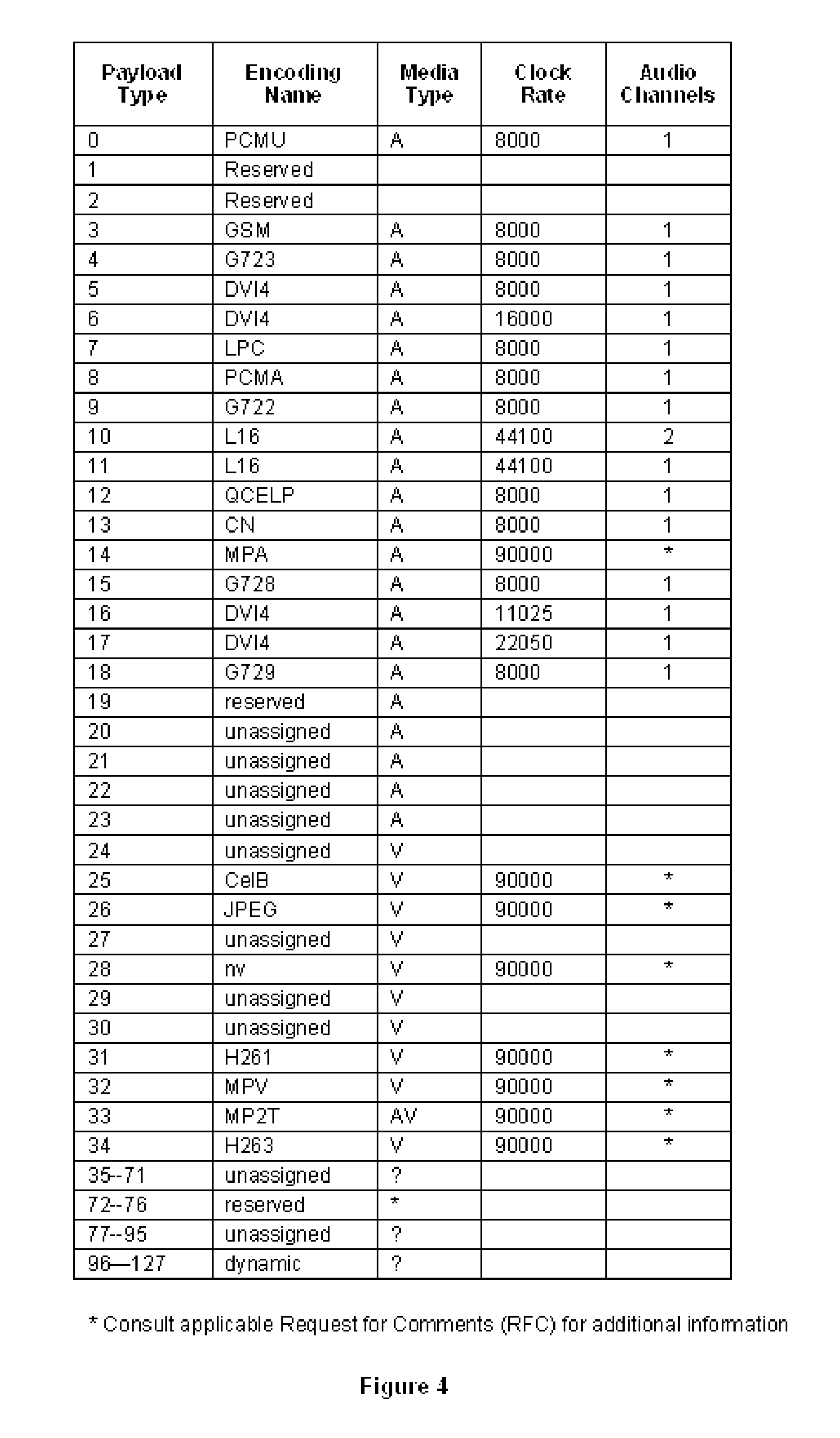
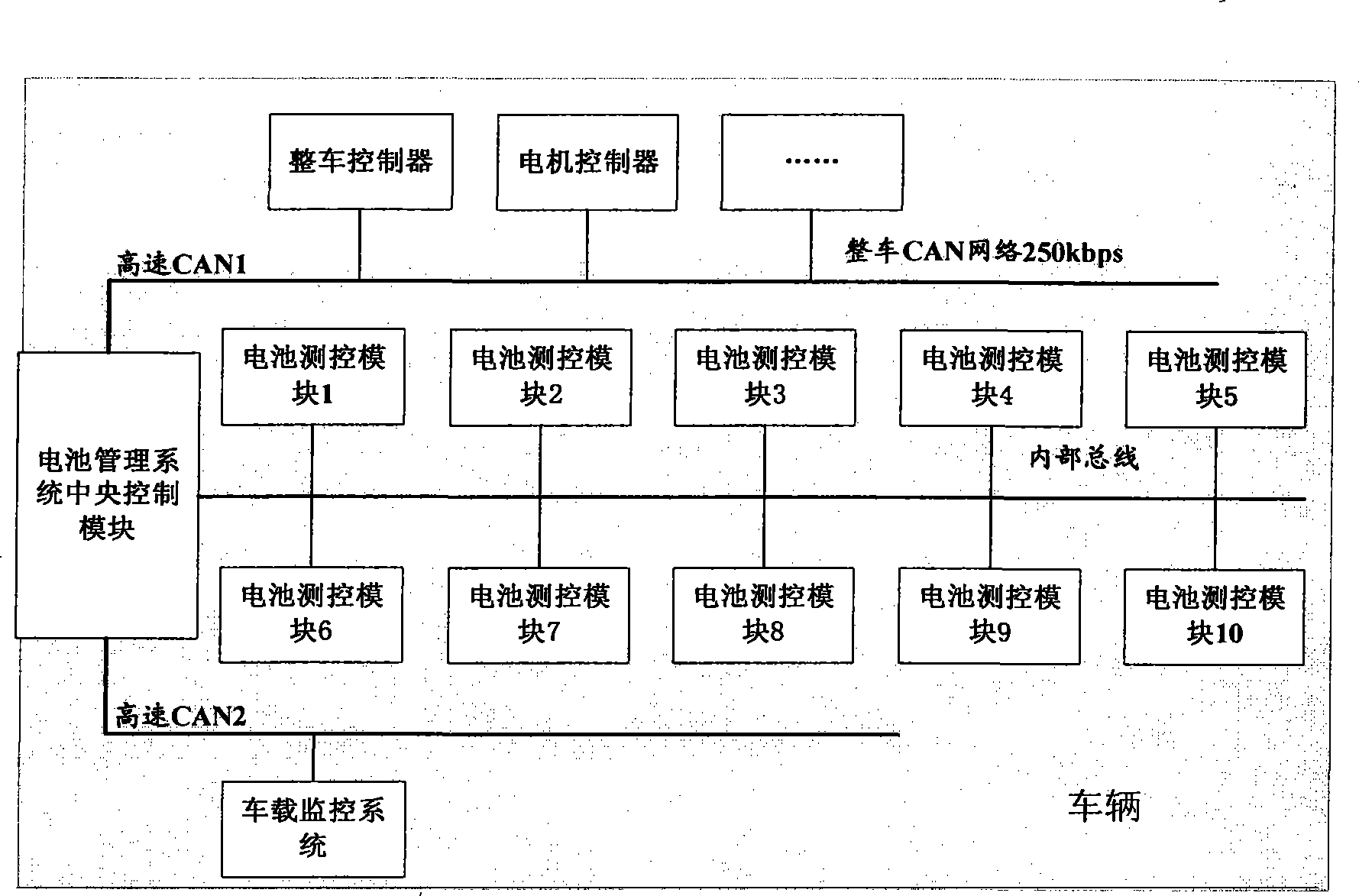
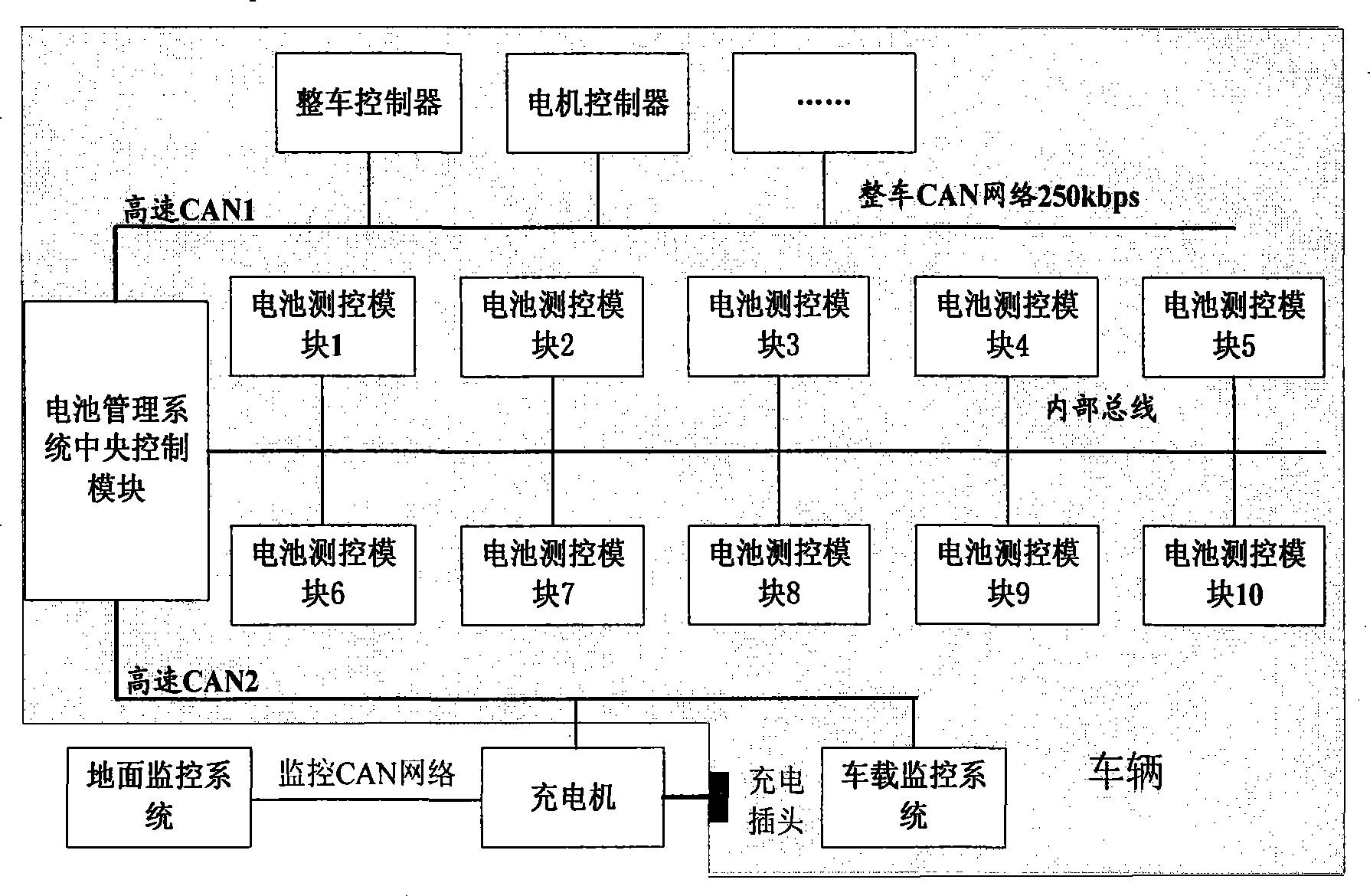
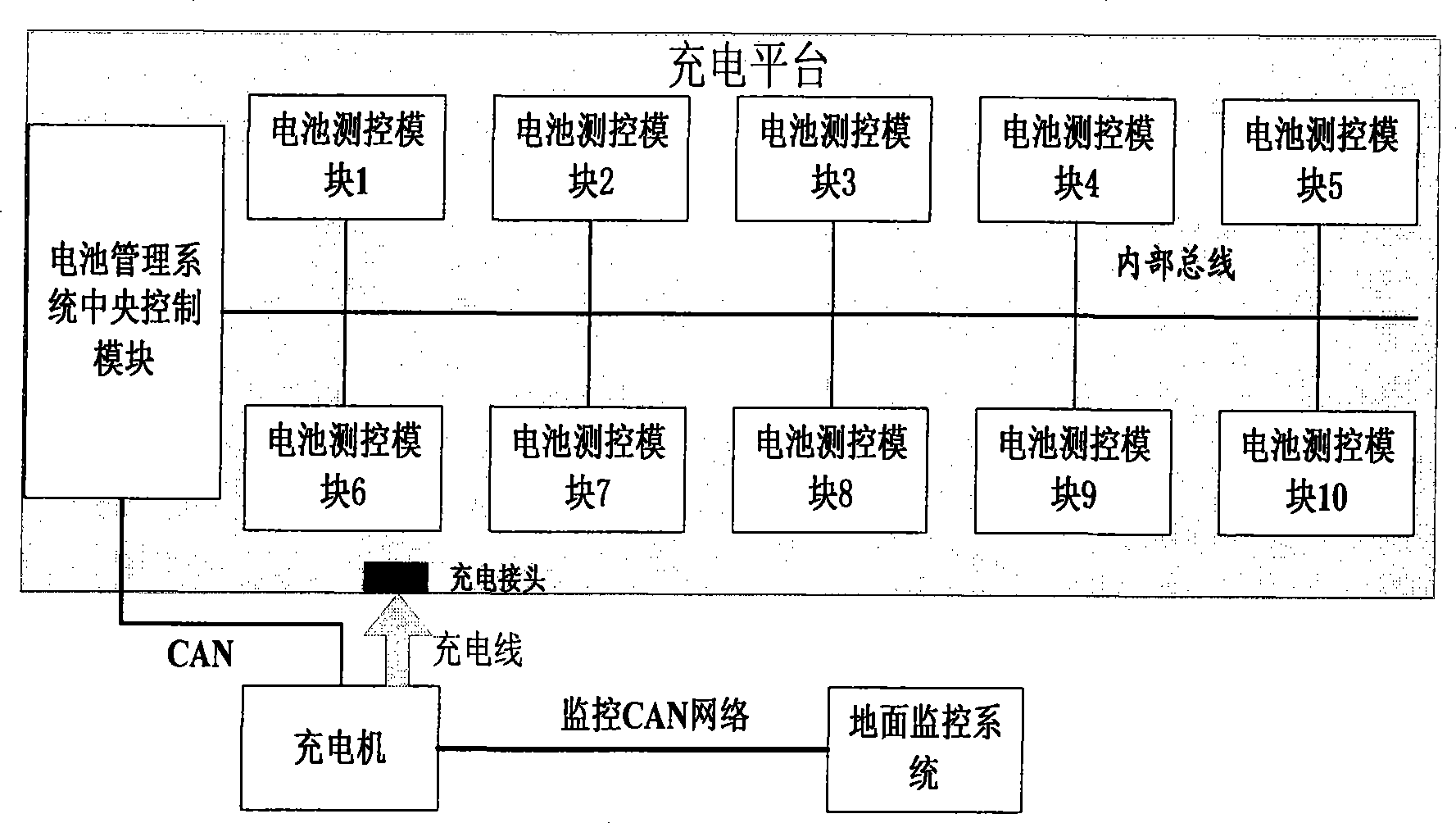
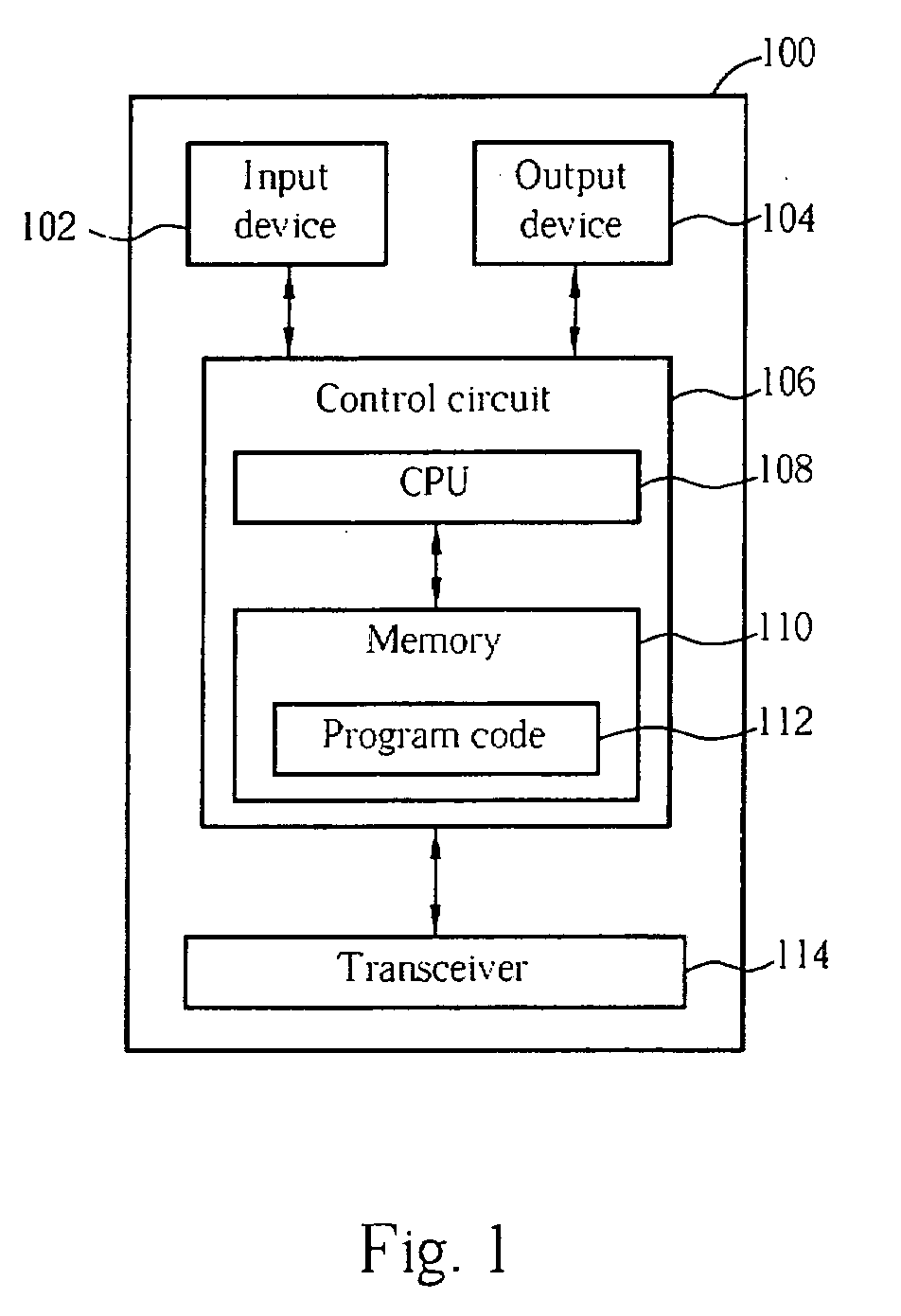
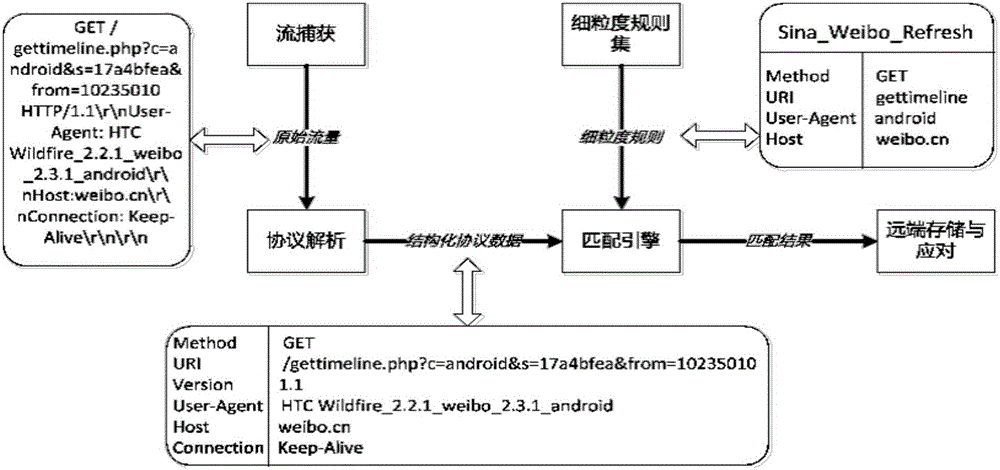
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
317 results about "Protocol specification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Communication Protocol Specification is a means by which the rules and formats of a communication protocol can be described at a formal level, and it is often part of (indeed, the largest part of) a communication protocol standard.
Adaptive Network Traffic Classification Using Historical Context
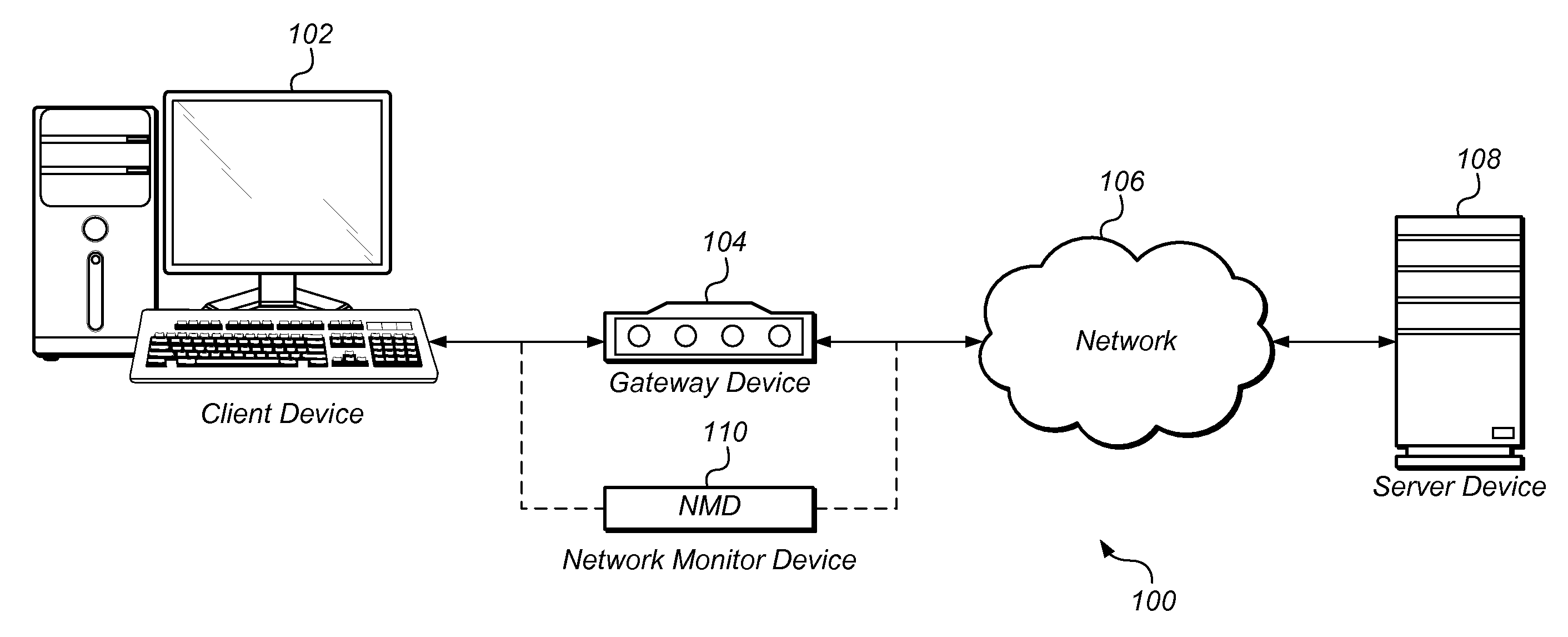
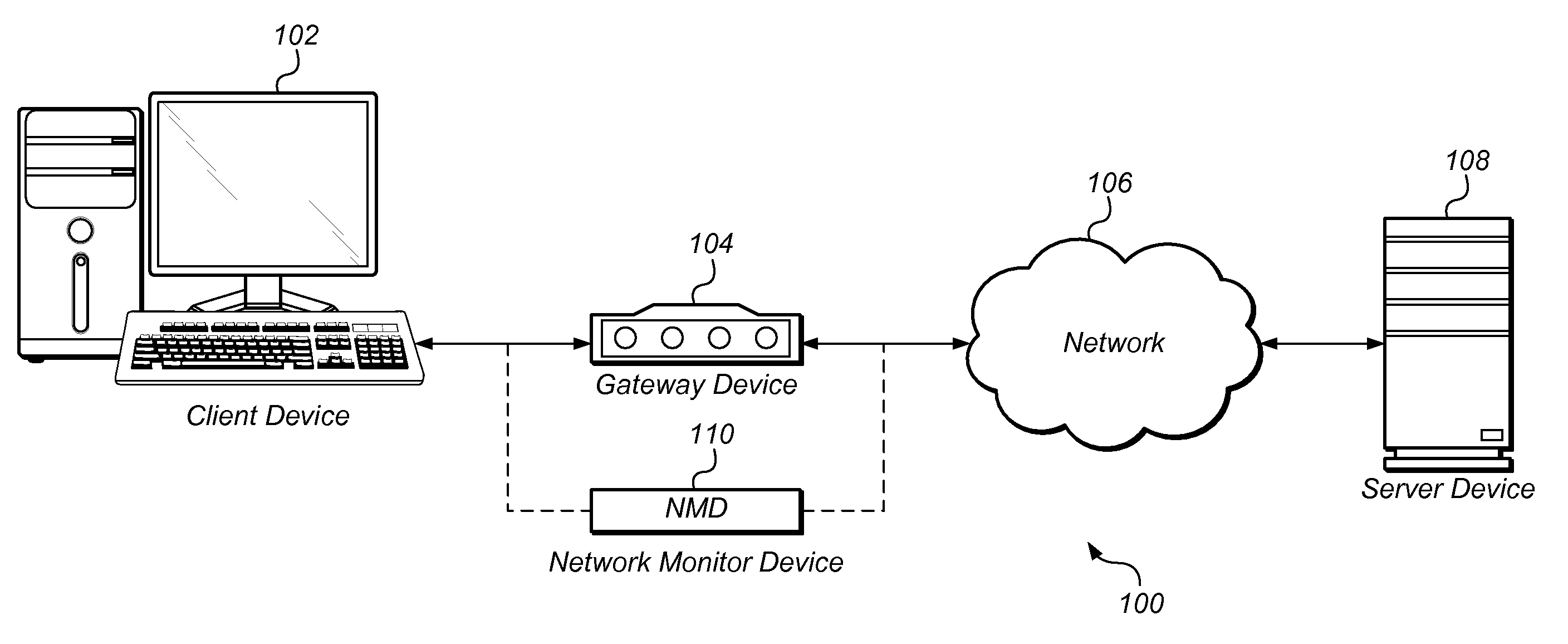
Adaptive network traffic classification using historical context. Network traffic may be monitored and classified by considering several attributes using packet filters, regular expressions, context-free grammars, rule sets, and / or protocol dissectors, among other means and by applying a variety of techniques such as signature matching and statistical analysis. Unlike static systems, the classification decisions may be reexamined from time to time or after subsequent processing determines that the traffic does not conform to the protocol specification corresponding to the classification decision. Historical context may be used to adjust the classification strategy for similar or related traffic.
Owner:EXTRAHOP NETWORKS
Adaptive network traffic classification using historical context
Adaptive network traffic classification using historical context. Network traffic may be monitored and classified by considering several attributes using packet filters, regular expressions, context-free grammars, rule sets, and / or protocol dissectors, among other means and by applying a variety of techniques such as signature matching and statistical analysis. Unlike static systems, the classification decisions may be reexamined from time to time or after subsequent processing determines that the traffic does not conform to the protocol specification corresponding to the classification decision. Historical context may be used to adjust the classification strategy for similar or related traffic.
Owner:EXTRAHOP NETWORKS
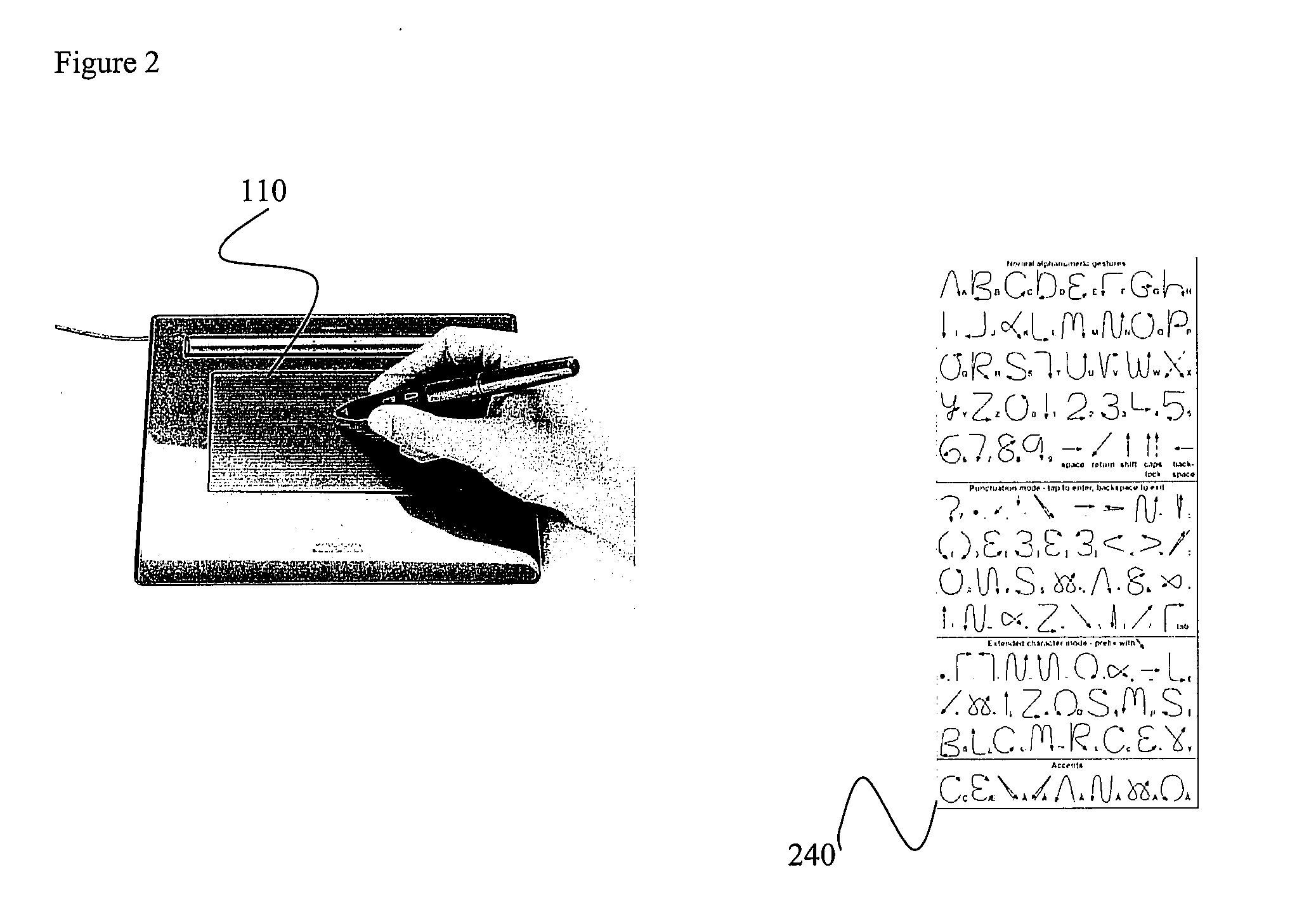
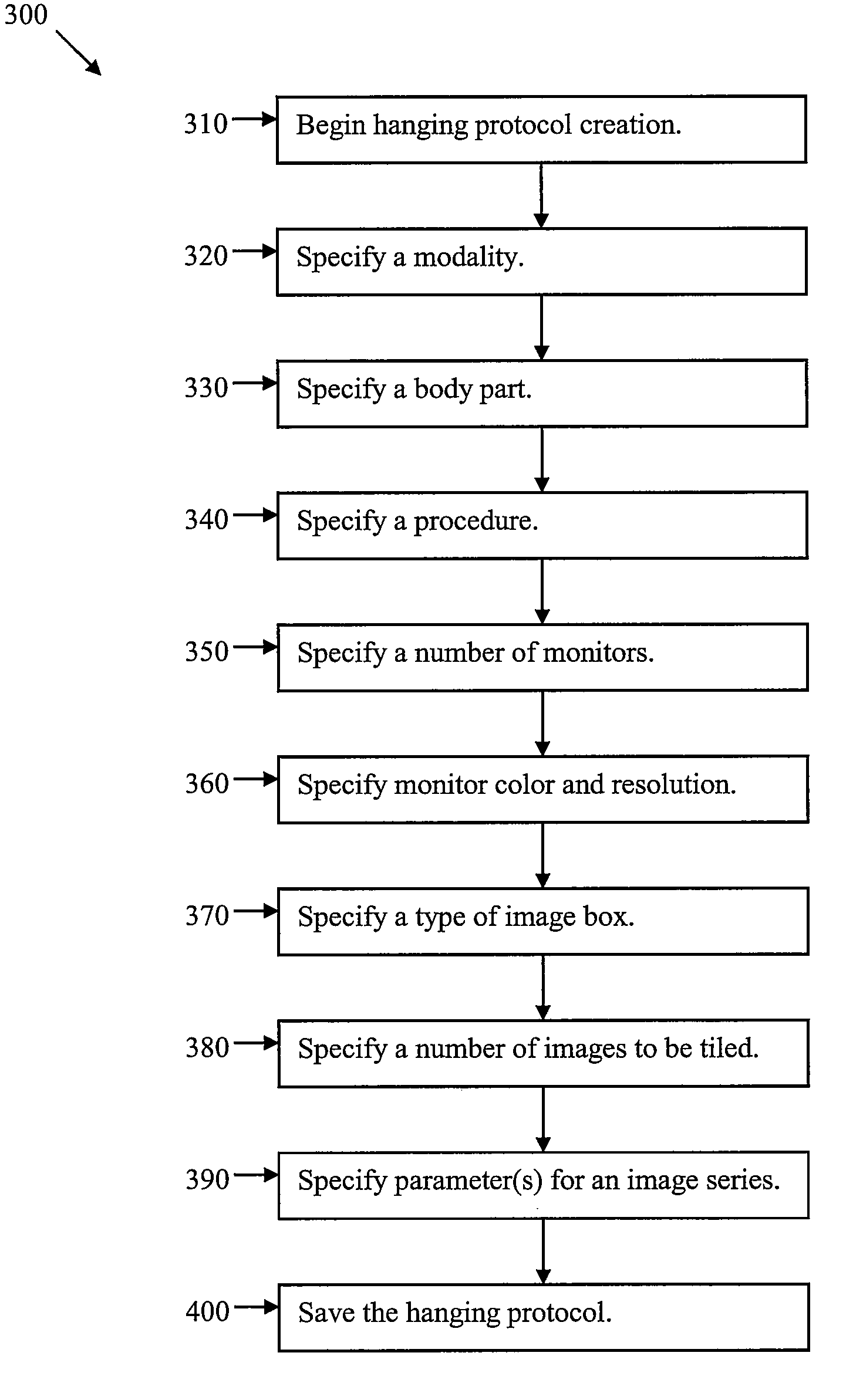
Methods and systems for creation of hanging protocols using graffiti-enabled devices
InactiveUS20080120576A1Easy to displayInput/output for user-computer interactionGraph readingClinical informationHuman–computer interaction
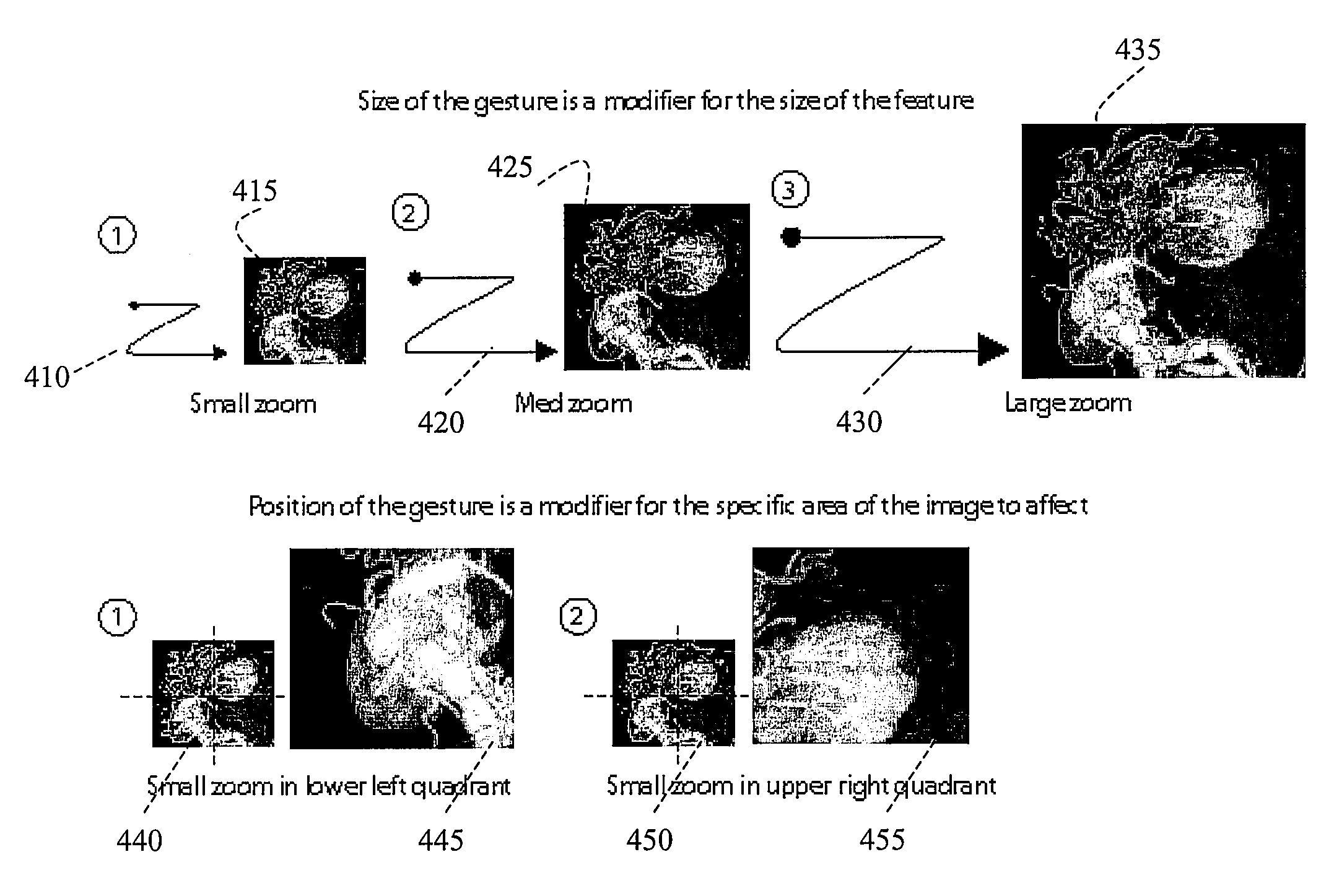
Certain embodiments of the present invention provide methods and systems for hanging protocol generation using gesture recognition. Certain embodiments provide a method for creating a hanging protocol based on gesture input in a clinical environment. The method includes specifying a hanging protocol specification using gesture-based input. The method also includes translating the gesture-based input into a hanging protocol. The method further includes facilitating display of clinical information based on the hanging protocol. Certain embodiments provide a gesture detection system. The system includes a sensor surface configured to detect gesture-based input made on the sensor surface. The gesture-based input specifies a hanging protocol layout. The system also includes a processor configured to identify the gesture-based input and translate the gesture to a corresponding hanging protocol definition for display of image and clinical data.
Owner:GENERAL ELECTRIC CO
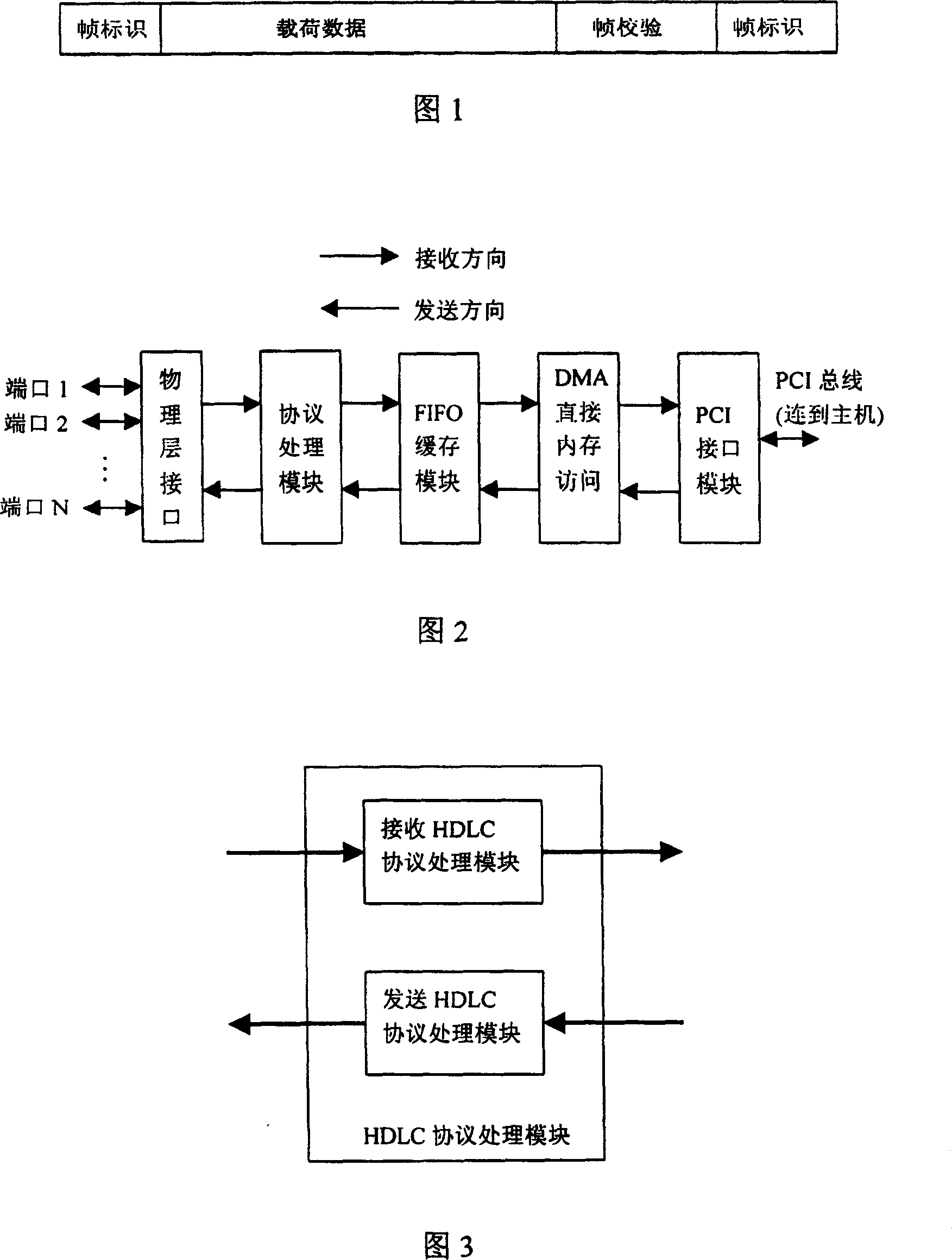
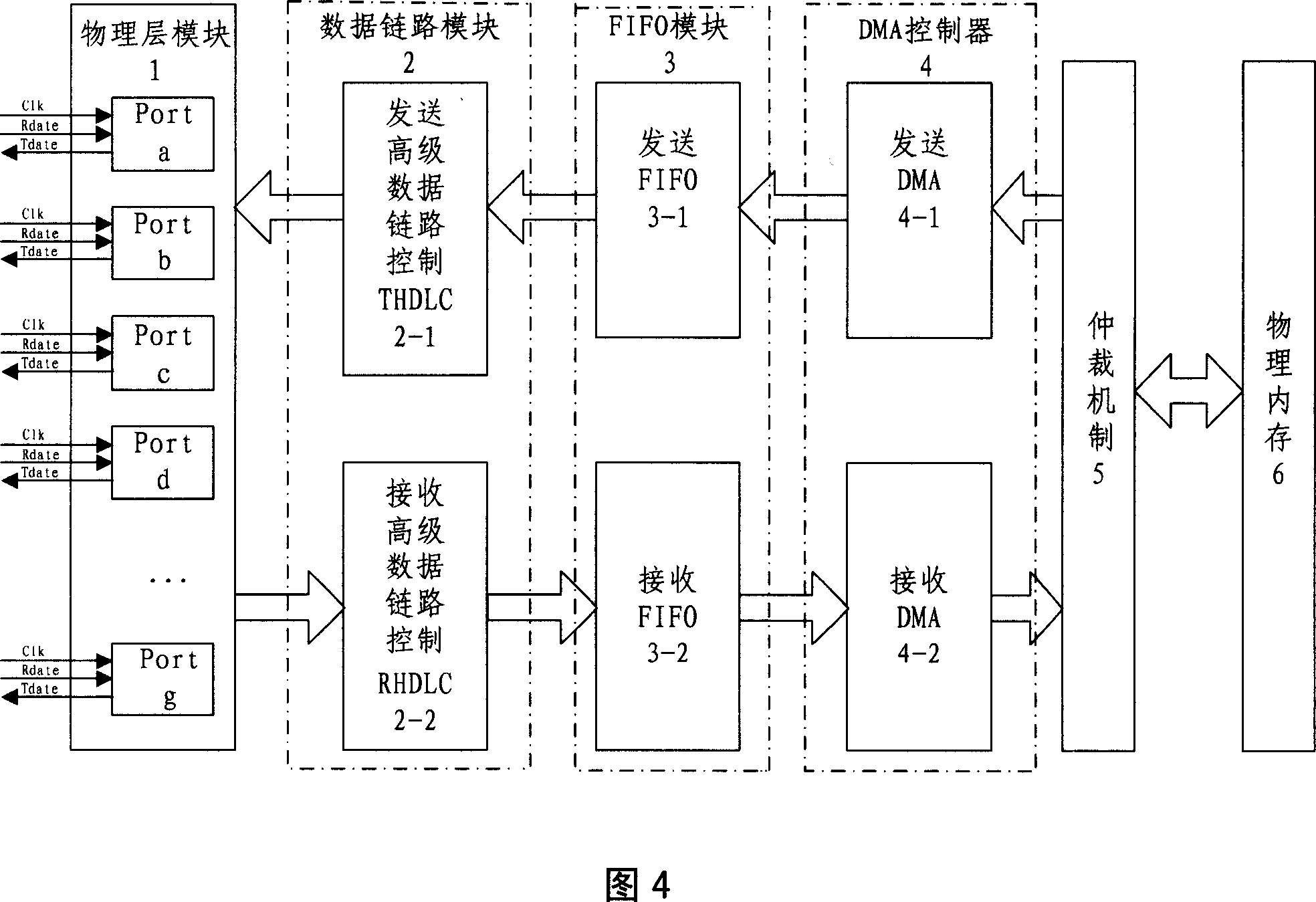
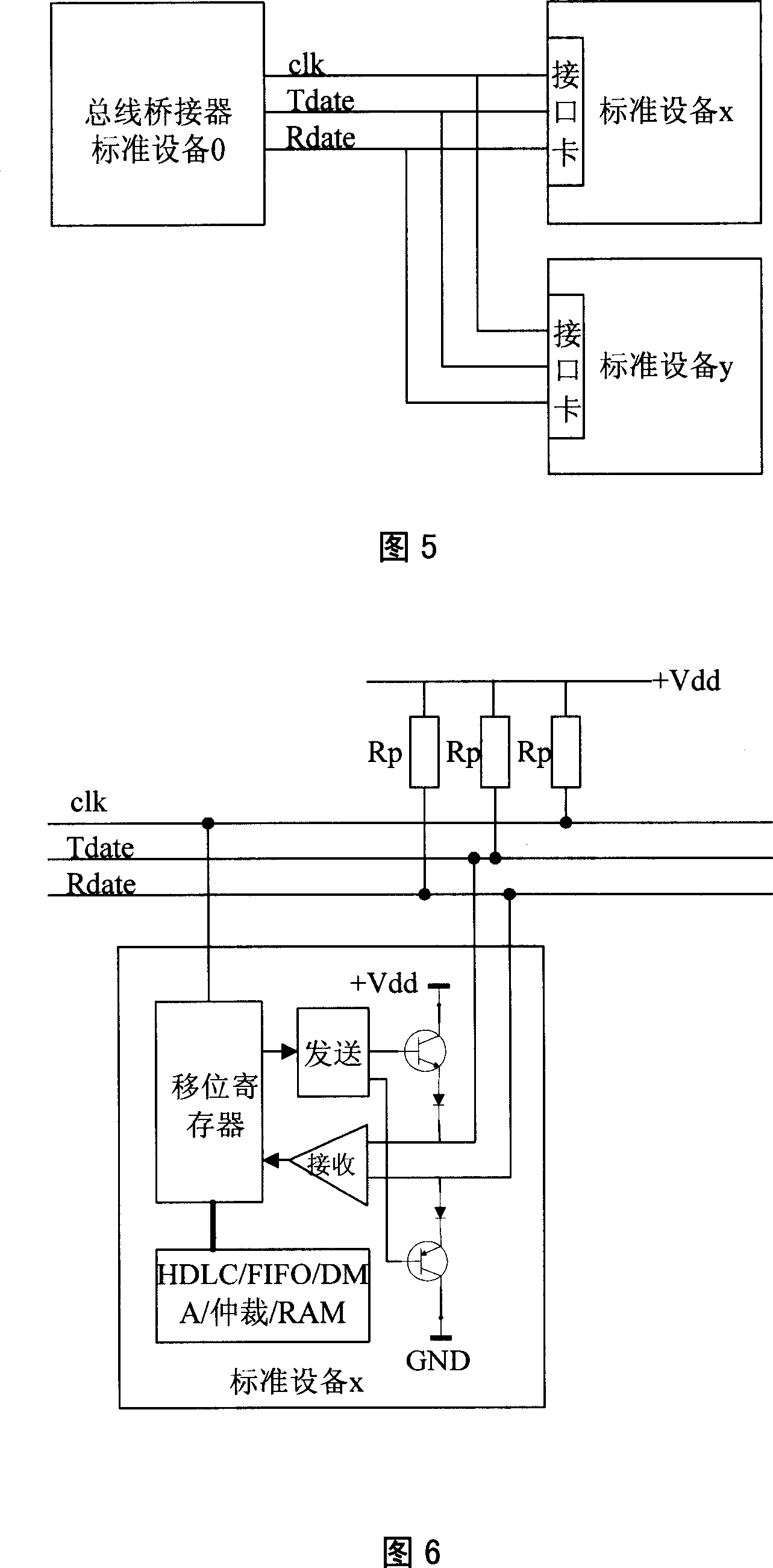
Data bus bridge and its working method
ActiveCN101018179ADoes not affect normal workIncrease data transfer rateBus networksWorking setData transmission
The related data bus bridge comprises: a physical interface connected with external standard device to transmit data according to different logic channel, a data link unit to execute HDLC protocol for data on different logic channel, a FIFO unit for data buffer, an arbitrating mechanism unit to ensure physical interfaces exclusive visit the share data in memory and make the data read and write accord with protocol specification, and a DMA control unit to build high-speed data transmission between physical interface and physical memory. This invention is real-time and reliable, and fit to negotiate control device and monitor device.
Owner:CHANGZHOU TELEVIC KTK ELECTRONICS
Concealing a network connected device
ActiveUS20060089994A1Increase in sizeDigital data processing detailsMultiple digital computer combinationsAuthorizationConnected device
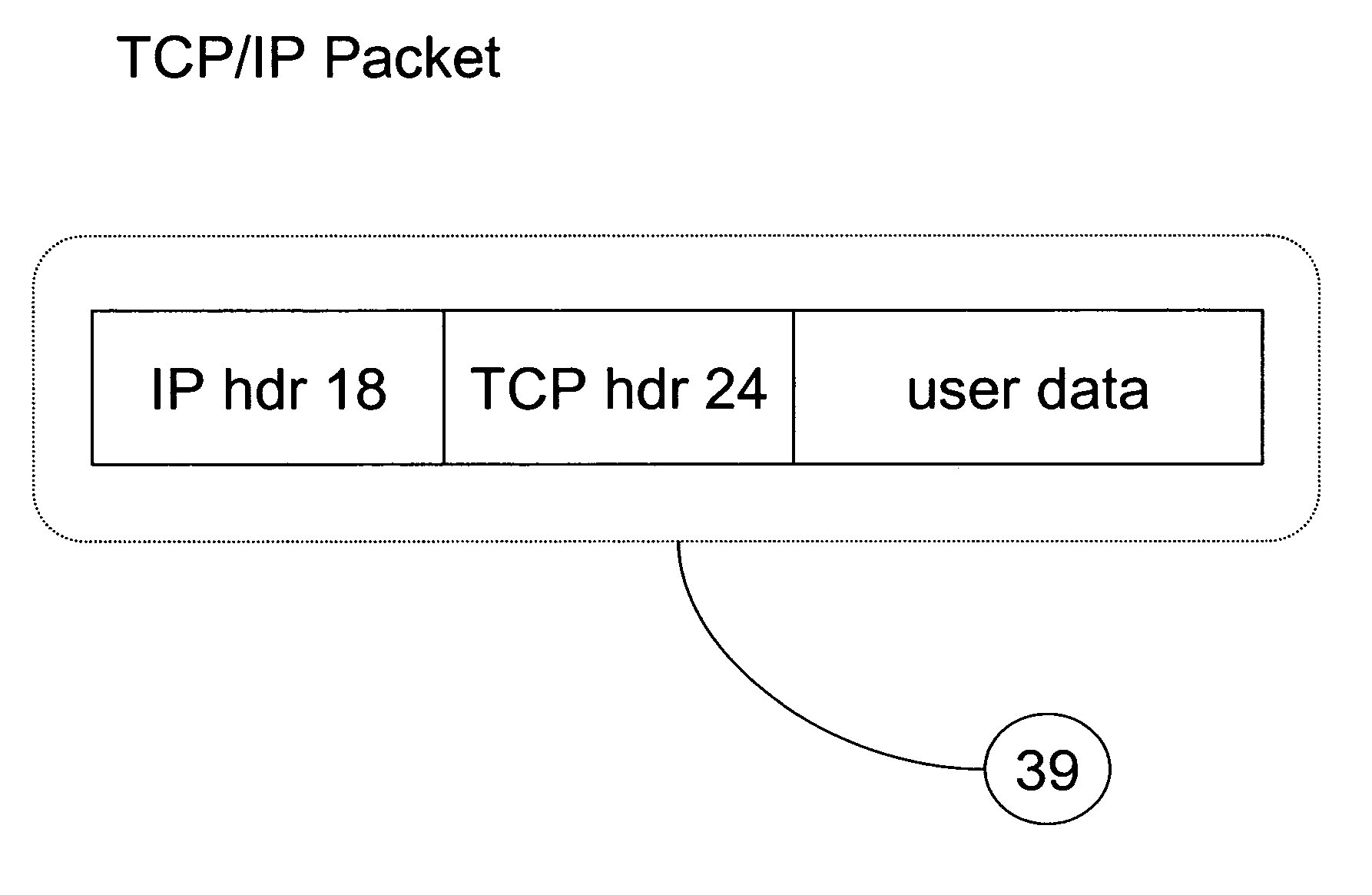
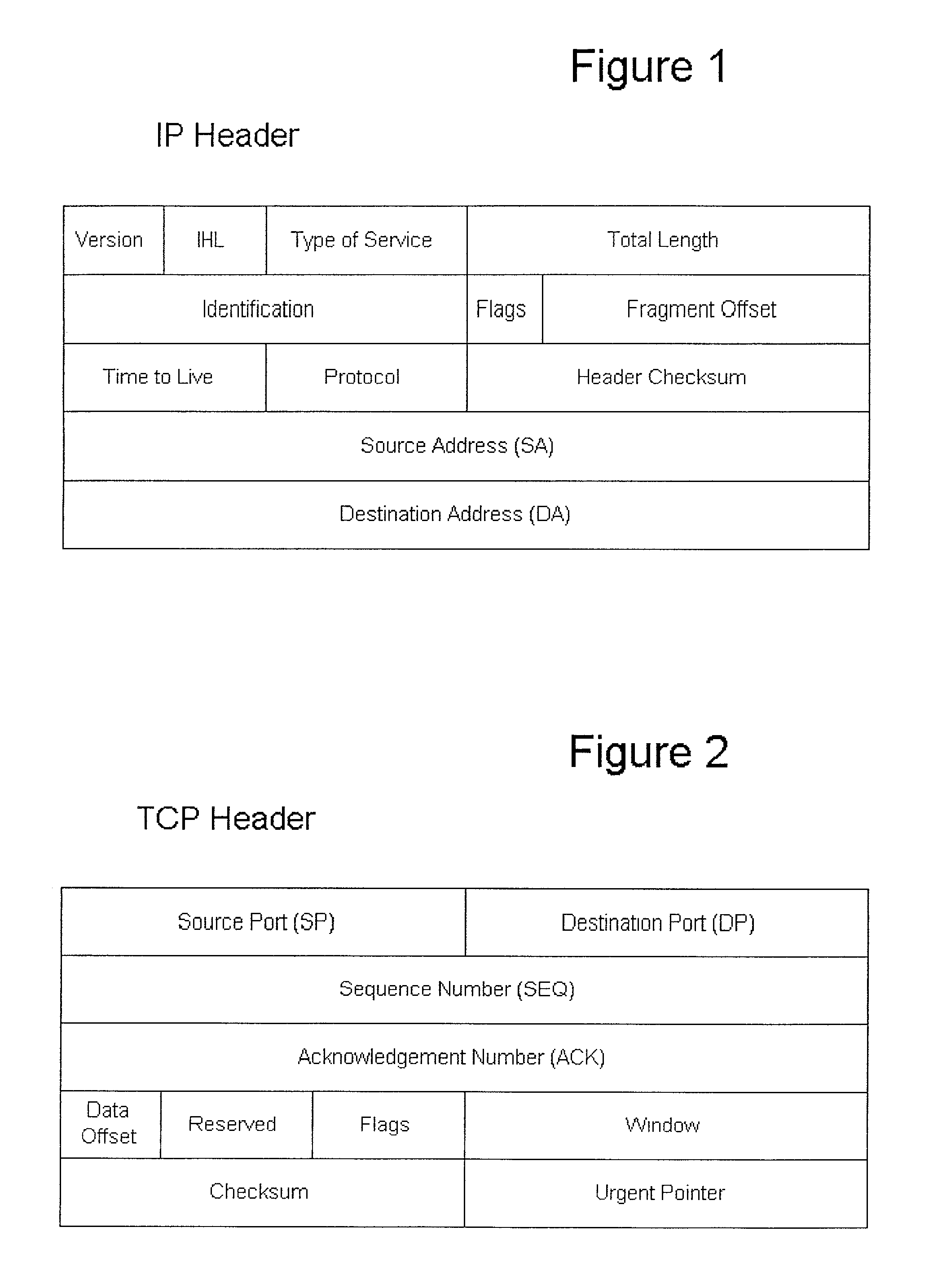
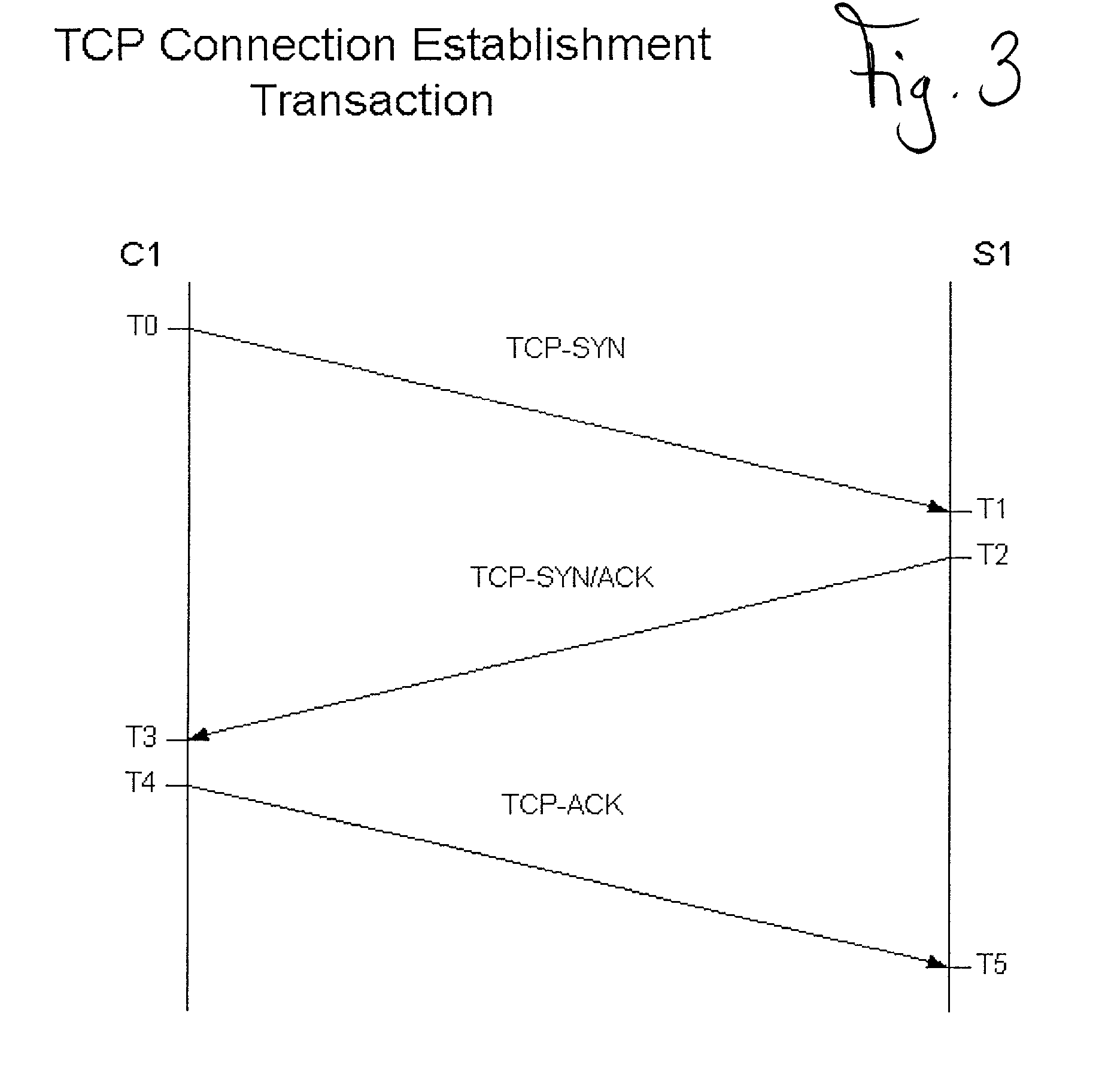
In a preferred embodiment of the invention, a network client (42) inserts an authorization key (38) into the SEQ (30) and ACK (32) fields of a TCP connection request (56). The TCP connection request (56) is sent to a authorizing server (46). The authorizing server (46) extracts the authorization key (38) and uses the authorization key (38), with other implicit and explicit data contained within the TCP connection request (56) to authorize the TCP connection request (56). If the TCP connection request (56) is authorized, the authorizing server (46) sends a TCP-SYN / ACK (58) back to the network client (42) as described in the TCP protocol specification. If the TCP connection request (56) is denied, the TCP connection request (56) is discarded and nothing is sent back to the network client (42).
Owner:INVISINET TECH LLC
System for improving overall battery life of a GSM communication device
InactiveUS20070184836A1Extend battery lifeMaximizing lifetime of battery cellPower managementEnergy efficient ICTDefinite periodLogical process
Disclosed is a system for improving the overall battery life of a GSM device according to an optimization mechanism for suspending neighbor-cell scanning in a GSM wireless communication system, the system having a wireless device including: (a) a Central Processing Unit (CPU) executing software programs intended to comply with GSM protocol specifications; (b) an RF transmission unit and an RF reception unit functioning either independently or as a single unit; (c) a specialized Digital Signal Processor being able to process received signal at a corresponding receiving antenna and offering estimates of the received signal level and quality; (d) a logic process by which the mobile terminal powers off an RF module thereof for a definite period of time and wakes up at a pre-determined interval to listen to paging messages transmitted thereto; and (e) firmware / software performing neighbor cell monitoring in compliance with a protocol mandated by GSM standards.
Owner:SAMSUNG ELECTRONICS CO LTD
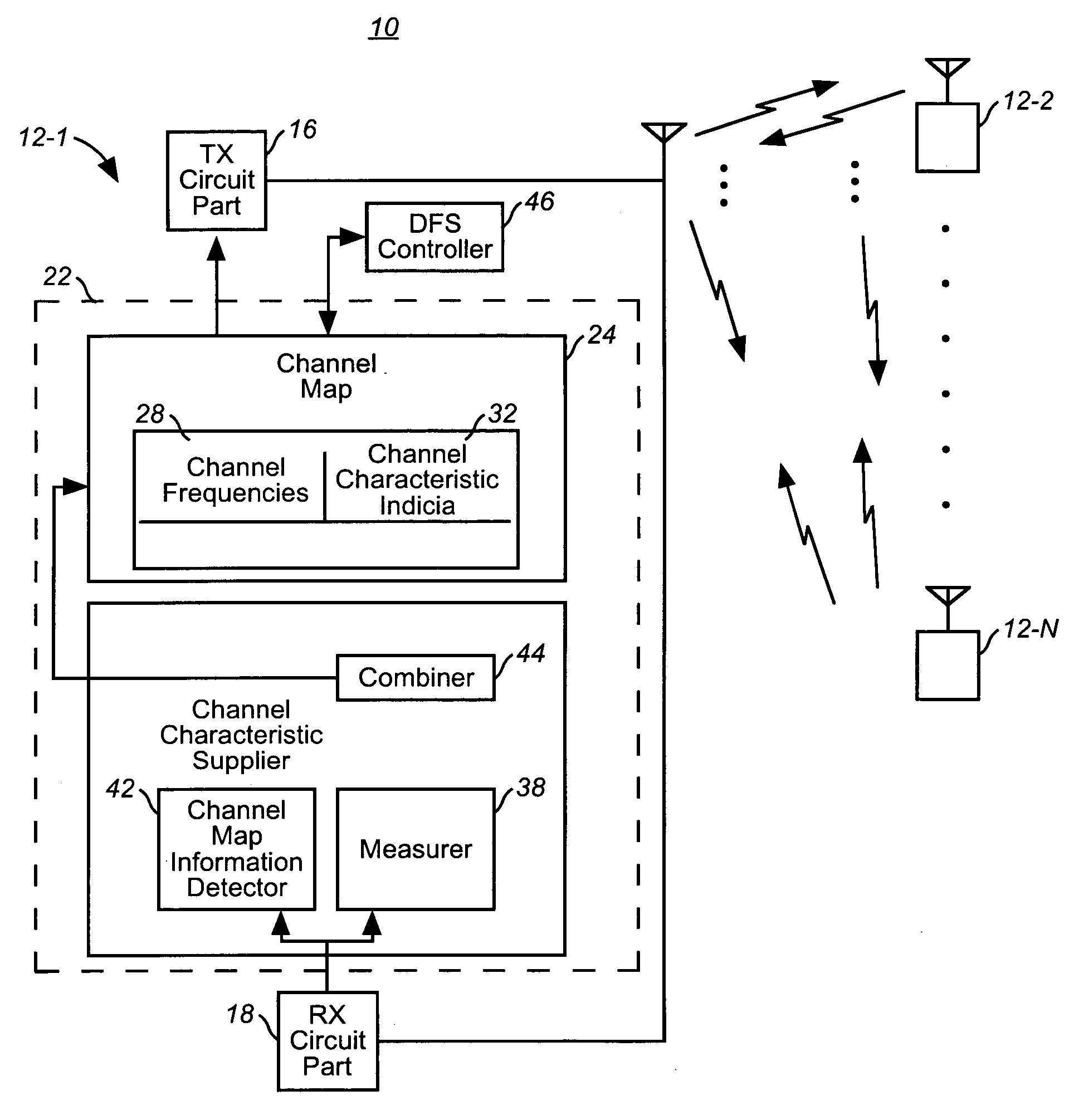
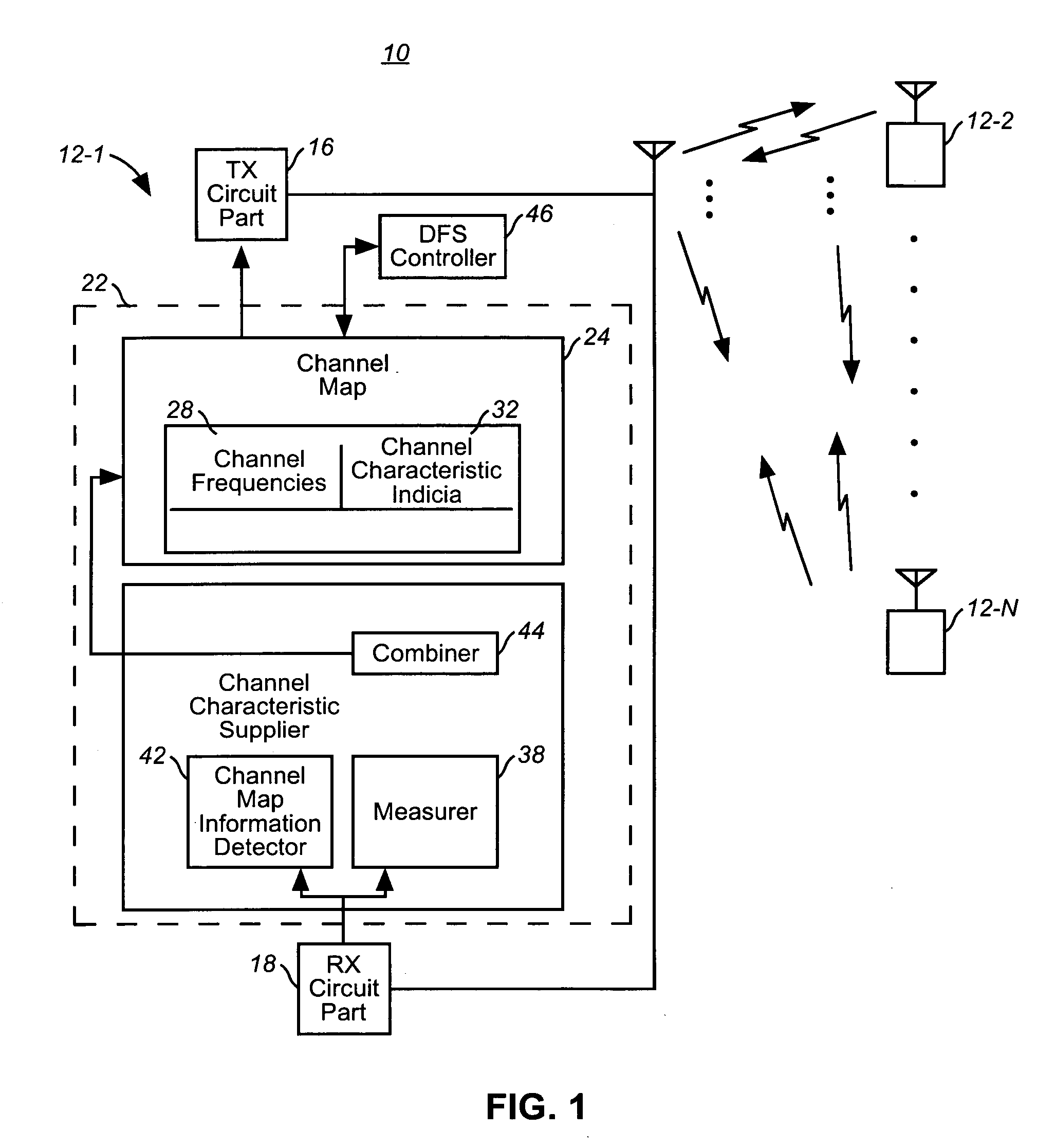
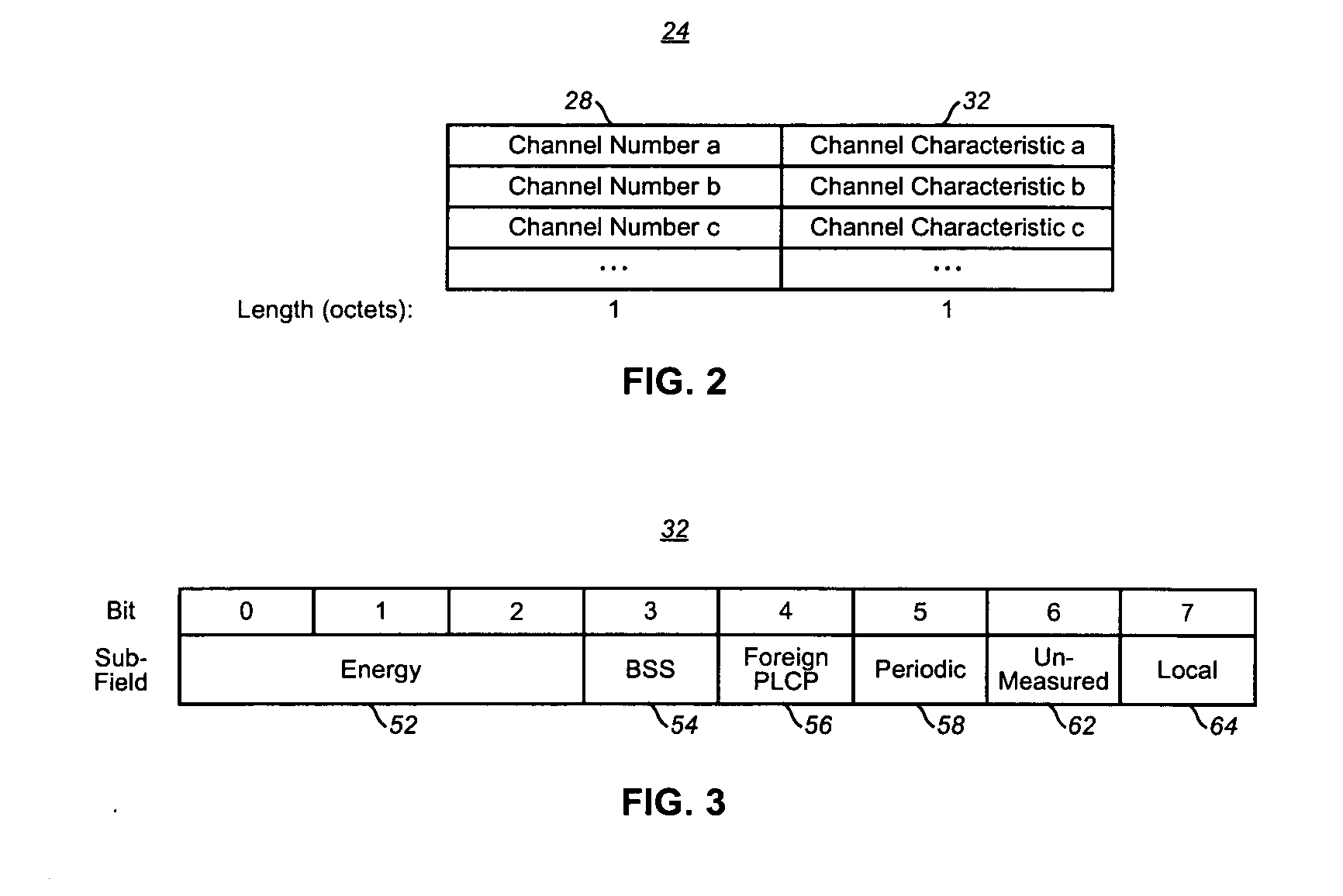
Assembly, and associated method, for facilitating channel frequecy selection in a communication system utilizing a dynamic frequency selection scheme
An assembly, and an associated method, for an ad hoc network, such as an independent basic service set defined in an IEEE 802.11 protocol specification. A channel map is created and maintained at each mobile station of the ad hoc network. The channel map is populated with channel characteristic indicia of channel frequencies that might be available upon which to be used in the ad hoc network to effectuate communications between the mobile stations. Information related to the channel map created and maintained at each of the mobile stations is exchanged, and any of the mobile stations is selectable to form a DFS owner that defines the channel frequency to be used upon which to define a communication channel for communications in the network.
Owner:NOKIA TECHNOLOGLES OY
Methods and systems for creation of hanging protocols using eye tracking and voice command and control
ActiveUS20080120141A1Easy to displayData processing applicationsLocal control/monitoringComputer hardwareClinical information
Certain embodiments of the present invention provide methods and systems for hanging protocol generation using eye tracking and / or voice command and control. Certain embodiments provide a method for creating a hanging protocol based on at least one of eye tracking and voice command and control input in a clinical environment. The method includes specifying a hanging protocol specification using input including at least one of eye tracking and voice command and control. The method also includes translating the input into a hanging protocol. The method further includes facilitating display of clinical information based on the hanging protocol.
Owner:GENERAL ELECTRIC CO
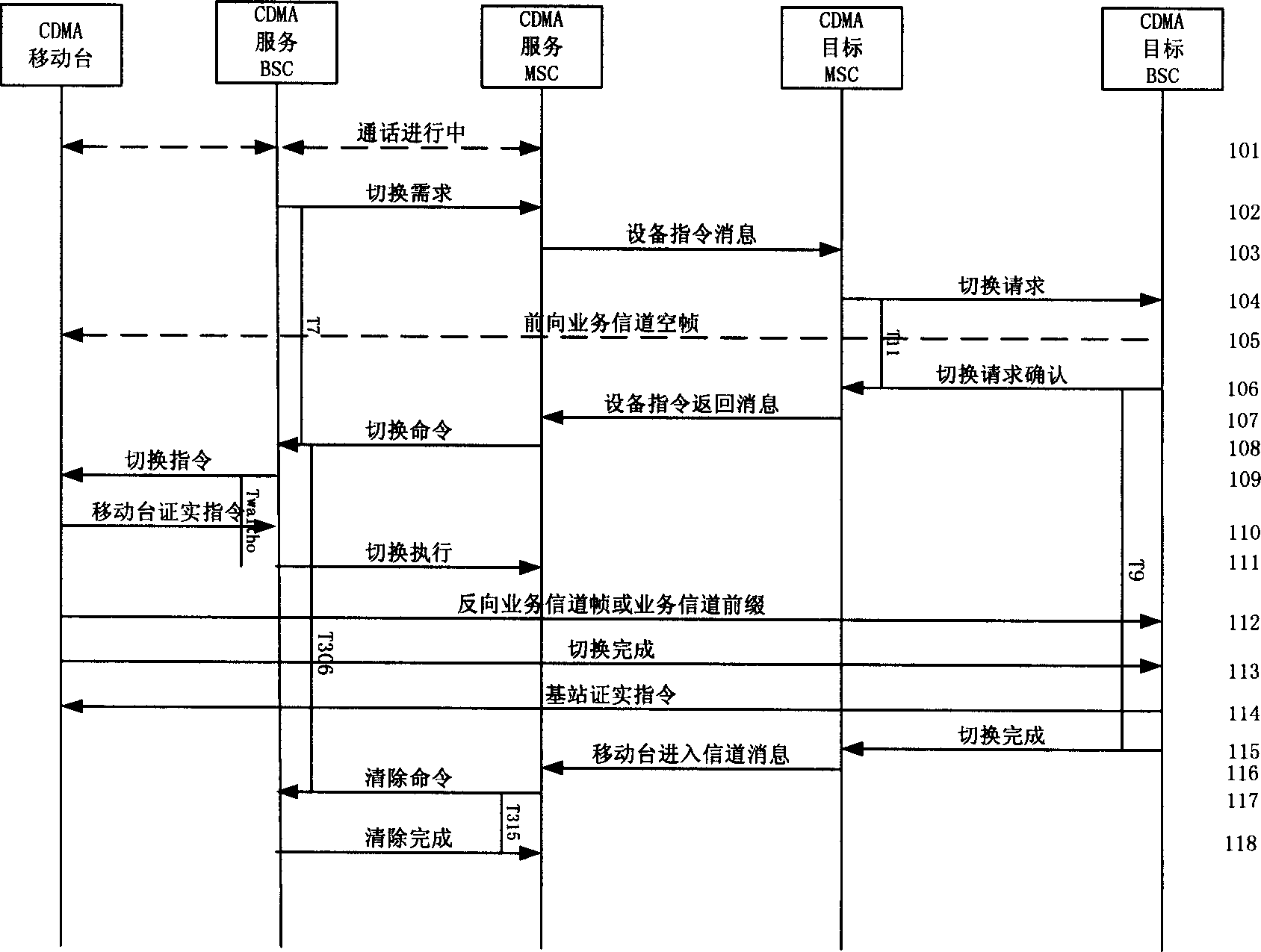
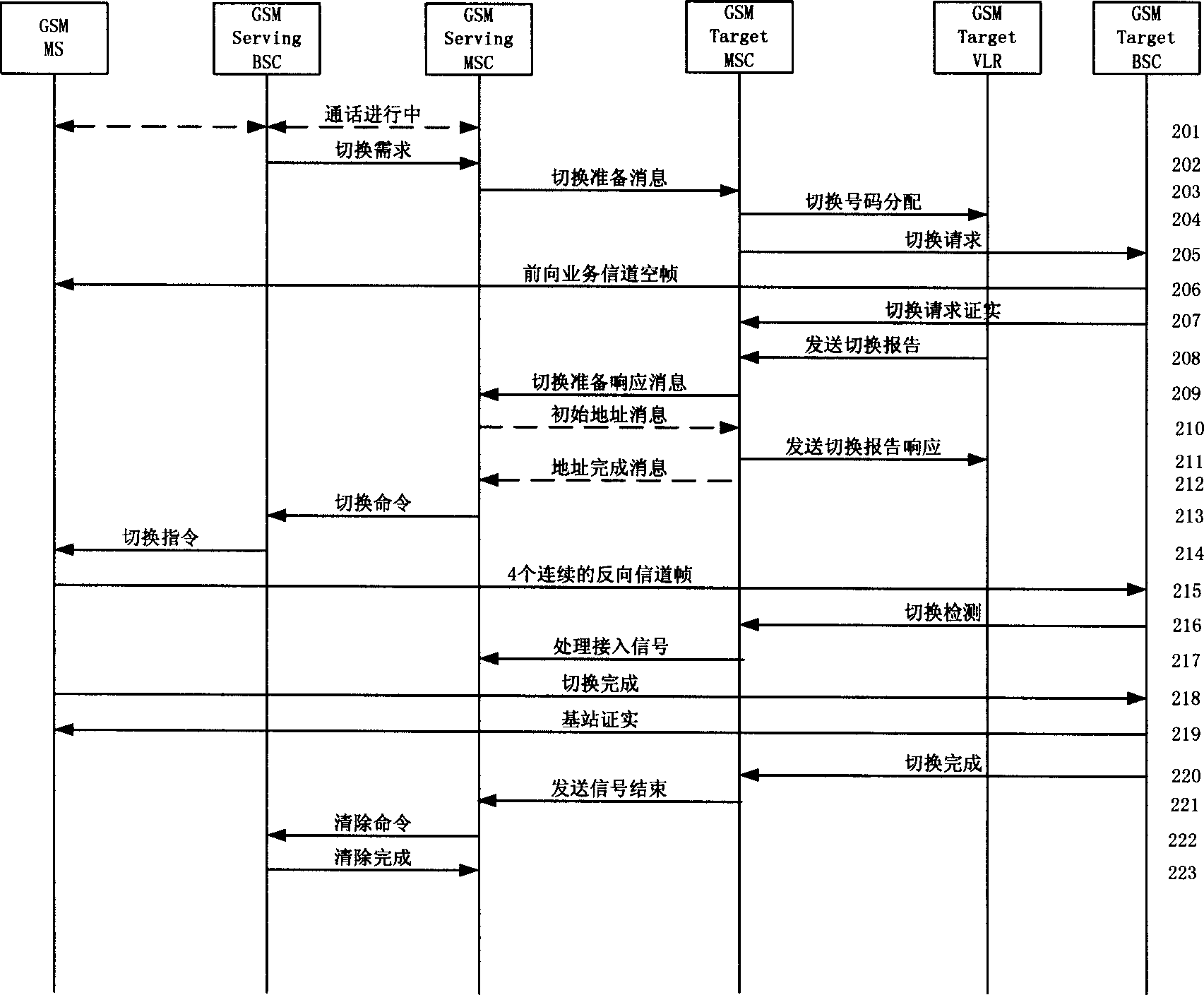
Method of switching between CDMA system and GSM system for dual mode mobile station
InactiveCN1505413AGuaranteed continuityLoad balancingRadio/inductive link selection arrangementsWireless communicationResource informationDual mode
The invention is a switch method between CDMA system and GSM system which supporting CDMA / GSM double model mobile station, the invention uses the interconnecting function entity (IIF) in the core network of CDMA system and GSM system, masks the core networks of the two basic different protocol standard, each MSC of each system uses the IIF as the MSC belonging to the same system, the parameter of measurement and service needed by the core network MSC and the wireless chain resources information of target network needed by the service core network are added into the switch instruction information correspondent to the service core network E interface, and they are transmitted to the correspondent target MSC through IIF entity by service MSC, realizes the E interface instruction chain and instruction message translation converting function between the CDMA system core network instruction and the GSM system core network, it provides voice service chain relay function between CDMA service MSC and GSM target MSC.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
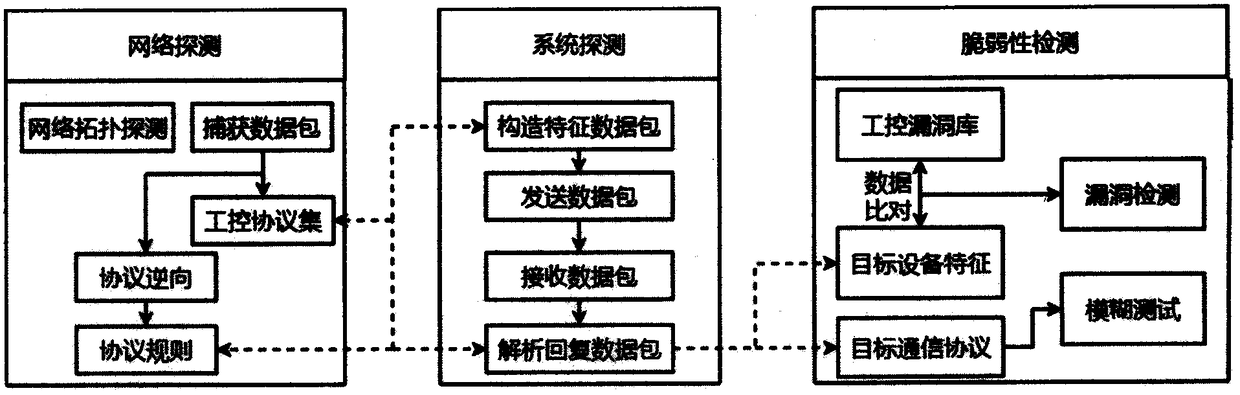
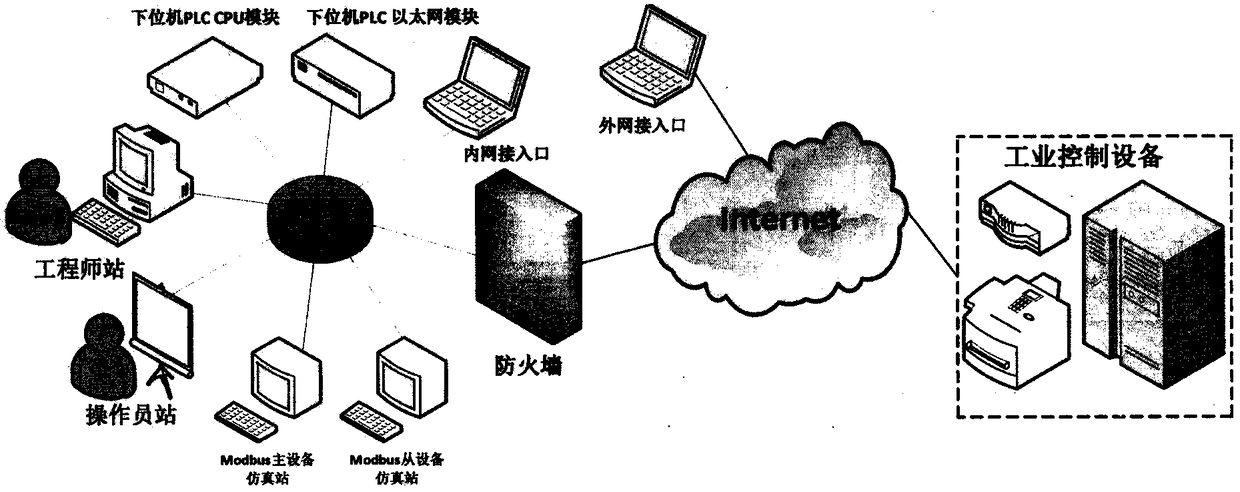
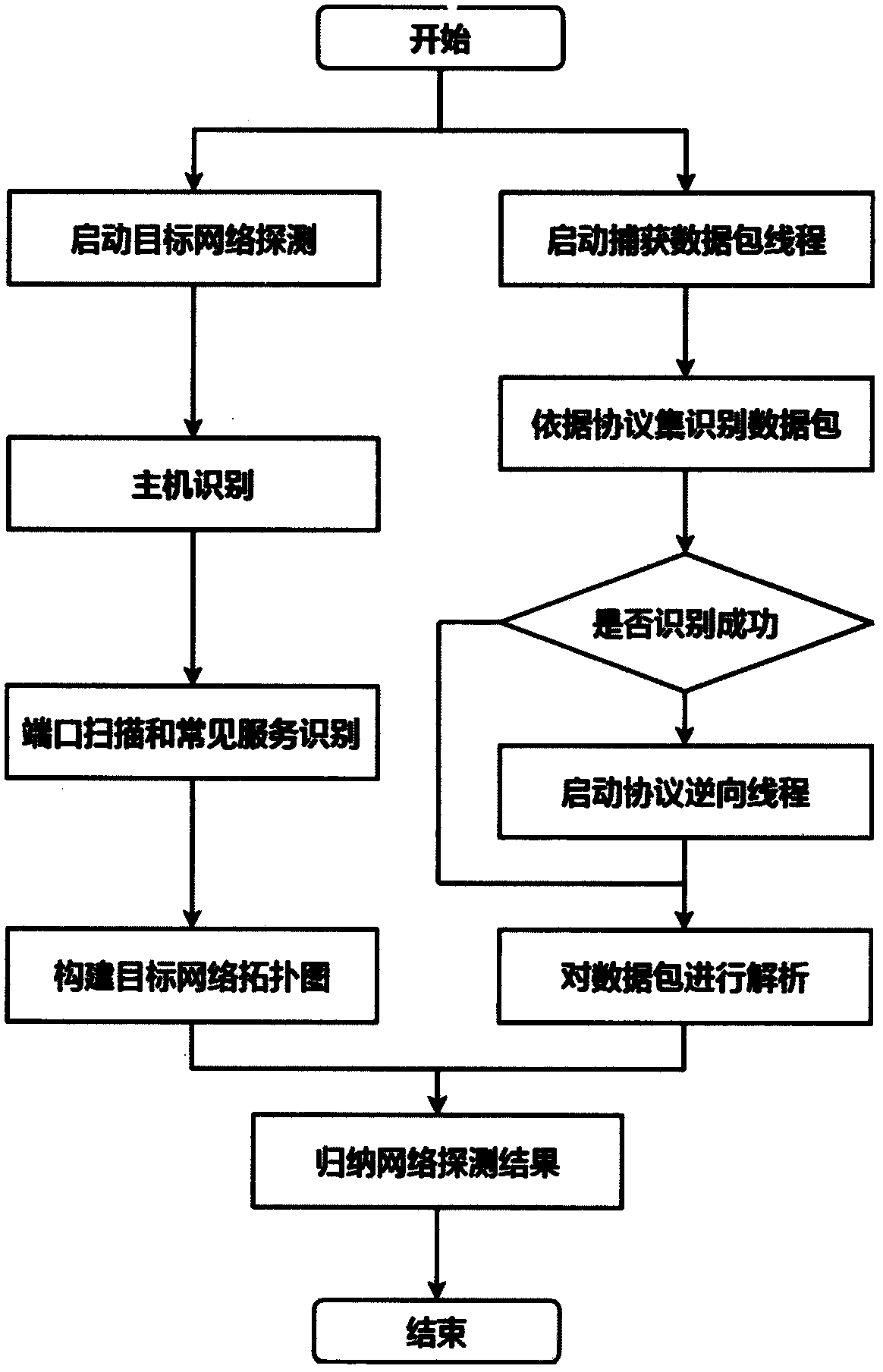
Vulnerability detection method for industrial control system
InactiveCN108737417AGain advantageImprove applicabilityTransmissionIndustrial EthernetNetwork packet
The invention provides a vulnerability detection method for an industrial control system. The method comprises the following steps: performing network detection on a target environment based on industrial Ethernet features, identifying an industrial control device, and capturing a session data packet; parsing the data packet according to the industrial control protocol specification and the private protocol reverse technology, and constructing a feature code data packet to perform further system detection to obtain specific fingerprint information; comparing the vulnerability information of amatching target based on the features of an industrial control dedicated vulnerability database, and performing related vulnerability detection based on strategy drive; and performing a fuzzy test based on the industrial control protocol vulnerability, and mining the security vulnerabilities of the industrial control system network, and detecting the security vulnerability. According to the vulnerability detection method provided by the invention, the vulnerability detection is performed on the industrial control target to detect the security vulnerabilities before the network attackers so asto improve the security and reliability of the industrial control system.
Owner:NANJING UNIV +3
Method and device for producing test case
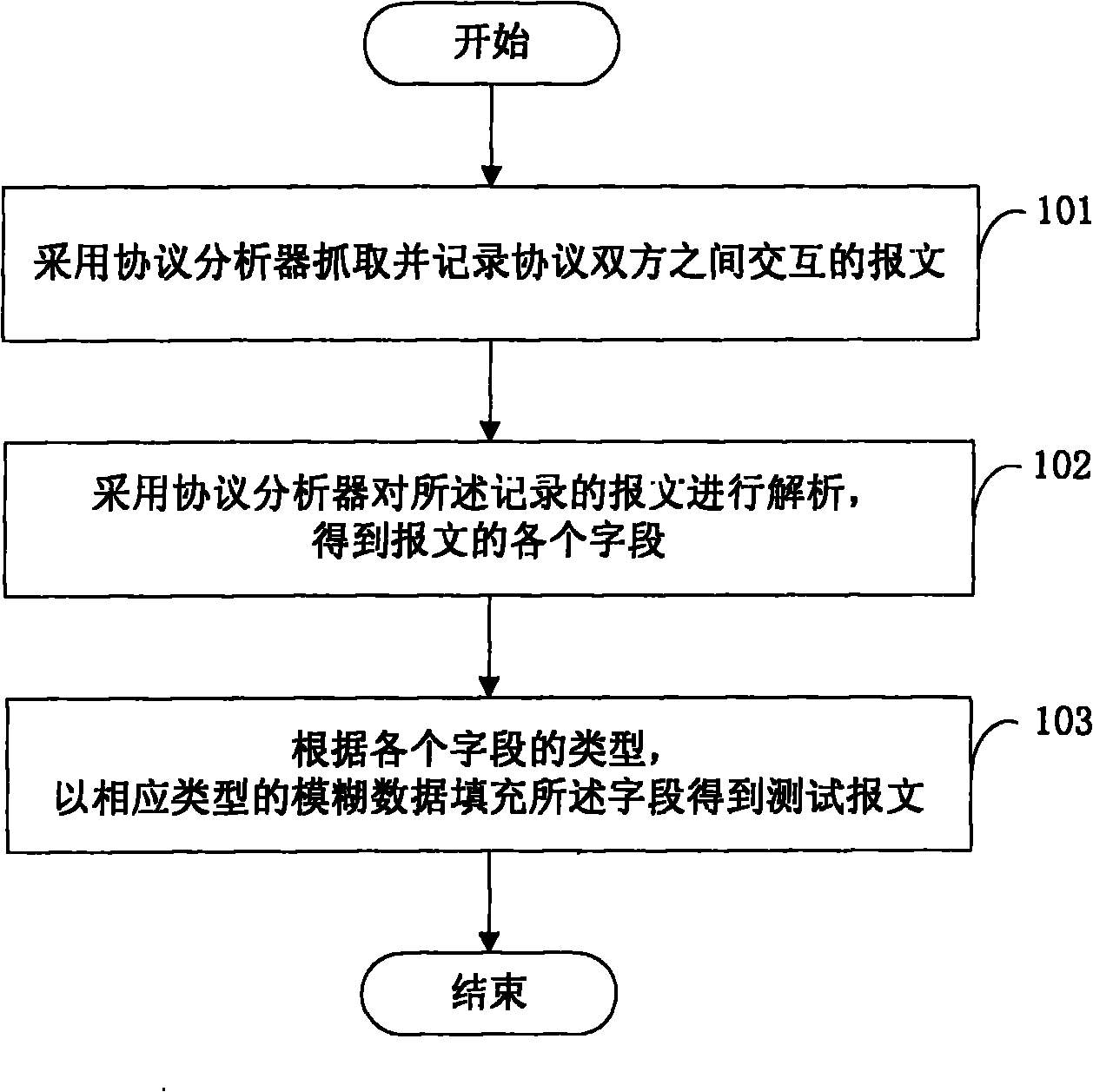
InactiveCN101902367AImprove effectivenessSave time and costData switching networksComputer hardwareComputer science
The invention discloses a method for producing a test case, which is used for performing fuzz testing on protocols and comprises the following steps: grabbing and recording interactive messages between both sides of a protocol by a protocol analyzer; analyzing the recorded messages by the protocol analyzer to obtain each field of the messages; and filling each field by fuzzy data with corresponding types to obtain test messages according to the type of each field. The invention also discloses a system for producing a test case. By the invention, a complete and effective test case can be produced in no need of understanding the relative knowledge of protocol specifications so as to completely and effectively evaluate the safety of a protocol product.
Owner:SIEMENS CHINA
Method and system for controlling media sessions in networks that use communication protocols with distinct signaling and media channels
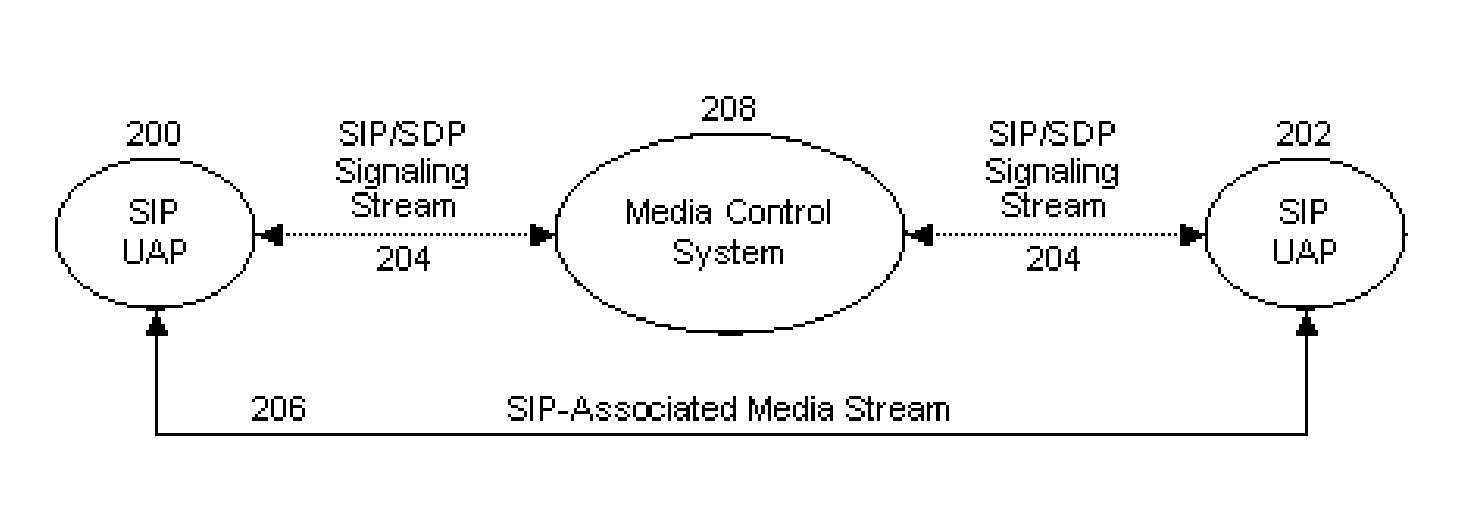
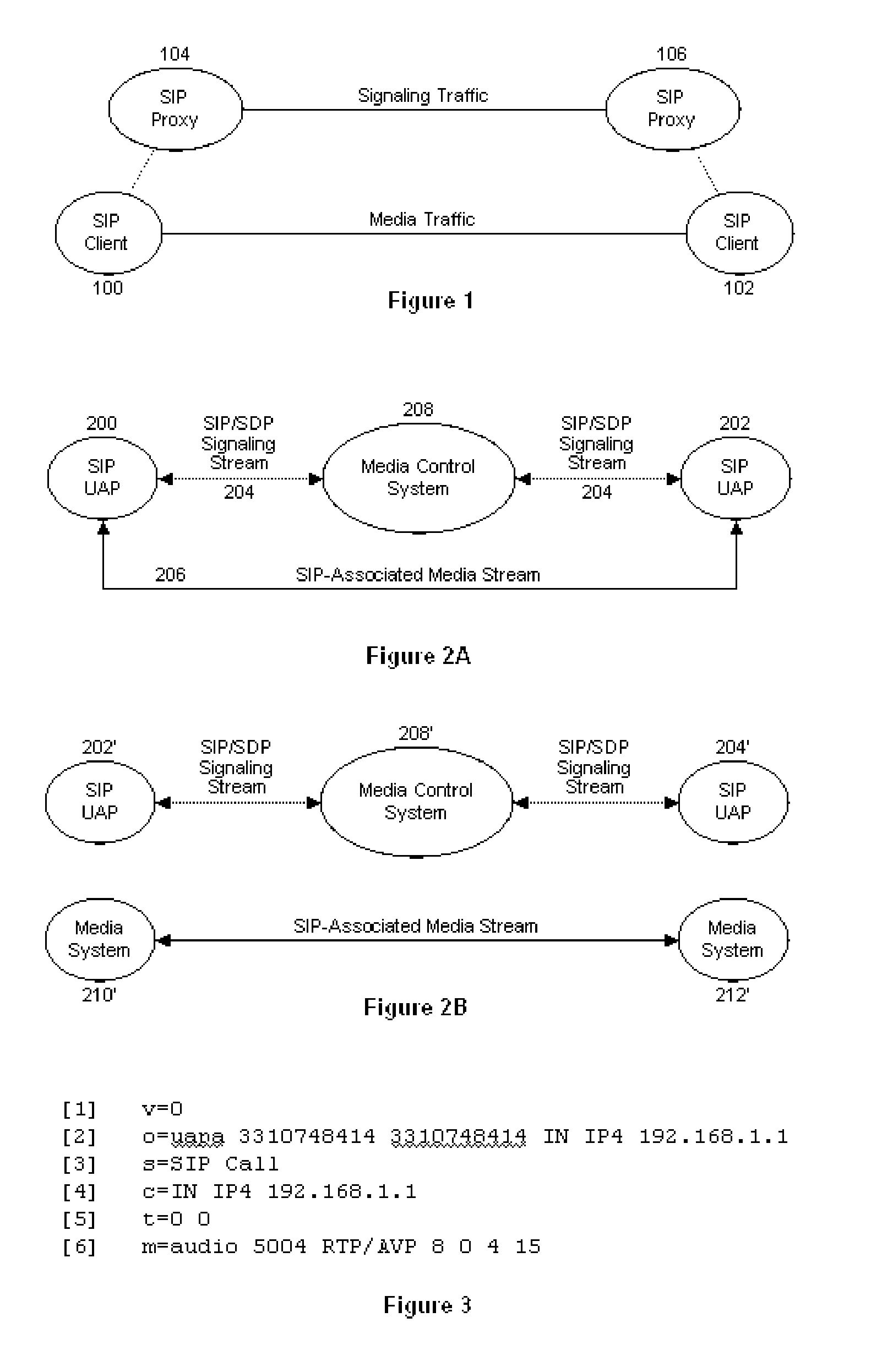
ActiveUS7796603B1Increase heightOptimize networkData switching by path configurationMedia controlsControl system
A media control system (MCS) enforces media control policies on systems that conform to the relevant protocol specifications (such as SIP and SDP), for example, by interpreting and potentially modifying or destroying the SDP offers embedded in the SIP signaling messages that traverse it. This enables the MCS to exercise control over SIP-associated media sessions without necessarily inserting itself into the media streams themselves. The MCS can enforce media control policies that are based either directly on information that is explicitly contained in SDP message bodies or on secondary information that can be derived from information that is contained in the SDP messages.
Owner:ACME PACKET
Communications system for pure electric motor coach power cell management system and management method thereof
InactiveCN101417637ARealize managementImplement charge managementTransmissionElectric/fluid circuitCommunications systemElectric-vehicle battery
The invention relates to a communication system used for a pure electric passenger vehicle battery management system. The communication system comprises a plurality of battery monitoring and controlling modules, a battery management system central control module, a whole vehicle controller, a vehicle-loading monitoring and controlling system, a ground monitoring and controlling system, and a charger. The communication system utilizes SAE J1939 as reference for formulating the communication protocol specification of a pure electric passenger vehicle battery management system and the communication content and formula of main key components, and meets the needs of the management and the fault diagnosis communication protocol of the electric vehicle battery system.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
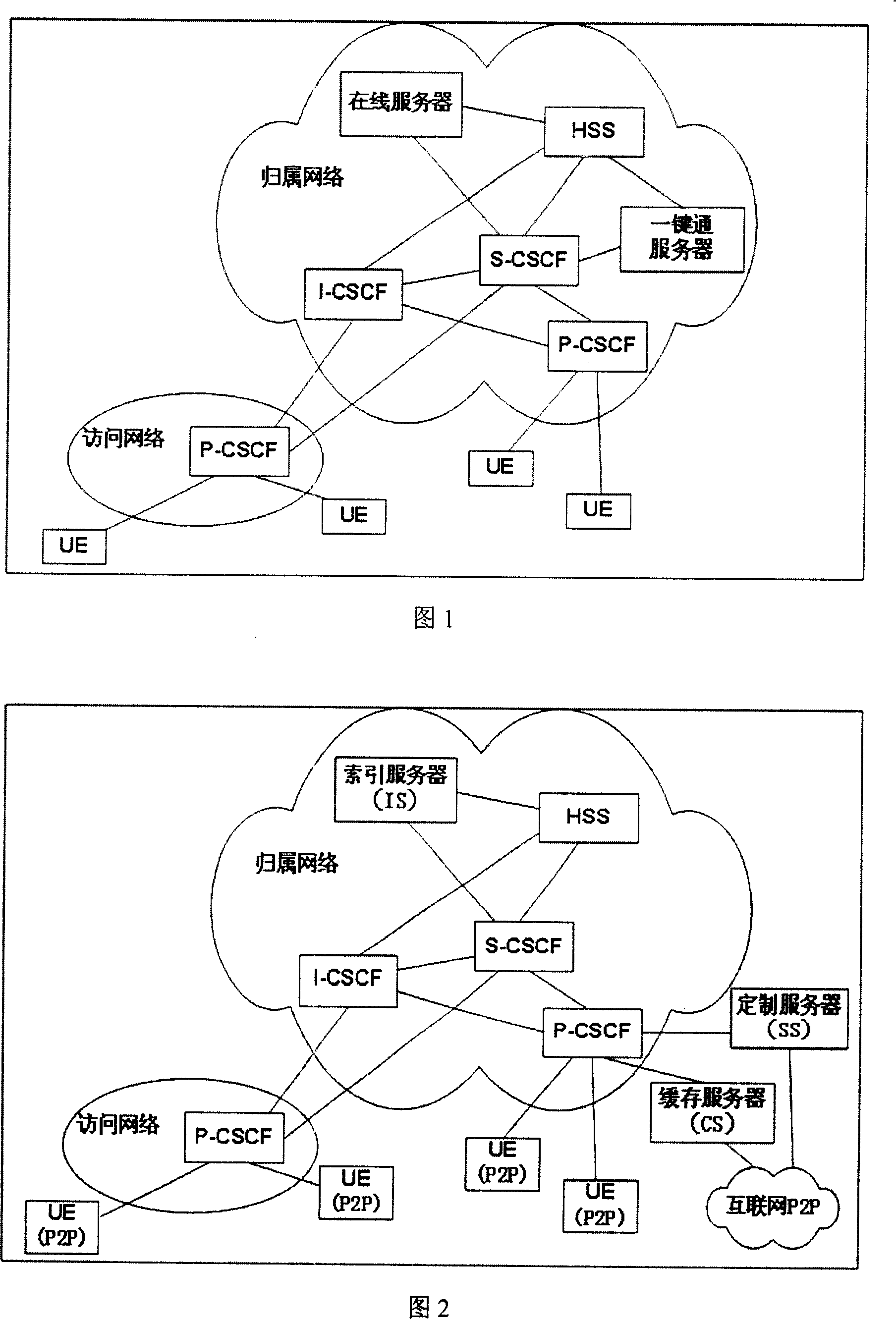
Peer-to-peer networking file sharing service network structure
InactiveCN101115019AEasy to crossGood continuityAutomatic exchangesData switching networksApplication serverSession control
The invention relates to a P2P file-sharing service network framework, comprising a user entity, an Agent-Call Session Control Function entity, a Timetable-Call Session Control Function entity, a Service-Call Session Control Function entity, an application server, and an attribution user server. The invention is characterized in that the application server is an index server to realize P2P file-sharing service. The user entity is provided with a P2P file-sharing service function module; the index server is respectively connected with the attribution user server and the Service-Call Session Control Function entity; the user entity is connected with the Agent-Call Session Control Function entity. The invention can effectively realize the discontinuity of the mobile and roaming services of the users, allow wired and wireless users to participate simultaneously, and realize uniform standard protocol specification, provide effective management and copyright protection, improve service performance by a buffer, and expand service contents by a custom server.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
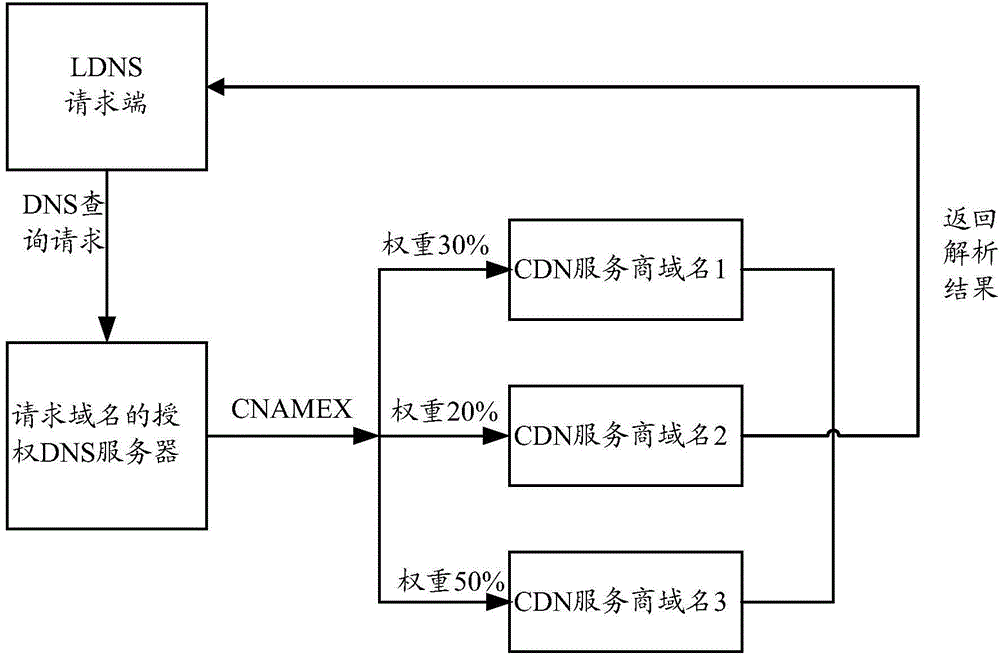
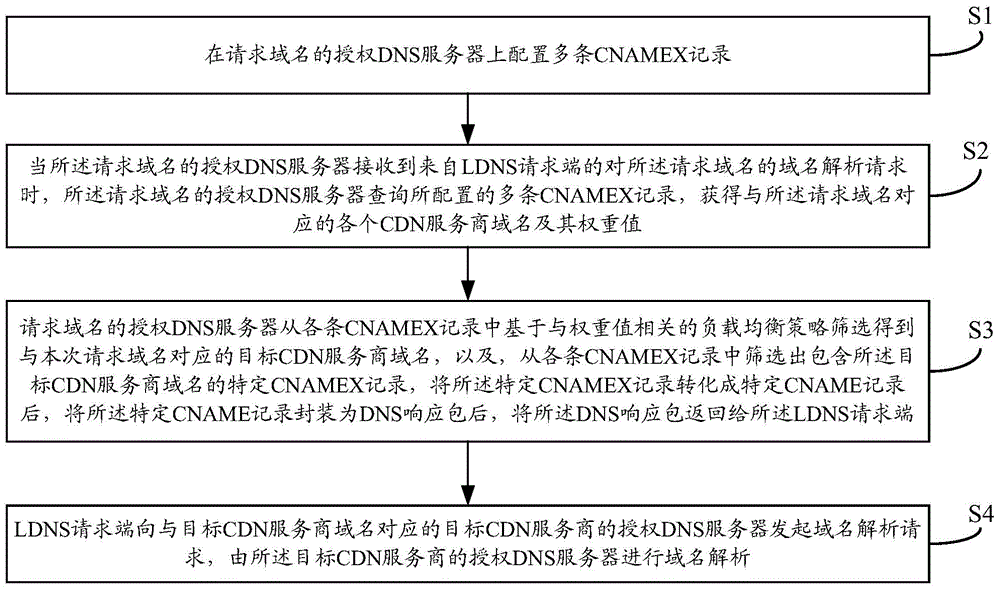
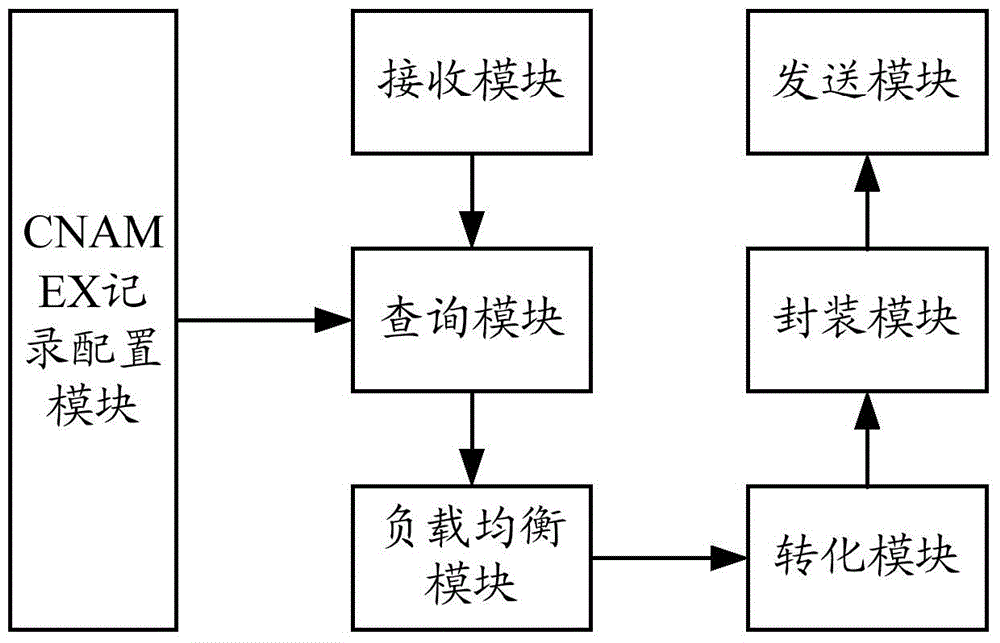
Method and system for load balancing in DNS system based on alias record
The invention provides a method and system for load balancing in a DNS system based on an alias record. The method includes the steps that a CNAMEX record is revised and added according to DNS protocol specifications, the aliases of the same domain name under the same view point to multiple other domain names, and therefore the same service website domain name in the same VIEW has access to multiple CDN service providers to conduct acceleration. In addition, weight indexes of traffic loads are added for the CNAMEX record, a user can reasonably share traffics to the different service providers according to the performance and the bearing capabilities of the CDN service providers, and the quality of CDN application services is optimized.
Owner:江苏友普信息技术有限公司
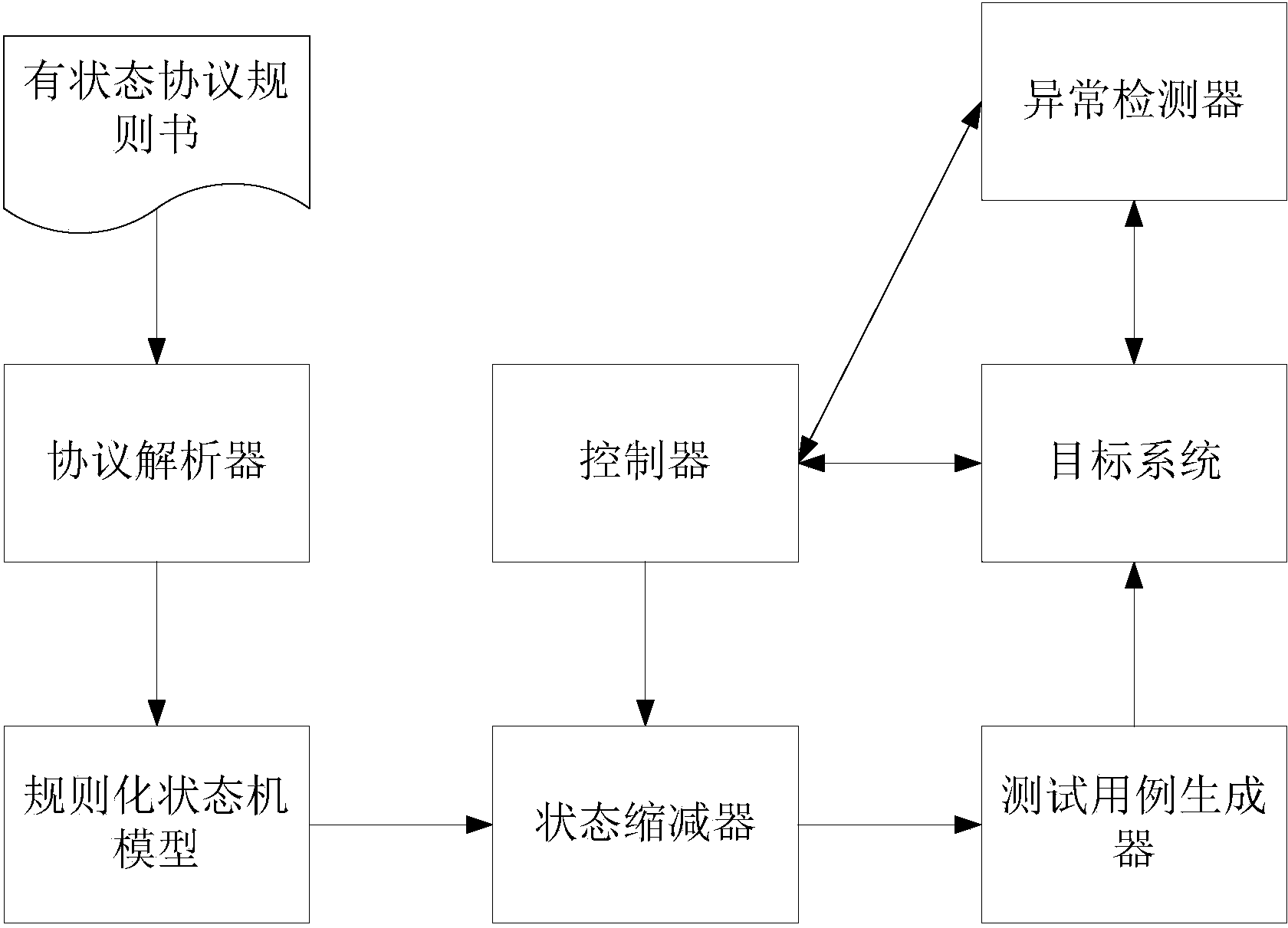
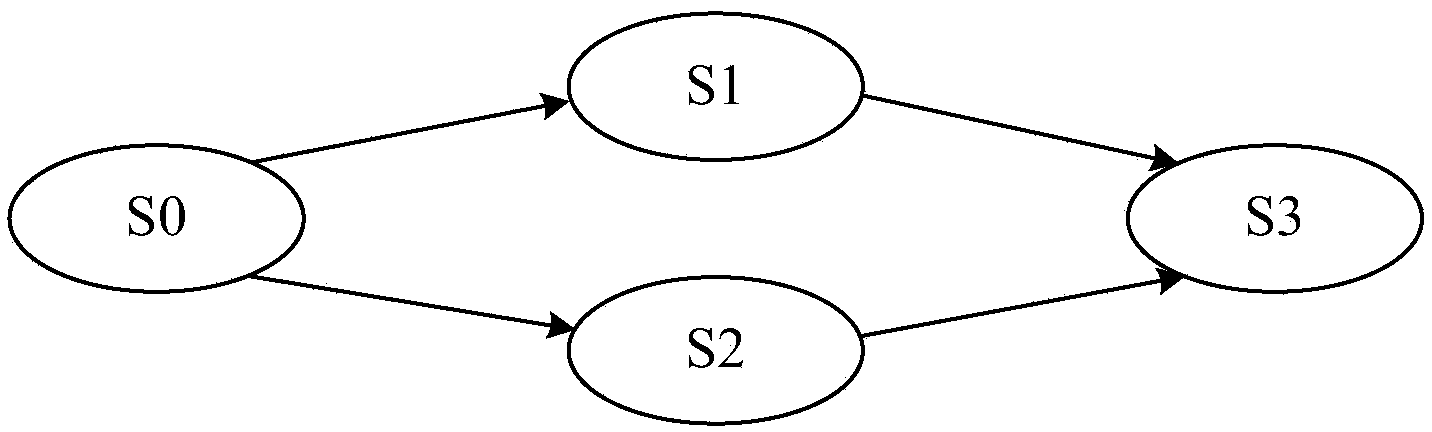
Regularization state machine model design method with stateful protocol
ActiveCN104142888AIncrease coverageEfficient testingSoftware testing/debuggingState spaceTheoretical computer science
The invention discloses a regularization state machine model design method with a stateful protocol. The regularization state machine model design method is used for improving a traditional fuzz test aiming at a stateful network protocol, enables a test case generated by the traditional fuzz test to be targeted but not indigested, has a wide cover range and is efficient. The regularization state machine model design method comprises the steps of step 1, obtaining the protocol specifications of a to-be-tested network protocol, and obtaining the protocol rules and a preliminary protocol state machine model through format analysis on the to-be-tested network protocol; step 2, generating a regularization state machine model for simplifying state space according to the preliminary protocol state machine model and the information of the state rules; step 3, generating a state generating tree combined with a state and the rules according to the protocol rules and the regularization state machine model, simplifying the relation between the state and a message through the state generating tree, and eliminating insignificant combinations; step 4, generating a preliminary test case; step 5, carrying out regular variation on the preliminary test case, and obtaining a final test case set.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Abnormal behavior detection method for unknown industrial communication protocol specification
The invention discloses an abnormal behavior detection method for an unknown industrial communication protocol specification. The abnormal behavior detection method is divided into an online self-learning stage and a real-time detection stage, wherein the online self-learning stage mainly completes the analysis and feature extraction of network original network communication data, forms an event sequence, takes the event sequence as the input of a hidden Markov model to train the model, and finally obtains the optimized hidden Markov model and a behavior probability threshold through iteration; and the real-time detection stage uses the optimized hidden Markov model to perform behavior probability calculation on the event sequence which is processed in real time, and completes the abnormal detection of an industrial communication behavior by comparing the behavior probability with the behavior probability threshold. The abnormal behavior detection method for the unknown industrial communication protocol specification provided by the invention can detect the legitimacy of an industrial communication data stream using the unknown industrial communication protocol specification, and detect the abnormal industrial communication behavior and give an alarm in real time, so as to guarantee the network communication security of an industrial control system.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
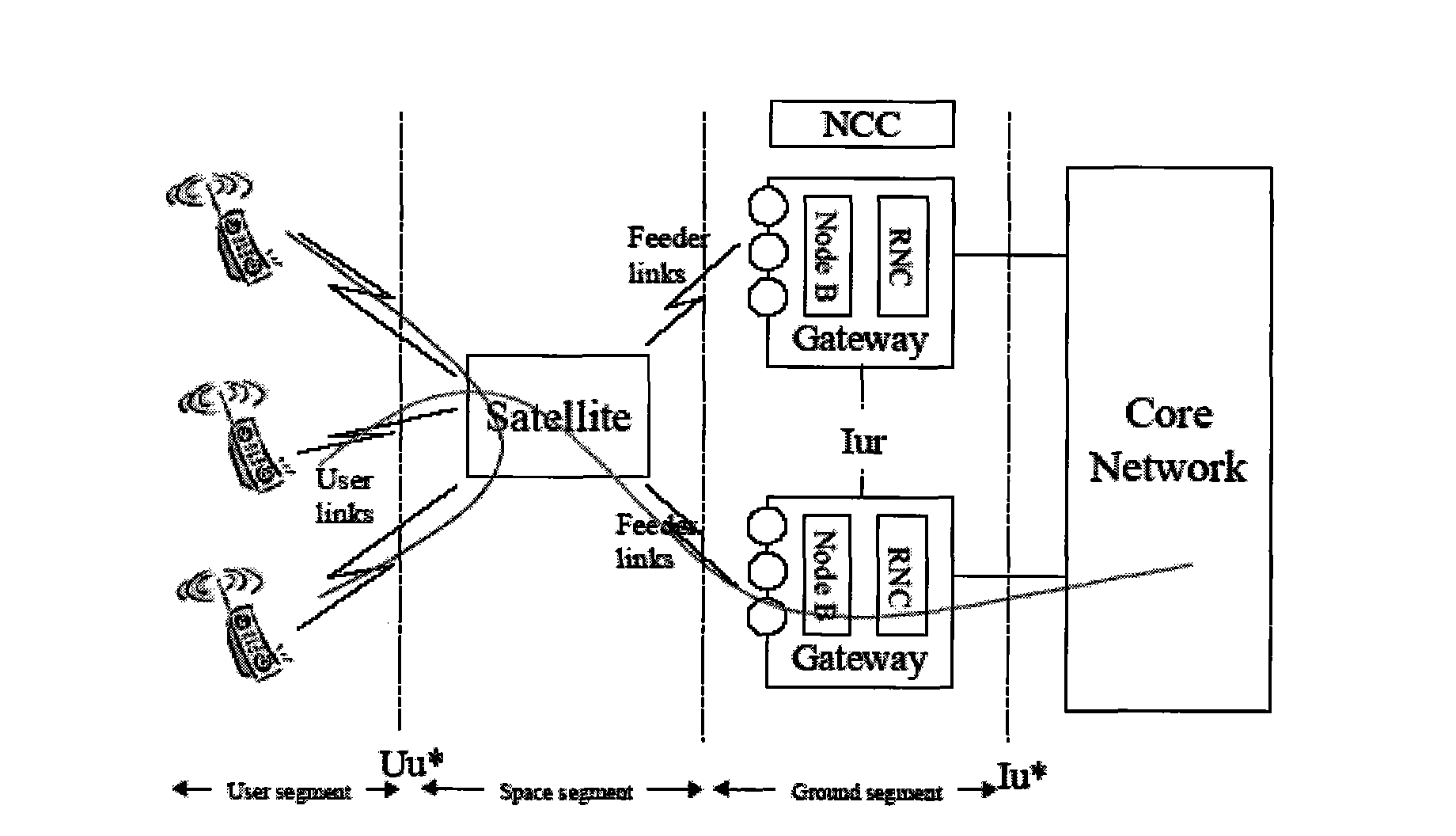
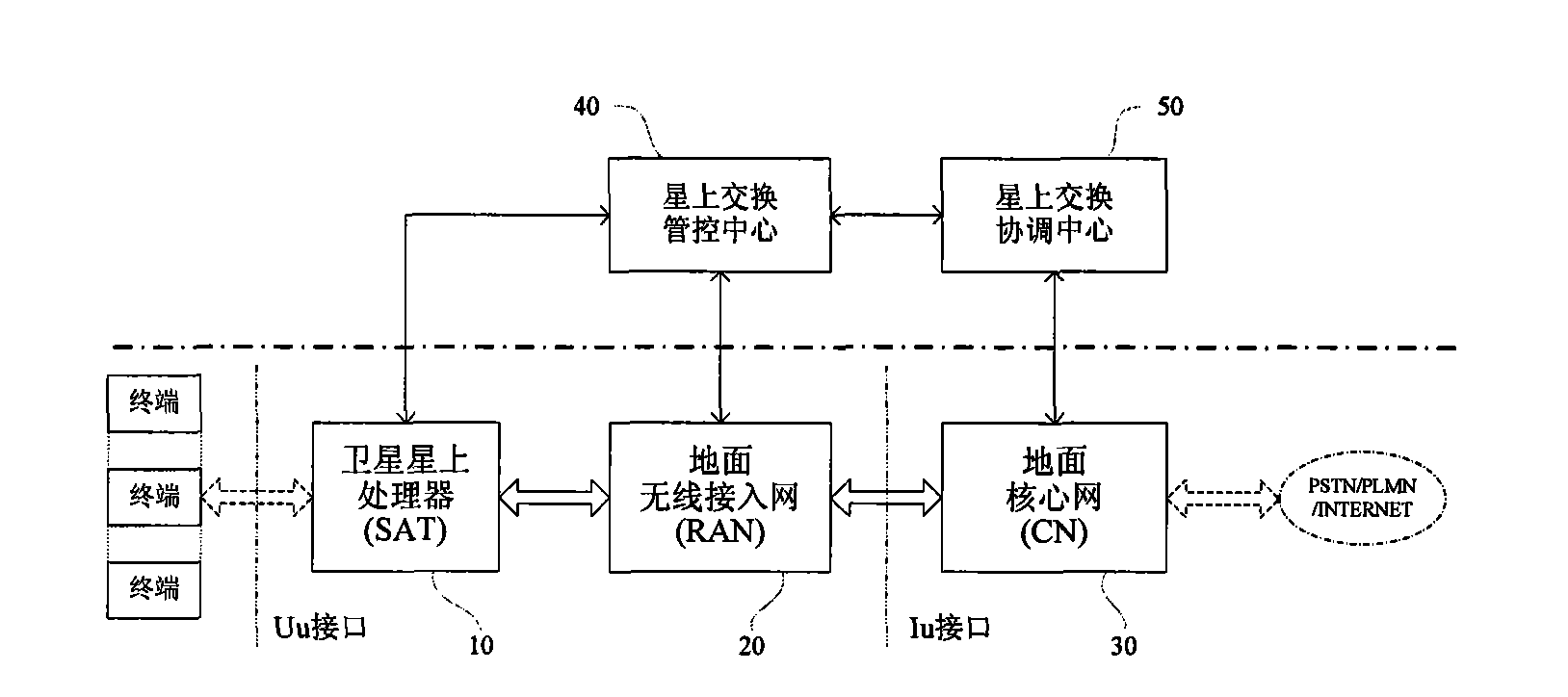
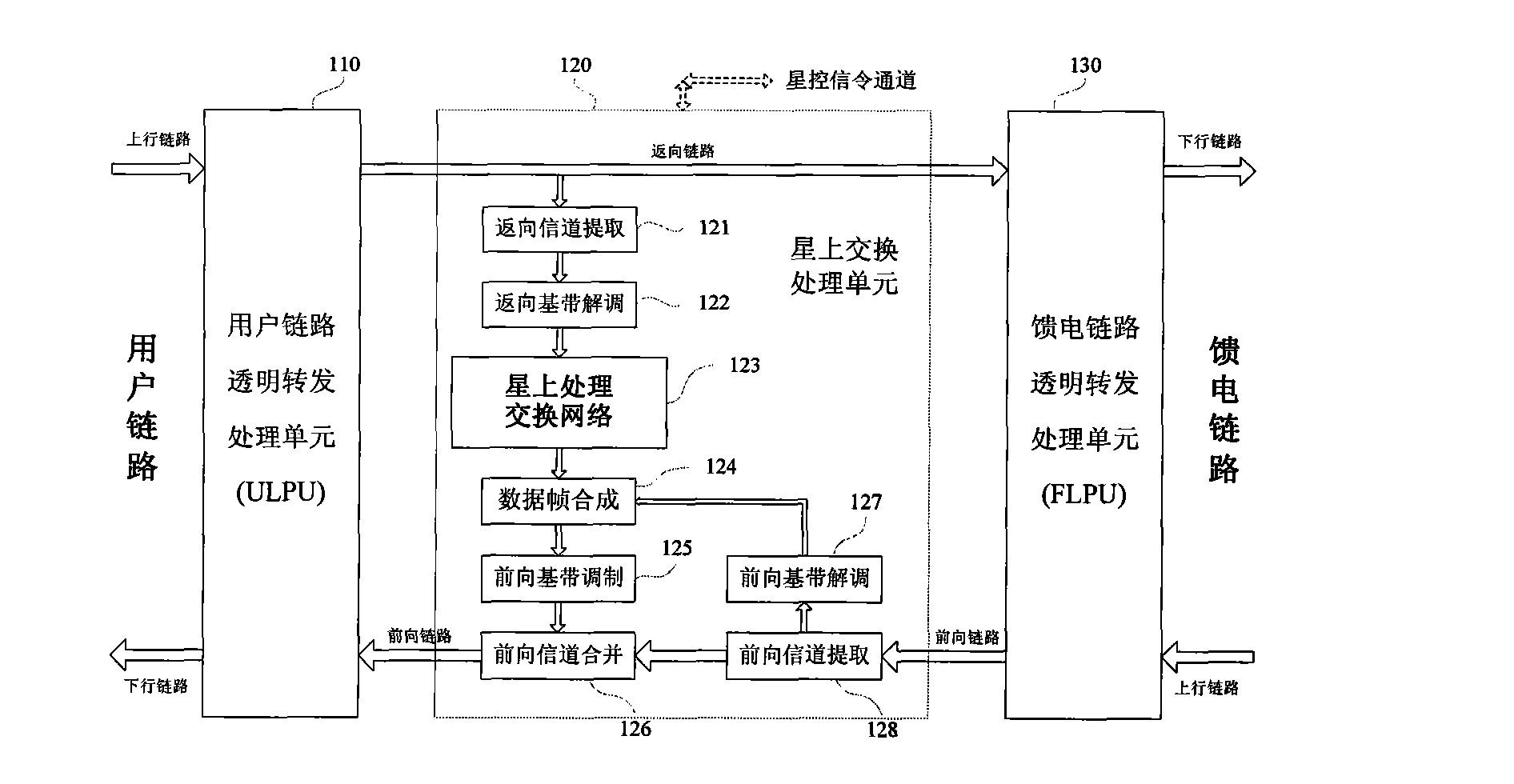
Satellite mobile communication system based on partial satellite baseband switching
InactiveCN101635594AReduce service transmission delayEasy to transformRadio transmissionWireless commuication servicesControl signalBaseband
The invention discloses a satellite mobile communication system based on partial satellite baseband switching, which belongs to the technical field of satellite communication. The satellite mobile communication system comprises a communication network body branch and a satellite switching management control branch which are discrete and parallel. A management control signal of satellite switchingprocessing is produced and transmitted by the satellite switching management control branch. A satellite processor in the system has the complete function of satellite transparent forwarding between a user link and a feeding link and also supports partial communication business for realizing satellite single-hop connection in the mode of bridging a bypass. A communication interface, a protocol specification and a processing course of the prior ground mobile communication system are not corrected basically; the prior scheme of the ground user terminal can be directly adopted by a satellite user terminal without considering double-module / multiple-module terminal design requirements; and simultaneously, the satellite mobile communication system is convenient for the further upgrade of a communication network body of the satellite system along with the development of the network technique of the ground mobile communication system.
Owner:PEKING UNIV
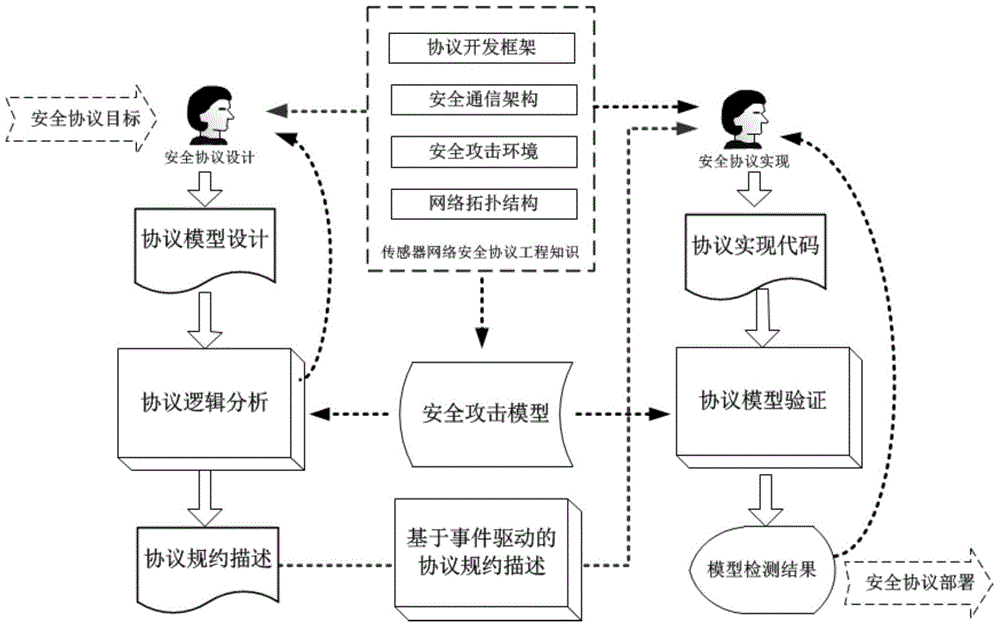
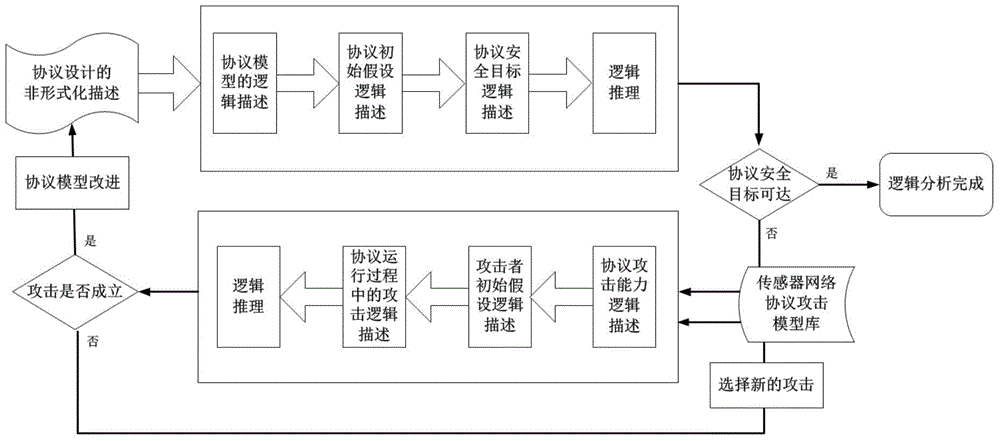
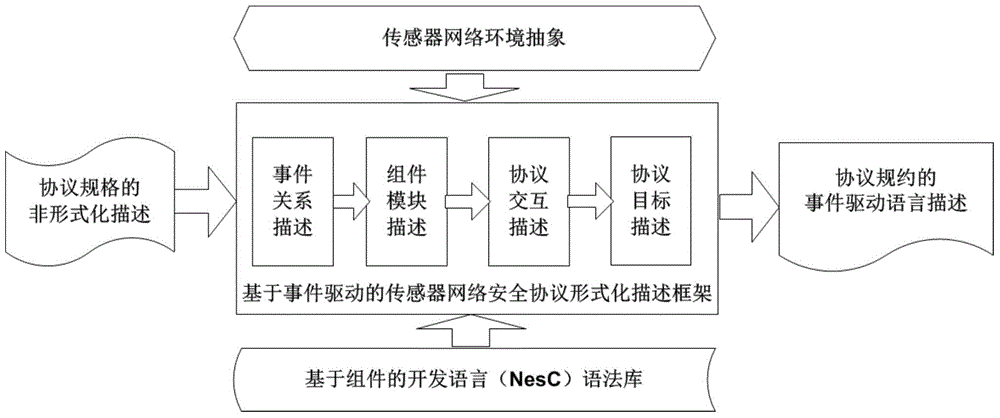
Formal verification method for facing design and accomplishment of wireless sensing network safety protocol
ActiveCN104135397ASimple designImprove development efficiencyData switching networksProtocol designValidation methods
A formal verification method for facing design and accomplishment of a wireless sensing network safety protocol, comprises the following steps: (1) a sensing network safety protocol design method based on logical analysis: a designer of the sensor network safety protocol accepting a protocol design goal, and designing a protocol rudiment based on analysis of sensor network environmental factors; establishing a logical reasoning system to accomplish protocol modeling and logical analysis, amending the protocol design plan according to the analysis result, and repeating logical analysis until the logic of the protocol is correct; and giving description of the protocol specification which is not formalized finally; (2) a safety protocol specification description language facing the sensing network developing environment; and (3) a safety protocol code automatic verification method based on model checking. The present invention effectively ensures safety and efficiency of the design and development and has good expansibility.
Owner:ZHEJIANG UNIV OF TECH
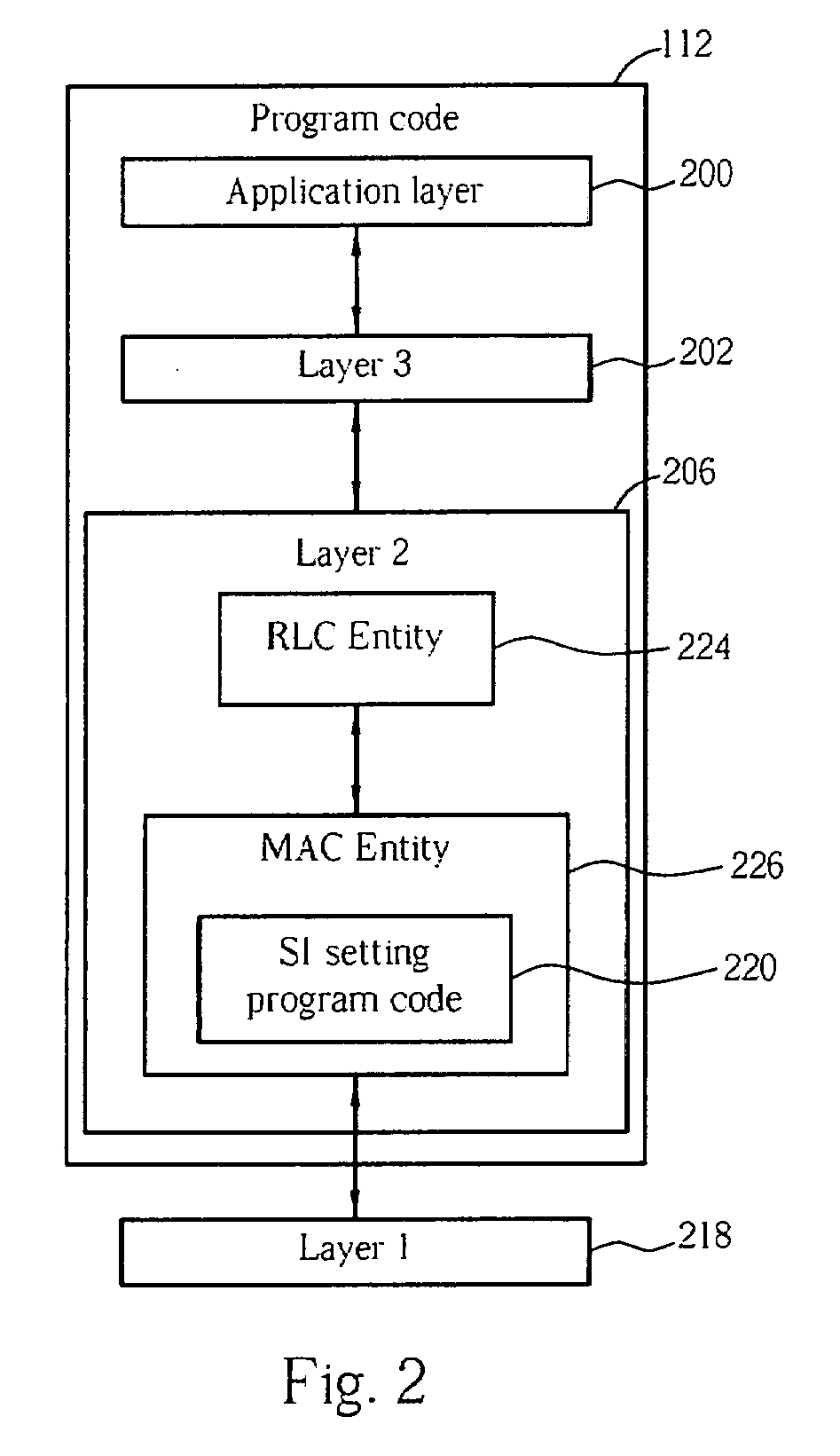
Method and apparatus for setting field data of scheduling information in a wireless communications system
InactiveUS20080026738A1Accurate settingNetwork traffic/resource managementRadio/inductive link selection arrangementsCommunications systemField data
A method for setting field data of a scheduling information in a wireless communications system according to the Medium Access Control protocol specification of the 3rd Generation Partnership Project is disclosed. The scheduling information comprises at least a Highest priority Logical channel Buffer Status field, called HLBS field hereinafter, for storing an HLBS index. The method comprises setting a value of the HLBS index to be a second value when an HLBS value is greater than a first value, and storing the value of the HLBS index into the HLBS field. Figures.
Owner:INNOVATIVE SONIC
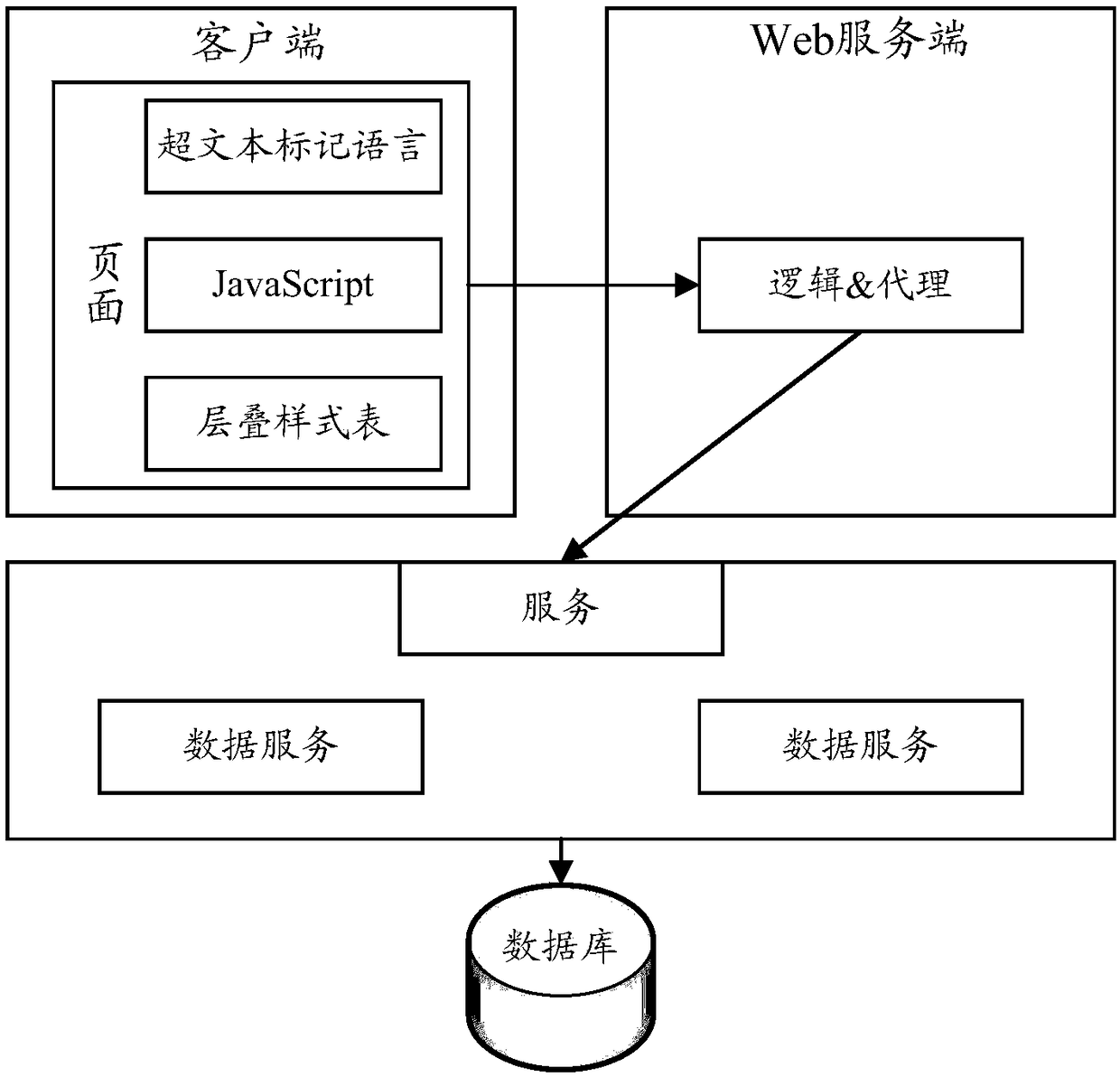
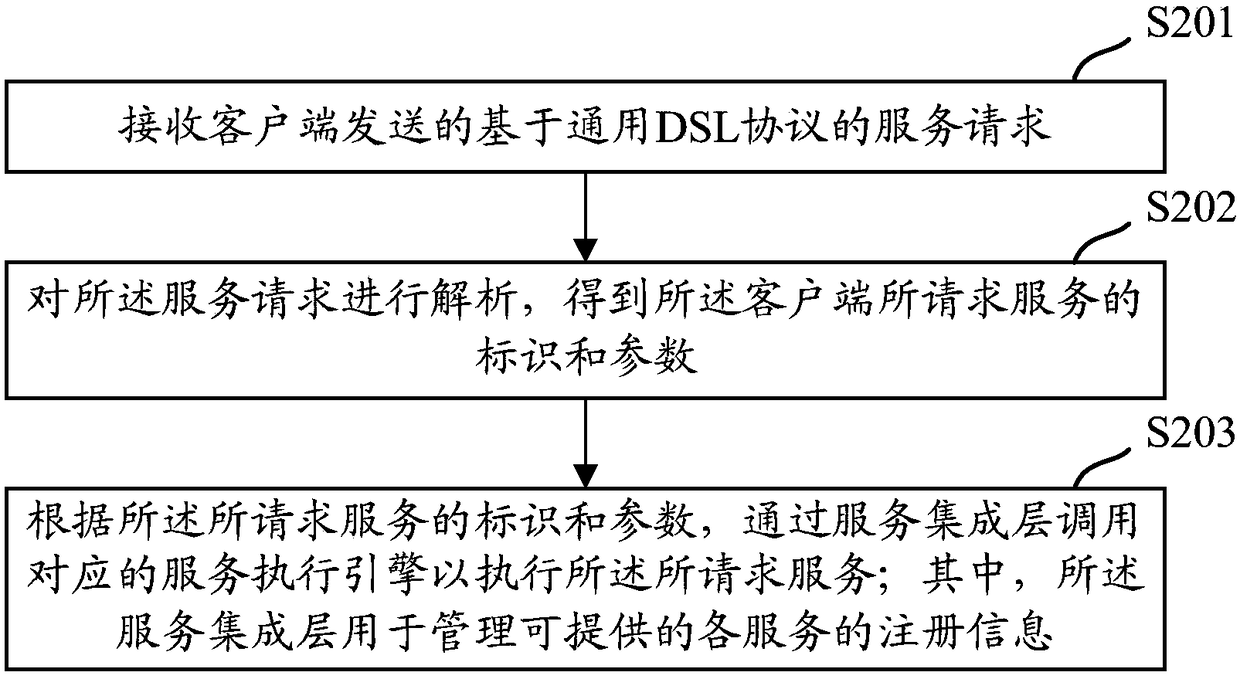
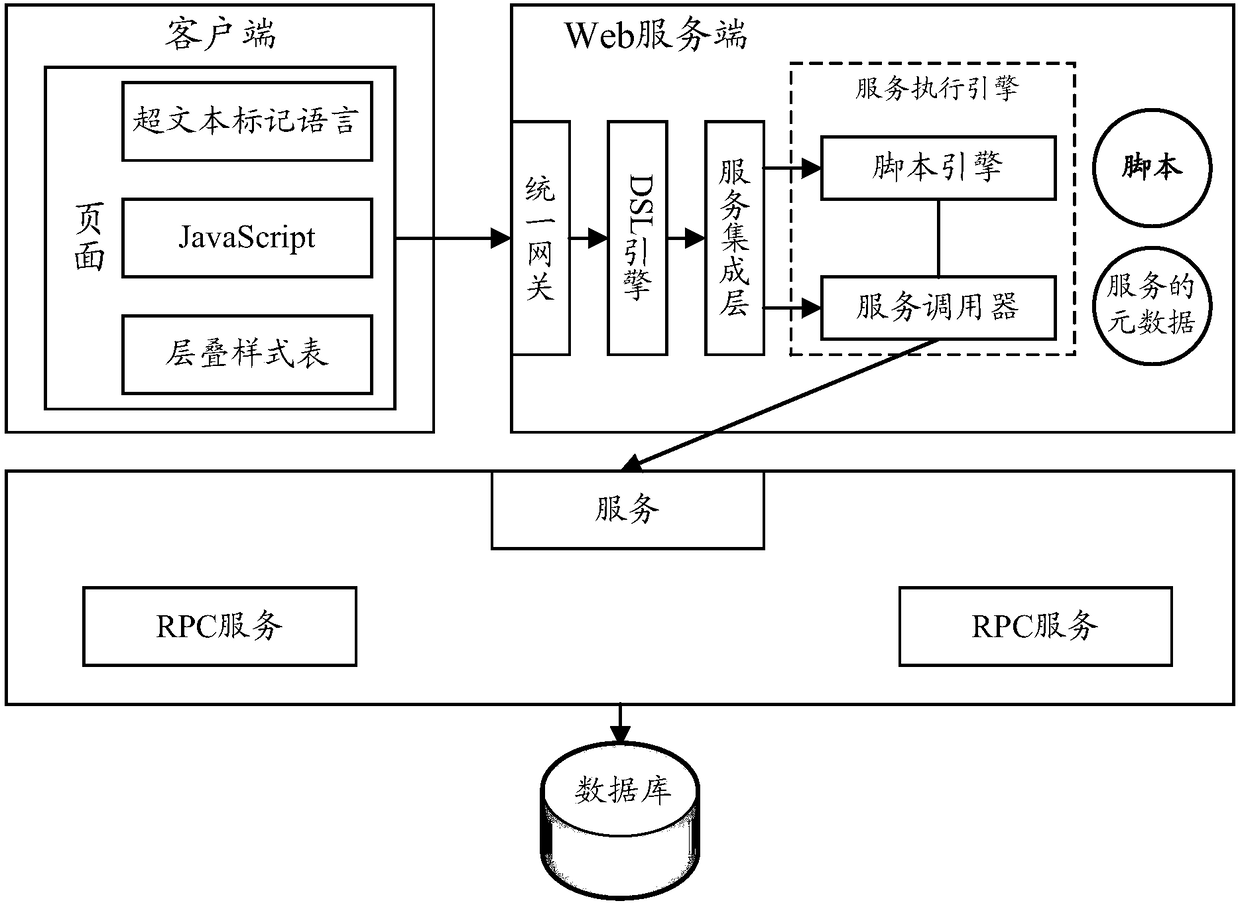
Service method, device and system, and electronic apparatus
ActiveCN109002362AAchieve integrationReduce hardcodingInterprogram communicationTransmissionHard codingClient-side
A service method, device and system, and an electronic apparatus are disclosed. The method comprises the following steps of: receiving a service request based on a common DSL protocol sent by a client; analyzing the service request to obtain the identifier and parameters of the service requested by the client; invoking a corresponding service execution engine through a service integration layer toexecute the requested service according to the identifier and parameters of the requested service, wherein the service integration layer is configured to manage registration information of each service that can be provided. With the embodiment of the present application, the registration information of each service can be uniformly managed based on the common DSL protocol specification request and through the service integration layer so as to effectively realize the service integration, and hard coding can be reduced, so that error is reduced and service efficiency is improved.
Owner:ADVANCED NEW TECH CO LTD
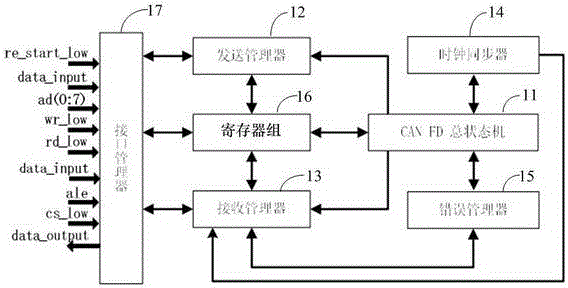
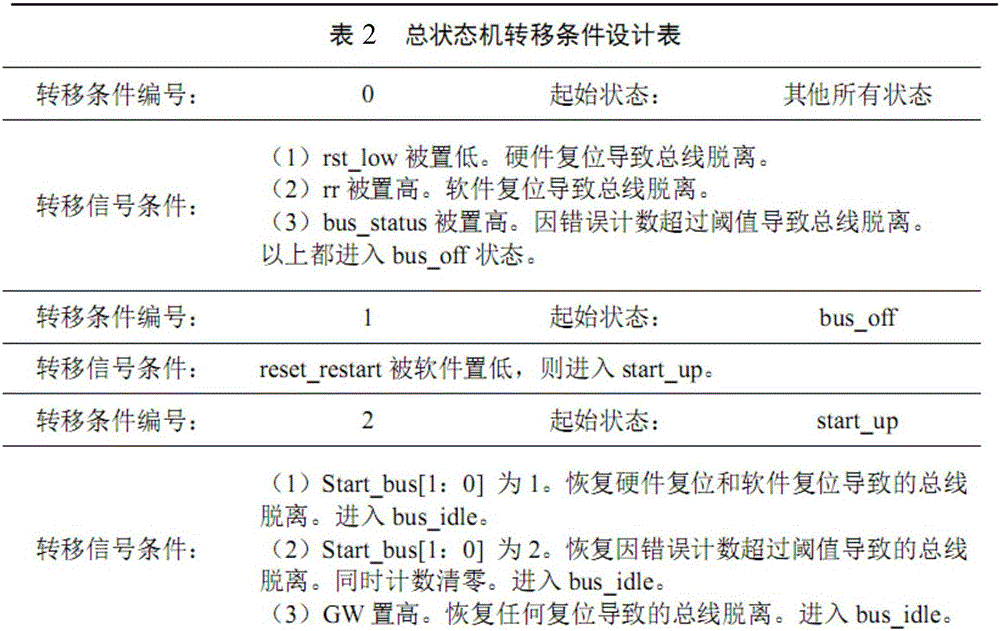
Novel CAN FD controller
The invention discloses a novel CAN FD controller. A CAN FD total state machine regulates an overall function and working state of a CAN FD controller; a sending management device sends all types of frames and ACK signals; a receiving management device monitors a bus and analyzes data received by the bus; a clock synchronizer control a bit clock cycle according to user setting and a bus signal and provides a bus value sampling point and a sampling value; an error management module carries out statistic counting on node errors and reflects counting values into node error state (ES) and bus state (BS) information; a register group manages registers in a centralized mode; and an interface management device parses an instruction from a microcontroller and decodes address information into a gating signal corresponding to a register. The novel CAN FD controller based on a CAN FD bus communication protocol specification and a practical demand of a microwave power distributed control system has excellent performances and has the important practical engineering significance.
Owner:SICHUAN UNIV
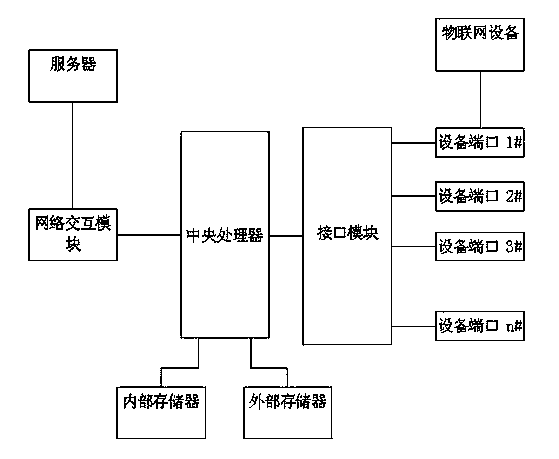
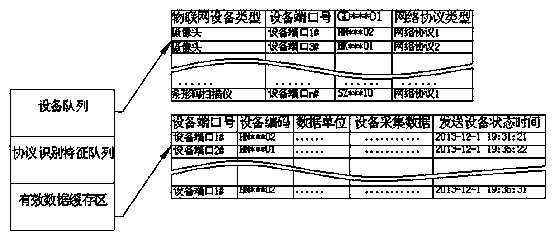
Internet of things multi-protocol access transform device and control method thereof
The invention discloses an internet of things multi-protocol access transform device which comprises an interface module, a network interaction module, an internal storage, an external storage and a central processor, wherein the interface module is in network connection with an internet of things device, and the network interaction module is in network connection with a server. The central processor can recognize network protocols used by the internet of things device and screen out effective data conforming to data acquisition requirements; a device array for recording access device network information, a protocol recognition feature array for recoding unified protocol specifications and an effective data cache region are established in the internal storage; protocol recognition feature data are stored in the protocol recognition feature array; the central processor is connected with the interface module connected with the network, the network interaction module, the internal storage and the external storage. The traditional device access mode of the internet of things can be replaced, and the devices can be concentrated accessed in and managed. The problem that no unified communication language and communication protocol exists in the internet of things device connection is solved.
Owner:GUANGDONG FUTURE INFORMATION TECHN CO LTD
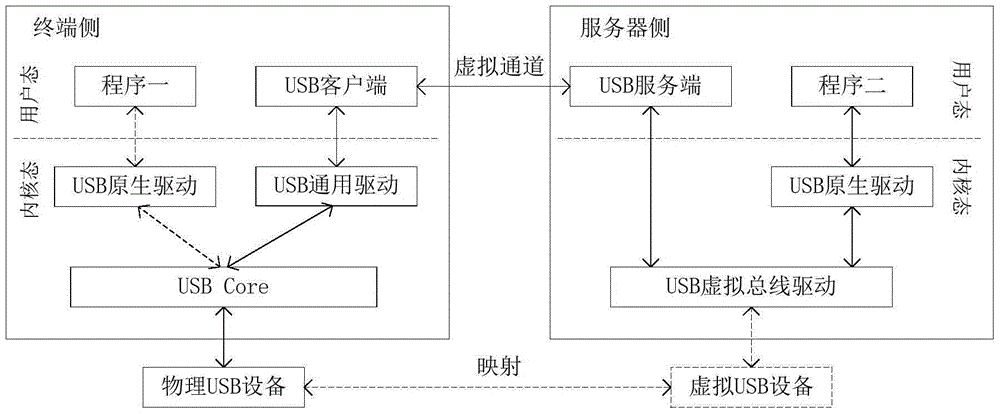
USB equipment access method, device and system, terminal and server
ActiveCN105183675ASolve the problem that cannot be redirectedImprove compatibilityProgram controlAccess methodTechnical standard
The invention discloses a USB equipment access method, device and system, a terminal and a server, and belongs to the technical field of computers. The method comprises the steps that an access request issued by the server is received; whether an access operation indicated by the access request is a first access operation or not is judged; if the access request indicates that the terminal conducts the first access operation on physical USB equipment, a first processing operation corresponding to the first access operation is executed according to compatible strategies so that an execution result of the first processing operation can be fed back to the server. Due to the fact that actions executed when the terminal responds to the first access operation when the physical USB equipment does not support the first access operation are set in the compatible strategies, the physical USB equipment can still conduct correct redirection according to the access request even when the physical USB equipment is not designed on the basis of certain standard USB protocol specifications, the problem that some physical USB equipment which is not designed on the basis of a certain standard USB protocol specification cannot be redirected is solved, and guarantees are provided for users to normally use the physical USB equipment.
Owner:HUAWEI TECH CO LTD
Concealing a network connected device
ActiveUS6973496B2Comprehensive understandingUser identity/authority verificationMultiple digital computer combinationsNetwork connectionThe Internet
In a preferred embodiment of the invention, a network client inserts a validation key into the SEQ and ACK fields of a TCP connection request (TCP-SYN). The TCP connection request is sent to a validating server. The validating server extracts the validation key and uses it, with other implicit and explicit data contained within the TCP connection request to validate the connection establishment request. If the connection request is validated, the validating server responds with a TCP-SYN / ACK as described in the TCP protocol specification. If the TCP connection request is denied, the request is discarded and nothing is sent back to the requestor, in this case the network client. When an internet port scanner sends a TCP connection request to a validating network server without the proper key, the request is silently discarded or “black-holed.” This makes the validating server appear to the Internet port scanner to not exist. The validating server has completely concealed itself from unauthorized and unvalidated connections.
Owner:INVISINET TECH LLC
Case generation method for semi-legalized fuzz test of network protocol based on finite-state machine
ActiveCN105095075AQuality improvementReduce sizeSoftware testing/debuggingGranularityFinite-state machine
The invention discloses a case generation method for a semi-legalized fuzz test of a network protocol based on a finite-state machine. The case generation method comprises following steps: analyzing a protocol interaction process based on the network protocol of the finite-state machine and according to a network protocol specification and constructing a network protocol model based on the finite-state machine; establishing the complete test sequence aimed at the finite-state machine, wherein the test sequence is a set composed of all state transition paths of the finite-state machine; constructing a message set of deformity agreements after variation in protocol messages md; sequentially selecting one of the message set of deformity agreements from md as a md used for substituting the complete test sequence in order to obtain one fuzz test sequence related to md so that p fuzz test sequences related to md can be obtained; and finally obtaining all fuzz test sequences from m0 to m(n-1) as cases for the fuzz test. The case generation method is utilized such that cases, with finer granularity, for the fuzzy test of the network protocol can be obtained.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
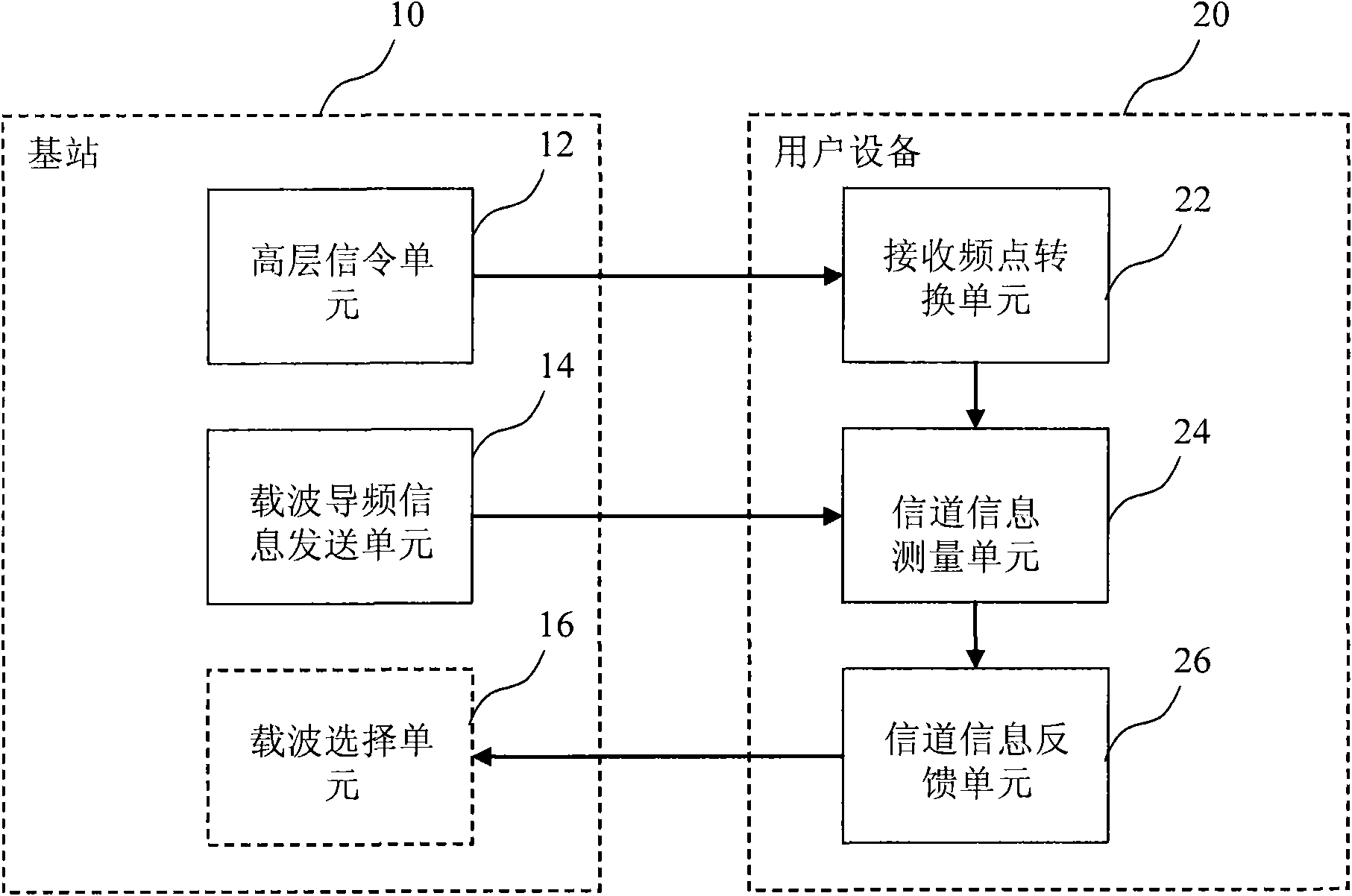
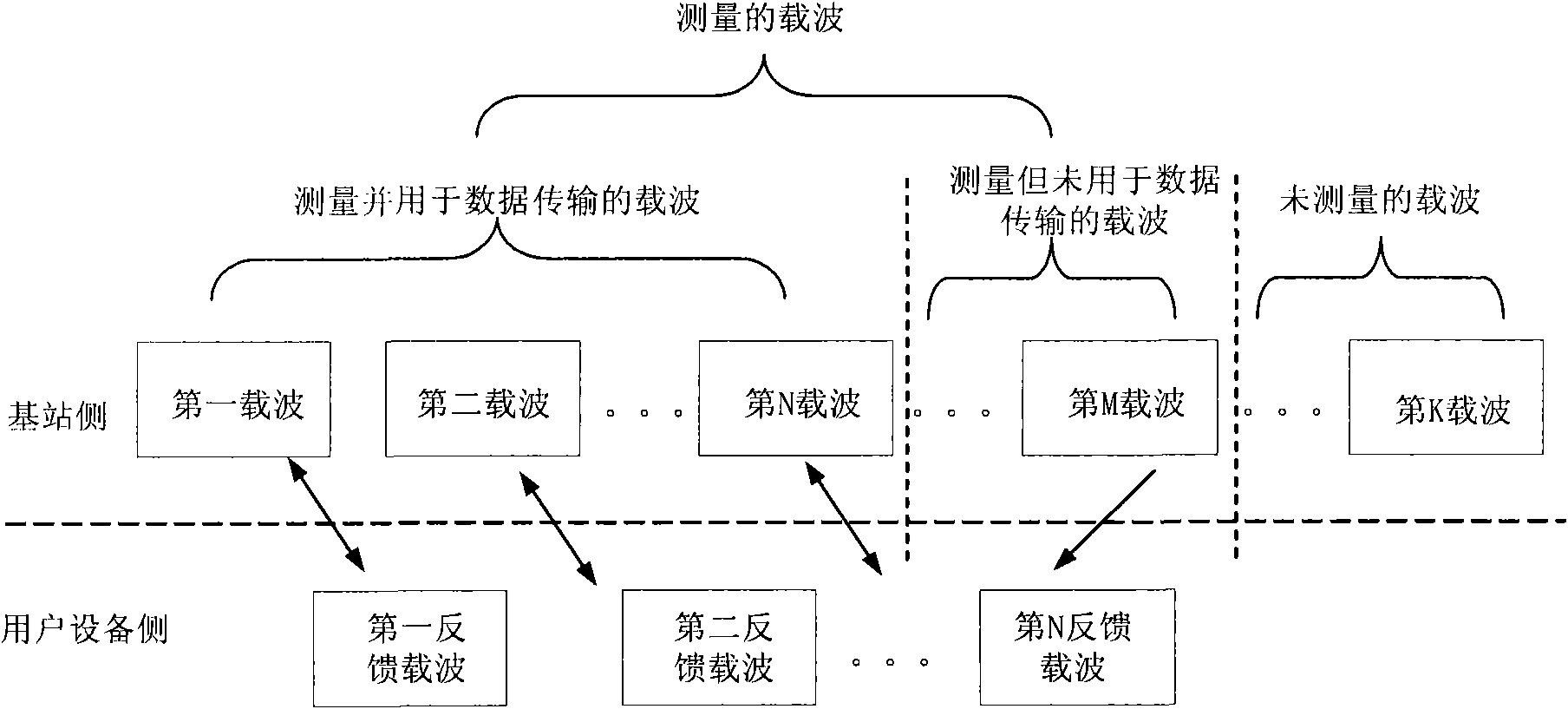
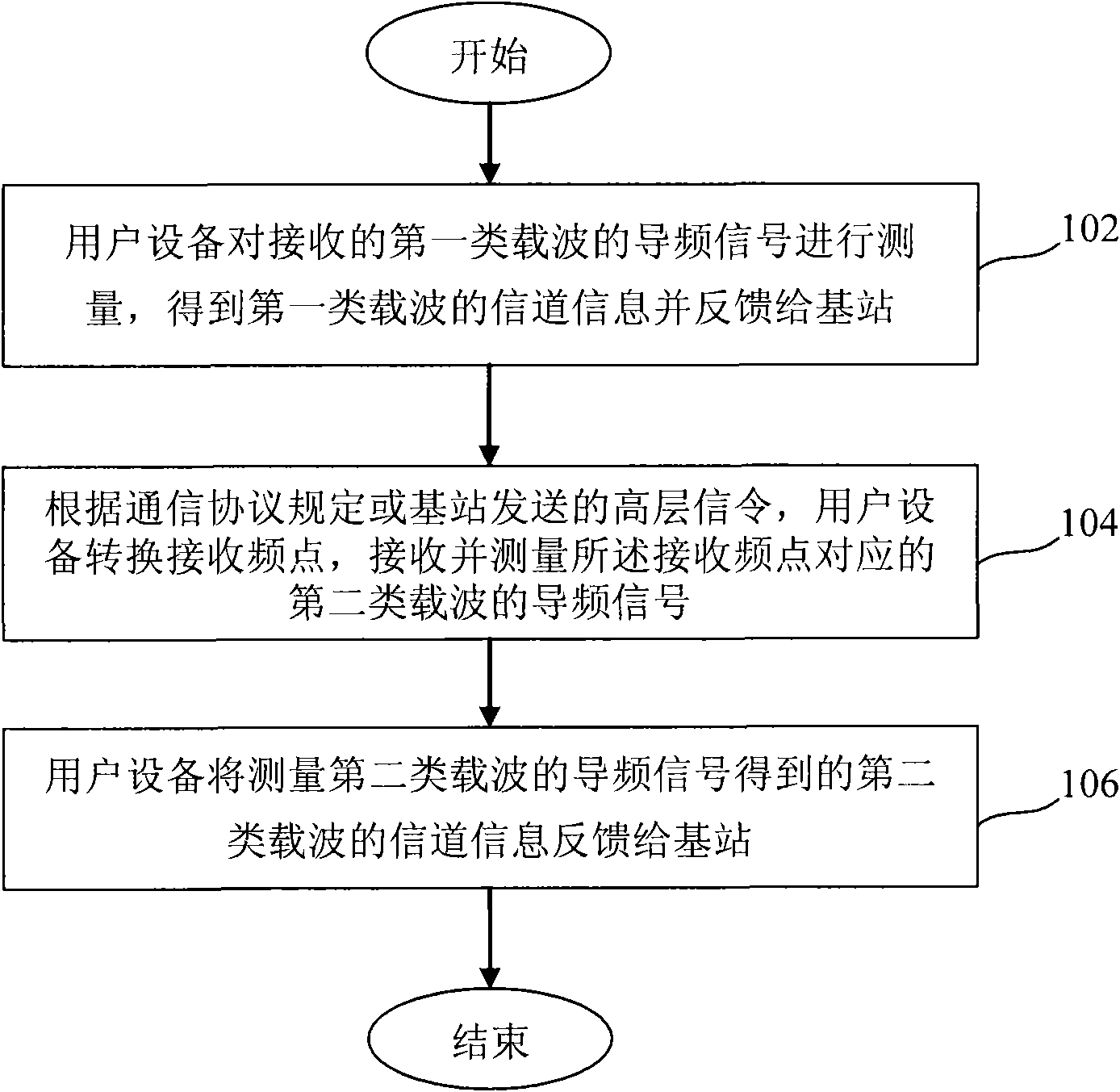
Carrier selection/channel information measurement and feedback system and method of long-term evolution multi-carrier system
ActiveCN101772050AImplement feedbackQuality improvementTransmission monitoringWireless communicationCarrier signalEngineering
The invention relates to a carrier channel information measurement and feedback method of a long-term evolution multi-carrier system. User equipment measures a pilot signal of a received first carrier, obtains the channel information of the first carrier and feeds back to a base station; the user equipment converts a receiving frequency point according to a communication protocol specification ora high-level signaling transmitted by the base station and receives and measures a pilot signal of a second carrier corresponding to the receiving frequency point; and the user equipment feeds back the channel information of the second carrier obtained by measuring the pilot signal of the second carrier to the base station. The invention can realize the channel information feedback of the currentused carrier and an unused carrier in a multi-carrier system, is beneficial to the modulation coding way selection and the frequency resource dispatch of a base station system and the user equipment in the process of data transmission and embodies the frequency selective gain of the long-term evolution multi-carrier system to the greatest extent. The invention also provides a carrier selection system / method of the long-term evolution multi-carrier system, the base station and the user equipment.
Owner:DATANG MOBILE COMM EQUIP CO LTD
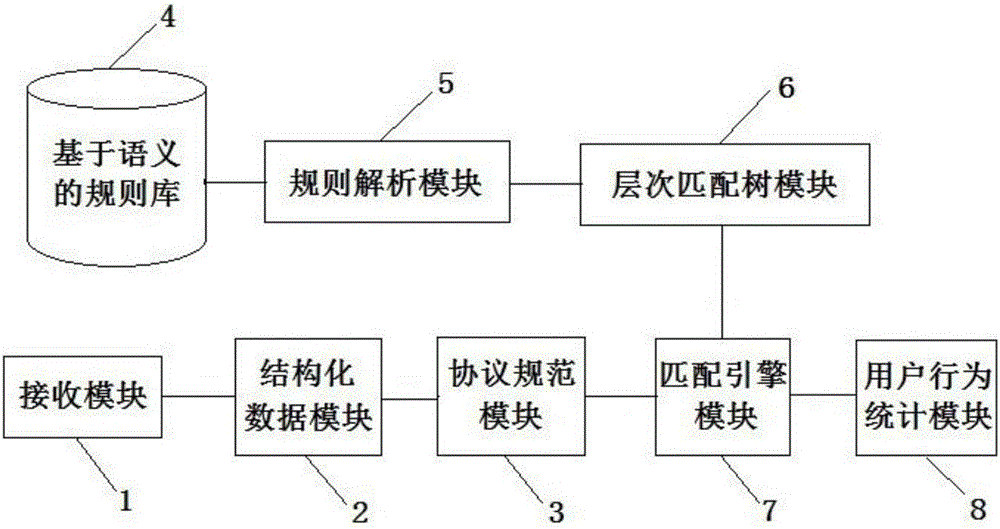
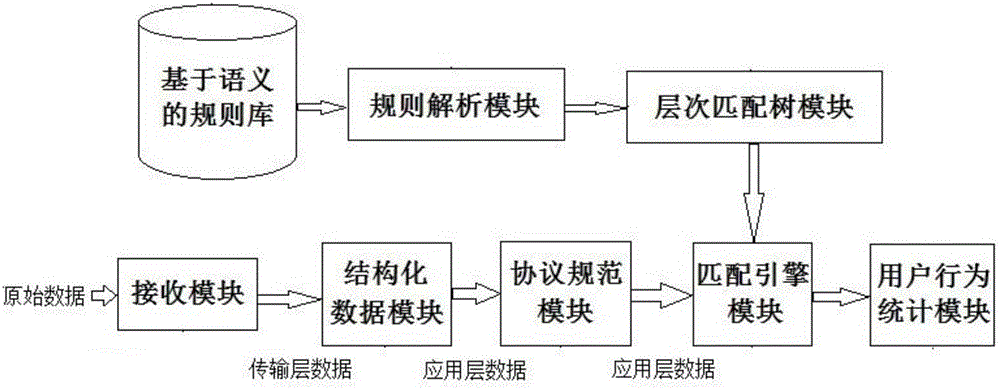
Network traffic depth identification system and method based on many-core processor
InactiveCN105162626AImplementation of deep recognitionMeet real-time online processing capabilitiesData switching networksTransport layerNetwork data
The invention discloses a network traffic depth identification system based on a many-core processor and a corresponding identification method. The identification method comprises: firstly, establishing a semantic-based rule base by use of a semantic-based rule module, analyzing rules in the rule base by use of a rule analysis module and then generating a hierarchy match tree by use of a hierarchy match tree module; obtaining original network data by virtue of a receiving module and orderly performing IP fragment recombination processing and TCP recombination processing to obtain transport layer data; identifying the type of a protocol used by the transport layer data at an application layer according to a protocol specification regular expression defined by a protocol specification module and then performing structuring processing on the application layer data by virtue of a structured protocol data module; and finally, performing rule matching on the structured application layer data according to the hierarchy match tree by virtue of a matching engine module, sending a successful matching result to a user behavior statistical module for statistics, and then completing the network traffic depth identification.
Owner:XI'AN POLYTECHNIC UNIVERSITY
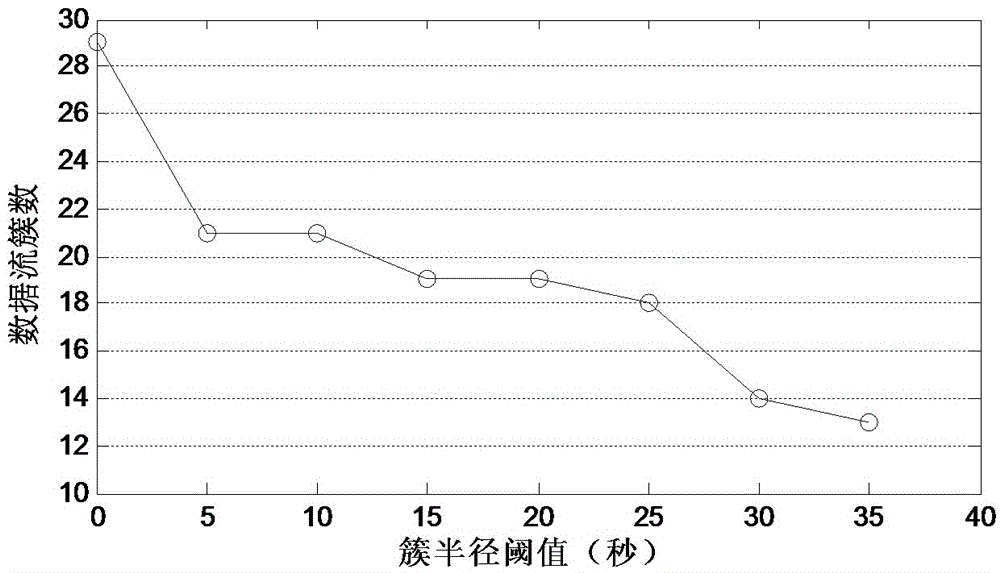
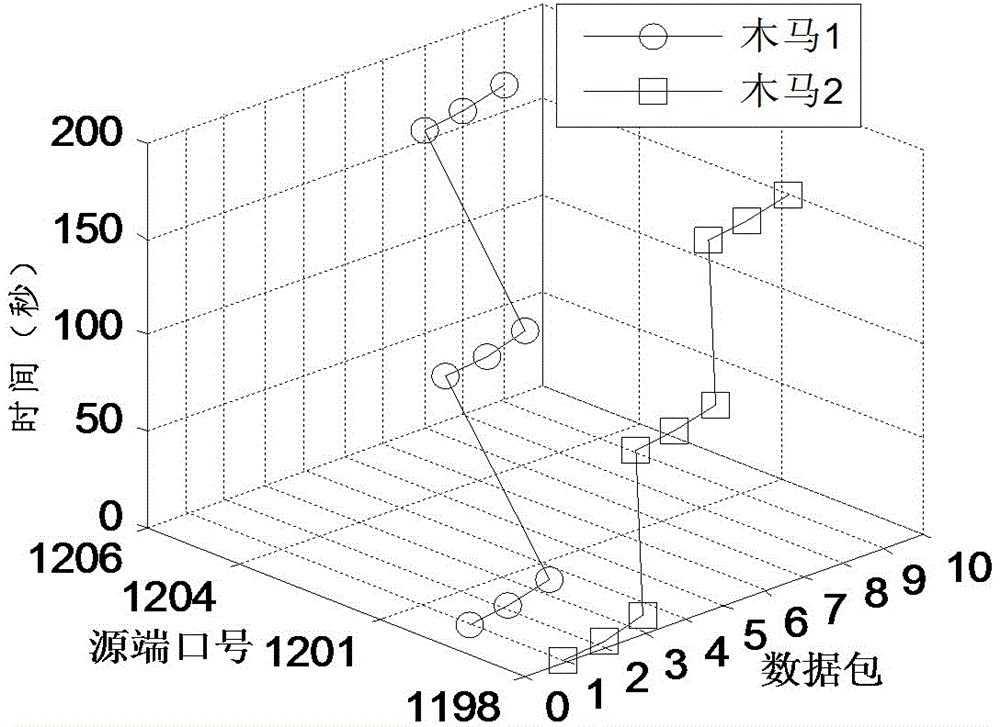
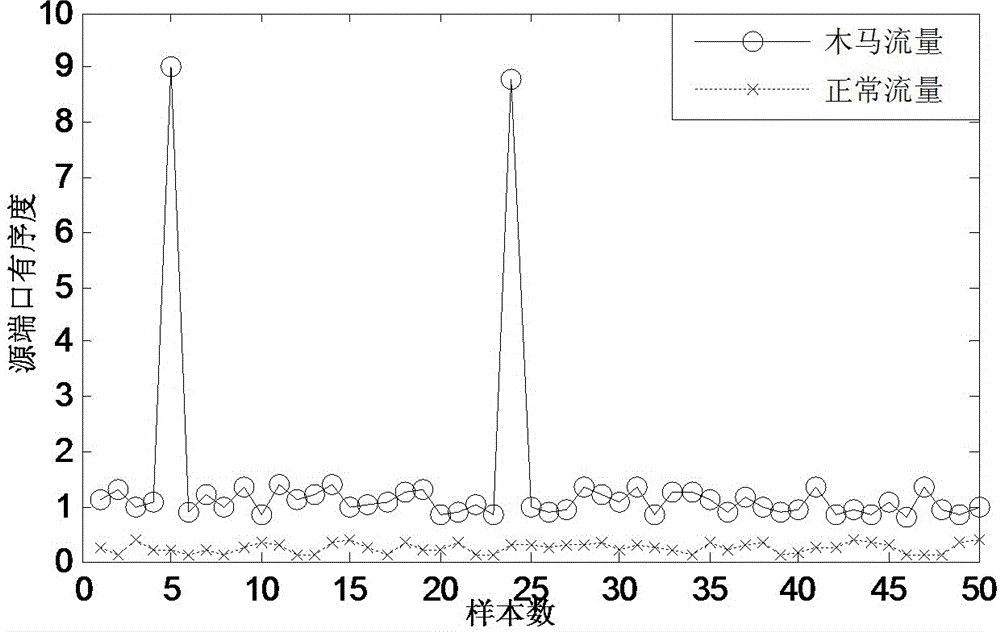
Torjan detection method based on uncontrolled end flow analysis
The invention discloses a torjan detection method based on uncontrolled end flow analysis. The method includes the steps that firstly, a captured network data package is processed; secondly, the network data package is organized into data flows according to quintuple information and requirements of protocol specifications; then, the data flows are classified according to equivalent tetrads to form data flow sets identified by the tetrads; finally the data flows in the data flow sets are clustered to form data flow clusters by the adoption of a data flow clustering algorithm based on timestamps. According to the torjan detection method based on the uncontrolled end flow analysis, on the basis of carrying out clustering on the network data flows to form the data flow clusters, the data flows are processed with the data flow cluster as a unit to analyze the difference between torjan communication behaviors and normal network communication behaviors, in addition, the difference between the torjan communication behaviors and the normal network communication behaviors are deeply dug in combination with the technologies of statistic analysis and data mining, and therefore uncontrolled end torjan flow in a network can be detected.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
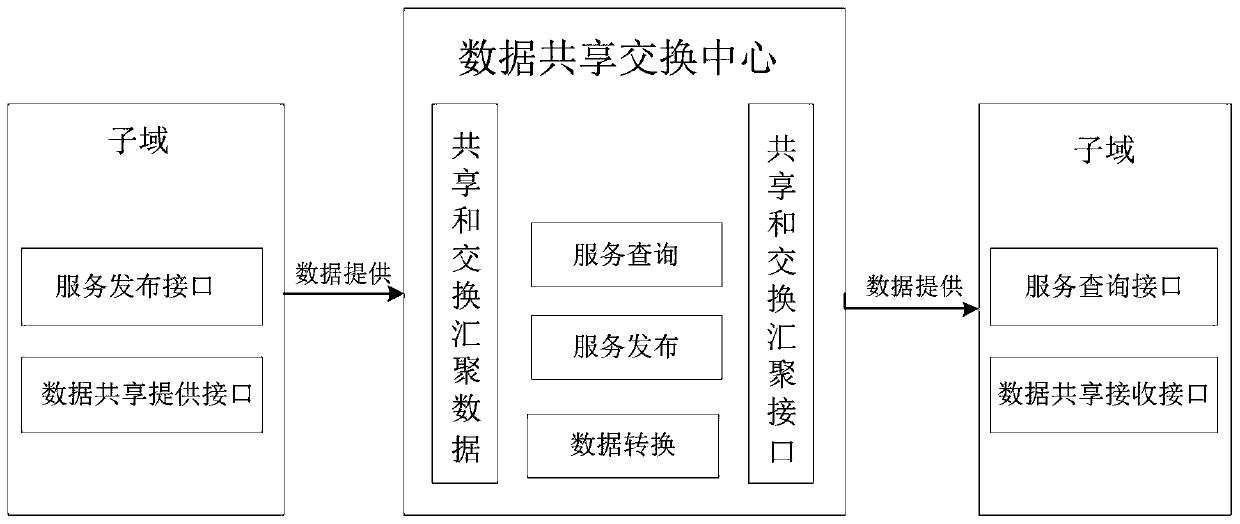
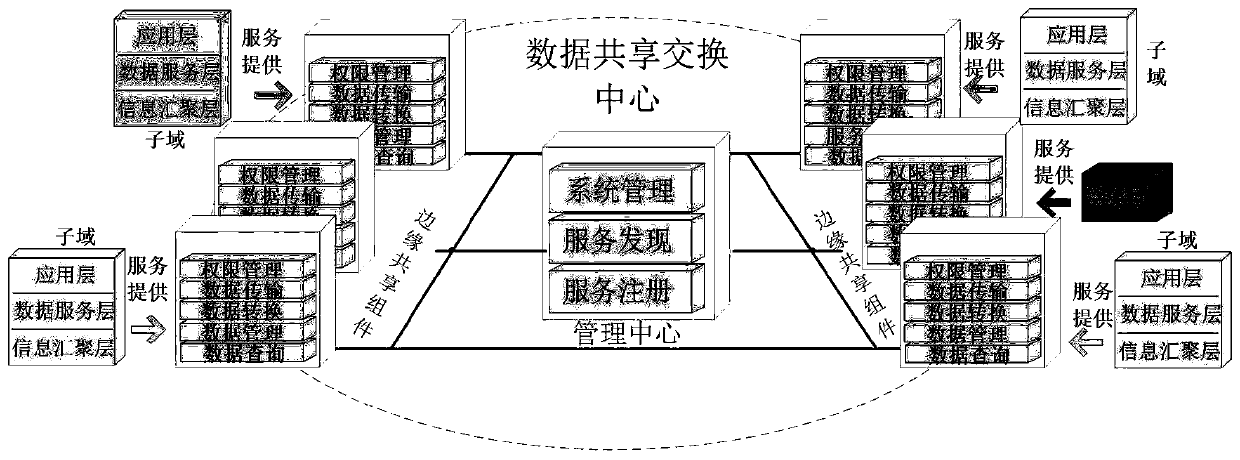
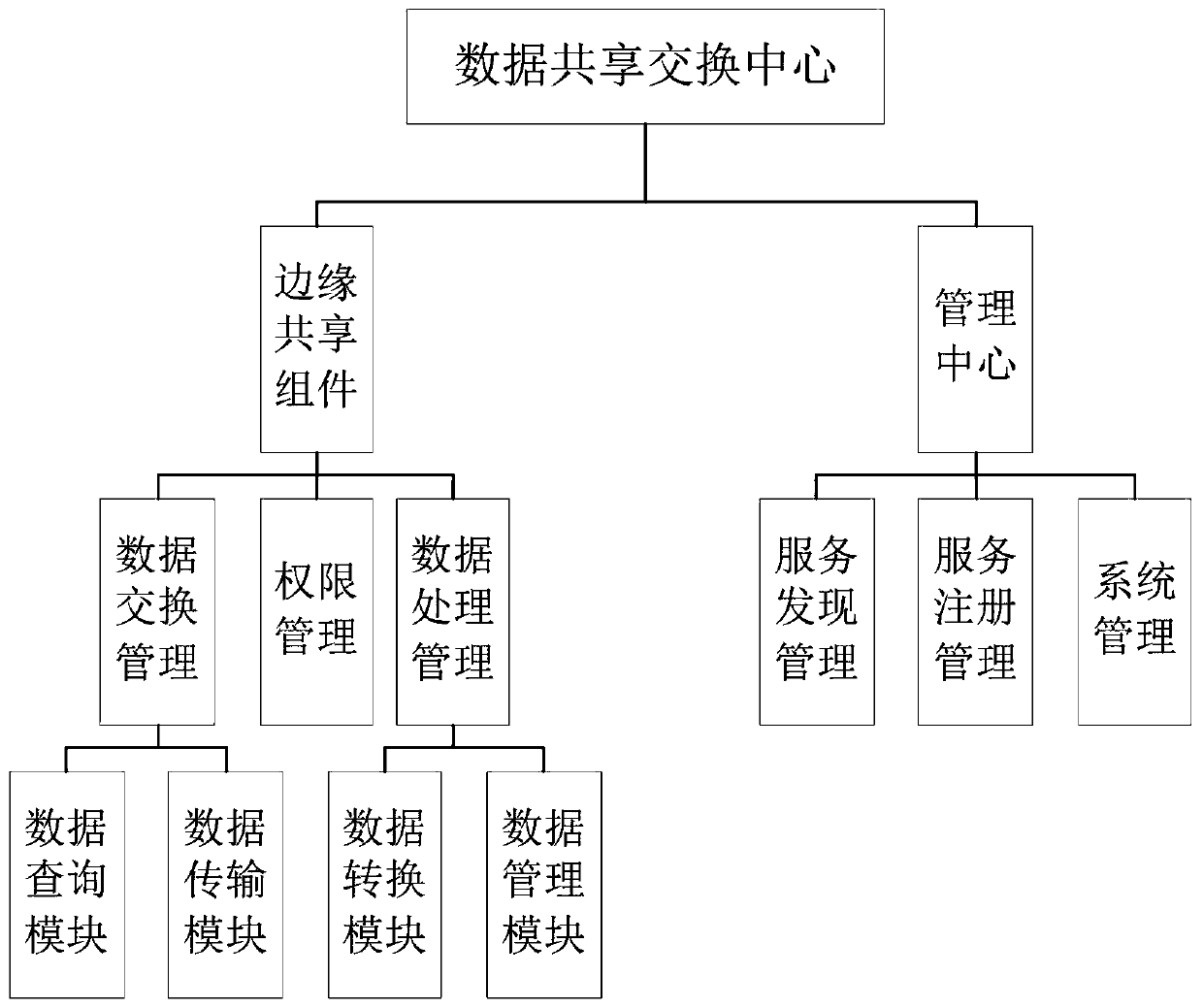
Multi-domain data sharing exchange platform architecture based on block chain
The invention belongs to the technical field of data exchange of the Internet of Things, and discloses a multi-domain data sharing exchange platform architecture based on a block chain, which comprises a data sharing exchange center module used for connecting other subdomain modules in series so as to achieve interconnection and intercommunication among subdomains and the sharing exchange of dataamong the subdomain, and managing sub-domain services and sub-domain data, and integrating all Internet of Things resources into a unified Internet of Things data and service providing platform; subdomains, each domain being customized by a local service provider to meet the protocol specification implementation of the data sharing exchange center. The data generated by the subdomains are stored locally, when data sharing is needed, the data needs to be opened or obtained from other domains, and the idea of taking the data as the center is achieved; when data sharing exchange needs to be carried out between domains, authority judgment is carried out through the data sharing exchange center, interconnection and intercommunication are carried out, the subdomain coupling degree is low, and data sharing with other subdomains can be flexibly carried out.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com