Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
103 results about "Protocol Status" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
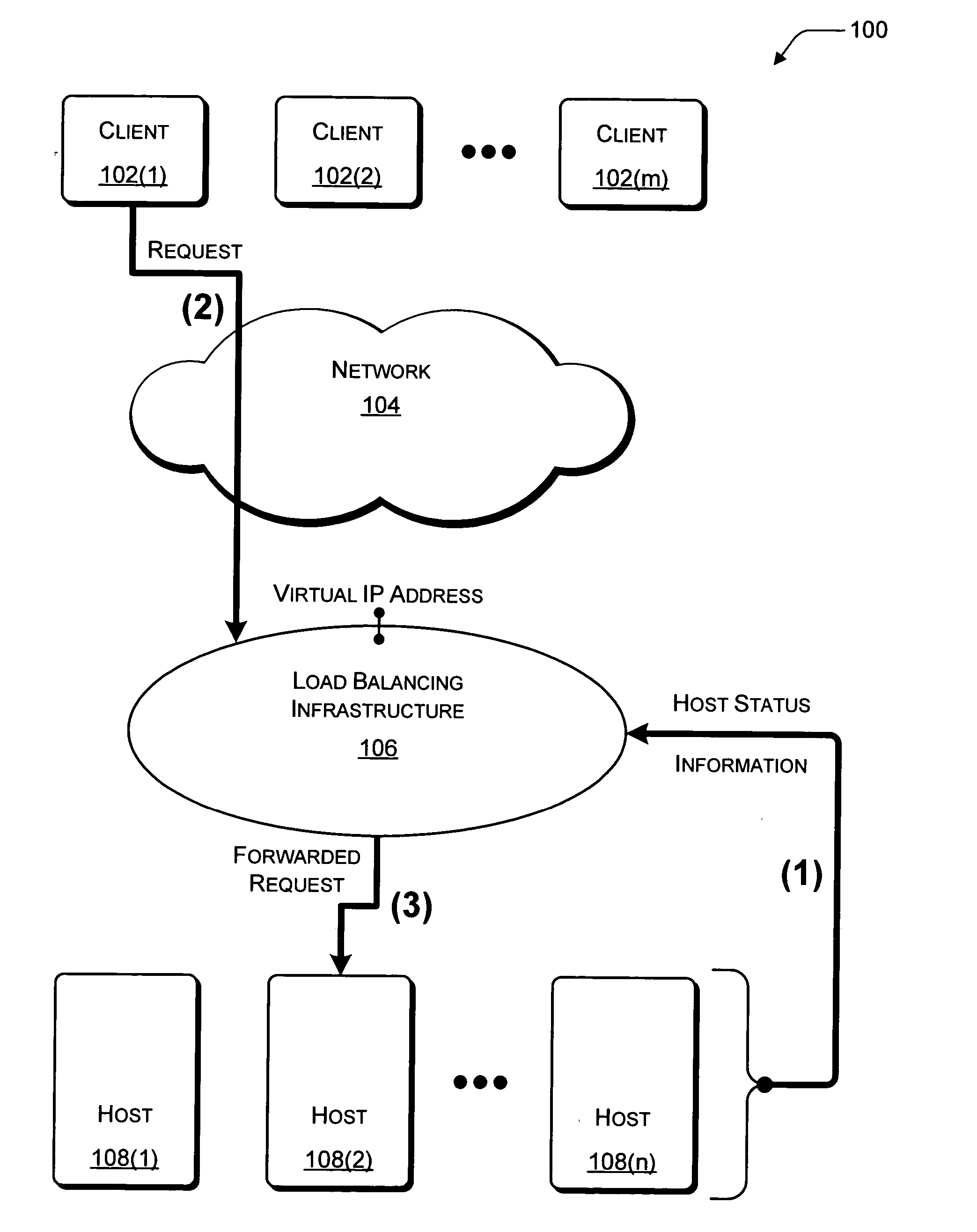
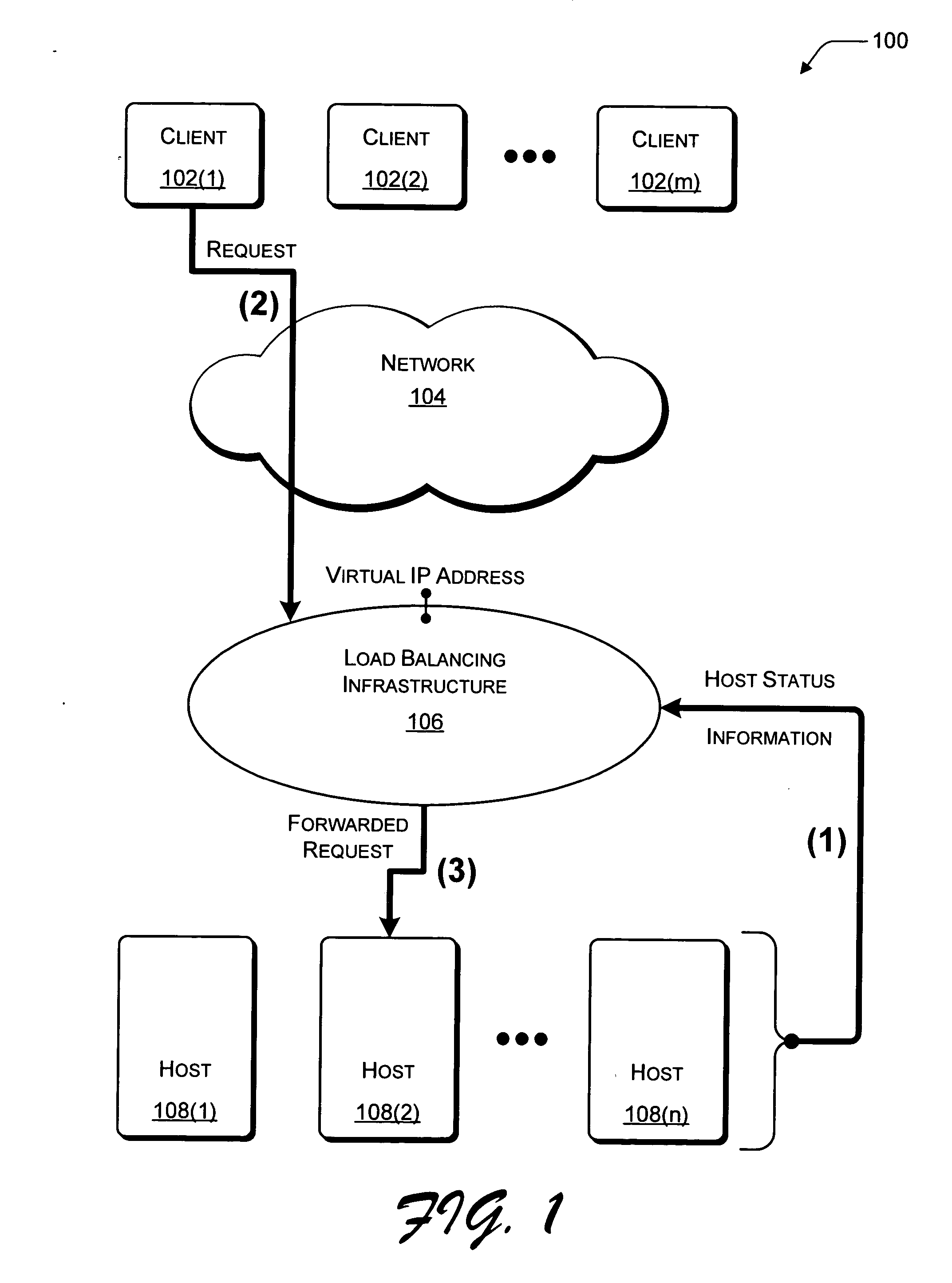
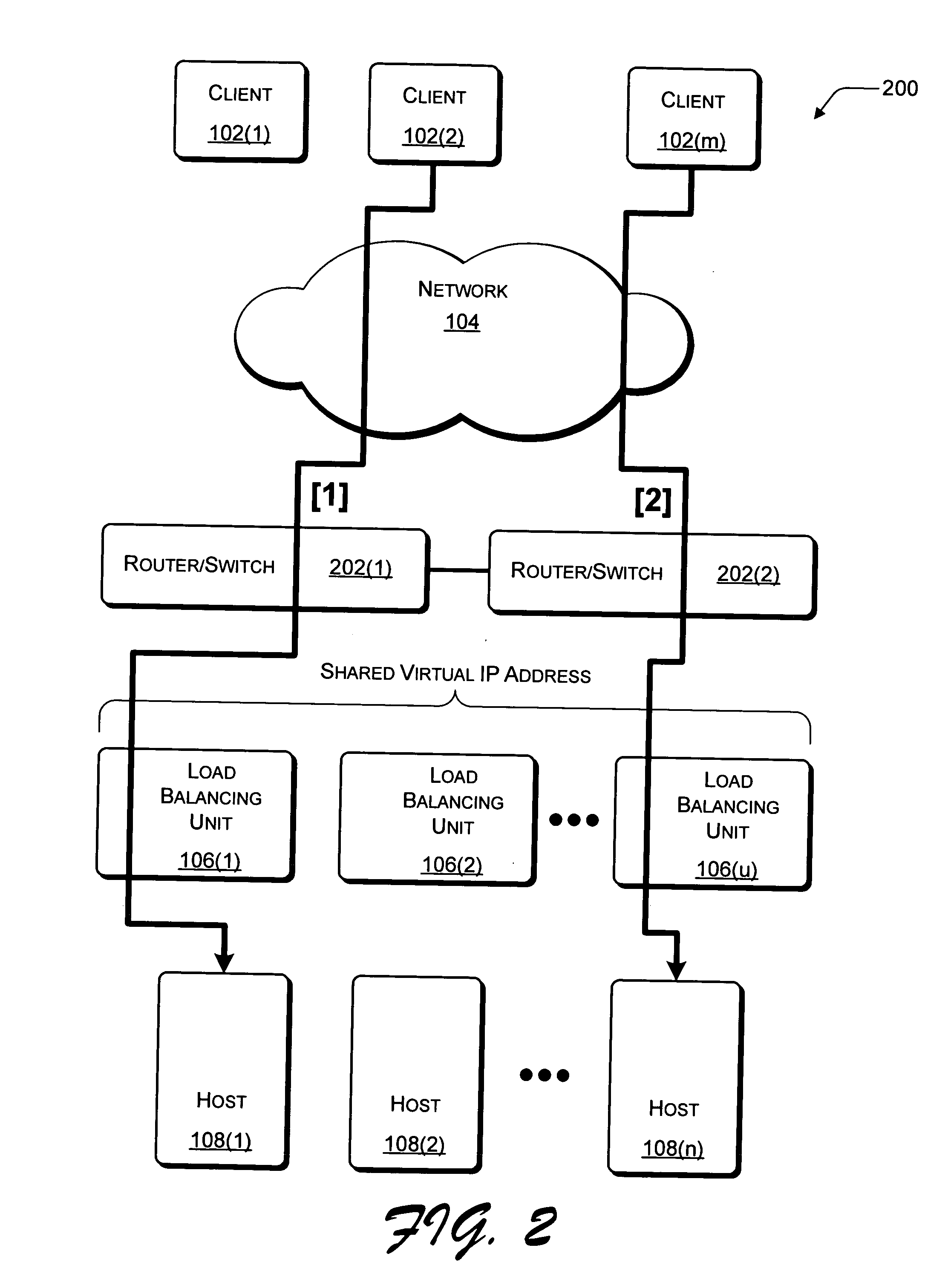
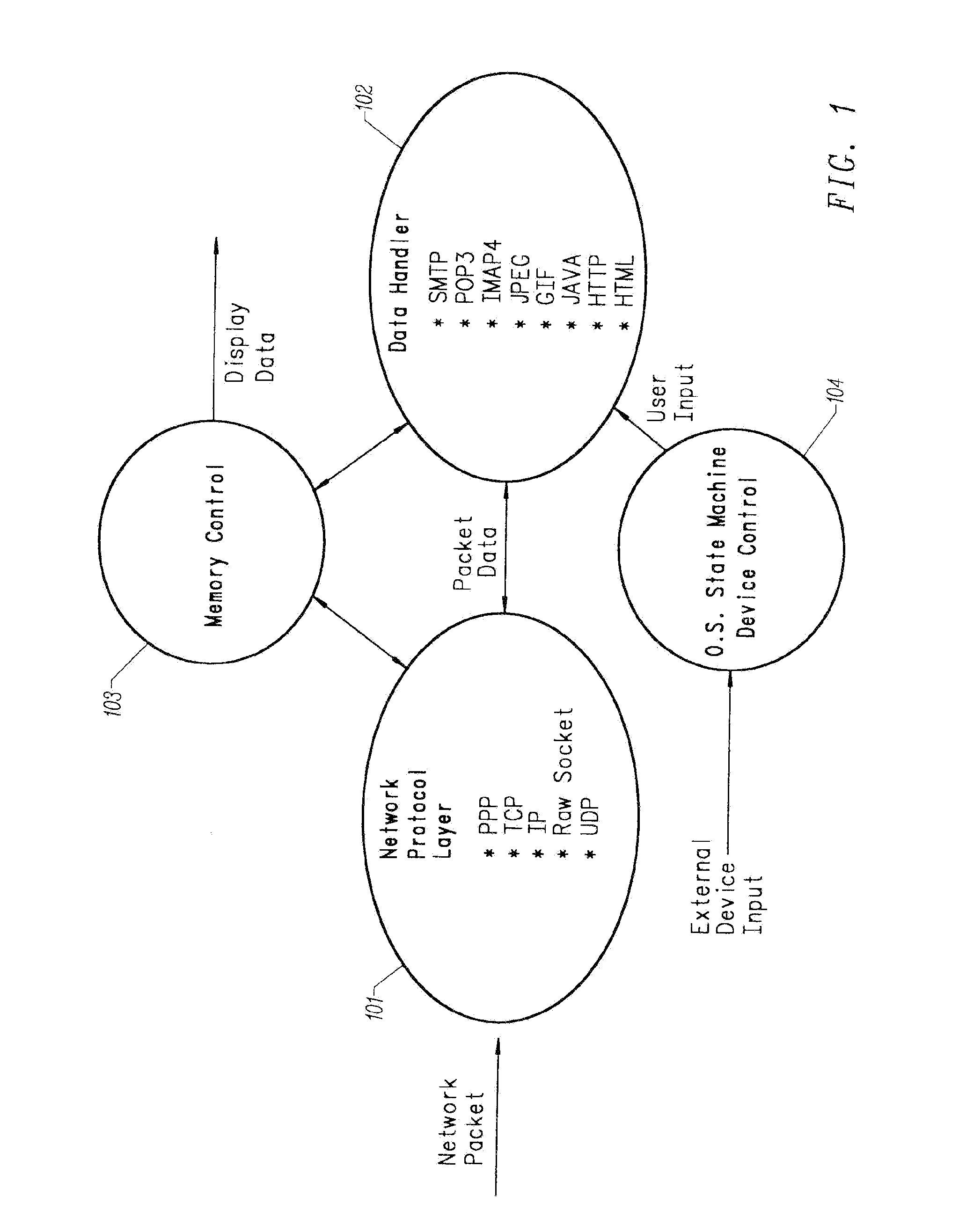
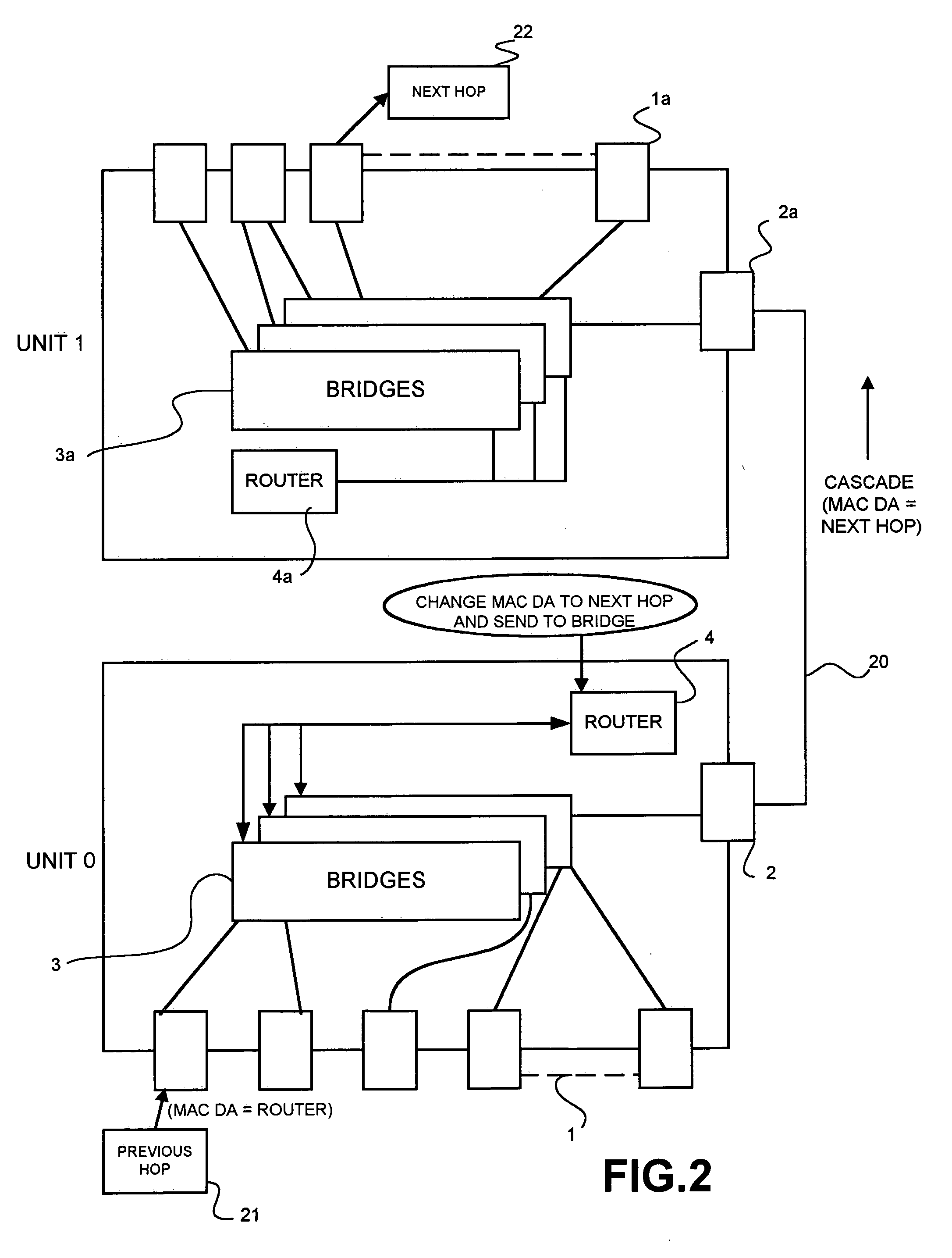
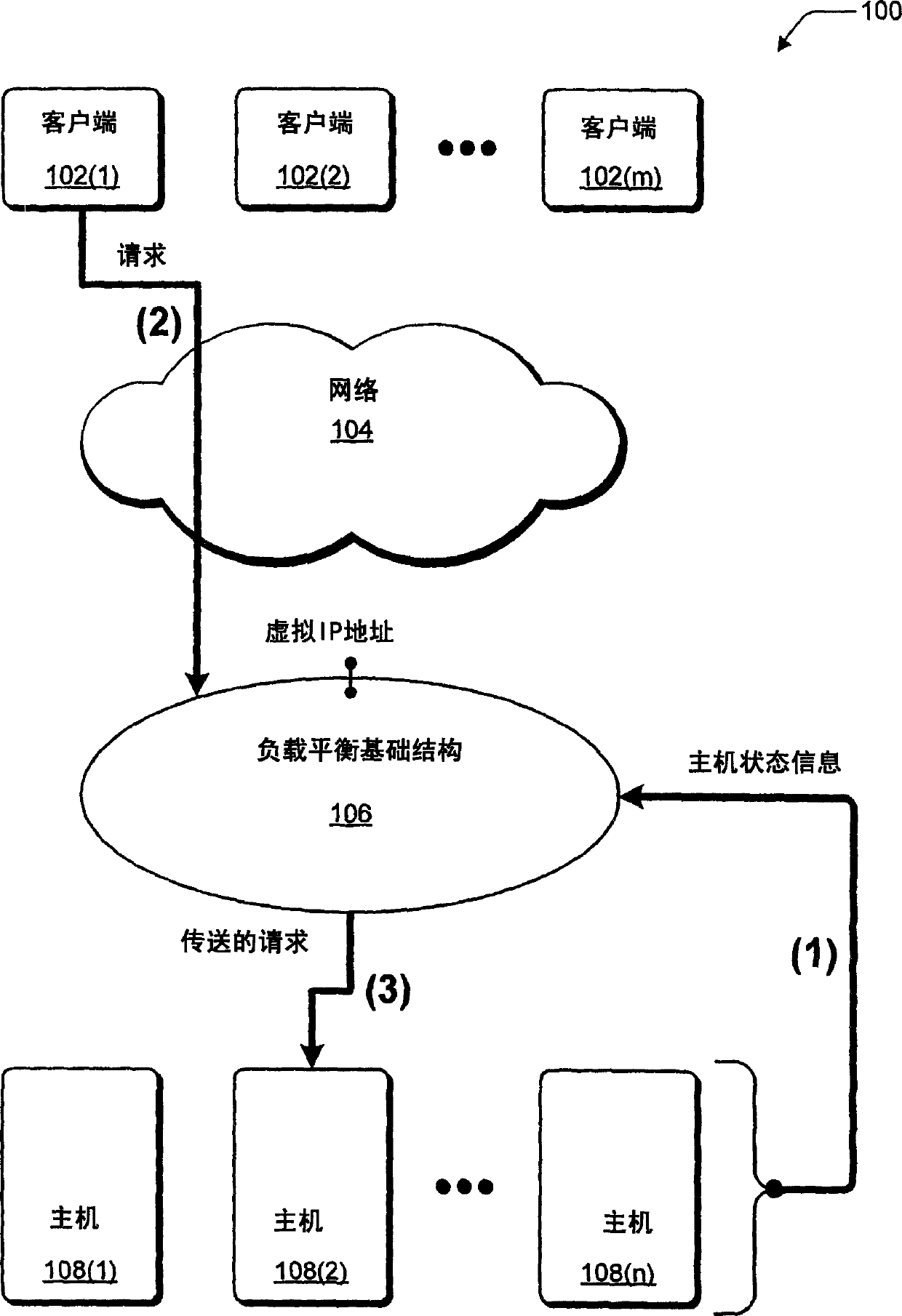
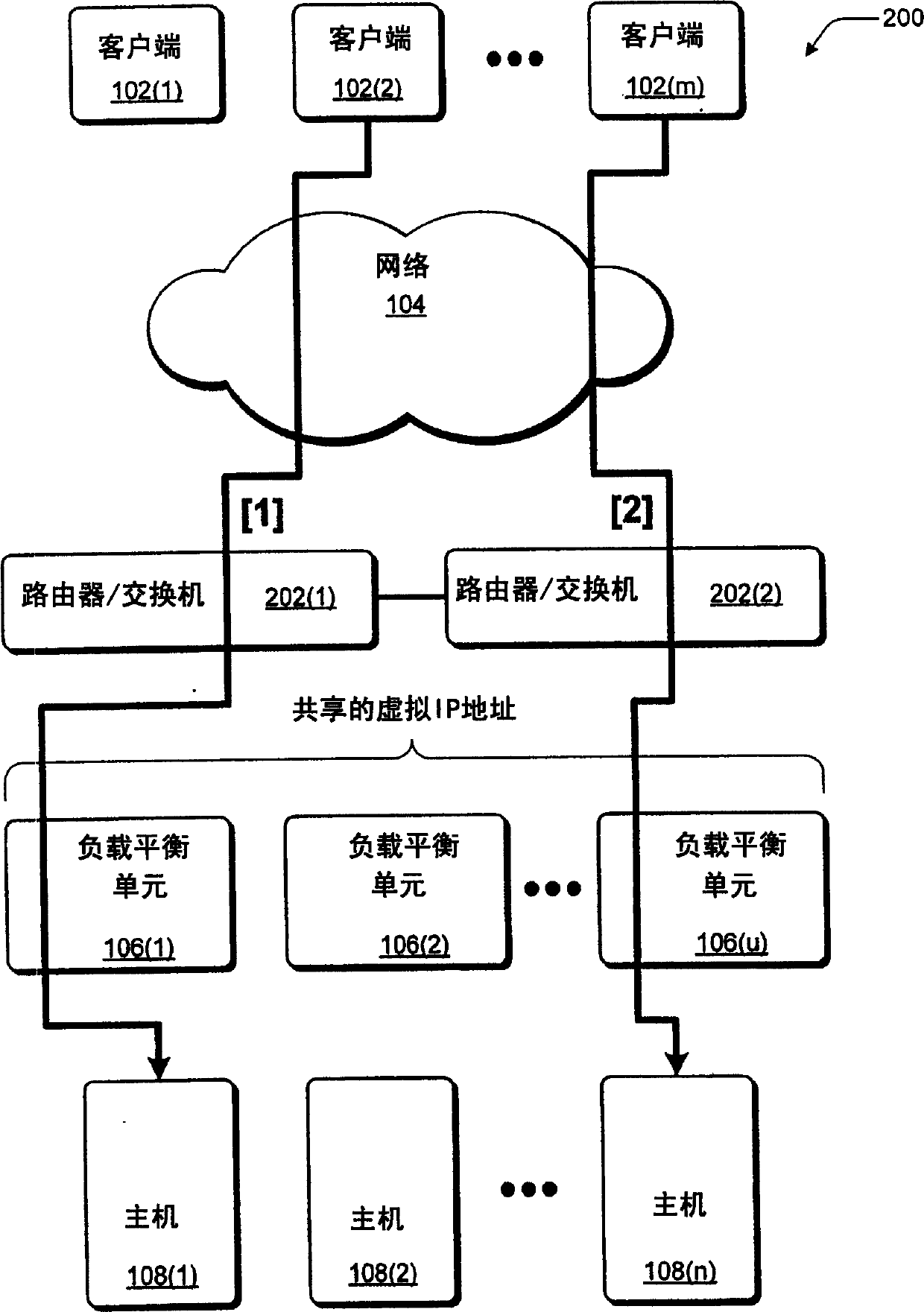
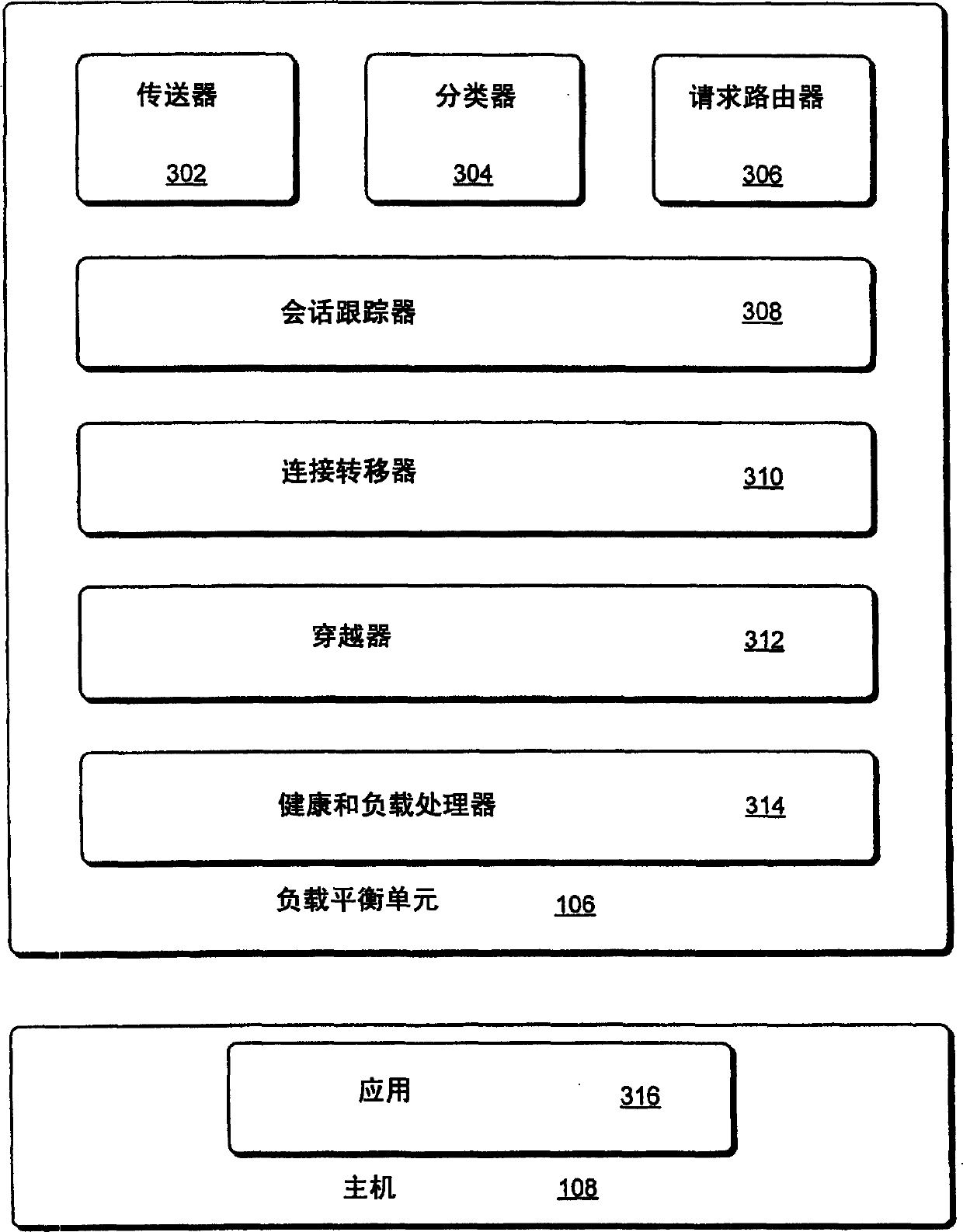
Network load balancing with connection manipulation
ActiveUS20050055435A1Multiple digital computer combinationsData switching networksEncapsulated dataProtocol stack
In an exemplary device implementation, a device includes: a connection migrator that is configured to migrate connections away from the device; the connection migrator capable of precipitating a compilation of protocol state for a connection across a protocol stack; the connection migrator adapted to aggregate the compiled protocol state with data for the connection into an aggregated connection state; the connection migrator further capable of causing the aggregated connection state to be sent toward a target device. In an exemplary media implementation, processor-executable instructions direct a device to perform actions including: obtaining at least a portion of a source / destination pair from a packet; accessing an encapsulation mapping table using the at least a portion of the source / destination pair to locate an encapsulation mapping entry; extracting a flow identifier from the encapsulation mapping entry; and replacing part of the packet with the flow identifier to produce an encapsulated packet.
Owner:MICROSOFT TECH LICENSING LLC
Router and routing protocol redundancy
InactiveUS6910148B1Reduce service outageReduce degradationData switching networksRedundant hardware error correctionSoftwareRouting protocol
A router and routing protocol redundancy are disclosed to reduce service outage or degradation for a network device and thus to increase service availability on a network due to software and hardware failures of the network device. A network device such as router includes a redundancy platform having an active controller system and a standby controller system. A routing protocol state change is received or generated by the active controller system. The received or generated routing protocol state change is replicated to the standby controller system. By replicating the routing protocol state change, the standby controller system can maintain the routing protocol sessions for the network device if a failure occurs in the active controller system. Furthermore, the routing protocol states are maintained in realtime to handle the dynamic changes created by routing protocols.
Owner:RPX CORP
Router and routing protocol redundancy
InactiveUS20050265346A1Reduce service outage and degradationImprove service availabilityData switching by path configurationSoftwareRouting protocol
A router and routing protocol redundancy are disclosed to reduce service outage or degradation for a network device and thus to increase service availability on a network due to software and hardware failures of the network device. A network device such as router includes a redundancy platform having an active controller system and a standby controller system. A routing protocol state change is received or generated by the active controller system. The received or generated routing protocol state change is replicated to the standby controller system. By replicating the routing protocol state change, the standby controller system can maintain the routing protocol sessions for the network device if a failure occurs in the active controller system. Furthermore, the routing protocol states are maintained in realtime to handle the dynamic changes created by routing protocols.
Owner:RPX CORP
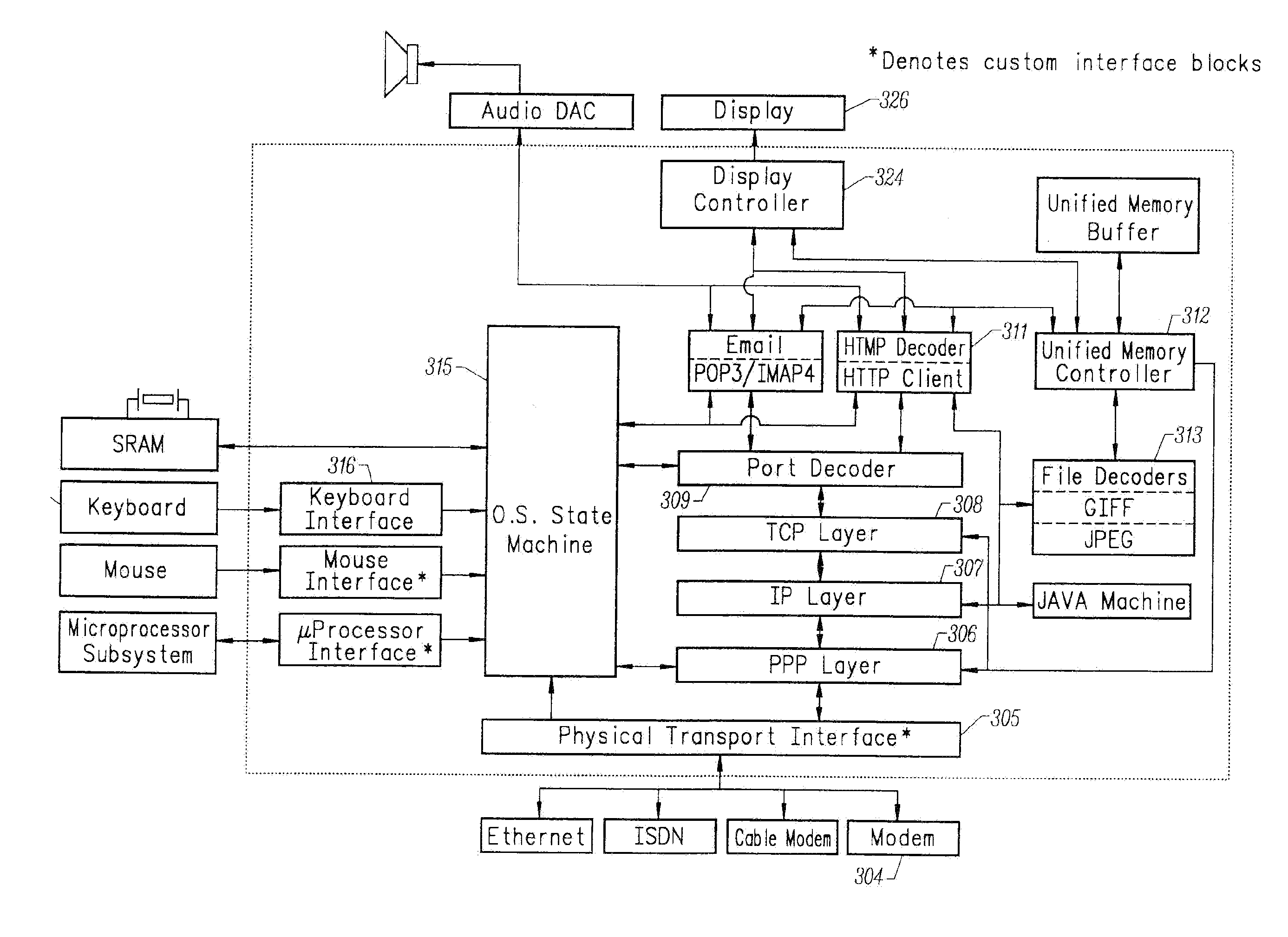
Gigabit Ethernet Adapter
InactiveUS20070253430A1Fast communication speedCompact solutionWide area networksRaw socketSmall form factor
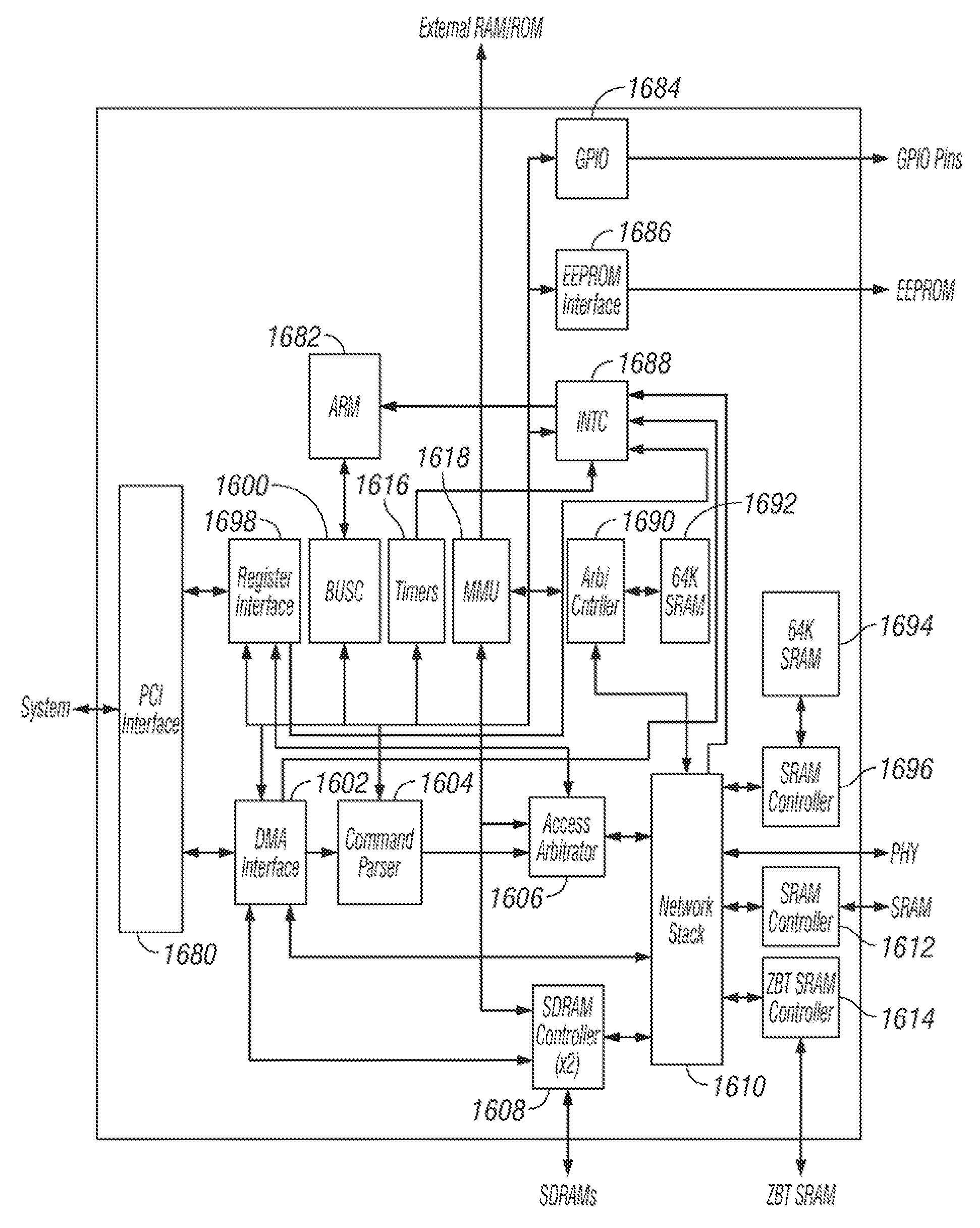
A gigabit Ethernet adapter provides a provides a low-cost, low-power, easily manufacturable, small form-factor network access module which has a low memory demand and provides a highly efficient protocol decode. The invention comprises a hardware-integrated system that both decodes multiple network protocols byte-streaming manner concurrently and processes packet data in one pass, thereby reducing system memory and form factor requirements, while also eliminating software CPU overhead. A preferred embodiment of the invention comprises a plurality of protocol state machines that decode network protocols such as TCP, IP, User Datagram Protocol (UDP), PPP, Raw Socket, RARP, ICMP, IGMP, iSCSI, RDMA, and FCIP concurrently as each byte is received. Each protocol handler parses, interprets, and strips header information immediately from the packet, requiring no intermediate memory. The invention provides an internet tuner core, peripherals, and external interfaces. A network stack processes, generates and receives network packets. An internal programmable processor controls the network stack and handles any other types of ICMP packets, IGMP packets, or packets corresponding to other protocols not supported directly by dedicated hardware. A virtual memory manager is implemented in optimized, hardwired logic. The virtual memory manager allows the use of a virtual number of network connections which is limited only by the amount of internal and external memory available.
Owner:NVIDIA CORP
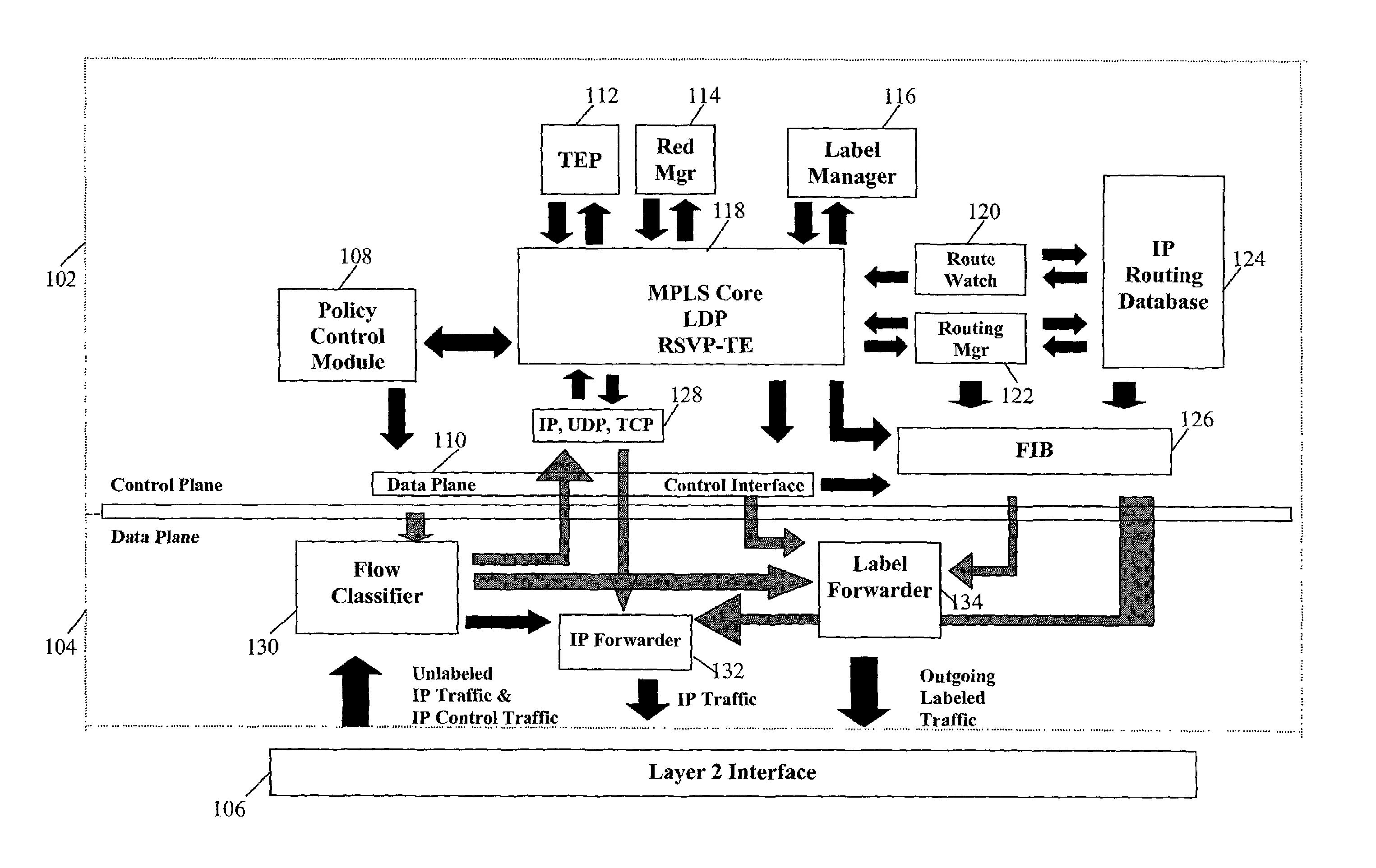
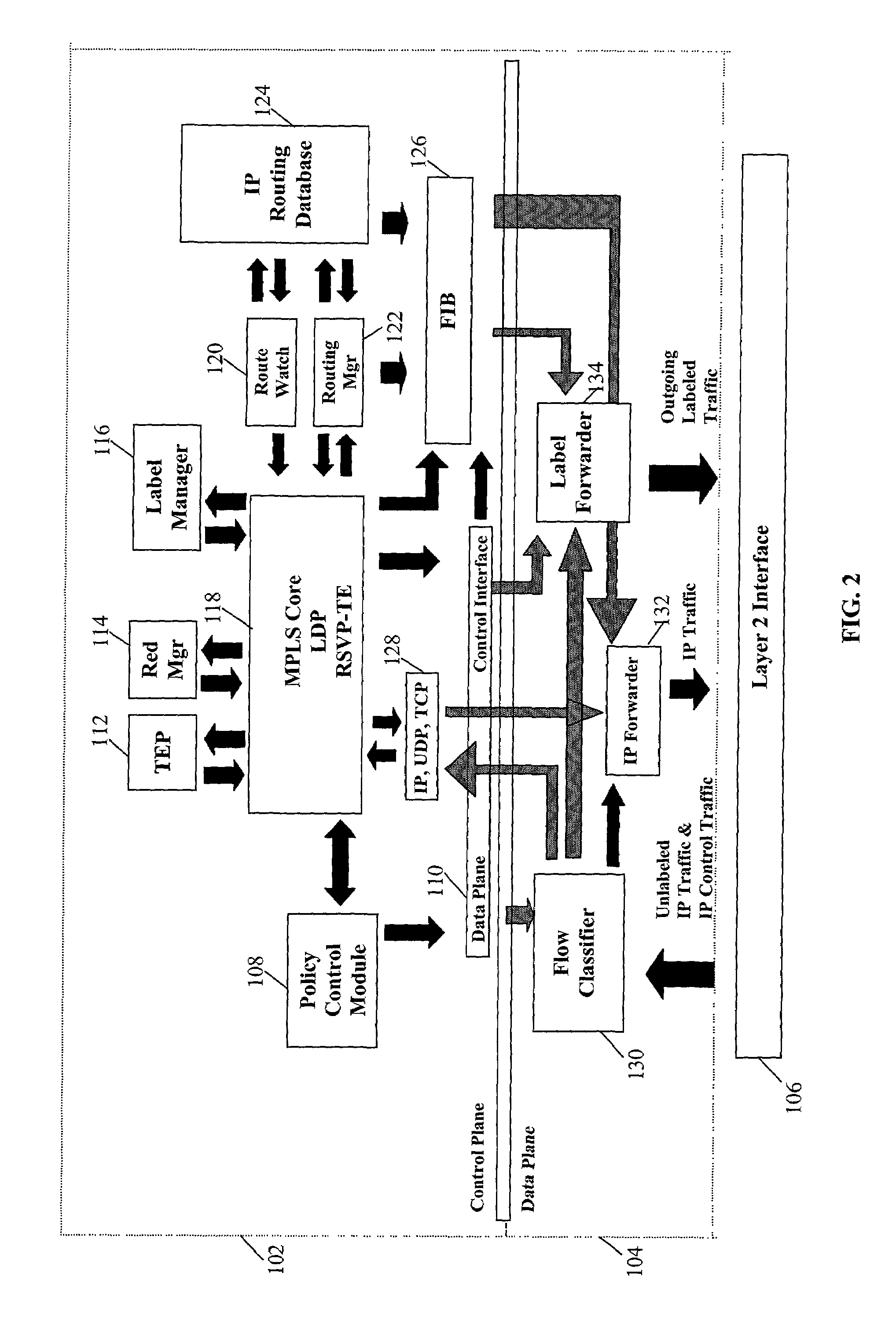
Method and system for implementing MPLS redundancy
The present invention relates to a method and system for implementing protocol redundancy in a router. In particular, the invention relates to providing redundancy of multi protocol label switching (MPLS). In one aspect, the present invention provides MPLS redundancy wherein all protocol states are mirrored. An active processor provides MPLS operations. In the present invention, a standby processor is coupled to the active processor. During the initial synchronization, all protocol information from the active processor is forwarded to the standby processor. The protocol information can include event information and state information. Thereafter, any updates of protocol information are immediately forwarded to the standby processor in an orderly and controlled manner. Upon failure of the active processor, the standby processor takes over as the active processor. All MPLS protocol operations are performed on the new active processor.
Owner:NOKIA TECH OY
Stackable routers employing a routing protocol
ActiveUS20050135357A1Reduce bandwidth requirementsMaintain relationshipData switching by path configurationPrimary stationNetwork router
A stack of network routers is composed of at least one (elected) master unit and one or more slave units each capable of running a routing protocol. Only the master unit runs the entire routing protocol at a given time. It forwards direct update messages via a transmission control protocol to each of the slave units. These direct update messages may include specific packet formats for the protocol state machinery where such machinery is required by the routing protocol, e.g. the interface state machine and the neighbor state machine for the OSPF protocol, and for the net databases, e.g. the link state databases for the OSPF protocol, in each of the slave units. Each slave unit may run its protocol state machinery (where provided) based purely on the direct update messages received from the master. The synchronisation of the net databases may be based on snooping net update packets and a comparison of the information received thereby with verification data messages sent from the master unit. The synchronization allows the running of the routing protocol on multiple physical routers in a stack without requiring the overhead of a back-up unit that would not perform routing unless a master router unit became unavailable.
Owner:VALTRUS INNOVATIONS LTD
Method for Acquiring Packet Data Convergence Protocol Status Report and Packet Data Convergence Protocol Entity
ActiveUS20120224525A1Quality improvementError preventionFrequency-division multiplex detailsQuality of serviceCommunications system
The present invention discloses a method for acquiring a Packet Data Convergence Protocol (PDCP) status report and a packet data convergence protocol entity. The method comprises the steps of: a PDCP entity transmitting to an opposite PDCP entity a PDCP Protocol Data Unit (PDU) used to request the transmission of a PDCP status report; and the PDCP entity receiving the PDCP status report which is transmitted from the opposite PDCP entity according to the PDCP PDU. By the present invention, the quality of service and the performance of the wireless communication system are improved.
Owner:ADVANCED STANDARD COMM LLC
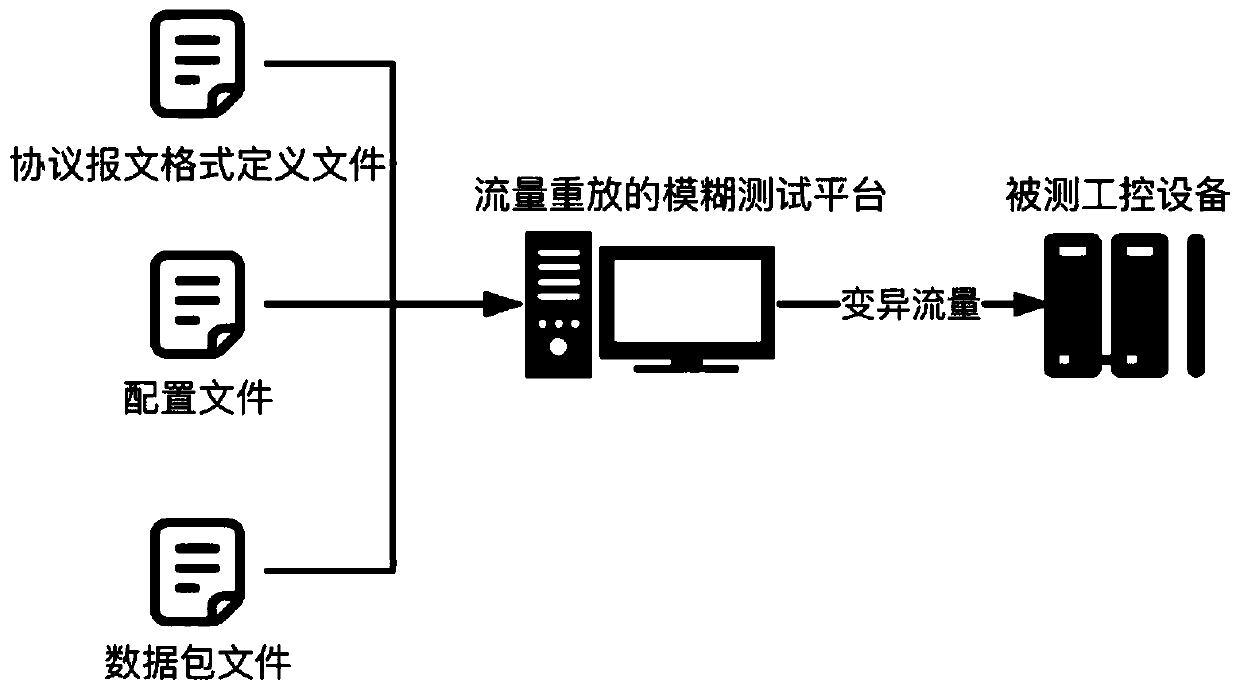
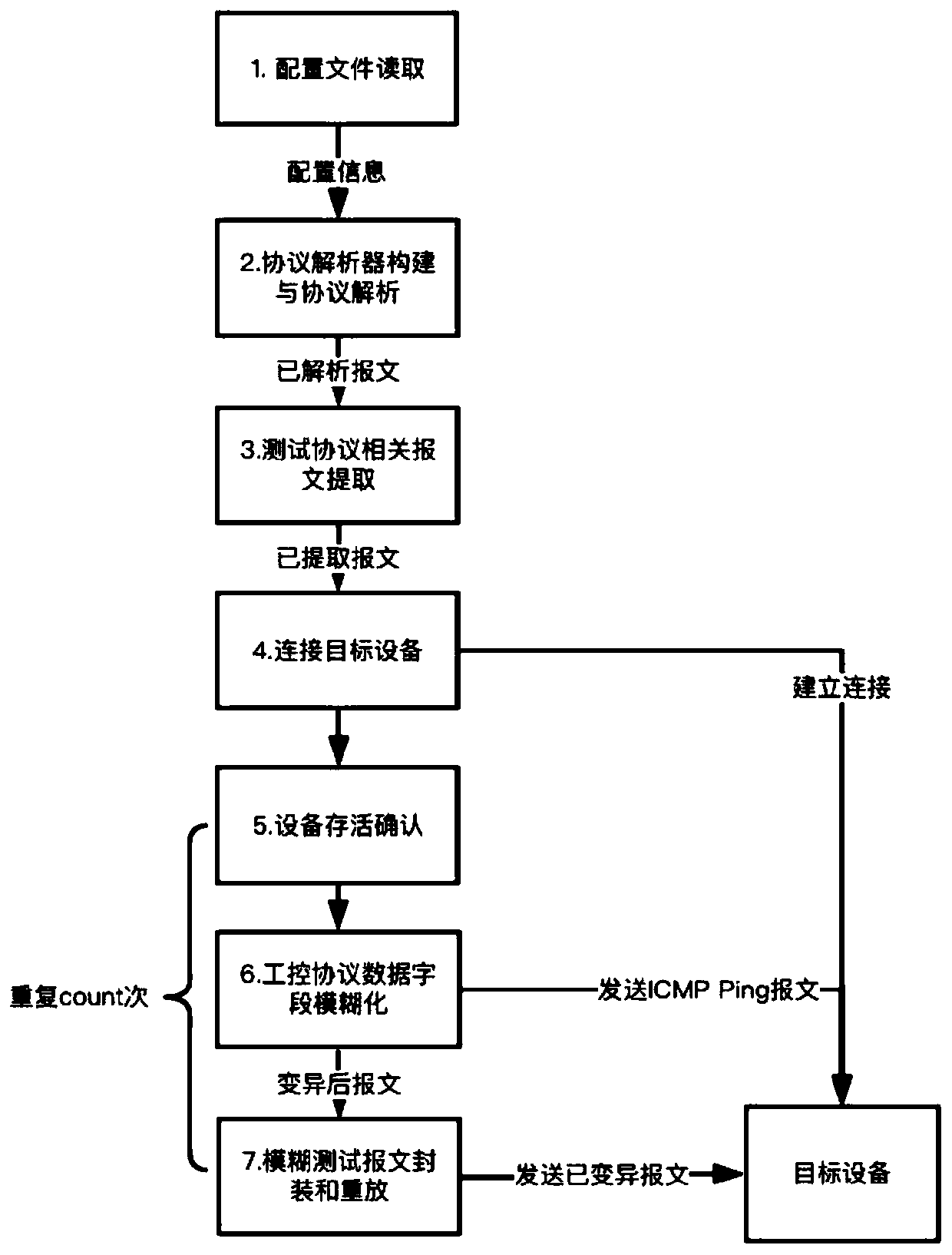
Industrial control protocol fuzzy test method based on flow replay
ActiveCN110505111AShorten the test preparation phaseData switching networksTraffic capacityProtocol Application
The invention relates to the field of industrial network security, in particular to an industrial control protocol fuzzy test method based on flow replay. The invention aims to provide an industrial control protocol fuzzy test method based on flow replay. Real protocol flow data of an operation environment of industrial control equipment is taken as a basis. A format is defined through a simple configuration file format and an industrial control protocol message. A corresponding protocol analyzer is constructed. An device protocol state message is extracted to fuzzify an industrial control protocol field specified by a user. Message application layer data is extracted. The message application layer data is packaged and replayed. An industrial control protocol fuzzy test is quickly and efficiently carried out on the premise of ensuring effective input and complete establishment of a protocol session. The invention is suitable for automatic testing of existing industrial control protocolvulnerability mining and industrial control protocol research and development and the like.
Owner:HANGZHOU DIANZI UNIV
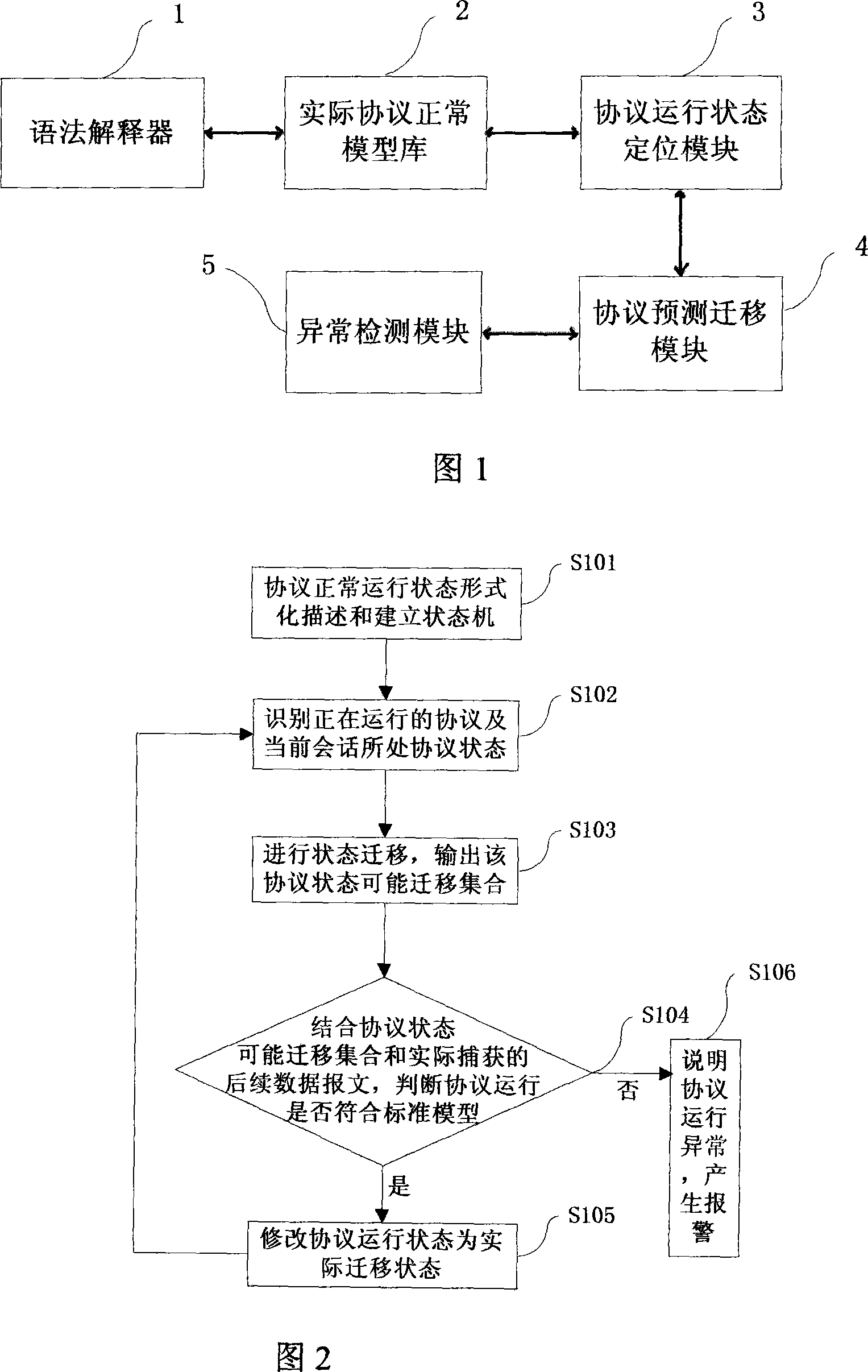
Condition detection based protocol abnormity detecting method and system
The present invention relates to a based on a status measure protocol abnormal measure method and system. The foundation of a protocol normal running state model comprises the examination of a protocol formal description expression and the making of a correlation protocol state machine; a protocol running state orientation moment realizes the exact orientation of the used protocol state in the present conversation towards the exact network communication data message; a protocol running state moving moment realizes the forecast of the next likely ongoing state moving and makes a normal state running concourse of the after-orientation protocol state; an abnormal examination moment judges whether the present protocol running accords with the protocol standard model and return the examination result by the gained subsequent message and the forecast running concourse. The present invention can check the correlative abnormal protocol in the network protocol communication process according to the exact protocol of the practically gained message and can conveniently expand the protocol normal running model according to the practical requirement.
Owner:BEIJING VENUS INFORMATION TECH +1
Method for detecting unknown abnormal behaviors of website
ActiveCN107438079AAvoid paralysisEarly warning of network problemsData switching networksDirected graphAccess time
The invention relates to a method for detecting the unknown abnormal behaviors of a website, and the method comprises the steps: obtaining original website information, carrying out the preprocessing and learning, and completing a directed graph and a webpage in-degree table of the website; detecting the access abnormal data of a single page; giving an alarm if the abnormality is detected, and adding one to the number of alarm times; detecting the access abnormality data of a key service; giving an alarm if the abnormality is detected, and adding one to the number of alarm times; detecting the access abnormality data of a single user; giving an alarm if the abnormality is detected, and adding one to the number of alarm times; counting the alarm times, and detecting the number of alarm times of a website HTTP protocol status code; giving an alarm to a website with the number of alarm times of the website HTTP protocol status code being greater than 20 in each half of an hour, carrying out the statistics of abnormal webpage URLs, and carrying out the sorting according to the number of access times; and carrying out the inspection. The method is used for detecting the security flaws of the website and various types of known threats, analyzing the unknown illegal connection and access, carrying out the early warning for a network problem, avoiding the paralysis of a user's network to the greatest extent, and facilitating the subsequent inspection, treatment and maintenance.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Network load balancing with connection manipulation
ActiveCN1607781AData switching by path configurationMultiple digital computer combinationsComputer scienceProtocol stack
Owner:MICROSOFT TECH LICENSING LLC
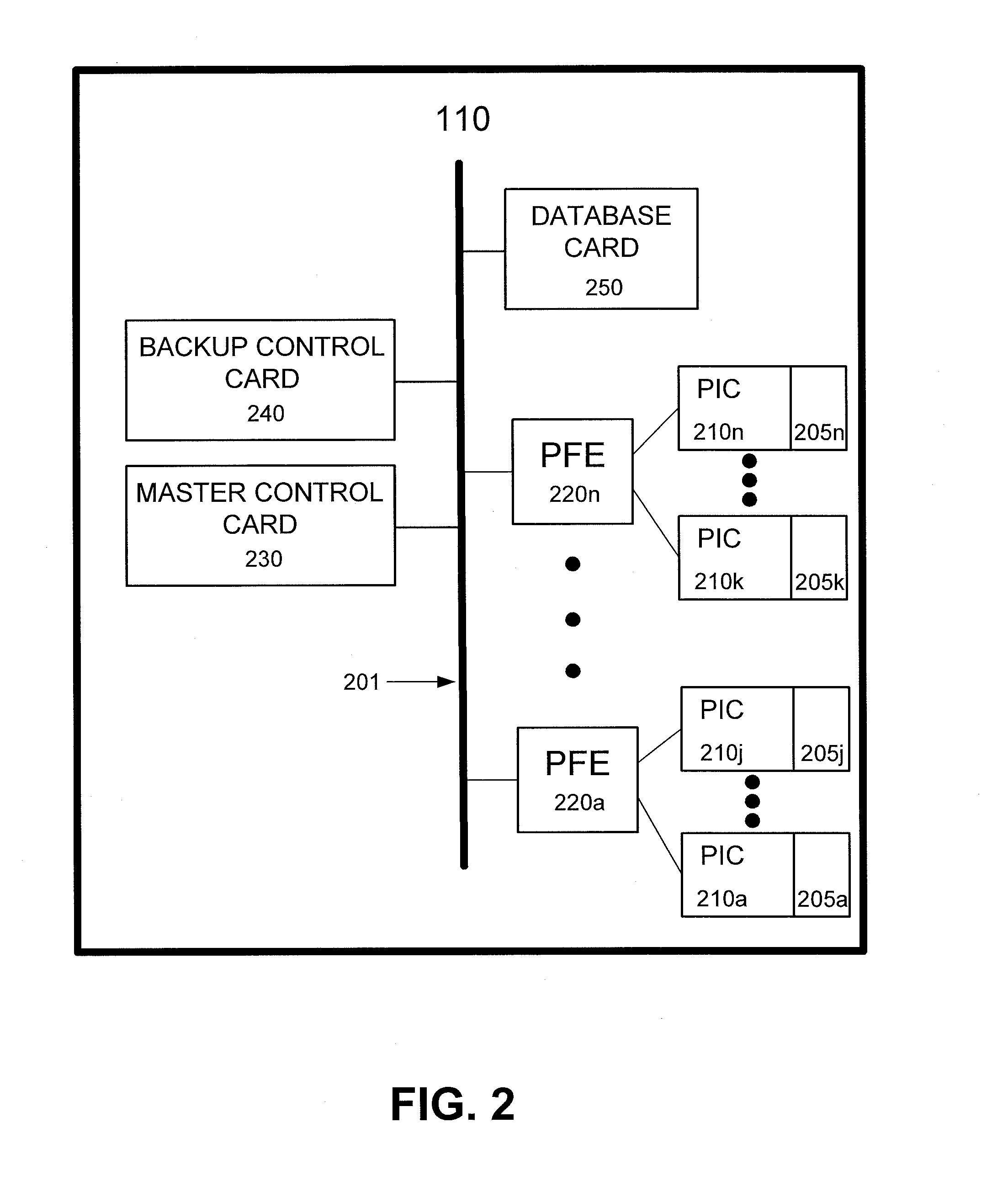
Method and apparatus for hitless failover in networking systems using single database
A device includes a master control card that performs control plane processing, a backup control card, where the backup control card takes over control plane processing if the master control card goes out of service, and a database card that connects to the master control card and the backup control card, where the database control card stores information relating to control plane processing. A method of achieving hitless failover in a network element includes detecting that a master control card of the network element has gone out of service, designating the backup control card as a new master control card of the network element, establishing communication with a database card of the network element, and retrieving protocol states information from the database card.
Owner:JUMIPER NETWORKS INC
Efficient marking of shared cache lines
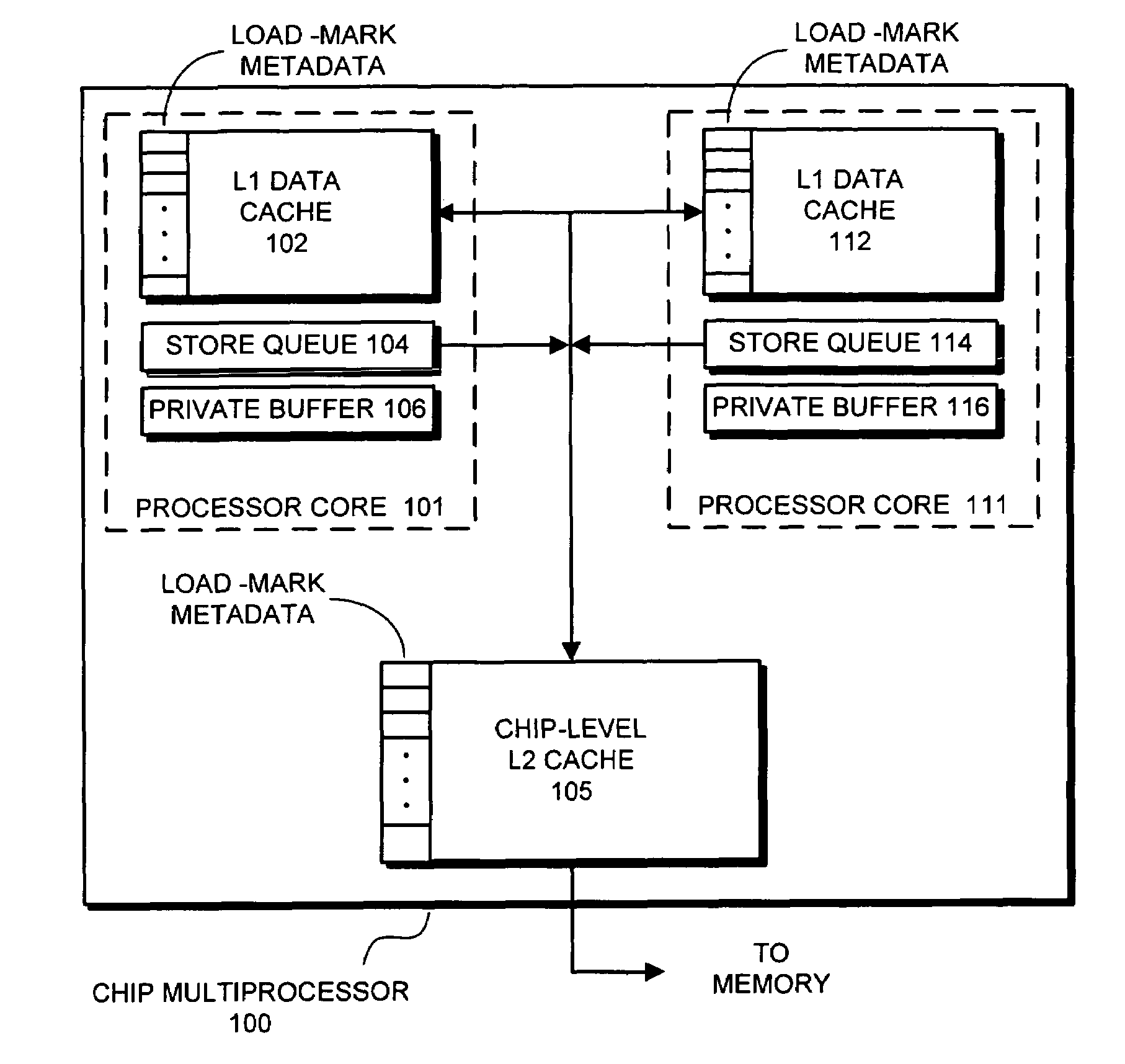
ActiveUS20080140935A1Effective markingMemory architecture accessing/allocationMemory adressing/allocation/relocationMulti processorParallel computing
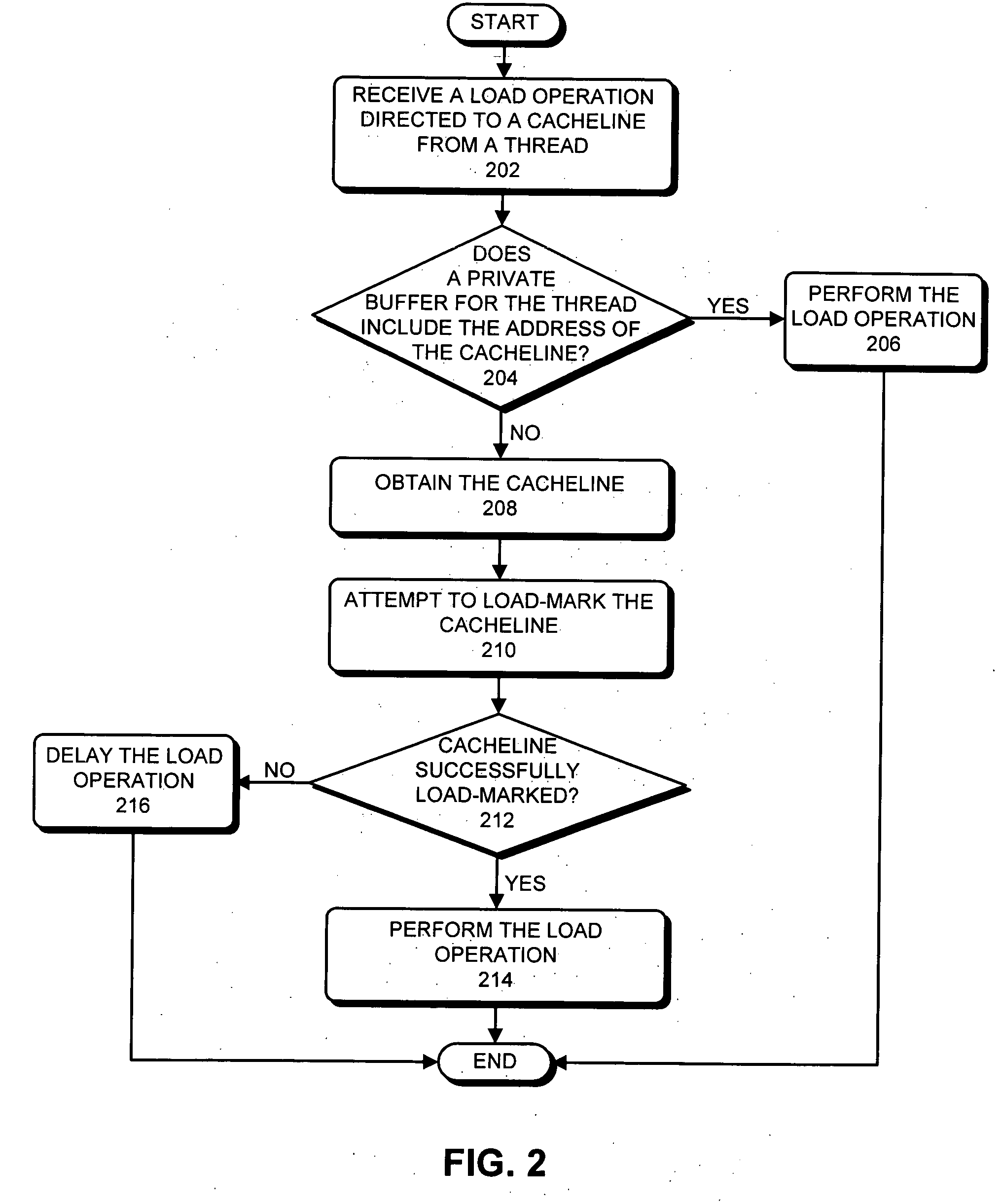
One embodiment of the present invention provides a system that efficiently marks cache lines in a multi-processor computer system. The system starts by receiving a load request for a cache line from a requesting thread. Upon receiving the load request, the system loads a copy of the cache line into a local cache for the requesting thread. The system then load-marks the copy of the cache line in the local cache by incrementing a reader count value contained in metadata for the copy of the cache line, regardless of the cache coherency protocol status of the copy of the cache line, whereby the system updates the metadata in the local copy of the cache line without obtaining exclusive access to the cache line.
Owner:ORACLE INT CORP
Annular mimicry architecture without protocol state, defense method and readable storage medium
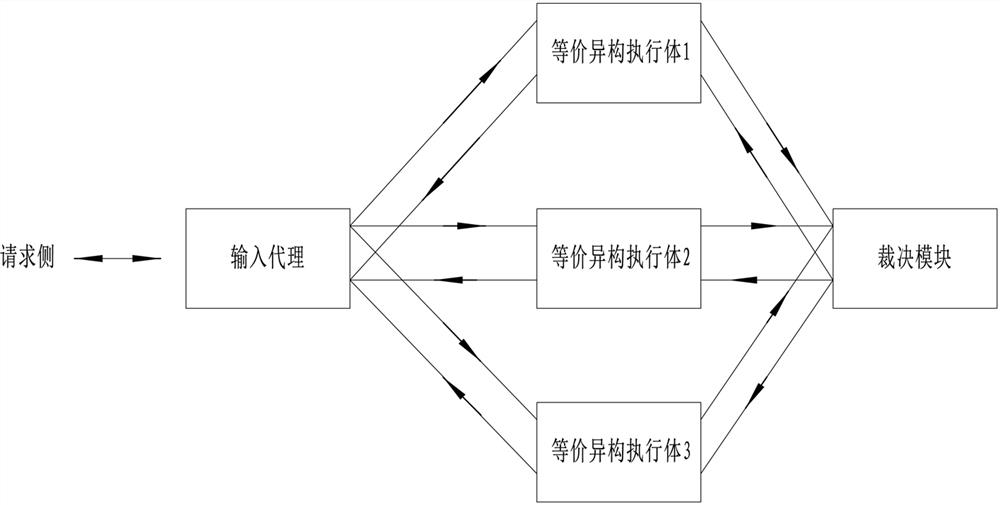
The invention provides a mimicry defense method for an annular mimicry architecture without a protocol state. The method comprises the following steps that: a request side sends request information toan input agent, and the input agent copies and distributes the request information to each equivalent heterogeneous execution body through a one-way communication channel after normalizing a protocol; each equivalent heterogeneous execution body processes the request information and sends response information to a judgment module through a one-way communication channel; and the judgment module judges the response information, sends the response information to a request side through a one-way request side communication channel if judgment succeeds, and sends the judgment information to a feedback controller if judgment fails so as to adjust the state of each heterogeneous execution body. According to the mimicry defense method, the requirement on the input agent is reduced, the structure of the agent is simplified, the agent is prevented from becoming a performance bottleneck, the problem that the agent is easily attacked is solved, and the security of the whole mimicry architecture isimproved.
Owner:河南信大网御科技有限公司 +1
Electric power communication protocol exception detection method based on dynamic extensible finite state
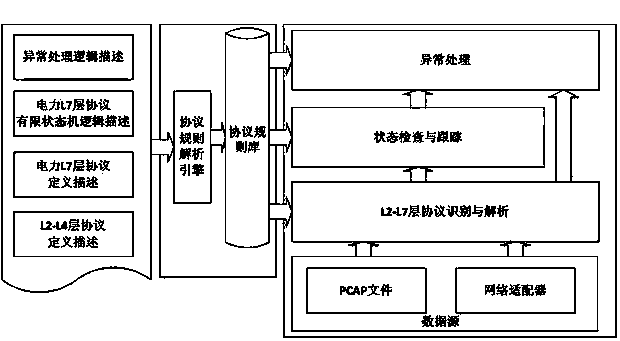
The invention discloses an electric power communication protocol exception detection method based on a dynamic extensible finite state. The method includes describing definitions of L2 to L7 (link layer to the application layer) of an electric power communication protocol, protocol state machine logic and exception handling logic according to protocol description rules, acquiring protocol rule definition files, translating the protocol rule definition files to form a protocol rule database through a protocol rule analytic engine, and performing protocol analysis, state detection and exception processing on network data packages according to the protocol rule database. The dynamic extensible support is provided for various application layer protocols and is further provided for application layer context state detection and exception processing, electric power communication protocol exception detection is facilitated, and the method has promised application prospect.
Owner:STATE GRID CORP OF CHINA +3
Security testing method and device for protocol implementation
InactiveCN102624574AImprove execution efficiencyLow costData switching networksComputer hardwareState model
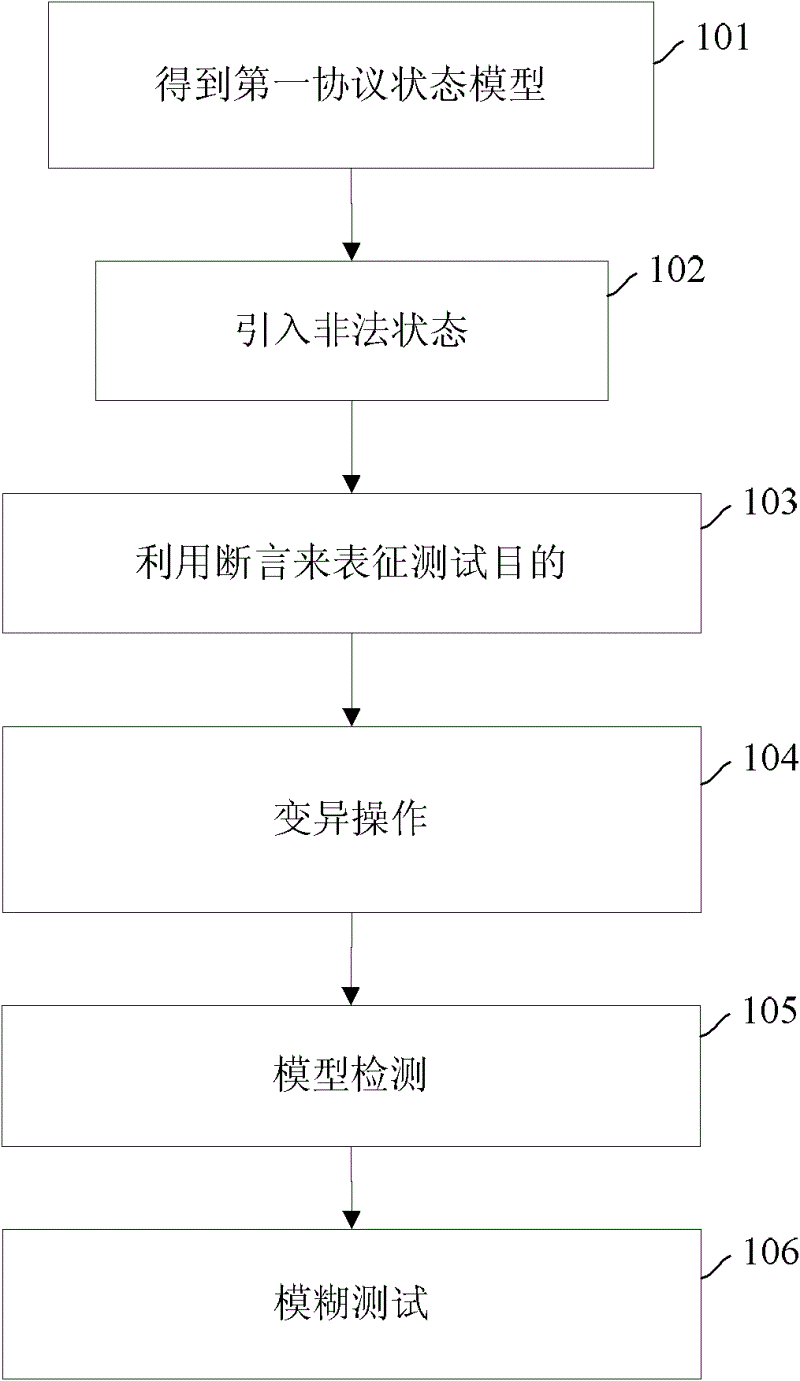
The embodiment of the invention provides a security testing method for protocol implementation, and comprises: mapping a protocol specification on which the protocol implementation is based to a first protocol state model; forming a second protocol state model by introducing an illegal state that corresponds to security failure into the first protocol state model; characterizing the testing purposes of the first protocol state model and the second protocol state model by utilizing an assertion; generating a mutated protocol state model by carrying out a mutative operation on the second protocol state model; performing a model test on the mutated protocol state model according to the assertion to generate a testing suite obtained from mapping a counter-example in the mutated protocol state model that violates the assertion; and carrying out a fuzzing test on the protocol implementation by a testing suite to test security holes in protocol implementation. The invented embodiment further provides a corresponding testing device. According to the invented embodiment, efficient and low-cost protocol security test is realized.
Owner:SIEMENS AG
Protocol test generating method of parallel expansion finite-state machine based on variable dependence
ActiveCN102404167AReflect characteristicsFix non-executable issuesData switching networksPathPingParallel Extensions
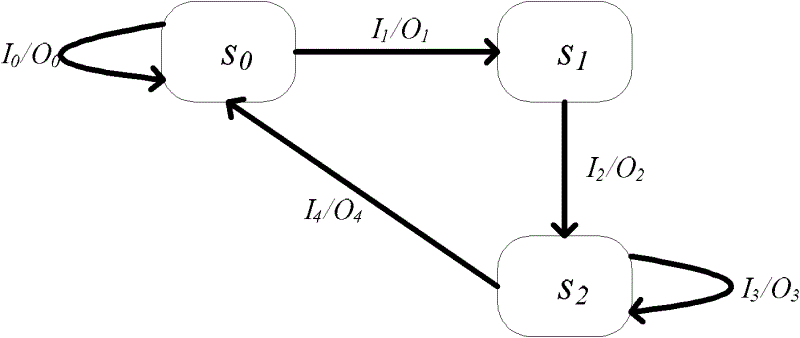
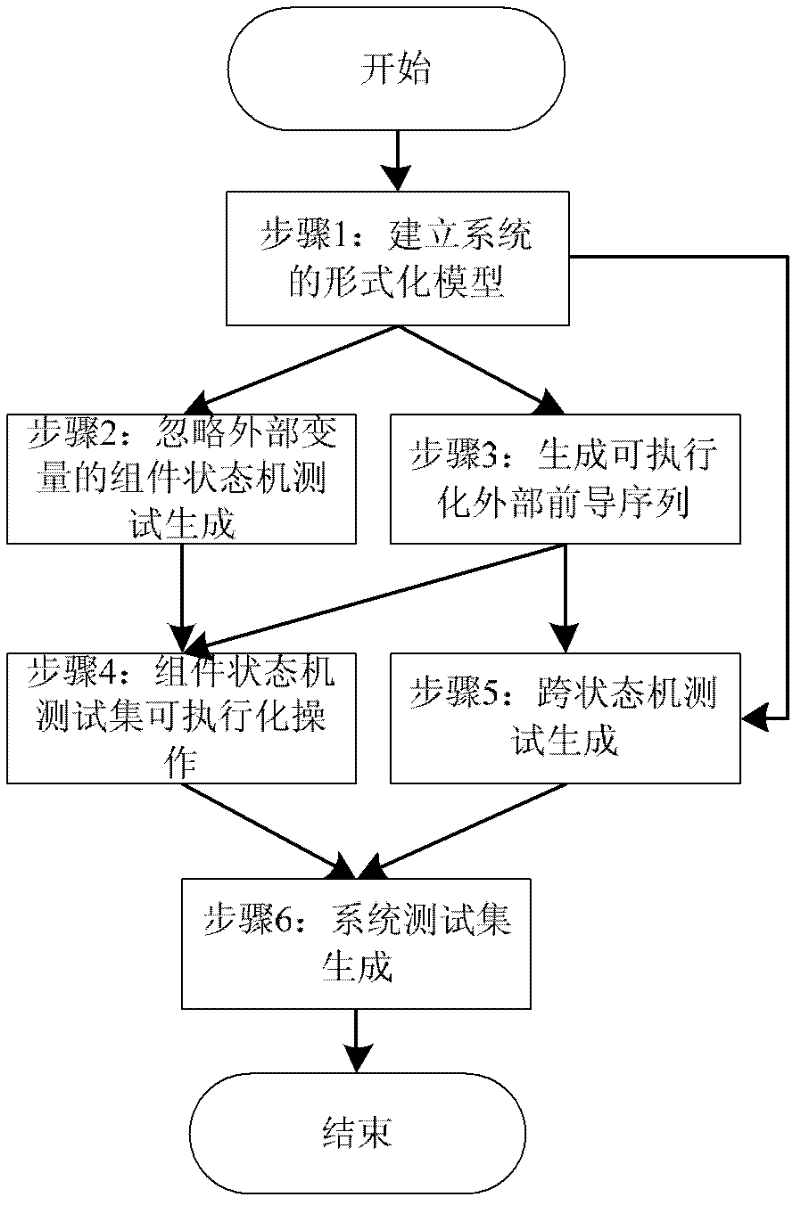
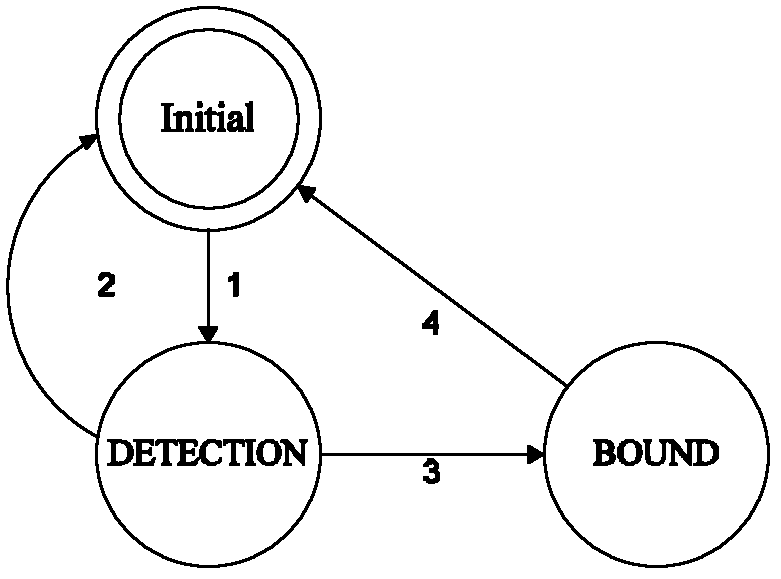
The invention relates to the technical field of a network protocol test and discloses a protocol test generating method of a parallel expansion finite-state machine based on variable dependence. The protocol test generating method comprises the following steps of 1. in a computer, describing a protocol specification of tested network equipment as a parallel expansion finite-state machine model; 2. generating a component state machine abstract test set by adopting a test generation technology of the expansion finite-state machine ignoring the variable dependence; 3. aiming at external variables, generating an executable external leader sequence; 4. carrying out executable processing on the component state machine abstract test set by linking the external leader sequence; 5. generating a cross-state machine abstract test set with respect to the external variables; and 6. combining the abstract test set processed in the step 4 and the abstract test set generated in the step 5, deleting a repeated or an included test sequence and obtaining the abstract test set of a protocol state machine. By adopting the protocol test generating method, the non-executable problem of the path caused by the variable dependence is solved, and the state explosion is avoided.
Owner:TSINGHUA UNIV
Method and system of accurate recognition in P2P protocol based on behavior characteristics
In the network protocol communication process, the invention can extracts the behavior feature from the information carried by the captured message, and based on the behavior feature, realizes the accurate identification to P2P protocol. The method comprises behavior feature model base, protocol state location multi mode match module, protocol state migration module, attach detection / audit module. Said protocol behavior feature model base is used to create the matching feature of protocol dedicated state; the protocol state location module is used to use multi mode matching approach to realize the location for protocol state of data message; the protocol state migration module is used to realize the migration tracing for the protocol running state; the attack detection / auditing module is used to call the relevant detection or auditing function according to the pre-stage output result.
Owner:BEIJING VENUS INFORMATION TECH
Virtual multicast routing for a cluster having state synchronization
InactiveCN1798105ALoad balancingSpecial service provision for substationNetwork packetExchange protocol
A system, apparatus, and method are directed to managing multicast routing using a network cluster. A cluster master actively participates in multicast control protocol communications with the cluster neighbors, while non-master member nodes, do not participate in the protocols' operation outside of the cluster. However, each cluster member maintains virtually the same protocol state, such that should the master become unavailable, another cluster member may assume the master role with minimum delay. New members to the cluster are synchronized by receiving initial protocol state information from the master. After the initial protocol state synchronization, cluster members actively monitor the network to acquire new protocol state information. In addition, cluster members exchange protocol state information between themselves that may not be obtainable off the network. Filtering of multicast data packets is performed by each cluster member, to load balance multicast data traffic across the cluster members.
Owner:NOKIA CORP
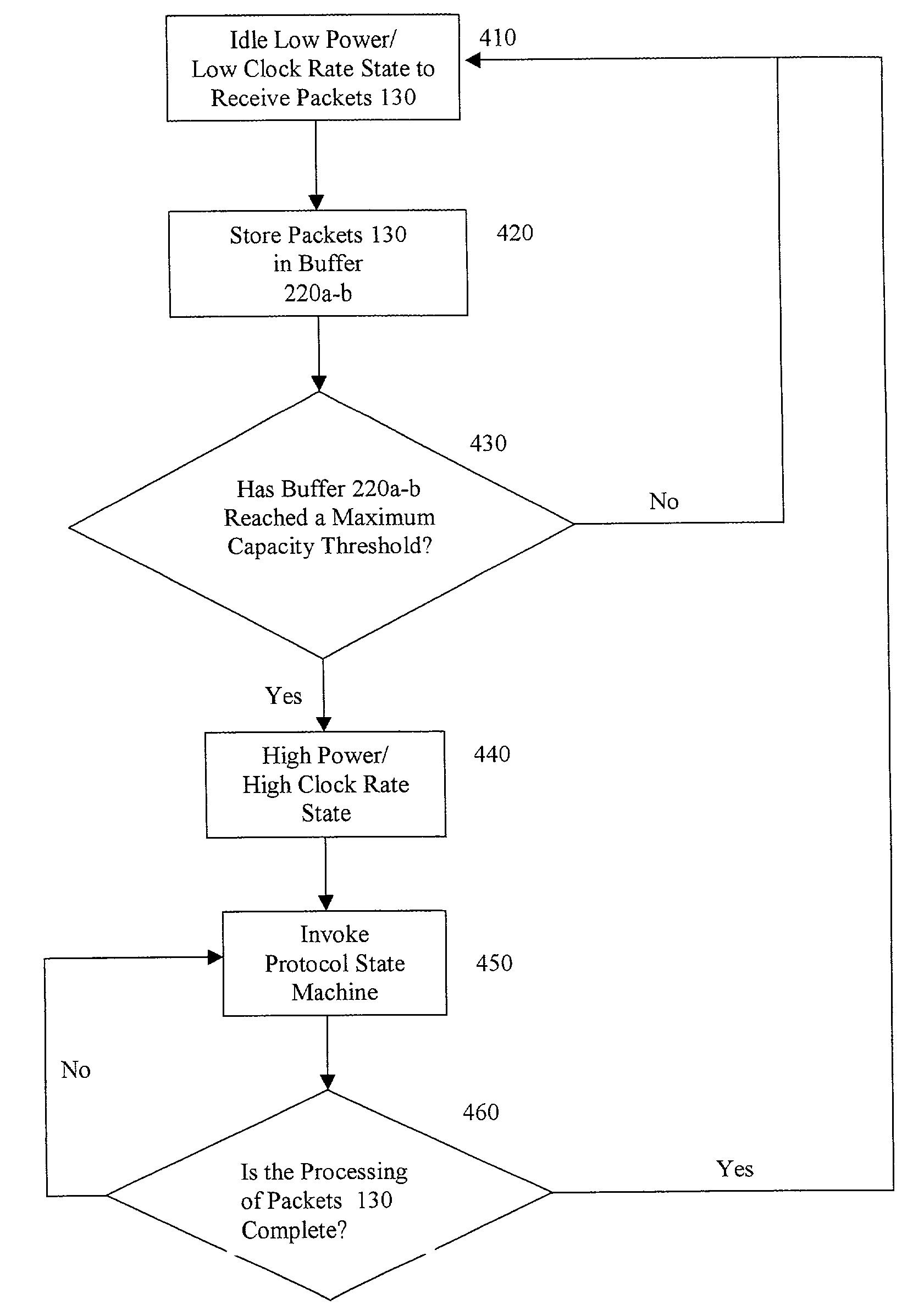
Method and apparatus for managing energy usage of processors while executing protocol state machines
A method and apparatus of implementing protocol state machines that conserve energy on energy conscious devices is disclosed. Under this method, most of the energy consuming protocol state machine context invocations or operations are aggregated in time and are scheduled at regular intervals. Such an aggregation leads to many contexts executing concurrently in a burst prior to entering a dormant state. Thus, resource usage can reach a predictable rate pattern of idle and active cycles. With such a pattern, it is possible to take advantage of the energy saving features of processors by downshifting the processor clock speed and use of other resources such as peripherals and buses. The intervals are configured to achieve a tradeoff between timely execution and energy consumption. The aggregation operates across two dimensions, namely, multiple instances of a protocol state machine and multiple layers of protocols in a layered architecture.
Owner:INTEL CORP
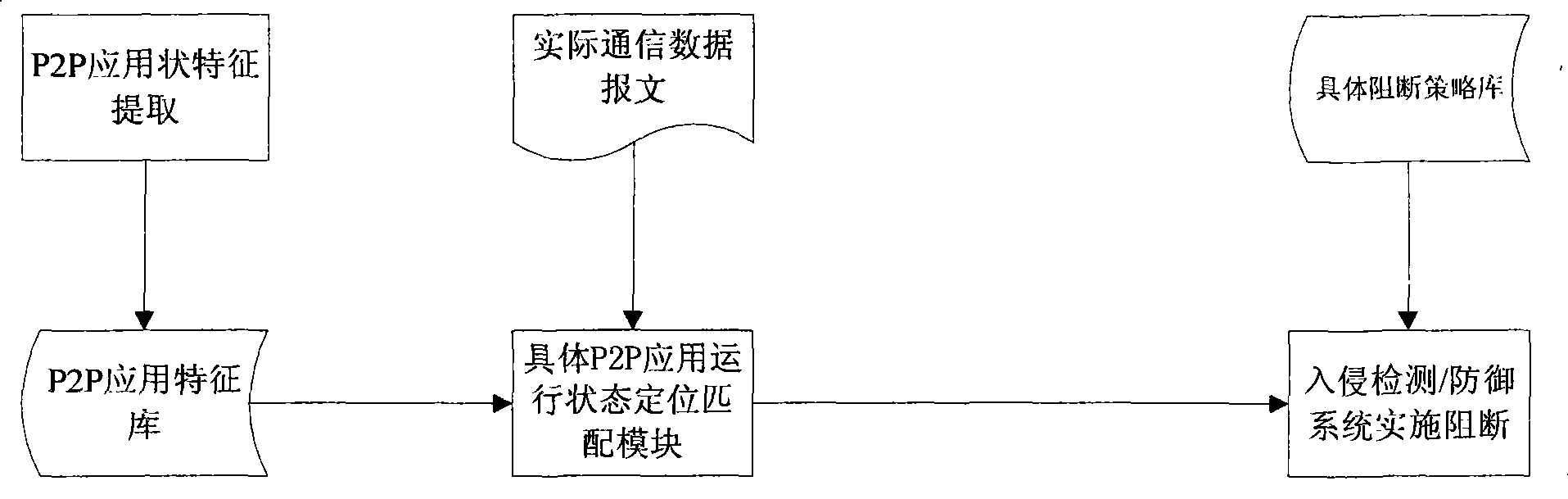
Method and system for monitoring P2P software
InactiveCN101442519AResolve accuracyImprove accuracyData switching networksNetworking protocolPattern matching
The invention relates to a P2P software monitoring method and a P2P software monitoring system capable of being used in network products. The method and the system can extract various protocol features during network protocol communication according to information carried by actually captured messages, so as to realize monitoring of P2P application, and can implement interdiction of different strategies according to actual demands and aiming at different running states. The method and the system comprise three stages of establishment of a protocol feature model, application stage identification and positioning, and implementation of corresponding interdiction strategies, wherein a module for establishing the protocol feature model works out matching features of specific states of detailed P2P application; an application stage identification and positioning module realizes positioning of application states and protocol states affiliated to detailed data messages in the multi-pattern matching mode; and a corresponding interdiction strategy module realizes establishment and correlation of related strategies and corresponding monitoring function.
Owner:BEIJING VENUS INFORMATION TECH
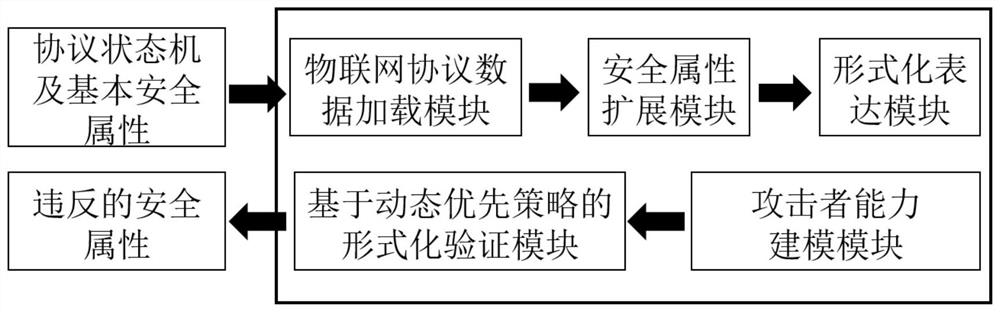
Internet of Things protocol security automatic analysis method and system based on formal verification
ActiveCN112153030AReduce manual burdenImprove securityData switching networksAttackSoftware engineering
The invention discloses an Internet of Things protocol security automatic analysis method and system based on formal verification, and the method comprises the steps: building a security attribute needing to be satisfied by a protocol based on an Internet of Things protocol state machine, and automatically achieving the formal description of an Internet of Things protocol and the security attribute needing to be satisfied by the Internet of Things protocol; modeling attacker ability by applying two attack scenes, and formal verification being realized based on a dynamic priority strategy. According to the Internet of Things protocol security automatic analysis method based on formal verification, protocol state machines, deployed on a plurality of Internet of Things platforms, of MQTT, CoAP and AMQP protocols can be efficiently converted into formal languages, and automatic and systematic security analysis is carried out.
Owner:杭州智达融信科技有限公司
Gigabit ethernet adapter
ActiveUS8218555B2Fast communication speedHighly efficient protocol decodeTime-division multiplexData switching by path configurationOne passRaw socket
A gigabit Ethernet adapter provides a provides a low-cost, low-power, easily manufacturable, small form-factor network access module which has a low memory demand and provides a highly efficient protocol decode. The invention comprises a hardware-integrated system that both decodes multiple network protocols in a byte-streaming manner concurrently and processes packet data in one pass, thereby reducing system memory and form factor requirements, while also eliminating software CPU overhead. A preferred embodiment of the invention comprises a plurality of protocol state machines that decode network protocols such as TCP, IP, User Datagram Protocol (UDP), PPP, Raw Socket, RARP, ICMP, IGMP, iSCSI, RDMA, and FCIP concurrently as each byte is received. Each protocol handler parses, interprets, and strips header information immediately from the packet, requiring no intermediate memory. The invention provides an Internet tuner core, peripherals, and external interfaces. A network stack processes, generates and receives network packets. An internal programmable processor controls the network stack and handles any other types of ICMP packets, IGMP packets, or packets corresponding to other protocols not supported directly by dedicated hardware. A virtual memory manager is implemented in optimized, hardwired logic. The virtual memory manager allows the use of a virtual number of network connections which is limited only by the amount of internal and external memory available.
Owner:NVIDIA CORP
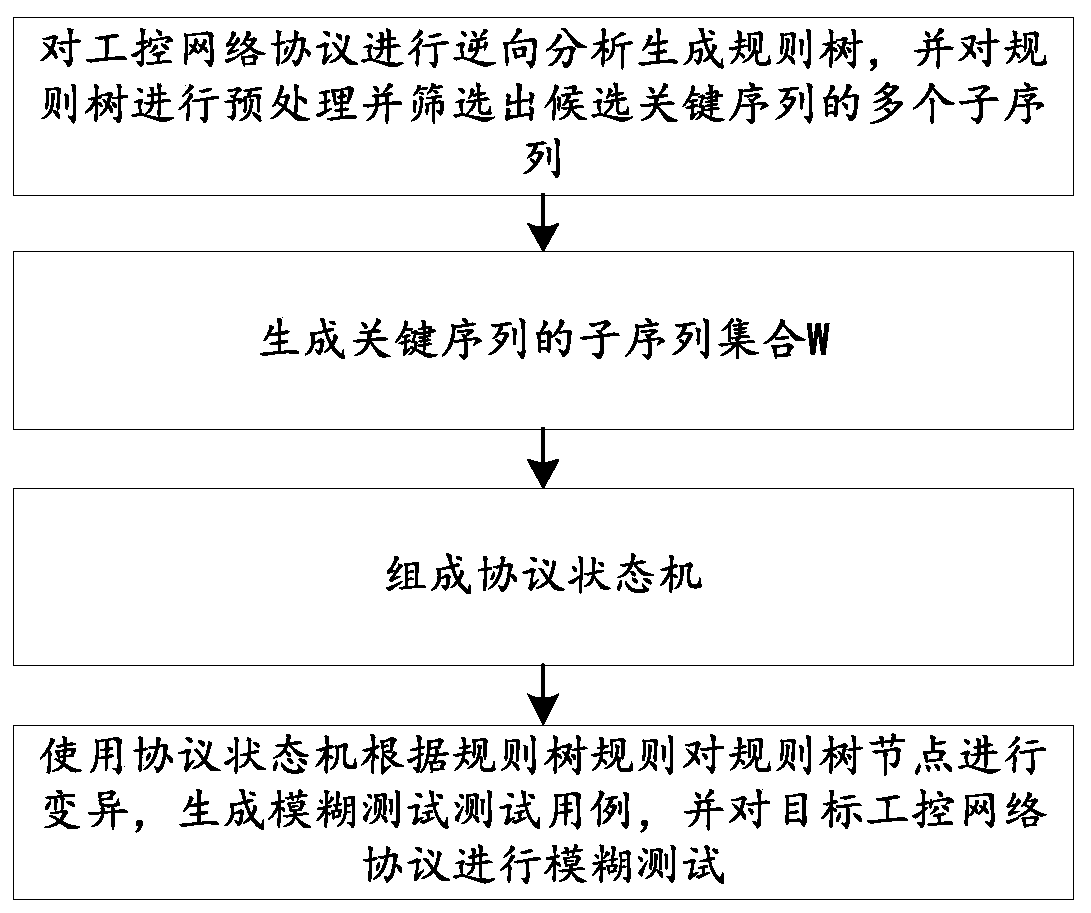
Method and system for fuzzy test of industrial control network protocol based on reverse analysis
InactiveCN110661778APromote generationSolve the problem of not being able to mine vulnerabilities in industrial control proprietary protocolsData switching networksGeneration processReverse analysis
The invention discloses a method and a system for fuzzy test of an industrial control network protocol based on reverse analysis, and belongs to the technical field of network security. The method comprises the following steps: performing reverse analysis on an industrial control network protocol to generate a rule tree, preprocessing the rule tree, and screening out a plurality of sub-sequences of candidate key sequences; generating a subsequence set W of the key sequences; forming a protocol state machine; and using a protocol state machine to perform variation on the rule tree nodes according to the rule tree rules, generating a fuzzy test case, and performing fuzzy test on the target industrial control network protocol. The problem that a traditional fuzzy test method cannot perform vulnerability mining on an industrial control proprietary protocol is solved, and the test case generation process is optimized.
Owner:CHINA ELECTRIC POWER RES INST +3
Graceful restart method based on PIM SM protocol and system thereof
ActiveCN101895475AImprove reliabilitySave bandwidthSpecial service provision for substationComputer hardwareIp address
The invention provides a graceful restart method based on a PIM SM protocol, which can realize faster convergence of multicast protocol states, and a system for realizing the method. In the method, neighbor equipment checks all interfaces connected with restart equipment, and if any IGMP member exists on the interfaces, an IGMP host member report is forged and sent to the restart equipment; the restart equipment recovers an IGMP member state under the interface corresponding to the IGMP host member report by analyzing the IP address of a multicast group in the IGMP host member report; the neighbor equipment on all the interfaces of the restart equipment checks IGMP member information on network segments connected with the restart equipment, and if any IGMP member exists, the IGMP host member report is constructed; and thus, the restart equipment can fast recover the IGMP member information on each interface without waiting for the IGMP member report respectively sent by the host on each interface. The invention enables the restart equipment control plane to quicken the recovery rate of the IGMP member state.
Owner:MAIPU COMM TECH CO LTD
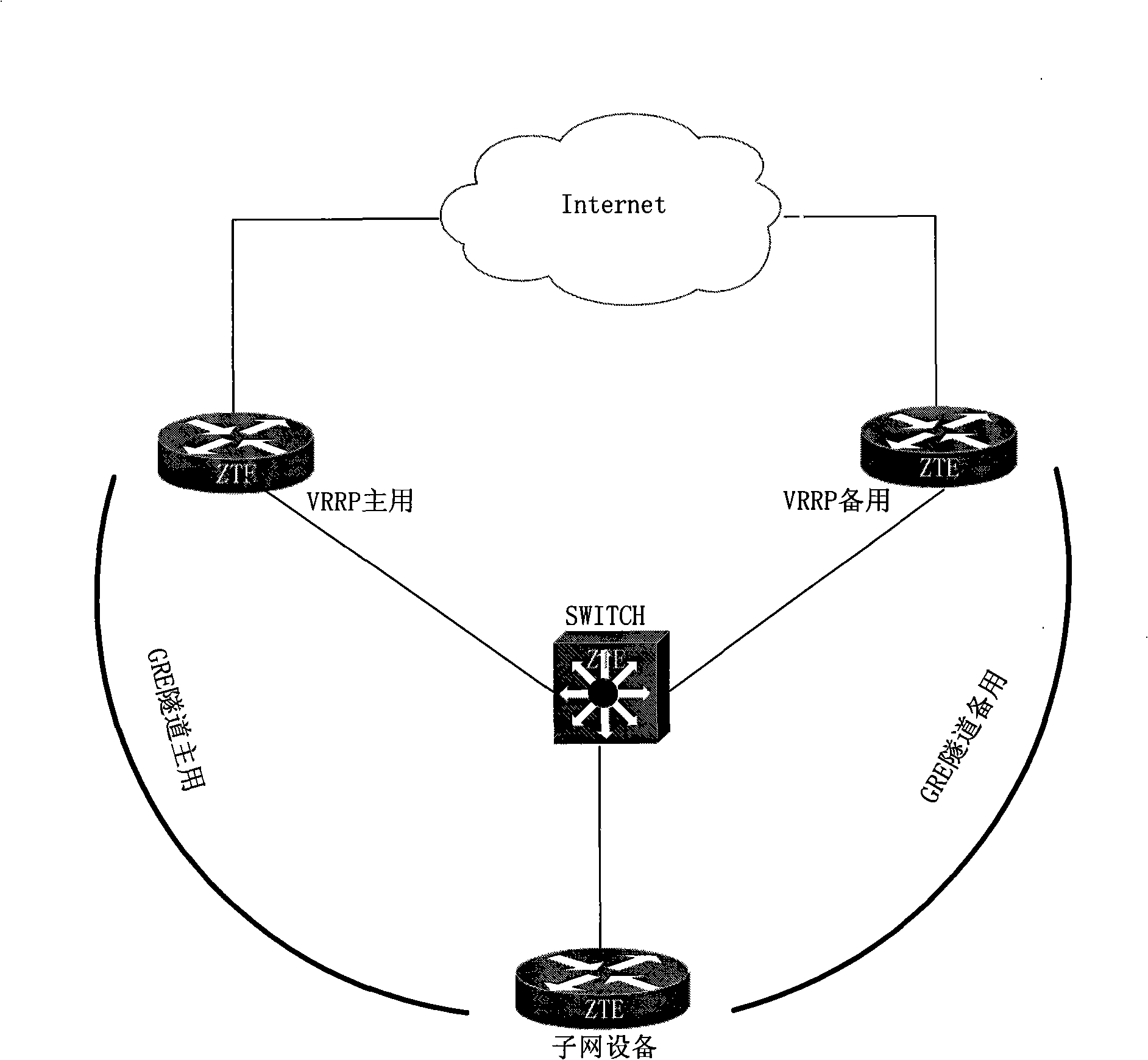
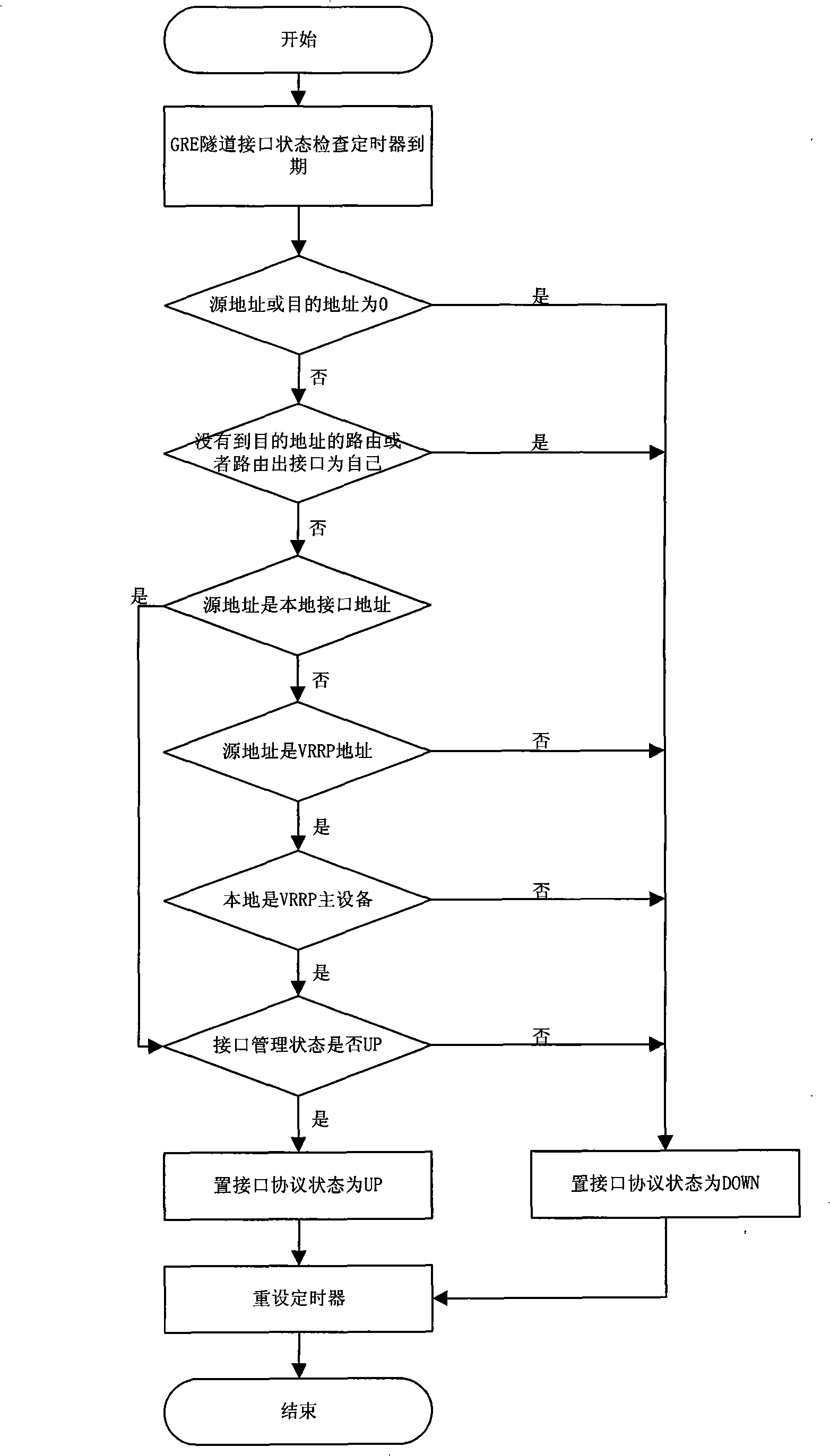
A method for virtual router to establish tunnel
The invention discloses a method for a virtual router to establish channels. The method comprises the steps of configuring universal router packaging channel information to a redundancy protocol equipment of a virtual router, setting a timer for inspecting the status of a channel port, regularly checking a source address and a destination address of the channel, and further checking the source address information of the channel if the source address and the destination address of the channel are not zero and the destination address of the channel is provided with a router, setting the protocol status of the channel port to be Up if an administrative status of the channel is Up, otherwise setting the administrative status of the channel to be Down and setting the timer for inspecting the status of the channel port again. By adopting the interaction of a GRE module and a VRRP module, the method provides a redundancy backup gateway which is supported by the VRRP technology when a subnet equipment adopts a GRE channel as a static default gateway, and improves the reliability and continuity of the running service to an access equipment when the GRE channel is adopted by a network system to forward data.
Owner:ZTE CORP
Network protocol fuzzy test method based on state migration traversal
ActiveCN109525457AGuaranteed to be comprehensiveReduce deliveryData switching networksComputer hardwareNetworking protocol
The invention provides a network protocol fuzzy test method based on state migration traversal, which comprises the following steps: protocol state machine obtaining, state machine optimal traversal path obtaining, traversal path marking and dynamic fuzzy testing. Based on the shortest path of all migrations of a traversal protocol state machine, the invention sequentially tests each state migration to ensure the comprehensiveness of the test range. The invention sends a test case according to the protocol state of the protocol entity, reduces the invalid message interaction, and improves thevalidity of the fuzzy test. The invention combines the input of the test case with the judgement of the protocol state, timely discovers the state abnormality of the protocol entity according to the UIO sequence of the protocol state and improves the working efficiency of the fuzzy test.
Owner:ARMY ENG UNIV OF PLA
Efficient marking of shared cache lines
ActiveUS7549025B2Effective markingMemory architecture accessing/allocationMemory adressing/allocation/relocationMulti processorParallel computing
One embodiment of the present invention provides a system that efficiently marks cache lines in a multi-processor computer system. The system starts by receiving a load request for a cache line from a requesting thread. Upon receiving the load request, the system loads a copy of the cache line into a local cache for the requesting thread. The system then load-marks the copy of the cache line in the local cache by incrementing a reader count value contained in metadata for the copy of the cache line, regardless of the cache coherency protocol status of the copy of the cache line, whereby the system updates the metadata in the local copy of the cache line without obtaining exclusive access to the cache line.
Owner:ORACLE INT CORP
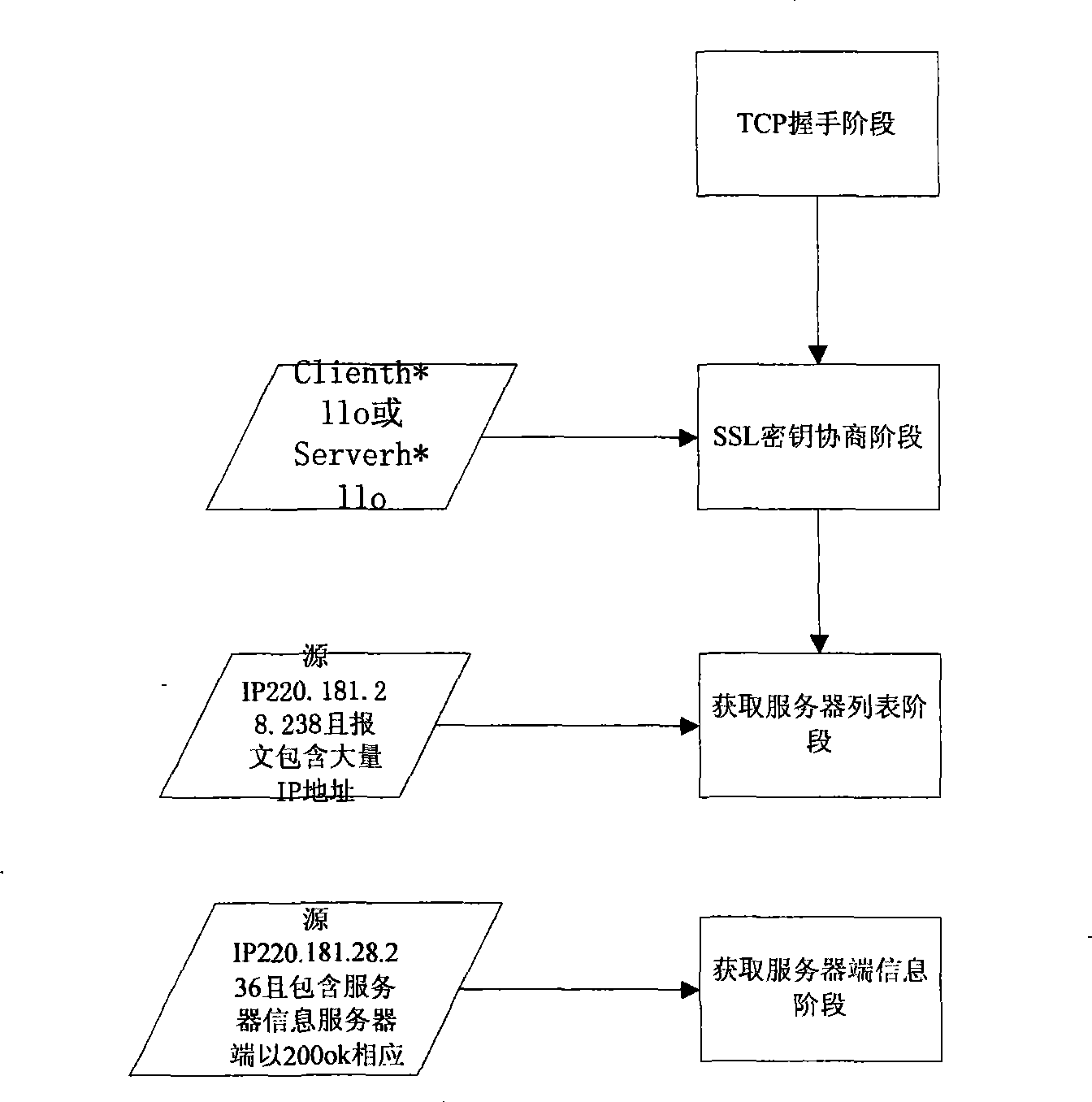
Systems and methods for evaluating encrypted data packets in a networked environment
Systems, methods, and apparatuses enable evaluating encrypted or obfuscated data packets being transmitted over a connection in a networked environment. In an embodiment, a security service utilizes one or more microservices operating as detectors to analyze characteristics of an encrypted or obfuscated network connection. Using the information from the detectors, the security service classifies the type of encryption protocol used on an encrypted connection and determines an extrapolated protocol state. Using the extrapolated protocol state with additional information received from the detectors, the security service determines a risk level associated with the connection and executes security actions on the connection based on the risk level.
Owner:FORTINET
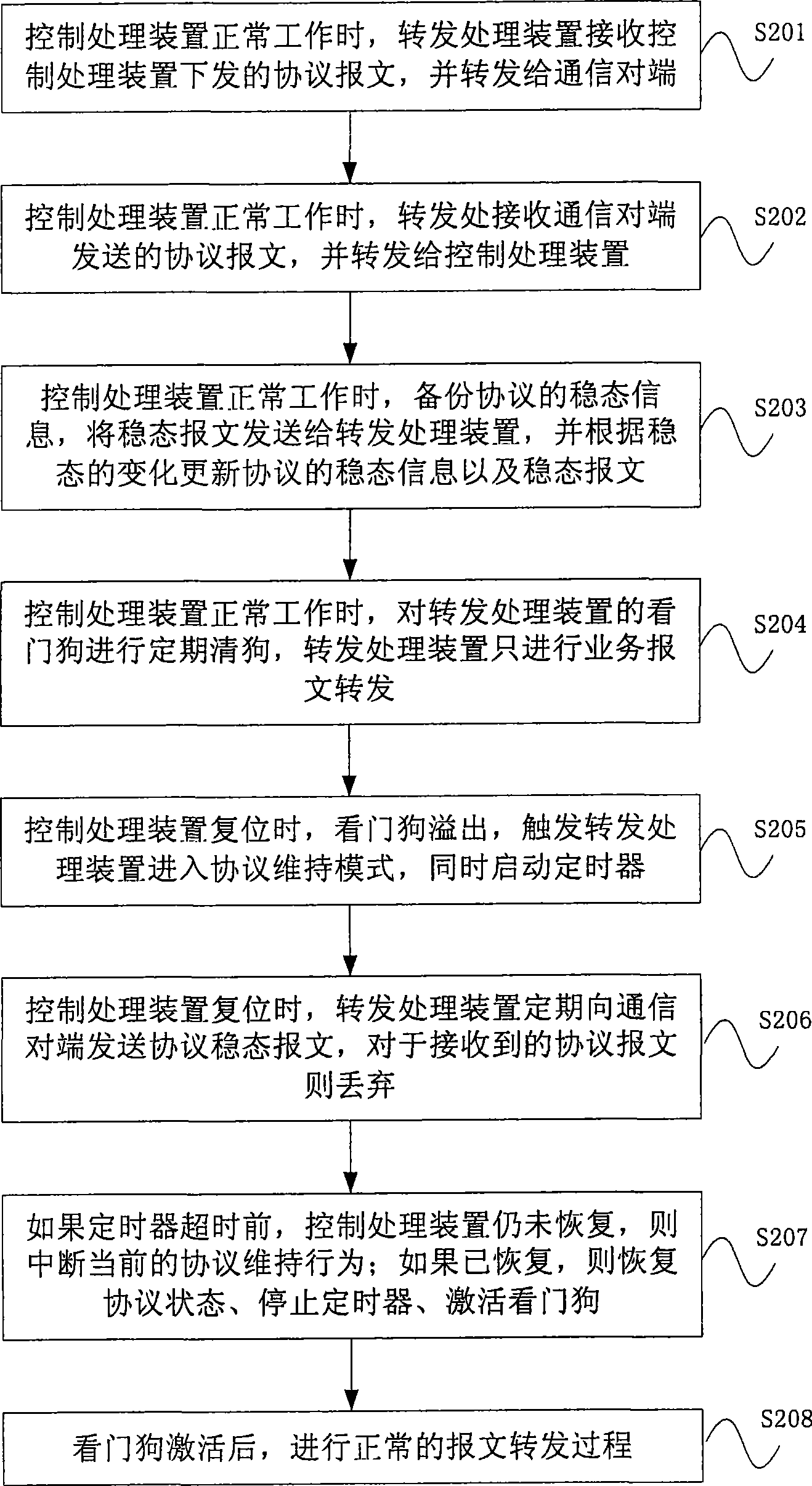
Method and communication equipment for holding protocol state
The embodiment of the invention provides a method for maintaining protocol state and communication equipment thereof, wherein the communication equipment comprises a control management device and a transmission processing device; the control management device is used for generating a protocol stable state message corresponding to the stable state of a protocol and issuing the protocol stable state message and corresponding transmission information thereof to the transmission processing device; the transmission processing device is used for receiving and storing the protocol stable state message and the corresponding transmission information issued by the control management device; and when the control management device is reset, a protocol stable state message which is stored and corresponds to the stable state of the protocol when the control management device is reset is periodically sent to a communication opposite end according to the transmission information. The communication equipment continues to periodically send the protocol stable state message through the transmission processing device to keep the current protocol session state away from interruption when the control management device is reset.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com