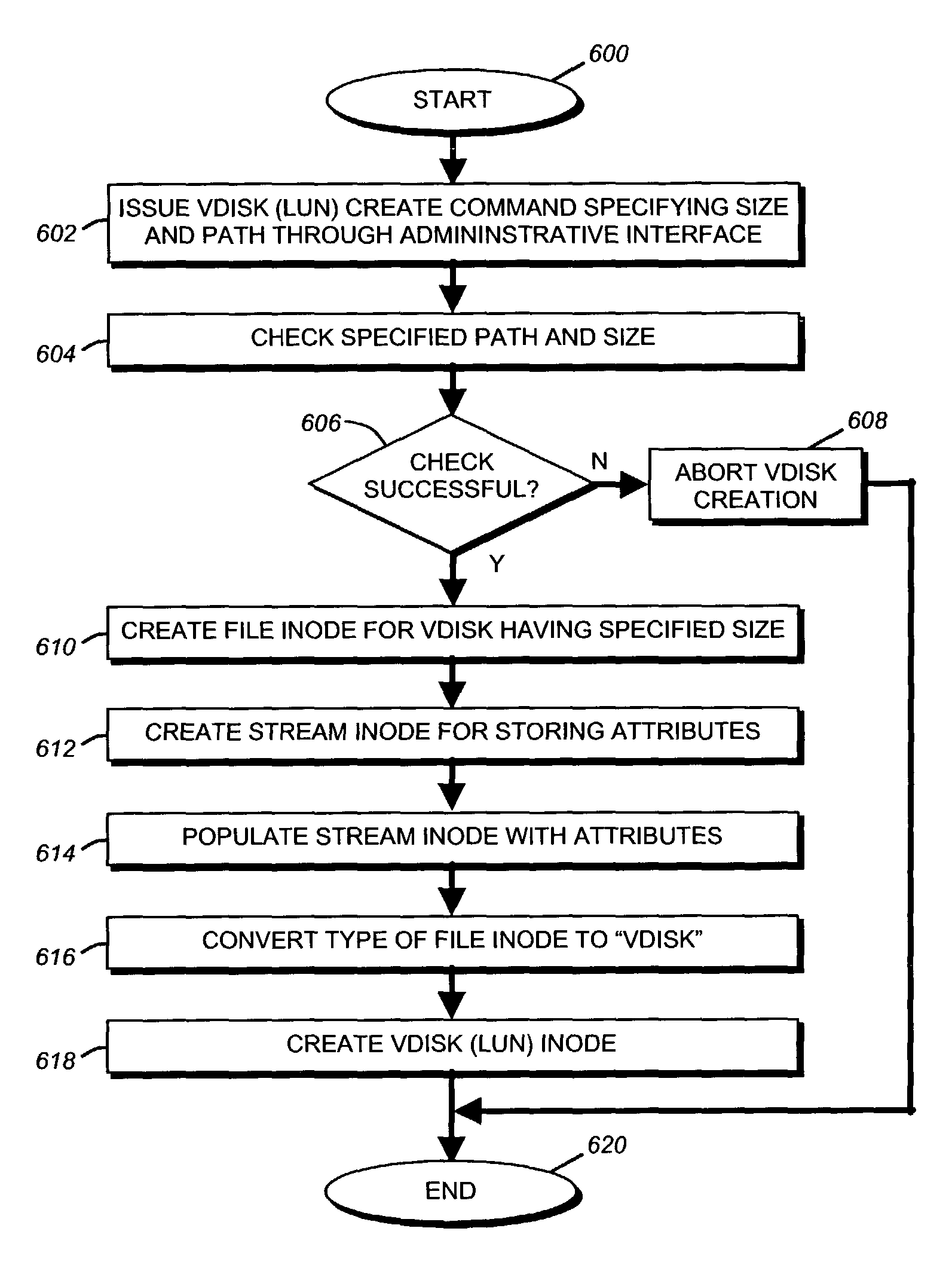
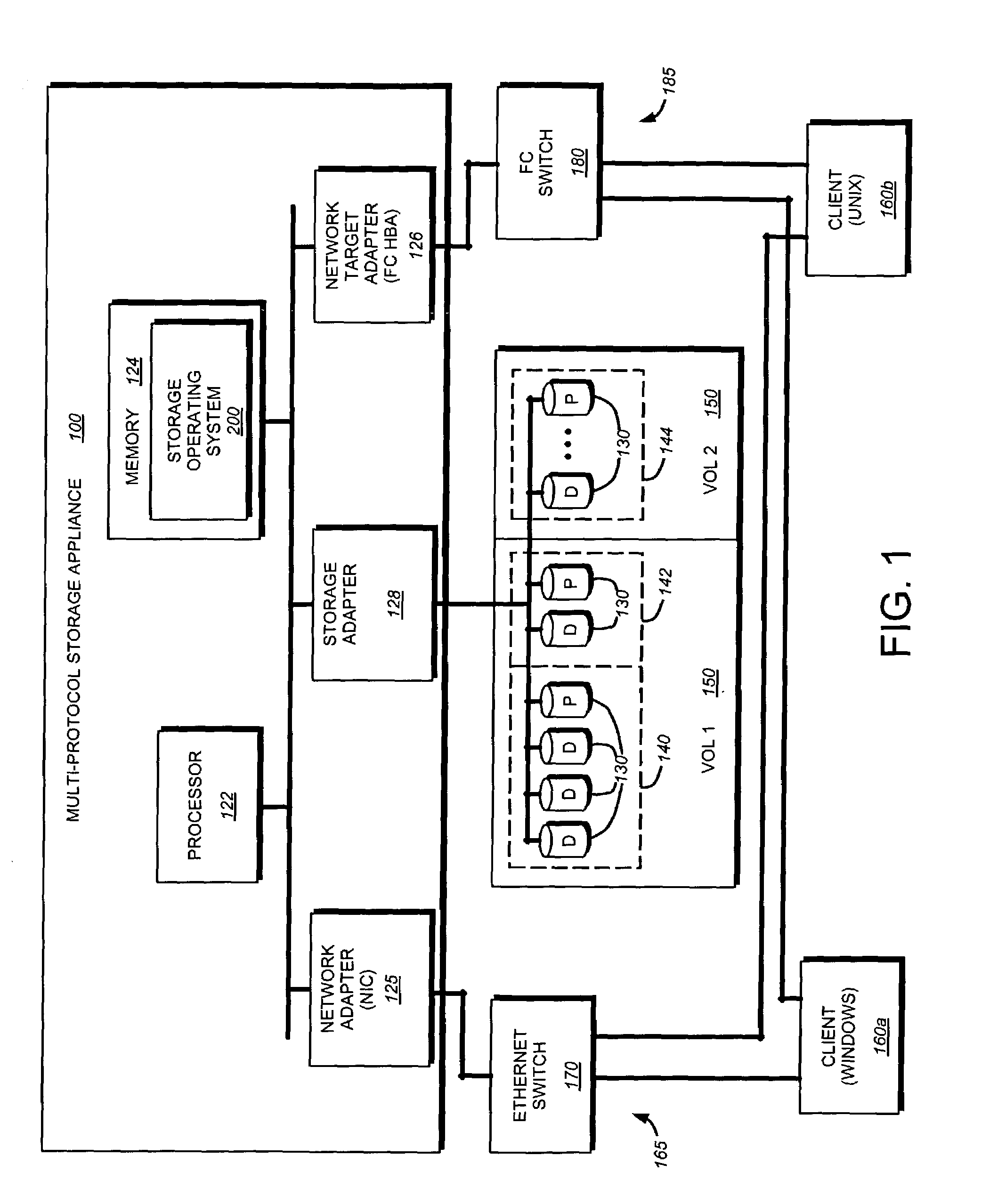
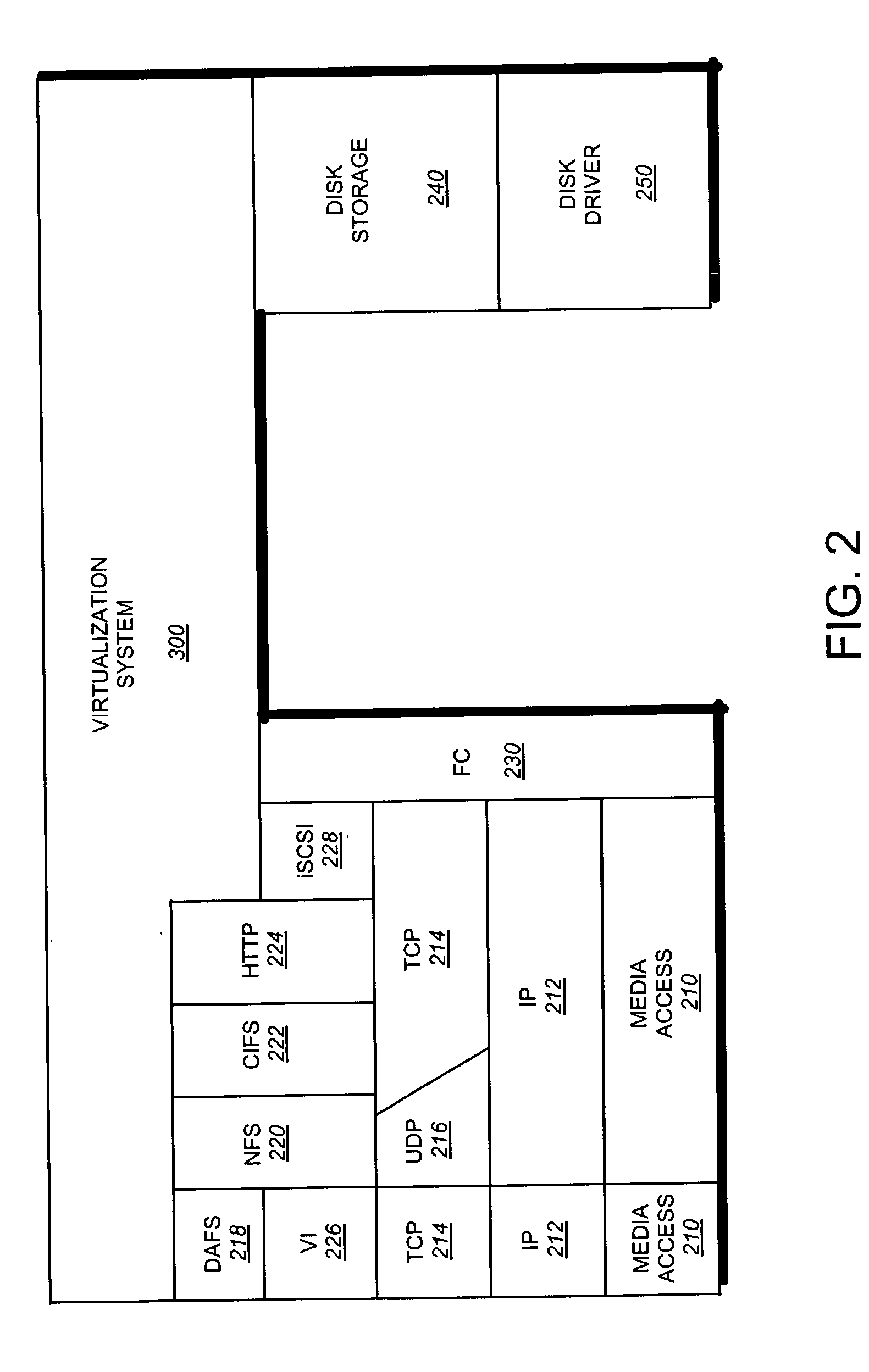
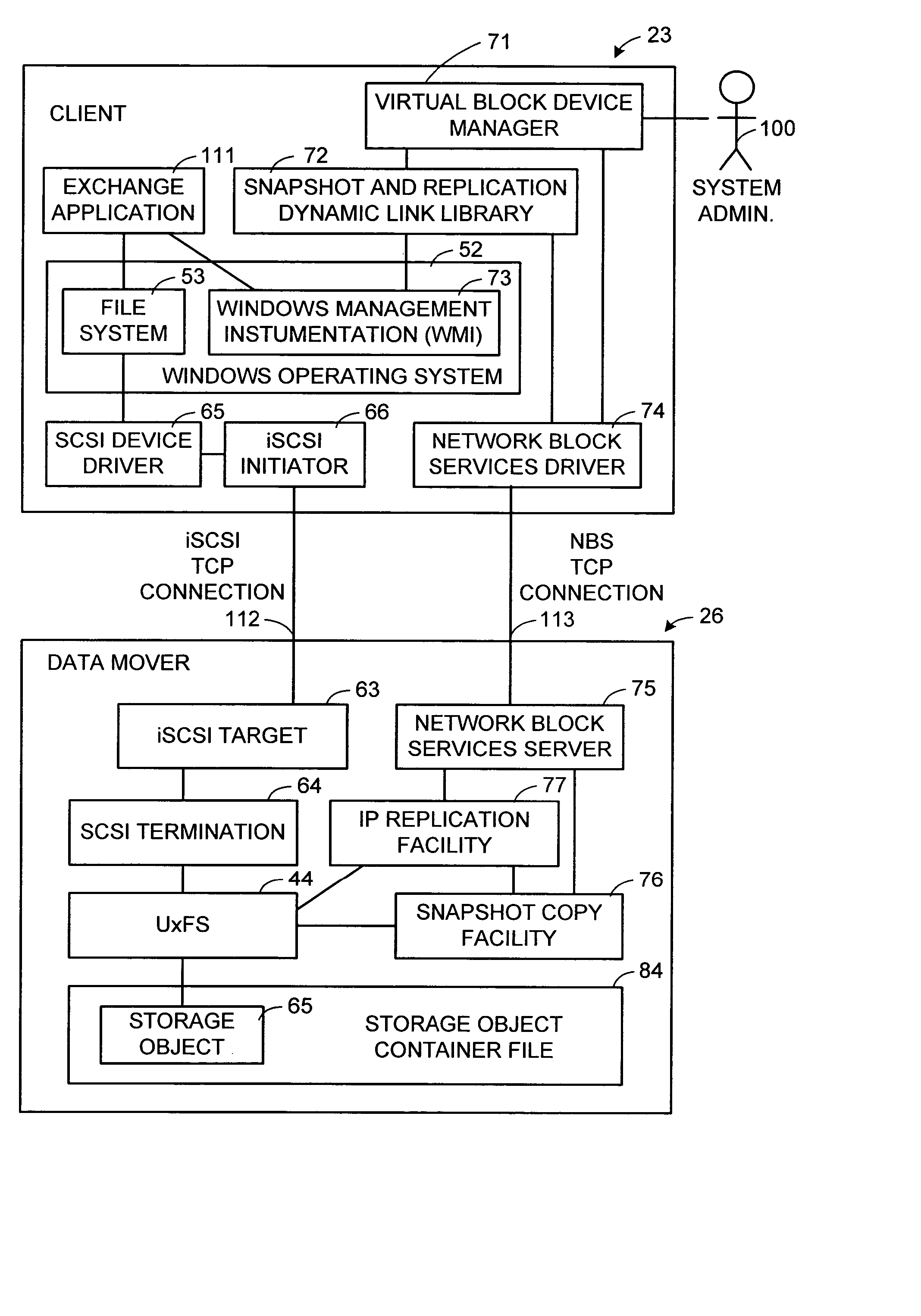
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2101results about "File systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
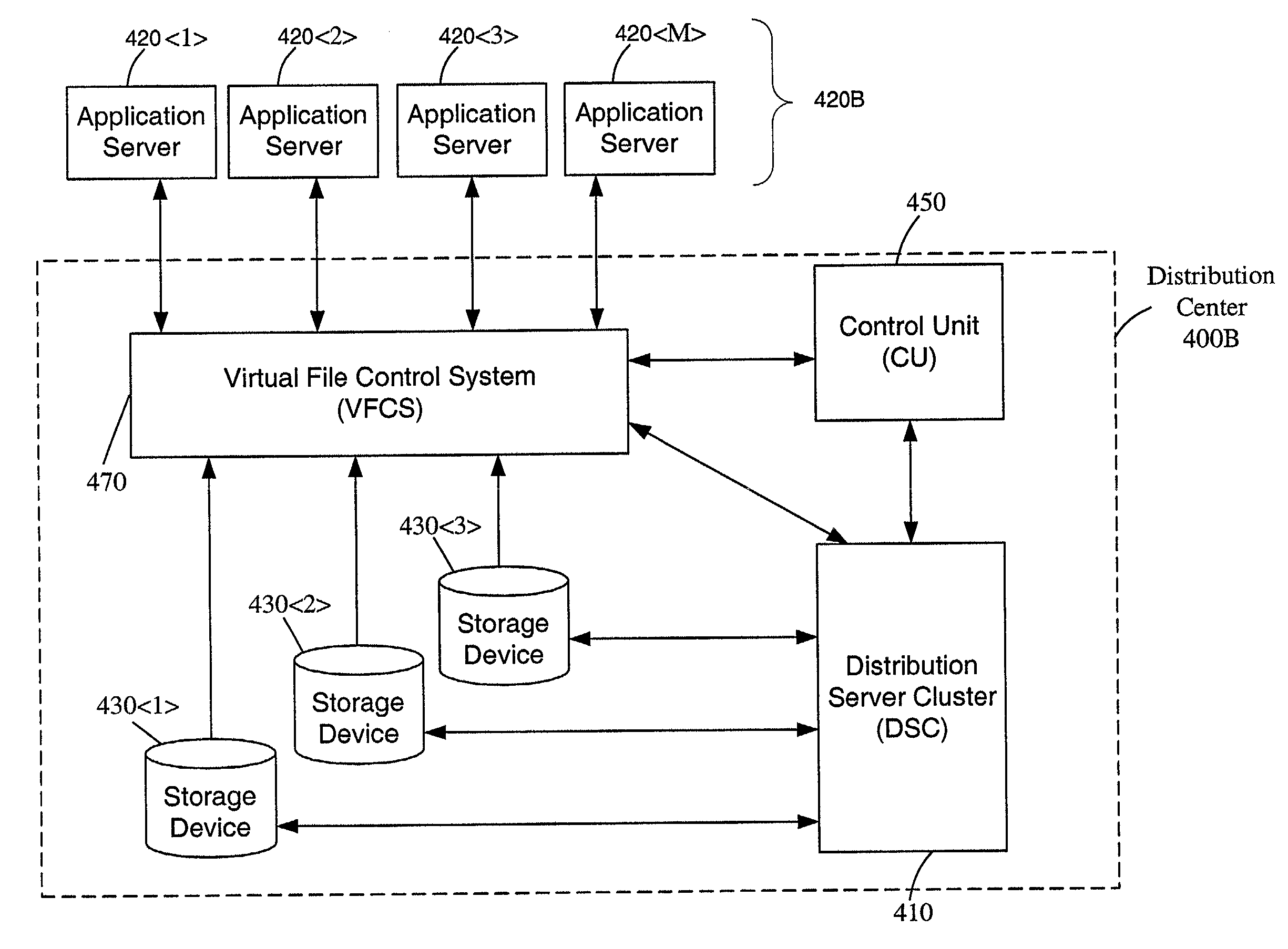
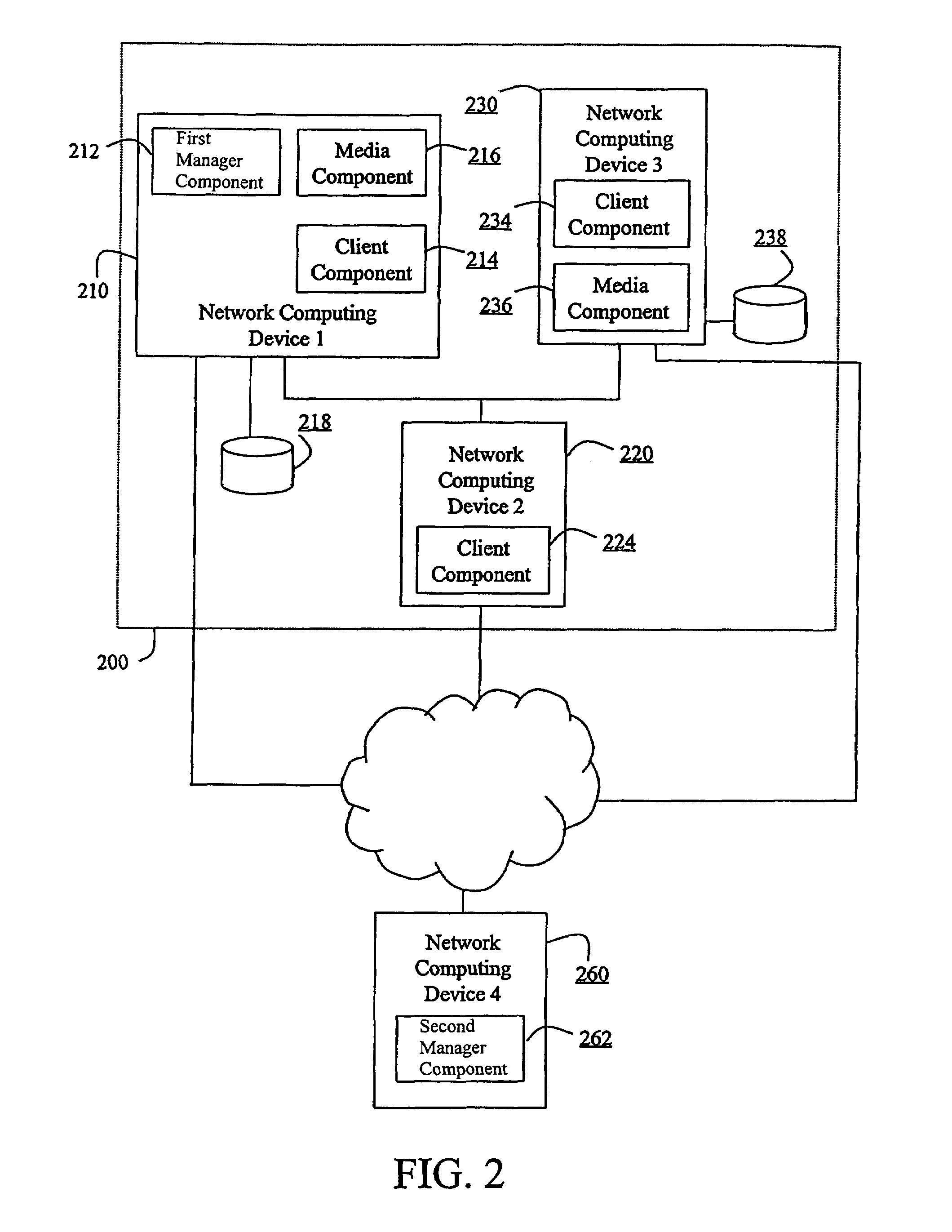
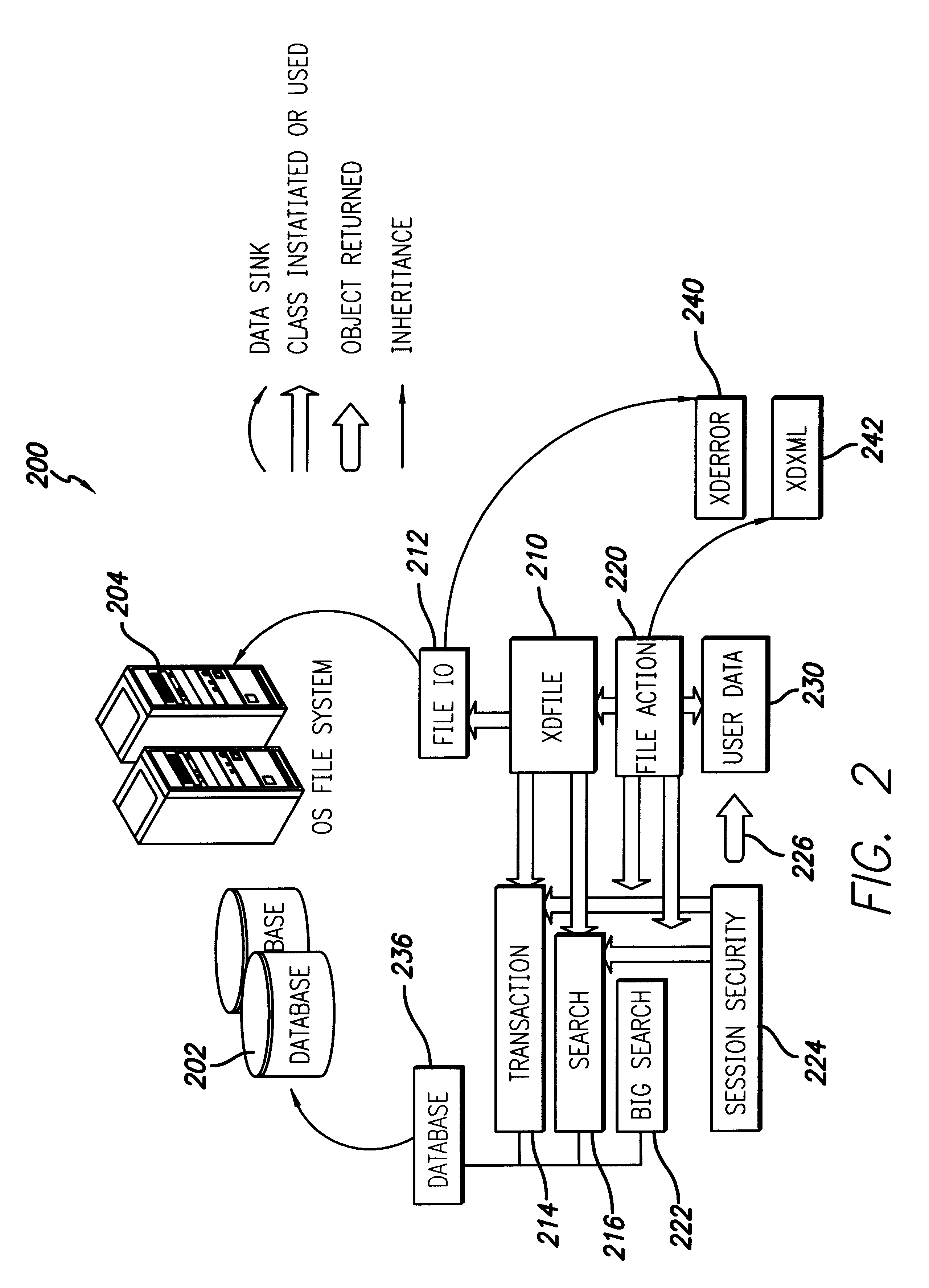
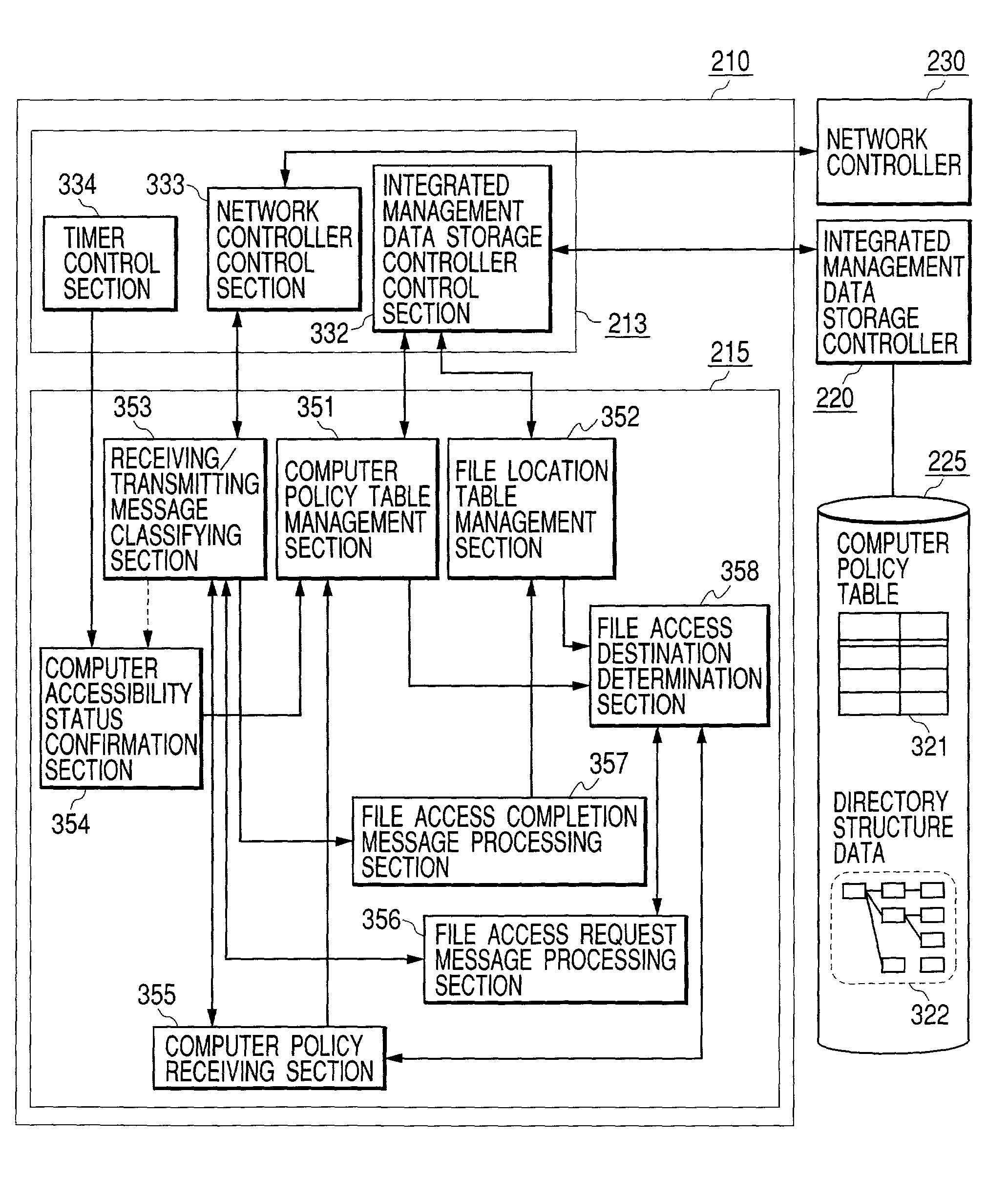
Method and system for managing distributed content and related metadata
InactiveUS7272613B2Reduce storage requirementsReduce amountData processing applicationsError detection/correctionControl systemFile system
The invention provides a method and system for creating an innovative file system that separates its directory presentation from its data store. The method and system include processing, division, distribution, managing, synchronizing, and reassembling of file system objects that does not delay the presentation of the content to the user, but also uses a reduced amount of storage space. The invention includes the ability to manage and control the integrity of the files distributed across the network, and the ability to serve and reconstruct files in real time using a Virtual File Control System.
Owner:PRISMEDIA NETWORK +1
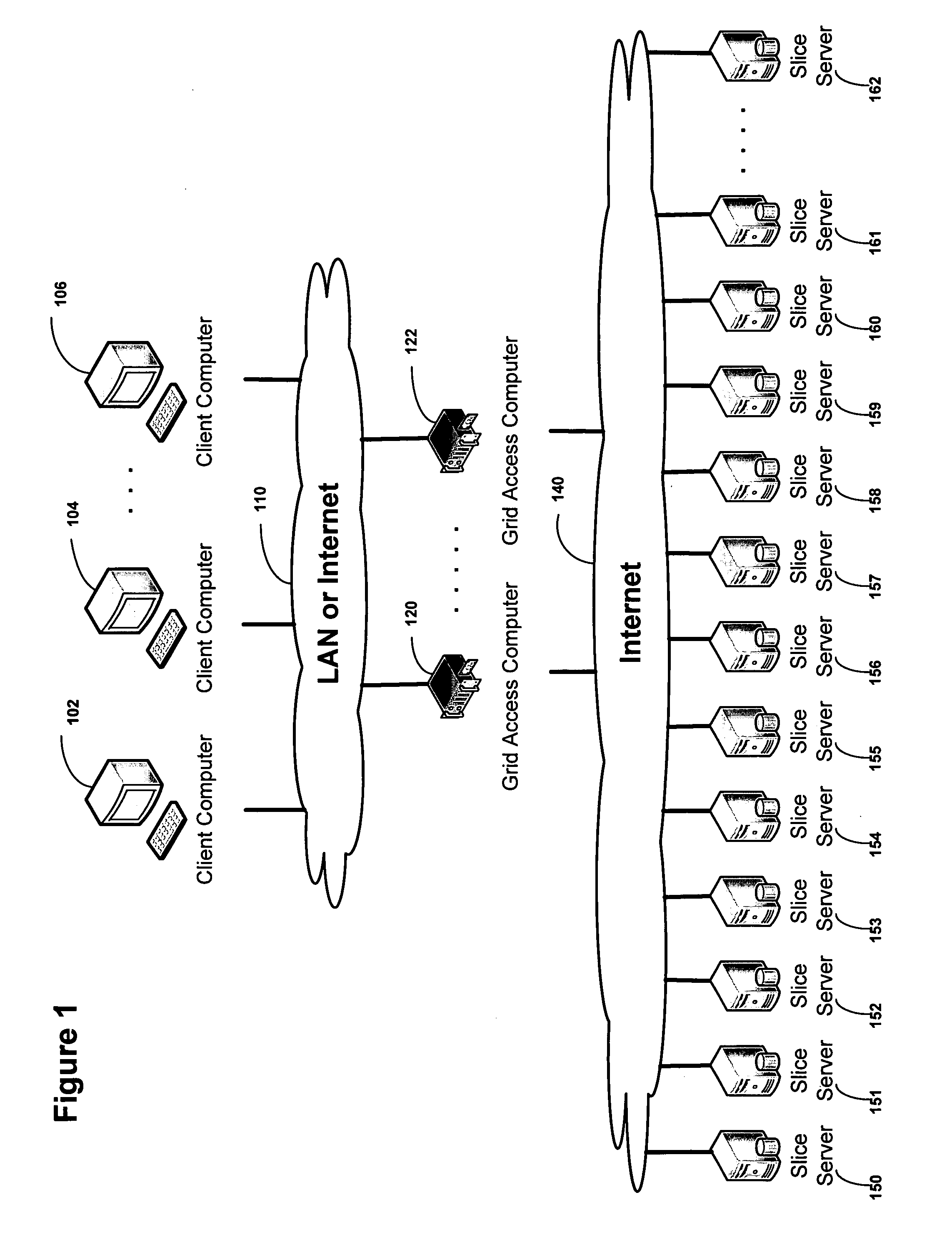
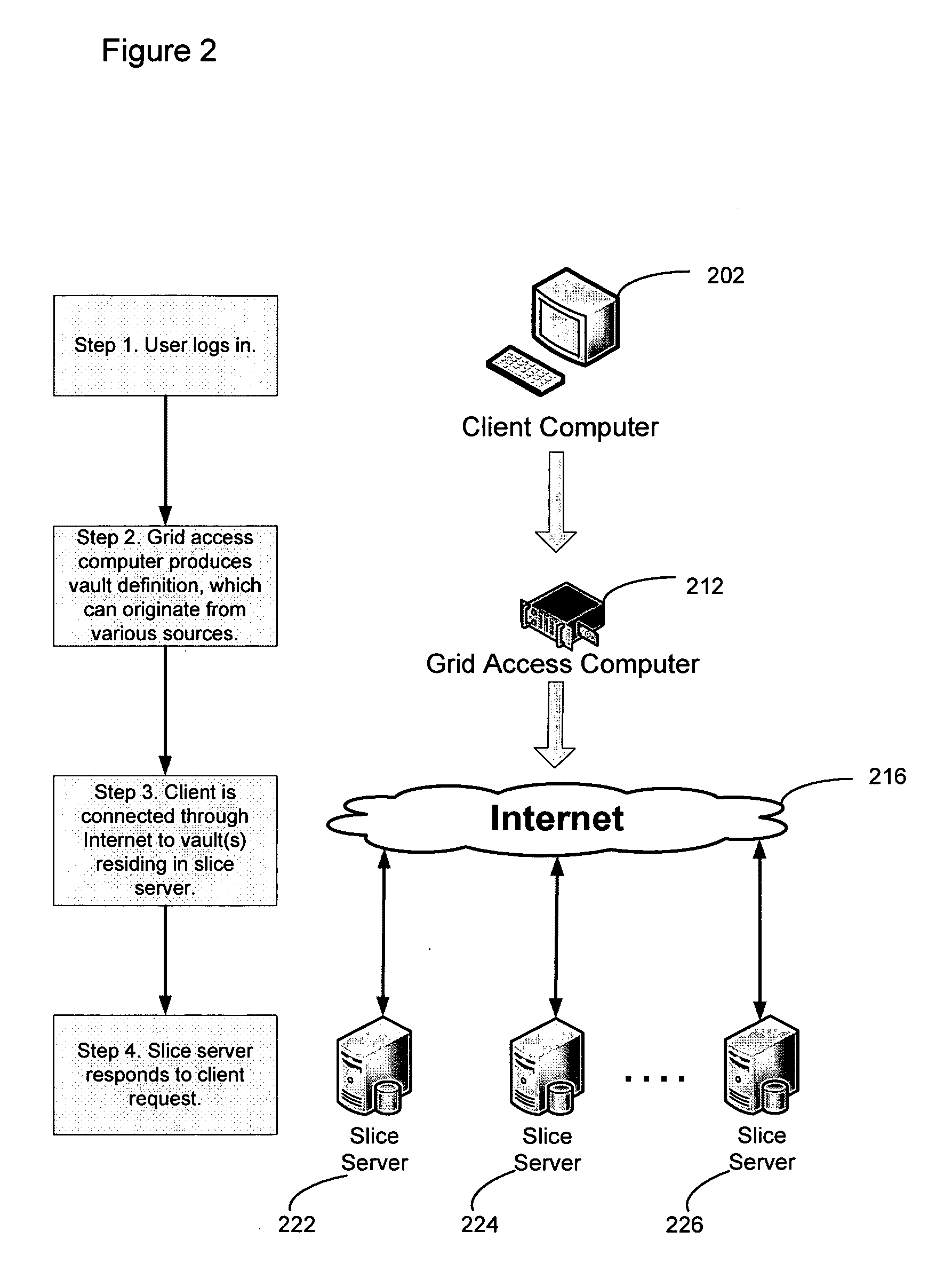
Virtualized data storage vaults on a dispersed data storage network
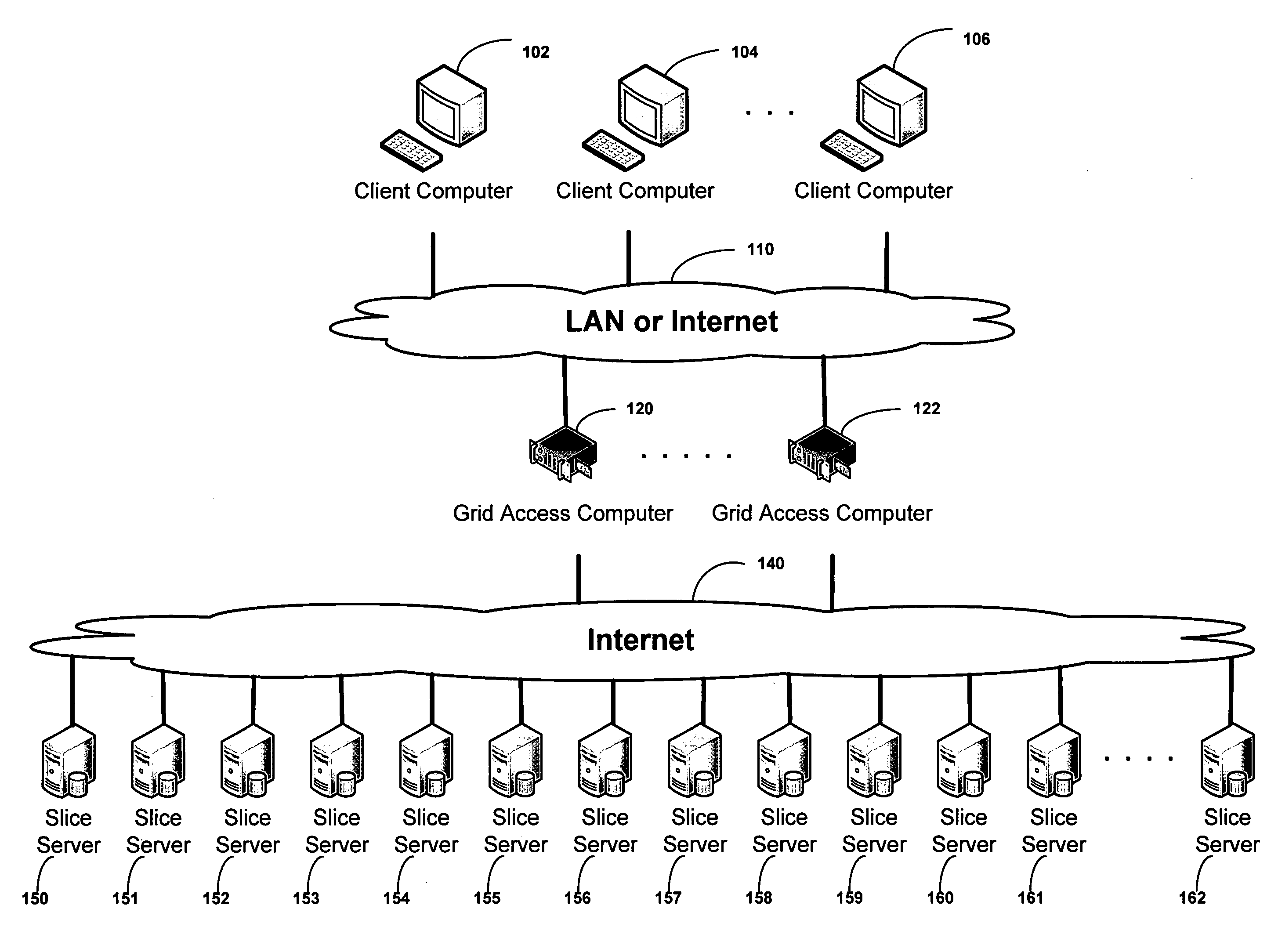
ActiveUS20090094251A1Efficient managementData processing applicationsDigital data processing detailsInformation dispersalVirtualization
A system, method, and apparatus for implementing a plurality of dispersed data storage networks using a set of slice servers are disclosed. A plurality of information records are maintained, with each information record corresponding to a dispersed data storage network. The information record maintains what slice servers are used to implement the dispersed data storage network, as well as other information needed to administer a DDSN, such as the information dispersal algorithm used, how data is stored, and whether data is compressed or encrypted.
Owner:PURE STORAGE
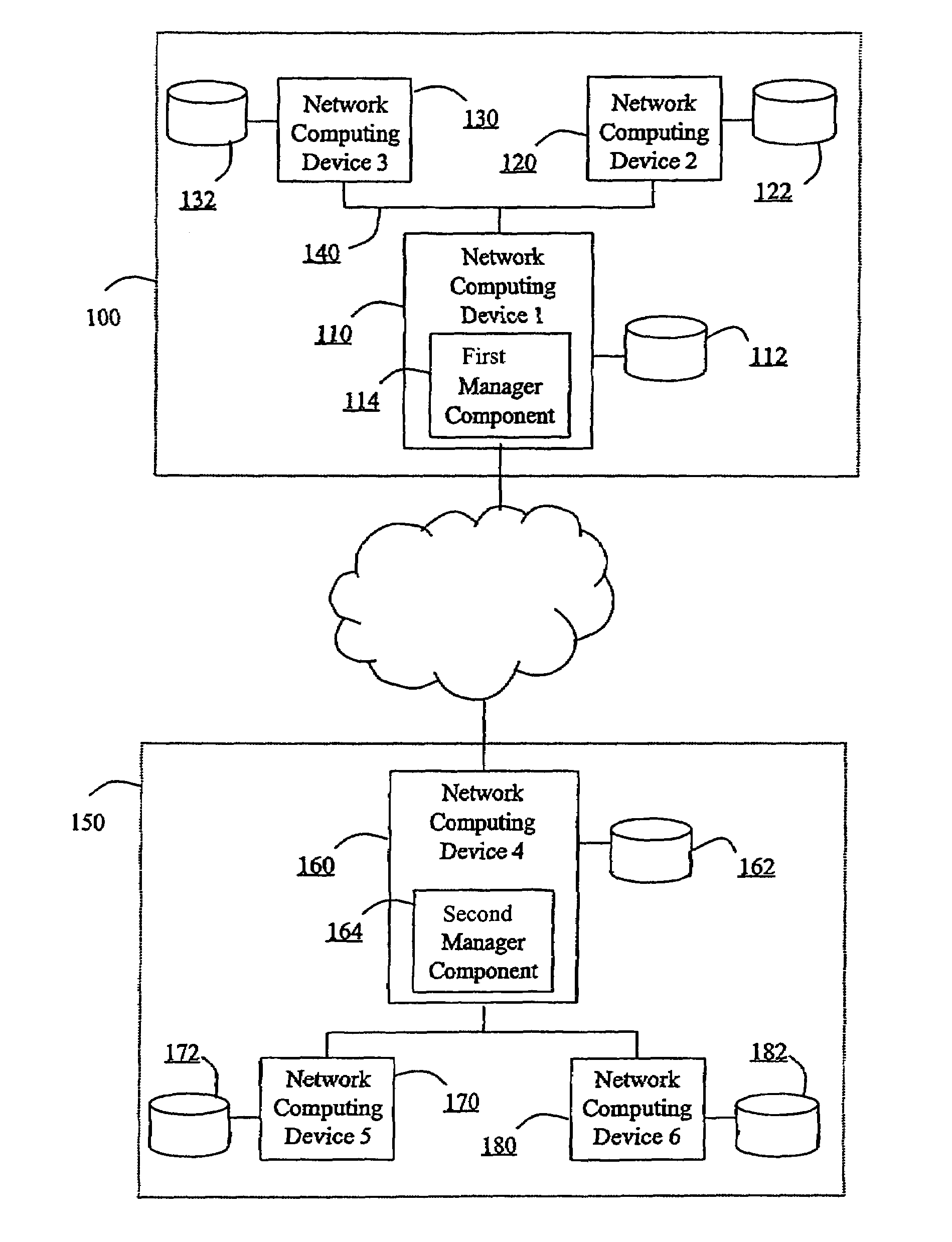
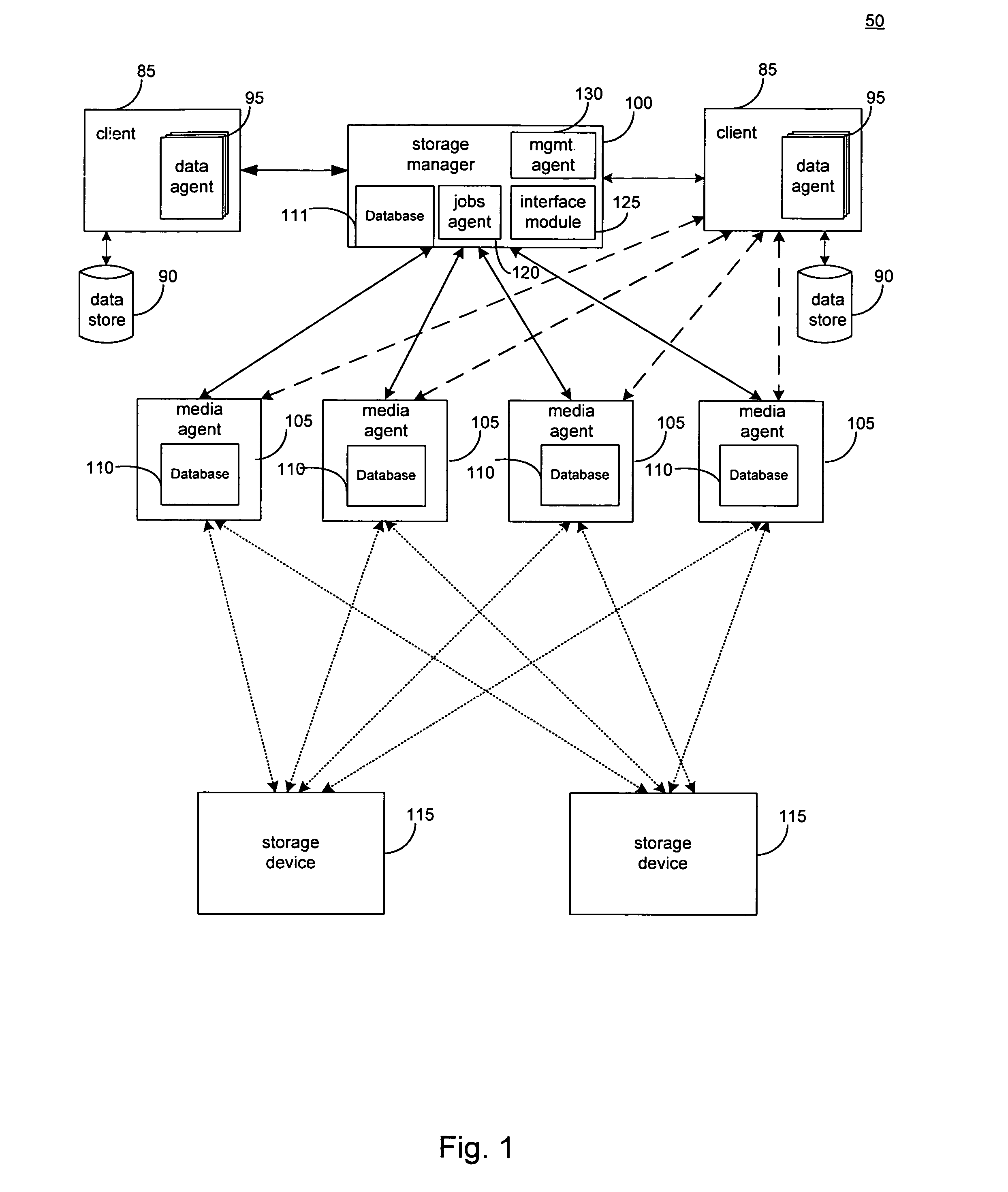
Hierarchical backup and retrieval system
InactiveUS7395282B1Data processing applicationsDigital data processing detailsSoftware agentAdministrative controls
The invention is a hierarchical backup system. The interconnected network computing devices are put into groups of backup cells. A backup cell has a manager software agent responsible maintaining and initiating a backup regime for the network computing devices in the backup cell. The backups are directed to backup devices within the backup cell. Several backup cells can be defined. A manager software agent for a particular cell may be placed into contact with the manager software agent of another cell, by which information about the cells may be passed back and forth. Additionally, one of the software agents may be given administrative control over another software agent with which it is in communication.
Owner:COMMVAULT SYST INC
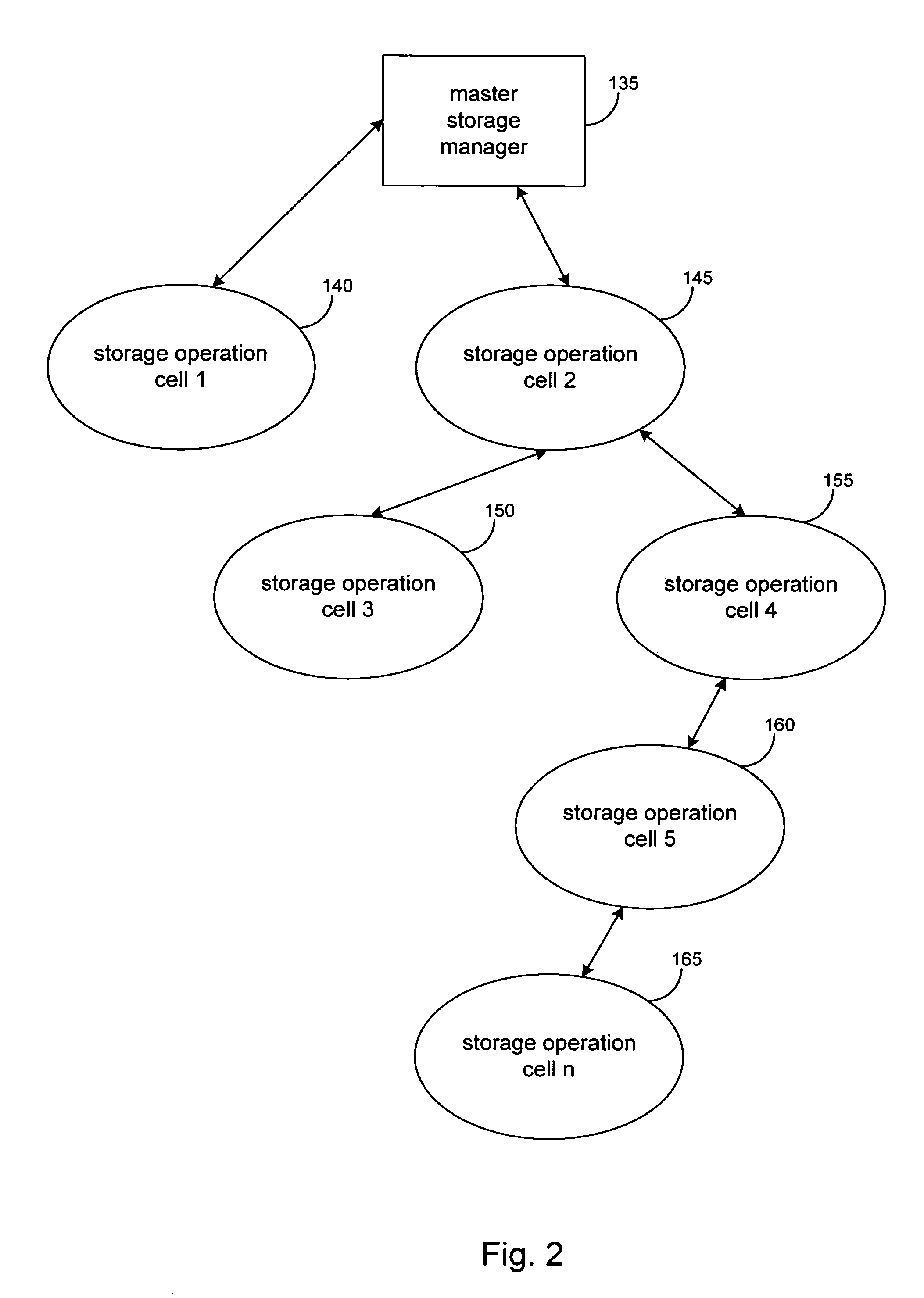
Hierarchical systems and methods for providing a unified view of storage information
The present invention provides systems and methods for data storage. A hierarchical storage management architecture is presented to facilitate data management. The disclosed system provides methods for evaluating the state of stored data relative to enterprise needs by using weighted parameters that may be user defined. Also disclosed are systems and methods evaluating costing and risk management associated with stored data.
Owner:COMMVAULT SYST INC
Computer graphic display visualization system and method
InactiveUS6868525B1Improve compactnessIncrease flexibilityDrawing from basic elementsAdvertisementsGraphicsCollaborative filtering
An improved human user computer interface system, providing a graphic representation of a hierarchy populated with naturally classified objects, having included therein at least one associated object having a distinct classification. Preferably, a collaborative filter is employed to define the appropriate associated object. The associated object preferably comprises a sponsored object, generating a subsidy or revenue.
Owner:RELATIVITY DISPLAY LLC
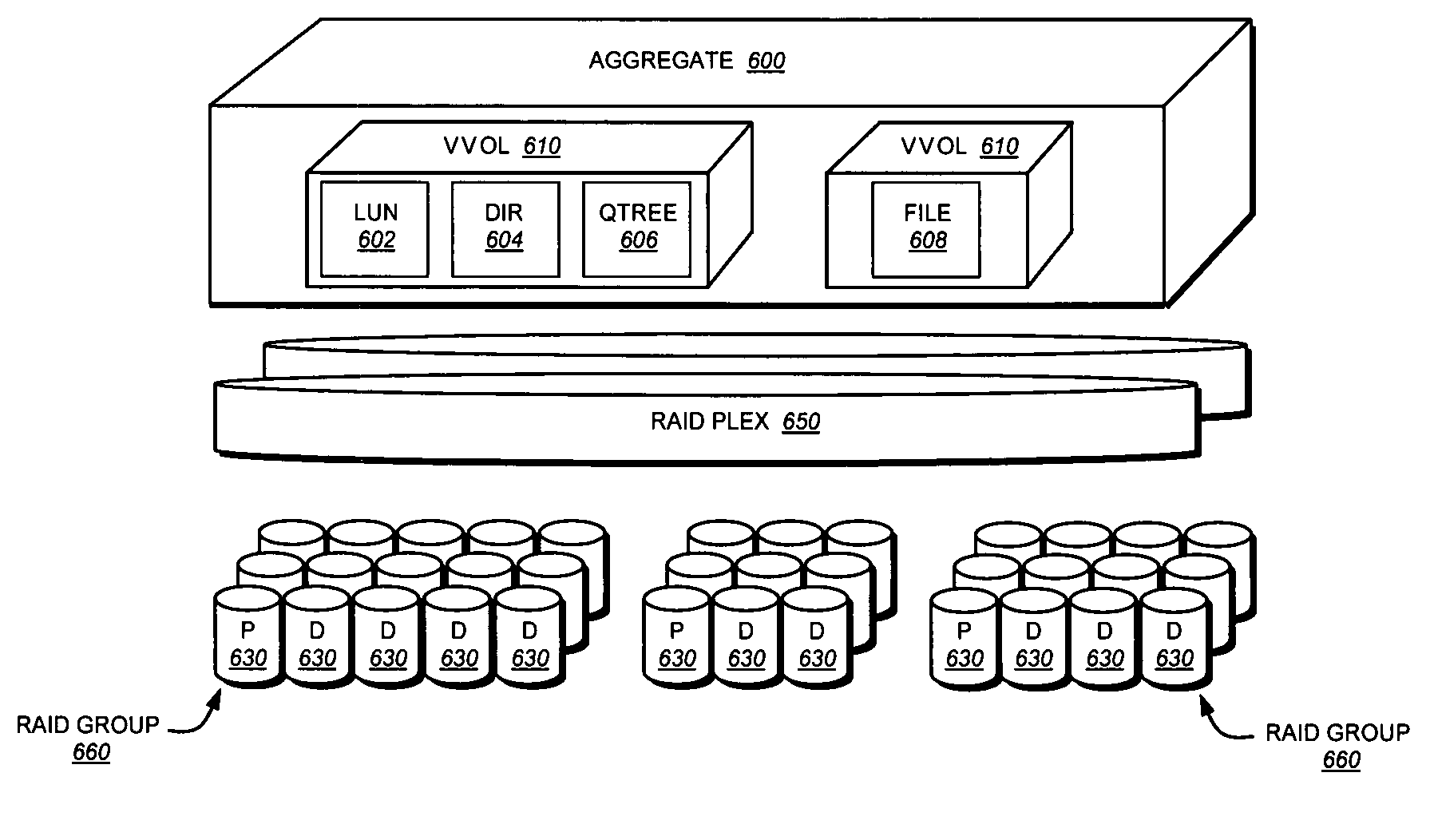
Architecture for supporting sparse volumes
ActiveUS7689609B2Faster exportMinimal write operationDigital data processing detailsSpecial data processing applicationsData storingData store
Owner:NETWORK APPLIANCE INC
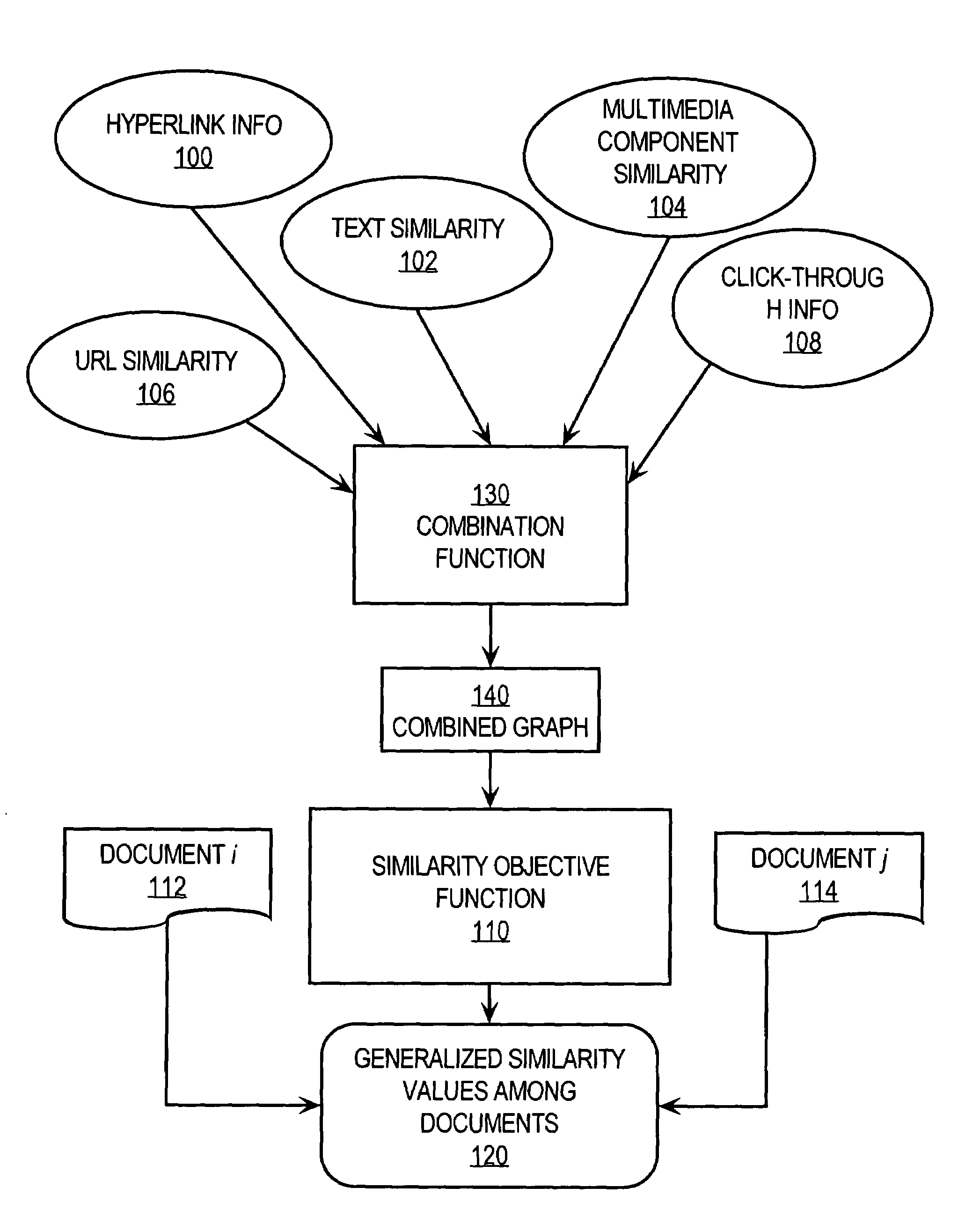
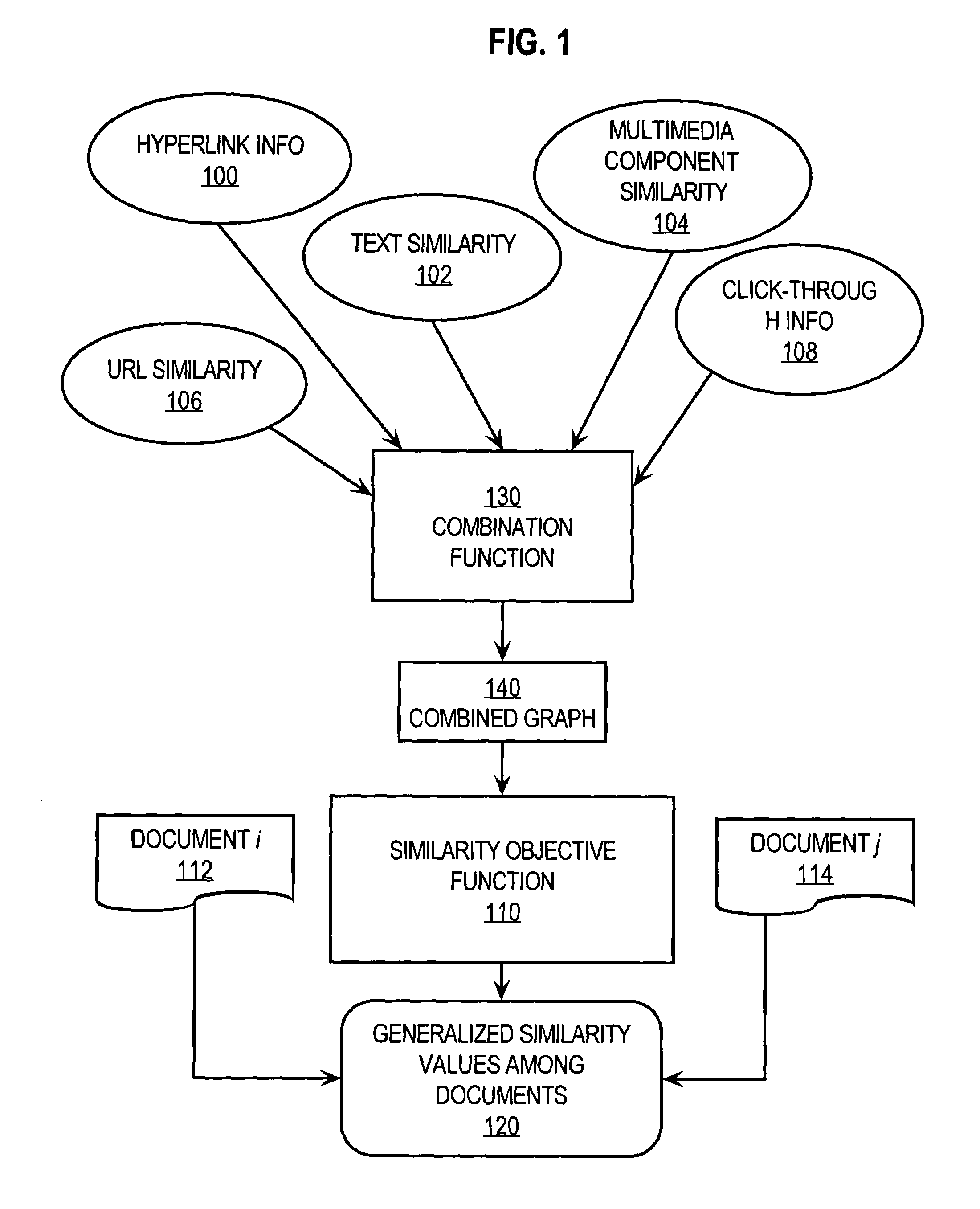
Method and apparatus for measuring similarity among electronic documents
A method and apparatus are provided for determining when electronic documents stored in a large collection of documents are similar to one another. A plurality of similarity information is derived from the documents. The similarity information may be based on a variety of factors, including hyperlinks in the documents, text similarity, user click-through information, similarity in the titles of the documents or their location identifiers, and patterns of user viewing. The similarity information is fed to a combination function that synthesizes the various measures of similarity information into combined similarity information. Using the combined similarity information, an objective function is iteratively maximized in order to yield a generalized similarity value that expresses the similarity of particular pairs of documents. In an embodiment, the generalized similarity value is used to determine the proper category, among a taxonomy of categories in an index, cache or search system, into which certain documents belong.
Owner:YAHOO INC
Method and apparatus for transparent distributed network-attached storage with web cache communication protocol/anycast and file handle redundancy
ActiveUS7254636B1Data processing applicationsDigital data processing detailsContent distributionNetwork connection
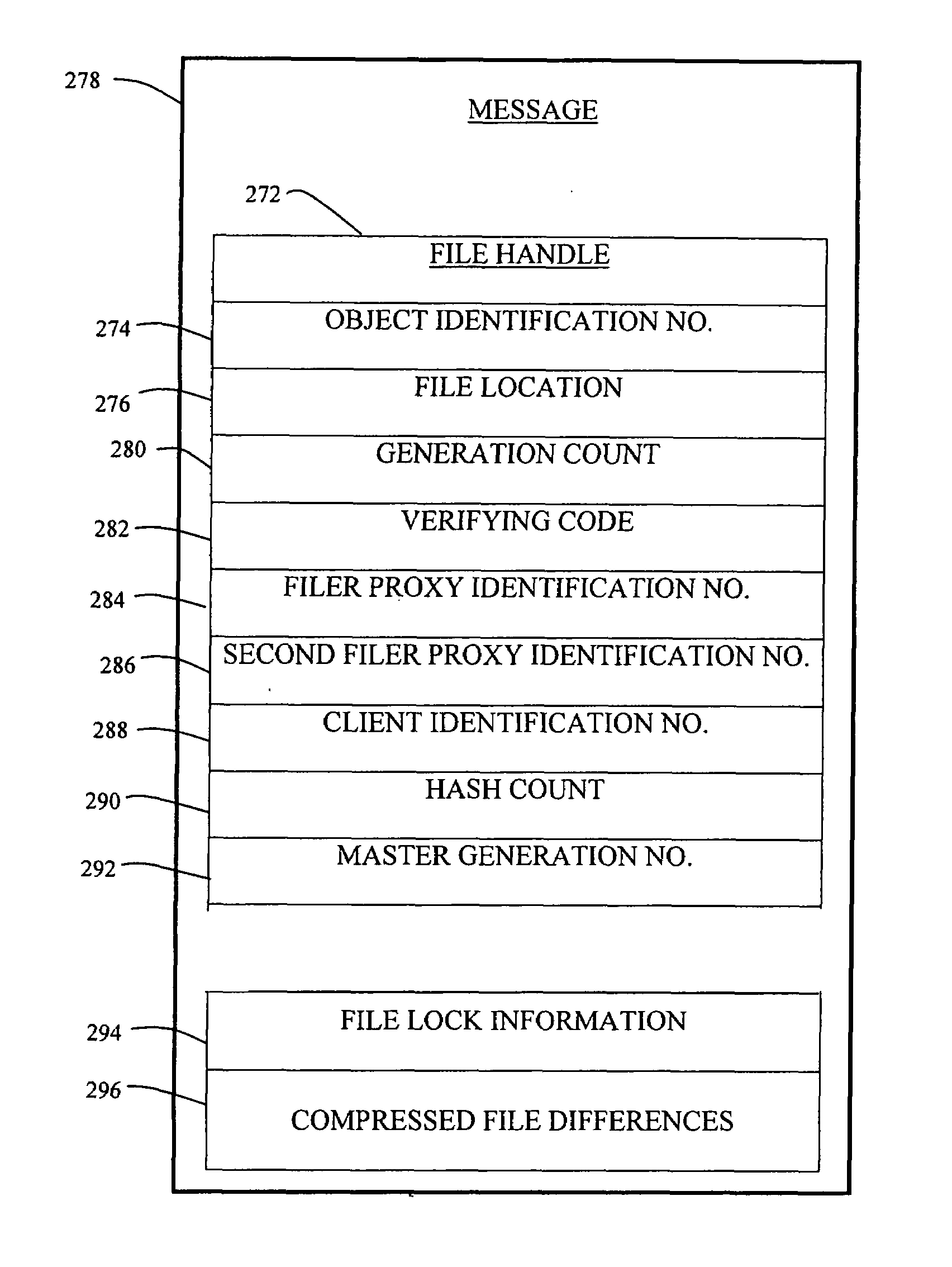
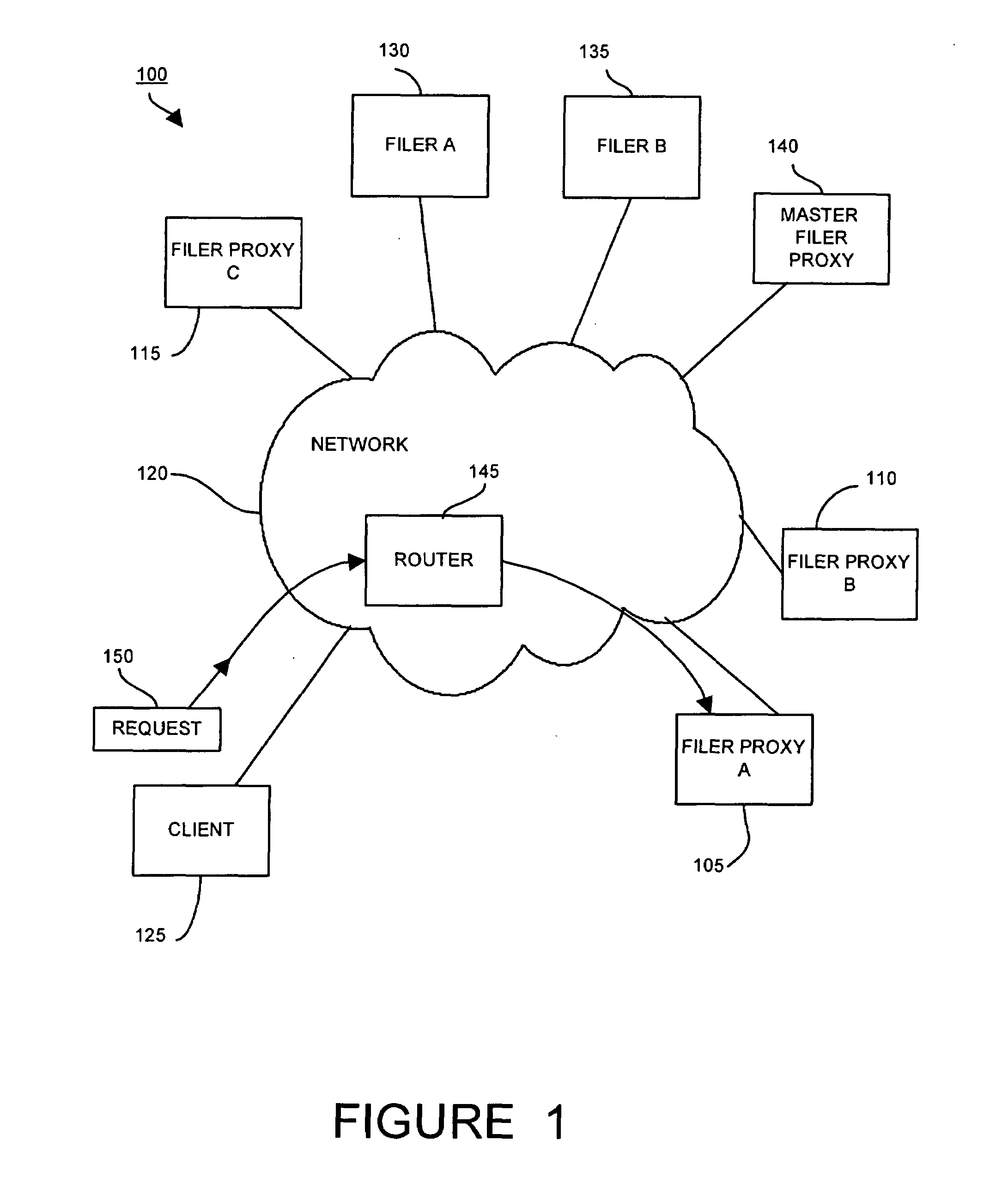
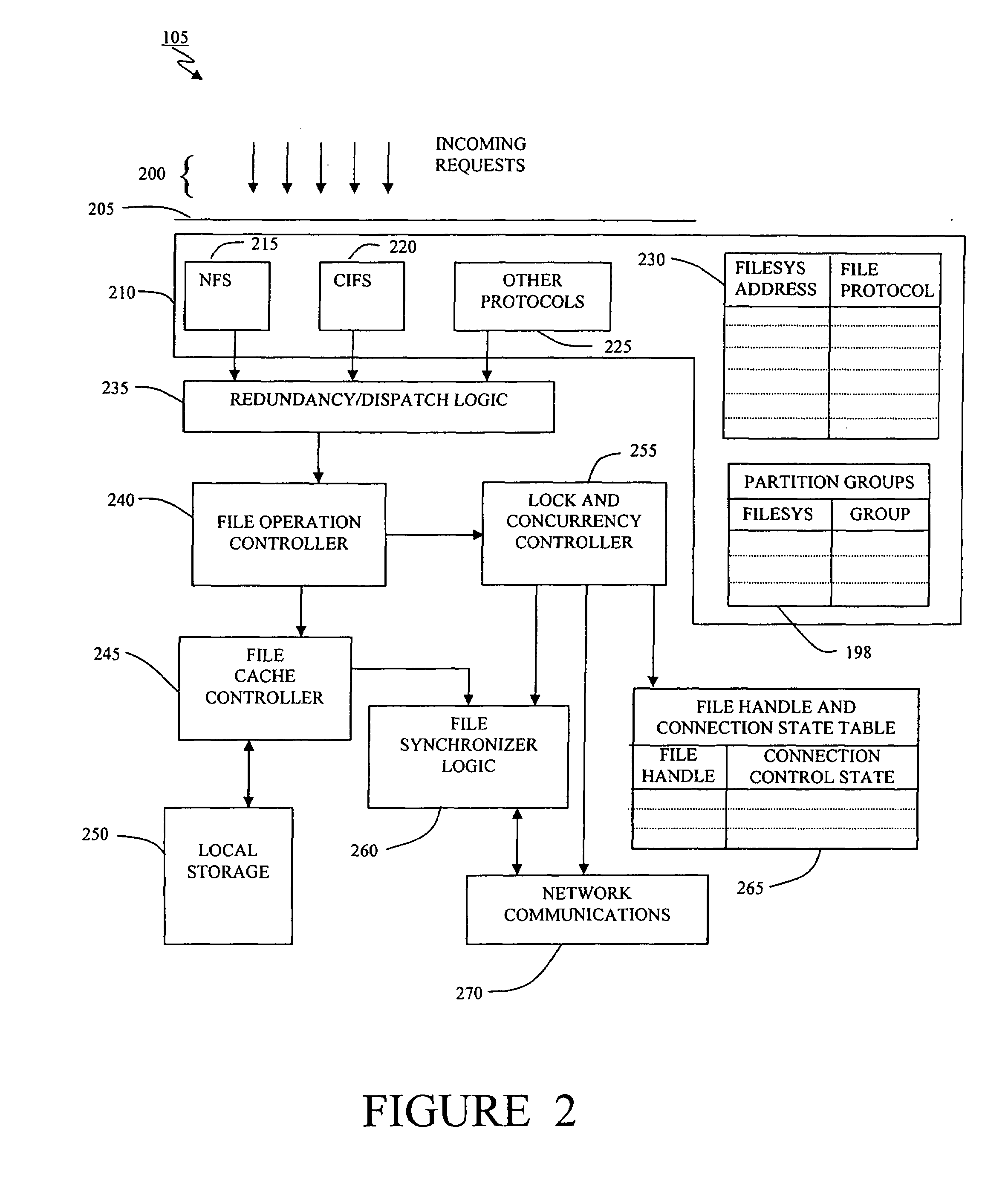
A distributed network-attached storage network provides content distribution using conventional file transfer protocols such as NFS and CIFS. A filer proxy accepts a client request and translates the client request to a file transfer protocol accepted at the file system having the file requested in the client request. The filer proxy generates a file handle for the file containing redundant filer proxy information to be used for failover to a backup filer proxy in the event of a network error or failure of an original filer proxy. The file handle also contains information for network security purposes such as detection of forged file handles.
Owner:CISCO TECH INC
System and method for mapping file block numbers to logical block addresses
ActiveUS7437530B1Improve performanceRaise transfer toMultiple digital computer combinationsTransmissionOperational systemLogical block addressing
A system and method for mapping file block numbers (FBNs) to logical block addresses (LBAs) is provided. The system and method performs the mapping of FBNs to LBAs in a file system layer of a storage operating system, thereby enabling the use of clients in a storage environment that have not been modified to incorporate mapping tables. As a result, a client may send data access requests to the storage system utilizing FBNs and have the storage system perform the appropriate mapping to LBAs.
Owner:NETWORK APPLIANCE INC
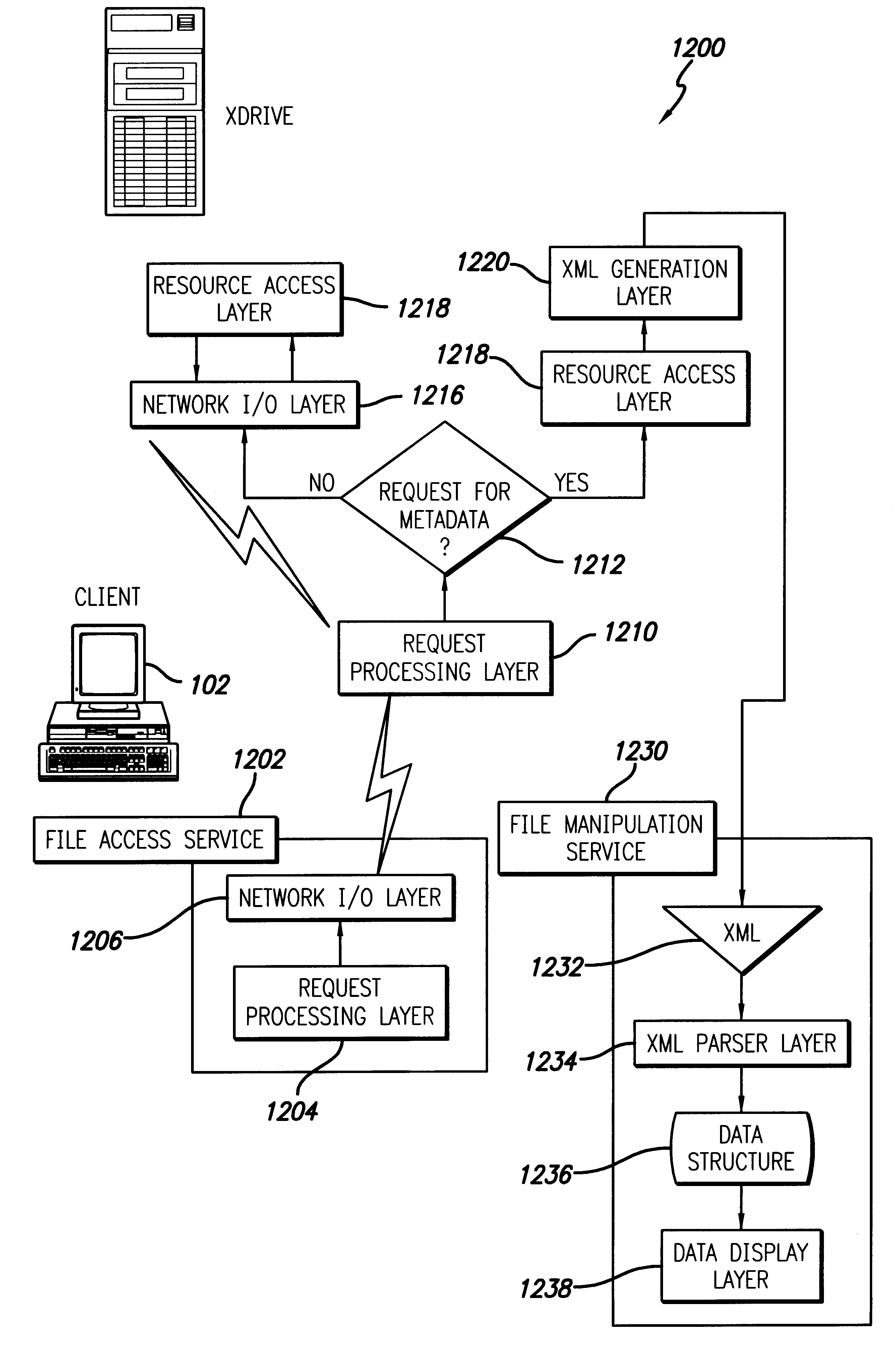
Shared internet storage resource, user interface system, and method
InactiveUS6351776B1Easy to understandData processing applicationsWeb data indexingData streamWeb service
The Shared Internet Storage Resource provides Internet-based file storage, retrieval, access, control, and manipulation for a user. Additionally, an easy-to-use user interface is provided both for a browser or stand-alone application. The entire method provides means by which users can establish, use, and maintain files on the Internet in a manner remote from their local computers yet in a manner that is similar to the file manipulation used on their local computers. A high capacity or other storage system is attached to the Internet via an optional internal network that also serves to generate and direct metadata regarding the stored files. A web server using a CGI, Java(R)-based, or other interface transmits and retrieves TCP / IP packets or other Internet information through a load balancer / firewall by using XML to wrap the data packets. File instructions may be transmitted over the Internet to the Shared Resource System. The user's account may be password protected so that only the user may access his or her files. On the user's side, a stand-alone client application or JavaScript object interpreted through a browser provide two means by which the XML or other markup language data stream may be received and put to use by the user. Internet-to-Internet file transfers may be effected by directly downloading to the user's account space.
Owner:TIME WARNER
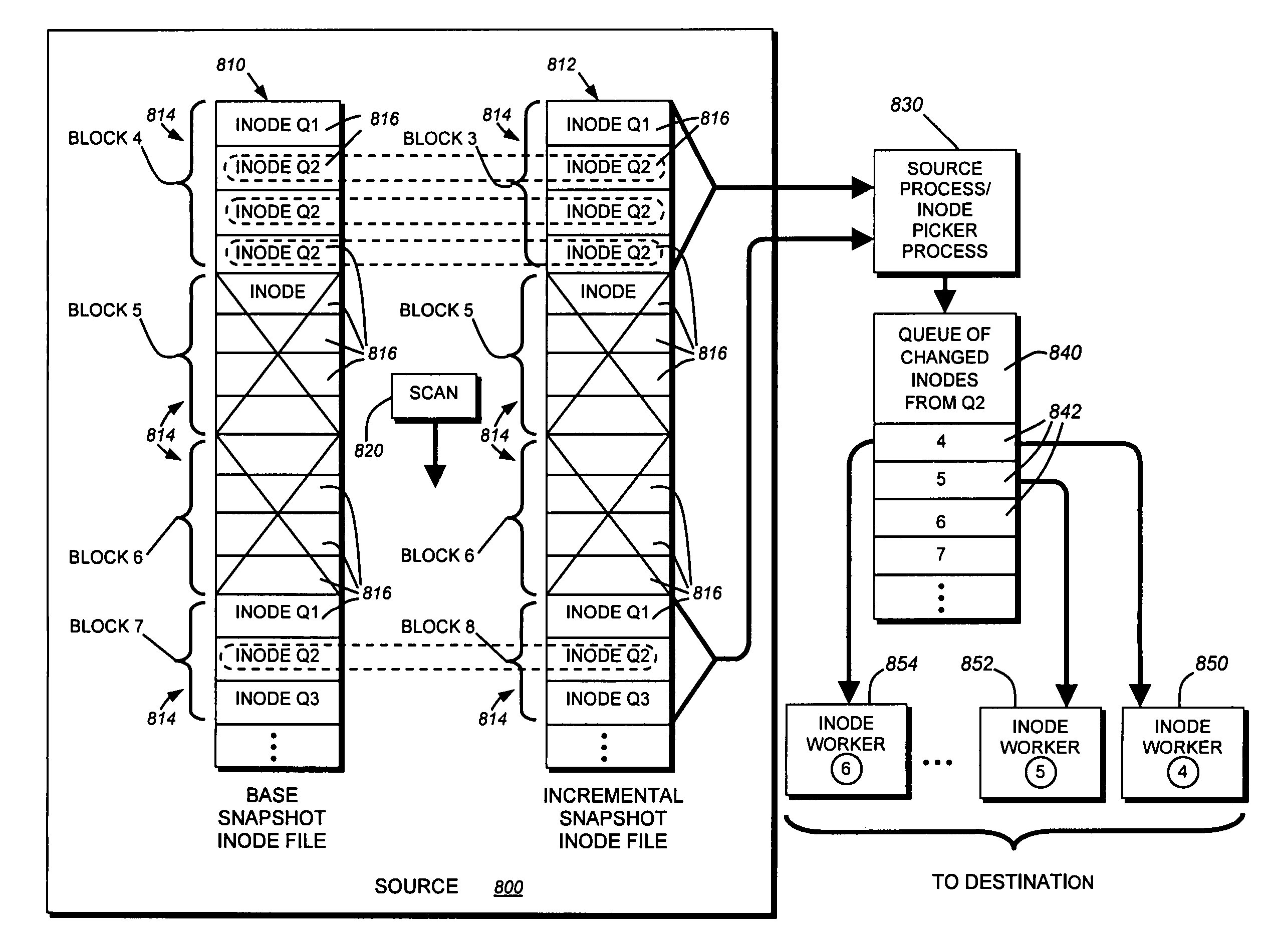
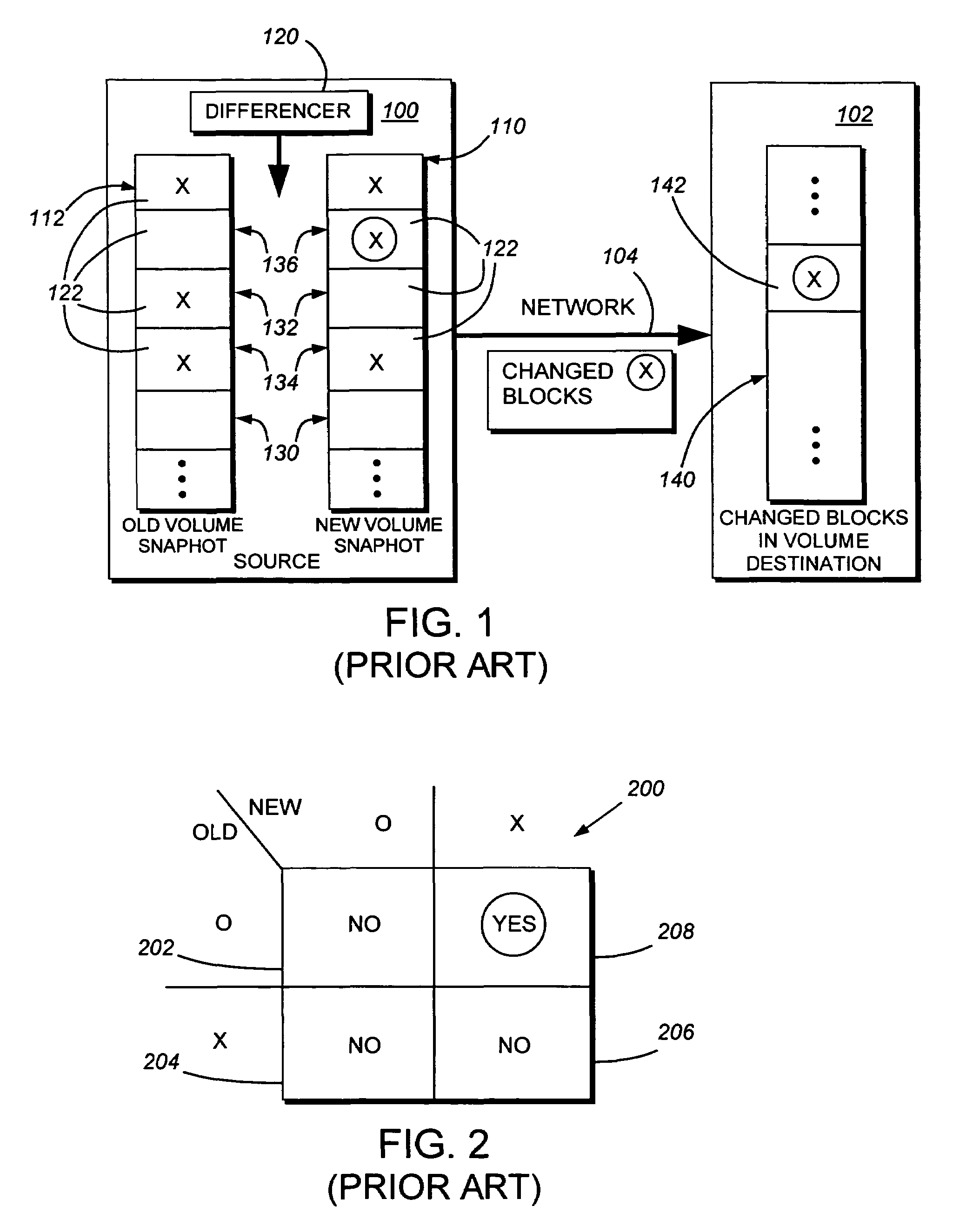
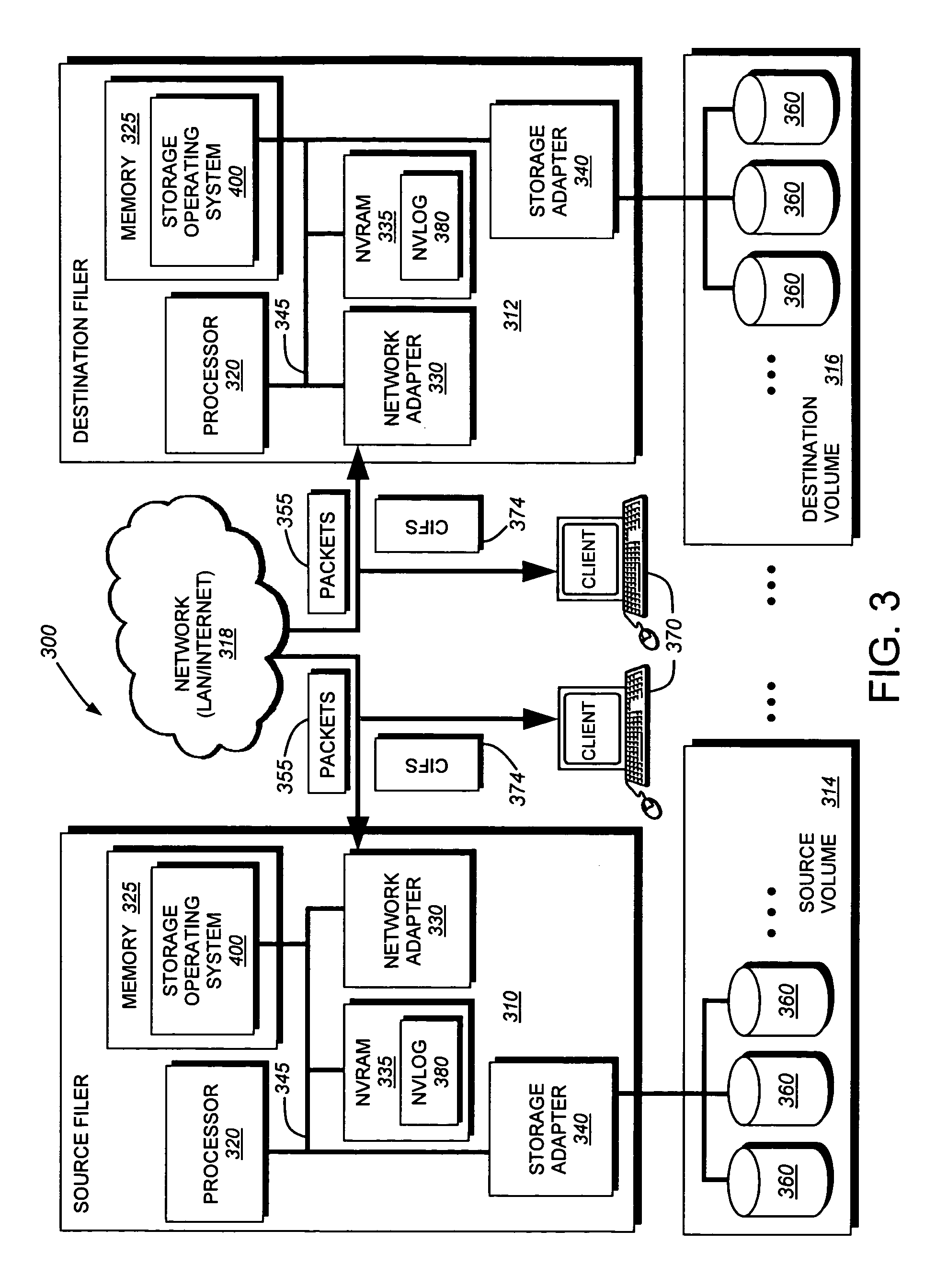
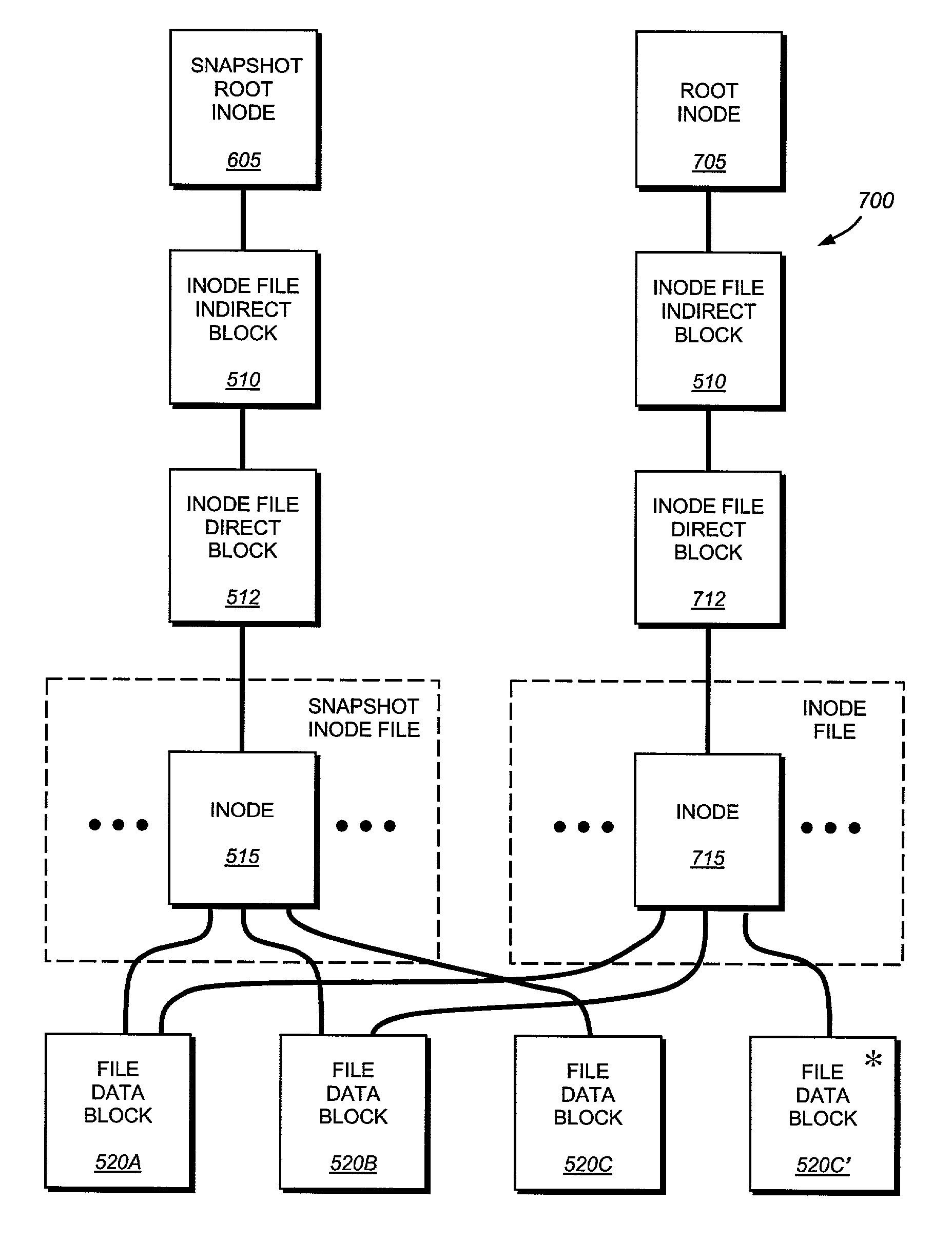
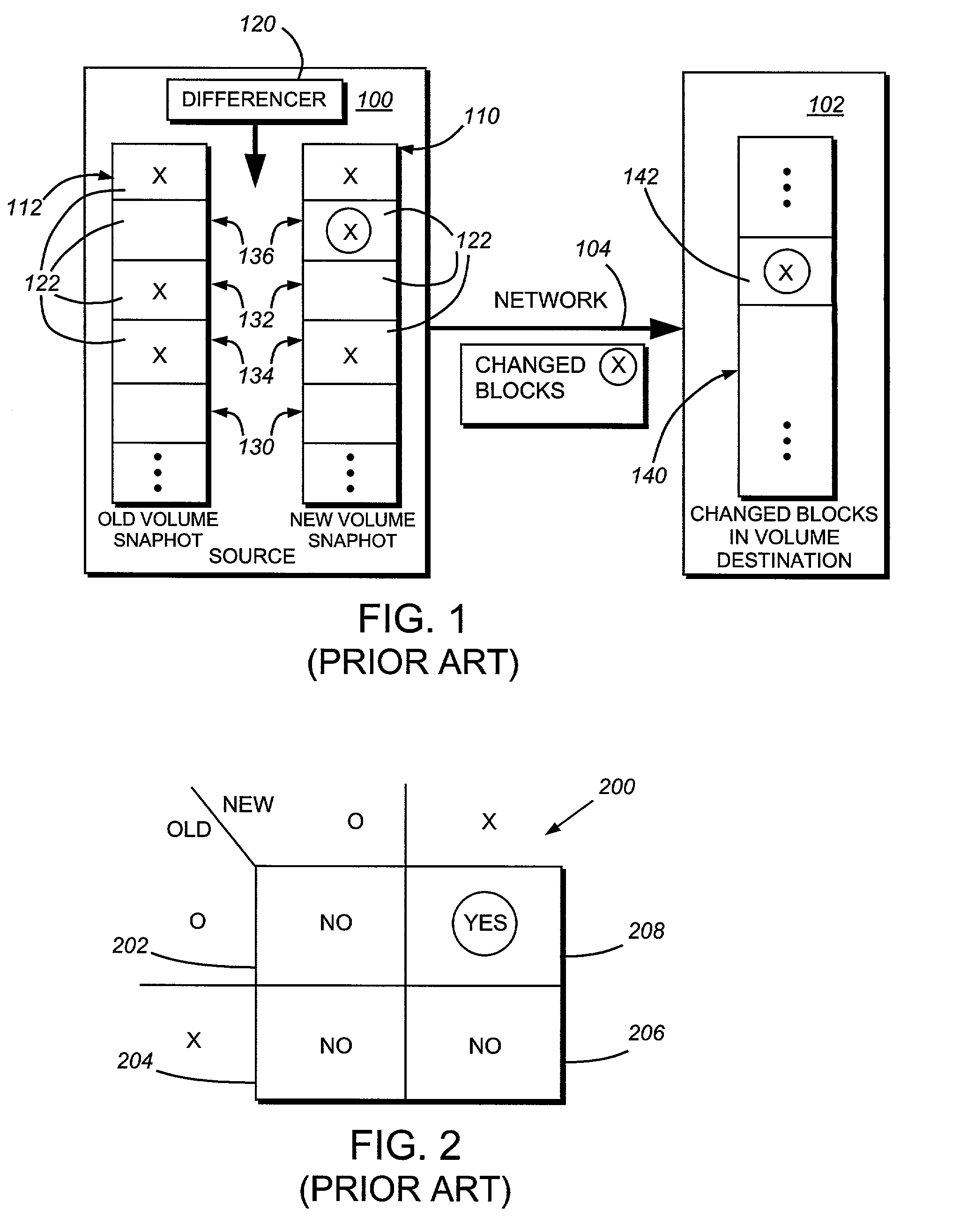
System and method for determining changes in two snapshots and for transmitting changes to destination snapshot
InactiveUS6993539B2Efficient scanningOvercome disadvantagesData processing applicationsSpecial data processing applicationsData streamInode
A system and method for remote asynchronous replication or mirroring of changes in a source file system snapshot in a destination replica file system using a scan (via a scanner) of the blocks that make up two versions of a snapshot of the source file system, which identifies changed blocks in the respective snapshot files based upon differences in volume block numbers identified in a scan of the logical file block index of each snapshot. Trees of blocks associated with the files are traversed, bypassing unchanged pointers between versions and walking down to identify the changes in the hierarchy of the tree. These changes are transmitted to the destination mirror or replicated snapshot. This technique allows regular files, directories, inodes and any other hierarchical structure to be efficiently scanned to determine differences between versions thereof. The changes in the files and directories are transmitted over the network for update of the replicated destination snapshot in an asynchronous (lazy write) manner. The changes are described in an extensible, system-independent data stream format layered under a network transport protocol. At the destination, source changes are used to update the destination snapshot. Any deleted or modified inodes already on the destination are moved to a temporary or “purgatory” directory and, if reused, are relinked to the rebuilt replicated snapshot directory. The source file system snapshots can be representative of a volume sub-organization, such as a qtree.
Owner:NETWORK APPLIANCE INC
System and method for asynchronous mirroring of snapshots at a destination using a purgatory directory and inode mapping
ActiveUS7225204B2Improve versatilityImprove utilizationData processing applicationsDigital data processing detailsInodeComputer science
A system and method for updating a replicated destination file system snapshot with changes in a source file system snapshot, facilitates construction of a new directory tree on the destination from source update information using a temporary or “purgatory” directory that allows any modified and deleted files on the destination active file system to be associated with (e.g. moved to) the purgatory directory if and until they are reused. In addition, an inode map is established on the destination that maps source inode numbers to destination inode numbers so as to facilitate building of the destination tree using inode / generation number tuples. The inode map allows resynchronization of the source file system to the destination. The inode map also allows association of two or more destination snapshots to each other based upon their respective maps with the source.
Owner:NETWORK APPLIANCE INC
System and method for managing versions
InactiveUS20050027757A1Improve consistencyOvercomes drawbackData processing applicationsDigital data processing detailsDigital contentUser interface
A system and method for electronic file management includes an object-oriented file management database, a volume manager, and a coherency manager. The volume manager manages electronic files and metadata relating to the files of one or more volumes. Each volume may include folders, files, and / or other digital content. The file management system may also automatically manage versions of electronic files. This version management may be based on opening, saving, and changing of files. A user interface facilitates user interaction with the file management system. The user interface may enable a user to view, within the file management system, one or more versions of the electronic files.
Owner:MATHON SYST
Internet-based shared file service with native PC client access and semantics and distributed access control
InactiveUS7136903B1Web data retrievalPublic key for secure communicationWide area networkAccess control
A multi-user file storage service and system enable each user of a pre-subscribed user group to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Additionally, an encrypted key is transferred from the file server node to a particular client node via a secure channel. The encrypted key uses an encryption function and a decryption function not known locally at the remote file server. Furthermore, both privileged access control rights and file sharing mode access control to a particular file of the group of files are delegated to one or more distributed nodes other than the remote file server node which provides the data.
Owner:GOOGLE LLC
Storage virtualization by layering virtual disk objects on a file system
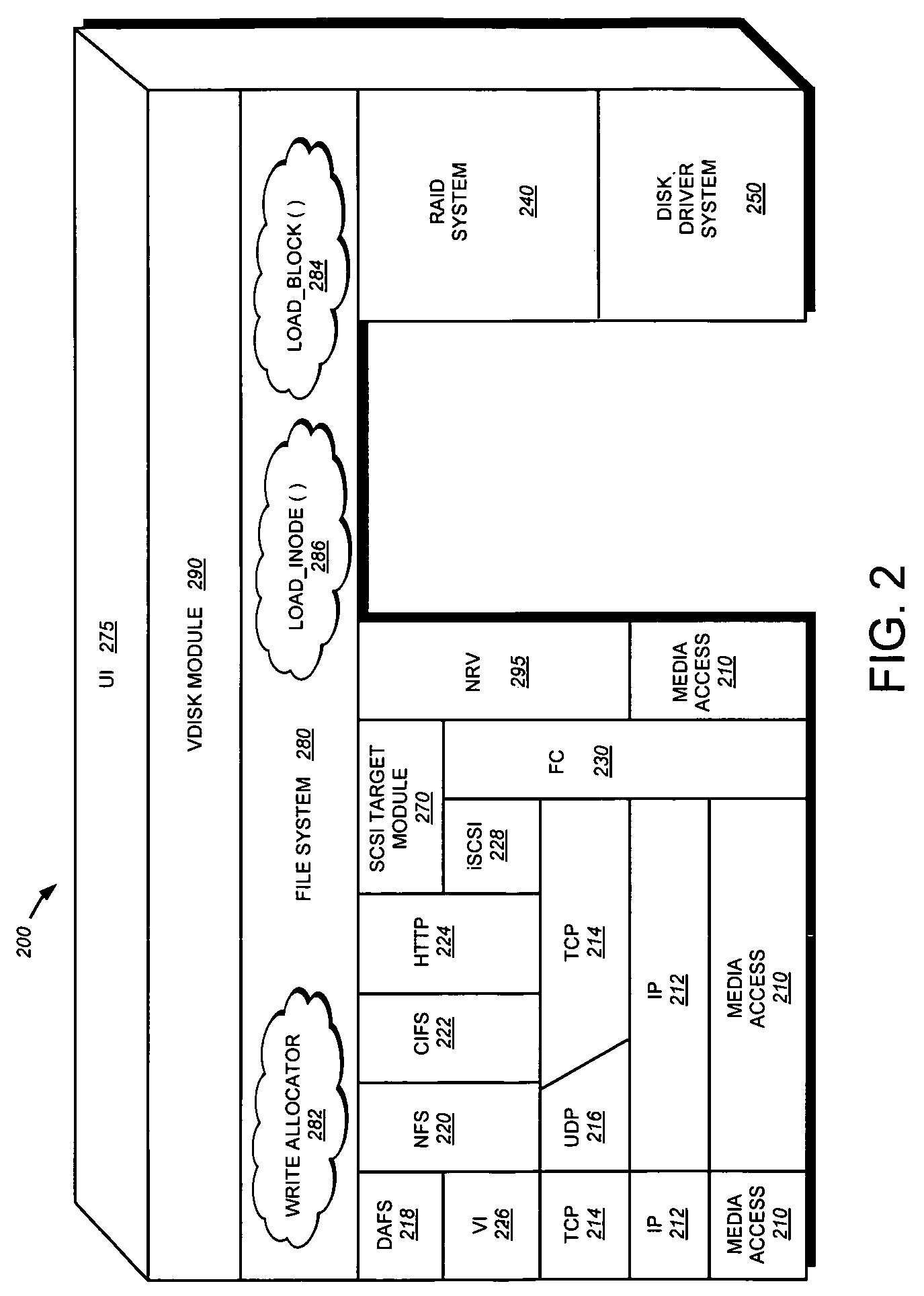
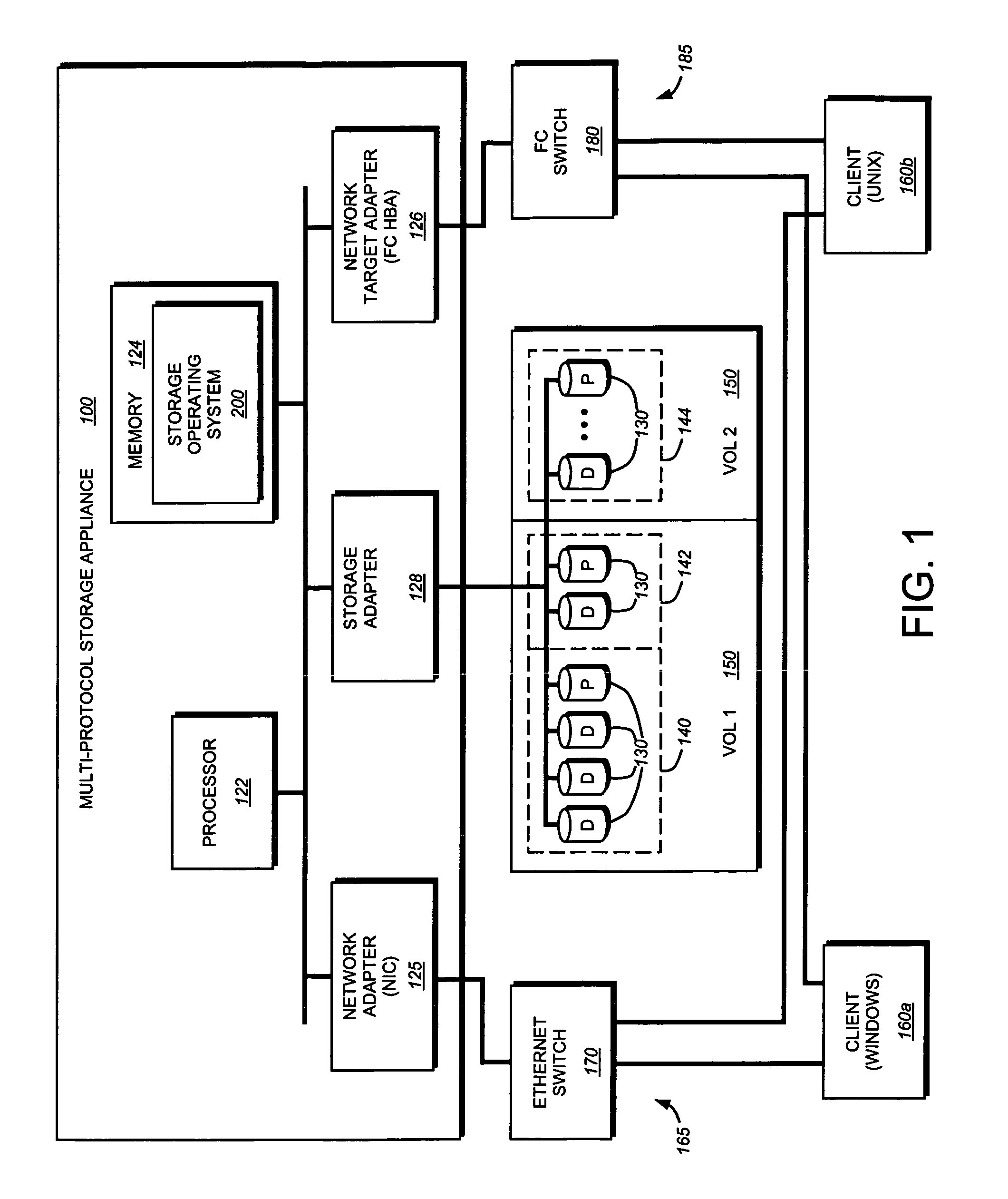
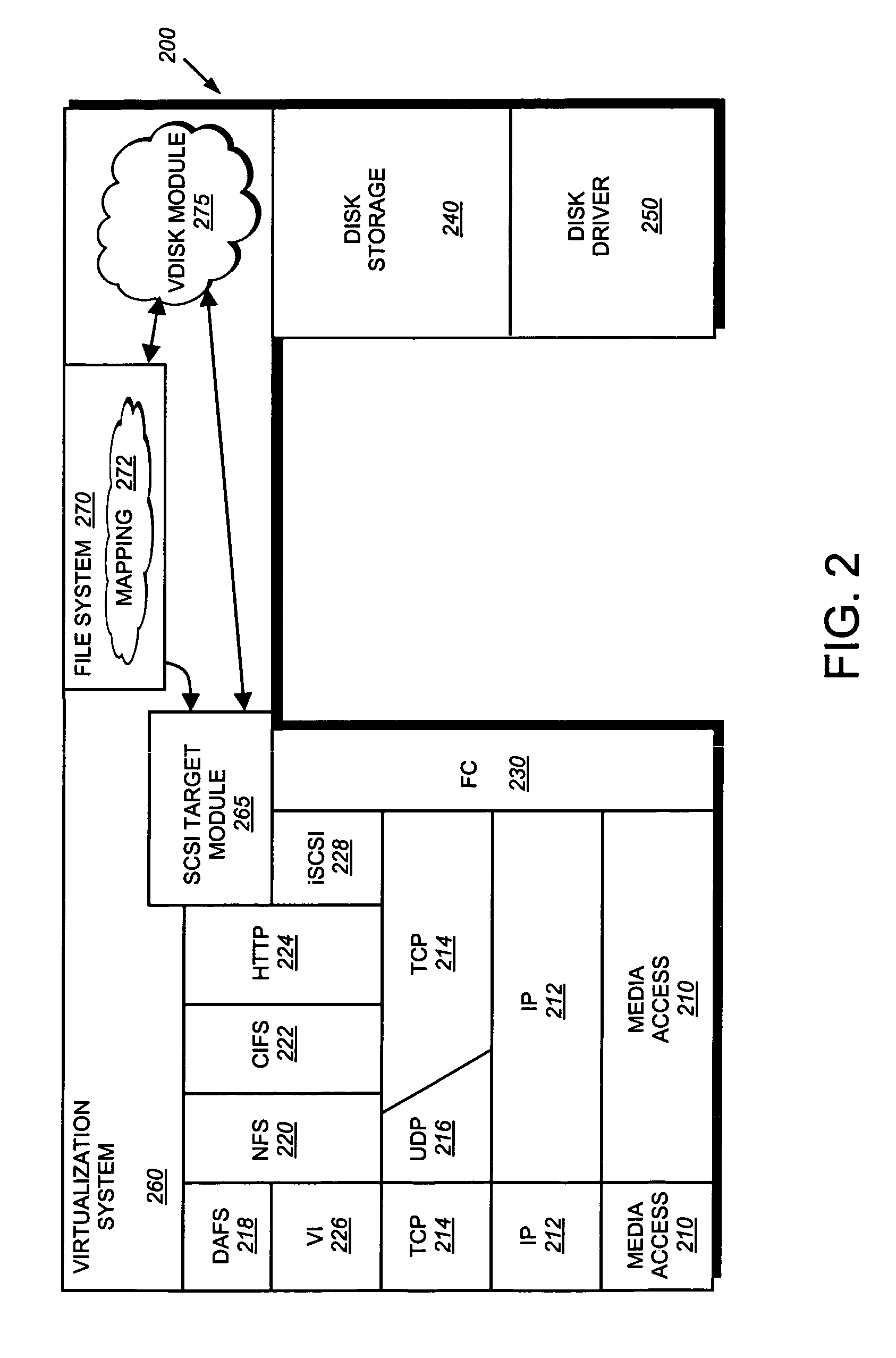
InactiveUS7107385B2Input/output to record carriersData processing applicationsOperational systemFile system
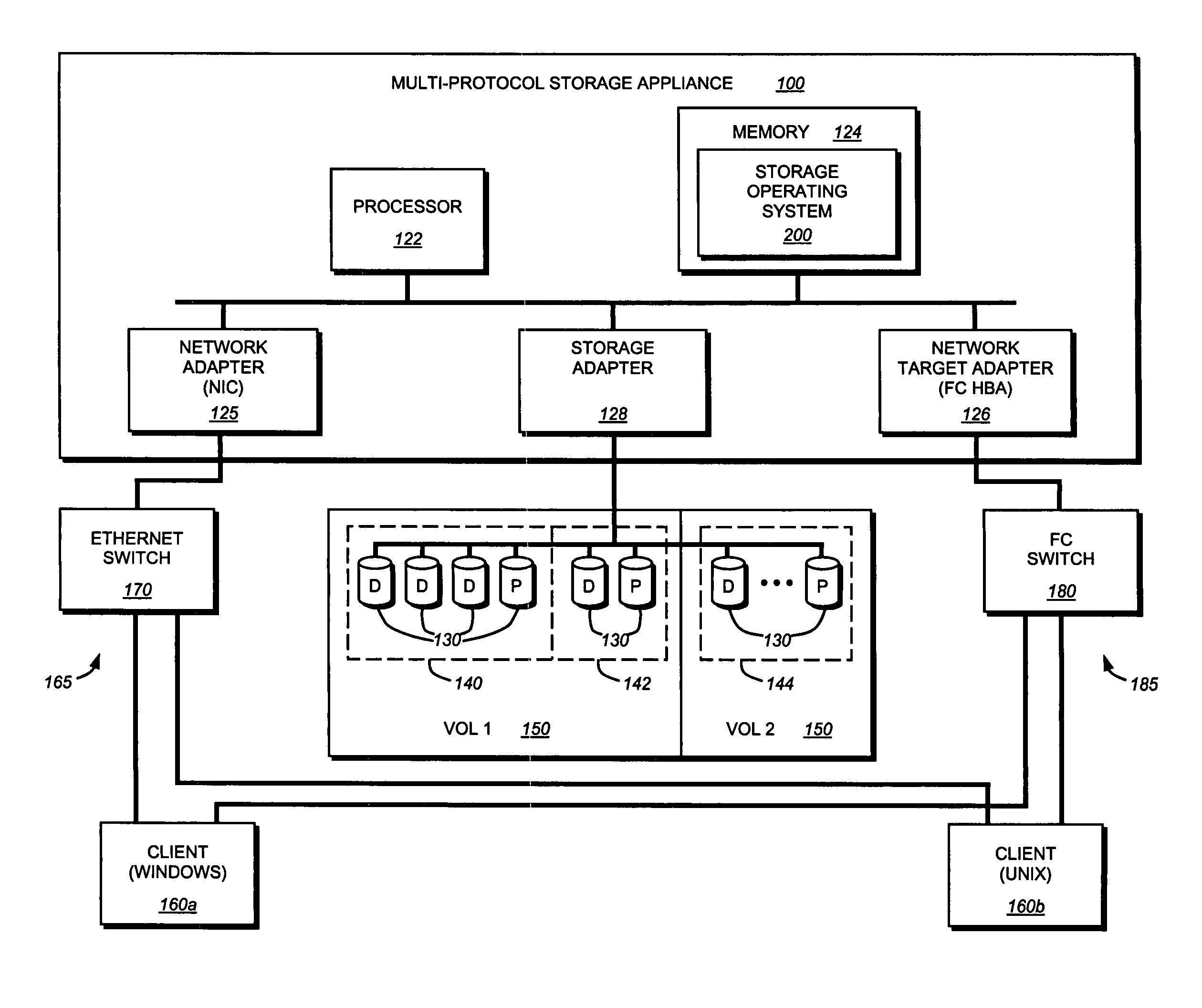
A storage virtualization selection technique “automates” a virtualization selection process to create virtual disk (vdisk) storage objects over a volume of a file system implemented by a storage operating system of a multi-protocol storage appliance. The file system provides a virtualization system that aggregates physical storage of a set of disks or portions (e.g., extents) of disks into a pool of blocks that can be dynamically allocated to form a vdisk. The file system also provides reliability guarantees for the vdisks in accordance with its underlying architecture. That is, the file system organizes its storage within volumes created among the managed disks. The vdisk is thereafter created as a storage object within a volume and, thus, inherits the underlying reliability configuration associated with that volume. The portions are aggregated and allocated as a vdisk with reliability guarantees in response to a request to create the vdisk from a user of the storage appliance and without further user involvement.
Owner:NETWORK APPLIANCE INC
Multi-protocol sharable virtual storage objects
ActiveUS20050044162A1Digital data processing detailsMultiple digital computer combinationsUnixFile replication
A storage object such as a virtual disk drive or a raw logical volume is contained in a UNIX compatible file so that the file containing the storage object can be exported using the NFS or CIFS protocol and shared among UNIX and MS Windows clients or servers. The storage object can be replicated and backed up using conventional file replication and backup facilities without disruption of client access to the storage object. For client access to data of the storage object, a software driver accesses the file containing the storage object. For example, a software driver called a virtual SCSI termination is used to access a file containing a virtual SCSI disk drive. Standard storage services use the iSCSI protocol to access the virtual SCSI termination. An IP replication or snapshot copy facility may access the file containing the virtual SCSI disk drive using a higher-level protocol.
Owner:EMC IP HLDG CO LLC
Method for allocating files in a file system integrated with a raid disk sub-system
A method is disclosed for integrating a file system with a RAID array that exports precise information about the arrangement of data blocks in the RAID subsystem. The file system examines this information and uses it to optimize the location of blocks as they are written to the RAID system. Thus, the system uses explicit knowledge of the underlying RAID disk layout to schedule disk allocation. The method uses separate current-write location (CWL) pointers for each disk in the disk array where the pointers simply advance through the disks as writes occur. The algorithm used has two primary goals. The first goal is to keep the CWL pointers as close together as possible, thereby improving RAID efficiency by writing to multiple blocks in the stripe simultaneously. The second goal is to allocate adjacent blocks in a file on the same disk, thereby improving read back performance. The method satisfies the first goal by always writing on the disk with the lowest CWL pointer. For the second goal, a new disks chosen only when the algorithm starts allocating space for a new file, or when it has allocated N blocks on the same disk for a single file. A sufficient number of blocks is defined as all the buffers in a chunk of N sequential buffers in a file. The result is that CWL pointers are never more than N blocks apart on different disks, and large files have N consecutive blocks on the same disk.
Owner:NETWORK APPLIANCE INC
Internet-based shared file service with native PC client access and semantics
A multi-user file storage service and system enables each user of a user group to operate an arbitrary client node at an arbitrary geographic location to communicate with a remote file server node via a wide area network. More than one user of the user group is permitted to access the file group at the remote file server node simultaneously, but the integrity of the files is maintained by controlling access so that each access to one of the files at the remote file server is performed, if at all, on a respective portion of that file as most recently updated at the remote file server node.
Owner:GOOGLE LLC
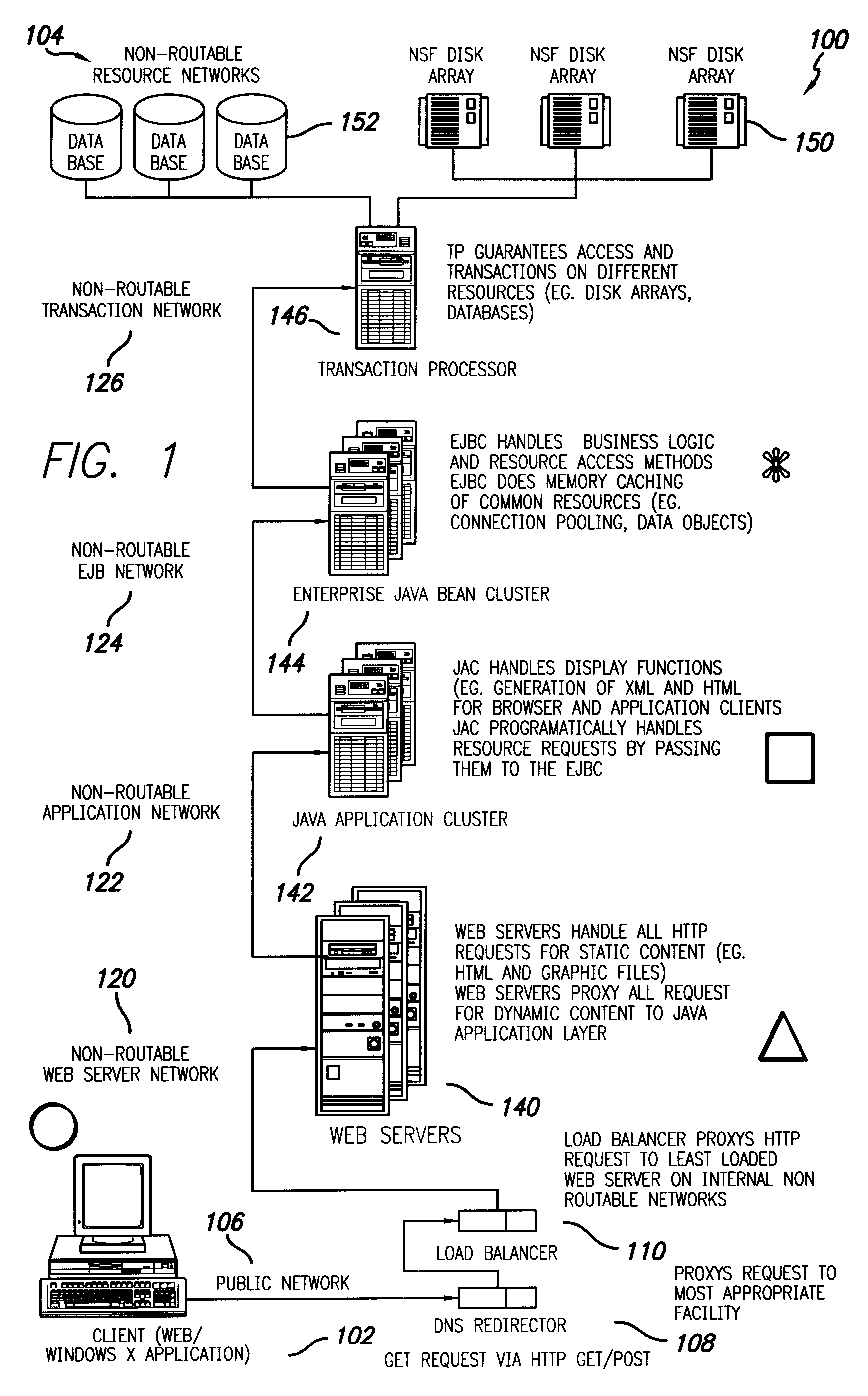
Storage management integrated system and storage control method for storage management integrated system
InactiveUS7120757B2Easy to implementImprove fitInput/output to record carriersDigital computer detailsStorage managementAccessibility
It is intended to achieve an arrangement wherein, when file information of shared disks which are distributed in a plurality of computers connected to a network are used, operating conditions at the time of accessing shared disks can be defined, thus enabling users to easily share files without being bothered by setting-up, or operations of computers located on the other side when they are to perform file sharing.In order to achieve the above-stated arrangement, a storage management integrated server 100 is provided in a network, and respective computers register conditions, an accessibility states and use types pertaining to shared volume to be offered to the server. Thereafter, when a certain computer is to make a file accessing to a shared volume, the computer makes an inquiry to the storage management integrated server for an adequate access destination, determines, on the basis of a response from the server, computers which are suitable to the access source, and makes direct accesses to such computers.
Owner:HITACHI LTD
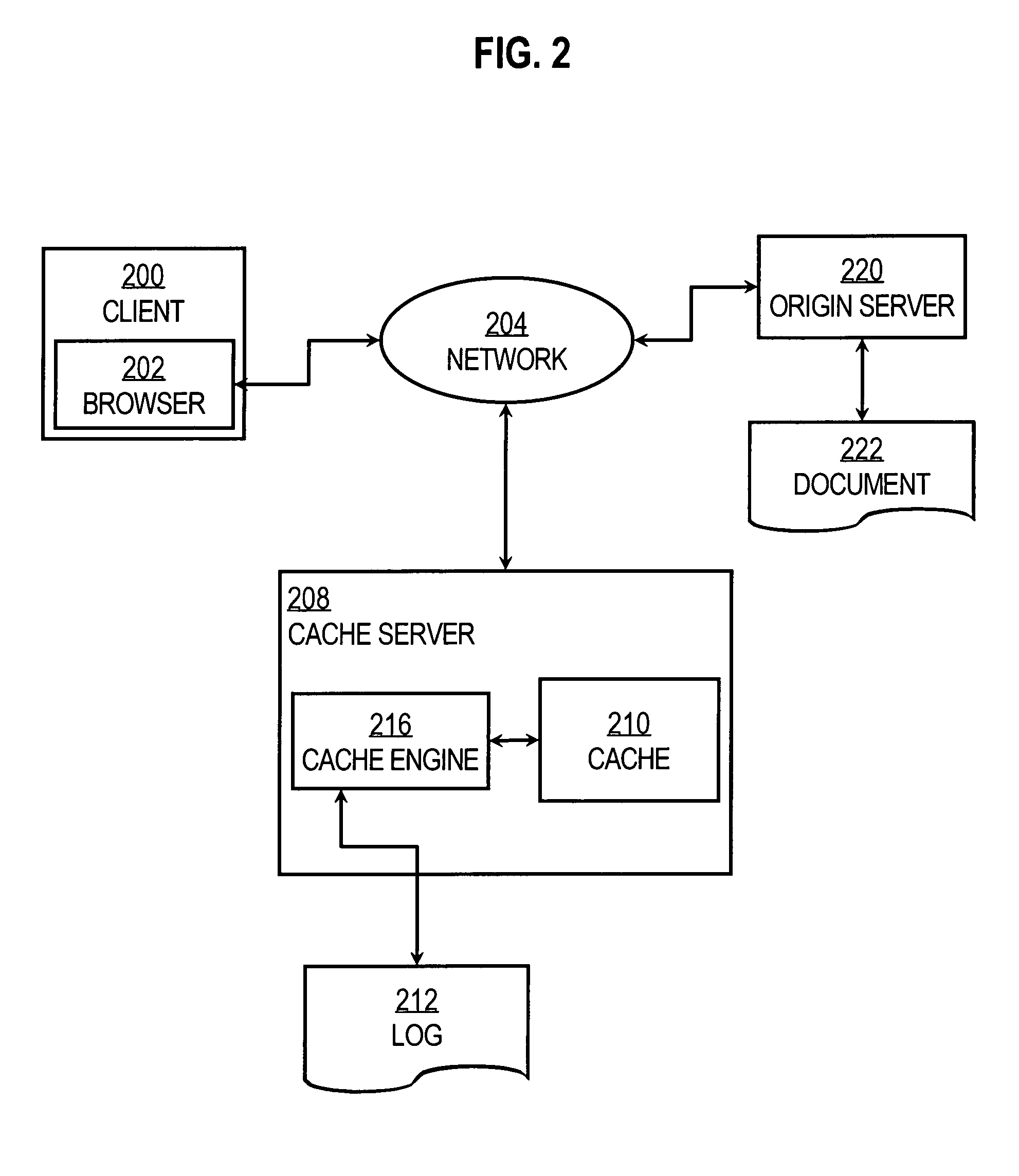
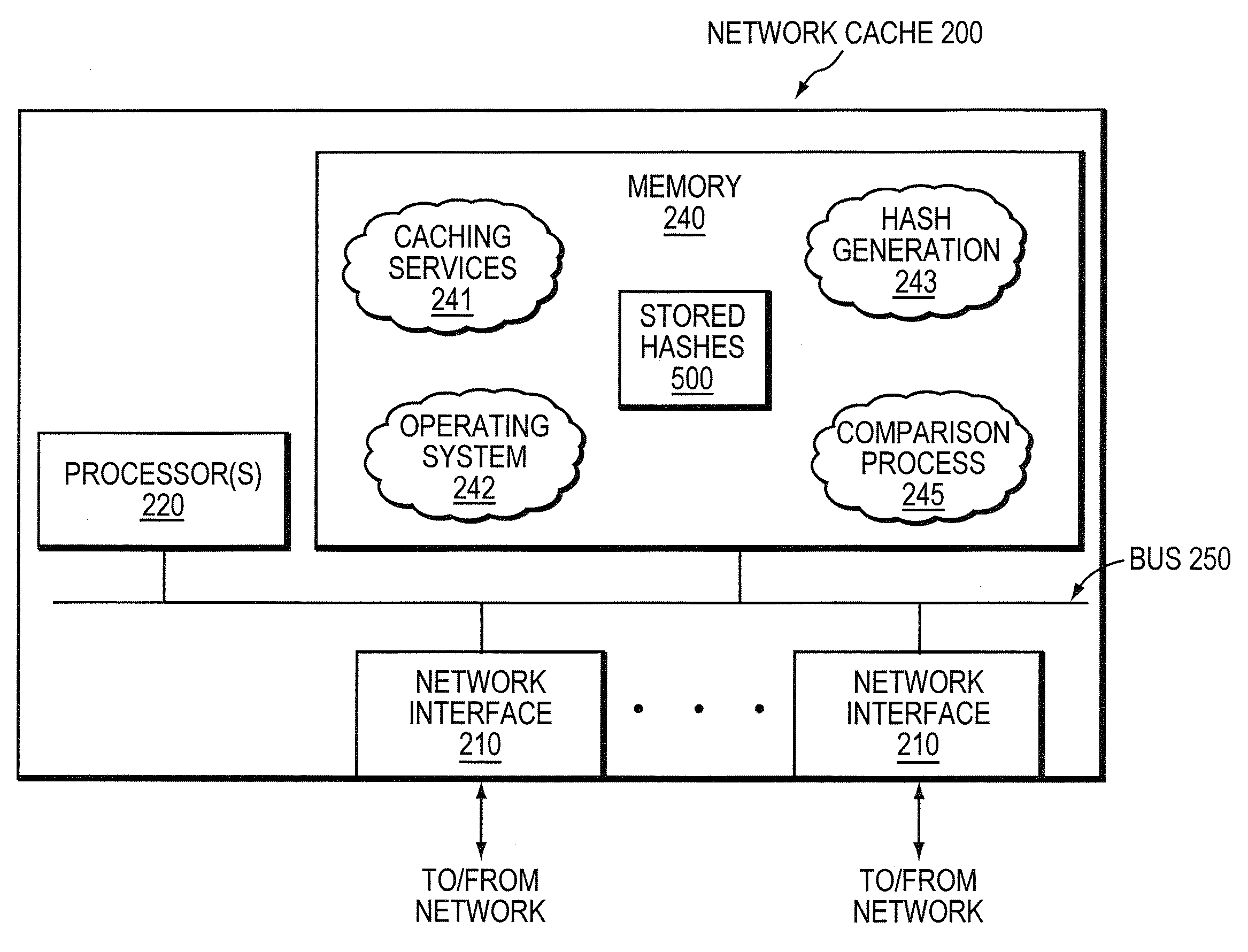
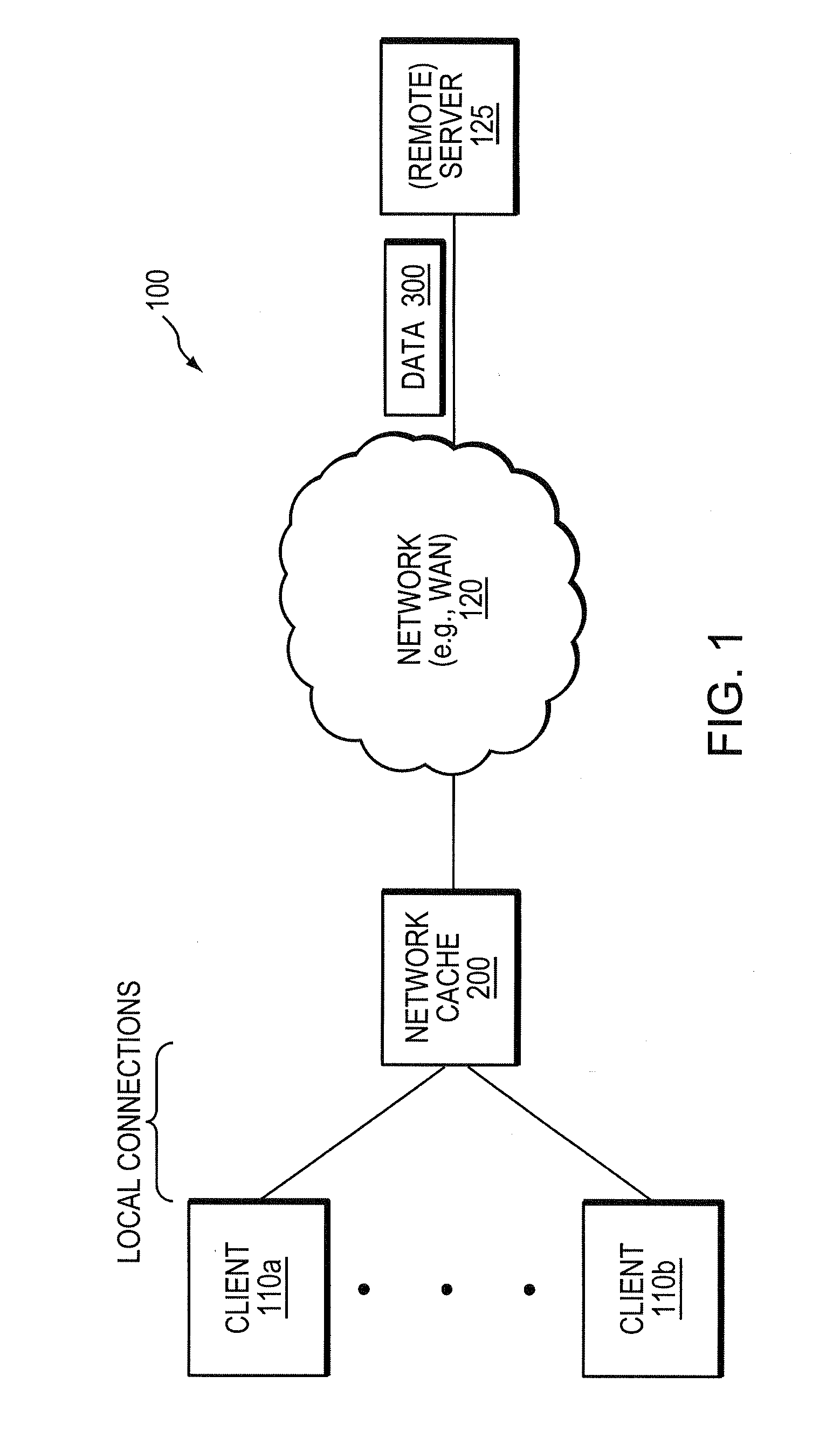
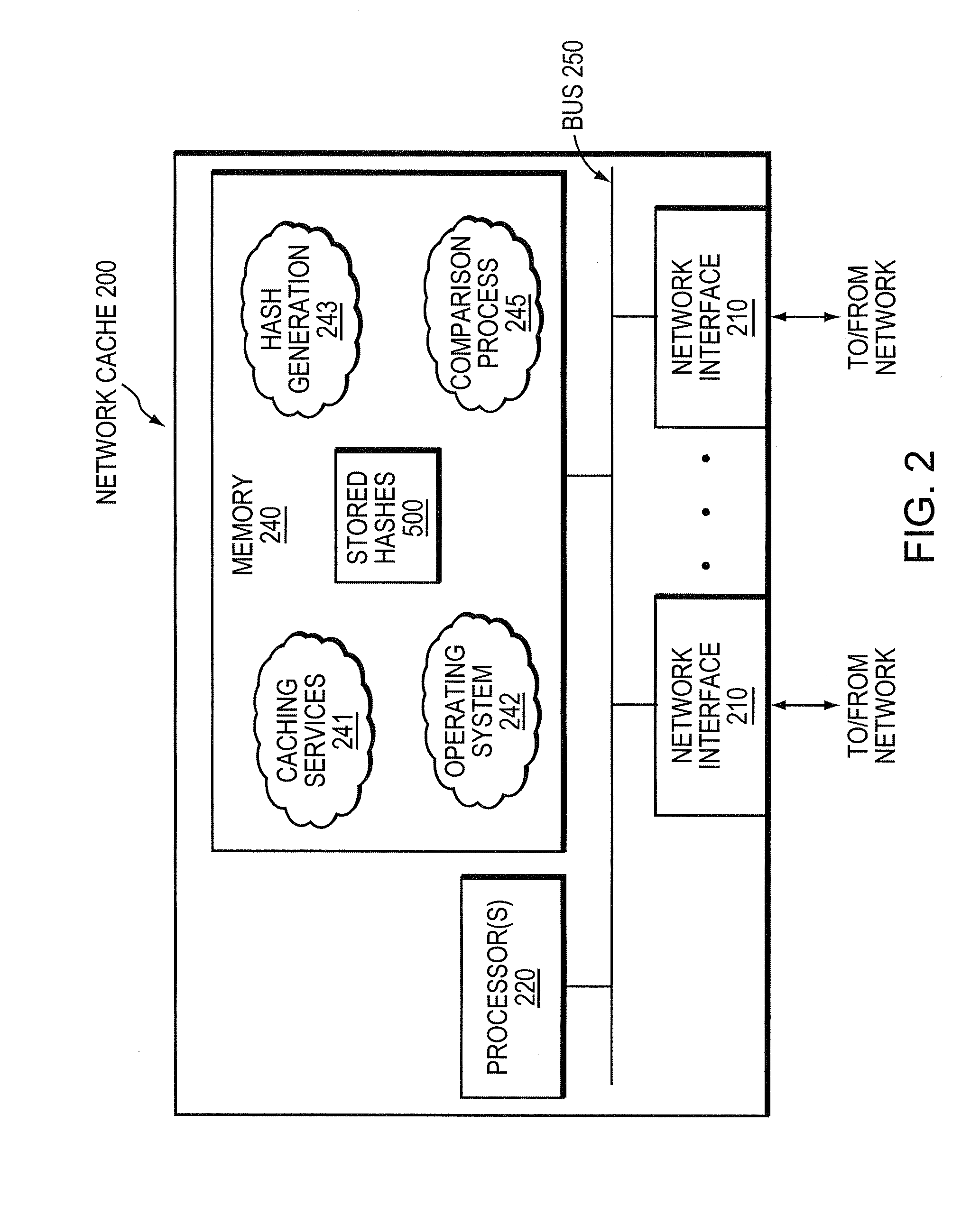
System and method for bandwidth optimization in a network storage environment
ActiveUS20080243992A1Optimized network bandwidth utilizationResource can be very expensiveMultiple digital computer combinationsSpecial data processing applicationsClient-sideData store
According to one or more embodiments of the present invention, a network cache intercepts data requested by a client from a remote server interconnected with the cache through one or more wide area network (WAN) links (e.g., for Wide Area File Services, or “WAFS”). The network cache stores the data and sends the data to the client. The cache may then intercept a first write request for the data from the client to the remote server, and determine one or more portions of the data in the write request that changed from the data stored at the cache (e.g., according to one or more hashes created based on the data). The network cache then sends a second write request for only the changed portions of the data to the remote server.
Owner:NETWORK APPLIANCE INC
Cache system and method for generating uncached objects from cached and stored object components
InactiveUS7006099B2Memory architecture accessing/allocationImage memory managementExternal storageParallel computing
Methods and apparatus for constructing objects within a cache system thereby allowing the cache system to respond to requested objects that are not initially available within the cache system. One embodiment of the invention caches image files, where the images are divided into components and stored in a format that allows identification and access to the components. The cache system determines that an object, such as an image file, is missing from the cache memory, locates sufficient components from the cache memory and / or external storage, and constructs the object from the located components.
Owner:AWARE INC
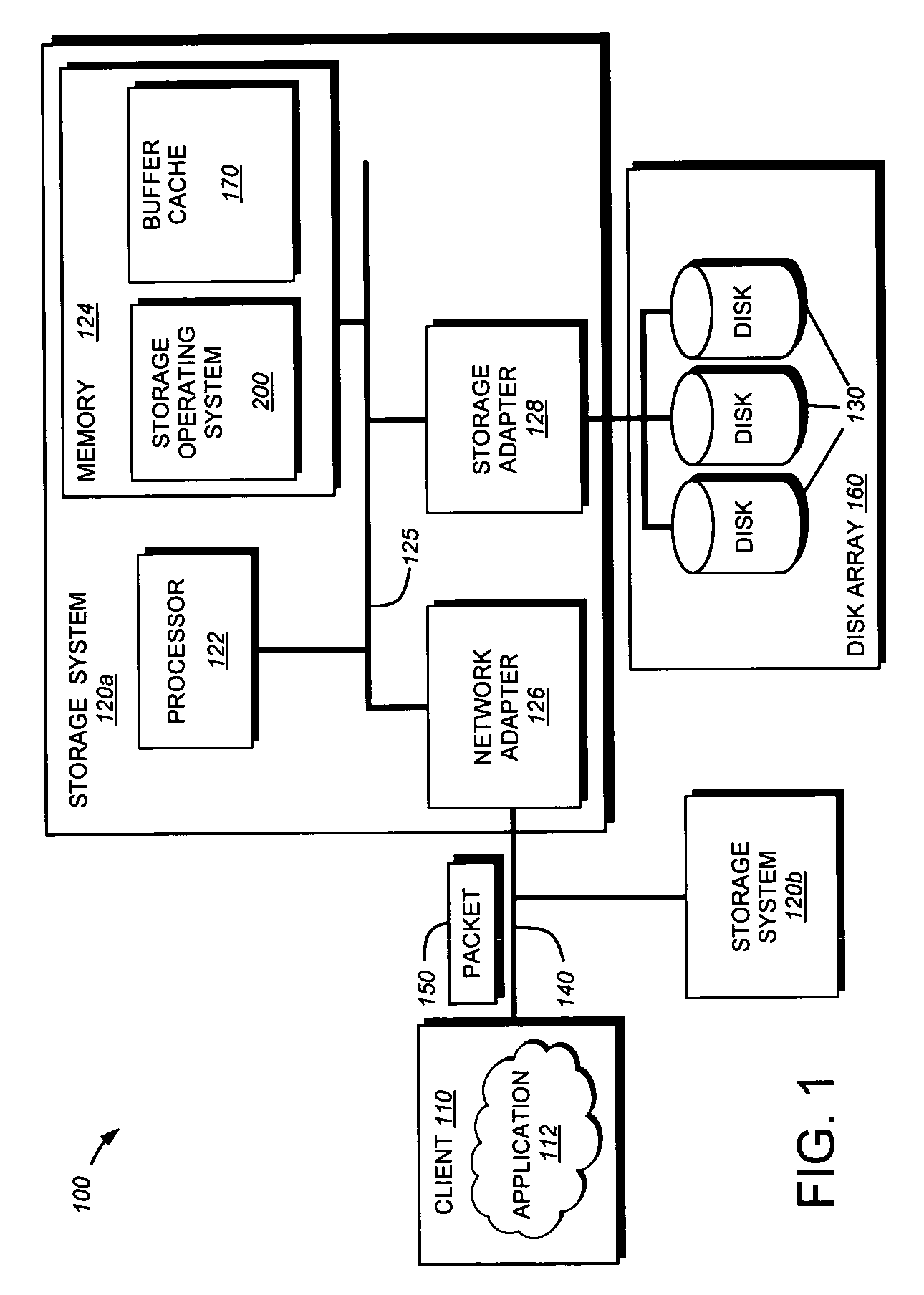
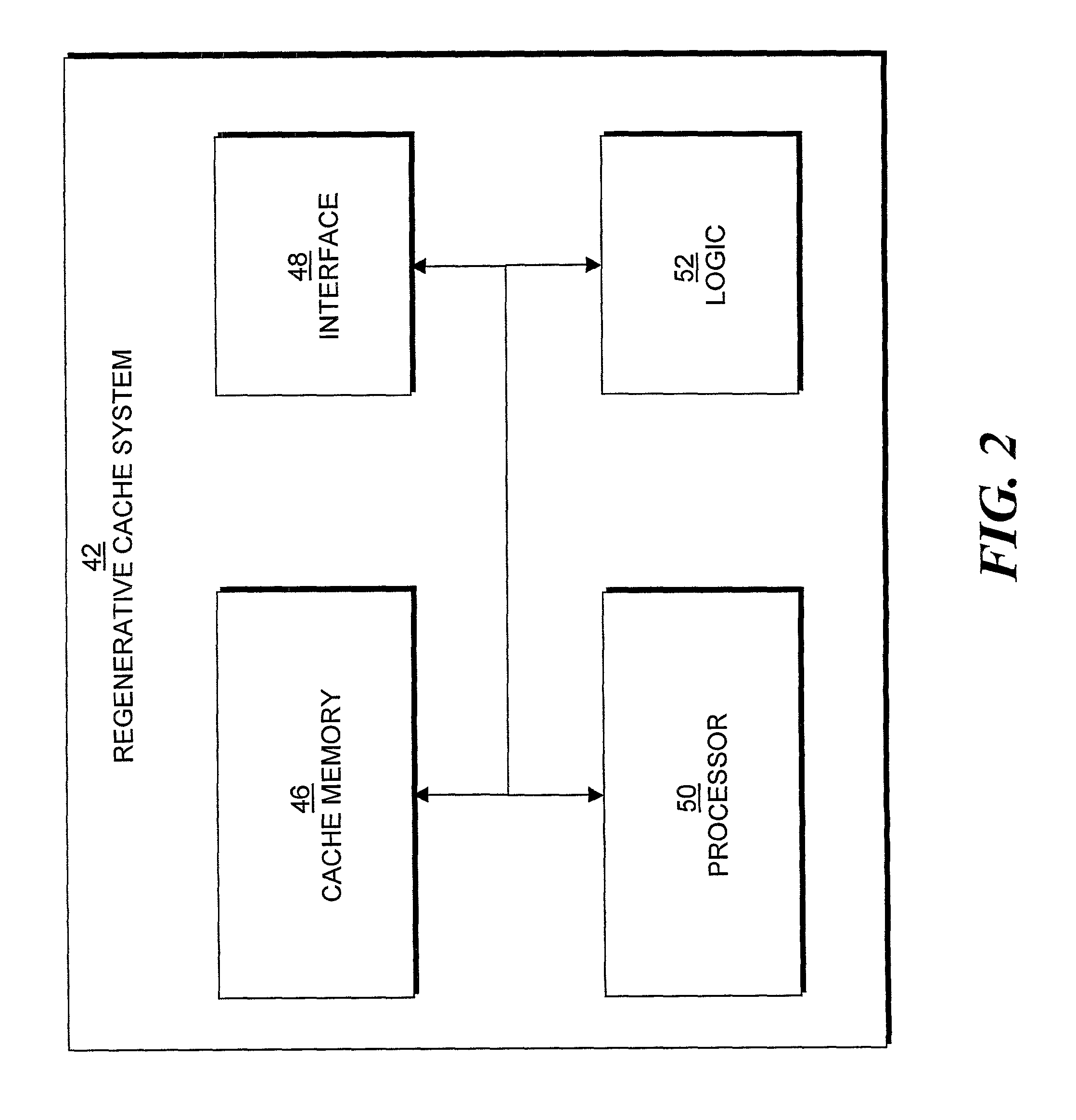
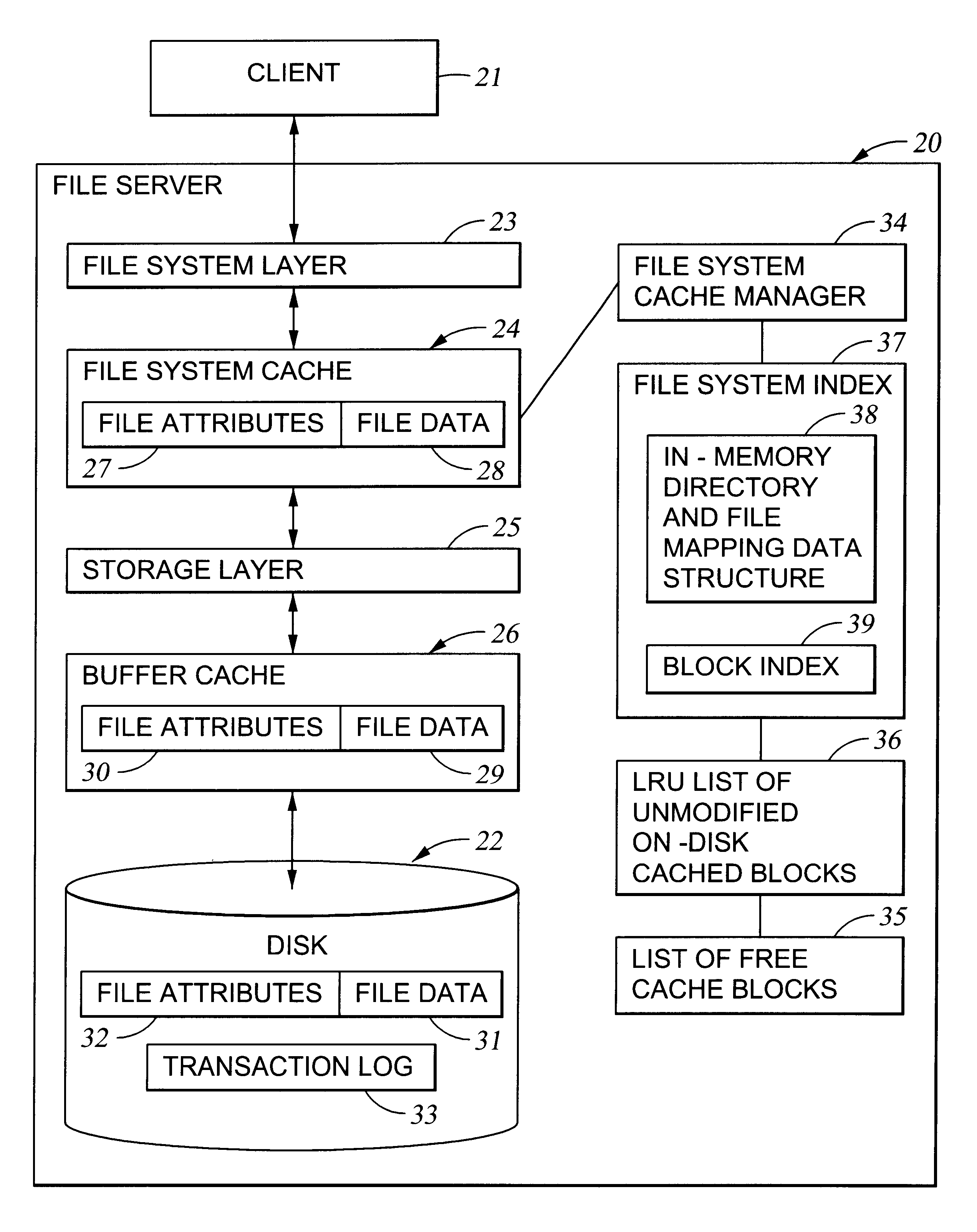
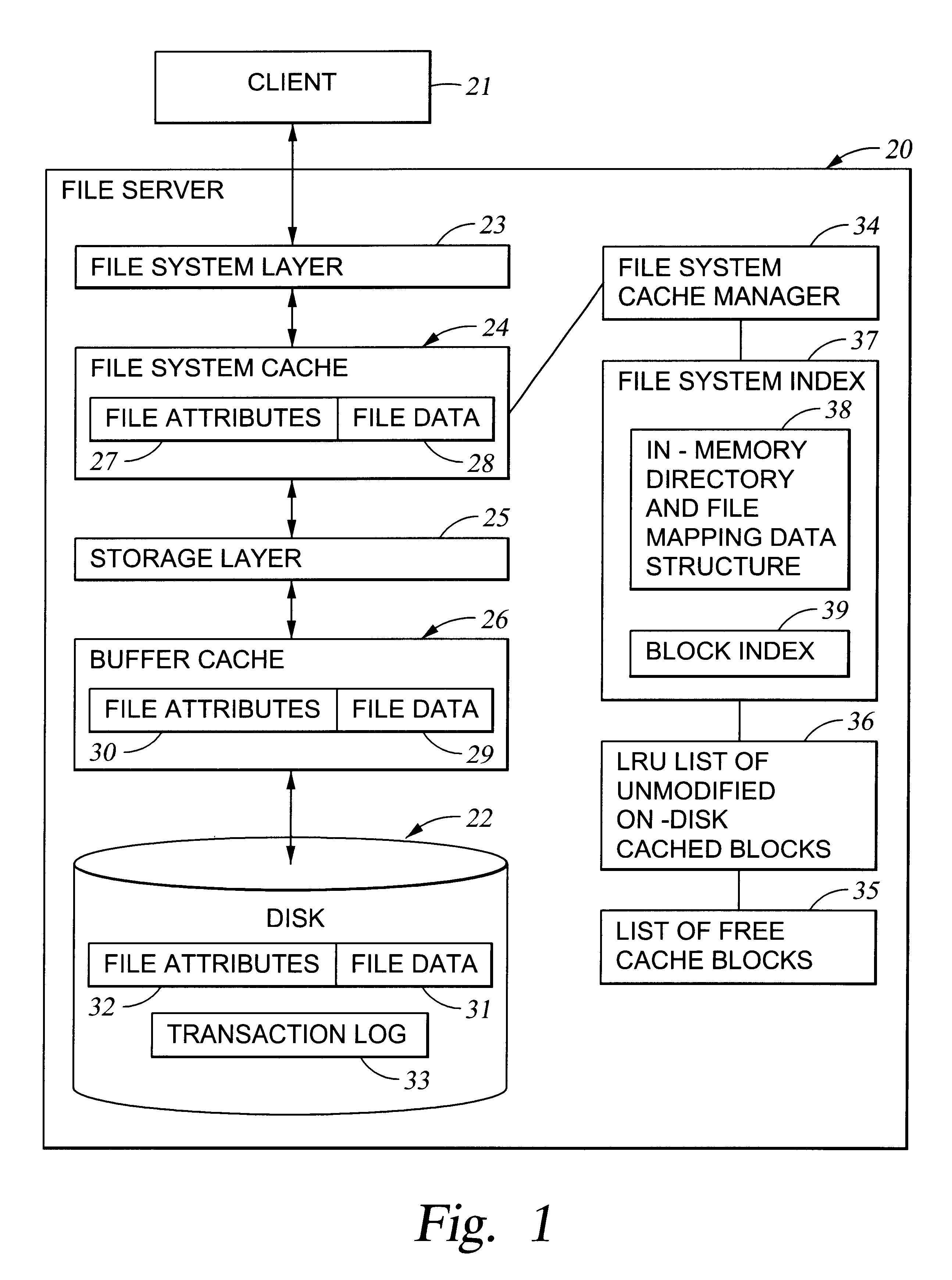
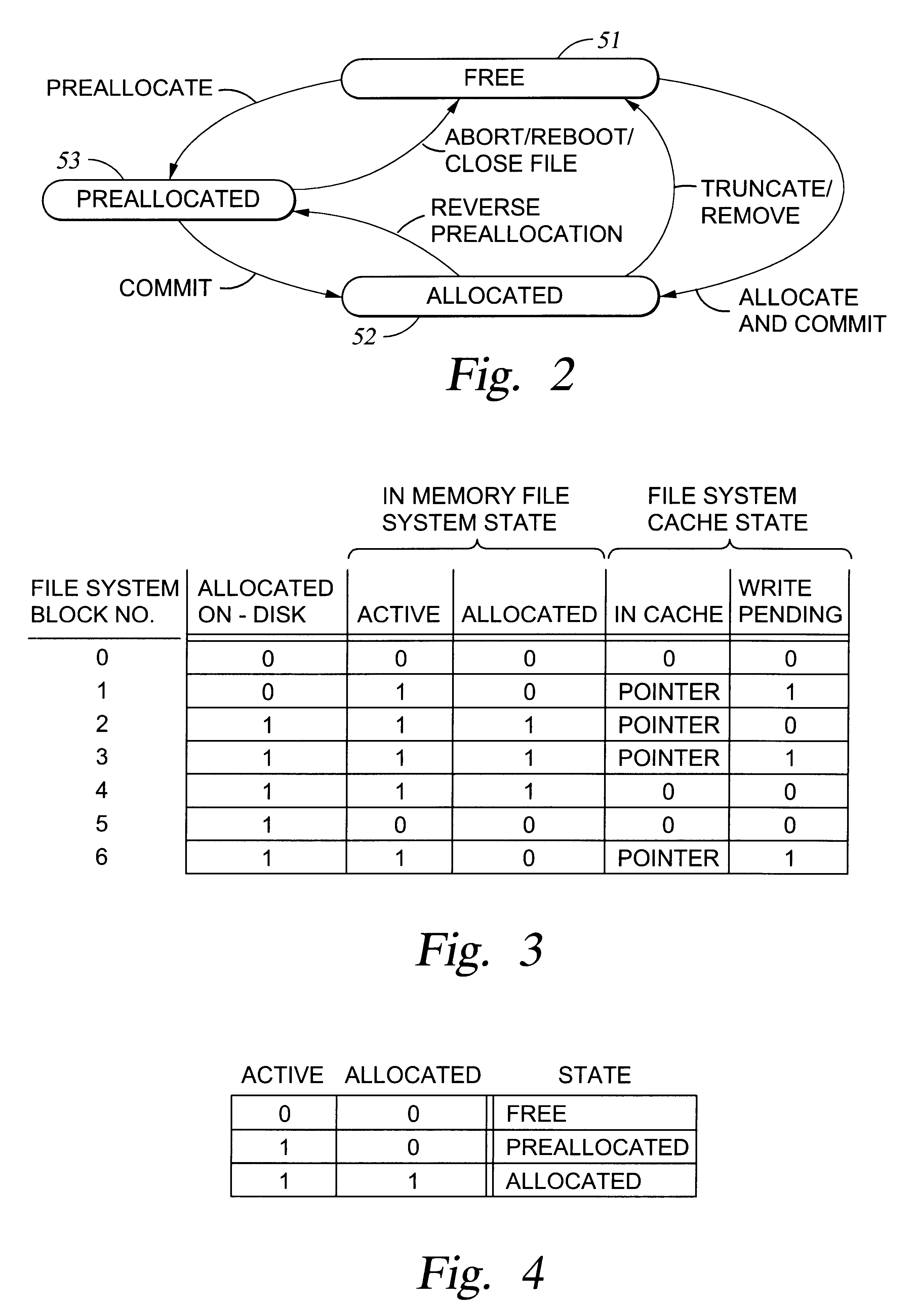
Preallocation of file system cache blocks in a data storage system
InactiveUS6571259B1Data processing applicationsSpecial data processing applicationsOperational systemTransaction log
A file server provides transaction processing capabilities previously supplied by the operating system of a host computer. On-disk file system metadata is changed only at commit time, and a transaction log protects the transition. The disk state can only be a consistent state, resulting from a commit operation. All disk-block reservation and pre-allocation mapping are in the memory, and after a crash, they are automatically discarded. The file server therefore relieves the client of processing burden and also reduces network traffic. In addition, the file server can more efficiently perform the transaction processing capabilities and reduce the frequency of access to storage by judicious allocation of file system blocks and transfer of file system blocks between file system objects, cache memory, and the transaction log. The differentiation between preallocation states and allocation states of in-memory file system blocks also permits application programs to more efficiently transfer data between files.
Owner:EMC IP HLDG CO LLC
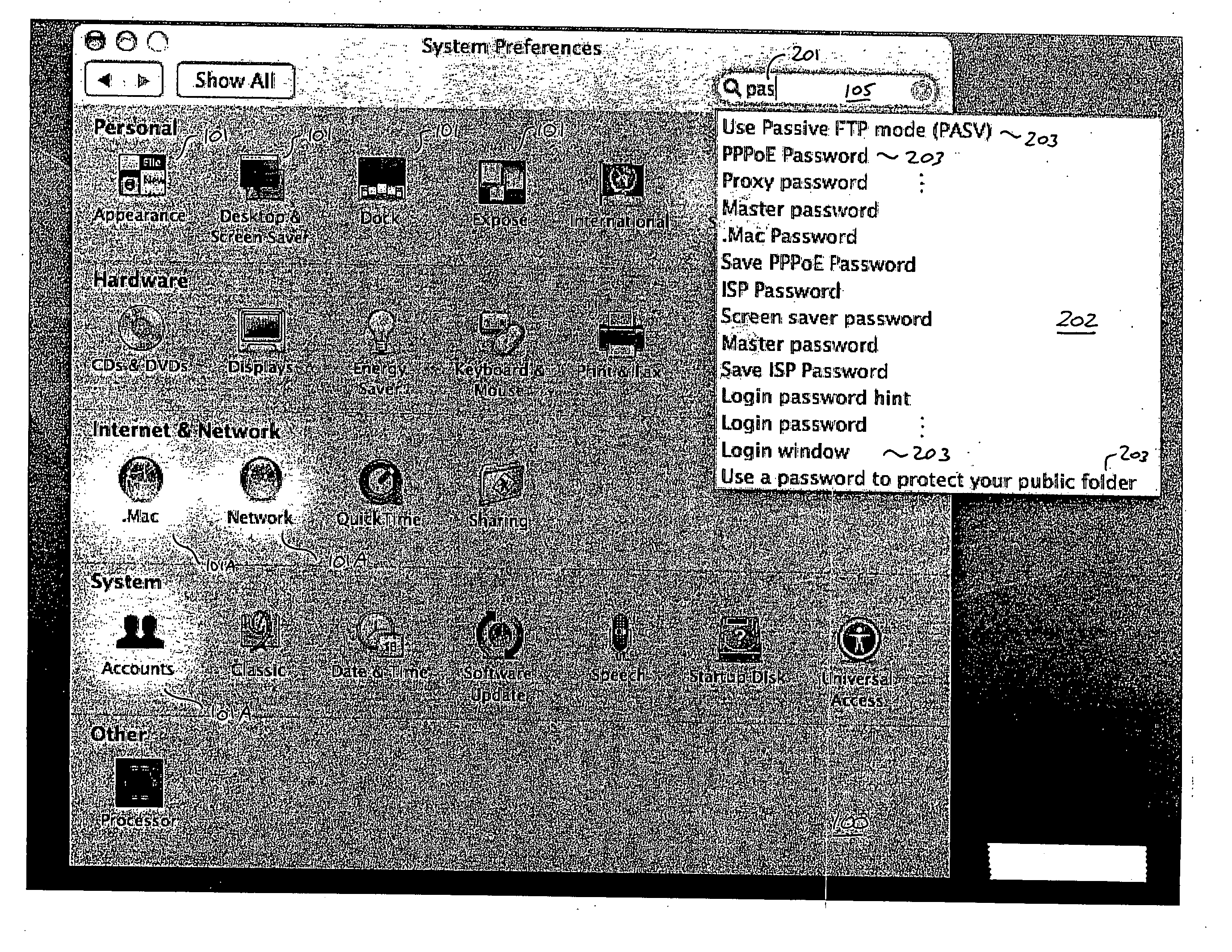
Highlighting icons for search results
ActiveUS20060101347A1Precise positioningProgram controlSpecial data processing applicationsUser inputDegree of certainty
The present invention provides a search capability to allow a user to easily locate a preference control, file, folder, control, or other system resource or data item associated with a search result. In one embodiment, a user enters a search term (or a portion thereof) in a search field associated with one or more resource types that may be searched. The user may be presented with a pop-up menu containing a list of likely matches. The user selects the desired preference control from the pop-up menu, and the corresponding preference pane, or other container, containing the selected data item, control, or other resource is displayed. In one aspect, as the user enters the search term (or portion thereof), certain icons are highlighted. Specifically, those icons that represent containers containing matching data items (such as preference panes having controls that match the search term) are highlighted. Different types of highlighting can be used depending on the degree of certainty as to which container is likely to contain the correct match.
Owner:APPLE INC
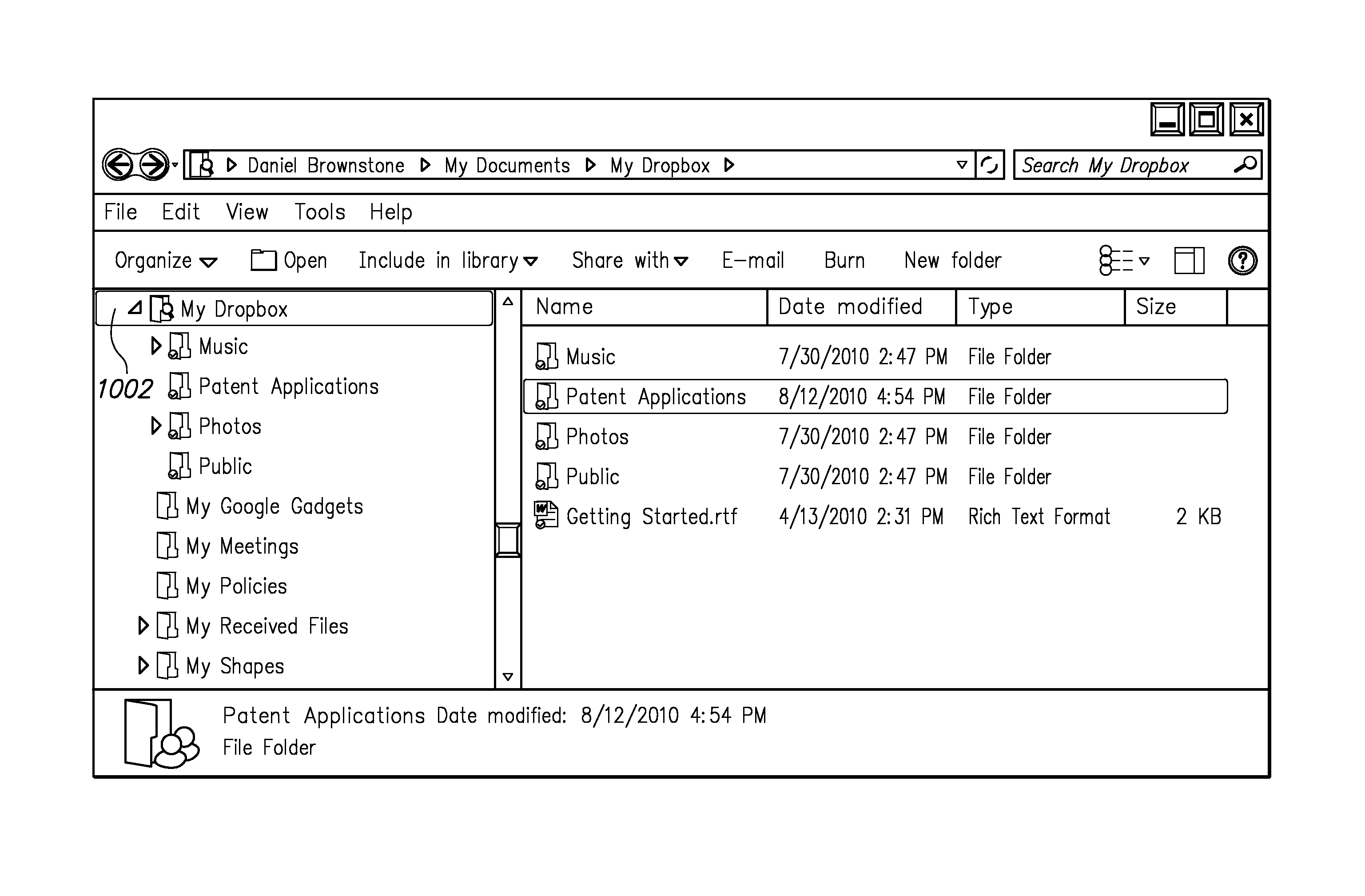
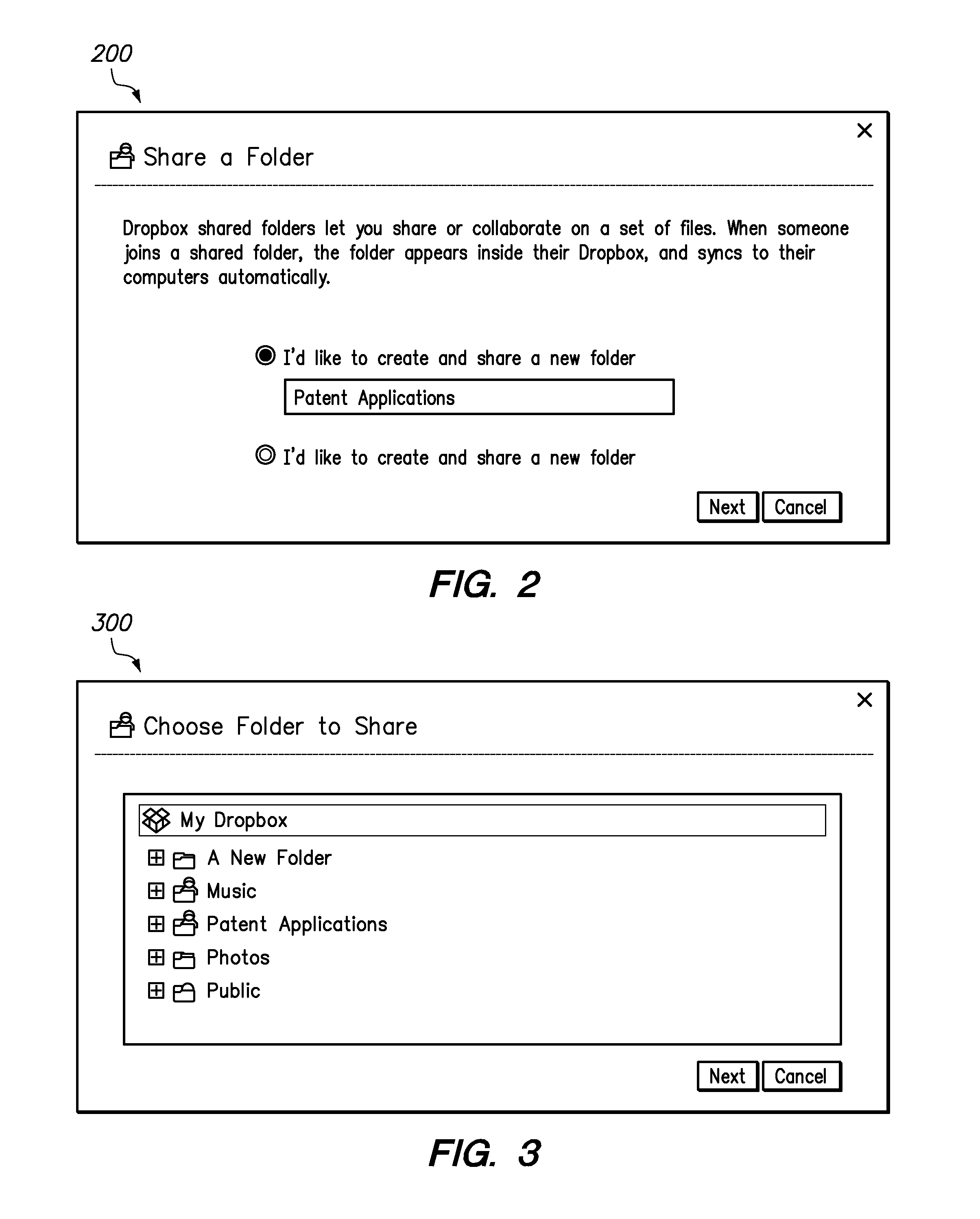
Network folder synchronization
ActiveUS8825597B1Reduce network utilizationReduce utilizationDigital data processing detailsTransmissionClient-sideDistributed computing
Synchronization of folders shared among multiple clients over a network is provided. A first user of a first client instantiates a folder to be shared, and the folder and its contents are synchronized with a host system. As the user makes changes to the folder and its contents on the first client, those changes are propagated to the synchronized version on the host server. Other clients who will be sharing the synchronized folder register with the host system and obtain a current version of the synchronized folder and contents. As the contents of the synchronized folder are changed by any of the clients, the changes are propagated to the host system, which in turn delivers the changes to each of the clients registered as sharing that folder. In this way, each client participating in the share has a current version of the folder and its contents.
Owner:DROPBOX
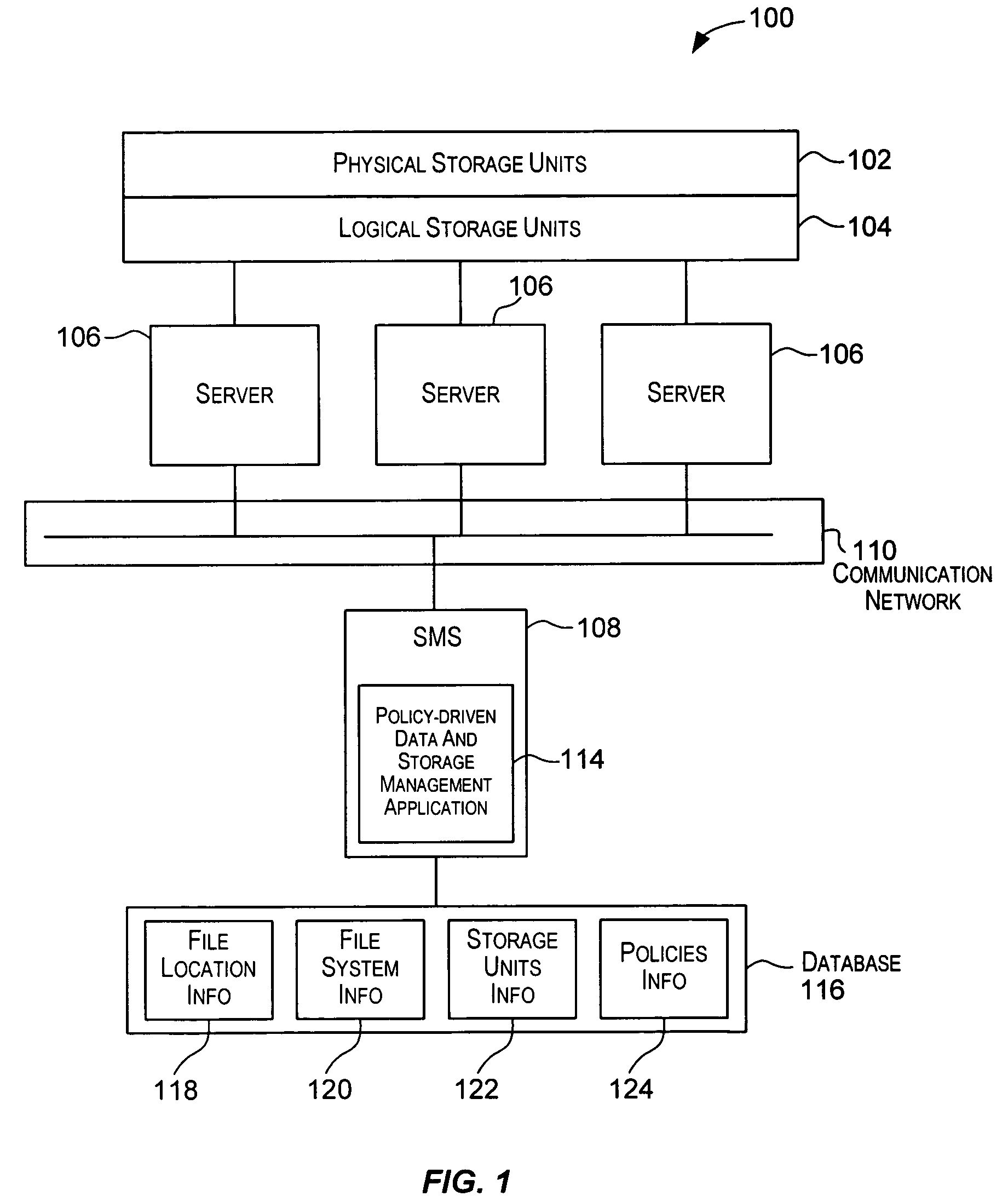
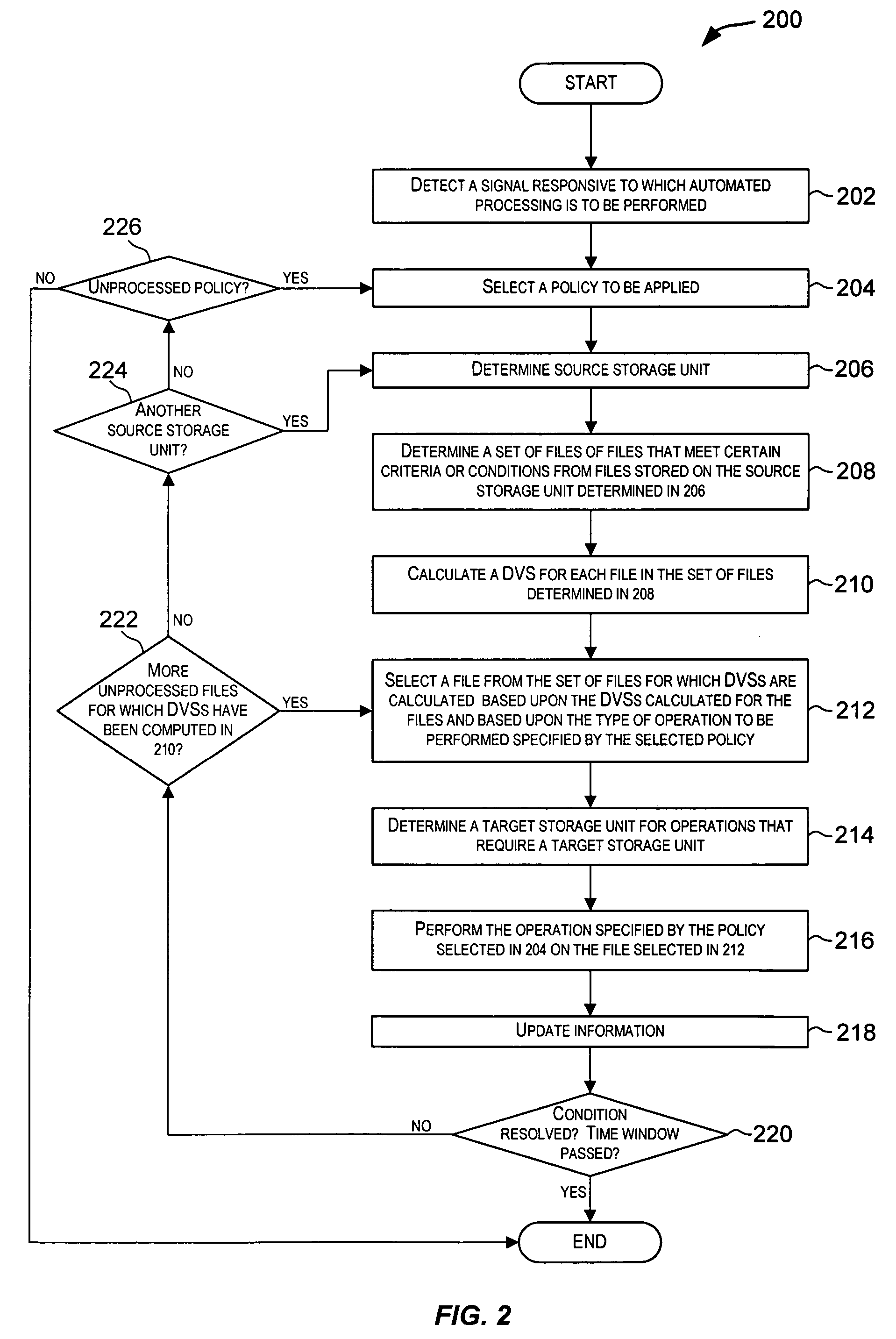
Techniques for performing policy automated operations
ActiveUS7509316B2Data processing applicationsDigital data processing detailsStorage managementDatabase
Techniques for automatically performing various data and storage management operations in a storage environment. The operations to be performed are automatically determined based upon policies configured for the data and storage environment. For a selected operation, one or more files on which the operation is to be performed are also automatically determined. The one or more files may be selected using different techniques based upon characteristics of the files and also based upon the operation to be performed. Target storage units, if need for the operation, are also automatically determined. The operations are then performed on the selected files. Examples of policy-driven operations include copying a file, moving a file, deleting a file, archiving a file, backing-up a file, restoring a file, migrating a file, recalling a file, etc.
Owner:ROCKET SOFTWARE
File sharing in P2P group shared spaces
InactiveUS20050091289A1Reduce usageManaged quickly and effectivelySpecial service provision for substationData processing applicationsVisual presentationSystem usage
A computer implemented method and system enable users to share files in a server-less shared space. By providing access to such spaces via a visual presentation, the system renders content available for access by other group members. Access is sometimes provided through propagation of metadata or other uniquely identifying indicia associated with the shared space to all group members.
Owner:MICROSOFT TECH LICENSING LLC
Consistency methods and systems
InactiveUS20070214194A1Maintain data consistencyError detection/correctionSpecial data processing applicationsTimestampDistributed data store
Embodiments of the present invention are directed to methods for maintaining data consistency of data blocks during migration or reconfiguration of a current configuration within a distributed data-storage system to a new configuration. In one embodiment of the present invention, the current configuration is first determined to be reconfigured. The new configuration is then initialized, and data blocks are copied from the current configuration to the new configuration. Then, the configuration states maintained by component data-storage systems that store data blocks of the current and new configurations are synchronized. Finally, the current configuration is deallocated. In a second embodiment of the present invention, a current configuration is determined to be reconfigured, and, while carrying out continuing READ and WRITE operations directed to data blocks of the current configuration in a data-consistent manner, the new configuration is initialized, data blocks are copied from the current configuration to the new configuration, and the timestamp and data states for the data blocks of the current and new configurations are synchronized.
Owner:HEWLETT PACKARD DEV CO LP
Method and apparatus for adaptive services networking
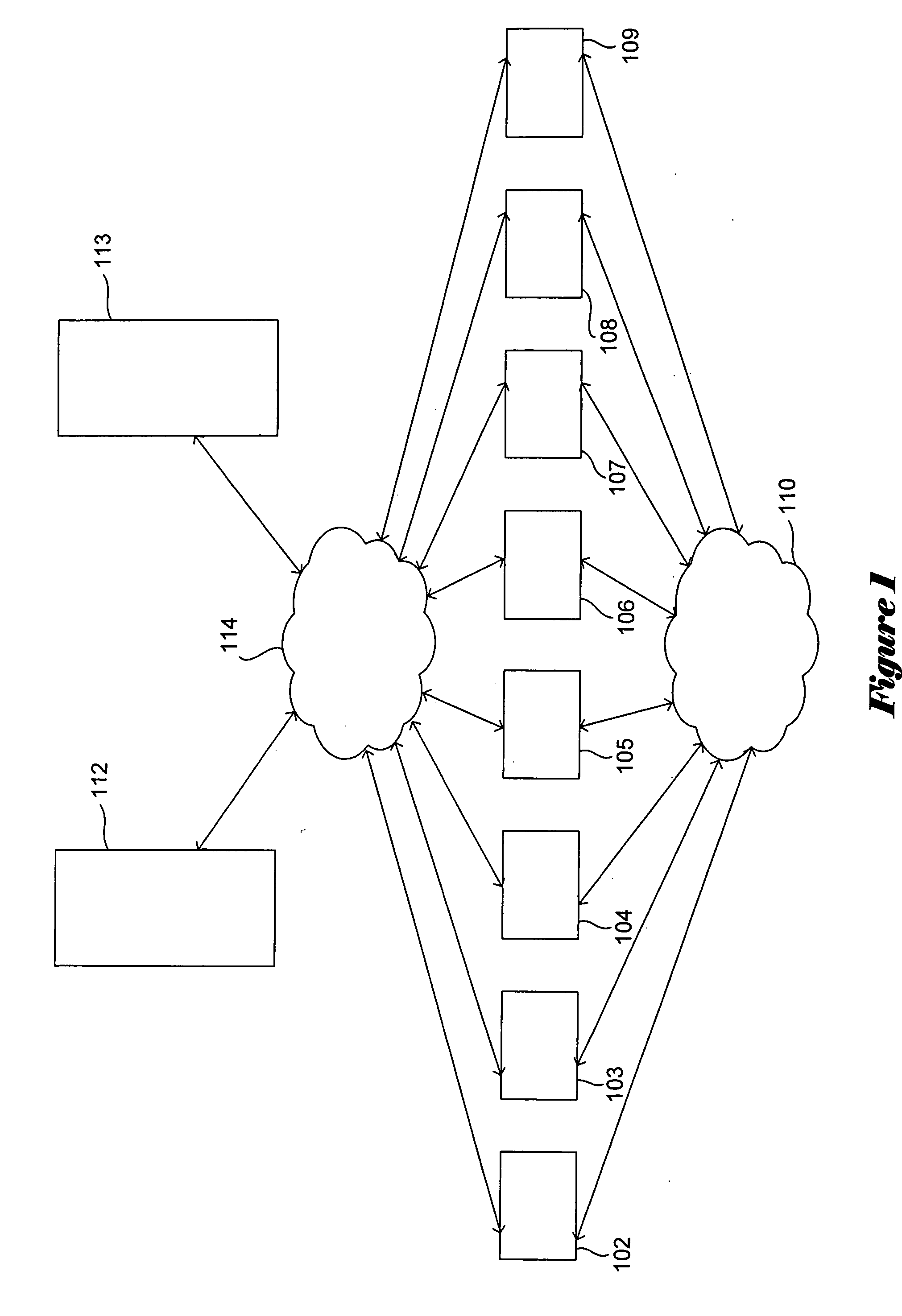
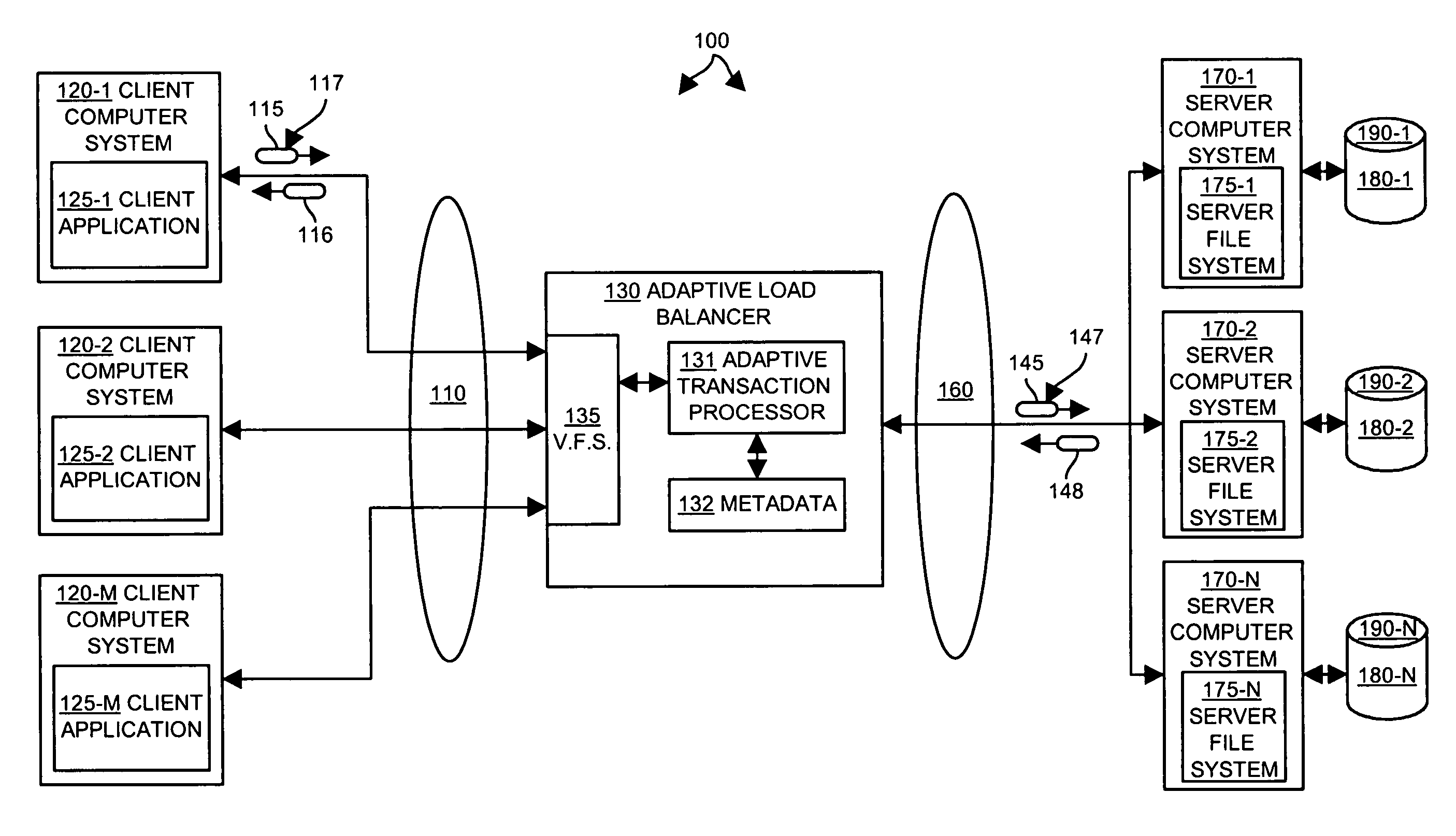
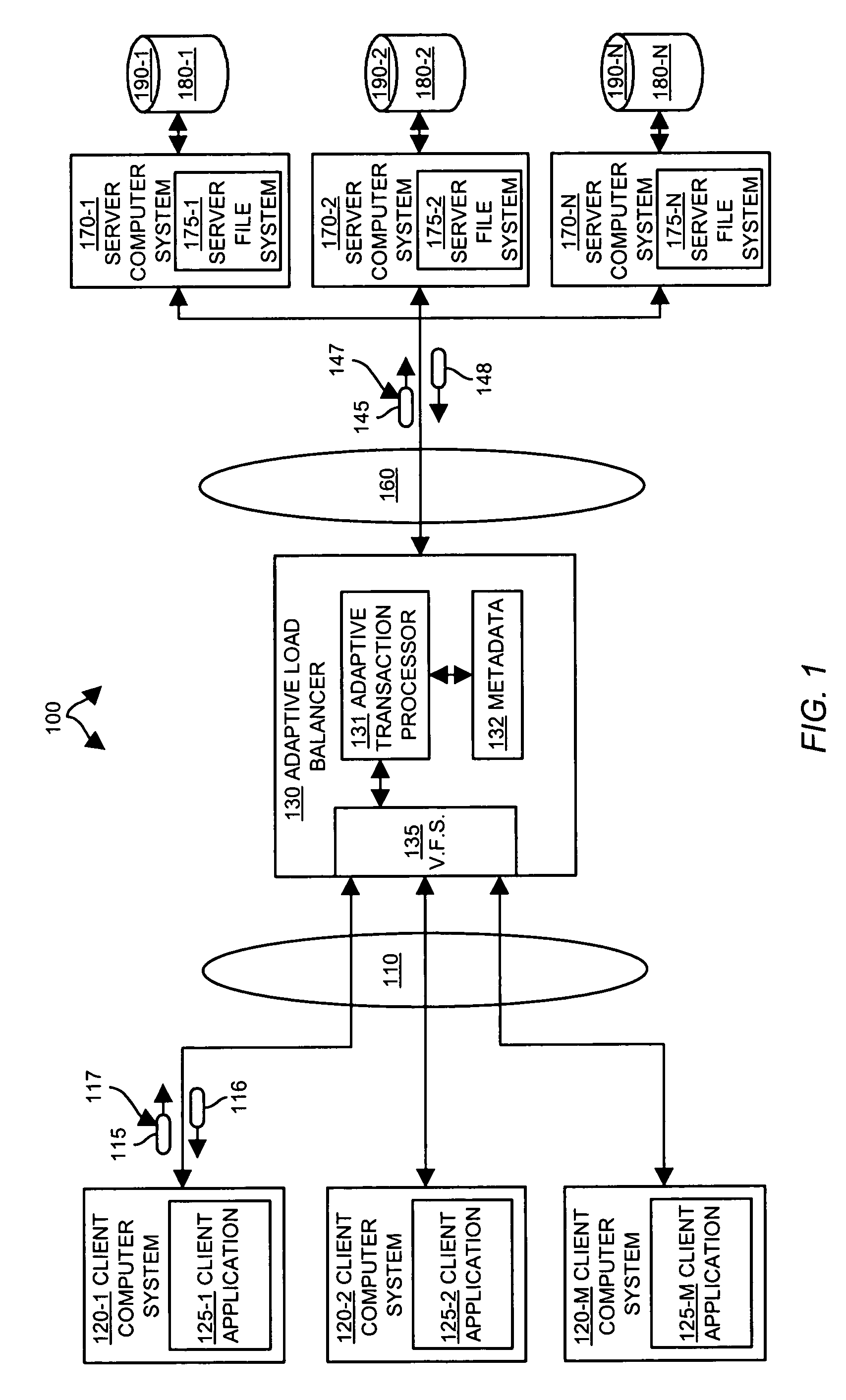
InactiveUS7877511B1Effective serviceExpand accessMultiple digital computer combinationsTransmissionAdaptive servicesData set
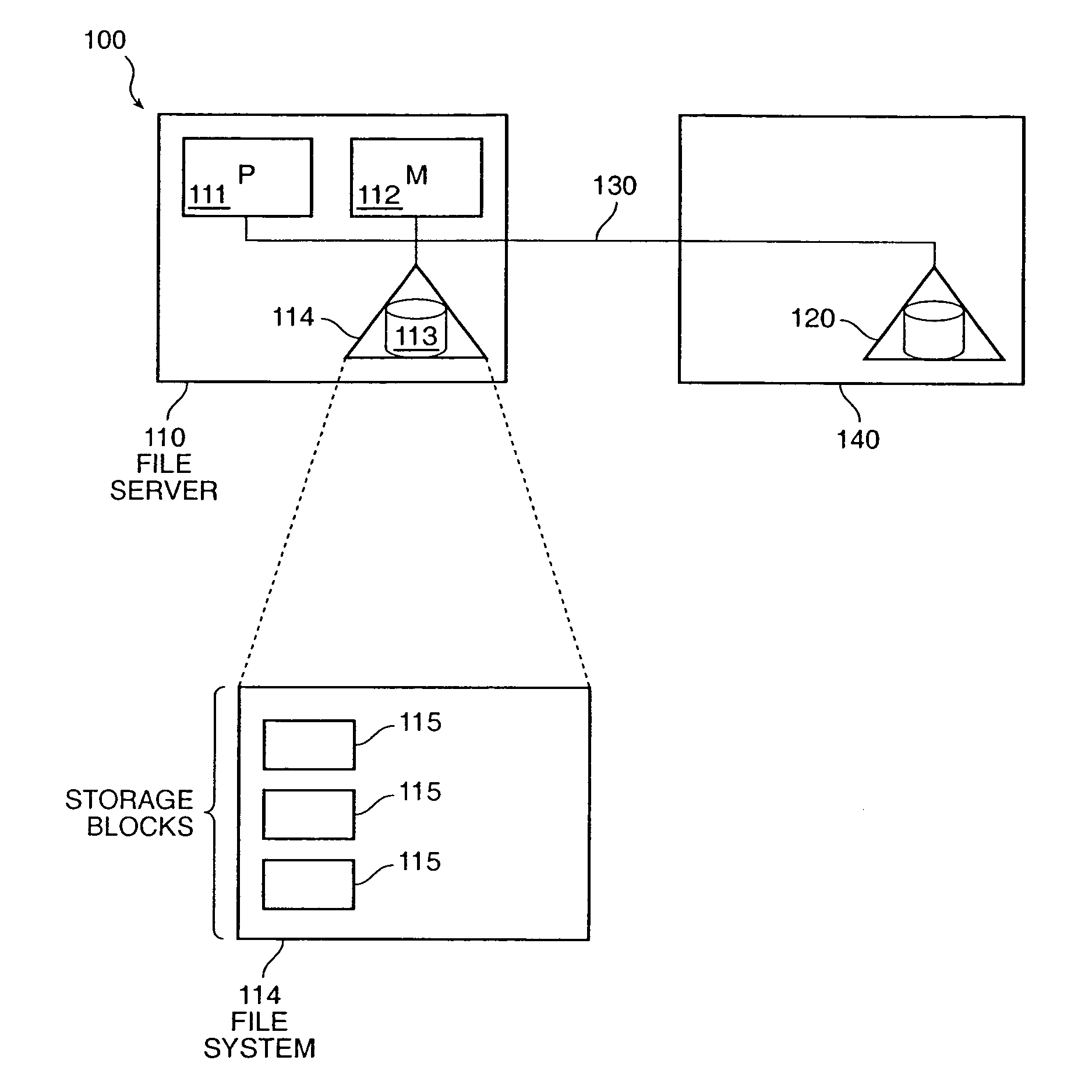
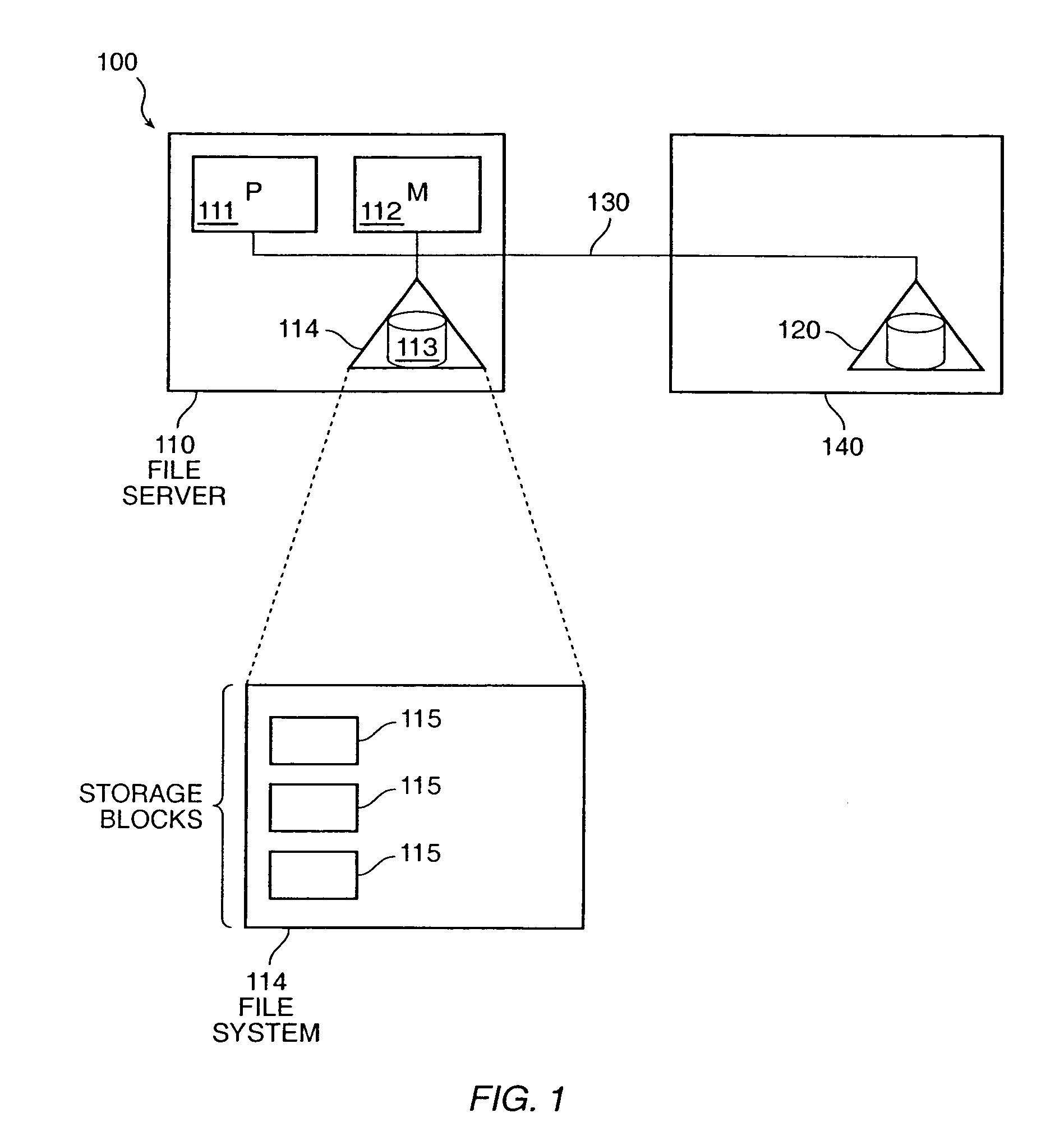
Methods and apparatus provide an adaptive load balancer that presents a virtual data system to client computer systems. The virtual data system provides access to an aggregated set of data, such as files or web service objects, available from a plurality of server data systems respectively operating within a plurality of server computer systems. The adaptive load balancer receives a client data access transaction from a client computer system that specifies a data access operation to be performed relative to the virtual data system presented to the client computer system. The adaptive load balancer processes the client data access transaction in relation to metadata associated with the virtual data system to provide access to the file or service object within a server computer system, or to access the metadata. The adaptive load balancer can work in conjunction with other adaptive load balancers to dynamically adjust to demands for access to data by replicating and migrating data such as files or service objects as needed between the server computer systems to accommodate data access demands.
Owner:F5 NETWORKS INC
File system image transfer
InactiveUS7174352B2Data processing applicationsSpecial data processing applicationsFile systemImage transfer
Owner:NETWORK APPLIANCE INC
Systems and methods for a search-based email client
InactiveUS20050144241A1Eliminating cogitationExpand the scope ofDigital data processing detailsMultiple digital computer combinationsUser needsRelevant information
A search-based email client may incorporate a number of useful features. A search function can default to a search of all email contexts, thereby eliminating user cogitation over which context an email message may be stored in. Furthermore, the search function can automatically search for related personal content and / or related information on the internet or other computer network, and present this useful information to the user in addition to the returned emails. The search function can be integrated into a user interface to allow for one-click searches on any likely search field. The search function can search the body of email messages by default, thereby widening the scope of default searches and eliminating potentially missed information and user need to proactively widen their search. A search function can search attachments, which also provides a wider search scope.
Owner:OATH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com