Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
8937results about How to "Efficient management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
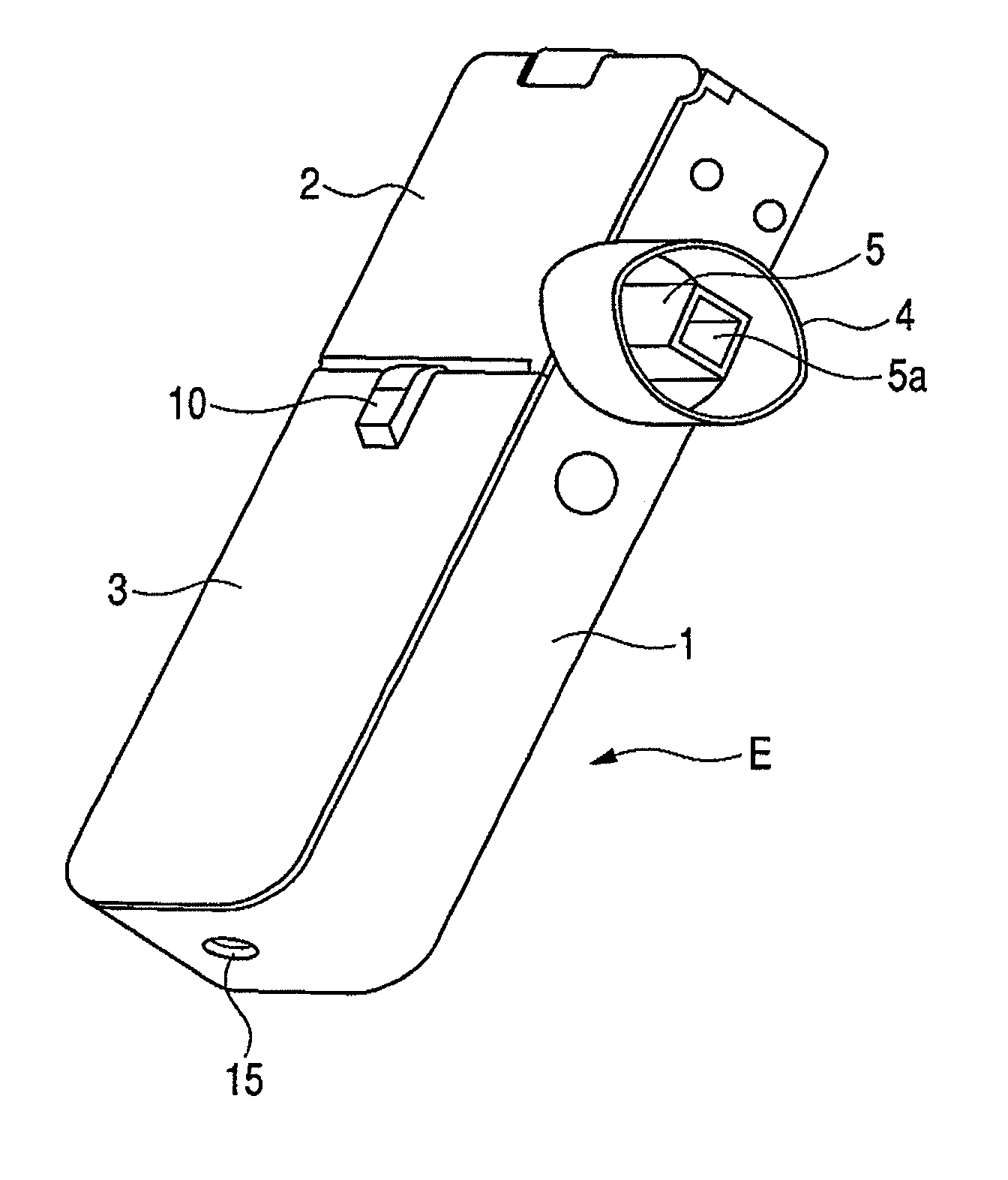
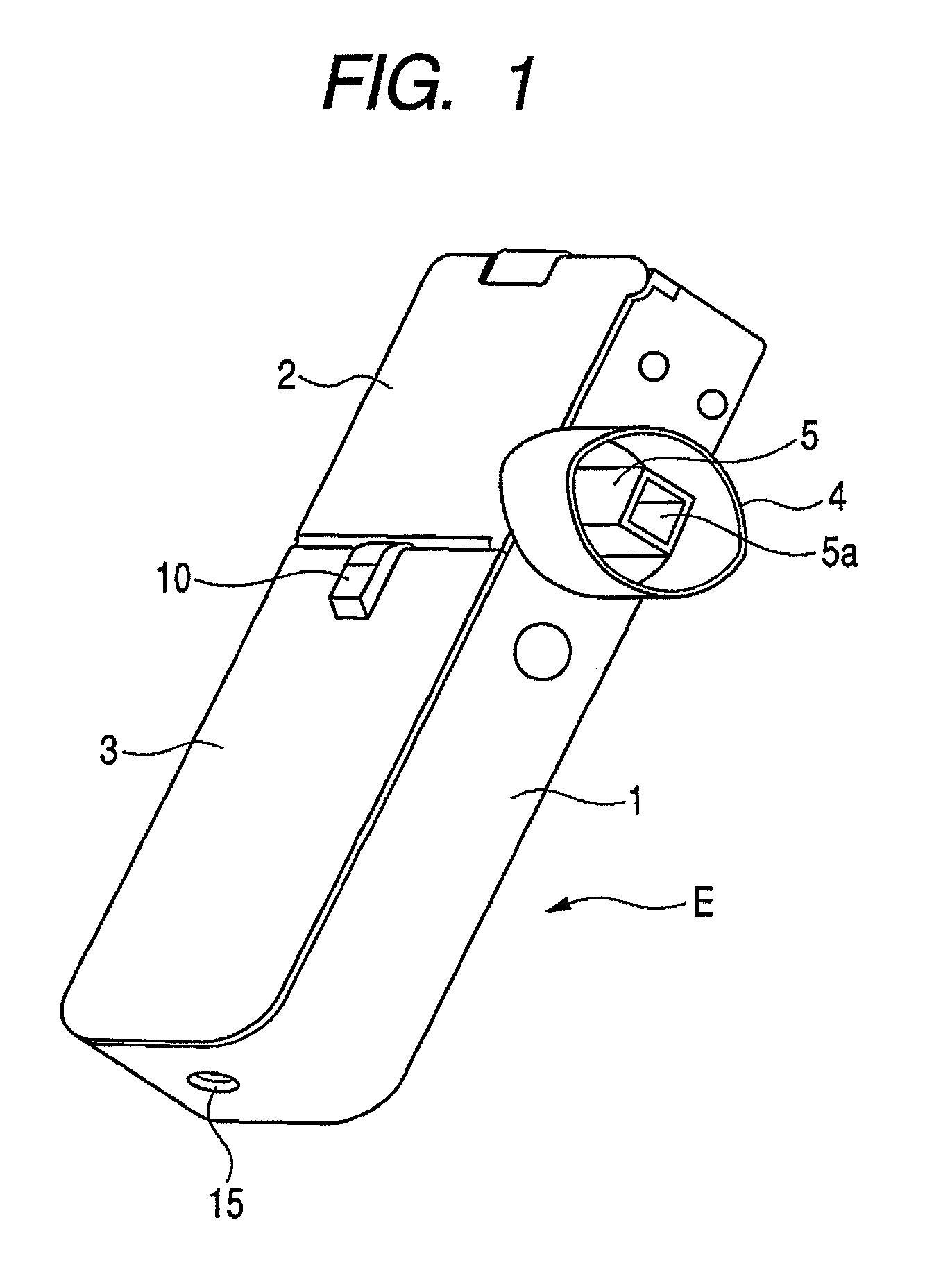
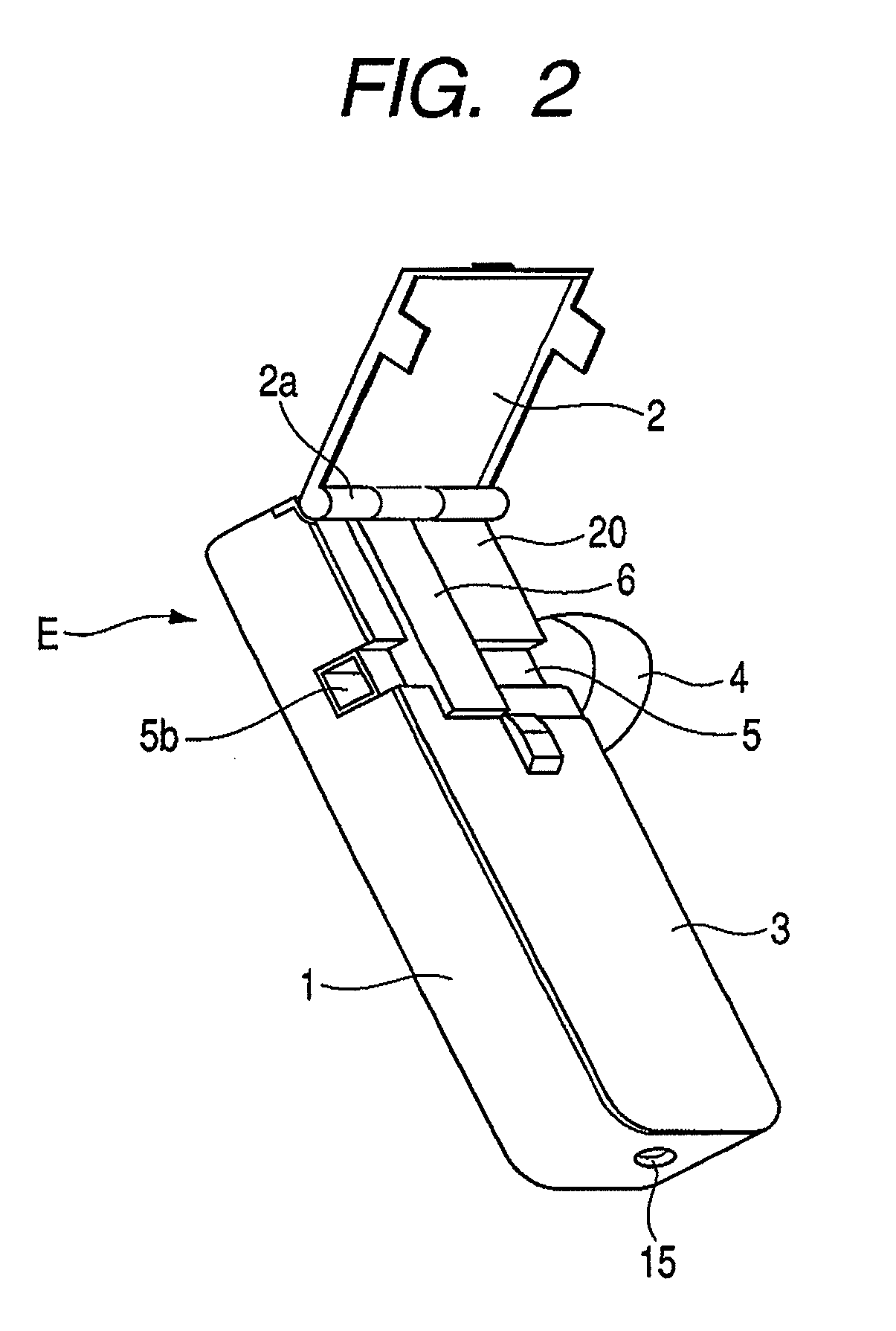
Medicine inhaler and medicine ejection method
InactiveUS7896006B2Efficiently inhaledAccurate doseRespiratorsOperating means/releasing devices for valvesOpen air environmentBiomedical engineering
A medicine ejection device is provided allowing a medicine with a desired droplet diameter to be inhaled at a constant rate. The medicine ejection device has a decision part at which the ejection operating conditions of a medicine ejection part for ejecting the medicine are decided in accordance with at least one of an open-air environment or a state of the medicine during use of the device. The device ejects the medicine according to the ejection operating conditions decided by the decision part.
Owner:CANON KK
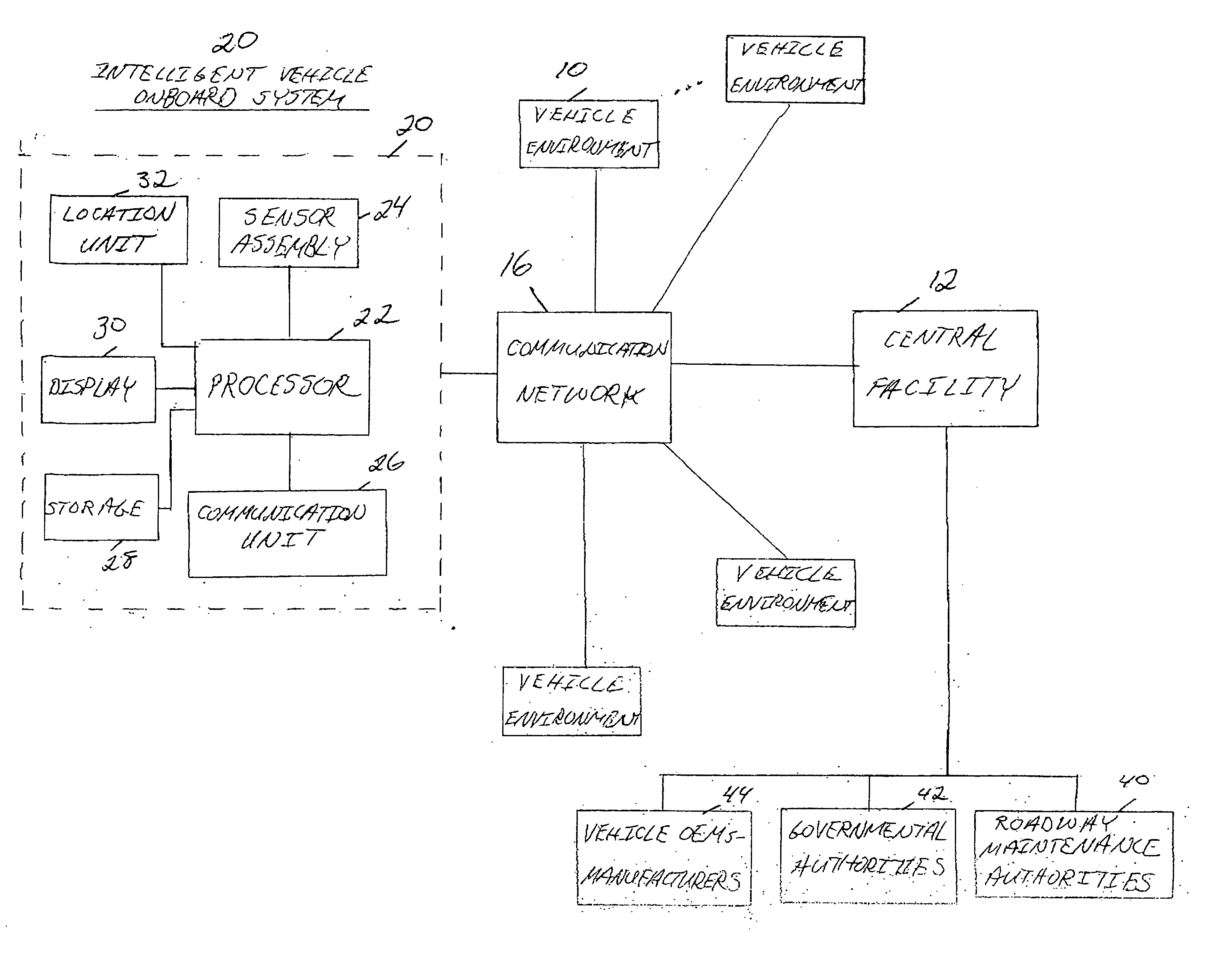
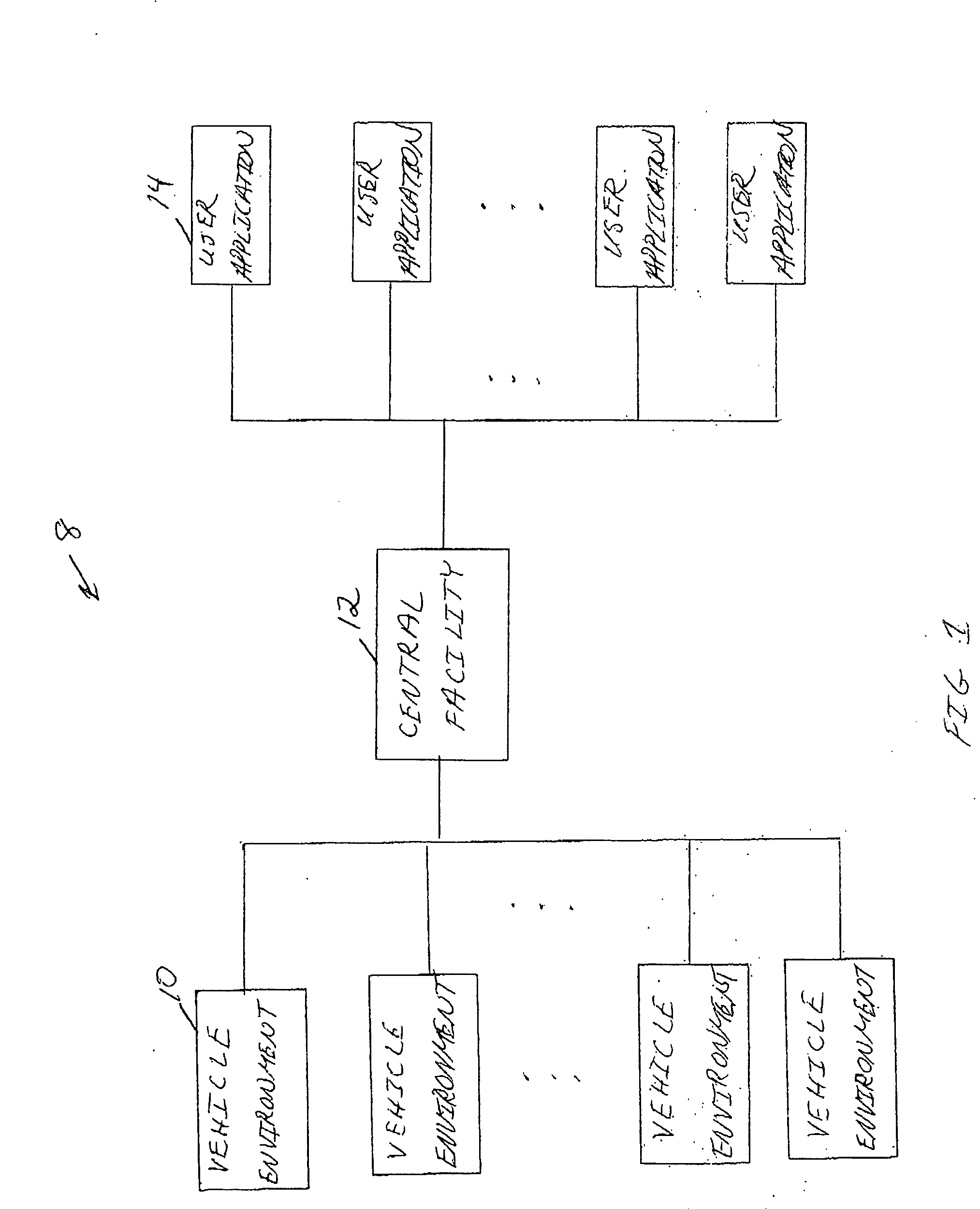
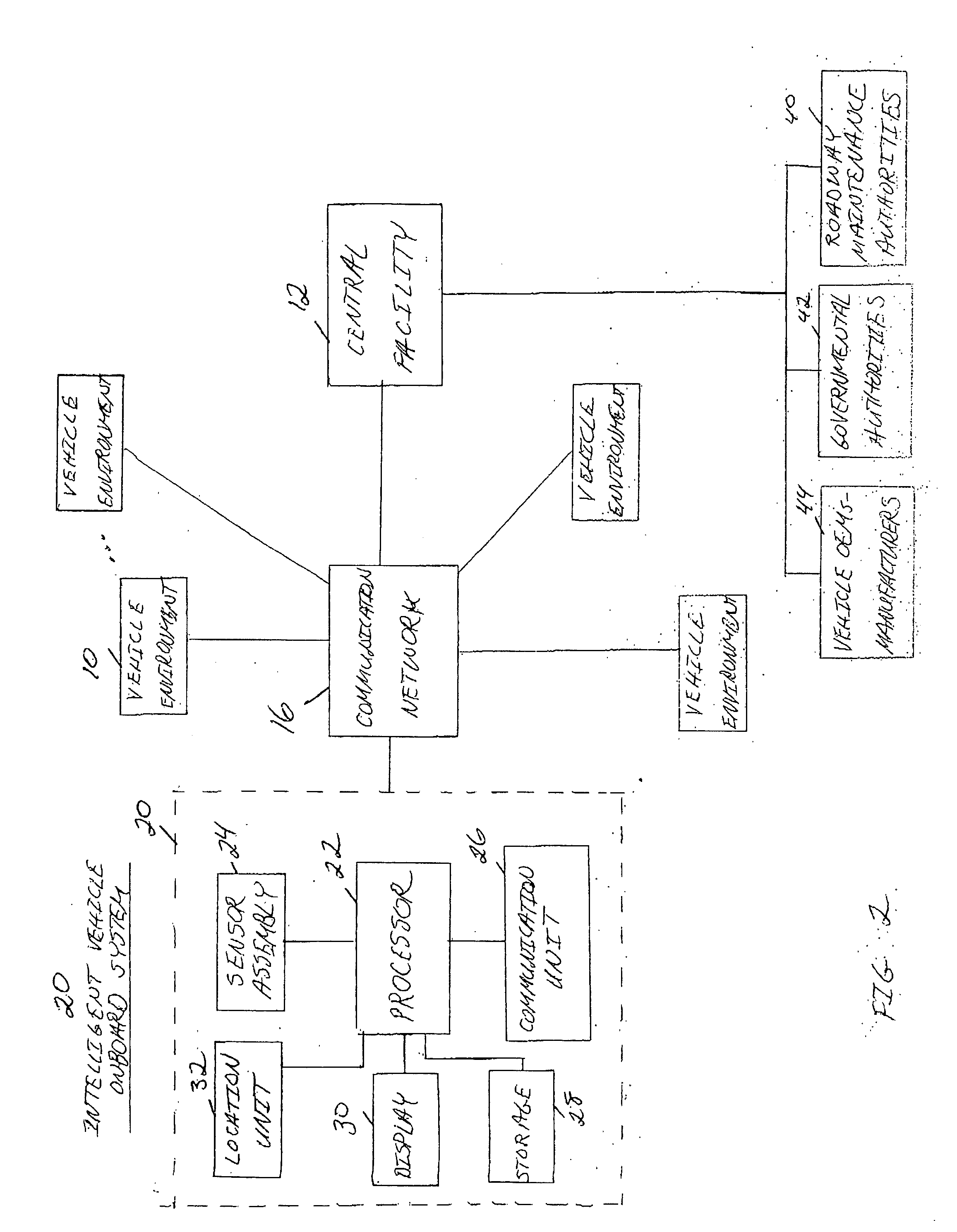
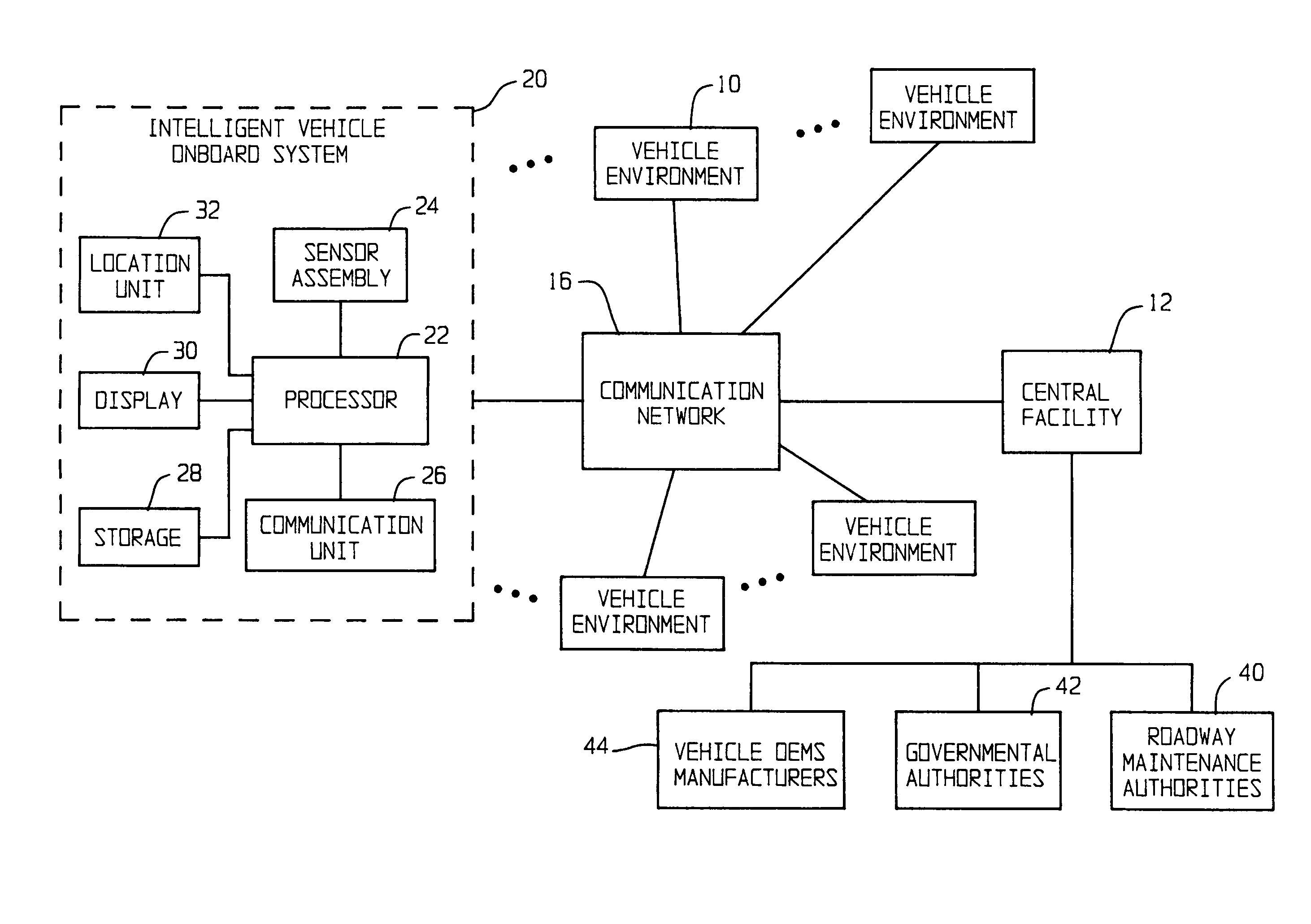
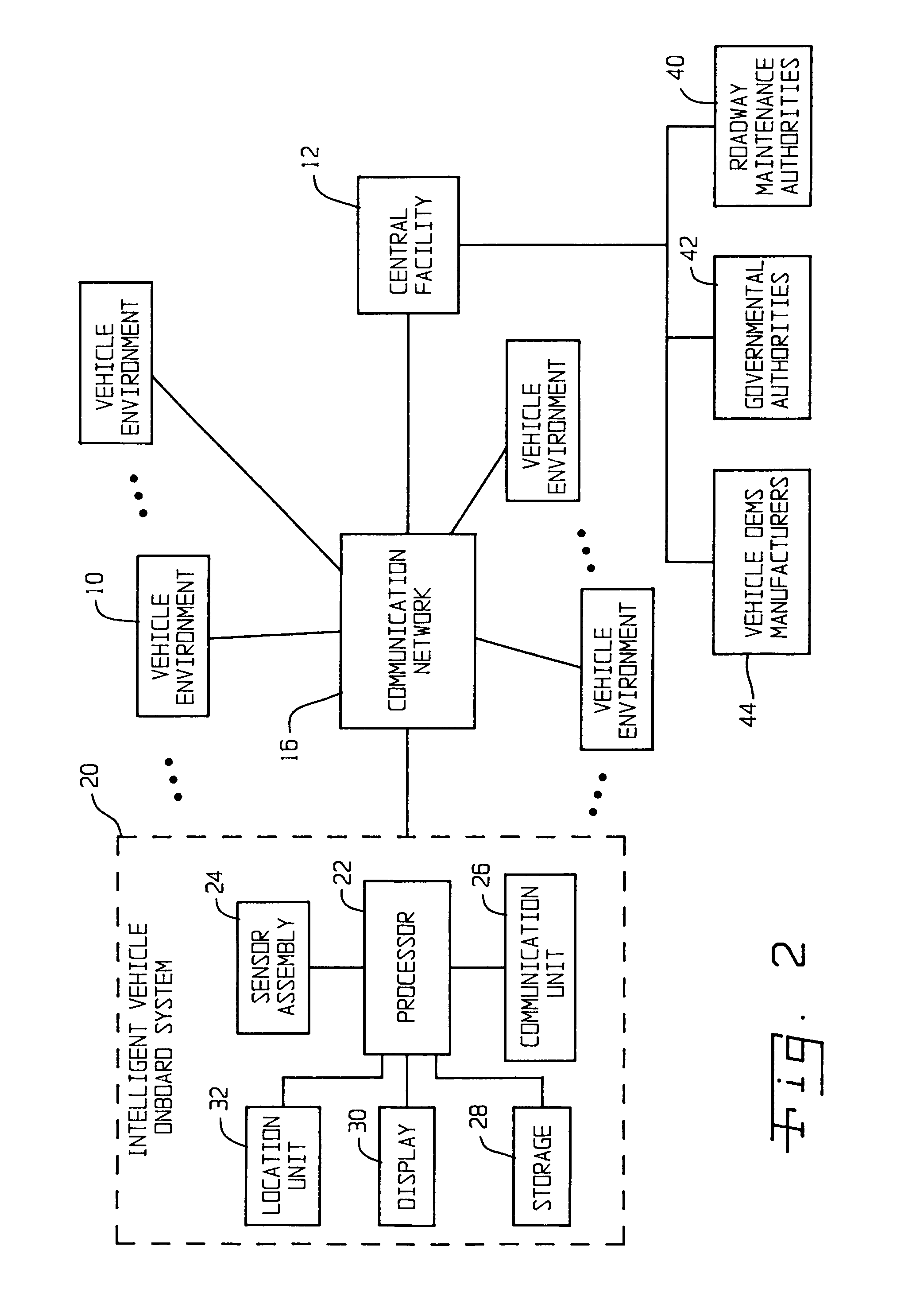
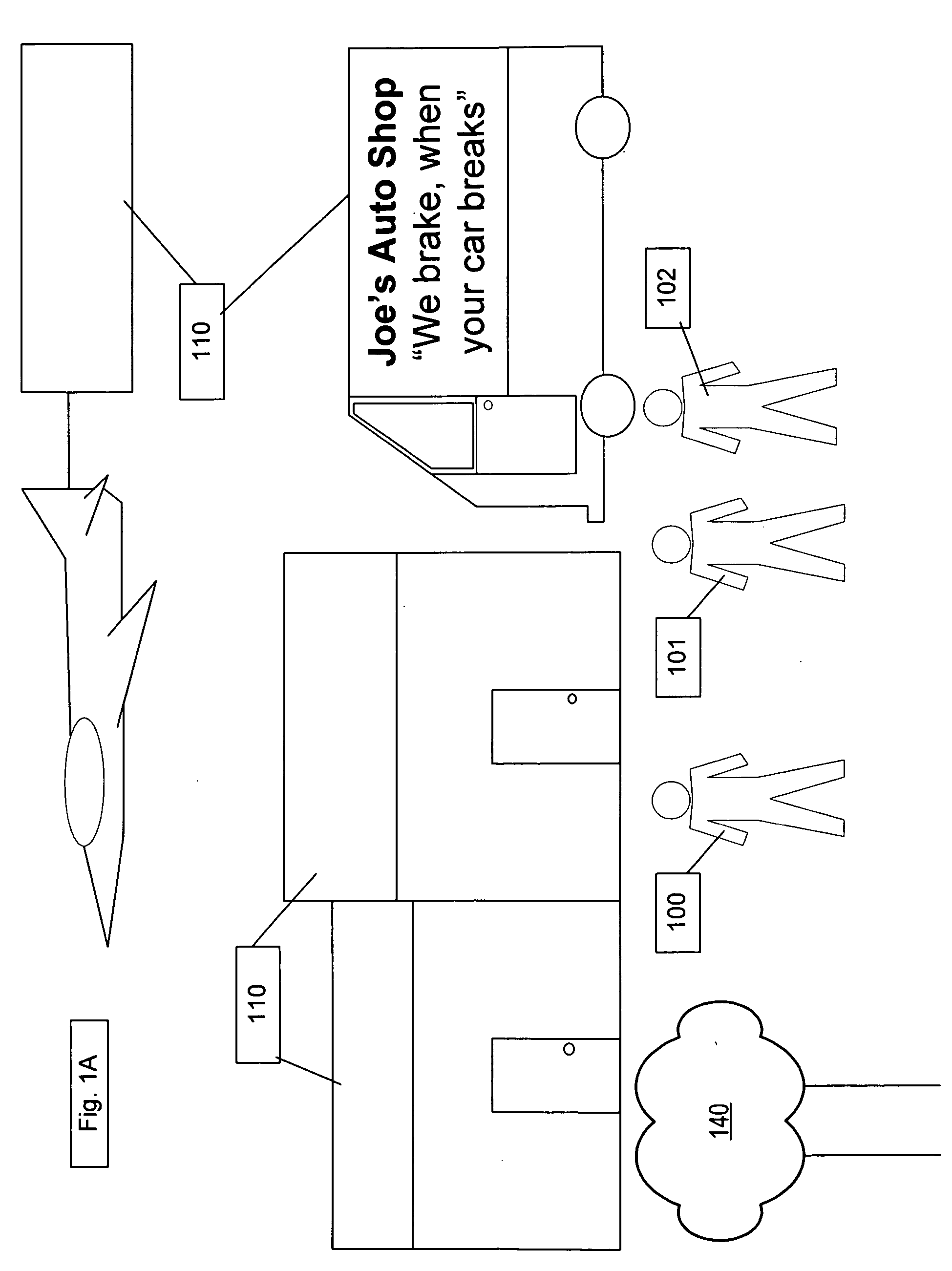
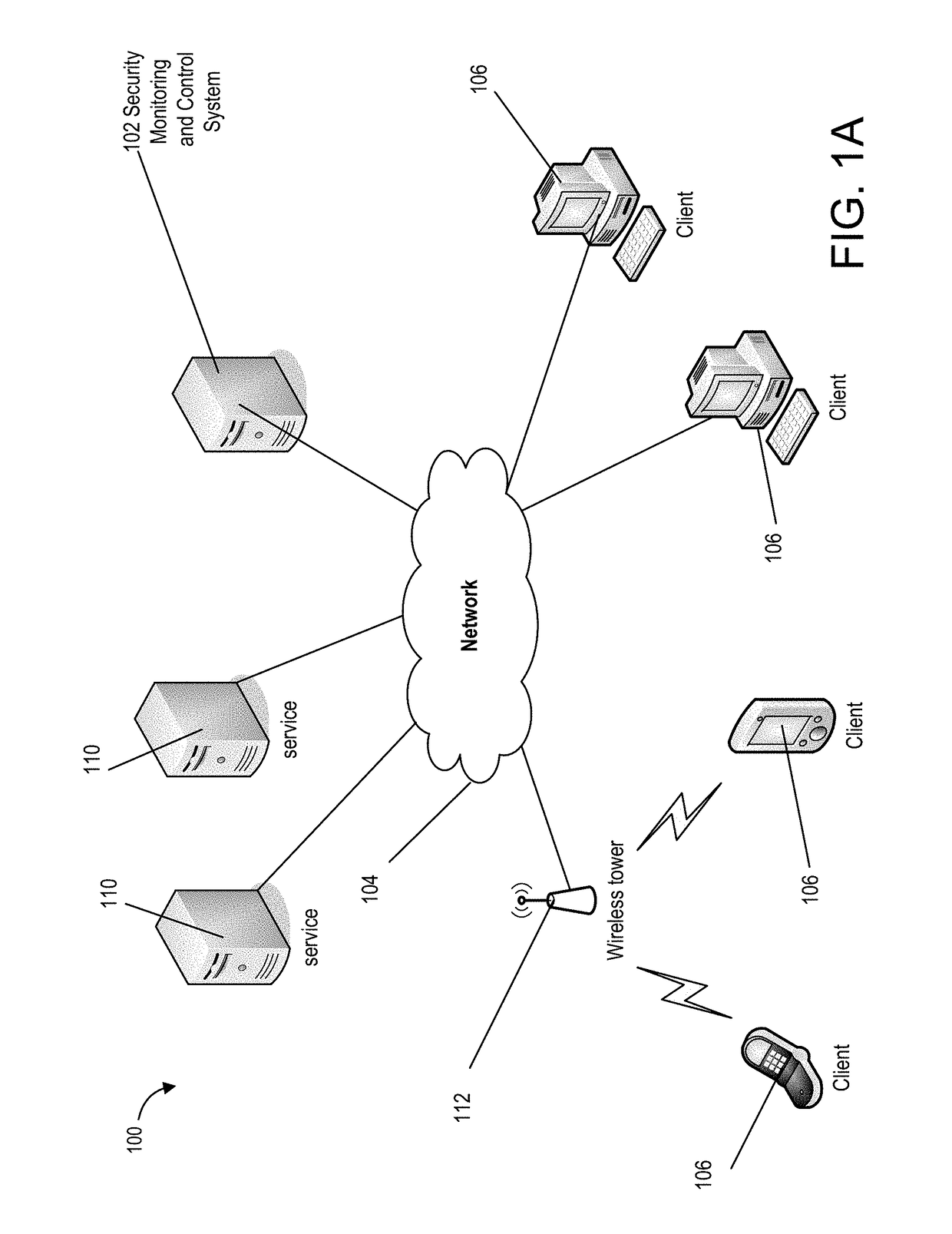
Centralized facility and intelligent on-board vehicle platform for collecting, analyzing and distributing information relating to transportation infrastructure and conditions
ActiveUS20050065711A1Effectively conditionEfficient designAnalogue computers for vehiclesInstruments for road network navigationTransportation infrastructureIn vehicle
An on-board intelligent vehicle system includes a sensor assembly to collect data and a processor to process the data to determine the occurrence of at least one event. The data may be collected from existing standard equipment such as the vehicle communication bus or add-on sensors. The data may be indicative of conditions relating to the vehicle, roadway infrastructure, and roadway utilization, such as vehicle performance, roadway design, roadway conditions, and traffic levels. The detection of an event may signify abnormal, substandard, or unacceptable conditions prevailing in the roadway, vehicle, or traffic. The vehicle transmits an event indicator and correlated vehicle location data to a central facility for further management of the information. The central facility sends communications reflecting event occurrence to various relevant or interested users. The user population can include other vehicle subscribers (e.g., to provide rerouting data based on location-relevant roadway or traffic events), roadway maintenance crews, vehicle manufacturers, and governmental agencies (e.g., transportation authorities, law enforcement, and legislative bodies).
Owner:ZOOM INFORMATION SYST
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
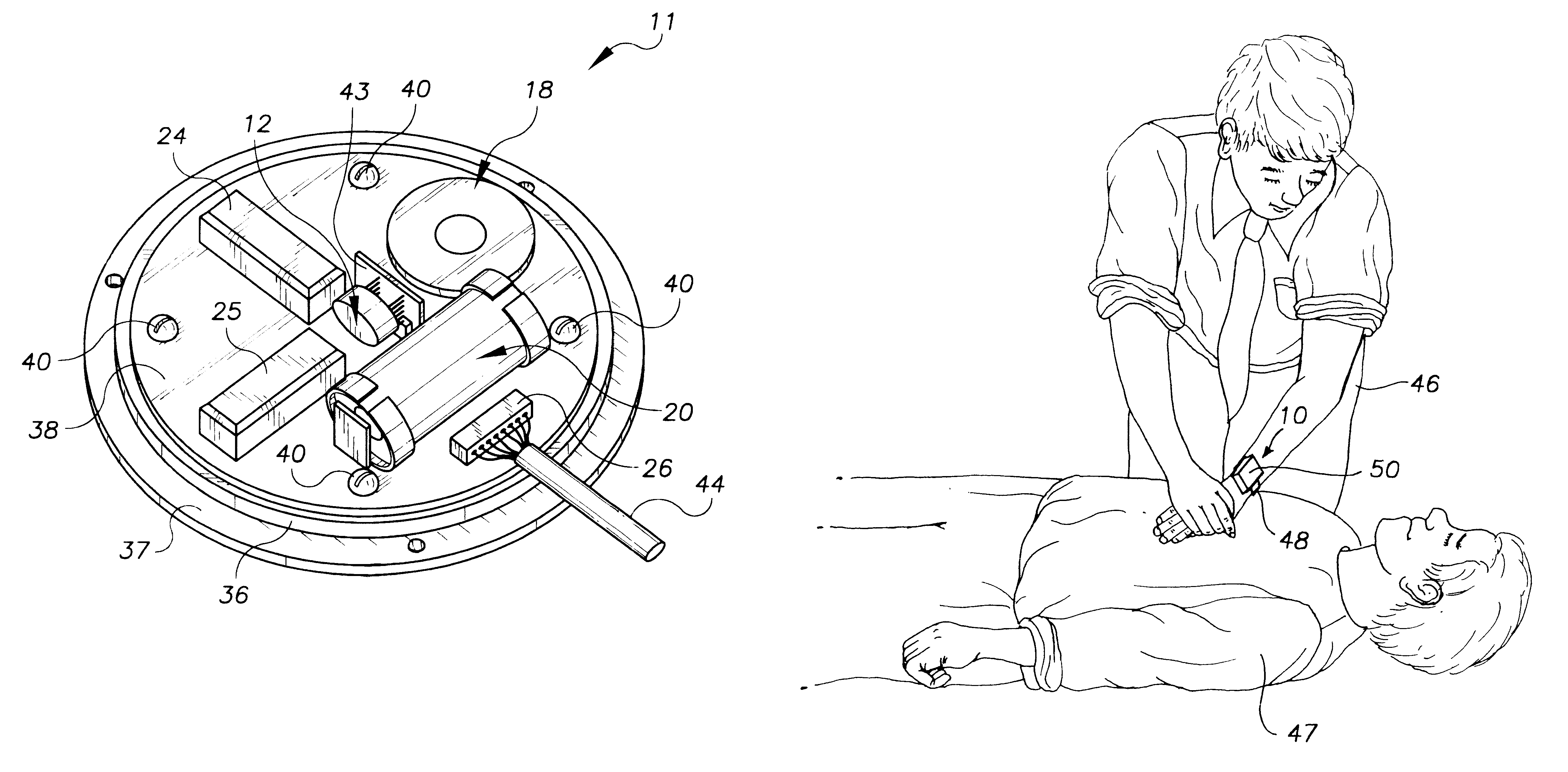
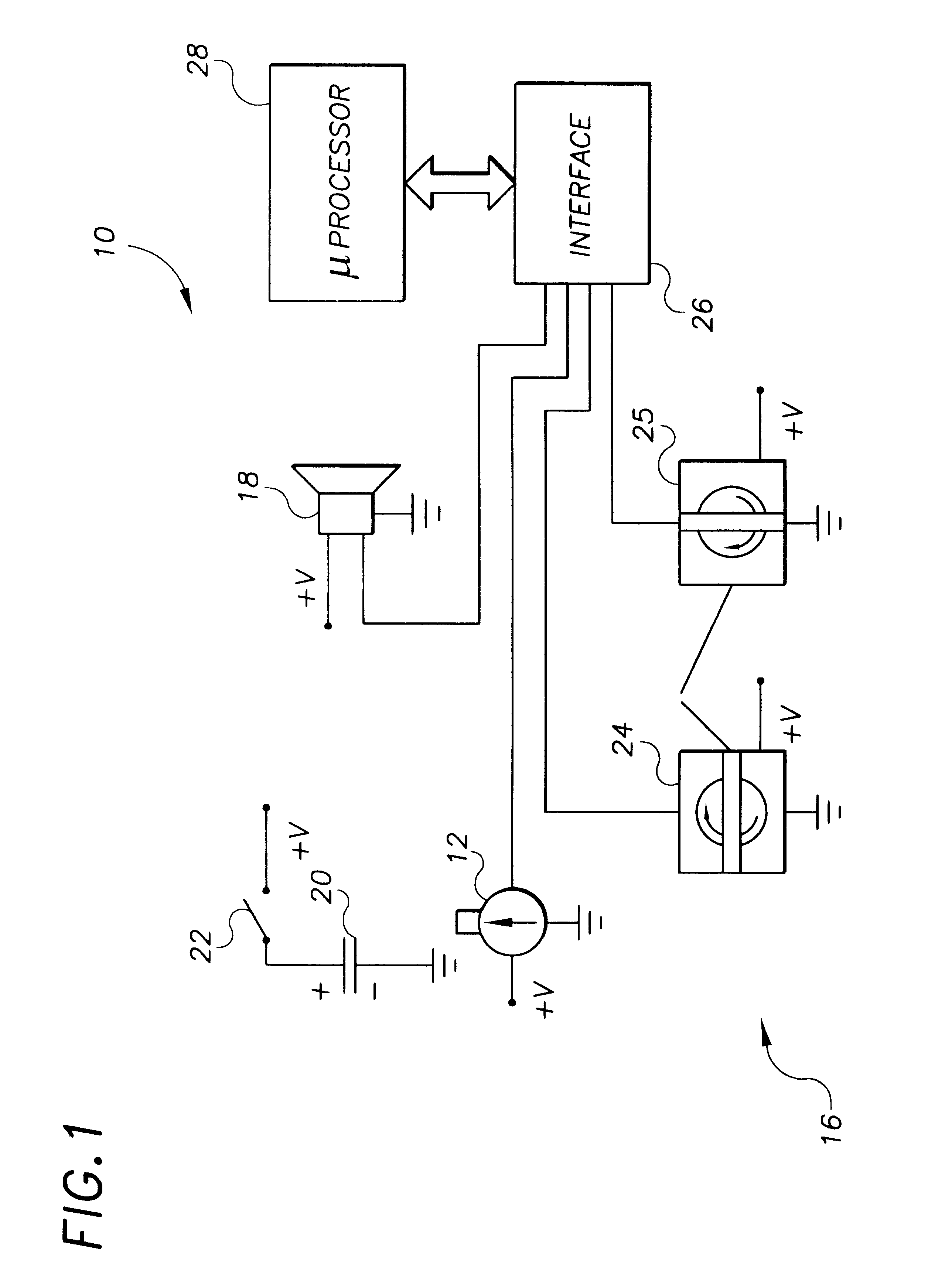
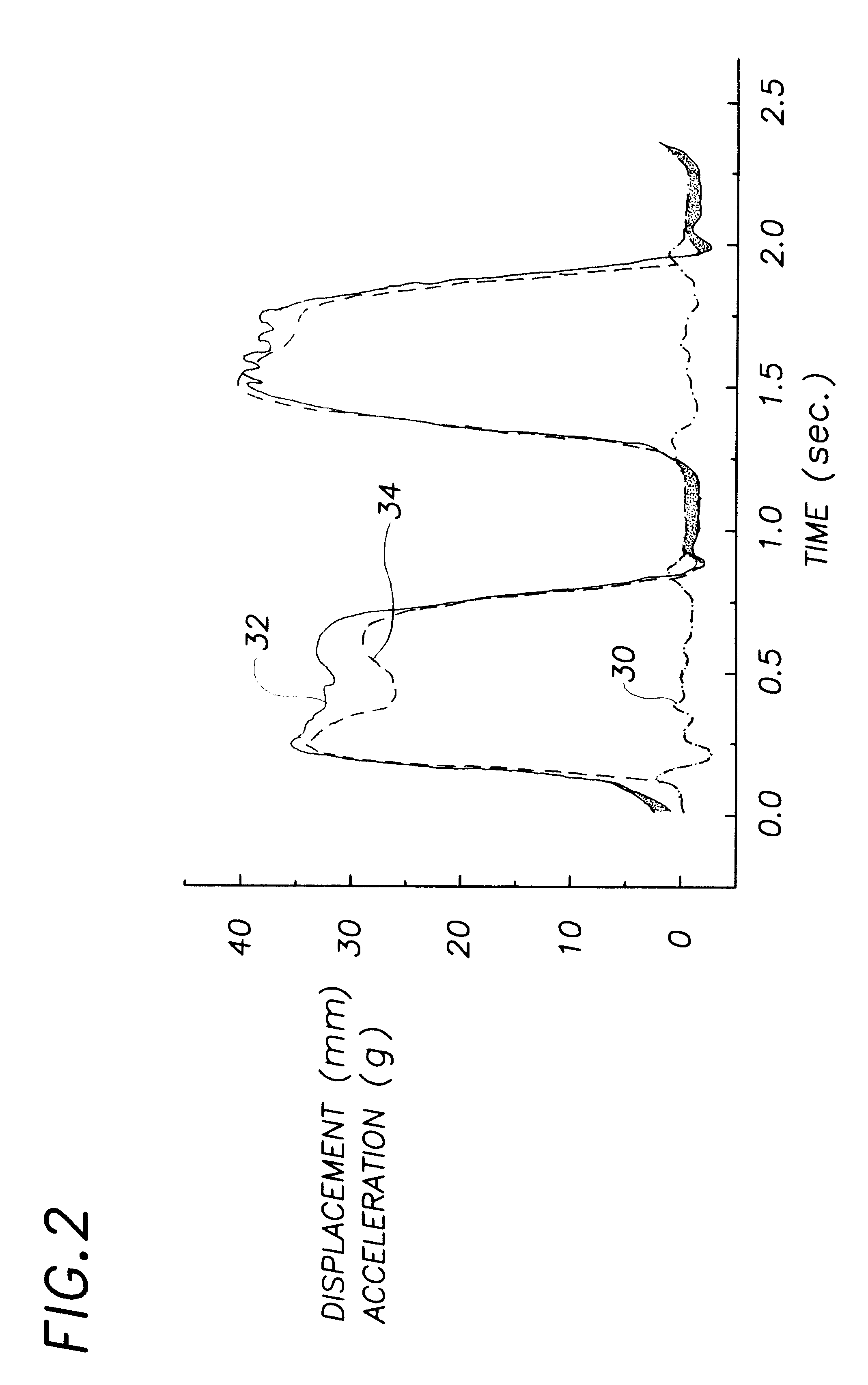
CPR chest compression monitor
InactiveUS6390996B1Accurate measurementSmall sizeHeart defibrillatorsInertial sensorsEcg signalEmergency medicine
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
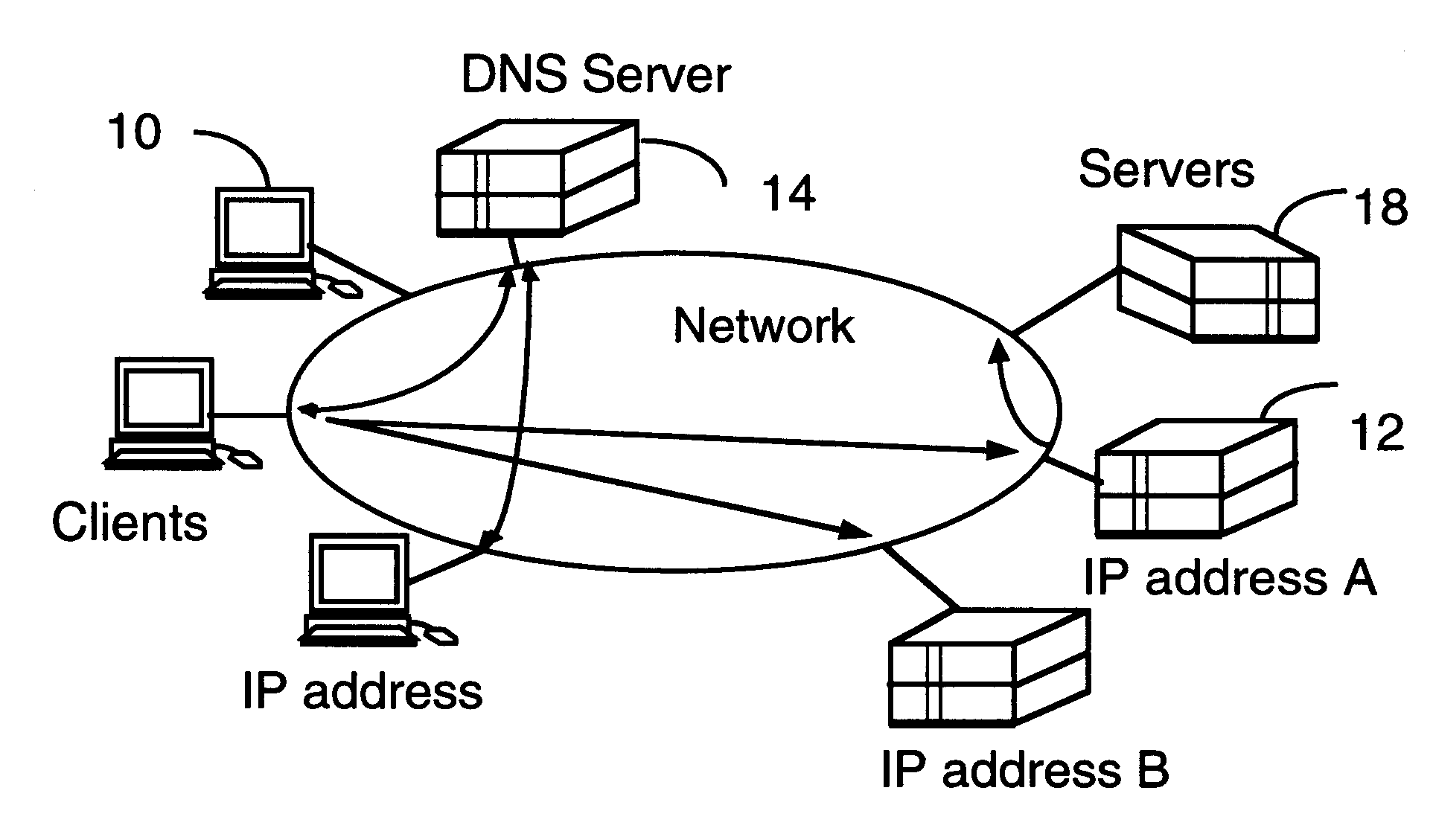
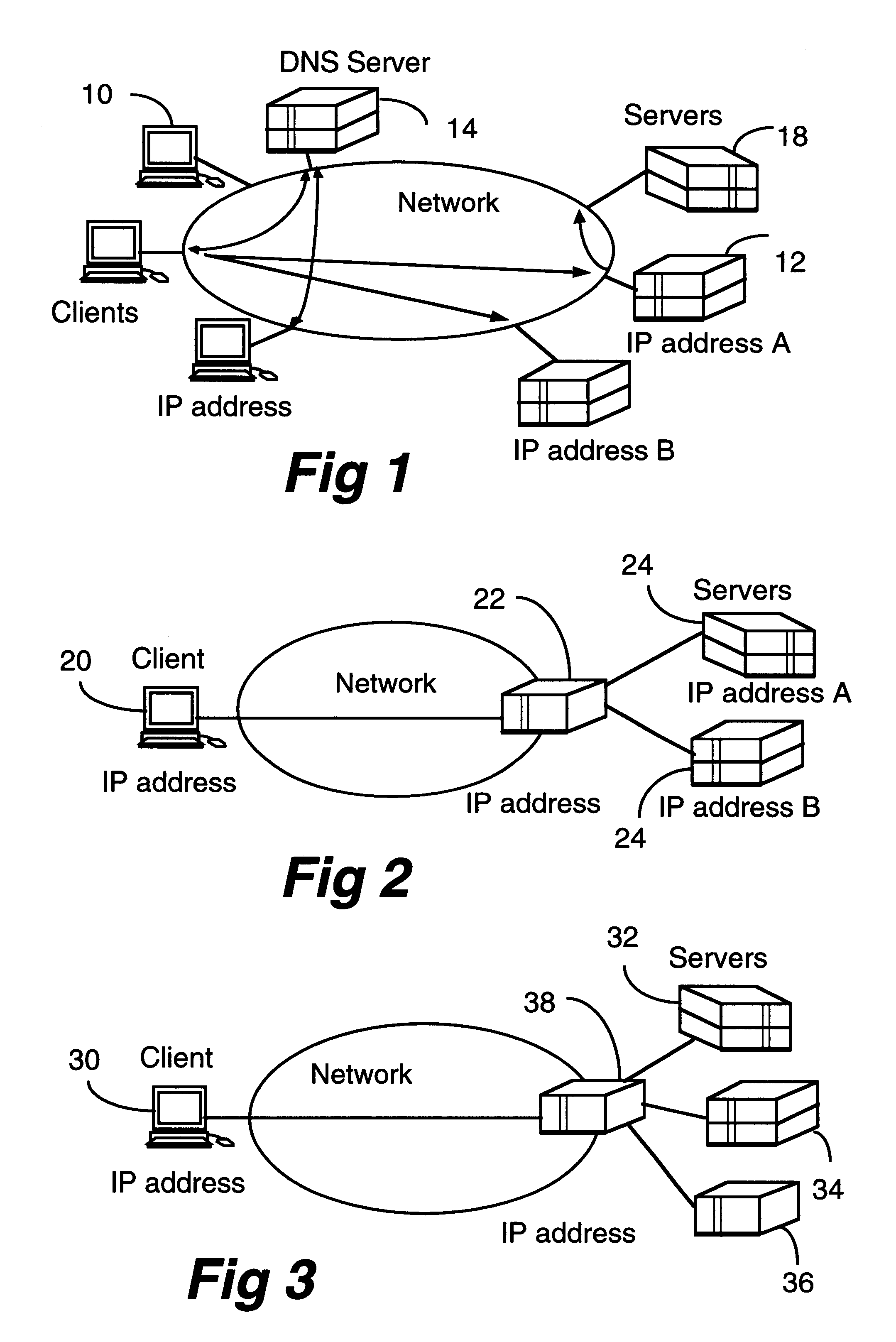
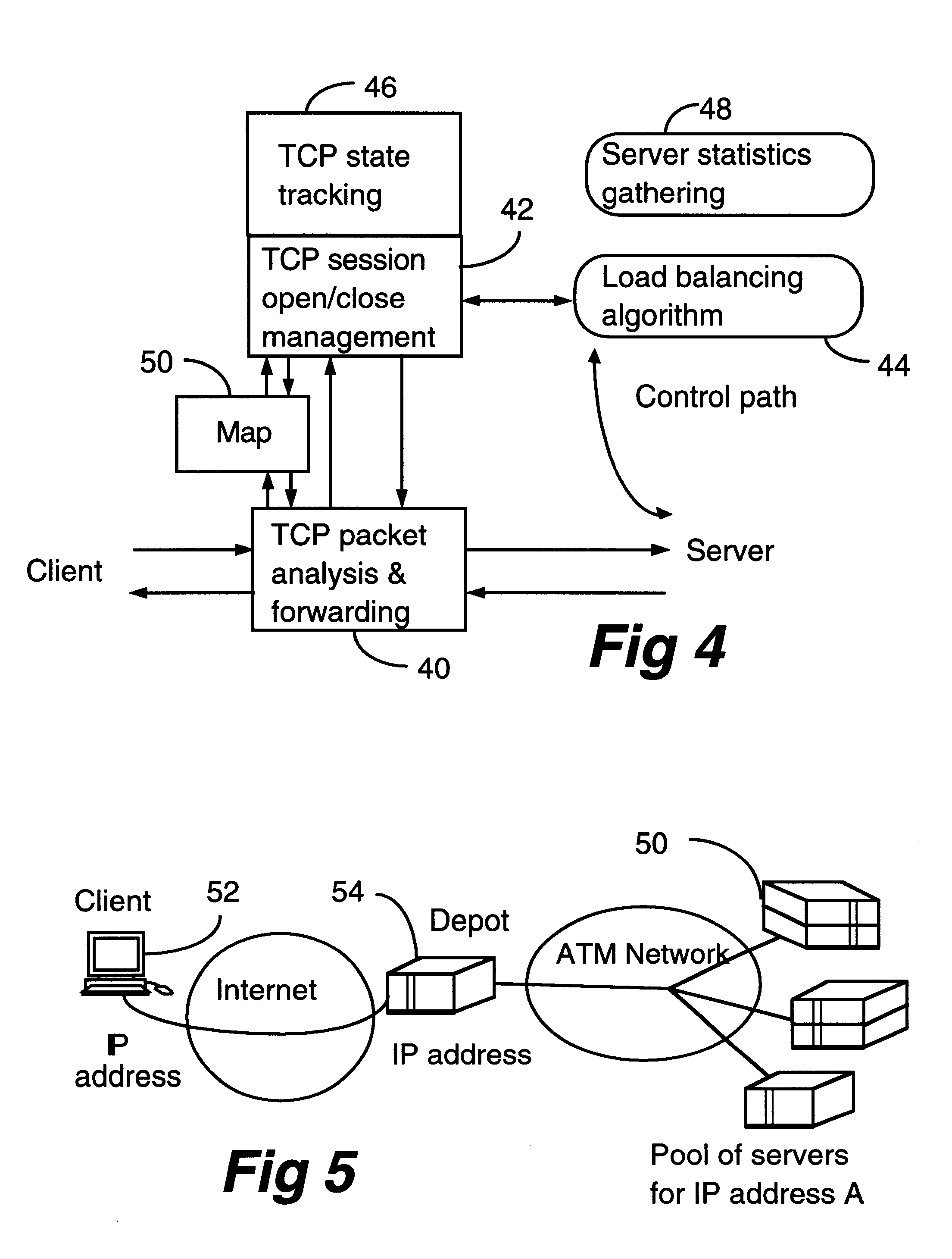
Scaleable web server and method of efficiently managing multiple servers
InactiveUS6330602B1Improve performanceEfficient managementData switching by path configurationMultiple digital computer combinationsInformation resourceWeb service
A client-server architecture includes a plurality of clients and a plurality of servers. Information resources are replicated among the servers. According to one aspect, the invention includes an intermediary device called a "depot" sitting transparently between a client and a pool of servers which have the replicated information resources. The depot dynamically distributes multiple sessions contained in a client request among the servers. This architecture realizes a good granular scaleability of servers, and improved server throughput with a good response time. Multiple depots also realize robustness.
Owner:AVAYA INC
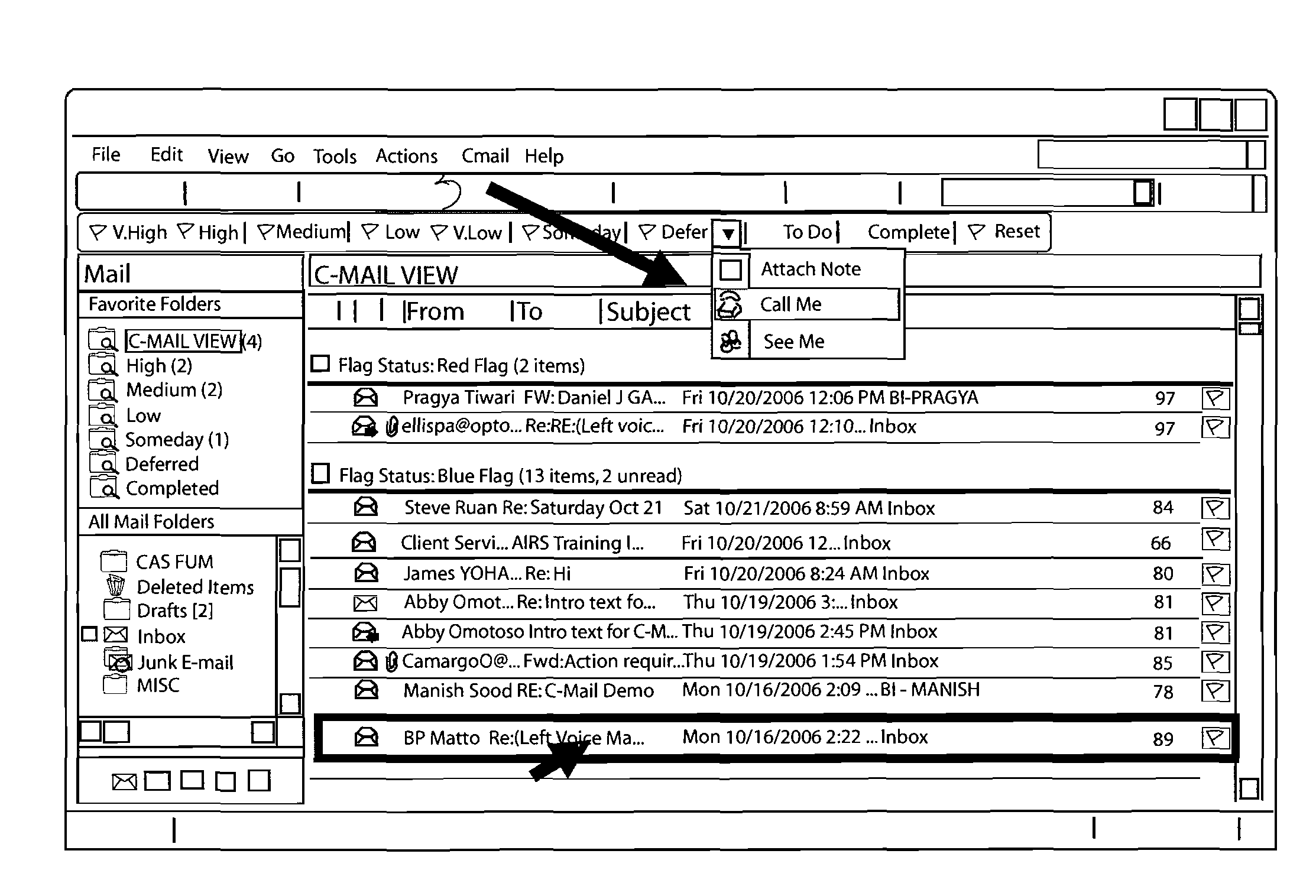
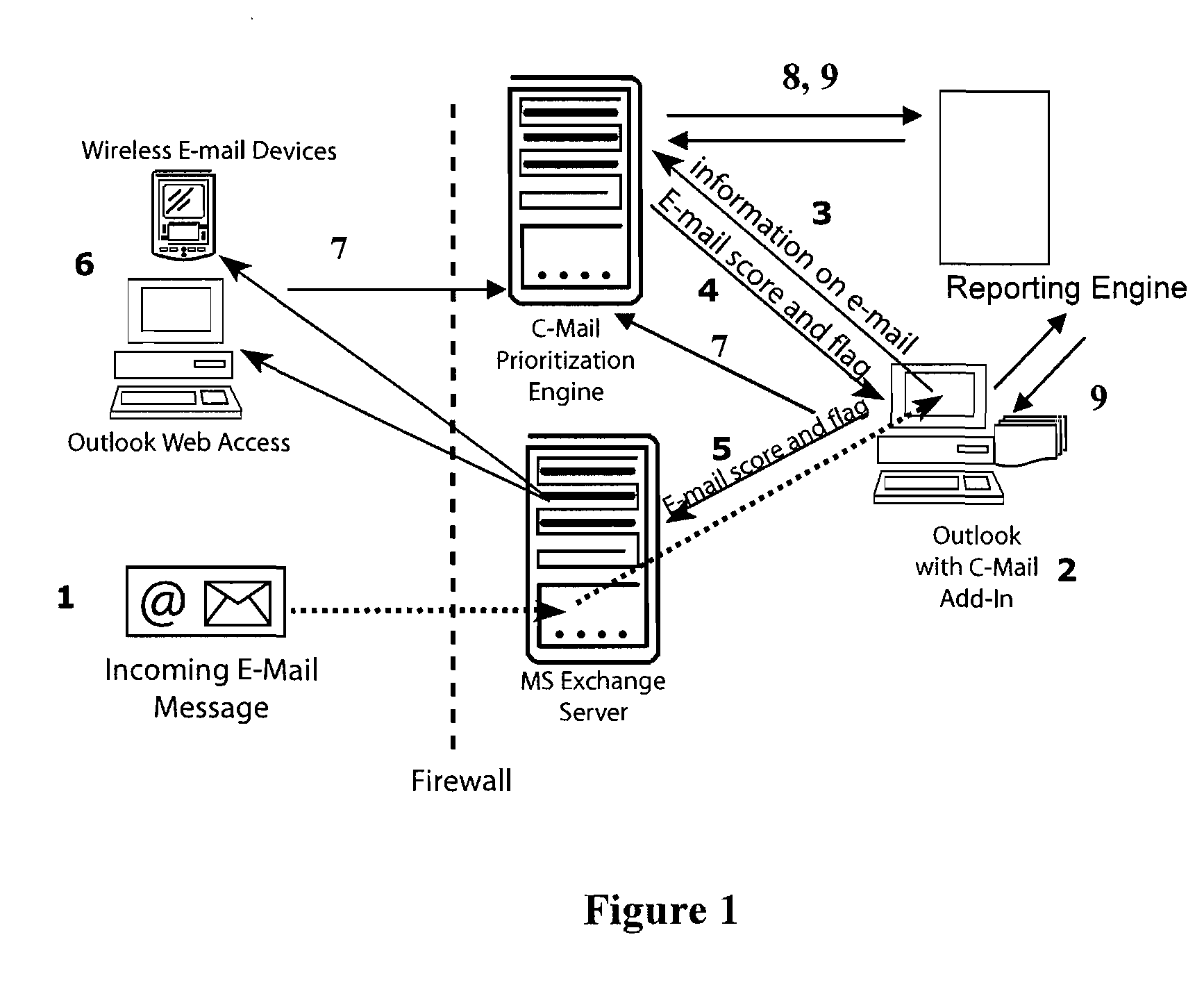
System and method of dynamically prioritized electronic mail graphical user interface, and measuring email productivity and collaboration trends
InactiveUS20080126951A1Efficient use ofEfficient managementTransmissionInput/output processes for data processingGraphicsProduction rate
A system and method for managing electronic communications more effectively utilizes electronic communications. The method assigns a prioritization score and category to each electronic communication so that a user can more effectively manage the communications. The user interacts with a graphical user interface to effectively manage electronic communications. The system arranges and displays the electronic communications according to prioritization scores and categories, and includes interactive modules to override a system assigned prioritization scores and assign any score or category the user selects. The method also measures productivity of users as a function of at least three different metrics, a decision-making metric; a communication metric; and a processing metric, and takes into account prioritization scores and the amount of time it takes users to effectively utilize the electronic communications. The method also generates reports of the productivity of individual users, and the productivity of relationships between multiple users of electronic communications.
Owner:MESSAGEMIND LLC
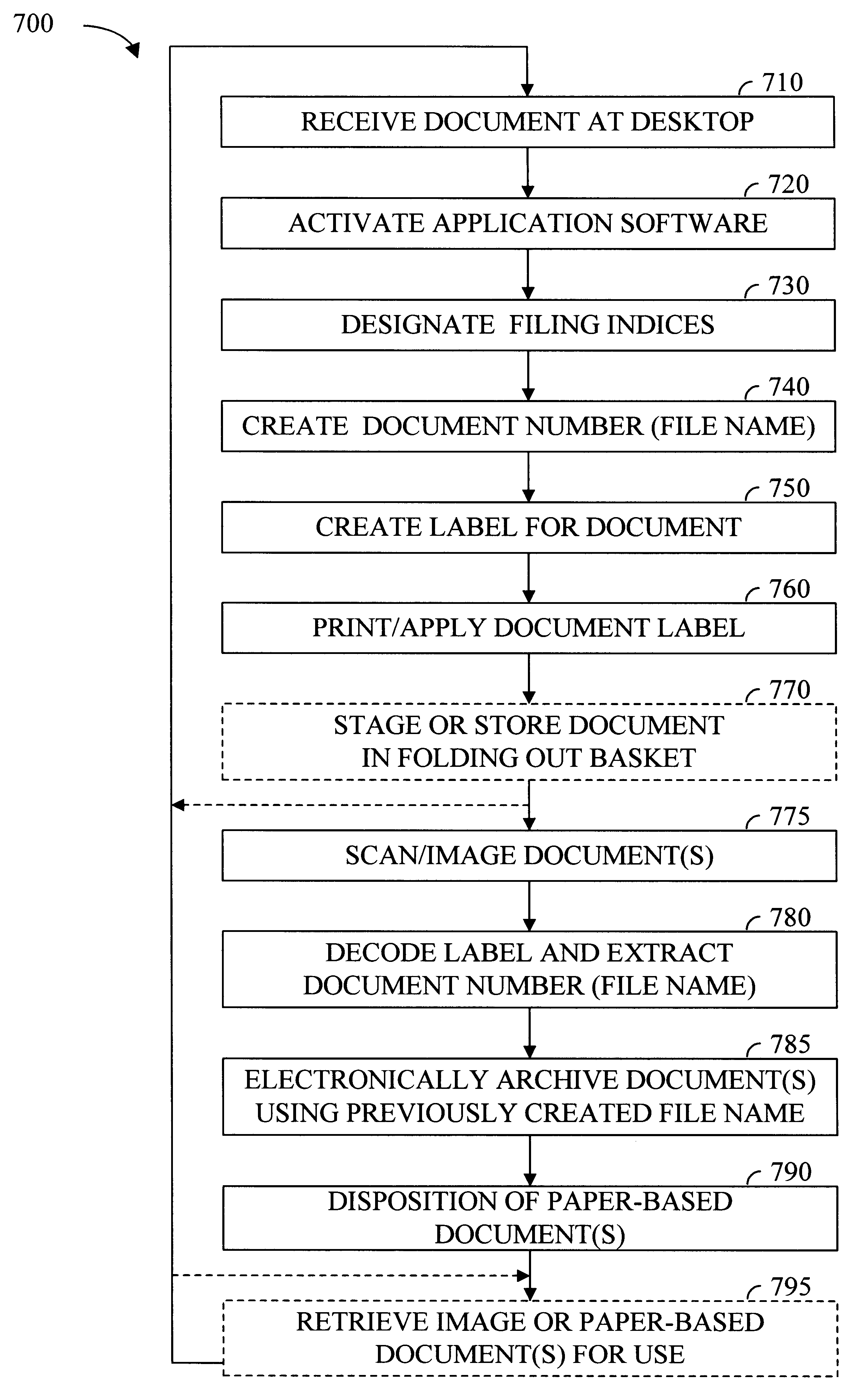
Apparatus and method for digital filing
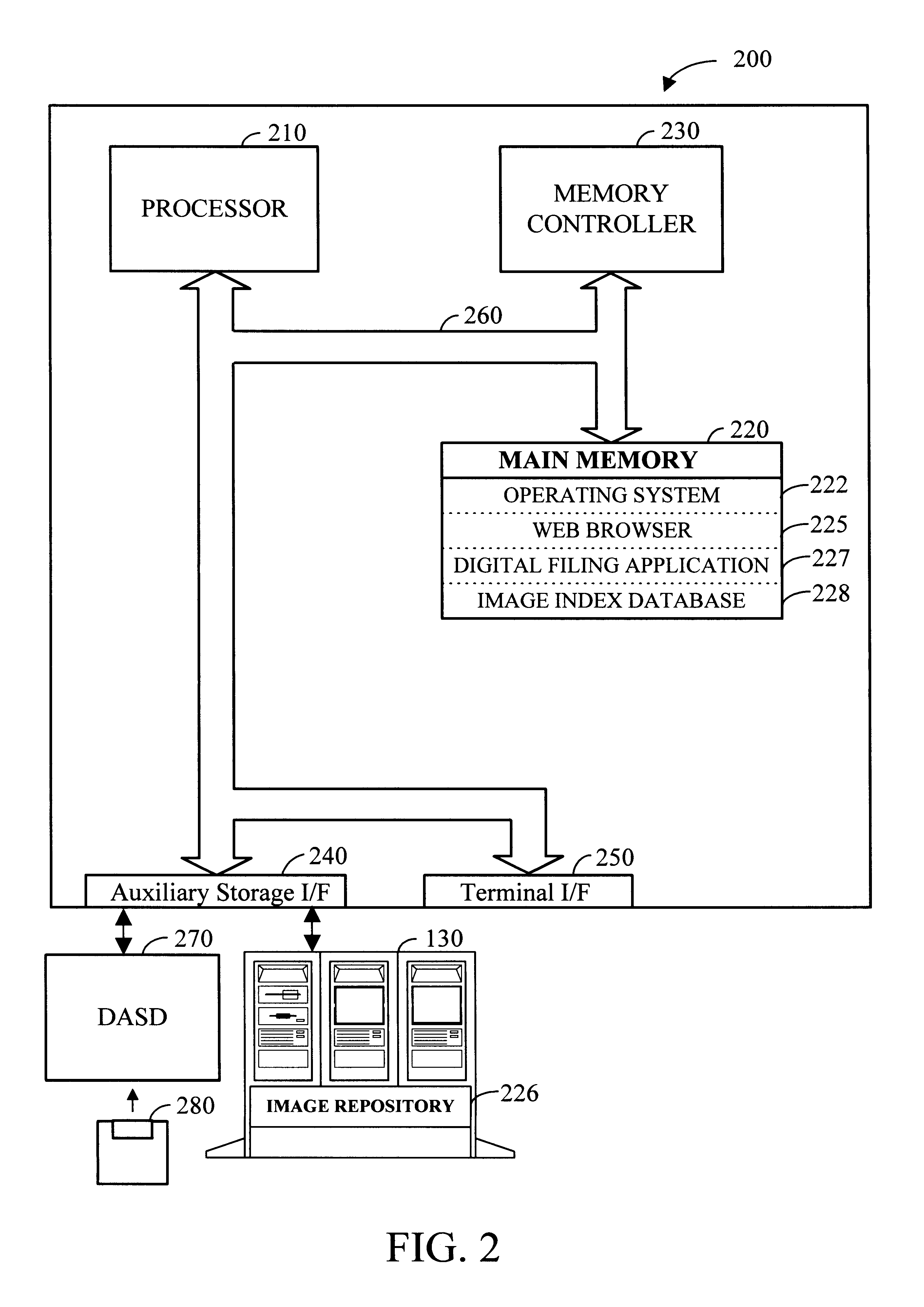
InactiveUS6192165B1Easy and effective and imagingEasy and effective indexingData processing applicationsDigital computer detailsElectronic documentWeb browser
According to the preferred embodiments of the present invention, an apparatus and method for a digital filing system is disclosed. In this context, digital filing refers to the efficient management of paper-based information from its receipt at the desktop through an indexing, scanning, image storage and image retrieval process. The preferred embodiments of the present invention provide for easy and effective indexing, imaging, storing, retrieving and managing of paper-based documents, transforming them into electronic documents using a system which incorporates many existing office resources. The proposed system and method implements a desktop solution for digital filing, which can be made available to each worker. In one embodiment of the present invention, an individual has complete control over the electronic storage and retrieval of their documents from a standard desktop computer, using a standard web browser application. Uniquely, the digital filing system of the present invention also allows users to index and label documents prior to scanning / imaging by using a dedicated desktop labeling mechanism.
Owner:IMAGETAG
Centralized facility and intelligent on-board vehicle platform for collecting, analyzing and distributing information relating to transportation infrastructure and conditions
ActiveUS7421334B2Efficient managementAnalogue computers for vehiclesInstruments for road network navigationTransportation infrastructureIn vehicle
An on-board intelligent vehicle system includes a sensor assembly to collect data and a processor to process the data to determine the occurrence of at least one event. The data may be collected from existing standard equipment such as the vehicle communication bus or add-on sensors. The data may be indicative of conditions relating to the vehicle, roadway infrastructure, and roadway utilization, such as vehicle performance, roadway design, roadway conditions, and traffic levels. The detection of an event may signify abnormal, substandard, or unacceptable conditions prevailing in the roadway, vehicle, or traffic. The vehicle transmits an event indicator and correlated vehicle location data to a central facility for further management of the information. The central facility sends communications reflecting event occurrence to various relevant or interested users. The user population can include other vehicle subscribers (e.g., to provide rerouting data based on location-relevant roadway or traffic events), roadway maintenance crews, vehicle manufacturers, and governmental agencies (e.g., transportation authorities, law enforcement, and legislative bodies).
Owner:ZOOM INFORMATION SYST
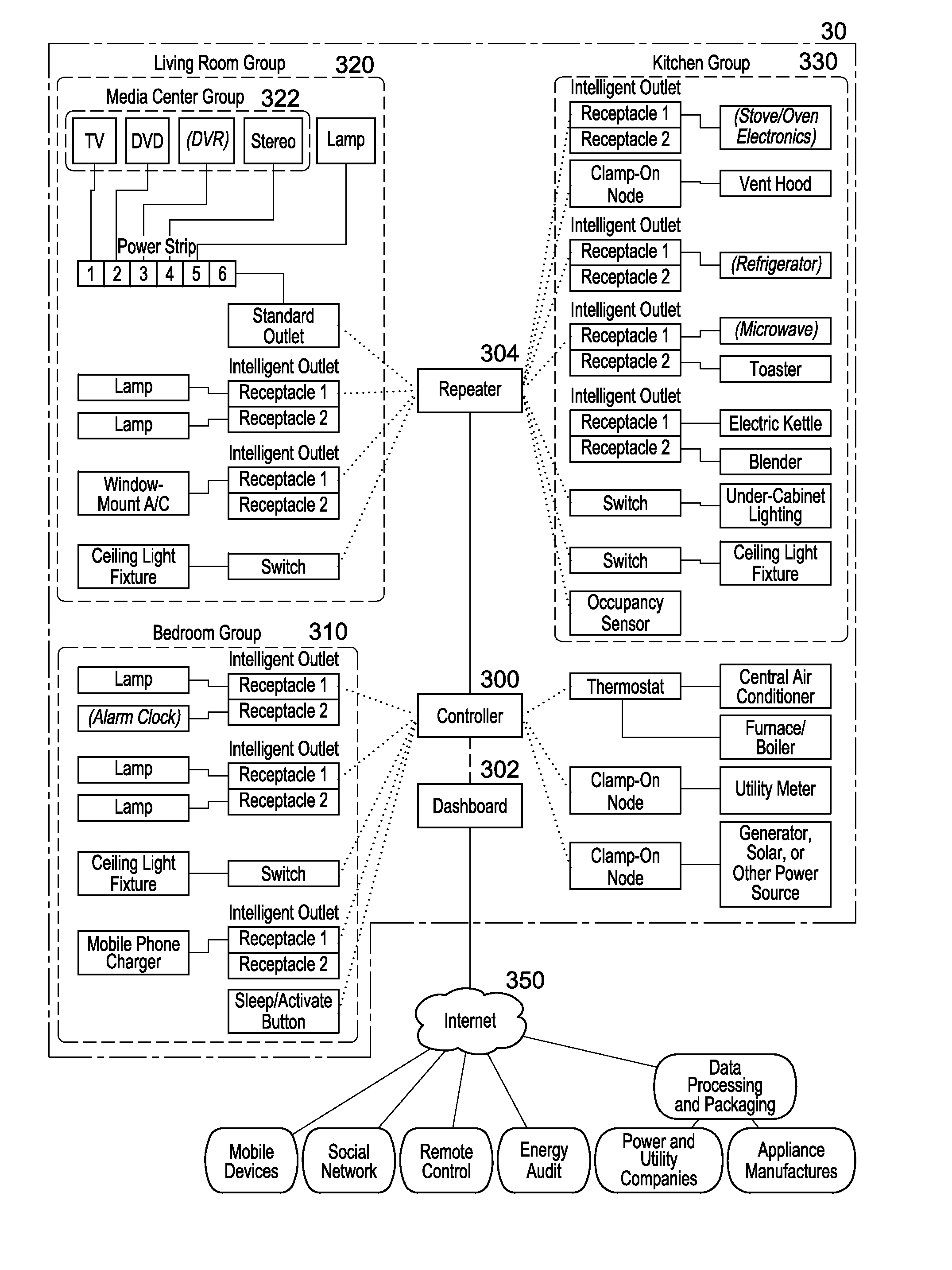
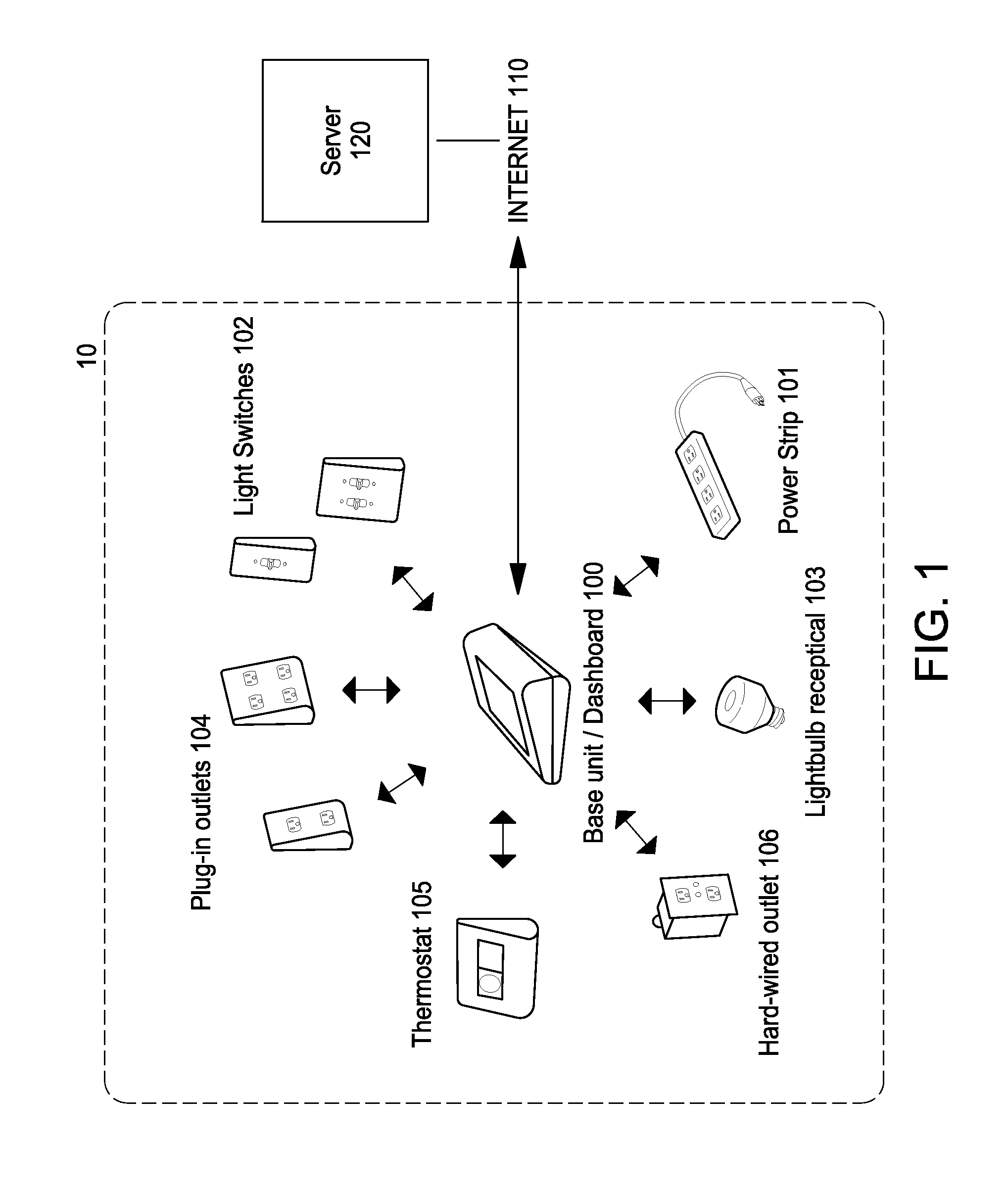
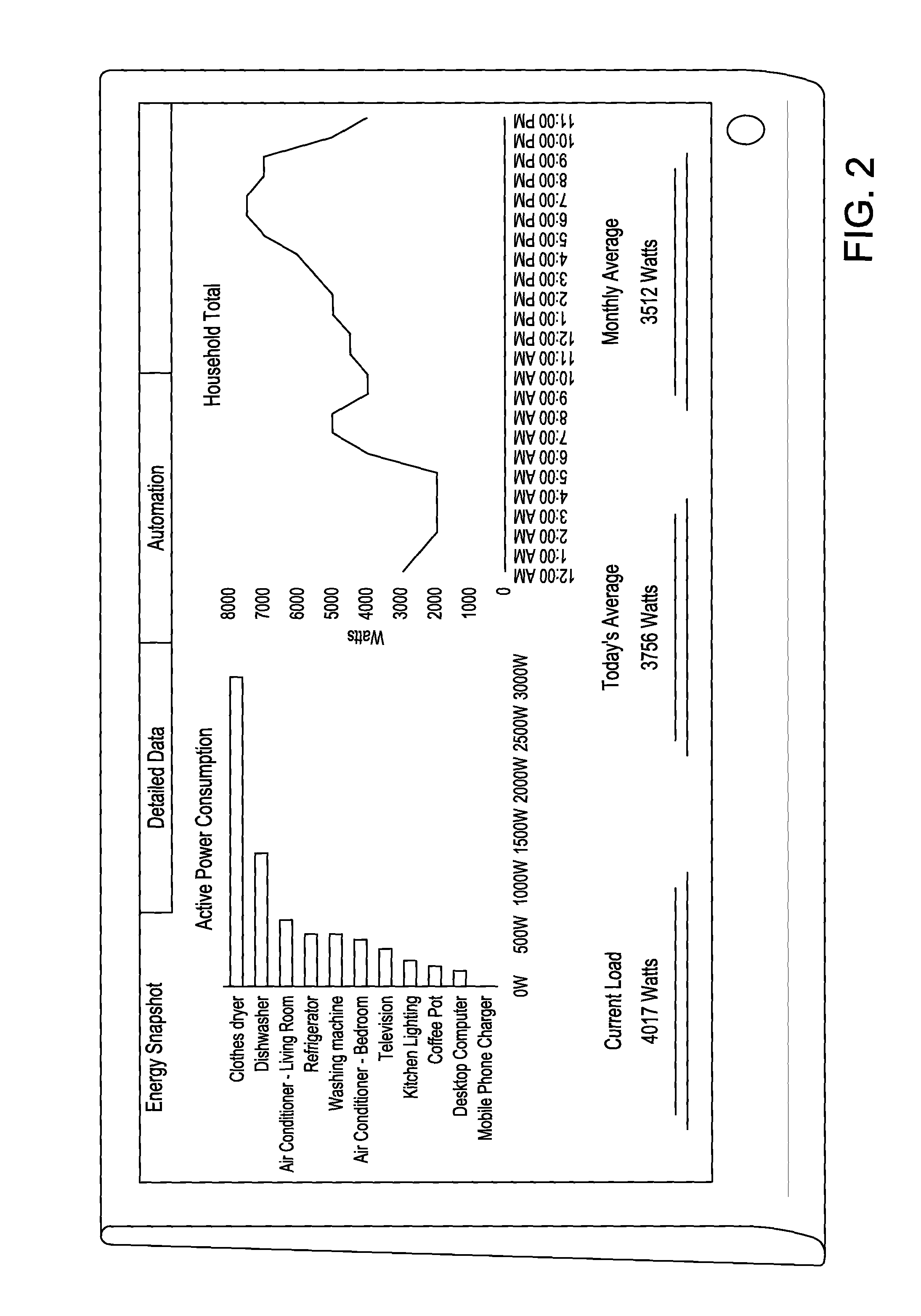
System and method for home energy monitor and control
ActiveUS8255090B2Increase powerEfficient managementLevel controlPayment architectureCommunity basedMonitoring system
The invention generally concerns systems and methods for monitoring and controlling the power consumption of a power-consuming device. The system and method may connect to a power source and a power-consuming device, connecting the power-consuming device to the power source. The power usage of the power-consuming device may then be measured and monitored. This monitoring data may then be stored and optionally sent to a controlling device on a data network. The location of the power-consuming device may also be determined, recorded, and sent to a controlling device. The system may also control the power usage of the power-consuming device. In some cases, a remote server may connect multiple energy monitoring systems in order to gain additional efficiencies and foster a community-based social network.
Owner:ENERGYHUB
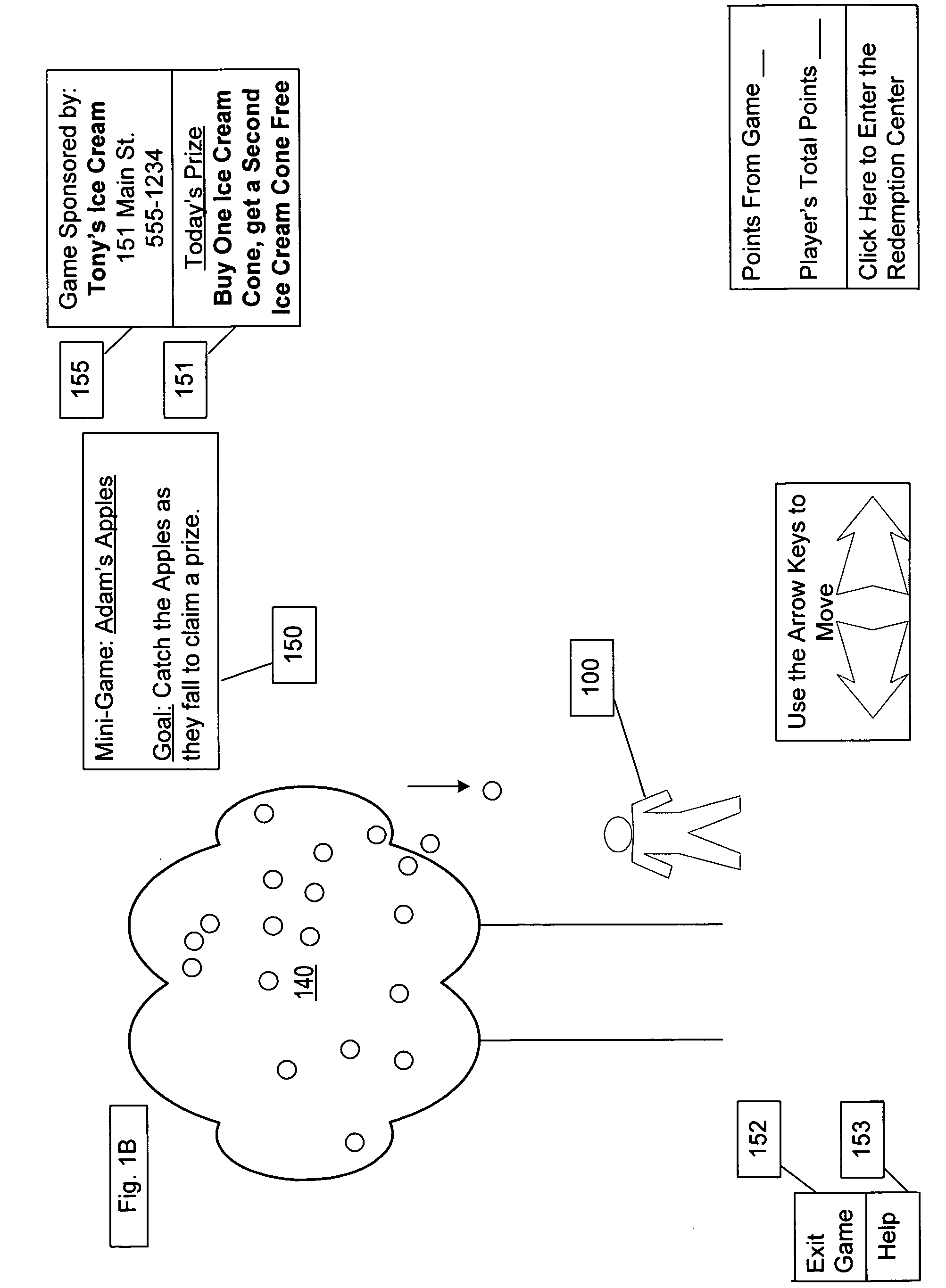
Method, system and apparatus for location based advertising
InactiveUS20060155597A1Good curative effectOvercome deficienciesDiscounts/incentivesFile systemUser profile
The invention relates to a method, system and apparatus for managing a small business' advertising. More specifically, the system creates and administers a virtual online world accessible to users (players) within a virtual environment. A player interacts with various elements of the virtual environment and during those interactions the advertising is displayed to the user. To subscribe to the virtual environment, a player provides user information through a registration process to create a user profile. The system selects and displays advertisements that are correlated to a given user. The correlation between advertisement and user in one embodiment of the invention is based on a user's zip code. Further, in order to facilitate the quick adoption of the system among small business owners, a fundraising paradigm is implemented. More specifically, people volunteer to sell advertising opportunities within a virtual environment in exchange for a share of sales revenues.
Owner:GLEASON DAVID MARTIN
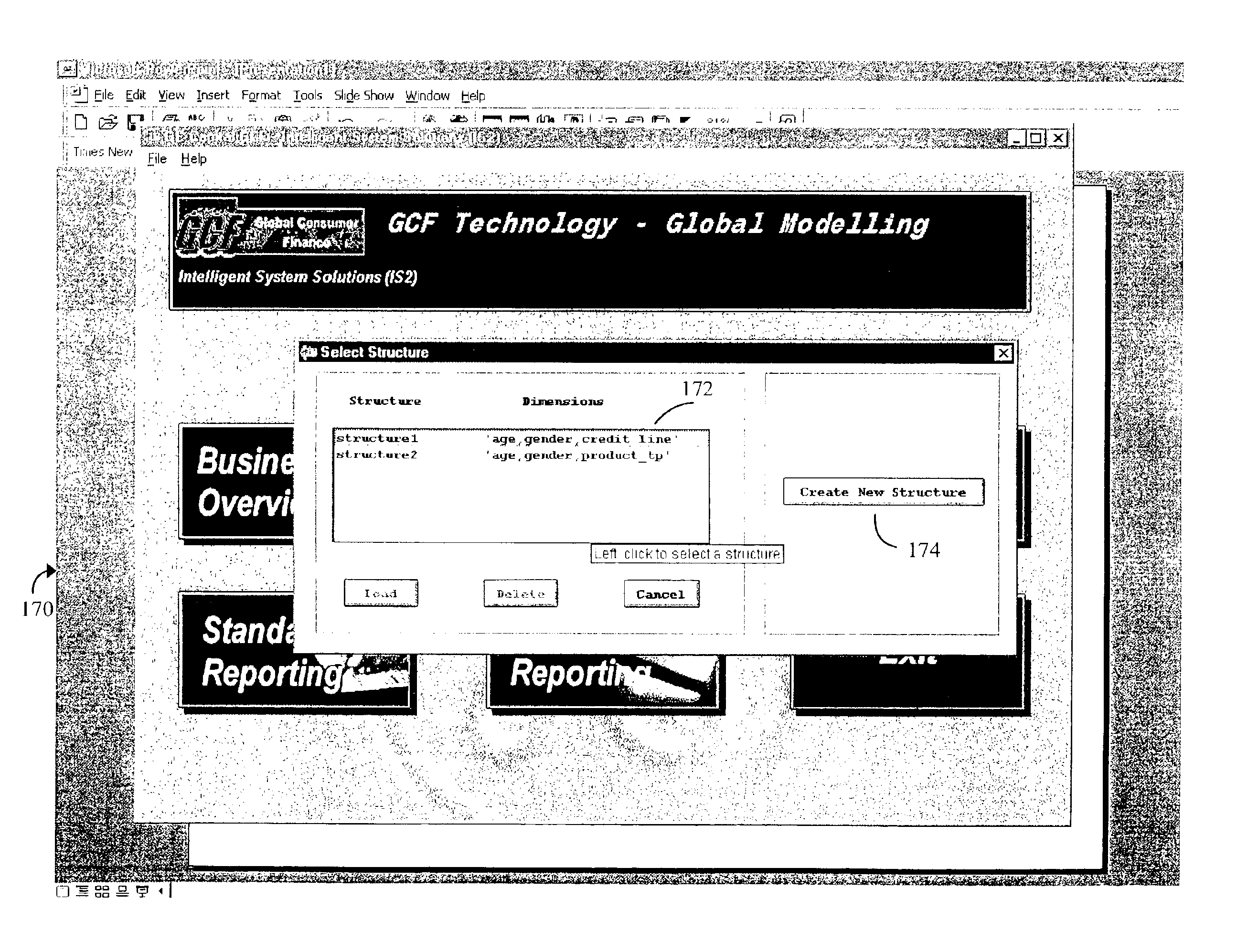
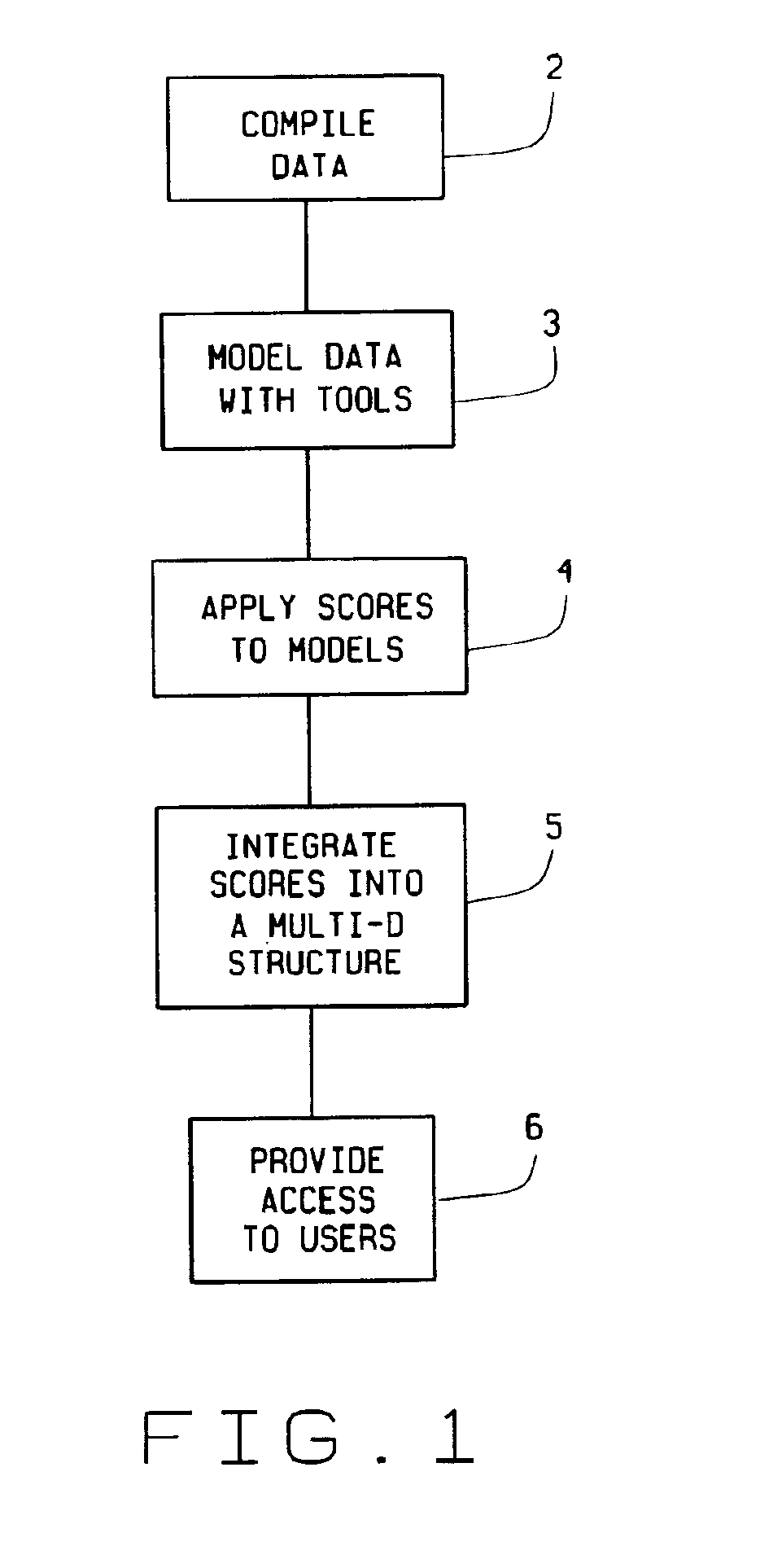
Methods and systems for accessing multi-dimensional customer data
InactiveUS6901406B2Efficiently targetEfficient managementFinanceDigital data processing detailsMultiple dimensionRelational database
Methods and systems for modeling customer data into a multi-dimensional structure for access to enable efficient customer targeting are described. The method includes the steps of compiling data from multiple sources to create a relational database, using tools to model data within the relational database, scoring the modeled data, integrating scores into a multi-dimensional structure and providing access to end users to the multi-dimensional structure.
Owner:GE CAPITAL US HLDG INC +1
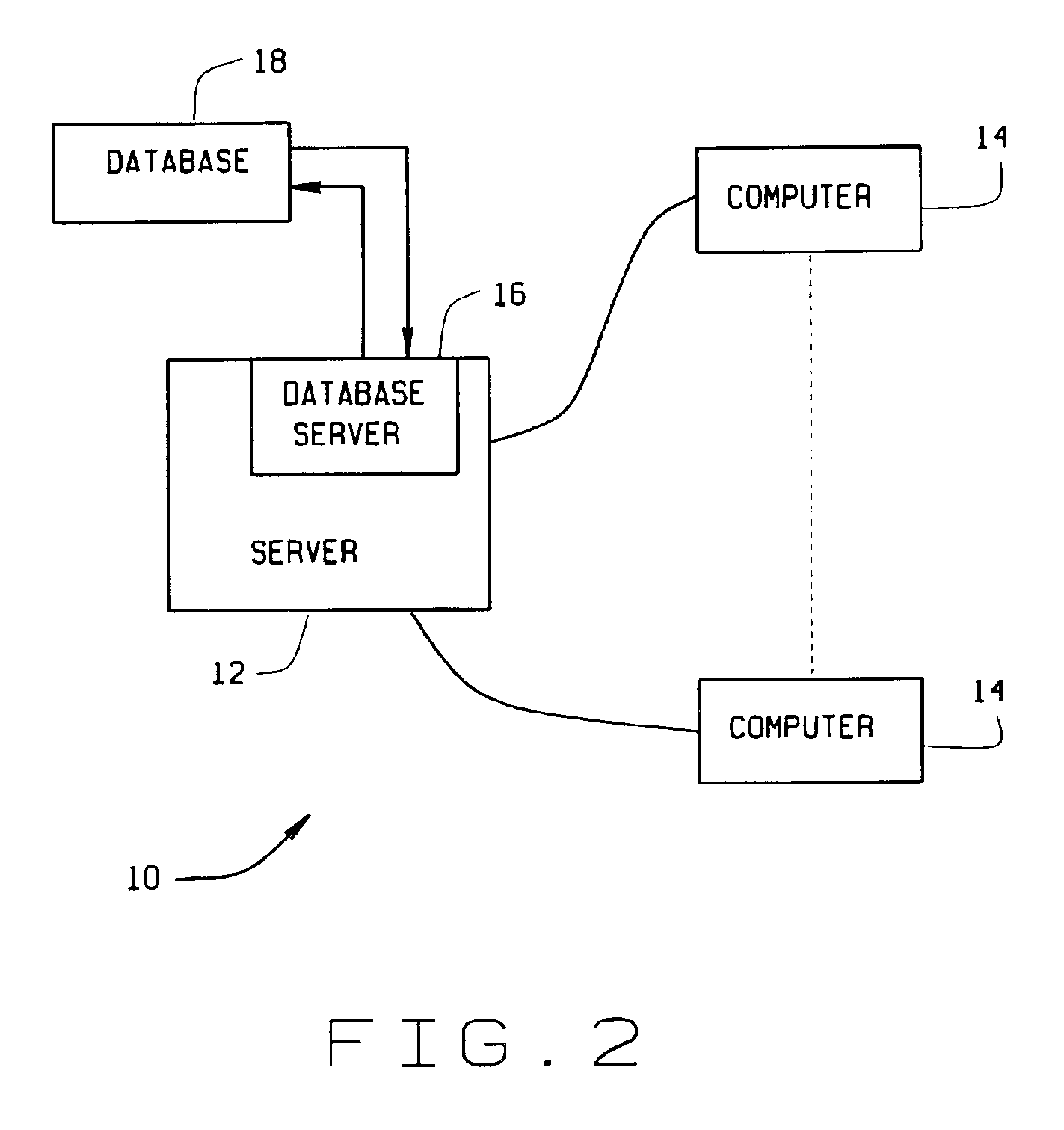
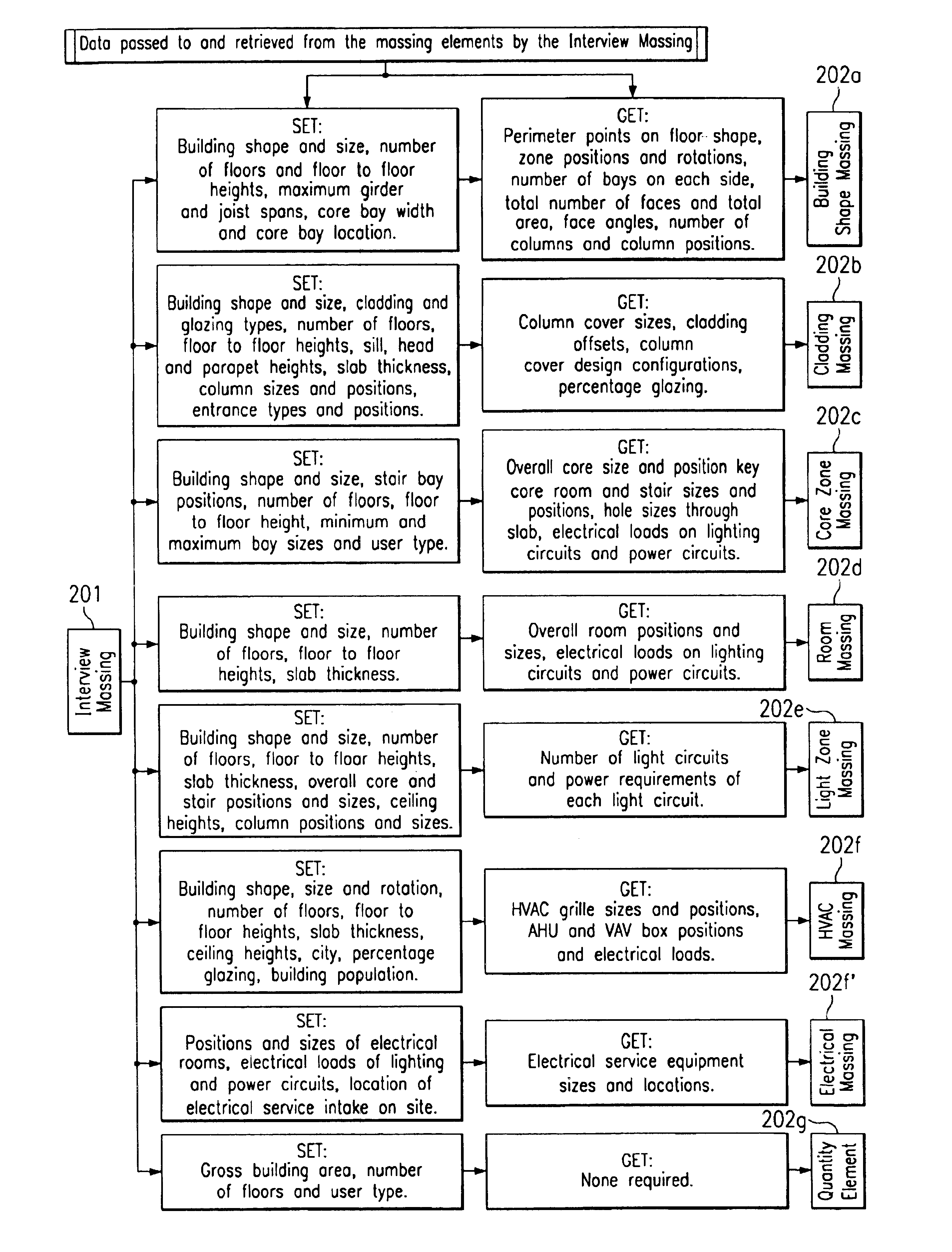
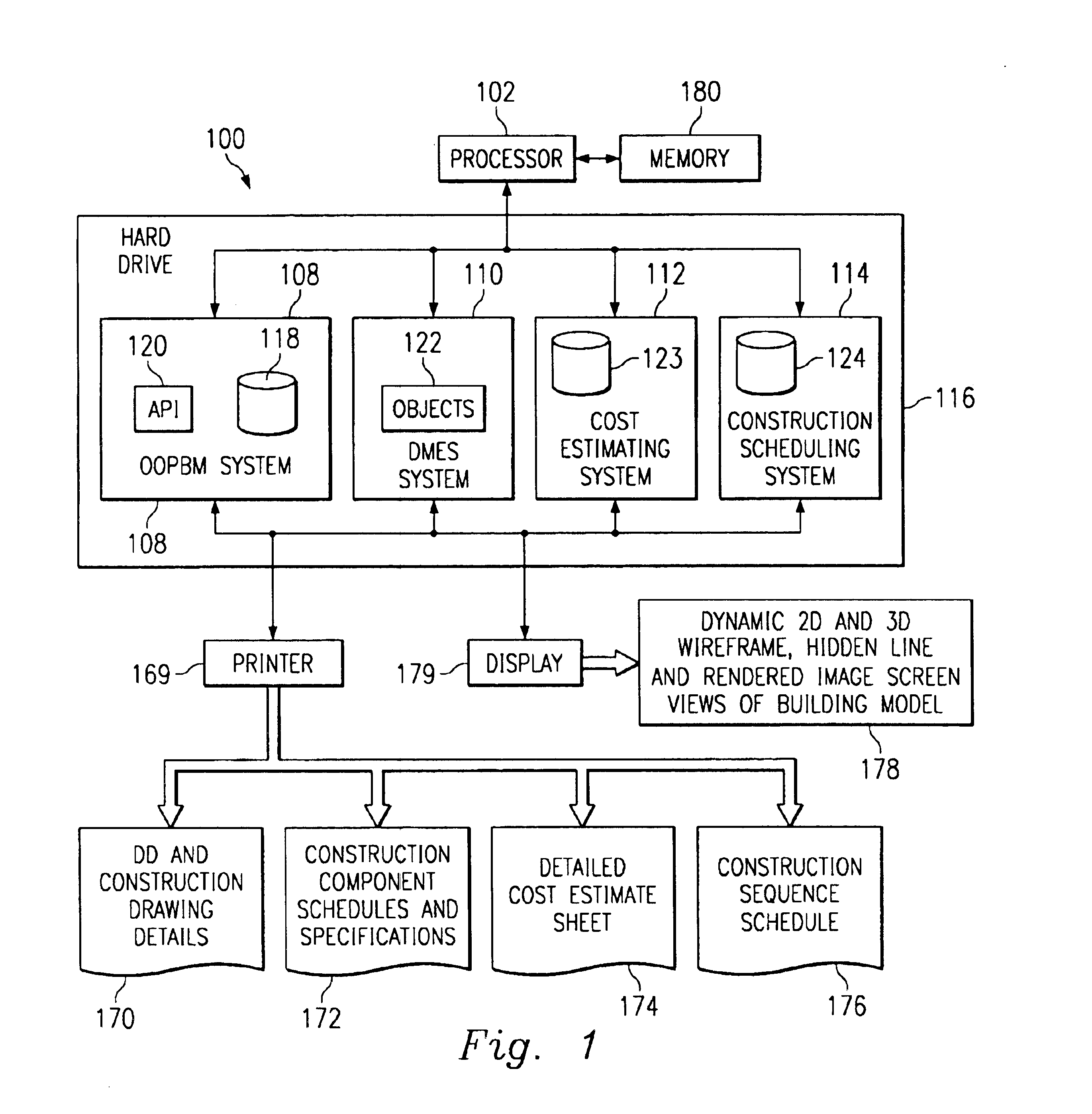
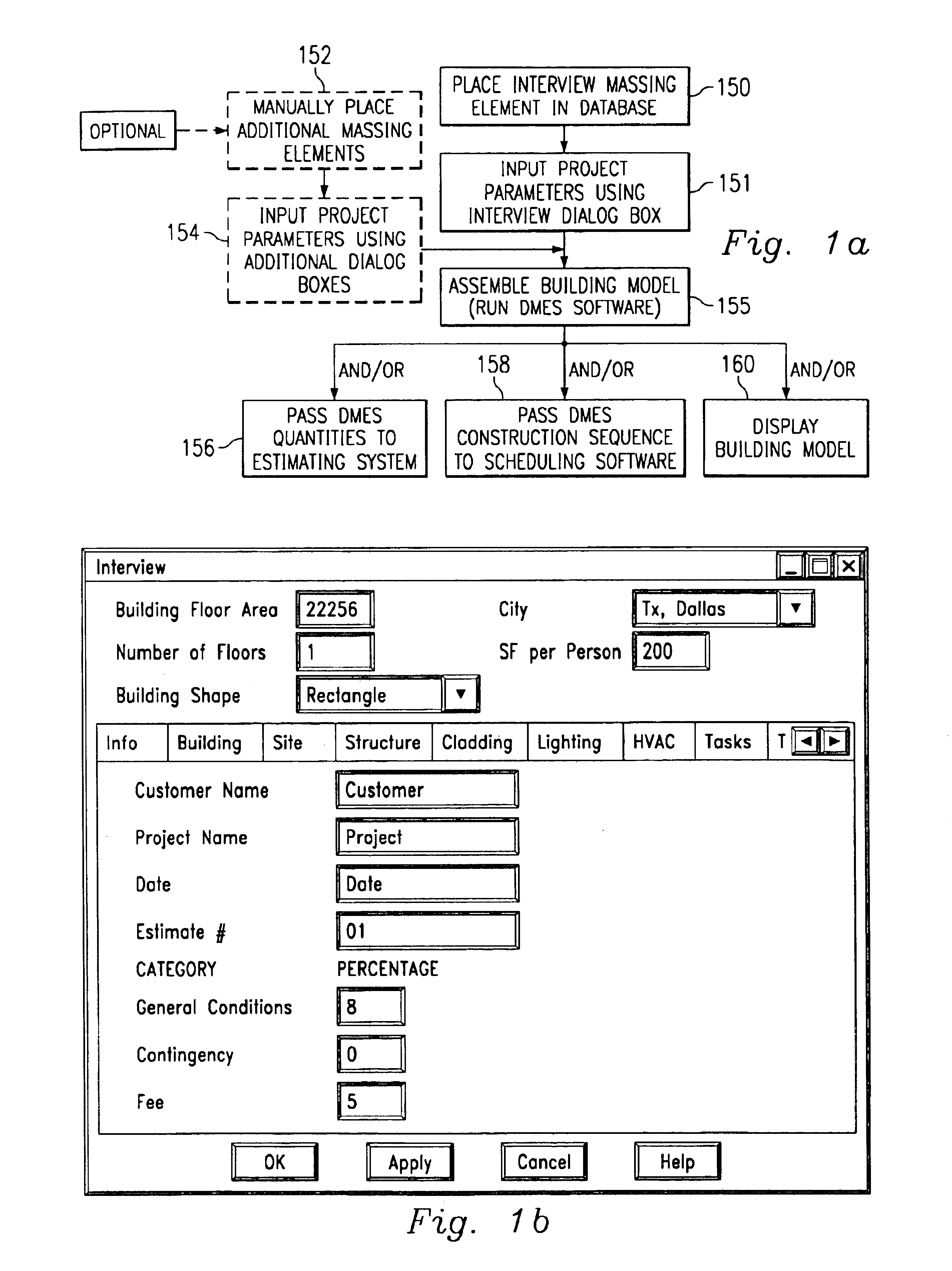
Computer-implemented automated building design and modeling and project cost estimation and scheduling system
InactiveUS6859768B1Reduction in building delivery timeProductionGeometric CADBuying/selling/leasing transactionsObject compositionBuilding design
A computer-implemented automated building design and modeling and construction project cost estimating and scheduling system (“DMES system”) is described. The DMES system provides a central source for all of the design and construction information for a construction project in a coordinated two-dimensional and three-dimensional spatial database that is freely accessible by all of the members of an interdisciplinary construction project team as a means to produce automatically coordinated design development and construction document information. The DMES system acquires and stores all of the appropriate design, engineering, and construction expertise and information available for any building type for use in automatically assembling and coordinating the design, cost-estimating, and scheduling for a construction project. In one embodiment, the DMES system consists of a plurality of objects, comprising elements and massing elements arranged in an assembly hierarchy. Each of the objects includes programming code that defines an interface and discrete internal functions that define its behavior. When instantiated in the database, the objects automatically create further instances of other objects in the hierarchy, which in turn do the same, thus assembling a complete building model automatically from the initial manually-placed instance. The building model enables automatic generation of drawings and cost and scheduling information. By running automatic iterations of the building model, multiple designs may be evaluated to determine the optimum design.
Owner:BECK TECH
Method and apparatus for consumer interaction based on spend capacity
ActiveUS20060242046A1Efficient use ofEfficient managementFinancePayment architectureBalance transferInsurance life
Share of Wallet (“SoW”) is a modeling approach that utilizes various data sources to provide outputs that describe a consumer's spending capability, tradeline history including balance transfers, and balance information. These outputs can be appended to data profiles of customers and prospects and can be utilized to support decisions involving prospecting, new applicant evaluation, and customer management across the lifecycle. In addition to credit card companies, SoW outputs may be useful to companies issuing, for example: private label cards, life insurance, on-line brokerages, mutual funds, car sales / leases, hospitals, and home equity lines of credit or loans. “Best customer” models can correlate SoW outputs with various customer groups. A SoW score focusing on a consumer's spending capacity can be used in the same manner as a credit bureau score.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
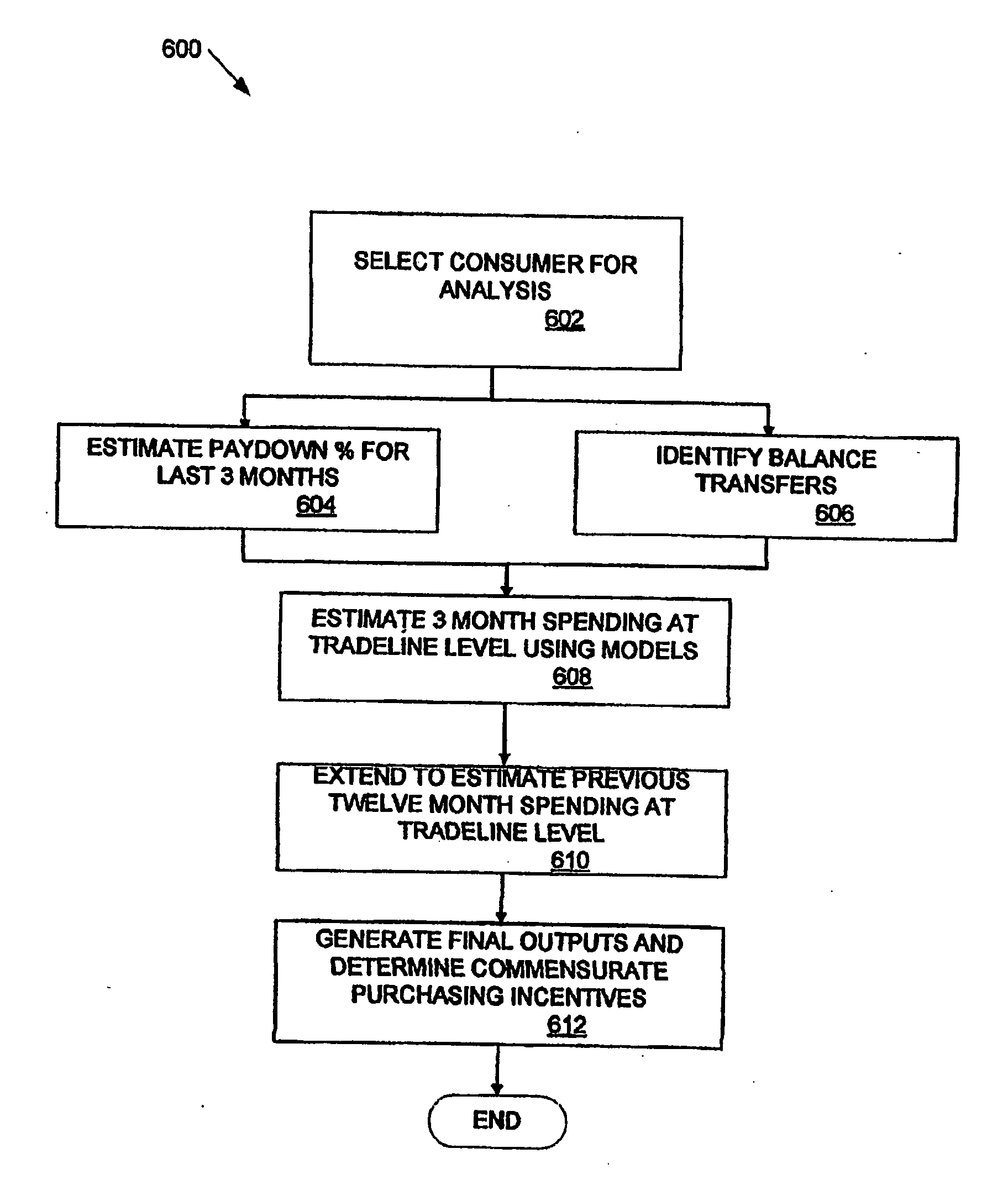
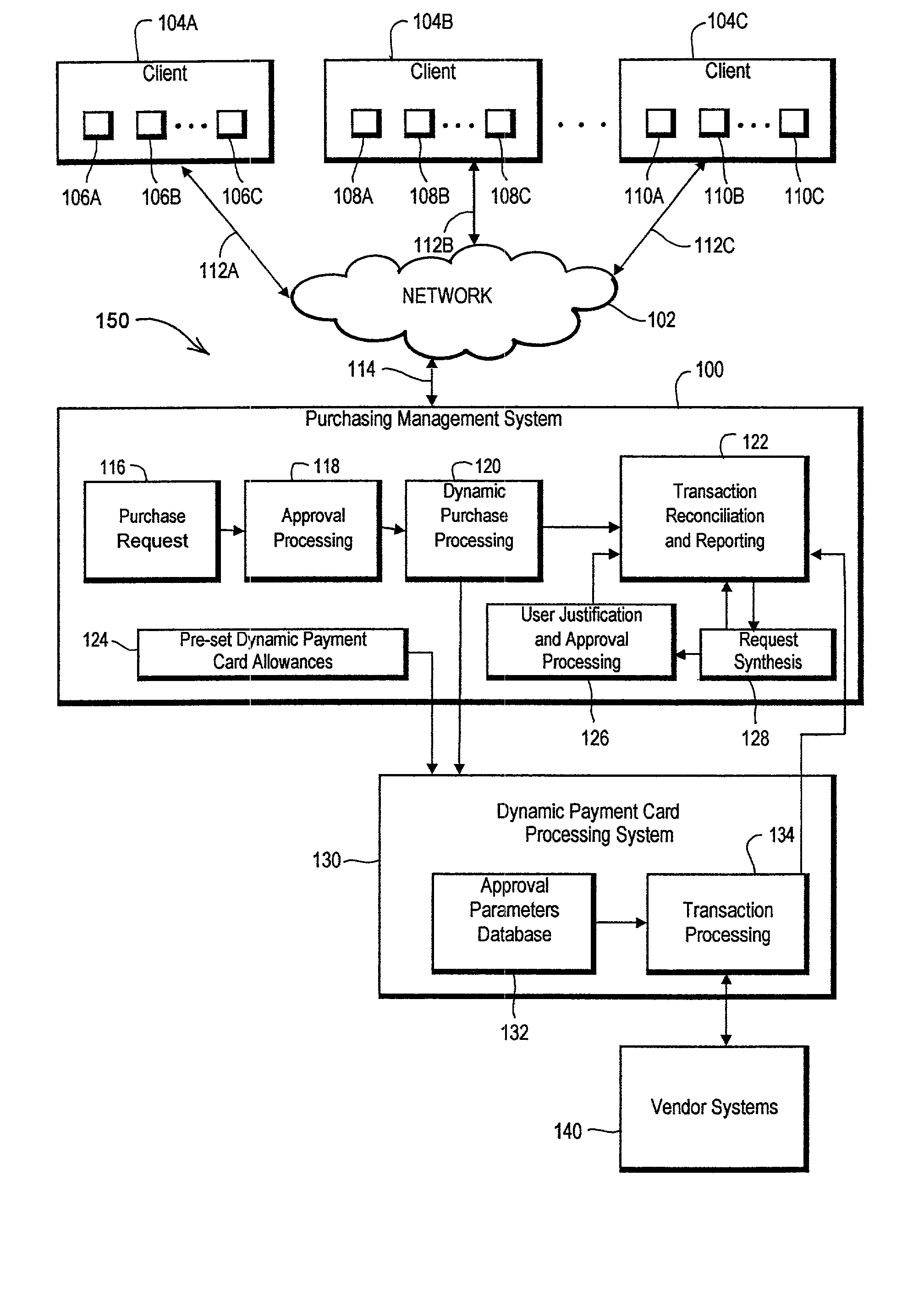
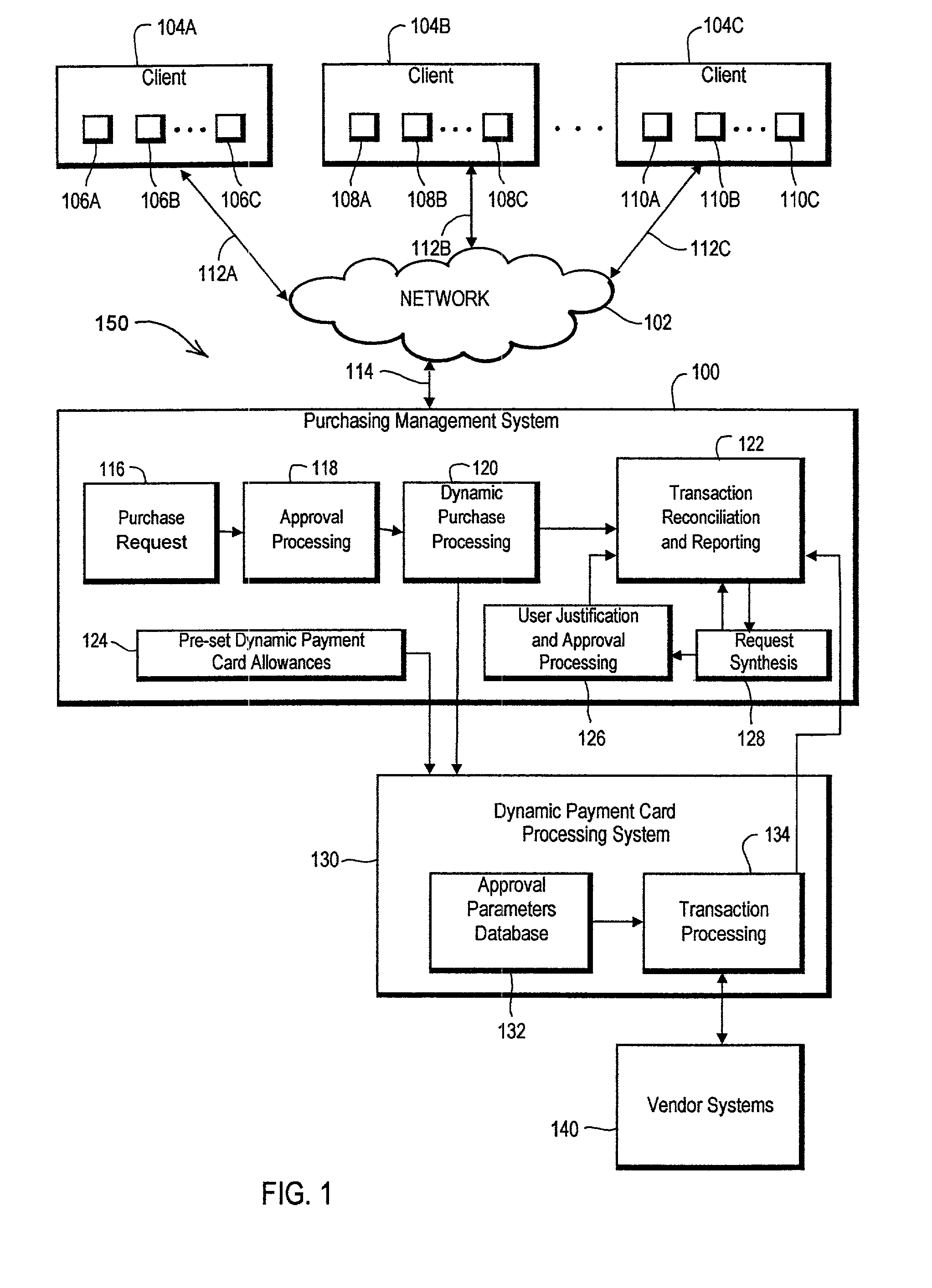
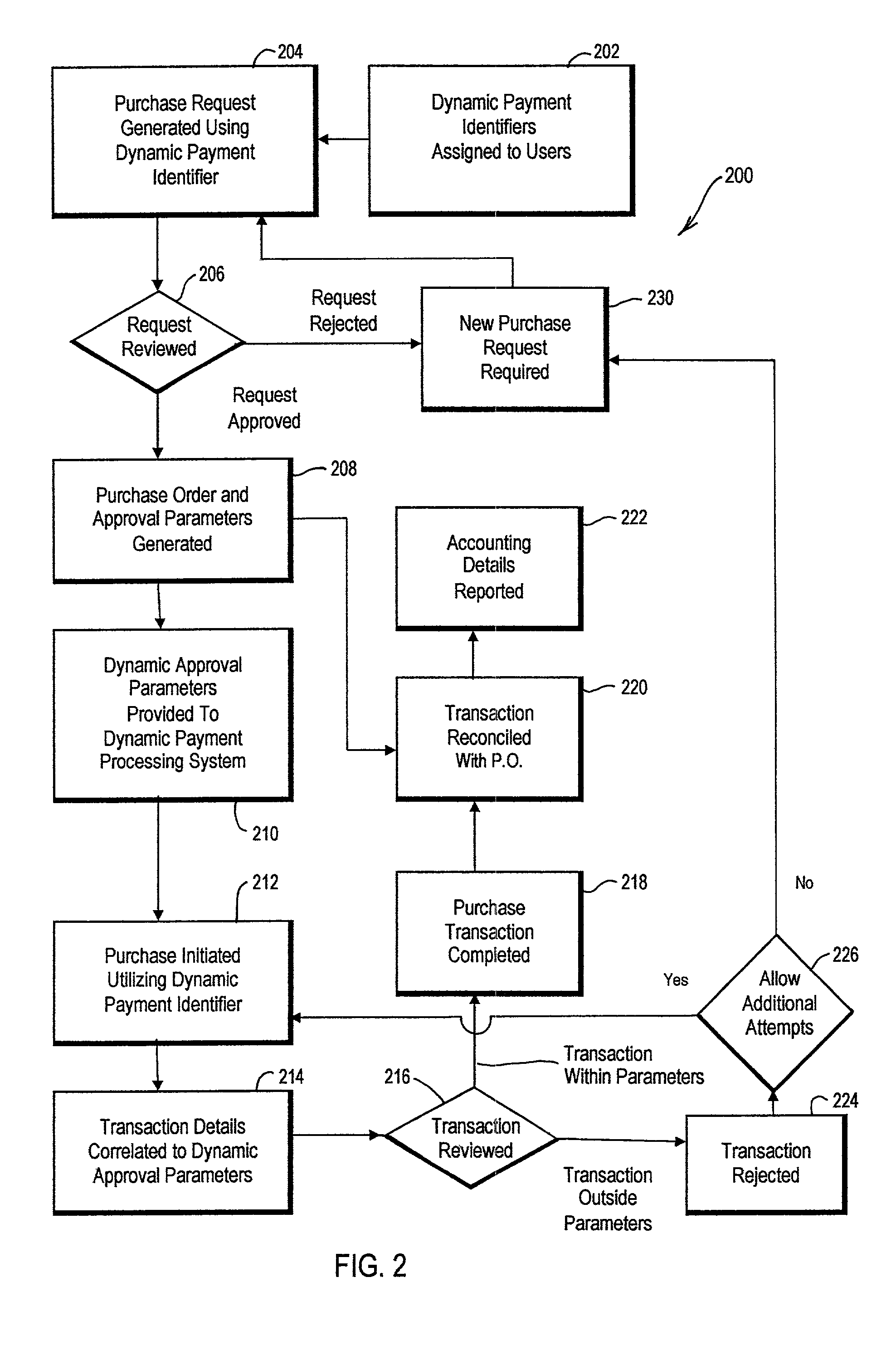
Dynamic payment cards and related management systems and associated methods
InactiveUS7319986B2Efficient managementEasy to manageFinanceCoded identity card or credit card actuationPaymentDynamic management
Dynamic payment cards and related dynamic payment card management systems and associated methods are disclosed that allow for the efficient management of corporate purchasing needs. The dynamic payment cards can be traditional payment cards with card control settings that are dynamically managed. In addition, a dynamic card management system can automatically interface with card processor systems to dynamically modify these card control settings, and a purchasing management system or other request and approval workflow engine can provide an interface between a company and the dynamic card management system. More generally, an advantageous solution for purchasing management is disclosed that utilizes dynamically or actively managed approval parameters to help control transaction authorization determinations associated with purchasing mechanisms. These dynamic approval parameters can be generated and / or managed through the application of configurable company purchasing policies and rules, and these dynamic approval parameters can be stored, for example, by a processing system that makes authorization determinations when transactions are initiated using the purchasing mechanisms.
Owner:BANK OF AMERICA CORP
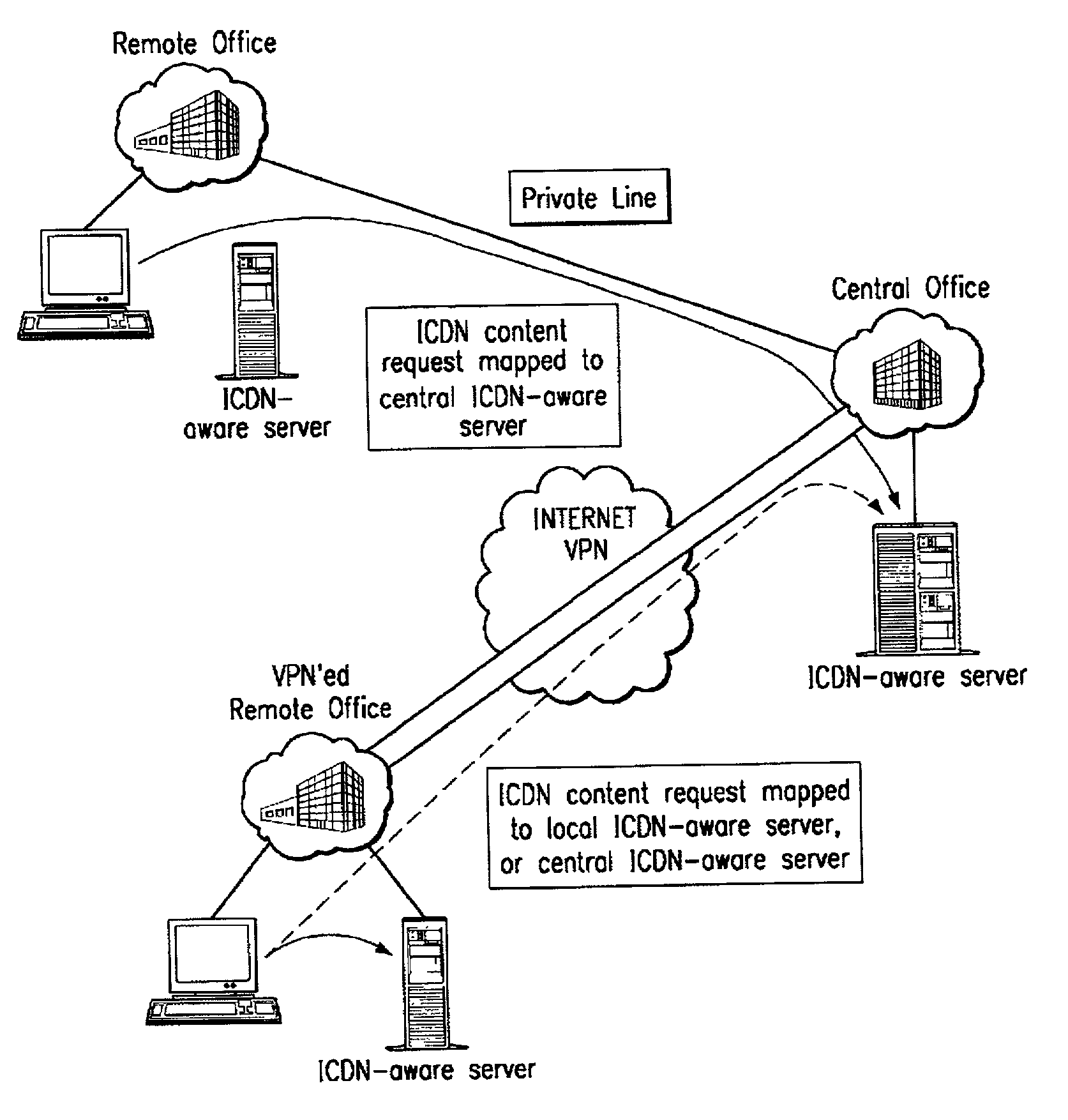
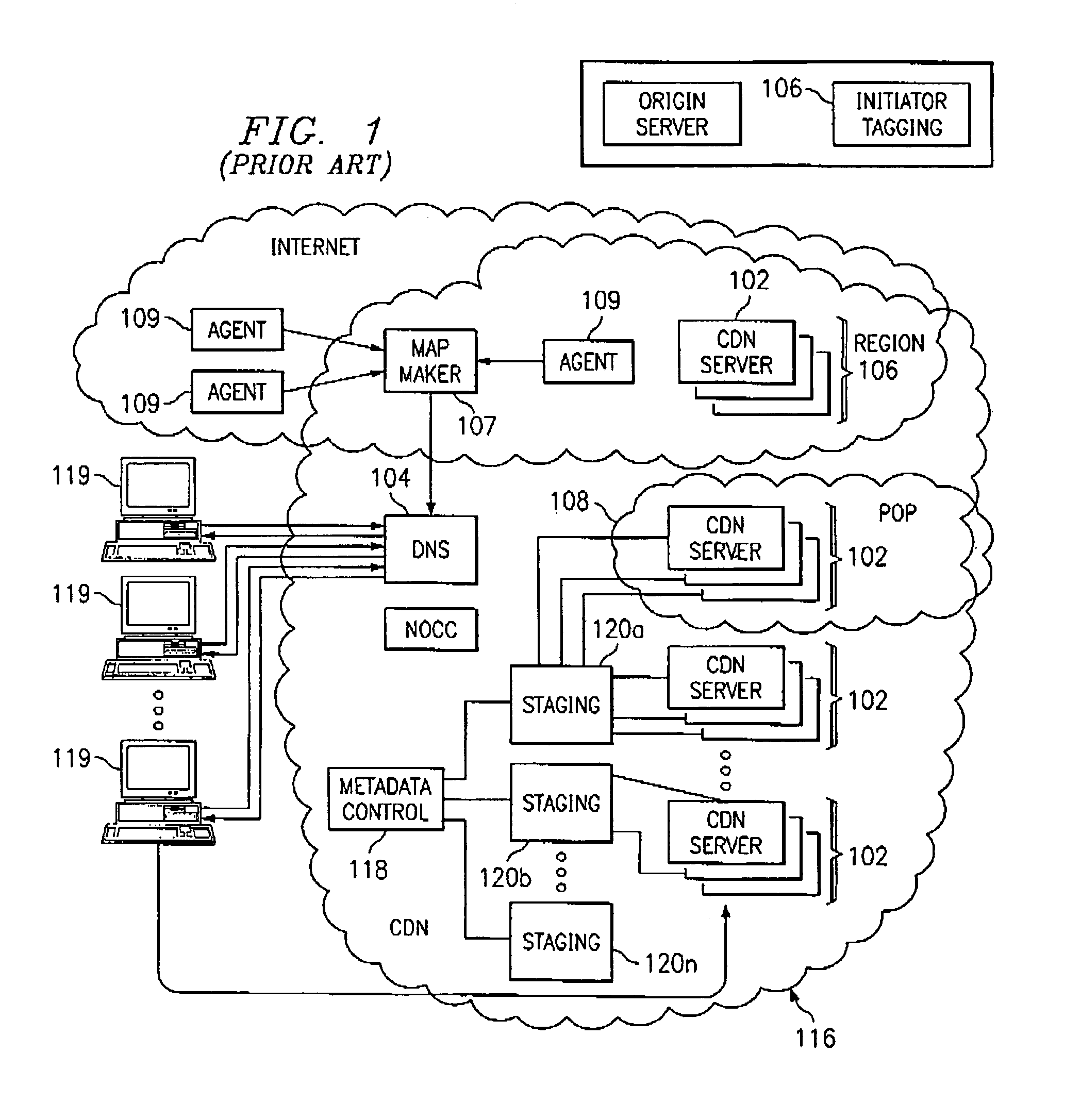
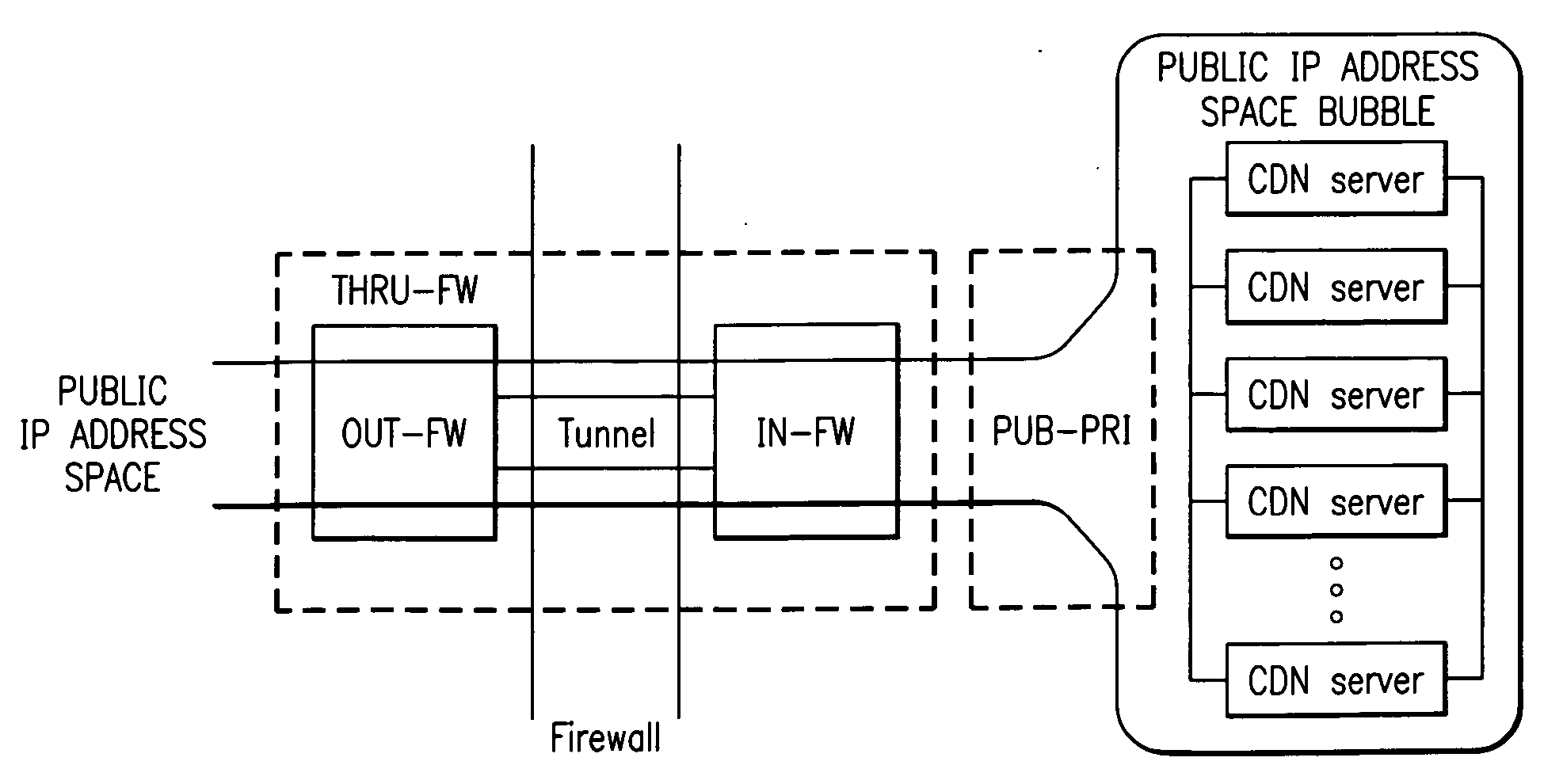
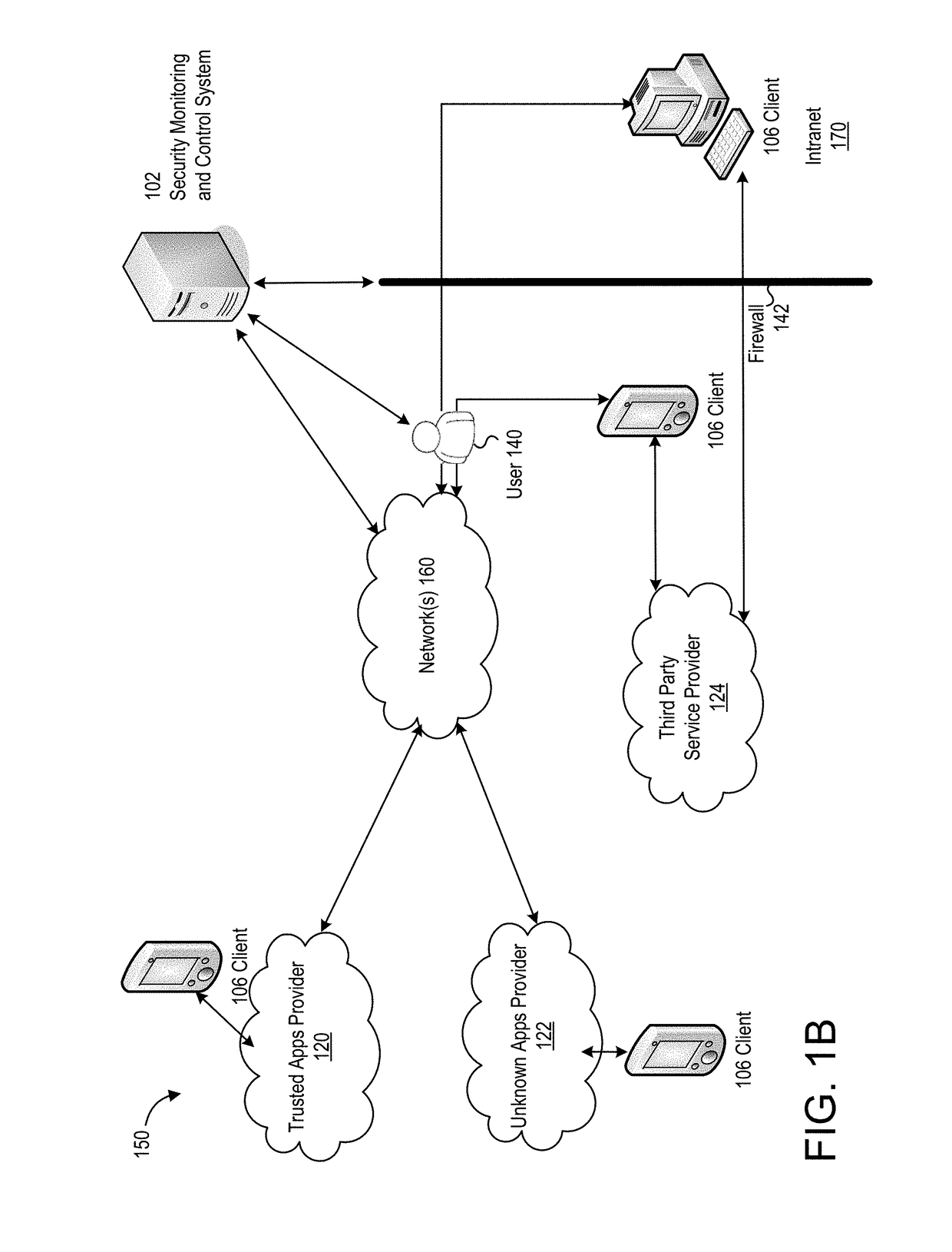
Extending an Internet content delivery network into an enterprise
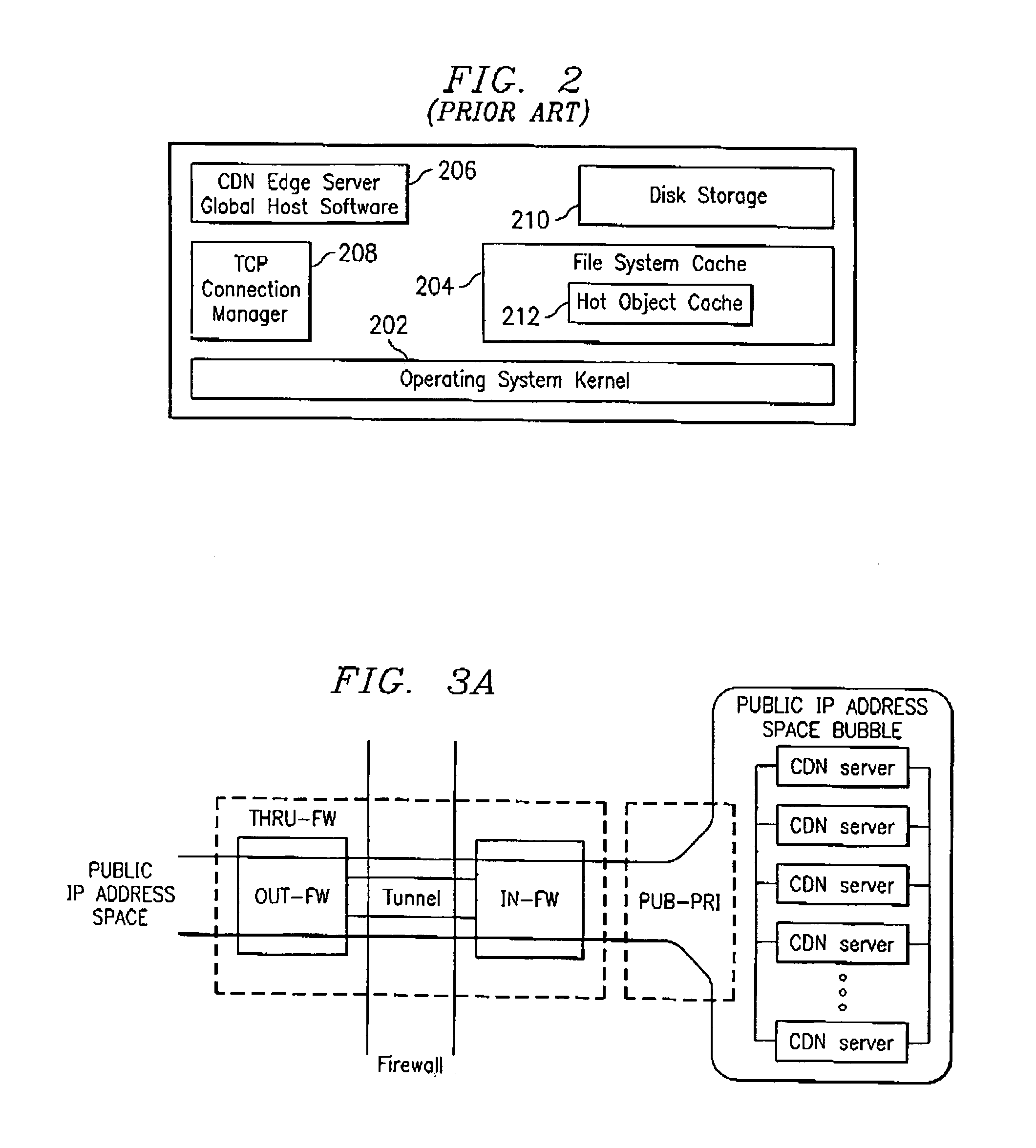
ActiveUS7096266B2Efficient and cost-effectiveEfficient managementMultiple digital computer combinationsSecuring communicationInternet contentPrivate network
An Internet content delivery network deploys one or more CDN server regions in an enterprise and manages those regions as part of the Internet CDN. In one aspect of the invention, a CDN service provider (CDNSP) deploys one or more CDN regions behind an enterprise's corporate firewall(s). The regions are used to deliver Internet content—content that has been tagged or otherwise made available for delivery over the Internet from the CDN's content servers. This content includes, for example, content that given content providers have identified is to be delivered by the CDN. In addition, the enterprise may tag intranet content, which is then also served from the CDN regions behind the firewall. Intranet content remains secure by virtue of using the enterprise's existing security infrastructure. In accordance with another aspect of the invention, the CDNSP implements access controls and deploys one or more CDN regions outside an enterprise's firewall(s) such that intranet content can be served from regions located outside the firewall(s). In this embodiment, the CDNSP can provide granular control, such as permissions per groups of users. In this way, the CDNSP, in effect, extends a conventional virtual private network (VPN) to all or a portion of the ICDN, thereby enabling the CDNSP to use multiple regions and potentially thousands of content servers available to serve the enterprise's internal content. In addition to making internal content available from the edge of the network, the CDNSP provides a mechanism by which an enterprise may share secure data with its business partner(s) without setting up any special infrastructure.
Owner:AKAMAI TECH INC
Thermoformed apparatus having a communications device
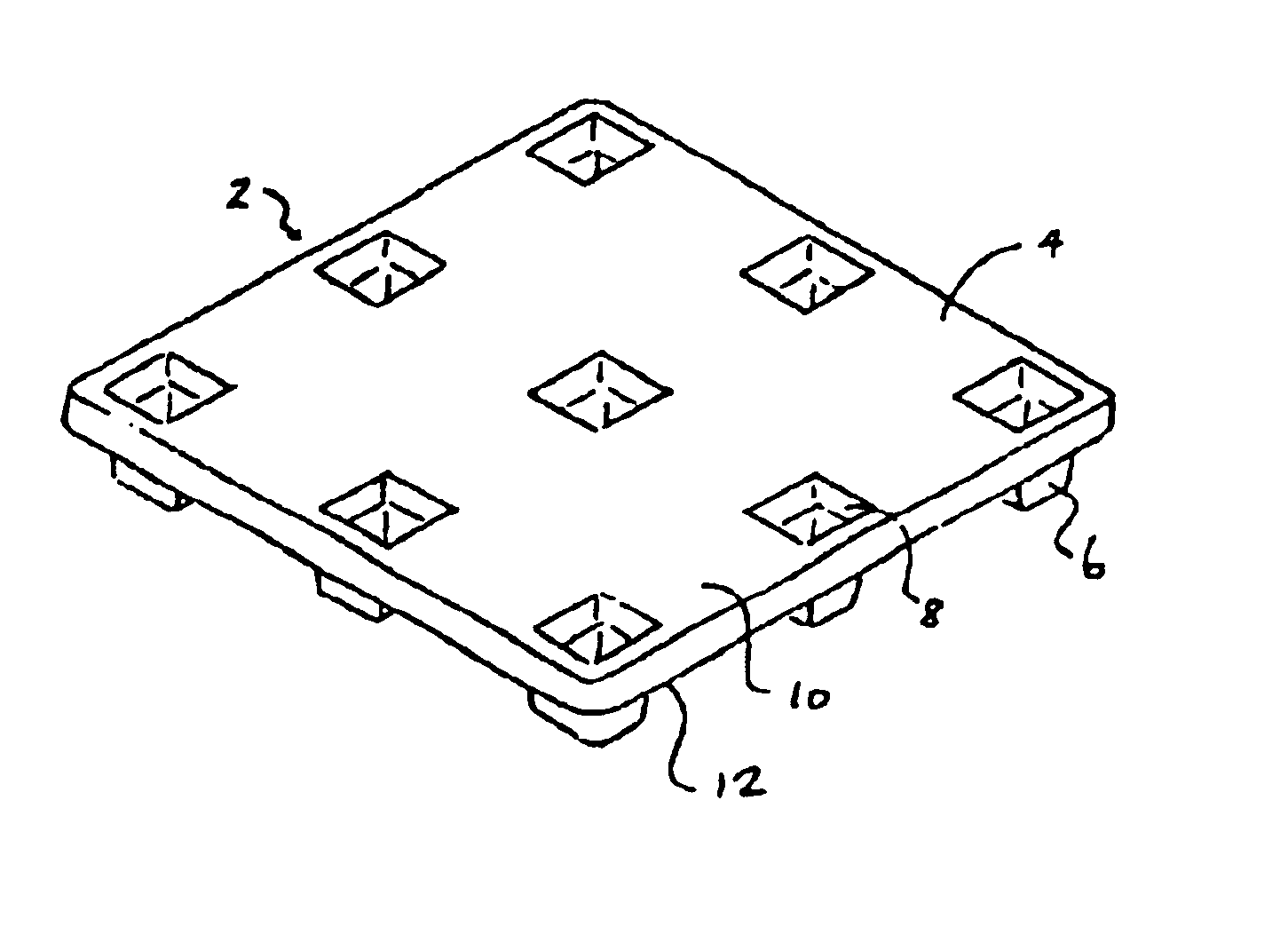
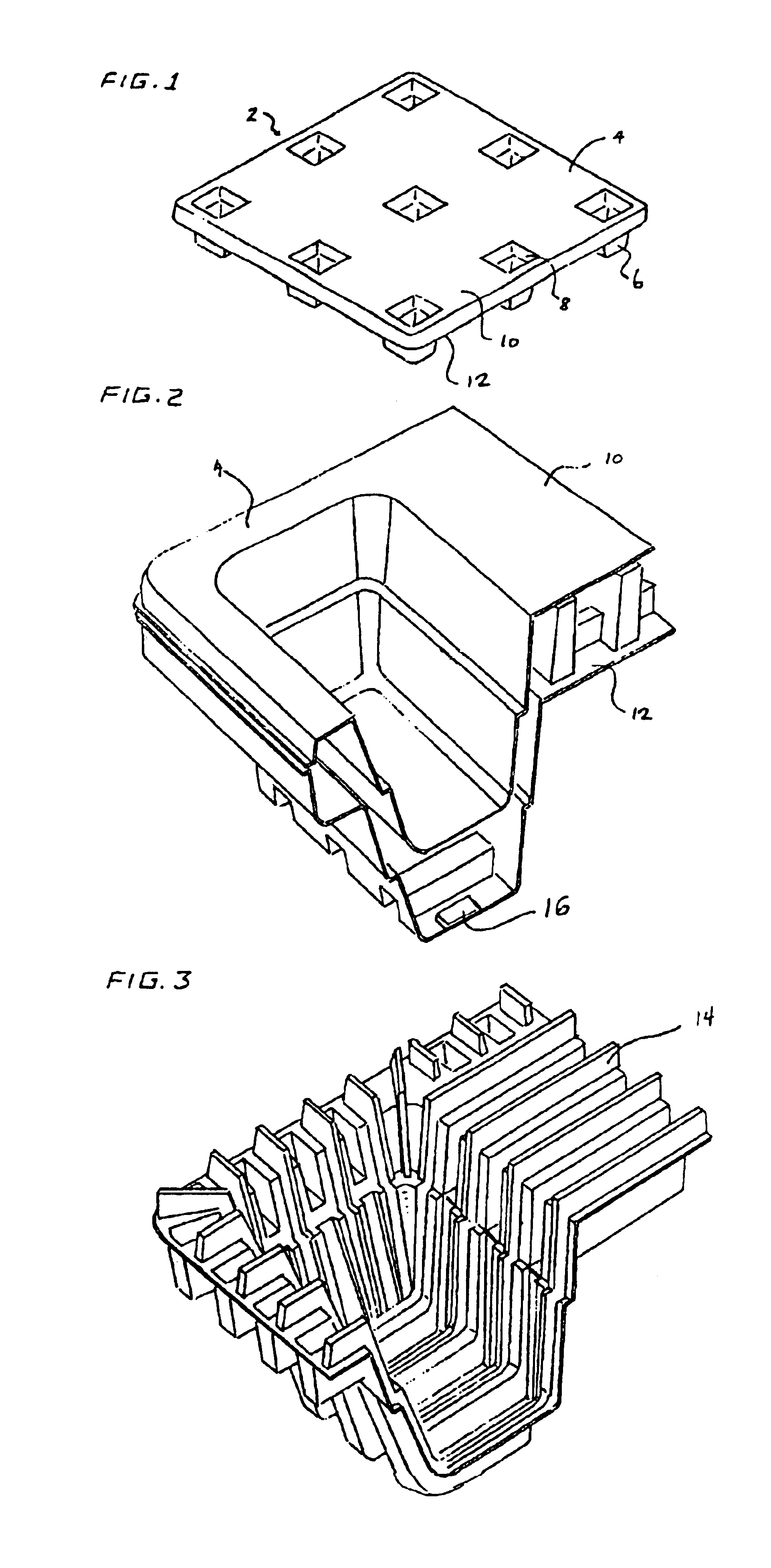
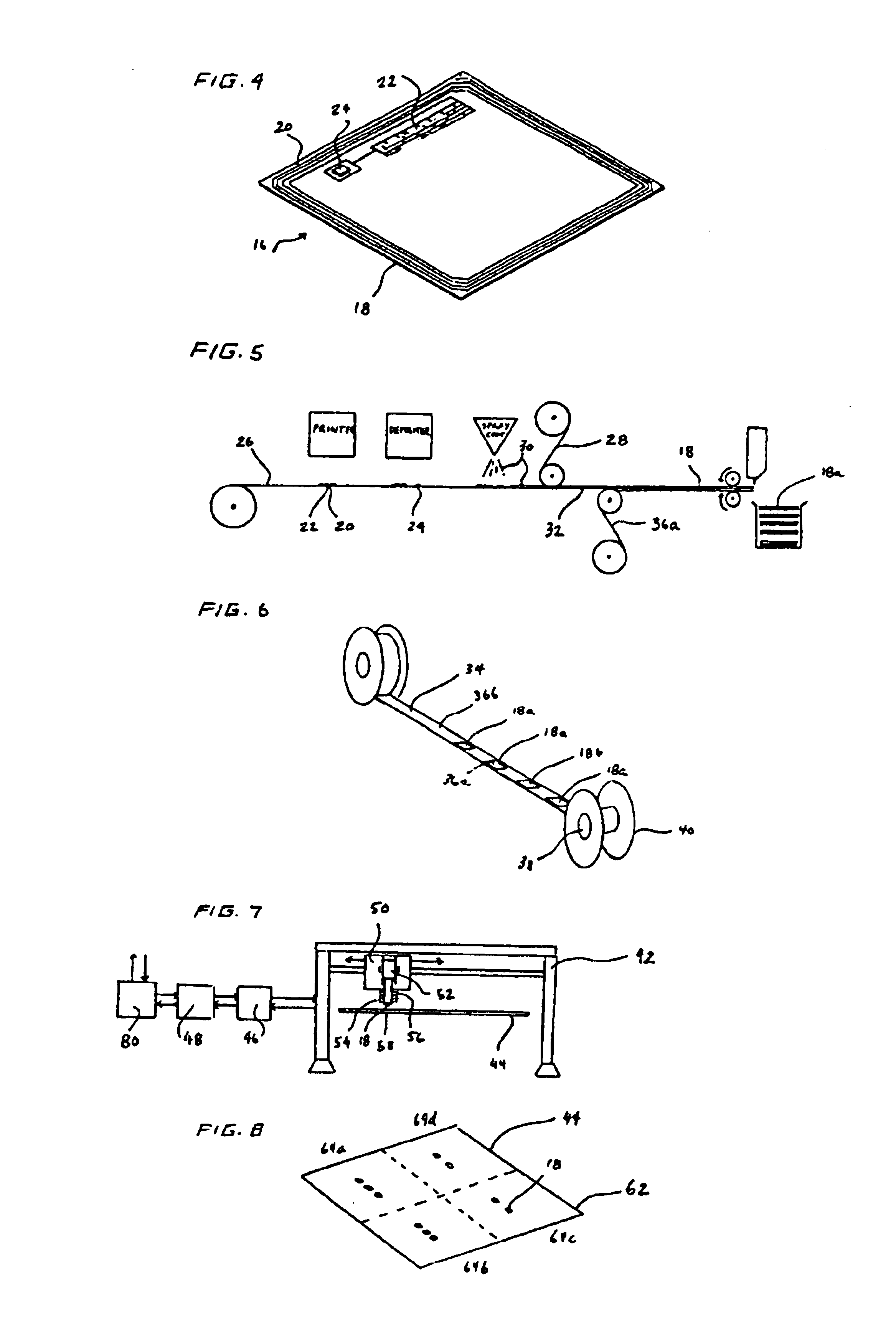
InactiveUS6943678B2Improve protectionIncreased durabilityRecord carriersDigital data processing detailsThermoformingEngineering
An apparatus has a communications device associated therewith. In another aspect of the present invention, a pallet is made from thermoformed polymeric sheets with an attached communications device. A further aspect of the present invention provides a radio frequency identification device attached to an apparatus. In still another aspect of the present invention, a communications device is incorporated into one or more sheets of a pallet or other container prior to forming. Methods of making and using a thermoformed pallet and container, having a communications device, are also provided.
Owner:NEXTREME
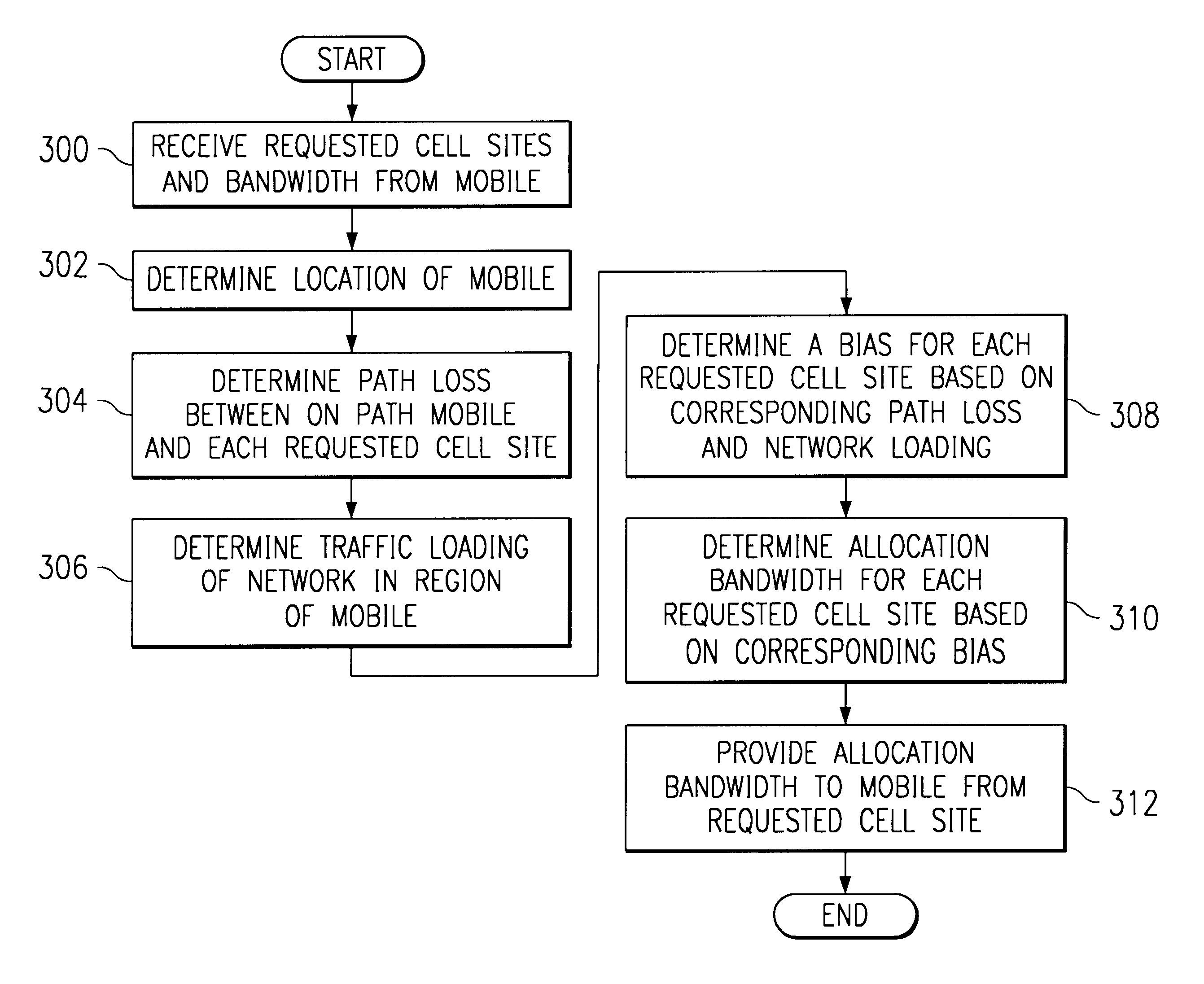
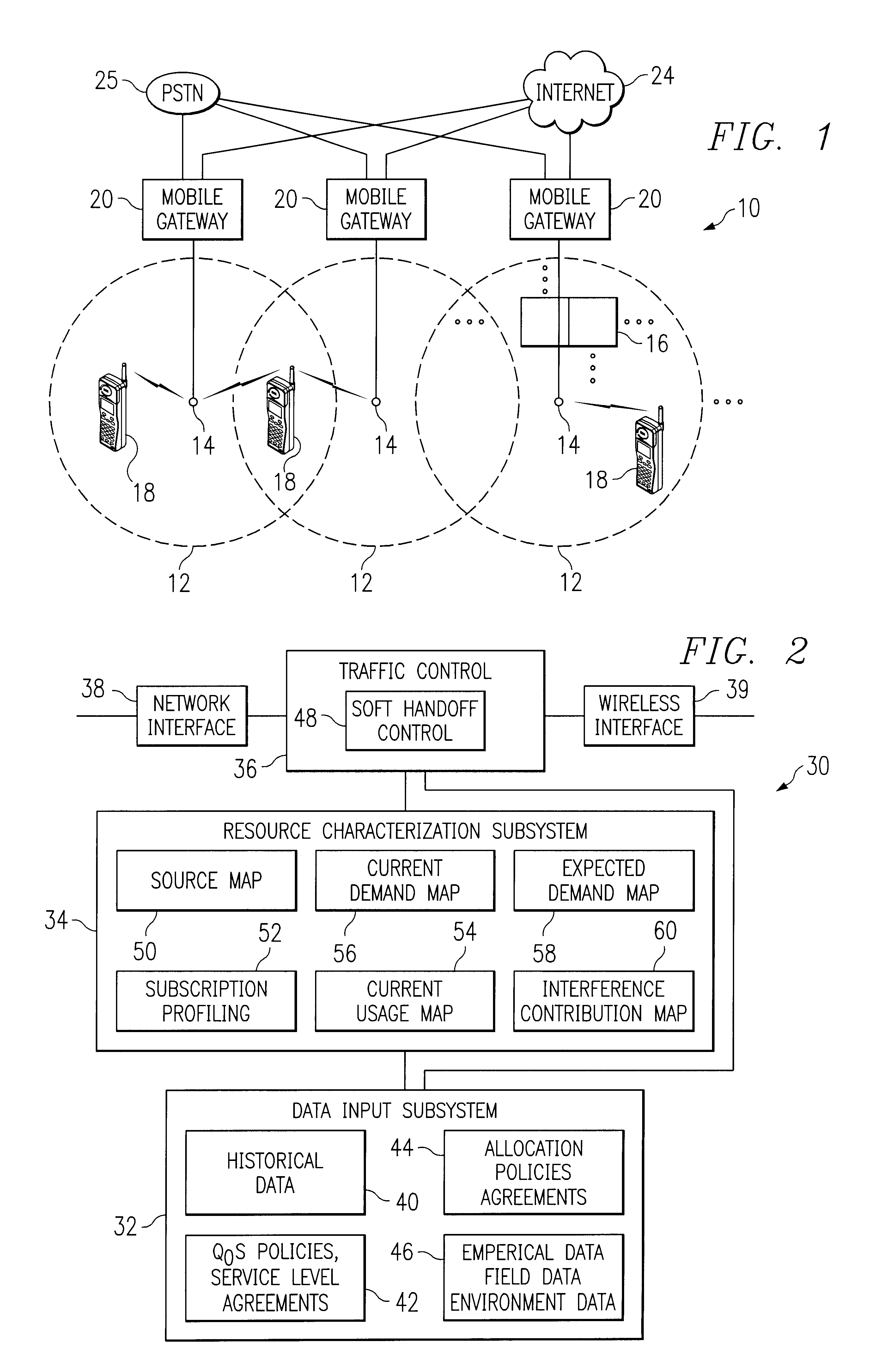
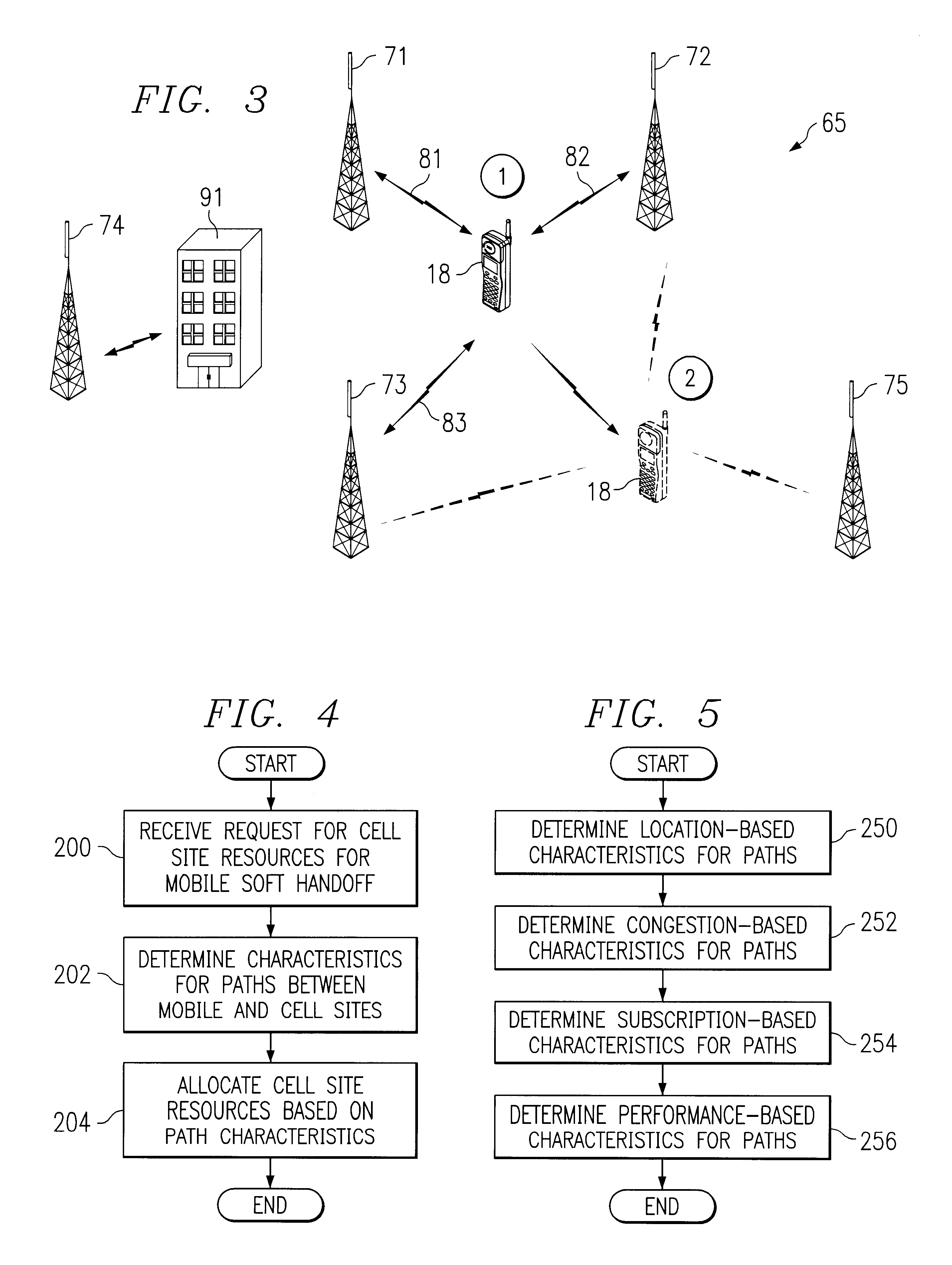
Method and system for dynamic soft handoff resource allocation in a wireless network
InactiveUS6907243B1Resource allocatedMinimize air-link congestionPower managementAccounting/billing servicesTelecommunicationsMobile device
A method and system for dynamic soft handoff resource allocation in a wireless communications network includes determining a wireless path characteristic individually for each path of a macro diversity connection between a mobile device and a plurality of wireless sites. Wireless resources are allocated for the macro diversity connection between the mobile device and the wireless sites based on the wireless path characteristic. The wireless path characteristic includes a location-based characteristic, a congestion-based characteristic, a subscriber-based characteristic and / or a performance-based characteristic.
Owner:CISCO TECH INC
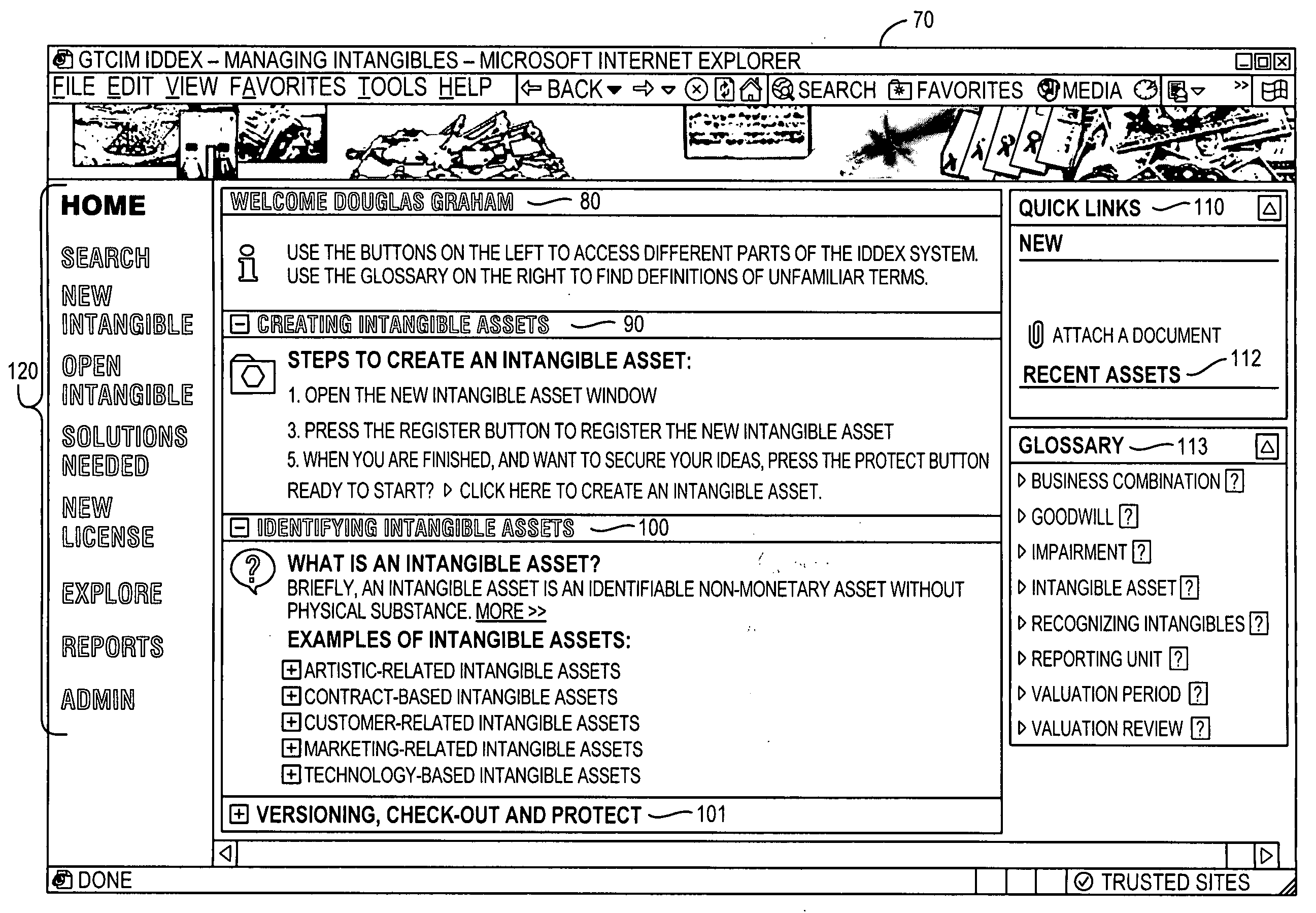
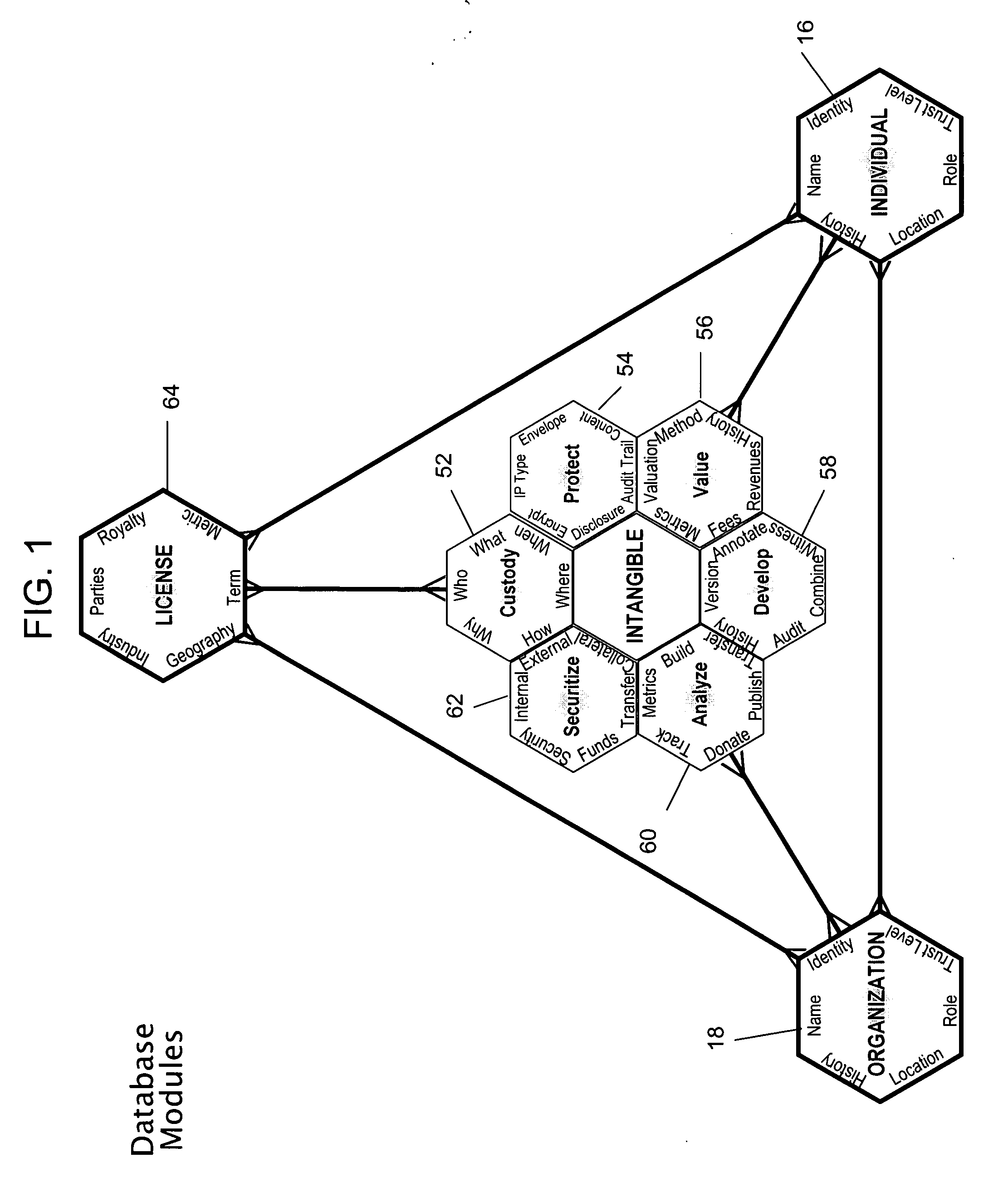
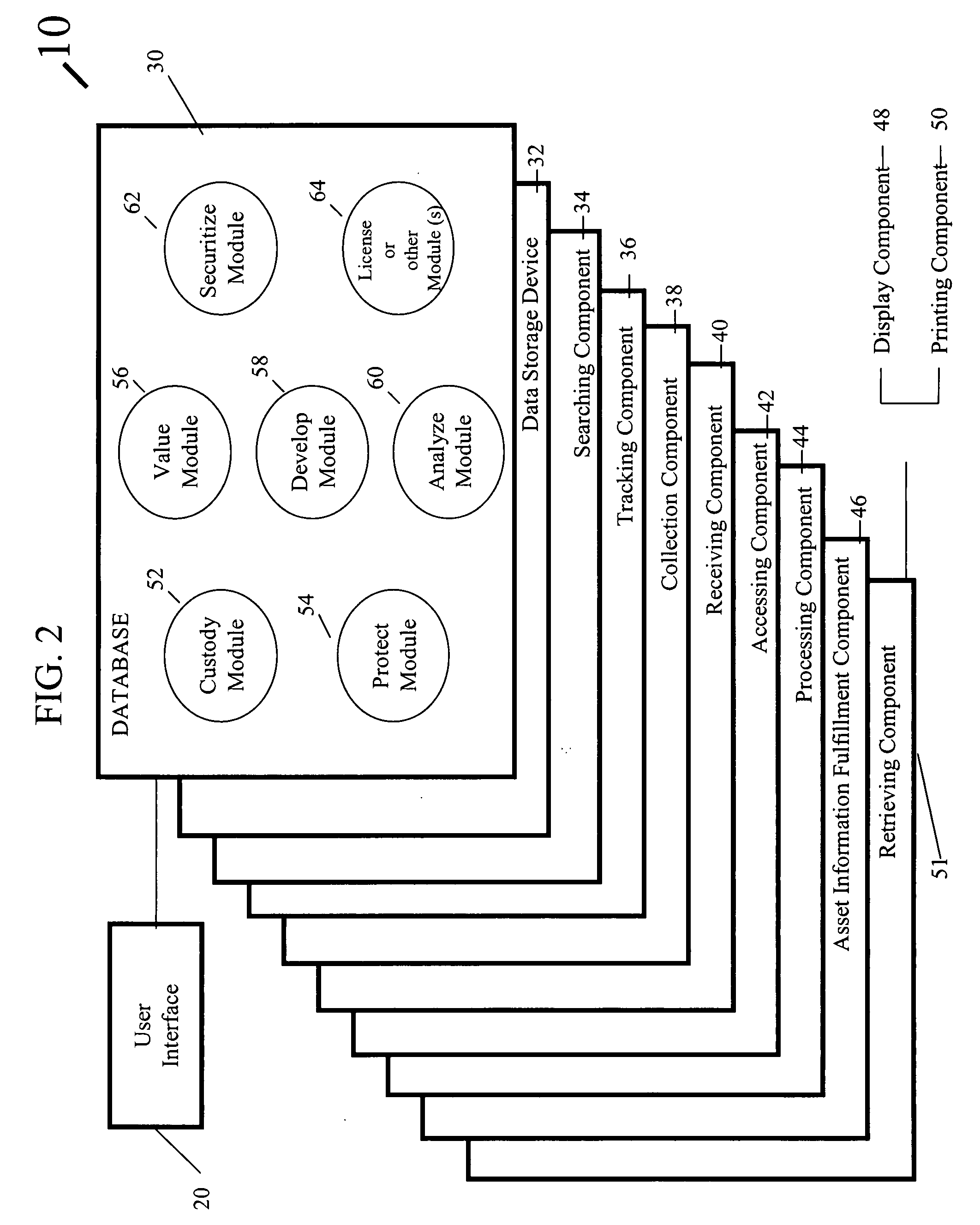
Systems and methods for management of intangible assets
InactiveUS20080215474A1Facilitating versioningPromote collaborationFinanceOffice automationKnowledge organizationEffective management
Systems and methods for management of intangible assets are provided that allow effective management of intangible assets. The intangible asset management system and method include a computer based intangible asset management system for storing, managing, disseminating and sharing intangible asset information of an entity among users, the system comprising: a user interface that displays options for a user to enter, view, and edit some or all of the intangible asset information from one or more modules; a database coupled to the user interface for storing the intangible asset information and a processor coupled to the user interface and the database, the processor to: receive intangible asset information from the user; process and organize the intangible asset information into at least one module; store the intangible asset information in the database by module; update the database with any new intangible asset information received from the user; and provide the updated intangible asset information in response to an inquiry from a second user.
Owner:INNOVATION INT AMERICAS
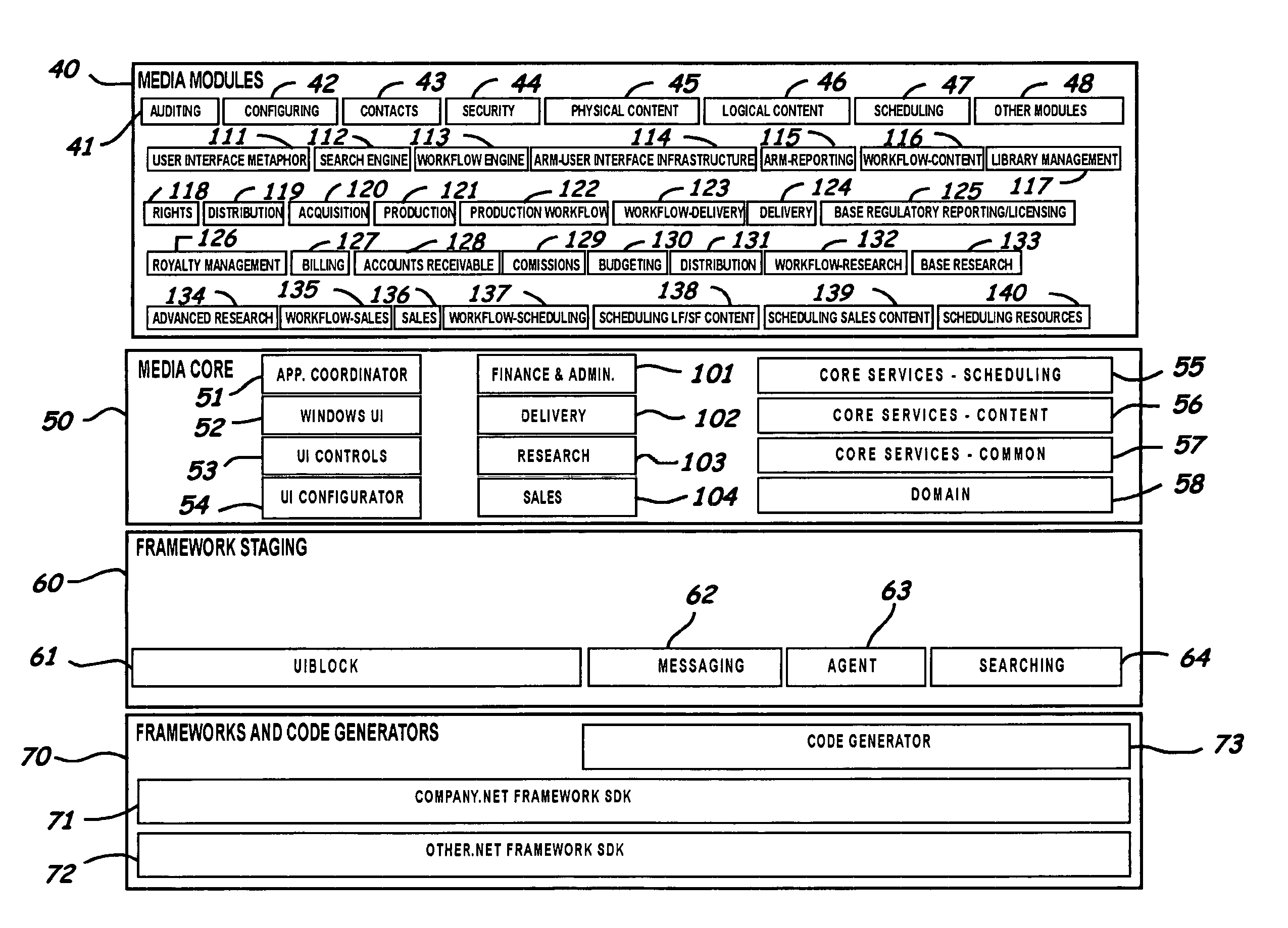
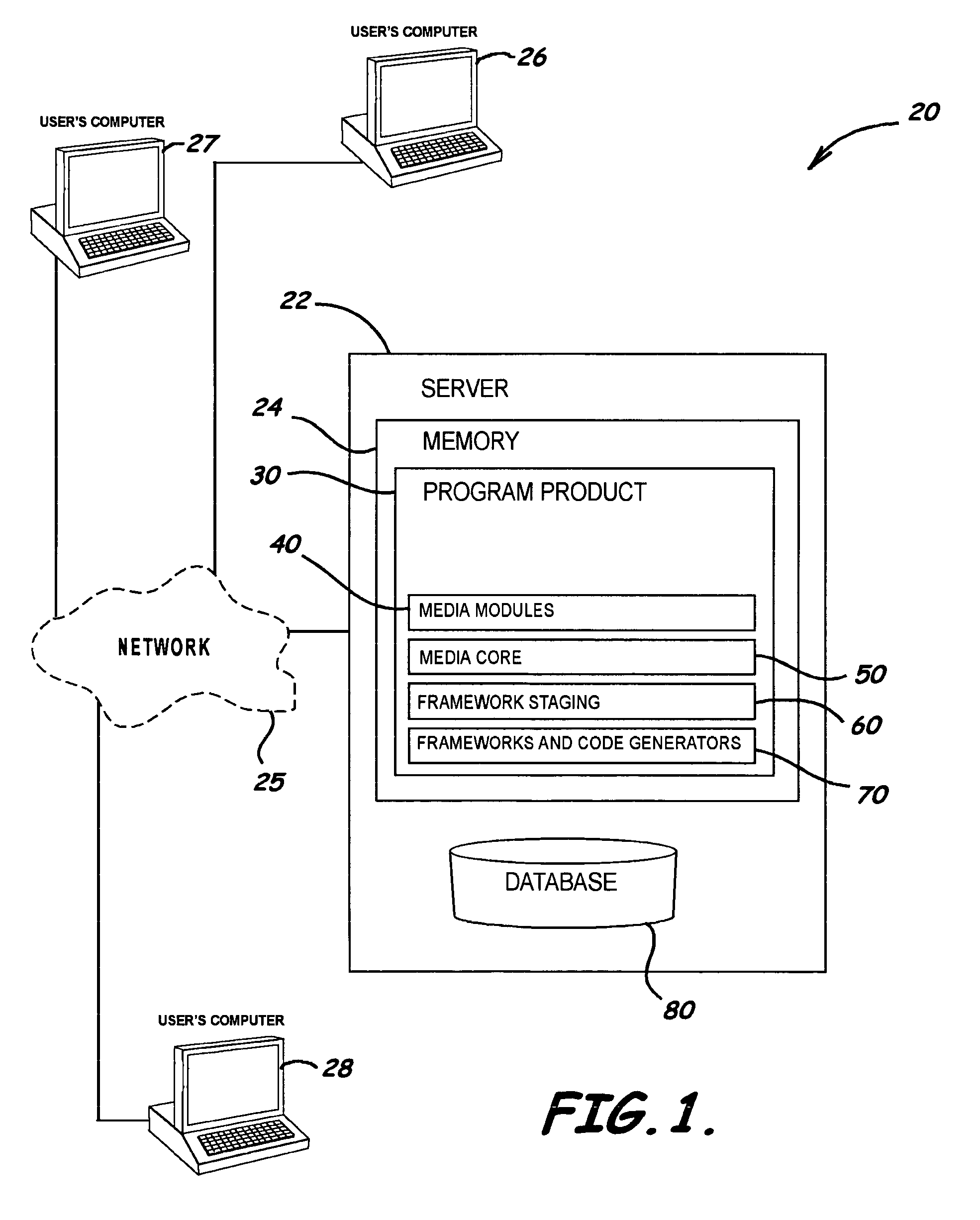
System, program product, and methods to enhance media content management
ActiveUS8250051B2Efficient managementEasy to integrateDigital data processing detailsApparatus for meter-controlled dispensingContent managementDatabase access
Embodiments of systems, program products, and methods to enhance and more effectively manage media content are provided. An embodiment of a method, for example, can include analyzing a user assigned role to allow access to specific data in a database in response to the user assigned role, capturing and storing metadata from multiple sources accessible by a plurality of different types of users, and tracking access to and changes in data in a database in response to user database access to thereby form transaction activity trails describing access and changed data to enhance digital file management and allow a plurality of media content management services to be performed.
Owner:HBC SOLUTIONS
Network distributed tracking wire transfer protocol
InactiveUS20070011267A1Efficient changeEfficient managementDigital data information retrievalMultiple digital computer combinationsData acquisitionWire transfer
A network distributed tracking wire transfer protocol for storing and retrieving data across a distributed data collection. The protocol includes a location string for specifying the network location of data associated with an entity in the distributed data collection, and an identification string for specifying the identity of an entity in the distributed data collection. According to the protocol, the length of the location string and the length of the identification string are variable, and an association between an identification string and a location string can be spontaneously and dynamically changed. The network distributed tracking wire transfer protocol is application independent, organizationally independent, and geographically independent. A method for using the protocol in a distributed data collection environment and a system for implementing the protocol are also provided.
Owner:KOVE IO INC
Snapshot storage and management system with indexing and user interface
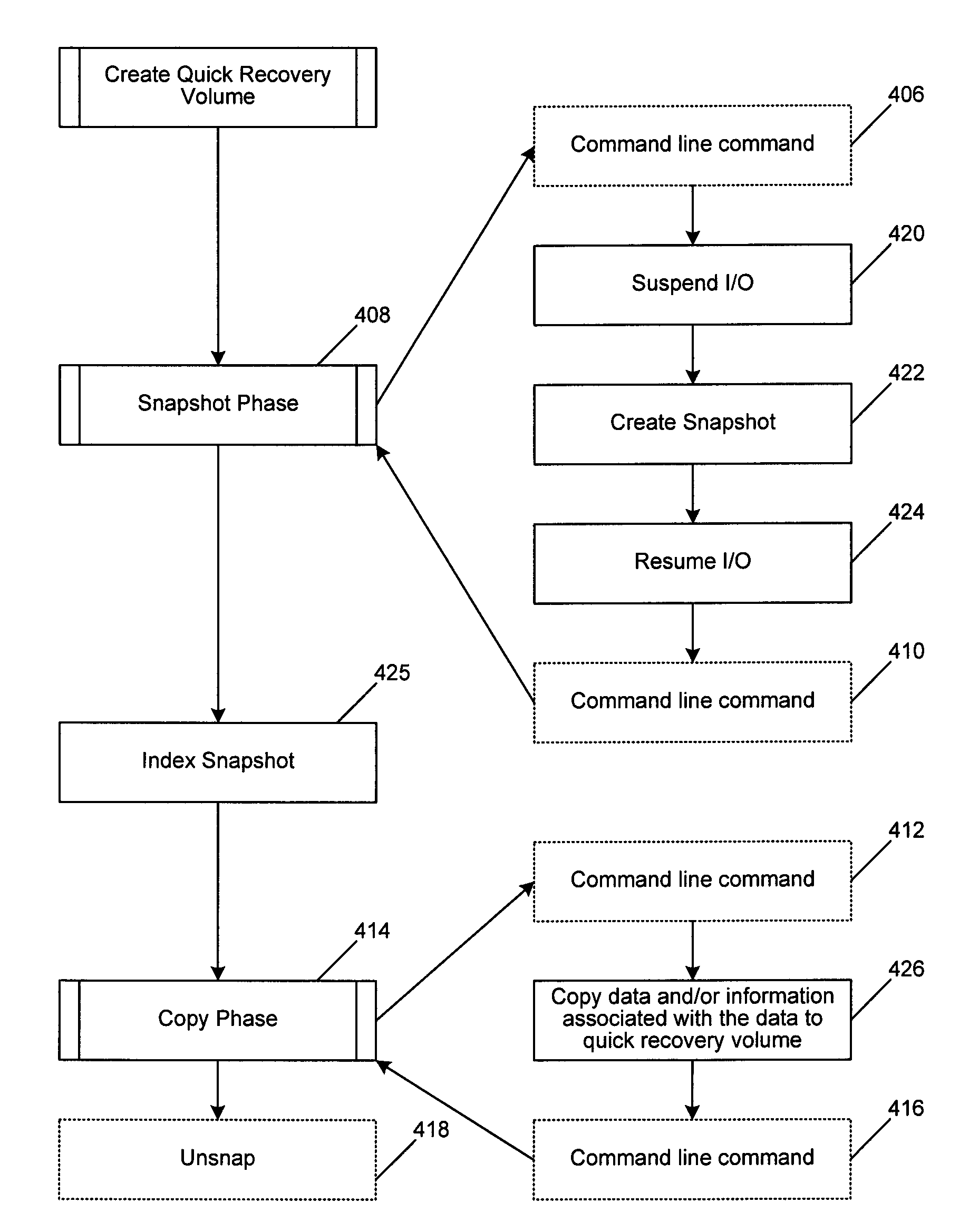
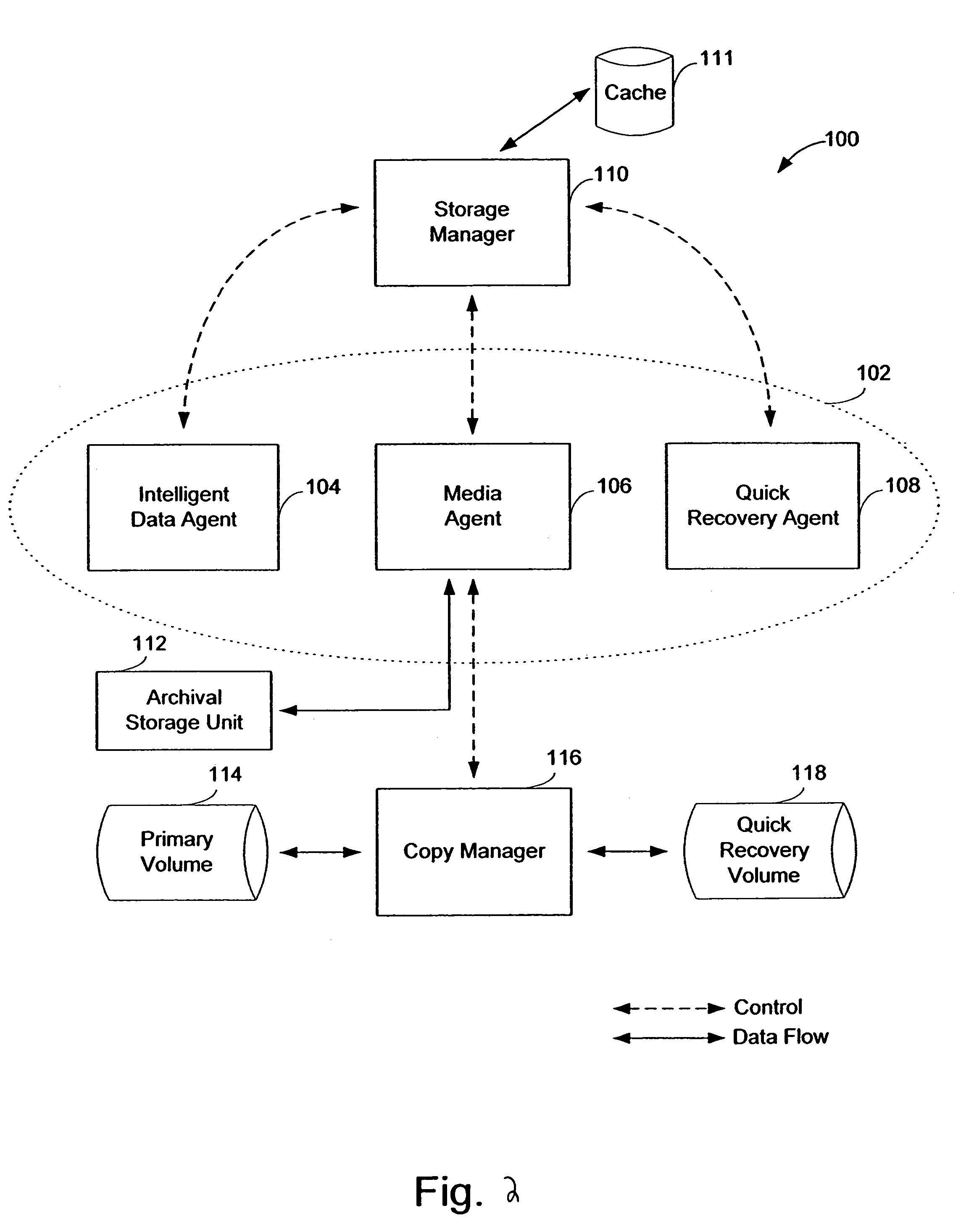
InactiveUS7568080B2Create efficientlyEfficient managementData processing applicationsInput/output to record carriersStorage managementApplication software
A system and method of managing stored data in a storage management system. The storage management system includes a storage manager, a media agent connected to the storage manager, and a primary volume connected to the media agent. A plurality of snapshots are taken of the primary volume. The snapshots are indexed by associating respective information with the snapshot. The indexed snapshots are copied to a recovery volume. In this way, browsing features are enabled for the user. The user may view the snapshots in a hierarchical format, and may even view snapshot data in association with the corresponding application. The resultant recovery volume may be used to replace a primary volume.
Owner:COMMVAULT SYST INC
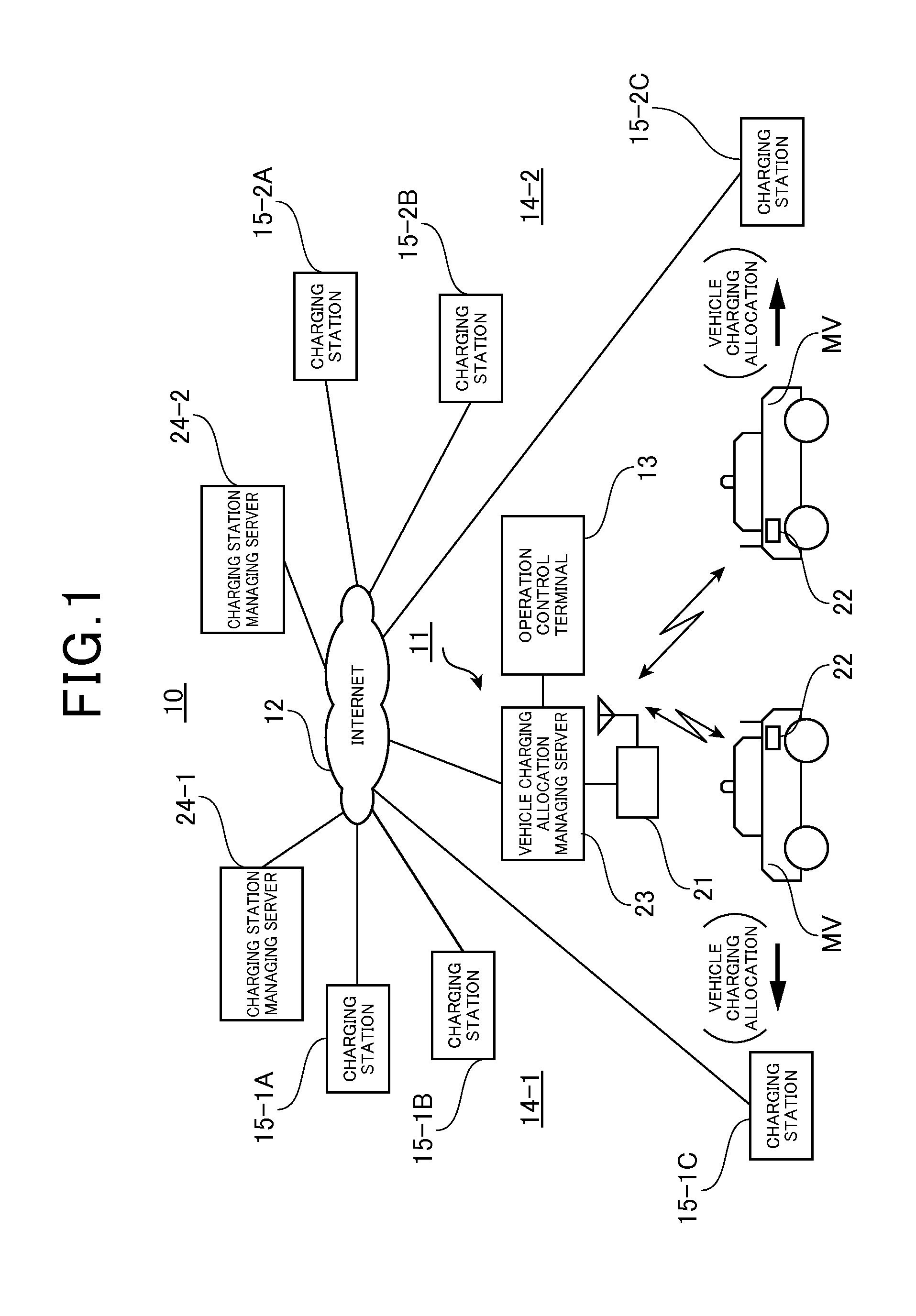
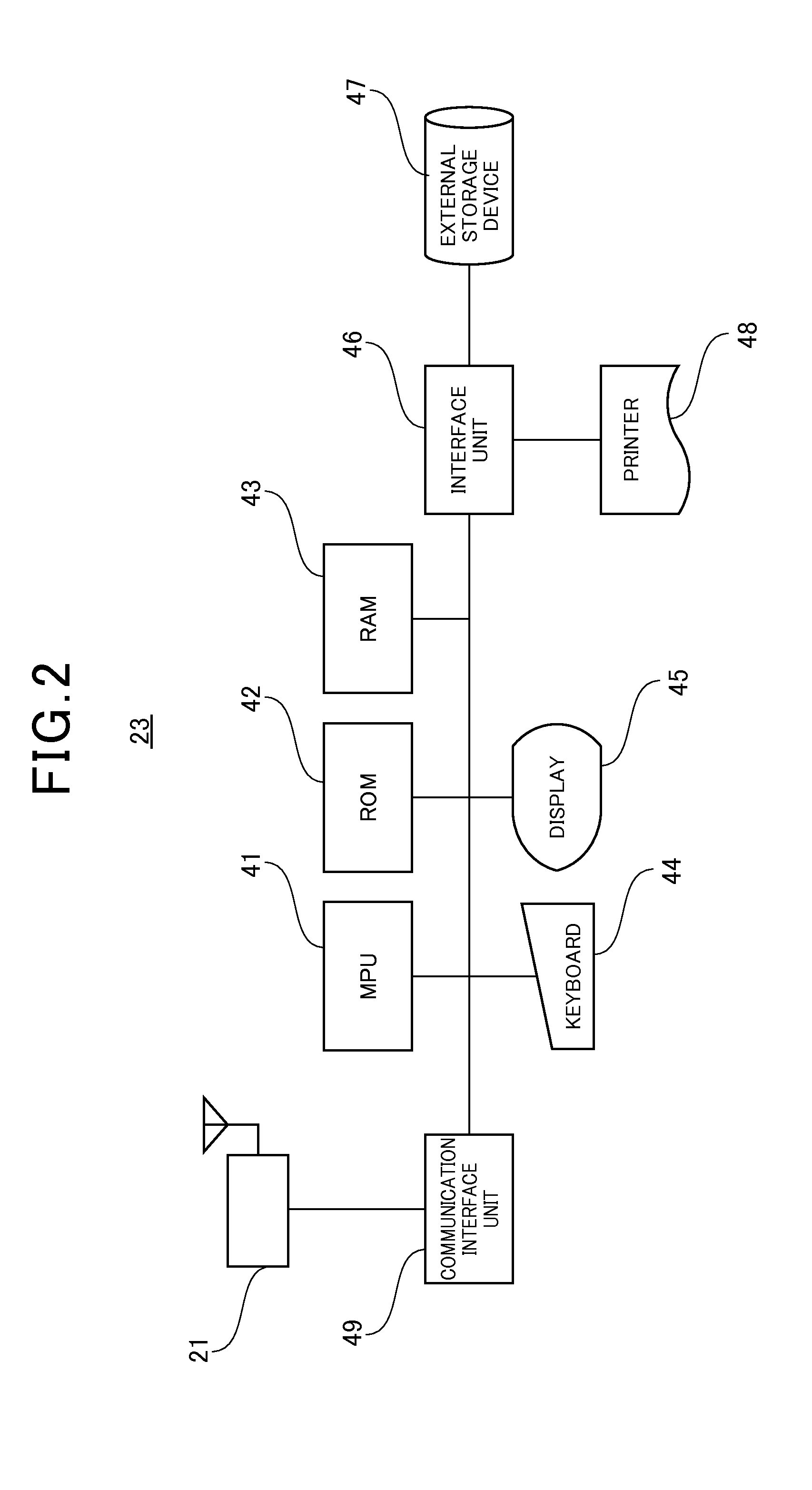
Vehicle charging allocation managing server and vehicle charging allocation managing system
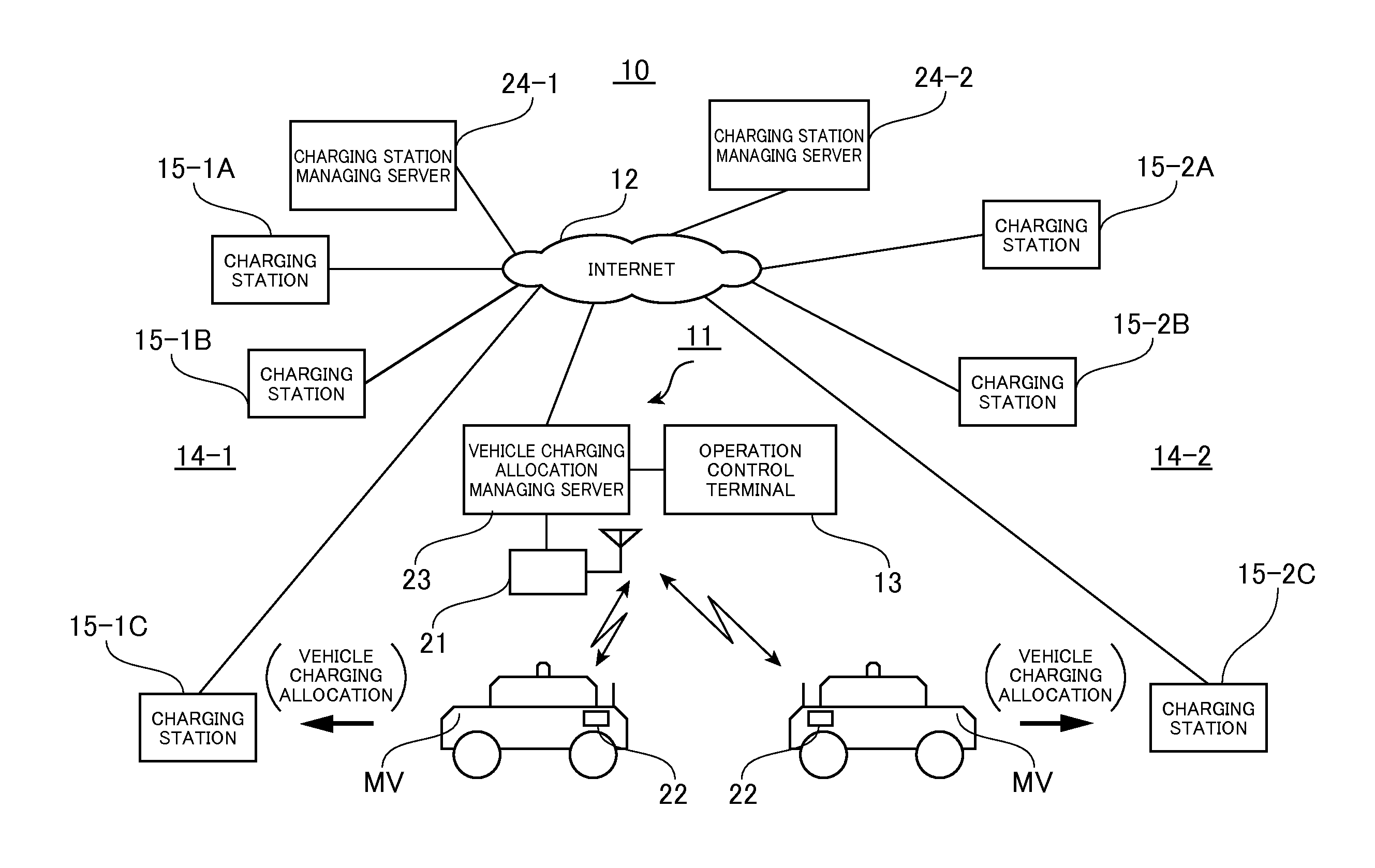
InactiveUS20110246252A1Efficient managementReduce the effectInstruments for road network navigationVehicle position indicationCharging stationEngineering
A vehicle charging allocation managing system containing plural charging stations each having a battery charger to charge a vehicle, a charging station managing server for managing the charging stations, and a vehicle charging allocation managing server that is connected to the charging station managing server through a communication network, and instructs vehicle allocation to allocate each of the vehicles to an appropriate one of the charging stations for charging. The vehicle charging allocation managing server has a controller for setting a vehicle charging allocation schedule for specifying a charging station and a charting time zone to charge each of the vehicles on the basis of a battery residual capacity and a battery capacity consumption plan, thereby performing vehicle allocation for charging.
Owner:MOTION SRL +2
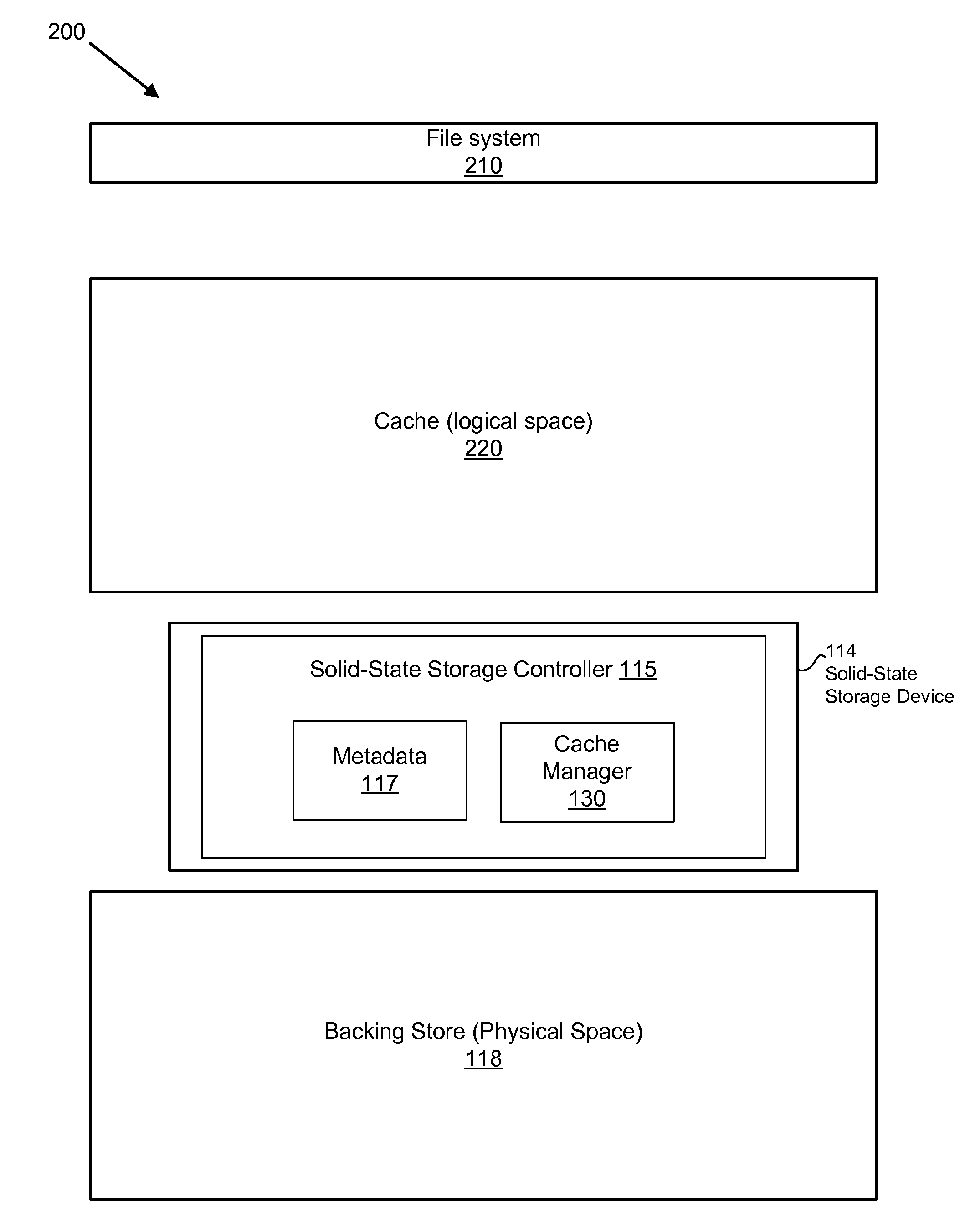
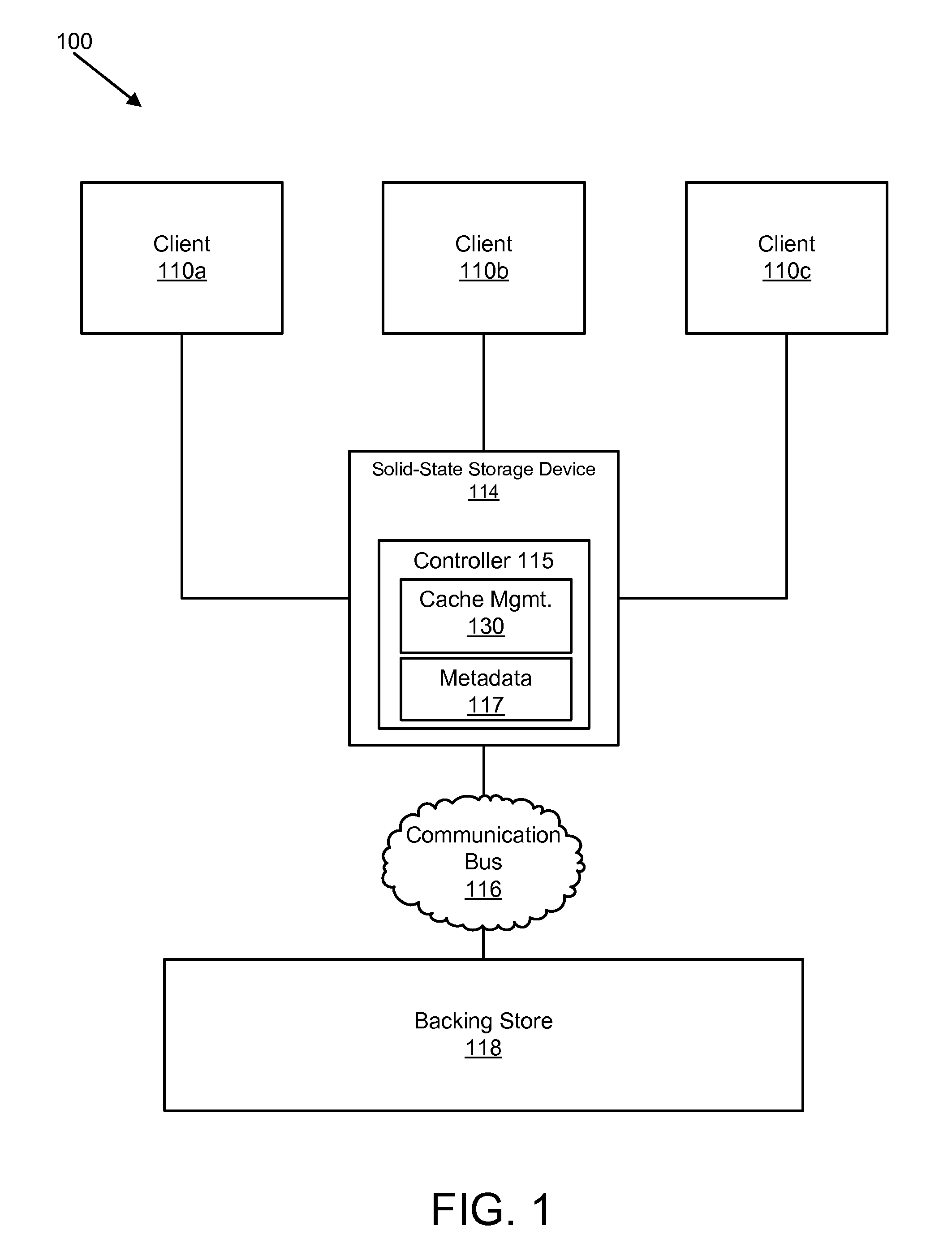
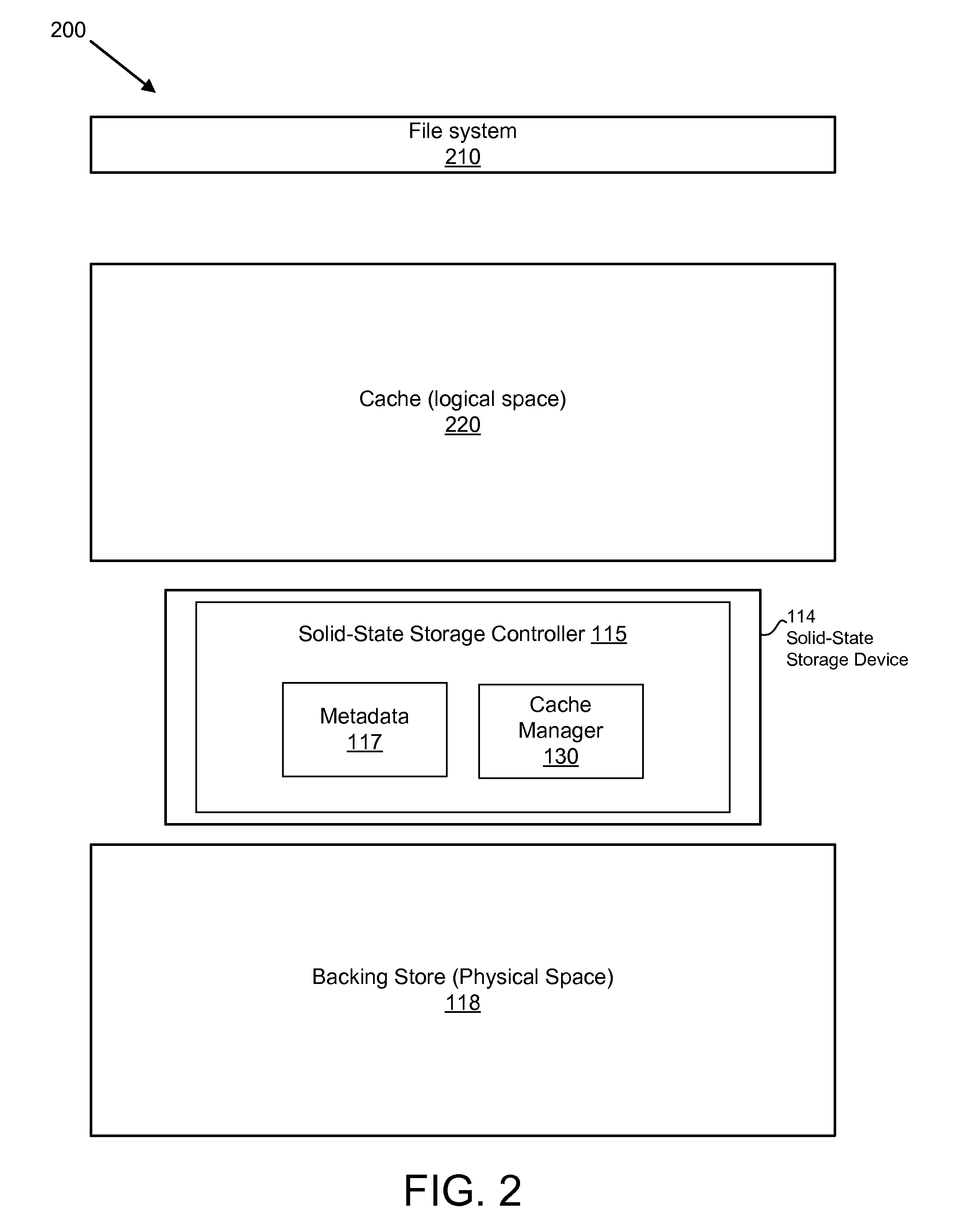
Apparatus, System, and Method for Caching Data on a Solid-State Storage Device
ActiveUS20110066808A1Reduce in quantityServiced quickly and efficientlyMemory architecture accessing/allocationMemory adressing/allocation/relocationSolid-state storageMetadata
An apparatus, system, and method are disclosed for caching data on a solid-state storage device. The solid-state storage device maintains metadata pertaining to cache operations performed on the solid-state storage device, as well as storage operations of the solid-state storage device. The metadata indicates what data in the cache is valid, as well as information about what data in the nonvolatile cache has been stored in a backing store. A backup engine works through units in the nonvolatile cache device and backs up the valid data to the backing store. During grooming operations, the groomer determines whether the data is valid and whether the data is discardable. Data that is both valid and discardable may be removed during the grooming operation. The groomer may also determine whether the data is cold in determining whether to remove the data from the cache device. The cache device may present to clients a logical space that is the same size as the backing store. The cache device may be transparent to the clients.
Owner:SANDISK TECH LLC
Extending an internet content delivery network into an enterprise
InactiveUS20060282522A1Efficient and cost-effectiveEfficient managementMultiple digital computer combinationsElectric digital data processingInternet contentPrivate network
An Internet content delivery network deploys one or more CDN server regions in an enterprise and manages those regions as part of the Internet CDN. In one aspect of the invention, a CDN service provider (CDNSP) deploys one or more CDN regions behind an enterprise's corporate firewall(s). The regions are used to deliver Internet content—content that has been tagged or otherwise made available for delivery over the Internet from the CDN's content servers. This content includes, for example, content that given content providers have identified is to be delivered by the CDN. In addition, the enterprise may tag intranet content, which is then also served from the CDN regions behind the firewall. Intranet content remains secure by virtue of using the enterprise's existing security infrastructure. In accordance with another aspect of the invention, the CDNSP implements access controls and deploys one or more CDN regions outside an enterprise's firewall(s) such that intranet content can be served from regions located outside the firewall(s). In this embodiment, the CDNSP can provide granular control, such as permissions per groups of users. In this way, the CDNSP, in effect, extends a conventional virtual private network (VPN) to all or a portion of the ICDN, thereby enabling the CDNSP to use multiple regions and potentially thousands of content servers available to serve the enterprise's internal content. In addition to making internal content available from the edge of the network, the CDNSP provides a mechanism by which an enterprise may share secure data with its business partner(s) without setting up any special infrastructure.
Owner:AKAMAI TECH INC
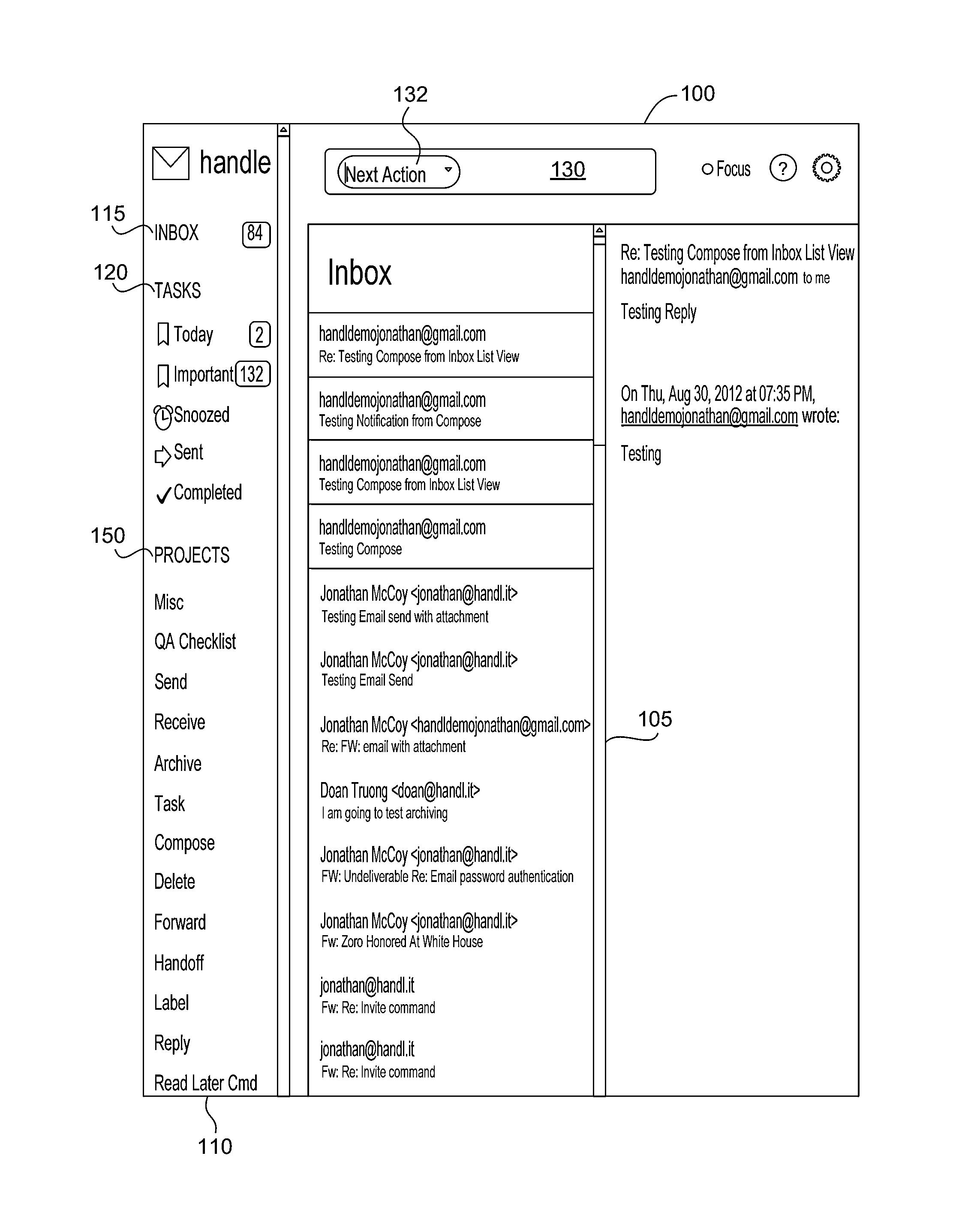
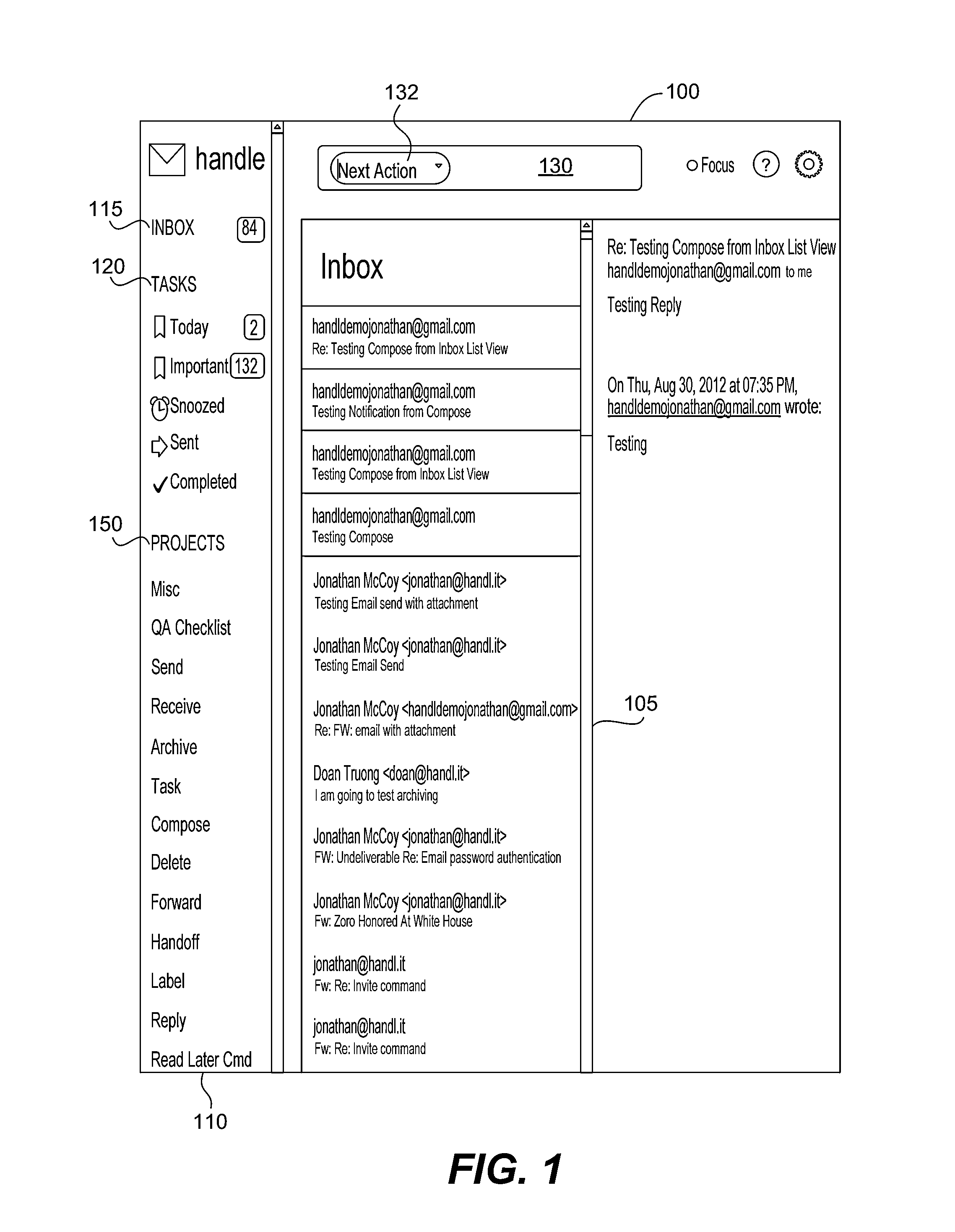
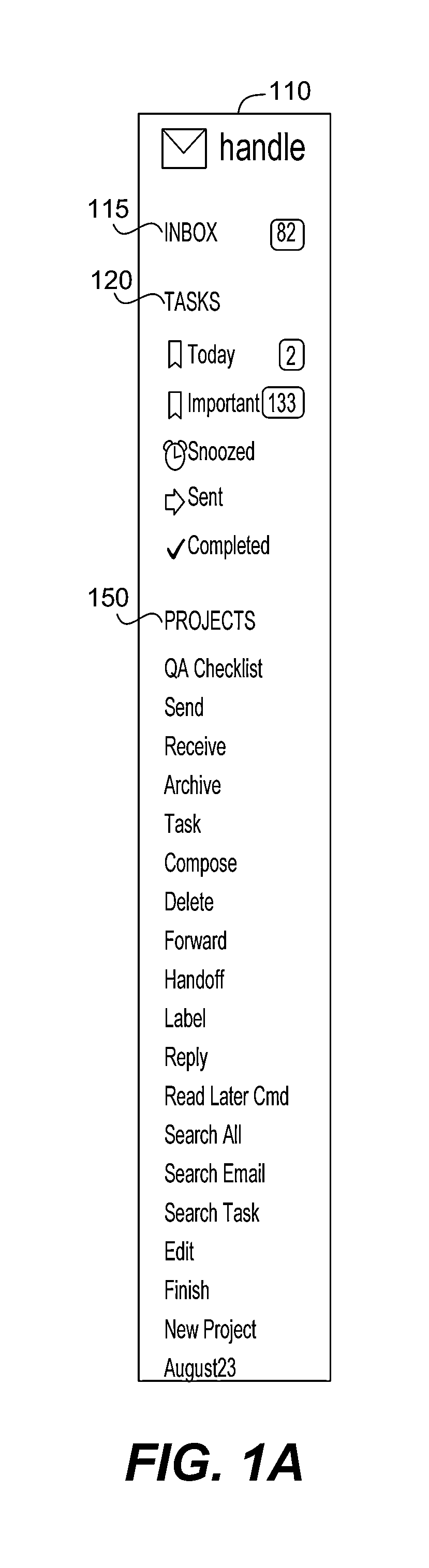
Email and task management services and user interface
InactiveUS20150143258A1Efficient processing of emails and tasksEfficient managementData switching networksInput/output processes for data processingThird partyContext based
A system, method, service, user interface, and computer readable medium to integrate email and task management is disclosed. Users are provided with options to convert an email into a task, including one-click command options. Efficient triaging of incoming emails is supported. Integration with different email systems and third party services is also supported. Additionally, context aware operation supports features such as adapting operation for efficient use of mobile device in combination with desktop computers. An option is provided to convert an email into a To-Do item, which may include a contextually based reminder. Another option includes adding an email item to an electronic calendar.
Owner:HANDLE
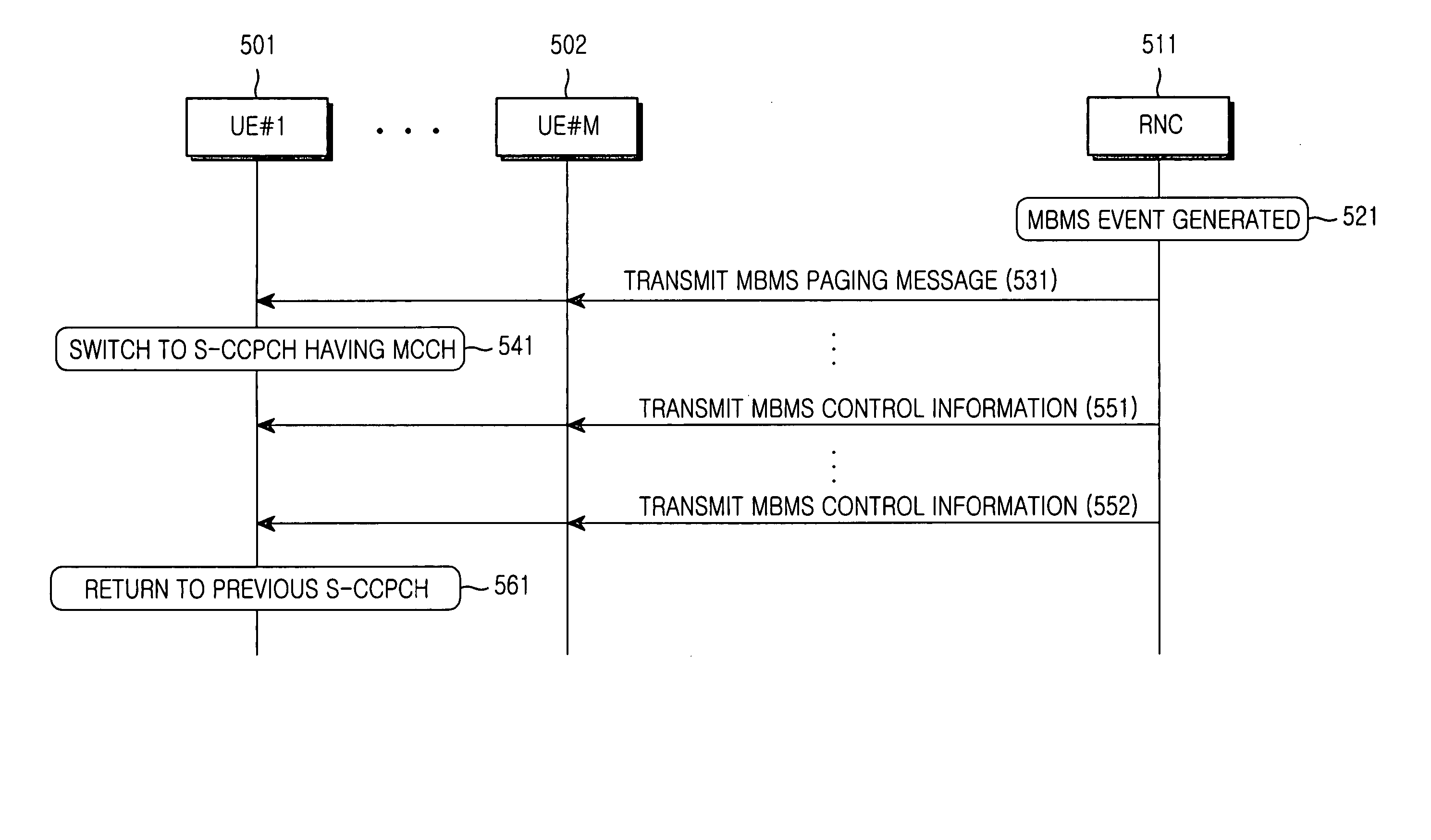
Apparatus and method for transmitting/receiving MBMS control information in a mobile communication system
InactiveUS20050020260A1Efficiently manageEfficiently supportBroadcast service distributionRadio transmission for post communicationTelecommunicationsMobile communication systems
A method and apparatus for transmitting and receiving MBMS control information in an MBMS mobile communication system are provided. An RNC transmits MBMS control information for an MBMS service on an MCCH mapped to one of a plurality of CCPCHs available in a cell of the mobile communication system, and transmits a paging message on a logical channel mapped to each of the CCPCHs. Here, the paging message requests reception of the MBMS control information. A UE monitors one of the plurality of the CCPCHs, receives the paging message on the monitored CCPCH, switches to the CCPCH having the MCCH, and receives the MBMS control information on the switched to CCPCH. Therefore, resource consumption is minimized in transmitting MBMS control information in a cell and the reception reliability of the MBMS control information in the UE is increased.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for providing service or adding benefit to social networks
InactiveUS20100145771A1Increase adoptionEfficient and cost-effective administrationDrawing from basic elementsOffice automationGraphicsRanking
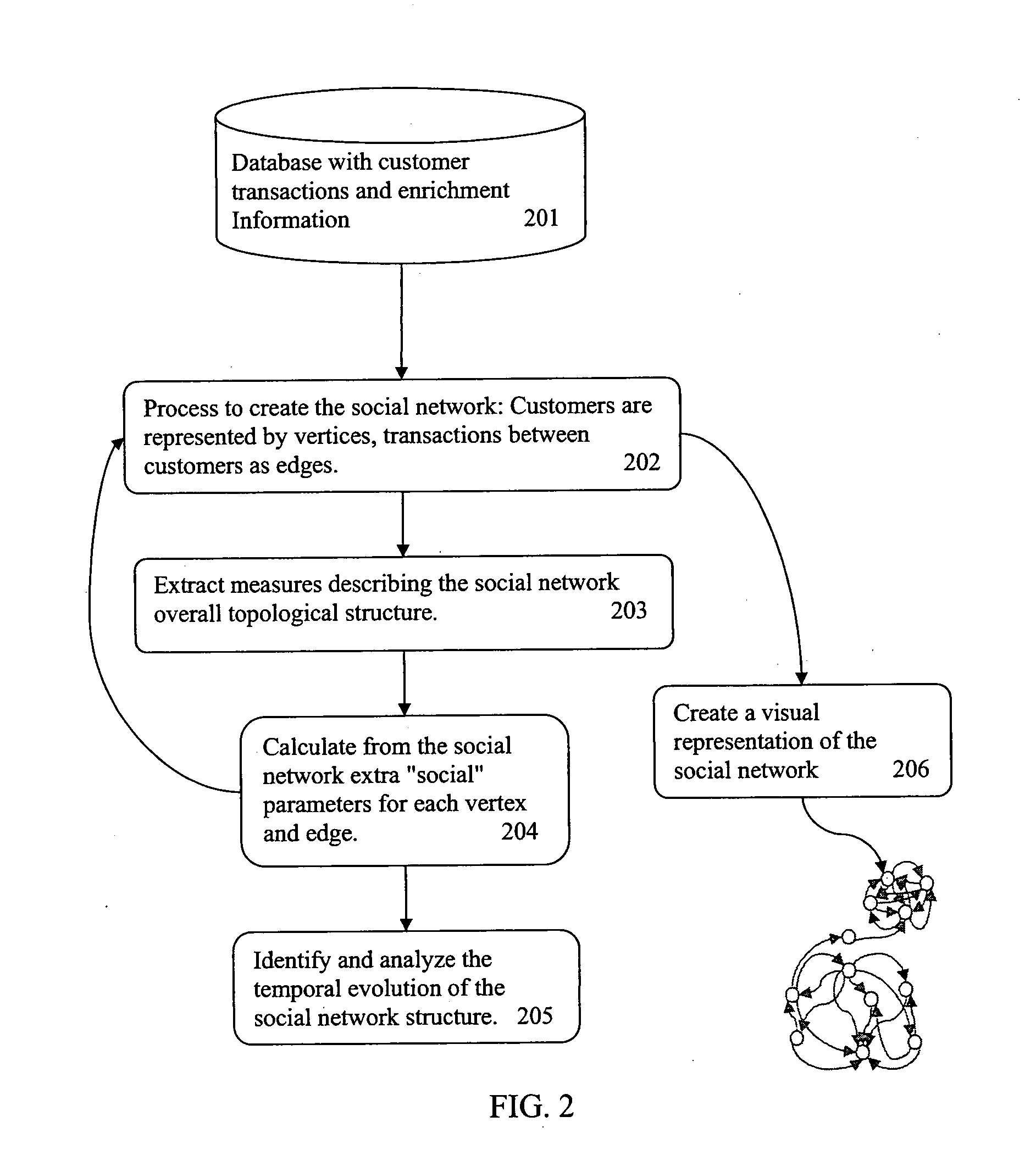
A system and method for enhancing the revenue and / or efficiency of a network service is disclosed. The system constructs a graph of a social network in which users are capable of two-way communication with other users, the network service provider, or other entities such as advertisers. Using such methods as social VIP ranking, the system is capable of performing a variety of analyses, the results of which provide the network service provider insights on how to best perform such tasks as monitoring and enhancing campaign effectiveness, identify fraud, optimize resource allocation and ensure the quality of network management.
Owner:MARA ISON CONNECTIVE +1
Flash memory management system and method utilizing multiple block list windows
InactiveUS6895464B2Improve performanceImprove reliabilityInput/output to record carriersMemory loss protectionRapid accessBlock detection
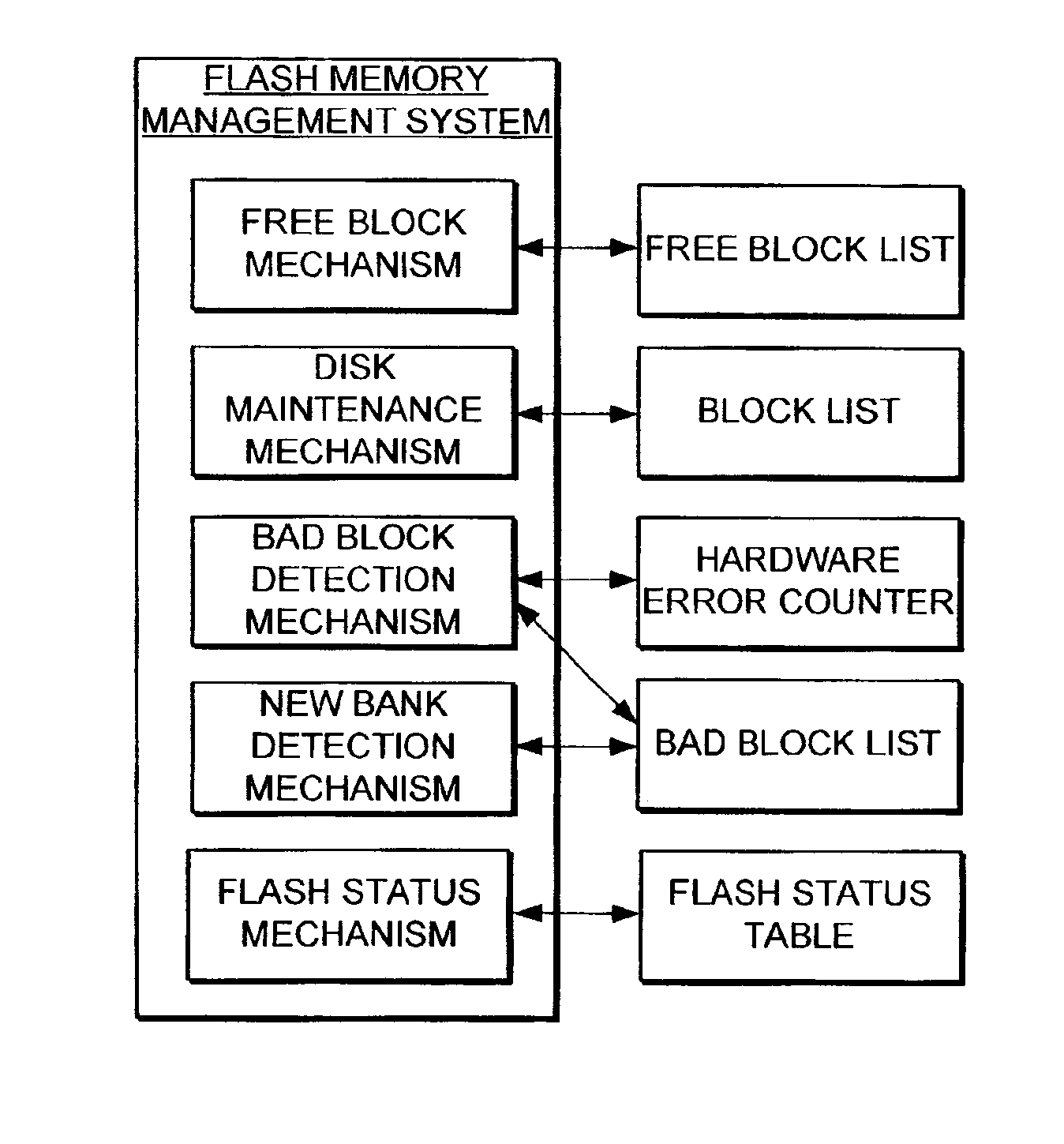
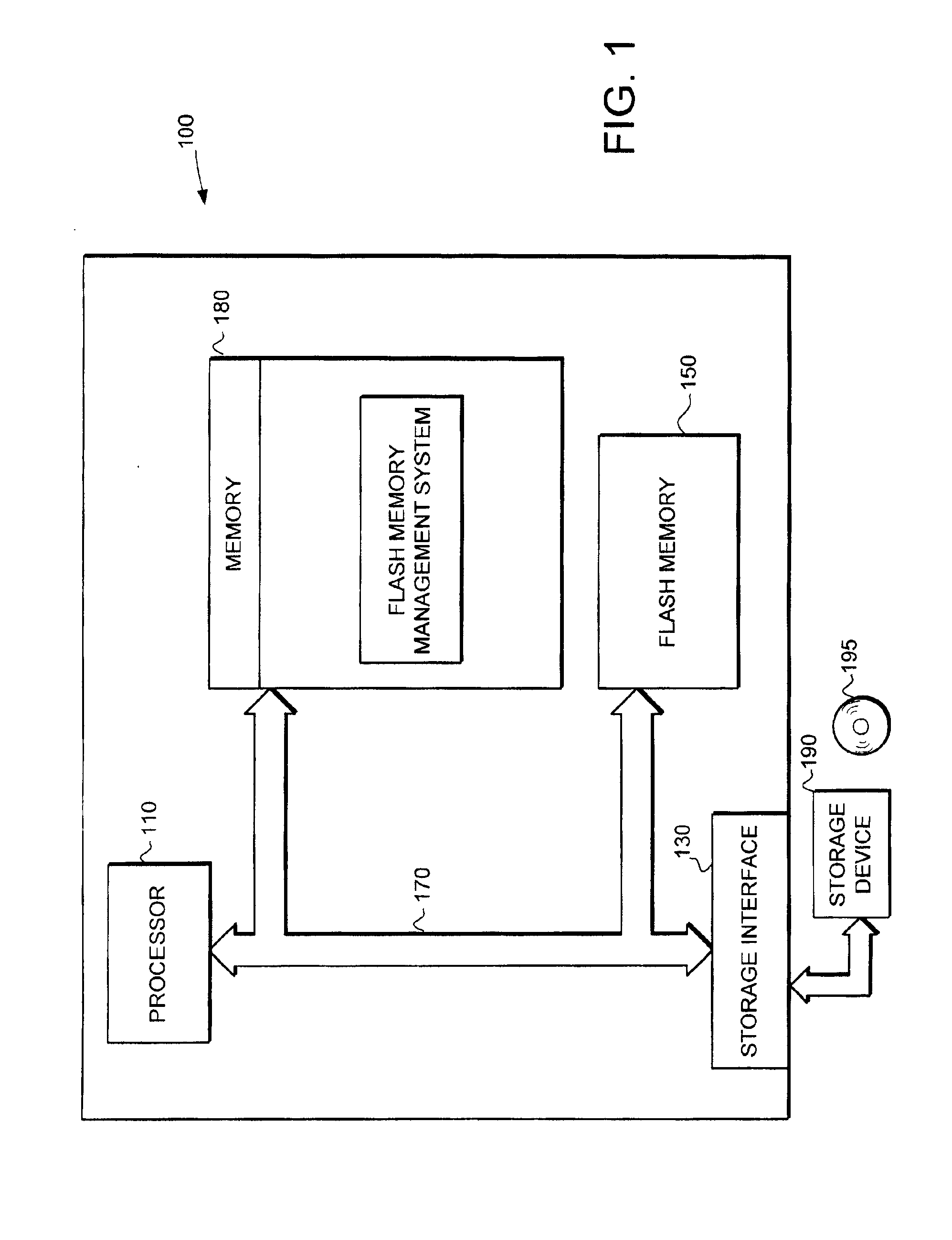
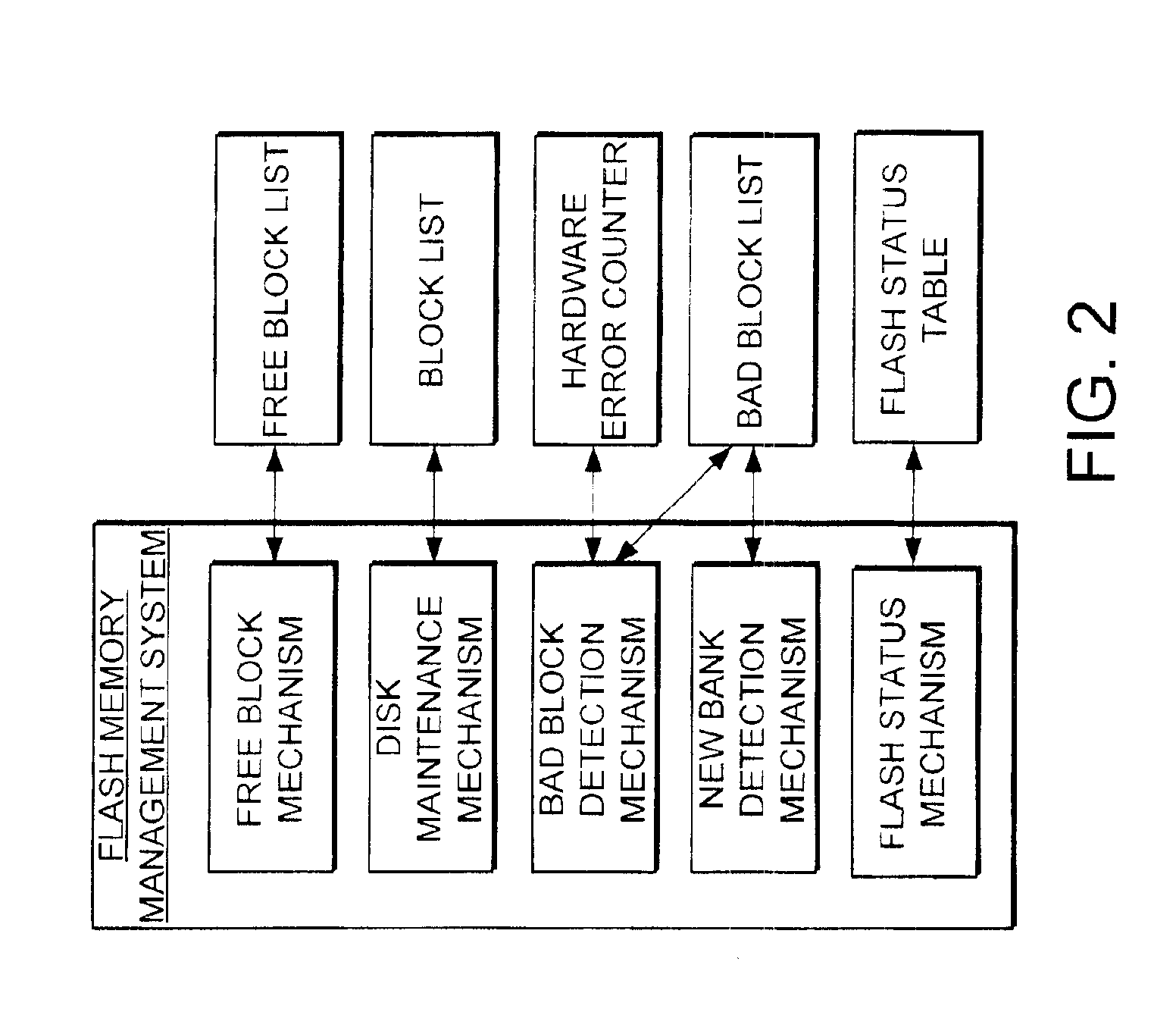
The present invention provides a flash memory management system and method with increased performance. The flash memory management system provides the ability to efficiently manage and allocate flash memory use in a way that improves reliability and longevity, while maintaining good performance levels. The flash memory management system includes a free block mechanism, a disk maintenance mechanism, and a bad block detection mechanism. The free block mechanism provides efficient sorting of free blocks to facilitate selecting low use blocks for writing. The disk maintenance mechanism provides for the ability to efficiently clean flash memory blocks during processor idle times. The bad block detection mechanism provides the ability to better detect when a block of flash memory is likely to go bad. The flash status mechanism stores information in fast access memory that describes the content and status of the data in the flash disk. The new bank detection mechanism provides the ability to automatically detect when new banks of flash memory are added to the system. Together, these mechanisms provide a flash memory management system that can improve the operational efficiency of systems that utilize flash memory.
Owner:III HLDG 12 LLC
Method and system for performing distributed verification with respect to measurement data in sensor network
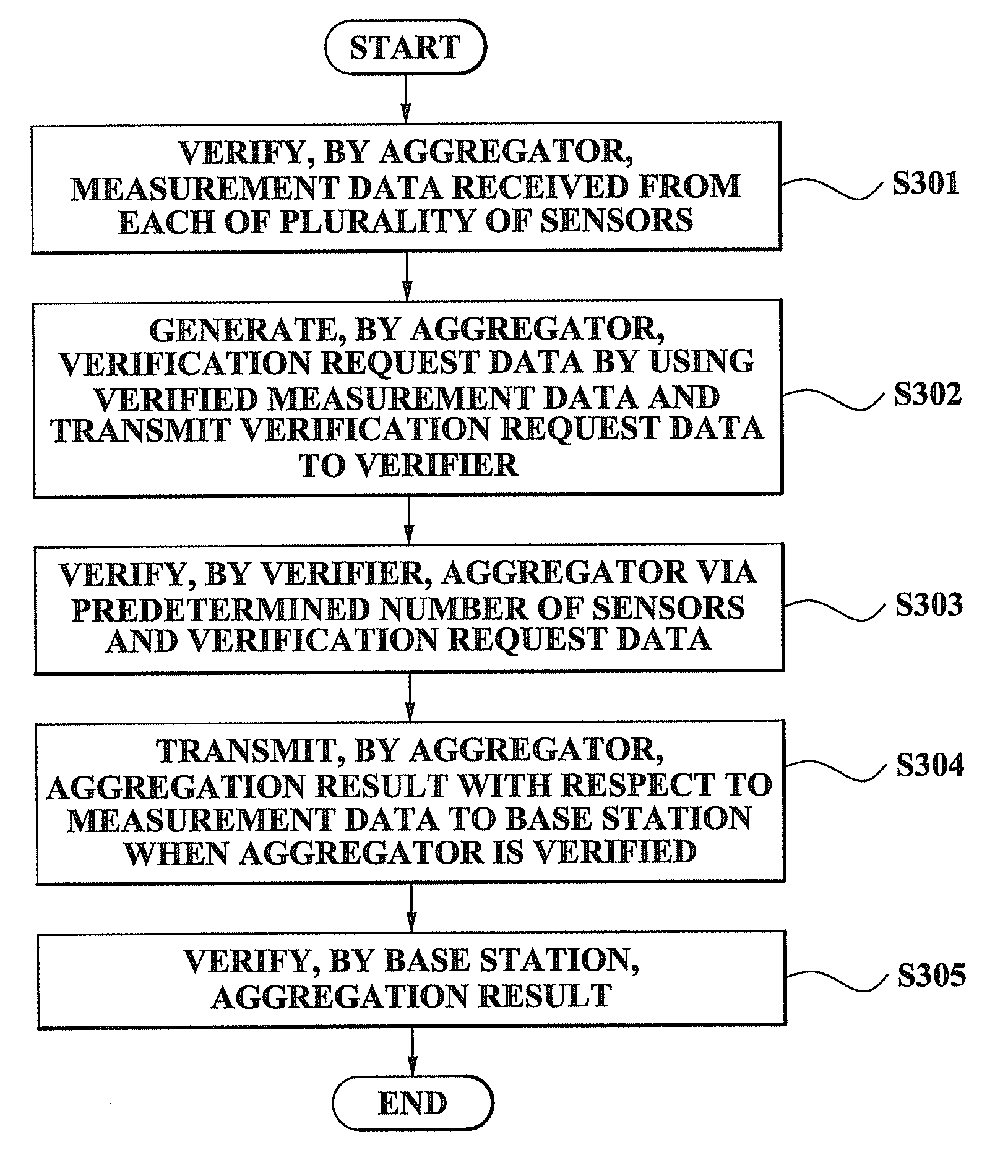
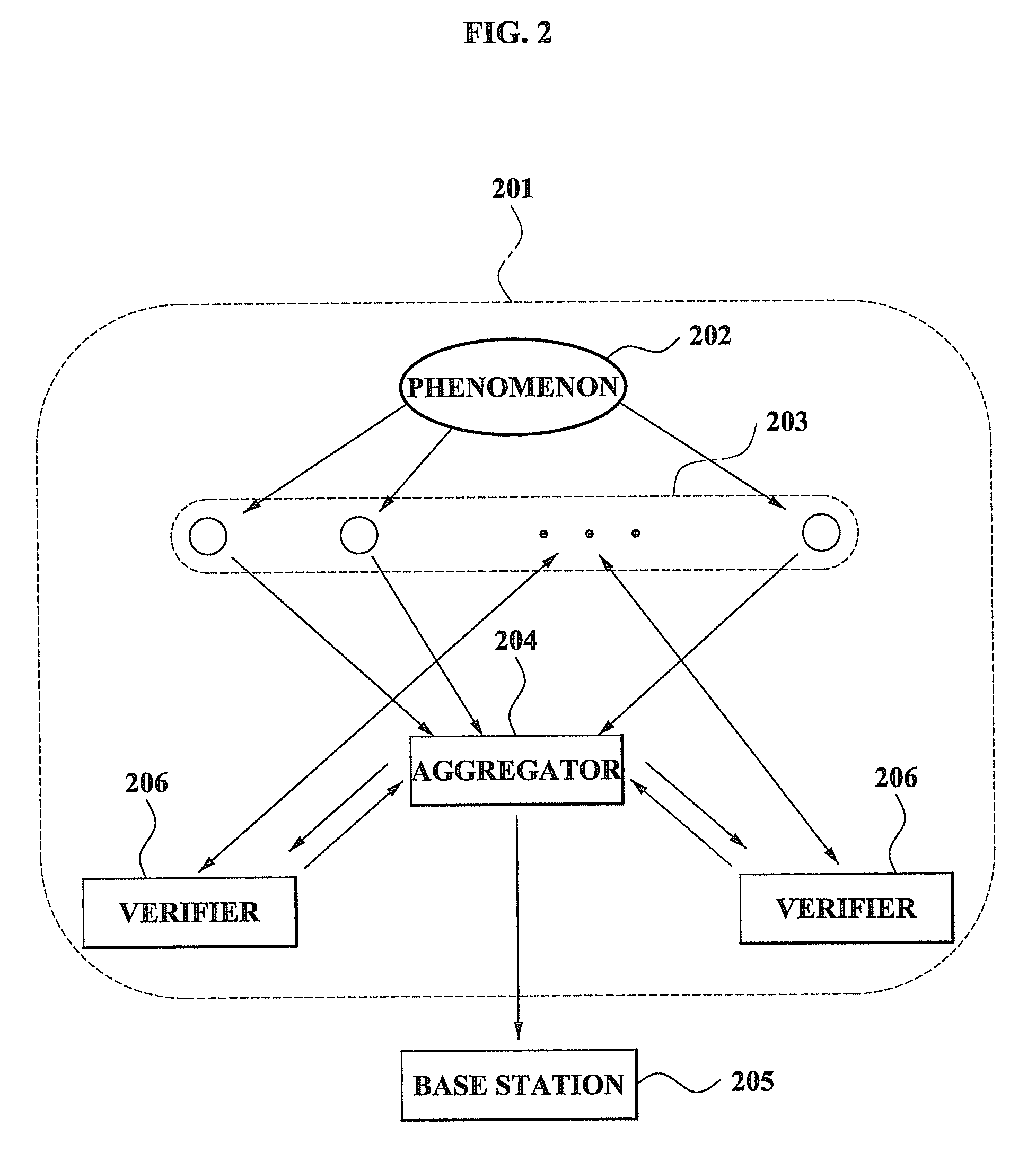
ActiveUS20080262798A1Efficient managementImprove securityAmplifier modifications to reduce noise influenceDigital data processing detailsData validationSource Data Verification
A method and system for performing a distributed verification with respect to measurement data in a sensor network. The method of performing the distributed verification with respect to measurement data in a sensor network includes: verifying, by an aggregator, the measurement data received from each of a plurality of sensors; generating, by the aggregator, verification request data by using the verified measurement data; transmitting the verification request data to a verifier; and verifying, by the verifier, the aggregator via a predetermined number of sensors of the plurality of sensors and the verification request data. The method of performing a distributed verification with respect to measurement data in a sensor network further includes transmitting, by the aggregator, an aggregation result with respect to the measurement data to a base station when the aggregator is verified; and verifying, by the base station, the aggregation result.
Owner:SAMSUNG ELECTRONICS CO LTD
Techniques for discovering and managing security of applications
ActiveUS20170251013A1Minimizing security threatMinimizing riskTransmissionSafety management systemsData source
Techniques for discovery and management of applications in a computing environment of an organization are disclosed. A security management system discovers use of applications within a computing environment to manage access to applications for minimizing security threats and risks in a computing environment of the organization. The security management system can obtain network data about network traffic to identify unique applications. The security management system can perform analysis and correlation, including use of one or more data sources, to determine information about an application. The system can compute a measure of security for an application (“an application risk score”) and a user (“a user risk score”). The score may be analyzed to determine a threat of security posed by the application based on use of the application. The security system can perform one or more instructions to configure access permitted by an application, whether access is denied or restricted.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com