Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
17714 results about "Information handling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information handling is a skill which is essential in this information rich age. This skill or set of skills must be taught in an integrated way, not in isolation, seen as a part of all learning not just taught in one lesson.
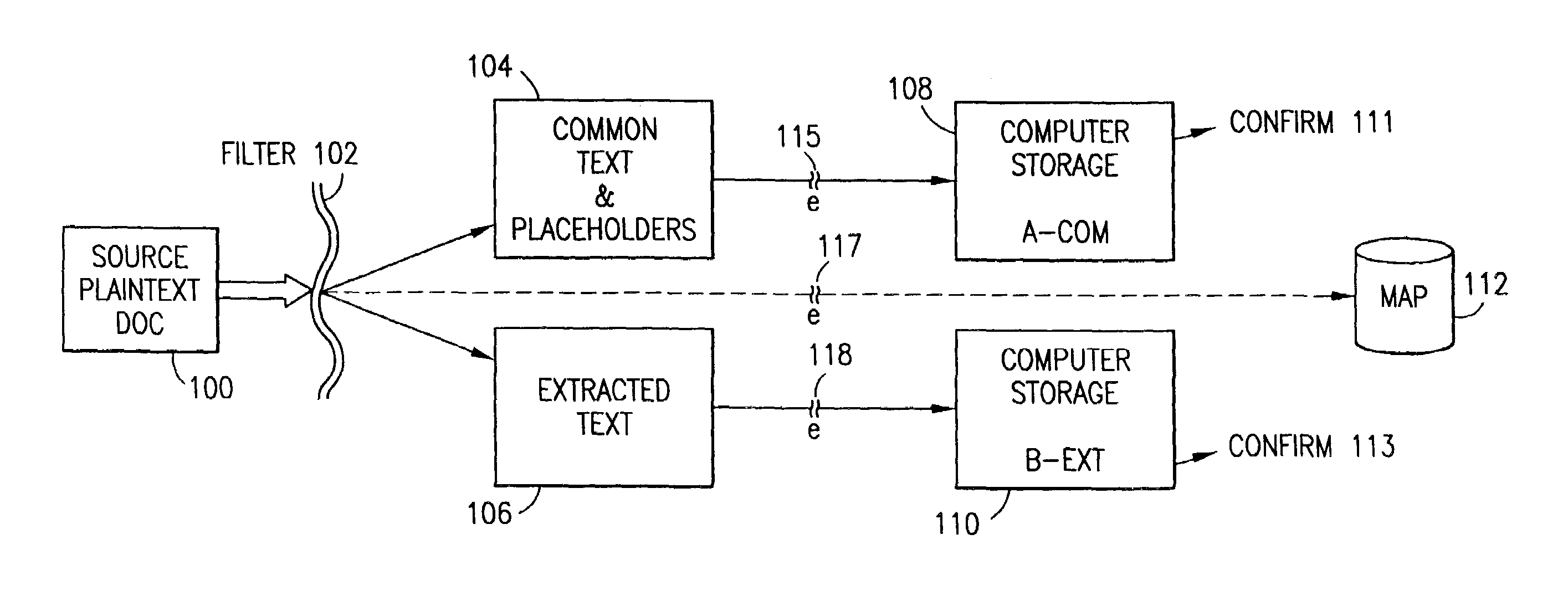
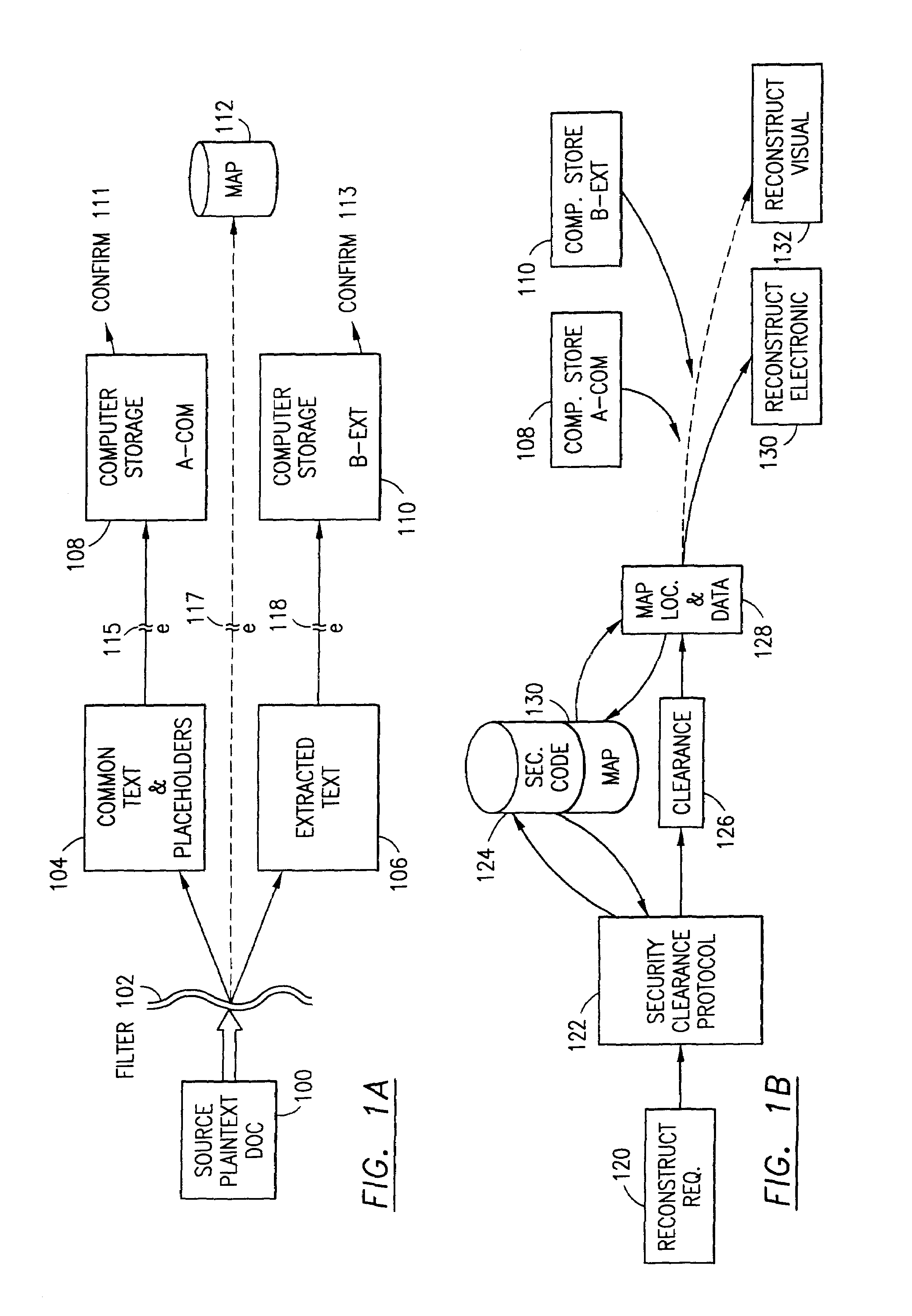
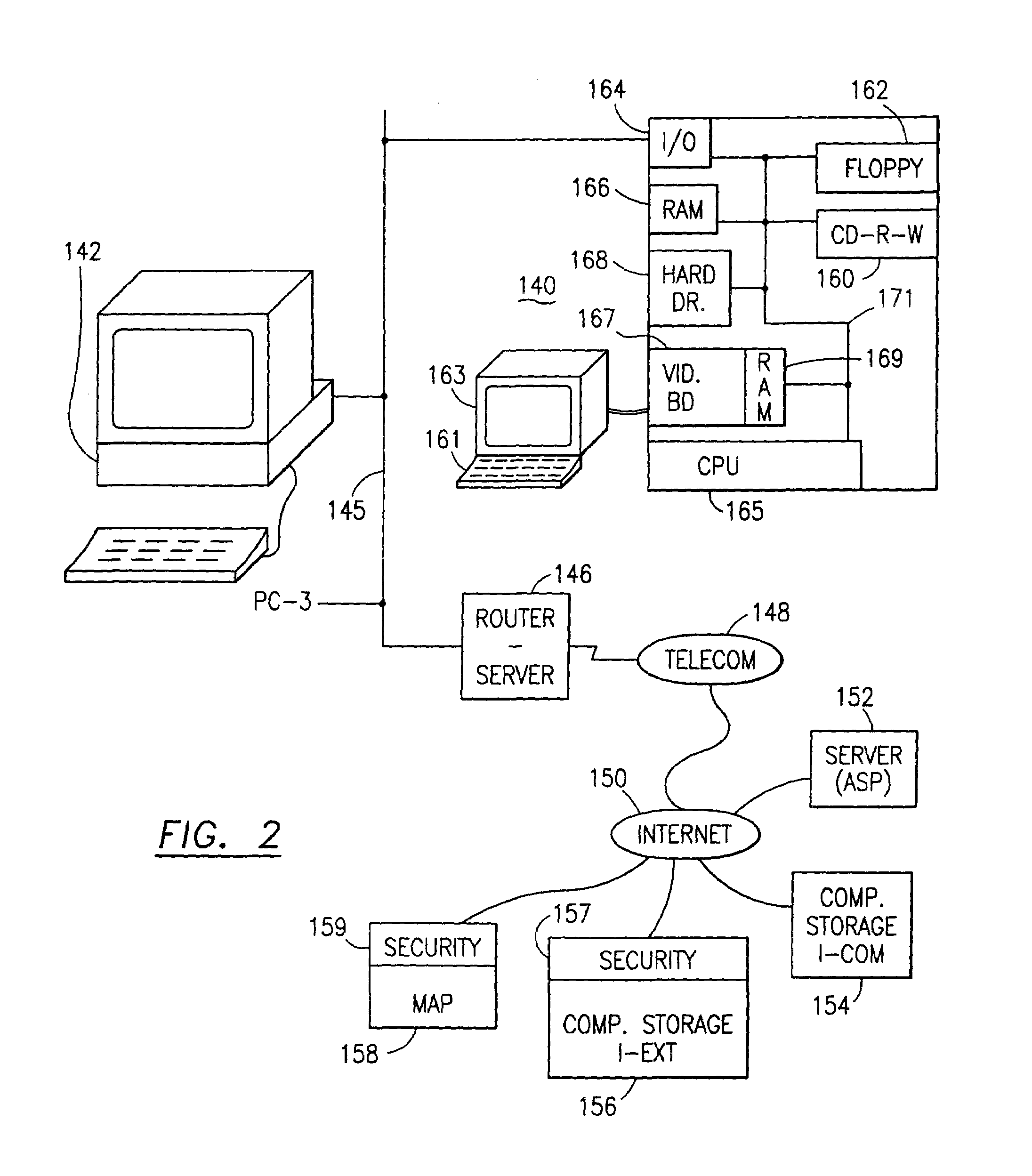
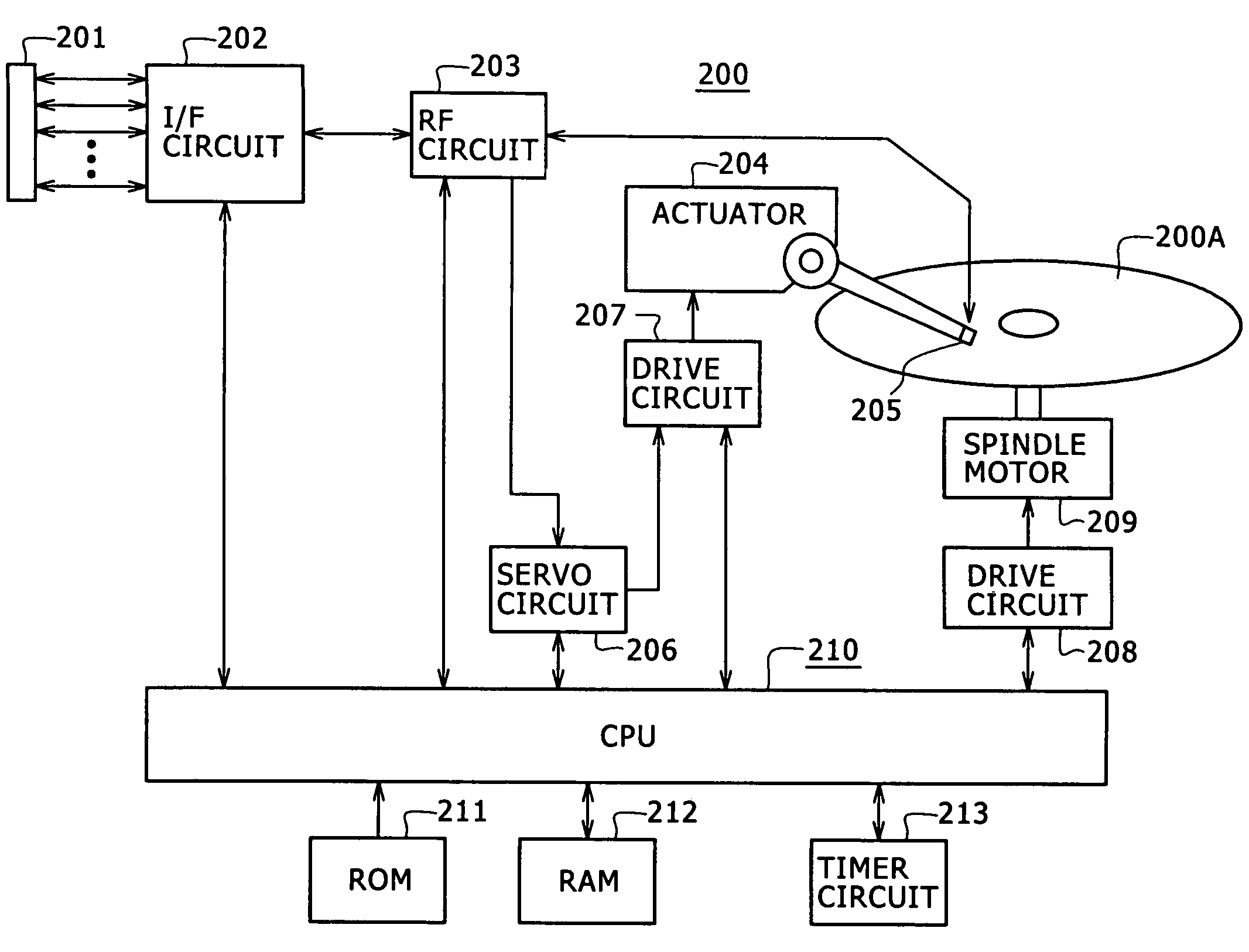
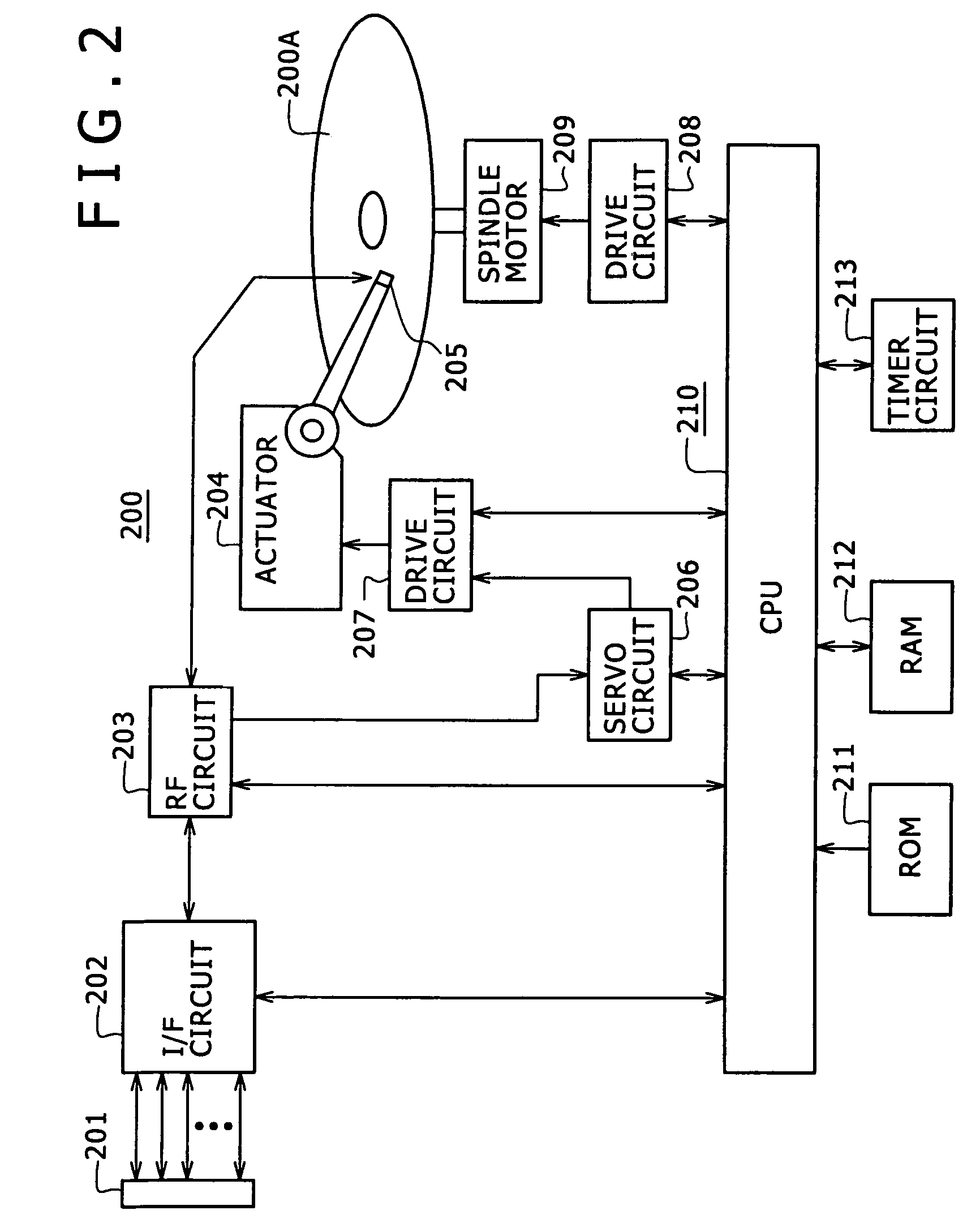
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
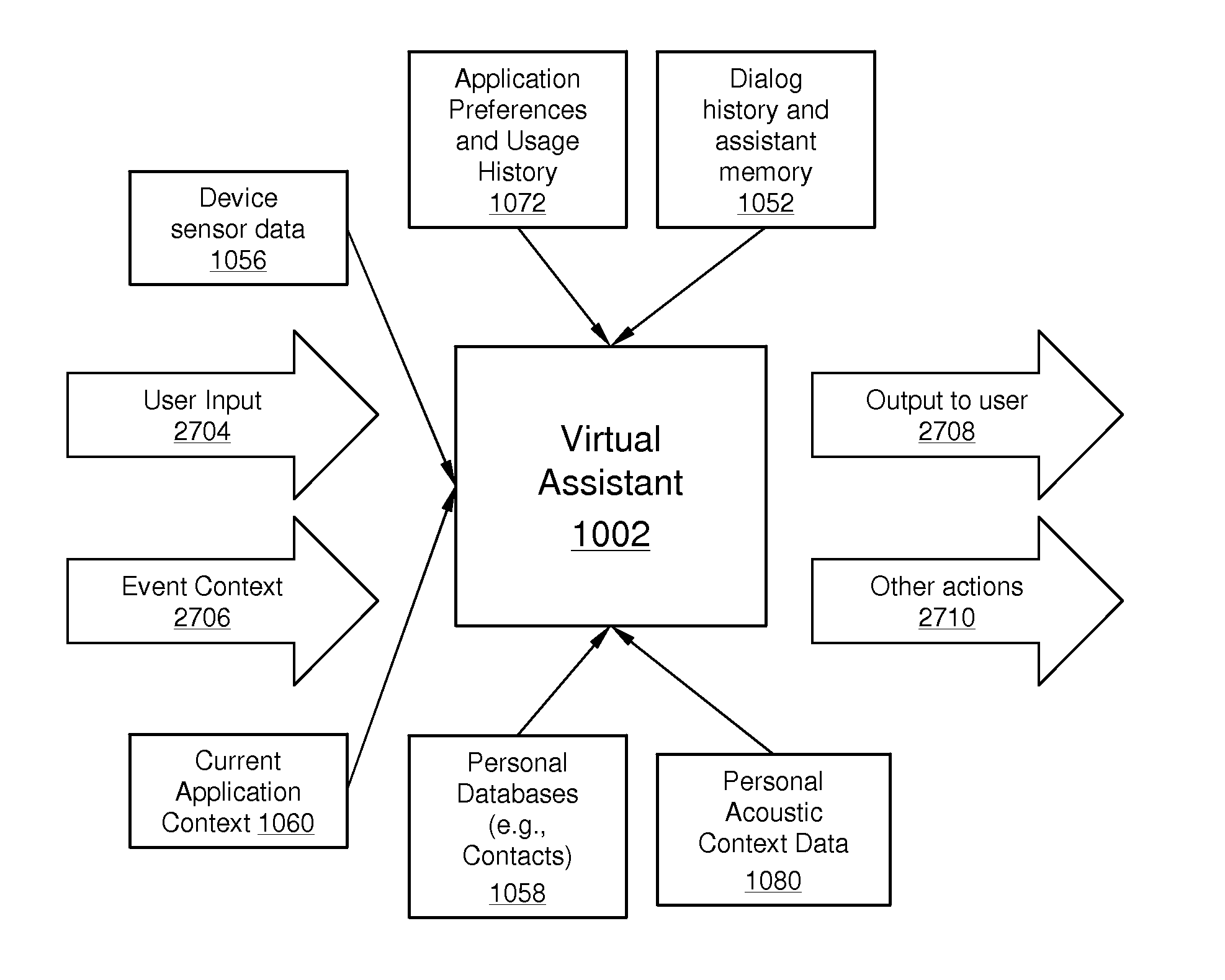
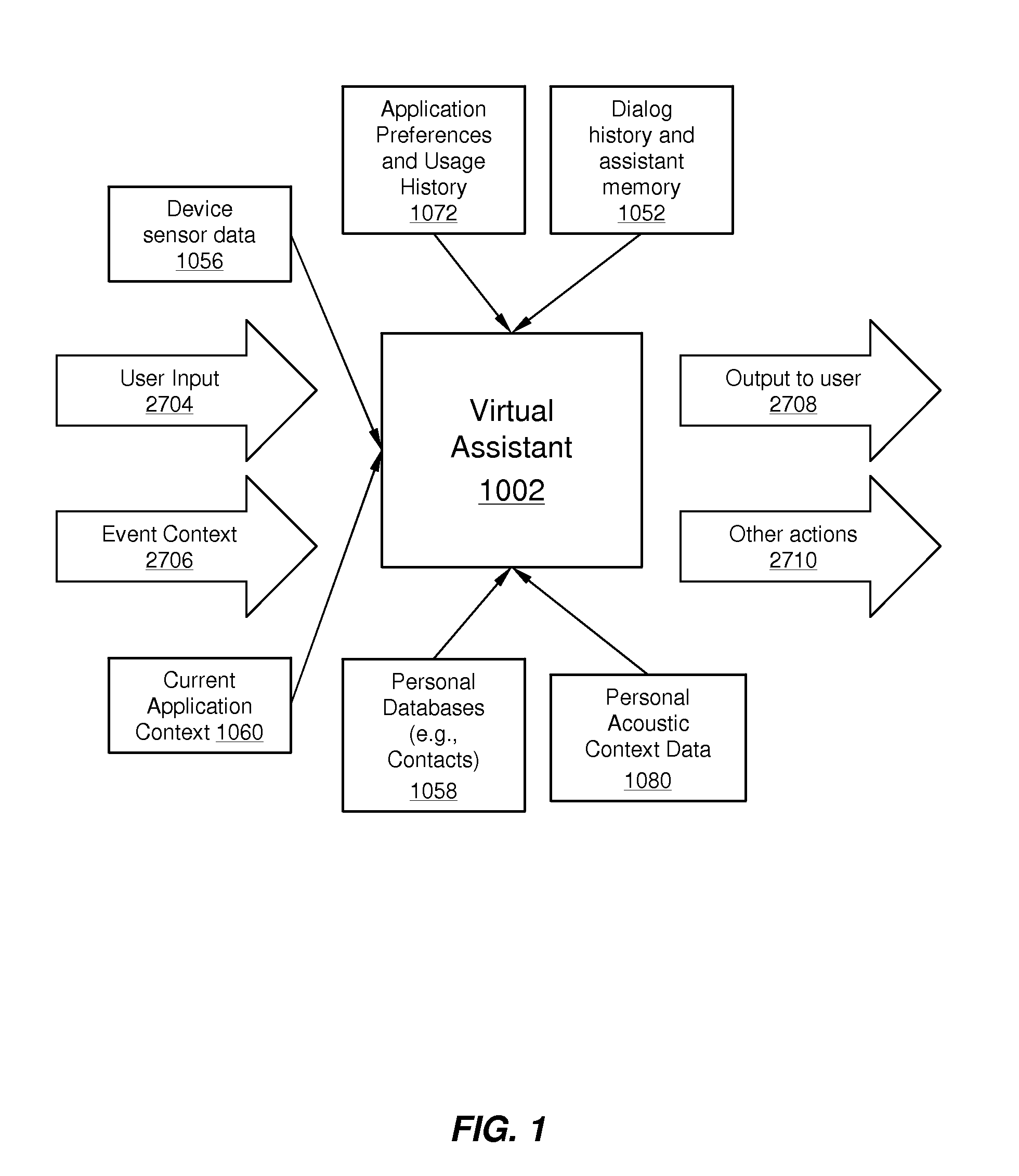
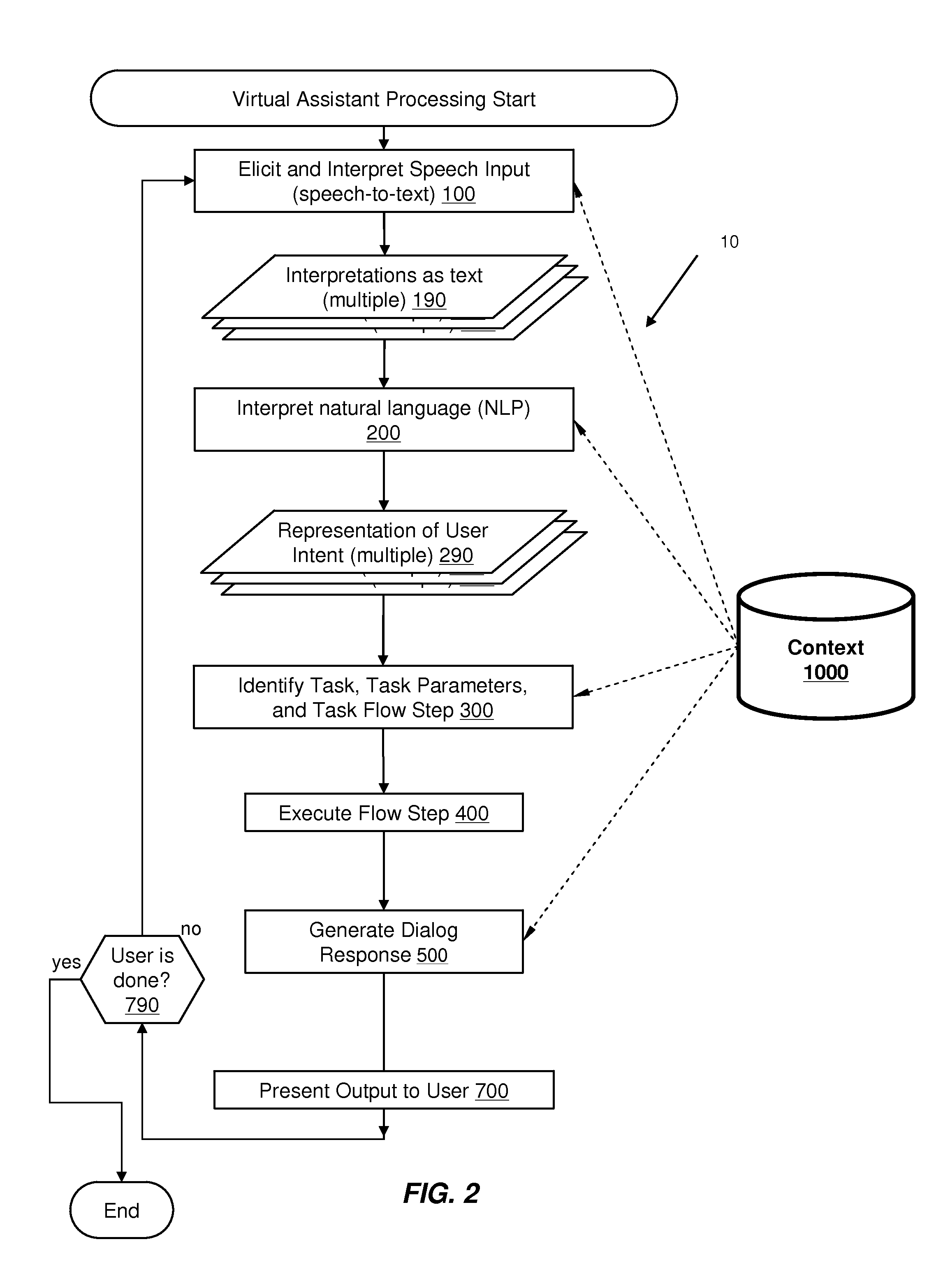
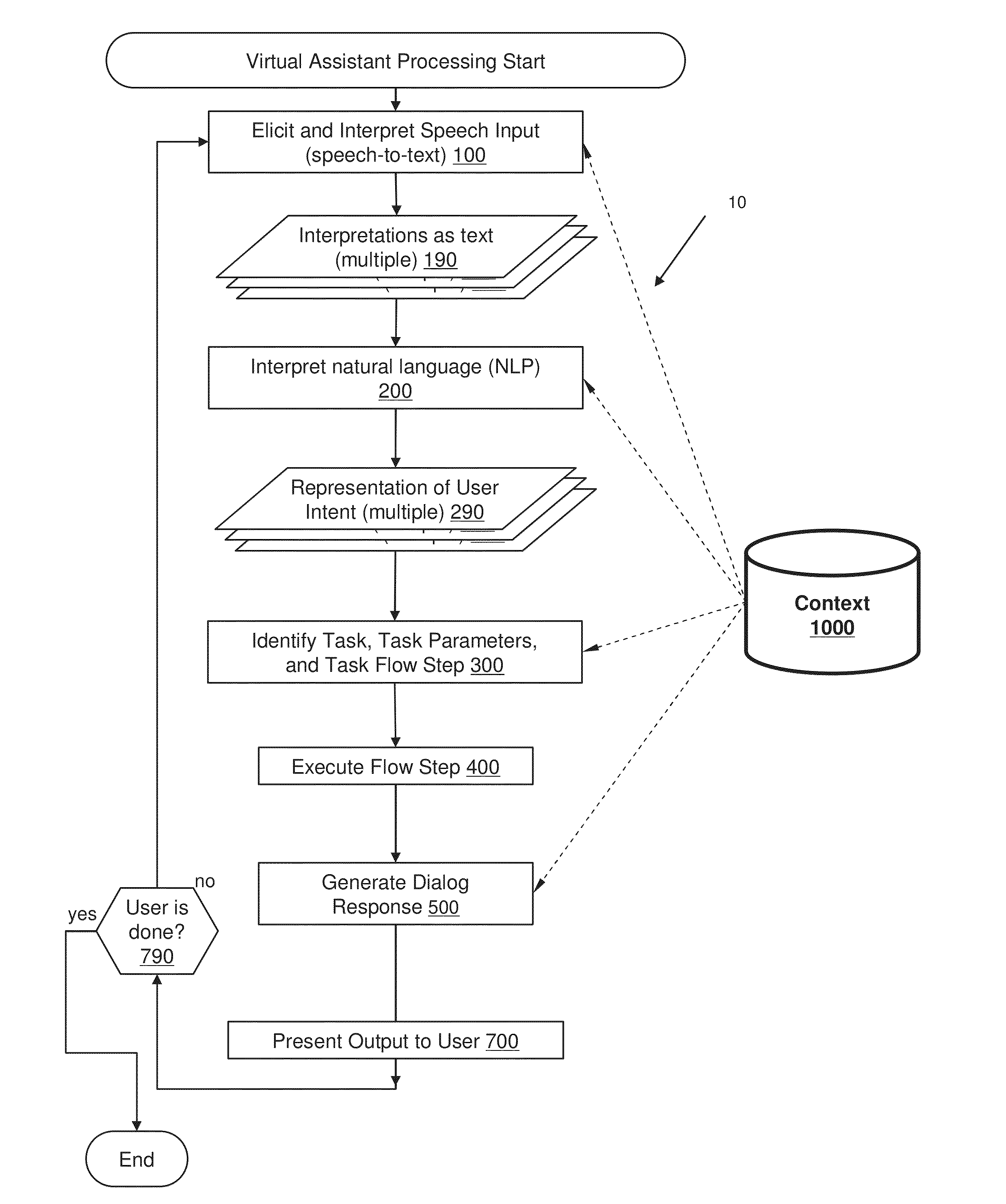
Using Context Information To Facilitate Processing Of Commands In A Virtual Assistant
ActiveUS20120265528A1Clarify userReduce in quantityNatural language data processingSpeech recognitionPersonalizationInformation processing
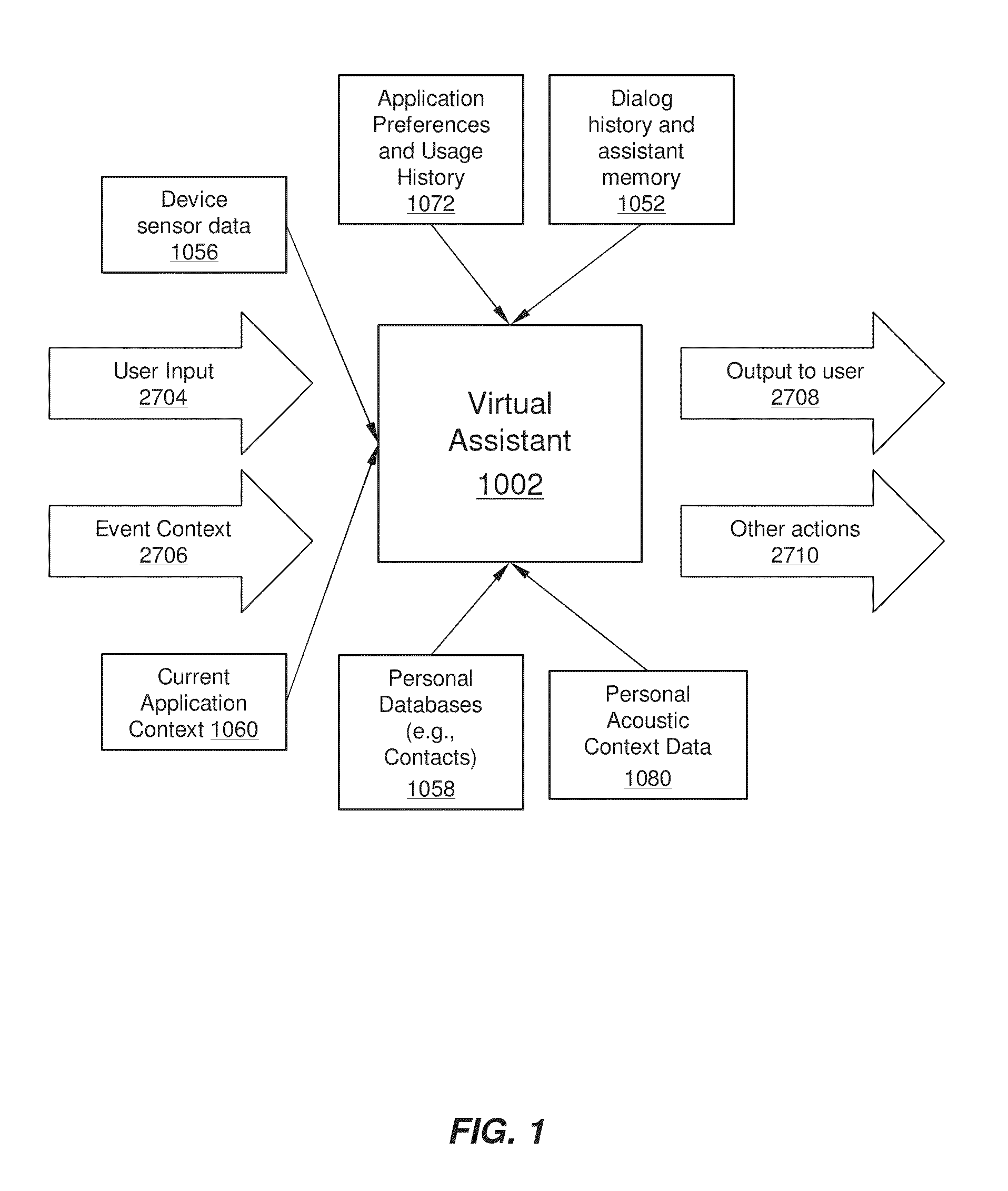
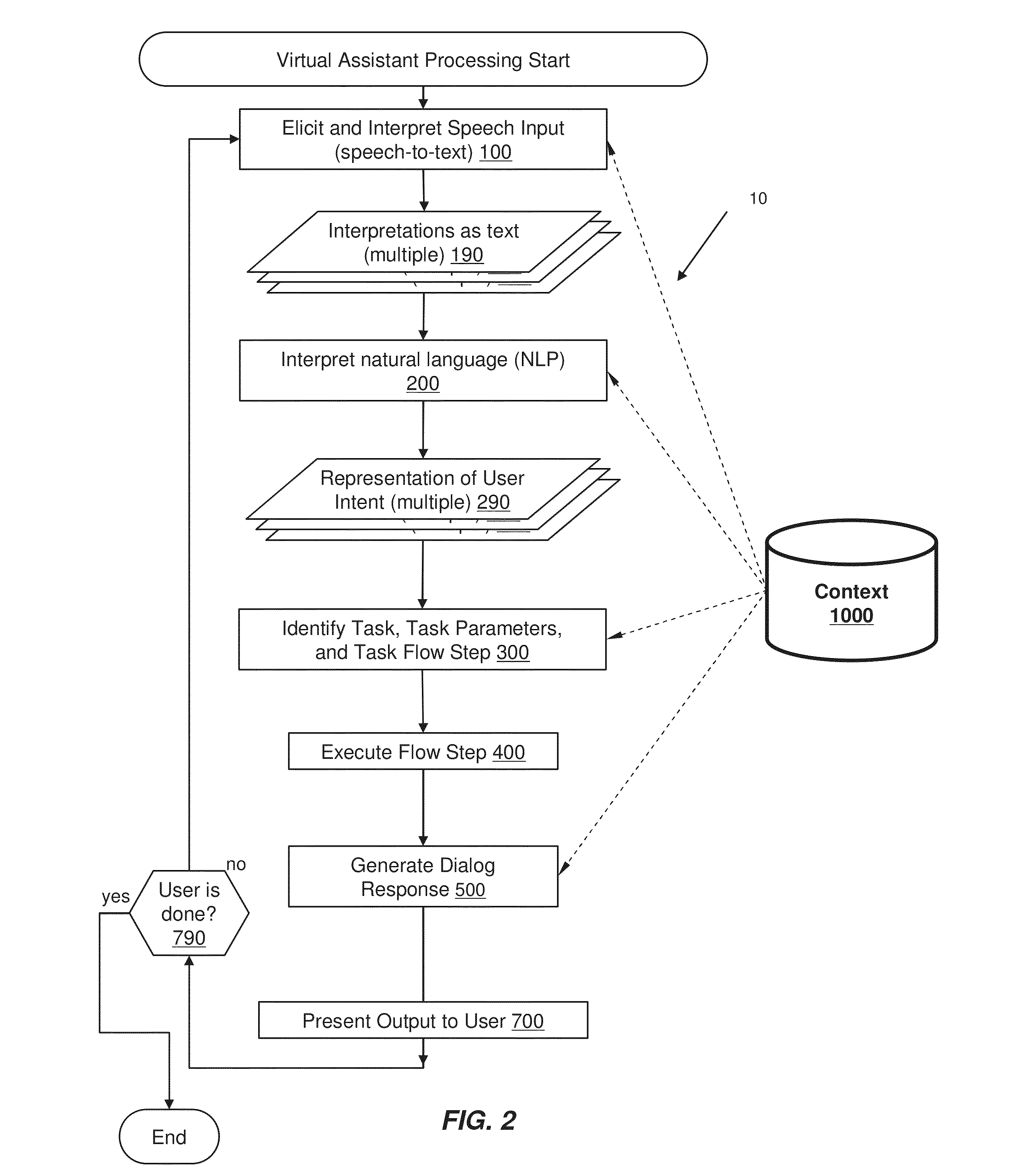
A virtual assistant uses context information to supplement natural language or gestural input from a user. Context helps to clarify the user's intent and to reduce the number of candidate interpretations of the user's input, and reduces the need for the user to provide excessive clarification input. Context can include any available information that is usable by the assistant to supplement explicit user input to constrain an information-processing problem and / or to personalize results. Context can be used to constrain solutions during various phases of processing, including, for example, speech recognition, natural language processing, task flow processing, and dialog generation.
Owner:APPLE INC
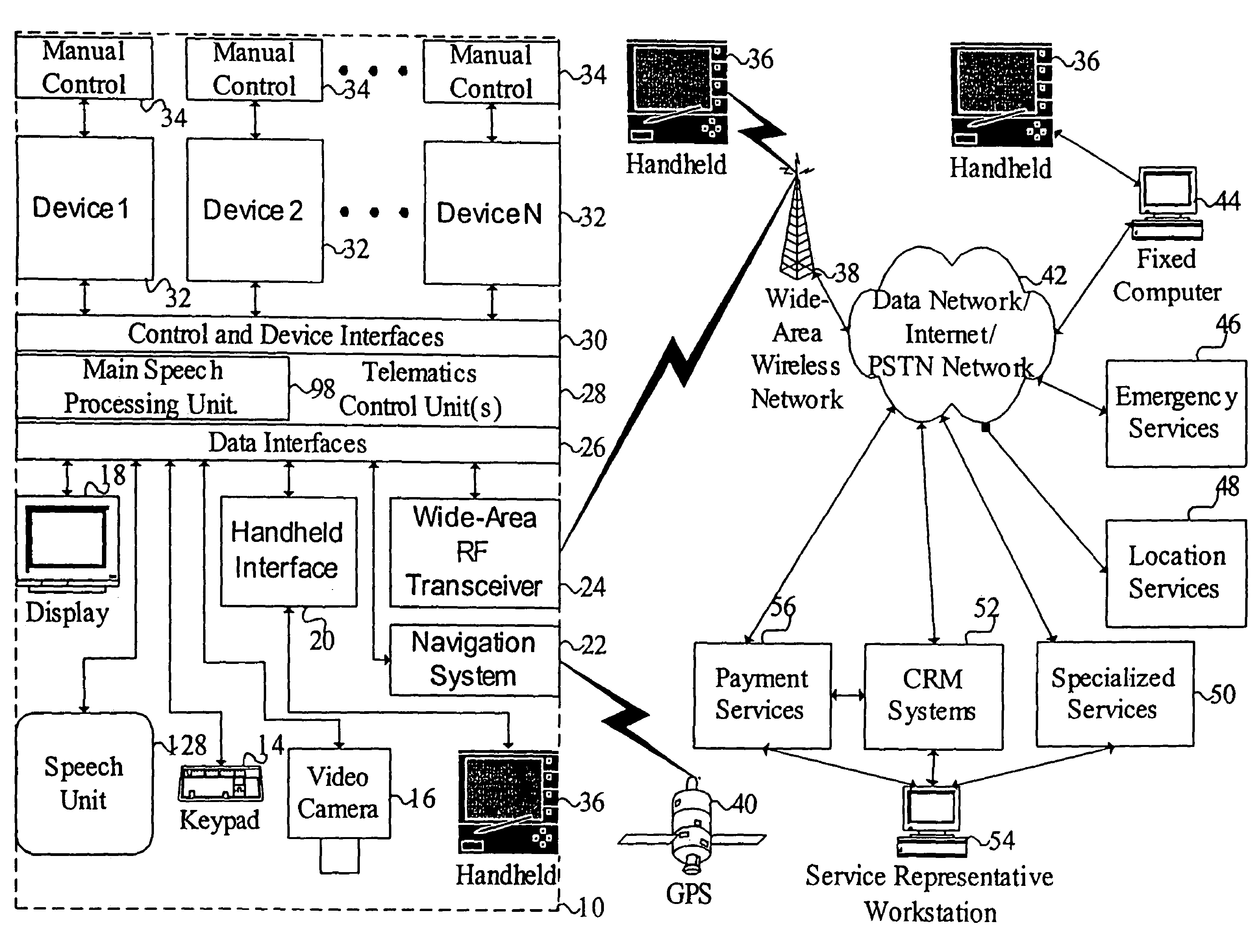
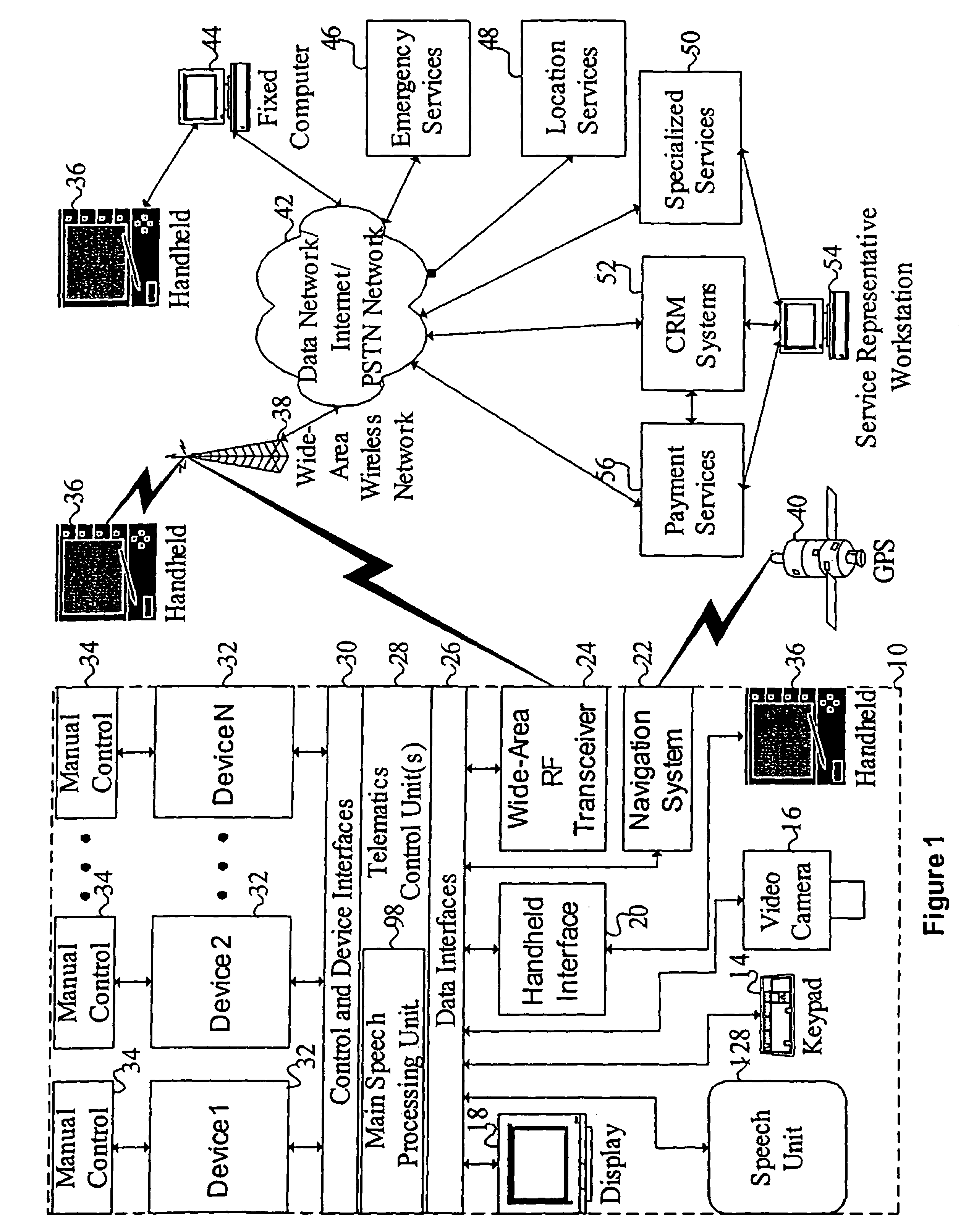
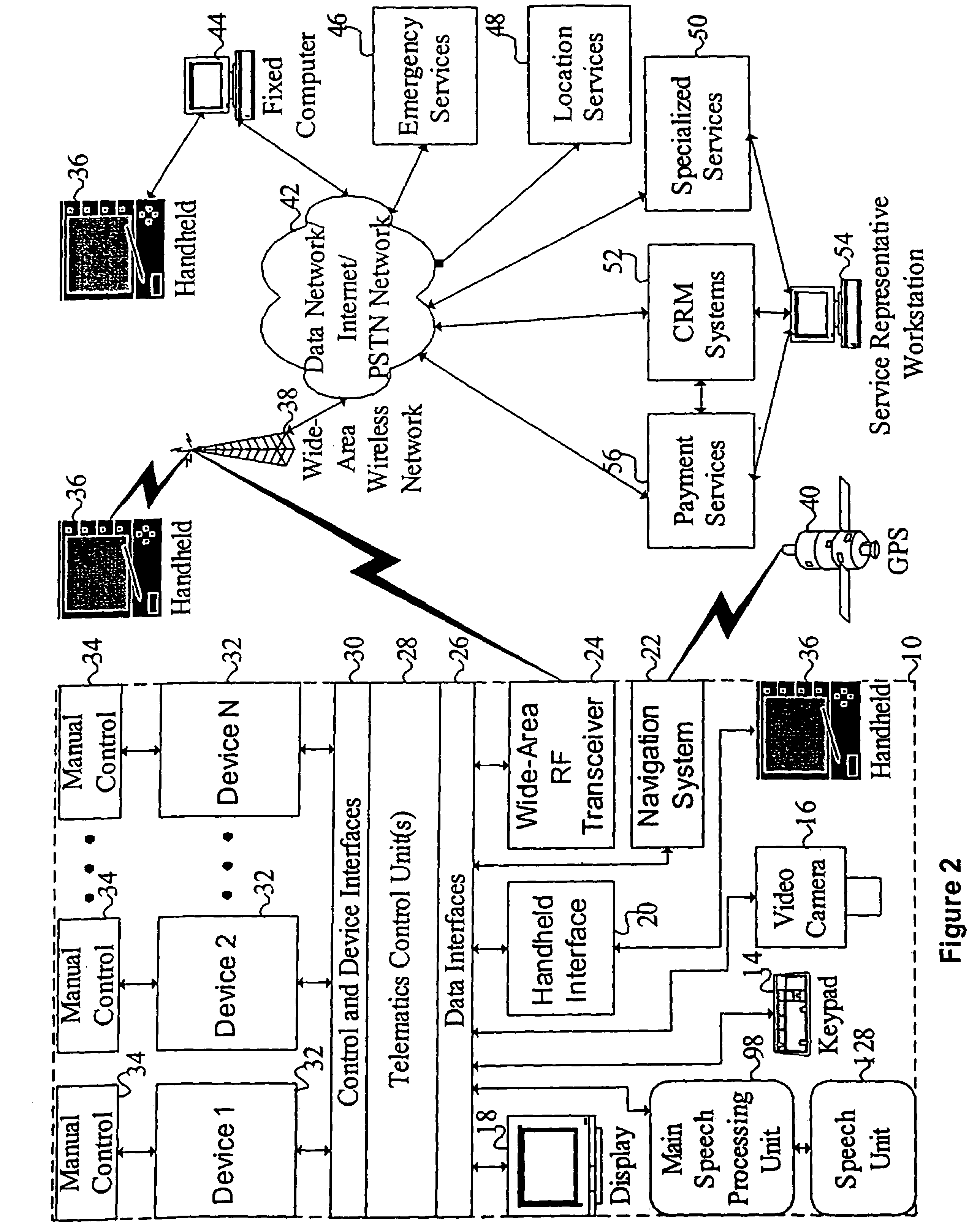
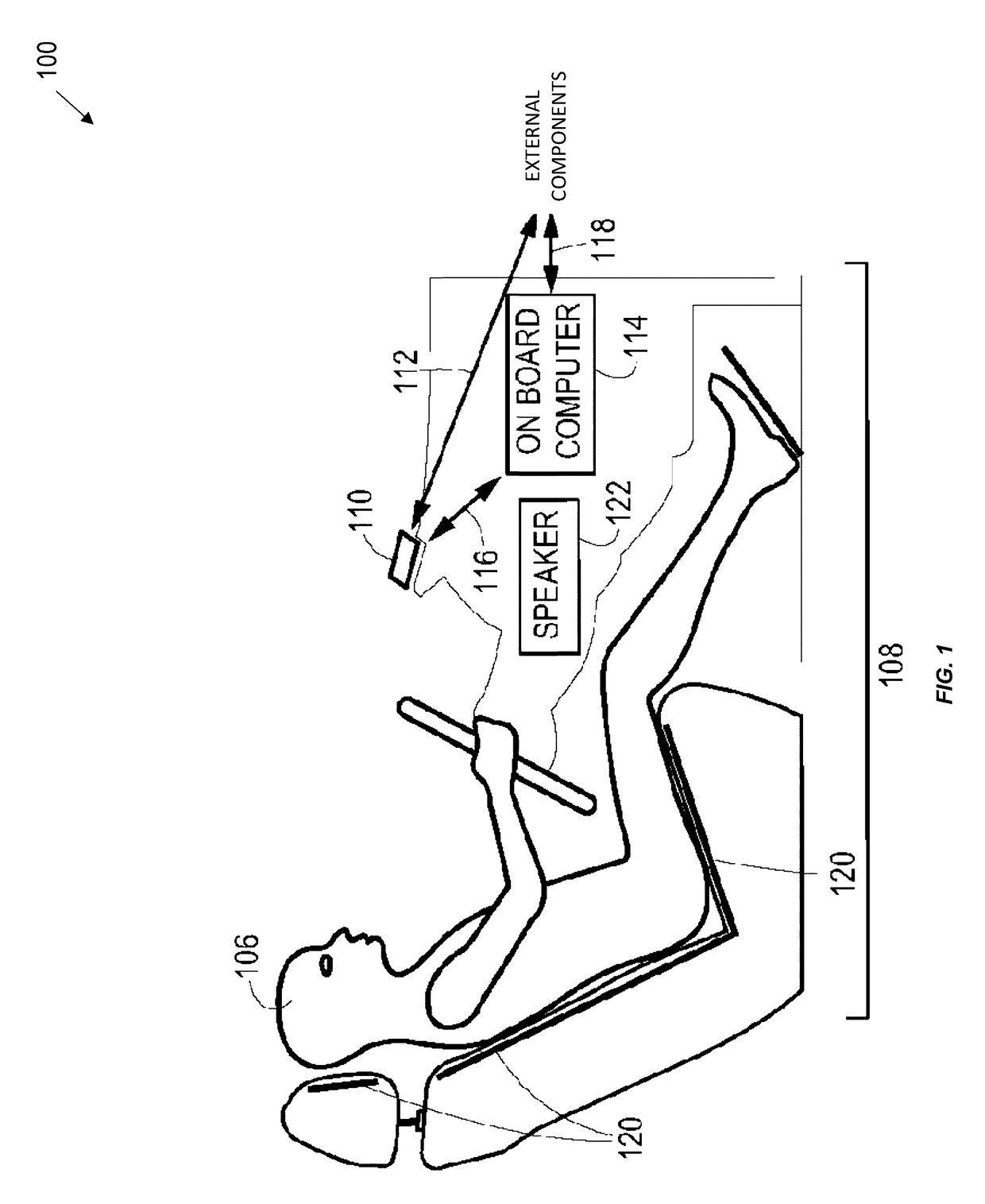
Mobile systems and methods of supporting natural language human-machine interactions
ActiveUS7949529B2Promotes feeling of naturalConvenient timeWeb data indexingDevices with voice recognitionTelematicsWide area network
A mobile system is provided that includes speech-based and non-speech-based interfaces for telematics applications. The mobile system identifies and uses context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for users that submit requests and / or commands in multiple domains. The invention creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context and presenting the expected results for a particular question or command. The invention may organize domain specific behavior and information into agents, that are distributable or updateable over a wide area network.
Owner:DIALECT LLC
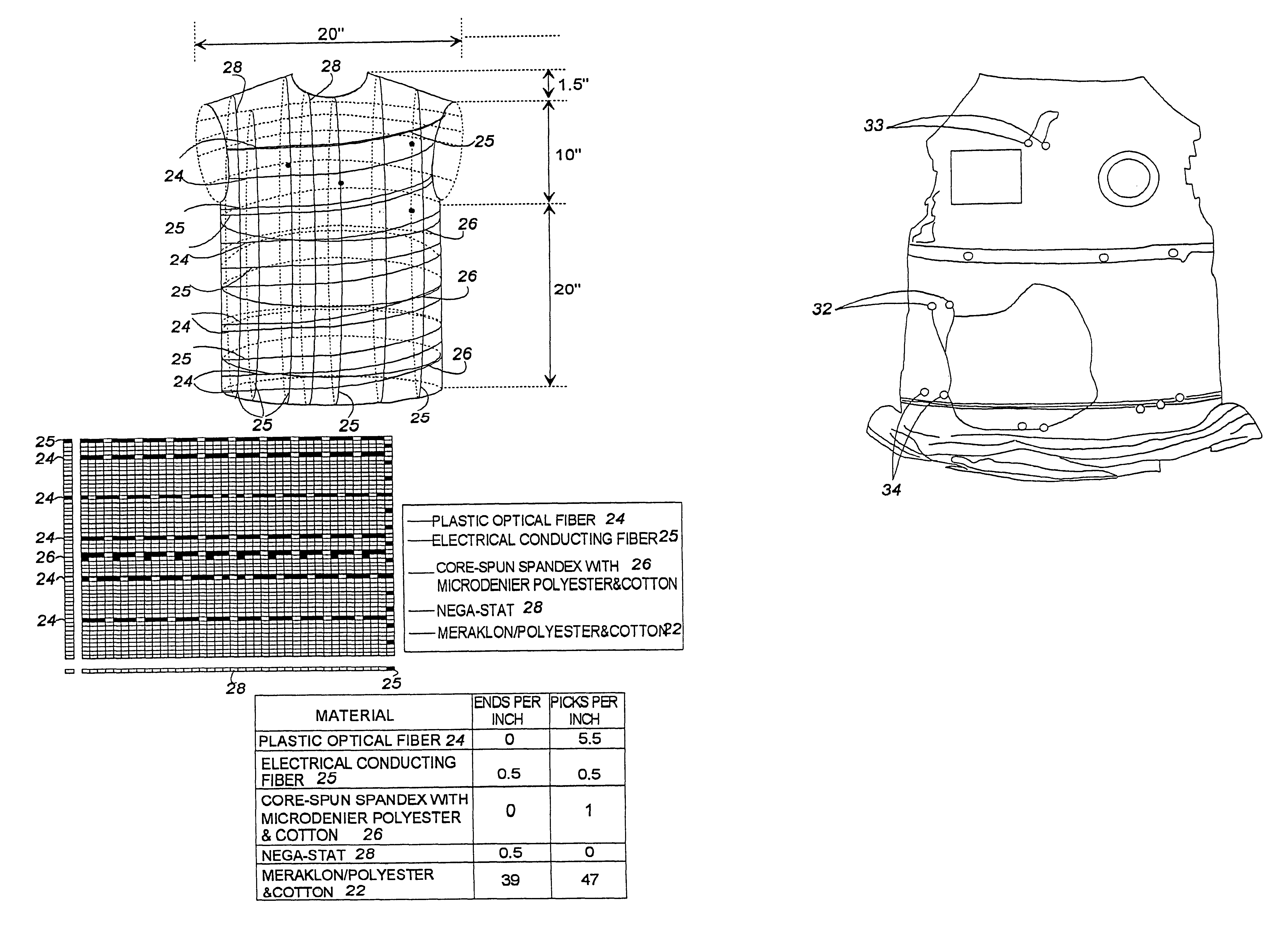
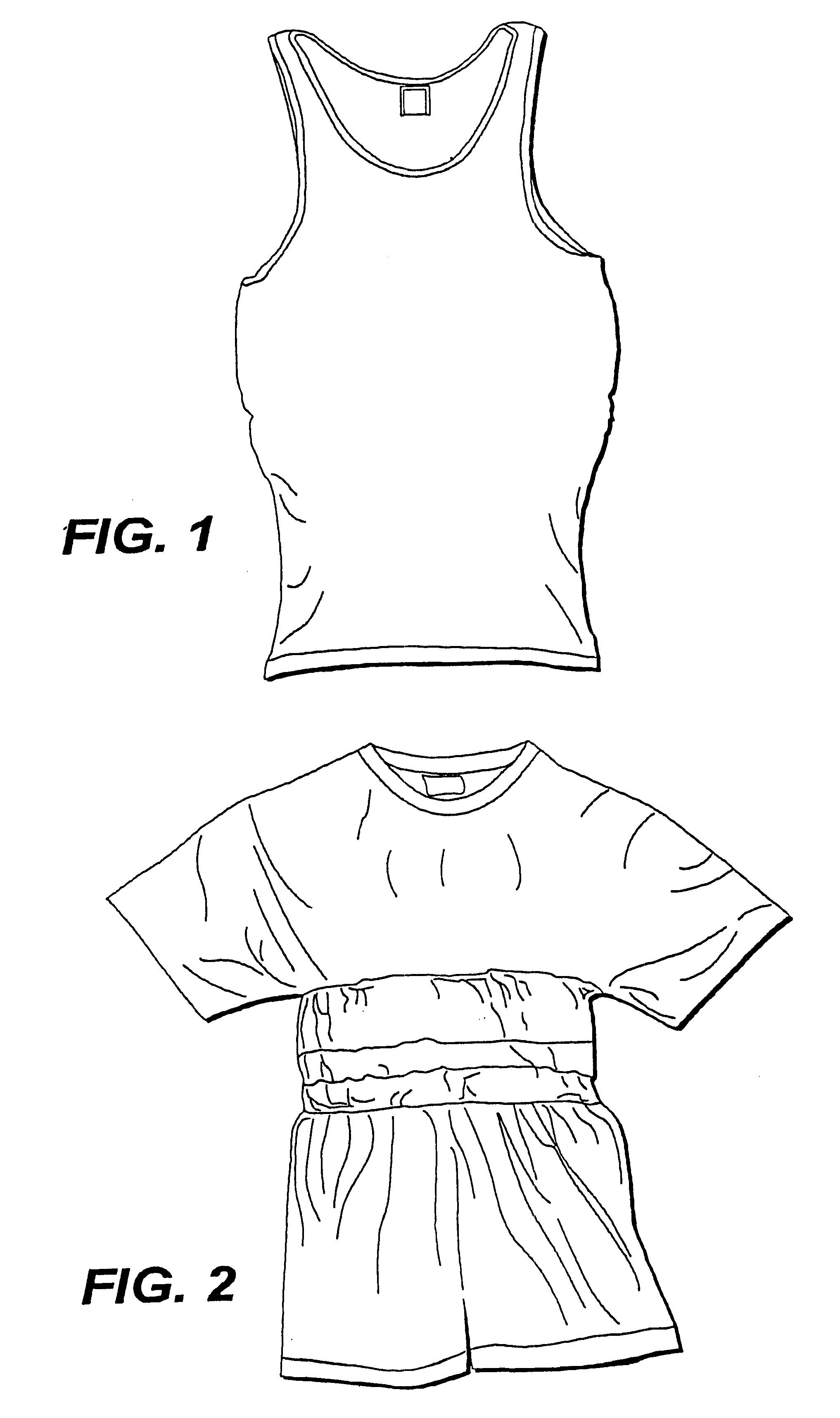
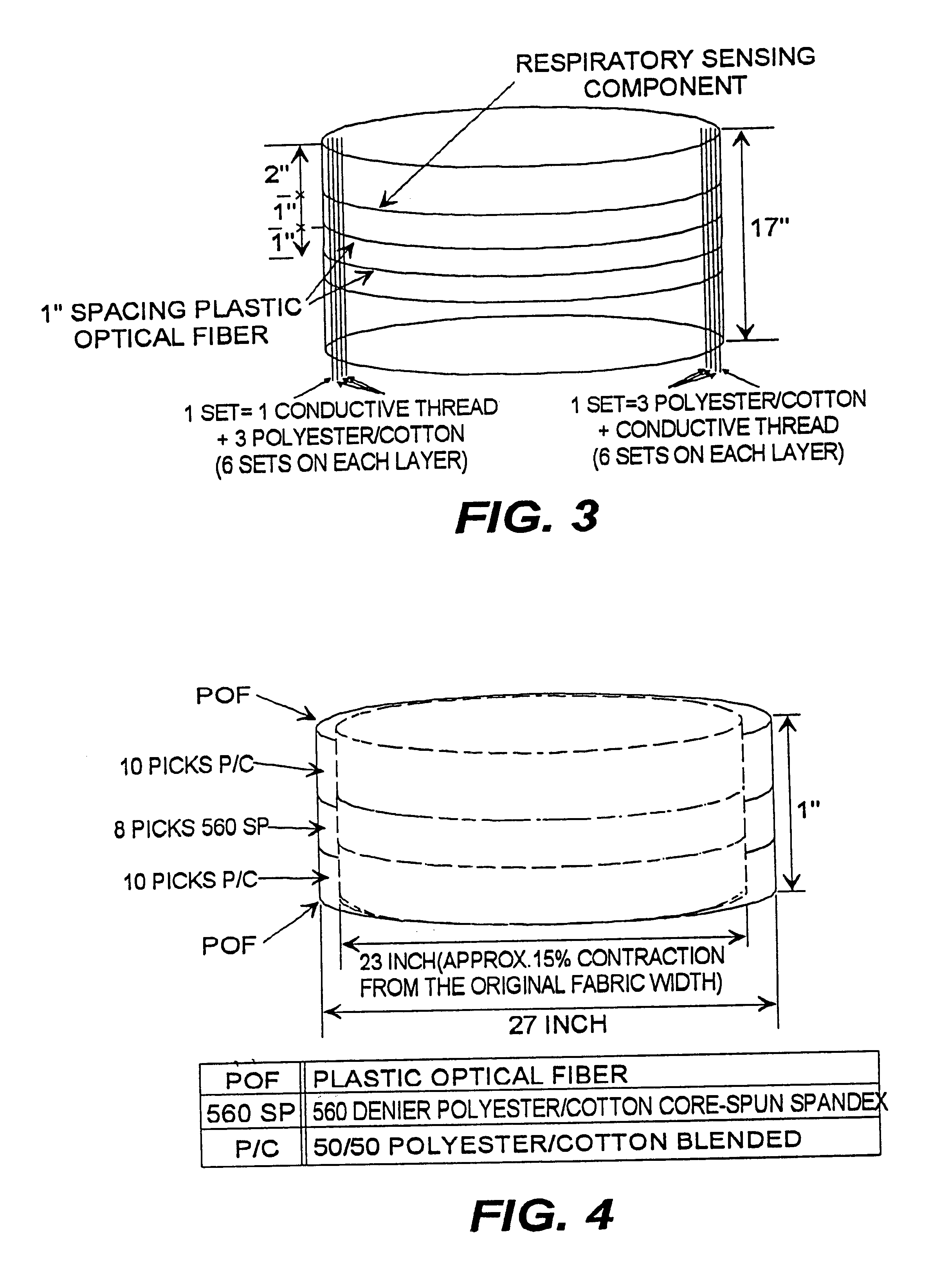
Fabric or garment with integrated flexible information infrastructure
InactiveUS6381482B1Raise the ratioImprove high temperature stabilityWeft knittingOrnamental textile articlesInformation processingEngineering
A fabric, in the form of a woven or knitted fabric or garment, including a flexible information infrastructure integrated within the fabric for collecting, processing, transmitting and receiving information concerning-but not limited to-a wearer of the fabric. The fabric allows a new way to customize information processing devices to "fit" the wearer by selecting and plugging in (or removing) chips / sensors from the fabric thus creating a wearable, mobile information infrastructure that can operate in a stand-alone or networked mode. The fabric can be provided with sensors for monitoring physical aspects of the wearer, for example body vital signs, such as heart rate, EKG, pulse, respiration rate, temperature, voice, and allergic reaction, as well as penetration of the fabric. The fabric consists of a base fabric ("comfort component"), and an information infrastructure component which can consist of a penetration detection component, or an electrical conductive component, or both. The preferred penetration detection component is a sheathed optical fiber. The information infrastructure component can include, in addition to an electrically conductive textile yarn, a sensor or a connector for a sensor. A process is provided for making an electrical interconnection between intersecting electrically conductive yarns. Furthermore, a process is established for sheathing the plastic optical fiber and protecting it.
Owner:GEORGIA TECH RES CORP
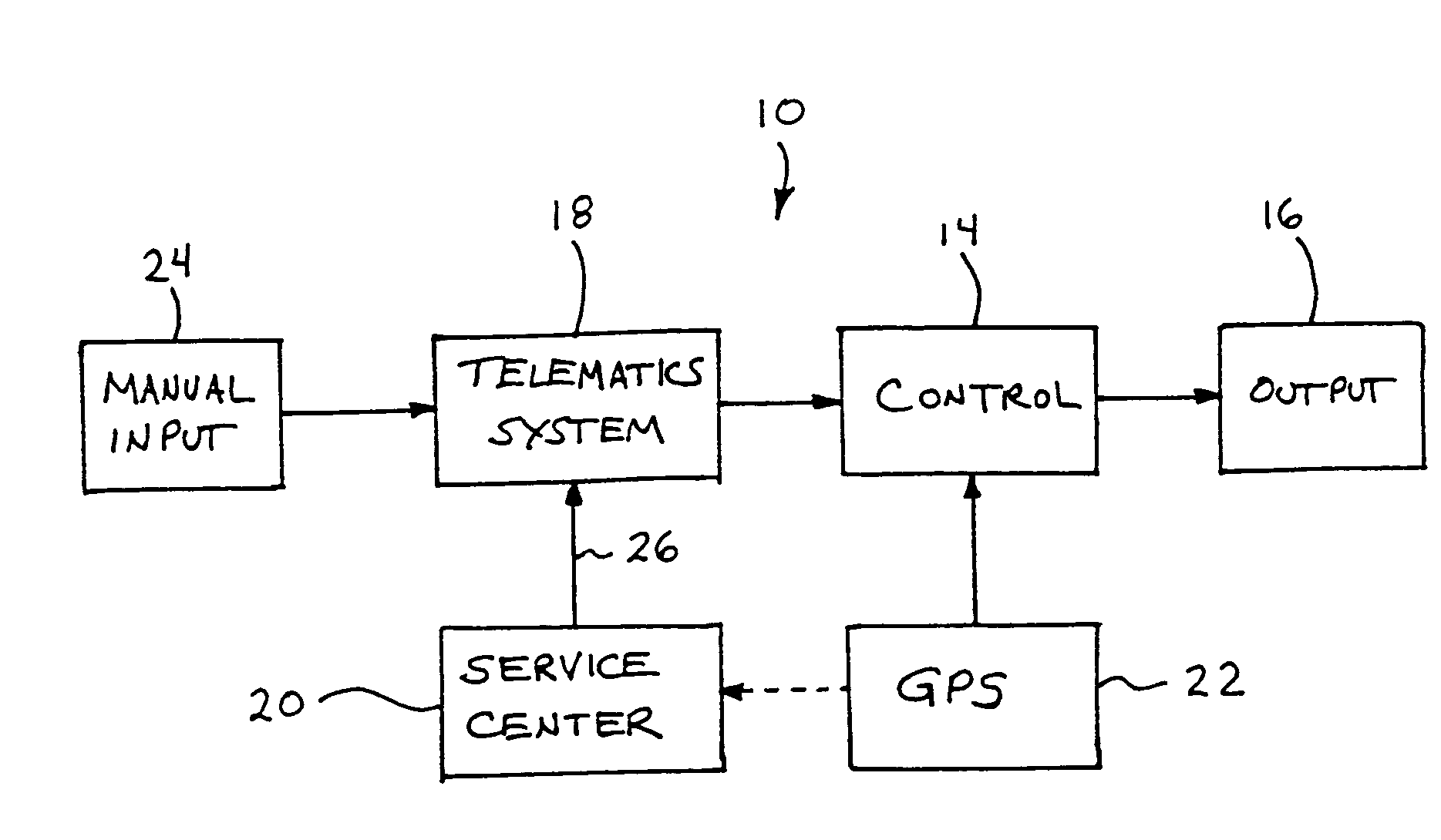
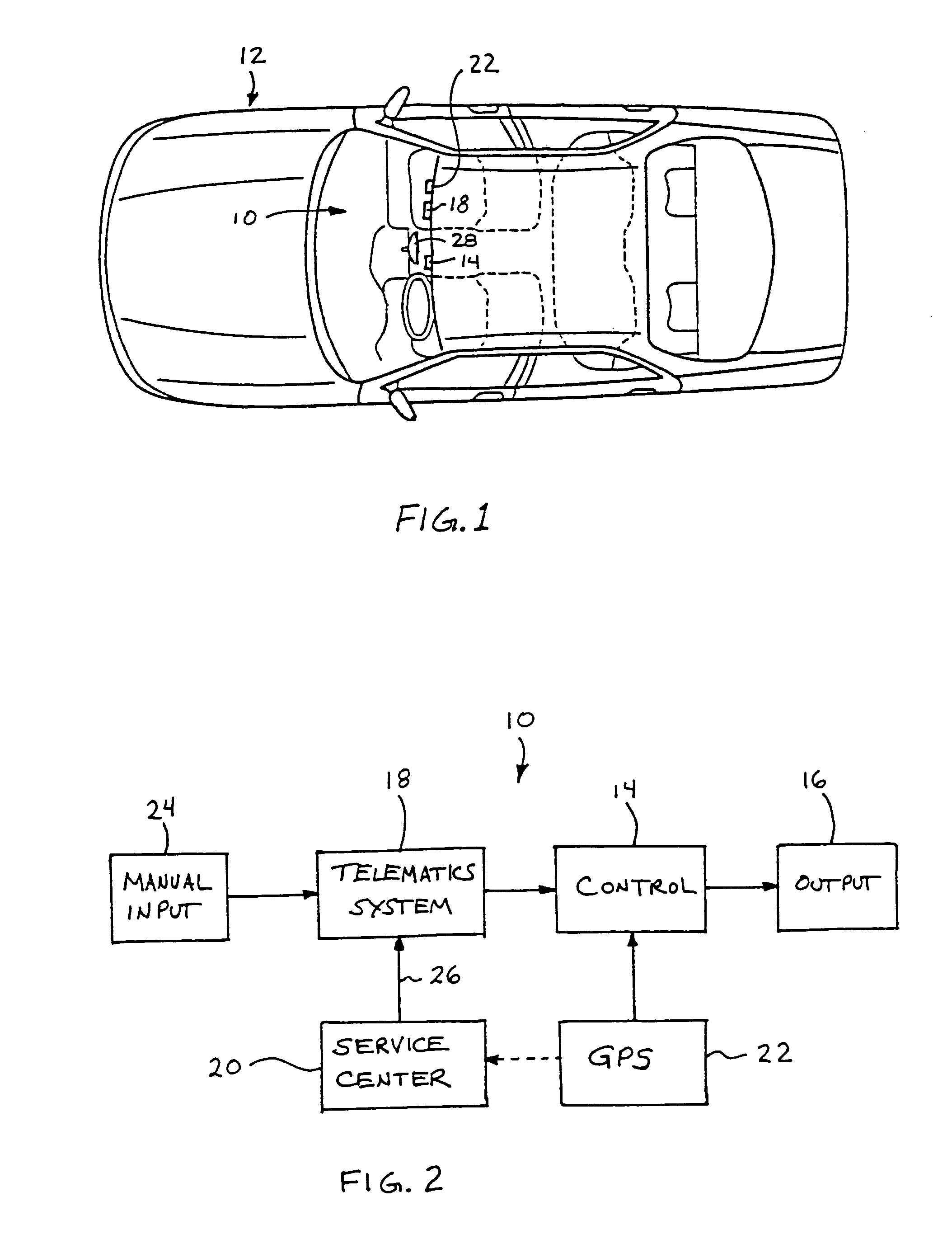
Vehicle navigation system for use with a telematics system
InactiveUS7167796B2Low costImage enhancementTelevision system detailsDriver/operatorService provision
A navigation system for a vehicle includes a vehicle-based telematics system, a vehicle-based global positioning system and a control. The telematics system is operable to receive a user input from a driver of the vehicle and to download directional information from an external service provider to the control in response to the user input and an initial geographic position of the vehicle. The directional information comprises at least two instructions with each of the instructions being coded or associated with or linked to a respective geographic location. The control is operable to provide an output corresponding to each of the instructions in response to a current actual geographic position of the vehicle. The control is operable to provide each instruction only when the then current actual geographic position of the vehicle at least generally corresponds to the particular geographic location associated with the instruction.
Owner:DONNELLY CORP
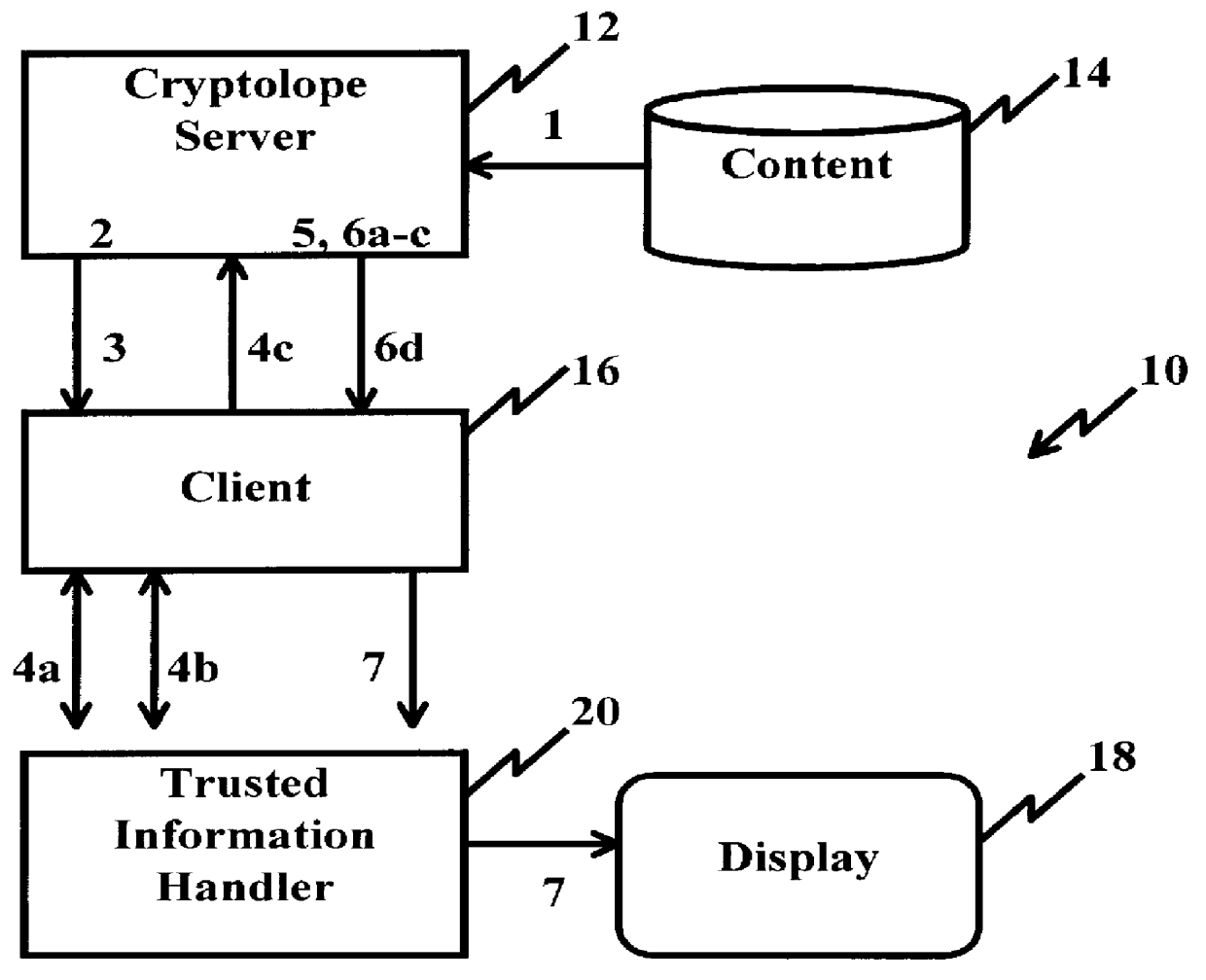
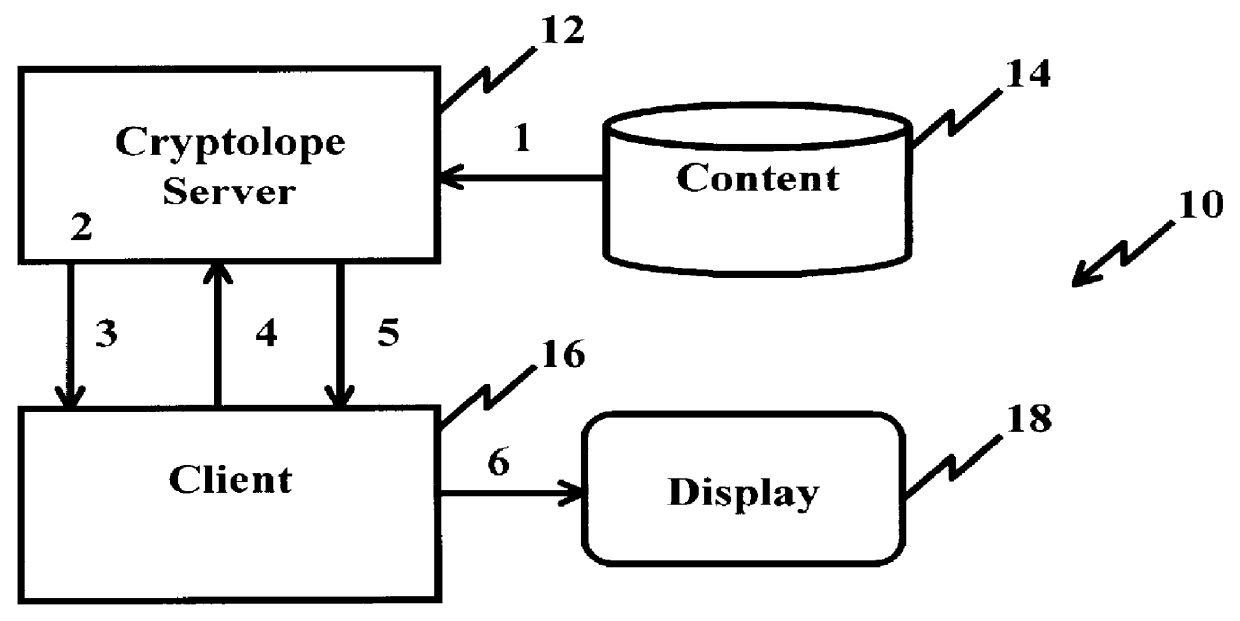
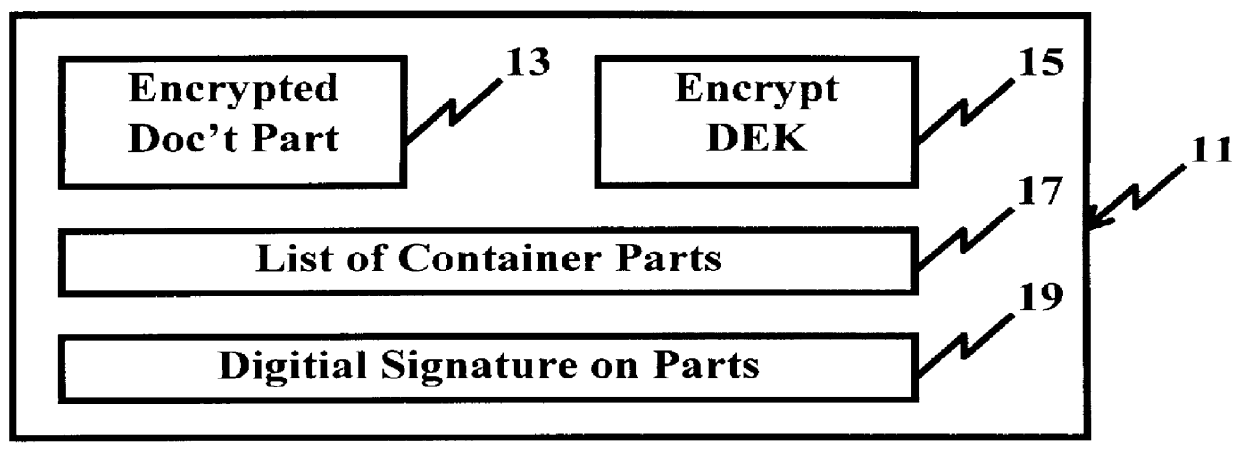
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
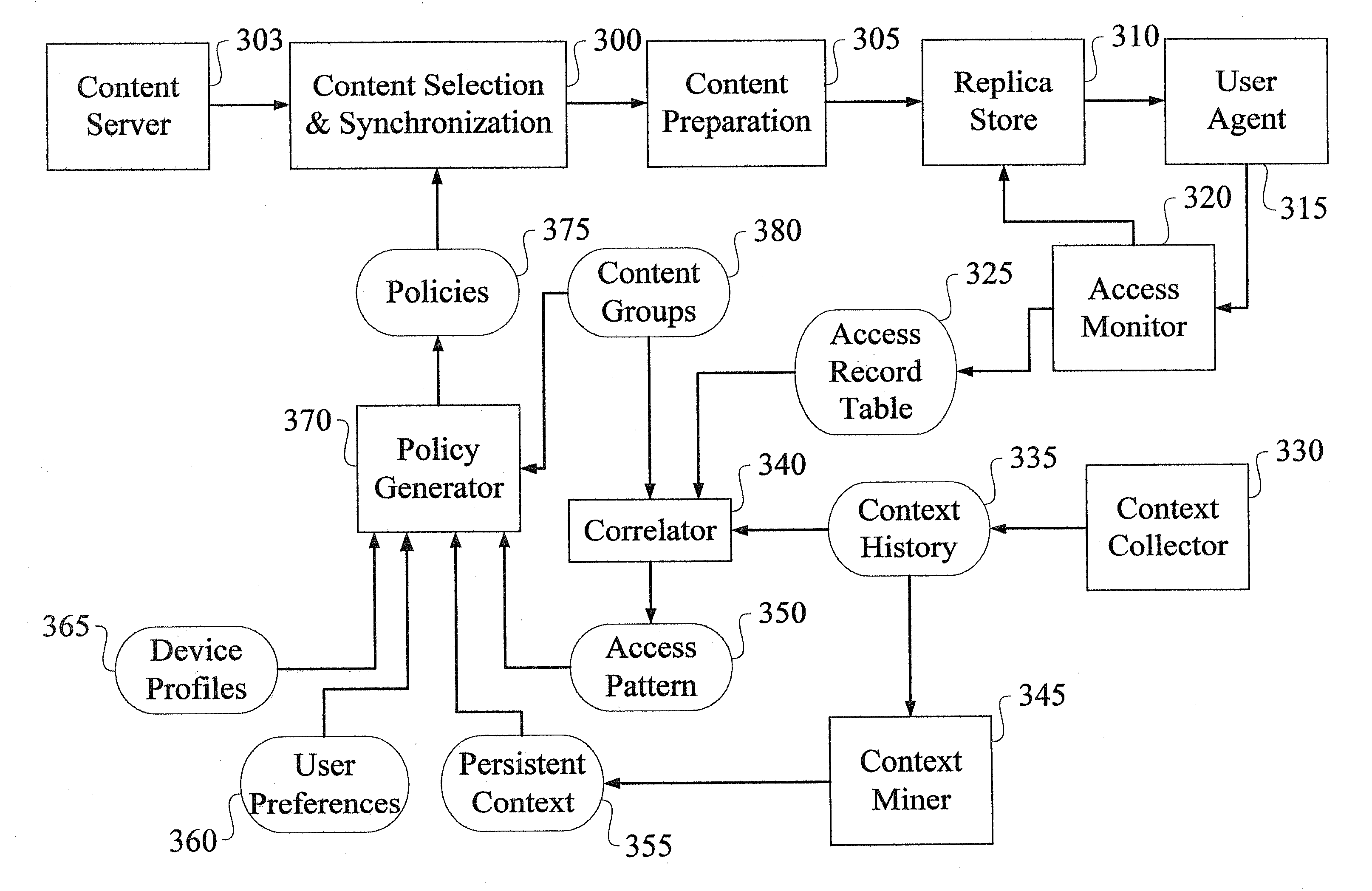
Method and Apparatus for Content Pre-Fetching and Preparation
InactiveUS20090287750A1Improve responsivenessMemory adressing/allocation/relocationInformation formatInformation processingProgram planning
A method of pre-fetching and preparing content in an information processing system is provided. The method includes the steps of generating at least one content pre-fetching policy and at least one content preparation policy, wherein each of the policies are at least in part a function of context information associated with a user. The content is pre-fetched based on information contained within the at least one content pre-fetching policy. Once the content has been pre-fetched, it is prepared based on information contained within the at least one content preparation policy. The context information associated with the user includes at least one of the user's usage patterns, current location, future plans and preferences.
Owner:IBM CORP
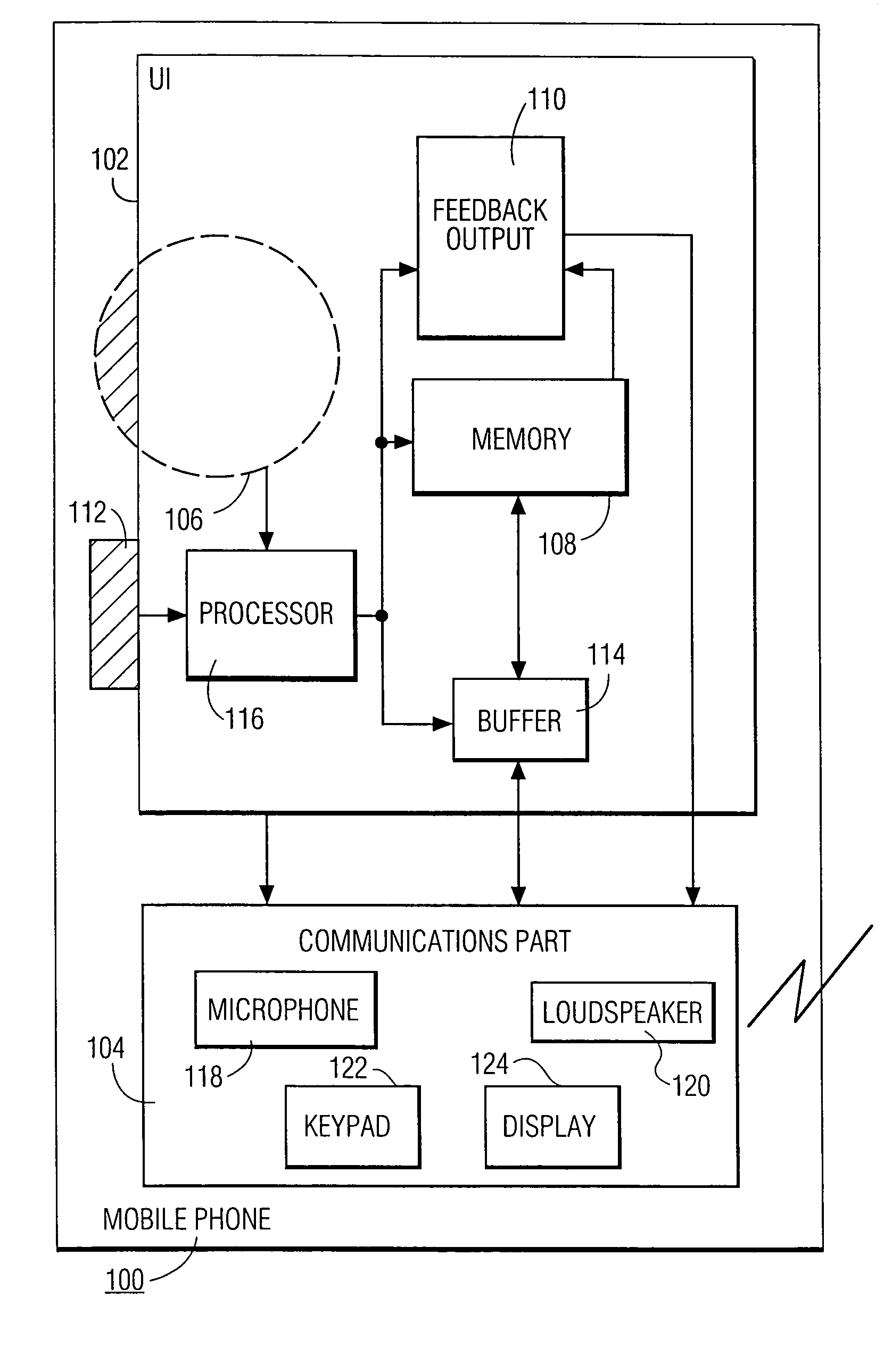
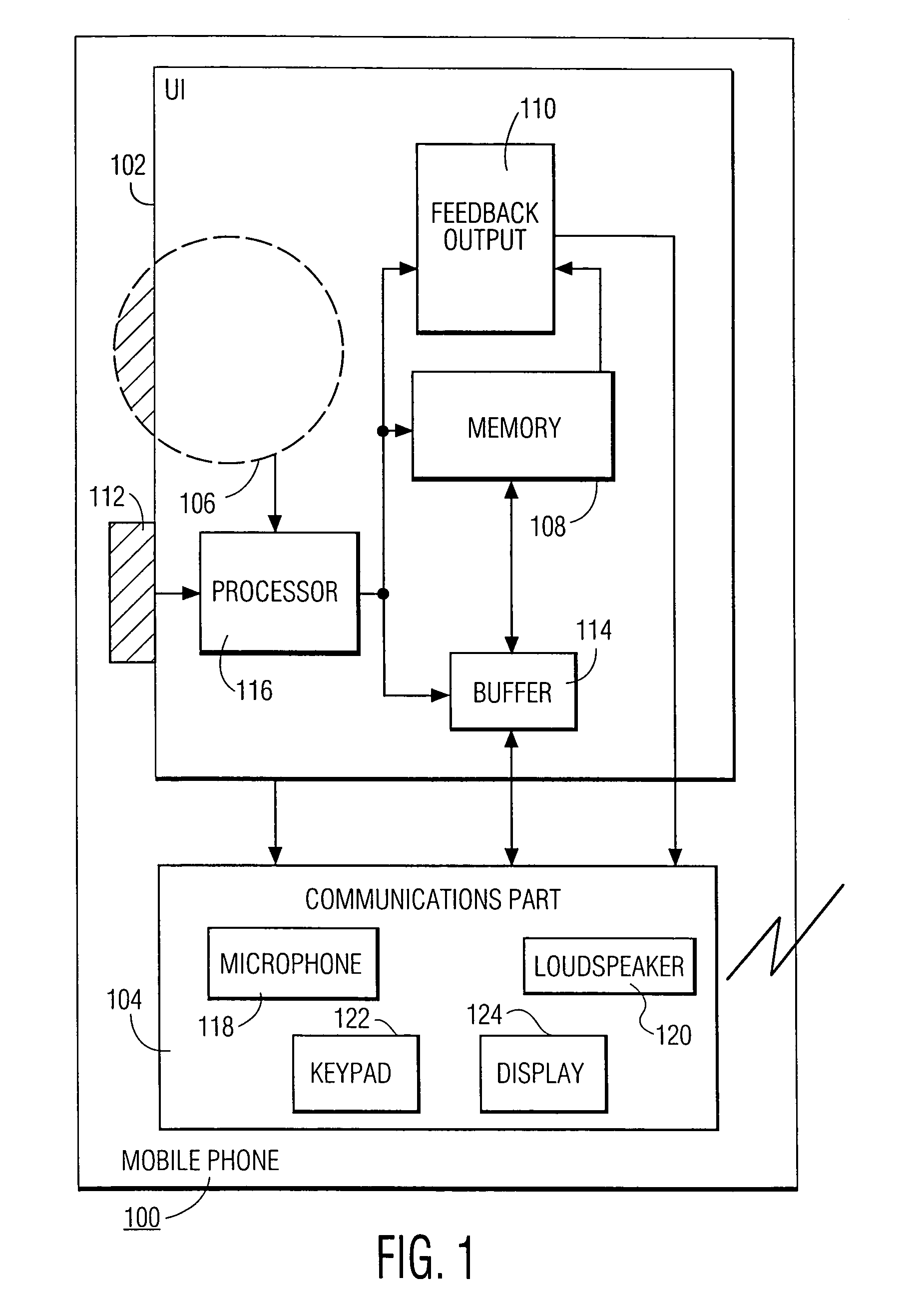
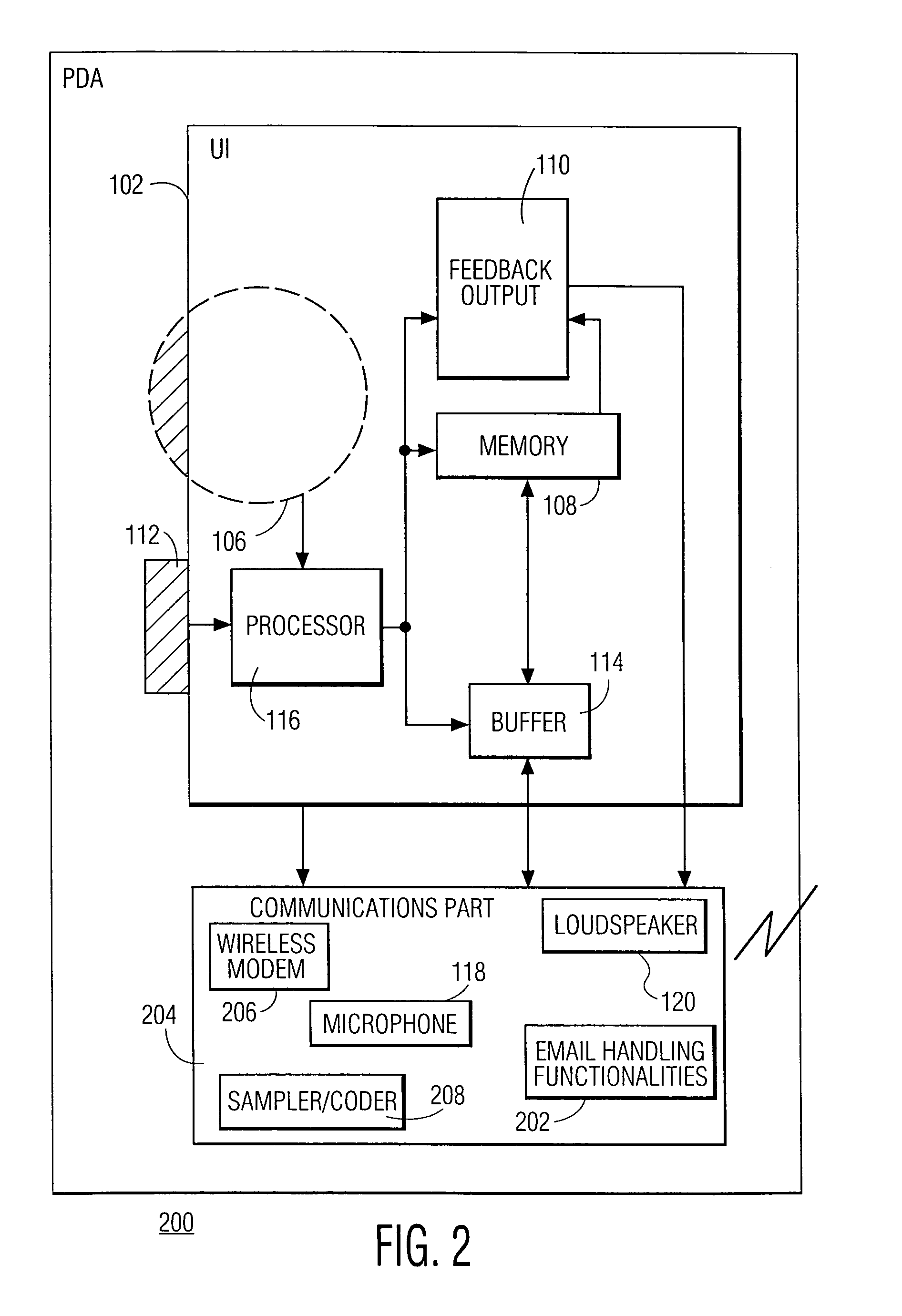
Hand-ear user interface for hand-held device
InactiveUS6978127B1Small sizeInput/output for user-computer interactionInterconnection arrangementsInformation processingPersonalization
A hand-held information processing device, such as a mobile phone, has a thumb wheel that lets the user scan a circular array of options. Each respective one of the options is represented by a respective audio output that gets played out when the wheel is turned a notch up or down. This enables the user to select an option with one hand and without having to look at the device. It also allows for a form factor smaller than that of a conventional mobile phones since a keypad is not needed for entering digits to make a call from a personalized directory.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
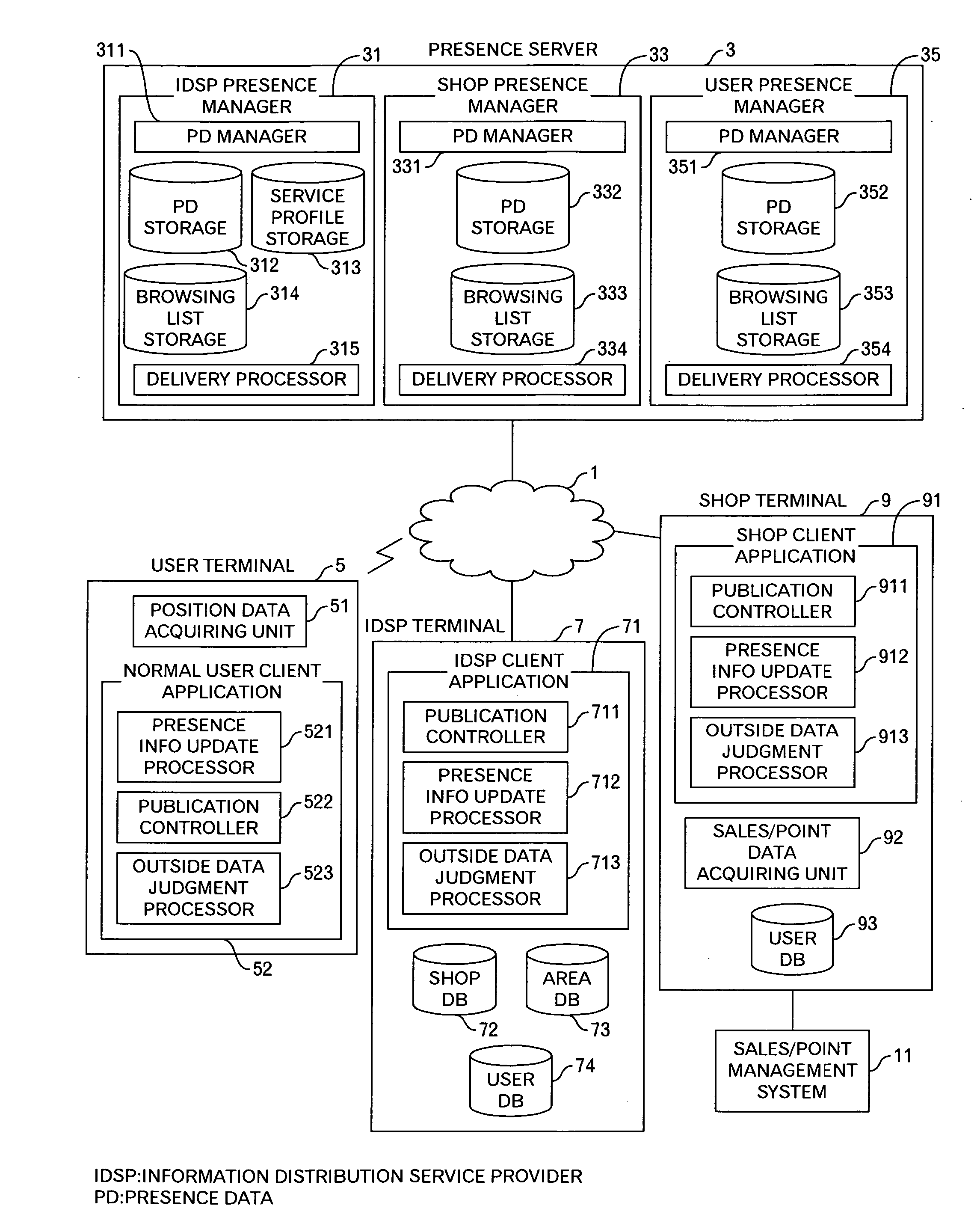
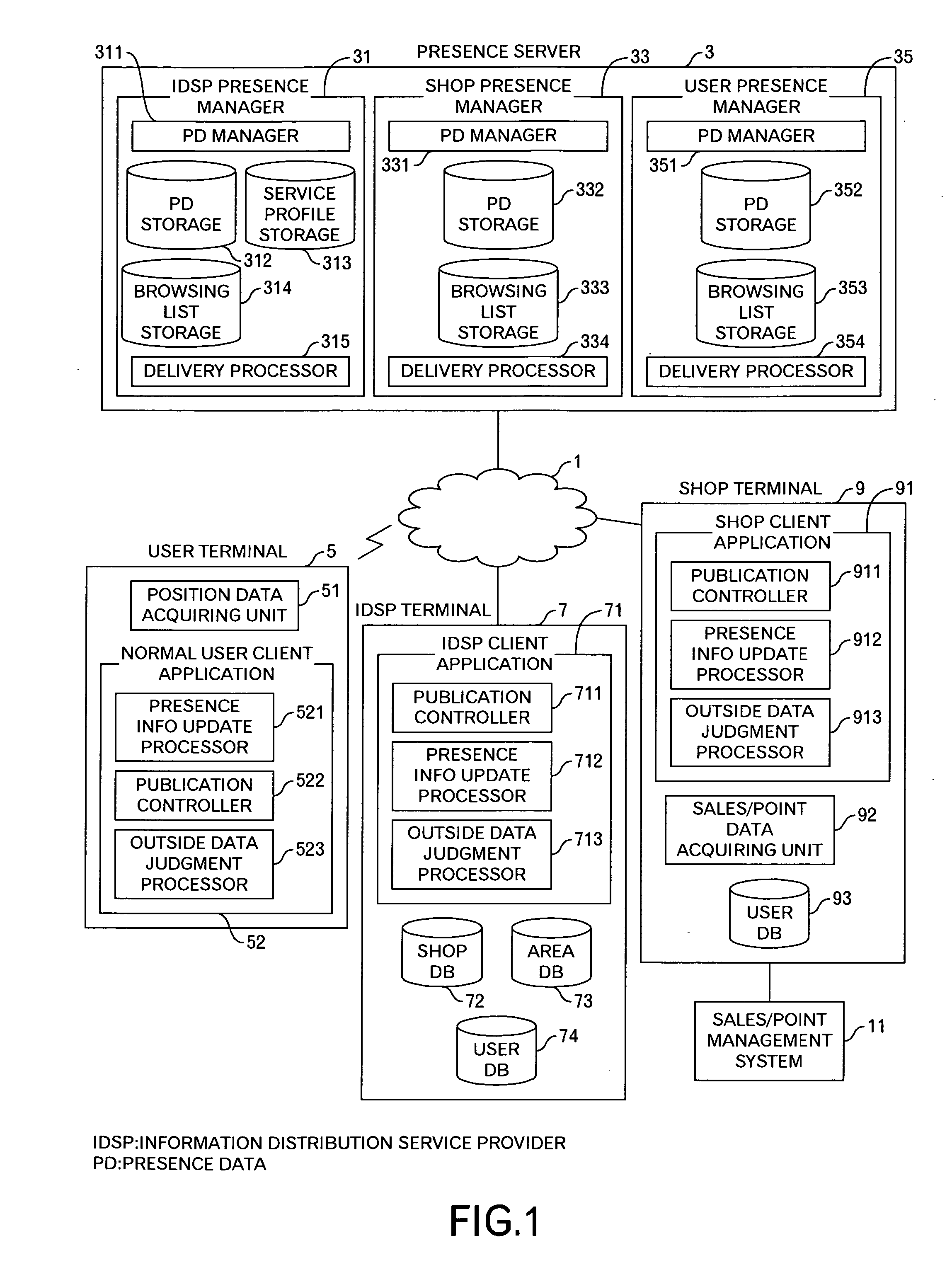
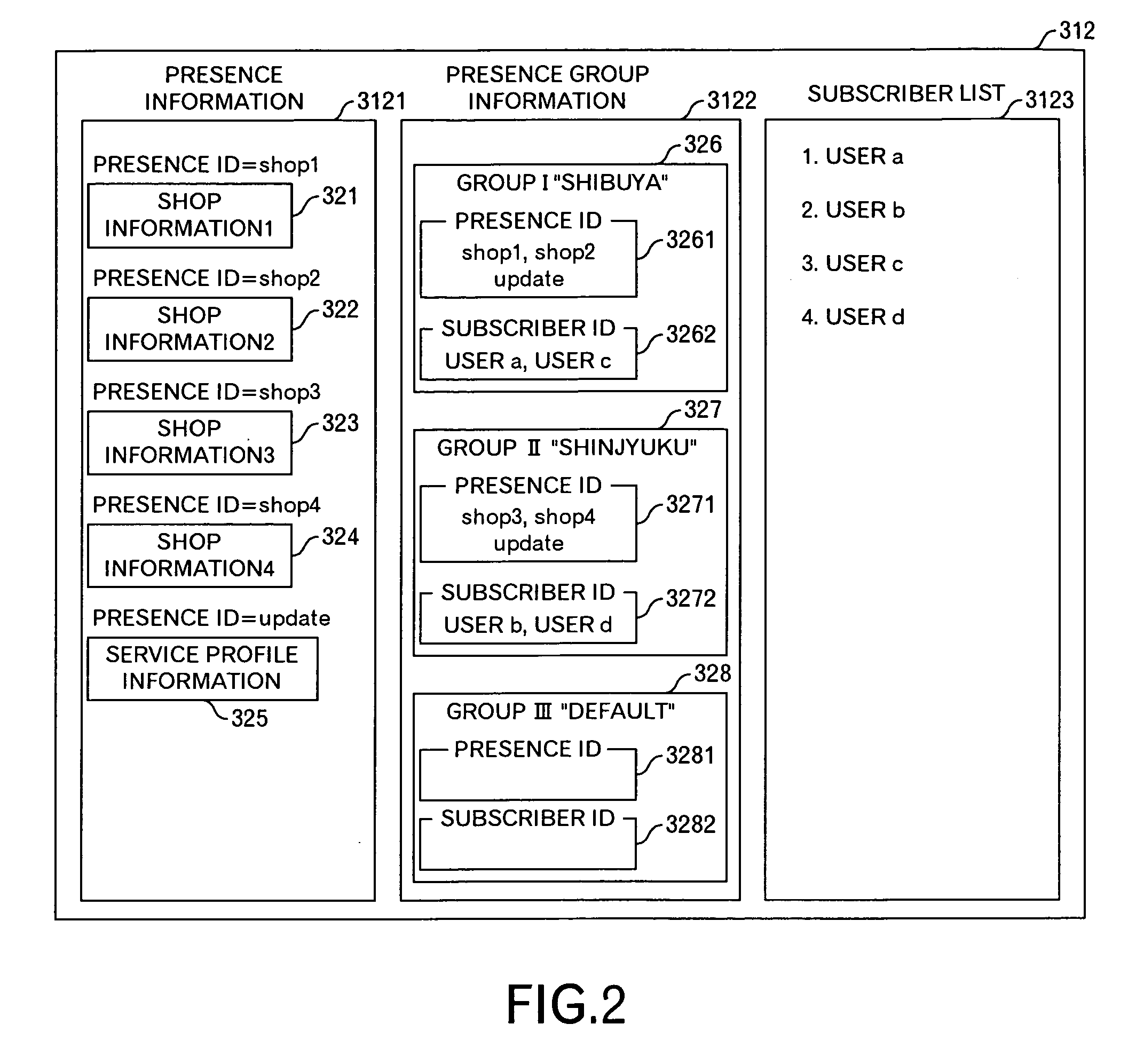
Presence information processing method and computer
InactiveUS20060242239A1Easy delivery settingSpecial service provision for substationMultiple digital computer combinationsInformation processingUser management
The presence information delivery system according to this invention manages, for each user, data of one or plural presence group so as to associate one or plural presence information items for the presence information to be delivered with an ID or IDs of one or plural delivery destination user of the presence information relating to the presence information item. With this configuration, by generating a new presence group associating the presence information item with the delivery destination user, by registering the presence information item to another presence group, and by registering the delivery destination user into another presence group, the flexible information delivery is enabled according to characteristics or the like of the delivery destination user and presence information.
Owner:FUJITSU LTD
Using context information to facilitate processing of commands in a virtual assistant
ActiveUS20140297284A1Clarify userReduce in quantityNatural language data processingSpeech recognitionPersonalizationInformation processing
A virtual assistant uses context information to supplement natural language or gestural input from a user. Context helps to clarify the user's intent and to reduce the number of candidate interpretations of the user's input, and reduces the need for the user to provide excessive clarification input. Context can include any available information that is usable by the assistant to supplement explicit user input to constrain an information-processing problem and / or to personalize results. Context can be used to constrain solutions during various phases of processing, including, for example, speech recognition, natural language processing, task flow processing, and dialog generation.
Owner:APPLE INC
Insider threat detection
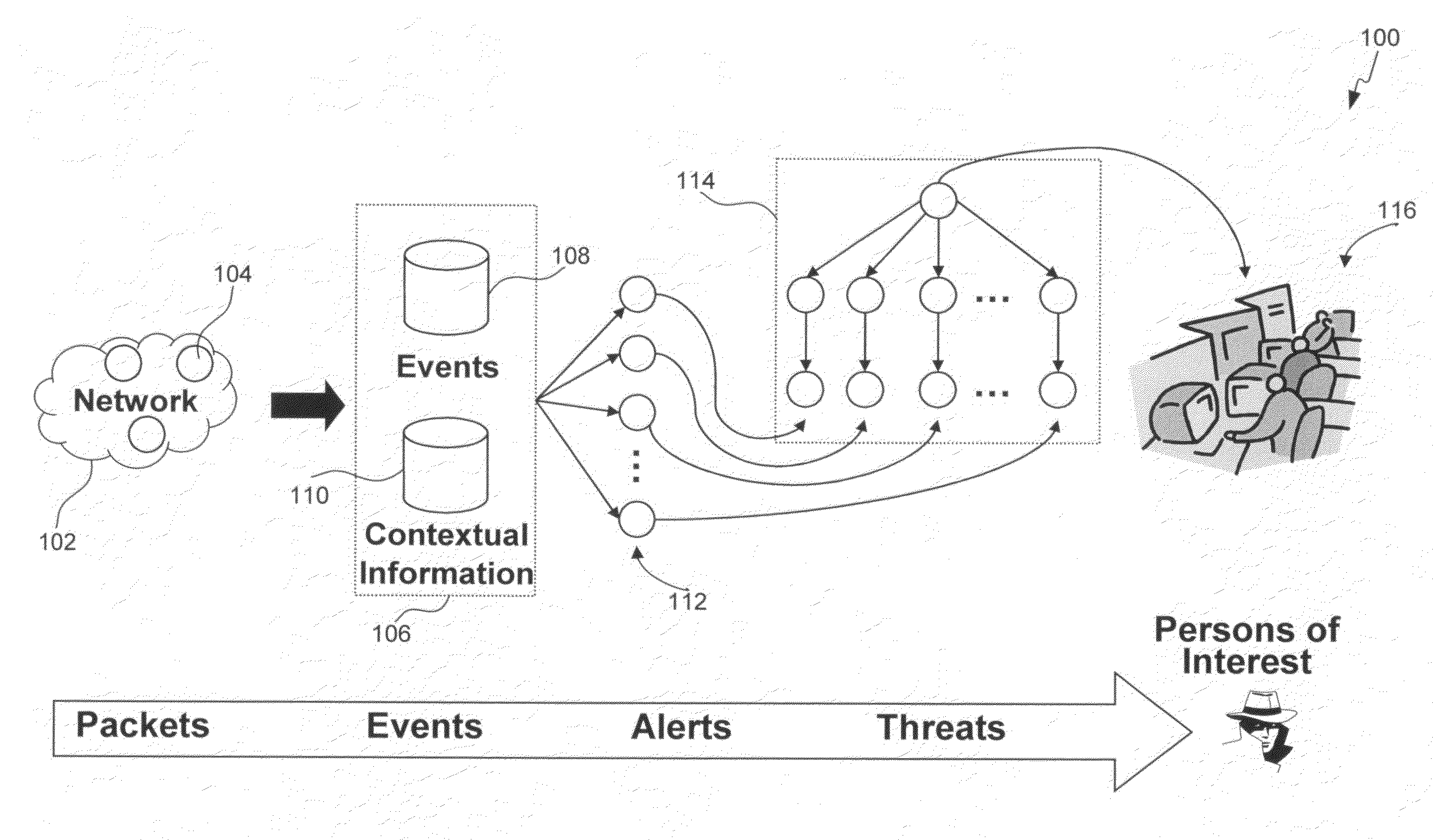
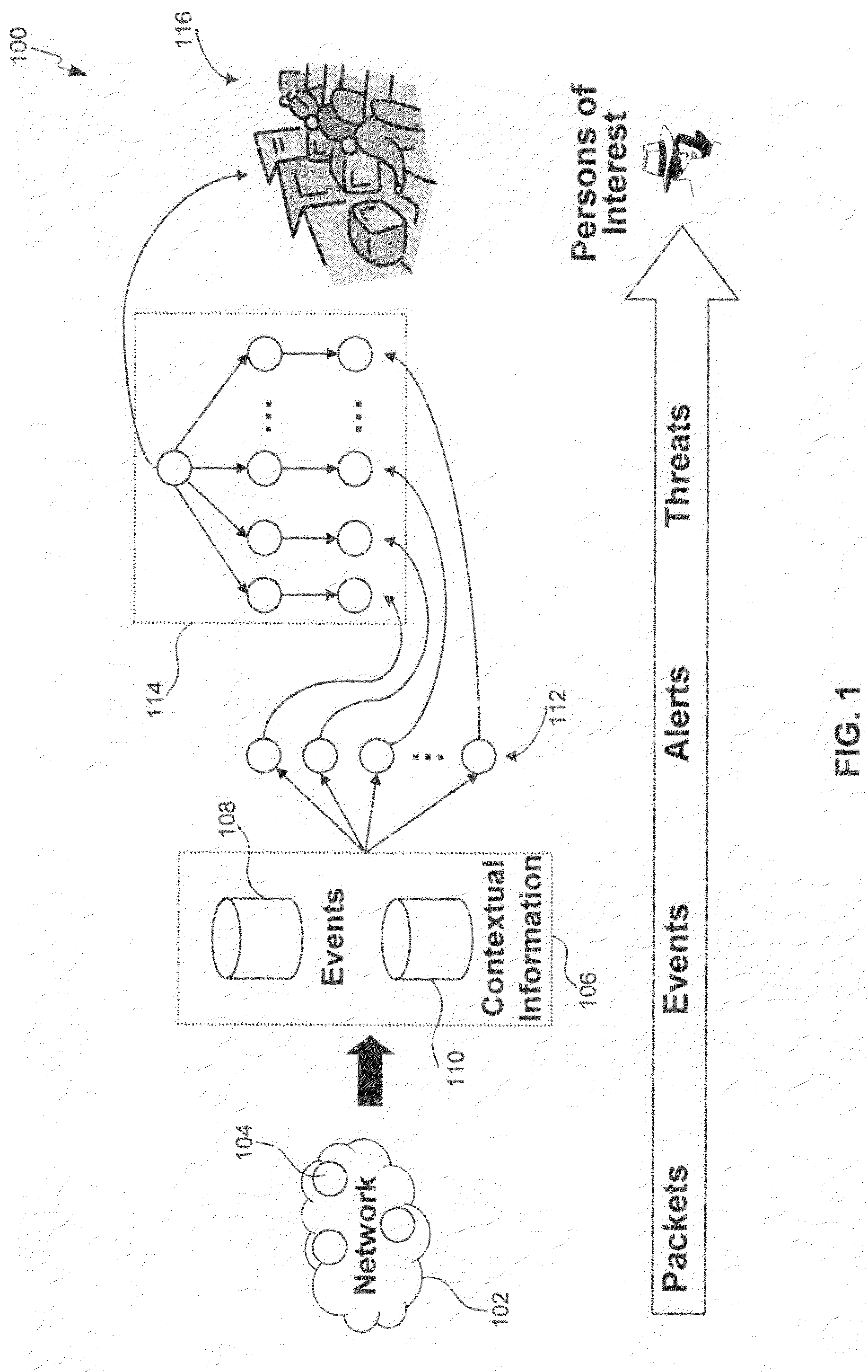
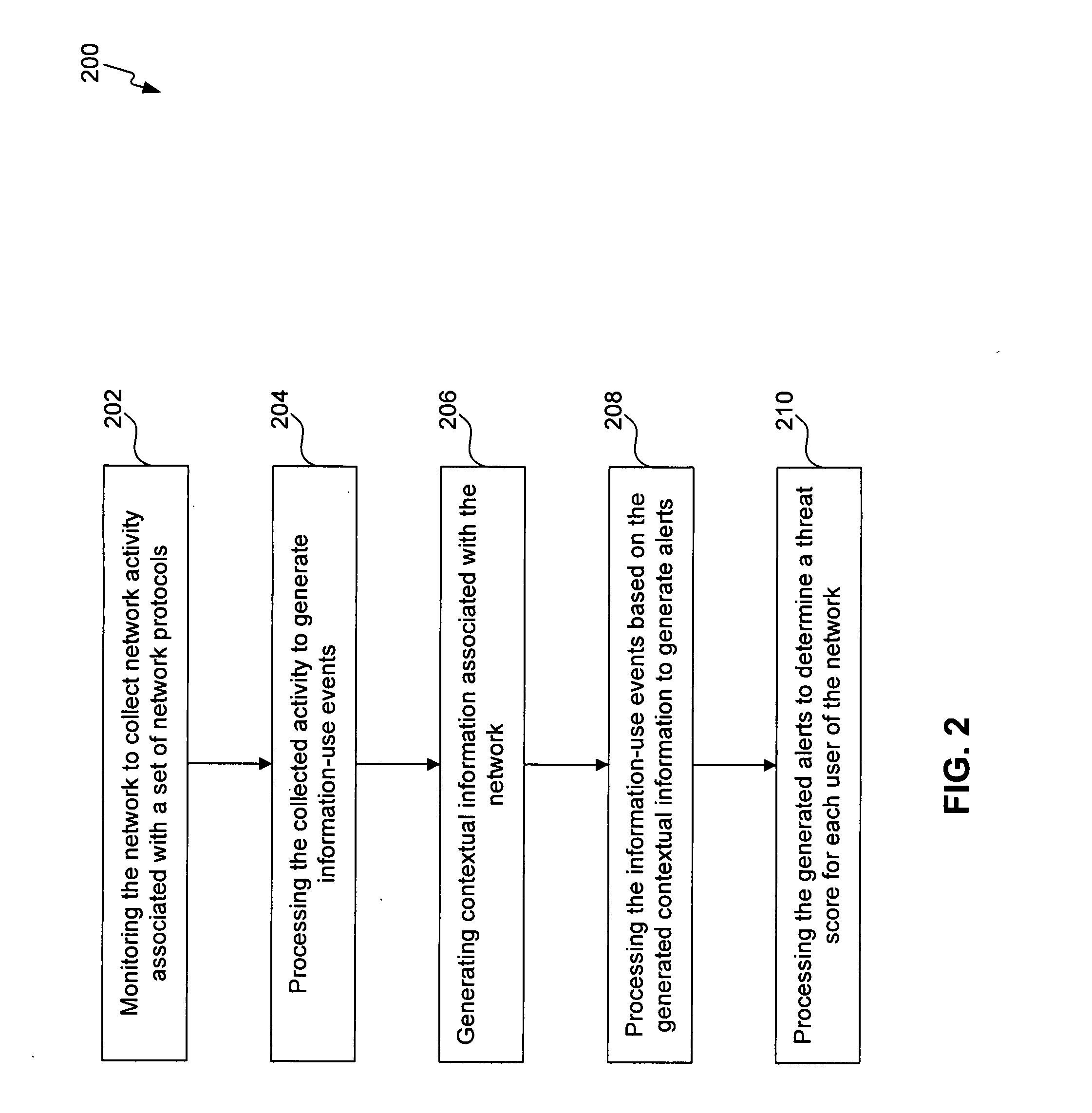
Methods, systems, and computer program products for insider threat detection are provided. Embodiments detect insiders who act on documents and / or files to which they have access but whose activity is inappropriate or uncharacteristic of them based on their identity, past activity, and / or organizational context. Embodiments work by monitoring the network to detect network activity associated with a set of network protocols; processing the detected activity to generate information-use events; generating contextual information associated with users of the network; and processing the information-use events based on the generated contextual information to generate alerts and threat scores for users of the network. Embodiments provide several information-misuse detectors that are used to examine generated information-use events in view of collected contextual information to detect volumetric anomalies, suspicious and / or evasive behavior. Embodiments provide a user threat ranking system and a user interface to examine user threat scores and analyze user activity.
Owner:MITRE SPORTS INT LTD
Information processing apparatus and control method thereof, and computer program
InactiveUS8112716B2Input/output processes for data processingInformation processingComputer hardware
An information processing apparatus comprising display unit configured to display a window, accepting unit configured to accept a resize instruction of the displayed window together with a scroll instruction indicating whether or not to scroll display contents within the window, and control unit configured to control a size of the window and a scrolling of the display contents within the window based on contents of the resize instruction and the scroll instruction, wherein when the scroll instruction indicates that the display contents are to be scrolled, the control unit changes the window to a size indicated by the resize instruction, and scrolls the display contents according to a change amount of the window, and when the scroll instruction indicates that the display contents are not to be scrolled, the control unit changes the window to a size indicated by the resize instruction, and suppresses a scrolling of the display contents.
Owner:CANON KK
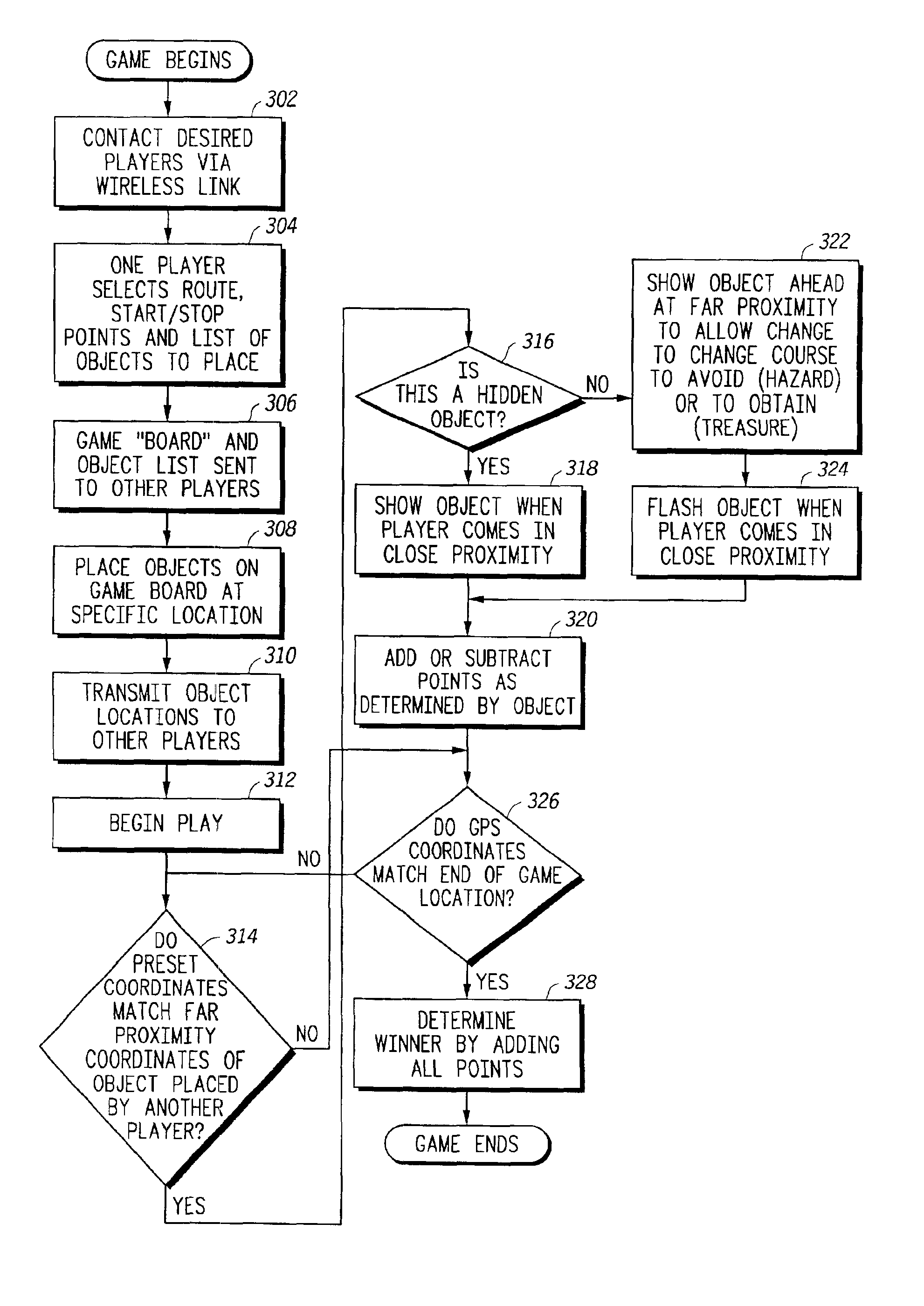
Method for providing entertainment to a portable device
InactiveUS6895238B2Broadcast with distributionInstruments for road network navigationIn vehicleComputer science
A unique method for providing entertainment to a portable device, such as a wireless communication device, is disclosed. The method includes steps of receiving location information related to said wireless communication device; providing challenges associated with a game to a user of a wireless communication; providing rewards in response to answers based upon the location of said wireless communication device. The method finds particular application in vehicles having telematics communications products.
Owner:GOOGLE TECH HLDG LLC
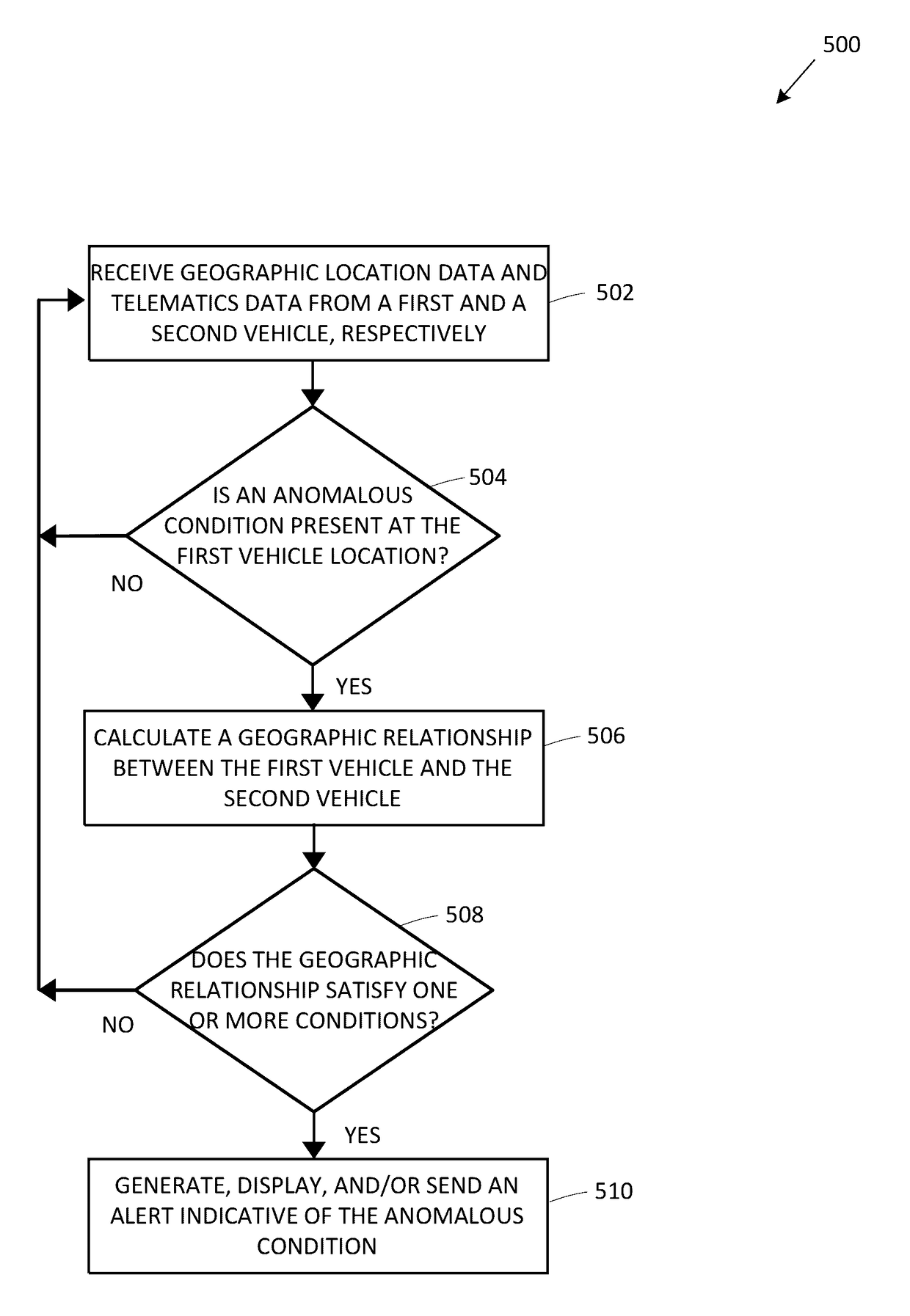
Alert notifications utilizing broadcasted telematics data
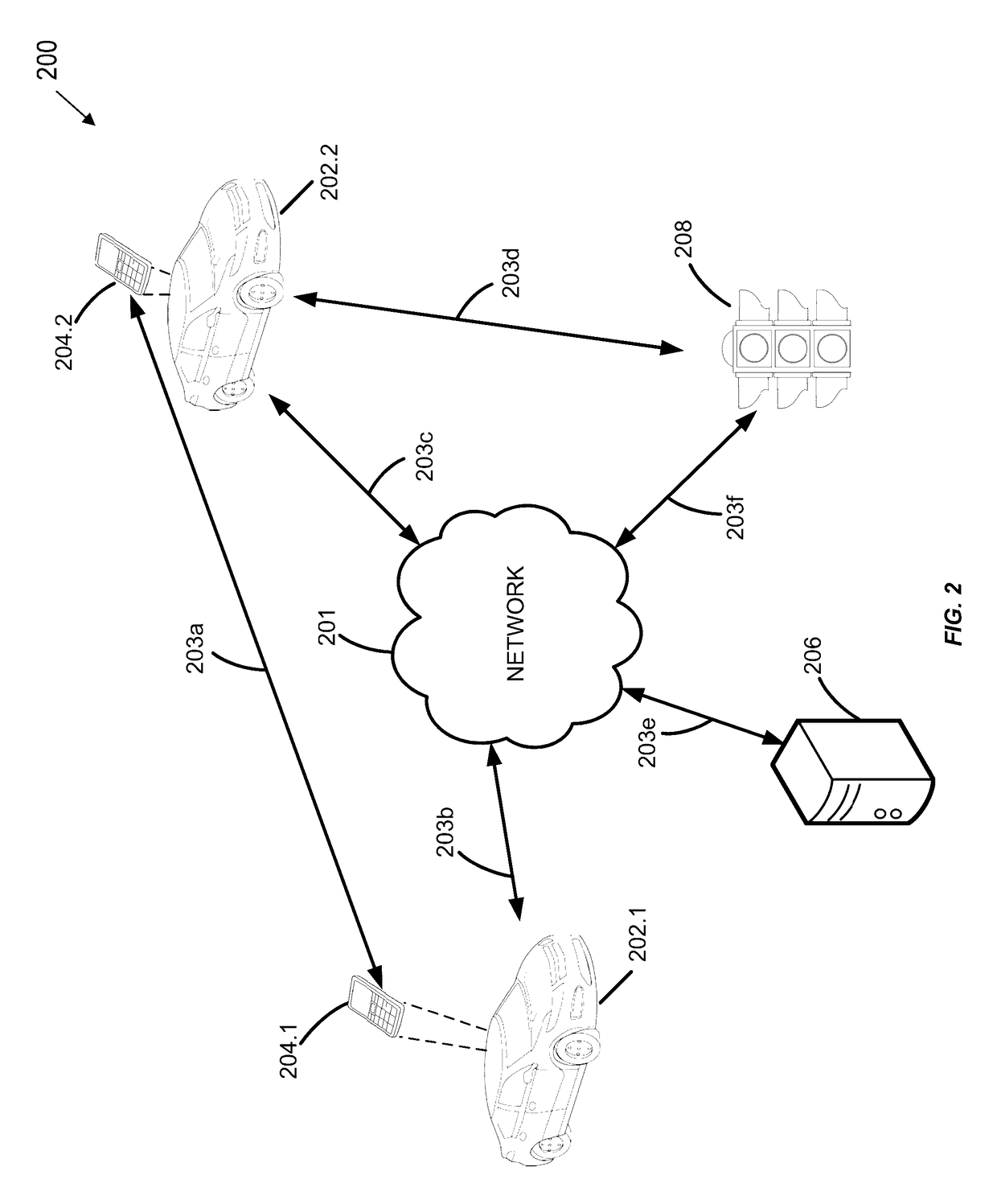
ActiveUS9679487B1Easy to driveReduce riskInstruments for road network navigationRegistering/indicating working of vehiclesGeolocationEngineering
Geographic location data and telematics data may be collected in real-time by a mobile device within a vehicle, or the vehicle itself. The telematics data may indicate vehicle direction, speed, motion, etc., as well as traffic hazards in the surrounding environment. A remote server may receive the location and telematics data from two vehicles. If an anomalous or hazardous condition exists in the vicinity of the first vehicle, a geographic relationship with the second vehicle is determined, and if within a predetermined distance, an alert or alternate route for the second vehicle is determined and transmitted to the second vehicle. As a result, a negative impact or risk of collision caused by the anomalous condition on the second vehicle is alleviated. The amount of the insured's usage of the telematics data-based risk mitigation or prevision functionality may be used to calculate or adjust insurance premiums, rates, or discounts.
Owner:HYUNDAI MOTOR CO LTD +1
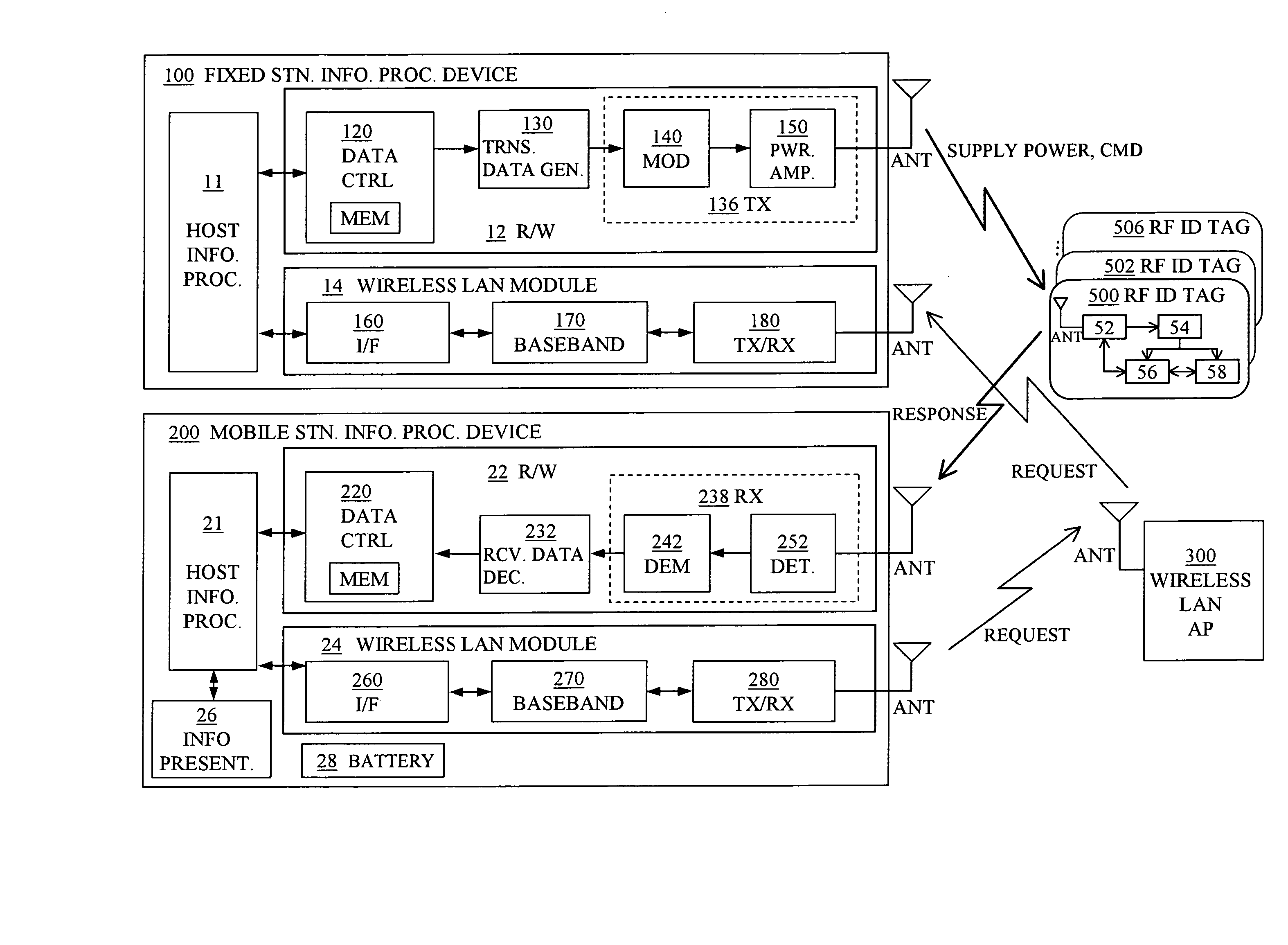
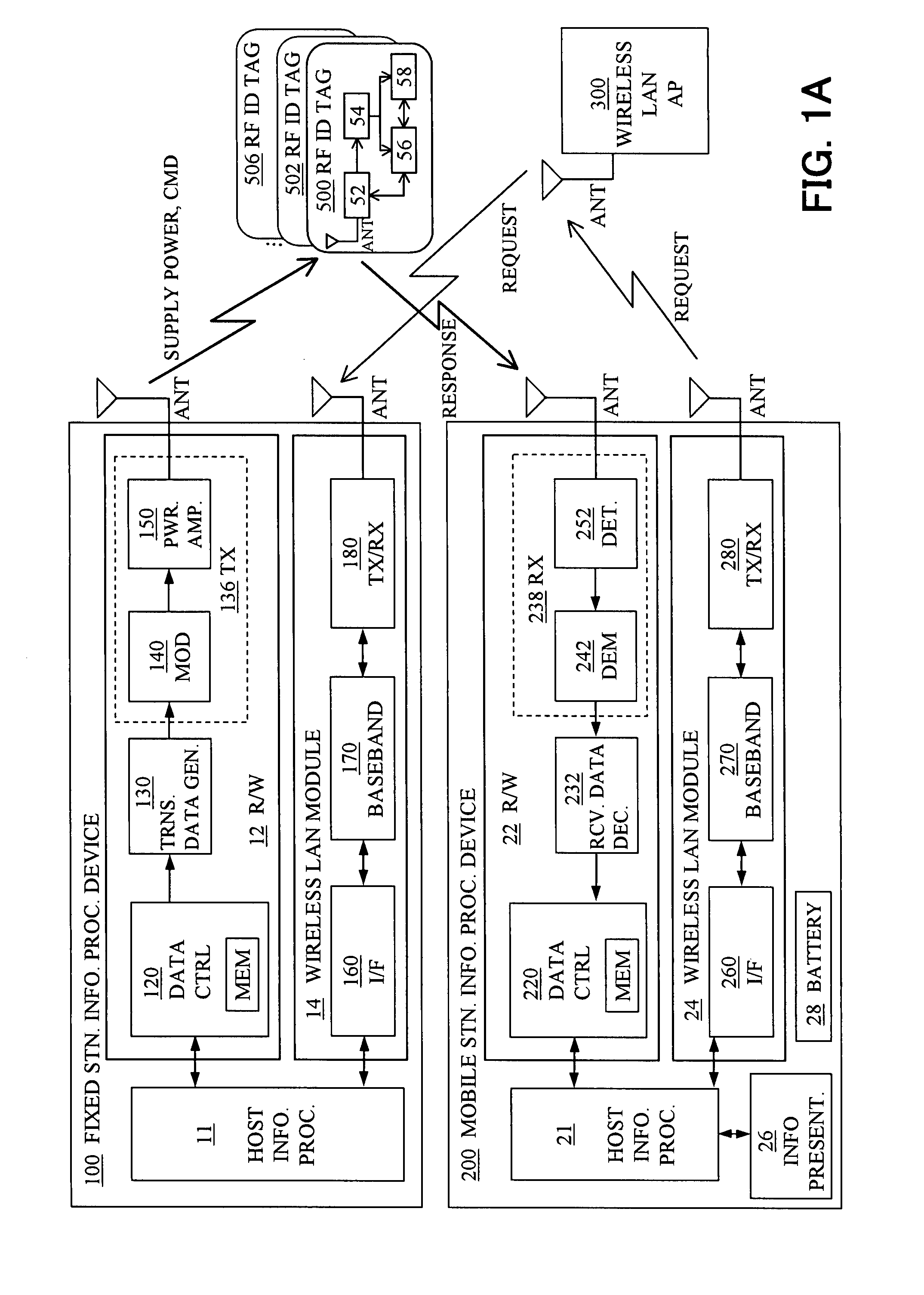
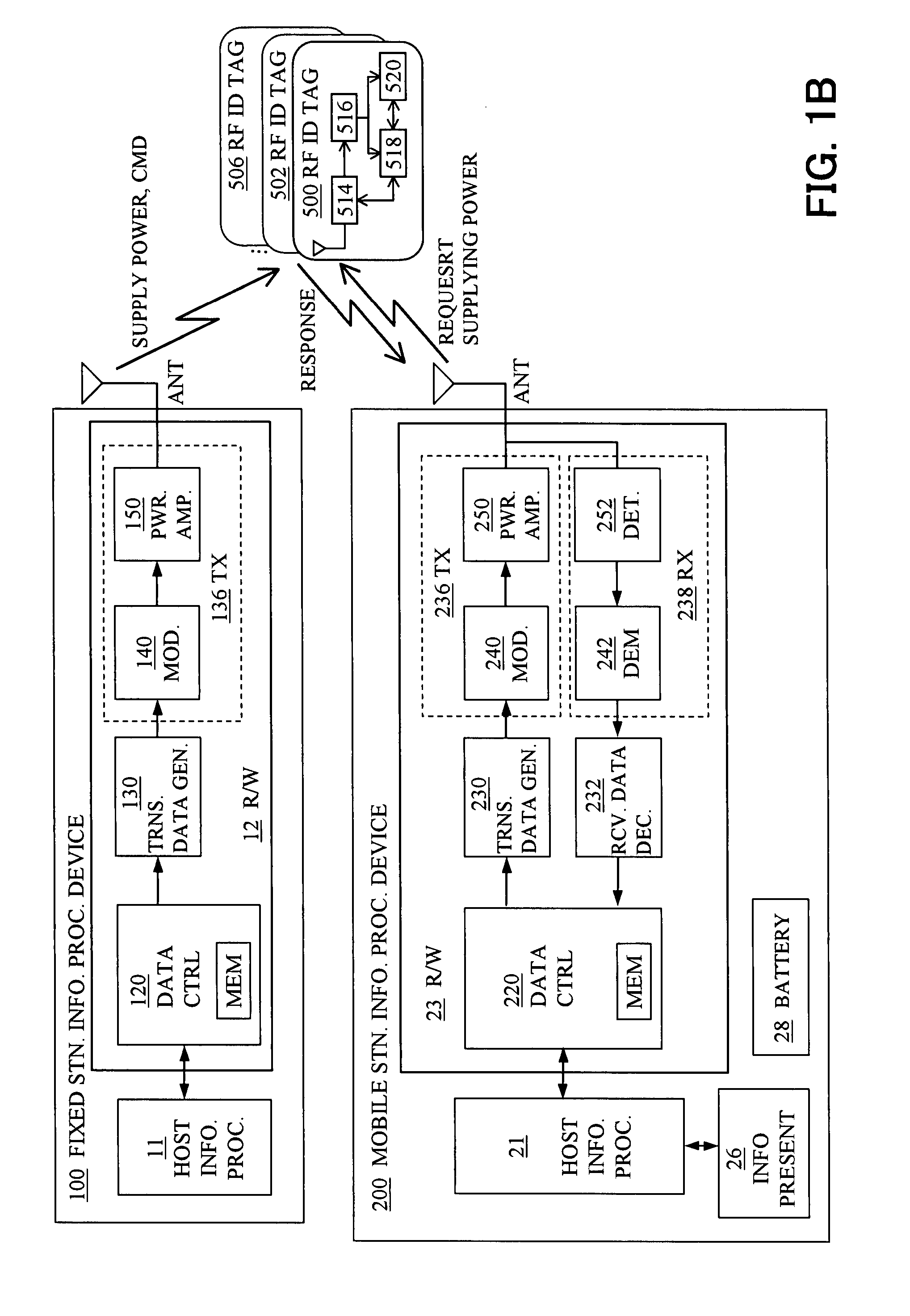
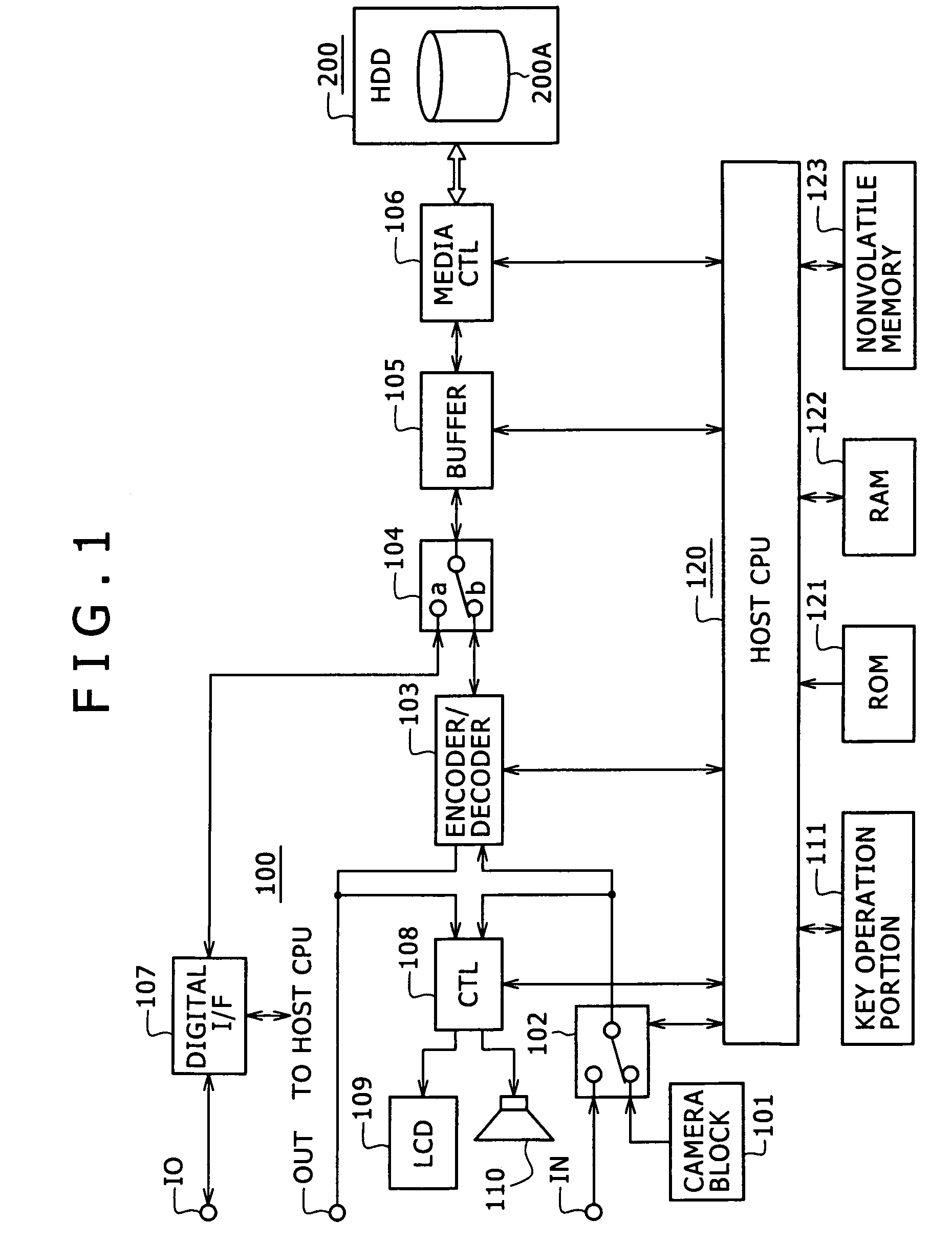
Information access system for accessing information in contactless information storage device, and method therefor
InactiveUS20070273486A1Reduce power consumptionAvoid collisionElectric signal transmission systemsDigital data processing detailsInformation processingComputer hardware
An information access system includes: a passive contactless information storage device (500) capable of transmitting and receiving signals; a fixed-station information processing device (100) having an information processing unit, and a wireless transmitter for transmitting, in a contactless manner, a command signal for requesting transmission of information stored in the information storage device and supplying power in a contactless manner to the information storage device; and a mobile-station information processing device (200) having an information processing unit, an information presenting unit, a battery, and a wireless receiver for receiving a response signal for response to the command signal, from the information storage device in a contactless manner. While the fixed-station device is supplying power to the information storage device in the contactless manner, the information storage device transmits, in response to the command signal, the response signal to the mobile-station device in the contactless manner.
Owner:FUJITSU LTD
Automated microfabrication-based biodetector
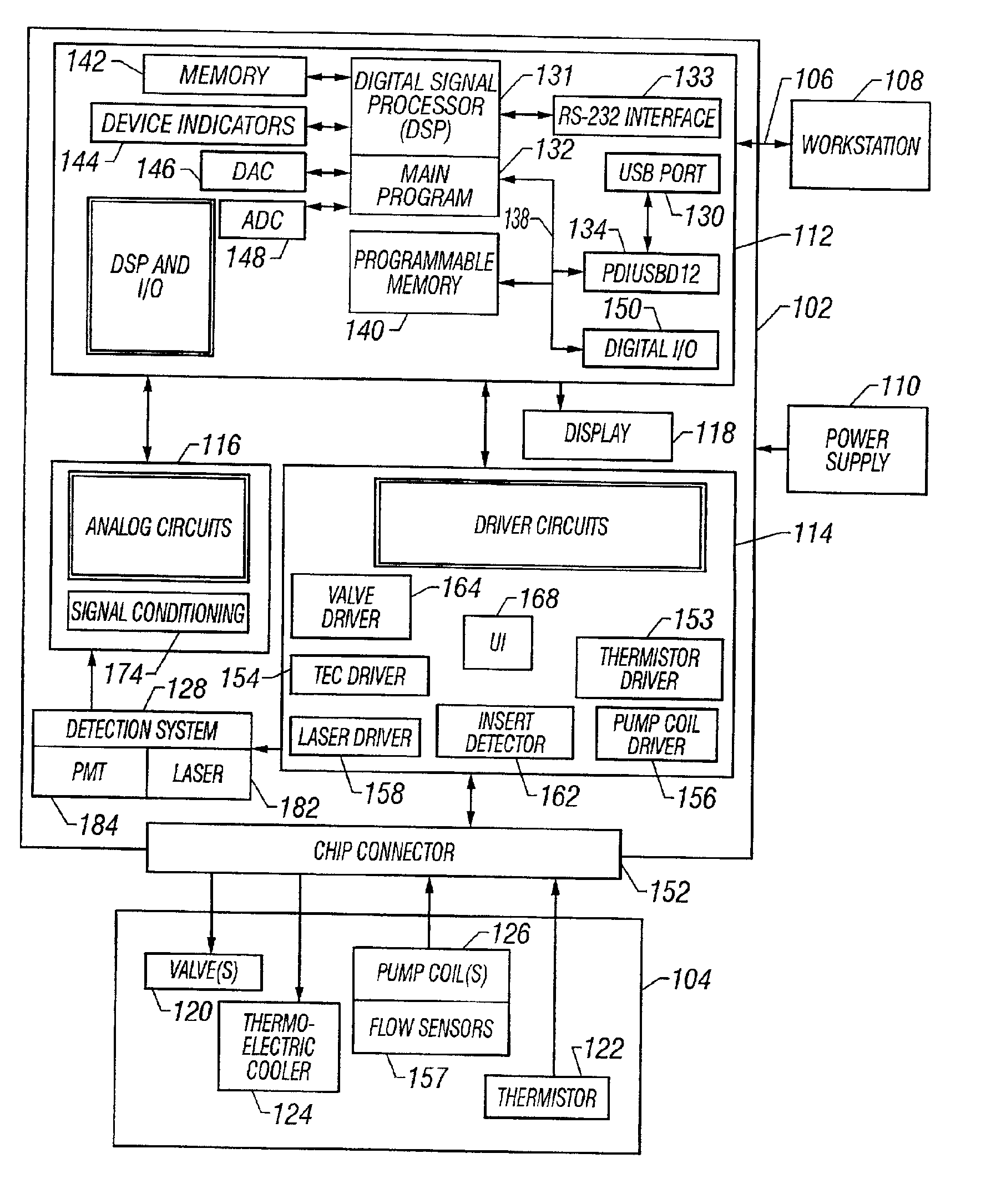
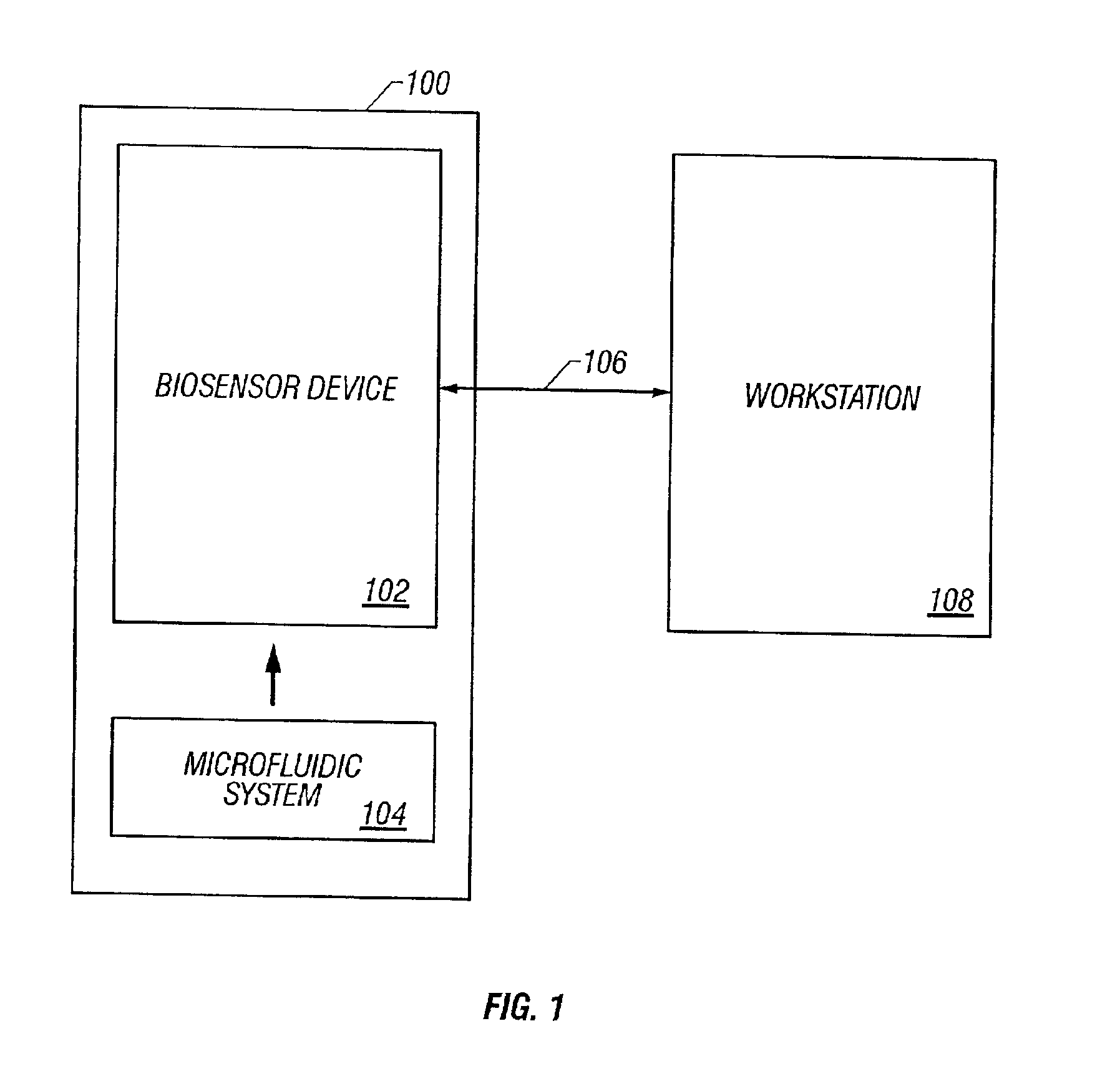
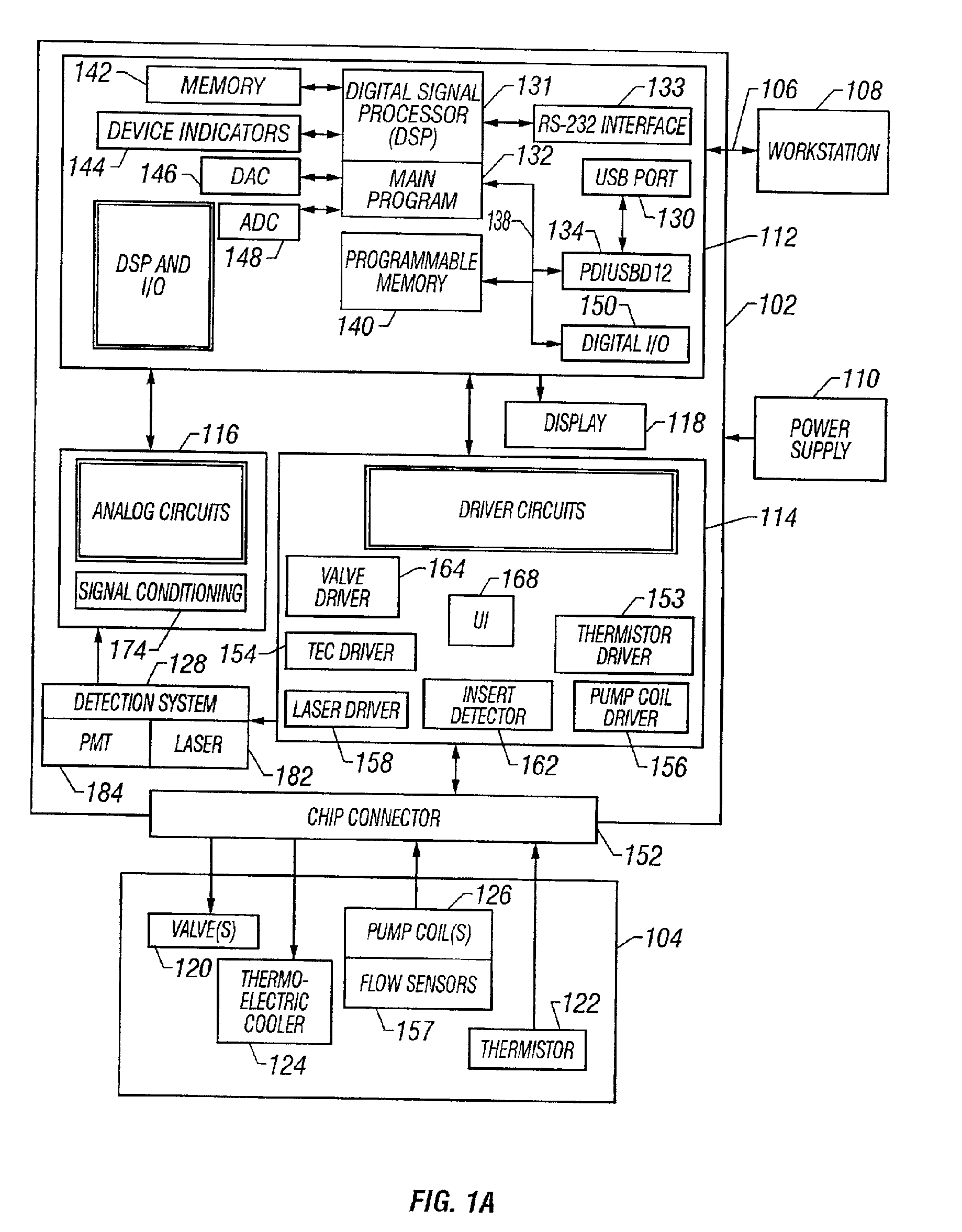
InactiveUS6878755B2Reduce riskHeating or cooling apparatusMicrobiological testing/measurementInformation processingChannel coupling
A system, apparatus, and method for processing a sample for chemical and / or biological analysis, and detecting one or more target substances. A first system of microfabricated components includes at least a reservoir and a channel, and a second system of detection components including at least a lens. The lens is focused on a sensing platform of the first system. The sensing platform is coupled to the reservoir by the channel. Various types of detection systems can be utilized with the present invention including fluorescence detection systems with a laser that is positioned to illuminate a sample in the sensing platform. The microfabricated components include one or more pumps, valves, mixers, and filters. A thermoelectric cooler can be positioned to control the temperature of at least one of the microfabricated components. A variety of component configurations can be implemented, and a variety of different processes can be performed, depending on the configuration of components. The device can also be networked with other information processing devices and share data regarding substances detected from the sample.
Owner:MICROGEN SYST
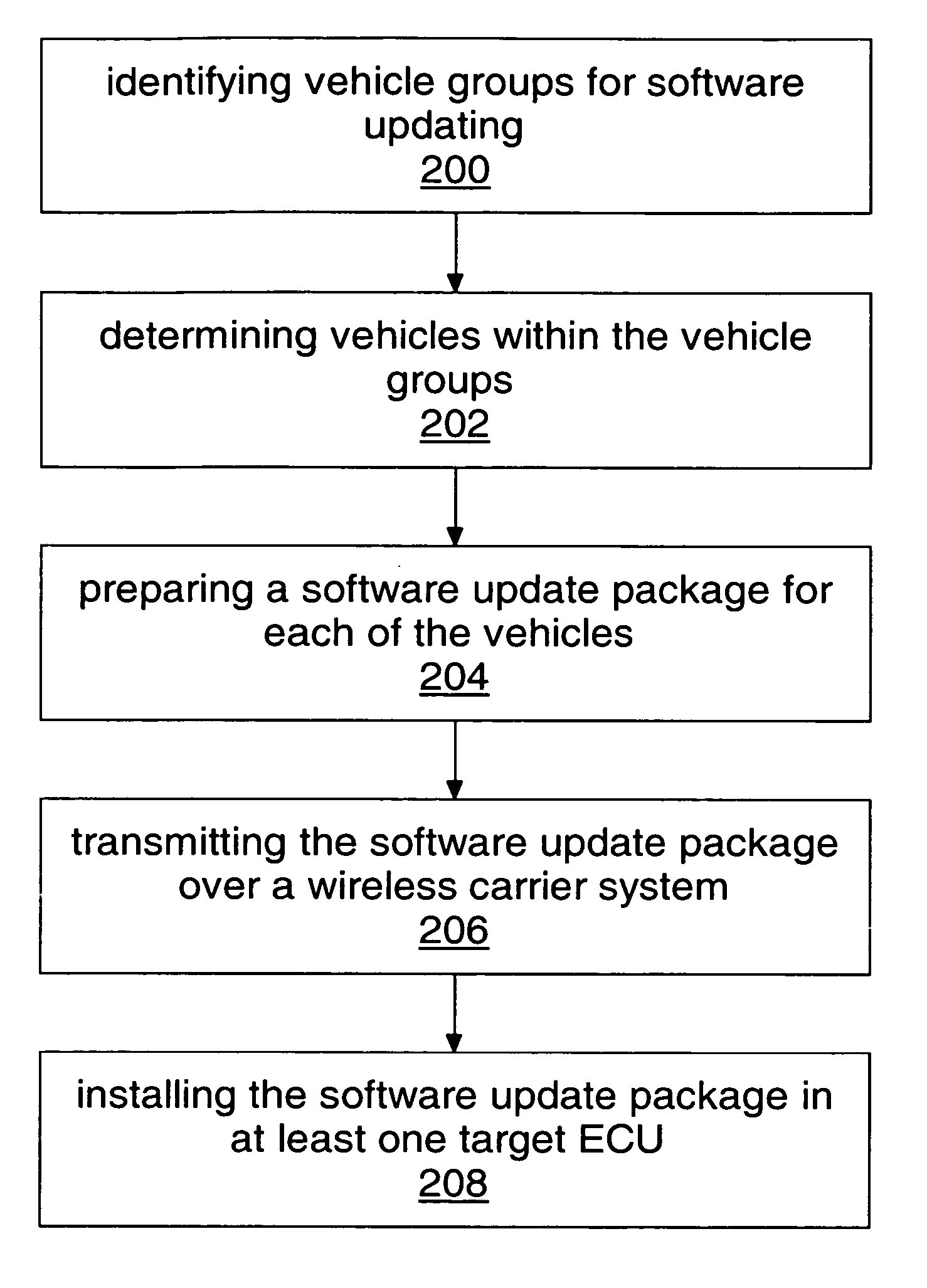
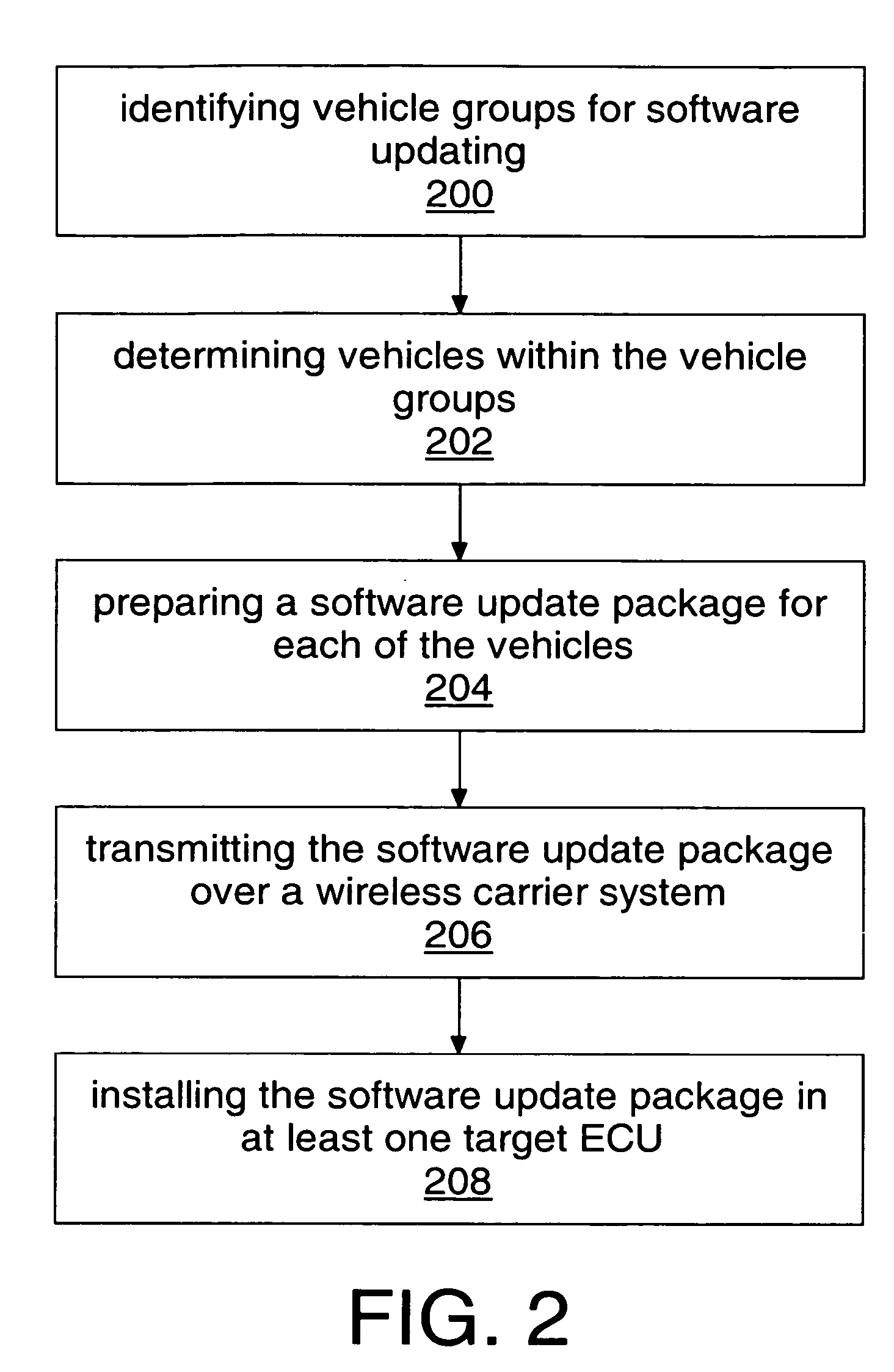
Method and system for remote reflash
A system and method for remote reflashing of software for electronic control units (ECUs). A method includes identifying vehicle groups for software updating 200, determining vehicles within the vehicle groups, each of the vehicles having a telematics device and a plurality of ECUs 202, preparing a software update package for each of the vehicles 204, transmitting the software update package over a wireless carrier system to the telematics device of each of the vehicles 206, and installing the software update package in at least one target ECU for each of the vehicles 208.
Owner:GENERA MOTORS LLC
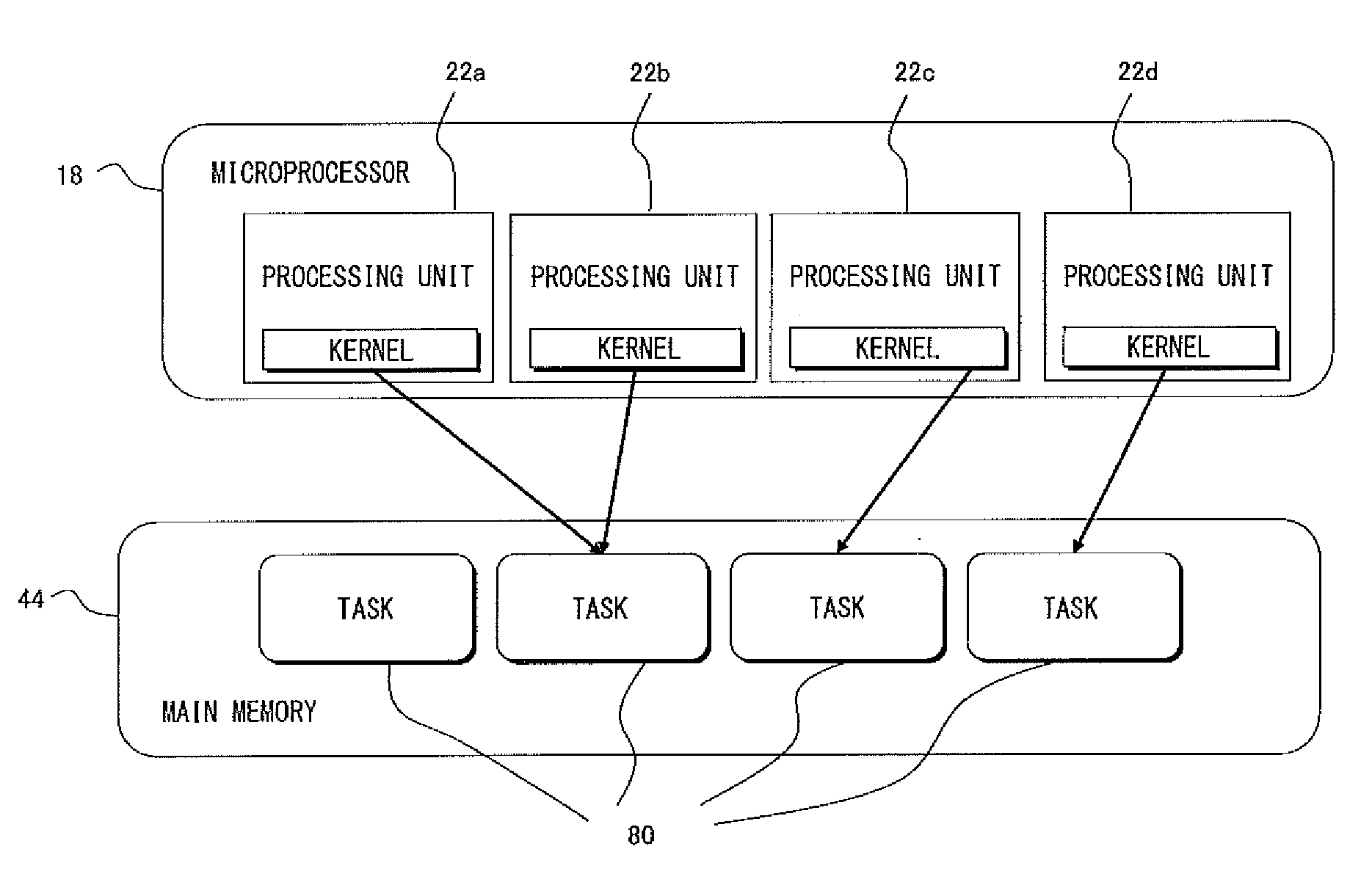
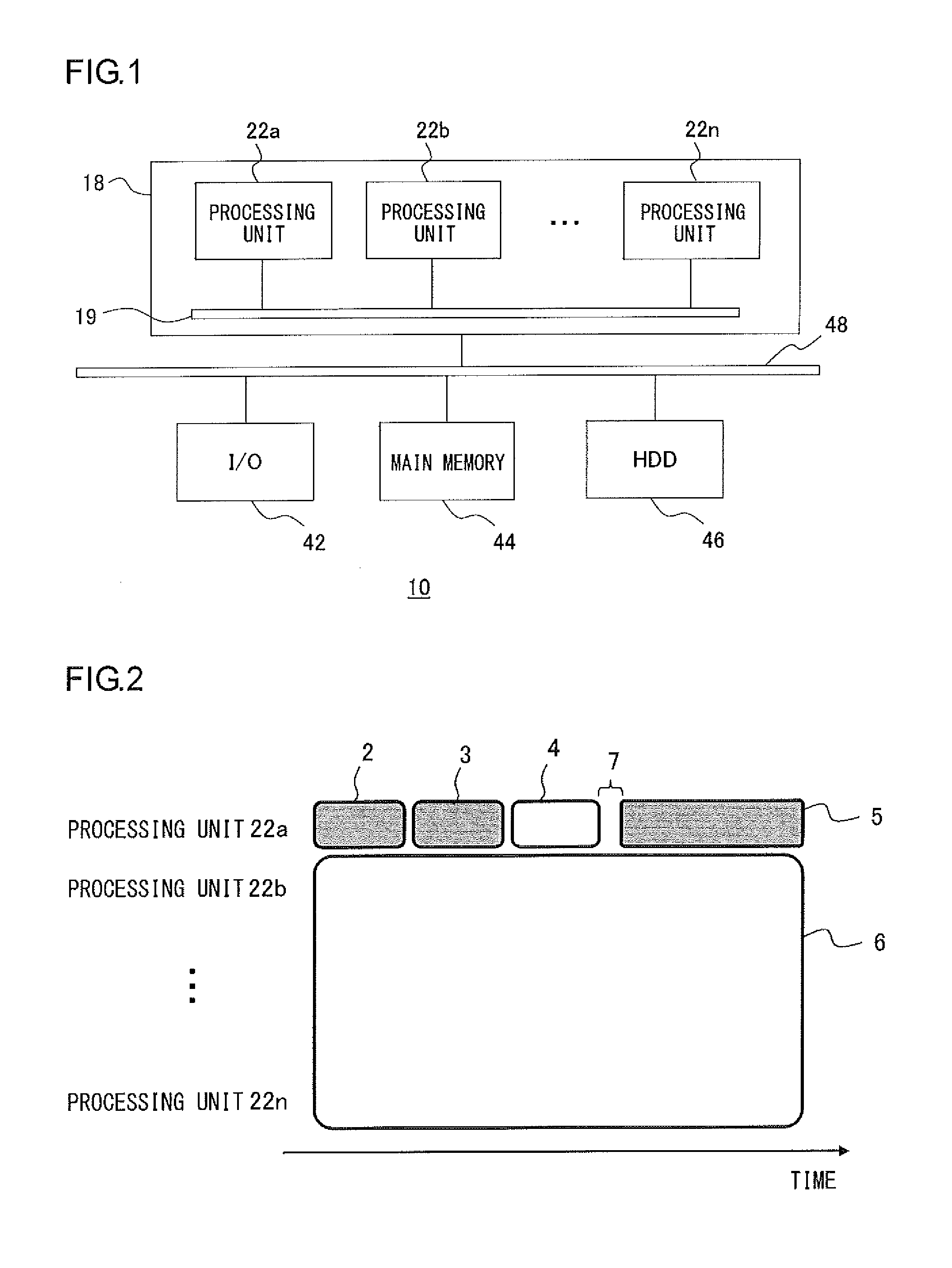
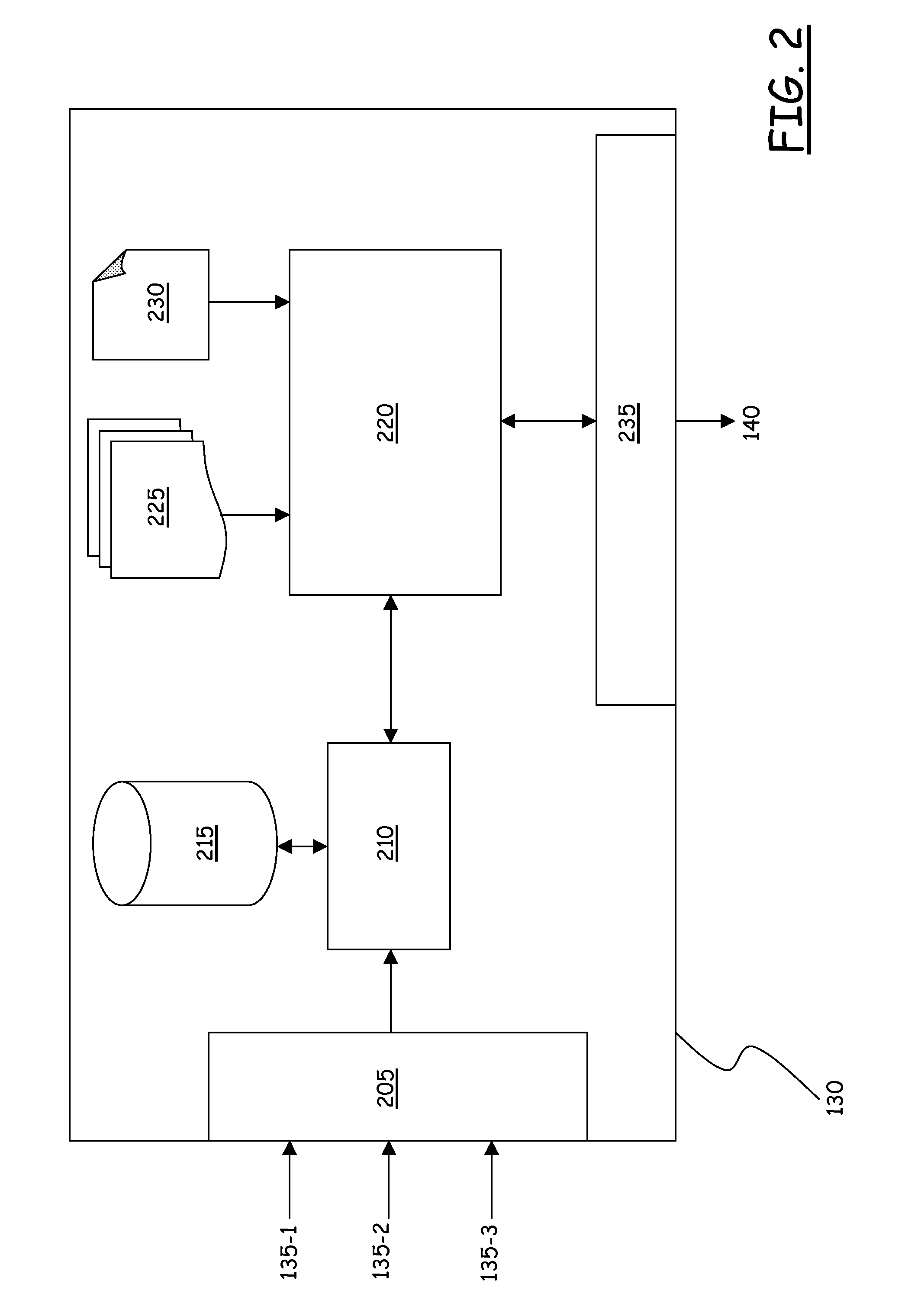
Information processing device and information processing method
ActiveUS20110302587A1Efficient execution of parallelEfficient executionMultiprogramming arrangementsMemory systemsMain processing unitInformation processing
A system-level management unit generates a system processing and makes a processing request to a task allocation unit of a user-level management unit. The task allocation unit schedules the system processing according to a procedure of an introduced user-level scheduling. A processing unit assigned to execute the system processing sends a notification of acceptability of the system processing to a main processing unit, by halts an application task in appropriate timing or when the processing of the current task is completed. When the notification is received within the time limit for execution, the system-level management unit has the processing unit start the system processing.
Owner:SONY COMPUTER ENTERTAINMENT INC
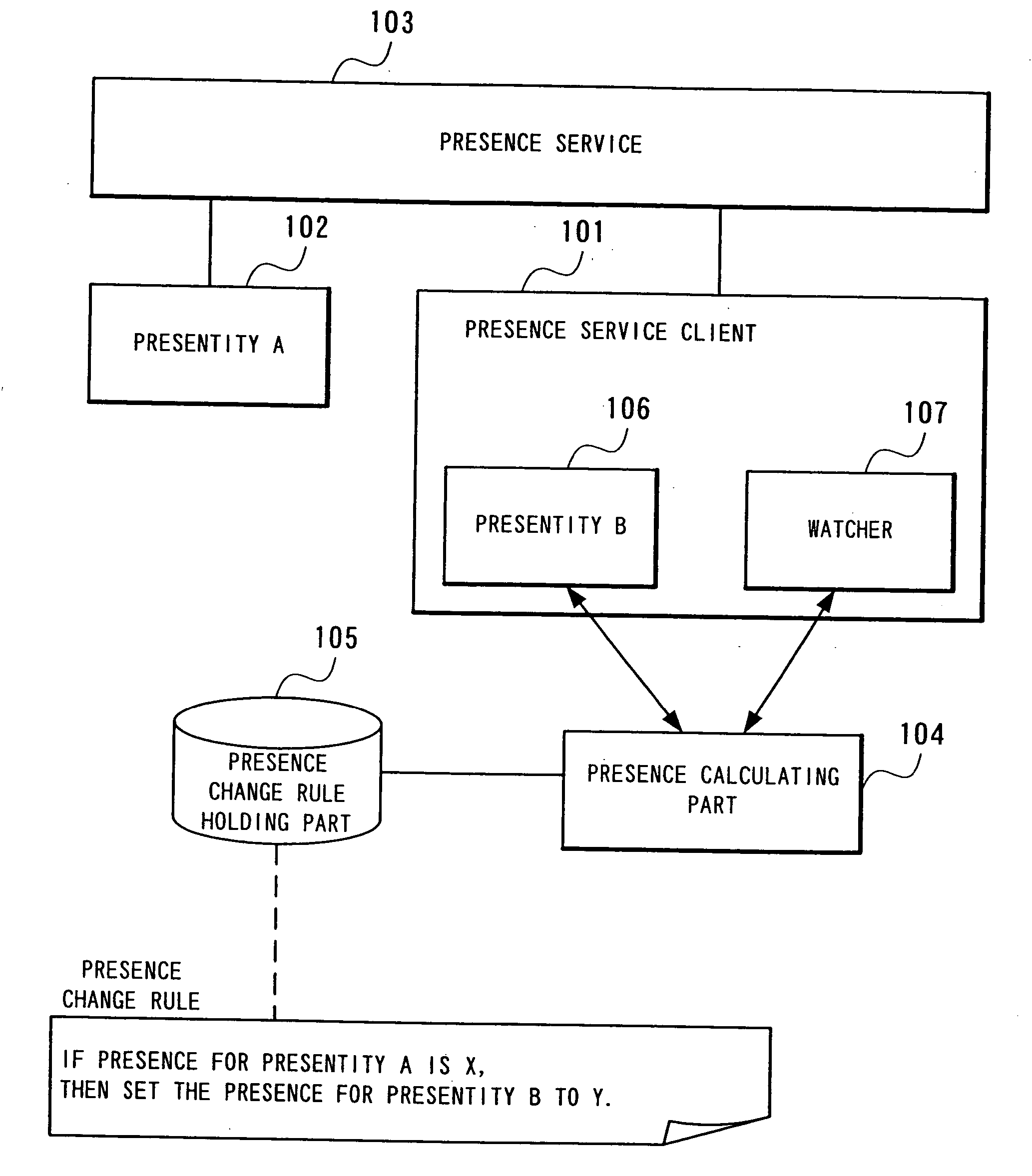
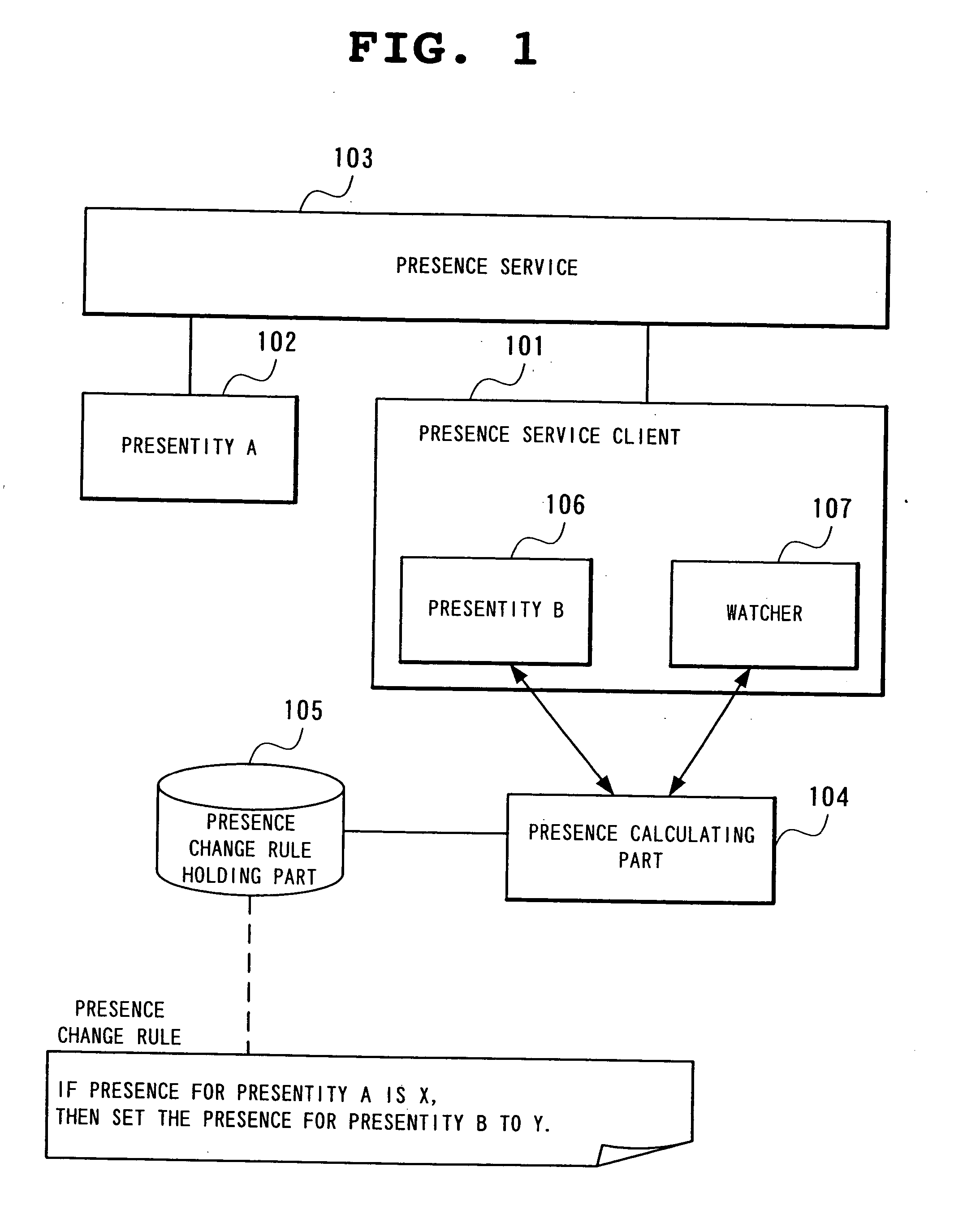
Presence system and information processing equipment, dynamic buddy list generation method in presence system, and presence notification destination controlling method and its program for use with presence system
ActiveUS20040153506A1Easy to seeEnsure normal communicationInformation formatContent conversionInformation processingPresence service
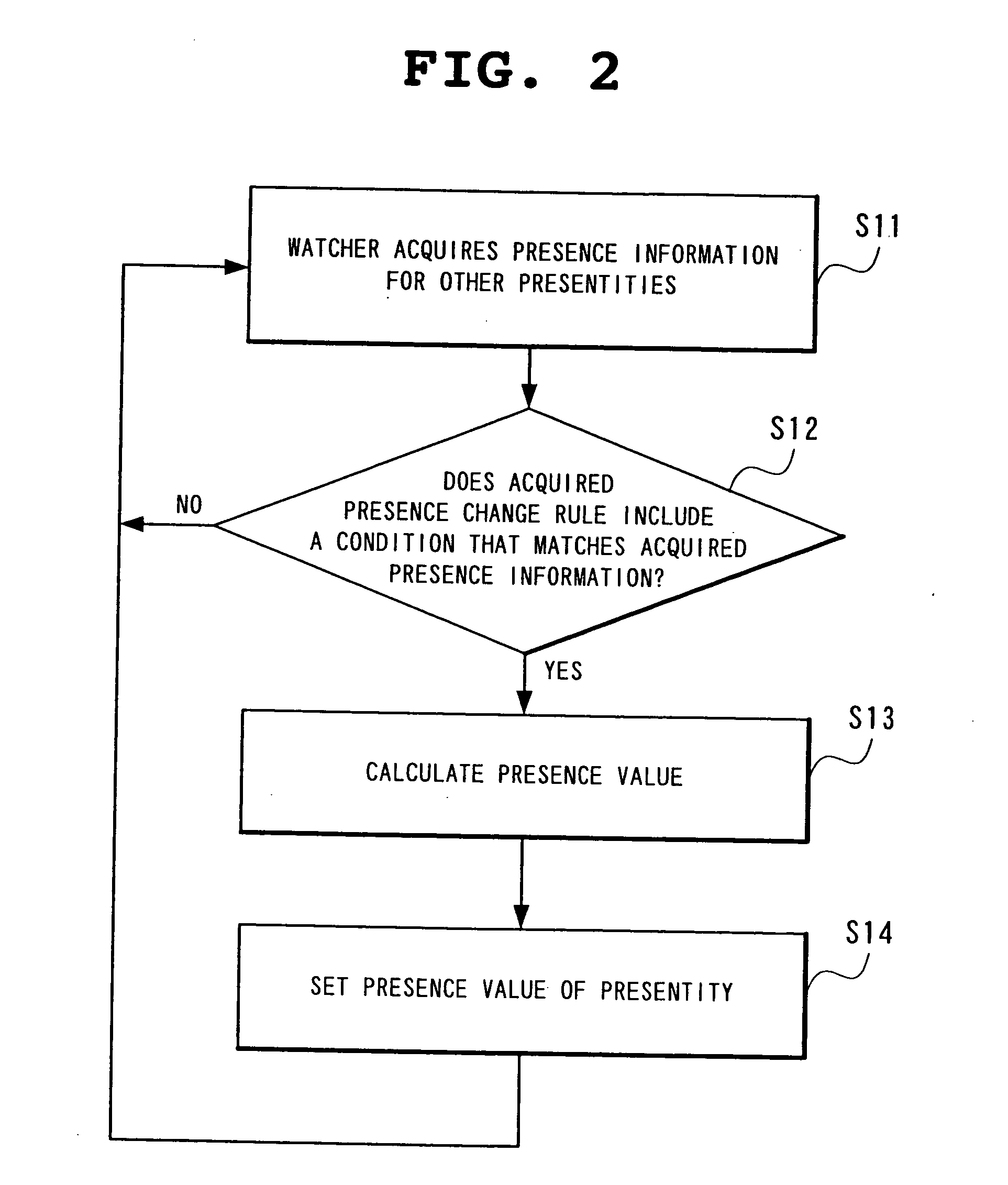
A presentity service client has a presentity that issues presence information to a presence service and a watcher which observes presence information for other presentities; a presence change rule holding part holds a presence change rule; and a presence calculating part changes the presence information for the presentity, using as a trigger a change in presence information of other presentities, based on the presence information of other presentity acquired by the watcher and in accordance with the presence change rule held by a presence change rules holding part.
Owner:NEC CORP
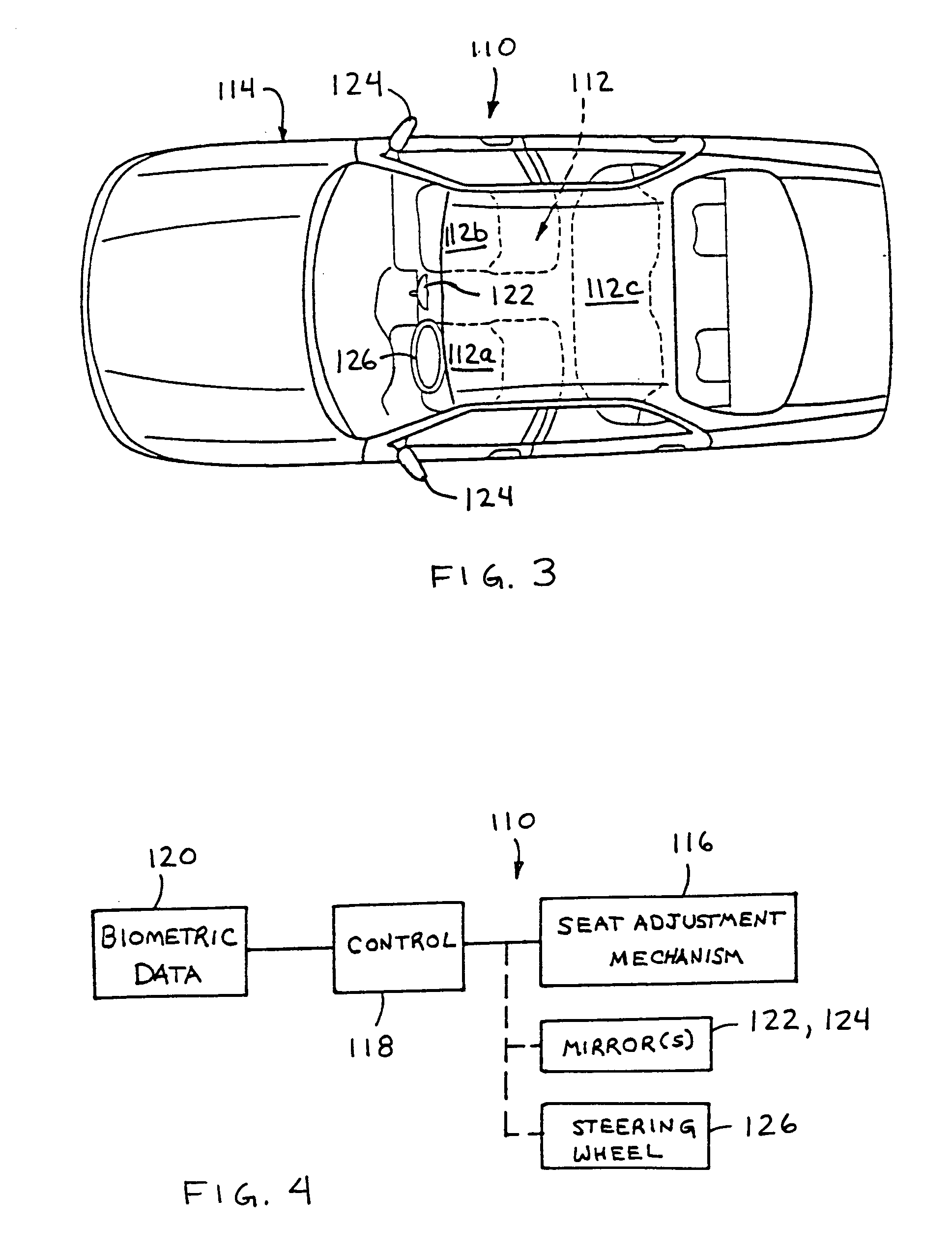
Adaptive drive supporting apparatus and method
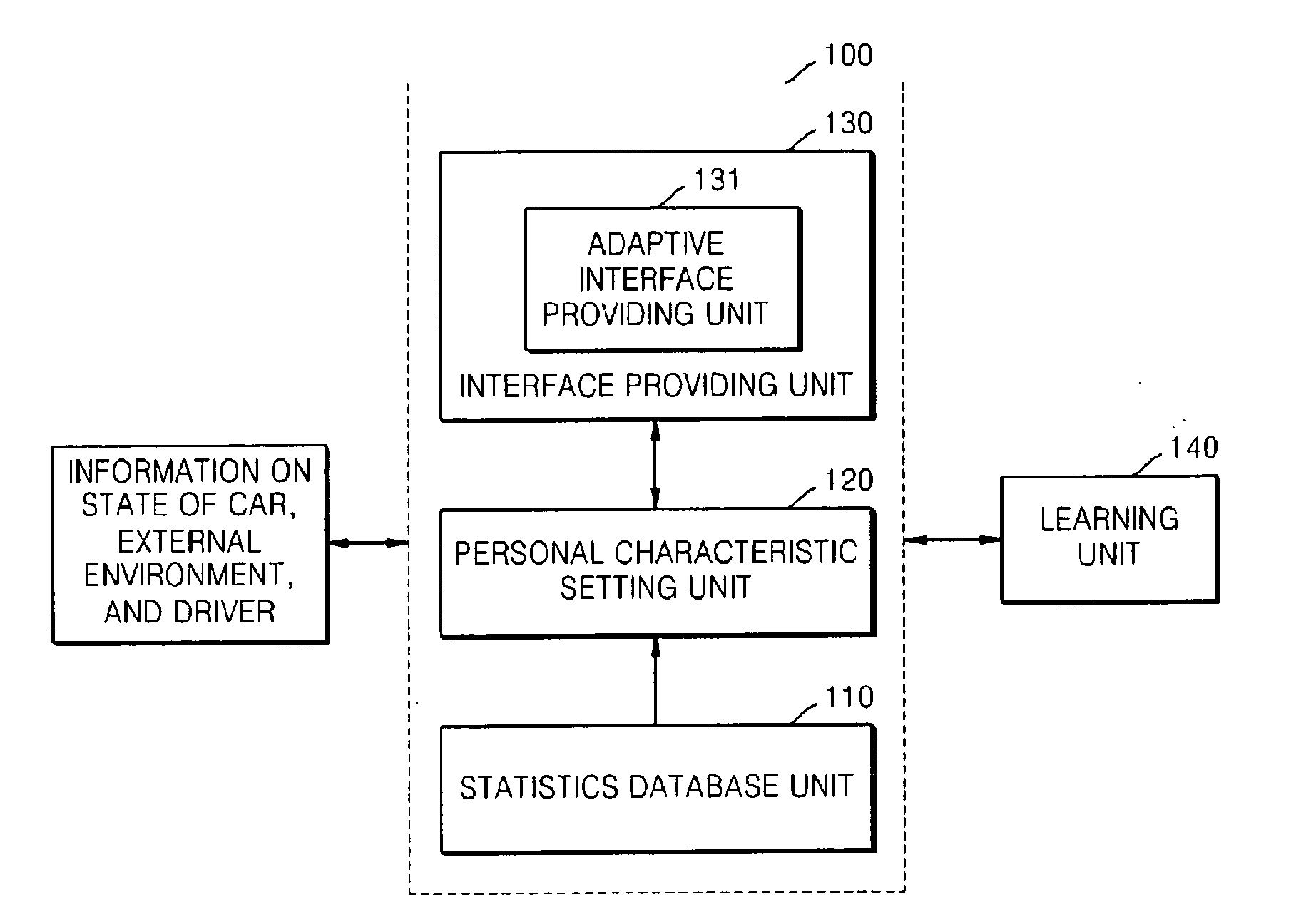
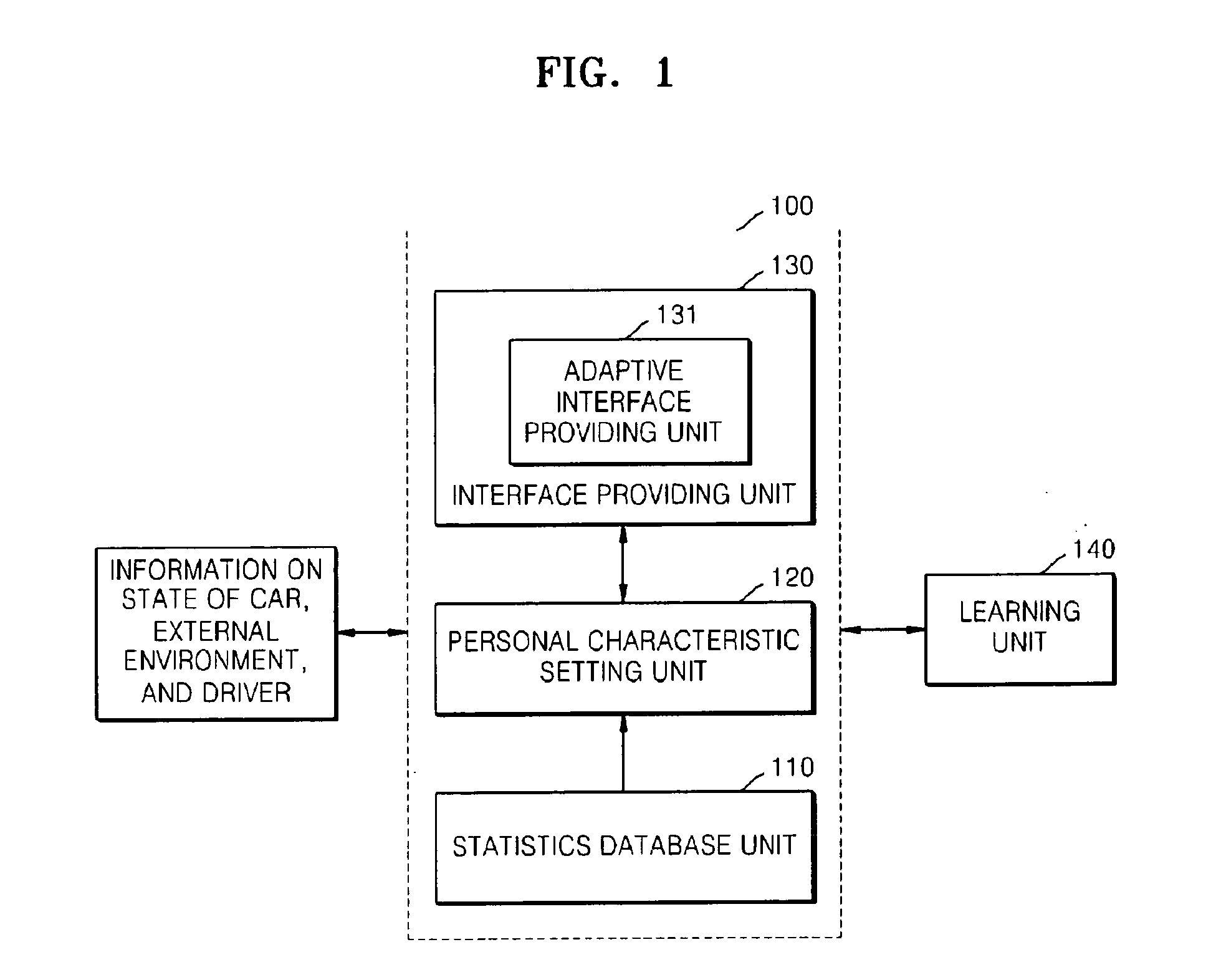
InactiveUS20100179932A1Overcome limitationsReduce decreaseRoad vehicles traffic controlDigital computer detailsPersonalizationStatistical database
Provided are an adaptive drive supporting apparatus and method that provide a personalized telematics user interface capable of supporting safe driving and convenient use. The adaptive drive supporting apparatus includes: a statistics database unit which stores and manages information on an average degree of attention required when a driving operation, a state of a car, or an external environment changes, information on degrees of attention required for manipulations of interfaces of the car, and a similarity between the functions of the interfaces; a personal characteristic setting unit which sets an individual degree of attention for each driver based on the average degree of attention according to a change in at least one of the driving operation, the state of the car, and the external environment; and an interface providing unit which determines whether or not a sum of the individual degree of attention and the degree of attention required when each driver manipulates a requested interface is larger than a predetermined threshold degree of attention required for safe driving.
Owner:ELECTRONICS & TELECOMM RES INST
RFID systems and methods for automatically detecting and/or directing the physical configuration of a complex system
ActiveUS8138925B2Less timeAvoid excessive errorServersAutomatic card filesInformation processingRadio frequency
A radio-frequency identification (RFID)-based configuration detection system for automatically detecting, directing, and / or configuring the physical configuration of a complex system constituted by a set of one or more types of mateable components. The RFID configuration detection system utilizes a set of mateable RFID tags arranged so that each mateable component includes at least one mateable RFID tag. Each RFID tag includes information about its associated component and is arranged so that when the components are mated, their associated RFID tags also are mated. The system uses at least one RFID reader to read RFID tag signals from the RFID tags. The RFID tag signals provide information about mating status of the component, as well as information about components themselves. An information processing system operably connected to the RFID reader receives and process information concerning the number and type of mated connections and thus the configuration. Changes to the configuration, such as mated connections being unmated, can be tracked to provide real-time configuration information.
Owner:FIBER MOUNTAIN INC
Method and system for estimating road traffic
ActiveUS8340718B2Analogue computers for vehiclesAnalogue computers for trafficInformation typeInformation processing
A method of estimating road traffic on a roads network, comprising: receiving information from at least one information source, wherein the information received from the at least one information source is one among a first information type and a second information type; defining at least two different information processing methods, each one associated with a respective one of said information type; selecting the information processing method based on the available information type and on predefined criteria; and processing with the selected information processing method the corresponding available information type; and providing an estimation of the road traffic based on the result of said processing.
Owner:TELECOM ITALIA SPA
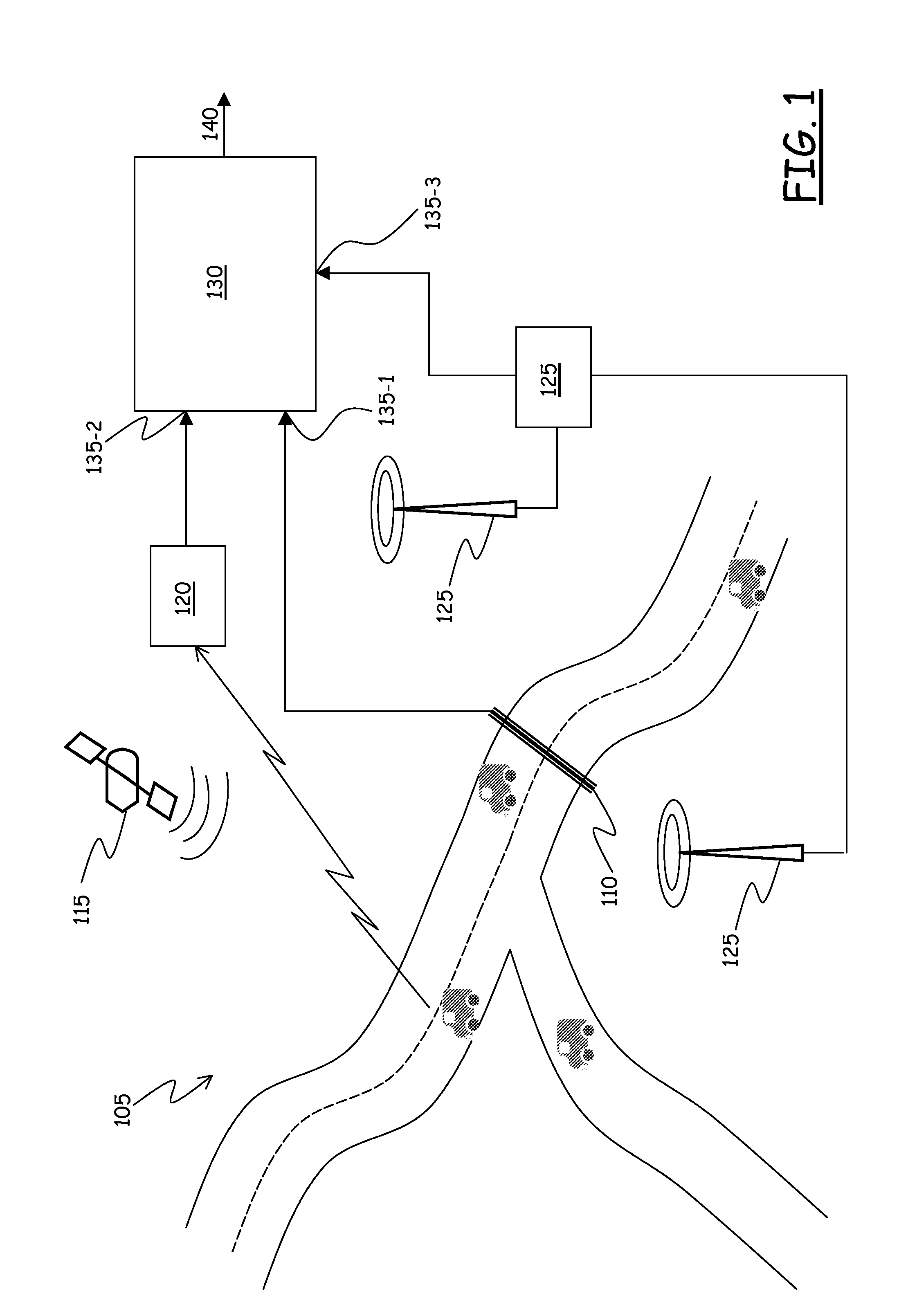
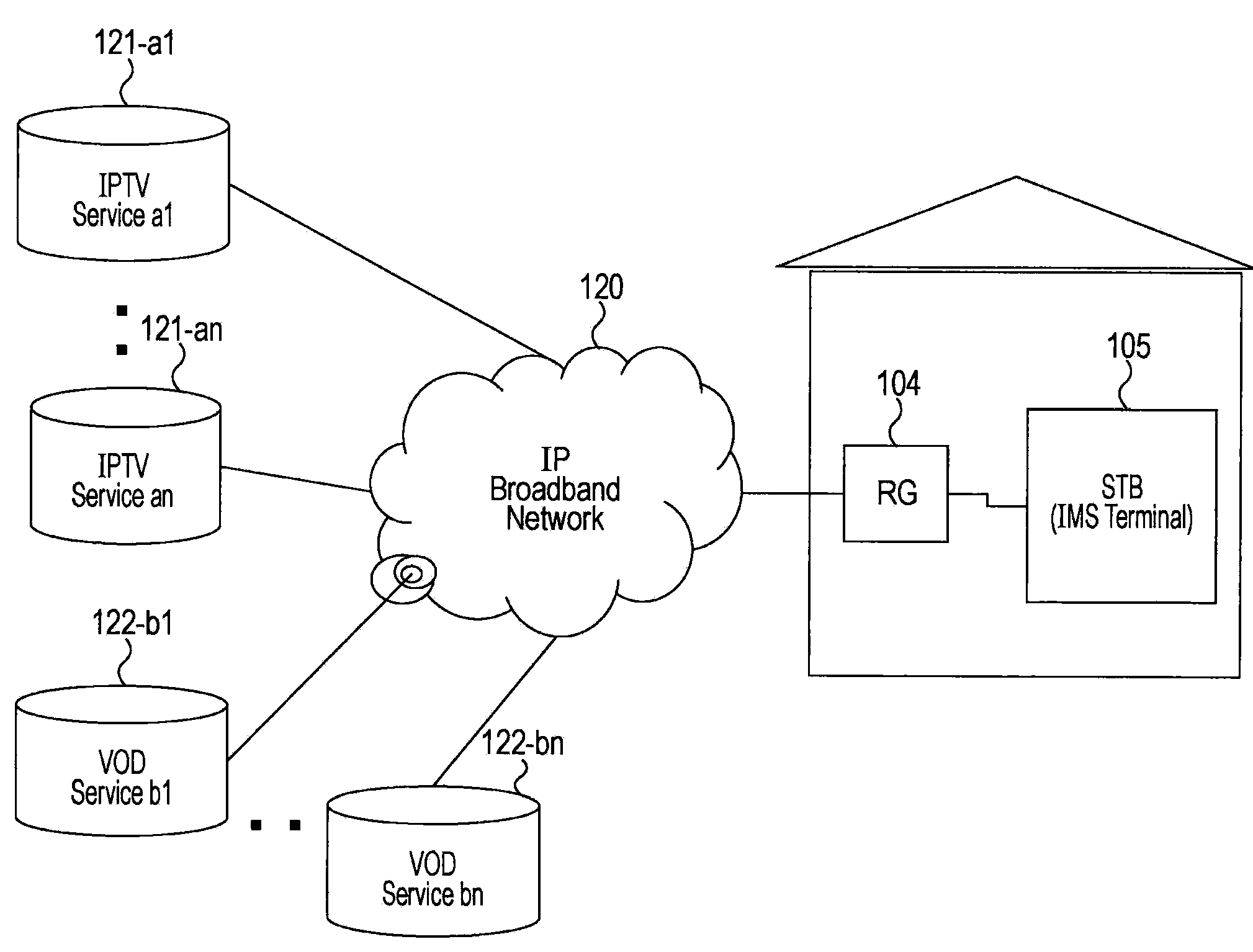
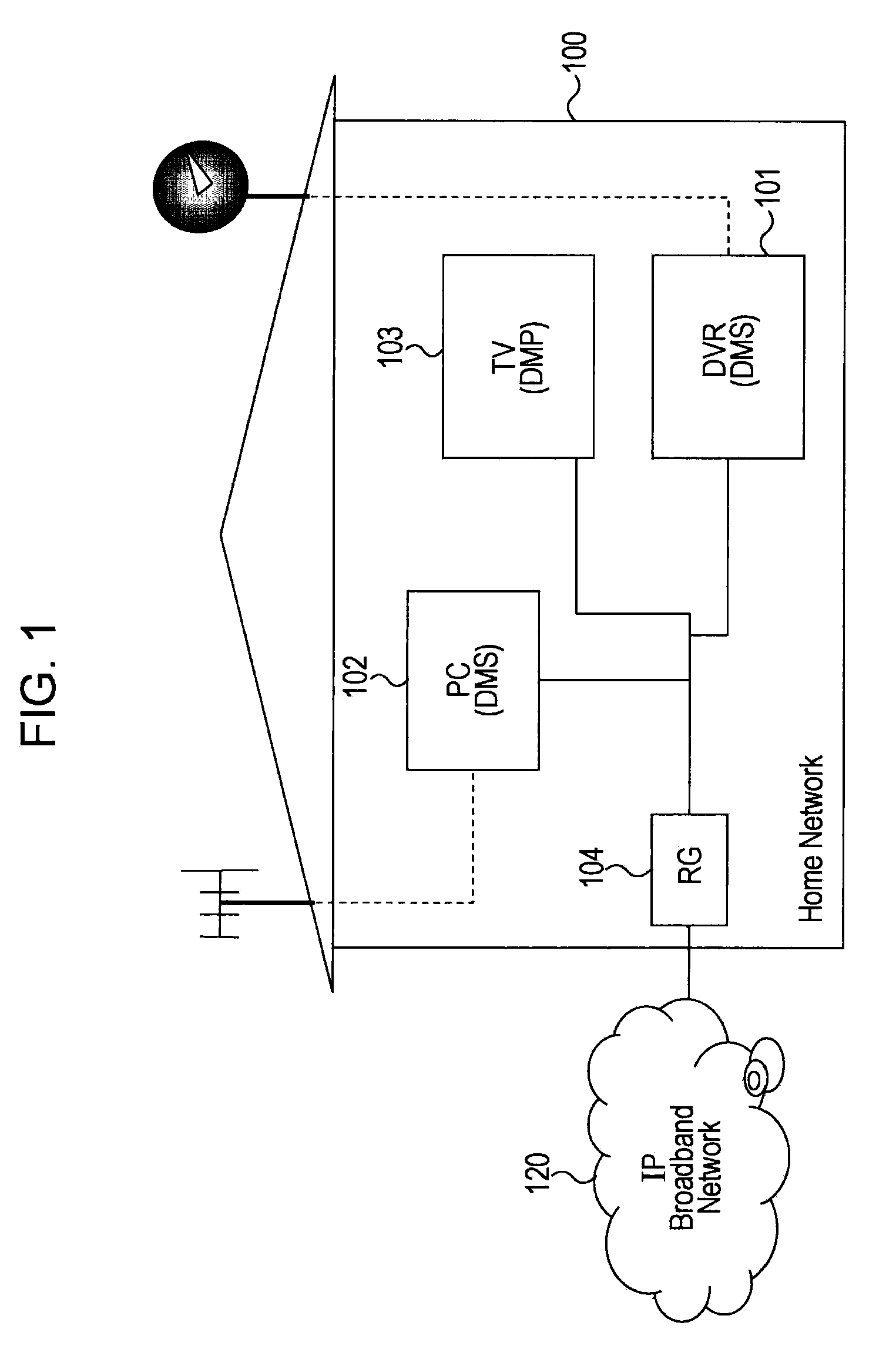
Information Processing Apparatus, Information Processing Method, and Computer Program
InactiveUS20090100147A1Increase flexibilityMultiple digital computer combinationsTwo-way working systemsInformation processingComputer network
A configuration is provided in which a device in a home network receives content from a server outside the home network and plays the content. A home IMS gateway maps an external server outside the home network as a virtual home network device, and executes a process of receiving a content providing service provided by the external server by using mapping information. Furthermore, switched reception of multicast distribution content provided by the external server and unicast distribution content is executed.
Owner:SONY CORP
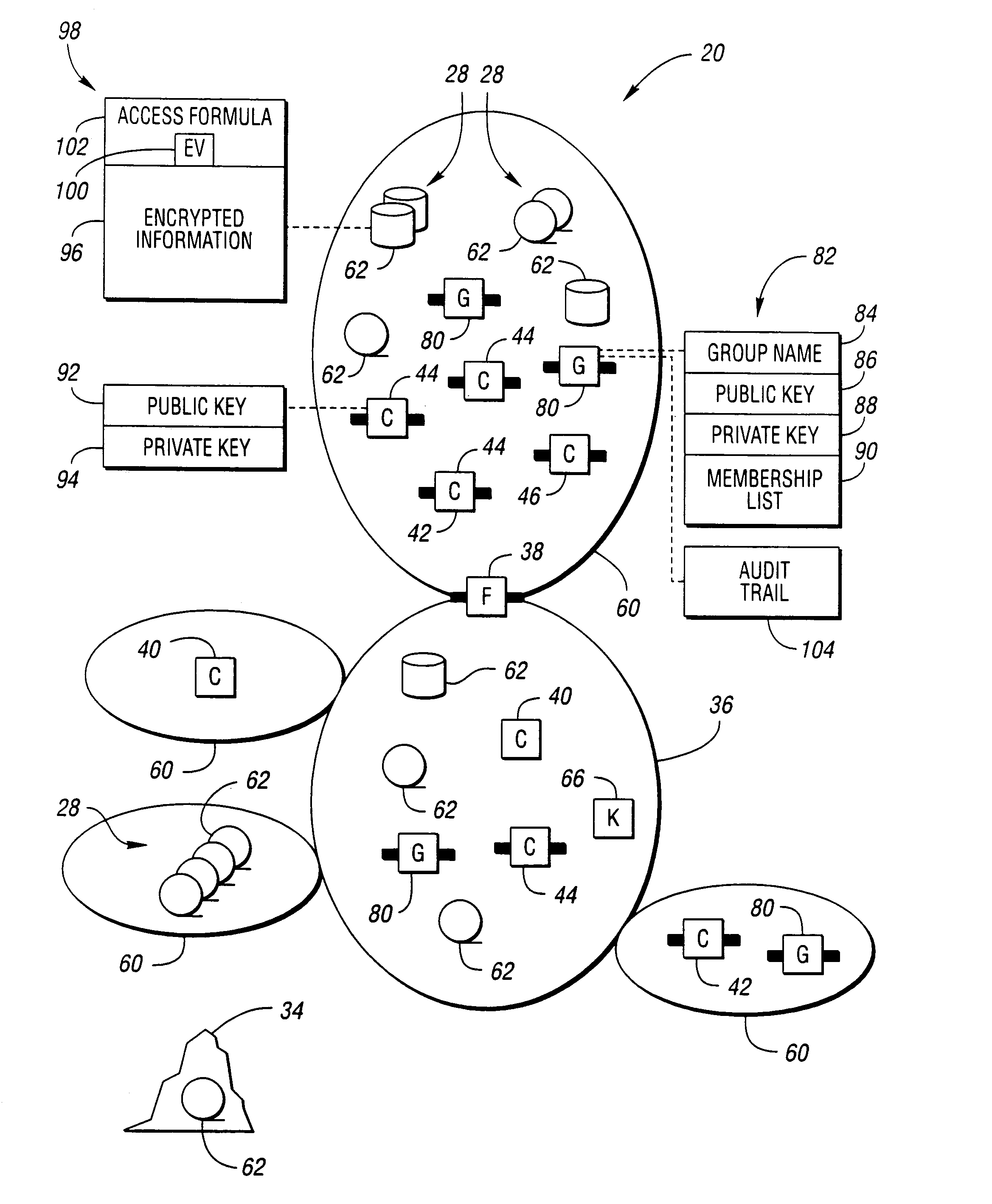
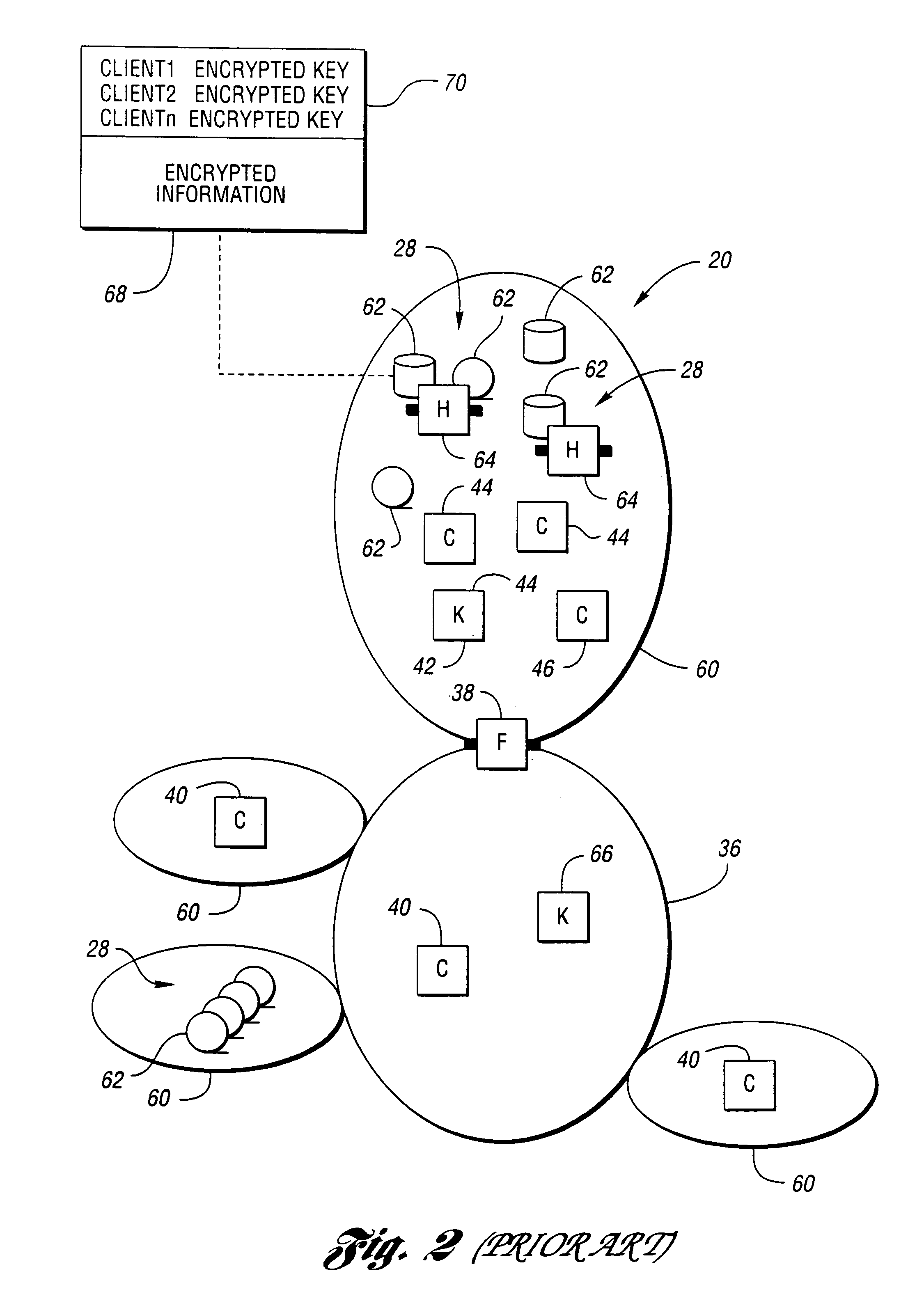
Method and system for secure information handling
InactiveUS6957330B1Safe handlingSafe storageKey distribution for secure communicationUser identity/authority verificationClient-sideSecurity information
Information that must remain secure is often stored on untrusted storage devices. To increase security, this information is encrypted by an encryption value prior to storing on the untrusted storage device. The encryption value itself is then encrypted. The encryption value is decrypted by correctly solving an access formula describing a function of groups. Each group includes a list of at least one consumer client. A requesting consumer client is granted access to the information if the requesting consumer client is a member of at least one group which correctly solves the access formula.
Owner:ORACLE INT CORP
Information processing equipment and power consumption control method
InactiveUS7412615B2Average power consumptionEnergy efficient ICTTelevision system detailsComputer hardwareInformation processing
Owner:SONY CORP
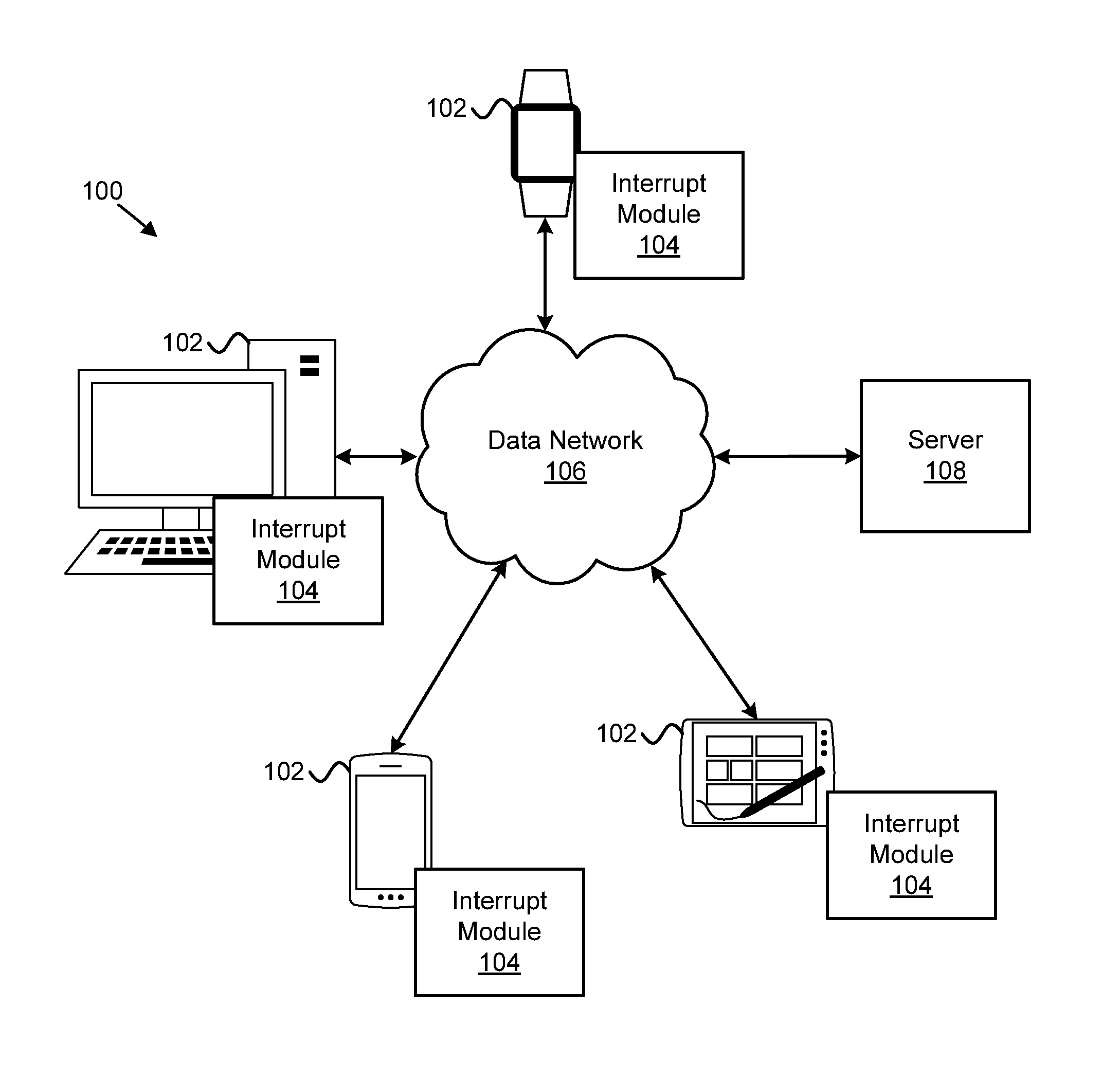
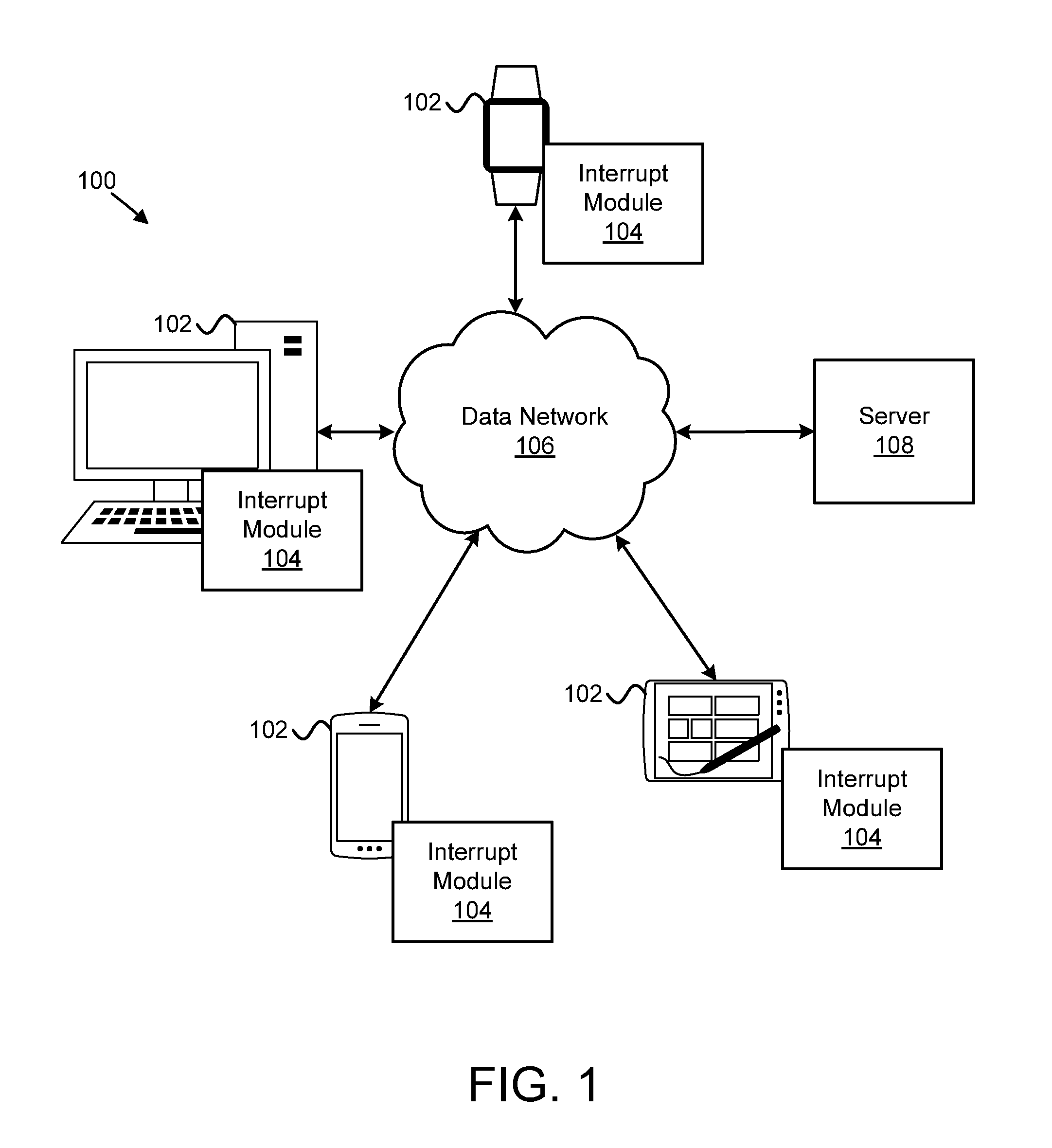
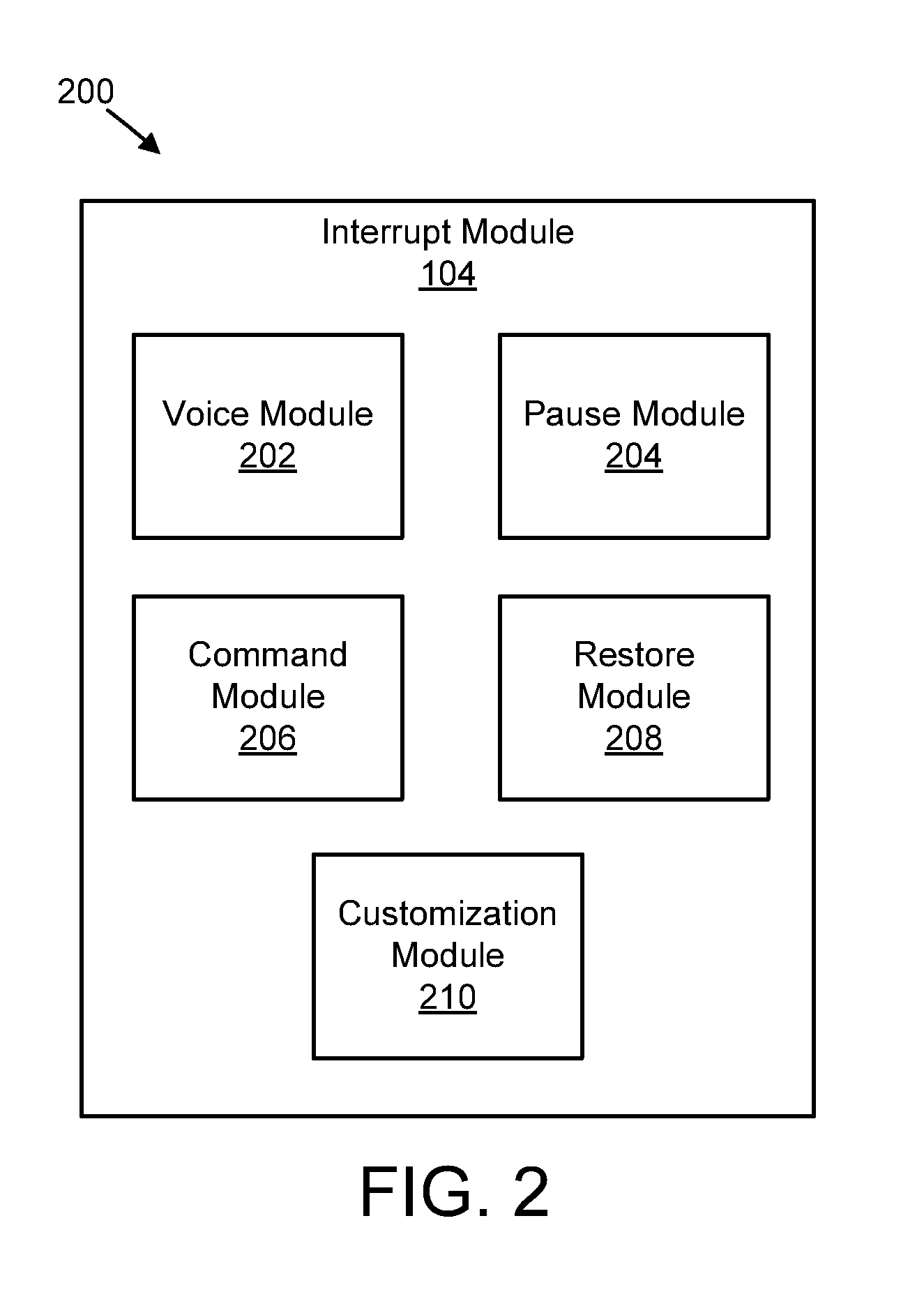
Executing a voice command during voice input
Apparatuses, methods, systems, and program products are disclosed for executing a voice command during voice input. A voice module detects a voice command intended to interrupt a first voice-related task using a voice input device associated with an information handling device. A pause module pauses the first voice-related task in response to the interrupt voice command. A command module executes a second voice-related task associated with the interrupt voice command. The second voice-related task does not correct voice input received by the first voice-related task.
Owner:LENOVO PC INT
Interactive computer program for measuring and analyzing mental ability
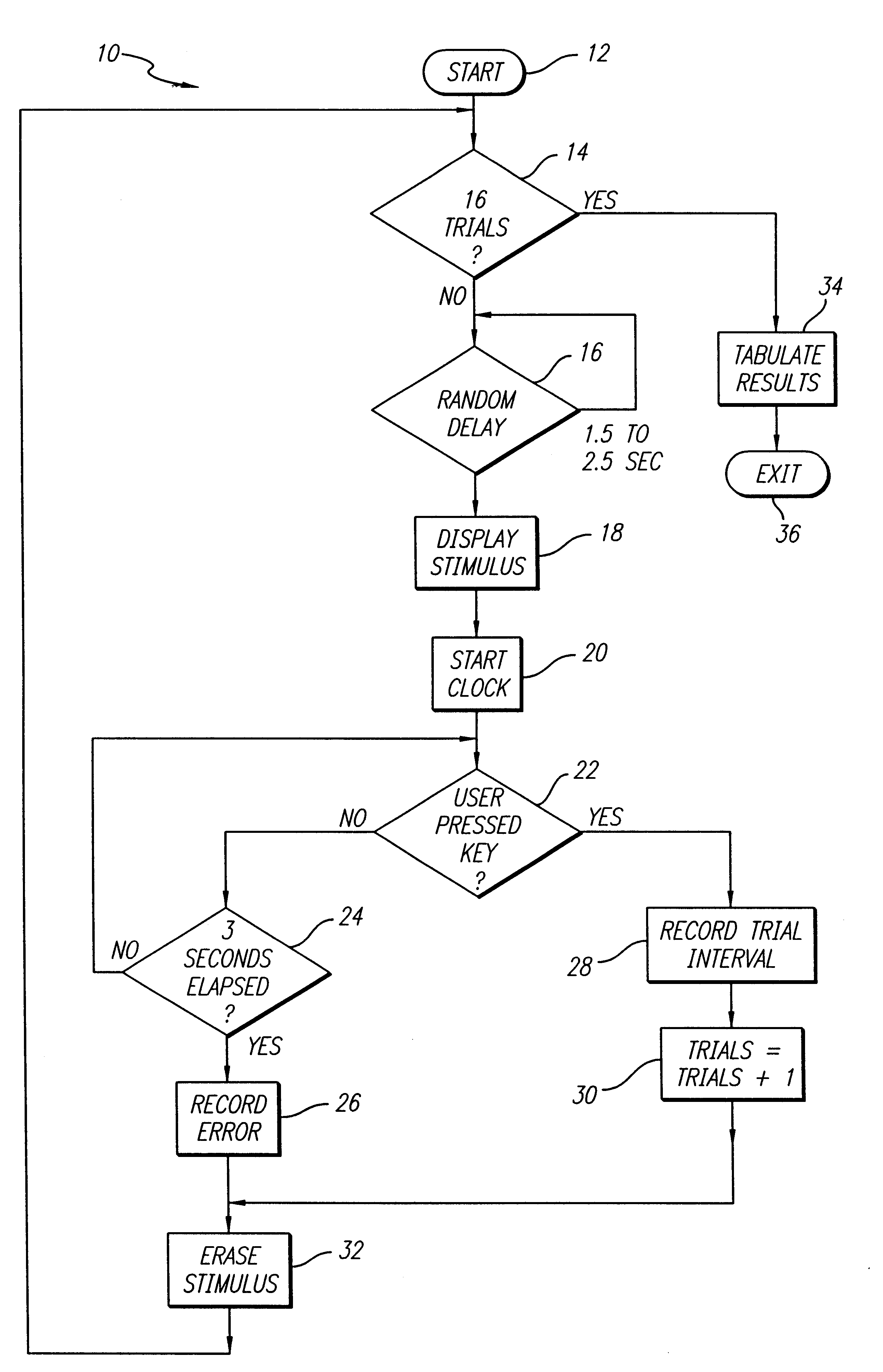
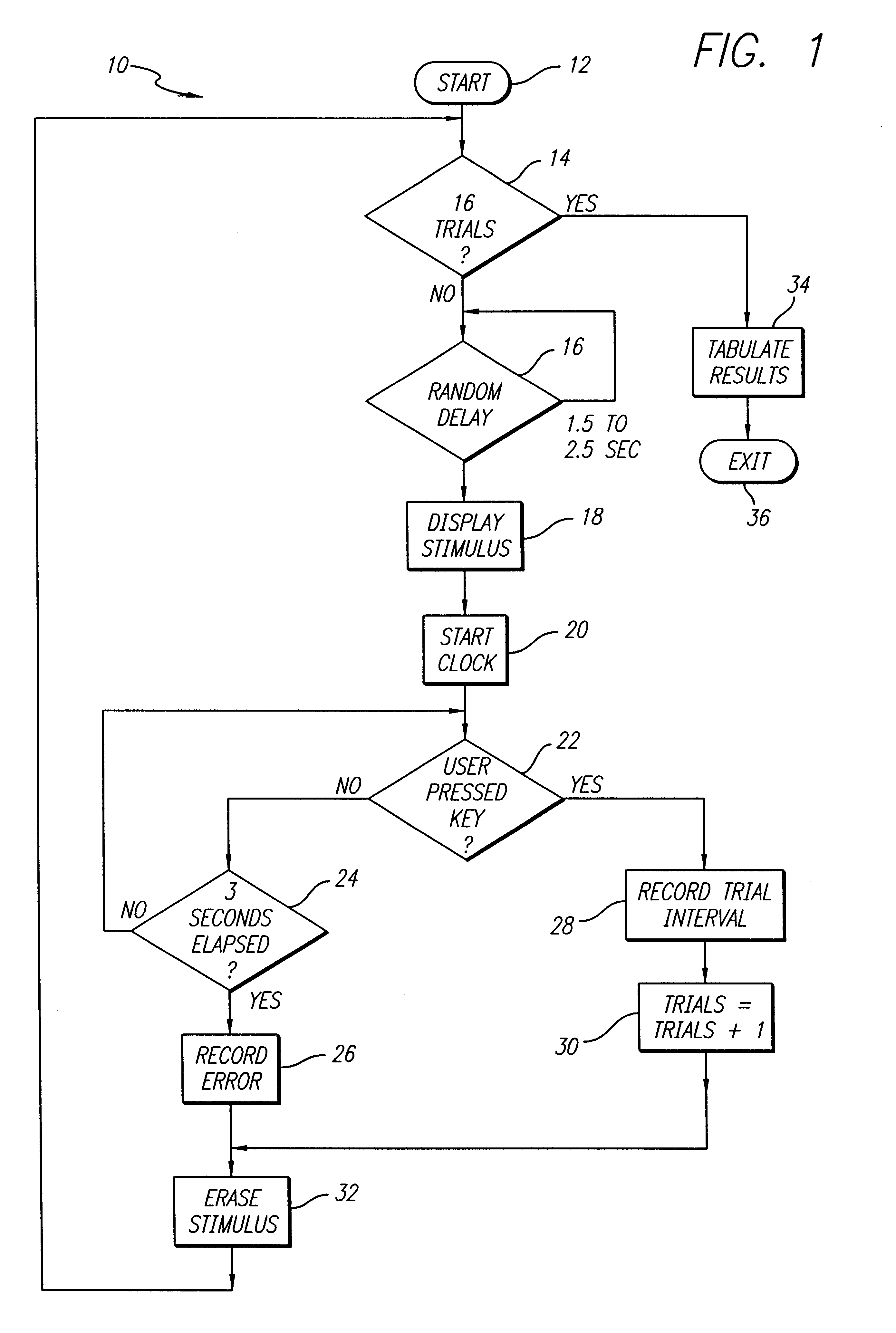
An interactive automatic system and technique for measuring and training of mental ability. In the illustrative embodiment, the invention is implemented on a computer which automatically presents a variety of visual and auditory stimuli. The system then measures reaction to the stimuli, adjusts certain stimulus parameters, and provides scores in response thereto. The scores are tabulated and displayed for analysis. In particular embodiments, the invention tests for physical reaction time, perceptual awareness thresholds, attention level, speed, efficiency and capacity of information processing by the brain and elementary cognitive processes, including memory, memory access and decision-making speed. The invention measures, identifies and quantifies noise in the subject's brain and elementary cognitive processing system, and the information exchange rate between the subject's left and right brain hemispheres. The inventive system compiles a history of the test scores, renders an overall performance rating, and delivers comments based on the subject scores. The complexity of the tests are adjusted based on the scores to optimally challenge cognitive capacities, thereby rendering more accurate evaluations of cognitive capacity, and optimizing learning of desired improvements in perceptual, physical and mental response speeds and efficiencies.
Owner:BCI
Information processing apparatus and method, and computer program
InactiveUS8935236B2High-quality data playbackSure easyTelevision system detailsData processing applicationsInformation processingImage resolution
An apparatus and method allowing for high-quality data acquisition and playback processing based on content information transmitted from a server to a client are provided. Property information constituting meta-information corresponding to content-associated attribute information stores data-scheme information on original content held by the server, such as file format information, codec information representing an encoded-data scheme, and resolution information. In response to a content information acquisition request from the client, content information including the data-scheme information on the original content is generated and is transmitted to the client. This structure allows the client to output a content transmission request in which the optimum data scheme is determined based on the data scheme of the original content. Therefore, high-quality data acquisition and playback can be achieved.
Owner:SONY CORP
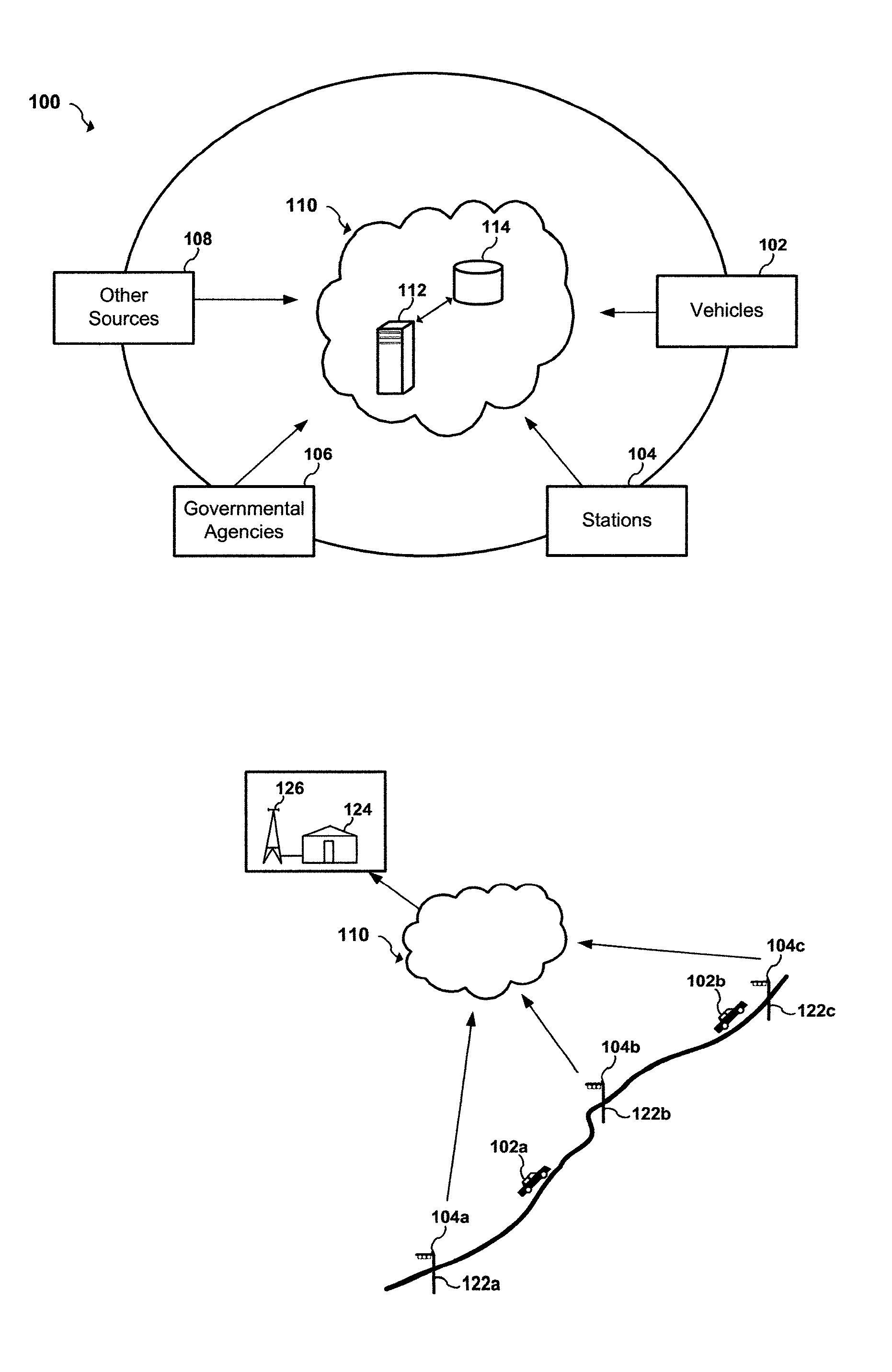
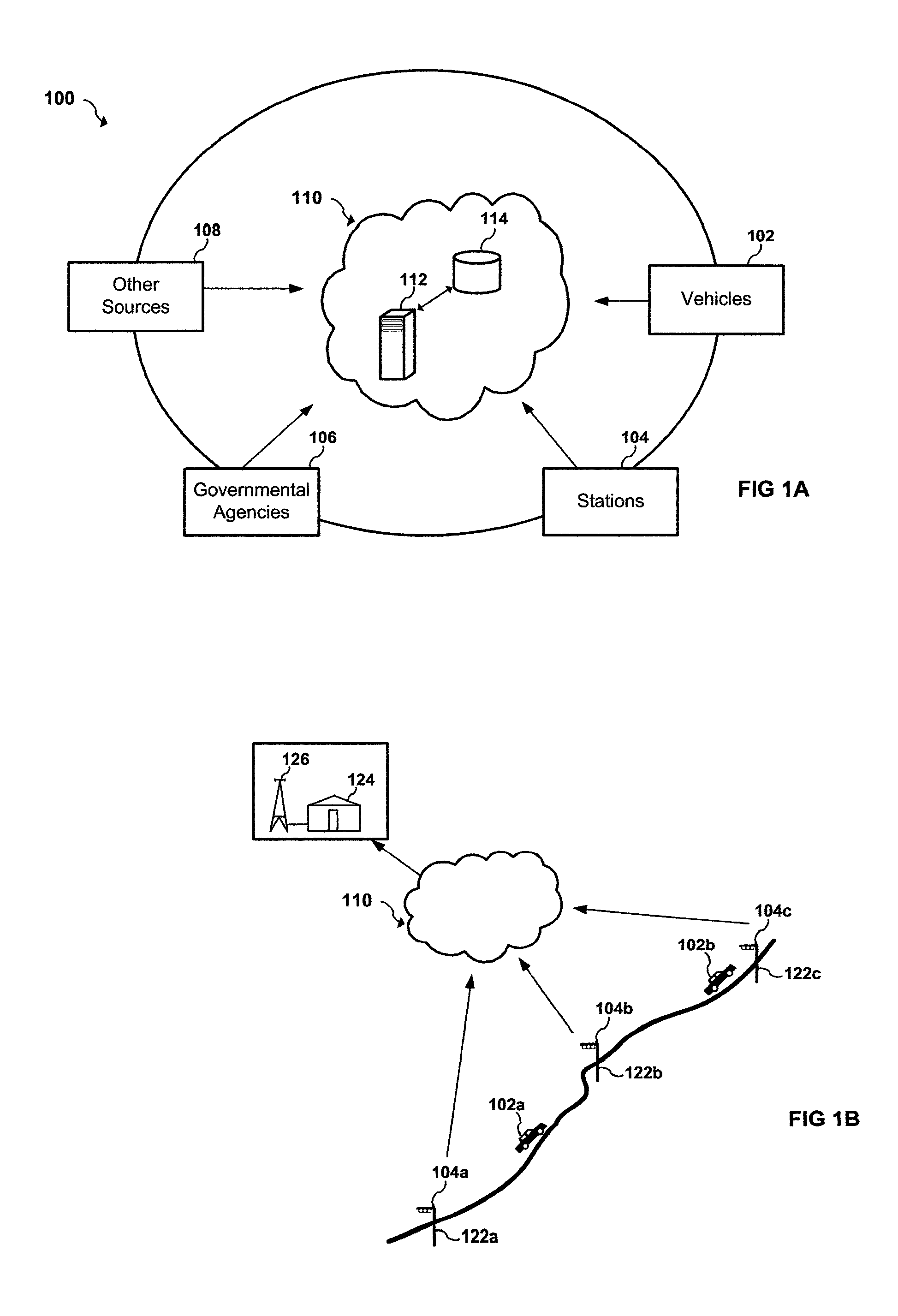
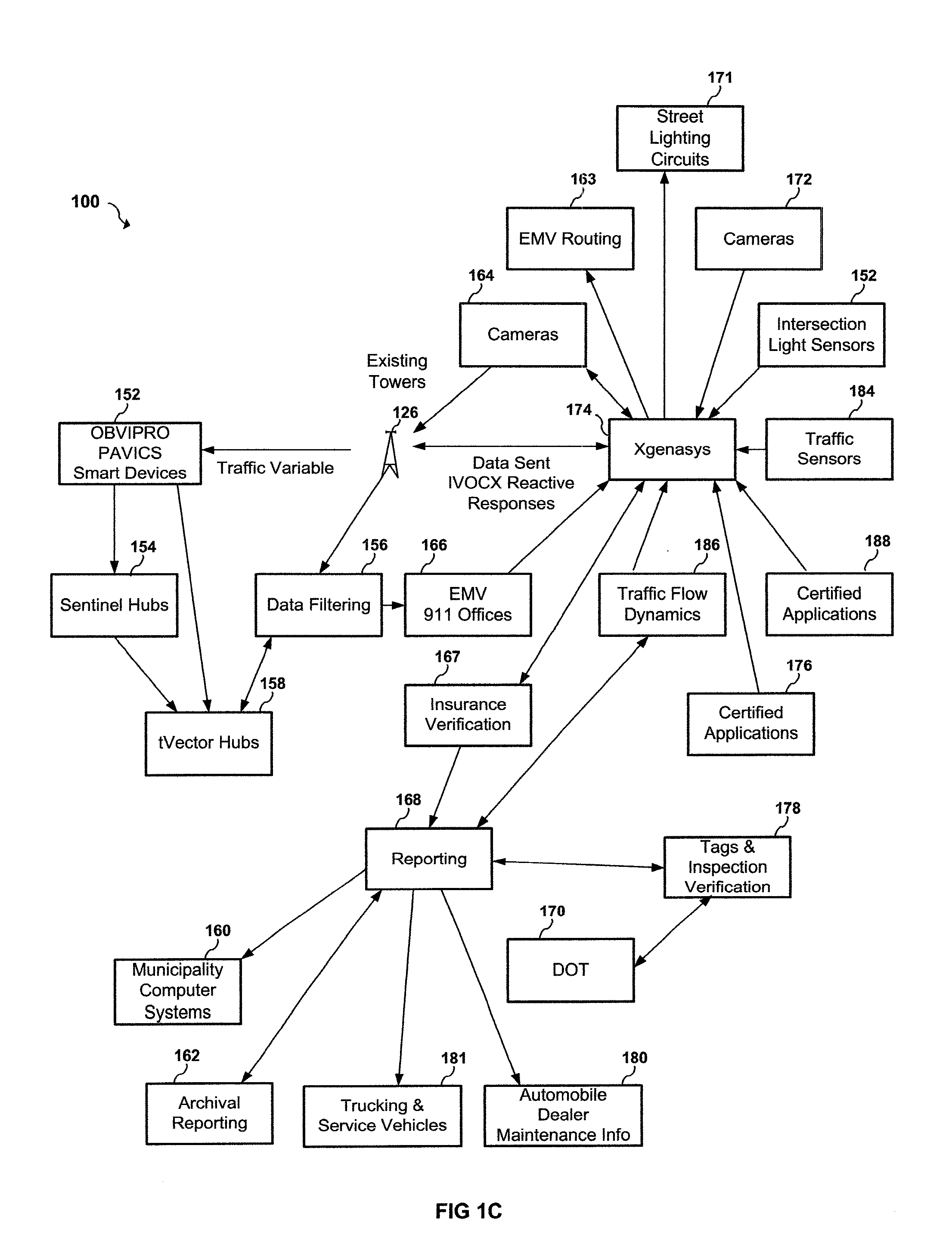
Apparatus and system to manage monitored vehicular flow rate
ActiveUS20160379486A1Solve the excessive calculationEfficient inputControlling traffic signalsArrangements for variable traffic instructionsPrivate networkEngineering
An apparatus and system to manage monitored traffic density in relationship to spatial locational flow rates. The system includes a variety of mobile and / or stationary transmitting and receiving comm-devices utilizing certified comm-devices equipped Avics iChipset arranged in a polarity of vehicles, in communication with stationary and / or mobile hub comm-devices and / or other certified comm-devices, strategically arranged within and / or along one or more roadways and in communication with a server channel networked to a central server. Configured to receive and / or transmit encrypted traffic data from the diversity of stationary and / or mobile transmitting and receiving comm-devices over the network, update traffic data in the non shared database, continuously calculate optimal traffic density flow for one or more of vehicles traveling along the one or more roadways based on the updated vehicular transit data, transmitting variations in speed adjustments in a network infrastructure to one or more vehicles; adjusting traffic light intersections based on traffic density traversing such roadways based on the optimal traffic flow suggestions combined with Predicated Traffic Artifacts transmitted via system generated encrypted digital comm-advice directives; and in turn share extracted and / or transmitted data with each state an federal DOT departments and other stack holders, including insurance companies and vehicle manufacturers and dealers with information to assist with making the traffic network safer. The present invention presents an Intuitive ITS engaged in Channeled Vehicular Telematics conveying statistical data, from an plurality of network devices, providing informational services forecasting safety-critical features and more, in return gathering and disseminating connected channelled intelligence between vehicles from within and surrounding infrastructures and other shareholders. Such data includes vehicle Phase-Change Spatial analytics from traffic congestion artifacts, along with Consumption Variable Analysis that provides real-time Energy Summation Data from combined vehicle exhausted energy by adjusting traffic flow based on traffic density in relationship with the human factor, vehicle capacity to navigate and topography and climatic variations in relationship with any area being traversed, and most importantly the use of the unique string identification. USIN acknowledged as ‘tMarker Audit Trail’ or simply tMarker Trail as to data inception creation point. Managed within a secure private network infrastructure, each comm-device is synchronized with localized cloud servers in communication will a central server. This invention embarks on a new era in vehicle management, further enhancing time sensitive movements, leaving no doubt as to Vehicle Symmetry Orientation, especially once you move your vehicle and additional particulars currently not beyond the scope of this art presented herein. ITTS will throughly reduce the worlds fossil fuel supply consumption rate and on many other fronts availed by extracted data, transmitted from each vehicles onboard vehicle processor equipped with Avics iChipSet on certified comm-devices, reducing navigational concerns to elementary variables creating a safe traffic network.
Owner:TAYLOR DONALD WARREN
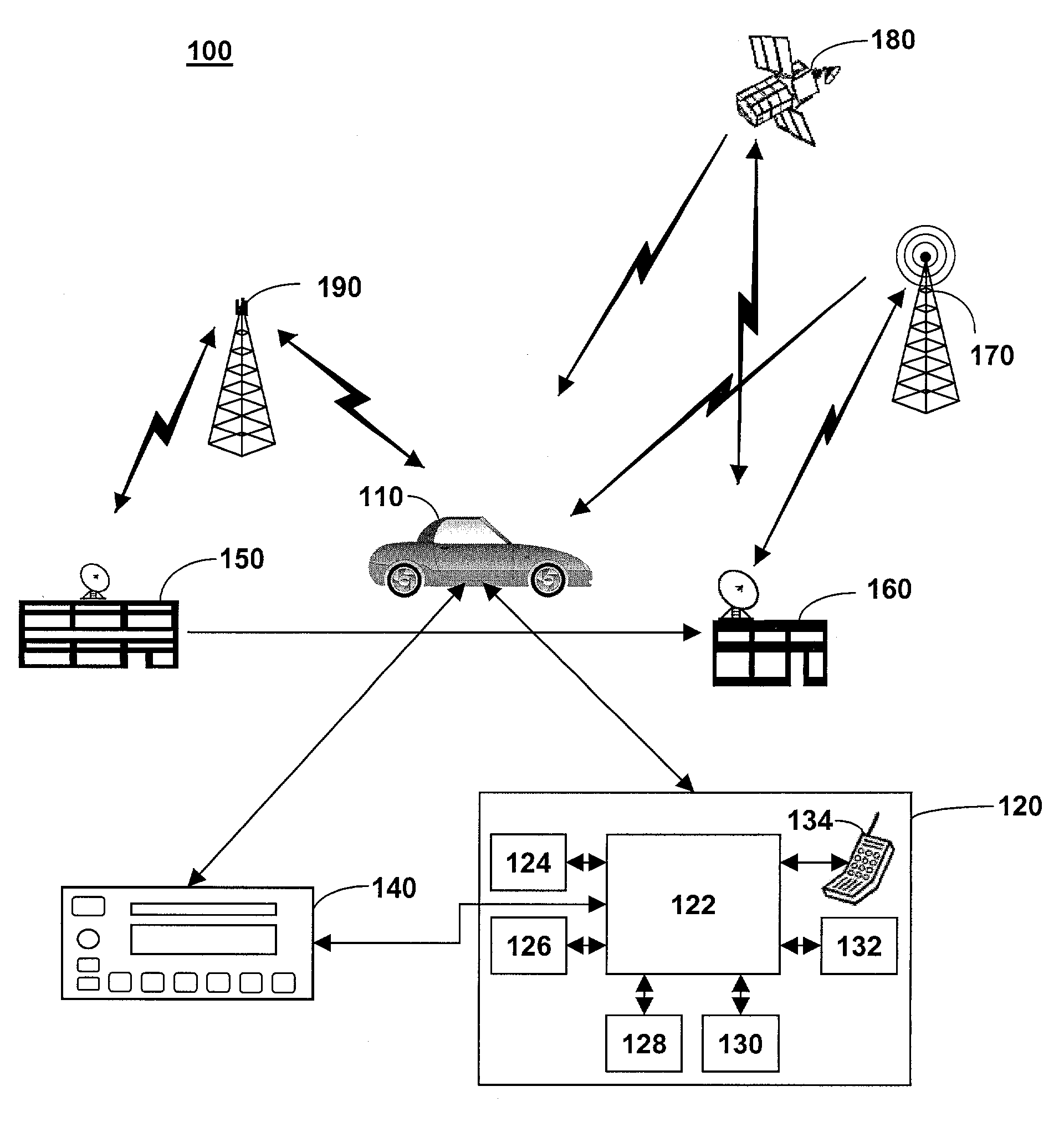
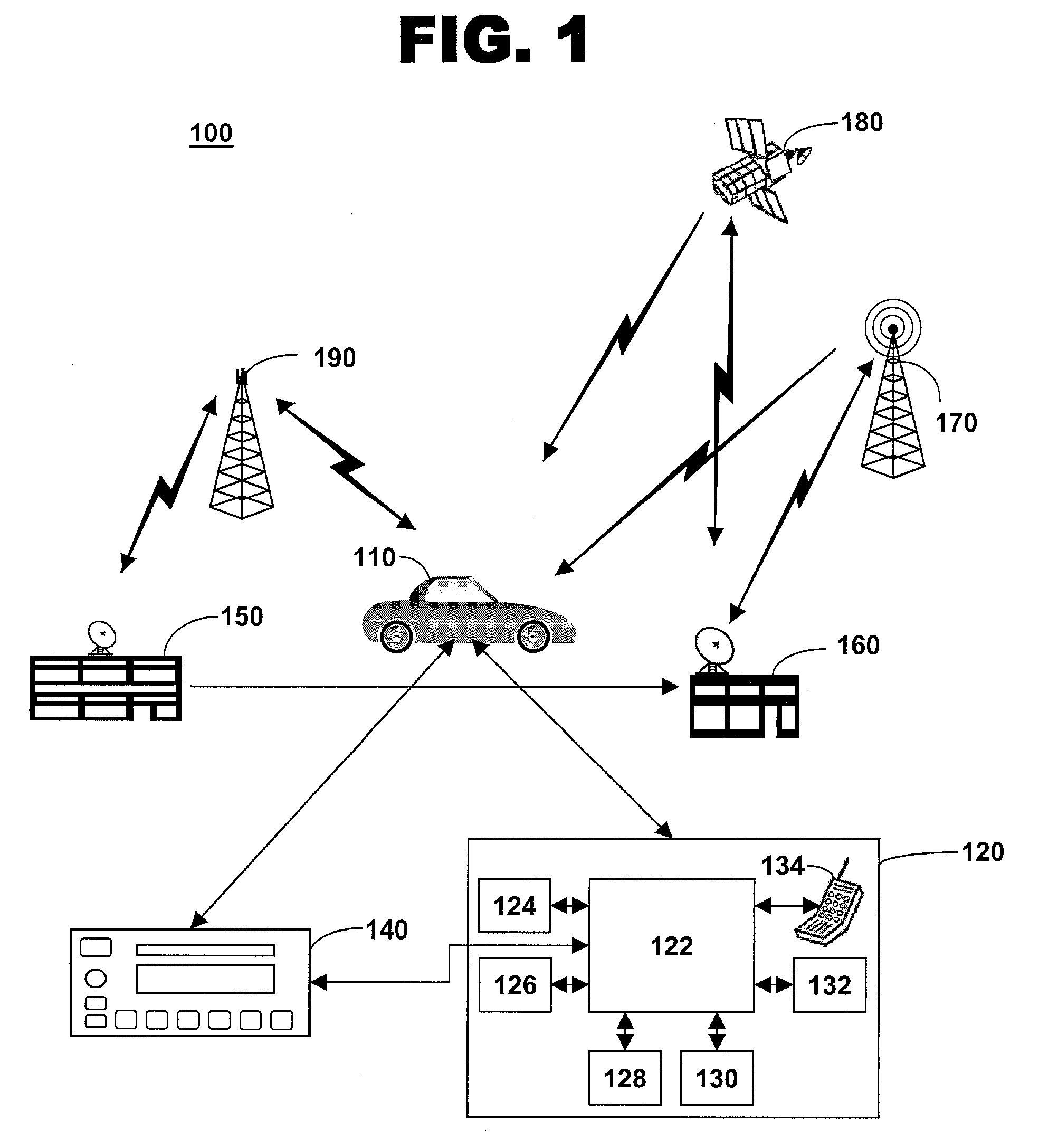
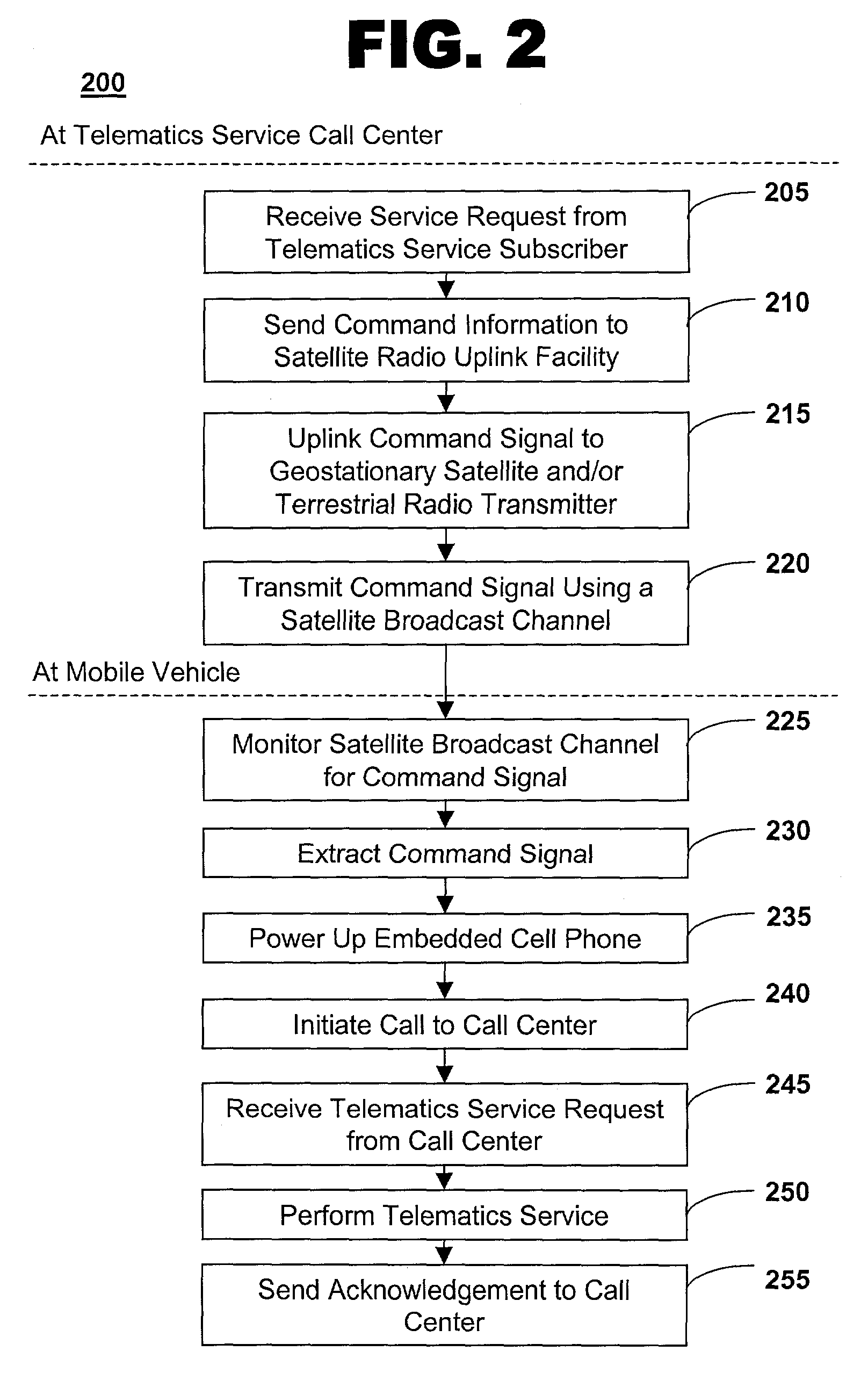
Method of communicating with a quiescent vehicle
ActiveUS7142810B2Registering/indicating working of vehiclesSpecial service for subscribersBroadcast channelsSatellite radio
The invention provides a method for establishing communications with a quiescent mobile vehicle. A satellite radio system broadcast channel is monitored for a command signal. The command signal is extracted from the broadcast channel. A cell phone in a telematics unit is powered up based on the command signal.
Owner:GENERA MOTORS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com