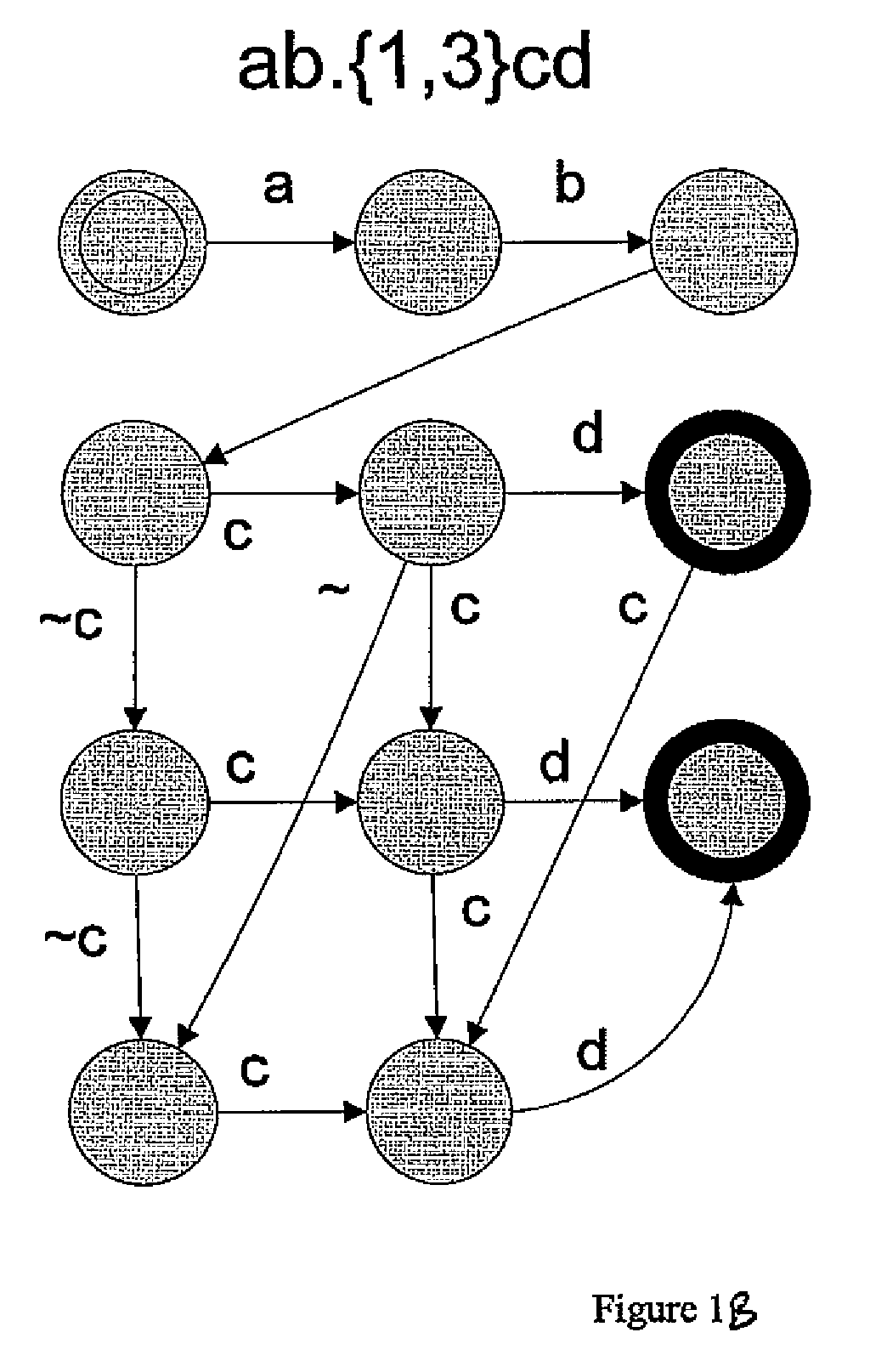
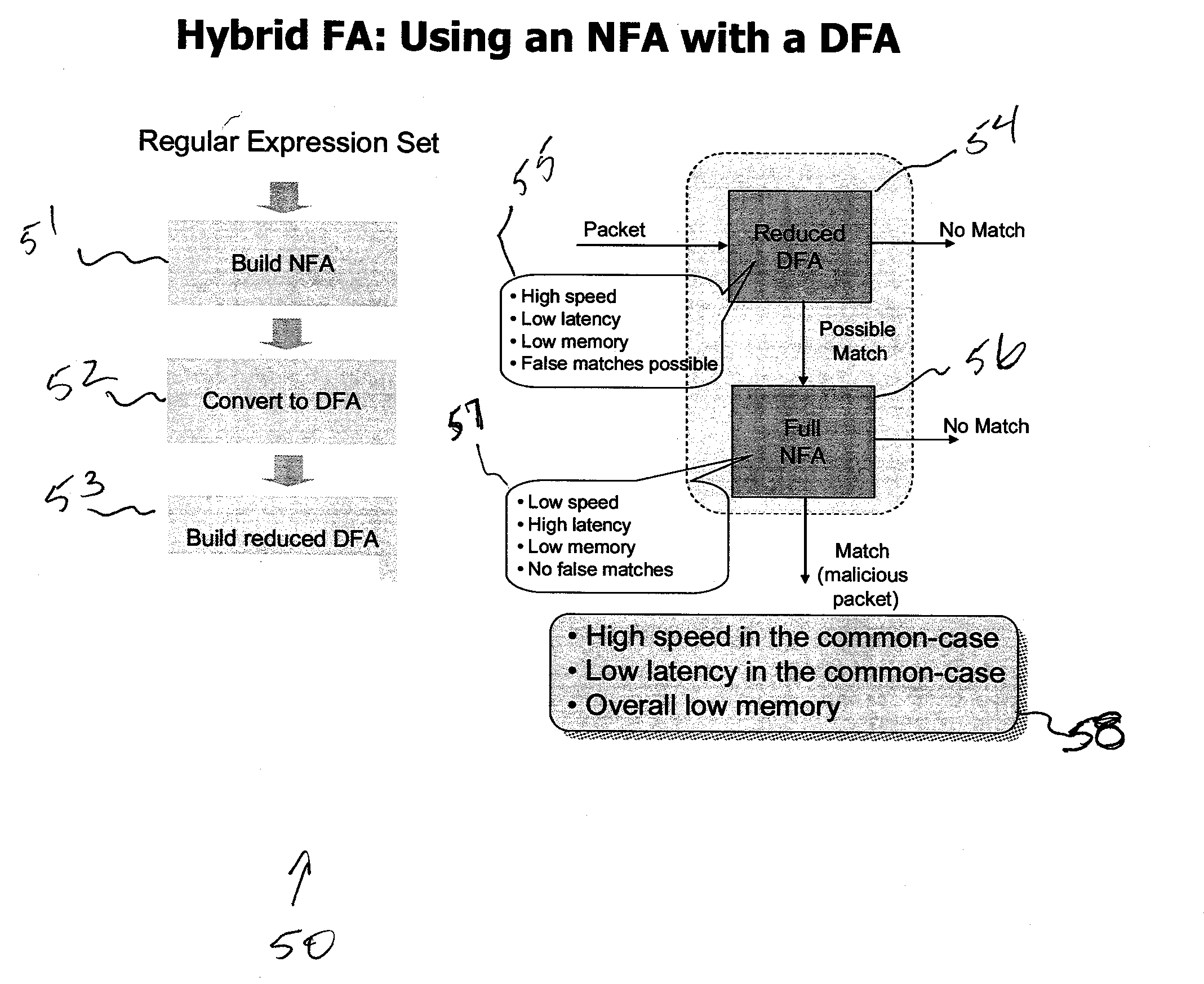
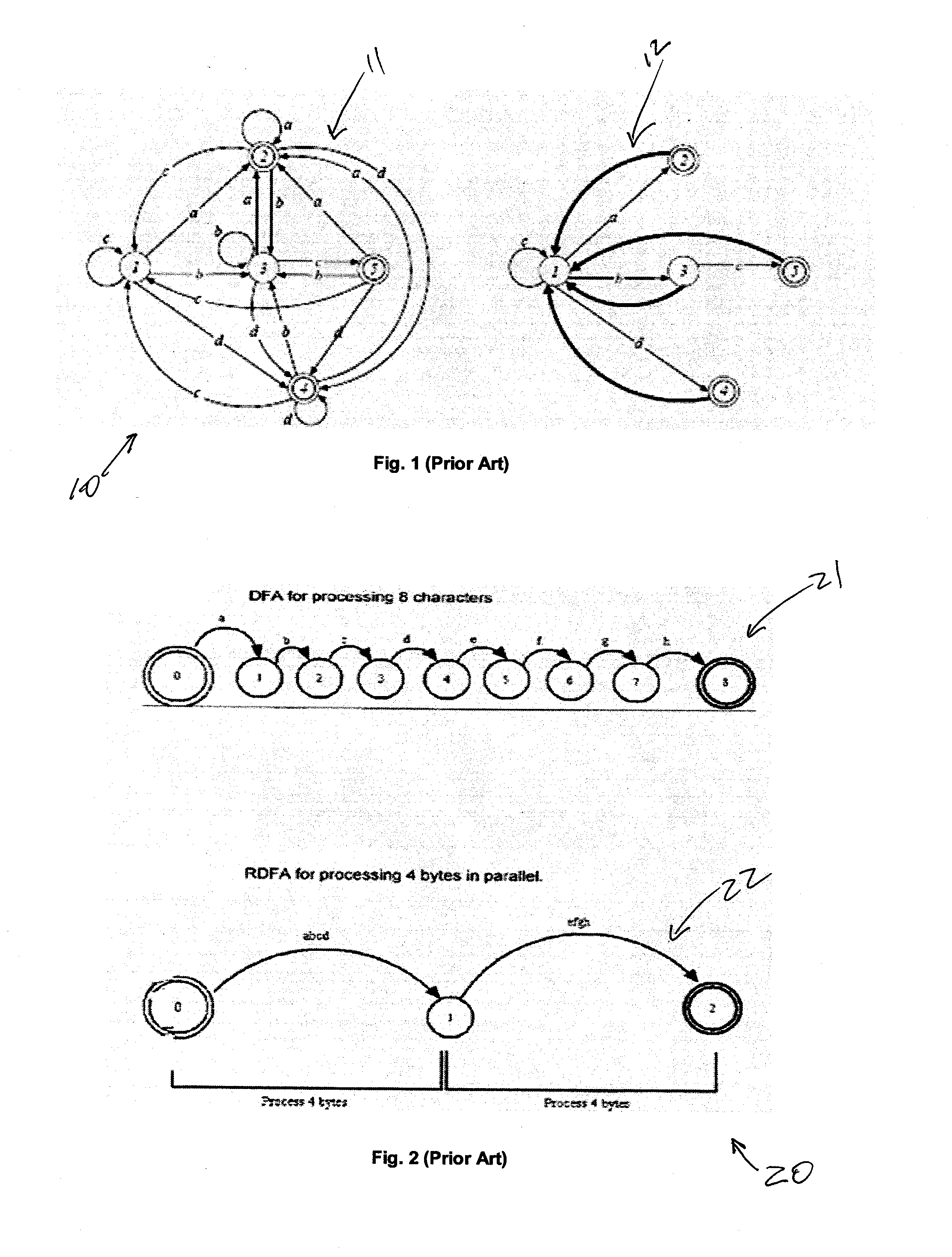
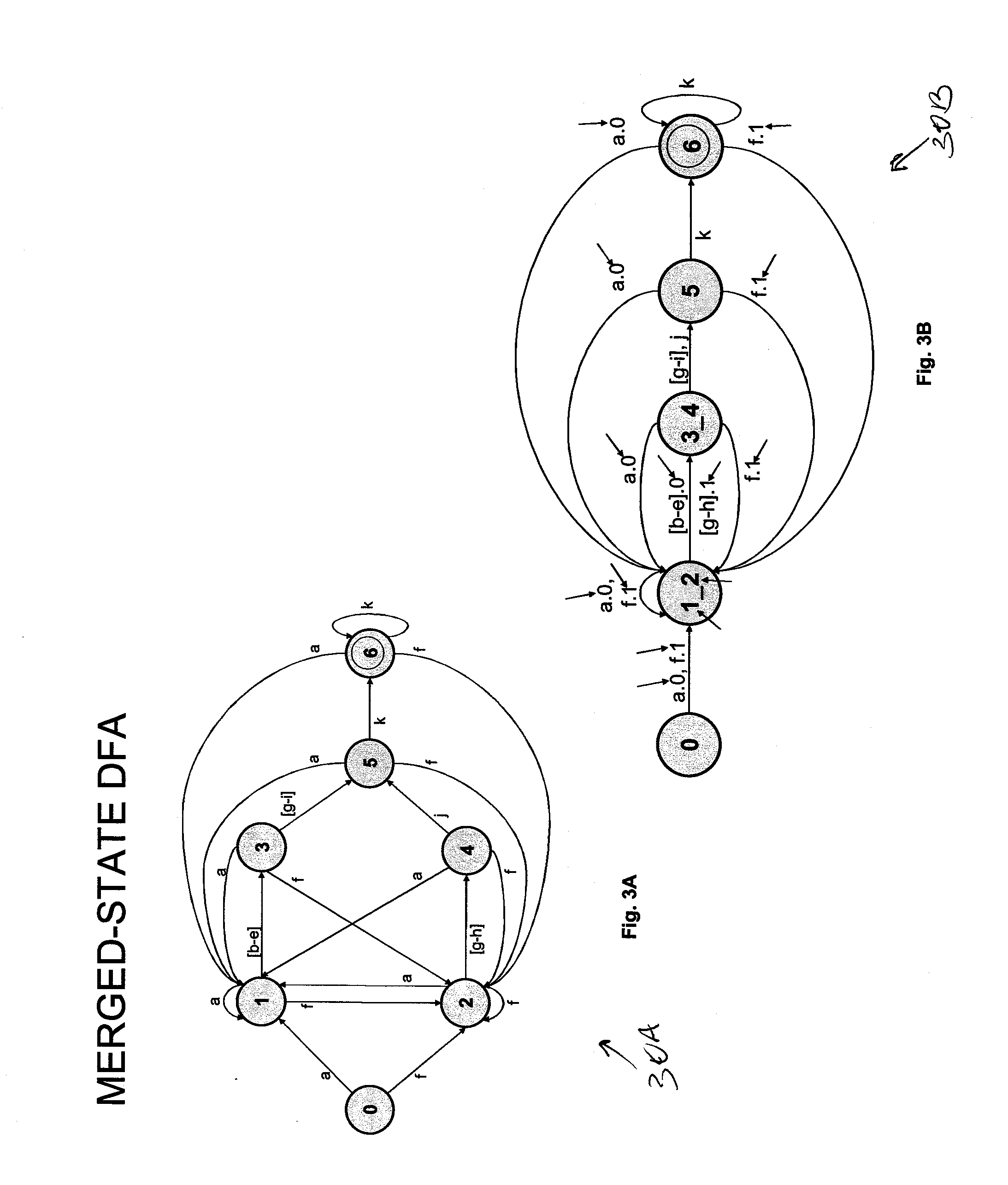
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
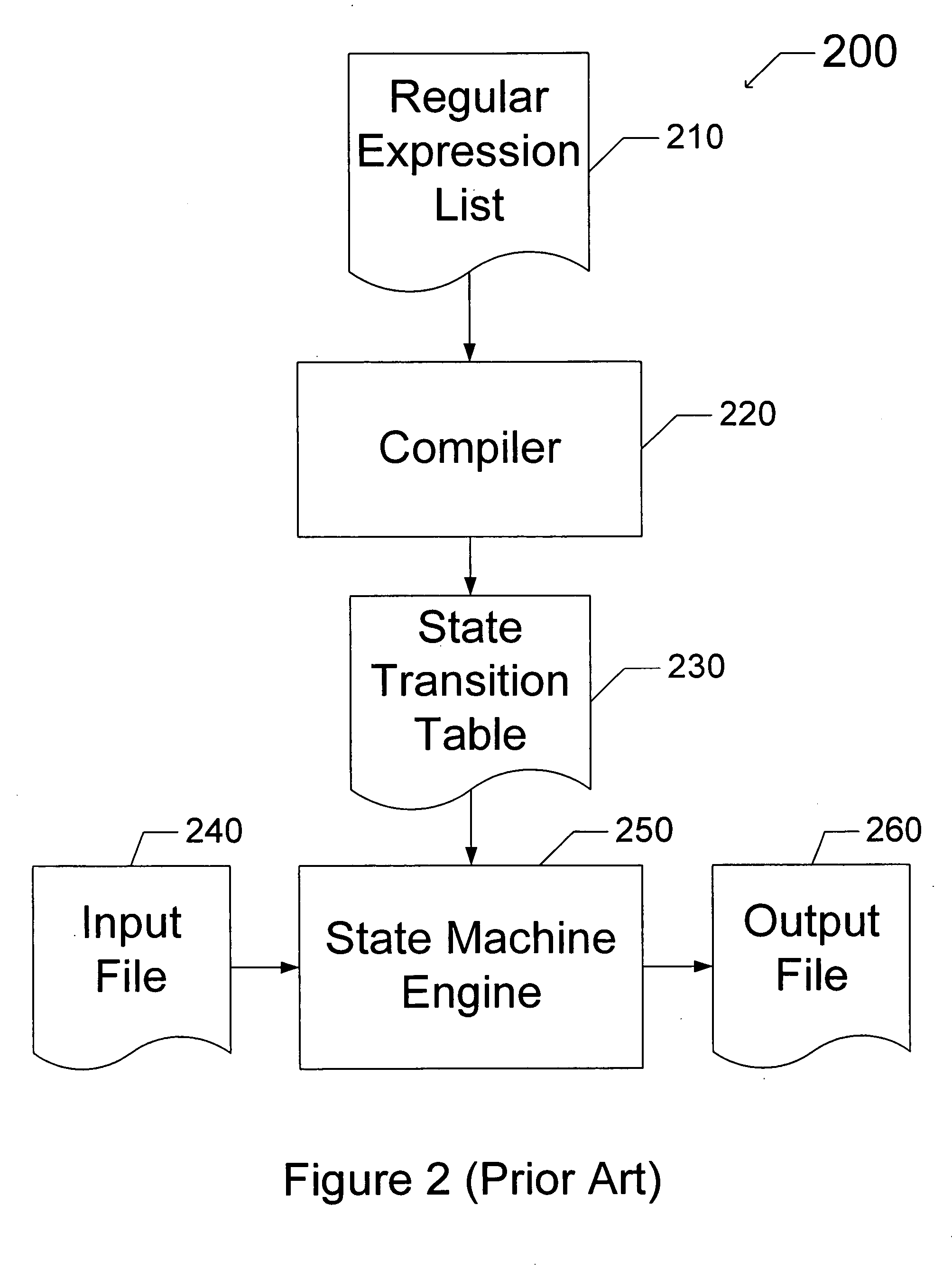
1686 results about "Regular expression" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
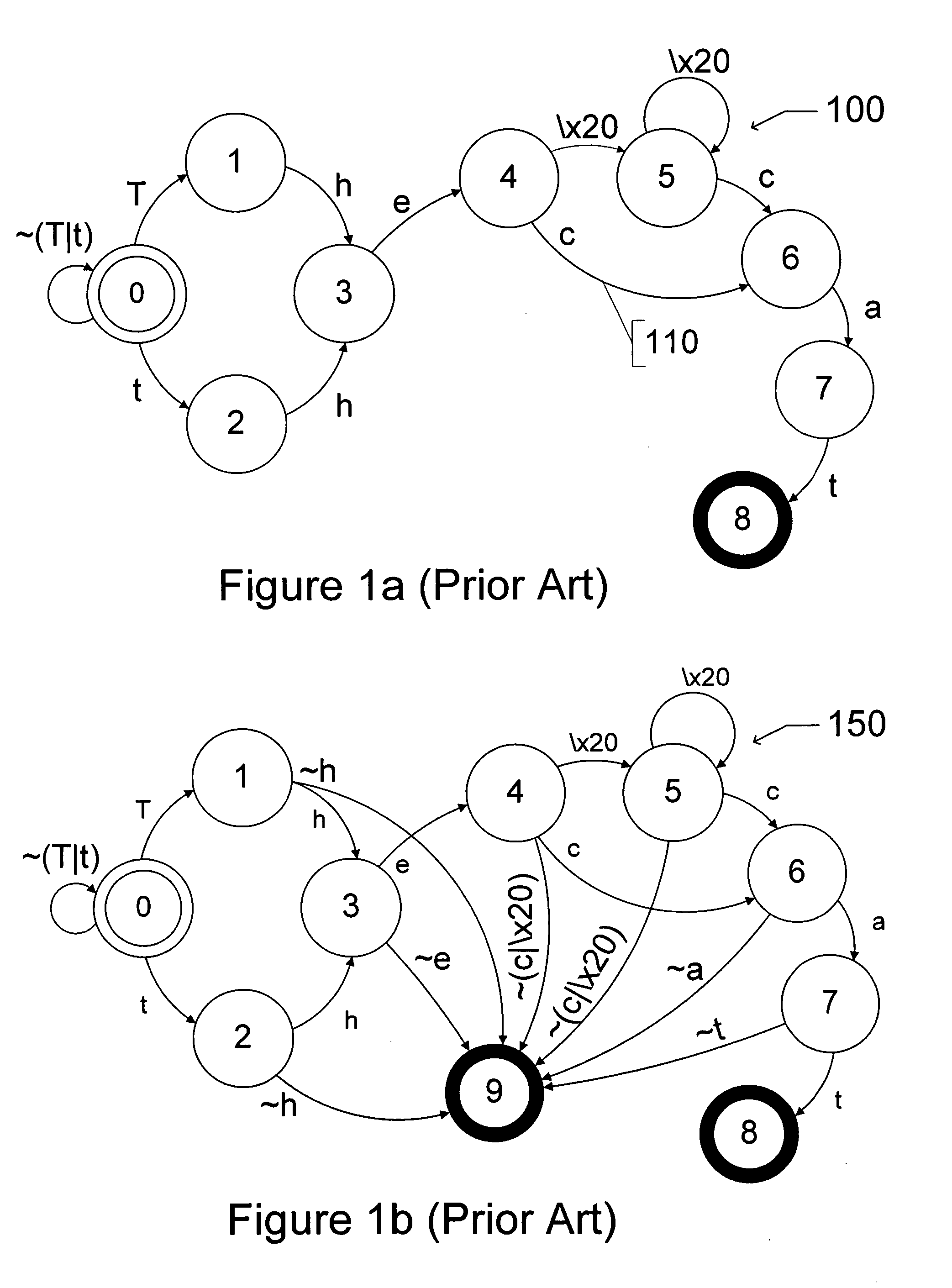
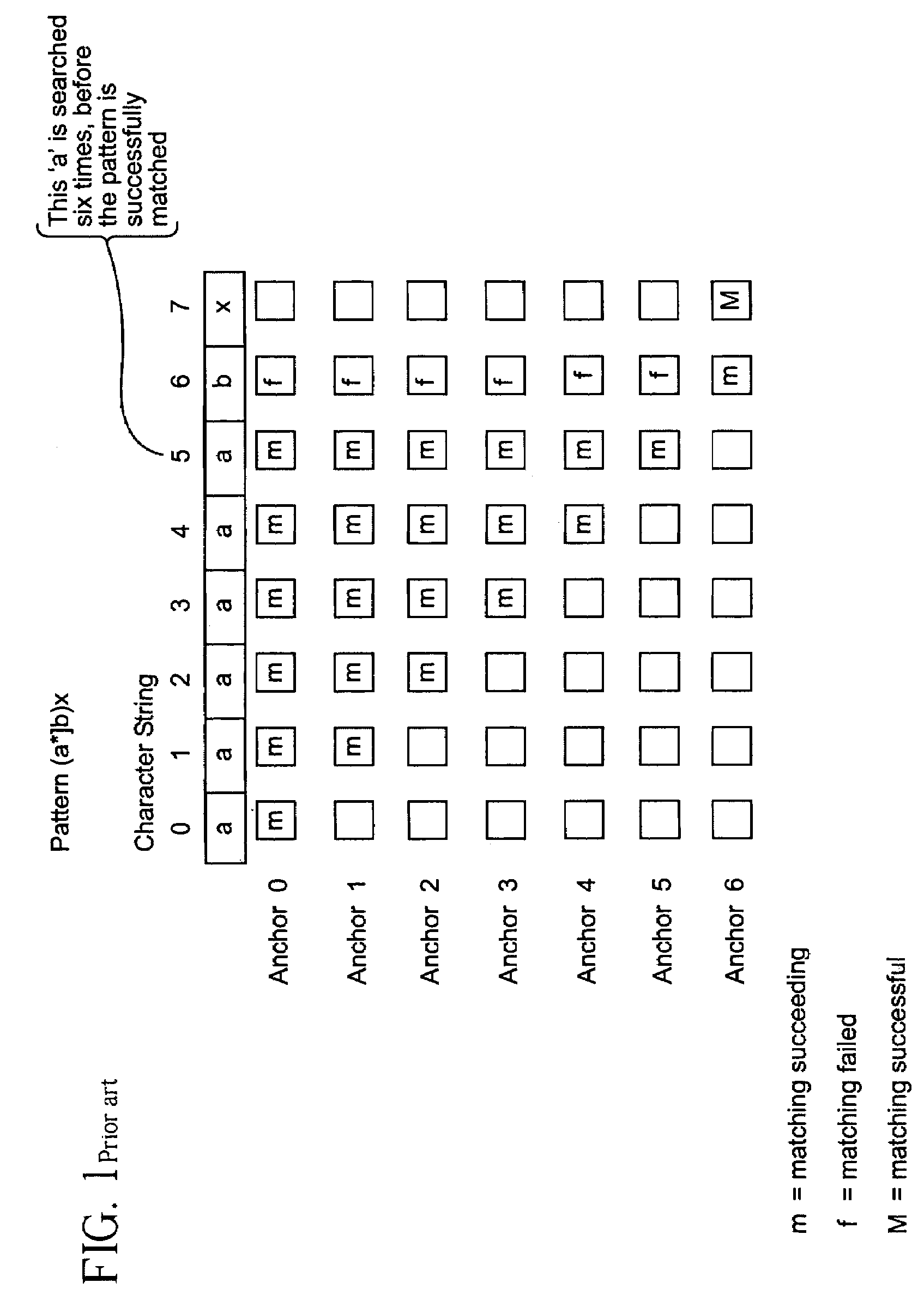
A regular expression, regex or regexp (sometimes called a rational expression) is a sequence of characters that define a search pattern. Usually such patterns are used by string searching algorithms for "find" or "find and replace" operations on strings, or for input validation. It is a technique developed in theoretical computer science and formal language theory.
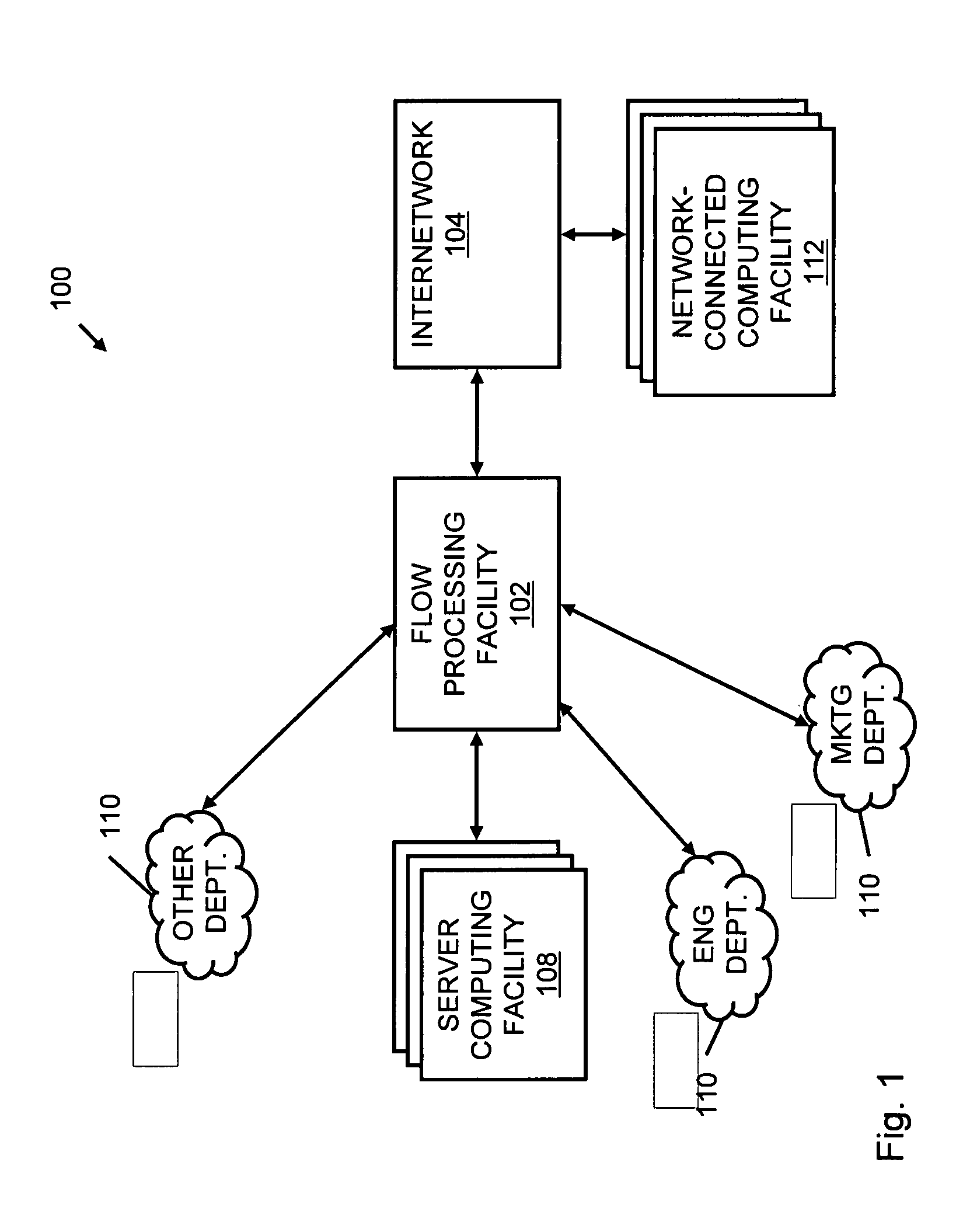
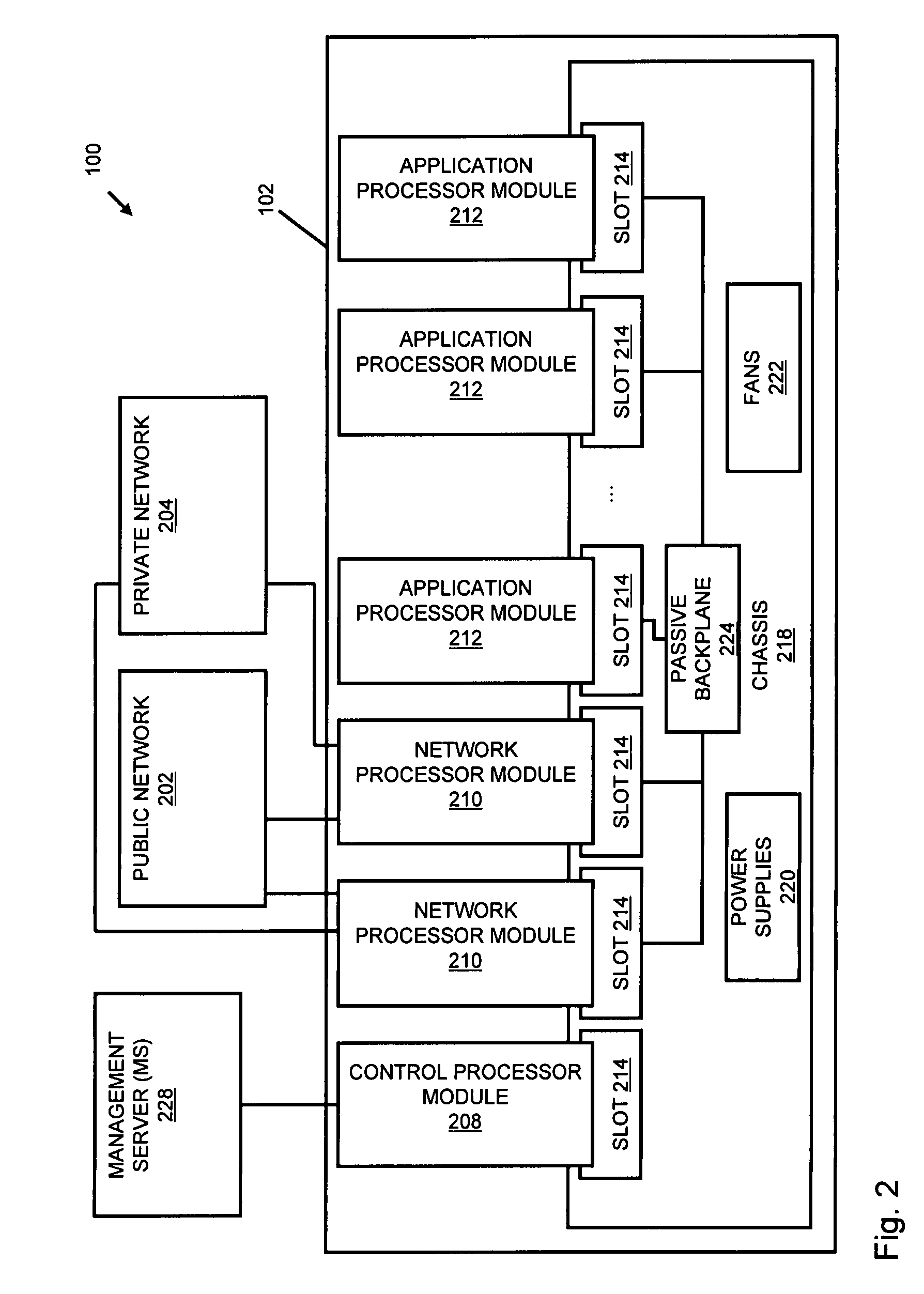
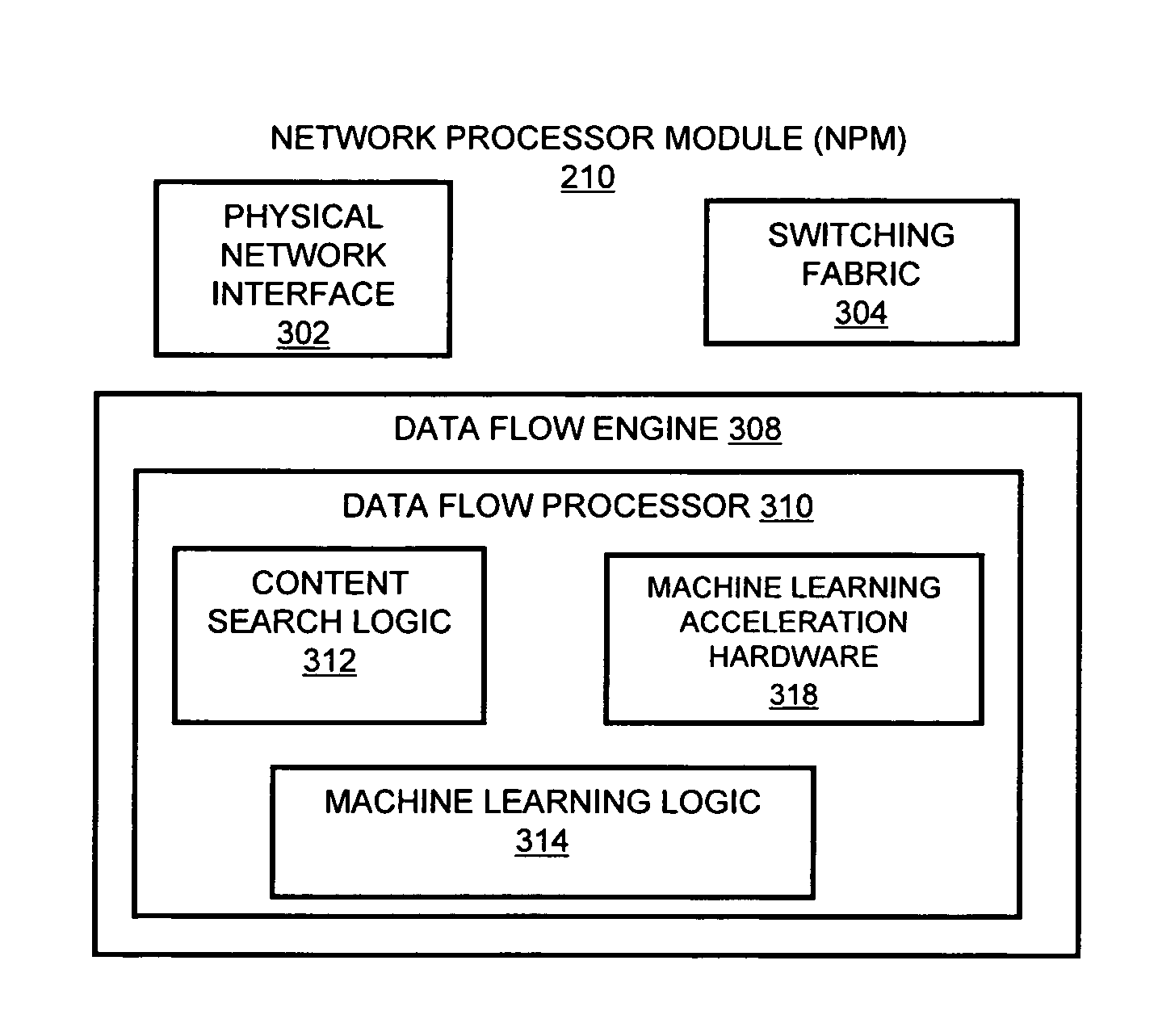
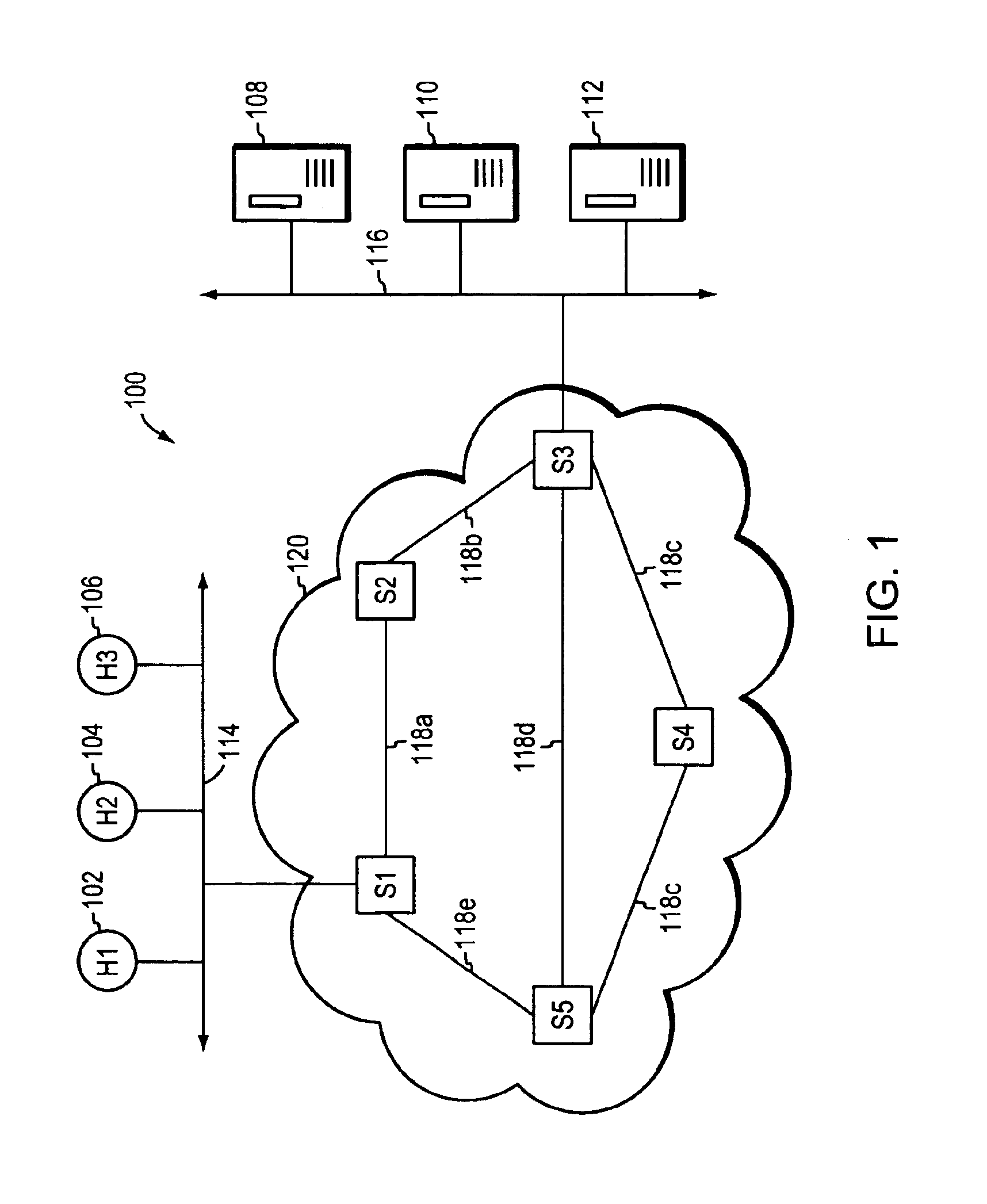
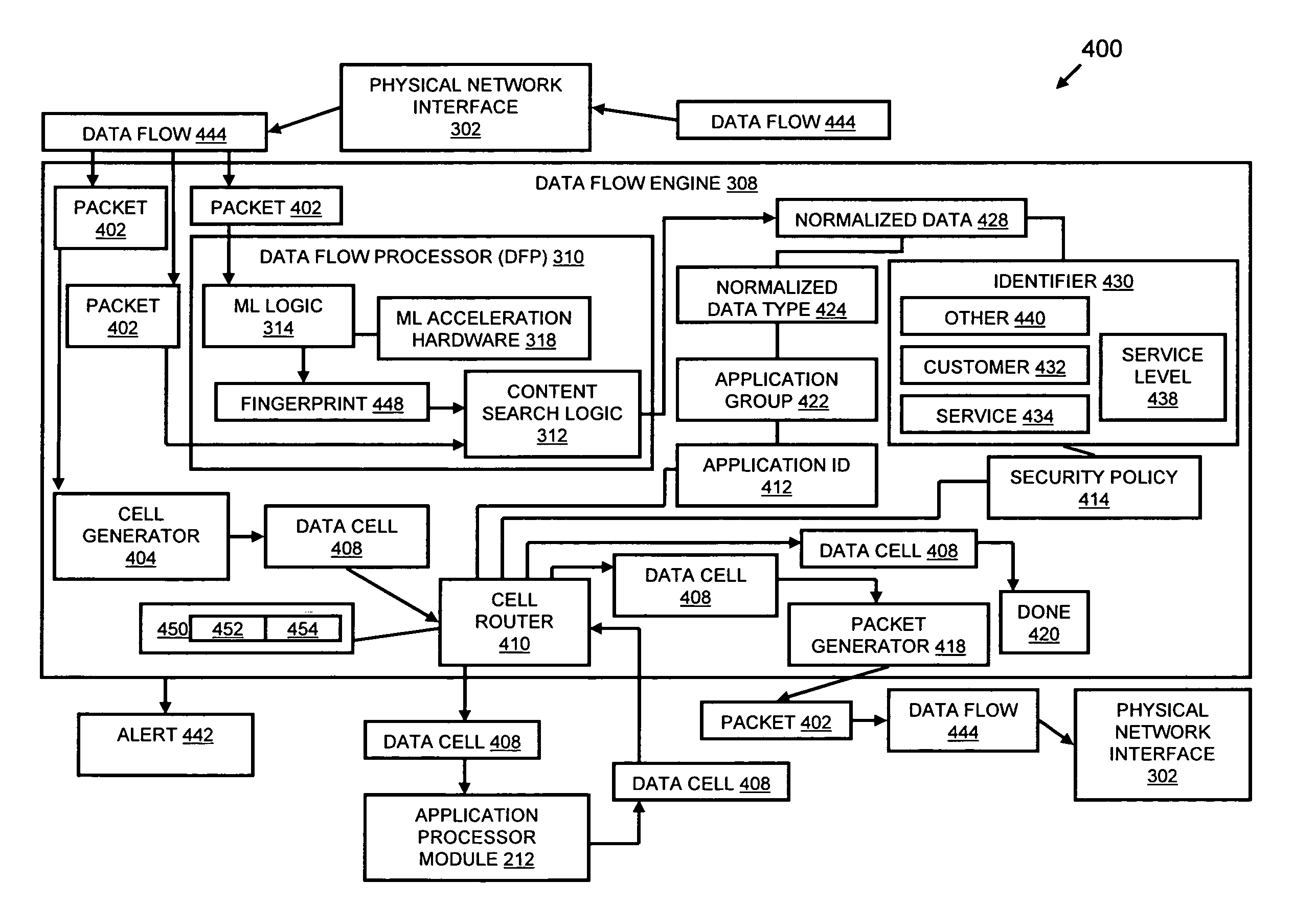
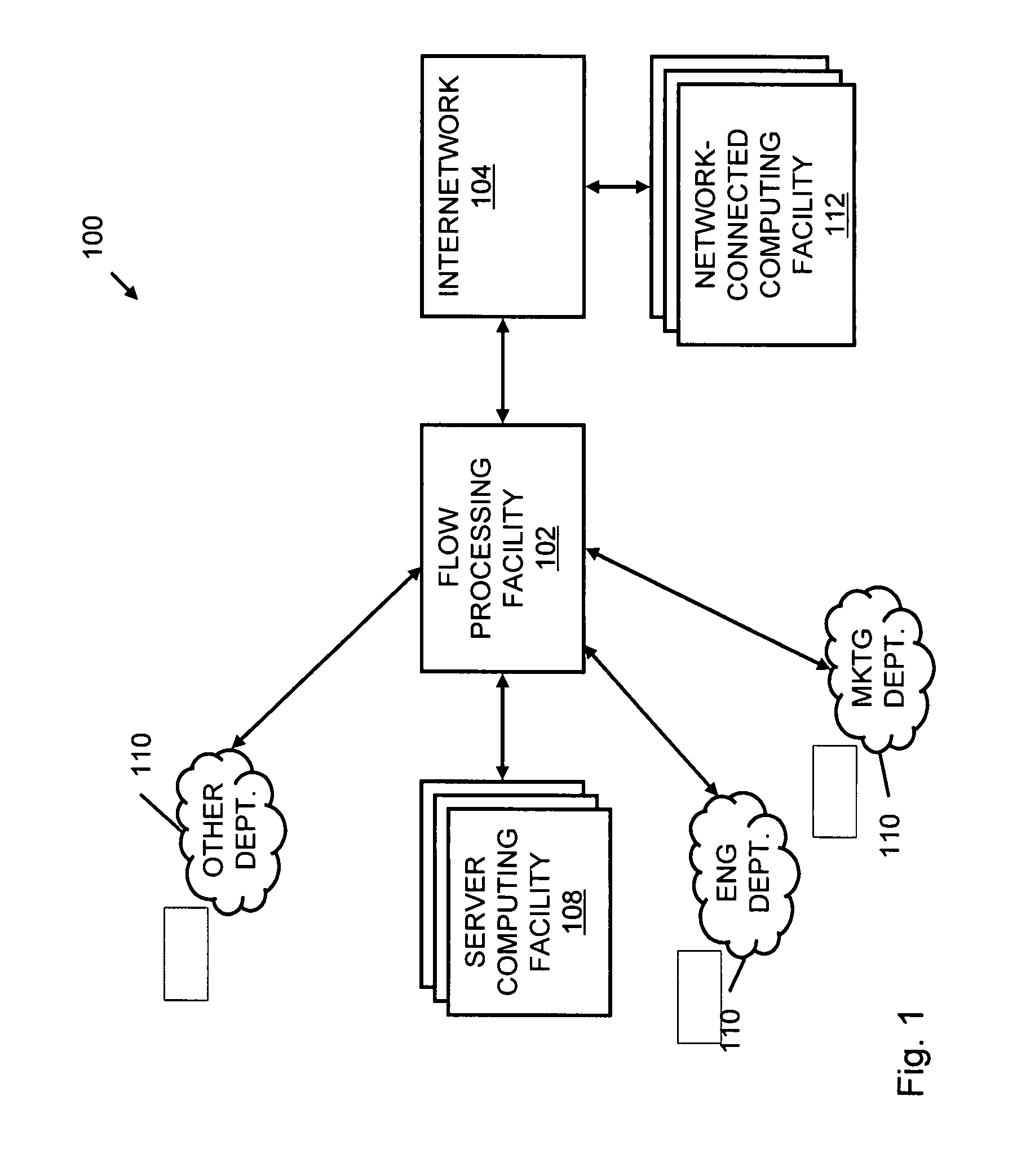
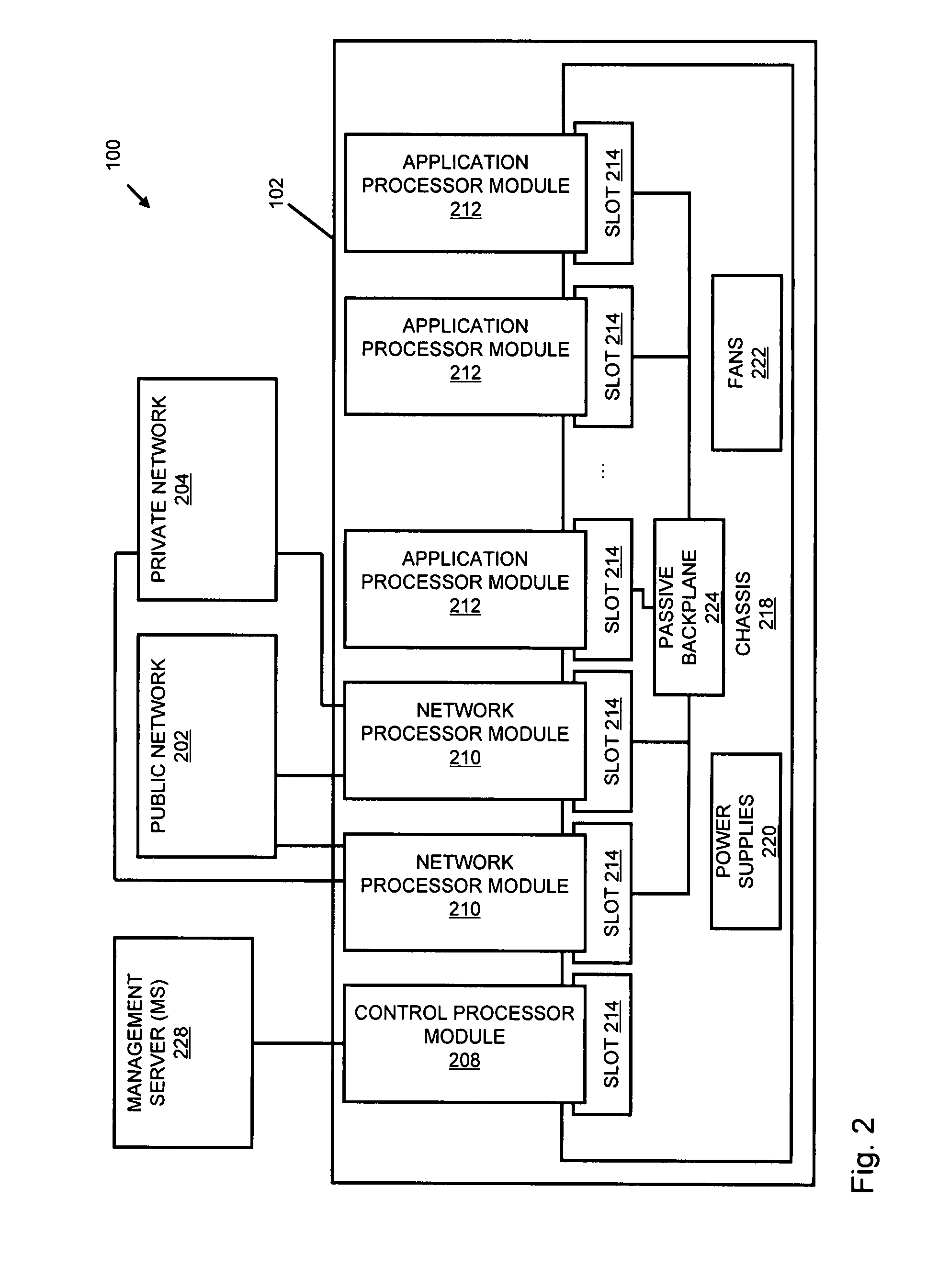
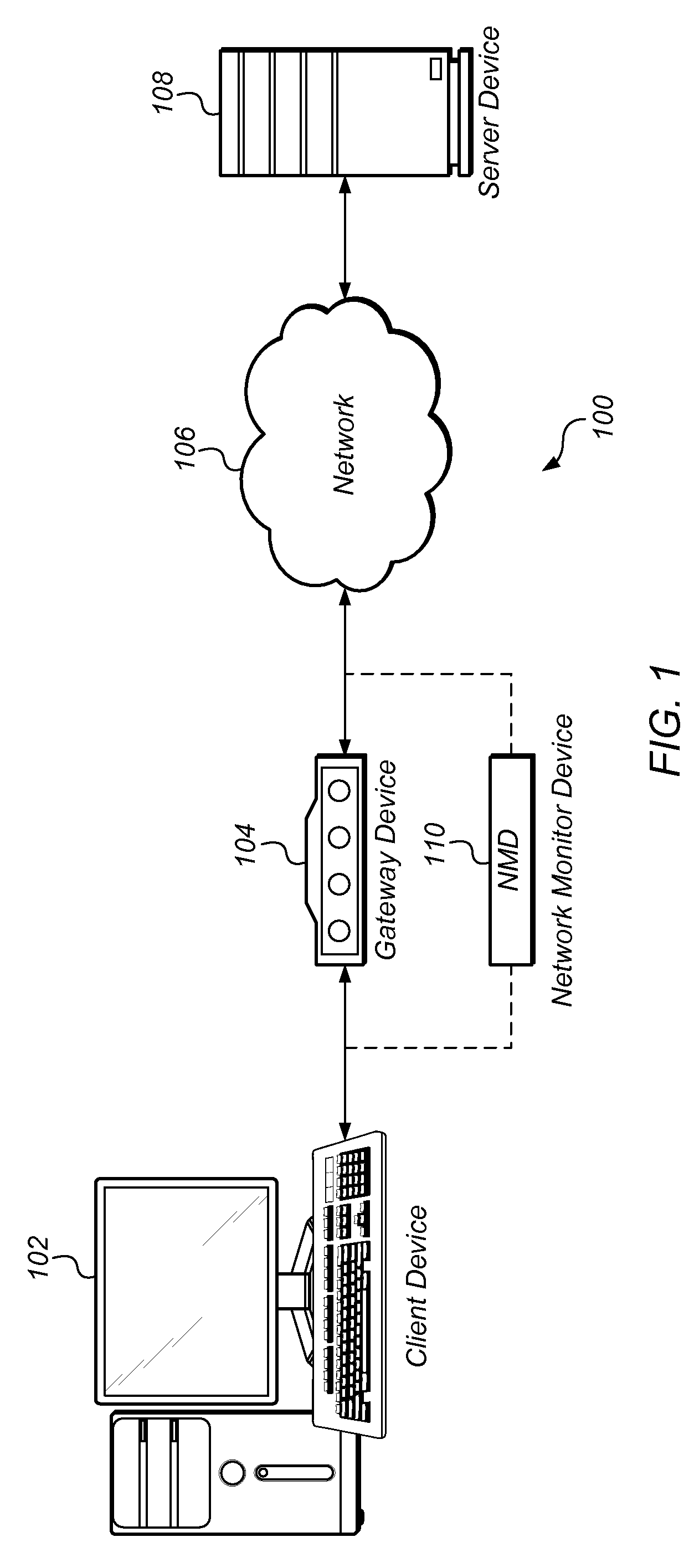
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
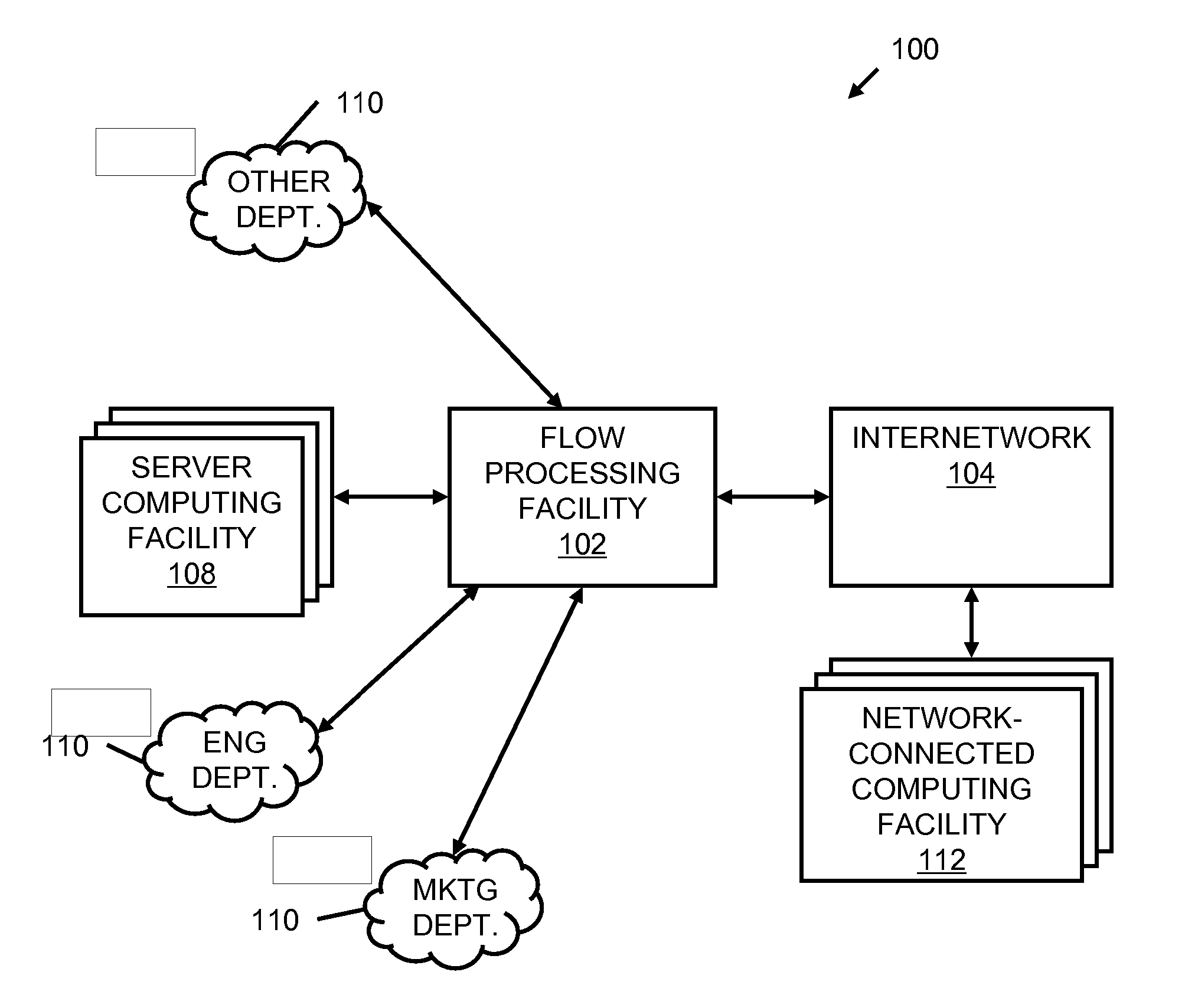
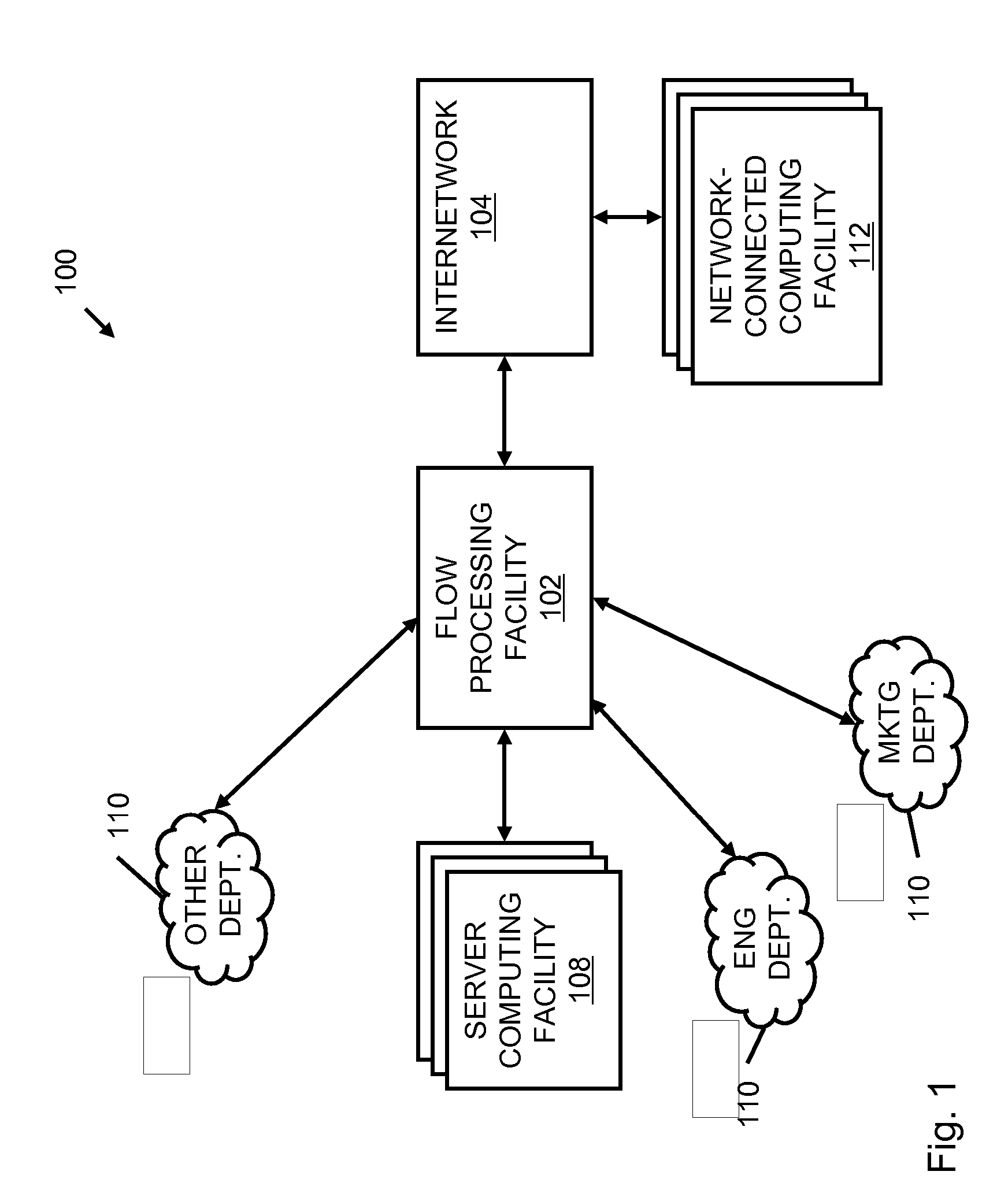
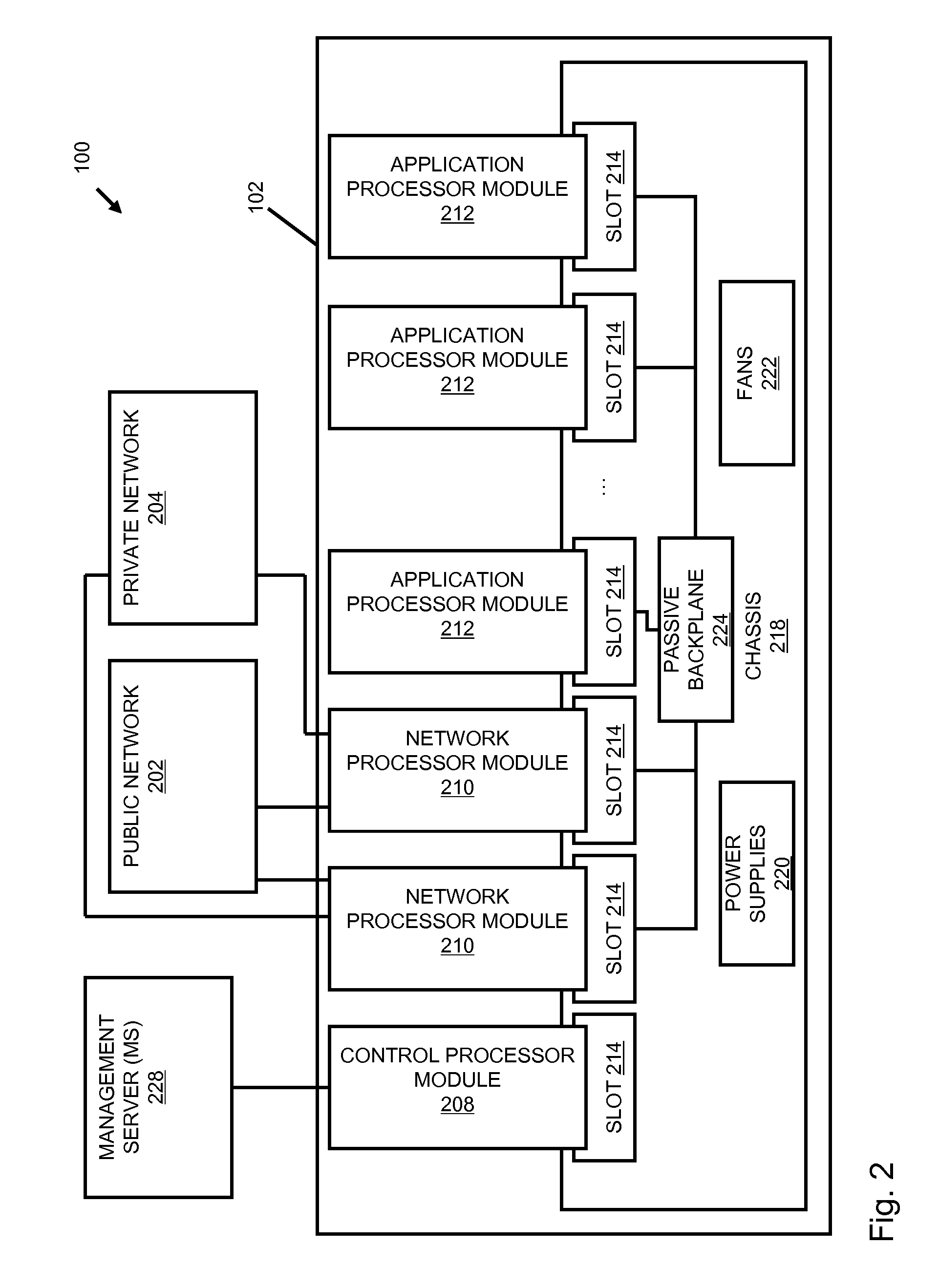
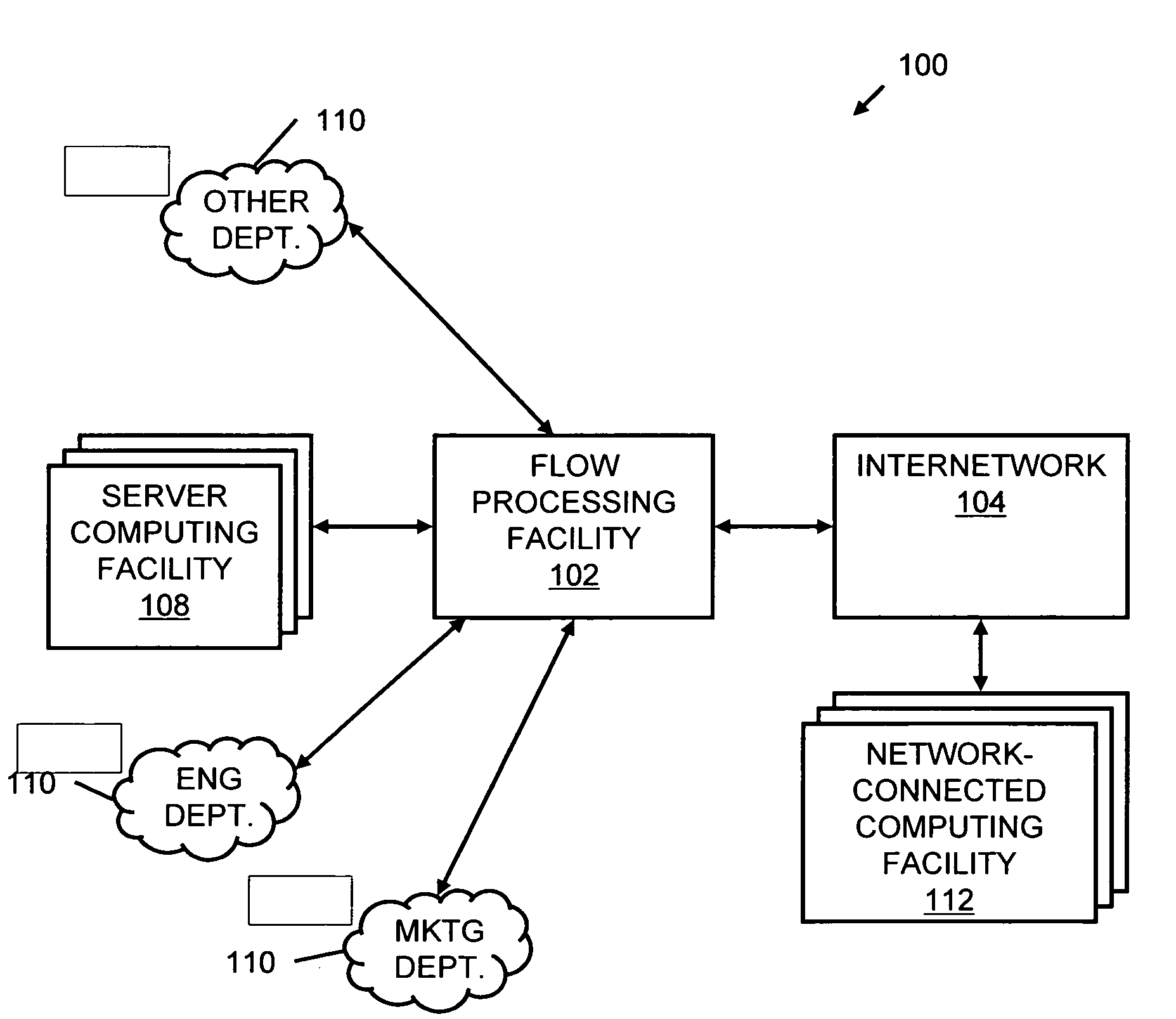
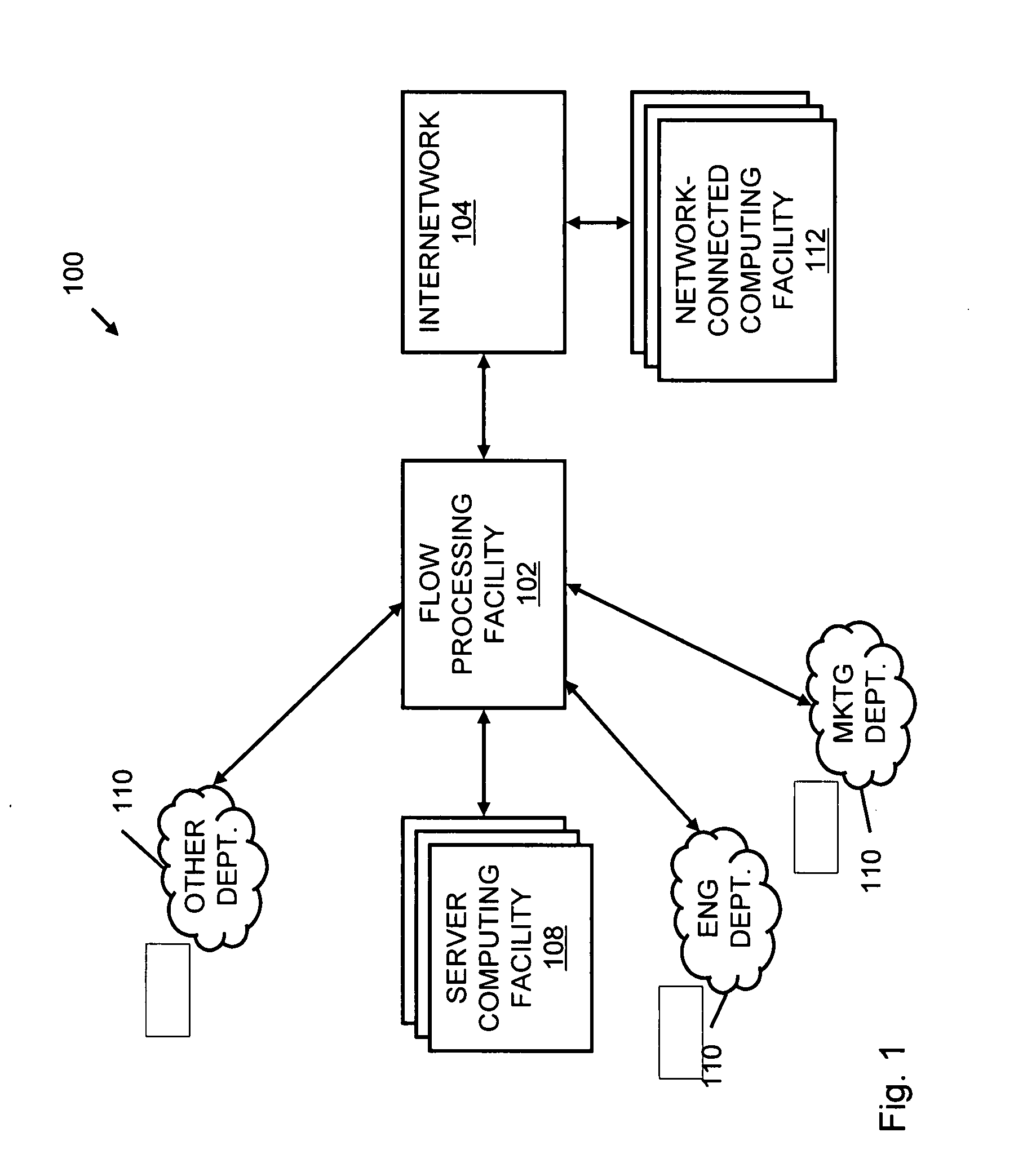
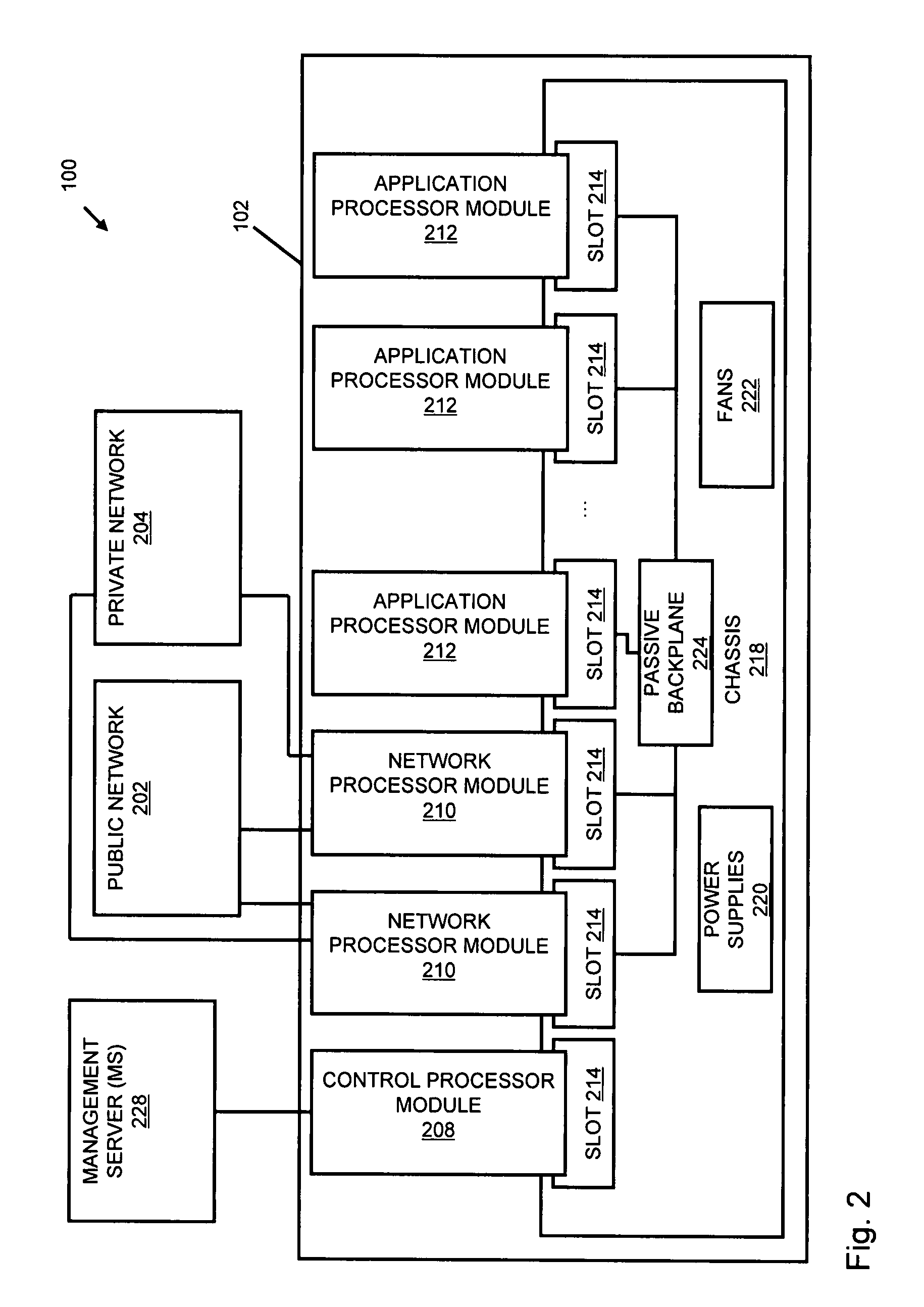
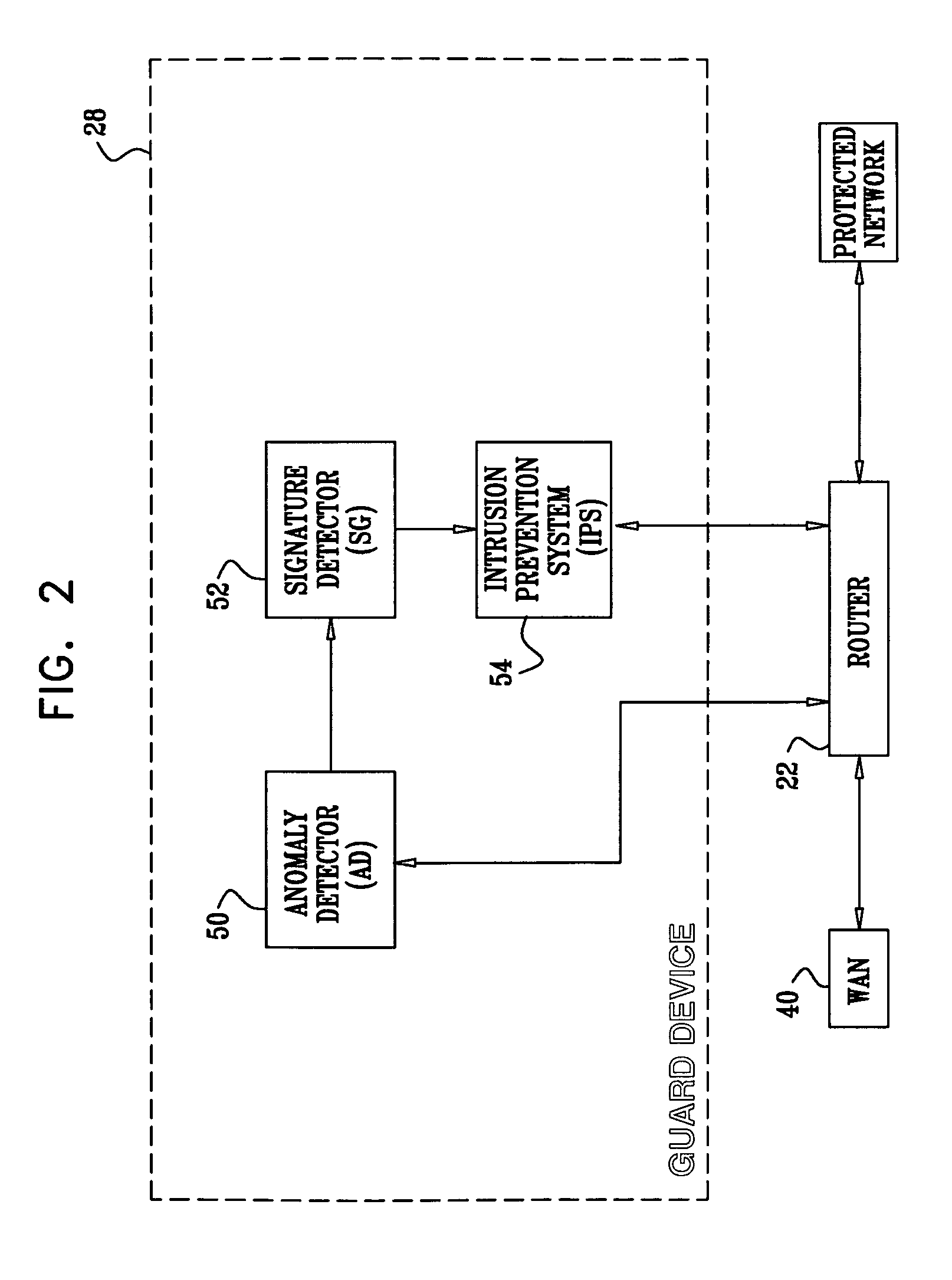
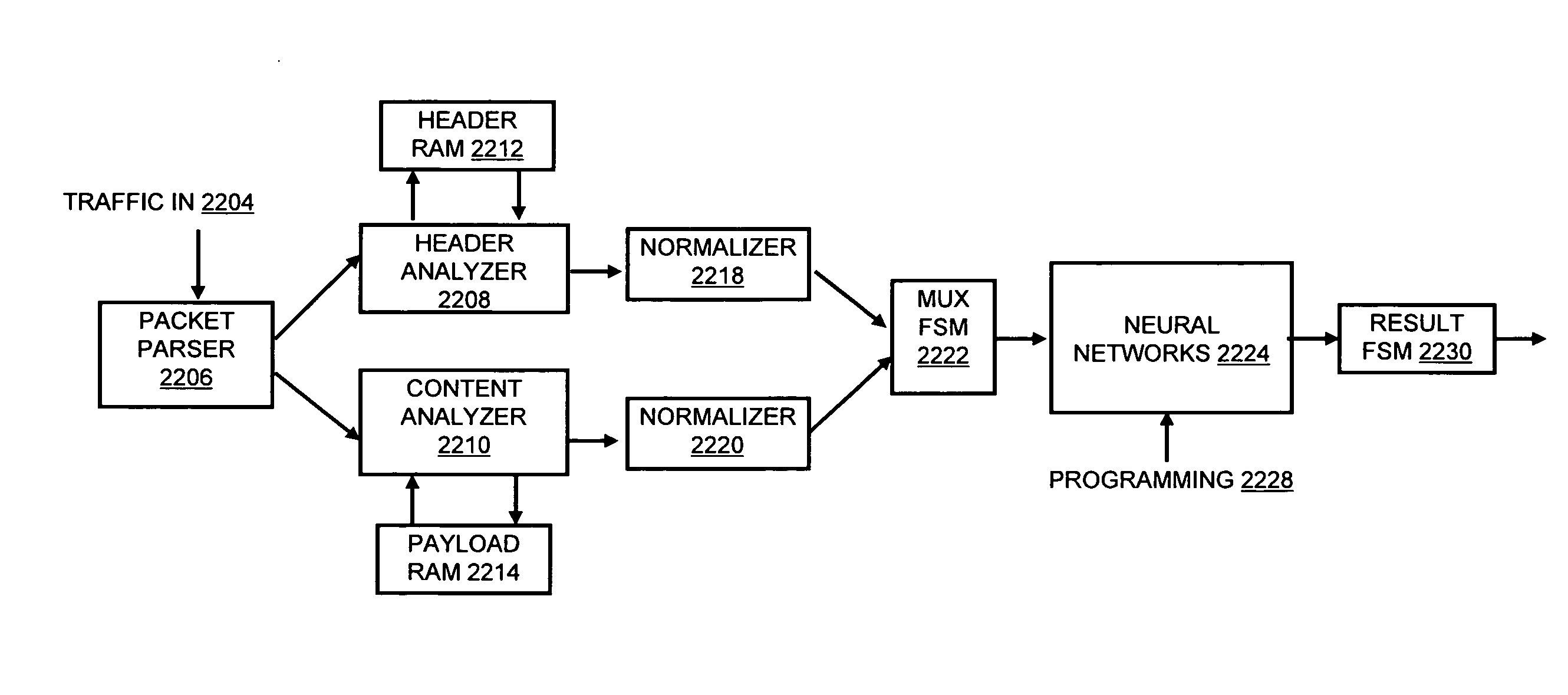
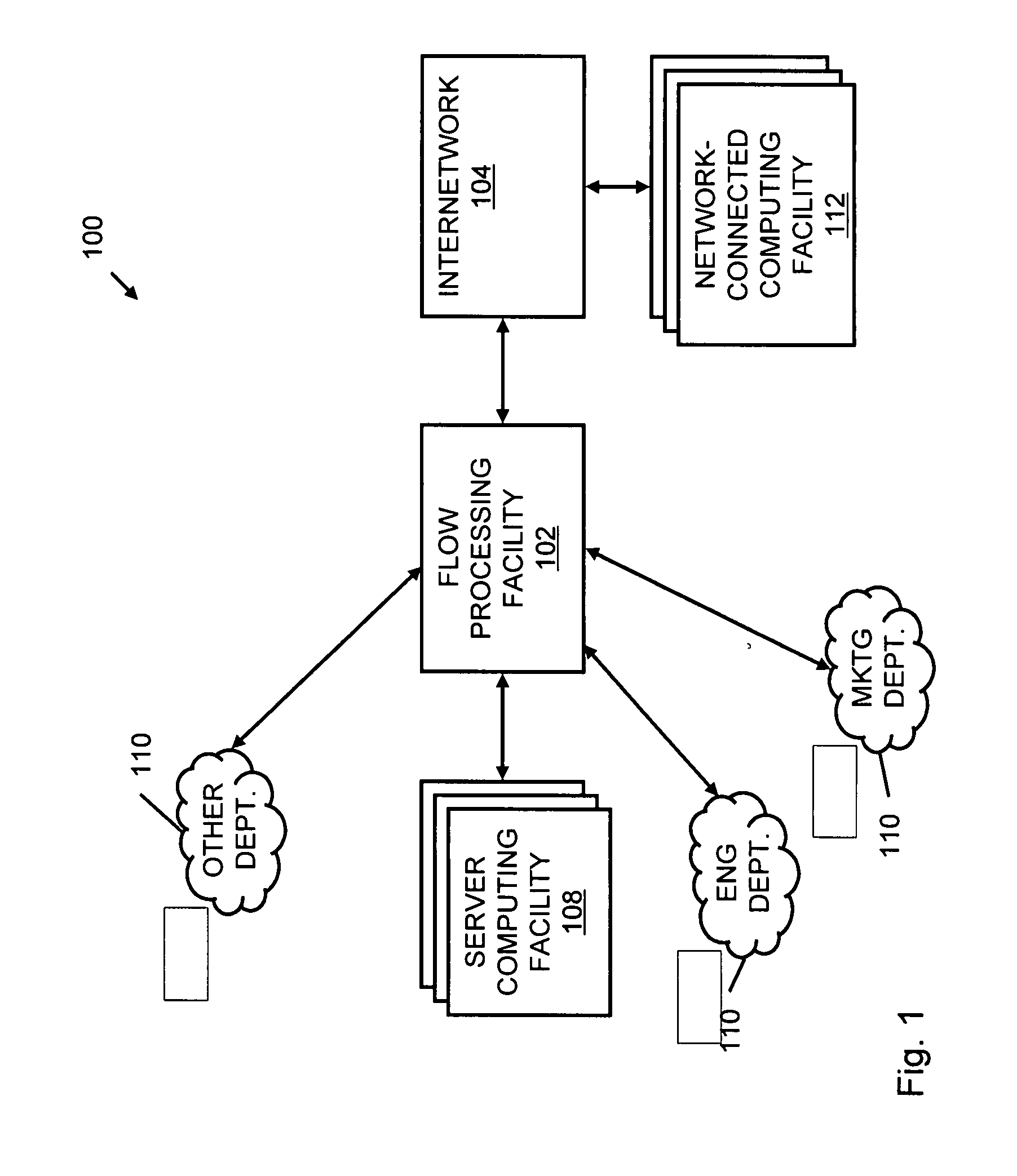
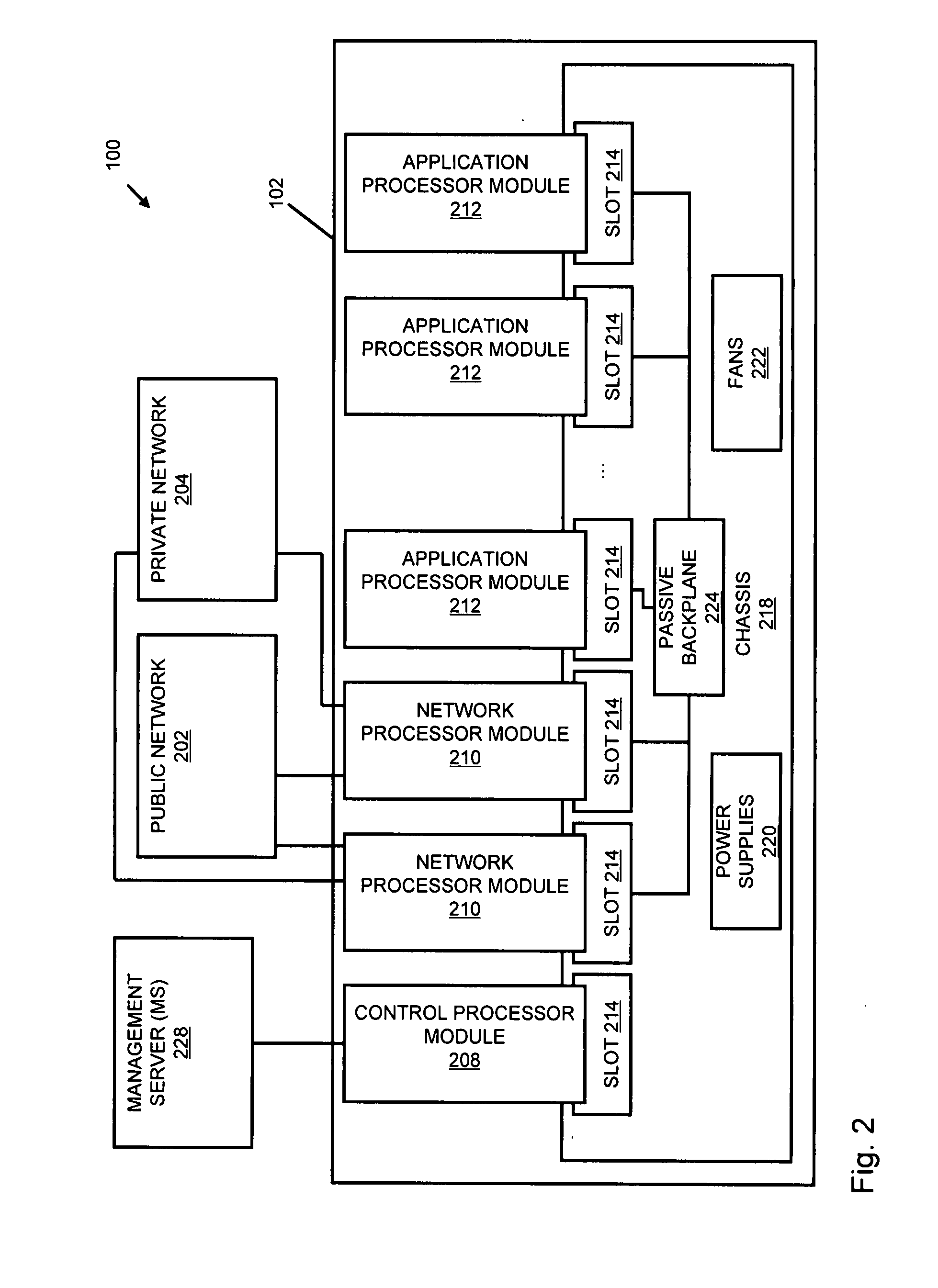
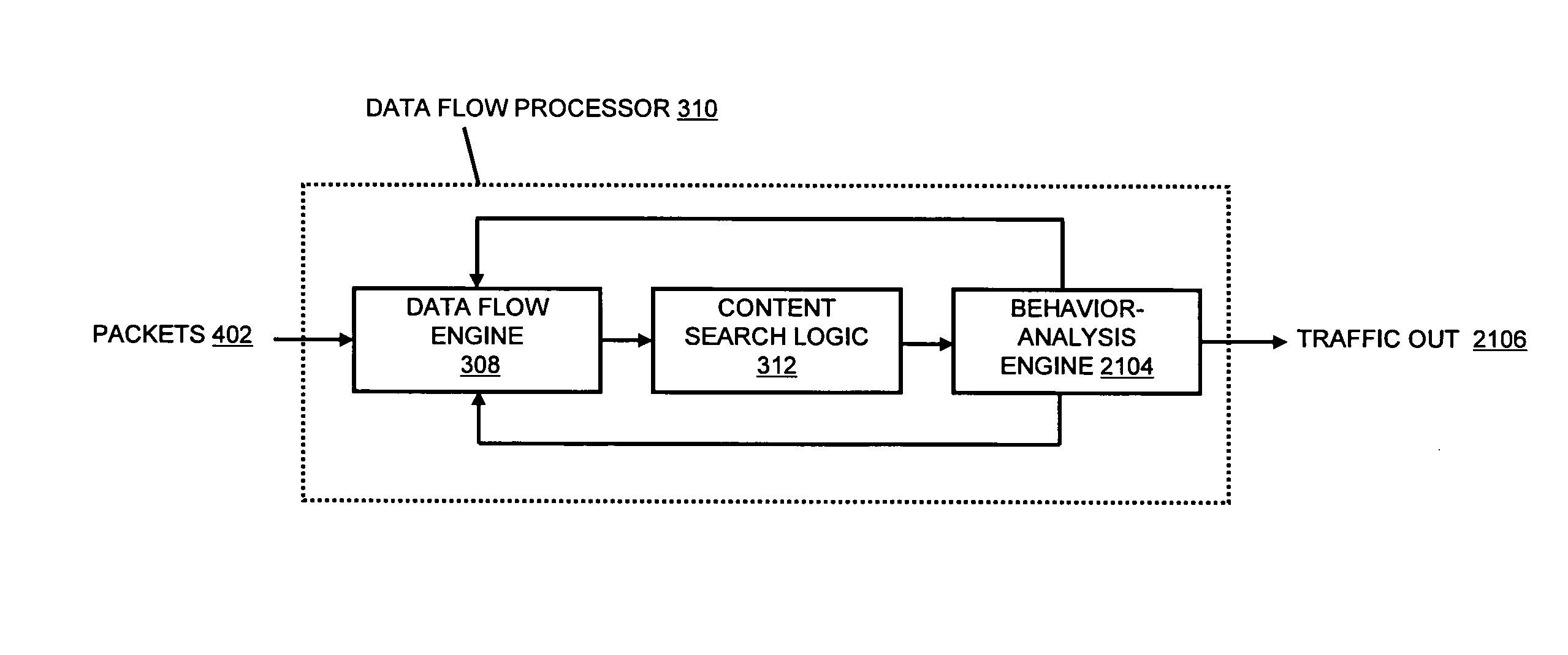
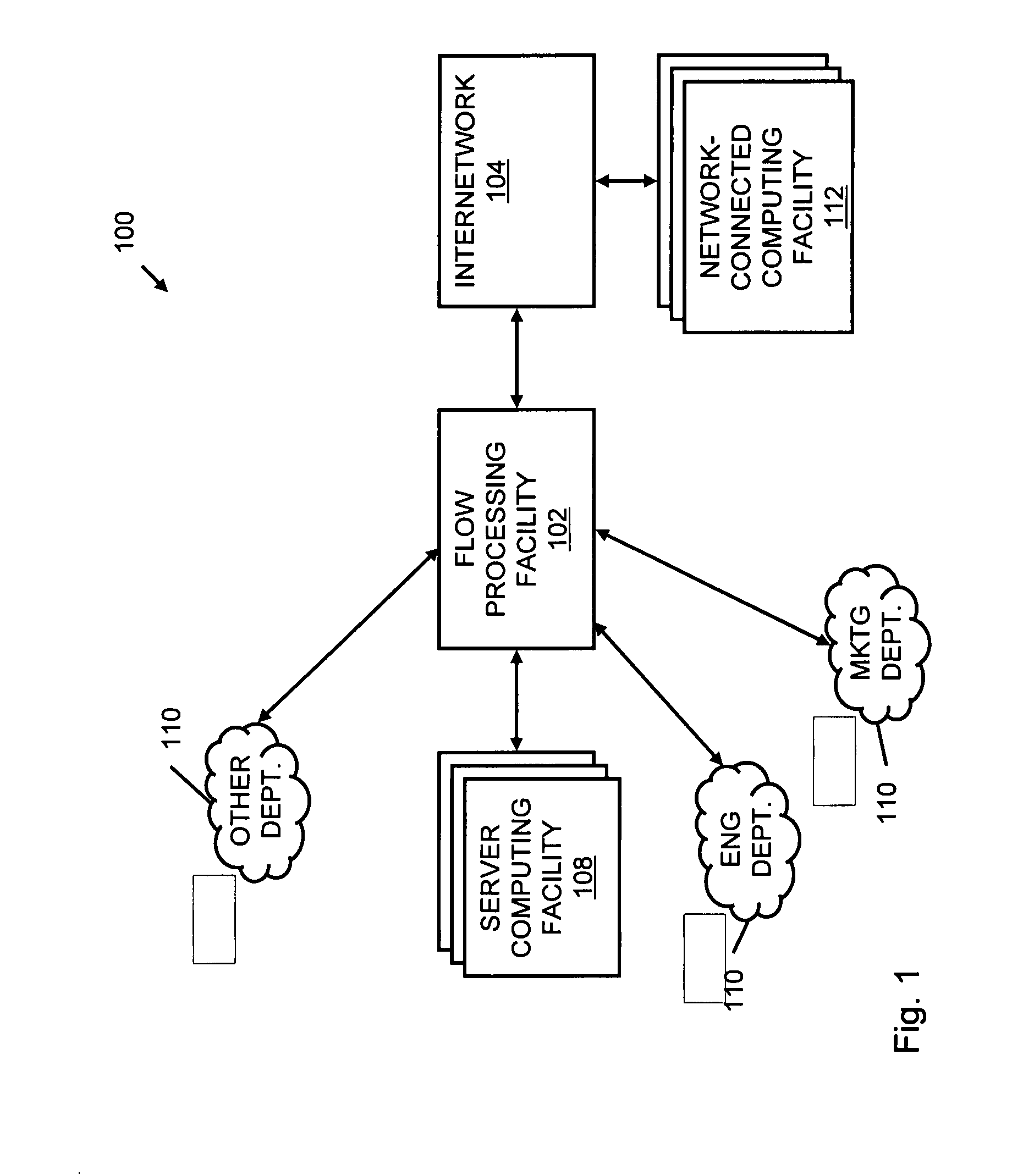
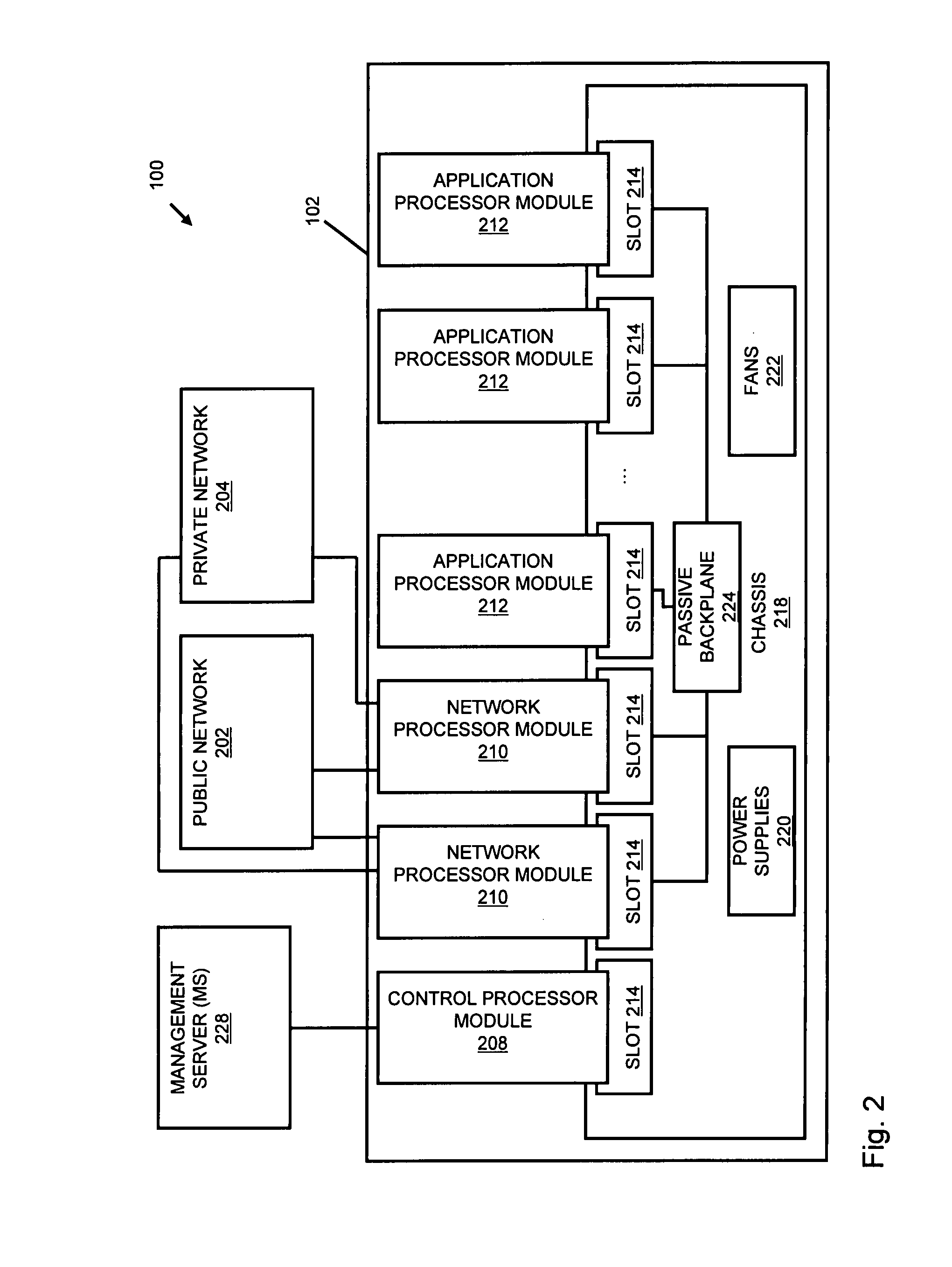
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Mitigating network attacks using automatic signature generation
A computer-implemented method for mitigating attacks of malicious traffic in a computer network includes receiving a set of attack sequences, including first traffic sequences suspected of containing the malicious traffic, analyzing the attack sequences so as to automatically extract a regular expression that matches at least a portion of the attack sequences in the set, and comparing second traffic sequences to the regular expression in order to identify the second traffic sequences that contain the malicious traffic.
Owner:CISCO TECH INC
System and method for performing regular expression matching with high parallelism
InactiveUS7225188B1Digital data information retrievalData processing applicationsPattern matchingTheoretical computer science
A system and method for searching data strings, such as network messages, for one or more predefined regular expressions is provided. Regular expressions are programmed into a pattern matching engine so that multiple characters, e.g., 32, of the data strings can be searched at the same time. The pattern matching engine includes a regular expression storage device having one or more content-addressable memories (CAMs) whose rows may be divided into sections. Each predefined regular expression is analyzed so as to identify the “borders” within the regular expression. A border is preferably defined to exist at each occurrence of one or more predefined metacharacters, such as “.*”, which finds any character zero, one or more times. The borders separate the regular expression into a sequence of sub-expressions each of which may be one or more characters in length. Each sub-expression is preferably programmed into a corresponding section of the pattern matching engine. The system may also be configured so as to search multiple regular expressions in parallel.
Owner:CISCO TECH INC
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
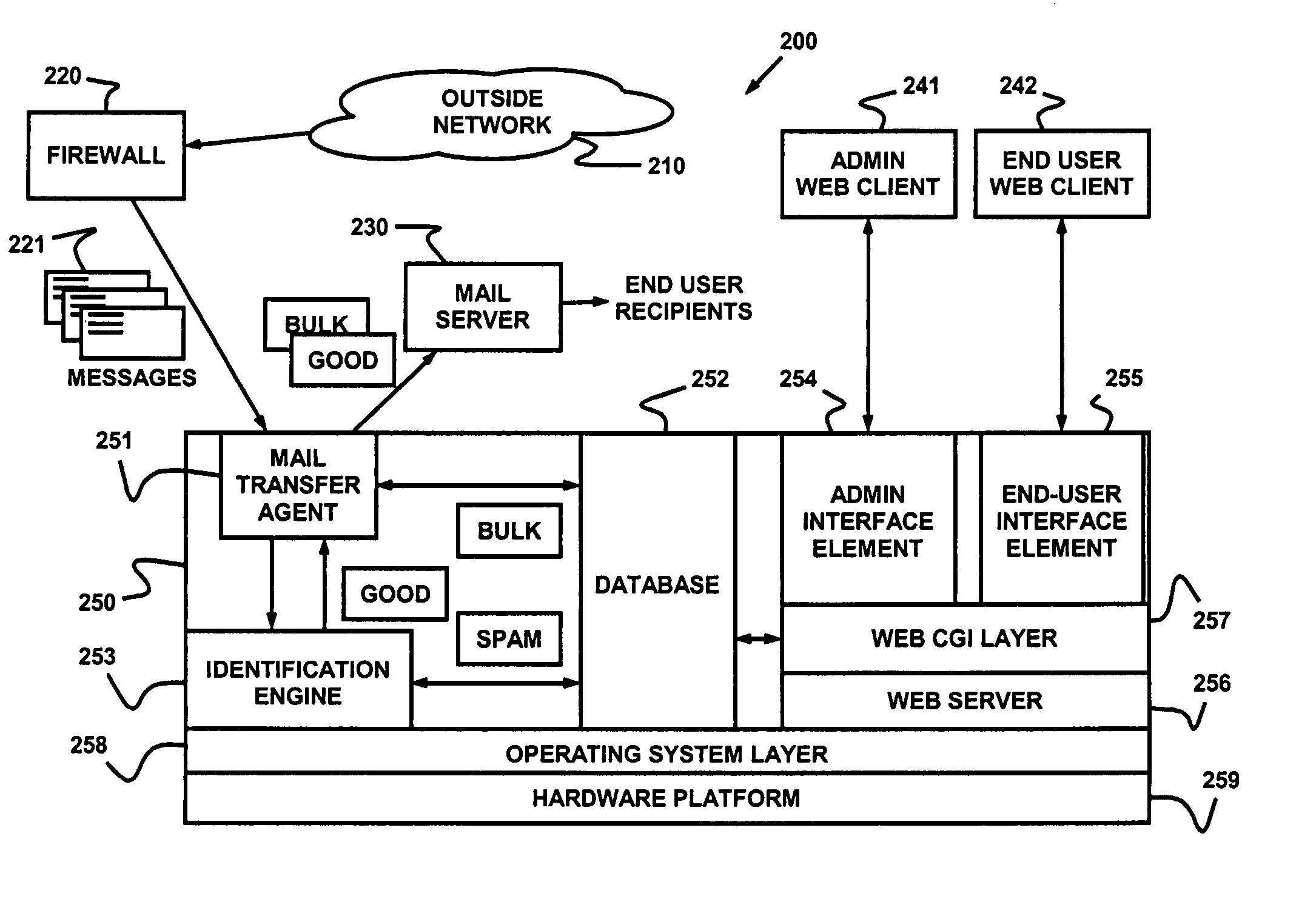
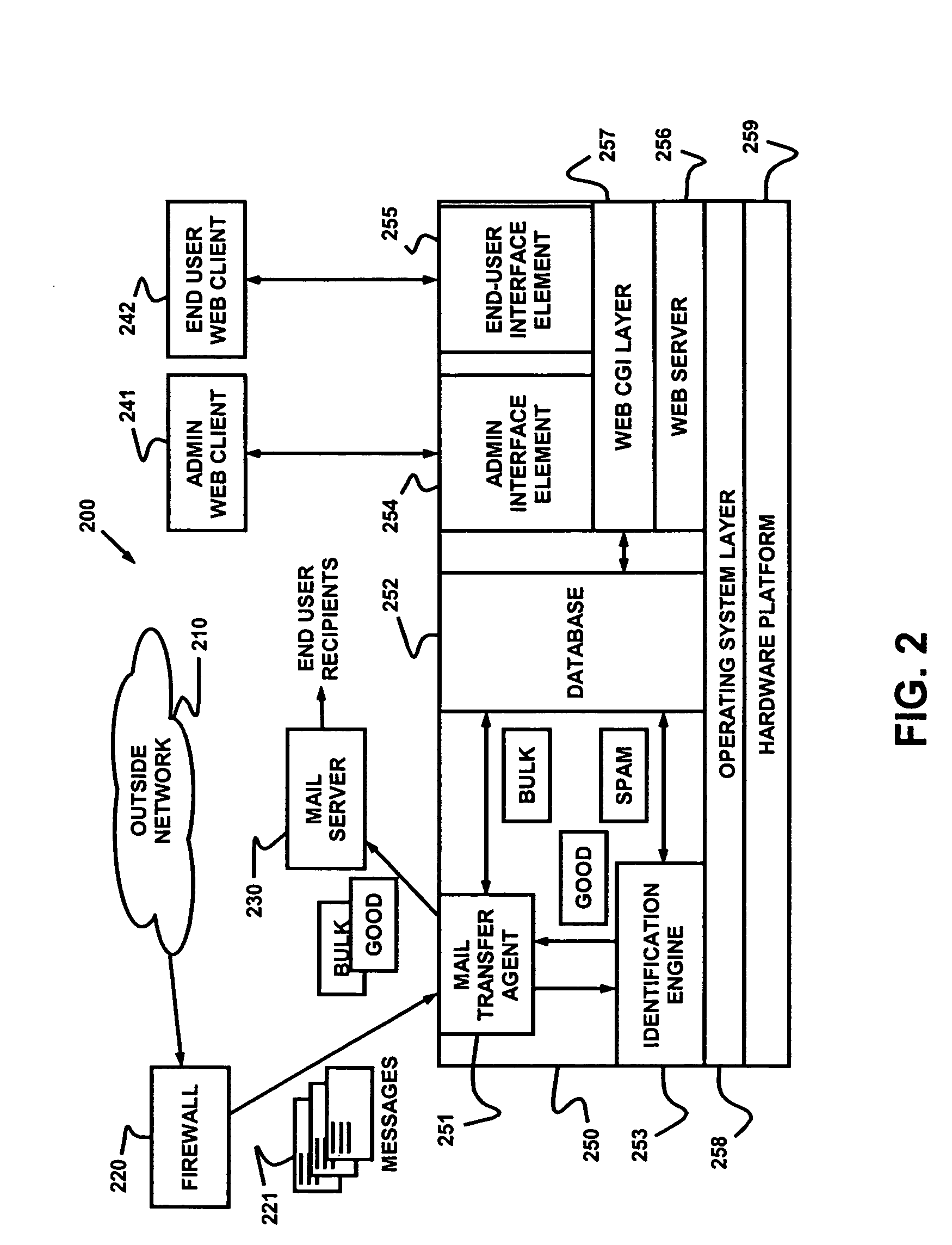
Dynamic message filtering
ActiveUS20050076084A1Reduce in quantityMake fastError detection/correctionGenetic modelsSpammingWhitelist
Dynamically filtering and classifying messages, as good messages, bulk periodicals, or spam. A regular expression recognizer, and pre-trained neural networks. The neural networks distinguish “likely good” from “likely spam,” and also operate at a more discriminating level to distinguish among the three categories above. A dynamic whitelist and blacklist; sending addresses are collected when the number of their messages indicates the sender is good or a spammer. A dynamically selected set of regular expressions input to the neural networks.
Owner:MAILGATE LLC
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
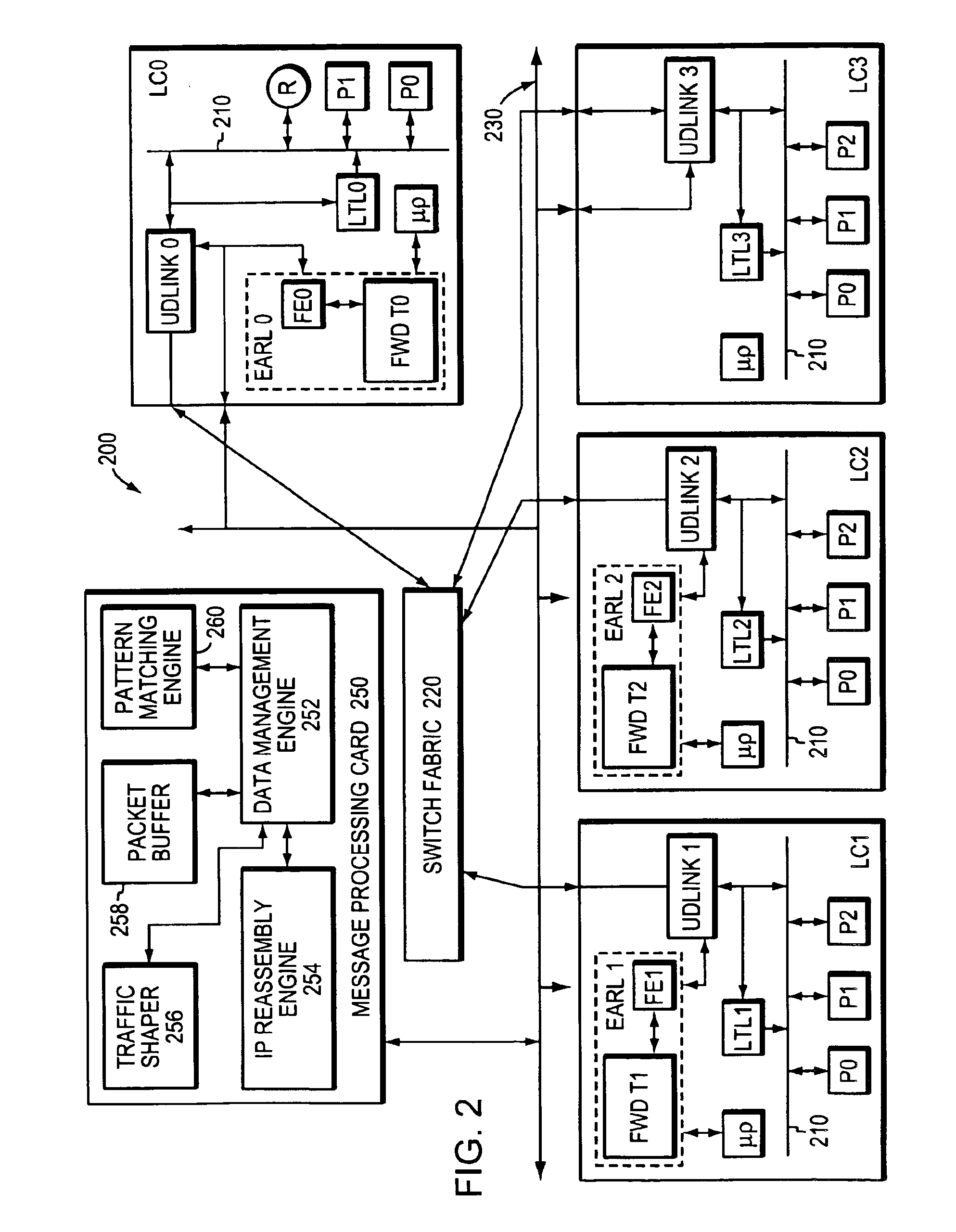
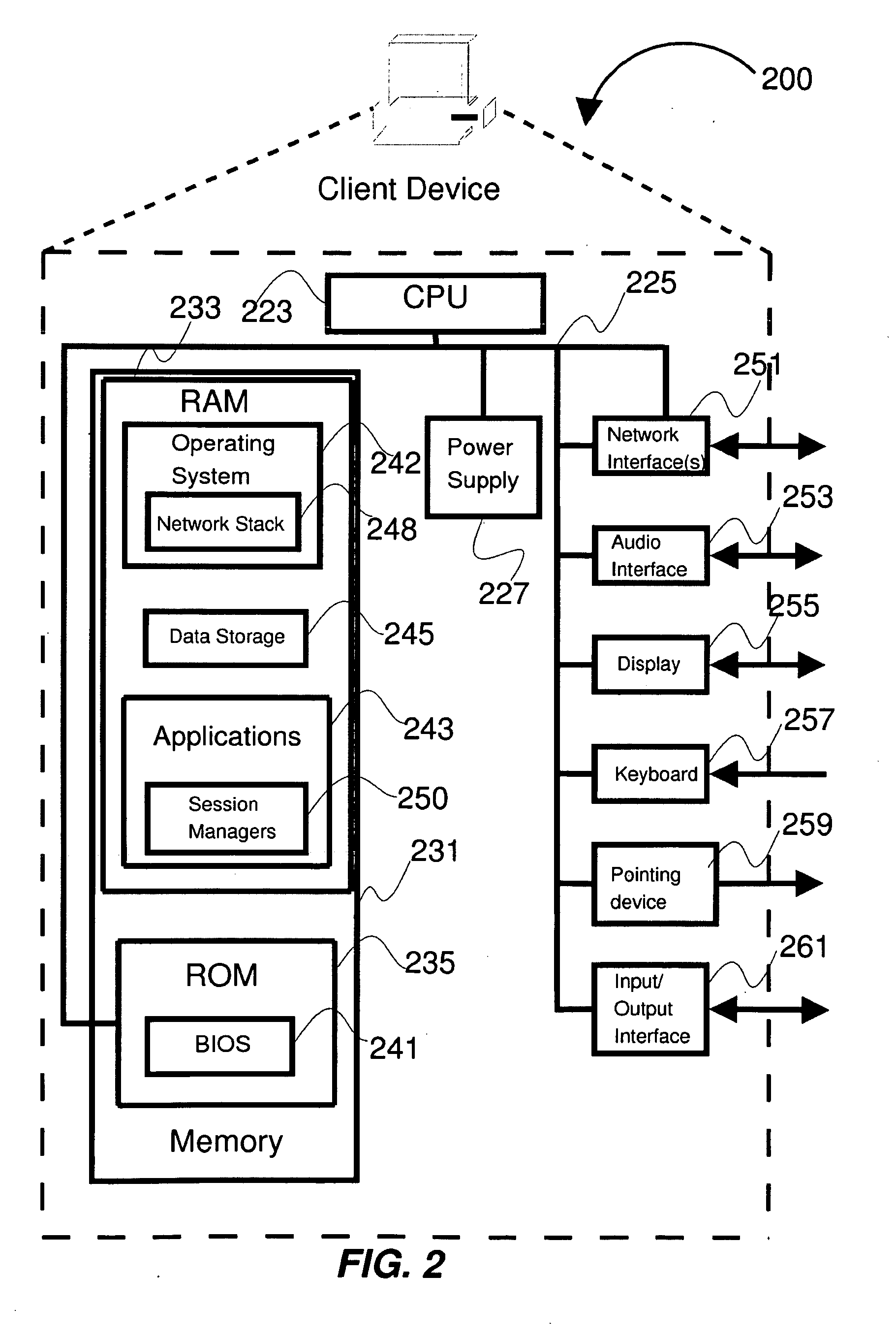
Method and apparatus for high-speed parsing of network messages
InactiveUS6892237B1Efficient analysisIncrease speedMultiple digital computer combinationsData switching networksPattern matchingRandom access memory
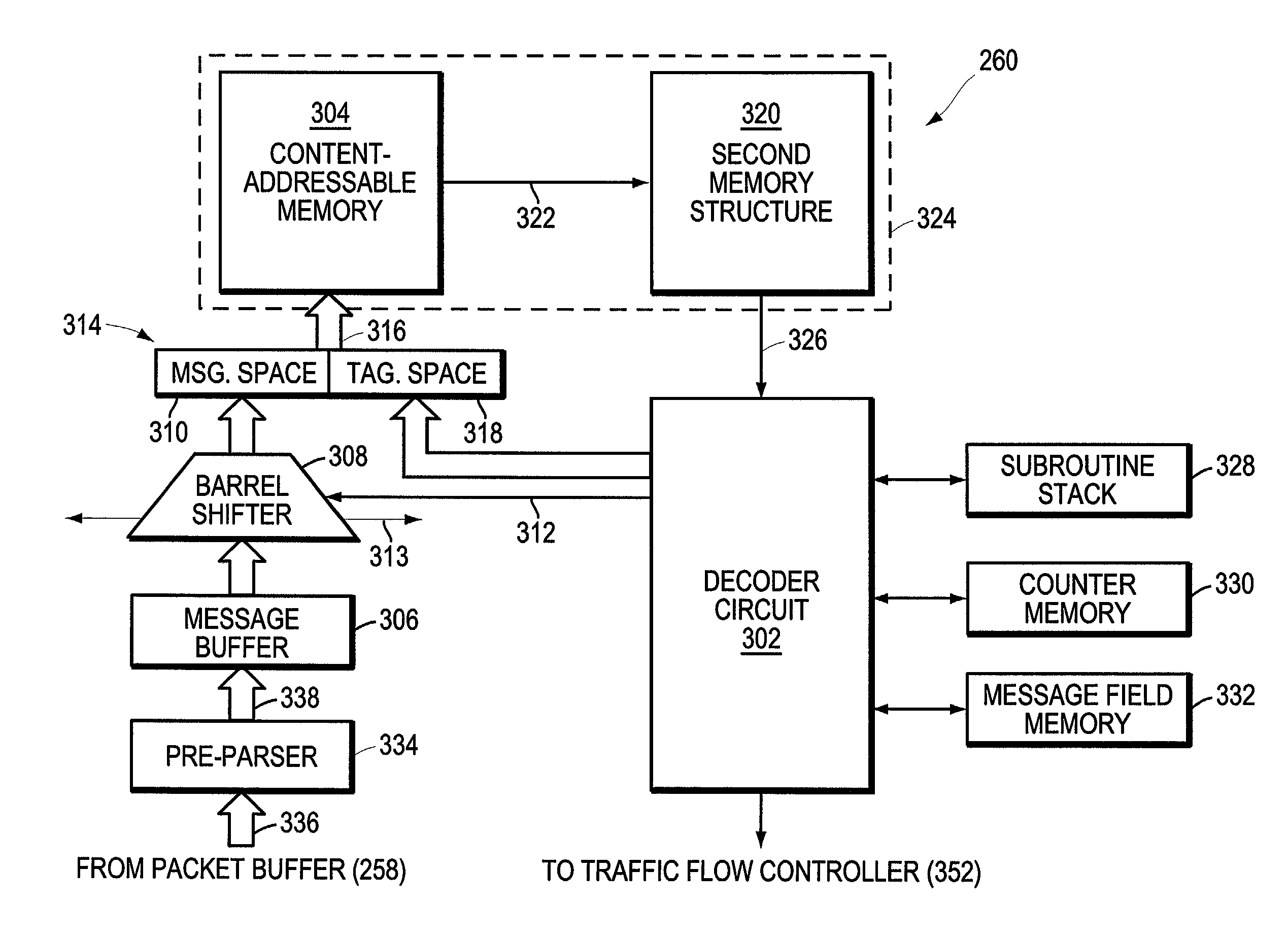
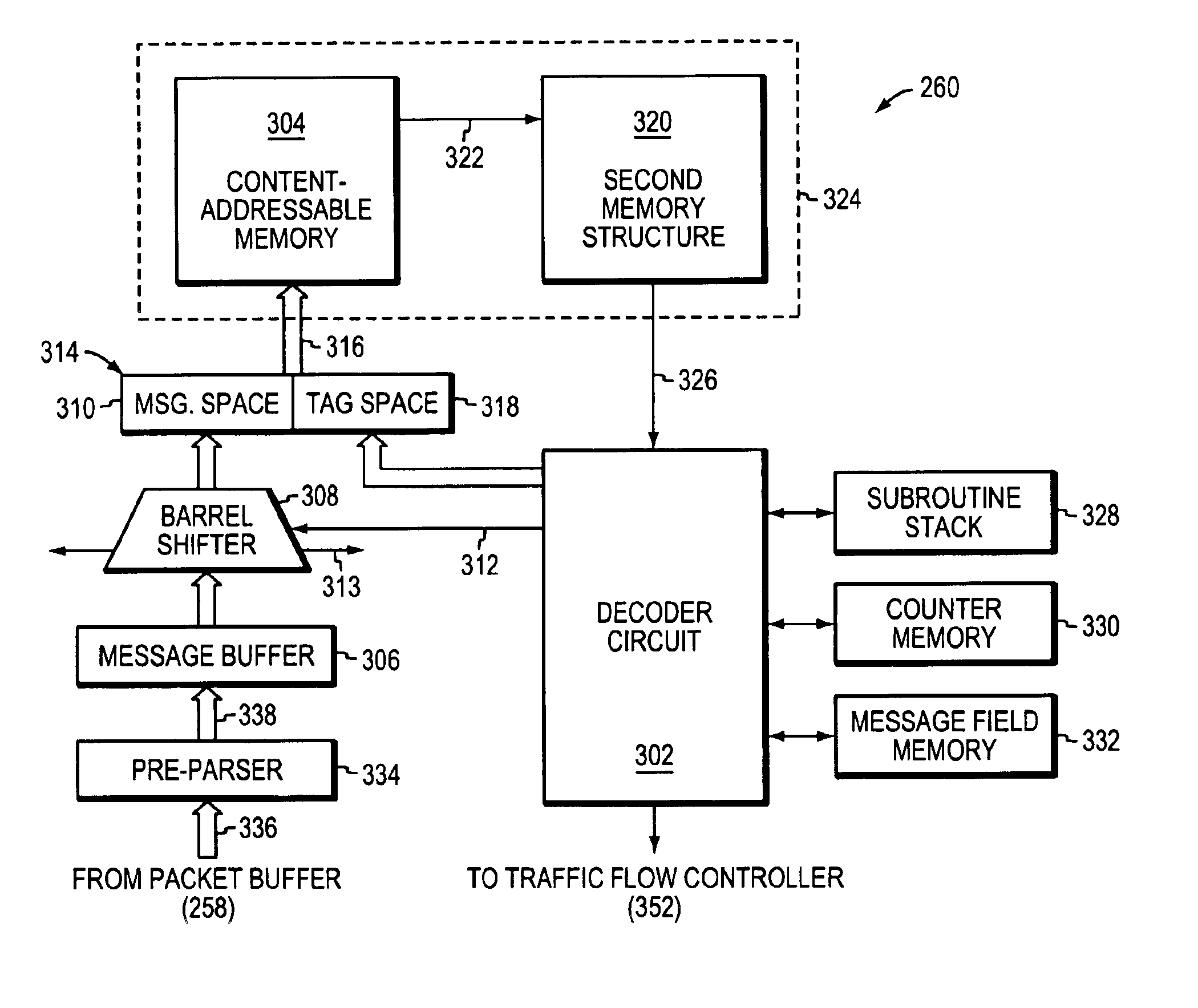
A programmable pattern matching engine efficiently parses the contents of network messages for regular expressions and executes pre-defined actions or treatments on those messages that match the regular expressions. The pattern matching engine is preferably a logic circuit designed to perform its pattern matching and execution functions at high speed, e.g., at multi-gigabit per second rates. It includes, among other things, a message buffer for storing the message being evaluated, a decoder circuit for decoding and executing corresponding actions or treatments, and one or more content-addressable memories (CAMs) that are programmed to store the regular expressions used to search the message. The CAM may be associated with a second memory device, such as a random access memory (RAM), as necessary, that is programmed to contain the respective actions or treatments to be applied to messages matching the corresponding CAM entries. The RAM provides its output to the decoder circuit, which, in response, decodes and executes the specified action or treatment.
Owner:CISCO TECH INC
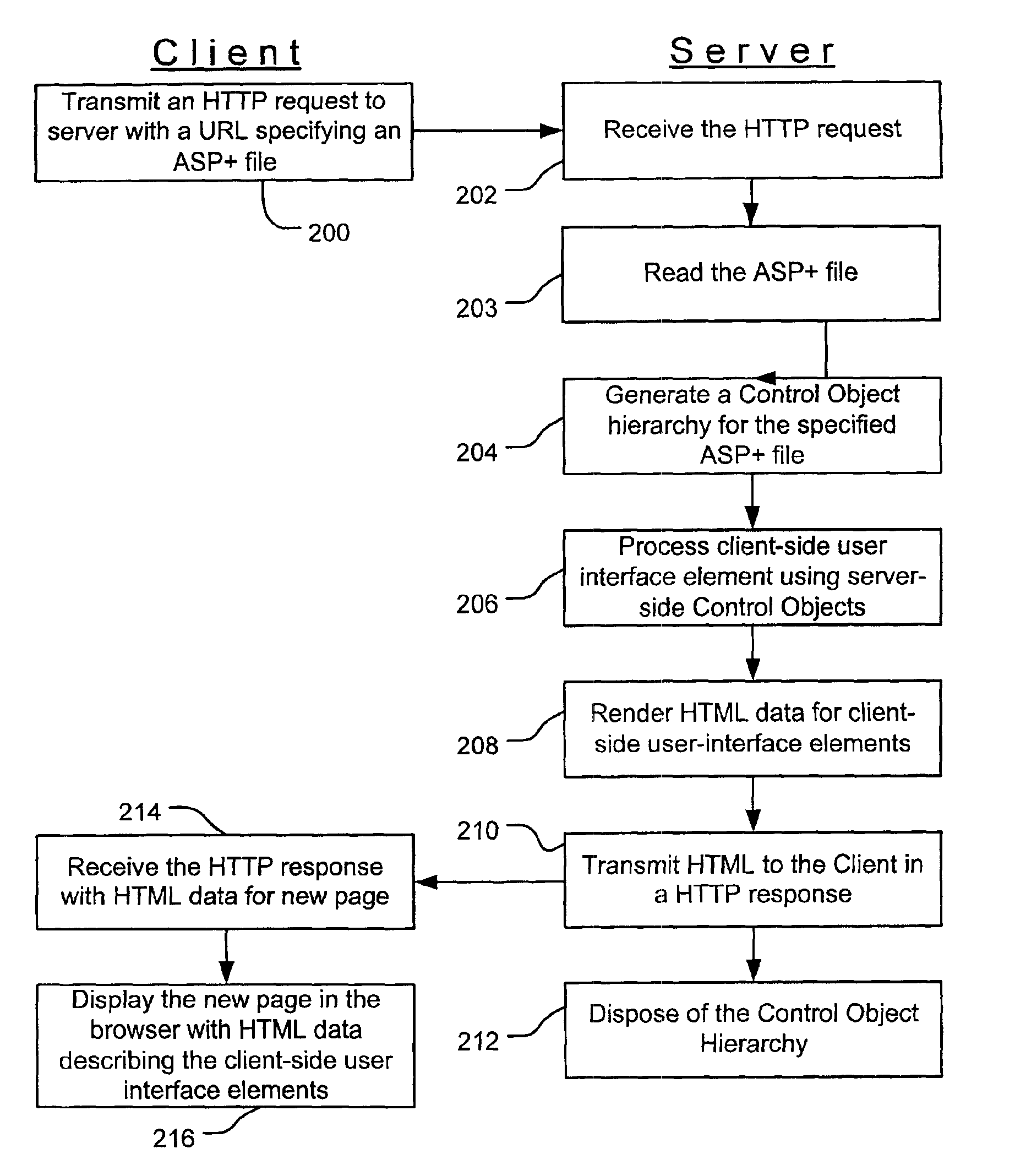
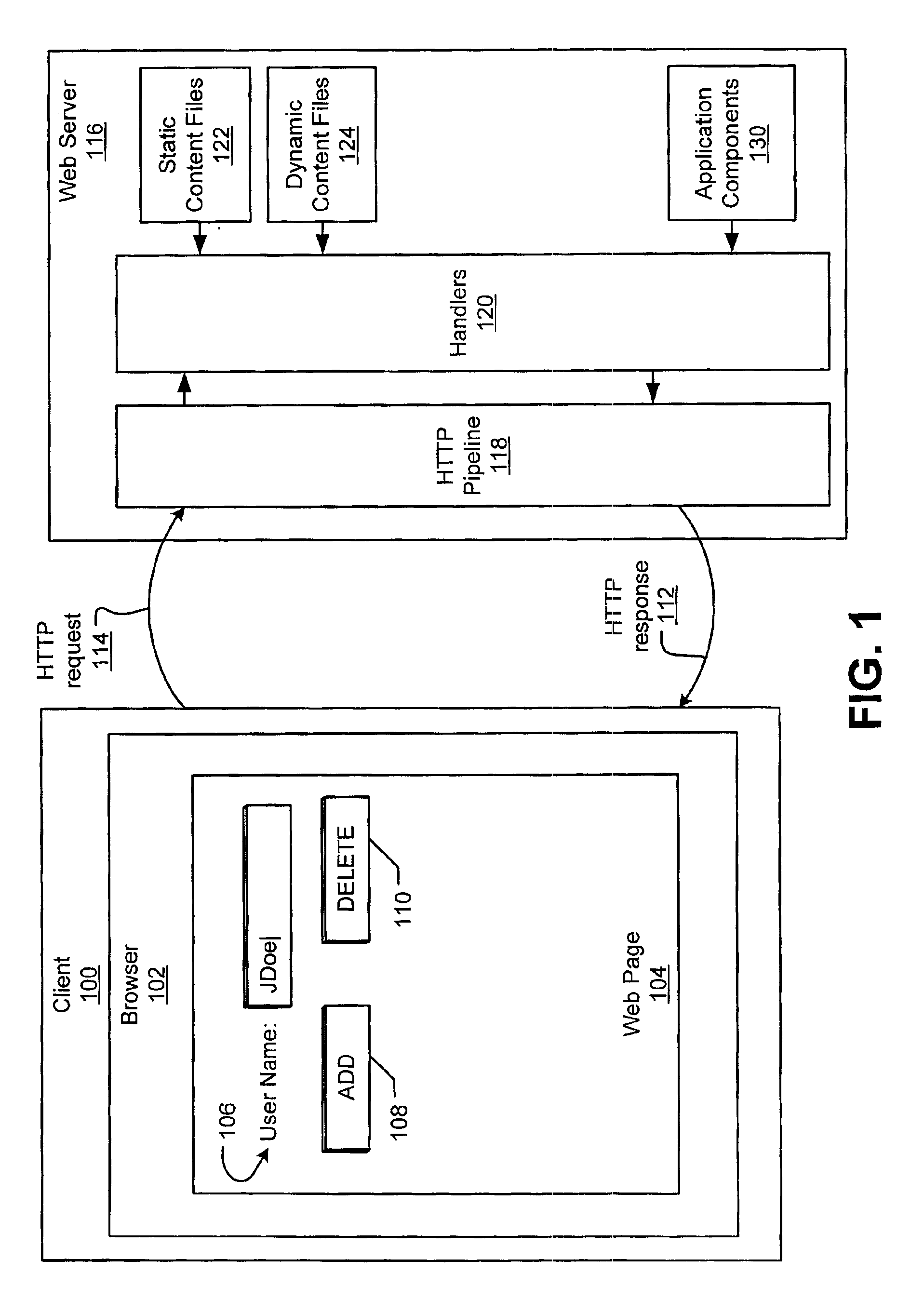
Web controls validation
InactiveUS6915454B1Receipt is inhibitedNon-redundant fault processingSpecific program execution arrangementsError processingFile comparison
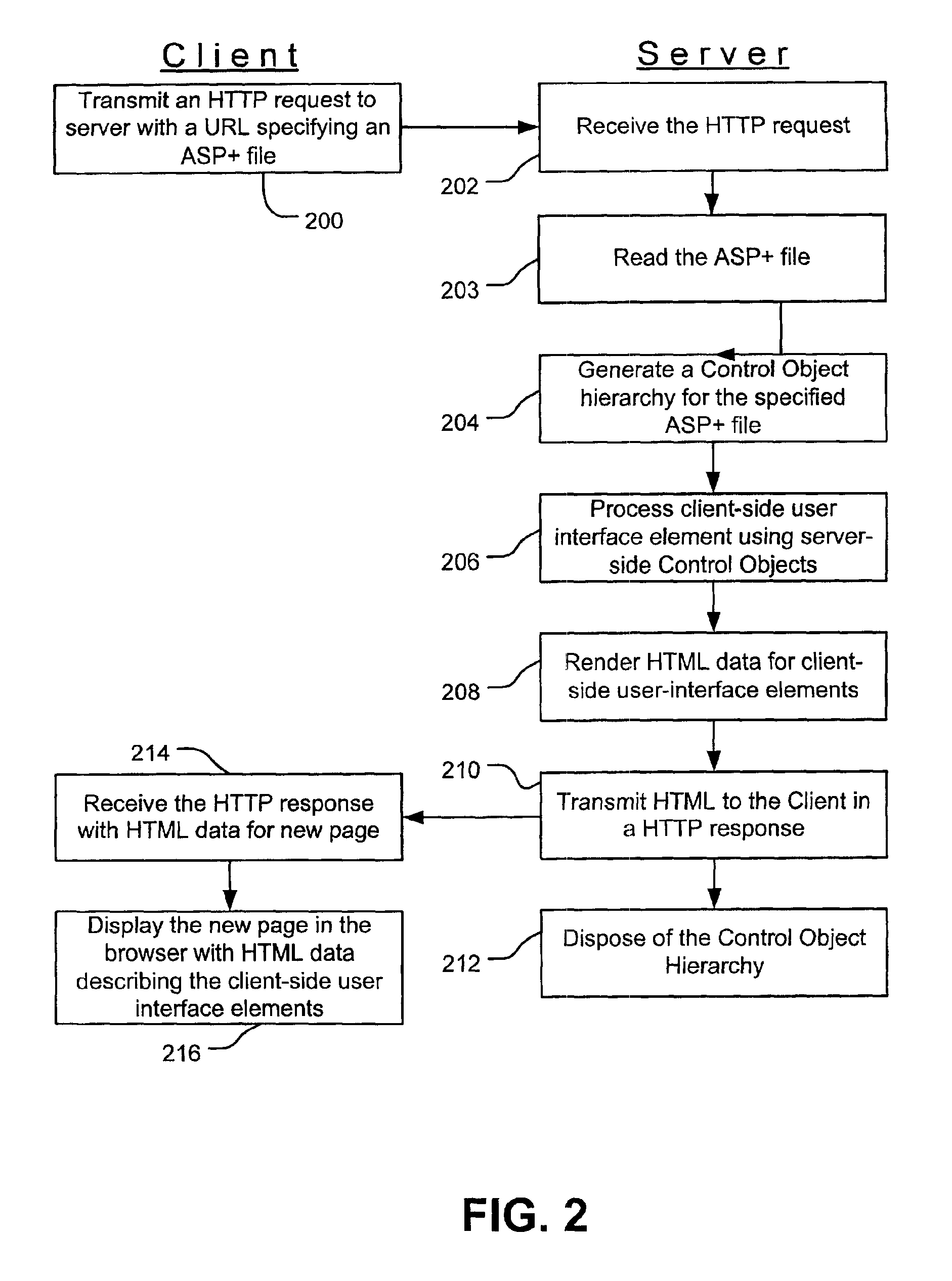
Web control validation may be defined using one or more declarations that are included in an ASP+ file by the web page author. The declarations specify server-side objects that validate the input data received in the web page and provide error handling in the event of a validation failure error. Validation declaration parameters specify the validation criteria against which the input data is validated. Example validation operations involve regular expressions, required fields, data comparison, range comparison and custom validation. Validation parameters can also specify- either server-side validation or client-side validation, depending on the client browser's capabilities. In a server-side scenario, a server-side validation object processes the input data received in an HTTP request from the client. In a client-side scenario, a server-side validation object renders the appropriate client-side code to validate the input data without a round trip between the client and the server.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
Method and device for high performance regular expression pattern matching
ActiveUS7702629B2Minimize the numberData processing applicationsDigital data information retrievalState dependentPattern matching
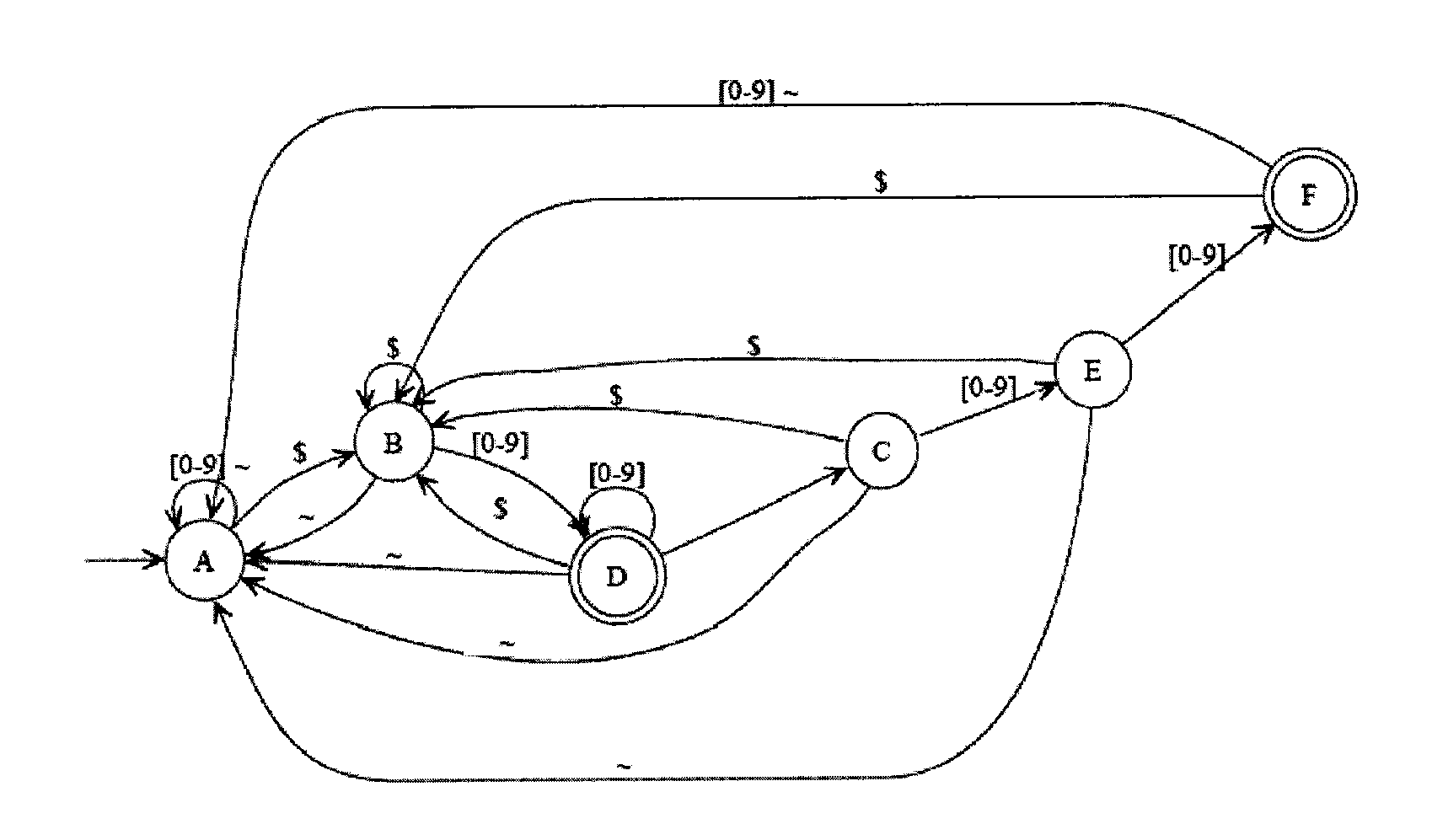
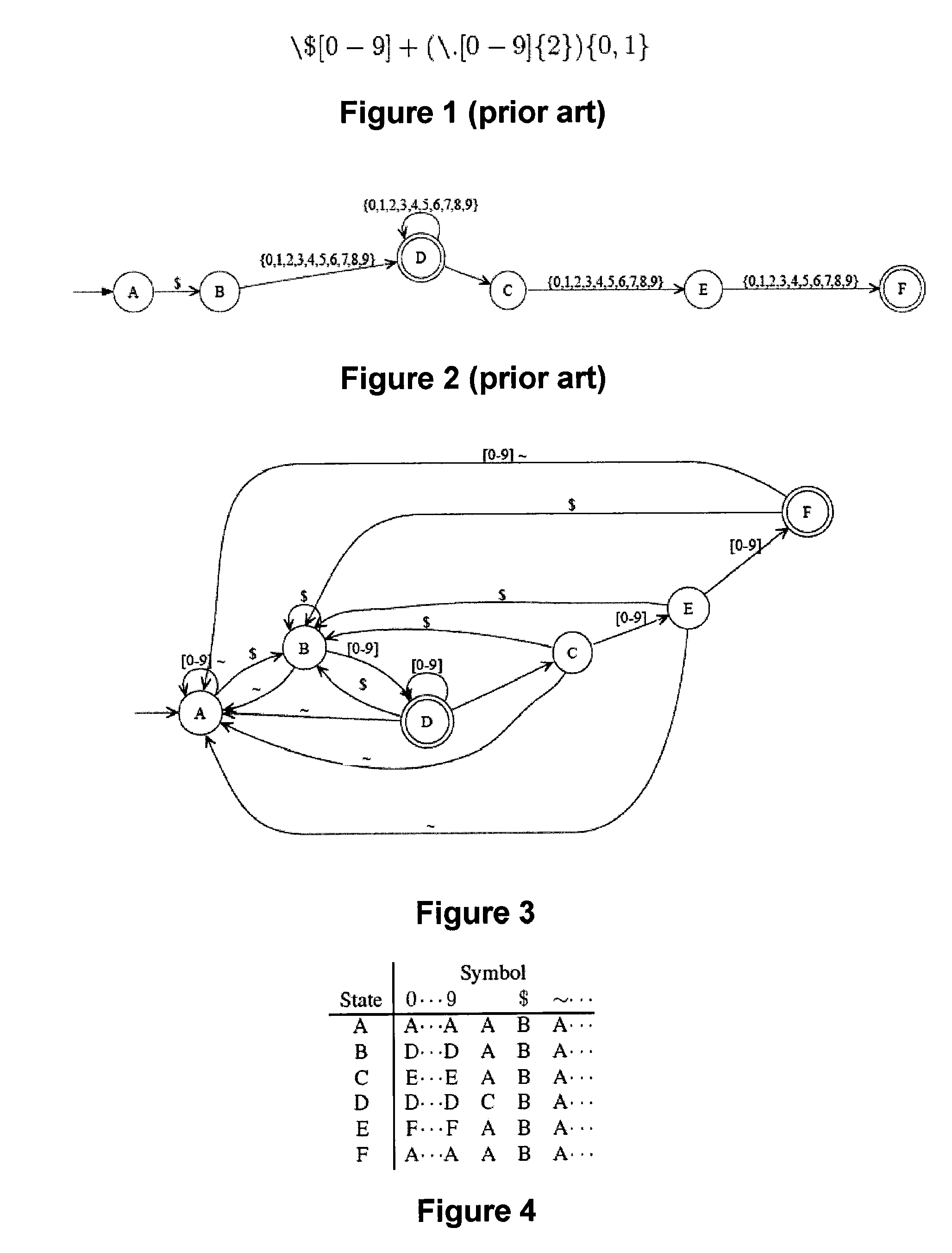
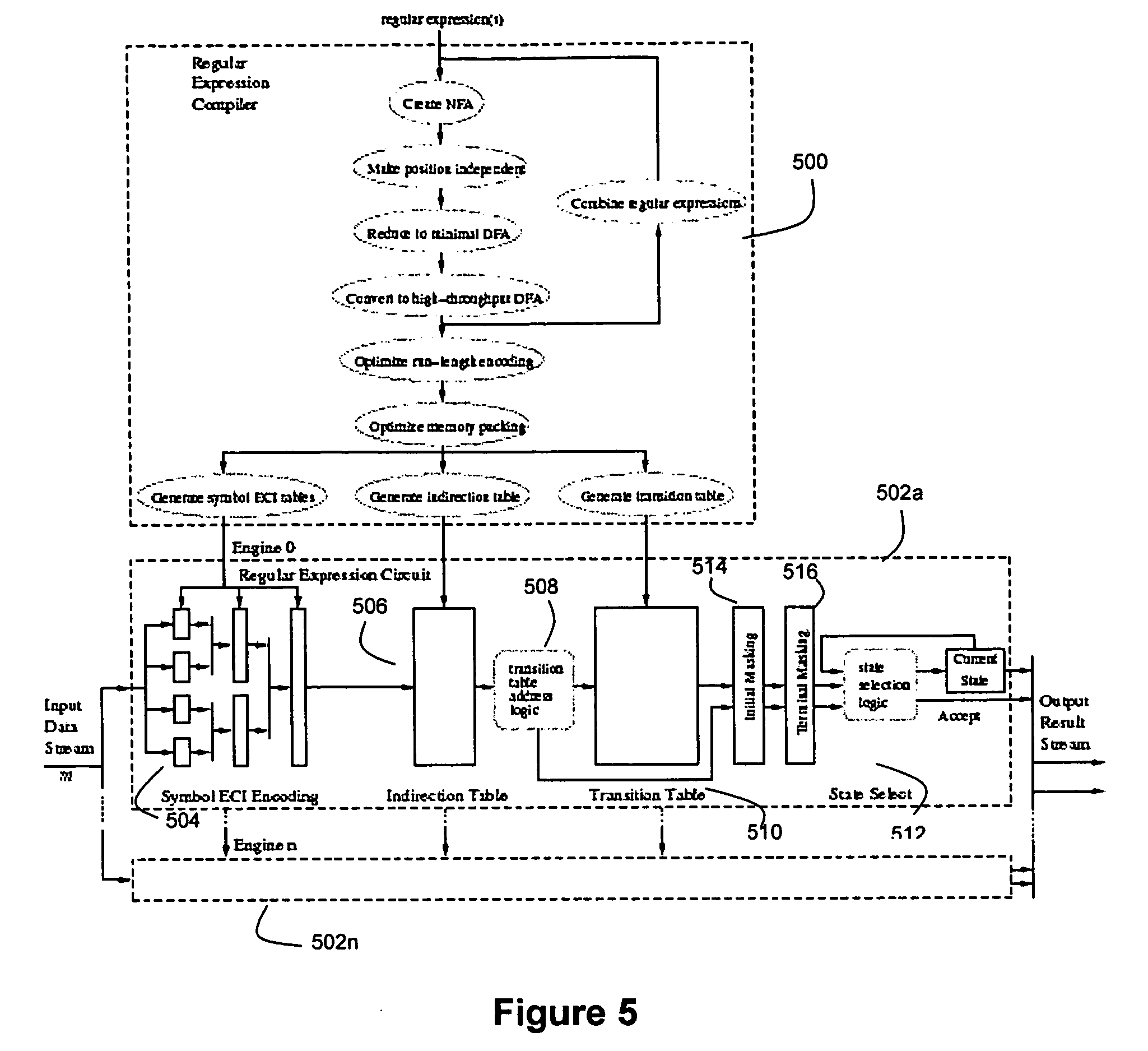
Disclosed herein is an improved architecture for regular expression pattern matching. Improvements to pattern matching deterministic finite automatons (DFAs) that are described by the inventors include a pipelining strategy that pushes state-dependent feedback to a final pipeline stage to thereby enhance parallelism and throughput, augmented state transitions that track whether a transition is indicative of a pattern match occurring thereby reducing the number of necessary states for the DFA, augmented state transition that track whether a transition is indicative of a restart to the matching process, compression of the DFA's transition table, alphabet encoding for input symbols to equivalence class identifiers, the use of an indirection table to allow for optimized transition table memory, and enhanced scalability to facilitate the ability of the improved DFA to process multiple input symbols per cycle.
Owner:IP RESERVOIR
Method and System for High Performance Data Metatagging and Data Indexing Using Coprocessors
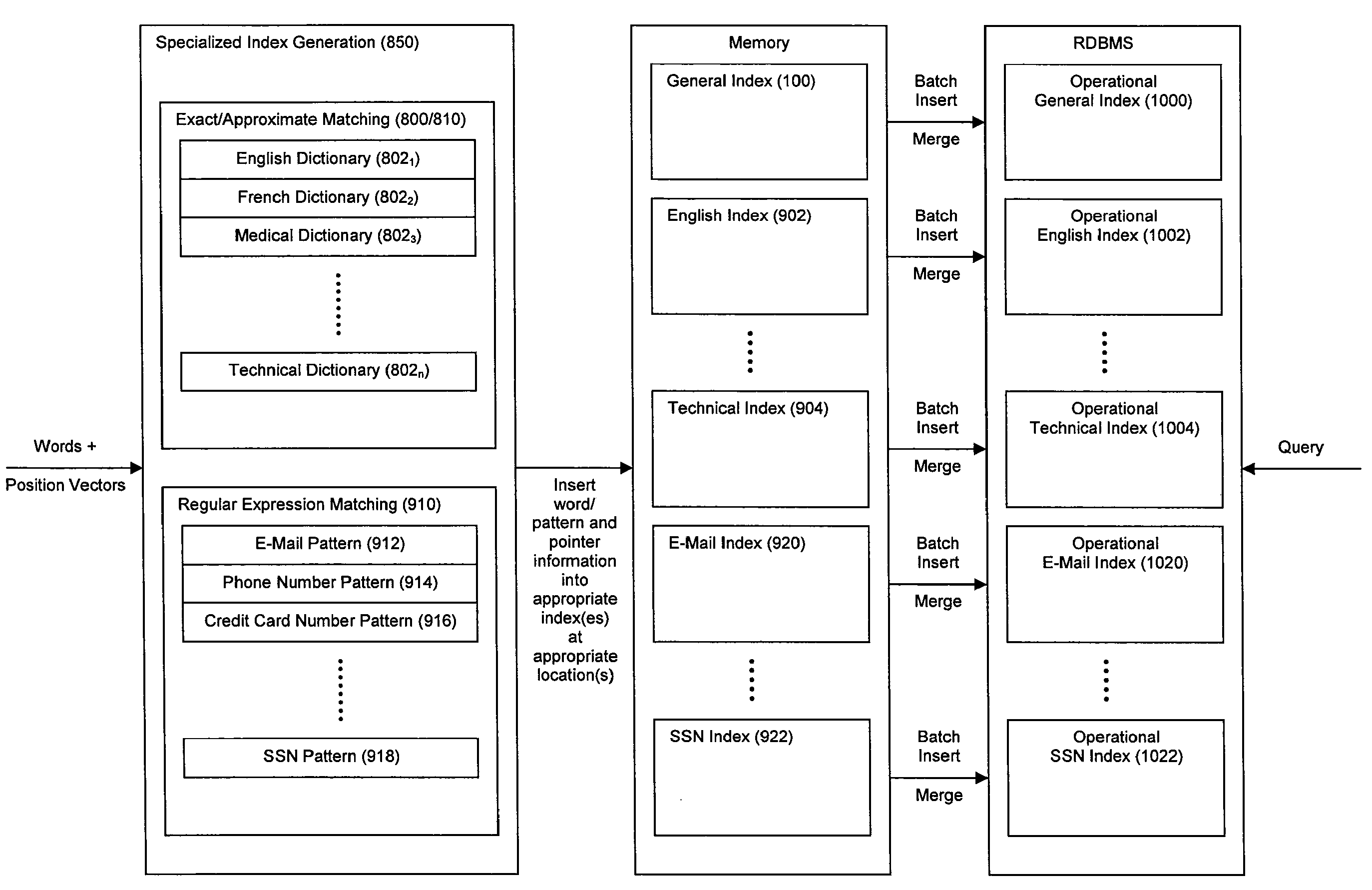
ActiveUS20080114725A1Robust and high performance data searchingHigh indexWeb data indexingFile access structuresData streamCoprocessor
Disclosed herein is a method and system for hardware-accelerating the generation of metadata for a data stream using a coprocessor. Using these techniques, data can be richly indexed, classified, and clustered at high speeds. Reconfigurable logic such a field programmable gate arrays (FPGAs) can be used by the coprocessor for this hardware acceleration. Techniques such as exact matching, approximate matching, and regular expression pattern matching can be employed by the coprocessor to generate desired metadata for the data stream.
Owner:IP RESERVOIR
Method and device for high performance regular expression pattern matching
ActiveUS20070130140A1Minimize the numberData processing applicationsDigital data information retrievalAlgorithmPattern matching
Disclosed herein is an improved architecture for regular expression pattern matching. Improvements to pattern matching deterministic finite automatons (DFAs) that are described by the inventors include a pipelining strategy that pushes state-dependent feedback to a final pipeline stage to thereby enhance parallelism and throughput, augmented state transitions that track whether a transition is indicative of a pattern match occurring thereby reducing the number of necessary states for the DFA, augmented state transition that track whether a transition is indicative of a restart to the matching process, compression of the DFA's transition table, alphabet encoding for input symbols to equivalence class identifiers, the use of an indirection table to allow for optimized transition table memory, and enhanced scalability to facilitate the ability of the improved DFA to process multiple input symbols per cycle.
Owner:IP RESERVOIR
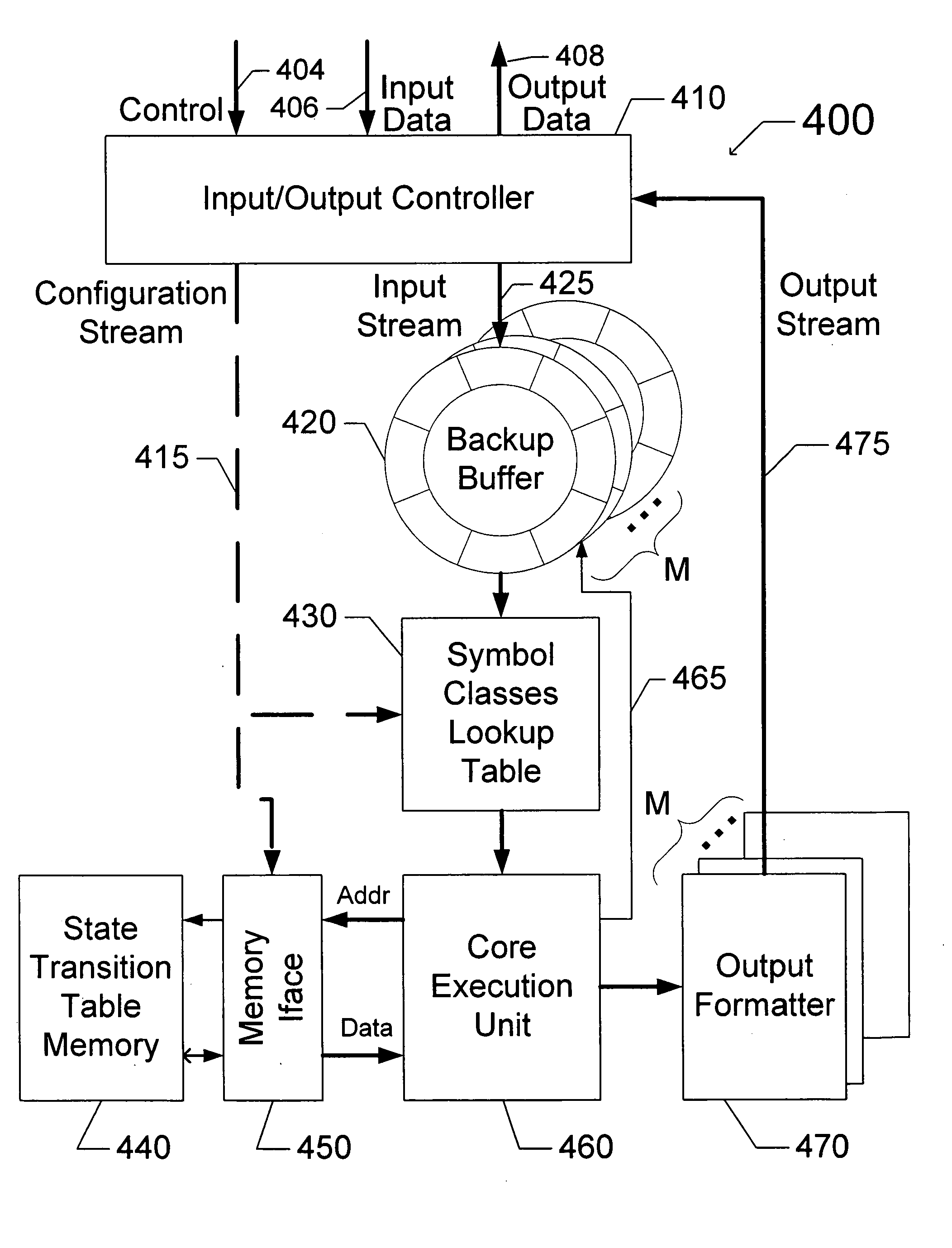
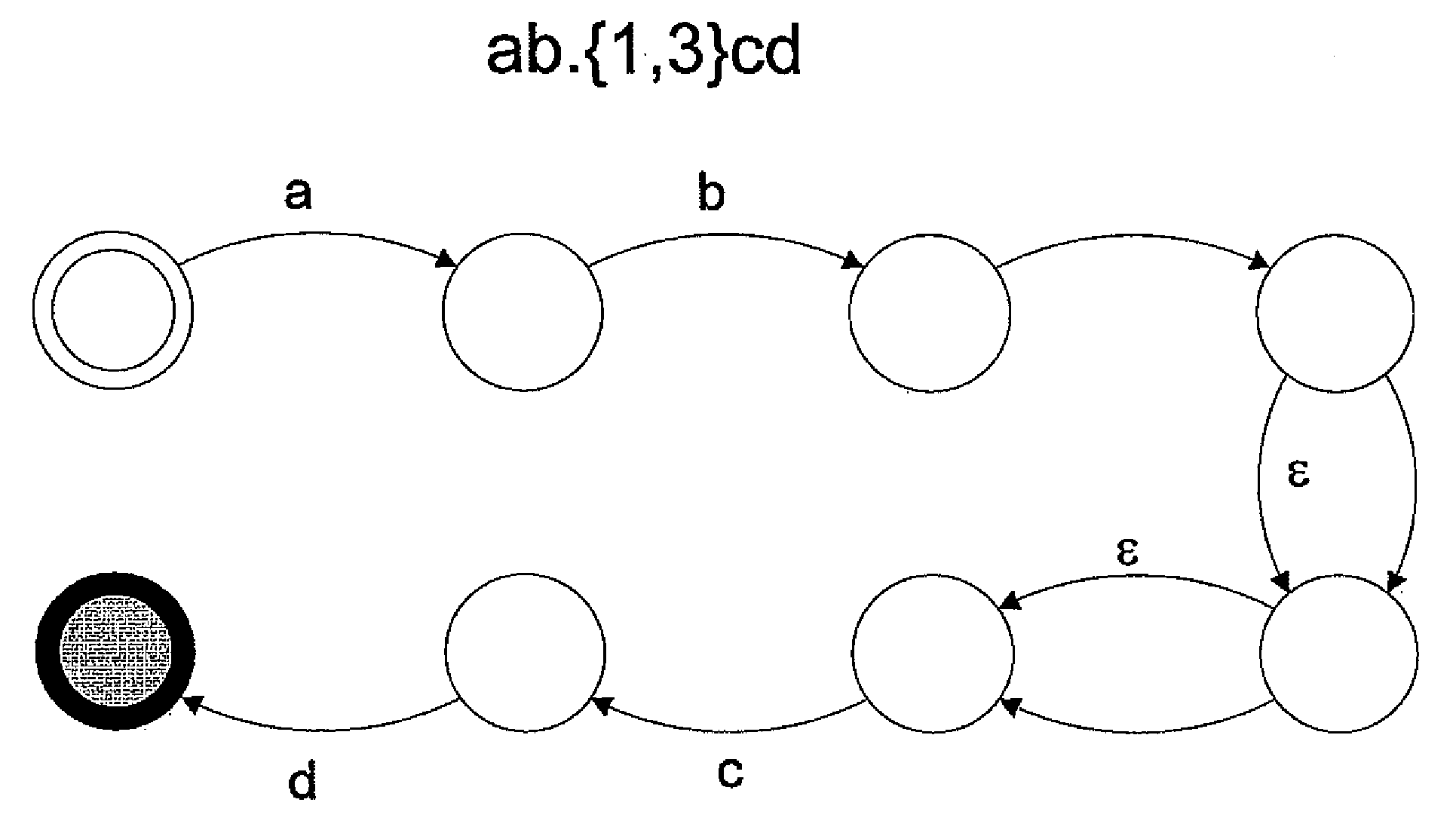
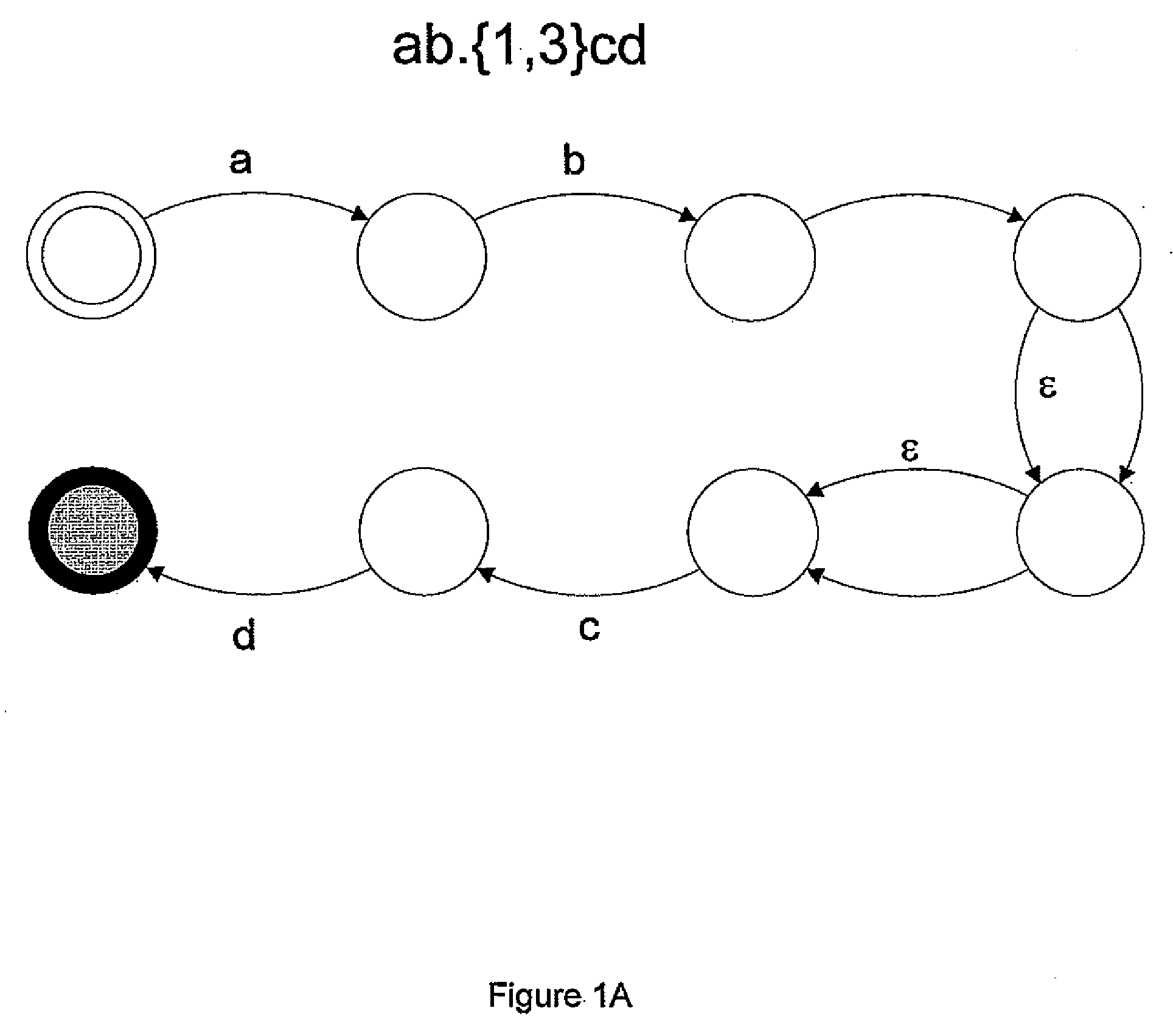
Regular expression acceleration engine and processing model
InactiveUS20050273450A1Digital data processing detailsCharacter and pattern recognitionVirtual terminalTheoretical computer science
Optimization for improved construction and execution of state machines configured to identify lexemes in data files is disclosed. This optimization includes, for example, systems and methods for disambiguating between overlapping matches found in data files, using trailing context regular expressions, removing stall states from state machines, selecting between a plurality of sets of regular expressions, analyzing multiple data files concurrently, analyzing portions of a single data file concurrently, representing state machines using instructions representative of transitions between states, and using virtual terminal instructions.
Owner:LSI CORPORATION
Apparatus and method for parsing unstructured data
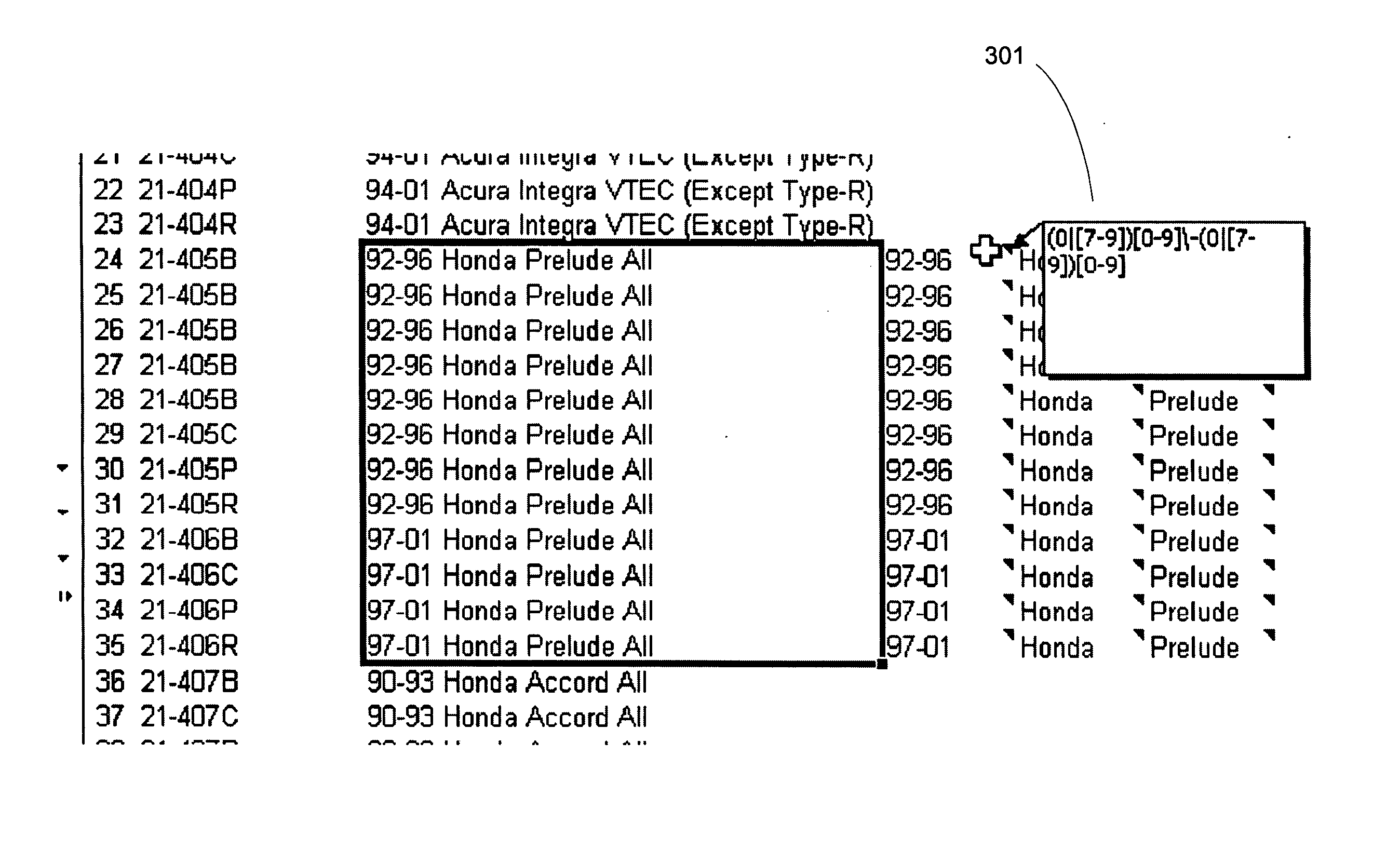
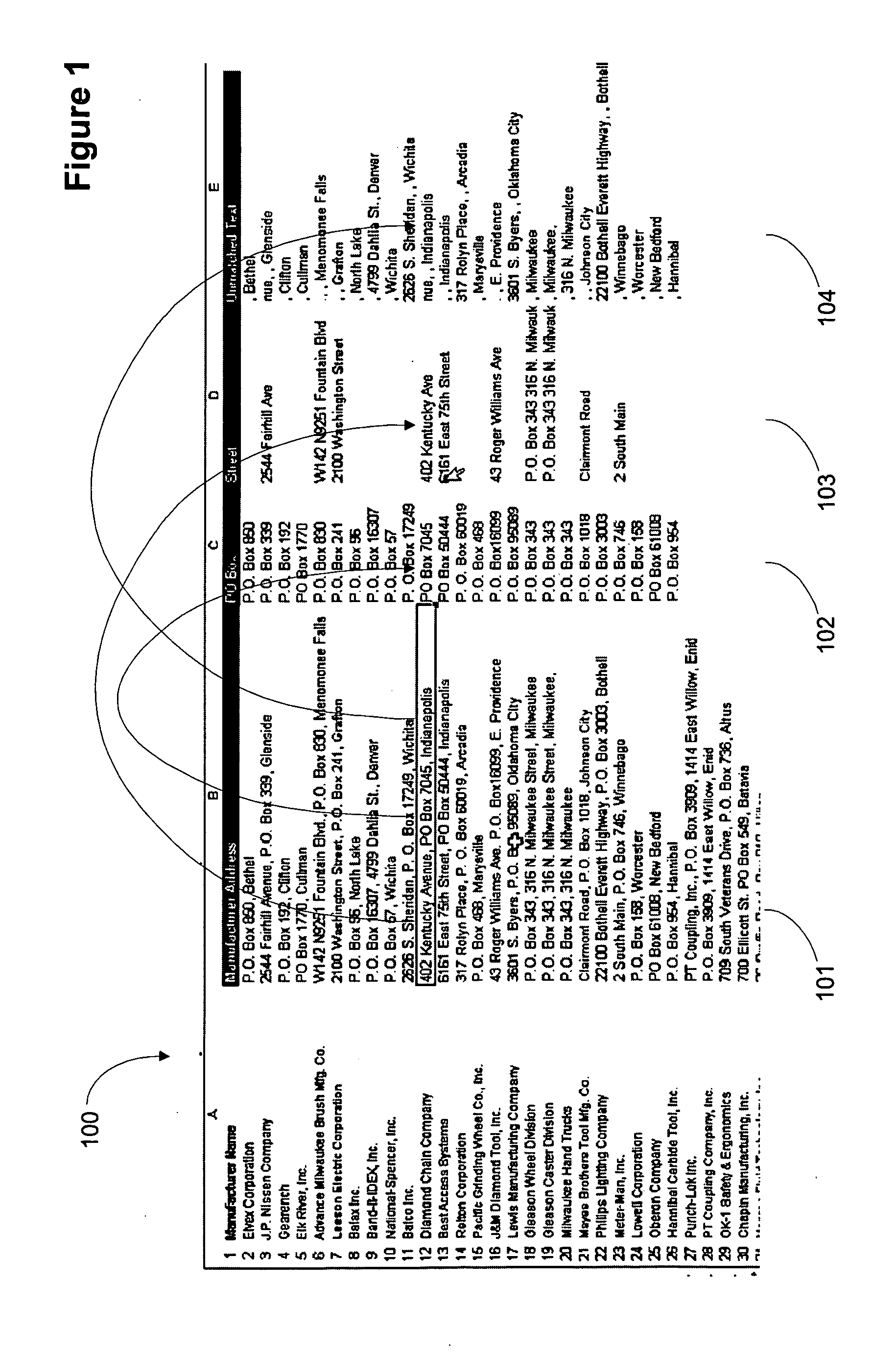
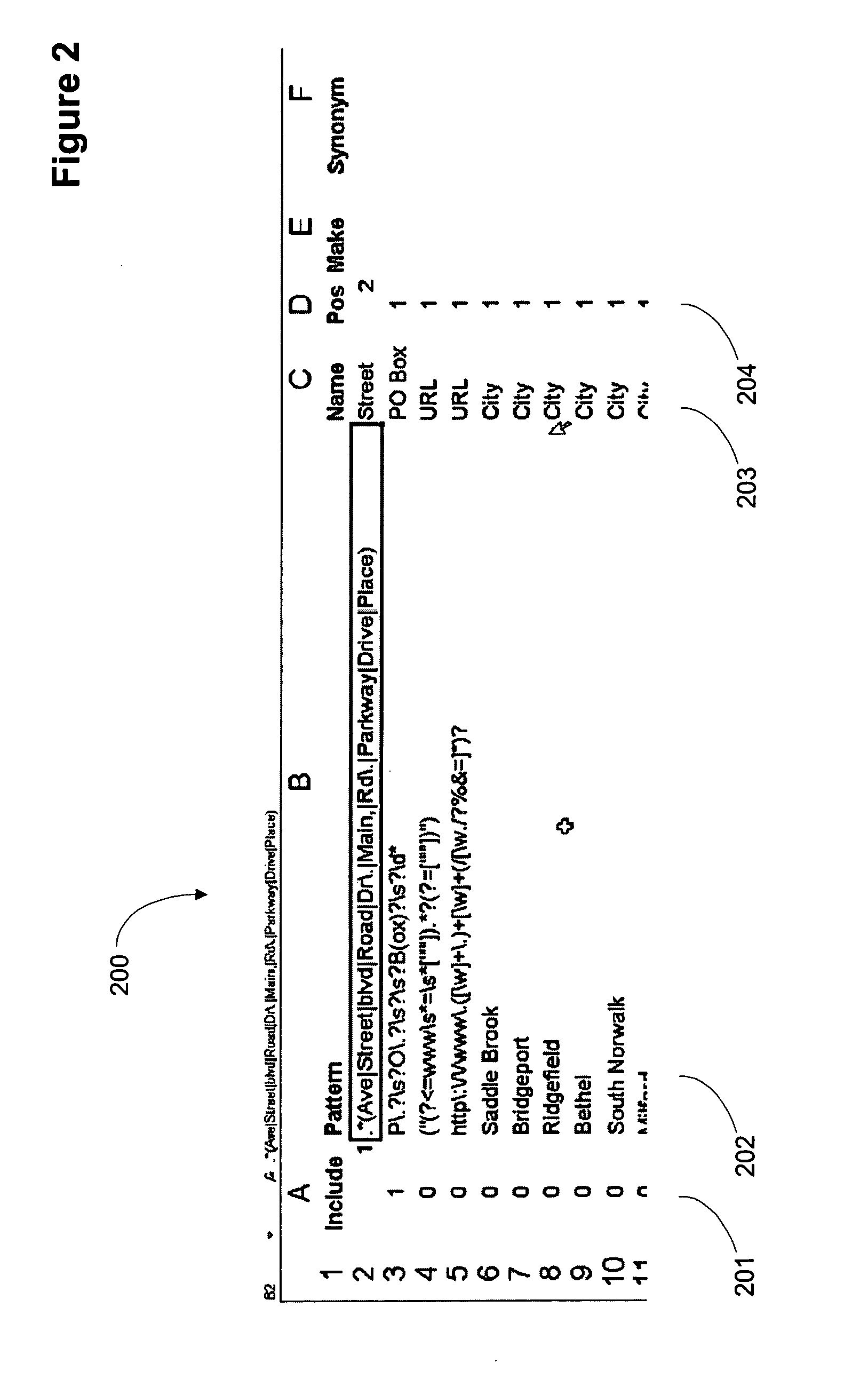
ActiveUS20070078872A1Quick implementationEliminates more and more unmatched textDigital data information retrievalDigital data processing detailsPattern matchingPosition dependent
A user interface for parsing unstructured data using pattern recognition. The patterns used in parsing data are formed from regular expressions. The parsed data may be displayed in a first format and unmatched strings in the unstructured text may be displayed in a second format. A format may comprise a desired color, font or any other user interface parameter. In addition, the data that parses according to a pattern may be placed in a column associated with the pattern in a tabular user interface, for example a spreadsheet like Excel™. Associating a pattern with a position to display successful matches in allows for breaking unstructured text into pieces associated with a particular field or column. Modification of the patterns allows for more and more of the unstructured text to match the patterns and when the data has been parsed to the desired level, the data may be imported into a database.
Owner:REGIONAL RESOURCES LTD
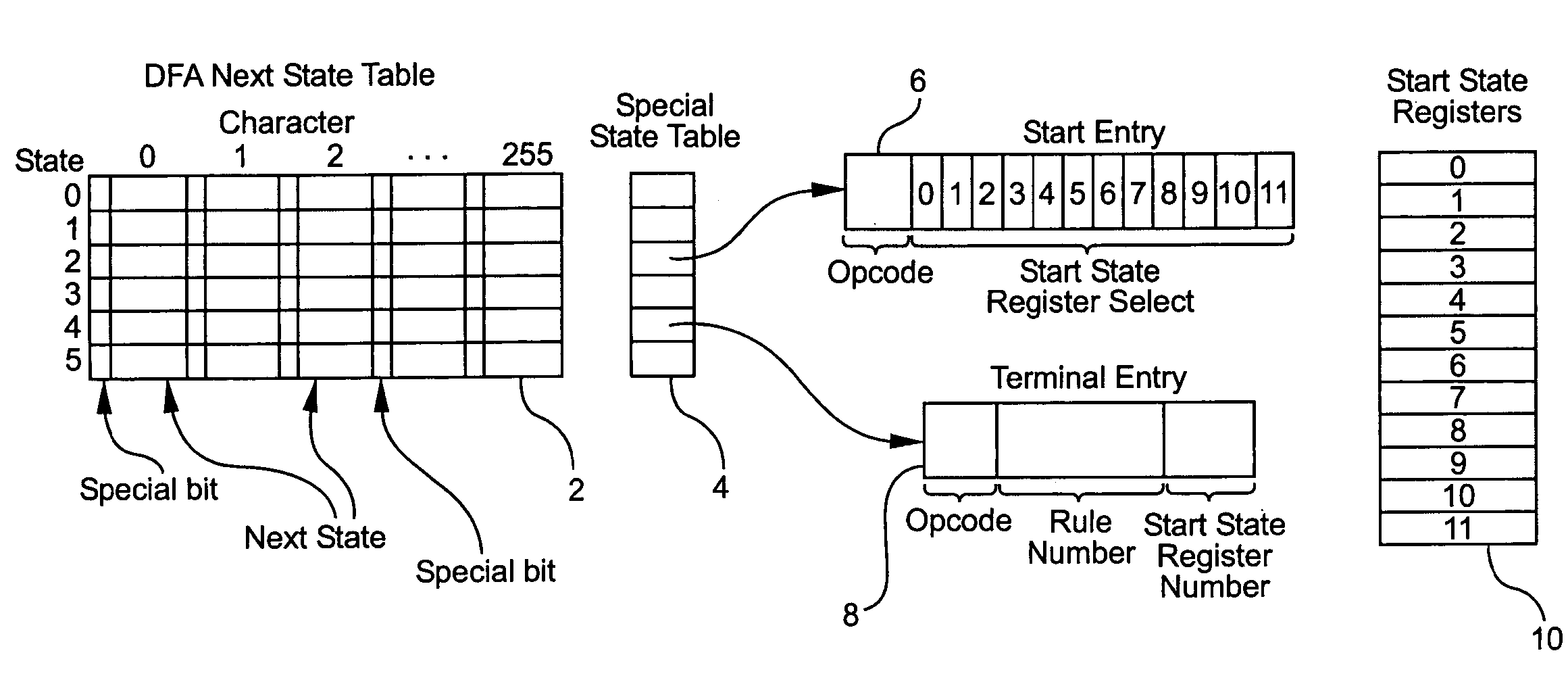
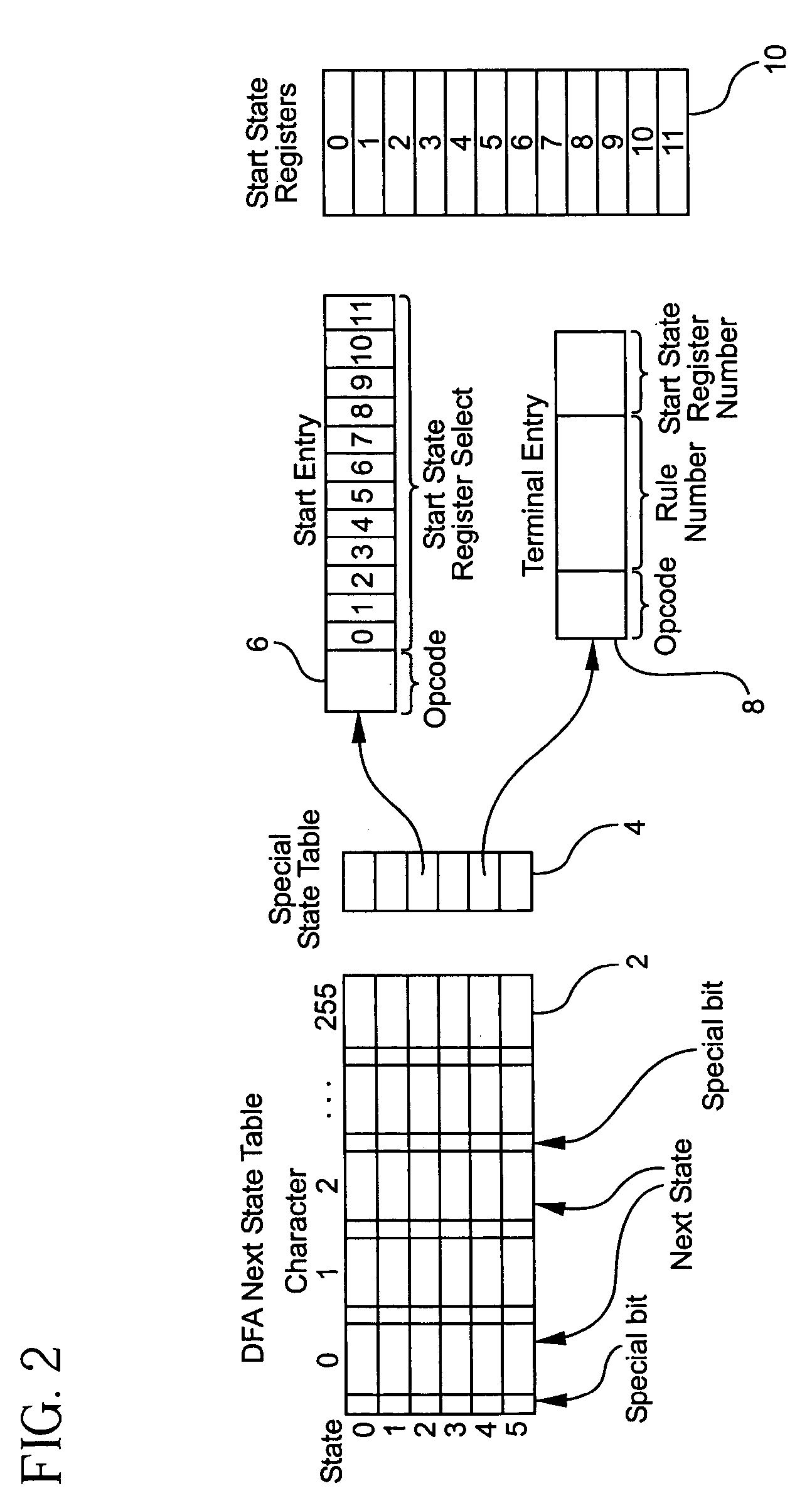
System and method for determining the start of a match of a regular expression
InactiveUS7305391B2Overcome disadvantagesDigital data information retrievalData processing applicationsProcessor registerTheoretical computer science
A method for determining the start of a match of a regular expression using the special state table, the set of start state registers and the DFA next state table, includes the step of determining from the regular expression each start-of-match start state and each end-of-match terminal state. For each start state, a start state entry is loaded into the special state table. For each terminal state, a terminal state entry is loaded into each special state table. The next state table is used to return the next state from the current state and an input character. When a start state is encountered, the current offset from the beginning of the input character string is loaded into the start state register. When a terminal state is encountered, the terminal state entry is retrieved from the special state table, and the value of the start state register corresponding to the rule number of the terminal entry in the special state table is further retrieved. The value of the start state register which is retrieved indicates the location in the character string where the start-of-match occurred for a particular rule.
Owner:RAMBUS INC
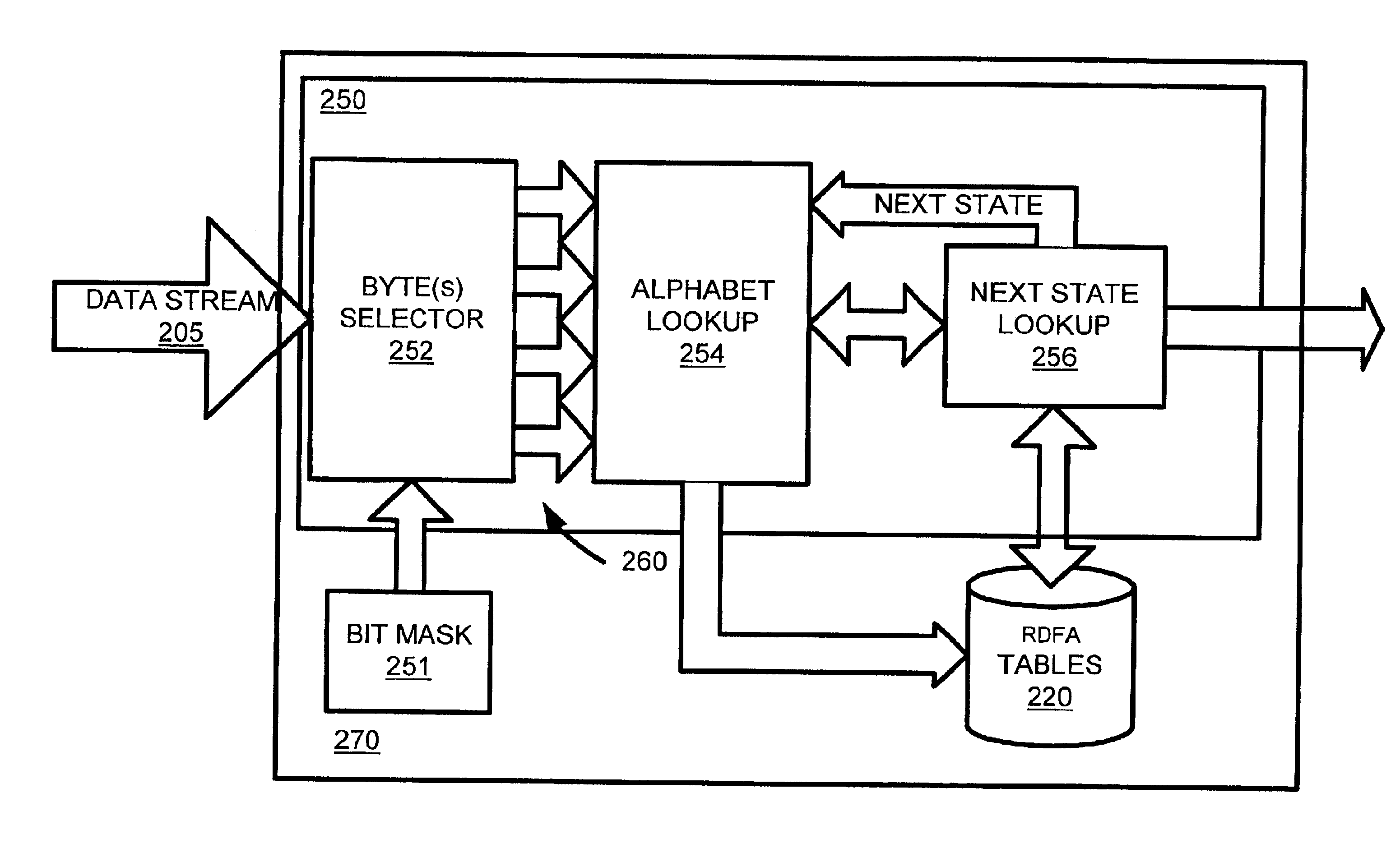
High speed data stream pattern recognition
InactiveUS6856981B2Increase speedLow memory storage requirementDigital data information retrievalMultiple digital computer combinationsData streamState dependent
A system and method in accordance with the present invention determines in real-time the portions of a set of characters from a data or character stream which satisfies one or more predetermined regular expressions. A Real-time Deterministic Finite state Automaton (RDFA) ensures that the set of characters is processed at high speeds with relatively small memory requirements. An optimized state machine models the regular expression(s) and state related alphabet lookup and next state tables are generated. Characters from the data stream are processed in parallel using the alphabet lookup and next state tables, to determine whether to transition to a next state or a terminal state, until the regular expression is satisfied or processing is terminated. Additional means may be implemented to determine a next action from satisfaction of the regular expression.
Owner:RAMBUS INC
Systems and methods for processing data flows
InactiveUS20080133517A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
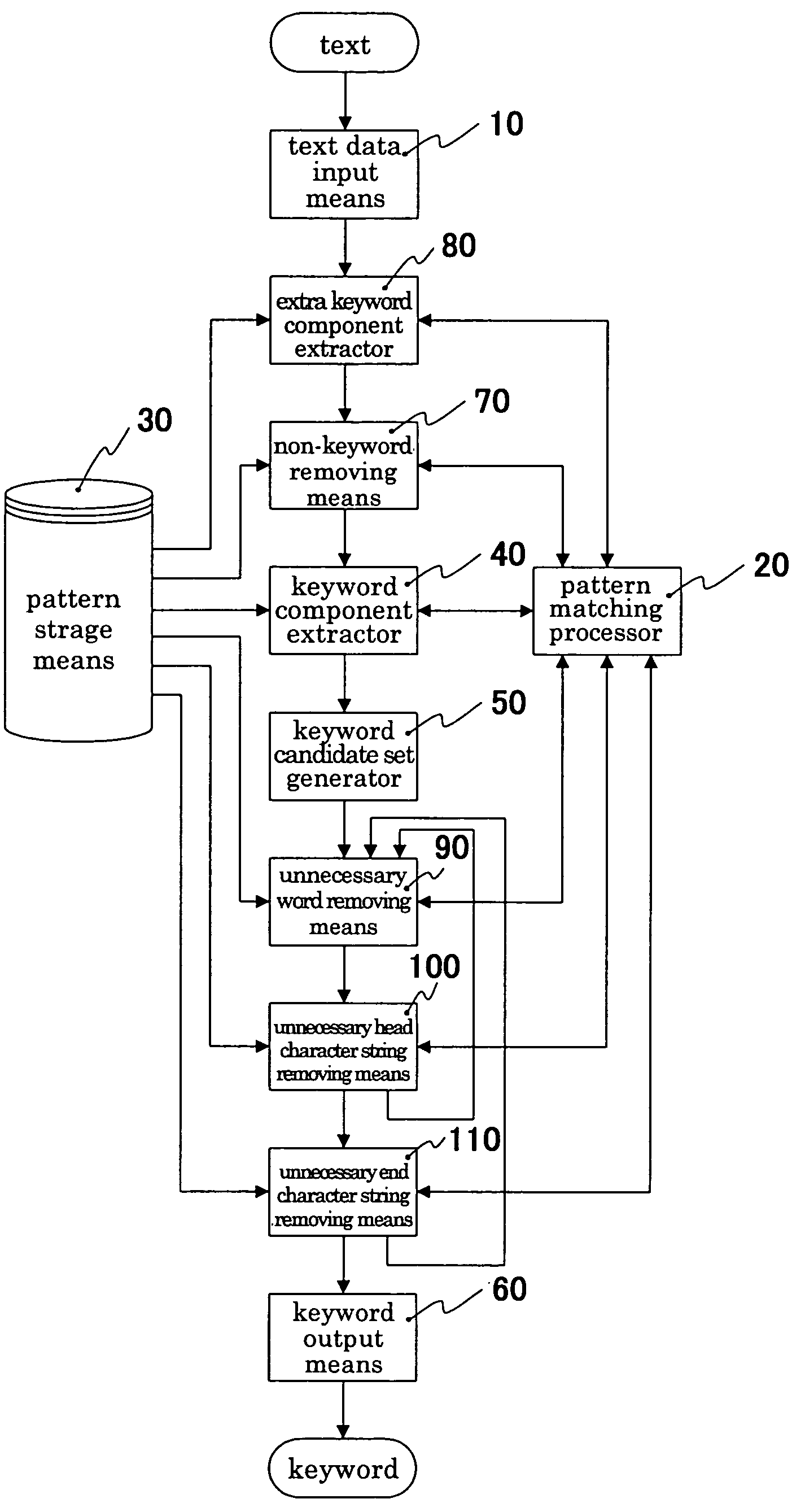
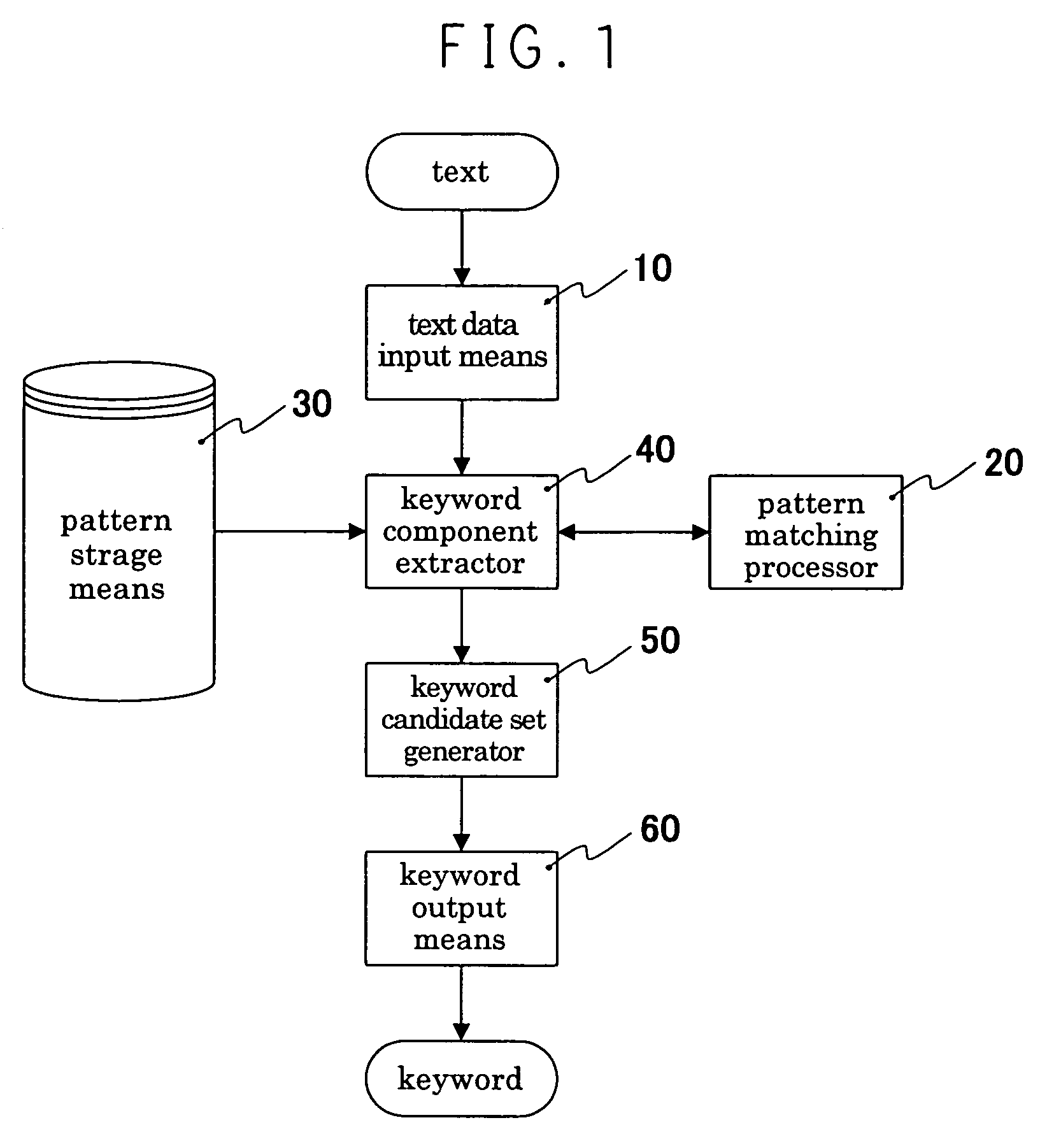
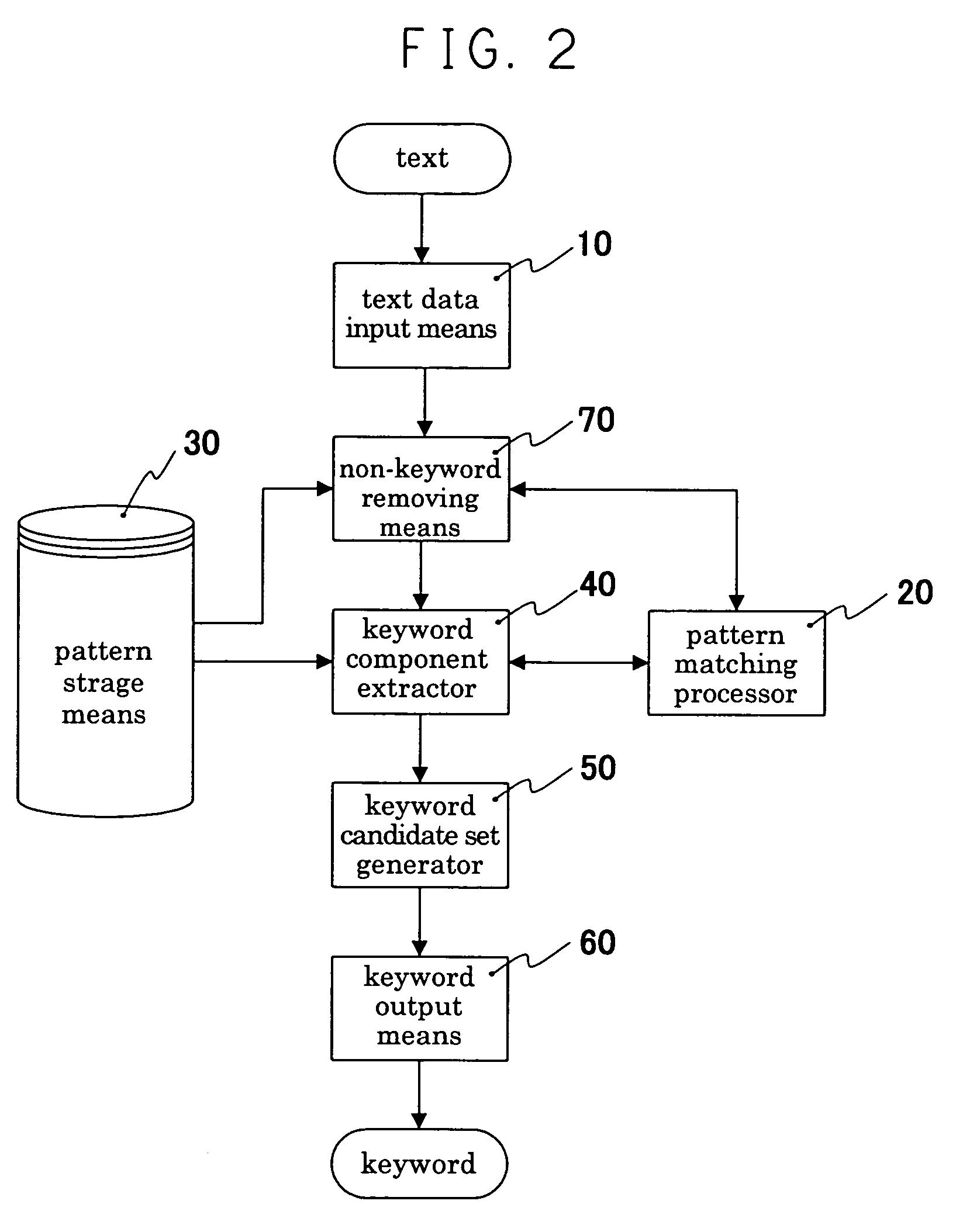
Keyword extracting device
InactiveUS7191177B2Data processing applicationsDigital data information retrievalPattern matchingText mode
A keyword extracting device which extracts keywords collectively and efficiently while improving descriptive property and reusability of the information for keyword extracting. A text data input inputs a text. A pattern processor carries out matching and replacement of a character string based on a pattern in regular expression or its equivalent. A pattern storage stores at least a keyword component pattern representing a character string capable of being a component of a keyword. A keyword component extractor extracts, as keyword components, all character strings which are matched with a keyword component pattern and are not overlapped with each other by using the pattern processor for a text. A keyword candidate set generator generates a keyword candidate set from each keyword. And, a keyword output outputs each keyword candidate of a keyword candidate set as a keyword.
Owner:MITSUBISHI ELECTRIC CORP
Systems and methods for processing data flows
InactiveUS8010469B2Increased complexityAvoid problemsMemory loss protectionError detection/correctionData streamSelf-organizing map
Methods and systems for flow processing and switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security are described. Such flow processing facilities may be used for inspecting network traffic packet payloads to detect security threats and intrusions across accessible layers of the network IP stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources.
Owner:CA TECH INC
Systems and methods for processing regular expressions
InactiveUS20070282833A1Data processing applicationsProgram controlData streamTheoretical computer science
A method for reducing the size of a DFA associated with a regular expression separates the functions of locating subexpressions within the DFA and determining if the located subexpressions satisfy a regular expression. For example, the functions of (1) locating subexpressions in a range asserting expression and, (2) determining whether the subexpressions satisfy the range of the range asserting expression are partitioned. In one embodiment, a first component may locate the subexpressions in a data stream using one or more DFAs, while a second component determines if the located subexpressions satisfy the range. In this embodiment, because the DFAs are not configured to determine a relationship between subexpressions, such as a range between subexpressions, the size of the resultant DFA may be significantly reduced.
Owner:INTEL CORP
Fast and scalable process for regular expression search
InactiveUS20080034427A1Reducing required for pattern matchingReducing deterministic finite automata (DFA)Memory loss protectionError detection/correctionPattern matchingAutomaton
A method includes reducing a deterministic finite automata DFA representative of an expression to provide a smaller DFA, and subjecting information that matches the smaller DFA to non-deterministic finite automata NFA representative of the expression for reducing memory required for pattern matching of the information.
Owner:NEC LAB AMERICA
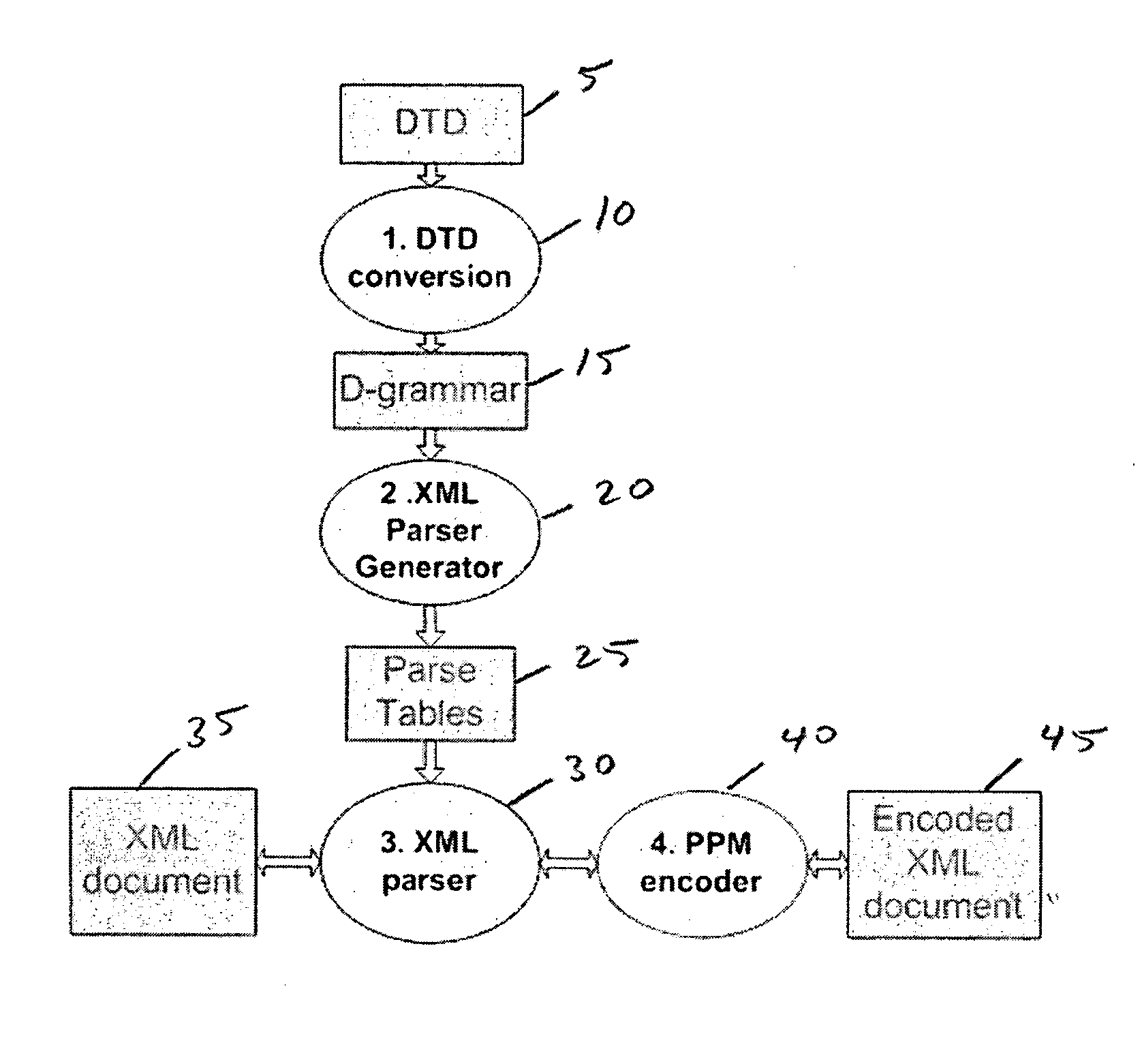
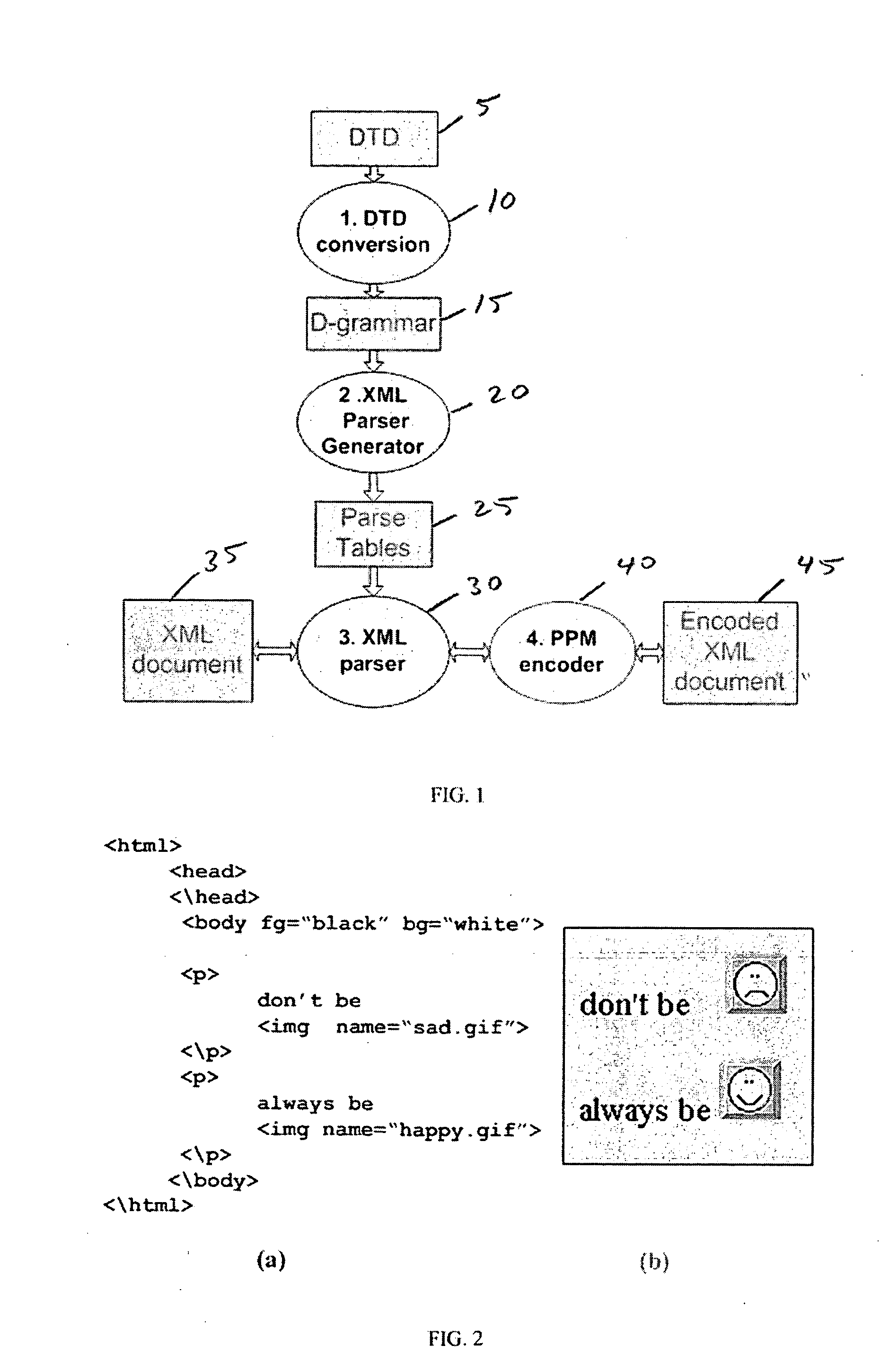
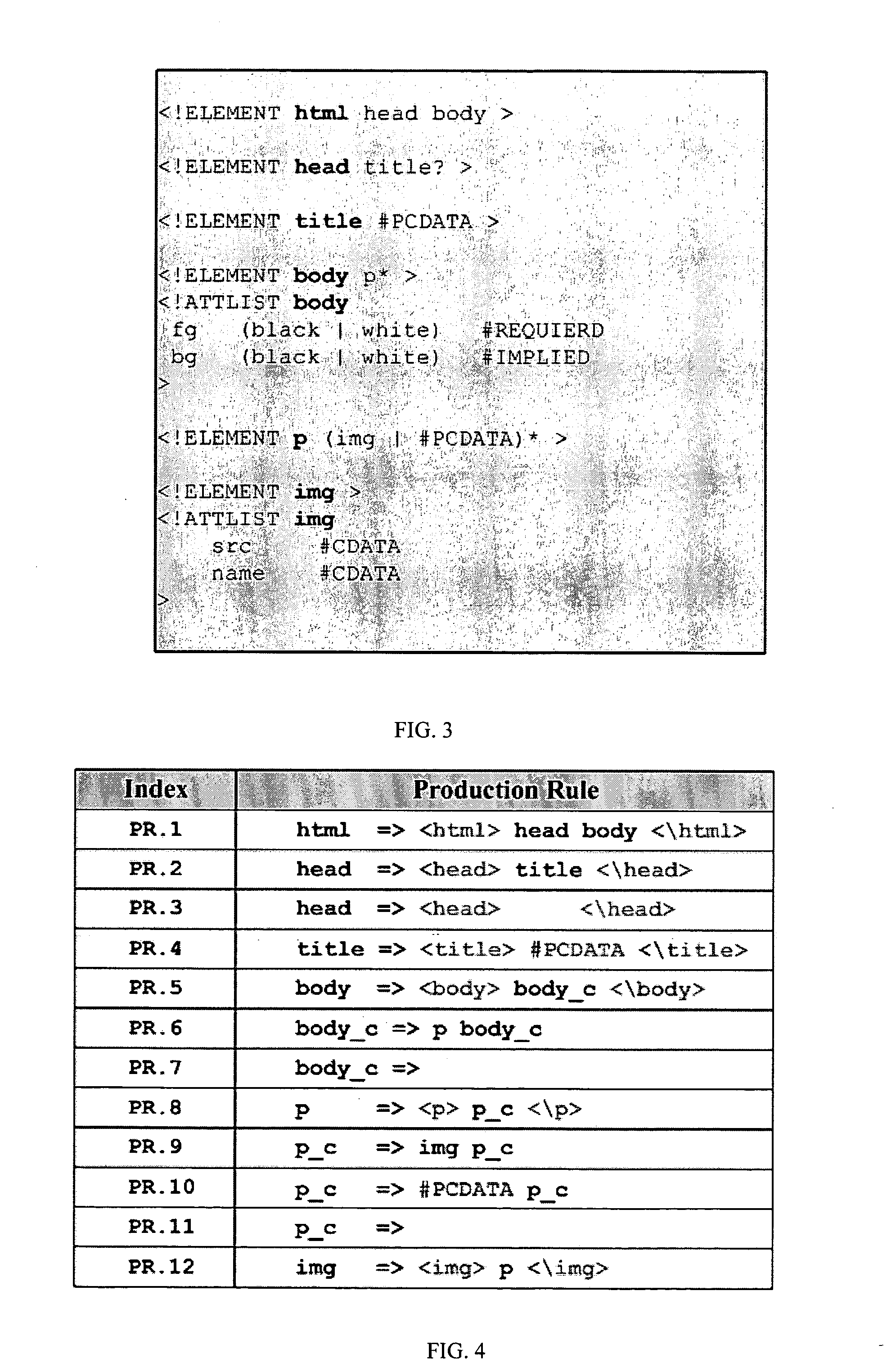
XML parser
InactiveUS20060117307A1Easy to compressFacilitates top down parsingNatural language data processingProgram controlDocument type declarationMultiple context
A method of generating a parser of a source code file that references a syntactic dictionary, a method of compressing the file, and apparatuses that use the methods. The syntactic dictionary is converted into a corresponding plurality of expressions, of a context-free grammar, that are a grammar of the source code. The parser is constructed from the expressions. The source code is compressed using the parser. Preferably, the grammar of the source code file is a D-grammar and the expressions are regular expressions. Preferably, the parser is a deterministic pushdown transducer. An important case of the present invention is that in which the source code is XML code and the syntactic dictionary is the document type declaration of the XML code. Apparatuses that use a parser of the present invention include compressors, decompressors, validators, converters, editors, network devices and end-user / hand-held devices.
Owner:RAMOT AT TEL AVIV UNIV LTD
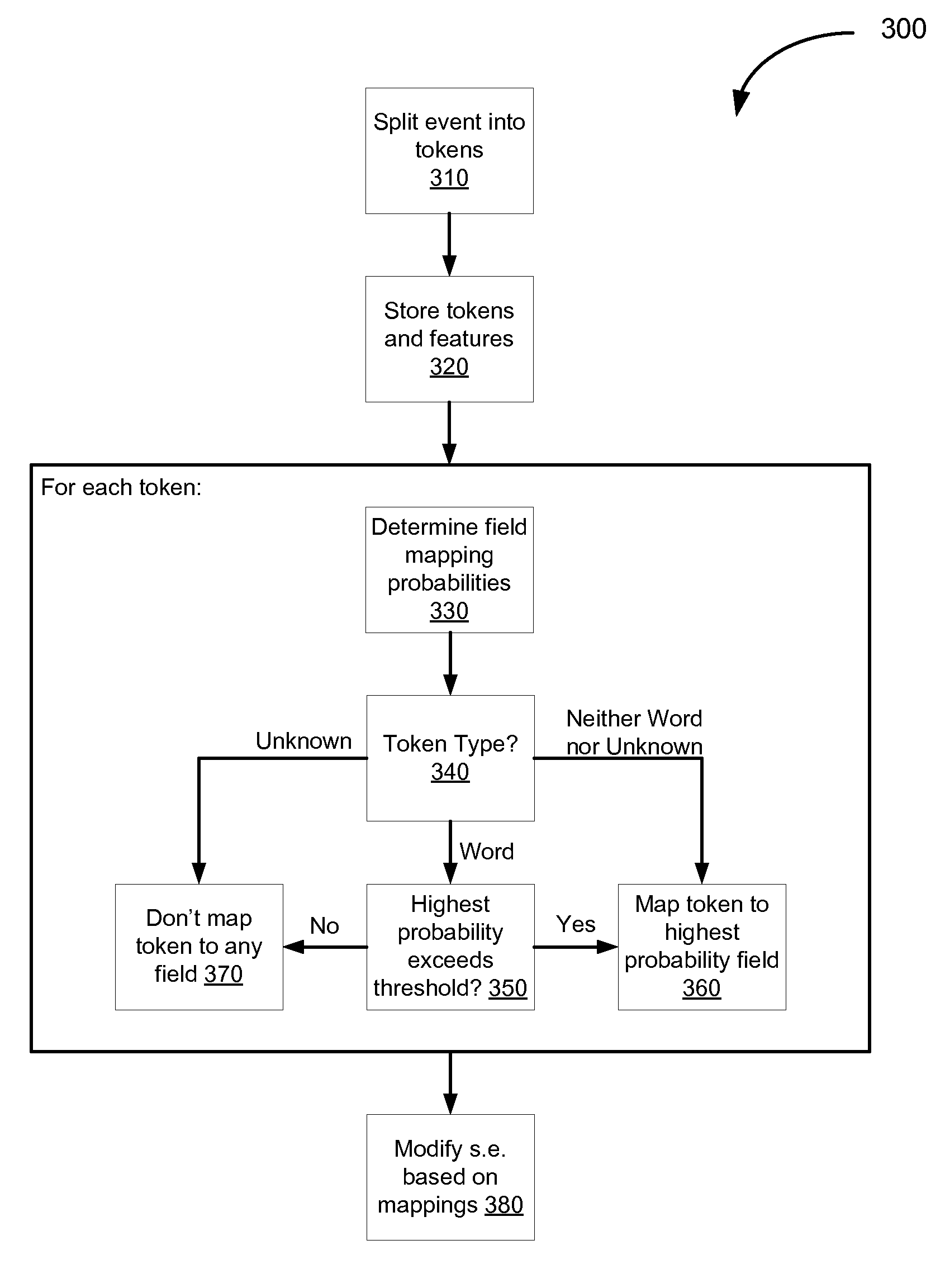
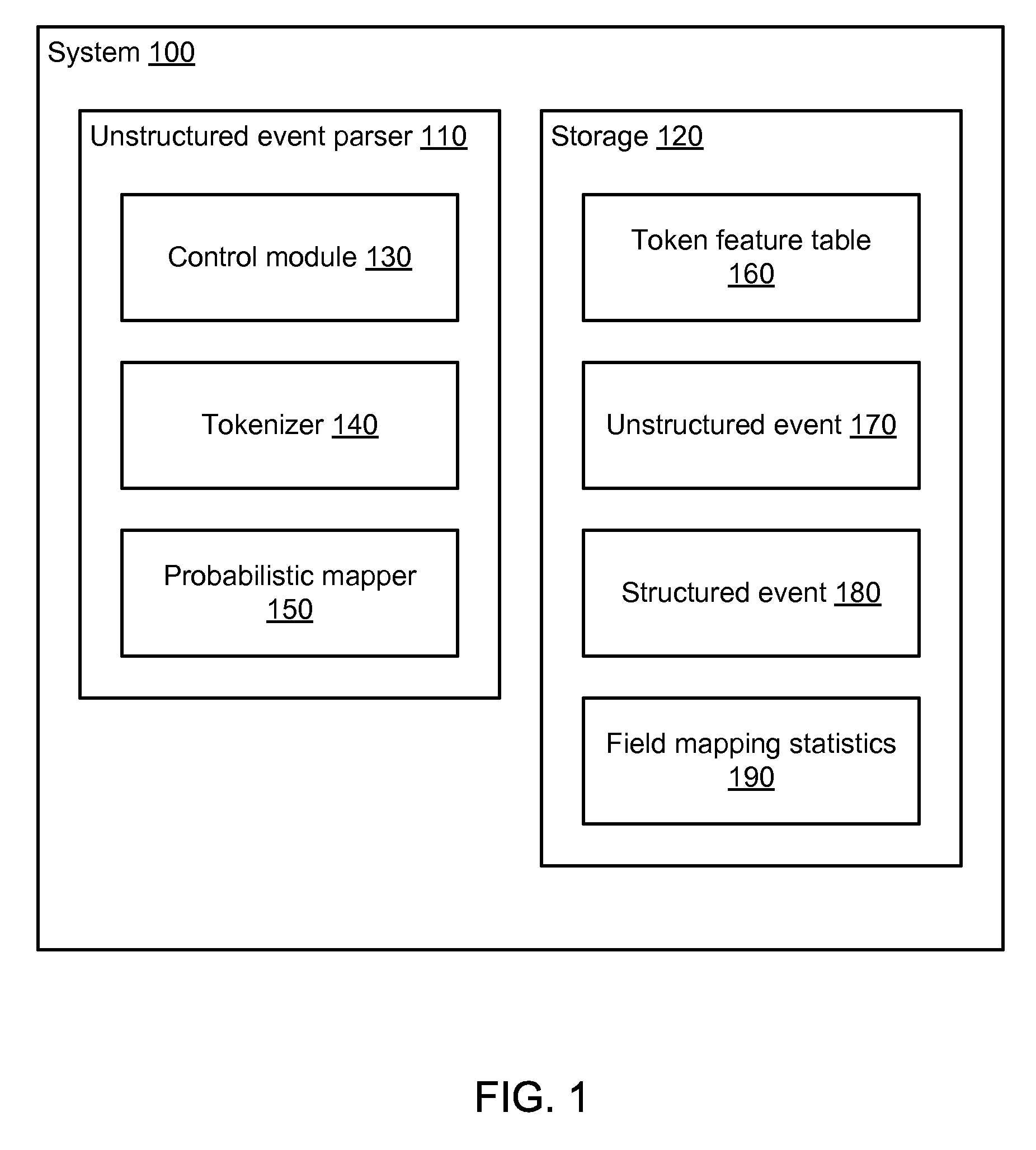
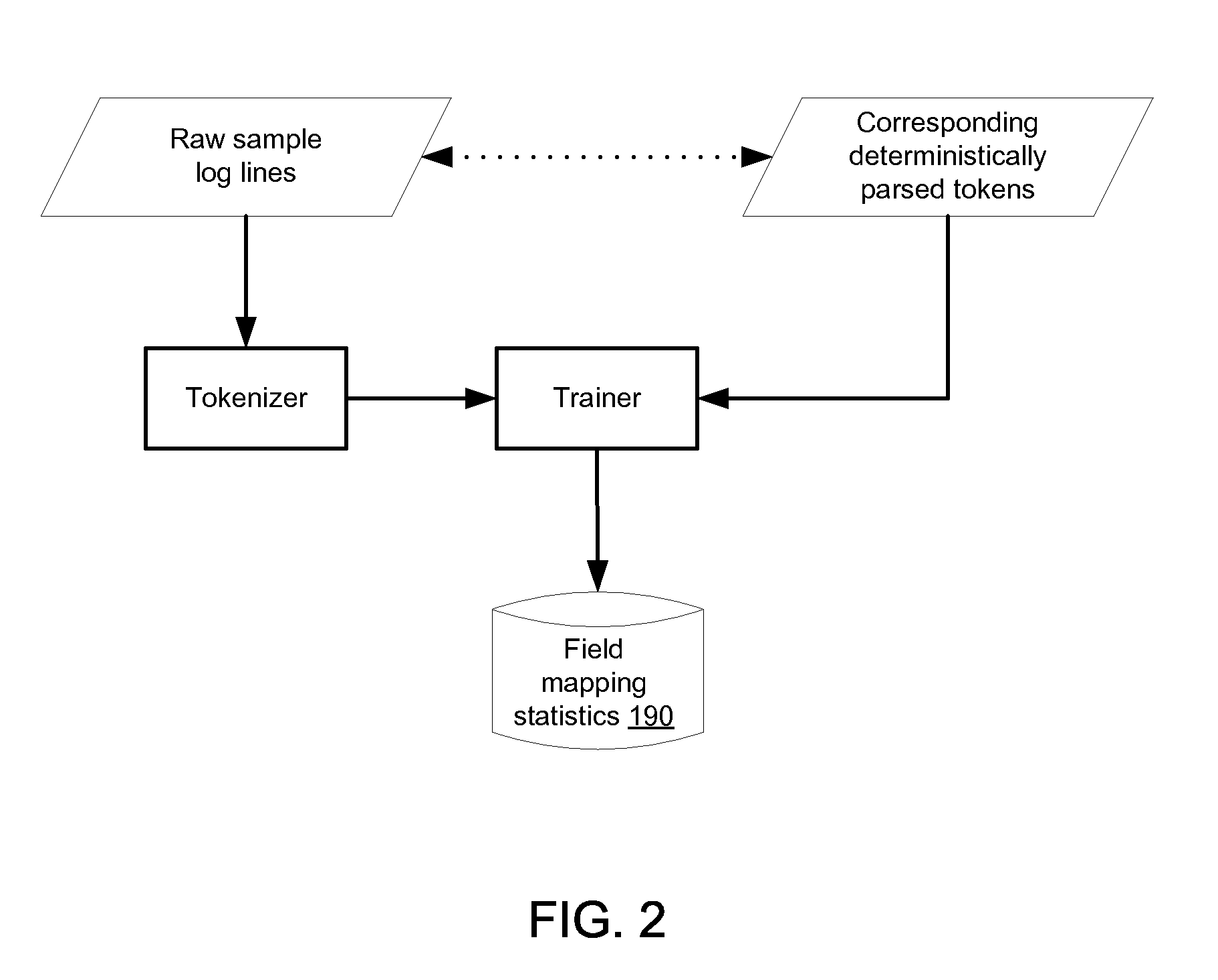
Extracting information from unstructured data and mapping the information to a structured schema using the naïve bayesian probability model
An “unstructured event parser” analyzes an event that is in unstructured form and generates an event that is in structured form. A mapping phase determines, for a given event token, possible fields of the structured event schema to which the token could be mapped and the probabilities that the token should be mapped to those fields. Particular tokens are then mapped to particular fields of the structured event schema. By using the Naïve Bayesian probability model, a “probabilistic mapper” determines, for a particular token and a particular field, the probability that that token maps to that field. The probabilistic mapper can also be used in a “regular expression creator” that generates a regex that matches an unstructured event and a “parameter file creator” that helps a user create a parameter file for use with a parameterized normalized event generator to generate a normalized event based on an unstructured event.
Owner:MICRO FOCUS LLC
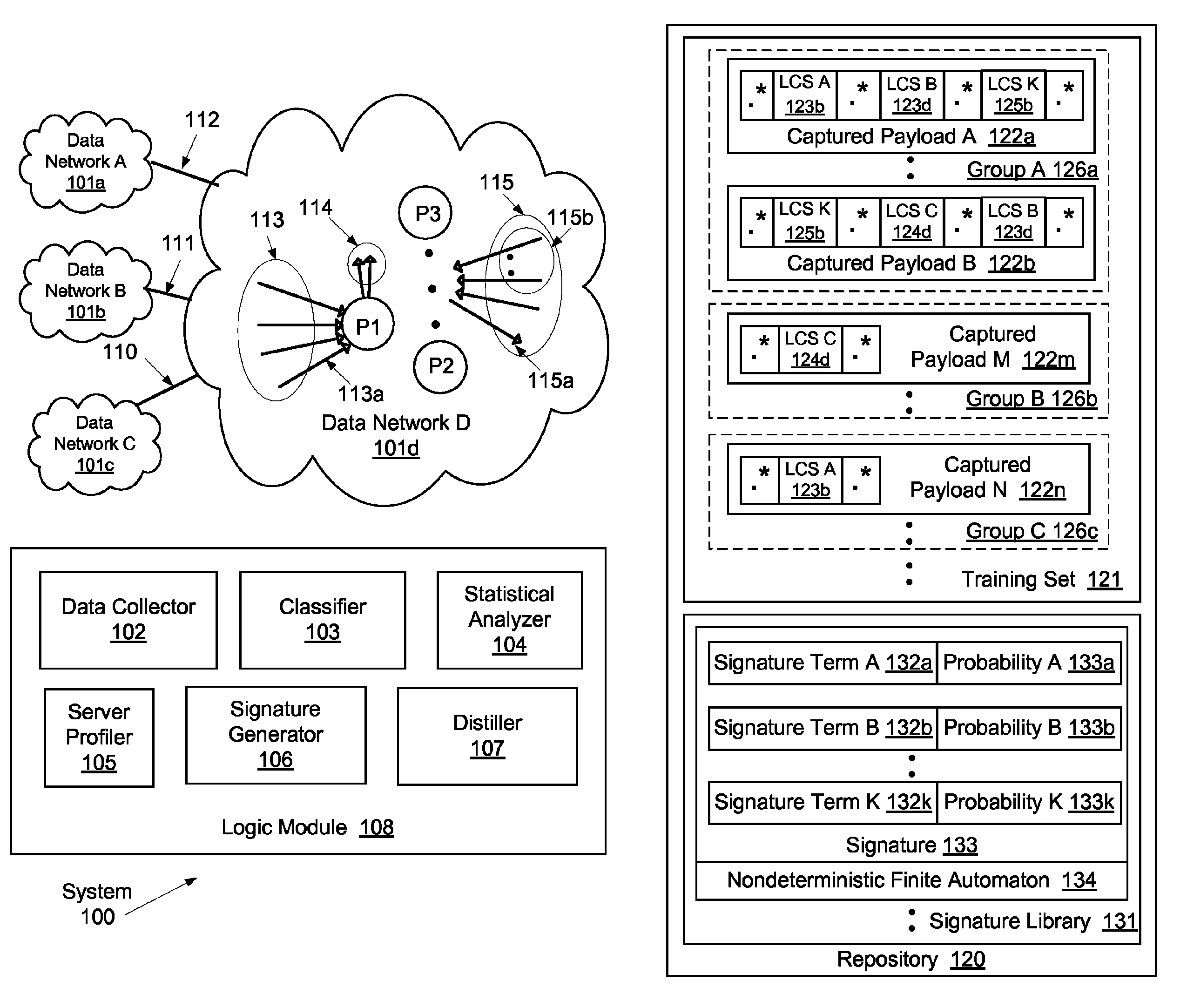
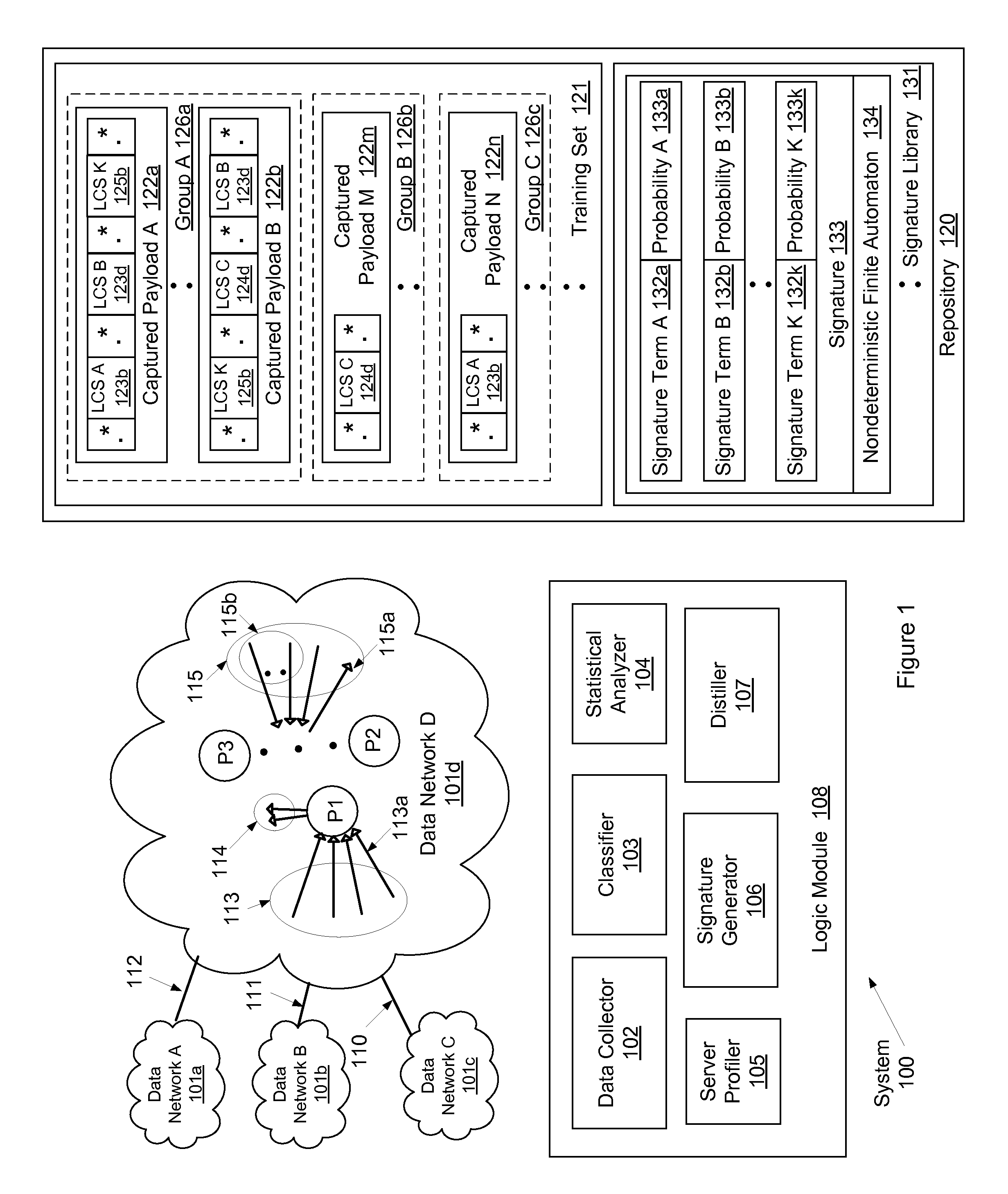
System and method for determining network application signatures using flow payloads
ActiveUS8964548B1Error preventionTransmission systemsNondeterministic finite automatonComputer science
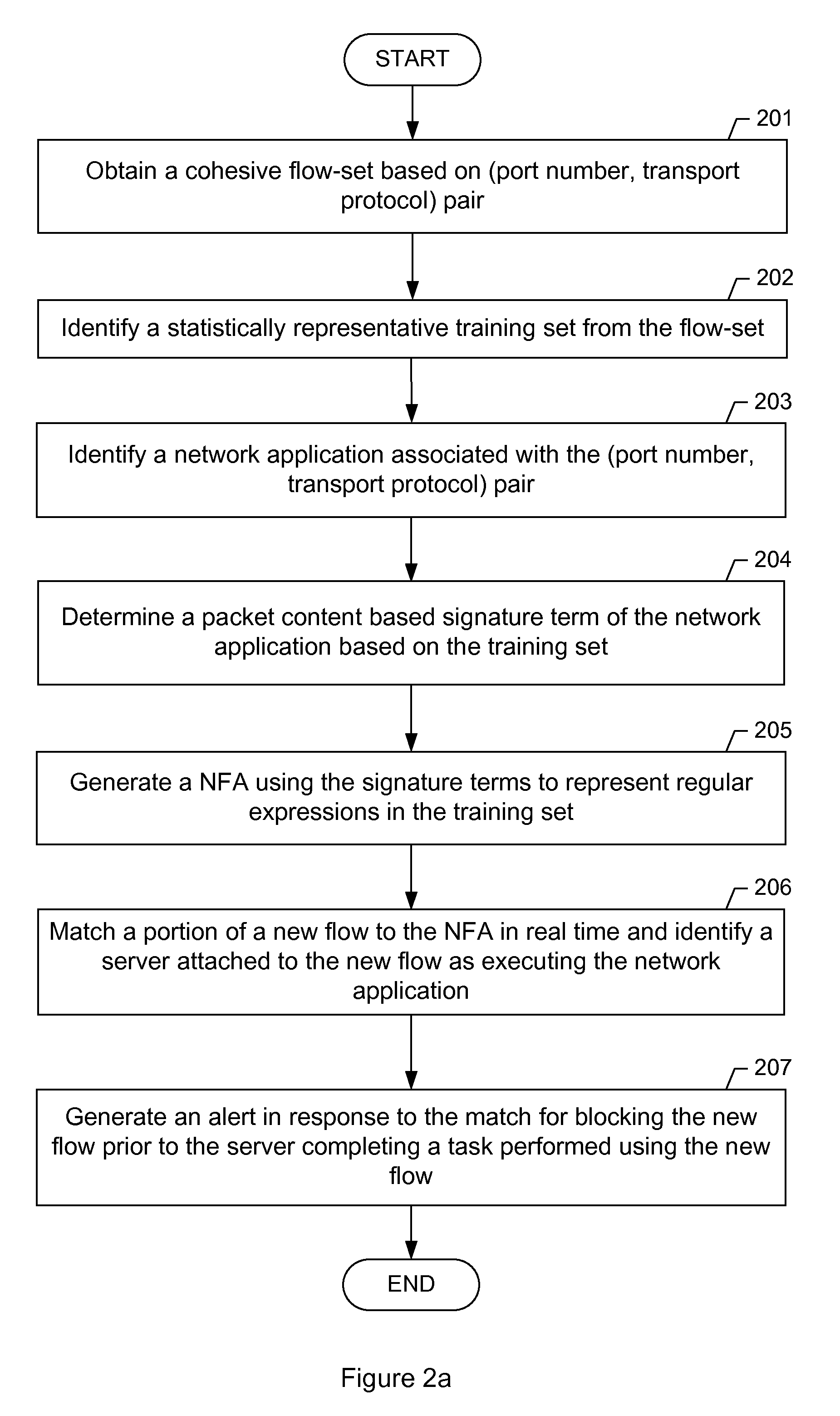
A method for profiling network traffic of a network is presented. The method includes obtaining a cohesive flow-set based on a (port number, transport protocol) pair, identifying a statistically representative training set from the flow-set, identifying a network application associated with the (port number, transport protocol) pair, determining a packet content based signature term of the network application based on the training set, generate a nondeterministic finite automaton (NFA) using the signature terms to represent regular expressions in the training set, matching a portion of a new flow to the NFA in real time and identify a server attached to the new flow as executing the network application, and generate an alert in response to the match for blocking the new flow prior to the server completing a task performed using the new flow.
Owner:THE BOEING CO
Complex symbol evaluation for programmable intelligent search memory
ActiveUS7827190B2Efficient and compact realizationDigital data information retrievalDigital data processing detailsTerm memoryMemory architecture
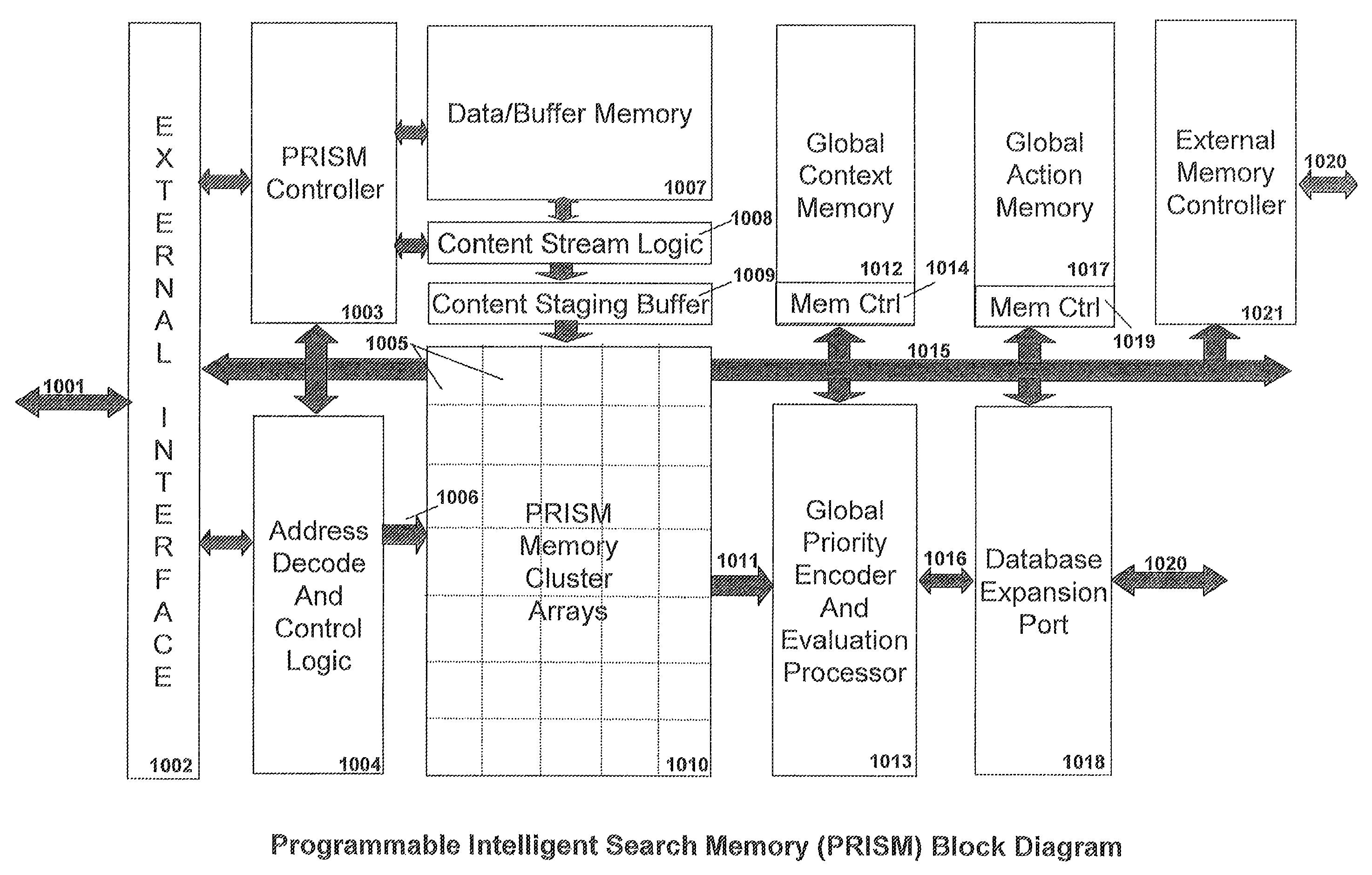
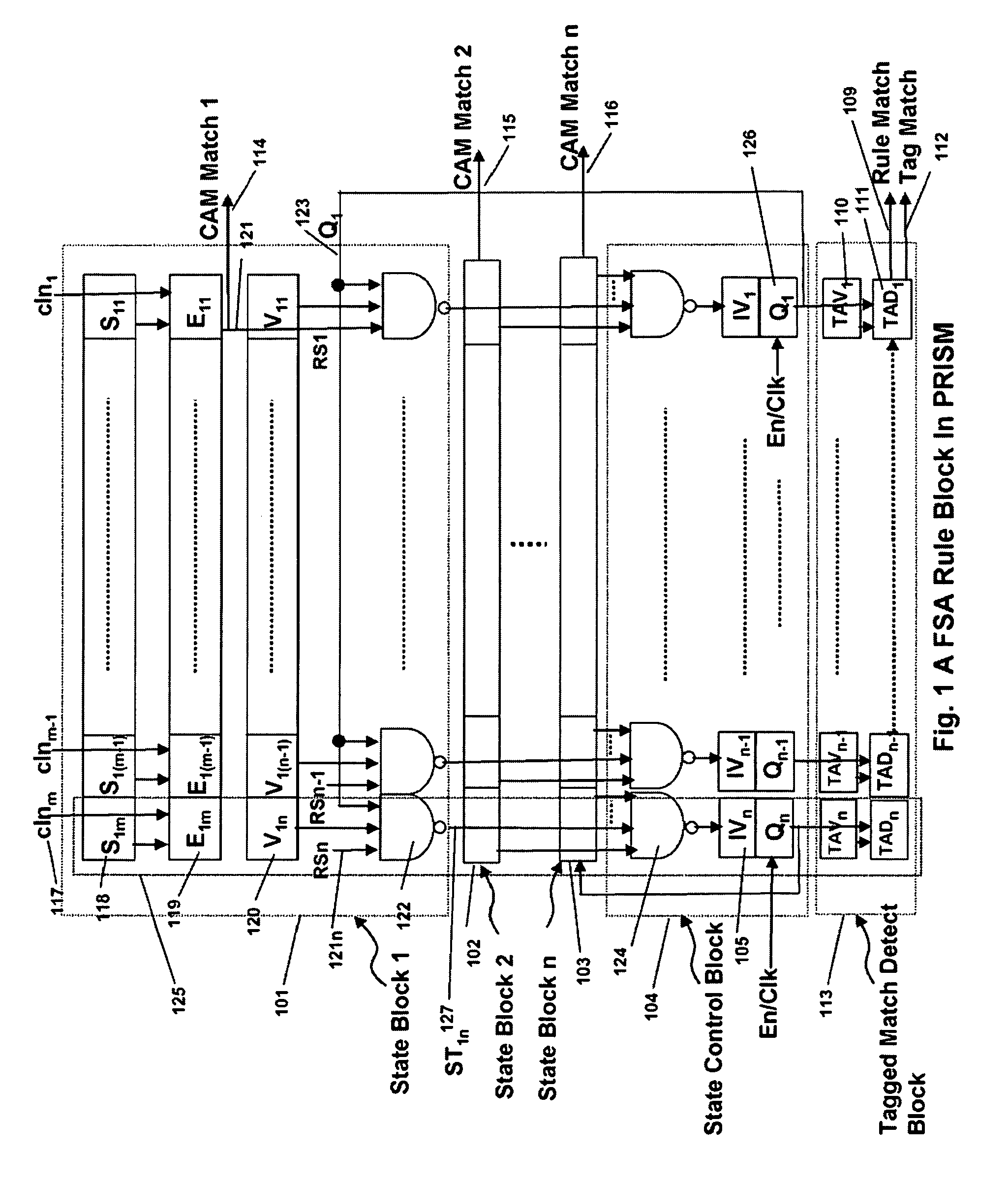
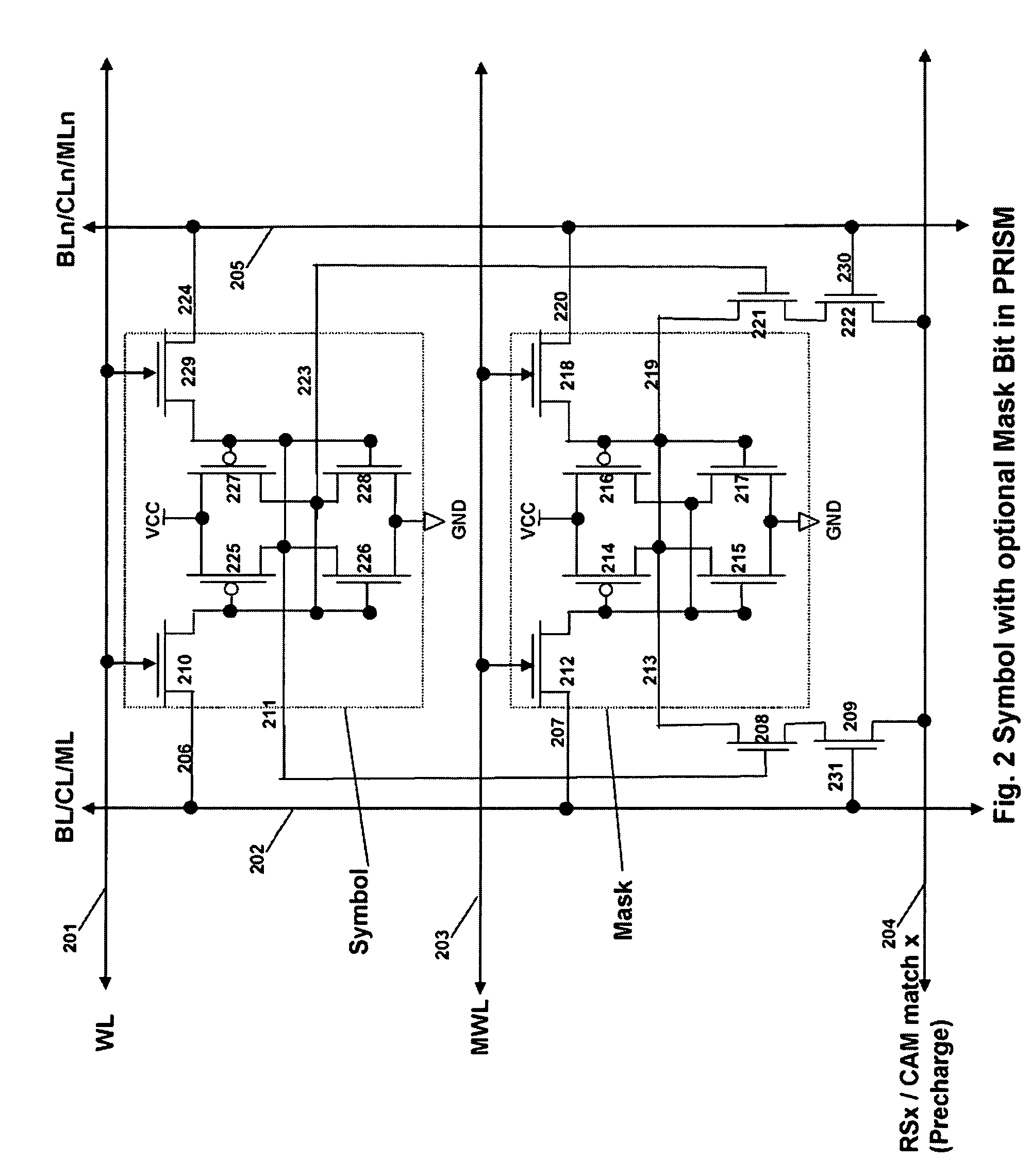
Memory architecture provides capabilities for high performance content search. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM) action(s) associated with the matched rule(s) are taken. Content search rules comprise of regular expressions which are converted to finite state automata and then programmed in PRISM for evaluating content with the search rules. The PRISM memory provides features for complex regular expression symbols like range detection, complement control, bit masking and the like and enables complex symbols and compact regular expression representation.
Owner:INFOSIL INC
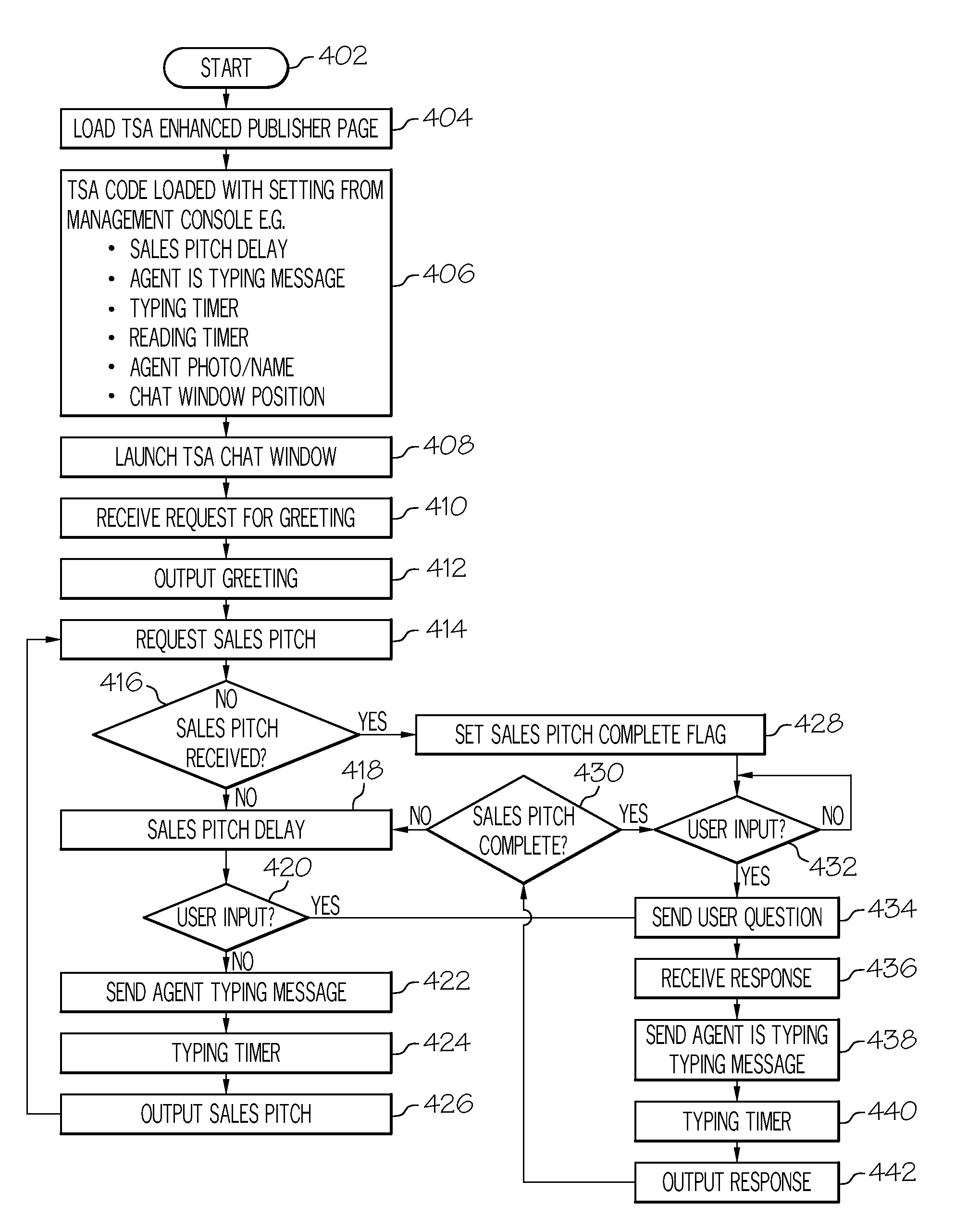
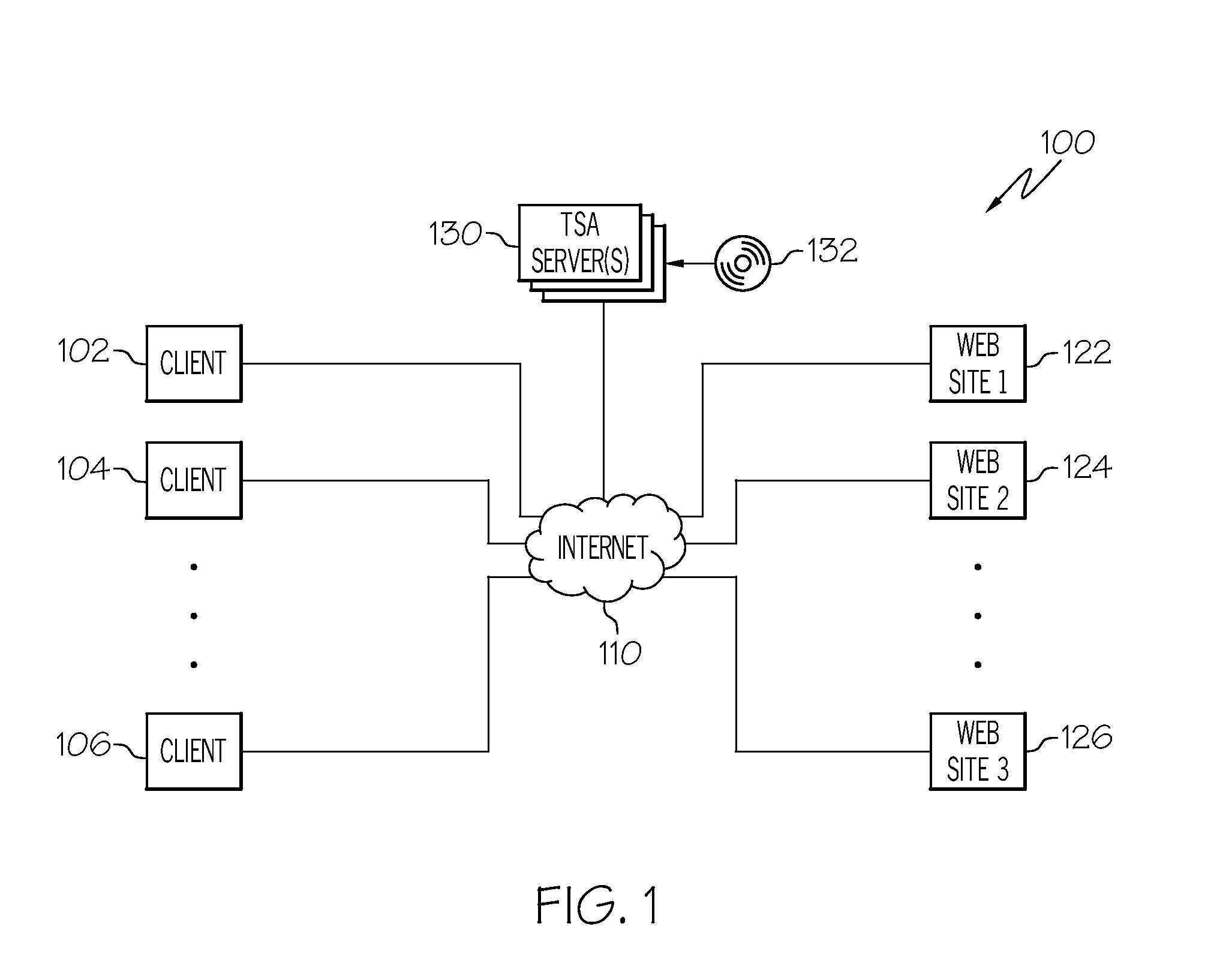
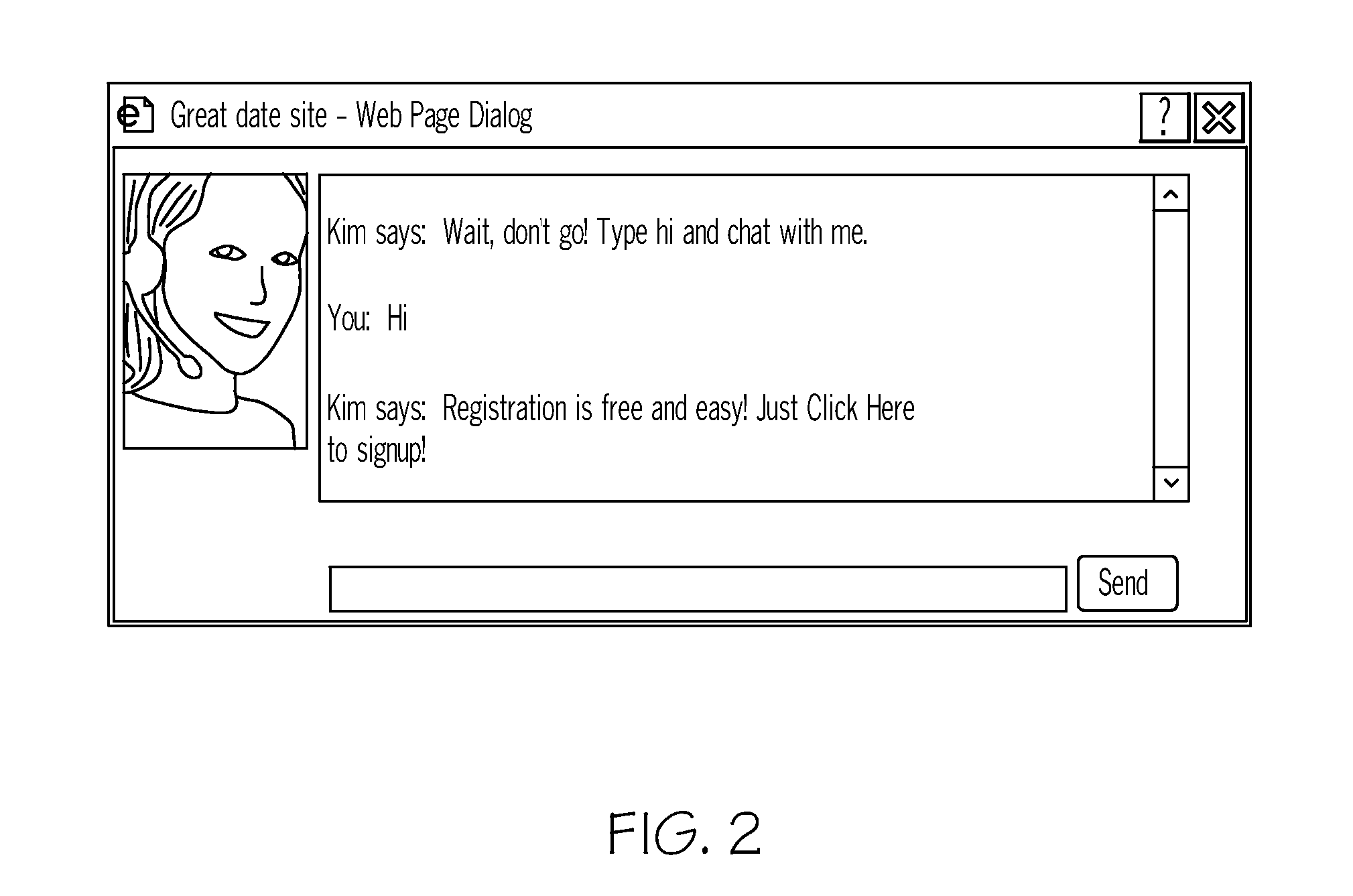
Management system for a conversational system
InactiveUS20110213642A1Increase salesImprove the level ofDigital data information retrievalSemantic analysisThird partyClient-side
The present invention is uniquely designed to interact with web retailer's customers with real agent reaction times as they give astute answers directly concerning web retailer's products and goals. The entire process is manageable through a third-party website which includes scripting, settings and other parameters selected by the web retailer. An artificial intelligence engine uses the combination of Bayesian probability keyword selection, natural language parsing and regular expression processing. The technology updates its response database with every client interaction-learning always takes place as it simulates a live agent, in real time. Every client interaction is recorded and analyzed, and as a result of the analysis the changes in the answer database are made.
Owner:PLEASE DONT GO LLC
Adaptive Network Traffic Classification Using Historical Context
Adaptive network traffic classification using historical context. Network traffic may be monitored and classified by considering several attributes using packet filters, regular expressions, context-free grammars, rule sets, and / or protocol dissectors, among other means and by applying a variety of techniques such as signature matching and statistical analysis. Unlike static systems, the classification decisions may be reexamined from time to time or after subsequent processing determines that the traffic does not conform to the protocol specification corresponding to the classification decision. Historical context may be used to adjust the classification strategy for similar or related traffic.
Owner:EXTRAHOP NETWORKS
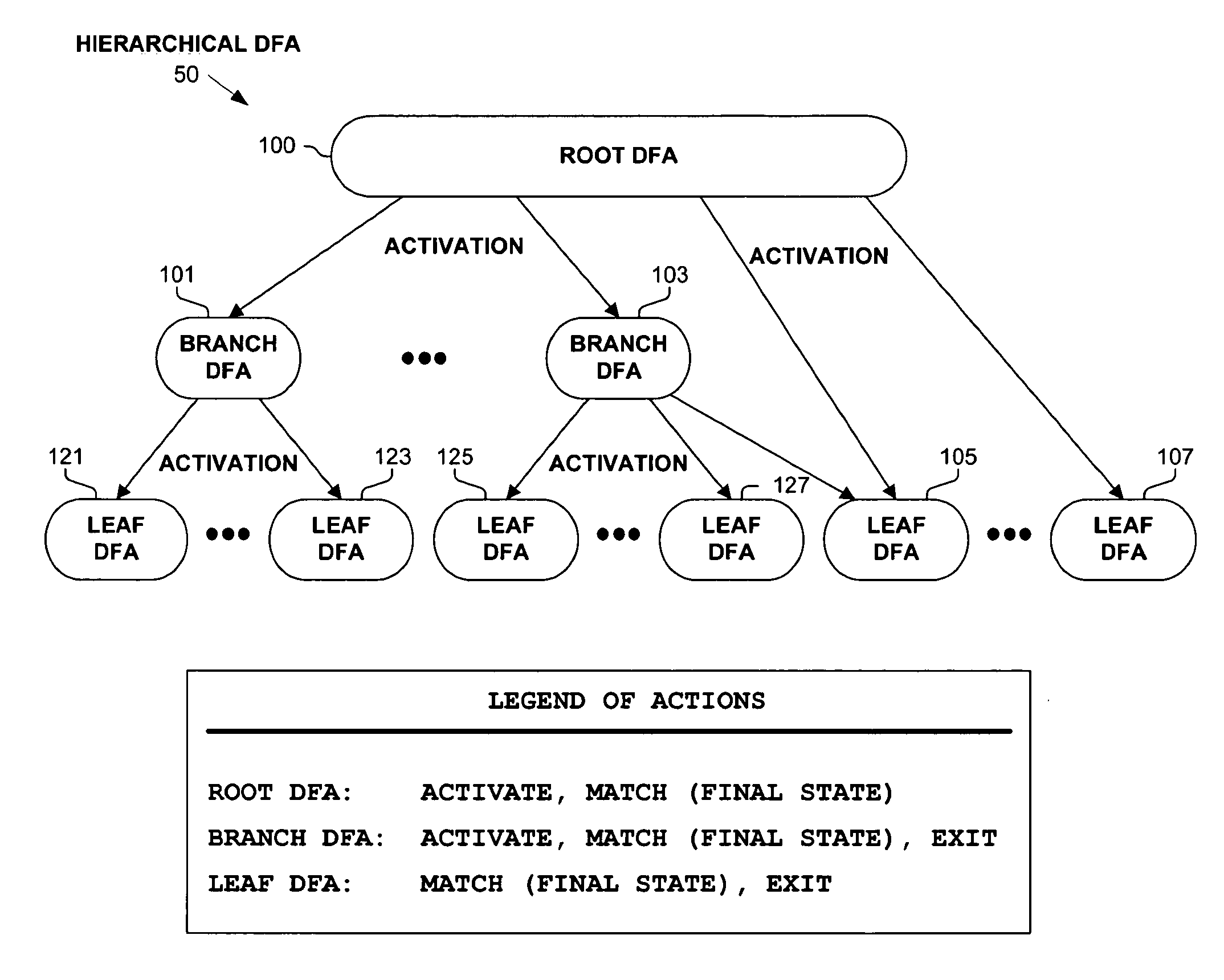
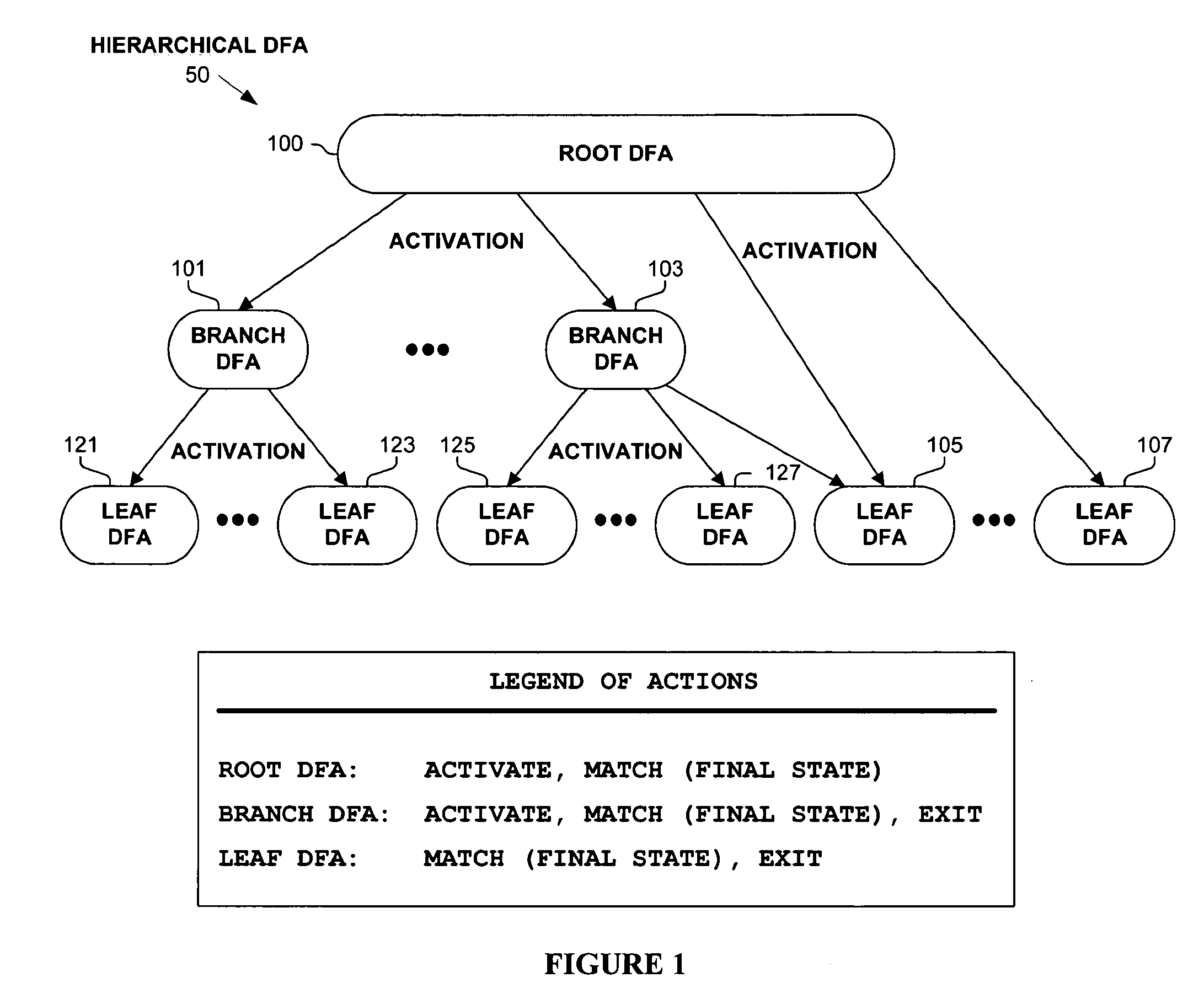
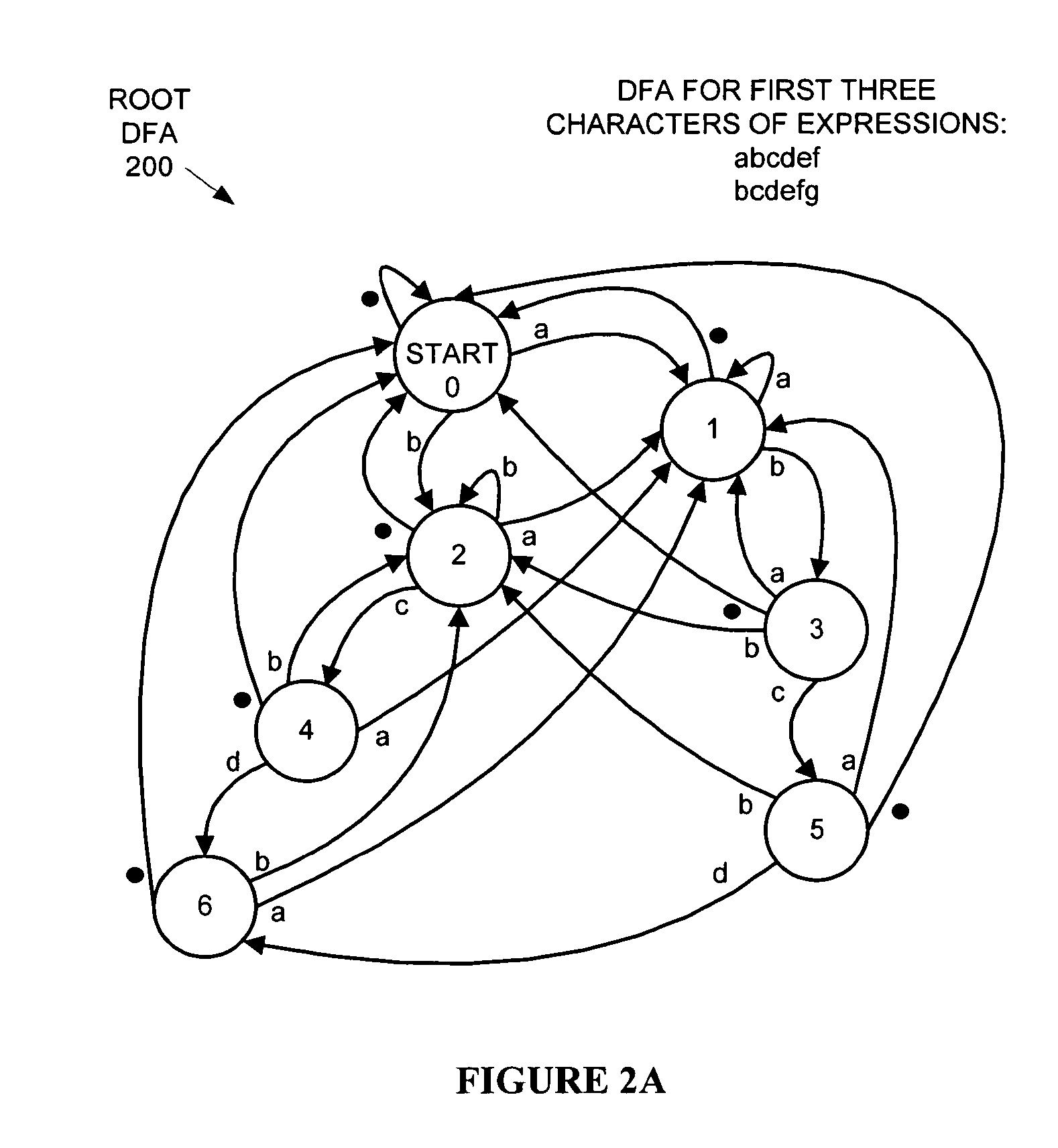
Hierarchical tree of deterministic finite automata
ActiveUS20060242123A1Avoid explosionDigital data information retrievalDigital data processing detailsBiological activationAutomaton
A hierarchical tree of deterministic finite automata (DFA) is traversed and / or generated based on a set of regular expressions. The hierarchical DFA includes a root DFA linked together with a set of leaf DFAs, and possibly a set of branch DFAs. The root DFA is always active and is responsive to an input string, as are any currently active branch and leaf DFAs. When a final state or arc is reached or traversed in any active DFA, a regular expression has been matched. The branch and leaf DFAs are activated in response to the root DFA or a branch DFA reaching or traversing an activation state or arc corresponding to the branch or leaf DFA. Active branch and leaf DFAs will become inactive when a termination state or arc is reached or traversed within the branch or leaf DFA. State explosion in the hierarchical DFA can typically be avoided by selectively grouping similar portions of the regular expressions together in branch and leaf DFAs.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com