Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
714 results about "Novel technique" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A novel technique developed by MIT researchers compresses “objects” in memory for the first time, freeing up more memory used by computers, allowing them to run faster and perform more tasks simultaneously. Image: Christine Daniloff, MIT.
System and method for dynamically generating, maintaining, and growing an online social network
InactiveUS20060048059A1Grows and increase in functionalityOvercomes drawbackDigital data information retrievalCharacter and pattern recognitionCommunity systemSocial web
Owner:CONCERT TECH
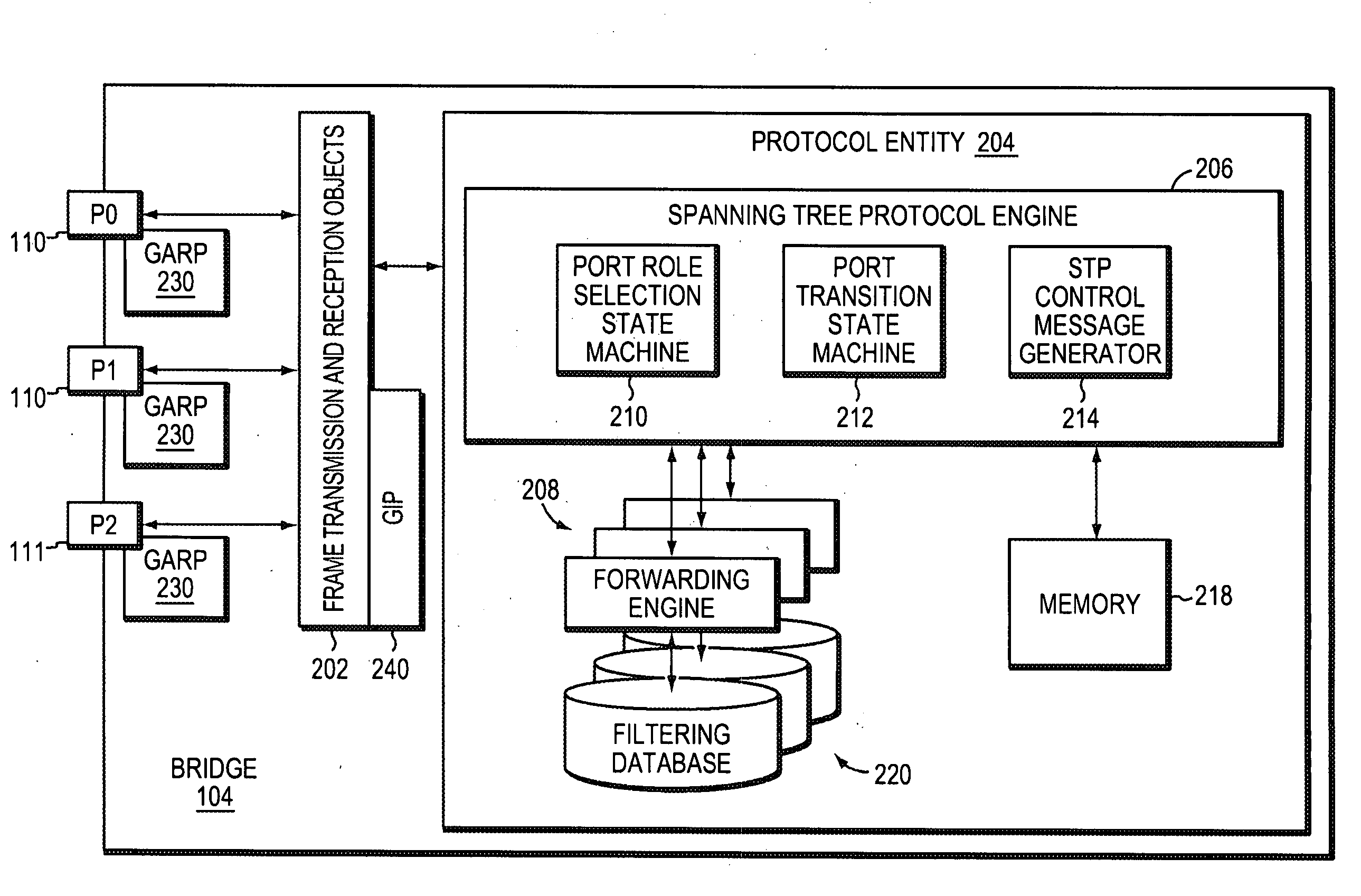
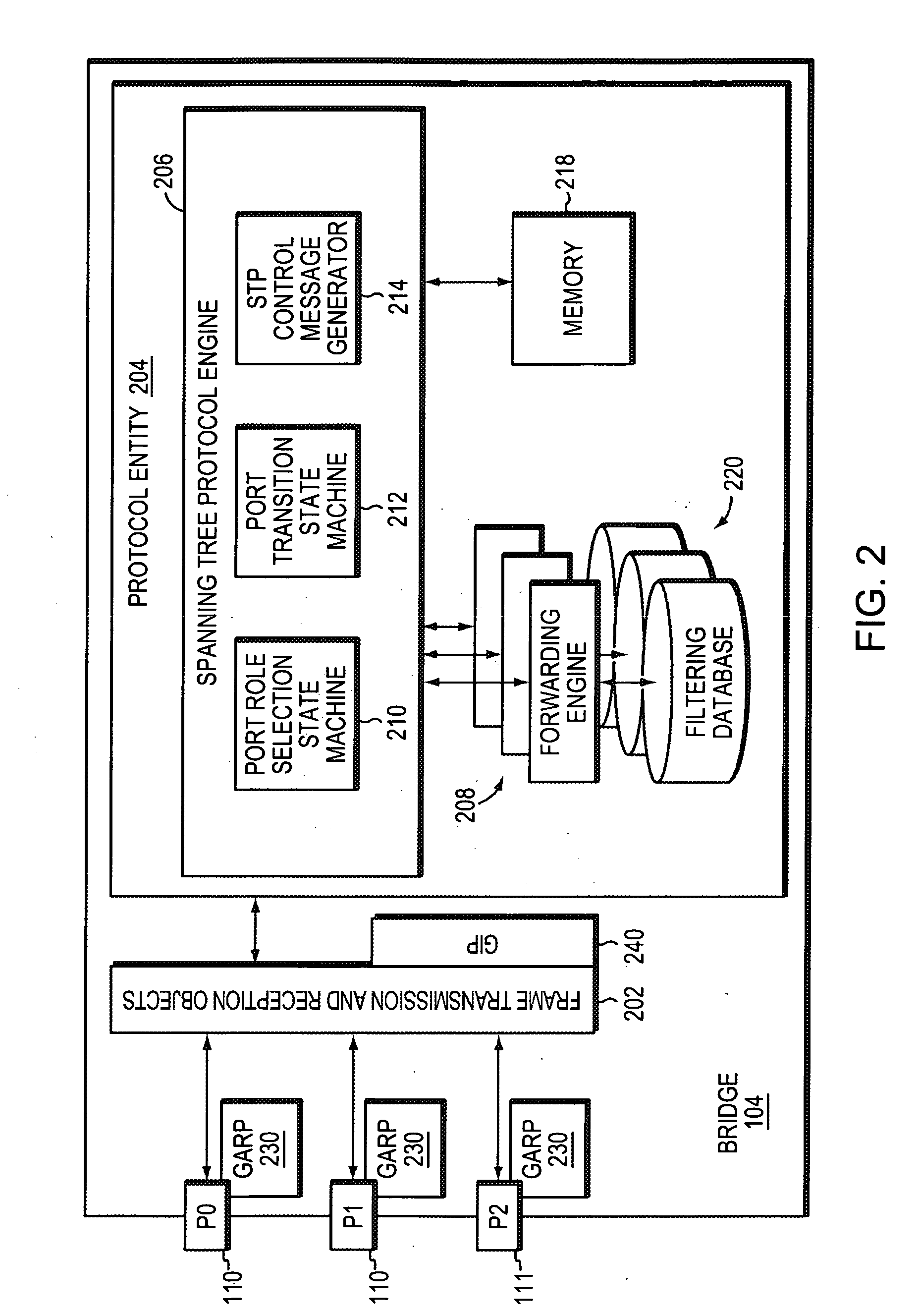
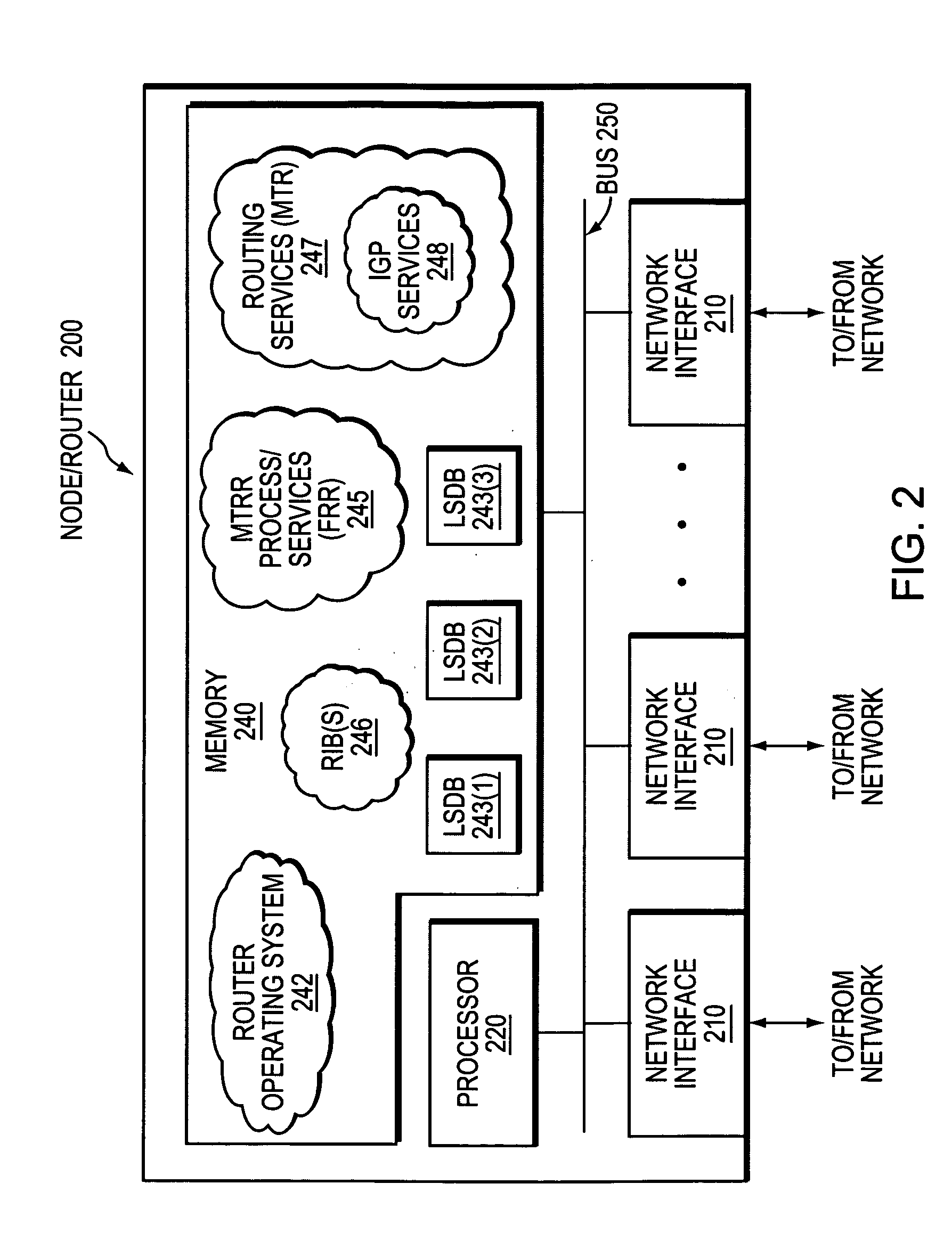
Dynamically configuring and verifying routing information of broadcast networks using link state protocols in a computer network
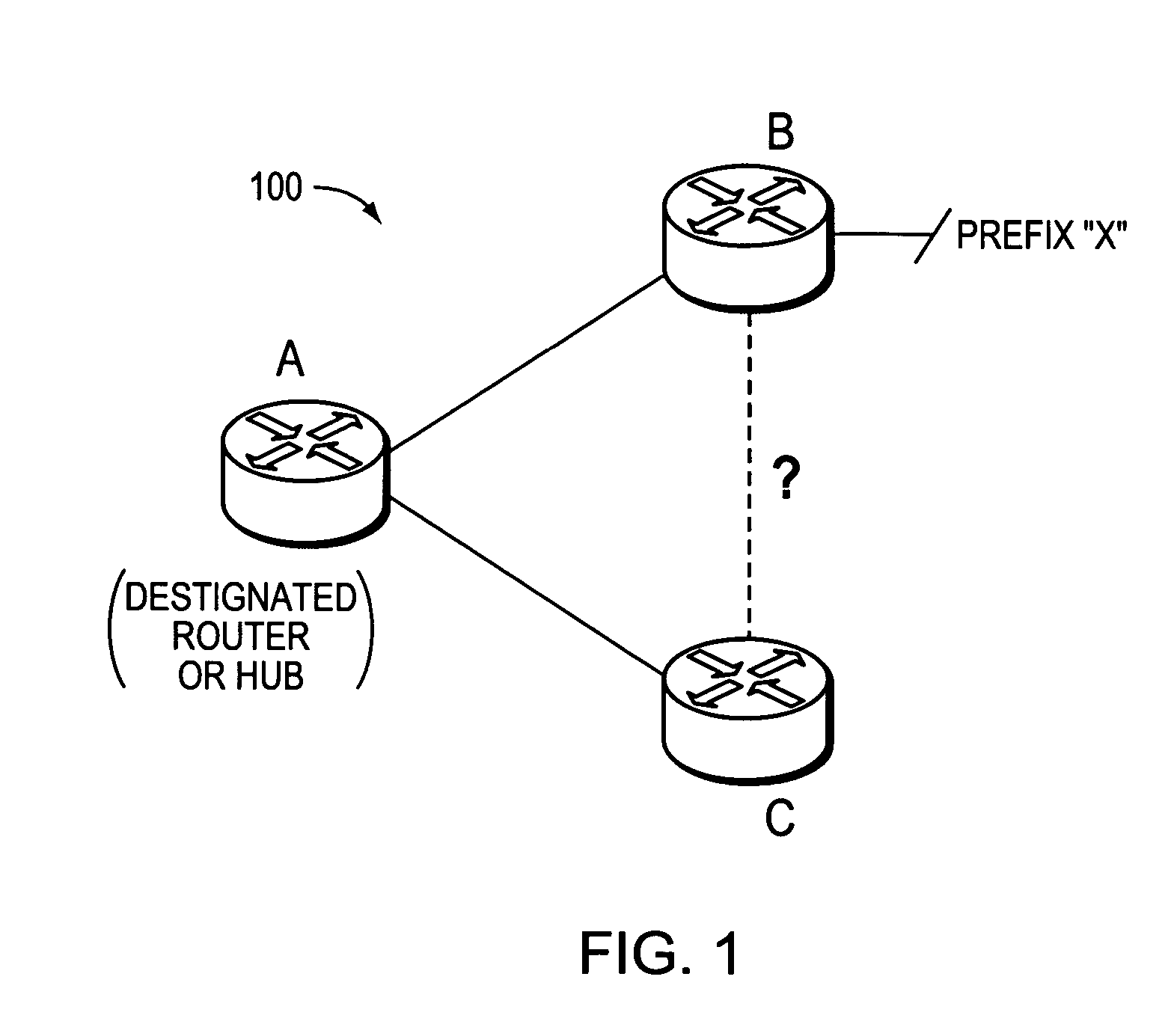
ActiveUS20070245034A1Reduce needAvoid installationDigital computer detailsData switching by path configurationBroadcastingComputer science
A technique dynamically configures and verifies routing information of broadcast networks using link state protocols in a computer network. According to the novel technique, a router within the broadcast network receives a link state protocol routing information advertisement from an advertising router, e.g., a designated router or other adjacent neighbor. The router learns of a next-hop router (“next-hop”) to reach a particular destination from the advertisement, and determines whether the next-hop is located within the same broadcast network (e.g., subnet) as the designated router. If so, the router further determines whether the next-hop is directly addressable (i.e., reachable), such as, e.g., by checking for link adjacencies to the next-hop or by sending request / reply messages (e.g., echo messages or “ping” messages) to the next-hop. In the event the next-hop for the destination is not directly addressable by the router (e.g., no adjacency or reply), the router installs a route to the destination via the designated router. Otherwise, the router installs a route to the destination via the next-hop.
Owner:CISCO TECH INC
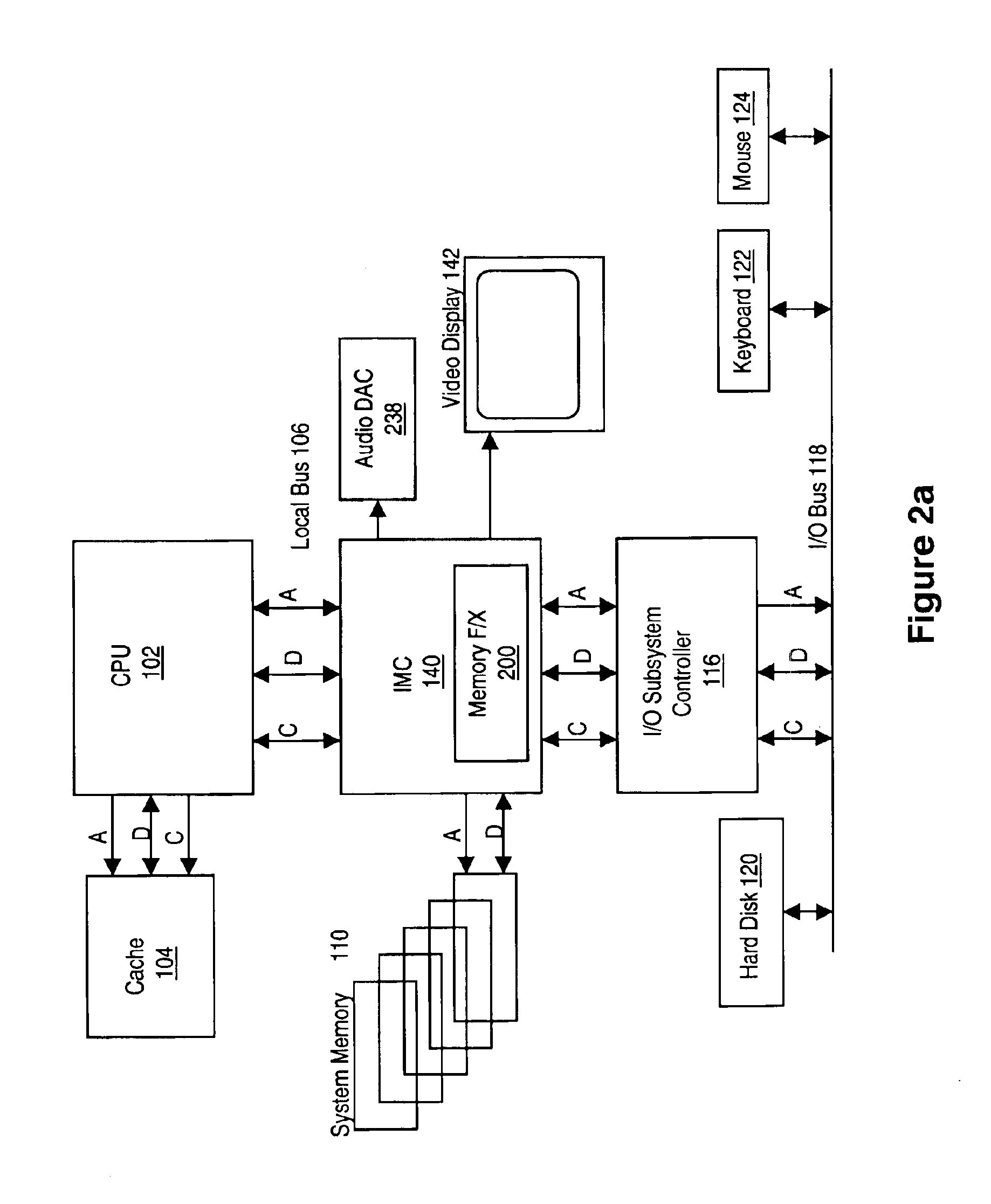
Memory module including scalable embedded parallel data compression and decompression engines
InactiveUS6879266B1Low costSmall data storage requirementMemory architecture accessing/allocationEnergy efficient ICTParallel compressionParallel computing
An memory module including parallel data compression and decompression engines for improved performance. The memory module includes MemoryF / X Technology. To improve latency and reduce performance degradations normally associated with compression and decompression techniques, the MemoryF / X Technology encompasses multiple novel techniques such as: 1) parallel lossless compression / decompression; 2) selectable compression modes such as lossless, lossy or no compression; 3) priority compression mode; 4) data cache techniques; 5) variable compression block sizes; 6) compression reordering; and 7) unique address translation, attribute, and address caches. The parallel compression and decompression algorithm allows high-speed parallel compression and high-speed parallel decompression operation. The memory module-integrated data compression and decompression capabilities remove system bottlenecks and increase performance. This allows lower cost systems due to smaller data storage, reduced bandwidth requirements, reduced power and noise.
Owner:INTELLECTUAL VENTURES I LLC
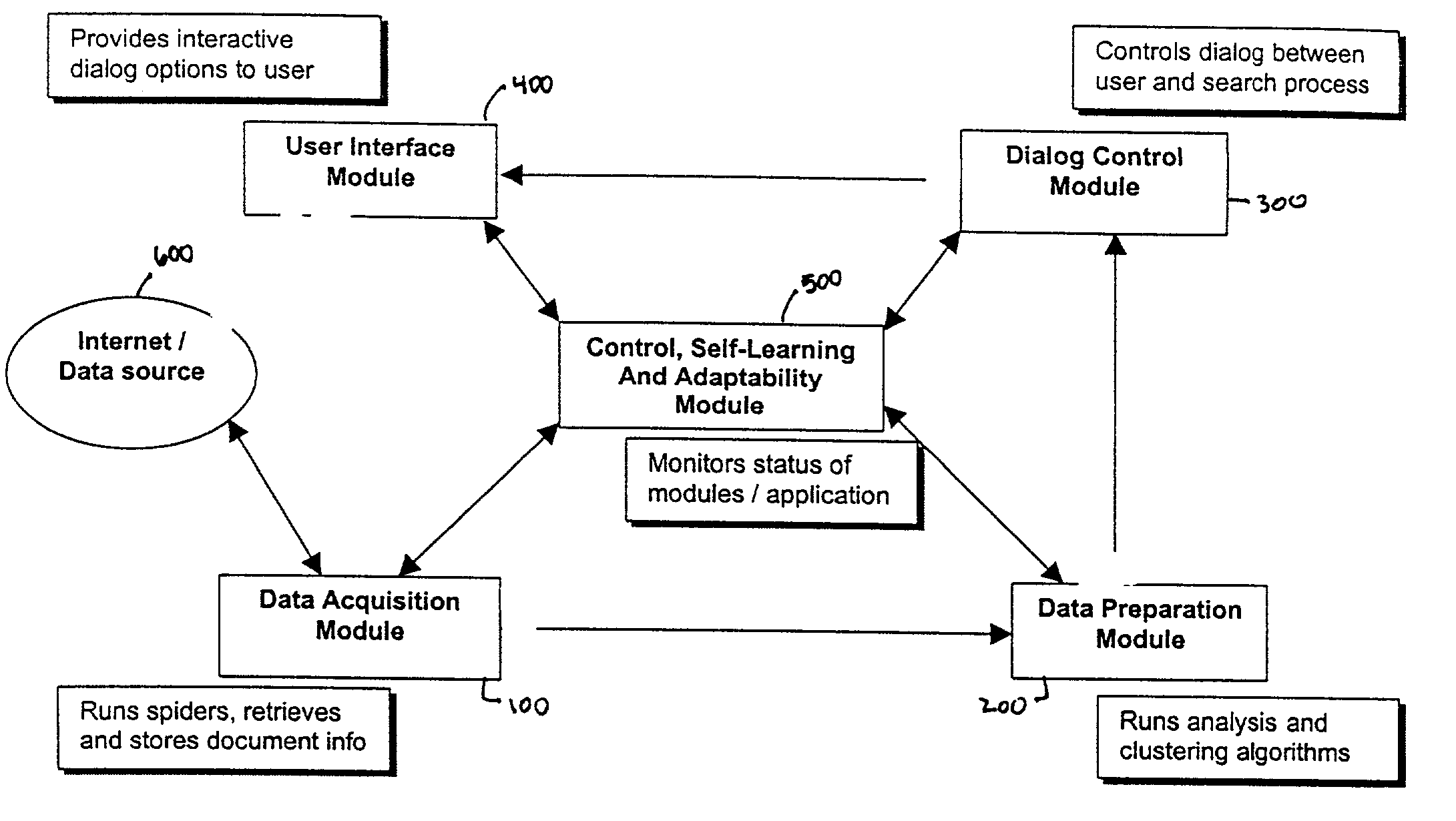
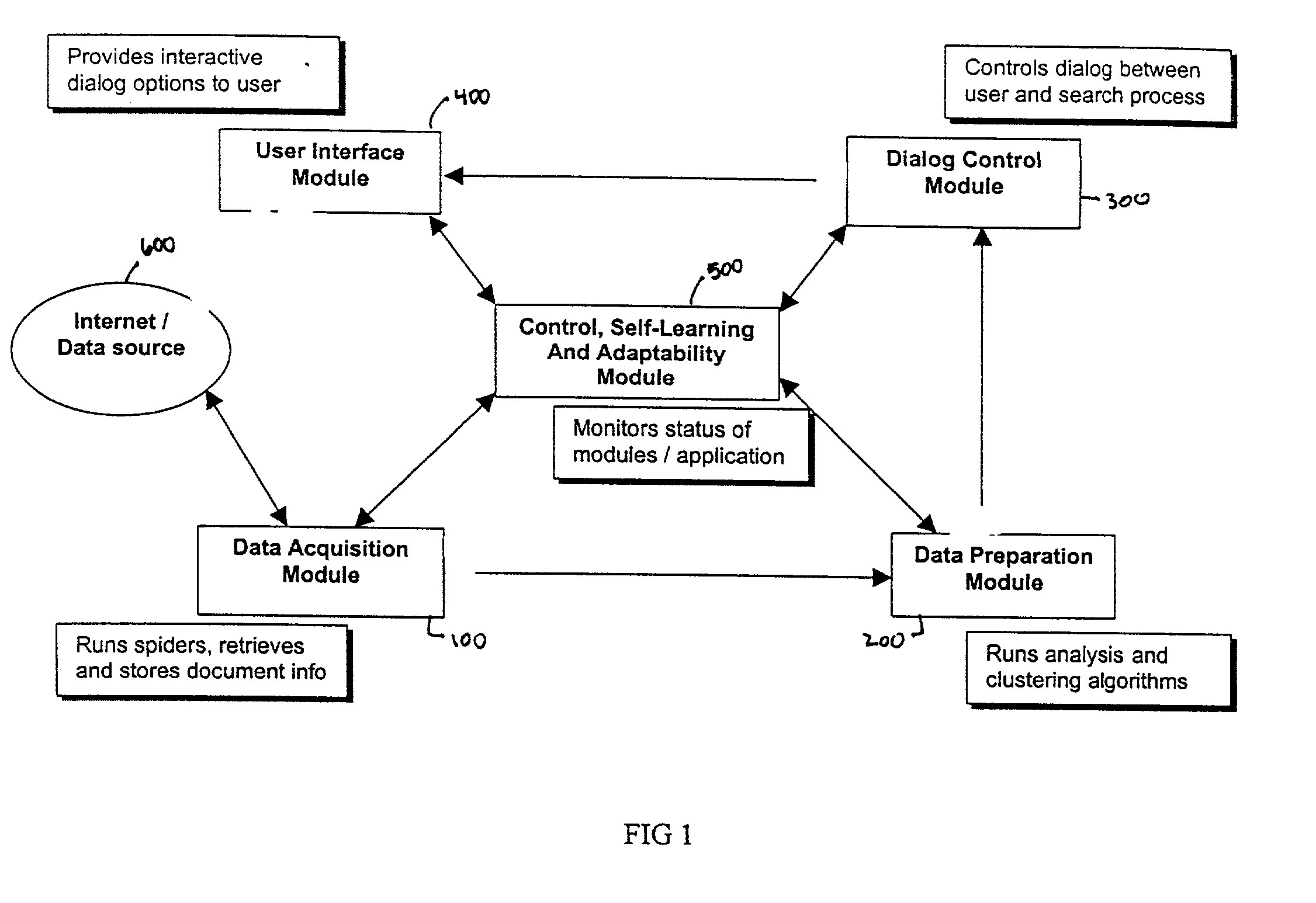
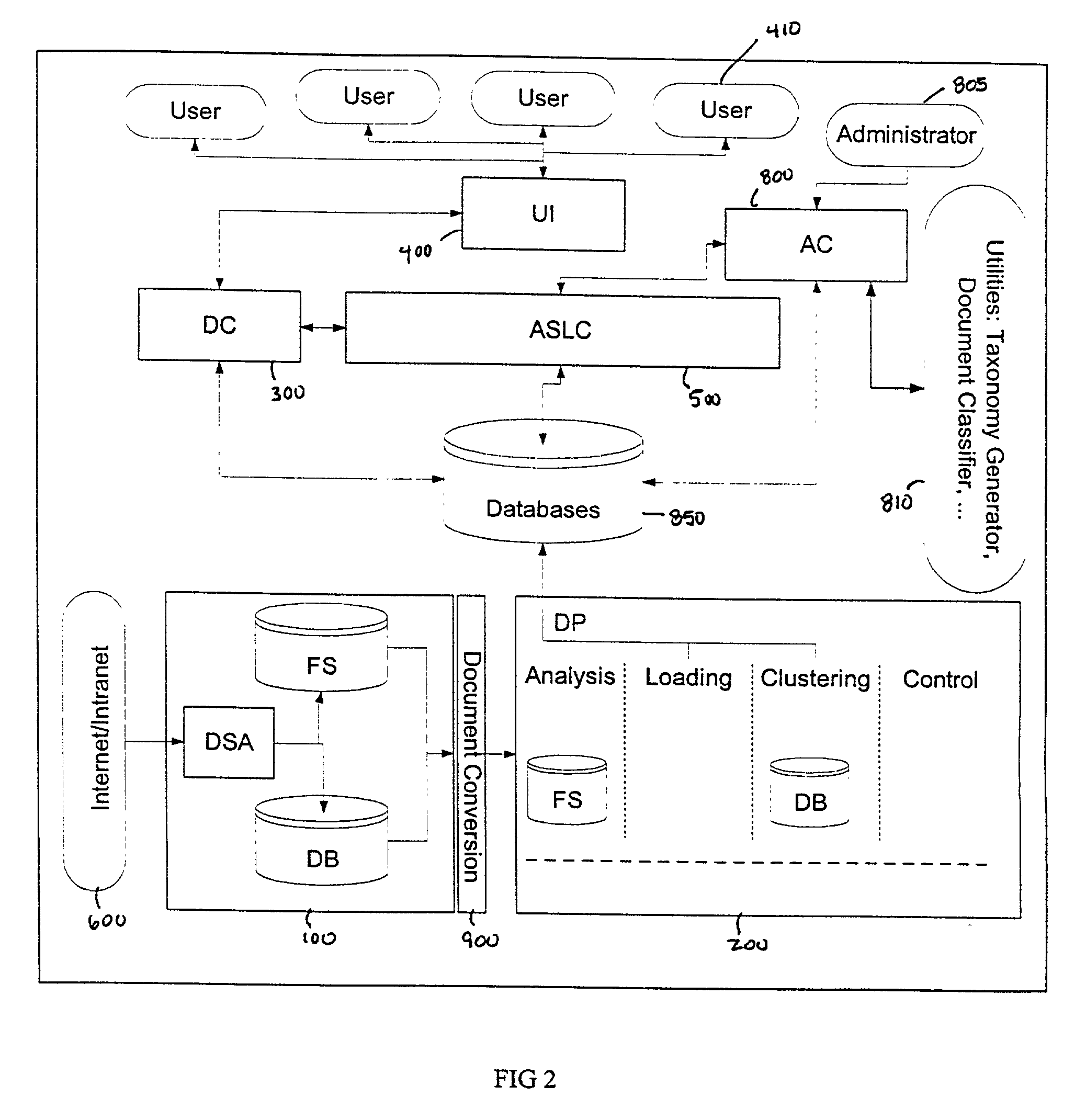
System and method for analysis and clustering of documents for search engine
InactiveUS20020065857A1Digital data information retrievalSpecial data processing applicationsDocument analysisComputational intelligence
A system and method for searching documents in a data source and more particularly, to a system and method for analyzing and clustering of documents for a search engine. The system and method includes analyzing and processing documents to secure the infrastructure and standards for optimal document processing. By incorporating Computational Intelligence (CI) and statistical methods, the document information is analyzed and clustered using novel techniques for knowledge extraction. A comprehensive dictionary is built based on the keywords identified by the these techniques from the entire text of the document. The text is parsed for keywords or the number of its occurrences and the context in which the word appears in the documents. The whole document is identified by the knowledge that is represented in its contents. Based on such knowledge extracted from all the documents, the documents are clustered into meaningful groups in a catalog tree. The results of document analysis and clustering information are stored in a database.
Owner:NUTECH SOLUTIONS
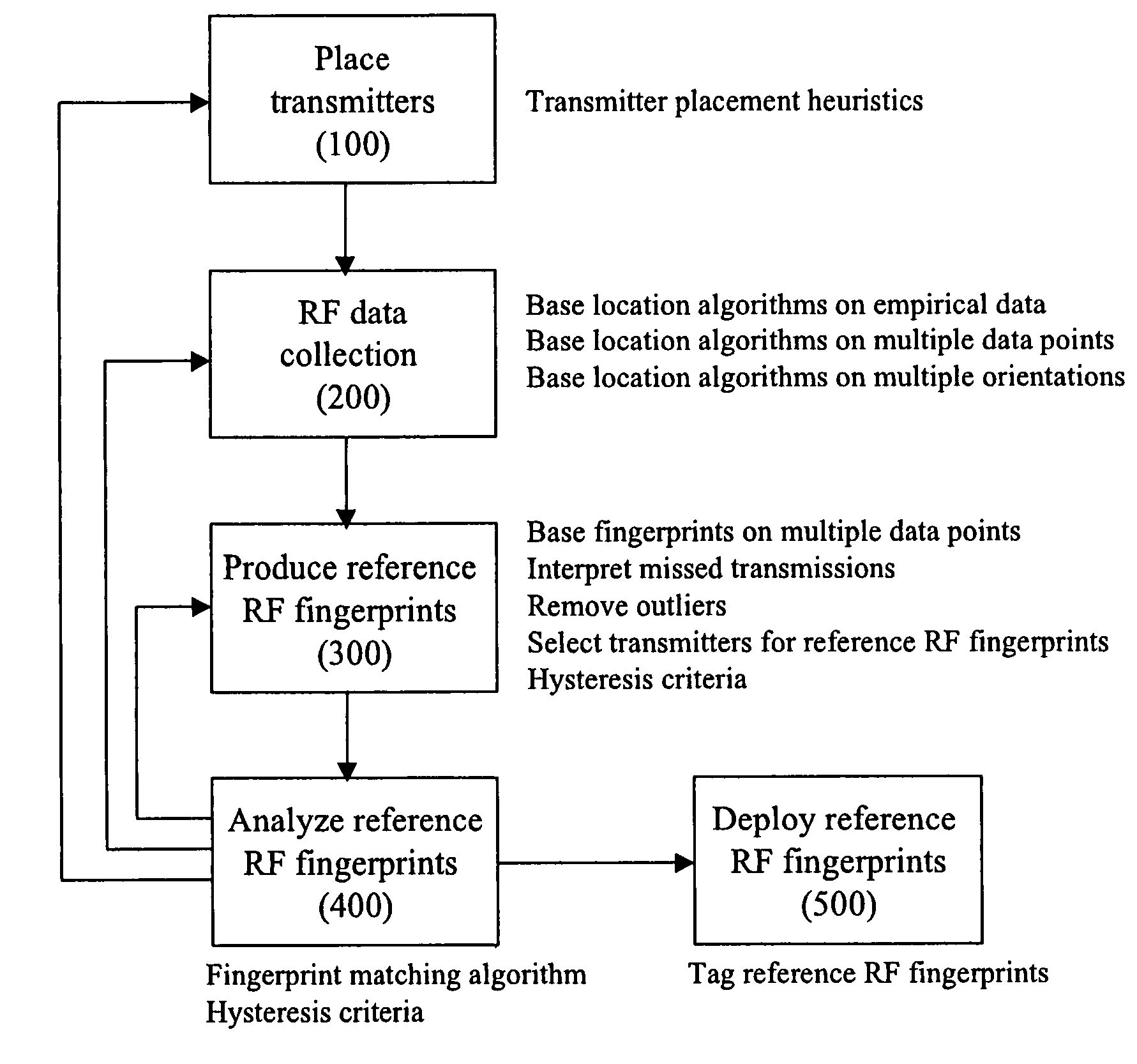
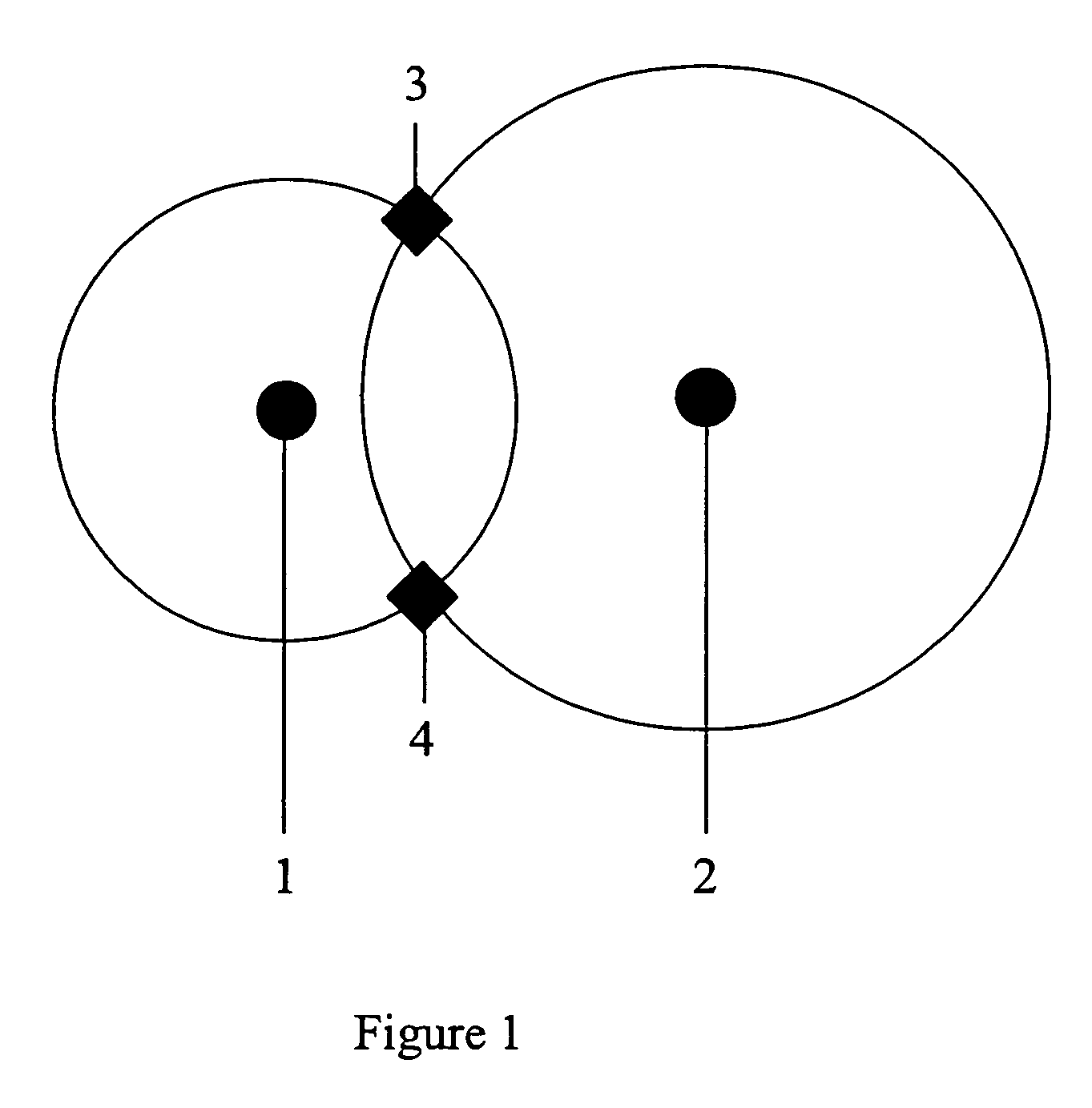
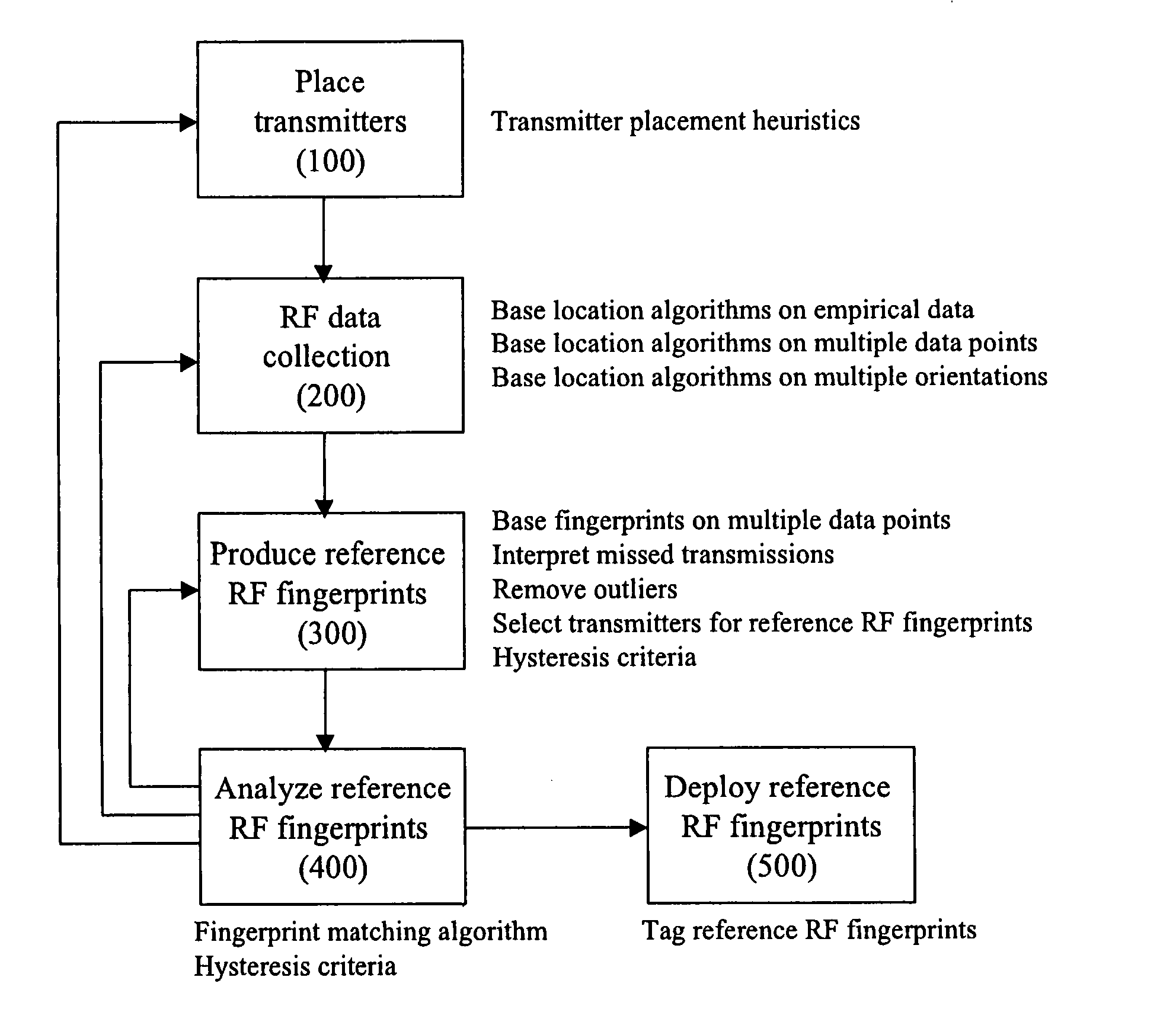
Method for RF fingerprinting
InactiveUS7346359B2Improve accuracyAccurate locationElectric signal transmission systemsImage analysisEngineeringLocation determination
The invention provides a novel method for preparing a wireless environment for location determination of a wireless mobile unit, and for location determination of a wireless mobile unit. In preparing the physical environment, the invention utilizes novel techniques, including novel techniques to place transmitters, the removal of outlying data in the creation of reference RF fingerprints, and algorithms to obtain accurate reference RF fingerprints. In determining the location of a wireless mobile unit, the invention utilizes novel techniques, including novel techniques to select transmitters, the removal of outlying data in the creation of reference RF fingerprints, and algorithms to obtain accurate reference RF fingerprints.
Owner:INNERWIRELESS
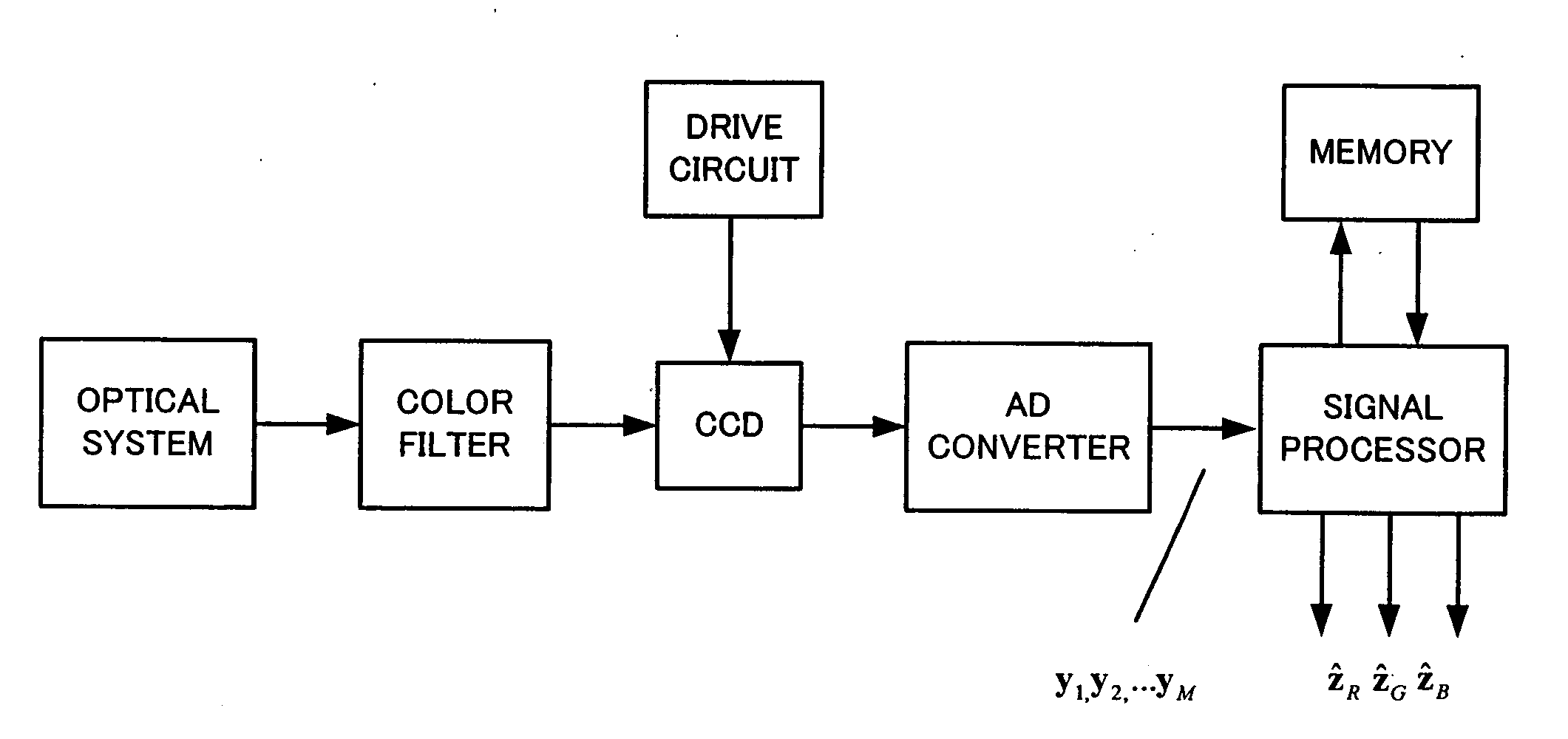
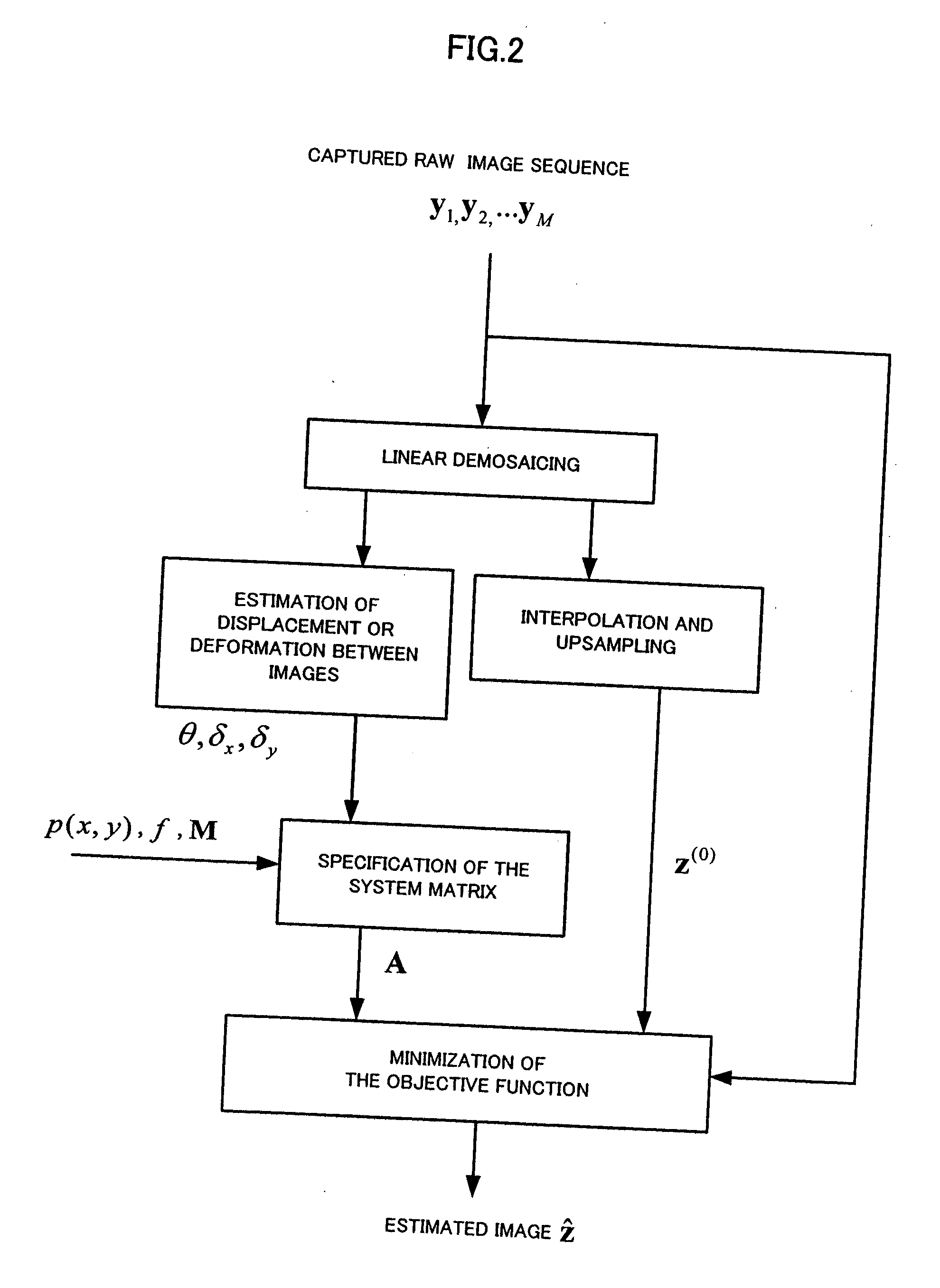
Method for creating high resolution color image, system for creating high resolution color image and program creating high resolution color image
InactiveUS20060038891A1Evaluates smoothnessEfficient implementationTelevision system detailsCharacter and pattern recognitionColor imageImage resolution
A limitation in the physical resolution of an image sensor offers a motivation to improve the resolution of an image. Super-resolution is mainly applied to gray scale images, and it has not been thoroughly investigated yet that a high resolution color image is reconstructed from an image sensor having a color filter array. An object of the invention is to directly reconstruct a high resolution color image from color mosaic obtained by an image sensor having a color filter array. A high resolution color image reconstruction method according to the invention is based on novel technique principles of color image reconstruction that an increase in resolution and demosaicing are performed at the same time. The verification and effective implement of the invention are also described.
Owner:TOKYO INST OF TECH
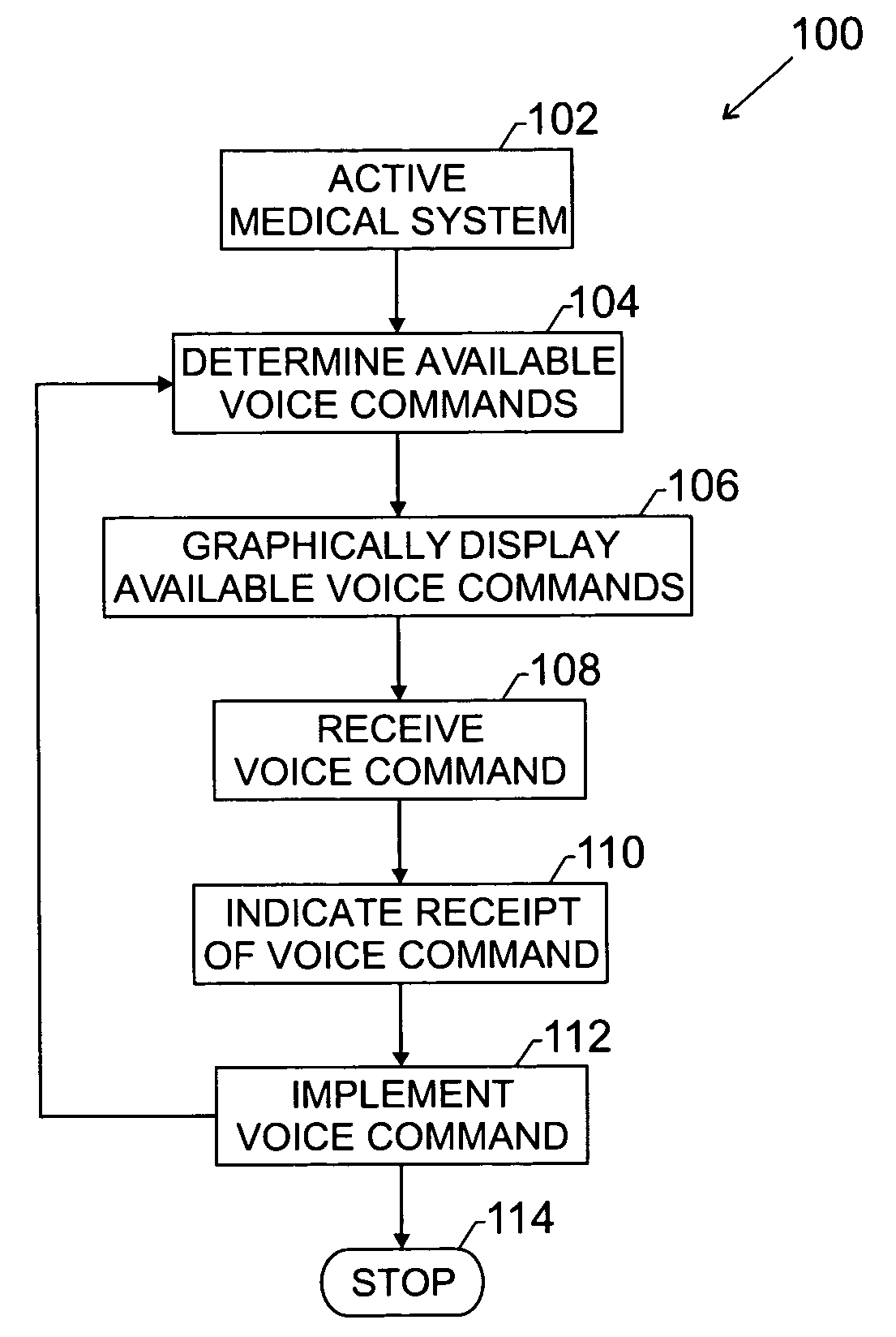
Method and apparatus for contextual voice cues
InactiveUS20050114140A1Increase adoptionImprove advancedLocal control/monitoringSpeech recognitionGraphicsSonification
The present invention provides a novel technique designed to provide a front-end graphical user interface for voice interaction, displaying a list of voice commands that can be used within a control scope of a medical system and that change depending on where the user is in the system. The user is presented with a quick reference guide to available commands without being overwhelmed. “Contextual voice cues” (CVC) provide a non-intrusive dynamic list of available commands to the user which automatically pop-up and change depending on the screen or mode the user is in. An indicator, such as a feedback light, may show whether a voice command is accepted. The technique may be utilized with medical information and diagnostic systems such as picture archival communication systems (PACS), ultrasound modalities, and so forth. Implementation of the technique should increase clinician adoption rates of voice recognition control and thus advance improvements in clinician workflow.
Owner:GE MEDICAL SYST INFORMATION TECH
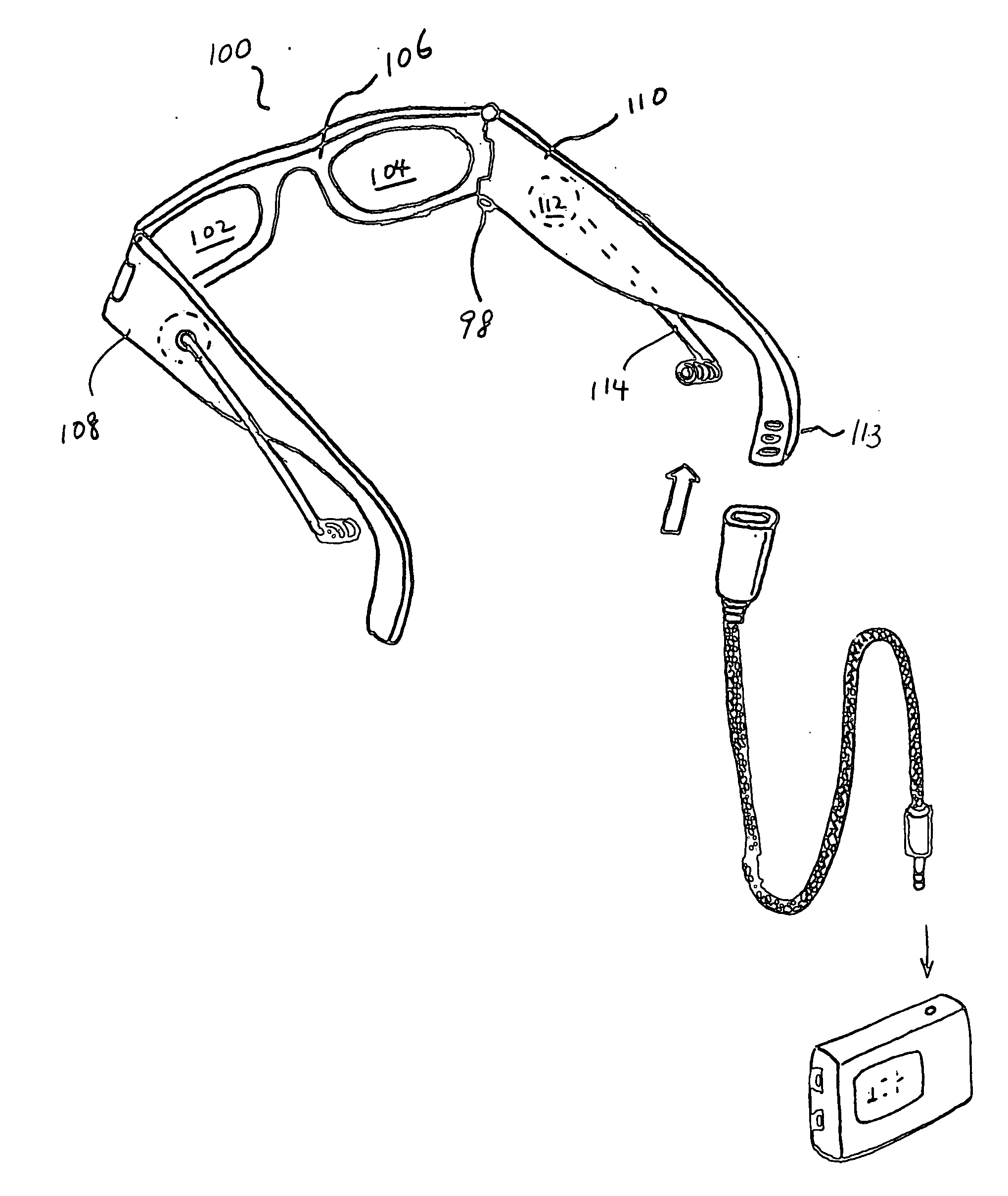
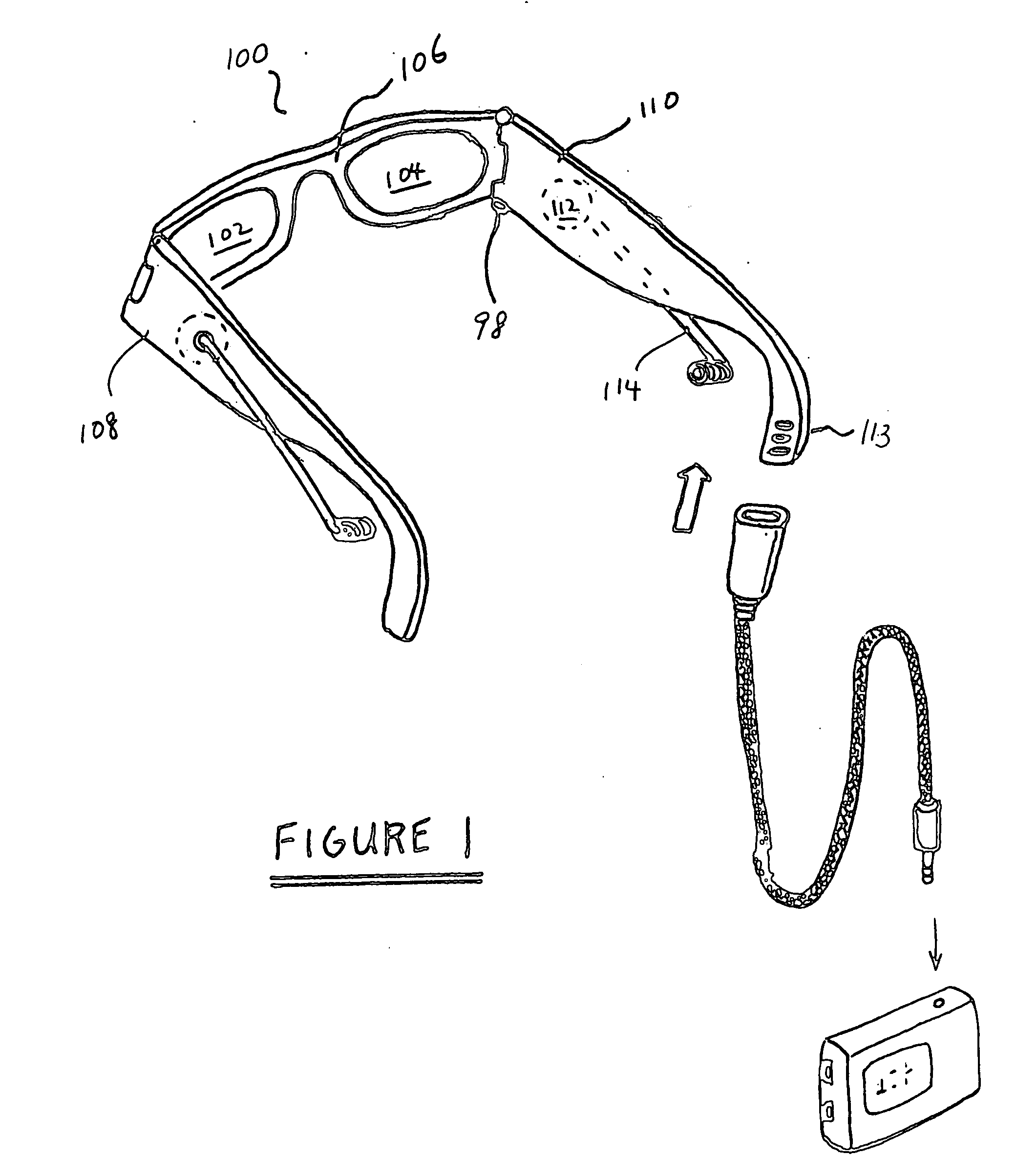
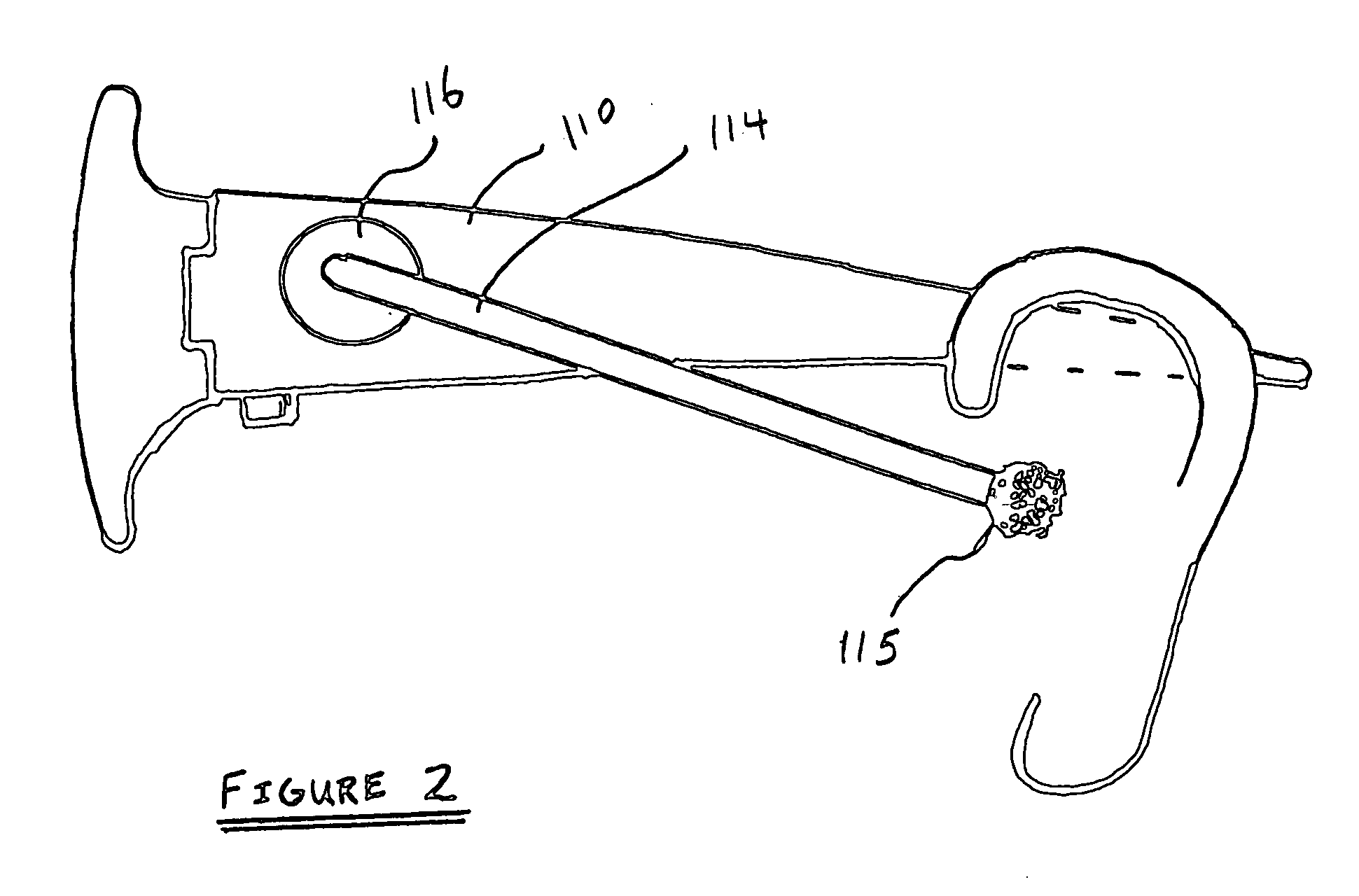
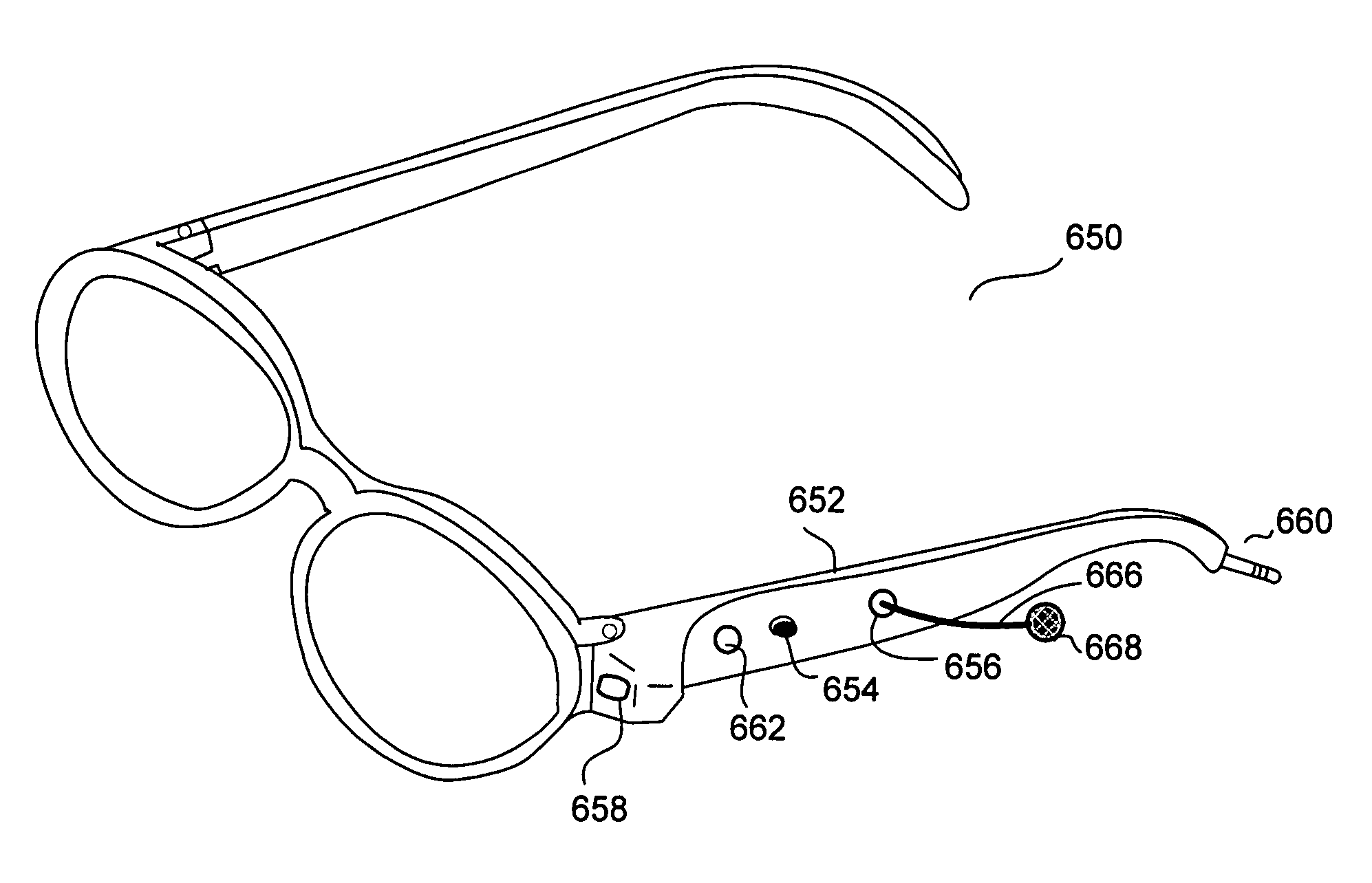
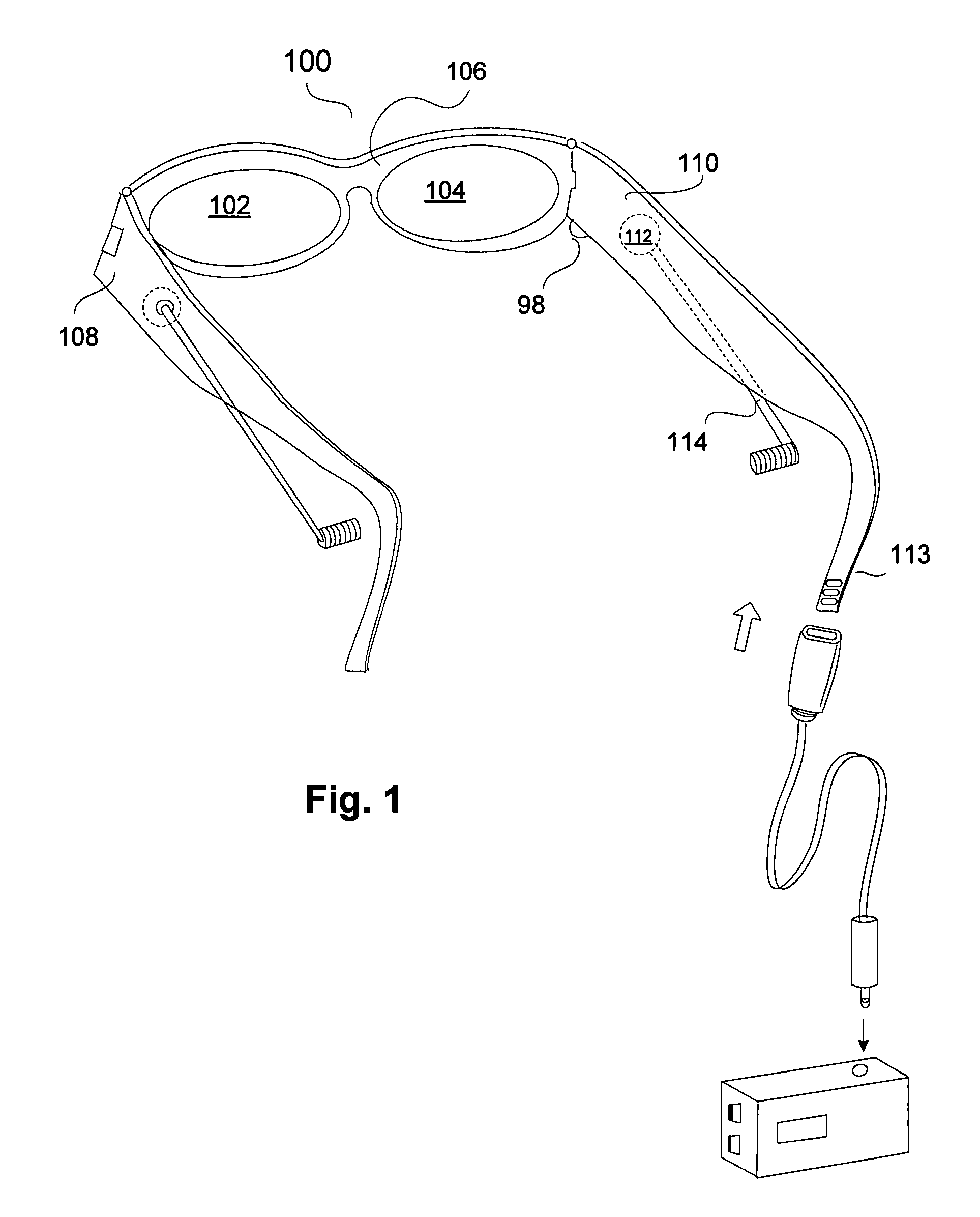
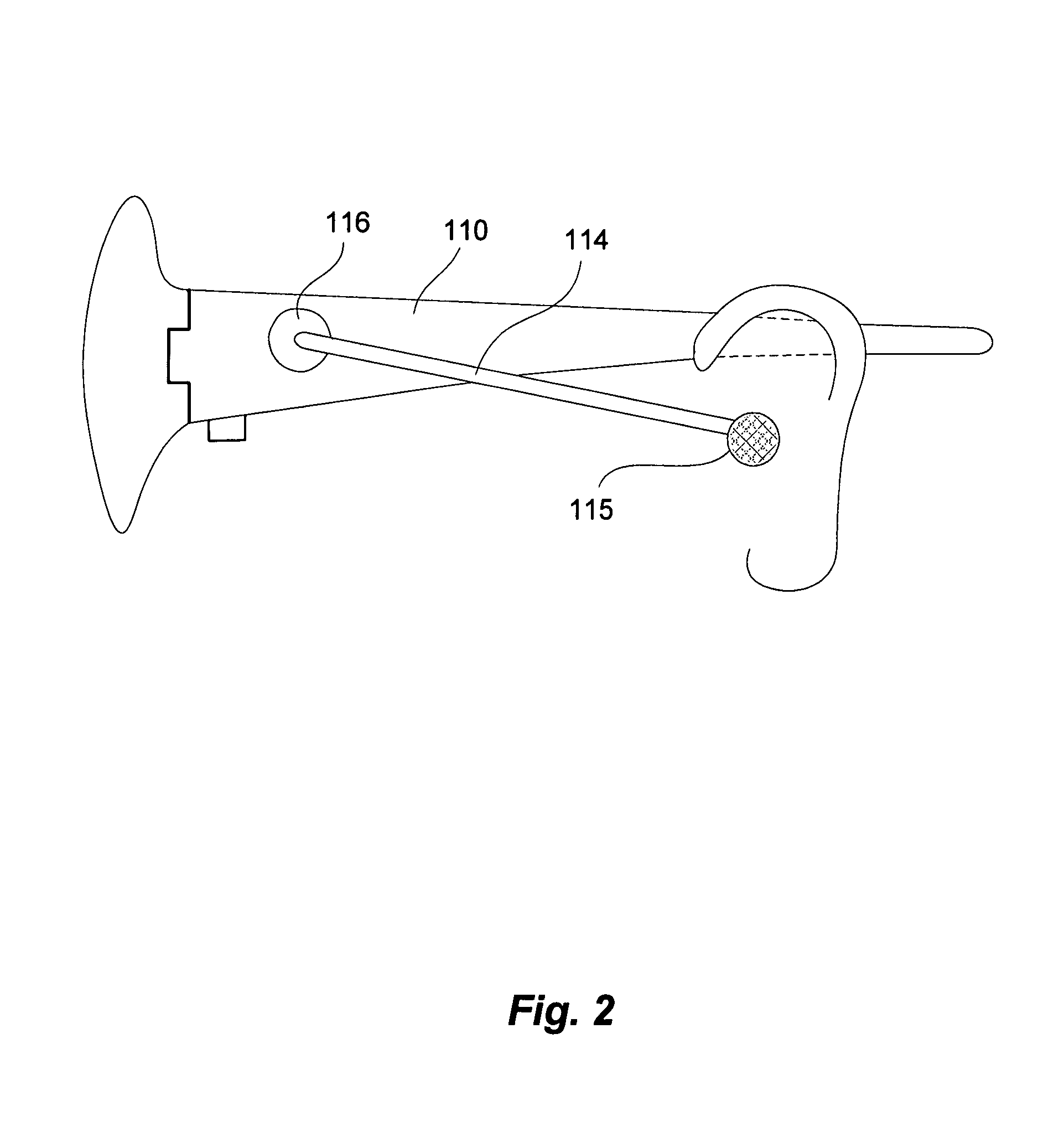
Eyeglasses with hearing enhanced and other audio signal-generating capabilities
InactiveUS20050248717A1Space minimizationReduce the amount requiredNon-optical adjunctsNon-optical partsThird partyEyewear
Novel techniques for hearing enhancement based on a pair of glasses are disclosed. In one embodiment, the glasses include a first lens holder, a second lens holder, a bridge element, a first temple, a second temple, a first speaker, a second speaker, a microphone and at least one electrical component that performs a hearing enhanced function to enhance audio signals from the microphone to be sent to the speakers for the user to hear. At least one electrical component in the glasses is for generating other audio signals by the speakers, with the other audio signals originating from signals other than audio signals captured by the microphone. In another embodiment, some of the electrical components are in a portable device, wired or wirelessly, coupled to the glasses. In yet another embodiment, the glasses function as a headset, with other electrical components in the portable device. In such embodiment, since the glasses can provide a number of different hearing functions, a third party may not be able to tell whether the user is wearing the glasses to have his hearing enhanced, or for hearing other audio signals.
Owner:INGENIOSPEC
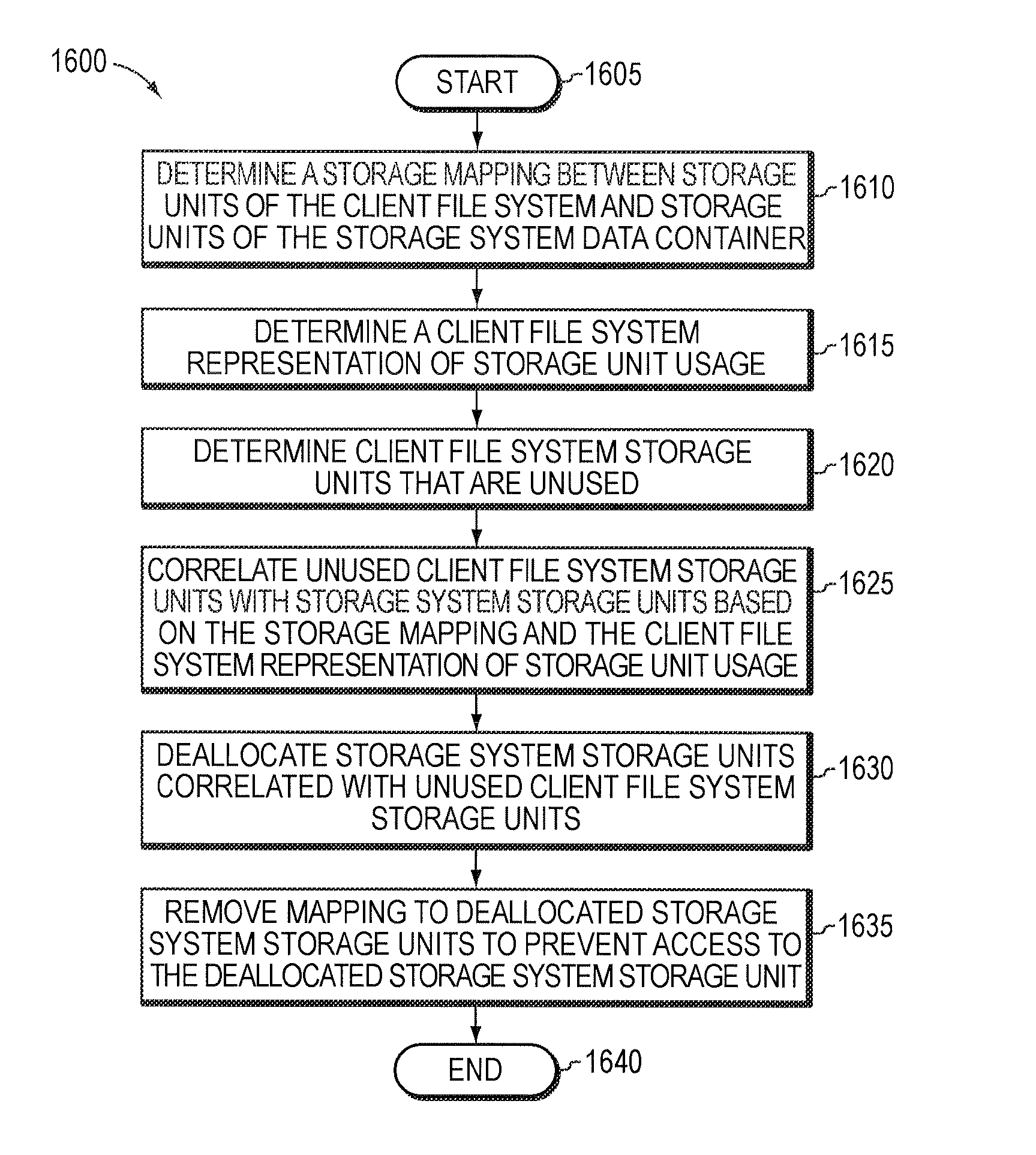
Storage system-based hole punching for reclaiming unused space from a data container
ActiveUS8086652B1Maintain integrityOvercome disadvantagesMemory adressing/allocation/relocationSpecial data processing applicationsFile systemSystem maintenance
A system and method reclaims unused storage space from a data container, such as a logical unit number (LUN) of a storage system. In particular, a novel technique is provided that allows a storage system to reclaim storage space not used by a client file system for which the storage system maintains storage, without requiring assistance from the client file system to determine storage usage. In other words, storage system may independently reclaim storage space not used by the client file system, without that file system's intervention.
Owner:NETWORK APPLIANCE INC
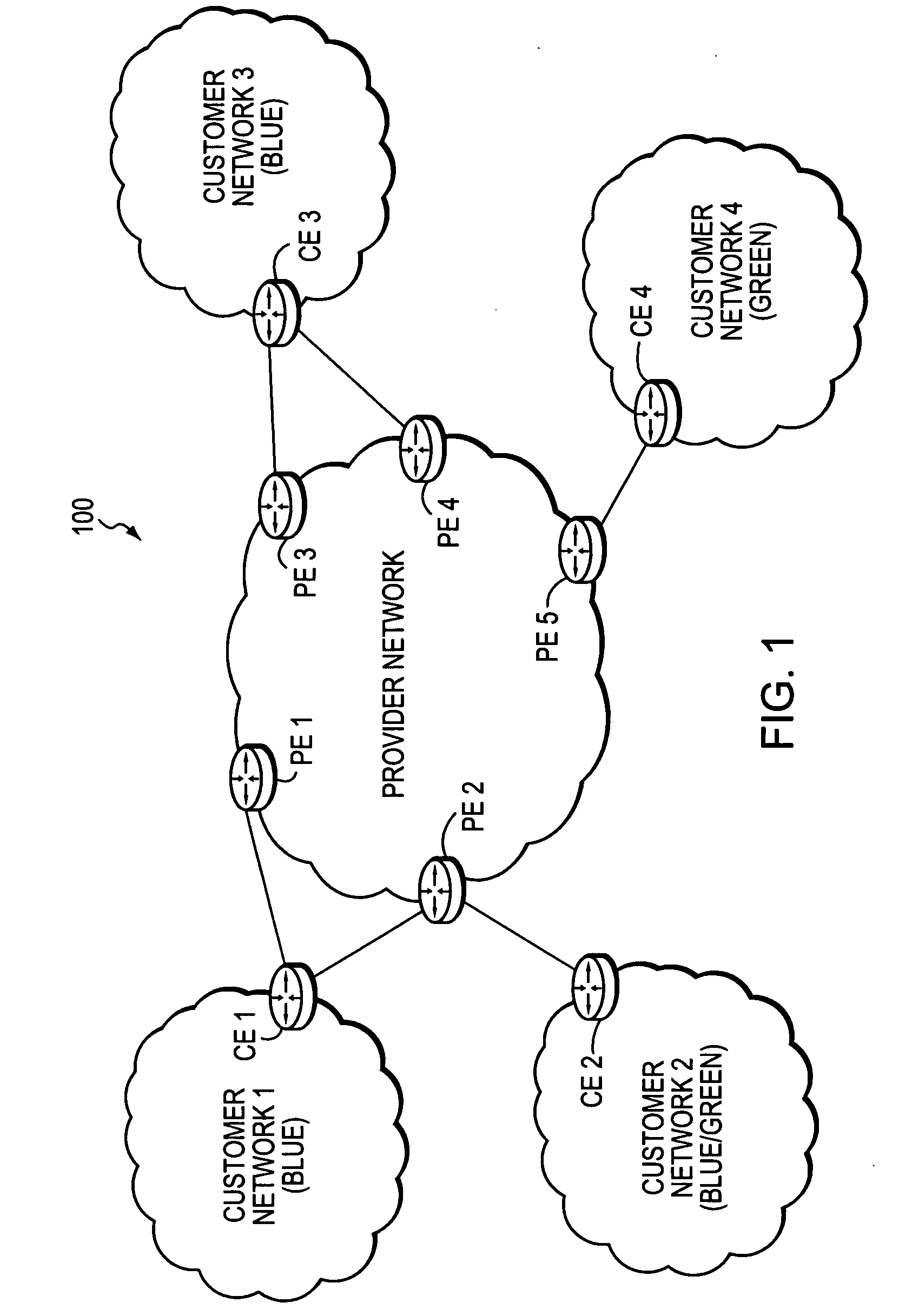
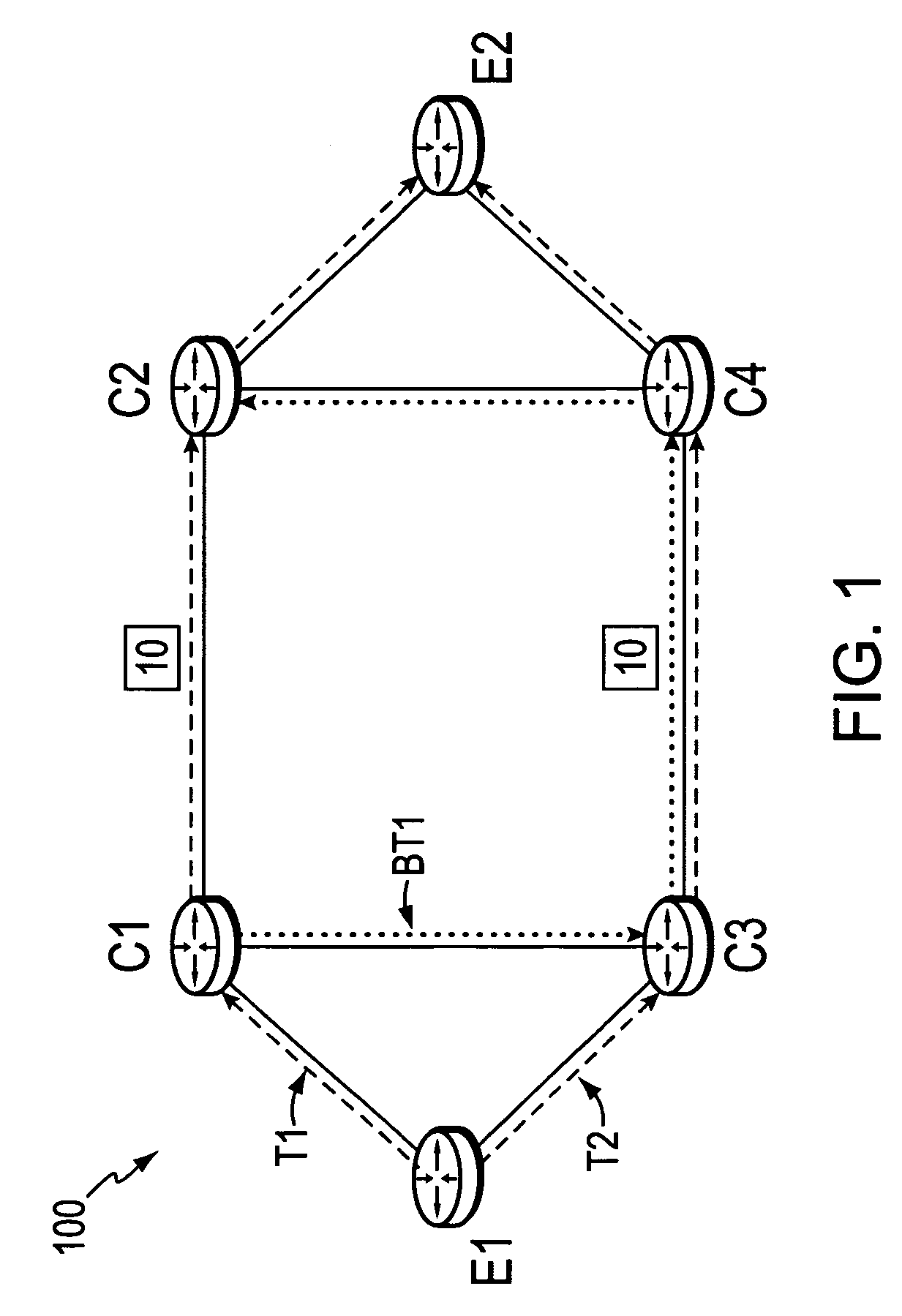
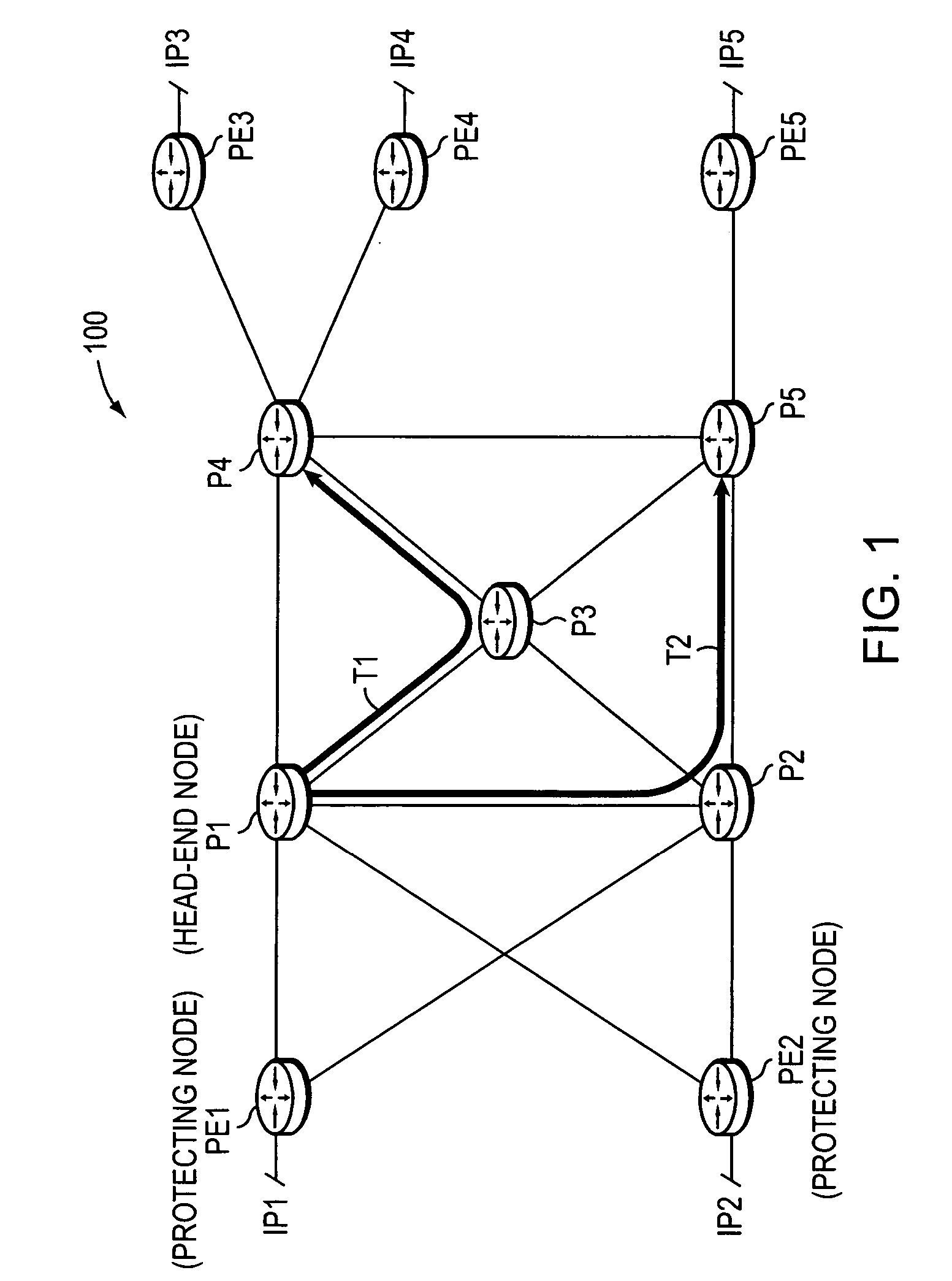
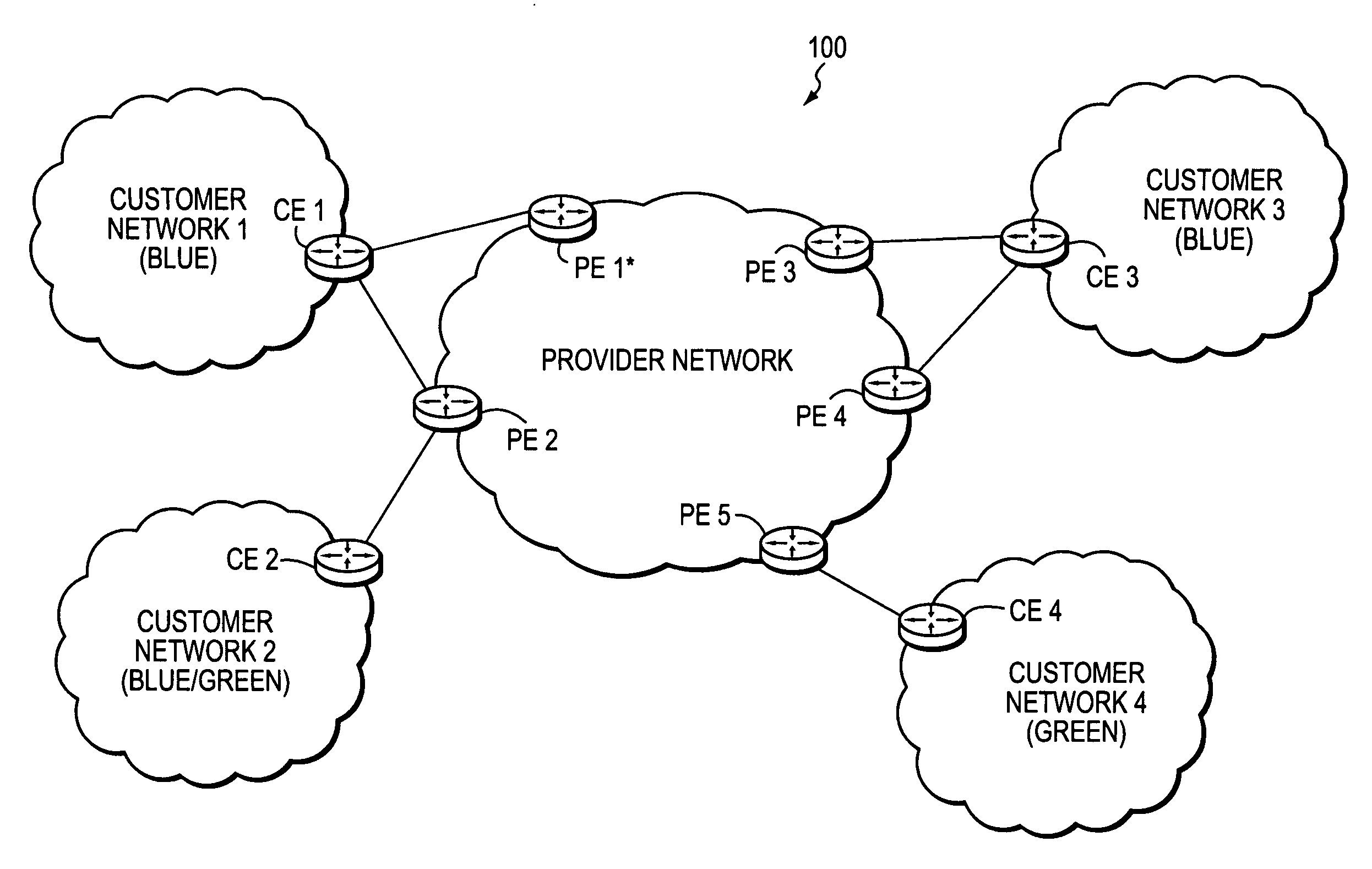
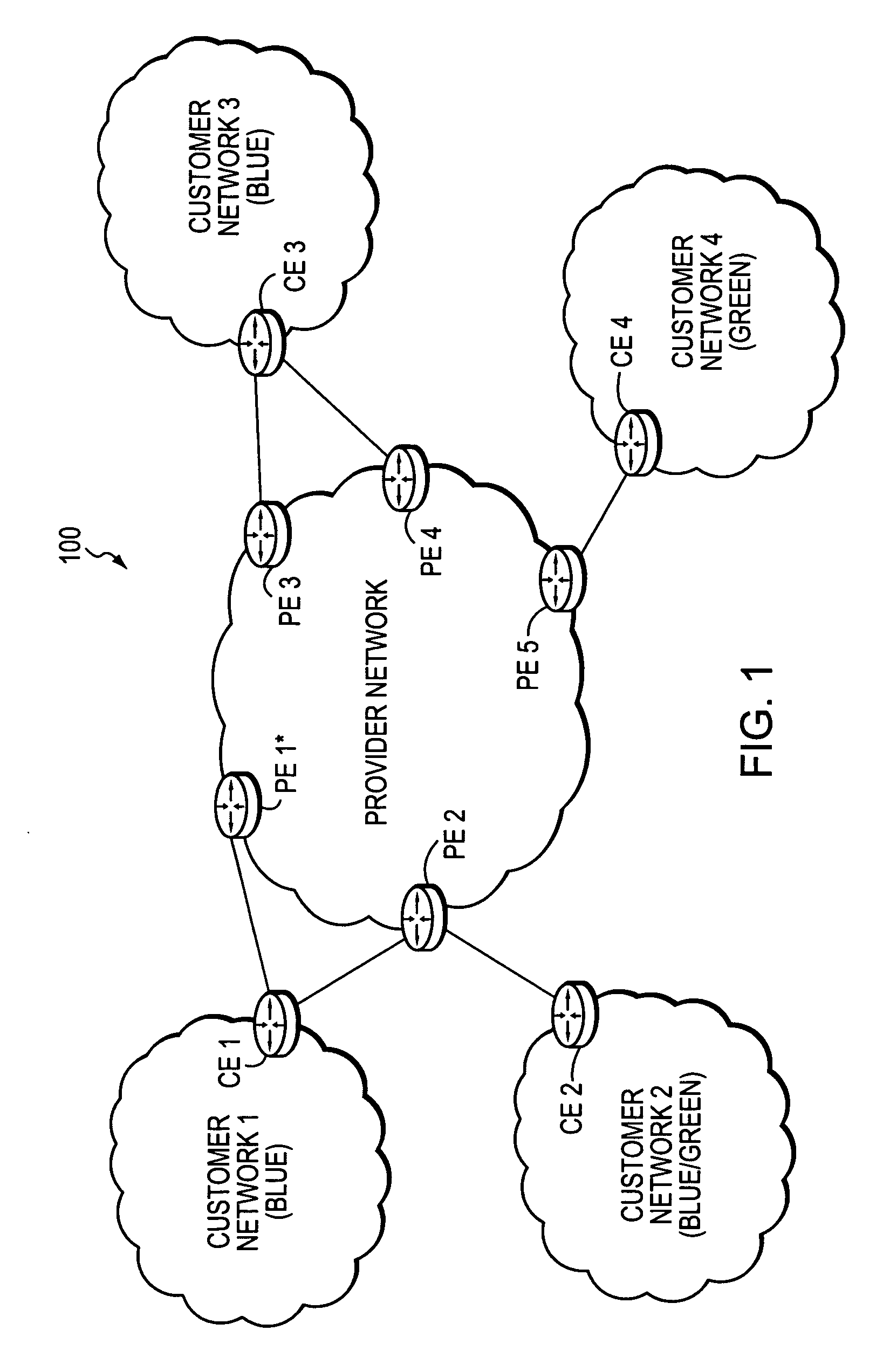
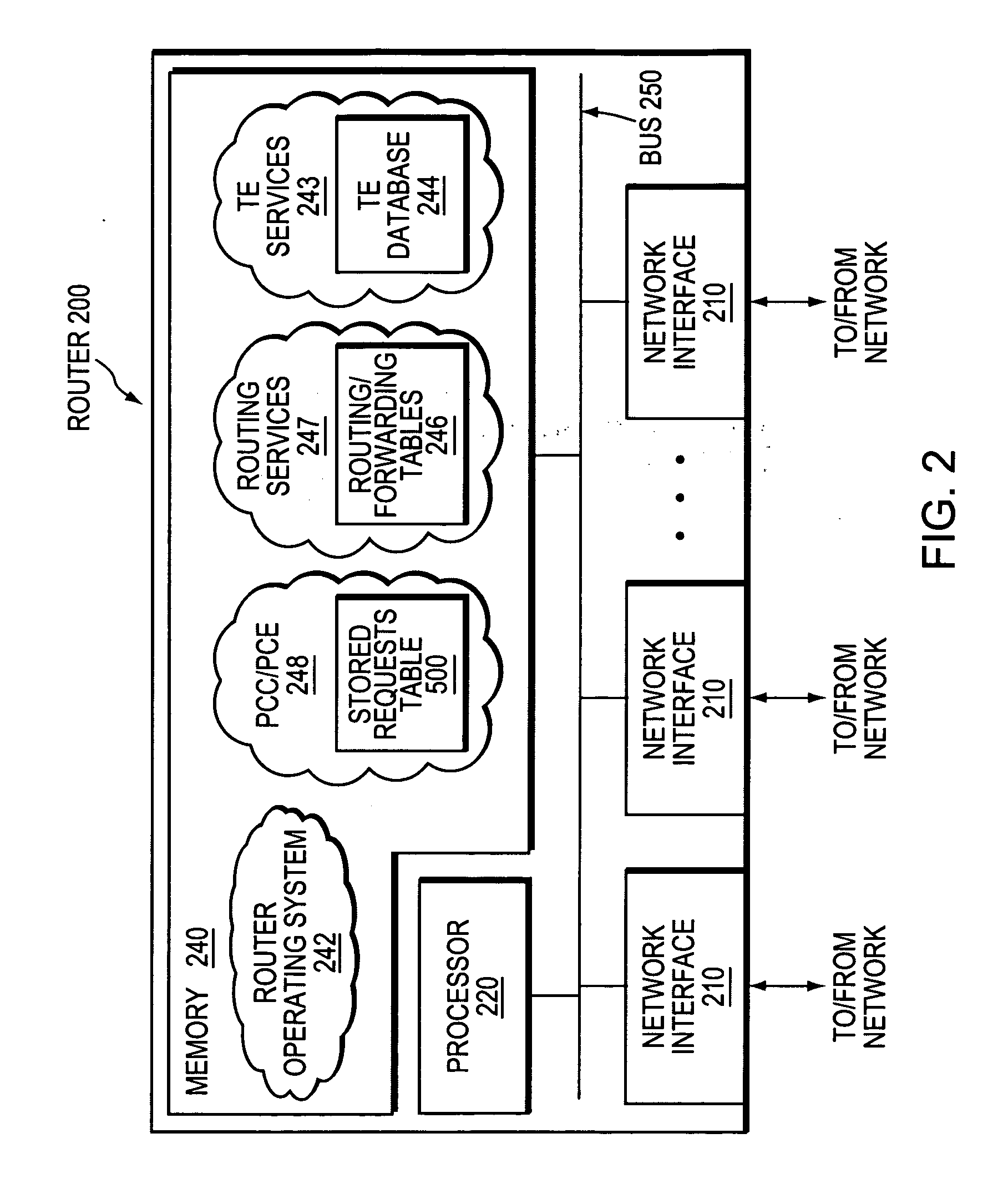
Technique for enabling traffic engineering on CE-CE paths across a provider network
ActiveUS20070133406A1Create efficientlyReduce needError preventionTransmission systemsPrivate networkDistributed computing
A technique enables Traffic Engineering (TE) on paths between customer edge devices (CEs) across a provider network (“CE-CE paths”) in a computer network. According to the novel technique, TE is configured on a link from a sending provider edge device (PE) to a first CE (“PE-CE link”), e.g., a CE of one or more virtual private networks (VPNs). The sending PE conveys TE information of the PE-CE link to one or more receiving PEs in the provider network. Upon receiving the TE information, each receiving PE expands a TE database (TED) for information regarding the provider network (i.e., a “core TED”) to include TE-configured PE-CE links, e.g., by updating one or more corresponding VPN TEDs (VTEDs) for each VPN maintained by the receiving PE. Once the receiving PEs have the TE information for configured PE-CE links from the provider network, one or more TE techniques may be applied to paths from a second CE of the receiving PE to the first CE (a CE-CE path) to thereby facilitate, e.g., establishment of TE-LSPs along CE-CE paths.
Owner:CISCO TECH INC
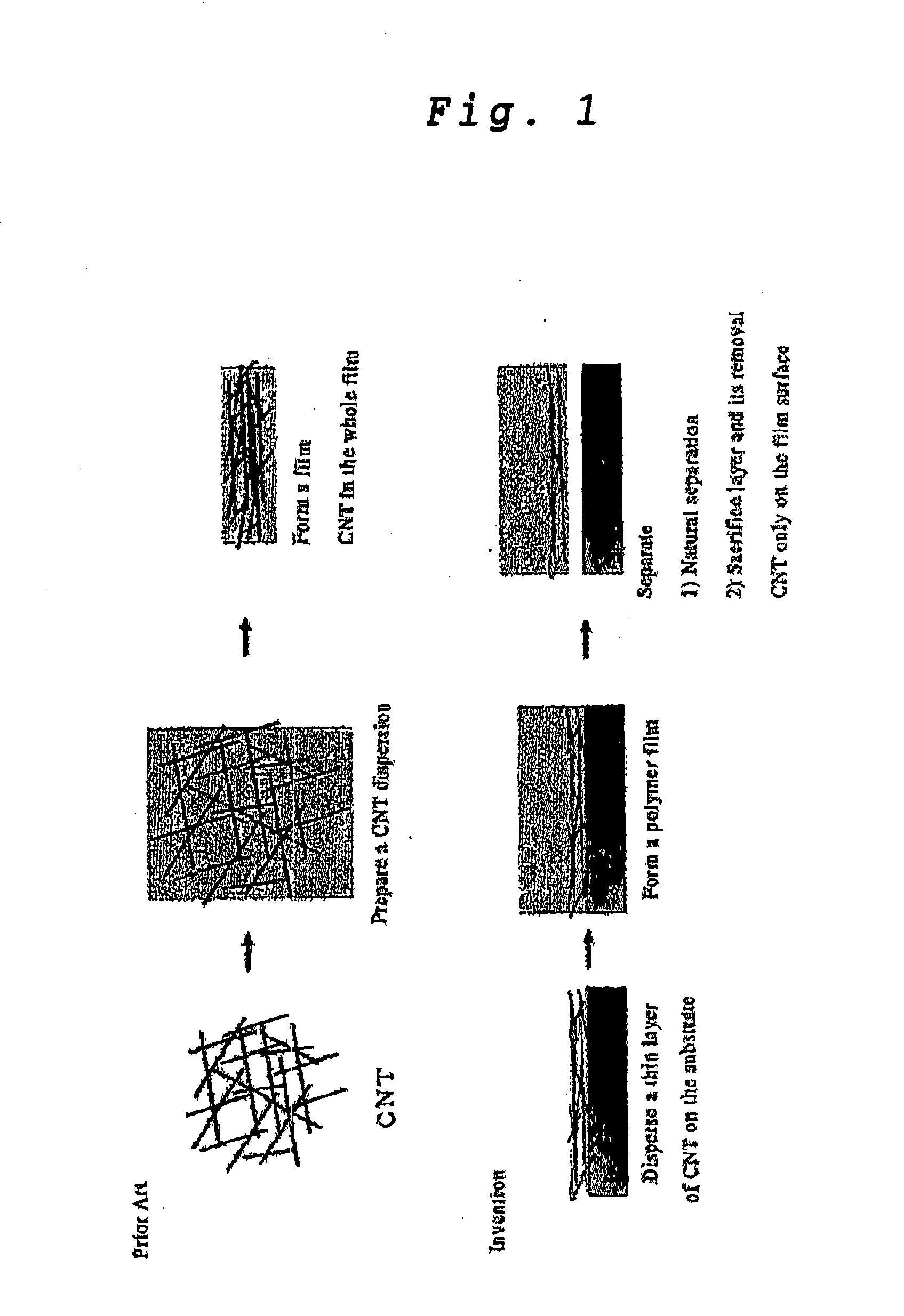
Transparent Conductive Carbon Nanotube Film and a Method for Producing the Same
InactiveUS20070298253A1Conductive and soft and flexibleImprove conductivityMaterial nanotechnologyConductive layers on insulating-supportsCarbon nanotubeTransparent conducting film
A transparent conductive film wherein carbon nanotubes are discursively embedded in the surface portion of a resin film is produced by (A) dispersing carbon nanotubes on a substrate surface, (B) forming a transparent resin film over the substrate on which the carbon nanotubes are dispersed, and then (C) separating the thus-formed resin film. This is a novel technique for realizing a highly transparent conductive film which is flexible and highly conductive even when amount of carbon nanotubes used therefor is small.
Owner:NAT INST OF ADVANCED IND SCI & TECH
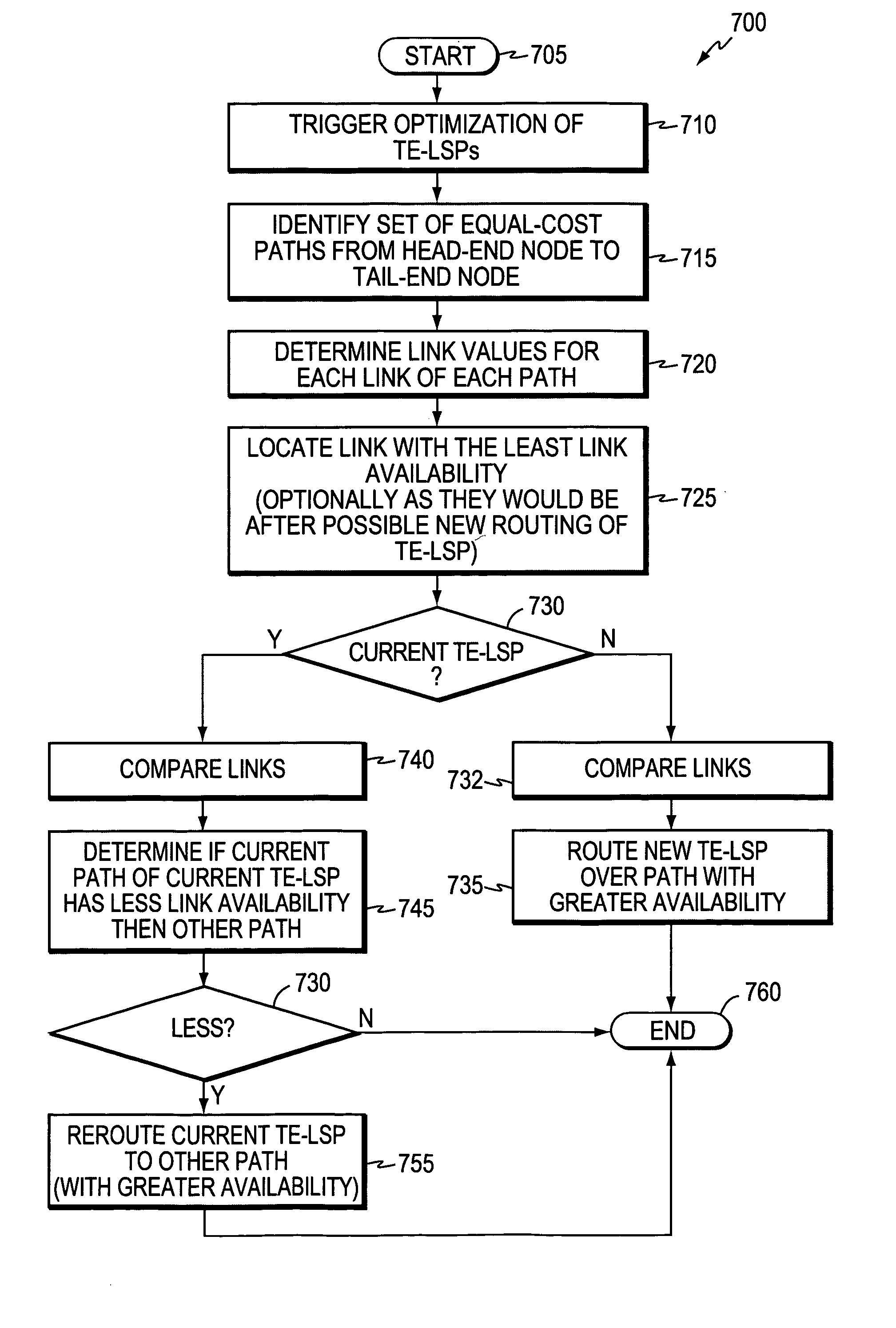
Technique for efficient load balancing of TE-LSPs
ActiveUS20060182035A1Efficient load balancingEqual-cost pathError preventionFrequency-division multiplex detailsPath computation elementLabel switching
A technique efficiently load balances traffic engineering (TE) label switched paths (LSPs) from a head-end node to a tail-end node of a computer network. The novel load balancing technique identifies (e.g., at the head-end node or a path computation element, PCE) a set of paths with equal costs from the head-end node to the tail-end node, where each path of the set is composed of one or more associated links. “Link values” such as, e.g., the number of unconstrained TE-LSPs on the link, the amount of available bandwidth on the link, or the percent of total available bandwidth already in use on the link, are applied to each link of each path. The most restrictive link values (link availability) of each path of the set, such as, e.g., the link with the lowest amount of available bandwidth, etc., are then compared. Upon comparing the link availability, the novel technique load balances established and / or new TE-LSPs from the head-end node to the tail-end node over the set of paths accordingly.
Owner:CISCO TECH INC
Dynamic protection against failure of a head-end node of one or more TE-LSPs
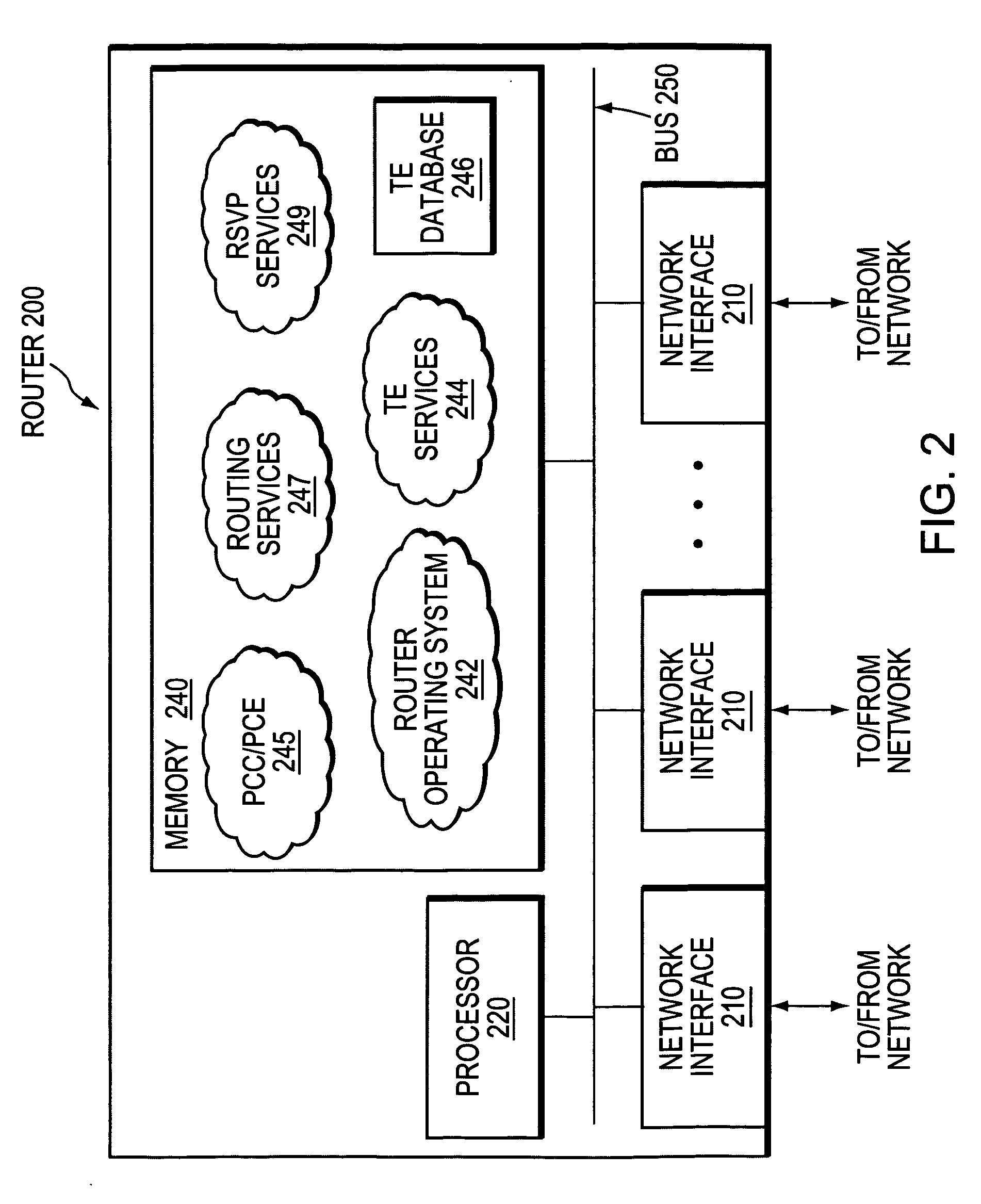
ActiveUS20070165515A1Preserving scalabilityReduce needError preventionTransmission systemsTraffic capacityLabel switching
A technique dynamically protects against failure of a head-end node of one or more primary Traffic Engineering Label Switched Paths (TE-LSPs) in a computer network. According to the novel technique, a neighboring upstream node (“protecting node”) of the head-end node learns of the primary TE-LSPs (and their respective state control blocks) extending from the head-end node to one or more address prefixes. The protecting node establishes a repair TE-LSP for each of the primary TE-LSPs to a corresponding downstream neighboring node of the head-end node (a “next-next-hop”). In response to detecting a failure of the head-end node, the protecting node locally reroutes traffic destined for the address prefixes to an appropriate repair TE-LSP. Due to the failure of the head-end node, the protecting node then refreshes the states of the primary TE-LSPs using replicated state control blocks accordingly, until the repair TE-LSPs are no longer needed.
Owner:CISCO TECH INC
Method for RF fingerprinting
InactiveUS20050040968A1Improve accuracyAccurate locationElectric signal transmission systemsImage analysisEngineeringLocation determination
The invention provides a novel method for preparing a wireless environment for location determination of a wireless mobile unit, and for location determination of a wireless mobile unit. In preparing the physical environment, the invention utilizes novel techniques, including novel techniques to place transmitters, the removal of outlying data in the creation of reference RF fingerprints, and algorithms to obtain accurate reference RF fingerprints. In determining the location of a wireless mobile unit, the invention utilizes novel techniques, including novel techniques to select transmitters, the removal of outlying data in the creation of reference RF fingerprints, and algorithms to obtain accurate reference RF fingerprints.
Owner:INNERWIRELESS
Color translating UV microscope
A color translating UV microscope for research and clinical applications involving imaging of living or dynamic samples in real time and providing several novel techniques for image creation, optical sectioning, dynamic motion tracking and contrast enhancement comprises a light source emitting UV light, and visible and IR light if desired. This light is directed to the condenser via a means of selecting monochromatic, bandpass, shortpass, longpass or notch limited light. The condenser can be a brightfield, darkfield, phase contrast or DIC. The slide is mounted in a stage capable of high speed movements in the X, Y and Z dimensions. The microscope uses broadband, narrowband or monochromat optimized objectives to direct the image of the sample to an image intensifier or UV sensitive video system. When an image intensifier is used it is either followed by a video camera, or in the simple version, by a synchronized set of filters which translate the image to a color image and deliver it to an eyepiece for viewing by the microscopist. Between the objective and the image intensifier there can be a selection of static or dynamic switchable filters. The video camera, if used, produces an image which is digitized by an image capture board in a computer. The image is then reassembled by an overlay process called color translation and the computer uses a combination of feedback from the information in the image and operator control to perform various tasks such as optical sectioning and three dimensional reconstruction, coordination of the monochromater while collecting multiple images sets called image planes, tracking dynamic sample elements in three space, control of the environment of the slide including electric, magnetic, acoustic, temperature, pressure and light levels, color filters and optics, control for microscope mode switching between transmitted, reflected, fluorescent, Raman, scanning, confocal, area limited, autofluorescent, acousto-optical and other modes.
Owner:RICHARDSON TECH
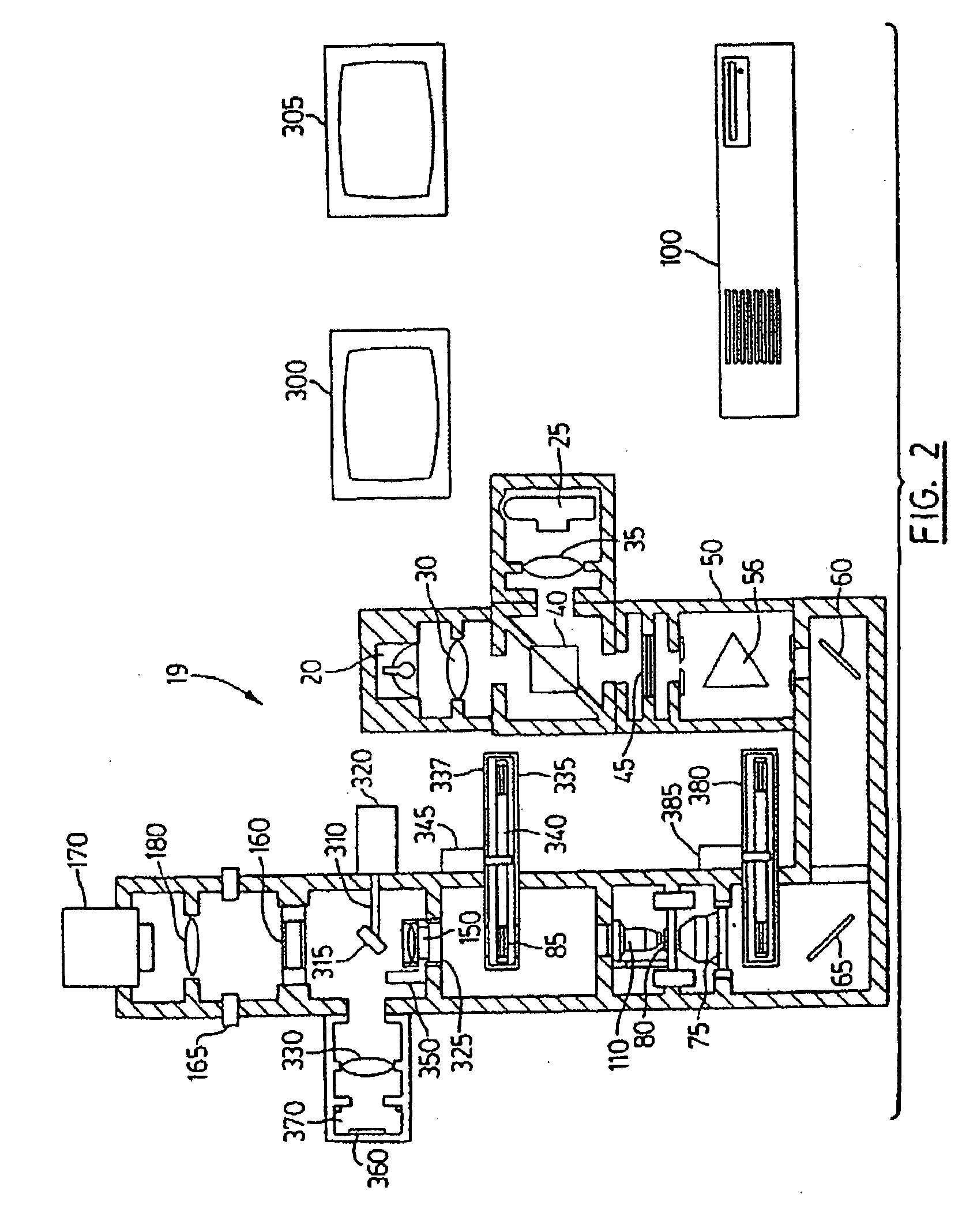
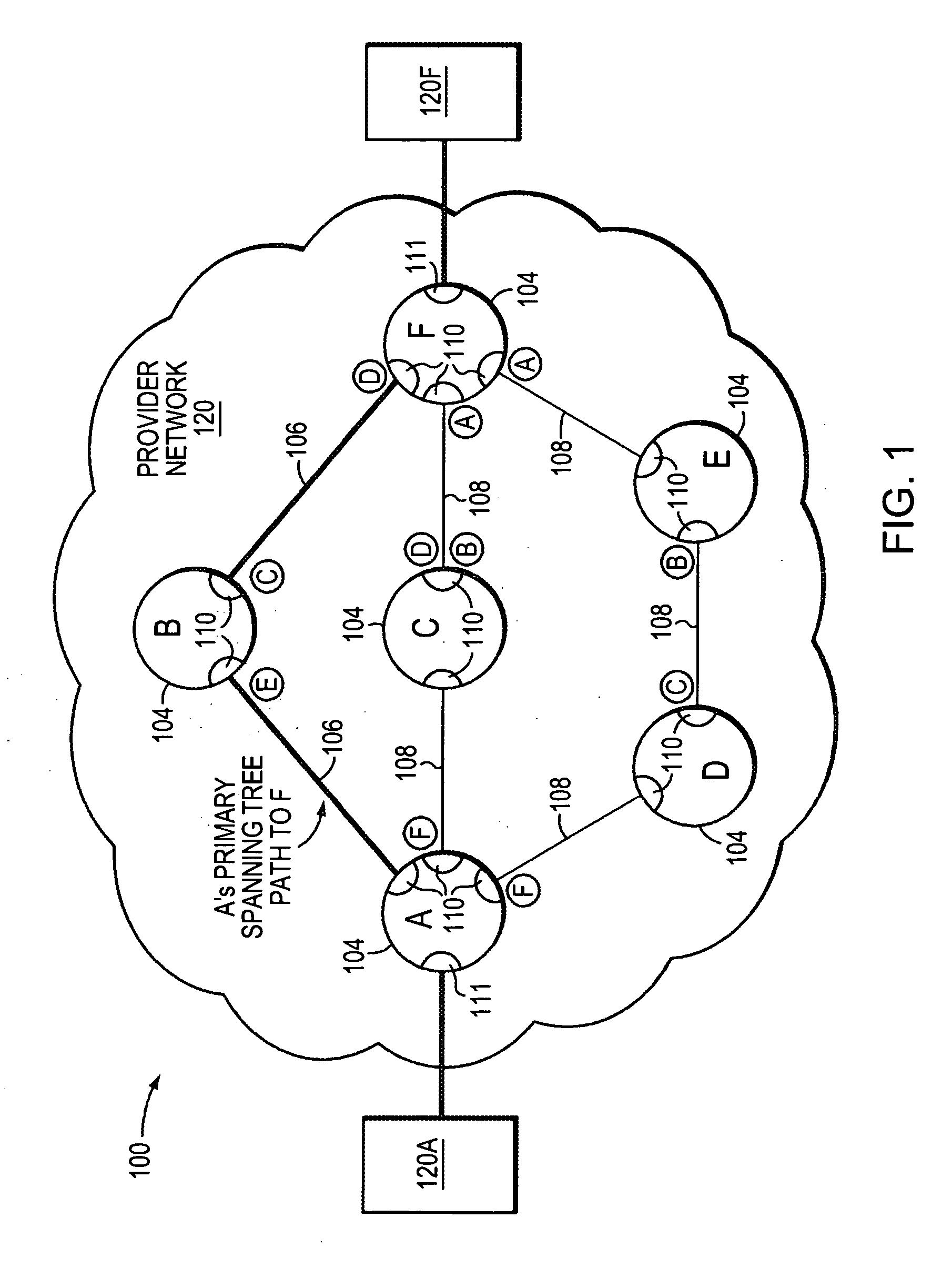
Technique for efficiently managing bandwidth registration for multiple spanning tree options
ActiveUS20070263554A1Efficient managementGreat opportunityData switching by path configurationData streamComputer network
A technique efficiently manages bandwidth (BW) registration for multiple spanning tree options in a computer network. According to the novel technique, an entry bridge determines multiple spanning tree paths to other bridges of the network (namely, one or more available spanning trees rooted at one or more bridges of the network) and determines a utilized (registered) BW on each of those paths. Upon receiving a request to initiate BW registration for a data flow to a destination end point, e.g., from an application source end point, the entry bridge selects one of the spanning tree paths to utilize for the data flow. Selection of the spanning tree path from among the multiple available paths may be based on (i) available bandwidth of the paths, (ii) a shortest of the paths, and (iii) a lowest bridge identifier ID for the bridge root for the path. The entry bridge sends a registration message for the data flow towards the destination end point along the selected spanning tree path. If successful, the data flow is transmitted on the selected path. If not, the entry bridge attempts to register the data flow on a next best alternate spanning tree, e.g., until a successful registration or until a determination that no further alternate spanning trees exist.
Owner:CISCO TECH INC
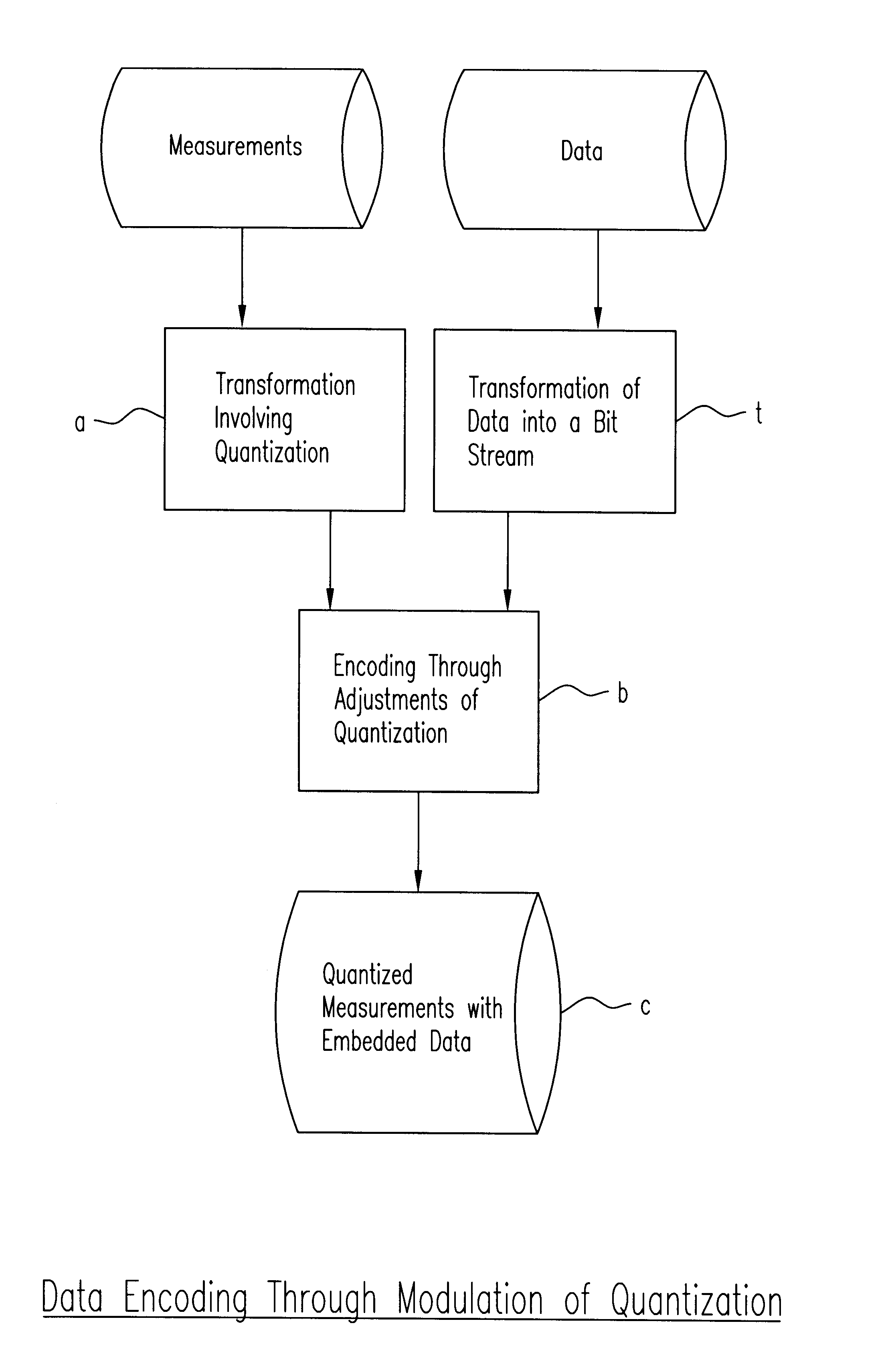
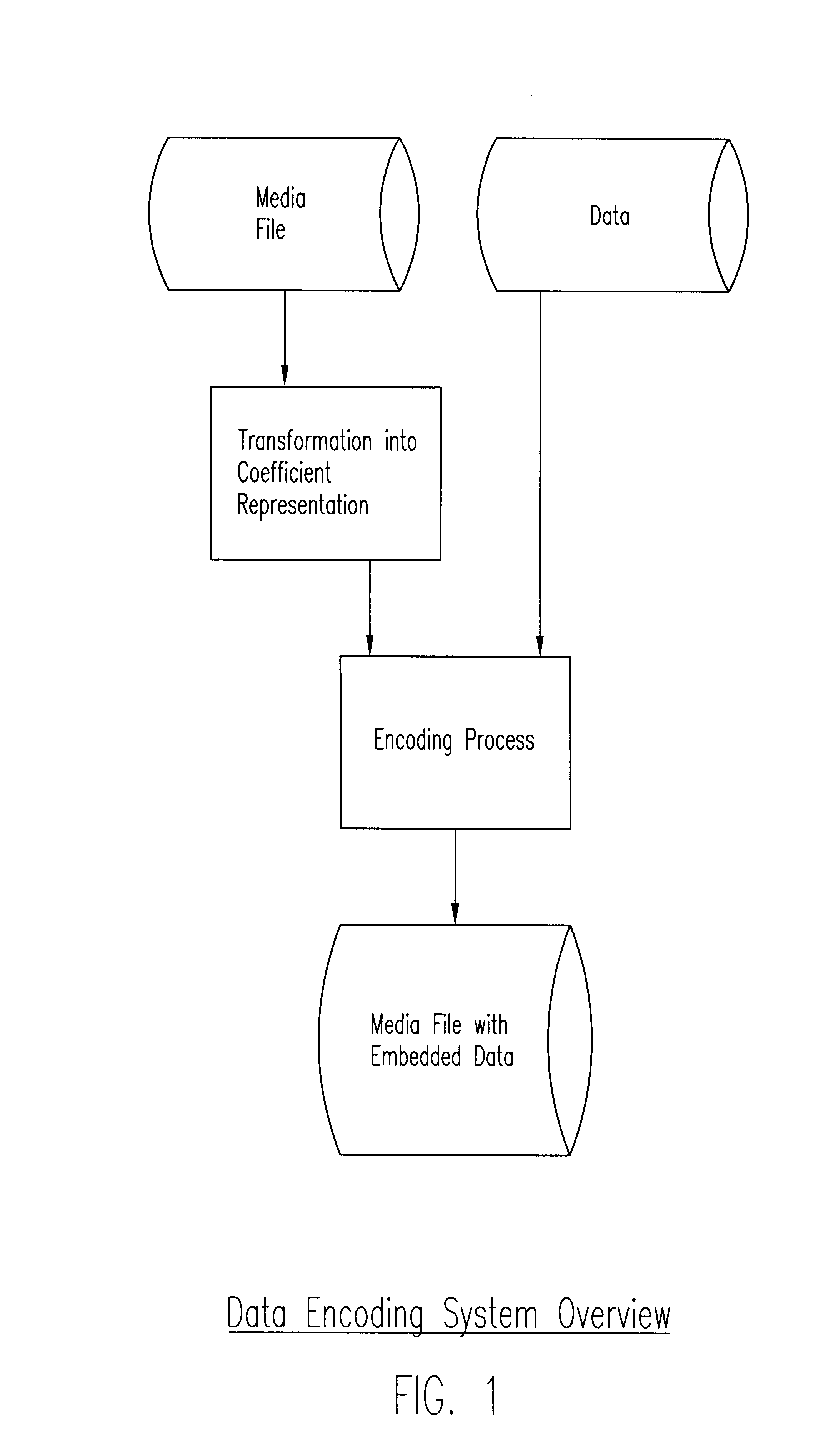
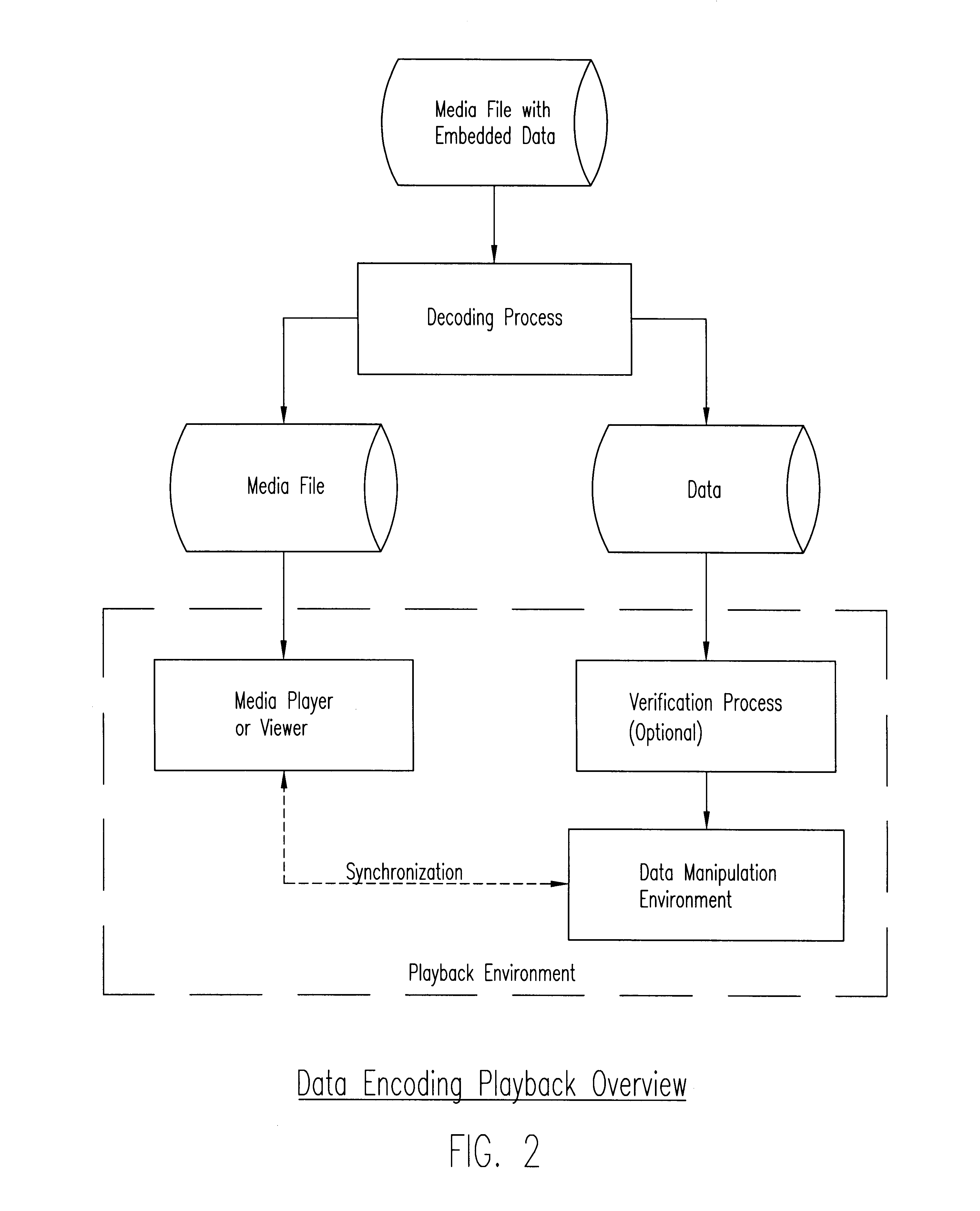
Method of and apparatus for high-bandwidth steganographic embedding of data in a series of digital signals or measurements such as taken from analog data streams or subsampled and/or transformed digital data
InactiveUS6768980B1Pulse modulation television signal transmissionSpeech analysisDigital dataData stream
A novel technique for high-bandwidth steganographic embedding of supplemental data in a series of digital signals or measurements, such as taken from analog data streams or subsampled and / or transformed digital data, wherein the series of measurements are derived through functional transformations and involving quantization and / or aliasing, with the supplemental data bits modulating or modifying the quantized and / or aliased components with only slight adjustments thereof to embed the supplemental data without substantially affecting the quality of the measurements; and all, preferably, through not exclusively, with the use of least-significant-bit parity encoding designed to choose the appropriate components to be so modulated or modified
Owner:TIME WARNER CABLE ENTERPRISES LLC
Eyeglasses with hearing enhanced and other audio signal-generating capabilities
InactiveUS7760898B2Remove associated stigmaImprove hearingNon-optical adjunctsNon-optical partsCamera lensEngineering
Novel techniques for hearing enhancement based on a pair of glasses are disclosed. In one embodiment, the glasses include a first lens holder, a second lens holder, a bridge element, a first temple, a second temple, a first speaker, a second speaker, a microphone and at least one electrical component that performs a hearing enhanced function to enhance audio signals from the microphone to be sent to the speakers for the user to hear. At least one electrical component in the glasses is for generating other audio signals by the speakers, with the other audio signals originating from signals other than audio signals captured by the microphone. In another embodiment, some of the electrical components are in a portable device, wired or wirelessly, coupled to the glasses. In yet another embodiment, the glasses function as a headset, with other electrical components in the portable device. In such embodiment, since the glasses can provide a number of different hearing functions, a third party may not be able to tell whether the user is wearing the glasses to have his hearing enhanced, or for hearing other audio signals.
Owner:INGENIOSPEC
Technique for efficiently routing IP traffic on CE-CE paths across a provider network
InactiveUS20070217419A1Efficient routingImprove overall utilizationError preventionTransmission systemsTraffic capacityPath computation element
A technique efficiently routes Internet Protocol (IP) traffic on paths between customer edge devices (CEs) across a provider network (“CE-CE paths”) in a computer network. According to the novel technique, a path computation element (PCE), e.g., a provider edge device (PE), may learn dynamic link attribute information of remote links from the provider network to one or more remote CEs (e.g., “PE-CE links” or “CE-PE links”). A multi-homed requesting CE requests from the PCE a set of CE-CE path metrics (e.g., costs) to one or more remote destination address prefixes, e.g., via each multihomed CE-PE link from the requesting CE. In response to the request, the PCE computes the set of available CE-CE paths and current metrics to the remote destination address prefixes and returns the corresponding CE-CE path metrics to the requesting CE. The requesting CE modifies its IP forwarding entries accordingly in order to perform IP traffic routing corresponding to the CE-CE path metrics (e.g., asymmetrical load balancing) across its multi-homed CE-PE links.
Owner:CISCO TECH INC
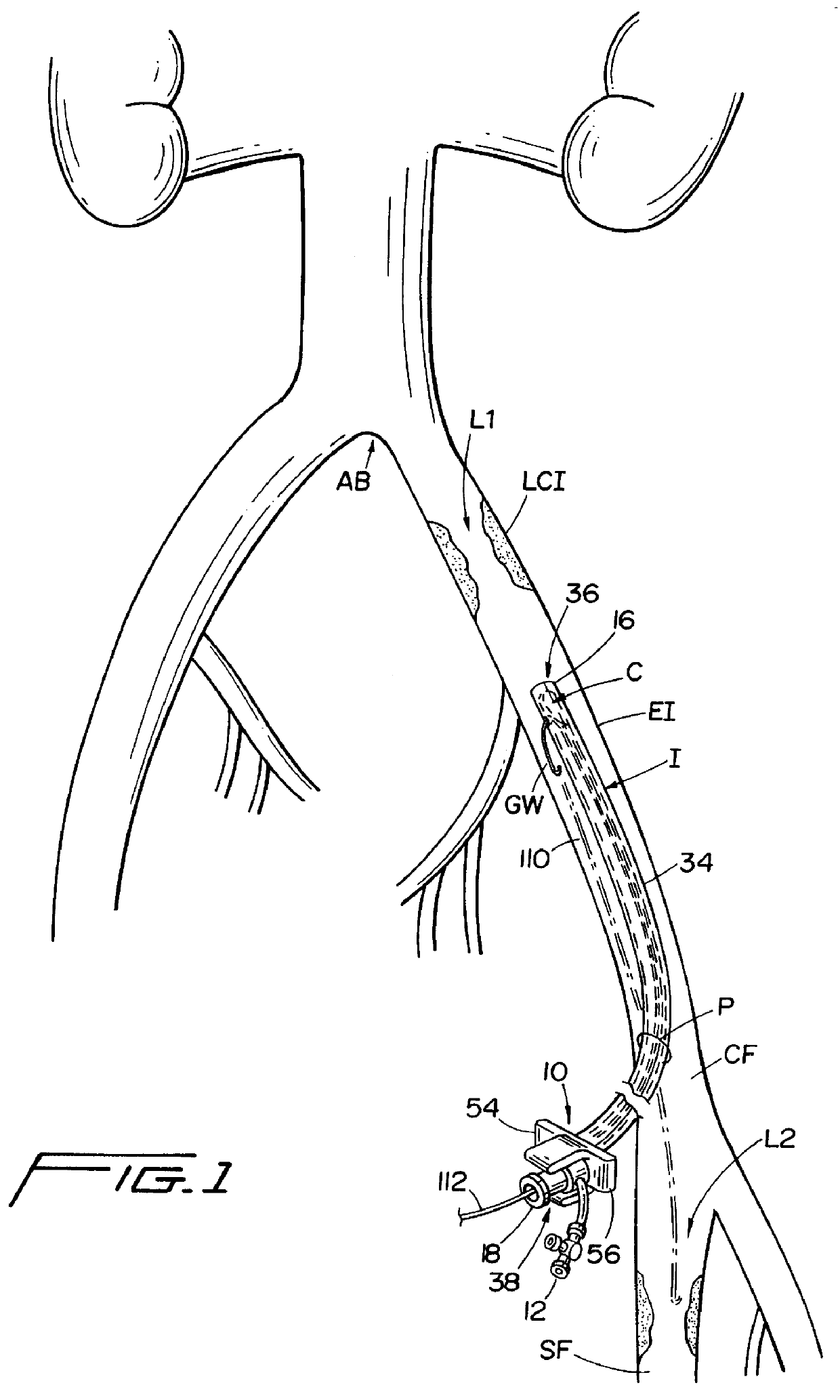
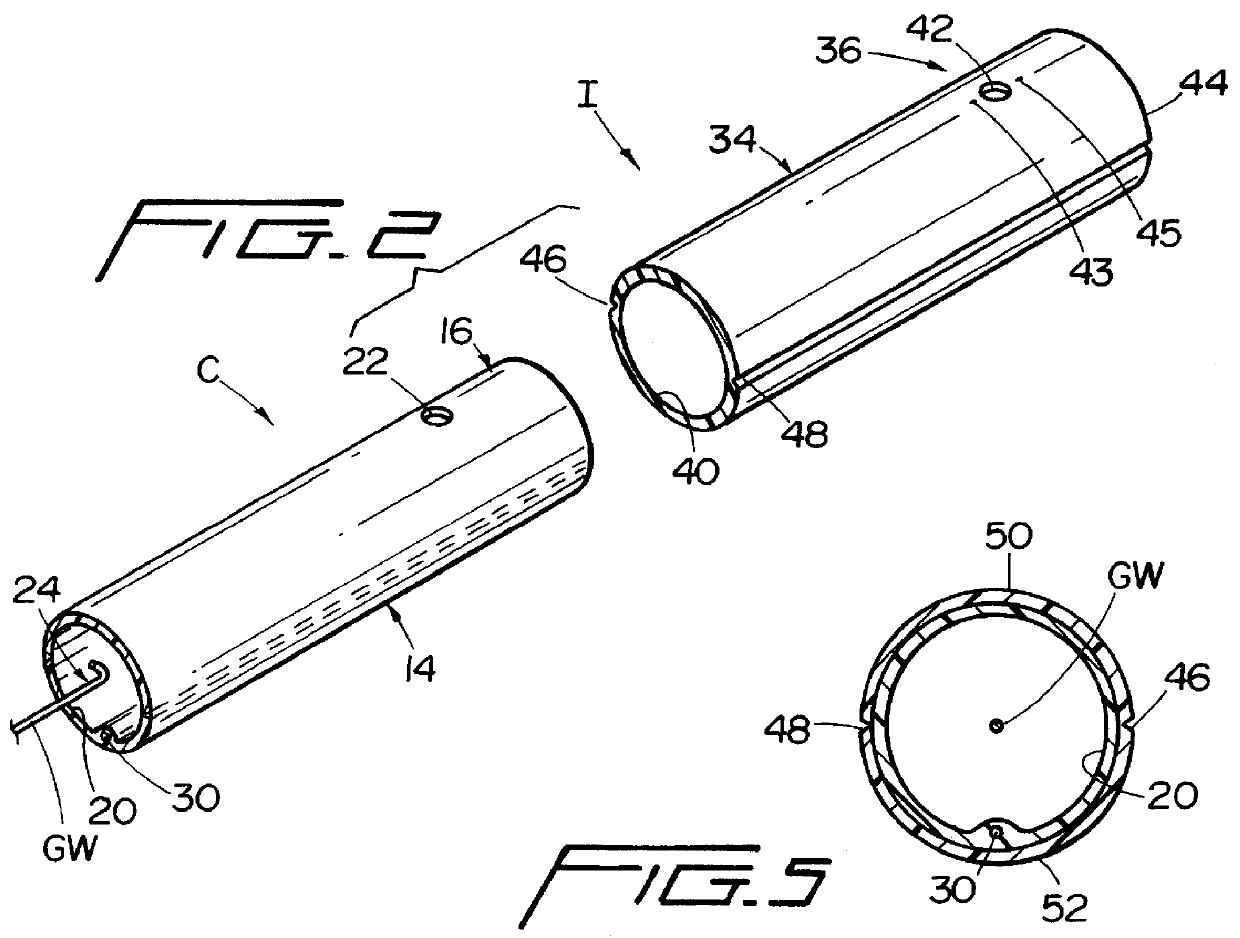
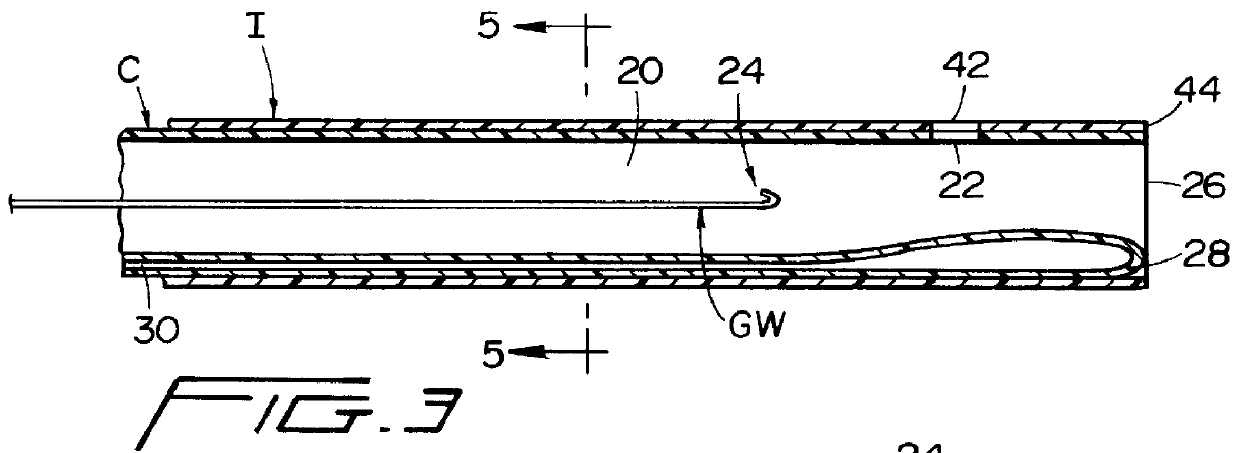
Catheter introducer for antegrade and retrograde medical procedures
InactiveUS6022342AAvoid delayEasy to implementGuide wiresSurgeryPercutaneous angioplastyCatheter introducer
A catheter introducer for antegrade and retrograde medical procedures includes a generally tubular introducer member having proximal and distal ends. The introducer member includes a lumen for receiving a guidewire during a medical procedure, which guidewire includes a distal end traveling in a first direction. The catheter introducer further includes an occlusion member adjacent the distal end thereof for altering the traveling direction of the distal end of the guidewire to a second direction. The catheter introducer of the invention can be easily used for performing angioplasty on tandem or segmental lesions in one procedure using antegrade and retrograde approaches. The novel technique of the present invention involves performing angioplasty on one lesion using one of the antegrade and retrograde approaches, and then using the other of the antegrade and retrograde approaches to perform angioplasty on the second lesion. Both lesions are attended to during one medical procedure.
Owner:MUKHERJEE DIPANKAR
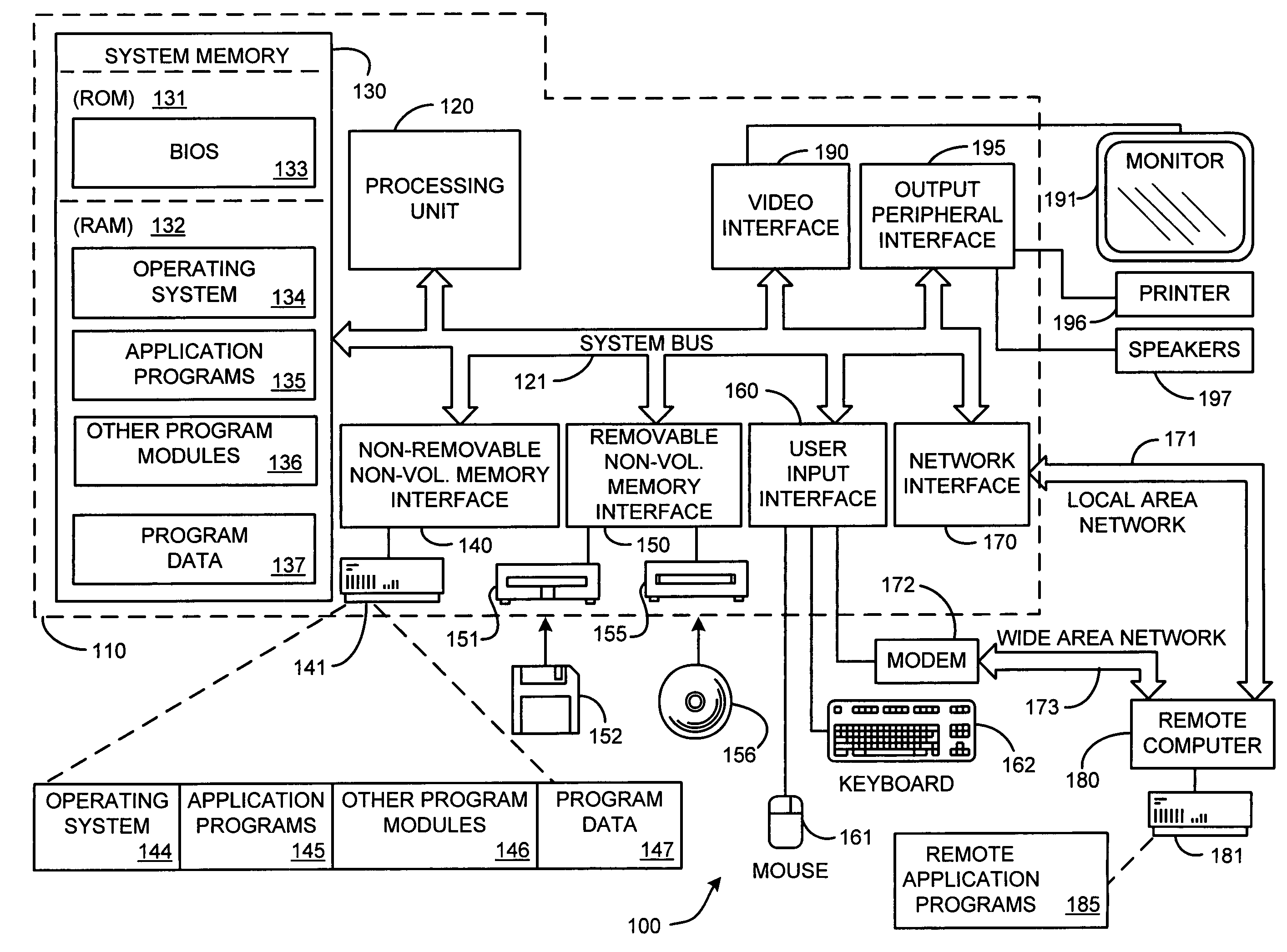
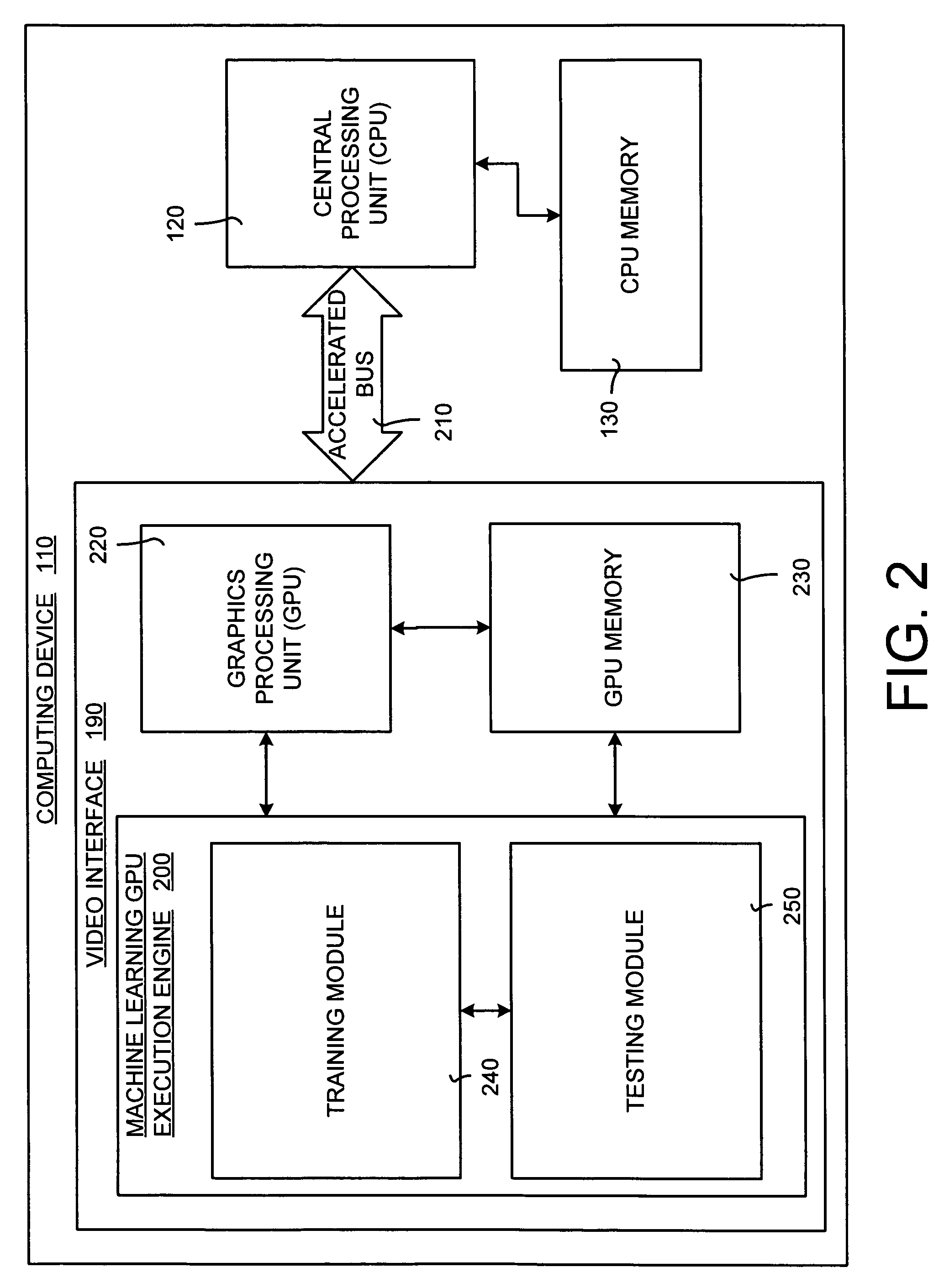
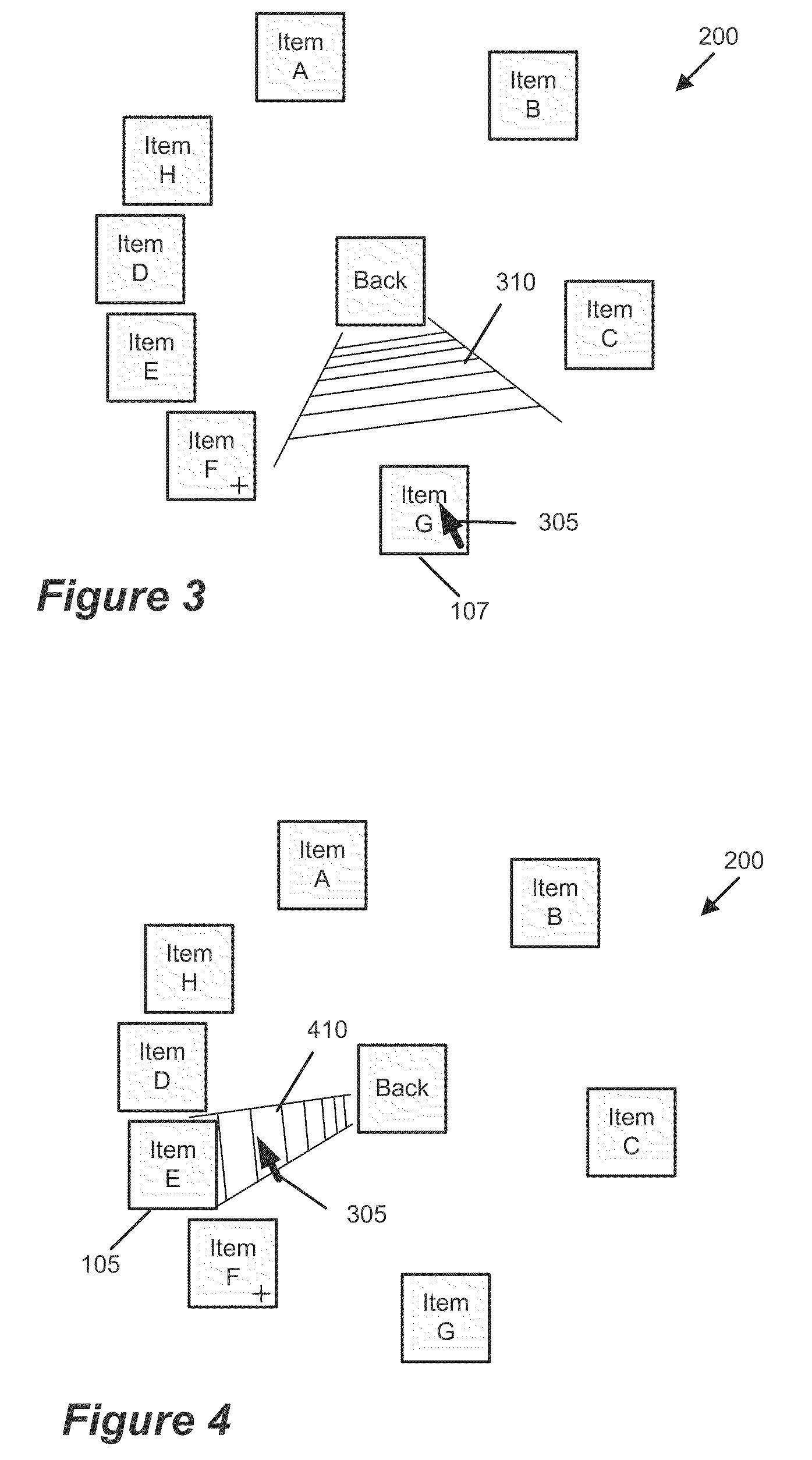
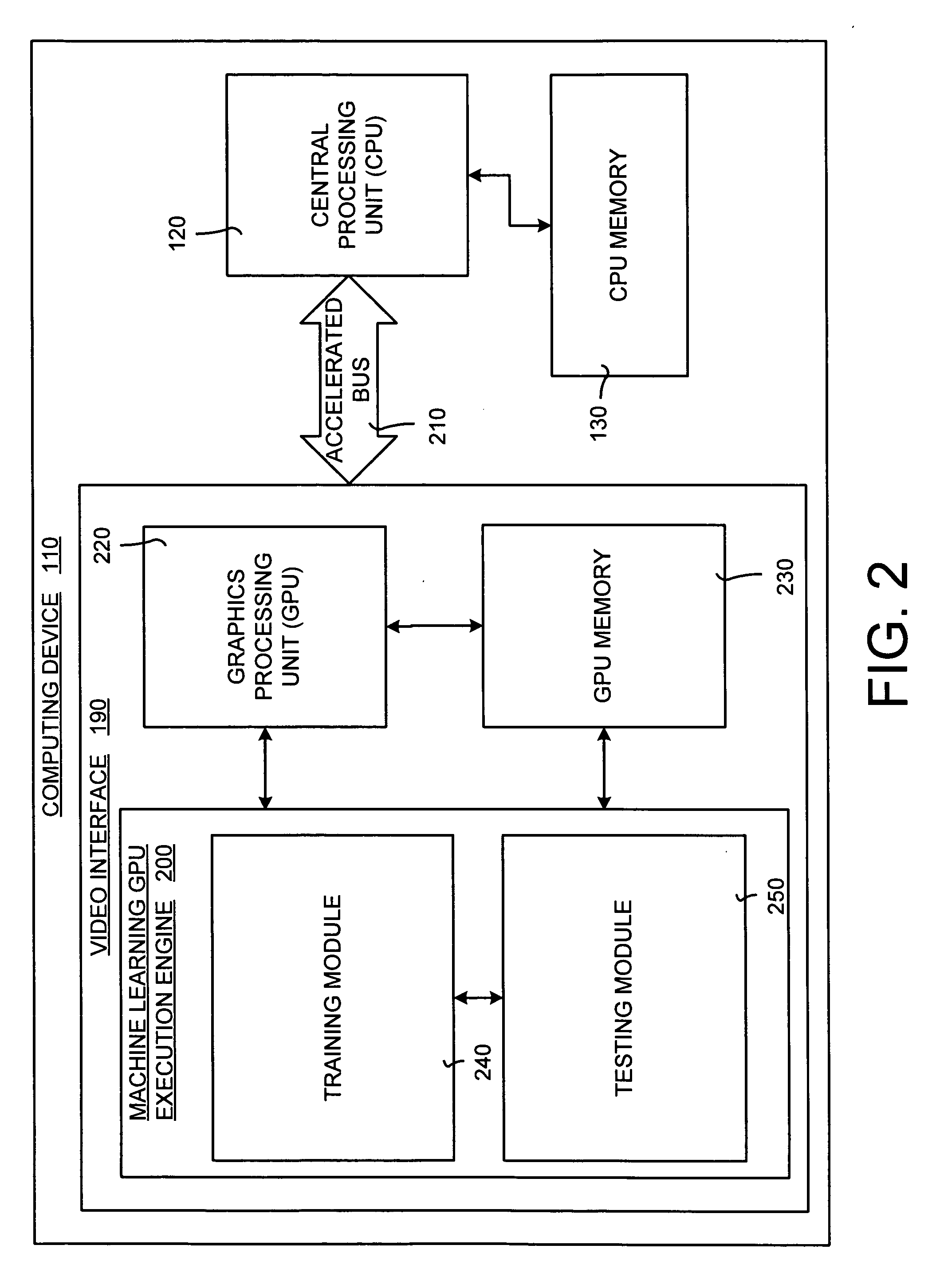
System and method for accelerating and optimizing the processing of machine learning techniques using a graphics processing unit
ActiveUS7219085B2Alleviates computational limitationMore computationCharacter and pattern recognitionKnowledge representationGraphicsTheoretical computer science
A system and method for processing machine learning techniques (such as neural networks) and other non-graphics applications using a graphics processing unit (GPU) to accelerate and optimize the processing. The system and method transfers an architecture that can be used for a wide variety of machine learning techniques from the CPU to the GPU. The transfer of processing to the GPU is accomplished using several novel techniques that overcome the limitations and work well within the framework of the GPU architecture. With these limitations overcome, machine learning techniques are particularly well suited for processing on the GPU because the GPU is typically much more powerful than the typical CPU. Moreover, similar to graphics processing, processing of machine learning techniques involves problems with solving non-trivial solutions and large amounts of data.
Owner:MICROSOFT TECH LICENSING LLC
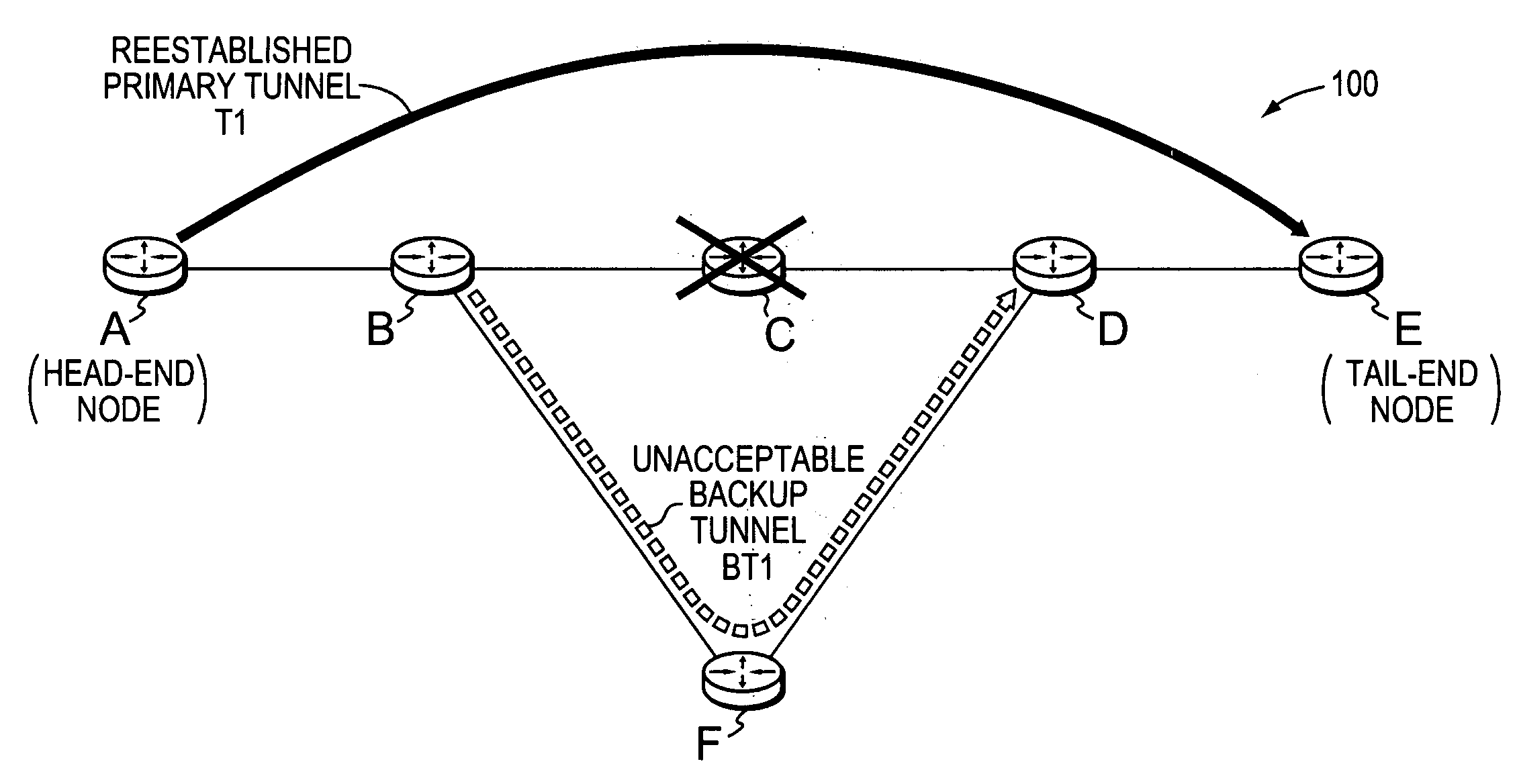
Technique for determining whether to reestablish fast rerouted primary tunnels based on backup tunnel path quality feedback
ActiveUS20070183317A1Promote recoveryReduce needError preventionTransmission systemsNodal analysisDistributed computing
A technique dynamically determines whether to reestablish a Fast Rerouted primary tunnel based on path quality feedback of a utilized backup tunnel in a computer network. According to the novel technique, a head-end node establishes a primary tunnel to a destination, and a point of local repair (PLR) node along the primary tunnel establishes a backup tunnel around one or more protected network elements of the primary tunnel, e.g., for Fast Reroute protection. Once one of the protected network elements fail, the PLR node “Fast Reroutes,” i.e., diverts, the traffic received on the primary tunnel onto the backup tunnel, and sends notification of backup tunnel path quality (e.g., with one or more metrics) to the head-end node. The head-end node then analyzes the path quality metrics of the backup tunnel to determine whether to utilize the backup tunnel or reestablish a new primary tunnel.
Owner:CISCO TECH INC
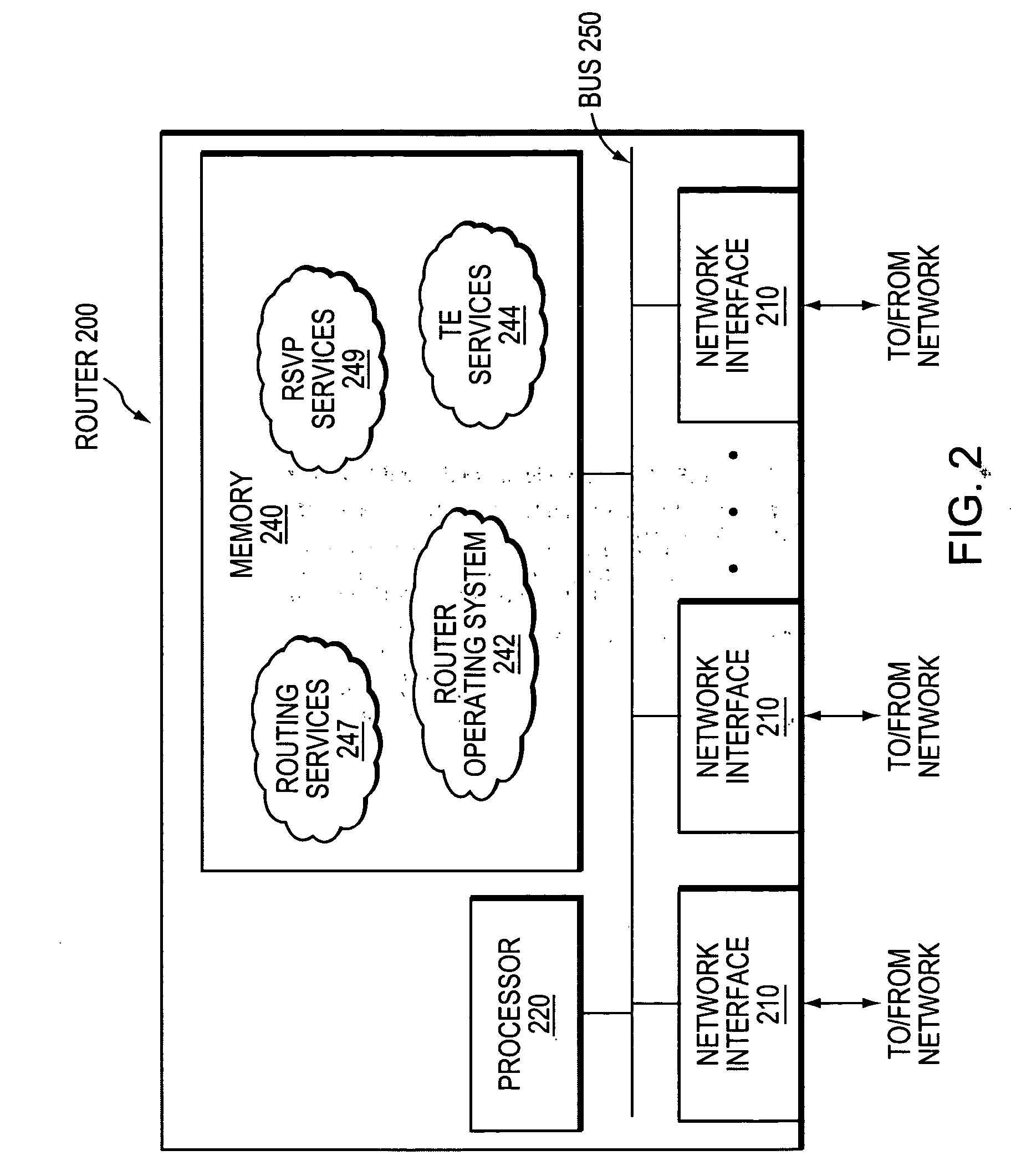
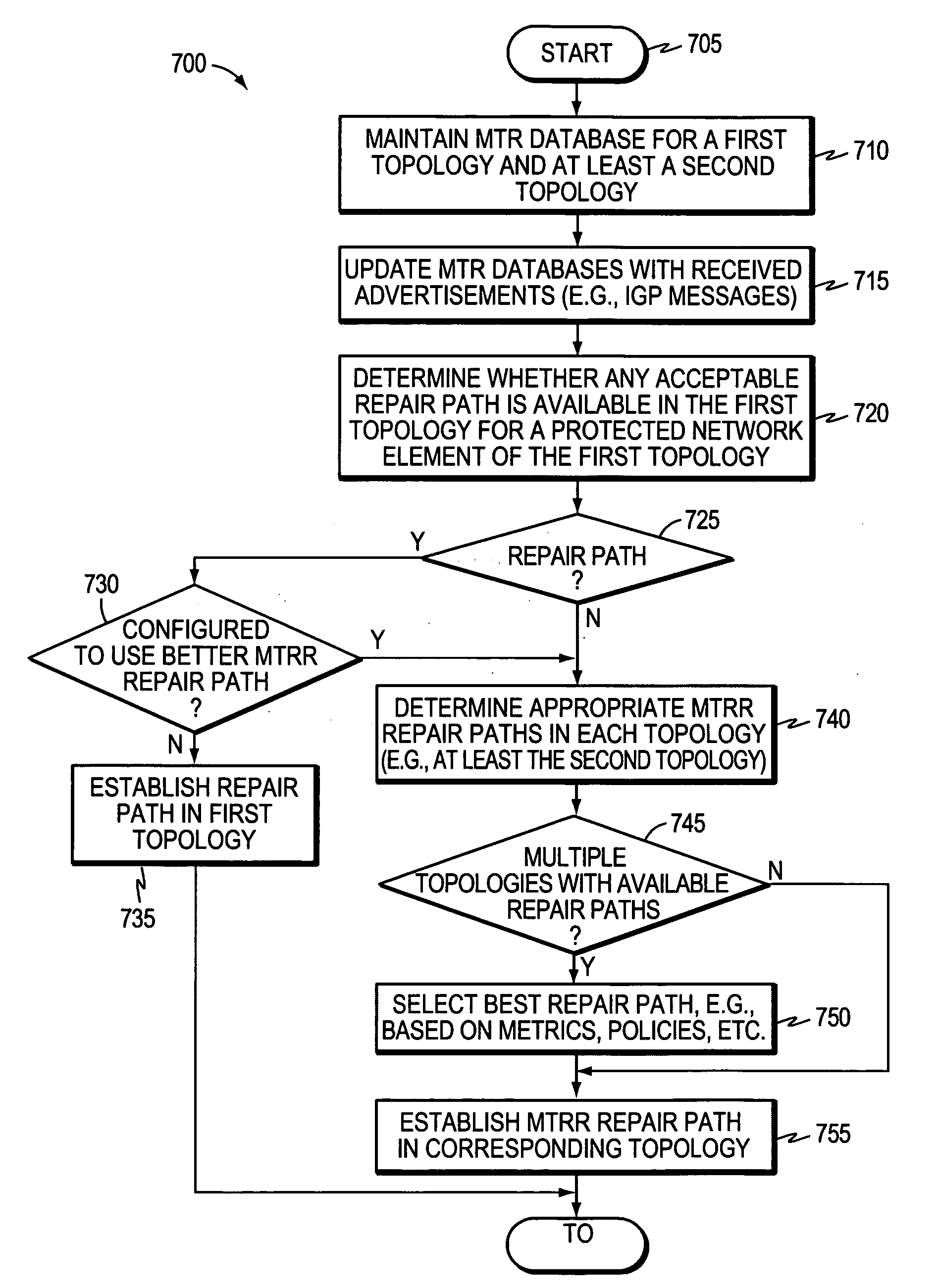
Technique for protecting against failure of a network element using Multi-Topology Repair Routing (MTRR)
ActiveUS20080049622A1Prevent extensionReduce needError preventionTransmission systemsTopological routingDistributed computing
A technique protects against failure of a network element using Multi-Topology Repair Routing (MTRR) in a computer network. According to the novel technique, a protecting node (e.g., a router) maintains Multi-Topology Routing (MTR) databases for a first topology and at least a second topology. The protecting node determines whether any acceptable repair paths are available in the first topology for a protected network element (e.g., node, link, etc.) of the first topology. If not, the protecting node may establish a repair path (e.g., for Fast ReRoute, FRR) in the second topology for the protected network element.
Owner:CISCO TECH INC
Wavelocker for Improving Laser Wavelength Accuracy in WDM Networks
InactiveUS20110135301A1Easy mappingMaintaining full visibilityMultiplex system selection arrangementsWavelength-division multiplex systemsLasing wavelengthOptoelectronics
The present invention includes novel techniques, apparatus, and systems for optical WDM communications. Various wavelocker apparatus and methods are disclosed that measure the frequency offsets between signal lasers and reference lasers. The measured offsets are used to adjust the signal laser frequencies to meet their target frequencies. The absolute accuracy of the reference laser frequency is improved by measuring the absorption of the reference laser by a gas cell with known fixed absorption lines versus the reference laser frequency. Apparatus and methods are disclosed to cover scenarios in which the reference laser polarization is aligned with the signal lasers, as well as those in which the reference laser polarization is not aligned with the signal lasers. The wavelocker apparatus may or may not be located at the same network site as the signal lasers.
Owner:VELLO SYST +1
Radial menus
Owner:APPLE INC
System and method for accelerating and optimizing the processing of machine learning techniques using a graphics processing unit
ActiveUS20050125369A1Alleviates computational limitationImprove data accessCharacter and pattern recognitionKnowledge representationGraphicsArtificial intelligence
A system and method for processing machine learning techniques (such as neural networks) and other non-graphics applications using a graphics processing unit (GPU) to accelerate and optimize the processing. The system and method transfers an architecture that can be used for a wide variety of machine learning techniques from the CPU to the GPU. The transfer of processing to the GPU is accomplished using several novel techniques that overcome the limitations and work well within the framework of the GPU architecture. With these limitations overcome, machine learning techniques are particularly well suited for processing on the GPU because the GPU is typically much more powerful than the typical CPU. Moreover, similar to graphics processing, processing of machine learning techniques involves problems with solving non-trivial solutions and large amounts of data.
Owner:MICROSOFT TECH LICENSING LLC
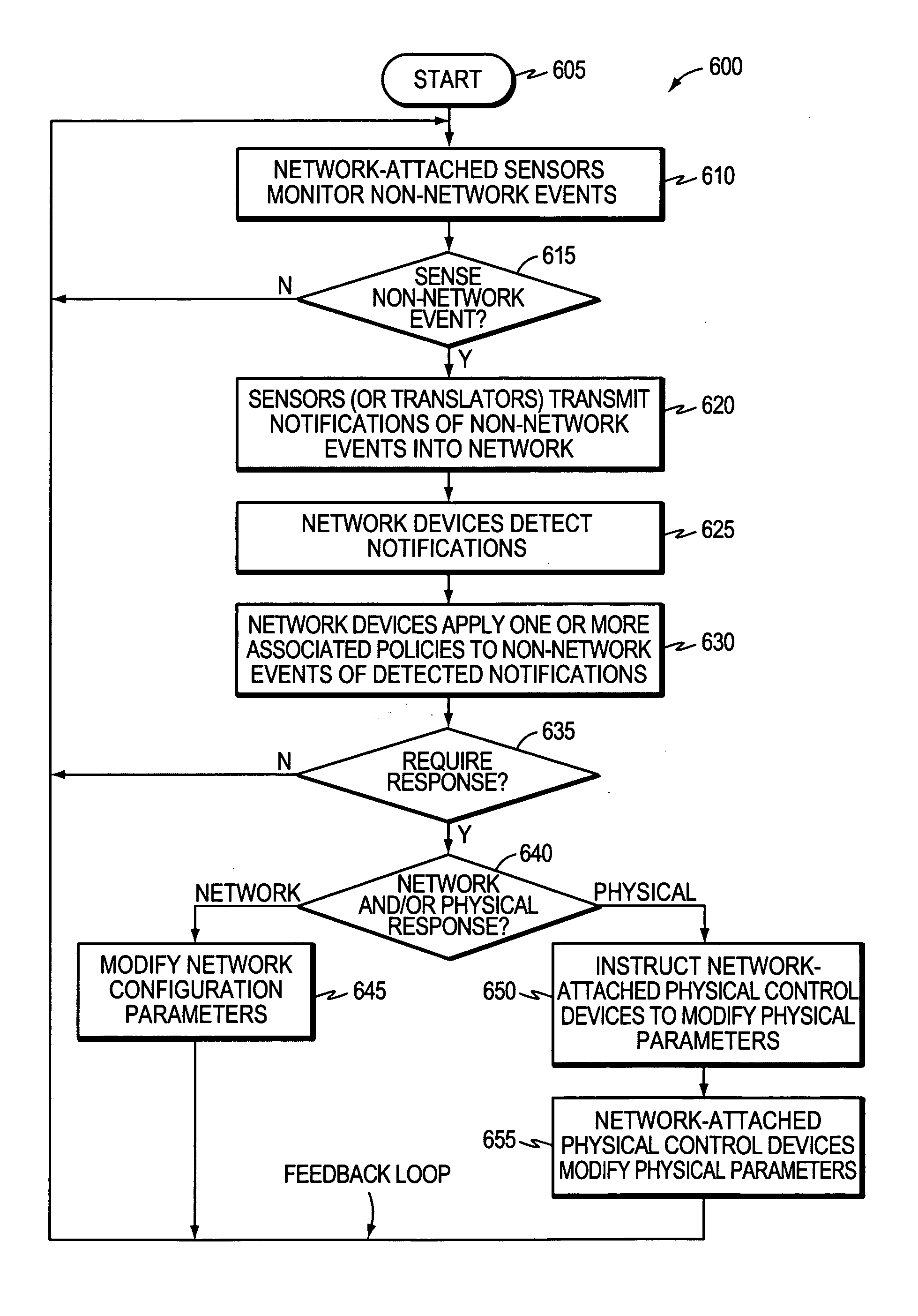
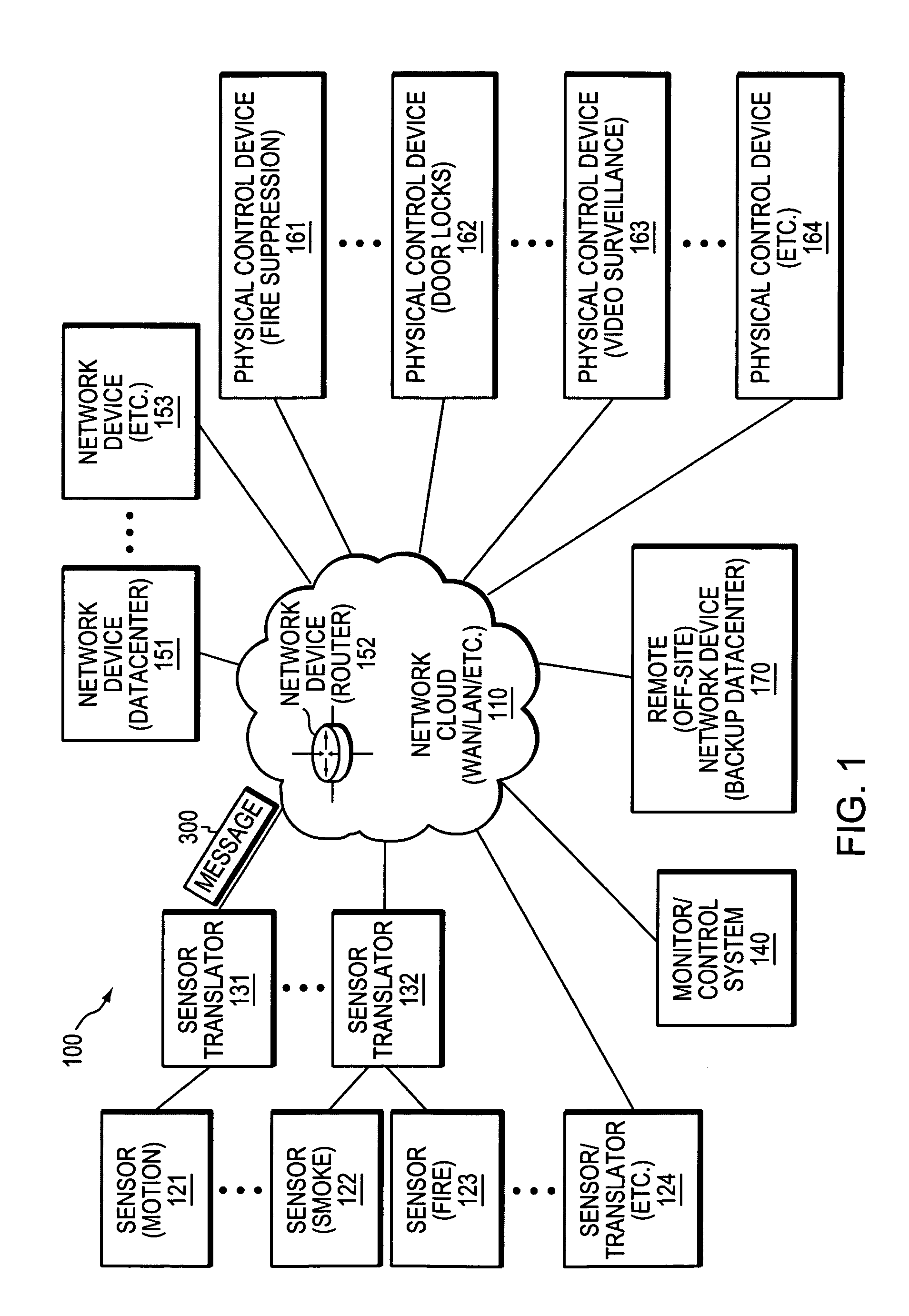
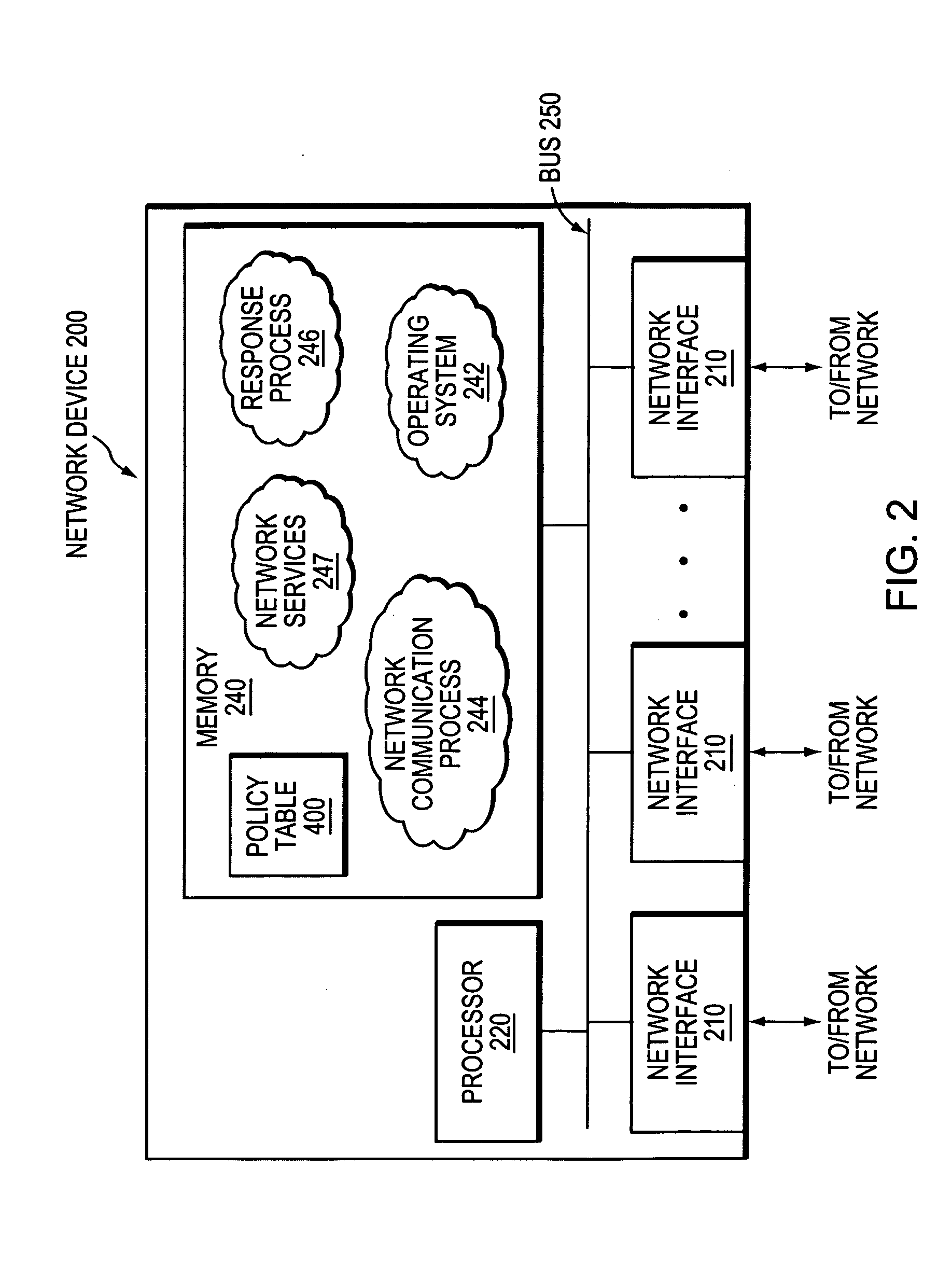
Dynamically responding to non-network events at a network device in a computer network
ActiveUS20070283005A1Improve responsivenessGuaranteed uptimeServersDigital computer detailsData centerNetwork connection
A technique dynamically responds to non-network events at a network device in a computer network. According to the novel technique, one or more sensors automatically detect (sense) one or more non-network events, and notifications of the non-network events are then transmitted over the network. One or more network devices (e.g., data centers, servers, routers, etc.) detect the notifications of the network events, and dynamically respond to the non-network events based on one or more associated policies. For example, one or more network-based policies may be defined that modify one or more network configuration parameters in response to the non-network events. Alternatively or in addition, one or more physical-based policies may be defined that instruct one or more network-attached physical control devices to modify one or more physical parameters.
Owner:CISCO TECH INC
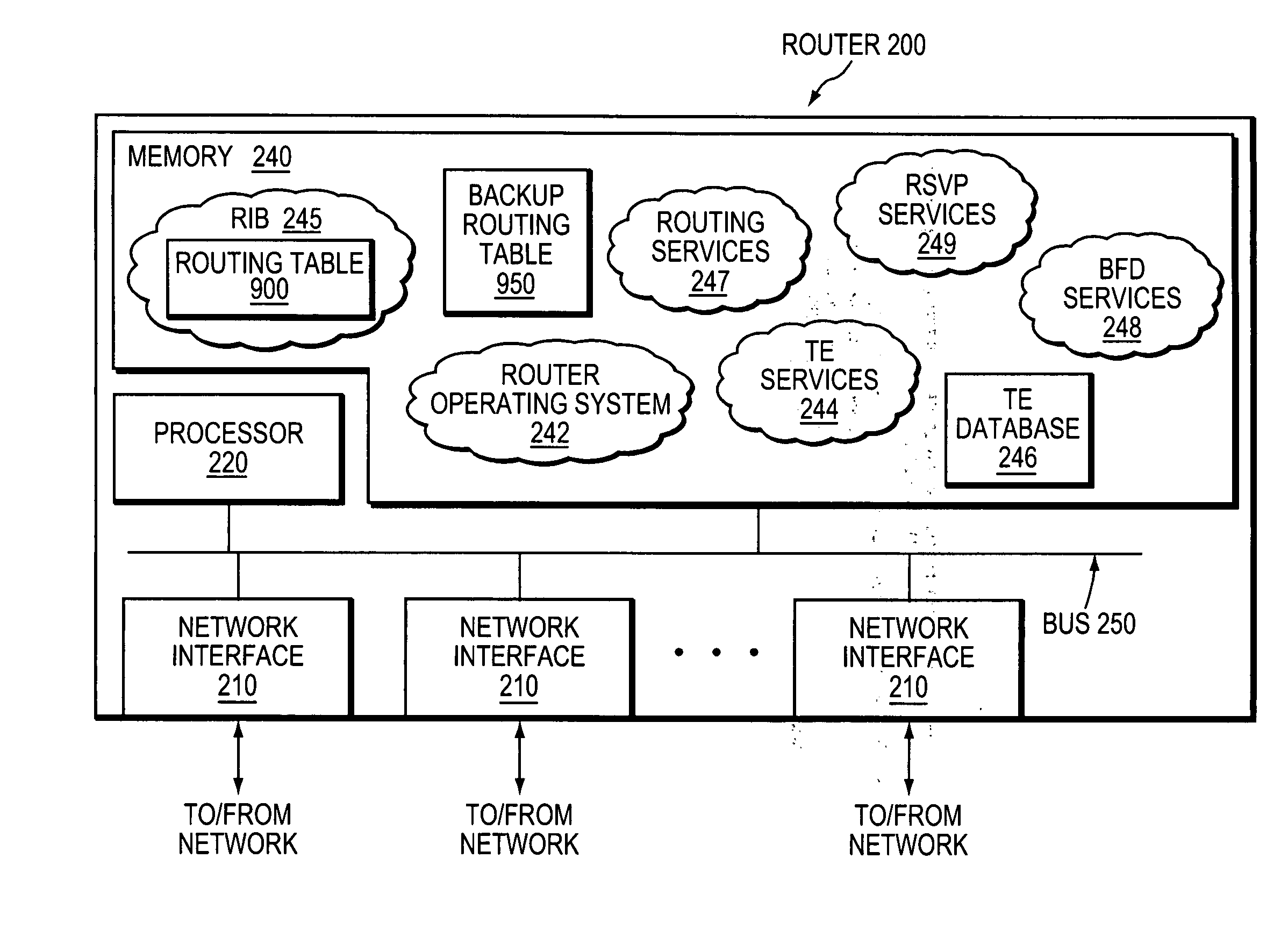
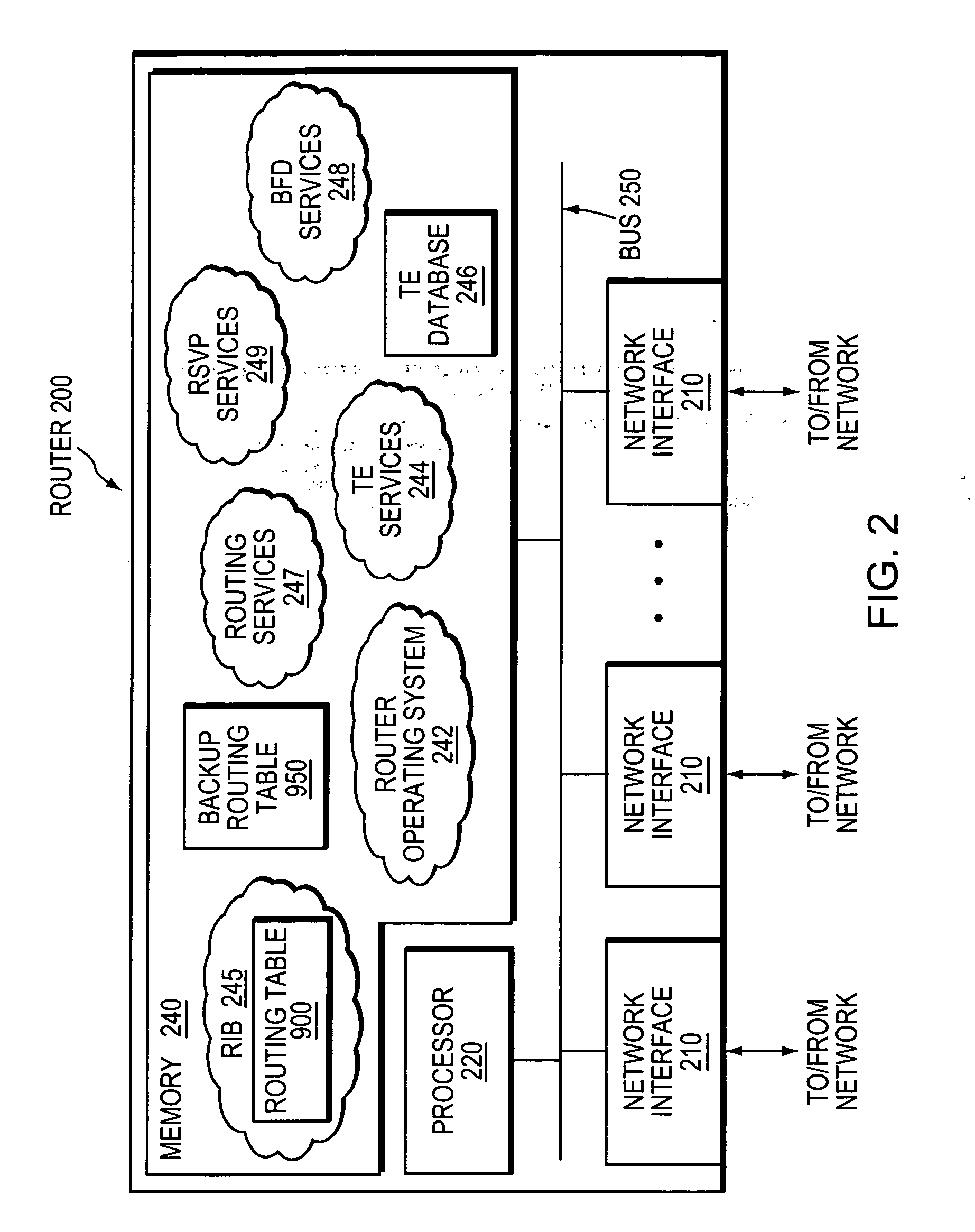
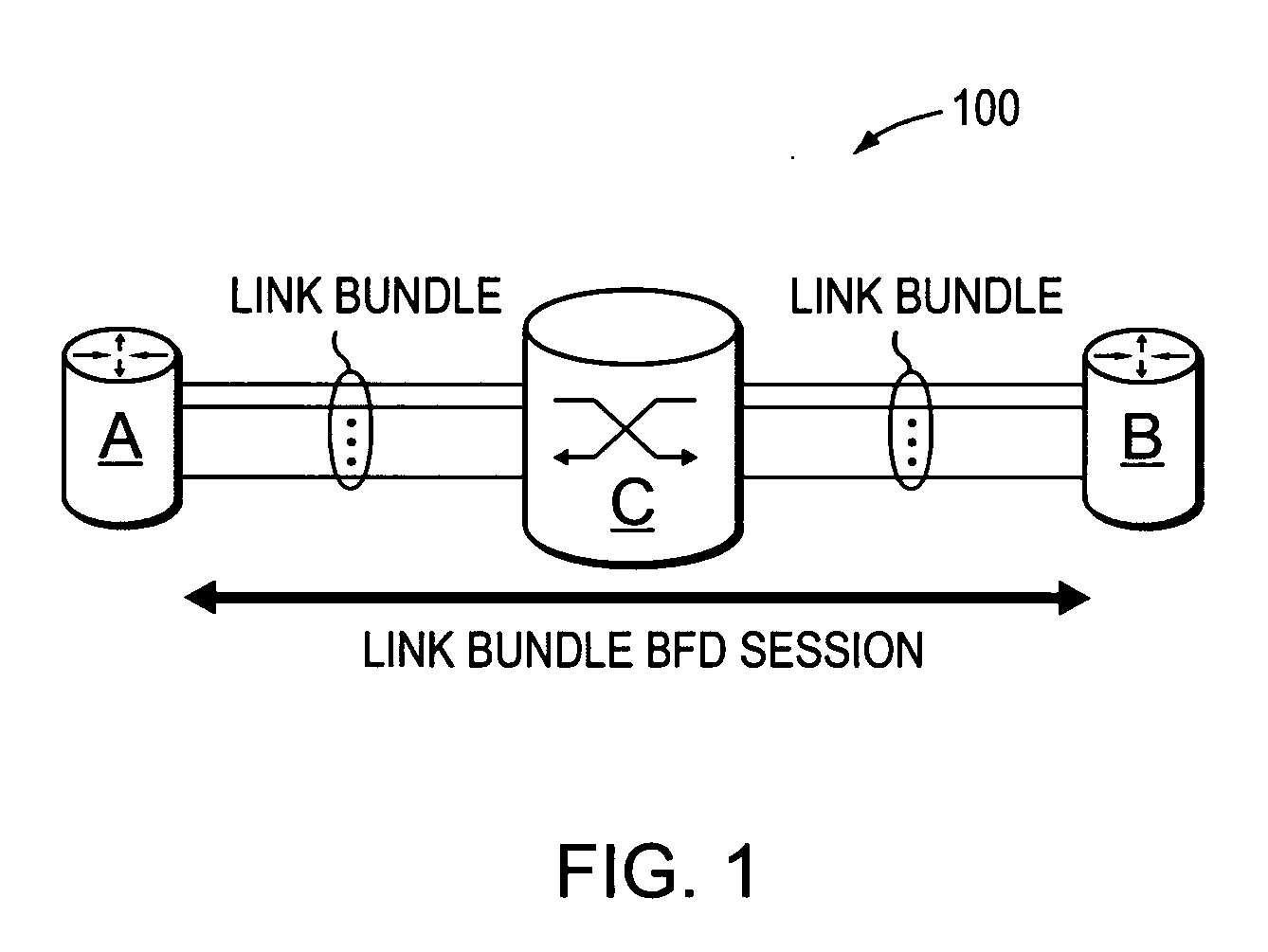
Technique for efficiently and dynamically maintaining bidirectional forwarding detection on a bundle of links
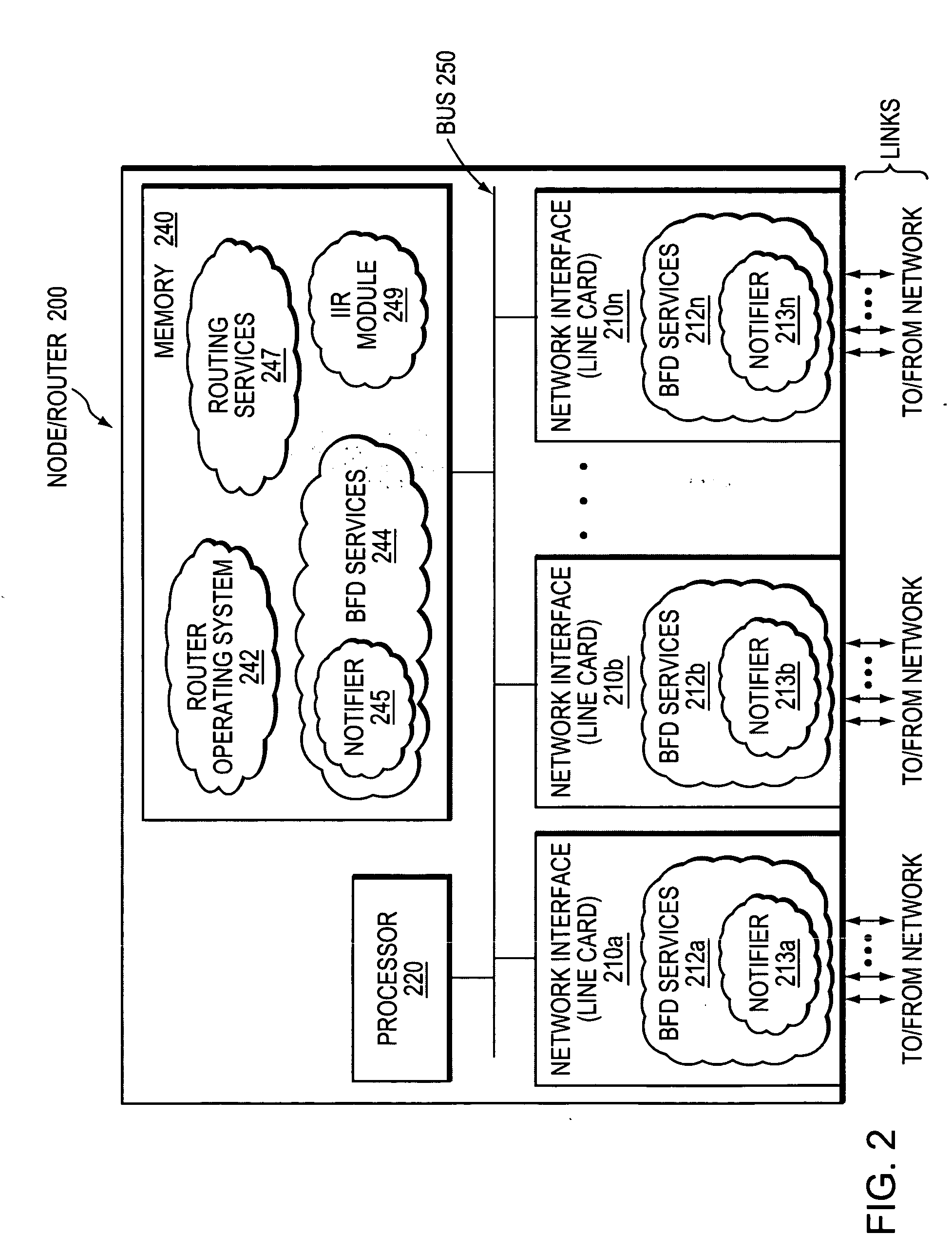
ActiveUS20070207591A1Improve performanceImprove scalabilityMultiplex system selection arrangementsEnergy efficient ICTComputer networkBidirectional Forwarding Detection
A technique efficiently and dynamically maintains bidirectional forwarding detection (BFD) on a bundle of links in a computer network. According to the novel technique, one or more “standby” BFD sessions may be established on one or more corresponding line cards (LCs), the LCs having one or more links of the bundle (bundle links). Once established, one of the standby BFD sessions may be selected as an “active” BFD session based on activity of one of the bundle links of the corresponding LC. Also, BFD messages may be transmitted from one of the bundle links of the active BFD session, e.g., the link receiving BFD messages. In response to inactivity of the transmitting link (e.g., failure, removal, etc.), the active BFD session may switch to another available active bundle link, and if no other active bundle links are available to the active BFD session, one of the standby BFD sessions is selected as the new active BFD session. In the event no other standby BFD sessions exist, the link bundle is determined to have failed.
Owner:CISCO TECH INC
Graphite intercalation and exfoliation process
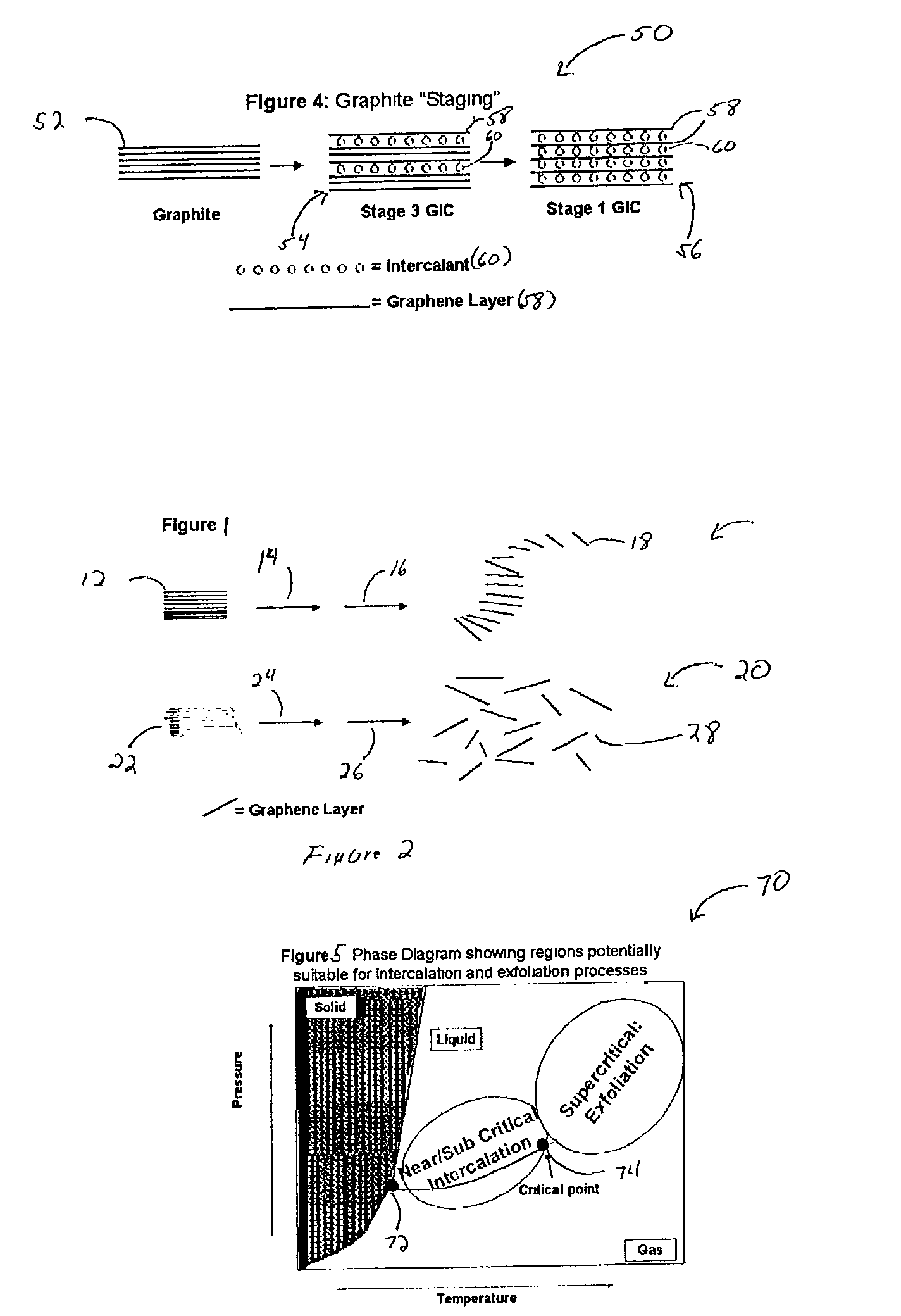
InactiveUS7105108B2Improve volume expansionReduce needMaterial nanotechnologyGraphiteConductive polymerGraphite particle
The invention relates to expanded graphite and methods of making the graphite and products that can be made from the graphite made from the inventive process. The invention includes the step of introducing a fluid into at least one of a plurality of interstices of graphite flake, wherein the fluid comprises at least one of a sub-critical point fluid, a near critical point fluid, or a supercritical fluid. The graphite flake is also intercalated with an intercalant and optionally an oxidizing agent. The invention may further include novel techniques of exfoliating the graphite. The invention may be practiced to make nano-sized graphite particles and also graphite composites. Preferred composites which may be made in accordance with the invention include conductive polymeric composites (thermally or electrically), paint composites, battery composites, capacitor composites, and pollution abatement catalyst support composites.
Owner:GRAFTECH INT HLDG INC
Systems and methods for detecting skin, eye region, and pupils
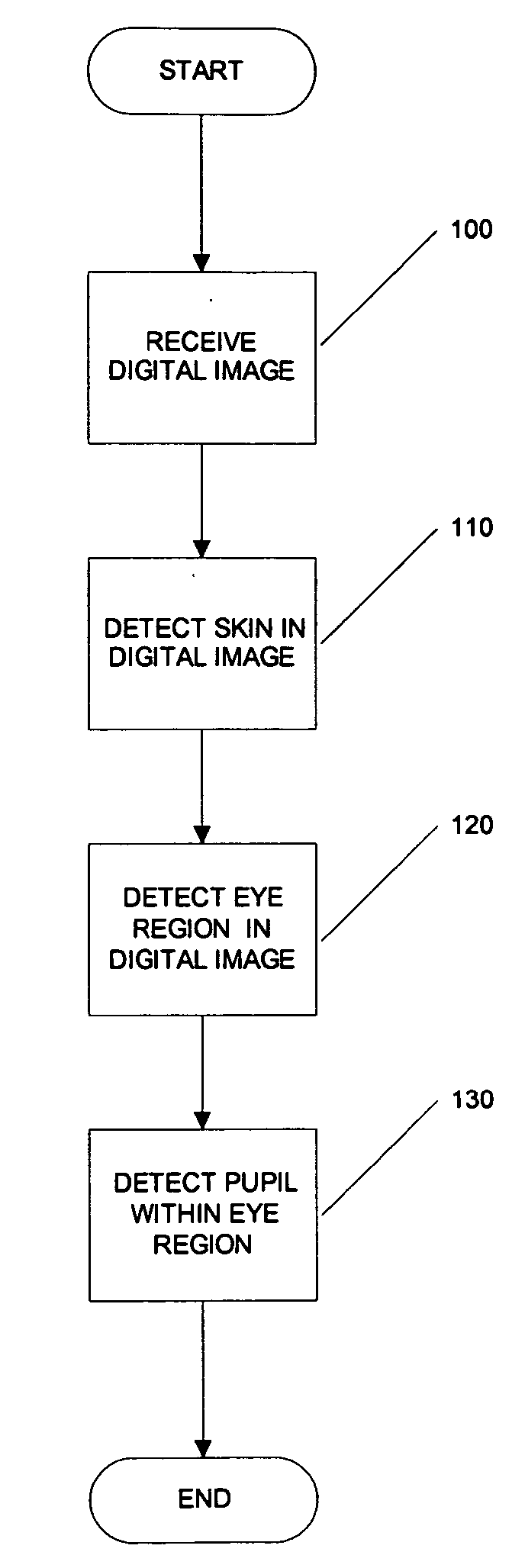
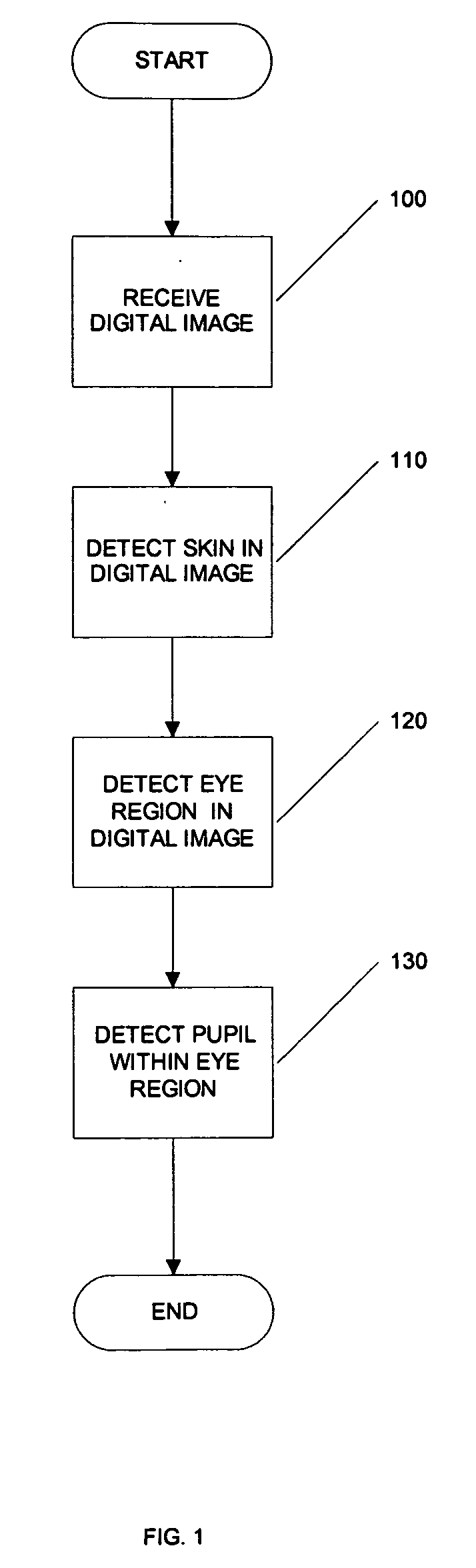
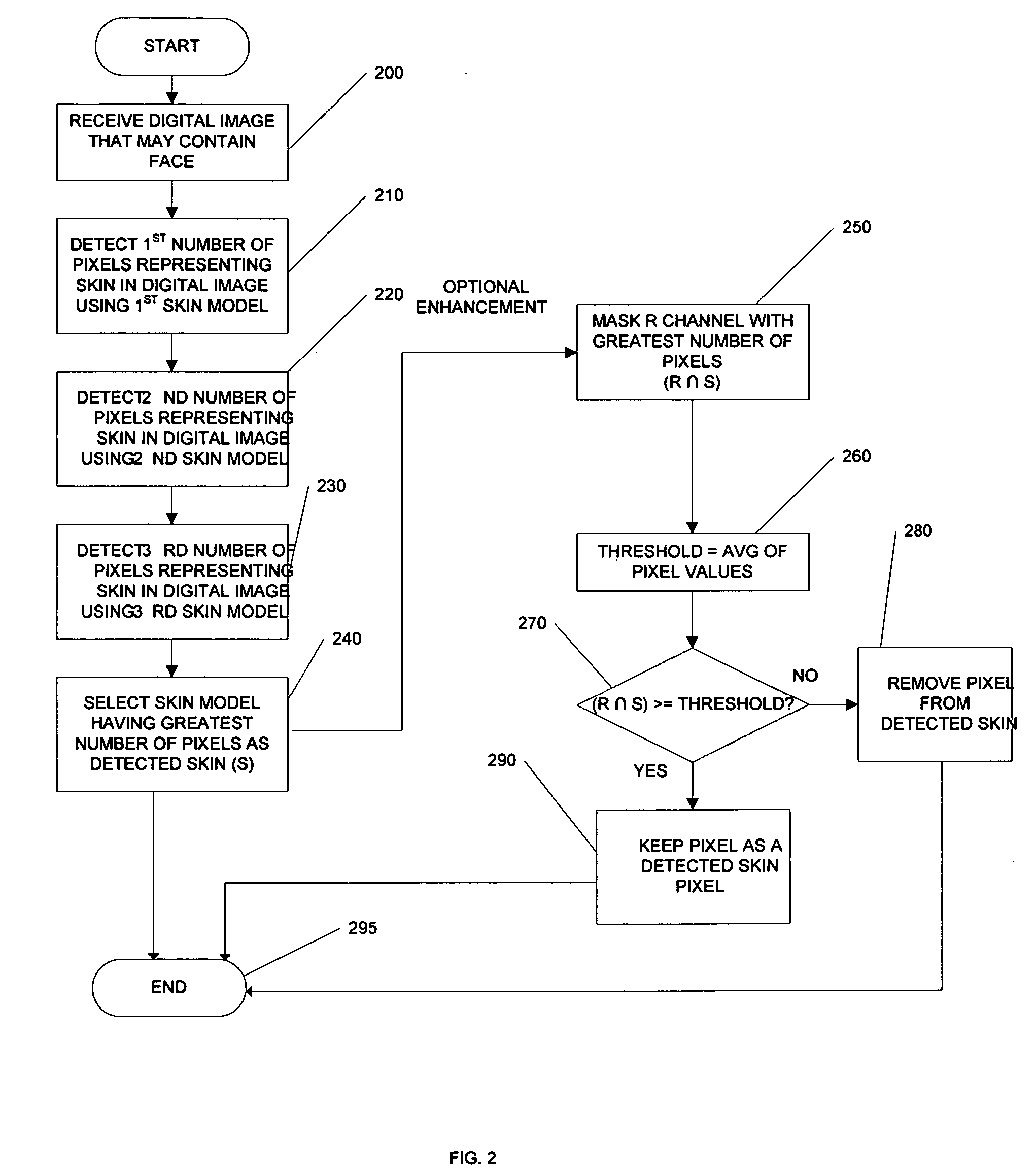
InactiveUS20050031173A1Improve security levelReduce chanceCharacter and pattern recognitionPattern recognitionJPEG
Systems, methods, and processes are provided for locating pupils in a portrait image for applications such as facial recognition, facial authentication, and manufacture of identification documents. One proposed method comprises three steps; skin detection, eye detection, and pupil detection. In the first step, the skin detection employs a plurality of Gaussian skin models. In the second step, coarse eye locations are found by using the amount of deviation in the R (red) channel with an image that has been cropped by skin detection. A small block centered at an obtained coarse location is then further processed in pupil detection. The step of pupil detection involves determining a Pupil Index that measures the characteristics of a pupil. Experiments tested on highly jpeg compressed images show that the algorithm of this embodiment successfully locates pupil images. It is believed that this novel technique for locating pupils in images can improve the accuracy of face recognition and / or face authentication.
Owner:L 1 SECURE CREDENTIALING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com