Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
319 results about "User involvement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
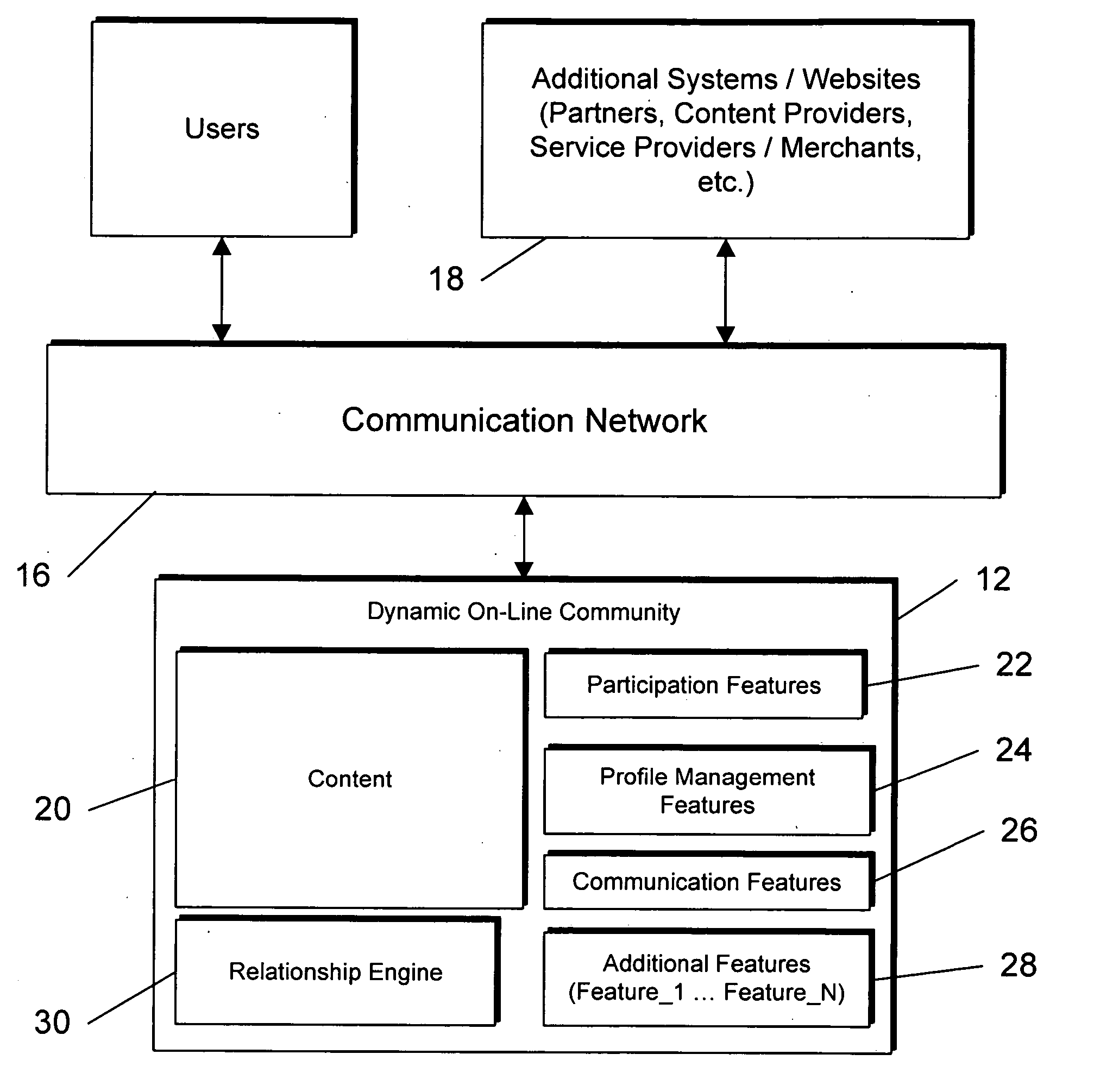
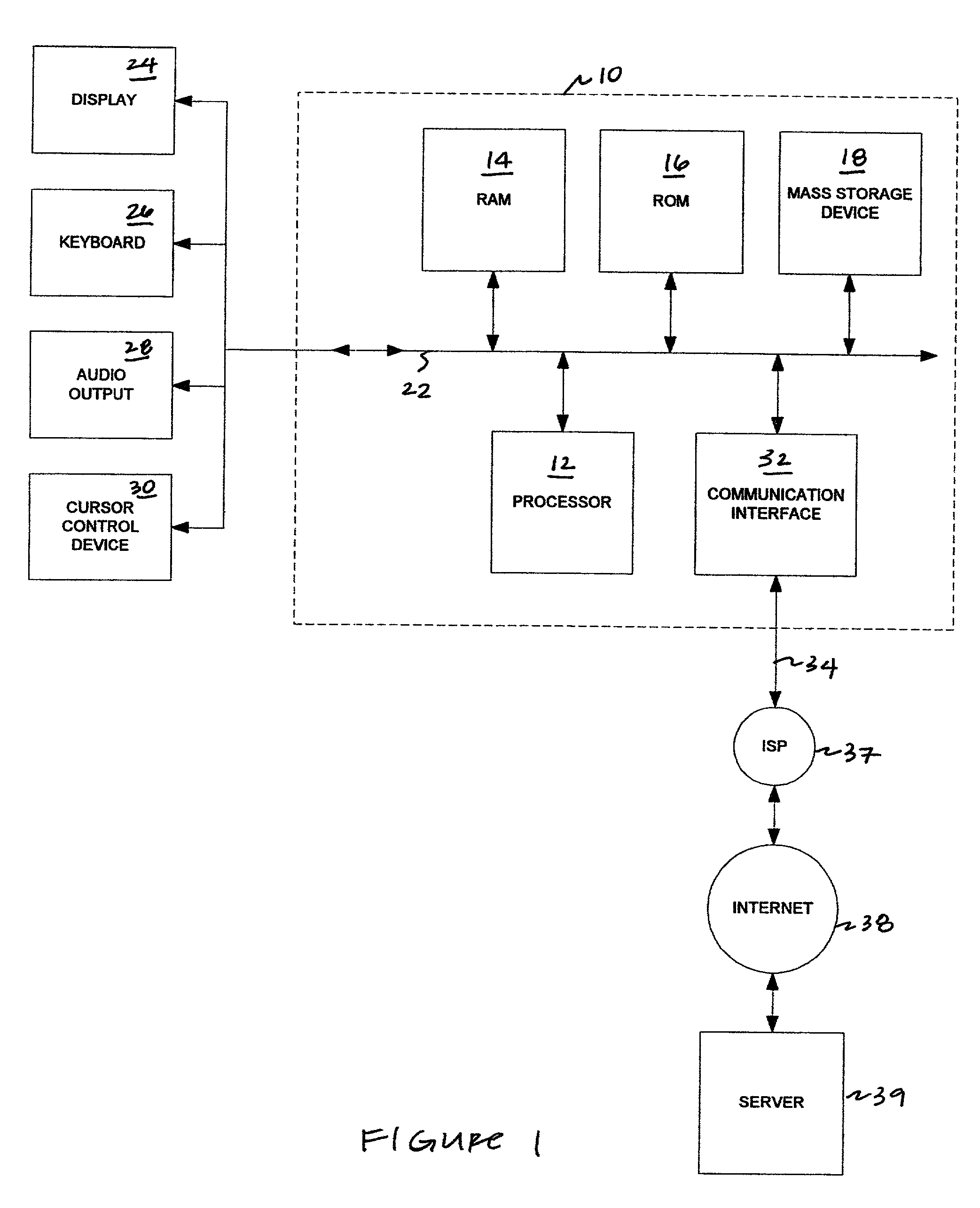
System and method for dynamically generating, maintaining, and growing an online social network
InactiveUS20060048059A1Grows and increase in functionalityOvercomes drawbackDigital data information retrievalCharacter and pattern recognitionCommunity systemSocial web
Owner:CONCERT TECH
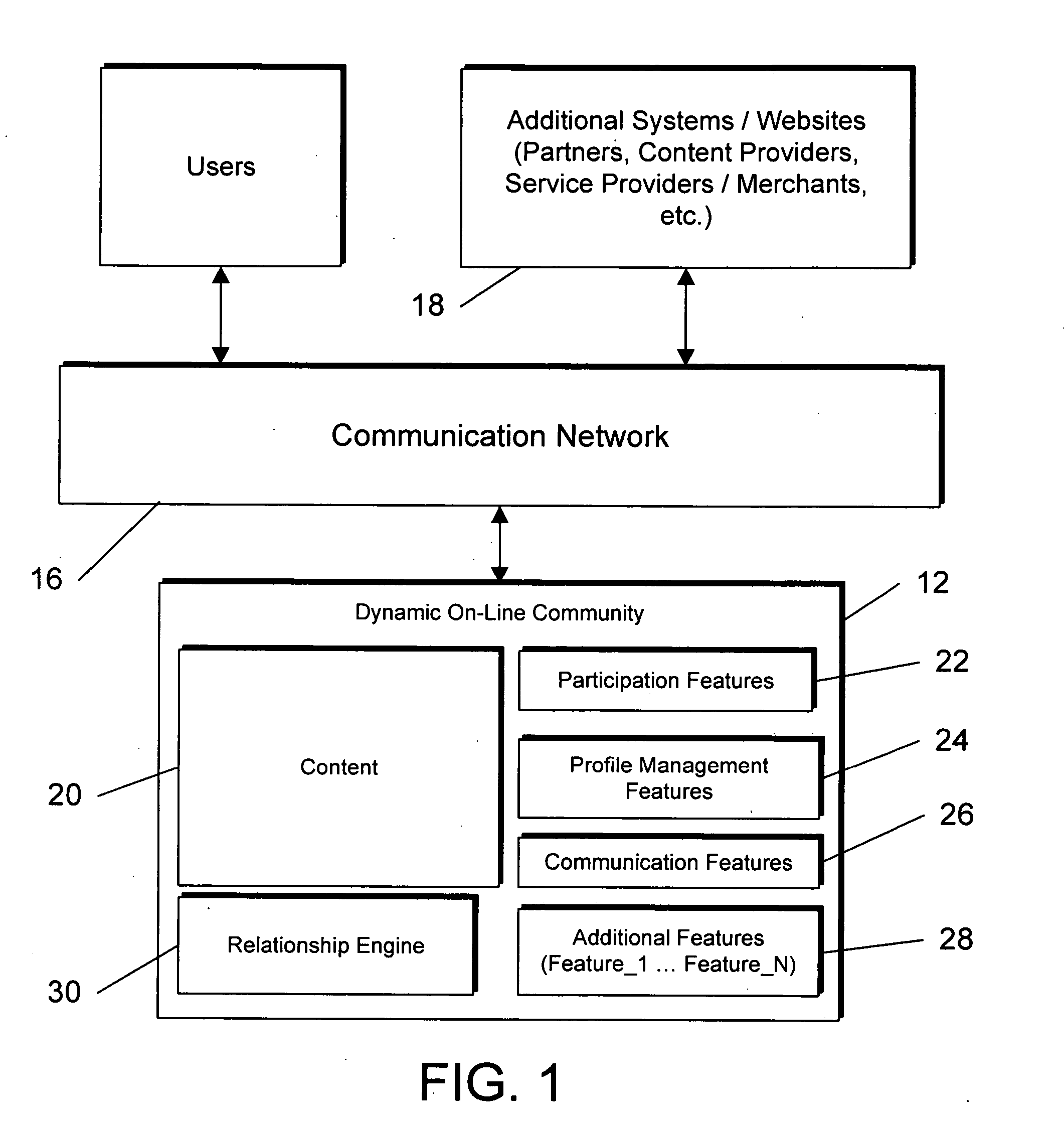
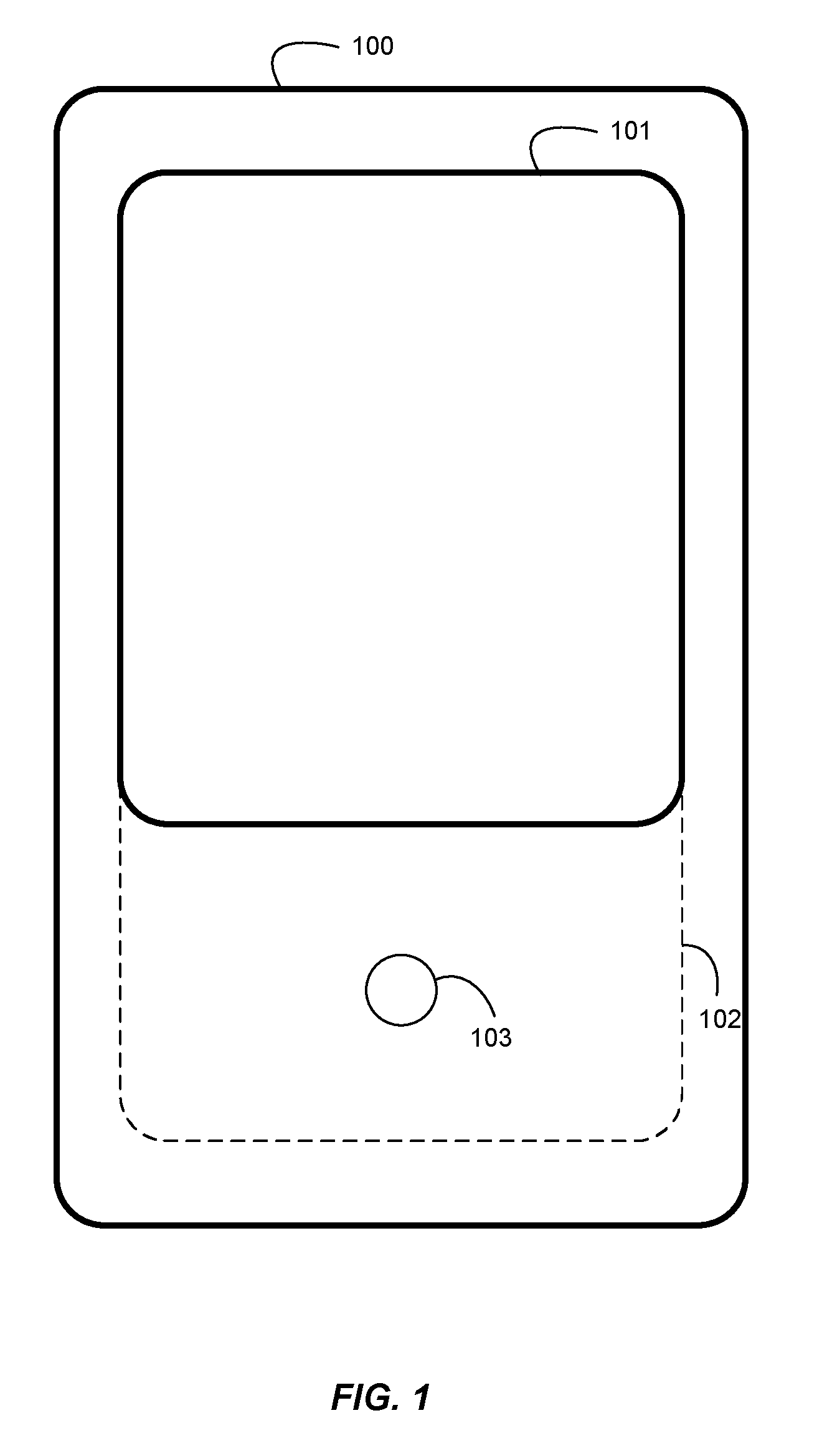
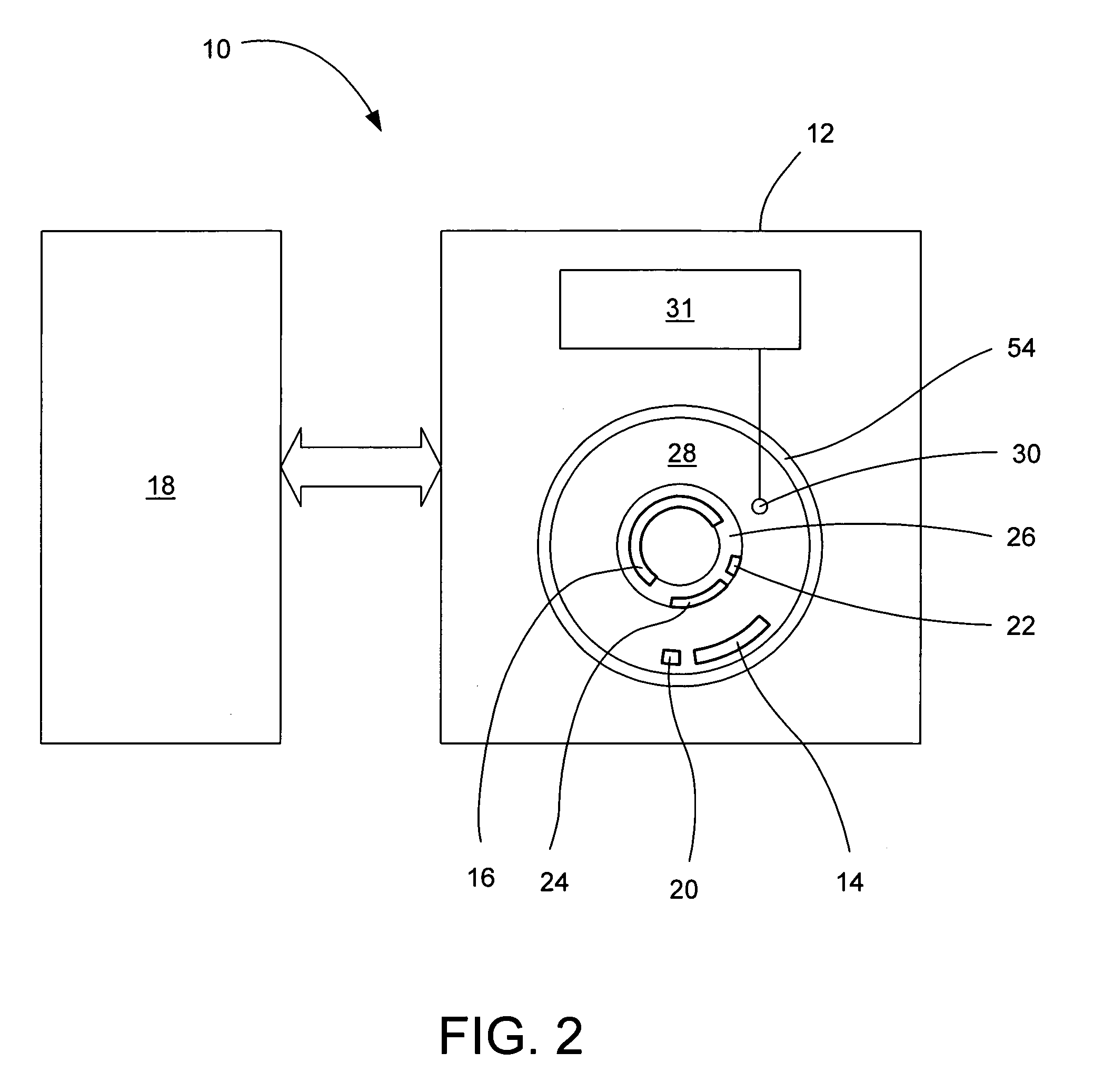
User Interface For Initiating Activities In An Electronic Device
ActiveUS20100185989A1Improve expediencyImprove convenienceCathode-ray tube indicatorsInput/output processes for data processingHome screenTouchscreen
In one embodiment, a user interface is presented for initiating activities in an electronic device. The user interface includes an element referred to as a “launch wave”, which can be activated at substantially any time, even if the user is engaged with an activity, without requiring the user to first return to a home screen. In various embodiments, the user can activate the launch wave by performing a gesture, or by pressing a physical button, or by tapping at a particular location on a touchscreen, or by activating a keyboard command. In one embodiment, activation of the launch wave and selection of an item from the launch wave can be performed in one continuous operation on a touch-sensitive screen, so as to improve the expediency and convenience of launching applications and other items.
Owner:QUALCOMM INC
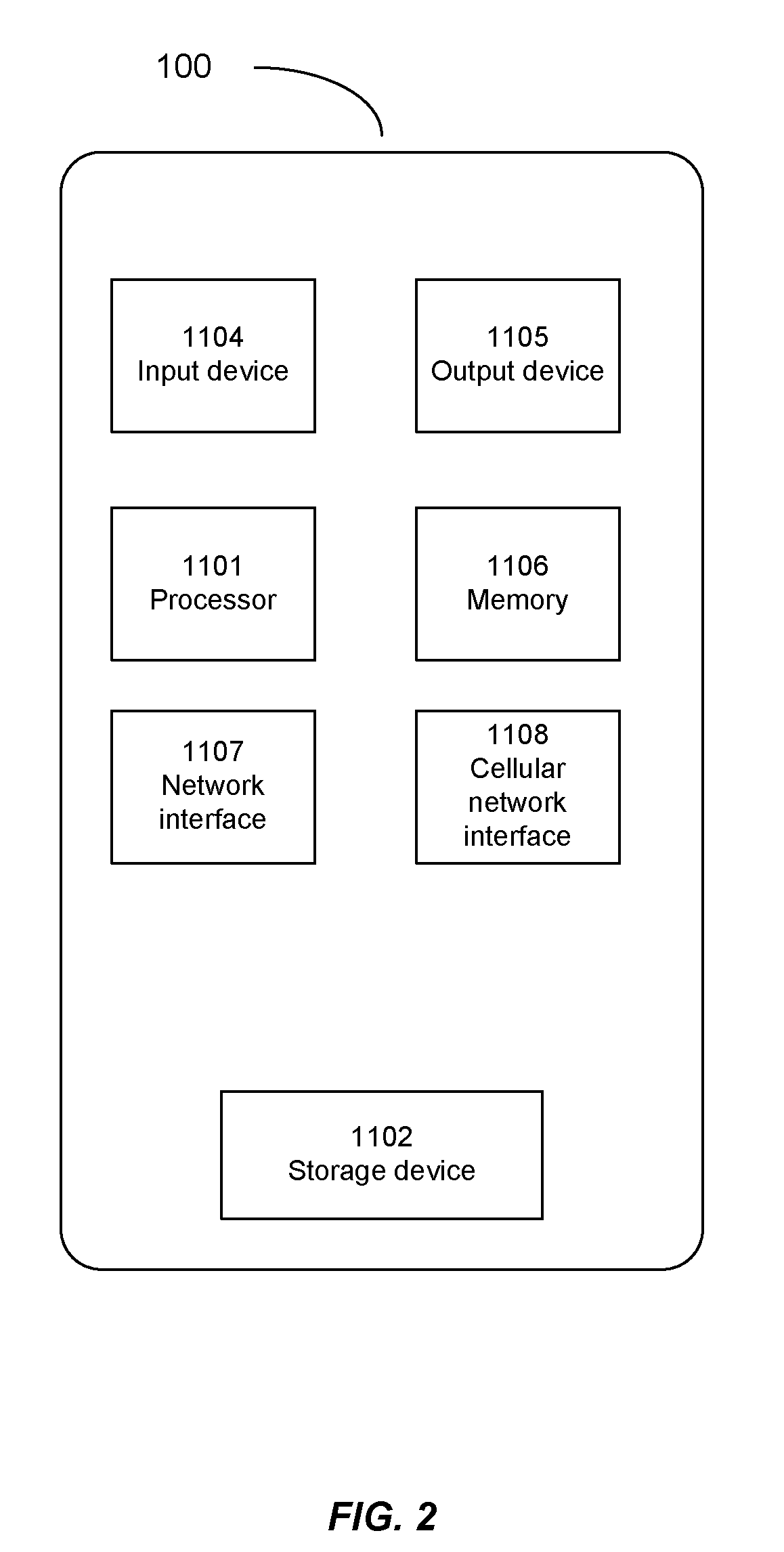
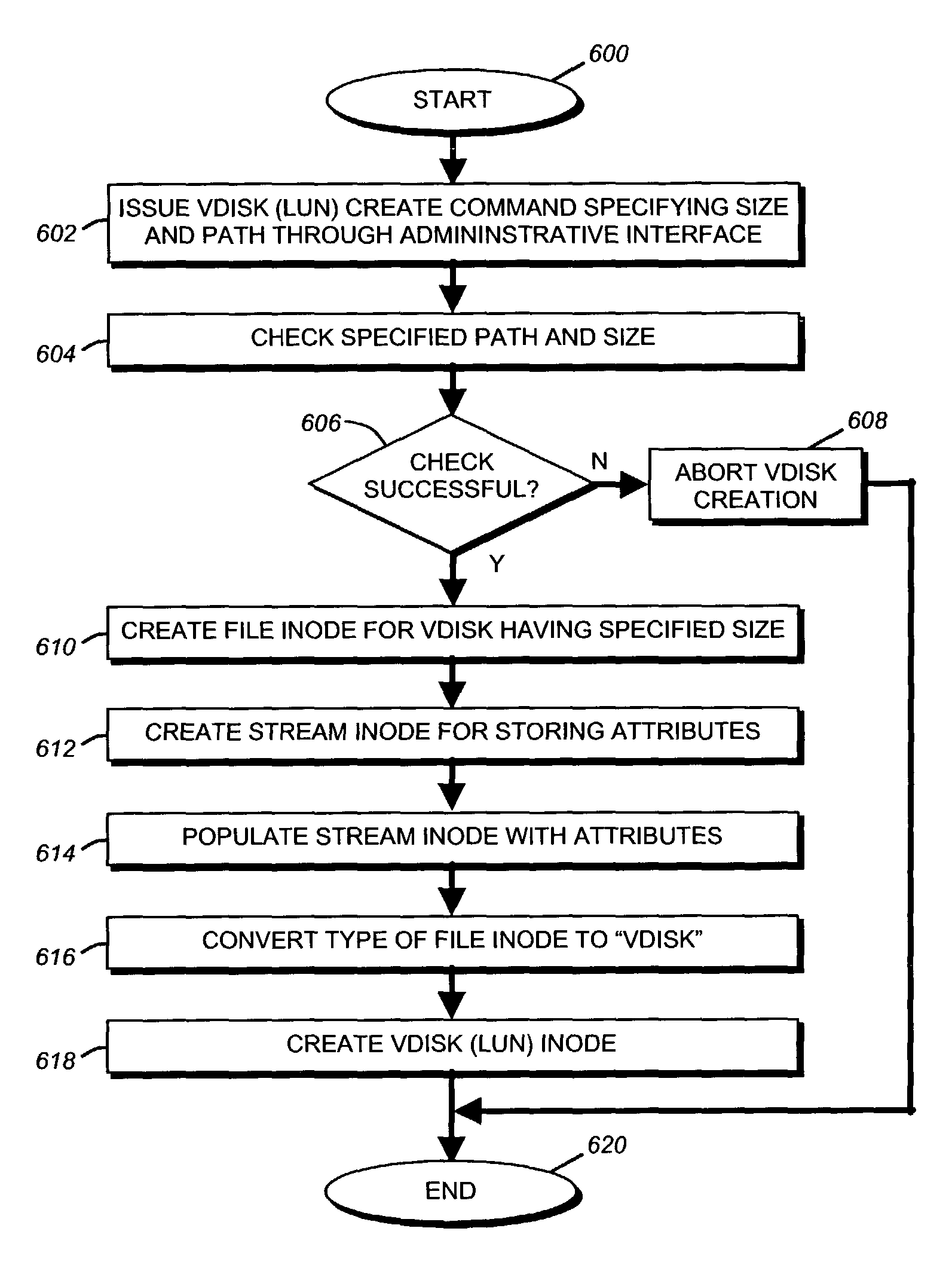
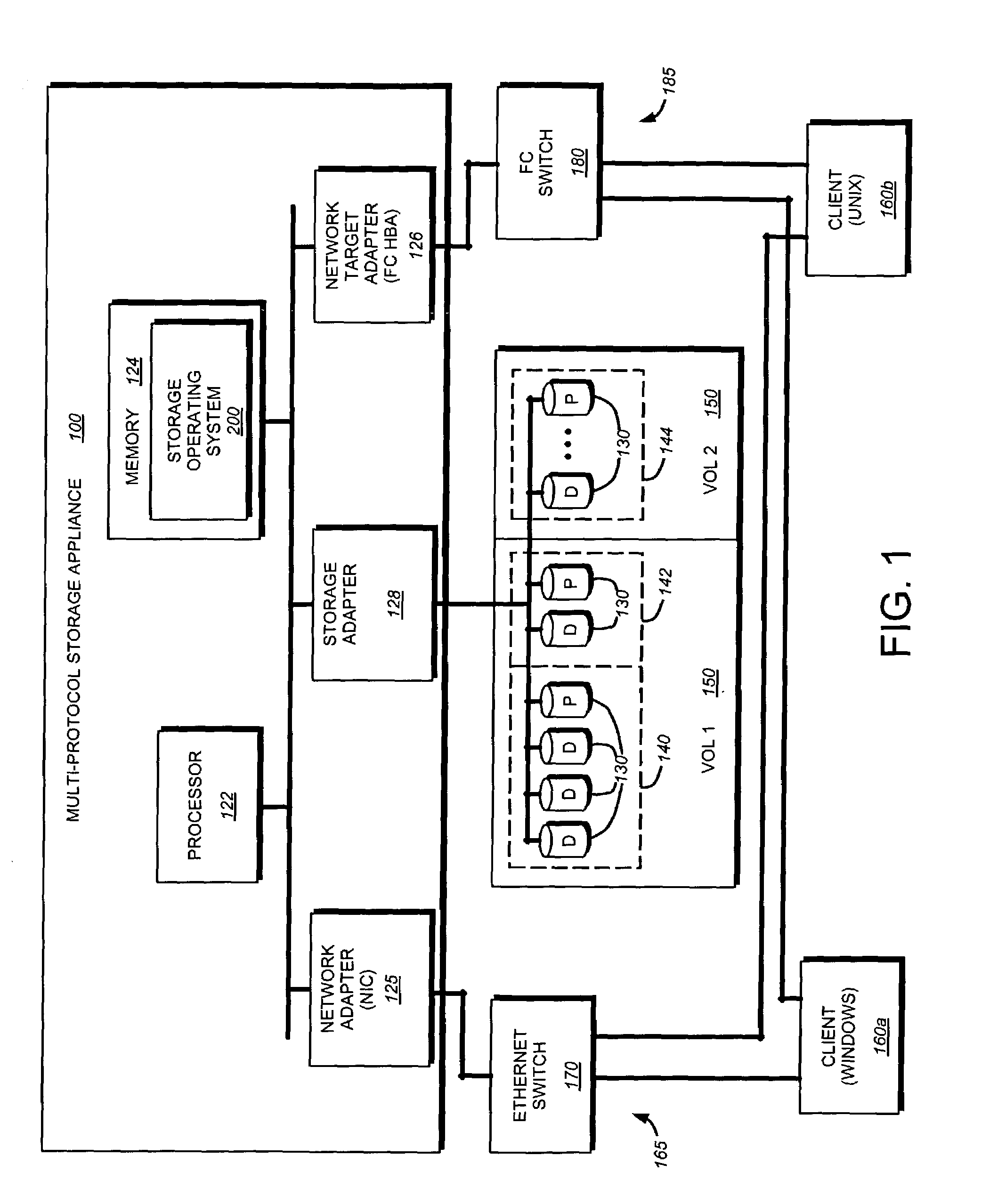
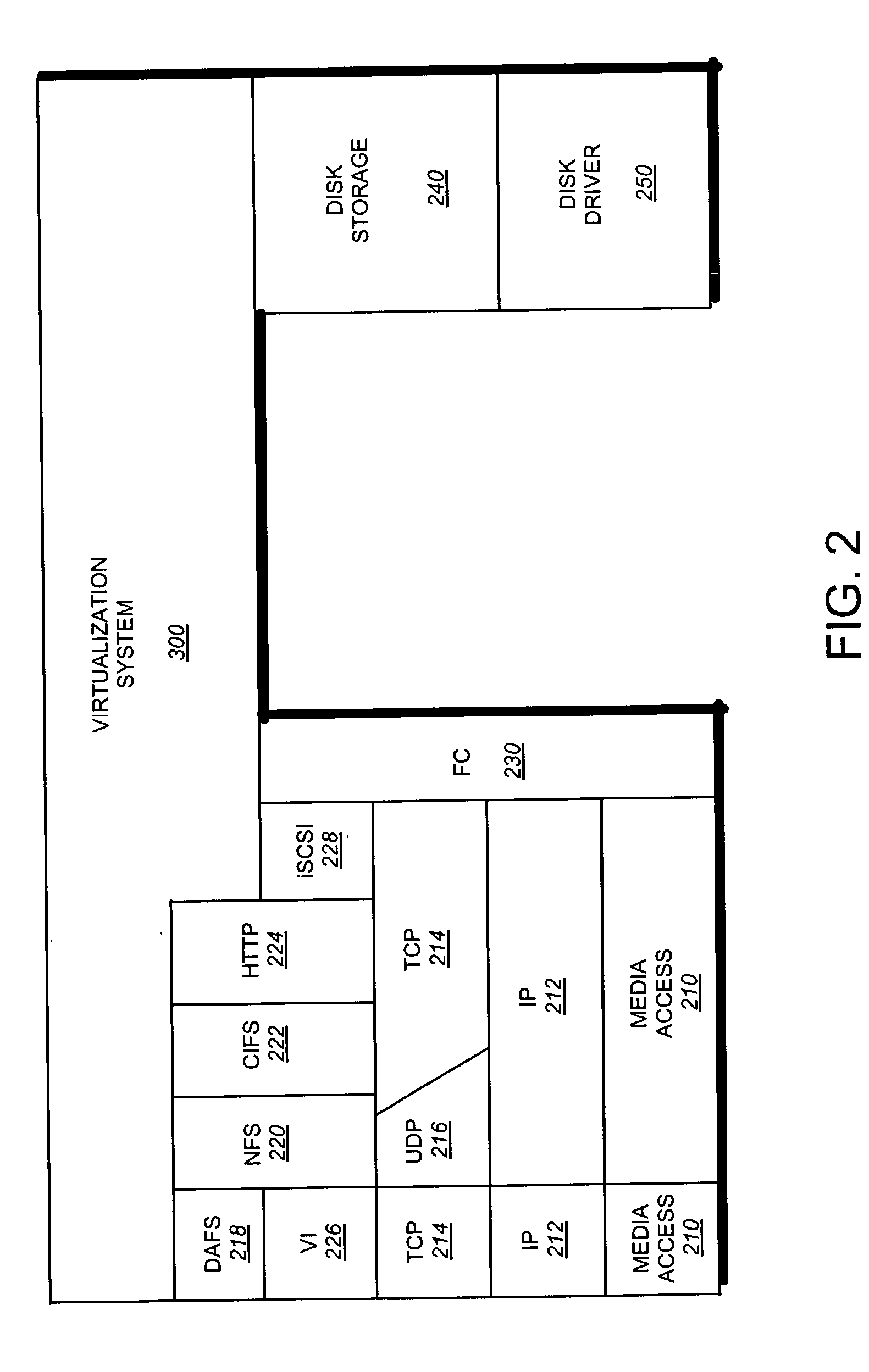
Storage virtualization by layering virtual disk objects on a file system
InactiveUS7107385B2Input/output to record carriersData processing applicationsOperational systemFile system
A storage virtualization selection technique “automates” a virtualization selection process to create virtual disk (vdisk) storage objects over a volume of a file system implemented by a storage operating system of a multi-protocol storage appliance. The file system provides a virtualization system that aggregates physical storage of a set of disks or portions (e.g., extents) of disks into a pool of blocks that can be dynamically allocated to form a vdisk. The file system also provides reliability guarantees for the vdisks in accordance with its underlying architecture. That is, the file system organizes its storage within volumes created among the managed disks. The vdisk is thereafter created as a storage object within a volume and, thus, inherits the underlying reliability configuration associated with that volume. The portions are aggregated and allocated as a vdisk with reliability guarantees in response to a request to create the vdisk from a user of the storage appliance and without further user involvement.
Owner:NETWORK APPLIANCE INC
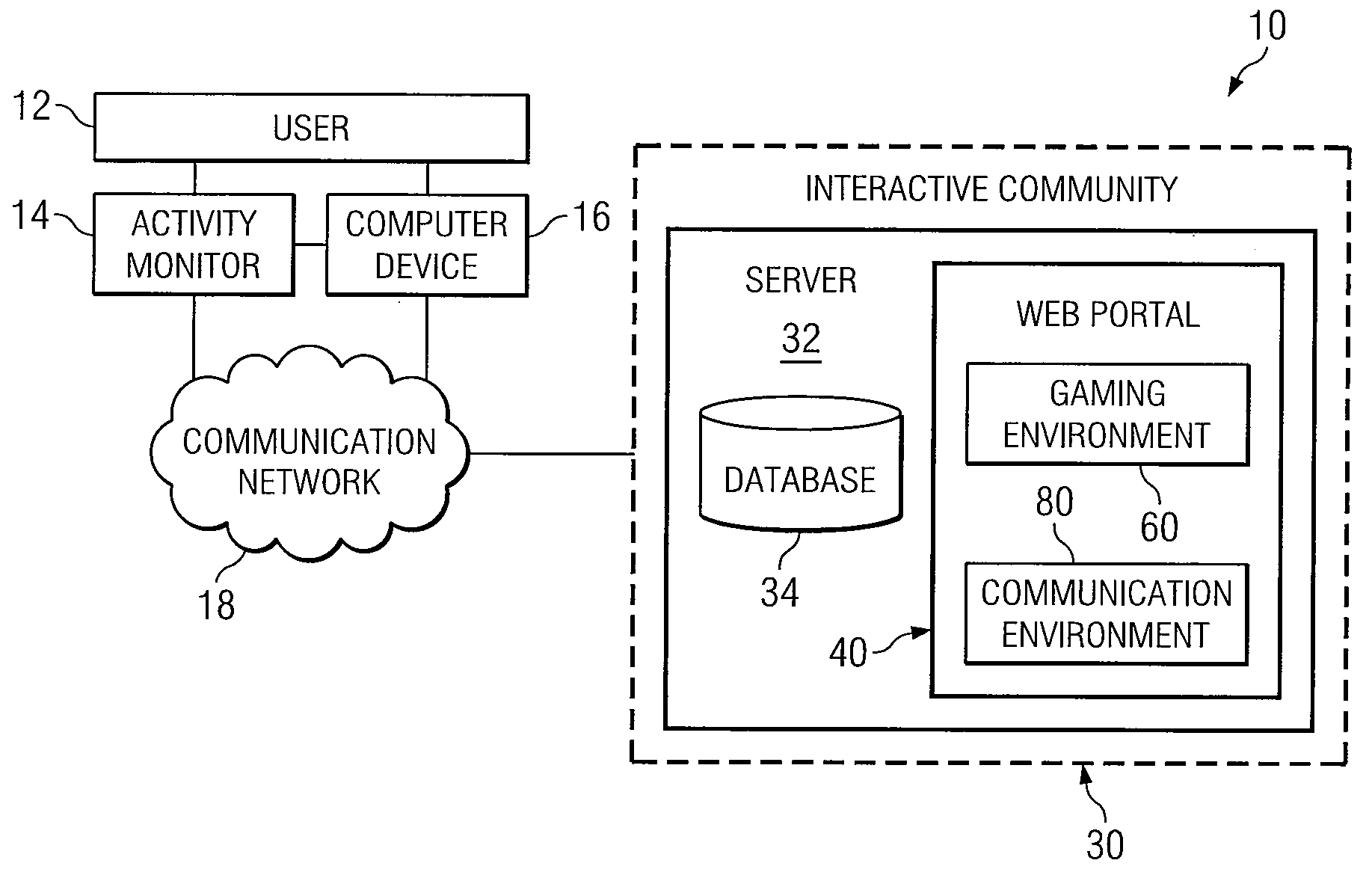
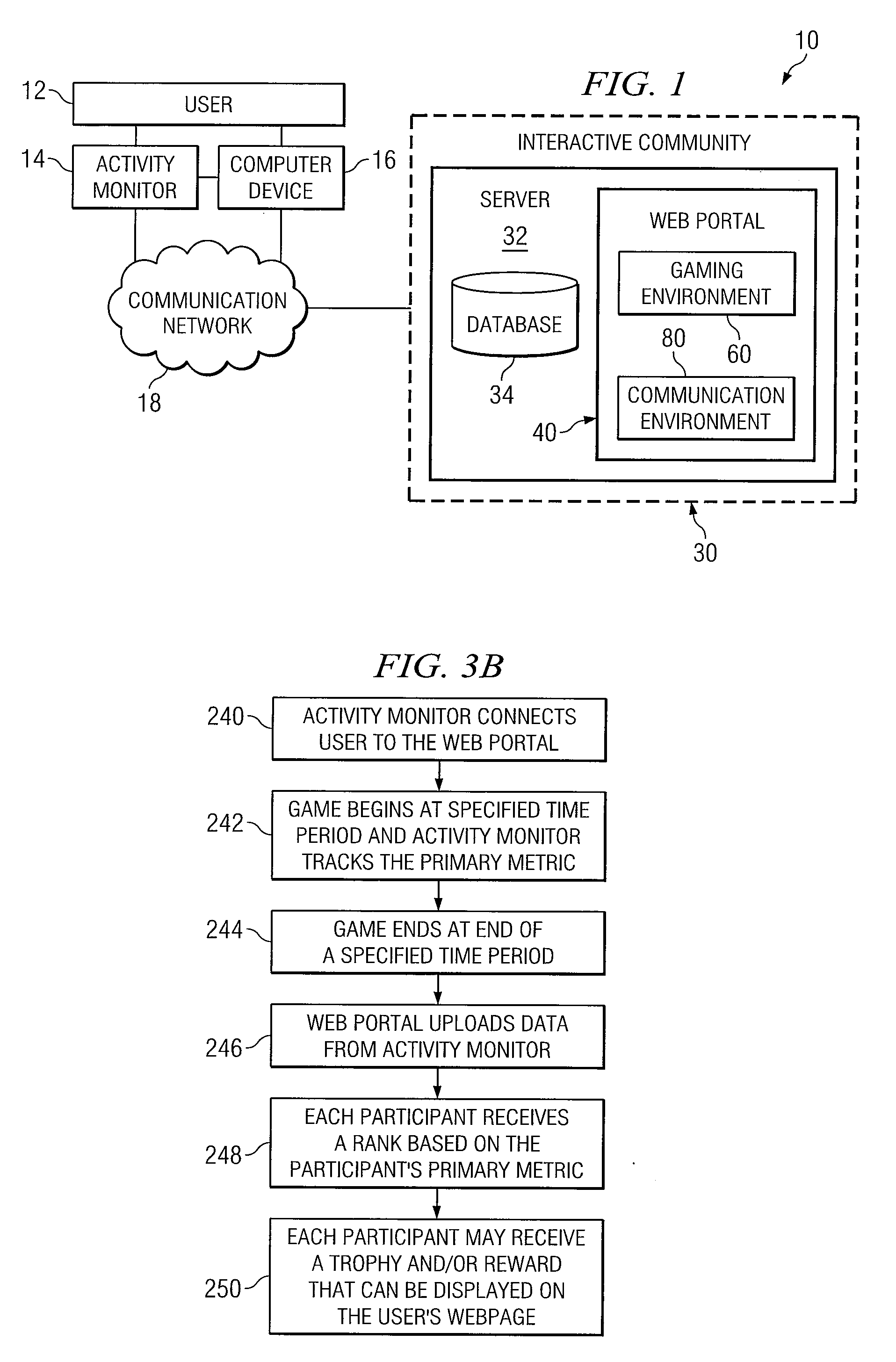
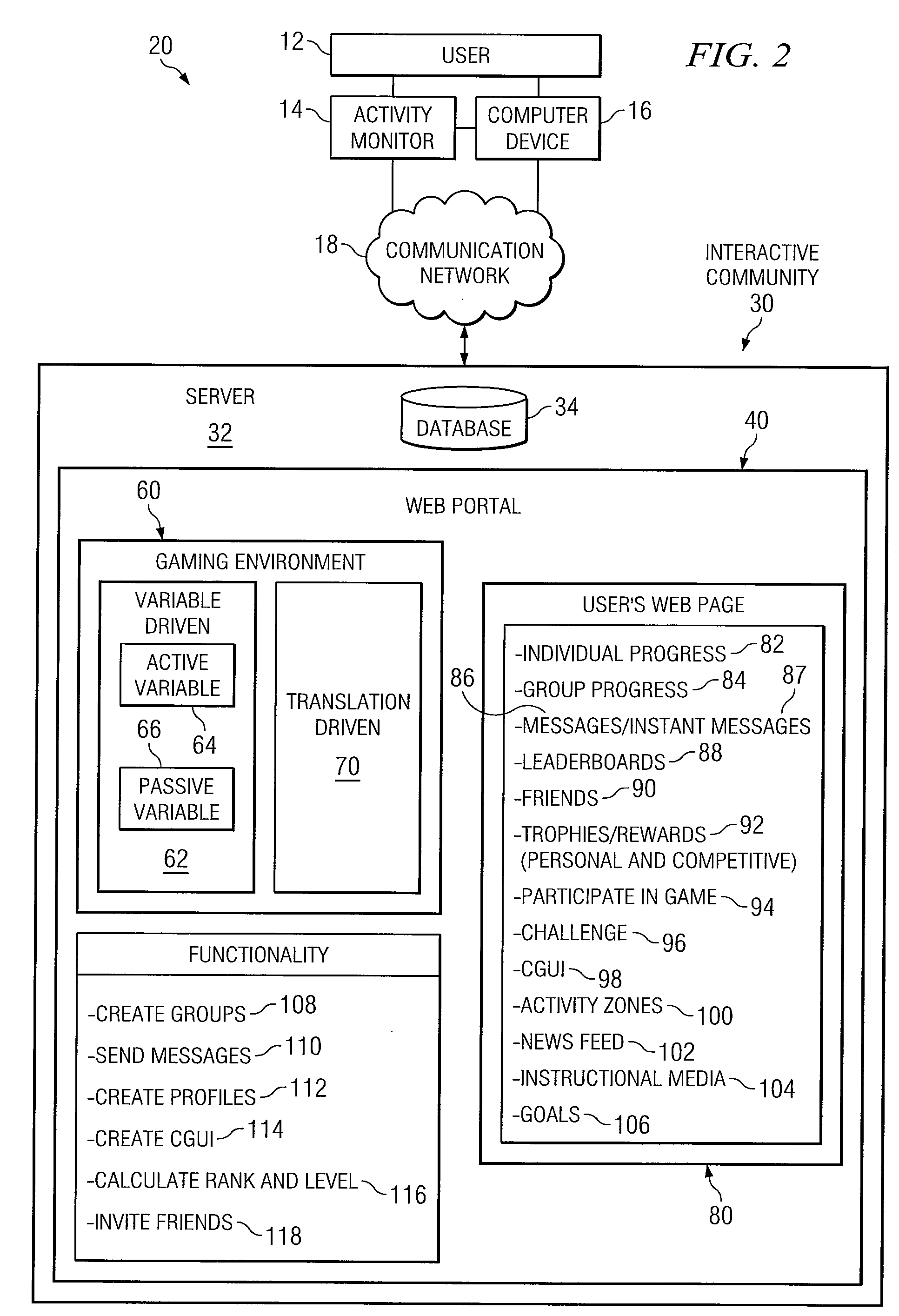
System and Method for Implementing an Interactive Online Community Utilizing an Activity Monitor
InactiveUS20080176655A1Eliminates and reduces disadvantageEliminates and reduces and problemPhysical therapies and activitiesMedical communicationData transmissionUser involvement
An interactive online community utilizes an activity monitor that is operable to measure data, transmit data, and receive data. One or more servers coupled to a communication network provide access to the World Wide Web (“web”). A web portal located on one or more servers is operable to transmit data to the activity monitor and receive data from the activity monitor. The web portal includes a gaming and communication environment that utilizes the data from the activity monitor. Users engage in physical activity and participate in the gaming and communication environment with other users.
Owner:JAMES TERRY L +1
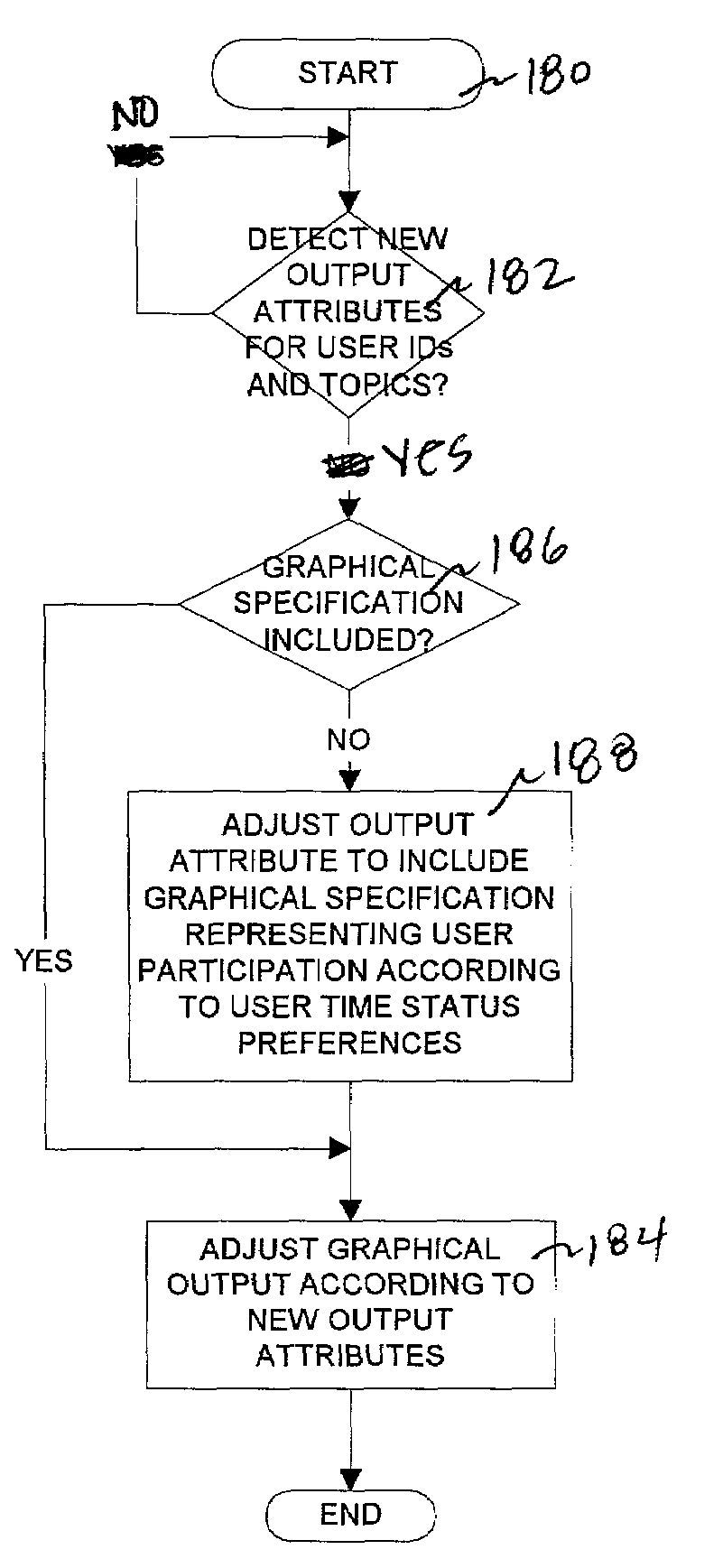
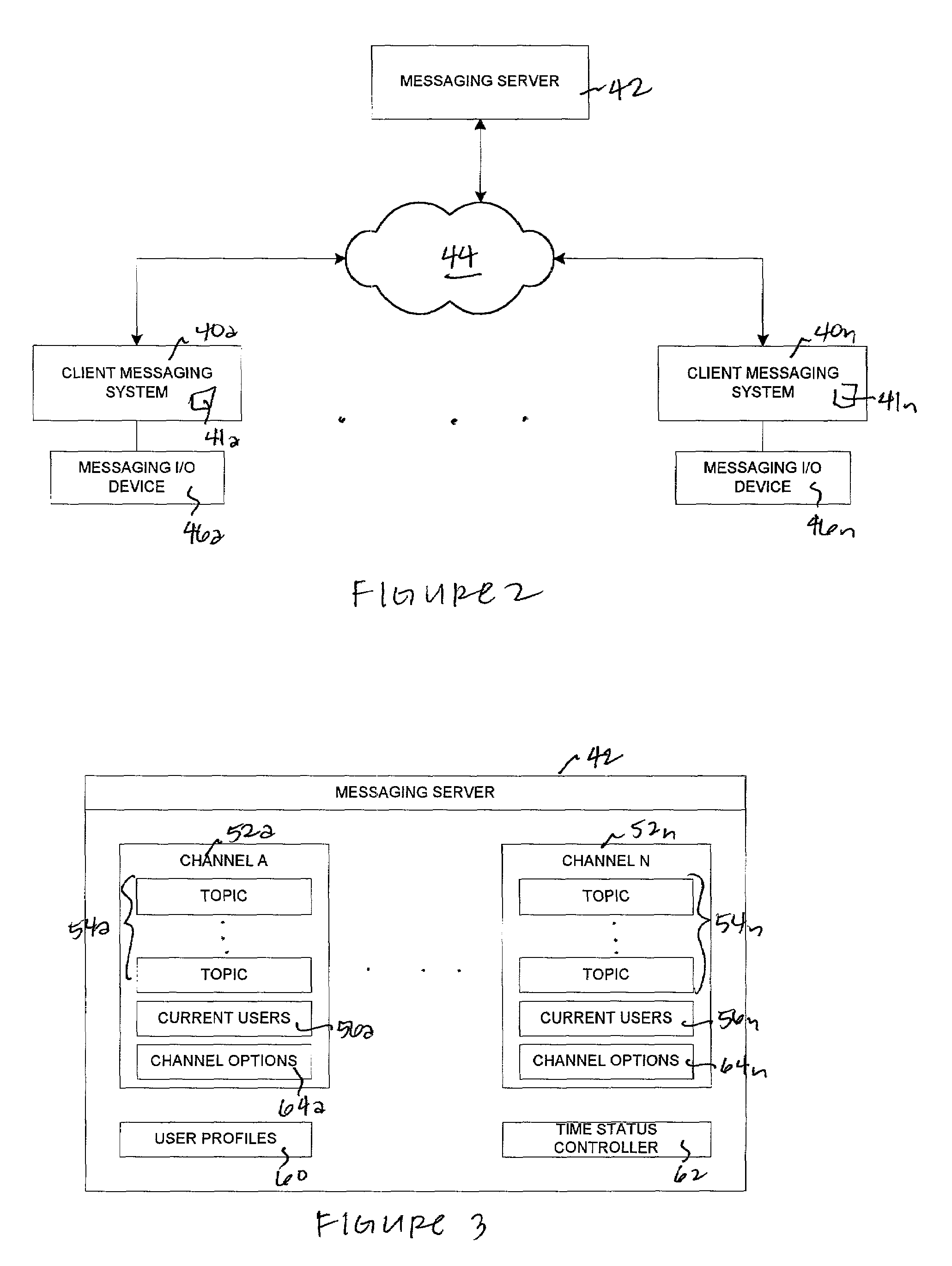
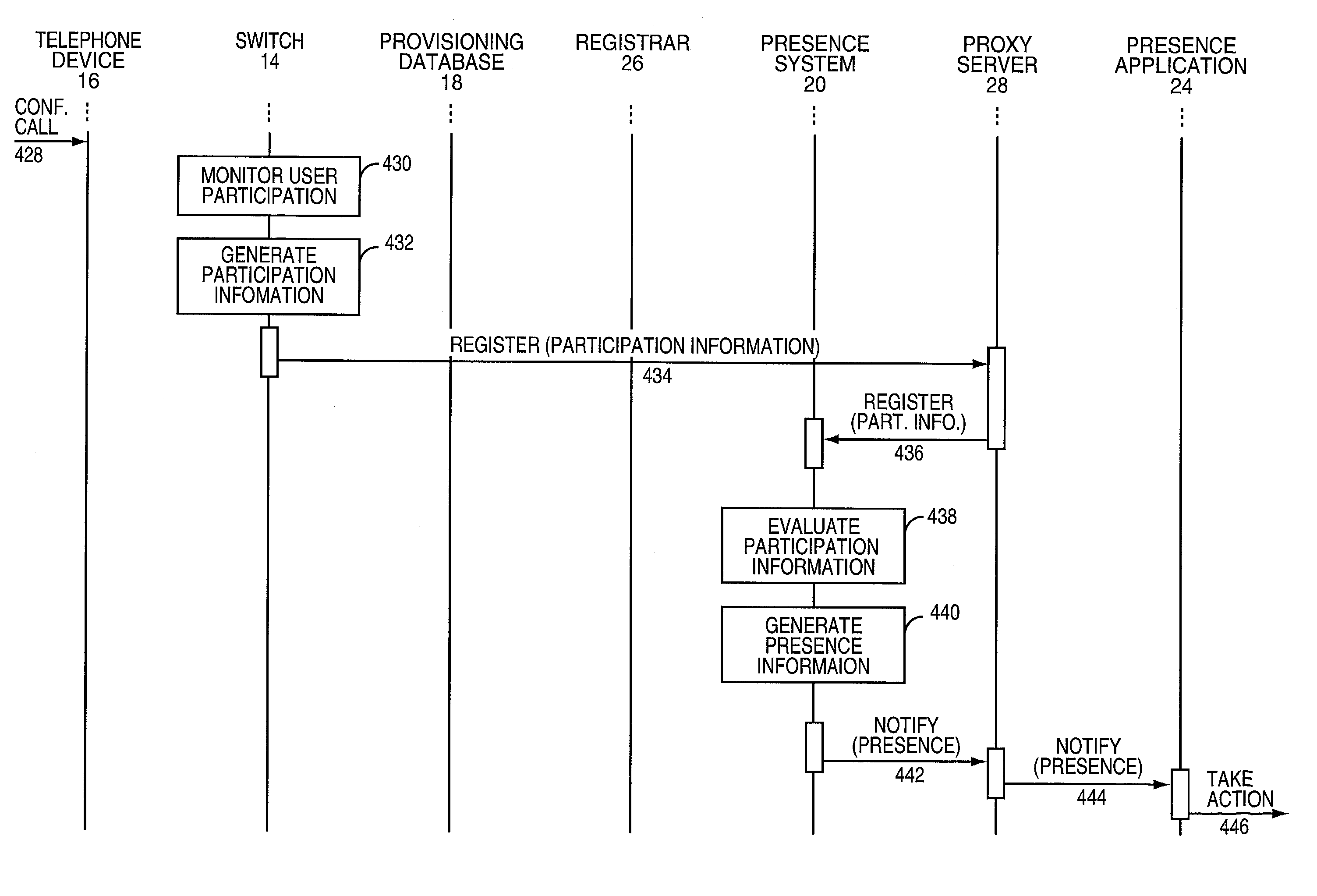
Specifying monitored user participation in messaging sessions
ActiveUS7062533B2Multiple digital computer combinationsData switching networksGraphicsUser participation
A method, system, and program for specifying monitored user participation in a messaging session is provided. A time status for a messaging system element is determined. The time status corresponds to a type of participation by at least one user in a messaging session. An output attribute is assigned to the messaging system element according to the time status, such that output of the messaging system element is specified to depict time status for the messaging session. A client messaging system, receiving the messaging system element with the output attribute, graphically displays the messaging system element in order to graphically reflect user participation in a messaging session.
Owner:ACTIVISION PUBLISHING
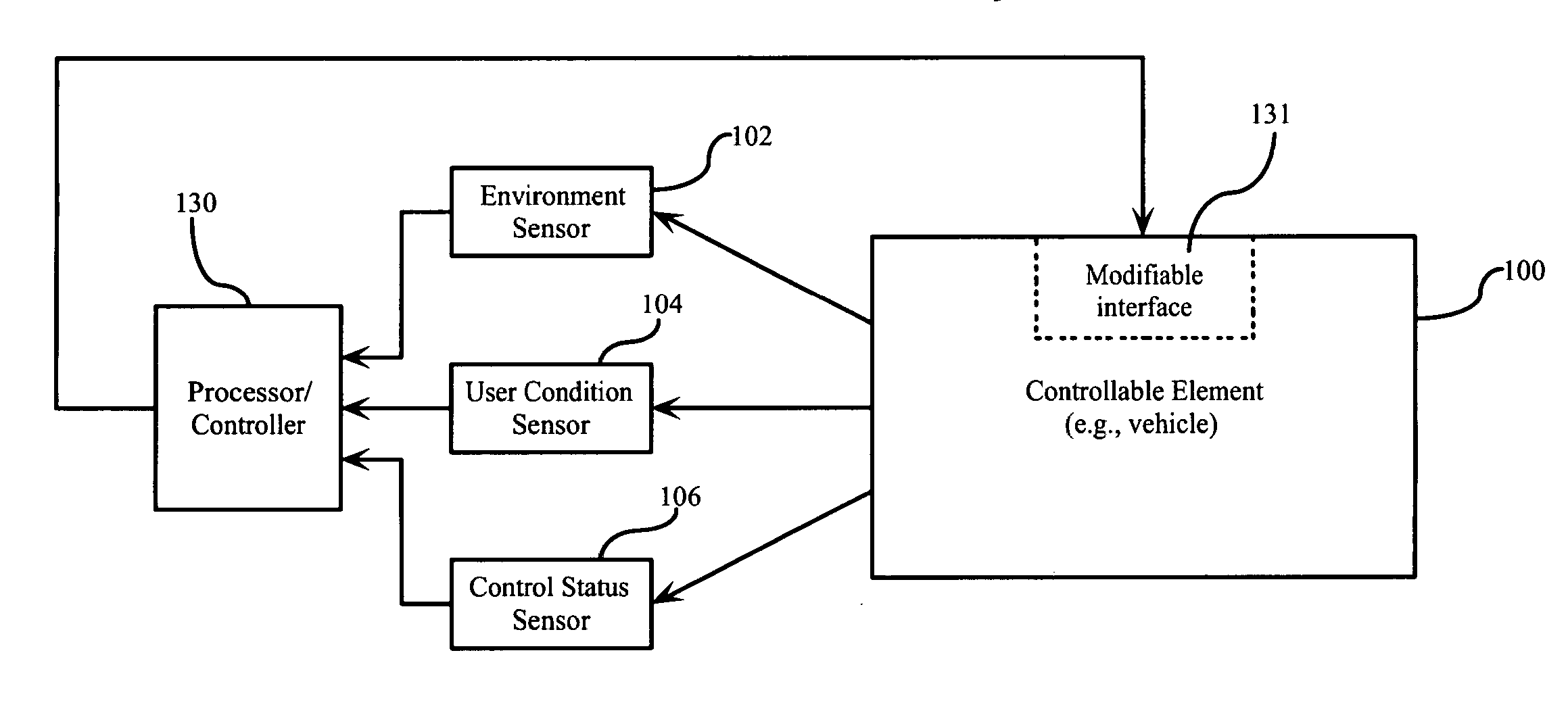
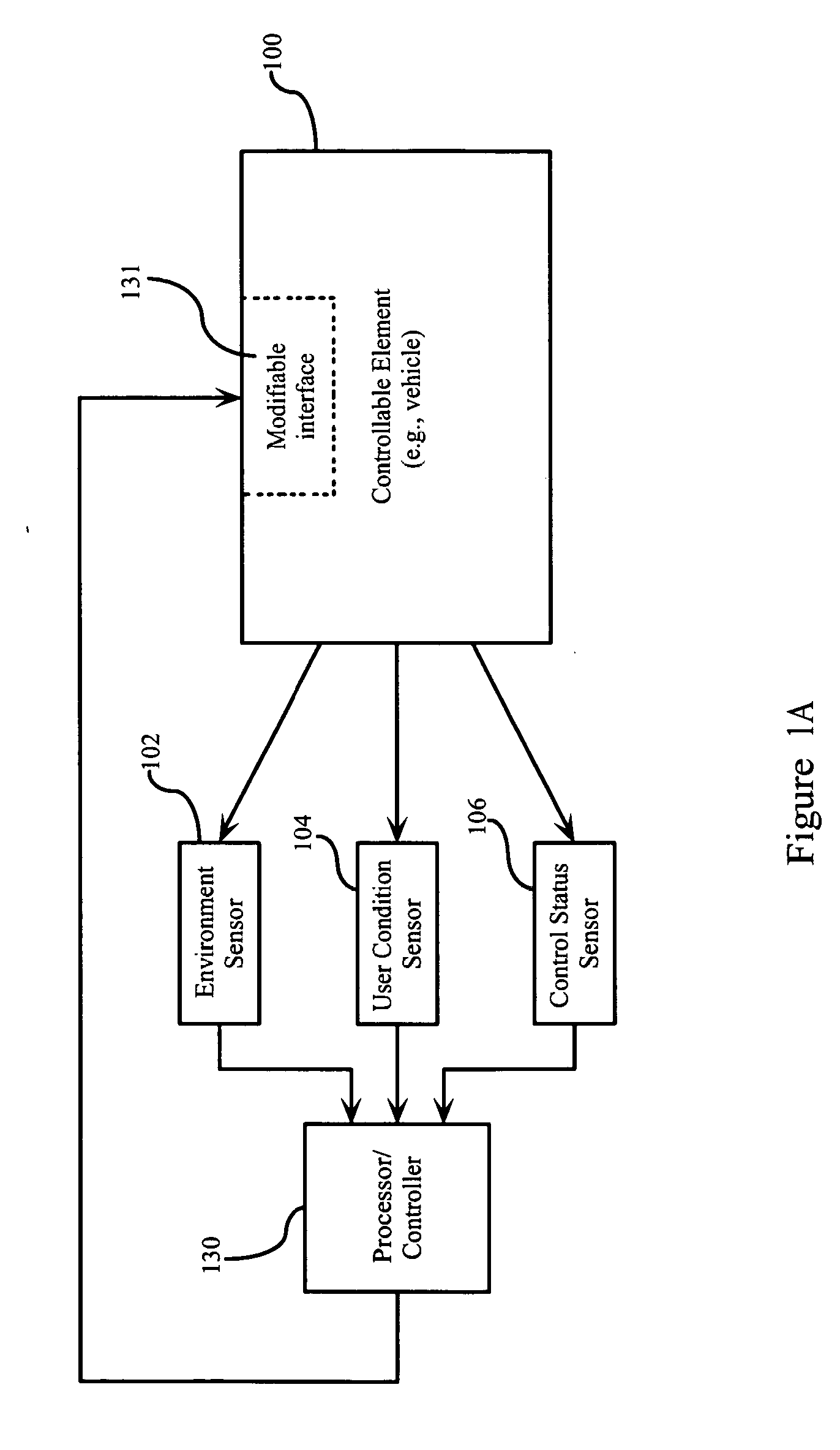
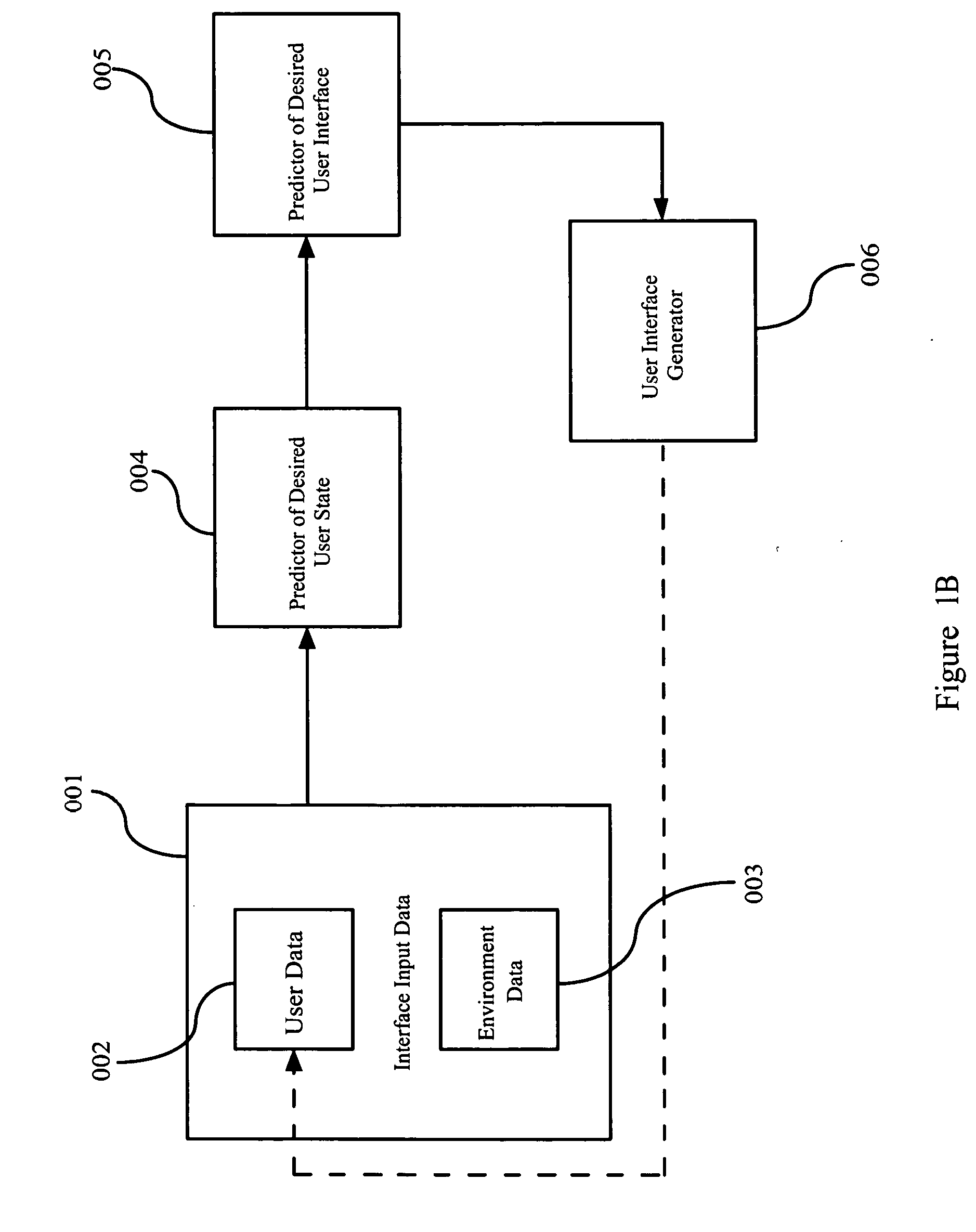
Predictive user modeling in user interface design
Dynamic modification of user interfaces is disclosed, based upon identification of the current state of the user and the sensing of a particular situation in which the user is involved and / or environment in which the user is situated. In particular, emotional and mental states of a user are identified and these states are taken into consideration when creating and / or adapting an interface to be used by the user. The interface is modified / created automatically based on identified user biometrics, that is, measured physical properties of the user.
Owner:IBM CORP
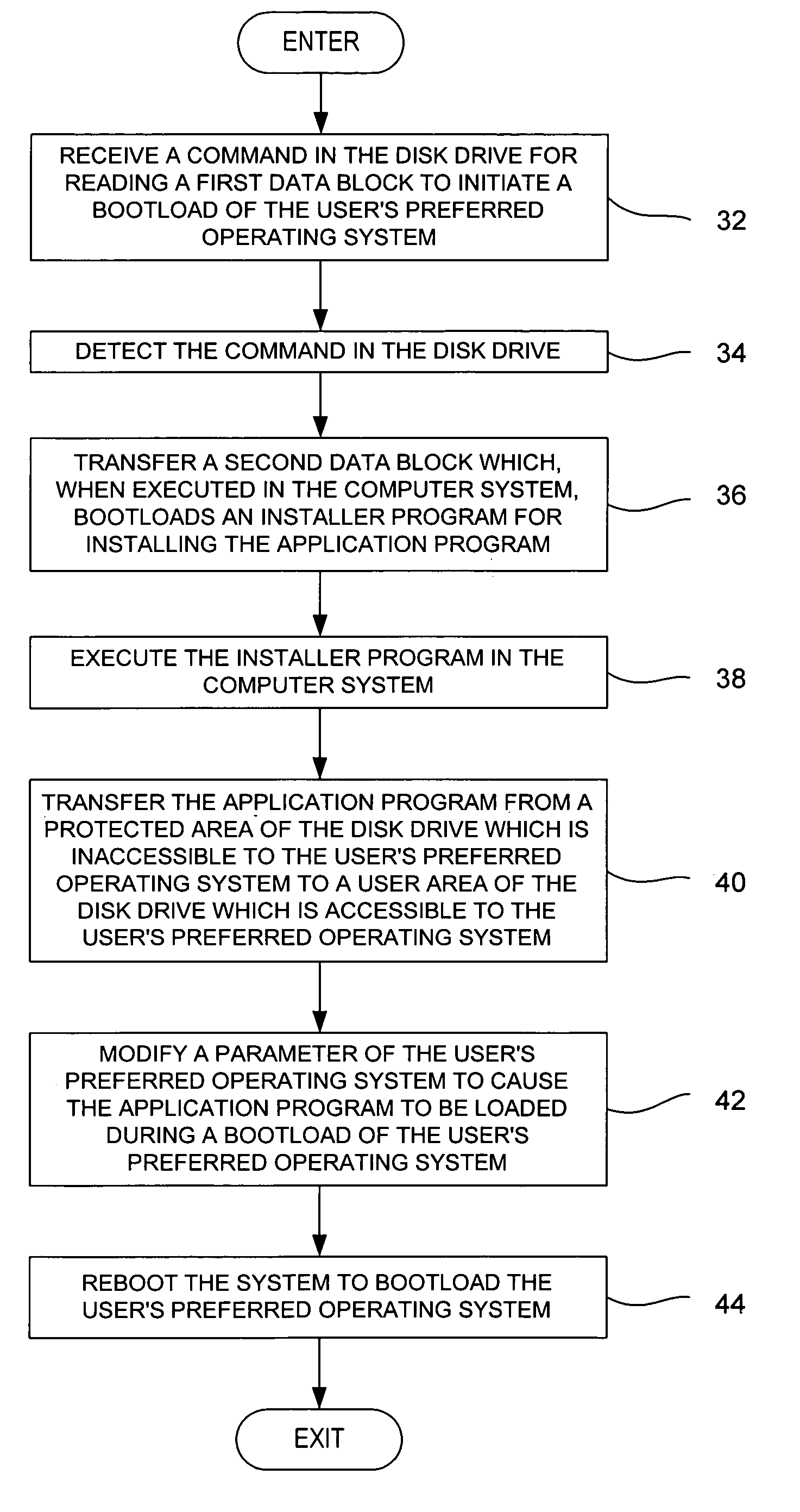
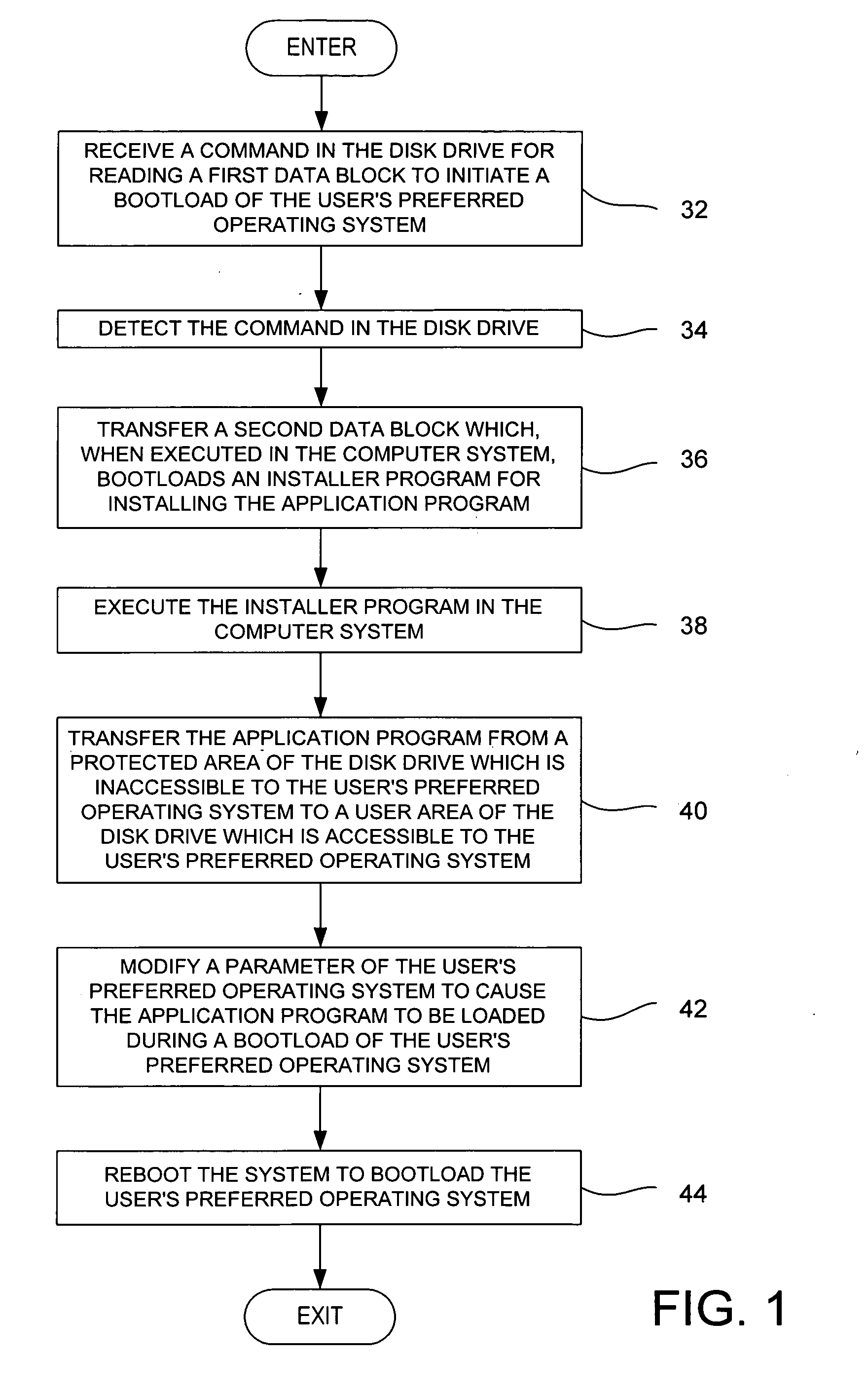
Method for installing an application program, to be executed during each bootload of a computer system for presenting a user with content options prior to conventional system startup presentation, without requiring a user's participation to install the program
The present invention may be embodied in a method, performed in a computer system having a disk drive, for installing an application program for execution under a user's preferred operating system without requiring user intervention. A command is received by the disk drive for reading a first data block to initiate a bootload of the user's preferred operating system. The disk drive detects the command and transfers a second data block which bootloads an installer program for installing the application program. The installer program is executed in the computer system to transfer the application program from a protected area of the disk drive to a user area of the disk drive, to modify a parameter of the user's preferred operating system to cause the application program to be loaded during a bootload of the user's preferred operating system, and to reboot the system to bootload the user's preferred operating system.
Owner:WESTERN DIGITAL TECH INC
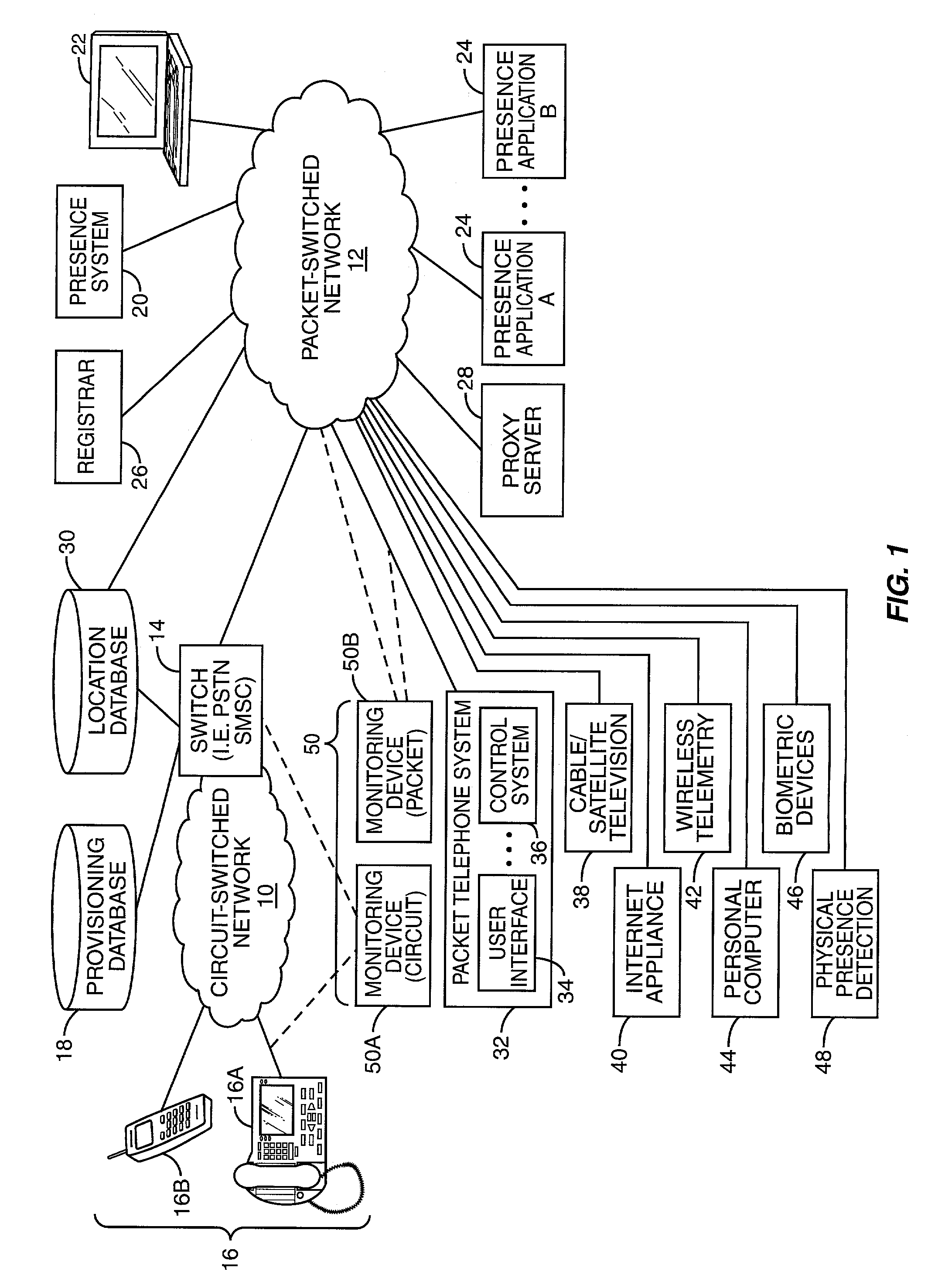
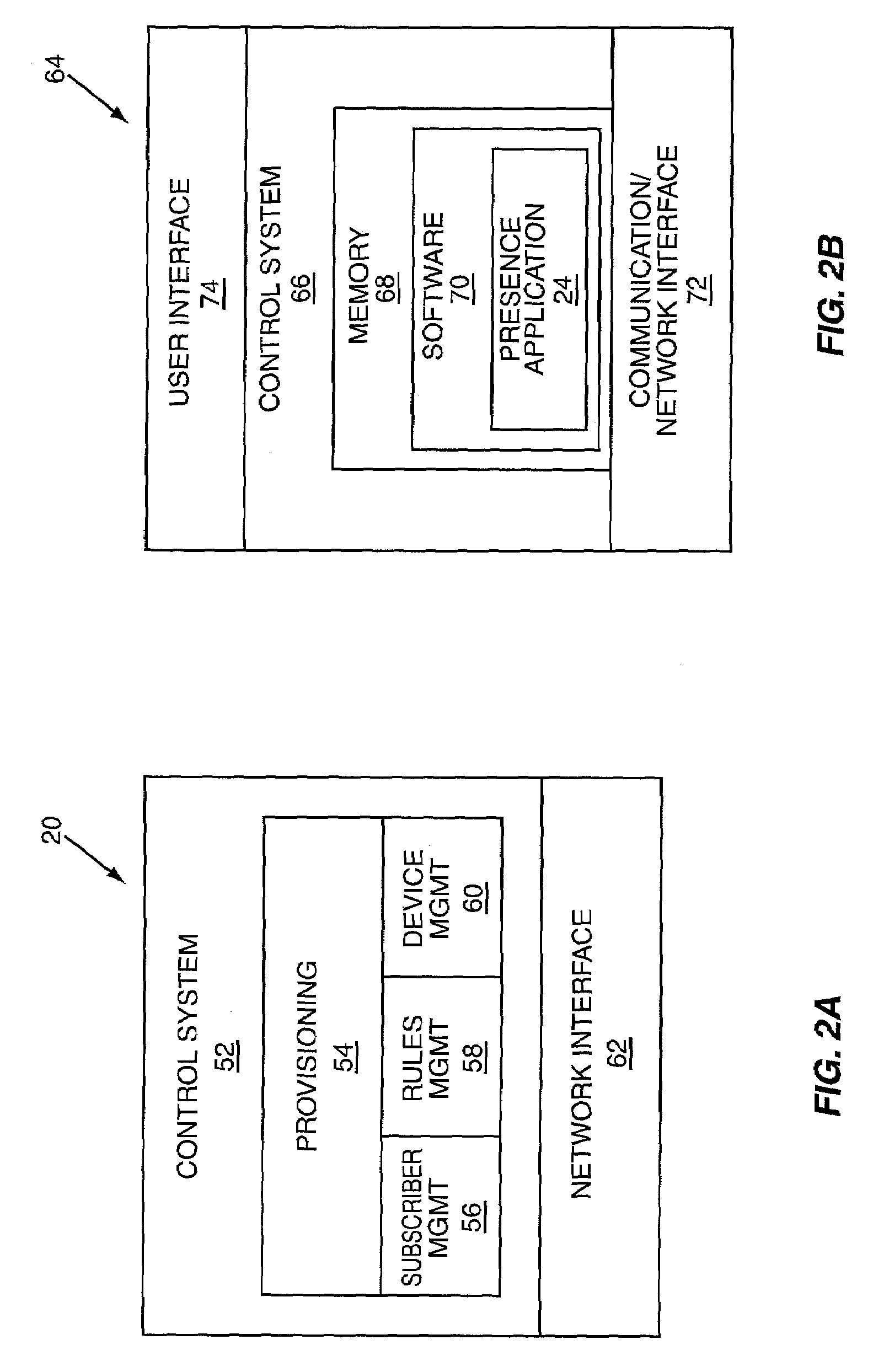
Presence information based on media activity
InactiveUS7139797B1Multiple digital computer combinationsTransmissionProviding presenceUser involvement
The present invention provides presence information to a subscriber indicative of the availability of a user who is already actively participating in a communication session. A presence system receives and processes participation information, which bears on the degree in which the user is participating in the communication session, and generates the presence information based on defined processing rules. The resultant presence information may indicate whether the user can be interrupted to accept other communications while engaged in the communication session. If the user can be interrupted, the presence information may also identify the most appropriate methods to contact the user during the communication session.
Owner:RPX CLEARINGHOUSE
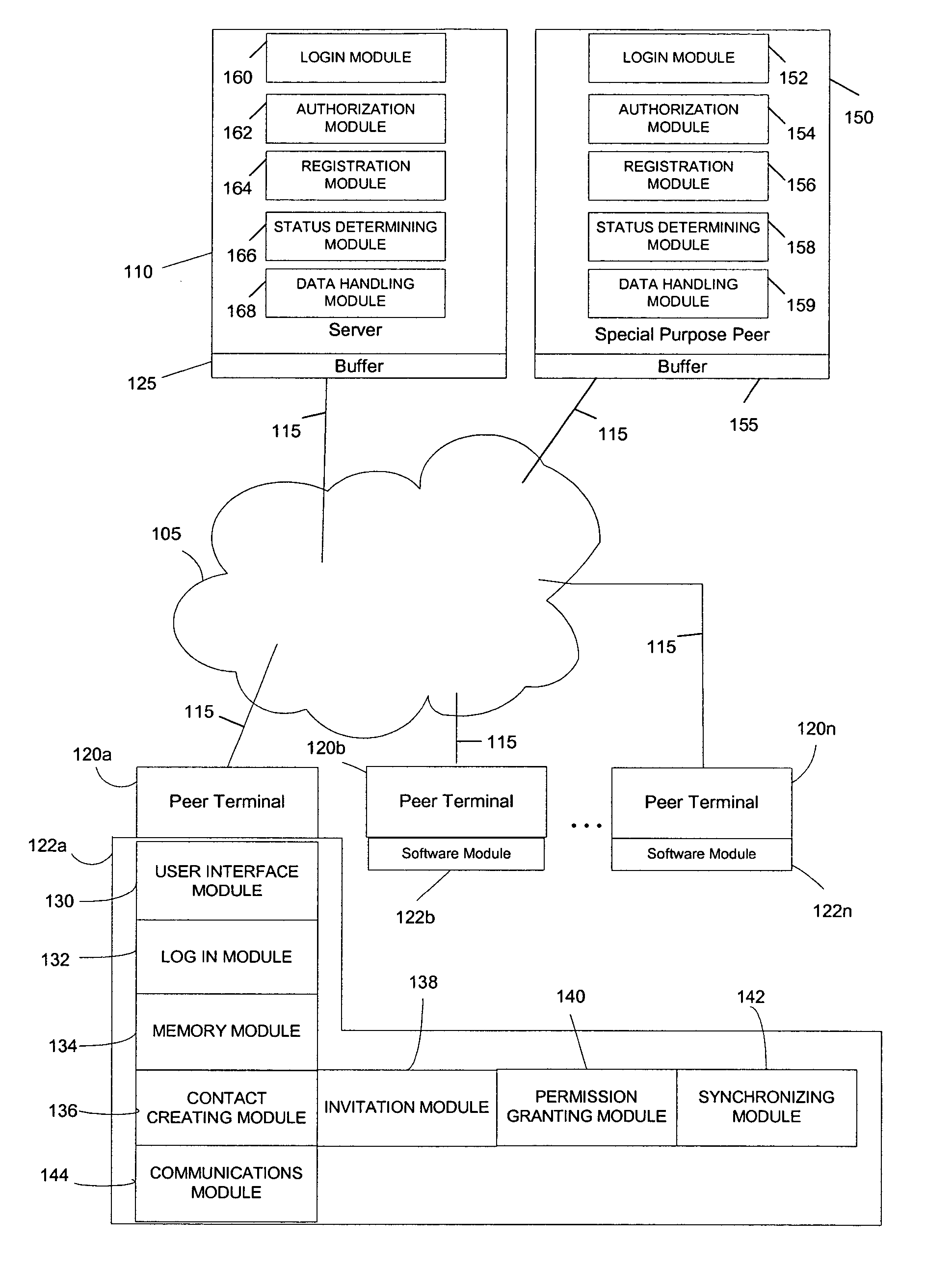
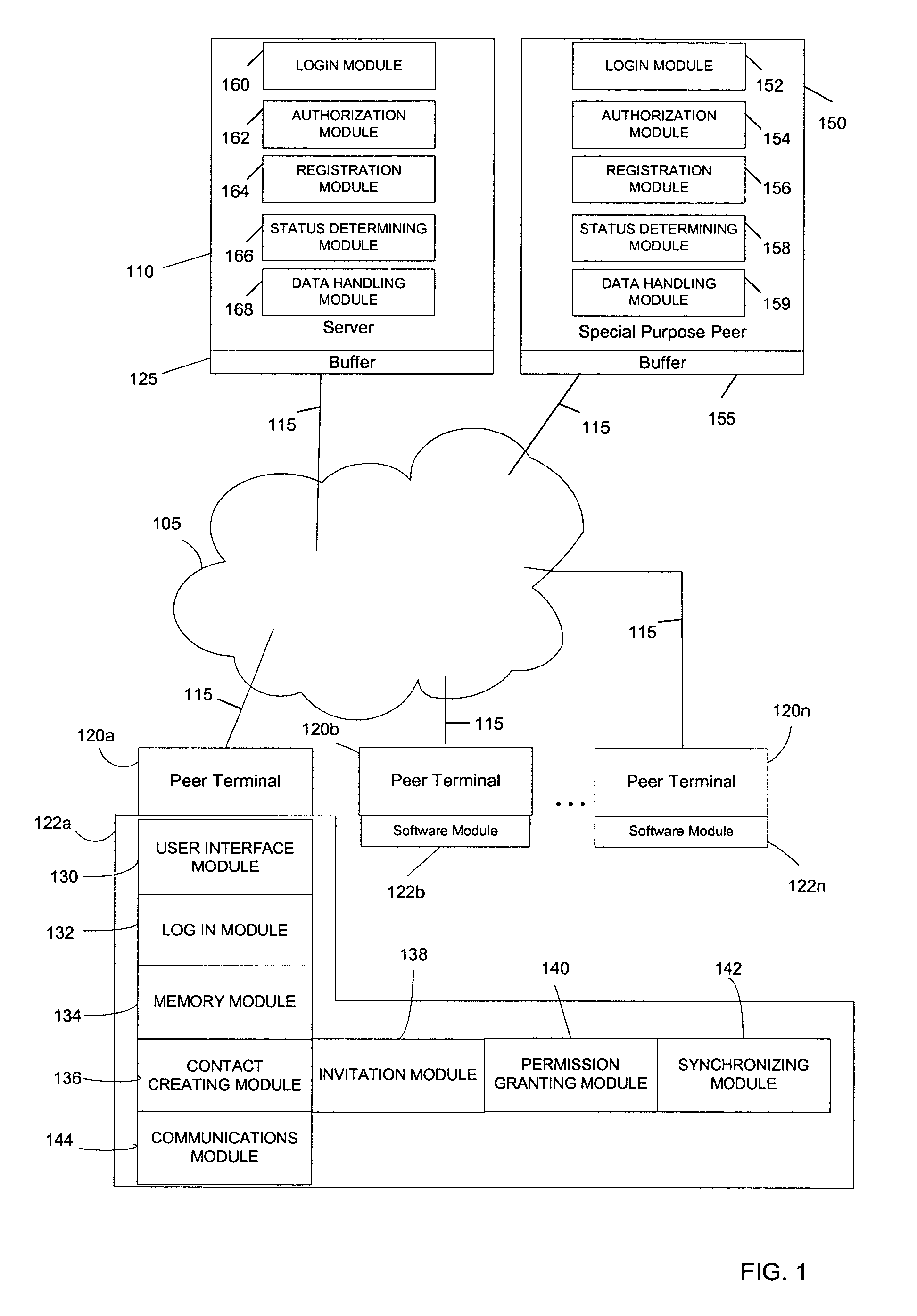
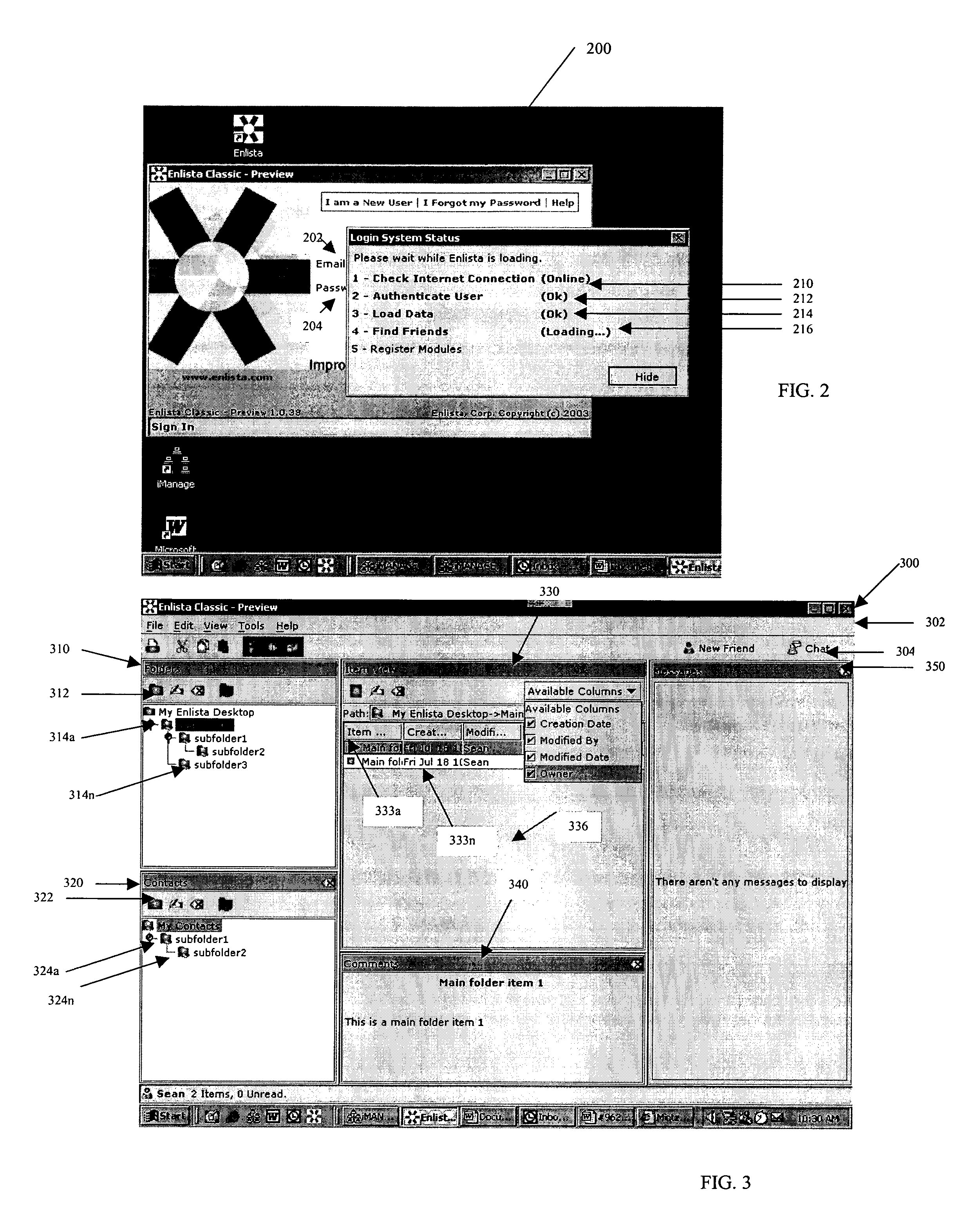
System and method for creating and selectively sharing data elements in a peer-to-peer network
InactiveUS20050091316A1Facilitate communicationFacilitate automatic synchronizationMultiple digital computer combinationsTransmissionInformation sharingData element
A system and method are provided for sharing information in a distributed peer-to-peer network wherein an information owner invites one or more trusted users to participate in information sharing and wherein the information owner designates permission levels for each of one or more trusted users. Upon accepting the invitation, the one or more trusted users may be granted with complete access, read only access, or blocked access to the shared information. The one or more trusted users may selectively decide to accept or decline to share information on a folder-to-folder basis. Any modifications made to the shared information may be disseminated to all the trusted users in real-time, upon log-in to a central server, or after a predetermined time delay.
Owner:ENLISTA
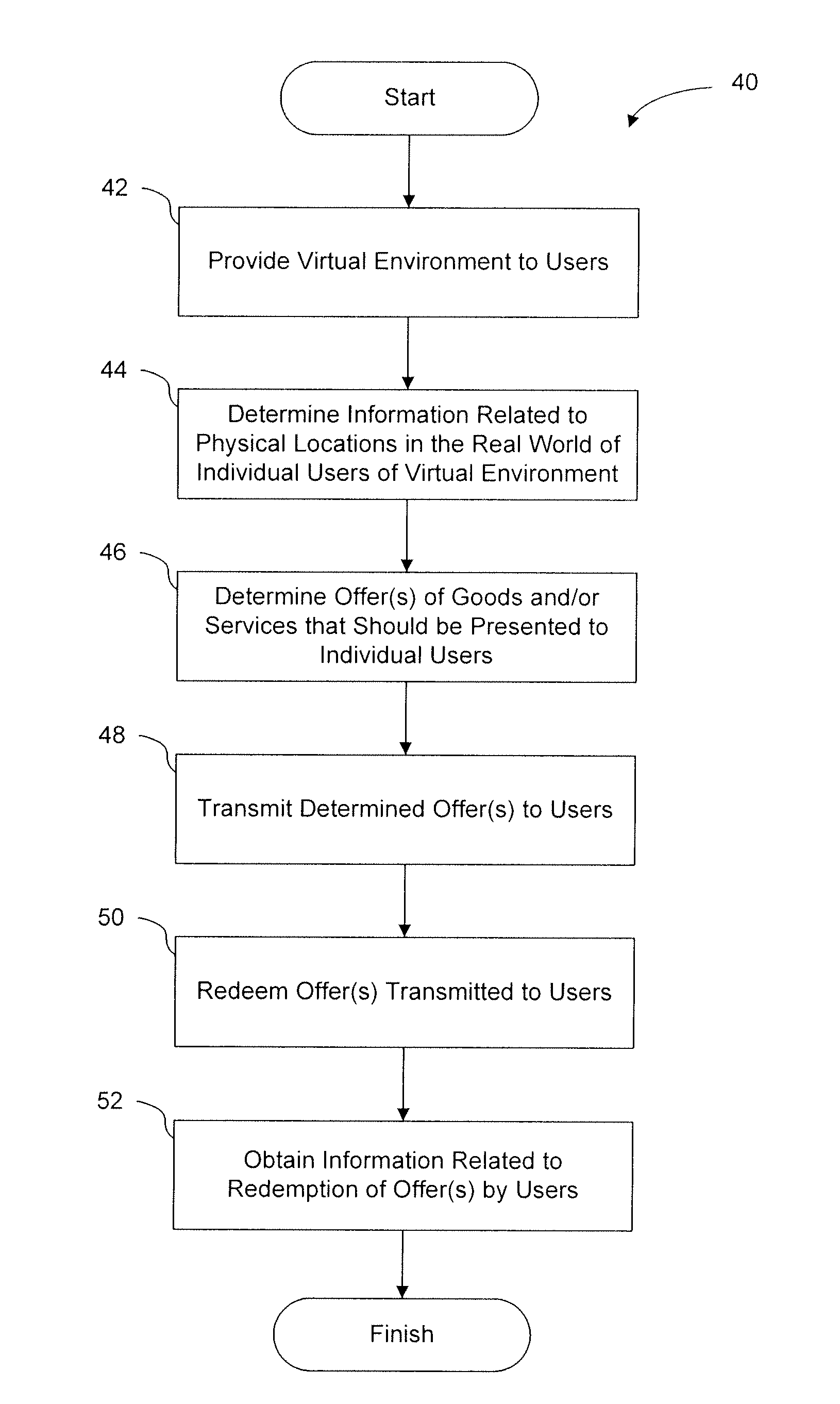
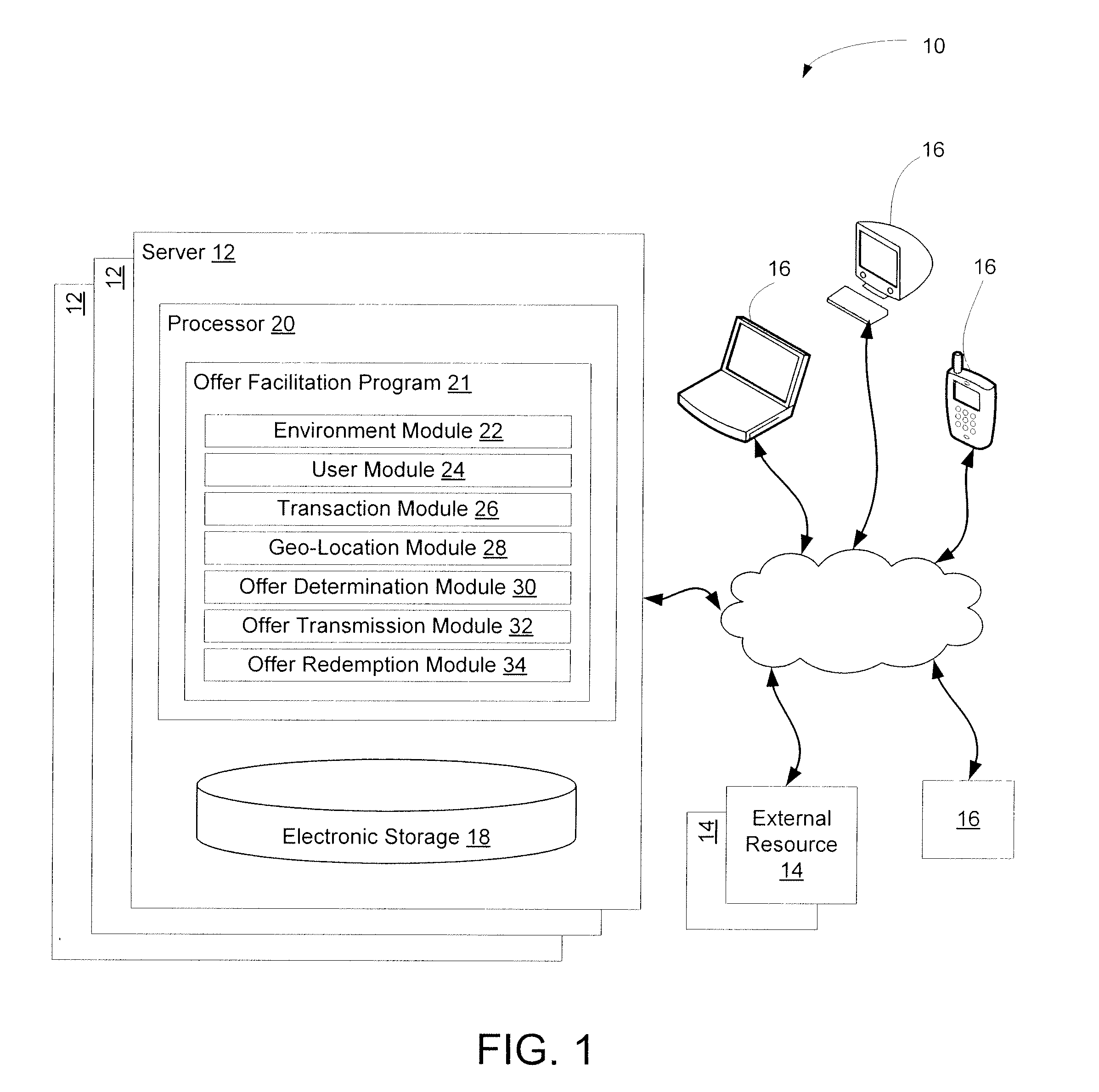
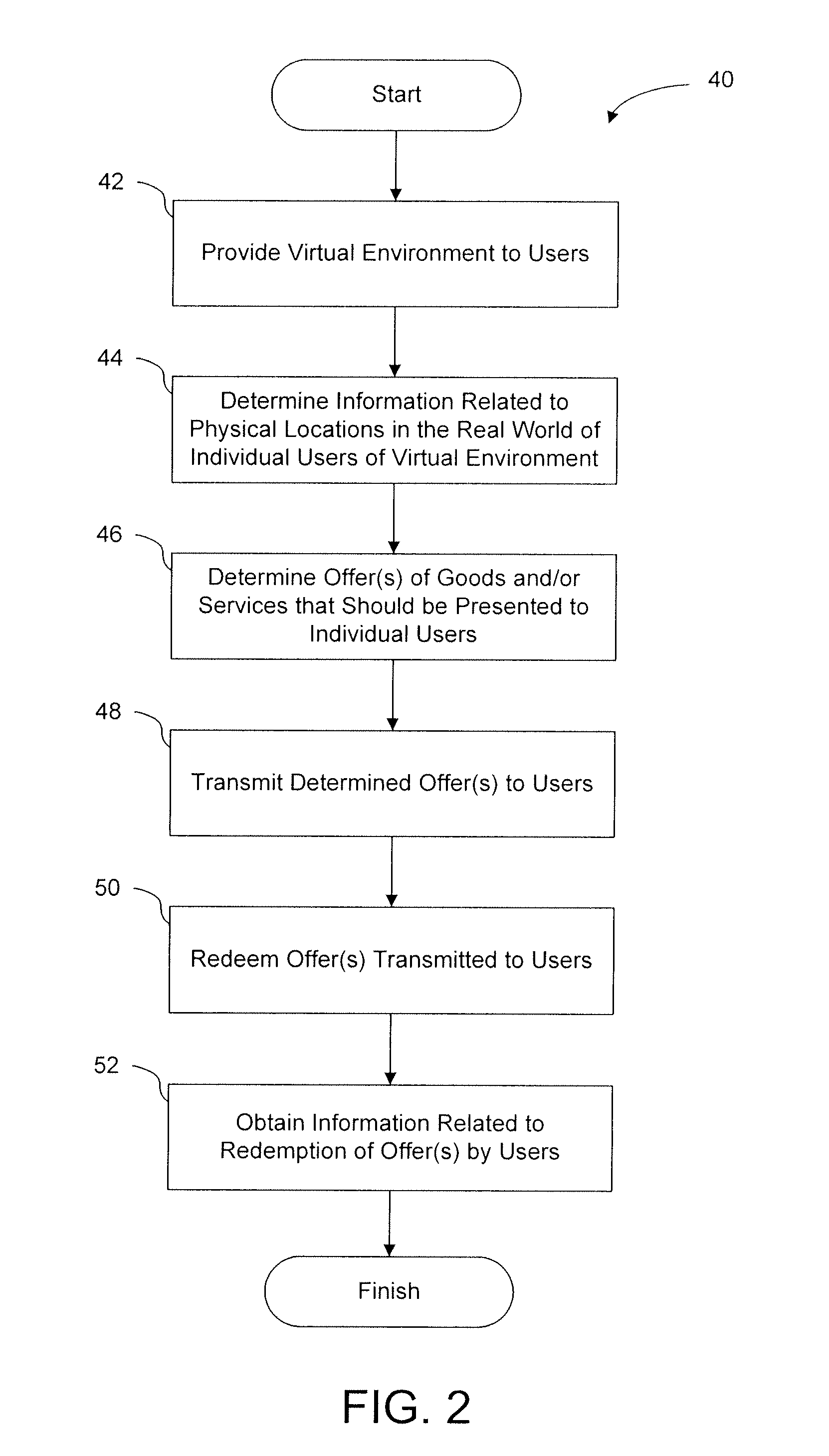
Providing offers based on locations within virtual environments and/or the real world
InactiveUS20120047002A1Improve immersionEnhance user retention and user enjoyment and other featureDiscounts/incentivesEnvironmental standardHuman–computer interaction
Owner:ENVIE INTERACTIVE
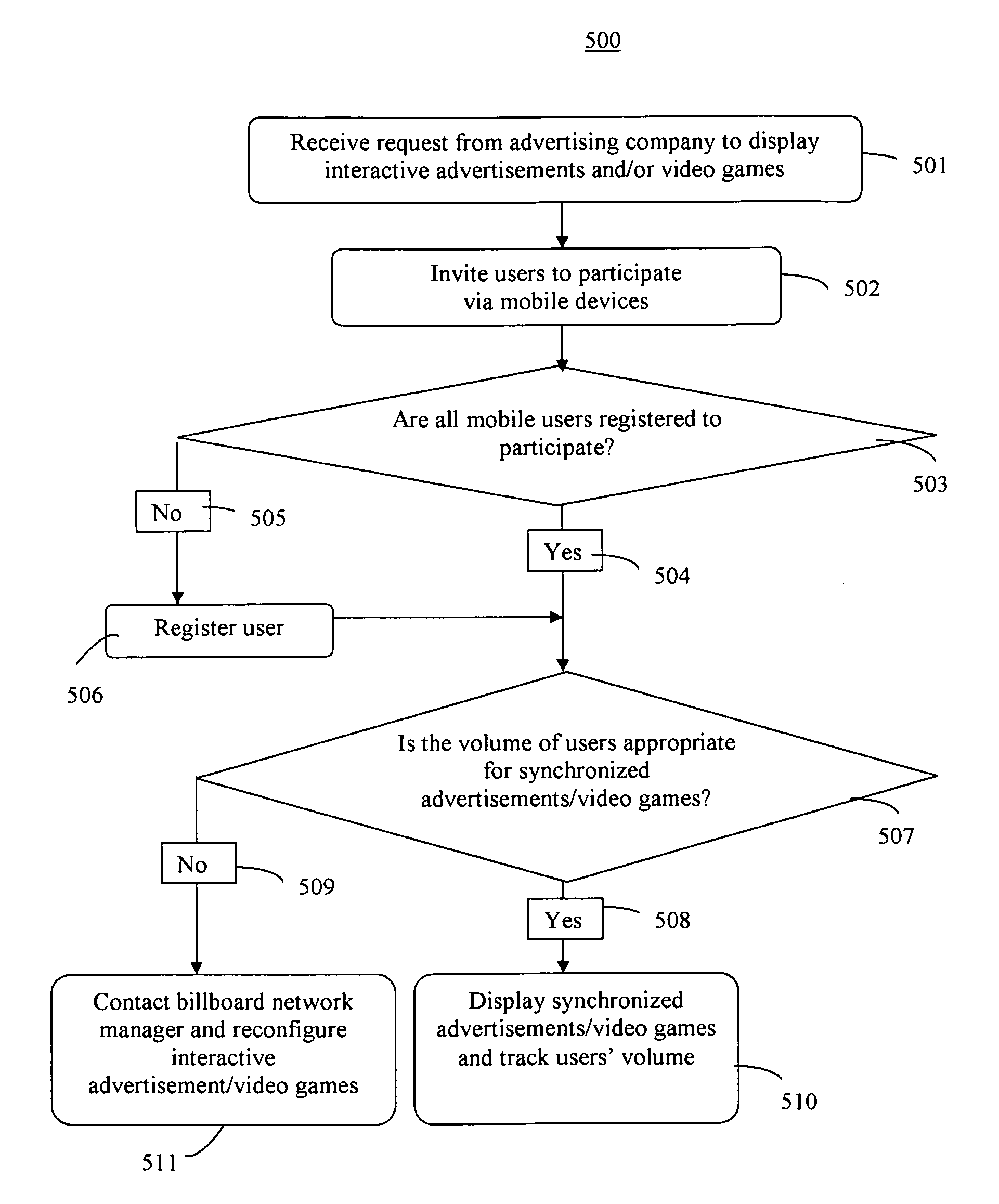
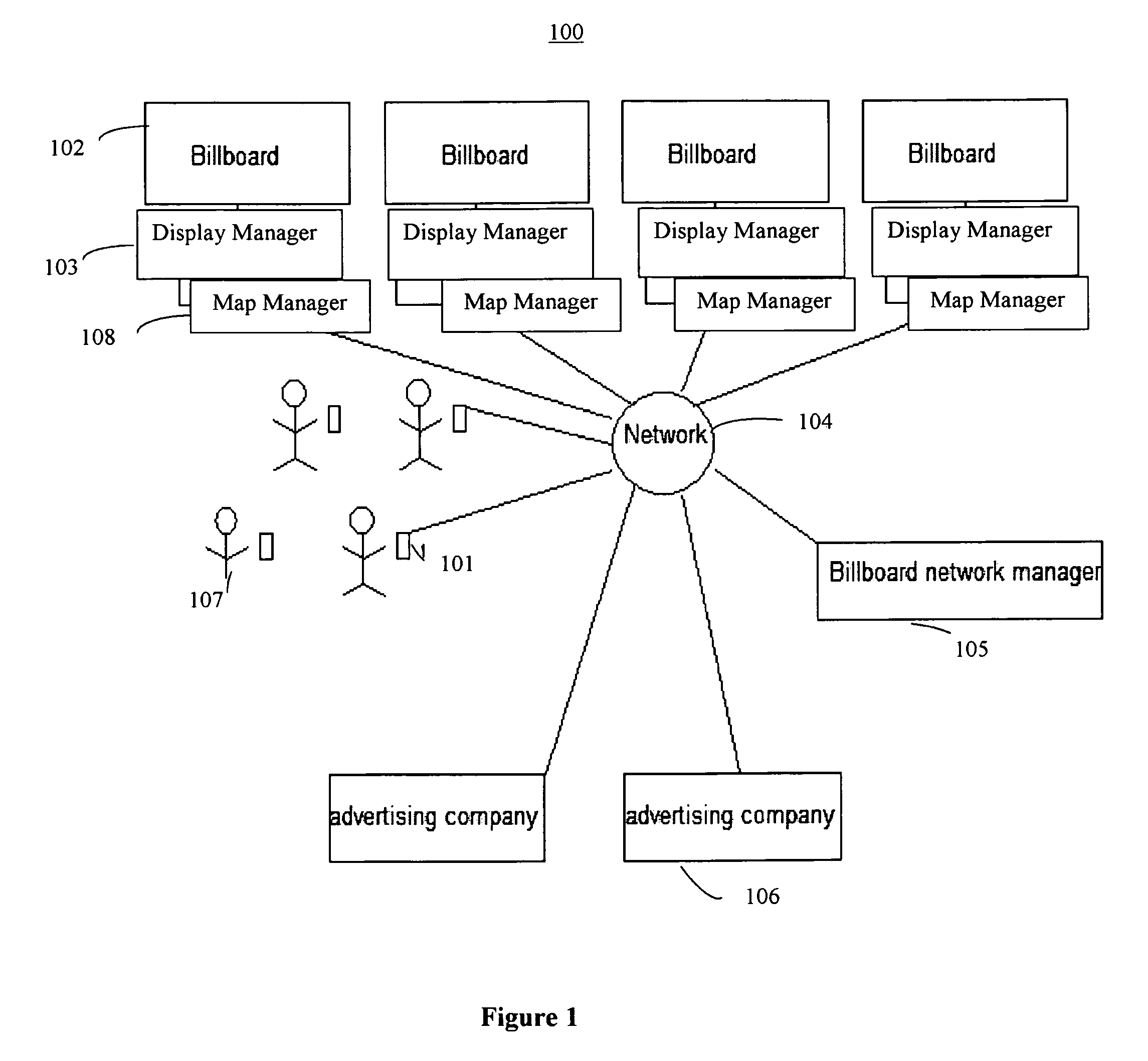
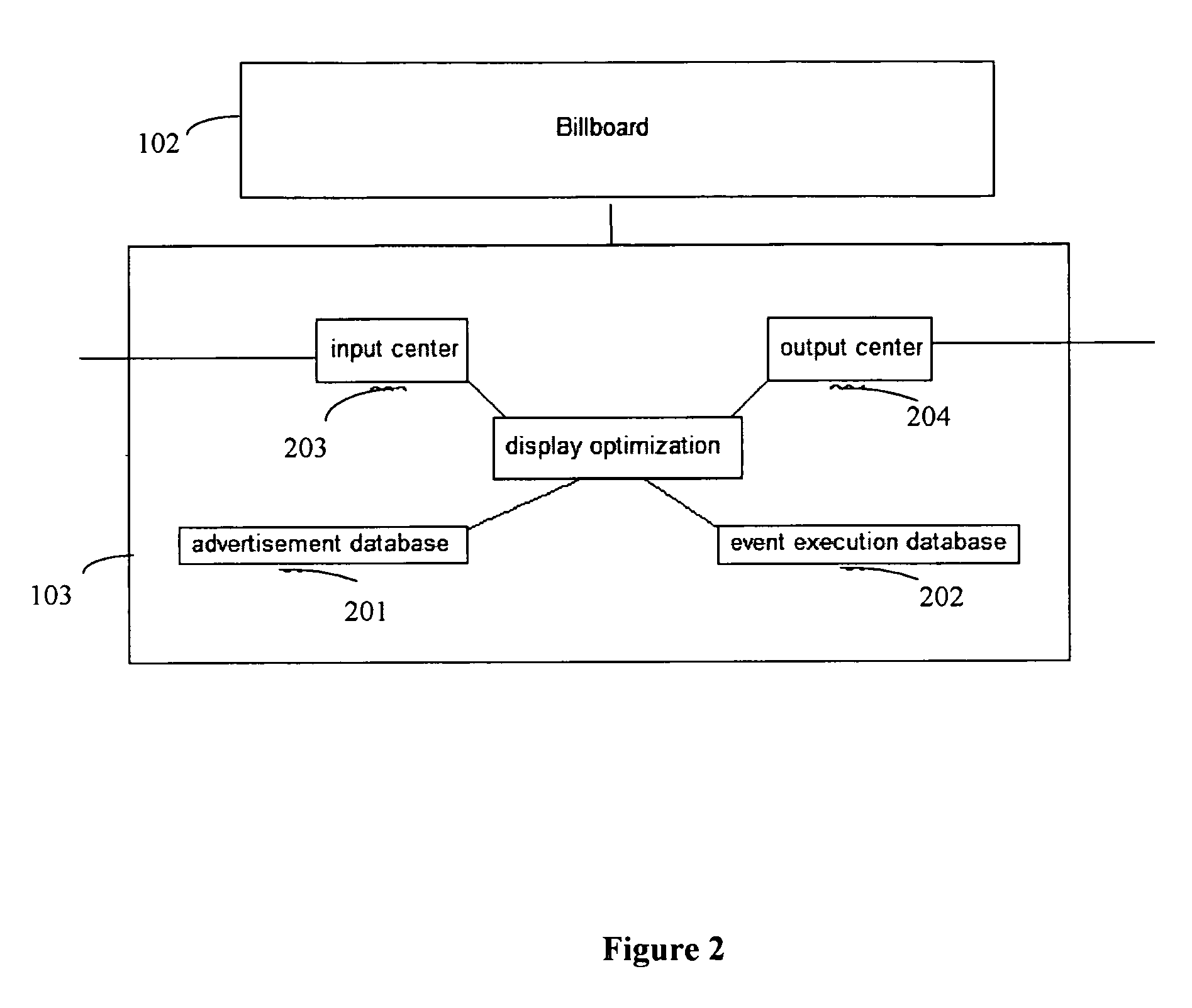
Collaborative and situationally aware active billboards
InactiveUS7515136B1Television system detailsCathode-ray tube indicatorsNetwork managementMobile device
A method of collaborative interactions with billboards includes receiving a request, by a billboard network manager, from an advertisement company to display synchronized interactive advertisements and video games on billboards in an area, inviting users in the area to participate in the advertisements and video games through the billboards and mobile devices of the users via a network, checking registration of the users to participate in the collaborative interactions with billboards, and checking a volume of the users in the area for appropriate synchronized advertisements and video games. If the volume of users is appropriate for synchronized advertisements and video games, then the billboard network manager displays the synchronized advertisements and video games, and continues to track the volume of the users in the area. If the volume of users is not appropriate for synchronized advertisements and video games, then the billboard network management reconfigures synchronized billboard content for more appropriate advertisements and video games by one of randomly changing a content, and propagating and extending through synchronized billboards a particular content of some billboard section that brought more interest from the users.
Owner:ACTIVISION PUBLISHING
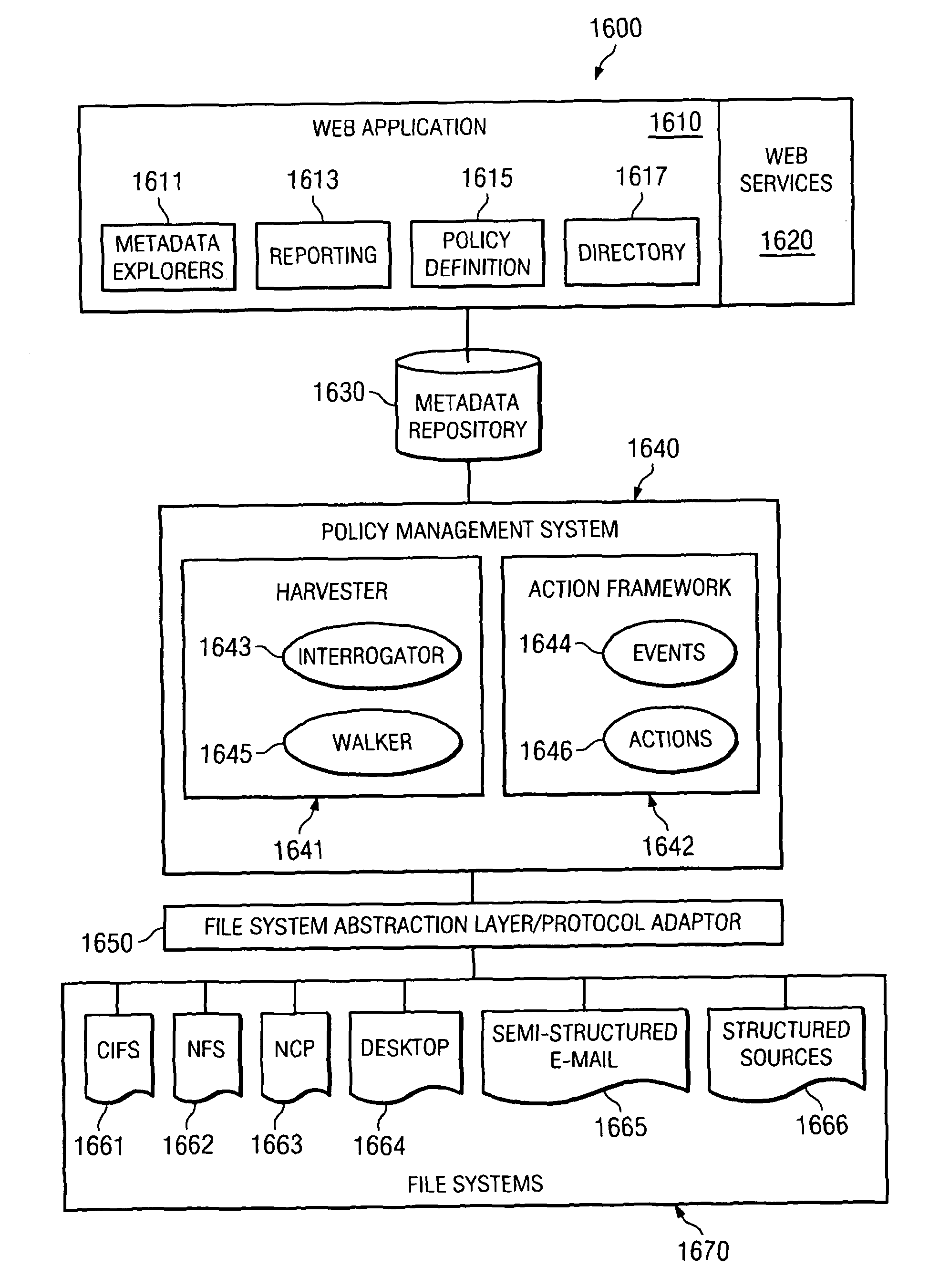
System and method for involving users in object management
InactiveUS7844582B1Digital data information retrievalDigital data processing detailsManagement systemUser involvement
Systems and methods for identifying objects in a managed storage environment with a user and involving the user with policy implementations or decisions associated with these objects are disclosed. These systems and methods may allow a single user identity for the managed storage environment to be assigned to a user and associated with a set of user identities, each of the set of user identities corresponding to the user's identity with respect to a particular domain. Previous or subsequent to establishing a user's enterprise wide identity, data and metadata may be obtained about objects residing in one or more of the domains in the enterprise as described in detail above. Objects within these domains can then be associated with a user using the set of user identities and a report generated for the user based upon these objects, including the policies associated with these objects.
Owner:IBM CORP
User interface for initiating activities in an electronic device
ActiveUS20120216143A1Improve expediencyImprove convenienceInput/output processes for data processingHome screenTouchscreen
In one embodiment, a user interface is presented for initiating activities in an electronic device. The user interface includes an element referred to as a “launch wave”, which can be activated at substantially any time, even if the user is engaged with an activity, without requiring the user to first return to a home screen. In various embodiments, the user can activate the launch wave by performing a gesture, or by pressing a physical button, or by tapping at a particular location on a touchscreen, or by activating a keyboard command. In one embodiment, activation of the launch wave and selection of an item from the launch wave can be performed in one continuous operation on a touch-sensitive screen, so as to improve the expediency and convenience of launching applications and other items.
Owner:QUALCOMM INC
System and method for identification of automated browser agents
Disclosed herein are methods and systems for evaluating web browser behavior to report on human versus non-human activity, based on varying analyses of detectable properties. By passively detecting the code of a webpage engaged by a browsing user, the present invention evaluates the browsing user's activity in order to predict the type of user with a degree of confidence. The predictions are formed by acquiring information on how a user loads, navigates, and interacts with a webpage and comparing that information with known and unknown properties in various control groups. If the prediction yields a high likelihood of automated activity, additional active detection may be performed. Reports are compiled by analysis servers and made available to the operators of webpages. By compiling performance metrics and informing operators of fraudulent versus normal activity, the invention combats malicious automated traffic directed at any aspect of a given webpage.
Owner:HUMAN SECURITY INC
Virtual universe subject matter expert assistance
ActiveUS8127236B2Knowledge representationInput/output processes for data processingSubject-matter expertSubject matter
Owner:ACTIVISION PUBLISHING
Method and system for providing a user interface application and presenting information thereon
InactiveUS20070214123A1Information obtainedSpecial data processing applicationsInput/output processes for data processingThe InternetUser interface
A presentation system and method provides a GUI application that allows presenting Internet information on electronic devices such as consumer electronic devices with minimal user key presses / commands. The user is enabled to browse / search for Internet information without having to enter queries, using a small number of key presses. Further the user is enabled to obtain desired Internet information with no or minimal user involvement in query construction.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for secure electronic communication in a partially keyless environment
InactiveUS7640427B2Reduce the burden onImprove securityPublic key for secure communicationMultiple digital computer combinationsDigital identityPlaintext
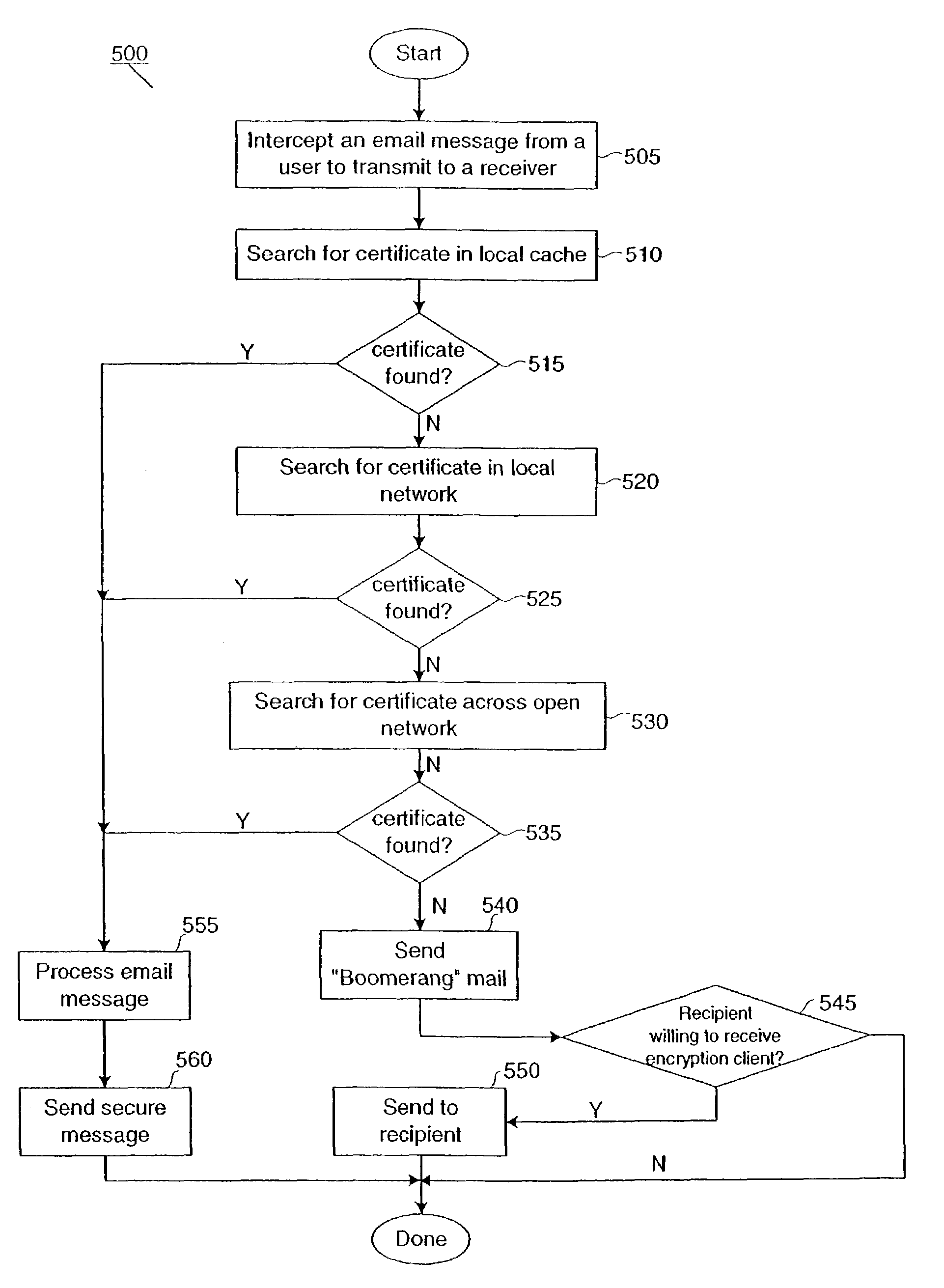
This present invention provides users with secure transparent electronic communication, allowing them to send and receive encrypted and / or signed messages with little or no user involvement. In various embodiments, the present invention provides a user with e-mail security via automated hierarchical techniques for transparently sending and receiving secure messages, and lowers the burden on administrators. Such a system can also manage cryptographic keys and certificates for the users, and creates such keys and certificates for the users when necessary. A server according to the present invention can intercept unsecured messages from a user, automatically transform those messages into secured messages, and transmit those secure messages to the intended recipients. The server can also automatically transform messages after the recipient sends a digital identity to the server and downloads the software necessary for transforming the secured messages back into readable messages (i.e., from ciphertext into plaintext). The server can further intercept an unsecured message from a user, search for a digital identity of the intended recipient, secure the unsecured message upon finding such a digital identity, and transparently send the secured message to the intended recipient.
Owner:CA TECH INC
System for Integrated Teleconference and Improved Electronic Medical Record with Iconic Dashboard
InactiveUS20080243548A1Easy fashionComputer-assisted medical data acquisitionOffice automationDashboardMedical record
A method for conveying complex or large amounts of data to a user in a readily understandable fashion. The method includes providing a computerized graphical user interface for displaying information to a user of the method, providing a reference database containing data pertaining to a field of endeavor engaged in by a user of the method, the reference database being stored on an electronic medium in communication with the computerized graphical user interface, streamlining by an automated process the data contained in the reference database such that at least a portion of the data is identified as being that which is pertinent to a problem being addressed by the user, displaying with the computerized graphical user interface at least a portion of the data identified as being that which is pertinent to a problem being addressed by the user, and displaying to the user with the computerized graphical user interface a graphical timeline illustrating a history of the problem being addressed by the user.
Owner:ICONIC HEALTH
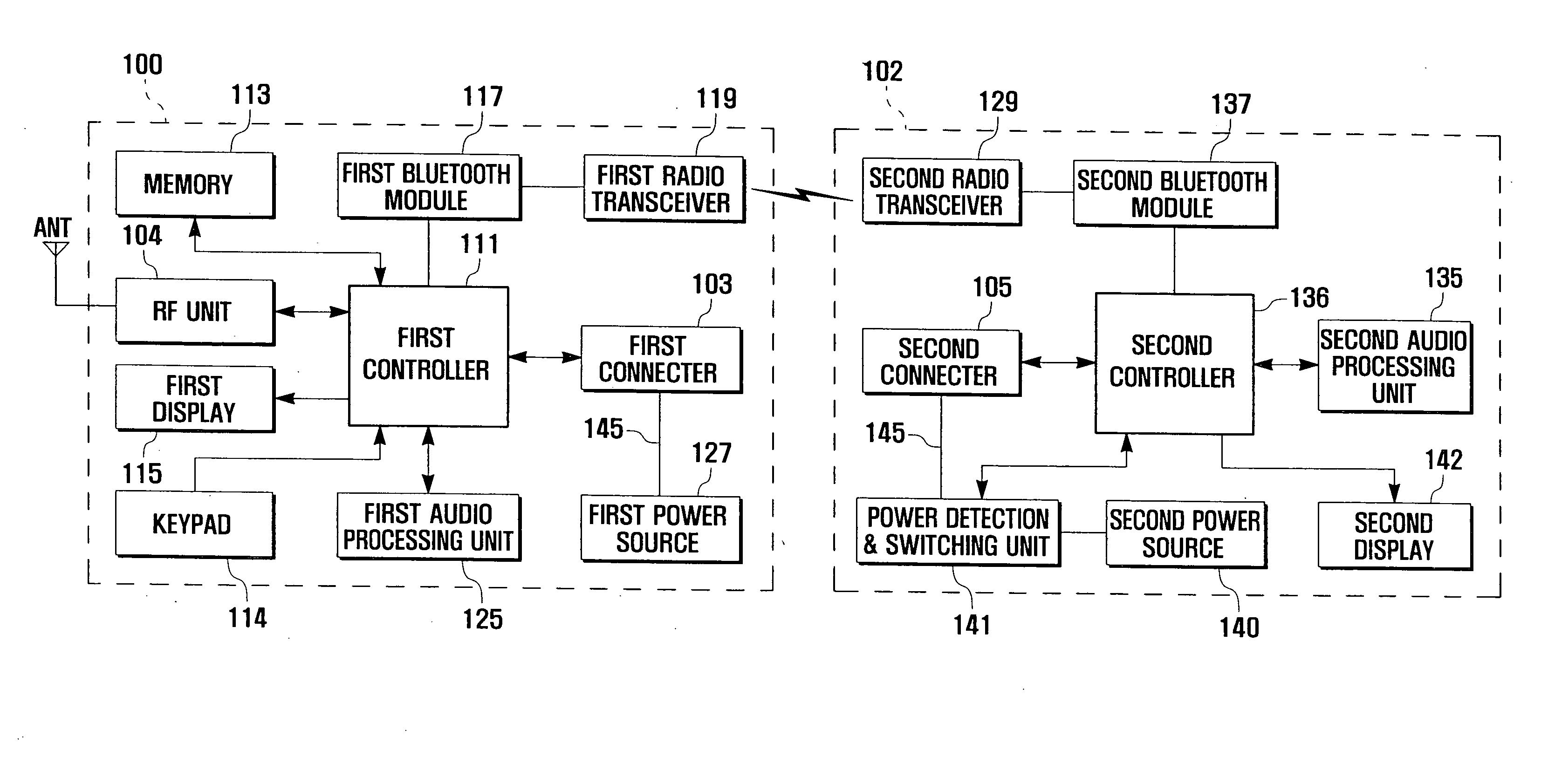
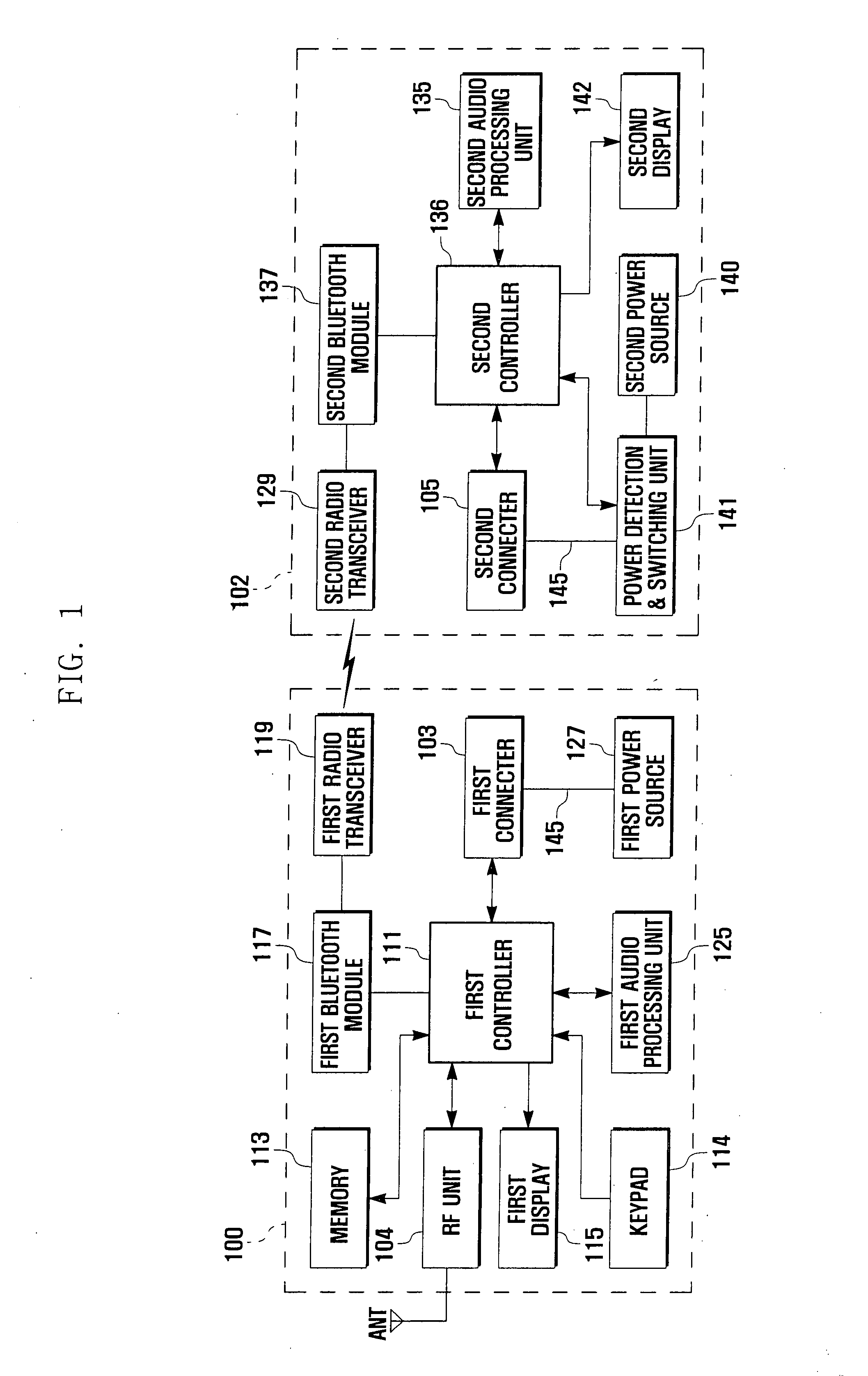
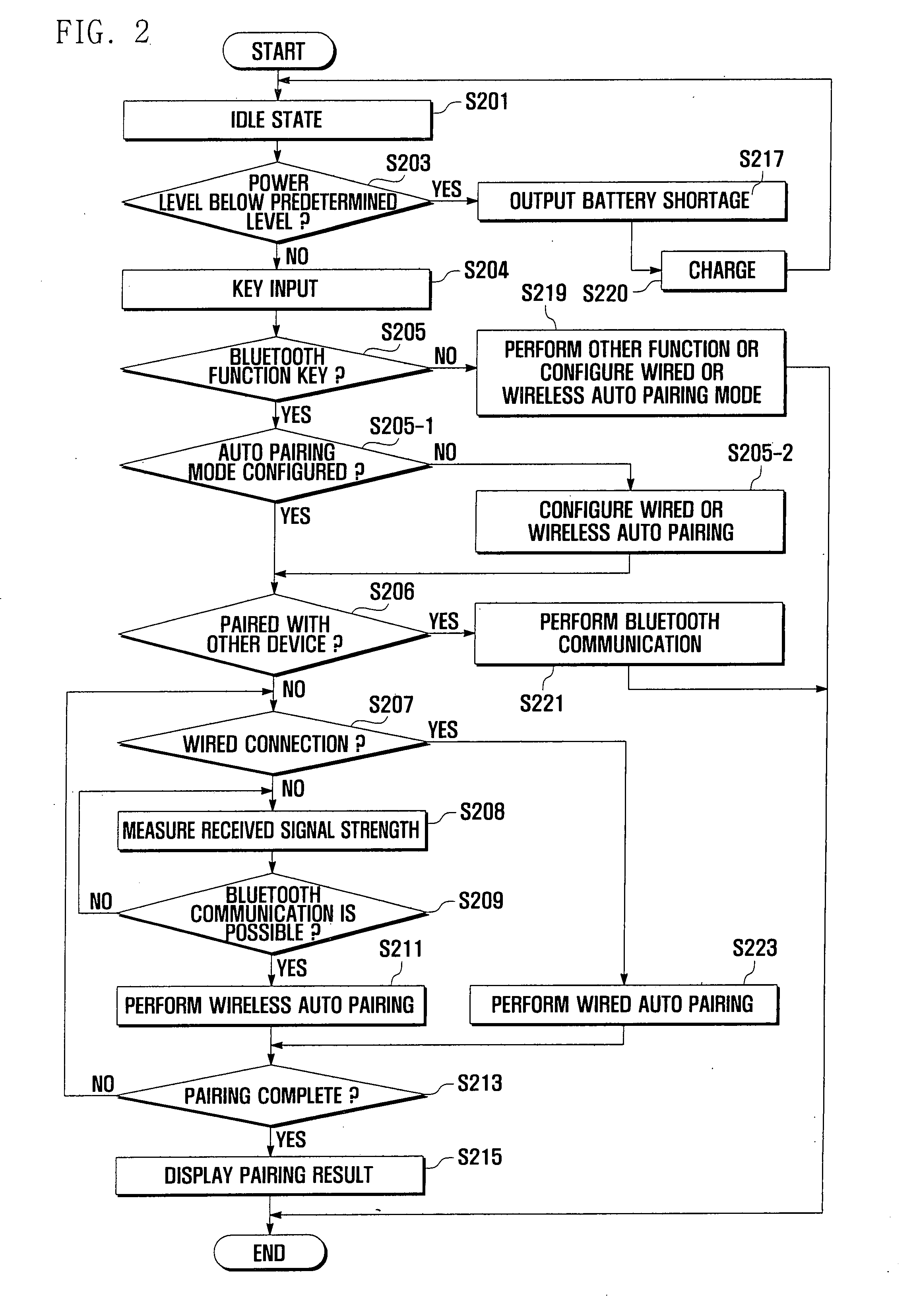
Auto pairing system and method for bluetooth network
An auto pairing system and method for a Bluetooth network is provided through a wired or wireless coupling. The method for pairing two devices of a short range wireless communication network includes configuring, at each device, a wired and wireless auto pairing of the devices; determining whether the devices are physically coupled with each other; and performing pairing between the devices if the devices are physically coupled. The auto pairing system and method for Bluetooth devices of the present invention enables Bluetooth devices to automatically perform an on-going pairing process through a wired connection or wirelessly in close proximity without a user involvement, thereby improving user convenience.
Owner:SAMSUNG ELECTRONICS CO LTD
Recovering data from arrays of storage devices after certain failures
InactiveUS6990611B2Reduce amountReduce the amount requiredRedundant hardware error correctionRAIDArray data structure
A method is disclosed for recovering data from a RAID system after a transient failure. After a transient failure, the cause of the failure is corrected and a user initiates a trust array command. The RAID controller receives the trust array command and performs several modifications to the disk metadata. First, the partition age metadata field is synchronized. Second, the primary dead partition map metadata field is cleared. Third, the partition status metadata field is set to initialized. Following the metadata modifications, the RAID controller verifies that it can access all of the drives in the array. If all drives are accessible, the array is on-line and fault tolerant without the need for re-constructing a drive within the array, or re-creating the array. If one drive remains inaccessible, data is available from the array, and the array is in a critical state. If two or more drives remain inaccessible, the array remains off-line and a partial recovery may be attempted. The trust array command may, in certain instances, be initiated automatically by the RAID system without any user involvement.
Owner:DOT HILL SYST
Information processing apparatus, information processing method, service providing system, and computer program thereof
InactiveUS7058897B2Easy to operateOffice automationInput/output processes for data processingInformation processingDrag and drop
An invention allowing the exchange of community cards within a virtual space by an easy operation. A display screen shown on the display section of the user terminal device is composed of a virtual space display for displaying three-dimensional objects in a virtual space, and a list window of belongings displayed by the user's own community cards. The user can move freely within the virtual space while referring to the virtual space display, and when conversing with other users within the virtual space and the user wants to let another user participate in the community the user himself belongs to, the user can present community cards corresponding to the avatar, to a user for newly participating in the community, by drag-and-drop of any of the community cards on the avatar.
Owner:SONY CORP
System and method for traffic violation avoidance
InactiveUS20180174446A1Avoid violationsData processing applicationsDetection of traffic movementDriver/operatorTraffic violation
A system and method for providing traffic violation avoidance guidance by categorizing traffic data into data types or user types corresponding to one another, the data and user types including one of commercial vehicle, non-commercial vehicle, vehicle type, vehicle plate type, motorcyclist, cyclist, or pedestrian, and generating notifications of potential traffic violations based on the user's location and type. A summary of differences between a first set of traffic rules associated with a first location and a second set of traffic rules associated with a second location may be generated based on the data type or the user type. The system and method may also analyze traffic data to predict potential traffic violations based on a user's location and type, and to provide a notification regarding the potential traffic violations to the user through a user engagement panel associated with a user's remote computing device.
Owner:OPERR TECH INC
Search method and system and system using the same
Information regarding the structure of information in a content database is maintained in a structure database. The structure database is used to correlate the data structure of a query to the structure of the content database, in order to determine that information in the content database which needs to be provided to a searcher in response to the query. In one embodiment, this search method is used in an online forum, and the forum maintains a reputation score for users with respect to given subject matter. The reputation score is dependent upon the quality of a user's participation in the forum. A user's reputation score depends upon the evaluation by others of information he posts and upon the user evaluating information posted by others.
Owner:TRANSPARENSEE SYST
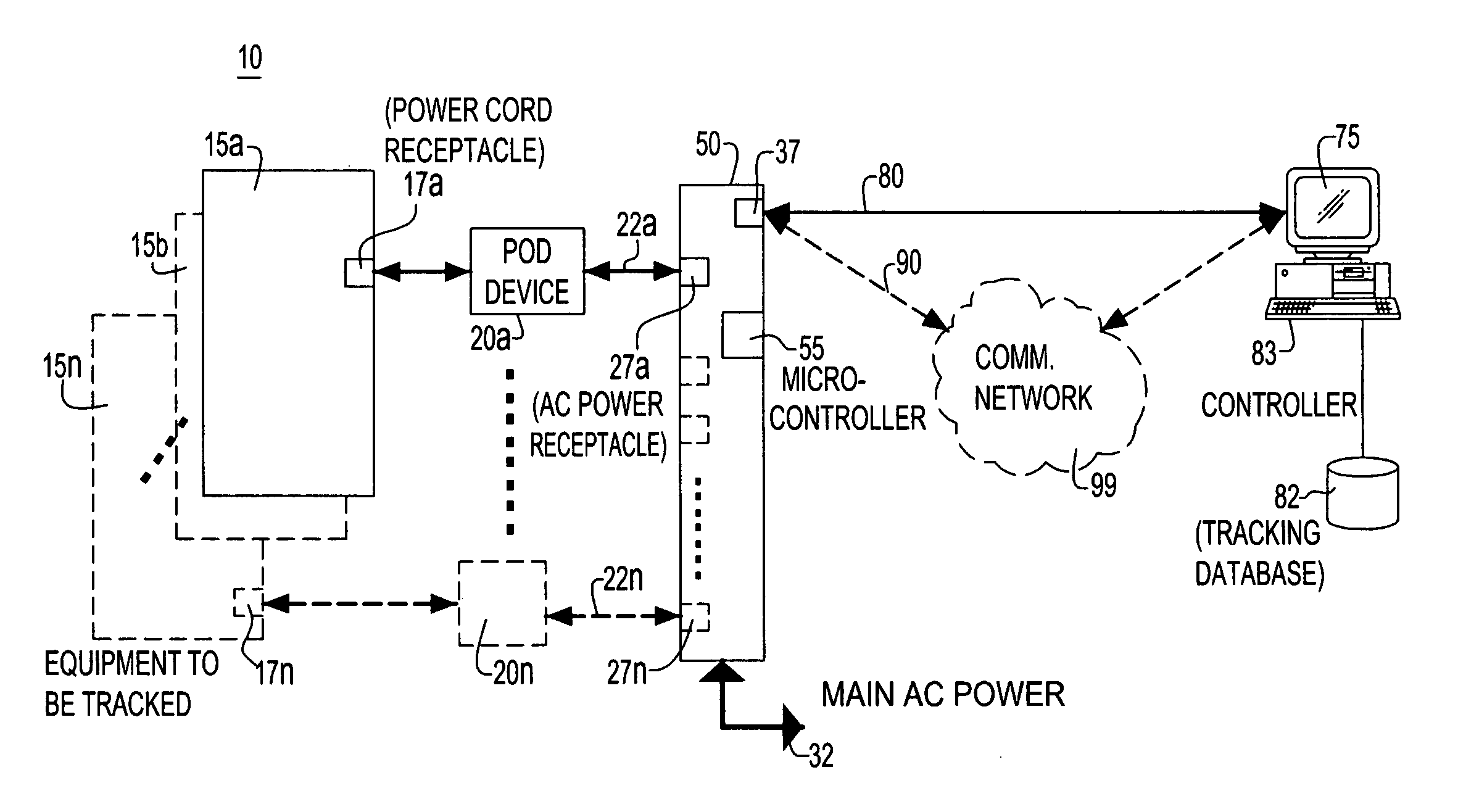
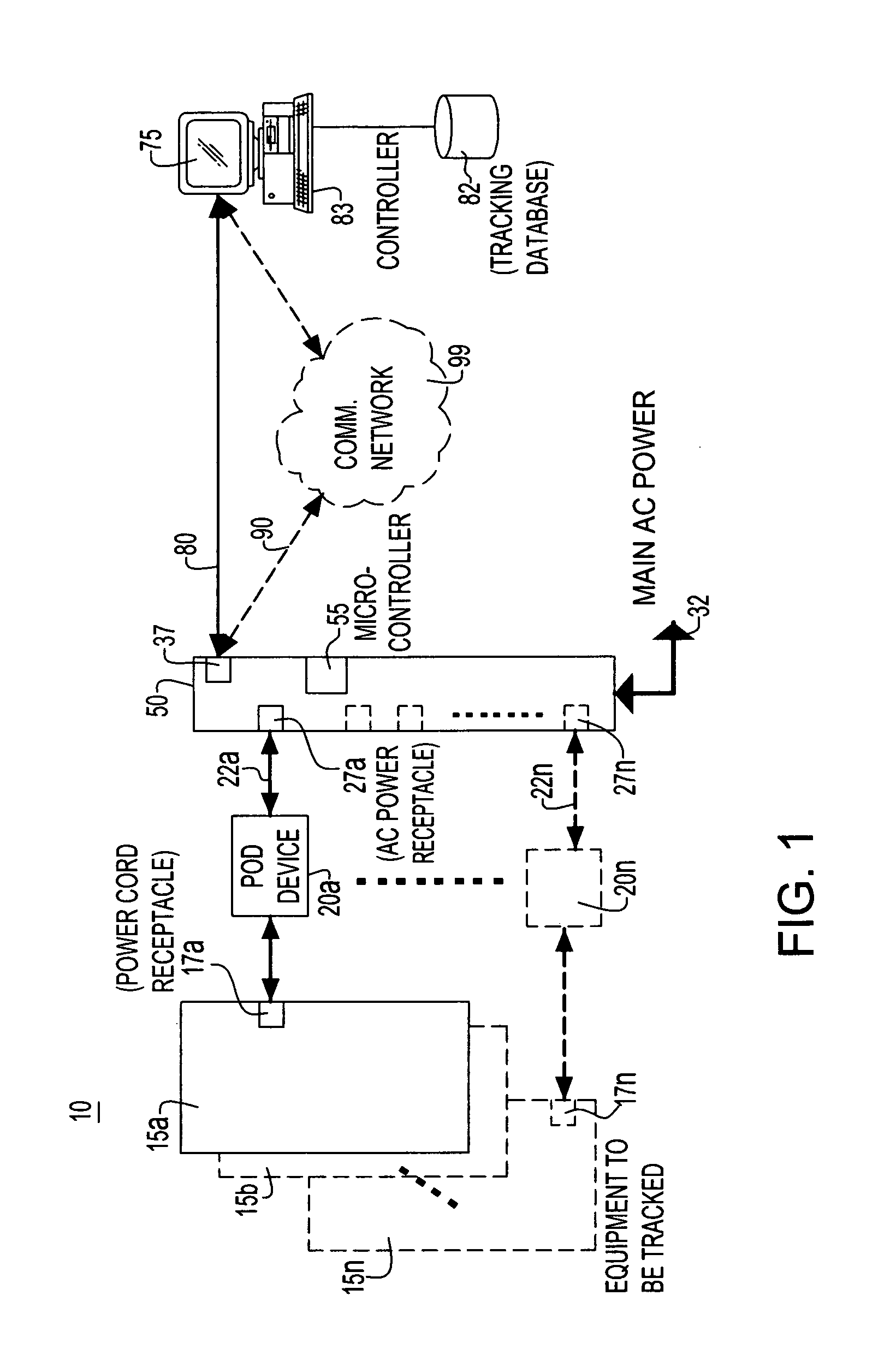
Tracking system and method for electrically powered equipment
InactiveUS7333000B2Simplify the management processProgramme controlElectric signal transmission systemsCommunications systemPower equipment
A novel system and method for simplifying the management of electronic equipment such as computers, networks, and equipment and communications systems. The system tracks equipment that has been registered in an inventory database without any user involvement. Once registered and connected into the system's power source device, the equipment's location will be easily tracked without human intervention. This information may be used to locate systems in need of up grade, repair or relocation, and further can verify that the correct equipment was moved and that it was moved to the correct location.
Owner:SICORE TECH
Method, system, and program for allocating storage resources
InactiveUS20040230317A1Computer controlInput/output processes for data processingComputerized systemResource based
Provided are a method, system, and program for allocating resources, wherein the resources are capable of being configured from a computer system. User interface elements are rendered enabling user selection of a plurality of strategies concerning allocation of computational resources, including a participation strategy having one of at least two values indicating a degree of user involvement in the allocation of computational resources and at least one configuration strategy specifying a configuration for the resource allocation. Selection of a plurality of resource allocation constraints is enabled if the selected value for the participation strategy is a first value. Selection of one of a plurality of configuration modes is enabled if the selected value for the participation strategy is a second value. An allocation is made of the resources based on the selected at least one configuration strategy and one of the selected resource allocation constraints or the selected configuration mode.
Owner:SUN MICROSYSTEMS INC
Detecting sexually predatory content in an electronic communication
InactiveUS7444403B1Efficient detectionEfficiently provideData processing applicationsComputer security arrangementsElectronic communicationMessage passing
A system and method for detecting an electronic communication such as an email, an instant messaging session, or a chat session that relates to an unsafe behavior directed to or engaged by a user. Instructions are adapted to analyze one or more features of the electronic communication, which is sent or received by the user. Instructions are adapted to categorize the electronic communication as relating to the unsafe behavior based on the analyzed features. A report is generated if the electronic communication is categorized as relating to the unsafe behavior. Instructions are adapted to send the report to a responsible person such as a parent, guardian, or other responsible person of the user. The report informs the responsible person that the electronic communication possibly relates to the unsafe behavior.
Owner:MICROSOFT TECH LICENSING LLC
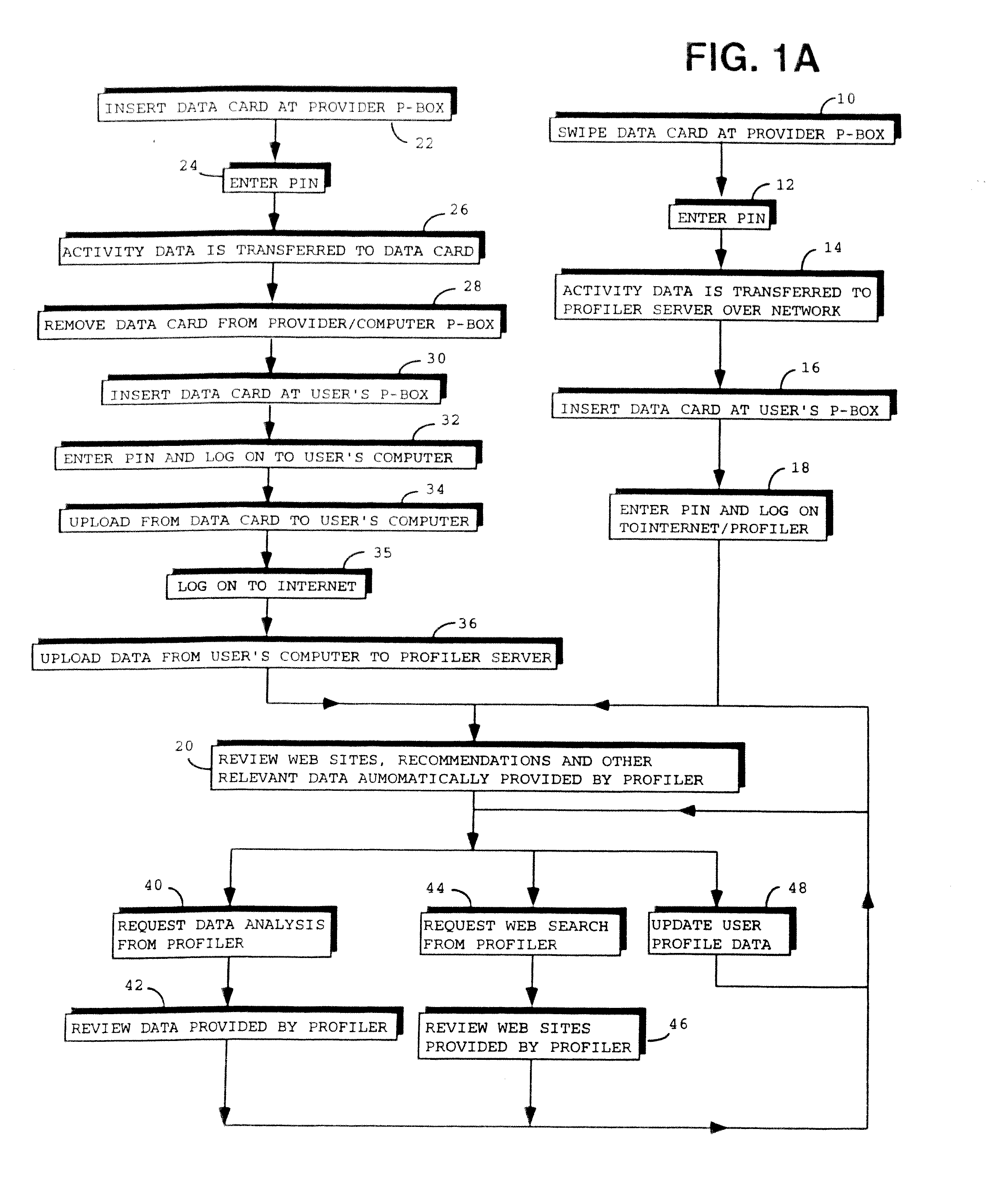
Method for Providing Information and Recommendations Based on User Activity
A method for providing recommendations to a user based on user activity. A plurality of activity data tracking a plurality of activities of a user is obtained. The activity data may be obtained over a wide area network such as the internet or downloaded from a data card which stores activity data whenever the user participates in an activity. The activity data is either stored on the data card or transmitted over the network whenever the user uses a card when participating in any activity such as when making a purchase of goods, paying for services, watching television, etc. The activity data is processed to identify a plurality of user patterns. The user patterns are used to form a user profile and may include user habit data. Recommendations specific to the user based on the user patterns are then created for and provided to the user. The recommendations are provided to a user when the user logs onto a computer network such as the internet. The recommendations may also be provided by electronic mail, electronic pager or other methods. The recommendations are provided by various data analysis techniques including rule based inference engines and other forms of artificial intelligence.
Owner:PERSONAL DATA NETWORK CORP
Edge detection in ultrasound images
InactiveUS20090080738A1Easy to detectMinimal user involvementUltrasonic/sonic/infrasonic diagnosticsImage enhancementPattern recognitionImaging processing
Embodiments of the present invention improve edge detection in 2-dimensional image data that may be carried out automatically with minimal user involvement. The invention is carried automatically, using an image processing technique that results in generation of a segmented edge contour, which may then be used in 3-dimensional reconstruction and segmentation.
Owner:BIOSENSE WEBSTER INC
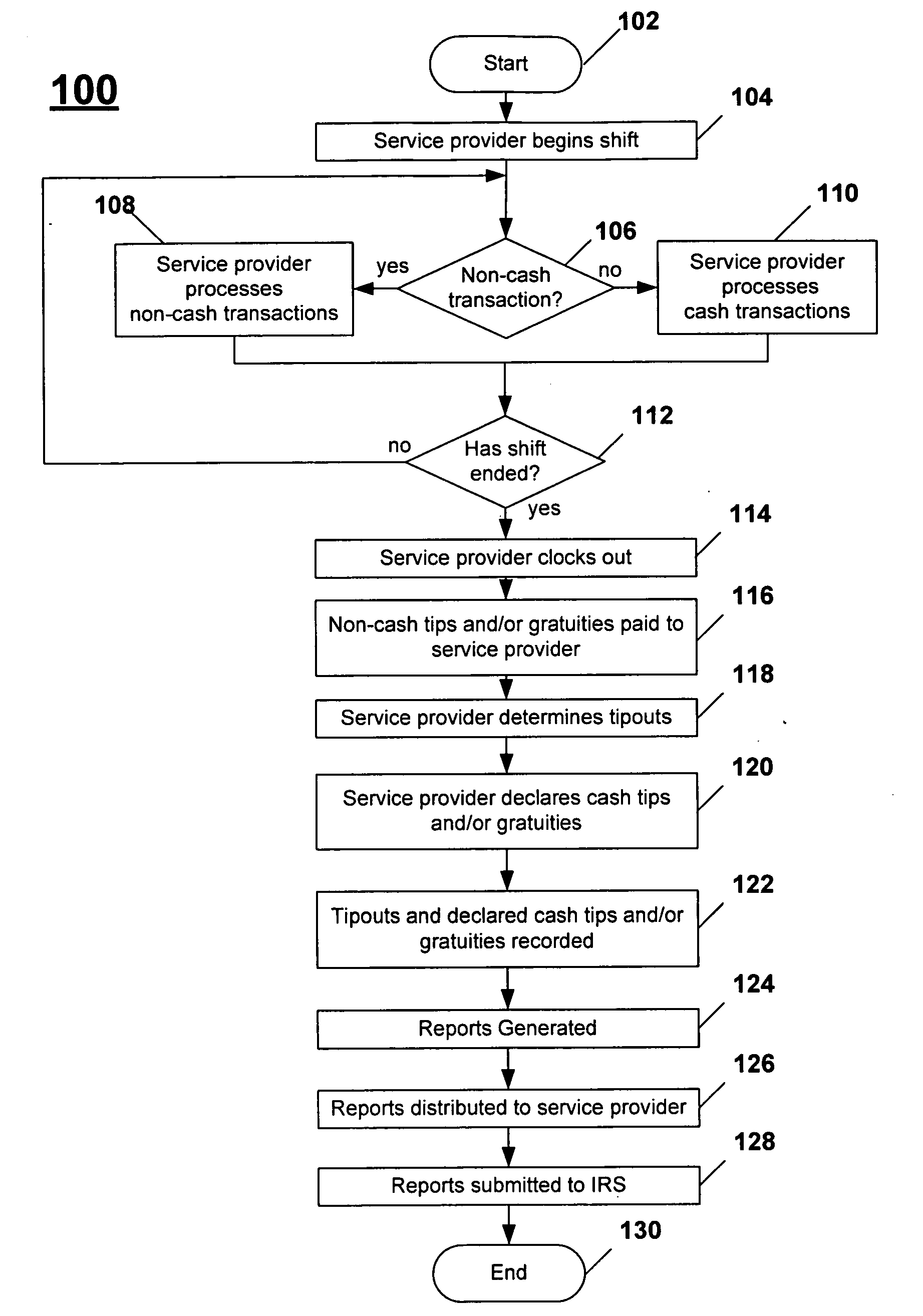
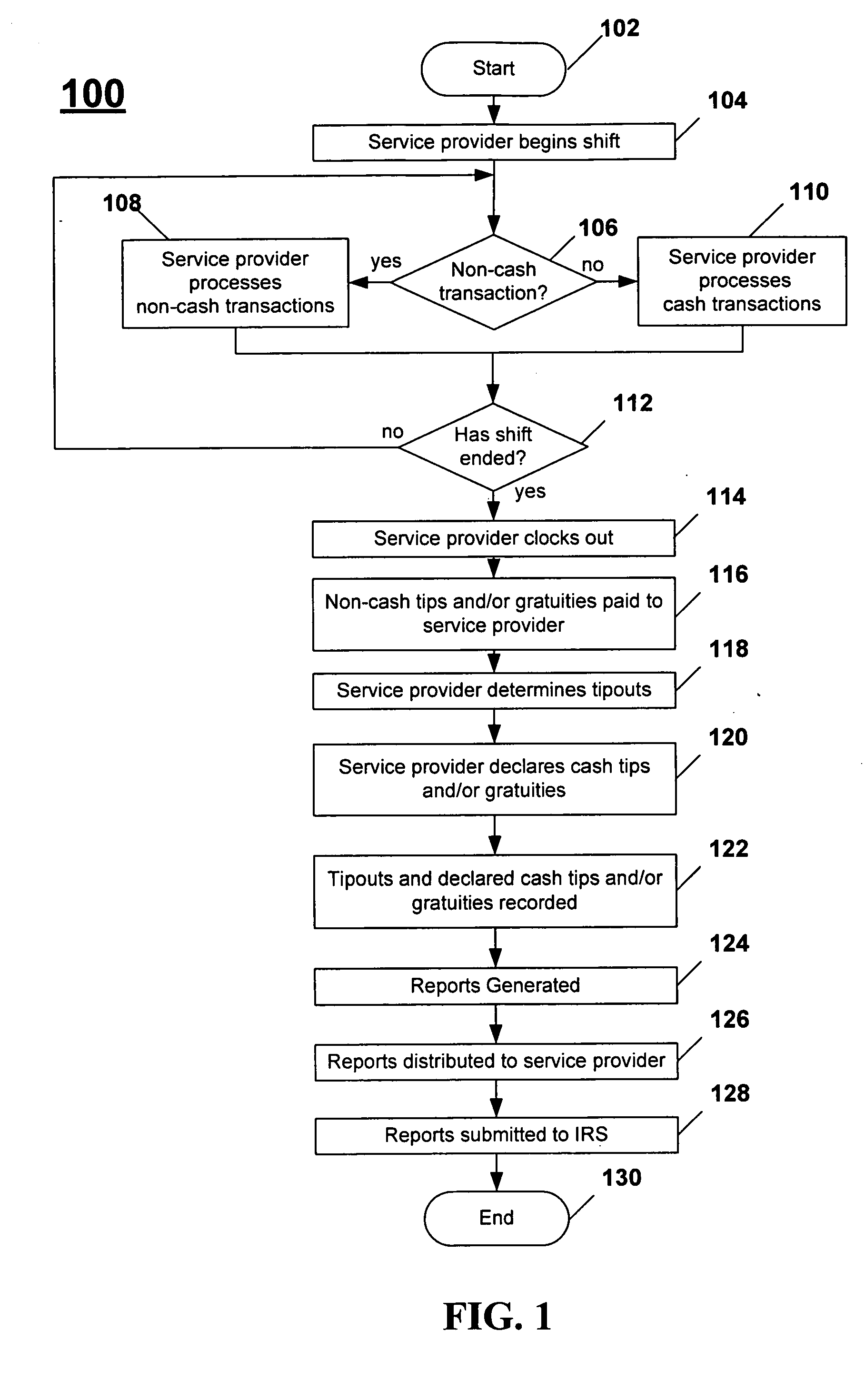
Systems and methods for managing tips and gratuities
Disclosed are systems and methods for recording, maintaining, and reporting tips and gratuities, optionally including details such as employee, task performed, and shift. In one aspect, inter-employee tip and gratuity transactions are tracked and verified. In another aspect, taxing authority forms and / or returns are automatically generated with substantially decreased administration time and cost, thereby facilitating a user's participation in voluntary taxing authority programs. Additionally, the training required by such programs is automatically monitored. In yet another aspect, tips and / or gratuities may be paid as wages. In another aspect of the present invention, employees are provided an opportunity to increase declared tips if the originally declared tips place employee in jeopardy of an audit. In another aspect, interfaces to third-party systems such as POS systems, payroll systems, and the like are provided to further minimize system administration time and data accuracy. In another aspect, Web-based systems are provided.
Owner:MARSHALL JOHN STEVEN
Group Electronic Purchase
InactiveUS20120226614A1Facilitates social ecommerceEncourage online purchasesFinanceCommercePaymentFinancial transaction
Payment for a purchase is facilitated wherein members of a group contribute to the payment. A memory can store account information for a plurality of contributing users and for a purchasing user. A processor can be operable to receive a communication indicating an agreement of each of the contributing users to participate in a group purchase transaction. The participation can include transferring money from the contributing users to the purchasing user. The processor can be further operable to access accounts of the contributing users and the purchasing user, transfer money from the accounts of the contributing users into the account of the purchasing user, and authorize the group purchase transaction with a merchant for the purchasing user. In this manner, a more expensive item may be purchased, such as for a gift, than may be purchase by an individual member of the group.
Owner:PAYPAL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com