Patents
Literature
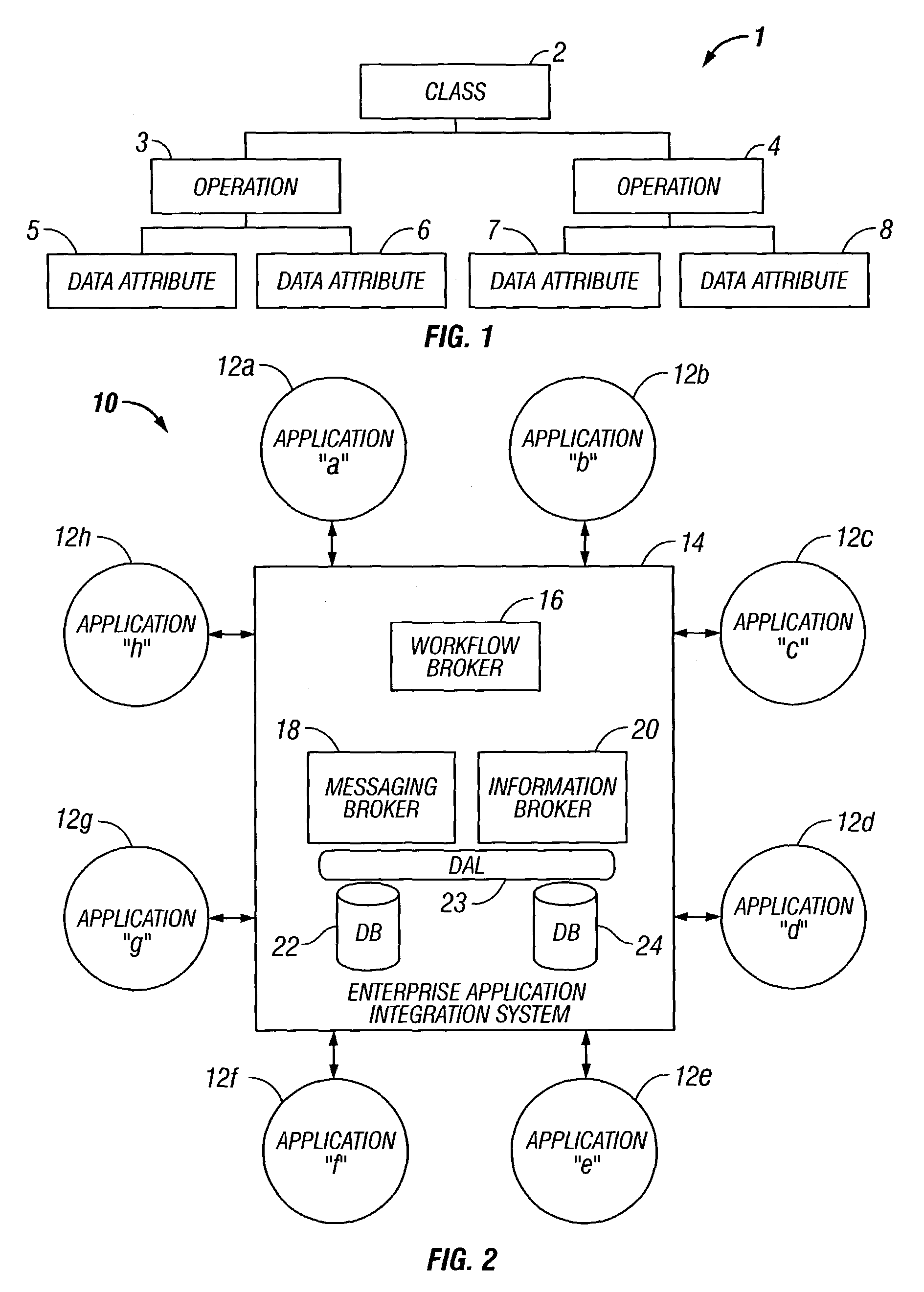
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
436 results about "Shared database" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
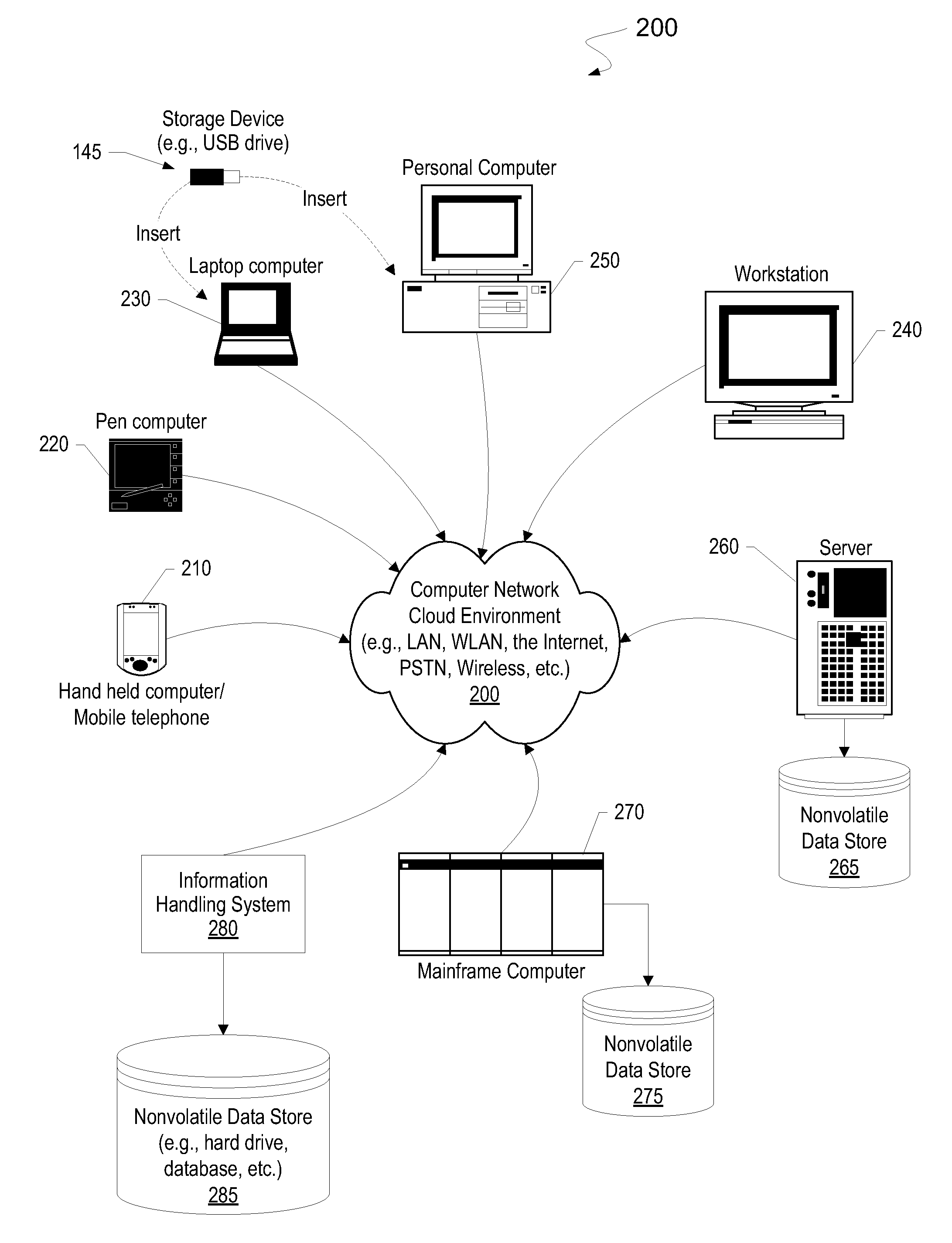
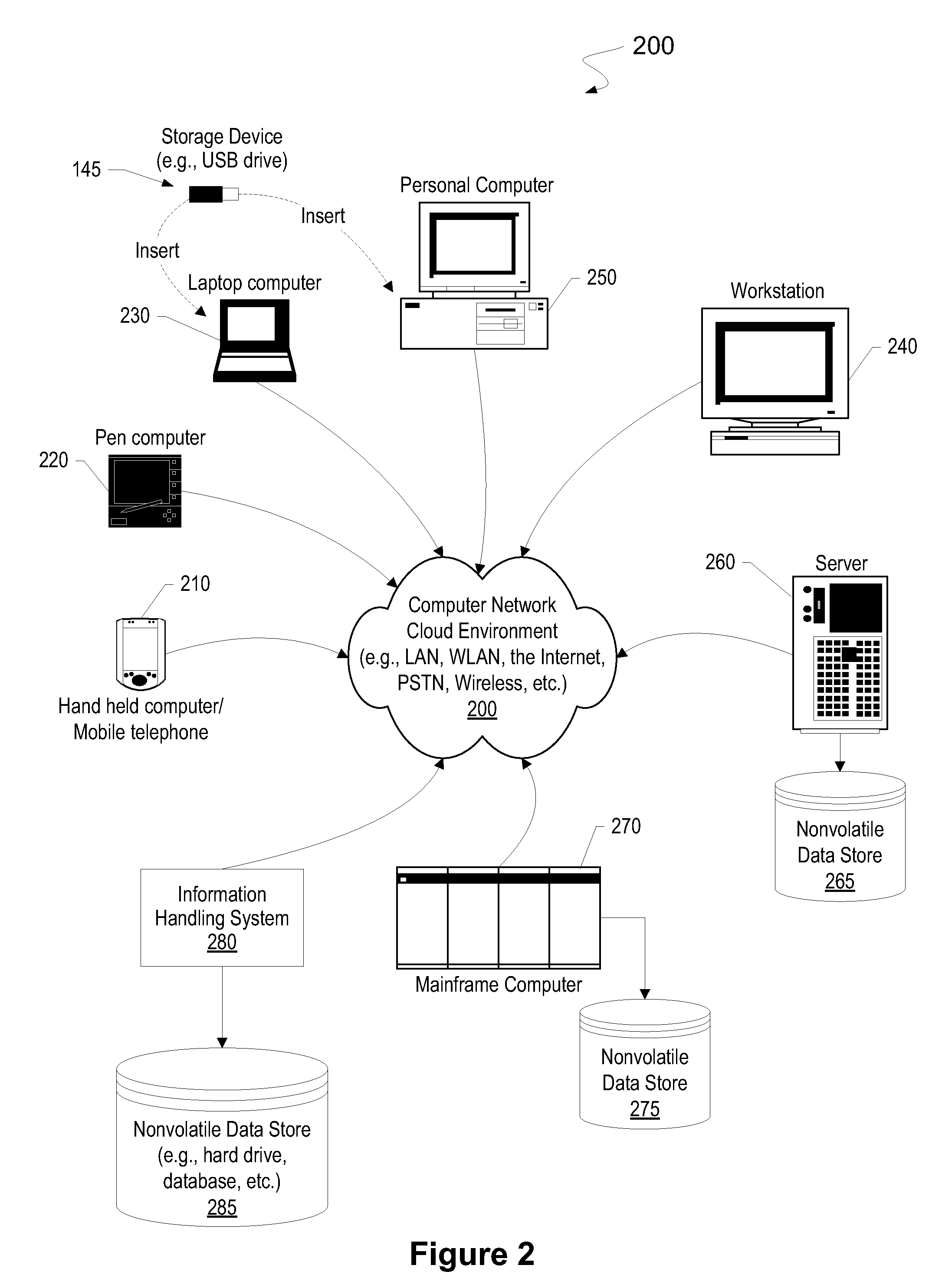
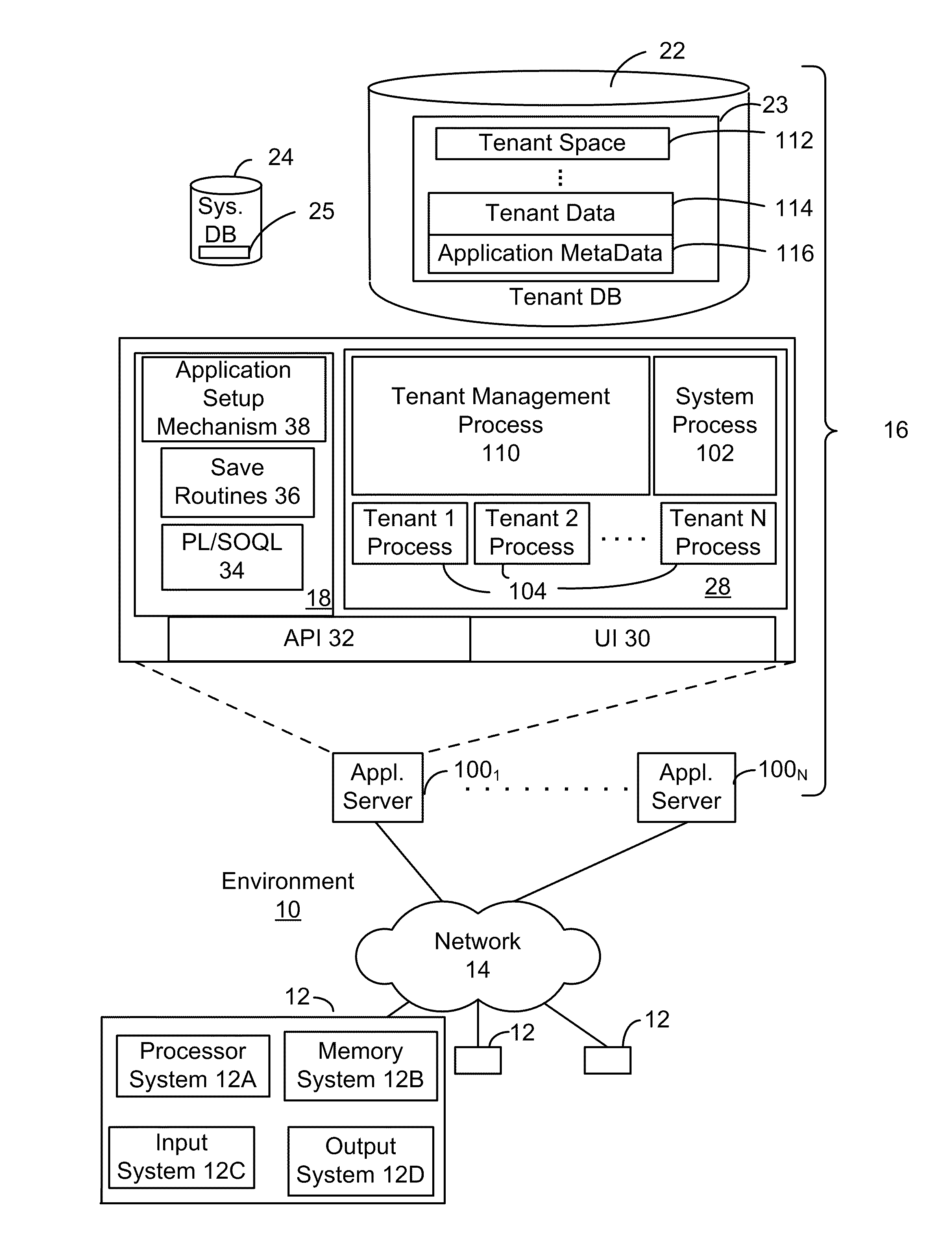
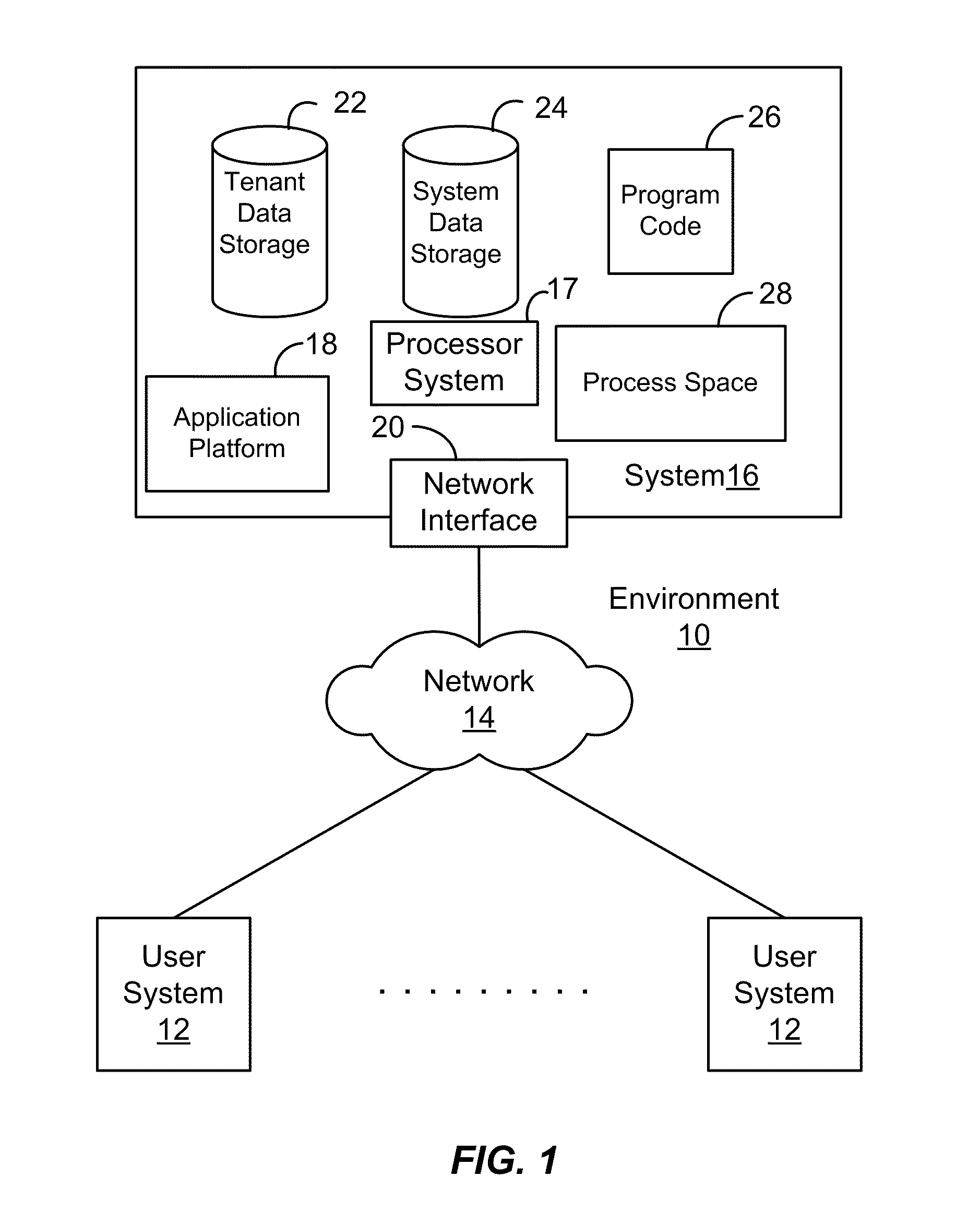
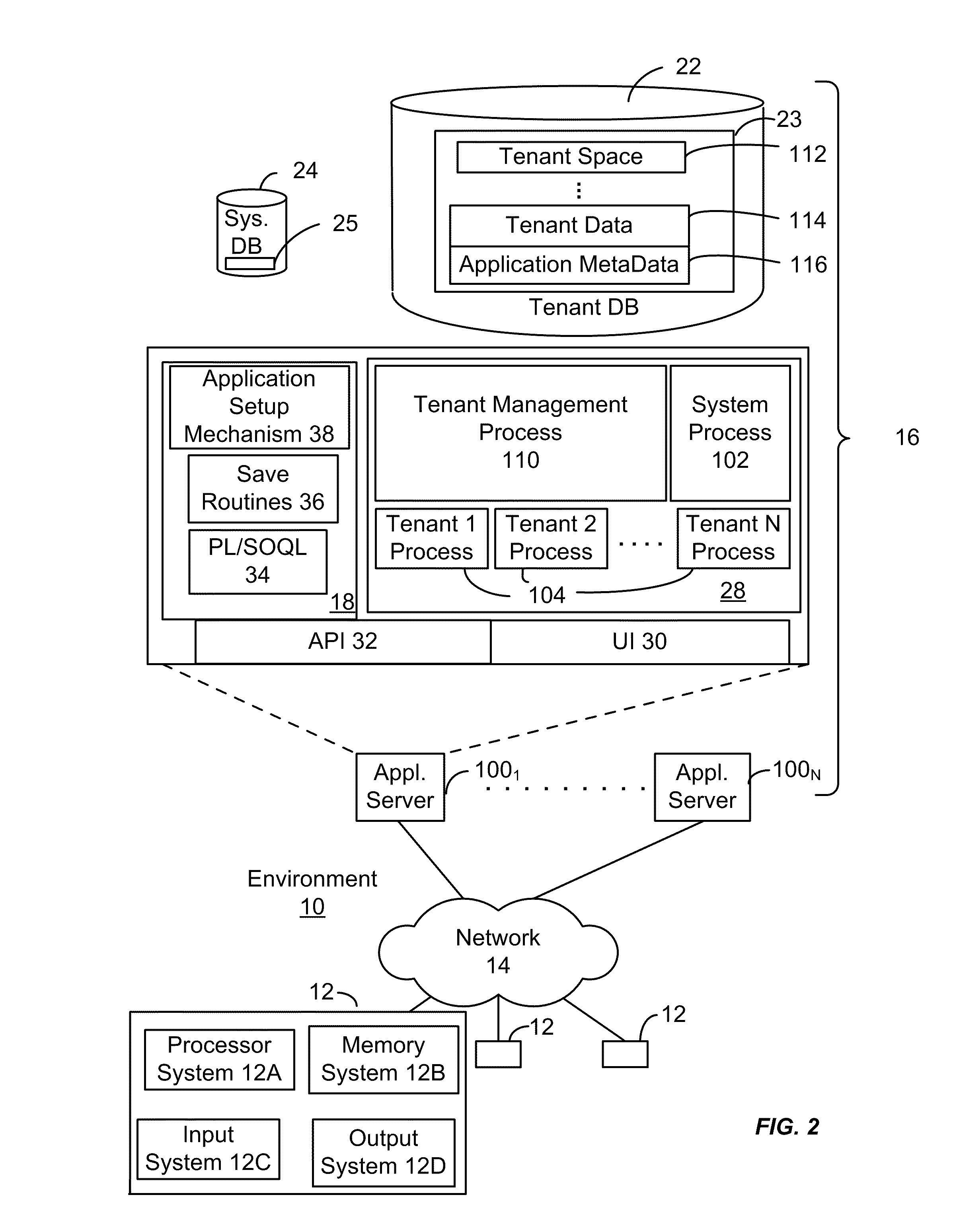
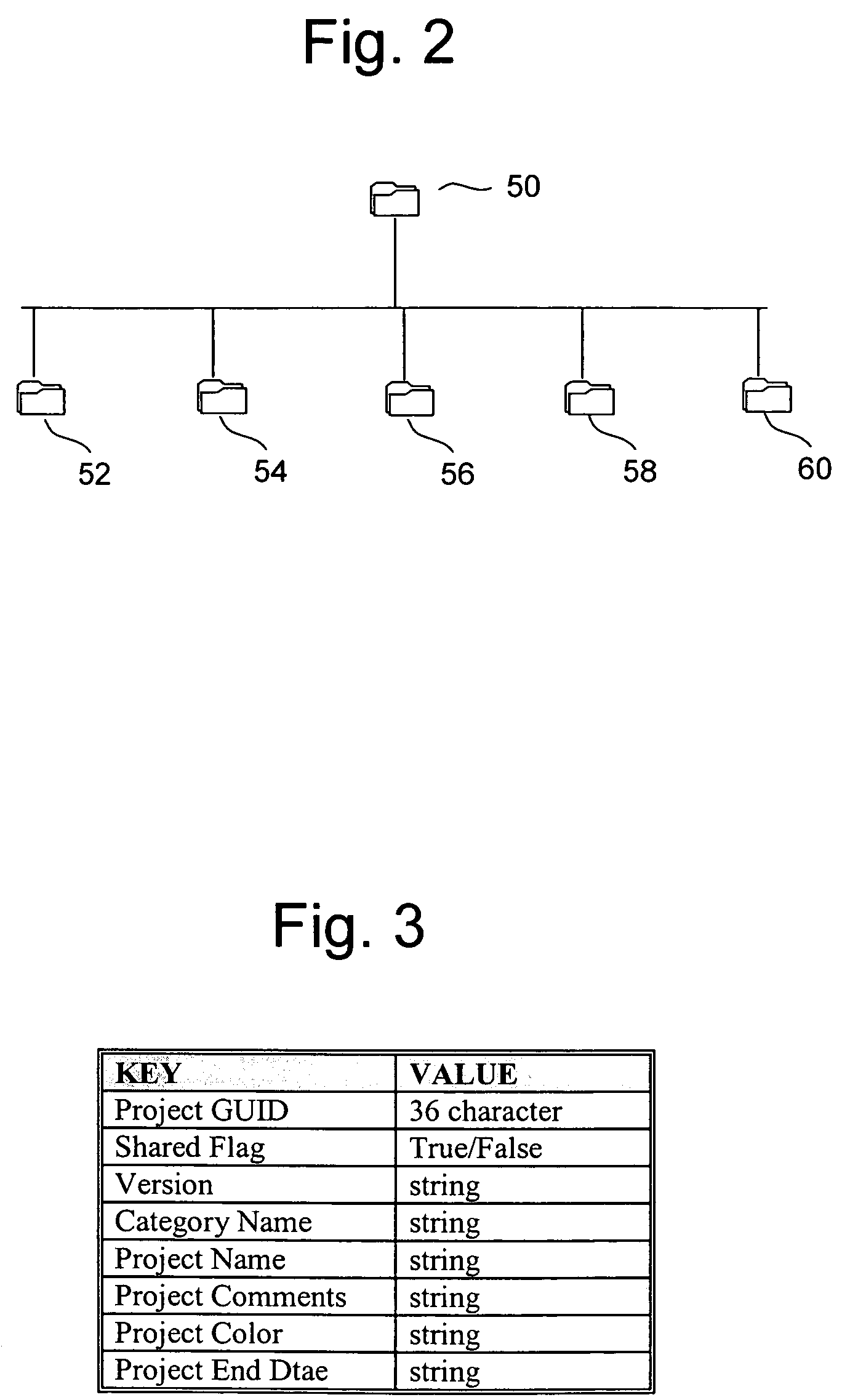
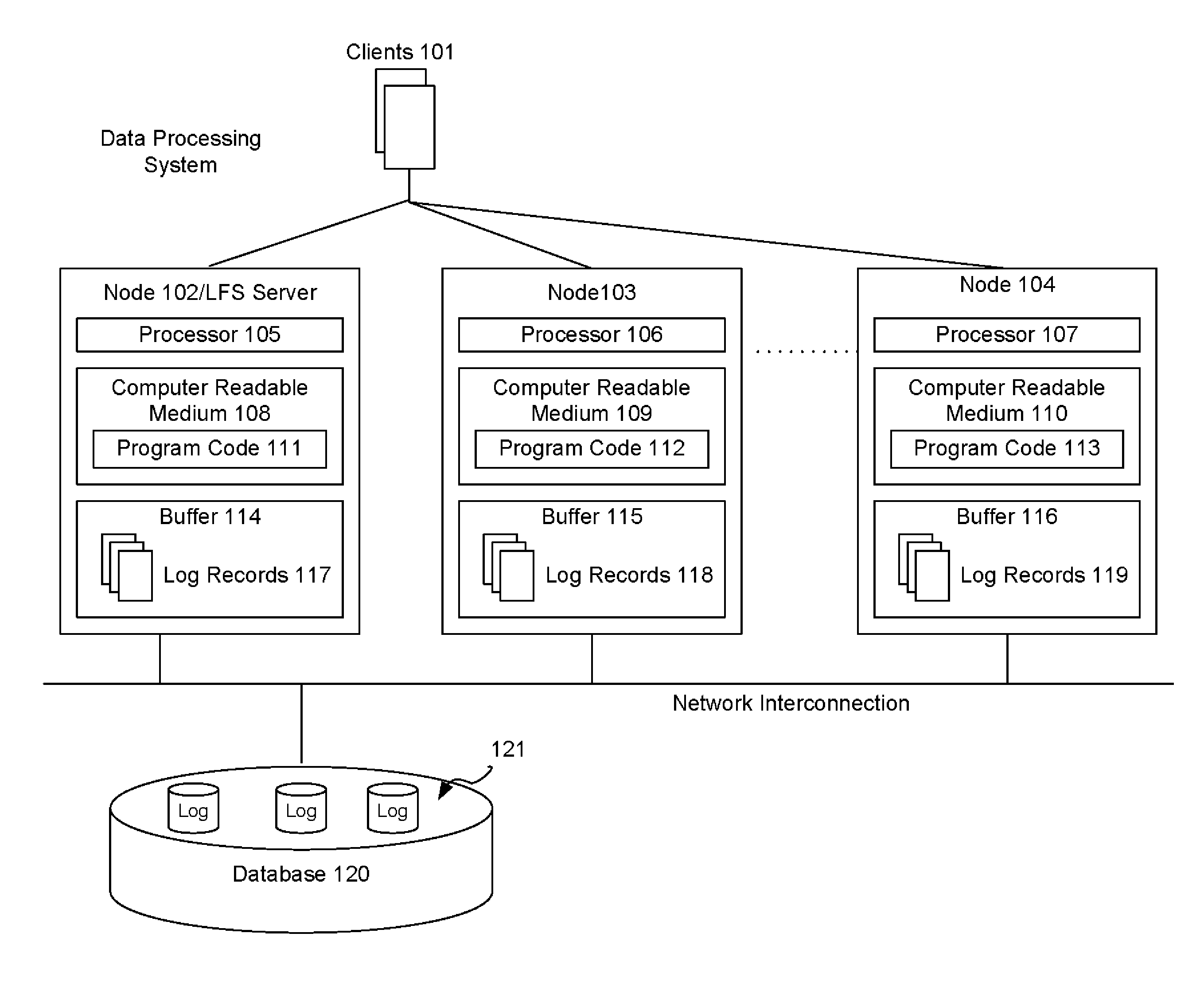
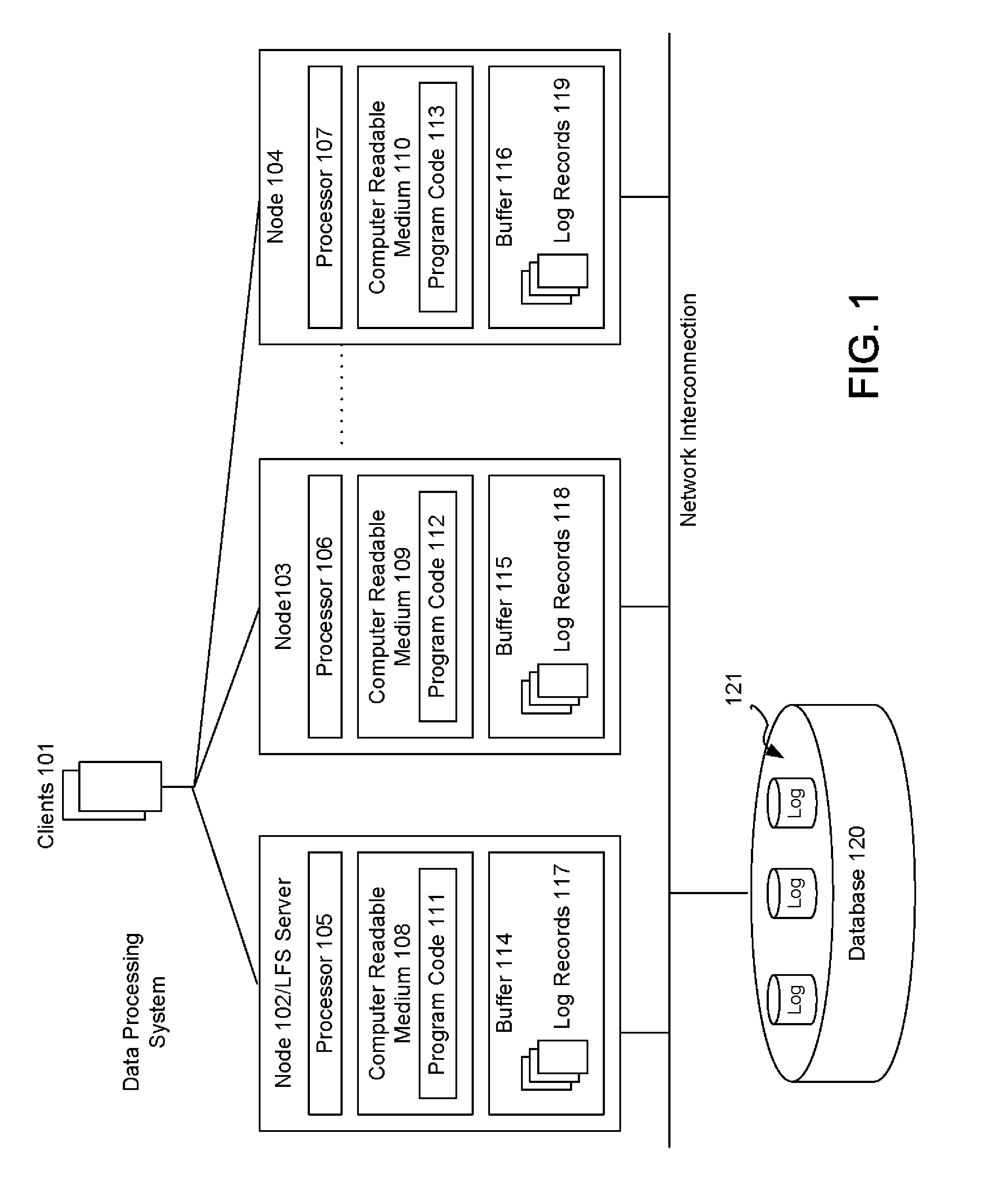
The shared database can be on the same computer (local) or on a different computer (remote). If you have been granted access and you connect to the shared database, you can view and update records and communication history items, create new records, and move records to and from the Deleted Items folder.
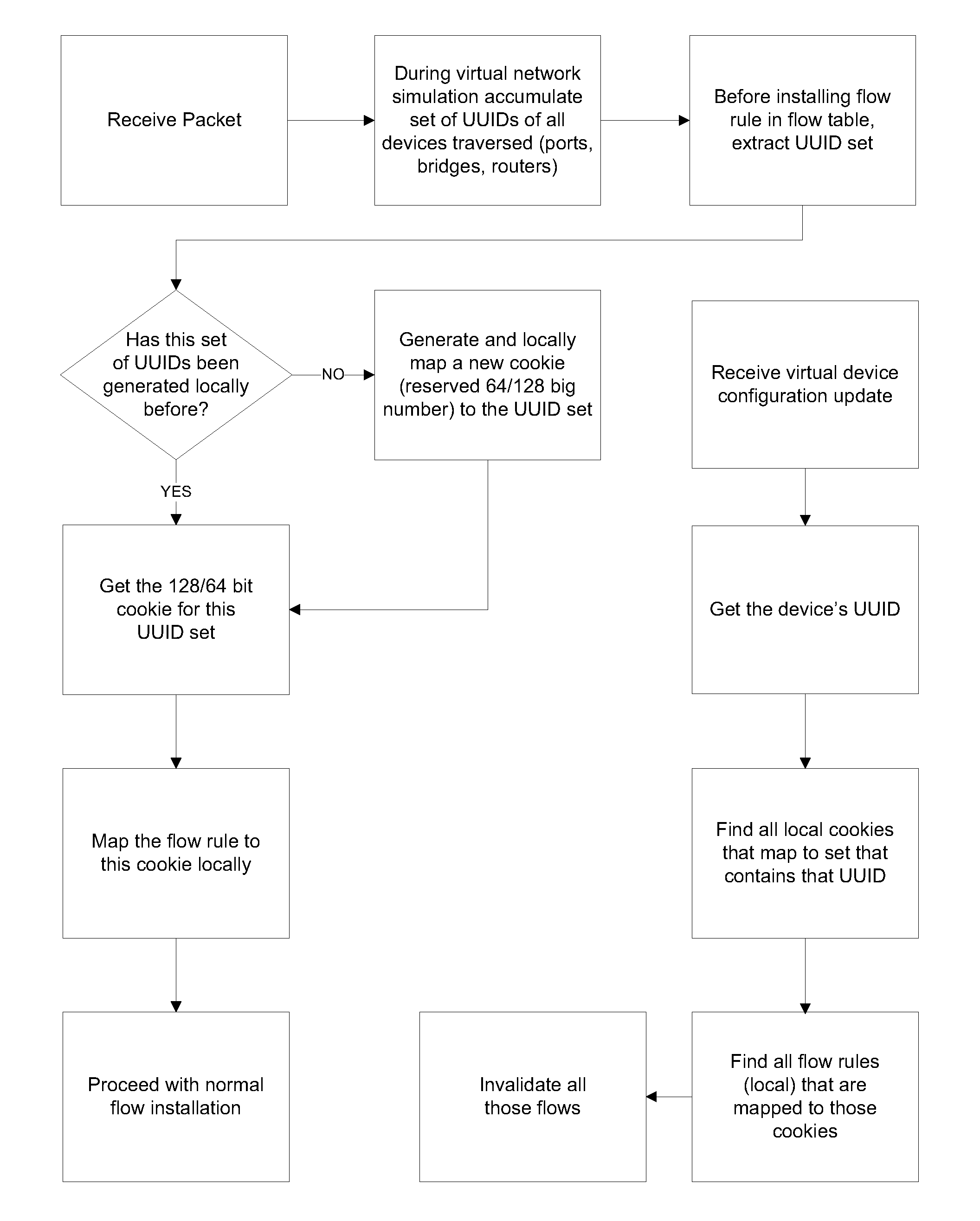
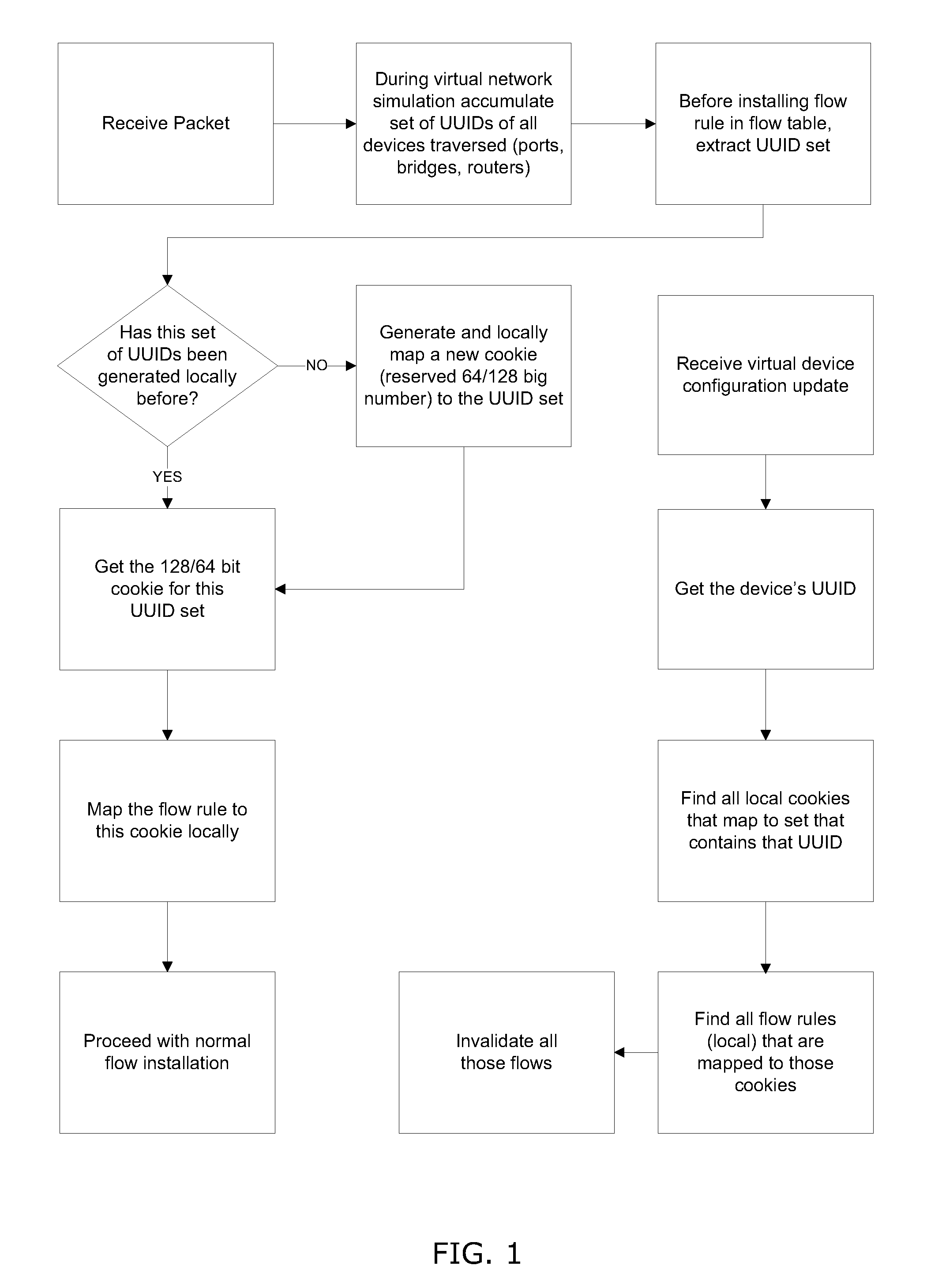
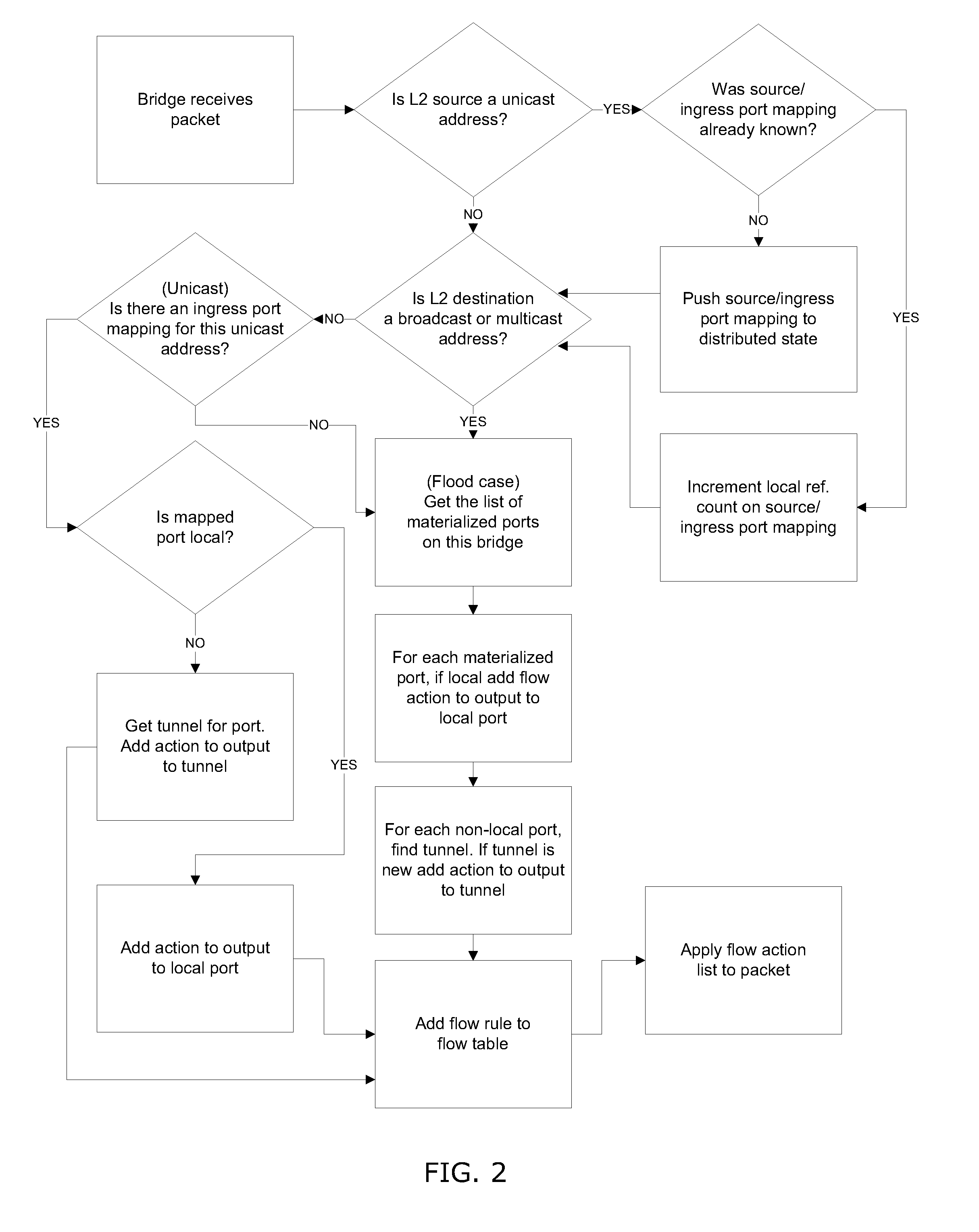
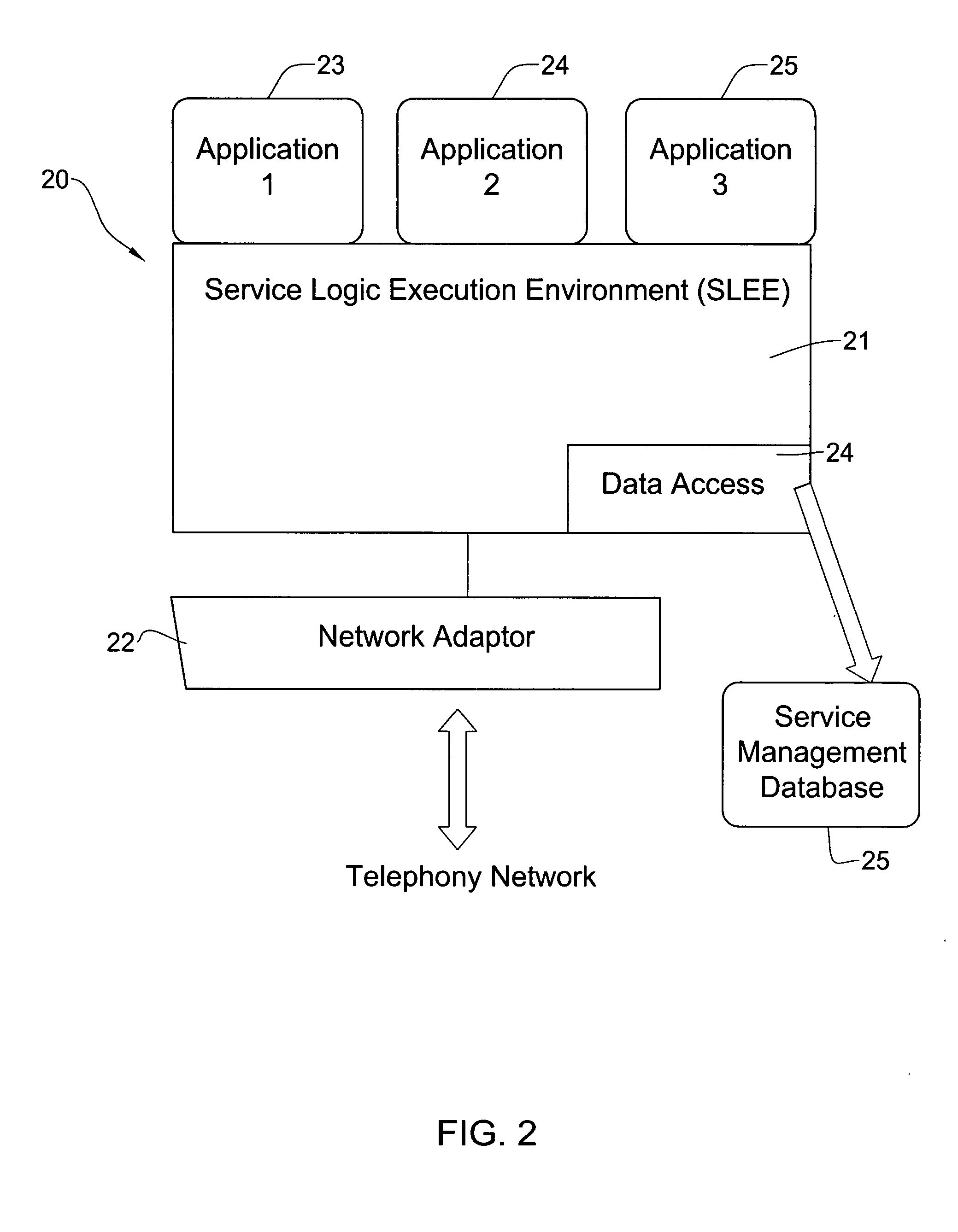
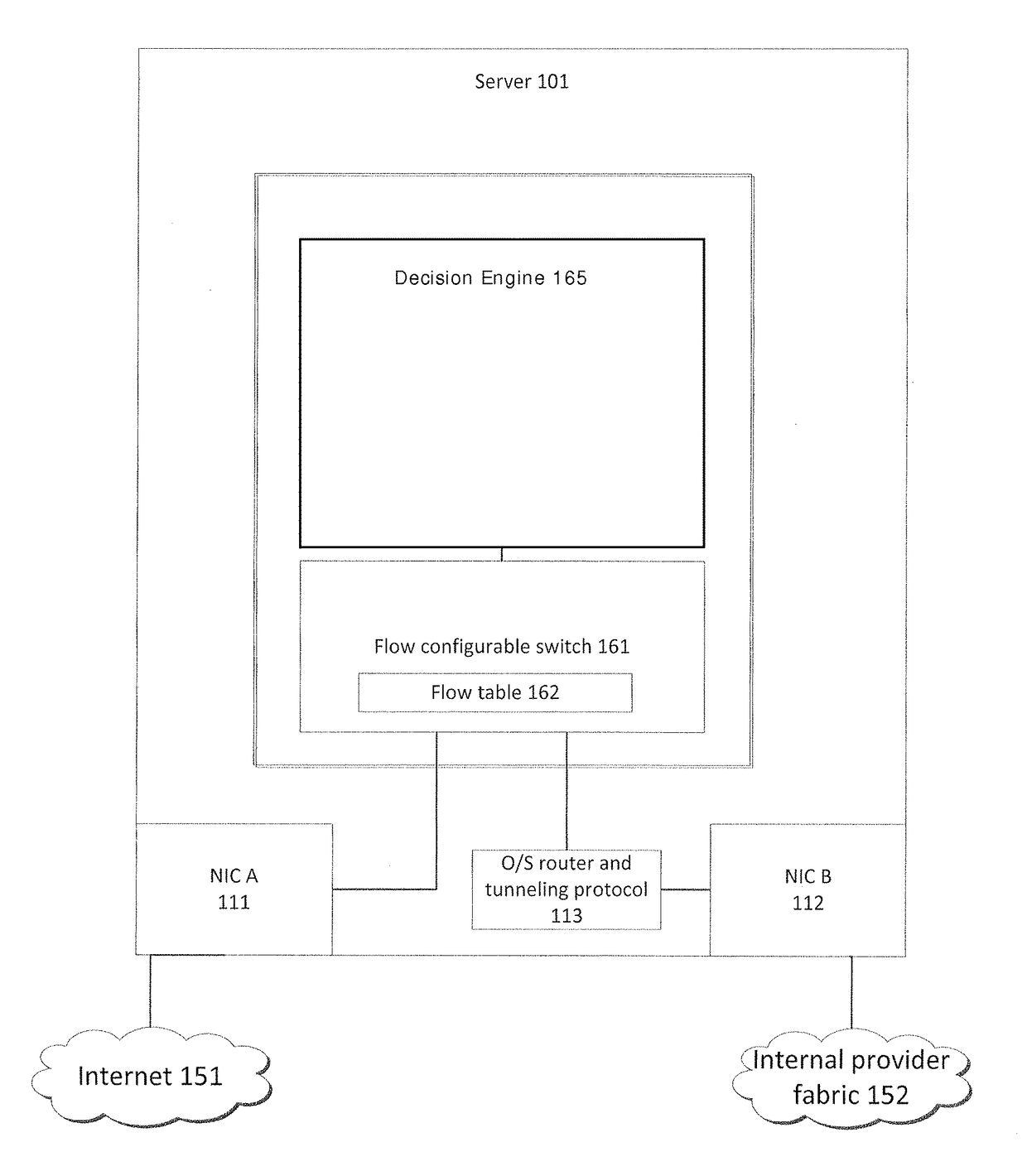
System and method for implementing and managing virtual networks
ActiveUS20140195666A1Digital computer detailsData switching networksVirtual network topologyDecision taking
A system and method for implementing and management virtual networks is disclosed. A method includes receiving a network packet arriving at a first network interface of a first node of an underlying network, communicating at least the packet and an identifier of the first network interface to a decision engine, determining how the packet should be processed based on a simulation by the decision engine of a traversal of a virtual network topology including a plurality of virtual network devices, wherein the decision engine communicates with a shared database accessible from the underlying network that stores the virtual network topology and virtual device configurations for the plurality of virtual network devices; and processing the packet based upon the simulation.
Owner:MIDO HLDG LTD
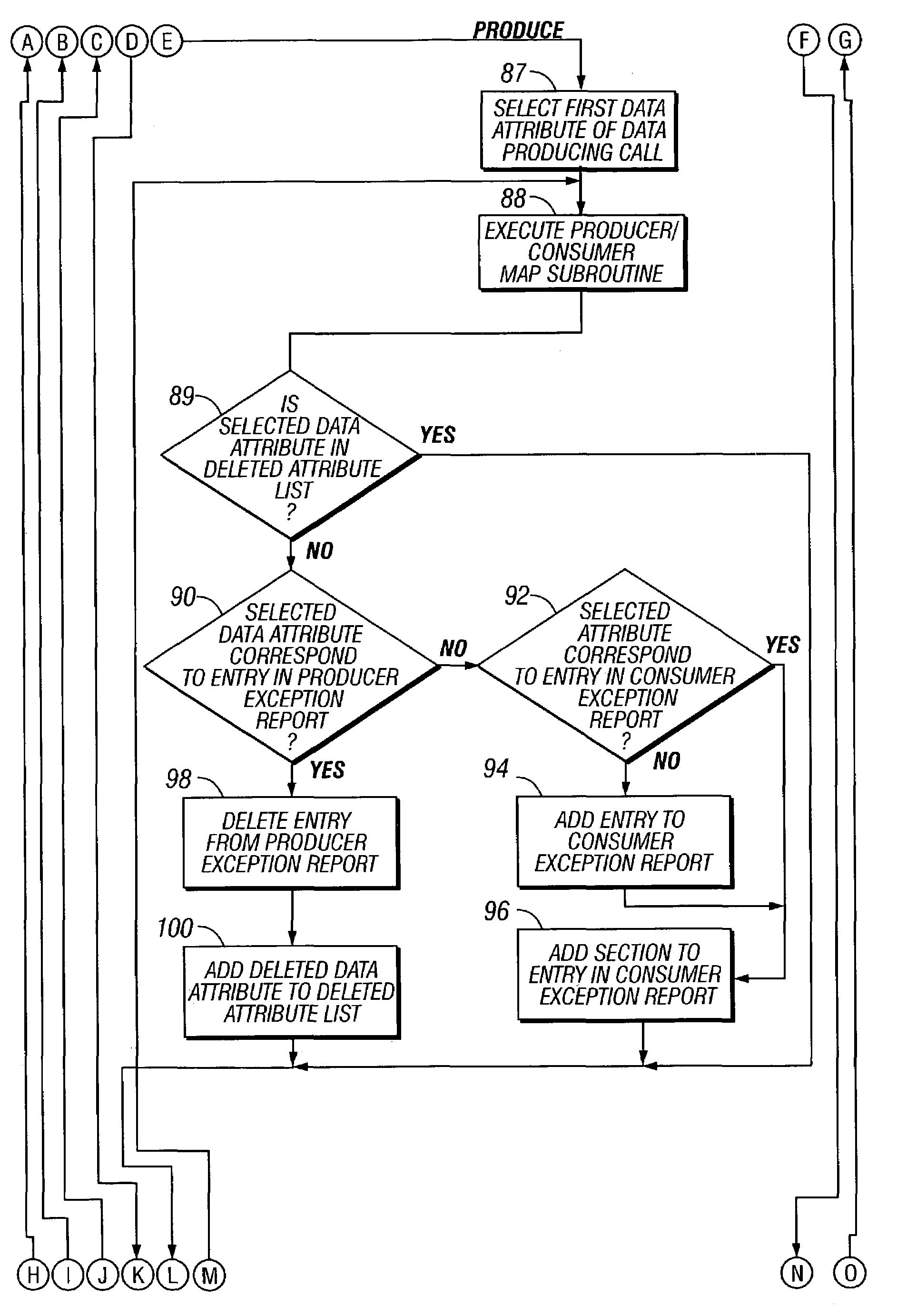
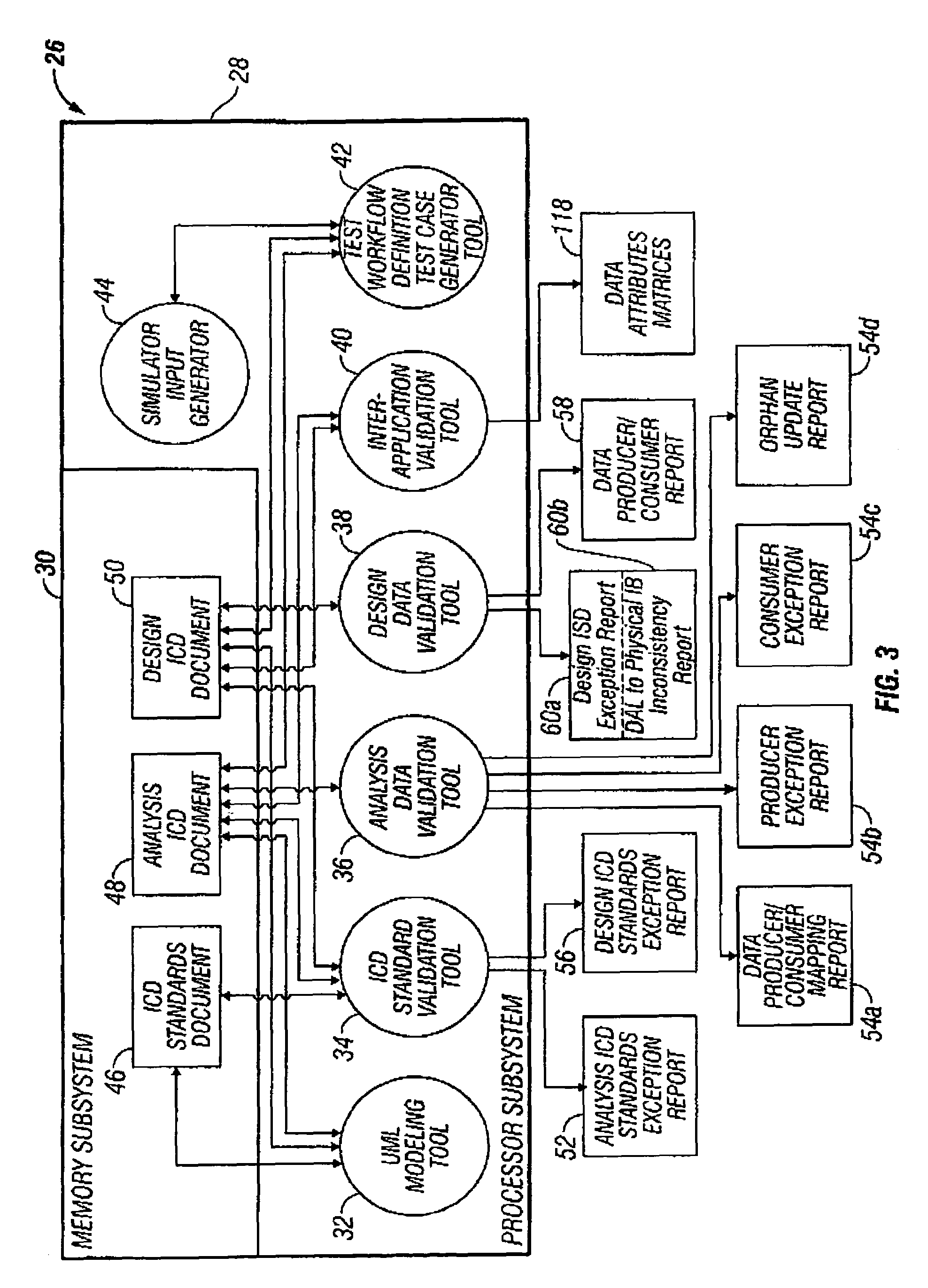
Analysis data validation tool for use in enterprise architecture modeling with result based model updating
InactiveUS7216340B1Digital data information retrievalSpecial data processing applicationsAnalysis dataEnterprise architecture
A device for modeling an integrated enterprise includes a first tool for constructing a model of the integrated enterprise and a second tool for analyzing calls, contained in the constructed model, between applications of the integrated enterprise and a database shared thereby. The call analysis tool identifies data attribute imbalances in calls between the applications of the integrated enterprise and the shared database. Data attribute imbalances result if the calls attempt to consume data which was never produced or if the calls produce data which is never consumed. The call analysis tool also generates producer / consumer maps of the data attributes used in the model, producer exception reports which identify data attributes which are consumed but never produced and consumer exception reports which identify data attributes which are produced but never consumed.
Owner:SPRINT CORPORATION
Automated method for identifying and repairing logical data discrepancies between database replicas in a database cluster
InactiveUS8126848B2Digital data processing detailsDatabase distribution/replicationData differencingTransaction log
A method and system for monitoring and maintaining the consistency of replicated databases in a shared-nothing database cluster architecture is presented. The method involves the continuous monitoring of the database transaction logs that are maintained by the autonomous database managers that manage the individual database replicas in the cluster. In the event that data discrepancies are detected via the comparison of the transaction logs of the individual database replicas, remedial action is carried out according to configured rules in the main cluster controller. These remedial actions may include, but are not limited to, making a database node inactive within the cluster, or automatically repairing any data discrepancies that are detected among the database replicas in the cluster.
Owner:WAGNER ROBERT EDWARD
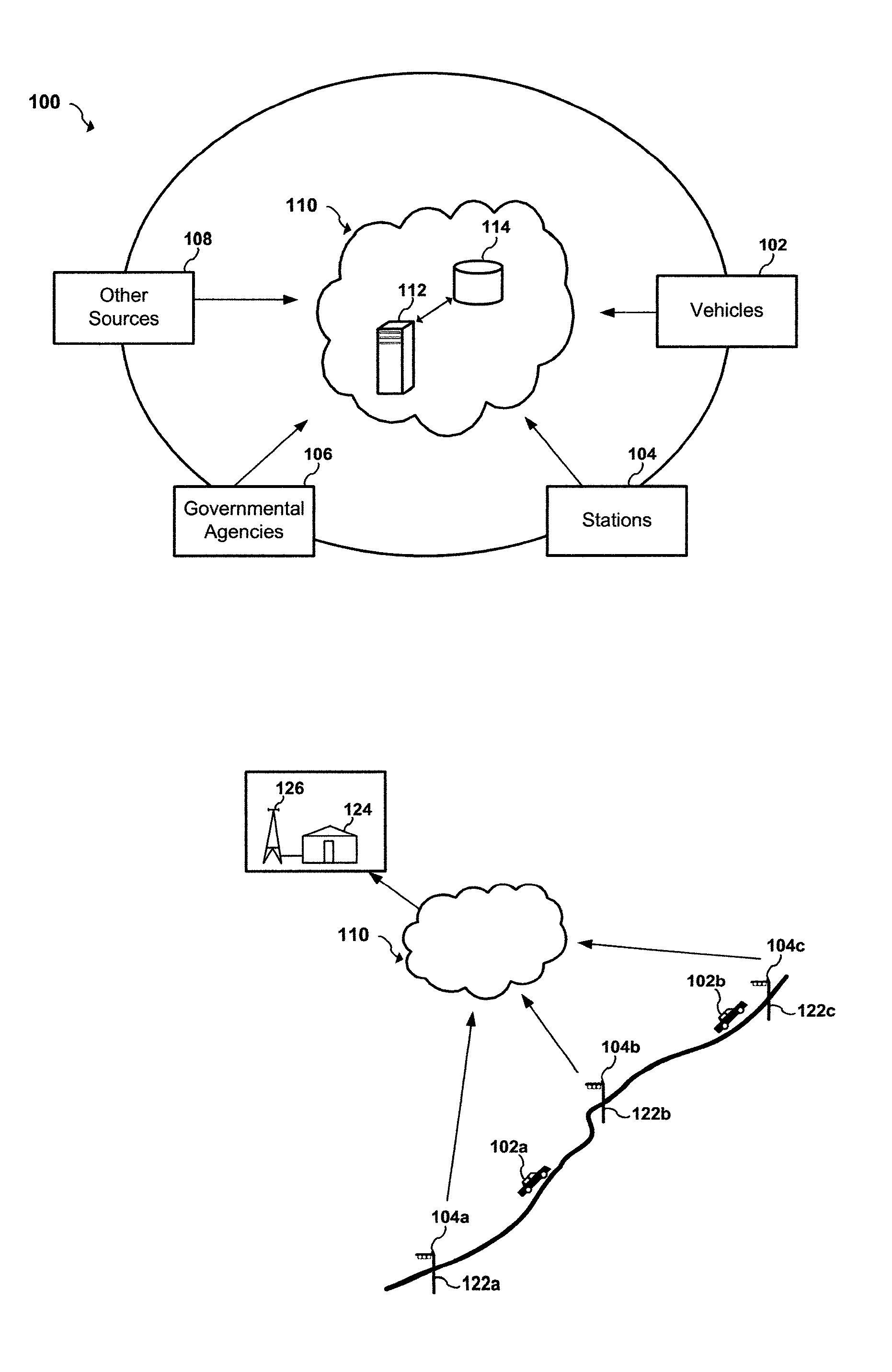
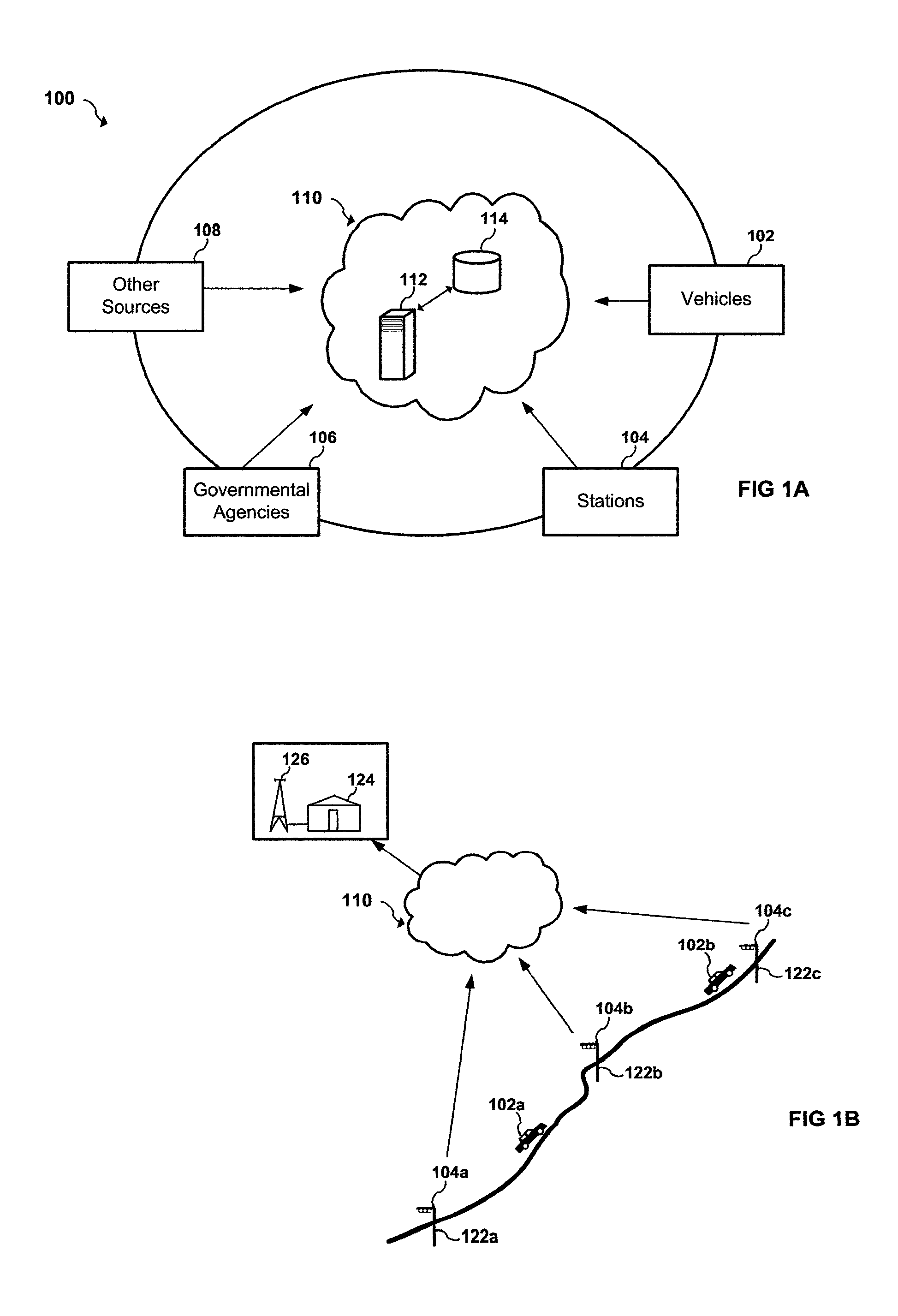
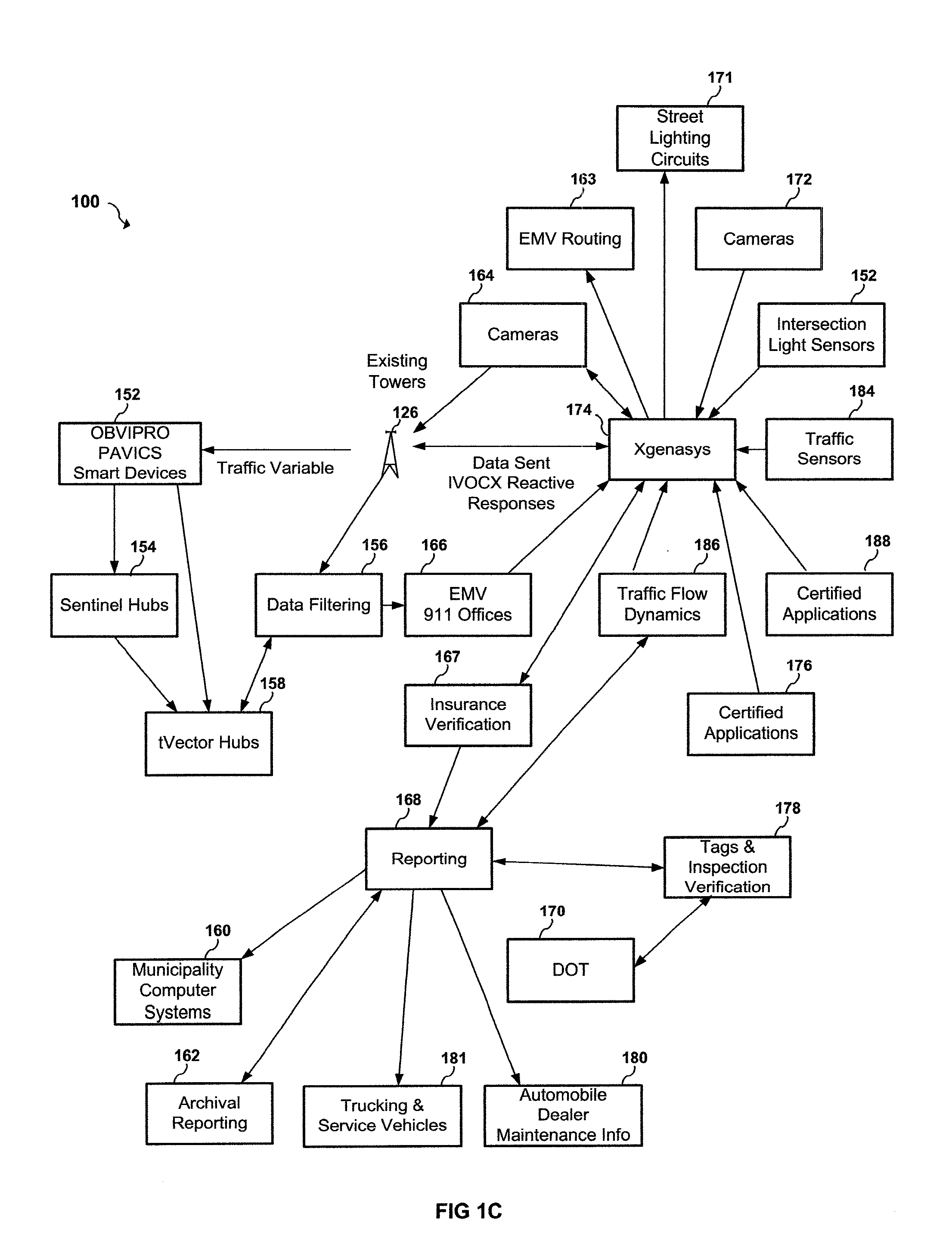
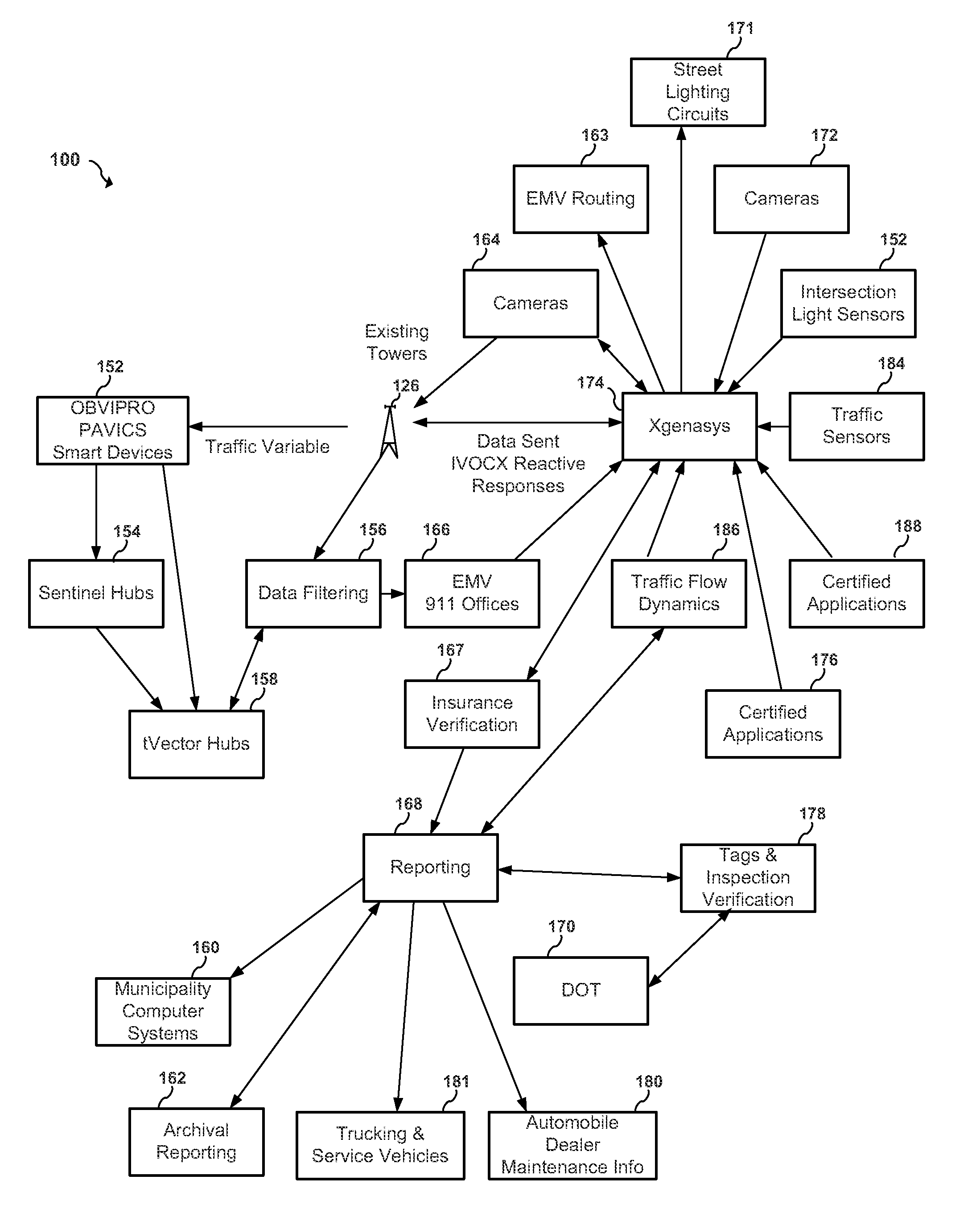
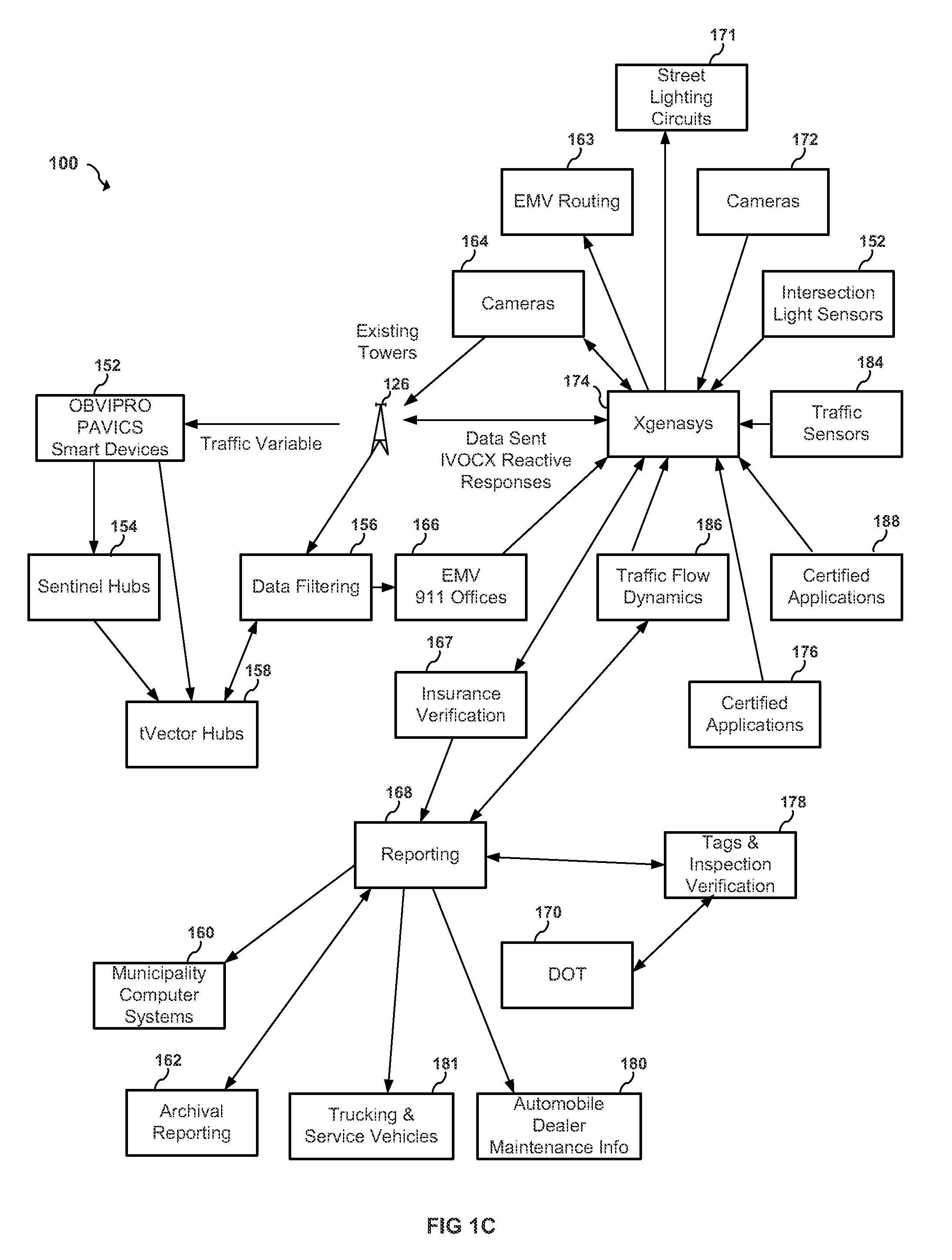
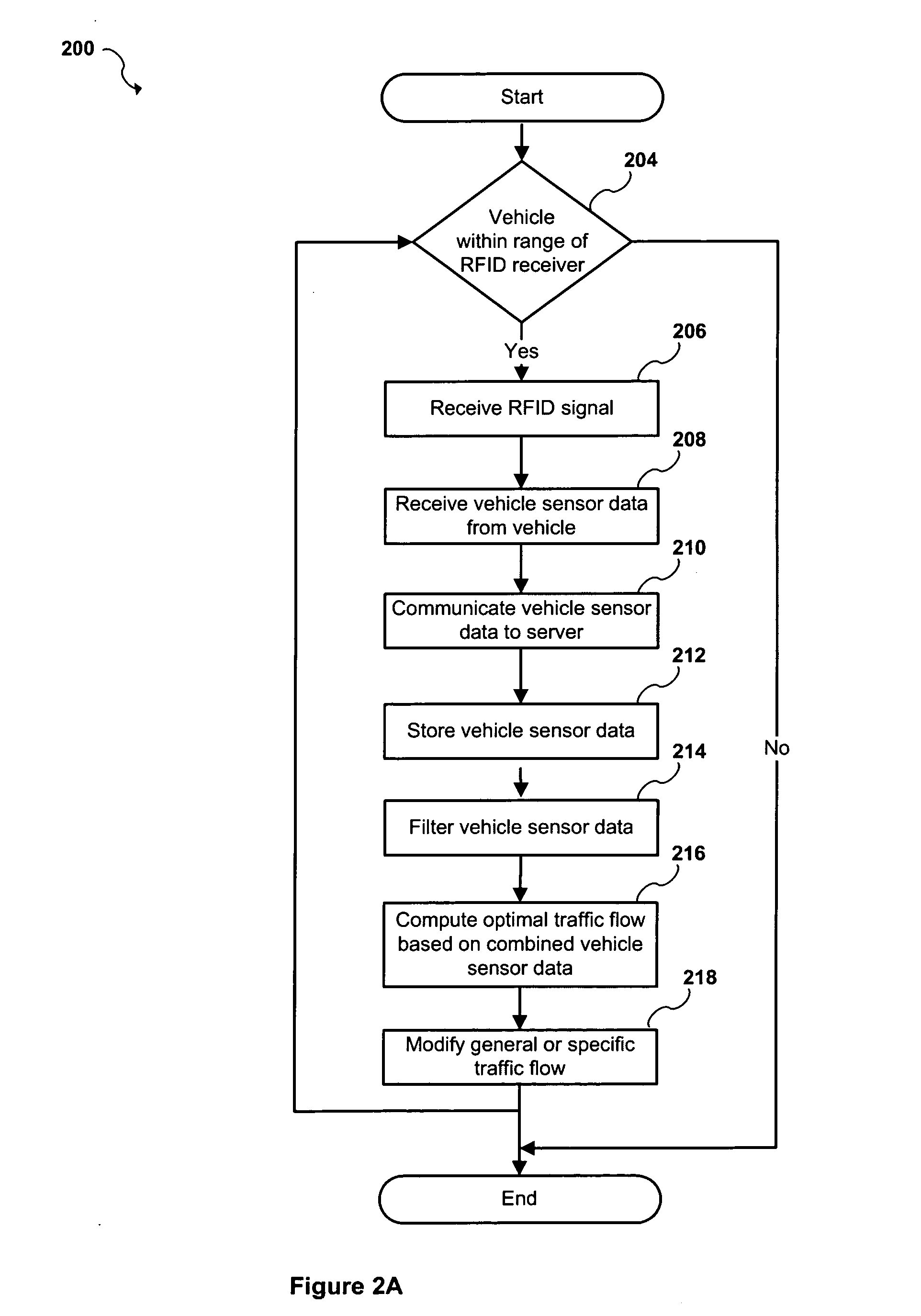
Apparatus and system to manage monitored vehicular flow rate
ActiveUS20160379486A1Solve the excessive calculationEfficient inputControlling traffic signalsArrangements for variable traffic instructionsPrivate networkEngineering
An apparatus and system to manage monitored traffic density in relationship to spatial locational flow rates. The system includes a variety of mobile and / or stationary transmitting and receiving comm-devices utilizing certified comm-devices equipped Avics iChipset arranged in a polarity of vehicles, in communication with stationary and / or mobile hub comm-devices and / or other certified comm-devices, strategically arranged within and / or along one or more roadways and in communication with a server channel networked to a central server. Configured to receive and / or transmit encrypted traffic data from the diversity of stationary and / or mobile transmitting and receiving comm-devices over the network, update traffic data in the non shared database, continuously calculate optimal traffic density flow for one or more of vehicles traveling along the one or more roadways based on the updated vehicular transit data, transmitting variations in speed adjustments in a network infrastructure to one or more vehicles; adjusting traffic light intersections based on traffic density traversing such roadways based on the optimal traffic flow suggestions combined with Predicated Traffic Artifacts transmitted via system generated encrypted digital comm-advice directives; and in turn share extracted and / or transmitted data with each state an federal DOT departments and other stack holders, including insurance companies and vehicle manufacturers and dealers with information to assist with making the traffic network safer. The present invention presents an Intuitive ITS engaged in Channeled Vehicular Telematics conveying statistical data, from an plurality of network devices, providing informational services forecasting safety-critical features and more, in return gathering and disseminating connected channelled intelligence between vehicles from within and surrounding infrastructures and other shareholders. Such data includes vehicle Phase-Change Spatial analytics from traffic congestion artifacts, along with Consumption Variable Analysis that provides real-time Energy Summation Data from combined vehicle exhausted energy by adjusting traffic flow based on traffic density in relationship with the human factor, vehicle capacity to navigate and topography and climatic variations in relationship with any area being traversed, and most importantly the use of the unique string identification. USIN acknowledged as ‘tMarker Audit Trail’ or simply tMarker Trail as to data inception creation point. Managed within a secure private network infrastructure, each comm-device is synchronized with localized cloud servers in communication will a central server. This invention embarks on a new era in vehicle management, further enhancing time sensitive movements, leaving no doubt as to Vehicle Symmetry Orientation, especially once you move your vehicle and additional particulars currently not beyond the scope of this art presented herein. ITTS will throughly reduce the worlds fossil fuel supply consumption rate and on many other fronts availed by extracted data, transmitted from each vehicles onboard vehicle processor equipped with Avics iChipSet on certified comm-devices, reducing navigational concerns to elementary variables creating a safe traffic network.
Owner:TAYLOR DONALD WARREN
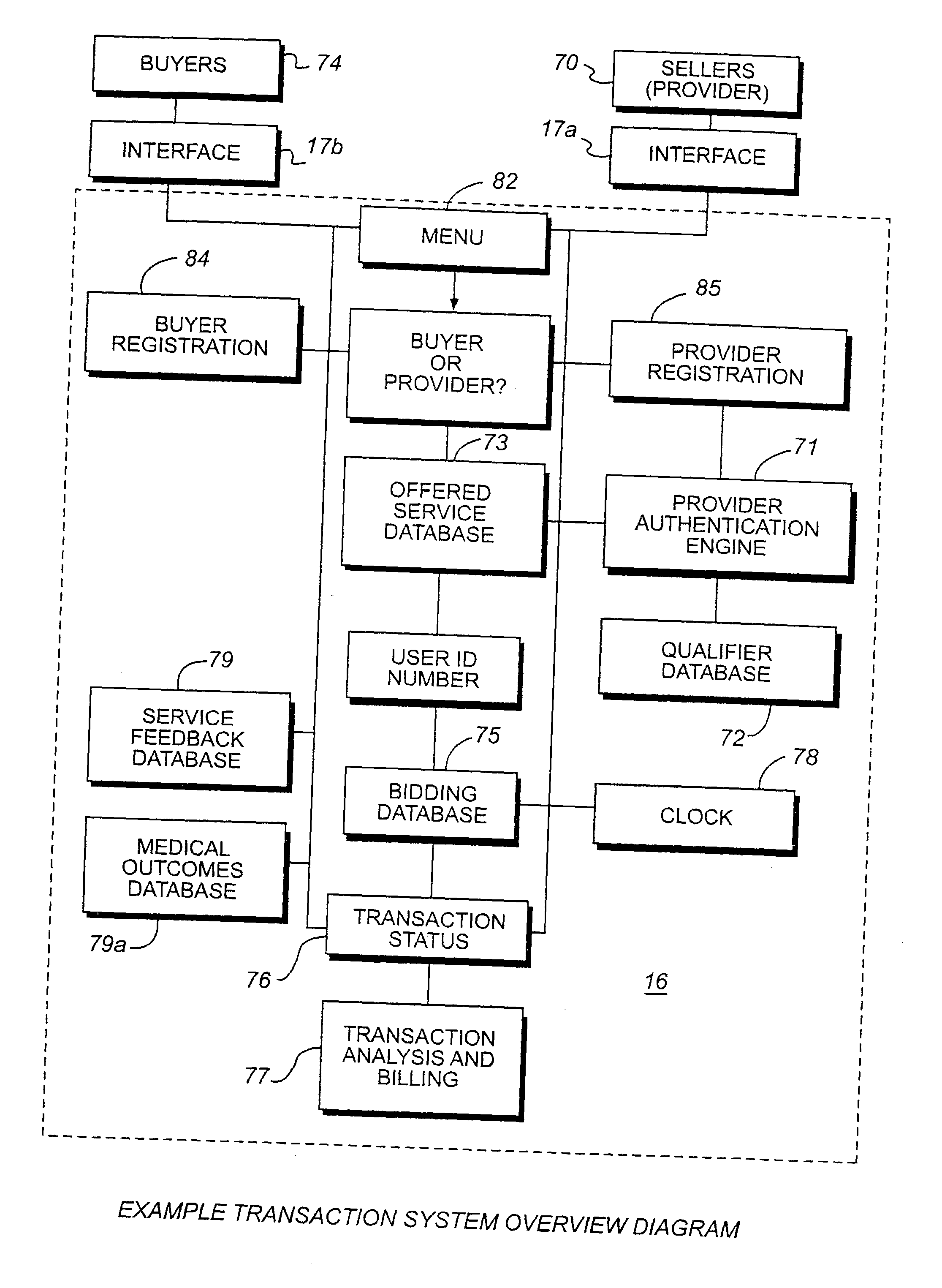
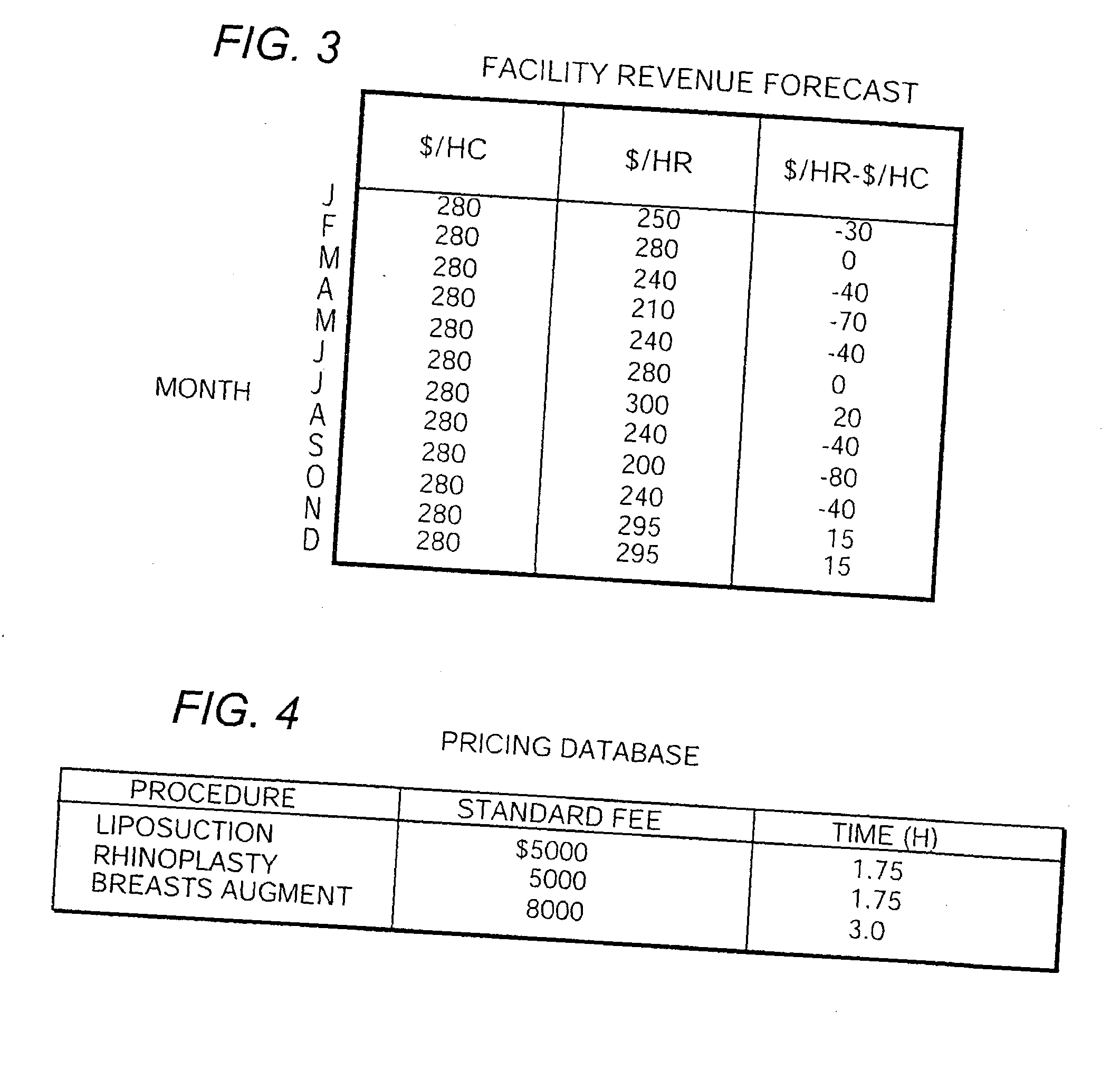
Method and system for provision and acquisition of medical services and products
InactiveUS20030195838A1More transactionDrive up costFinanceTelemedicineService provisionThe Internet
Transactional costs associated with providing professional services are reduced by enabling prospective clients / patients and professional service providers to competitively negotiate fees for proffered services through an interactive on-line professional services auction transaction system implemented over a publicly accessible communications network such as the Internet. A separate on-line auction transaction system, which shares database resources with the professional services auction transaction system, is also provided for implementing an arrangement for auctioning options to purchase services at a discount-such as discount coupons that are applicable toward fees charged for proffered professional services. A person-to-person network marketing arrangement for rewarding existing member professional service providers for recruiting prospective new service provider members and training them in the use of the on-line auction transaction systems is also fostered and supported via the on-line professional services auction transaction system.
Owner:HENLEY JULIAN L
Apparatus and system for monitoring and managing traffic flow
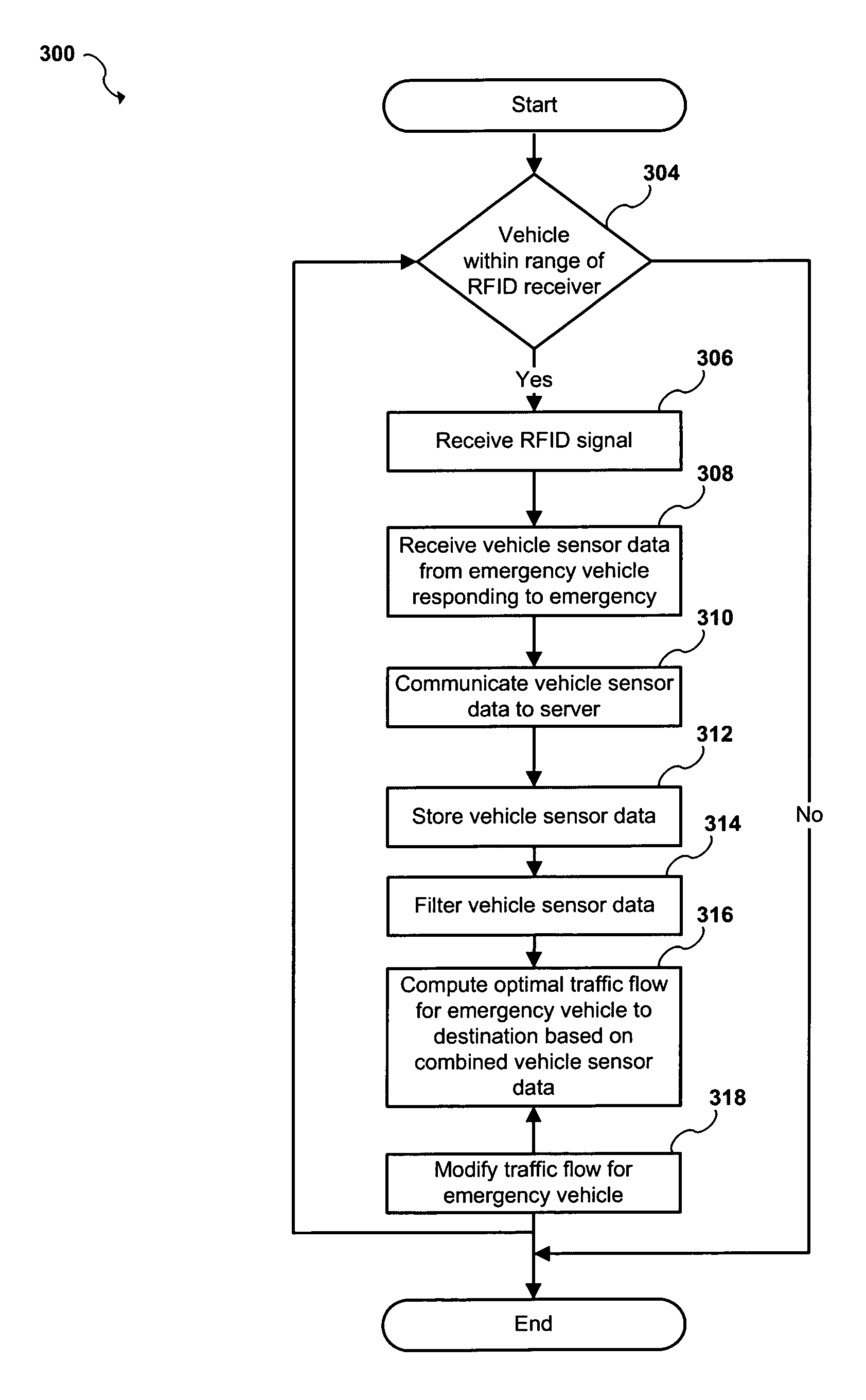
ActiveUS9224293B2Controlling traffic signalsDetection of traffic movementTraffic capacityTraffic congestion
An apparatus and system for monitoring and managing traffic flow. The system includes a plurality of remote sensor devices arranged in a plurality of vehicles, a plurality of remote communication hub devices operatively arranged along one or more roadways and in communication with the plurality of remote sensor devices, a central server, a network interface in communication with the central server and the plurality of remote communication hub devices over a network, and a shared database in communication with the central server. The central server is configured to receive traffic data from the plurality of remote sensor devices over the network, update traffic data in the shared database, periodically calculate an optimal traffic flow for one or more of vehicles traveling along the one or more roadways based on the updated traffic data, and transmit timing adjustments over the network to one or more traffic light intersections based on the optimal traffic flow calculations. The network interface is configured to send and receive traffic data. The traffic data includes vehicle location information and network traffic congestion information.
Owner:TAYLOR DONALD WARREN
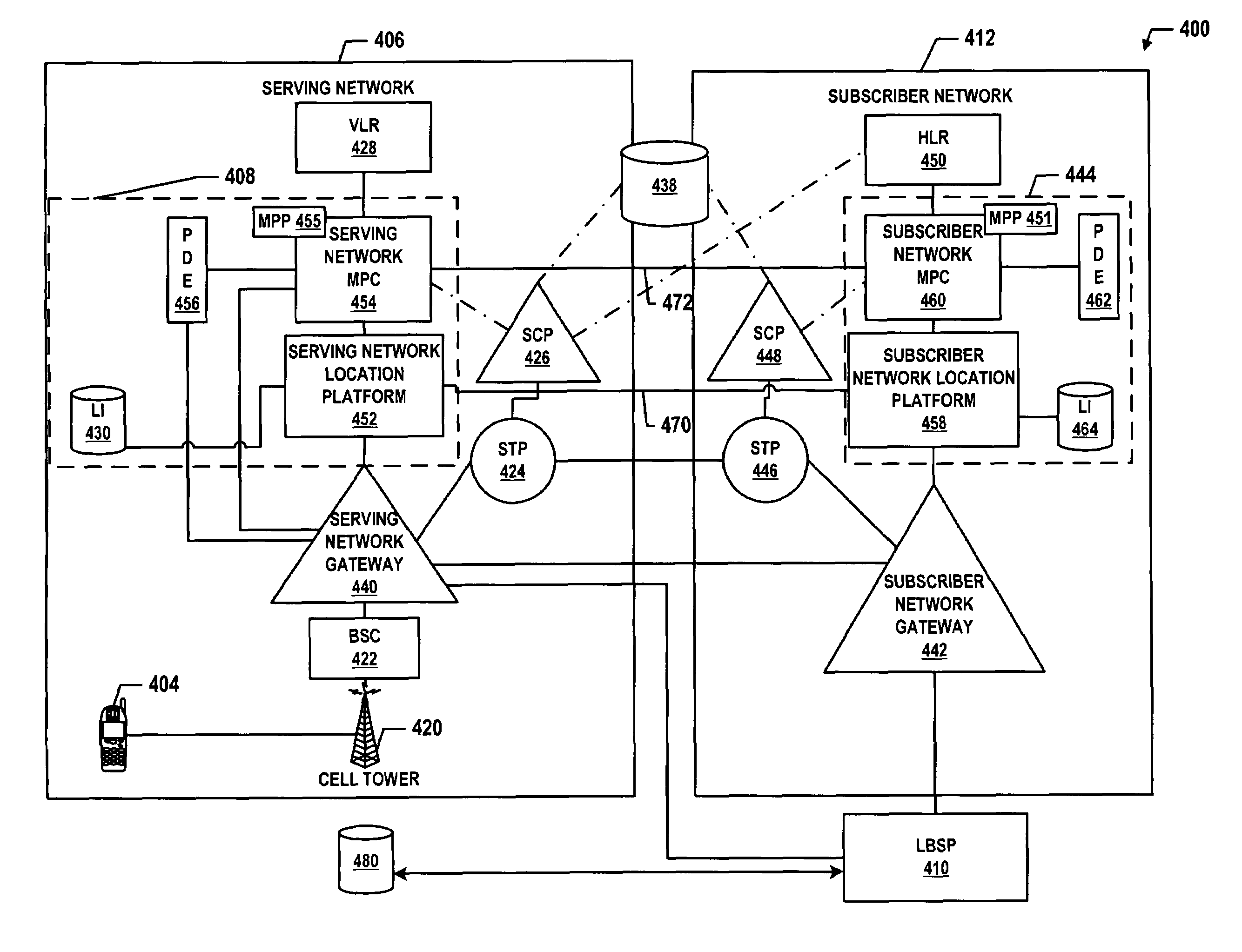
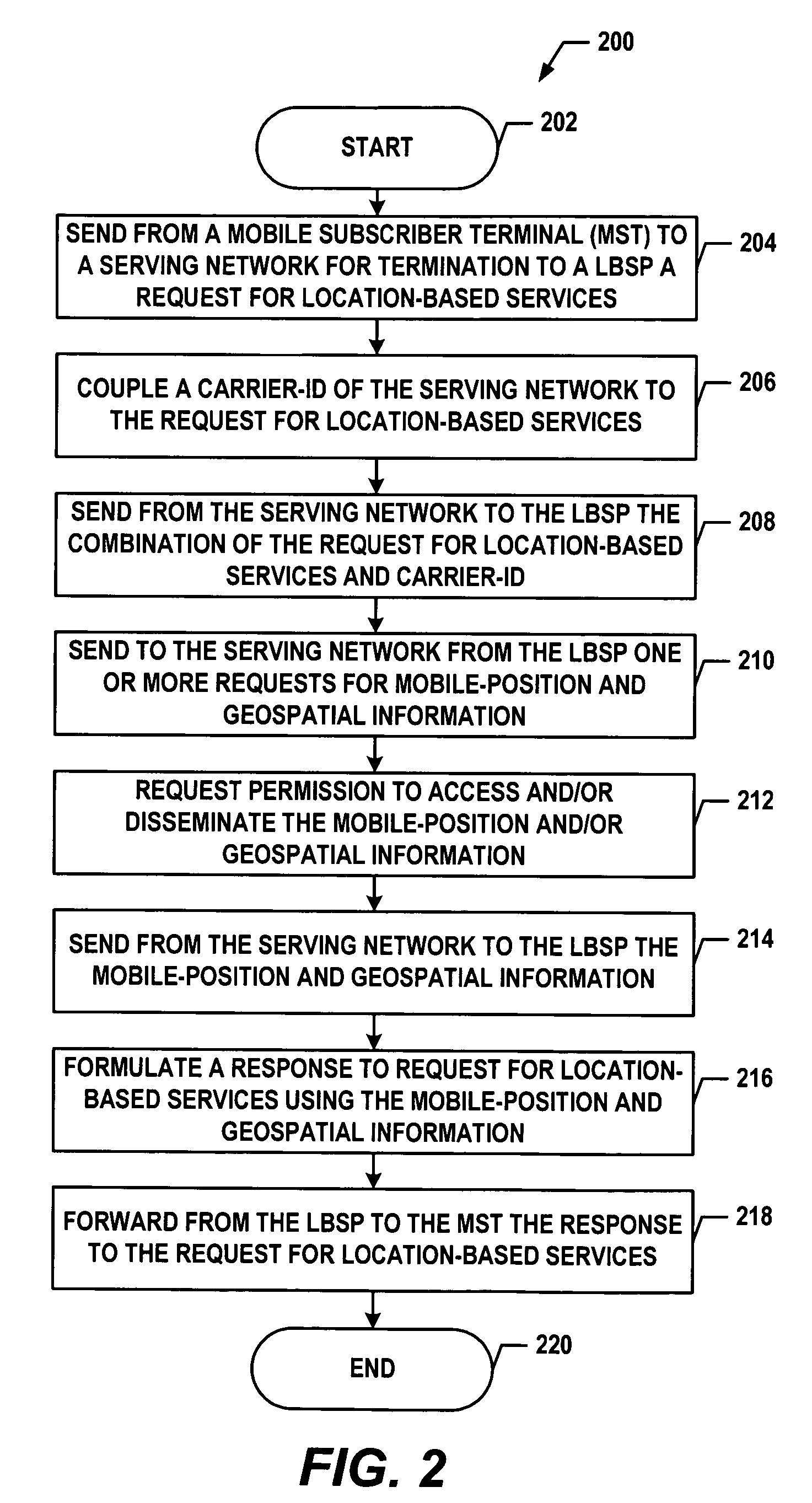
Method and system for sharing and/or centralizing mobile positioning information and geospatial data for roaming mobile subscriber terminals
ActiveUS7209758B1Position fixationRadio/inductive link selection arrangementsData libraryGeo spatial
A method and system for providing location based services (LBSs) to a mobile-subscriber terminal (MST) roaming in a serving network is provided. A location based service provider (LBSP) that is outside of the serving network receives from the serving system an MST-initiated request for LBSs and an identifier of a first location system (LS1) that is associated with the serving network. Responsive to the MST-initiated request, the LBSP sends to a second location system (LS2) (i) a request for mobile positioning information (MPI) for the MST, and (ii) the identifier. Using the identifier, the LS2 addresses and sends the request for MPI to the LS1. Responsively, the LS1 populates a shared database with the MPI. The LS2 retrieves the MPI from the shared database and sends it to the LBSP. The LBSP sends to the MST a reply to the MST-initiated request for LBSs.
Owner:SPRINT SPECTRUM LLC
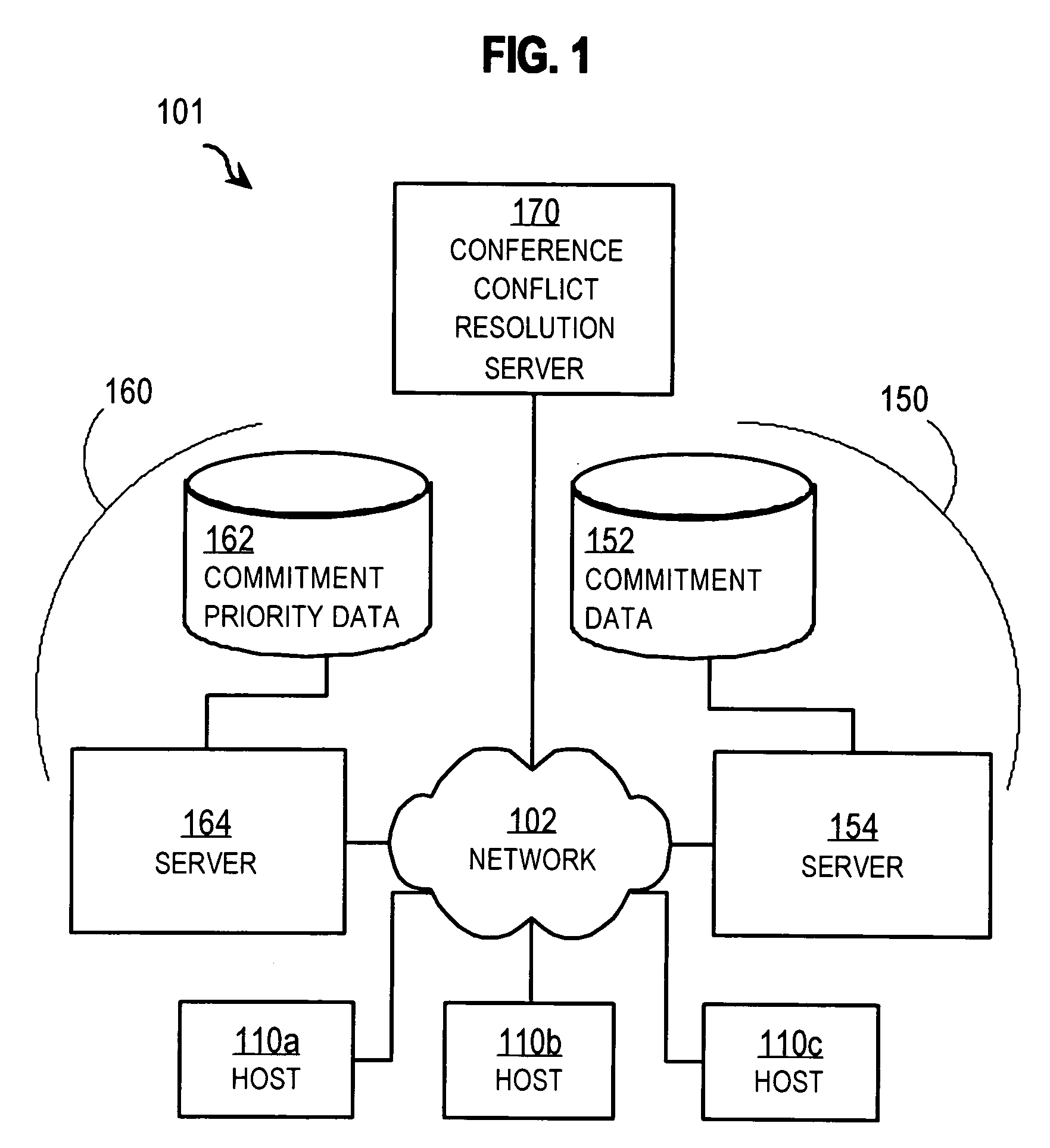
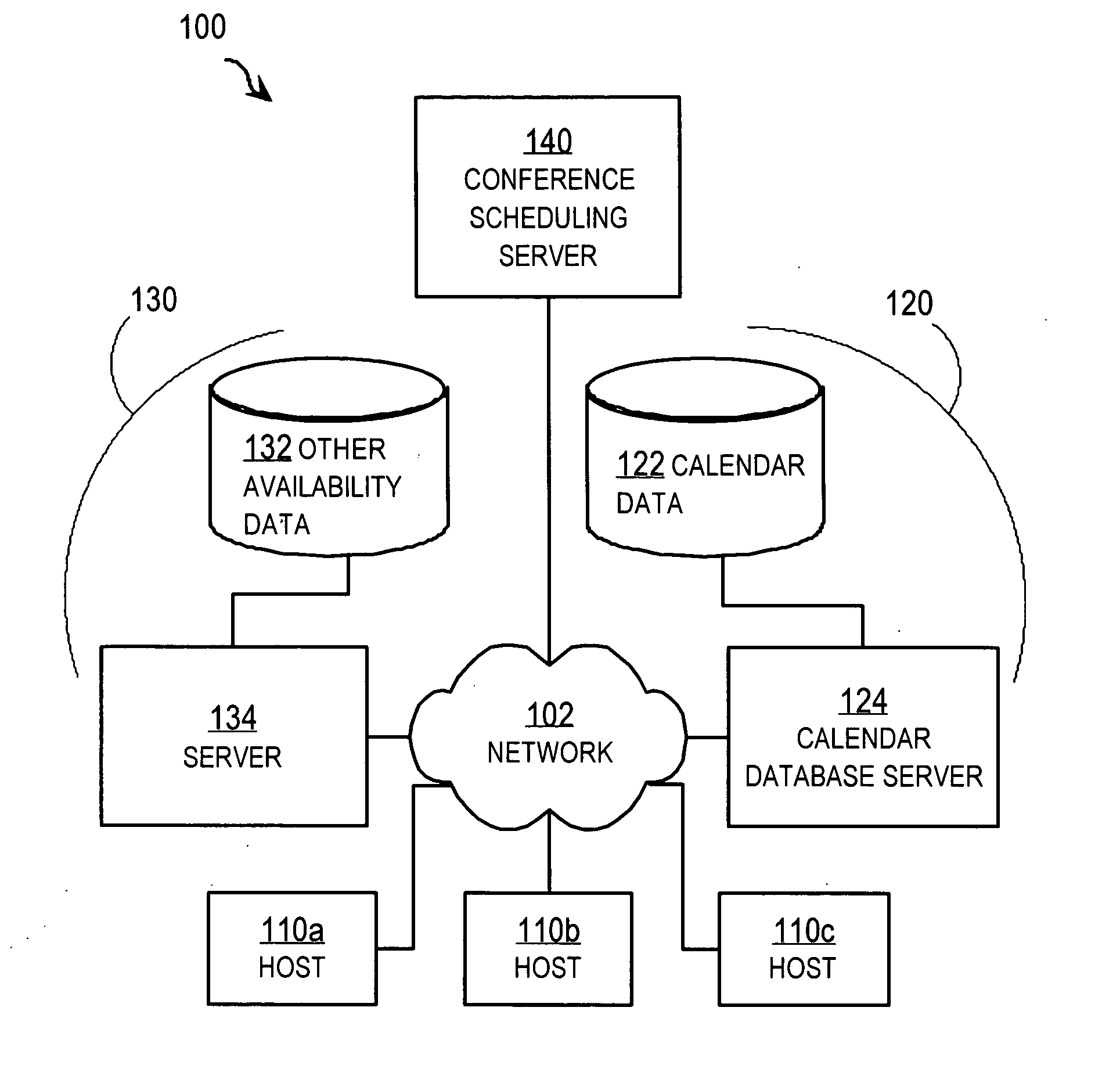
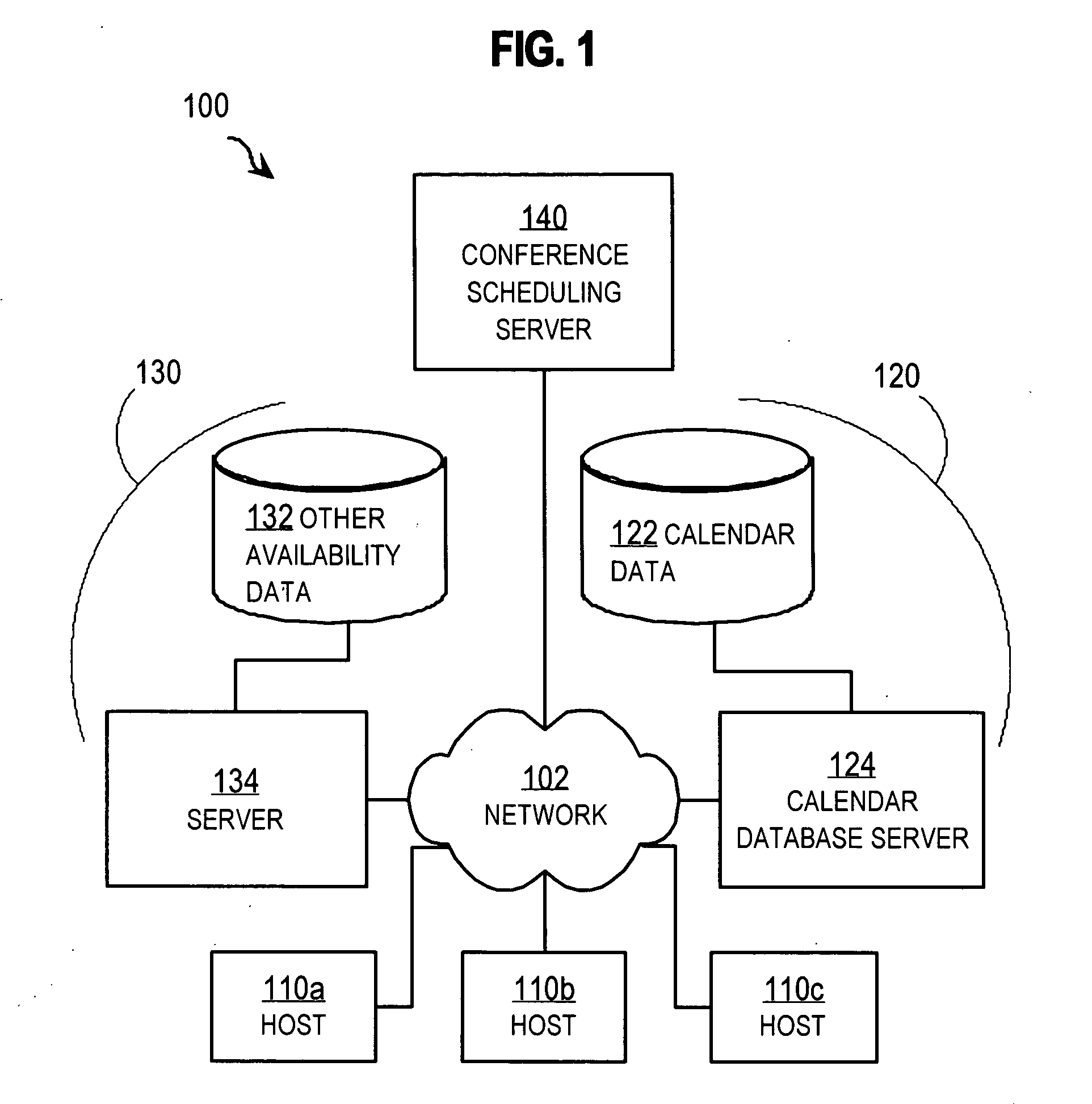
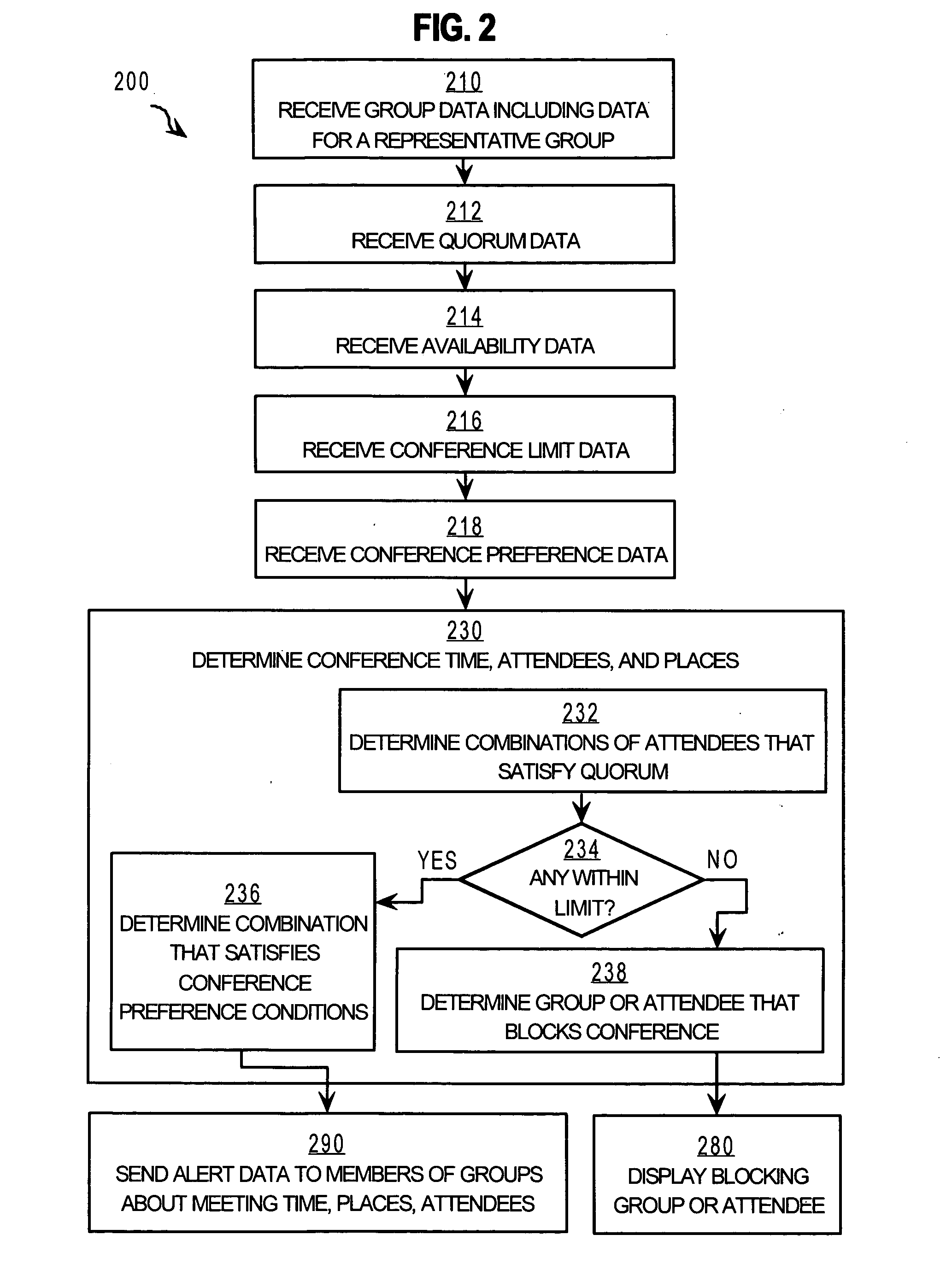
Techniques for resolving conflicts in scheduling conferences
InactiveUS20060047557A1Multiprogramming arrangementsData switching networksTravel costHuman language
Techniques for scheduling a conference among multiple persons includes receiving a conference request to schedule a particular conference. The conference request includes quorum data and limit data. The quorum data indicates a quorum of persons to conduct the particular conference. The limit data indicates a limit on a property of the particular conference, such as a limit on the date, time, location, language, or travel cost. The method also includes receiving availability data from a shared database that includes information about a recorded commitment of time for each person of a population. Also received is priority data that indicates an importance to an organization that a particular recorded commitment of a particular person is honored. A proposed time interval for the particular conference is determined based on the conference request and the availability data and the priority data.
Owner:CISCO TECH INC
Malware detection and analysis
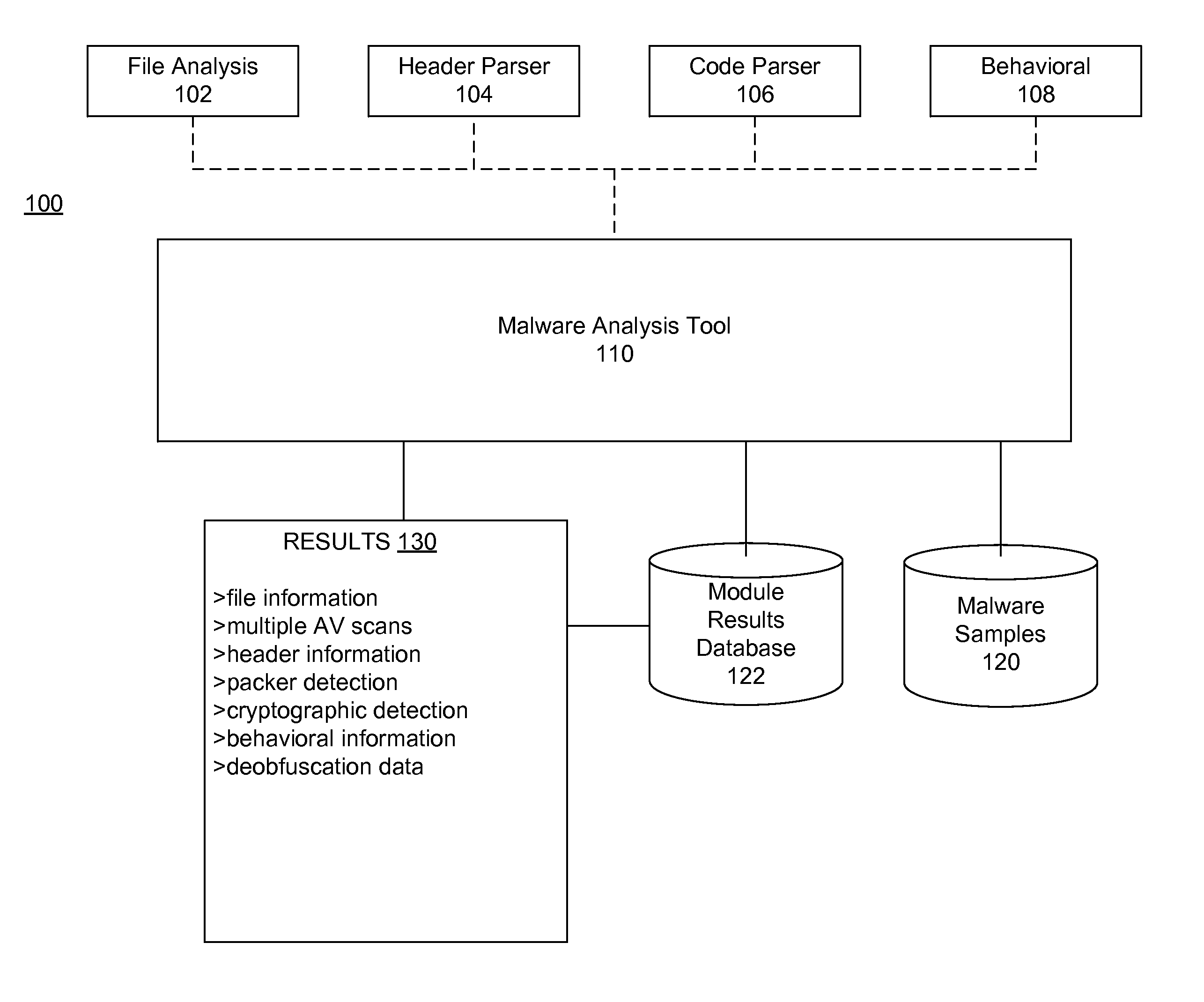
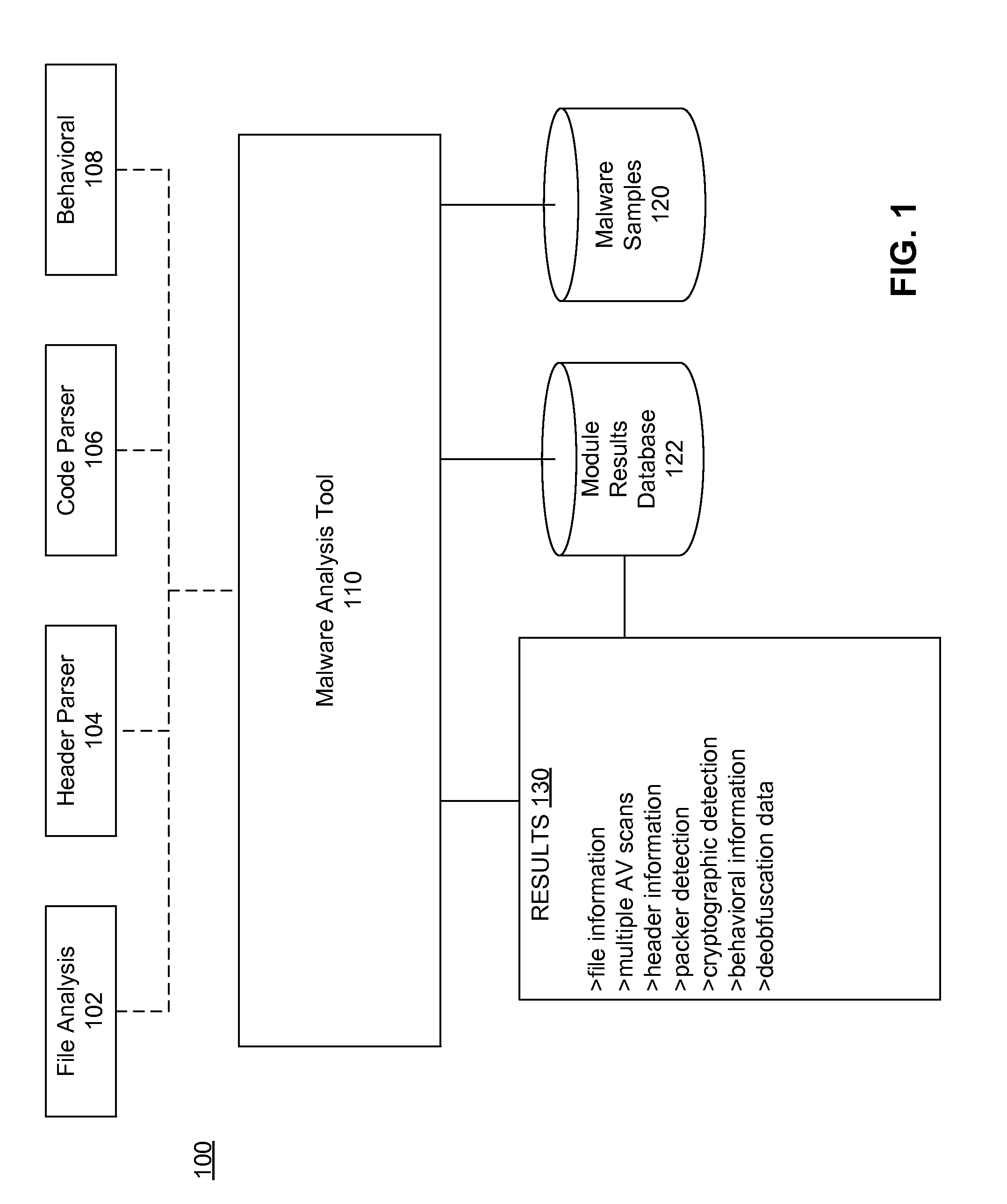
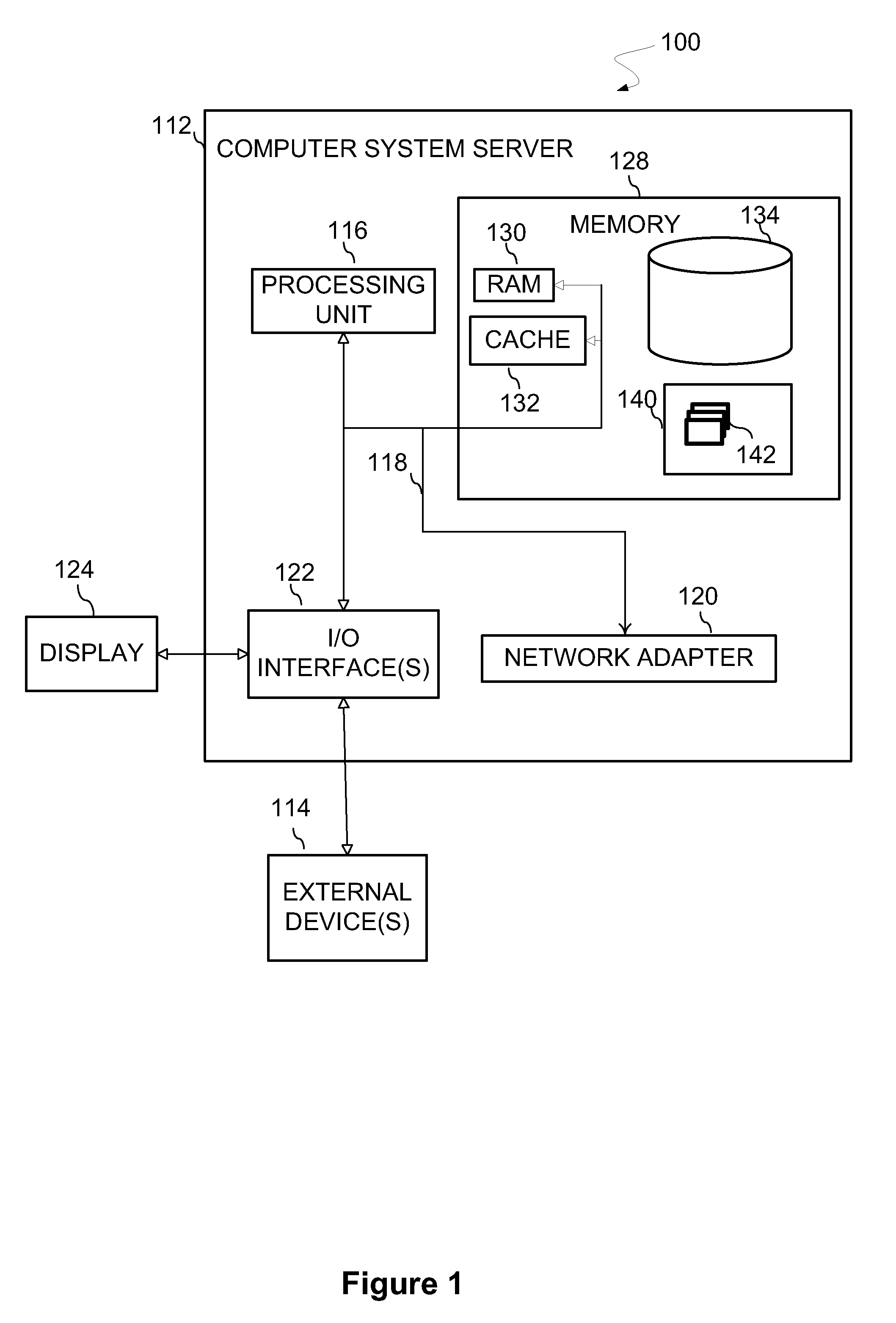
Embodiments of the invention describe systems and methods for malicious software detection and analysis. A binary executable comprising obfuscated malware on a host device may be received, and incident data indicating a time when the binary executable was received and identifying processes operating on the host device may be recorded. The binary executable is analyzed via a scalable plurality of execution environments, including one or more non-virtual execution environments and one or more virtual execution environments, to generate runtime data and deobfuscation data attributable to the binary executable. At least some of the runtime data and deobfuscation data attributable to the binary executable is stored in a shared database, while at least some of the incident data is stored in a private, non-shared database.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
Cloud database sharing
InactiveUS20130031136A1Digital data processing detailsDigital computer detailsAuthorization certificateResource pool
A method, system and computer program product is provided achieving database sharing by providing an interface to contribute a database and a set of resources to a resource pool in a first cloud environment. The interface further allowing a user to input parameters identifying a database, a set of resources, a set of authorization credentials, and a sharing policy. The interface further comprising responsive to the user using the interface and providing the interface parameters which identify the database, the set of resources, the set of authorization credentials, and the sharing policy, adding the database, the set of resources, the set of authorization credentials, and the sharing policy to the database resource pool in the cloud environment, sharing the database, the set of resources, according to the sharing policy, and utilizing the set of authorization credentials.
Owner:IBM CORP +1
Techniques for managing conference schedules using groups
ActiveUS20060045029A1Reduce conflictEasy to produceSpecial service provision for substationMultiplex system selection arrangementsCrowdsData availability
A method and apparatus for scheduling a conference among multiple persons includes receiving group data that indicates persons in a first group. Availability data is received from a shared database that includes information about availability for a conference of a population of persons that includes the persons from the first group. Quorum data is received that indicates that a quorum for a particular conference includes any one or more persons in the first group and less than all persons in the first group; thus the first group is a called a “representative group.” A proposed time interval that satisfies the quorum based on the group data, the availability data, and the quorum data is determined for the particular conference.
Owner:CISCO TECH INC
Method for identifying logical data discrepancies between database replicas in a database cluster
InactiveUS20080140734A1Database distribution/replicationSpecial data processing applicationsData differencingRemedial action
A method and system for monitoring the consistency of replicated databases in a shared-nothing database cluster architecture is presented. The method involves the continuous monitoring of the database transaction logs that are maintained by the autonomous database managers that manage the individual database replicas in the cluster. In the event that data discrepancies are detected via the comparison of the transaction logs of the individual database replicas, remedial action is carried out according to configured rules in the main cluster controller. Additionally, if the database management system running within each node of the cluster possesses a database history file that records key events pertaining to a database replica, such as the occurrence of non-logged bulk loads of table data, or the modification of tables, a method can be instituted for the monitoring of the history files for discrepancies between the database replicas.
Owner:WAGNER ROBERT EDWARD
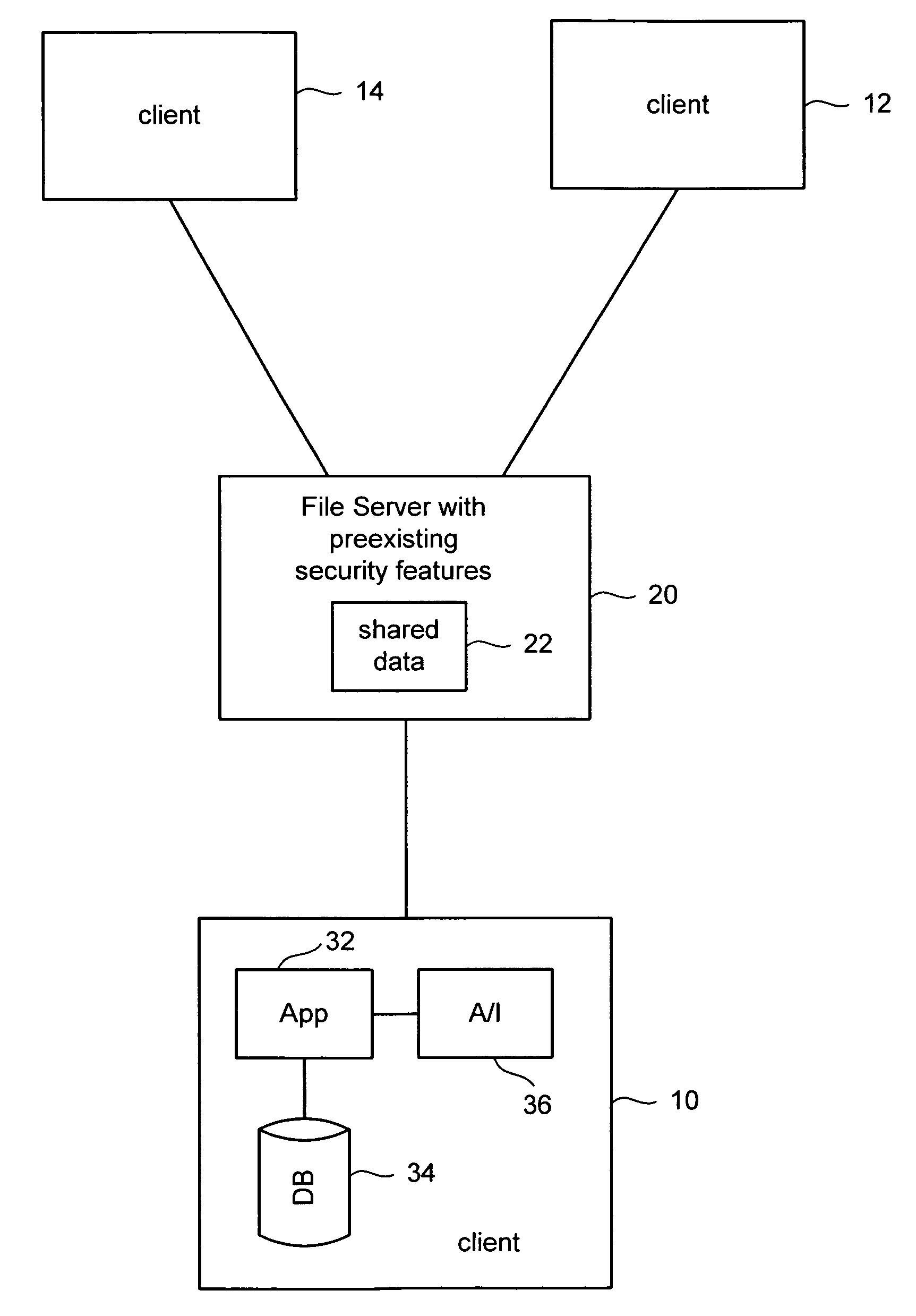
Using a file server as a central shared database
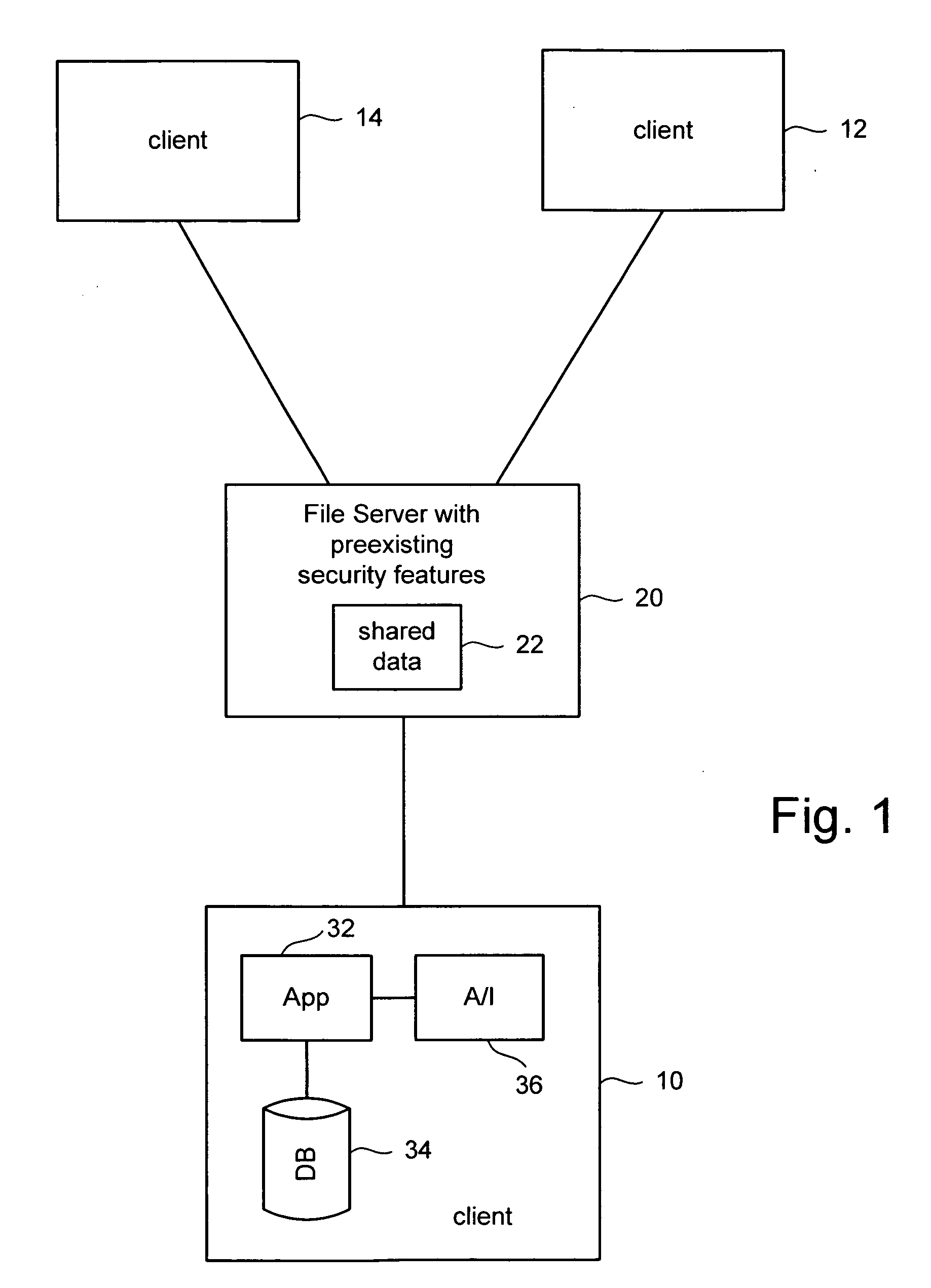
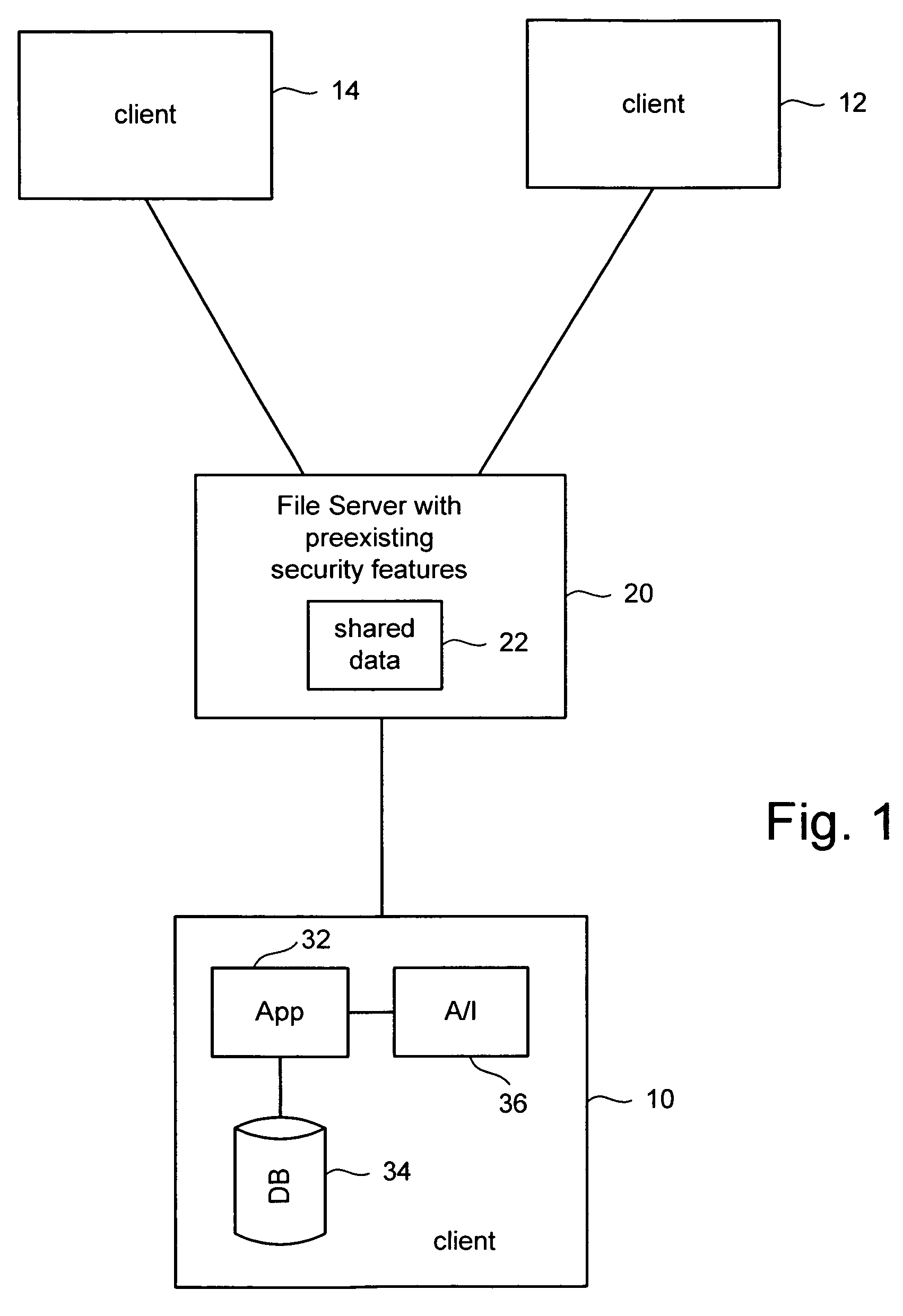
ActiveUS20060173932A1Data processing applicationsDigital data information retrievalClient-sideFile server
Various entities need to share data among team members working on the same project without investing in specialized server software. To address this need, an existing standard file server is used to host data for sharing among the team. The file server has not been customized to share the data for the particular application. A user creates a special folder for a project at a user specified location on the file server. Data associated with the project is converted to files and stored in a structure of folders used by the file server to represent the data that is shared. Each client that has subscribed to this shared data synchronizes the data on their local computing device with the data on the file server. Security is provided by using the file server's built-in access controls.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus and system for monitoring and managing traffic flow
InactiveUS20140278026A1Controlling traffic signalsAnalogue computers for vehiclesTraffic capacityRemote communication
An apparatus and system for monitoring and managing traffic flow. The system includes a plurality of remote sensor devices arranged in a plurality of vehicles, a plurality of remote communication devices arranged along one or more roadways and in communication with the plurality of remote sensor devices, a central server, a network interface in communication with the central server and the plurality of remote communication devices over a network, and a shared database in communication with the central server. The central server is configured to receive traffic data from the plurality of remote sensor devices over the network, update traffic data in the shared database, periodically calculate an optimal traffic flow for one or more of vehicles traveling along the one or more roadways based on the updated traffic data, and transmit timing adjustments over the network to one or more traffic light intersections based on the optimal traffic flow calculations. The network interface is configured to send and receive traffic data, wherein the traffic data includes vehicle location information.
Owner:TAYLOR DONALD WARREN
Sender authentication for difficult to classify email
InactiveUS20110271349A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyElectronic mail
The portion of email traffic that cannot be definitively determined to be spam or definitively determined to be ham (non-spam) is processed by sending a bounceback email to the sender, requiring the sender to reply using a sub-address created by the bounceback generator. The type of bounceback email depends on whether the domain of the received email indicates that the sender is or is not likely to be a spammer. When the sender is not likely to be a spammer, the bounceback email includes a sub-address in computer readable form. When the sender is likely to be a spammer, the bounceback email includes a test that must be solved to yield the sub-address; preferably, the test is very difficult for a computer to solve but reasonably easy for a human to solve. When a reply email to the bounceback email (“reply bounceback”) is received, the presence of the sub-address indicates that the sender is not a spammer, so the reply bounceback is determined to be ham and delivered to the destination mailbox. The bounceback can have the sub-address encoded in such a way that a human must be involved in decoding, which is appropriate for situations where the envelope sender domain of the original email is considered suspicious. The bounceback can have the sub-address presented in a computer readable format when the envelope sender domain of the original email is more trustworthy, if authenticated. Authentication information can be retained in a local private Sender Policy Framework (SPF) database, or shared in a centralized private SPF database.
Owner:KAPLAN MICHAEL GREGOR
Methods and Systems for Sharing Database Content
ActiveUS20100223467A1Digital data processing detailsUser identity/authority verificationThird partyNetwork addressing
Mechanisms and methods for sharing database content stored by a first organization with a third party are provided. A network address is provided to the third party, which can enable control of the access to the content and tracking of the views of the content. For example, the network address can include an encrypted key that contains information about the organization that created content and the specific distribution ID for delivering the content when requested by the third party using the address. A distribution can be created in numerous ways, with various restrictions on the access to the document of a distribution.
Owner:SALESFORCE COM INC
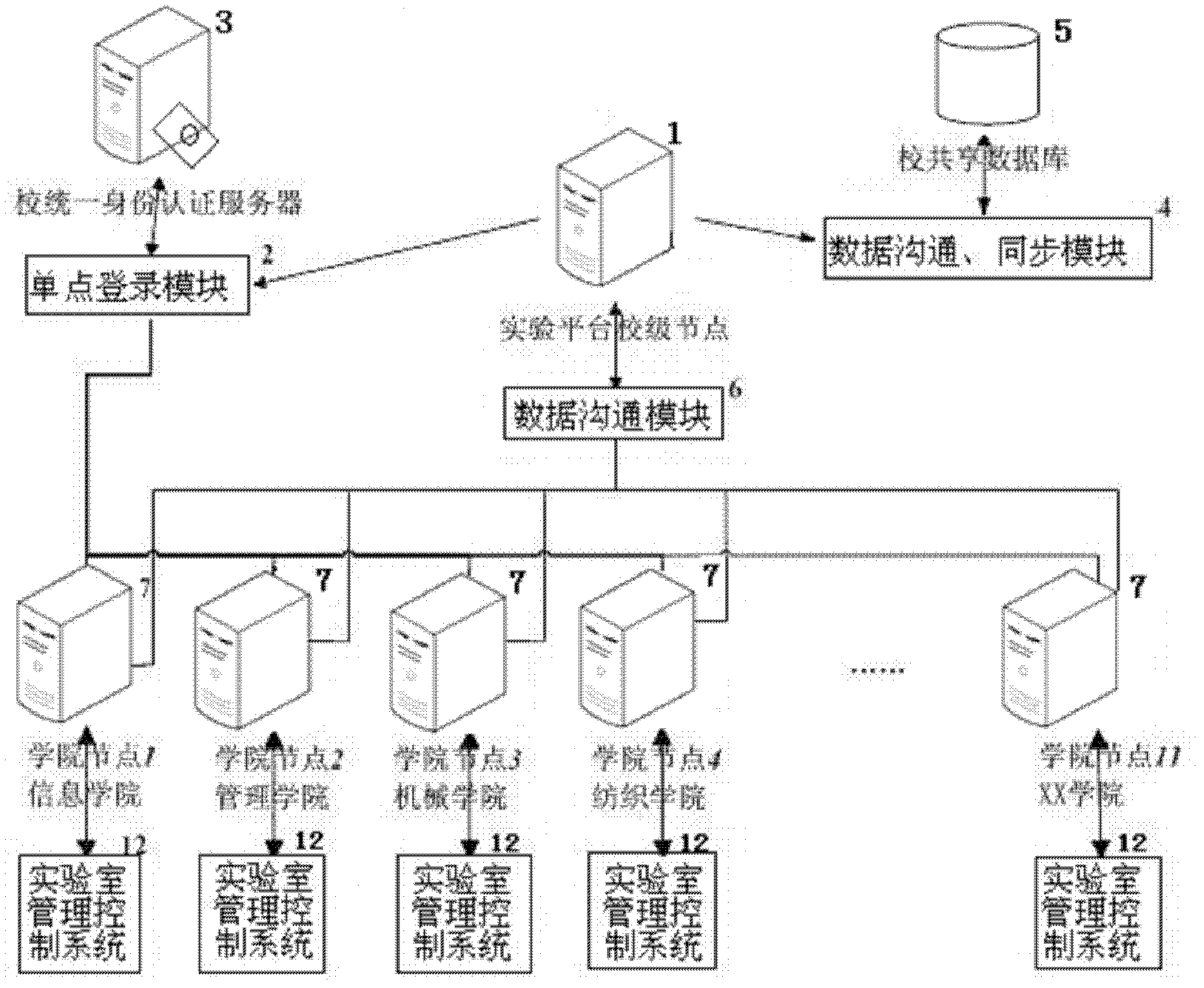
System and method for open intelligent management of laboratory
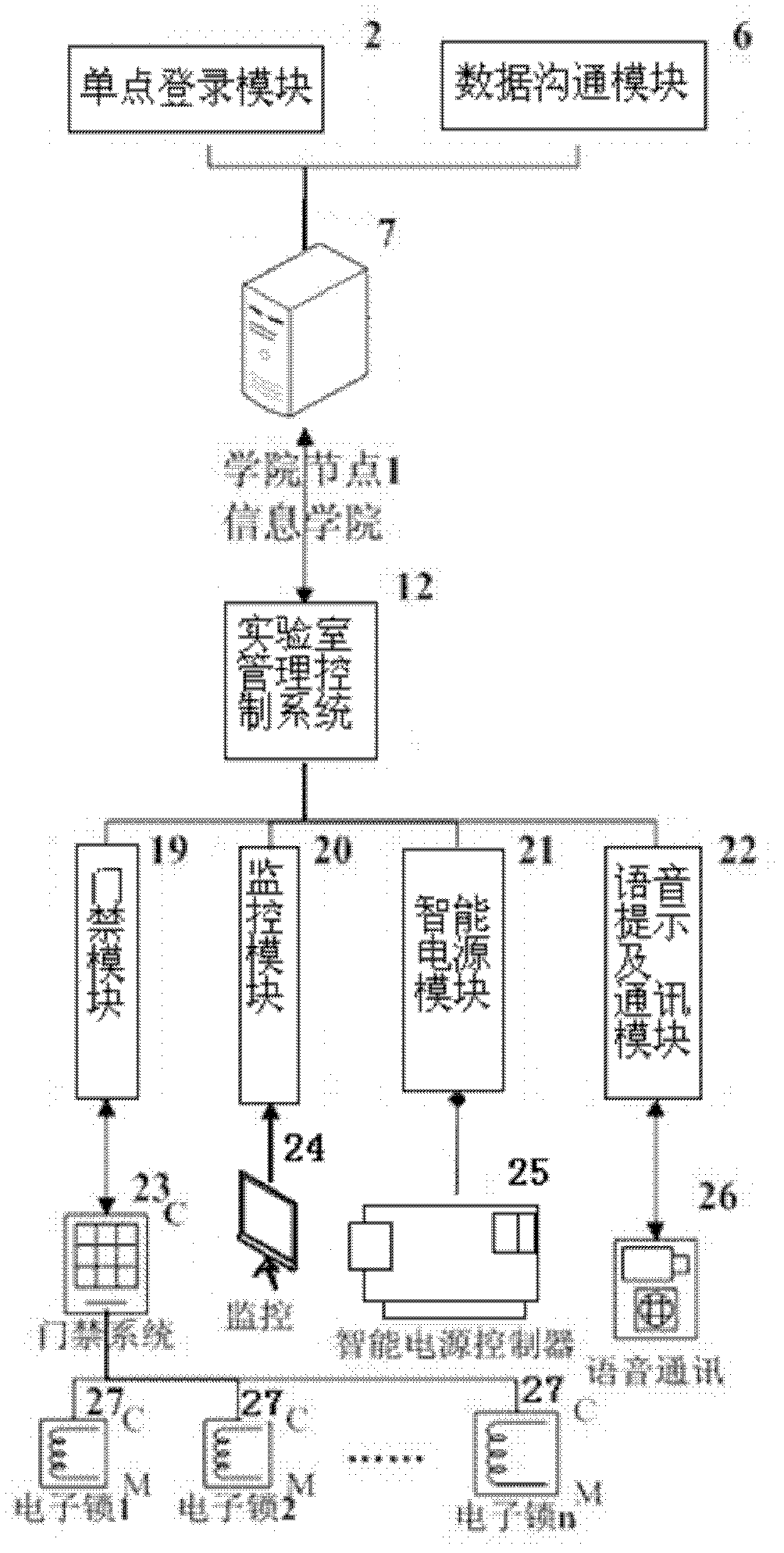
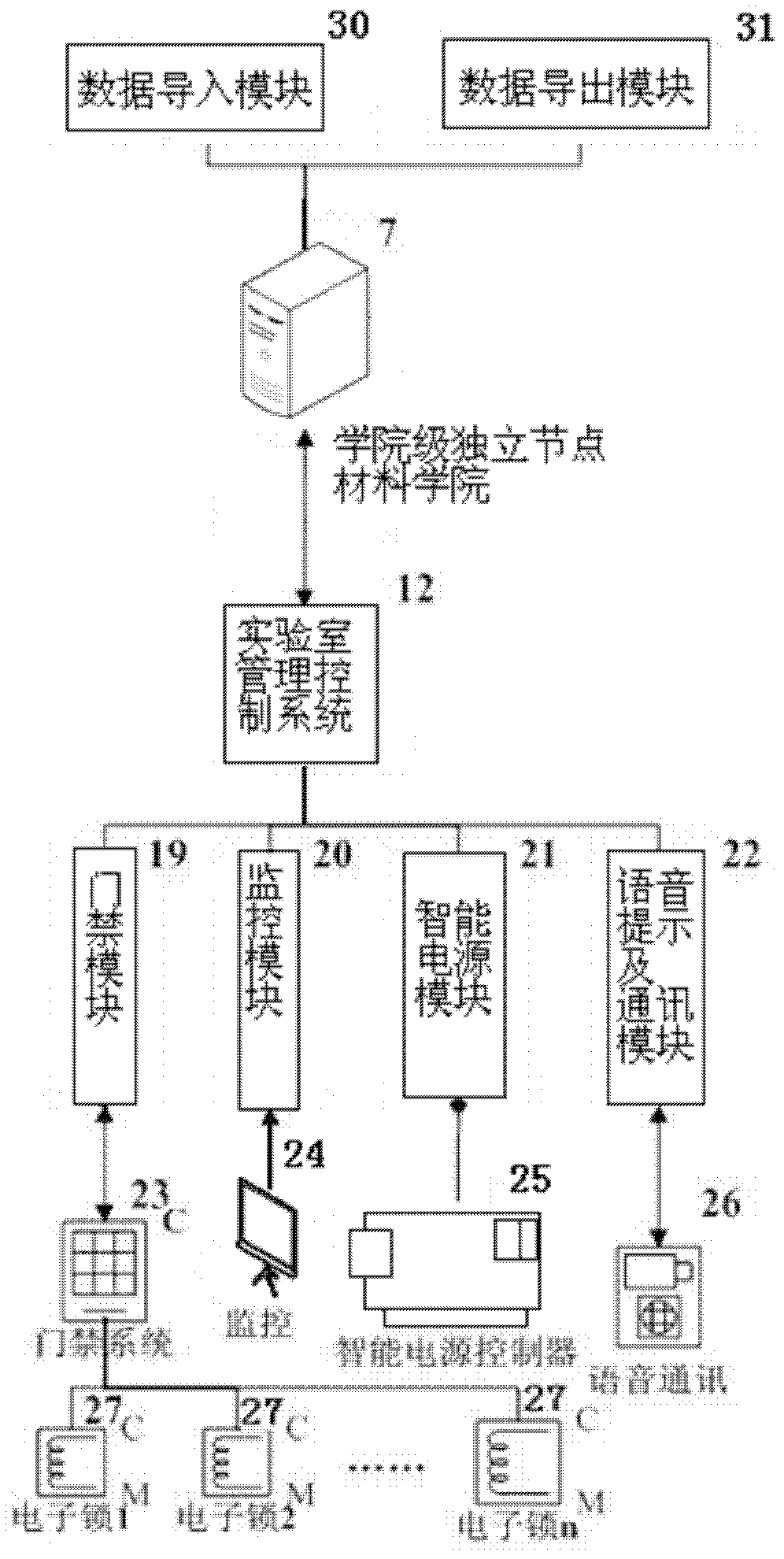
InactiveCN102306342AOpen implementationImprove work efficiencyData processing applicationsControl systemThe Internet
The invention relates to a system and a method for open intelligent management of a laboratory. The system comprises a server and a client, wherein the server comprises a university level platform node server and a plurality of college level platform node servers; the university level platform node server performs data communication with a university shared data base through a data communication module and a synchronous module, and performs data communication with the college level platform node servers through the data communication module; the client is connected with the server through a campus network inside a university and through the INTERNET outside the university; and the client comprises a laboratory management control system and an intelligent laboratory management system. The method comprises the management of experiments or experiment courses specified in a teaching program and the management of open experiments or equipment usage outside the teaching program. According to the invention, all-day open of the laboratory can be realized, and the working efficiency of laboratory management personnel can be greatly improved.
Owner:DONGHUA UNIV
Method And Apparatus Of Dynamic Spectrum Sharing In Cellular Networks
InactiveUS20130295946A1Network traffic/resource managementNetwork planningApplying knowledgeFrequency spectrum
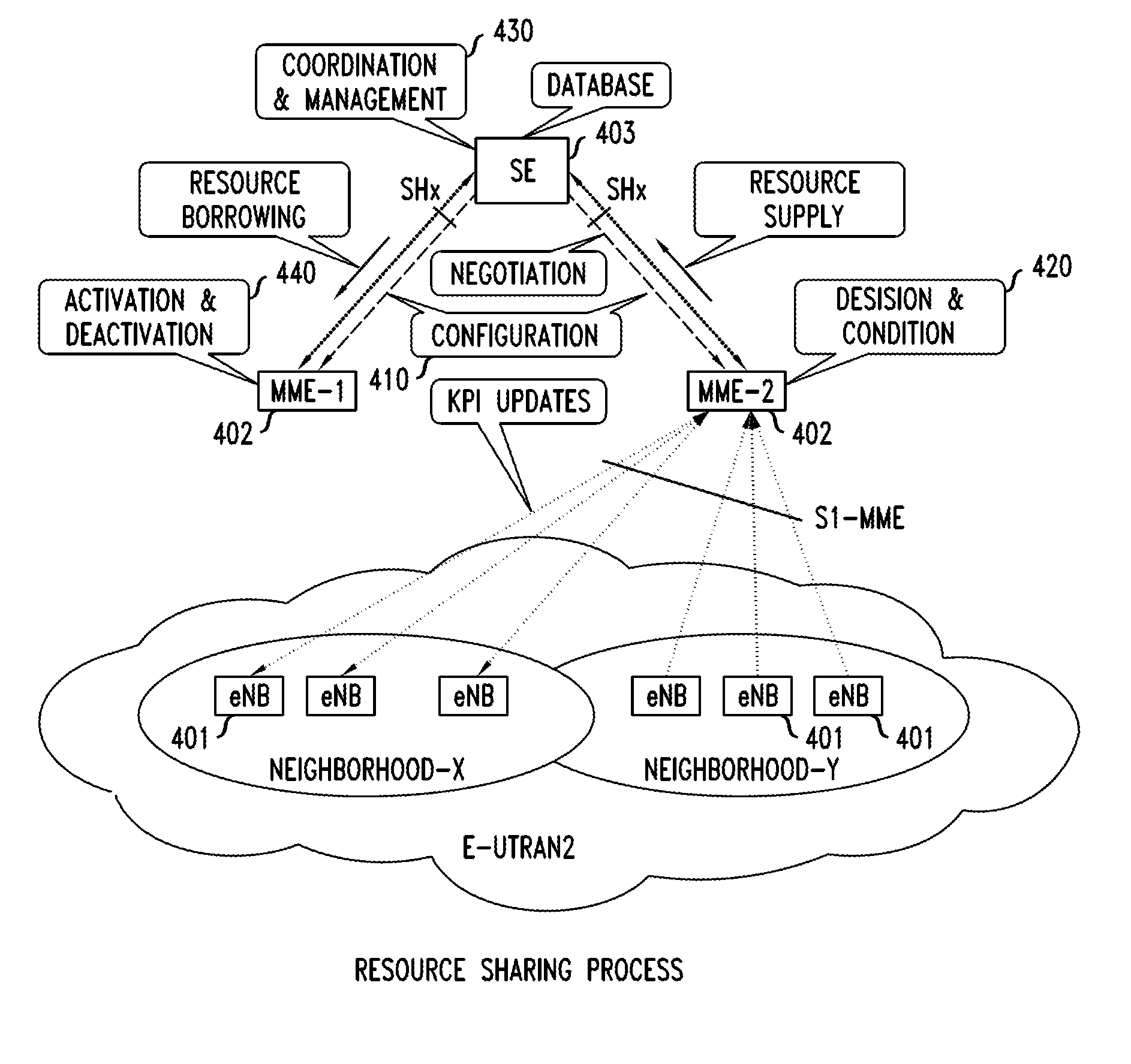
According to a disclosed method, an MME in a network analyzes KPIs from the cells it serves and based on the KPIs, it decides to engage in sharing. The MME then contacts a sharing entity (SE) to announce that it wants to supply spectrum for sharing. The MME obtains terms of a sharing agreement from the SE and the MME obtains the identity of the other network. In response to this information, the MME configures its base stations to support the supplying of spectrum to the other network. The SE applies knowledge of network topology and of services offered. This knowledge is obtained from a sharing database. At the expiration of the sharing agreement, the SE tells the MMEs to deactivate the sharing agreement.
Owner:WSOU INVESTMENTS LLC
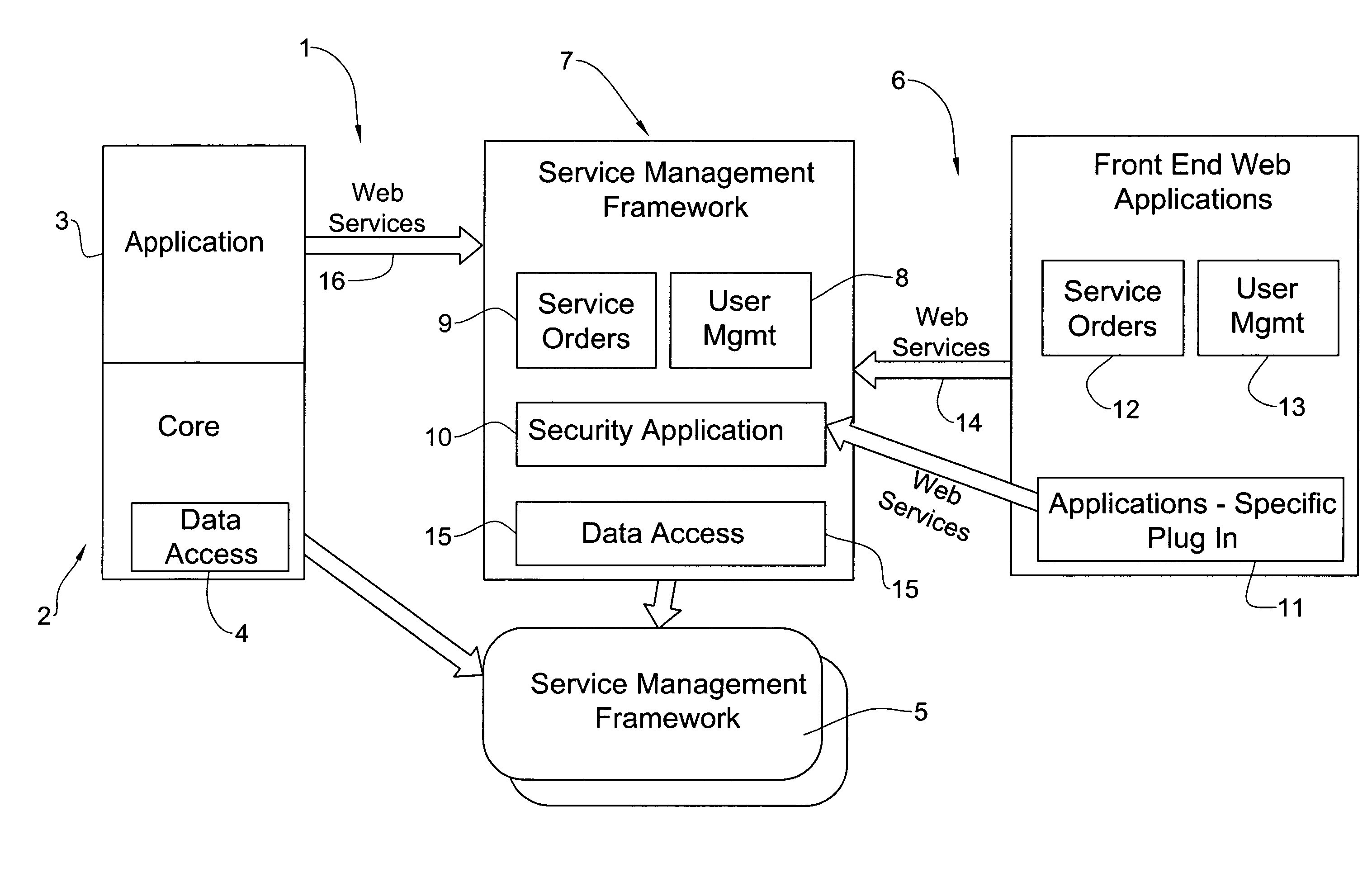
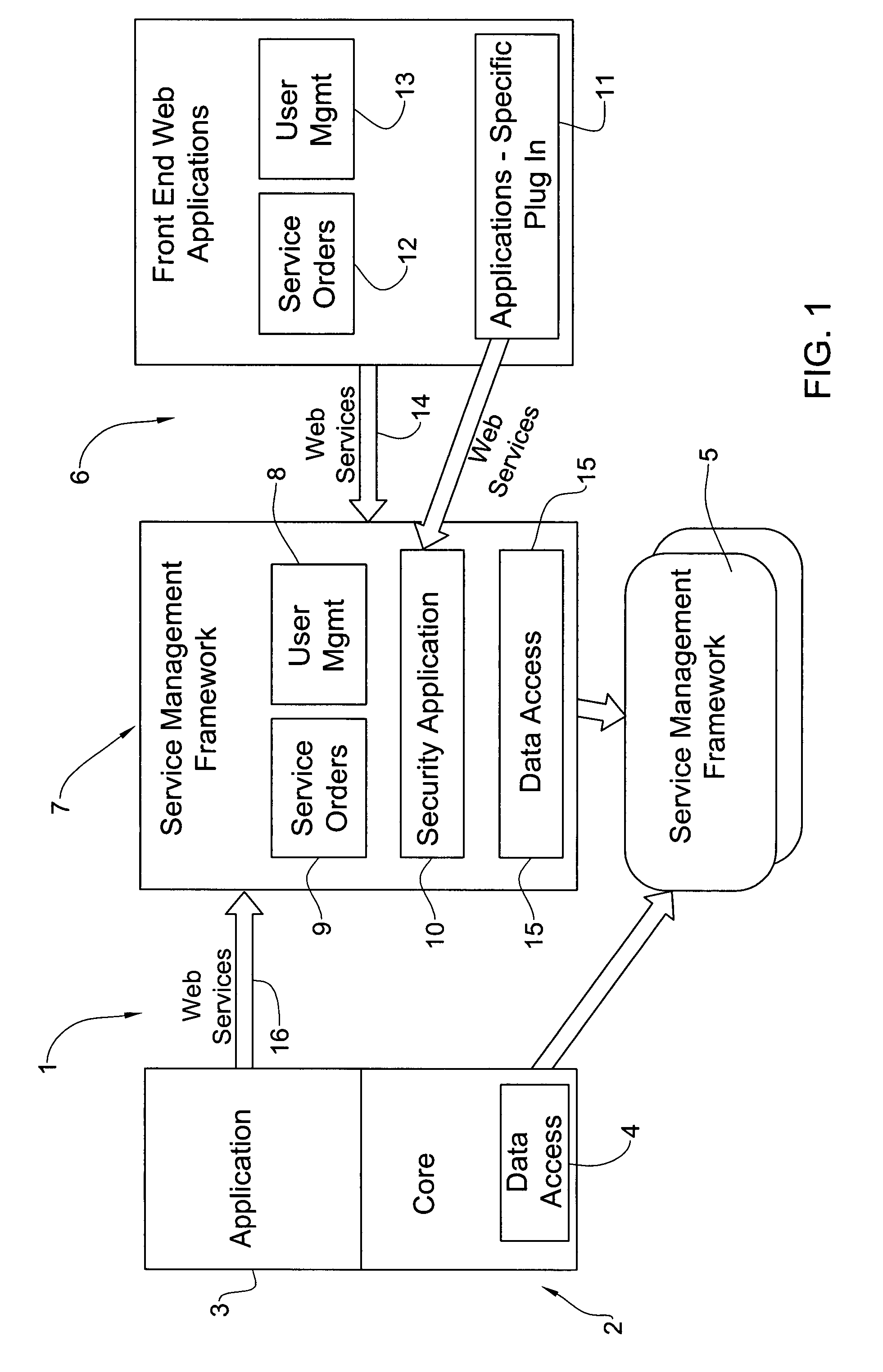
Service provisioning system
InactiveUS20080195622A1Easy accessDigital data information retrievalSpecial data processing applicationsService provisionShared database
A method for generating objects which facilitate access of application platform system and service provisioning system to a shared database. The method includes generating automatically objects for incorporating in the application platform system as well as objects for incorporating in the provisioning system. The generated objects facilitate access of the application platform system to the shared database, and further facilitate access of the service provisioning system to the shared database.
Owner:PERSONETA
Managing hierarchical authority to access files in a shared database
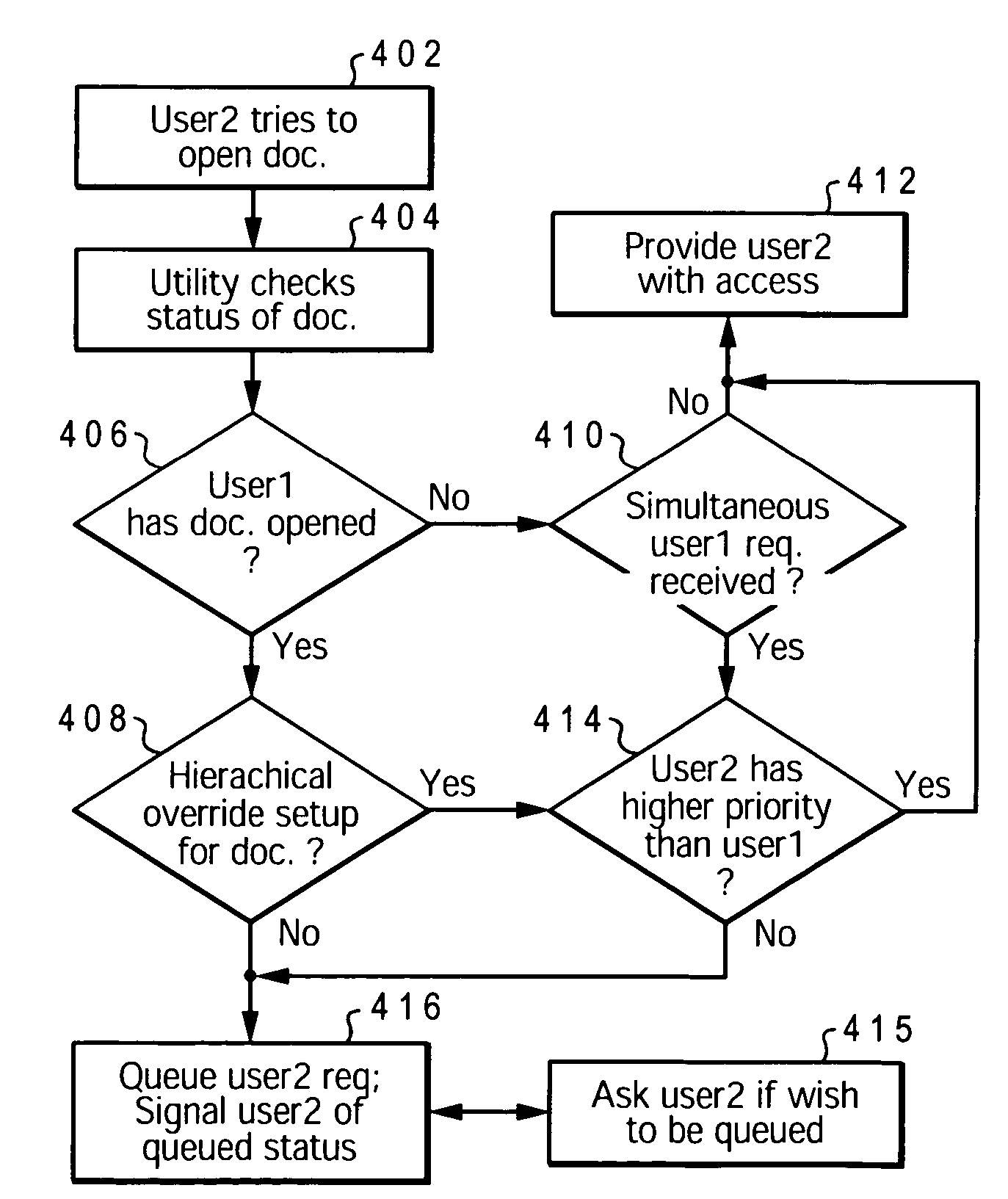
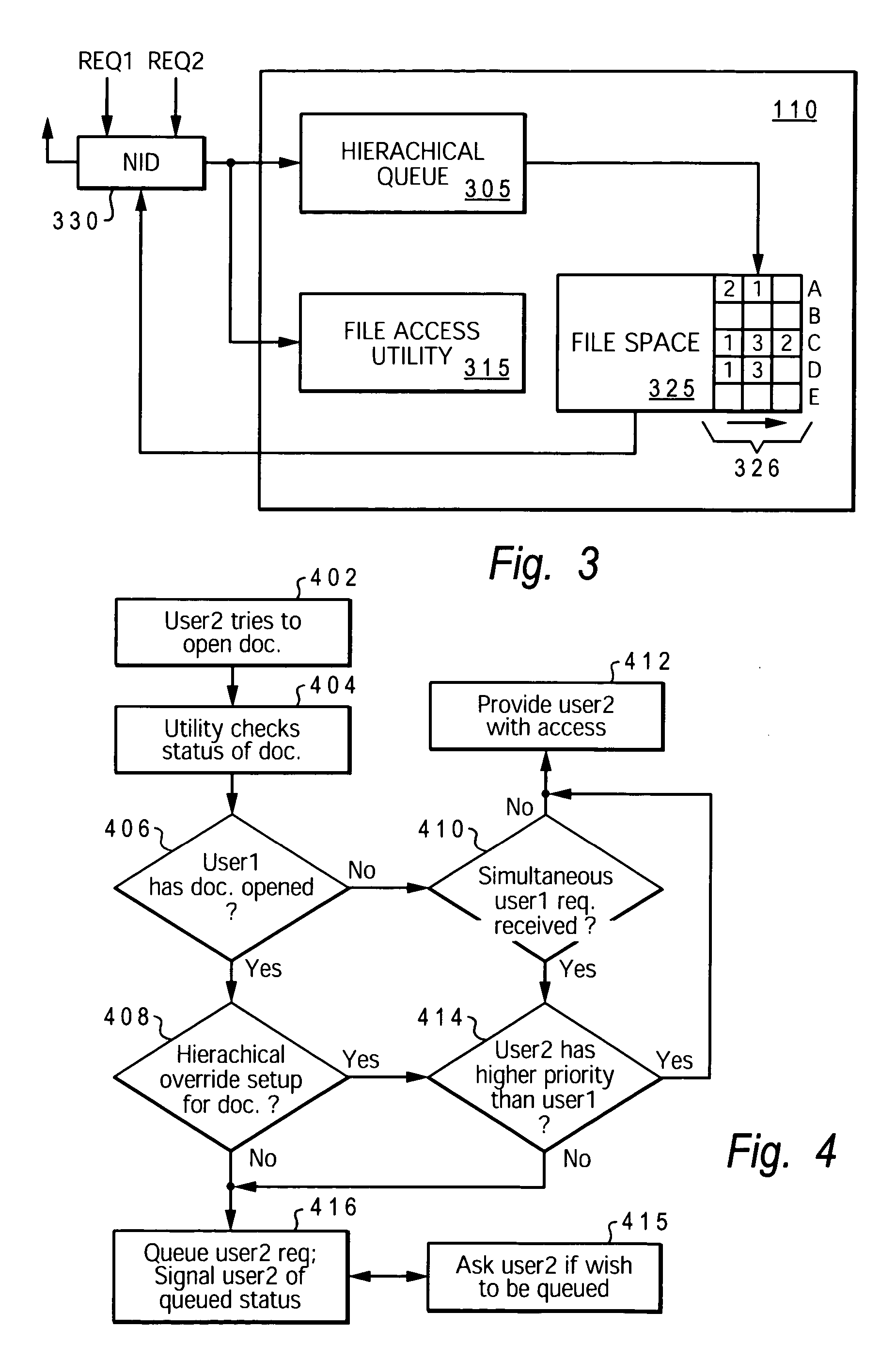
InactiveUS20060155705A1Timely controlSpecial data processing applicationsFile systemsNetwork dataUser identifier
A method, system, and program product that enable dynamic scheduling / arranging of access by multiple users to a single electronic file. A network-database access management utility (NAMU) is provided, which manages / schedules network-level access to the electronic file. NAMU includes an access-request queue that schedules / arranges the user identifier (IDs) for each of multiple users that have requested access to the file while the file was checked out to a previous user. When the first user completes his access to the file and closes the file, an alert is generated for the next user in queue. This alert informs the next user that the first user has closed the file and that he / she may now access the electronic file.
Owner:IBM CORP
Dynamic Resource Sharing Among Cellular Networks
InactiveUS20130090124A1Time-division multiplexSubstation equipmentApplying knowledgeDynamic resource
According to a disclosed method, an MME in a network analyzes KPIs from the cells it serves and based on the KPIs, it decides to engage in sharing. The MME then contacts a sharing entity (SE) to announce that it wants to borrow or to supply resources. The MME obtains terms of a sharing agreement from the SE and the MME obtains the identity of the other network. In response to this information, the MME configures its network elements to share. The MME's own network may be a supplier or a borrower. If the network is a supplier, the MME configures its base stations to support UEs subscribing to the other network. If the network is a borrower, the MME configures its UEs to accept service from the other network's base stations. The SE applies knowledge of network topology and of services offered. This knowledge is obtained from a sharing database. At the expiration of the sharing agreement, the SE tells the MMEs to deactivate the sharing agreement.
Owner:WSOU INVESTMENTS LLC
Method, device and system for implementing resource sharing
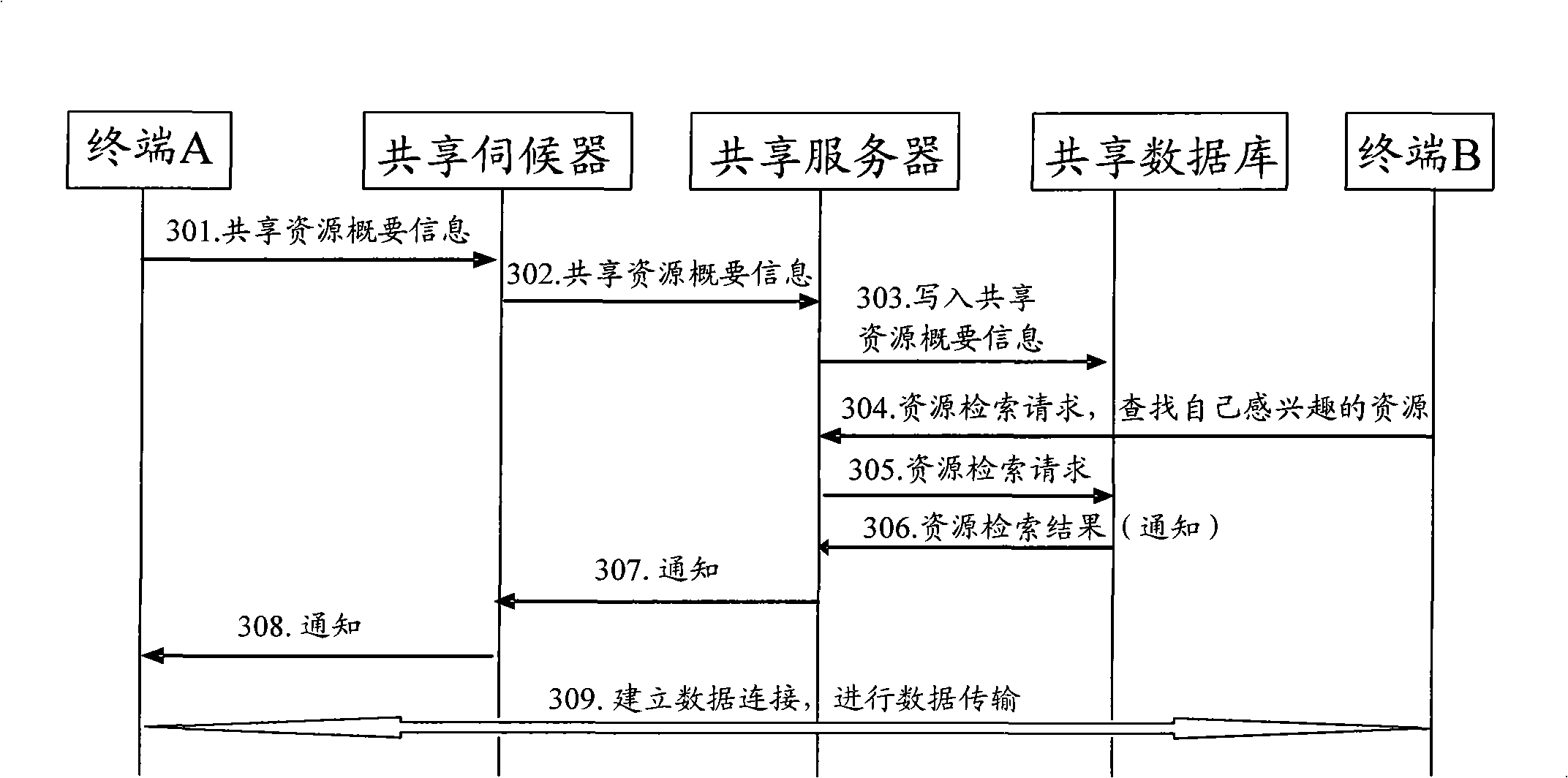
InactiveCN101321179AAchieve sharingReduce configuration requirementsTransmissionTerminal equipmentShared resource
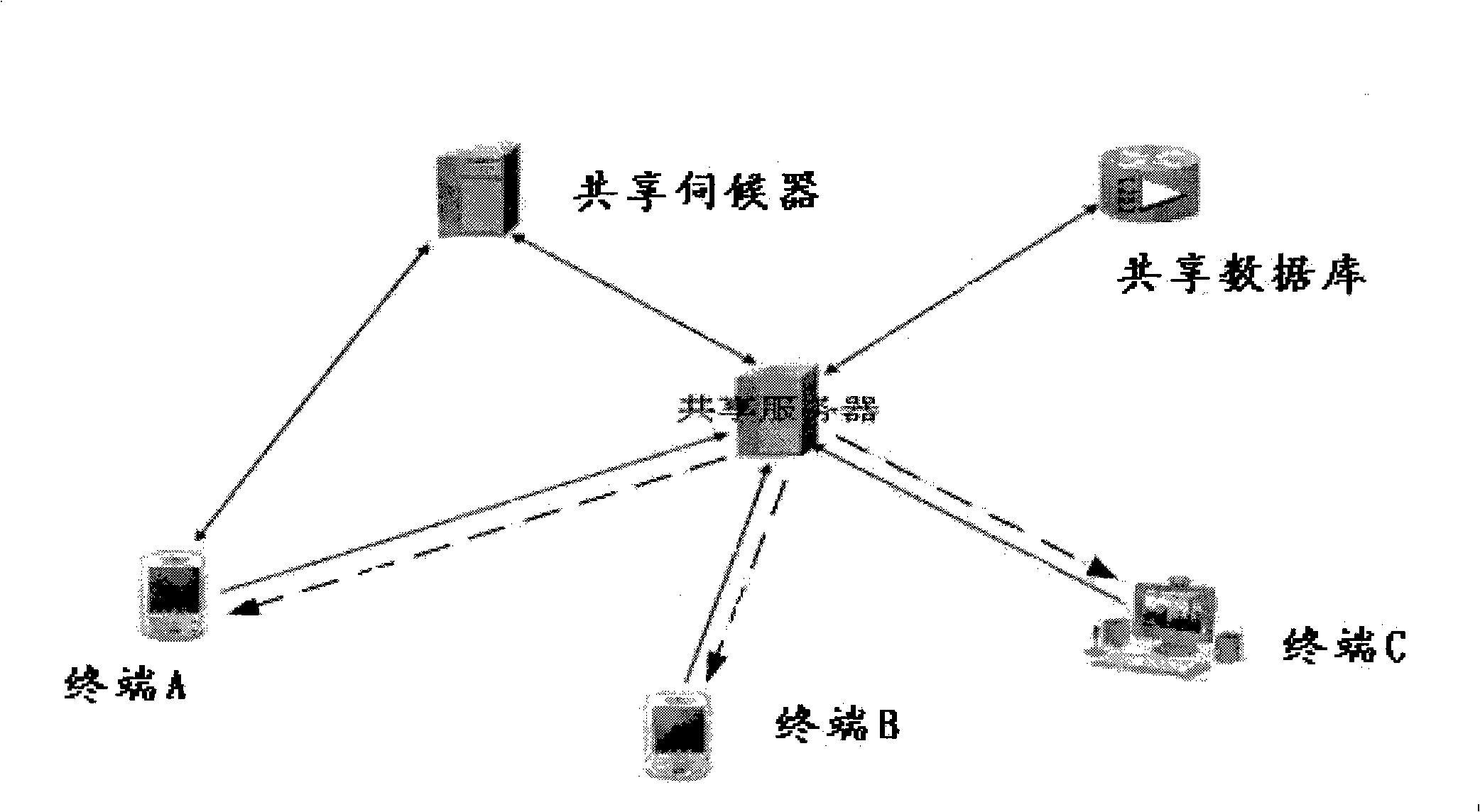
The invention provides a method for implementing resource sharing, which is applied in the resource sharing between mobile terminals or between a mobile terminal and a fixing terminal, comprising: receiving general information of sharing resource or the sharing resource from a first terminal, and writing them into a sharing database; receiving a resource retrieve request from a second terminal, obtaining a resource retrieve result from the sharing database, and sending the obtained sharing resource to the second terminal according to the information contained in the resource retrieve result. The invention synchronously provides a mobile terminal device and a system for implementing resource sharing. The invention is capable of implementing resource sharing between terminals and remote transmission of the shared resource. The terminals are able to freely select self-interested resources such that experience of terminals is strengthened.
Owner:HUAWEI TECH CO LTD
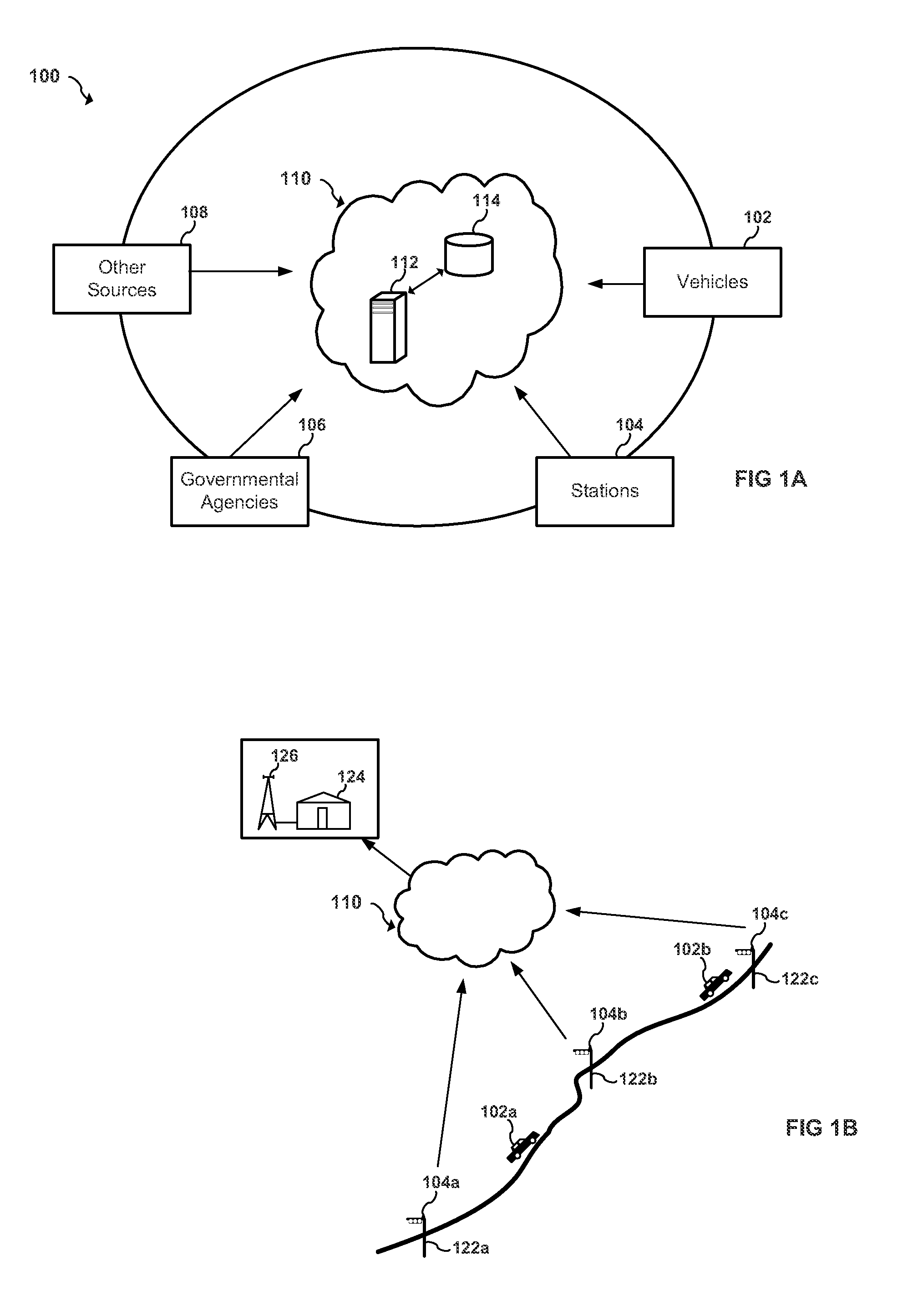
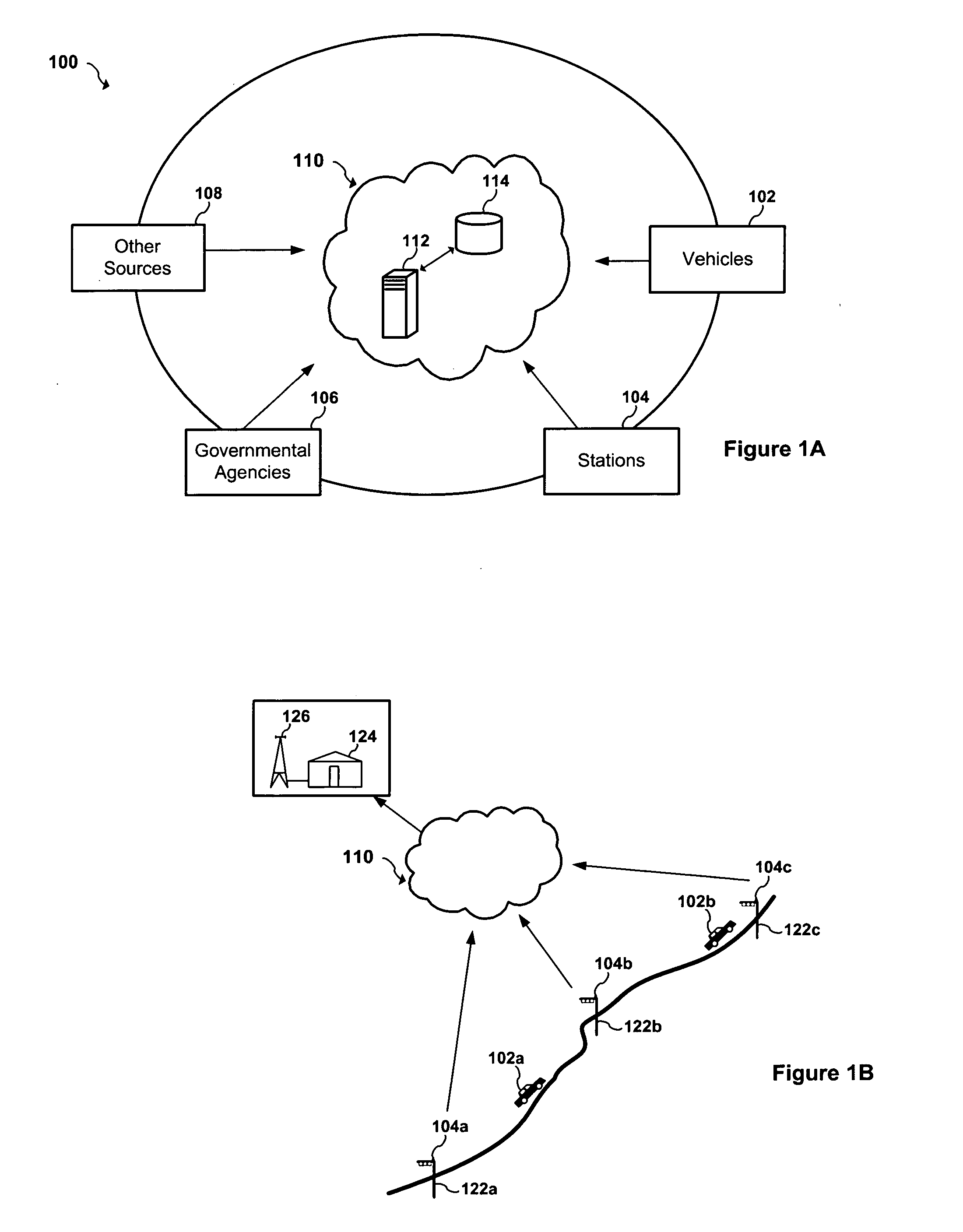
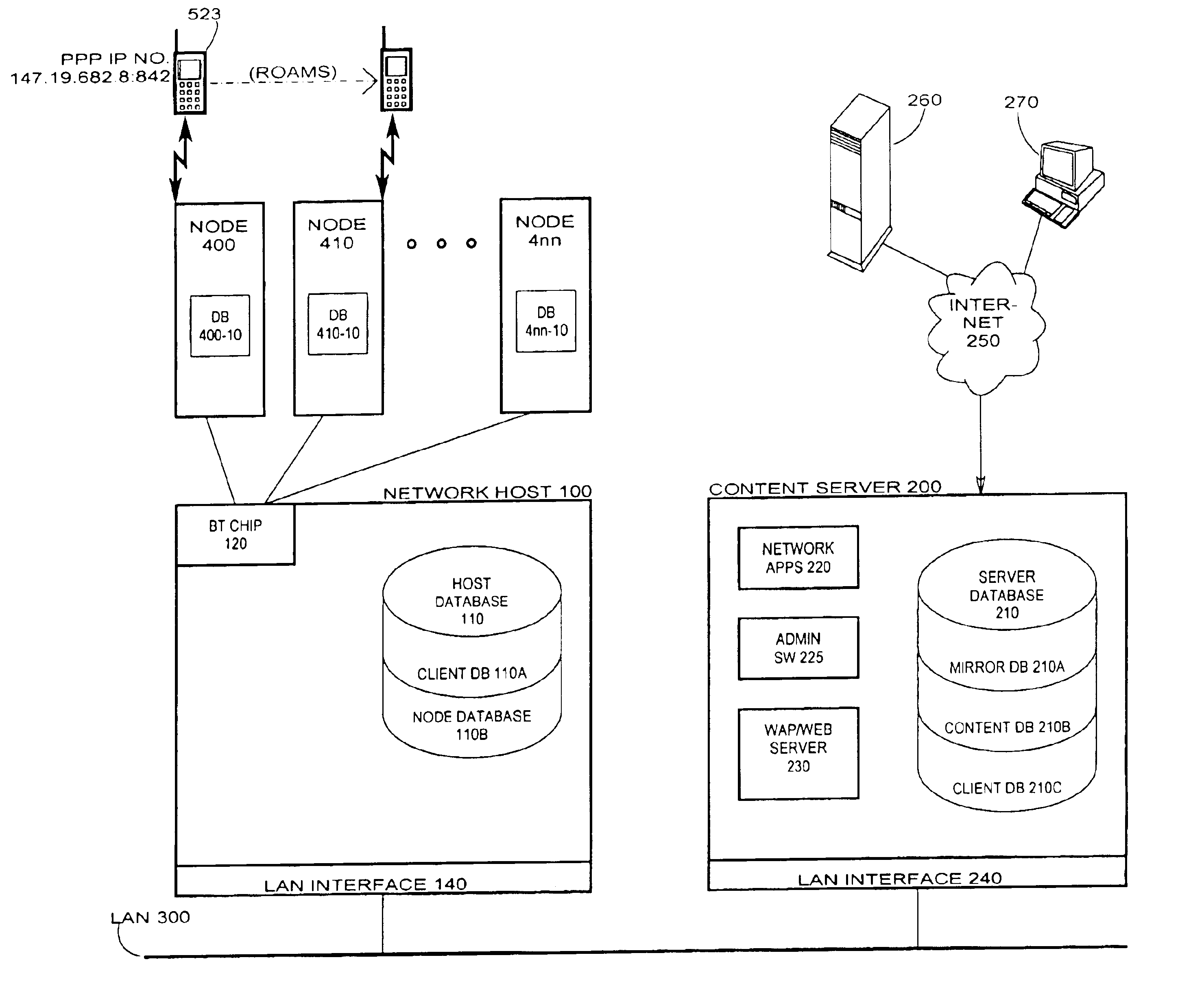
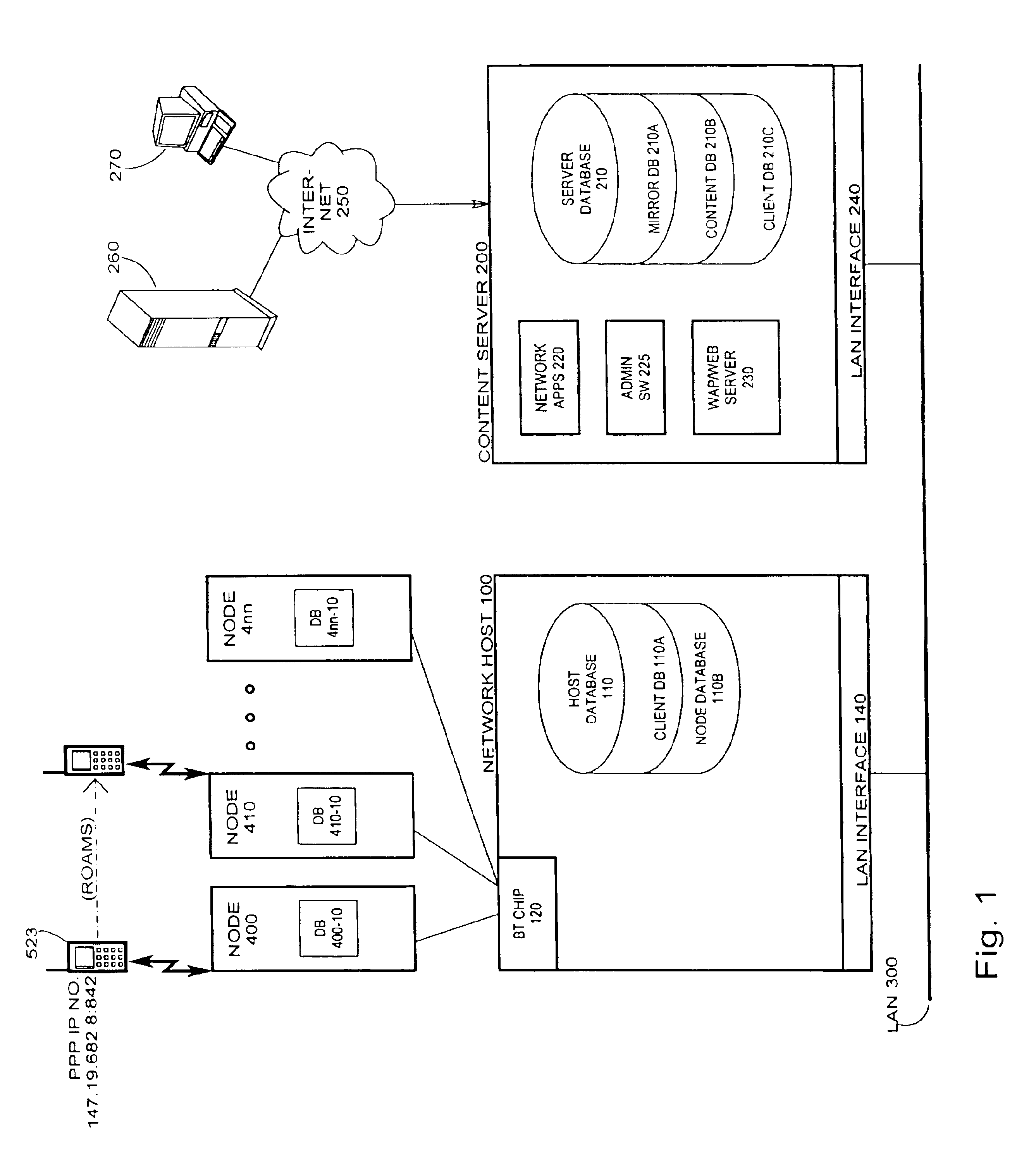
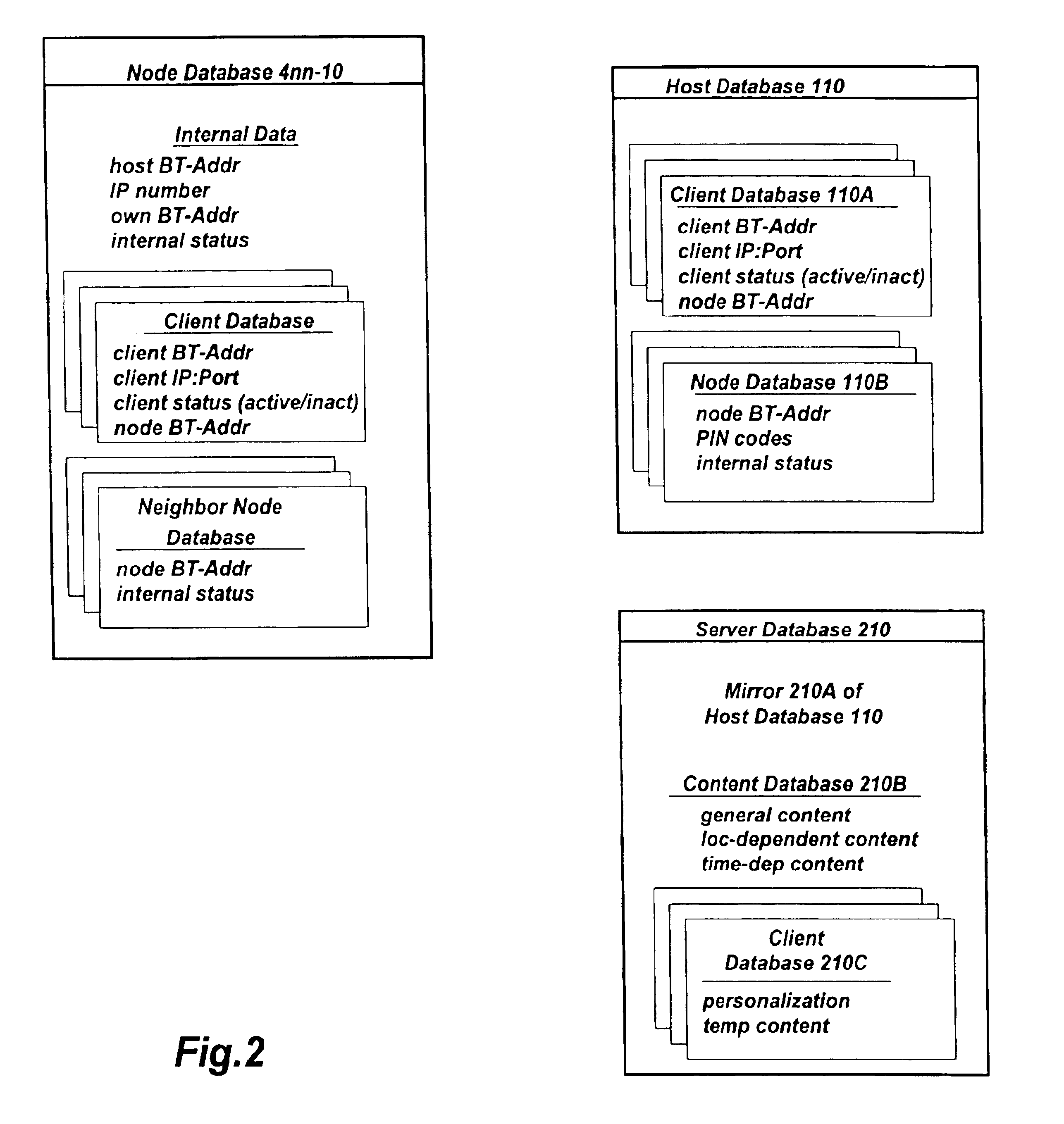
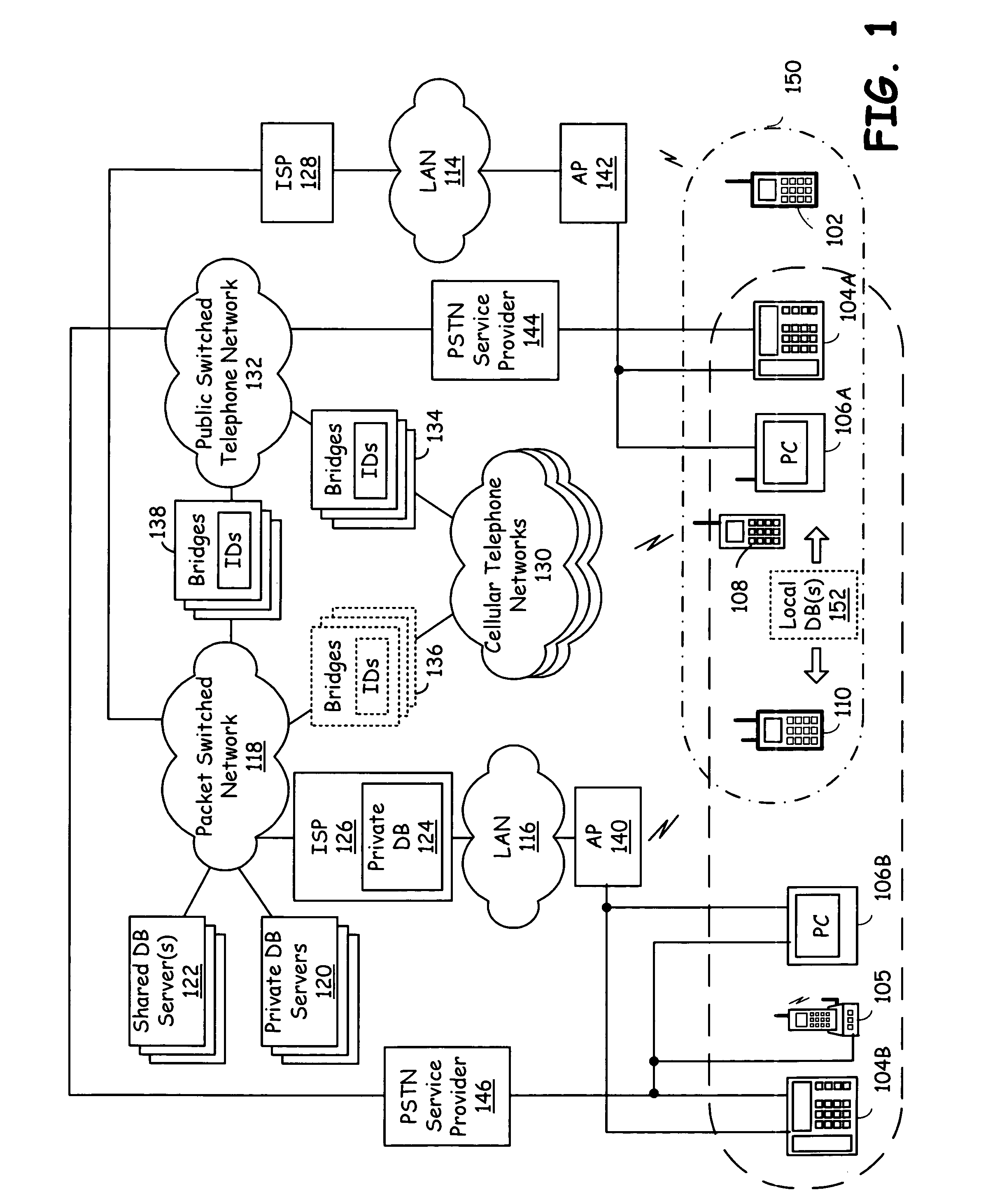
Short range RF network with roaming terminals
A short-range RF network deployed at a site larger than the coverage area of a single short-range RF transceiver includes a plurality of short-range RF transceivers deployed with overlapping coverage areas and accessible through a gateway, and accommodates terminal devices to establish communication through any transceivers with the gateway or with other of the terminal devices. The system further includes a WAP / Web server in communication with the Internet and in communication with the gateway. Terminal devices may establish Internet sessions through a node, the gateway, the WAP / Web server, and the Internet with remote Web servers or with remote users, and are assigned PPP IP numbers for such sessions. A terminal device which roams from the coverage area of one node to the coverage area of another node, and which is accordingly assigned a new PPP IP number, may continue in an Internet session by virtue of a shared database associated with the WAP / Web server and updated by the gateway. The shared database enables correlation of the terminal device's current location in the network with the PPP IP number by which Internet communications refer to it.
Owner:NOKIA CORP
System and method for implementing and managing virtual networks
A system and method for implementing and management virtual networks is disclosed. A method includes receiving a network packet arriving at a first network interface of a first node of an underlying network, communicating at least the packet and an identifier of the first network interface to a decision engine, determining how the packet should be processed based on a simulation by the decision engine of a traversal of a virtual network topology including a plurality of virtual network devices, wherein the decision engine communicates with a shared database accessible from the underlying network that stores the virtual network topology and virtual device configurations for the plurality of virtual network devices; and processing the packet based upon the simulation.
Owner:MIDO HLDG LTD
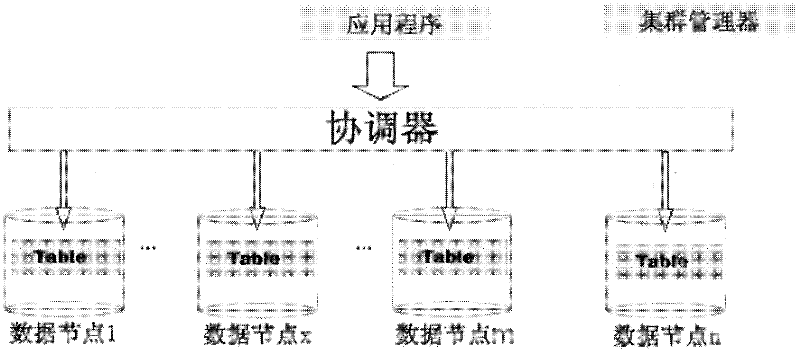
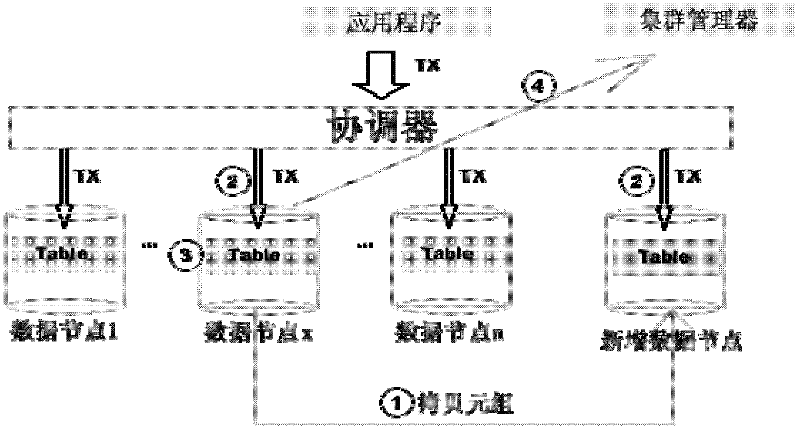
Method for achieving system dynamic expansion in shared-nothing database cluster
ActiveCN102521297ASolving the Dynamic Scalability ChallengeReduce the impactSpecial data processing applicationsHigh availabilityData node
The invention discloses a method for achieving system dynamic expansion in a shared-nothing database cluster, which includes the following steps: adding and detecting newly added data nodes and verifying connectivity of the newly added data nodes; initializing the newly added data nodes and synchronizing metadata information into the newly added data nodes; redistributing related tuples of a data table and distributed on the newly added data nodes in data nodes and the newly added data nodes, and leading operation on the data table in the redistributing process to be synchronous in the data nodes and the newly added data nodes; and modifying cluster configuration files in a cluster manager. The method solves the problem of difficulty in dynamic expansion of the shared-nothing database cluster, and greatly reduces influence on and loss of user service logic during expansion of the cluster. By means of the method, on-line expansion can be achieved, so that high expandability of a system can be ensured, and high availability of the system can further be ensured.
Owner:北京人大金仓信息技术股份有限公司
System and method of multiplex mode isomerous data integration
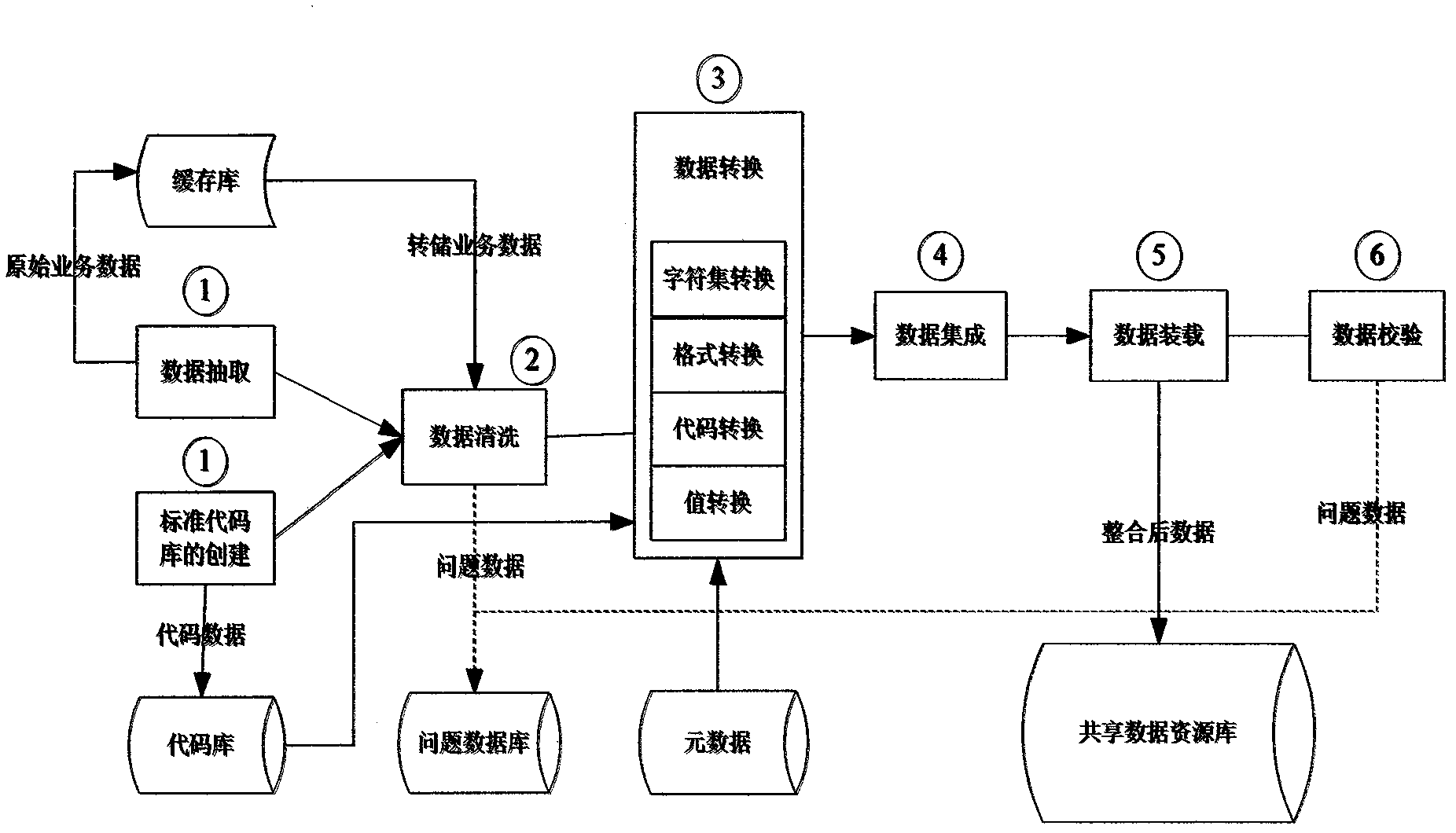
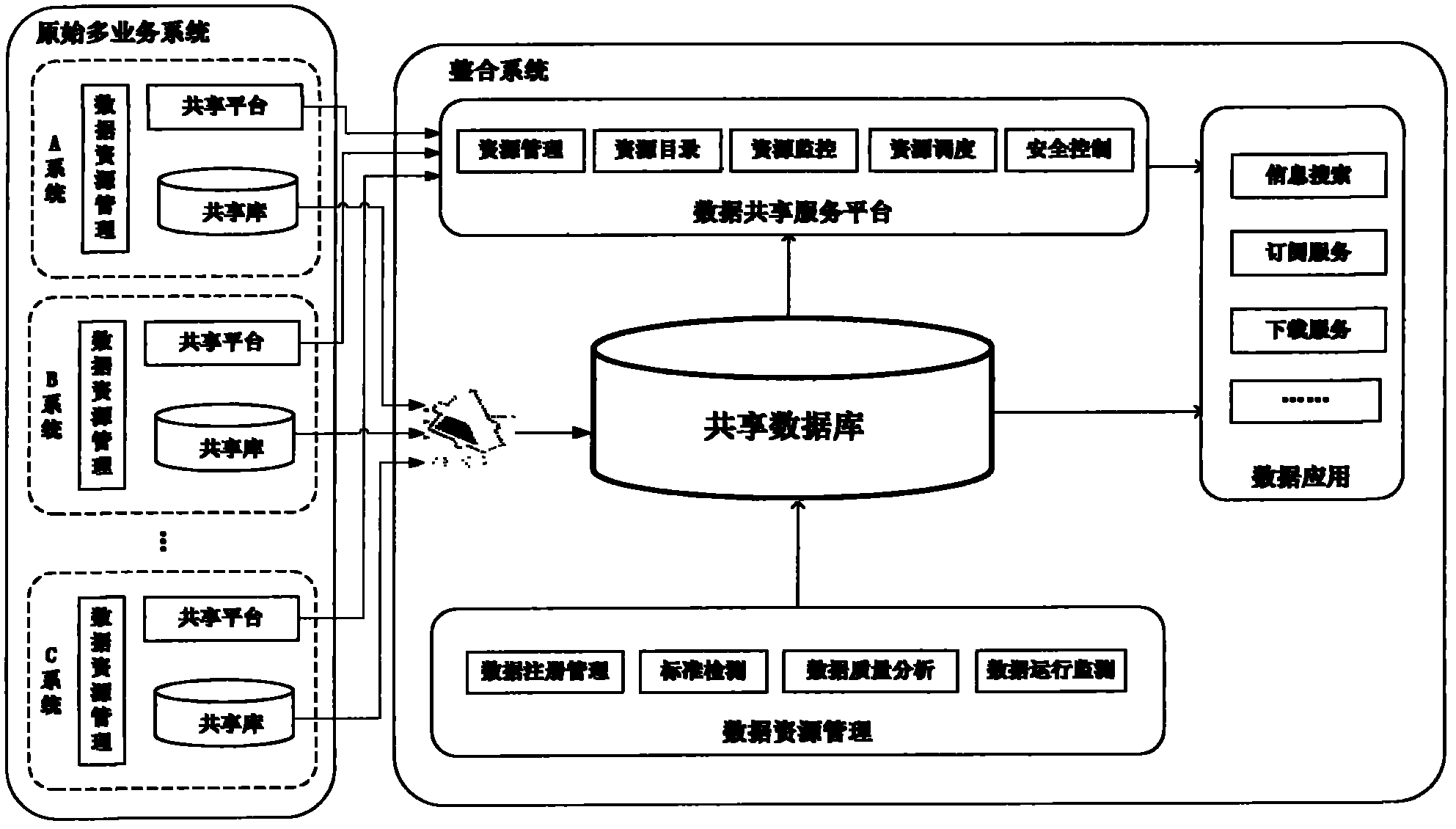
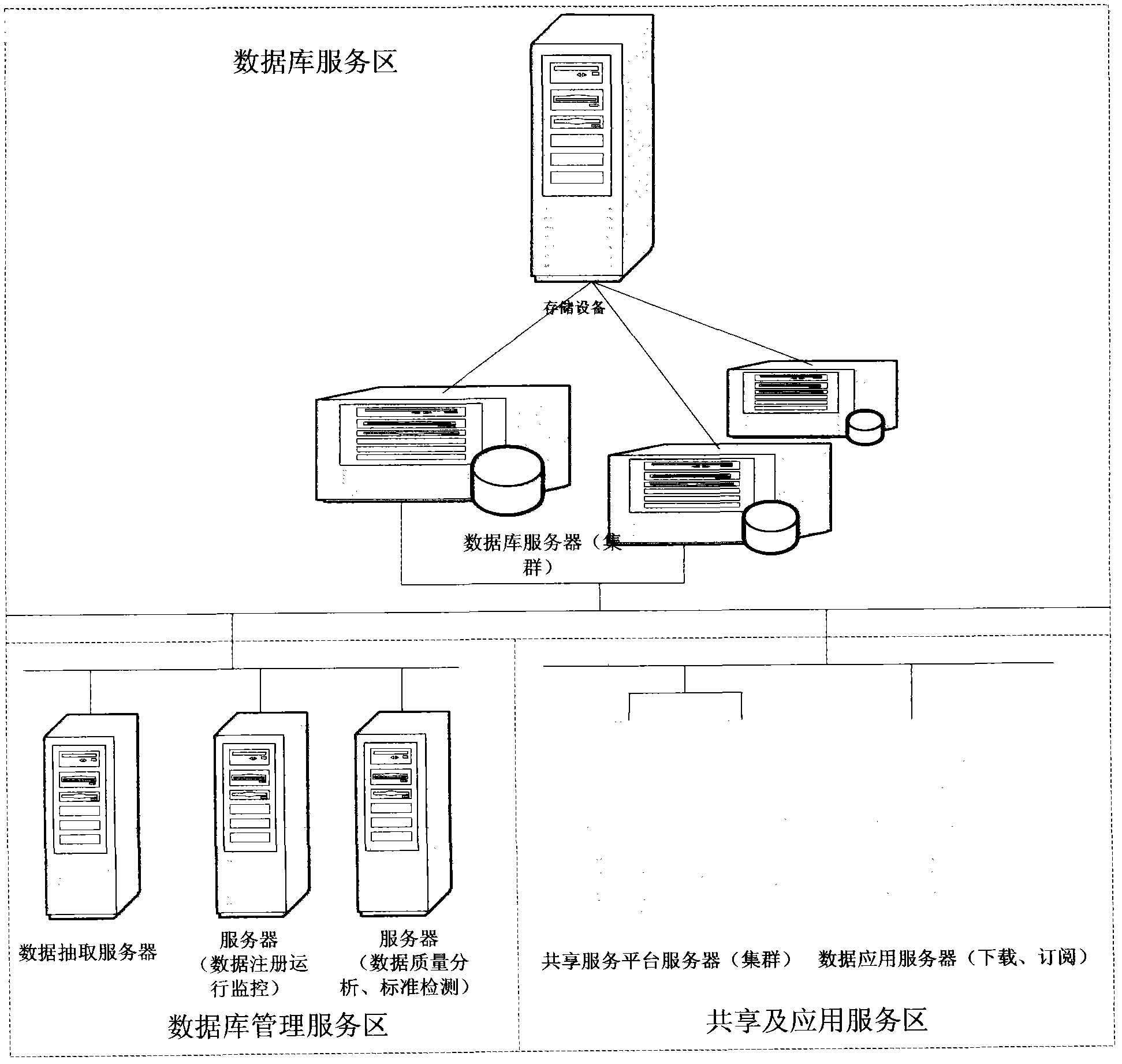
InactiveCN103136249AReduce difficultyReduce construction costsSpecial data processing applicationsOriginal dataData quality
The invention provides a system and a method of multiplex mode isomerous data integration. The system comprises an original data base, a data extracting tool, a shared data base, a data sharing platform, a data resource management module and a data application module. Various shared data resources distributed in different systems and departments are standardly converted, cleaned, filtered, related and indexed through the data extracting tool, and processing results are stored inside the shared data base; data login management, data standard detection, data quality management and data operation monitoring and controlling are conducted on the shared data base; a data sharing and inquiry channel inquiring the shared data base and the original data base through the data application module is provided; and an inquiry interface used for the shared data base and the original data base by a user is provided, and the inquire interface comprises intelligent data-resource search, data subscription and data downloading.
Owner:CHINA CHANGFENG SCI TECH IND GROUPCORP
Using a file server as a central shared database
ActiveUS7660809B2Digital data information retrievalData processing applicationsData synchronizationApplication software
Various entities need to share data among team members working on the same project without investing in specialized server software. To address this need, an existing standard file server is used to host data for sharing among the team. The file server has not been customized to share the data for the particular application. A user creates a special folder for a project at a user specified location on the file server. Data associated with the project is converted to files and stored in a structure of folders used by the file server to represent the data that is shared. Each client that has subscribed to this shared data synchronizes the data on their local computing device with the data on the file server. Security is provided by using the file server's built-in access controls.
Owner:MICROSOFT TECH LICENSING LLC
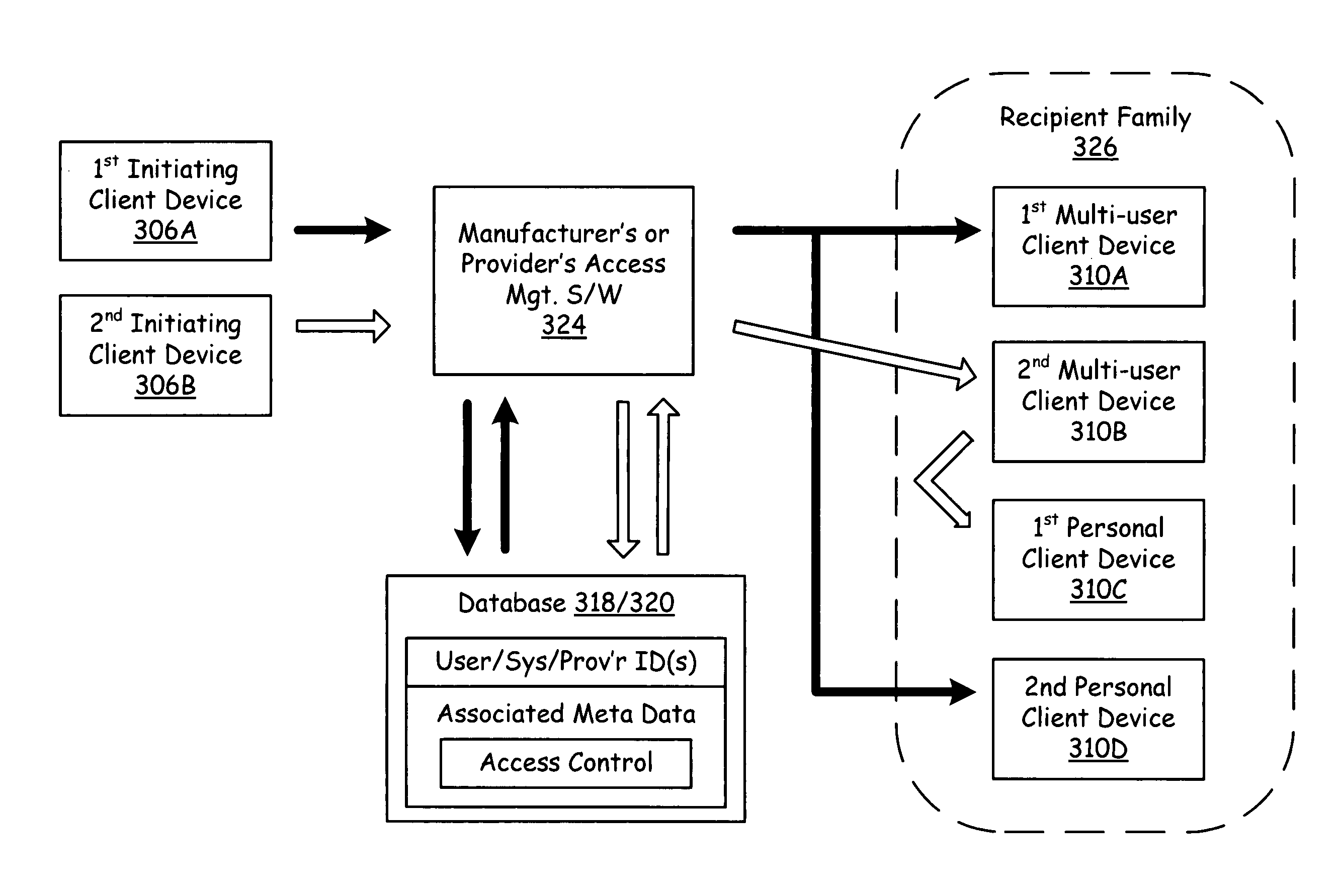
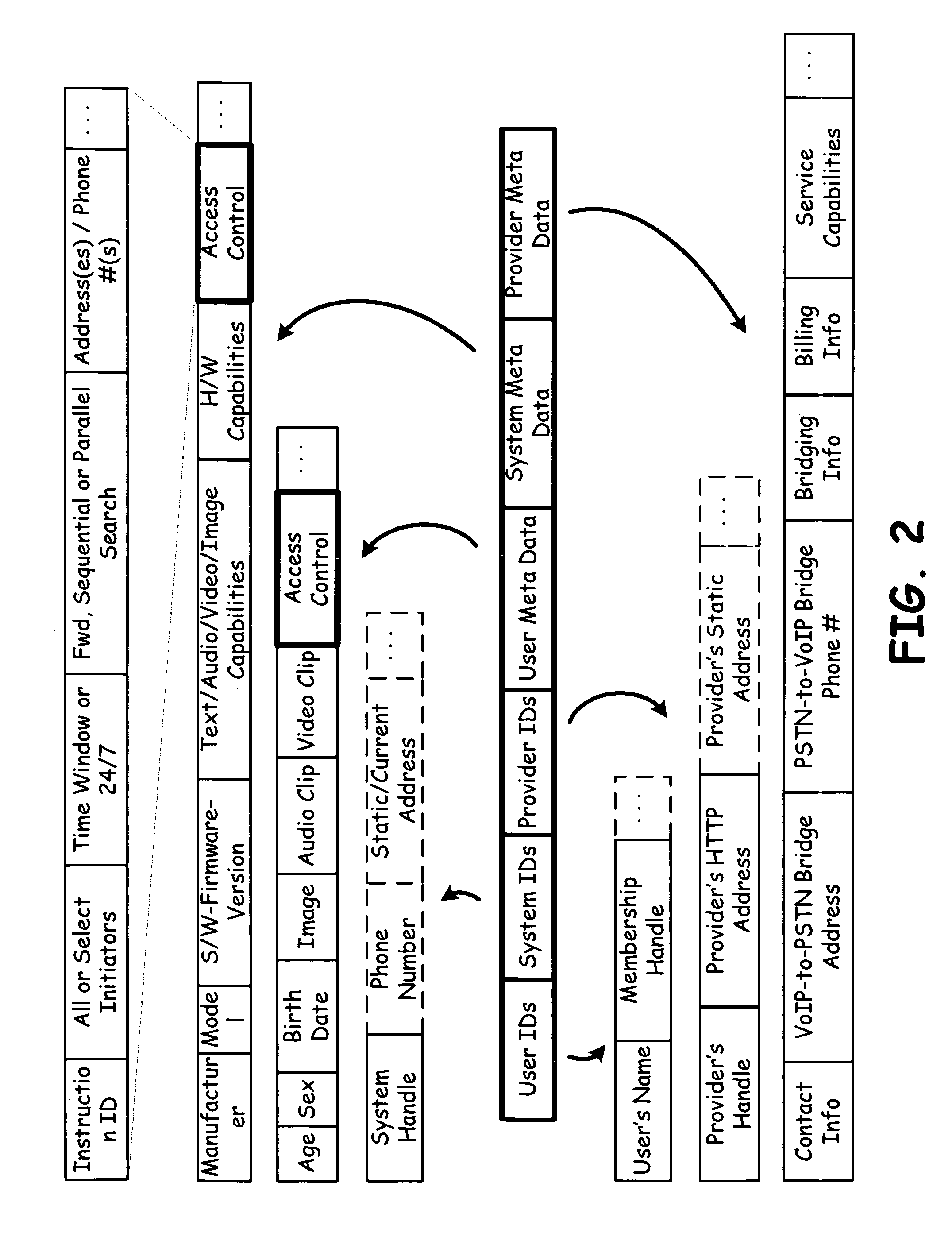
Multi user client terminals operable to support network communications
ActiveUS20070180123A1Multiple digital computer combinationsAutomatic exchangesVoice communicationNetwork communication
A network infrastructure operable to support the exchange of communications, such as voice communications, between a first client terminal having a first user identifier and a second (destination) client terminal associated with a second user identifier (handle). This second client terminal may be part of a family of client terminals. The network infrastructure includes a packet-switch network, a shared database and a number of client terminals serviced by one or more service providers. These terminals include a network interface and are identified by their service provider by a network address. The shared database associates user identifiers, metadata and network addresses. This allows a user to access the shared database in order to initiate a call request from the first client terminal to the second client terminal(s). The first client terminal receives the network address or vectoring information on the network address of the destination terminal through the shared database. This shared database may also have metadata used to manage the call. The destination terminal may receive or redirect the call within the family of client terminals based on metadata contained within the shared database or stored locally.
Owner:AVAGO TECH INT SALES PTE LTD
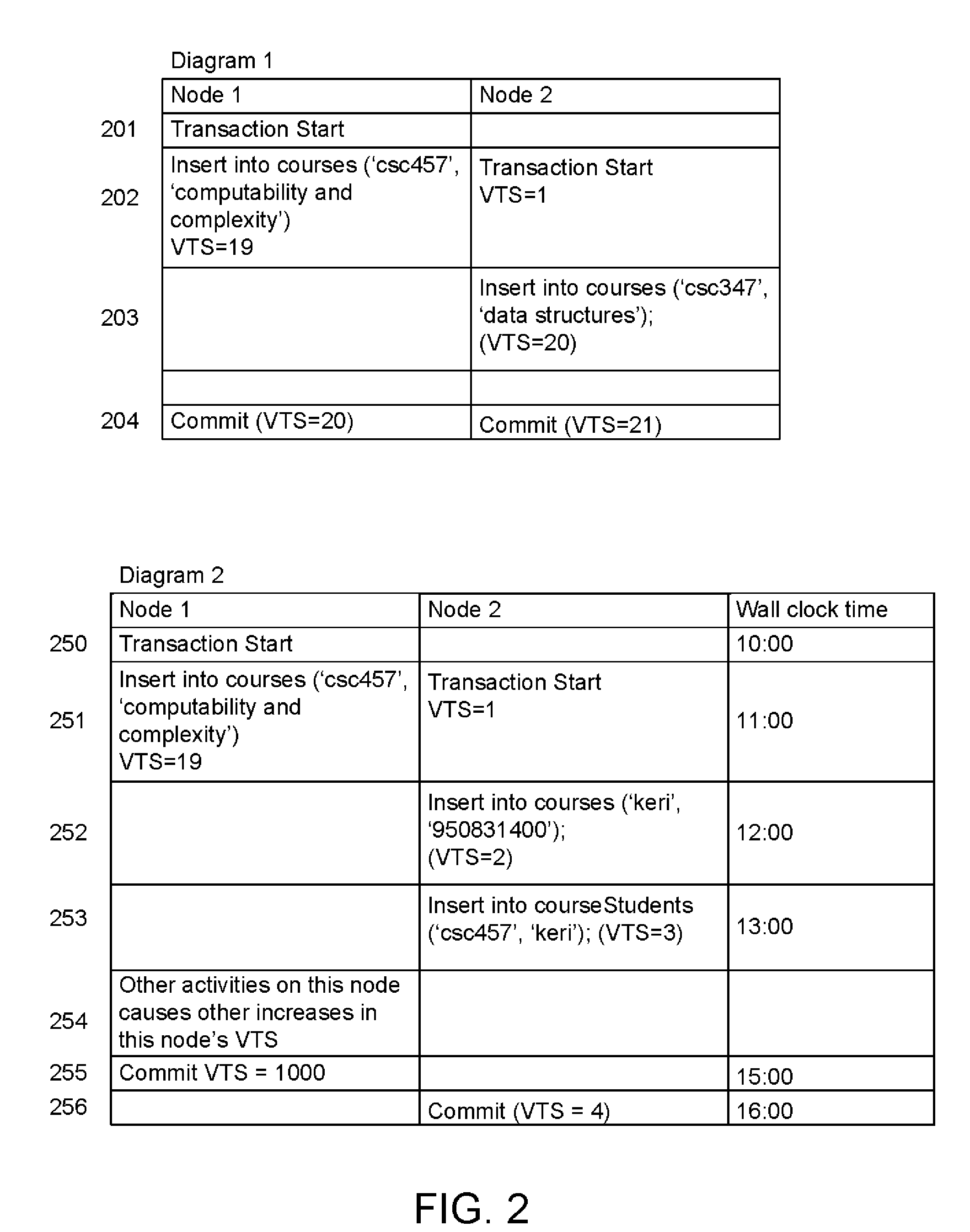
Methods to Minimize Communication in a Cluster Database System
ActiveUS20110137874A1Digital data information retrievalError detection/correctionTimestampSerial code
An ordering of operations in log records includes: performing update operations on a shared database object by a node; writing log records for the update operations into a local buffer by the node, the log records each including a local virtual timestamp; determining that a log flush to write the log records in the local buffer to a persistent storage is to be performed; in response, sending a request from the node to a log flush sequence server for a log flush sequence number; receiving the log flush sequence number by the node; inserting the log flush sequence number into the log records in the local buffer; and performing the log flush to write the log records in the local buffer to the persistent storage, where the log records written to the persistent storage comprises the local virtual timestamps and the log flush sequence number.
Owner:IBM CORP
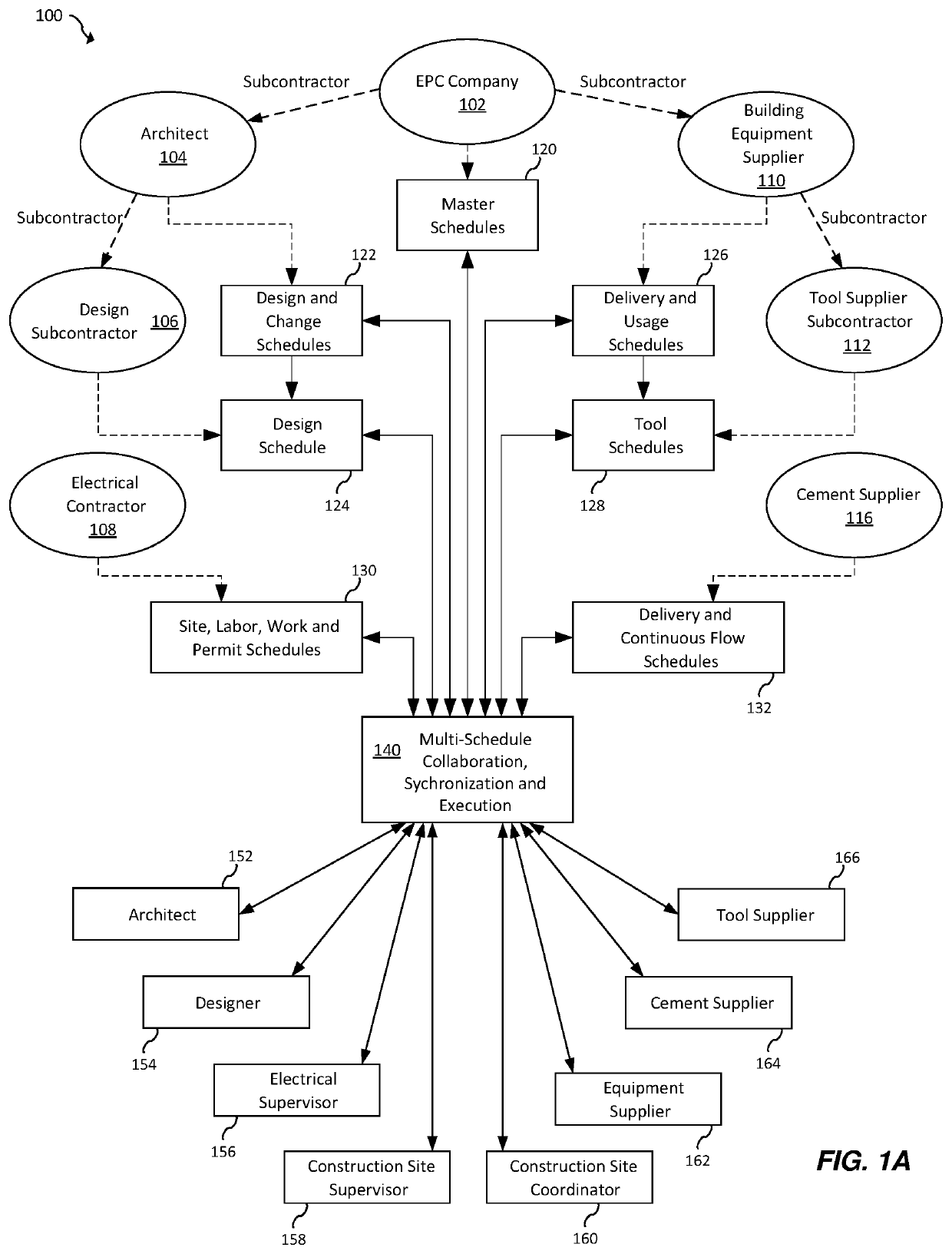
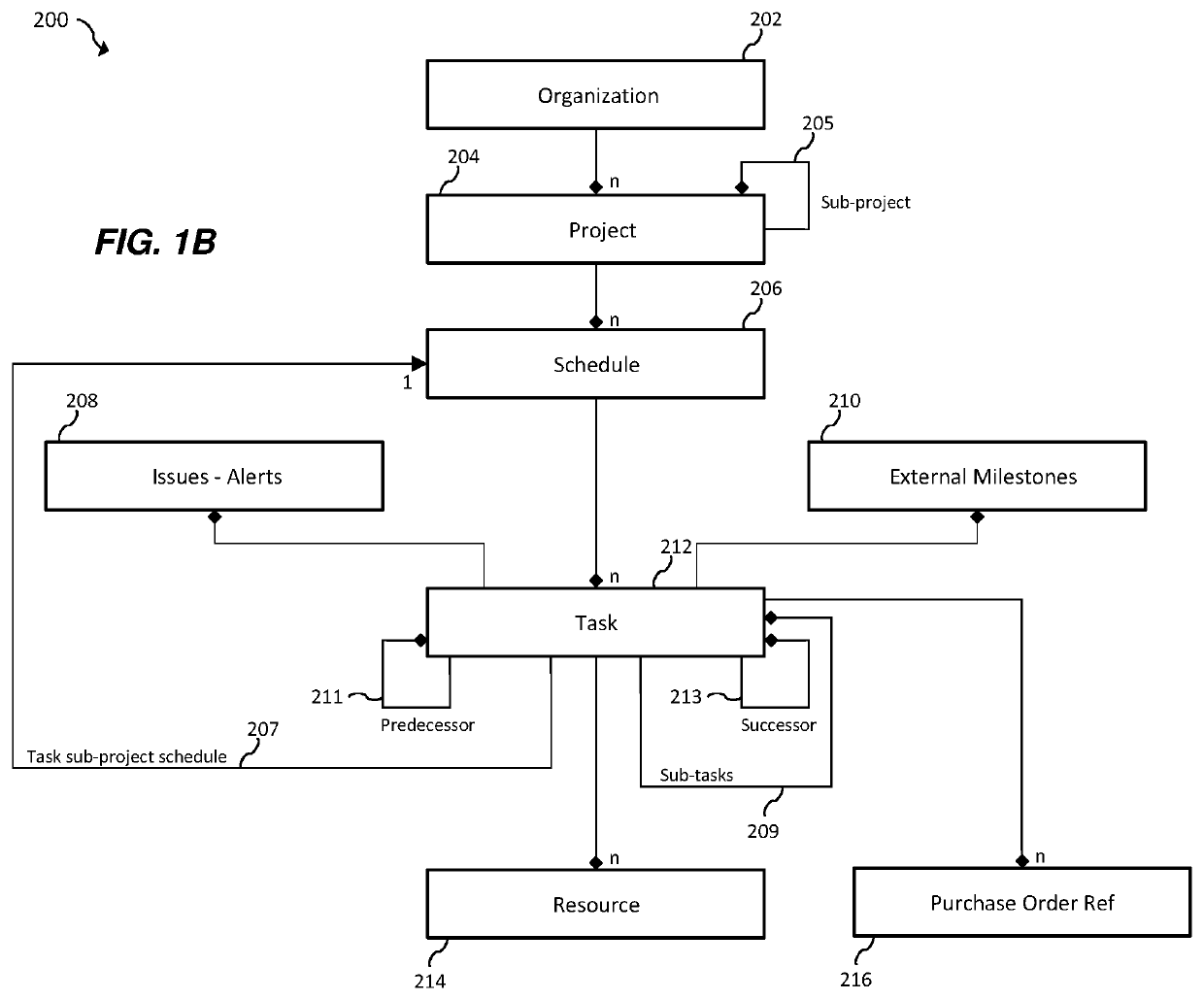
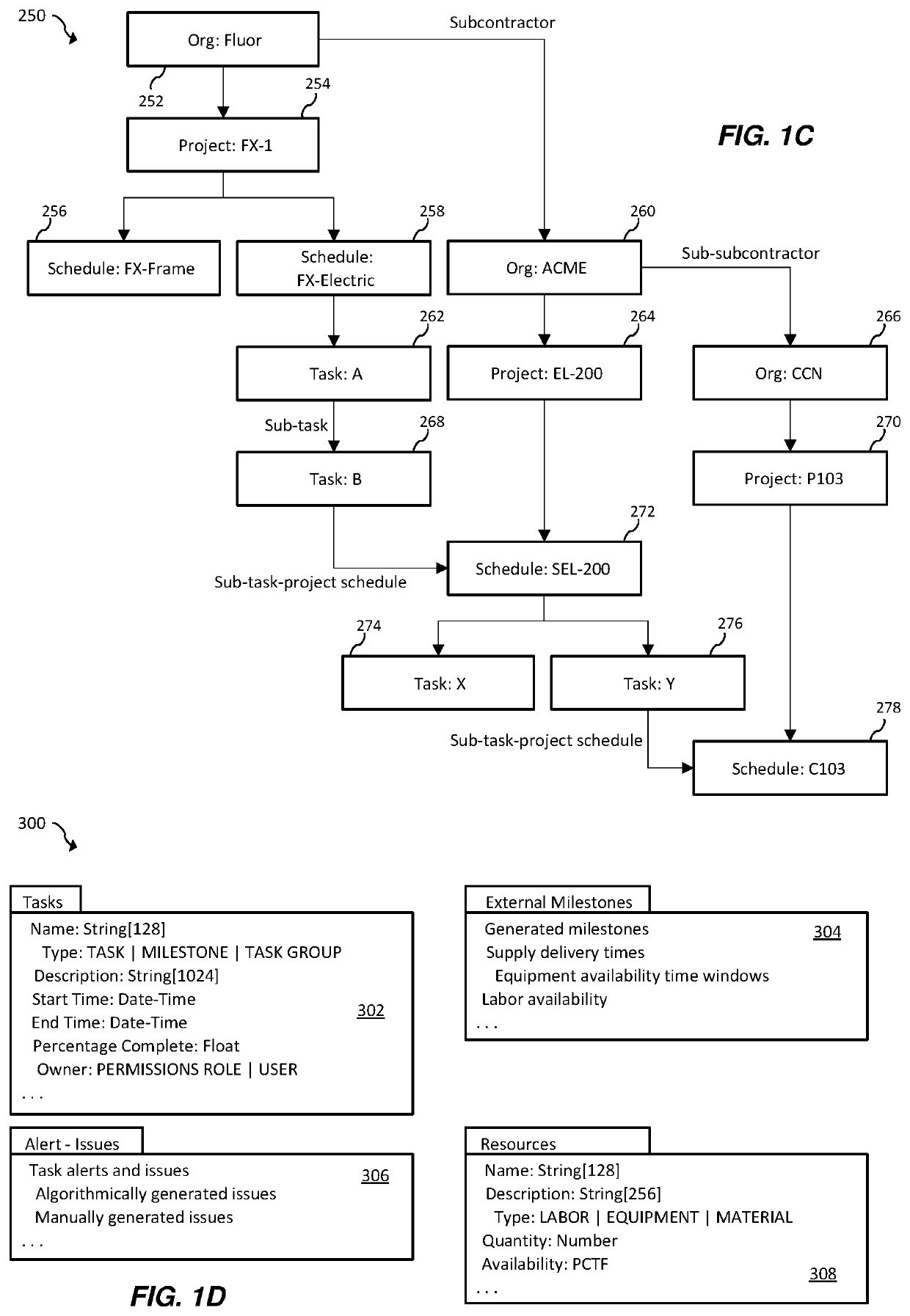
System and computer program for multi-party project schedule collaboration, synchronization and execution
Accordingly, one aspect of the present invention is to provide a system for multi-party project schedule collaboration, synchronization and execution in mega project operations across project and supporting supply chain networks. The system includes a plurality of remote computers in communication with a respective plurality of entities, a central server provided by a service provider over a network, a network interface in communication with the central server and the plurality of remote computers over a network, and a shared database in communication with the central server. The network interface being configured to receive one or more schedule updates via the network. The shared database a shared schedule having inter-shared relationships, one or more schedule tasks, a plurality of portions of the shared schedule and an execution plan to execute the shared schedule. Each of the one or more schedule updates includes a plurality of planned events impacting one or more of the plurality of portions. One or more of the plurality of portions being shared by at least two of the plurality of entities. The central server is configured to receive a schedule update from at least one of the plurality of entities in the supply chain network, update a first portion of the plurality of portions, compute and update a portion of the execution plan based on the updates to the first and second portions, wherein the update does not change the entirety of the execution plan, and notify the affected entities of the plurality of entities regarding the revised execution plan. The update results in a second portion of the plurality of portions also being updated. The one or more schedule updates are propagated to the supply chain network and the plurality of planned events and their respective timing are utilized to update the one or more schedule tasks.
Owner:ONE NETWORK ENTERPRISES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com