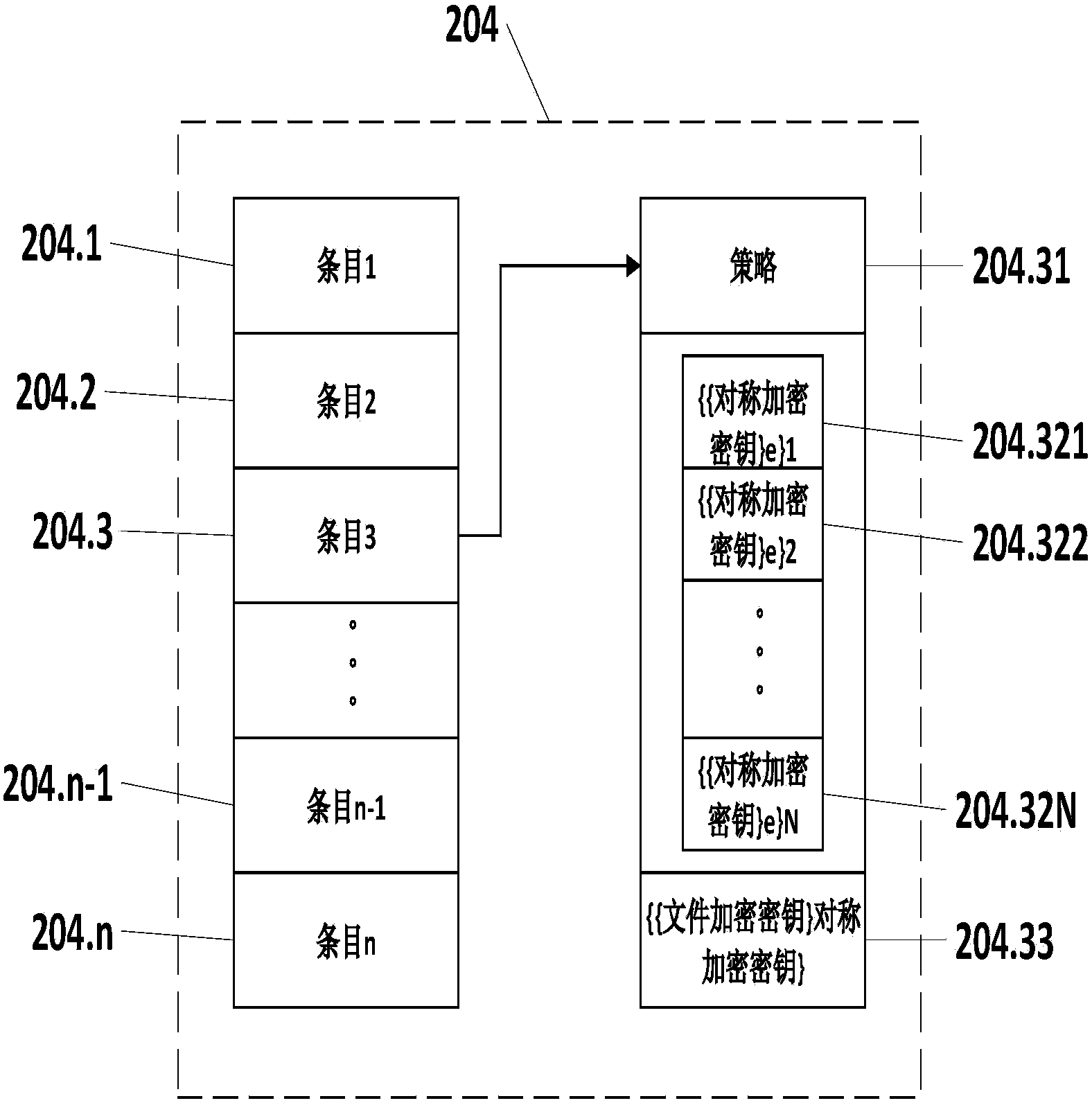
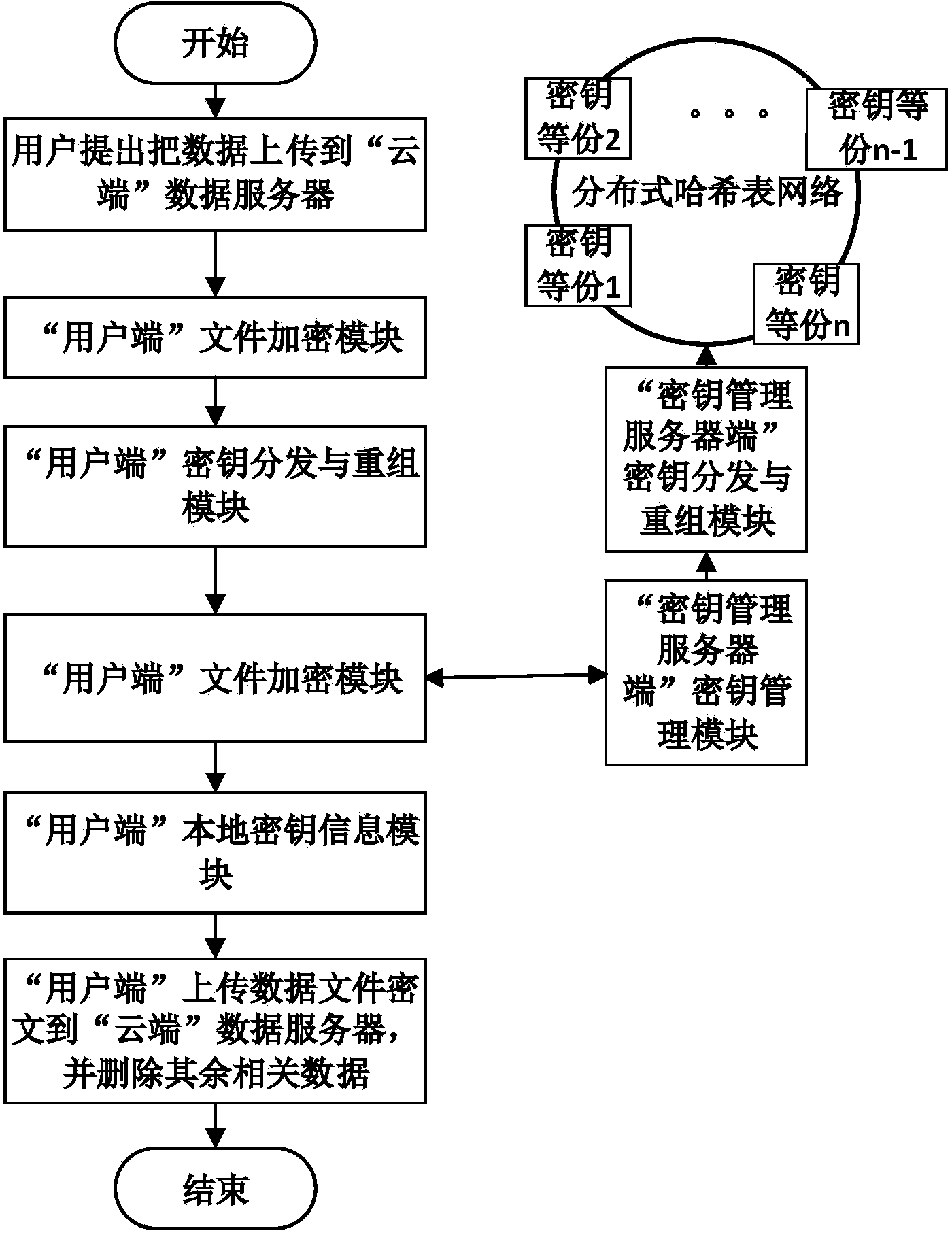
Cloud data safe deleting system and method without support of trusted third party
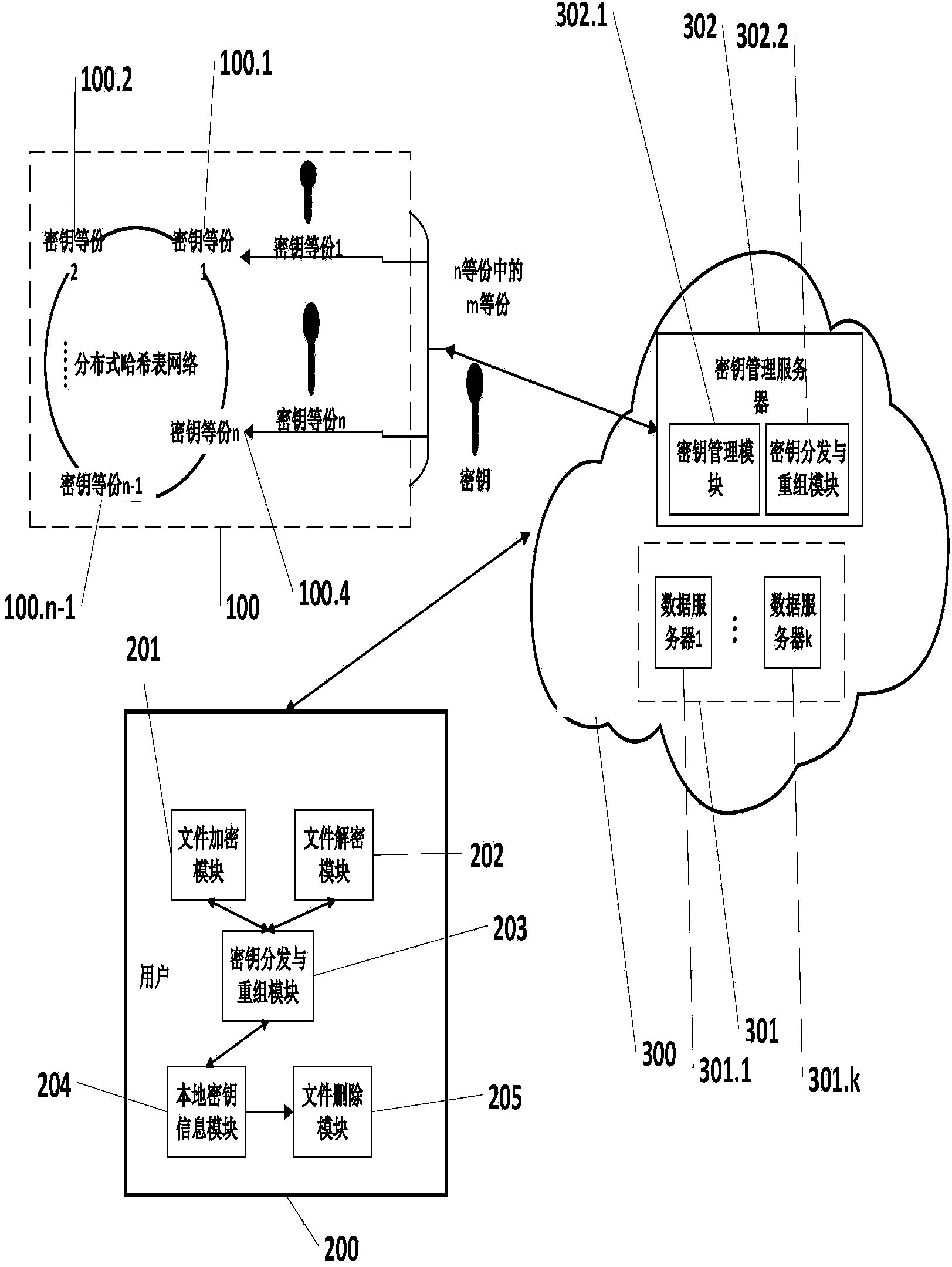
The invention discloses a cloud data safe deleting system and method without the support of a trusted third part. The system comprises a distributed hash table network, a user side and a cloud. The distributed hash table network is used for storing decryption key fragments. The user side is used for encrypting and decrypting files and deleting key information and comprises a file encryption module, a file decryption module, a key distribution and reorganization module, a local key information module and a file deletion module. The file encryption module and the file decryption module are used for encrypting and decrypting the files respectively; the key distribution and reorganization module is used for fragmenting and reorganizing keys; the local key information module is used for storing relevant key information; the file deletion module is used for deleting the key information. The cloud is provided with a data server and a key management server and used for storing data ciphertext information and key information and comprises the data server and the key management server, wherein the data server is used for storing file ciphertexts, and the key management server is used for managing key relevant information. The cloud data safe deleting system and method can be used for a cloud storage environment to protect data privacy of the user side.
Owner:HUAZHONG UNIV OF SCI & TECH
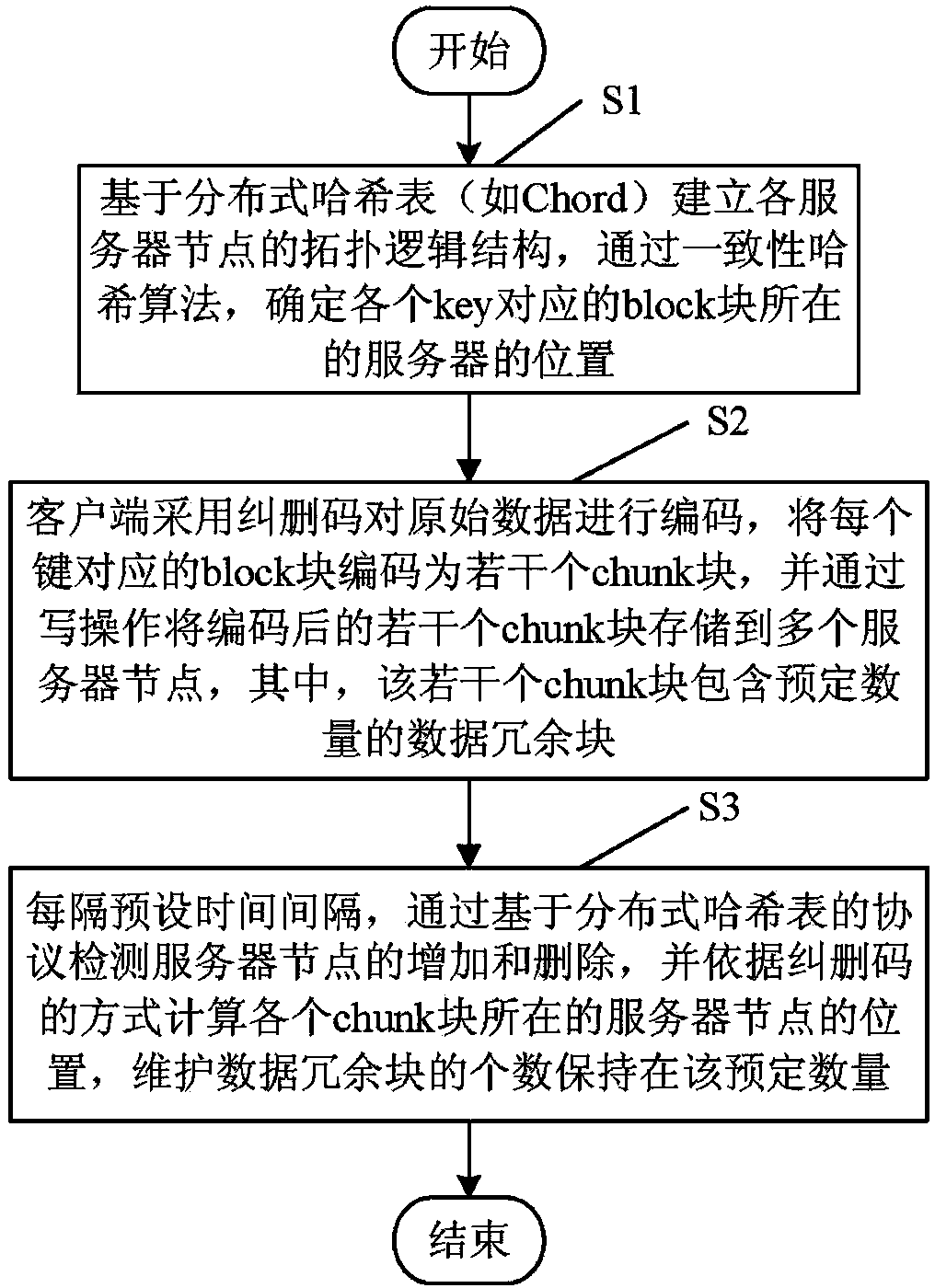
Data storage method based on distributed hash table and erasure codes
The invention discloses a data storage method based on a distributed hash table and erasure codes, and mainly relates to the field of distributed storage. The data storage method includes the following steps that a storage system manages data blocks wholly through a decentralized distributed hash table structure; in order to guarantee reliability, redundancy storage is conducted on the data blocks through erasure code coding; data are regularly scanned in a background process to maintain uniformity and redundancy of the data. According to the data storage method based on the distributed hash table and the erasure codes, the storage system has the decentralized structure and is better than a traditional distributed storage system in expansibility, and storage cost caused by data redundancy is reduced through the erasure codes on the premise that reliability of the data is guaranteed.
Owner:RESEARCH INSTITUTE OF TSINGHUA UNIVERSITY IN SHENZHEN
Distributed file system architectural method supporting mass data access
ActiveCN104008152AReduce complexityPromote migrationSpecial data processing applicationsRouting tableData access
The invention discloses a distributed file system architectural method supporting mass data access. The method is based on a distributed Hash table, and access nodes are obtained by conducting Hash mapping on a file path. By the adoption of the fully distributed type non-centralized architectural design, new nodes can join a cluster after several times of communications. A Kademlia algorithm is adopted for addressing among the nodes, and a routing table is divided and the distance between the nodes is obtained through exclusive-or operation to achieve skip of the most adjacent nodes. A leader is selected through a PaxosLease algorithm to handle the mapping operation on the nodes so as to solve the consensus problem. Block storage of fixed size is conducted on actual data of files, and redundant backup is conducted on the multiple nodes, so that the requirements for safety and distributed calculation are met. When an architectural system generated according to the architectural method processes mass files, the processing efficiency can be remarkably improved, and the good effect can be achieved in the environment with the low latency requirement.
Owner:SOUTH CHINA UNIV OF TECH
Utilizing peer-to-peer services with single instance storage techniques
A system and method for storing data in a peer-to-peer network. A computer system includes interconnected hosts configured to store data segments. A first host stores a first subset of the data segments received from other hosts. The first host maintains a portion of a distributed hash table corresponding to the first subset of data segments and de-duplicates the first subset of the data segments against the remaining data segments. The distributed hash table comprises entries corresponding to the data segments, each entry including a data segment fingerprint that unambiguously identifies the corresponding data segment. The first host selects and joins a group of hosts that maintains the distributed hash table. The first host conveys data to the selected group indicating its availability to own additional entries in the distributed hash table.
Owner:VERITAS TECH
System and method for theft and data recovery from lost portable devices
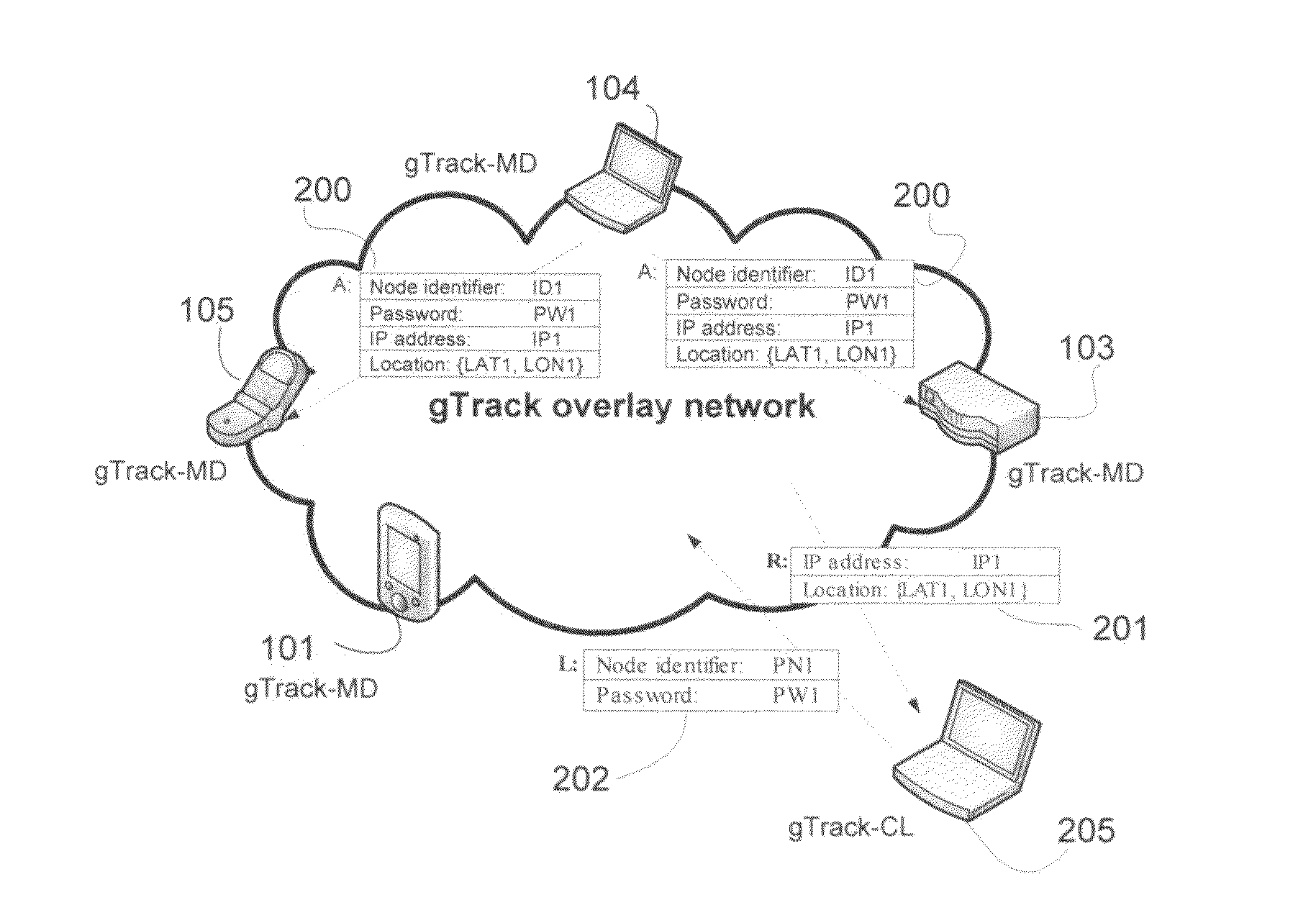
InactiveUS20100229220A1Preventing unauthorized uninstallsReduce operating expensesDigital data processing detailsMultiple digital computer combinationsIp addressPrivacy protection
A system and method for theft recovery, data recovery, and privacy protection for portable devices with IP connectivity is implemented either according to a peer-to-peer or client-server model, with a serverless or a server-based infrastructure. In the P2P model, a distributed hash table (DHT) algorithm is used for storing and retrieving the device IP addresses and the device location coordinates when available. An authorized user can set a protected device into a locked mode or the device automatically enters into a locked mode after the device has been operated without proper authorization. In a locked mode, private data is deleted, transferred to a pre-selected storage system, alerts and location coordinates, when available, are to be sent to preselected accounts. Data on a lost portable device can be synchronized with a pre-selected storage system and be restored when the lost device is recovered.
Owner:GRASSTELL NETWORKS
Method and apparatus for creating user-generated document feedback to improve search relevancy
InactiveUS20080154879A1Increased its relevancyImprove search relevancyDigital data information retrievalSpecial data processing applicationsDistributed hash tableDocument preparation
Method and system for improving relevancy of online search results are disclosed. The method includes collecting highlighted phrases from users who review one or more documents at one or more websites, aggregating the highlighted phrases about the one or more documents in a distributed hash table, ranking relevancy of the highlighted phrases according to frequency of occurrences of similar phrases, generating search relevancy data to be used by a search relevancy algorithm of a search engine, and generating search results in response to a search query using the search relevancy data.
Owner:OATH INC
Data prefetching method of DHT memory system and node and system
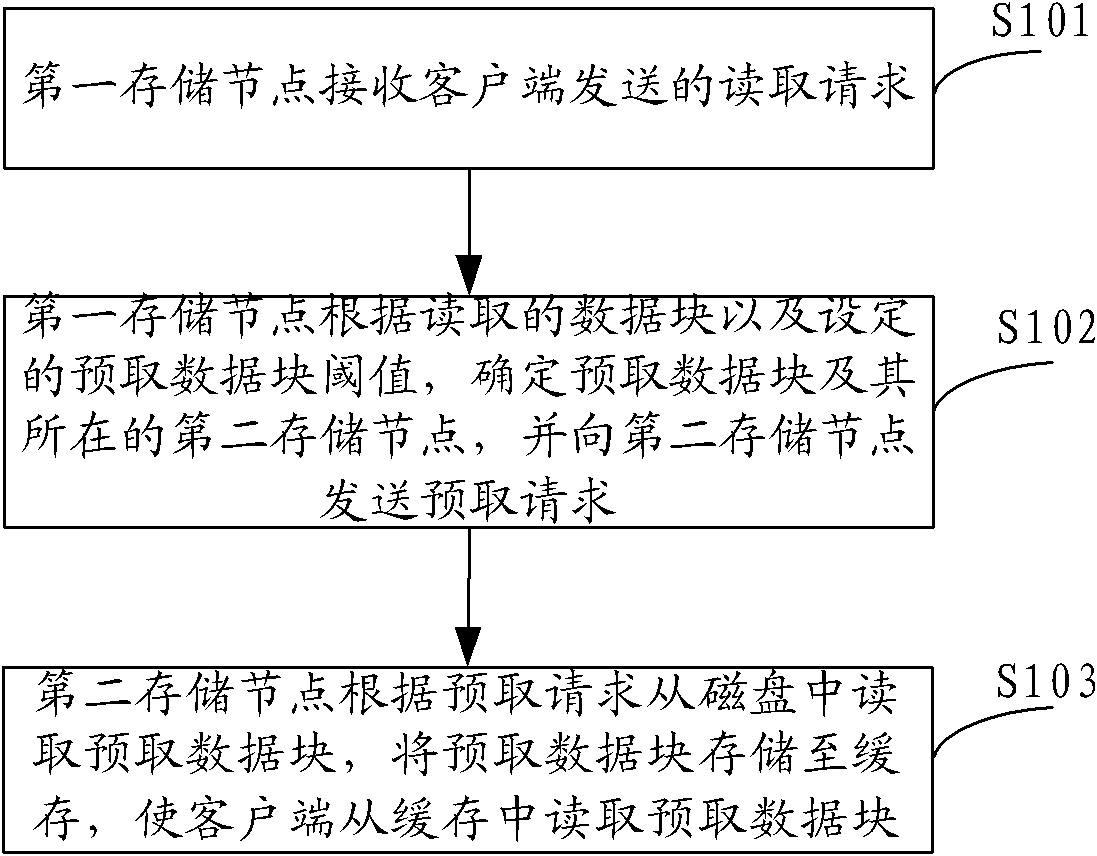
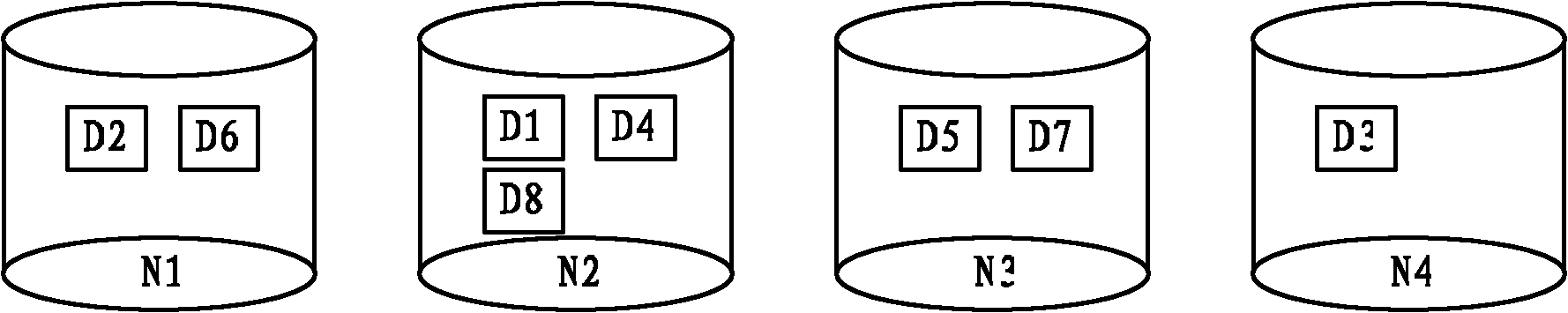
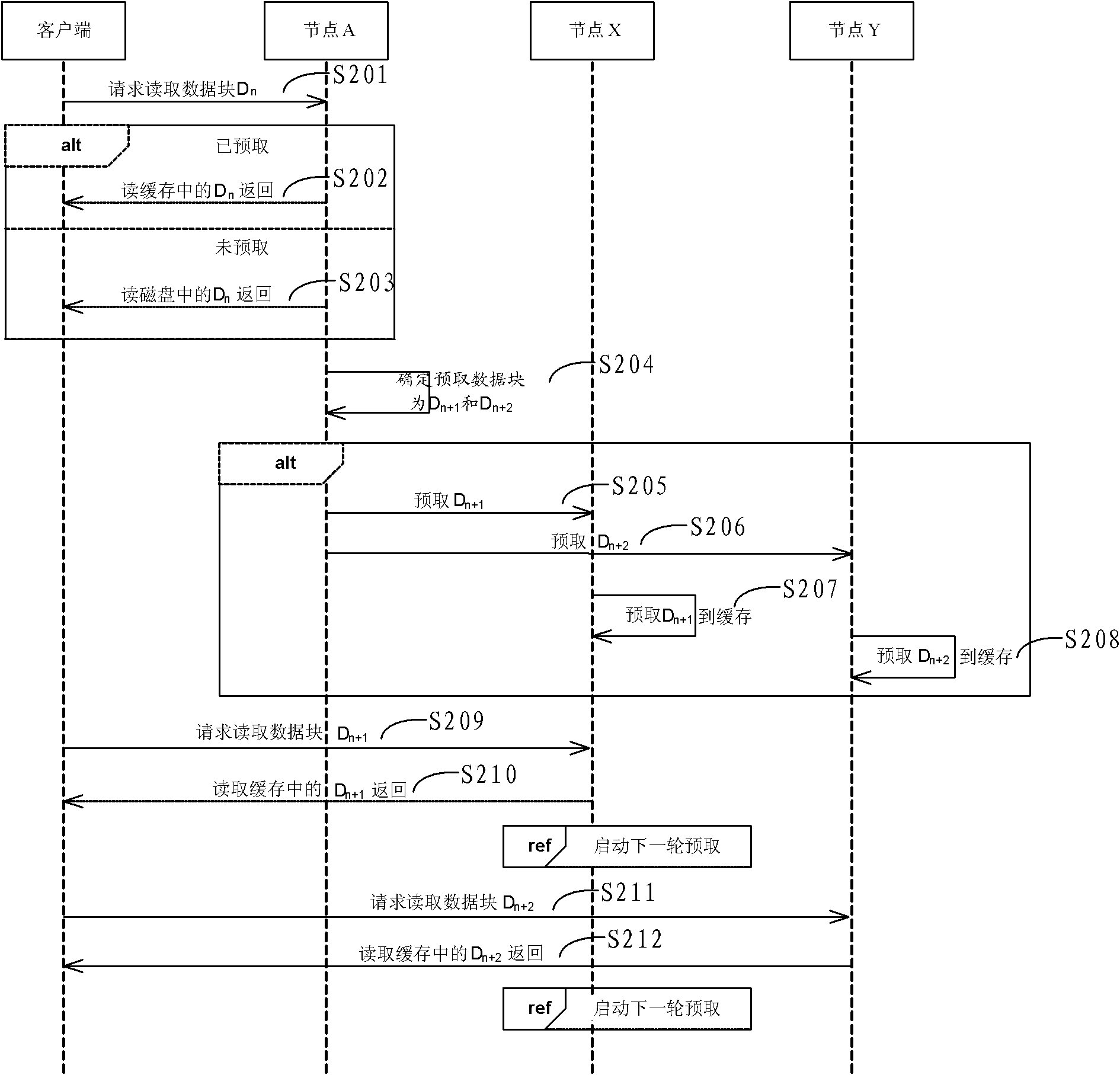
ActiveCN102111448AImprove data access efficiencySave resourcesMemory architecture accessing/allocationSoftware engineeringData accessClient-side
The embodiment of the invention provides a data prefetching method of a DHT (Distributed Hash Table) memory system, a node and a system. The method comprises the following steps: a first memory node receives a reading request sent by a client side, a prefetching data block and a second memory node where the prefetching data block is positioned are defined according to the read data block and a set threshold of the predetching data block, and a prefetching request is sent to the second memory node, wherein the first memory node and the second memory node are identical or different nodes, the prefetching request comprises identification information of the prefetching data block, and the identification information is exclusively used for identifying the prefetching data block; and the secondmemory node reads the prefeching data block from a disk according to the prefetching request, and stores the prefetching data block to a local cache, so that the client side can read the prefetching data block from the local cache of the second memory node. By adopting the embodiment of the invention, the prefetching data block can be directly read from the cache, so that the data visit efficiency of each memory node in the system can be improved.
Owner:HUAWEI TECH CO LTD
Distributed storage of routing information in a link state protocol controlled network
InactiveUS7684352B2Digital computer detailsData switching by path configurationIp addressLink-state routing protocol
A distributed hash table is implemented to store routing information on a network. Node IDs exchanged in connection with implementation of a link state routing protocol are used as keys in the distributed hash table, and routes are stored at one or more nodes on the network. When a route is learned, the route is processed against the set of keys to determine which nodes should store the route. When a route is needed, the route is processed against the set of keys to determine which nodes should have the route information. The manner in which the route is processed against the set of keys is the same in both instances, so that the DHT may be used to store and retrieve route information on the network. The DHT may be implemented to store MAC addresses, IP addresses, MPLS labels, or other information of interest to enable routes to be stored and learned by network elements on the network.
Owner:RPX CLEARINGHOUSE
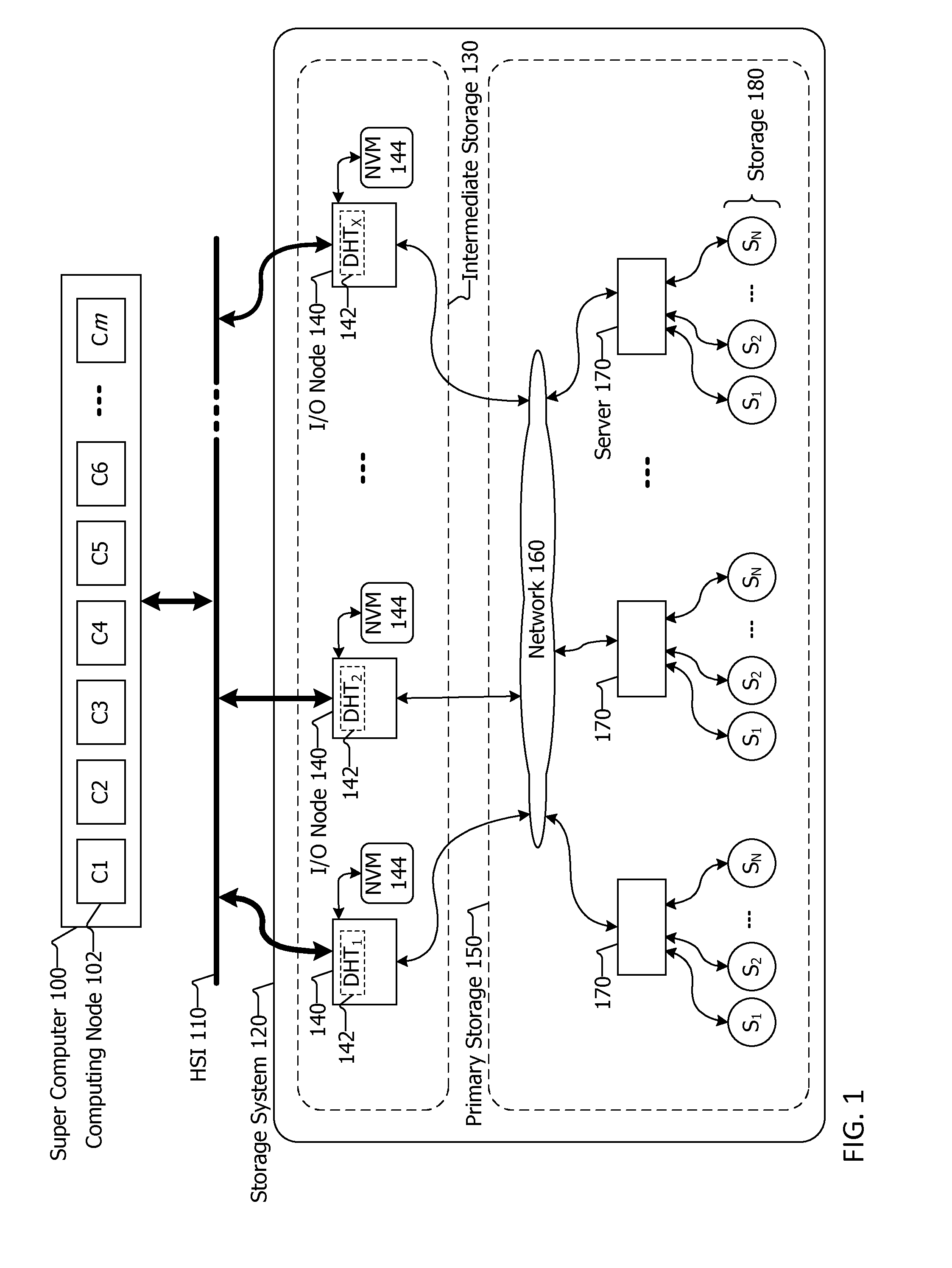
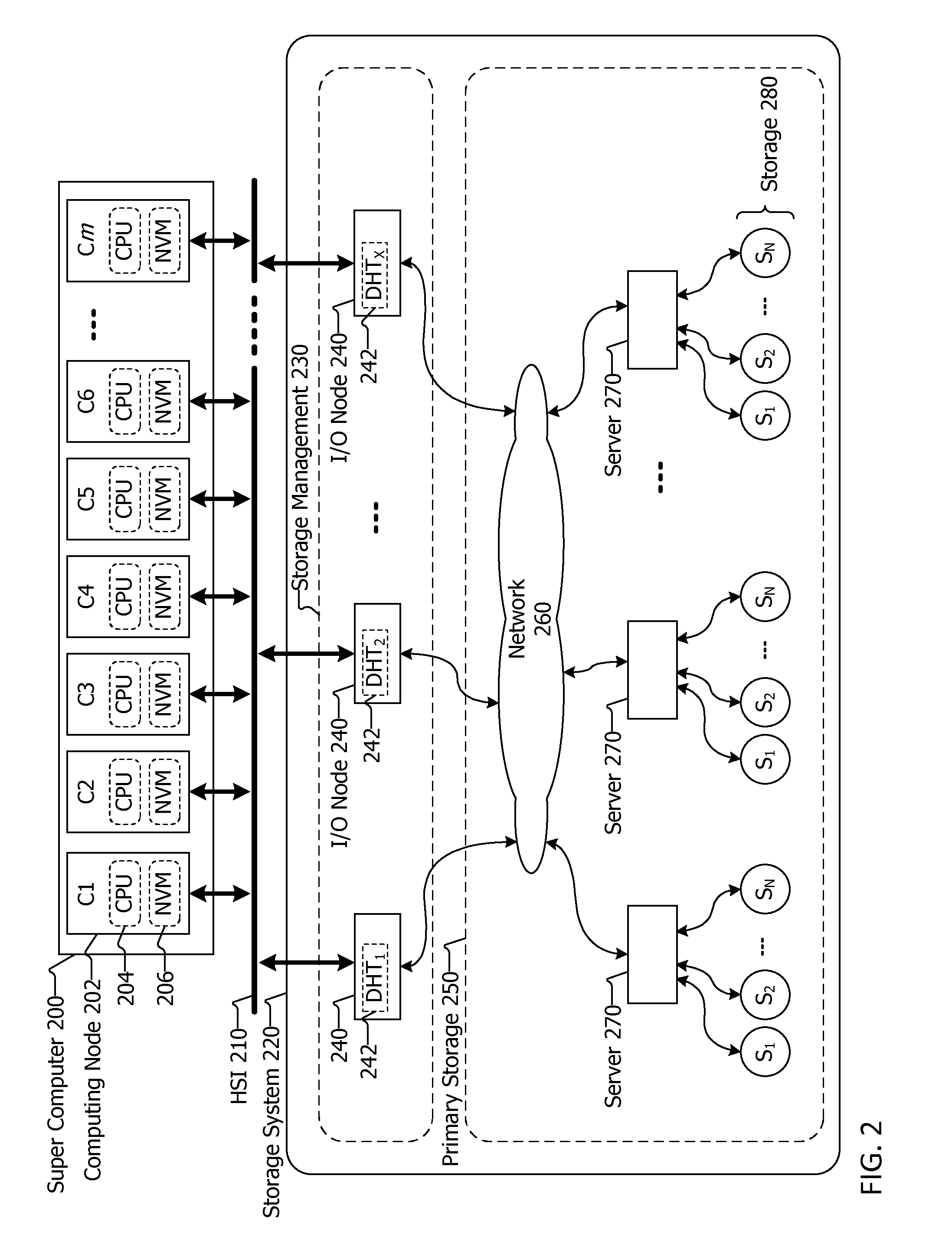
Data storage architecture and system for high performance computing
ActiveUS20140108707A1Memory adressing/allocation/relocationSpecial data processing applicationsPerformance computingRapid access
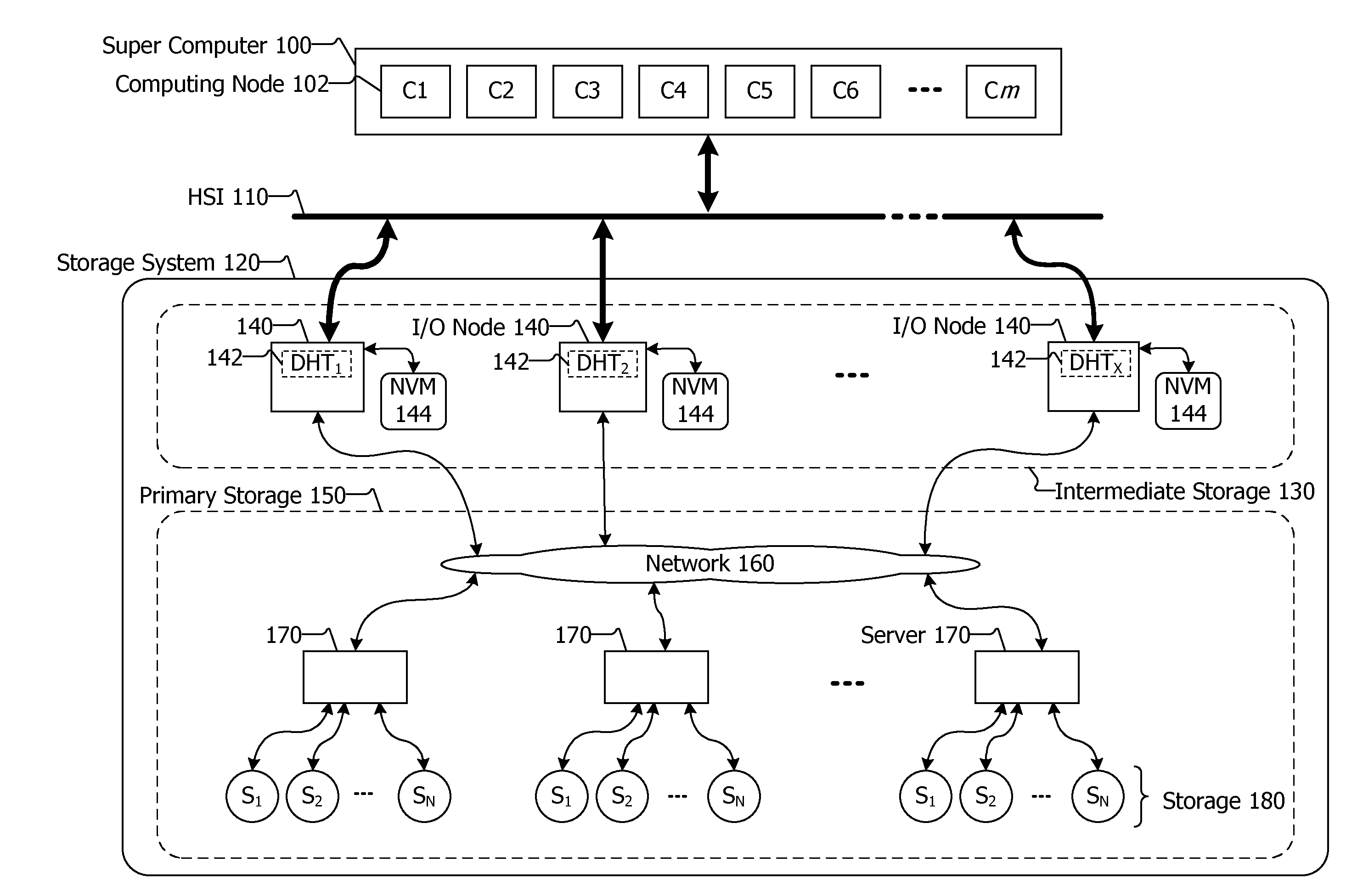
Data storage systems and methods for storing data are described herein. The storage system may be integrated with or coupled with a compute cluster or super computer having multiple computing nodes. A plurality of nonvolatile memory units may be included with computing nodes, coupled with computing nodes or coupled with input / output nodes. The input / output nodes may be included with the compute cluster or super computer, or coupled thereto. The nonvolatile memory units store data items provided by the computing nodes, and the input / output nodes maintain where the data items are stored in the nonvolatile memory units via a hash table distributed among the input / output nodes. The use of a distributed hash table allows for quick access to data items stored in the nonvolatile memory units even as the computing nodes are writing large amounts of data to the storage system quickly in bursts.
Owner:DATADIRECT NETWORKS
Distributed hash table in opposite account
InactiveCN1731742ARapid positioningImprove robustnessData switching networksClockwiseComputer science
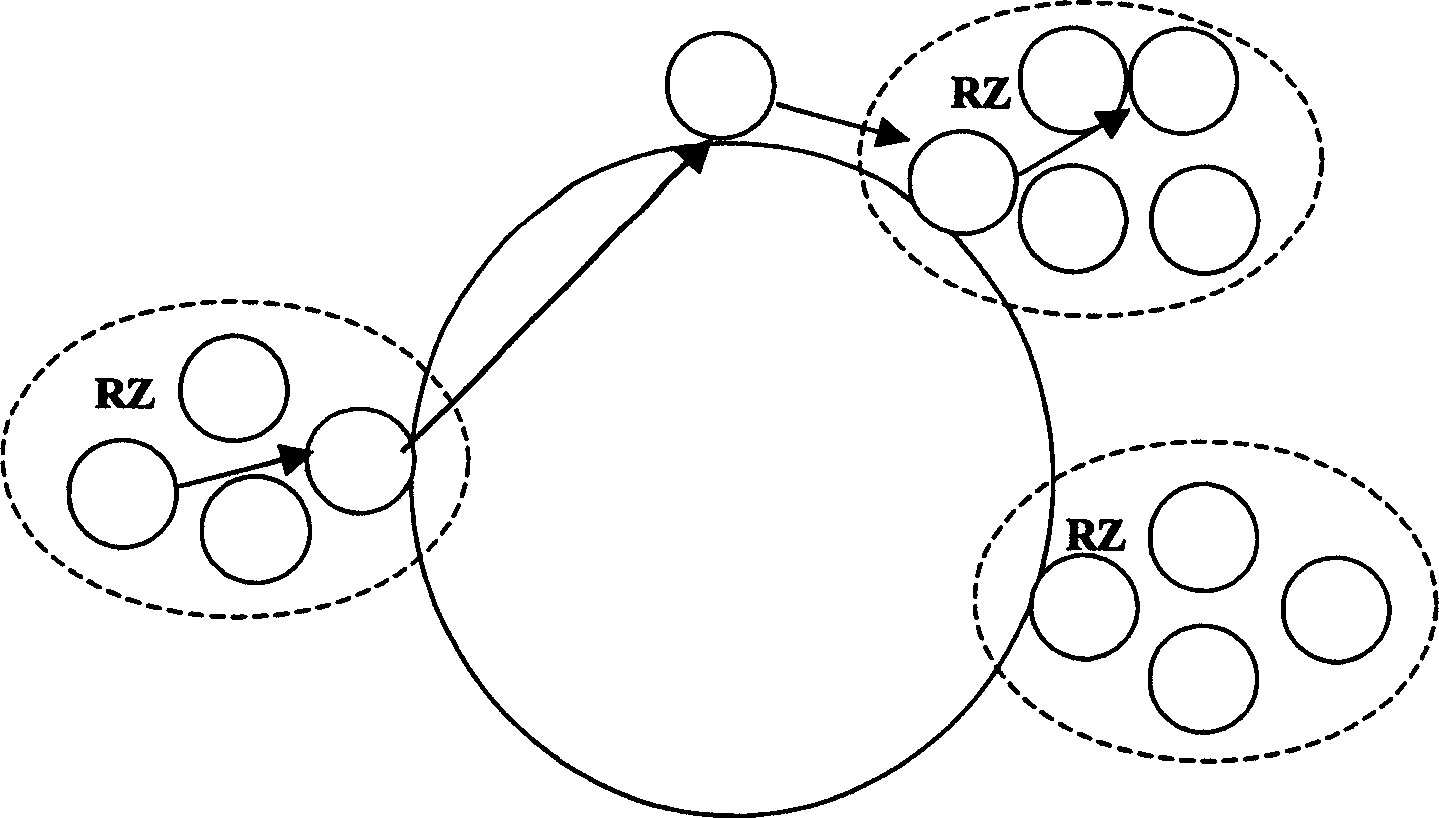
This invention relates to a distributed-type chord used in the condition of open peer-to-peer, which provides a rapid, effective and reliable source-locating technology to motivate the application of p2p. The invention is attained by mapping compatibly in clockwise and counter-clock wise directions in chord space ring to compensate for the non-uniform of source location in one direction, and makes the set points in p2p net form a distributed chord ring, every set points maps to several general homologue points, which can reduce the time of source location and expand effective management region of p2p net.
Owner:NANJING UNIV OF POSTS & TELECOMM
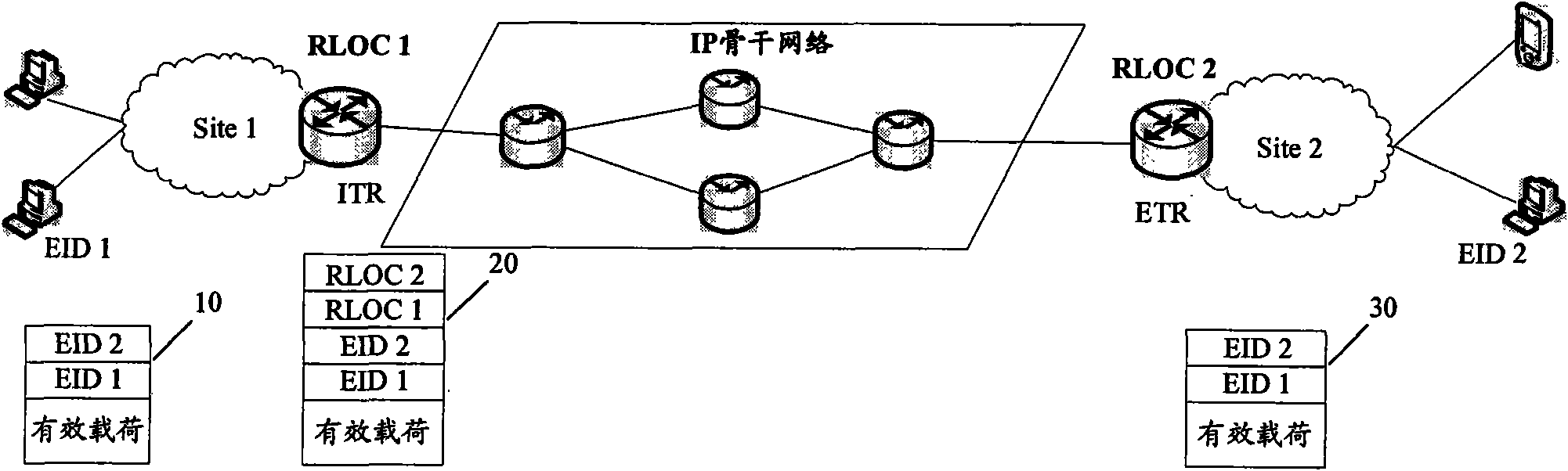
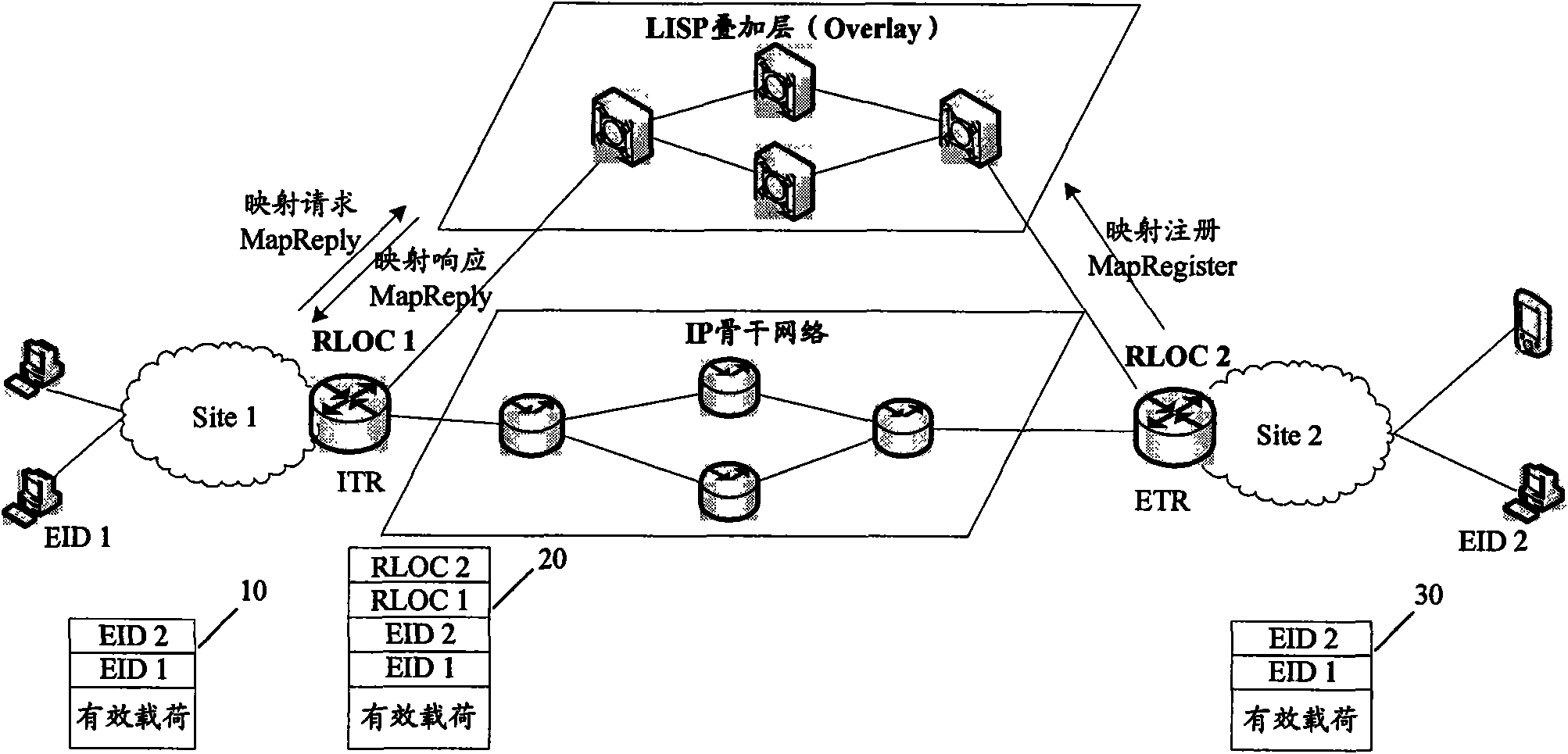
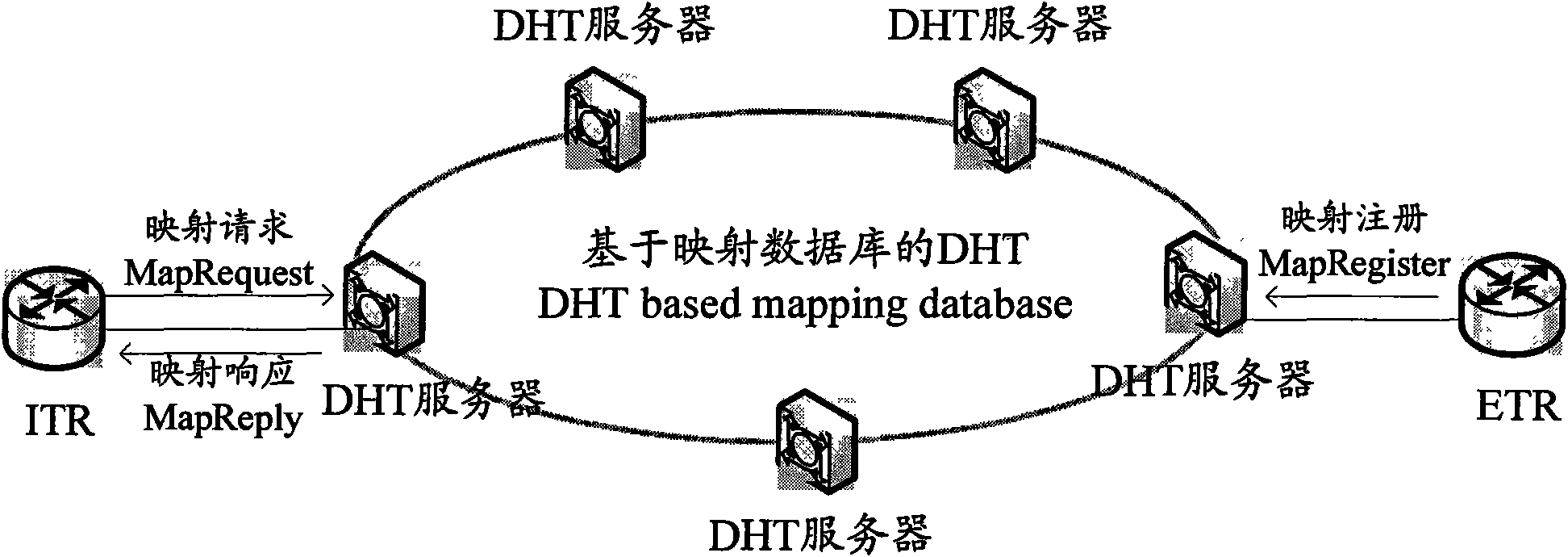
Data switching system and method based on locator identify separation protocol (LISP)
ActiveCN101945034AClear functionSimple data transferData switching networksComputer terminalProtocol for Carrying Authentication for Network Access
The invention discloses a data switching system based on a locator identify separation protocol (LISP), which comprises an IP backbone network and more than one tunneling router. The data switching system is characterized in that the system also comprises an LISP superimposed layer for storing the mapping relationship between an endpoint identifier (EID) and a routing locator (RLOC); the LISP superimposed layer comprises at least one distributed hash table (DHT) server; and the tunneling router is connected with the DHT server, and is used for transmitting a mapping request or a mapping register to the DHT server and receiving a mapping response from the DHT server. The invention also discloses an LISP data switching method. By using the invention, the mapping from the EID to the RLOC can be simply and conveniently realized, thereby flexibly completing the switching of LISP data.
Owner:HUAWEI TEHCHNOLOGIES CO LTD
Method and system for searching data in P2P network base on distributed Hash table
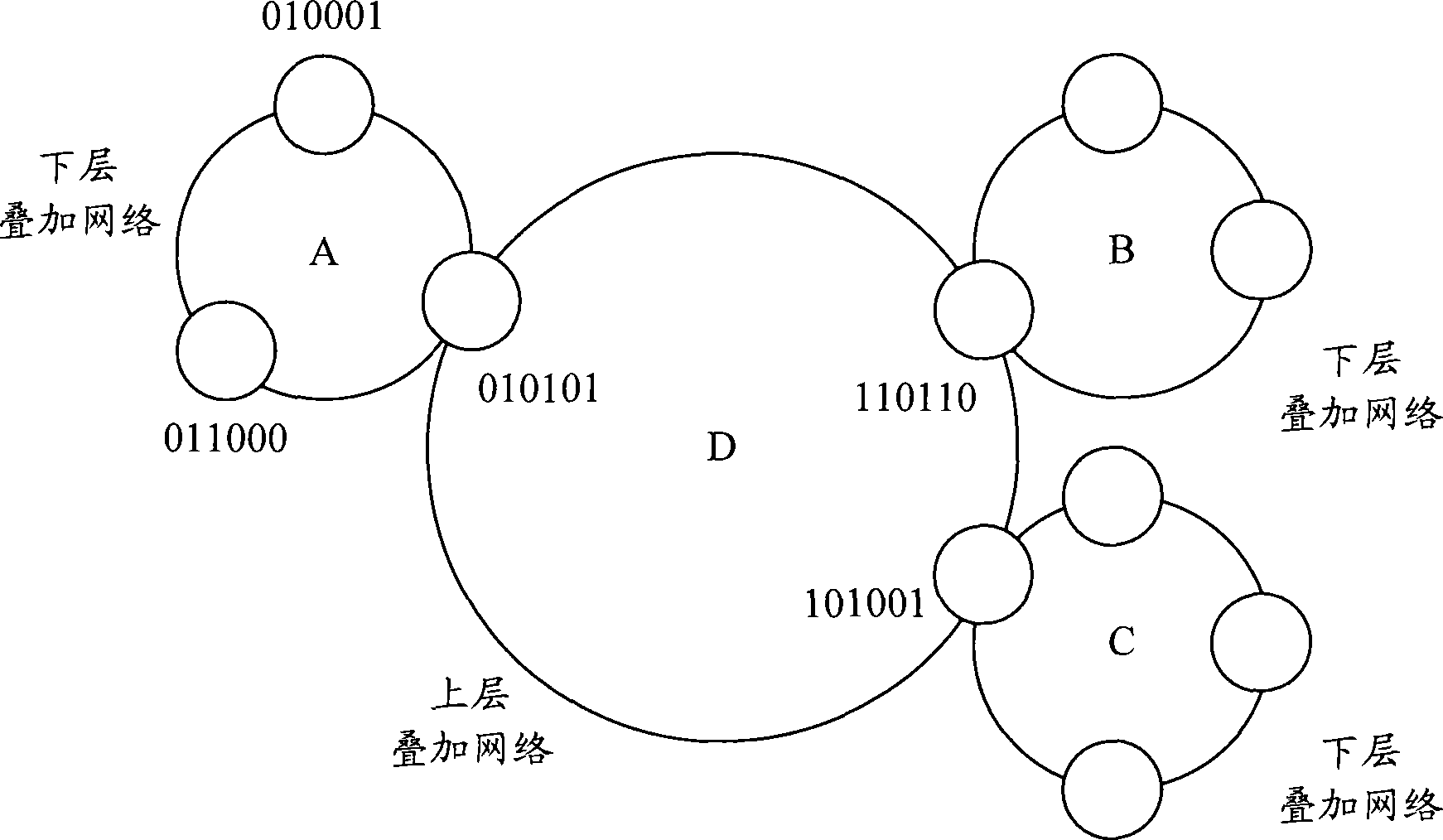
InactiveCN101399743AImprove query efficiencyStore-and-forward switching systemsNetworks interconnectionData nodeA domain
The invention discloses a method for searching data in the P2P network which is based on distribution hash table; the P2P network comprises at least two layers of networks which are overlapped; every overlapped network comprises at least one node and the identifier of the node comprises a domain identifier and a local identifier; the neighboring two overlapped networks transfer data by super-nodes; the method comprises that a first super-node of the upper overlapped network receives an inquiry request; the inquiry request comprises the domain identifier and local identifier of the data package which needs to be searched; a second super-node which is provided with the same domain identifier as the identifier of the inquiry request is searched from the first super-node in the upper overlapped network; the data node is searched according to the local identifier in the inquiry request in the lower overlapped network in which the second super-node is located. The invention also discloses the corresponding system and node. By adopting the invention, different key words are adopted for inquiring in different layers of the overlapped networks and the inquiry efficiency can be improved.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com