Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
747 results about "Application protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
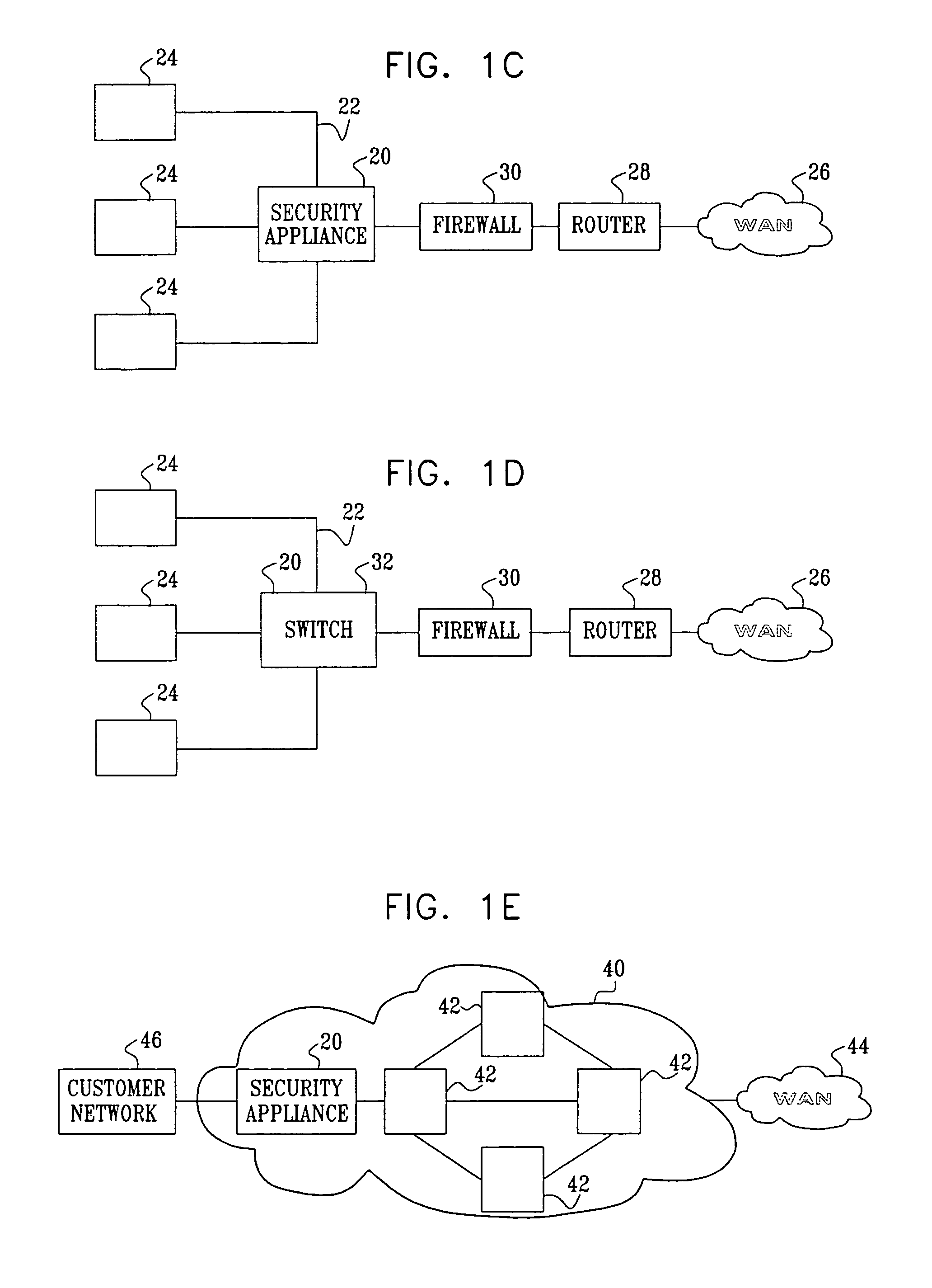
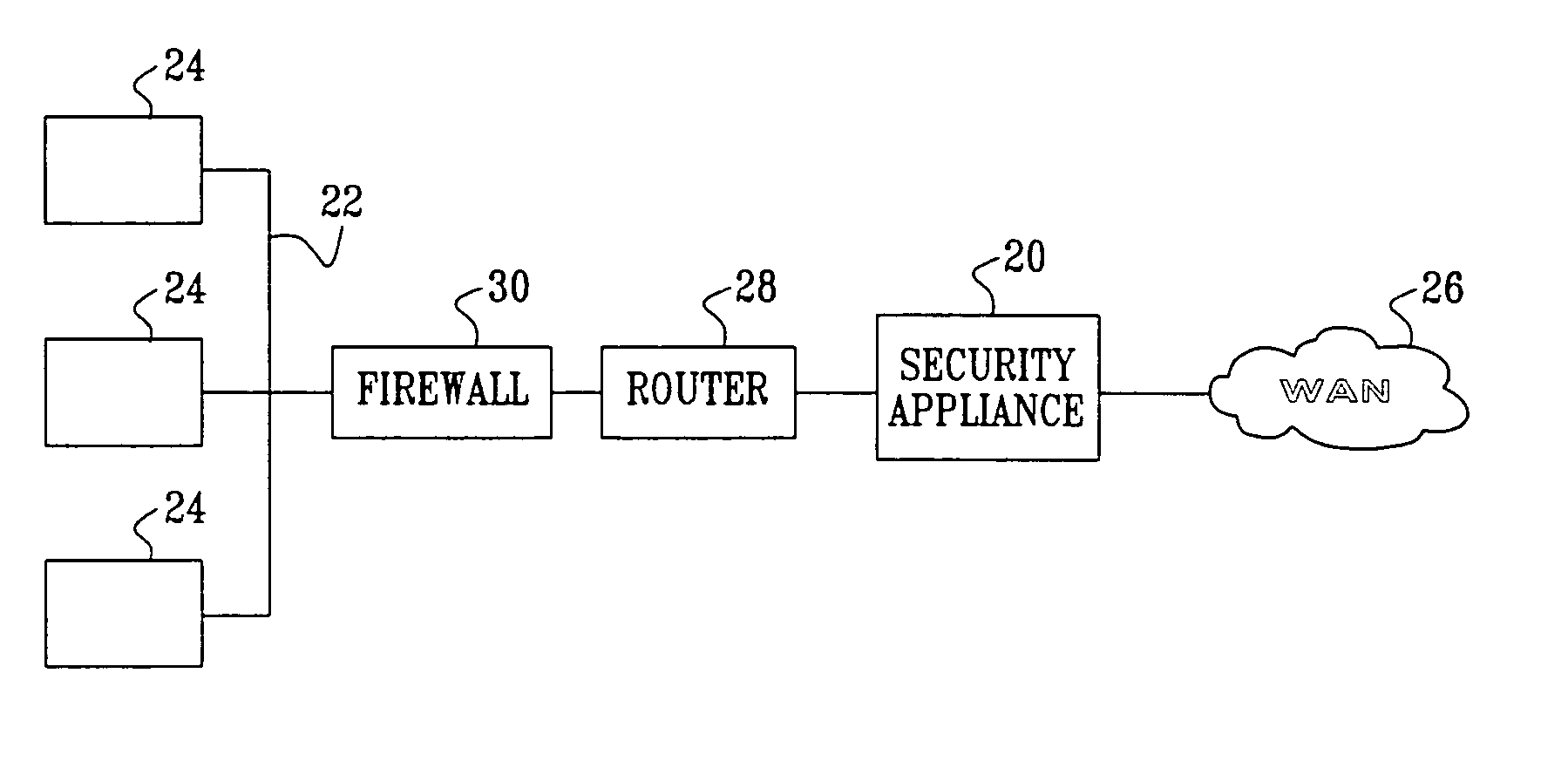
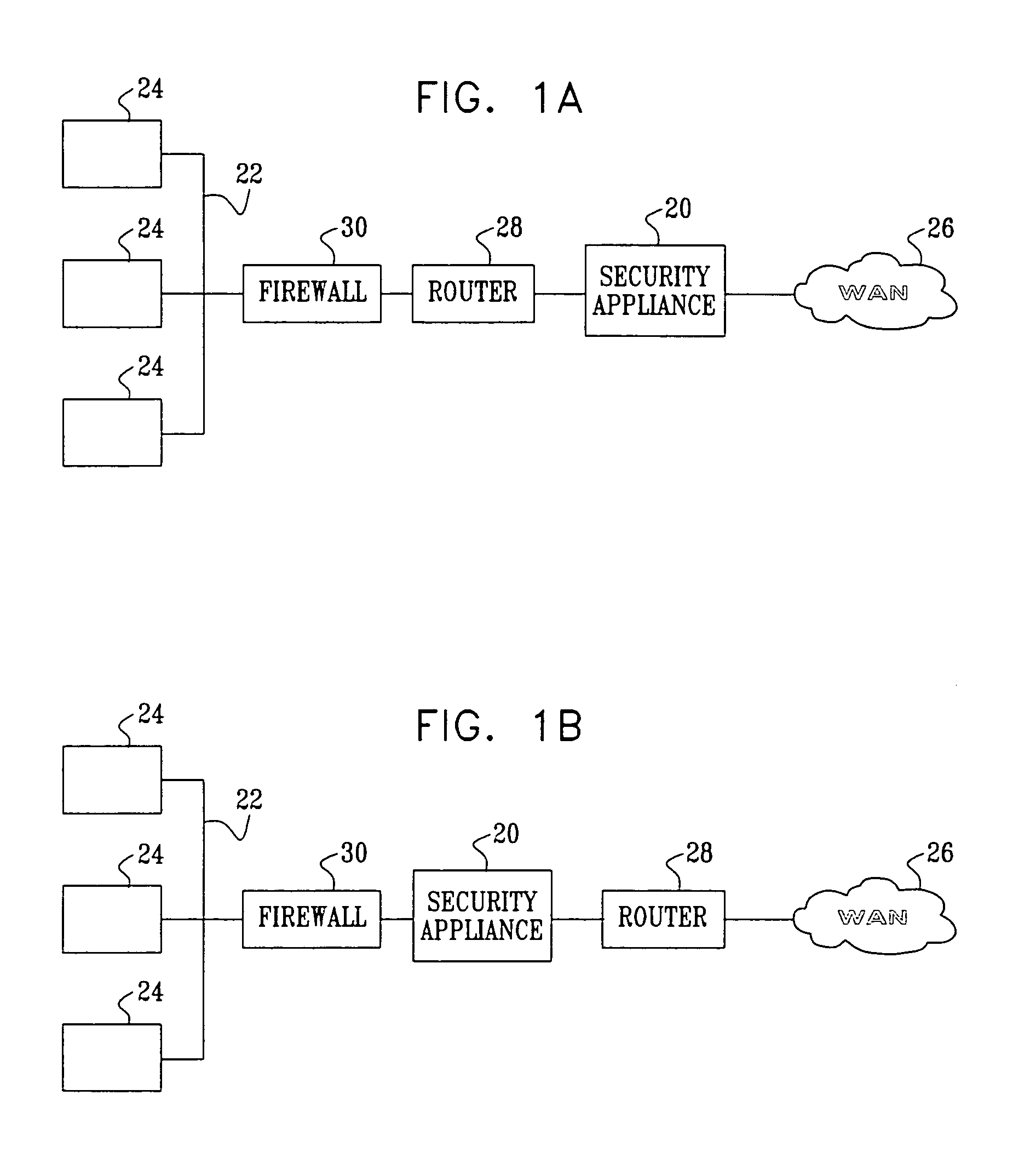
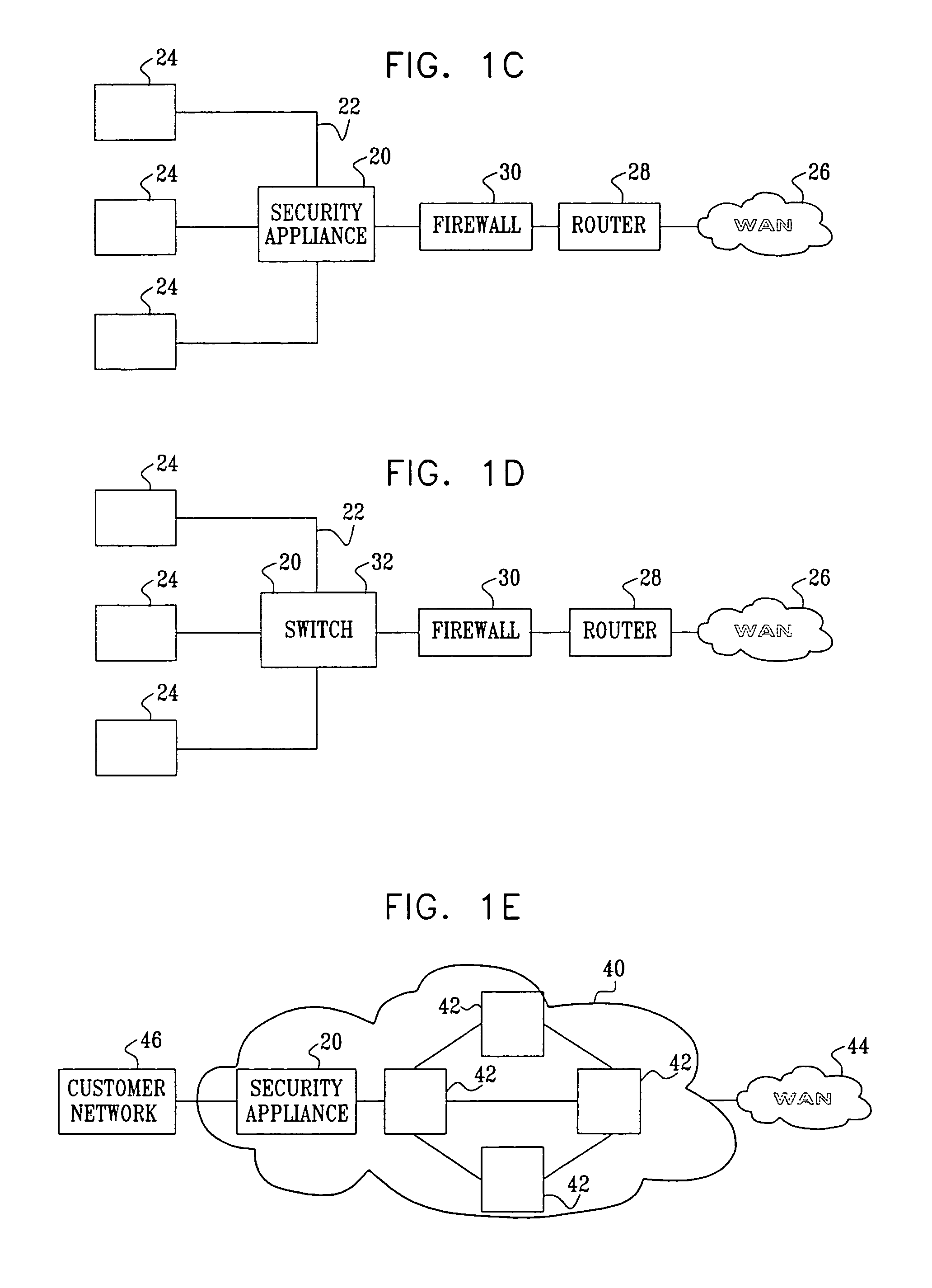
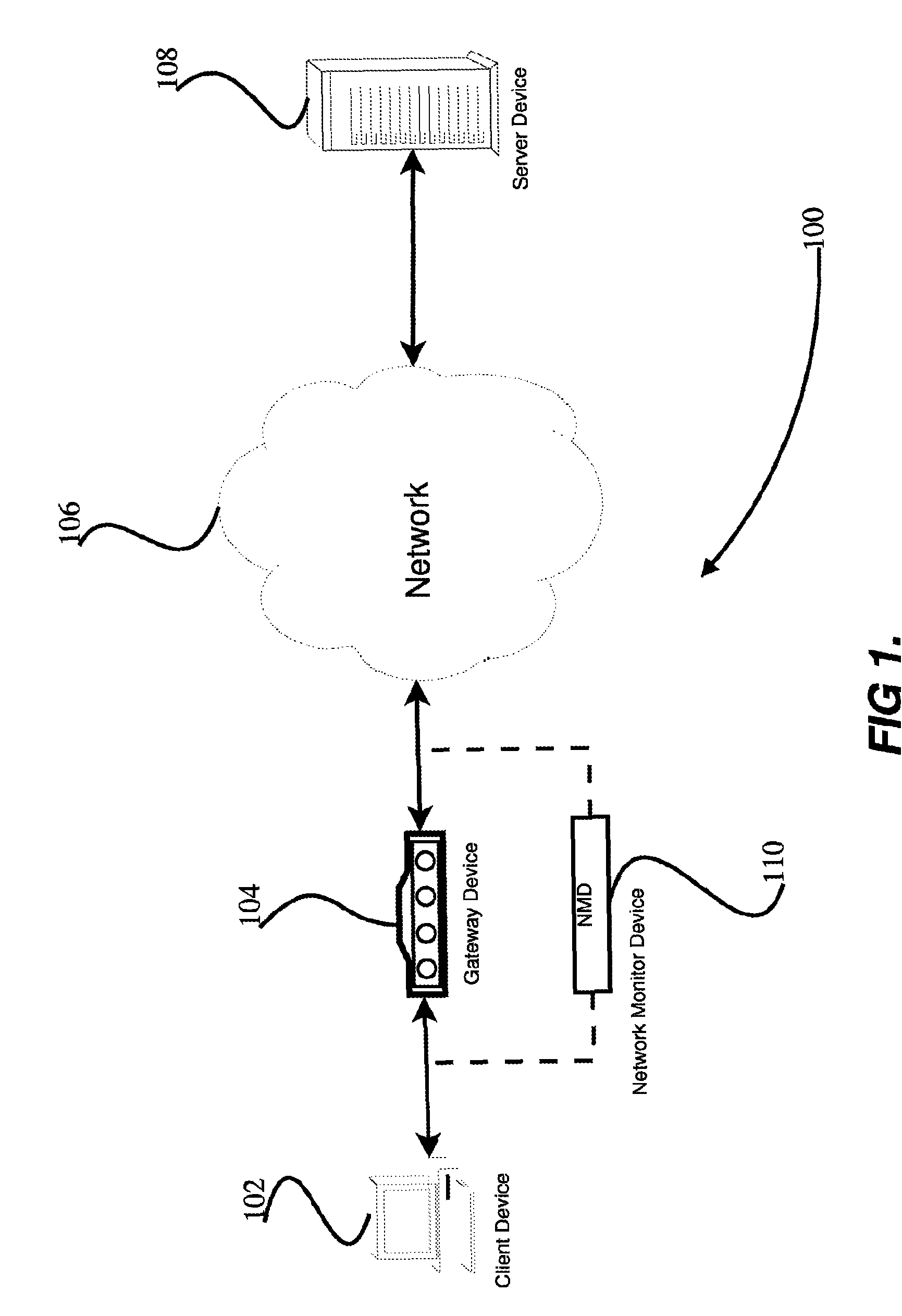
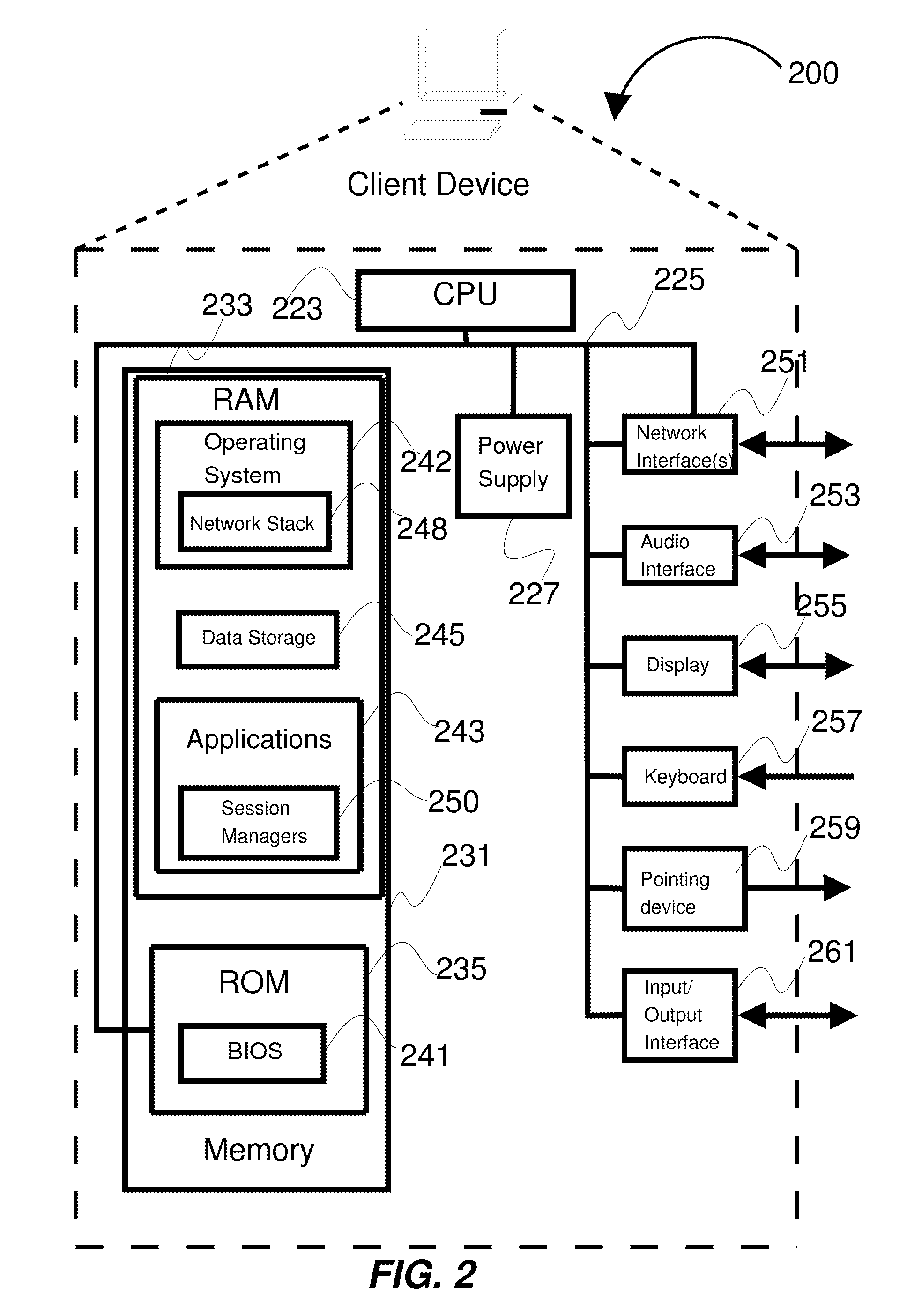
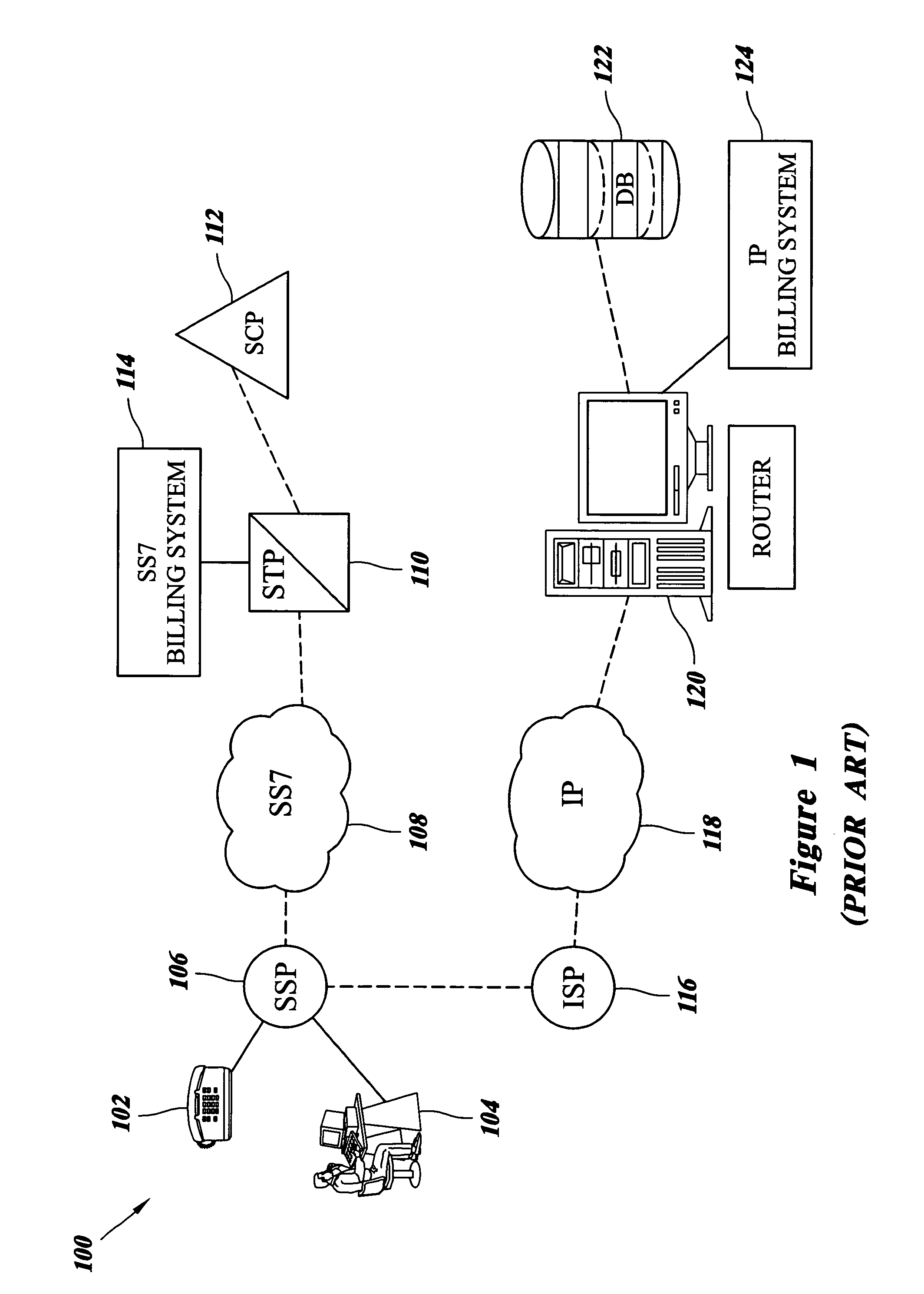
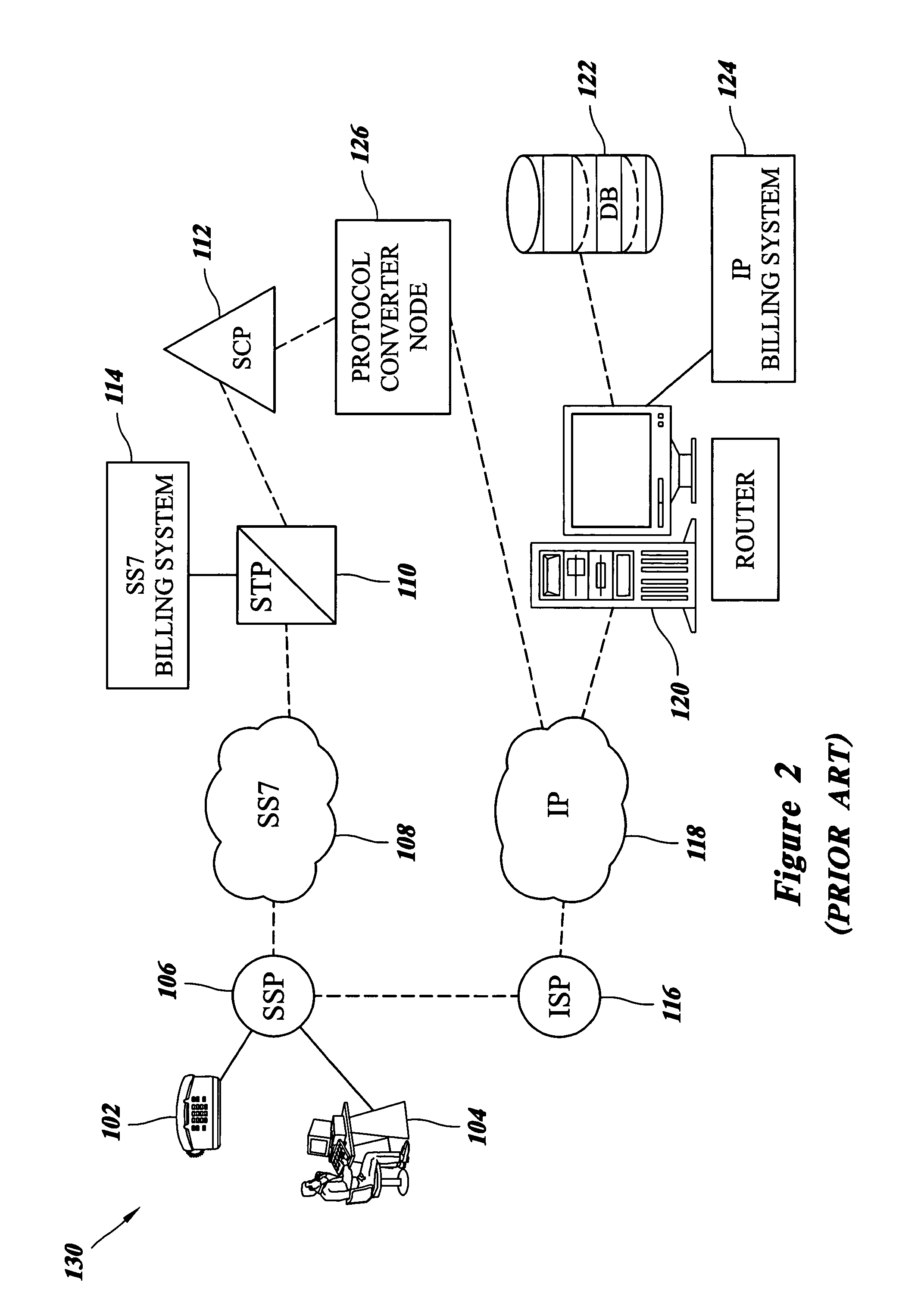
Application protocol is one such protocol. Application protocols govern various processes, such as the process for downloading a web page, or for sending e-mail. The application protocol directs how these processes are done.
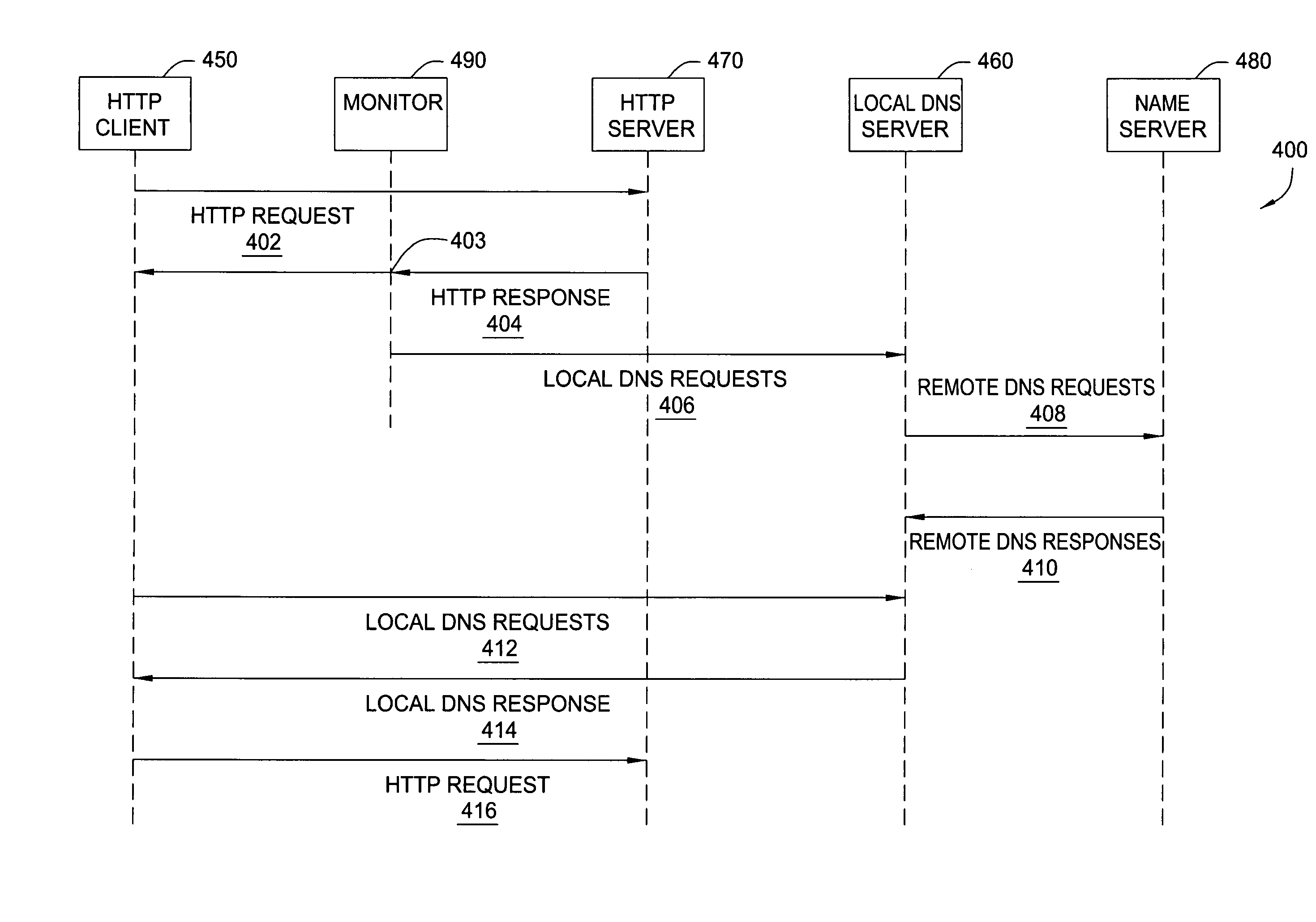
Method and apparatus for DNS pre-fetching for multiple clients
InactiveUS20050262248A1Quick responseQuick connectionMultiple digital computer combinationsTransmissionDomain nameData pack
In one embodiment, the present invention is a method and apparatus for DNS pre-fetching for multiple clients. In one embodiment, all packets coming into or going out of a local network are scanned for application protocol, domain names, and / or other information. If pre-defined criteria indicate that the network is interested in a particular domain name, a DNS lookup is performed and the corresponding IP address is cached by the local DNS server. The local DNS server is thereby able to quickly respond to future requests for the cached domain name. Moreover, because the IP address is cached at the local DNS server, any client connected to the local DNS server on the local network can request the cached domain name from the local DNS server and be quickly connected to the indicated domain name.
Owner:IBM CORP
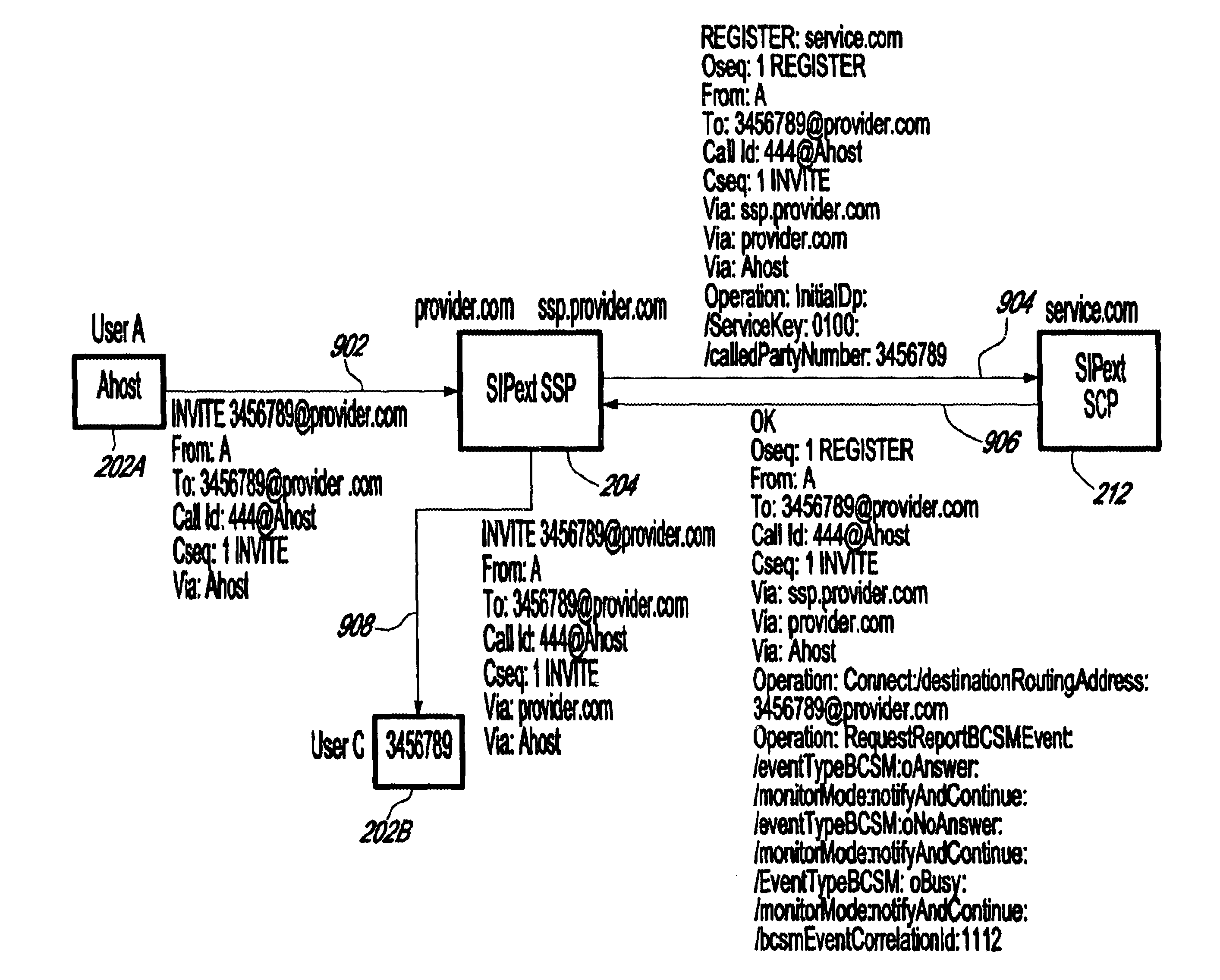
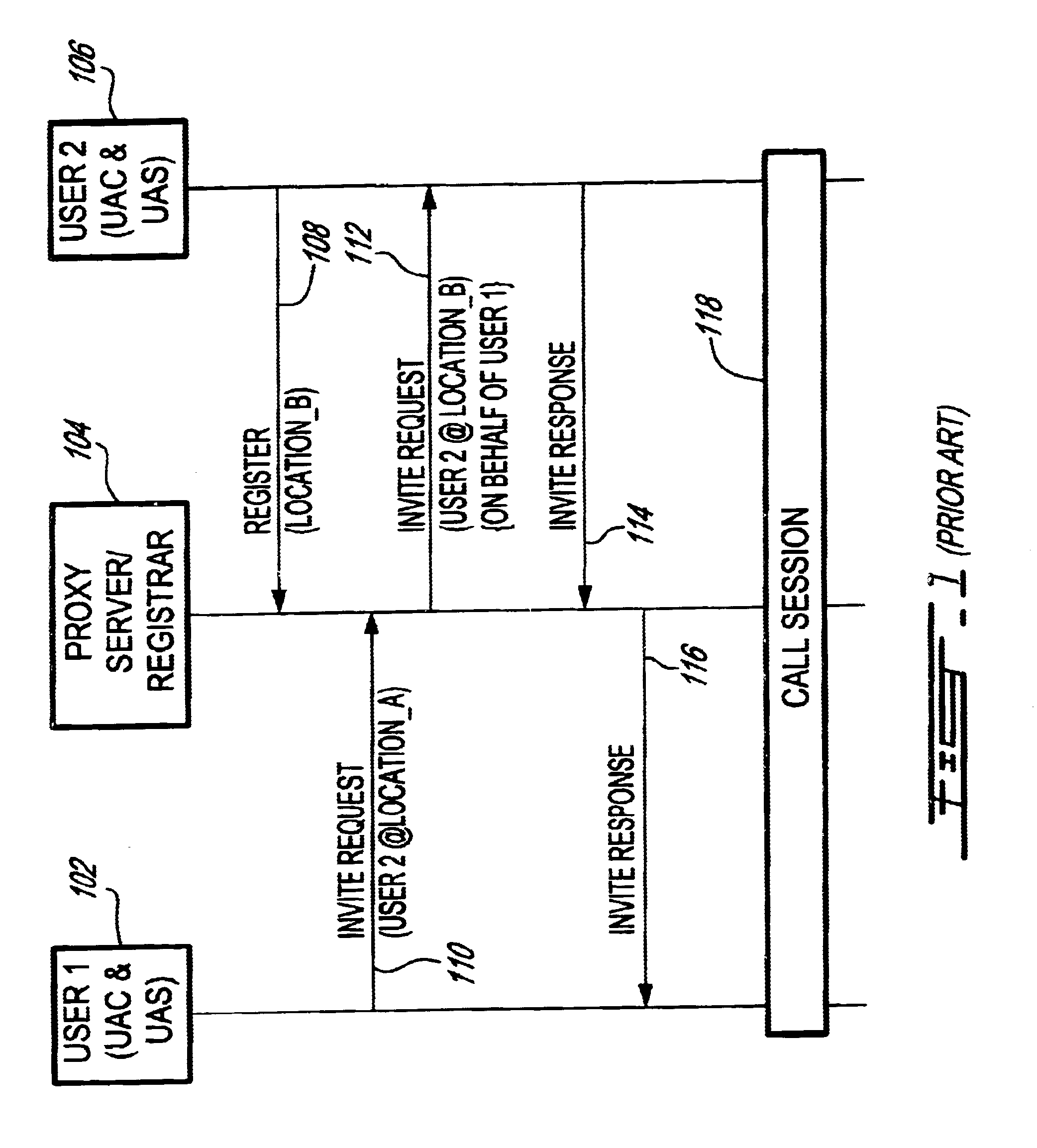
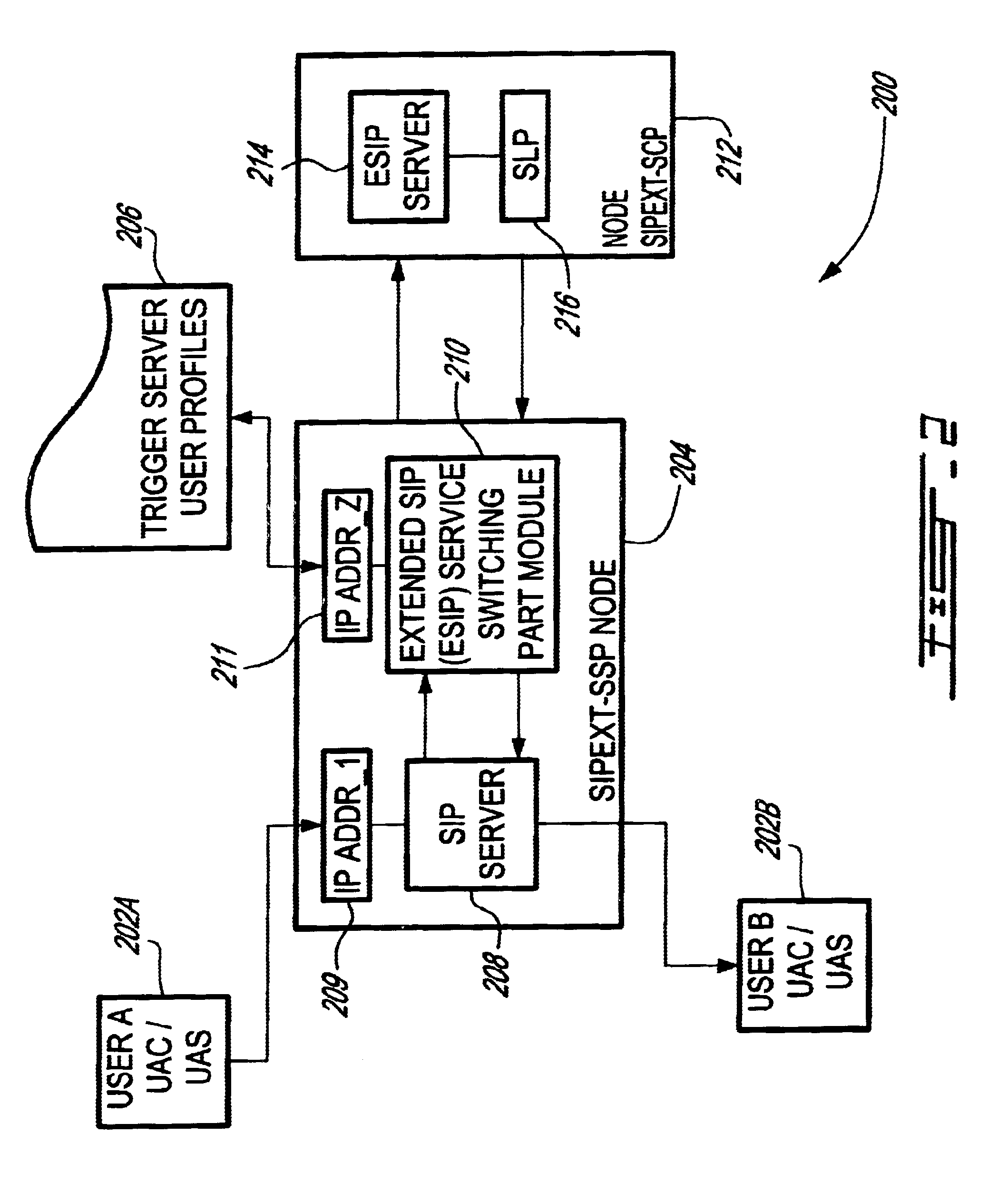
System and method for providing value-added services (VAS) in an integrated telecommunications network using session initiation protocol (SIP)
InactiveUS6625141B1Intelligent networksData processing applicationsSession Initiation ProtocolIntelligent Network
A system and method for providing Value-Added Services (VAS) in an integrated telecommunications network having a packet-switched network portion (PSN) operable with Session Initiation Protocol (SIP). The integrated telecommunications network includes a SIPext SSP server, a trigger server, and a service node having a Service Logic Program (SLP) that is operable with Intelligent Network Application Protocol (INAP). The SIPext SSP and service nodes are provided with the capability to communicate using SIP-compliant messaging. New header fields are provided that specify operations to be performed by the service node with respect to a service. INAP service parametric data is also provided in the header fields in a sequential form. When a call is received in the SIPext SSP server for a user having a subscription for a VAS, it queries the user profile stored in the trigger server. If the user is subscribed for a service, a SIP request message is formulated based on the user profile, wherein appropriate headers are populated with relevant parametric information and call context data. The service node launches the SLP based on the information provided in the request message and sends a SIP response message to the SIPext SSP server with an instruction concerning the provisioning of the VAS. The SIPext SSP server, thereafter, takes an appropriate action based on the response message and any parametric information contained therein.
Owner:TELEFON AB LM ERICSSON (PUBL)
Transmission of data within a communications network
ActiveUS20050063347A1Transmitter specific arrangementsRadio/inductive link selection arrangementsData transmissionControl parameters
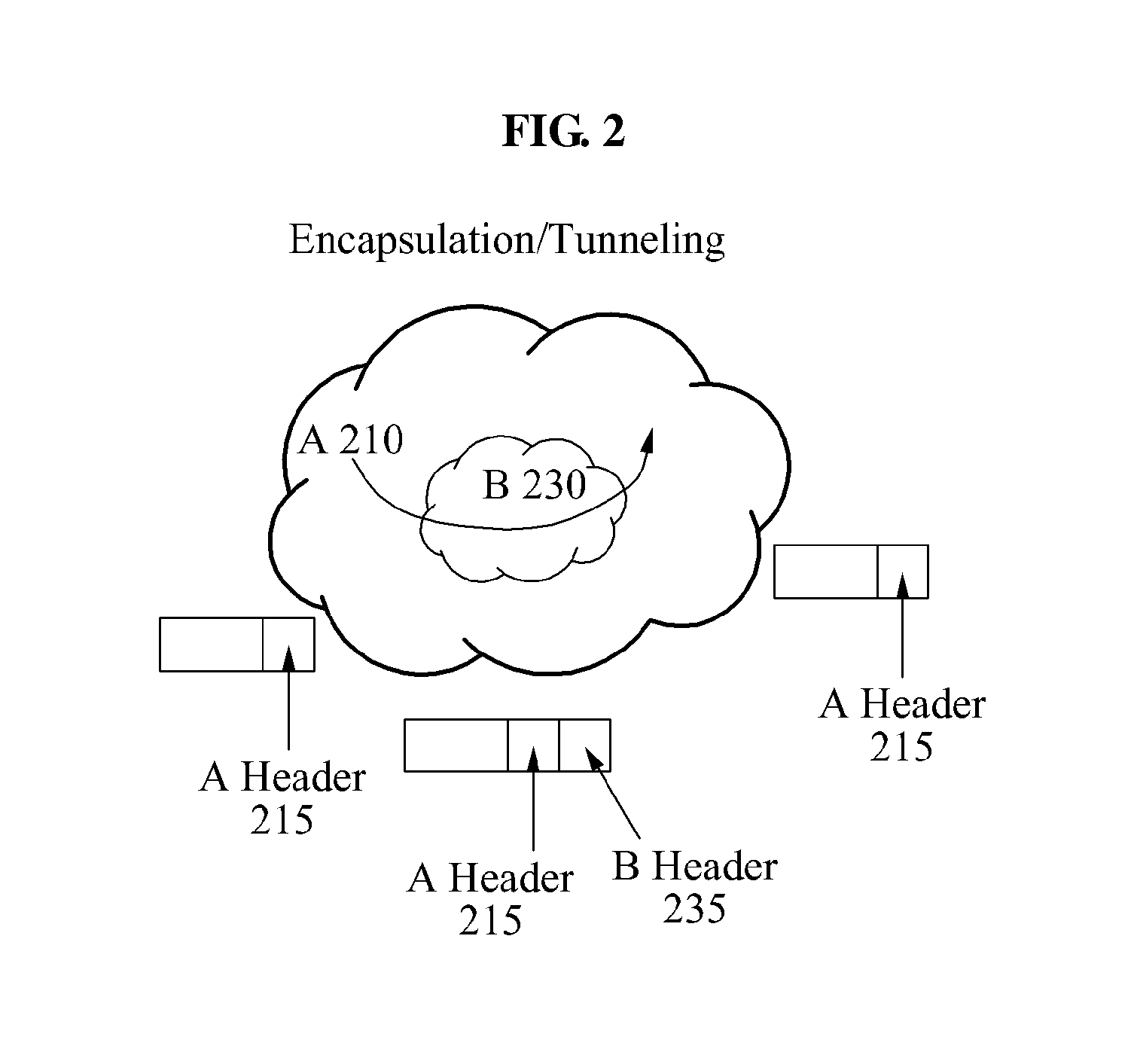
The invention relates to methods for providing a network element 5 of a communications network with data, in particular HSDPA related data. In order to enable the transmission of user data, it is proposed that a controller 4 of the network uses a dedicated frame structure for assembling frames with said user data. The frames can then be transmitted from the controller 4 via an interface to the network element 5. In order to enable the transmission of control parameters, it is further proposed that an interface application protocol is employed which allows the controller 4 to add control parameters to control messages transmitted from the controller 4 to a network element 5 via the interface.
Owner:MICROSOFT TECH LICENSING LLC
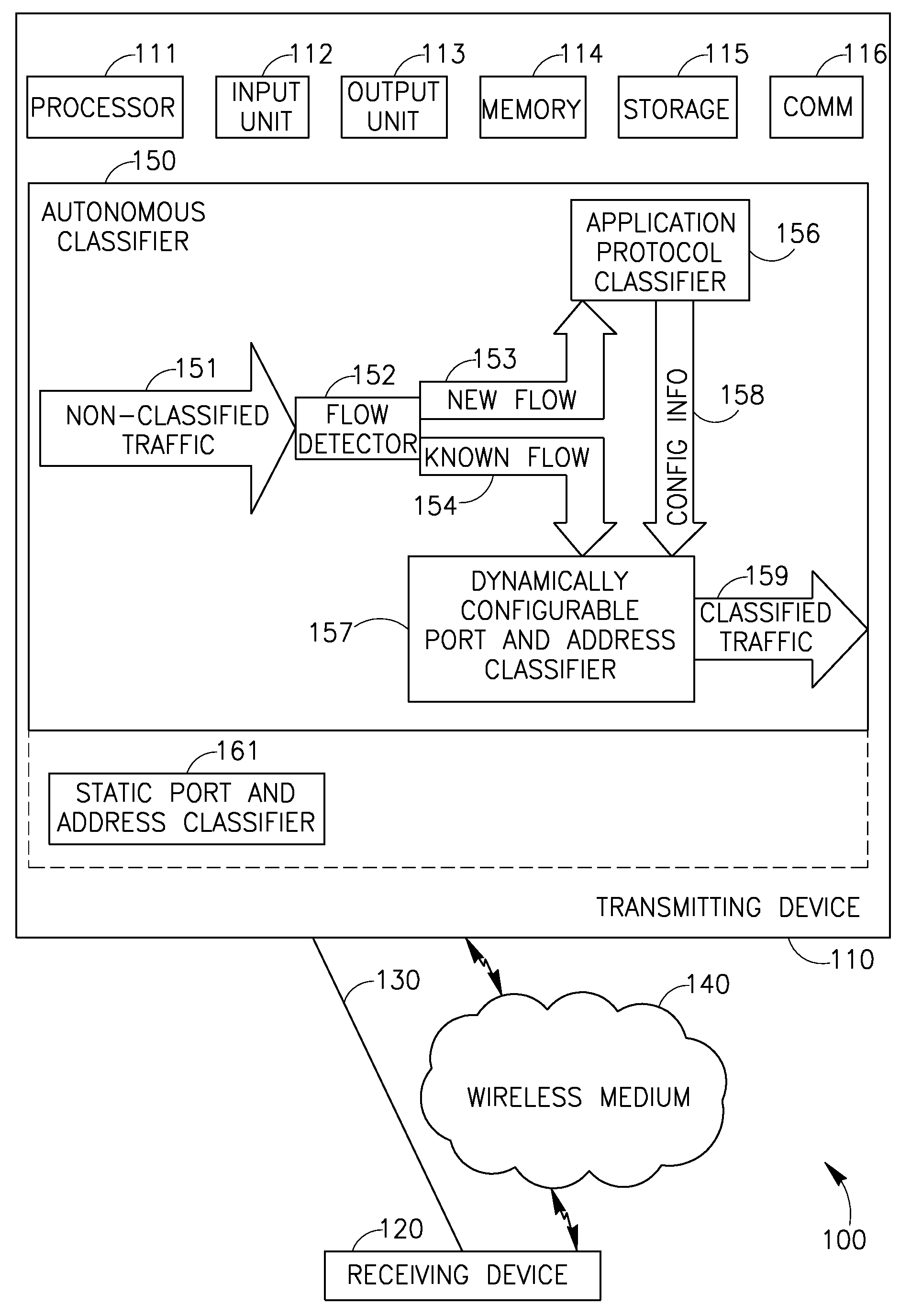
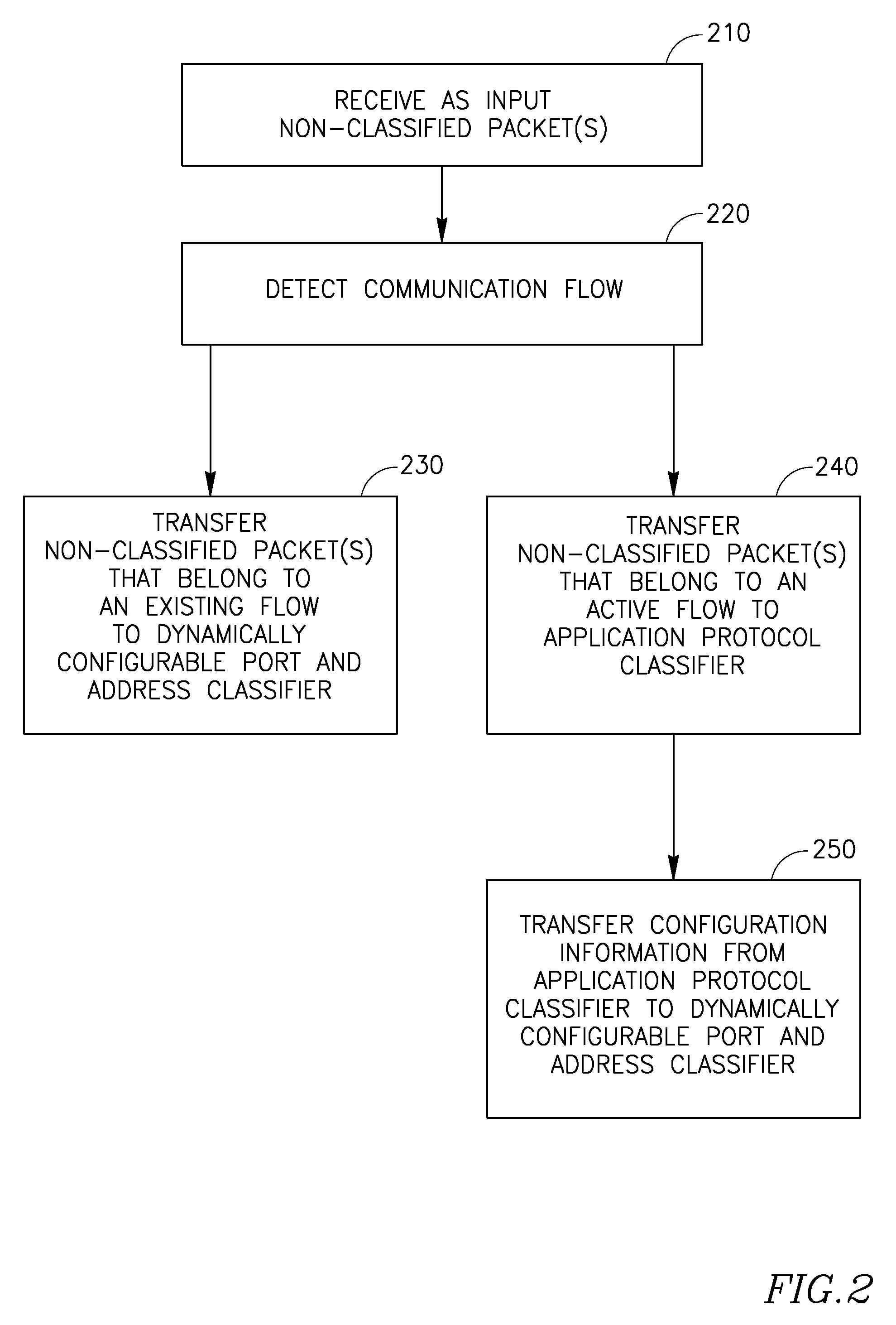
Device, system, and method of classification of communication traffic
Device, system, and method of classification of communication traffic. For example, a communication traffic classifier includes: a dynamically configurable port and address classifier to classify an unclassified packet based on port and address configuration information received from an application protocol classifier.
Owner:LANTIQ ISRAEL
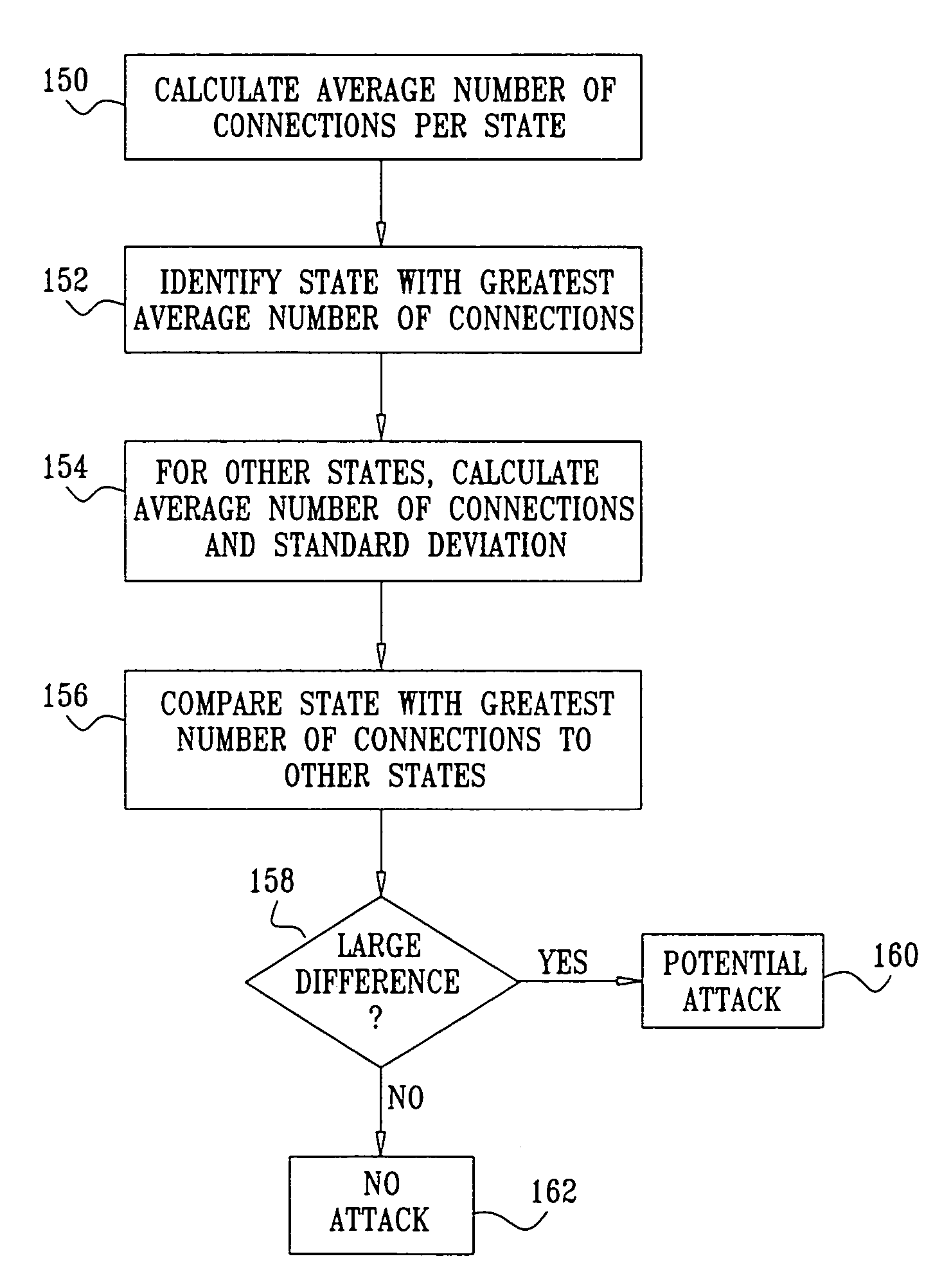
Stateful attack protection
ActiveUS7607170B2Reduces false positivesExtended durationMemory loss protectionError detection/correctionApplication protocol
A method for detecting an attack in a computer network includes monitoring communication traffic transmitted over connections on the network that are associated with a stateful application protocol so as to detect respective states of the connections, and analyzing a distribution of the states so as to detect the attack.
Owner:RADWARE
Stateful attack protection
ActiveUS20060137009A1Reduces false positiveExtended durationMemory loss protectionError detection/correctionApplication protocolTraffic volume
A method for detecting an attack in a computer network includes monitoring communication traffic transmitted over connections on the network that are associated with a stateful application protocol so as to detect respective states of the connections, and analyzing a distribution of the states so as to detect the attack.
Owner:RADWARE
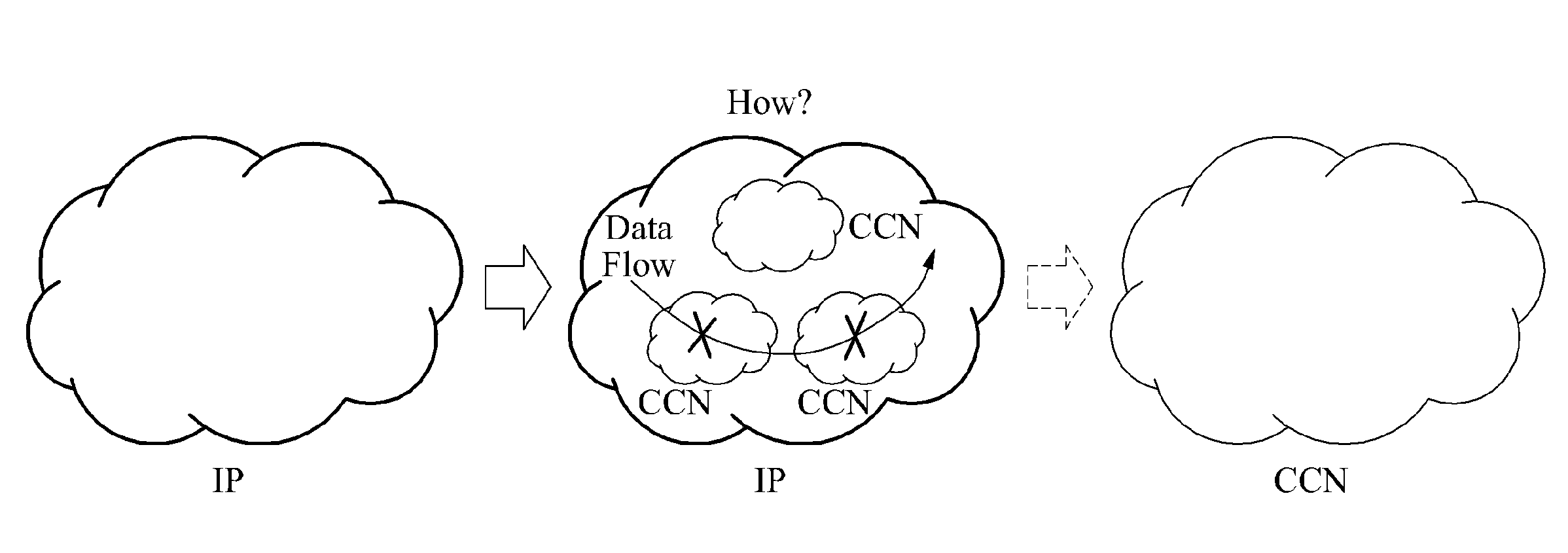
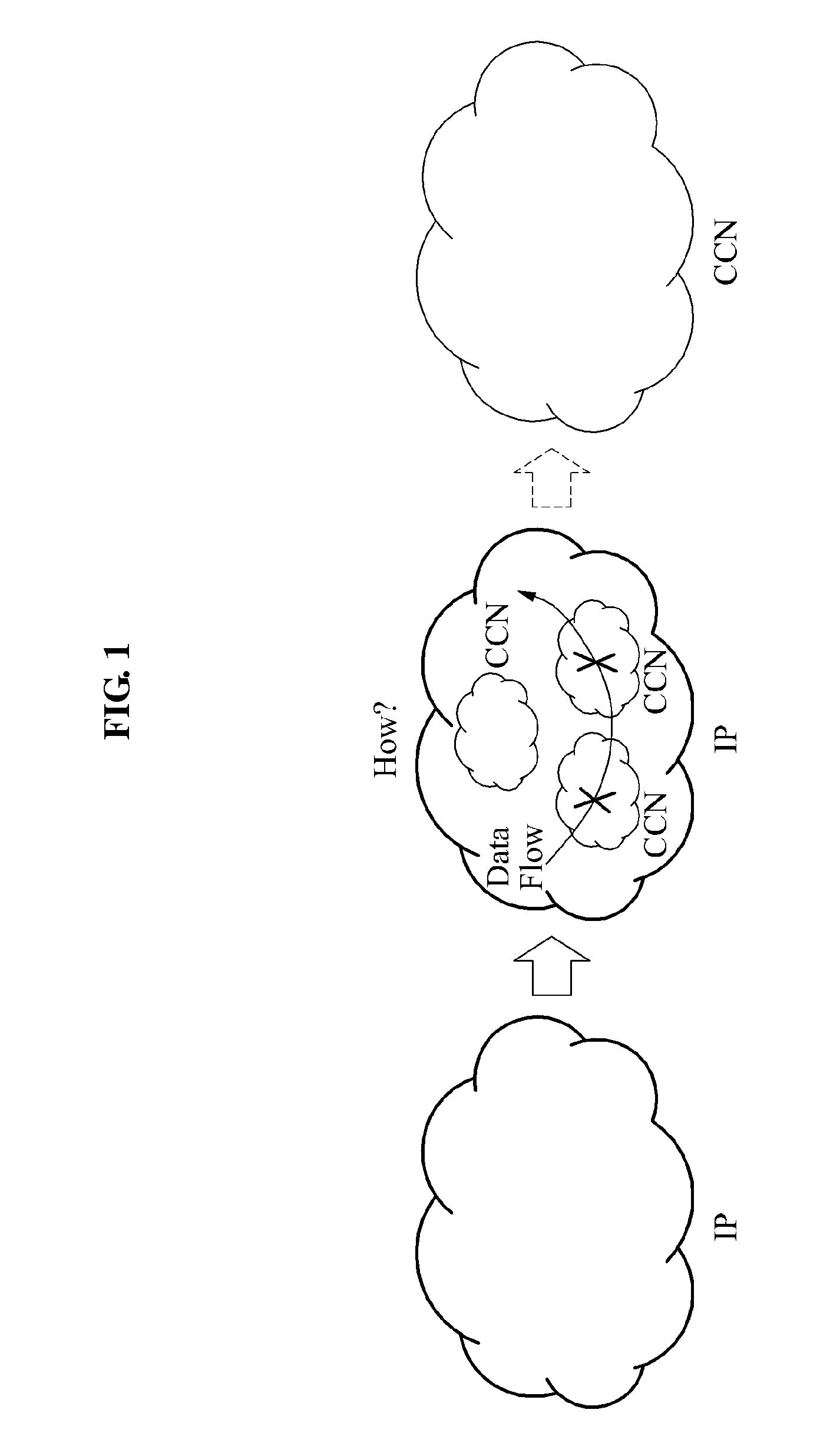
Method of implementing content-centric network (CCN) using internet protocol (IP)-based network in gateway, and gateway
ActiveUS20130173822A1Multiple digital computer combinationsNetwork connectionsInternet protocol suiteTTEthernet
A method of implementing a Content-Centric Network (CCN) using an Internet Protocol (IP)-based network, and a gateway that may implement such a method, are provided. A method of implementing a CCN using an IP-based network may involve: determining an application protocol and a packet type corresponding to the application protocol of an IP-based network, the application protocol being included in an IP packet of an IP-based network, and generating a content name corresponding to the IP packet, based on the application protocol and the packet type.
Owner:SAMSUNG ELECTRONICS CO LTD
Detecting anomalous network application behavior
ActiveUS8185953B2Memory loss protectionError detection/correctionInformation analysisInternet traffic
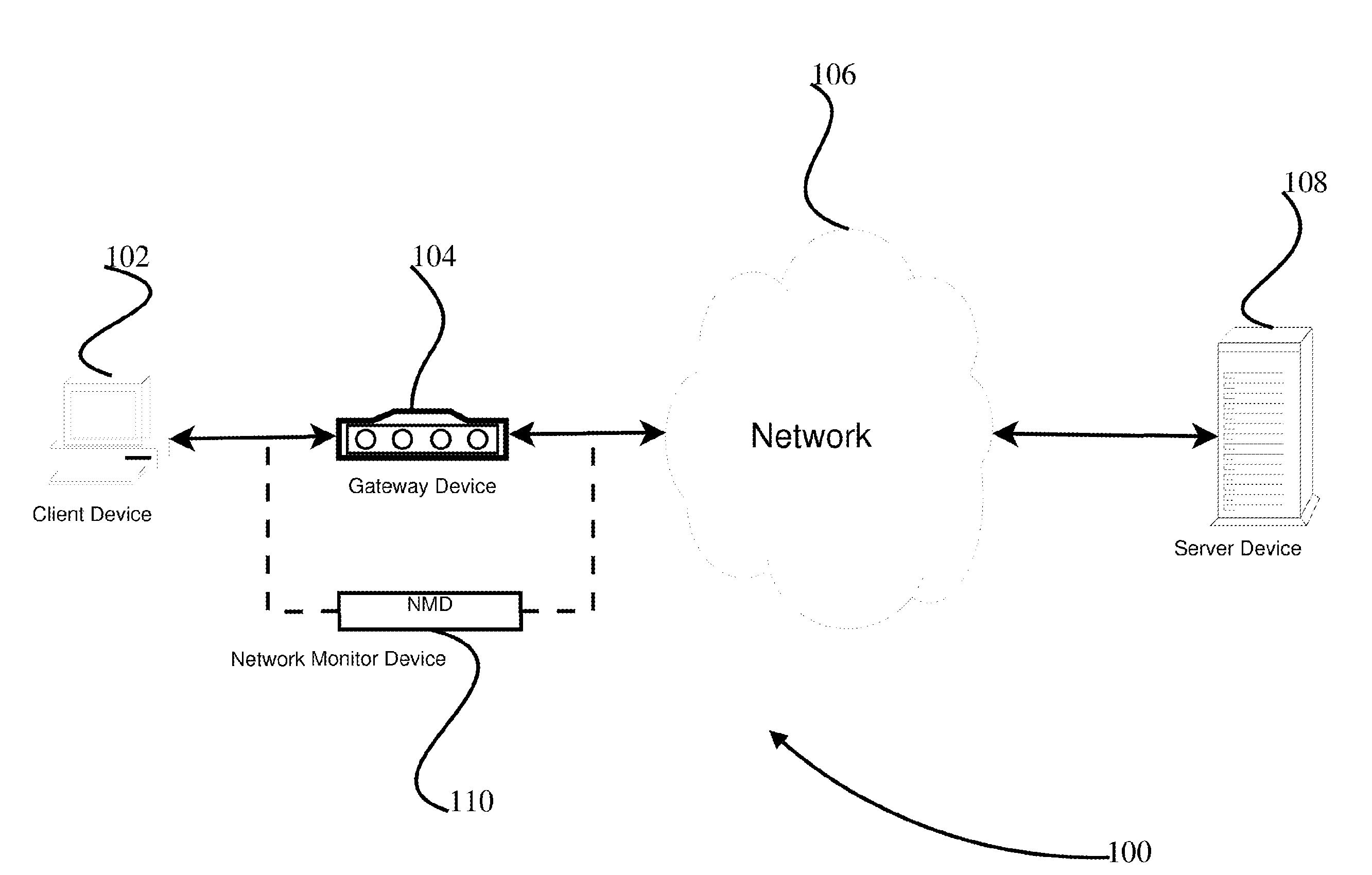
System and Method for detecting anomalous network application behavior. Network traffic between at least one client and one or more servers may be monitored. The client and the one or more servers may communicate using one or more application protocols. The network traffic may be analyzed at the application-protocol level to determine anomalous network application behavior. Analyzing the network traffic may include determining, for one or more communications involving the client, if the client has previously stored or received an identifier corresponding to the one or more communications. If no such identifier has been observed in a previous communication, then the one or more communications involving the client may be determined to be anomalous. A network monitoring device may perform one or more of the network monitoring, the information extraction, or the information analysis.
Owner:EXTRAHOP NETWORKS
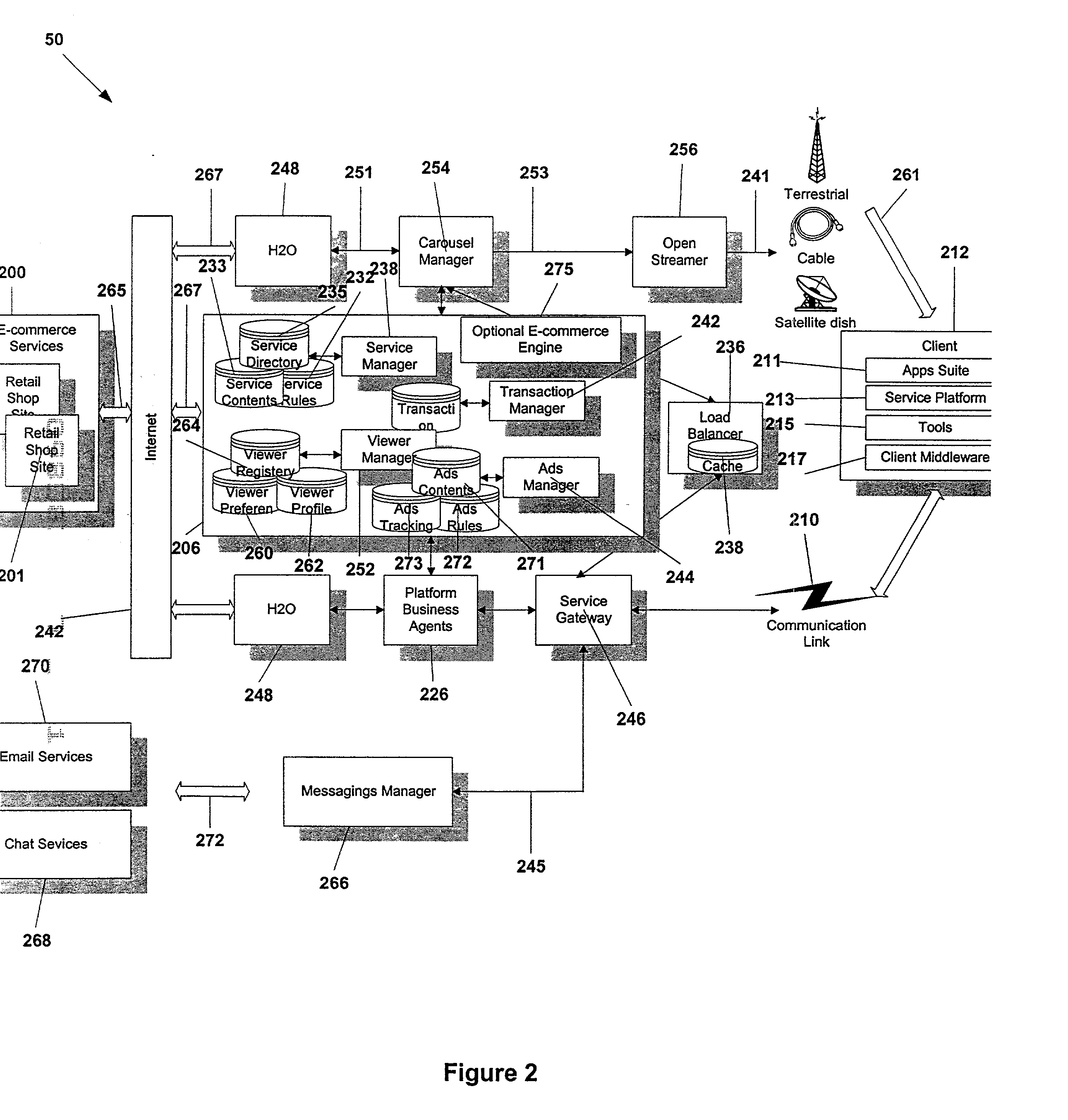
Digital television application protocol for interactive television
ActiveUS20020108122A1Easy to handleComplex communicationAnalogue secracy/subscription systemsMultiple digital computer combinationsOperational systemNetwork Communication Protocols
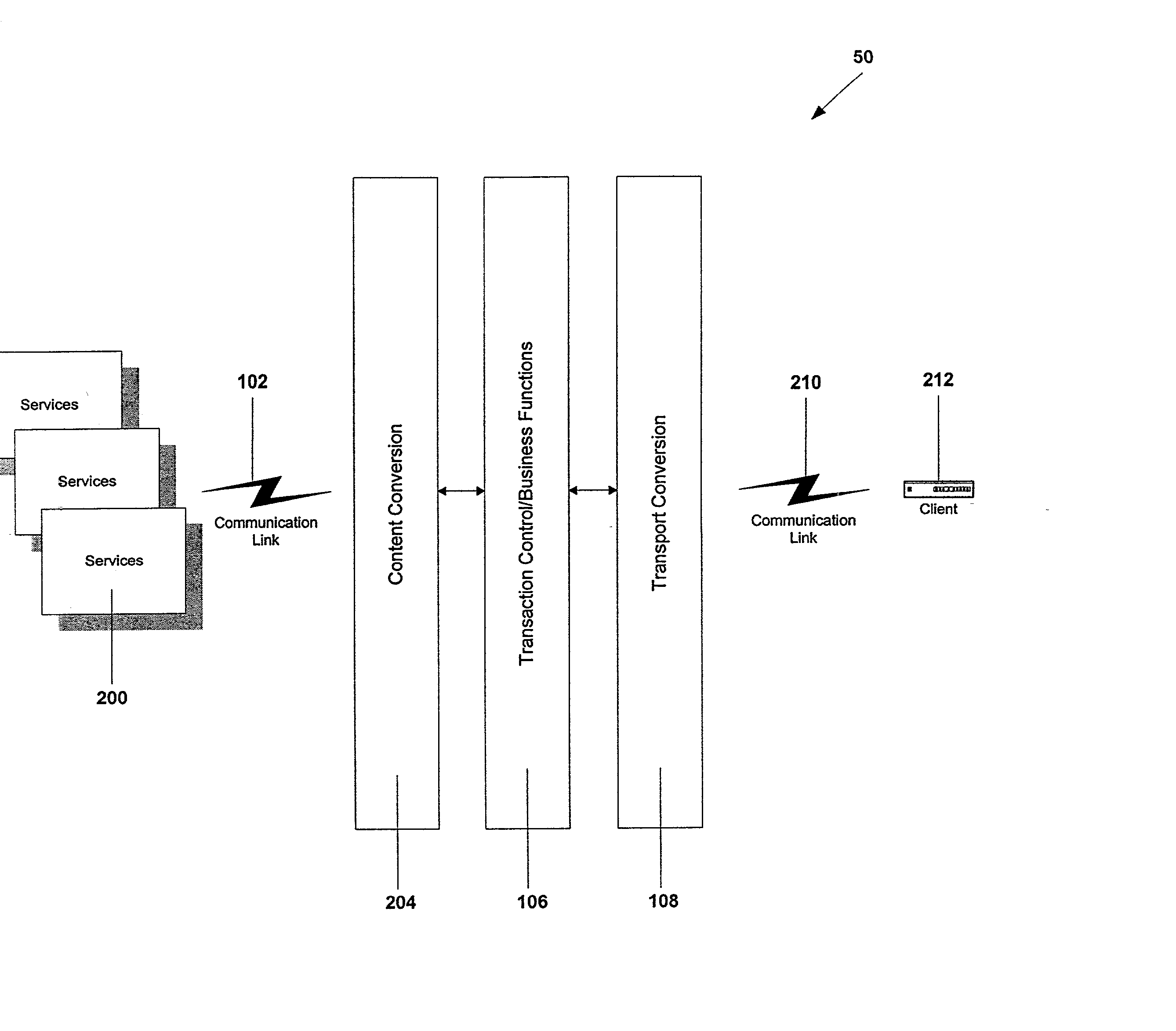
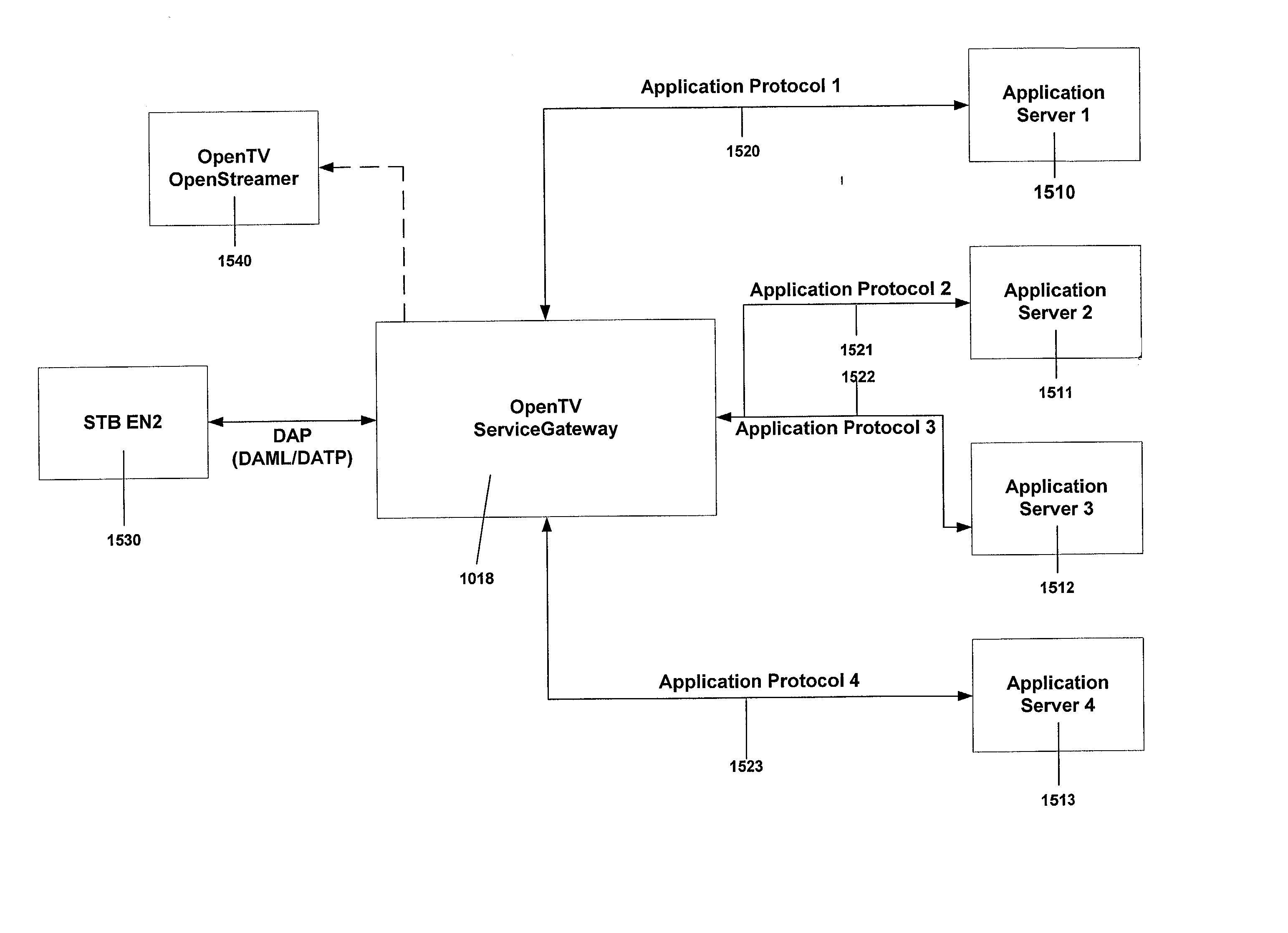
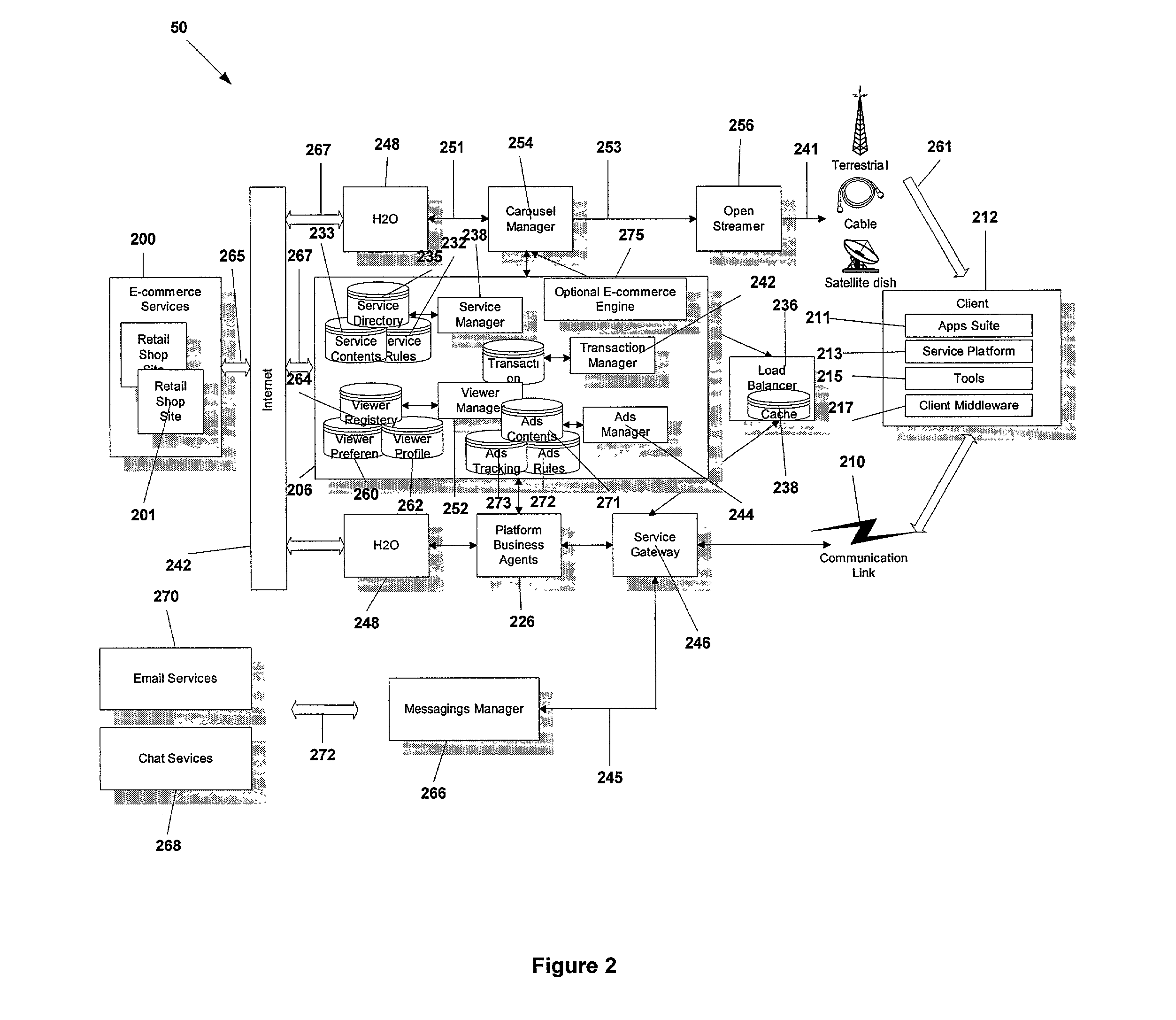
A common communication language that can address all the applications running in a multitude of set top boxes (STBs) or client devices and application servers. The present invention, DATP protocol encapsulates a meta language that provides a generic portable communication application programmer interface that requires light processor utilization and is well-suited for a typical STB possessing limited processing power. DATP requires relatively few processing cycles compared to typical Internet communication protocols. DATP reduces the overhead of the communication protocol handler at the STB and makes the communication protocol handler common for all STBs applications. The preferred DATP protocol is portable for all STBs since it is written in a native language that interfaces with the underlying operating system of the STB. A SGW (SGW) performs as a DATP server. The SGW translates between DATP messages and standard communication protocols. SGW enables SP clients at STBs utilizing DATP to communicate with service applications using a variety of communication protocols. A content converter is provided to convert standard Web content into content suitable for display on a client viewing device, e.g., a TV.
Owner:OPEN TV INC
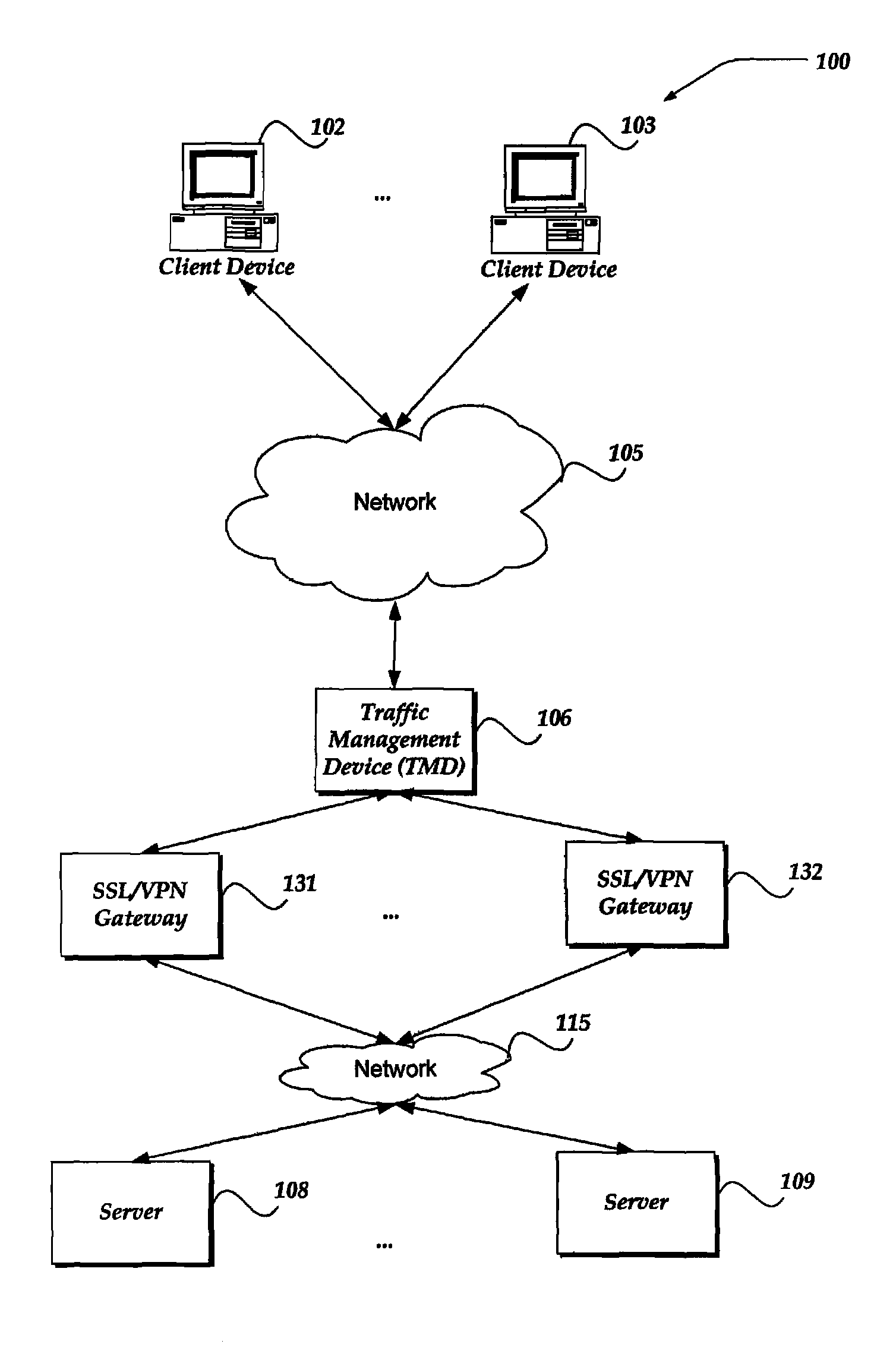
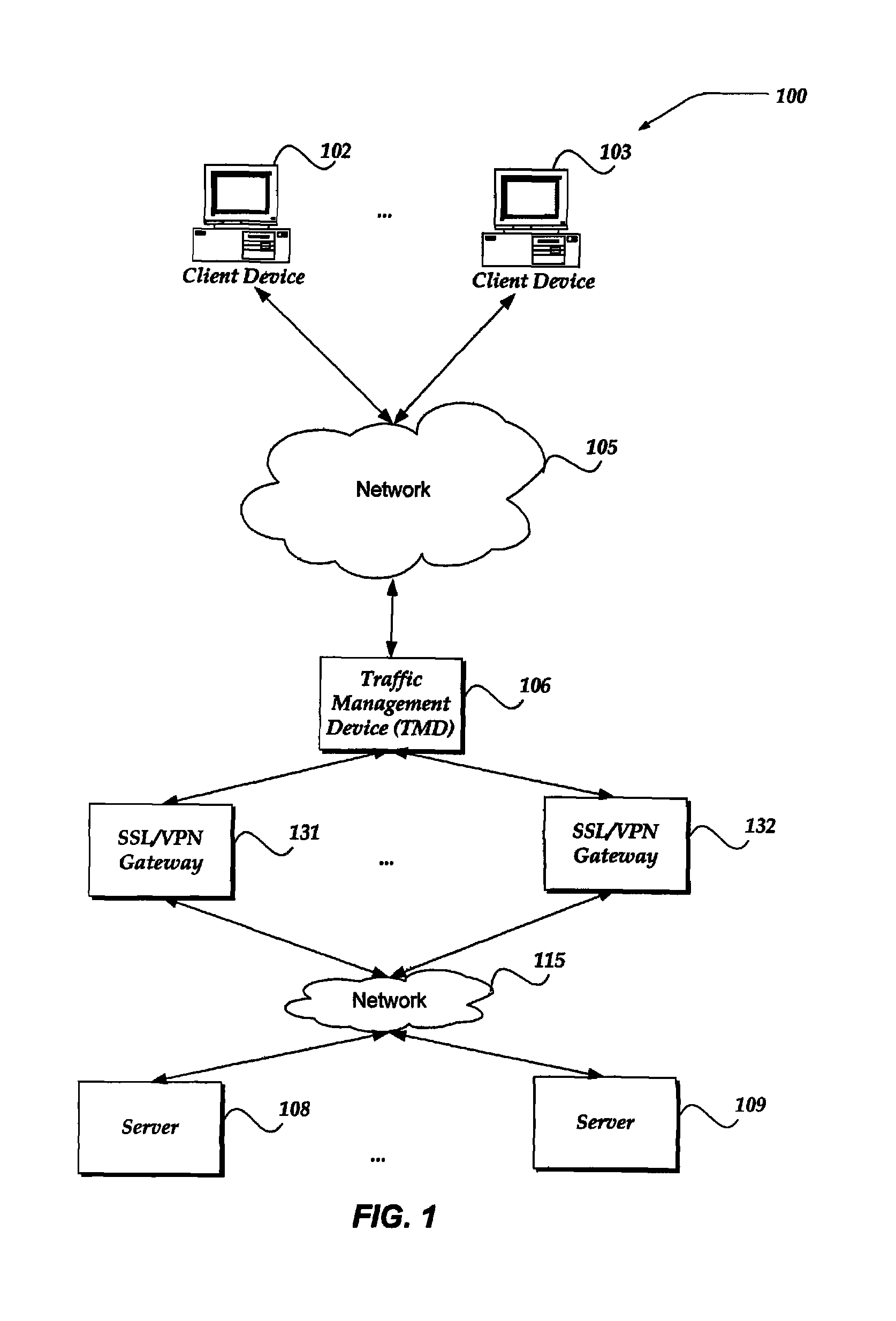
Intelligent HTTP based load-balancing, persistence, and application traffic management of SSL VPN tunnels
InactiveUS8566452B1Multiple digital computer combinationsTransmissionTraffic capacityApplication lifecycle management
A system, apparatus, and method are directed to converting from a use of a HTTPS connection to a tunnel connection while maintaining an underlying connection between a client and a server. An HTTPS connection is employed to establish a network connection between a client device and a network device. A gateway is selected to receive a request from the client device. In one embodiment, selecting may comprise using load-balancing, cookie-persistence, or the like. Subsequently, the HTTPS connection is transitioned to another application layer communication protocol connection. Transitioning may comprise converting from a use of a first protocol stack configured to process a HTTP connection to a second protocol stack configured to process a non-HTTP based application protocol connection, and establishing a tunnel between the client device and a server through the selected gateway.
Owner:F5 NETWORKS INC
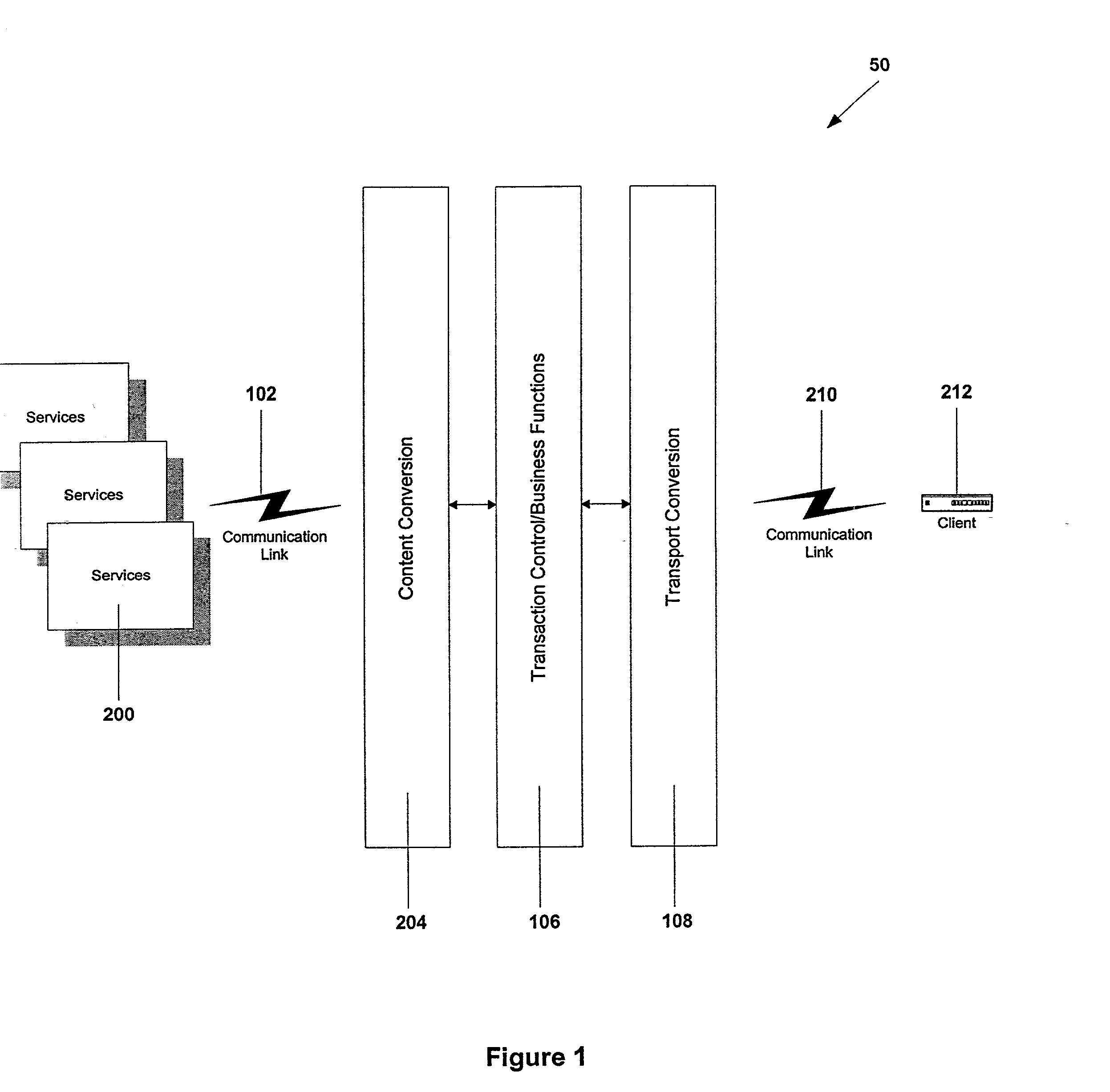
Digital television application protocol for interactive television
ActiveUS20020169885A1Easy to handleComplex communicationAnalogue secracy/subscription systemsMultiple digital computer combinationsOperational systemNetwork Communication Protocols
A common communication language that can address all the applications running in a multitude of set top boxes (STBs) or client devices and application servers. The present invention, DATP protocol encapsulates a Meta language that provides a generic portable communication application programmer interface that requires light processor utilization and is well suited for a typical STB possessing limited processing power. DATP requires relatively few processing cycles compared to typical Internet communication protocols. DATP reduces the overhead of the communication protocol handler at the STB and makes the communication protocol handler common for all STBs applications. The preferred DATP protocol is portable for all STBs since it is written in a native language that interfaces with the underlying operating system of the STB. A SGW (SGW) performs as a DATP server. The SGW translates between DATP messages and standard communication protocols. SGW enables SP clients at STBs utilizing DATP to communicate with service applications using a variety of communication protocols. A content converter is provided to convert standard Web content into content suitable for display on a client-viewing device, e.g., a TV.
Owner:OPEN TV INC
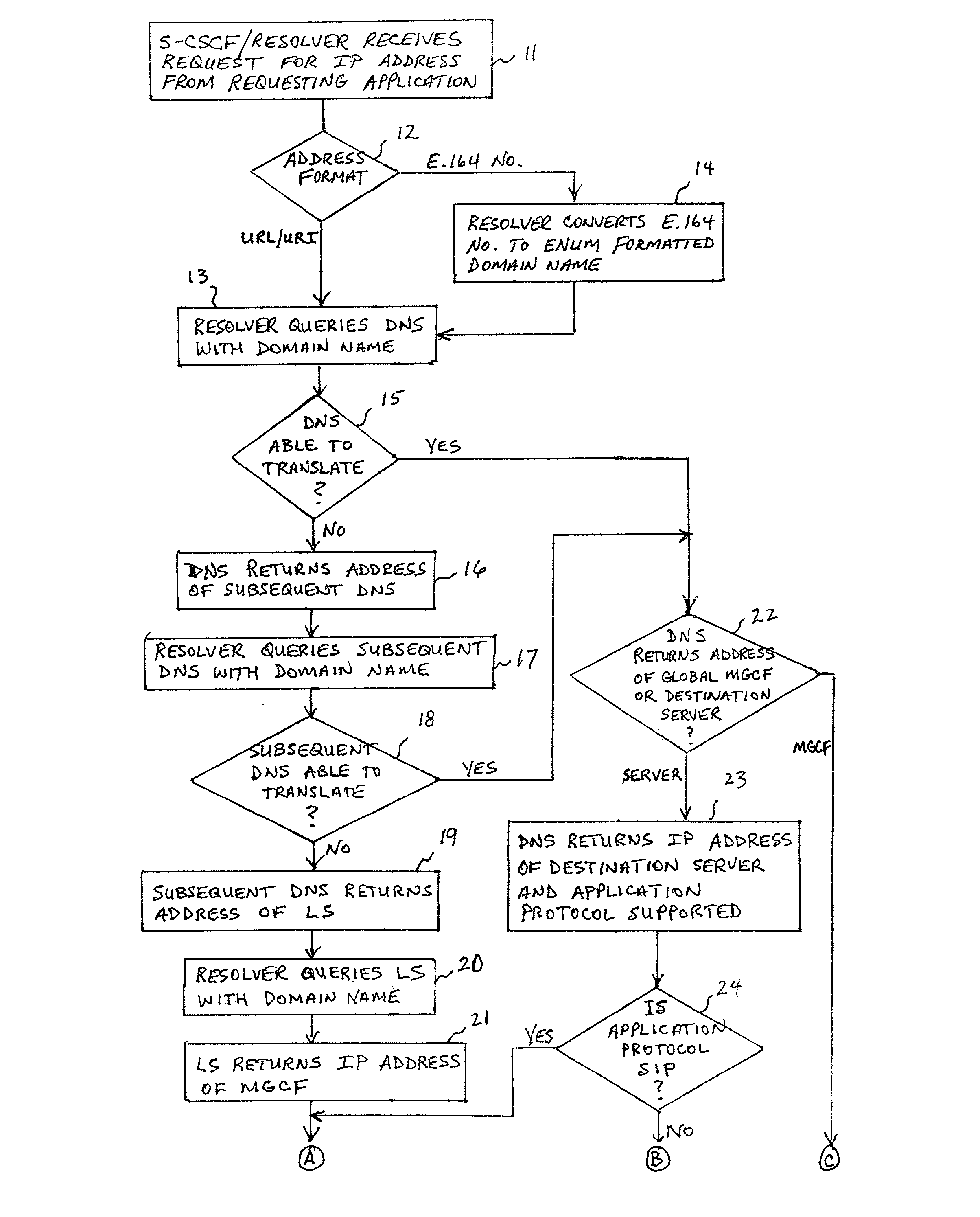
System and method for address resolution in internet protocol (IP) -based networks
ActiveUS20020027915A1Data switching by path configurationNetwork connectionsInternet protocol suiteDomain name
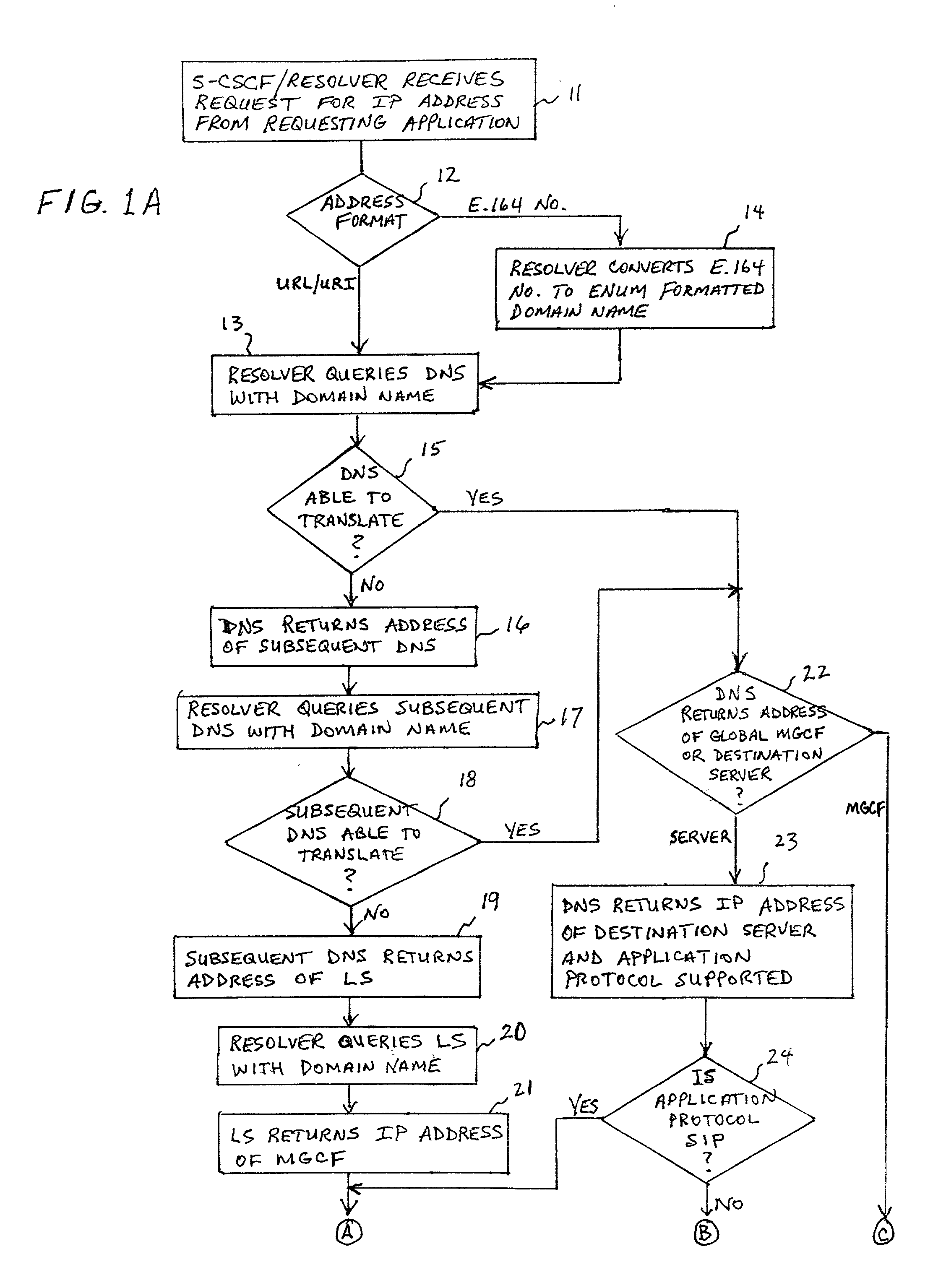
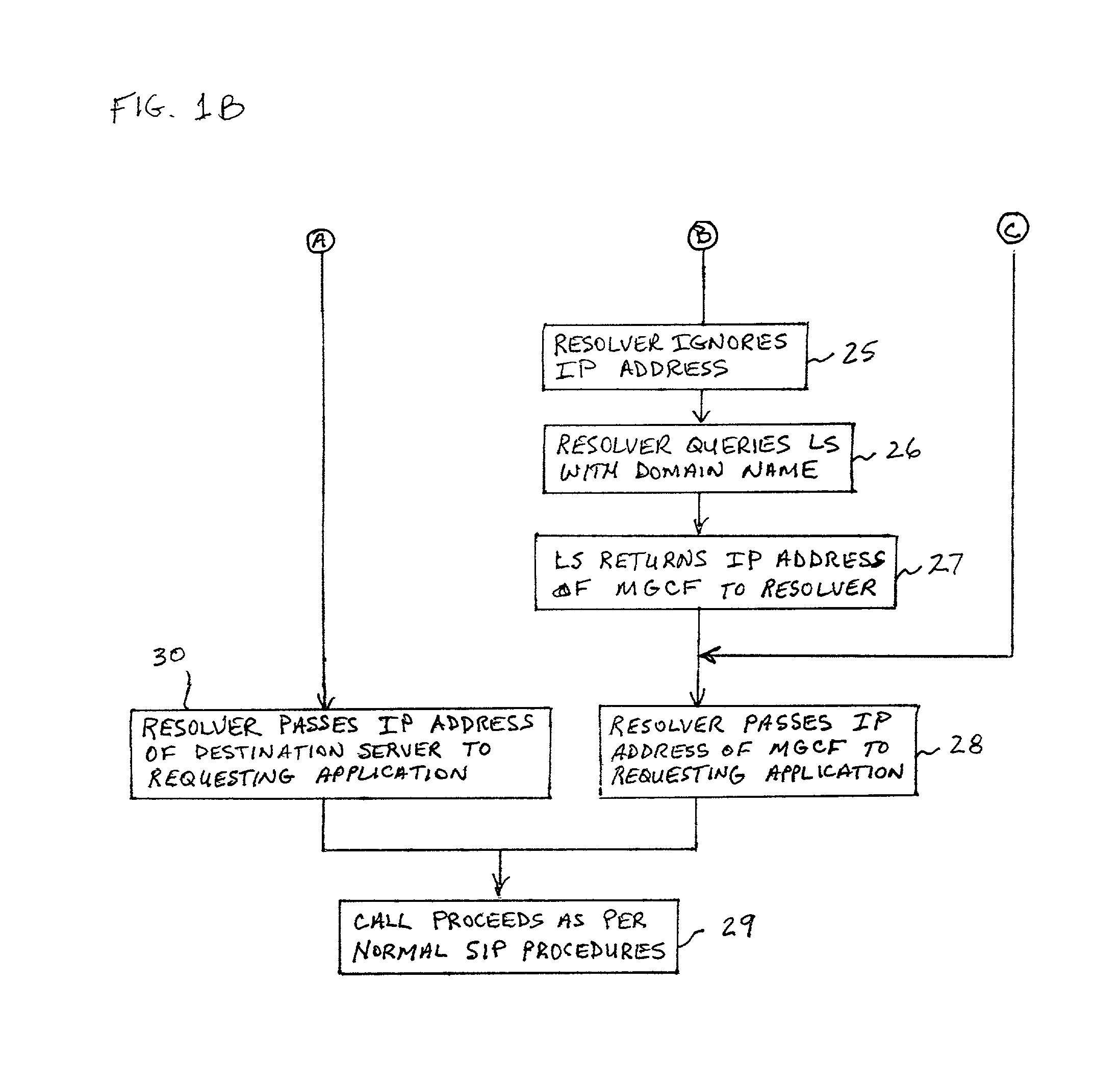
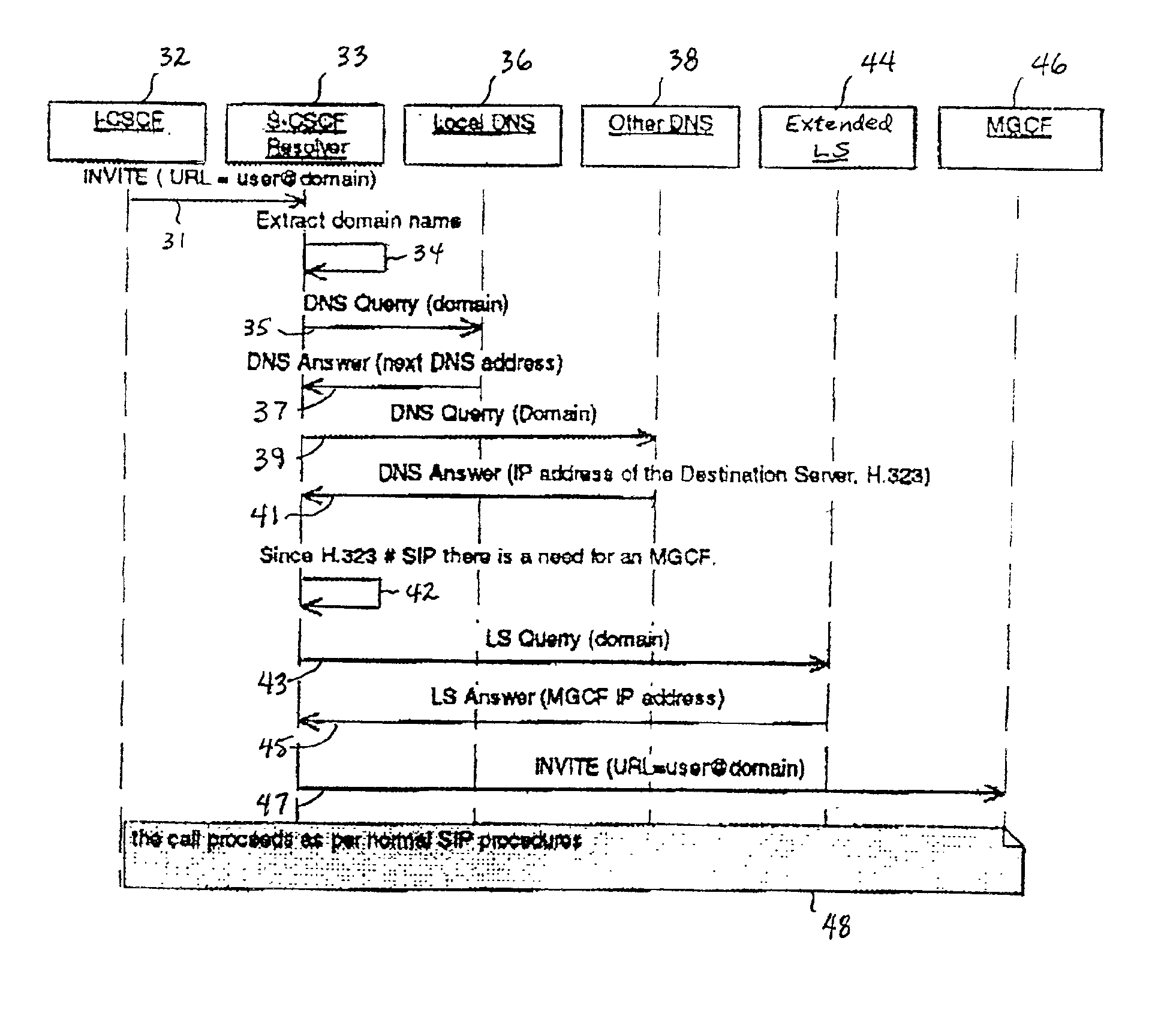
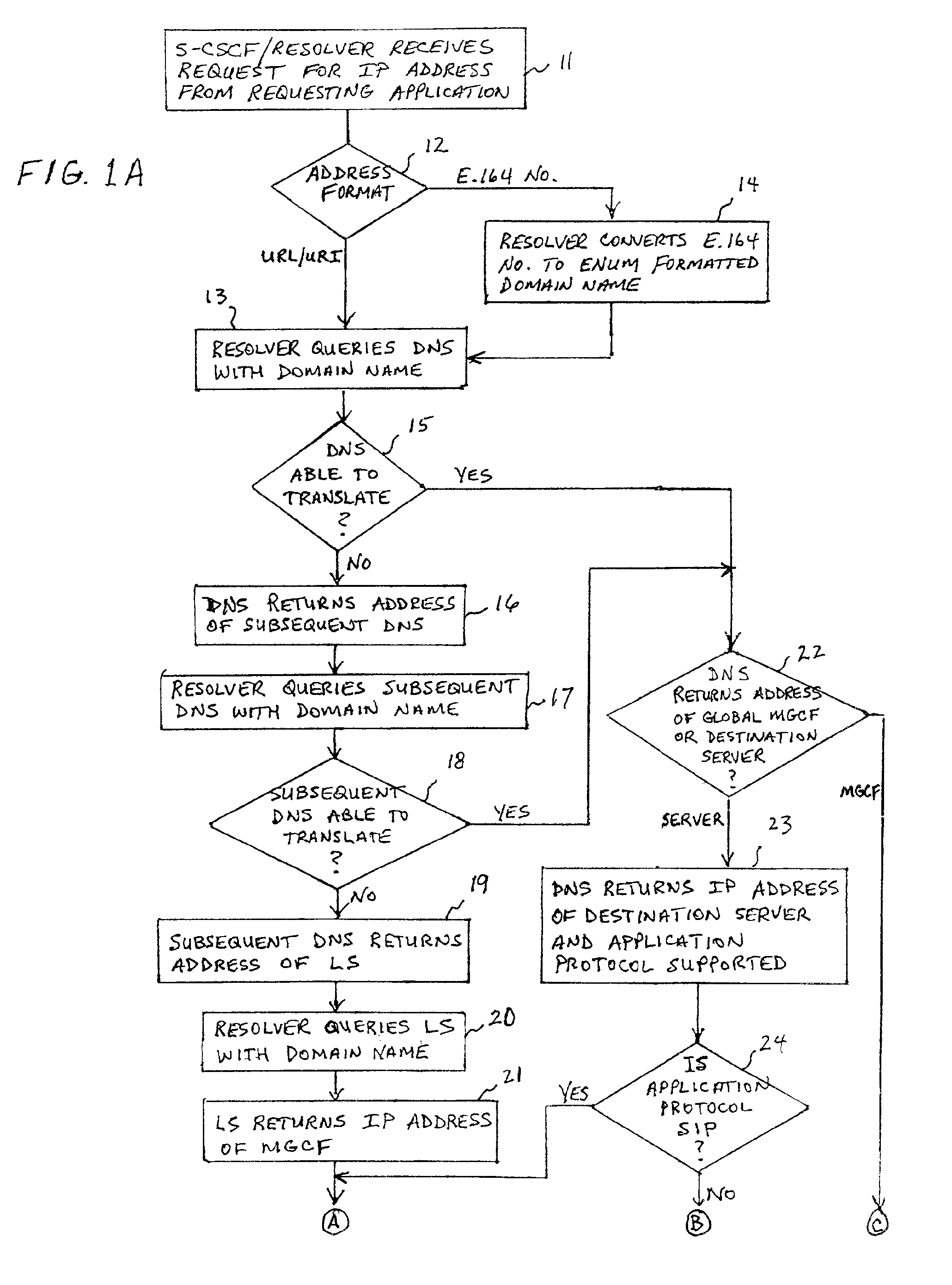
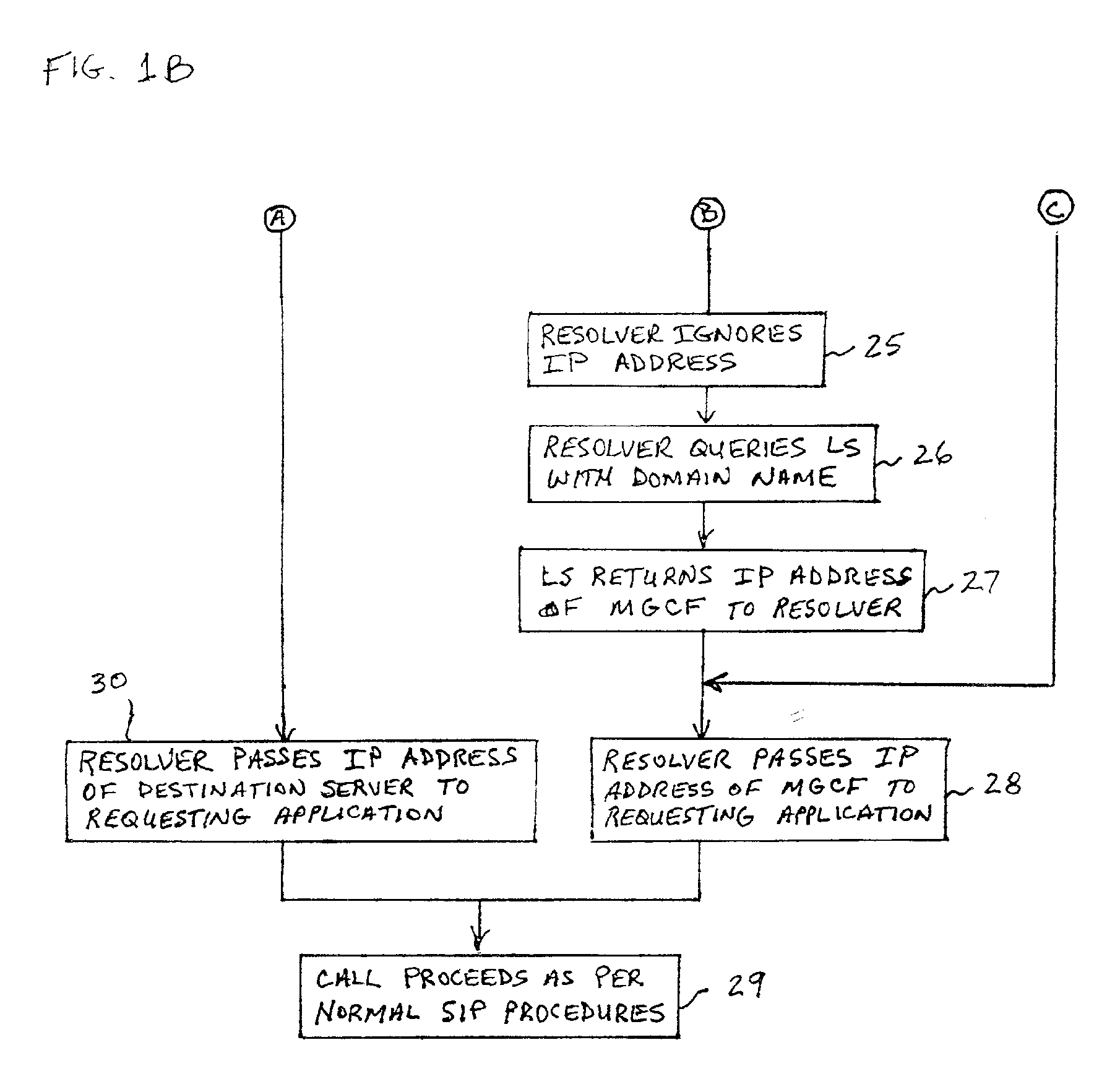
A system and unified method of address resolution in an IP-based network. A Resolver determines whether an input address is a URL / URI, and if so, extracts a domain name. If the input address is an E.164 number, the Resolver converts the E.164 number into a domain name in ENUM format. The Resolver then sends a domain name query to a DNS which, if able, returns the IP address for either a Global MGCF or a destination server along with a supported Application protocol. If the DNS is unable to perform the translation, or the Application protocol returned is not supported by the requesting application, the Resolver sends a domain name query to an extended Location Server (LS) to obtain an IP address of a gateway function capable of interfacing with the destination server.
Owner:TELEFON AB LM ERICSSON (PUBL)
Detecting Anomalous Network Application Behavior
ActiveUS20080222717A1Memory loss protectionError detection/correctionTraffic capacityInformation analysis
System and Method for detecting anomalous network application behavior. Network traffic between at least one client and one or more servers may be monitored. The client and the one or more servers may communicate using one or more application protocols. The network traffic may be analyzed at the application-protocol level to determine anomalous network application behavior. Analyzing the network traffic may include determining, for one or more communications involving the client, if the client has previously stored or received an identifier corresponding to the one or more communications. If no such identifier has been observed in a previous communication, then the one or more communications involving the client may be determined to be anomalous. A network monitoring device may perform one or more of the network monitoring, the information extraction, or the information analysis.
Owner:EXTRAHOP NETWORKS
Arrangement for sharing a single signaling point code between multiple hosts in an IP-based network
A Voice over IP network having multiple signaling message transfer nodes (e.g., call agents, signaling gateways), communicate with switched circuit network nodes using a single point code. A signaling gateway, upon receiving an SS7 signaling message specifying a destination point code corresponding to its provisioned point code and carrying a signaling application protocol message, selects a destination call agent based on the originating point code in the SS7 signaling message and independent of the destination point code. The signaling gateway selectively outputs to the selected destination call agent an IP-based message carrying the signaling application protocol message according to a prescribed IP-based signaling message transport protocol, based on a determined availability of the selected destination call agent. The signaling gateway uses the User Part Unavailable message to inform the originating PSTN switch that the selected destination call agent is unavailable.
Owner:CISCO TECH INC
System and method for address resolution in internet protocol (IP)-based networks
ActiveUS6917612B2Data switching by path configurationNetwork connectionsInternet protocol suiteDomain name
A system and unified method of address resolution in an IP-based network. A Resolver determines whether an input address is a URL / URI, and if so, extracts a domain name. If the input address is an E.164 number, the Resolver converts the E.164 number into a domain name in ENUM format. The Resolver then sends a domain name query to a DNS which, if able, returns the IP address for either a Global MGCF or a destination server along with a supported Application protocol. If the DNS is unable to perform the translation, or the Application protocol returned is not supported by the requesting application, the Resolver sends a domain name query to an extended Location Server (LS) to obtain an IP address of a gateway function capable of interfacing with the destination server.
Owner:TELEFON AB LM ERICSSON (PUBL)
Methods and systems for providing message translation, accounting and routing service in a multi-protocol communications network environment
InactiveUS6967956B1Easy to routeFacilitates accountingTime-division multiplexData switching by path configurationTransmission protocolMessage routing
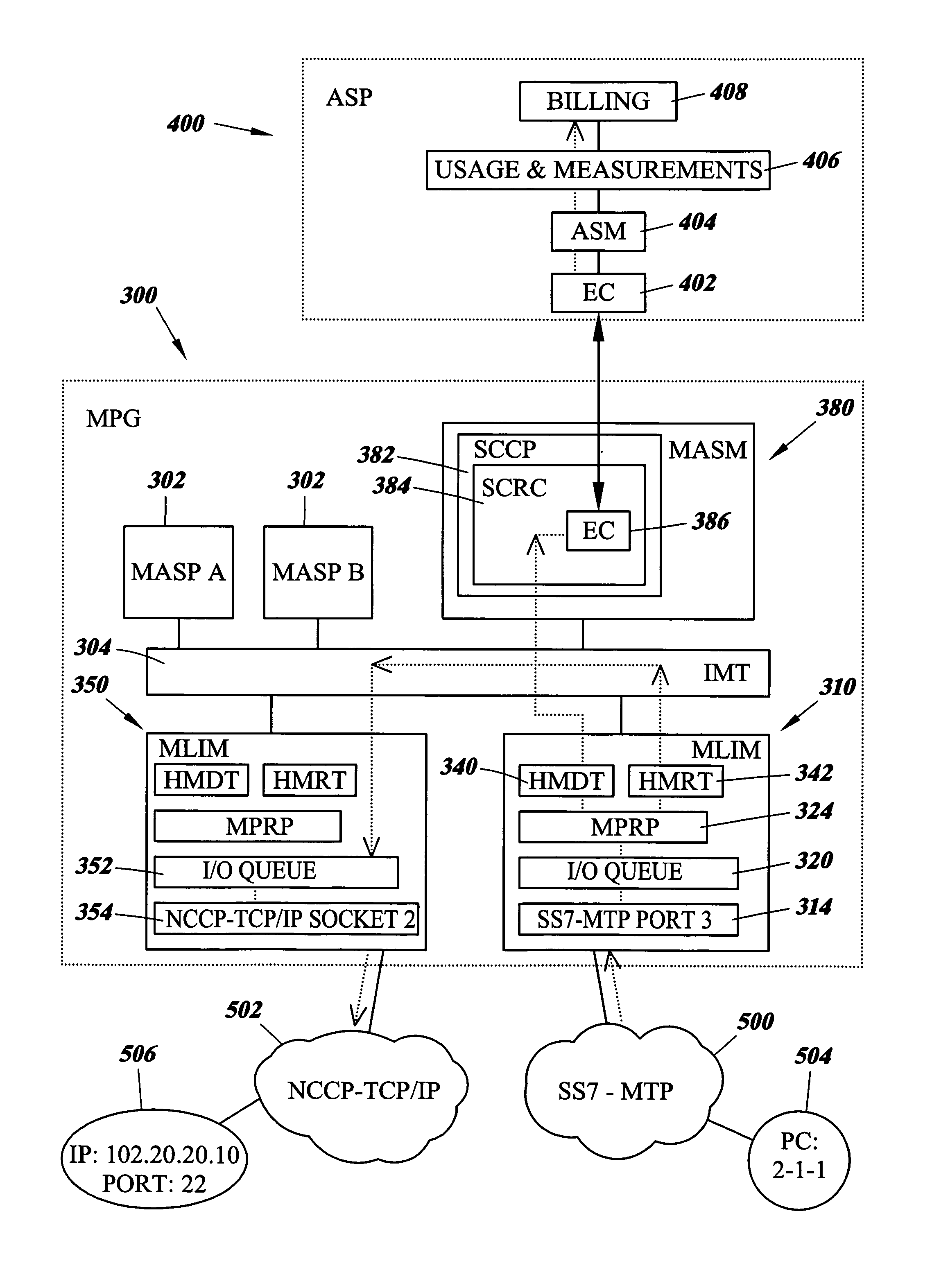
A network element that is capable facilitating the routing and accounting of messages between a plurality of network elements that do not share a common signaling application protocol nor a common transport protocol suite. In one embodiment of the present invention, a Multi-Protocol Gateway (MPG) is adapted to receive a signaling message and subsequently translate both the signaling and transport protocol suite prior to message routing. The MPG node is also configured to create and maintain usage and measurements data that may subsequently be used to produce billing records.
Owner:TEKELEC
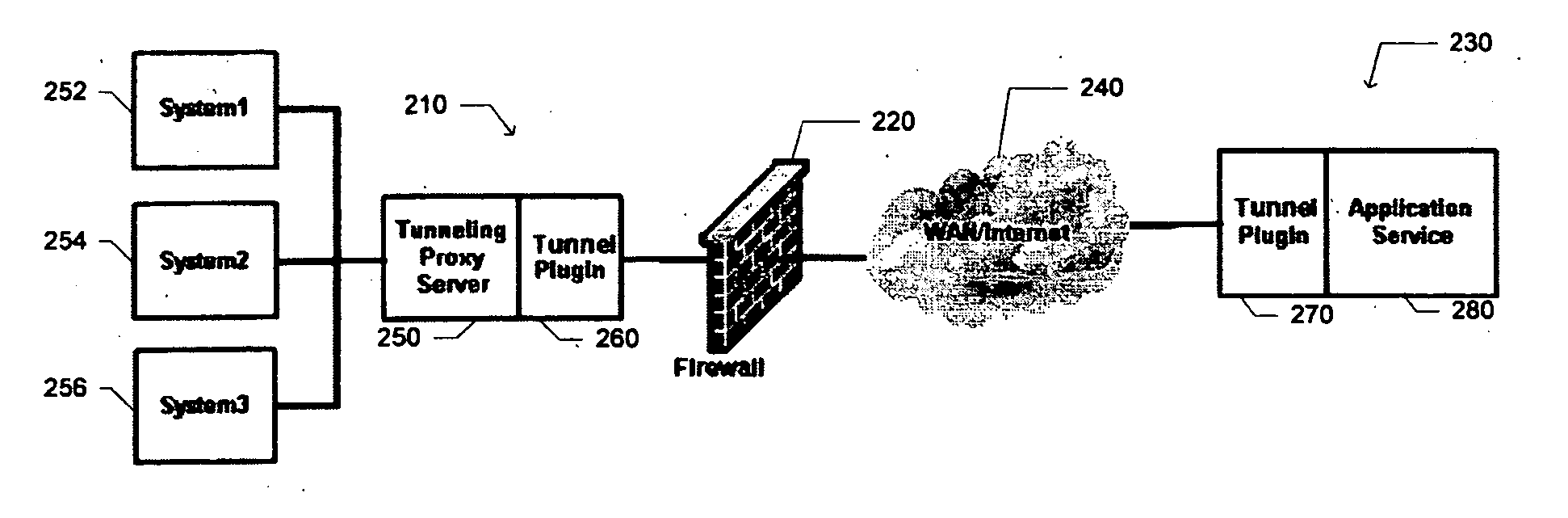
System and method for traversing firewalls, NATs, and proxies with rich media communications and other application protocols
InactiveUS20060168321A1Digital computer detailsSecuring communicationWireless Application ProtocolPrivate network
A tunneling system and method is described for traversing firewalls, NATs, and proxies. Upon a request from a device on the secure private network or on a public network such as the Internet, a connection to a designated or permitted device of the secure private network by way of the public network can be established, allowing selected devices of the private network to access devices on the public network. A bi-directional channel can be established where information such as rich multimedia and real-time voice and video can be accessed or communicated.
Owner:AVAYA INC
Device for classifying and recognizing network application flow quantity and method thereof
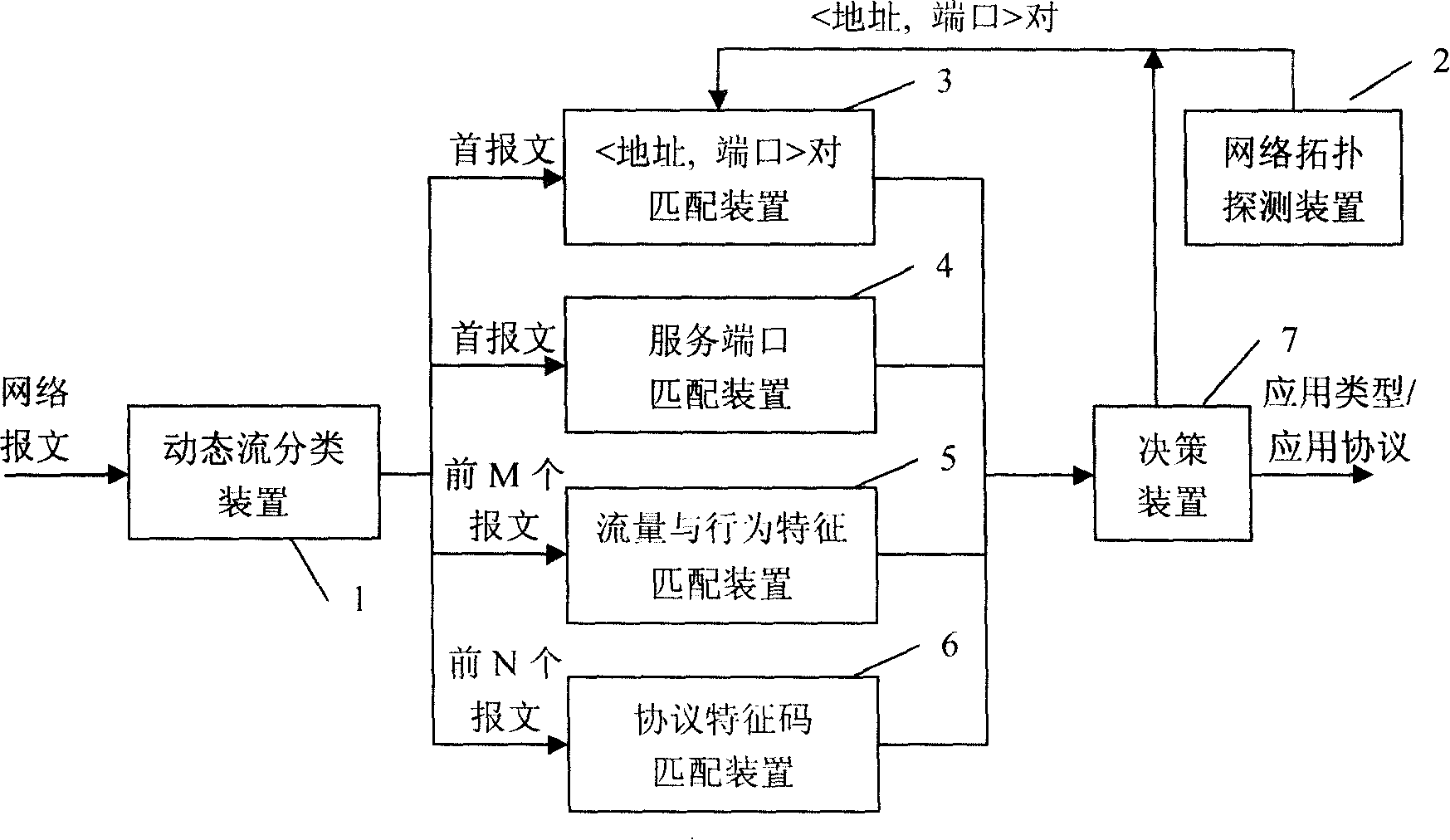
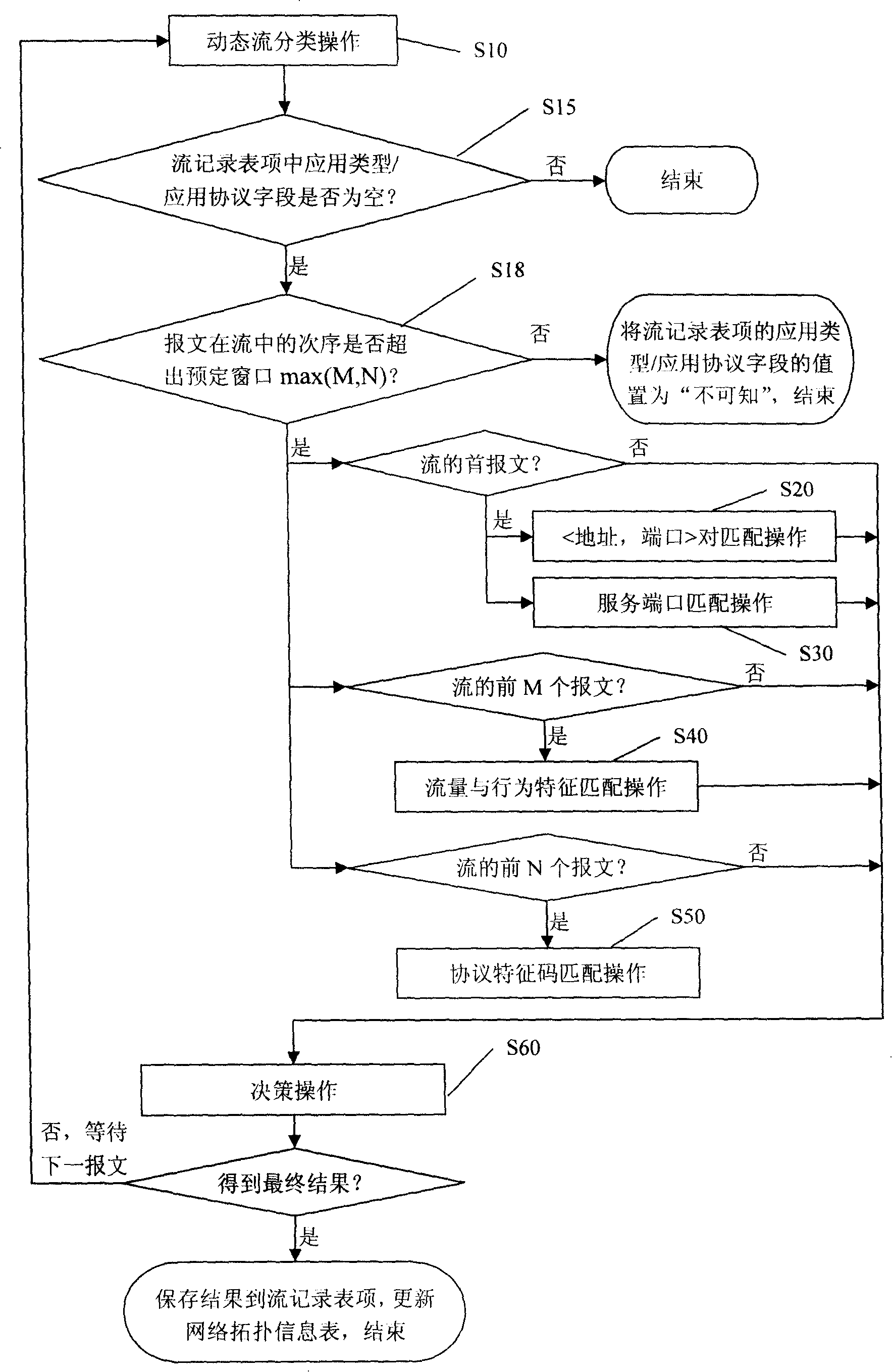
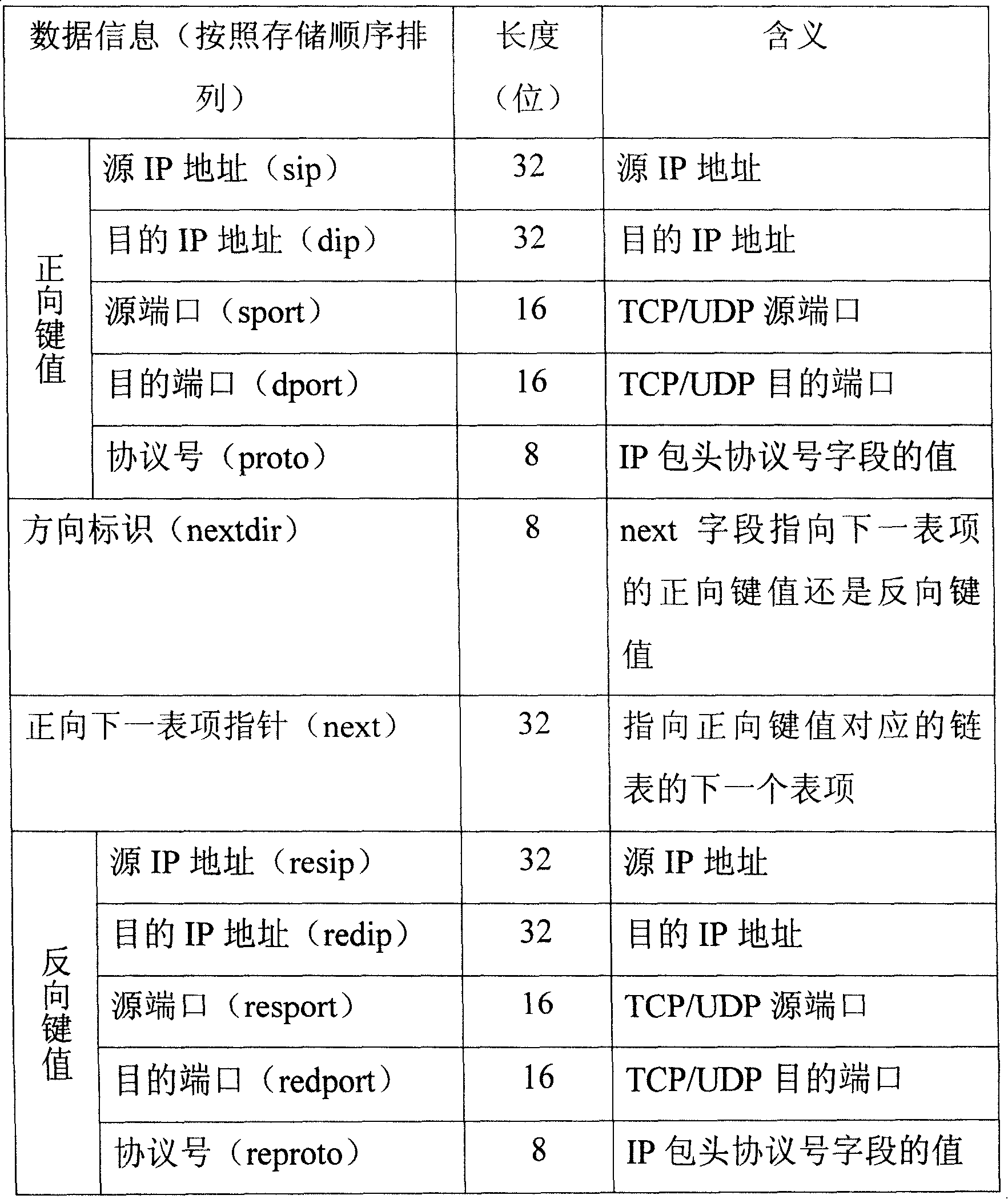
A network application flow classifying recognizing device includes a dynamic flow classifying device which builds a hash table by taking the IP five-tuple array contained in a massage as the key assignments and searches a network flow table by making use of the hash table; a (address, port ) checking matching device which searches an information table of the address to carry through matching on the received messages; a service terminal matching device which carries through matching on the received messages by searching a service port table, a flow / action characteristic matching device which counts the flow characteristic and action characteristic aiming at the front M messages of the flow and carries through matching with the information in a flow / action characteristic mode library; a protocol characteristic code matching device which carries through matching on the front L bytes of the message payload and the protocol characteristic codes of a protocol characteristic code library; a decision device which comprehensively analyzes and judges the application type or application protocol that a network flow belongs to; a network topology detecting device which searches the currently active nodes and uses a node information to dynamically update the information table of the address aiming at various application service.
Owner:PEKING UNIV
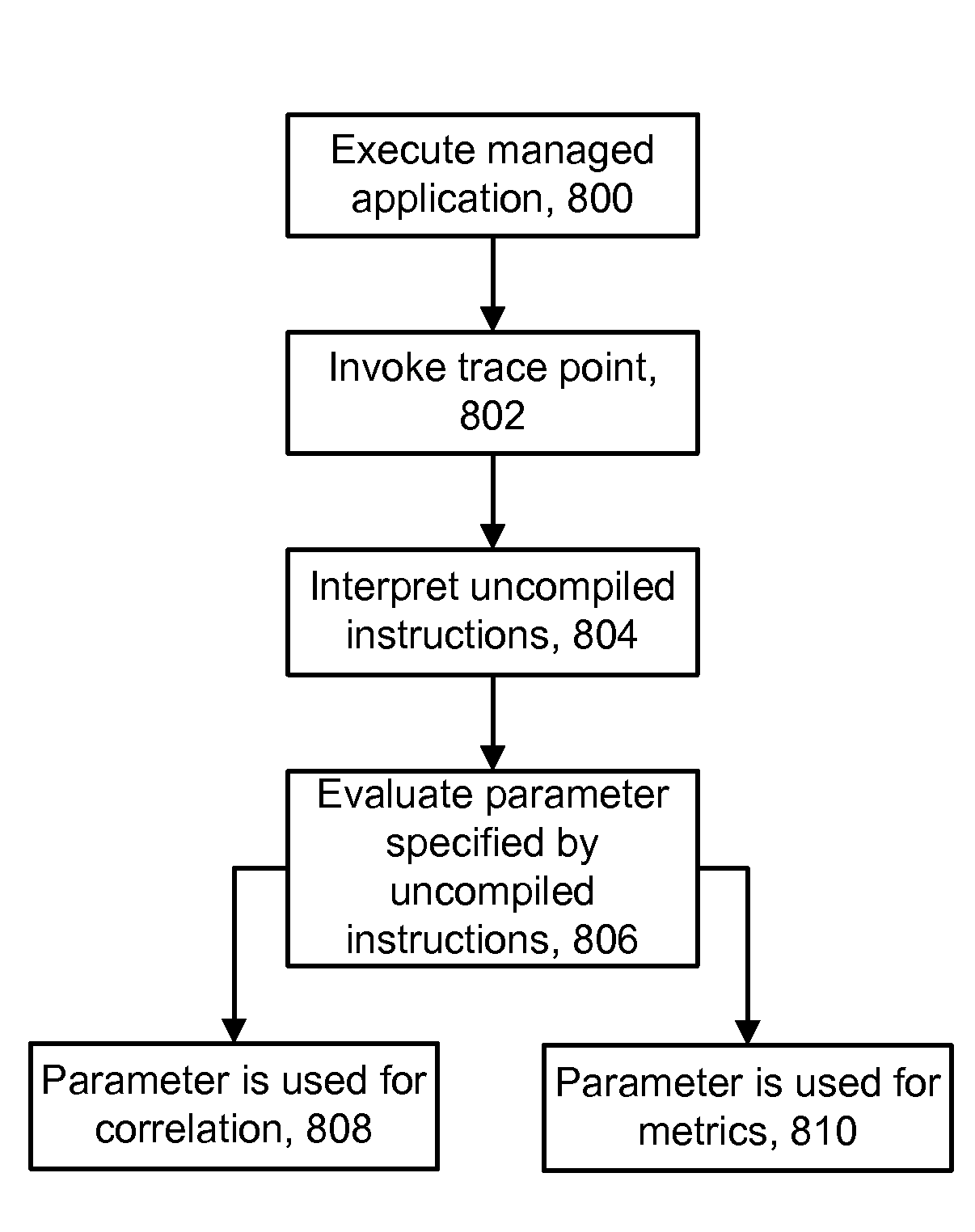
Instrumenting An Application With Flexible Tracers To Provide Correlation Data And Metrics
A technique for flexibly adding instrumentation to an application. A file is created which includes a dynamic parameter syntax. The file identifies a trace point in the application, such as a method, and the syntax includes one or more parameters which are evaluated when the method is invoked. The parameters can be used to provide cross-process correlation and / or performance metrics. A client process which calls a server process can include the parameter in a message header according to any desired transport protocol, such as HTTP or JMS. Different application protocols and implementation can be accommodated to track a transaction which executes on different platforms. The dynamic parameter syntax is interpreted as uncompiled code and is designed to be added by the user in the field to augment a package of pre-built instrumentation software after the package has been deployed.
Owner:CA TECH INC
Method for correlating and presenting network management data
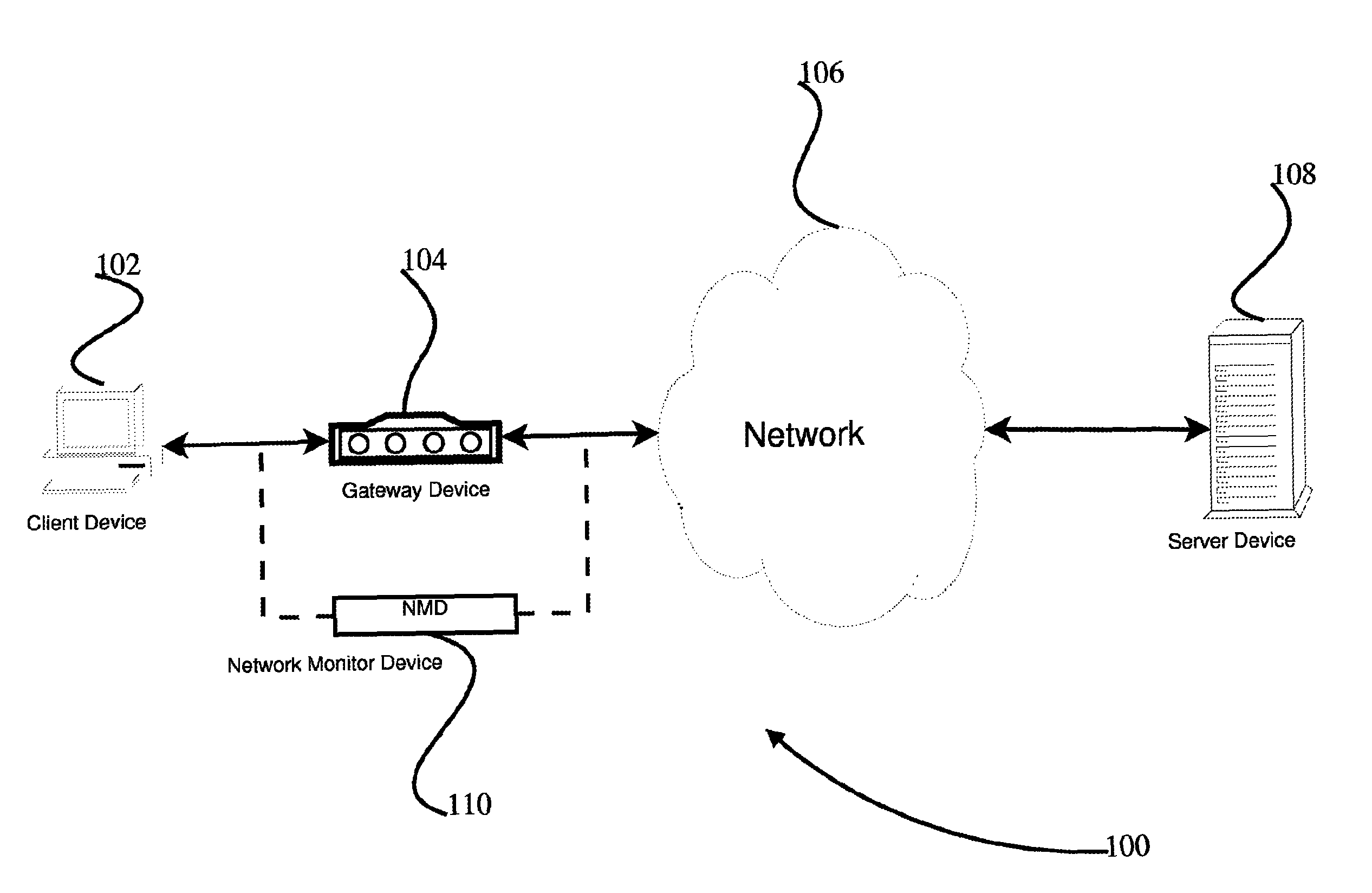
InactiveUS7143159B1Useful displayEfficiently presentedMultiple digital computer combinationsTransmissionTraffic capacitySplit window
NIC collected network statistics are captured by agent devices resident on Host machines of a network. A probe (software or hardware) retrieves the collected statistics from one or more monitored hosts (each host on the network, for example) and places them in RMON MIB and RMON extension MIB formats. The MIB data is retrieved by queries from a data correlation device that then correlates the queried data into useful statistics regarding network traffic. The useful statistics include network traffic in bytes per second for each application, application protocol, hosts, user logon id, etc. for each of the monitored hosts. Different views including a host to host matrix view are provided in a split window display.
Owner:VALTRUS INNOVATIONS LTD
System, base station and method for multi-standard base station intercommunication
ActiveCN101202974AImprove the success rate of switchingImprove switching performanceRadio/inductive link selection arrangementsTransmissionEngineeringInterconnection
The invention discloses a system and a method of multi-standard base station interconnection, wherein, multi-standard base stations are connected by means of uniform interface units which provide basic physical transport bearing and uniform transport protocol stacks, namely, uniform logic interfaces, which are used for transporting high-level application protocols to support the information interaction among multi-standard base stations, even among base station child nodes inside each multi-standard base station, such as load information, resource using information, interference information, switch process signaling messages, data forwarding and so on. The high-level application protocols born in the uniform transport protocol stacks are primarily user plane protocols and control plane protocols. The realizing function of the interface units is also provided among all the base station child nodes inside the multi-standard base stations. As the interface units which are internally provided by the multi-standard base stations adopt uniform transport protocol stacks, the system performance can be radically improved if similar uniform logic interfaces are provided among the multi-standard base stations.
Owner:HUAWEI TECH CO LTD
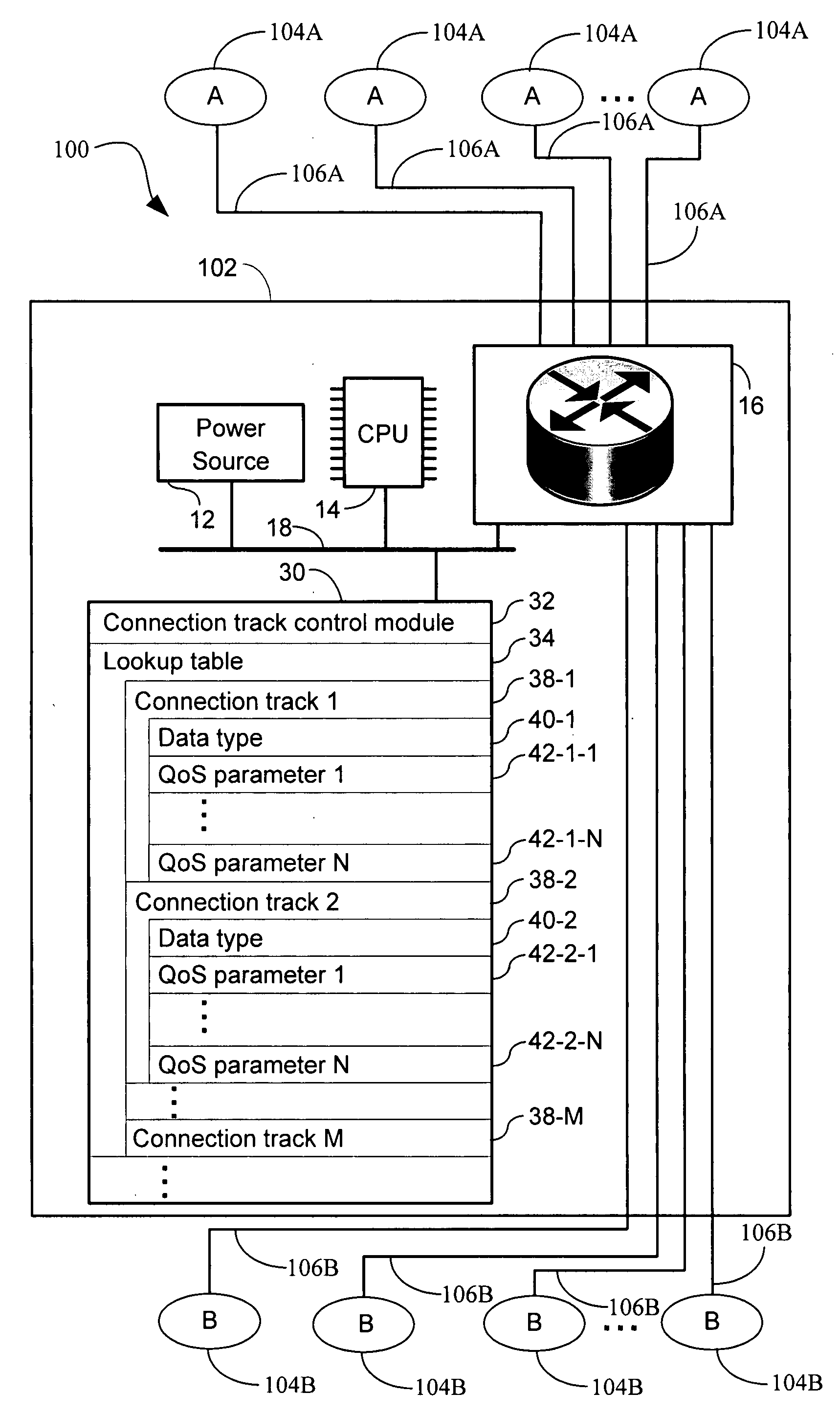
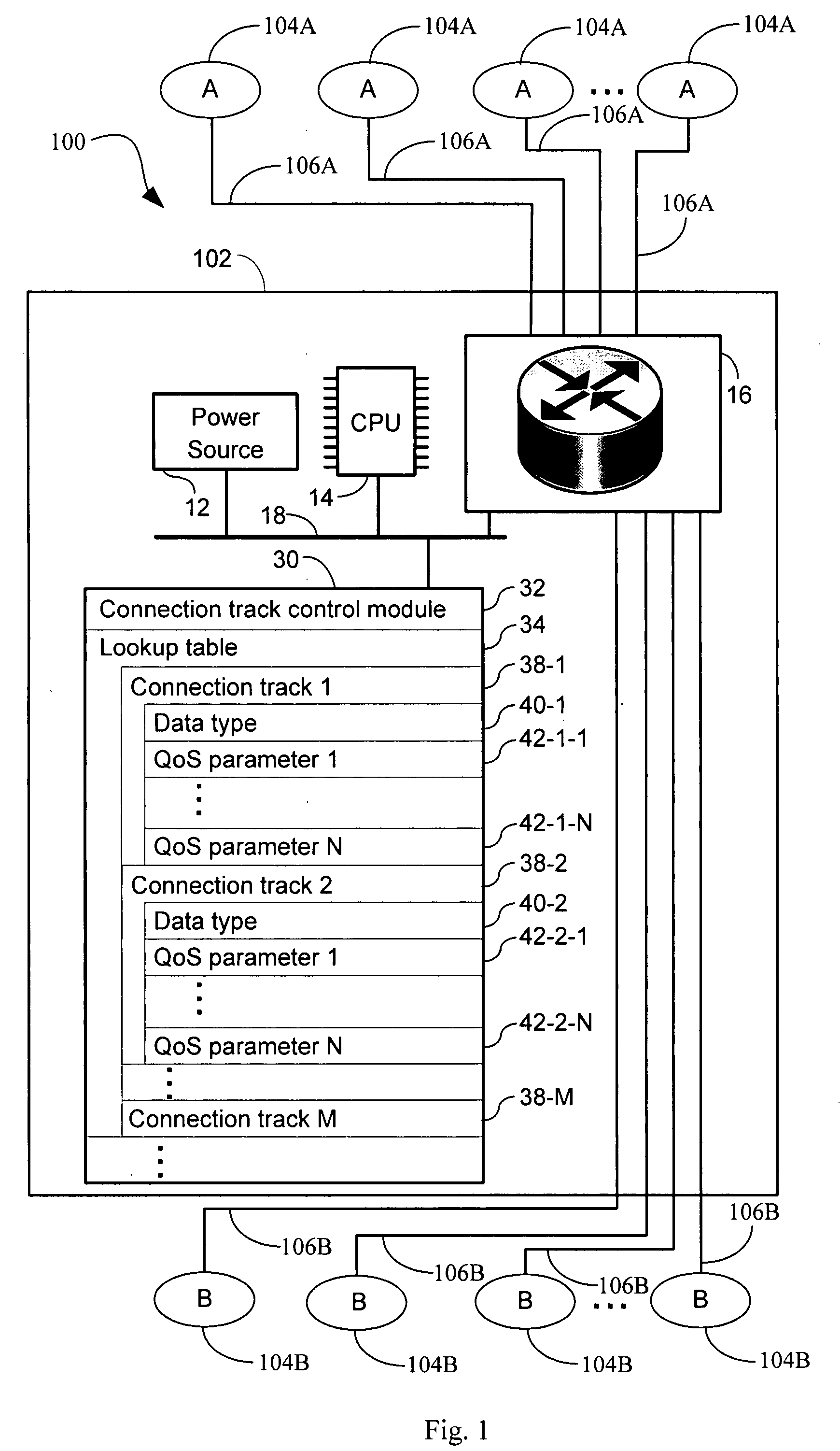
Systems and methods for dynamic quality of service
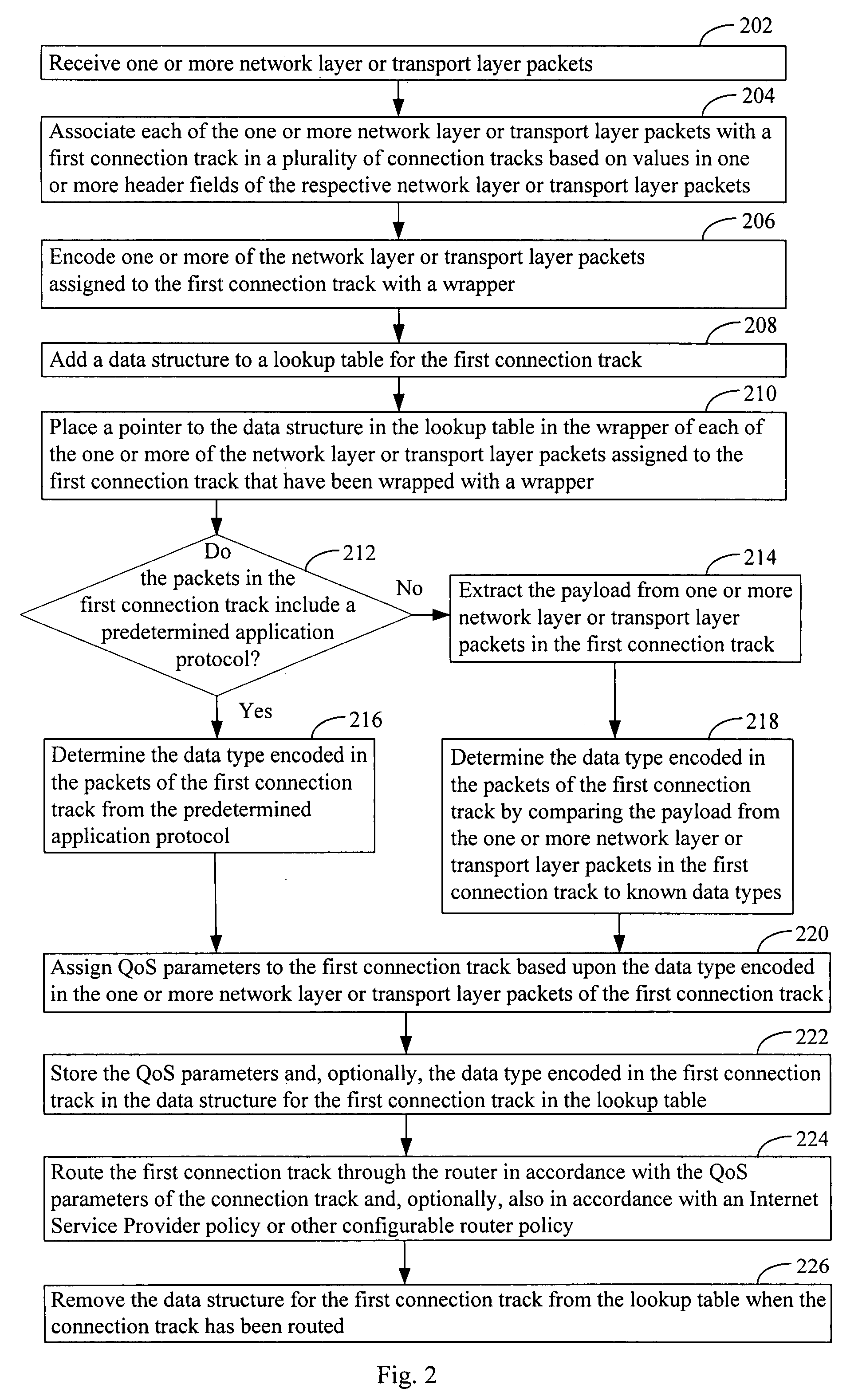
Systems, methods, and apparatus for routing are provided in which a connection track comprising a plurality of network or transport layer packets, received by a router, is identified by examination of header fields of one or more first packets in the plurality of packets. One or more quality of service (QoS) parameters is associated with the connection track by determining whether the track encodes a data type by (i) an identification of a predetermined application protocol used within the one or more first packets and / or (ii) a comparison of a payload of one or more packets in the plurality of packets to known data type formats. A first QoS parameter is set to a first value in a first value range when the connection track contains the first data type. The connection track is routed through the router in accordance with the one or more QoS parameters assigned to the connection track.
Owner:OAE TECH INC
System and method for communication of multi-mode base stations
InactiveUS20090253426A1Improve system performanceImprove performanceSubstation equipmentWireless commuication servicesTransmission protocolHandover
A system and method for communication of multi-mode base stations is provided. The multi-mode base stations are communicatively coupled to each other through a uniform interface unit that provides a basal physical transmission bearer and a uniform transmission protocol stack, namely uniform logic interface, for transmitting a higher layer application protocol to support information interaction, such as load information, resource usage information, interference information, handover flow signaling information, data forwarding, between multi-mode base stations even base station sub-nodes in each multi-mode base station. The higher layer application protocol borne by the uniform transmission protocol stack is mainly a user plane protocol and a control plane protocol. The implementation function of the interface unit between base station sub-nodes in the multi-mode base station is further provided. When the interface unit provided by the multi-mode base station uses a uniform protocol stack, if the similar uniform protocol stack is provided between multi-mode base stations, the performance of the system can be greatly improved.
Owner:HUAWEI TECH CO LTD
Systems, methods, and computer program products for managing communications
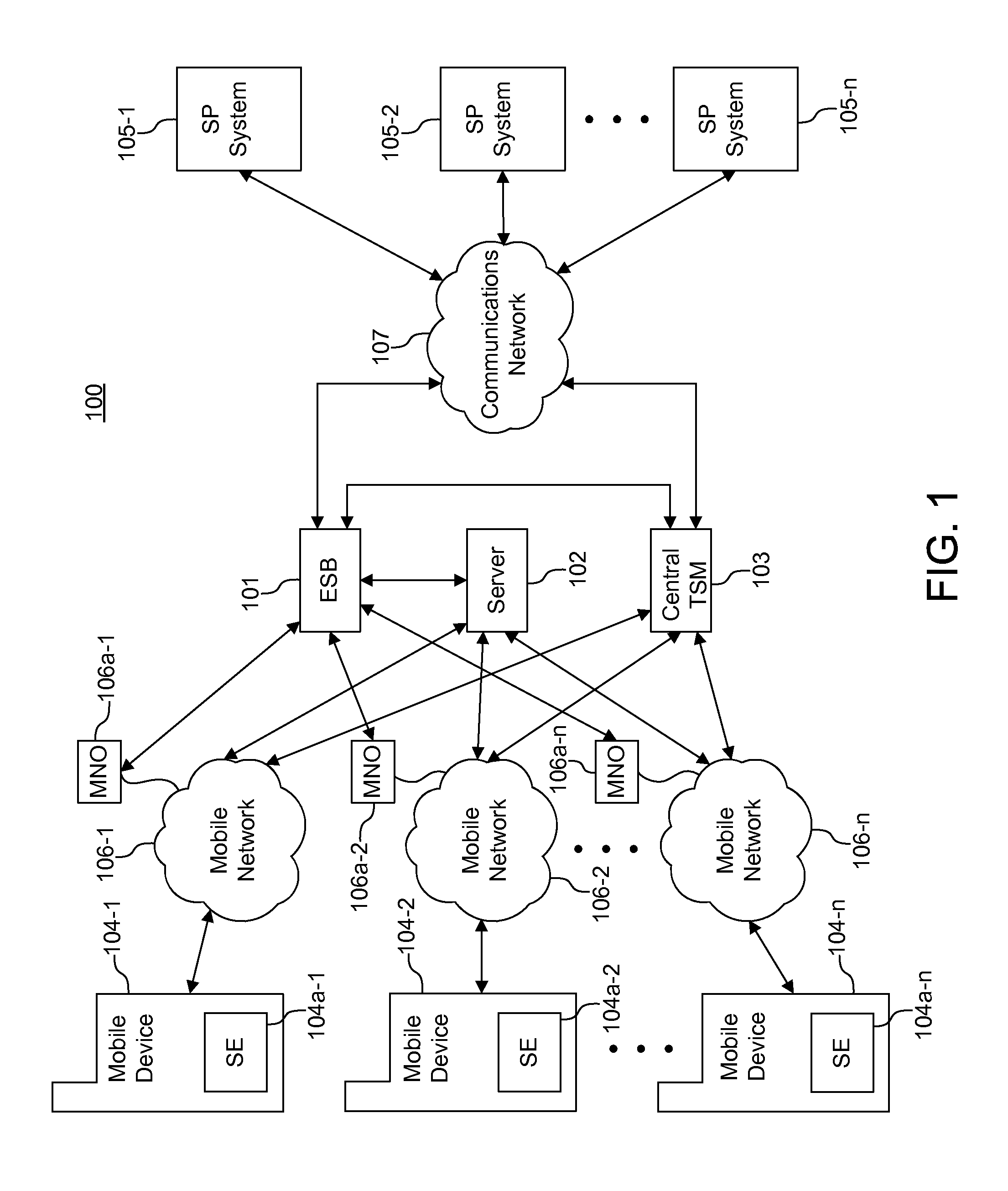
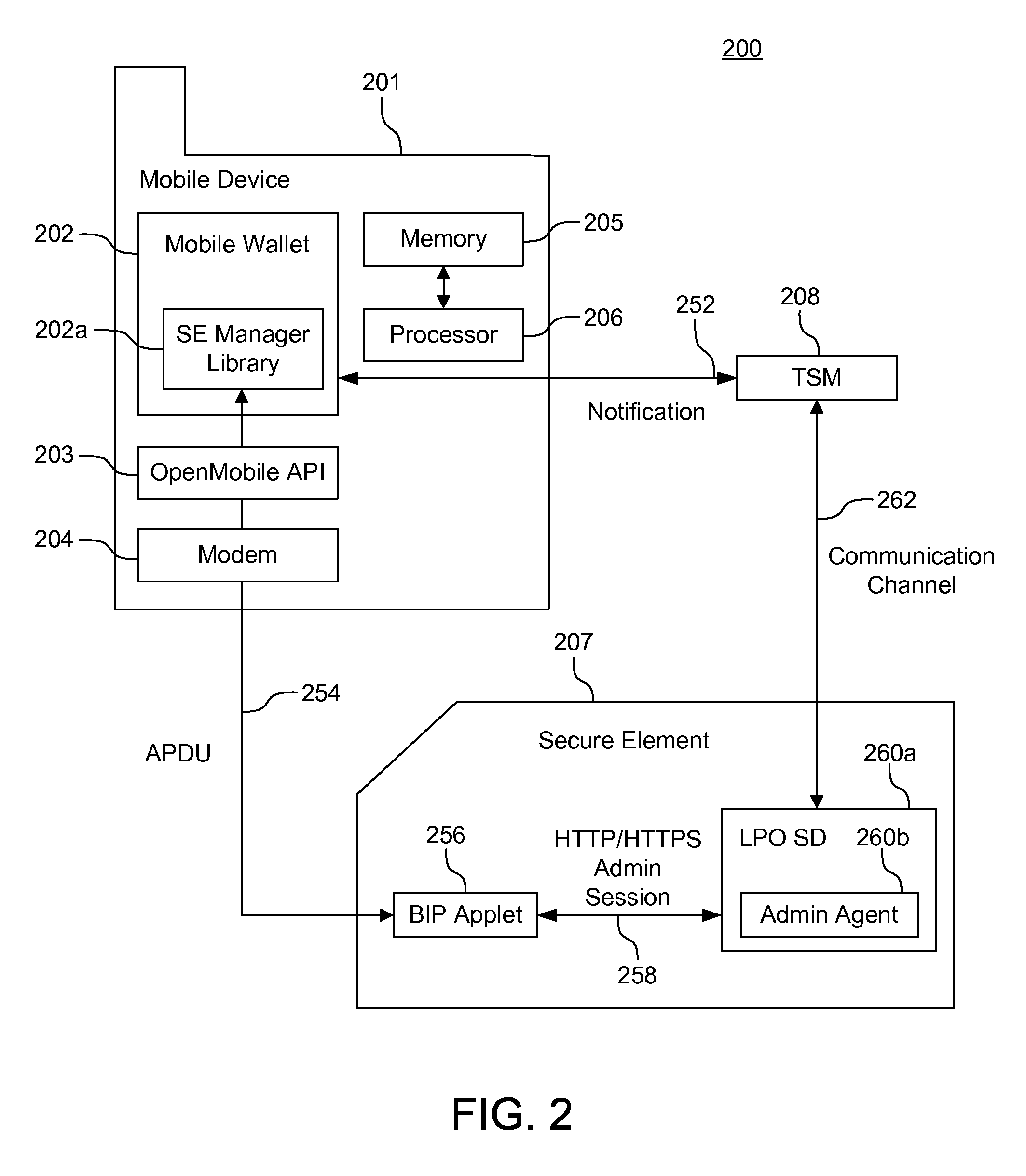
InactiveUS20150106456A1Increase awarenessLimited to componentMessaging/mailboxes/announcementsData switching networksCommunications systemComputer science
System, methods, and computer program products are provided for managing communications. A first applet and a second applet are operable receive and transmit application protocol data unit messages. The application protocol data unit messages include command-response message pairs. An application protocol data unit message is transmitted from the first applet to a second applet to trigger and establish a communication channel with a first device. Thus, messages may be comprehensively managed post-issuance. User experience is improved.
Owner:GOOGLE LLC
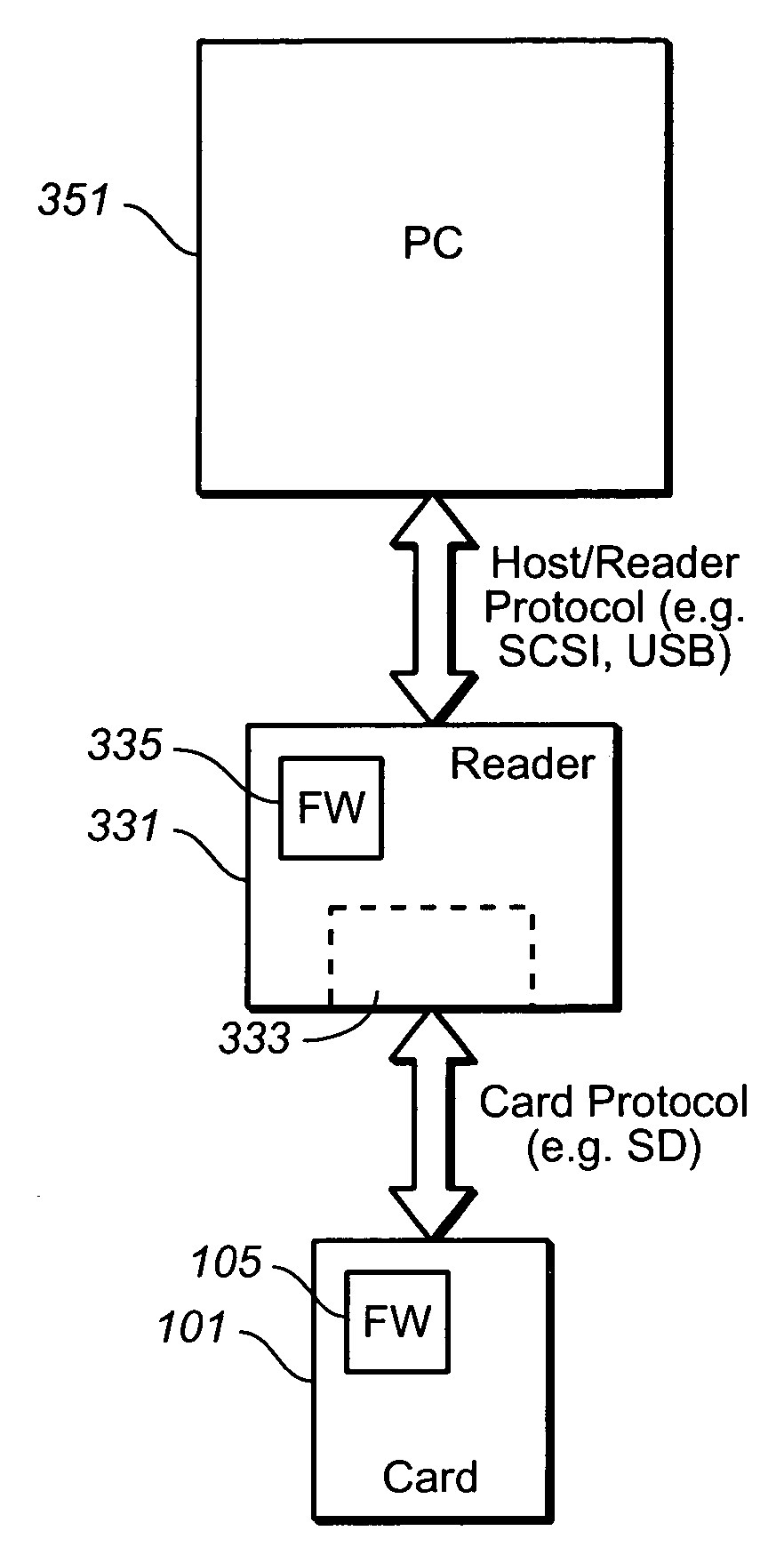
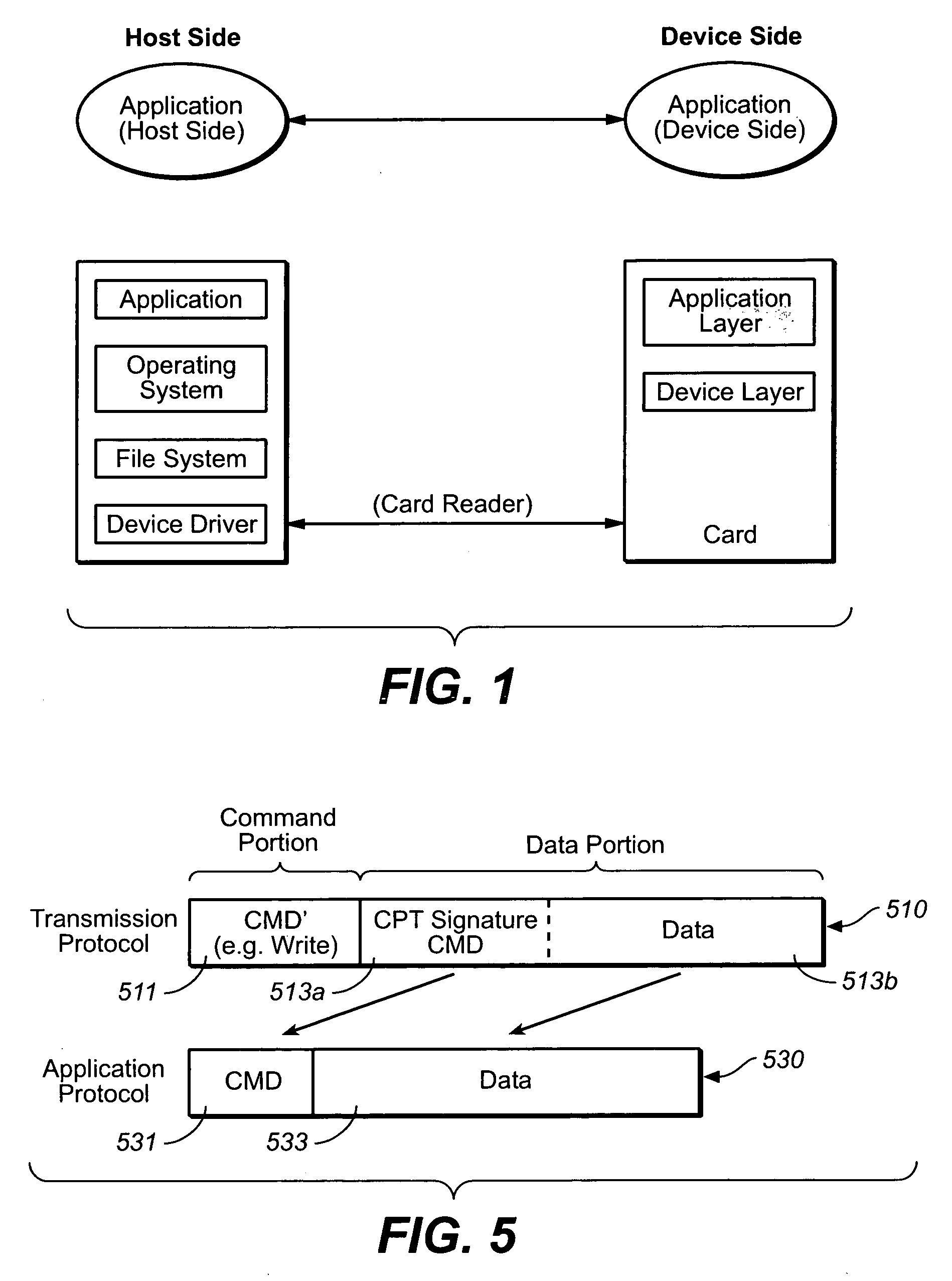
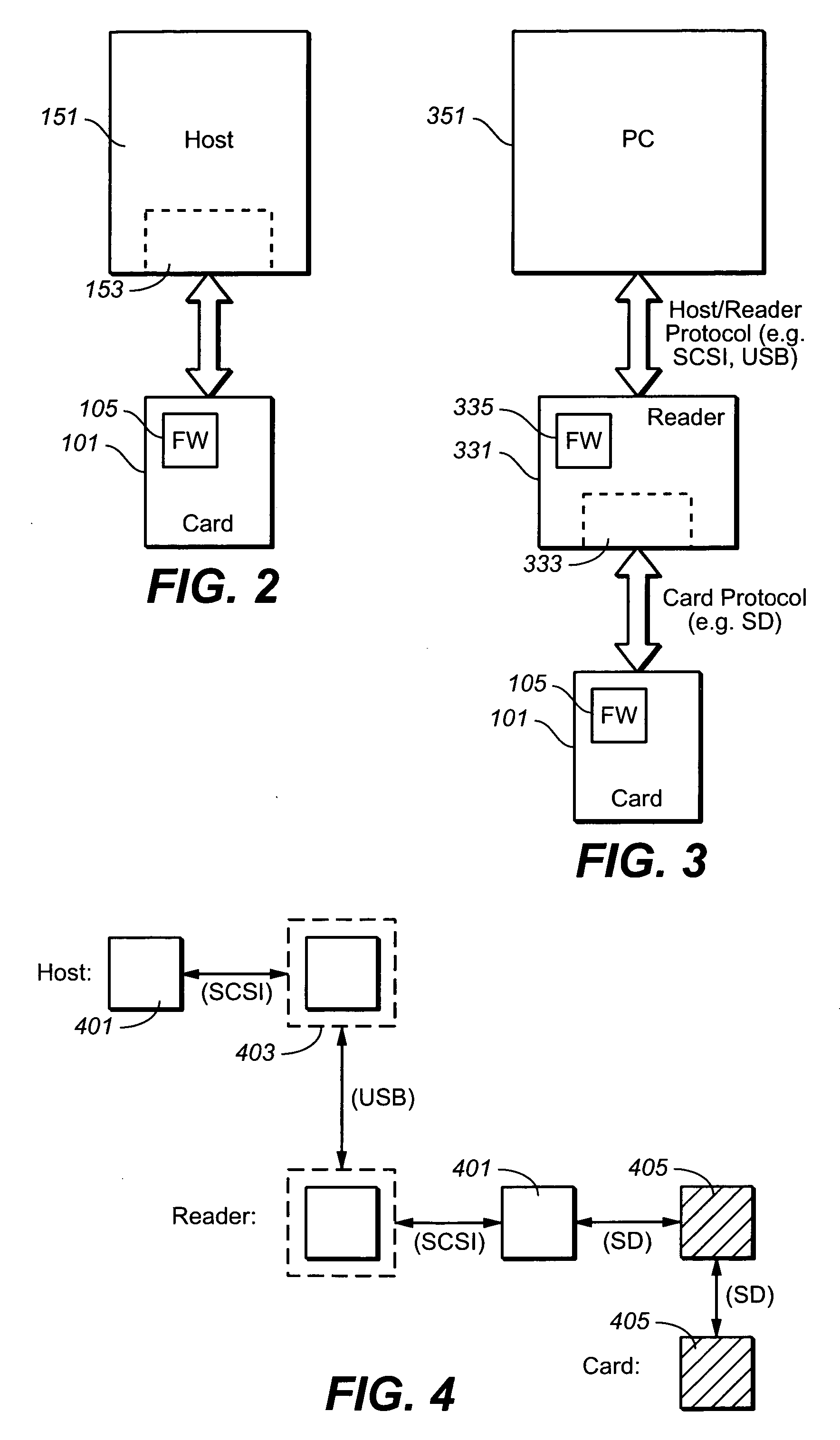
Media card command pass through methods
The present invention presents techniques for transmitting application specific instruction between a host and a memory card. The commands for the application specific protocol are embedded along with a signature in the data portion of a transmission protocol that is used to communicate between the host the memory card. This allows for the transmission of application specific commands that lack a corresponding command in the transmission protocol to still be transmitted in that protocol. The method can be implemented on the host side either at the device driver level or the file level. In order to implement a read command in the application specific protocol, a write command in the first protocol with an embedded read command is first sent to a logical address, followed by a second read command to the same logical address.
Owner:SANDISK TECH LLC
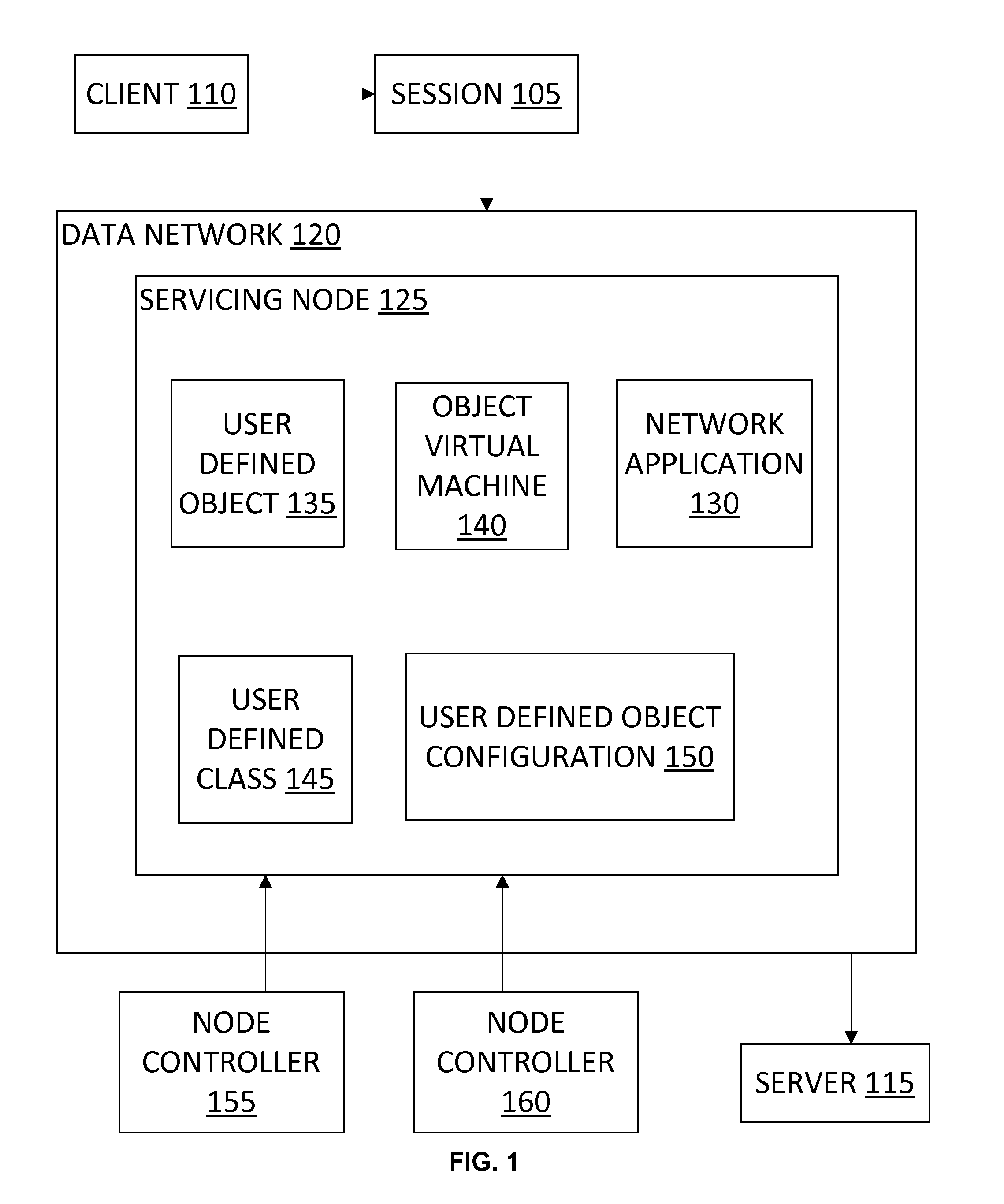
User Defined Objects for Network Devices
ActiveUS20150350048A1Well formedDigital computer detailsData switching networksProgramming languageNetwork packet
Systems and methods are provided herein. An exemplary servicing node may include: an interface to a data network, the interface coupled to an object machine; and the object machine, the object machine: receiving a data packet from the data network using the network interface, the data packet comprising at least one of a destination address, a destination port number, and an application protocol; determining a condition associated with the at least one of the destination address, the destination port number, and the application protocol; identifying a program name using the condition; executing a program using a name table, the name table linking each of a plurality of program names to a respective program, the executing comprising getting an instruction of the program, the instruction including object information.
Owner:A10 NETWORKS
Map-based remarks
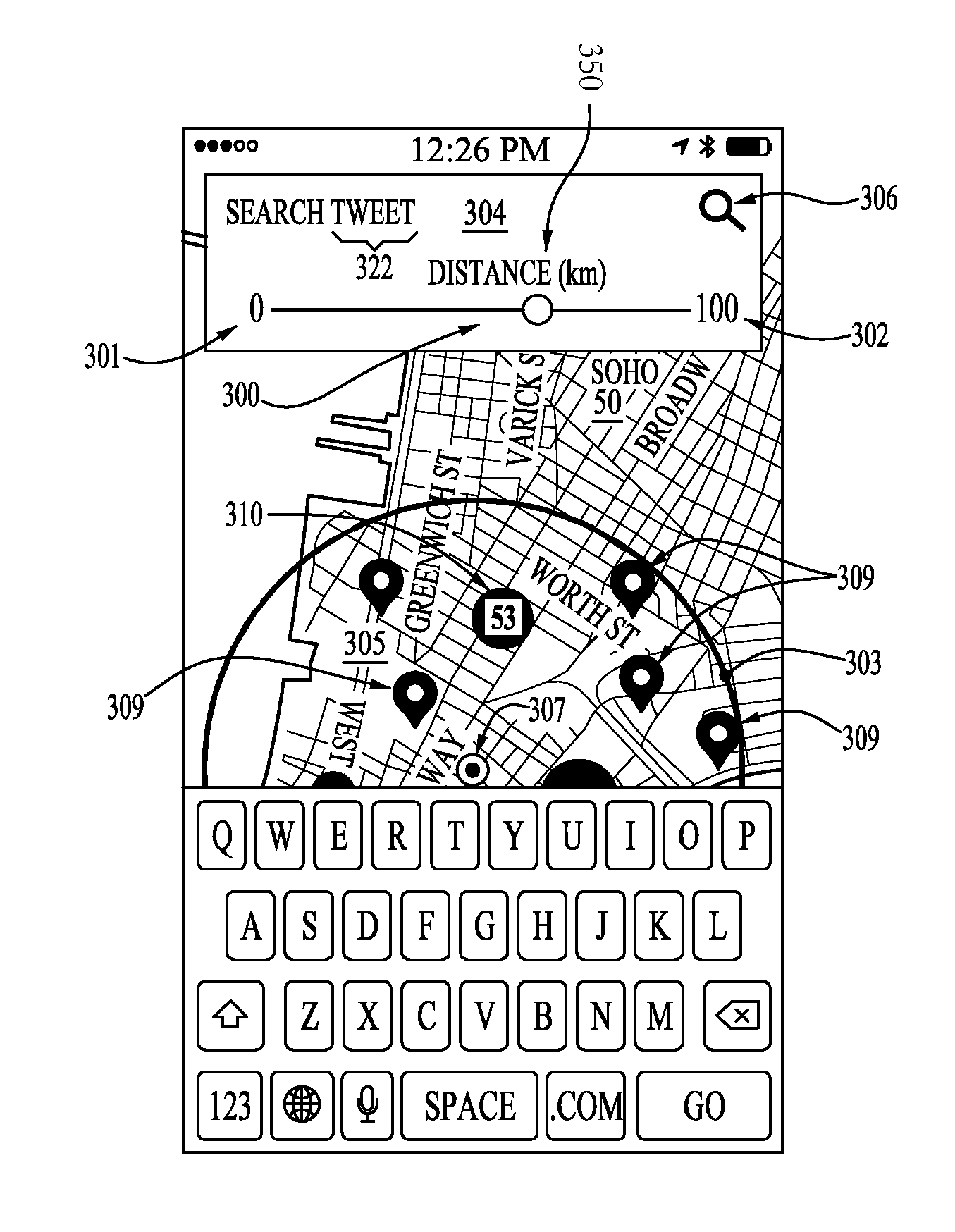
InactiveUS20150334077A1Simplify the release processSimple stepsData processing applicationsData switching networksThird partyInternet privacy
A method for sharing a geopost includes controlling a shared map image post via a sharing application, capable of sharing a post on a social network, wherein the sharing application comprises a map with a GPS location capable of being authenticated by at least two authentication inputs, providing a prebuilt application protocol which sends the at least two authentication inputs to the third party social network, authorizing a third party social network with a posting permission, where the posting is both shared and sharable, and the sharing application is stored on a non-transitory computer-readable medium, superimposing a semitransparent circle on a map in the user interface, around the GPS location, providing a search input filed and a search function, and providing a hidden posting function capable of publishing to the third party social network only upon touching a portion of the map via the user interface in the mobile software application.
Owner:FELDMAN DOUGLAS E
Multiple application protocol identification method and device
InactiveCN104038389AHigh precisionImprove finenessData switching networksTraffic capacityMultiple applications
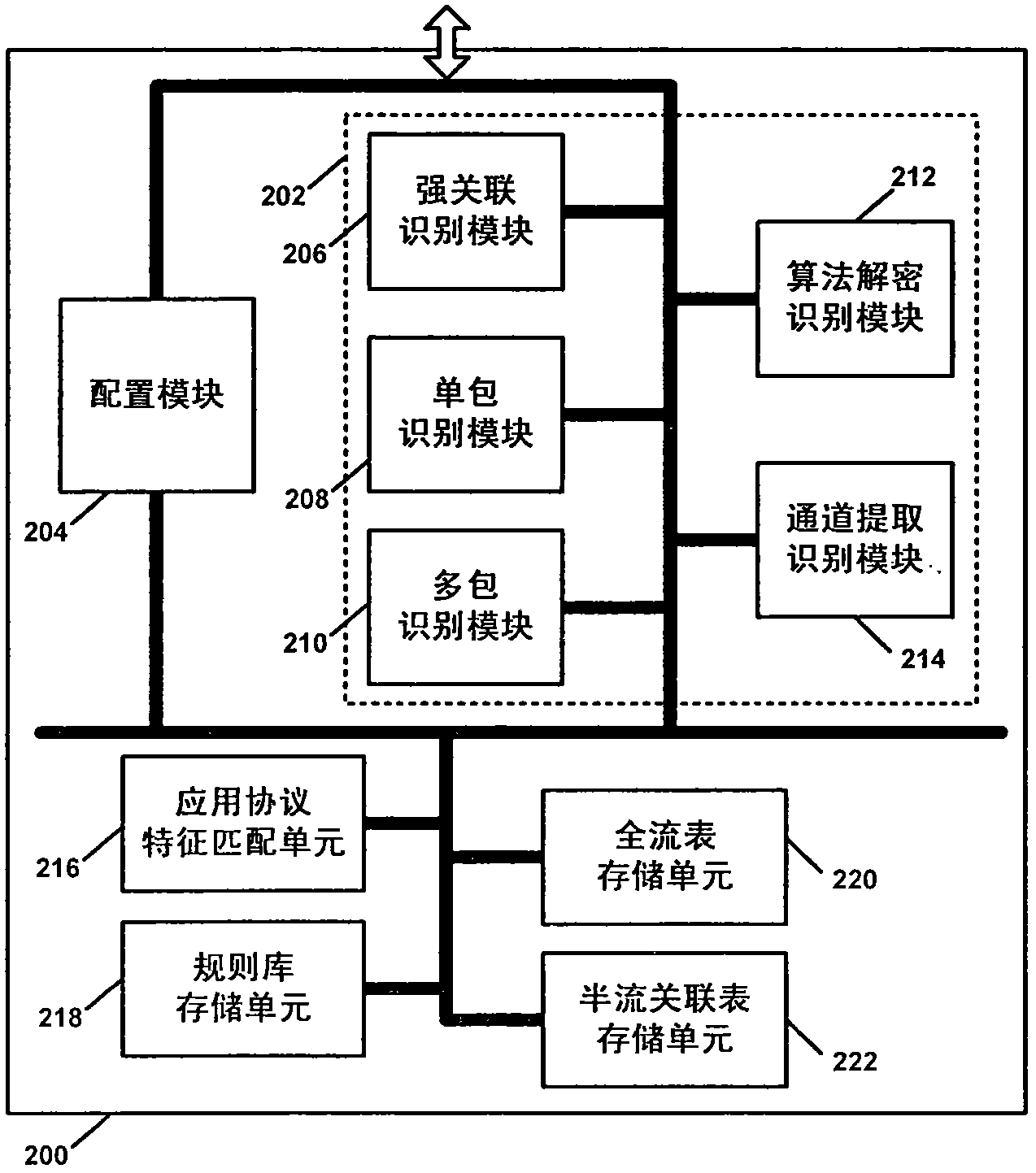
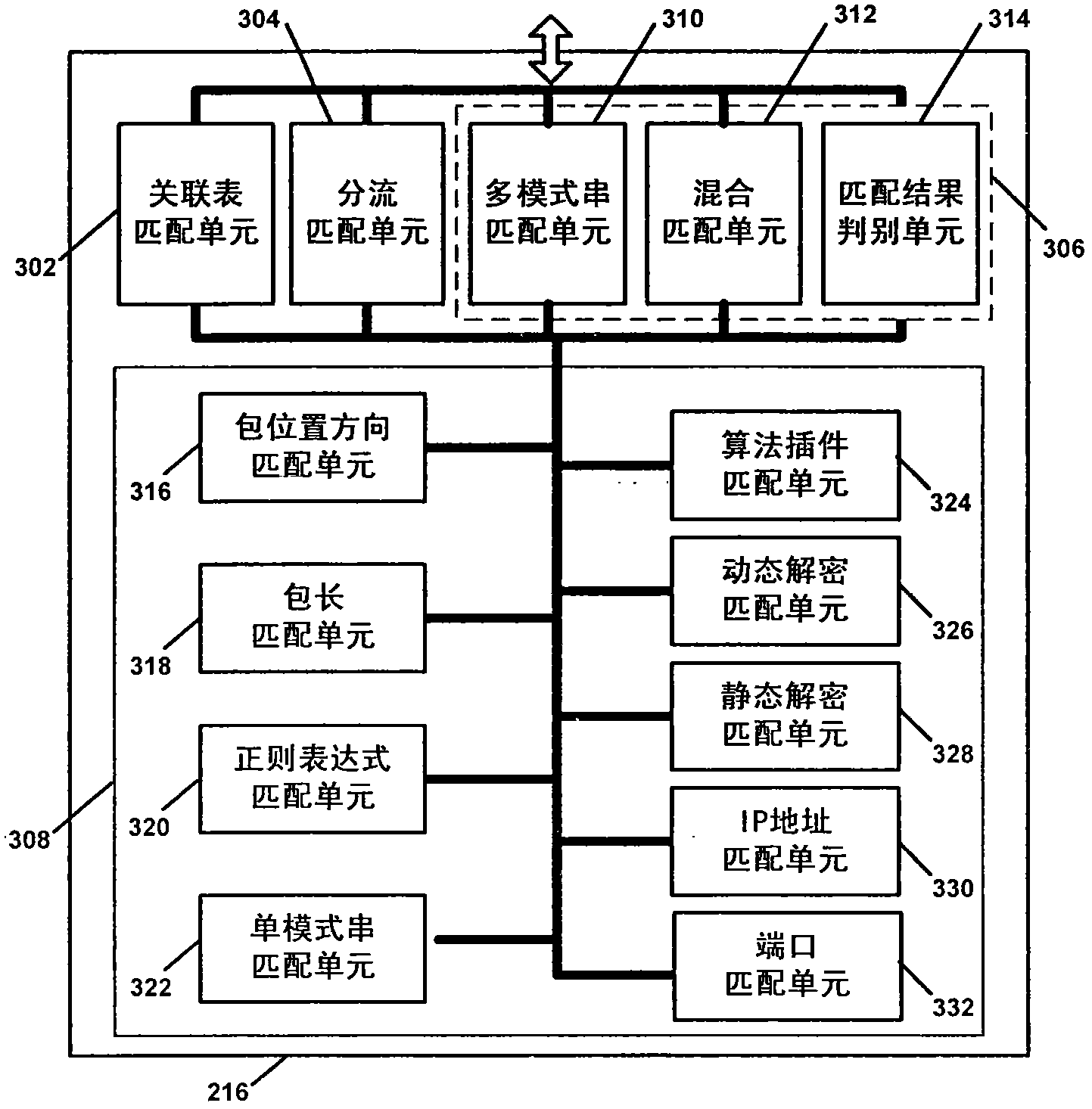
The invention discloses a multiple application protocol identification method and an application protocol identification engine. According to the multiple application protocol identification method, characteristic conditions, decryption suite conditions, application protocol characteristics, application protocol hit action, various detection identification modules and corresponding rule description methods are provided on the basis of XM language; the application protocol identification engine comprises identification modules, such as a strong correlation identification module, a single packet identification module, a multi-packet identification module, an algorithm decryption and identification module and a channel extraction and identification module; a configuration module; and an application protocol characteristic matching unit, a full-flow table storage unit, a half-flow association table storage unit, and a rule base storage unit. By the use of the multiple application protocol identification method and the application protocol identification engine, flexible rule description configuration mechanisms and online, accurate and comprehensive identification of application protocols and encrypted traffic are achieved.
Owner:BEIJING TOPSEC TECH +2
System and method for generating policy-based audio
ActiveUS8768494B1Easily enabledBroaden applicationBurglar alarmSpecial data processing applicationsLoudspeakerComputer science
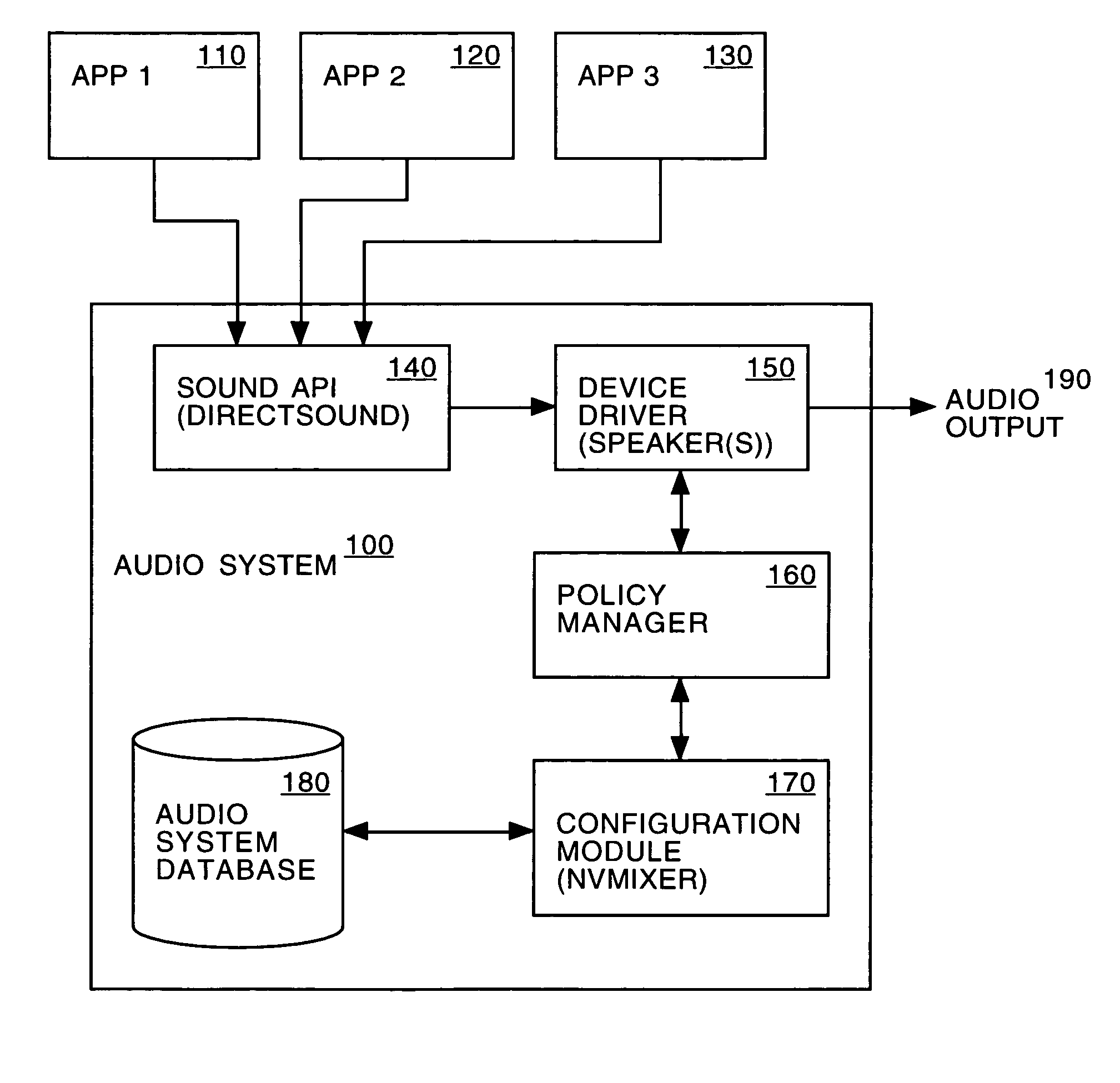
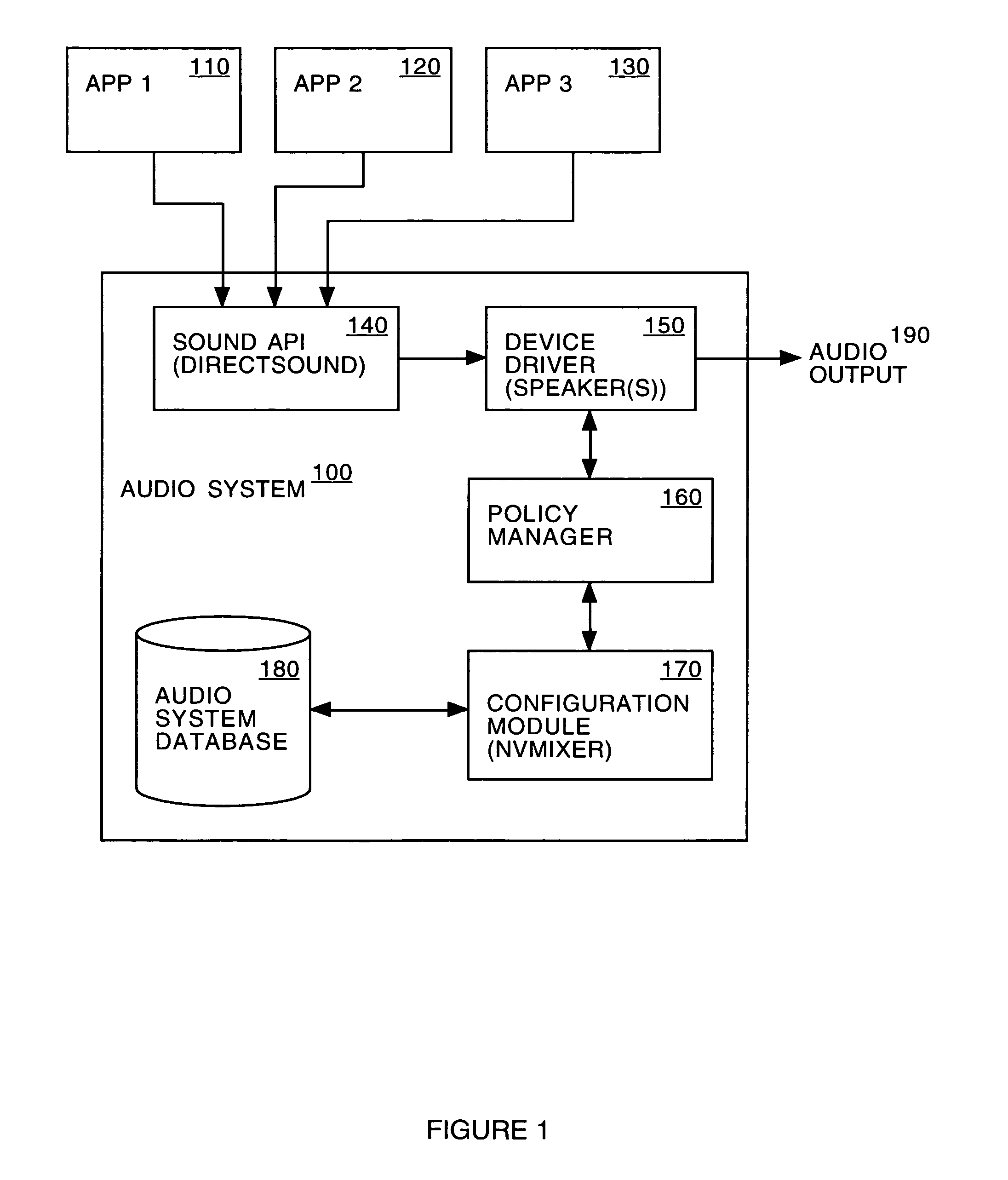
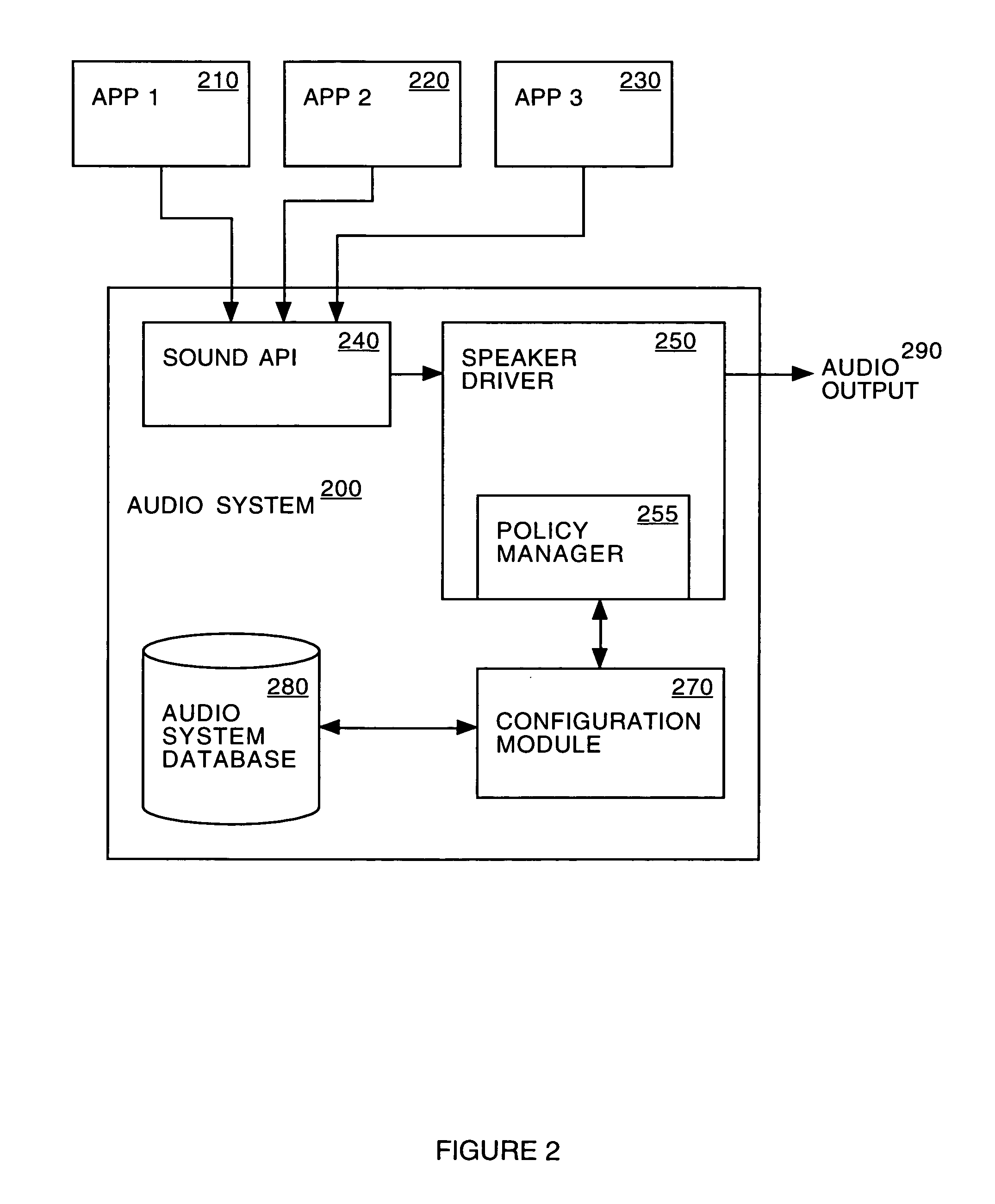
Embodiments of the invention provide a policy-based audio system. The system includes a sound application protocol interface, a configuration module and a speaker driver. The sound application protocol interface receives a set of sound samples generated by an application or event. The configuration module retrieves a first group of one or more parameters, rules and priorities applicable to the application or event. The speaker driver produces an audio output by processing the set of sound samples as a function of the group of one or more configuration parameters, rules and priorities.
Owner:NVIDIA CORP
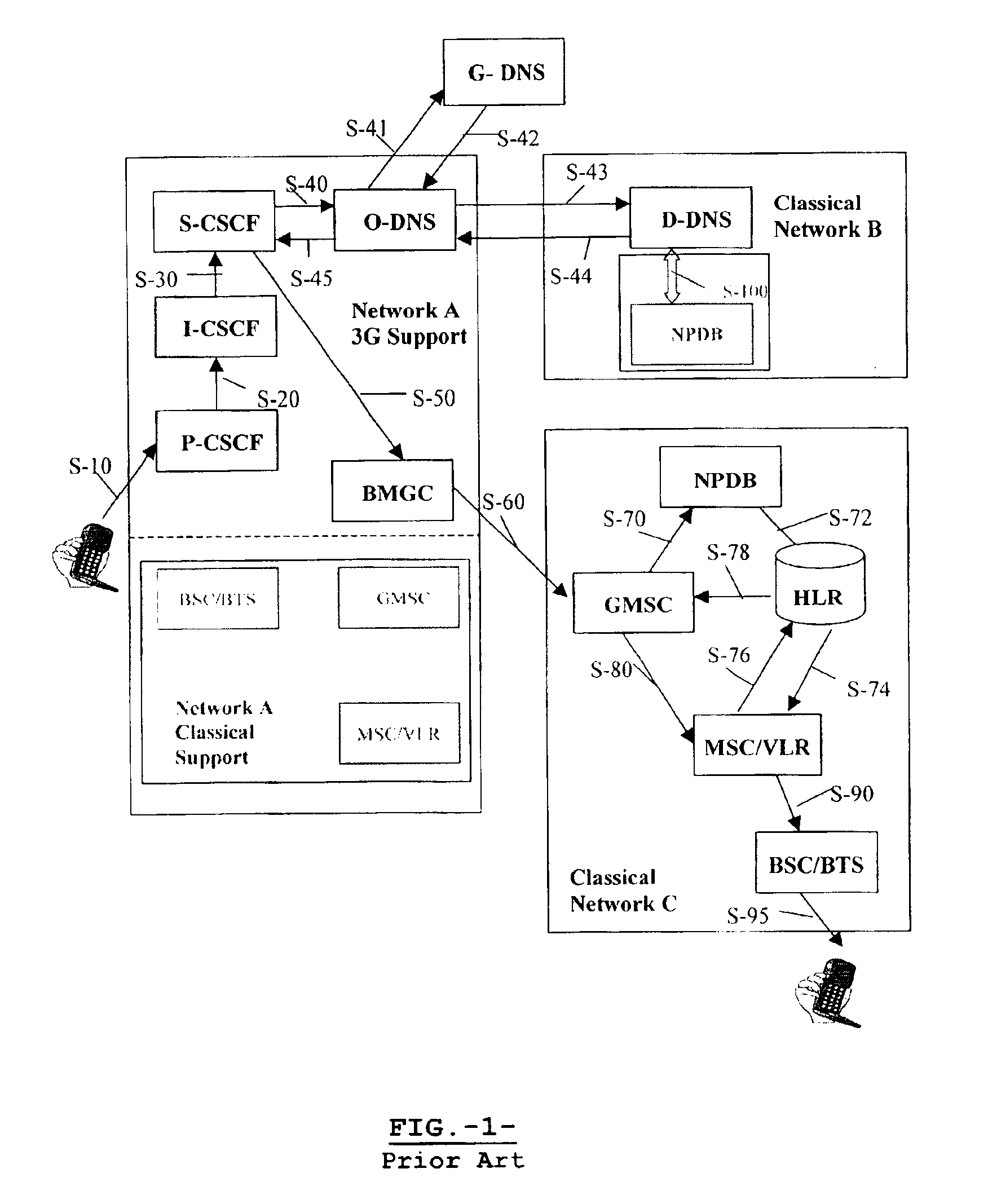
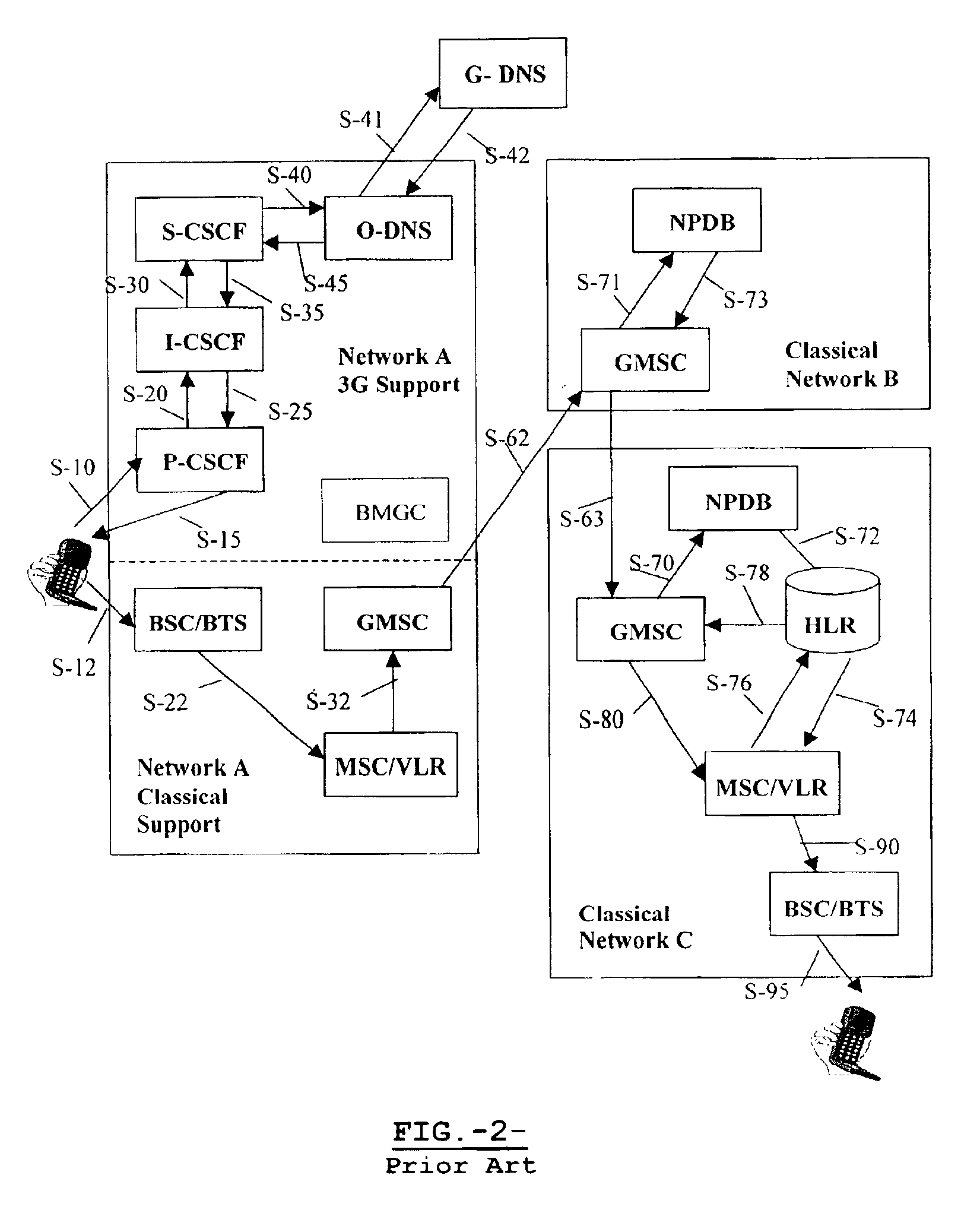
Method and apparatus for solving number portability in origin
InactiveUS6873849B2Interconnection arrangementsTime-division multiplexProtocol for Carrying Authentication for Network AccessInter-working function
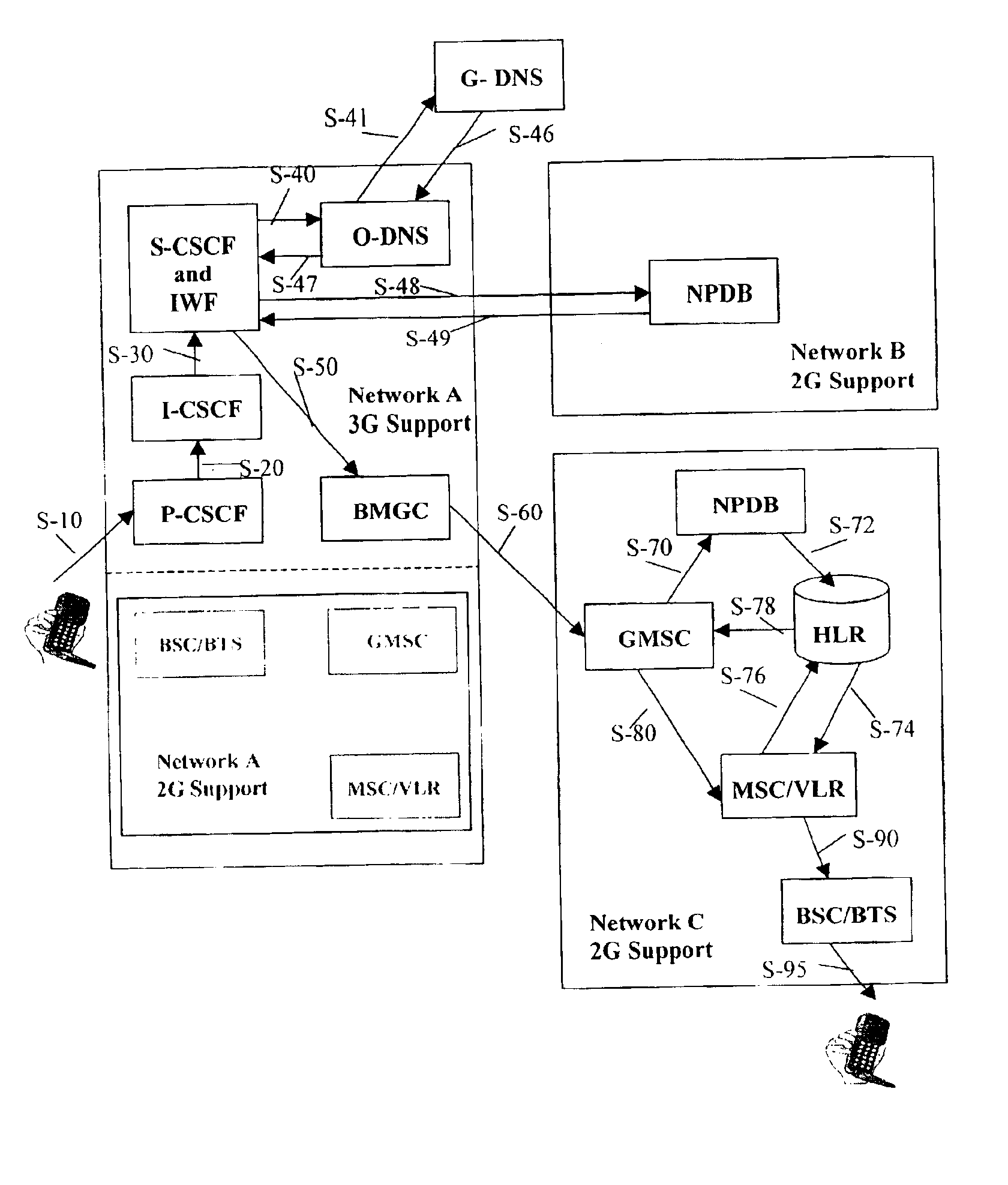
This invention provides a method intended to solve Number Portability in origin for calls to ported subscribers at a destination classical network, an inter-working function intended to provide the means to support said method, and a hierarchical DNS structure able to provide a new URI indicating interworking with an external database where routing data for said ported subscribers reside. This new URI specifies the Global Title address of the external database and the access protocol to said external database. The NAPTR resolution for that URI implies the use of an Inter-working Feature (IWF) placed in the DNS-resolver part of an S-CSCF, or in a close association, in the originating network. This IWF comprises a Protocol Translator and Controller adapting between DNS format and the external database access protocol format, at least one of a plurality of Application Protocol Handling Modules, and an SS7 Protocol Stack.
Owner:TELEFON AB LM ERICSSON (PUBL)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com