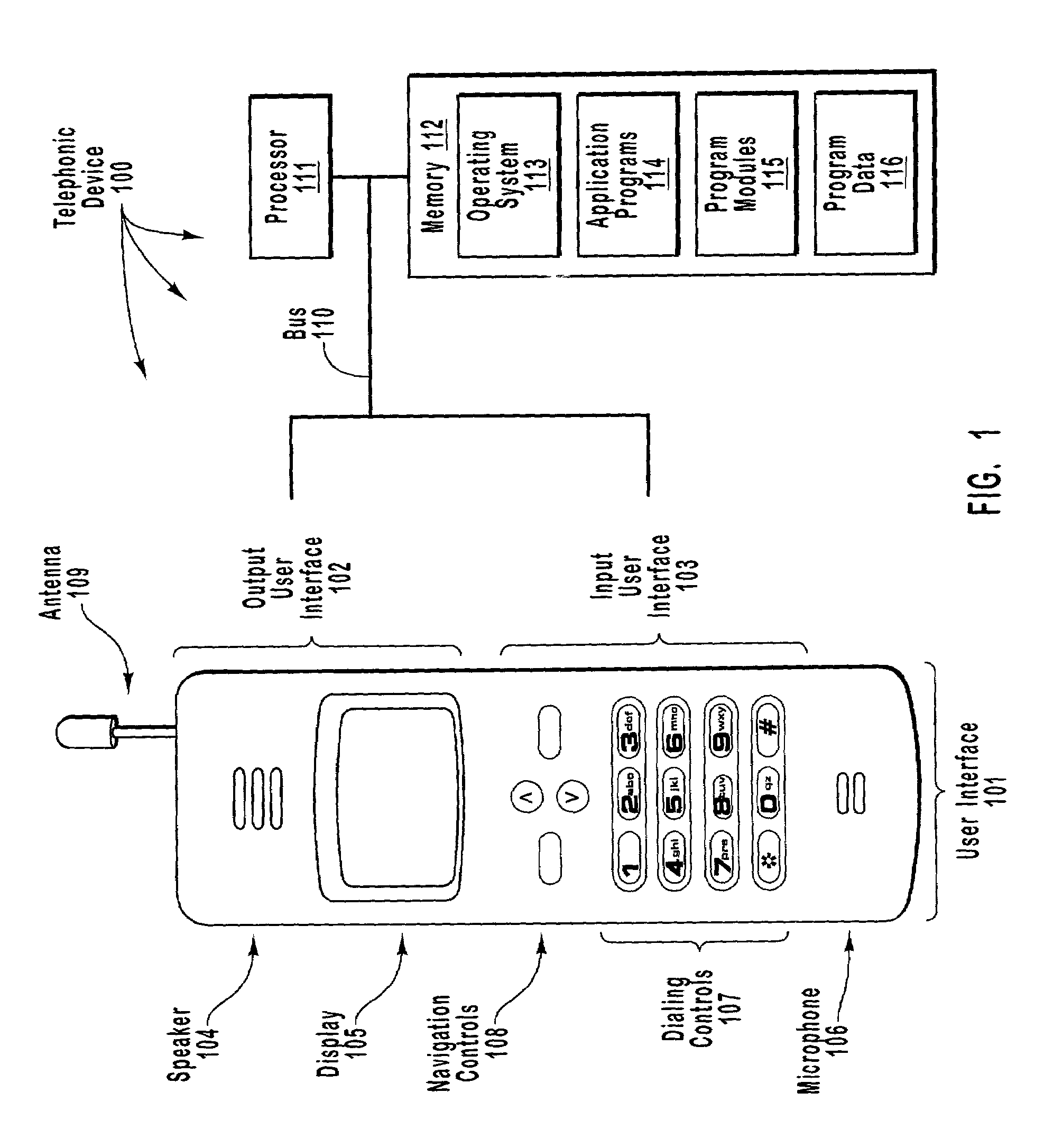
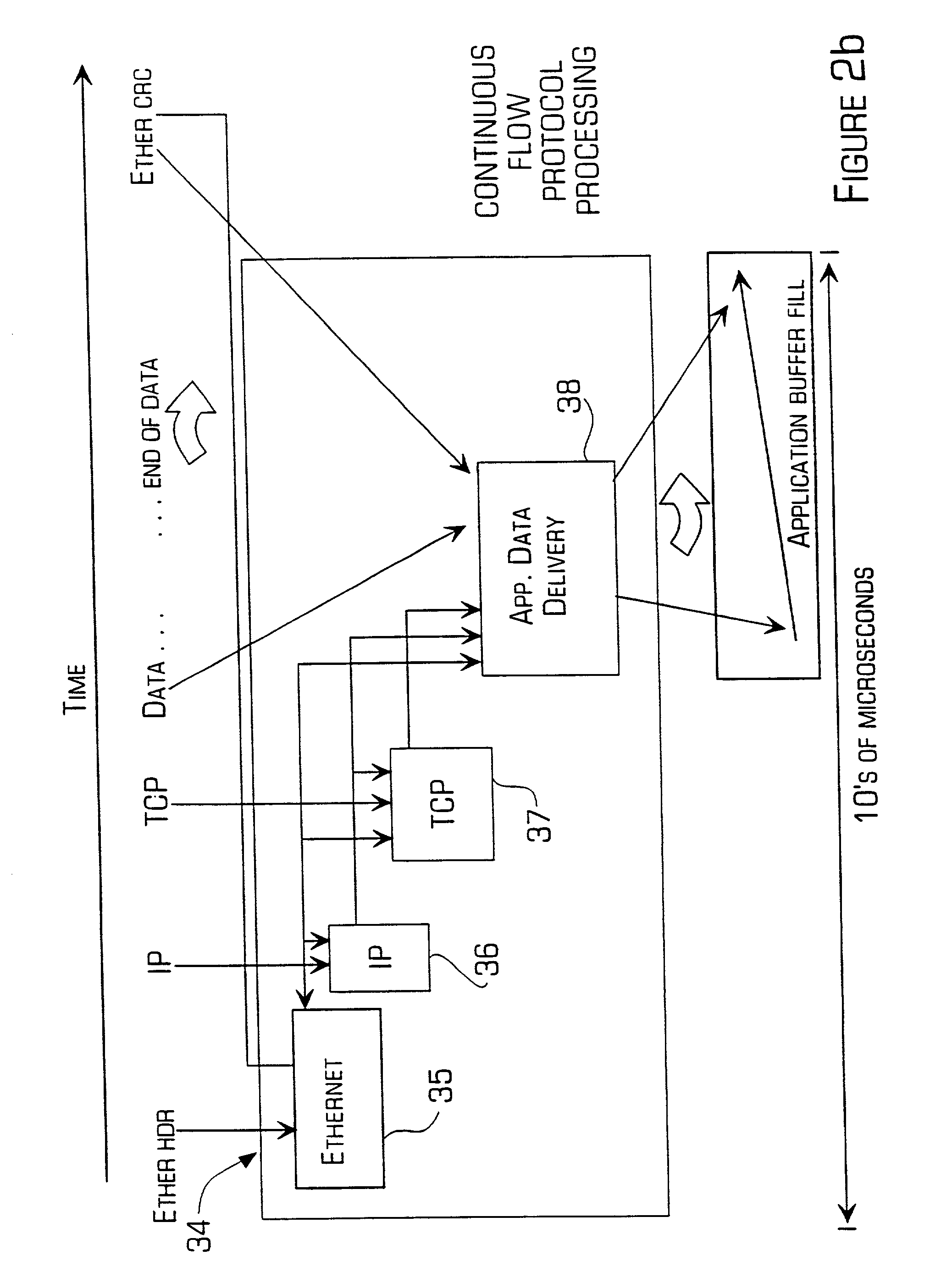
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3411 results about "Transmission protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
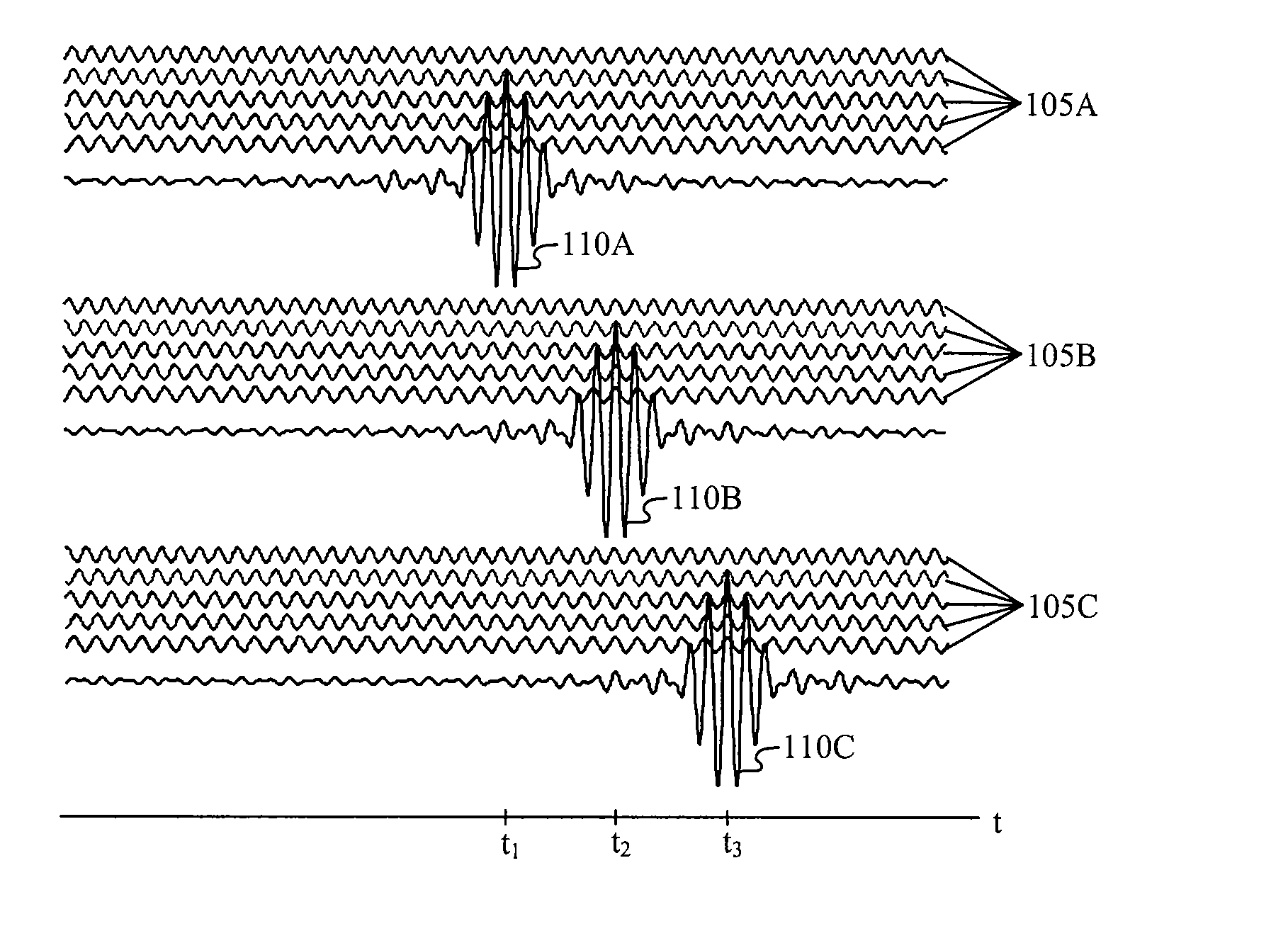
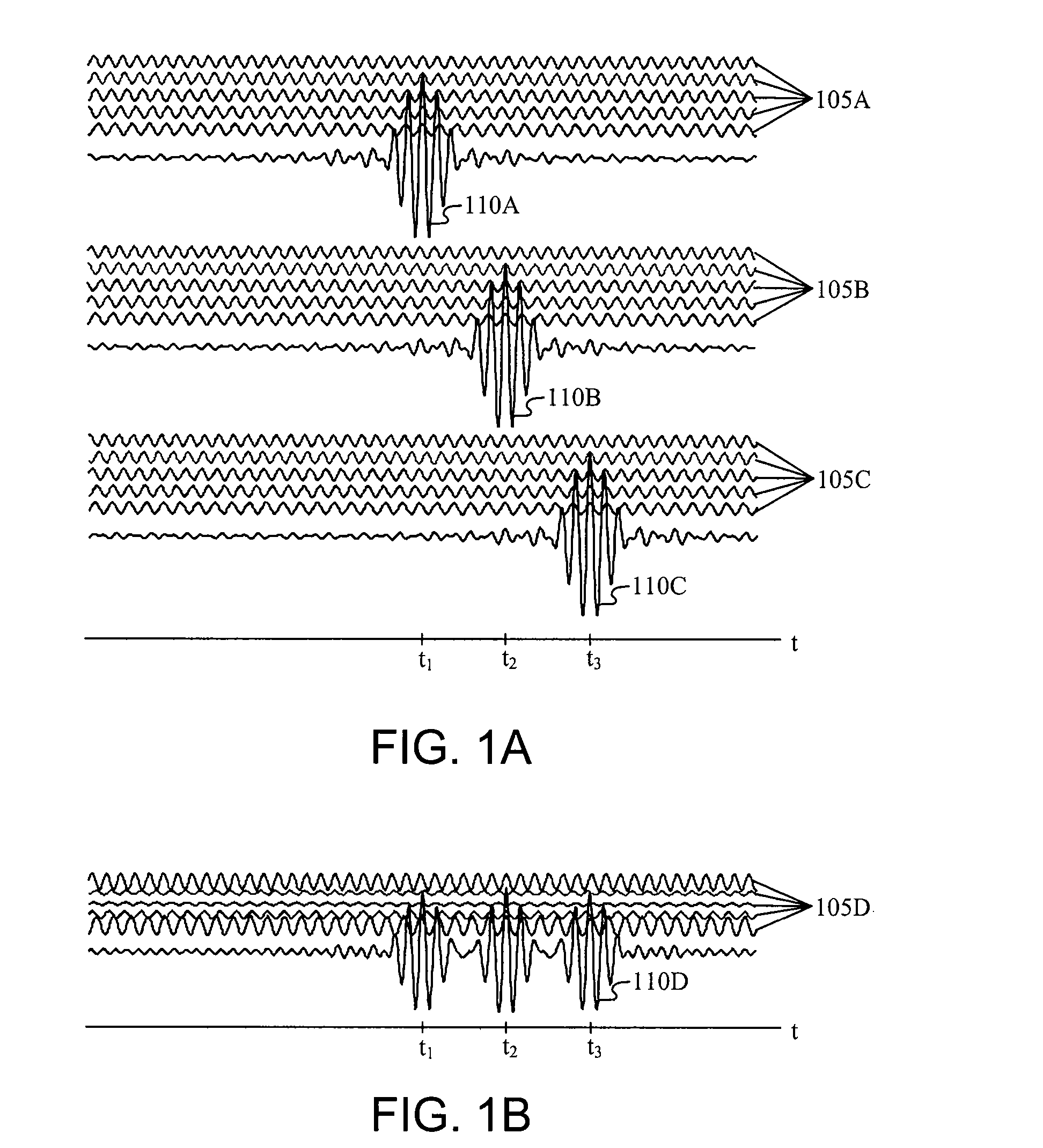
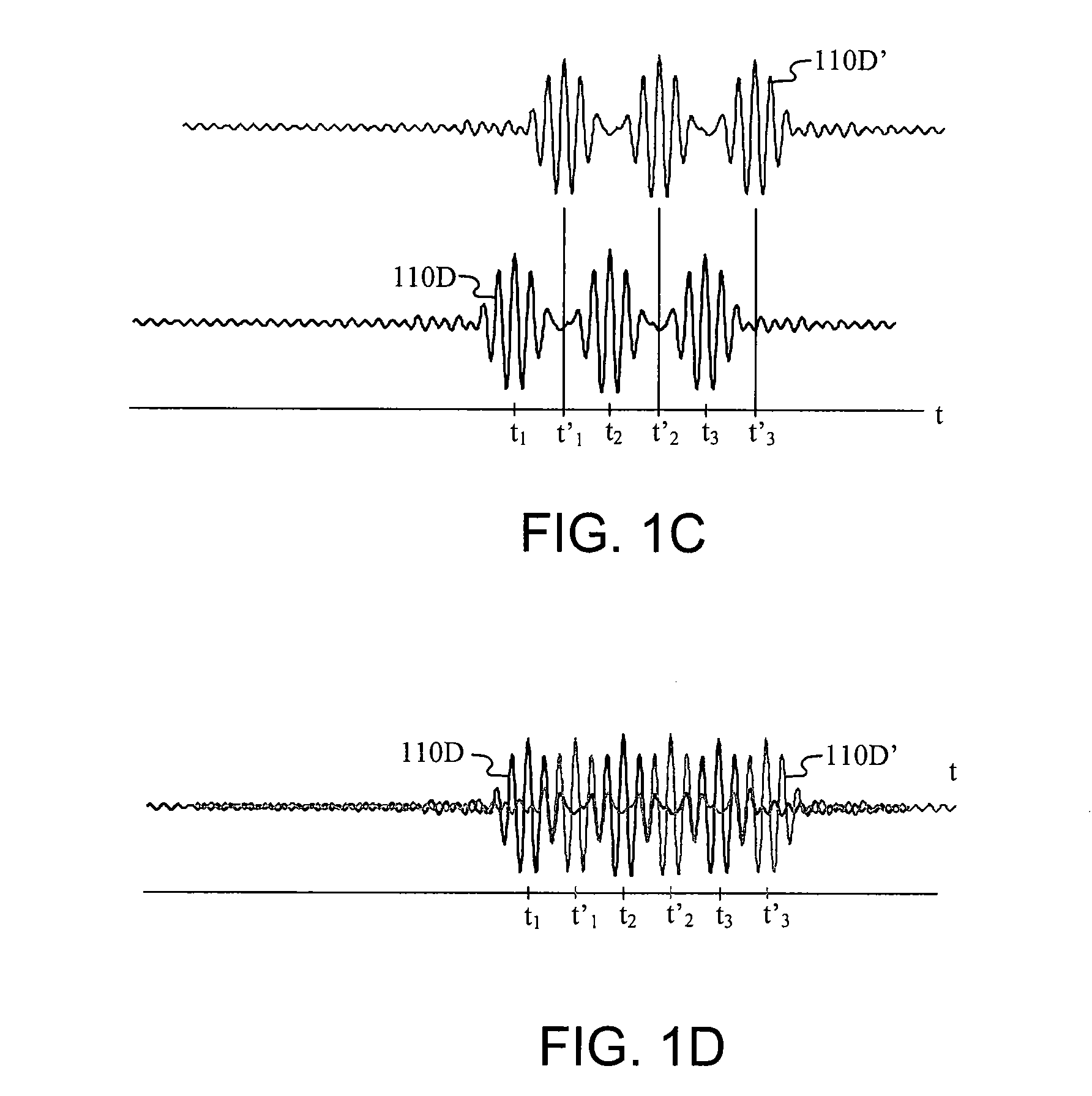
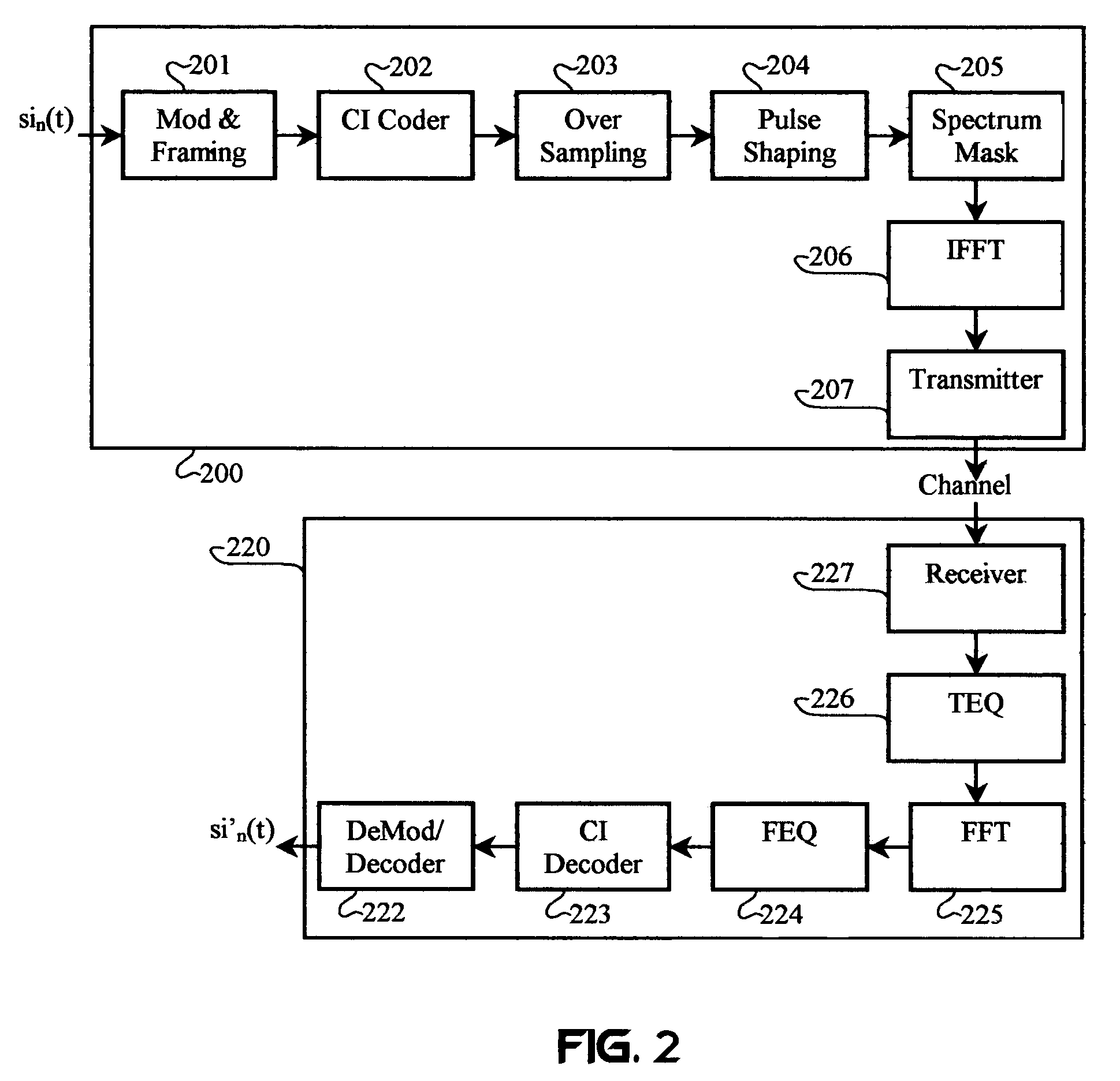
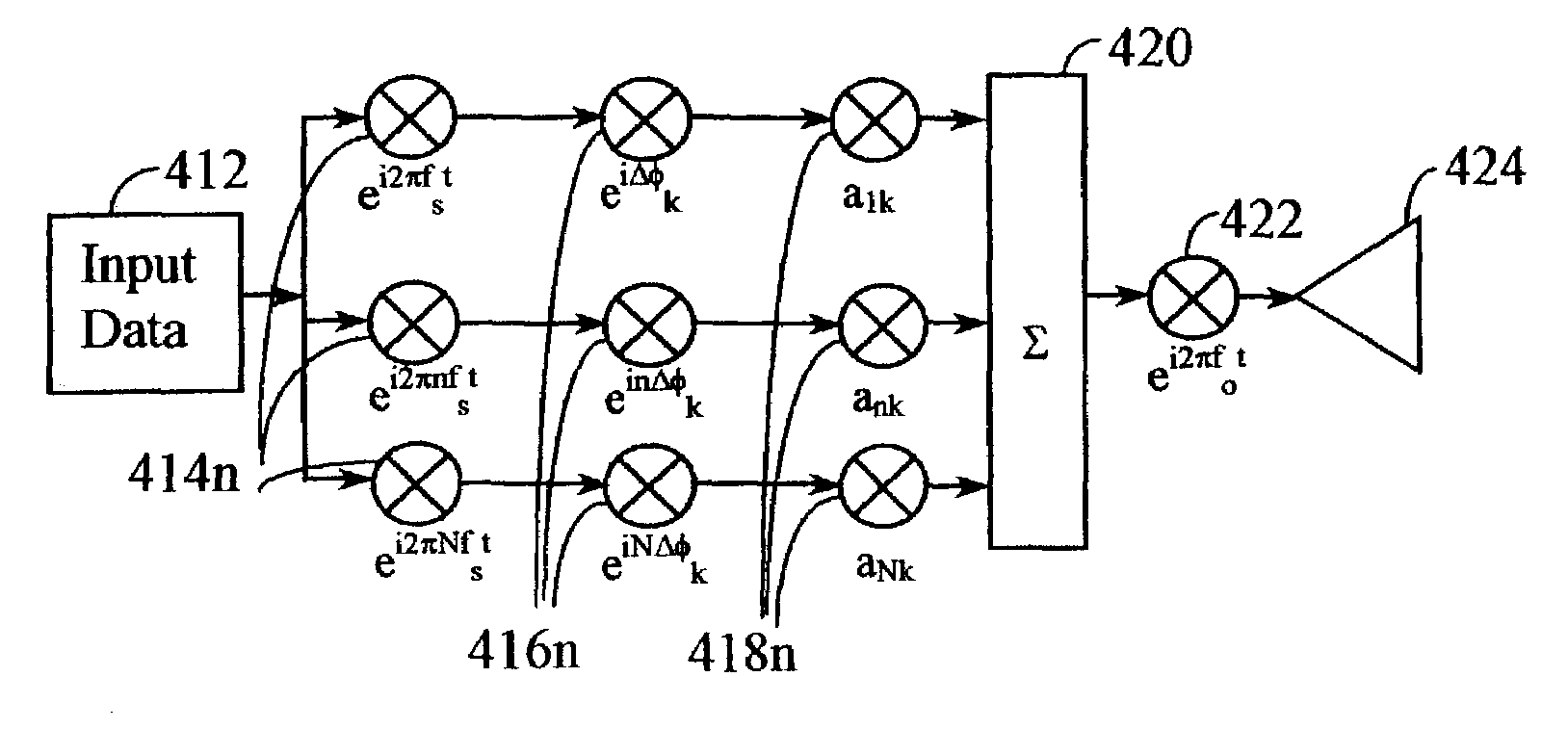
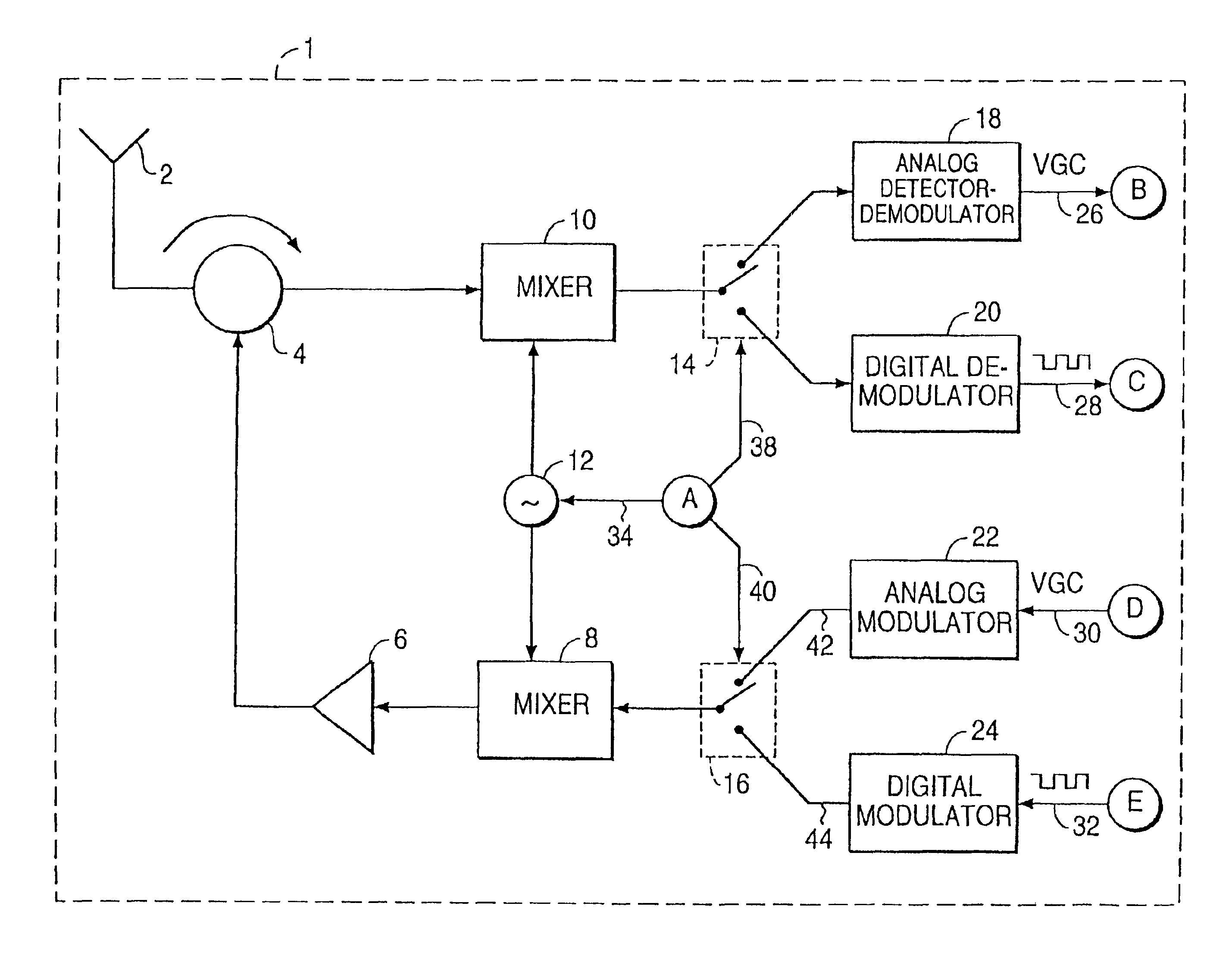
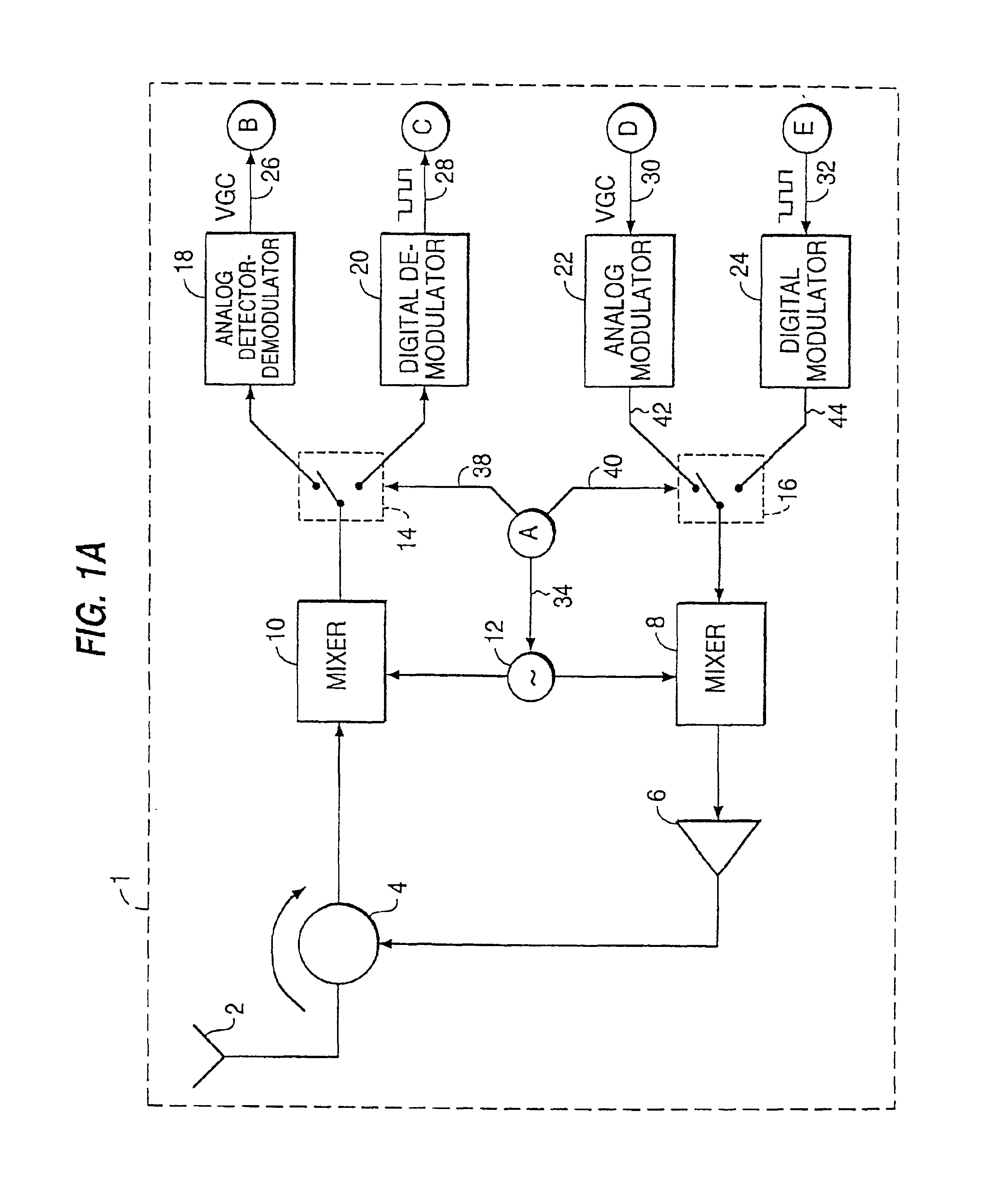
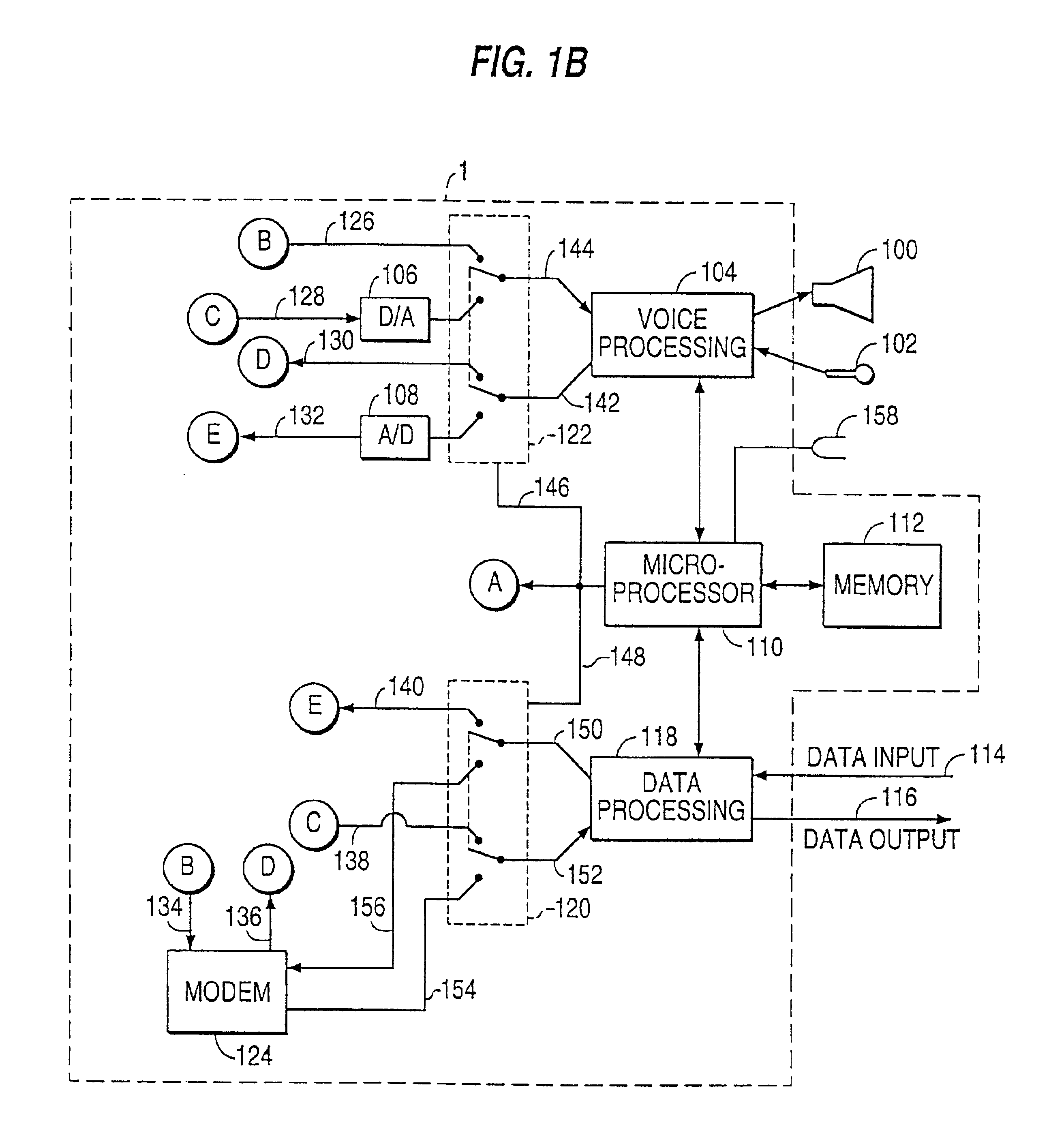
Multicarrier Sub-Layer for Direct Sequence Channel and Multiple-Access Coding
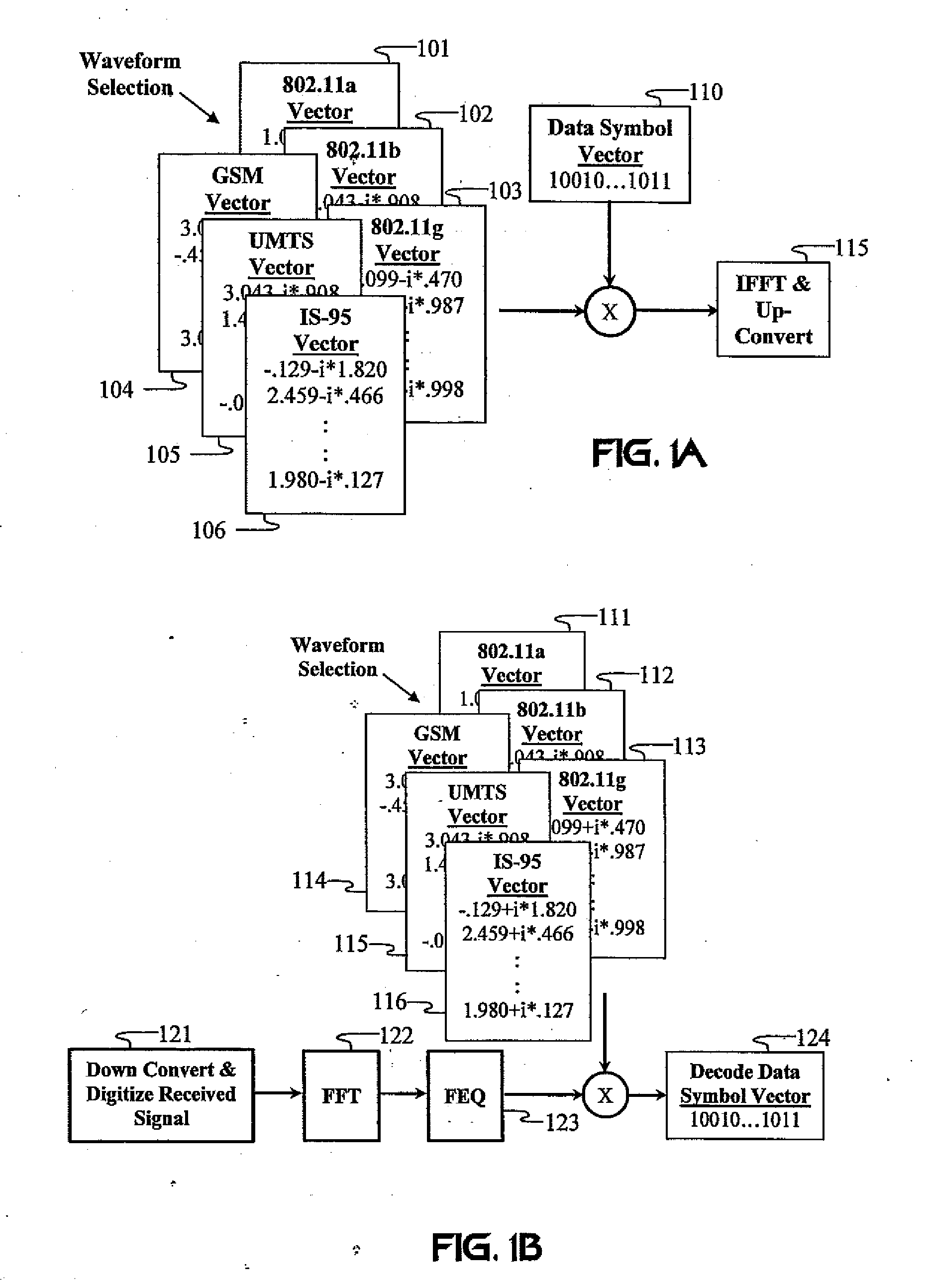
InactiveUS20070211786A1Low costImprove system performanceSecret communicationMultiplex code generationUltra-widebandTransmission protocol
Carrier Interferometry (CI) provides wideband transmission protocols with frequency-band selectivity to improve interference rejection, reduce multipath fading, and enable operation across non-continuous frequency bands. Direct-sequence protocols, such as DS-CDMA, are provided with CI to greatly improve performance and reduce transceiver complexity. CI introduces families of orthogonal polyphase codes that can be used for channel coding, spreading, and / or multiple access. Unlike conventional DS-CDMA, CI coding is not necessary for energy spreading because a set of CI carriers has an inherently wide aggregate bandwidth. Instead, CI codes are used for channelization, energy smoothing in the frequency domain, and interference suppression. CI-based ultra-wideband protocols are implemented via frequency-domain processing to reduce synchronization problems, transceiver complexity, and poor multipath performance of conventional ultra-wideband systems. CI allows wideband protocols to be implemented with space-frequency processing and other array-processing techniques to provide either or both diversity combining and sub-space processing. CI also enables spatial processing without antenna arrays. Even the bandwidth efficiency of multicarrier protocols is greatly enhanced with CI. CI-based wavelets avoid time and frequency resolution trade-offs associated with conventional wavelet processing. CI-based Fourier transforms eliminate all multiplications, which greatly simplifies multi-frequency processing. The quantum-wave principles of CI improve all types of baseband and radio processing.
Owner:GENGHISCOMM HLDG
Multicarrier sub-layer for direct sequence channel and multiple-access coding
InactiveUS7430257B1Low costPolarisation/directional diversityAmplitude-modulated carrier systemsUltra-widebandTransmission protocol
Carrier Interferometry (CI) provides wideband transmission protocols with frequency-band selectivity to improve interference rejection, reduce multipath fading, and enable operation across non-continuous frequency bands. Direct-sequence protocols, such as DS-CDMA, are provided with CI to greatly improve performance and reduce transceiver complexity. CI introduces families of orthogonal polyphase codes that can be used for channel coding, spreading, and / or multiple access. Unlike conventional DS-CDMA, CI coding is not necessary for energy spreading because a set of CI carriers has an inherently wide aggregate bandwidth. Instead, CI codes are used for channelization, energy smoothing in the frequency domain, and interference suppression. CI-based ultra-wideband protocols are implemented via frequency-domain processing to reduce synchronization problems, transceiver complexity, and poor multipath performance of conventional ultra-wideband systems. CI allows wideband protocols to be implemented with space-frequency processing and other array-processing techniques to provide either or both diversity combining and sub-space processing. CI also enables spatial processing without antenna arrays. Even the bandwidth efficiency of multicarrier protocols is greatly enhanced with CI. CI-based wavelets avoid time and frequency resolution trade-offs associated with conventional wavelet processing. CI-based Fourier transforms eliminate all multiplications, which greatly simplifies multi-frequency processing. The quantum-wave principles of CI improve all types of baseband and radio processing.
Owner:GENGHISCOMM HLDG
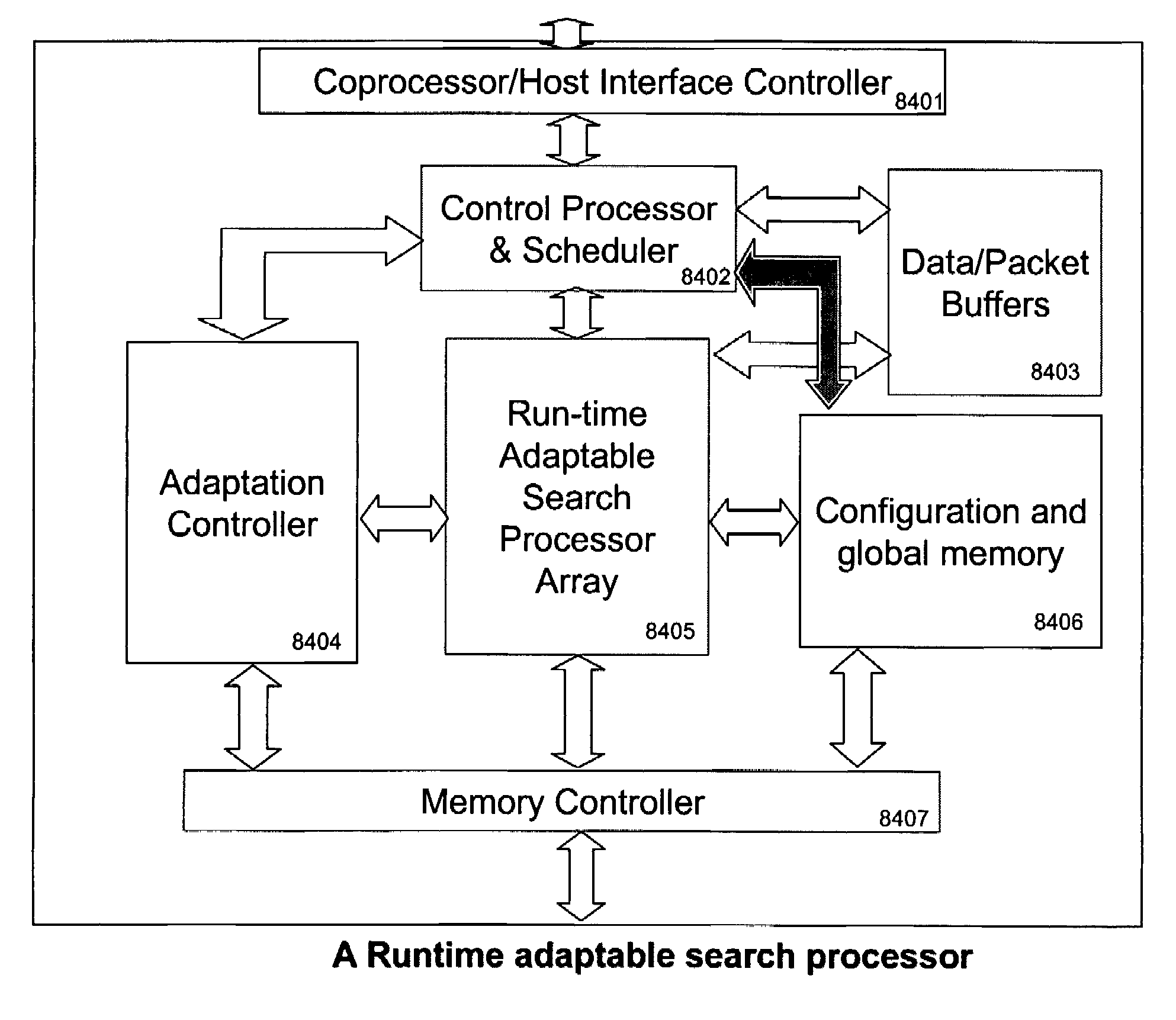
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Proxying hypertext transfer protocol (HTTP) requests for microservices
In various embodiments, a gateway application generates an outgoing Hypertext Transmission Protocol (HTTP) request based on an incoming HTTP request. In operation, the gateway application receives the incoming HTTP request and identifies an upstream service based on at least one of an HTTP method and a header included in the incoming HTTP request. Subsequently, the gateway application generates an outgoing HTTP request based on the upstream service and the incoming HTTP request. Finally, the gateway application issues the outgoing HTTP request. The outgoing HTTP request causes the upstream service to perform an action requested in the incoming HTTP request. Advantageously, the gateway application enables underlying upstream services to perform actions specified via incoming HTTP requests without directly exposing the upstream services to users.
Owner:SPLUNK INC
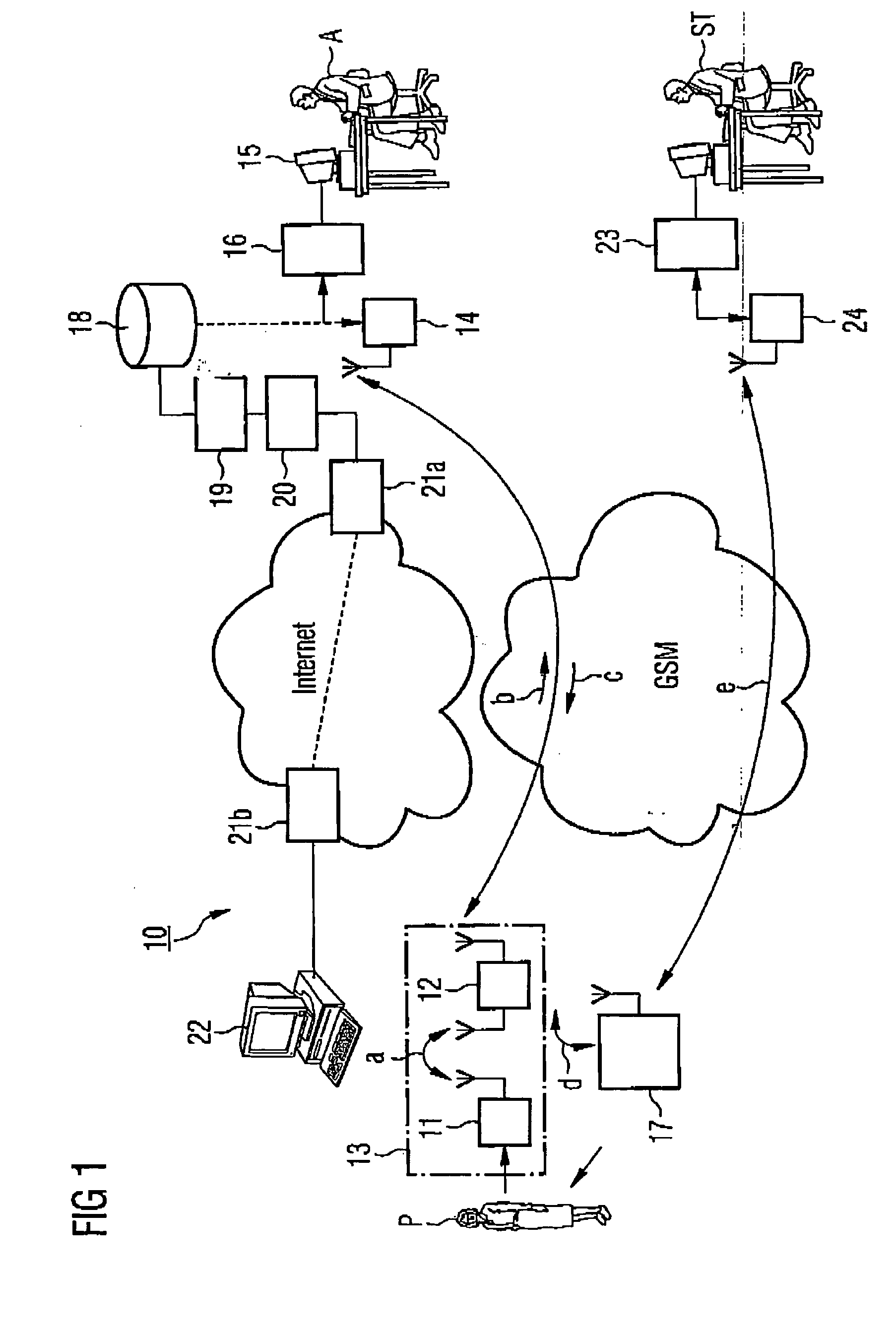
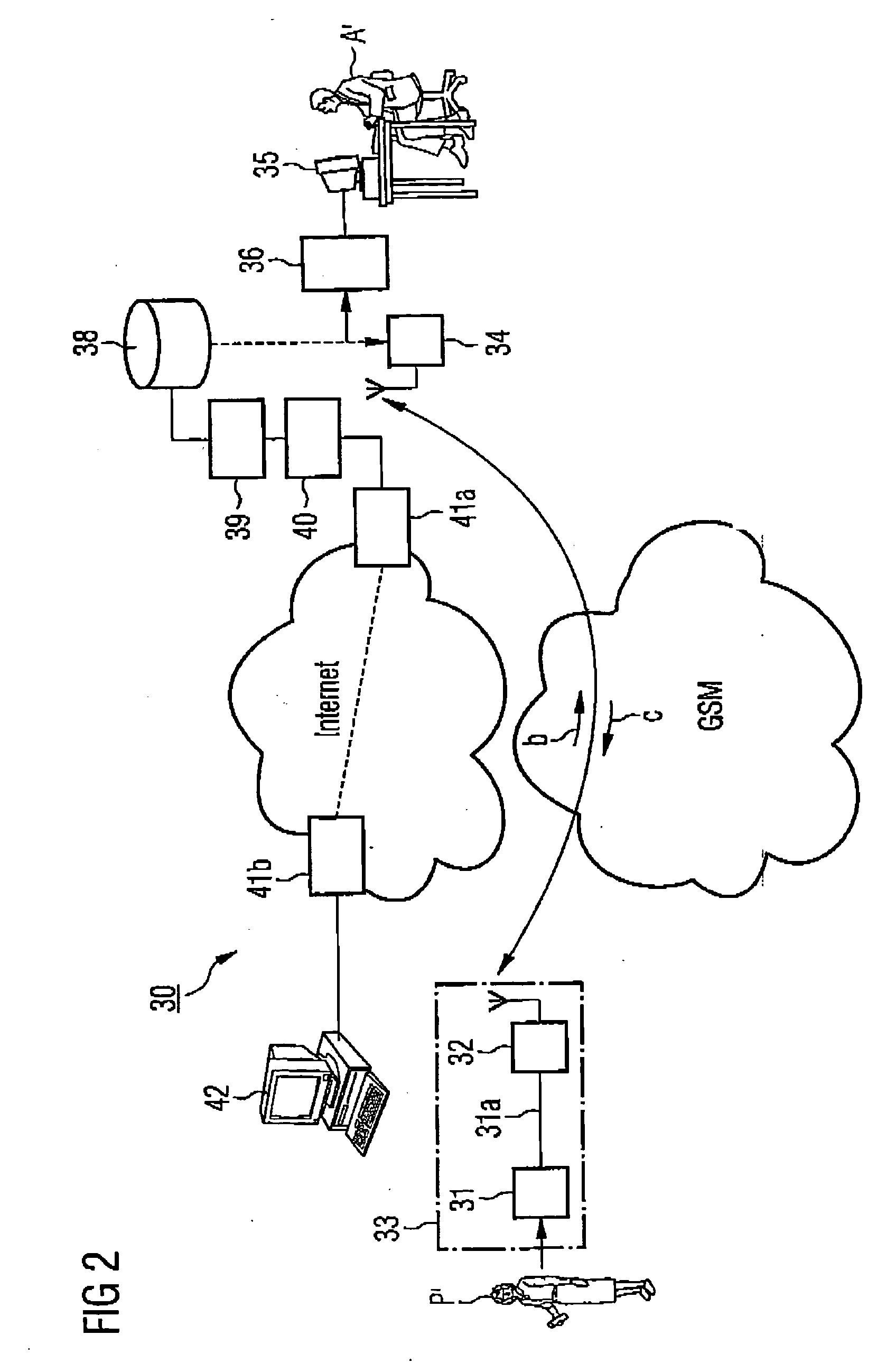
Arrangement of equipment for remote monitoring of bodily functions
InactiveUS20070282177A1Improve availabilityConvincing reliability of monitoringLocal control/monitoringDrug and medicationsTransmission protocolTelecommunications network
An arrangement of equipment for the remote monitoring of bodily functions of a mammal under medical care, comprises: a function-measurement device to measure a physiological quantity relevant to bodily function; a first display unit disposed remotely from the function-measurement device and monitored by a responsible medical person, to display the measured values of the measured physiological quantity and a function characterization derived therefrom; an input unit disposed remotely from the function-measurement device, for the input of control commands for the function-measurement device, and to input warning signals; and a bi-directional public telecommunication-network connection with an outward channel between the function-measurement device and the first display unit and a return channel between the input unit and the function-measurement device, where, for each connected device, there is provided an interface adapted to a transmission protocol of the telecommunication network.
Owner:UBICOM GES FUR TELEKOMMUNIKATION
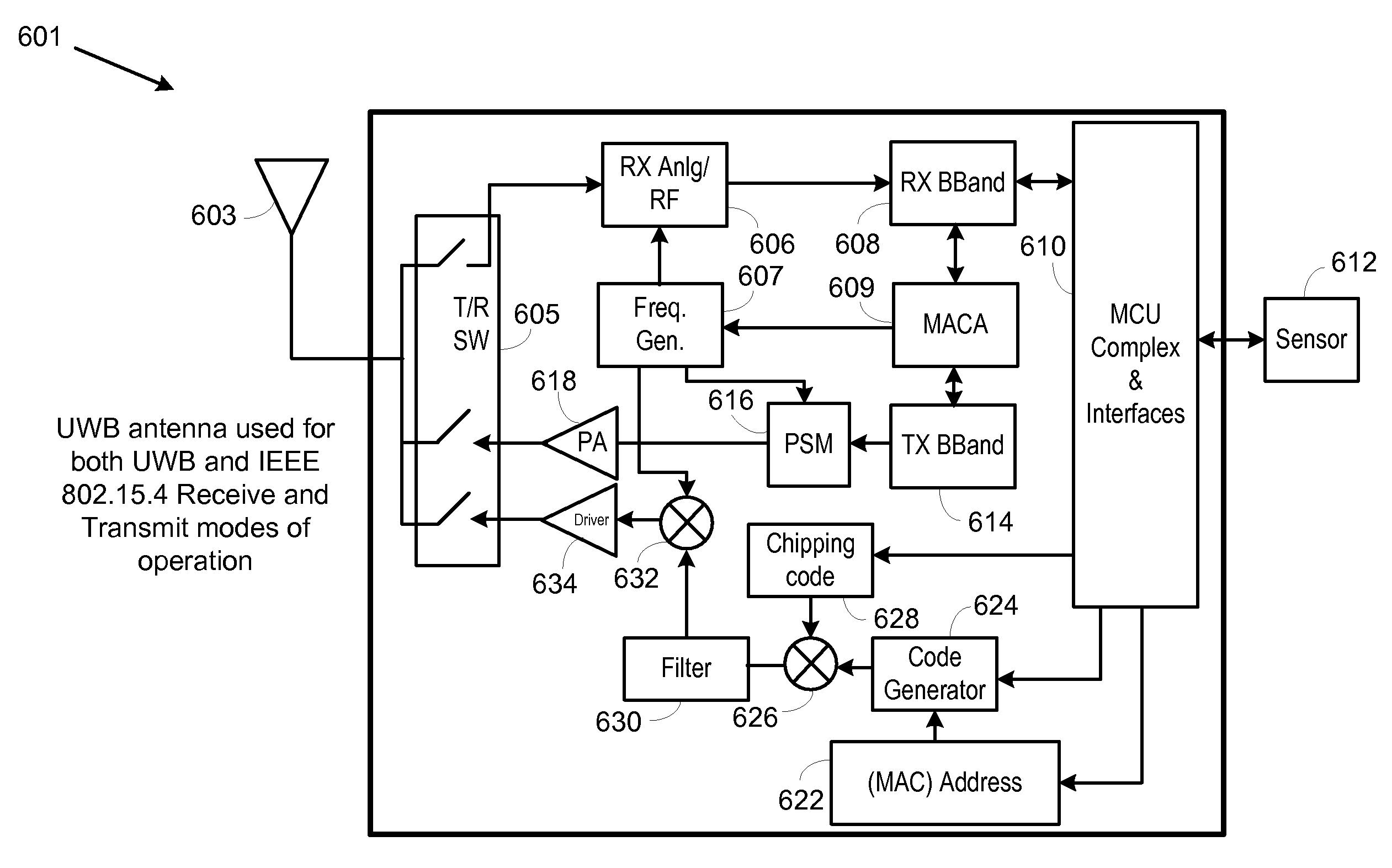
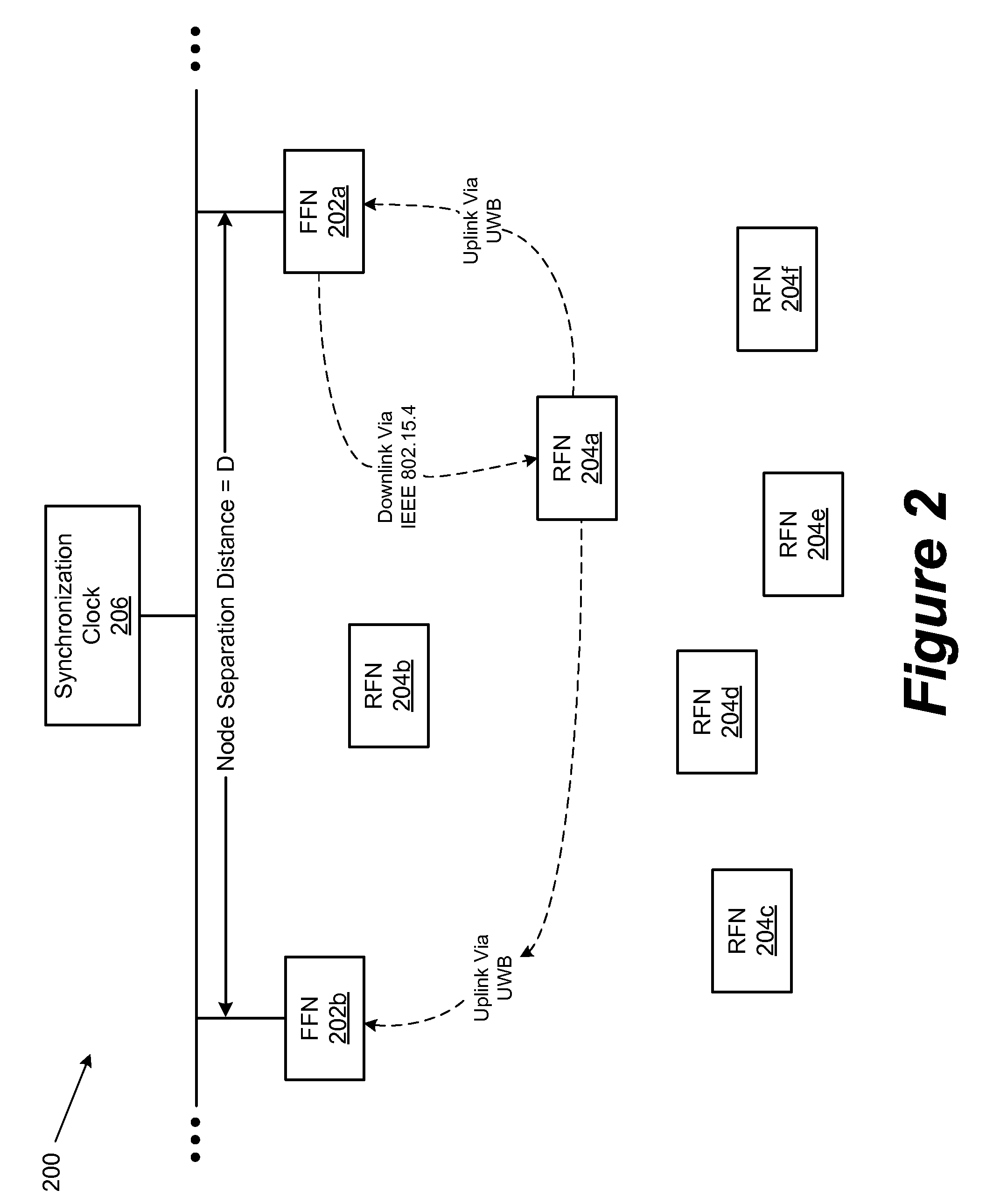
Smart/Active RFID Tag for Use in a WPAN
ActiveUS20090311960A1Near-field transmissionDirection finders using radio wavesTransmission protocolTransceiver
A system and method is provided for processing communication signals in a wireless personal area network (WPAN) using a transceiver comprising a first transmitter and a first receiver operable to transmit and receive signals using a first transmission protocol and a second transmitter operable to transmit signals using a second transmission protocol. In various embodiments, the first receiver is used to receive a first signal that was transmitted using the first communication protocol and the second transmitter is used to transmit a second signal using the second transmission protocol in response to receipt of the first signal. The second signal is then processed to determine the location of the object. In some embodiments, the first transmission protocol is compliant with an Institute of Electrical and Electronics Engineers 802.15.4 transmission protocol and the second transmission protocol is compliant with an Ultra-Wide Band (UWB) protocol.
Owner:NXP USA INC
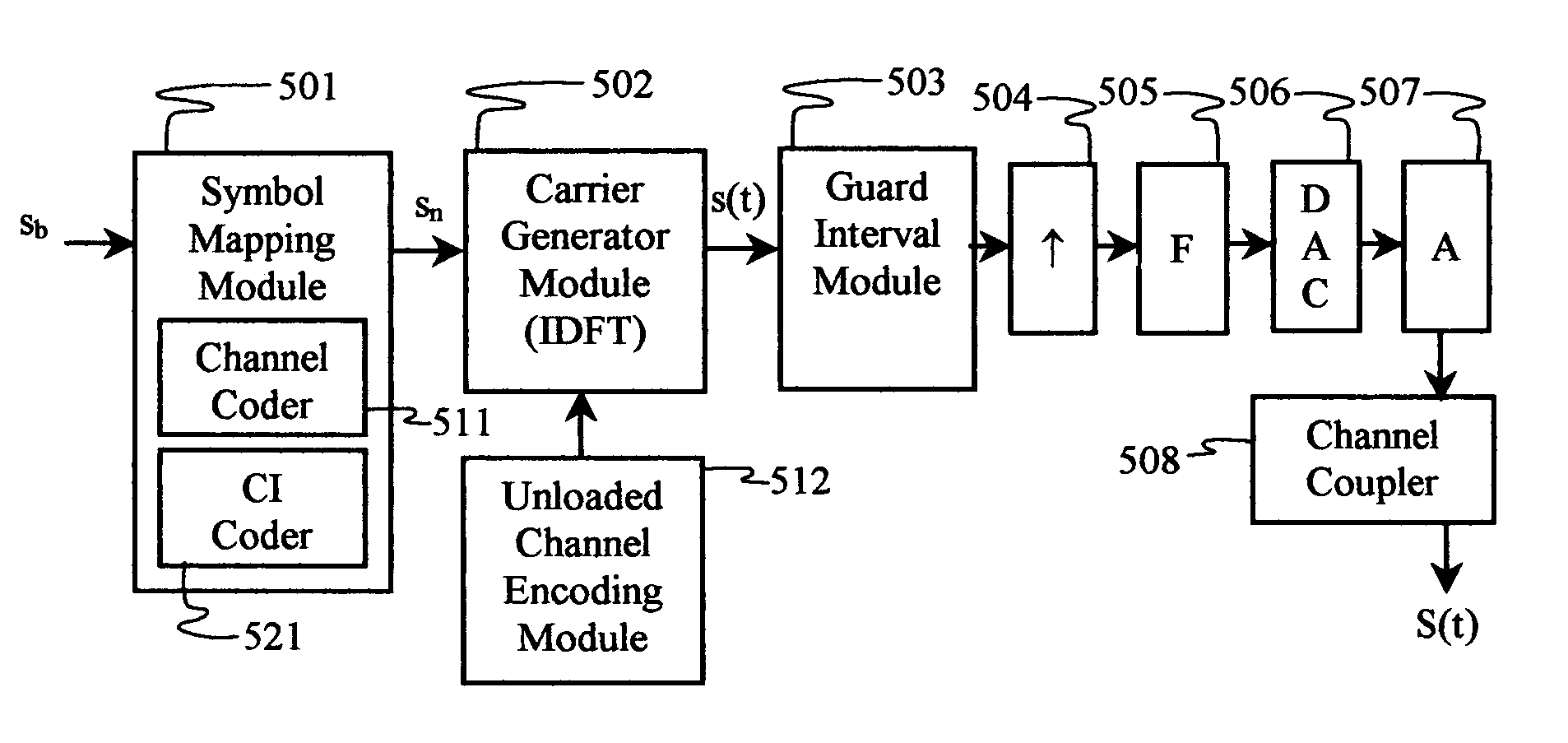
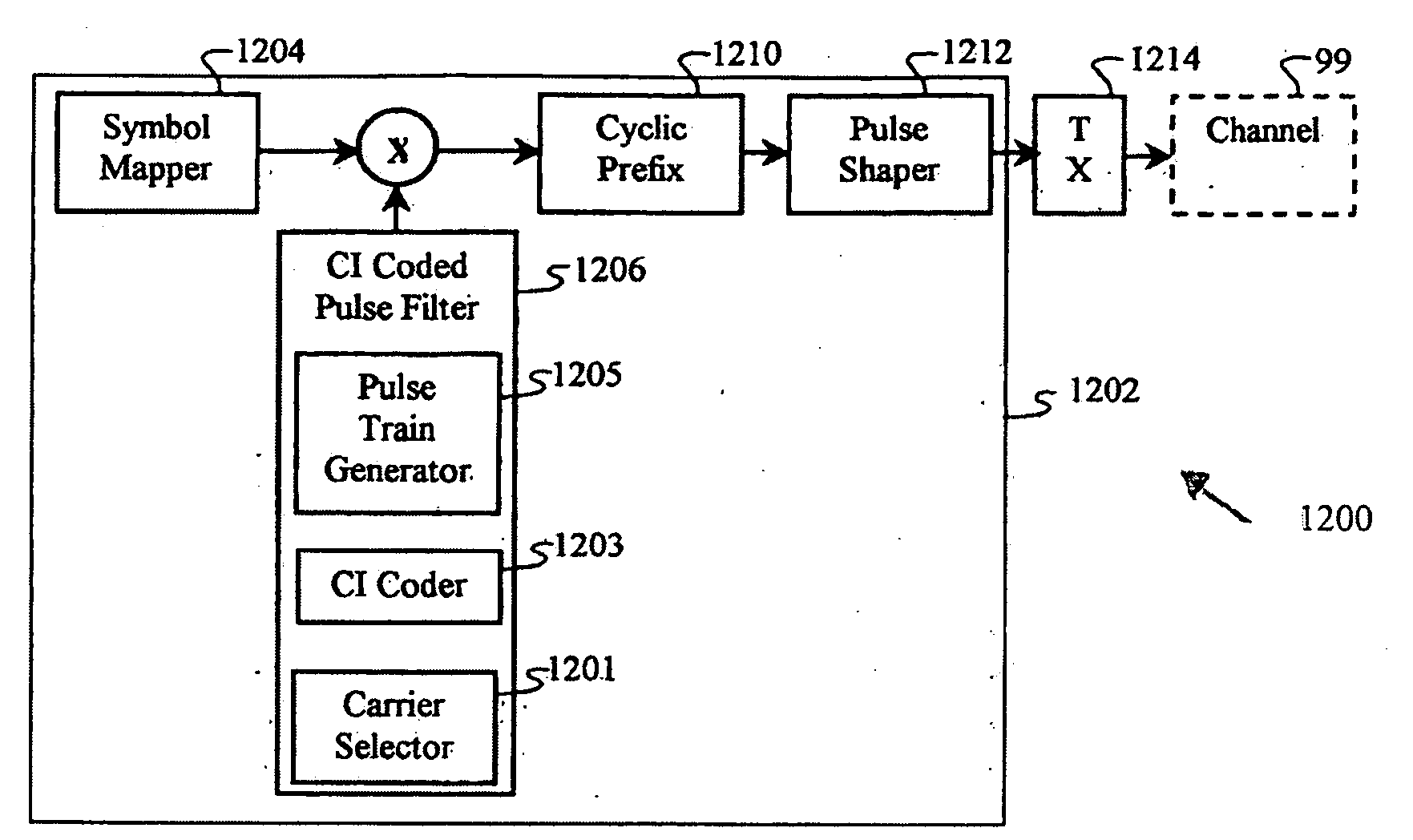
Software adaptable high performance multicarrier transmission protocol
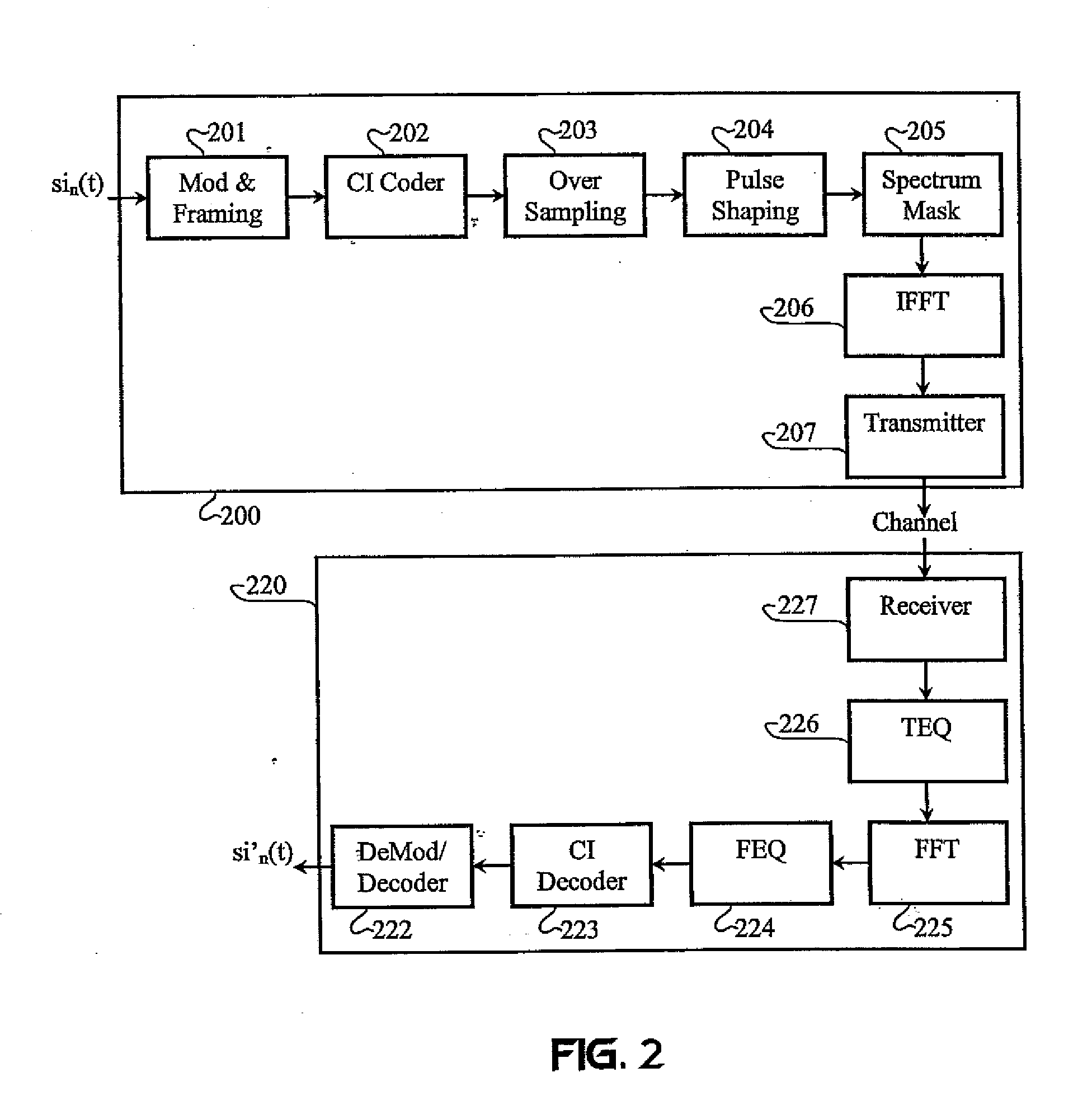
InactiveUS7418043B2Reduce PAPREnhance other technique used for PAPR mitigationModulated carrier system with waveletsSecret communicationTransmission protocolTime domain
Techniques for reducing peak-to-average power in multicarrier transmitters employ peak cancellation with subcarriers that are impaired by existing channel conditions. The use of Carrier Interferometry (CI) coding further improves the effectiveness of peak reduction. CI coding can also be impressed onto pulse sequences in the time domain, which enhances spectral selection and facilitates peak-power control.
Owner:DEPARTMENT 13 INC
Playlists for real-time or near real-time streaming
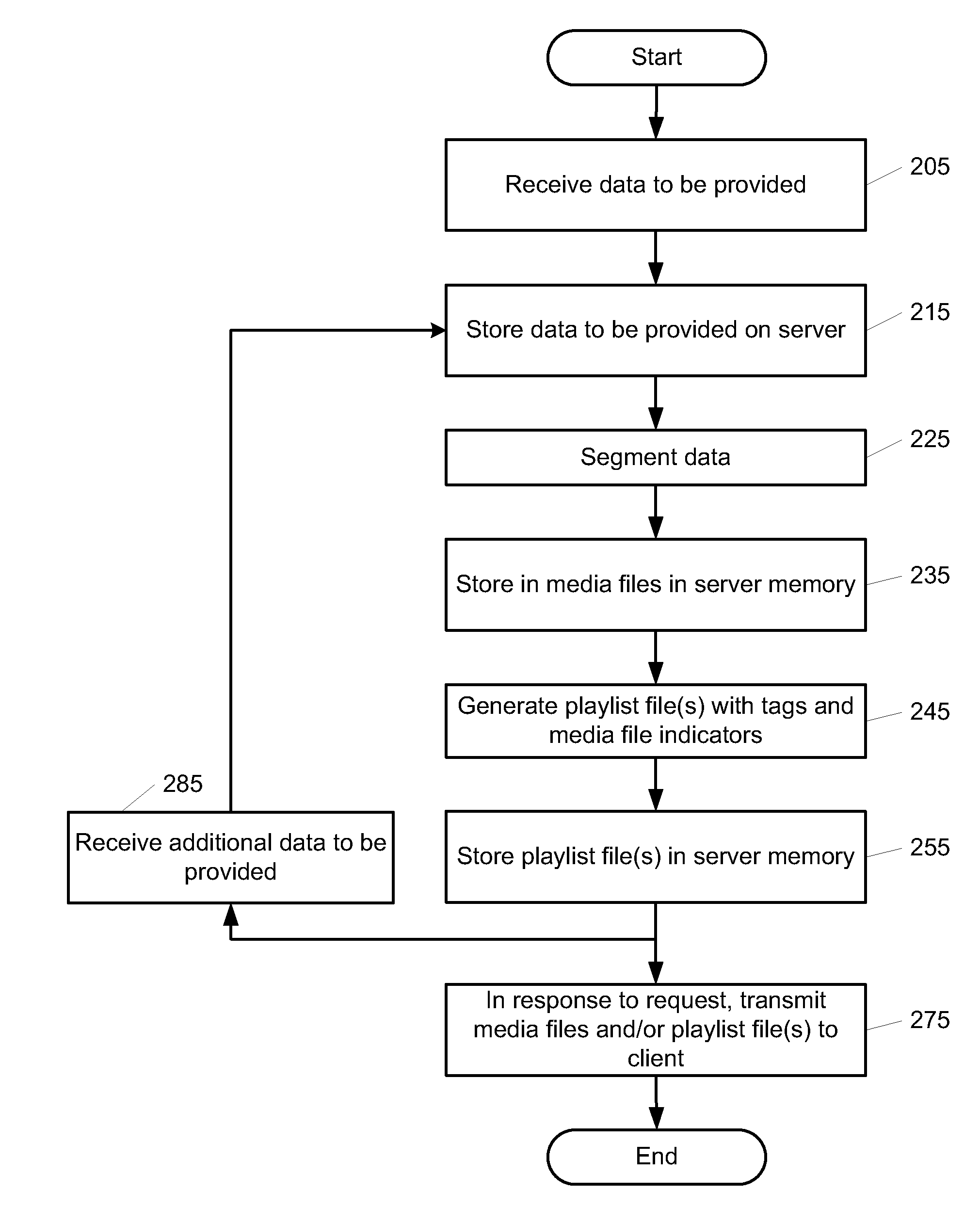
InactiveUS20100169303A1Easy retrievalFacilitate a client in presenting the segmented user dataDigital data processing detailsTelevision systemsData streamClient-side
Methods and apparatuses for real-time or near real-time streaming of content using transfer protocols such as an HTTP compliant protocol. In one embodiment, a method includes dividing a stream of data, representing the contiguous time based content of a program (e.g. a live video broadcast), into a plurality of distinct media files, and generating a playlist file having a plurality of tags and Universal Resource Indicators (URIs) indicating an order of presentation of the plurality of distinct media files. The plurality of media files and the playlist file can be made available for transmission to a client device which can retrieve the media files using the playlist file.
Owner:APPLE INC
TCP/IP processor and engine using RDMA
ActiveUS7376755B2Sharply reduces TCP/IP protocol stack overheadImprove performanceMultiplex system selection arrangementsMemory adressing/allocation/relocationTransmission protocolInternal memory
A TCP / IP processor and data processing engines for use in the TCP / IP processor is disclosed. The TCP / IP processor can transport data payloads of Internet Protocol (IP) data packets using an architecture that provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. The engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a TCP / IP session information database and may also store a storage information session database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer.
Owner:MEMORY ACCESS TECH LLC
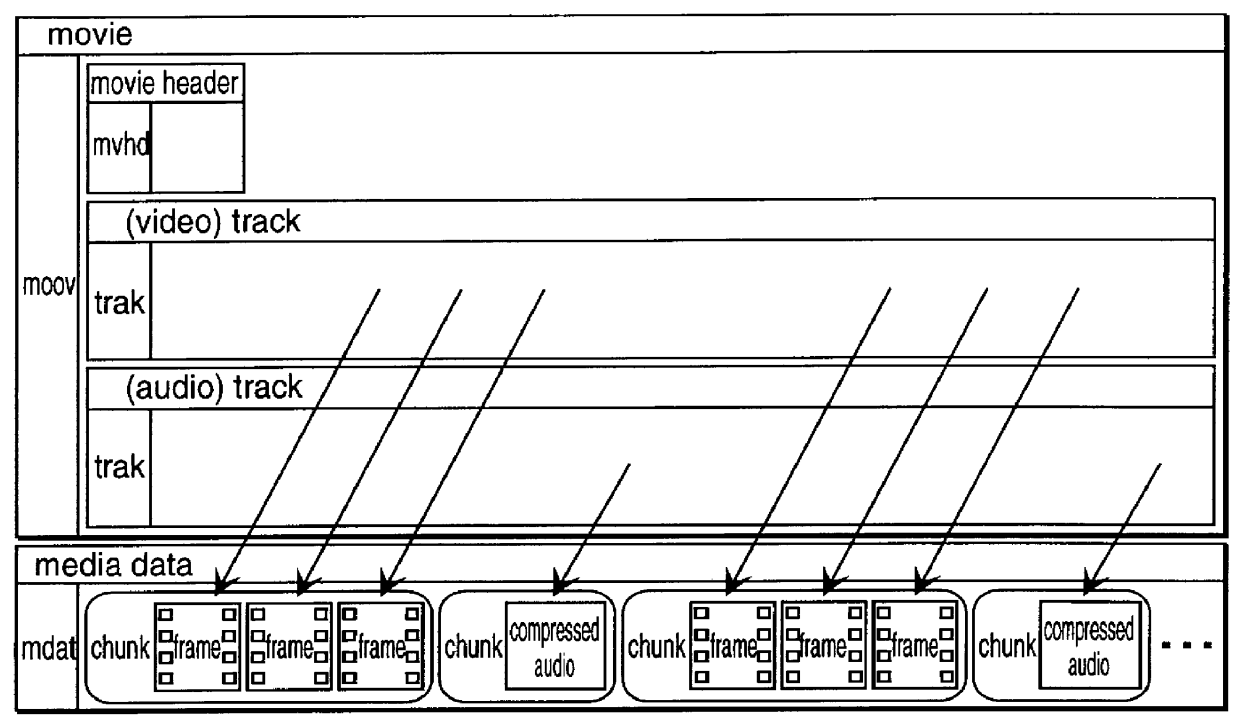
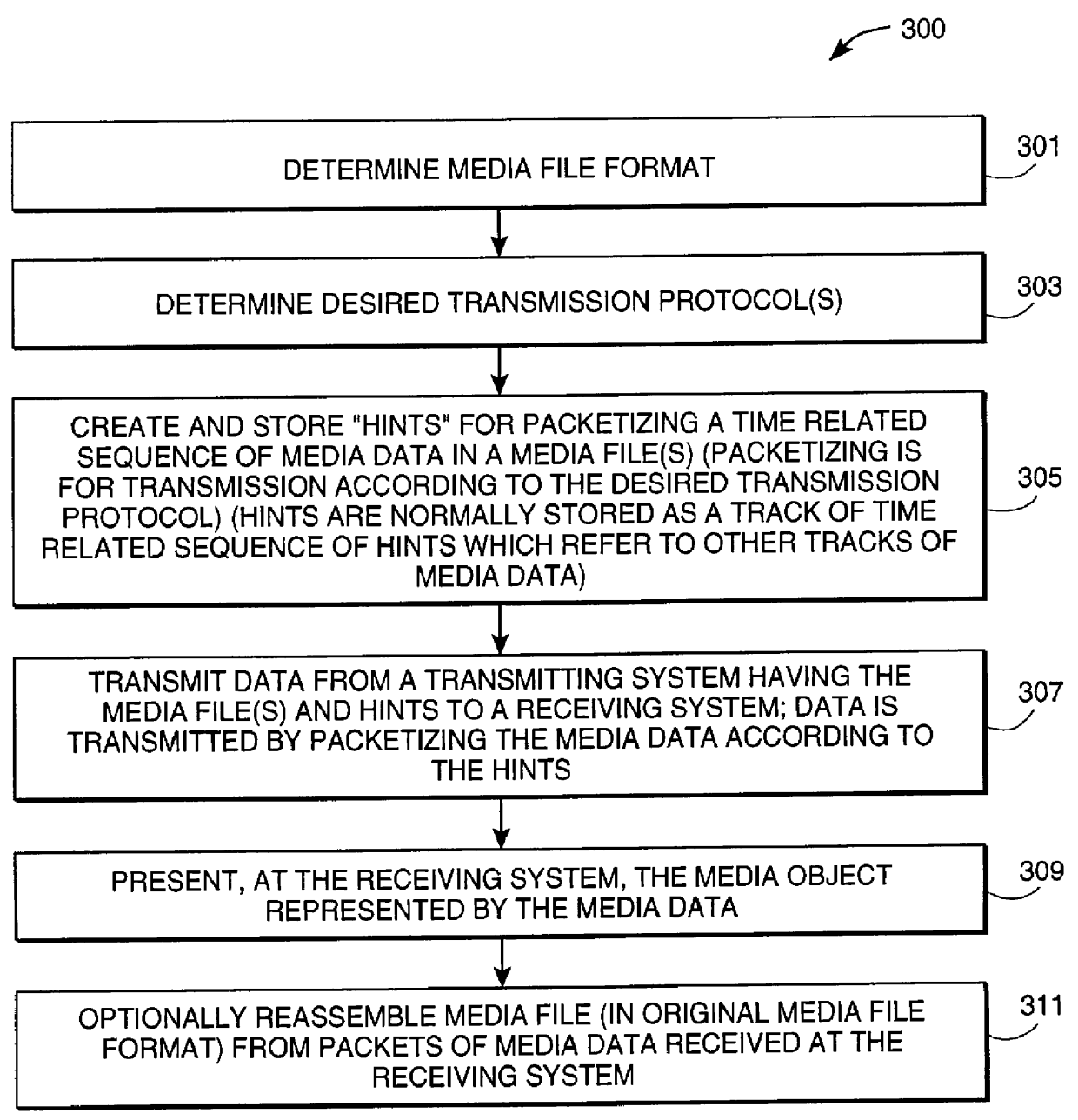
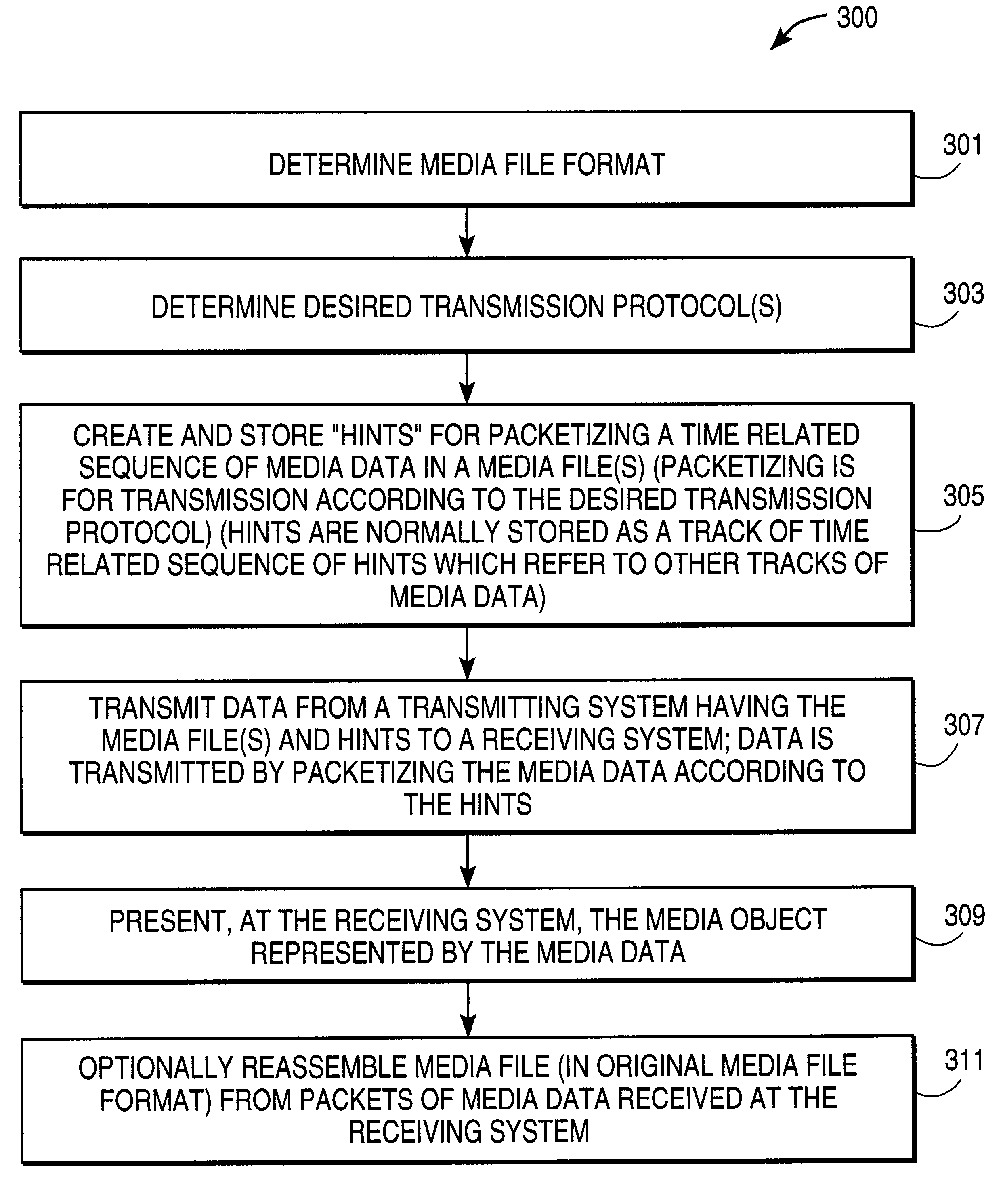
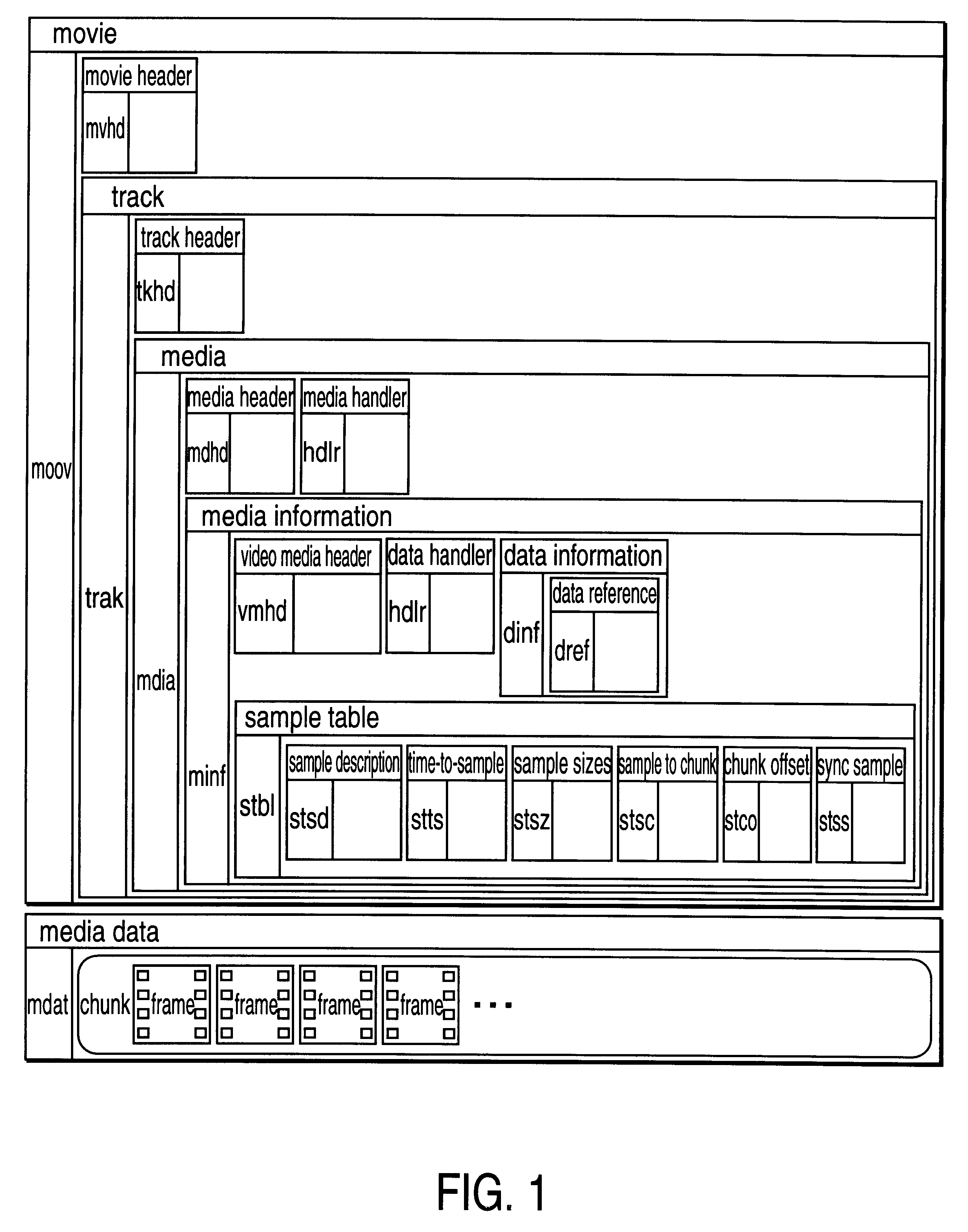
Method and apparatus for media data transmission
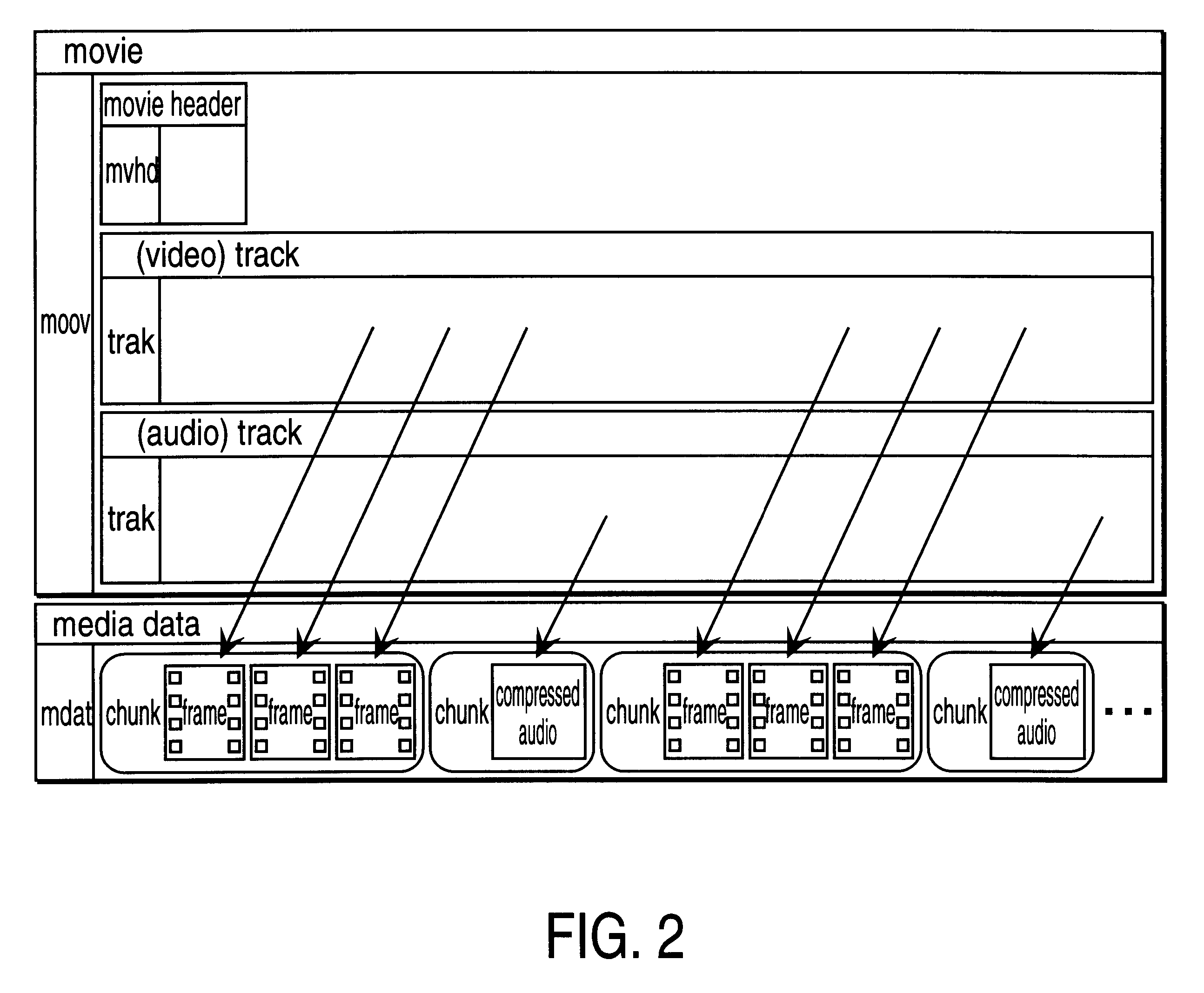
InactiveUS6134243ASpecial service provision for substationMultiplex system selection arrangementsTransmission protocolData set
Methods and apparatuses for processing media data for transmission in a data communication medium. A set of data indicates how to transmit a time related sequence of media data according to a transmission protocol. The set of data, includes a time related sequence of data which is associated with the time related sequence of media data. The set of data may be utilized by a digital processing system to transmit the time related sequence of media data (e.g., by packets generated according to the transmission protocol and the set of data).
Owner:APPLE INC
Method and apparatus for media data transmission
InactiveUS6453355B1Multiplex system selection arrangementsSpecial service provision for substationTransmission protocolData transmission
Methods and apparatuses for processing media data transmitted in a data communication medium. A digital processing system is provided with a time related sequence of media data provided to the digital processing system based on a set of data, wherein the set of data indicates a method to transmit the time related sequence of media data according to a transmission protocol. The set of data, itself, is a time related sequence of data associated with the time related sequence of media data. The time related sequence of media data may be presented and / or stored by the digital processing system.
Owner:APPLE INC
Method and apparatus for time and frequency transfer in communication networks
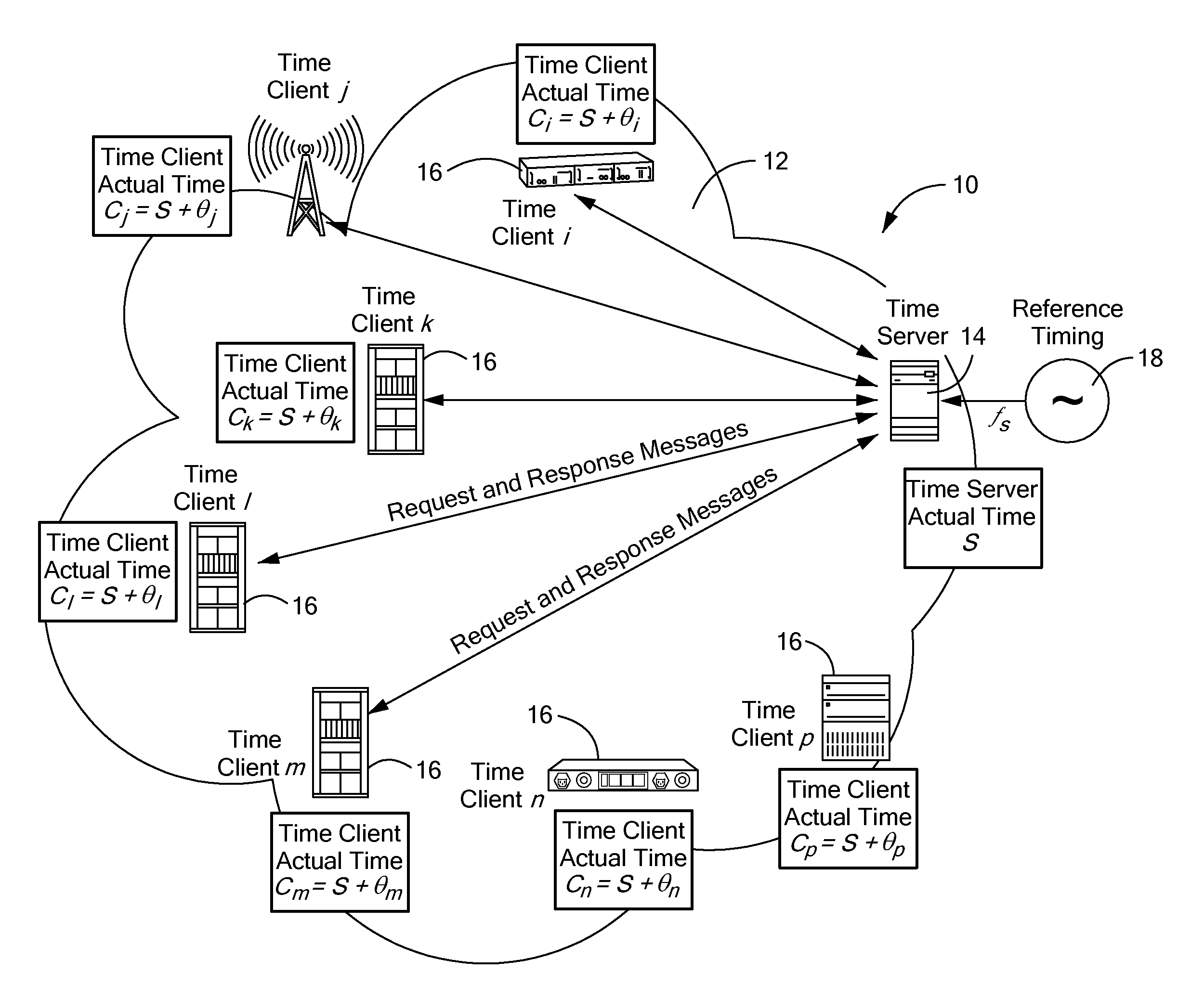
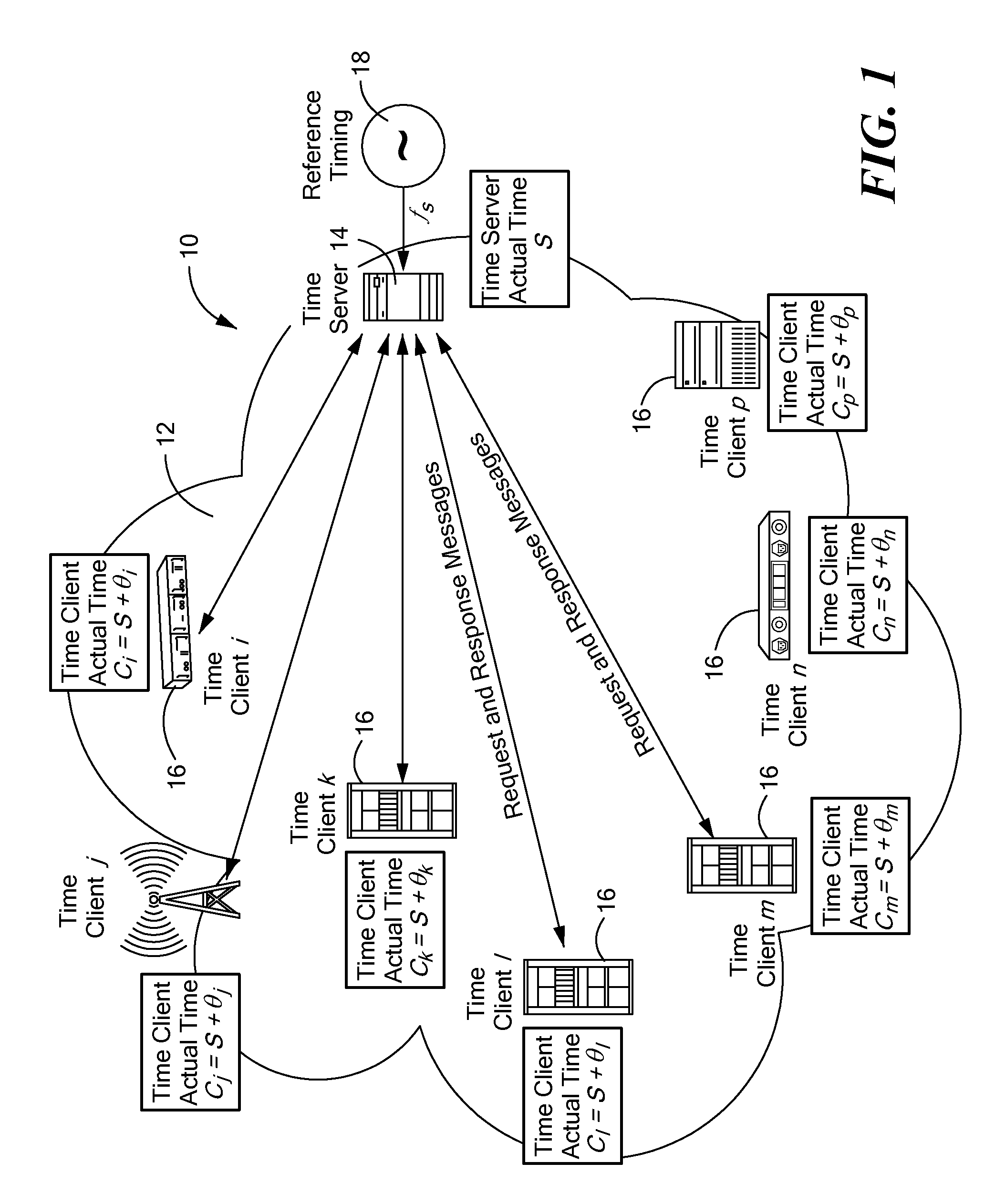
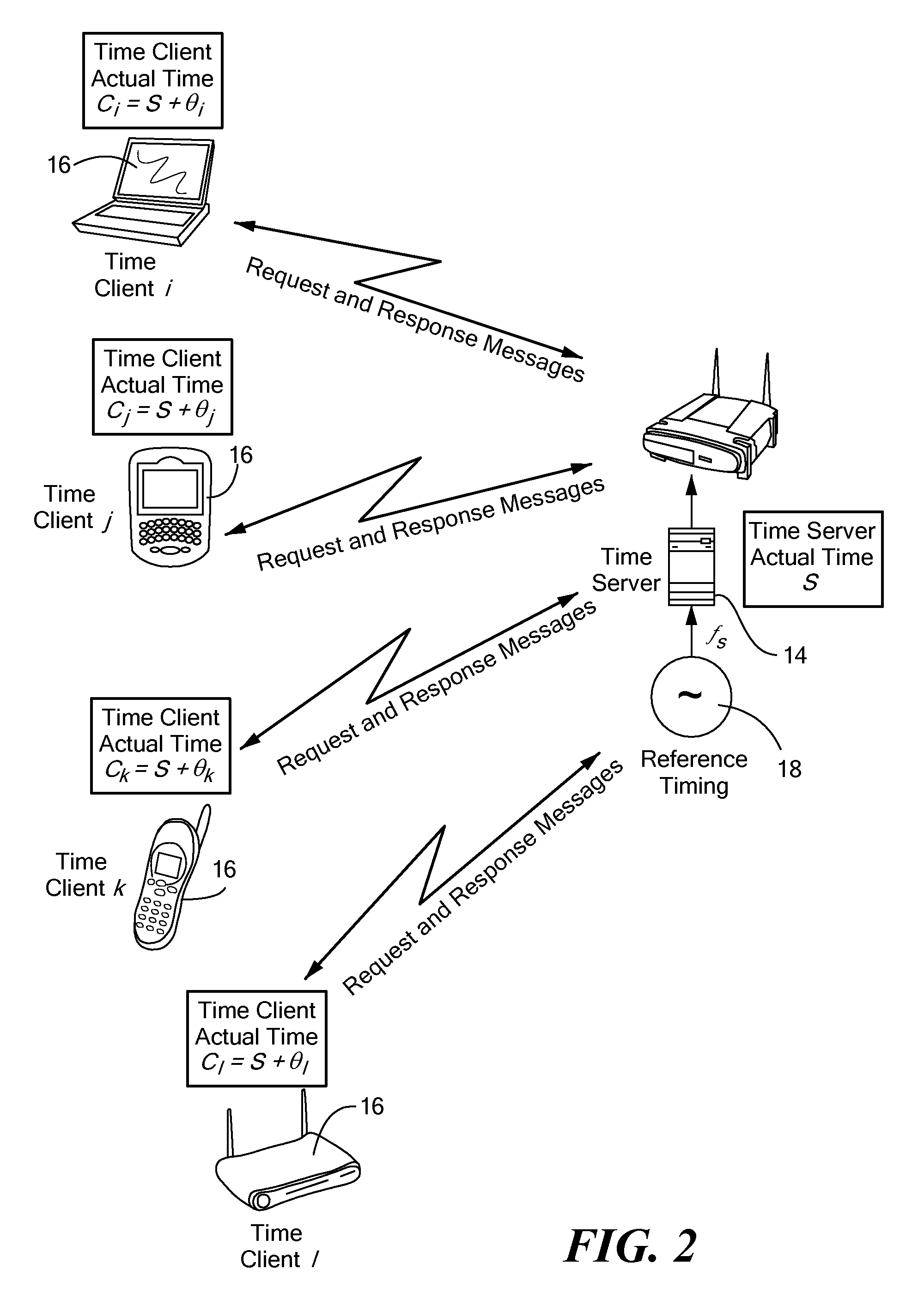
A timing system for time synchronization between a time server and a time client over a packet network. The timing system includes a time server for generating current timestamp information and a time client having a phase-locked loop driven client clock counter. The time client periodically exchanges time transfer protocol messages with the time server over the packet network, and calculates an estimated client time based on the timestamp information. The phase-locked loop in the time client receives periodic signals representing the estimated server time as its input and calculates a signal which represents the error difference between the estimated server time and the time indicated by the time client clock counter. The error difference eventually converges to zero or a given error range indicating the time presented by the client clock counter, which is driven by the phase-locked loop having locked onto the time of the time server.
Owner:RPX CLEARINGHOUSE +1
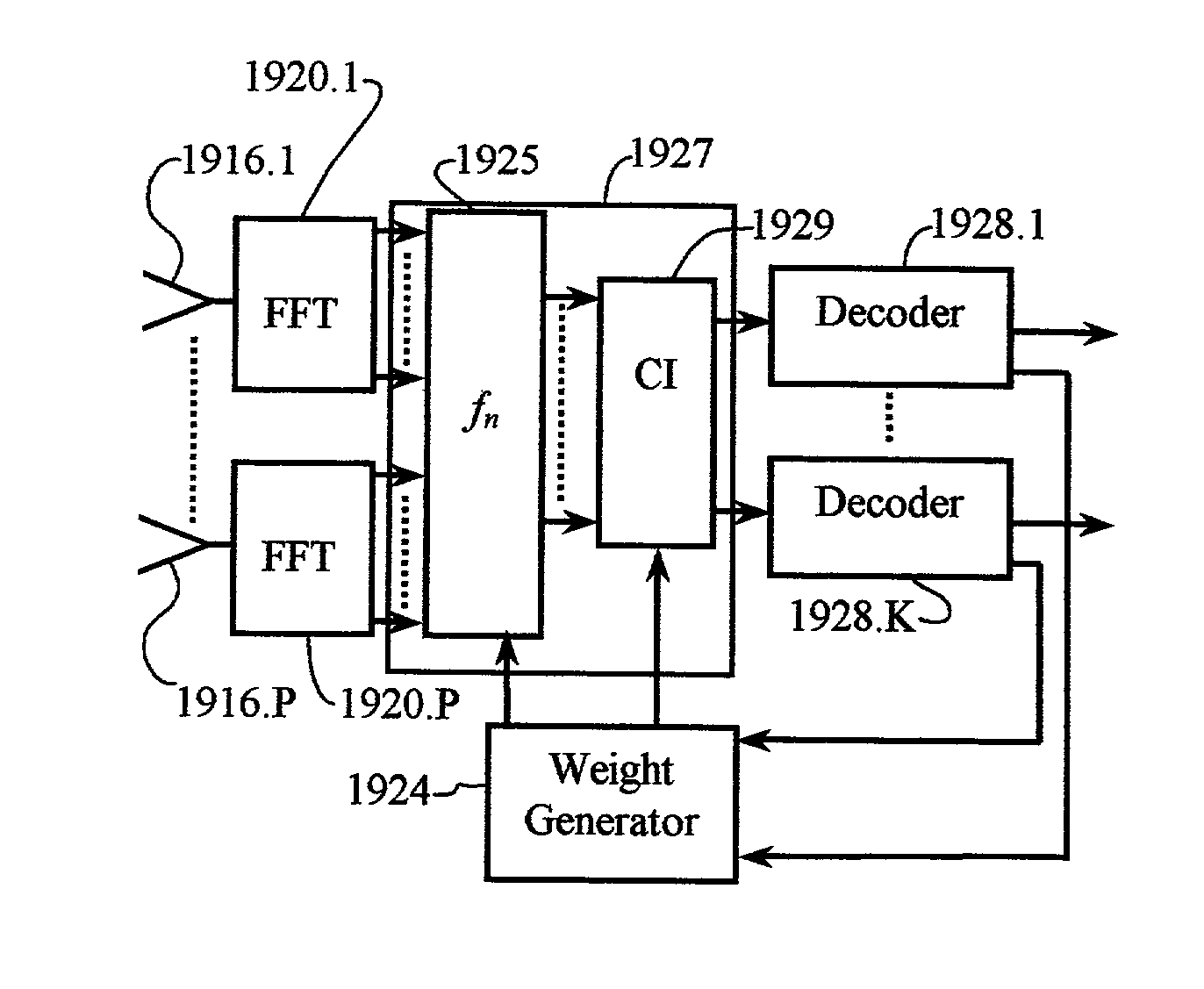
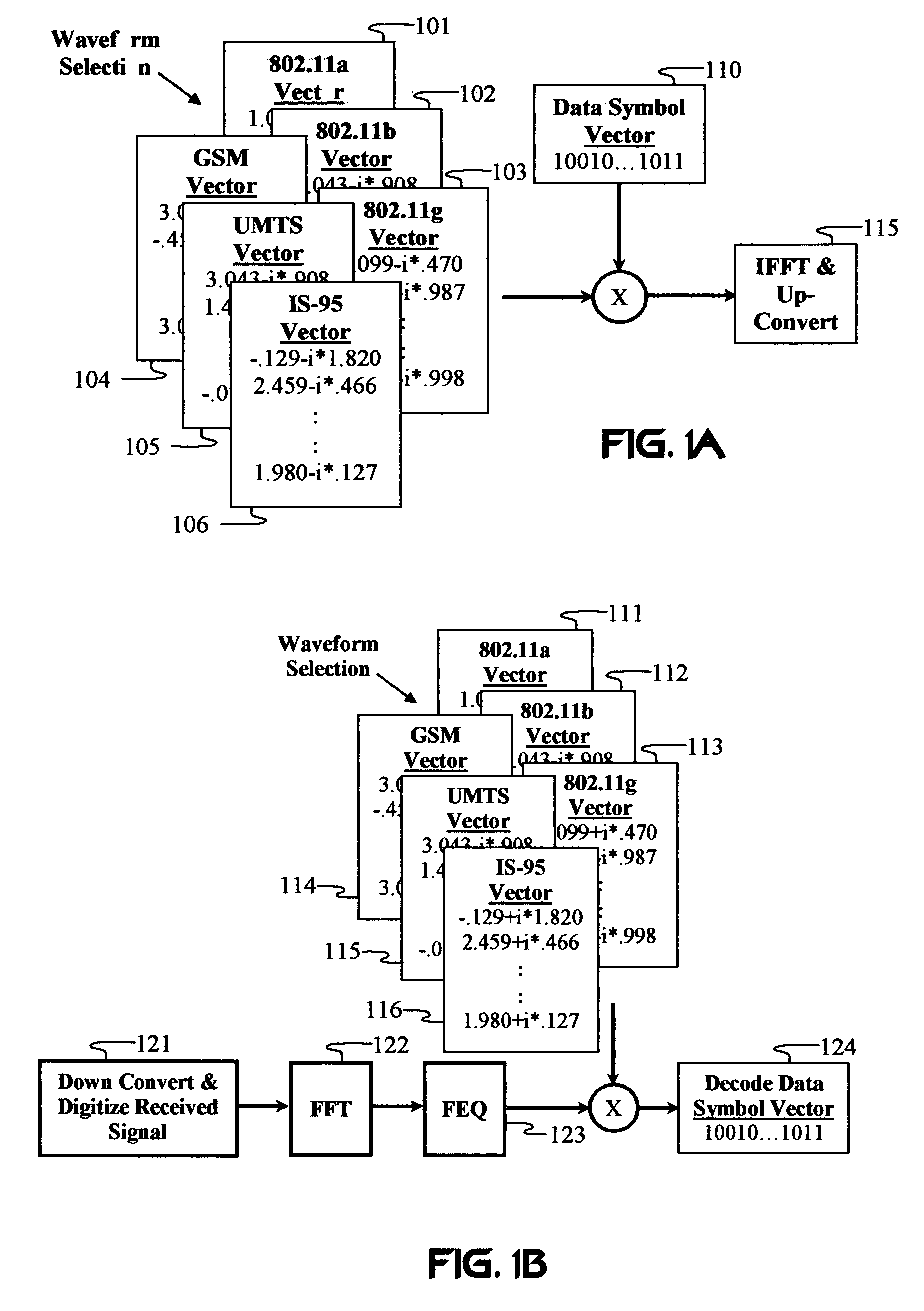
Unified multi-carrier framework for multiple-access technologies
InactiveUS7406261B2Reduce the impactReduce transmit powerModulated-carrier systemsOptical multiplexTransmission protocolCarrier signal
A wireless communication system transmits data on multiple carriers simultaneously to provide frequency diversity. Orthogonality is provided by carrier interference, which causes a narrow pulse in the time domain corresponding to each transmitted data symbol. Selection of the frequency separation and phases of the carriers controls the timing of the pulses. Equivalently, pulse waveforms may be generated from an appropriate selection of polyphase sub-carrier codes. Time division of the pulses and frequency division of the carriers may be employed for multiple access. Received signals are processed by combining frequency-domain components corresponding to a desired user's allocated carriers. Individual data symbols are processed by providing polyphase decoding, matched filtering, or time-domain shifting the received carriers. Carrier Interferometry components may be used to build various signals corresponding to other transmission protocols.
Owner:DEPARTMENT 13 INC
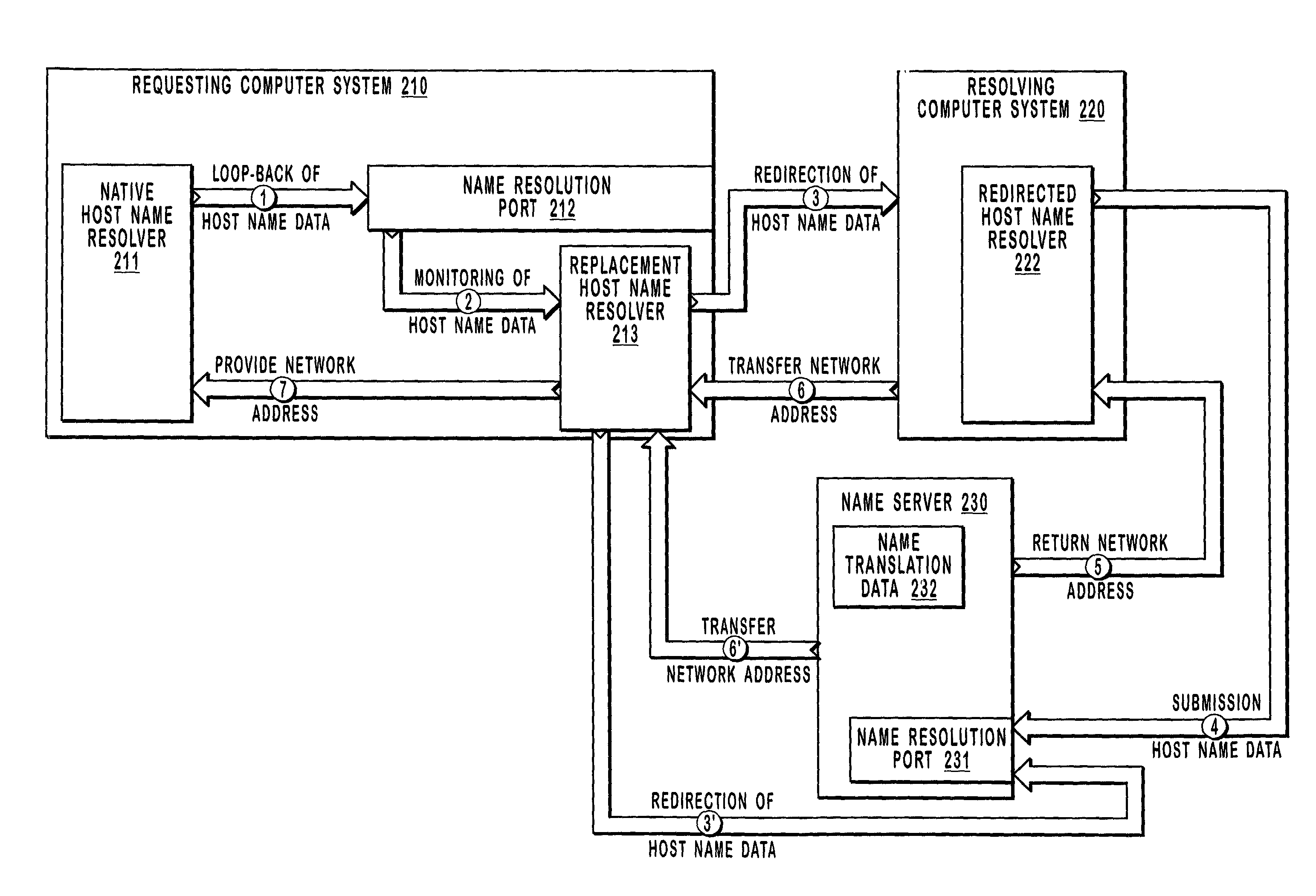
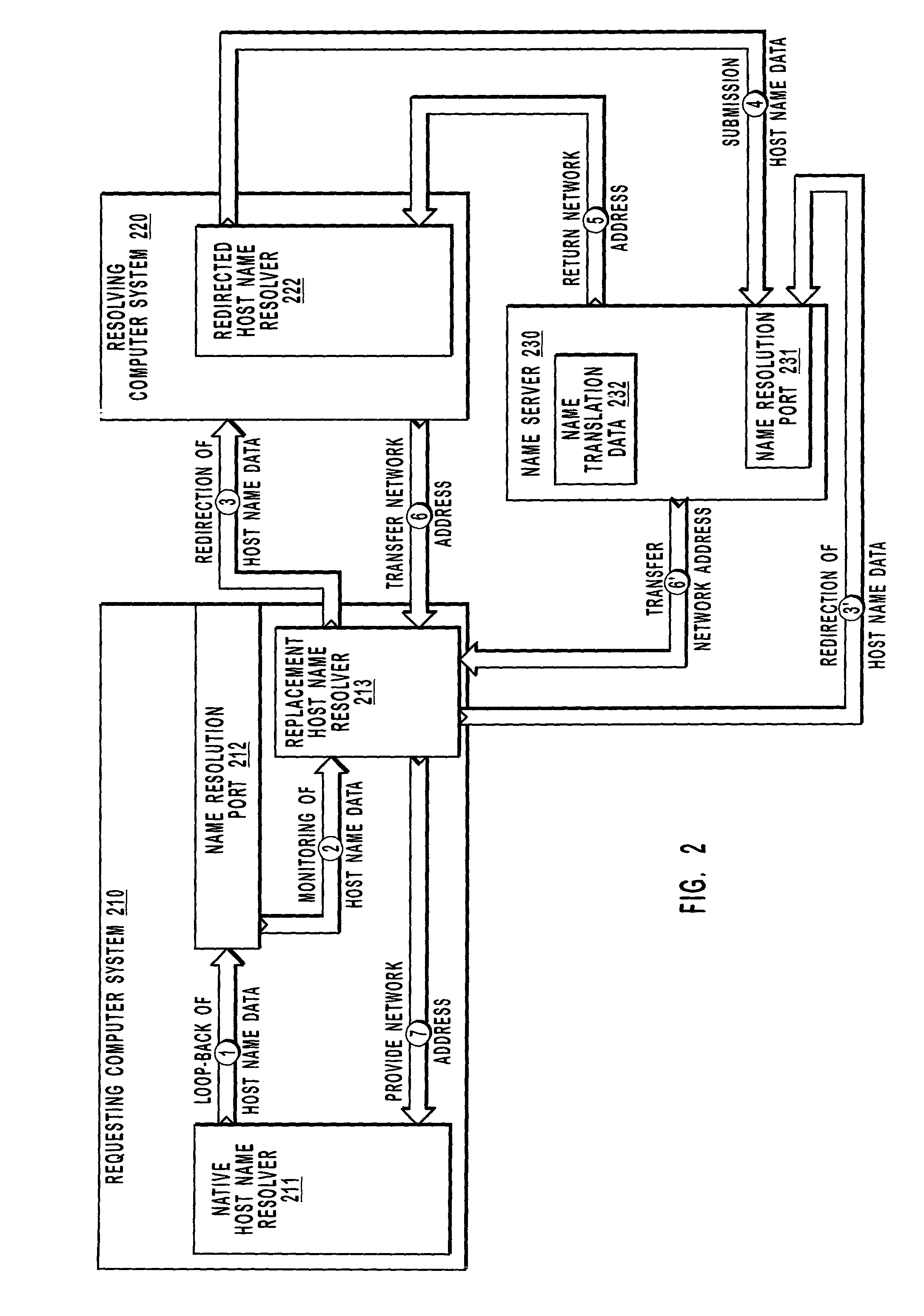
Resolving host name data
InactiveUS7284056B2Multiple digital computer combinationsTransmissionTransmission protocolSupplicant
Host name data is “looped-back” from a native host name resolver included in a requesting computer system to a name resolution port that is also included in the requesting computer system. A replacement host name resolver monitors the name resolution port for host name data that is incompatible with name resolution techniques utilized by a network. The replacement host name resolver modifies the otherwise incompatible host name data for compatibility with name resolution techniques utilized by the network. Modifying host name data may include changing a transmission protocol associated with the host name data or formatting non-secure host name data for resolution with secure host name resolution techniques. The replacement host name resolver redirects compatible host name data to a module that may cause the host name data to be resolved into a network address. The network address may be provided to the native host name resolver.
Owner:MICROSOFT TECH LICENSING LLC
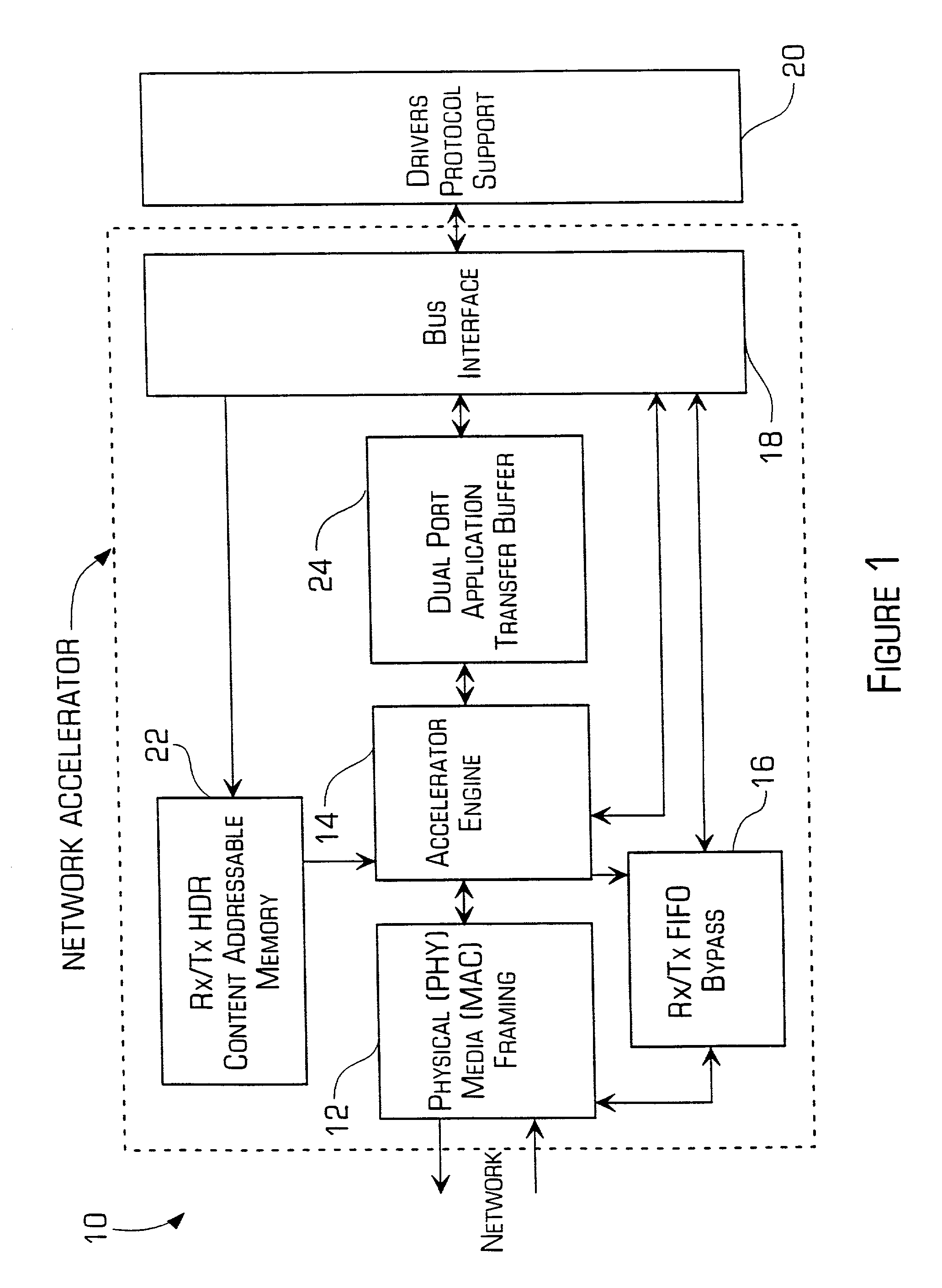
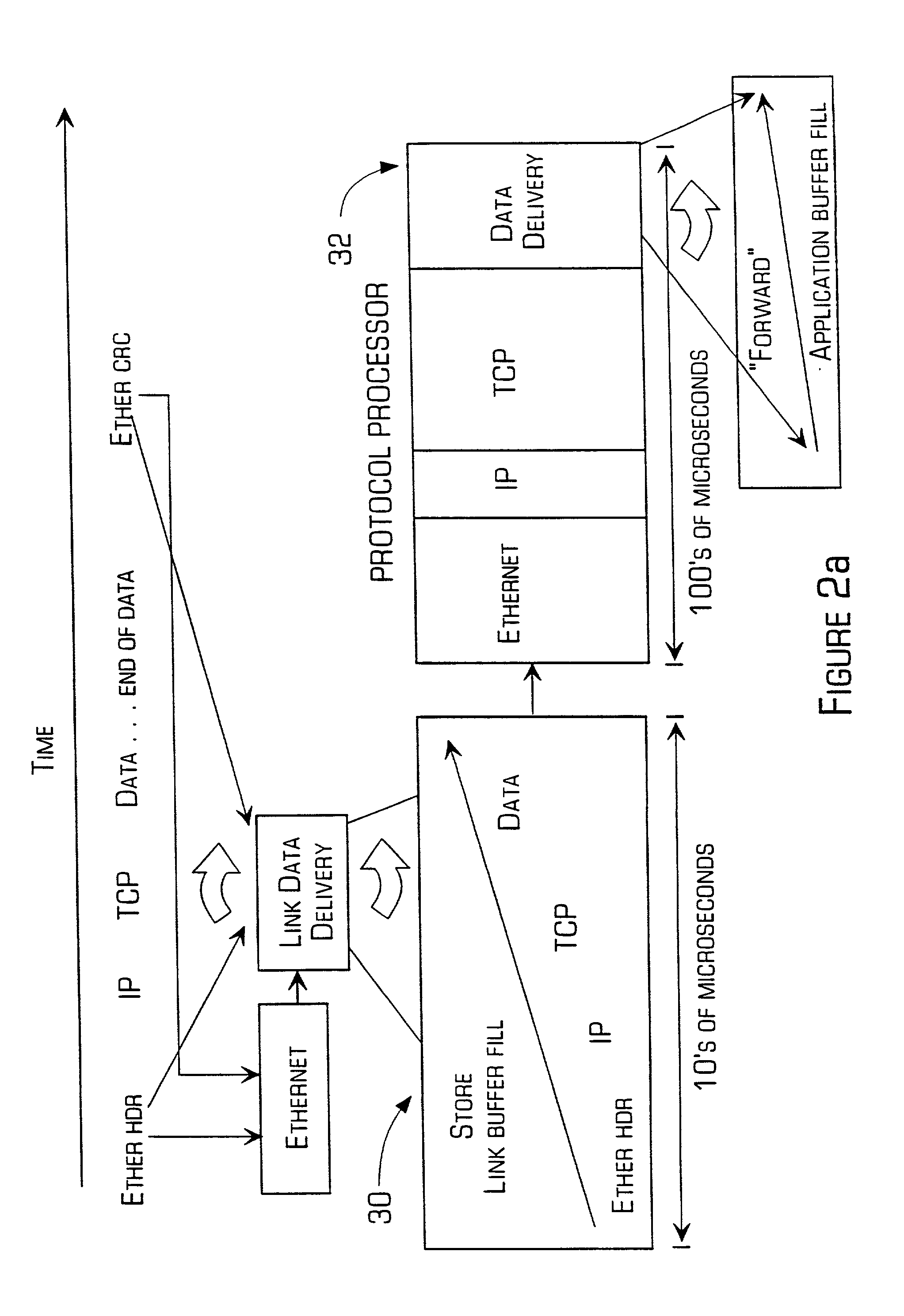
Accelerator system and method
InactiveUS20010004354A1Improve throughputFaster and less-expensive to constructTime-division multiplexRadio/inductive link selection arrangementsTransmission protocolComputer hardware
A network accelerator for TCP / IP includes programmable logic for performing transparent protocol translation of streamed protocols for audio / video at network signaling rates. The programmable logic is configured in a parallel pipelined architecture controlled by state machines and implements processing for predictable patterns of the majority of transmissions which are stored in a content addressable memory, and are simultaneously stored in a dual port, dual bank application memory. The invention allows raw Internet protocol communications by cell phones, and cell phone to Internet gateway high capacity transfer that scales independent of a translation application, by processing packet headers in parallel and during memory transfers without the necessity of conventional store and forward techniques.
Owner:JOLITZ LYNNE G
Method of and system for enabling access to consumer product related information and the purchase of consumer products at points of consumer presence on the world wide web (WWW) at which consumer product information request (CPIR) enabling servlet tags are embedded within HTML-encorded documents
InactiveUS20040153378A1Easy accessEasy to readDigital data information retrievalAdvertisementsTransmission protocolEngineering
An Internet-based electronic commerce (EC) enabled shopping system comprising: an Internet information server connected to the infrastructure of the Internet and supporting the hypertext transmission protocol (http); a Web-enabled client subsystem connected to the infrastructure of the Internet; and an EC-enabled WWW site comprising a plurality of interlinked HTML-encoded documents arranged and rendered to provide an electronic store environment for a consumer when served to the Web-enabled client subsystem, wherein the electronic store environment presenting a plurality of products for purchase and sale by an EC-enabled payment method supported over the Internet, wherein a Consumer Product Information Request (CPIR) enabling Server-side component tag, associated with each the product, is embedded within at least one of the HTML-encoded documents displayed on the Web-enabled client subsystem, and each the CPIR-enabling Server-side component tag being associated with a CPIR-enabling Server-side component encoded with a Universal Product Number (UPN) assigned to one the product, and whereby, when the consumer selects one the CPIR-enabling Server-side component tag, the associated CPIR-enabling Server-side component is automatically executed, enabling a search to be conducted against a product information database hosted on an Internet database server connected to the Internet, and the results from the search displayed in a graphical user interface (GUI) served to and displayed on the Web-enabled client subsystem.
Owner:PERKOWSKI THOMAS J
Adaptive omni-modal radio apparatus and methods
InactiveUS6934558B1Easily and conveniently identifyIntense competitionMetering/charging/biilling arrangementsAccounting/billing servicesTransmission protocolTransceiver
A frequency and protocol agile wireless communication product, and chipset for forming the same, including a frequency agile transceiver, a digital interface circuit for interconnecting the radio transceiver with external devices, protocol agile operating circuit for operating the radio transceiver in accordance with one of the transmission protocols as determined by a protocol signal and an adaptive control circuit for accessing a selected wireless communication network and for generating the frequency control signal and the protocol control signal in response to a user defined criteria Among the possible user defined criteria would be (1) the cost of sending a data message, (2) the quality of transmission link (signal strength, interference actual or potential), (3) the potential for being bumped off of the system (is service provider at near full capacity), (4) the security of transmnission, (5) any special criteria which the user could variably program into his omni-modal wireless product based on the user's desires or (6) any one or more combinations of the above features that are preprogrammed, changed or overridden by the user. The disclosed invention allows wireless service providers to broadcast electronically as part of any “handshaking” procedure with a omni-modal wireless product information such as (1) rate information and (2) information regarding system operating characteristics such as percent of system capacity in use and / or likelihood of being dropped. The disclosed invention creates a user oriented source enrollment and billing service in the wireless data market by establishing uniform standard for “handshakes” to occur between cell service providers and omni-modal wireless products. In addition, the disclosed invention can be implemented on a standard chip or chipset including a radio transceiver specifically designed to be used in all types of omni-modal wireless products.
Owner:ANTON INNOVATIONS INC
Software Adaptable High Performance Multicarrier Transmission Protocol
InactiveUS20080310484A1Reduce PAPRReduce complexityModulated carrier system with waveletsSecret communicationTransmission protocolFrequency spectrum
Techniques for reducing peak-to-average power in multicarrier transmitters employ peak cancellation with subcarriers that are impaired by existing channel conditions. The use of Carrier Interferometry (CI) coding further improves the effectiveness of peak reduction. CI coding can also be impressed onto pulse sequences in the time domain, which enhances spectral selection and facilitates peak-power control.
Owner:DEPARTMENT 13 INC
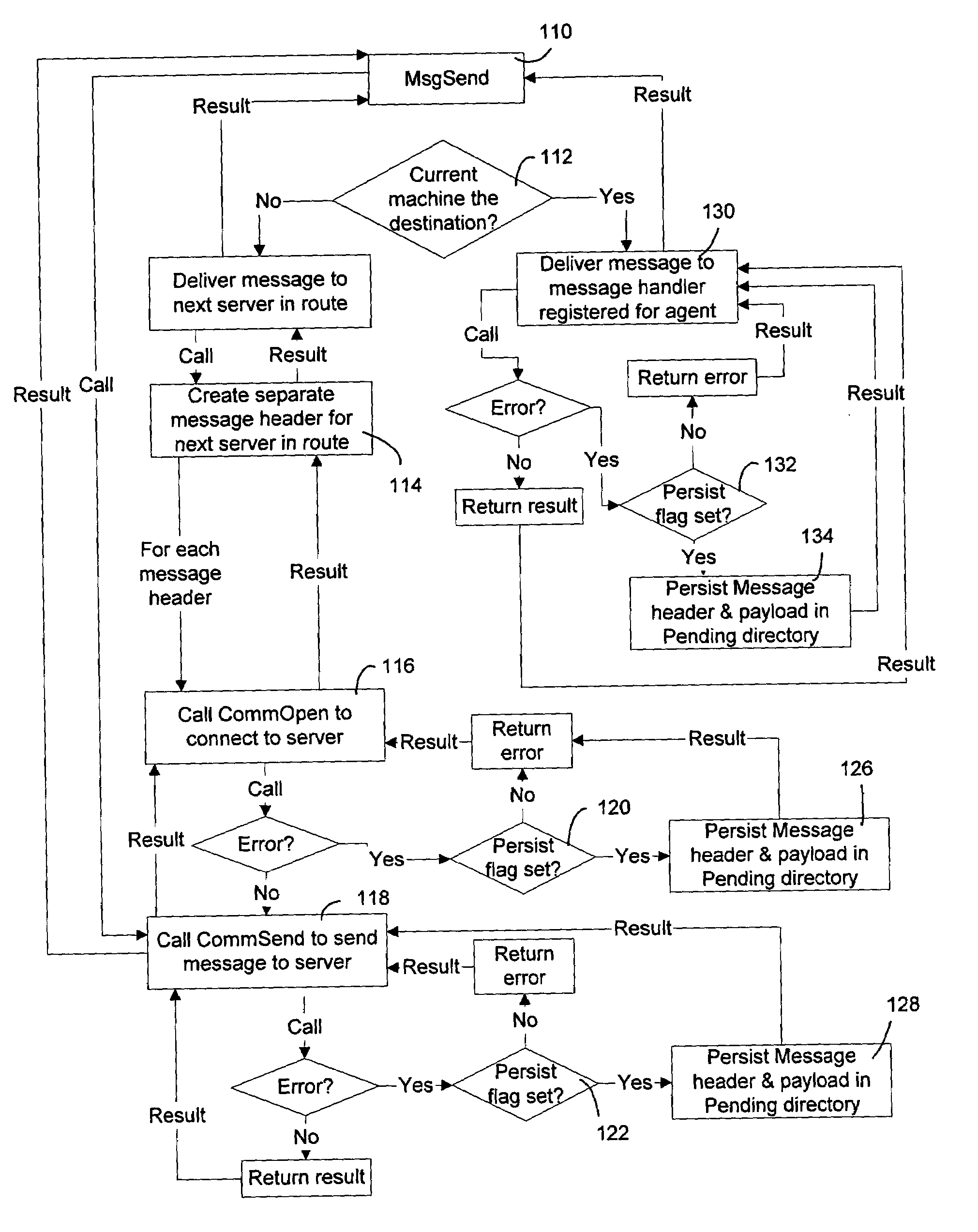
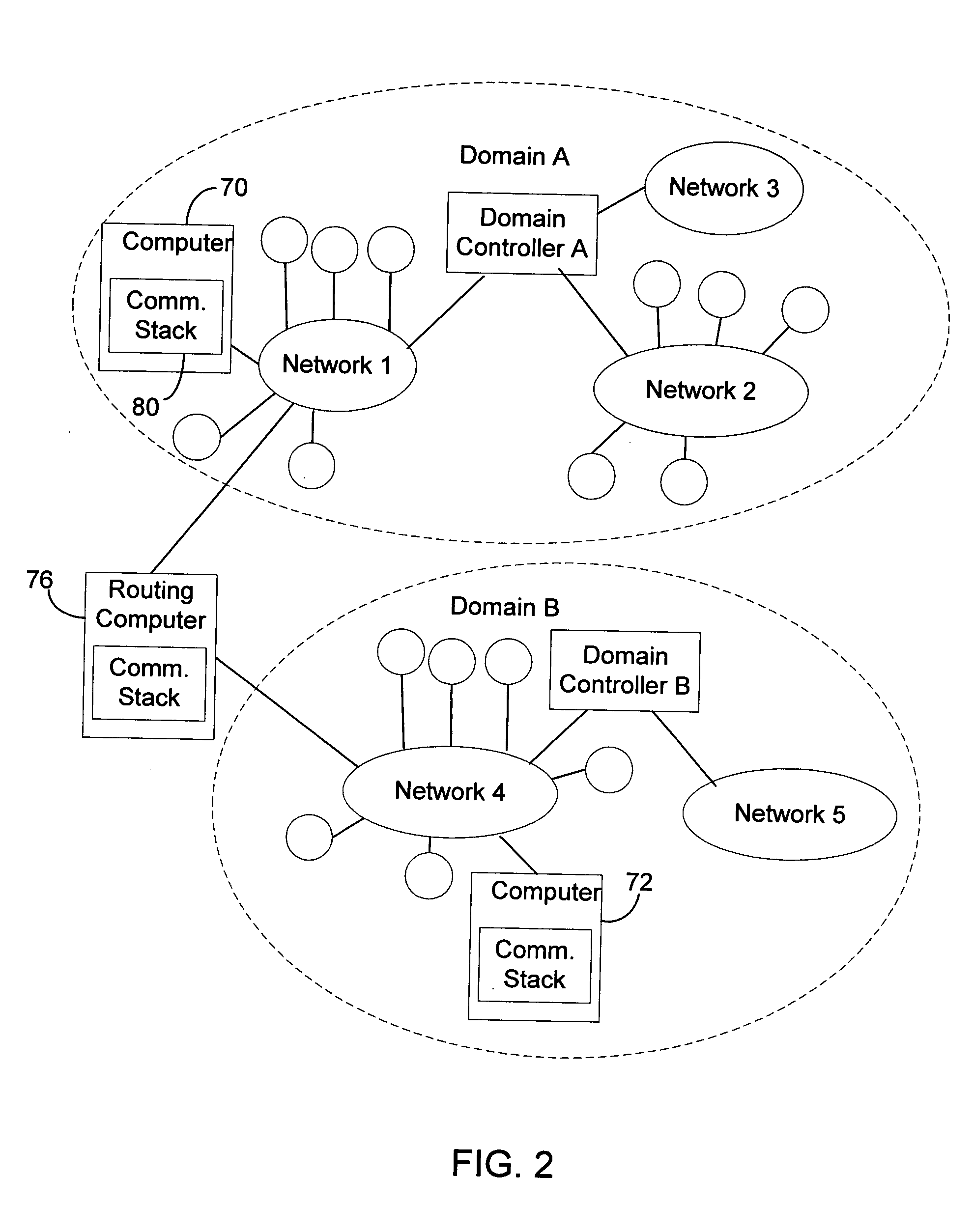
Communication stack for network communication and routing
ActiveUS7191248B2Imparts flexibilityImparts extensibilityMultiple digital computer combinationsSecuring communicationTransmission protocolCryptographic protocol
A communication stack enables computers implementing it to send, receive, or route network communications. The communication stack includes a message layer, a communication layer, a security layer, and a transport protocol layer, with plug-in transport protocol modules and plug-in security protocol modules. Each of the origin computer, target computer, and routing computers involved in delivering a message implements the communication stack. An application on the origin computer calls the message layer of the computer to send messages to a target computer and identifies routing computers on the route for delivering the message to the target computer. The message layer calls the communication layer to establish a connection to the target computer. The communication layer uses the transport protocol layer to establish an initial connection with the target computer, and uses the security layer to negotiate security parameters and to handle secured communications between the origin and target computers.
Owner:MICROSOFT TECH LICENSING LLC
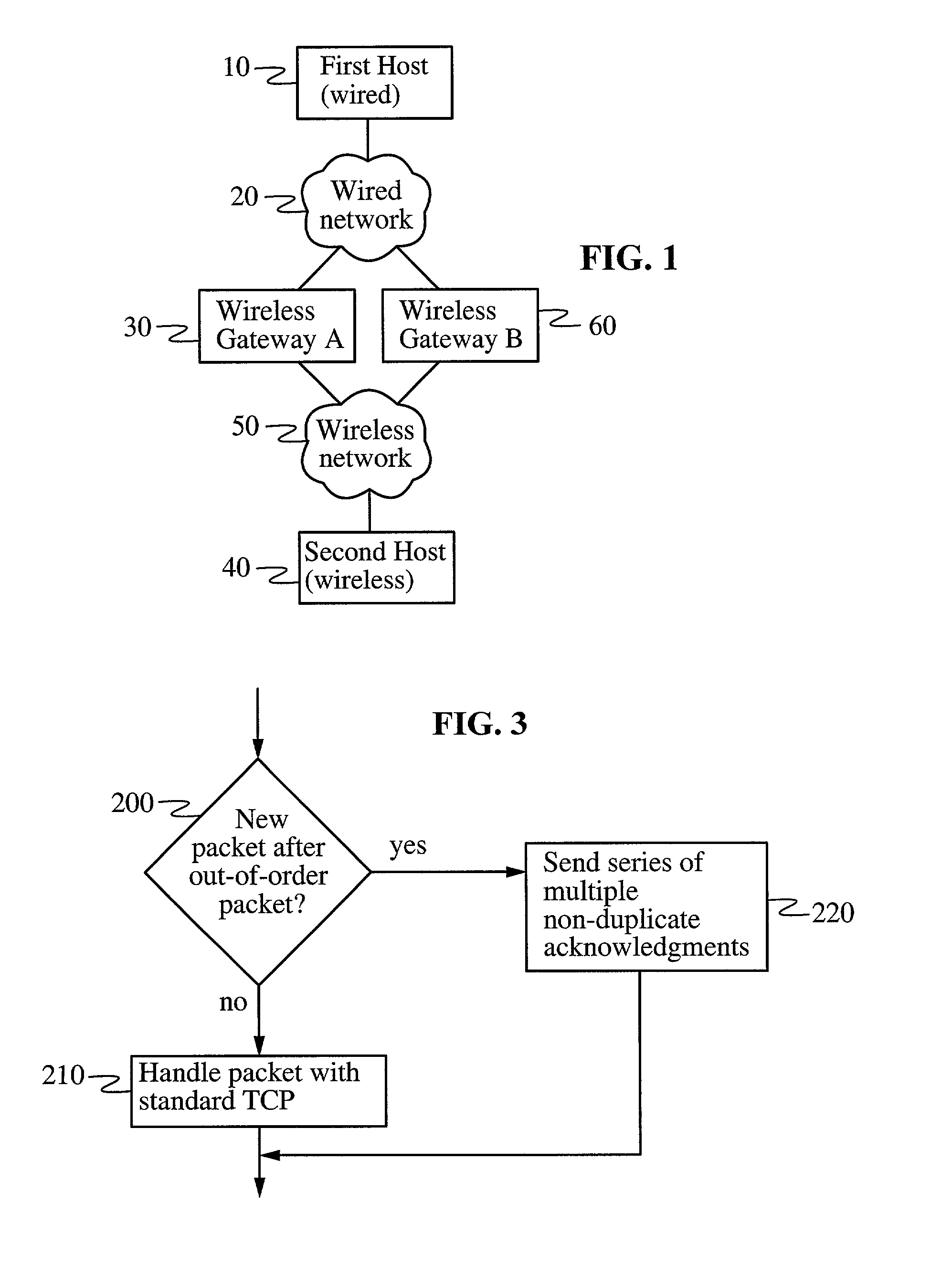
Data throughput over lossy communication links
InactiveUS7061856B2Promote recoveryError prevention/detection by using return channelFrequency-division multiplex detailsData connectionTelecommunications link
In a heterogeneous data network including both wired and wireless / lossy links, a transport protocol method implemented at the wireless host is fully compatible with existing wired networks and wireless gateways, and requires no modification to transport protocols at existing wired hosts. The wireless host calculates a temperament parameter [100] characterizing the error-proneness of the data connection and uses this parameter to determine whether error-induced losses or congestion-losses dominate the data connection [110]. If congestion-losses dominate the data connection, then the host uses a standard technique for acknowledging data packets [130]. If, on the other hand, error-induced losses dominate the connection, the host uses a modified technique for acknowledging data packets [120]. According to this modified technique, the wireless host sends a plurality of non-duplicate acknowledgements of a single packet whenever a packet is received after an out-of-order packet is received. By acknowledging distinct fragments of the packet, rather than identical (i.e., duplicate) acknowledgments of the packet, the acknowledgments have the effect of accelerating recovery of maximal window size at the wired host and increasing data throughput.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
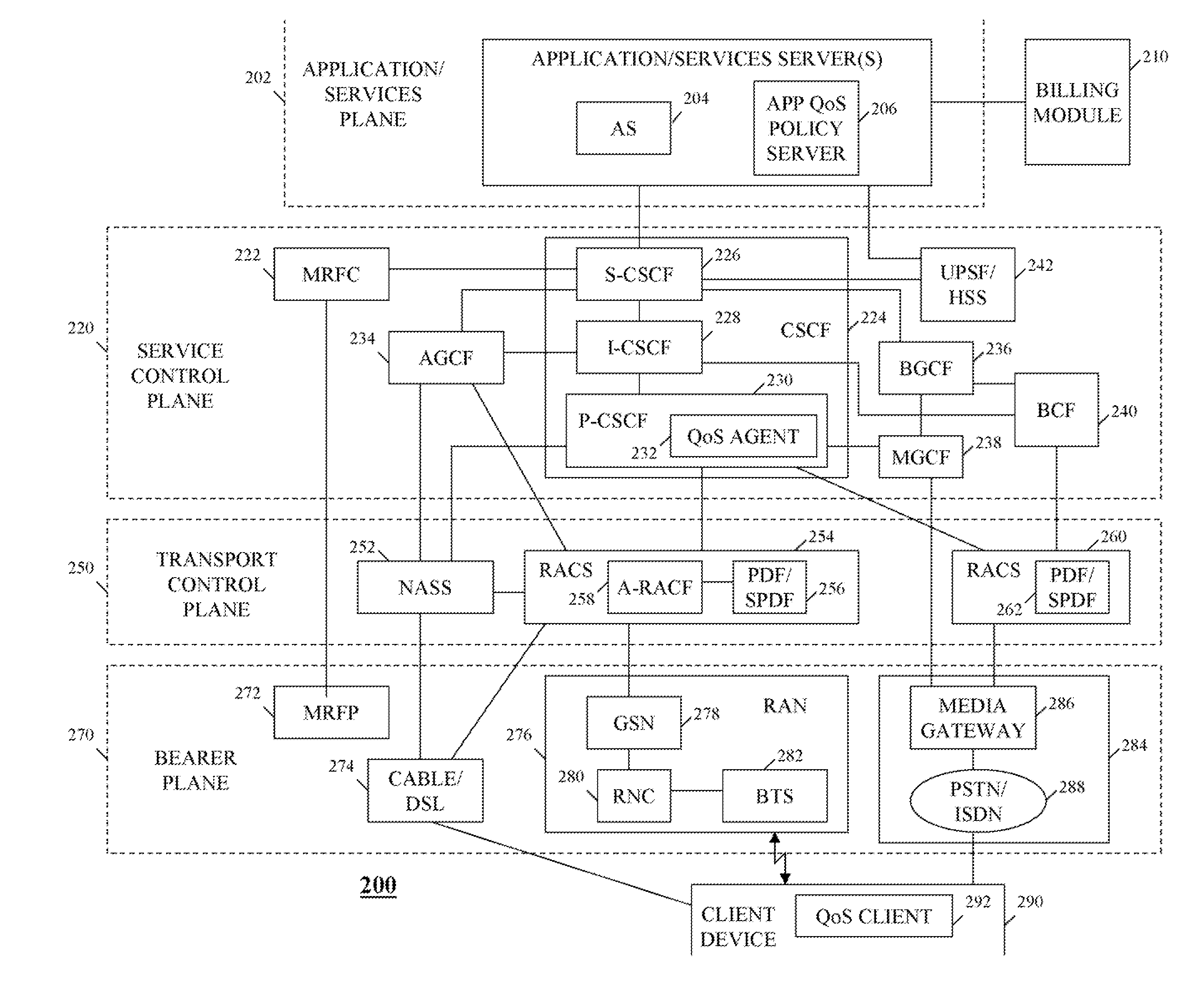
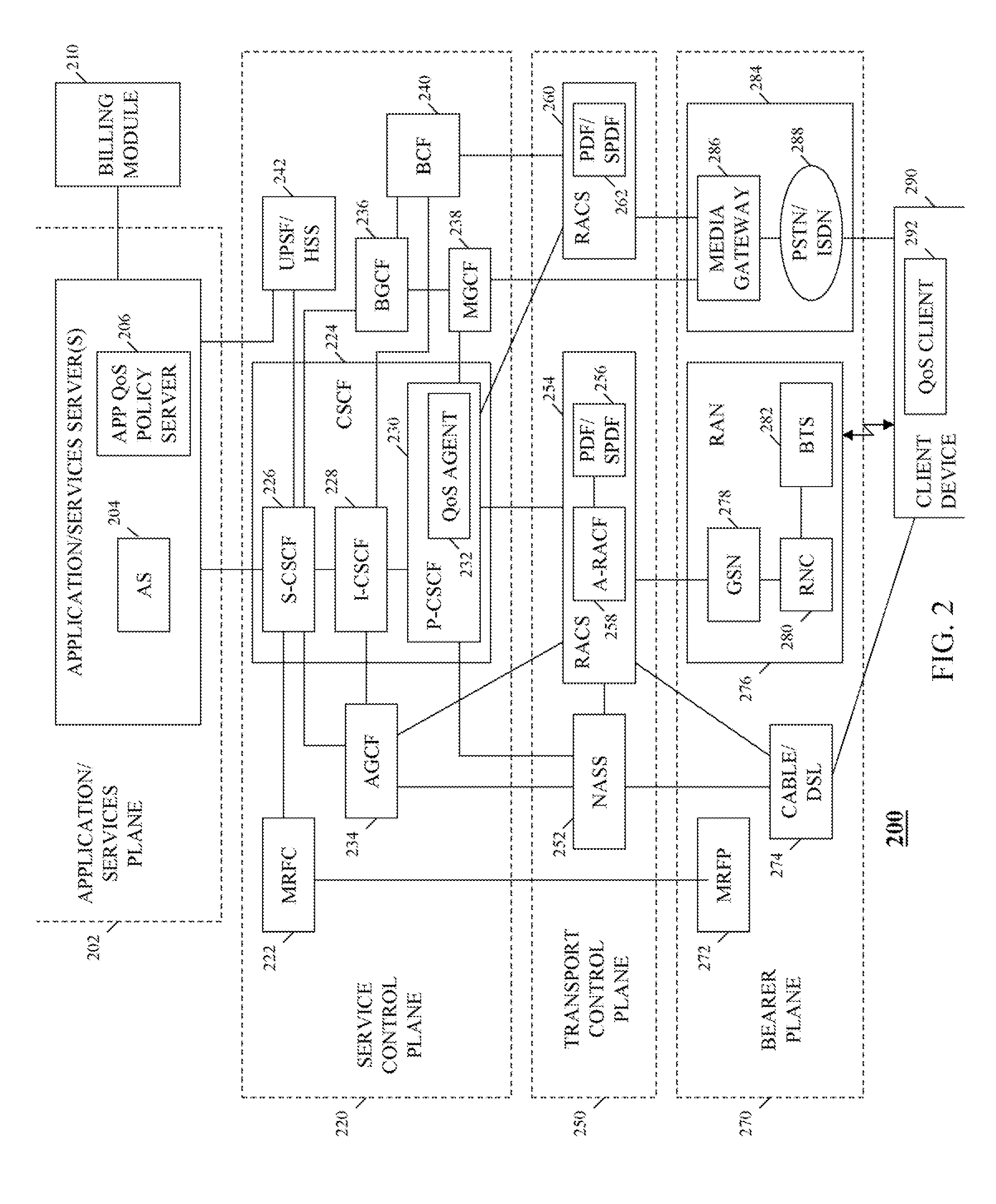
Method and apparatus for policy management for an internet protocol multimedia subsystem based wireless communication system
An Internet Protocol Multimedia Subsystem (IMS)-based communication system comprising multiple access networks, wherein each access network of the multiple access networks implements a different transport protocol than the other access networks of the multiple access networks, includes an application plane Quality of Service (QoS) policy server that, with the support of a Quality of Service (QoS) Agent, coordinates and manages QoS policies across the multiple transport networks, thereby providing for centrally consistently managed QoS policies, which policy management is transport control plane and network topology agnostic.
Owner:MOTOROLA SOLUTIONS INC
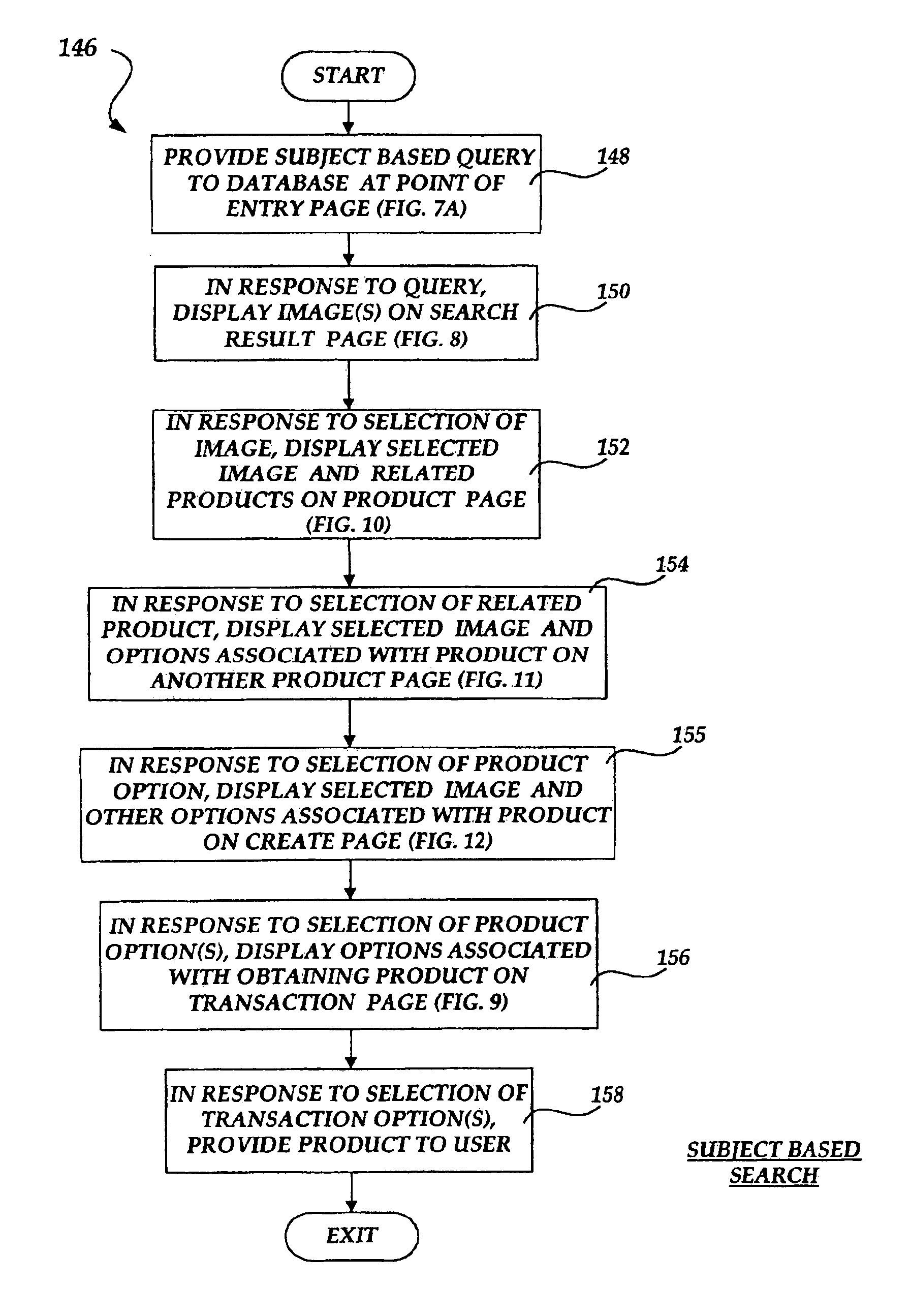
Method and system for automatically displaying an image and a product in a page based on contextual interaction and metadata
InactiveUS6901378B1Buying/selling/leasing transactionsMetadata still image retrievalTransmission protocolRelational database
The invention provides a method, system and computer-readable medium for storing images with related information in a relational database and using the information to order available products for a selected image over a network. Tag and business information may be associated with an image in the database and a unique image identifier is generated for each image. Different types of searches of the relational database may be performed including product based and image based. Affirmative results from searches are returned as images and / or products that are displayed in pages. The returned images also include information indicating available products. The selection of a returned image causes a cut-down version of the image and all of the available products to be displayed in the same page. When an available product is selected, a server enables a transaction for a user to order the selected product. A Hyper Text Transport Protocol (HTTP) Cookie is employed to store a copy of a client identifier at a client. Information associated with the client's behavior for each session is stored in a profile that is used to customize the particular options and products that are displayed to the user. A combination of user information, product information, image information and contextual interaction information is used to determine the display of the images and the products.
Owner:BEN GRP INC
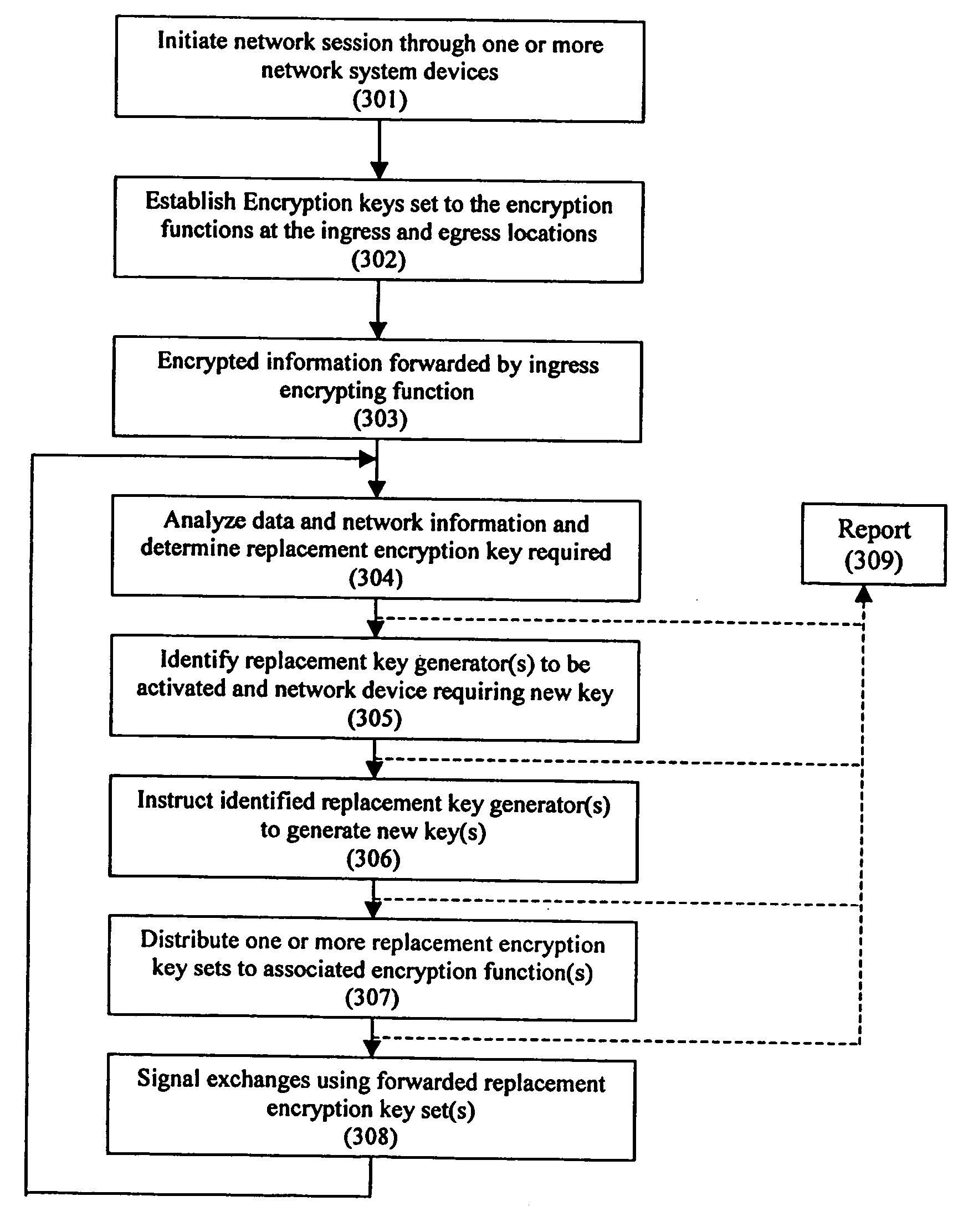
Encryption security in a network system
InactiveUS20060031936A1Improve network securityImprove securityMultiple keys/algorithms usageMemory loss protectionTransmission protocolTraffic capacity
A system and method for enhancing the security of signal exchanges in a network system. The system and method include a process and means for generating one or more replacement encryption key sets based on information and events. The information that may cause the generation of a replacement encryption key set includes, but is not limited to, a specified period of time, the level and / or type of signal traffic, and the signal transmission protocol and the amount of data sent. A key manager function initiates the replacement encryption key process based on the information. The replacement encryption key set may be randomly or pseudo-randomly generated. Functions attached to the network system required to employ encryption key sets may have encryption key sets unique to them or shared with one or more other attached functions. The system and method may be employed in a wireless, wired, or mixed transmission medium environment.
Owner:ENTERASYS NETWORKS
Method and transmitter for an efficient packet data transfer in a transmission protocol with repeat requests
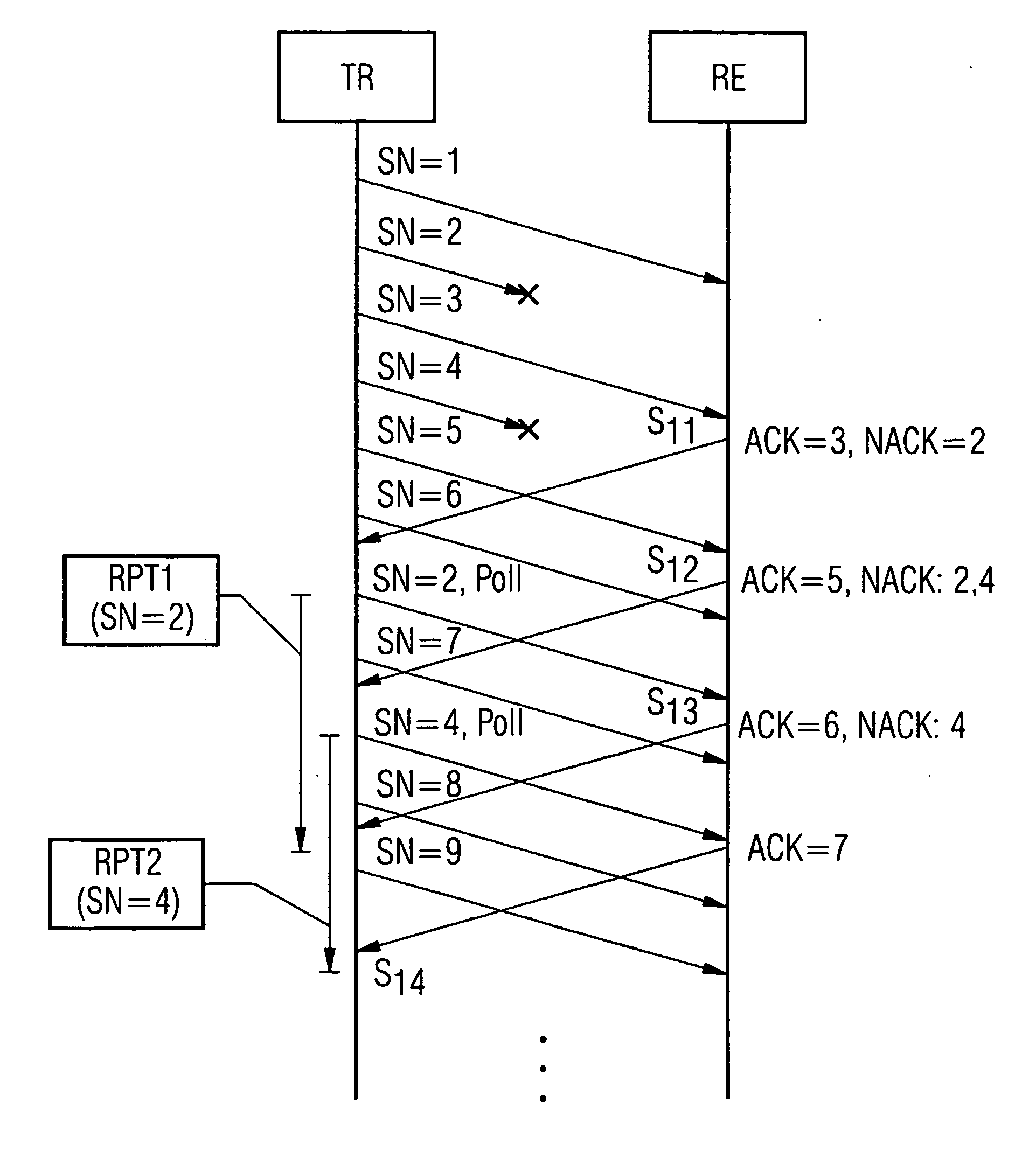
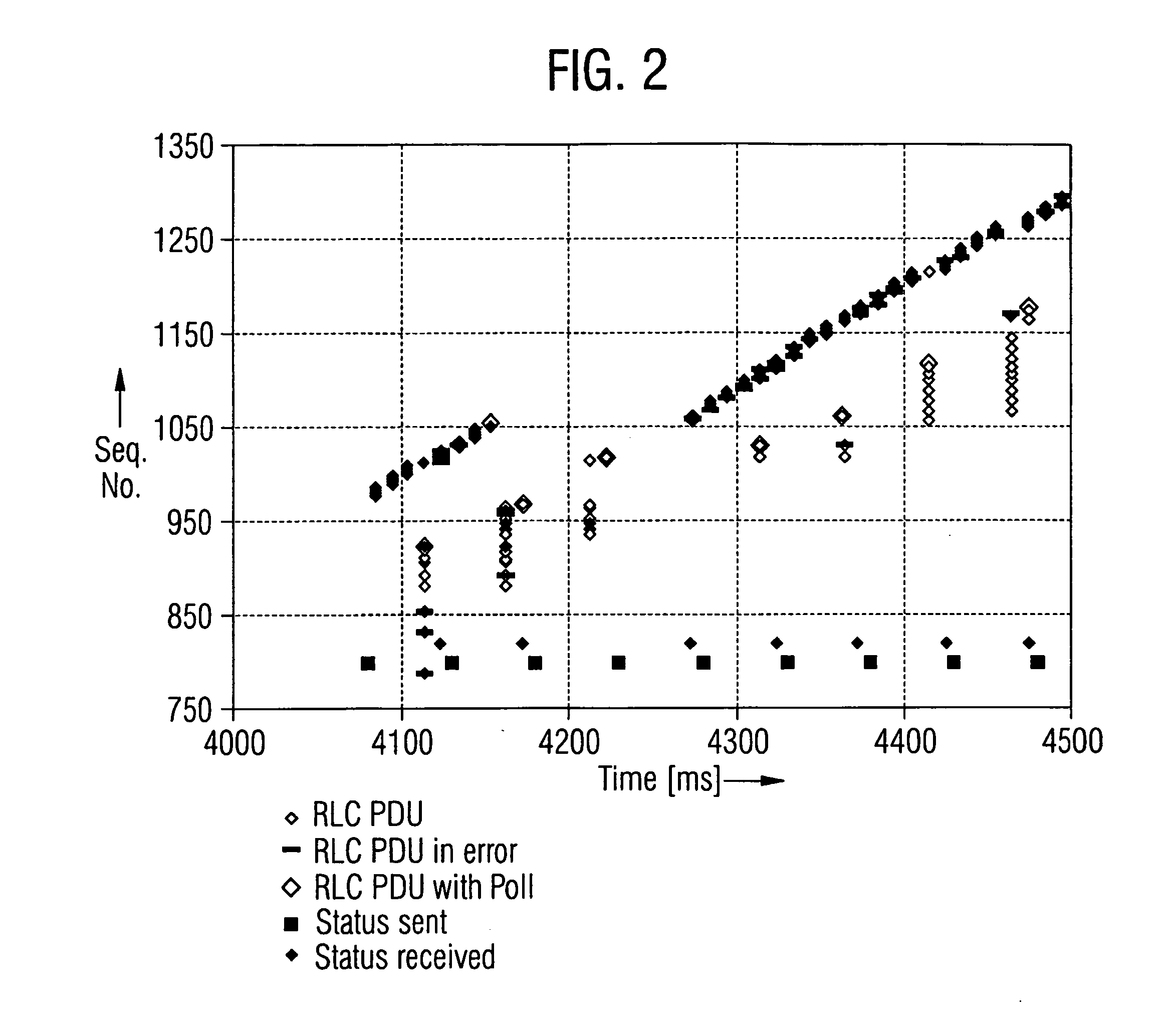
ActiveUS20040148396A1Spread the wordAvoid unnecessary multiple transmissionError prevention/detection by using return channelFrequency-division multiplex detailsTransmission protocolPacket data transmission
In a method for the transmission of data packets (D) from a transmitter (TR) to a receiver (RE) identification of transmitted data packets are stored. Defective data packets (D) are detected by the receiver (RE), status messages (S) which request defective data packets for retransmission are sent from the receiver (RE) to the transmitter (TR) and retransmissions of requested data packets are performed according to the status messages (S). The transmitter (TR) evaluates a first status message (S11) with an identification of at least one first requested data packet and retransmits the first data packet. The transmitter (TR) then initializes a timing unit according to the retransmission of the first data packet, wherein the timing unit or a threshold for the timing unit is attributable to the first data packet. When the transmitter evaluates a further status message (S12) and detects at least one further data packet that is requested for a retransmission, it selects the further data packet if the timing unit has reached the threshold or if the identification of the further data packet is different from the identification of the first data packets. Only the selected data packets are retransmitted. A transmitter and software programs embodying the invention are also described.
Owner:TELEFON AB LM ERICSSON (PUBL)
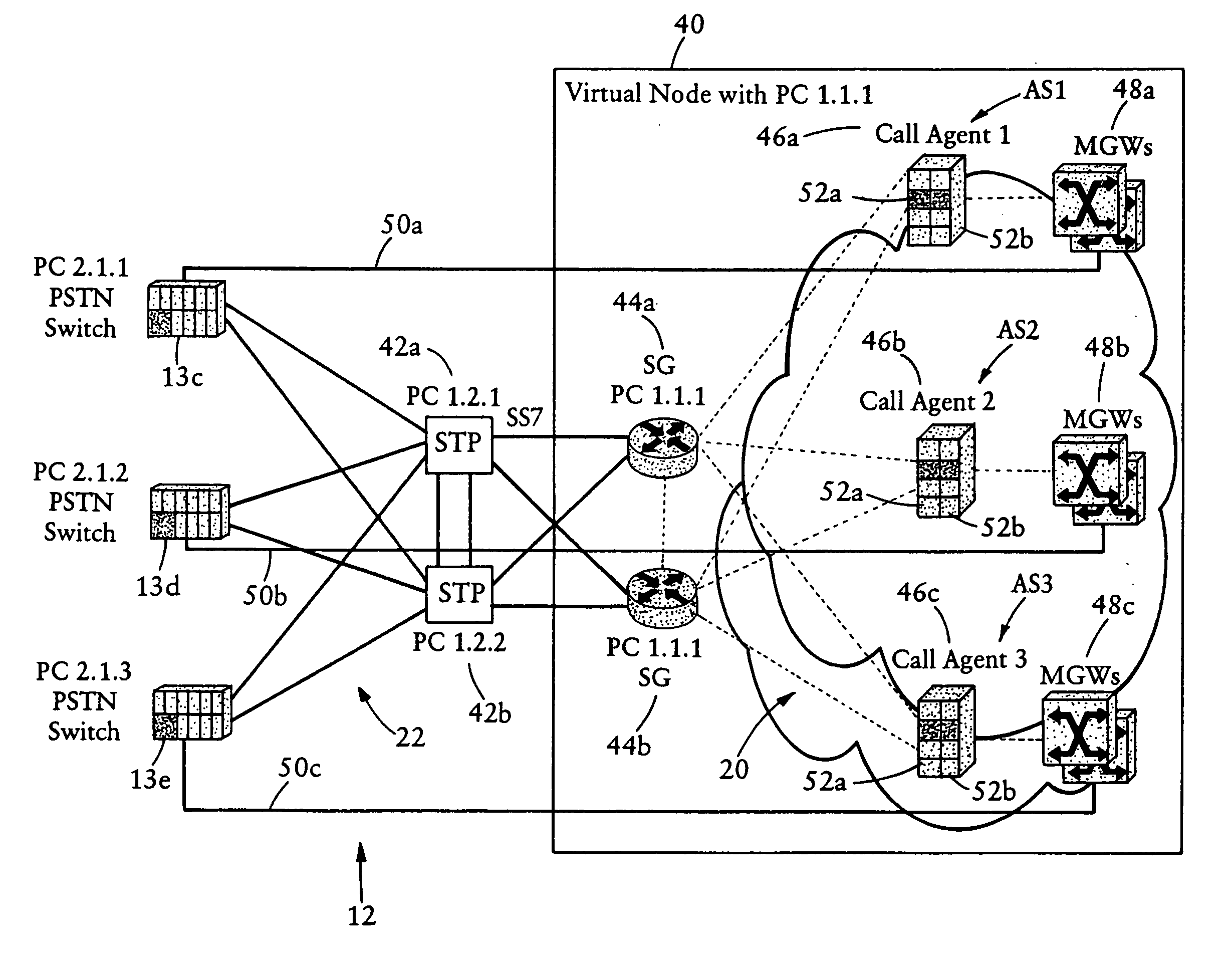
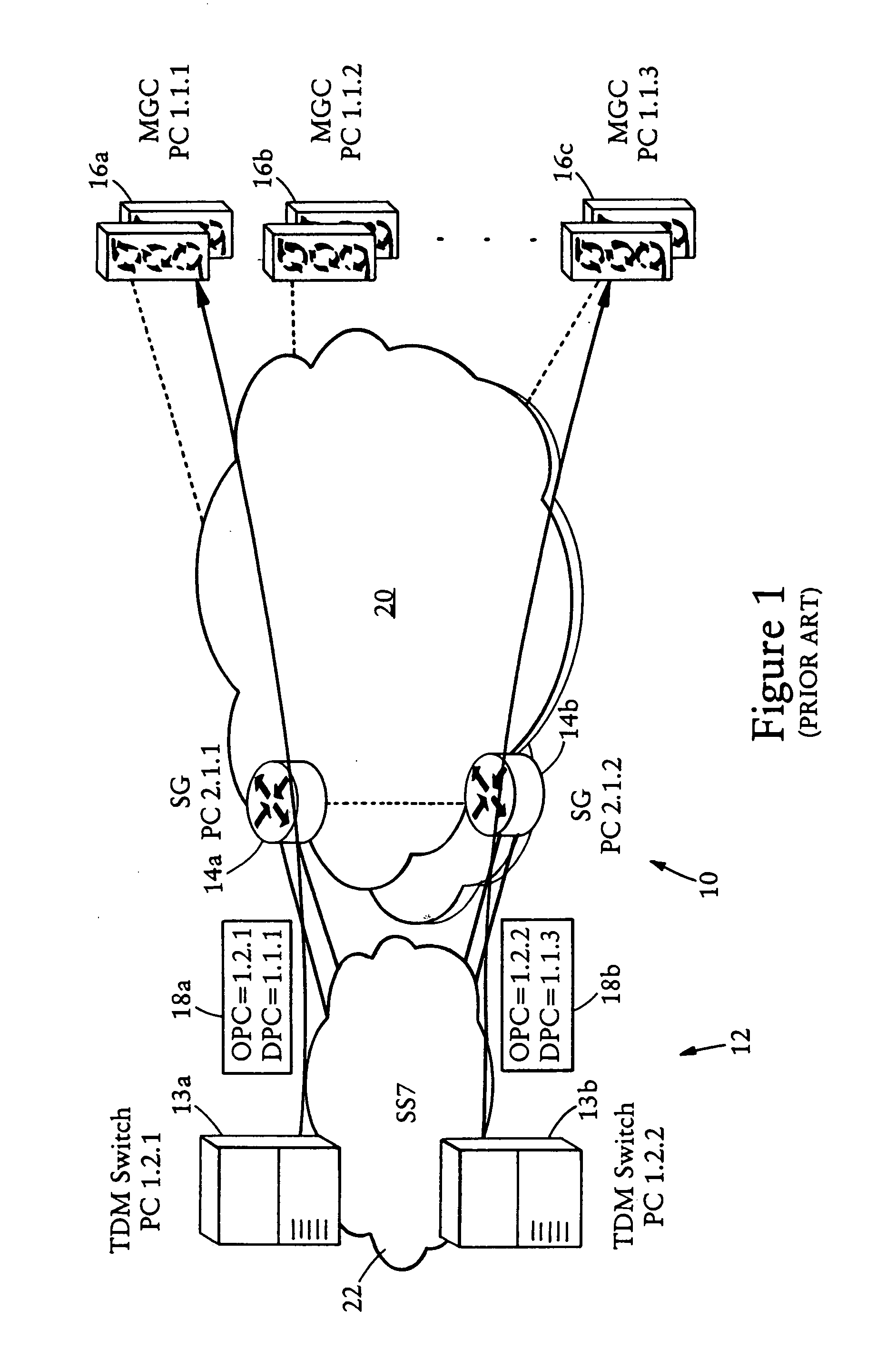
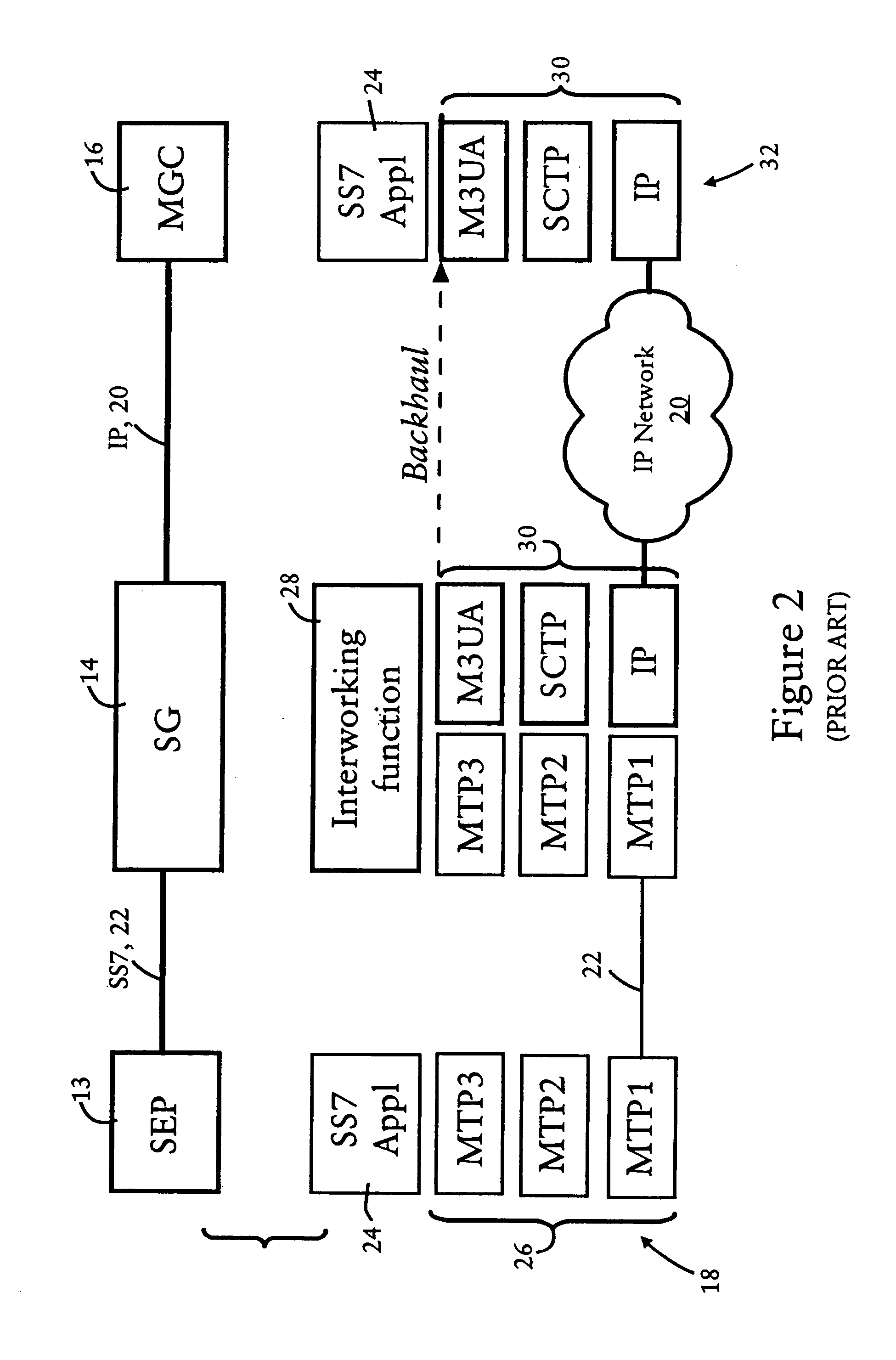
Arrangement for sharing a single signaling point code between multiple hosts in an IP-based network
A Voice over IP network having multiple signaling message transfer nodes (e.g., call agents, signaling gateways), communicate with switched circuit network nodes using a single point code. A signaling gateway, upon receiving an SS7 signaling message specifying a destination point code corresponding to its provisioned point code and carrying a signaling application protocol message, selects a destination call agent based on the originating point code in the SS7 signaling message and independent of the destination point code. The signaling gateway selectively outputs to the selected destination call agent an IP-based message carrying the signaling application protocol message according to a prescribed IP-based signaling message transport protocol, based on a determined availability of the selected destination call agent. The signaling gateway uses the User Part Unavailable message to inform the originating PSTN switch that the selected destination call agent is unavailable.
Owner:CISCO TECH INC
End-to-end publish/subscribe middleware architecture
InactiveUS7970918B2Guaranteed delivery qualityPromote resultsMultiprogramming arrangementsMultiple digital computer combinationsTransmission protocolMonitoring system
Owner:TERVELA INC
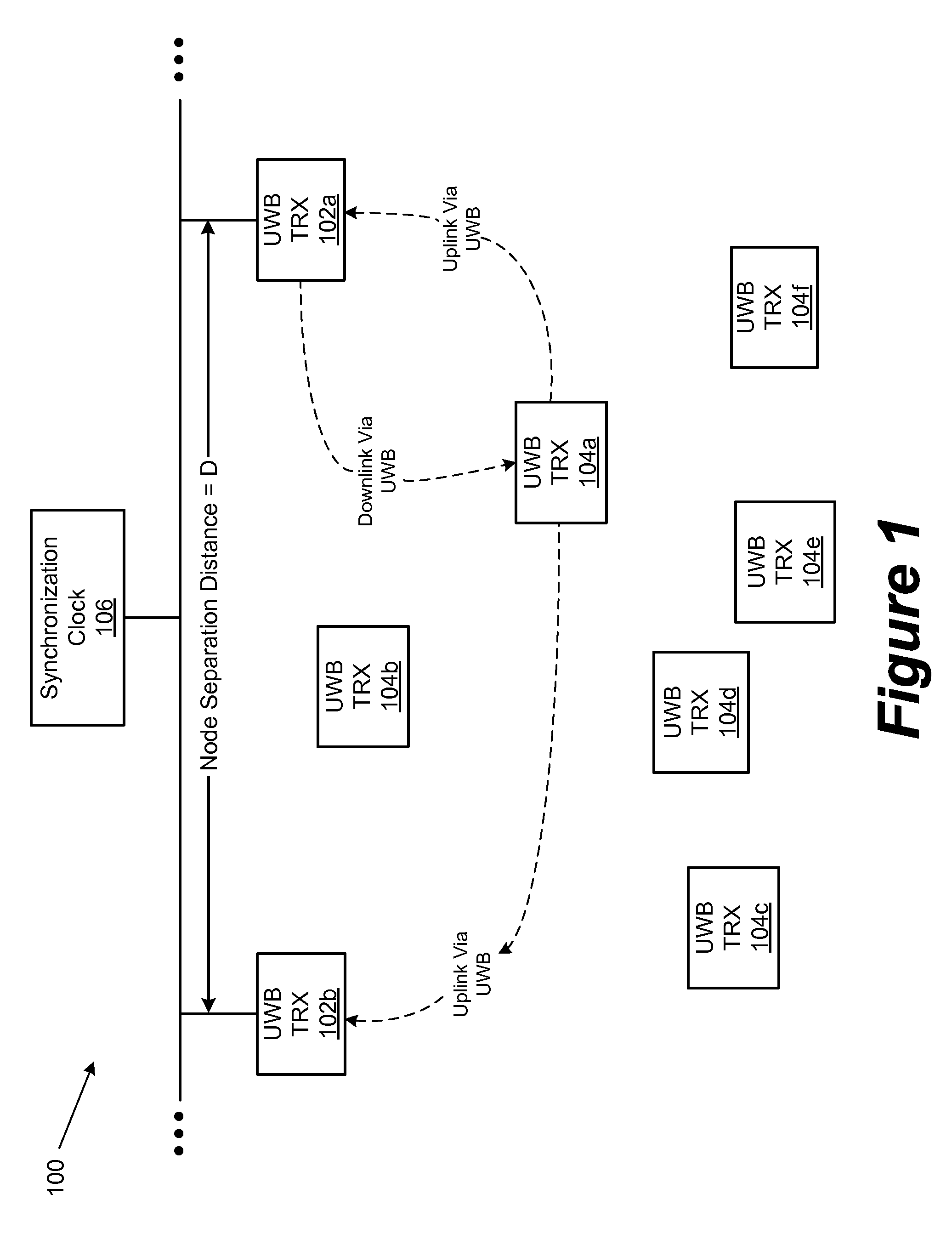
Communicating data between an access point and multiple wireless devices over a link
ActiveUS7512096B2Transmission control/equlisationError preventionTransmission protocolTelecommunications
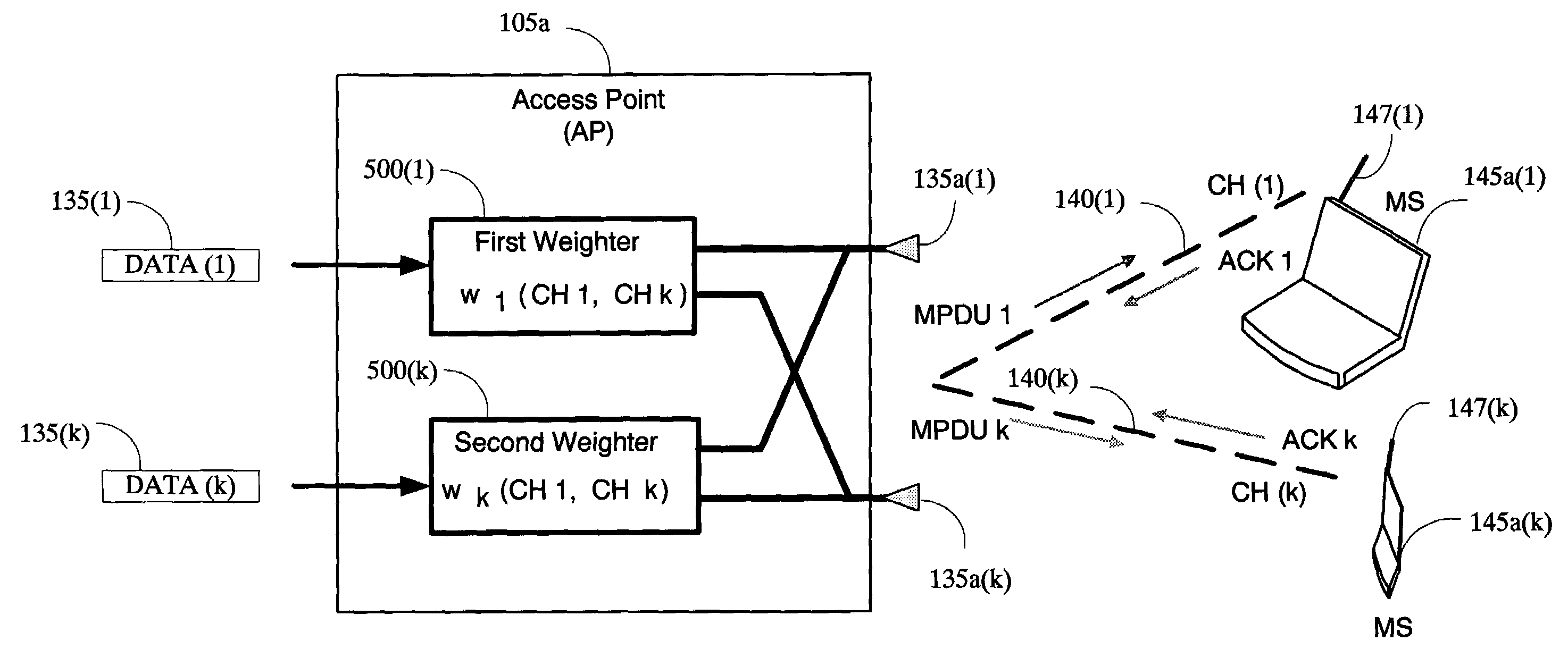
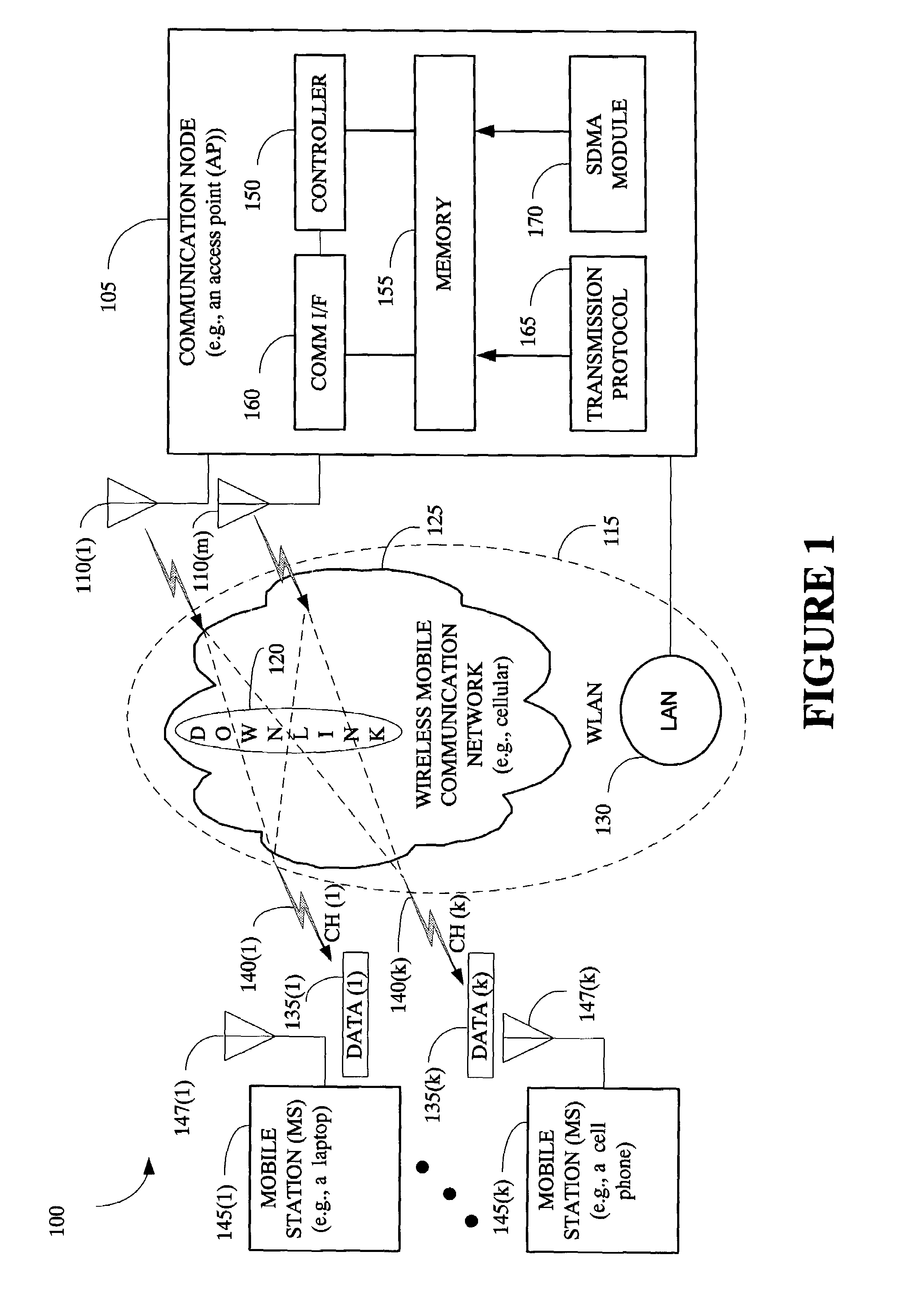
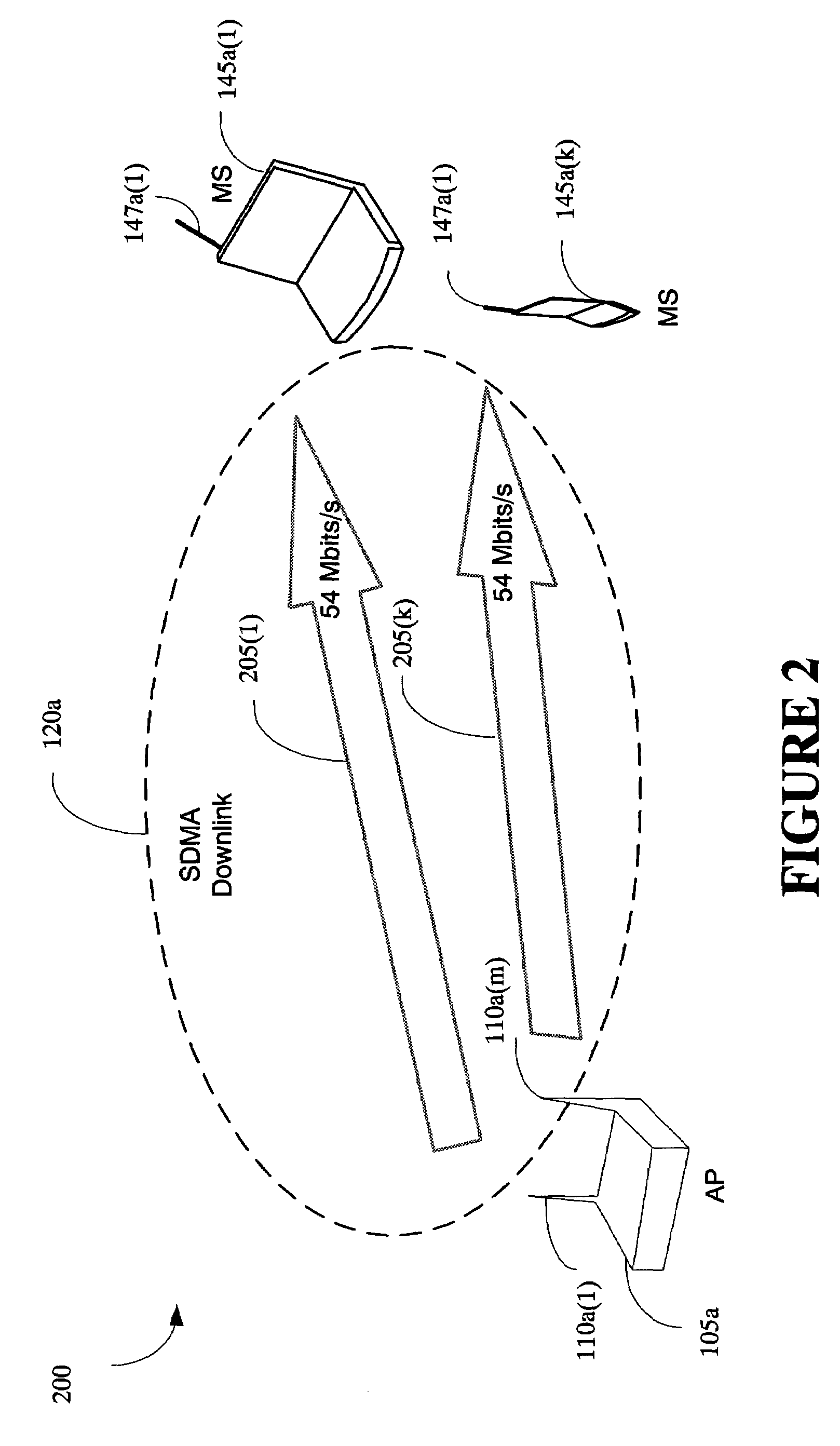
The present invention provides a method and an apparatus for communicating data over a network between a communication node, for example, an access point having a first and a second antenna and a first and a second mobile station. The method comprises weighting a first data at the access point to transmit the first data using the first and second antennas so that the first mobile station only receives the first data and weighting a second data at the access point to transmit the second data using the first and second antennas so that the second mobile station only receives the second data. A space division multiple access (SDMA) module may cause a transmission protocol to transmit the first data to the first mobile station on the downlink and transmit the second data to the second mobile station in parallel to the transmission of the first data on the downlink. In a telecommunication system, this substantially simultaneous transmission of the first and second data using a similar carrier frequency in a radio frequency communication over a wireless local area network (WLAN) may increase throughput of a downlink, for example, by a factor nominally equal to the number of antennas at an access point.
Owner:WSOU INVESTMENTS LLC
Method for multihop routing for distributed wlan networks
ActiveUS20050013253A1Error preventionFrequency-division multiplex detailsTransmission protocolMulti-hop routing
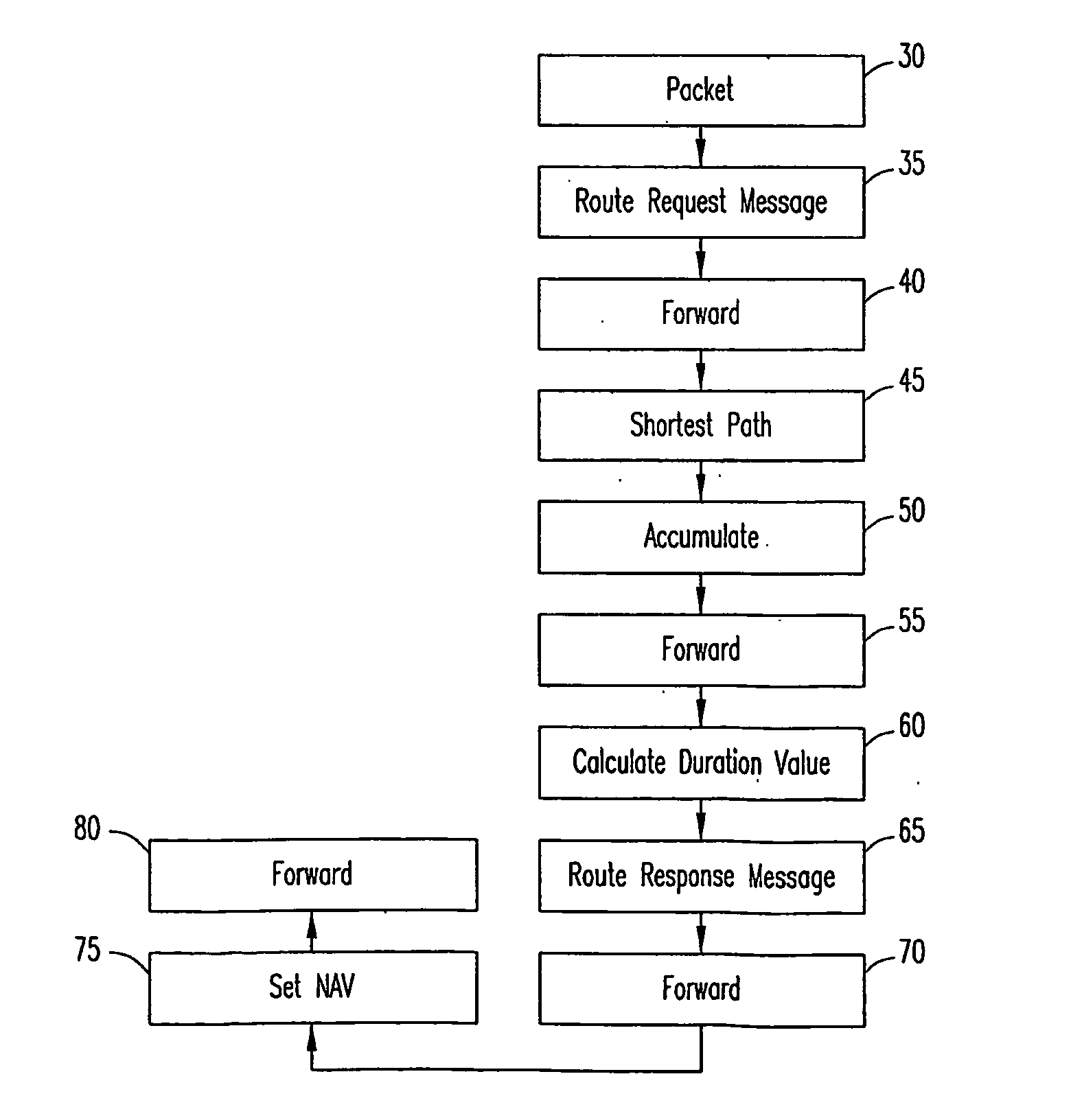
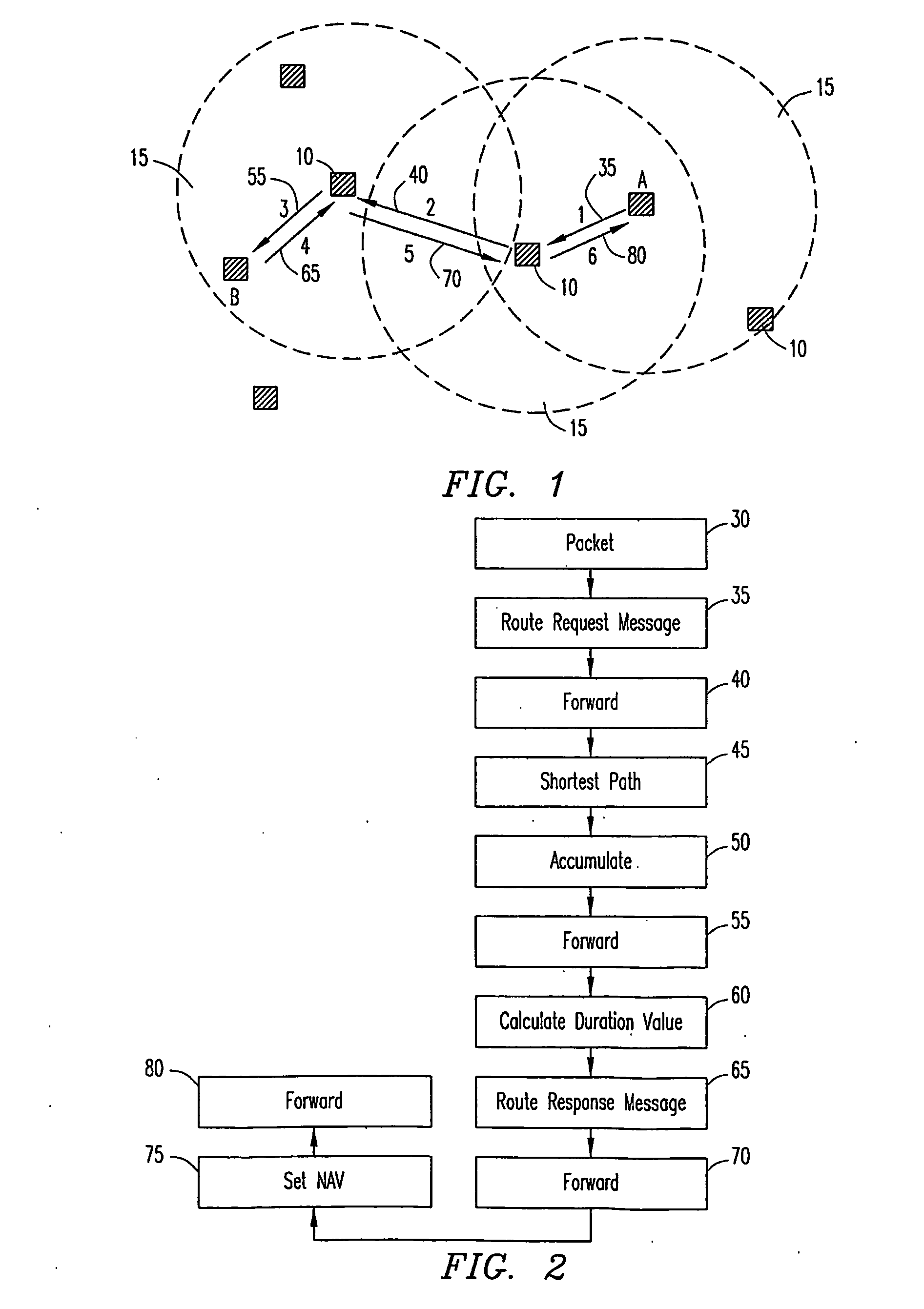
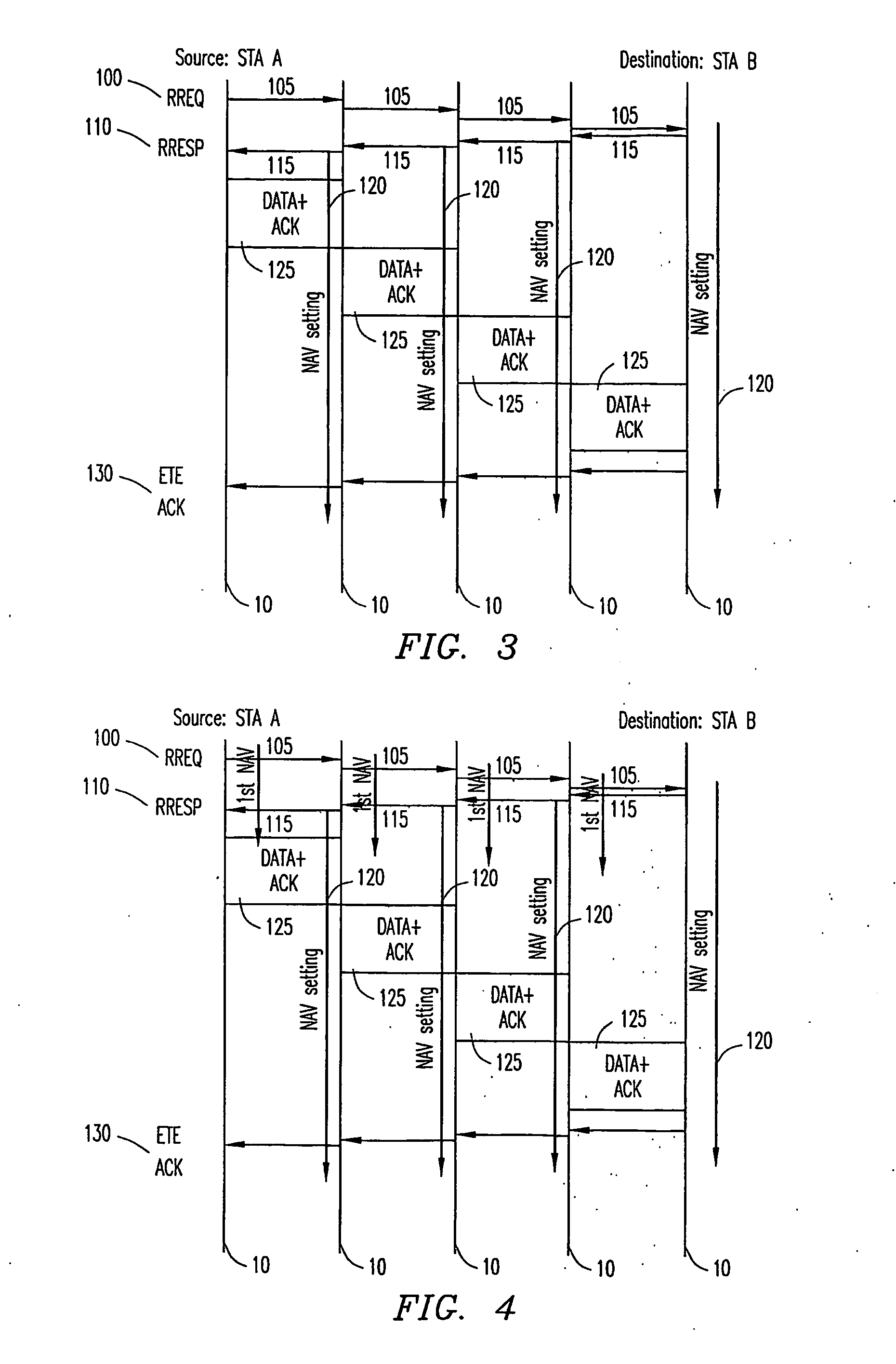
A method for multihop packet trasmissions in a wireless network involves establishing a multihop route through the wireless network. After establishment of the multihop route, transmission protocol parameter are altered to minimize delays for transmissions over the multihop route and at least one packet is transmitted over the multihop route according to the altered transmission protocol parameters. In a first embodiment, the altering of the transmission protocol parameters includes setting a NAV value at each node of the multihop route for a duration of the packet transmissions over the route. In an alternative embodiment, multihop packets are assigned a higher QoS value.
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method for generating selectable extension to media transport protocol
InactiveUS20060031545A1Special service provision for substationMultiple digital computer combinationsTransmission protocolExtension set
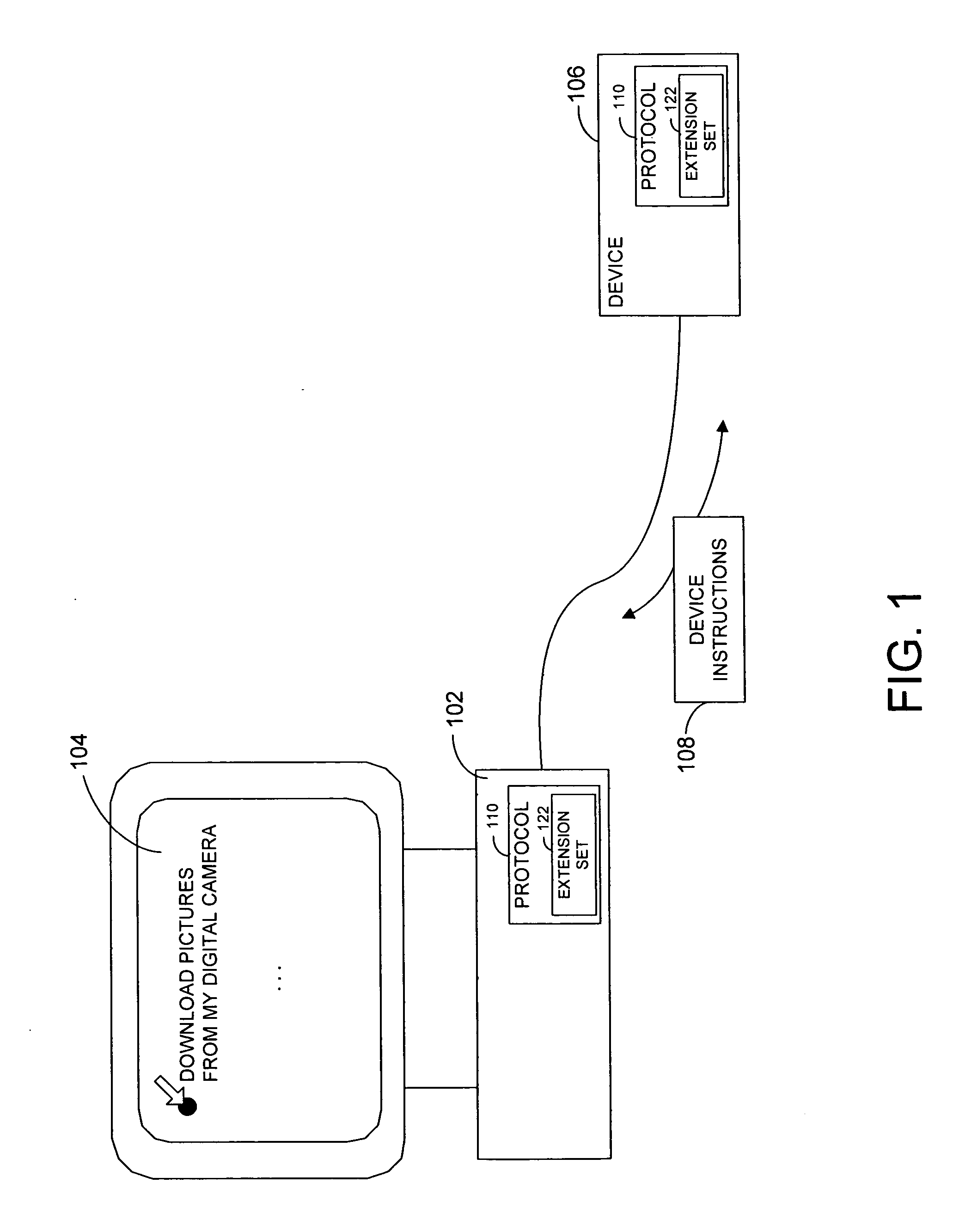
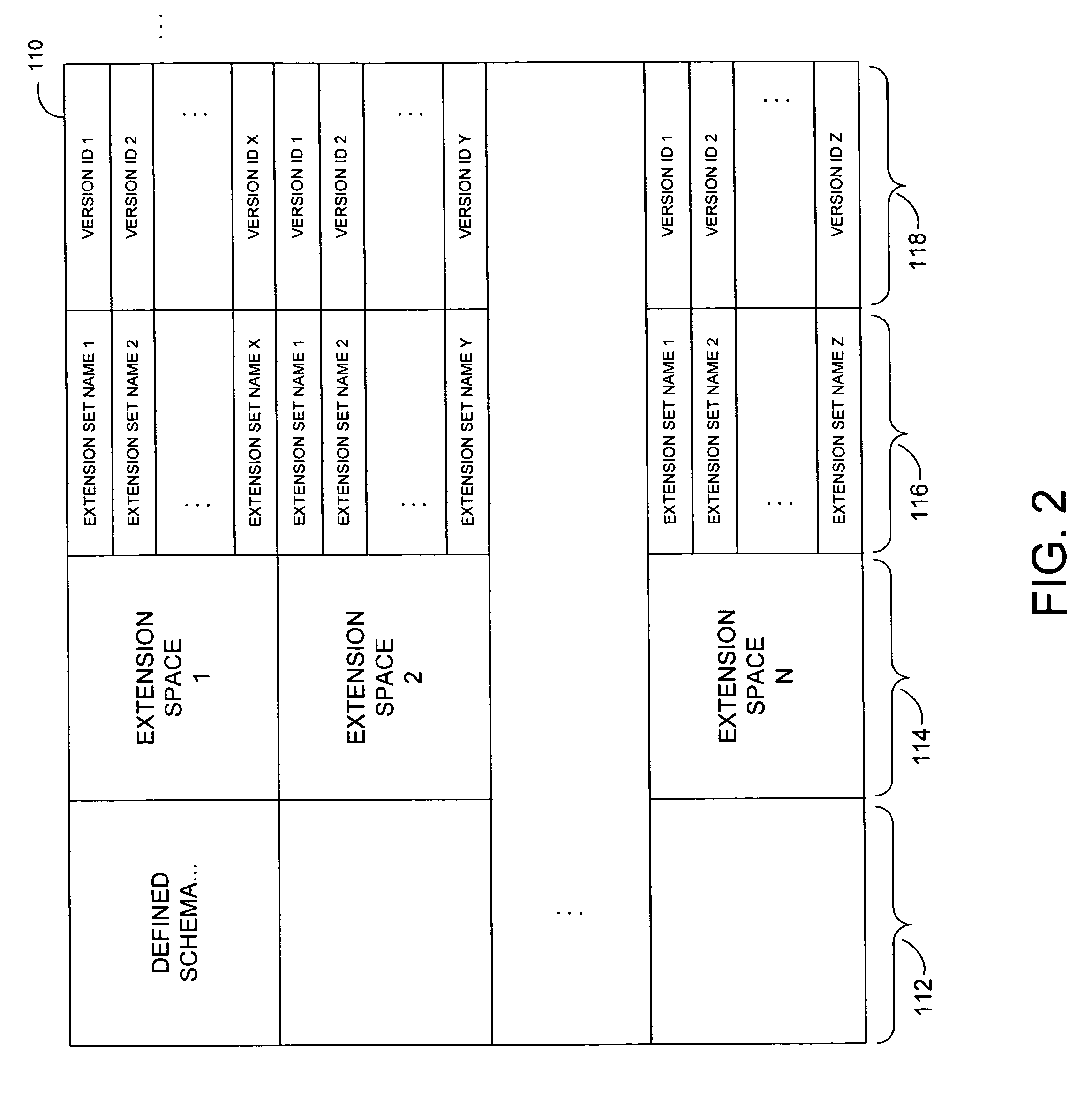
A protocol and related techniques and platforms allow vendors to selectably extend the Media Transport Protocol (MTP), or other defined protocols to implement vendor-specific commands, data fields, instructions and other extension sets. According to embodiments of the invention in one regard, one or more extension space may be utilized to derive independent extension sets, in part by separating the extension space according to a unique identifier assigned to or associated with a given vendor. In embodiments that unique identifier may be or include an Internet DNS (Domain Name System) domain name, or other extension set name or identifier. According to the invention in one regard, because a DNS domain name may be independently registered and secured by participating vendors or manufacturers and by definition uniquely assigned, the separation of vendor extension sets by that type of name may be automatic and free from conflict. Vendors or manufacturers, such as makers of digital cameras, digital video cameras, audio players such as MP3 or other players, software vendors or others may therefore freely design extensions to the Media Transport Protocol or other protocols, without a need to clear those extensions with a standards body and with confidence that their commands, data fields and other extensions may be free from overlap with that of other manufacturers.
Owner:MICROSOFT TECH LICENSING LLC
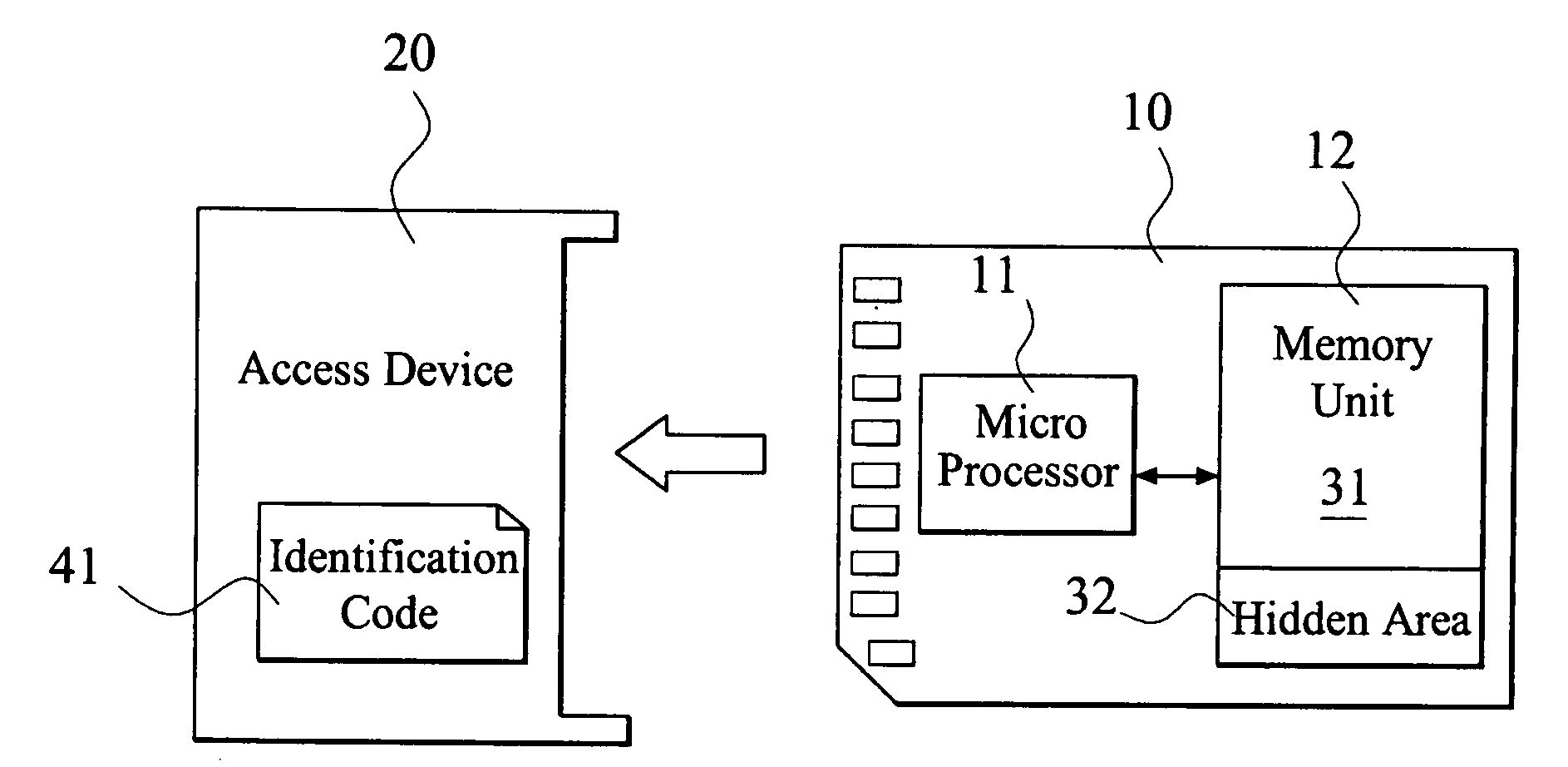
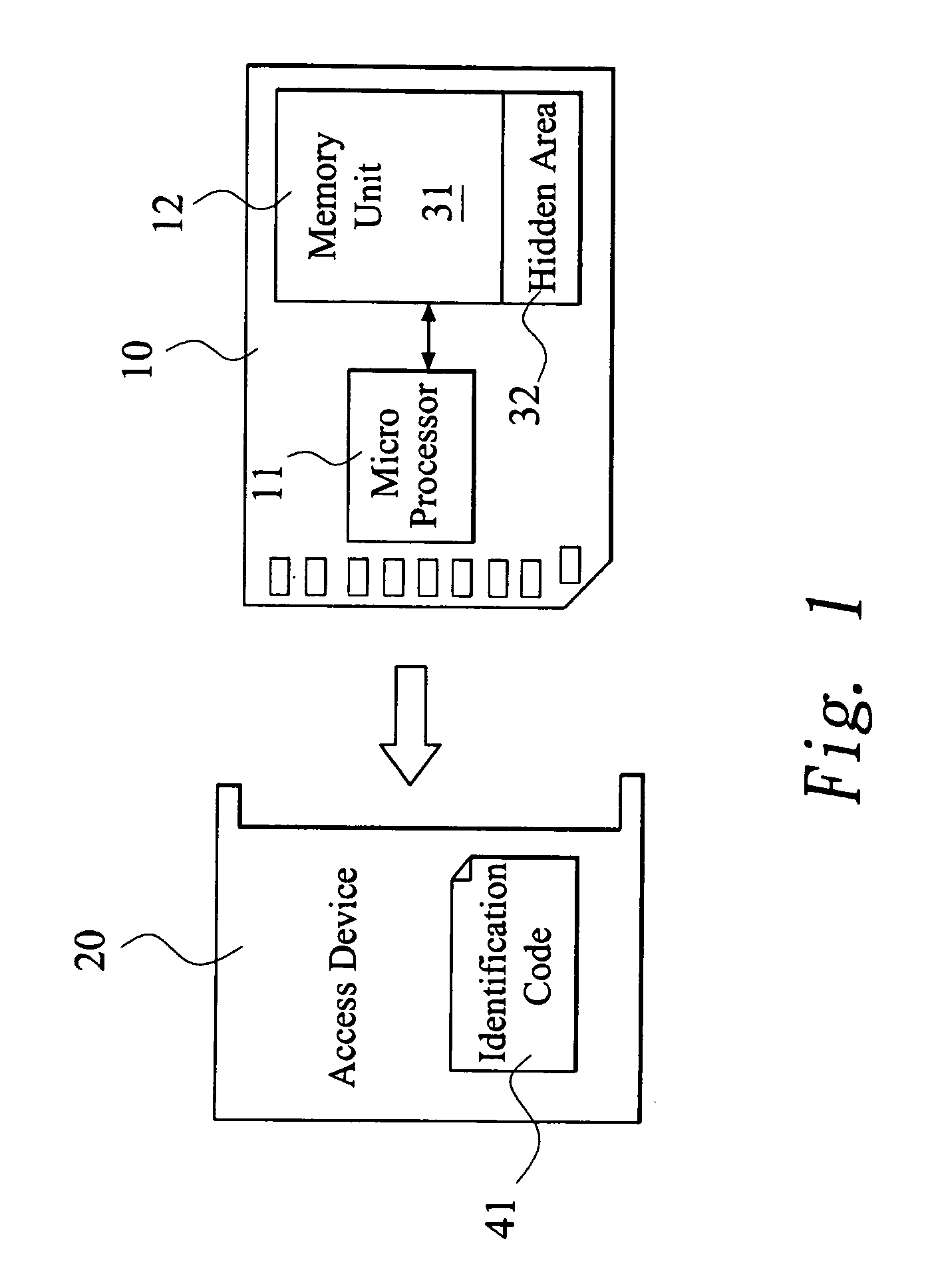
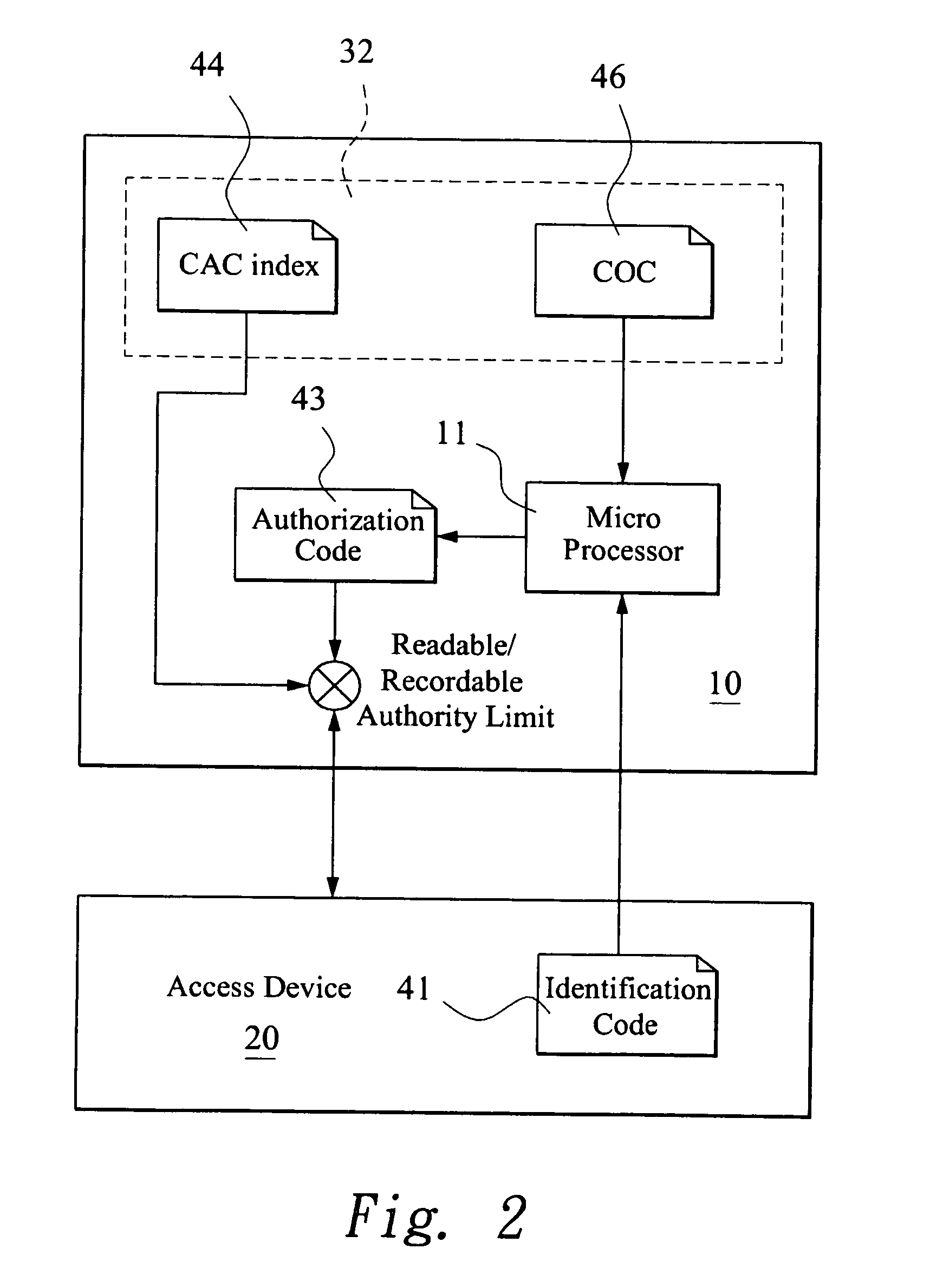
Authority limit management method
InactiveUS20080022415A1Avoid dataDigital data processing detailsAnalogue secracy/subscription systemsTransmission protocolIdentification device
An authority limit management method is proposed for a digital media storage. The digital media storage includes at least one micro processor and at least one memory unit and connected to an access device. A classification authorization code index (CAC index) and a plurality of classification operation commands (COC) is pre-stored in the digital media storage and an identification code is set for the access device. The classification operation commands is performed to calculate a classification authorization code when the digital media storage is connected to the access device for initial transmission protocol. The authority limit of the memory unit for the access device is granted to the access device according to the classification authorization code. Therefore, the data of the digital media storage can be prevented from illegal copy or hacker.
Owner:TRANSCEND INFORMATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com