Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4072 results about "Protocol stack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
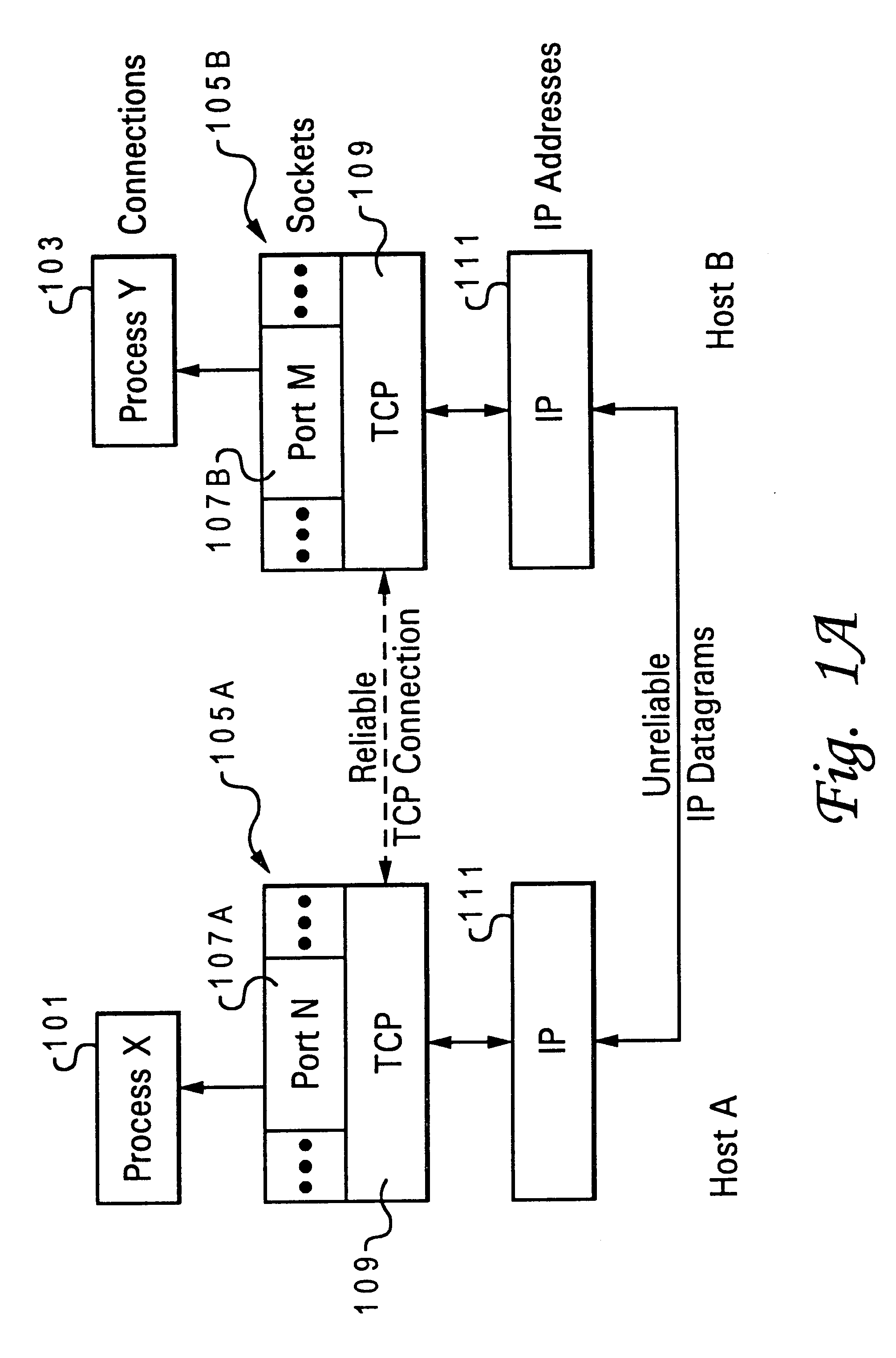
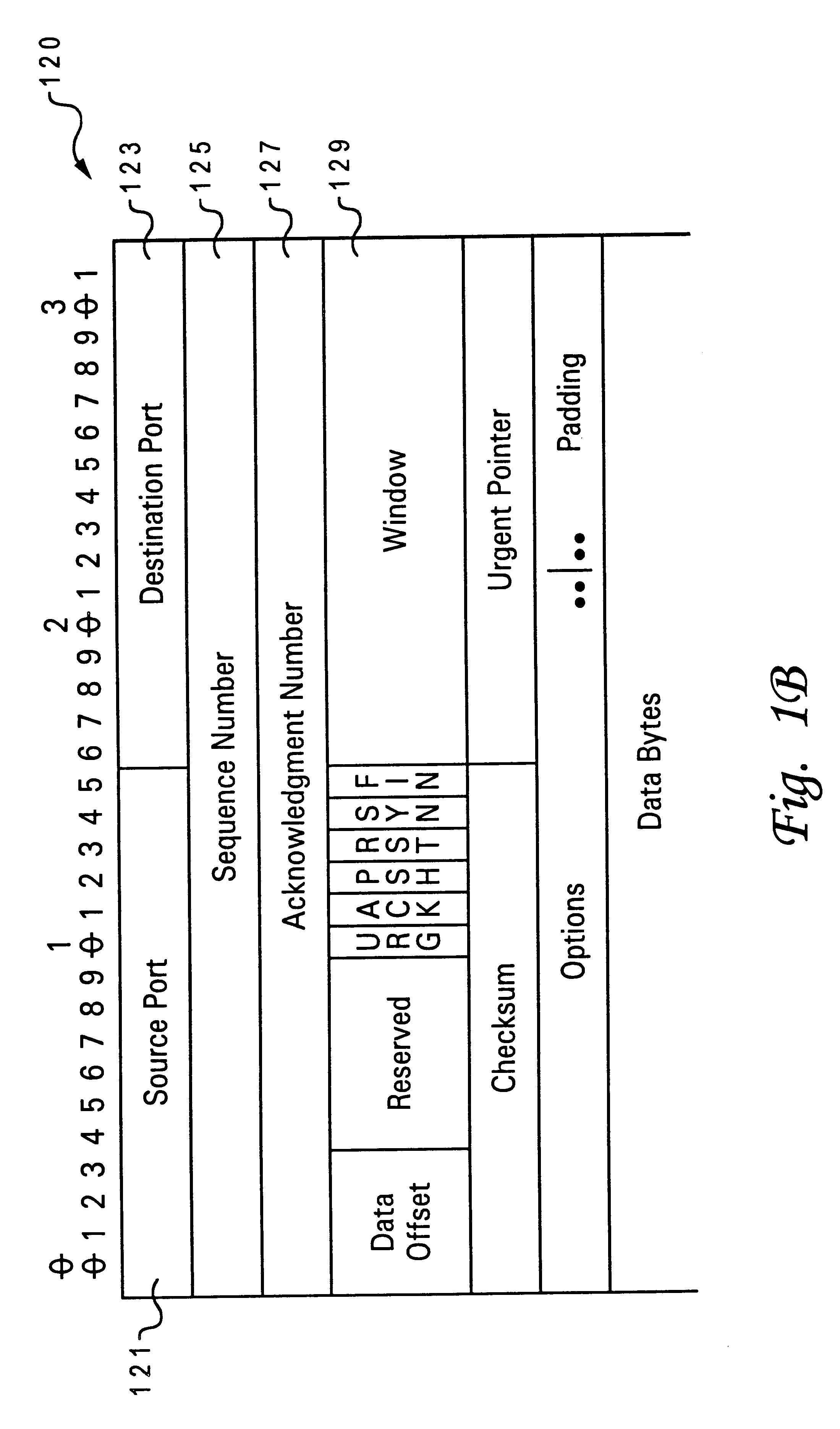
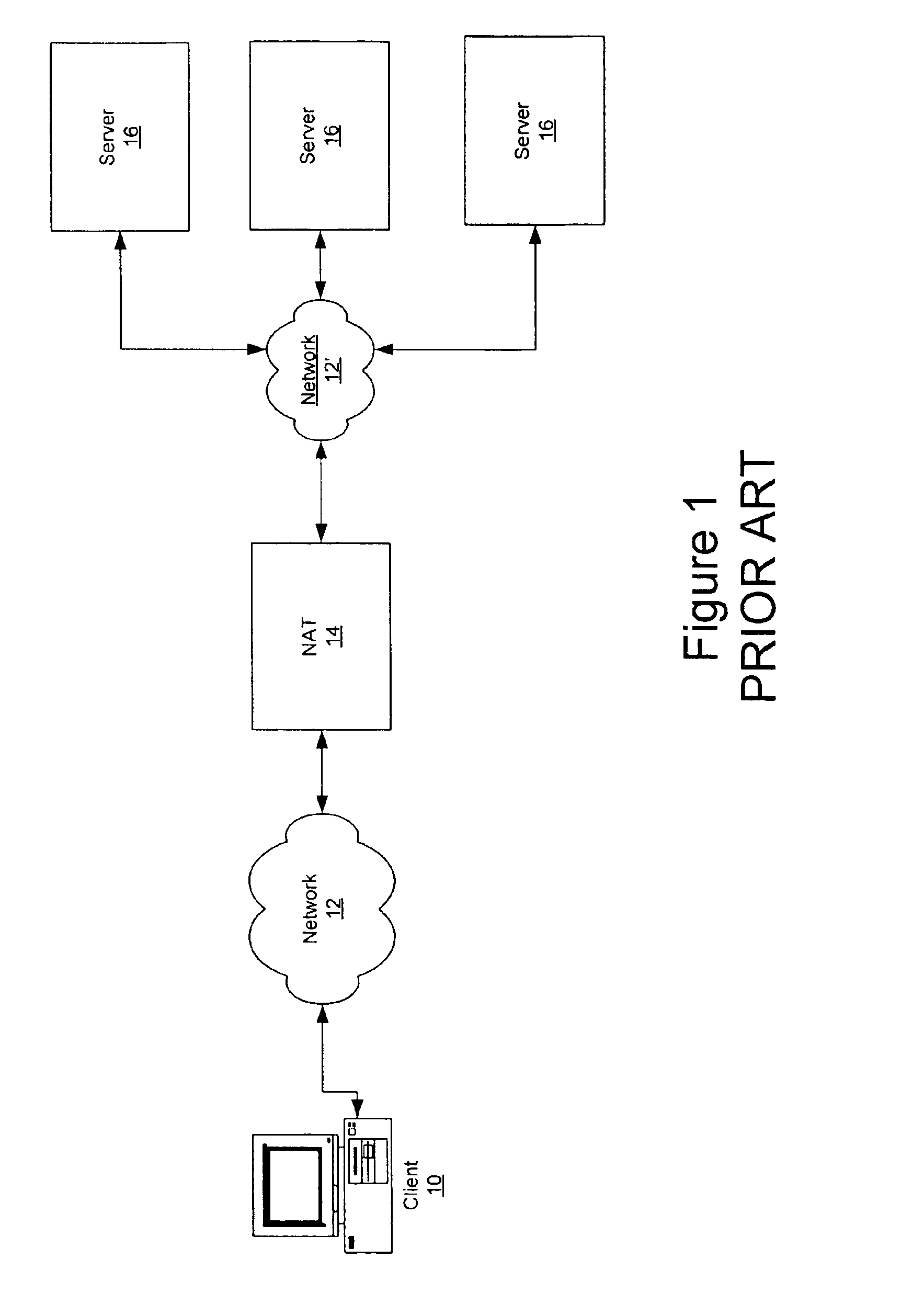
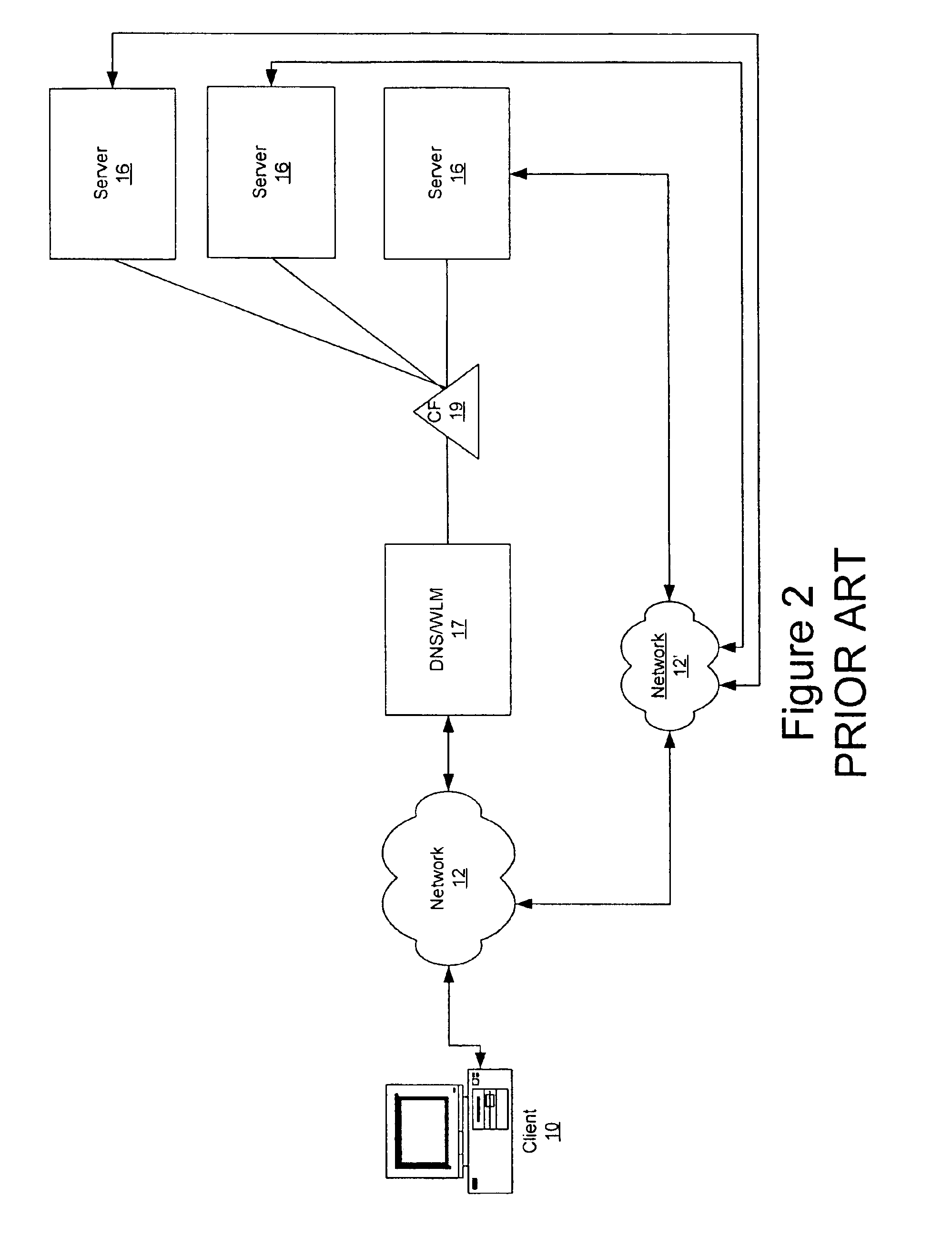
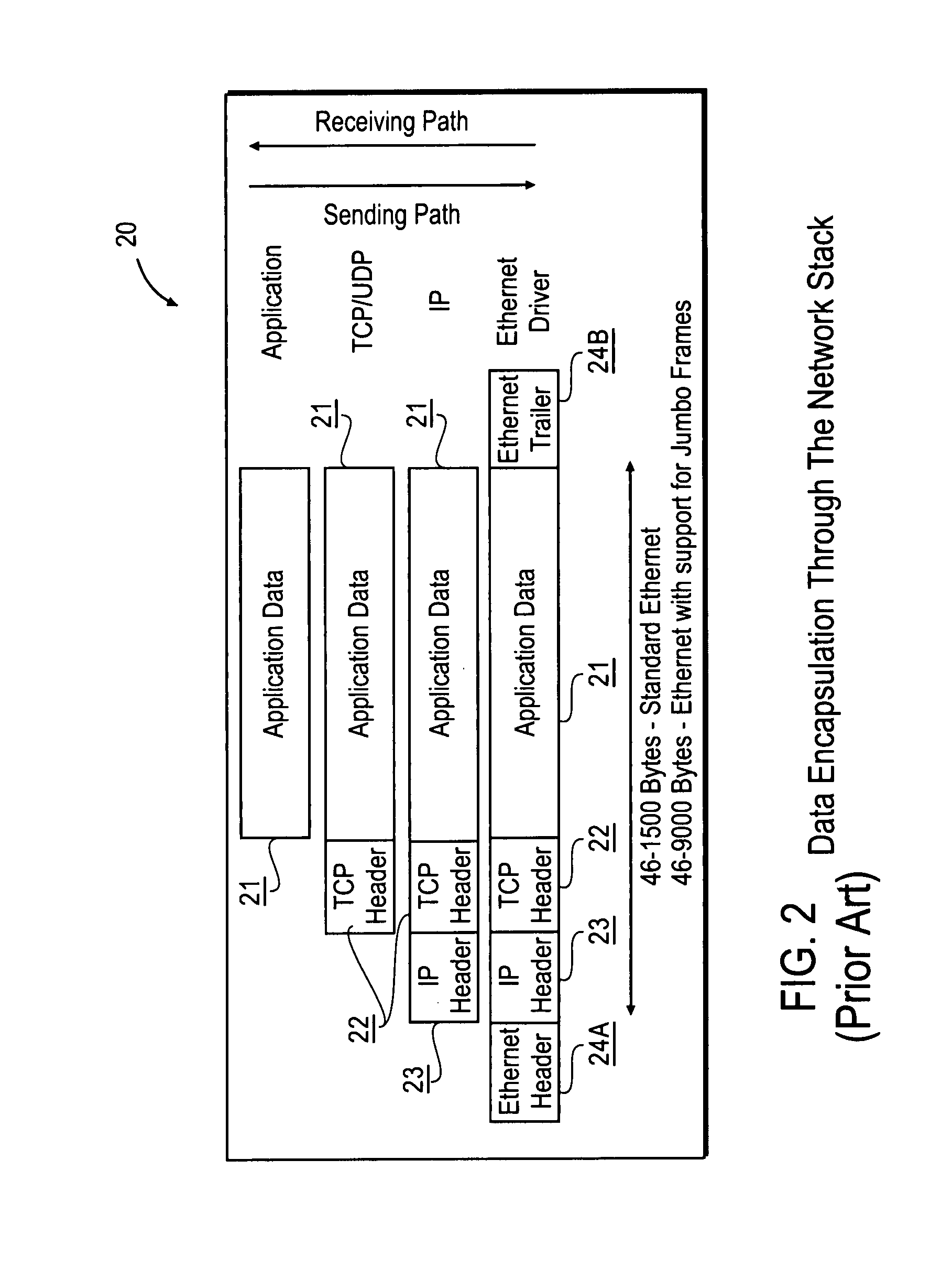
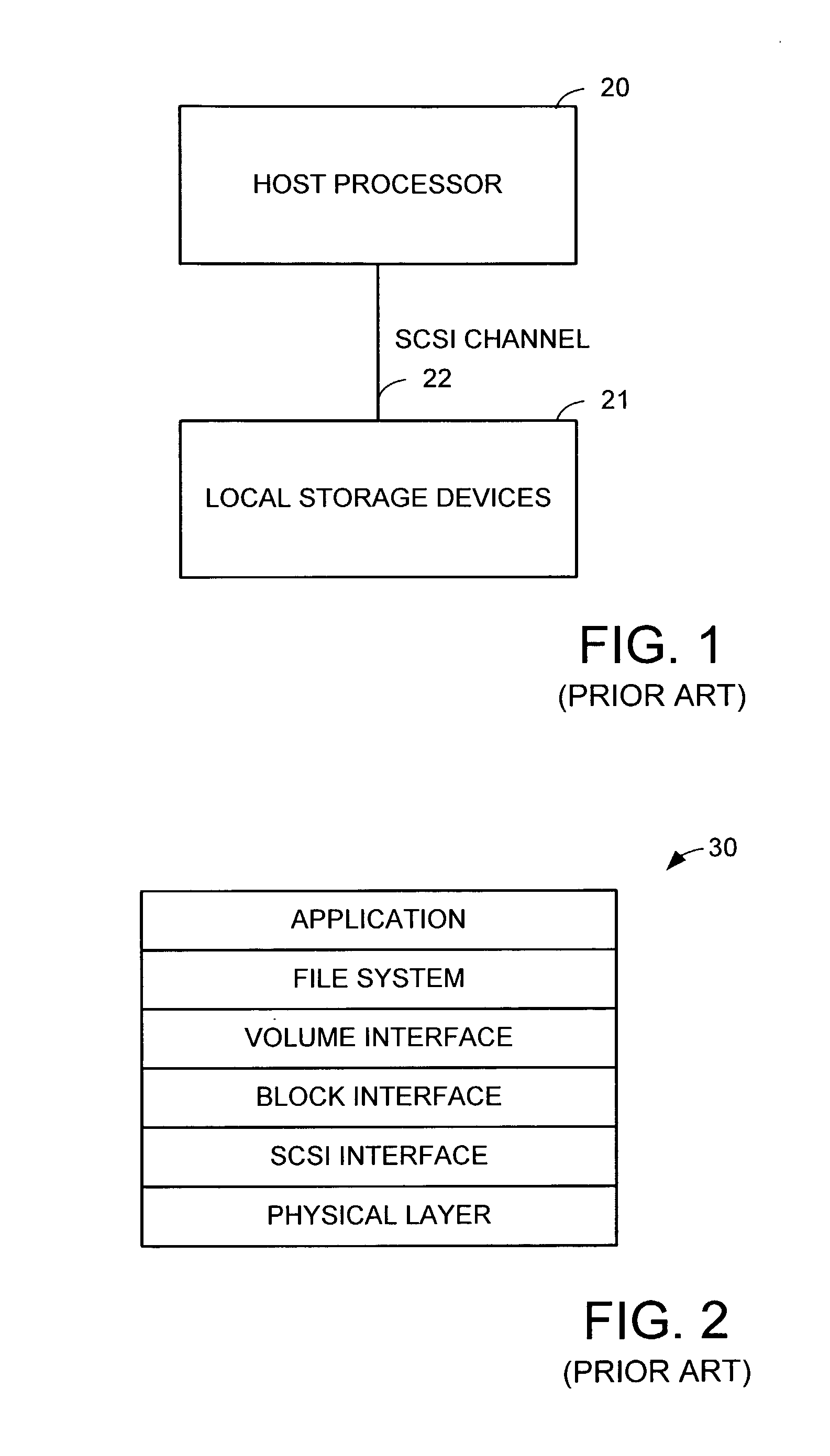
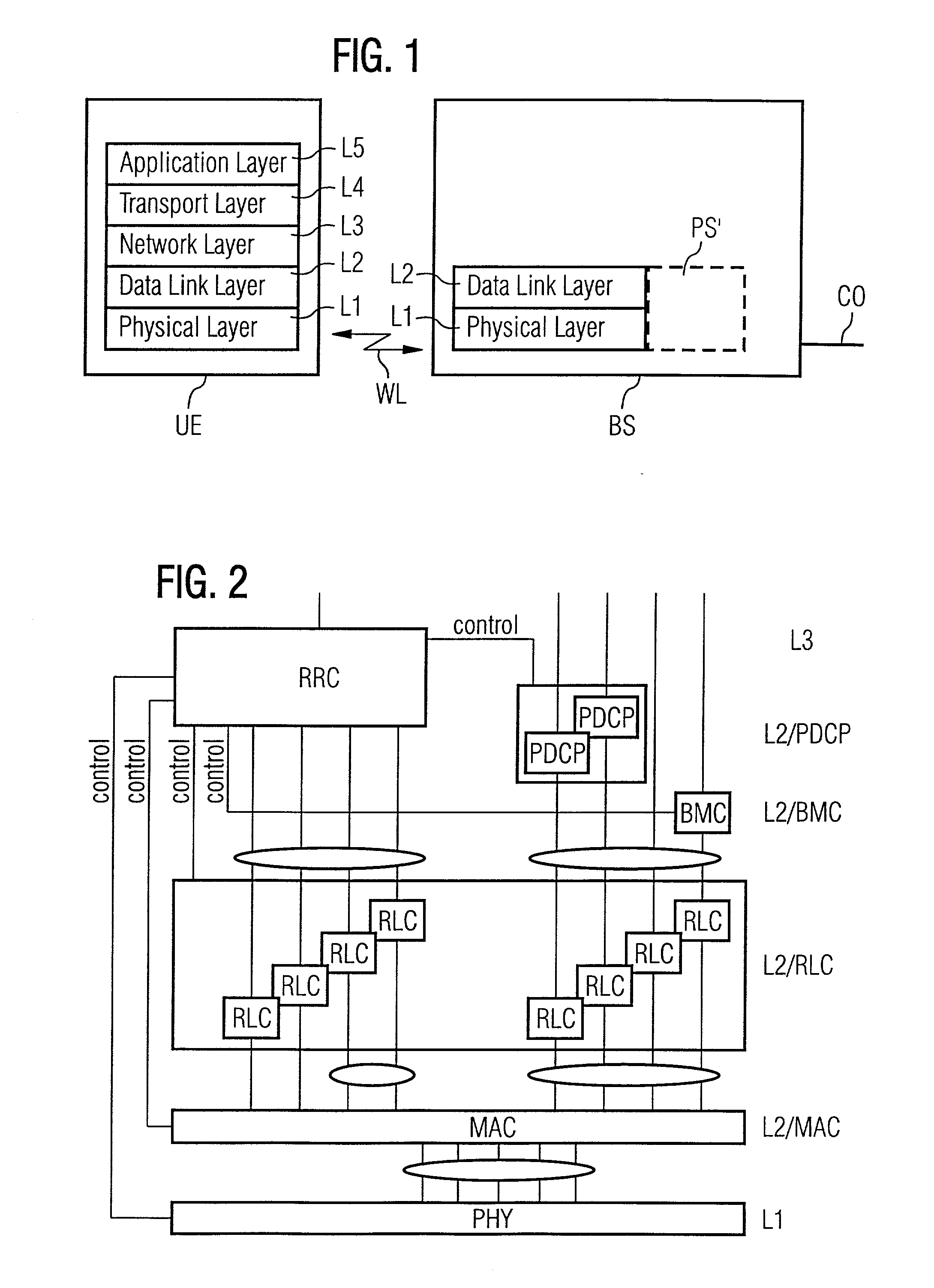
The protocol stack or network stack is an implementation of a computer networking protocol suite or protocol family. Some of these terms are used interchangeably but strictly speaking, the suite is the definition of the communication protocols, and the stack is the software implementation of them.
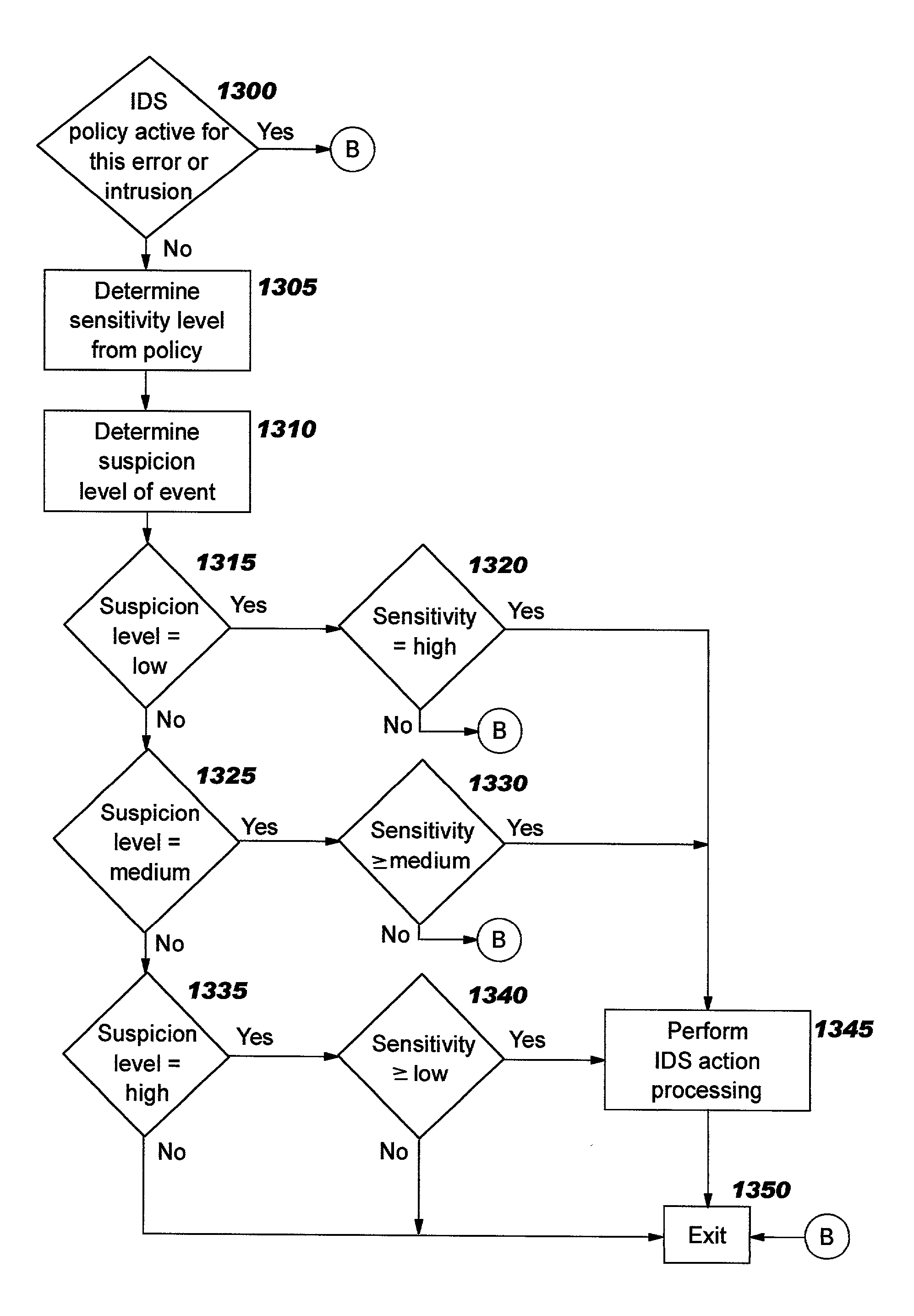
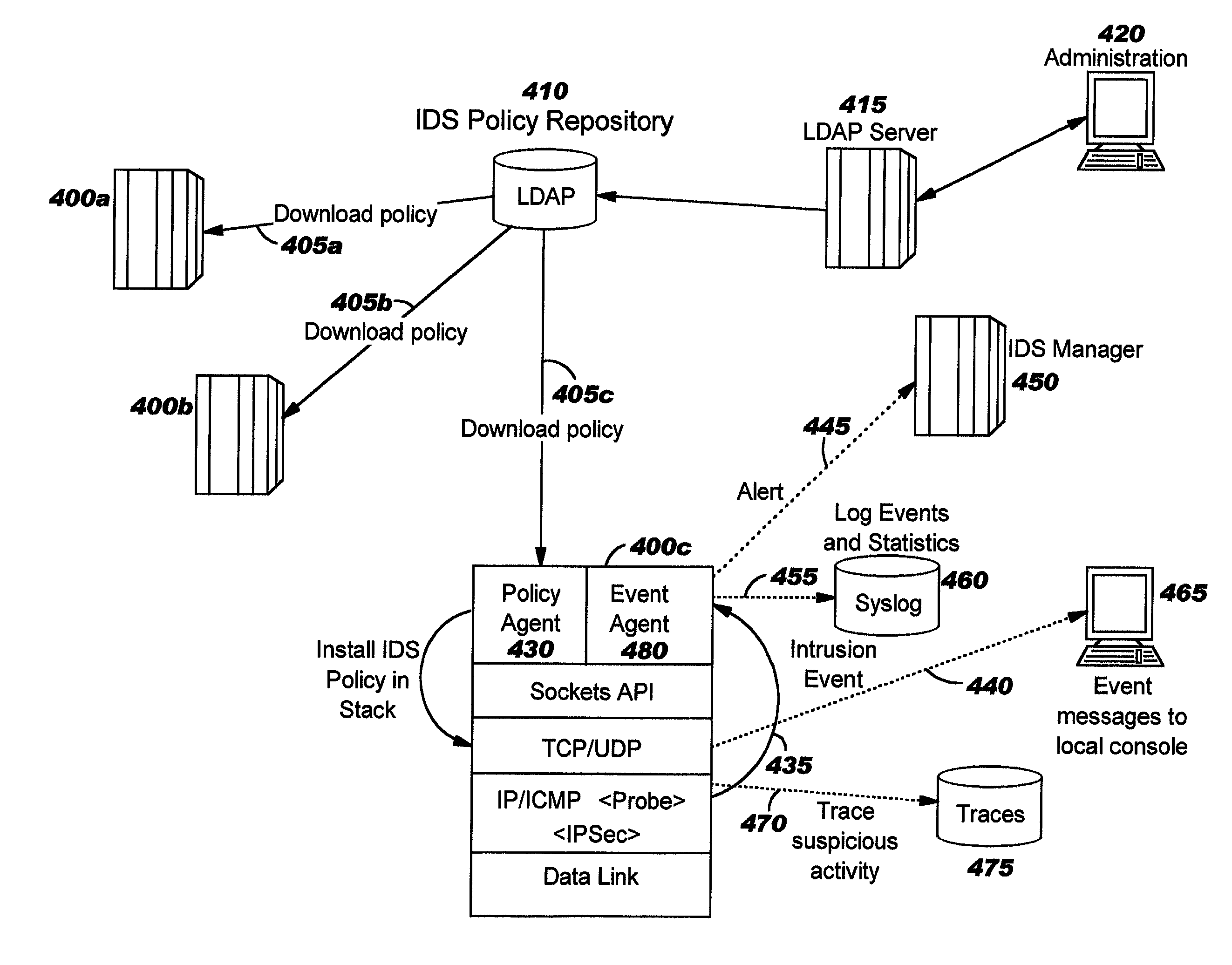
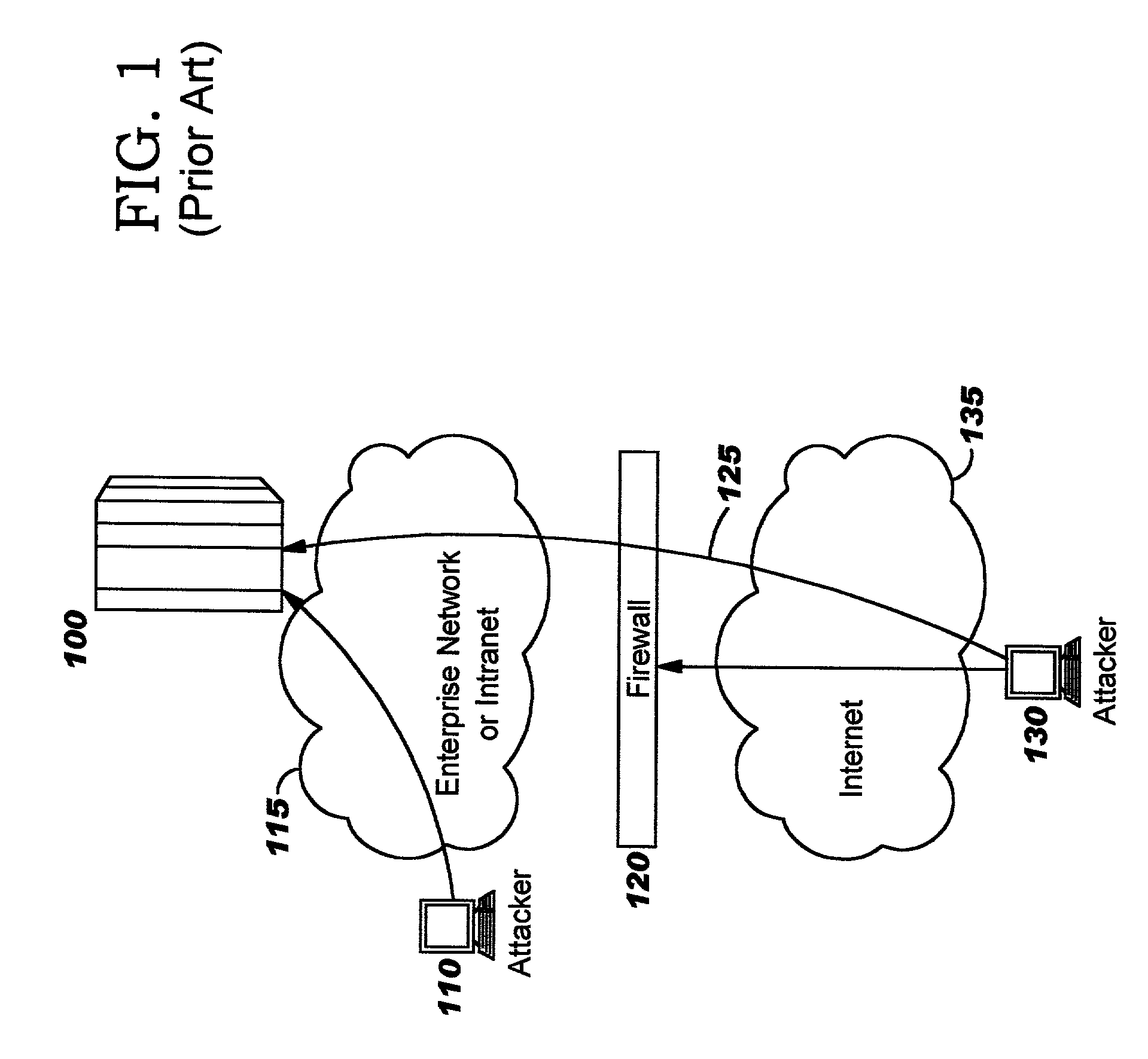
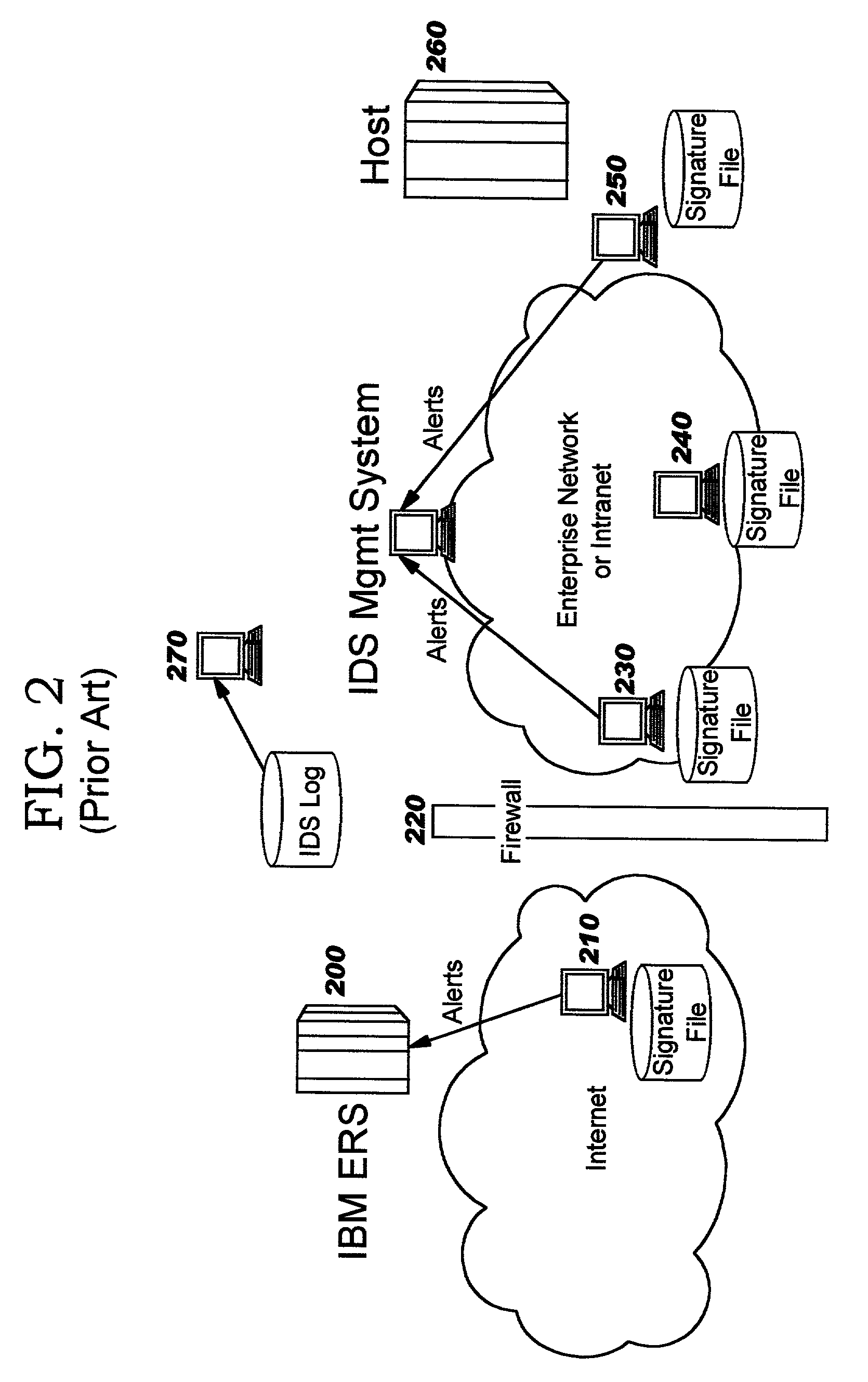
Integrated intrusion detection services
ActiveUS20030145226A1Memory loss protectionDigital computer detailsService improvementContext specific
Improvements in intrusion detection are disclosed by providing integrated intrusion detection services. Preferably, these services are integrated into a system or server that is the potential target of attack. Stack-based security processing is leveraged for access to cleartext data within the layers of the protocol stack. Layer-specific attacks may therefore be processed efficiently. Evaluation of incoming traffic for an intrusion is preferably performed only after an error condition of some type has been detected. This approach reduces the overhead of intrusion detection by reducing the number of packets to be inspected, and at the same time allows more efficient packet inspection through use of context-specific information that may be used to direct the inspection to particular candidate attacks. Generic attack class capability is also disclosed. Intrusion detection policy information may be used to direct the actions to be taken upon detecting an attack.
Owner:TREND MICRO INC
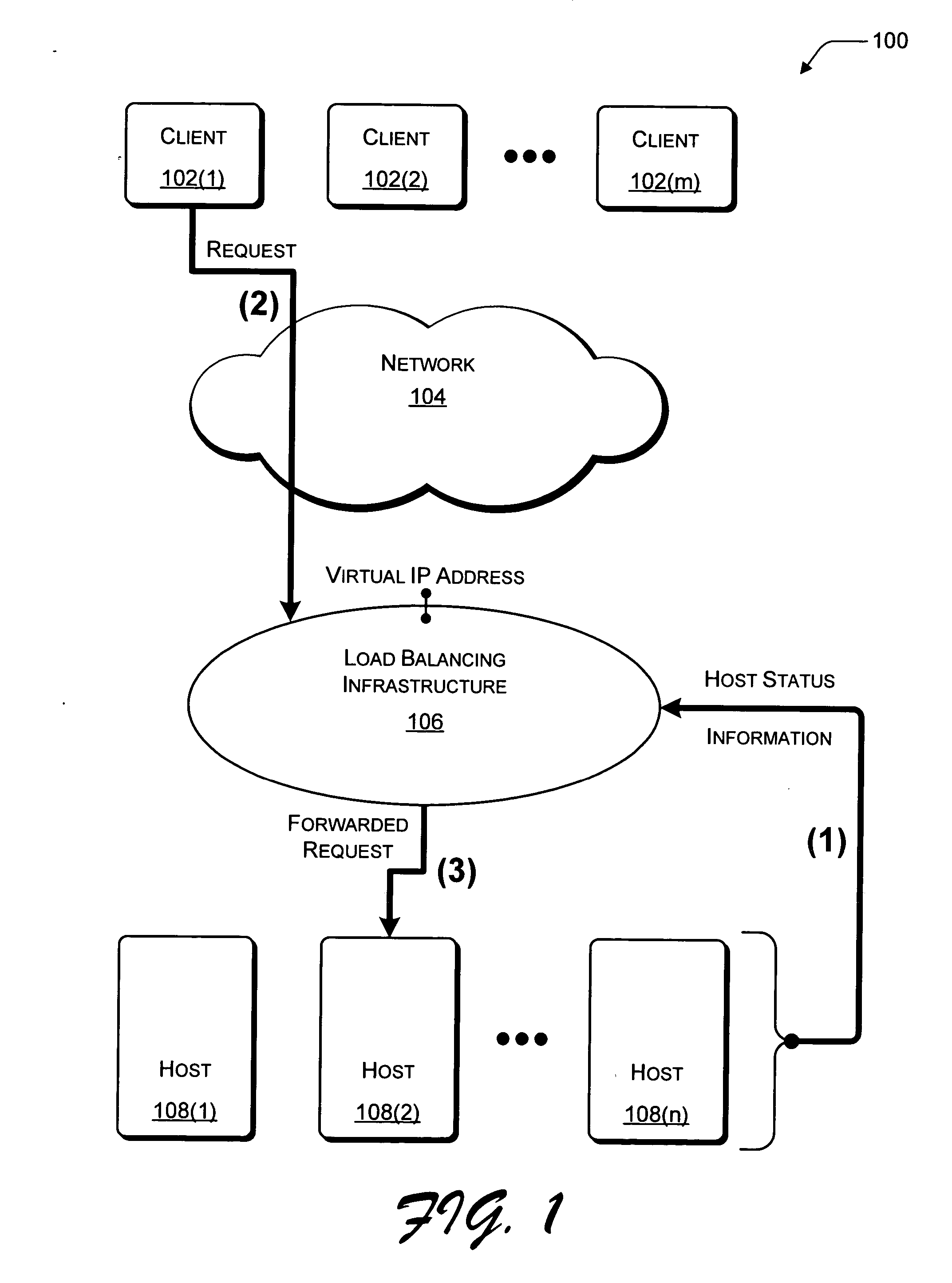
Network load balancing with connection manipulation
ActiveUS20050055435A1Multiple digital computer combinationsData switching networksEncapsulated dataProtocol stack
In an exemplary device implementation, a device includes: a connection migrator that is configured to migrate connections away from the device; the connection migrator capable of precipitating a compilation of protocol state for a connection across a protocol stack; the connection migrator adapted to aggregate the compiled protocol state with data for the connection into an aggregated connection state; the connection migrator further capable of causing the aggregated connection state to be sent toward a target device. In an exemplary media implementation, processor-executable instructions direct a device to perform actions including: obtaining at least a portion of a source / destination pair from a packet; accessing an encapsulation mapping table using the at least a portion of the source / destination pair to locate an encapsulation mapping entry; extracting a flow identifier from the encapsulation mapping entry; and replacing part of the packet with the flow identifier to produce an encapsulated packet.
Owner:MICROSOFT TECH LICENSING LLC
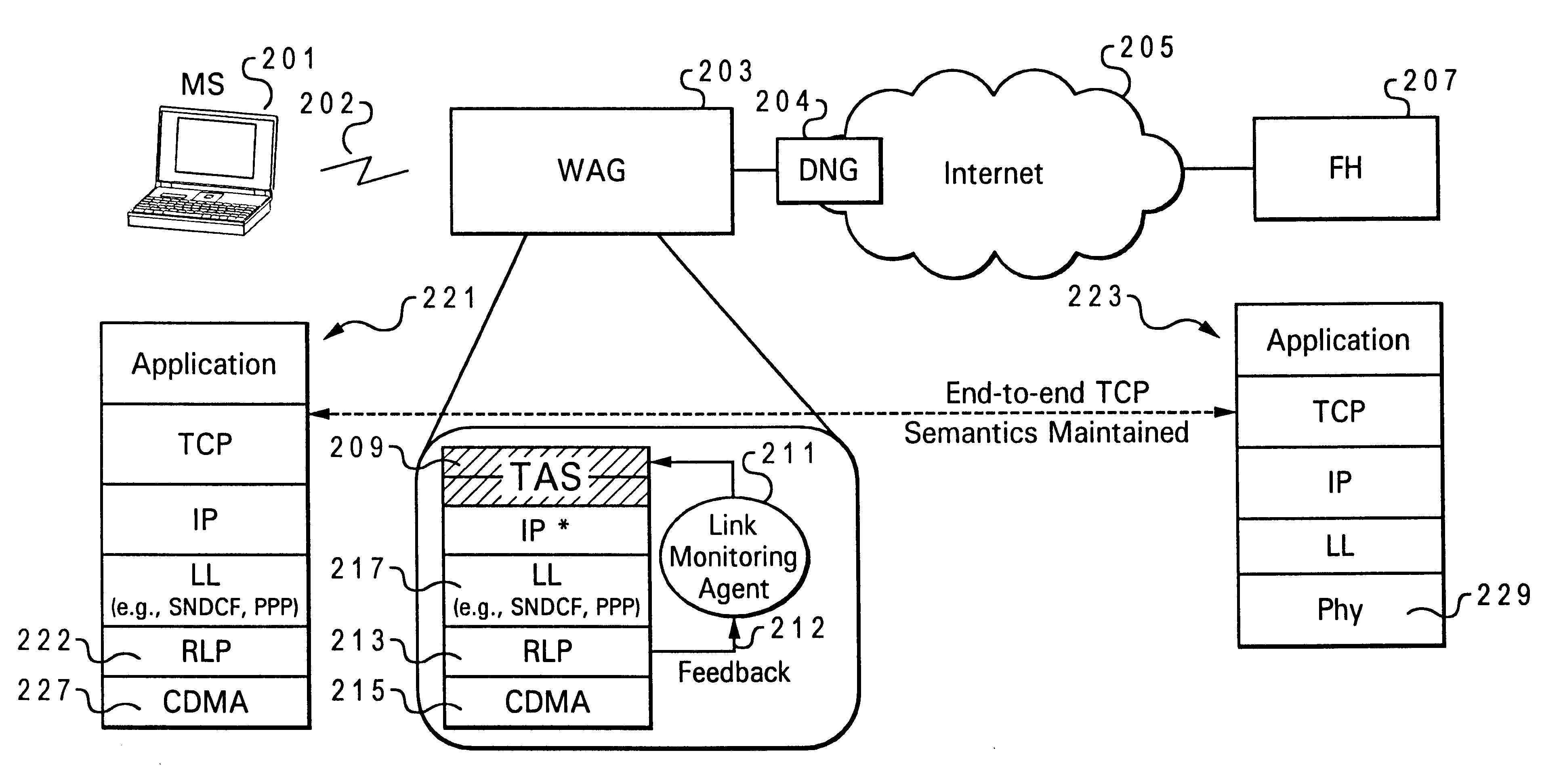
TCP-aware agent sublayer (TAS) for robust TCP over wireless
InactiveUS6208620B1Improve performanceMinimize impactError prevention/detection by using return channelTransmission systemsCongestion windowTransport control protocol
Disclosed is a system for minimizing the effects of faults over an air link of a wireless transmission channel utilizing Transport Control Protocol (TCP). The system includes a TCP-Aware Agent Sublayer (TAS) in a protocol stack, which has a mechanism for caching both TCP packets during forward transmission and acknowledgment (ACK) return packets. The caching mechanism is located near a wireless link of the wireless transmission channel. The system also includes a link monitoring agent coupled to the TAS. The link monitoring agent monitors the condition of the wireless transmission channel for an occurrence of a predefined fault. Once a predefined fault is detected, a system response is implemented based on the type of fault encountered. When the fault is an air link packet loss, an associated packet is immediately retransmitted from the cache, and when the fault is a temporary disconnect, a congestion window of the TCP source is closed.
Owner:NORTEL NETWORKS LTD
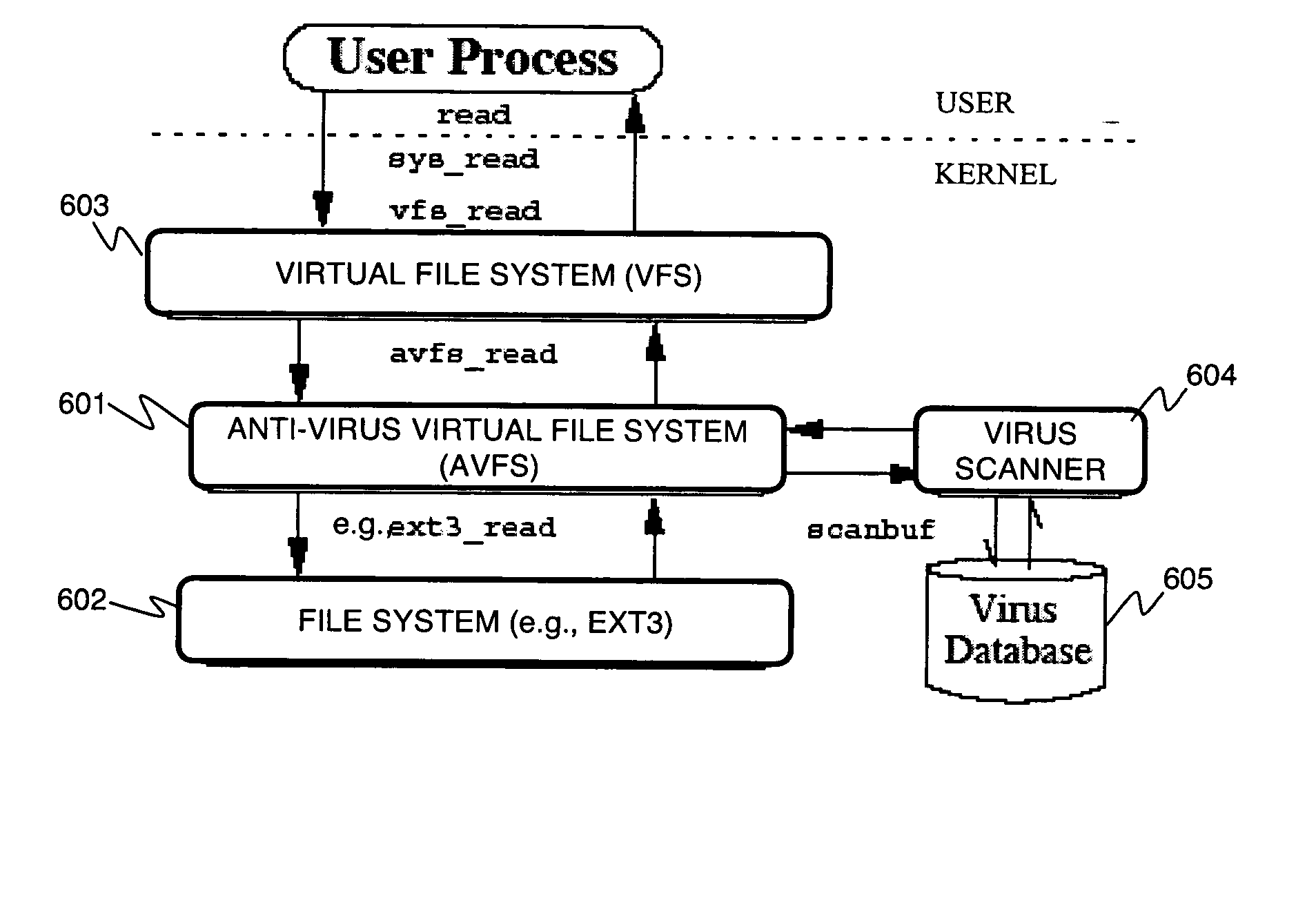
Stackable file systems and methods thereof
InactiveUS20050273858A1Memory loss protectionError detection/correctionOperational systemFile system
An operating system kernel, including a protocol stack, includes a network layer for receiving a message from a data network, a stackable file system layer coupled to the network layer for inspecting the message, wherein the stackable file system layer is coupled to a storage device, the stackable file system determining and storing file system level information determined from the message, and a wrapped file system comprising a file targeted by the message coupled to the stackable file system layer for receiving the message inspected by the stackable file system.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK +1
Service notification on a low bluetooth layer
InactiveUS7151764B1Fast contentFast processingAssess restrictionNetwork topologiesPointing deviceProtocol Application
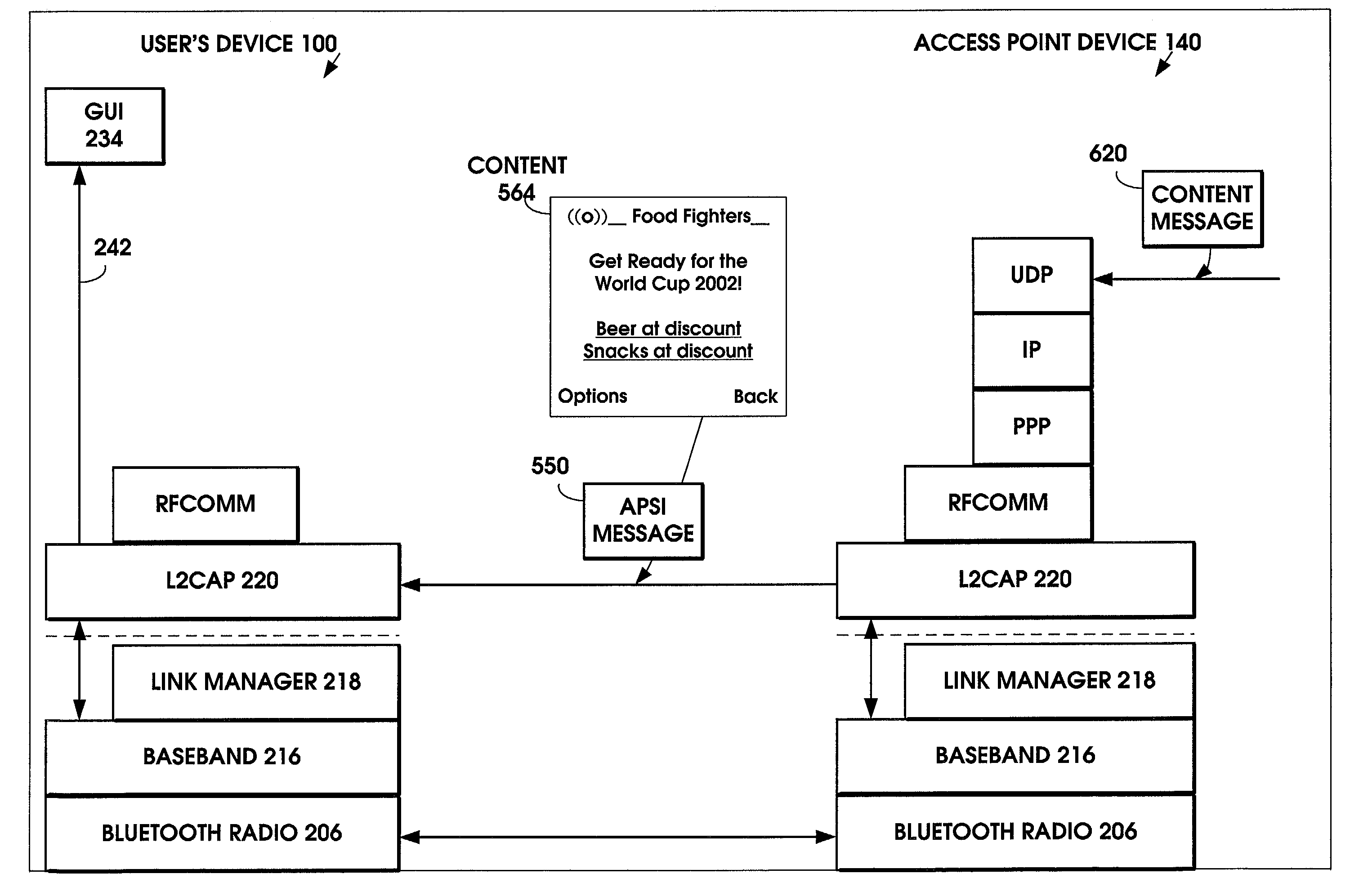
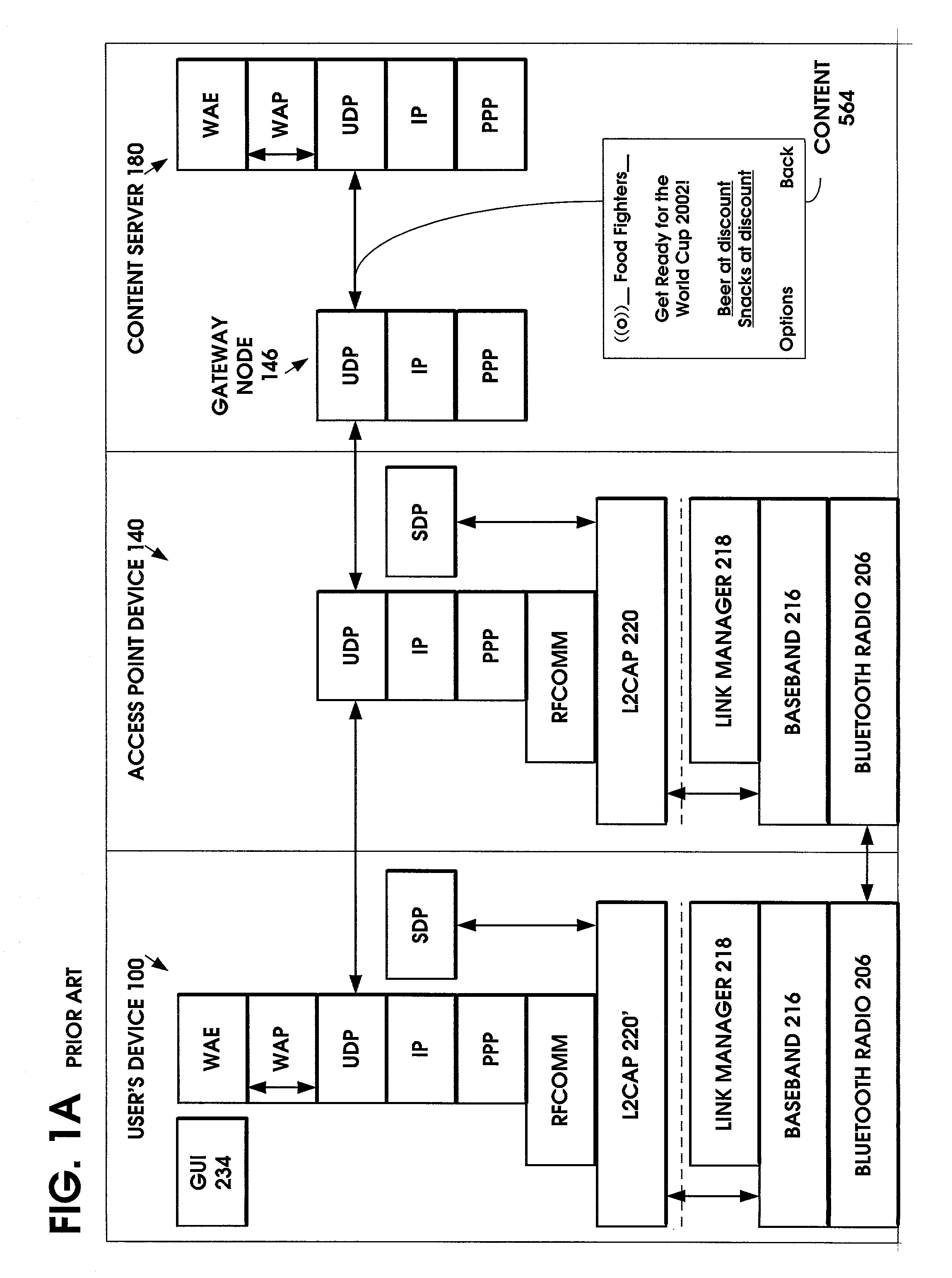
A method is provided to minimize the protocol stacks needed for a short range wireless access point to rapidly communicate a message to a short range wireless mobile device and display it to the user. The short range wireless access point device stores an Access Point Service Indicator (APSI) message characterizing the service platform offerings. The APSI message has a unique message ID in its header. The user device's transport protocol layer is modified to detect the unique message ID and load it into an APSI message buffer. The transport protocol layer passes the APSI message directly to the application layer, bypassing the middleware protocol layers. The method can be applied to communications between various types of wireless devices to enable rapid communication, such as between two mobile devices, between fixed and mobile devices, between short range devices or between long range devices.
Owner:NOKIA CORP
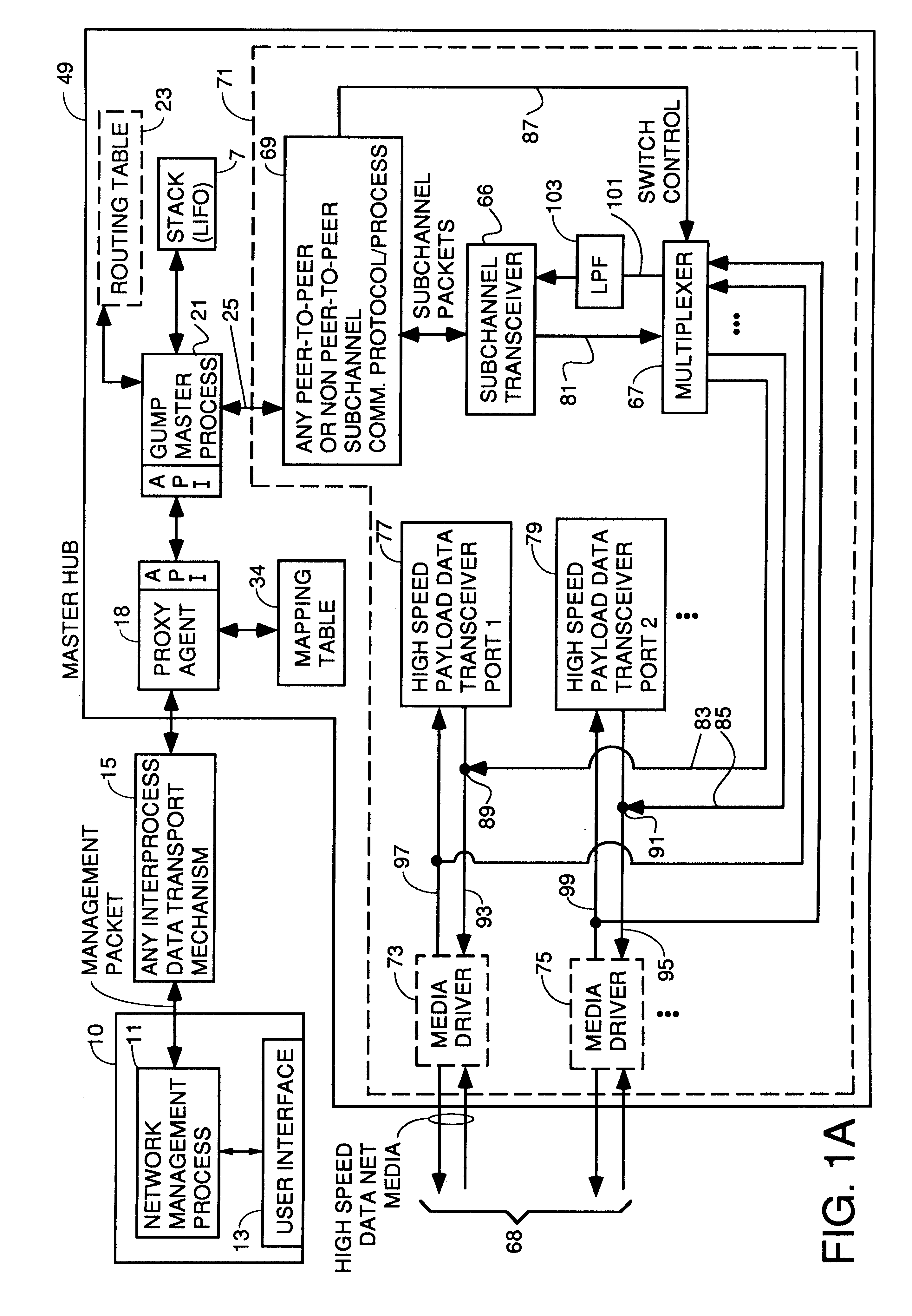
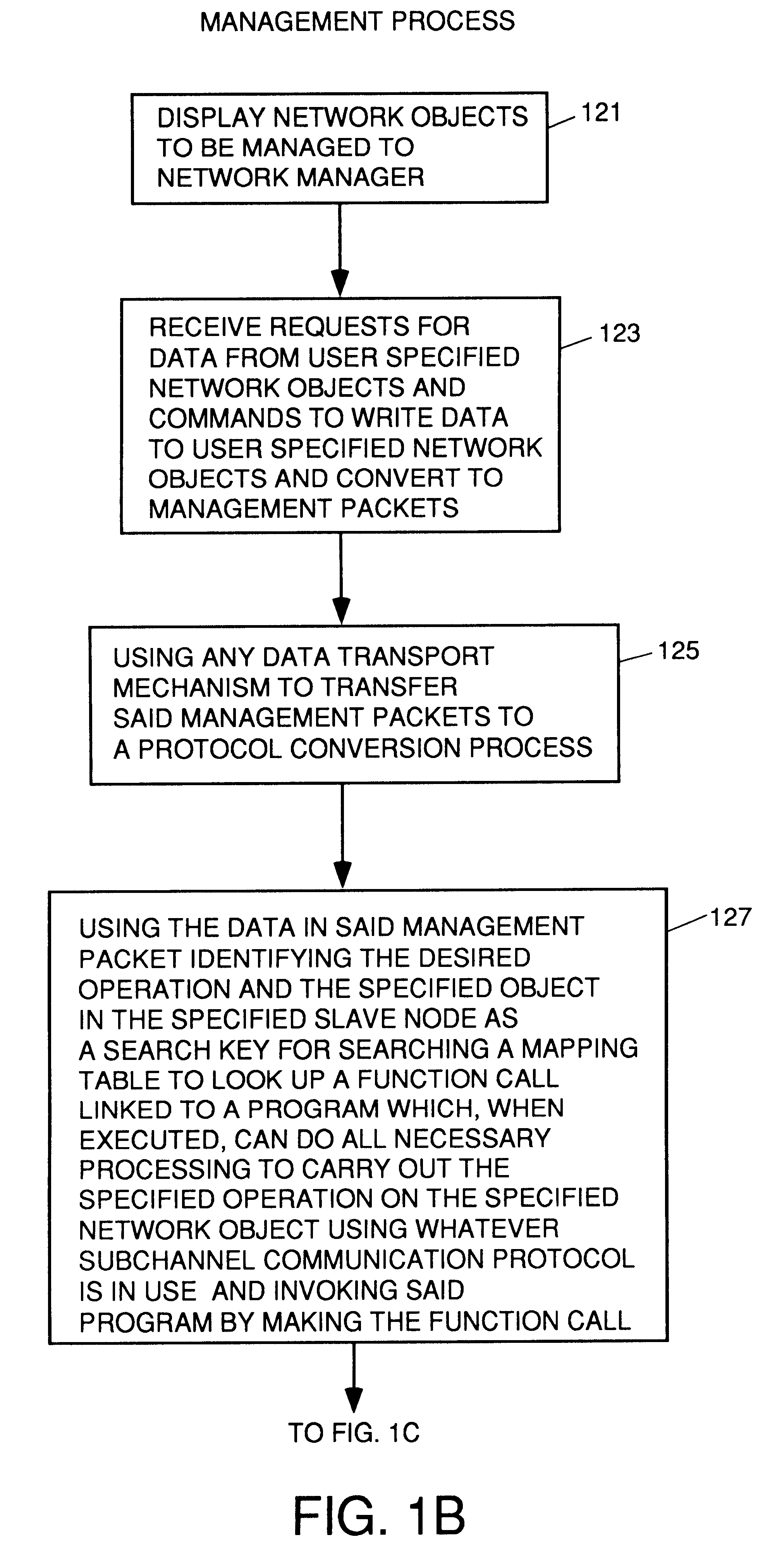
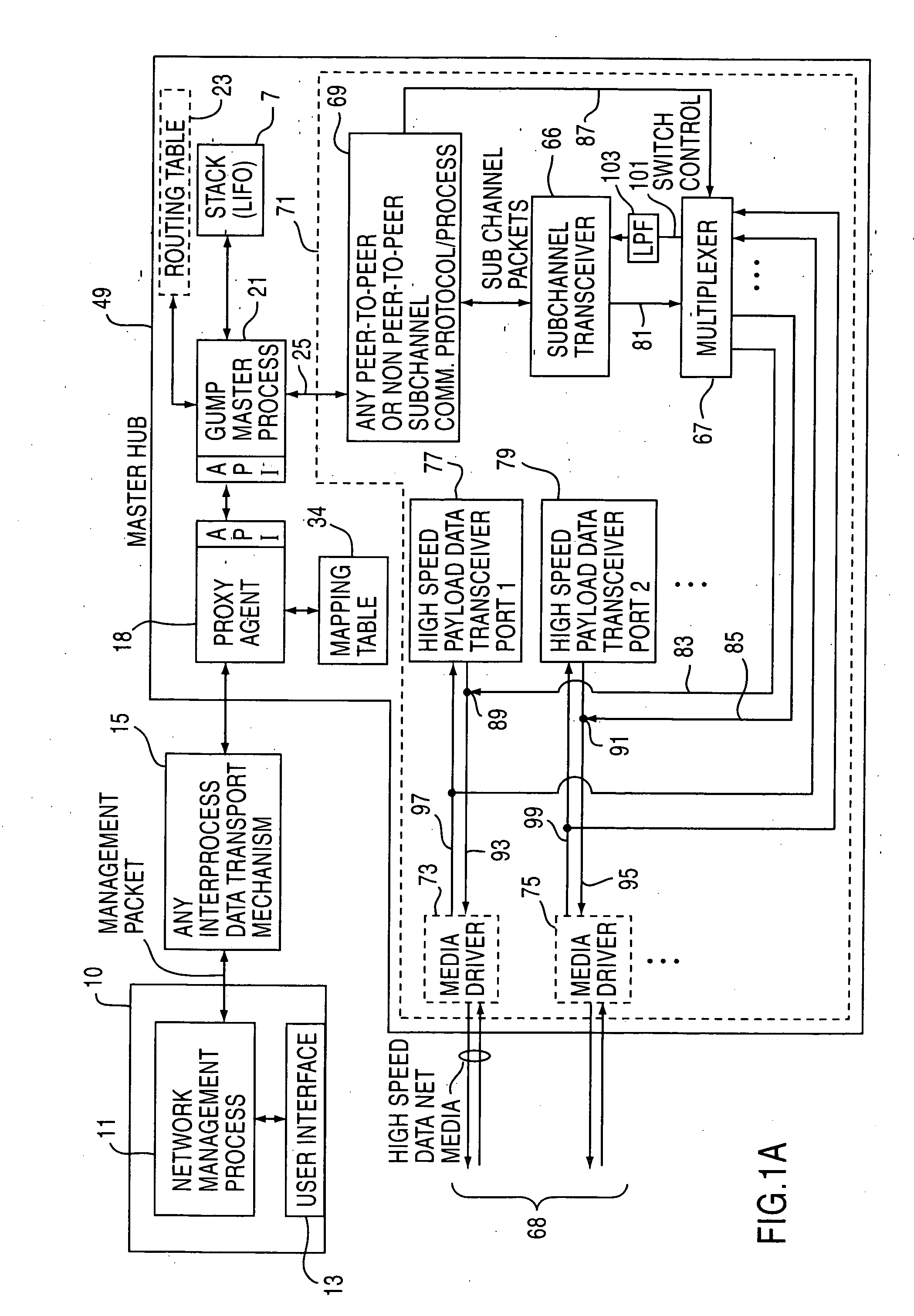
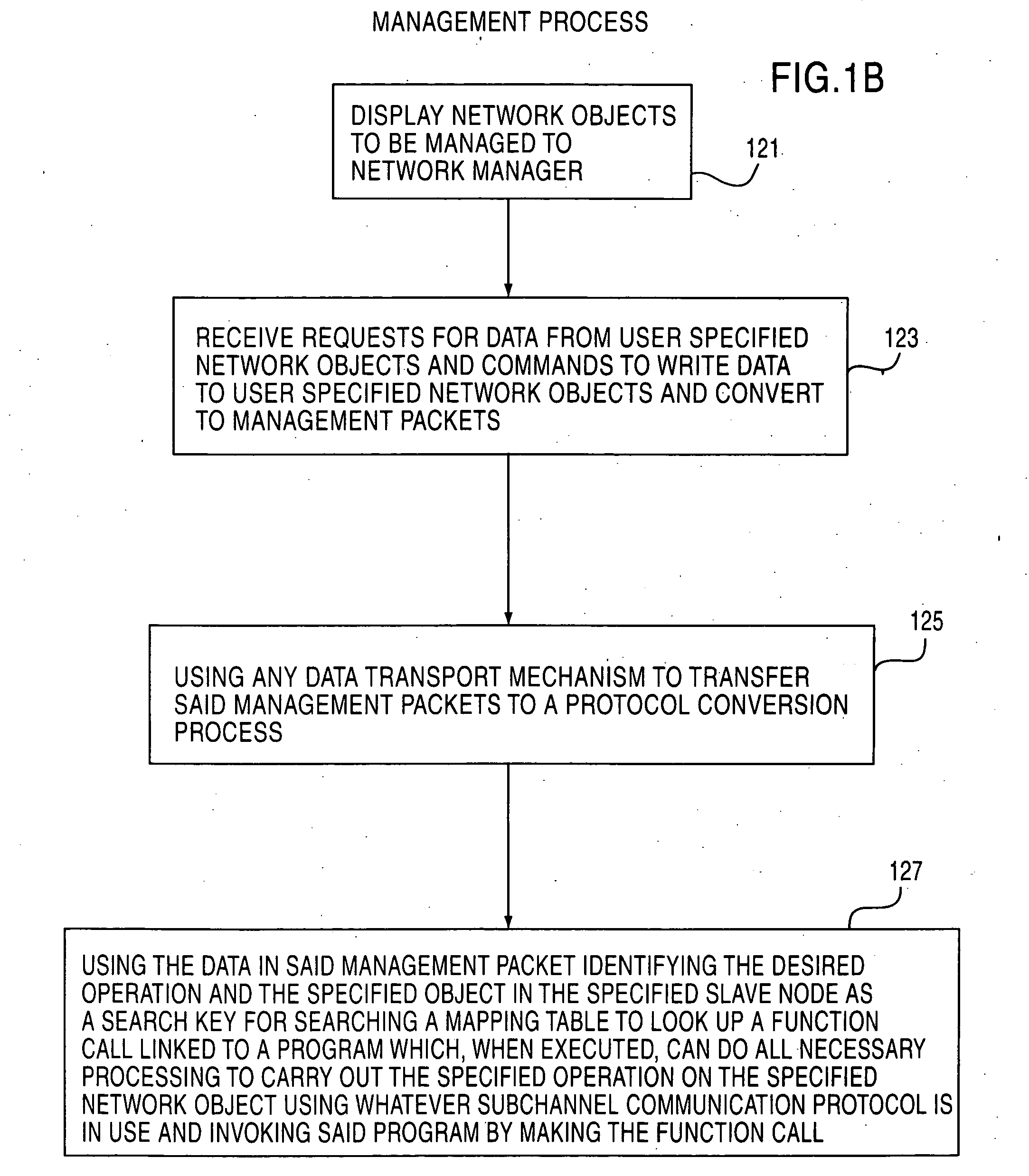
Apparatus and method for unilateral topology discovery in network management
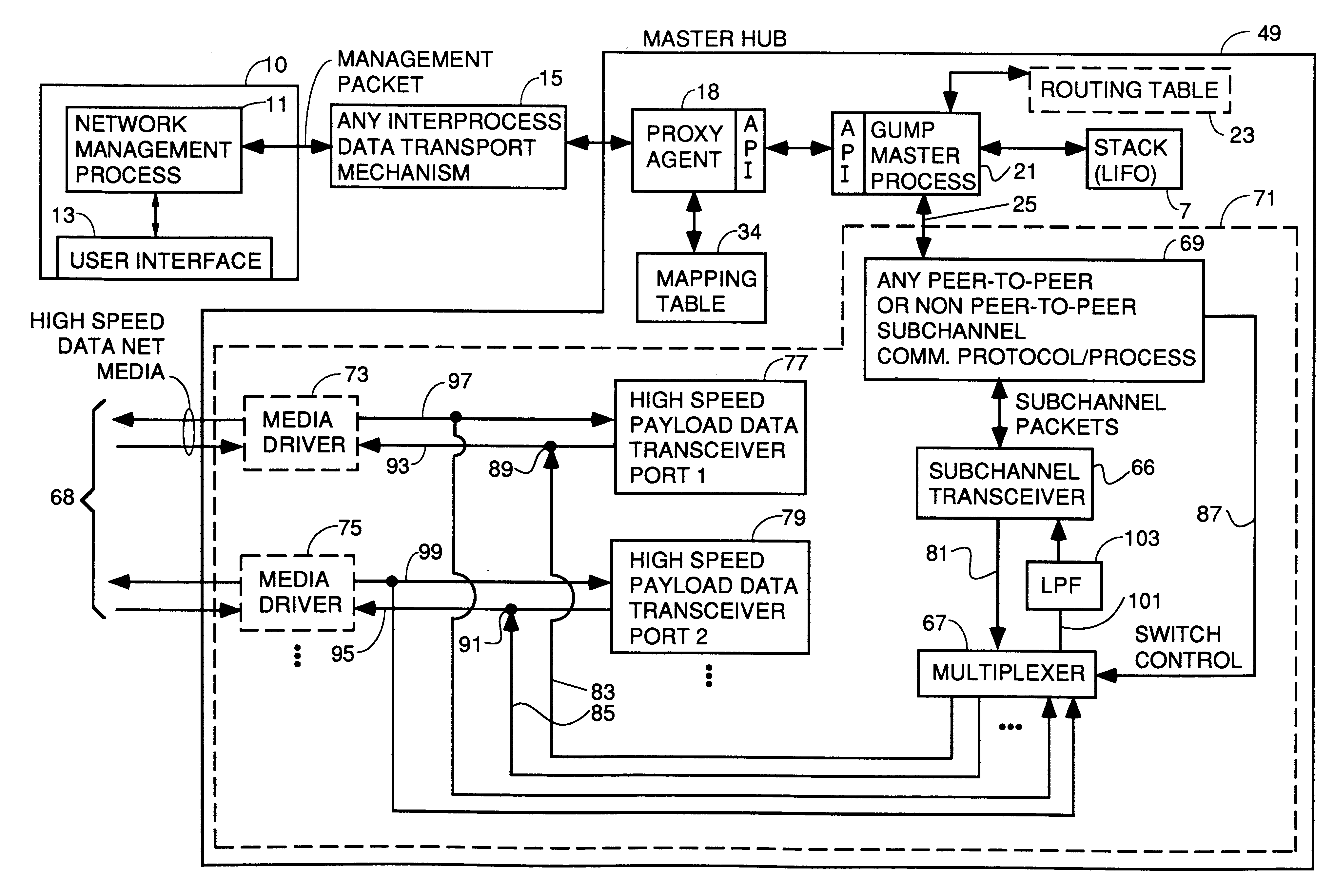
A system for reducing the cost of network managment by using a proxy agent and subchannel communications so fewer SNMP licenses and fewer protocol stacks are needed. Subchannel communication is achieved in a plurality of different embodiments. Embodiments having single subchannel transceivers, multiple transceivers, single multiplexer and multiple multiplexers are disclosed. An NMS process using routing table CRC to automatically detect when the NMS topology information is incorrect and automated topology discovery is disclosed. A process for automated discovery of redundant cables during automated topology discovery is disclosed.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
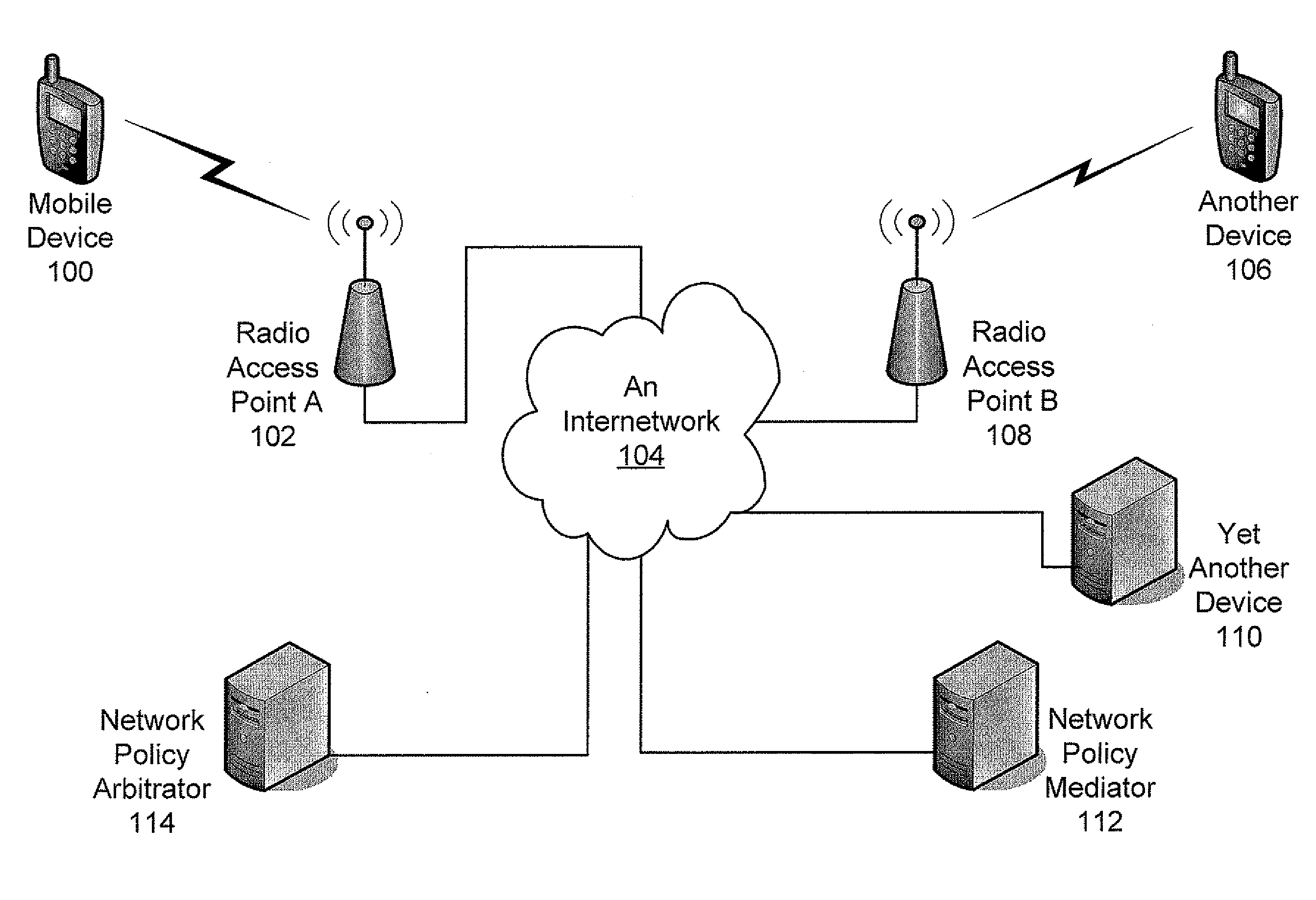
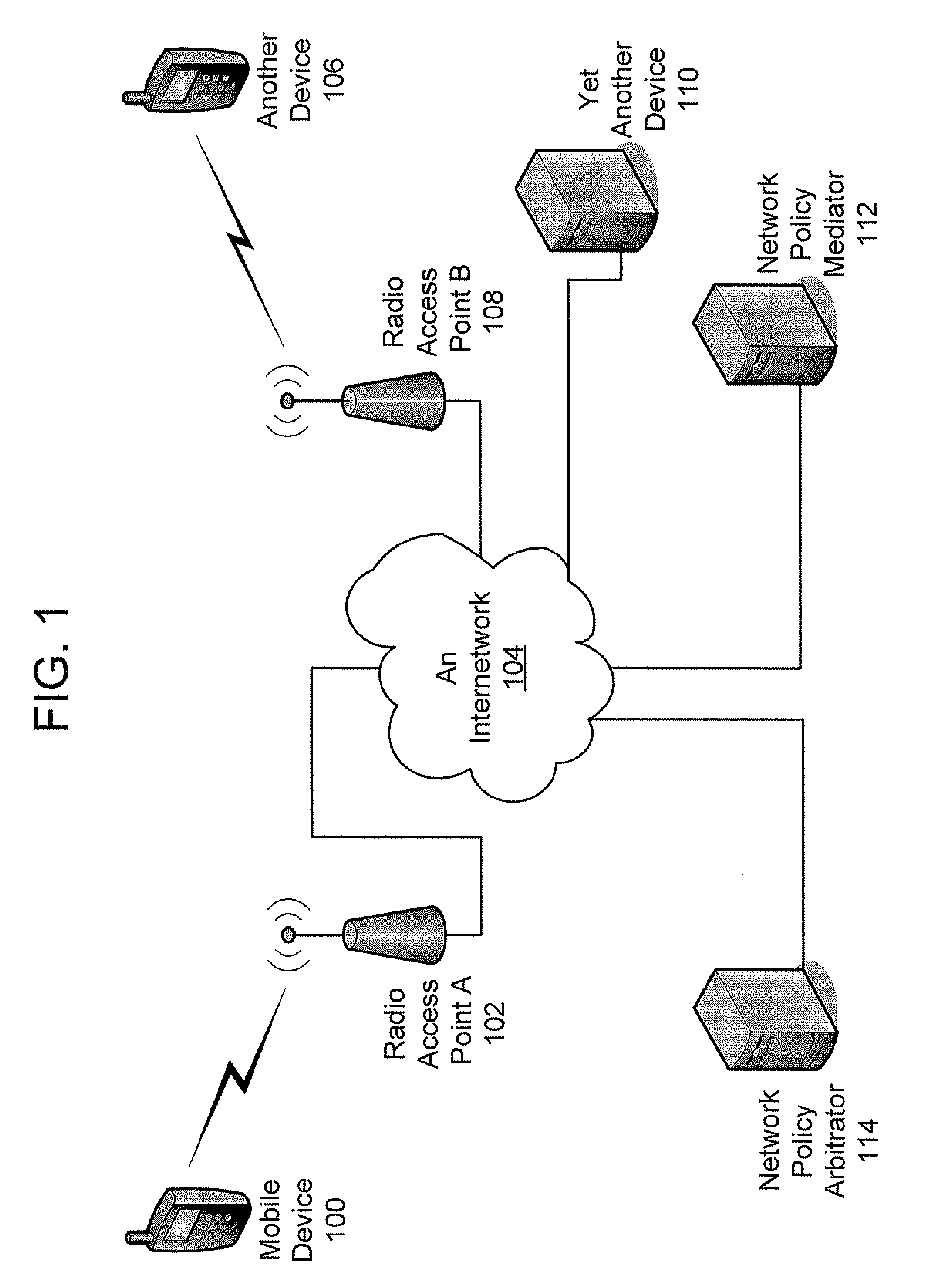
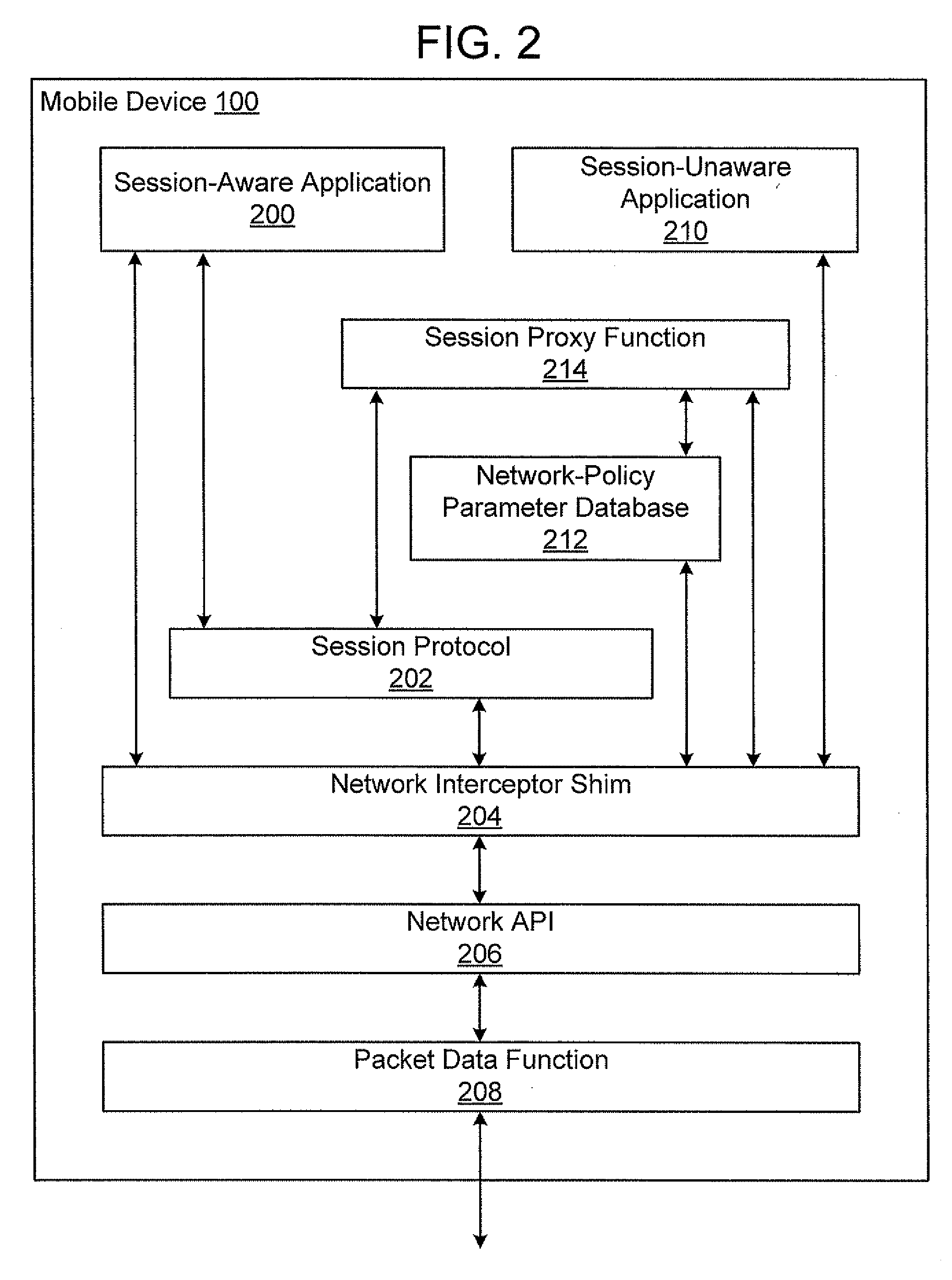
Establishing Network Policy For Session-Unaware Mobile-Device Applications
ActiveUS20080162704A1Network traffic/resource managementAssess restrictionNetworking protocolApplication software
The present invention provides the benefits of negotiated network resources to session-unaware applications. When a session-unaware application runs on a mobile device, the device, knowing that the application is session-unaware, negotiates appropriate network-policy parameters for the application. The application remains unaware, but it receives the benefits of the network-policy parameter negotiation. The network-policy parameter negotiation is carried on between the mobile device and a “network policy mediator” in the network. Together, they reserve the appropriate network resources and secure the appropriate guarantees. In some embodiments, a software “shim” runs in the network-protocol stack on the mobile device. By intercepting network-access attempts sent by the session-unaware application, the shim knows to begin the network-policy parameter negotiation. In some embodiments, the mobile device downloads information about session-unaware applications from the network. This information includes a list of which network-policy parameter guarantees would be most beneficial to each application.
Owner:U S CELLULAR
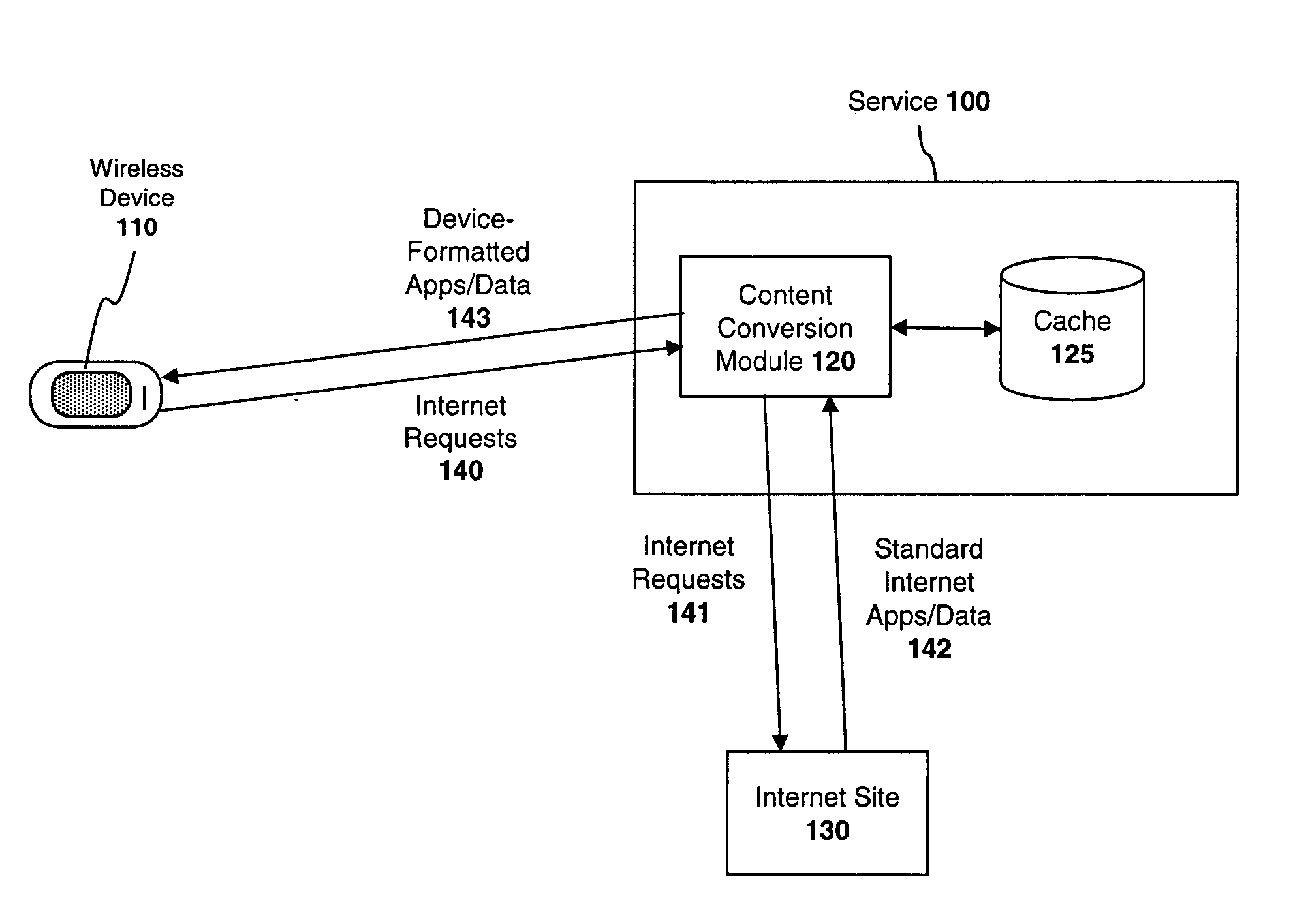
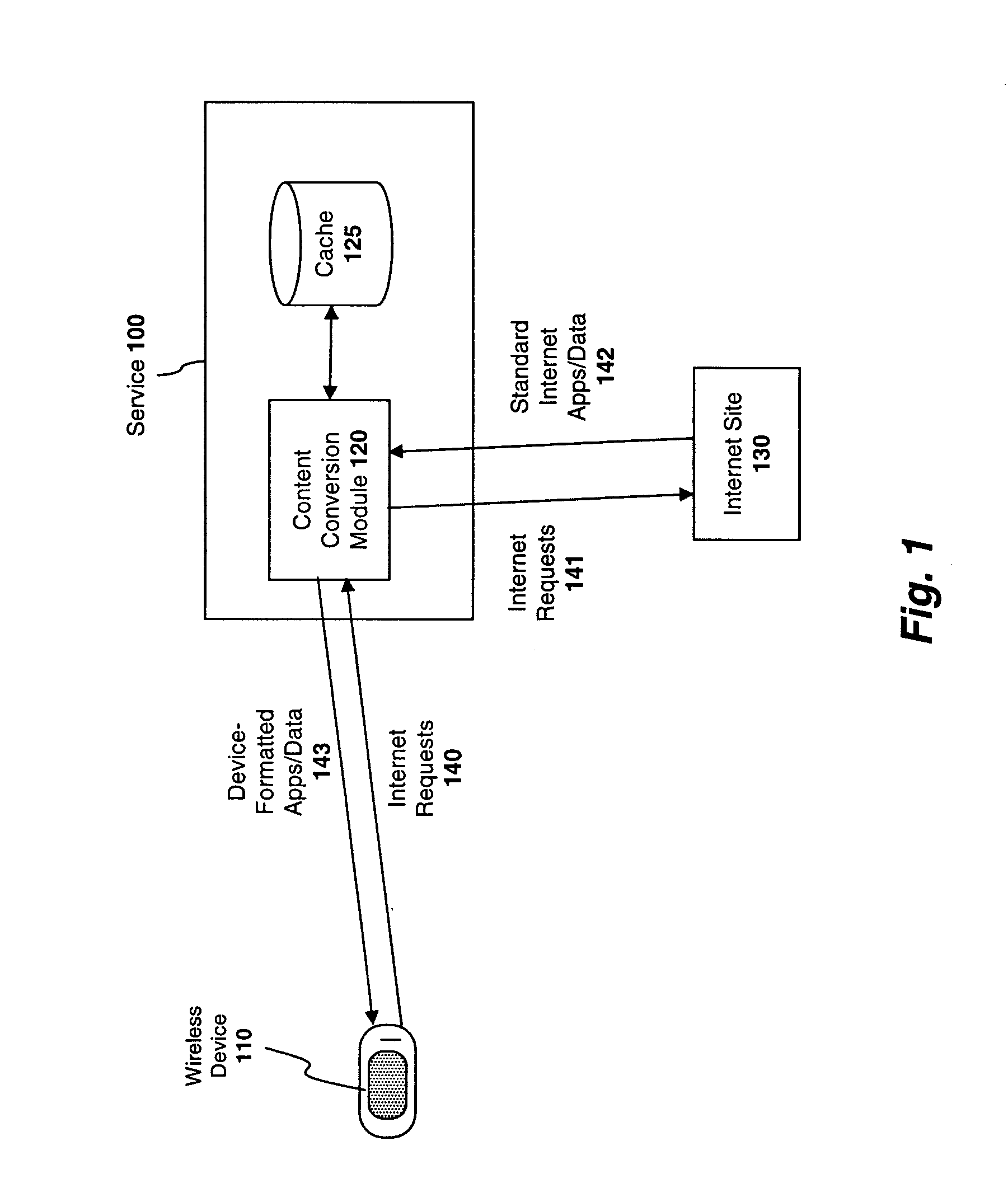
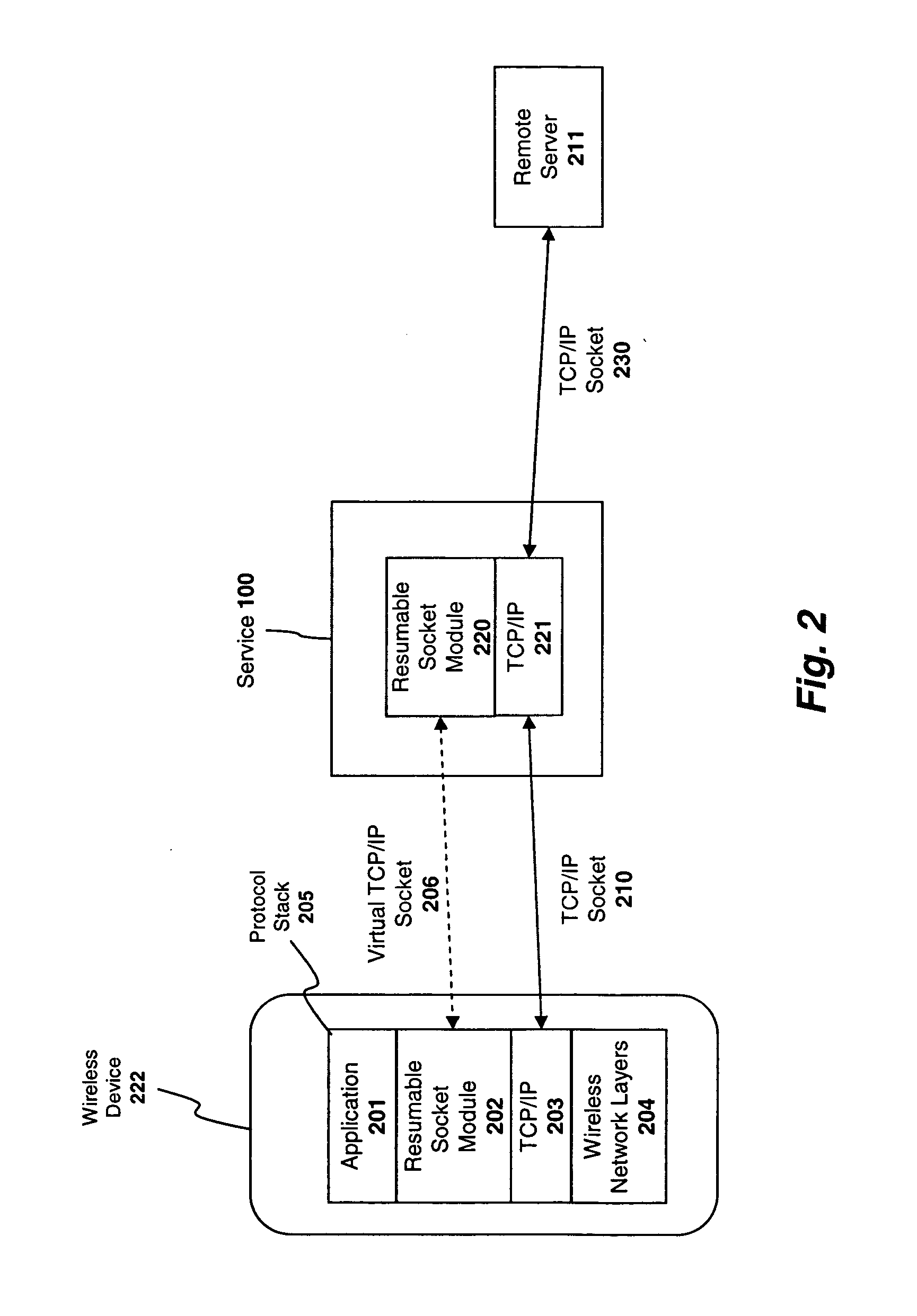
System and method for preserving socket connections over a wireless network
InactiveUS20090103515A1Time-division multiplexWireless commuication servicesNetworking protocolService provision
A system, apparatus, and method for maintaining a socket connection over a wireless network. For example, one embodiment of the invention is a wireless data processing device for emulating a socket connection comprising: a wireless radio for establishing a wireless communication channel with a wireless service provider over a wireless network; a network protocol stack including at least one layer configured to establish a socket connection with a remote server over the wireless network, the network protocol stack further including an application layer for executing applications capable of transmitting and receiving data over the socket connection; and a resumable socket module configured to emulate an open socket connection transparently to applications within the application layer, even when the wireless communication channel is temporarily lost, the resumable socket module counting a number of bytes transmitted or to be transmitted to the remote server and maintaining a buffer containing the bytes transmitted or to be transmitted.
Owner:MICROSOFT TECH LICENSING LLC
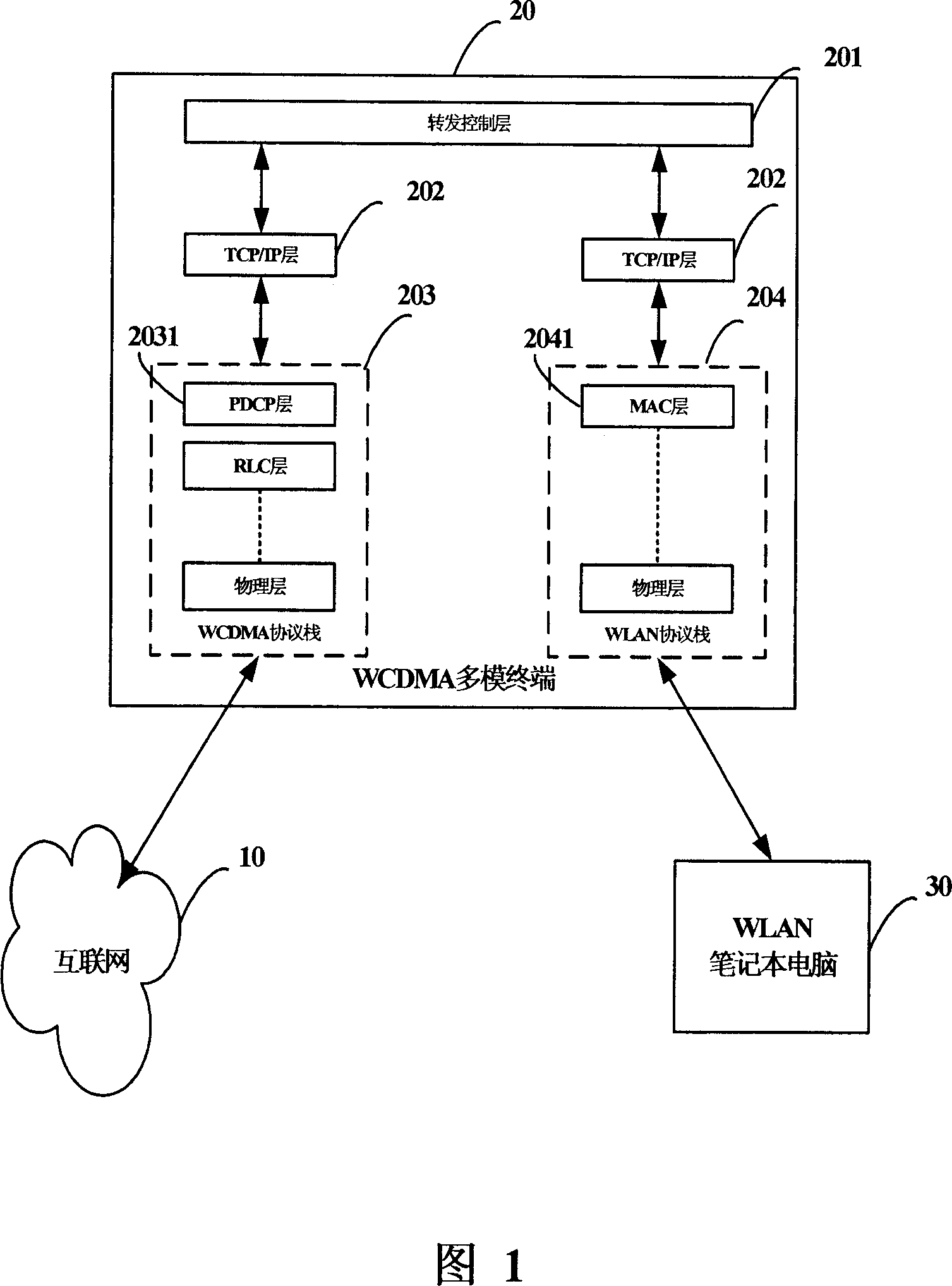
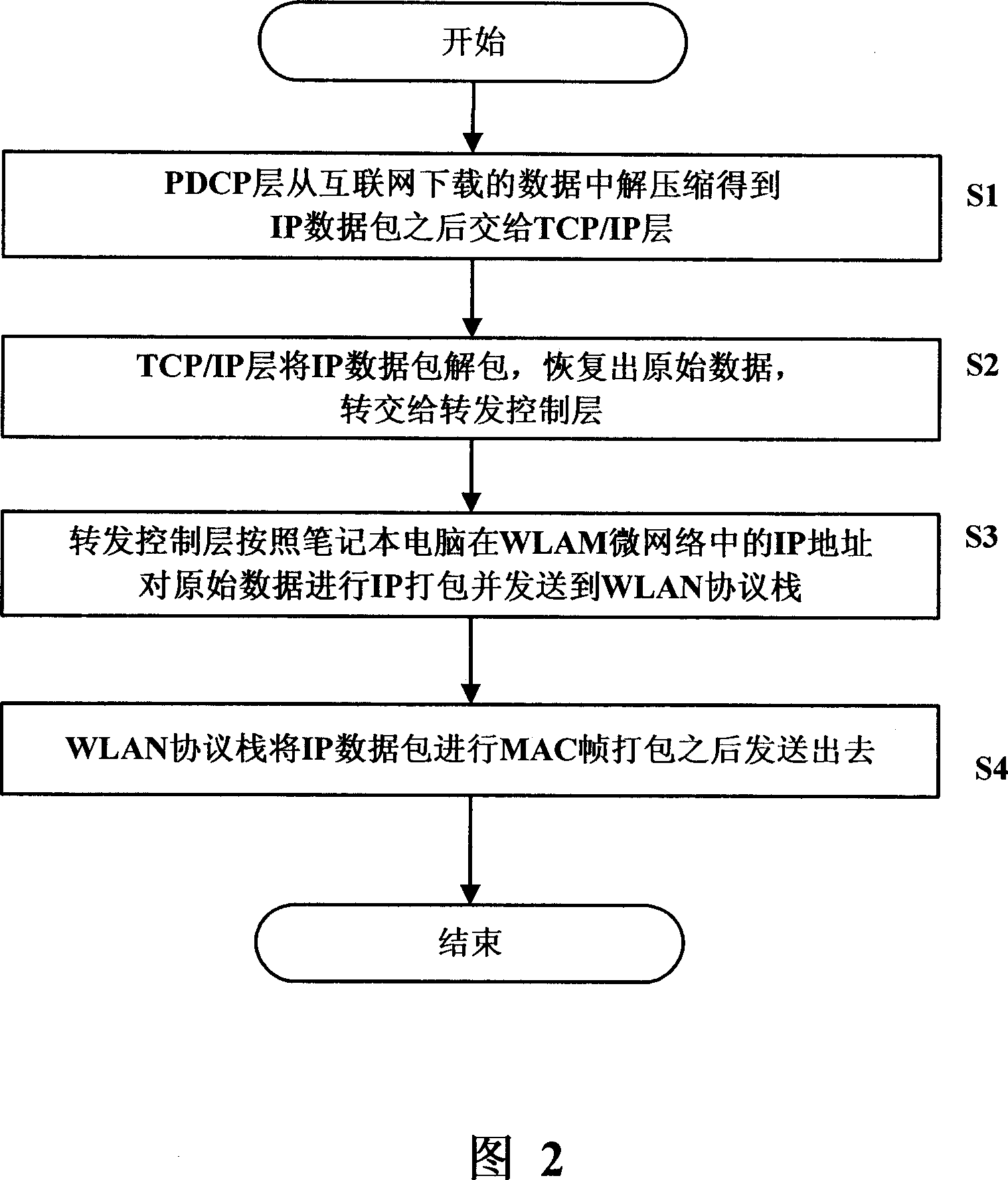
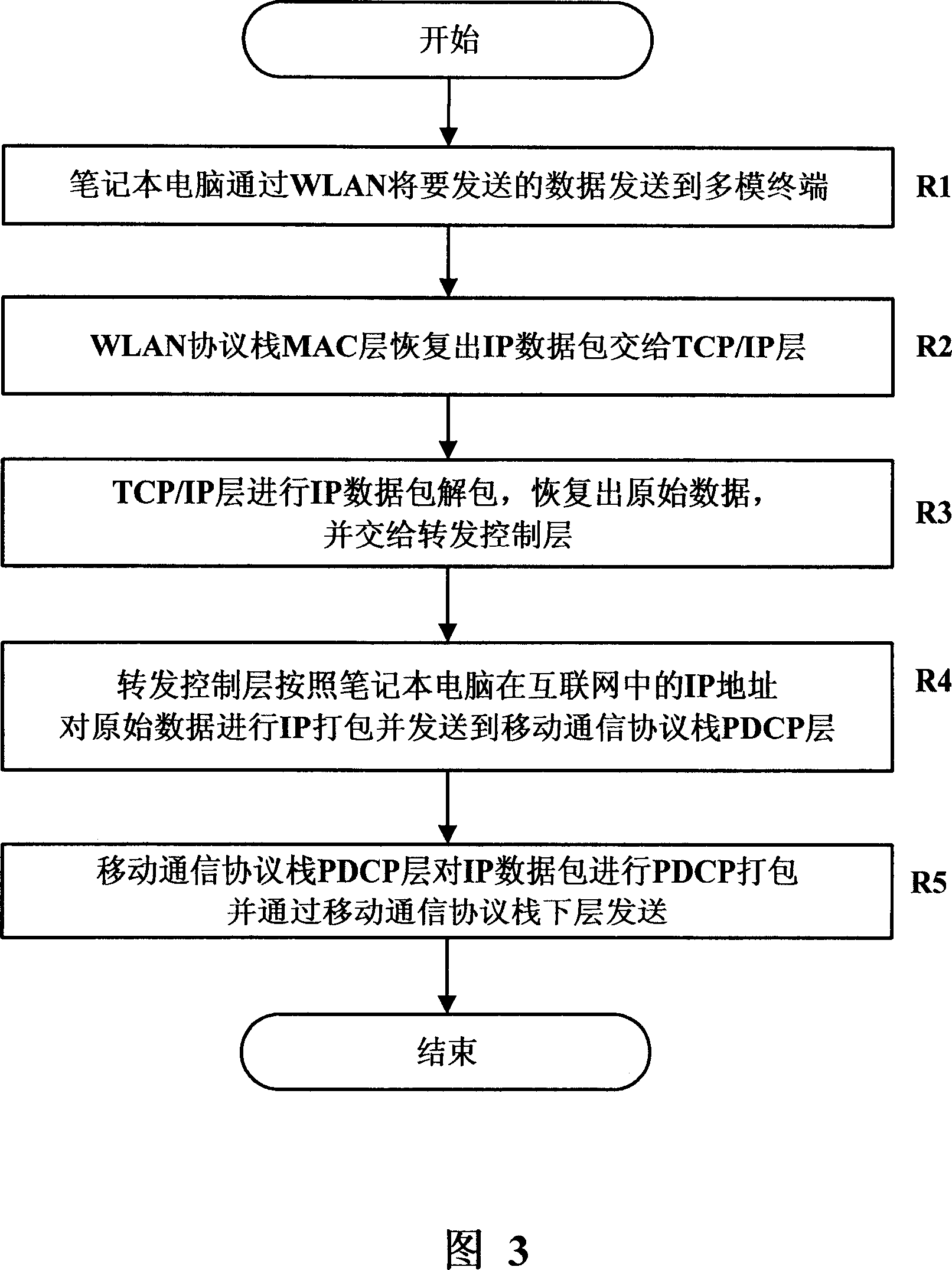
Multi-mode terminal and data forwarding method
The invention discloses a multimode terminal and a data transmitting method thereof. The multimode terminal of the invention is provided with at least one mobile communication protocol stack, one wireless local area network protocol stack, a shared buffer area and a transmitting controller, wherein, the mobile communication protocol stack is used for storing IP data packet received from the internet to the shared buffer area and then informing the transmitting control layer; the transmitting control layer is used for informing the wireless local area network protocol stack storage address of the IP data packet in the shared buffer area; the wireless local area network protocol stack is used for taking the IP data packet out of the share buffer area and sending the IP data packet to a radio installation, and anyone of the mobile communication protocol stack, the transmitting control layer and the wireless local area network protocol stack modifies target IP address of the IP data packet to be the IP address of the radio installation in the wireless local area network connection. The multimode terminal and data transmitting method of the invention can effectively improve data transmission utilization.
Owner:LENOVO (BEIJING) CO LTD
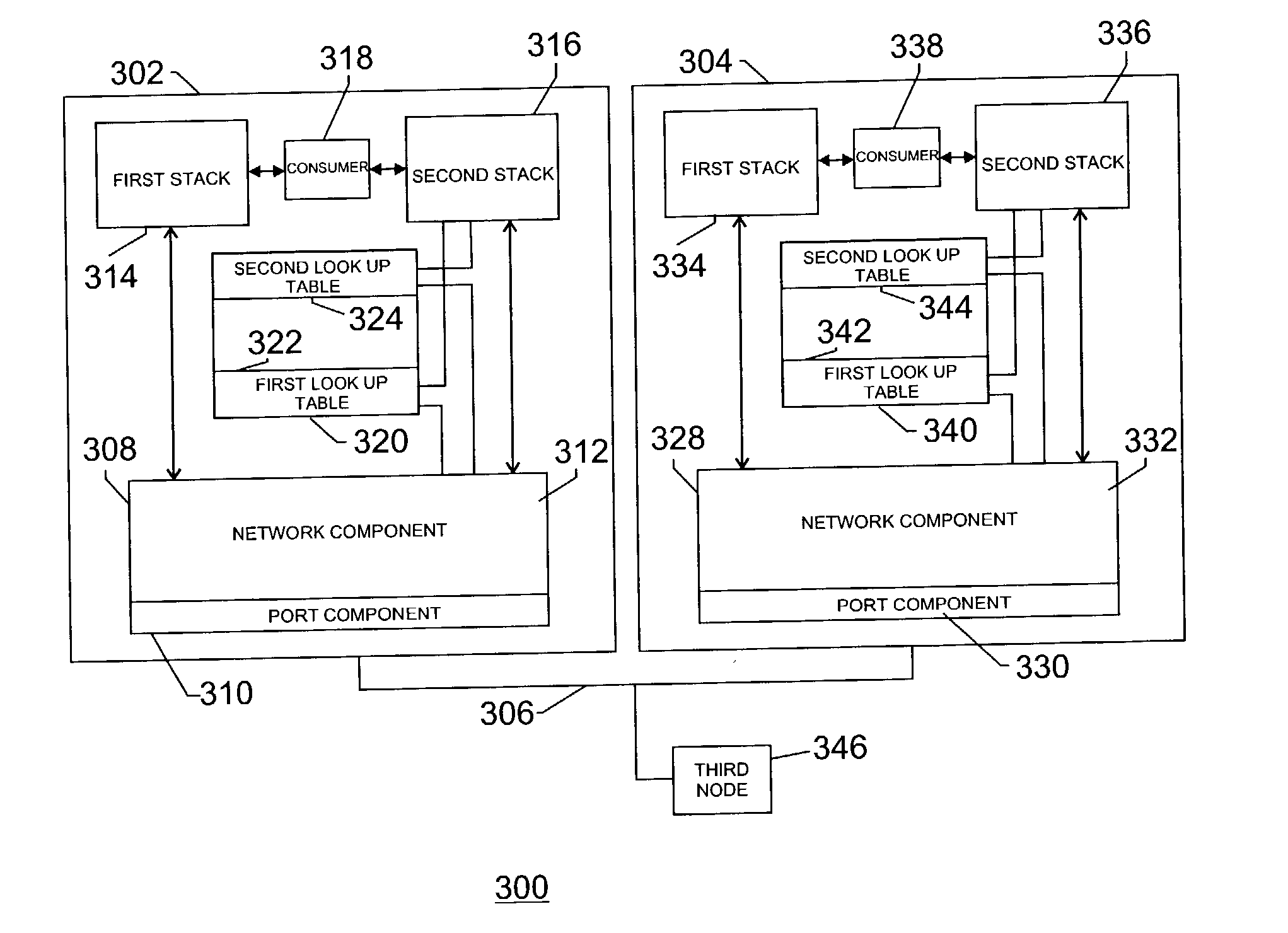
Aggregation over multiple processing nodes of network resources each providing offloaded connections between applications over a network
ActiveUS20060126619A1Time-division multiplexData switching by path configurationPrivate IPIp address
A computer system aggregates a plurality of network resources of a computer system. The computer system has a plurality of processing nodes. Each of the processing nodes includes one or more of the plurality of network resources. The one or more resources of each processing node makes up a bypass protocol stack operable to provide offloaded connections over a network to instances of one or more applications running on the system. Each of the applications is uniquely associated with a first port number. The system is identified on the network by a global IP address and each of the plurality of nodes is identified by a unique local IP address. Each of the plurality of resources is uniquely identified by an assigned private IP address. At each of the processing nodes, a listening socket is created for each instance of the plurality of applications running on the node. The listening socket is created by associating it with a first endpoint tuple that includes the public IP address uniquely identifying the node and the first port number associated with the application for which the listening socket is created. The first endpoint tuple associated with each listening socket created is translated to a set of bypass endpoint tuples, each of the set of bypass tuples including a different one of the assigned private IP addresses identifying the one or more network resources of the node. Each listening socket is associated with the set of bypass tuples. A global address translation map is maintained for each set of bypass tuples associated with each of the listening sockets created for an instance of each of the applications running on the plurality of processing nodes.
Owner:VALTRUS INNOVATIONS LTD
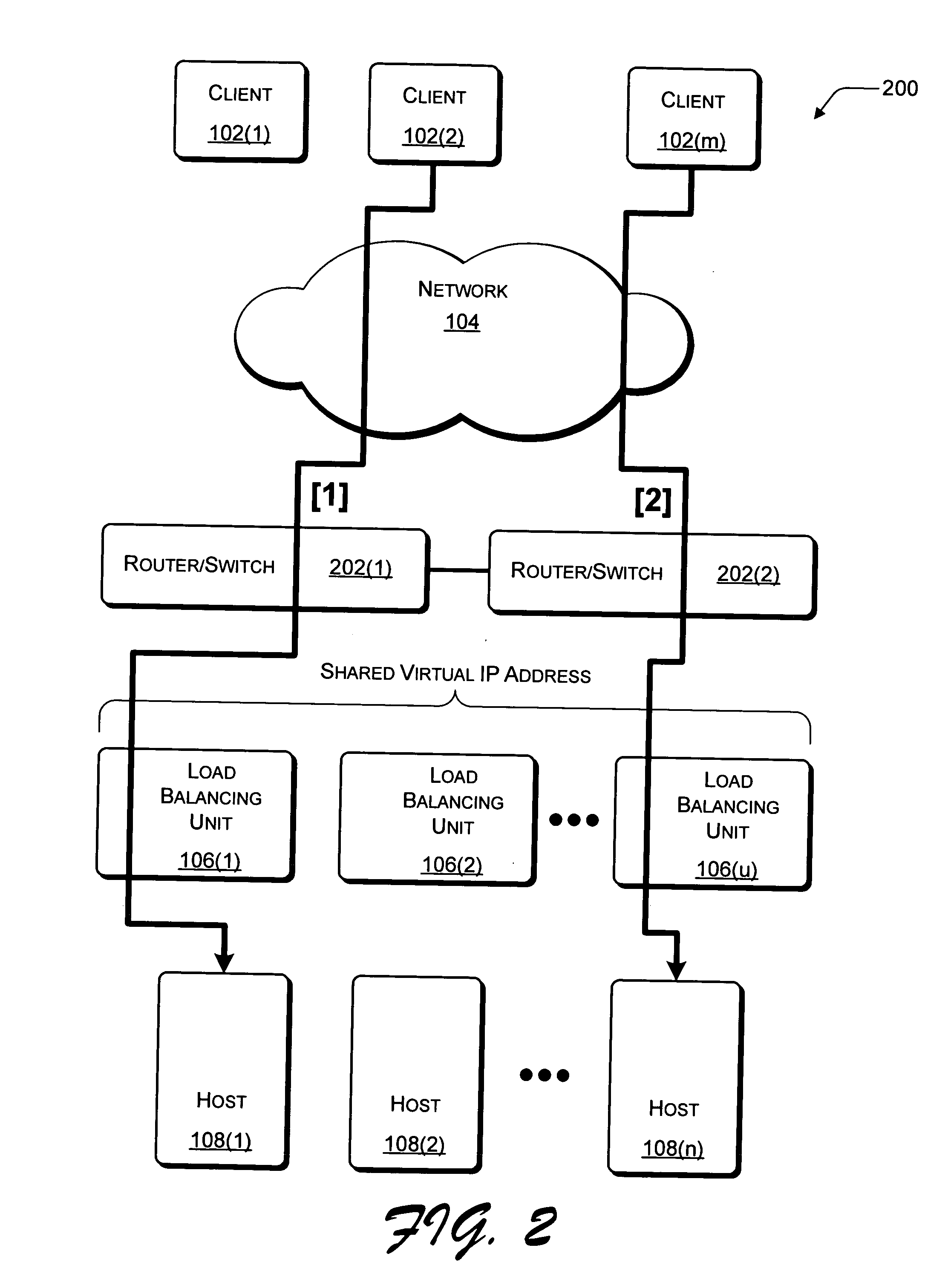
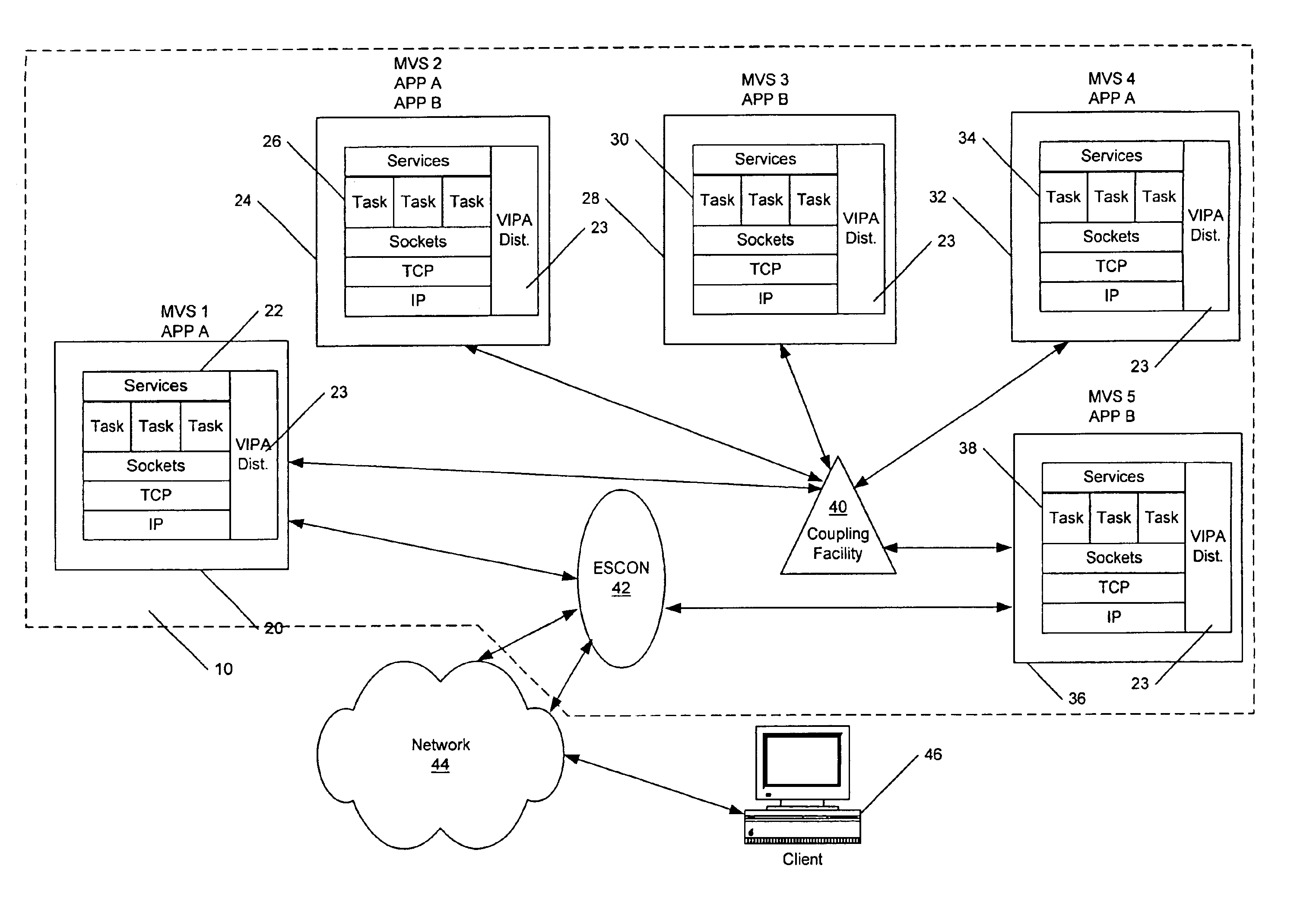
System having a single IP address associated with communication protocol stacks in a cluster of processing systems
Methods, systems and computer program products provide communications with a plurality of application instances using a plurality of communication protocol stacks and a single Internet Protocol (IP) address. A stack is established as a routing stack associated with the single IP address. Other stacks which are associated with the single IP address are defined as candidate target stacks and an identification of candidate target stacks and the routing stack is distributed to the stacks. The routing stack is notified when an application associated with a candidate target stack listens to a port of the IP address to establish a current actual target stack. A request to establish a connection to the IP address and the port of the IP address is received and a routing table entry corresponding to the current actual target stack is created to provide a routing path from the routing stack to the current actual target stack. Communications to the port of the IP address received by the routing stack are routed based on the routing table.
Owner:INT BUSINESS MASCH CORP
Media Access Control Data Plane System and Method for Wireless Communication Networks
ActiveUS20080285501A1Network traffic/resource managementFrequency-division multiplex detailsMedia access controlMobile station
A method and system for using a communication network having a relay node to provide wireless communication with a mobile station. A protocol stack is implemented in the relay node in which the protocol stack includes a media access control layer defining a media access control protocol. The media access control protocol defines a set of headers providing media access control layer data plane functions in the relay node.
Owner:APPLE INC
Integrated intrusion detection services
ActiveUS7076803B2Improve securityEasy to detectMemory loss protectionError detection/correctionTraffic capacityPlaintext
Improvements in intrusion detection are disclosed by providing integrated intrusion detection services. Preferably, these services are integrated into a system or server that is the potential target of attack. Stack-based security processing is leveraged for access to cleartext data within the layers of the protocol stack. Layer-specific attacks may therefore be processed efficiently. Evaluation of incoming traffic for an intrusion is preferably performed only after an error condition of some type has been detected. This approach reduces the overhead of intrusion detection by reducing the number of packets to be inspected, and at the same time allows more efficient packet inspection through use of context-specific information that may be used to direct the inspection to particular candidate attacks. Generic attack class capability is also disclosed. Intrusion detection policy information may be used to direct the actions to be taken upon detecting an attack.
Owner:TREND MICRO INC
Aggregation over multiple processing nodes of network resources each providing offloaded connections between applications over a network
A computer system aggregates a plurality of network resources of a computer system. The computer system has a plurality of processing nodes. Each of the processing nodes includes one or more of the plurality of network resources. The one or more resources of each processing node makes up a bypass protocol stack operable to provide offloaded connections over a network to instances of one or more applications running on the system. Each of the applications is uniquely associated with a first port number. The system is identified on the network by a global IP address and each of the plurality of nodes is identified by a unique local IP address. Each of the plurality of resources is uniquely identified by an assigned private IP address. At each of the processing nodes, a listening socket is created for each instance of the plurality of applications running on the node. The listening socket is created by associating it with a first endpoint tuple that includes the public IP address uniquely identifying the node and the first port number associated with the application for which the listening socket is created. The first endpoint tuple associated with each listening socket created is translated to a set of bypass endpoint tuples, each of the set of bypass tuples including a different one of the assigned private IP addresses identifying the one or more network resources of the node. Each listening socket is associated with the set of bypass tuples. A global address translation map is maintained for each set of bypass tuples associated with each of the listening sockets created for an instance of each of the applications running on the plurality of processing nodes.
Owner:VALTRUS INNOVATIONS LTD
Transmit-only and receive-only Bluetooth apparatus and method
Owner:CSR TECH INC
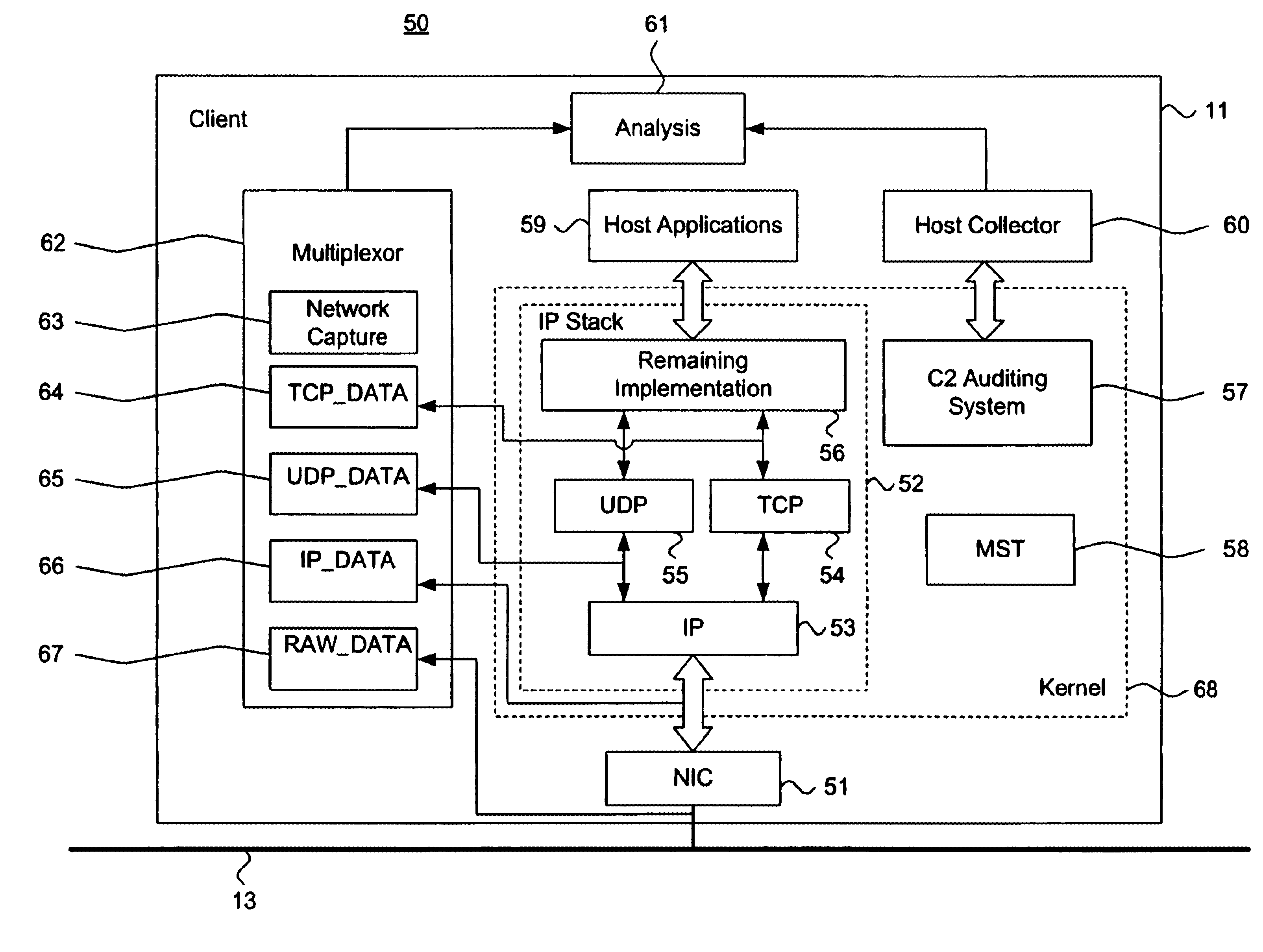
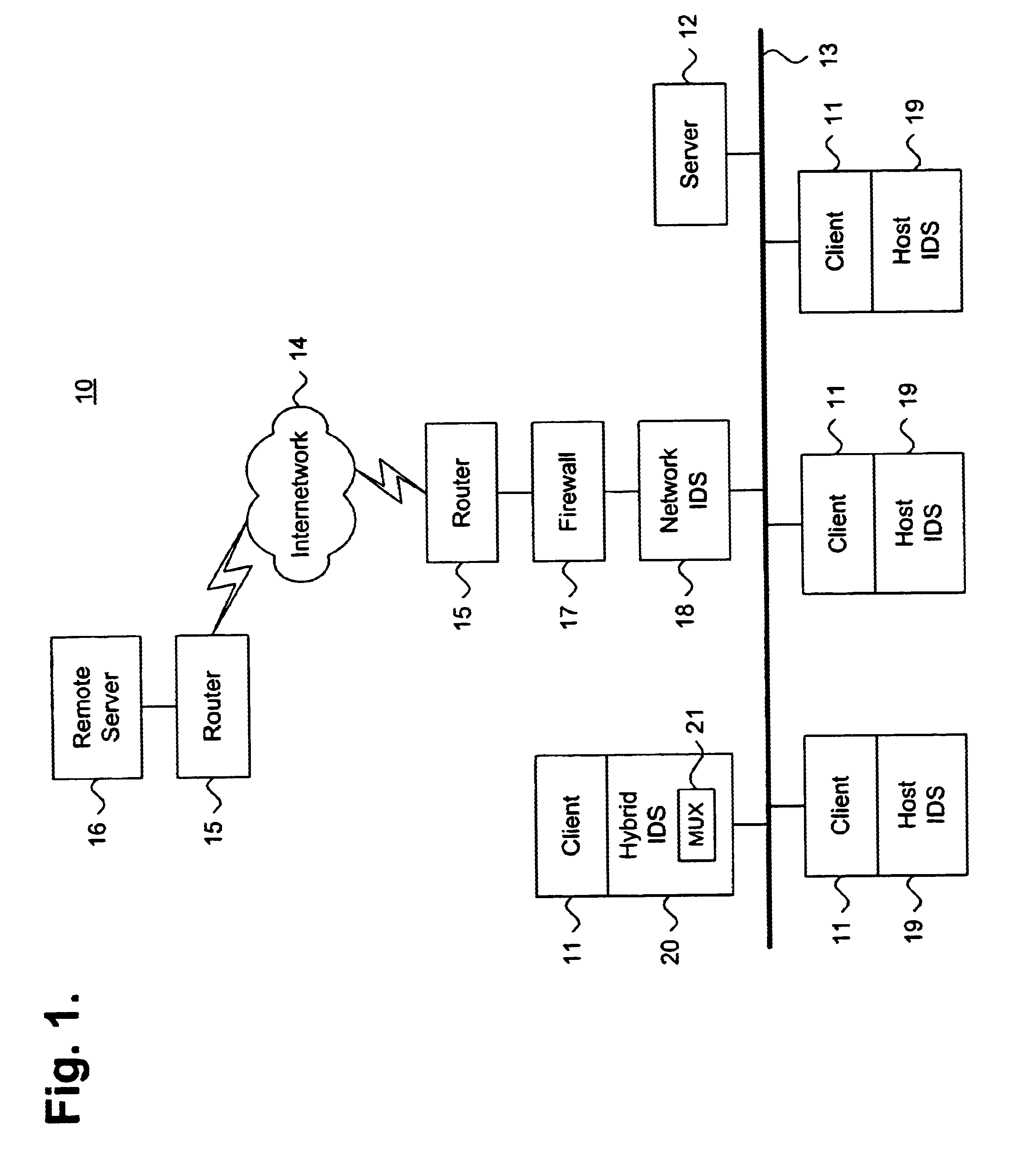
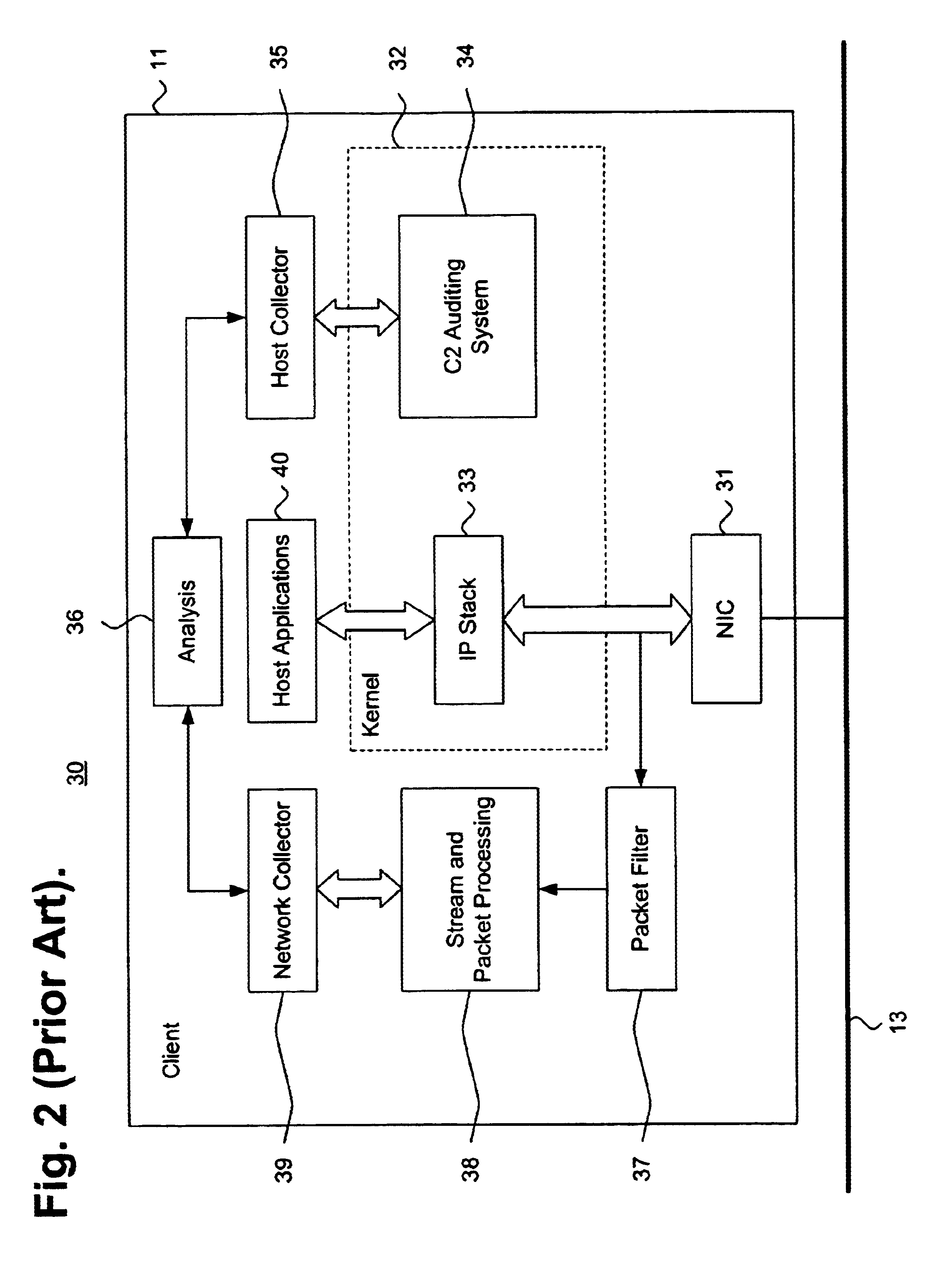
System and method for intrusion detection data collection using a network protocol stack multiplexor
InactiveUS6851061B1Memory loss protectionDigital computer detailsProtocol processingNetworking protocol
A system and method for detecting network intrusions using a protocol stack multiplexor is described. A network protocol stack includes a plurality of hierarchically structured protocol layers. Each such protocol layer includes a read queue and a write queue for staging transitory data packets and a set of procedures for processing the transitory data packets in accordance with the associated protocol. A protocol stack multiplexor is interfaced directly to at least one such protocol layer through a set of redirected pointers to the processing procedures of the interfaced protocol layer. A data packet collector references at least one of the read queue and the write queue for the associated protocol layer. A data packet exchanger communicates a memory reference to each transitory data packet from the referenced at least one of the read queue and the write queue for the associated protocol layer. An analysis module receives the communicated memory reference and performs intrusion detection based thereon.
Owner:MCAFEE LLC
Method and apparatus for performing connection management with multiple stacks
ActiveUS20040190533A1Time-division multiplexData switching by path configurationConnection managementNetwork interface controller
The disclosed embodiments relate to a communication device for use in a node of a system having a plurality of nodes. Each of the plurality of nodes may include network interface controllers ("NICs") and each of the NICs may have a public identifier and a private identifier associated therewith. A first protocol stack may operate according to a first protocol that is associated with the public identifier and a second protocol stack may operate according to a second protocol that is associated with the private identifier. A storage device may associate the public identifier of one or more of the NICs with the first protocol stack and the private identifier of one or more of the NICs with the second protocol stack. Received messages that incorporate the public identifier may be directed to the first protocol stack and messages that incorporate the private identifier may be directed to the second protocol stack.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
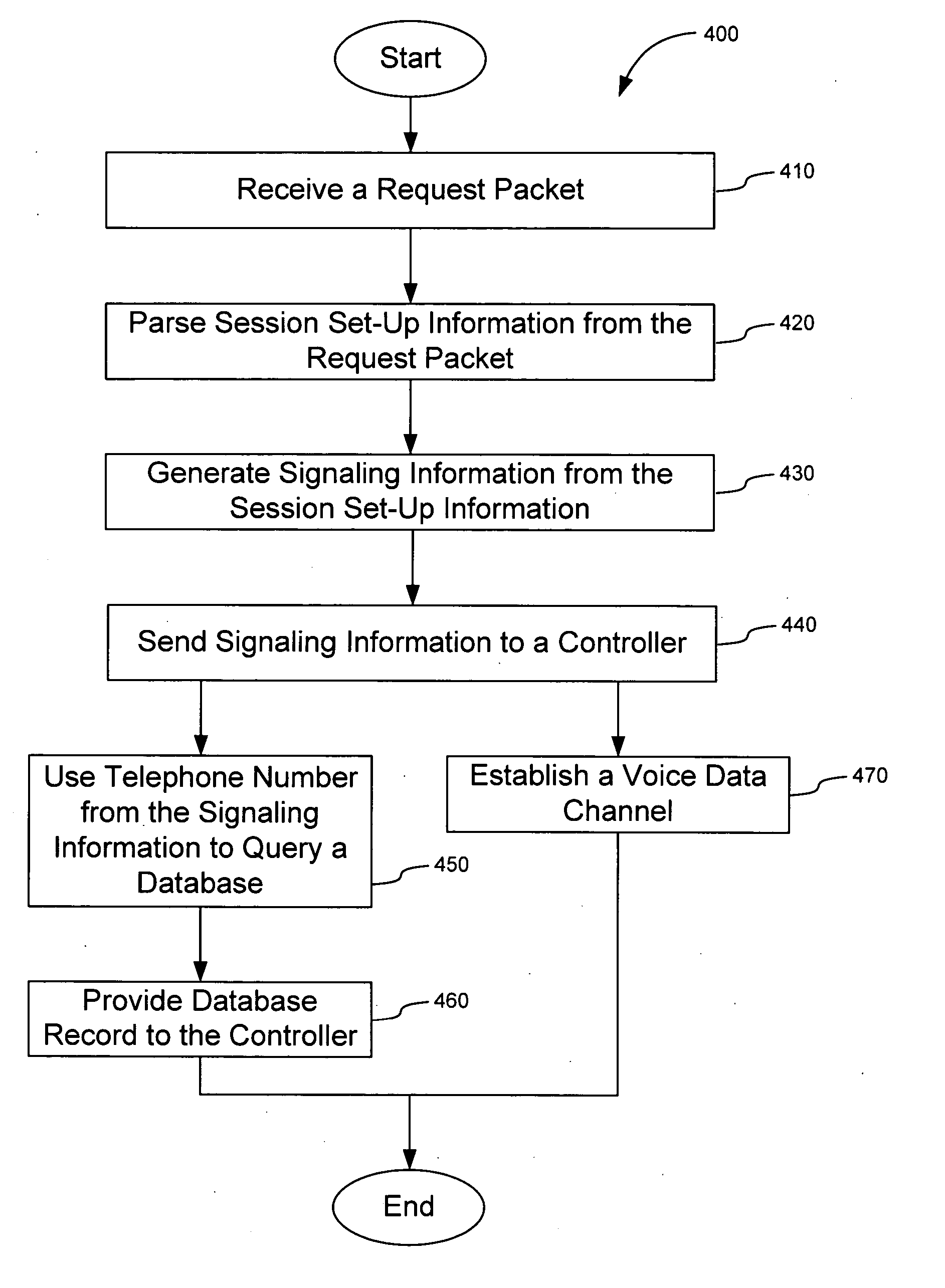
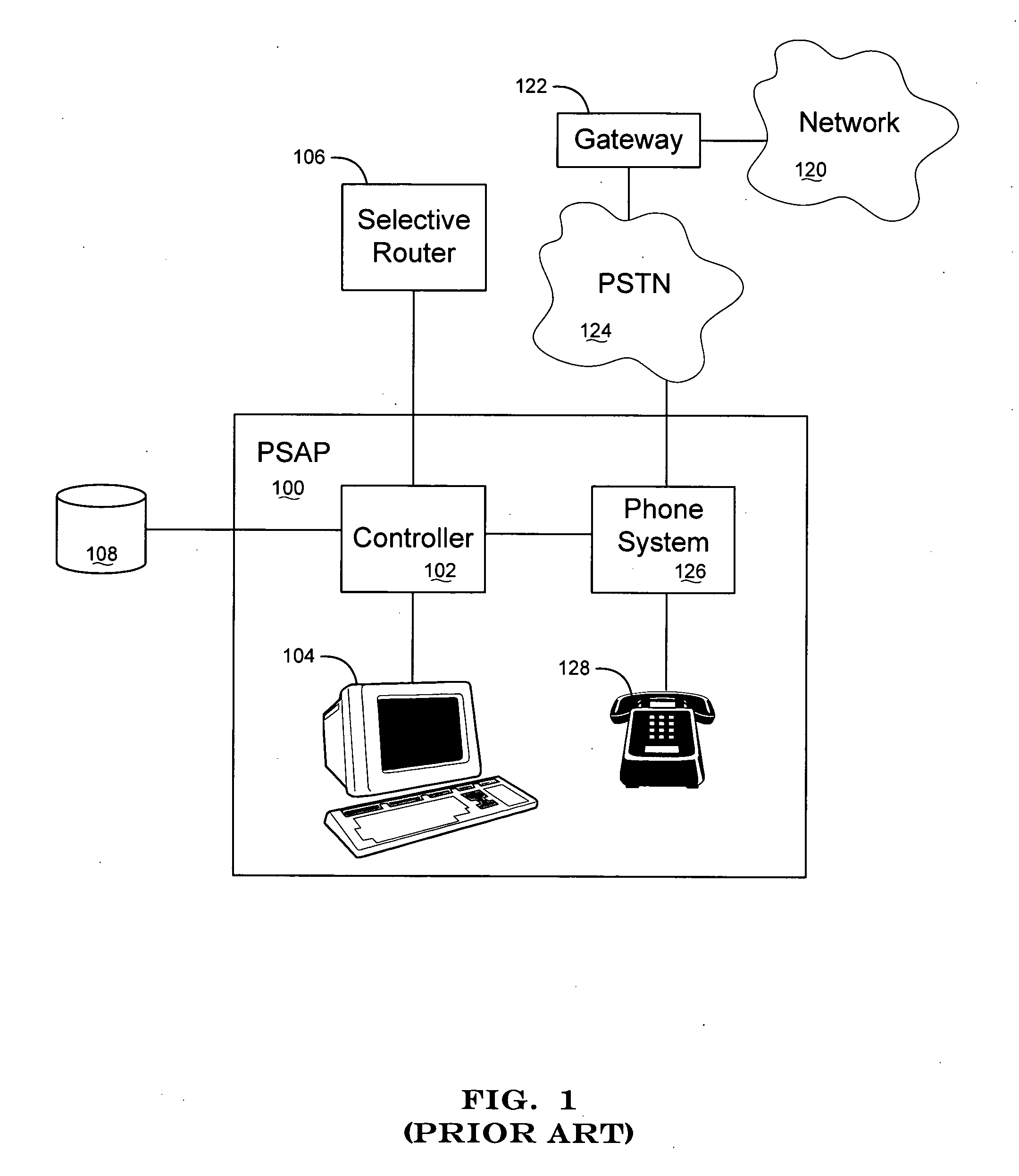
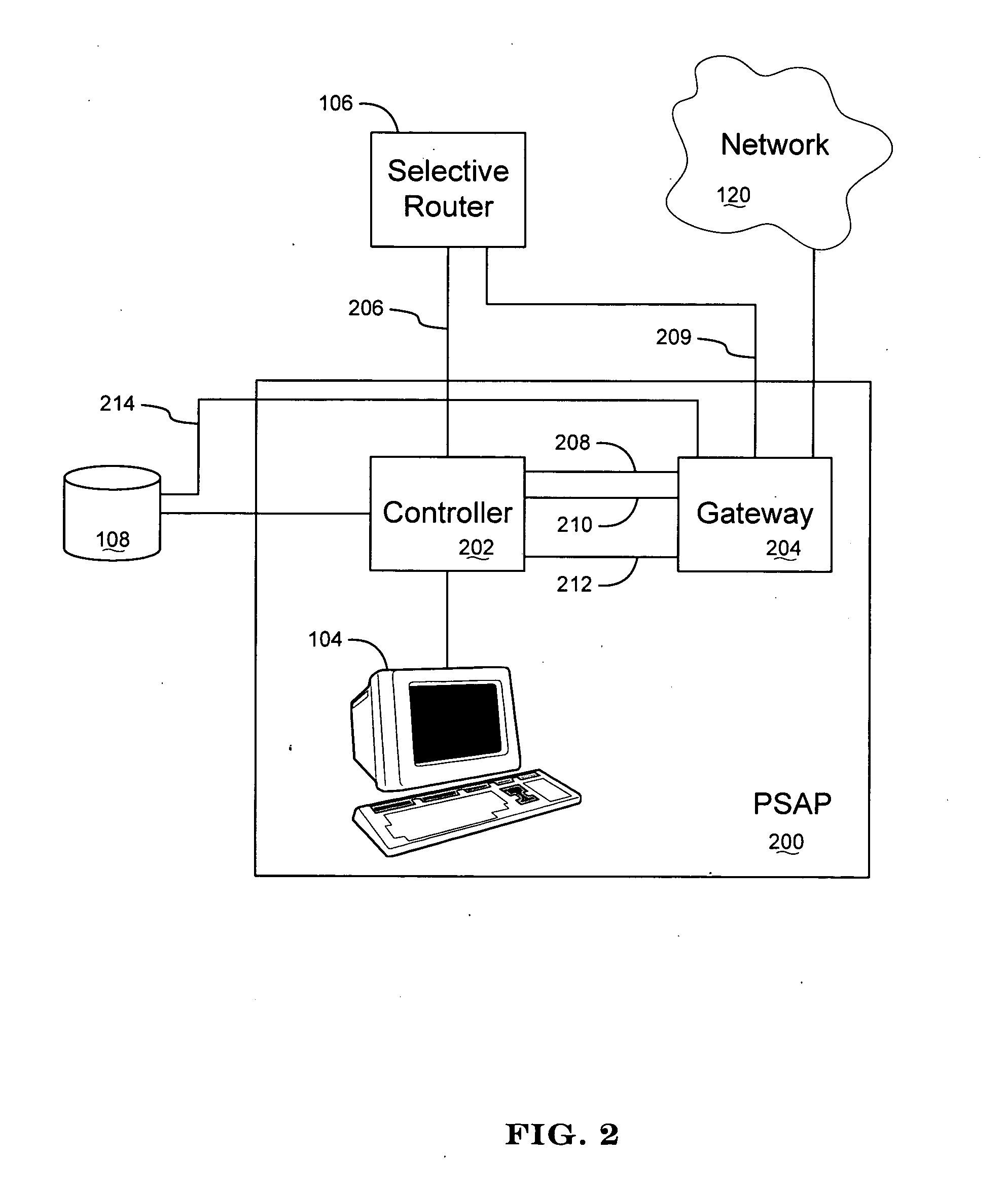
Apparatus and method for interfacing packet-based phone services with emergency call centers
InactiveUS7369530B2Telephonic communicationData switching by path configurationLogical frameworkComputer science
Owner:KEAGY SCOTT
Methods and systems for processing network data
InactiveUS7274706B1Time-division multiplexData switching by path configurationNetworking protocolNetwork packet
Methods and systems for processing data communicated over a network. In one aspect, an exemplary embodiment includes processing a first group of network packets in a first processor which executes a first network protocol stack, where the first group of network packets are communicated through a first network interface port, and processing a second group of network packets in a second processor which executes a second network protocol stack, where the second group of network packets is communicated through the first network interface port. Other methods and systems are also described.
Owner:RAMBUS INC +1
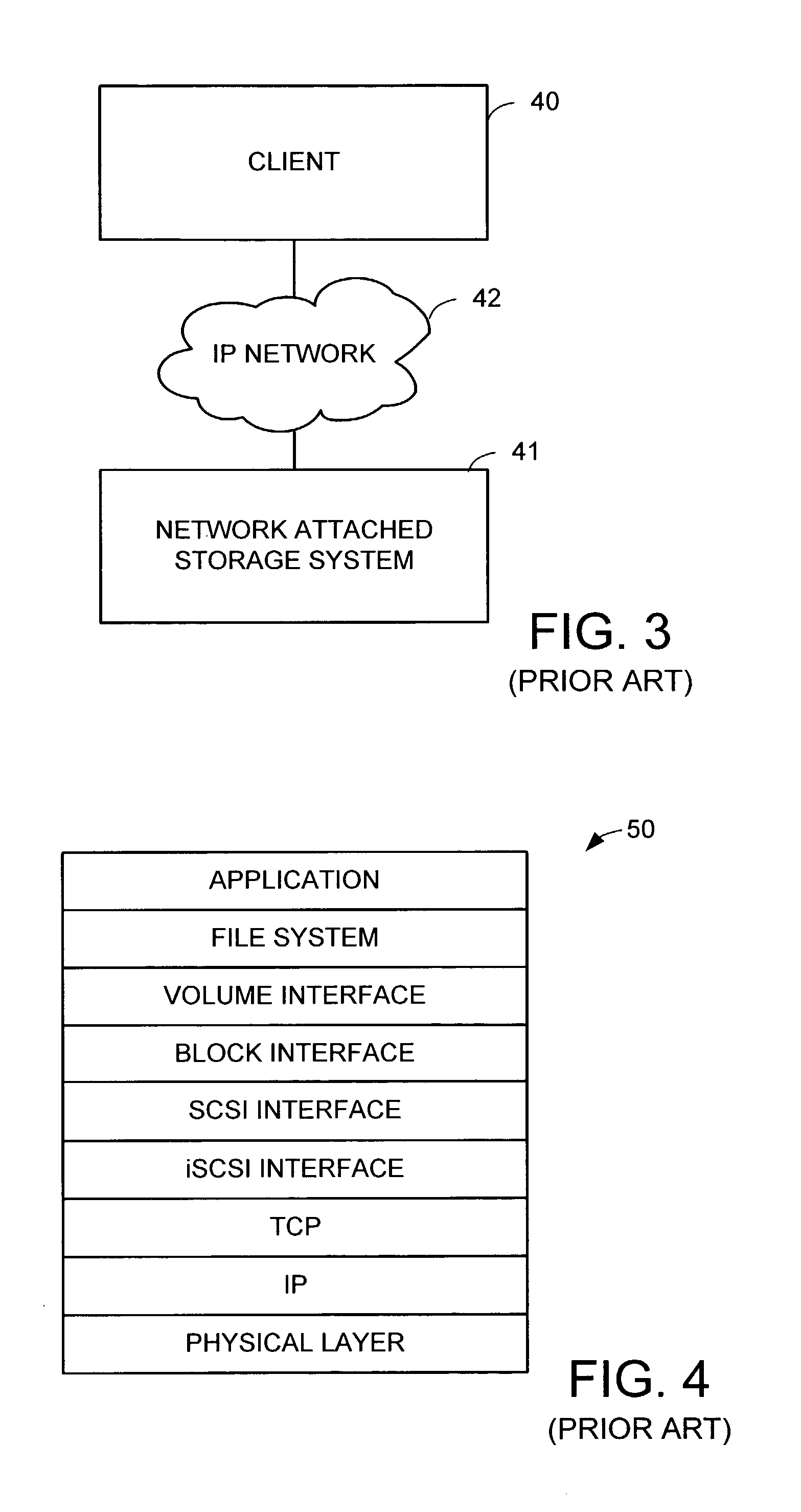
Network block services for client access of network-attached data storage in an IP network
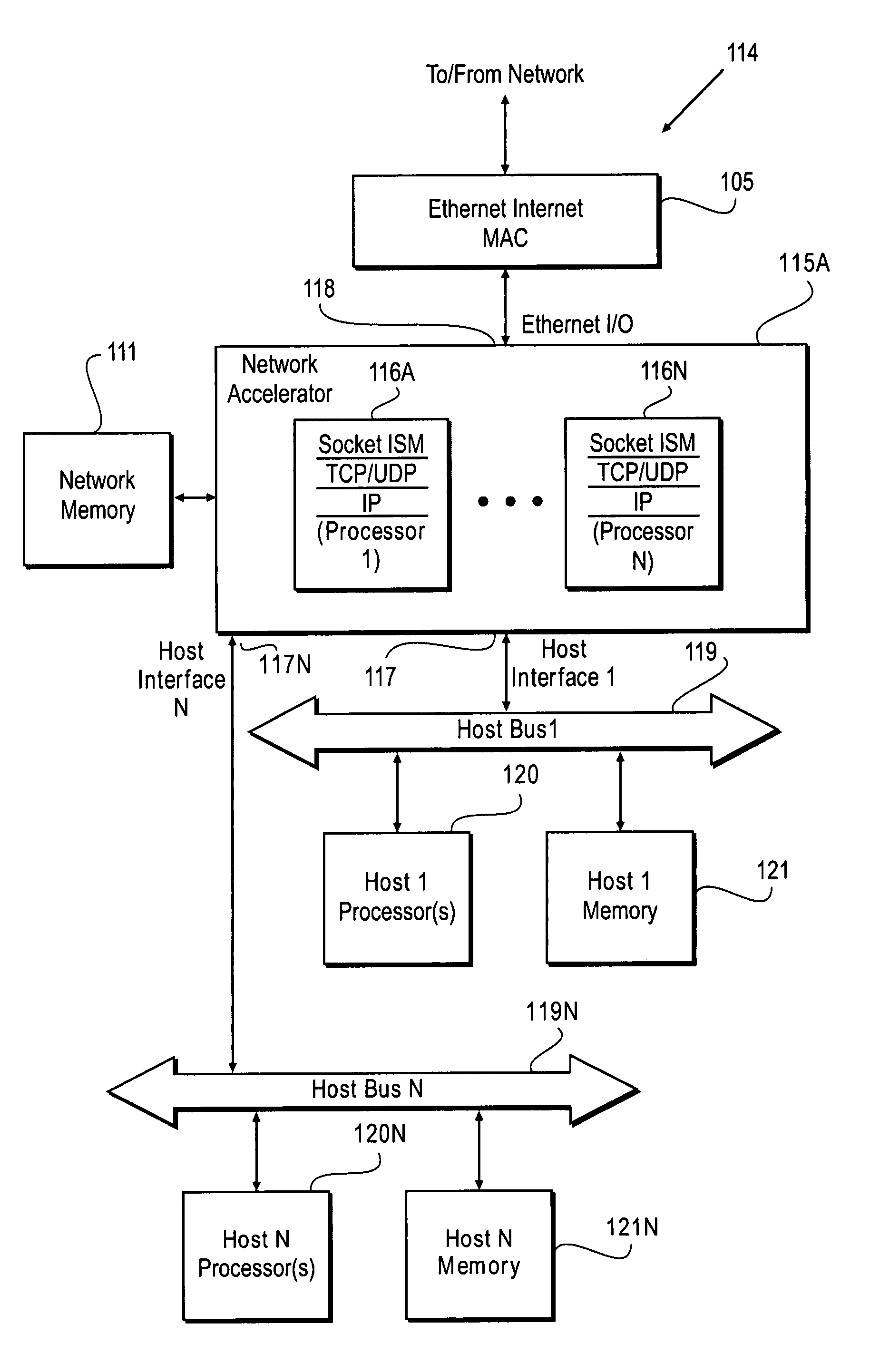
ActiveUS20040059822A1Multiple digital computer combinationsTransmissionService protocolOperational system
The SCSI and iSCSI layers over the TCP / IP layers of the protocol stack in an IP network client and in an IP network-attached storage server are replaced with a thin network block services layer. The network block services layer 71 implements a network block services protocol having a very reduced set of commands transmitted between the client and the storage server. The network block services protocol is used in a configuration process in which logical volumes of the network-attached storage are exported to the client and become local pseudo-disk instances. The client's operating system and application programs access the local pseudo-disk instances with what appears to be a standard device driver for a local disk device. The device driver maintains a TCP connection to each open device, and responds to connection failure by re-connecting with an alternative server IP port.
Owner:EMC IP HLDG CO LLC
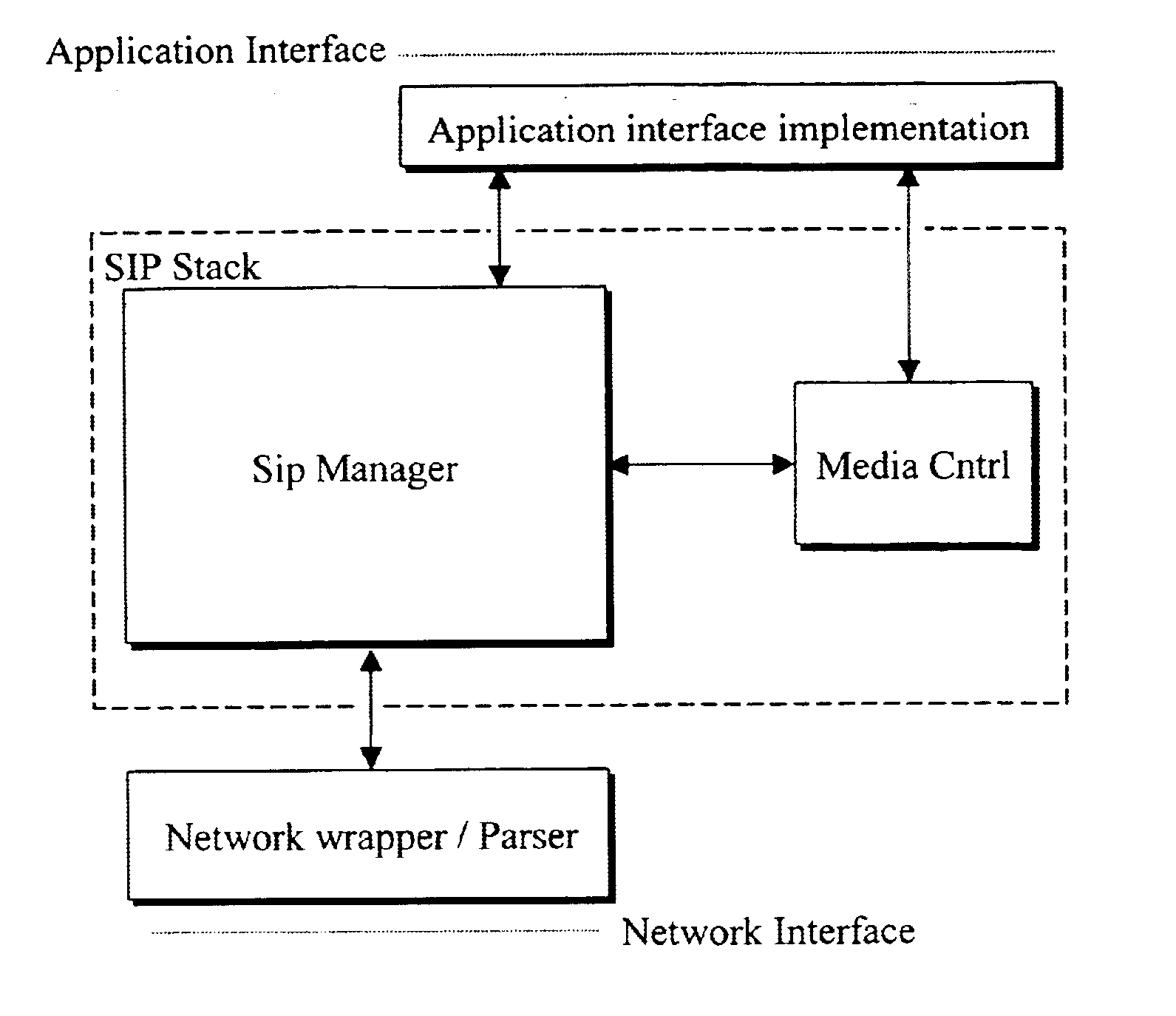
VoIP terminal security module, SIP stack with security manager, system and security methods
InactiveUS6865681B2Interconnection arrangementsUser identity/authority verificationModularitySecure voice
A secure voice over internet protocol (VoIP) terminal includes a modular security manager for use in conjunction with a protocol stack thereof, wherein the security manager includes a plurality of interfaces to the stack. In an SIP embodiment, these may include a security stack interface (SSA) between an SIP manager of an SIP stack and the security manager, a security terminal interface (SST) between a telephony application and the security manager, a security media interface (SSM) between the security manager and a media controller, and a security manager application interface (SMA) between the security manager and a security application (PGP) outside the stack.
Owner:NOKIA TECHNOLOGLES OY
Wireless extended proximity networks: systems, methods and program products
InactiveUS20050135286A1Network topologiesData switching by path configurationRouting tableNetworked system
A wireless proximity network is extended to provide peer-to peer communication among ad hoc networks. A mobile device (peer) coupled to an access point serves an adhoc network via a short-range communication link. The peer executes a Bluetooth protocol stack. Each peer has a routing table about all the peers in the adhoc network. A peer to peer software layer (P2P) runs on top of the Bluetooth protocol stack and beneath a multi-user application layer. The P2P software handles application deployment, peer management and communications for applications and provides information about existing peers on the adhoc network; routes messages between peers within an ad hoc network and from one peer to another in different adhoc networks. The access point is connected to a wireless LAN via a wireless router. The access point has an IP-BT address conversion table and communicates with other access points via wireless routers using TCP / IP protocols.
Owner:NOKIA SOLUTIONS & NETWORKS OY
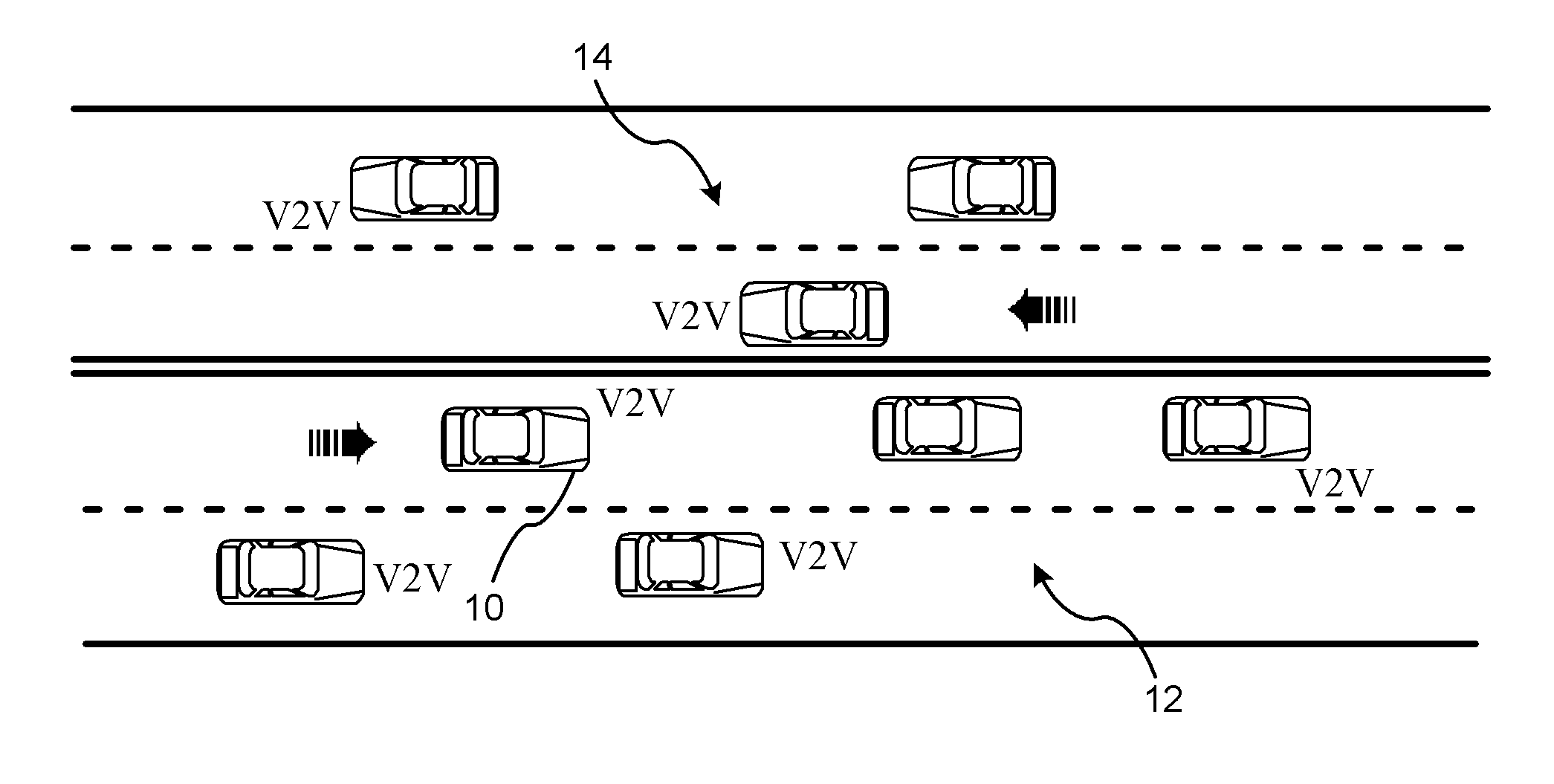
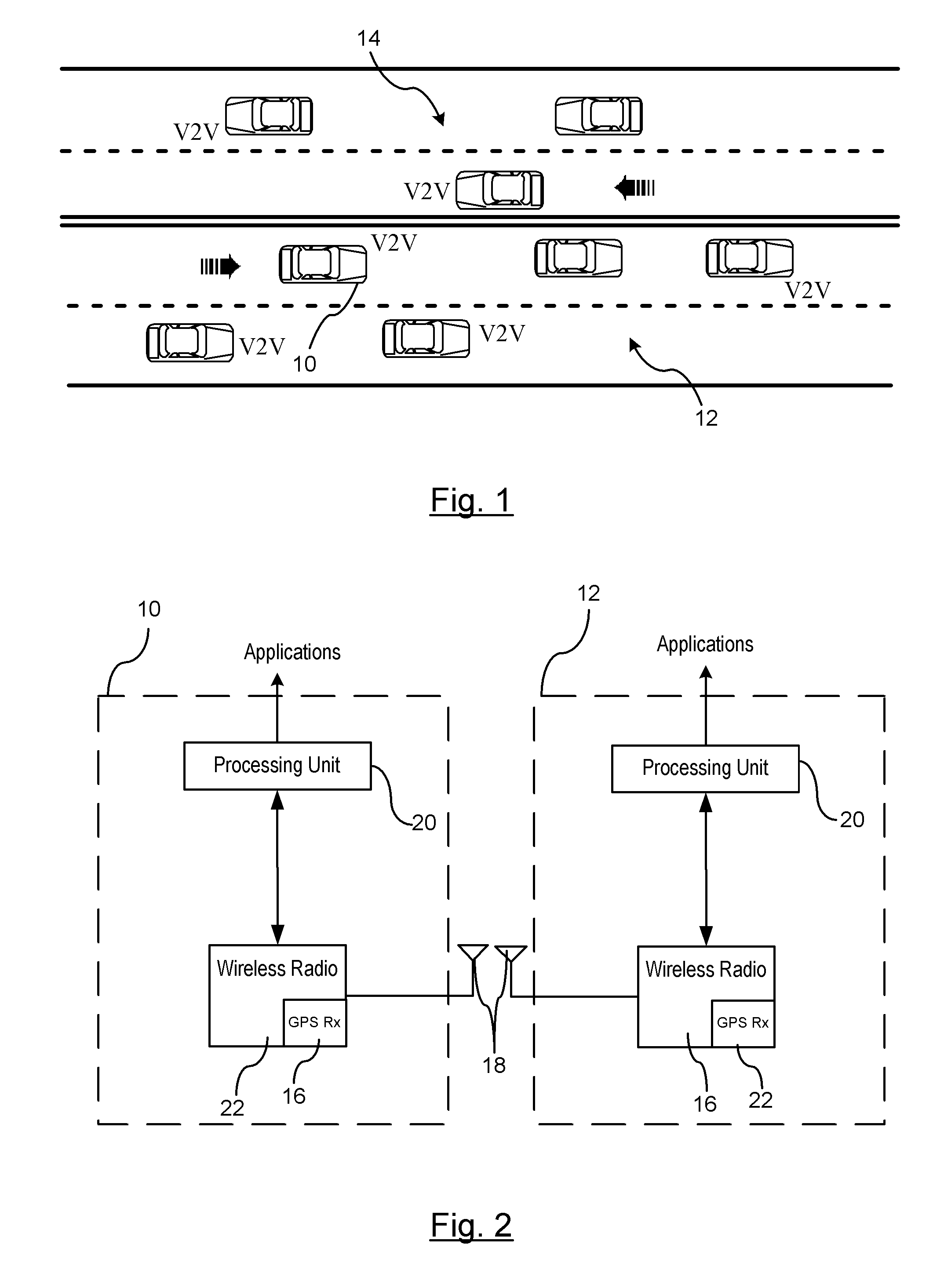
Reducing the Computational Load on Processors by Selectively Discarding Data in Vehicular Networks
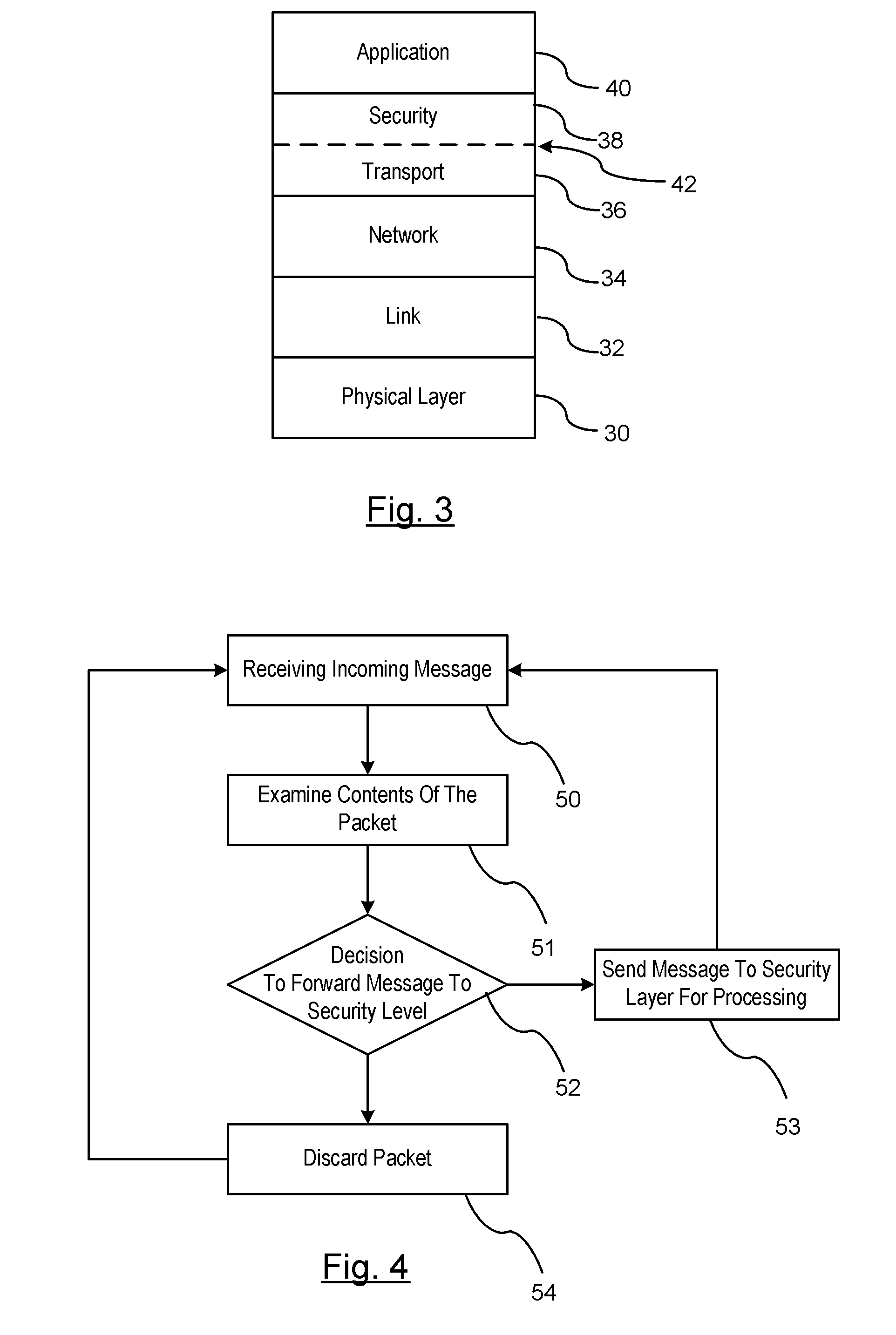
ActiveUS20110080302A1Efficient processingReduce computing loadService provisioningParticular environment based servicesCommunications systemProtocol stack
A method is provided for efficiently processing messages staged for authentication in a security layer of a protocol stack in a wireless vehicle-to-vehicle communication system. The vehicle-to-vehicle communication system includes a host vehicle receiver for receiving messages transmitted by one or more remote vehicles. The host receiver is configured to authenticate received messages in a security layer of a protocol stack. A wireless message broadcast by a remote vehicle is received. The wireless message contains characteristic data of the remote vehicle. The characteristic data is analyzed for determining whether the wireless message is in compliance with a predetermined parameter of the host vehicle. The wireless message is discarded prior to a transfer of the wireless message to the security layer in response to a determination that the wireless message is not in compliance with the predetermined parameter of the host vehicle. Otherwise, the wireless message is transferred to the security layer.
Owner:GM GLOBAL TECH OPERATIONS LLC
Apparatus and method for unilateral topology discovery in network management
InactiveUS20050013310A1Low costEliminate needTime-division multiplexData switching by path configurationRouting tableTopology information
A system for reducing the cost of network managment by using a proxy agent and subchannel communications so fewer SNMP licenses and fewer protocol stacks are needed. Subchannel communication is achieved in a plurality of different embodiments. Embodiments having single subchannel transceivers, multiple transceivers, single multiplexer and multiple multiplexers are disclosed. An NMS process using routing table CRC to automatically detect when the NMS topology information is incorrect and automated topology discovery is disclosed. A process for automated discovery of redundant cables during automated topology discovery is disclosed.
Owner:AVAGO TECH INT SALES PTE LTD
Apparatus and method for interfacing packet-based phone services with emergency call centers
InactiveUS20050174991A1Telephonic communicationData switching by path configurationLogical frameworkComputer science
A gateway is provided for interfacing packet-based phone services with controllers of emergency call centers. For each type of electronic medium to be interfaced, the gateway comprises a specific I / O interface and a specific module such as a protocol stack. The gateway also comprises an auxiliary information gateway application that integrates the I / O interfaces and modules into a logical framework that enables inter-working therebetween. A controller that includes the functionality of the gateway device is also provided. Methods for enabling emergency calls, and more generally for enabling a multi-media session, are also provided.
Owner:KEAGY SCOTT
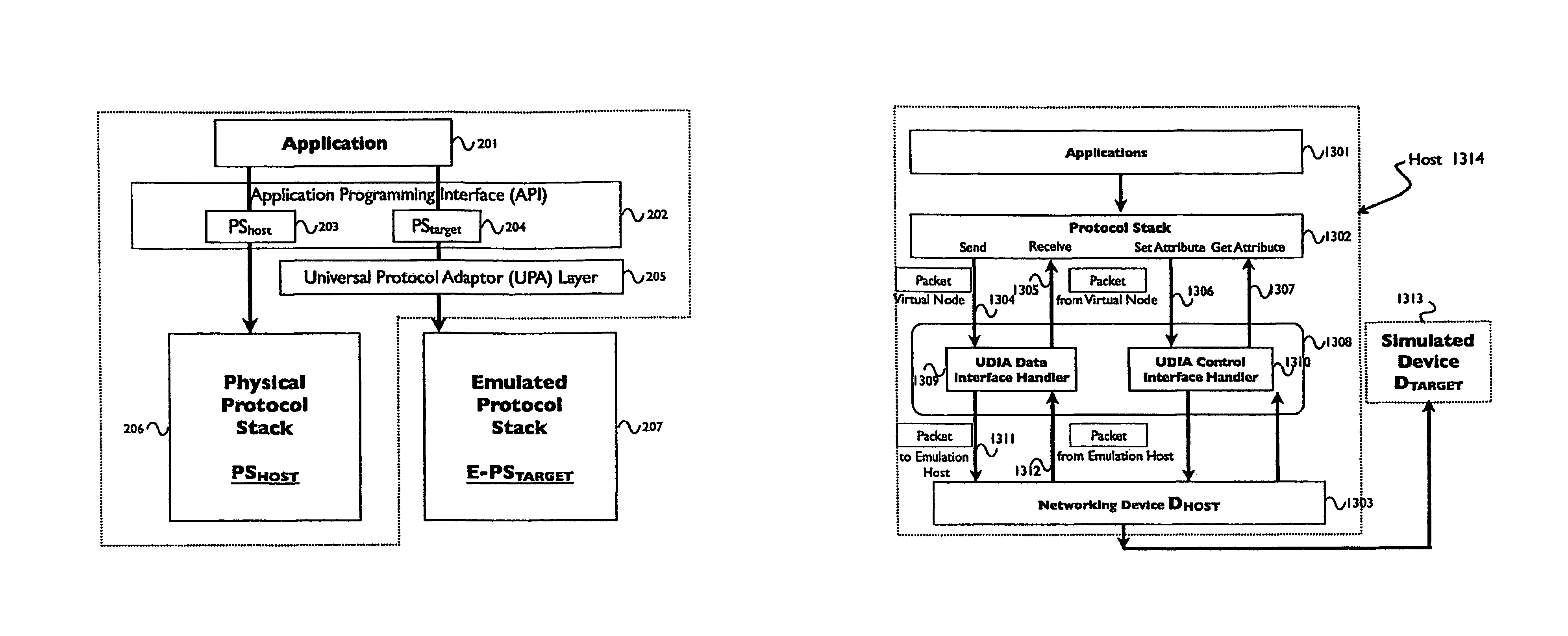
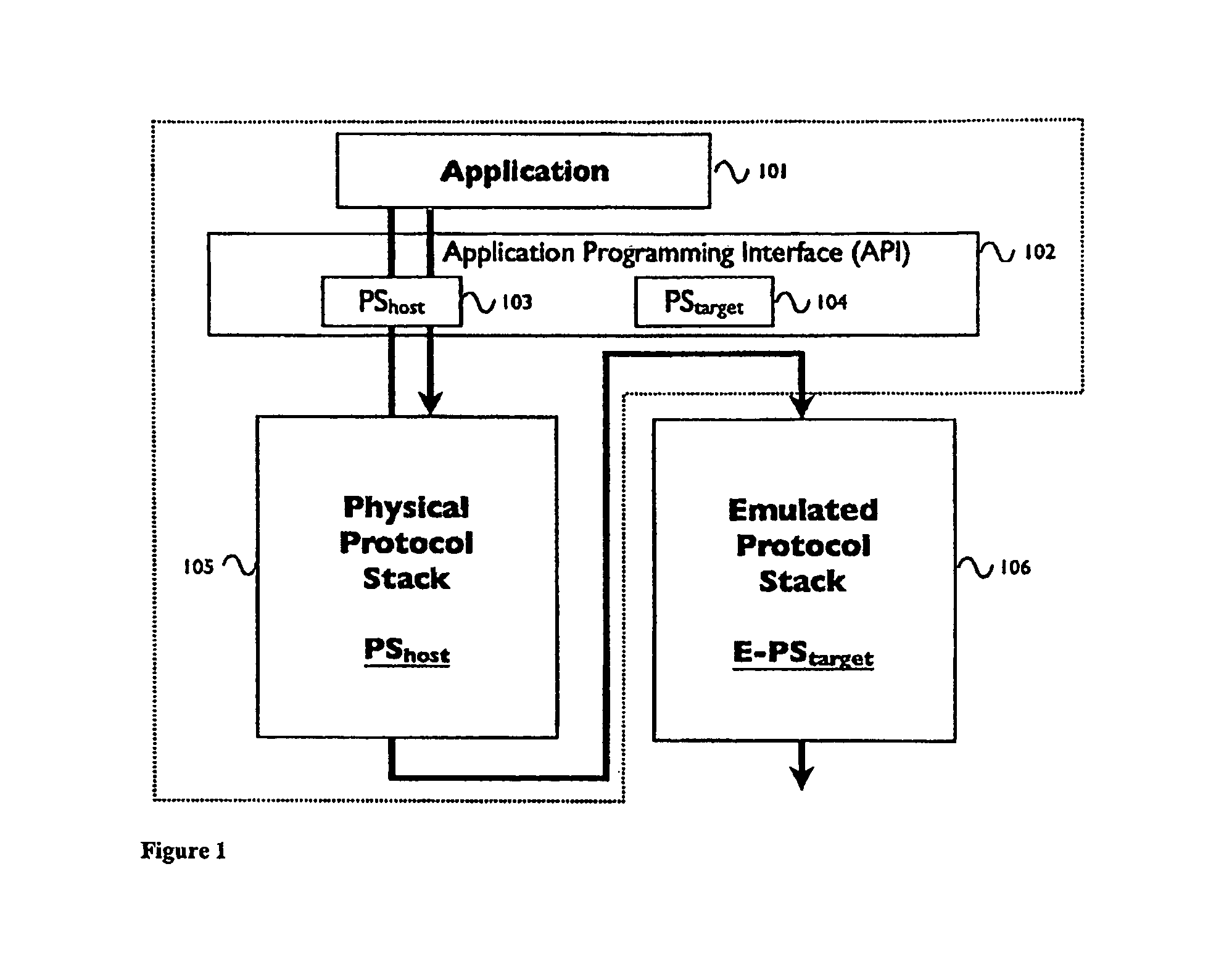
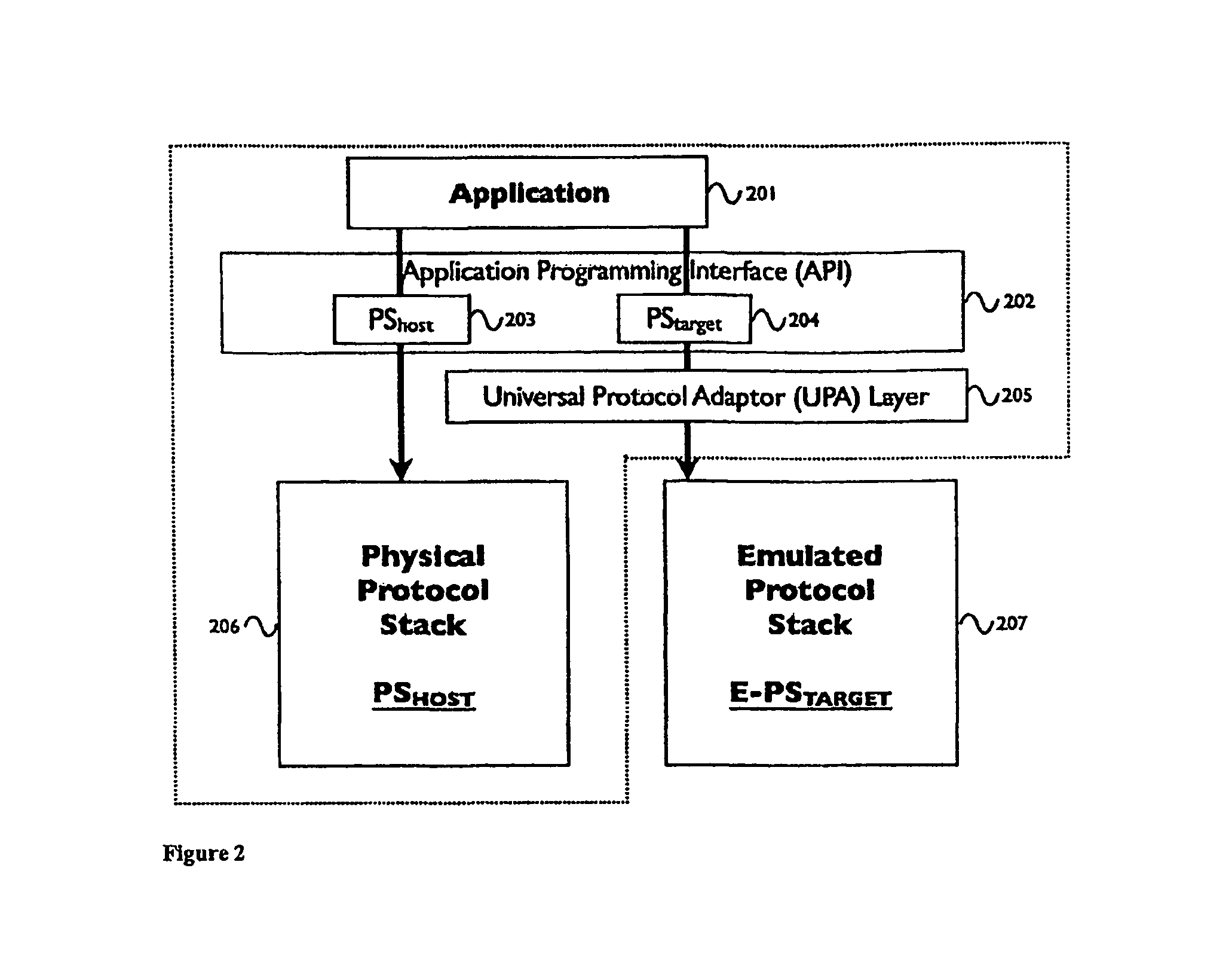
System and method for virtualization of networking system software via emulation
A method of running a target device in a hardware-in-the-loop network simulation via a host computer may include launching a network application on a host computer each having a protocol stack and a network device connected to a simulated network of target devices, interposing, on the host computer, a target device interface and adaptor between the protocol stack and the network device and transferring data and control information between the network application and the target device via the network device, whereby the target device runs on the host computer as if the target device were running directly on a host computer having a network device directly compatible with the target device.
Owner:KEYSIGHT TECH
Method and apparatus for secure internet protocol (IPSEC) offloading with integrated host protocol stack management
ActiveUS20060104308A1Requires minimizationDigital data processing detailsTime-division multiplexComputer hardwareSecurity association
The invention provides mechanisms for transferring processor control of secure Internet Protocol (IPSec) security association (SA) functions between a host and a target processing devices of a computerized system, such as processors in a host CPU and a NIC. In one aspect of the invention, the computation associated with authentication and / or encryption is offloaded while the host maintains control of when SA functions are offloaded, uploaded, invalidated, and re-keyed. The devices coordinate to maintain metrics for the SA, including support for both soft and hard limits on SA expiration. Timer requirements are minimized for the target. The offloaded SA function may be embedded in other offloaded state objects of intermediate software layers of a network stack.
Owner:MICROSOFT TECH LICENSING LLC
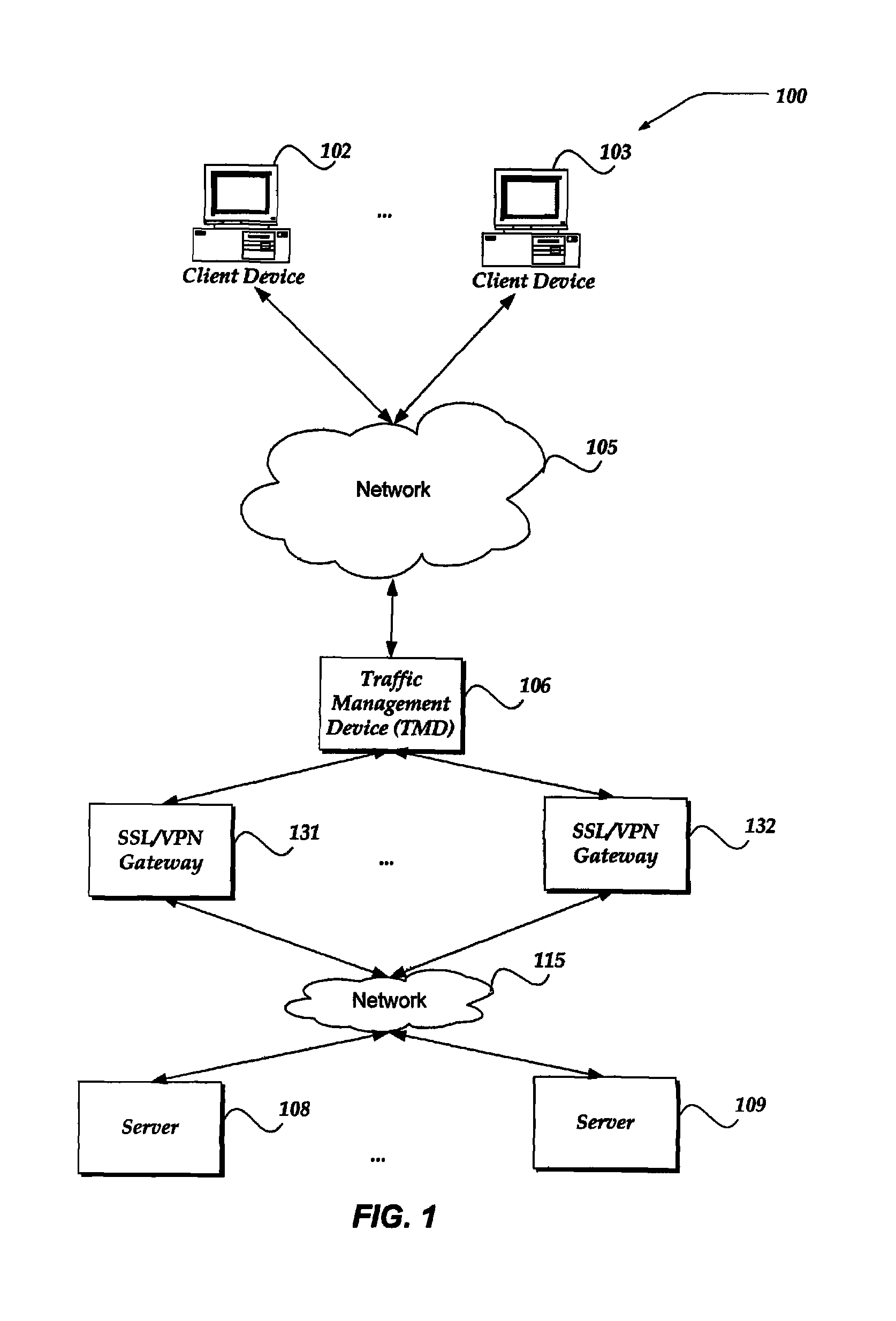
Intelligent HTTP based load-balancing, persistence, and application traffic management of SSL VPN tunnels
InactiveUS8566452B1Multiple digital computer combinationsTransmissionTraffic capacityApplication lifecycle management
A system, apparatus, and method are directed to converting from a use of a HTTPS connection to a tunnel connection while maintaining an underlying connection between a client and a server. An HTTPS connection is employed to establish a network connection between a client device and a network device. A gateway is selected to receive a request from the client device. In one embodiment, selecting may comprise using load-balancing, cookie-persistence, or the like. Subsequently, the HTTPS connection is transitioned to another application layer communication protocol connection. Transitioning may comprise converting from a use of a first protocol stack configured to process a HTTP connection to a second protocol stack configured to process a non-HTTP based application protocol connection, and establishing a tunnel between the client device and a server through the selected gateway.
Owner:F5 NETWORKS INC
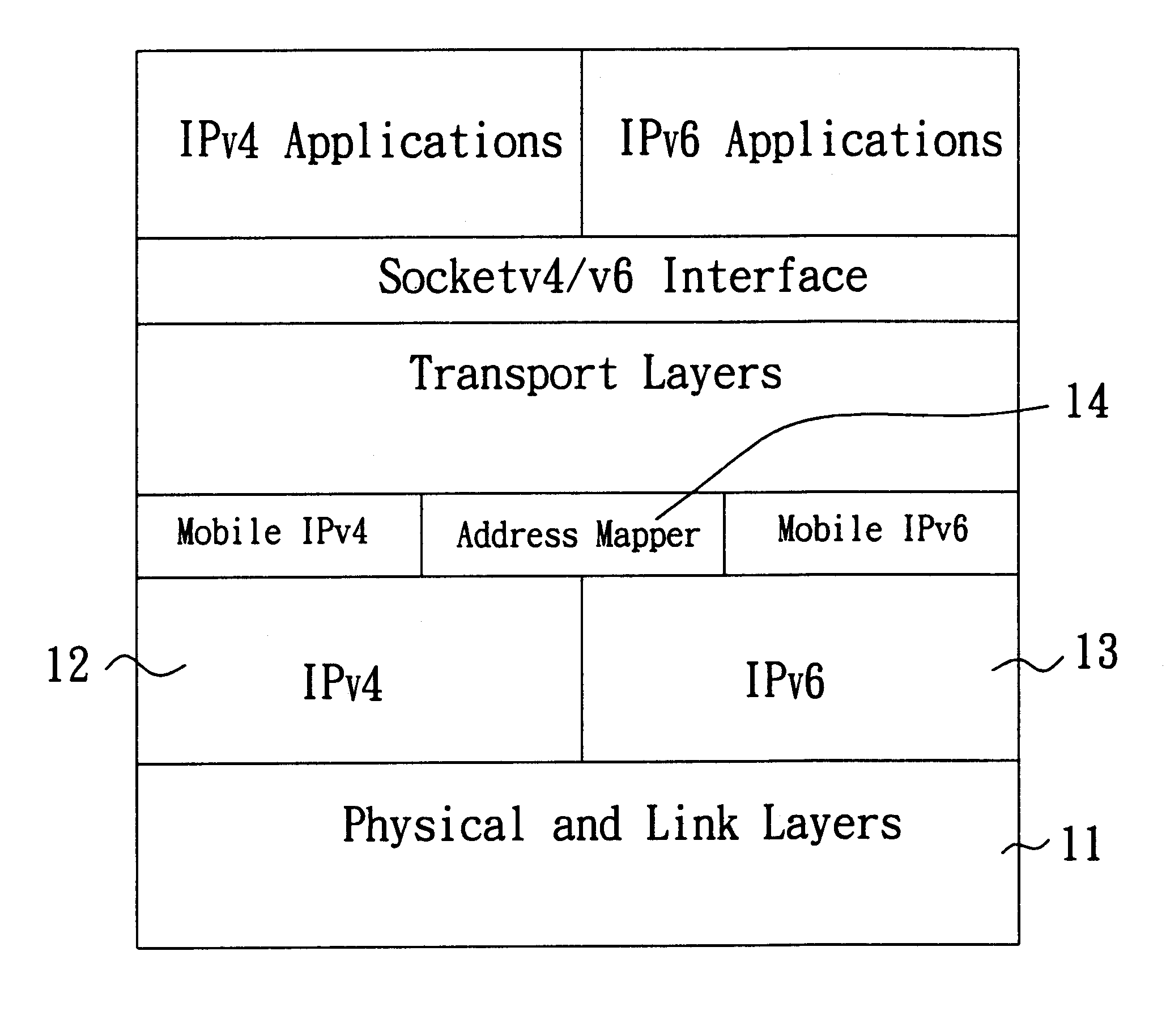
Method and system capable of providing mobility support for IPv4/IPv6 inter-networking
InactiveUS6862274B1Time-division multiplexData switching by path configurationNetwork packetForeign agent
A method and system capable of providing mobility support for IPv4 / IPv6 inter-networking to a mobile node is disclosed. The mobile node in the system has an address mapper, an IPv4 protocol stack and an IPv6 protocol stack in the network layer. When moving from IPv4 to IPv6 networks, the mobile node registered an IPv4 address receives router advertisement packets from an IPv6 router, so as to obtain a IPv6 care-of-address, and resolve the IPv6 care-of-address by an IPv4 care-of-address. The address mapper issues an IPv4 message to register the IPv4 care-of-address. When moving from IPv6 to IPv4 networks, the mobile node registered an IPv6 address receives agent advertisement messages from a foreign agent, so as to obtain an IPv4 care-of-address, resolve the IPv4 care-of-address by an IPv6 care-of-address. The address mapper issues an IPv6 message to register and update binding information by the IPv6 care-of-address.
Owner:IND TECH RES INST
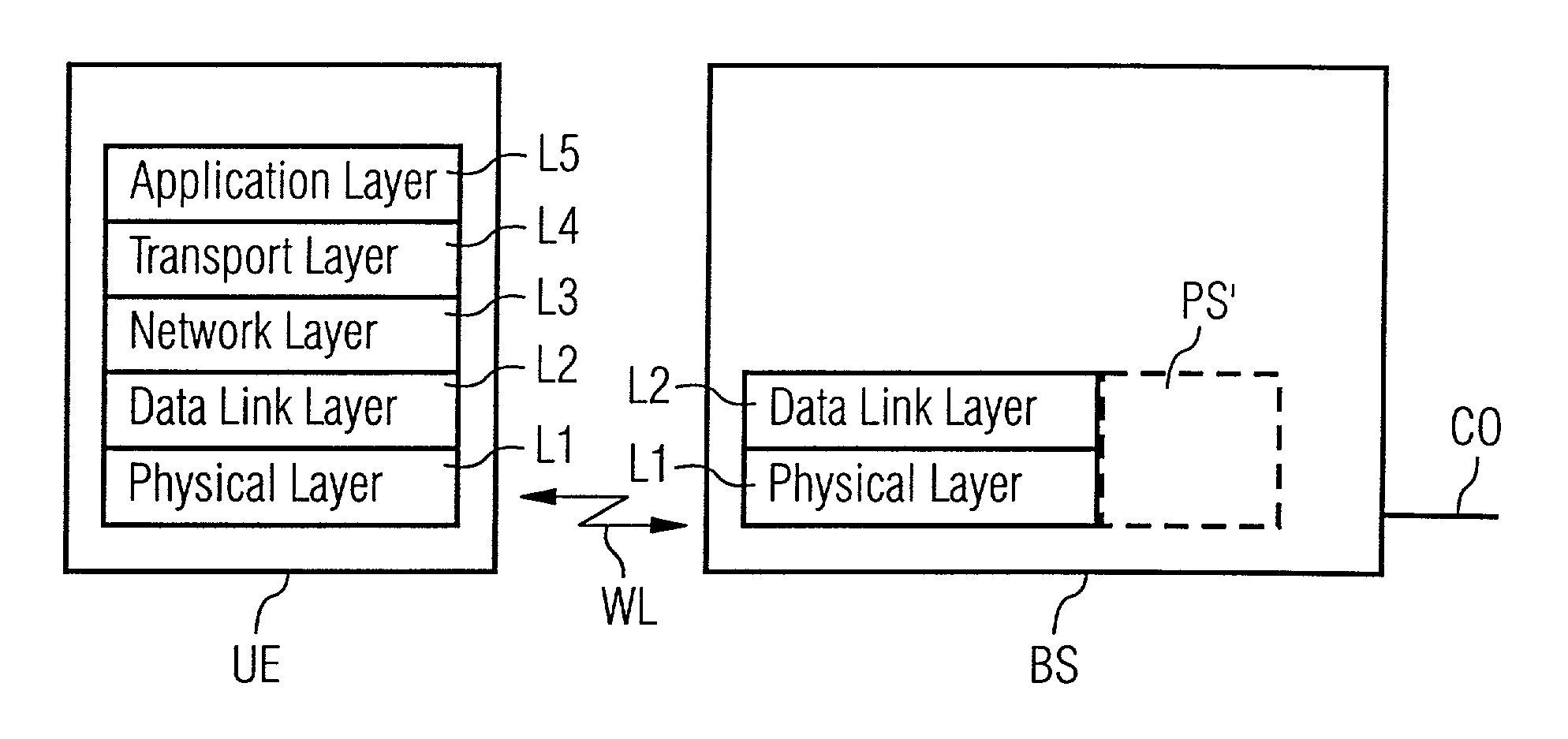
Method and device for improving the transmission efficiency in a communication system with a layered protocol stack
InactiveUS20020009067A1Easy to controlImprove efficiencyNetwork traffic/resource managementTime-division multiplexComputer hardwareCommunications system
In a method for improving the transmission efficiency in a communication system with a layered protocol stack, data packets are processed on an upper protocol layer. Data packets are forwarded to a lower protocol layer for transmission and the transmission is performed with variable channel access delays. The upper protocol layer is notified by the lower protocol layer when a transmission is started to allow a synchronization of timers in the upper protocol layer. If a layer performs a scheduling of data packets for the transmission, a rescheduling is performed alternatively or in addition during a channel access delay. Devices and software programs embodying the invention are also described.
Owner:HIGHBRIDGE PRINCIPAL STRATEGIES LLC AS COLLATERAL AGENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com