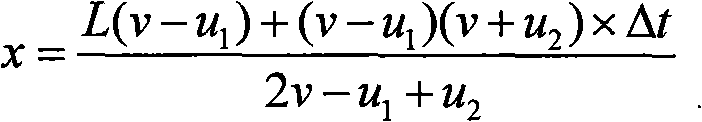Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2065 results about "File comparison" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
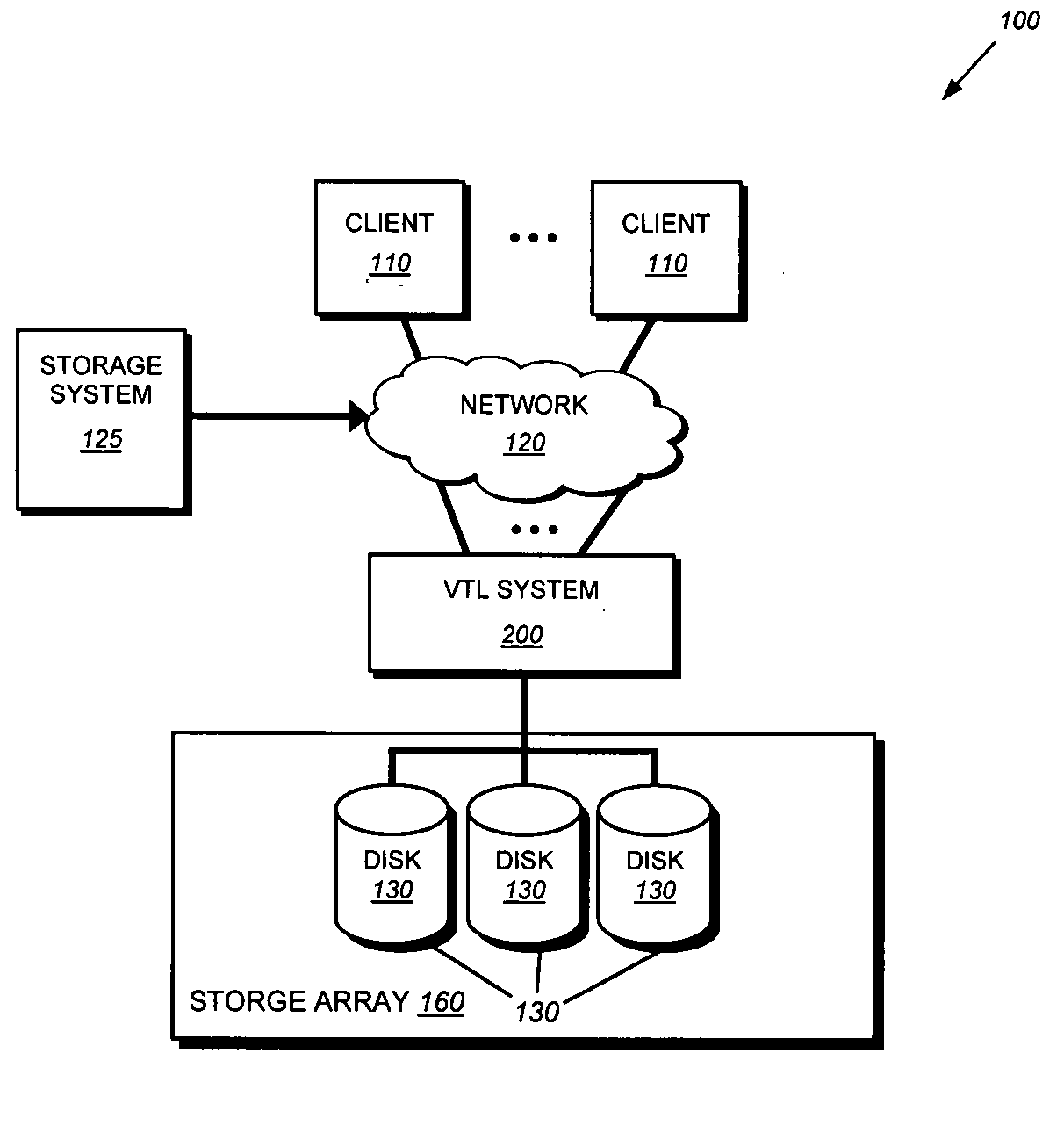
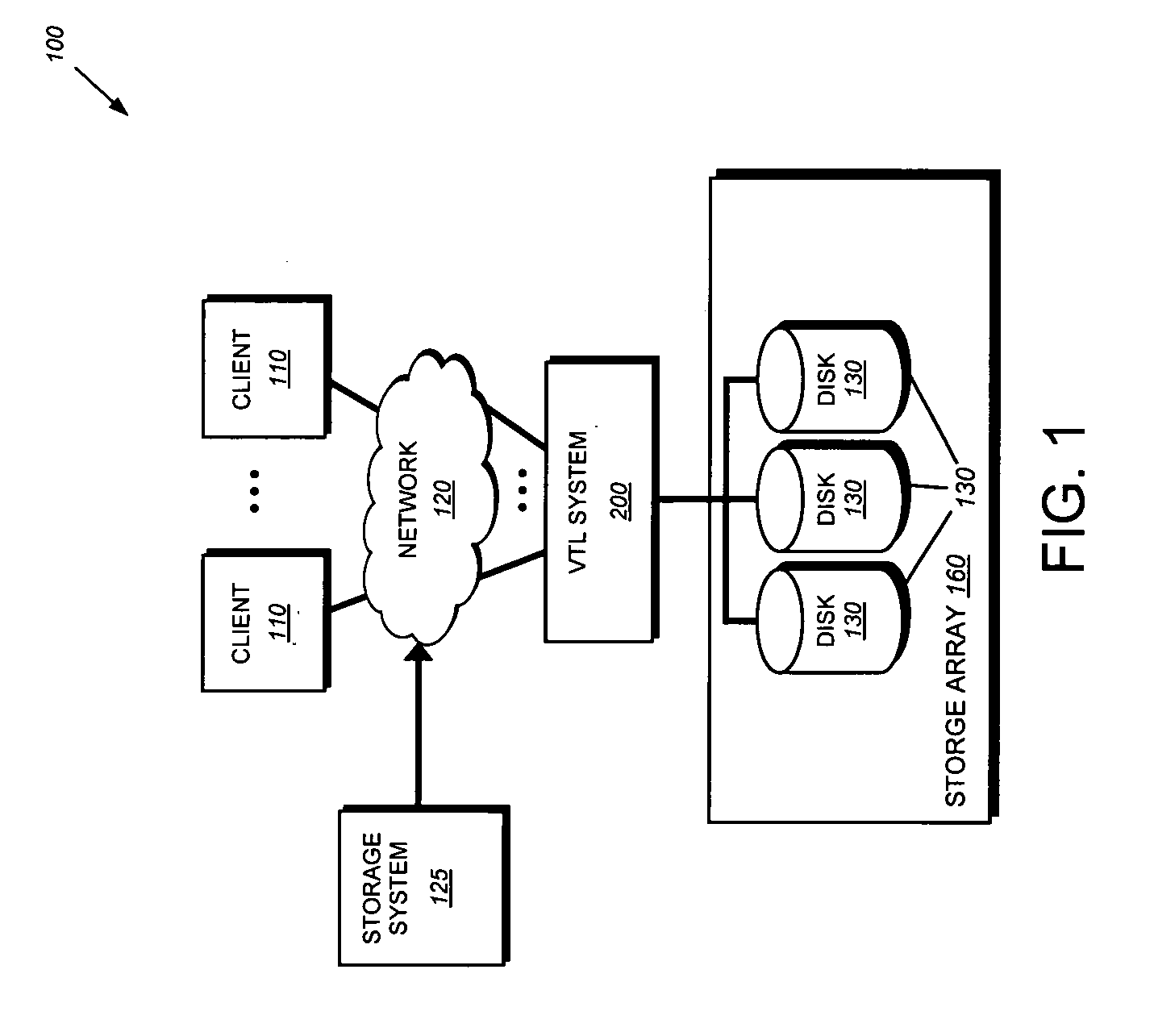
In computing, file comparison is the calculation and display of the differences and similarities between data objects, typically text files such as source code. The methods, implementations, and results are typically called a diff, after the Unix diff utility. The output may be presented in a graphical user interface or used as part of larger tasks in networks, file systems, or revision control.
Block chain data comparison and consensus method
ActiveCN105719185AWill not limit performanceNo capacity constraintsFinanceFinancial transactionFile comparison
The invention discloses a block chain data comparison and consensus method used for hash value calculation of content of each transaction. By changing the random numbers, the numbers of some bits of the hash values are set not to be repeated in a time period, and can be called as unrepeated serial numbers. Accounting servers are used to compare the numbers of the preset bits of the hash values to determine whether the transactions are identical or not. The unrepeated serial number comparison can be carried out in a way of establishing the Merkle-like tree, and because the numbers of the preset bits of the hash values of the transactions are not repeated, and can be used as the serial numbers, and can be disposed in the Merkle-like tree according to the certain rule, and therefore for different accounting servers, the positions of the hash values of the same transaction on the Merkle trees are totally identical, and the differences can be found out quickly, the data transfer amount can be reduced, and the time required by the consensus can be greatly accelerated.
Owner:HANGZHOU FUZAMEI TECH CO LTD
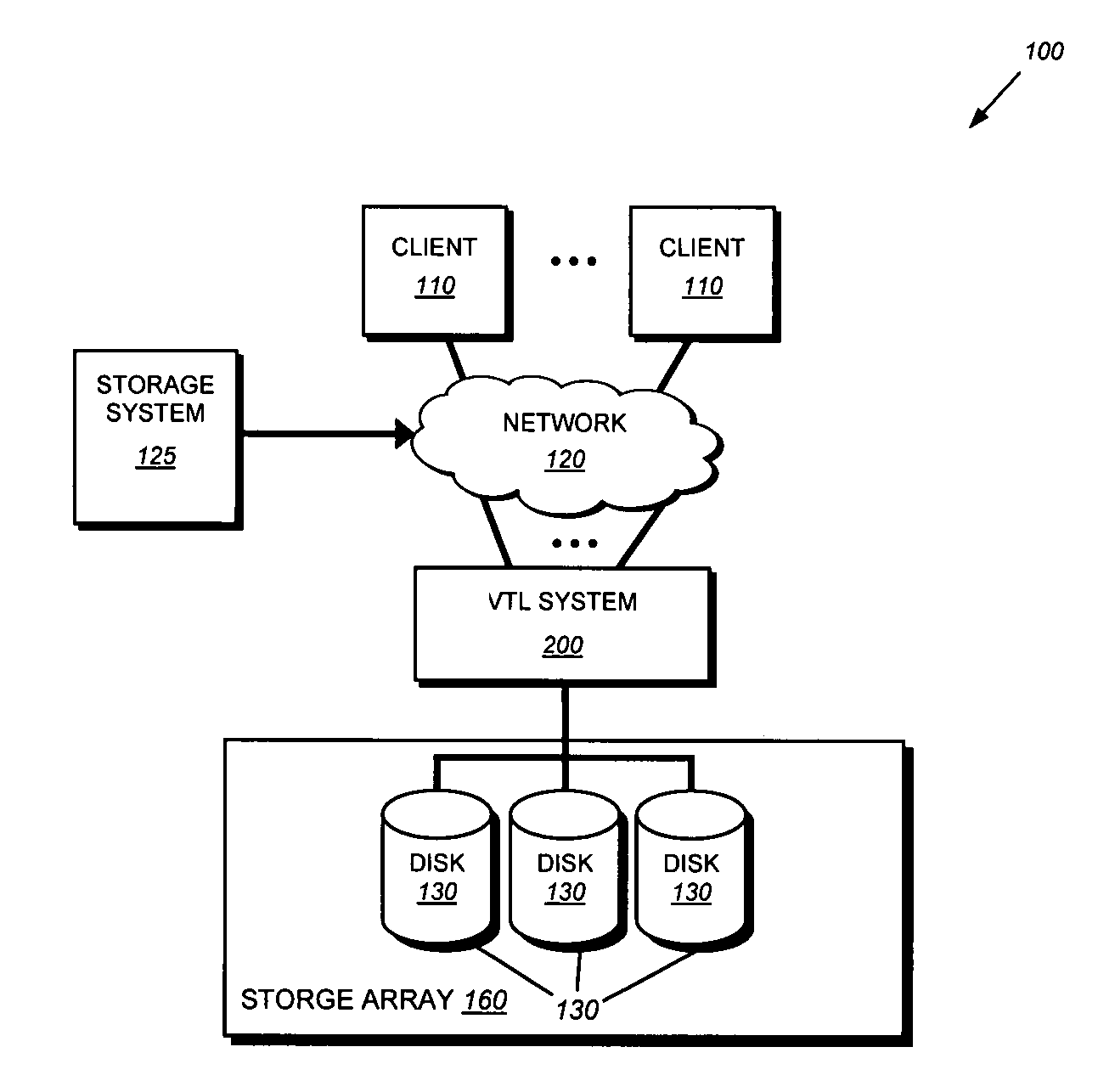
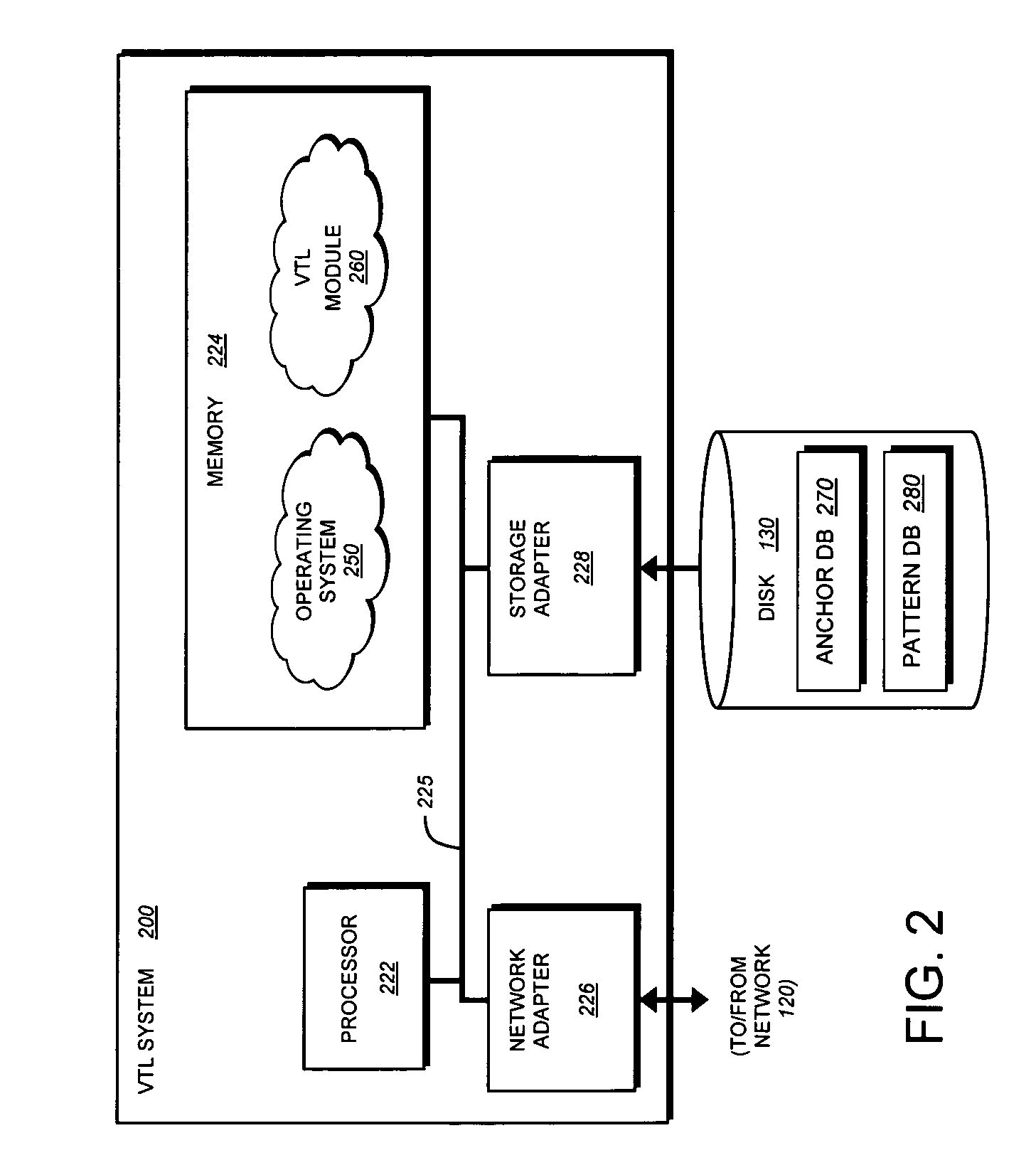
System and method for sampling based elimination of duplicate data
ActiveUS20070255758A1Overcome disadvantagesPicture reproducers using cathode ray tubesCode conversionData setFile comparison
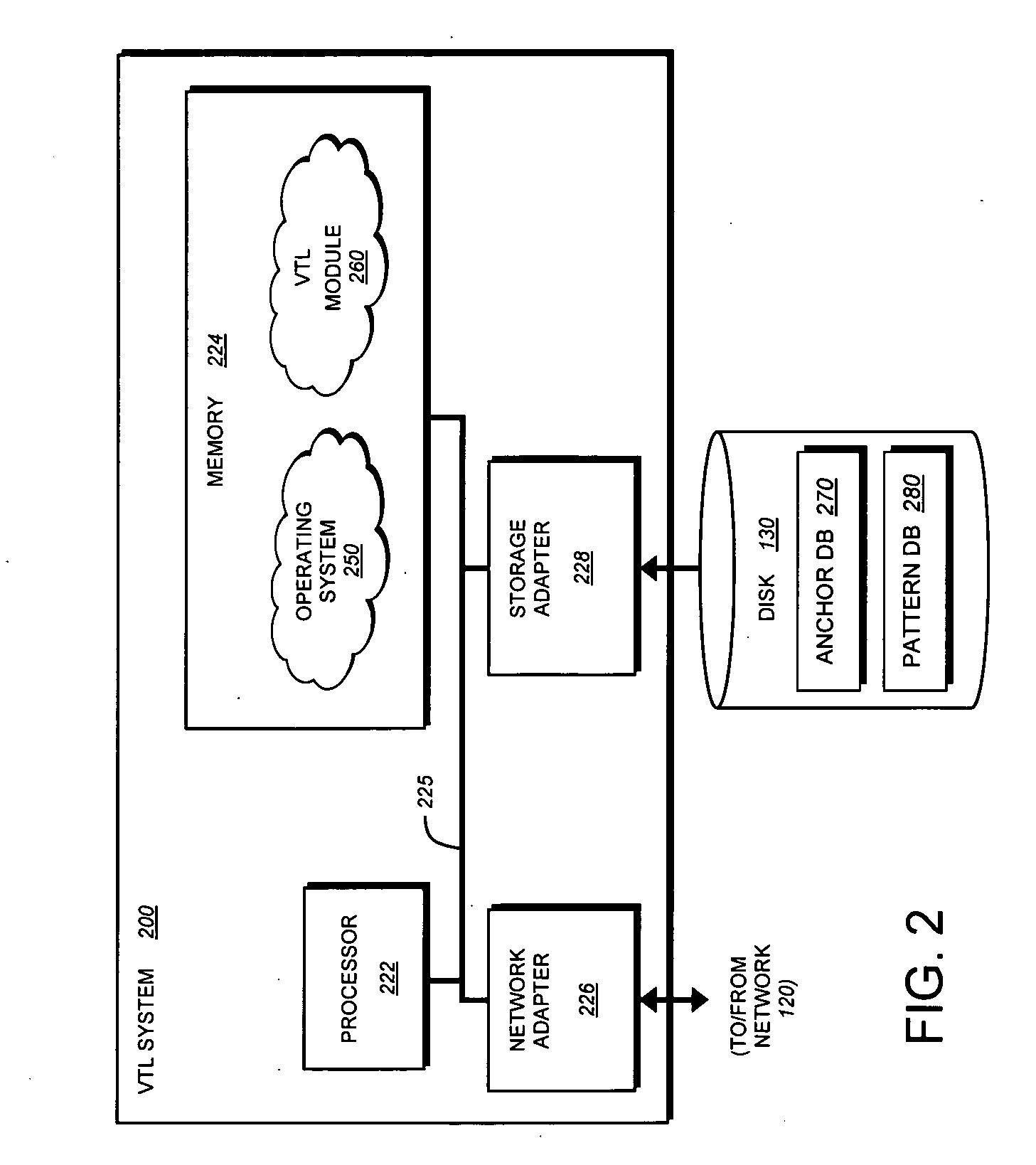
A technique for eliminating duplicate data is provided. Upon receipt of a new data set, one or more anchor points are identified within the data set. A bit-by-bit data comparison is then performed of the region surrounding the anchor point in the received data set with the region surrounding an anchor point stored within a pattern database to identify forward / backward delta values. The duplicate data identified by the anchor point, forward and backward delta values is then replaced in the received data set with a storage indicator.
Owner:NETWORK APPLIANCE INC
Systems and methods for client-based web crawling
InactiveUS20050071766A1The process is fast and accurateReducing server-client communication trafficData processing applicationsWeb data indexingData validationSource Data Verification
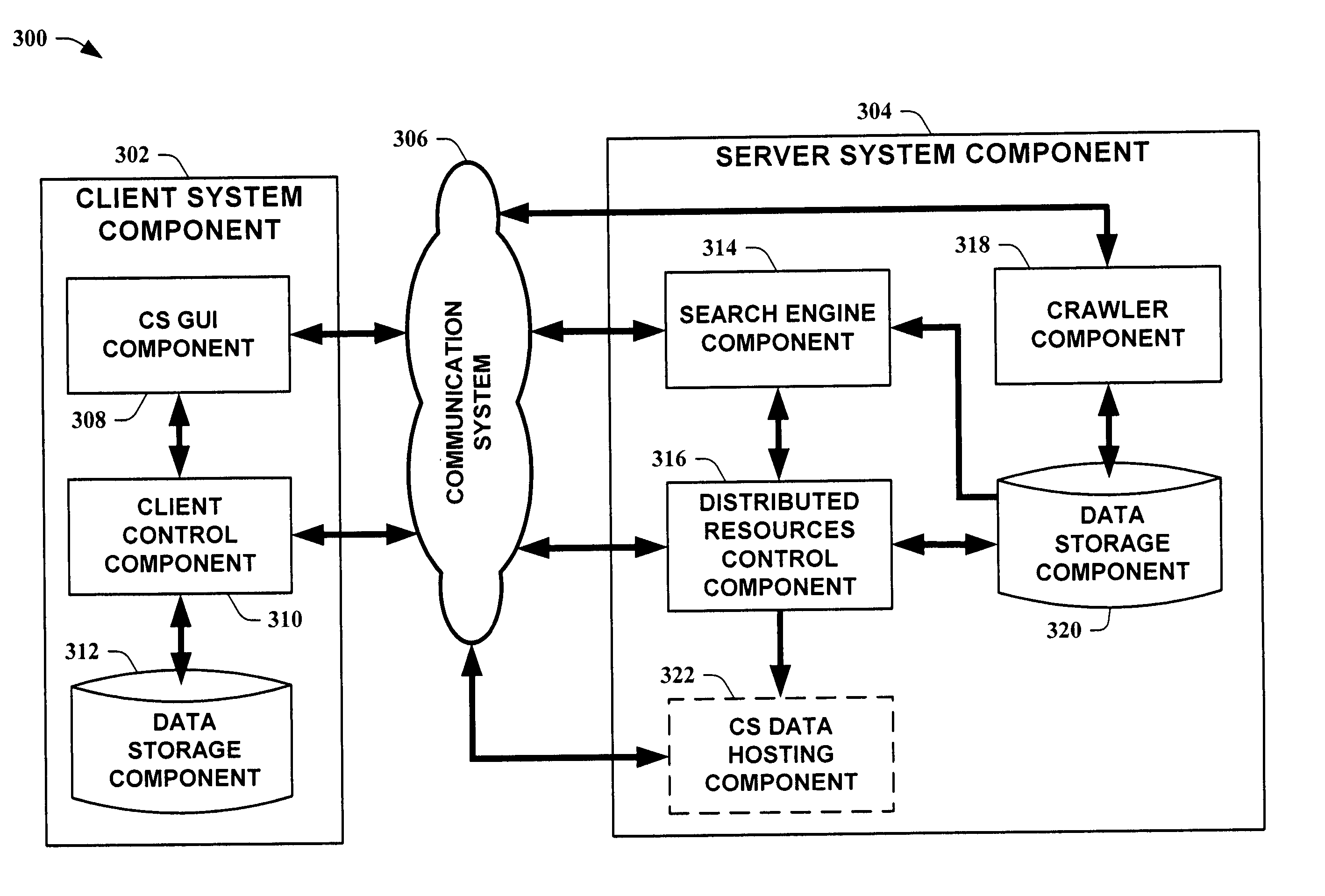
The present invention provides systems and methods for obtaining information from a networked system utilizing a distributed web crawler. The distributed nature of clients of a server is leveraged to provide fast and accurate web crawling data. Information gathered by a server's web crawler is compared to data retrieved by clients of the server to update the crawler's data. In one instance of the present invention, data comparison is achieved by utilizing information disseminated via a search engine results page. In another instance of the present invention, data validation is accomplished by client dictionaries, emanating from a server, that summarize web crawler data. The present invention also facilitates data analysis by providing a means to resist spoofing of a web crawler to increase data accuracy.
Owner:MICROSOFT TECH LICENSING LLC
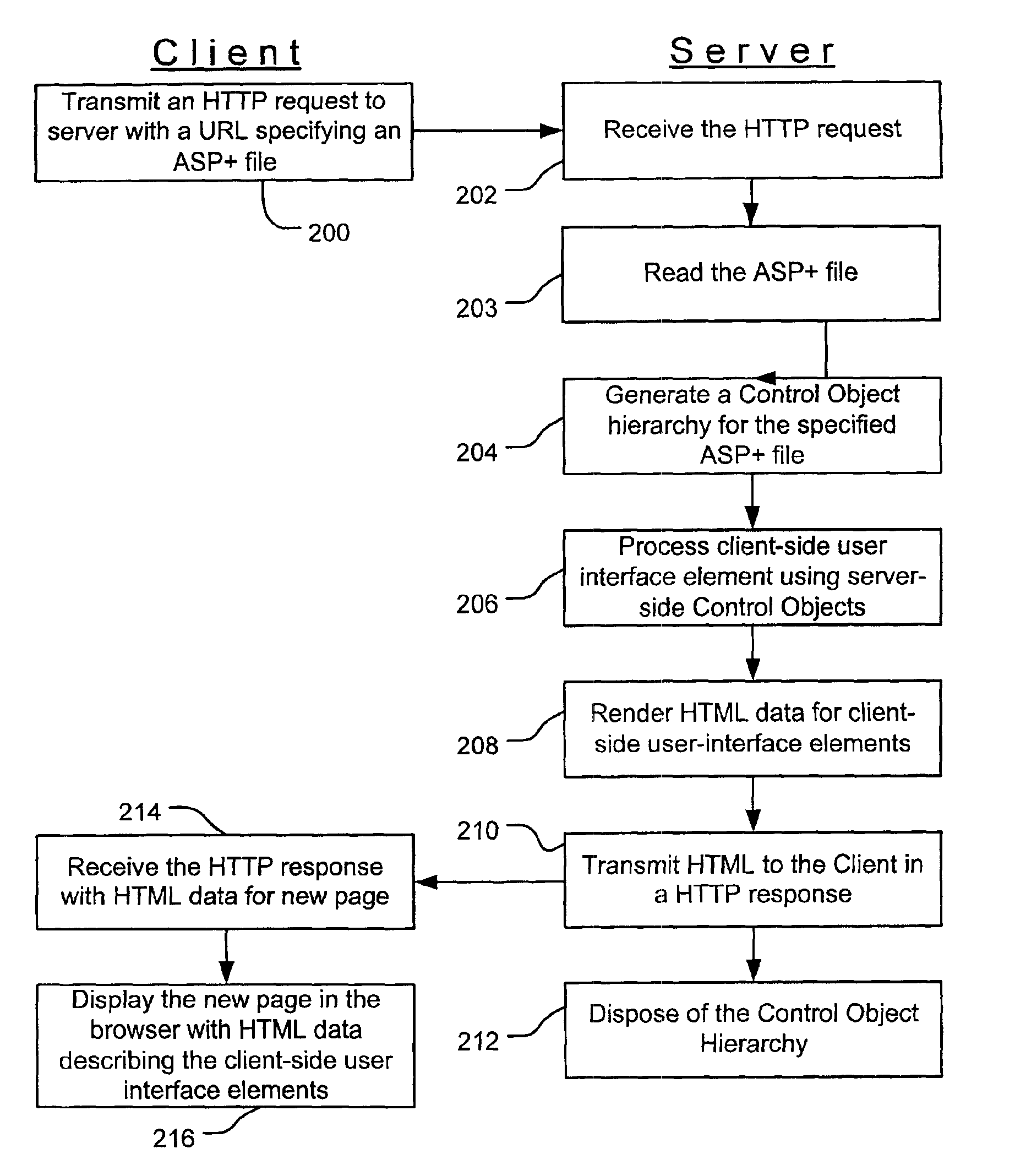
Web controls validation
InactiveUS6915454B1Receipt is inhibitedNon-redundant fault processingSpecific program execution arrangementsError processingFile comparison
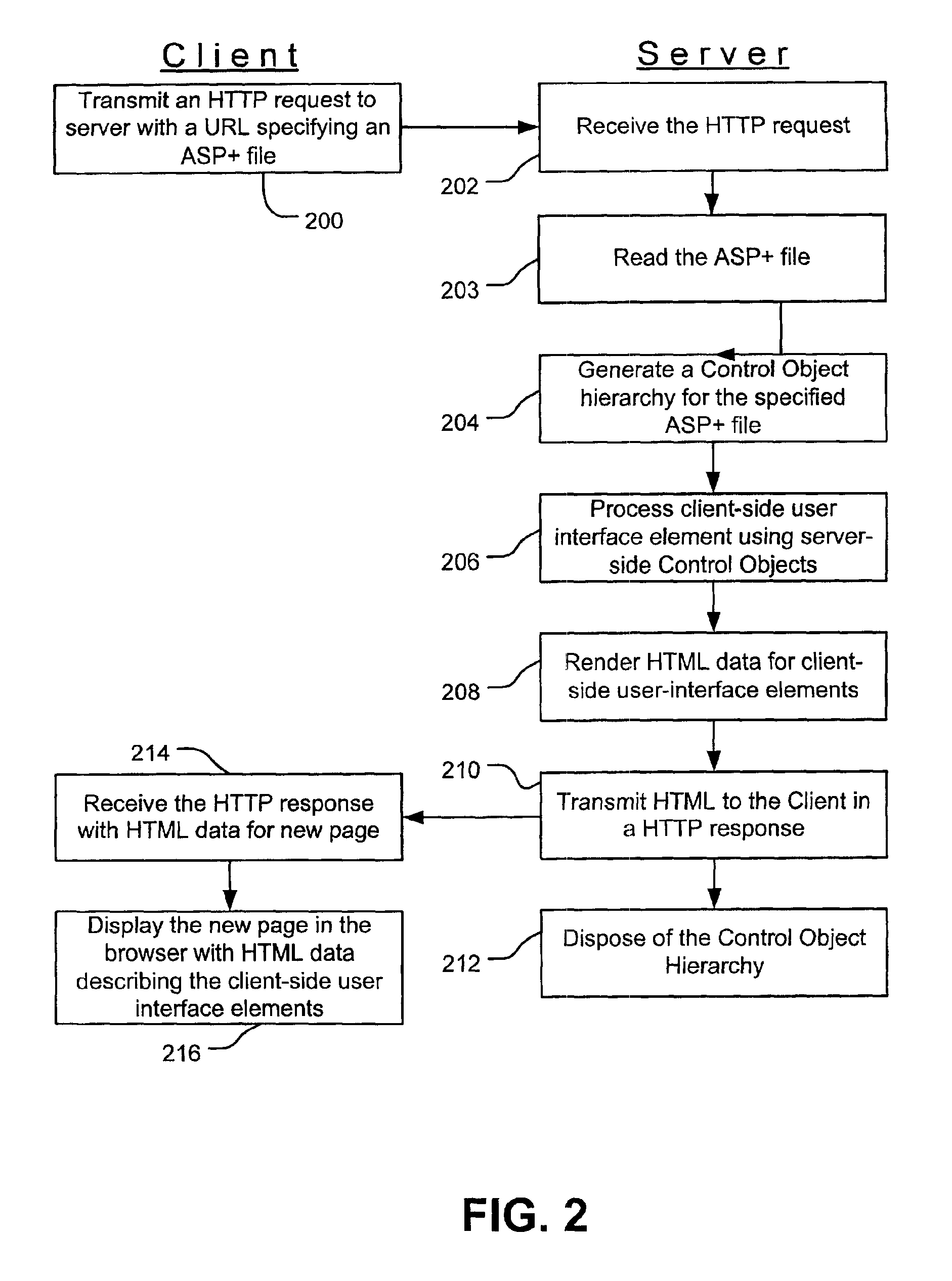
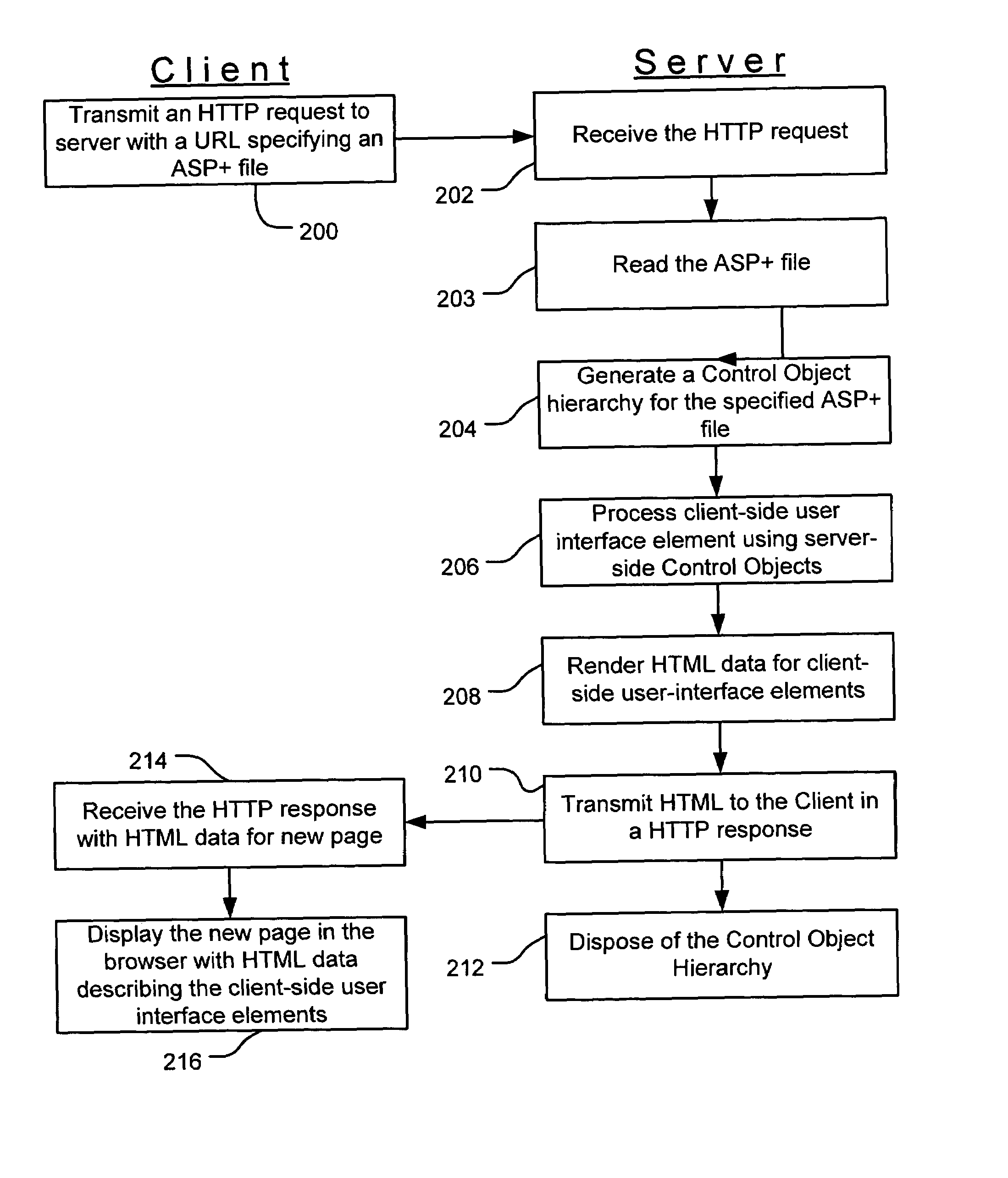
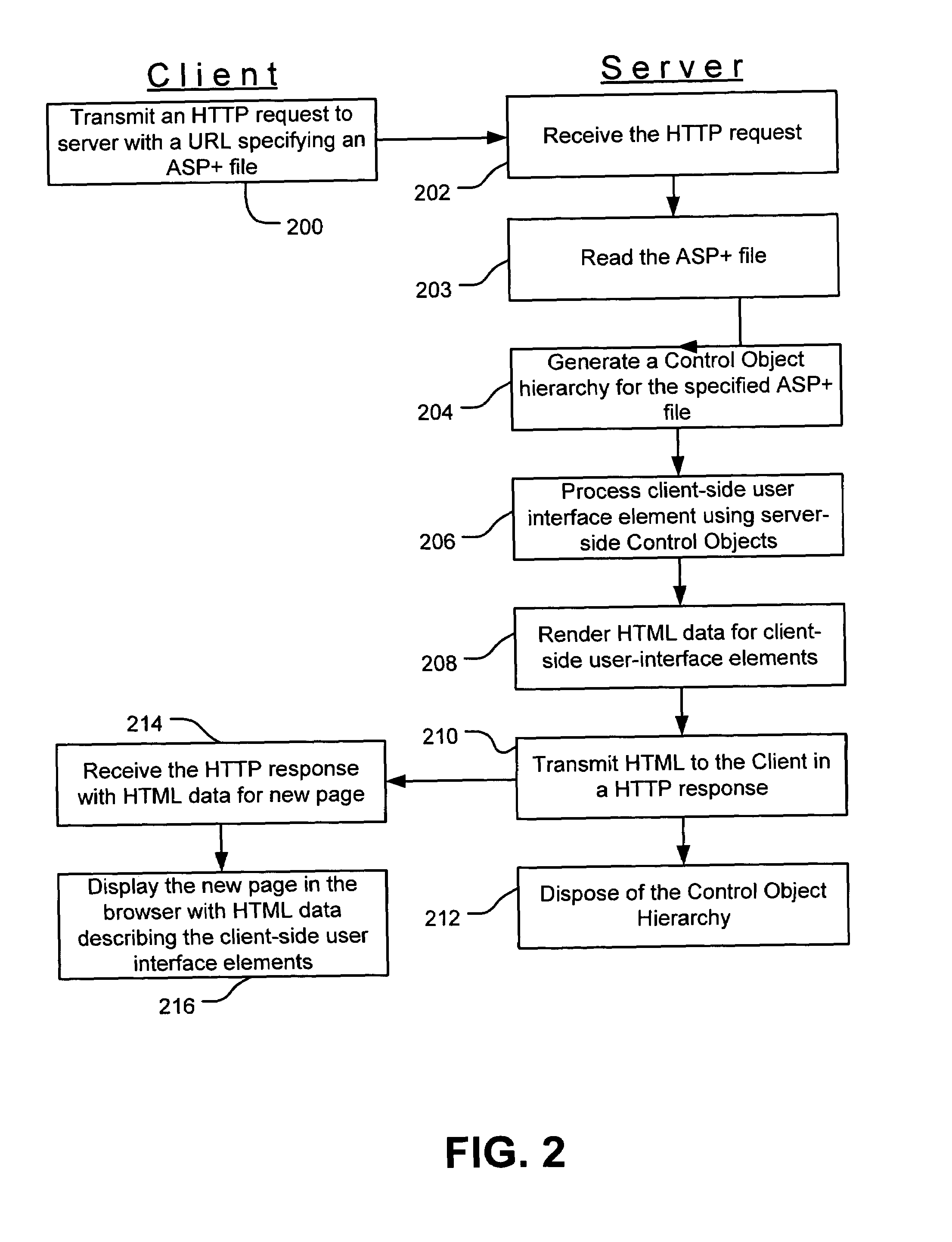
Web control validation may be defined using one or more declarations that are included in an ASP+ file by the web page author. The declarations specify server-side objects that validate the input data received in the web page and provide error handling in the event of a validation failure error. Validation declaration parameters specify the validation criteria against which the input data is validated. Example validation operations involve regular expressions, required fields, data comparison, range comparison and custom validation. Validation parameters can also specify- either server-side validation or client-side validation, depending on the client browser's capabilities. In a server-side scenario, a server-side validation object processes the input data received in an HTTP request from the client. In a client-side scenario, a server-side validation object renders the appropriate client-side code to validate the input data without a round trip between the client and the server.
Owner:MICROSOFT TECH LICENSING LLC
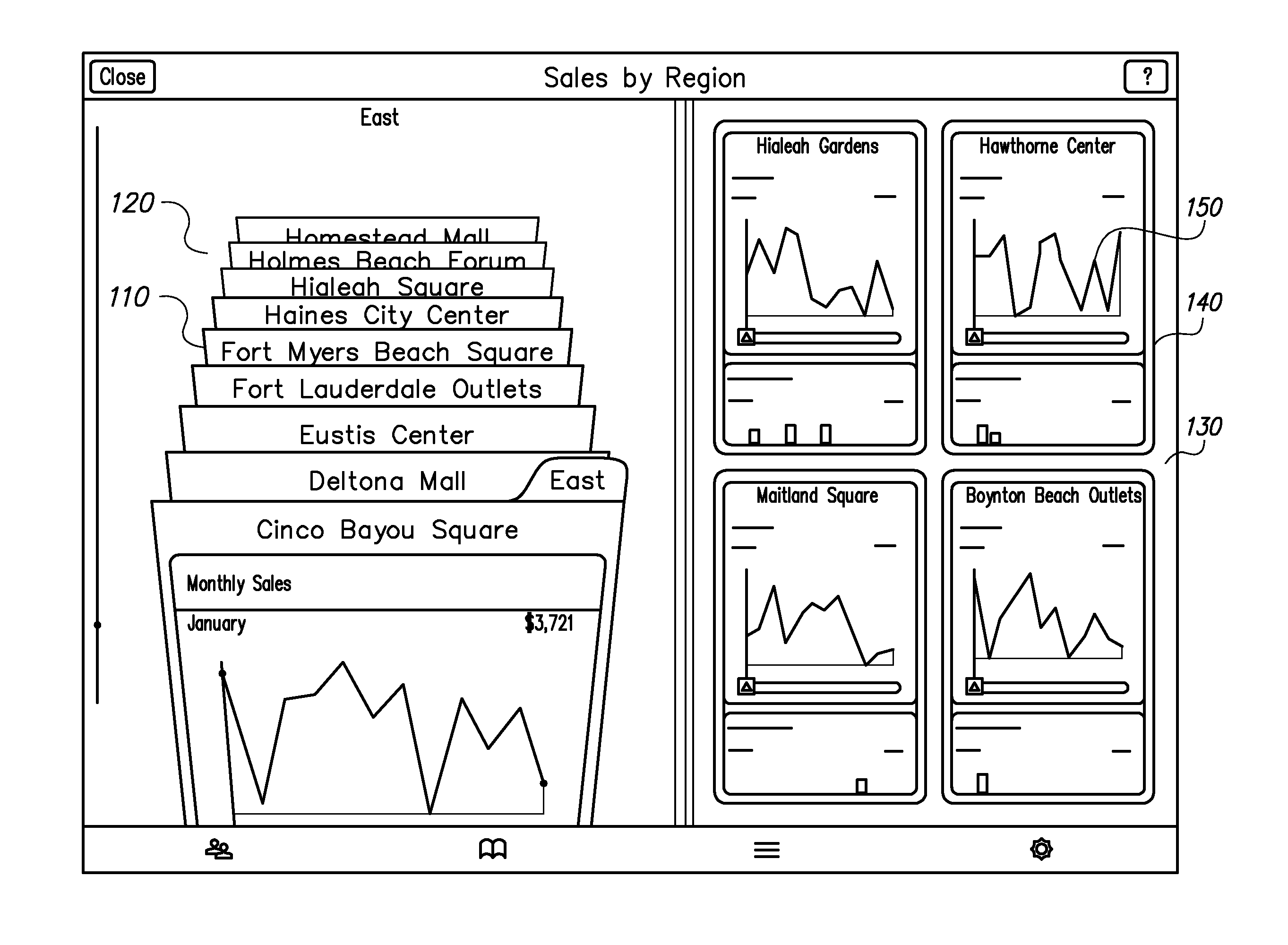
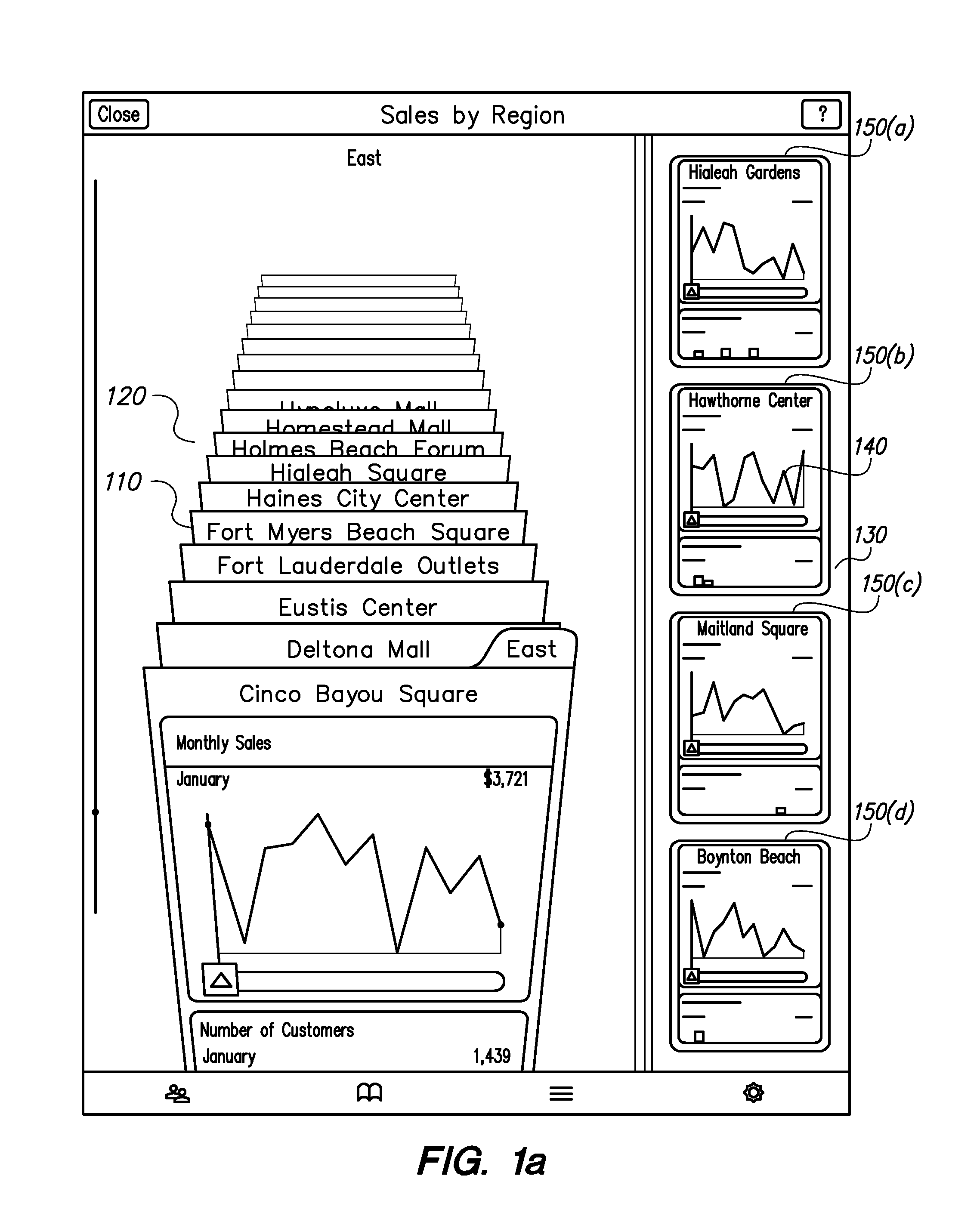
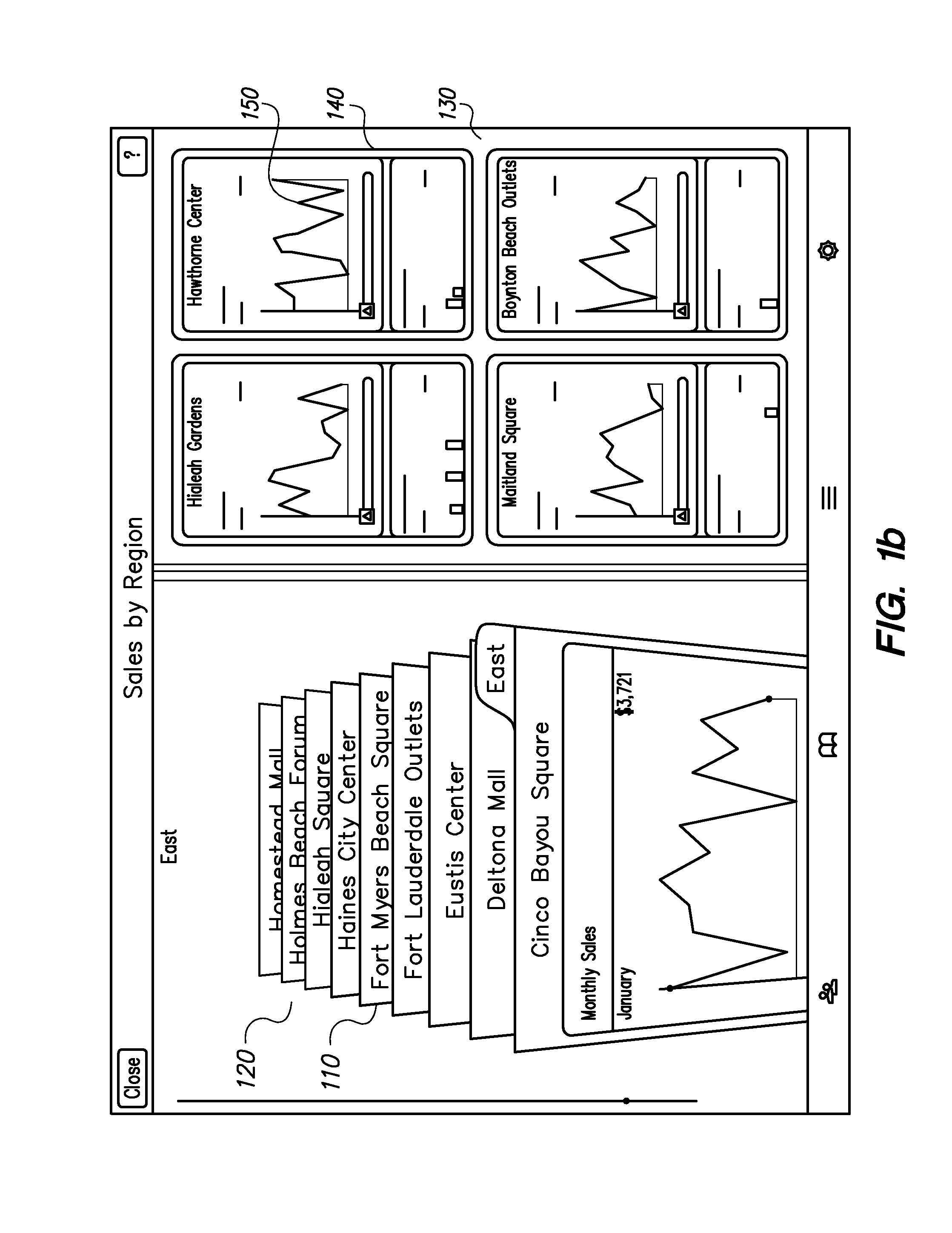
User Interface for Data Comparison
Systems and methods perform comparison of data represented as charts, for example, bar graphs, pie charts, line charts or stacked bar charts. The charts present visual representations mapping source values to target values. A user can select charts associated with a data records for comparison from an index of data records. The user selects a chart and a particular source value from the reference chart. The target values corresponding to the source value from other charts are compared against the target value from the reference chart. An aggregate of the target values associated with the source value from each chart may be presented to the user. The user can also use multi-touch input to select object representing data and drag them to perform actions associated with the objects. The actions performed on the objects depend on the locations of the objects as the user drags them.
Owner:SAP AG
Method and system for monitoring power supplies
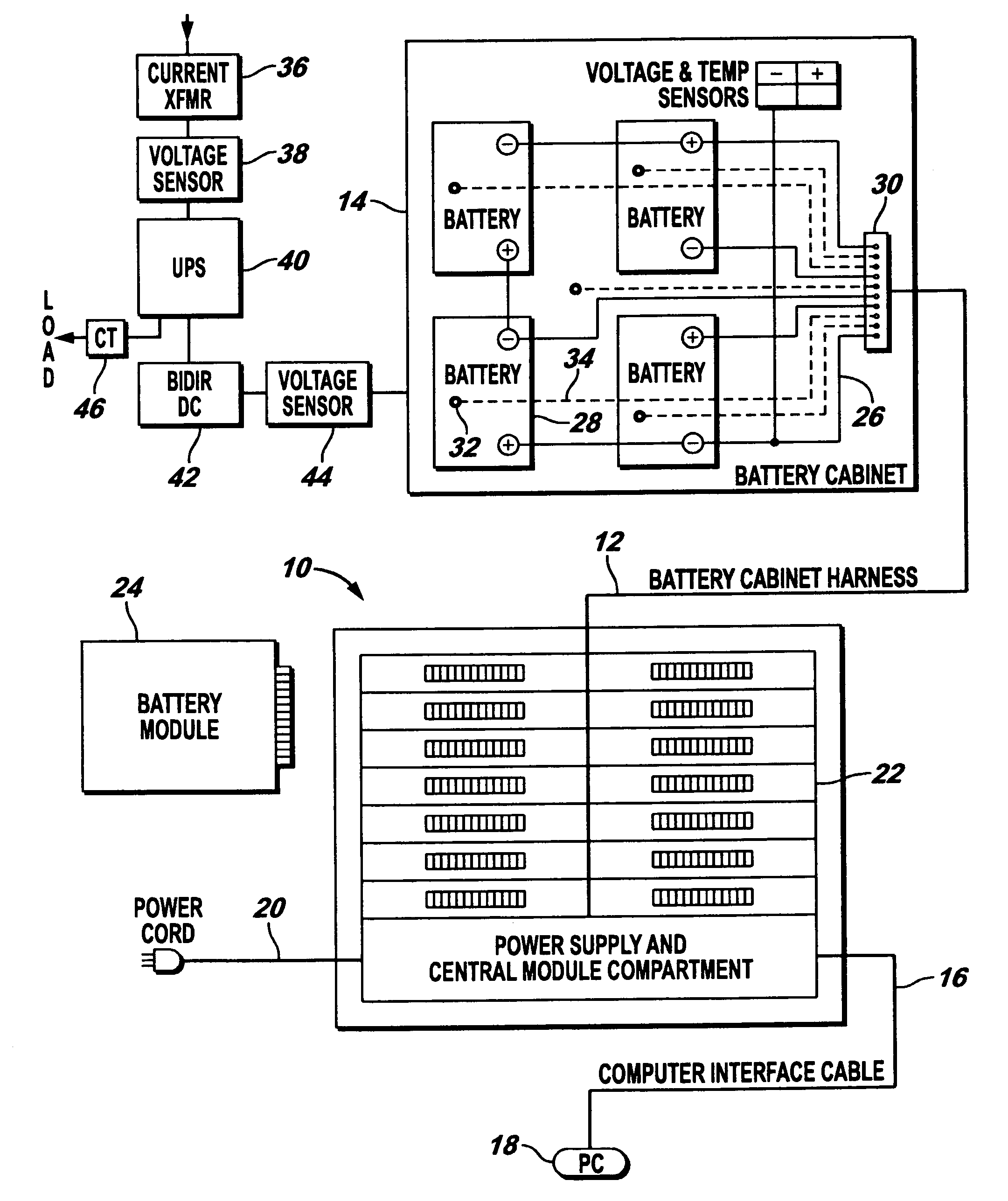
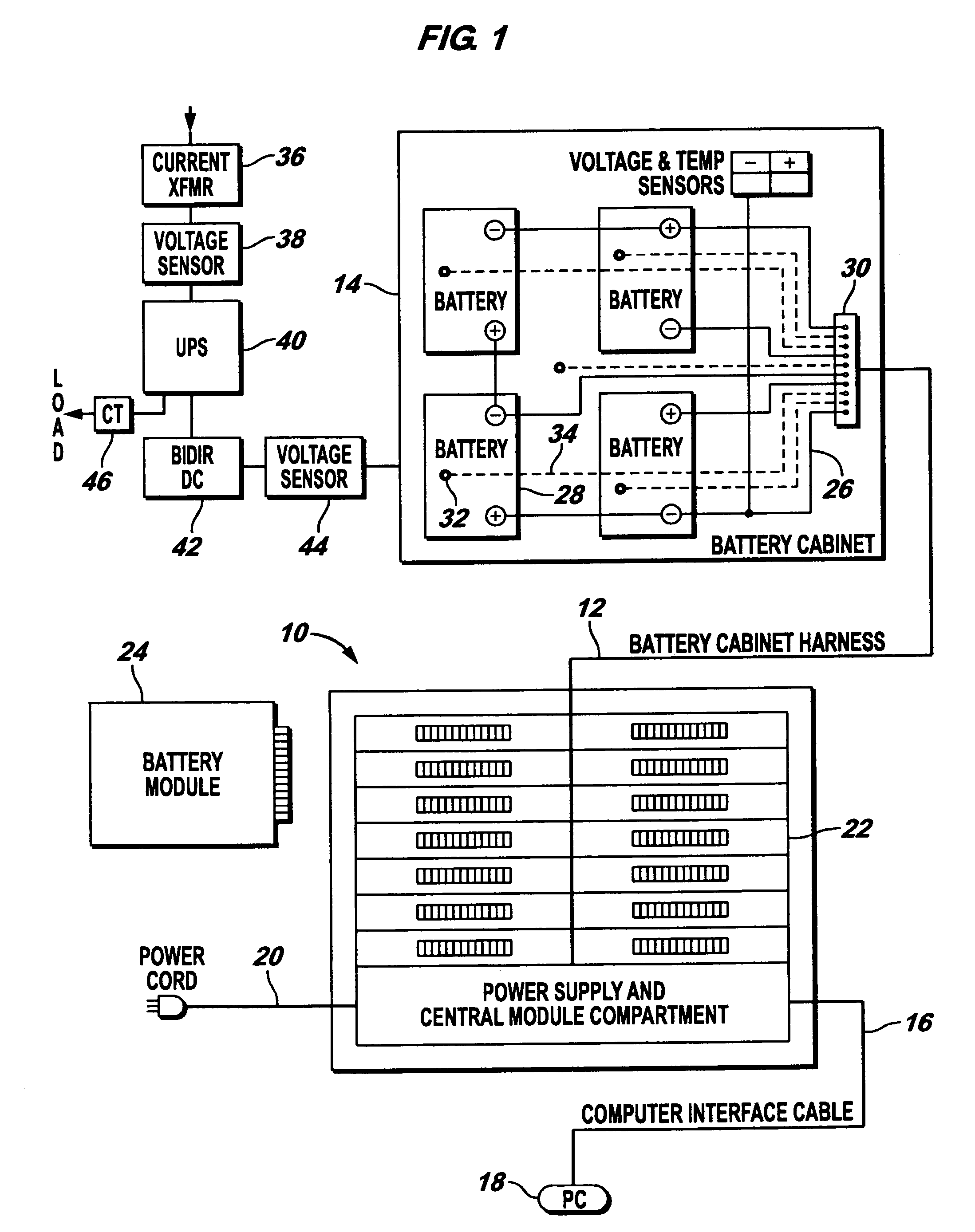
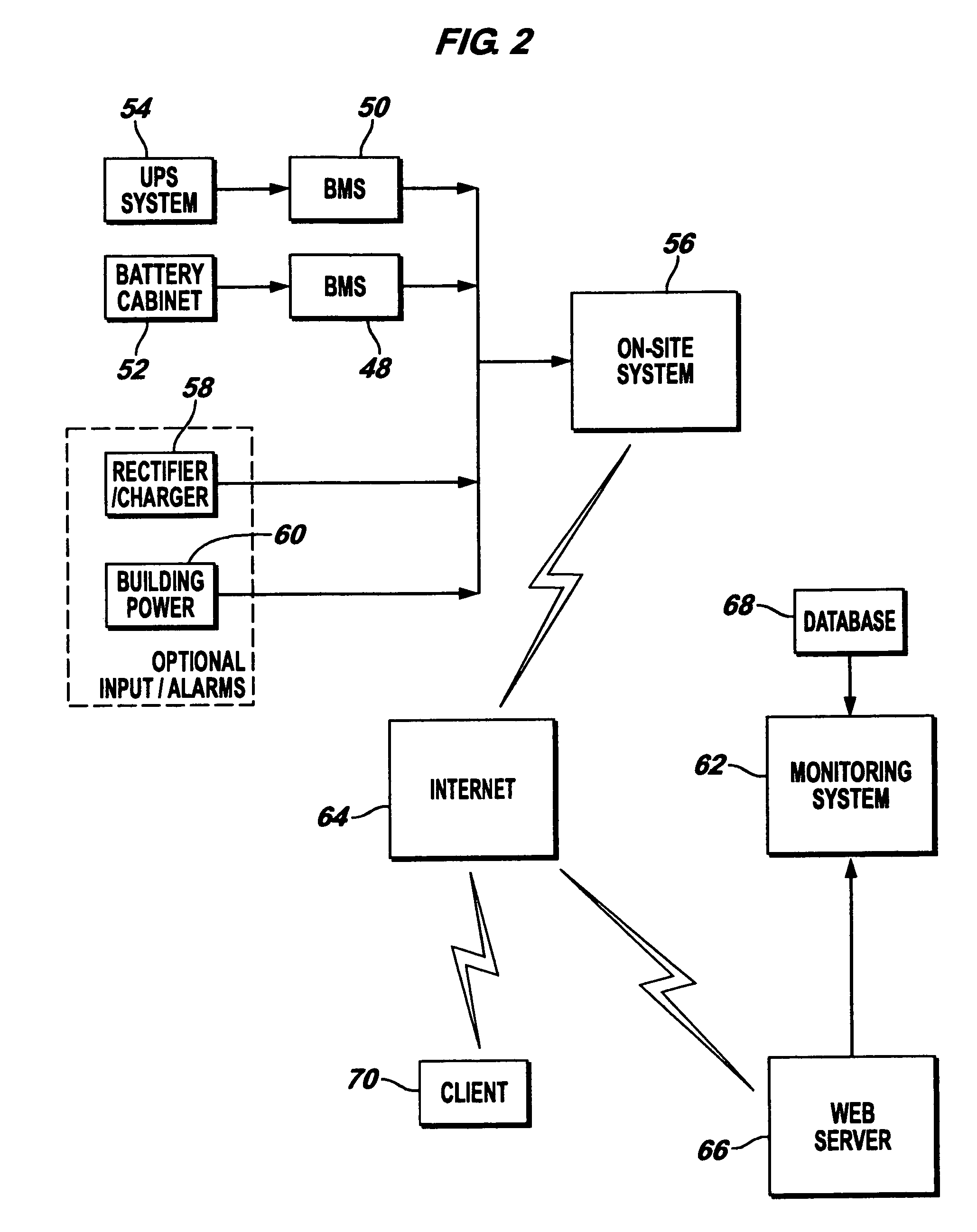
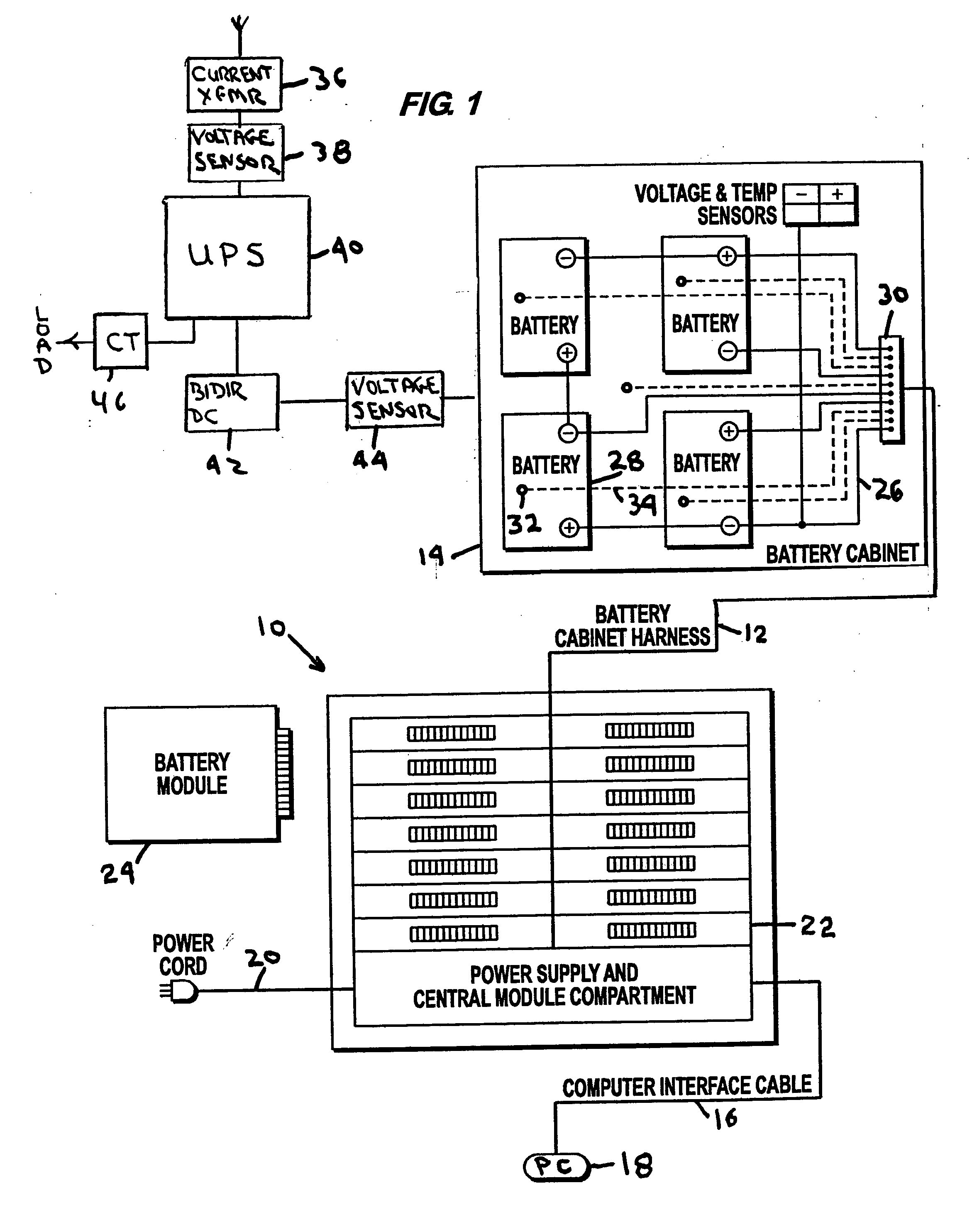
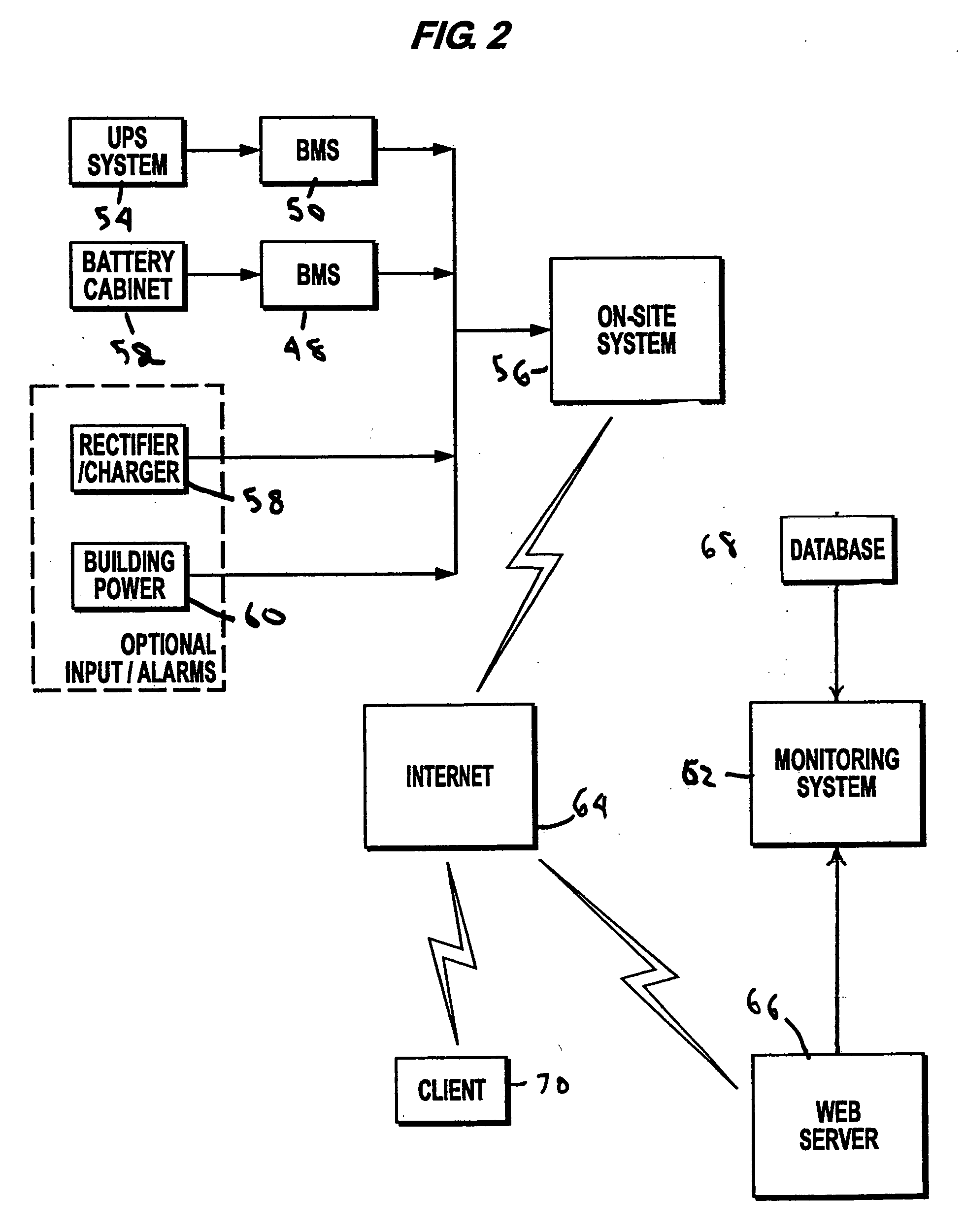
InactiveUS7184905B2Batteries circuit arrangementsElectric devicesElectrical batteryElectric power system
An electrical power (AC / DC) monitoring system remotely monitoring batteries and electrical power systems through a call center, providing continual monitoring, monthly reports, near real time viewing and service response. Modular by design, a plurality of individual input modules, which receive an analog voltage input, convert this signal to a digital format and send the digital signal to a central control which collects the data, then, at scheduled intervals, sends the collected data to a web server which contains the main software for the system. This software performs data comparisons, charts trends, predicts failures, plans and schedules service visits, then archives the data for future references. Alarm notifications are provided to the customer via Email, office phone (land line), cell phone (wireless), PDA, pager, etc. and can also be sent to a service provider to initiate the service response.
Owner:STEFAN DONALD A
Method and system for monitoring power supplies
An electrical power (AC / DC) monitoring system remotely monitoring batteries and electrical power systems through a call center, providing continual monitoring, monthly reports, near real time viewing and service response. Modular by design, a plurality of individual input modules, which receive an analog voltage input, convert this signal to a digital format and send the digital signal to a central control which collects the data, then, at scheduled intervals, sends the collected data to a web server which contains the main software for the system. This software performs data comparisons, charts trends, predicts failures, plans and schedules service visits, then archives the data for future references. Alarm notifications are provided to the customer via Email, office phone (land line), cell phone (wireless), PDA, pager, etc. and can also be sent to a service provider to initiate the service response.
Owner:STEFAN DONALD A
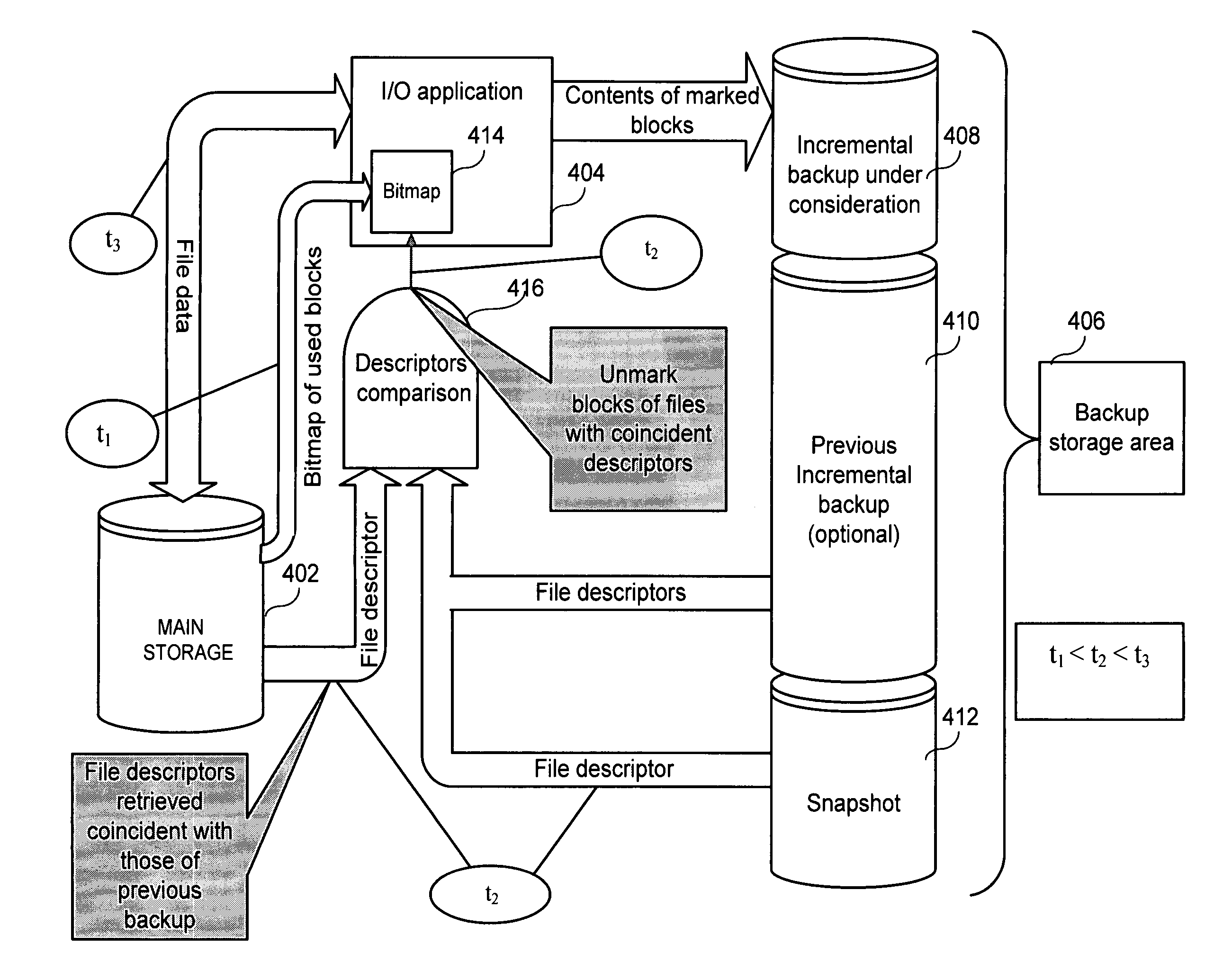
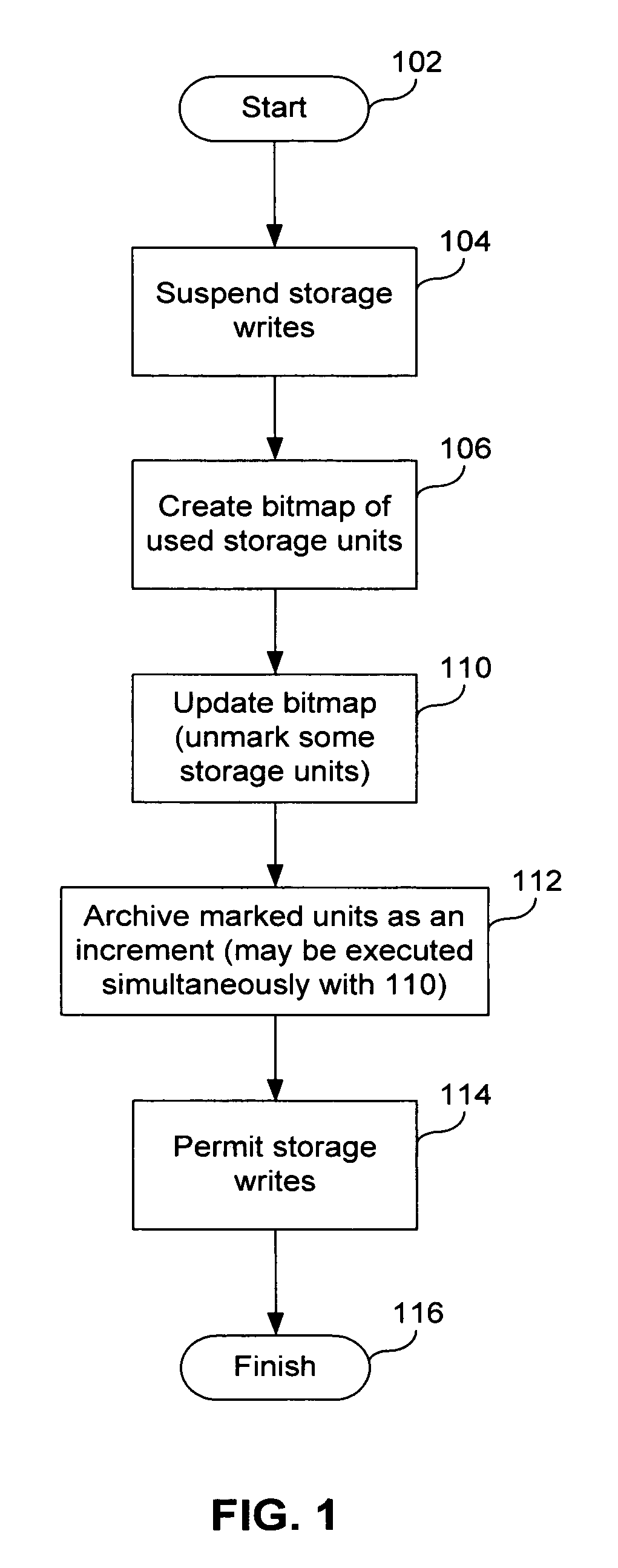
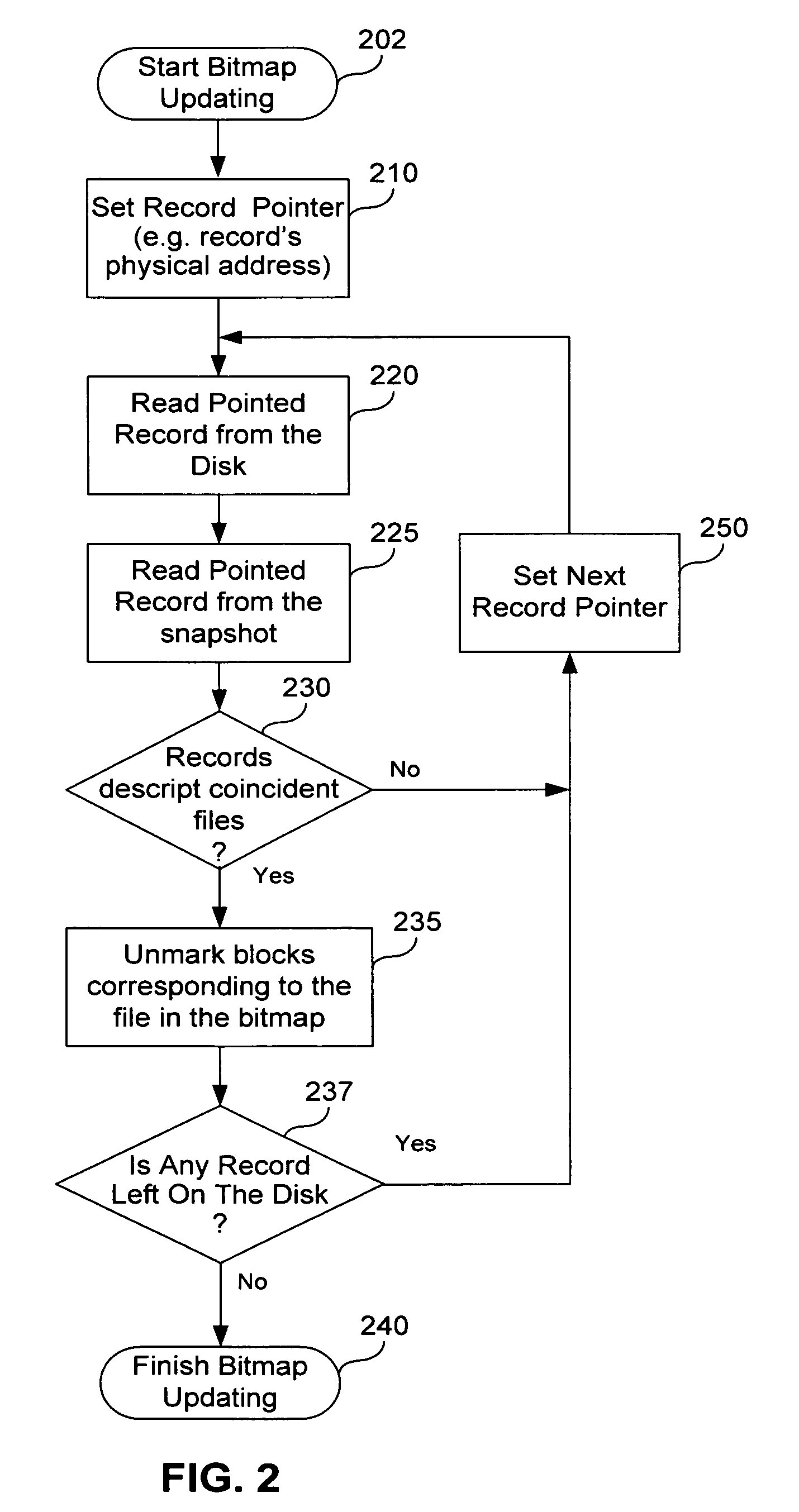
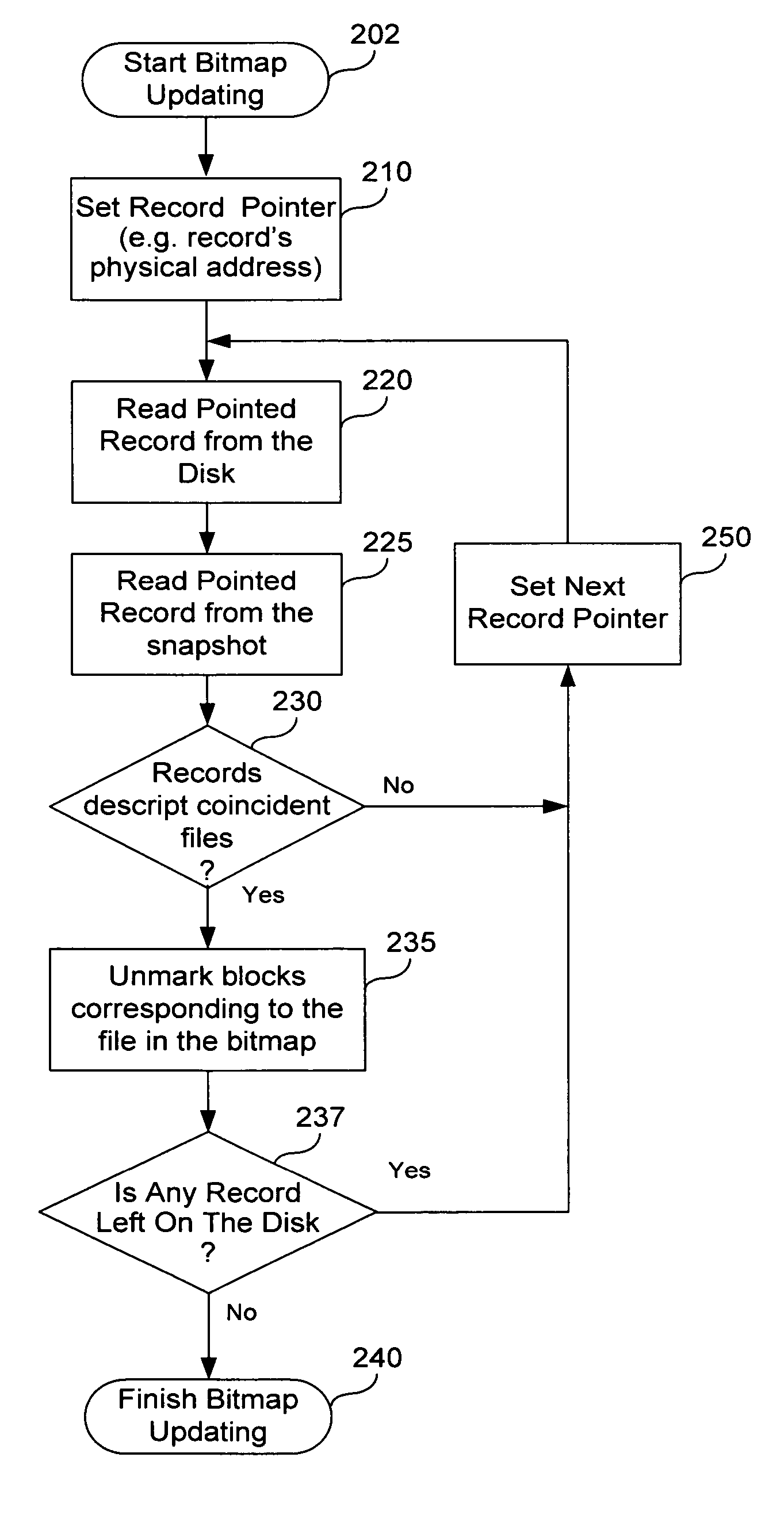
Fast incremental backup method and system
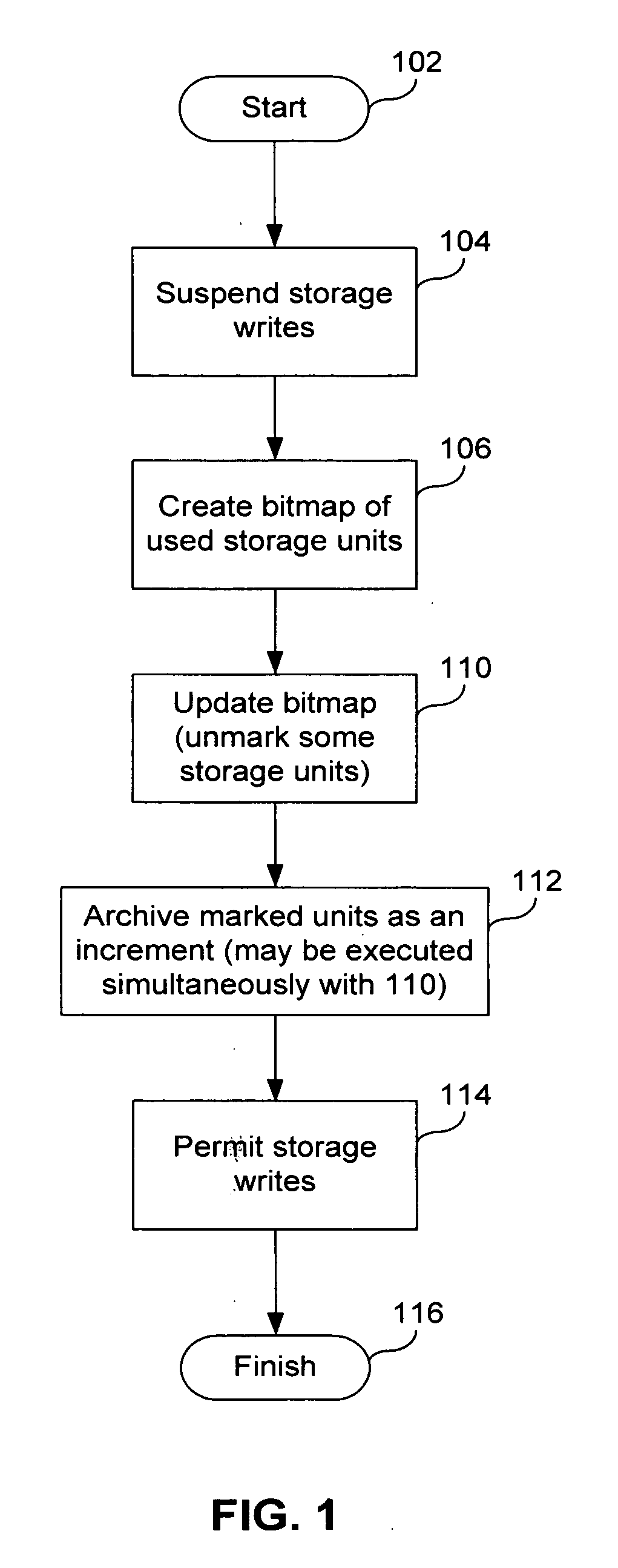
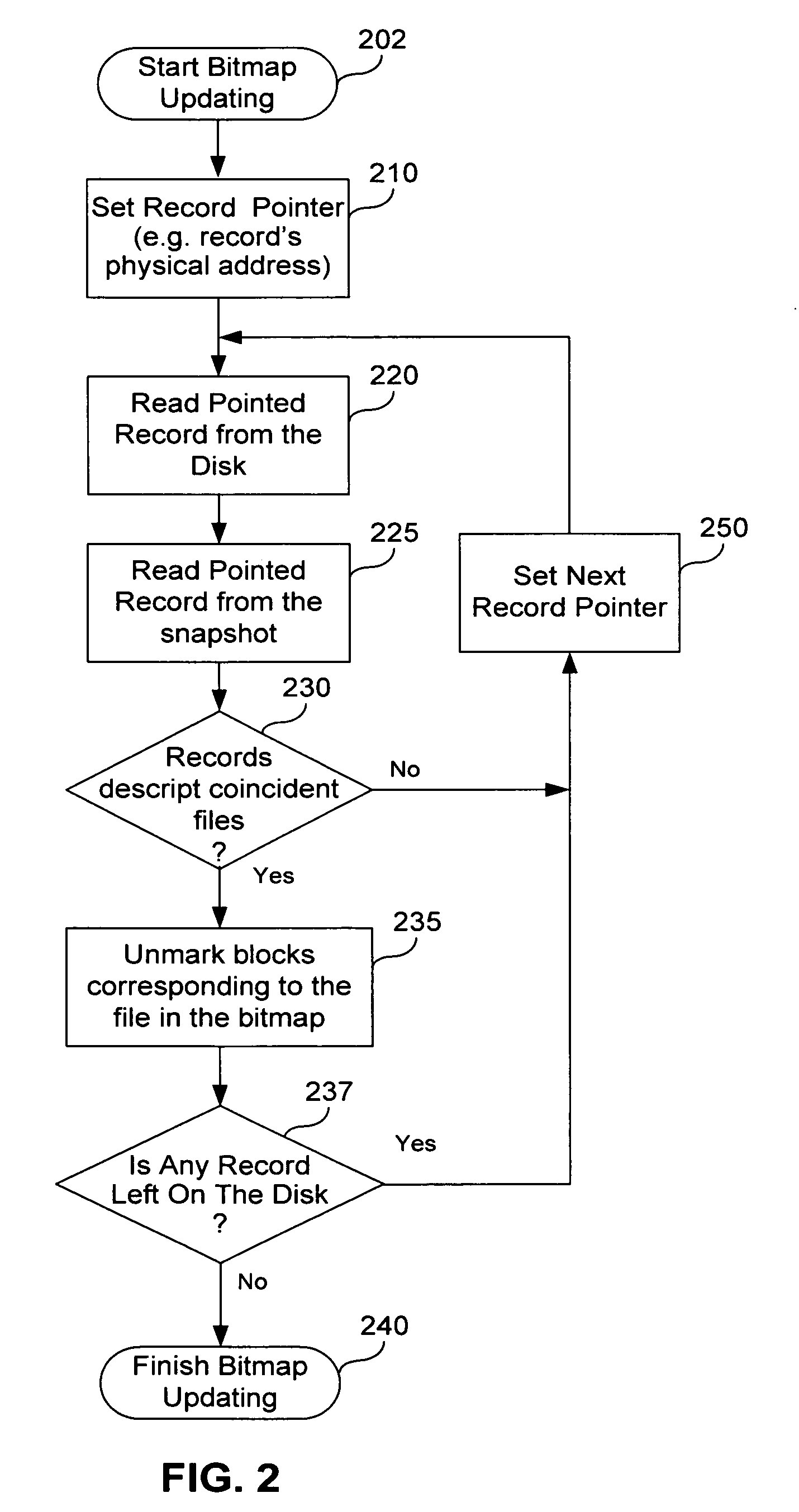
A method of incremental backup of a storage device includes reading descriptors of logical storage units of the storage device; comparing the descriptors of the logical storage units of the storage device with descriptors of archived logical storage units; for logical storage units of the storage device whose descriptors are not identical to the descriptors of the archived logical storage units, backing up contents of physical storage units that correspond to those logical storage units of the storage device; and, for logical storage units of the storage device whose descriptors are identical, performing a comparison step to check if these logical storage units need to be backed up. The logical storage units can be files. The comparison step can be, e.g., (1) bit-wise comparison of the logical blocks, (2) comparing control sums of the logical blocks, and (3) comparing log files relating to the logical storage units The physical storage units can be blocks. The descriptors can be, e.g., MFT entries, hash function values, timestamps, checksums, and file metadata. The descriptors can be compared on a physical storage unit basis. The method further can optionally include generating a bitmap of the physical storage units of the storage device; marking, in the bitmap, those physical storage units that correspond to logical storage units with different descriptors; and archiving content of the physical storage units marked in the bitmap. The method can further optionally include archiving logical storage units of the storage device having the same name as corresponding archived logical storage units of the storage device, but different time stamps.
Owner:MIDCAP FINANCIAL TRUST
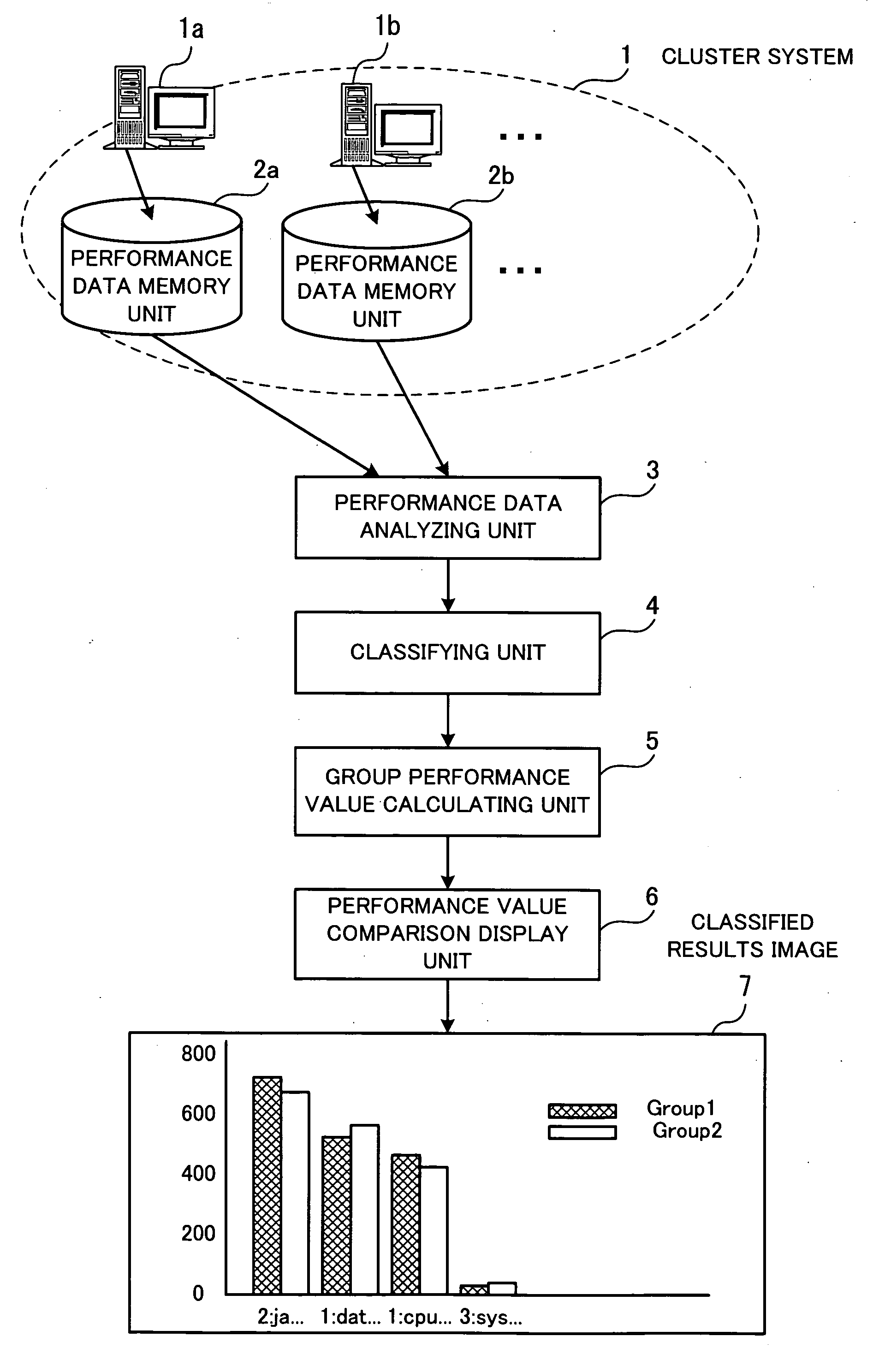
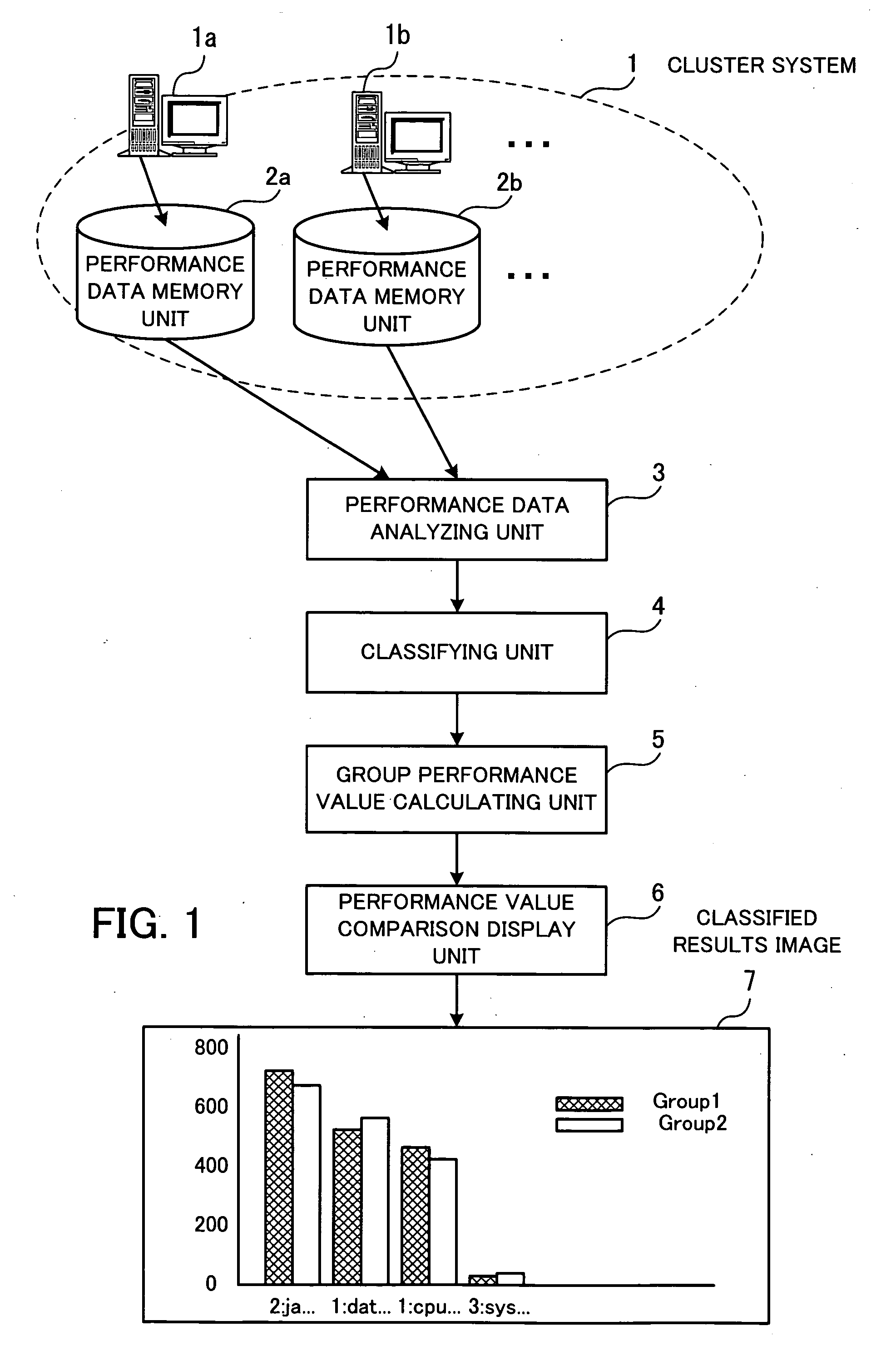
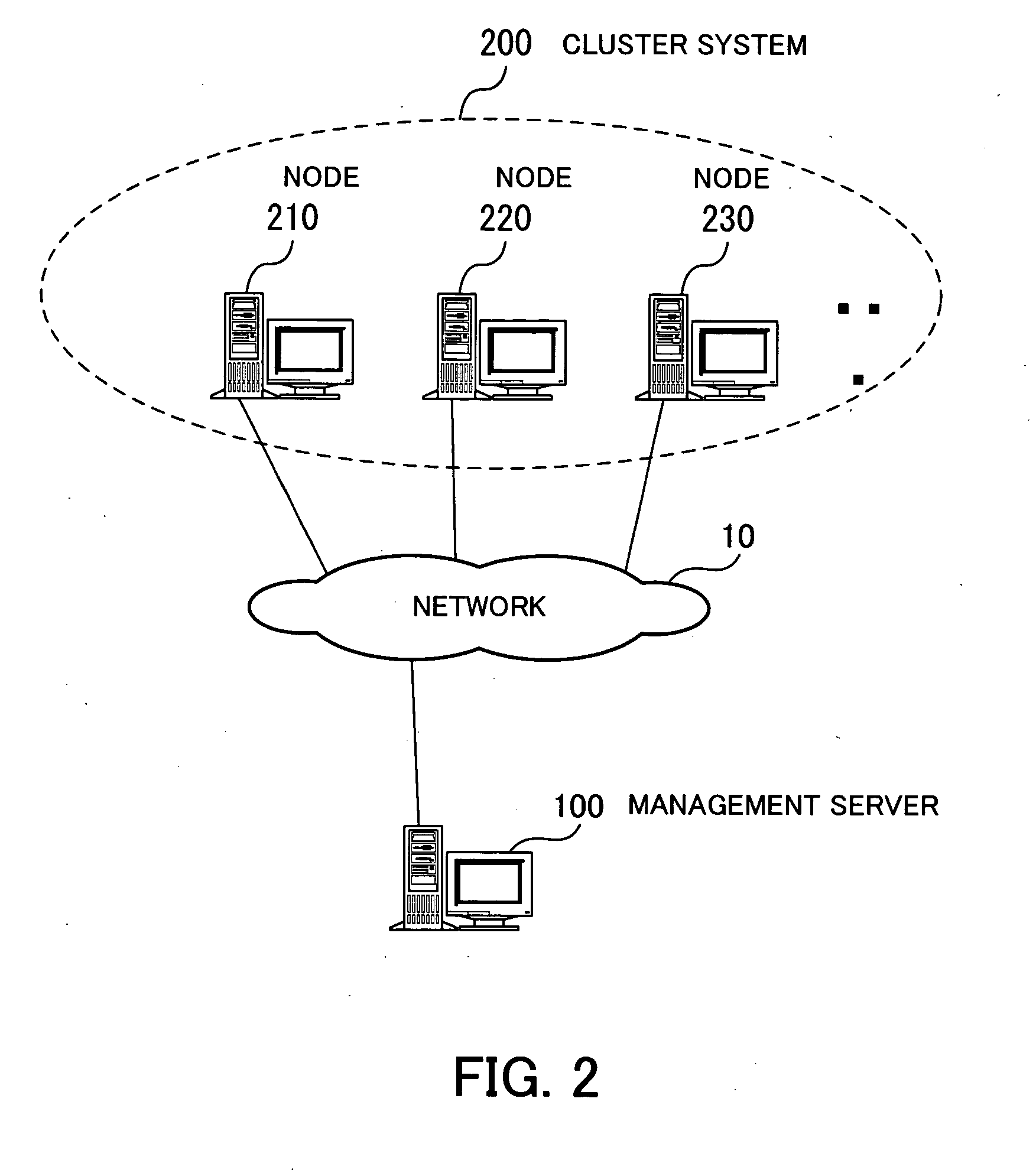
Computer-readable recording medium with recorded performance analyzing program, performance analyzing method, and performance analyzing apparatus
InactiveUS20070185990A1Efficiently investigatingError detection/correctionDigital computer detailsData displayCluster systems
A recording medium which is readable by a computer stores a performance analyzing program for searching for a node that is peculiar in performance in a cluster system, as well as unknown problems. The performance analyzing program enables the computer to function as various functional units. A performance data analyzing unit collects performance data of nodes which make up the cluster system from performance data storage unit for storing a plurality of types of performance data of the nodes, and analyzes performance values of the nodes based on the collected performance data. A classifying unit classifies the nodes into a plurality of groups by statistically processing the performance data collected by the performance data analyzing unit according to a predetermined classifying condition. A group performance value calculating unit statistically processes the performance data of the respective groups based on the performance data of the nodes classified into the groups, and calculates statistic values for the respective types of the performance data of the groups. A performance data comparison display unit displays the statistic values of the groups for the respective types of the performance data for comparison between the groups.
Owner:FUJITSU LTD
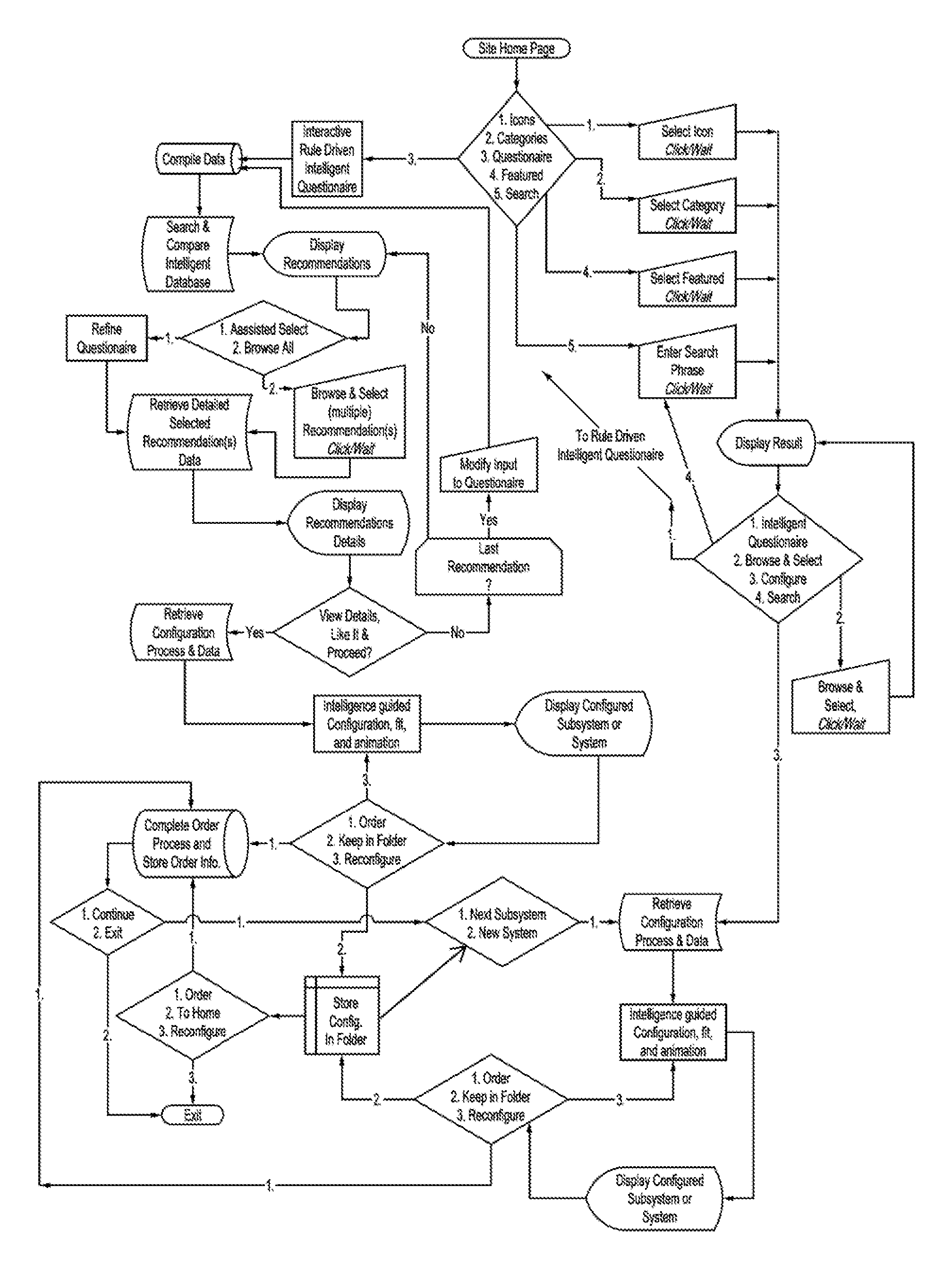
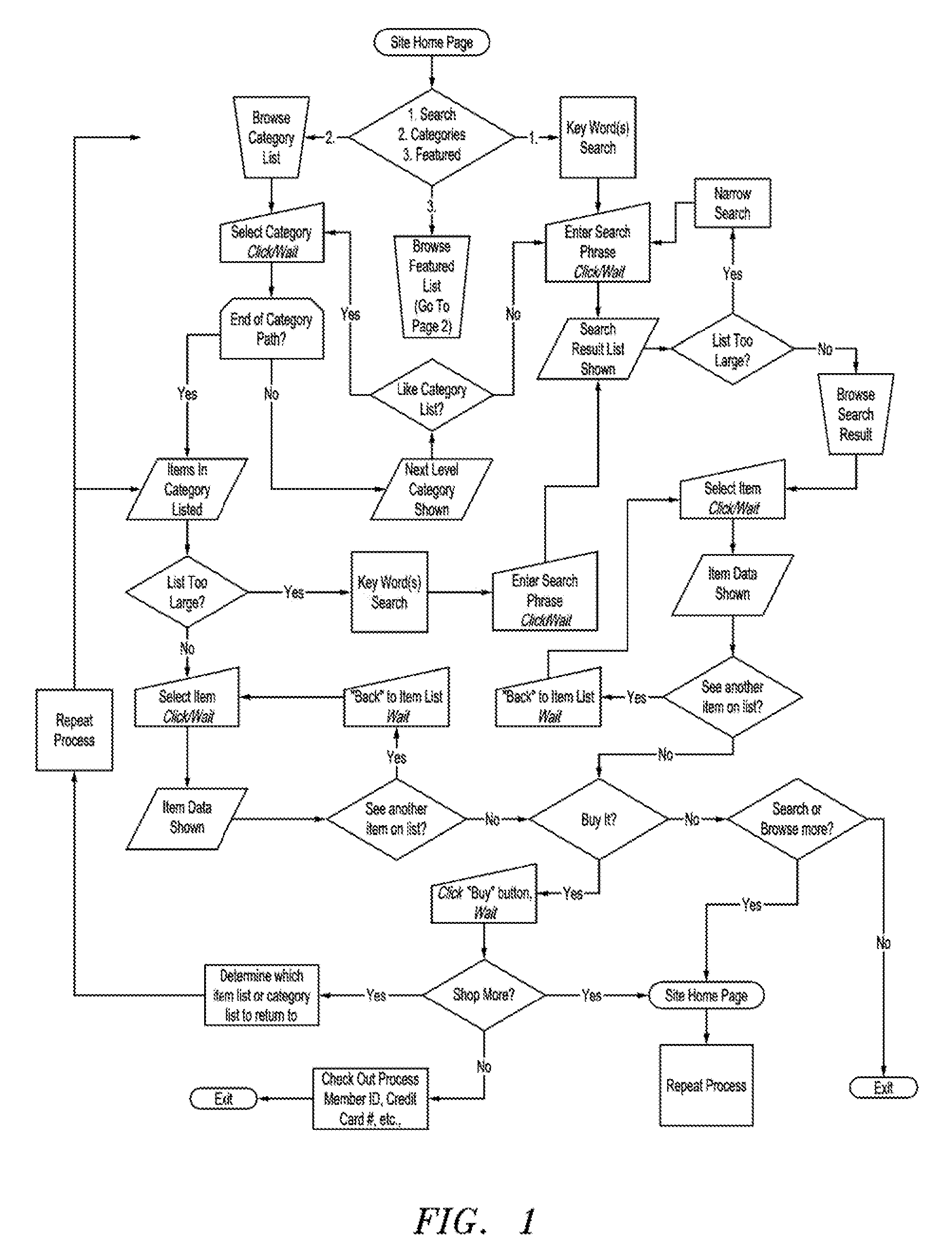
System and method for interactive, computer assisted personalization of on-line merchandise purchases
InactiveUS7328177B1Digital data information retrievalSpecial data processing applicationsPersonalizationGraphics
A system and method for enabling on-line purchasers to customize and personalize their purchasing options by prompting the customer to indicate customer preferences regarding merchandise and services to be purchased on-line. The system and method use intelligent process and rule-driven inquiry-databases, intelligent product databases, artificial intelligence rules, data comparison algorithms, animation software, graphics and video input and output hardware and software and / or video streaming to (1) guide consumers in specifying customer preferences, (2) make purchasing recommendations to consumers, (3) narrow selections of merchandise or services, (4) determine the fit of merchandise, (5) configure and optimize various options of subsystems into a complete system, (6) layout, compose and / or animate merchandise or models wearing merchandise, and (7) display the fitted system of multiple items with the recommended and / or selected settings.
Owner:LIN HENDEL CATHERINE
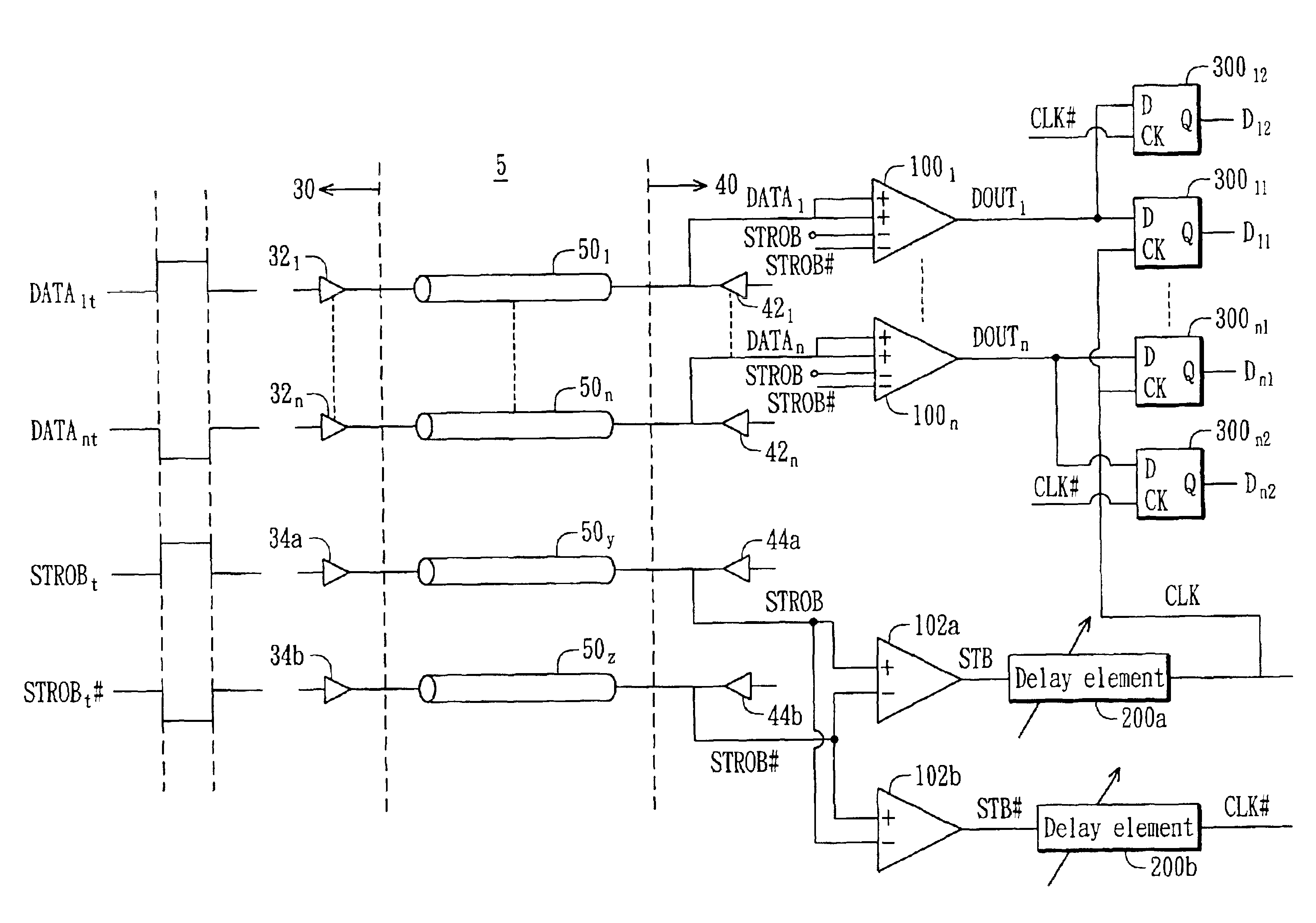
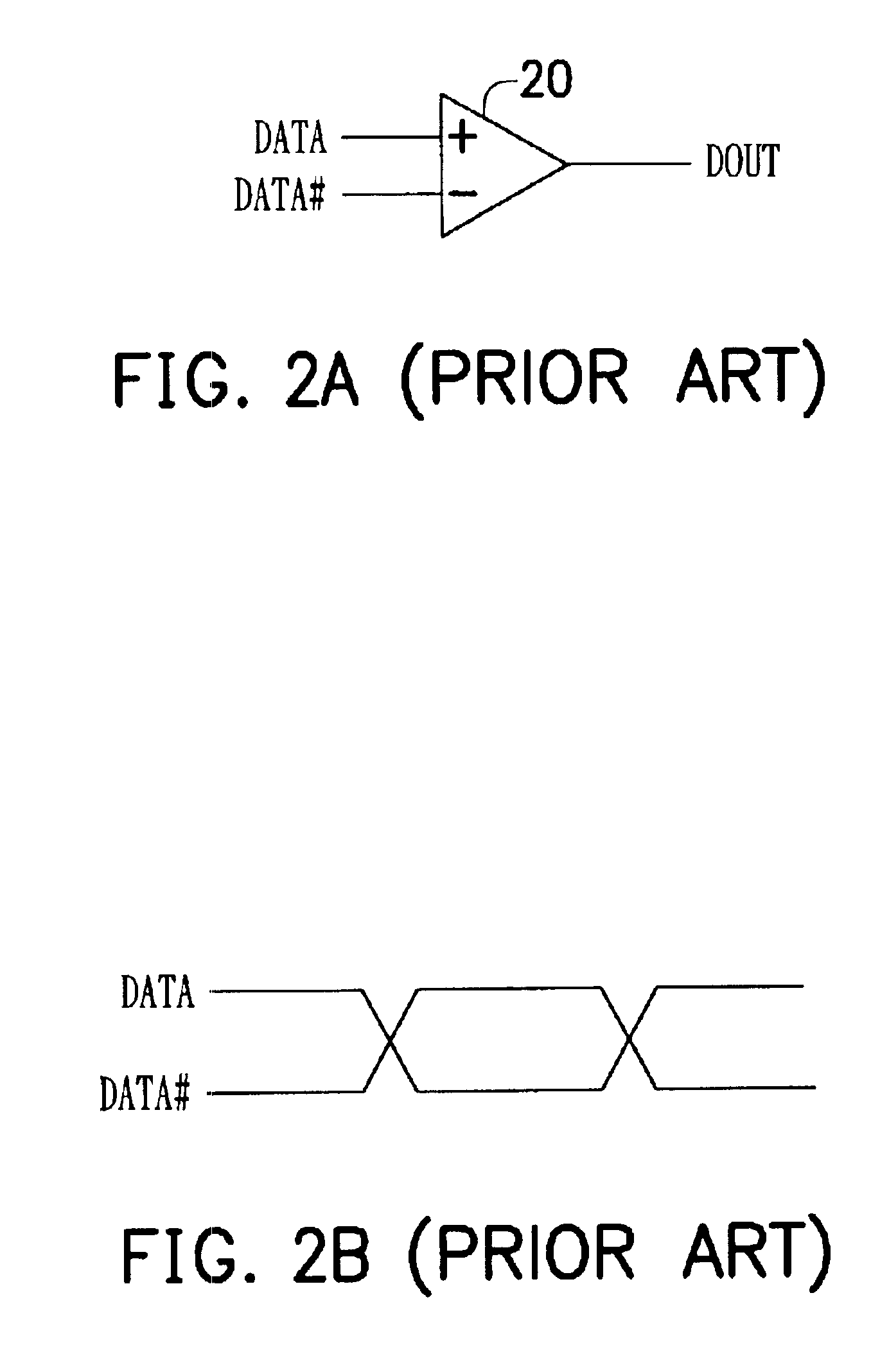
System for latching an output signal generated by comparing complimentary strobe signals and a data signal in response to a comparison of the complimentary strobe signals
ActiveUS6898724B2Prevent erroneous samplingOvercomes drawbackSynchronisation information channelsTime-division multiplexData signalOutput device
A data transmission system using a pair of complement signals (STROB / STROB#) as an edge-aligned strobe signal and input / output buffers therein. Several data signals and a pair of STROB / STROB# signals are transmitted from a data output device to a data input device therein. These data signals and the STROB / STROB# signals are edge-aligned and transmitted through the same transmission architecture. The data input device includes several data comparators for generating output signals from the received data signals using the received STROB / STROB# signals as a dynamic reference voltage. In addition, the data input device further includes several comparators and delay elements for generating a pair of non-inverting / inverting latch clock signals from the STROB / STROB# signals. Each of the output signals is sent to two data latch circuits for outputting two latched data based on the latch clock signals.
Owner:VIA TECH INC
Fast incremental backup method and system
ActiveUS20070083722A1Eliminate disadvantagesMemory loss protectionRedundant hardware error correctionHash functionChecksum
A method of incremental backup of a storage device includes reading descriptors of logical storage units of the storage device; comparing the descriptors of the logical storage units of the storage device with descriptors of archived logical storage units; for logical storage units of the storage device whose descriptors are not identical to the descriptors of the archived logical storage units, backing up contents of physical storage units that correspond to those logical storage units of the storage device; and, for logical storage units of the storage device whose descriptors are identical, performing a comparison step to check if these logical storage units need to be backed up. The logical storage units can be files. The comparison step can be, e.g., (1) bit-wise comparison of the logical blocks, (2) comparing control sums of the logical blocks, and (3) comparing log files relating to the logical storage units The physical storage units can be blocks. The descriptors can be, e.g., MFT entries, hash function values, timestamps, checksums, and file metadata. The descriptors can be compared on a physical storage unit basis. The method further can optionally include generating a bitmap of the physical storage units of the storage device; marking, in the bitmap, those physical storage units that correspond to logical storage units with different descriptors; and archiving content of the physical storage units marked in the bitmap. The method can further optionally include archiving logical storage units of the storage device having the same name as corresponding archived logical storage units of the storage device, but different time stamps.
Owner:MIDCAP FINANCIAL TRUST
System and method for automatically verifying storage of redundant contents into communication equipments, by data comparison
InactiveUS9130918B2Digital data processing detailsUser identity/authority verificationContent IdentifierRedundant code
A method is intended for verifying storage of contents into communication equipments connected to at least one communication network. This method consists, when a first communication equipment stores a content and wants to verify that this content is still stored into a second communication equipment: i) in transmitting a first request, comprising at least an identifier of this content and first data representative of this content and requiring verification of the storage of this content into the second communication equipment, to an auxiliary communication equipment acting as an interface between the communication network and the second communication equipment, ii) in transmitting a second request, comprising at least the content identifier, to the second communication equipment, to require transmission of second data representative of the content to the auxiliary communication equipment, and in triggering a timeout having a chosen duration, and iii) if the auxiliary communication equipment has received the second data before expiration of this timeout, in comparing these received second data, possibly after having processed them, to the received first data, and in transmitting a message representative of the result of this comparison to the first communication equipment.
Owner:THOMSON LICENSING SA
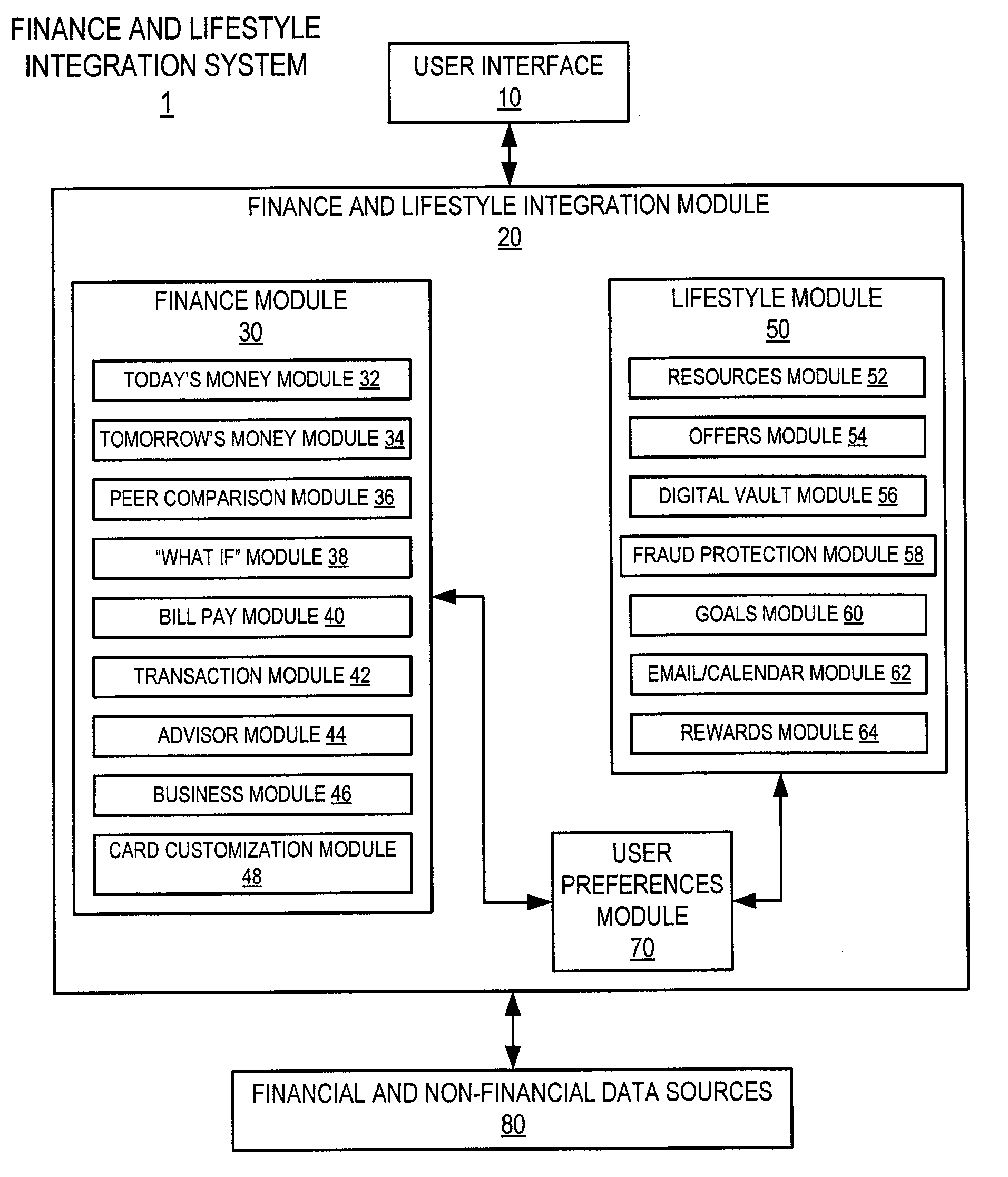
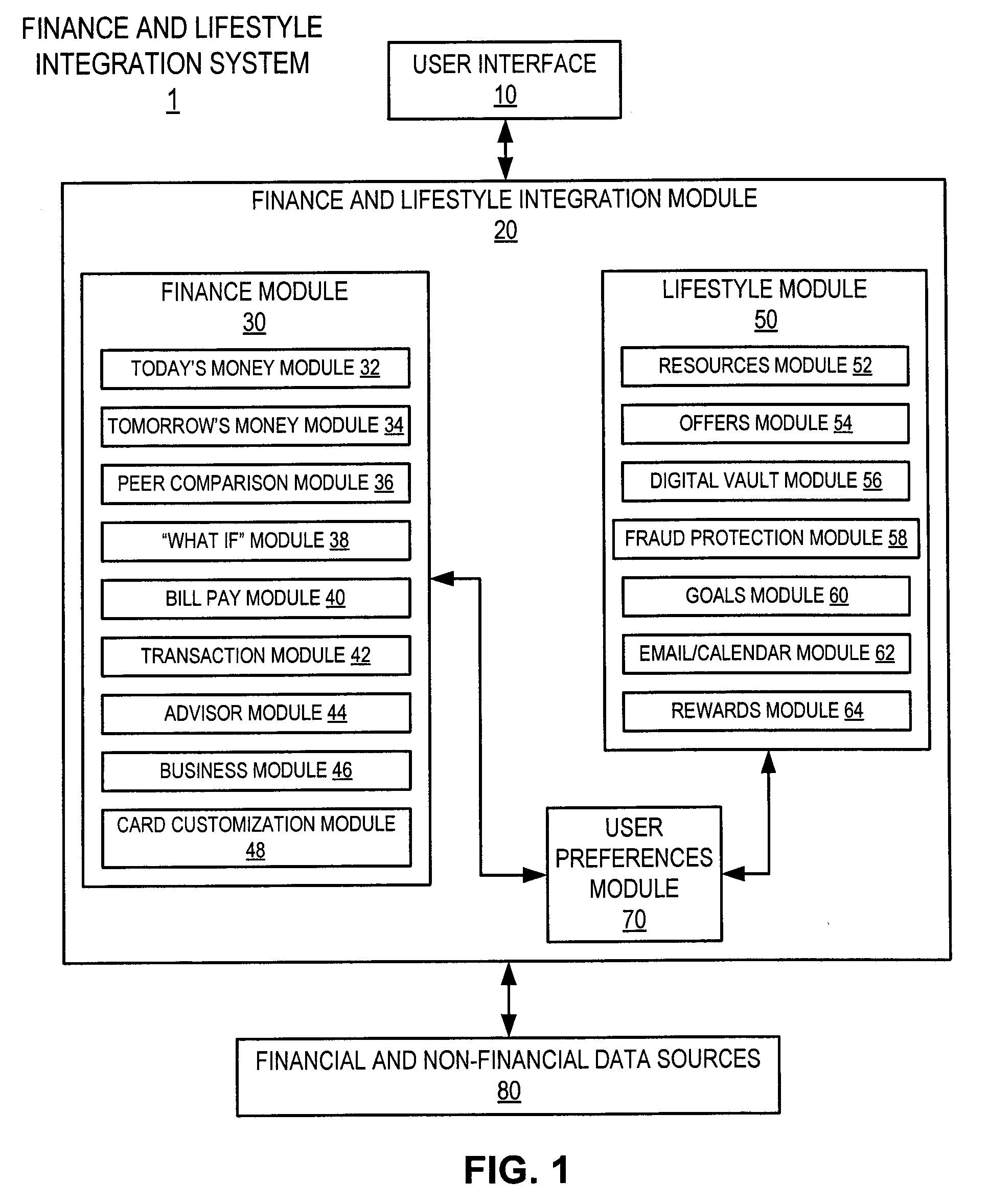
Financial data comparison tool
Embodiments of the present invention provide apparatuses and methods for allowing a user to compare his or her financial data to the financial data of a hypothetical peer person. For example, an apparatus is provided including: (a) a communication interface configured to communicate with a user terminal, wherein the communication interface is configured to receive user input from the user terminal; and (b) a processor configured to compare a user's finances with finances of an average member of a select group of people, the comparison based at least partially on the received user input, wherein the communication interface is configured to provide the user terminal with a visual comparison of the user's finances with the finances of an average member of the select group of people.
Owner:BANK OF AMERICA CORP
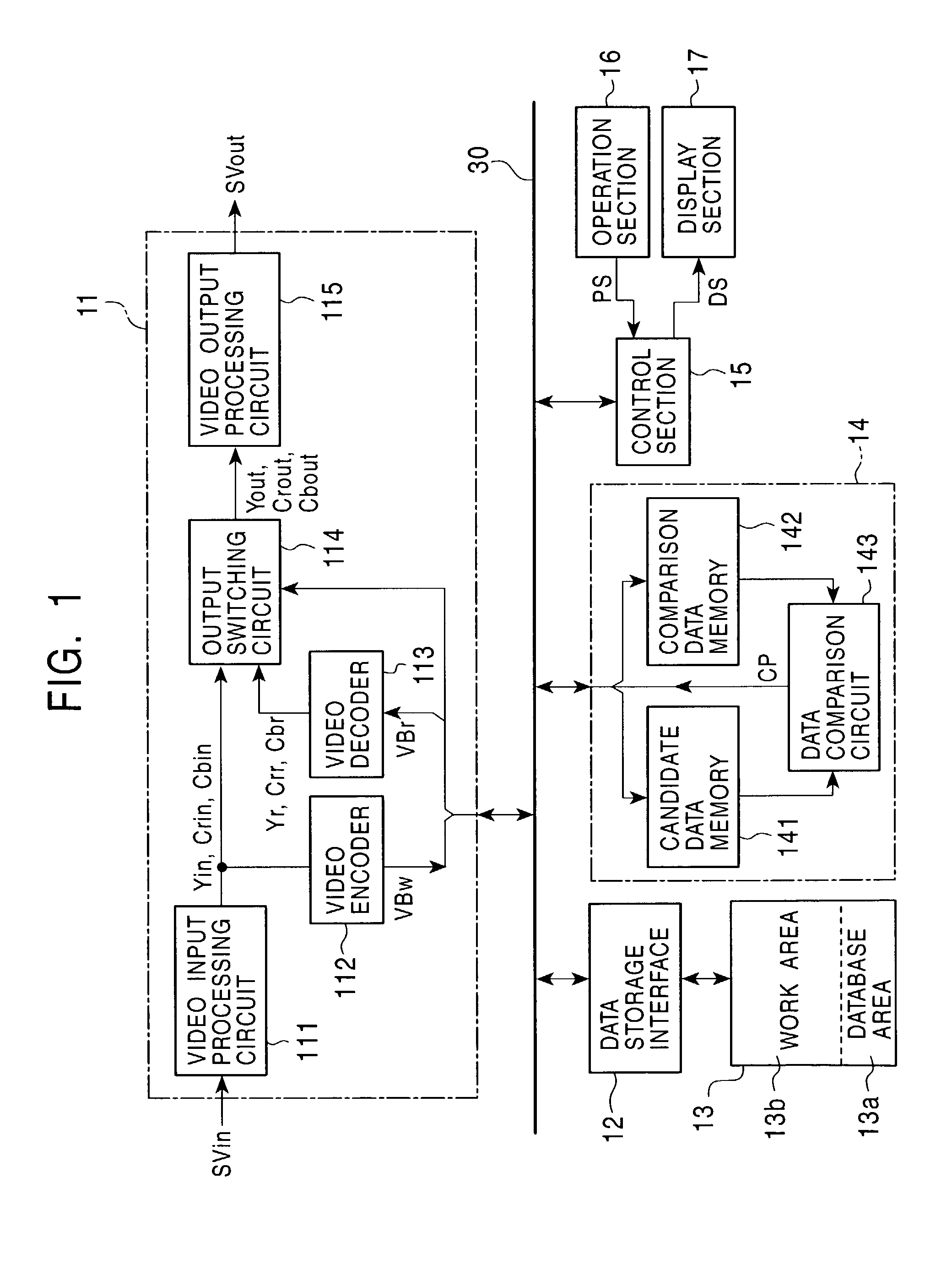
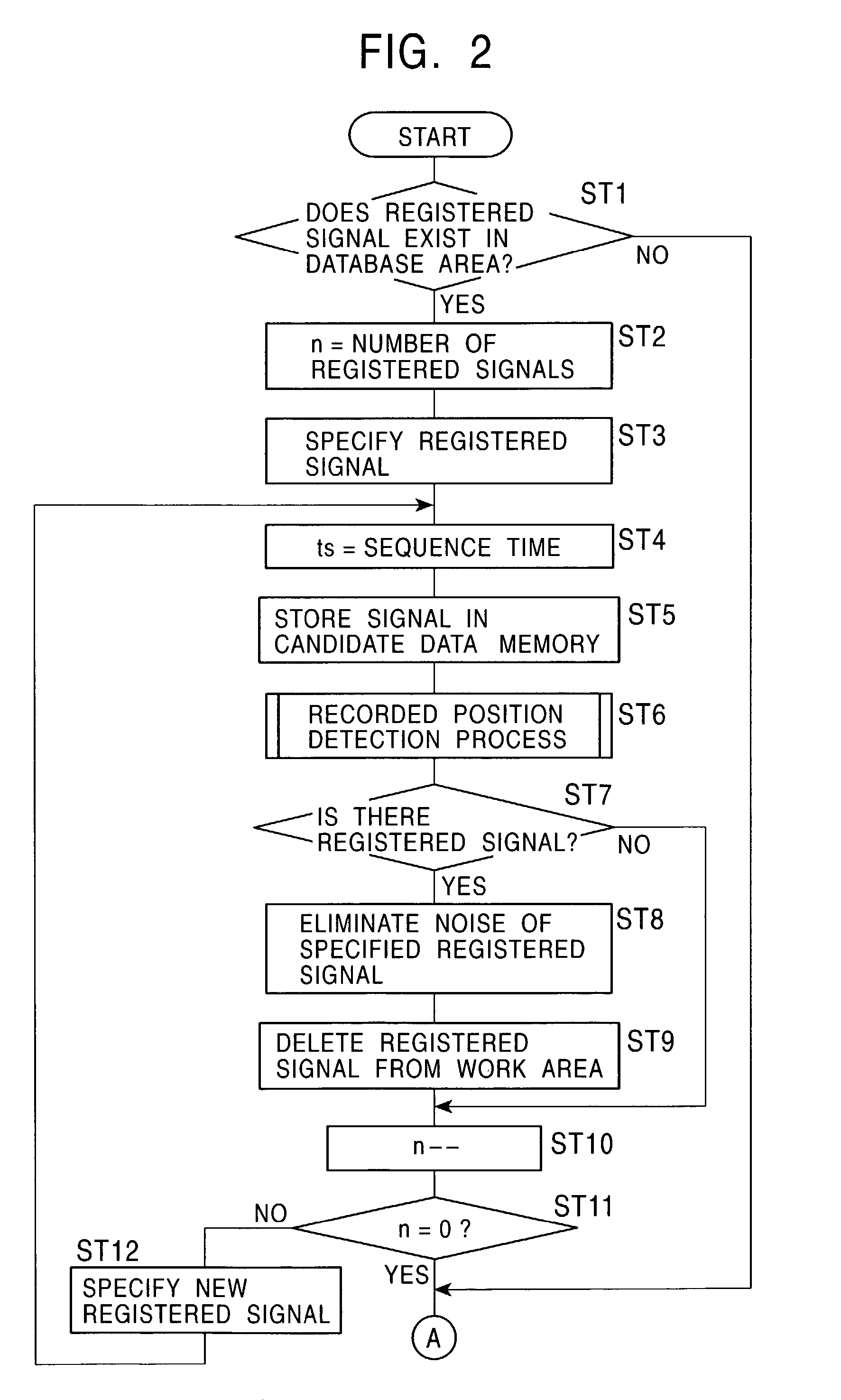
Signal processing method and signal processing apparatus
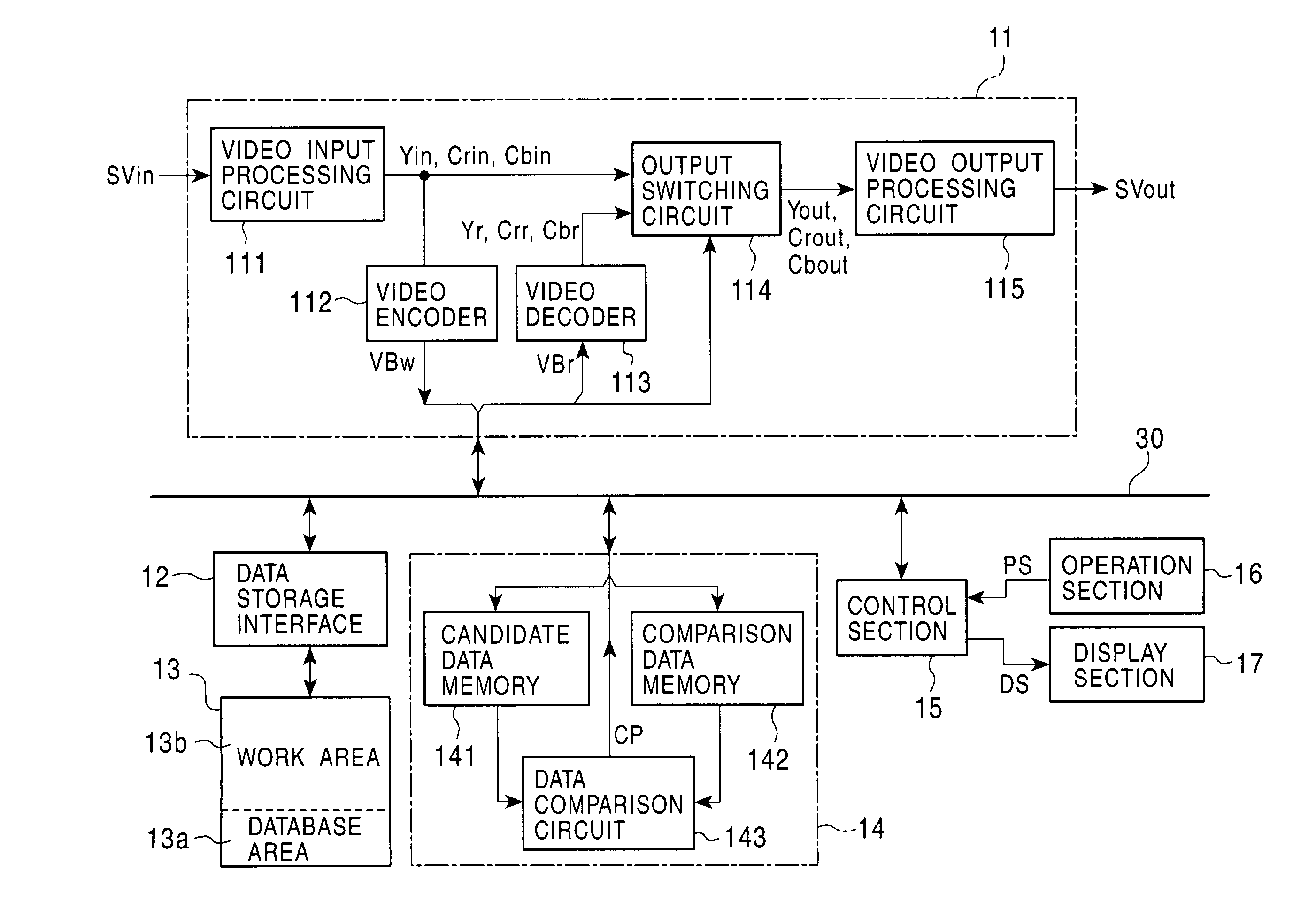
InactiveUS7529466B2Easy to detectEasy to useTelevision system detailsElectronic editing digitised analogue information signalsFile comparisonComputer science
A signal recorded in a work area is read for a predetermined time, the signal is assumed to be a candidate signal, and this signal is stored in a memory. A signal differing from the candidate signal is read for a predetermined time, the signal is assumed to be a comparison signal, and the signal is stored in another memory. A data comparison circuit determines whether or not the candidate signal and the comparison signal are signals with identical content are the same. When it is determined that the contents, the candidate signal is stored in a database area. A signal which is determined to have the same content as that of the candidate signal stored in the database area is deleted in such a manner that the signal can be recovered from the work area. A signal with identical content can easily be detected, and deletion of content recorded in a duplicate manner makes it possible to efficiently use a recording device.
Owner:SONY CORP
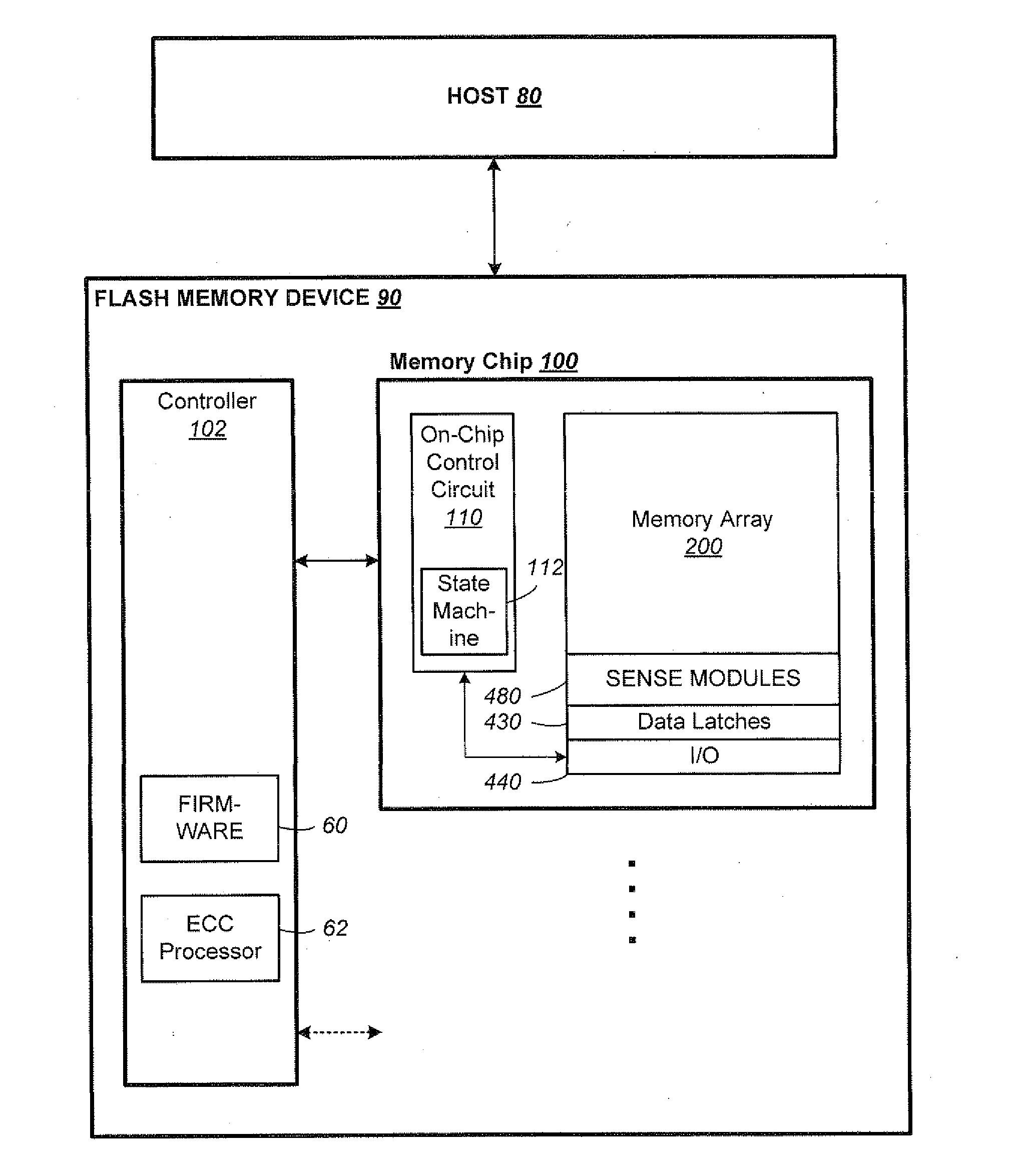
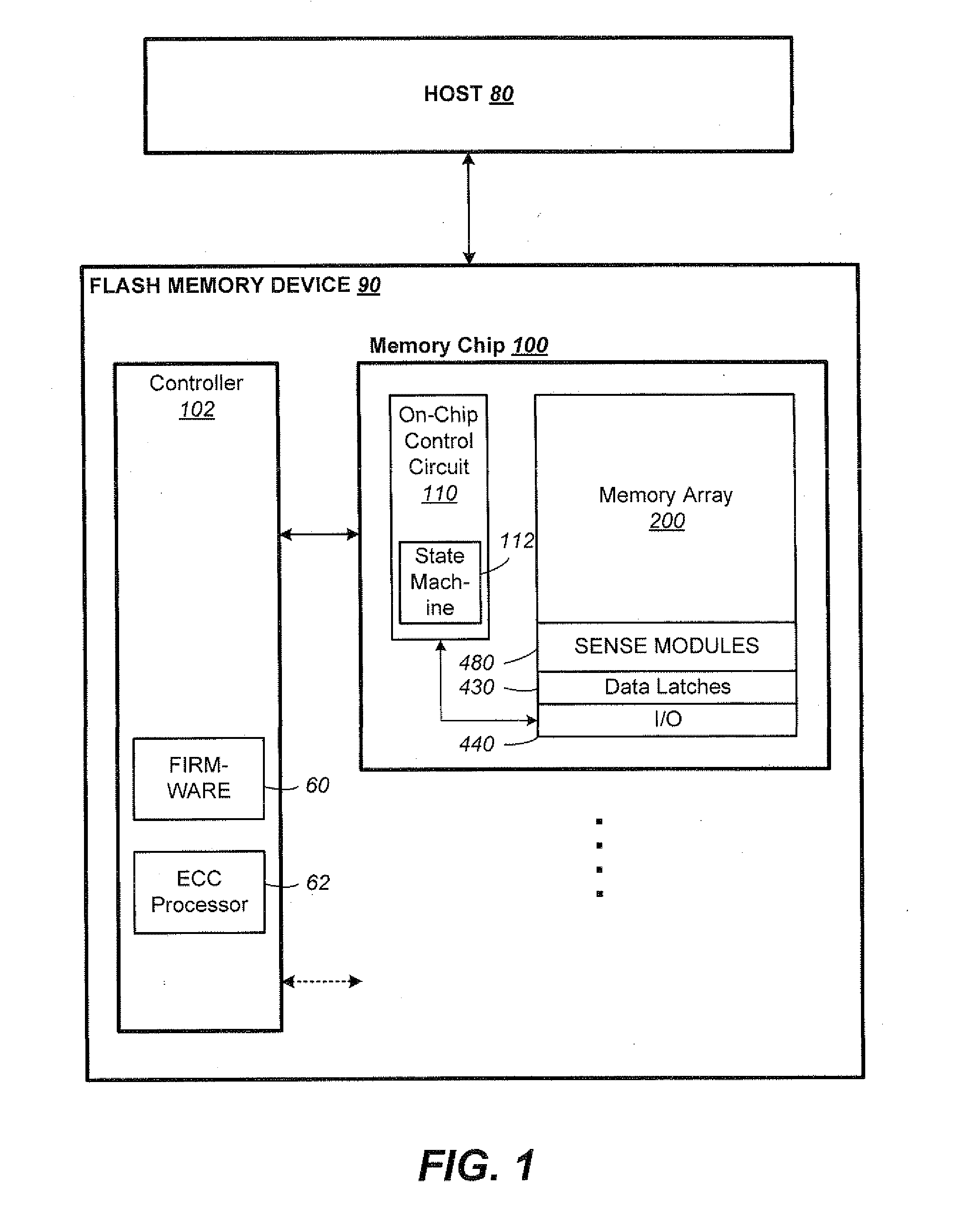
Post-Write Read in Non-Volatile Memories Using Comparison of Data as Written in Binary and Multi-State Formats
InactiveUS20130031431A1Error detection/correctionRead-only memoriesFile comparisonNon-volatile memory
Techniques for a post-write read are presented. In an exemplary embodiment, host data is initially written into the non-volatile memory in binary form, such as a non-volatile binary cache. It is then subsequently written from the binary section into a multi-state non-volatile section of the memory. After being written in multi-state format, pages of data from a multi-state block can then be checked against there source pages in the binary section to verify the quality of the multi-state write. This process can be performed on the memory device itself, without transferring the pages out to the controller.
Owner:SANDISK TECH LLC
Keyless entry system and keyless entry method
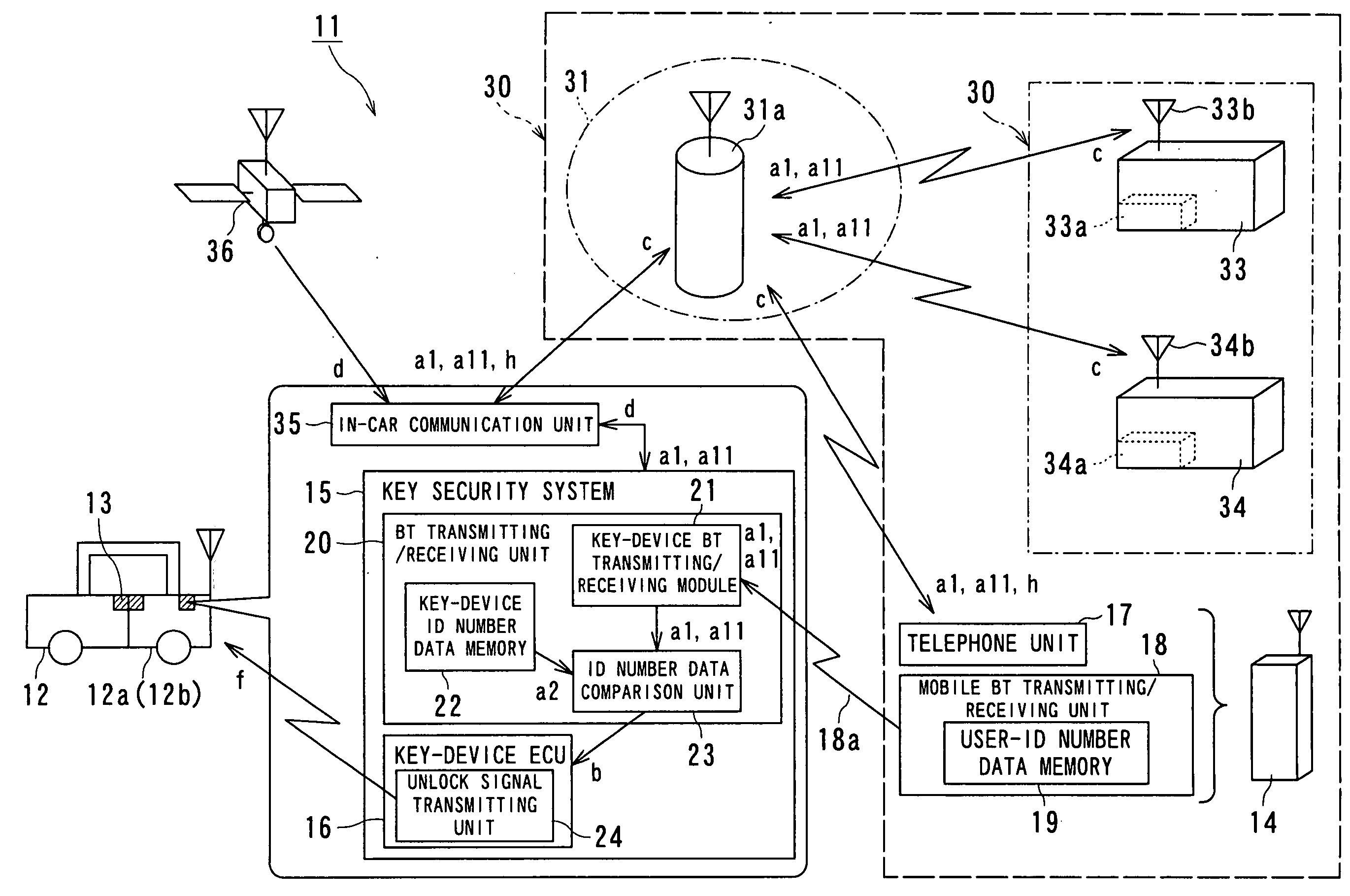
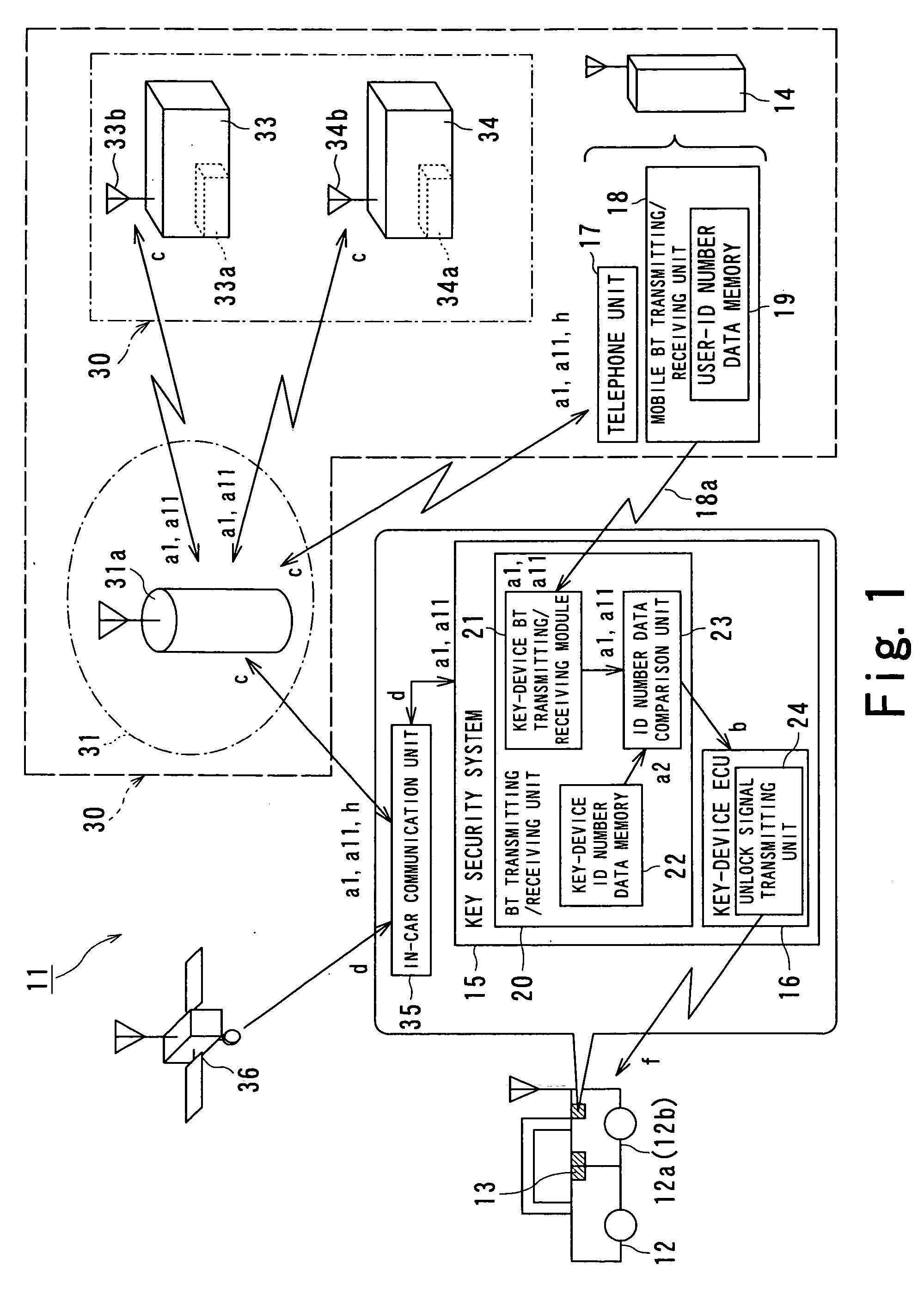
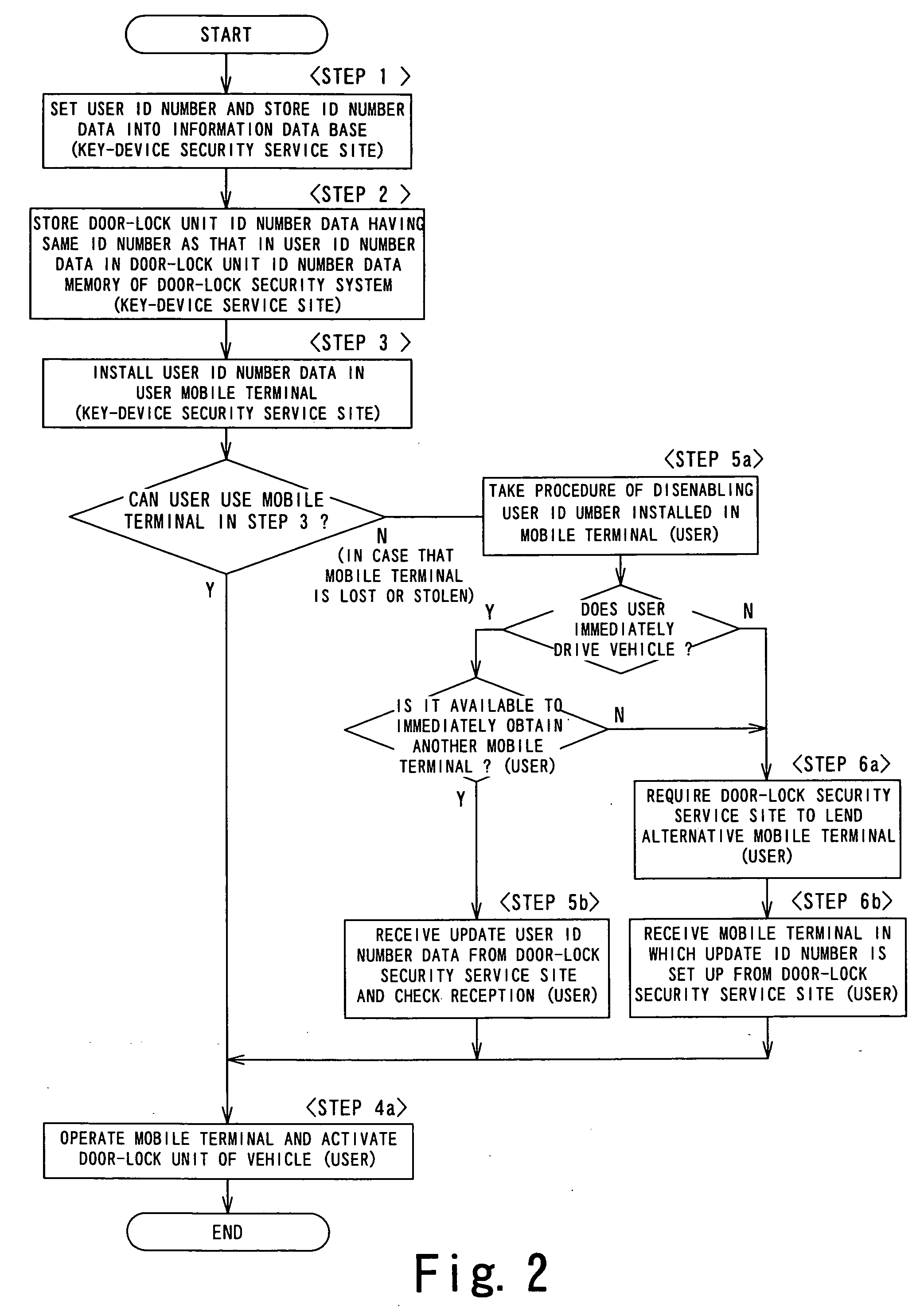
InactiveUS20060143463A1Maintain convenienceTelemetry/telecontrol selection arrangementsVehicle locksControl signalFile comparison
A keyless entry system include a key device 13 for carrying out locking and unlocking operations, a mobile terminal 14 including a mobile terminal transmitting / receiving unit 18 for transmitting user-ID number data a1 used for identifying a user of the key device 13, and a key security system 15 including a key device transmitting / receiving unit 20 for receiving the user-ID number data a1 from the mobile terminal 14. The key security system 15 includes an ID-number data comparison unit 23 for recognizing a fact that key-device ID number data a2 pre-stored in the key device 13 is identical to the user-ID number data a1 transmitted from the mobile terminal 14 and a key-device ECU 16 for receiving an unlock enable signal b and outputting a lock control signal f to the key device 13. According to the above-described configuration, when operating and activating the key device, such as a door lock device of a vehicle and a house, using a mobile terminal, such as a cell phone, which many people usually carry around with them, a keyless entry system and a keyless entry method that are reliable and convenient for users can be provided.
Owner:KK TOSHIBA
System and method for sampling based elimination of duplicate data
ActiveUS8165221B2Overcome disadvantagesColor television with pulse code modulationColor television with bandwidth reductionData setFile comparison
A technique for eliminating duplicate data is provided. Upon receipt of a new data set, one or more anchor points are identified within the data set. A bit-by-bit data comparison is then performed of the region surrounding the anchor point in the received data set with the region surrounding an anchor point stored within a pattern database to identify forward / backward delta values. The duplicate data identified by the anchor point, forward and backward delta values is then replaced in the received data set with a storage indicator.
Owner:NETWORK APPLIANCE INC
Method and system for updating client software
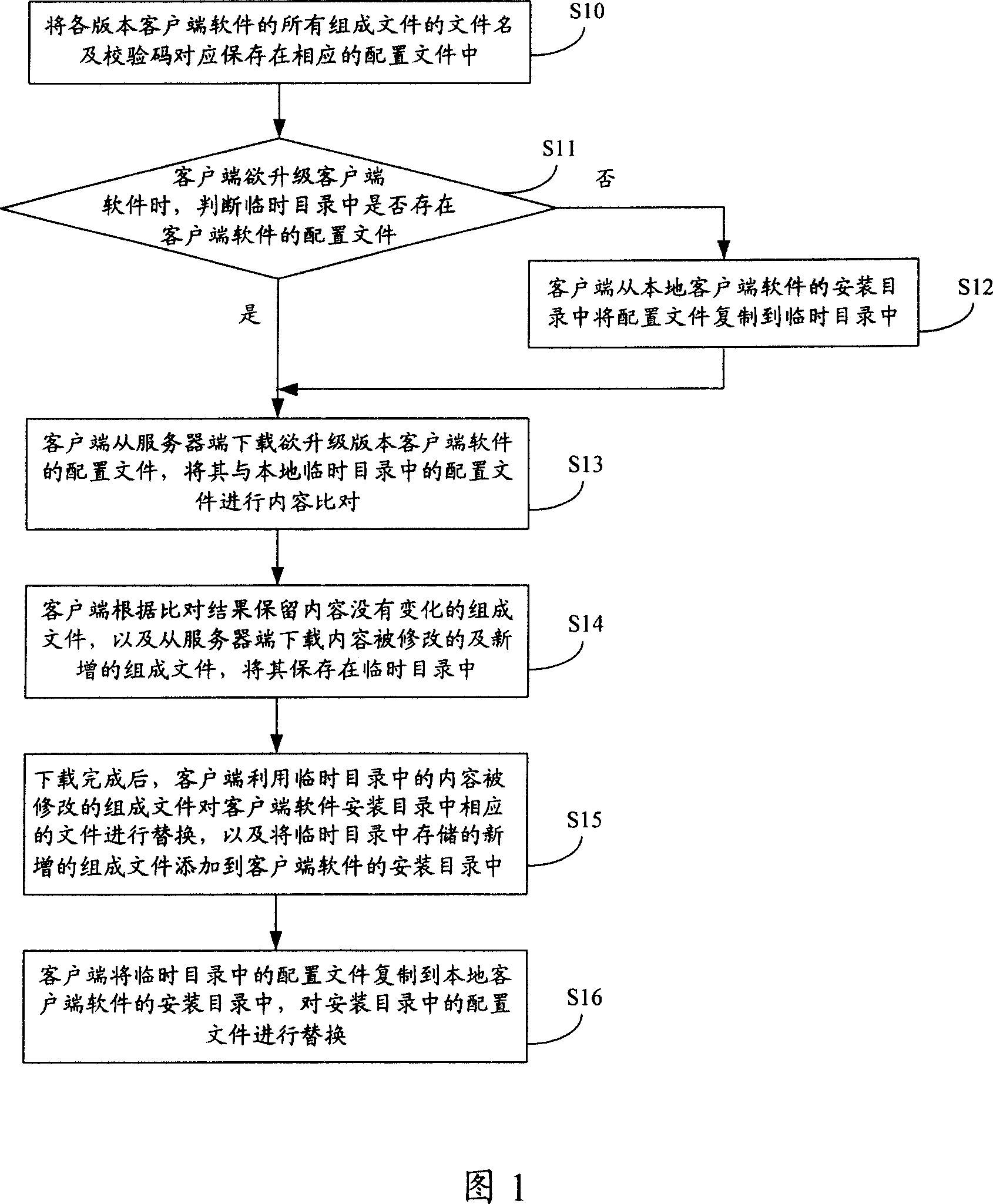
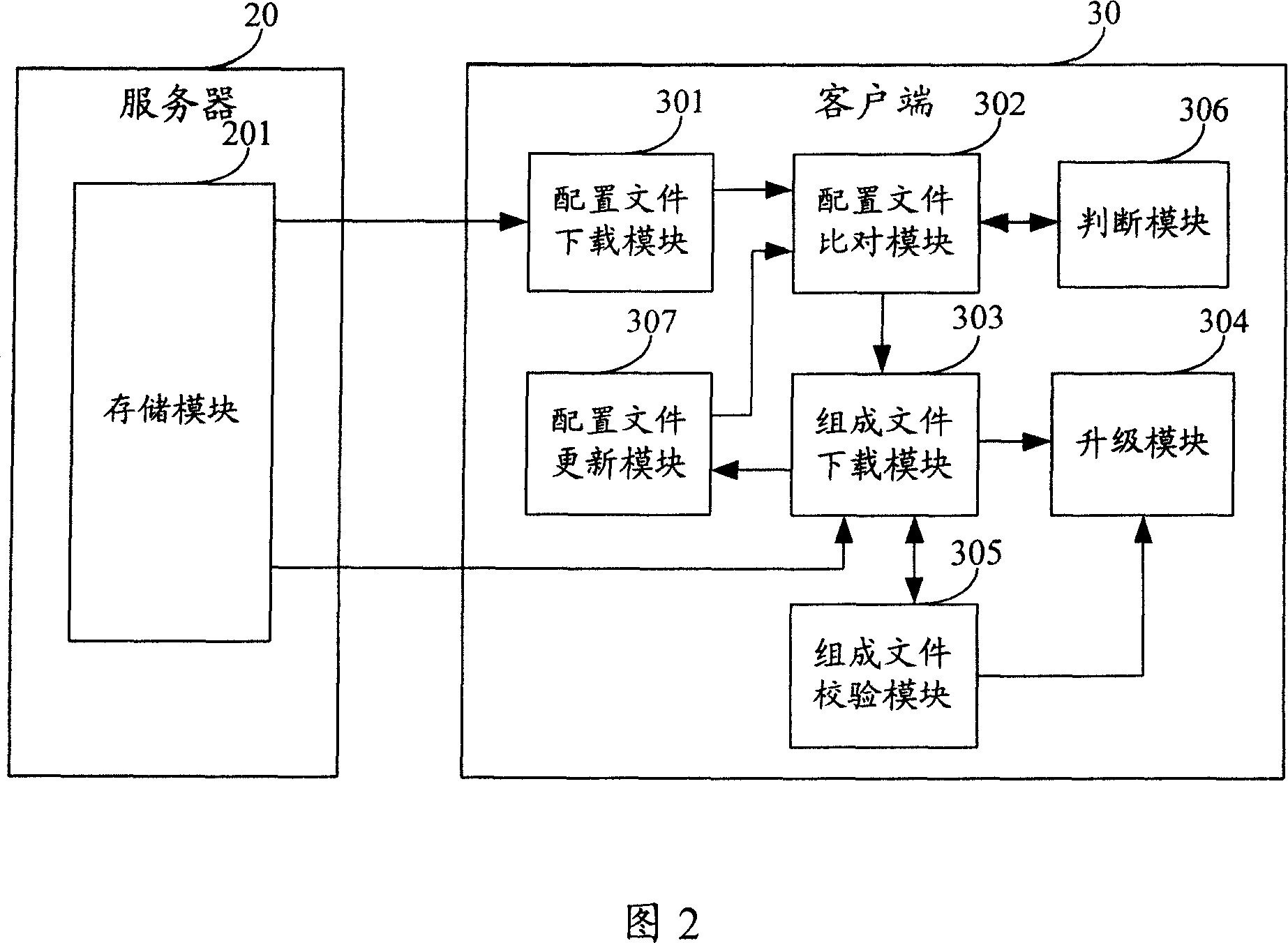
ActiveCN101110788AAvoid downloadingLower requirementProgram loading/initiatingData switching networksClient-sideFile comparison
The present invention discloses a method and a system for updating a client side software, which is used to solve the problem existing in the prior art that all bundle files contained in the new edition client side software need to be downloaded when the client side software is updated. The method comprises that the file names of the bundle files of the client side software of each edition and verification codes stored by a server side are correspondingly saved in the configuration files; when the client side software of local installation is updated by the client side, the configuration files of the specified edition client side software are downloaded from a server side, and are compared with the local corresponding configuration files in the content aspect, and according to the comparison results, the bundle files with unchanged contents and the bundle files revised and newly added in contents which are downloaded from a server side are retained locally. The system comprises a server and a client side, wherein the server comprises memory modules, and the client side comprises configuration file index modules, configuration file comparison modules, bundle file downloading modules and updating modules.
Owner:ALIBABA GRP HLDG LTD
Cache system in factory server for software dissemination
InactiveUS20050125524A1Minimizing size of cacheReduce the amount requiredCode conversionDigital computer detailsInformation processingFile comparison
A method and apparatus for minimizing the size of the cache that is required to store software packages for installation on an information handling system. An analysis is conducted on the individual program files contained in a software application file. In the analysis, the software application file is disassembled into the individual program files and each of the program files is decompressed and stored in temporary file directories. Files that are common to each of the software packages are identified. After the file comparison, the method and apparatus of the present invention is used to re-group the files to generate a composite program file library that contains all of the program files needed to regenerate the software application files. This composite program file library is then stored on a cache in a factory server used to manufacture information handling systems in a build to order process.
Owner:DELL PROD LP
System and method for comparing database data
InactiveUS7054891B2Data processing applicationsDigital data information retrievalImproved methodFile comparison
An improved method and system for comparing database data. Data comparison may be performed either within a database or between two databases. Sets of cyclical redundancy check values may be created, at various points in time. Corresponding cyclical redundancy check values may be compared with each other to determine if the underlying data is different; differences may be displayed. Each cyclical redundancy check value may correspond to a user-determined amount of data within the database. The user-determined amount of data may be: (1) user-specified columns within one of the plurality of tables within the database; (2) a row within one of the plurality of tables within the database; (3) a table within the database; (4) the database in its entirety; or (5) any other subset of the database. A user-determined number of bytes corresponding to a user-determined subset of the user-determined amount of data may be stored for future use.
Owner:BMC SOFTWARE
Method and system for implementing repeated data deletion
InactiveCN101882141AEnsure consistencyEfficient deletionSpecial data processing applicationsRedundant operation error correctionAlgorithm theoryData ingestion
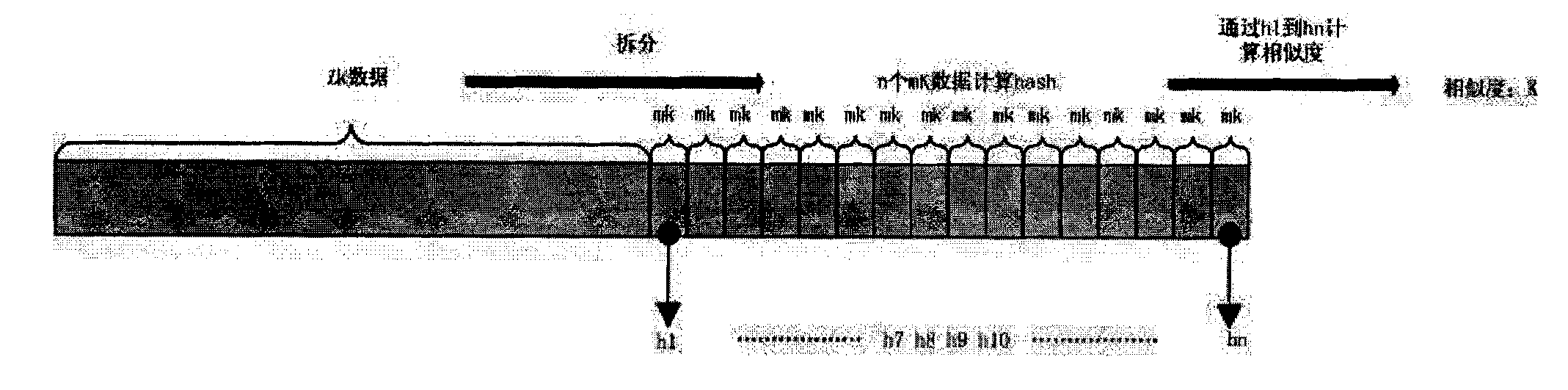
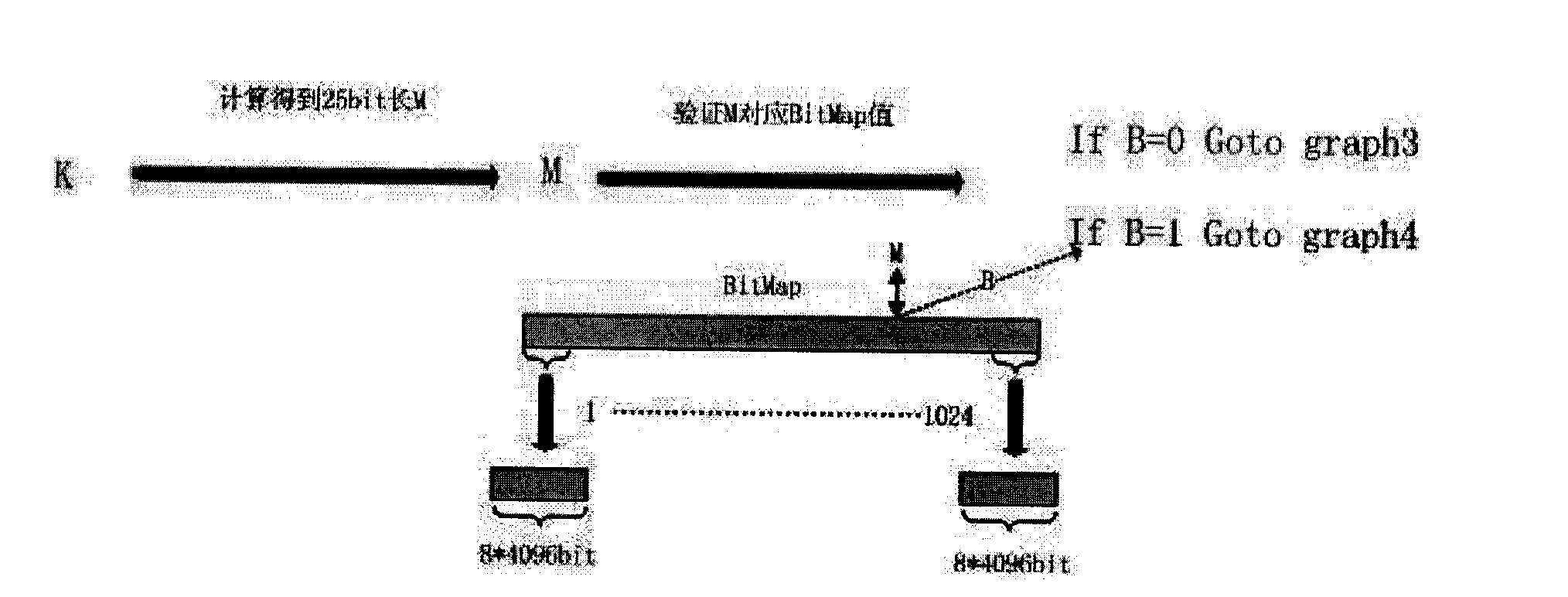
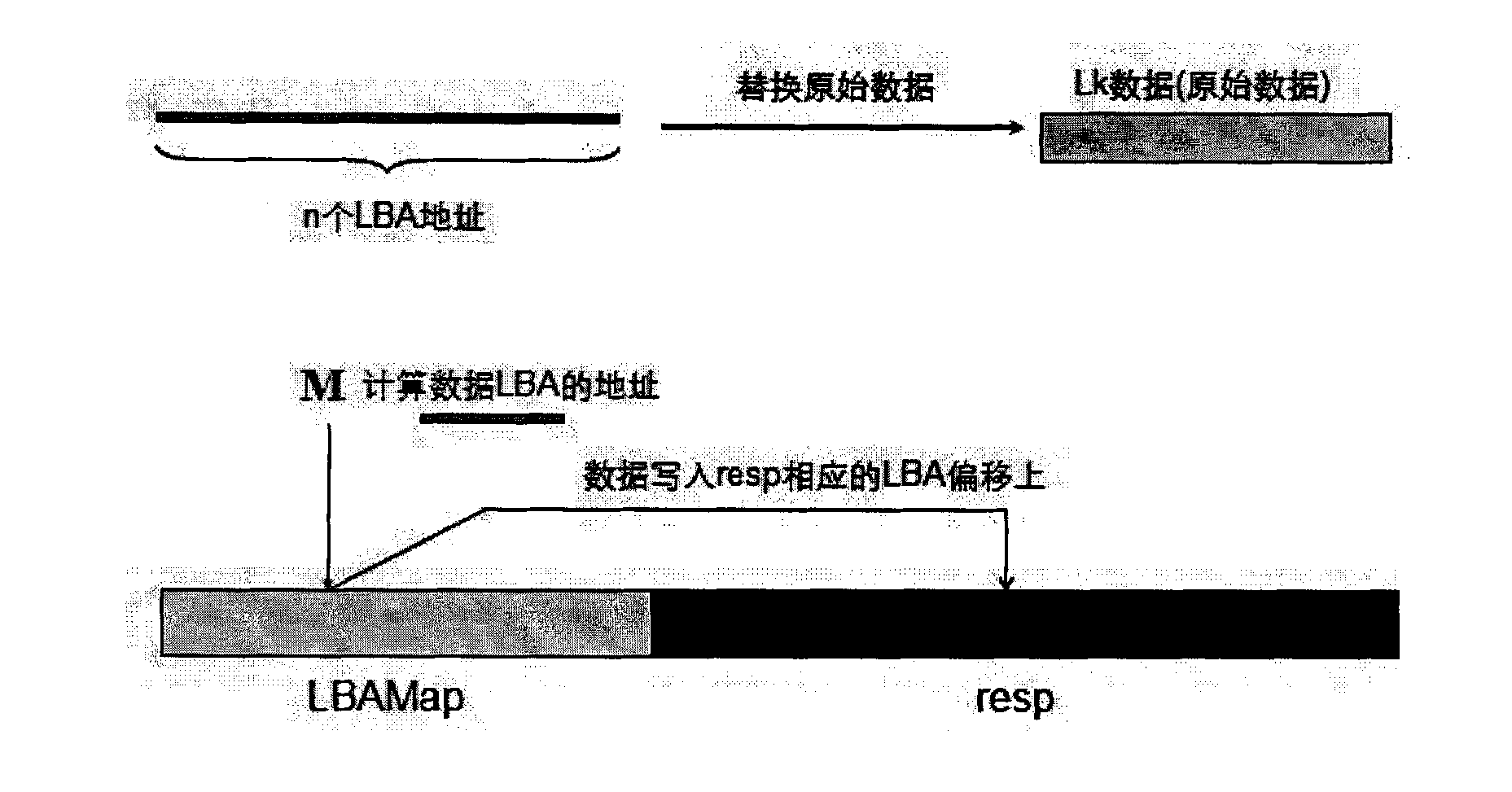
The invention provides a method for implementing repeated data deletion, which comprises the following steps of: calculating similarity of data by a simhash (similarity hash) algorithm; reckoning the similarity into an index library through a similarity positioning storage position; writing the data into a data warehouse; if the data with the same similarity enters the data warehouse, extracting the corresponding data in the data warehouse, and then performing binary comparison; and if the data are the same, recording indexes, otherwise, recording different data parts. The invention also provides a system for implementing the repeated data deletion, which comprises a similarity marking library (BitMap), a data offset marking library, the data warehouse (LBAMap) and a storage library (Resp) for recording initial data. The method and the system ensure data consistency by data comparison based on the simhash algorithm theory, efficiently finish the repeated data deletion, and ensure the consistency of the data.
Owner:无锡北方数据计算股份有限公司
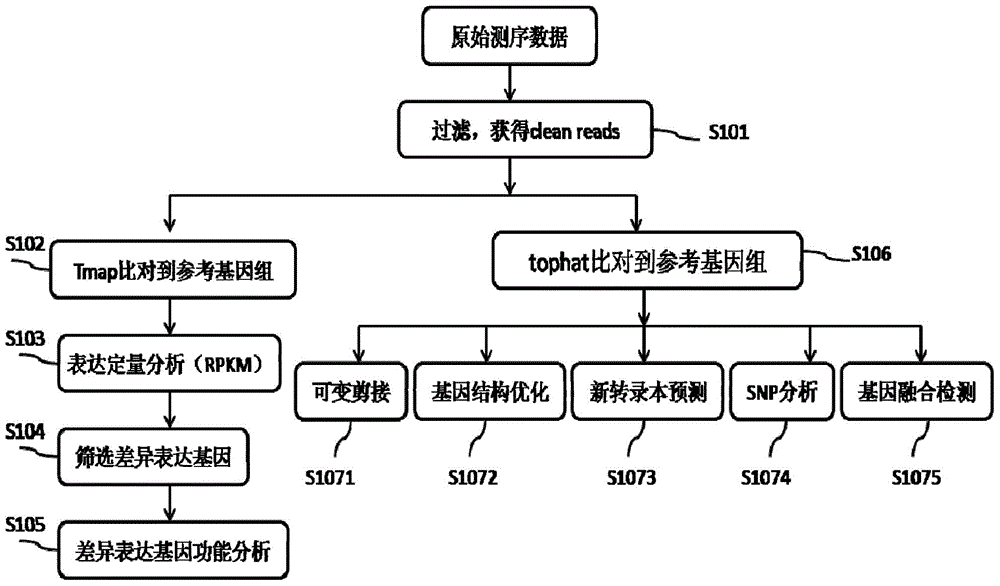
Proton-based transcriptome sequencing data comparison and analysis method and system
InactiveCN104657628AImprove accuracyImprove reliabilitySpecial data processing applicationsDifferentially expressed genesSingle-nucleotide polymorphism
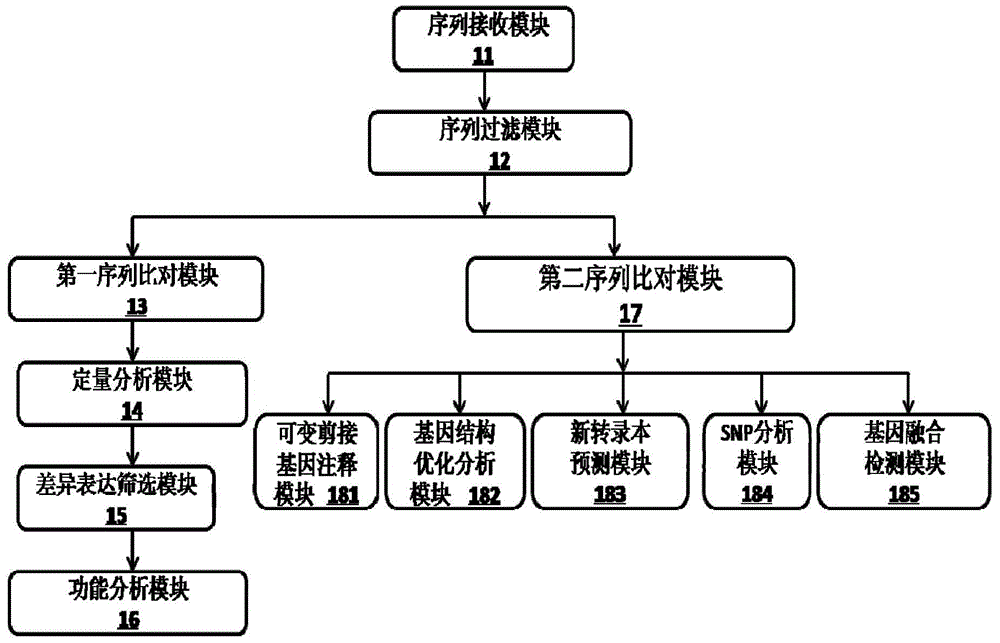
The invention provides a Proton-based transcriptome sequencing data comparison and analysis method and system. The method comprises the following steps: acquiring original sequencing data of at least two transcriptomes of a certain species by virtue of a Proton sequencing platform; filtering unqualified data to obtain clean reads; performing first-step analysis and second-step analysis, wherein the first-step analysis comprises the steps of comparing the clean reads with a reference genome of the species respectively, performing transcript quantitative analysis, screening significantly differently expressed genes and performing significantly differently expressed gene function analysis; the second-step analysis comprises the steps of comparing the clean reads to the reference genome of the species respectively, performing alternative splicing analysis, performing gene structure optimization analysis, performing new transcript prediction, performing SNP (Single Nucleotide Polymorphism) analysis and performing gene fusion detection. According to the method and the system, the transcriptome sequencing data comparison and analysis accuracy and reliability can be improved.
Owner:BGI TECH SOLUTIONS
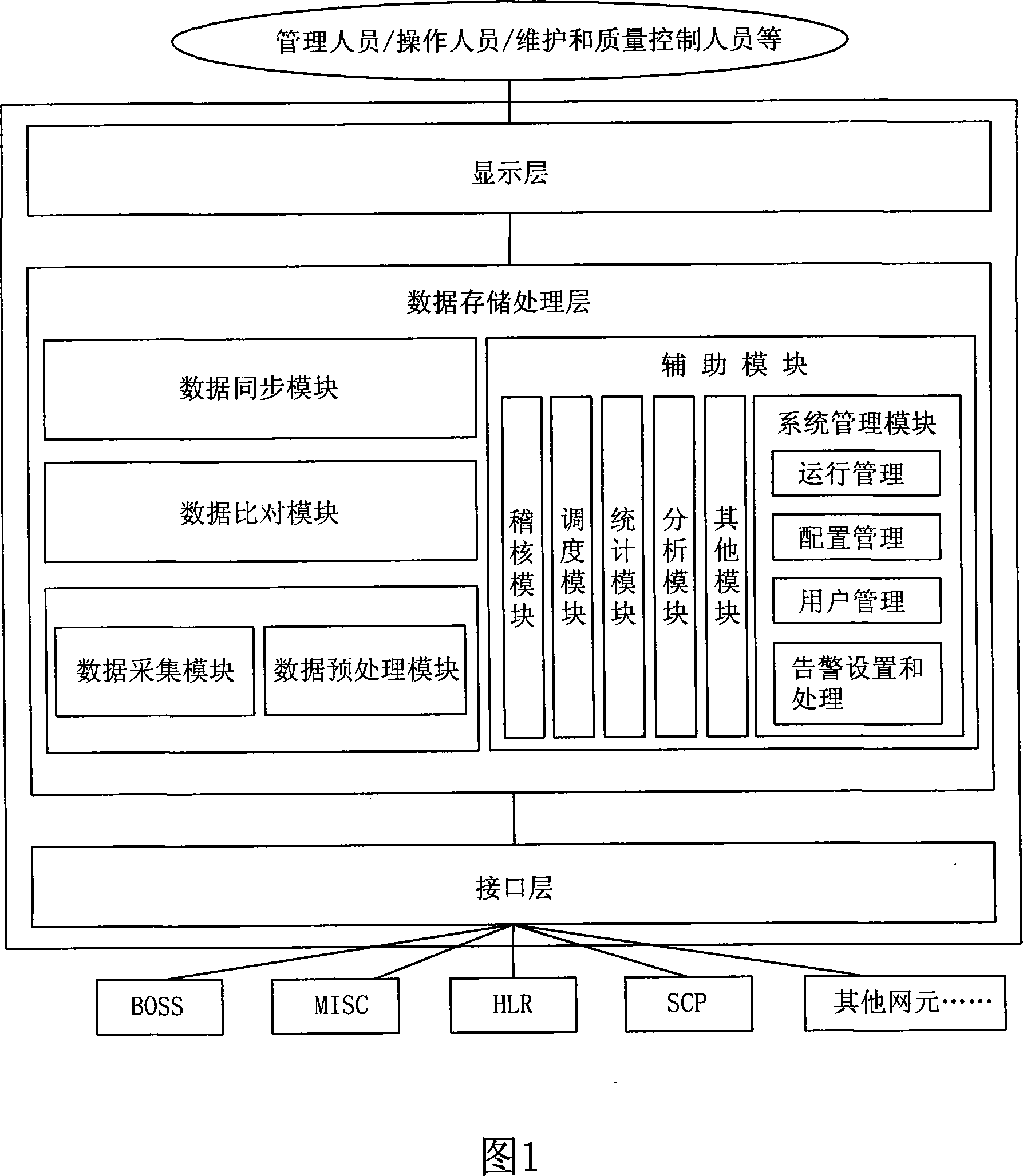
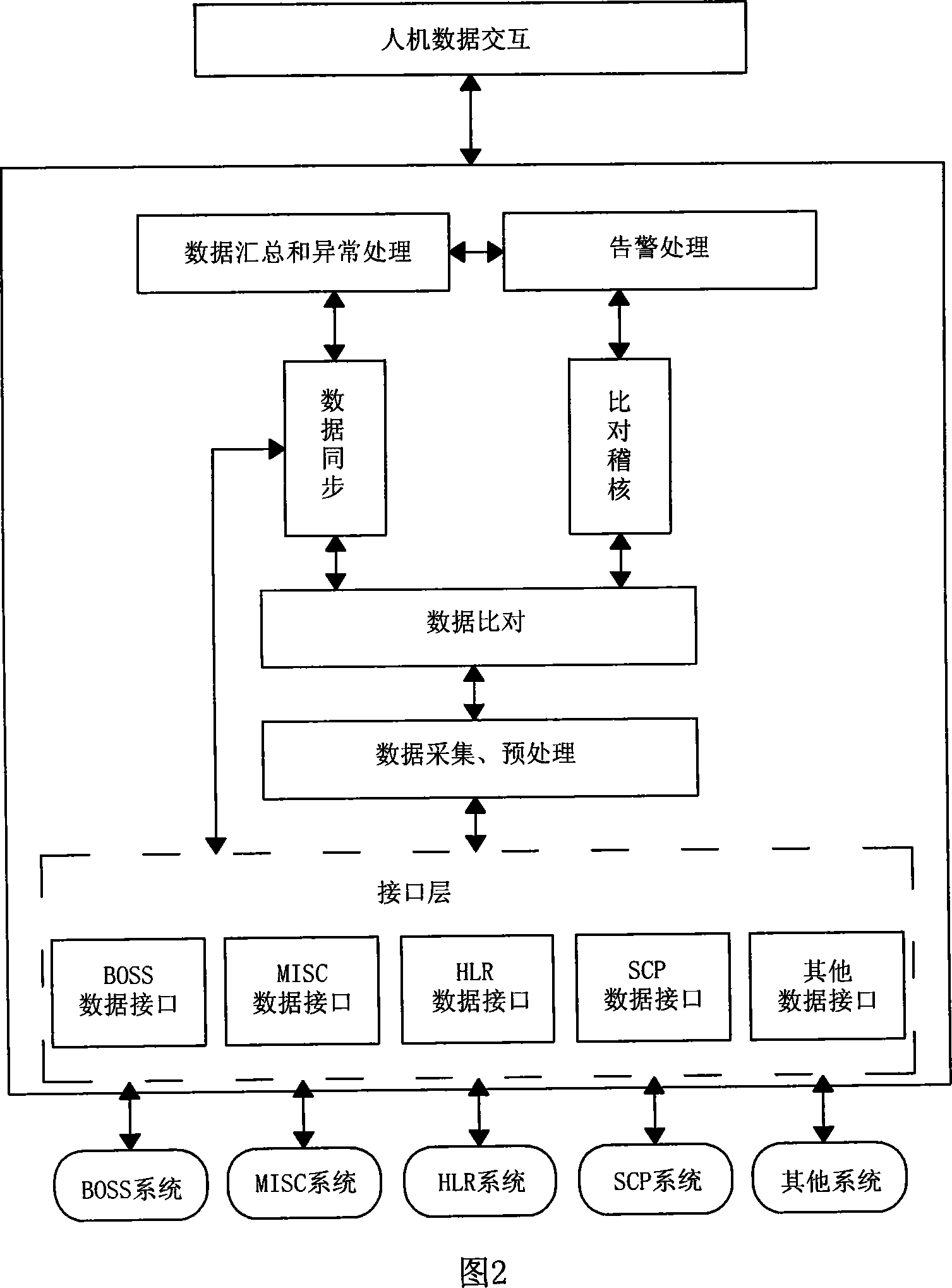
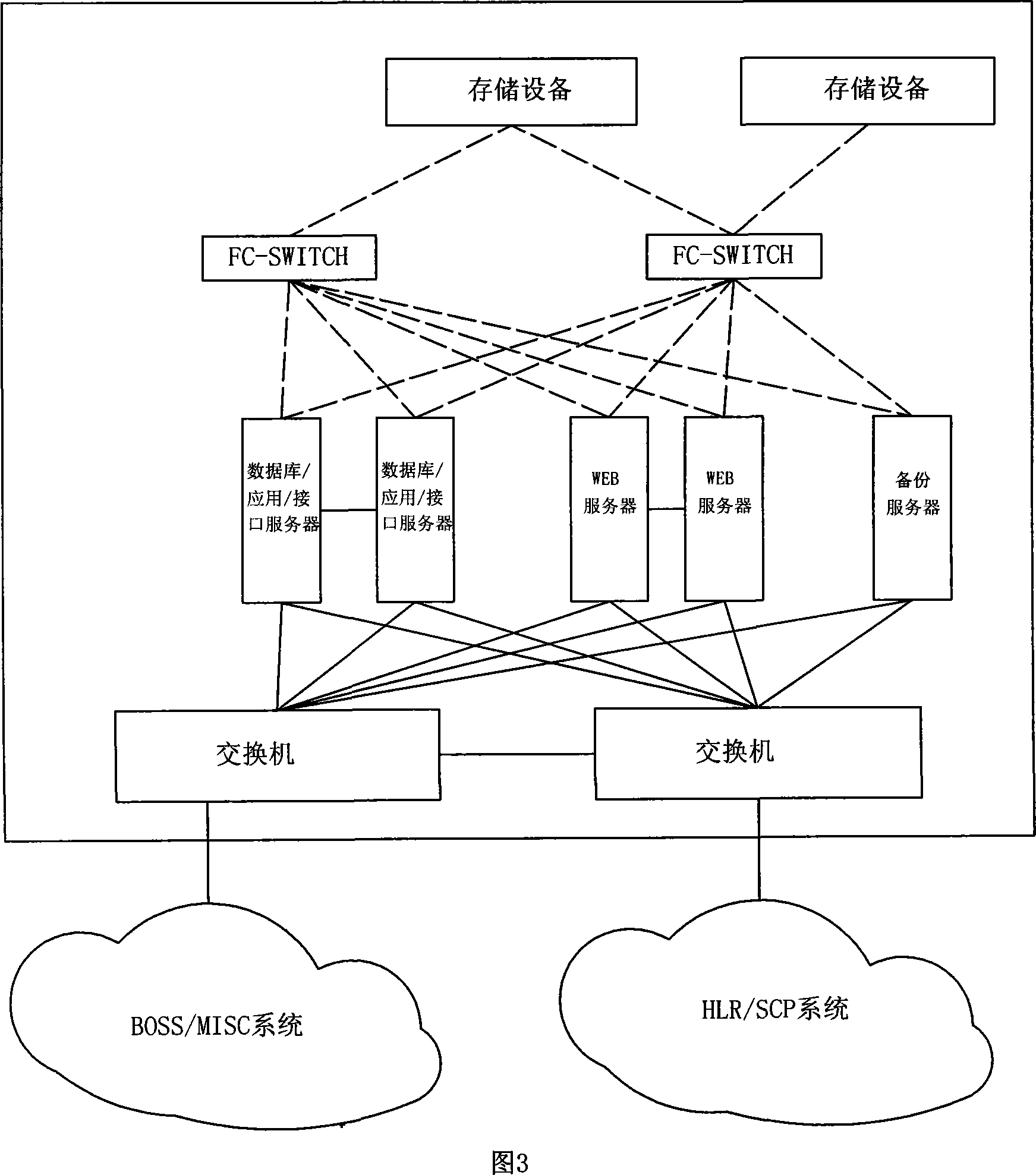
System and method for synchronizing comparison of data consistency
ActiveCN101094051AAvoid complaintsImprove effectivenessSynchronisation signal speed/phase controlData switching networksData synchronizationDifference list
It includes display layer, data storage / procession layer (SP) and system interface layer (SI). SP includes data collect module (DL), data pre-processing module (DP), data comparison module (DM), data sync, module (DS) and assistant module. Via SI, the business backup and bearing nets (BBB) realize mutual comm. between net elements (NE). From BBB, DL collects NE data requiring keeping coincident. DP / DM pre-processes and compares these data. Non-coincident data are recorded in the error list. According to availability test rule, DS verifies availability of data difference, generates corresponding synchronization data against valid data difference base on sync. rule and sends to related NE to keep coincidence of data between NEs. This invention raises data comparison synchronization level, system running efficiency and resource utilization. It ensures accuracy and coincidence of system data. It extensively is applied in multi-NE cooperation fields, such as comm., insurance and banking.
Owner:CHINA MOBILE GROUP SICHUAN
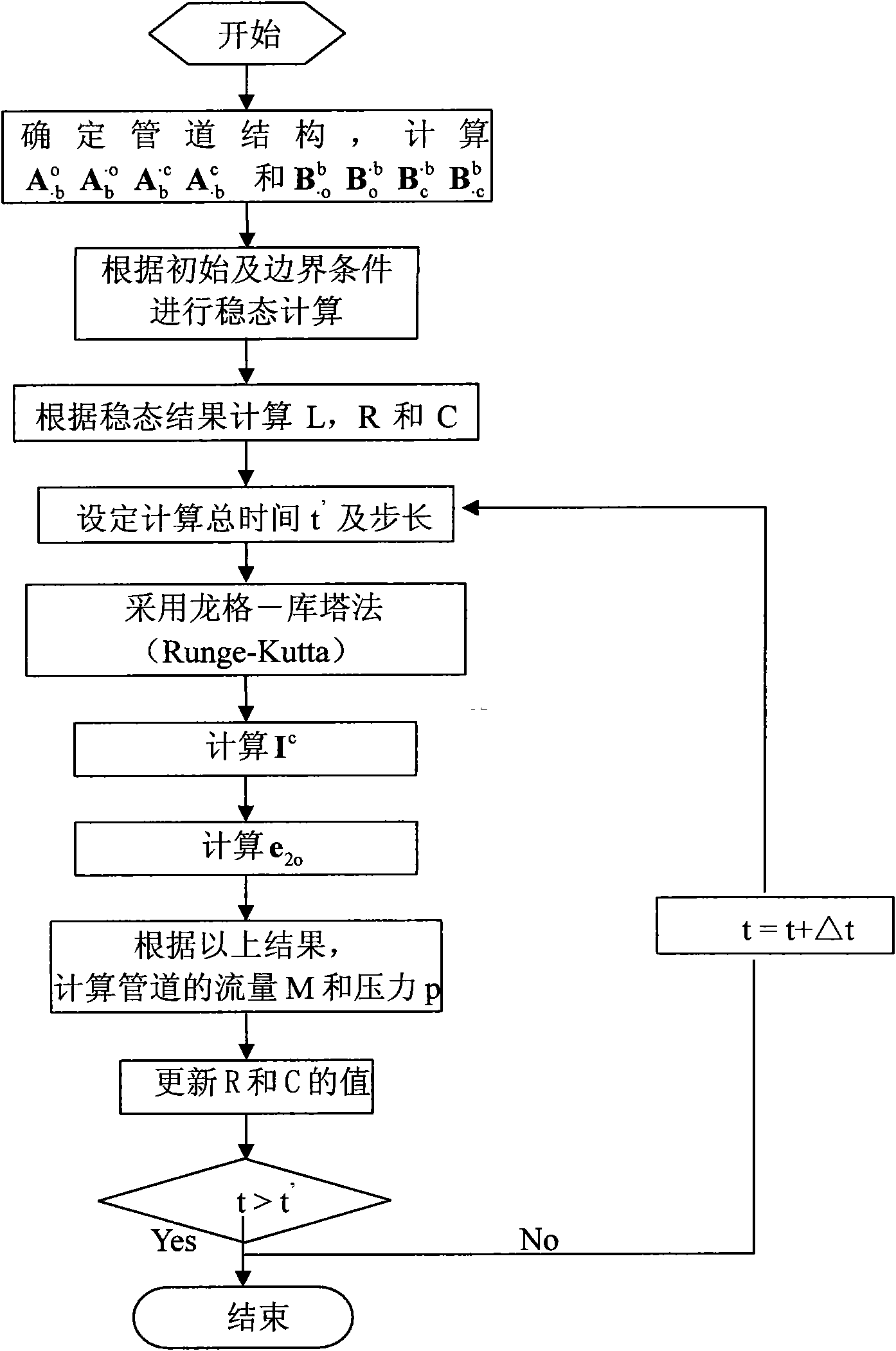
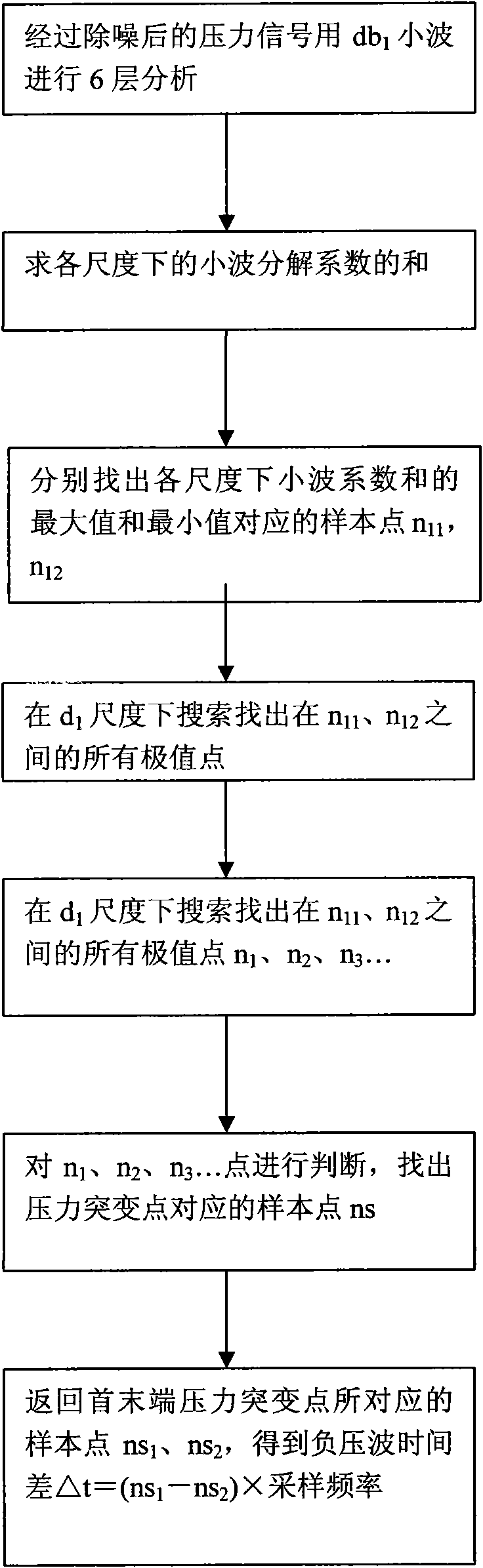
Method for measuring and locating leakage of gas pipelines
ActiveCN101625071ARealize the monitoring functionRealize the positioning functionPipeline systemsData acquisitionEngineering
The invention discloses a method for measuring and locating leakage of a gas pipeline network based on a geographic information system (GIS) and supervisory control and data acquisition technology (SCADA). The specific method comprises the following steps of establishing a gas pipeline network GIS system; reading and storing a pipe network graph, pipeline network attribute data and the like; collecting parameters of pressure, temperature and flow for each section of gas pipeline in real time by the SCADA system; comparing the collected parameters and the stored data and calculating; calculating the measuring values of the head end and the tail end of the pipeline and calculating the difference among parameter values; representing the abnormal pipeline information; searching extreme points and determining the pressure catastrophe points; calculating the position of the leakage point according to the parameters of gas consumption, temperature and pressure by using a leakage locating formula. By adopting SCADA, GIS and simulation calculations, the invention can realize self monitoring and locating of the gas pipelines with the advantages of quick measuring speed, high measuring precision, low missing report rate and false report rate and the like.
Owner:TIANJIN UNIV
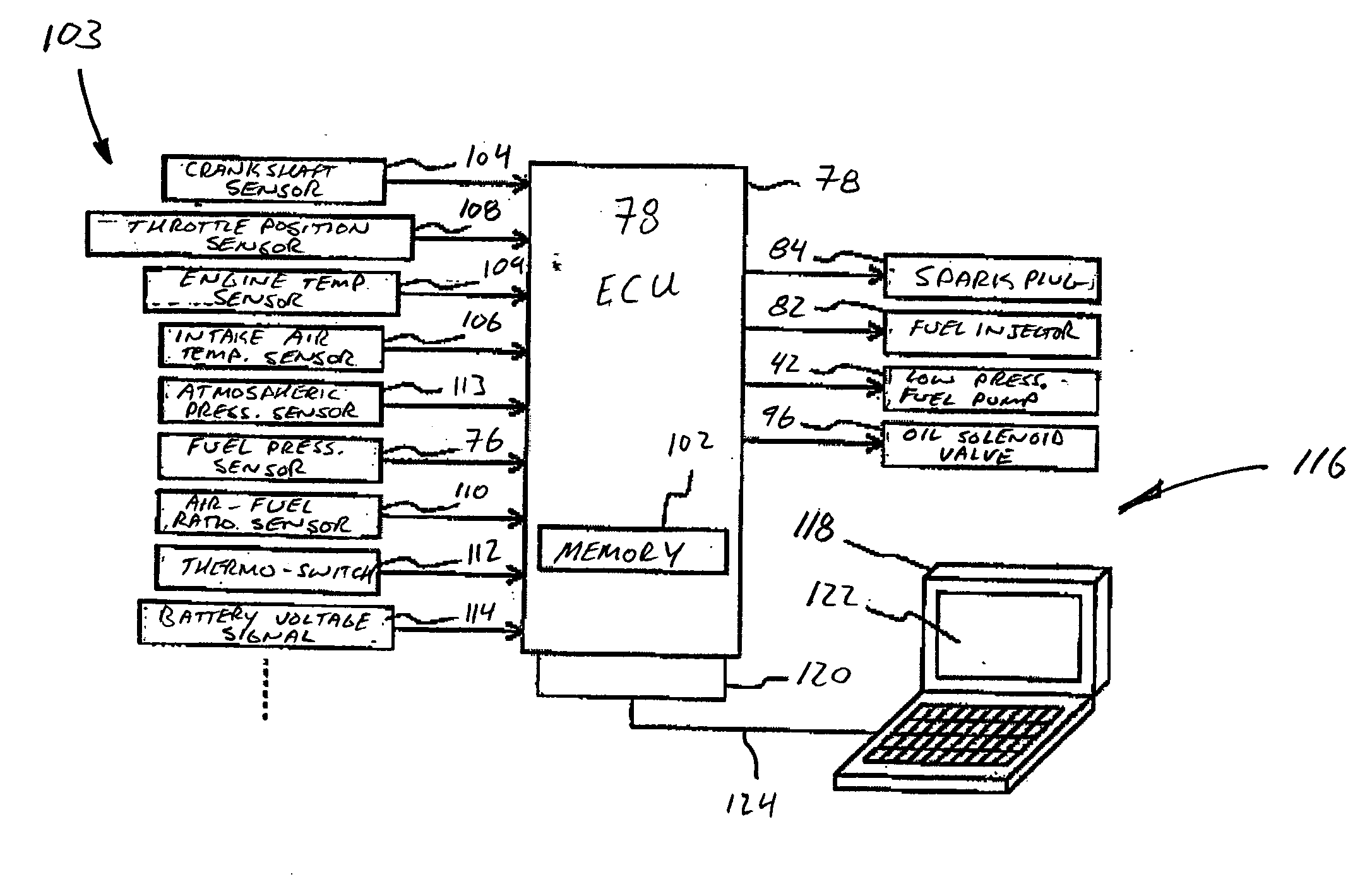
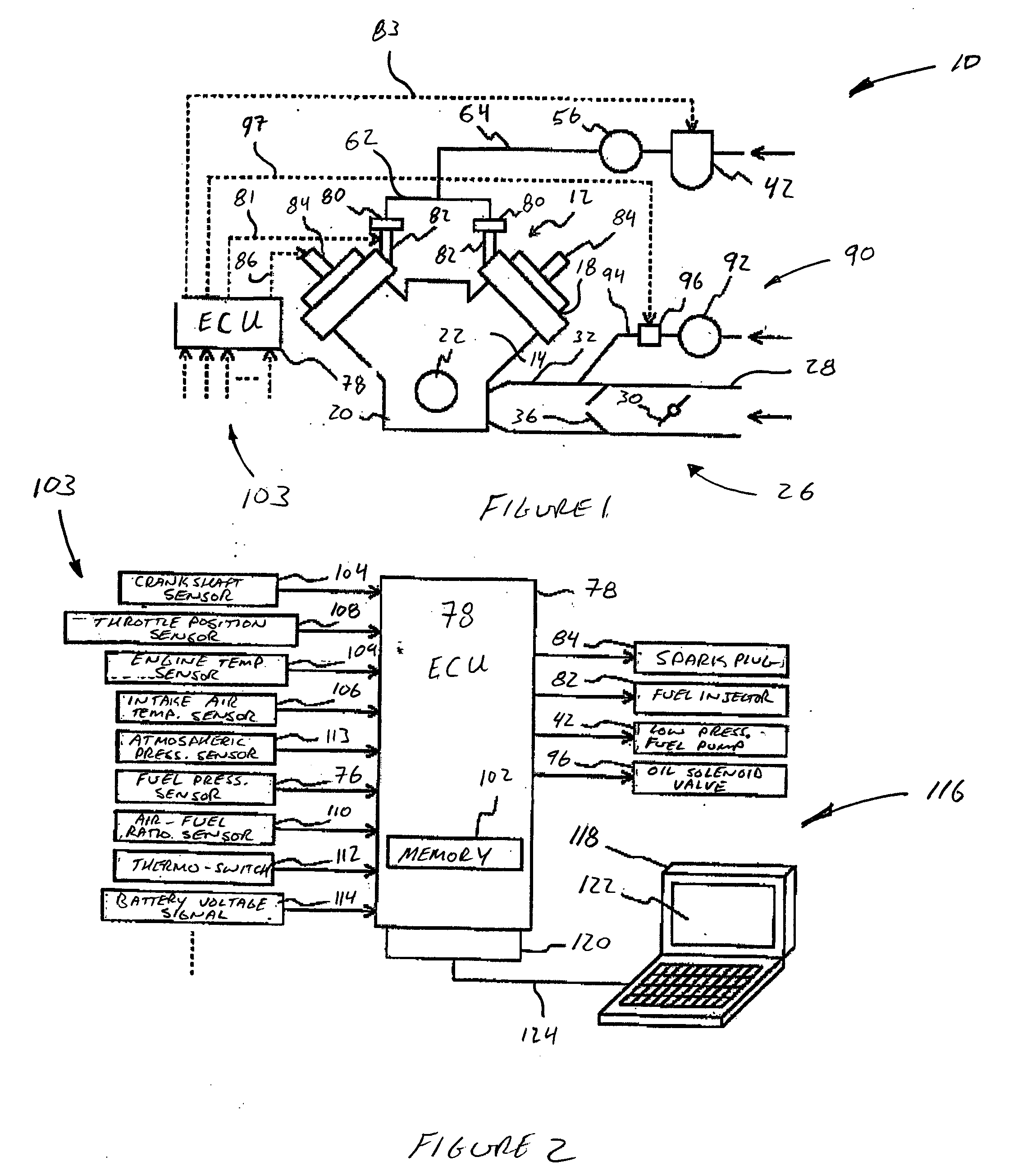
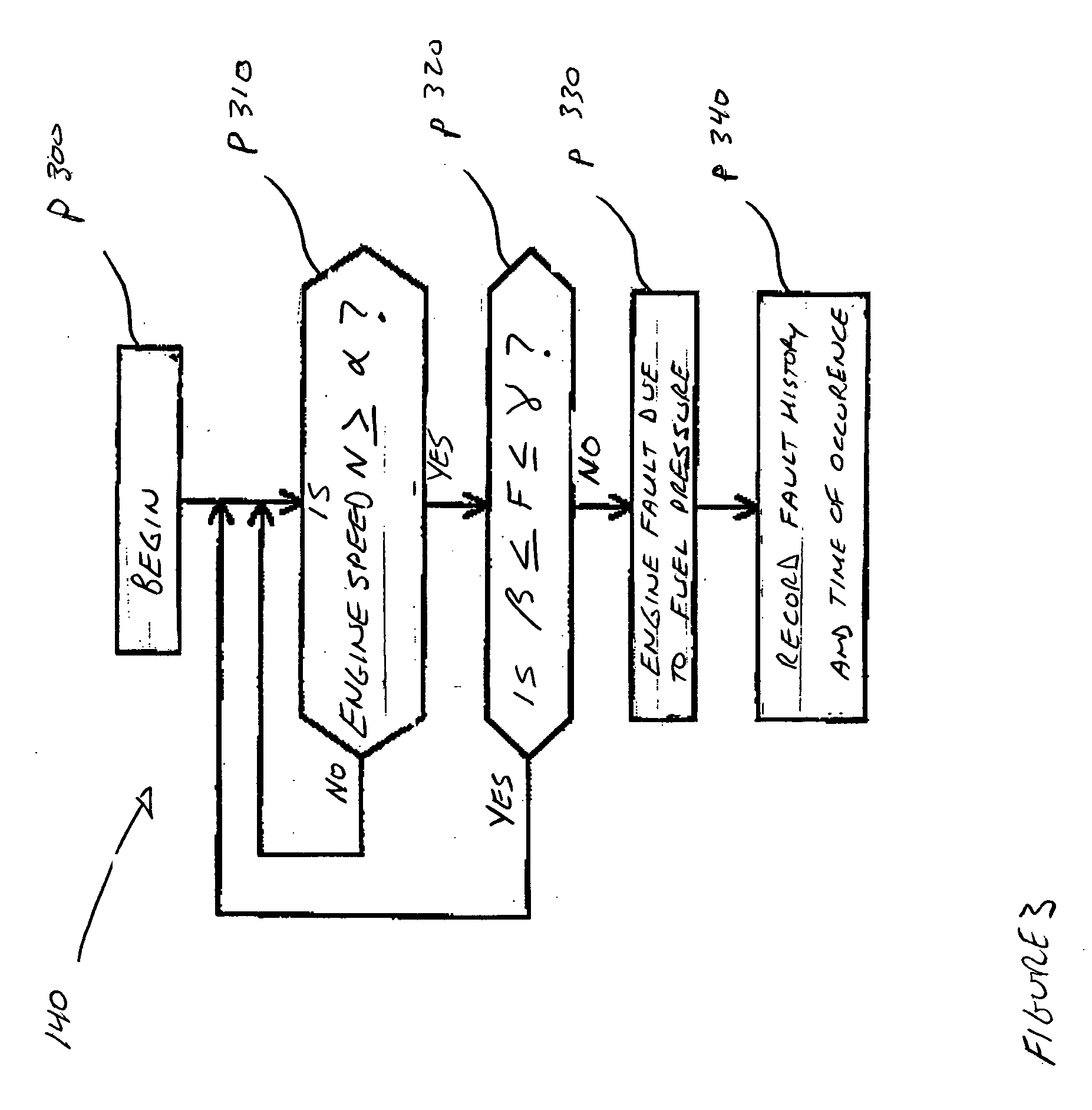
Malfunction diagnosis system for engine
InactiveUS20040002810A1Analogue computers for vehiclesInternal-combustion engine testingData setEngineering
A malfunction diagnosis system is provided to aid a technician or engineer in diagnosing an internal combustion engine. The diagnostic system comprises an electronic control unit that is operatively coupled to a data storage device and to one or more engine sensors. The electronic control unit is configured to collect data from the one or more engine sensors, compare the collected data with predetermined engine parameter values, and store the collected and compared data in the data storage device in various formats. A computer is selectively coupled to the data storage device. The computer program is configured to display specific sets of data and to clearly display any faulty engine parameter values resulting from the collected data comparison.
Owner:YAMAHA MARINE KK
Two-stage single-instance data de-duplication backup method
InactiveCN103324552AReduce consumptionEliminate redundant partsRedundant operation error correctionSpecial data processing applicationsEngineeringFile comparison
The invention discloses a two-stage single-instance data de-duplication backup method. De-duplication of data at two stages is performed during backup. The method comprises firstly, performing repeated data detection on a file scale, inquiring local logs to judge whether identical files are stored or not, and if the identical files are stored, informing users to complete the backup operation; if identical files are not stored locally, informing backup programs of server ends to inquire databases to judge whether files with identical content exist or not, if the files with identical content are searched, establishing links pointing to the files for clients only, and recording quotes of the files by clients by the server ends; if the files are new, uploading the files and recording information of the files by two ends; further processing the files after the files are uploaded to the server ends by background programs, and splicing small files together to avoid waste of space; storing large files respectively by type, comparing similar files regularly, and performing difference de-duplication at the second stage after grouping.
Owner:XI AN JIAOTONG UNIV
Enhanced data comparison tool
ActiveUS8819042B2Database management systemsDigital data processing detailsGraphicsGraphical user interface
Systems and methods are illustrated for transitioning data from one data store to another data store. The transition may occur according to comparison information received through a graphical user interface. For example, the comparison information may map data or columns in a source data store to data or columns in a target data store. A score may also be generated based on a comparison of the source and target. A report may indicate a successful or failed data transition based on the score.
Owner:BANK OF AMERICA CORP
Web controls validation
InactiveUS7451352B1Receipt is inhibitedNon-redundant fault processingError processingFile comparison
Owner:MICROSOFT TECH LICENSING LLC
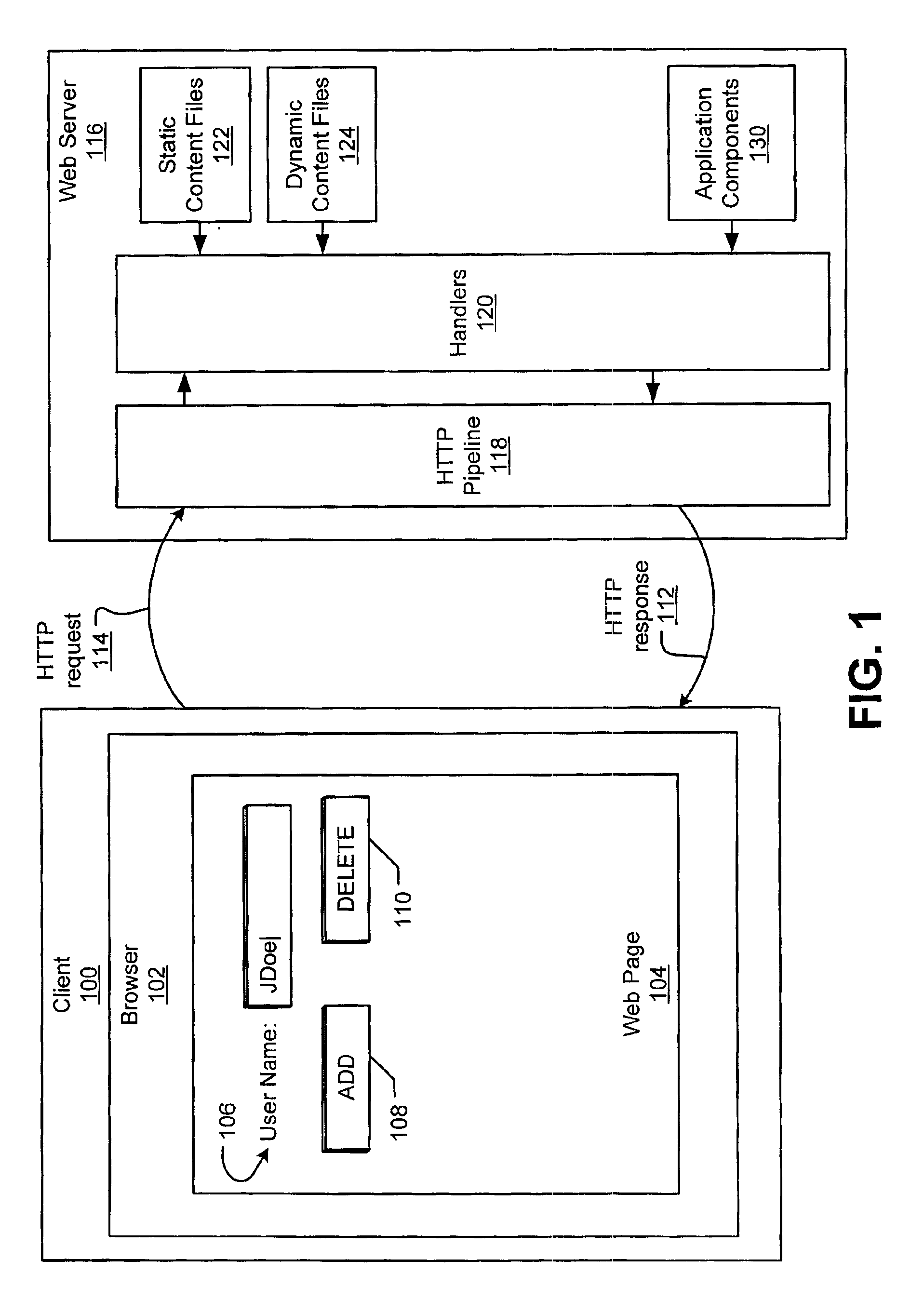
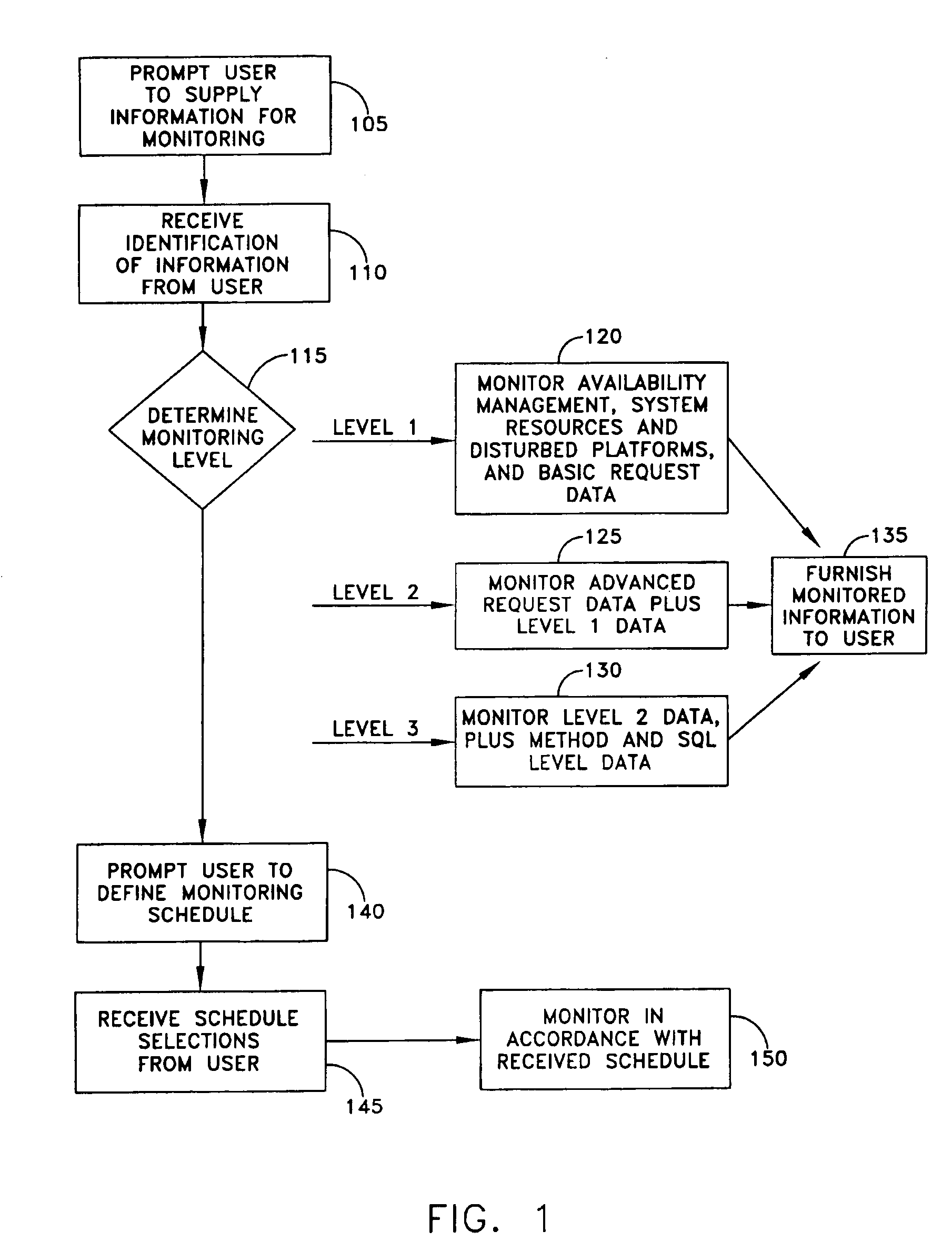
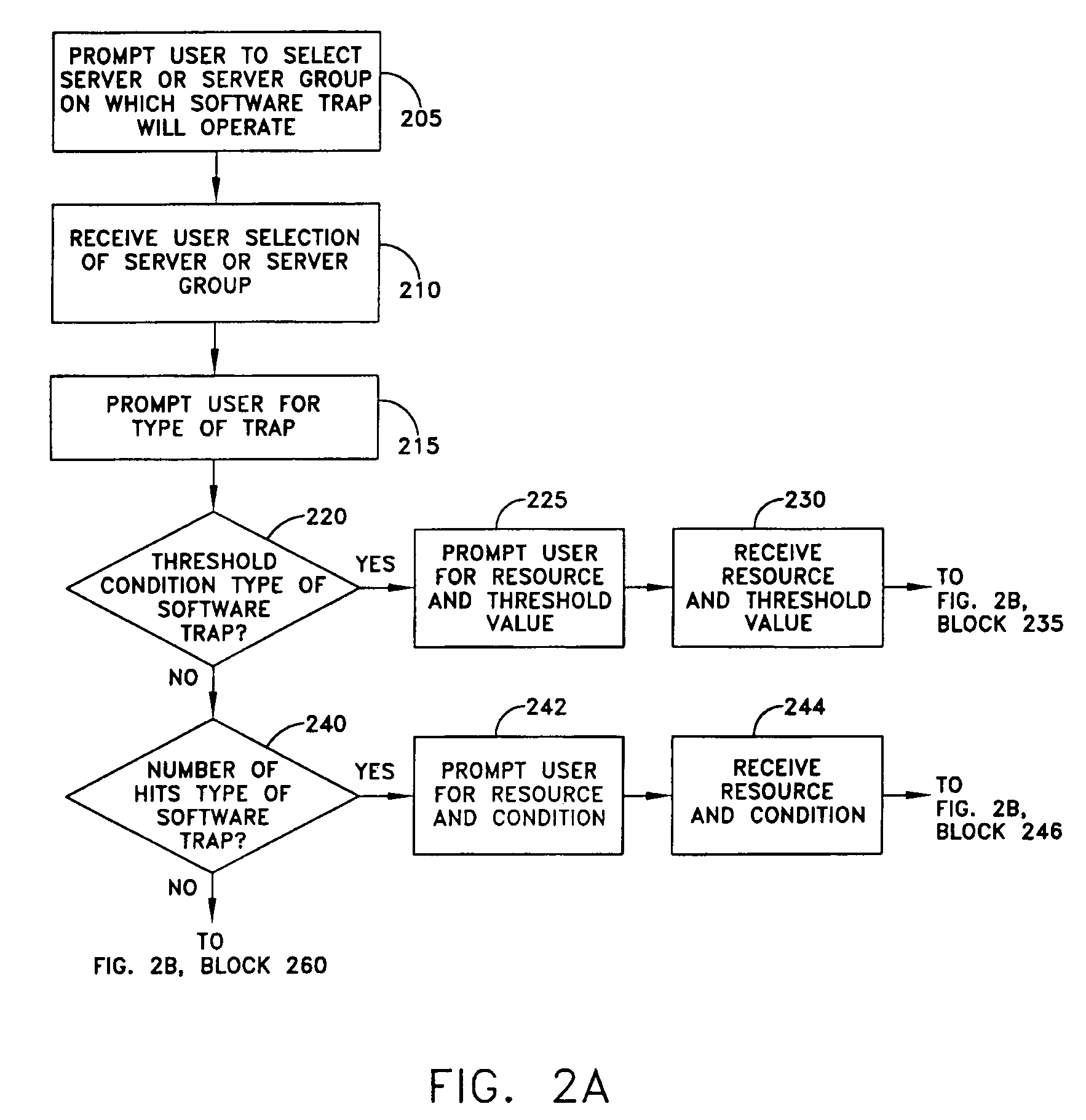
Monitoring performance of applications in a distributed environment
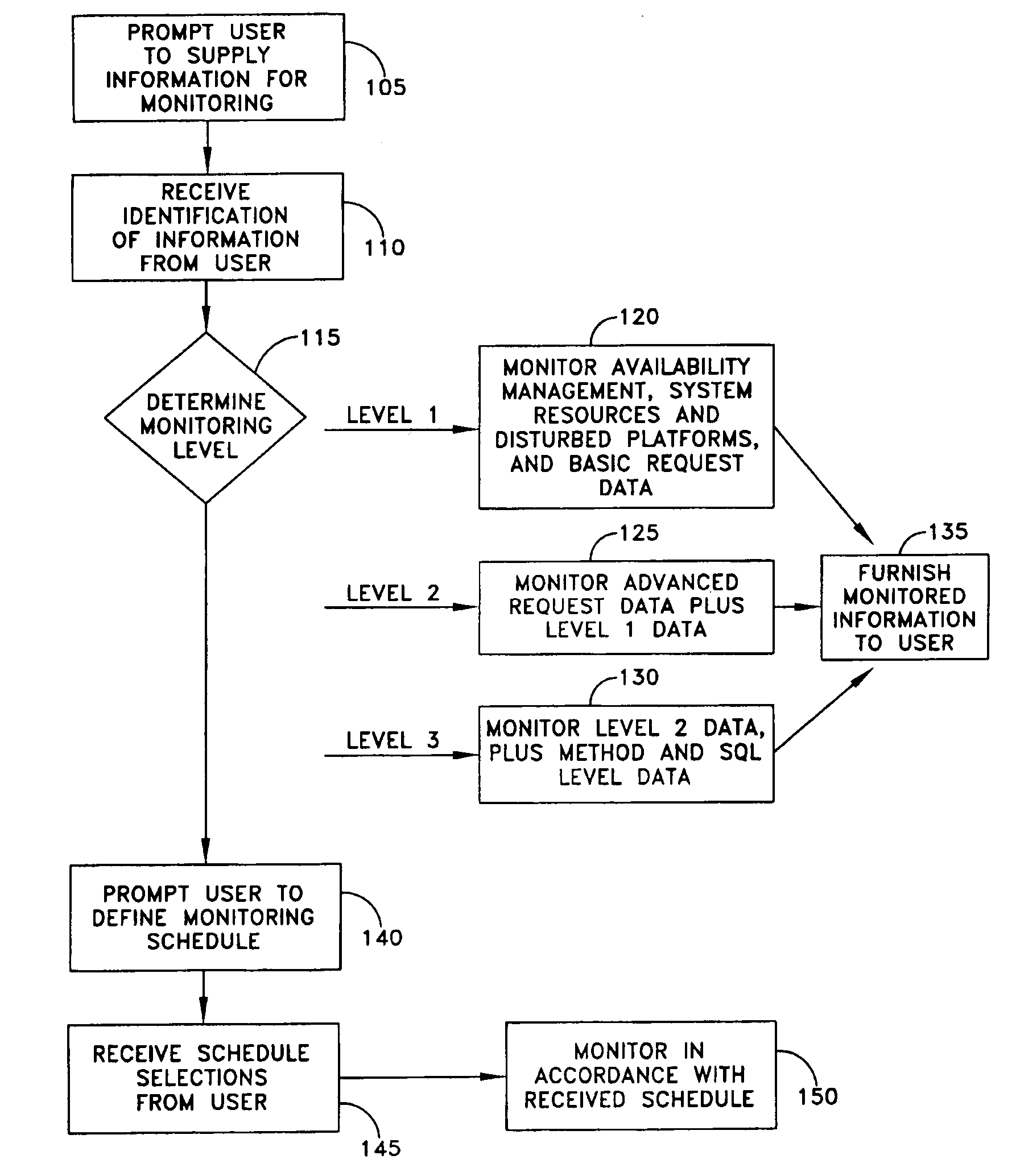
A method for management of performance of computer systems and applications includes prompting the user to select information for monitoring, monitoring the performance of applications running on servers, displaying data, and prompting users to input performance adjustments. A user is prompted to select a server or server group, a resource, and a threshold or condition for notification, and in response a system compares the value or quality of the parameter to the threshold or condition, and provides a notification to the user in the event that the parameter reaches the threshold or condition. A method includes the steps of providing the user with performance information, receiving from the user a request for more specific performance information, and providing more detailed performance information. A method according to the invention includes the steps of receiving from the user an identification of a server as an authoritative server, another server as a comparison server, comparing runtime environment data in the form of one or more of CPU data, server data and Java data between the selected servers, and displaying differences to a user. A method of the invention includes the steps of receiving from the user an identification of a server as an authoritative server, and another server as a comparison server, and providing a list of matching and differing file names. The method may further include the step of receiving from the user a selection of a file, conducting a comparison of the files, and providing a result to the user. A method of the invention includes the steps of assigning a role to each user, and mapping between access to functions and each user role by an access control list, whereby access to functions is limited depending on the assigned role of the user.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com