Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1805results about How to "Fast execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
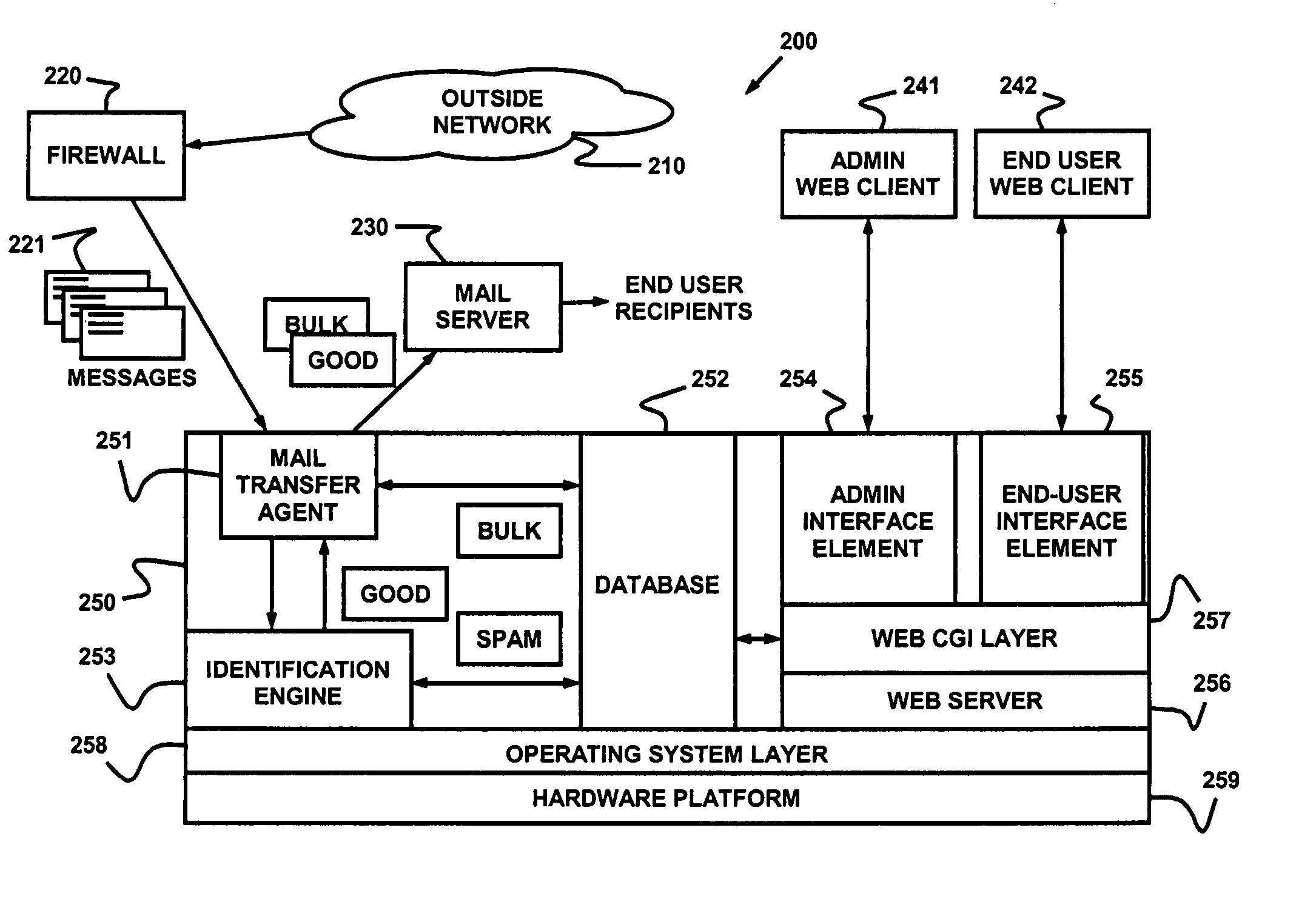
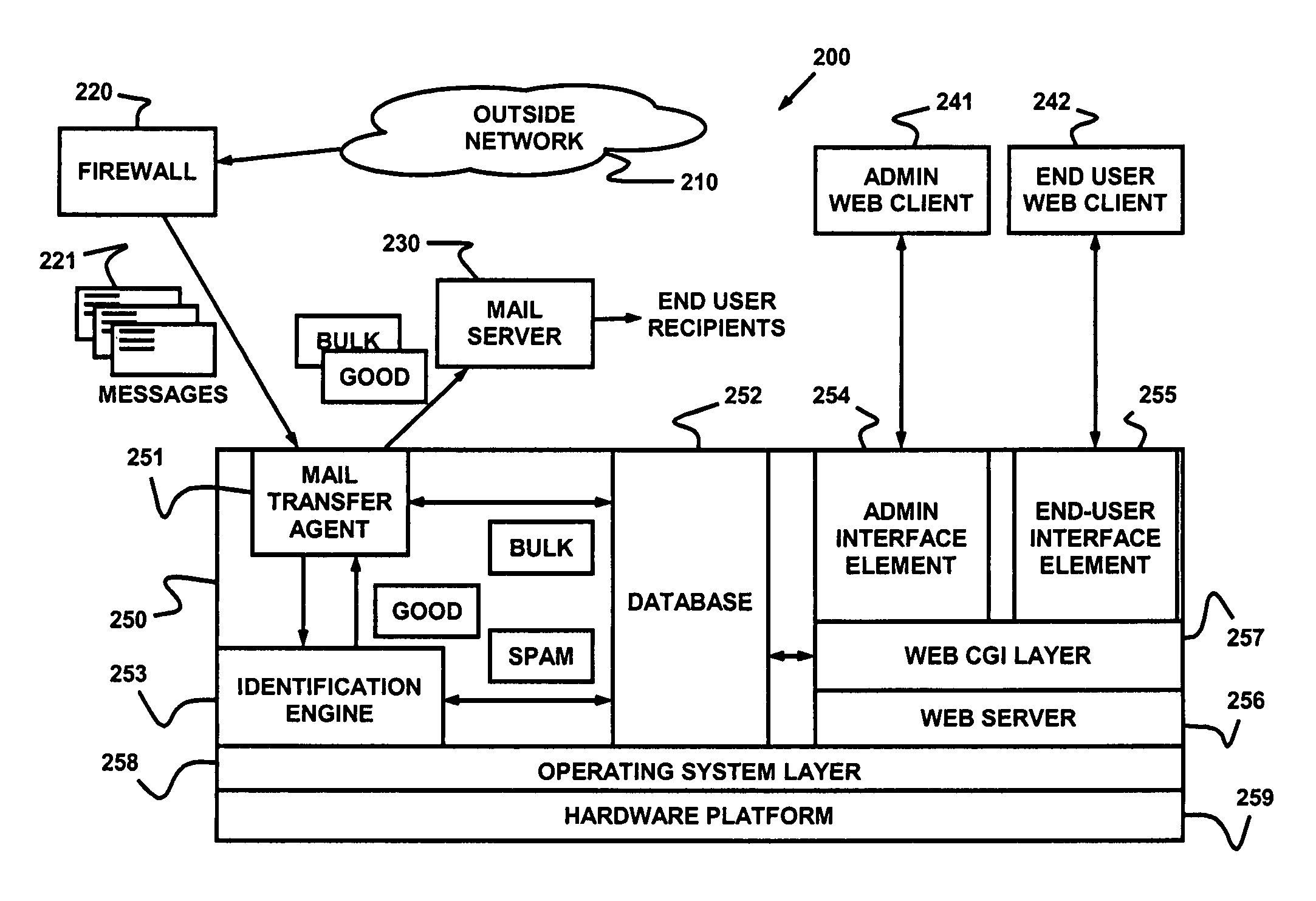
Dynamic message filtering
ActiveUS20050076084A1Reduce in quantityMake fastError detection/correctionGenetic modelsSpammingWhitelist
Dynamically filtering and classifying messages, as good messages, bulk periodicals, or spam. A regular expression recognizer, and pre-trained neural networks. The neural networks distinguish “likely good” from “likely spam,” and also operate at a more discriminating level to distinguish among the three categories above. A dynamic whitelist and blacklist; sending addresses are collected when the number of their messages indicates the sender is good or a spammer. A dynamically selected set of regular expressions input to the neural networks.
Owner:MAILGATE LLC
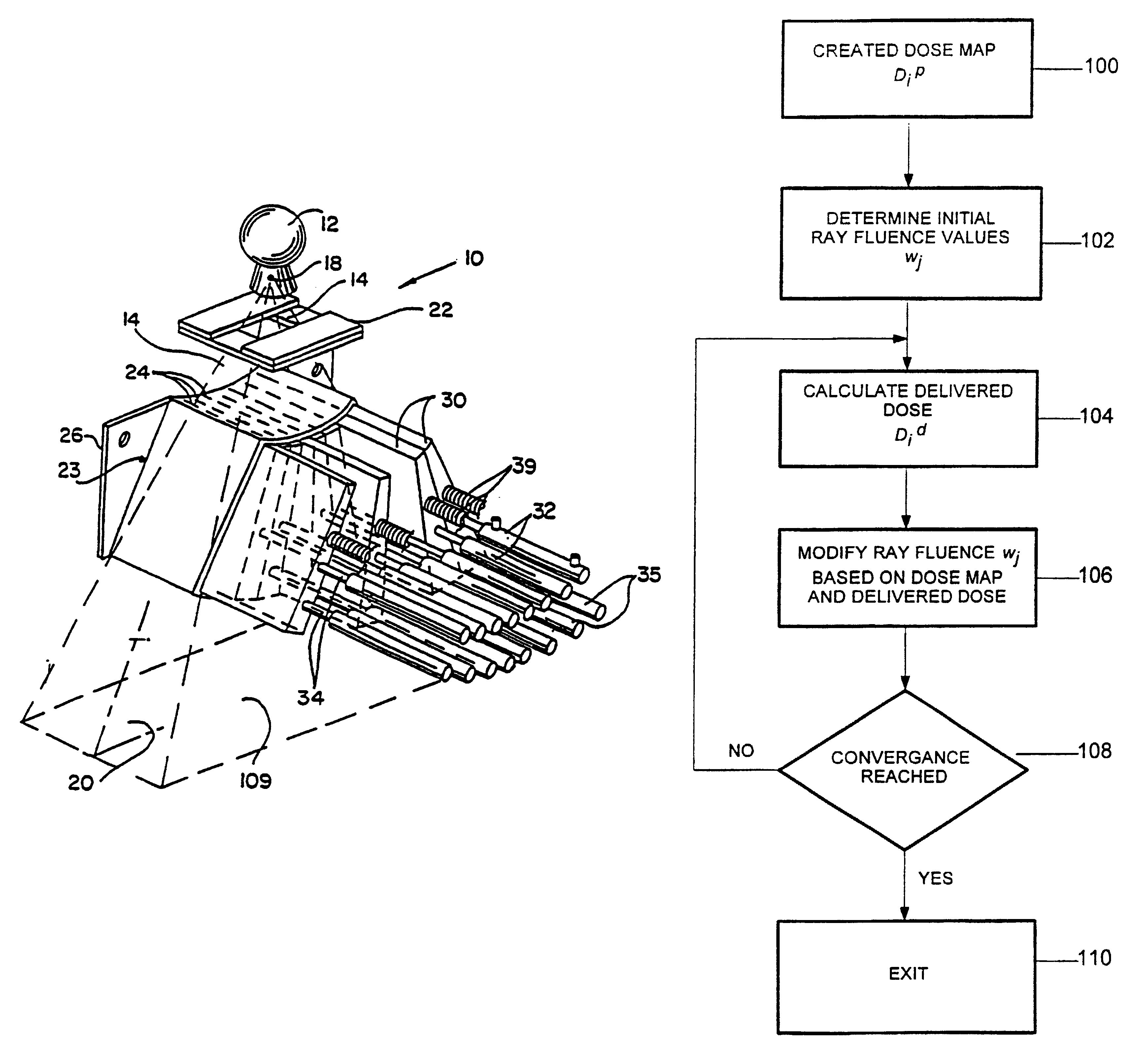
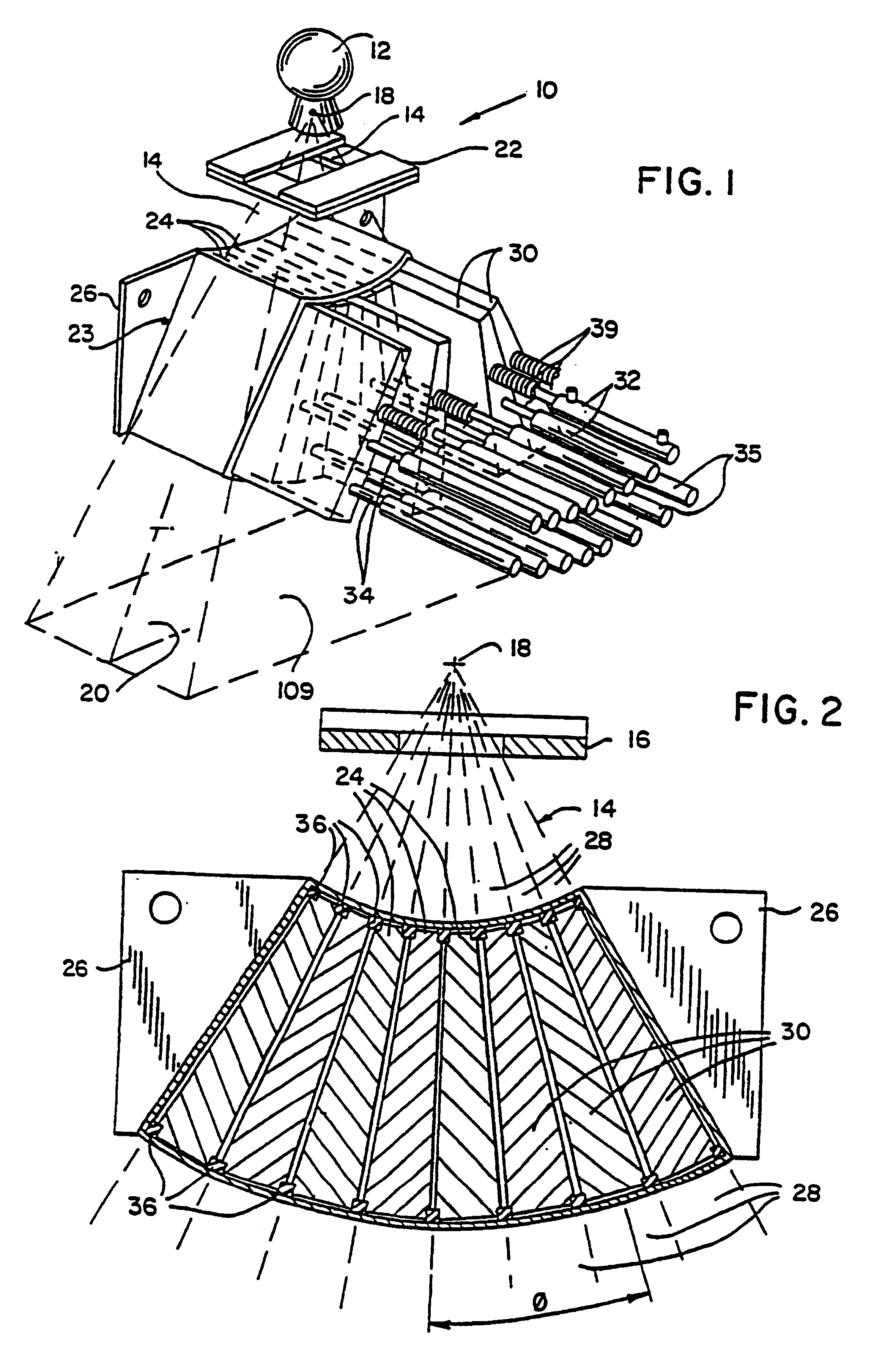
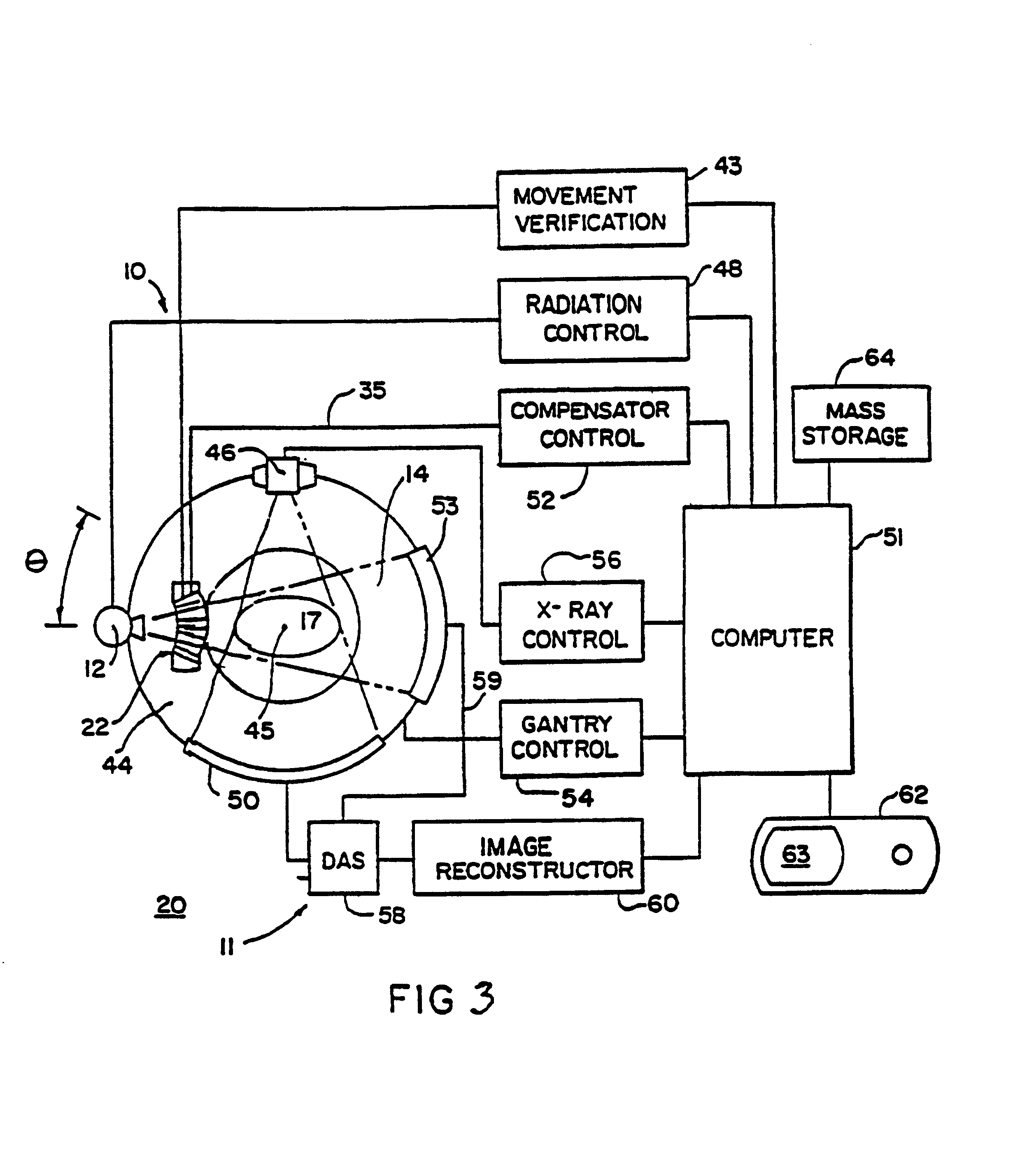
Method for preparing a radiation therapy plan
InactiveUS6560311B1Simple calculationFast executionMechanical/radiation/invasive therapiesComputer-assisted treatment prescription/deliveryDose profileIndividual dose
A method for determining a radiation treatment plan for a radiotherapy system providing multiple individual rays of intensity modulated radiation iteratively optimized the fluence of an initial set of such rays by a function that requires knowledge of only the prescribed dose and the dose resulting from the particular ray fluences. In this way, the need to store individual dose distributions of each ray are eliminated.
Owner:WISCONSIN ALUMNI RES FOUND
Mobile device for executing multiple applications and method for same
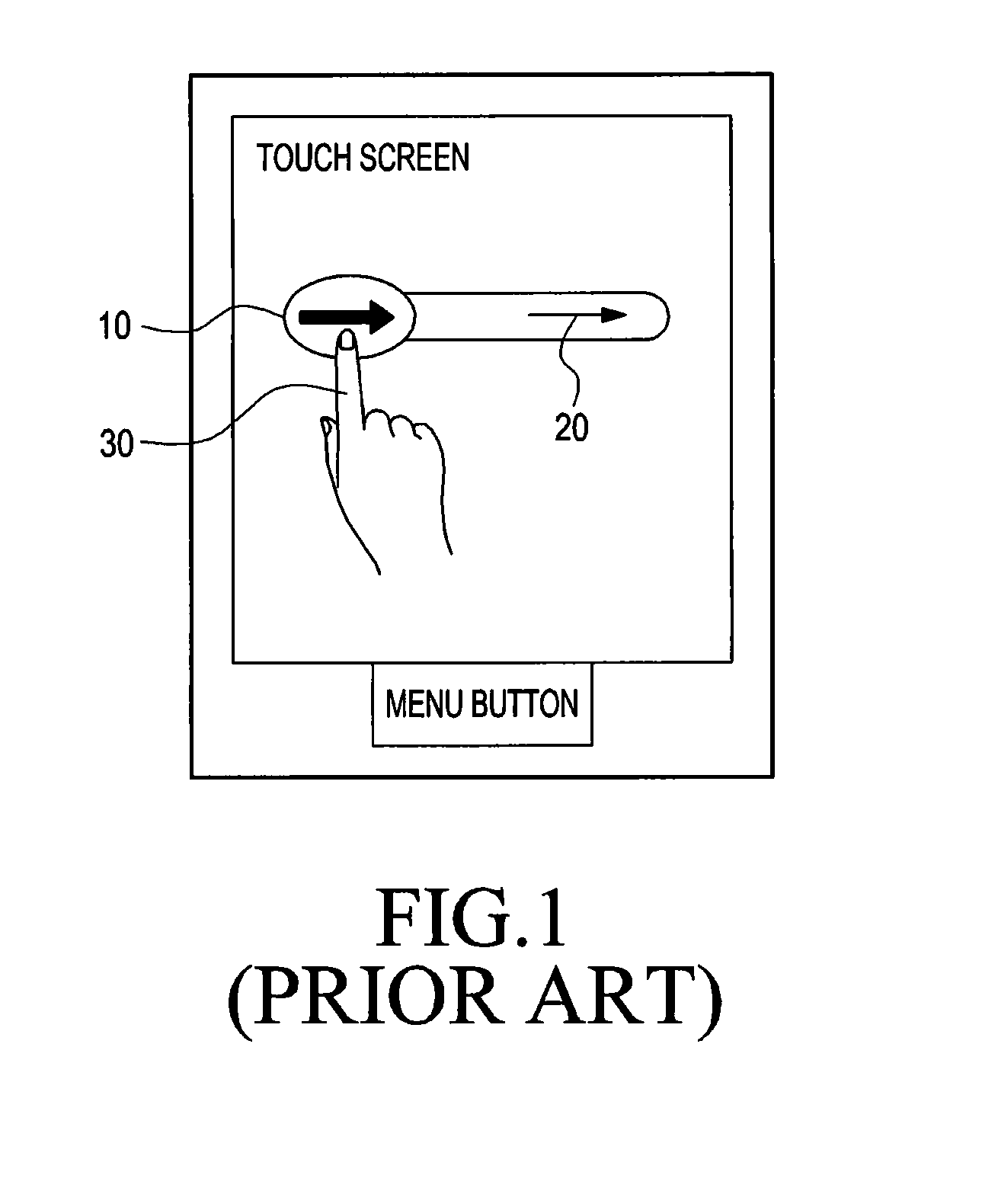
ActiveUS20130120295A1Quick displayReduce screen sizeInput/output for user-computer interactionCathode-ray tube indicatorsComputer hardwareTouchscreen
A mobile device for executing multiple applications is provided. The mobile device includes a touch screen for displaying a first window where a first application is executed, a second window where a second application different from the first application is executed, and a controller for displaying an execution keys for executing the multiple applications, determining whether a simultaneous execution input for the first application and the second application is input or not, and if the simultaneous execution input is input then displaying the first application on the first window and the second application on the second window.
Owner:SAMSUNG ELECTRONICS CO LTD
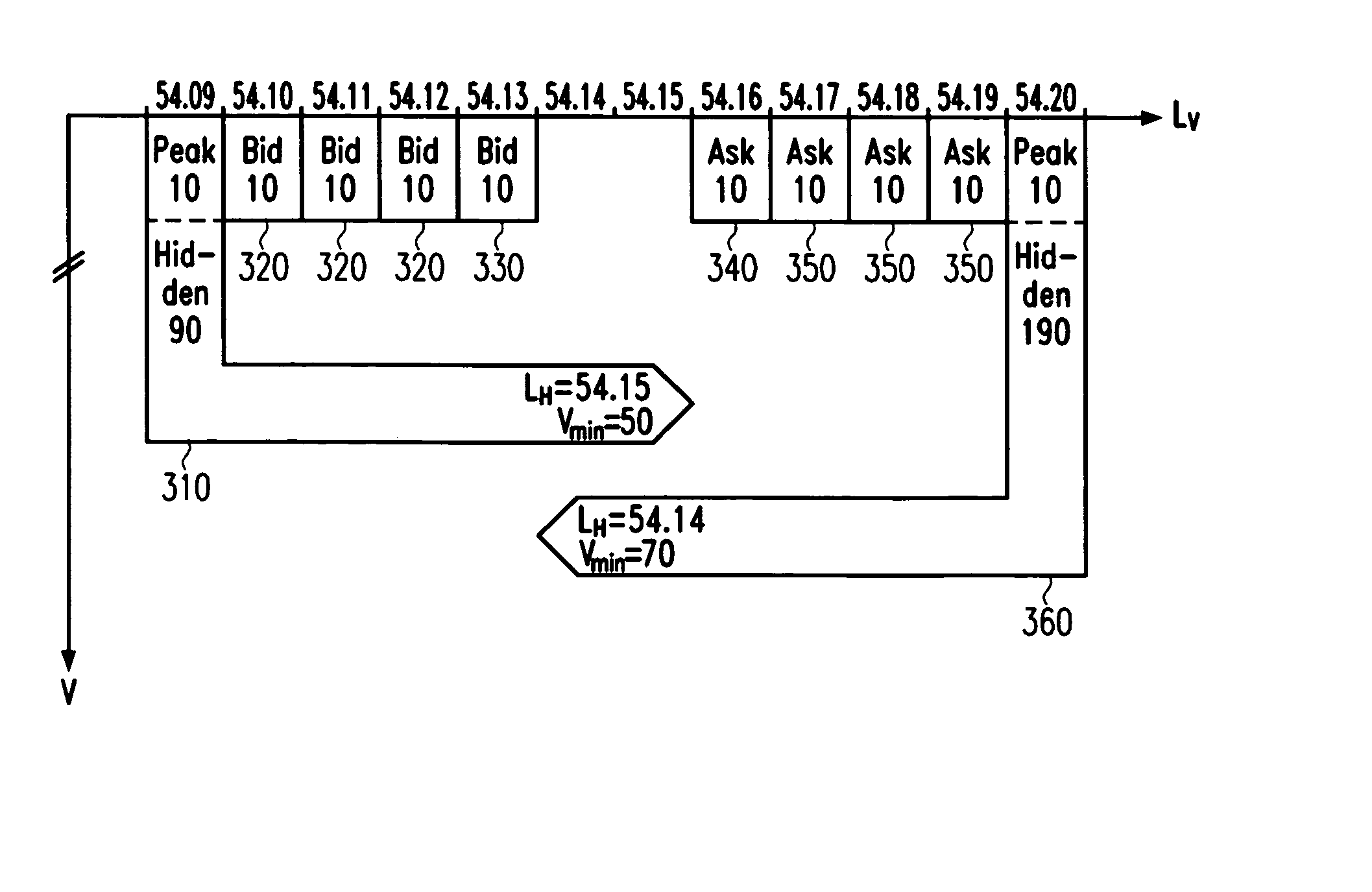
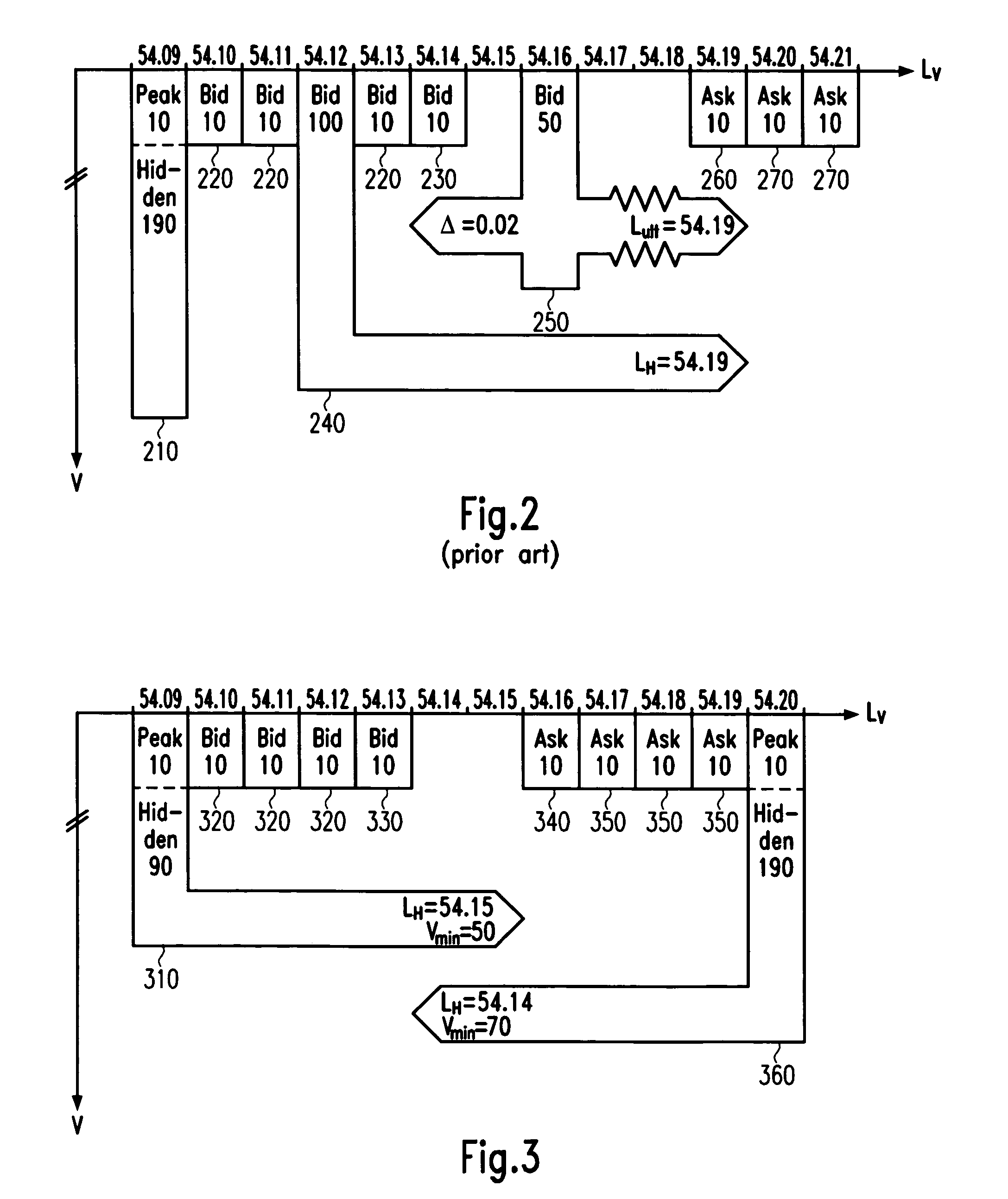
Integrated order matching system combining visible and hidden parameters
The invention provides back-end functionality for order processing in electronic order book trading. A sell / buy order is received comprising a lower / upper limit and a conditional lower / upper limit defining a conditional selling / buying price range for executing the sell / buy order under certain selling / buying conditions. A buy / sell order is received comprising an upper / lower limit, visible buy / sell volume parameter and hidden buy / sell volume parameter specifying a first part disclosed to all customers and a second part not disclosed to all customers, respectively, of the buy / sell order volume. It is determined whether the selling / buying conditions are fulfilled, including determining whether the sum of the first and second part of the buy / sell order is superior or equal to a threshold volume. The sell / buy order and the buy / sell order are executed against each other if at least the selling / buying conditions are fulfilled. Embodiments allow rapidly executing large trading interests with minimized market impact and opportunity costs.
Owner:DEUT BORSE
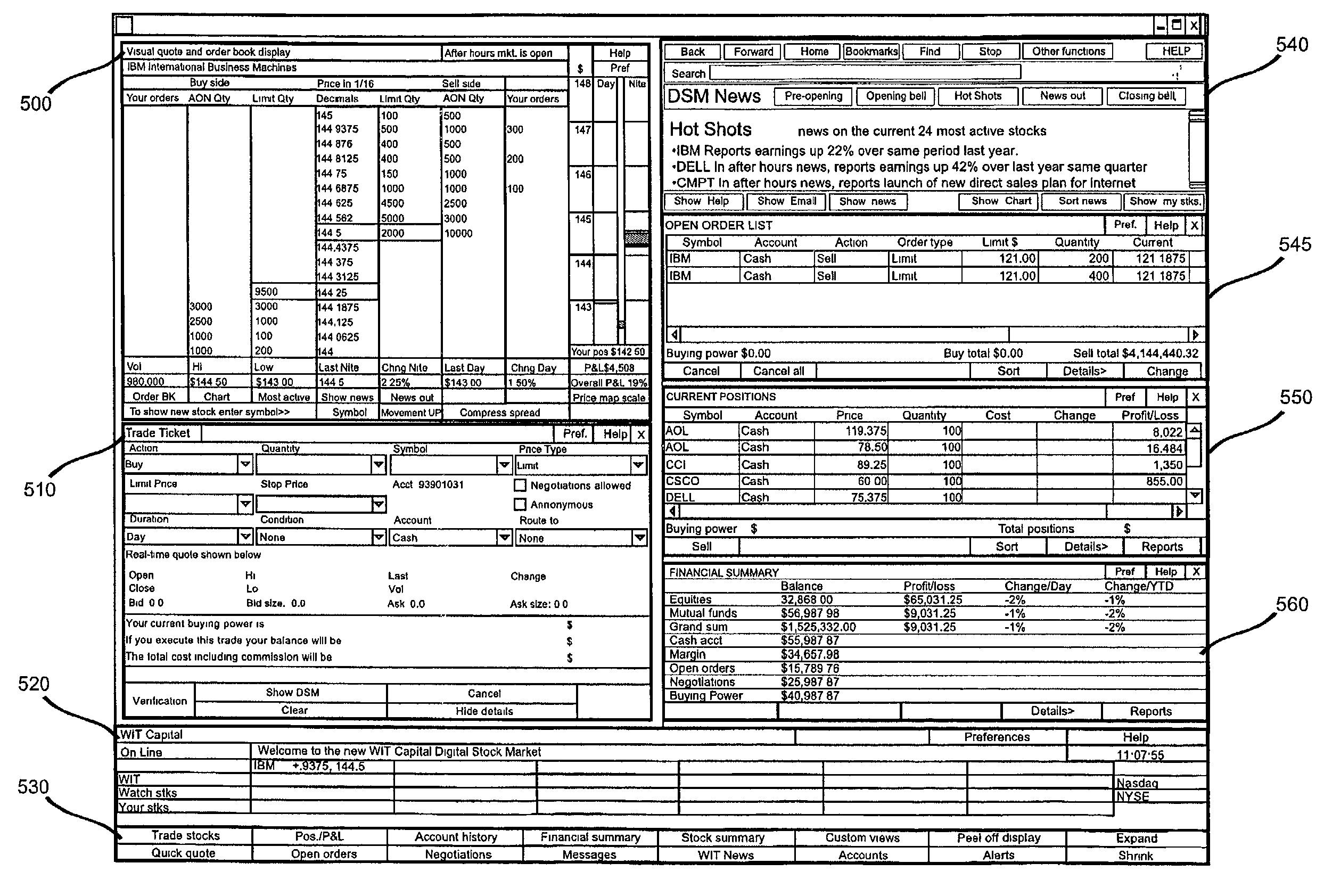
Computer trading system method and interface
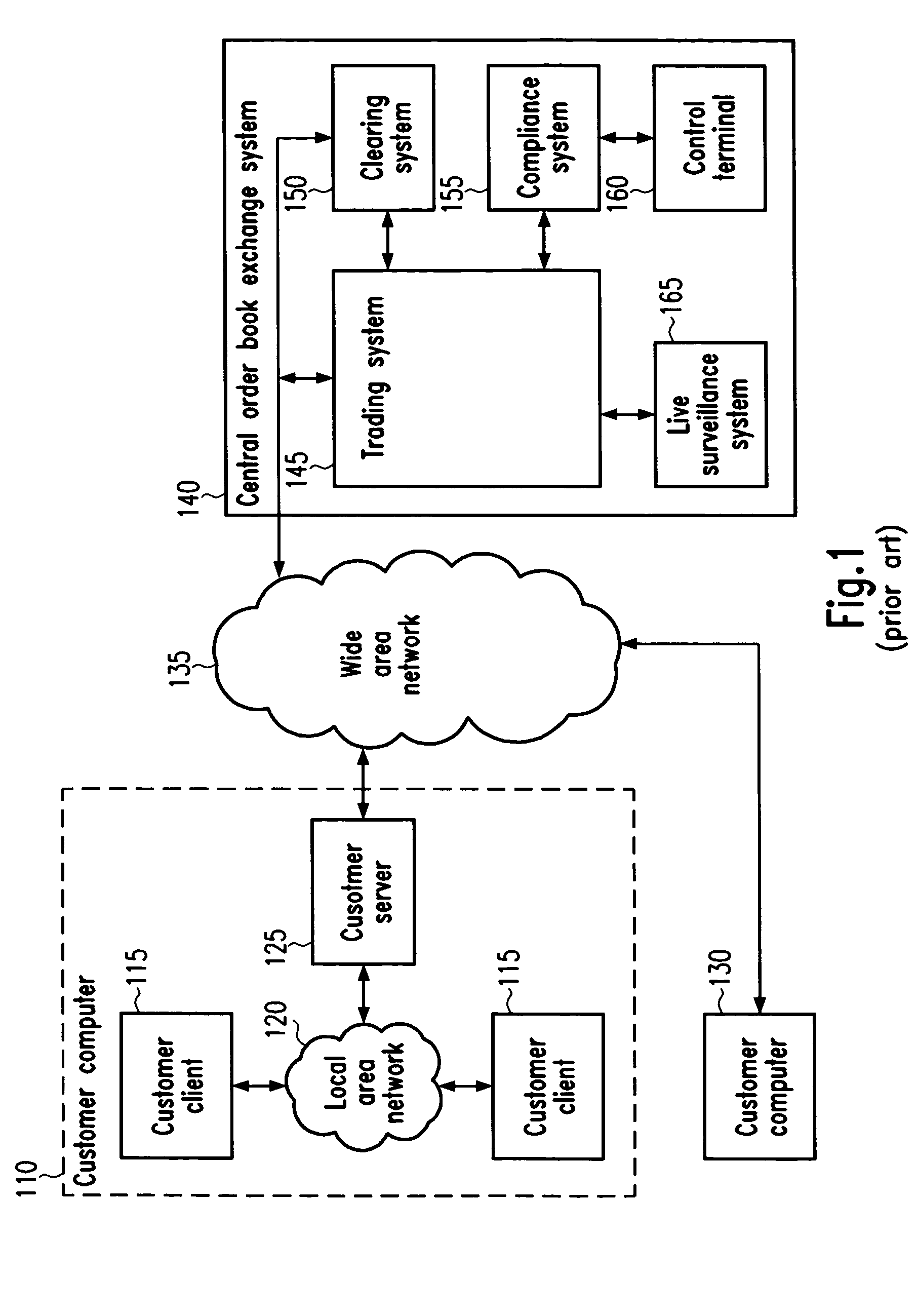
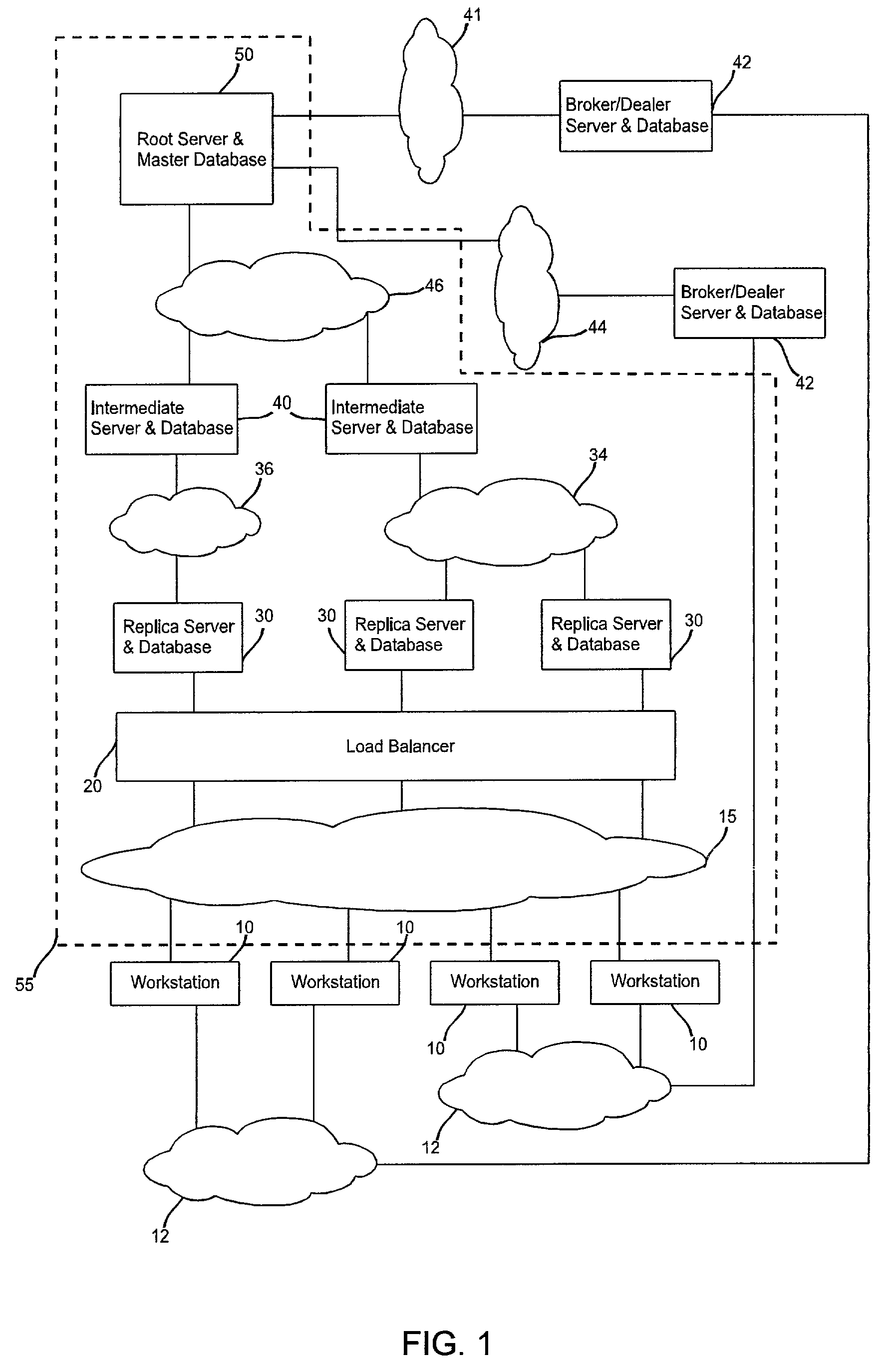
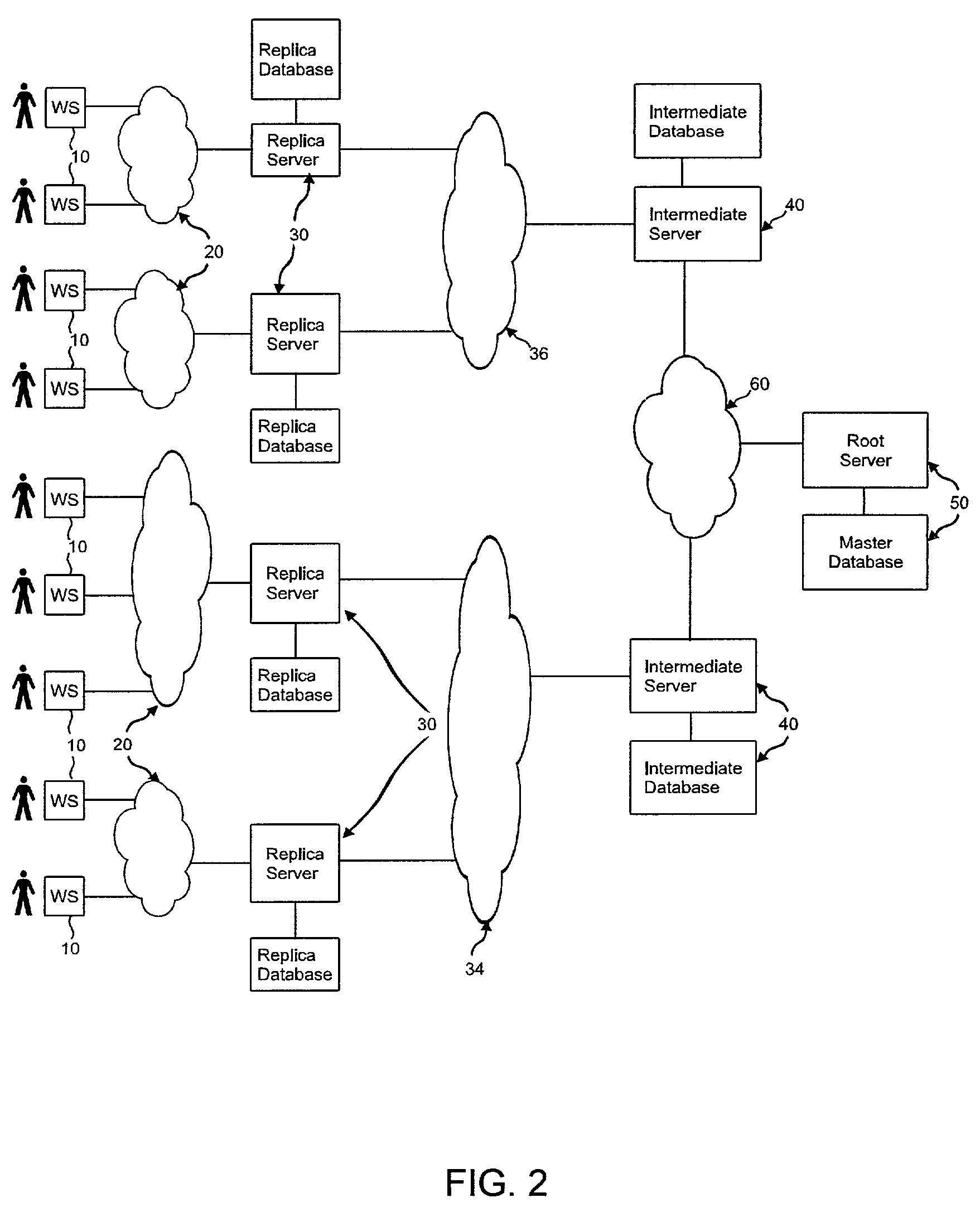
The system and method of the preferred embodiment supports trading of securities over the Internet both on national exchanges and outside the national exchanges. The preferred embodiment supports an improved human interface and a continuous display of real-time stock quotes on the user's computer screen. The ergonomic graphical user interface (GUI) of the preferred embodiment includes several functional benefits in comparison with existing on-line consumer trading systems. In the preferred embodiment, the users are subscribers to a securities trading service offered over the Internet. Preferably, each subscriber to this service is simultaneously connected from his own computer to a first system which provides user-to-user trading capabilities and to a second system which is a broker / dealer system of his / her choice. The system providing the user-to-user trading services preferably includes a root server and a hierarchical network of replicated servers supporting replicated databases. The user-to-user system provides real-time continuously updated stock information and facilitates user-to-user trades that have been approved by the broker / dealer systems with which it interacts. Users of the preferred system can trade securities with other users of the system. As part of this user-to-user trading, a user can accept a buy or sell offer at the terms offered or he can initiate a counteroffer and negotiate a trade.
Owner:UBS BUSINESS SOLUTIONS AG
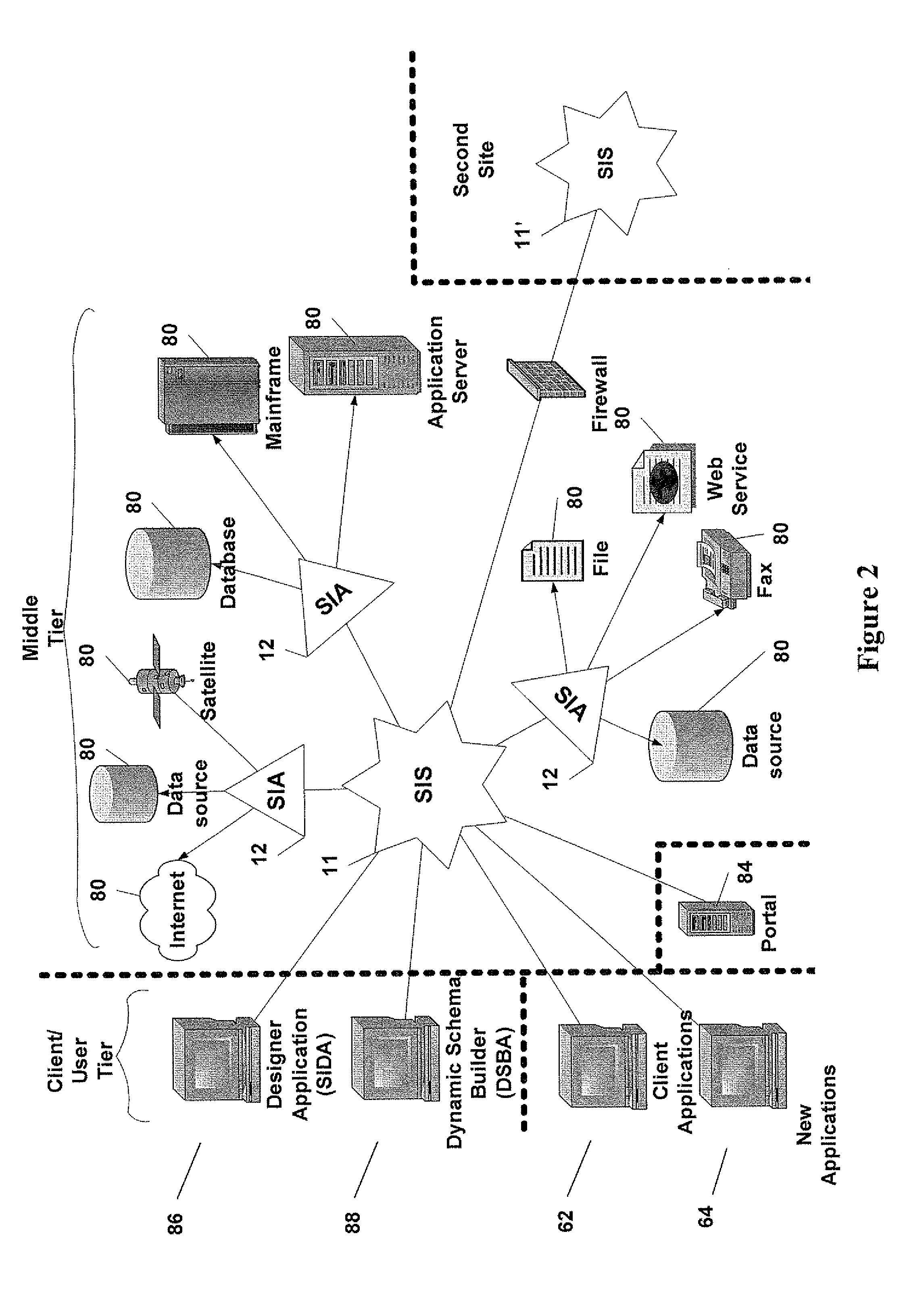
Smart Integration Engine And Metadata-Oriented Architecture For Automatic EII And Business Integration
InactiveUS20080082569A1Fast executionFull flexibilityOffice automationSpecial data processing applicationsData accessData source
The present invention discloses systems and methods for automating the EII, using a smart integration engine based on metadata. On-line execution (i.e. data access, retrieval, or update) is automated by integrating heterogeneous data sources via a centralized smart engine based on metadata of all data sources managed in a metadata repository. The data-source assets are mapped to business metadata (terminology) giving programmers the ability to use business terms, and overcome technical terms. IT departments can use the business-level terms for easy and fast programming of all services “at the business level”. The integration is performed by the engine (via pre-configuration) automatically, dynamically, and on-line, regardless of topology or technology changes, without user or administrator intervention. MDOA is a high-level concept in which the metadata maps the technical low-level terms to business high-level terms. MDOA is used for seamless integration of a fully-distributed organization with many data sources and technologies.
Owner:BIZWHEEL
Random number generator for electronic applications
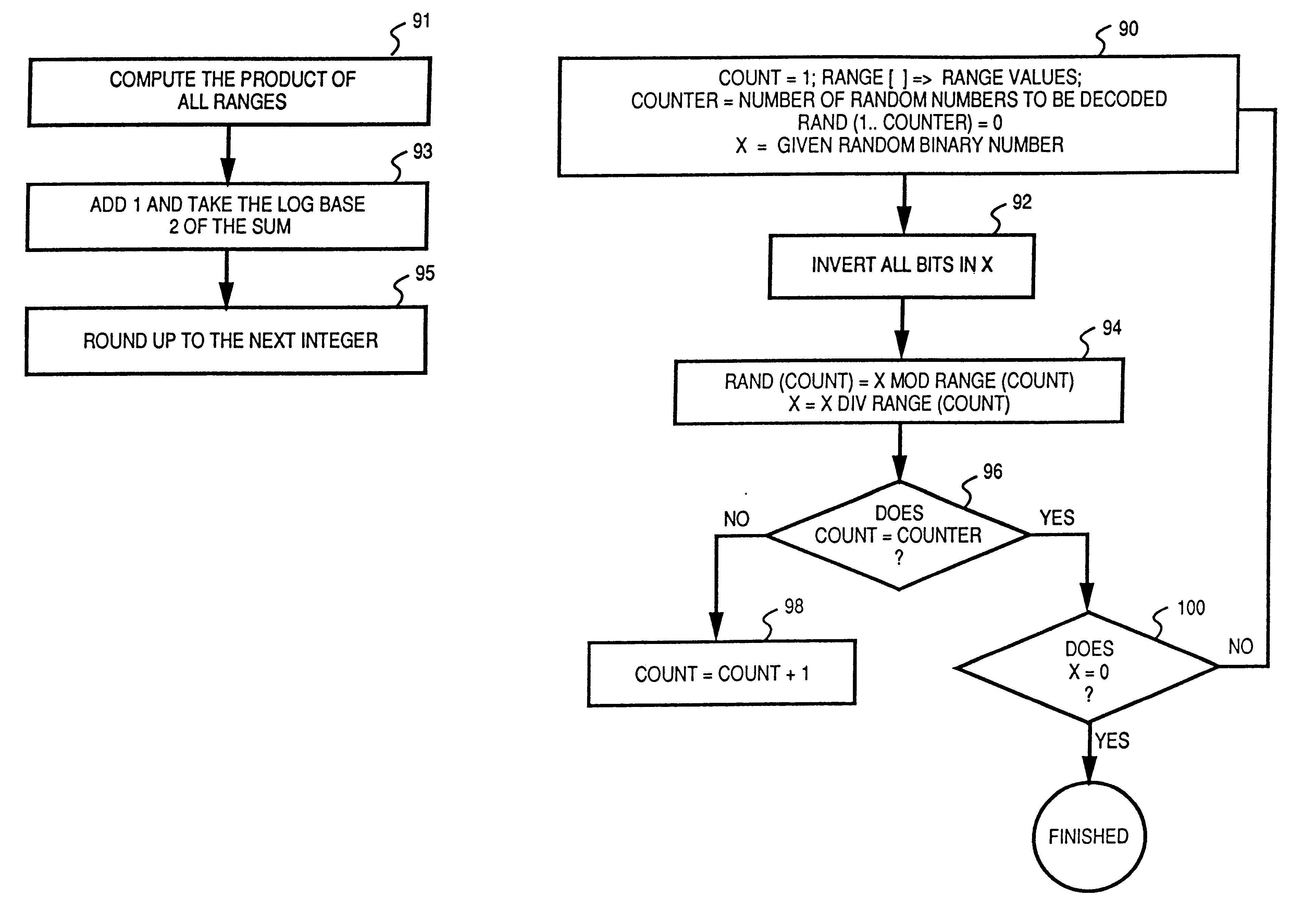
InactiveUS6193607B1Fast executionLottery apparatusRandom number generatorsGeneration processNumber generator
A method and apparatus for generating random numbers for use in electronic applications is disclosed. A given sequence of random binary numbers of a certain length can be decoded into several random numbers for a specific application. The upper range values of the random numbers to be decoded determine the number of bits required for the generation of the these random numbers. In the decoding process, the given random binary number divides a range value to generate a remainder and a quotient. The quotient becomes the new random binary number for the generation of other random numbers while the remainder is the generated random number. The process then repeats to generate other random numbers. At the end of the generation process, the last quotient determines the validity of the generated random numbers.
Owner:IGT
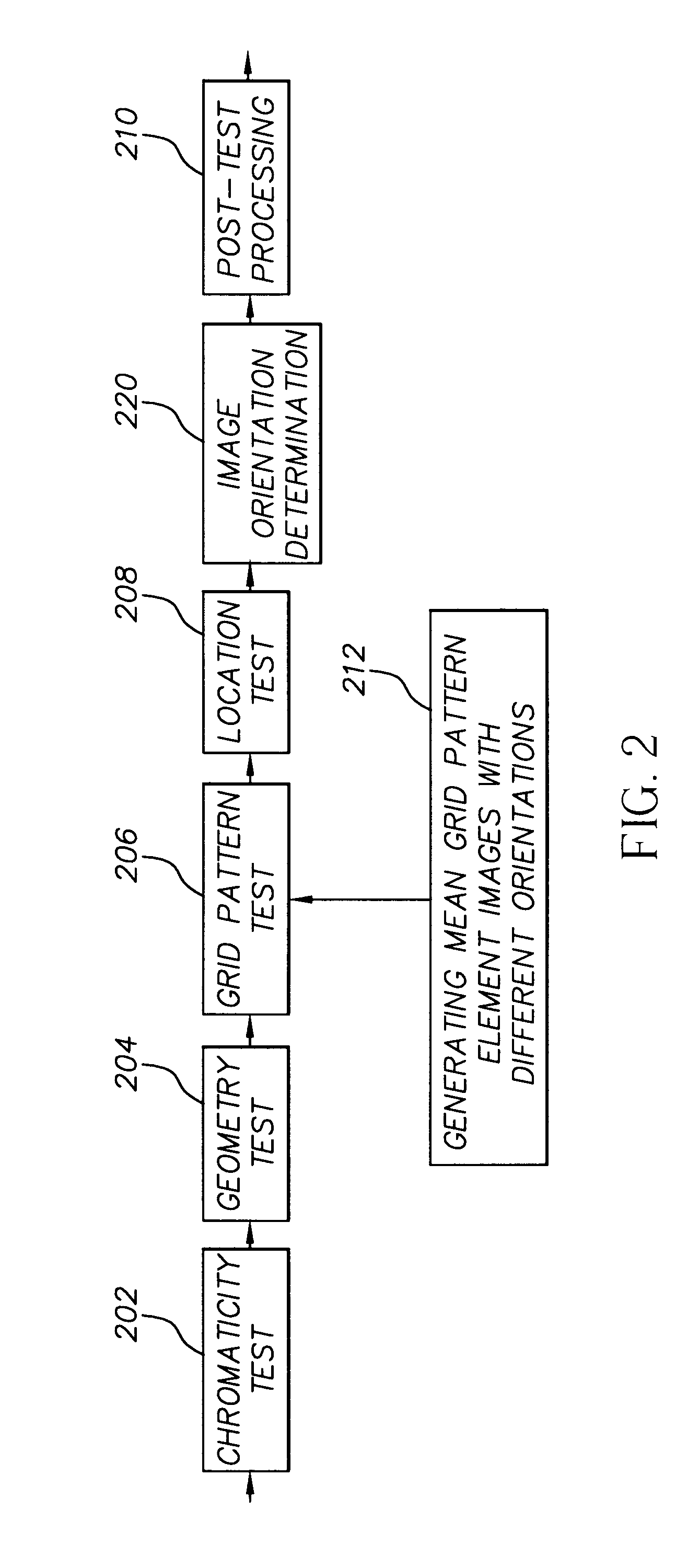
Method for face orientation determination in digital color images
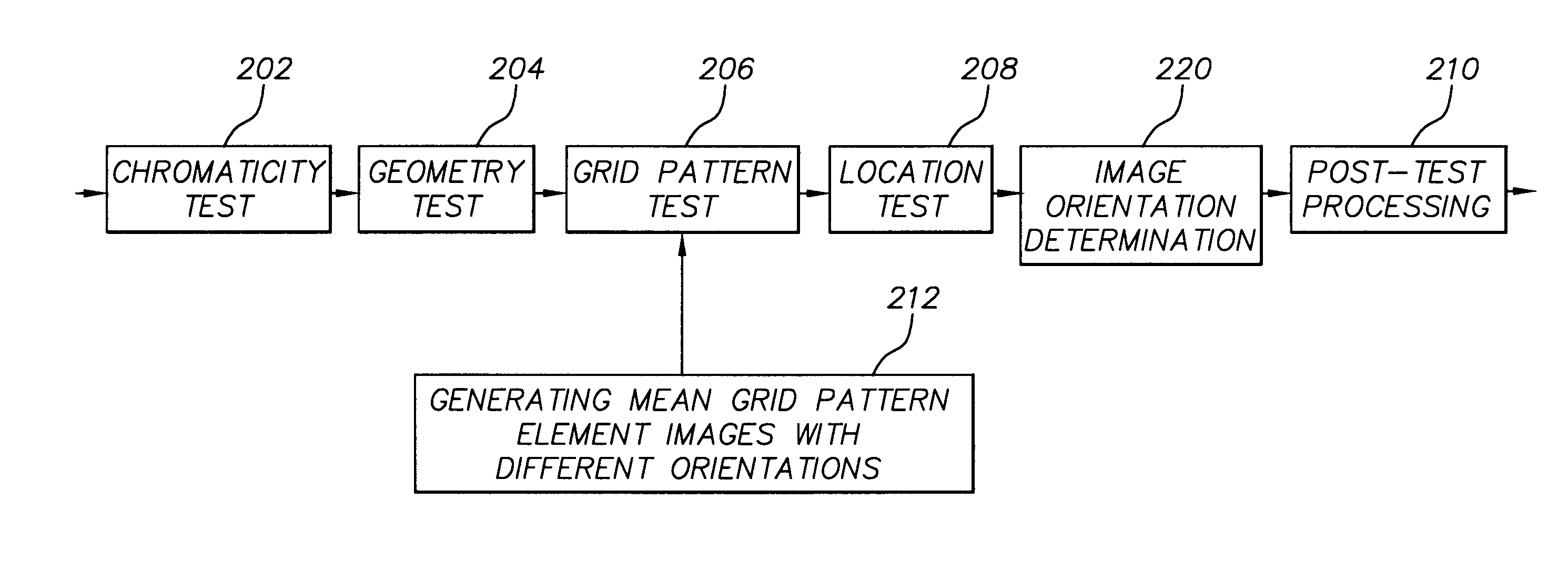
InactiveUS7120279B2Fast executionLittle memory spaceCharacter and pattern recognitionColor imageGrid pattern
A digital image processing method for determining an orientation of a face in a digital color image generates a mean grid pattern element image from a plurality of sample face images and an integral image from the digital color image. A face is located in the color digital image by using the integral image to perform a correlation test between the mean grid pattern element image and the digital color image at a plurality of effective resolutions by reducing the digital color image to a plurality of grid pattern element images at different effective resolutions and correlating the mean grid pattern element image with the plurality of grid pattern element images, whereby either the mean grid pattern element image or the grid pattern element images are provided at a plurality of different orientations. Accordingly, an orientation of the face in the color digital image is determined by using the images with different orientations in the correlation test.
Owner:MONUMENT PEAK VENTURES LLC
Network modeling system and method of simulating network operation with configurable node models
ActiveUS7765093B2Shorten speedFast executionAnalogue computers for electric apparatusDigital computer detailsGranularityModeling and simulation
Owner:HARRIS GLOBAL COMM INC
Method and system for virtual prototyping
ActiveUS7613599B2Reduce simulation overheadFast executionElectronic circuit testingError detection/correctionHuman–machine interfaceComputer architecture
An integrated design environment (IDE) is disclosed for forming virtual embedded systems. The IDE includes a design language for forming finite state machine models of hardware components that are coupled to simulators of processor cores, preferably instruction set accurate simulators. A software debugger interface permits a software application to be loaded and executed on the virtual embedded system. A virtual test bench may be coupled to the simulation to serve as a human-machine interface. In one embodiment, the IDE is provided as a web-based service for the evaluation, development and procurement phases of an embedded system project. IP components, such as processor cores, may be evaluated using a virtual embedded system. In one embodiment, a virtual embedded system is used as an executable specification for the procurement of a good or service related to an embedded system.
Owner:SYNOPSYS INC
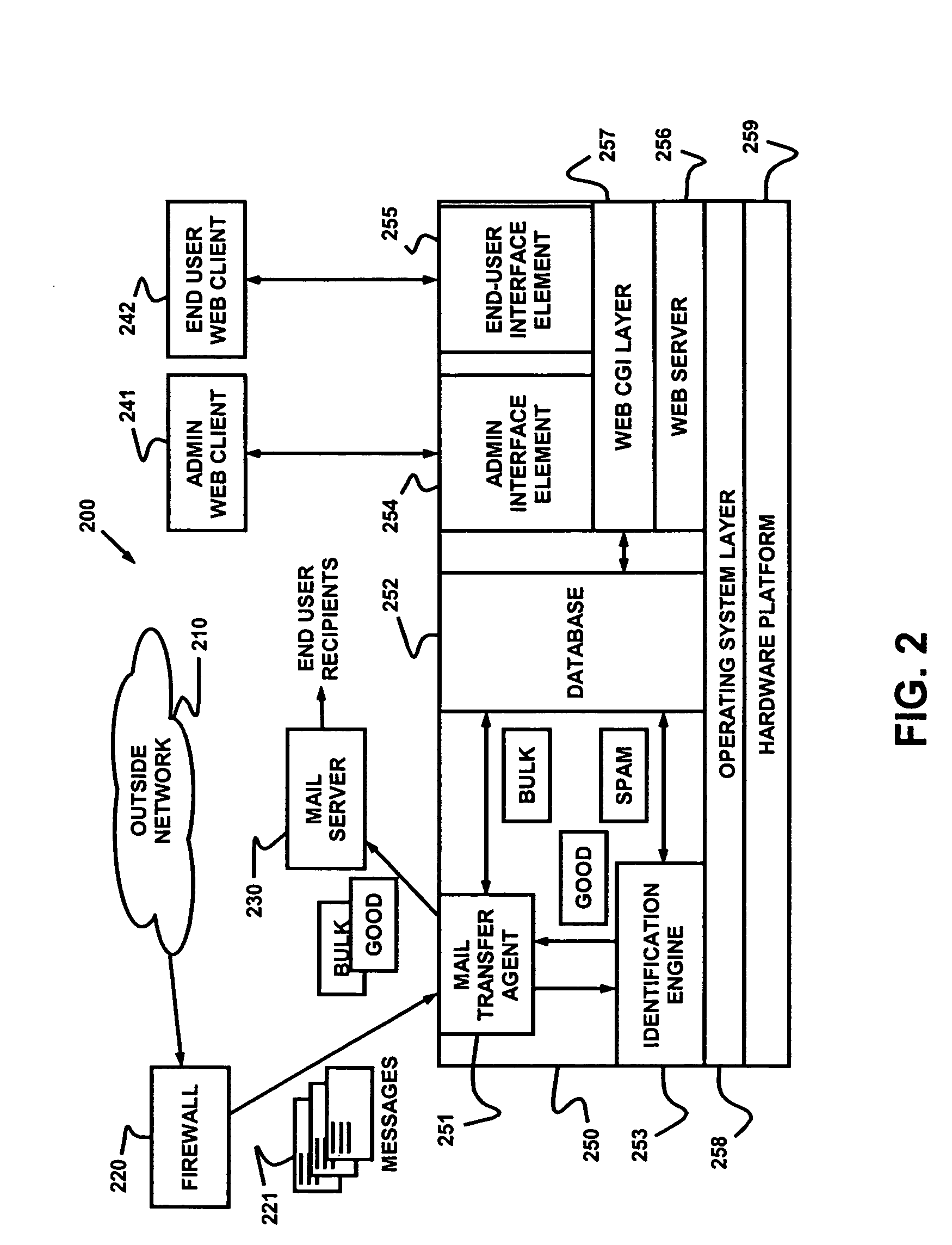
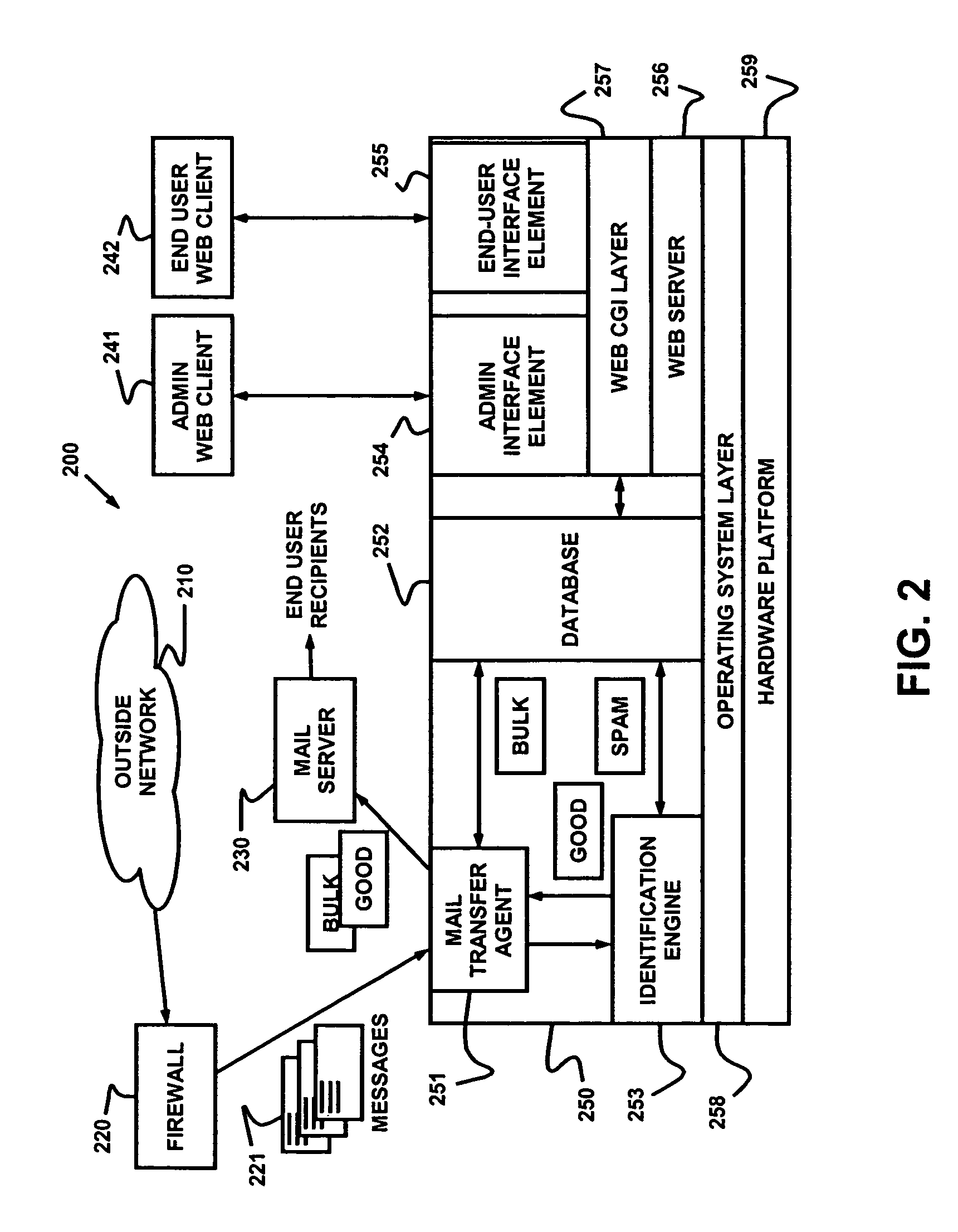
Dynamic message filtering
ActiveUS7257564B2Reduce in quantityMake fastError detection/correctionGenetic modelsWhitelistData mining
Dynamically filtering and classifying messages, as good messages, bulk periodicals, or spam. A regular expression recognizer, and pre-trained neural networks. The neural networks distinguish “likely good” from “likely spam,” and also operate at a more discriminating level to distinguish among the three categories above. A dynamic whitelist and blacklist; sending addresses are collected when the number of their messages indicates the sender is good or a spammer. A dynamically selected set of regular expressions input to the neural networks.
Owner:MAILGATE LLC
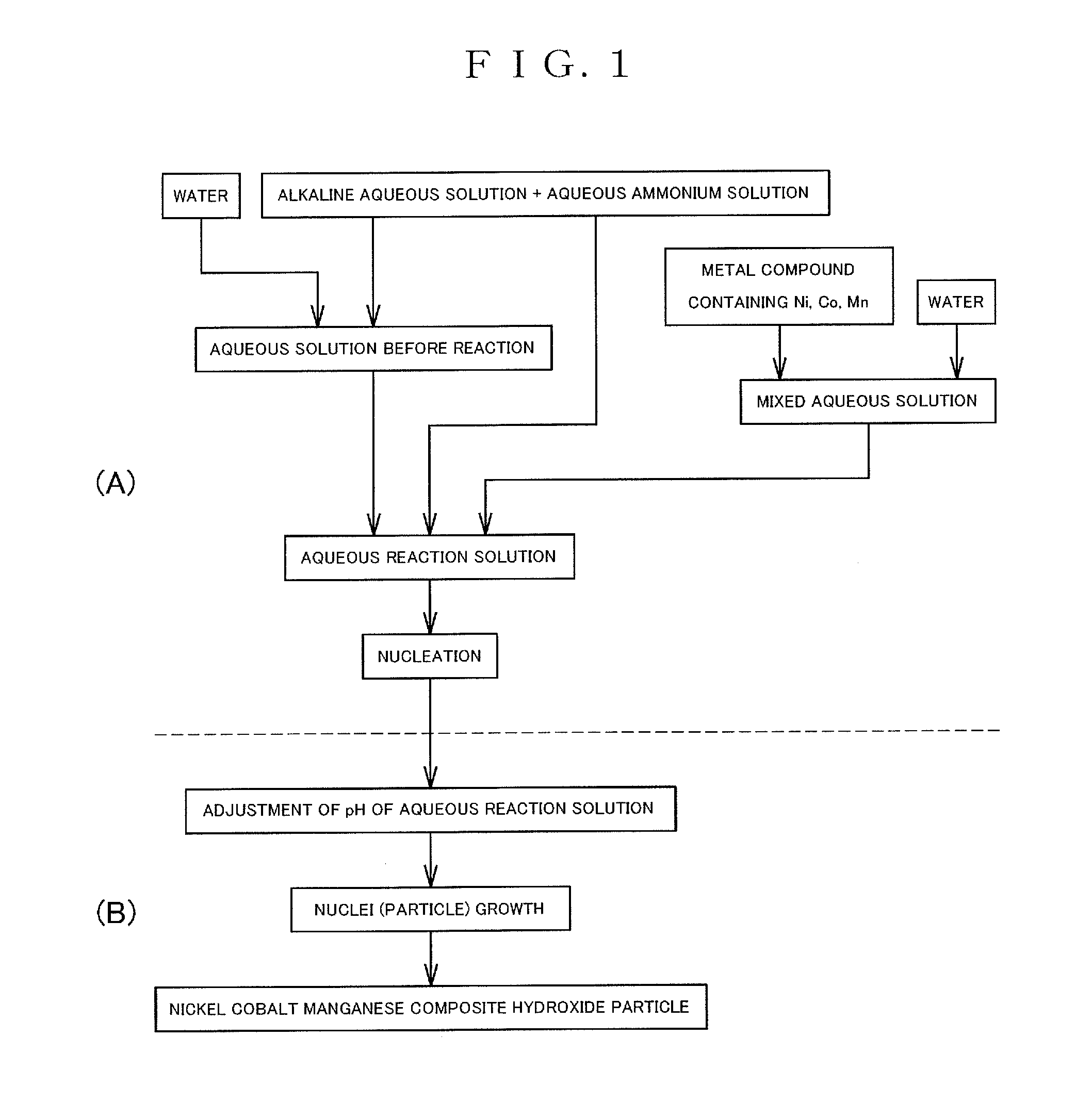
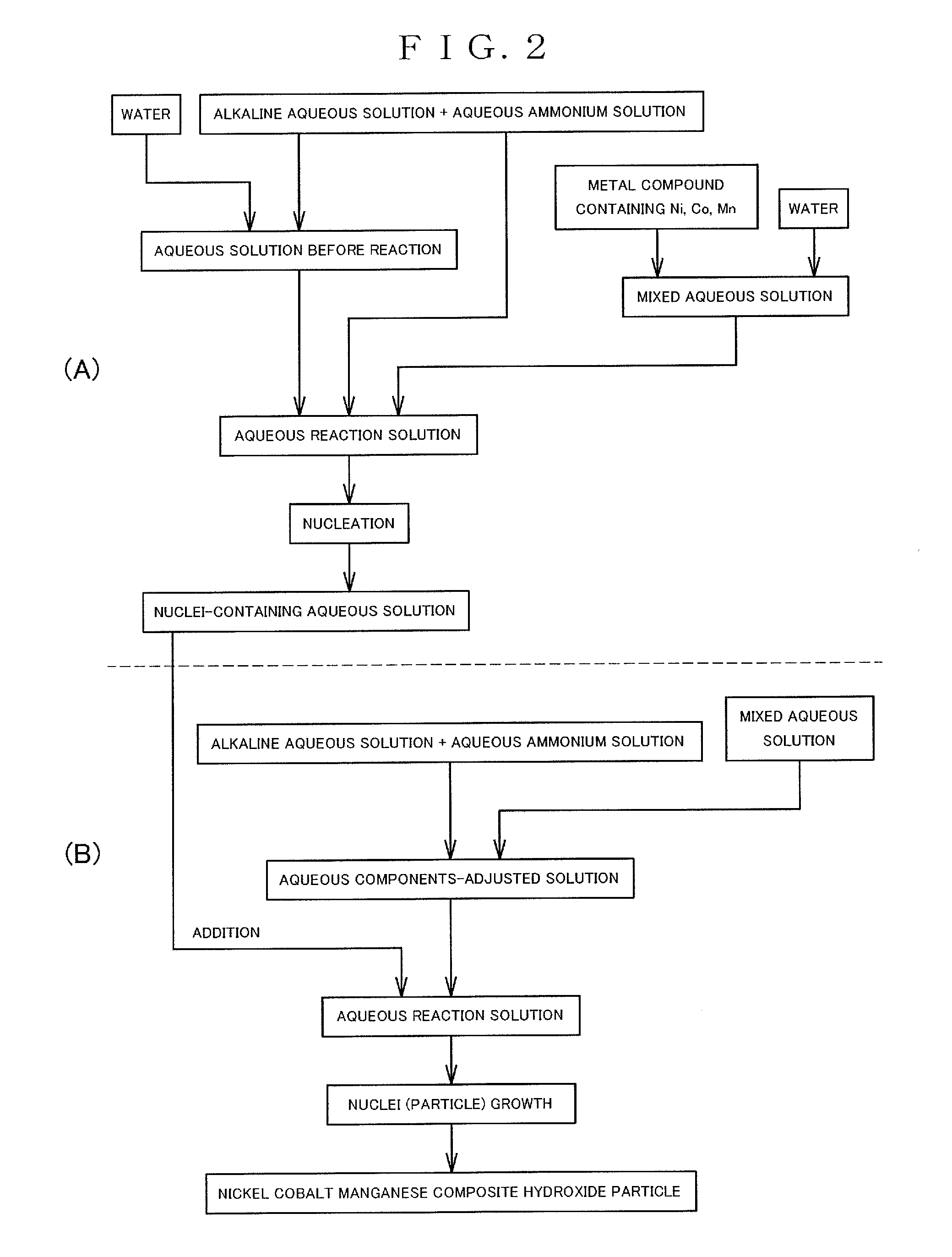
Nickel-cobalt-manganese complex hydroxide particles and method for producing same, positive electrode active material for nonaqueous electrolyte secondary battery and method for producing same, and nonaqueous electrolyte secondary battery
ActiveUS20120270107A1Growth inhibitionFast executionNon-aqueous electrolyte accumulator electrodesLi-accumulatorsLiquid temperatureManganese
An object of the present invention is to provide nickel cobalt manganese composite hydroxide particles having a small particle diameter and a uniform particle size distribution, and a method for producing the same.[Solution]A method for producing a nickel cobalt manganese composite hydroxide by a crystallization reaction is provided. The method includes: a nucleation step of performing nucleation by controlling a pH of an aqueous solution for nucleation including metal compounds containing nickel, cobalt and manganese, and an ammonium ion donor to 12.0 to 14.0 in terms of the pH as measured at a liquid temperature of 25° C. as a standard; and a particle growth step of growing nuclei by controlling a pH of an aqueous solution for particle growth containing nuclei formed in the nucleation step to 10.5 to 12.0 in terms of the pH as measured at a liquid temperature of 25° C. as a standard.
Owner:SUMITOMO METAL MINING CO LTD +1
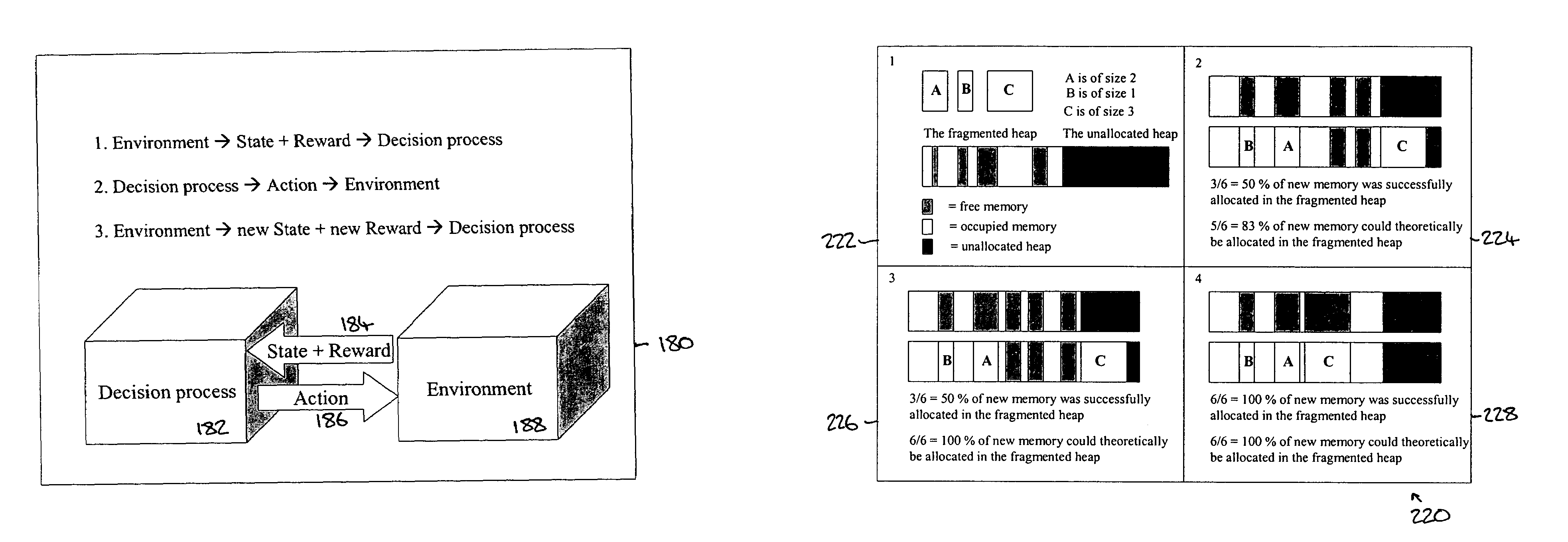
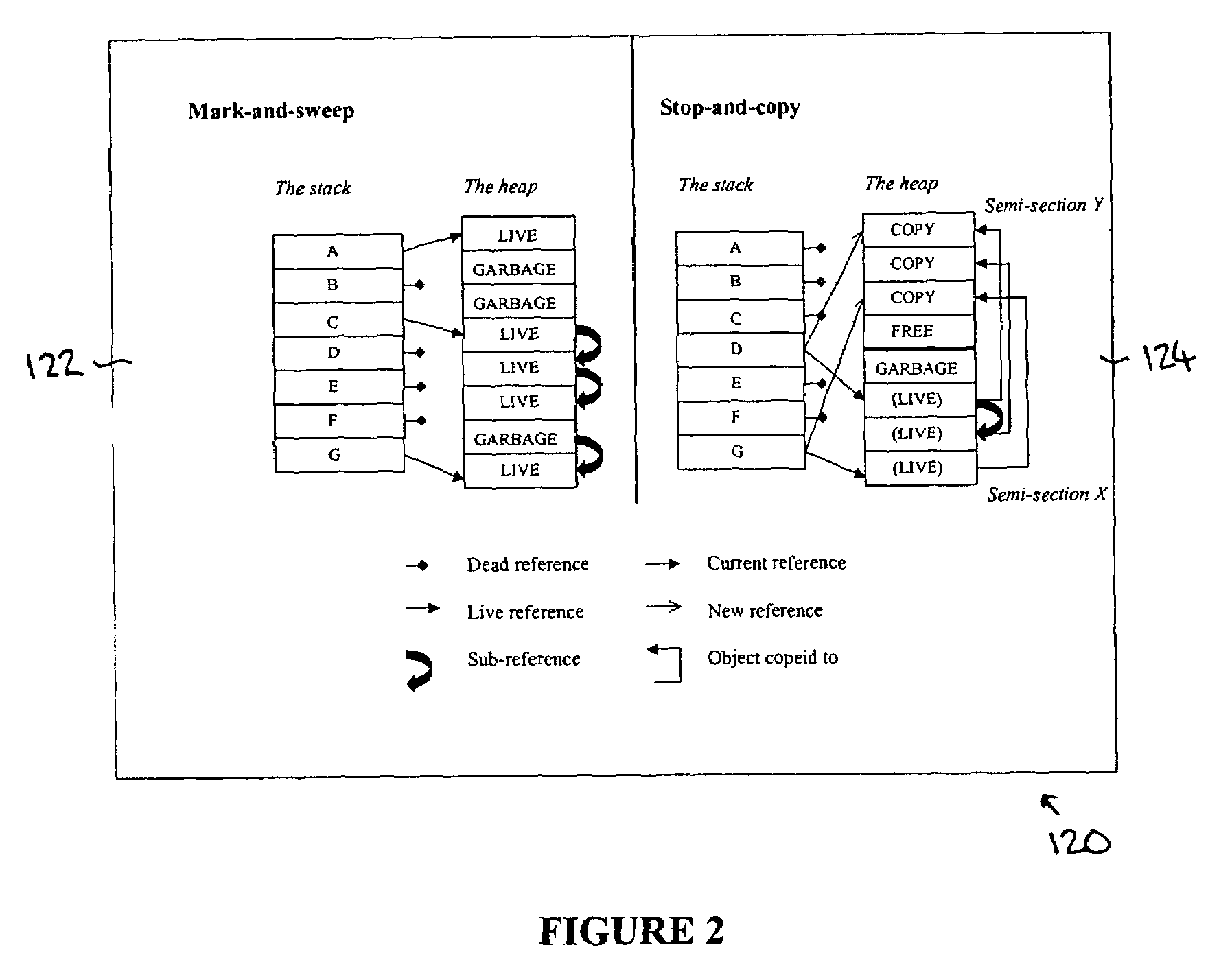
System and method for garbage collection in a computer system, which uses reinforcement learning to adjust the allocation of memory space, calculate a reward, and use the reward to determine further actions to be taken on the memory space
ActiveUS7174354B2Easy to collect and processSimple designData processing applicationsMemory adressing/allocation/relocationWaste collectionComputerized system
A system and method for use with a virtual machine, including an adaptive, automated memory management process that takes decisions regarding which garbage collector technique should be used, based on information extracted from the currently active applications. Reinforcement learning is used to decide under which circumstances to invoke the garbage collecting processing. The learning task is specified by rewards and penalties that indirectly tell the RLS agent what it is supposed to do instead of telling it how to accomplish the task. The decision is based on information about the memory allocation behavior of currently running applications. Embodiments of the system can be applied to the task of intelligent memory management in virtual machines, such as the Java Virtual Machine (JVM).
Owner:ORACLE INT CORP
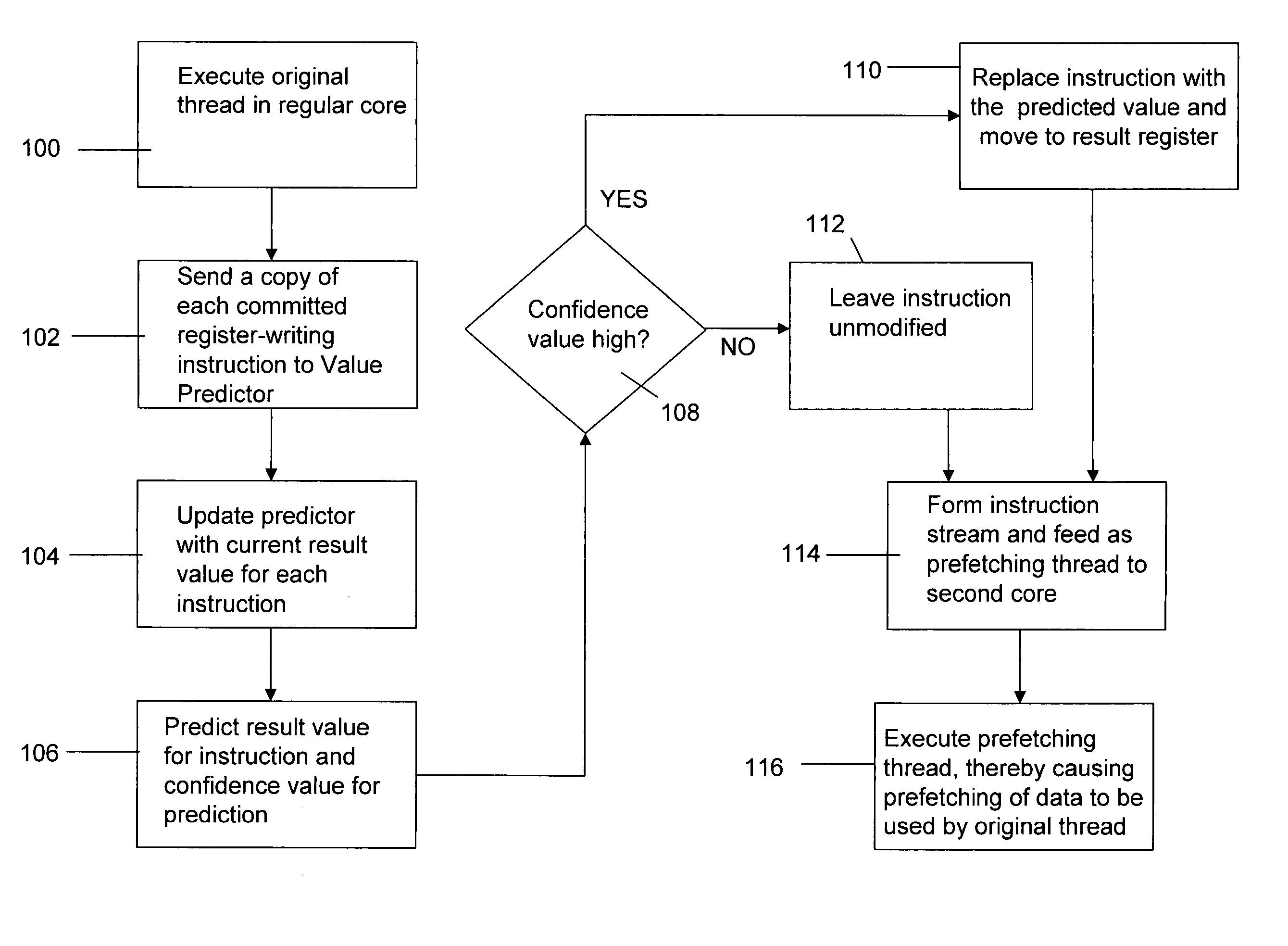
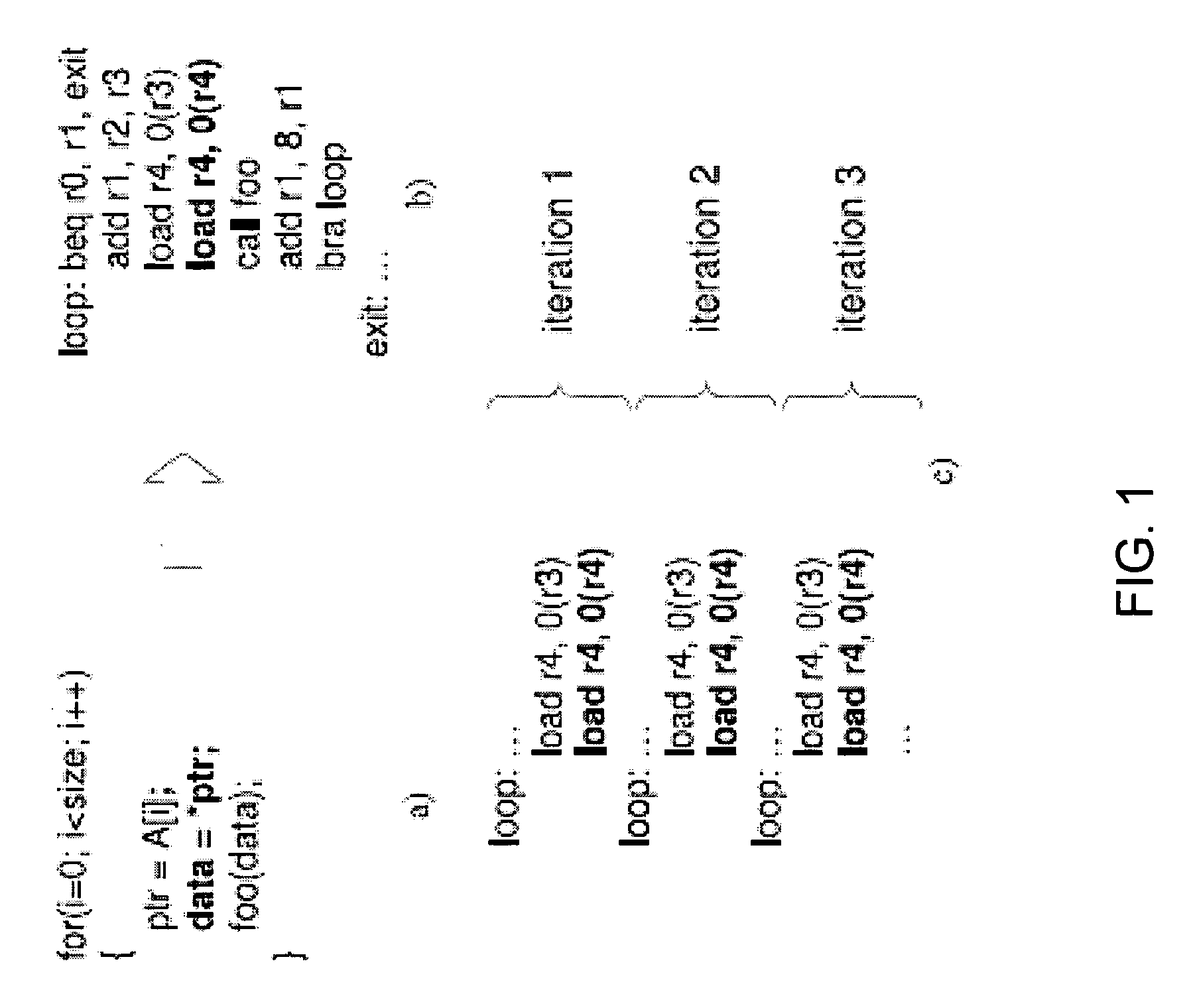
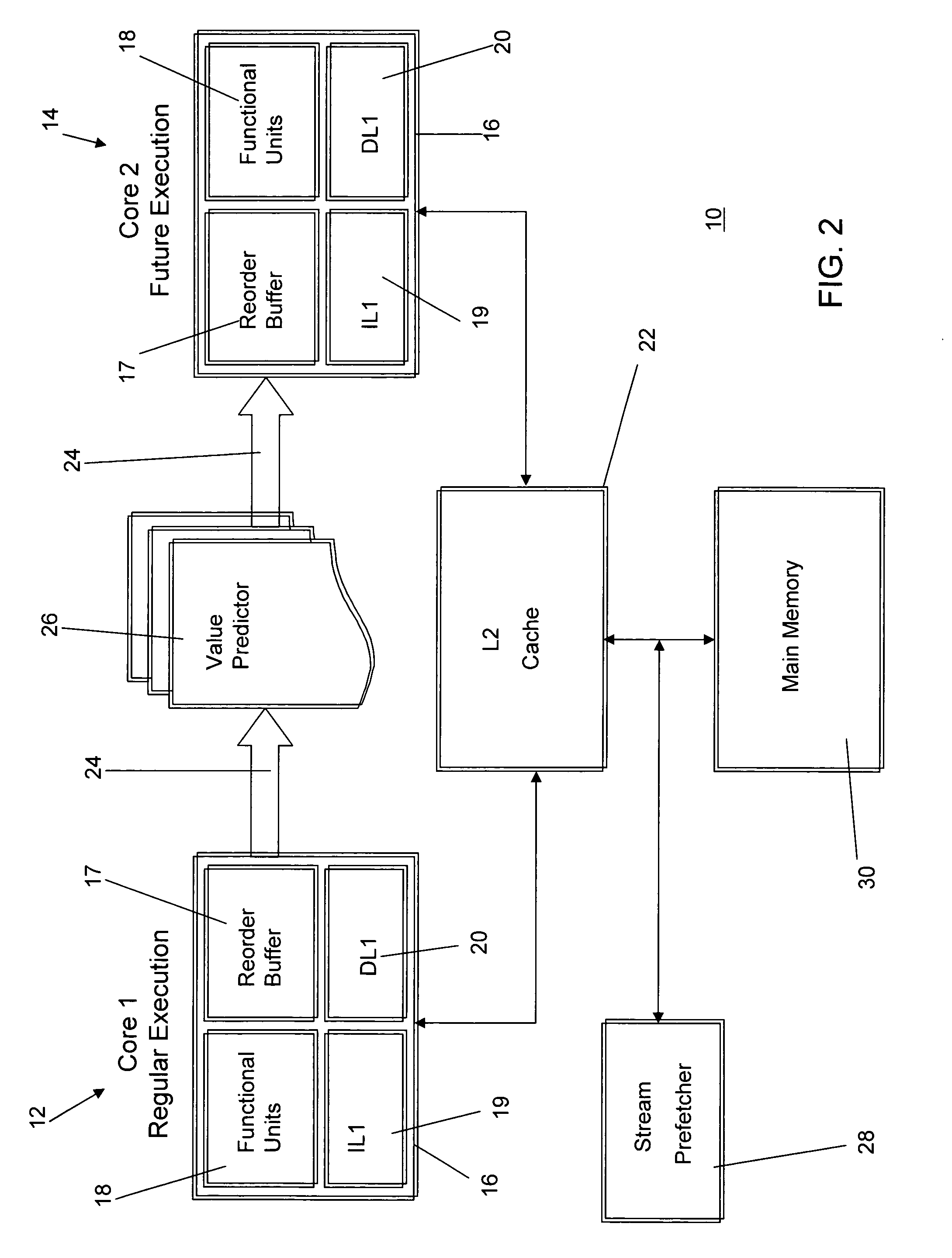
Future execution prefetching technique and architecture
ActiveUS20070174555A1Lower performance requirementsIncreased complexityRuntime instruction translationMemory systemsAccess timeTerm memory
A prefetching technique referred to as future execution (FE) dynamically creates a prefetching thread for each active thread in a processor by simply sending a copy of all committed, register-writing instructions in a primary thread to an otherwise idle processor. On the way to the second processor, a value predictor replaces each predictable instruction with a load immediate instruction, where the immediate is the predicted result that the instruction is likely to produce during its nth next dynamic execution. Executing this modified instruction stream (i.e., the prefetching thread) in another processor allows computation of the future results of the instructions that are not directly predictable. This causes the issuance of prefetches into the shared memory hierarchy, thereby reducing the primary thread's memory access time and speeding up the primary thread's execution.
Owner:CORNELL RES FOUNDATION INC
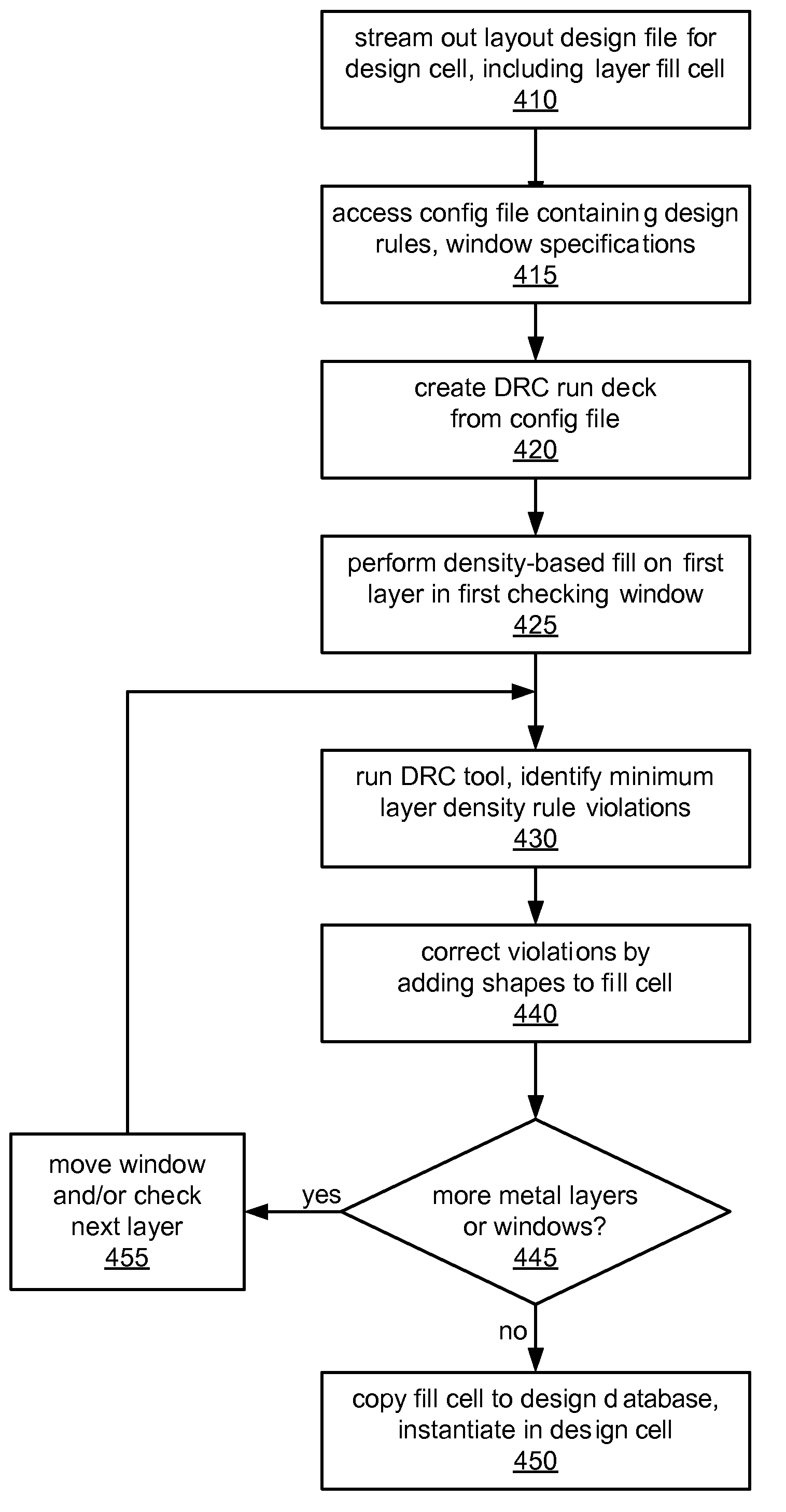
Density-Based Layer Filler for Integrated Circuit Design
ActiveUS20080120586A1Reduce riskExtended run timeCAD circuit designSoftware simulation/interpretation/emulationElectricityMinimum density
A system and method for performing density-based layer filling on a design layout encoding of an integrated circuit device is disclosed. In some embodiments, the density-based layer filler may identify open areas on a given design layer in which one or more minimum density rules are not met and may insert dummy shapes only in those identified areas. The dummy shapes may be constructed so as not to violate one or more other design rules. The density-based layer filler may access a configuration file comprising layer density rules and other design rules and may generate a run deck dependent on the contents of the configuration file. The density-based layer filler may be applied iteratively to a design in checking windows of various sizes according to multiple window sizes and step values specified in the configuration file. The dummy shapes may be electrically connected to an existing ground wire after insertion.
Owner:ORACLE INT CORP
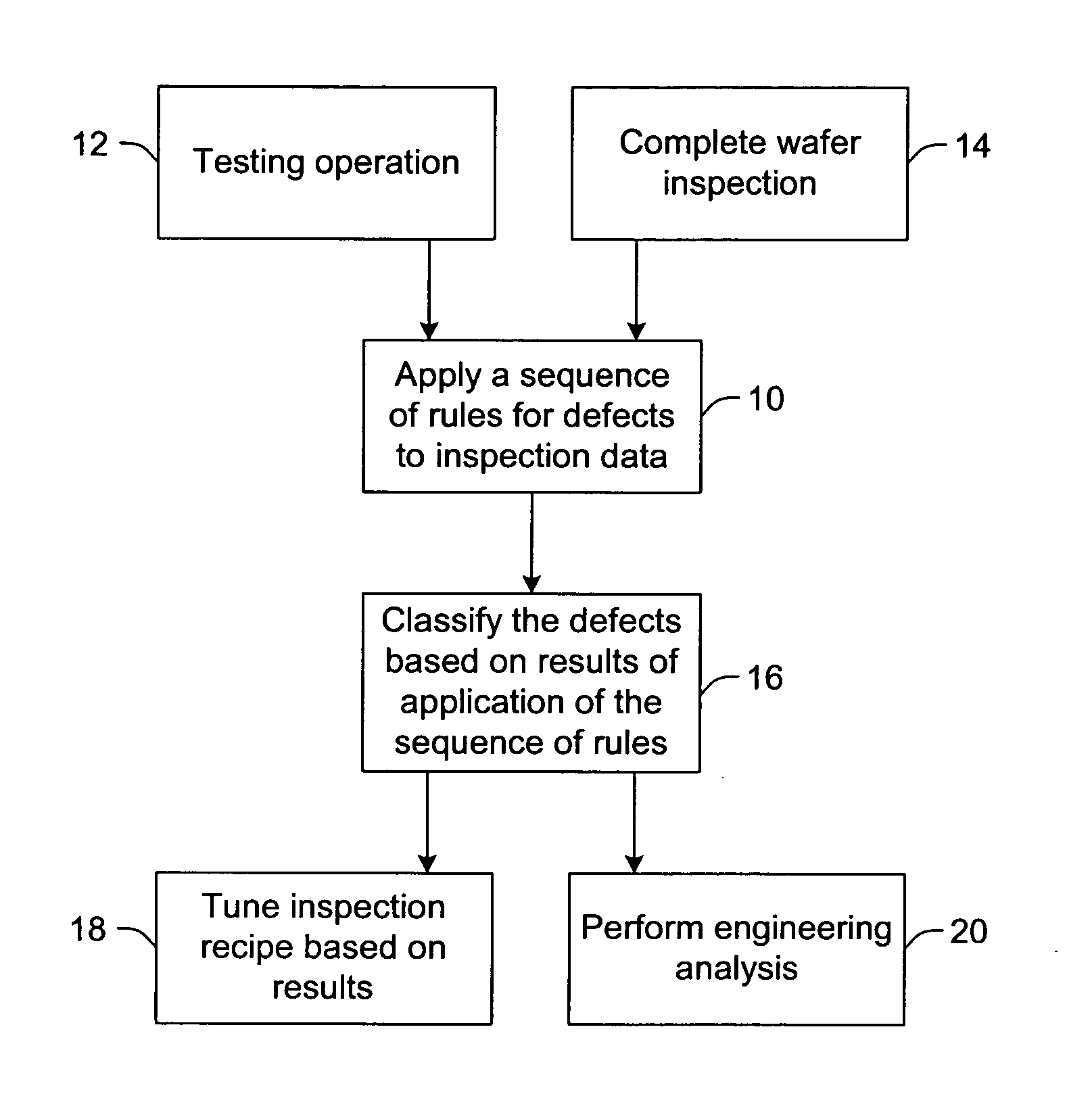
Flexible hybrid defect classification for semiconductor manufacturing
ActiveUS20060265145A1Fast executionSetup of such a classifier is relatively simpleImage enhancementImage analysisHybrid approachAlgorithm
Hybrid methods for classifying defects in semiconductor manufacturing are provided. The methods include applying a flexible sequence of rules for defects to inspection data. The sequence of rules includes deterministic rules, statistical rules, hybrid rules, or some combination thereof. The rules included in the sequence may be selected by a user using a graphical interface The method also includes classifying the defects based on results of applying the sequence of rules to the inspection data.
Owner:KLA TENCOR TECH CORP
System and method for processing transaction records suitable for healthcare and other industries
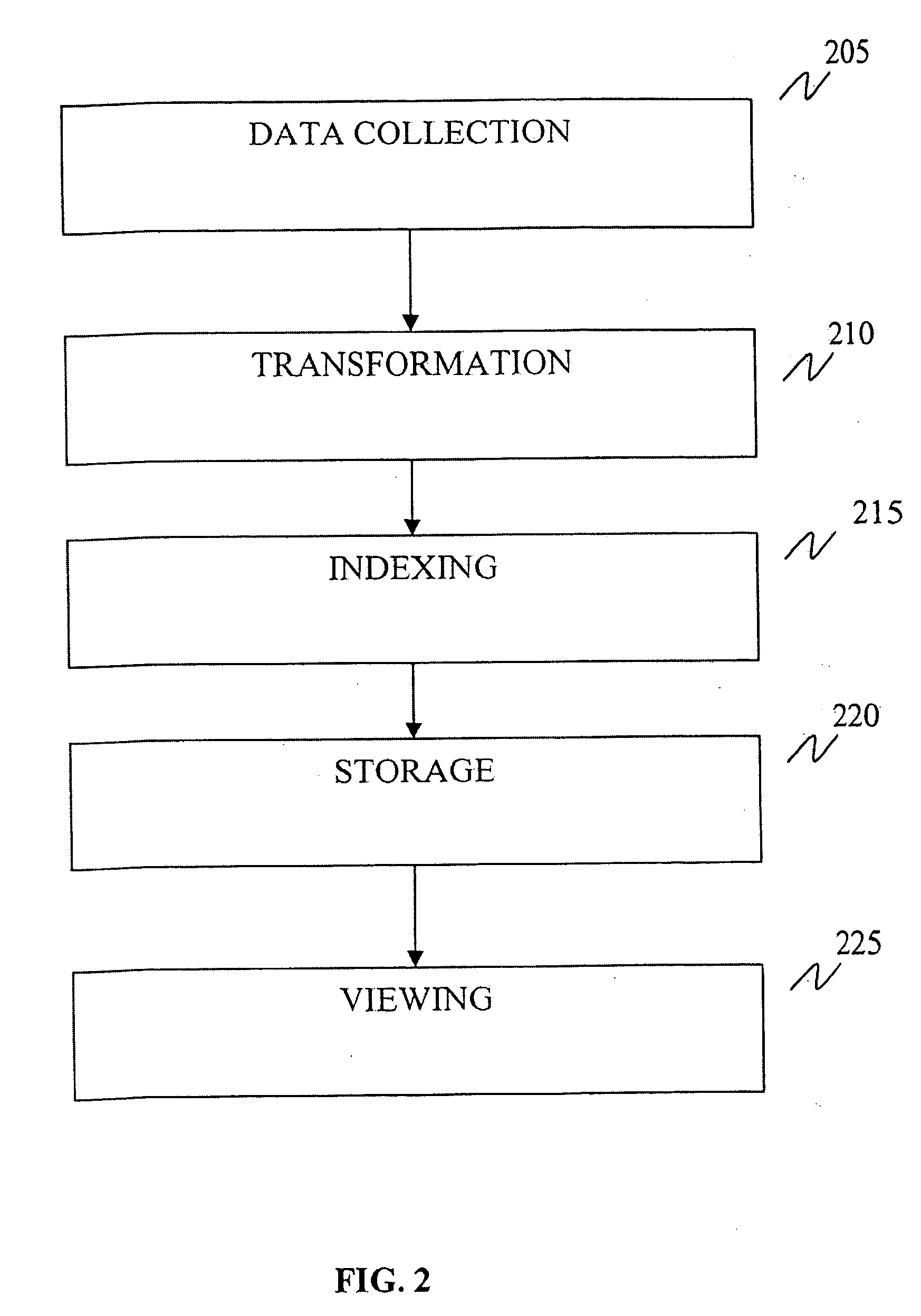
InactiveUS20050010452A1Easy to processEasy to viewOffice automationSpecial data processing applications
The system of the invention includes an interface processor for receiving transaction data in a first data format identifying transactions concerning financial reimbursement claim information communicated between two entities. The system also includes a transformation processor for converting the received transaction identification data from the first data format to a different second more generic, easily processed and readable second data format thereby allowing for customization and extensibility for different users. The system further includes an indexing processor that uses predetermined information concerning the second data format to identify and extract index information from the re-formatted transaction identification data. The index information is used to locate and retrieve the archived transaction data from a data repository included as part of the system upon user request. The system also includes a storage processor for storing records representing the re-formatted transaction identification data and the associated index information in the data repository. A display processor is also included for initiating display of the re-formatted transaction identification information in the second data format in response to a user command.
Owner:SIEMENS MEDICAL SOLUTIONS HEALTH SERVICES CORPORAT
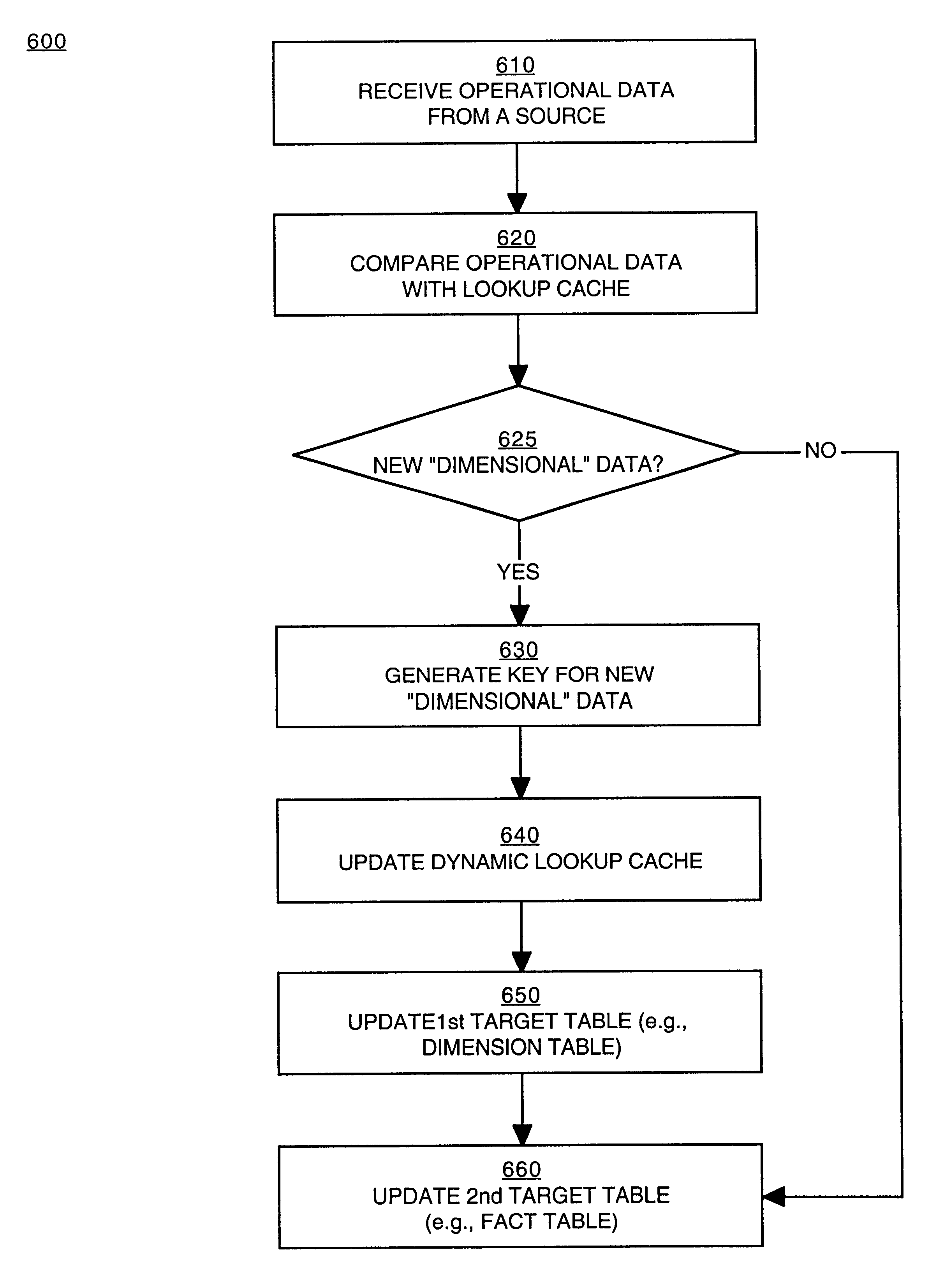
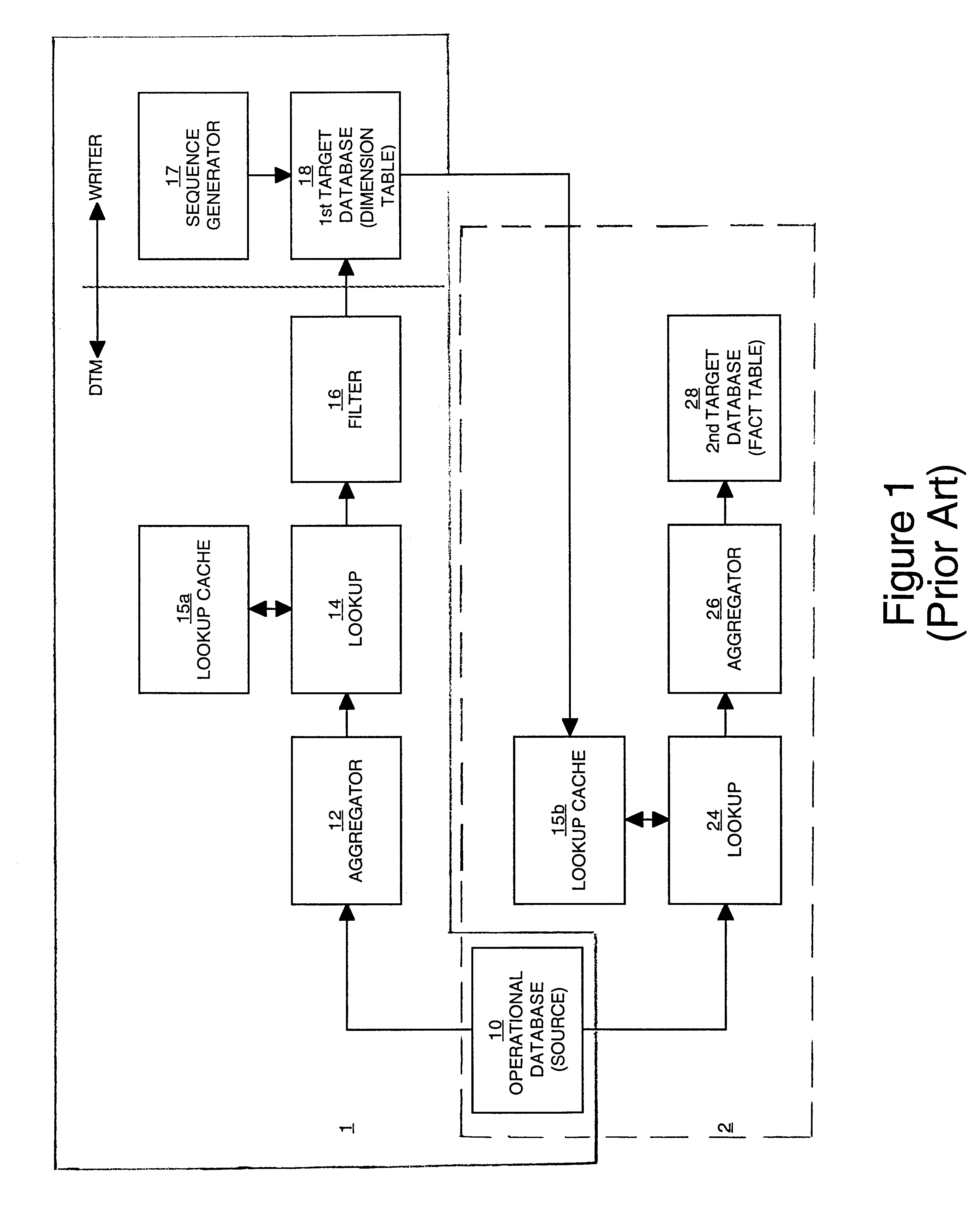
Method and apparatus for synchronizing cache with target tables in a data warehousing system
InactiveUS6895471B1Increase speedReduce loadDatabase updatingData processing applicationsData warehouseData set
A method and apparatus for processing (transporting) data, such as in a data warehouse system. In one embodiment, the data are received from a source and compared to data in a lookup cache comprising a subset of data from a first data set (e.g., a dimension table). Instances of the data not present in a lookup cache (that is, new data) are identified. Information corresponding to these instances are generated (e.g., a unique identifier is associated with each of these instances), and the first data set is updated accordingly. The lookup cache is then updated with the new data and the unique identifiers. Accordingly, the information (data) in the lookup cache and in the first data set are in synchronization. The lookup cache does not need to be rebuilt (e.g., to update a second data set such as a fact table).
Owner:INFORMATICA CORP
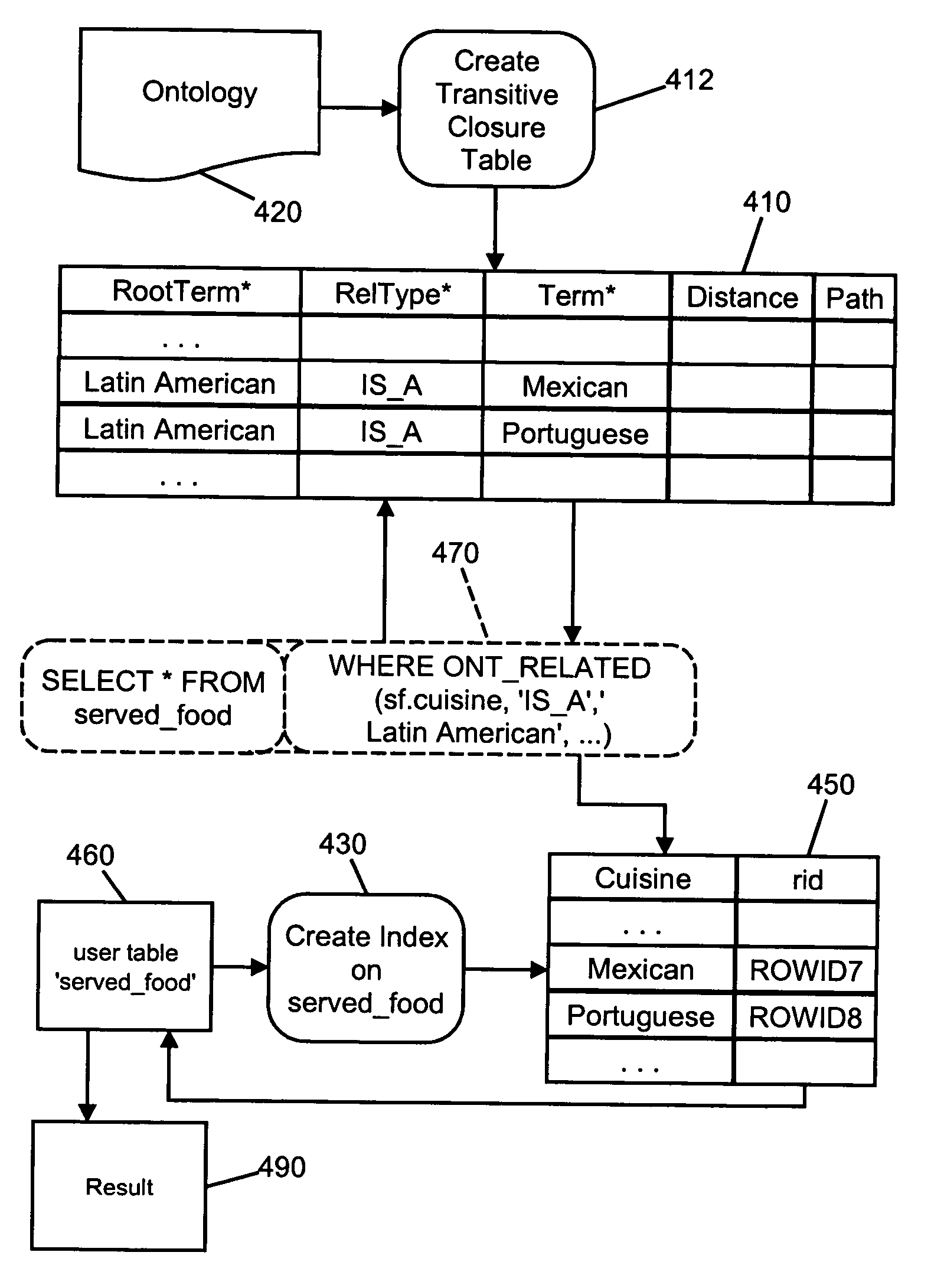
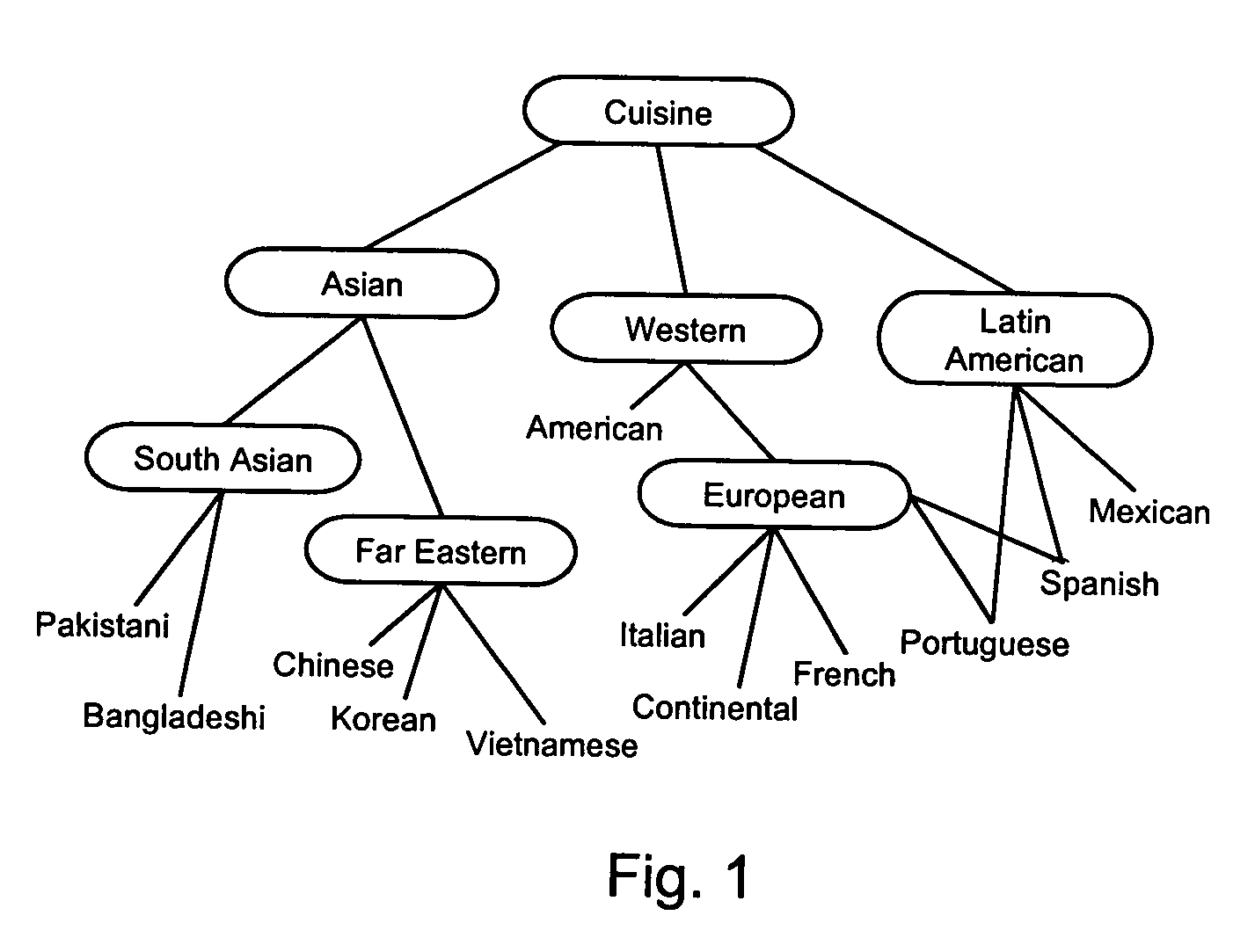
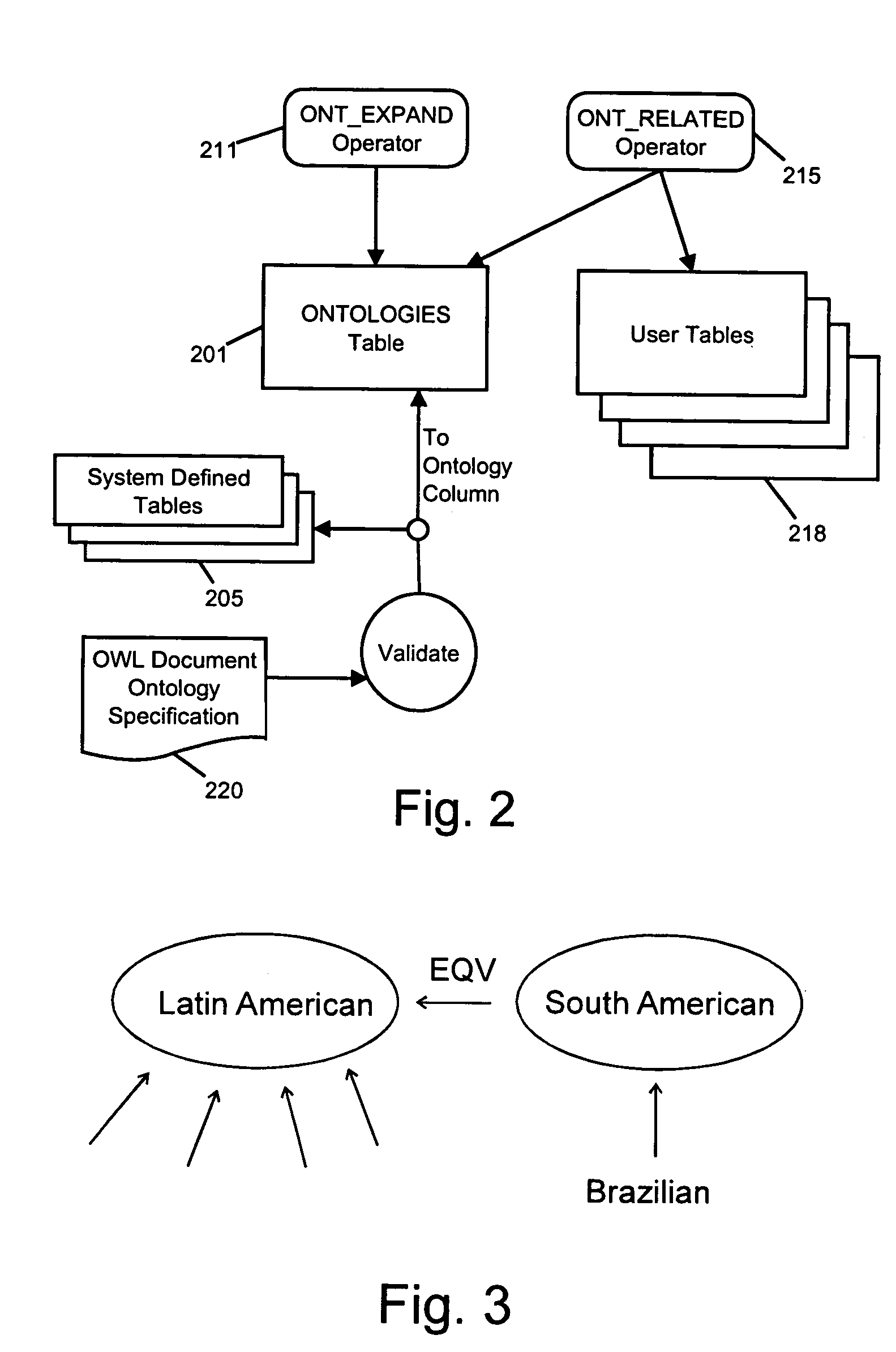
System for indexing ontology-based semantic matching operators in a relational database system
InactiveUS20060036633A1Quick identificationFast executionDigital data information retrievalDigital data processing detailsRelational databaseSemantic matching
A method for rapidly identifying terms that are associated with a given root term by a transitive relationship defined by hierarchical ontology data stored in a relational database. A transitive closure table is created that comprises a plurality of rows each of which specifies a term and an associated one of a plurality of root terms. The table is sorted and indexed by the root terms to group together rows associated with each of said root terms. The resulting transitive closure table may be consulted to rapidly identify terms associated with said given root term.
Owner:ORACLE INT CORP
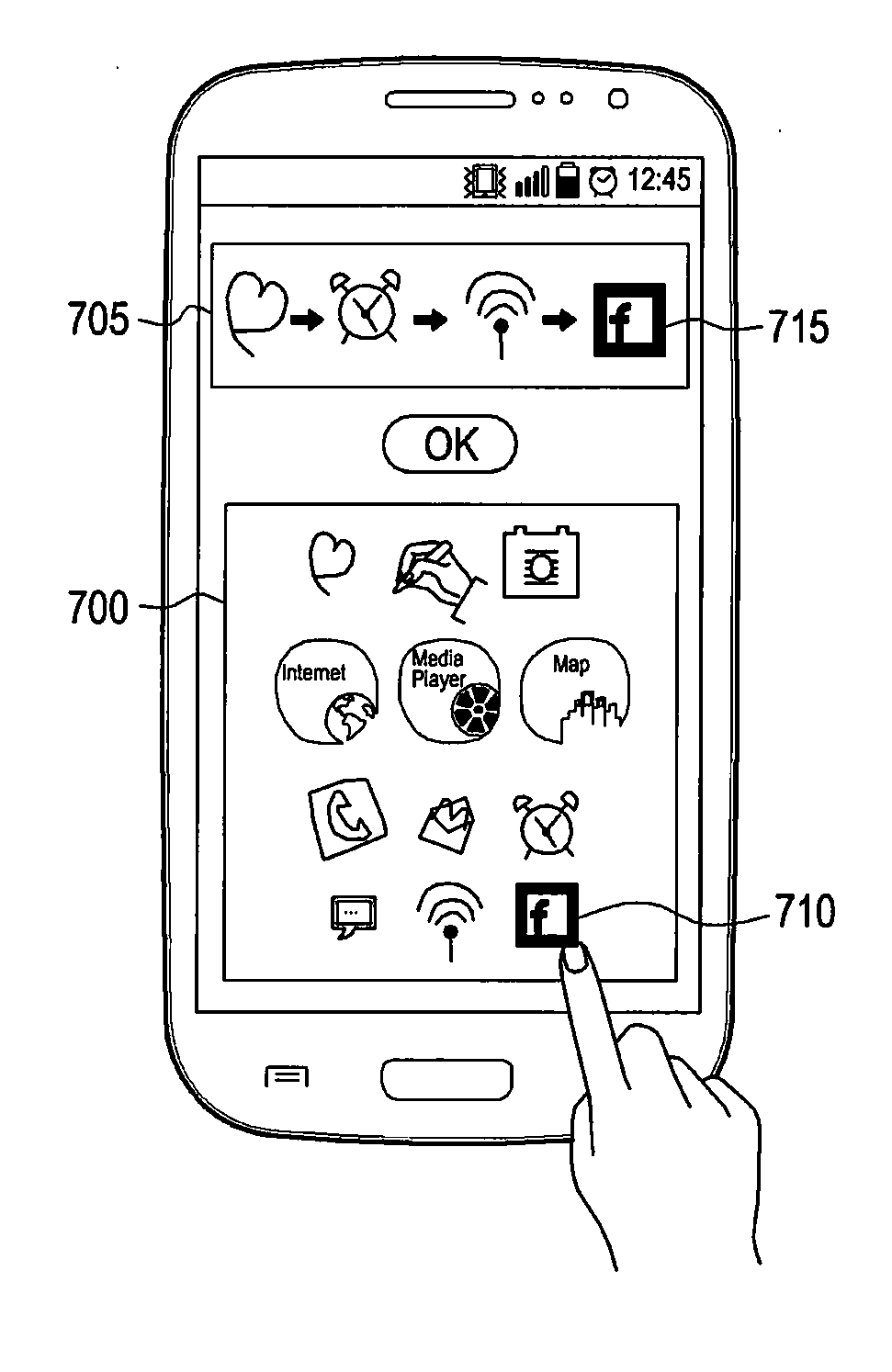
Method for quickly executing application on lock screen in mobile device, and mobile device therefor
InactiveUS20140365904A1Executed quickly and easilyFraudulent use of mobileInput/output for user-computer interactionUnauthorised/fraudulent call preventionLock screenMobile device
A method for quickly executing an application on a lock screen in a mobile device is provided. The method includes displaying a lock screen on which a plurality of executable objects are displayed; receiving an unlock command by an input means; determining whether the received unlock command coincides with a preset unlock command; unlocking the lock screen if the received unlock command coincides with the preset unlock command; and executing an application associated with an object corresponding to a last position of the input means. By doing so, the mobile device may quickly execute an application upon unlocking.
Owner:SAMSUNG ELECTRONICS CO LTD
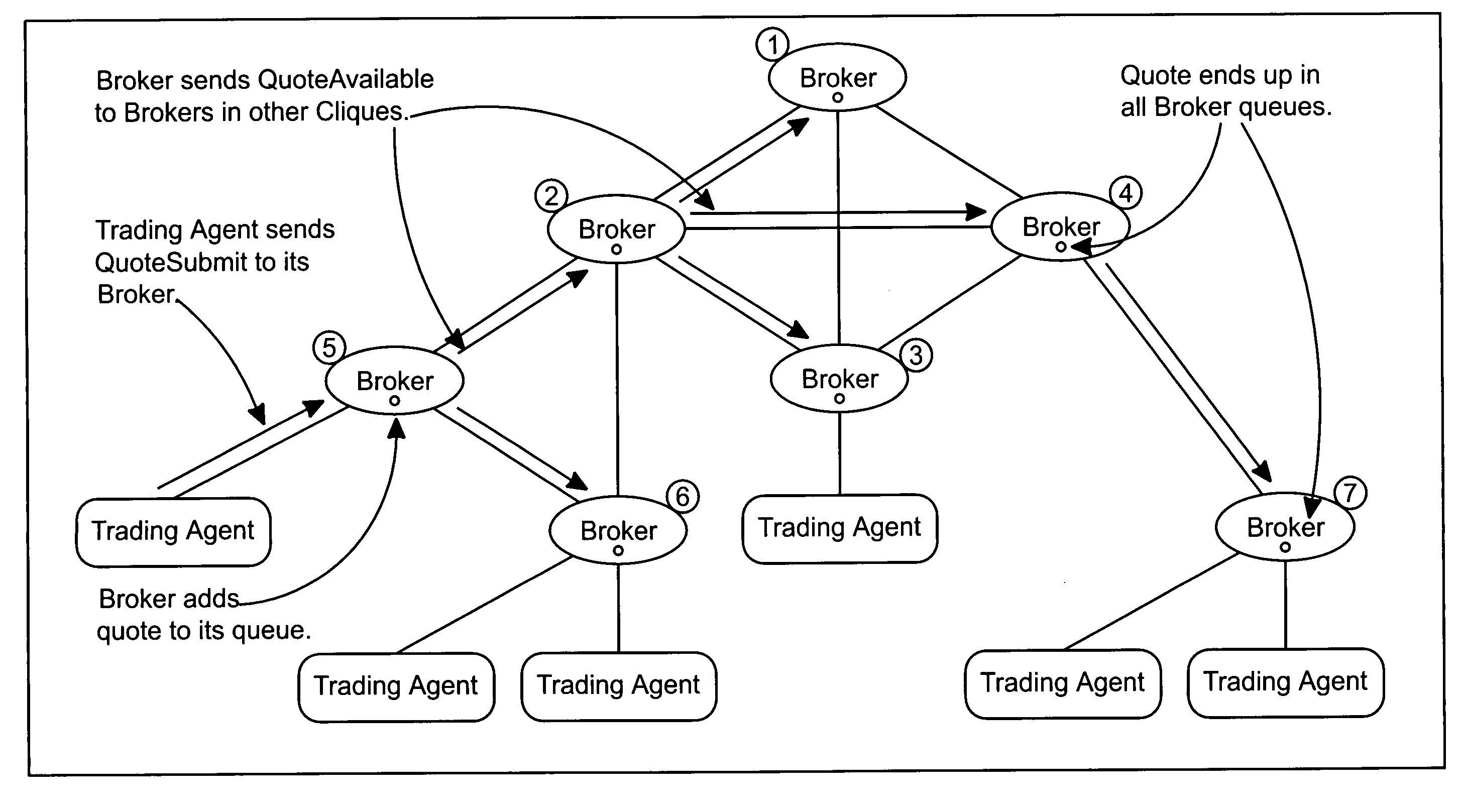
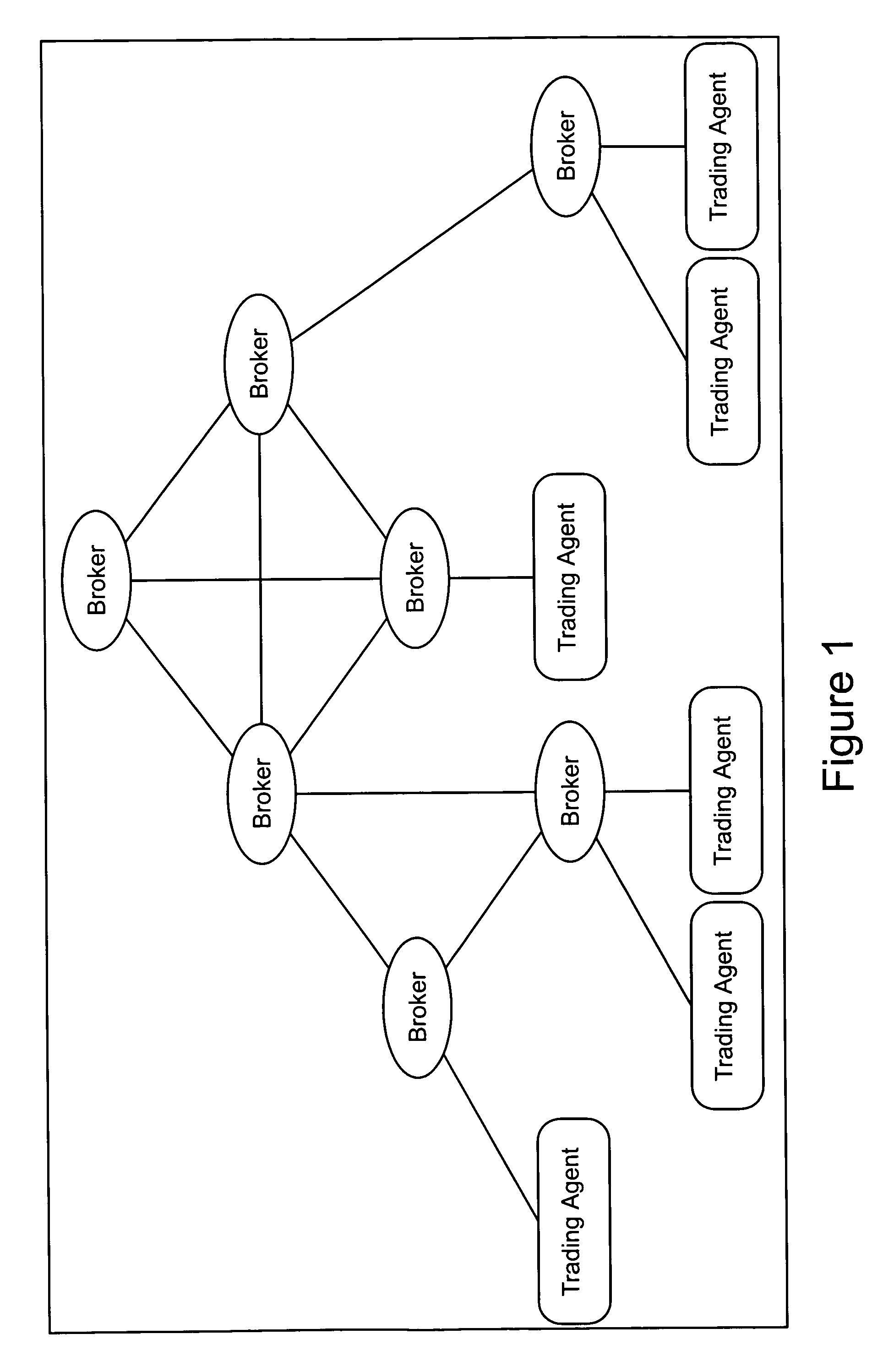
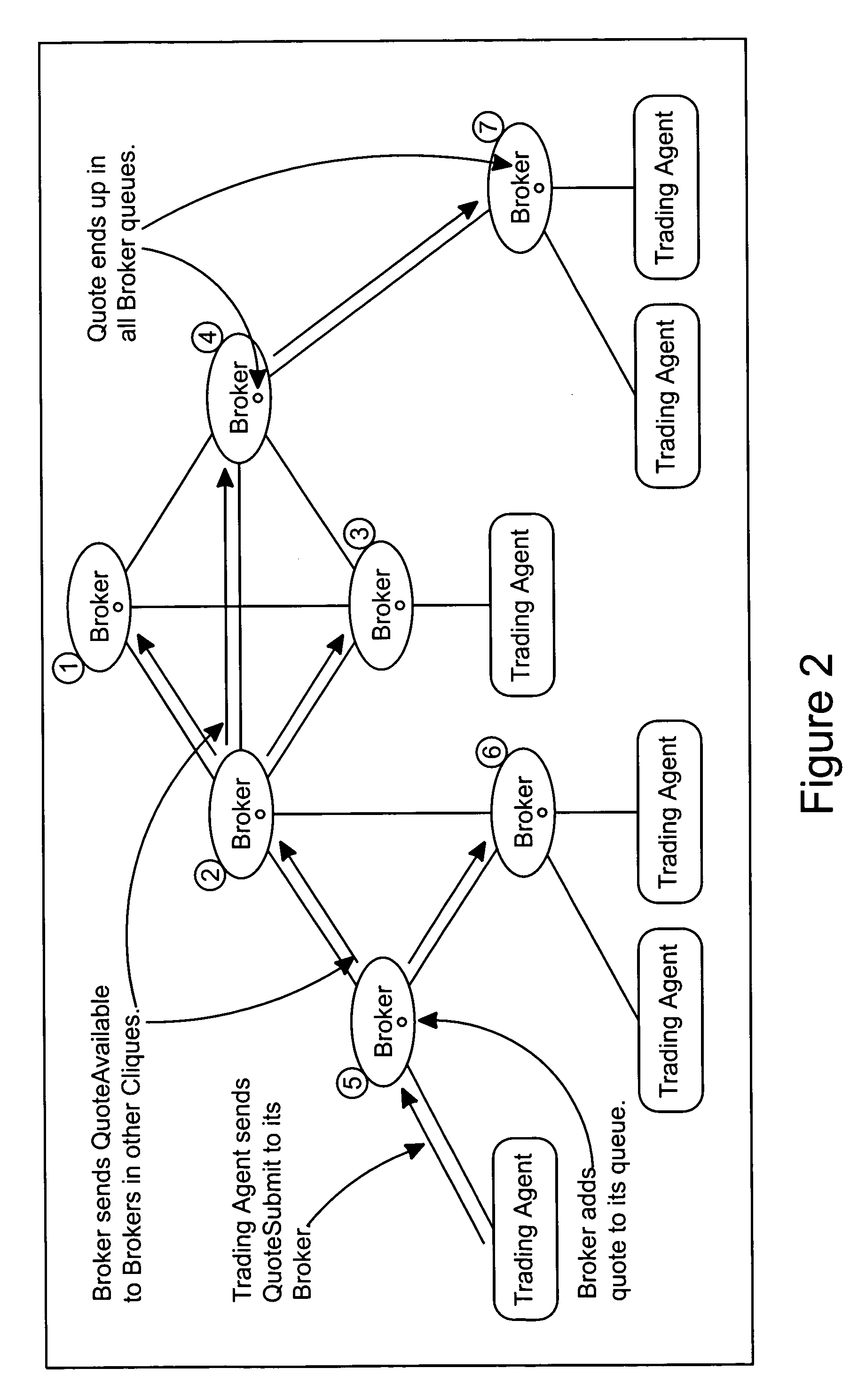
Architecture for anonymous trading system
InactiveUS7184982B1Increase performance benefitIncrease redundancyFinanceCommerceOrder entryComputer science
An anonymous trading system suitable for trading foreign exchange or other fungible instruments comprises a network of broking nodes each of which have equal status and each of which perform the function of matching orders input into the systems, executing trades and distributing market views. Trading agent nodes are connected to some or all of the broking nodes and act as an interface between trader terminals or other order input devices through which orders are submitted to the system, and the broking nodes. Orders may be input into the system as visible quotes or invisible hits.
Owner:CME GRP
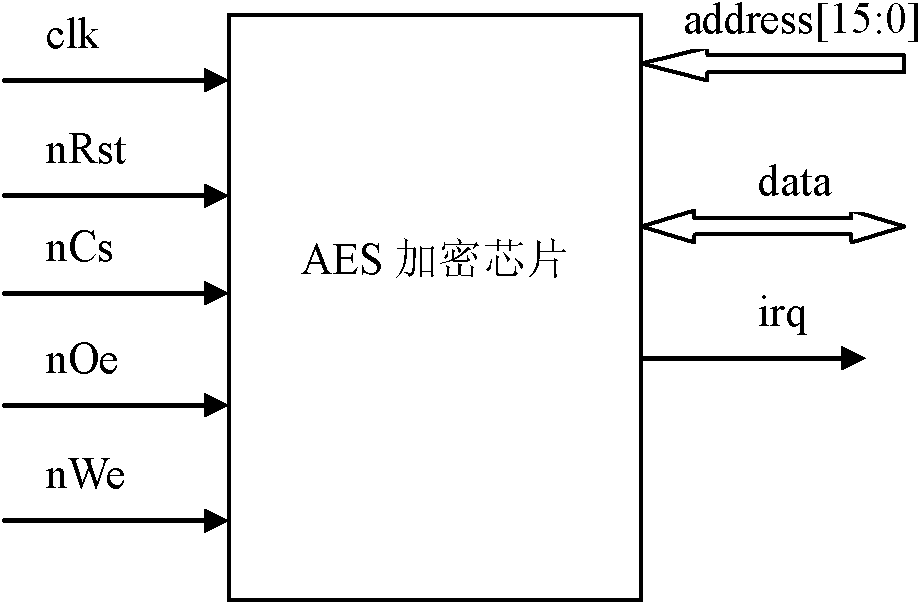
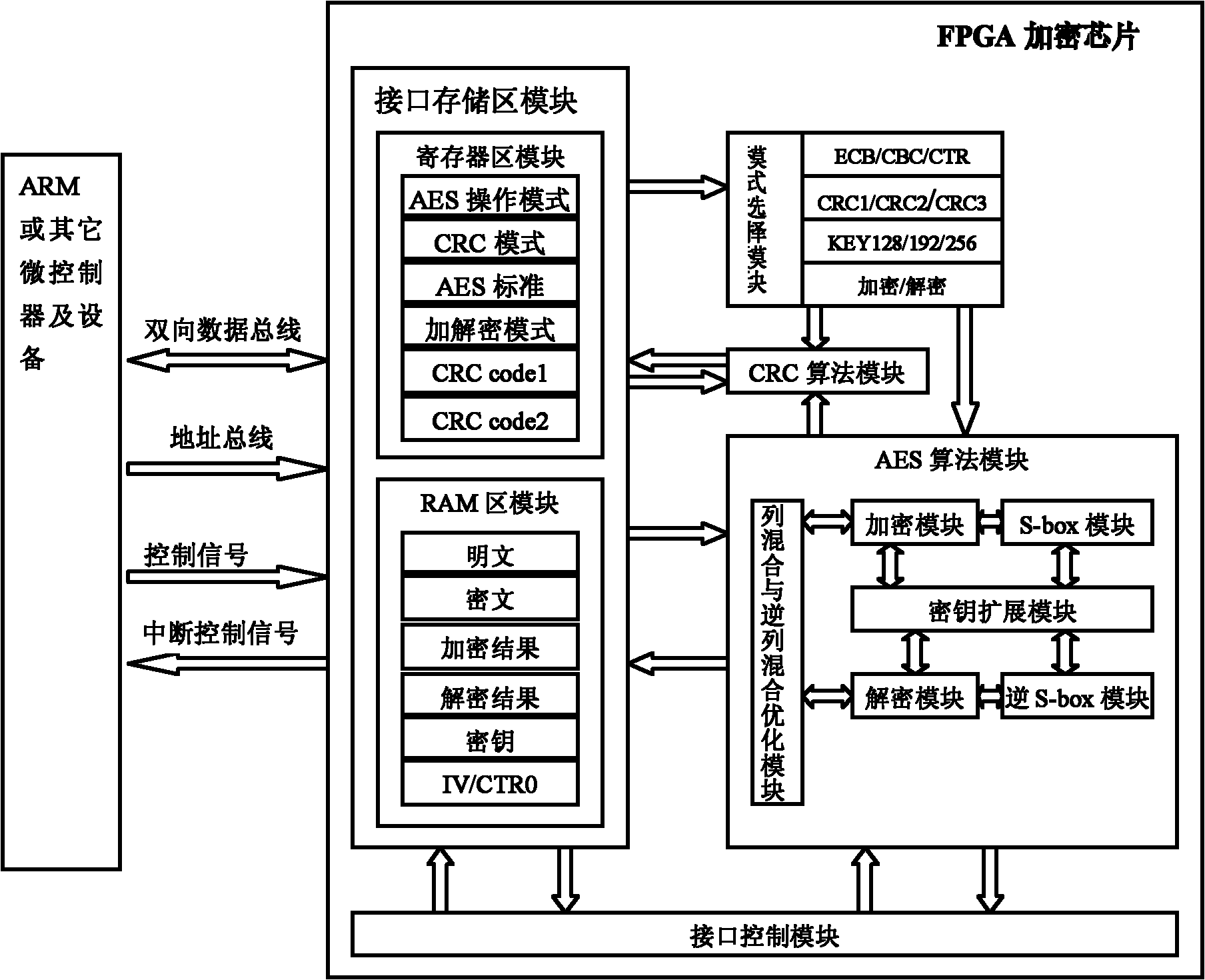
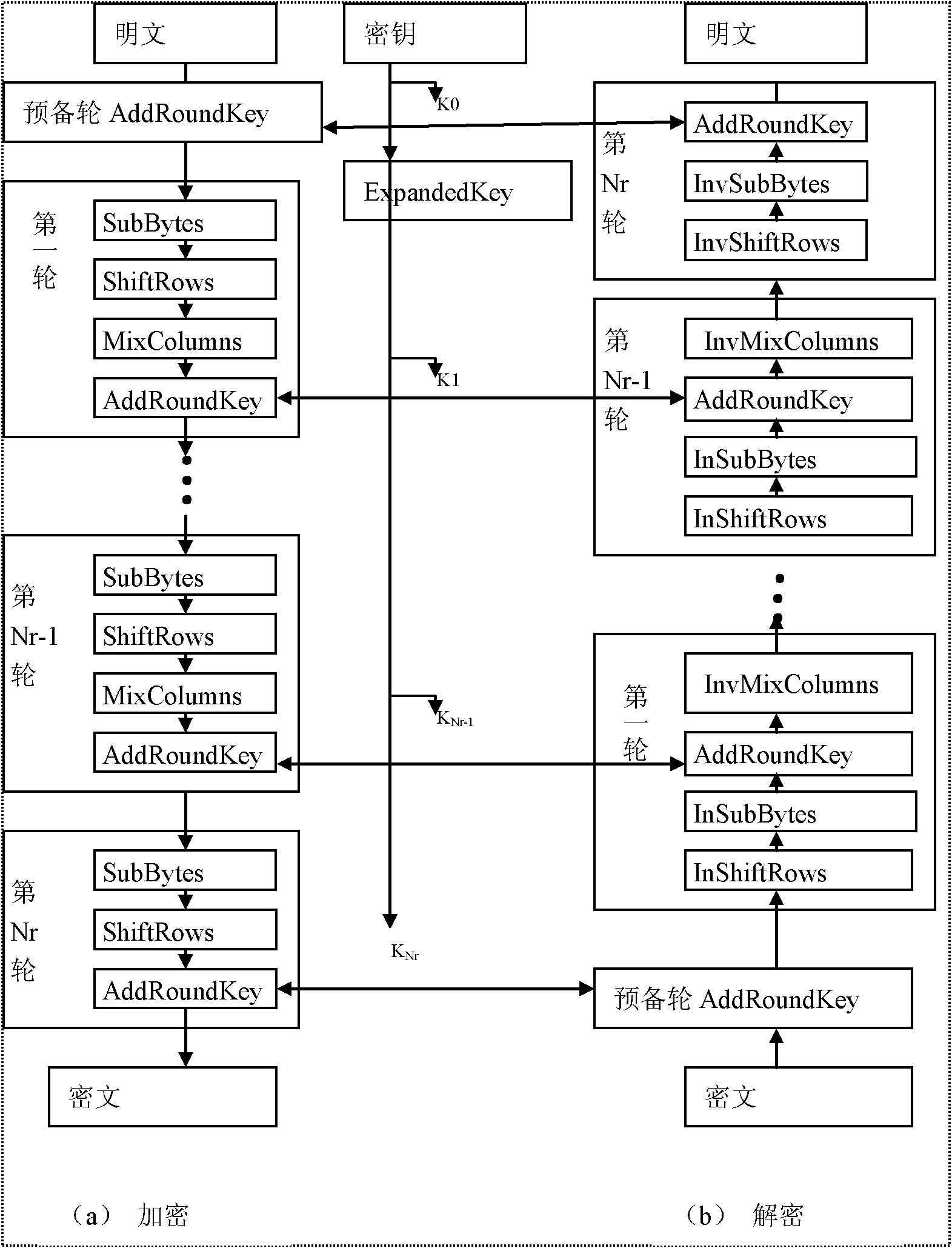
Method for designing AES (Advanced Encryption Standard) encryption chip based on FPGA (Field Programmable Gate Array) and embedded encryption system
InactiveCN102223228AFlexible useReduce areaEncryption apparatus with shift registers/memoriesInformation technologyEncryption system
The invention discloses a method for designing an AES (Advanced Encryption Standard) encryption chip based on an FPGA (Field Programmable Gate Array), which is designed for aiming at the requirement of an embedded system. The AES encryption chip not only can be used in a manner of a solid chip but also used in a manner of a software module. Three operation modes of ECB (Electronic Code Book), CBC (Cipher Block Chaining) and CTR (Counter Technical Requirement) are supported simultaneously. All standards of the AES can be encrypted and decrypted. The byte replacement and the key expansion are carried out by using a look-up table optimization algorithm. A column mixed optimization structure is provided. Device resources are saved while the operation speed is ensured. An RAM (Random-Access Memory) can be configured as a cache of information and a key through double ports of the FPGA. A problem for storing a time sequence and data of other devices or equipment and the FPGA is resolved. Safe and reliable communication with an FPGA interface joins CRC (Cyclic Redundancy Check) error detection in a manner of a memory bus. The AES encryption chip has the advantages of high safety, high encryption and decryption speeds, low device resource requirement, low cost and the like. The AES encryption chip can be widely used in information technology industries of intelligent card systems, ATMs (Automatic Teller Machines), wireless local area networks, wireless sensor networks and the like.
Owner:BEIHANG UNIV
Dynamic-based verification apparatus for verification from electronic system level to gate level, and verification method using the same
InactiveUS20110184713A1Reduce verification timeImprove verification efficiencyAnalogue computers for electric apparatusCAD circuit designElectronic systemsComputer architecture
The simulation consists of a front-end simulation and a back-end simulation. The front-end simulation can use an equivalent model at different abstraction level, or a simulation model for the back-end simulation. The back-end simulation uses the simulation result of front-end simulation so that it can run one or more simulation runs sequentially or in parallel. Alternatively, models at lower level of abstraction are simulated together with a model at higher level of abstraction in parallel using two or more simulators.
Owner:YANG SEI YANG
Indexing based on key ranges
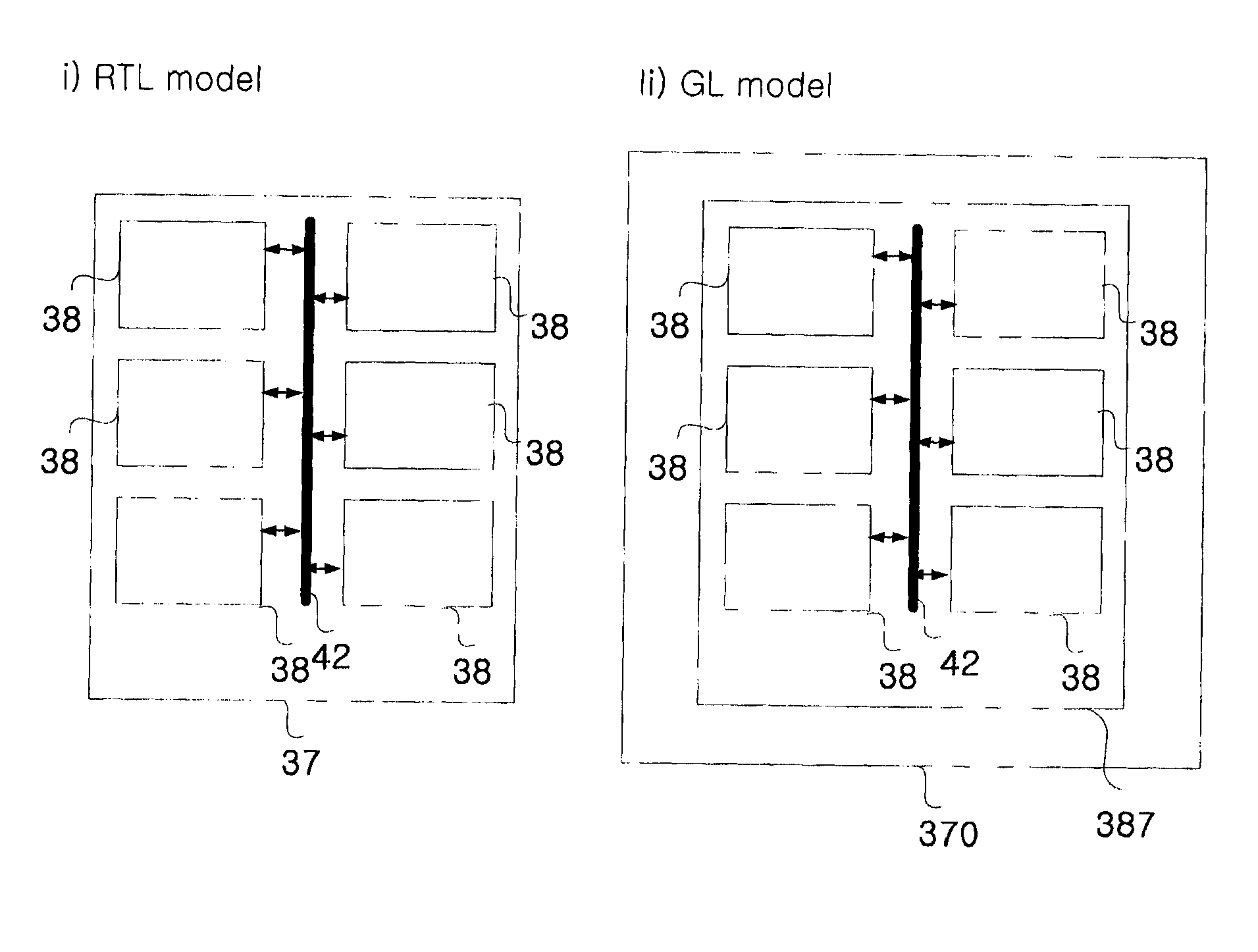
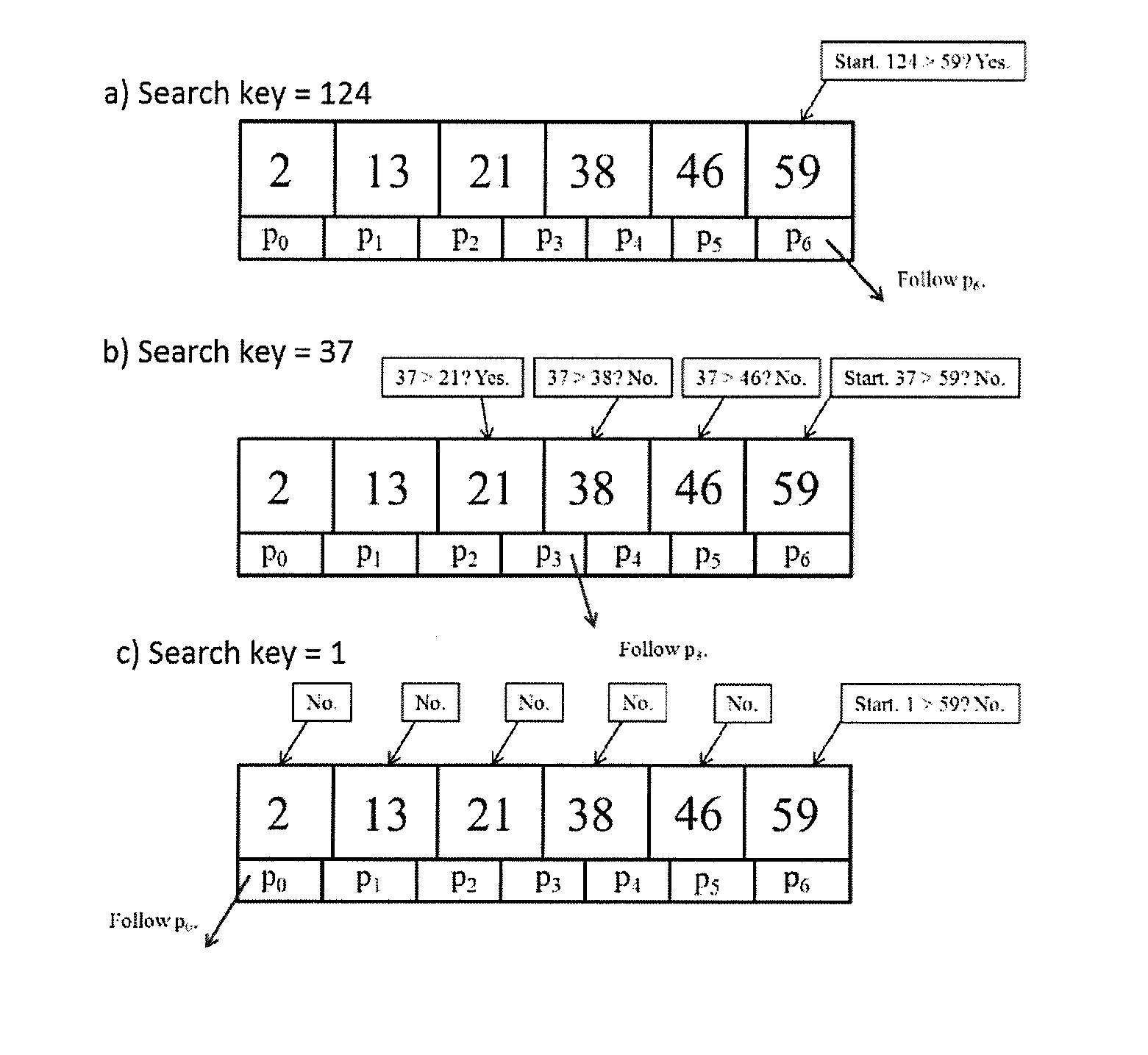
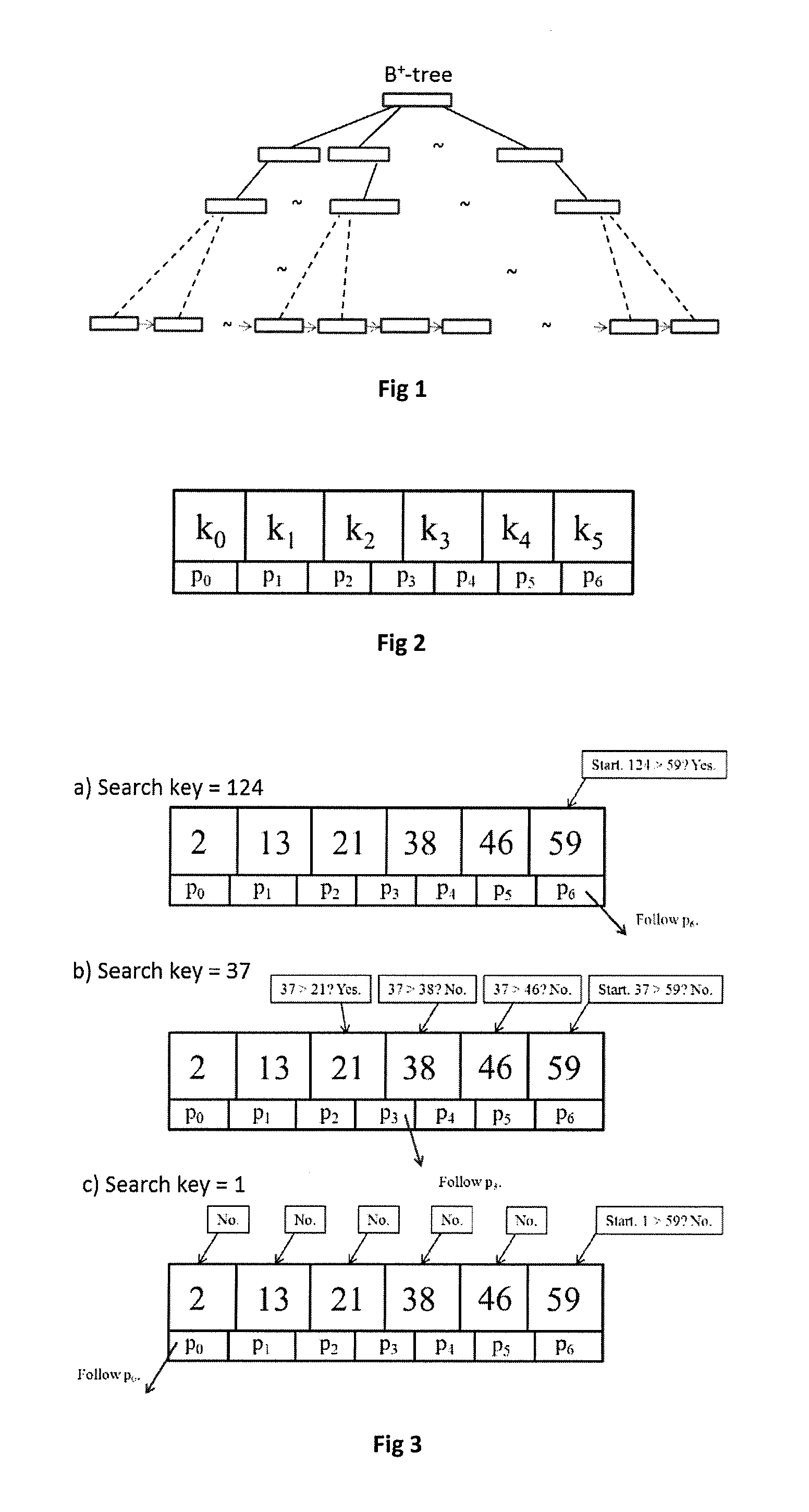
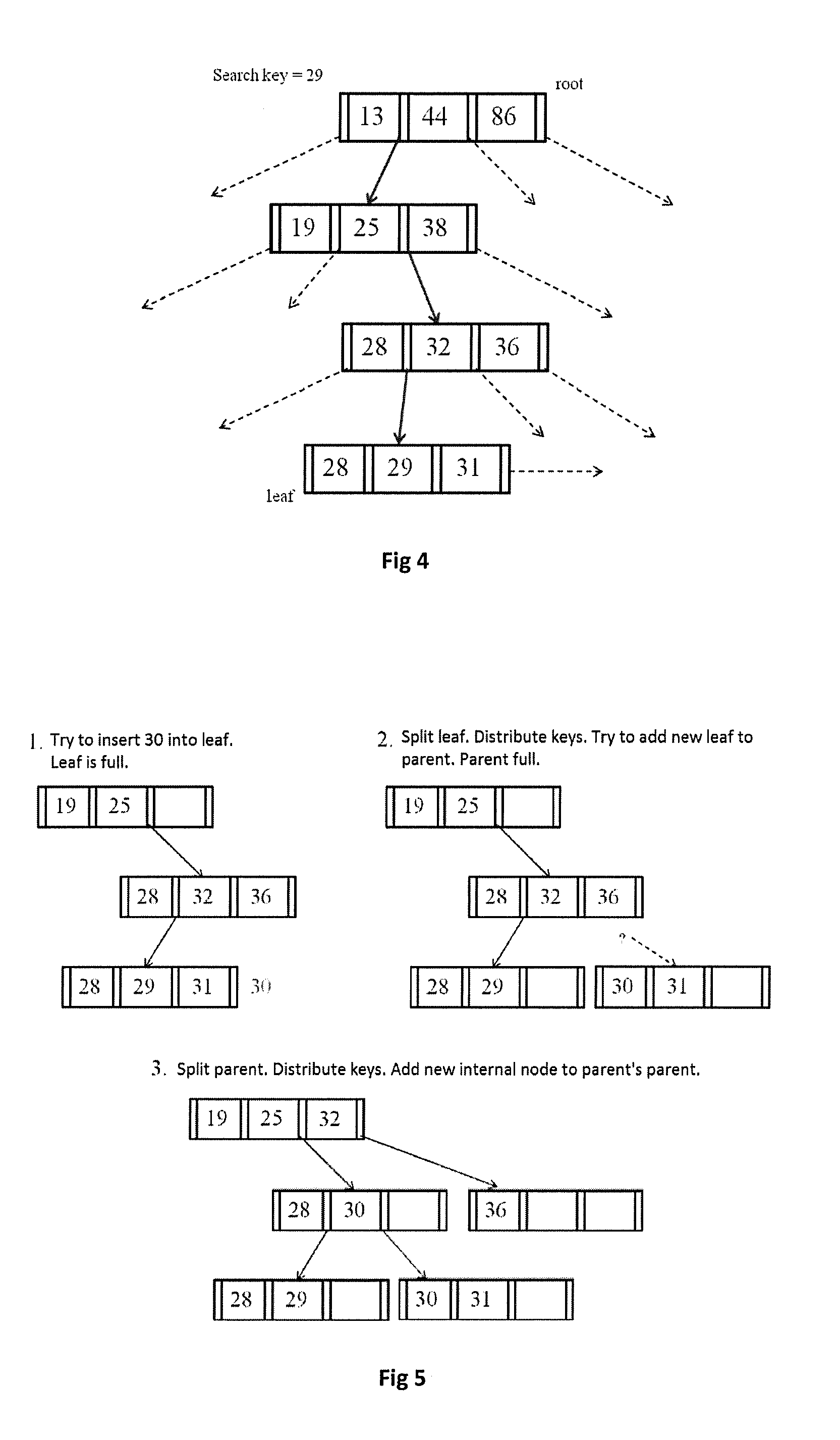
InactiveUS20130297613A1Fast executionLessDigital data processing detailsSpecial data processing applicationsOne passTheoretical computer science
The present invention is a fast indexing technique that builds an indexing structure based on multi-level key ranges typically for large data storage systems. The invention is explained based on the B+-tree. It is designed to reside in main memory. Point searches and range searches are helped by early termination of searches for non-existent data. Range searches can be processed depth-first or breath-first. One group of multiple searches can be processed with one pass on the indexing structure to minimize total cost. Implementation options and strategies are explained to show the flexibility of this invention for easy adaption and high efficiency. Each branch of any level has exact and clear key boundaries, so that it is very easy to build or cache partial index for various purposes. The inventive indexing structure can be tuned to speed up queries directed at popular ranges of index or index ranges of particular interest to the user.
Owner:MONMOUTH UNIVERSITY
Network configuration manager
InactiveUS7150037B2Fast executionDigital data processing detailsUnauthorized memory use protectionPasswordEngineering
Owner:INT BUSINESS MASCH CORP
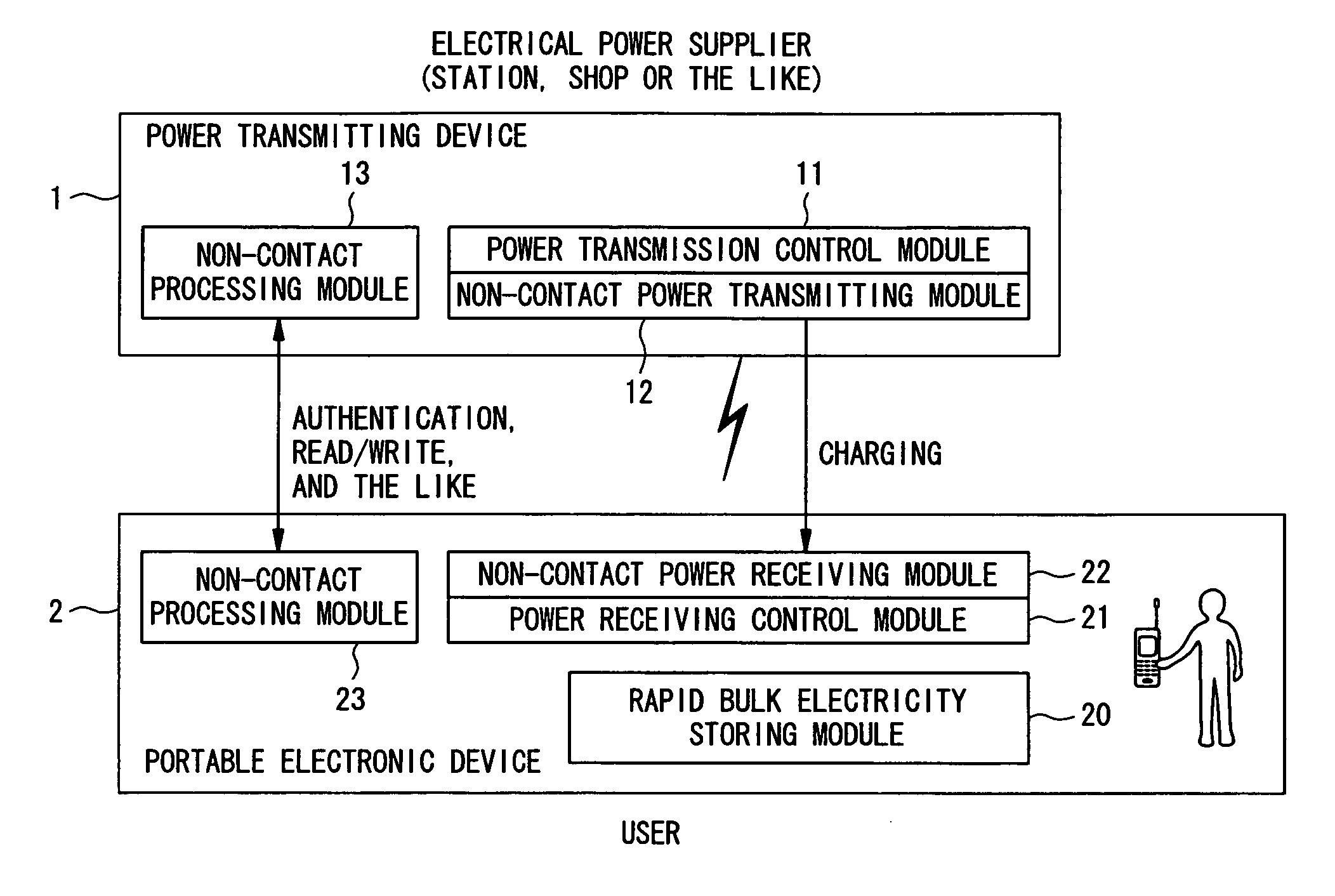
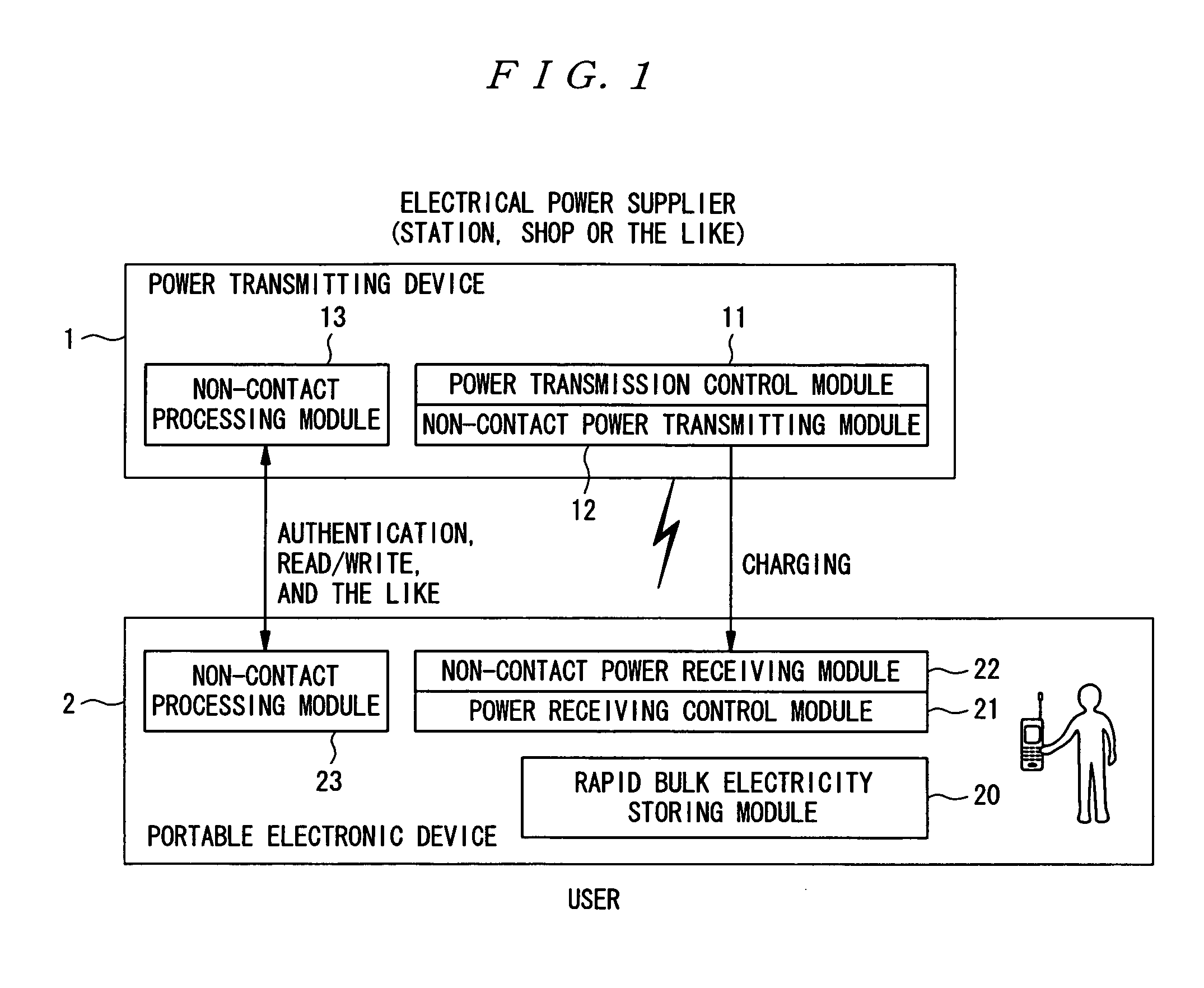
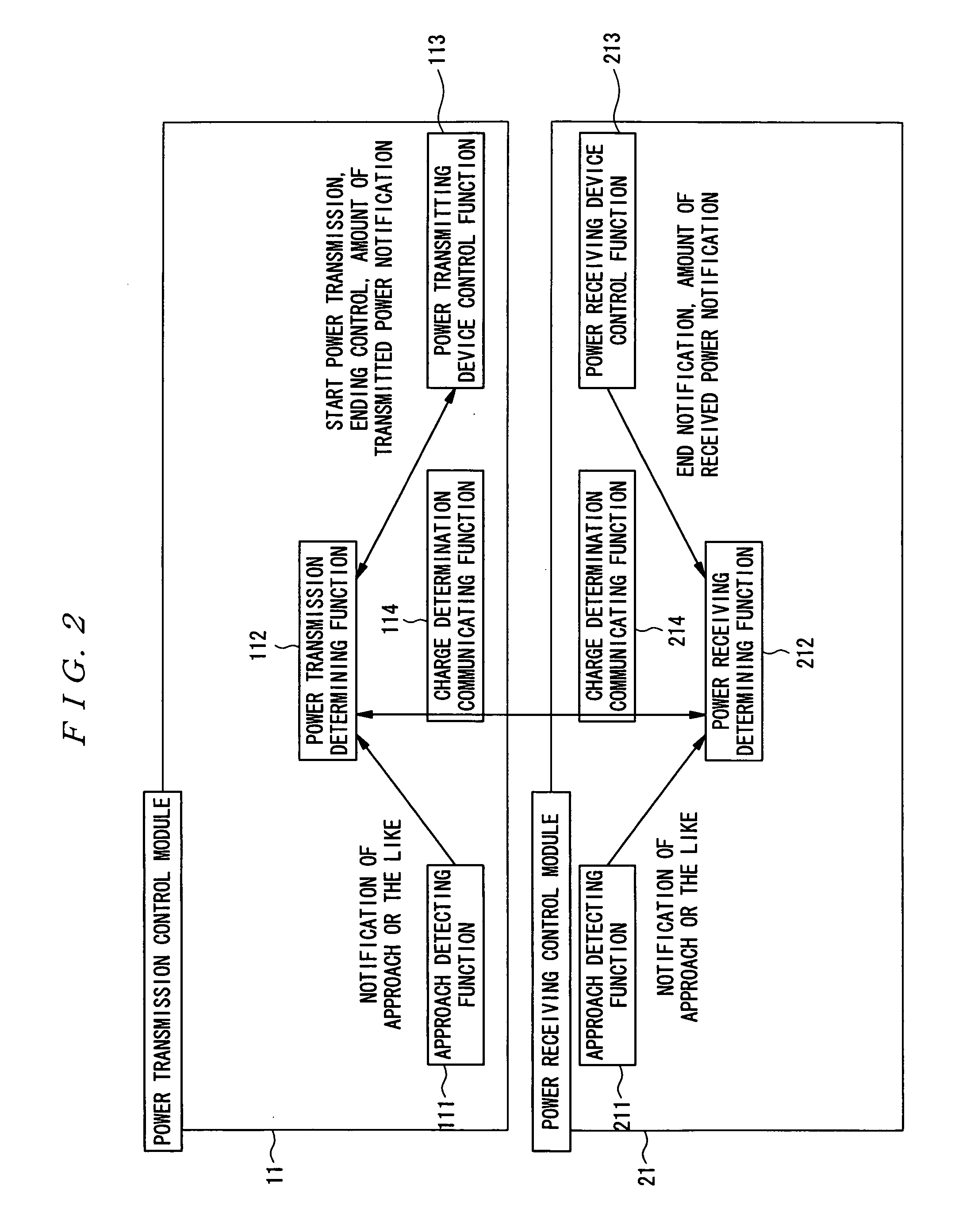
Power transmitting device, power receiving device, authentication/billing proxy device, electrical charging system, power transmitting method, power receiving method and electrical charging method
InactiveUS20060287763A1Reduce loadFast executionElectromagnetic wave systemFinanceElectric power transmissionElectricity
To realize charging while in non-contact processing operation for the purpose other than charging. An approach of a portable electronic device 2 with a rapid bulk electricity storing module 20, which is a chargeable power source, is detected at the side of a power transmitting device 1, and power transmission for charging the rapid bulk electricity storing module 20 is executed in response to the detection of the approach. A power source can be charged in operation for non-contact authentication which is executed when a device approaches an authentication device.
Owner:NTT DOCOMO INC
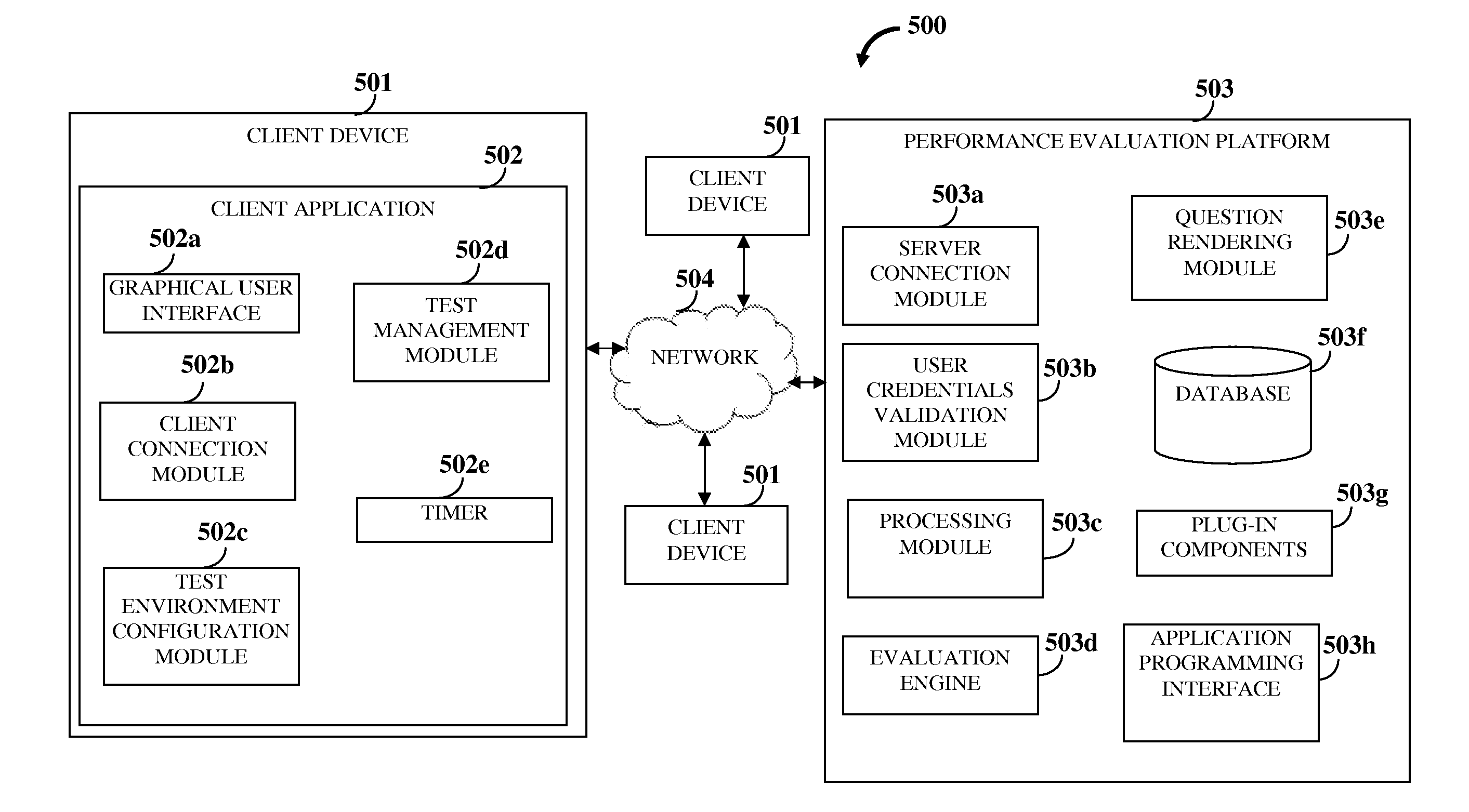
Performance Evaluation System
InactiveUS20120124559A1Fast executionFast evaluationMultiple digital computer combinationsElectrical appliancesClient-sideSelf adaptive
A computer implemented method and system for concurrently evaluating performance of multiple users in one or more tests provides a performance evaluation platform that is accessible to a client application on each of multiple client devices via a network. The client application manages interaction of the users with the performance evaluation platform via the network. The client application, in communication with the performance evaluation platform, configures an adaptive test environment at each of the client devices of the users based on one or more tests selected by the users. The client application on each of the client devices loads the selected tests from the performance evaluation platform and transmits solution responses to the selected tests acquired from the users to the performance evaluation platform. The performance evaluation platform configures processing elements for concurrently processing the solution responses and concurrently evaluates the performance of the users in the selected tests.
Owner:KONDUR SHANKAR NARAYANA
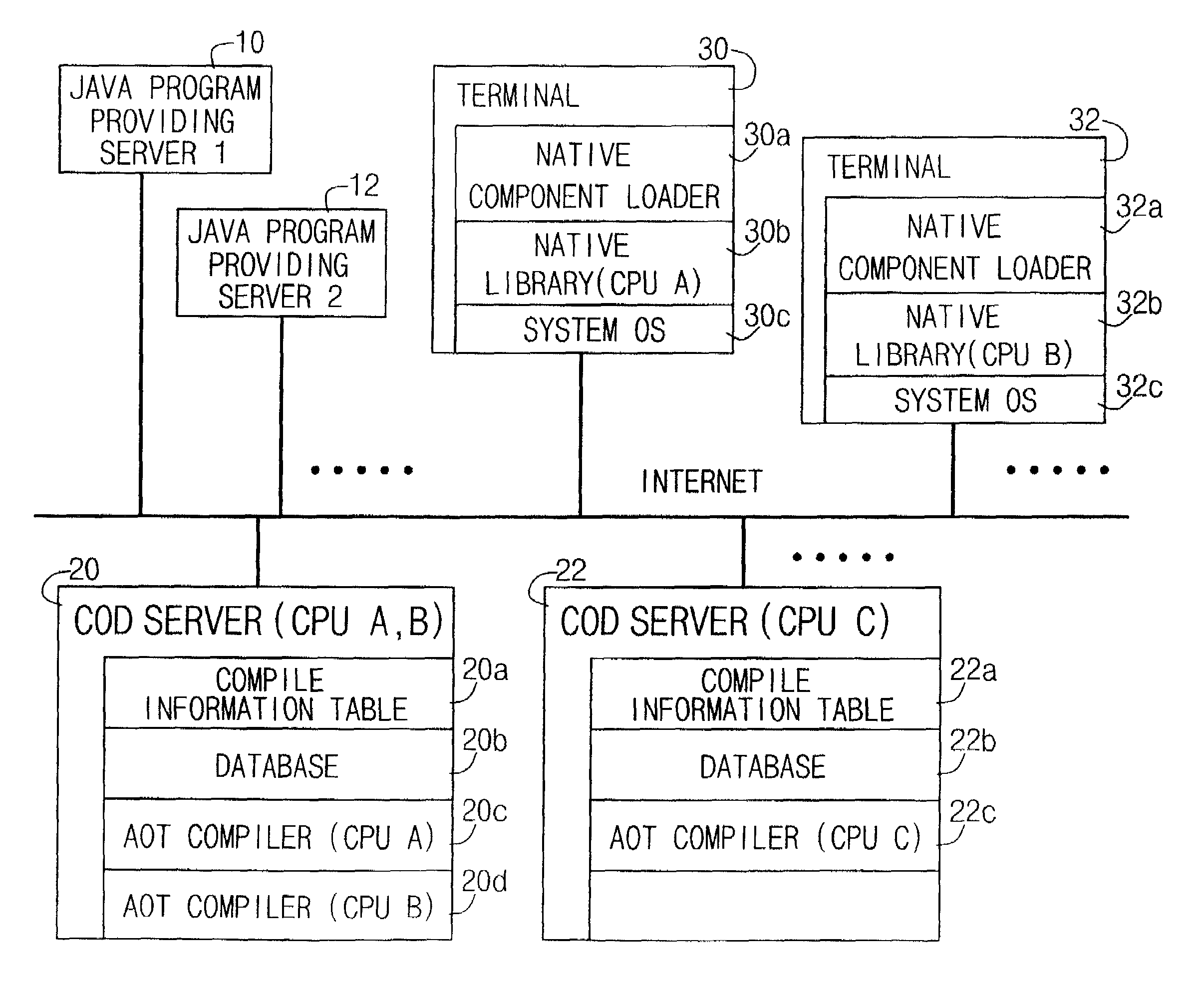
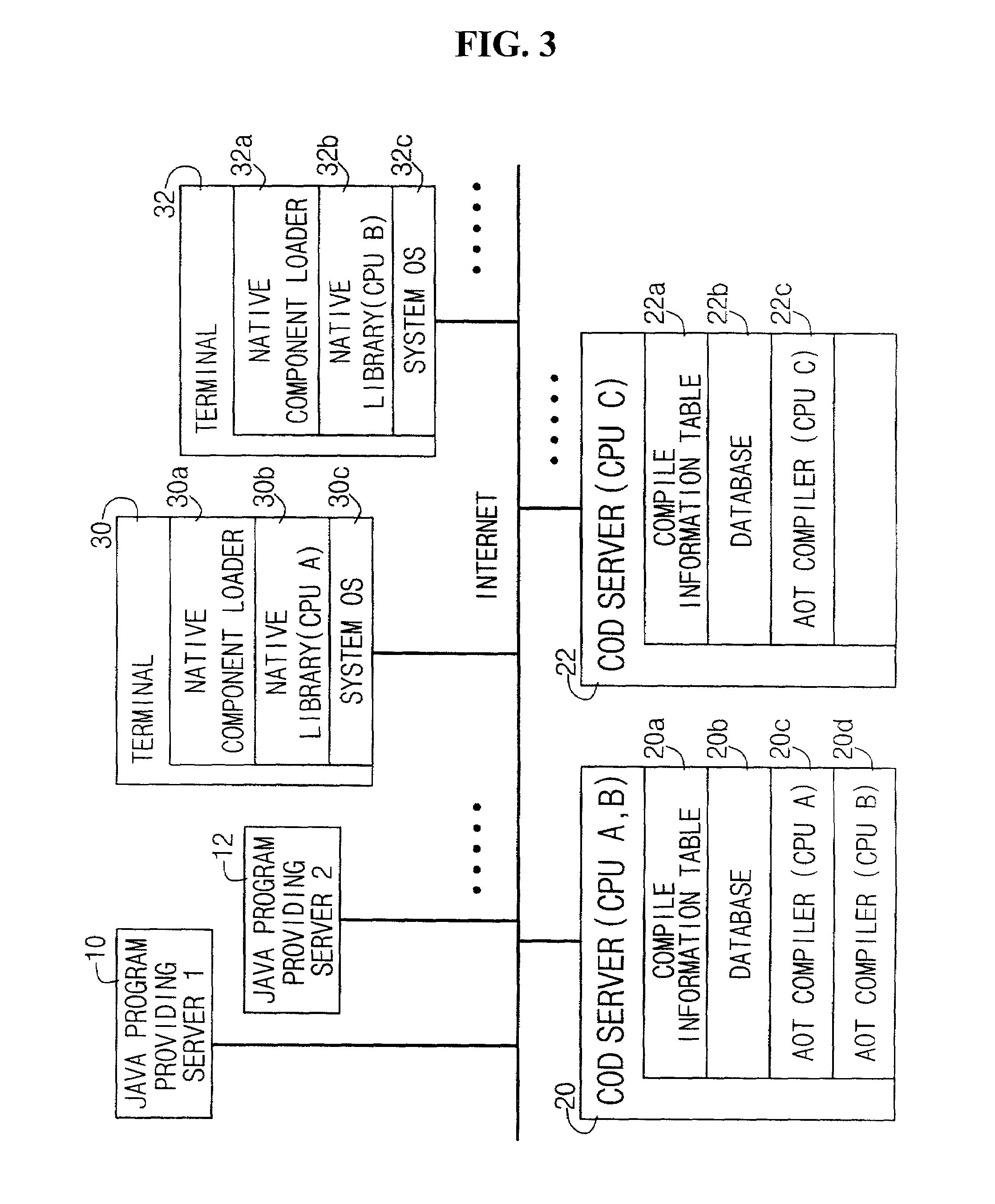
JAVA compile-on-demand service system for accelerating processing speed of JAVA program in data processing system and method thereof
ActiveUS7174544B2Reduce performanceHigh speedData processing applicationsProgram loading/initiatingData processing systemProgramming language
A JAVA program language compile-on-demand service system and method for accelerating a processing speed of a JAVA program in a data processing system having a relatively low performance is provided. The JAVA COD service system compiles a JAVA class file to be executed in a data processing system into a pattern which can be executed more speedily on the data processing system, and then transmits the compiled result, upon a request of the data processing system connected via a network in order to execute the JAVA program at a relatively faster speed. The system includes JAVA program providing servers, data processing systems, and a compile-on-demand server for receiving a service request, downloading a requested JAVA class file, compiling the downloaded JAVA class file, and transmitting the compiled result.
Owner:9FOLDERS INC
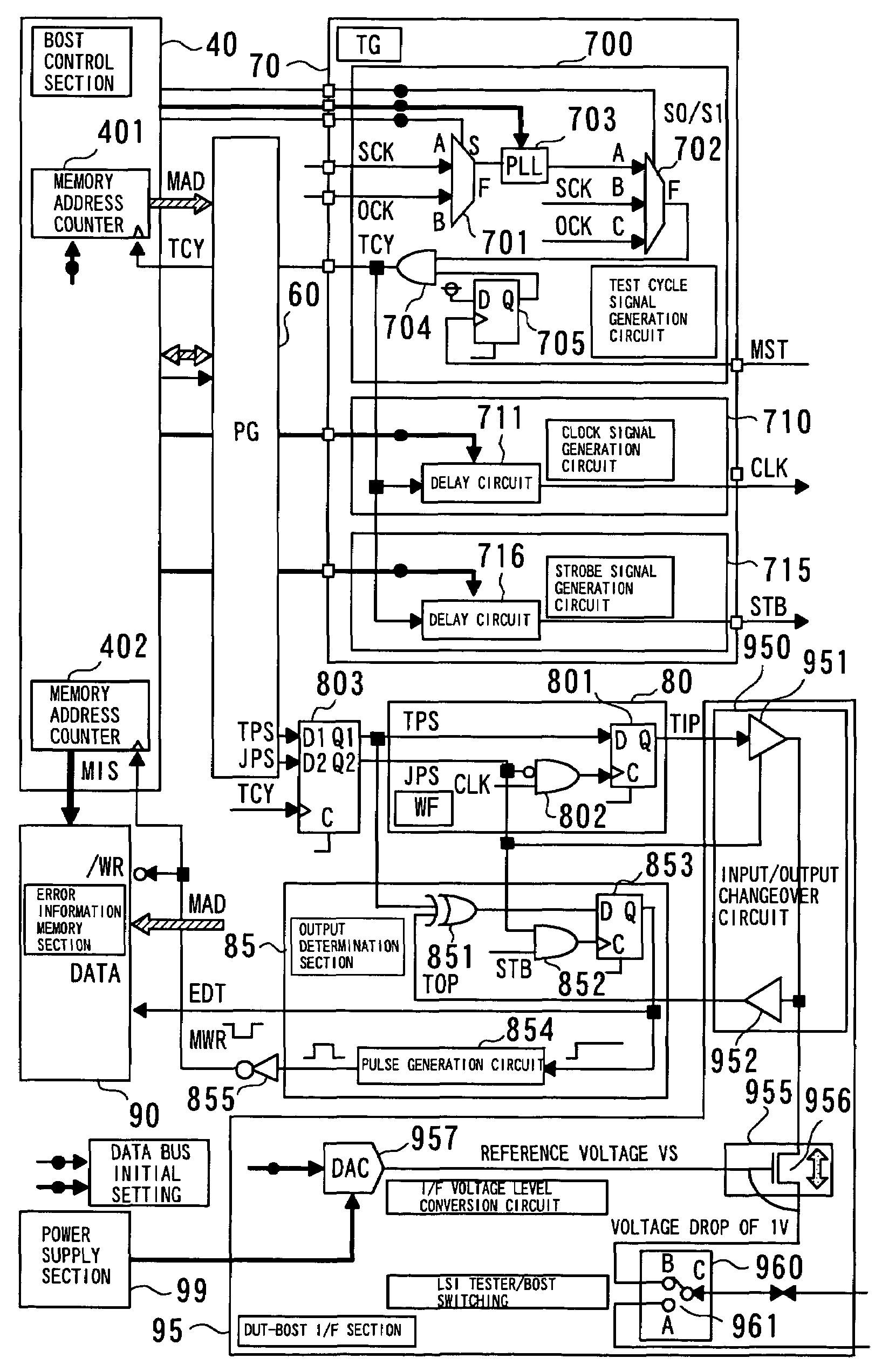
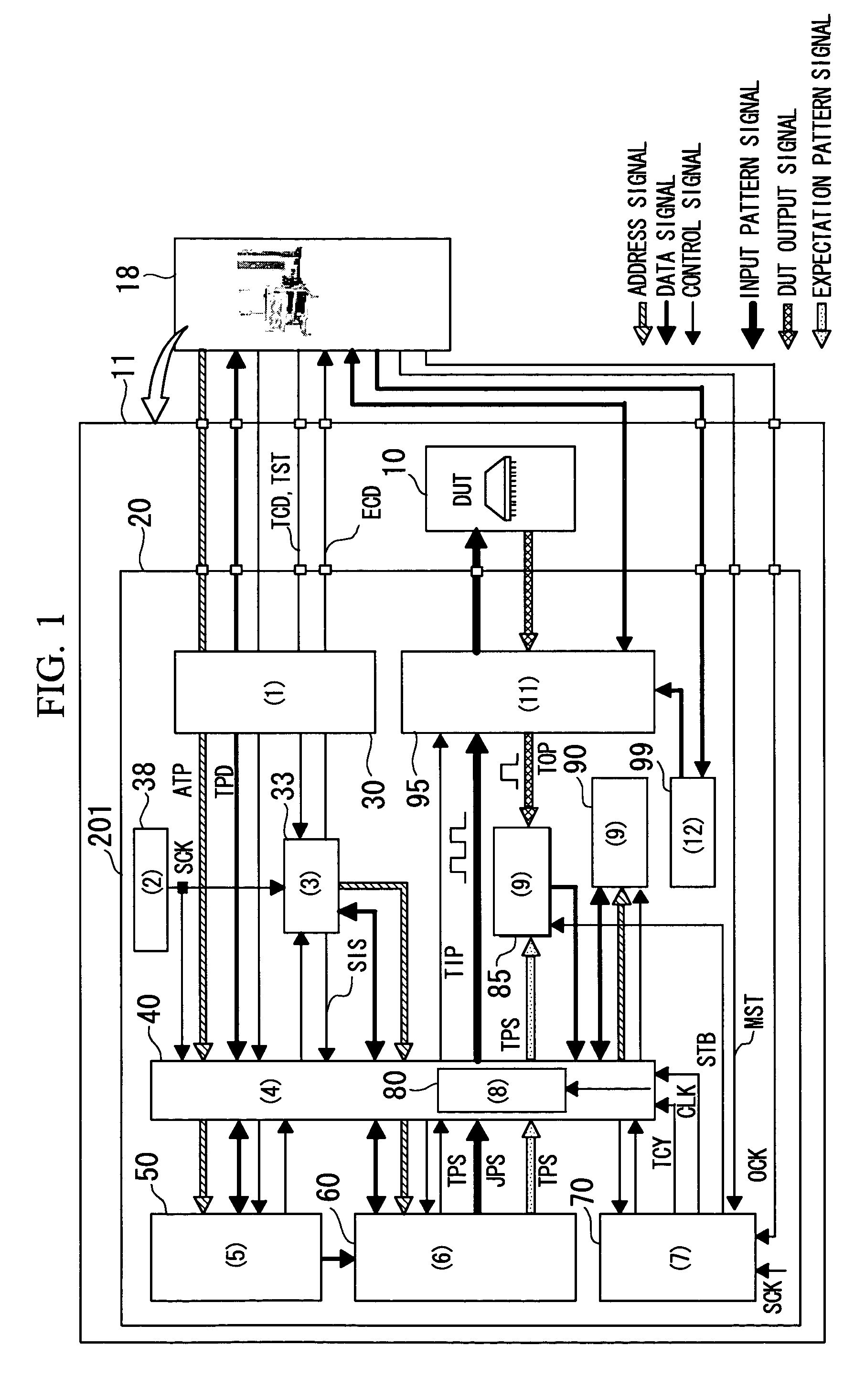
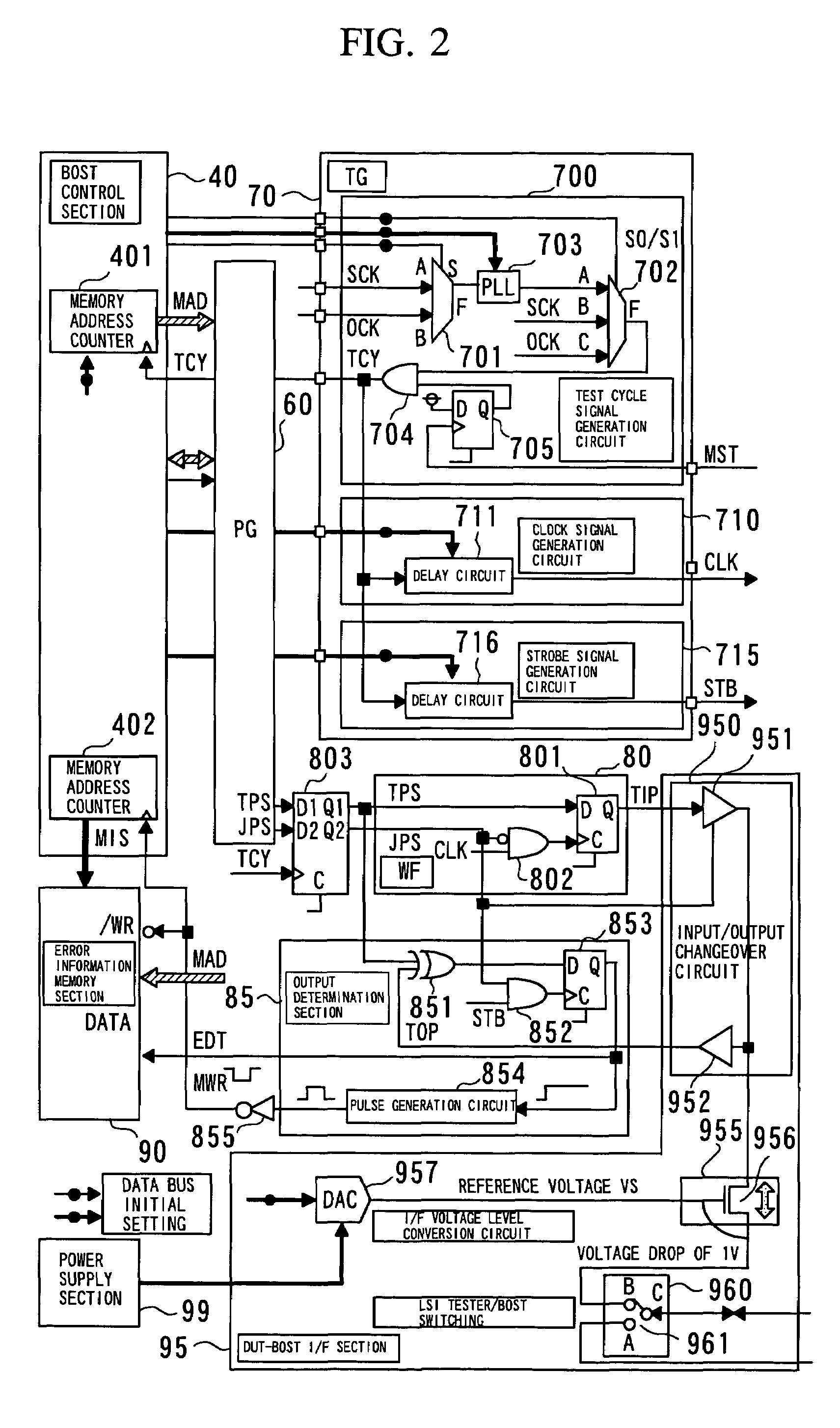
Apparatus for testing semiconductor integrated circuit
InactiveUS7058865B2Quickly testImprove scalabilityAnalog circuit testingDigital circuit testingSignal onIntegrated circuit
An apparatus for testing a semiconductor integrated circuit has a test circuit board and an ancillary test device. The ancillary test device can test a digital circuit. The ancillary test device has test pattern memory, a test pattern signal generator, and a control section for controlling an operation for the test pattern data selected from among the plurality of test pattern data sets stored in the test pattern memory and an operation for writing the selected test pattern data into the test pattern signal generator. The ancillary test device generates a test input pattern signal on the basis of test pattern data written in the test pattern signal generator and determines a test output pattern signal output from the semiconductor integrated circuit on the basis of the test input pattern signal, thereby testing a digital circuit.
Owner:RENESAS ELECTRONICS CORP
Lane change assist device
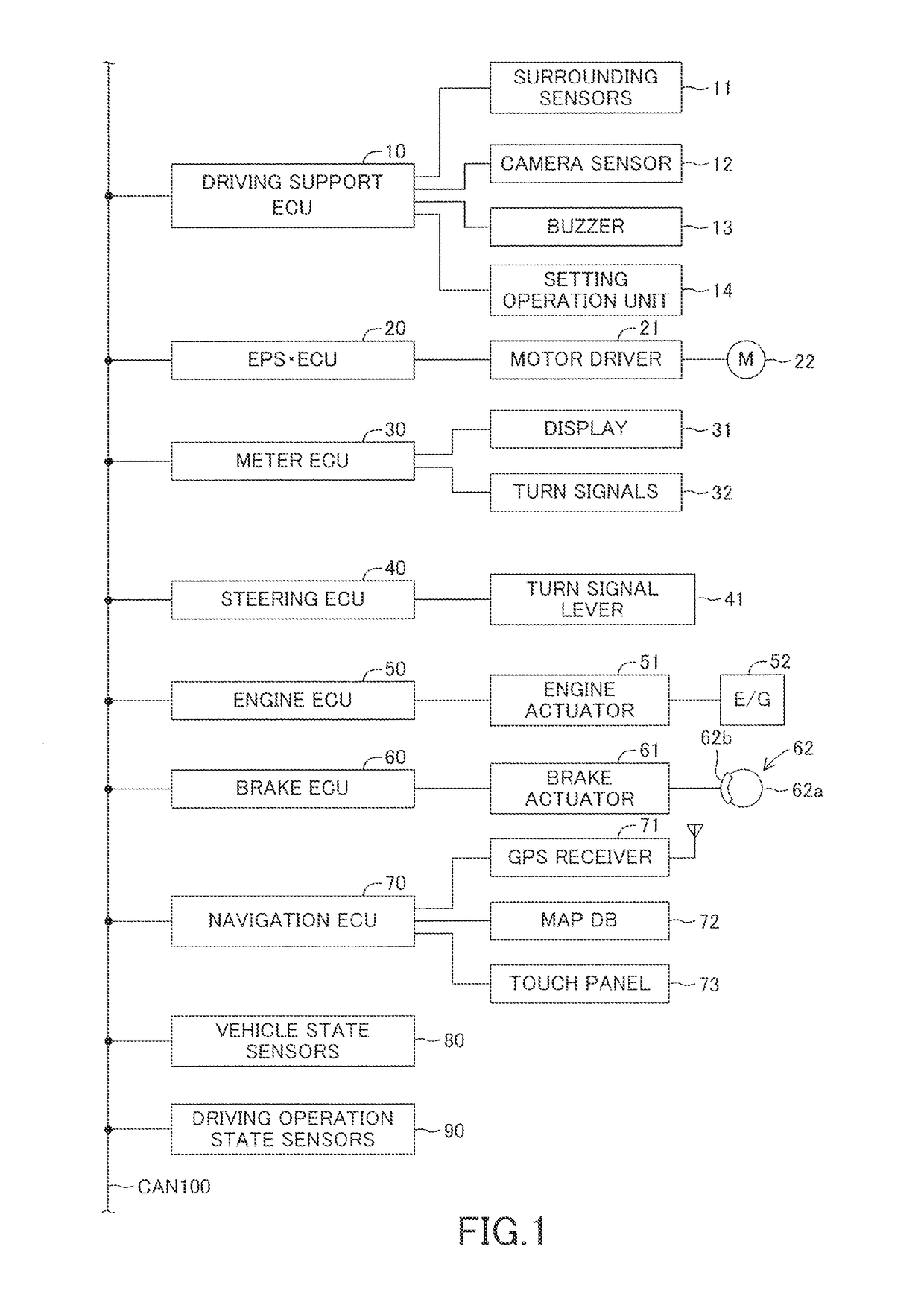
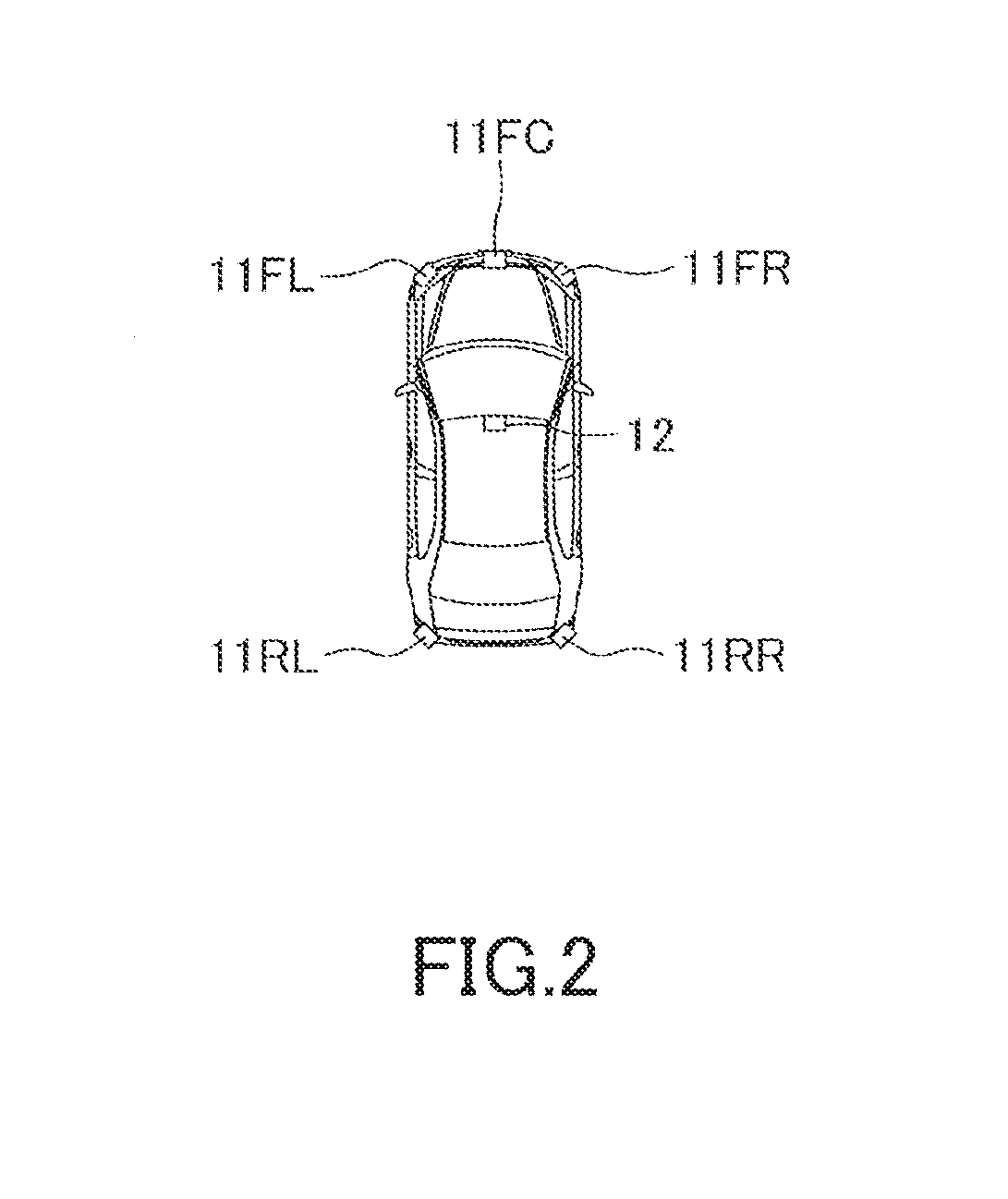
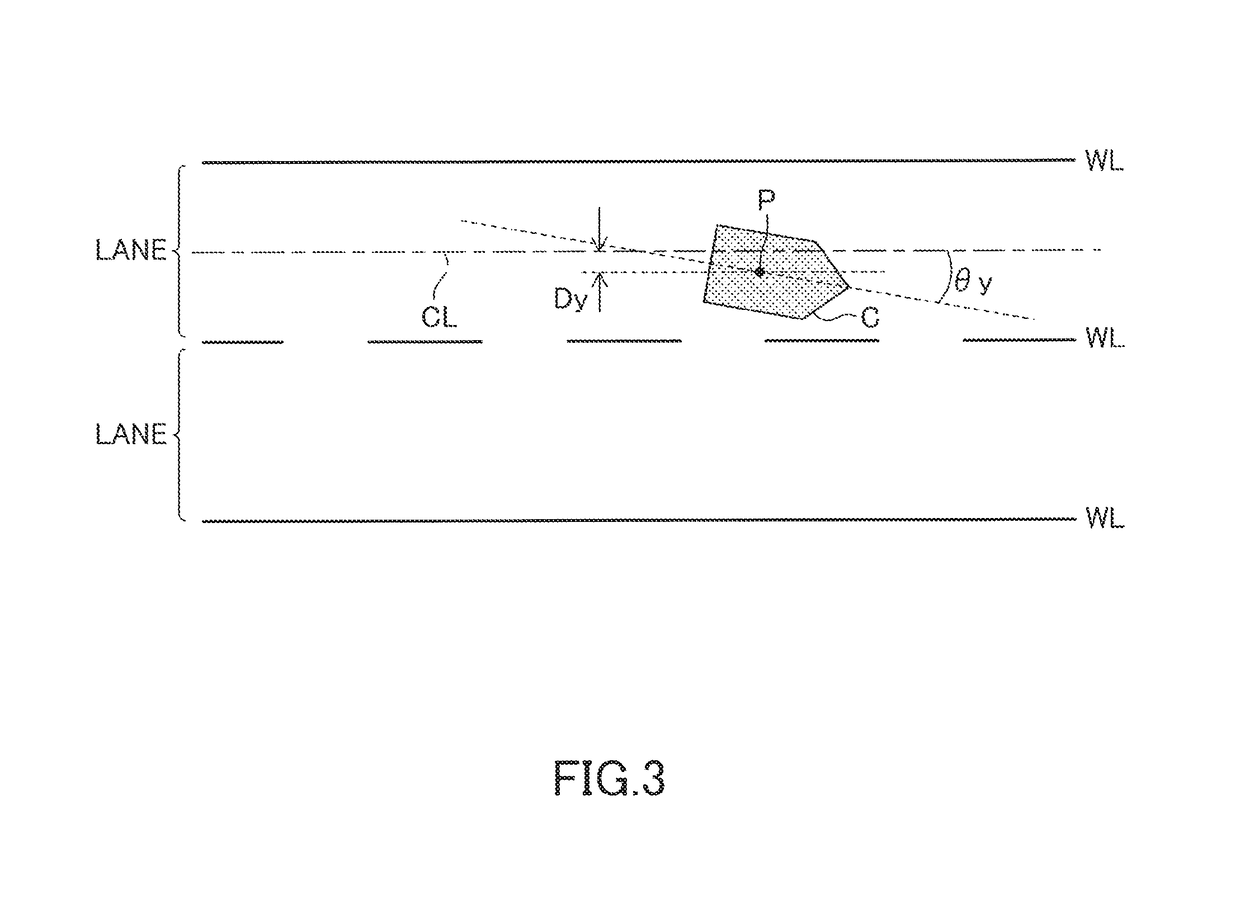
ActiveUS20180350242A1Fast executionAnti-collision systemsSteering partsAngular velocitySteering angle
A first limiter limits a first target steering angle correspondence value by a first steering angle correspondence value guard which defines the upper limit value of the steering angle correspondence value and is larger than a steering angle correspondence value guard at lane change time and limits a first target steering angular velocity correspondence value by a first steering angular velocity correspondence value guard which defines the upper limit value of the steering angular velocity correspondence value and is larger than a steering angular velocity correspondence value guard at lane change time. An actuator controller for first yaw angle return control which is configured to control an actuator to operate a steering wheel so that steering angle correspondence value becomes a first target steering angle correspondence value and a steering angular velocity correspondence value becomes a first target steering angular velocity correspondence value.
Owner:TOYOTA JIDOSHA KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com