Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1403 results about "Finite-state machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A finite-state machine (FSM) or finite-state automaton (FSA, plural: automata), finite automaton, or simply a state machine, is a mathematical model of computation. It is an abstract machine that can be in exactly one of a finite number of states at any given time. The FSM can change from one state to another in response to some external inputs and/or a condition is satisfied; the change from one state to another is called a transition. An FSM is defined by a list of its states, its initial state, and the conditions for each transition. Finite state machines are of two types – deterministic finite state machines and non-deterministic finite state machines. A deterministic finite-state machine can be constructed equivalent to any non-deterministic one.
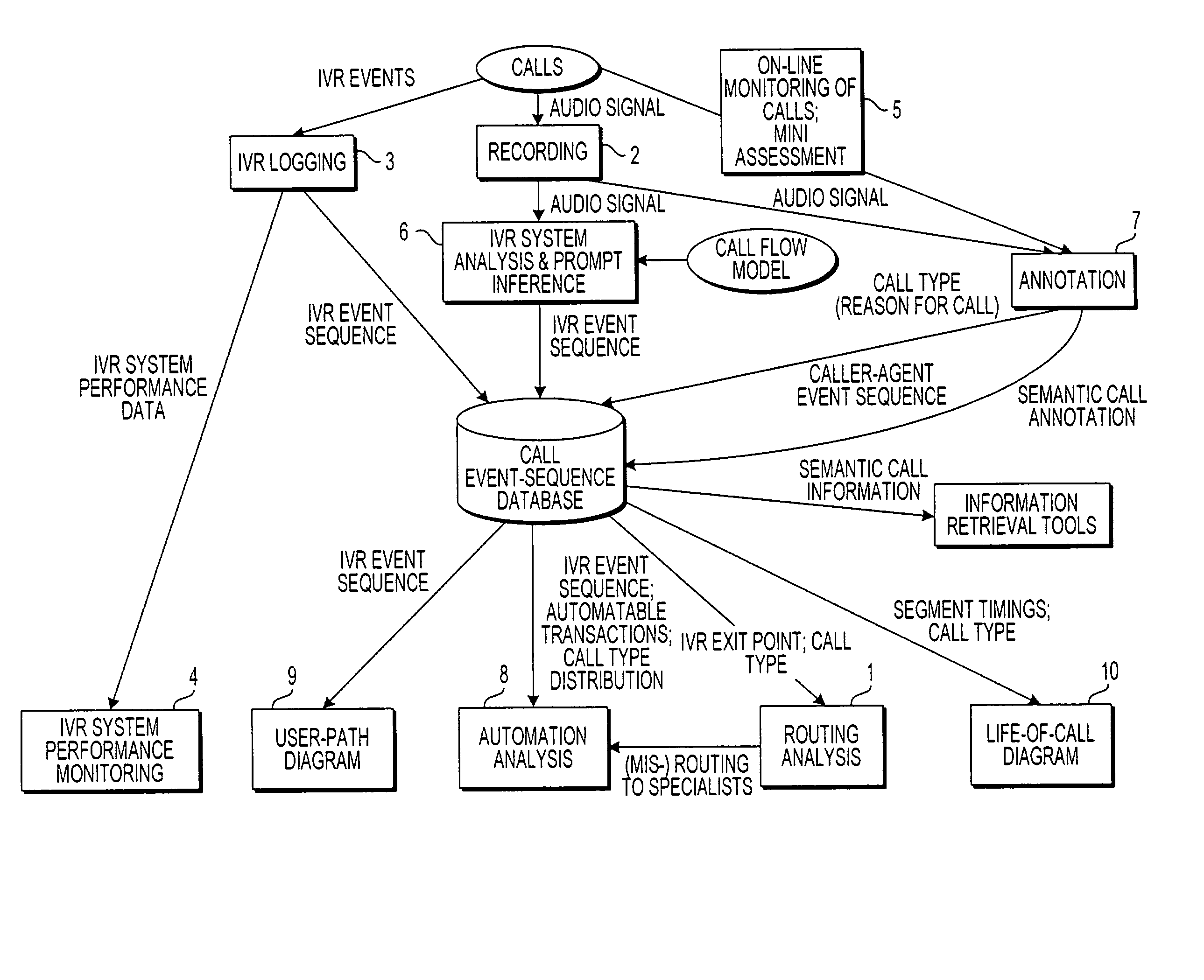
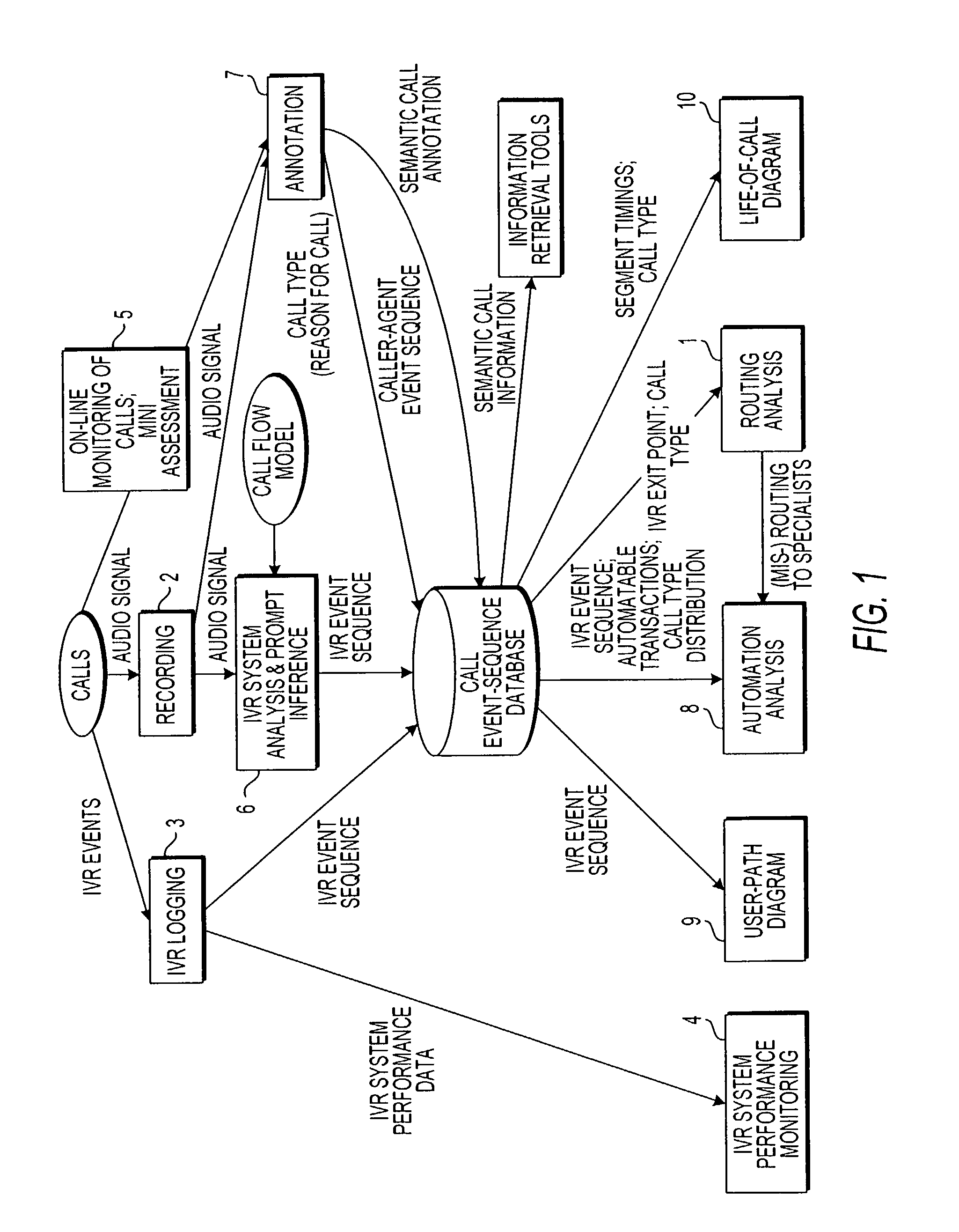
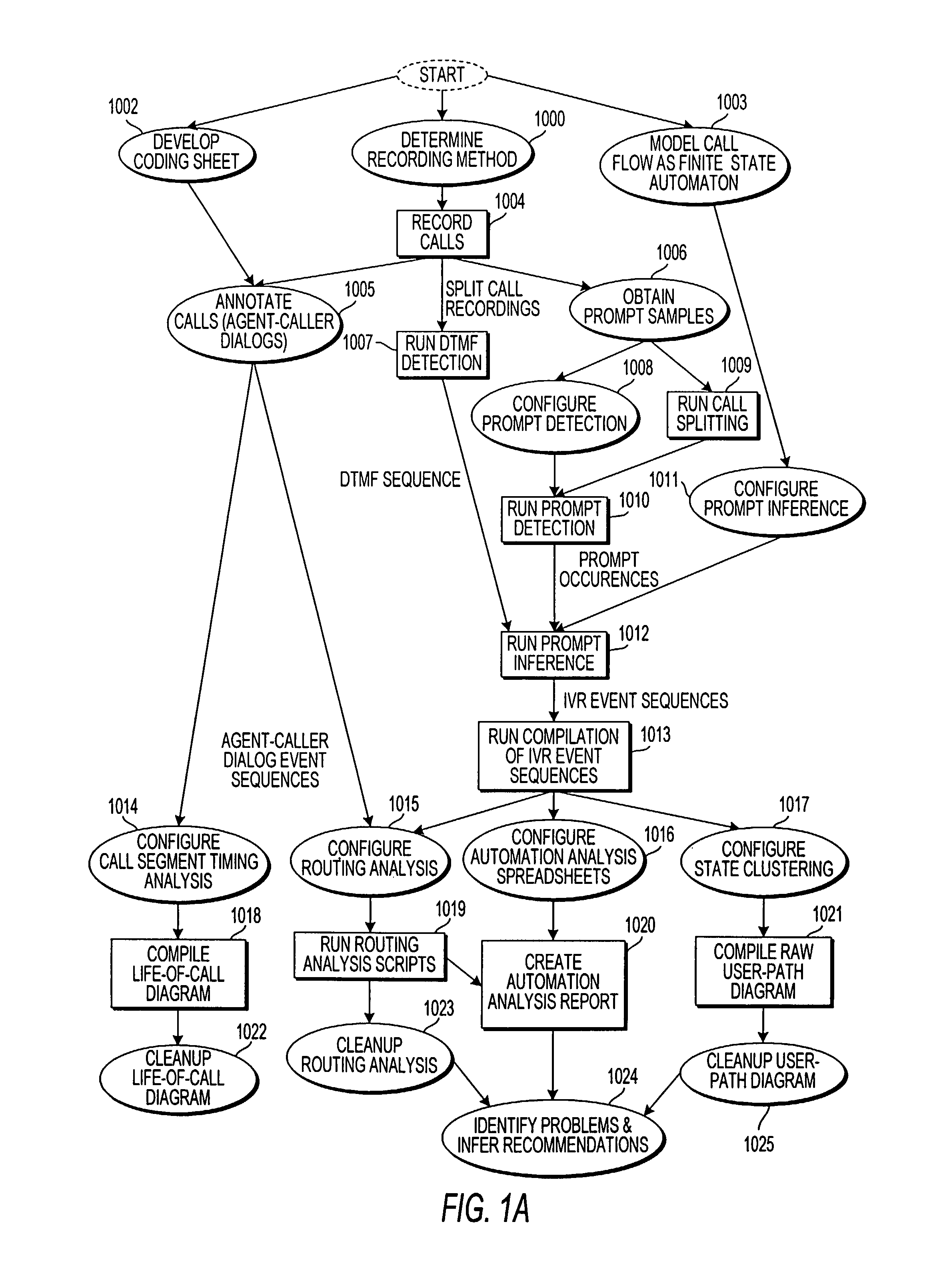
Apparatus and method for visually representing behavior of a user of an automated response system
InactiveUS7039166B1Overcome deficienciesSpeech analysisManual exchangesUser inputFinite-state machine
A system for visually representing user behavior within an interactive voice response (IVR) system of a call processing center generates a complete sequence of events within the IVR system for plural calls to the call processing center, the plurality of calls being recorded from end to end. A call flow of the IVR system is modeled as a non-deterministic finite-state machine, such that a start state of the finite-state machine represents a first prompt of the IVR system, other states of the finite-state machine represent subsequent prompts at which a branching occurs in the call flow of the IVR system, exit conditions are represented as end states, and transitions of the finite-state machine represent transitions between call flow states triggered by data inputted by a user or by internal processing of the IVR system. The complete sequences of events for the plural calls are provided to the finite-state machine to produce a two-way matrix of several counters. The data from the two-way matrix is represented as a state-transition diagram.
Owner:CX360 INC +1
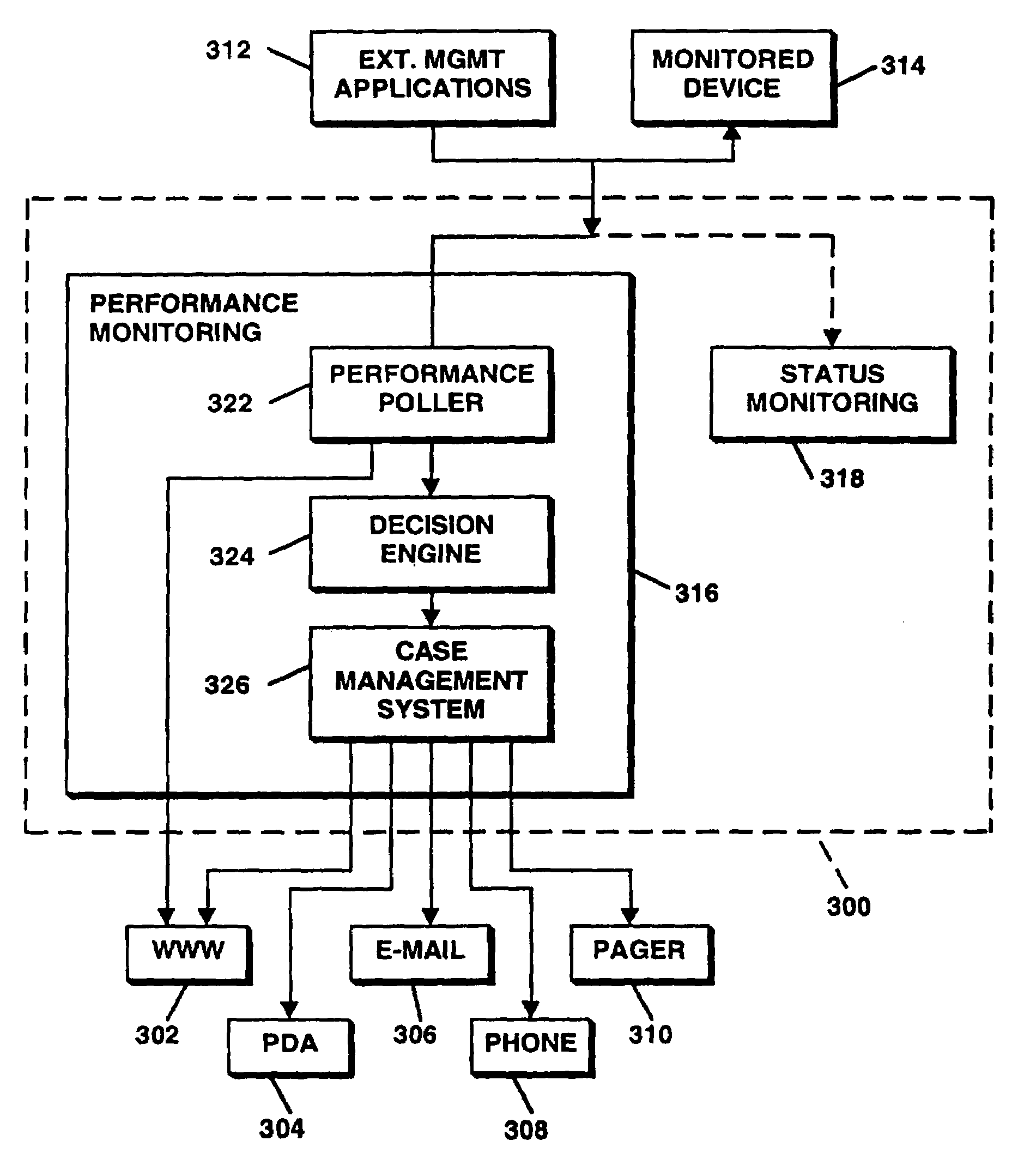
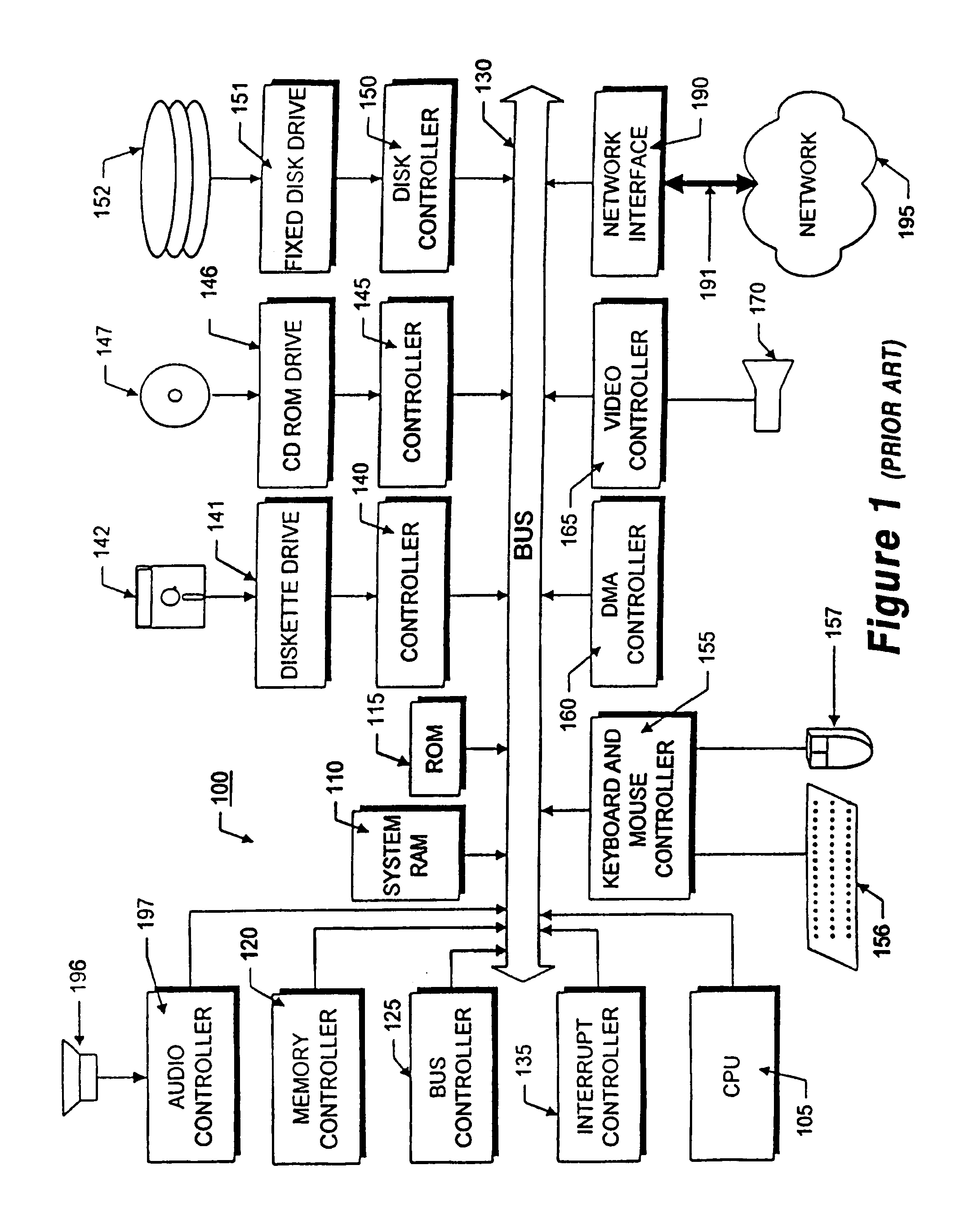
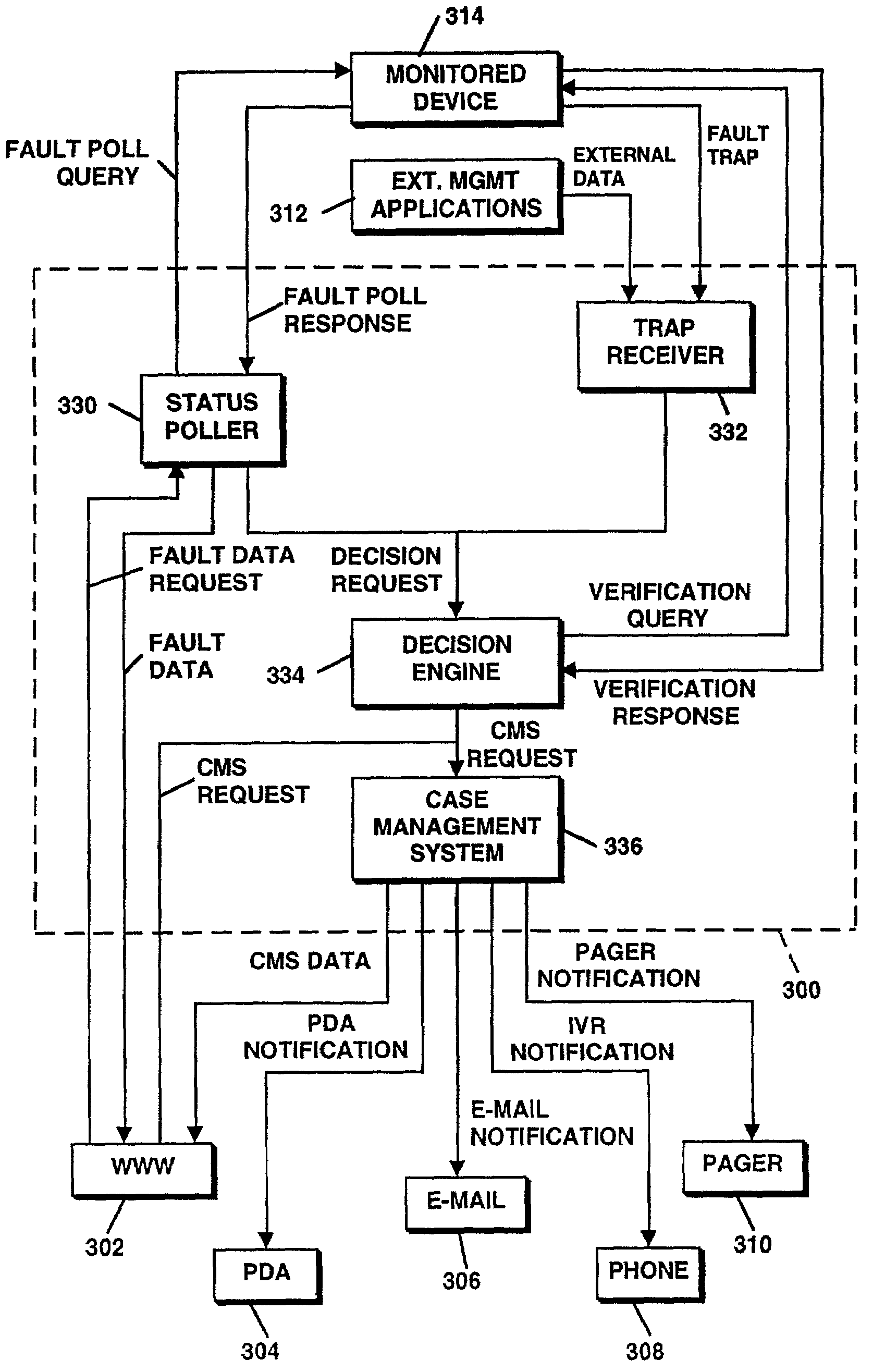
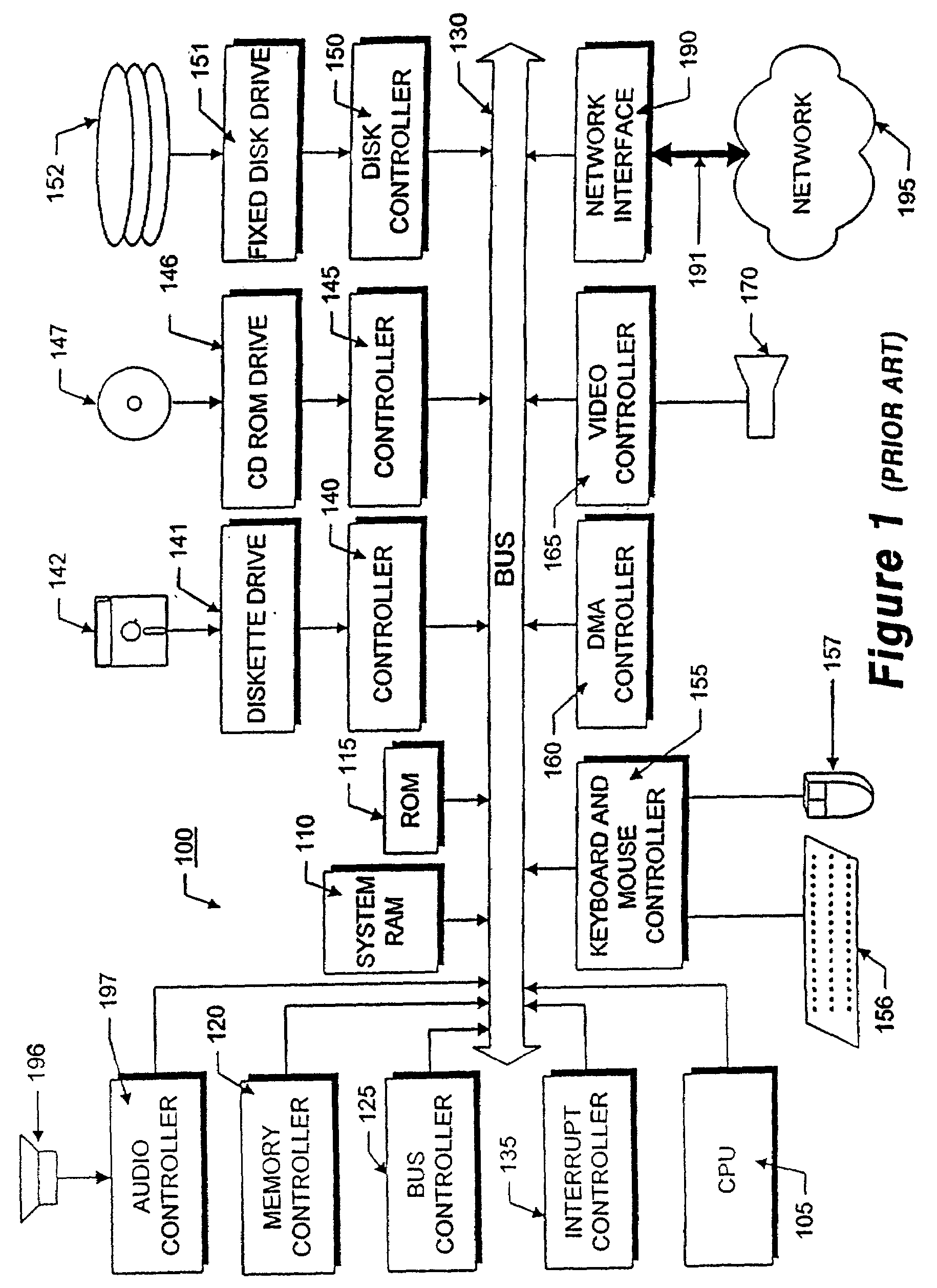
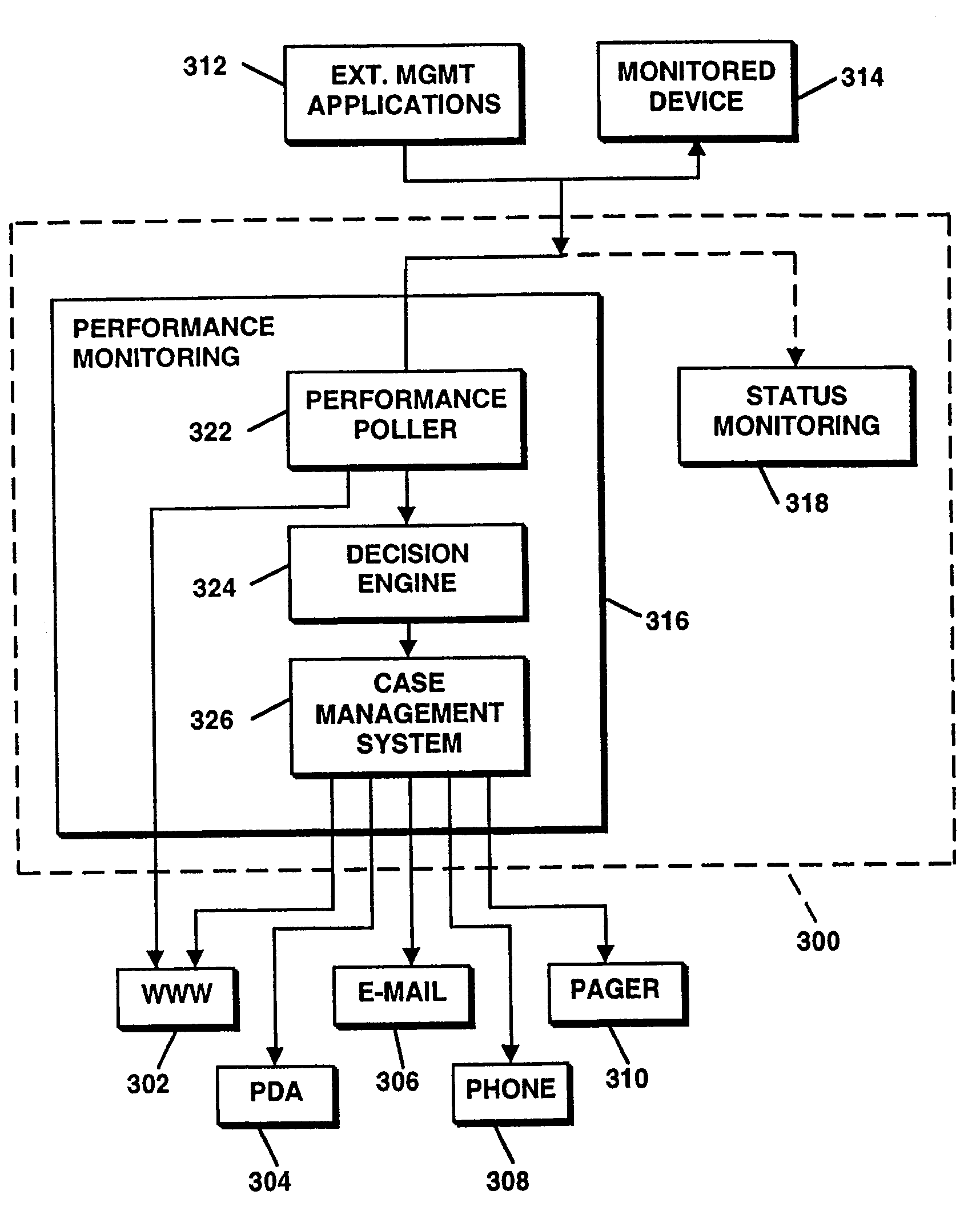
Method and apparatus for identifying problems in computer networks
A network appliance for monitoring, diagnosing and documenting problems among a plurality of devices and processes (objects) coupled to a computer network utilizes periodic polling and collection of object-generated trap data to monitor the status of objects on the computer network. The status of a multitude of objects is maintained in memory utilizing virtual state machines which contain a small amount of persistent data but which are modeled after one of a plurality of finite state machines. The memory further maintains dependency data related to each object which identifies parent / child relationships with other objects at the same or different layers of the OSI network protocol model. A decision engine verifies through on-demand polling that a device is down. A root cause analysis module utilizes status and dependency data to locate the highest object in the parent / child relationship tree that is affected to determine the root cause of a problem. Once a problem has been verified, a “case” is opened and notification alerts may be sent out to one or more devices. A user interface allows all objects within the network to be displayed with their respective status and their respective parent / child dependency objects in various formats.
Owner:OPTANIX INC
Method and apparatus for maintaining the status of objects in computer networks using virtual state machines
ActiveUS7197561B1Error detection/correctionMultiple digital computer combinationsVirtual finite-state machineFinite-state machine
A network appliance for monitoring, diagnosing and documenting problems among a plurality of devices and processes (objects) coupled to a computer network utilizes periodic polling and collection of object-generated trap data to monitor the status of objects on the computer network. The status of a multitude of objects is maintained in memory utilizing virtual state machines which contain a small amount of persistent data but which are modeled after one of a plurality of finite state machines. The memory further maintains dependency data related to each object which identifies parent / child relationships with other objects at the same or different layers of the OSI network protocol model. A decision engine verifies through on-demand polling that a device is down. A root cause analysis module utilizes status and dependency data to locate the highest object in the parent / child relationship tree that is affected to determine the root cause of a problem. Once a problem has been verified, a “case” is opened and notification alerts may be sent out to one or more devices. A user interface allows all objects within the network to be displayed with their respective status and their respective parent / child dependency objects in various formats.
Owner:OPTANIX INC
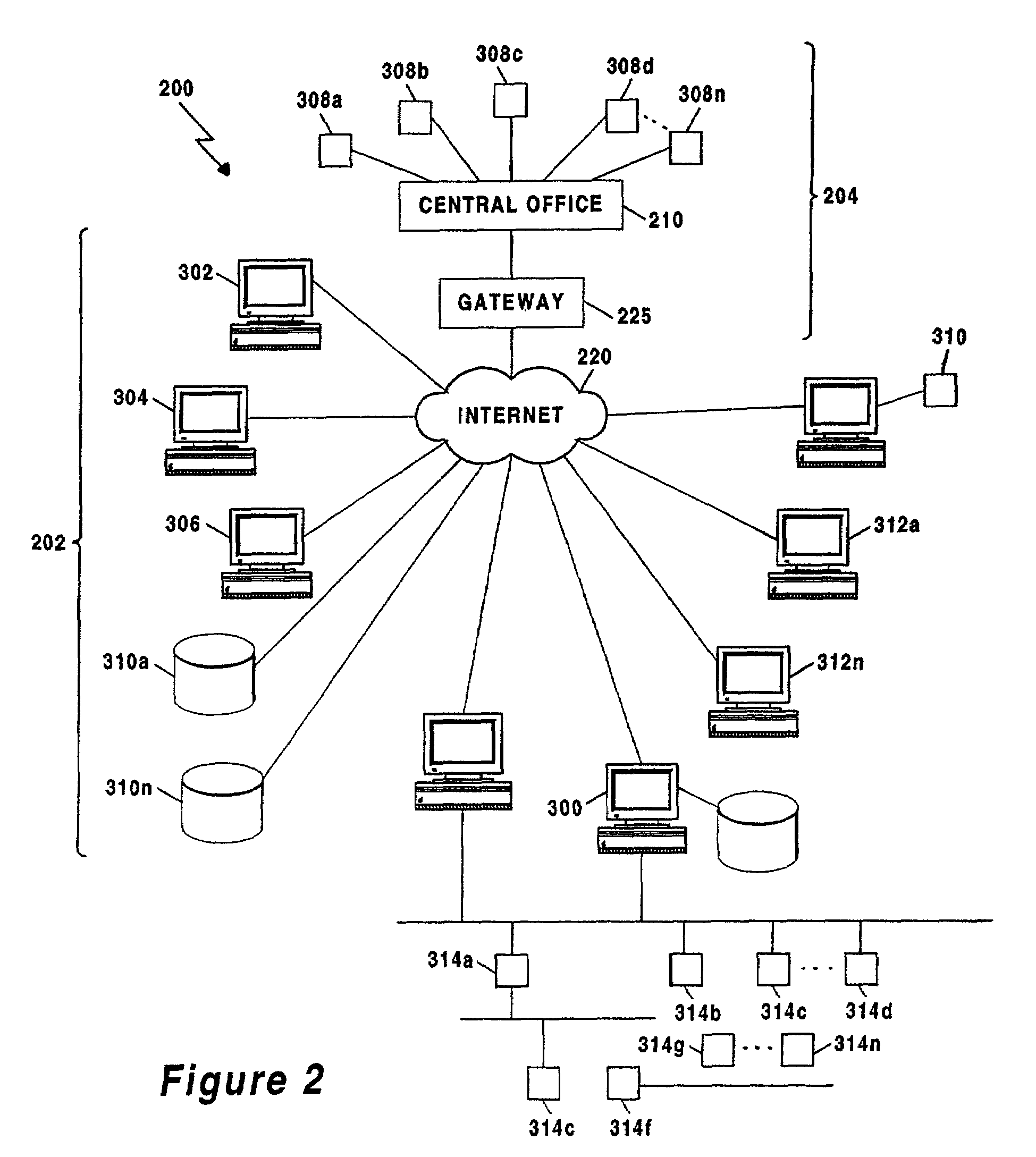
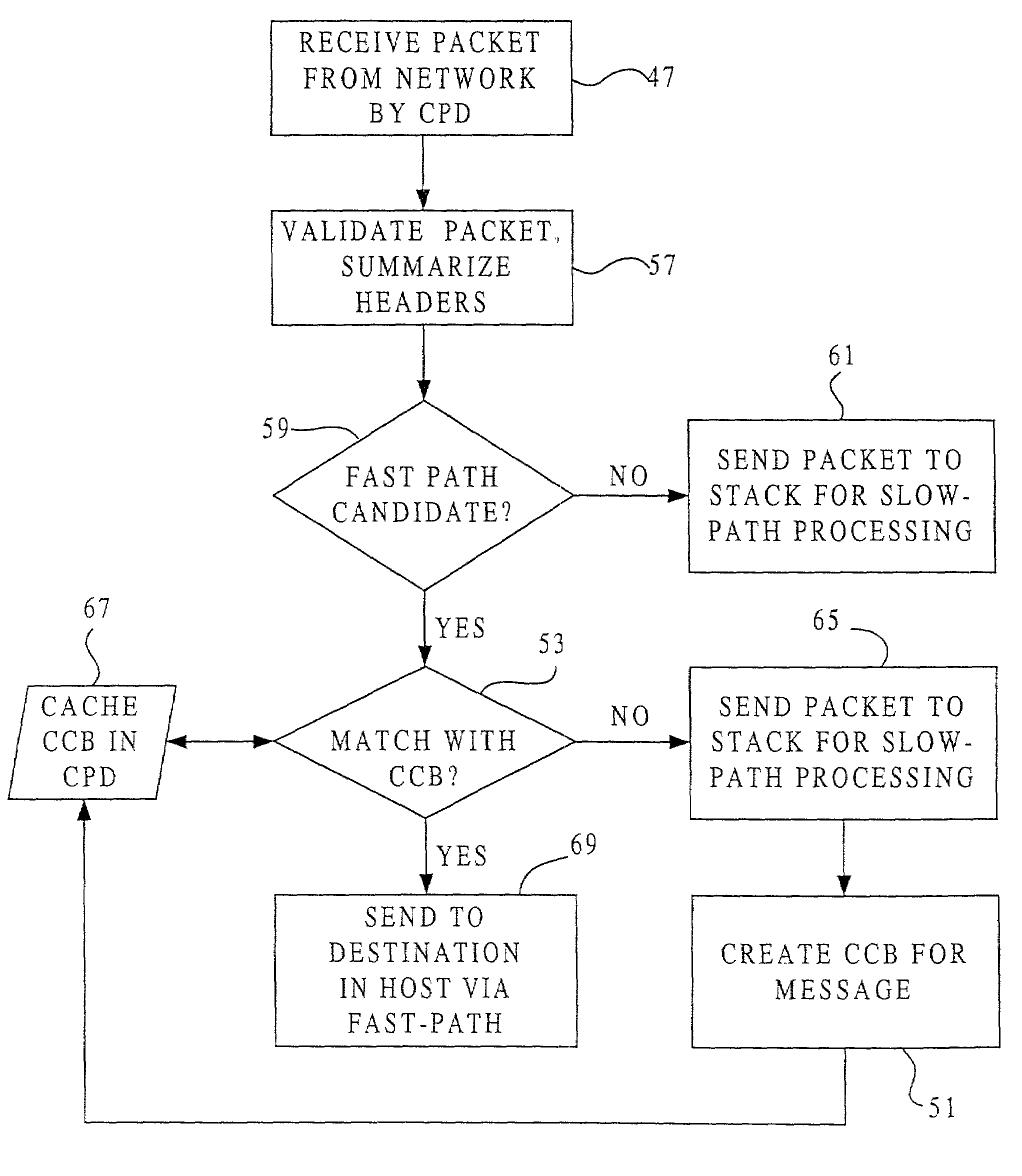
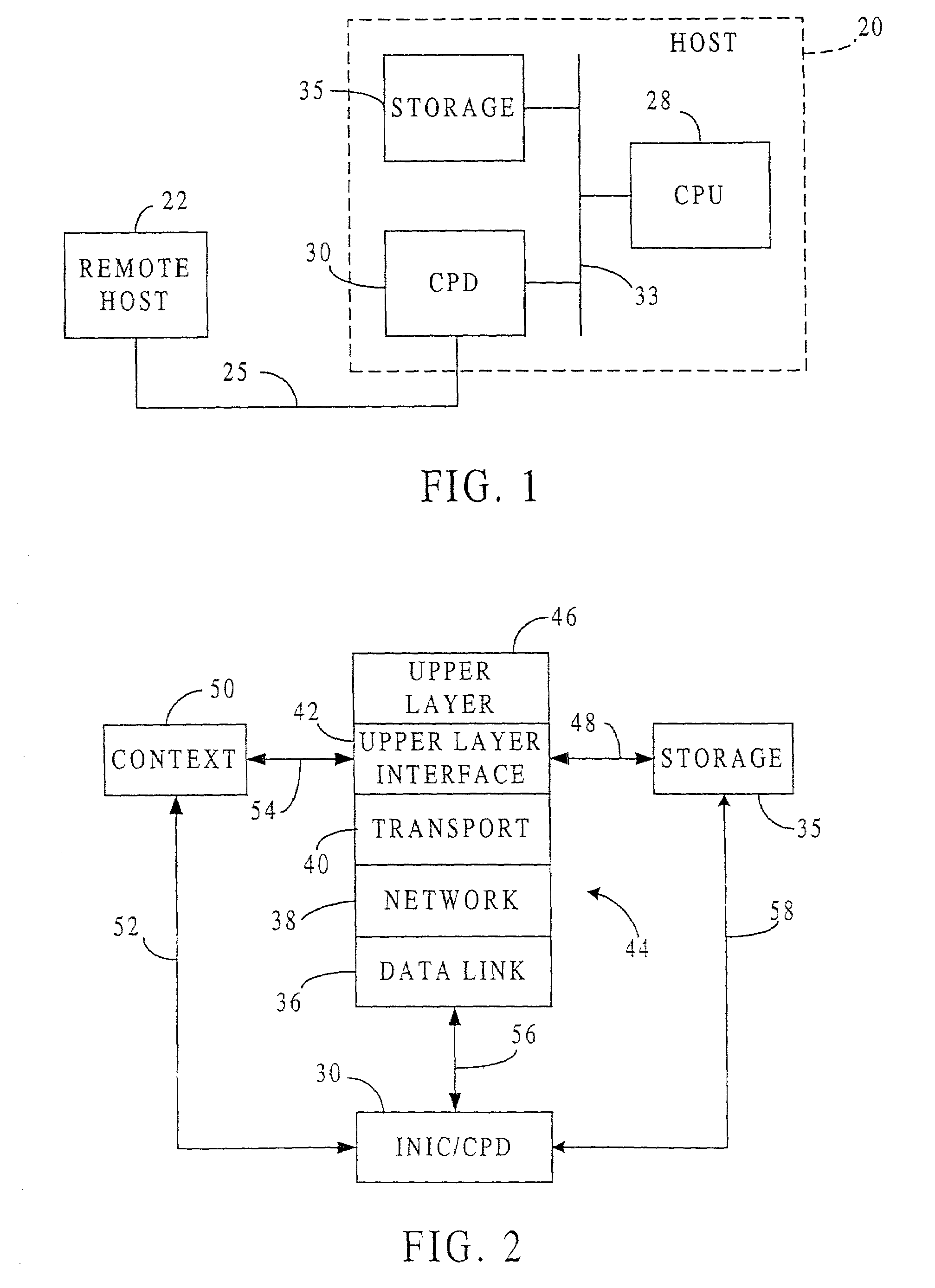
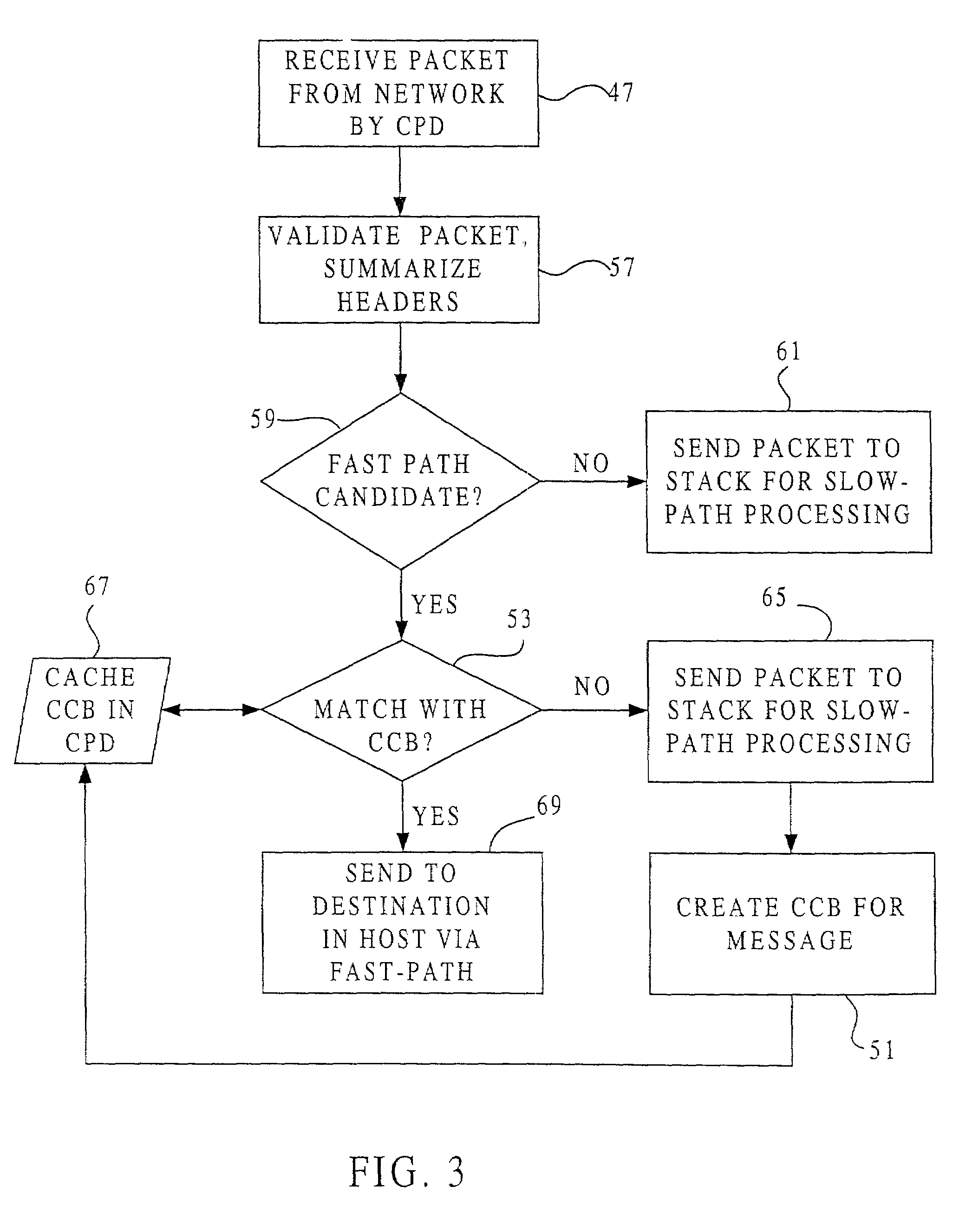
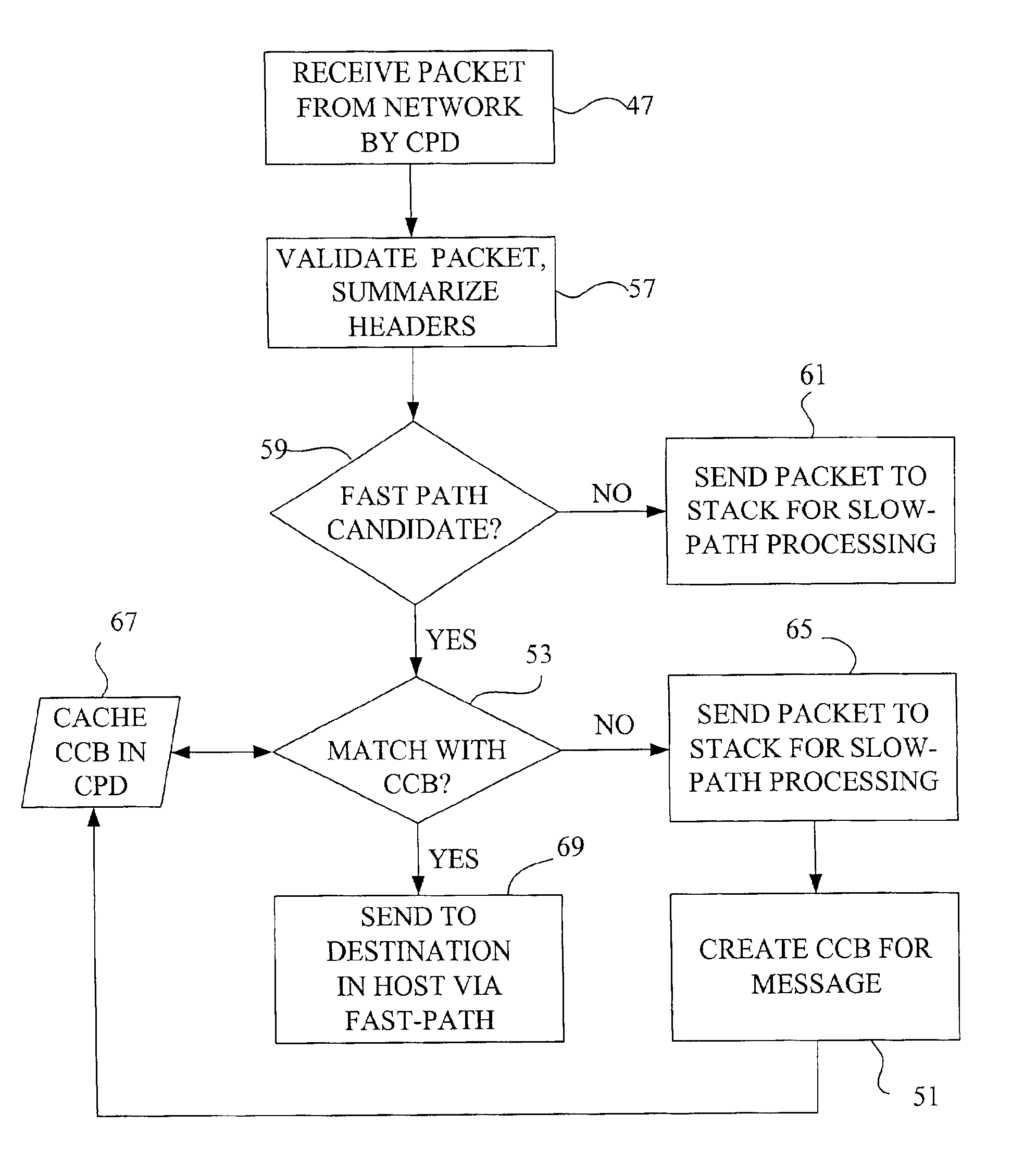
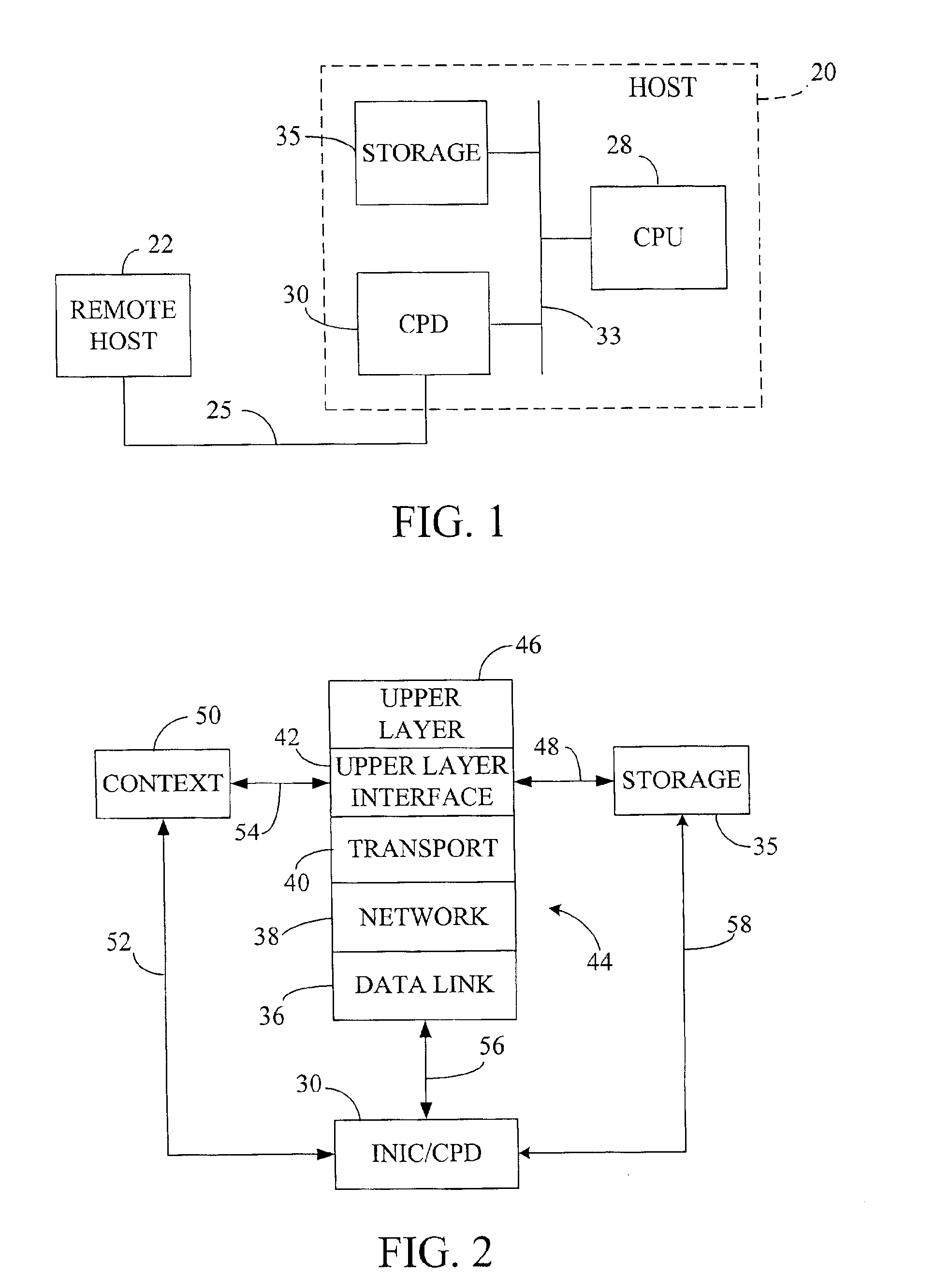
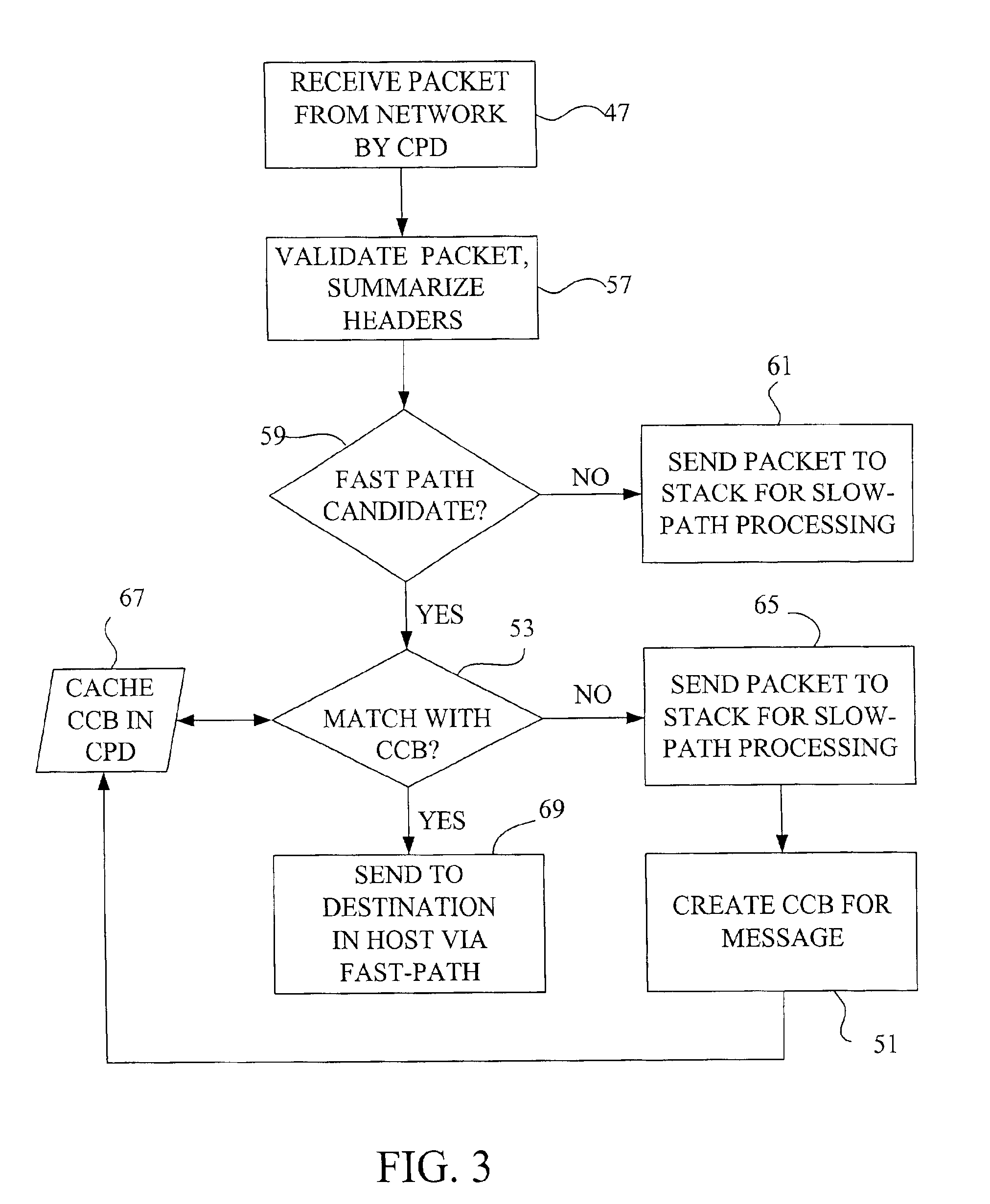
Fast-path processing for receiving data on TCP connection offload devices
ActiveUS7089326B2Negligibly effectMove quicklyMultiple digital computer combinationsData switching networksFast pathProtocol processing
A network interface device provides a fast-path that avoids most host TCP and IP protocol processing for most messages. The host retains a fallback slow-path processing capability. In one embodiment, generation of a response to a TCP / IP packet received onto the network interface device is accelerated by determining the TCP and IP source and destination information from the incoming packet, retrieving an appropriate template header, using a finite state machine to fill in the TCP and IP fields in the template header without sequential TCP and IP protocol processing, combining the filled-in template header with a data payload to form a packet, and then outputting the packet from the network interface device by pushing a pointer to the packet onto a transmit queue. A transmit sequencer retrieves the pointer from the transmit queue and causes the corresponding packet to be output from the network interface device.
Owner:ALACRITECH
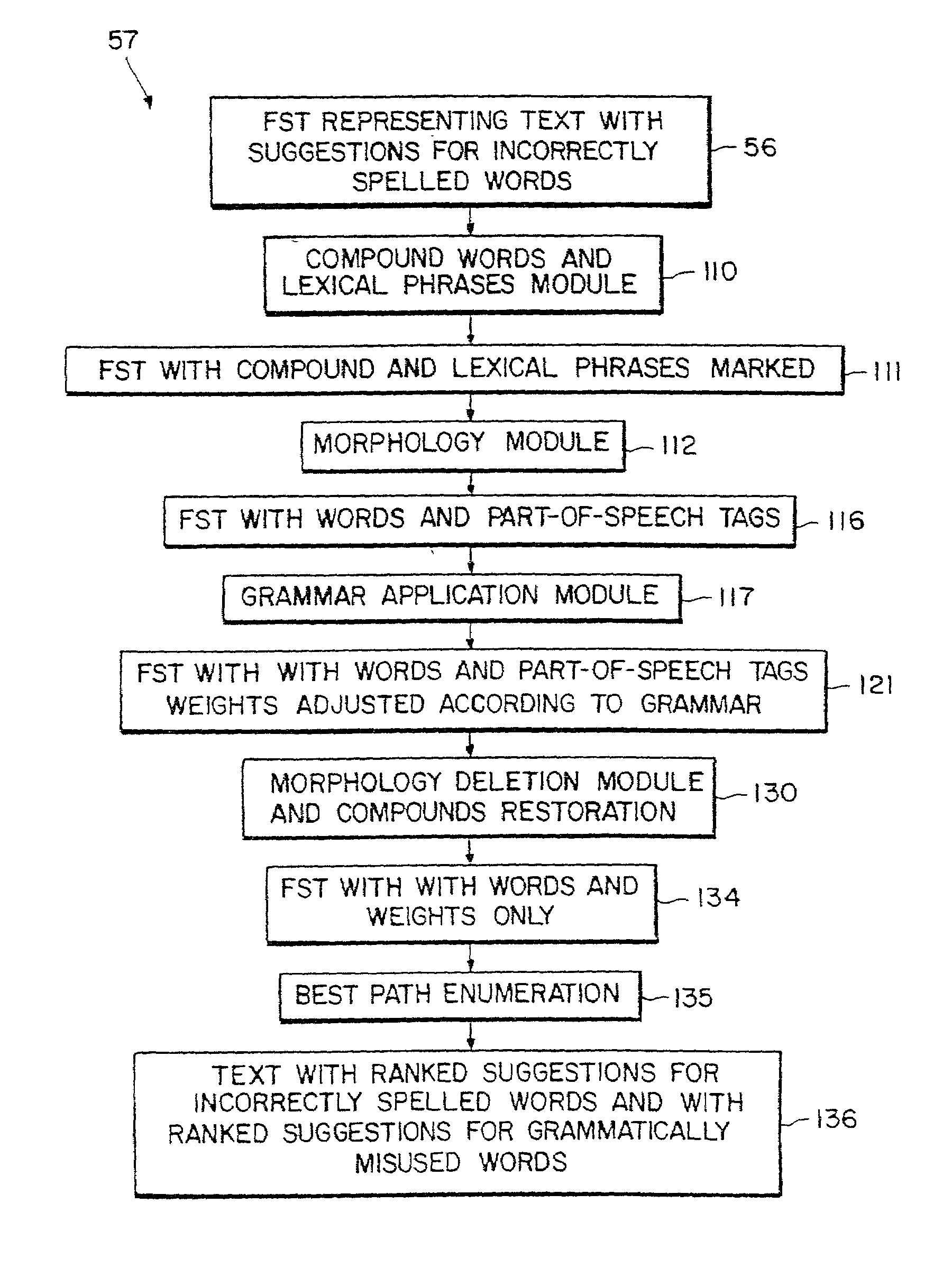
Spelling and grammar checking system
InactiveUS7243305B2Data processing applicationsDigital computer detailsFinite-state machineFinite state
System of correcting misspelled words in input text detects a misspelled word in the input text, determines a list of alternative words for the misspelled word, and ranks the list of alternative words based on a context of the input text. In certain embodiments, finite state machines (FSMs) are utilized in the spelling and grammar correction process, storing one or more lexicon FSMs, each of which represents a set of correctly spelled reference words. Storing the lexicon as one or more FSMs facilitates those embodiments of the invention employing a clinet-server architecture. The input text to be corrected may also be encoded as a FSM, which includes alternative word(s) for word(s) in need of correction along with associated weights. The invention adjusts the weights by taking into account the grammatical context in which the word appears in the input text. In certain embodiments the modification is performed by applying a second FSM to the FSM that was generated for the input text, where the second FSM encodes a grammatically correct sequence of words, thereby generating an additional FSM.
Owner:GLOBAL INFORMATION RES TECH
Transmit fast-path processing on TCP/IP offload network interface device
InactiveUS6965941B2Little and no performance benefitMove quicklyMultiplex system selection arrangementsMultiple digital computer combinationsFast pathProtocol processing
Owner:ALACRITECH
Spelling and grammar checking system
InactiveUS20040093567A1Data processing applicationsNatural language data processingFinite-state machineEngineering
System of correcting misspelled words in input text detects a misspelled word in the input text, determines a list of alternative words for the misspelled word, and ranks the list of alternative words based on a context of the input text. In certain embodiments, finite state machines (FSMs) are utilized in the spelling and grammar correction process, storing one or more lexicon FSMs, each of which represents a set of correctly spelled reference words. Storing the lexicon as one or more FSMs facilitates those embodiments of the invention employing a clinet-server architecture. The input text to be corrected may also be encoded as a FSM, which includes alternative word(s) for word(s) in need of correction along with associated weights. The invention adjusts the weights by taking into account the grammatical context in which the word appears in the input text. In certain embodiments the modification is performed by applying a second FSM to the FSM that was generated for the input text, where the second FSM encodes a grammatically correct sequence of words, thereby generating an additional FSM.
Owner:GLOBAL INFORMATION RES TECH
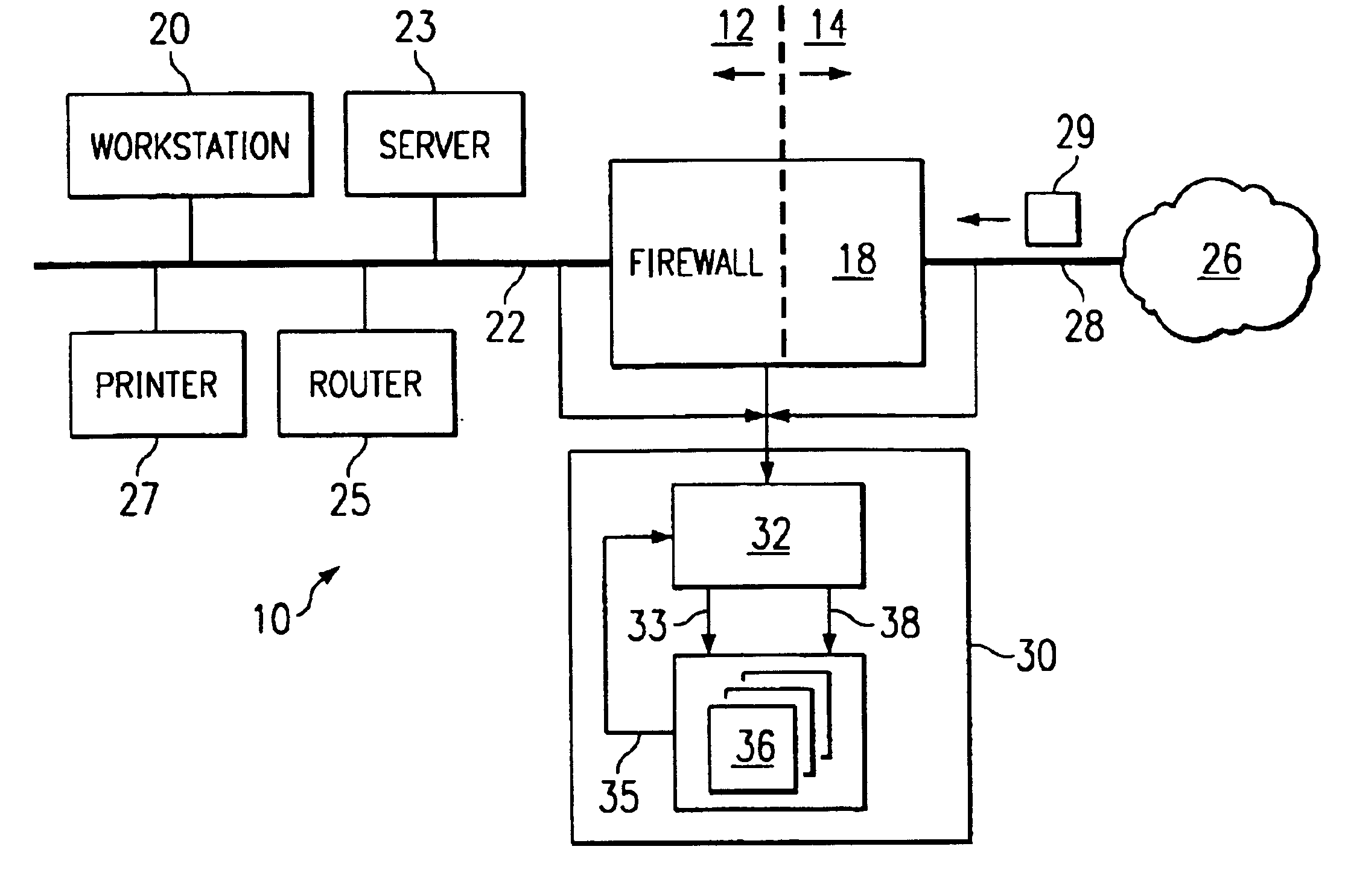
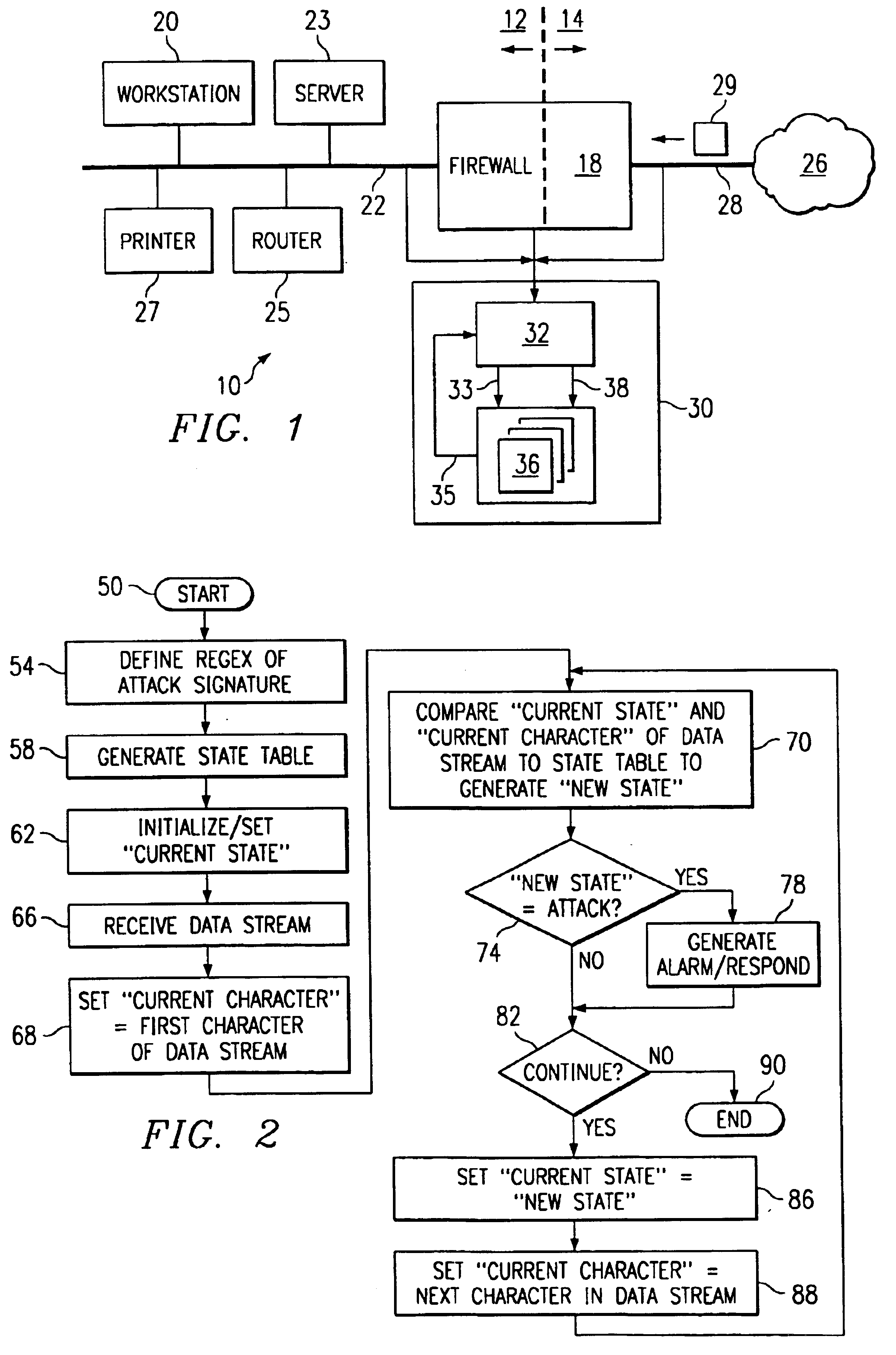
Binary state machine system and method for REGEX processing of a data stream in an intrusion detection system
InactiveUS6880087B1Reduce needPreserve memory resourceMemory loss protectionCode conversionData streamTheoretical computer science
A binary state machine system and method for REGEX processing of a data stream in an intrusion detection system are disclosed. The method comprises maintaining a state table. The state table is indexed such that inputs comprising a current state and a current character yield an output of a new state. The new state is related to an indication of an attack on a computer network. The method further includes maintaining the current state. An input stream comprising a plurality of characters is received. A first character of the input stream is selected as the current character. The current character and the current state are compared to the state table to generate a new state.
Owner:CISCO TECH INC
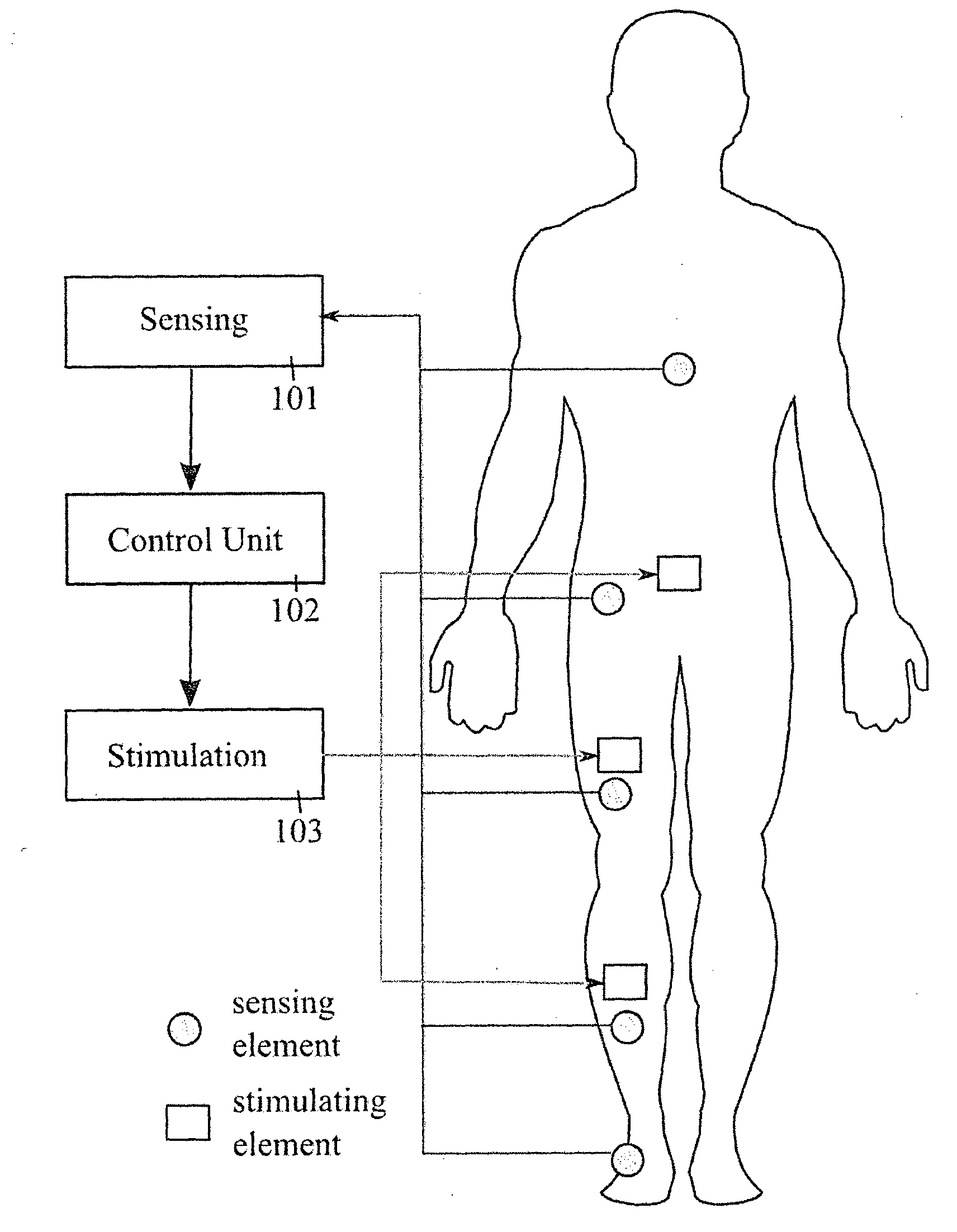
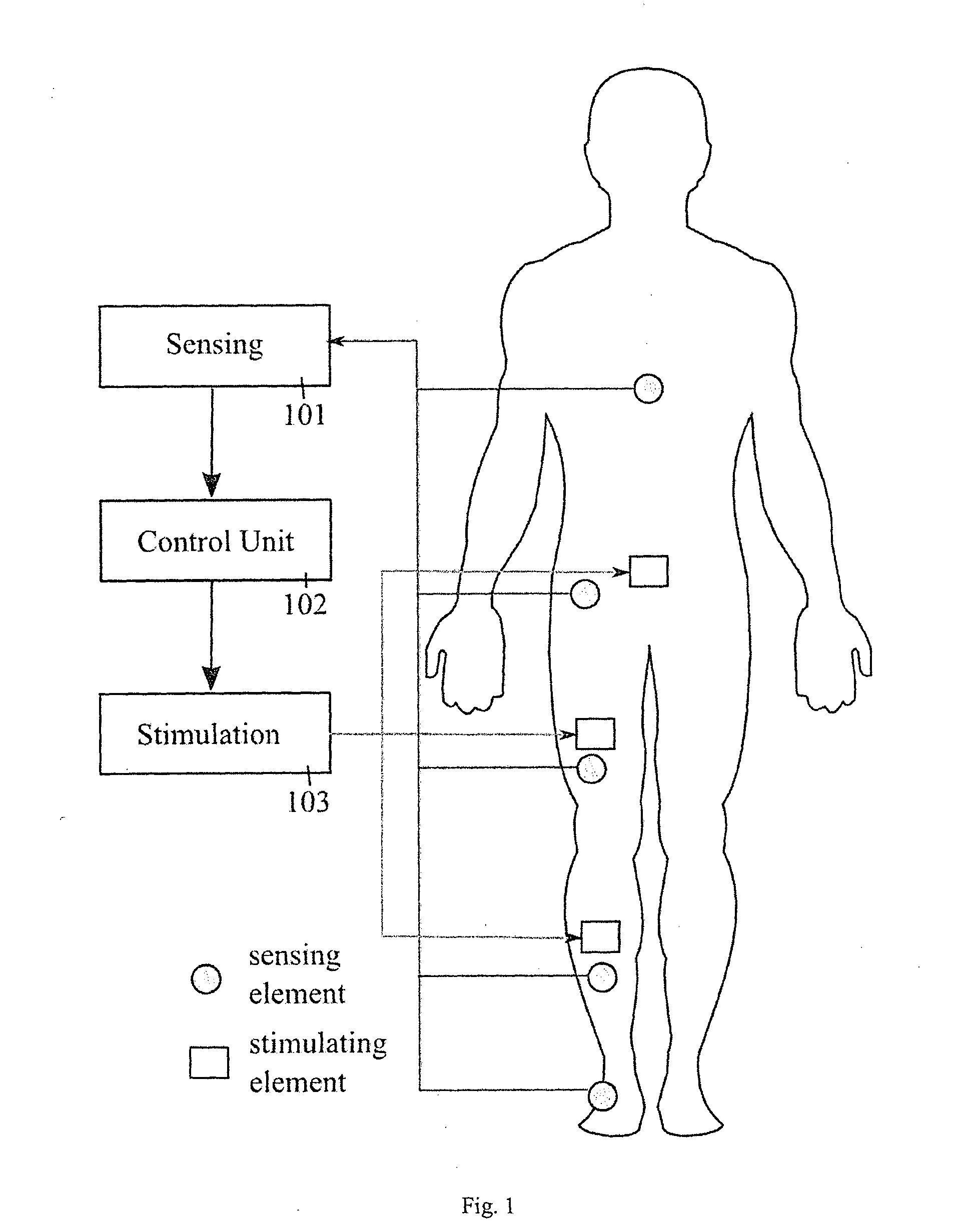
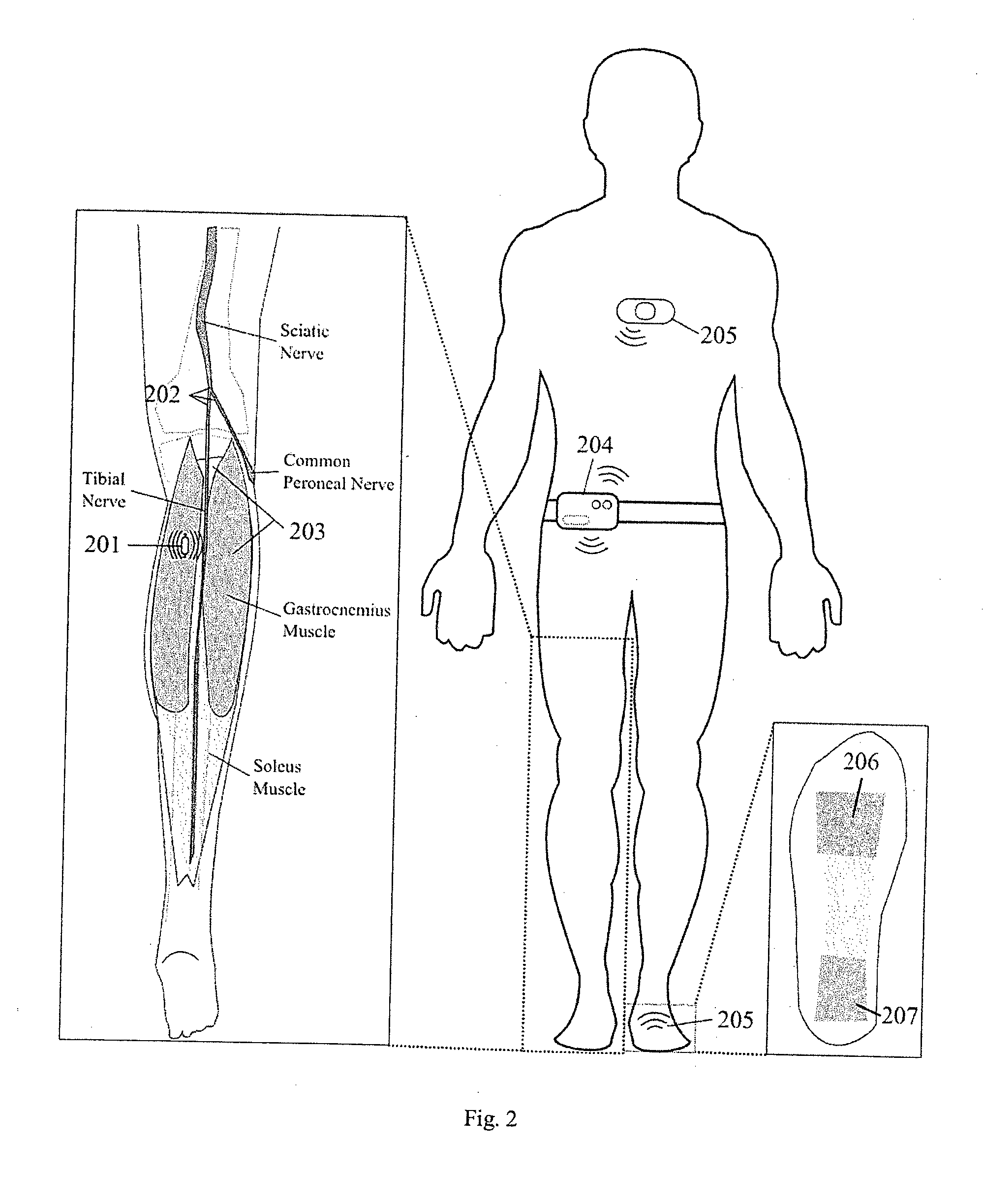
Apparatus and methods for prevention of syncope
ActiveUS20140358193A1Easy to installRemove changeSpinal electrodesElectrocardiographyMonitoring systemFinite-state machine
A monitoring system has biomechanical sensors, physiological sensors and a controller which receive sensory inputs from the sensors to provide output signals for the output device, and it detects from the sensory inputs risk of a syncopal event The bio-mechanical sensors include sensors arranged to allow the processor to detect a user postures and posture transitions. The processor operates a finite state machine, in which there is a state corresponding to each of a plurality of user physical postures and to each of a plurality of transitions between said postures, and the processor determines a relevant state depending on the sensory inputs. A device output may be muscle stimulation to prevent syncope, and there are stimulation permissions associated with the finite state machine states.
Owner:THE NAT UNIV OF IRELAND GALWAY +2
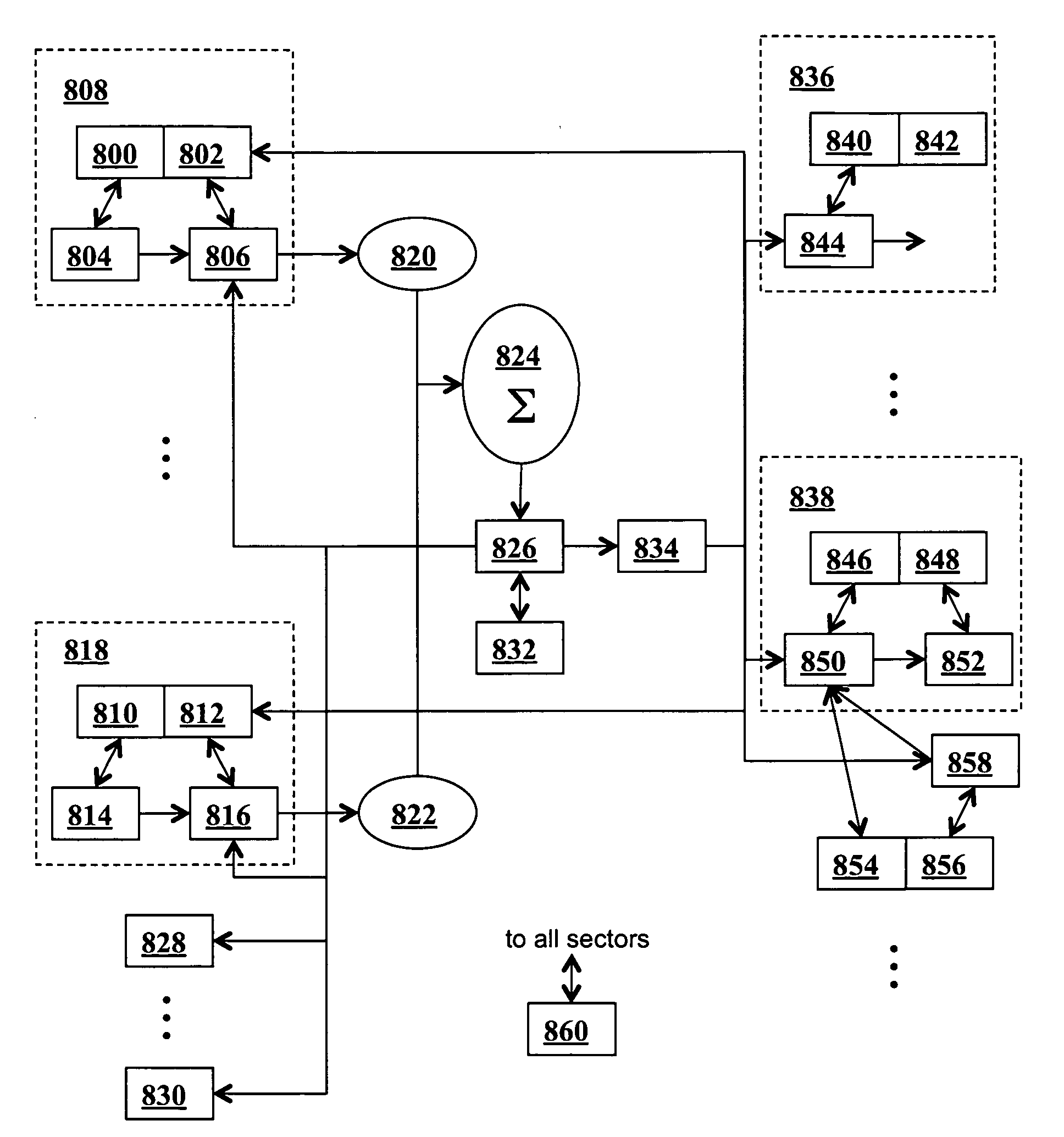
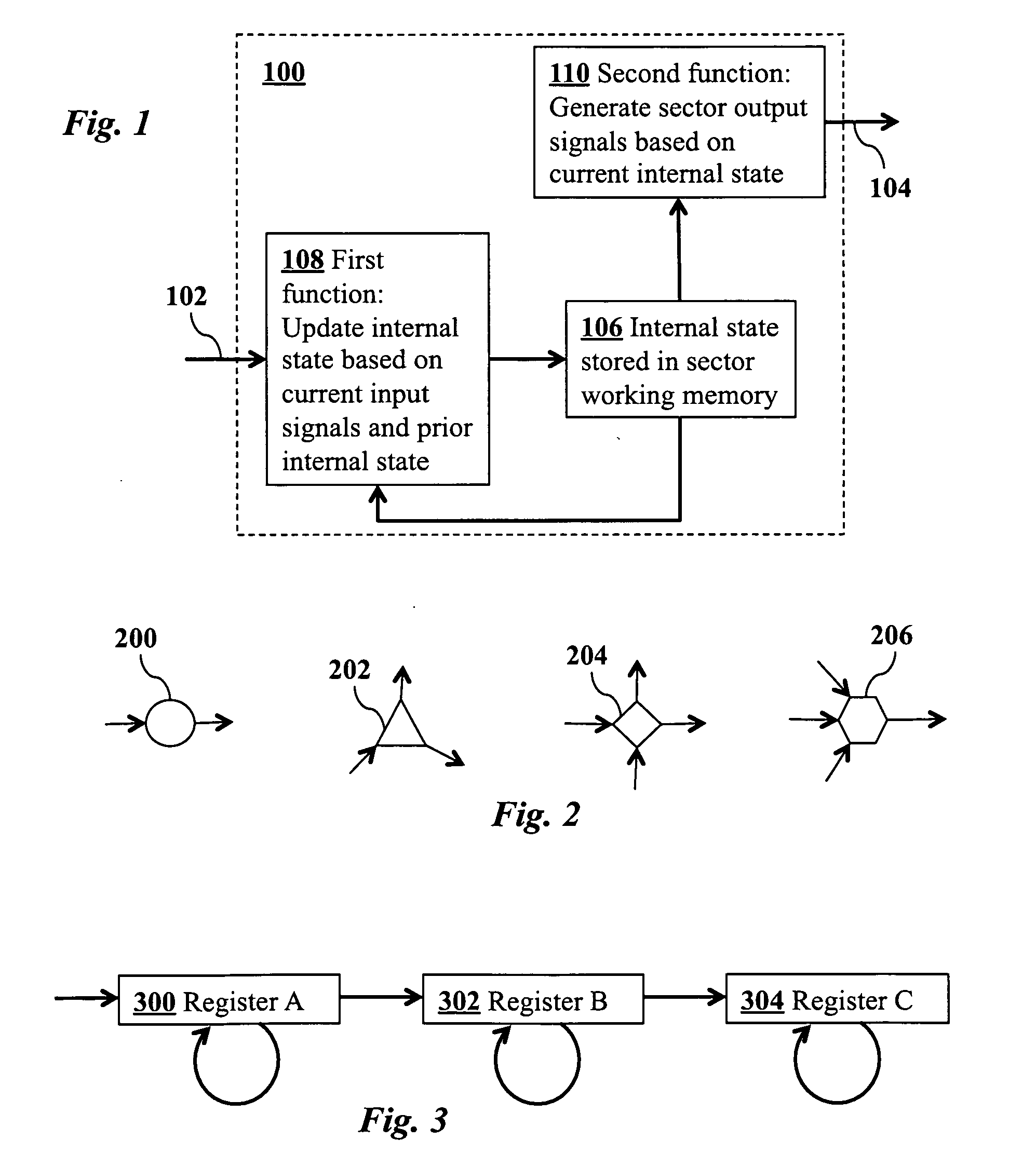
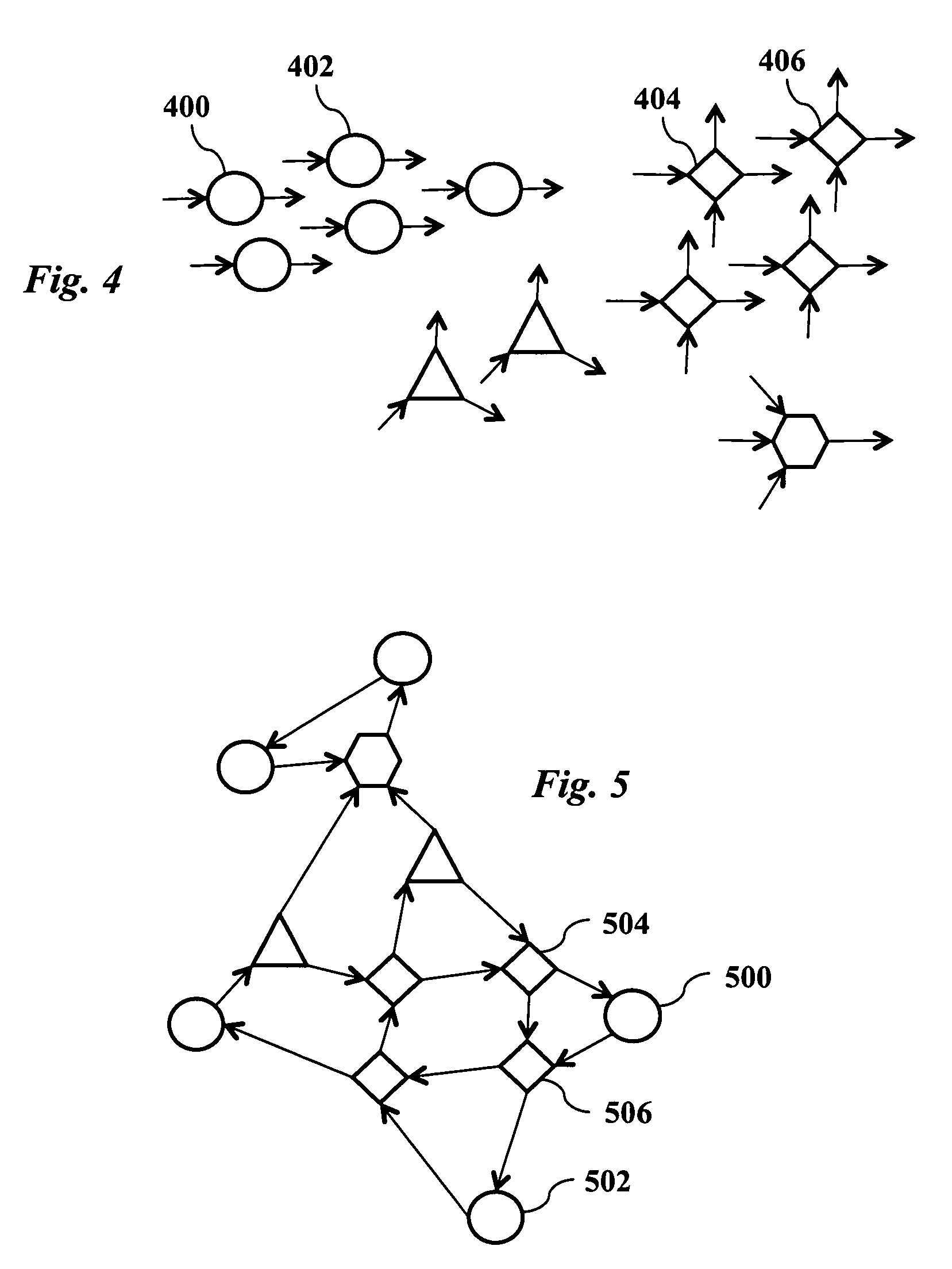
Method for efficiently simulating the information processing in cells and tissues of the nervous system with a temporal series compressed encoding neural network
ActiveUS20110016071A1Effective simulationExact reproductionDigital computer detailsDigital dataInformation processingNervous system
A neural network simulation represents components of neurons by finite state machines, called sectors, implemented using look-up tables. Each sector has an internal state represented by a compressed history of data input to the sector and is factorized into distinct historical time intervals of the data input. The compressed history of data input to the sector may be computed by compressing the data input to the sector during a time interval, storing the compressed history of data input to the sector in memory, and computing from the stored compressed history of data input to the sector the data output from the sector.
Owner:CORTICAL DATABASE
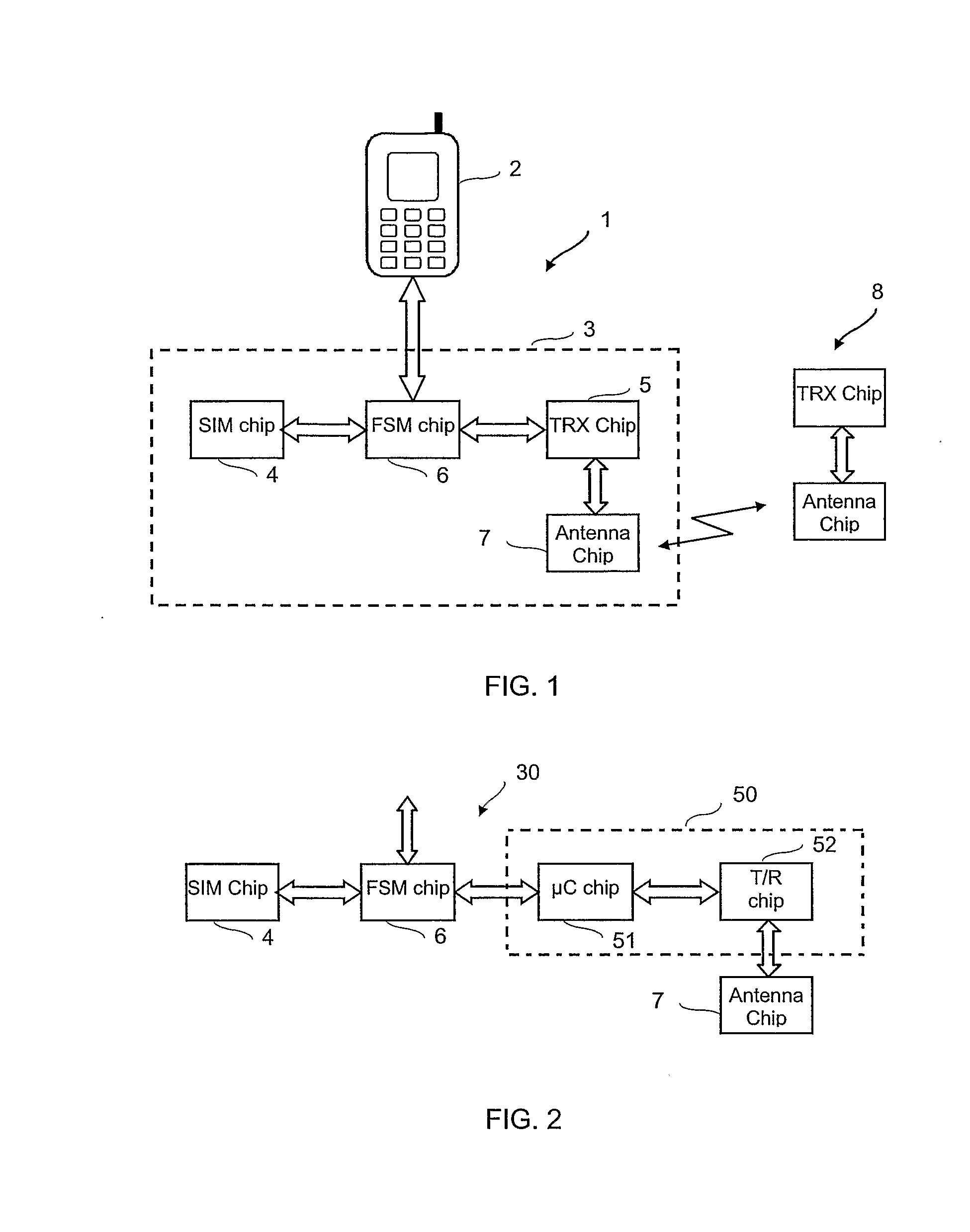
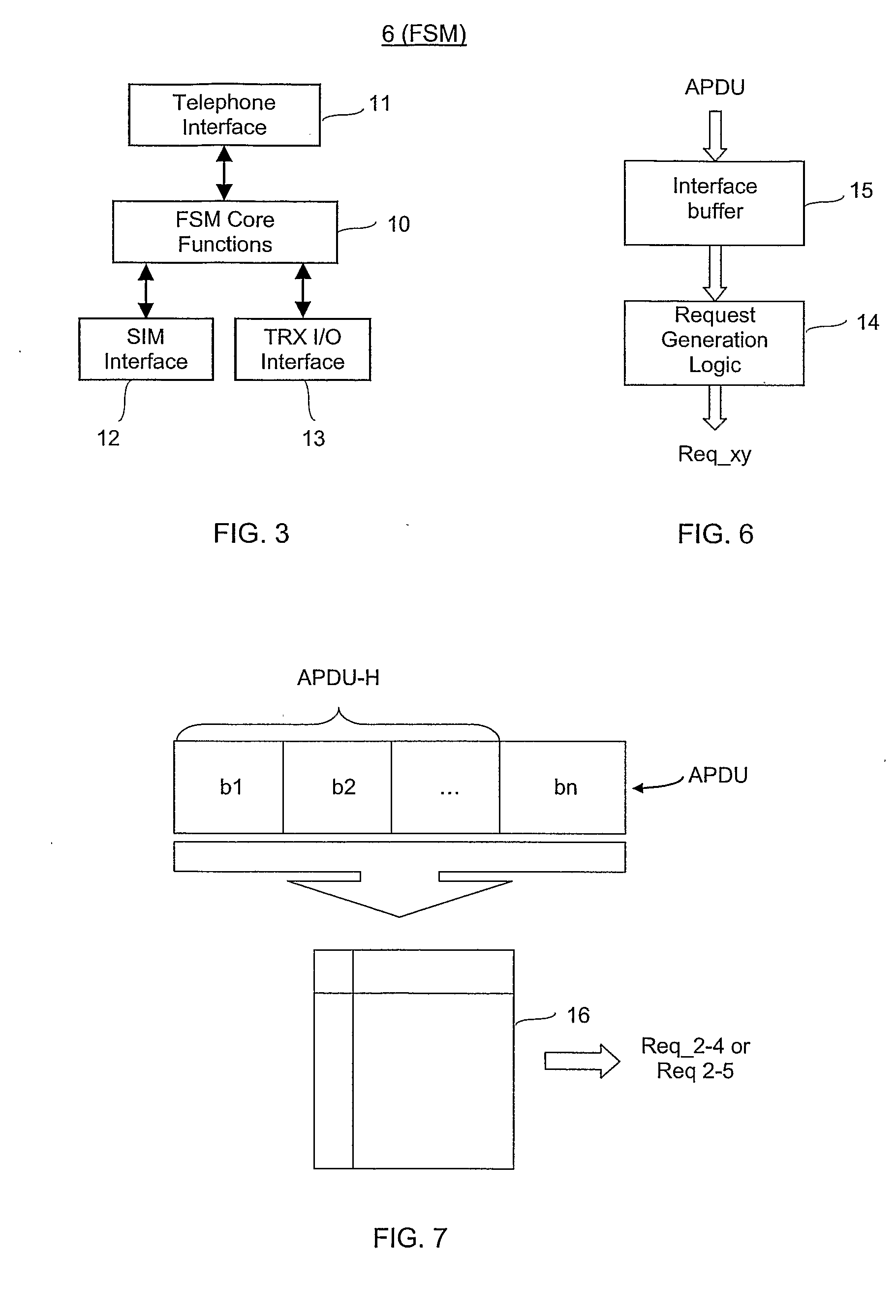
Joint Ic Card And Wireless Transceiver Module For Mobile Communication Equipment
InactiveUS20080261656A1Digital data processing detailsPayment architectureWireless transceiverTransceiver
Owner:TELECOM ITALIA SPA
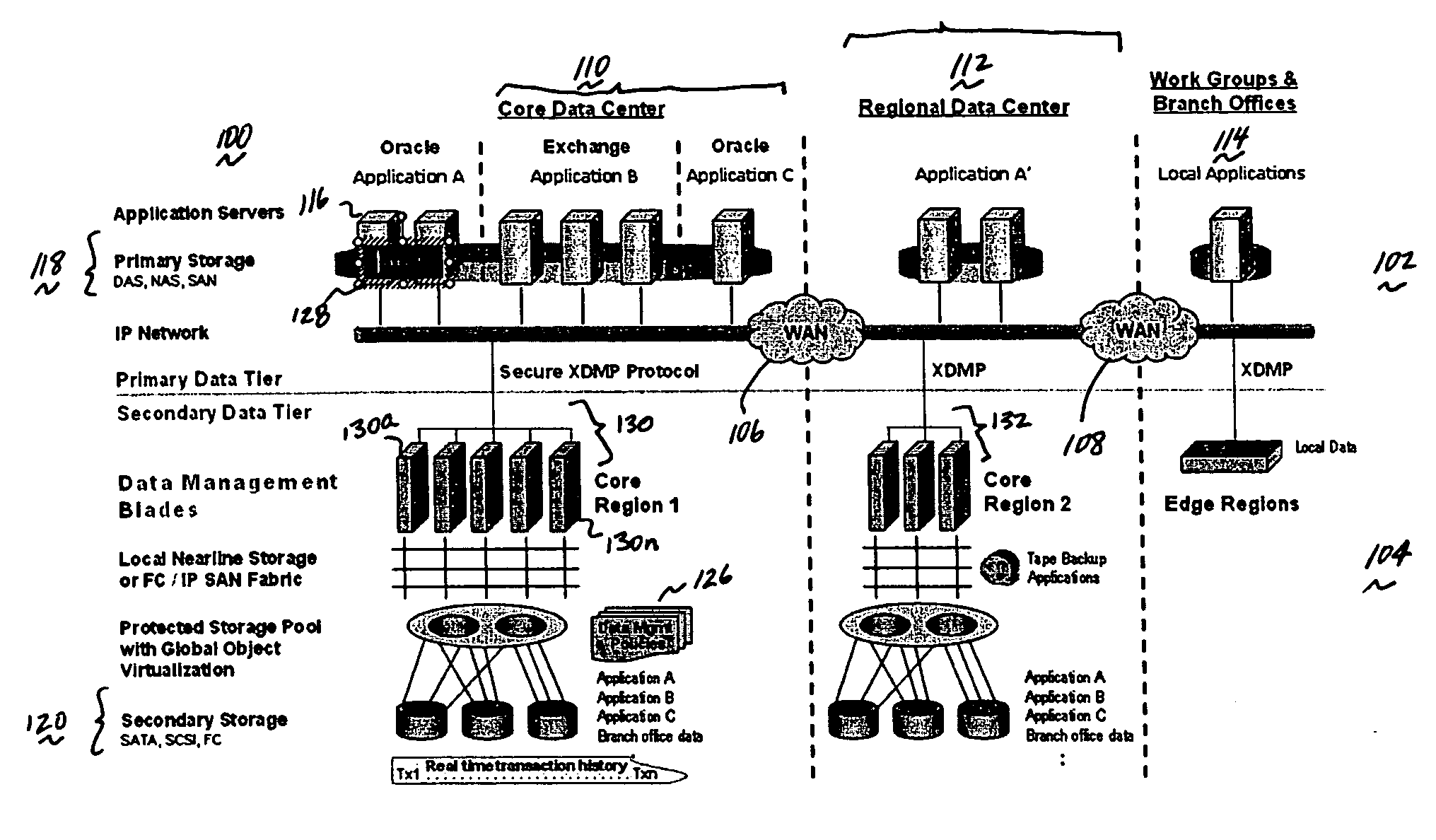
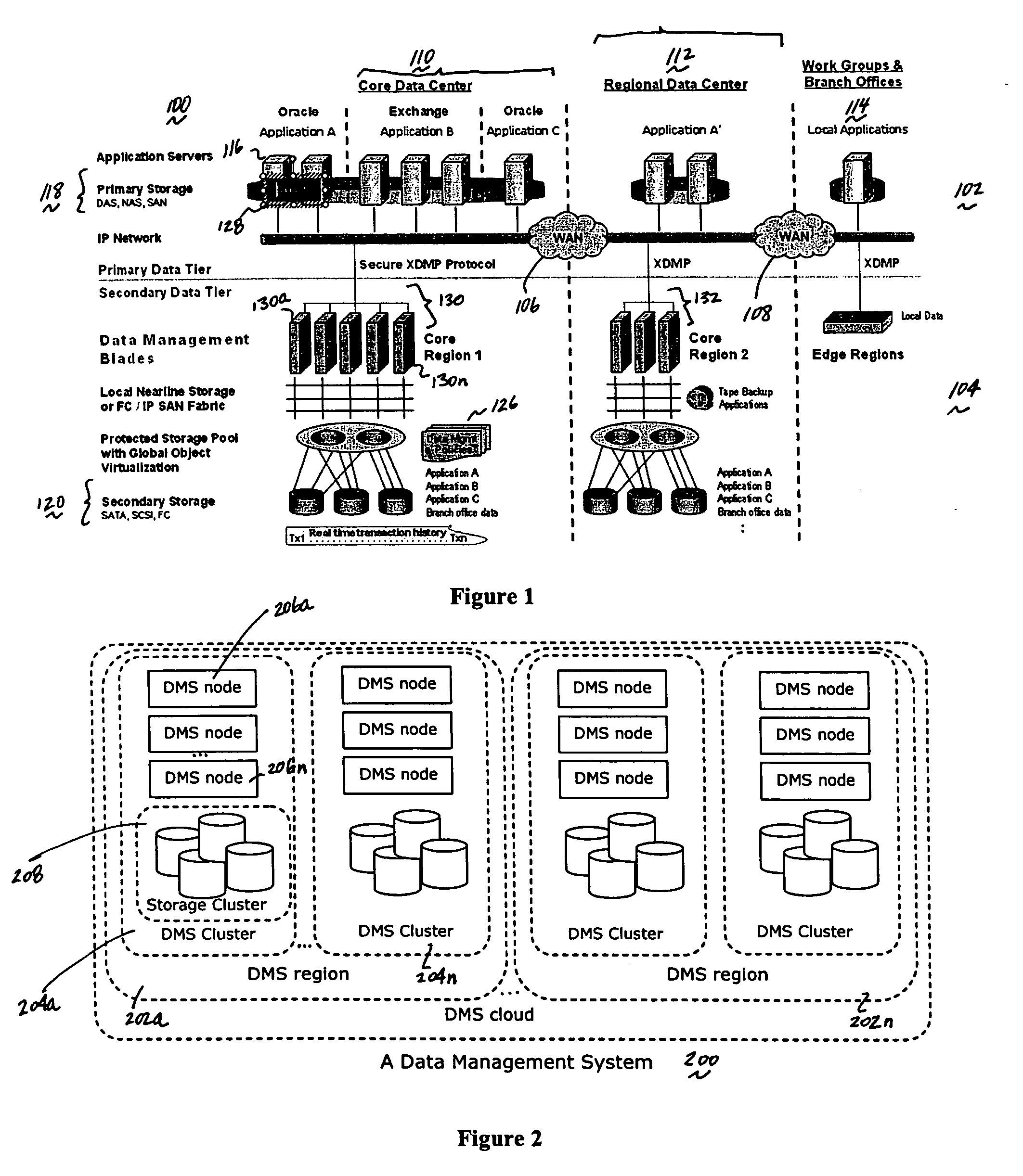
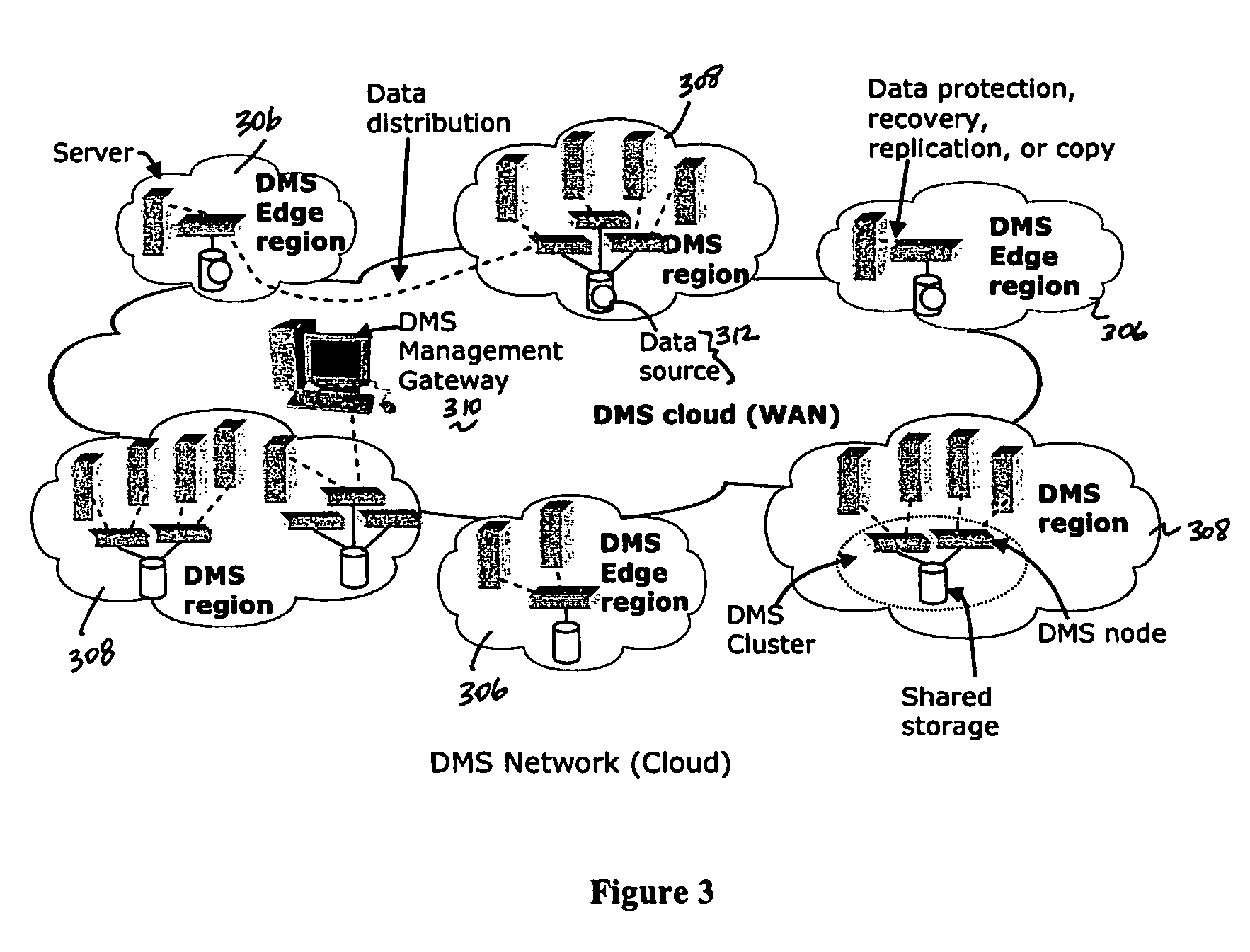
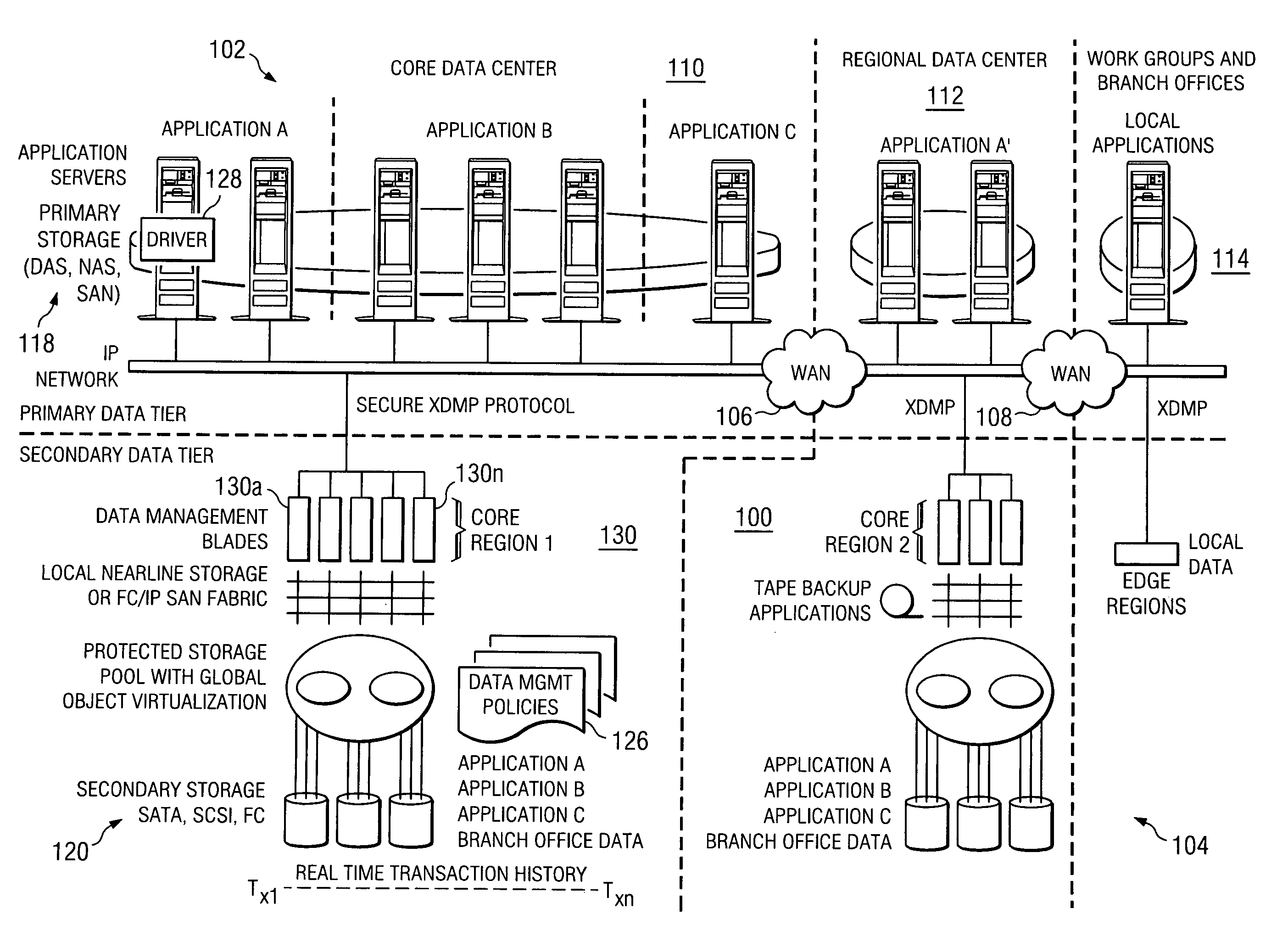
Method and system for automated, no downtime, real-time, continuous data protection
ActiveUS20050262377A1Easy to optimizeError detection/correctionGroup 6/16 element organic compoundsData streamFinite-state machine
A data management system or “DMS” provides an automated, continuous, real-time, substantially no downtime data protection service to one or more data sources associated with a set of application host servers. To facilitate the data protection service, a host driver embedded in an application server captures real-time data transactions, preferably in the form of an event journal that is provided to other DMS components. The driver functions to translate traditional file / database / block I / O and the like into a continuous, application-aware, output data stream. The host driver includes an event processor that provides the data protection service, preferably by implementing a finite state machine (FSM). In particular, the data protection is provided to a given data source in the host server by taking advantage of the continuous, real-time data that the host driver is capturing and providing to other DMS components. The state of the most current data in DMS matches the state of the data in the host server; as a consequence, the data protection is provided under the control of the finite state machine as a set of interconnected phases or “states.” The otherwise separate processes (initial data upload, continuous backup, blackout and data resynchronization, and recovery) are simply phases of the overall data protection cycle. As implemented by the finite state machine, this data protection cycle preferably loops around indefinitely until, for example, a user terminates the service. A given data protection phase (a given state) changes only as the state of the data and the environment change (a given incident).
Owner:QUEST SOFTWARE INC
Method and apparatus for identifying problems in computer networks
A network appliance for monitoring, diagnosing and documenting problems among a plurality of devices and processes (objects) coupled to a computer network utilizes periodic polling and collection of object-generated trap data to monitor the status of objects on the computer network. The status of a multitude of objects is maintained in memory utilizing virtual state machines which contain a small amount of persistent data but which are modeled after one of a plurality of finite state machines. The memory further maintains dependency data related to each object which identifies parent / child relationships with other objects at the same or different layers of the OSI network protocol model. A decision engine verifies through on-demand polling that a device is down. A root cause analysis module utilizes status and dependency data to locate the highest object in the parent / child relationship tree that is affected to determine the root cause of a problem. Once a problem has been verified, a “case” is opened and notification alerts may be sent out to one or more devices. A user interface allows all objects within the network to be displayed with their respective status and their respective parent / child dependency objects in various formats.
Owner:OPTANIX INC
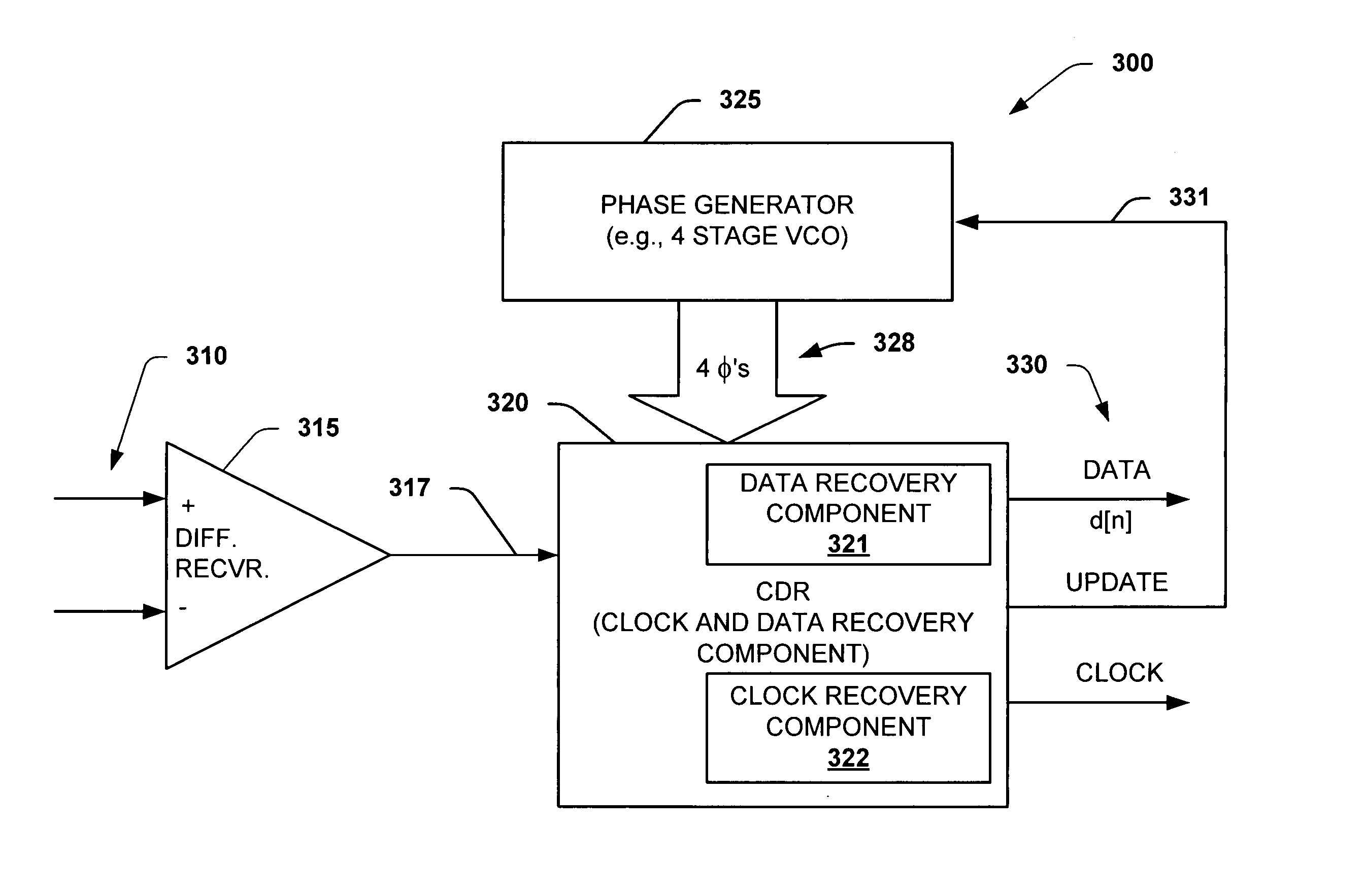
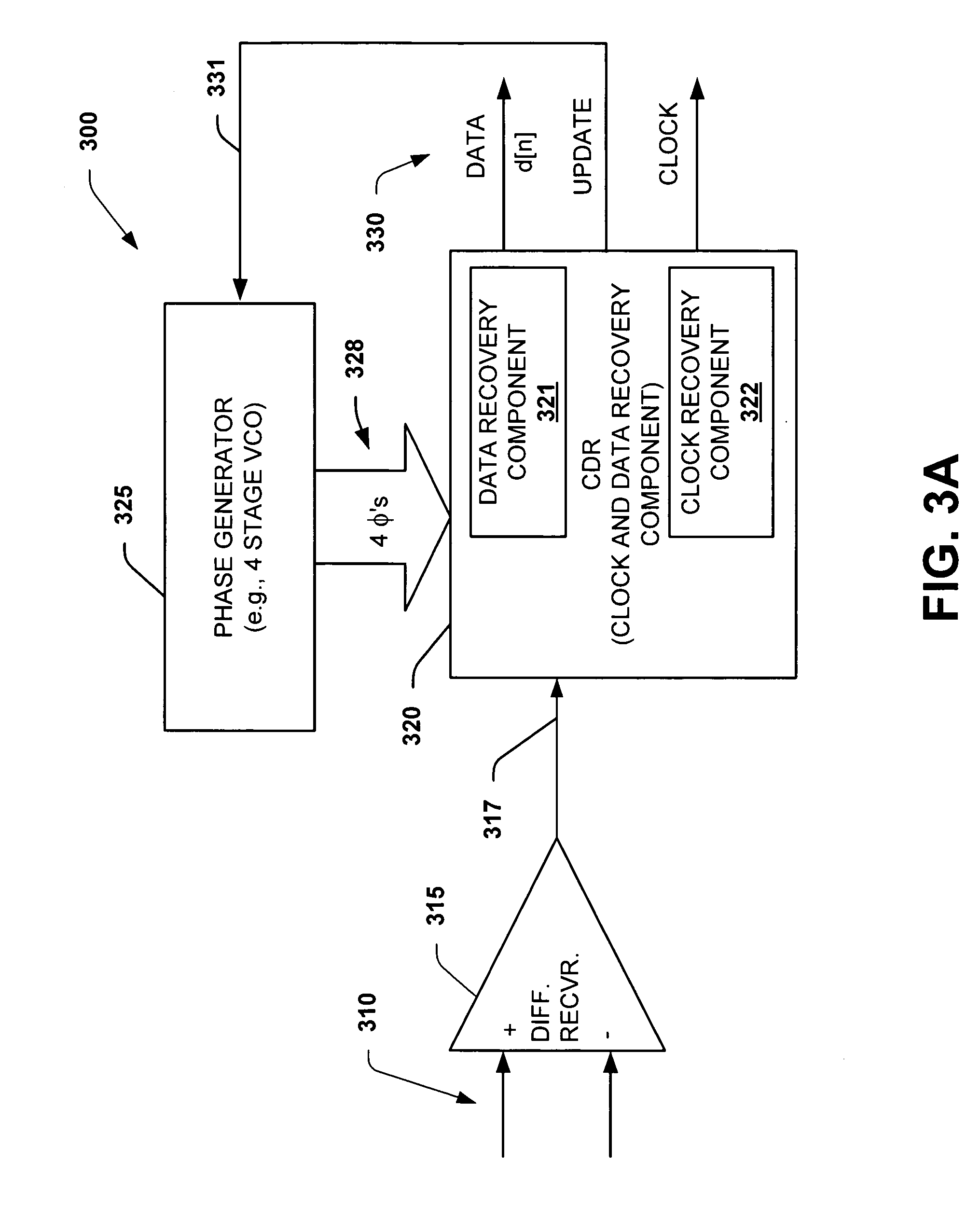
Interpolator based clock and data recovery (CDR) circuit with digitally programmable BW and tracking capability
ActiveUS20050180536A1High bandwidthLower latencyPulse automatic controlSynchronising arrangementPhase correctionData stream
The present invention facilitates clock and data recovery (330,716 / 718) for serial data streams (317,715) by providing a mechanism that can be employed to maintain a fixed tracking capability of an interpolator based CDR circuit (300,700) at multiple data rates (e.g., 800). The present invention further provides a wide data rate range CDR circuit (300,700), yet uses an interpolator design optimized for a fixed frequency. The invention employs a rate programmable divider circuit (606,656,706) that operates over a wide range of clock and data rates (e.g., 800) to provide various phase correction step sizes (e.g., 800) at a fixed VCO clock frequency. The divider (606,656,706) and a finite state machine (FSM) (612,662,712) of the exemplary CDR circuit (600,650,700) are manually programmed based on the data rate (614,667). Alternately, the data rate may be detected from a recovered serial data stream (718) during CDR operations (on-the-fly) utilizing a frequency detection circuit (725) to automatically program the divider (706) and FSM (712) to provide CDR circuit operation at the nearest base clock rate (716).
Owner:TEXAS INSTR INC
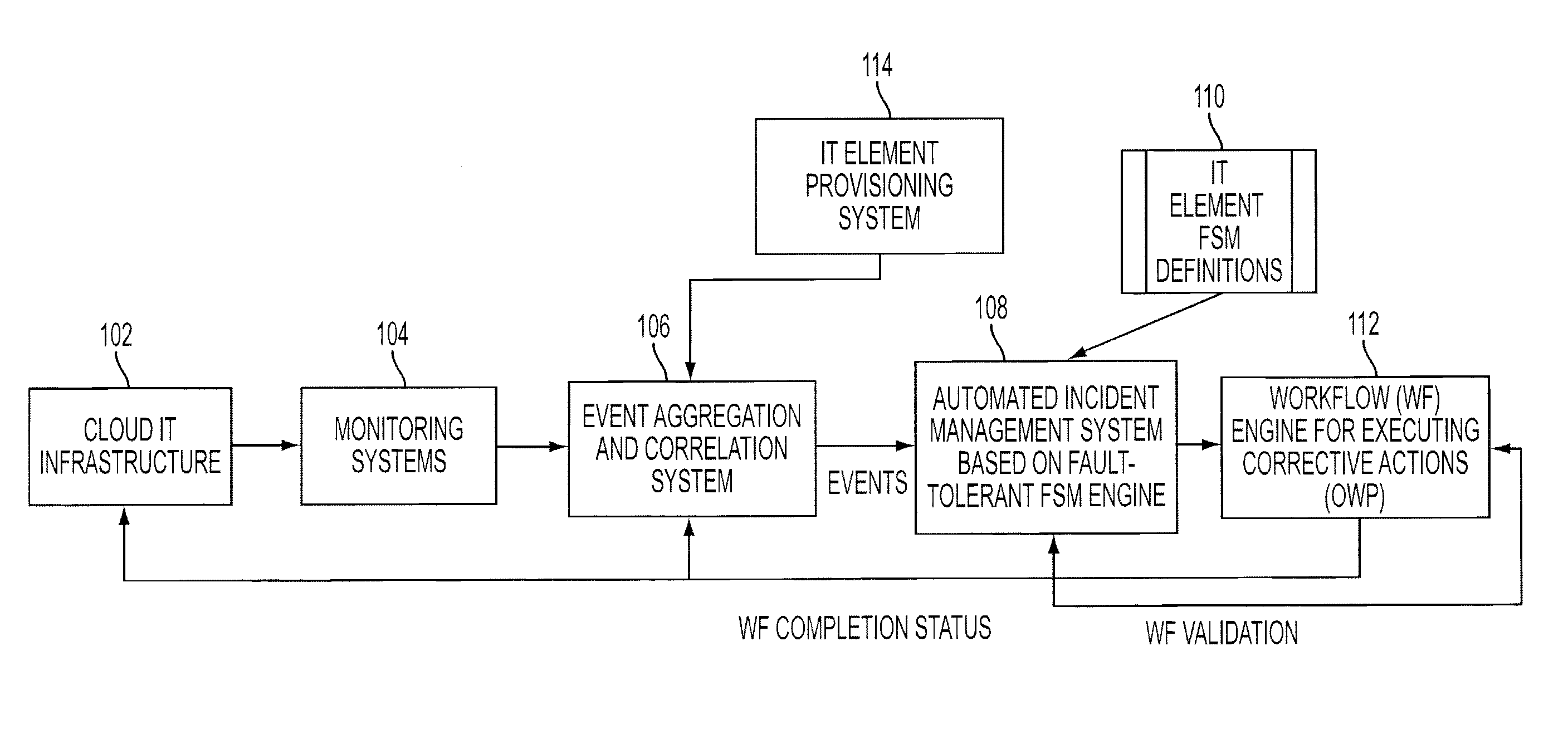
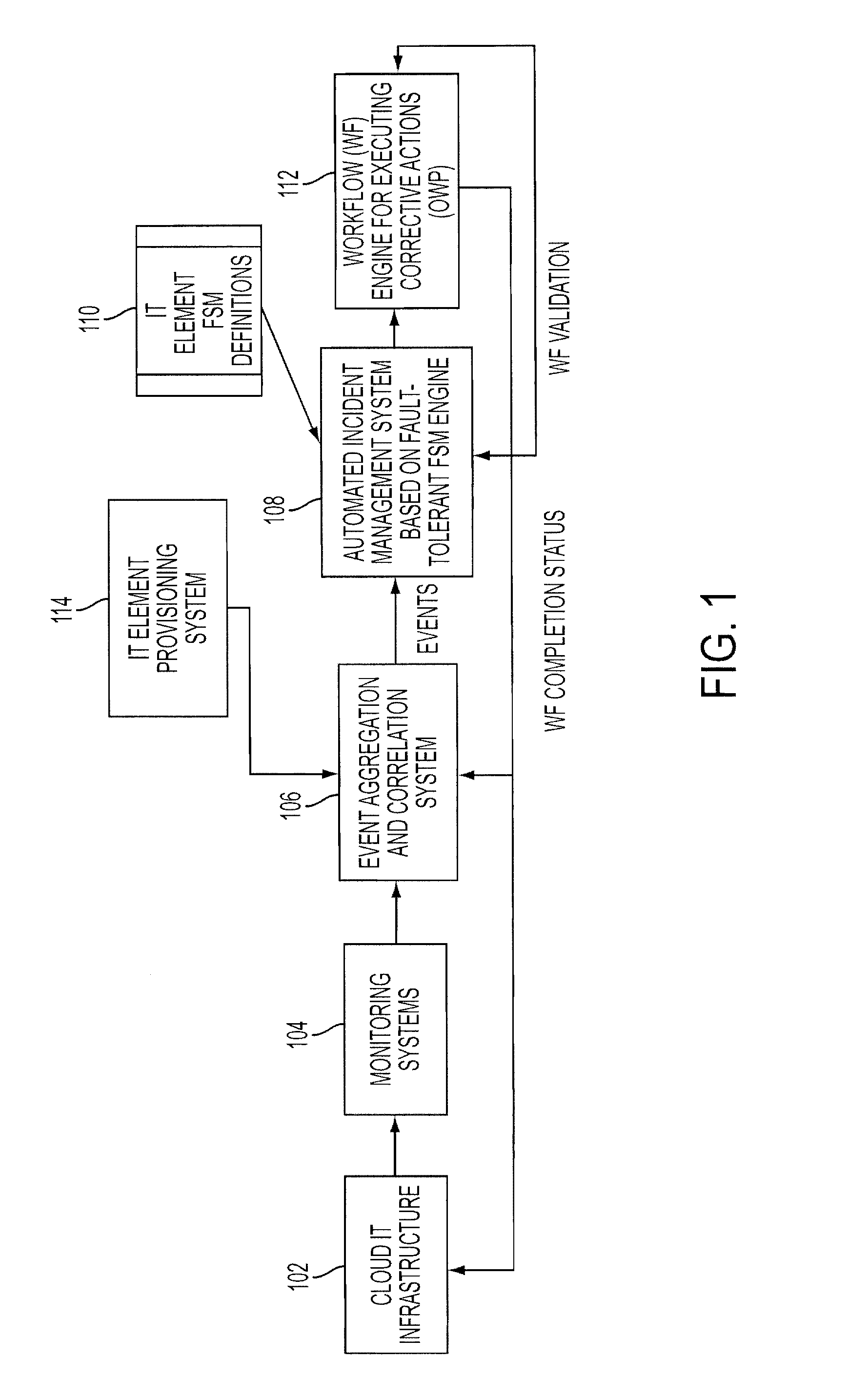
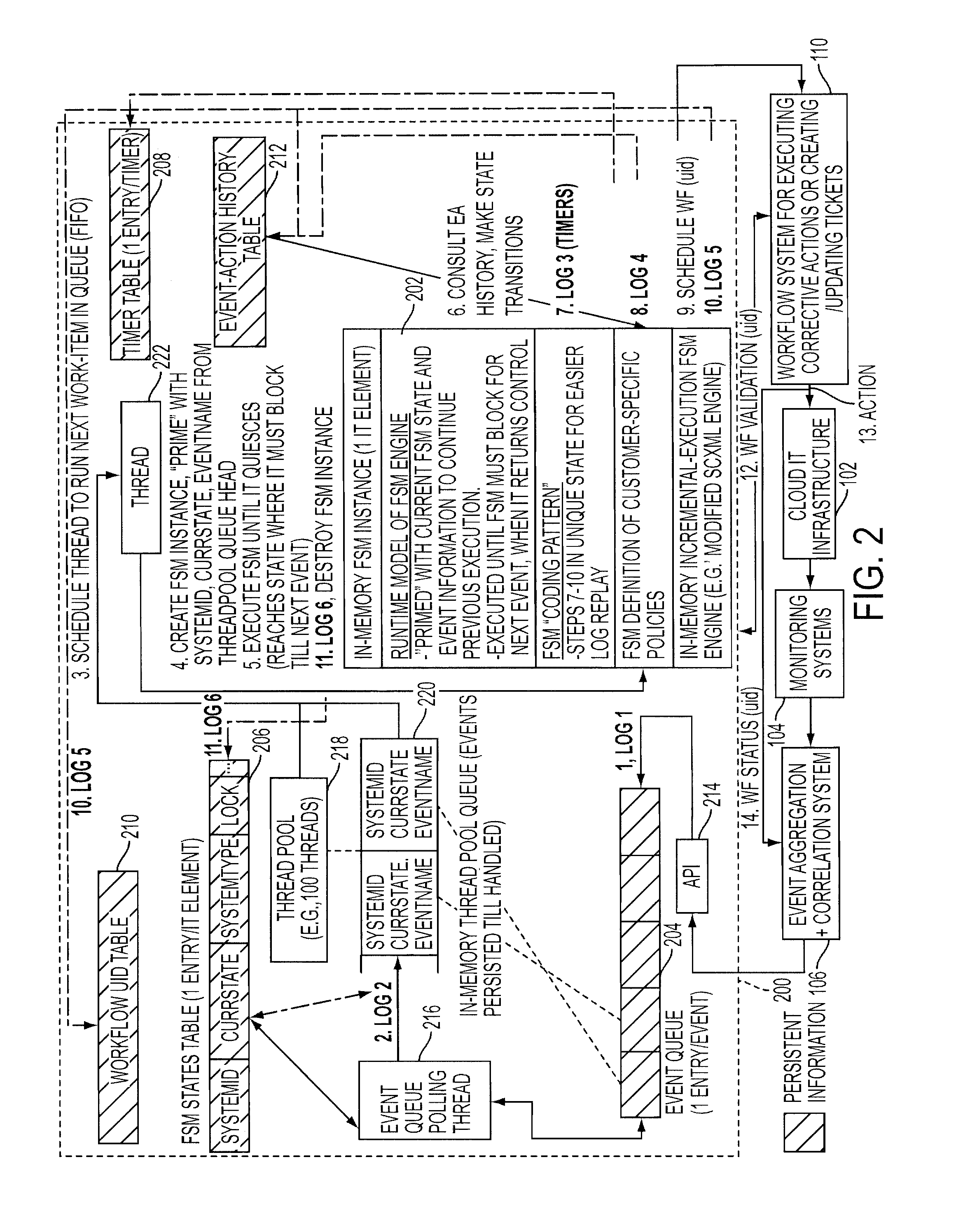
Adding scalability and fault tolerance to generic finite state machine frameworks for use in automated incident management of cloud computing infrastructures
InactiveUS20120151272A1Program controlRedundant operation error correctionFault toleranceExtensibility
A scalable and fault tolerant finite state machine engine, for example, for use in an automated incident management system, logs or records data in persistent storage at different points or levels during various internal processing of an event associated with an information technology element, and action taken associated with the event, by executing a finite state machine instance that encodes policies for handling incidents on such types of information technology elements. In the event that the finite state machine engine is shutdown during processing, the finite state machine engine is able to pick up from where it left off when it was shutdown, for each abnormally terminated finite state machine instance, by using the data logged in the persistent storage and determining a point of processing from where it should continue its execution.
Owner:GLOBALFOUNDRIES US INC
Method and system for power management in a gigabit Ethernet chip
InactiveUS20050097378A1Set clearEnergy efficient ICTPower managementControl registerFinite-state machine
Aspects of the invention for managing power in a single chip device may comprise, an internal finite state machine that, while in a communicating state, determines from within the single chip device whether a power management status is set and / or whether a first power management event is received. If the power management status is set, the finite state machine may transition from the communicating state to a power management event sent state. If the first power management event is received, the finite state machine may transition from the communicating state to a non-communicating state. The first power management event may be a turn off power management event. Furthermore, in instances where the power management status is set, it may be cleared, thereby causing the finite state machine to transition back to the communicating state. One or more power management control registers may be utilized for indicating power management status.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
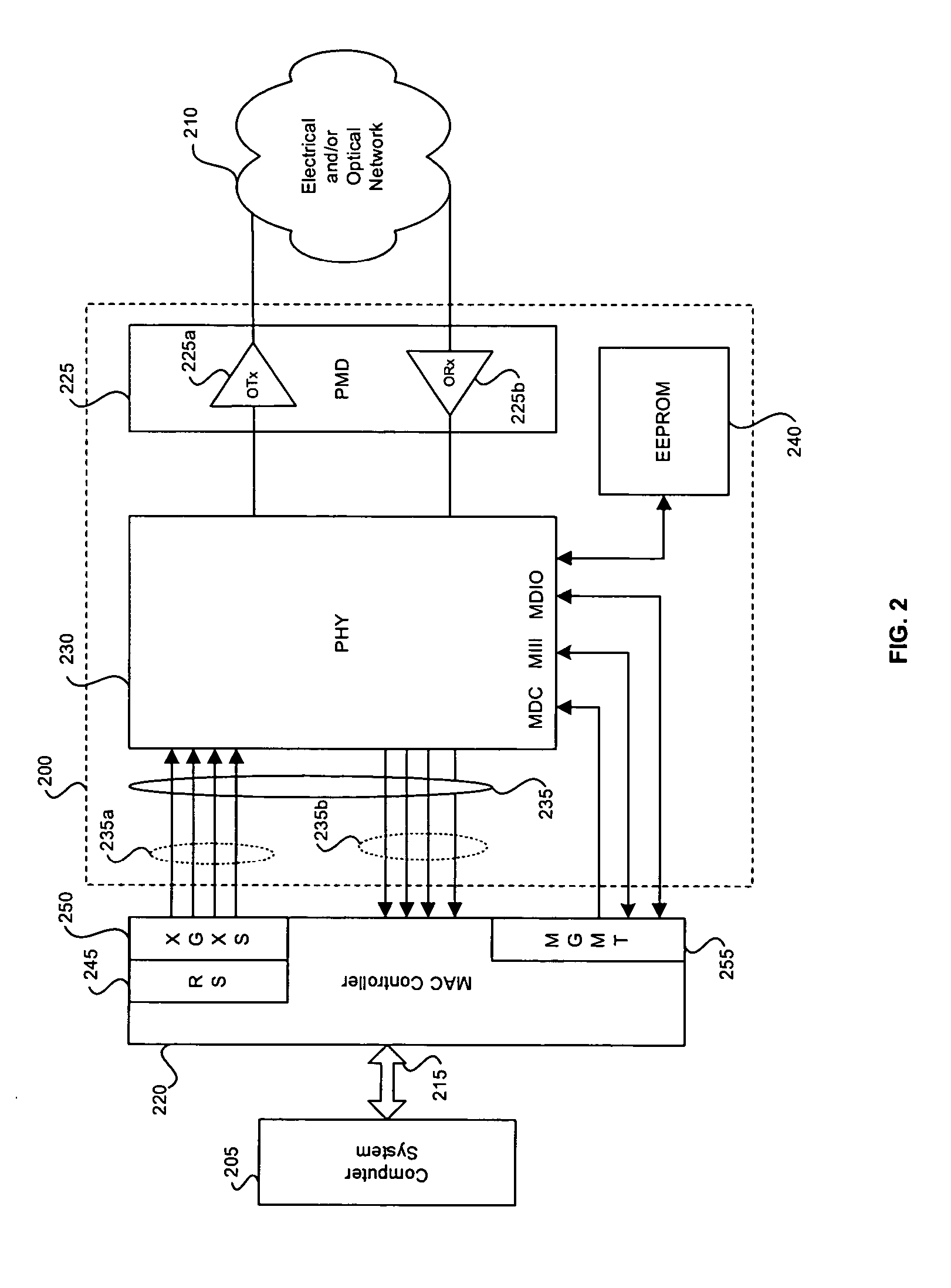
Method and system for virtual prototyping
ActiveUS7613599B2Reduce simulation overheadFast executionElectronic circuit testingError detection/correctionHuman–machine interfaceComputer architecture
An integrated design environment (IDE) is disclosed for forming virtual embedded systems. The IDE includes a design language for forming finite state machine models of hardware components that are coupled to simulators of processor cores, preferably instruction set accurate simulators. A software debugger interface permits a software application to be loaded and executed on the virtual embedded system. A virtual test bench may be coupled to the simulation to serve as a human-machine interface. In one embodiment, the IDE is provided as a web-based service for the evaluation, development and procurement phases of an embedded system project. IP components, such as processor cores, may be evaluated using a virtual embedded system. In one embodiment, a virtual embedded system is used as an executable specification for the procurement of a good or service related to an embedded system.
Owner:SYNOPSYS INC
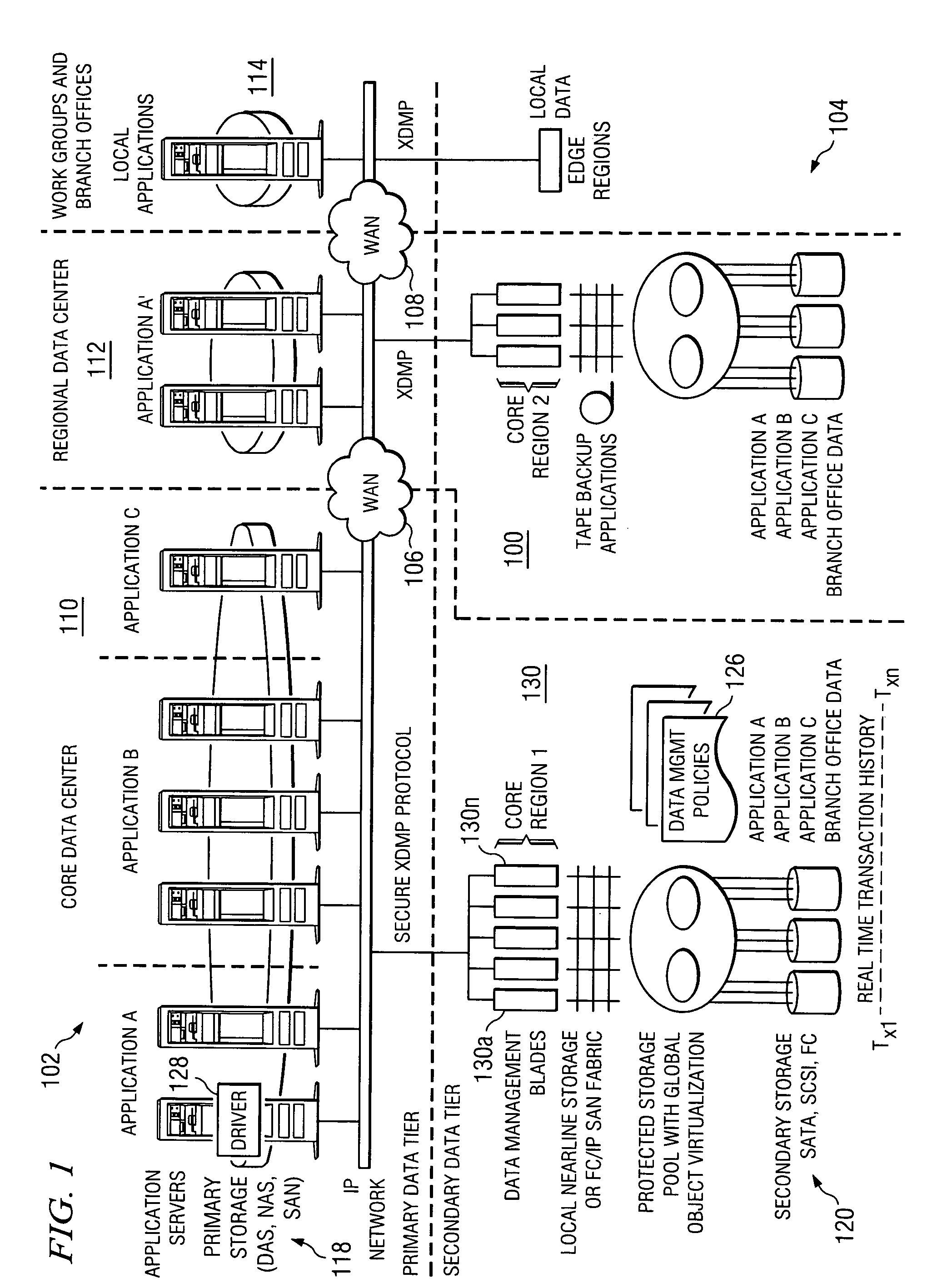
Method and system for automated, no downtime, real-time, continuous data protection
ActiveUS7096392B2Error detection/correctionGroup 6/16 element organic compoundsData streamFinite-state machine
A data management system or “DMS” provides an automated, continuous, real-time, substantially no downtime data protection service to one or more data sources associated with a set of application host servers. To facilitate the data protection service, a host driver embedded in an application server captures real-time data transactions, preferably in the form of an event journal that is provided to other DMS components. The driver functions to translate traditional file / database / block I / O and the like into a continuous, application-aware, output data stream. The host driver includes an event processor that provides the data protection service, preferably by implementing a finite state machine (FSM). In particular, the data protection is provided to a given data source in the host server by taking advantage of the continuous, real-time data that the host driver is capturing and providing to other DMS components. The state of the most current data in DMS matches the state of the data in the host server; as a consequence, the data protection is provided under the control of the finite state machine as a set of interconnected phases or “states.” The otherwise separate processes (initial data upload, continuous backup, blackout and data resynchronization, and recovery) are simply phases of the overall data protection cycle. As implemented by the finite state machine, this data protection cycle preferably loops around indefinitely until, for example, a user terminates the service. A given data protection phase (a given state) changes only as the state of the data and the environment change (a given incident).
Owner:QUEST SOFTWARE INC
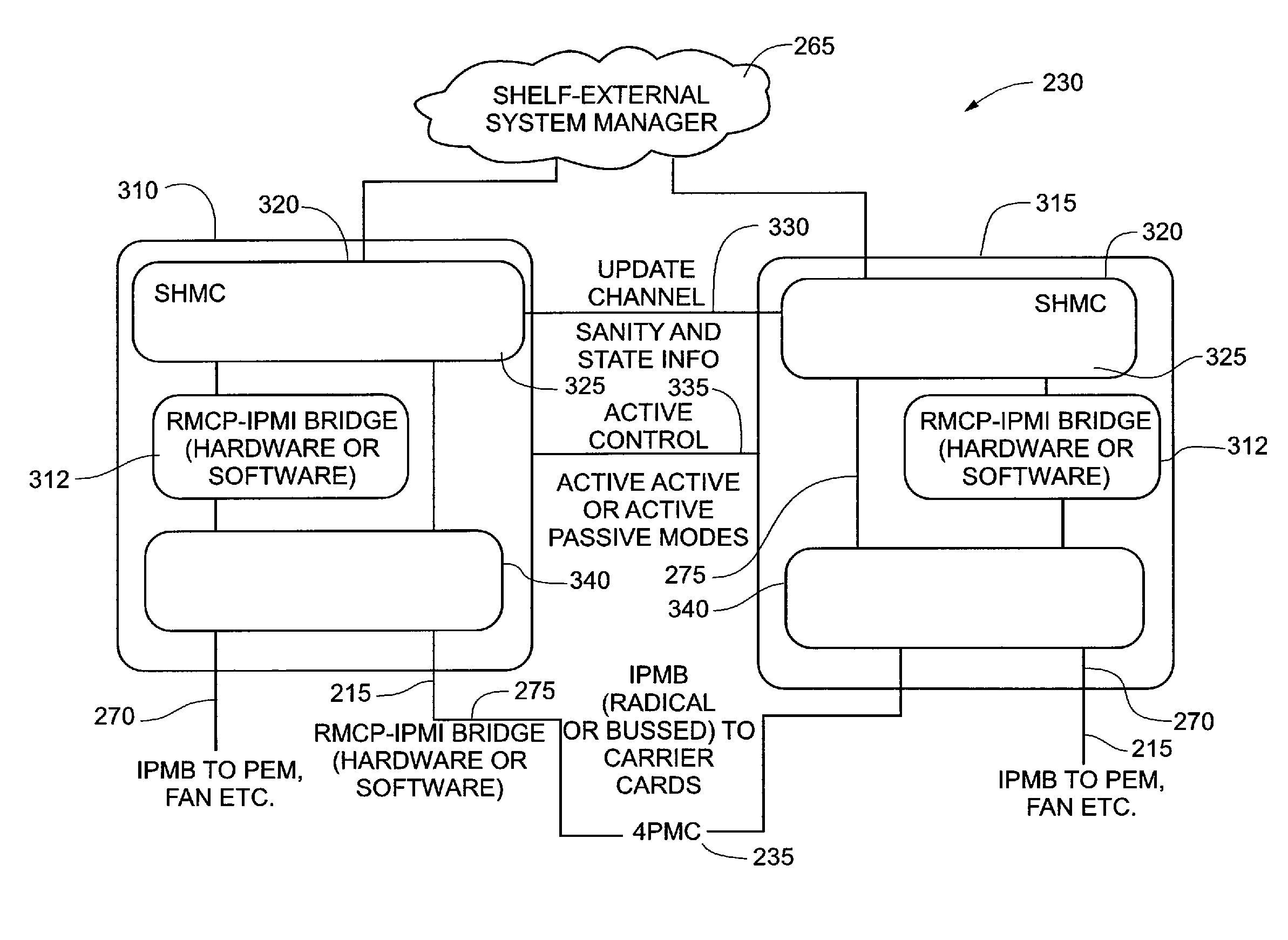
Shelf management controller with hardware/software implemented dual redundant configuration
InactiveUS7827442B2Safety arrangmentsElectric controllersController architectureIntelligent Platform Management Interface
A fault tolerant, multi-protocol shelf management controller architecture that is extensible provides an intelligent platform management interface that is version indifferent as well as programmable and reconfigurable. The shelf management controller is arranged in a dual redundant configuration in a client-server mode and has a message driven configuration with the messages conforming to the Intelligent Platform Management Interface (IPMI) specification as extended by PICMG 3.0. In one embodiment, each shelf management controller includes at least one bit stream processor comprising sequenced stage machines implementing one or more finite state machines associated with one or more devices that are under control of the shelf management controller. The finite state machines could be hardware or software based. The shelf management controller is also modeled as a layered architecture that includes an IPMI API layer. The IPMI API layer enables the shelf manager to interface with legacy and future IPMI specifications.
Owner:RPX CORP
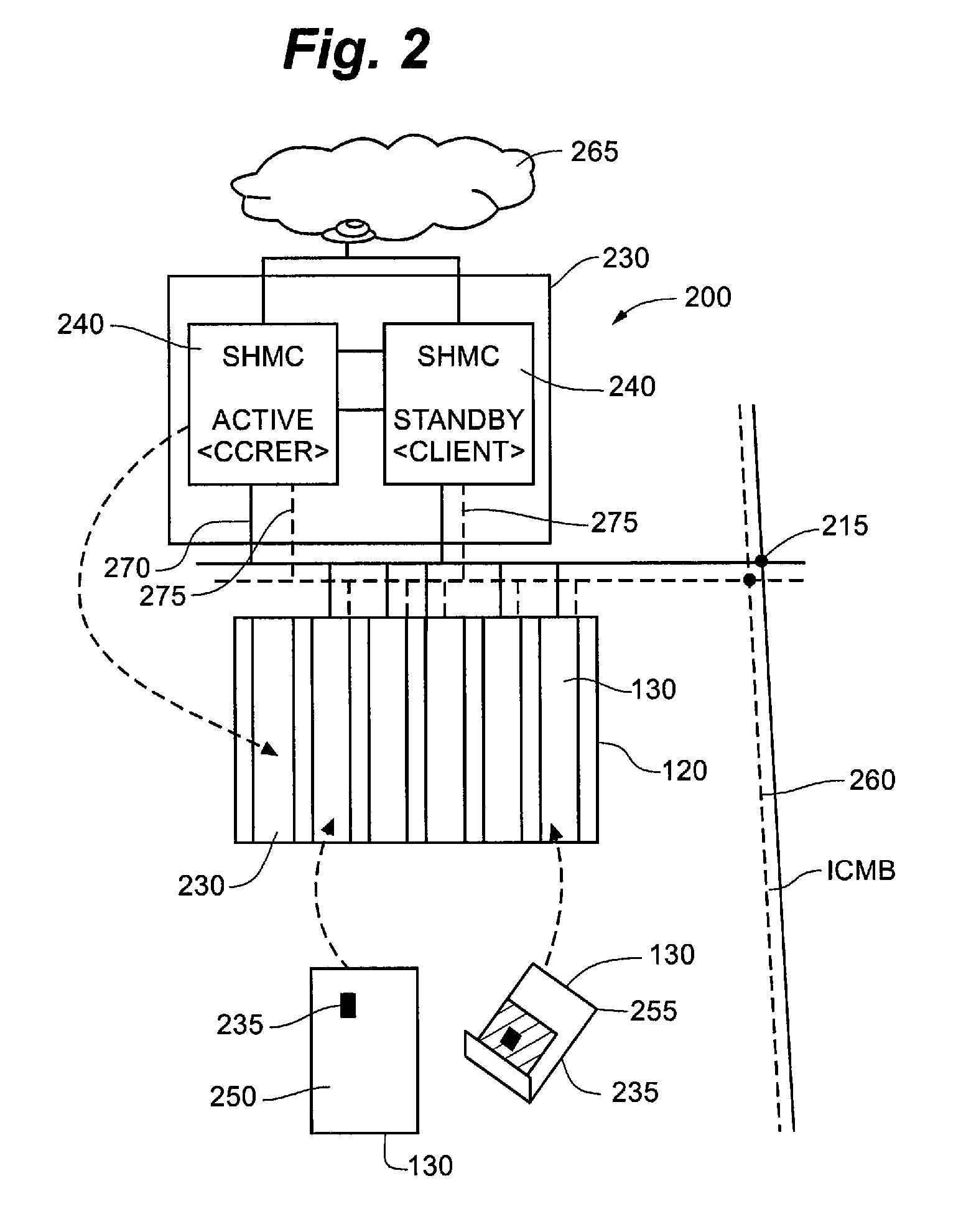
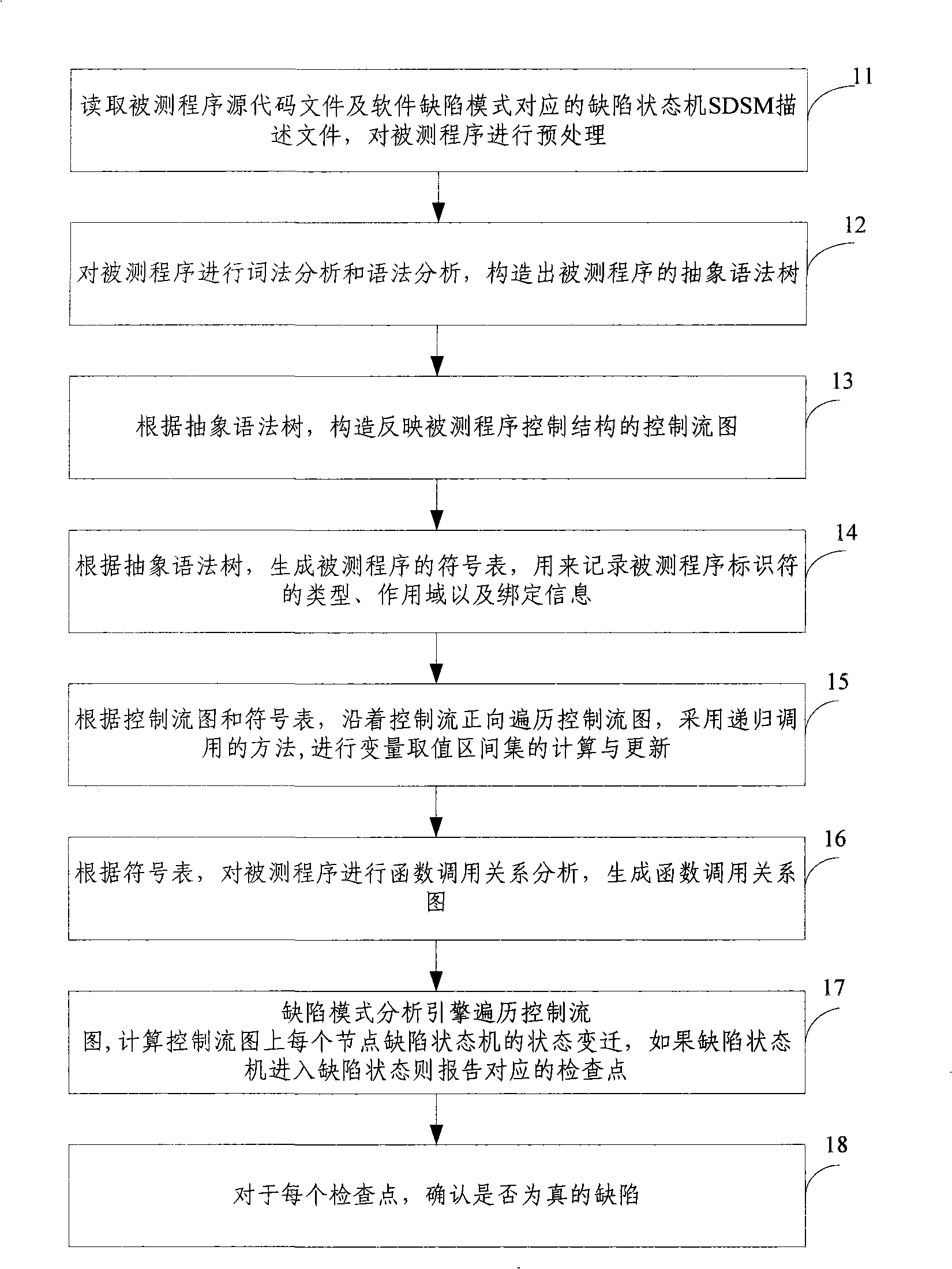
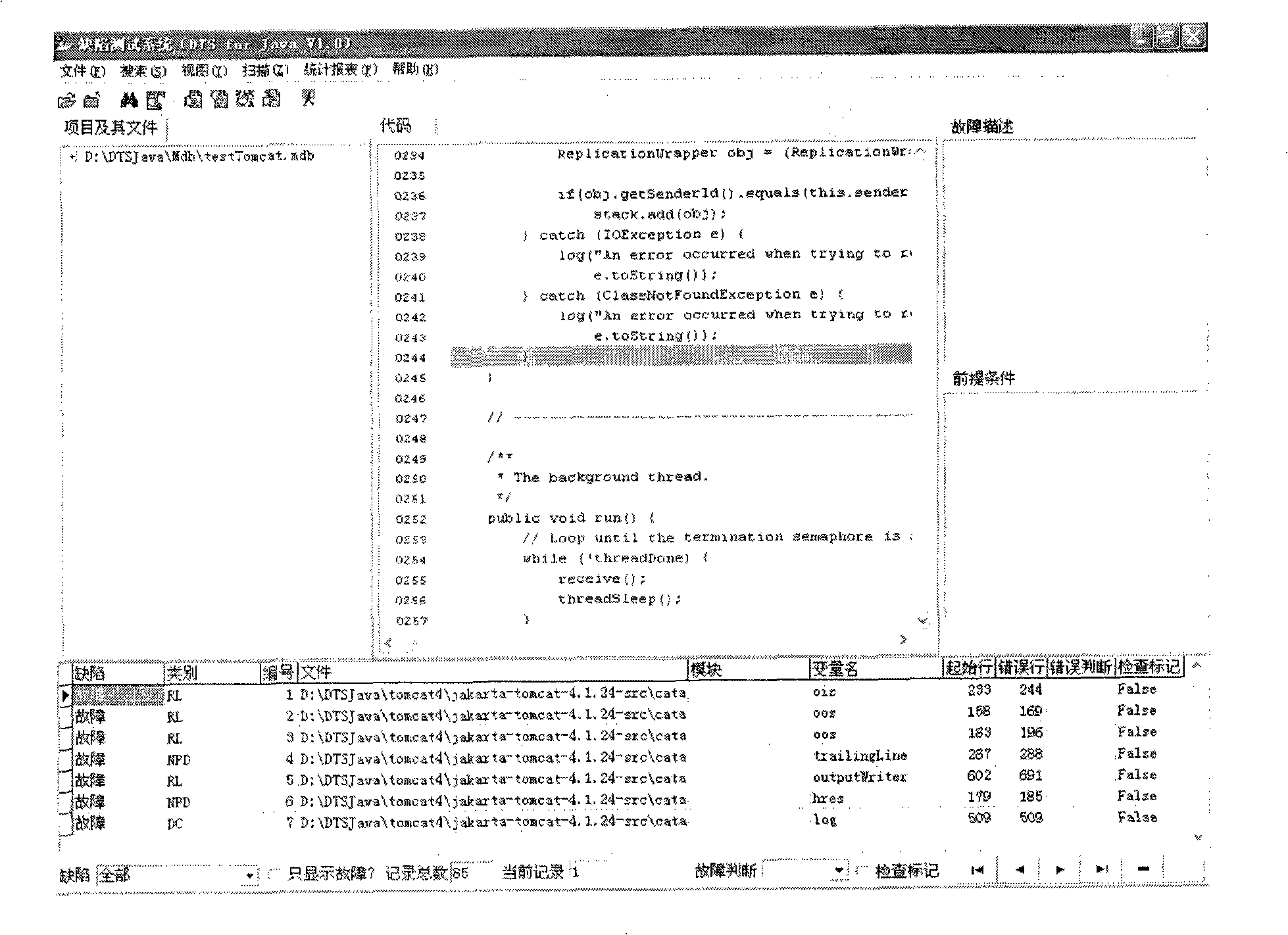
Test method and system based on software defect mode
InactiveCN101286132AReduce false positivesImprove test accuracySoftware testing/debuggingControl flowPresent method
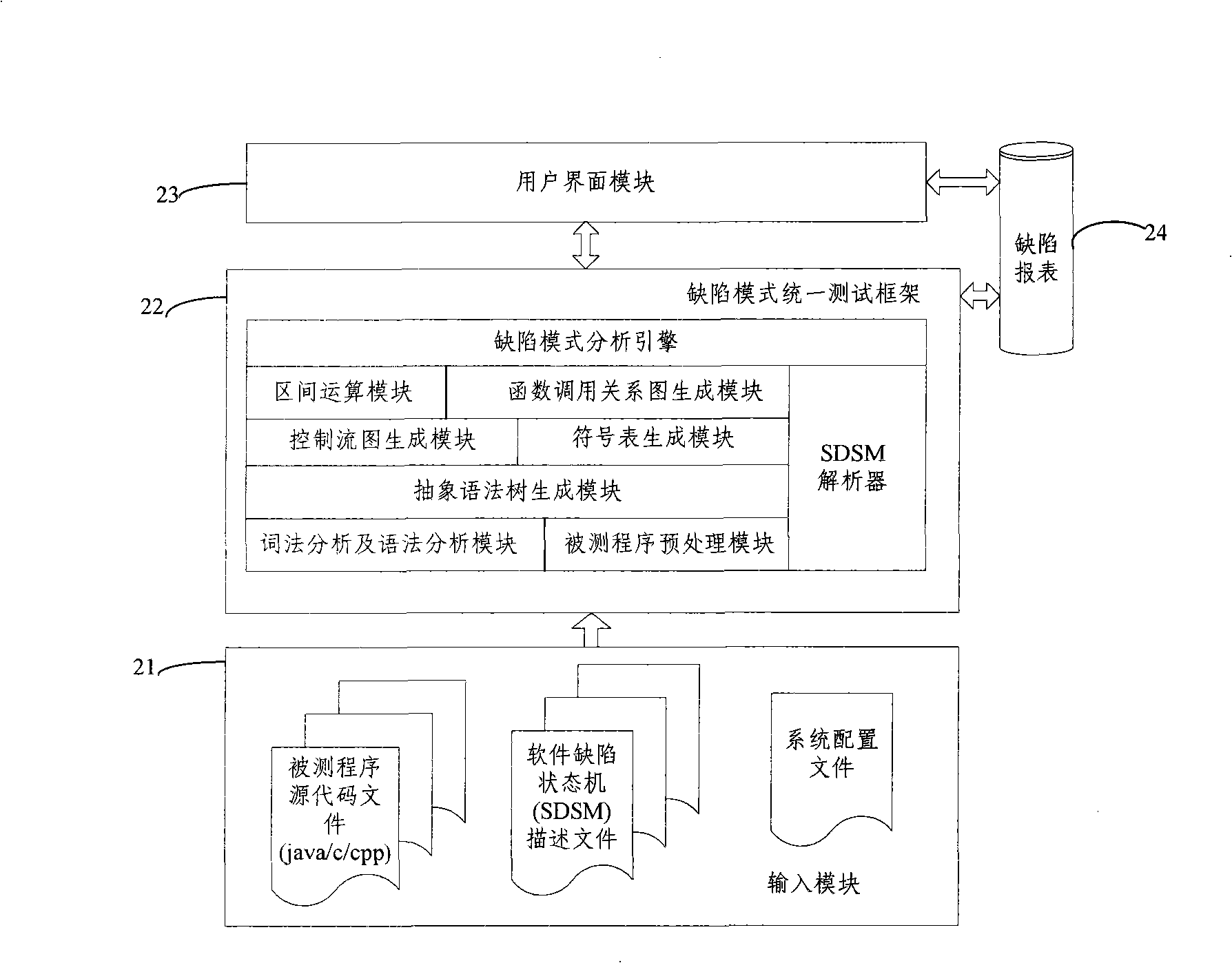
The invention discloses a testing method based on software defect mode, comprising the steps of: reading source code files of programs to be tested and SDSM description file of a defect state machine, carrying out pre-processing of the programs to be tested, analyzing the SDSM description file; carrying out lexical analysis and grammar analysis of the programs to be tested and constructing abstract syntax tree; generating a control flow graph and a symbol table according to the abstract syntax tree and carrying out the calculating and updating of variable value interval sets according to the control flow graph and the symbol table; carrying out function invoking relation analysis of the programs to be tested and generating a function invoking relation graph; searching the control flow graph by taking the function as unit according to the function invoking relation graph, calculating the state migration of each node defect state machine on the control flow graph, and reporting corresponding checking point when the defect state machine enters the defect state. The invention also discloses a testing system based on software defect mode, which comprises an input module, a defect mode uniformity testing frame and a user interface module and completes the uniform test on the programs to be tested.
Owner:BEIJING UNIV OF POSTS & TELECOMM
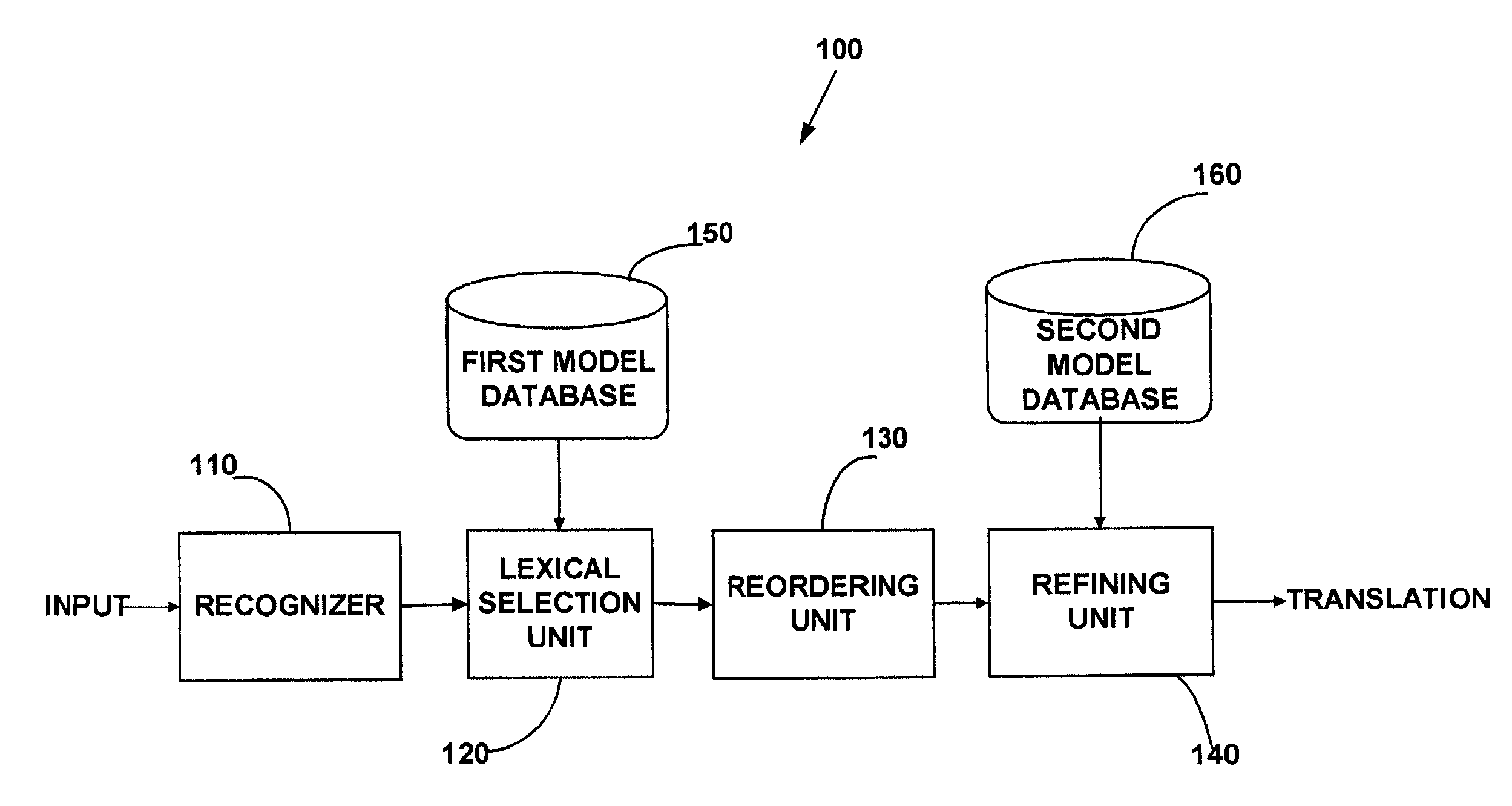
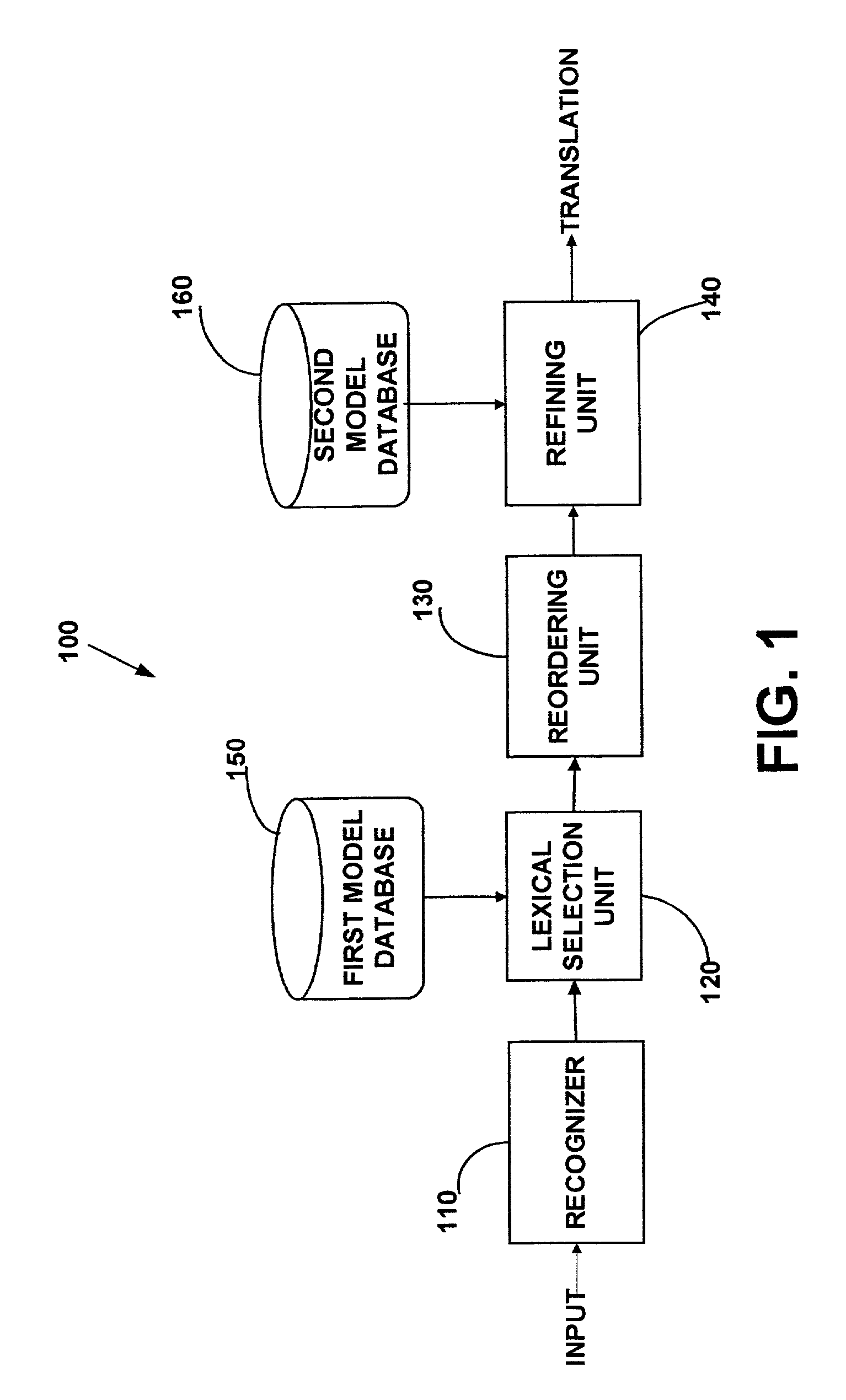
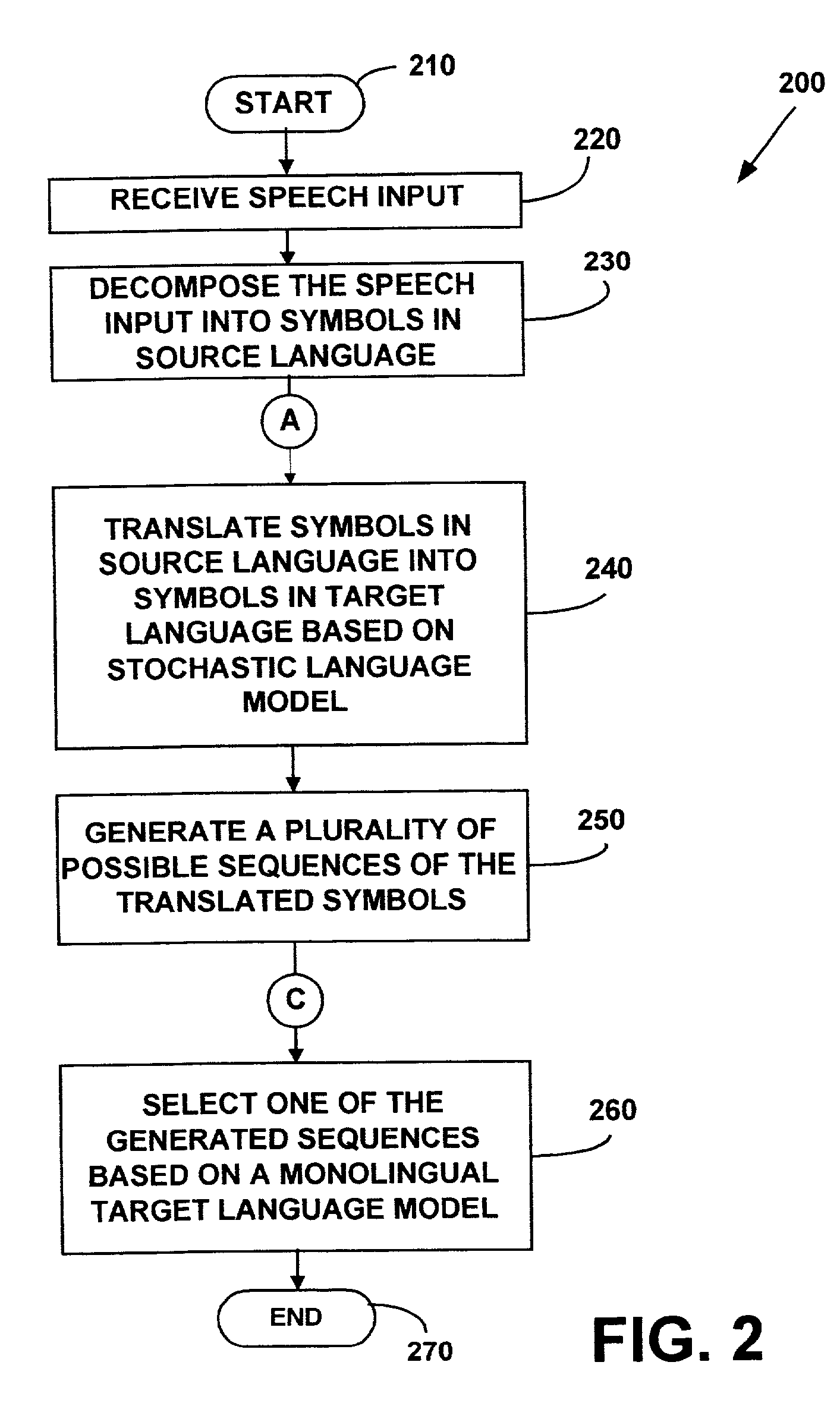
Method and apparatus for providing stochastic finite-state machine translation
A method and apparatus for stochastic finite-state machine translation is provided. The method may include receiving a speech input and translating the speech input in a source language into one or more symbols in a target language based on stochastic language model. Subsequently, all possible sequences of the translated symbols may be generated. One of the generated sequences may be selected based on a monolingual target language model.
Owner:NUANCE COMM INC
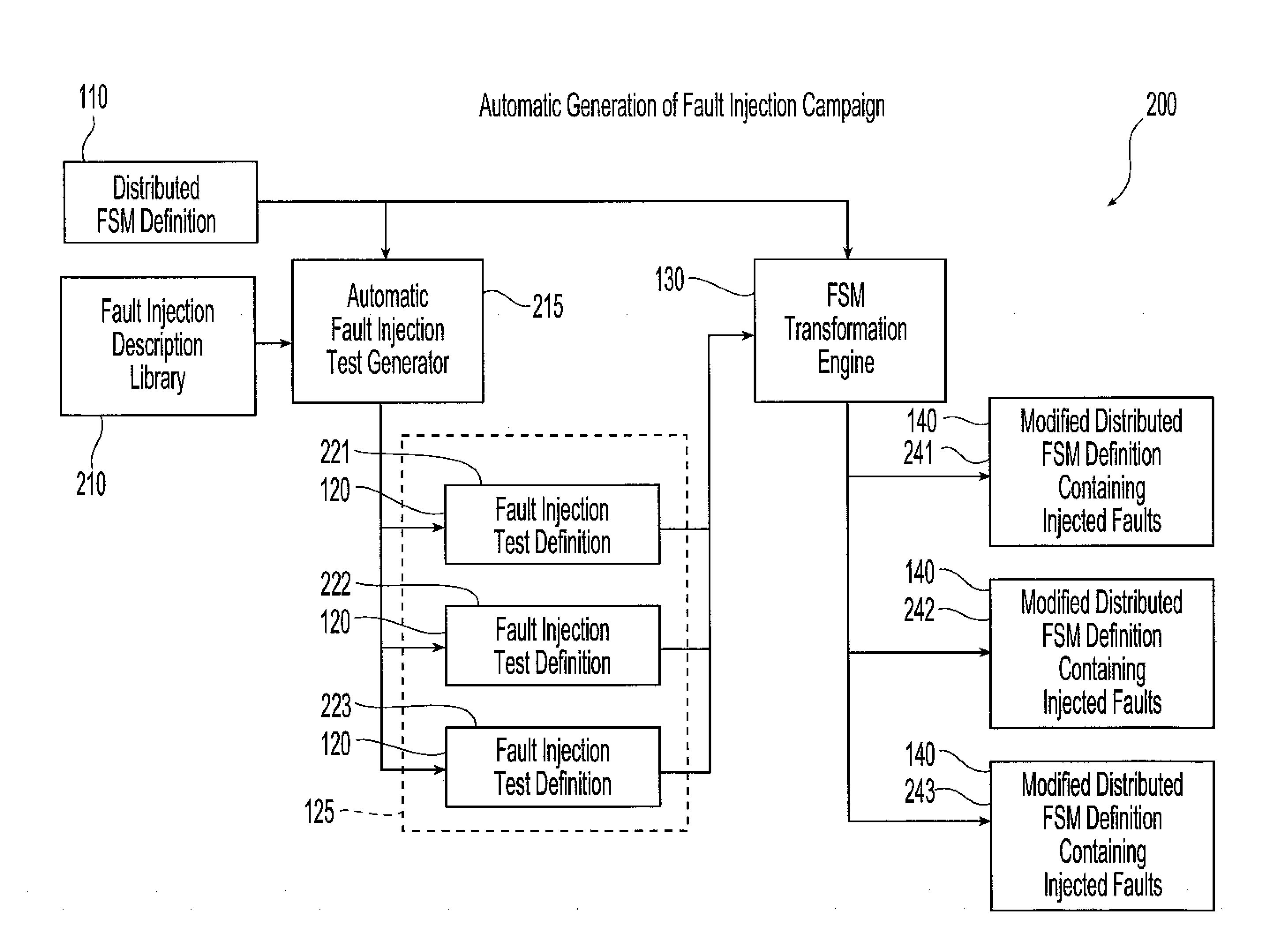
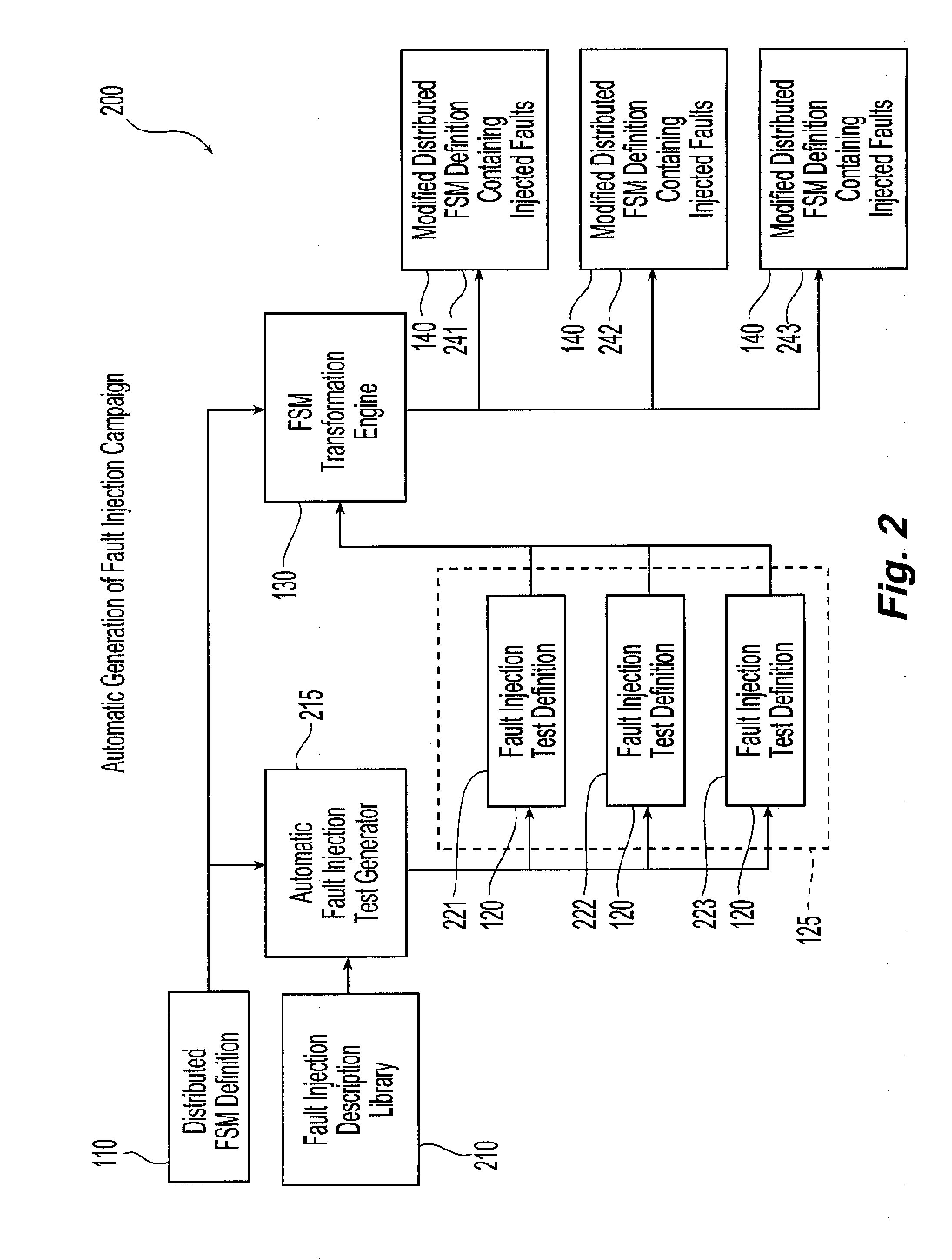
Distributed fault injection mechanism
InactiveUS20080215925A1Validating the robustness of a distributed computing systemEasy injectionError detection/correctionGraphicsGraphical user interface
Methods and systems are provided for testing distributed computer applications using finite state machines. A finite state machine definition for use in a distributed computer system is combined with the fault injections definitions contained within a fault injection campaign that is created for testing the computer application employing that finite state machine. The definition and combination of the finite state machine definition and the fault injection campaign is carried out automatically or manually, for example using a graphical user interface. This combination creates at least one modified finite state machine definition containing the desired injected faults. The modified finite state machine definition is separate from the originally identified finite state machine definition, and the originally identified finite state machine remains intact without injected faults. Trigger points within the finite state machine definition are identified for each fault injection test definition, and the modified finite state machine definition containing the fault injection test definition associated with a given trigger point are used in place of the original finite state machine definition upon detection of that trigger point during runtime of the finite state machine definition.
Owner:IBM CORP
Process and architecture of robotic system to mimic animal behavior in the natural environment
ActiveUS20050065651A1Programme-controlled manipulatorArtificial lifeBiomechanicsFinite-state machine
A robotic architecture for capturing the autonomous performance advantages the animal models enjoy in the natural environment is disclosed. A biomimesis process is employed to allow selective utilization of basic physical components and adaptation of a common control paradigm for each of different vehicle types. The biomimetic architecture involves five functional elements: a basic biomorphic plant for capturing the biomechanical advantages of the model organism; a neural circuit-based controller consisting of a finite state machine; myomorphic actuators producing linear graded force in response to trains of current pulses for mediating movements; labeled line code output by neuromorphic sensors; and a reactive behavioral sequencer executing command sequences defined within a behavioral library.
Owner:NORTHEASTERN UNIV
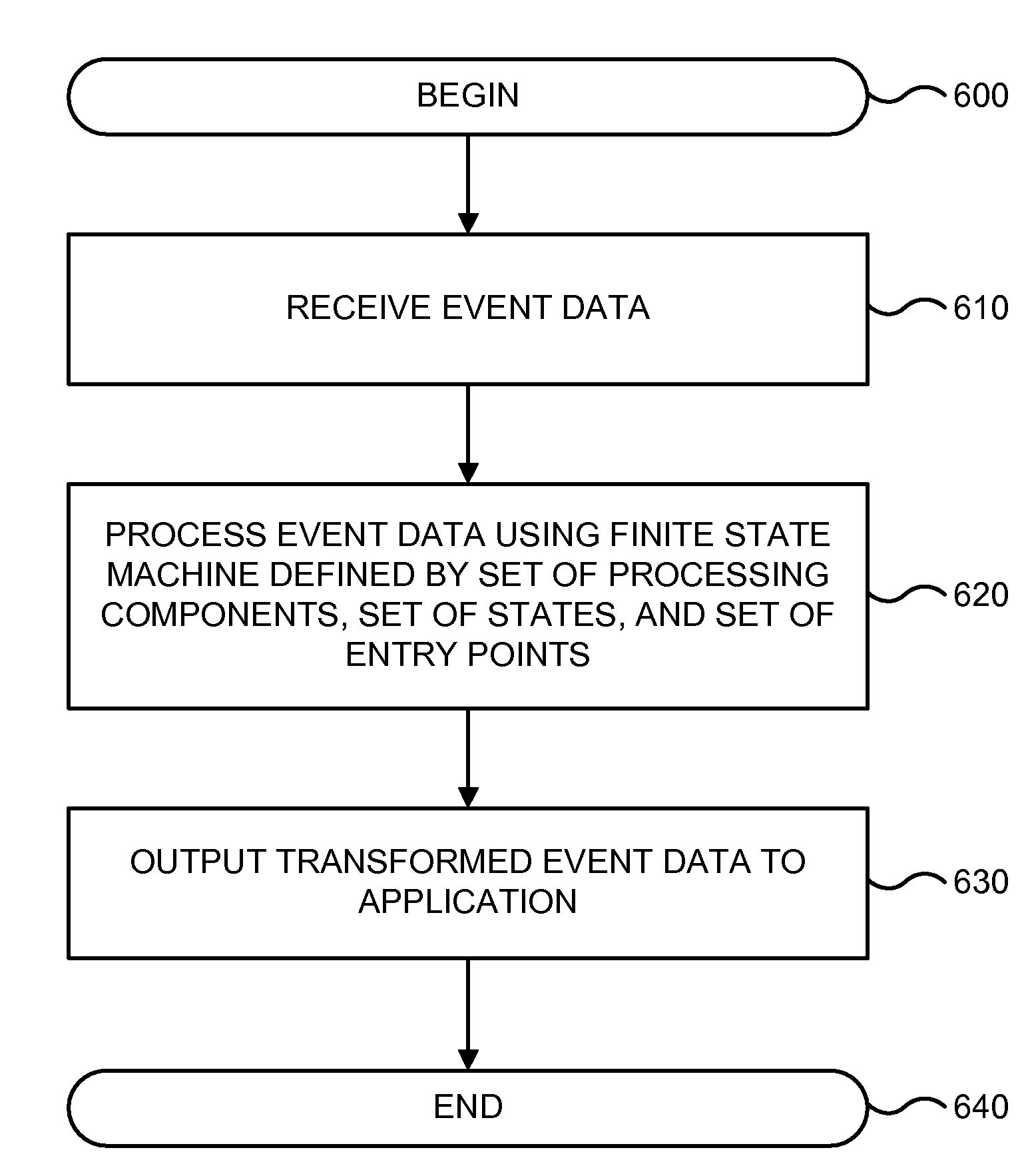
Event Processing Finite State Engine and Language
In various embodiments, a method for processing event streams includes receiving a finite state machine defined in response to a set of processing components, a set of states, and a set of entry points. Event data associated with an event stream is also received. The event data is processes according to the finite state machine to generate an event.
Owner:ORACLE INT CORP
Cooperative construction method for enhancing realistic table-tennis system based on real rackets
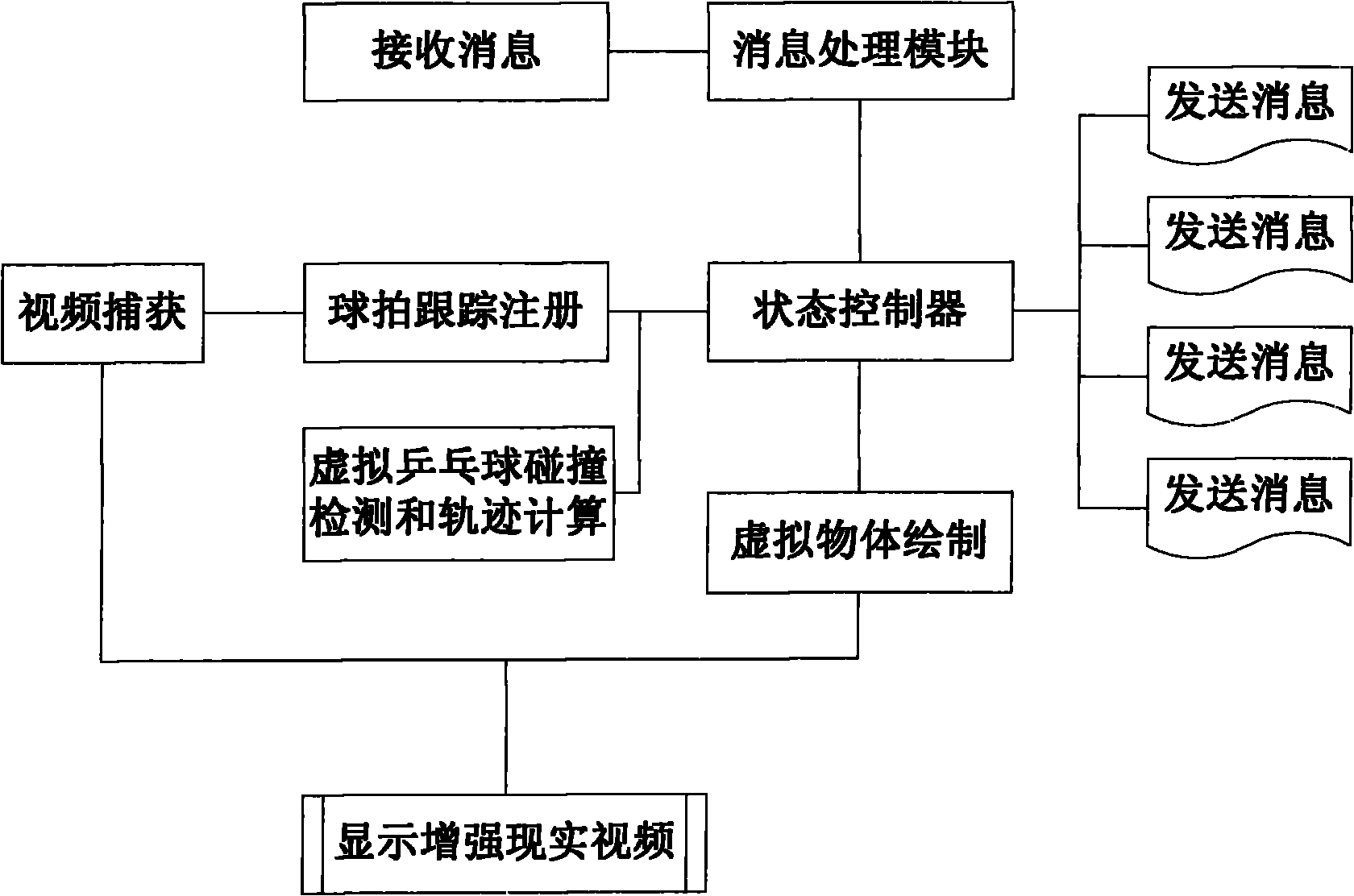
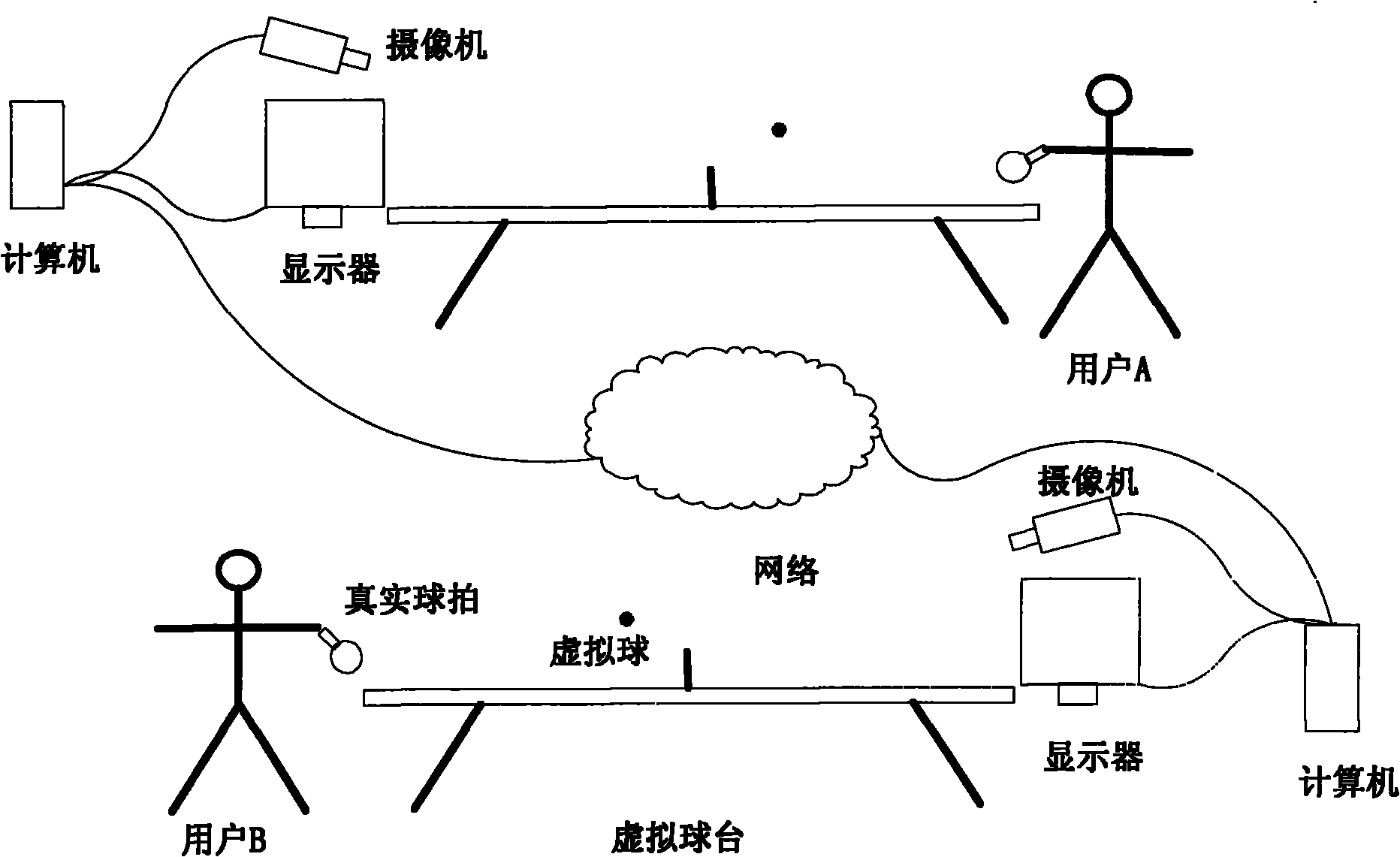
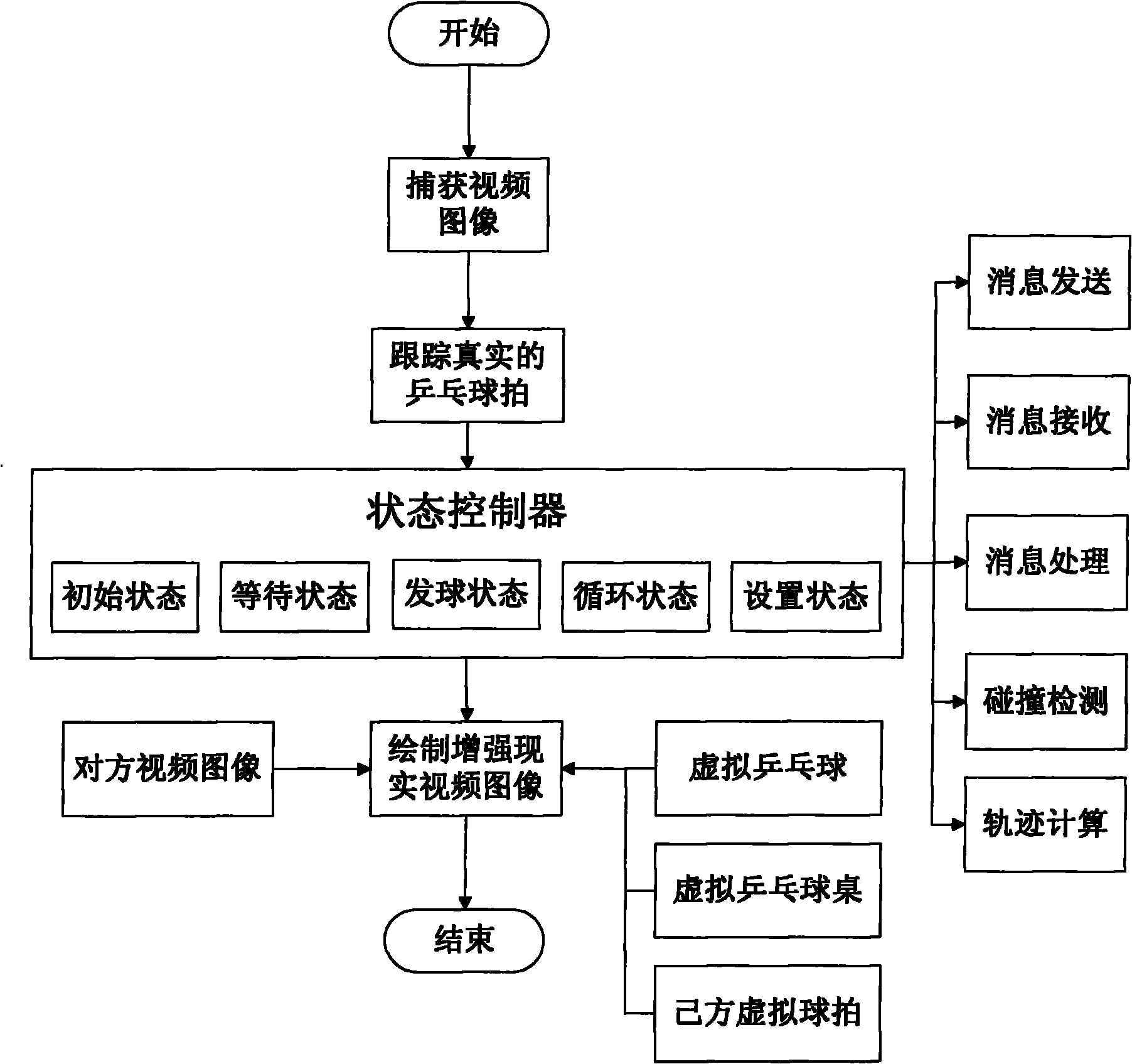
InactiveCN101893935AImprove developmentSimplify the development processInput/output for user-computer interactionTelevision systemsComputer graphics (images)Collision detection
The invention relates to a cooperative construction method for enhancing a realistic table-tennis system based on real rackets. The method comprises the following steps of: detecting and tracking a real table-tennis racket by utilizing the color characteristics according to a video image acquired by the system; designing and realizing the virtual-real three-dimensional registration of a virtual scene and a real scene, mapping the virtual scene to a video image coordinate system of the real rackets, participator users and real environment; designing and realizing the collision detection between a virtual table-tennis ball and objects, such as the real rackets, a virtual table-tennis table, a virtual table-tennis net, and the like according to the motion information of the real rackets and confirming and representing the motion trajectory of the virtual table-tennis ball after collision; and providing a finite state machine and a message-processing mechanism, controlling the conversion of various states of the table-tennis system in the operation process and ensuring a plurality of users to have the same table-tennis motion experience. The cooperative construction method can be widely applied to the fields, such as interactive digital entertainment, sports research, training simulation, remote education and training, and the like.
Owner:BEIHANG UNIV
Semantically-aware network intrusion signature generator
ActiveUS8065722B2Precision testingSolve the high false alarm rateError preventionFrequency-division multiplex detailsFinite-state machineComputer science
Owner:WISCONSIN ALUMNI RES FOUND
Scatter/gather accessing multiple cache lines in a single cache port
ActiveUS20120144089A1Memory adressing/allocation/relocationProgram controlProcessor registerParallel computing
Methods and apparatus are disclosed for accessing multiple data cache lines for scatter / gather operations. Embodiment of apparatus may comprise address generation logic to generate an address from an index of a set of indices for each of a set of corresponding mask elements having a first value. Line or bank match ordering logic matches addresses in the same cache line or different banks, and orders an access sequence to permit a group of addresses in multiple cache lines and different banks. Address selection logic directs the group of addresses to corresponding different banks in a cache to access data elements in multiple cache lines corresponding to the group of addresses in a single access cycle. A disassembly / reassembly buffer orders the data elements according to their respective bank / register positions, and a gather / scatter finite state machine changes the values of corresponding mask elements from the first value to a second value.
Owner:INTEL CORP
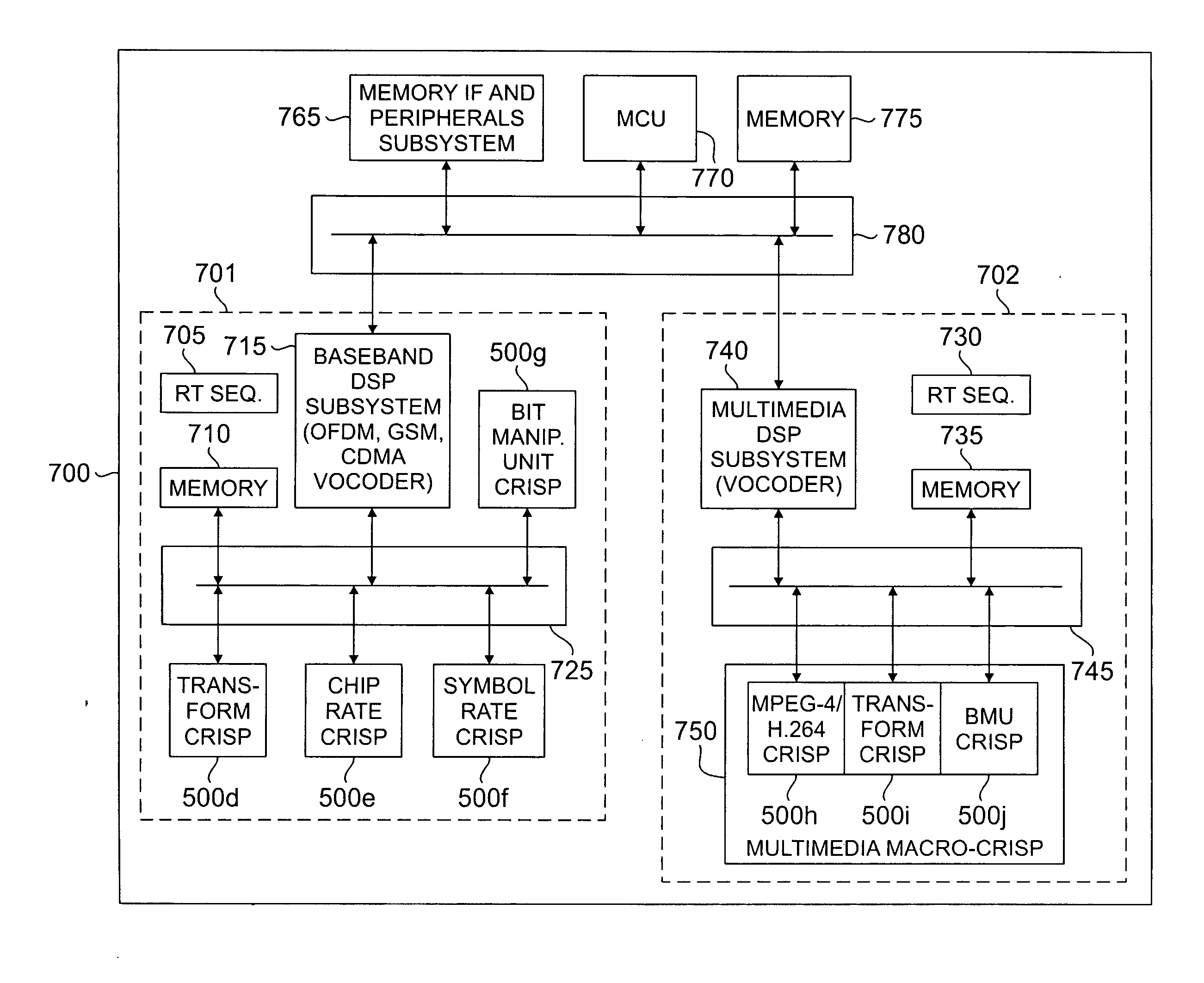
Multistandard SDR architecture using context-based operation reconfigurable instruction set processors
ActiveUS20060211387A1Energy efficient ICTGeneral purpose stored program computerComputer architectureSoftware define radio
A software-defined radio (SDR) system comprising: 1) a reconfigurable baseband subsystem for supporting a plurality of wireless communication standards comprising a first plurality of reconfigurable context-based operation instruction set processors; and 2) a reconfigurable application subsystem for supporting a plurality of end-user applications comprising a second plurality of reconfigurable context-based operation instruction set processors. Each of the first and second pluralities of reconfigurable context-based operation instruction set processors comprises: i) a reconfigurable data path comprising a plurality of reconfigurable functional blocks; and ii) a programmable finite state machine that controls the reconfigurable data path, wherein the programmable finite state machine is capable of executing a plurality of instructions associated with a particular function.
Owner:SAMSUNG ELECTRONICS CO LTD
Framework for flexible and scalable real-time traffic emulation for packet switched networks
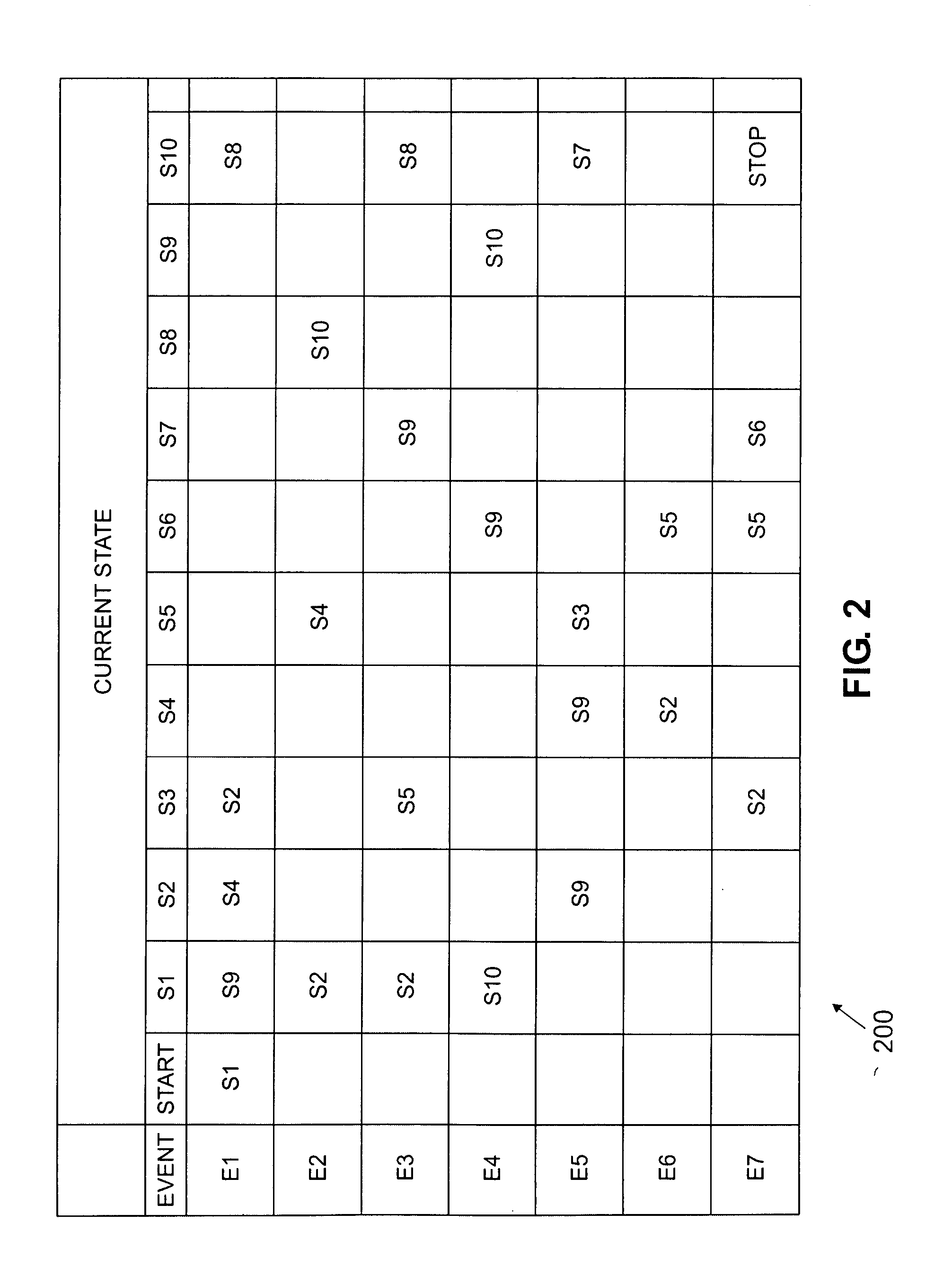
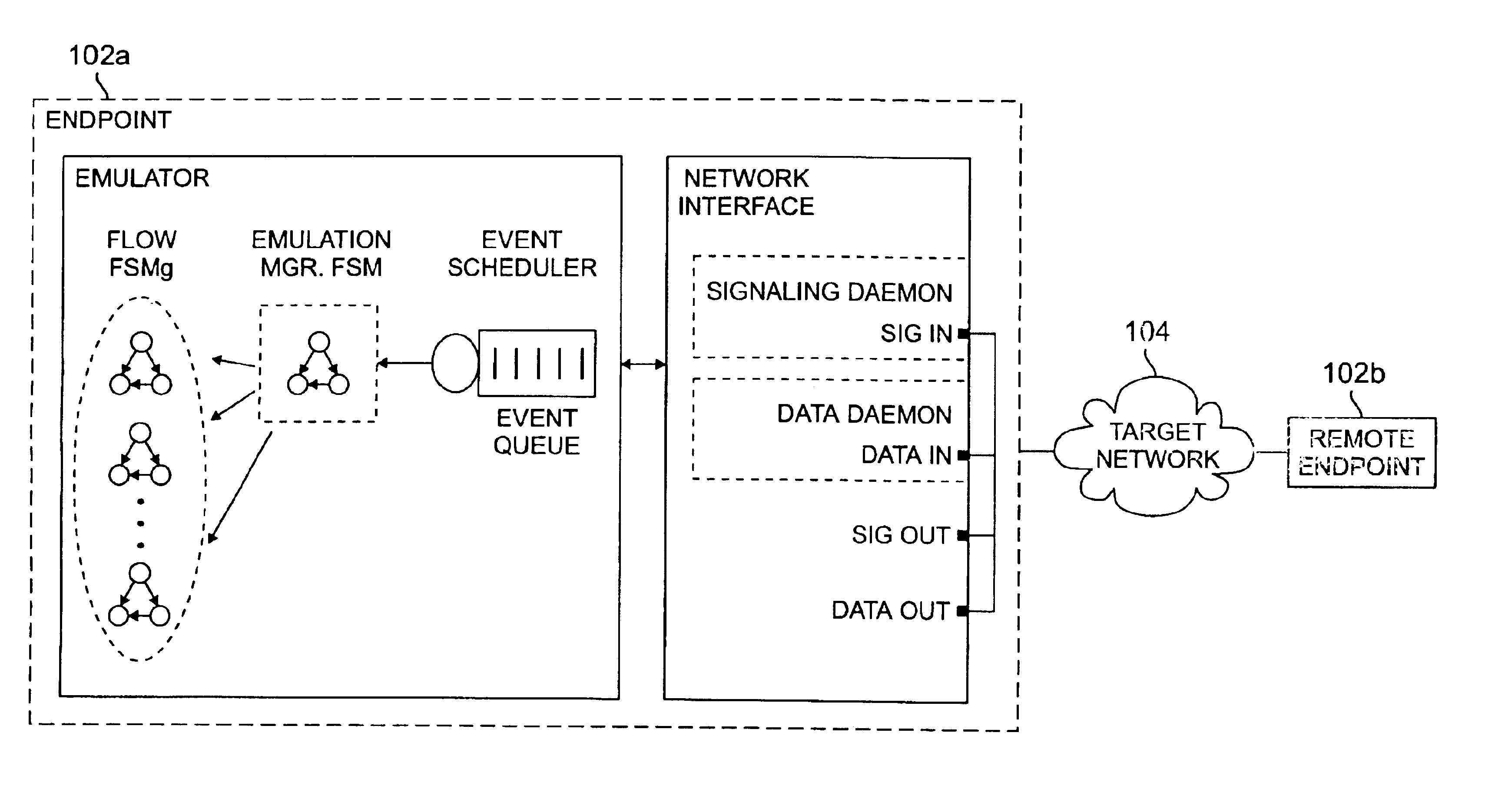
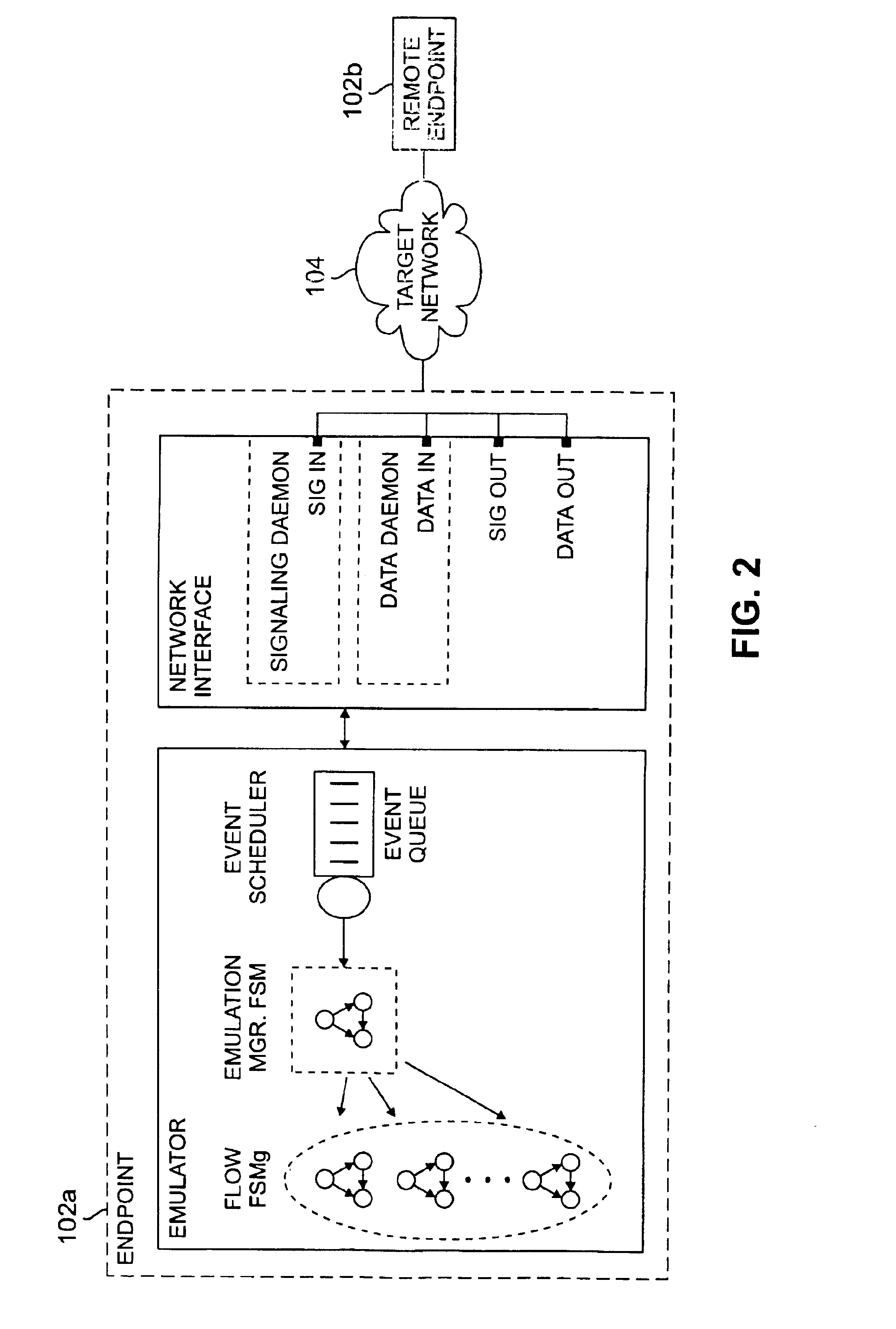
An implementation framework, including methodologies and the architecture, for a real-time traffic emulation for packet switched networks. The framework uses extended finite state machines to model the traffic flows that are to be emulated. A simple yet flexible FMS-based scripting language is proposed to describe these flows. An event-driven approach to schedule CPU among flows is also adopted.
Owner:LUCENT TECH INC +1
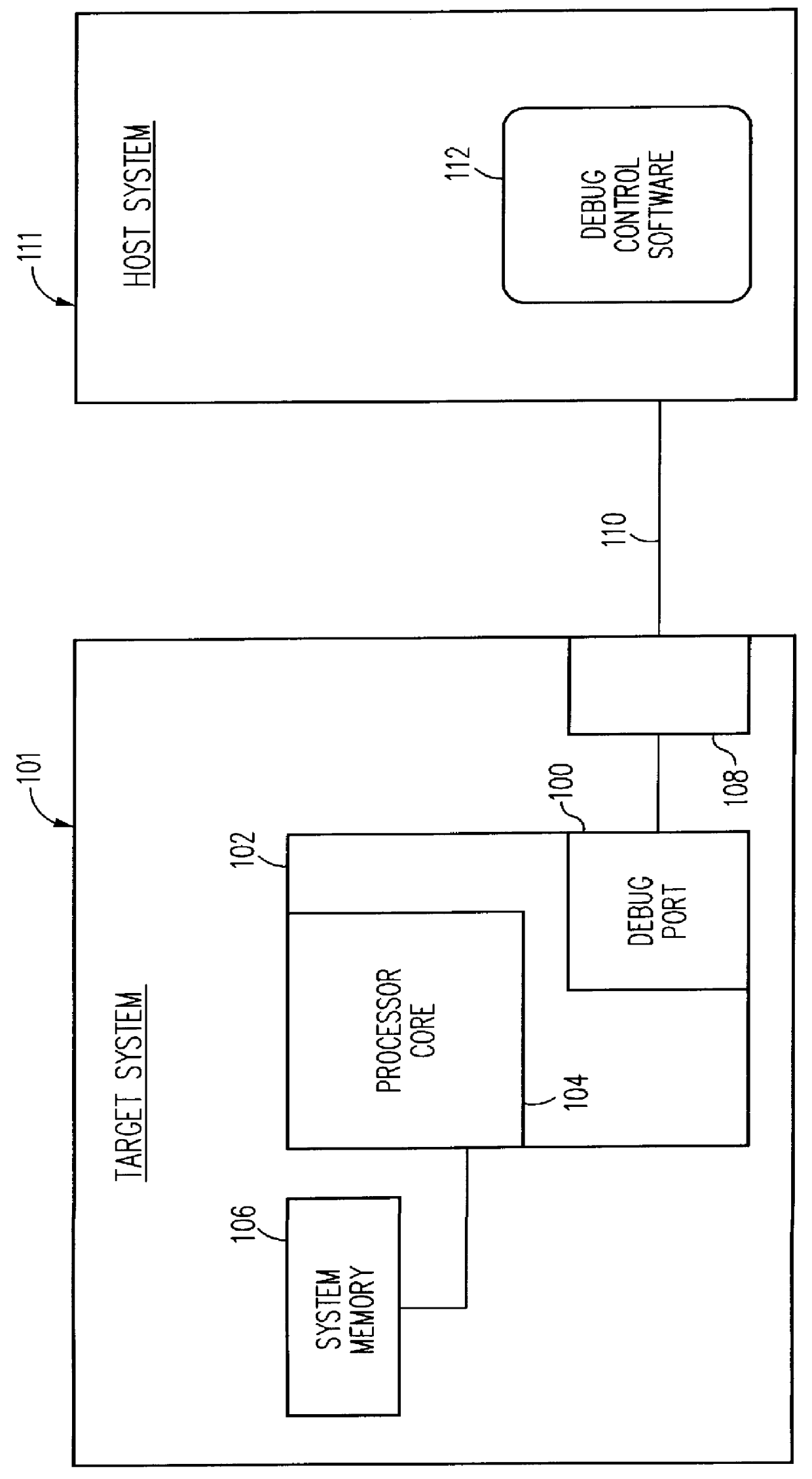
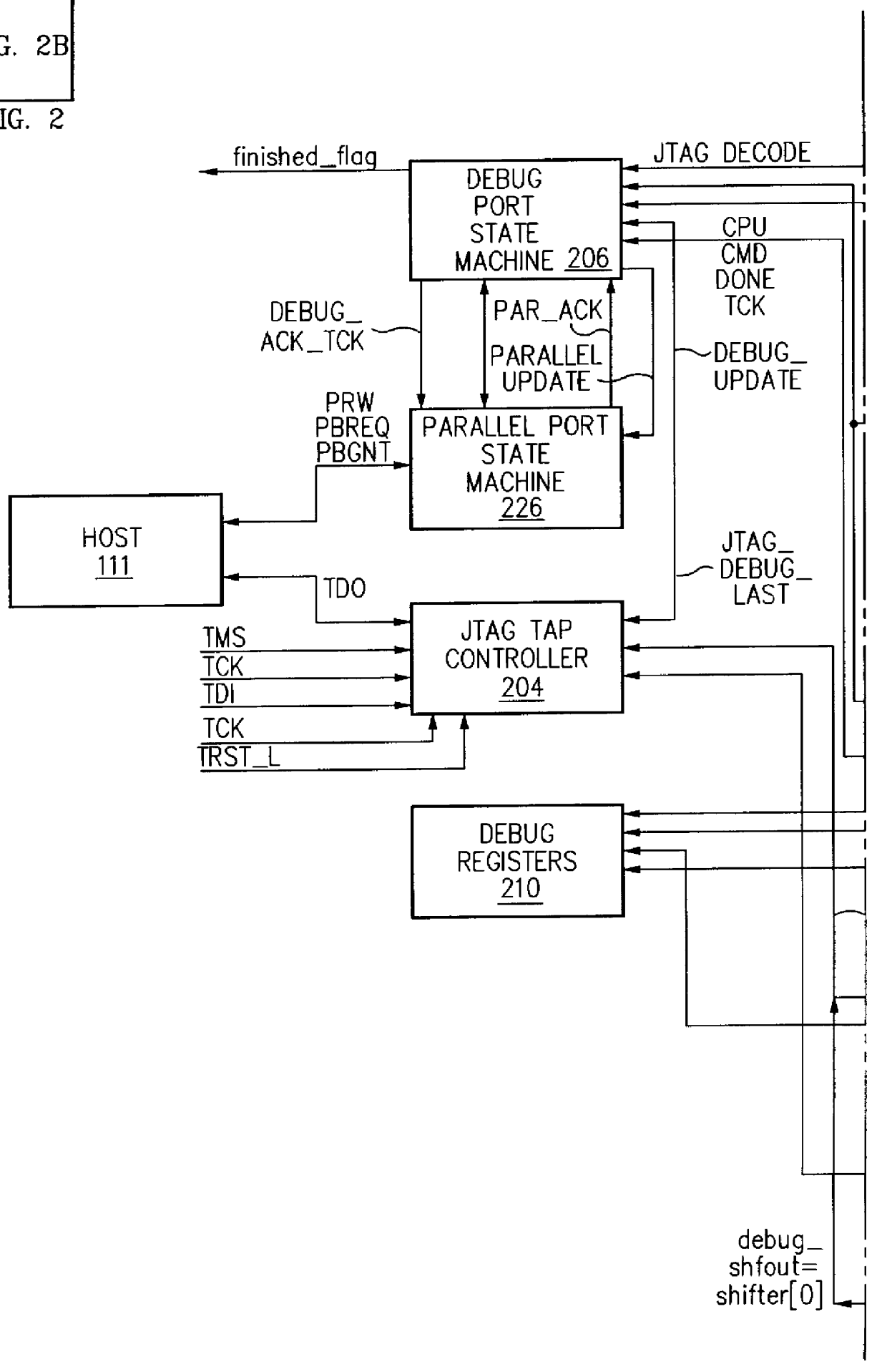
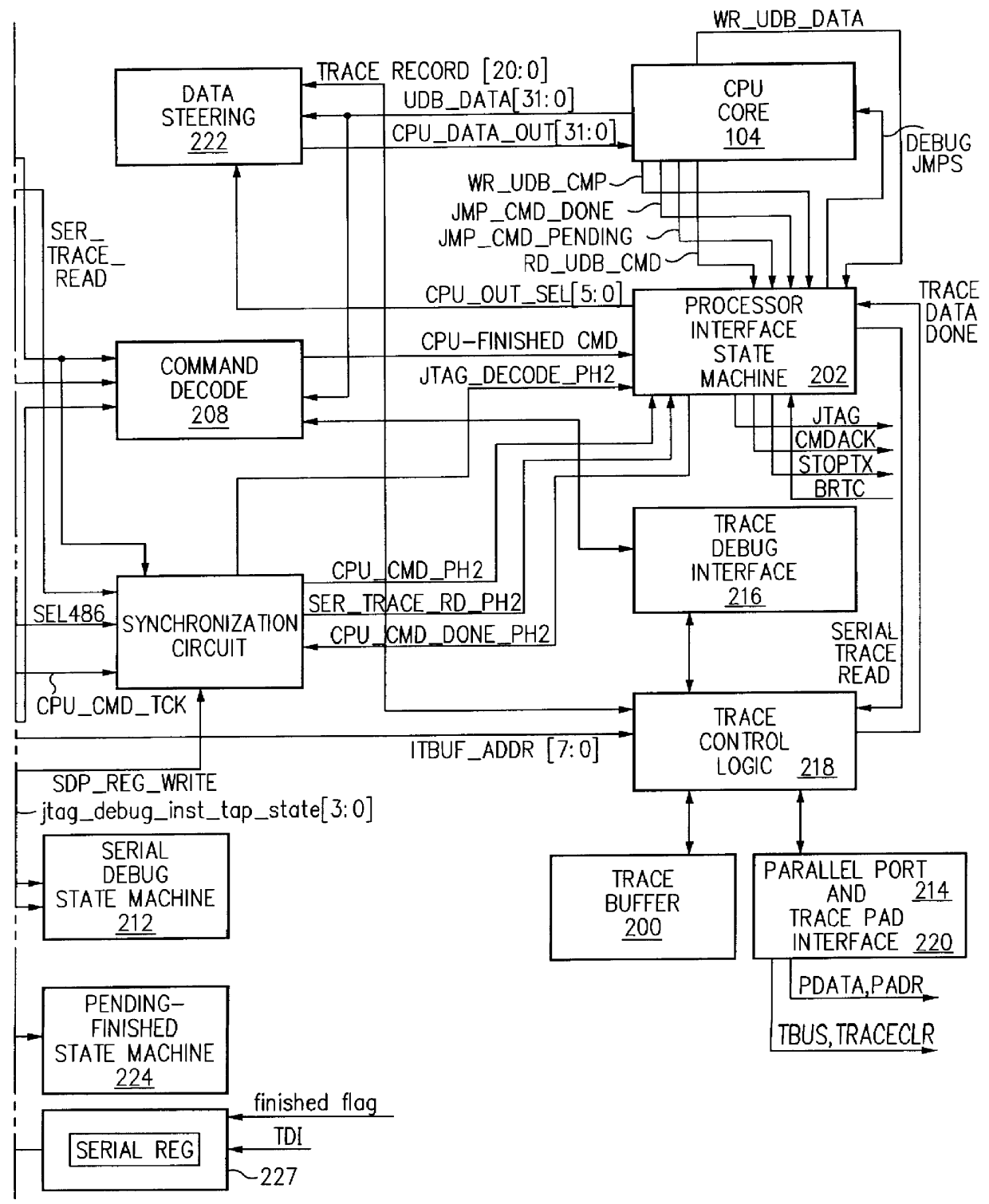
Debug interface including state machines for timing synchronization and communication
A system for debugging a processor includes logic circuits for communicating commands and data between a serial input / output port, a trace logic, and the processor. Some embodiments of the debugging system also include a parallel input / output port so that the logic circuits also communicate commands and data between the parallel input / output port, the trace logic, and the processor. The debug system includes a plurality of state machines that read the commands and data from the serial input / output ports. The commands are decoded by a decode logic. Some of the commands, such as commands for reading data from memory, utilize processor intervention and are transferred to the processor for execution. The state machines operate only on a single command at one time so that an active state machine does not accept additional commands until completion of the command that is currently executed. Once execution of the command is complete, the state machines generate an indication of the completion event or condition, typically by setting a flag in a debug register or by asserting a readable output pin. The completion event or condition is accessed by a debug tool such as a host processor, a monitoring tool, or the like.
Owner:ADVANCED MICRO DEVICES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com