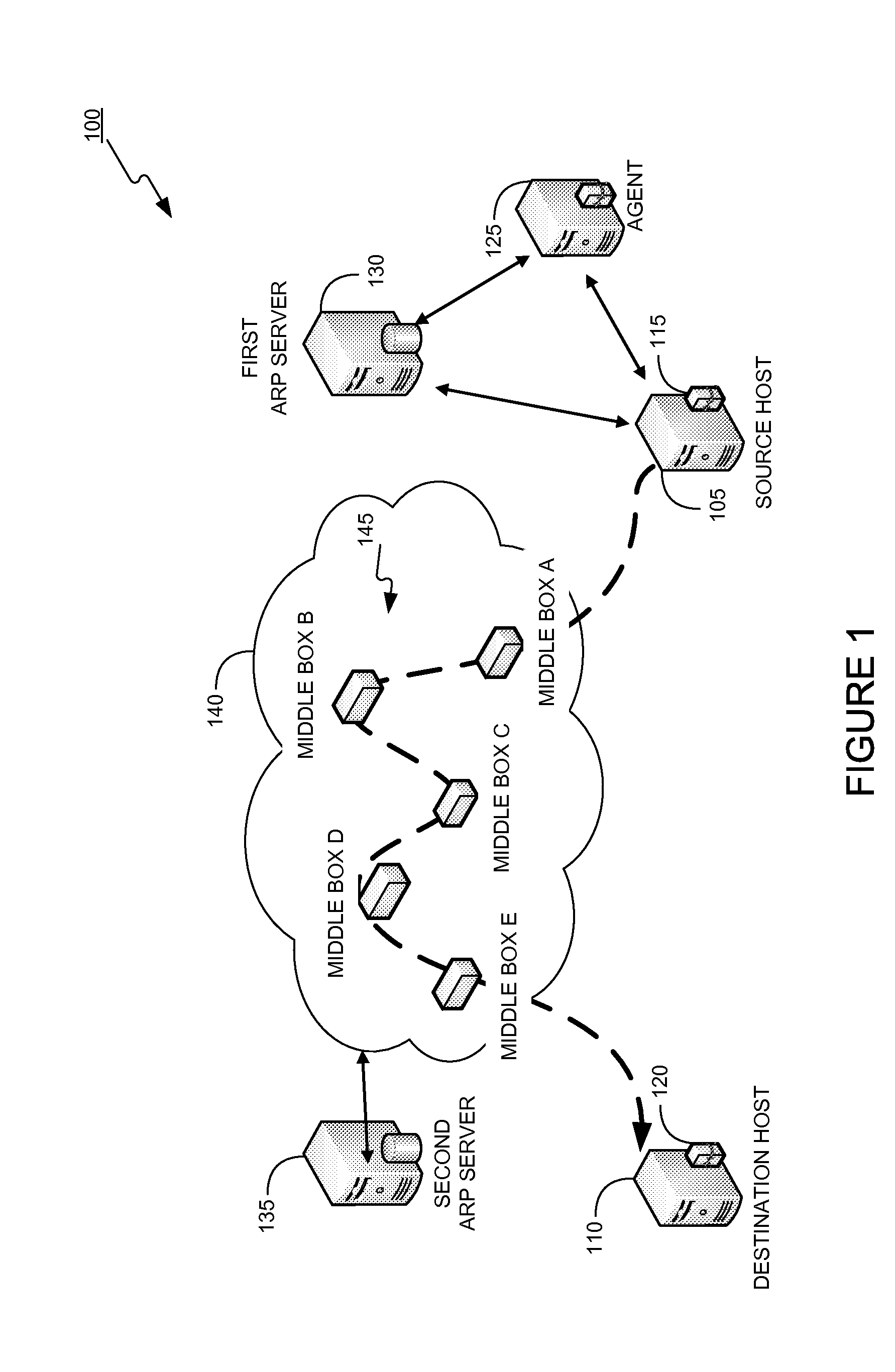
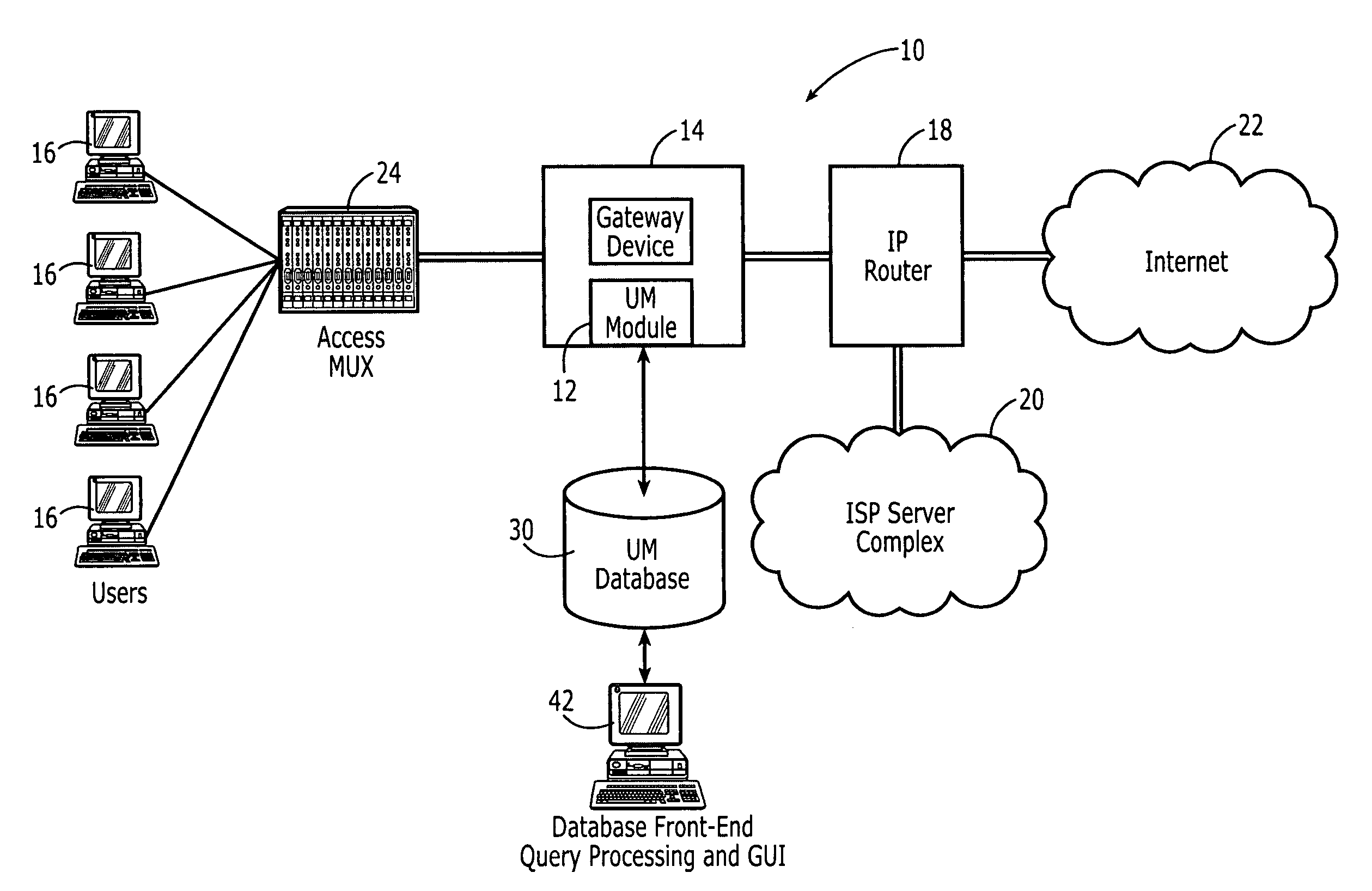
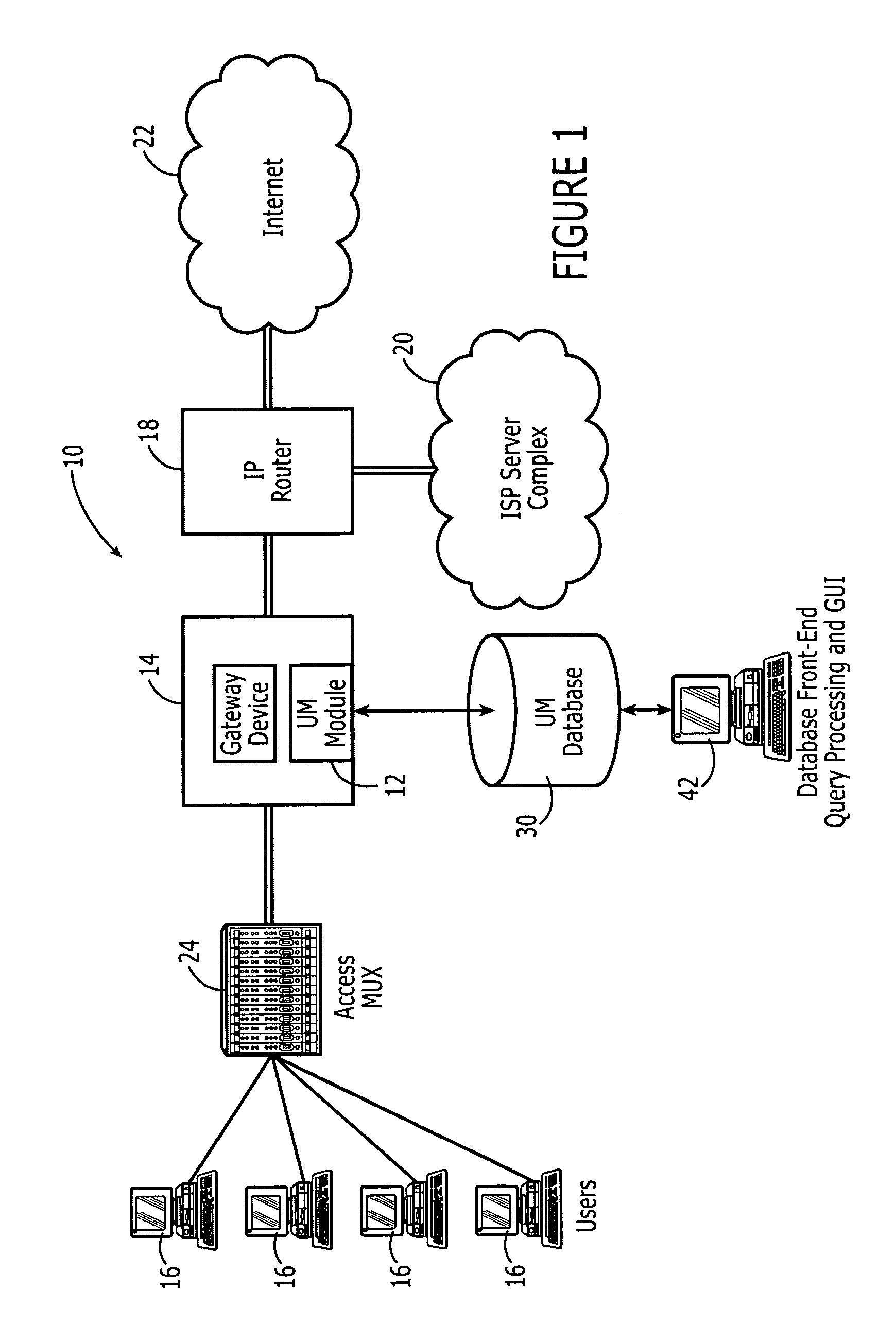
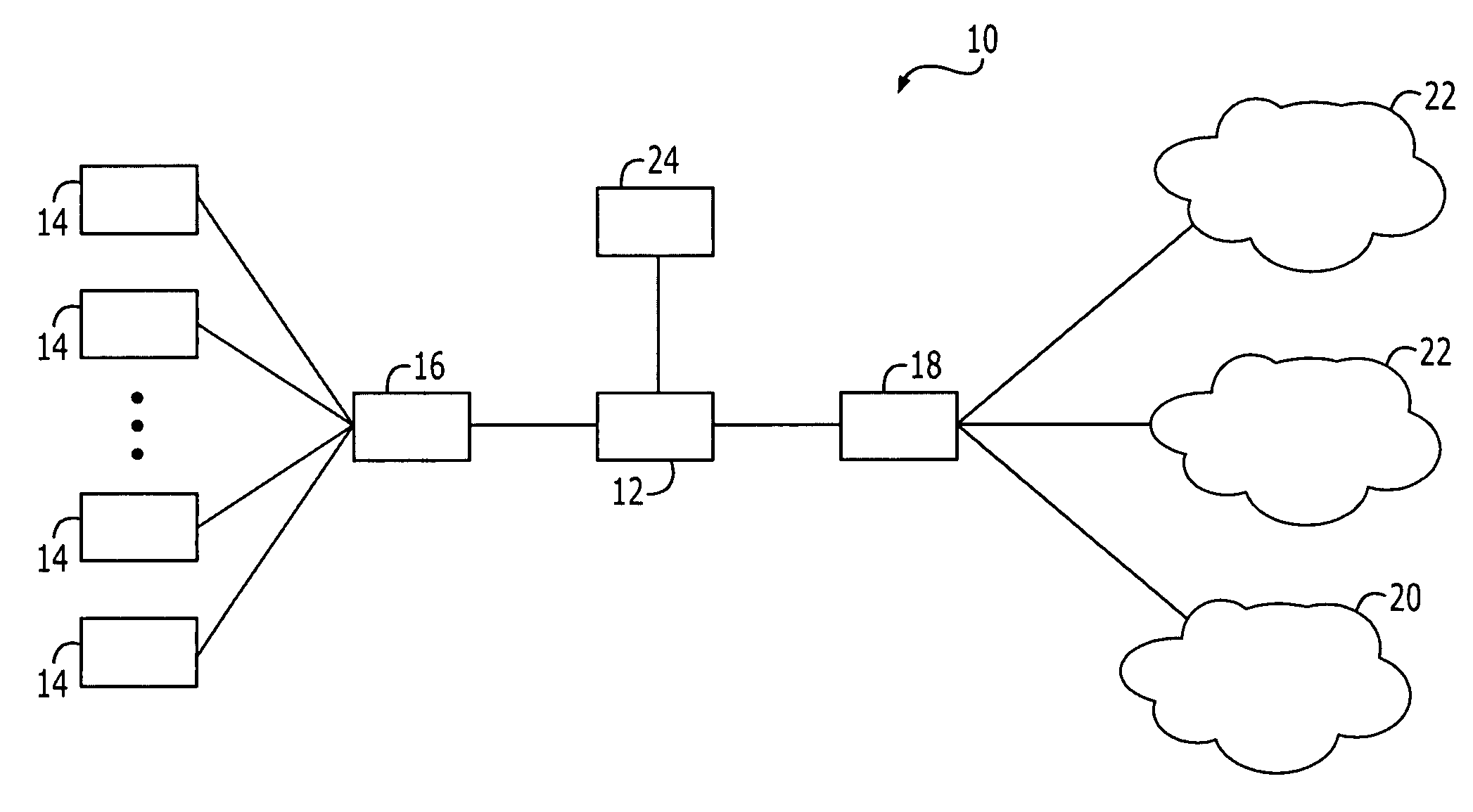
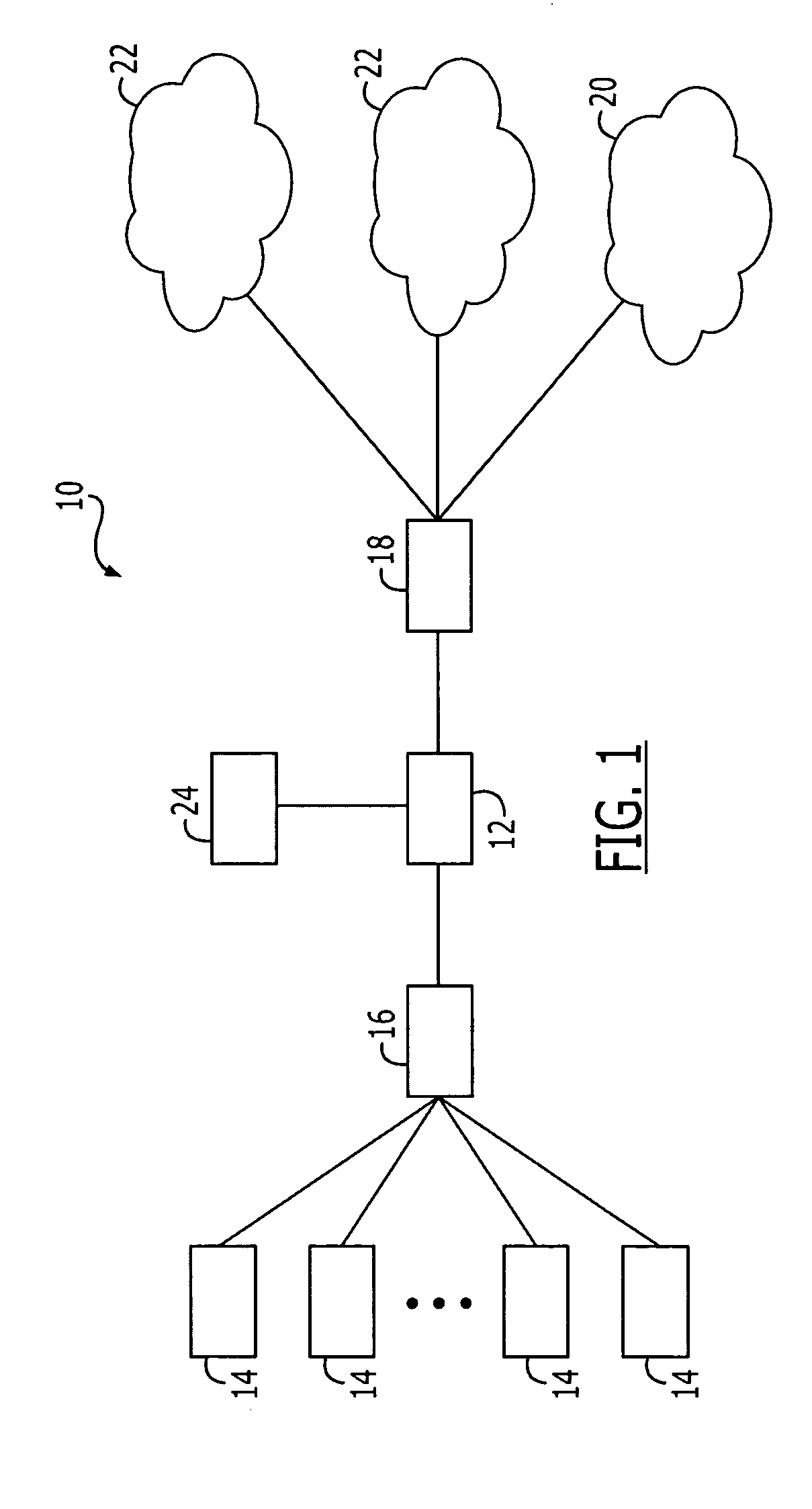
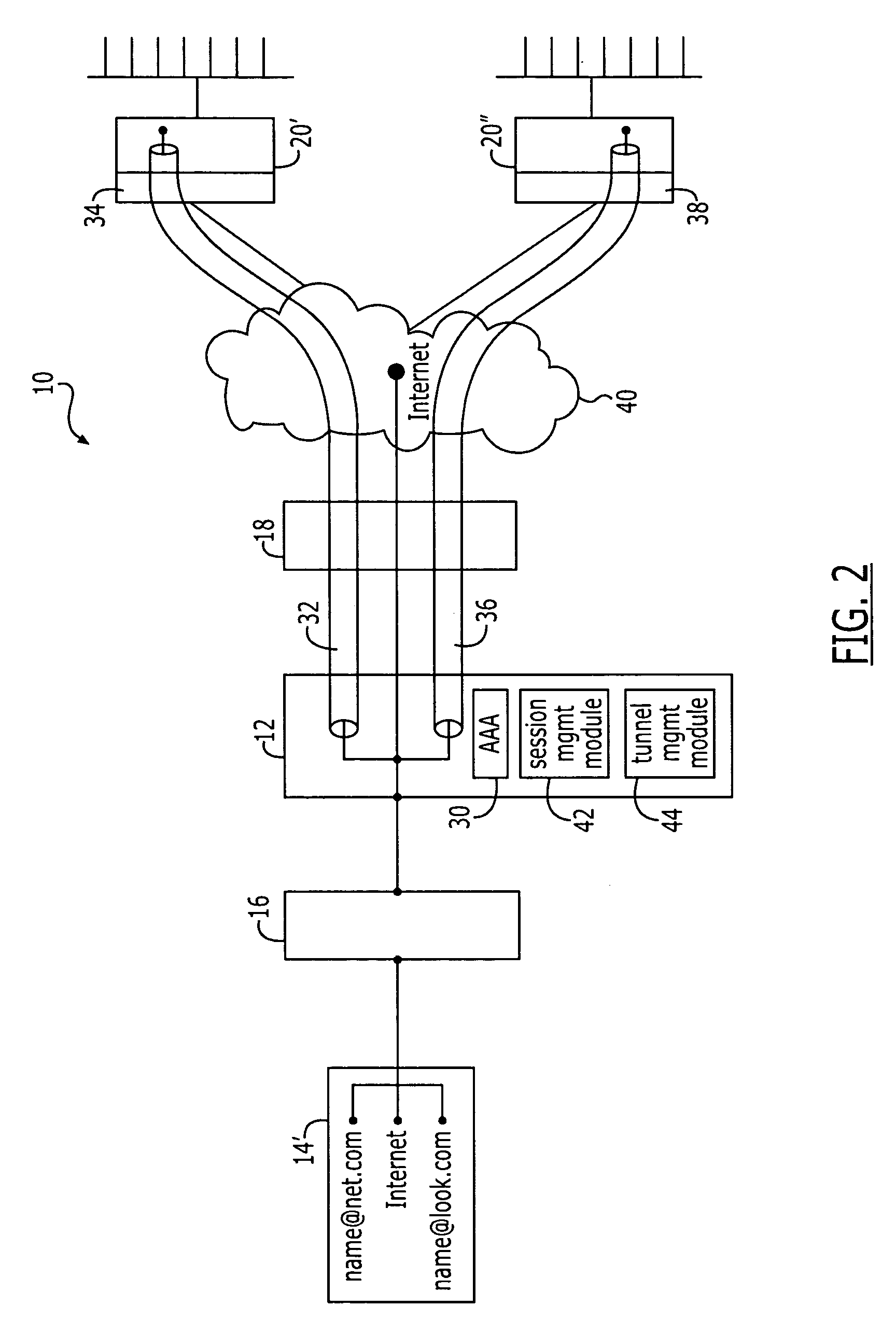
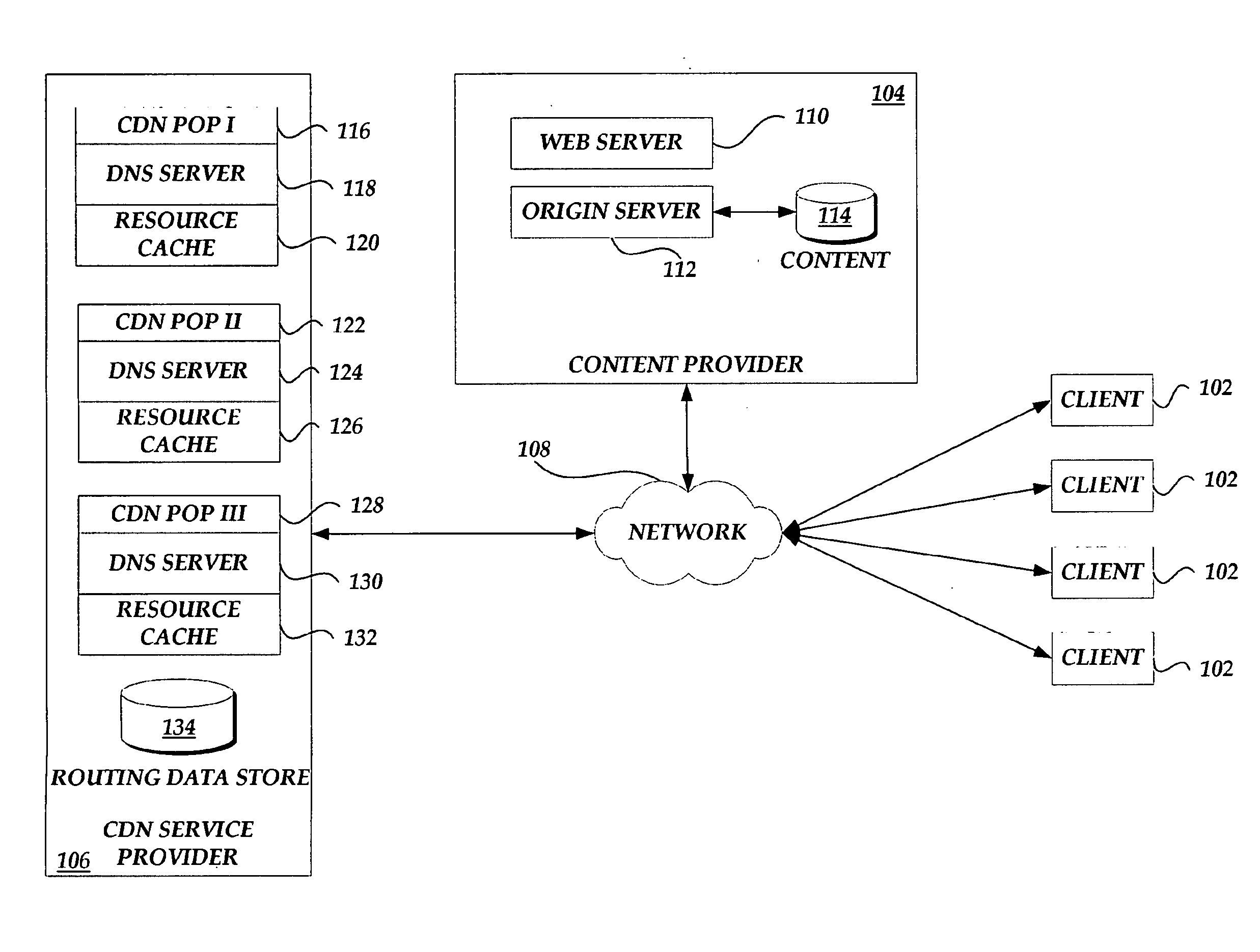
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
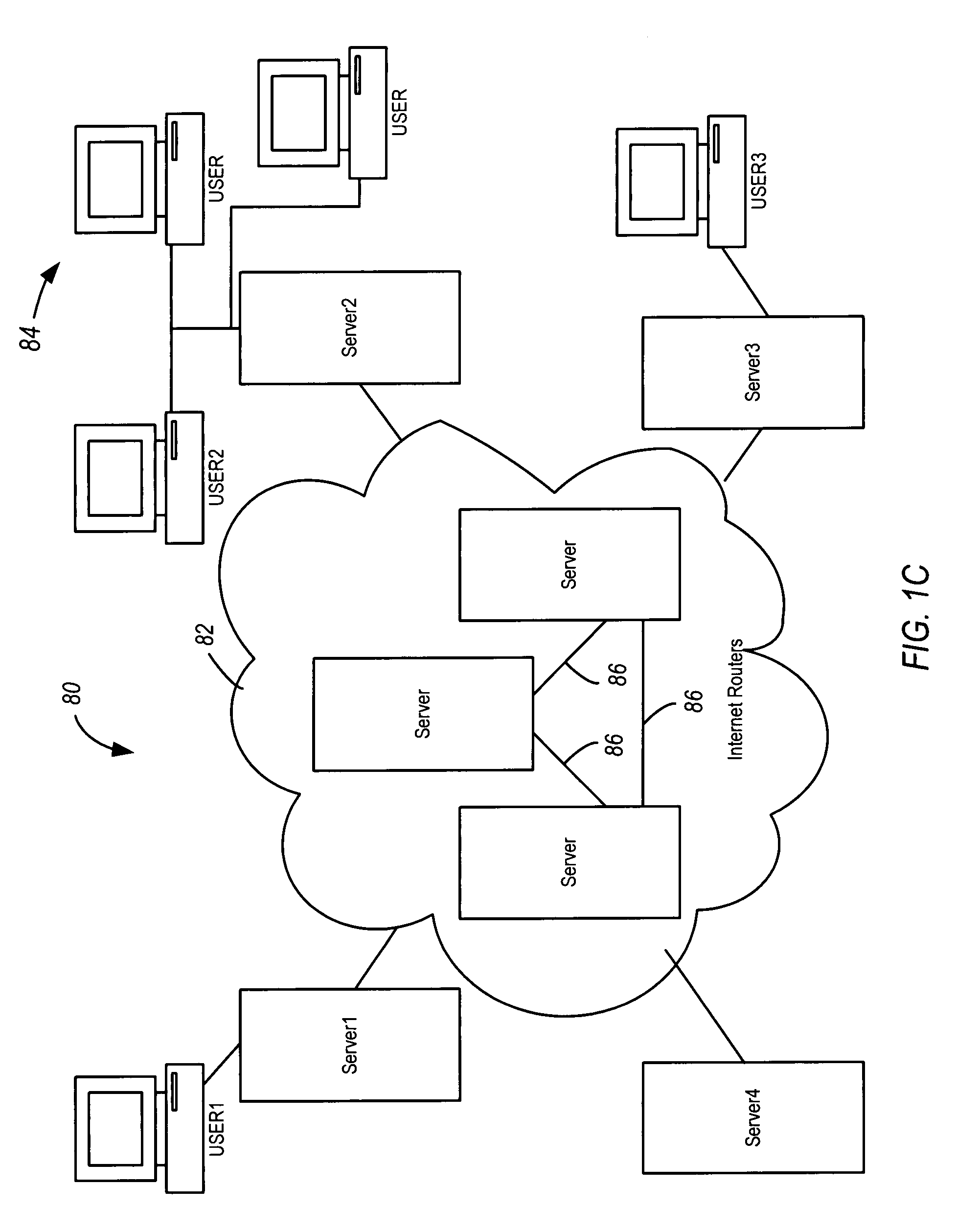
12693 results about "Network service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer networking, a network service is an application running at the network application layer and above, that provides data storage, manipulation, presentation, communication or other capability which is often implemented using a client-server or peer-to-peer architecture based on application layer network protocols.
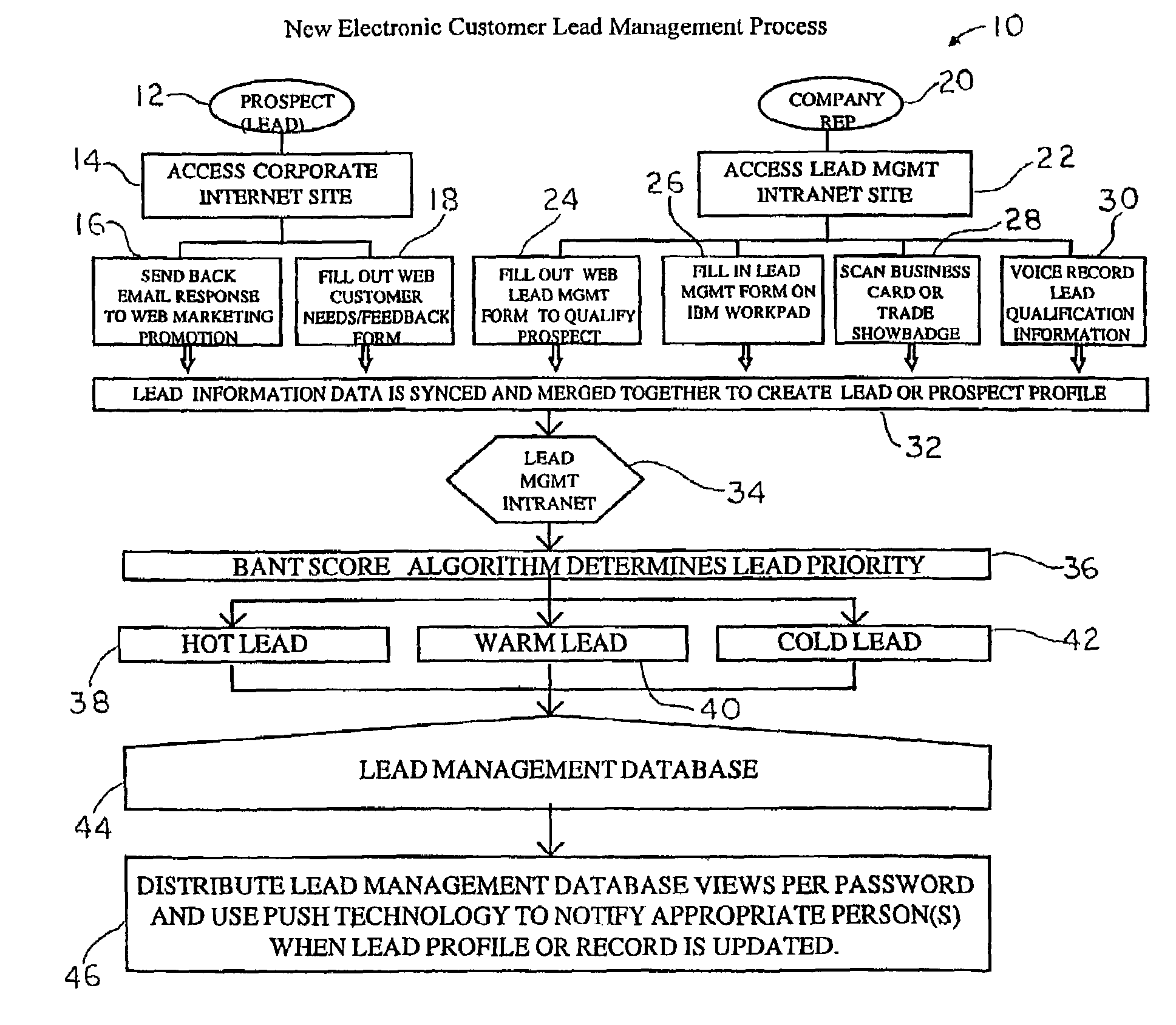
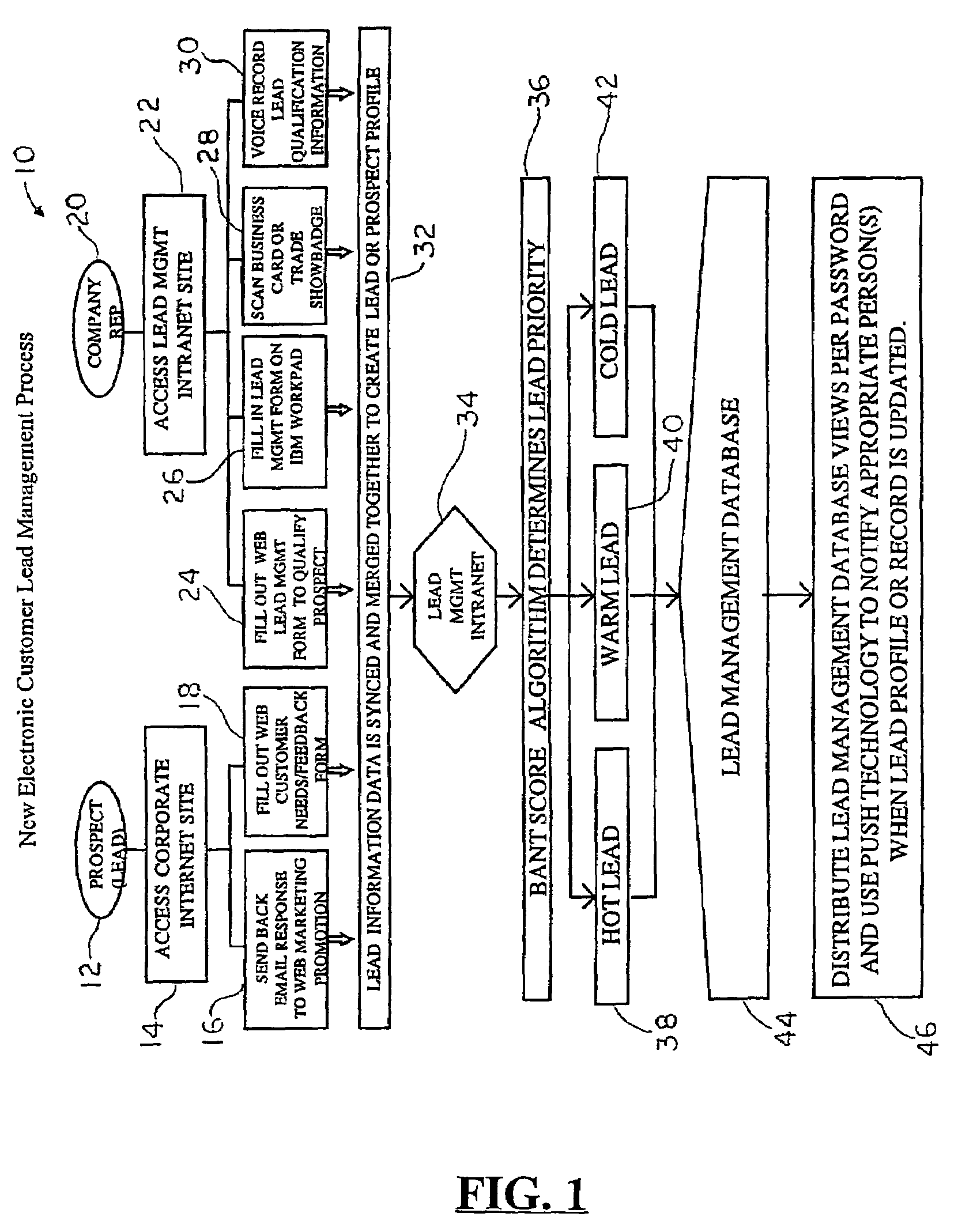
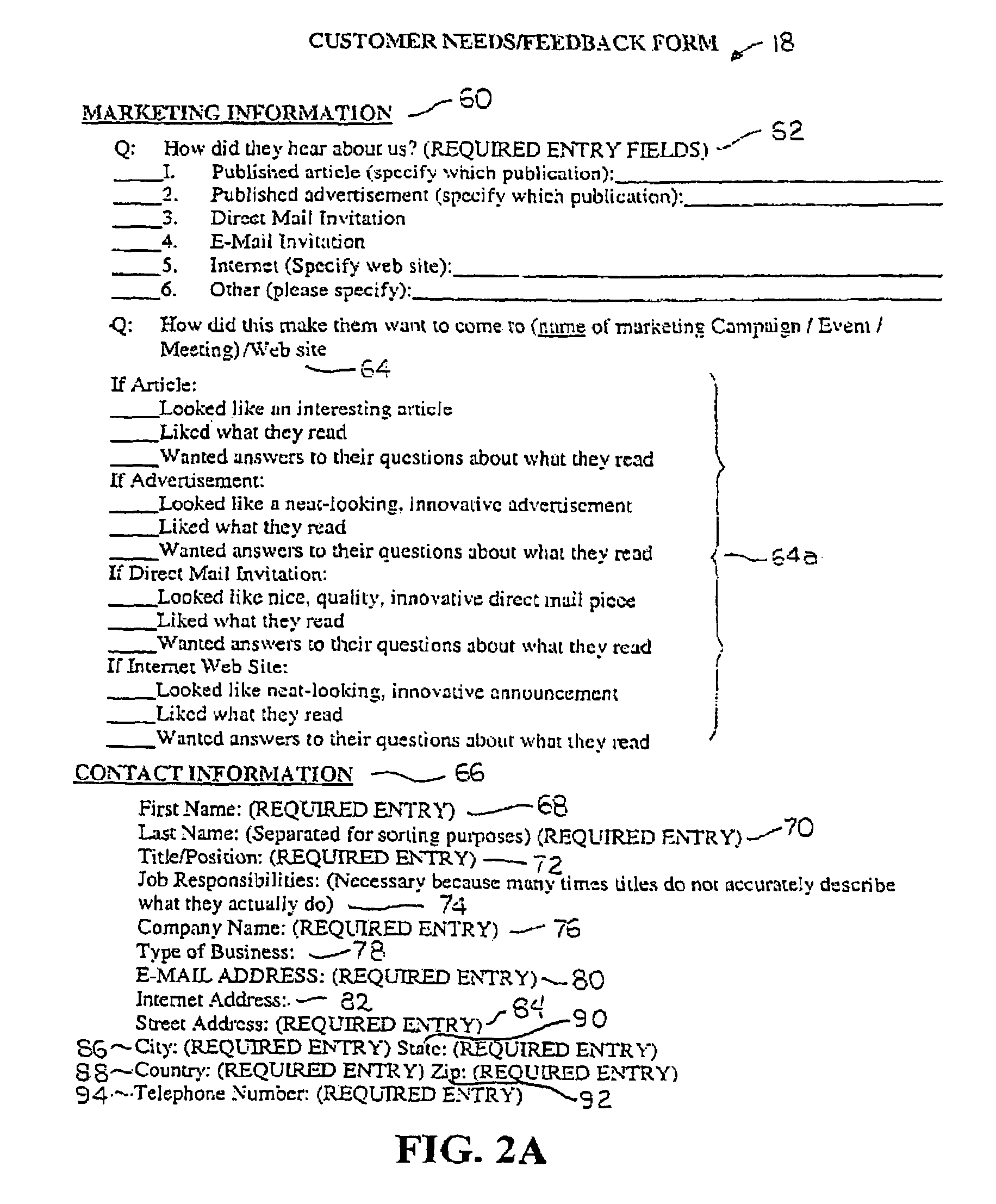
System and method for generating, capturing, and managing customer lead information over a computer network
A customer lead management system that relates to a system and method for collecting and organizing customer-marketing data, which is then made available to business representatives to assess. Specifically, using a computer network, and data on a potential customer's Budget, Authority, Needs, Timeframe, and other related customer data is collected. While this data is being collected, the customer lead management system stores the customer lead data in real-time instantly, automatically ranking the viability of the customer lead on the interest level of the customer lead and other variable criteria used in the web-based algorithm calculation, and automatically electronically notifies the appropriate company and / or company representative about the customer lead. The resulting customer lead profile record is located in a web server database, and can be accessed and undated in real-time by a portable computer or electronic device that has been web-enabled. The customer lead data is then capable of being accessed via a computer network by various companies that have goods / services that satisfy the needs and requirements of the customer lead. A company representative can be automatically notified when a customer lead profile has been updated.
Owner:CXT SYST INC
System and method to store and retrieve identifier associated information content
In one embodiment, information content files, such as text files, image files, XML files and the like, that provide information related to an identifier bearing item, such as a consumer item with a barcode, are stored on a data storage device such as network server. Identifier data entries, such as UPC data, are associated with file data entries, such as file names, in a database. General file access information that is used in accessing the information content files is stored on a terminal. In operation an identifier is read by the terminal and is used to extract one of the file data entries from the database based on database communication information stored on the terminal. The file data entry in combination with the general file access information is used to establish communication with the data storage device and to extract one of the information content files.
Owner:HAND HELD PRODS
System and Method to Store and Retrieve Indentifier Associated Information Content
In one embodiment, information content files, such as text files, image files, XML files and the like, that provide information related to an identifier bearing item, such as a consumer item with a barcode, are stored on a data storage device such as network server. Identifier data entries, such as UPC data, are associated with file data entries, such as file names, in a database. General file access information that is used in accessing the information content files is stored on a terminal. In operation an identifier is read by the terminal and is used to extract one of the file data entries from the database based on database communication information stored on the terminal. The file data entry in combination with the general file access information is used to establish communication with the data storage device and to extract one of the information content files.
Owner:HAND HELD PRODS
Systems, devices, agents and methods for monitoring and automatic reboot and restoration of computers, local area networks, wireless access points, modems and other hardware
ActiveUS20090013210A1Data switching networksRedundant operation error correctionDomain nameFully qualified domain name
An embodiment of the invention is a client on a local area network that periodically and automatically evaluates its physical connectivity with the local area network, exercises local-network services such as DHCP, and verifies Internet connectivity and function by pinging one or more numerically specified IP addresses and by pinging one or more IP addresses specified by an FQDN (Fully Qualified Domain Name) known to the assigned DNS servers. An embodiment of the invention may include a plurality of client elements monitoring one or more networks. Functionality according to embodiments of the invention can send notices, automatically initiate action, and otherwise assist in, among other things, remote monitoring and administration of networks, and particularly wireless networks.
Owner:SAND HLDG LLC
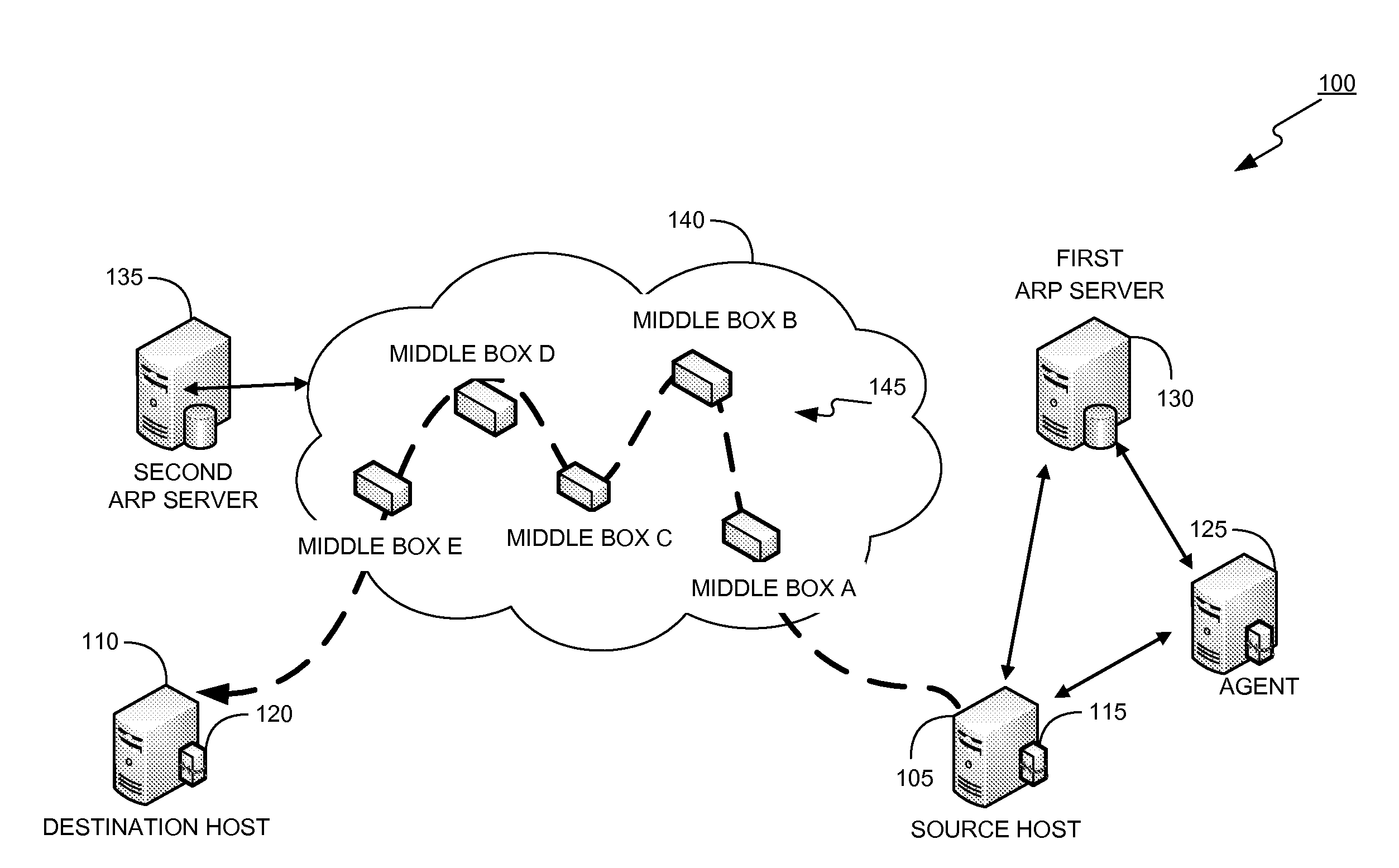
Network user authentication system and method
ActiveUS20070022469A1Removal difficult and impossibleThe certification process is reliableDigital data processing detailsUser identity/authority verificationUnique identifierAuthentication server
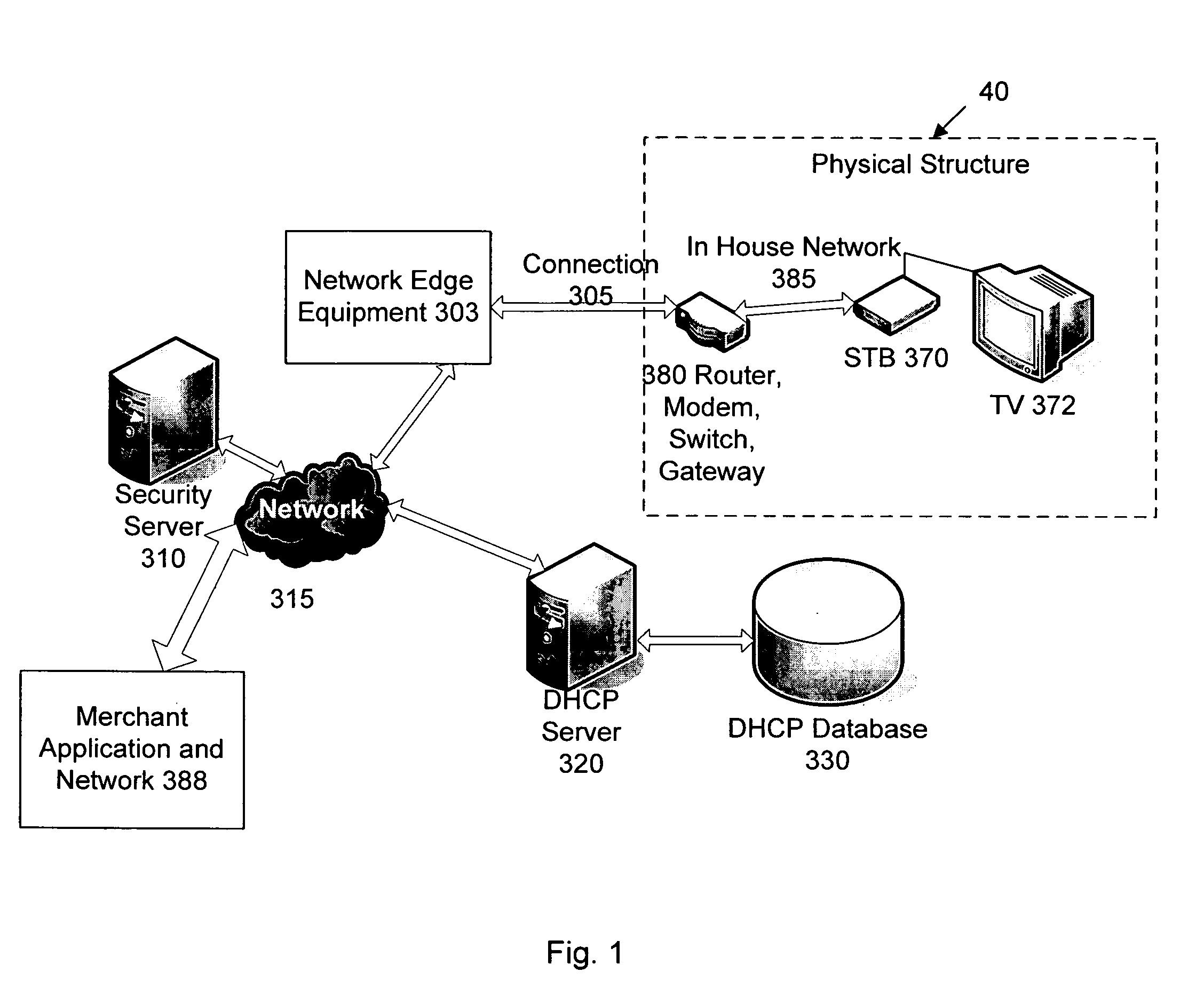
In a network user authentication system, a network user is identified for authentication purposes using the unique identifier for a dedicated physical communication line associated with the building in which the network user is located or a digital certificate which is associated with a secure component or communication line physically attached to a building. An authentication server initially verifies the identification of the dedicated communication line to be associated with a network service subscriber or issues a unique digital certificate to be associated with the dedicated communication line for authentication purposes. The digital certificate may be stored in a building gateway or in an edge site module which is connected to the secure components of a plurality of buildings and stores unique digital certificates for each building.
Owner:VERIMATRIX INC
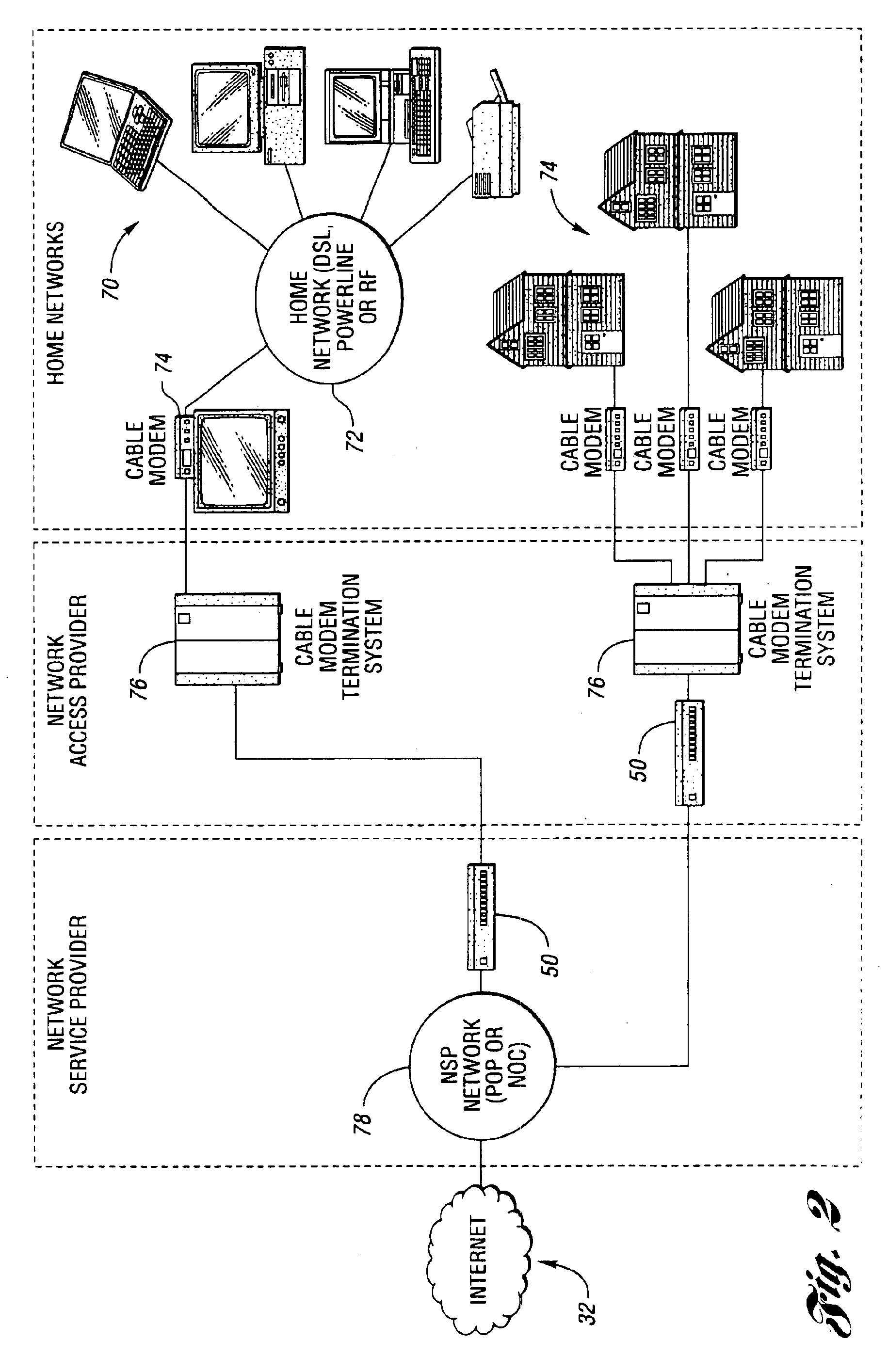
Apparatus and method for remotely monitoring a computer network
InactiveUS20060031476A1Easy to provideMinimize the possibilityDigital computer detailsTransmissionAnti virusPrivate network
There is provided an apparatus for remotely monitoring a computer network. Monitoring is performed using an inside out approach from behind firewalls and other security devices. The monitoring appliance is shipped to a client site preconfigured and typically requires no technically trained person for installation. Collected network data is periodically transmitted to a remote monitoring facility where it is recorded and analyzed. Both the monitoring appliance and the remote center maintain the configuration data. Typically, no client data is transmitted to the remote monitoring site. If the monitoring appliance fails, a completely configured replacement may be shipped to the site and easily installed. The monitoring appliance is optionally equipped to provide network services. Services such as web hosting, file server, print server, virtual private network (VPN), shared Internet access, web content filtering, anti-virus, spam e-mail elimination, and IP telephony services as well as other such services may be easily provided.
Owner:MATHES MARVIN LEE +1
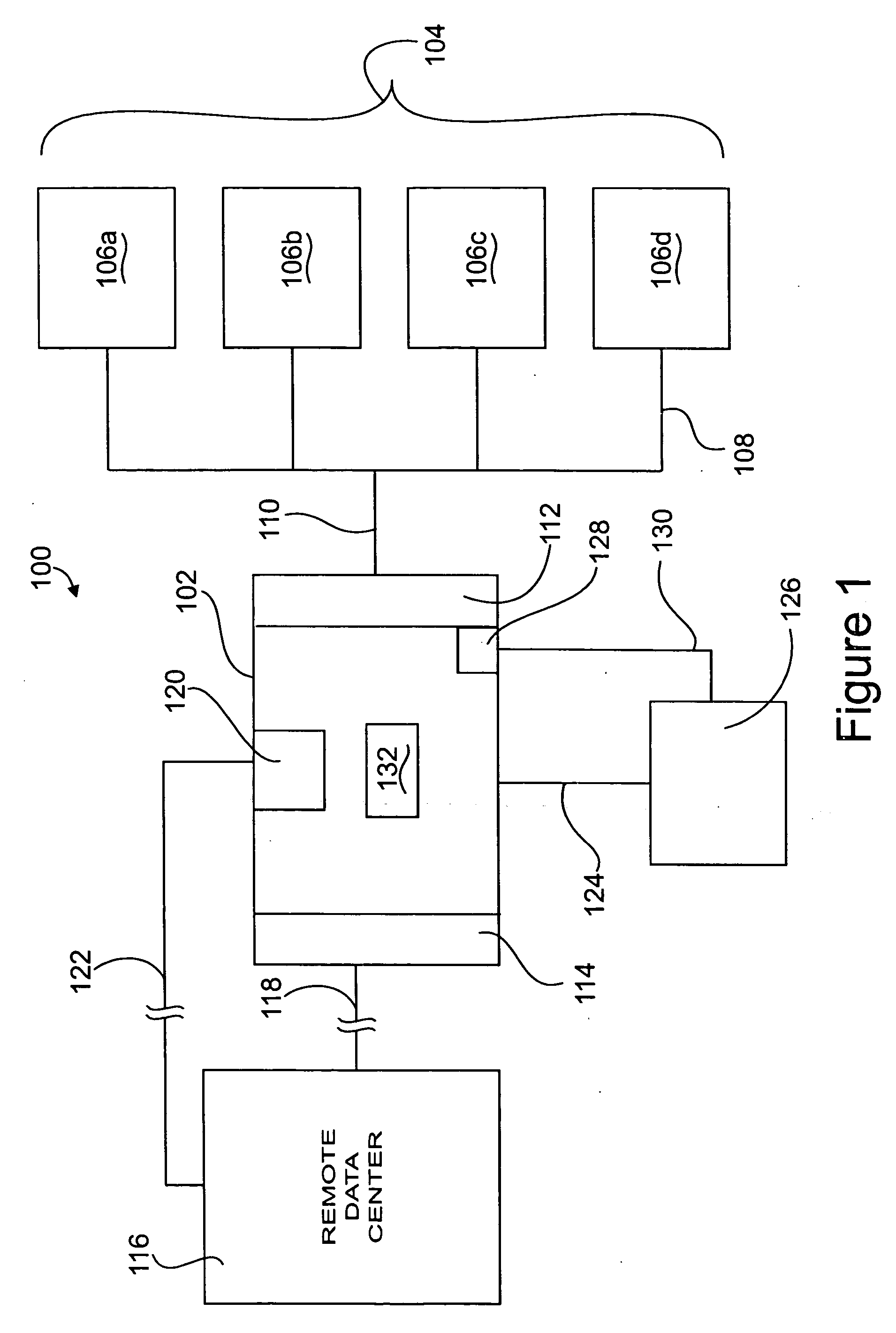
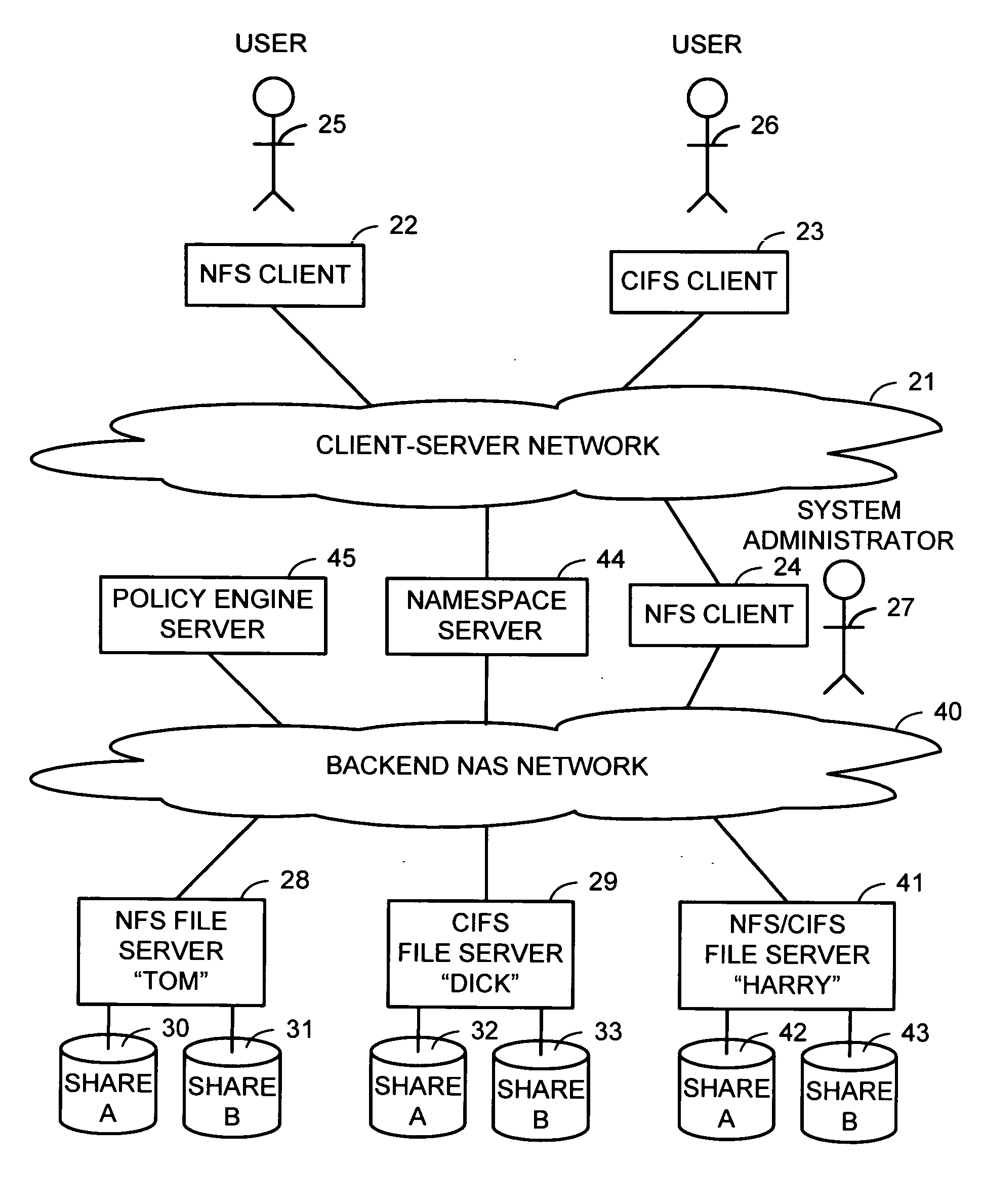
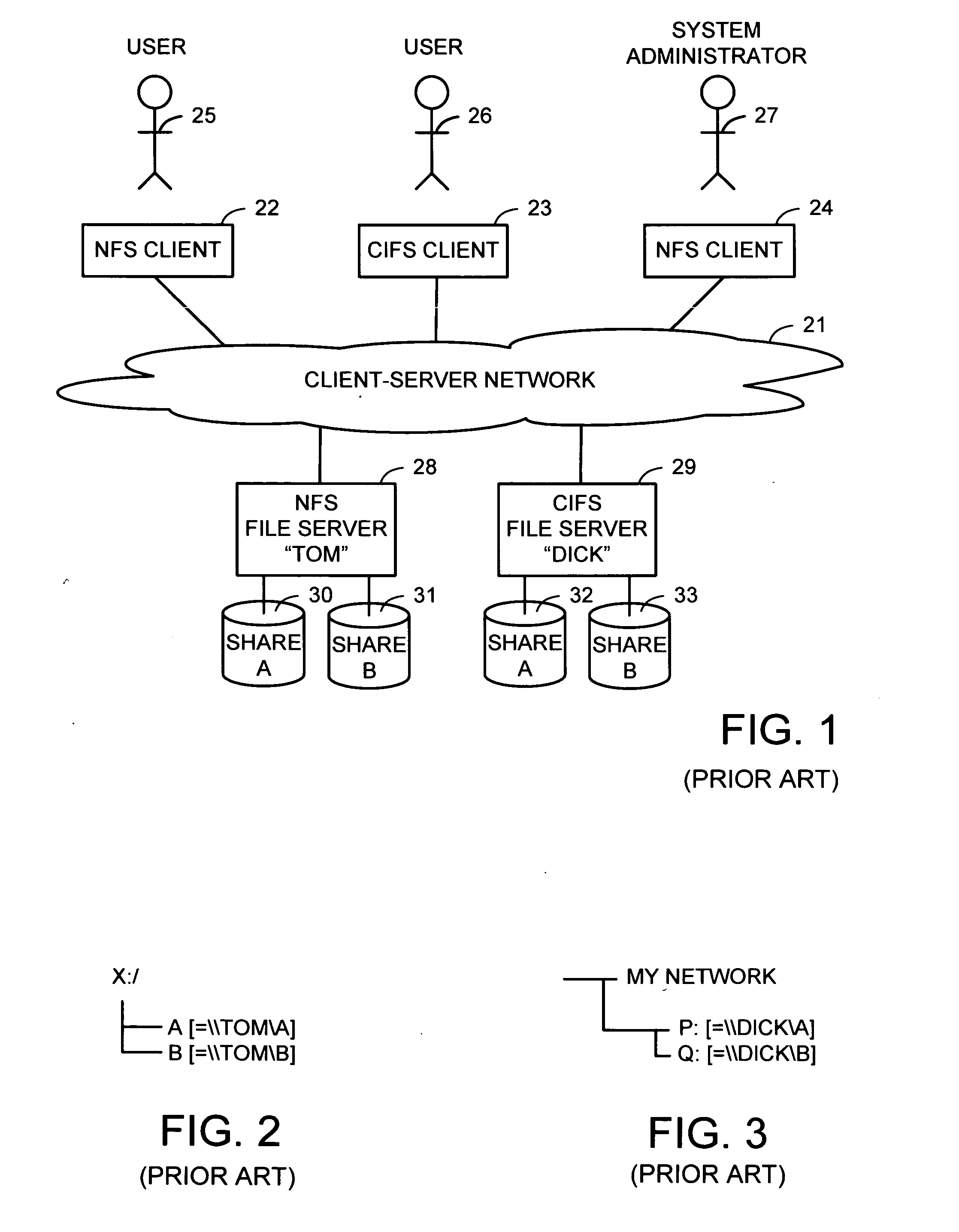
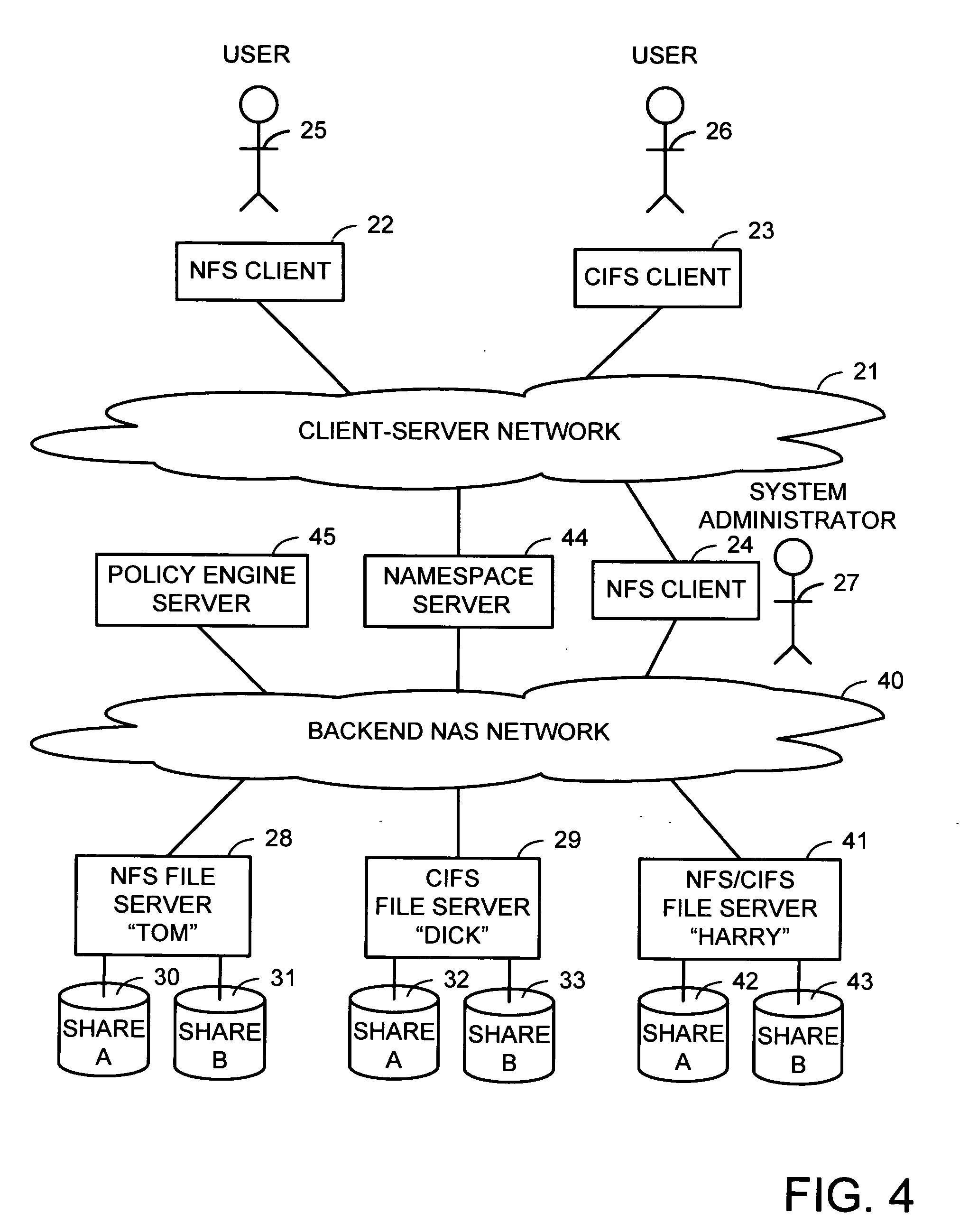
Intelligent network client for multi-protocol namespace redirection
InactiveUS20070088702A1Multiple digital computer combinationsTransmissionIntelligent NetworkEngineering
An intelligent network client has the capability of accessing a first network server in accordance with a first high-level file access protocol, and responding to a redirection reply from the first network server by accessing a second network server in accordance with a second high-level file access protocol. For example, the intelligent network client can be redirected from a CIFS / DFS server to a NFS server, and from an NFSv4 server to a CIFS server. Once redirected, the intelligent network client performs a directory mounting operation so that a subsequent client access to the same directory goes directly to the second network server. For example, the first network server is a namespace server for translating pathnames in a client-server network namespace into pathnames in a NAS network namespace, and the second network server is a file server in the NAS network namespace.
Owner:EMC CORP
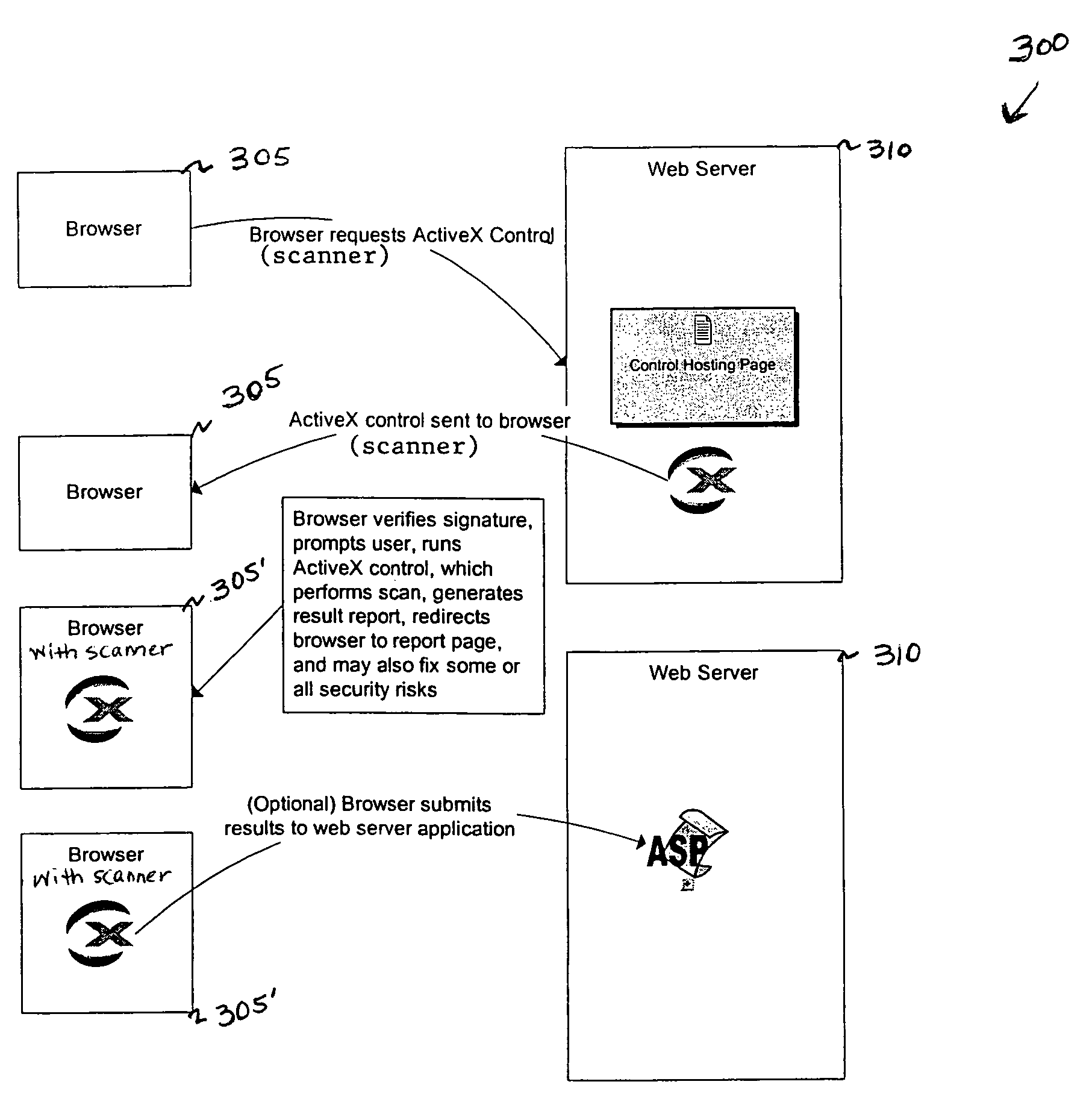
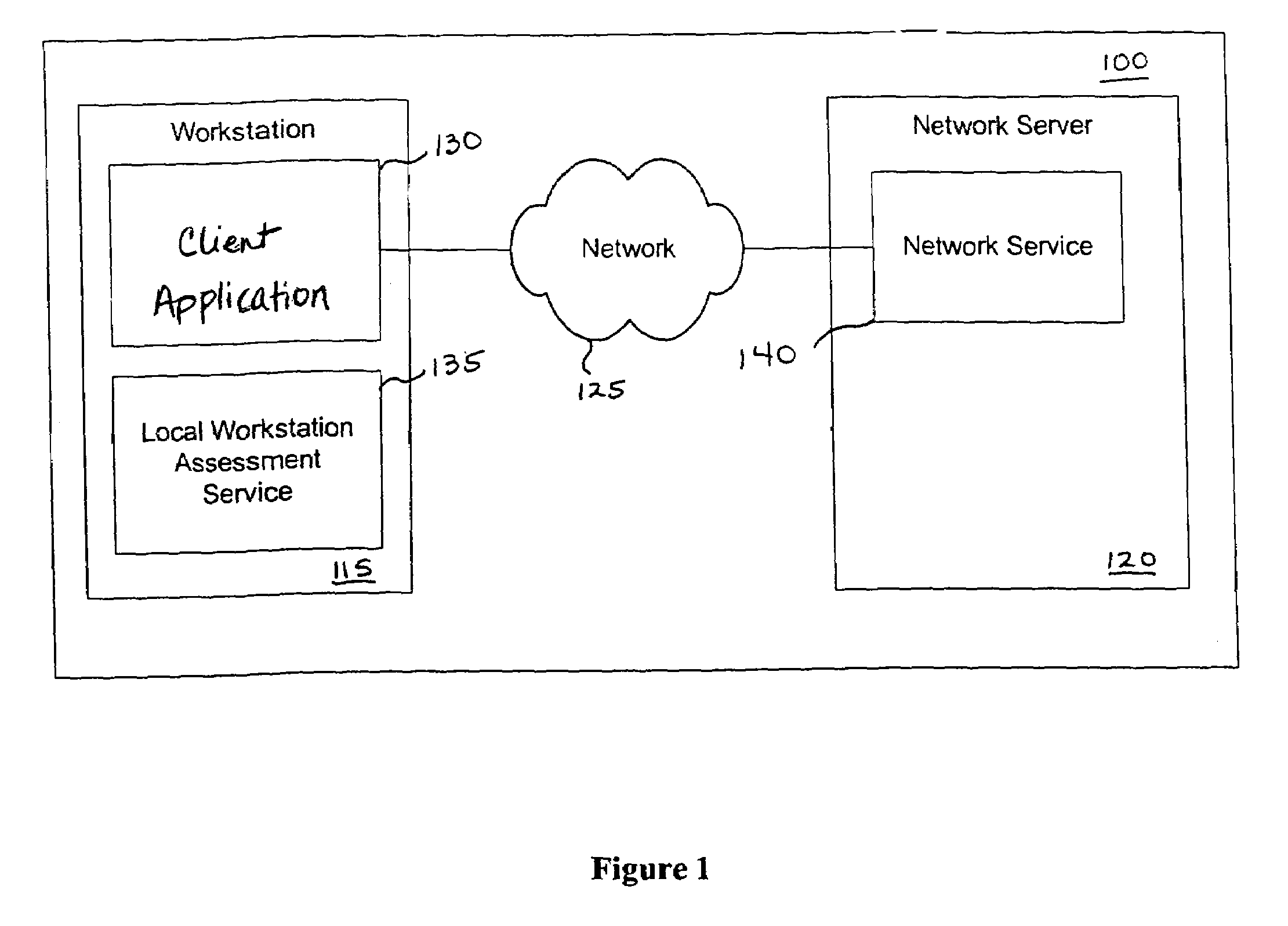
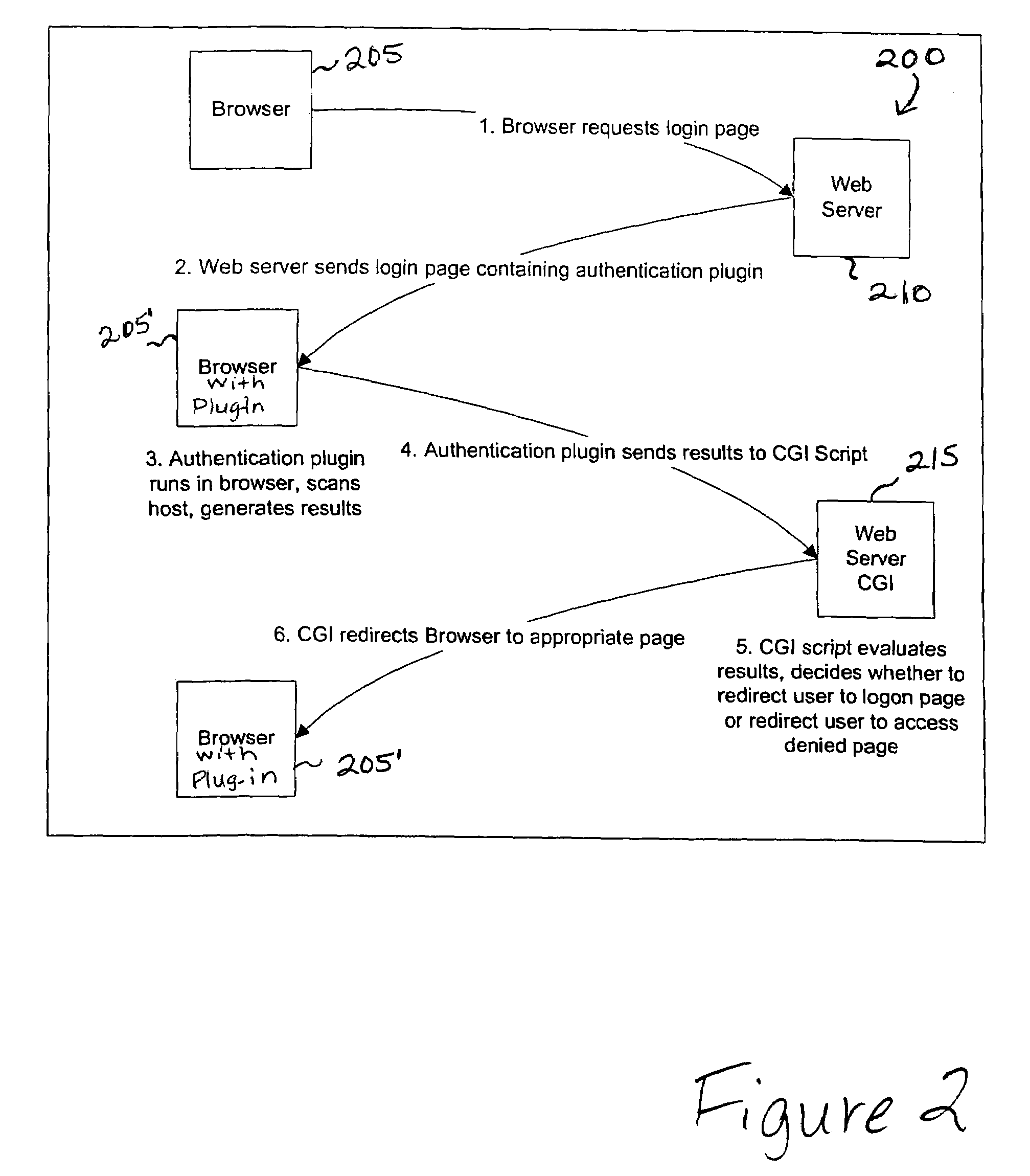
Vulnerability assessment and authentication of a computer by a local scanner
InactiveUS7178166B1Overcome disadvantagesMemory loss protectionDigital data processing detailsWorkstationNetwork service
Providing a user with assurance that a computer is secure based on a vulnerability assessment completed by a browser-compatible scanner operating on the computer. If the scanner finds a vulnerability, the scanner can inform the user that the machine is or may be compromised, or repair the vulnerability. For example, the scanner may be able to repair the vulnerability of the workstation. In the alternative, the scanner can provide the scan results to a network server. If the vulnerability assessment shows that the workstation is compromised, or if the possibility of remote compromise is high, the network server can decline to provide network services to the workstation.
Owner:KYNDRYL INC
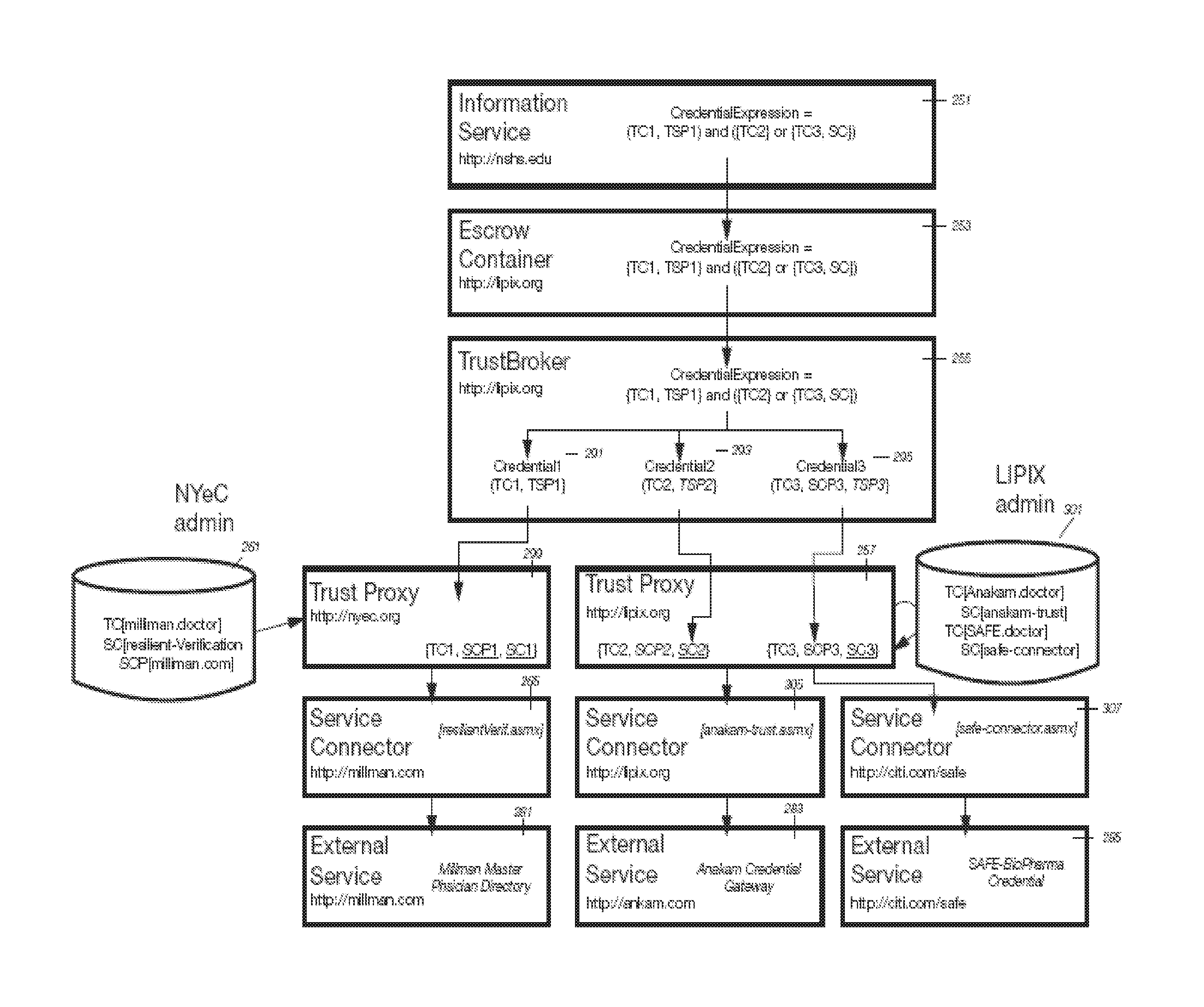
Resilient trust network services
ActiveUS8843997B1Digital data processing detailsUser identity/authority verificationComposite applicationIntegration platform
A Resilient Trust Network (RTN) is a set of servers that provide: an application integration platform for developing and publishing services and user interface for services, building derived services, subscribing to services, and embedding services into host applications, and building composite applications composed from multiple diverse services. The RST can also provide a platform for defining security requirements and accessing shared trust services that implement those requirements for services regardless of where or how those services are used.
Owner:DATA443 RISK MITIGATION INC
Dynamically provisioning middleboxes
Hybrid security architecture (HSA) provides a platform for middlebox traversal in the network. The HSA decouples the middlebox control from network forwarding. More specifically, such embodiments may receive a data packet having a packet header including an Ethernet header identifying source and destination addresses in the network. A traffic type of the data packet is determined. Then, layer-2 forwarding information, which encodes a set of non-forwarding network service provider middleboxes in the network to be traversed by the data packet, is determined based on the traffic type. The layer-2 forwarding information is inserted into the Ethernet header and the data packet is forwarded into the network. The data packet will then traverse, according to the layer-2 forwarding information, a sequence of the middleboxes in the network, wherein at least one non-forwarding network service will be provided by each of the middleboxes to the data packet in a sequence.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
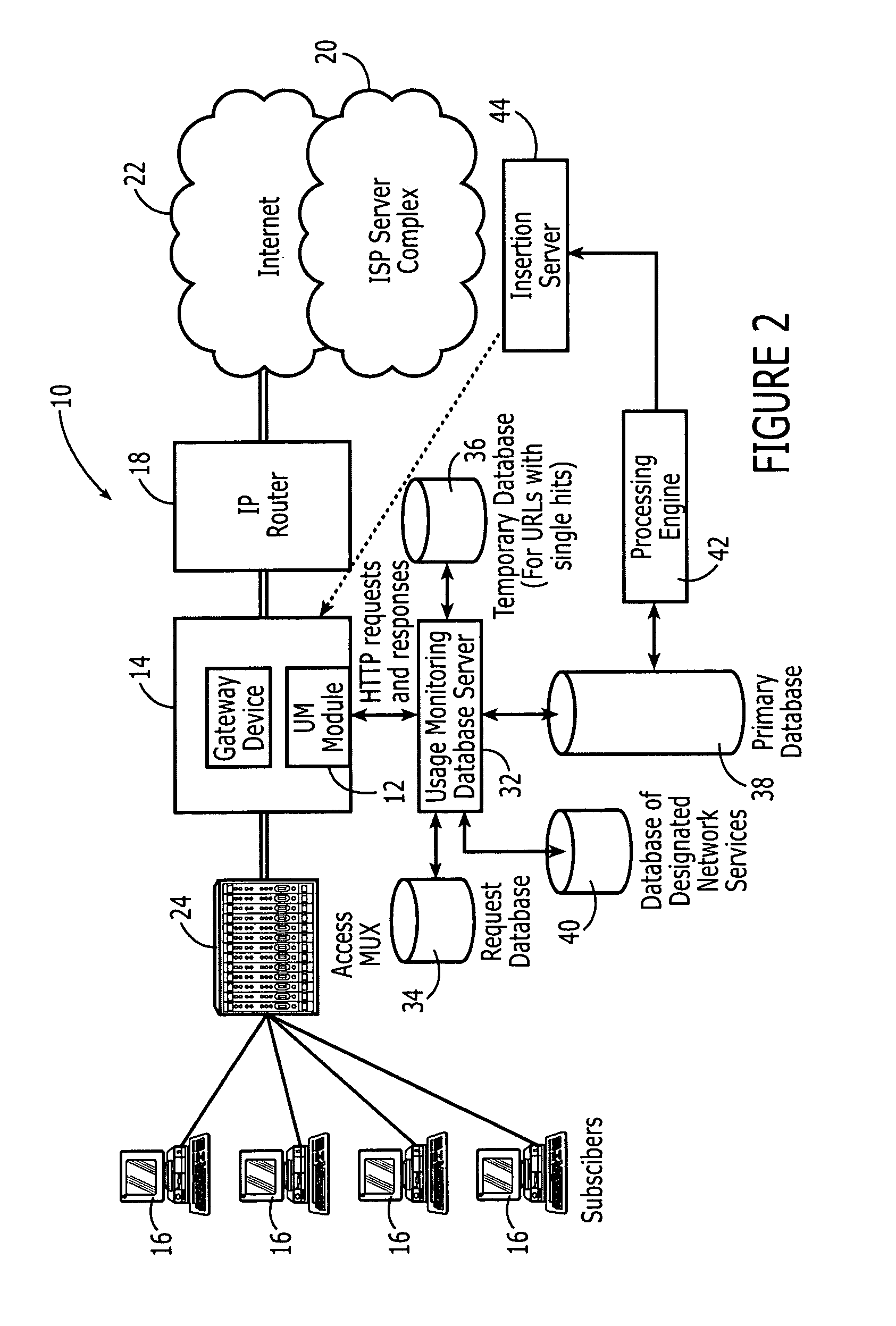
Network usage monitoring device and associated method
InactiveUS7020082B2Information can be usedIncrease valueError preventionFrequency-division multiplex detailsTraffic capacityNetwork interface device
A network usage monitoring module is provided for monitoring network usage at a network access point, i.e. network traffic aggregation point, typically at a gateway device or a similar network interface device. As such, the network usage monitoring module can monitor the usage of a number of network users who are attempting to access various network services provided via the gateway device. Thus, the usage information collected by the usage monitoring module is considerably more robust than that offered by conventional monitoring techniques. As such, the information is considerably more valuable to network service providers, network users, network beneficiaries and the like. In addition, the usage monitoring method and apparatus offers a number of particular features to improve the monitoring process as well as the value of the usage information that is collected.
Owner:NOMADIX INC
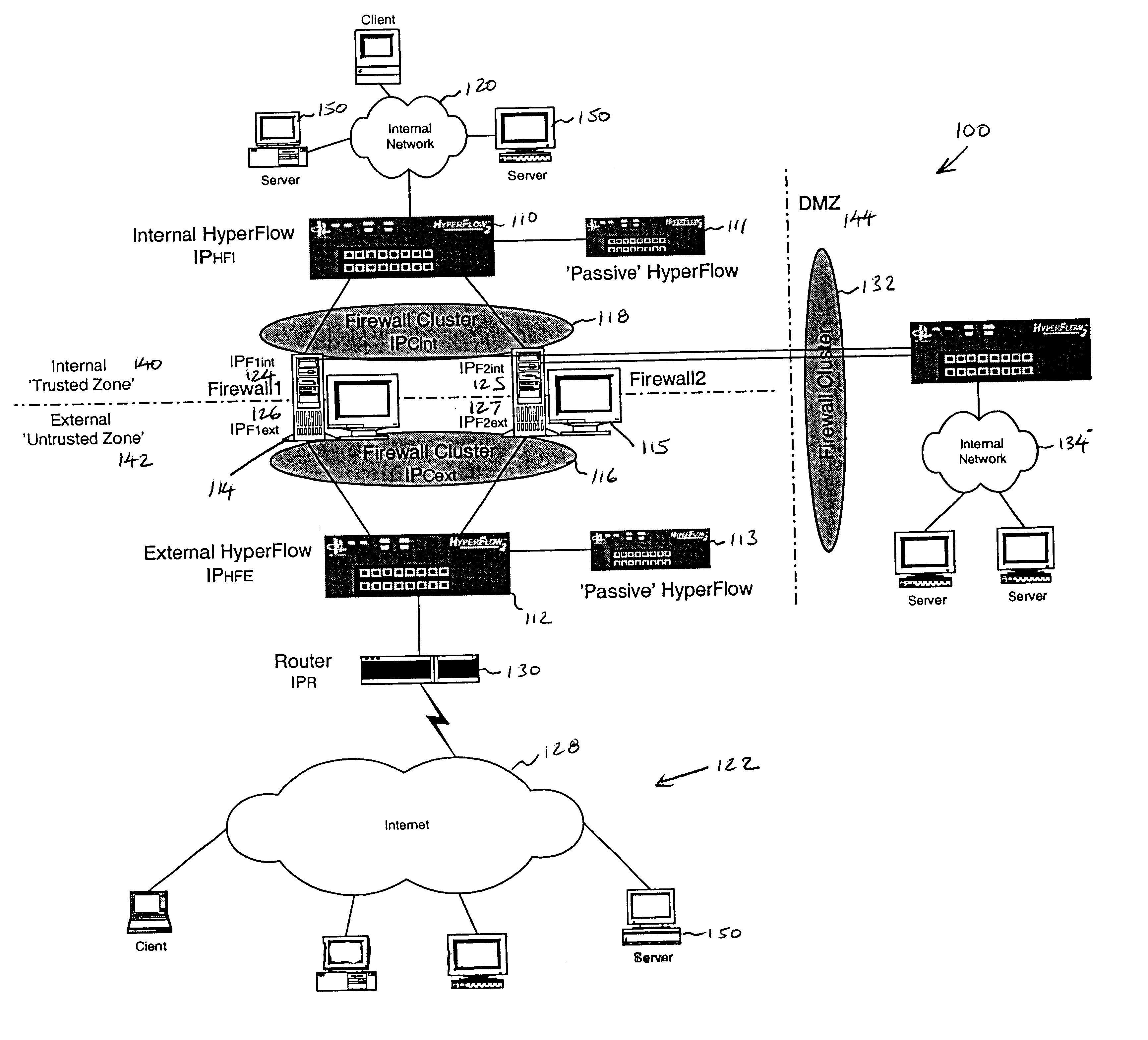
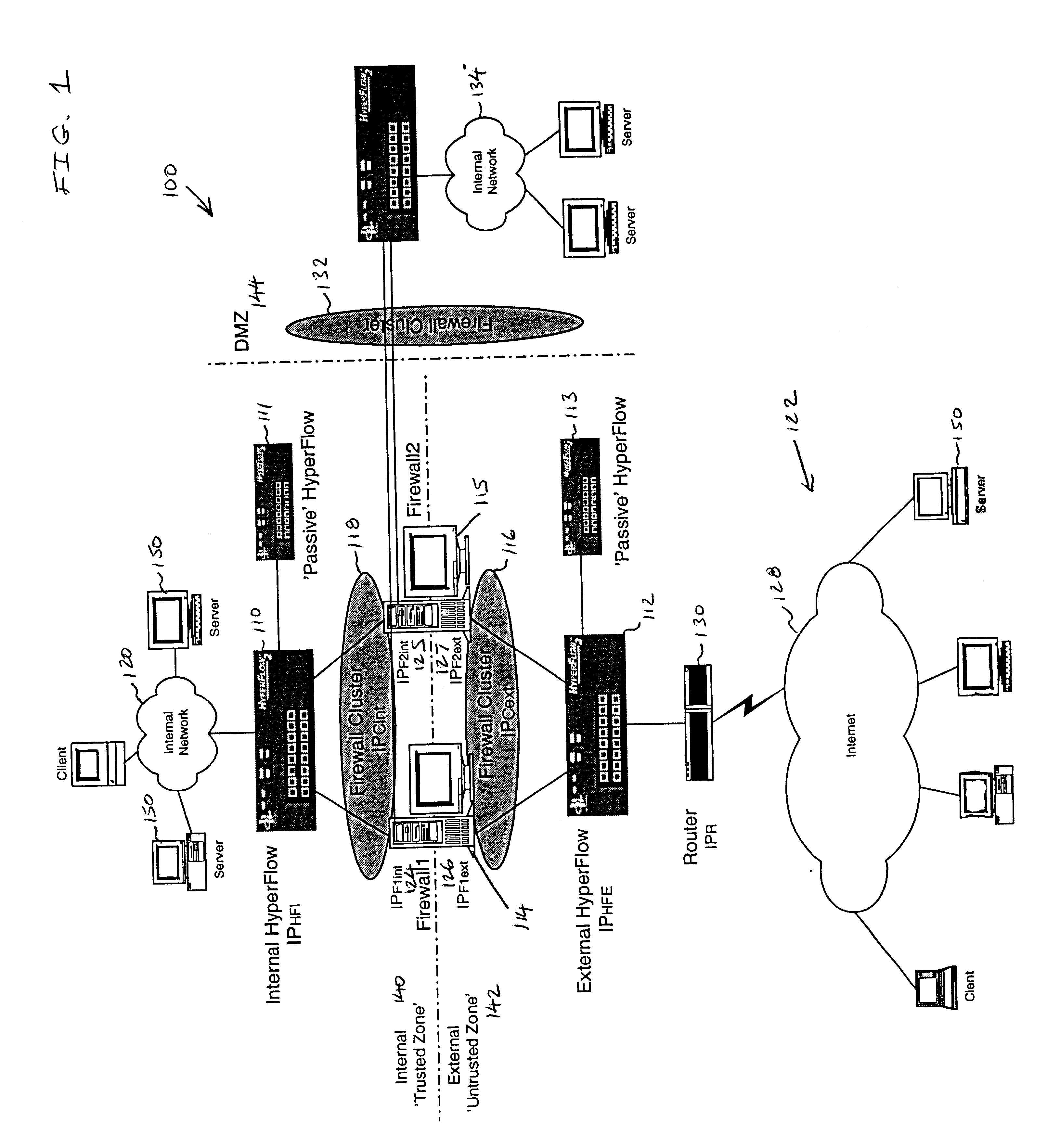
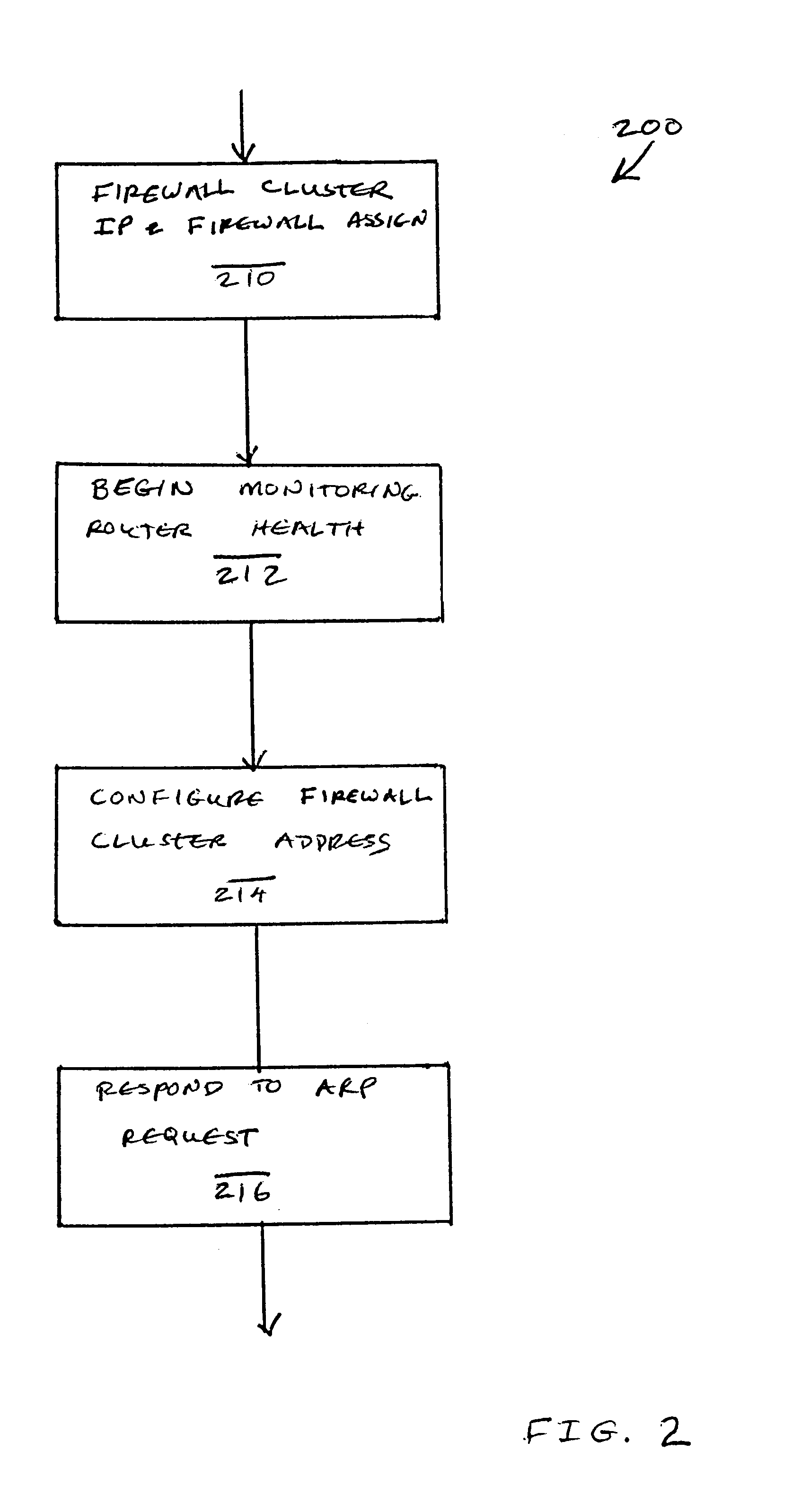
Firewall clustering for multiple network servers
InactiveUS6880089B1Increase capacityReduce calculationMultiple digital computer combinationsProgram controlTraffic capacityExtensibility
A firewall clustering system connects two or more firewalls between an internal network and an external network. The plurality of two or more firewalls are combined to supply high-availability and scaling of processing capacity. Firewalls maintain client-server state information. Flow controllers are connected to the firewalls and placed on both the internal “trusted” side and the external “untrusted” side of the firewalls. Flow controllers are placed on both sides of the firewalls to ensure that traffic for a given client-server session flows through the same firewall in both inbound and outbound directions. The firewalls perform filtering operations and / or network address translation (NAT) services. In both cases, the flow controllers supply high availability, scalability, and traffic distribution for the firewalls in the firewall cluster.
Owner:CITRIX SYST INC
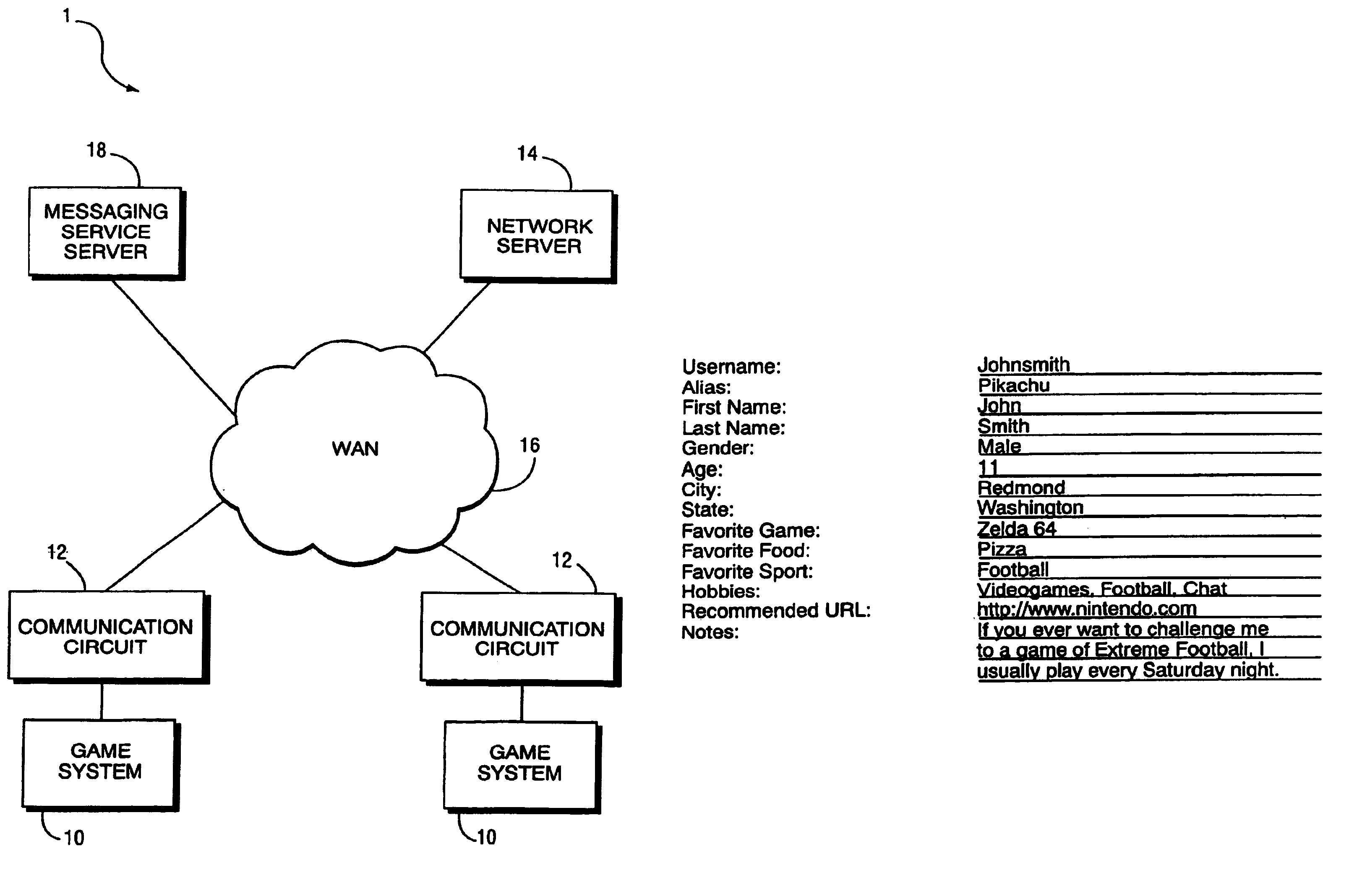
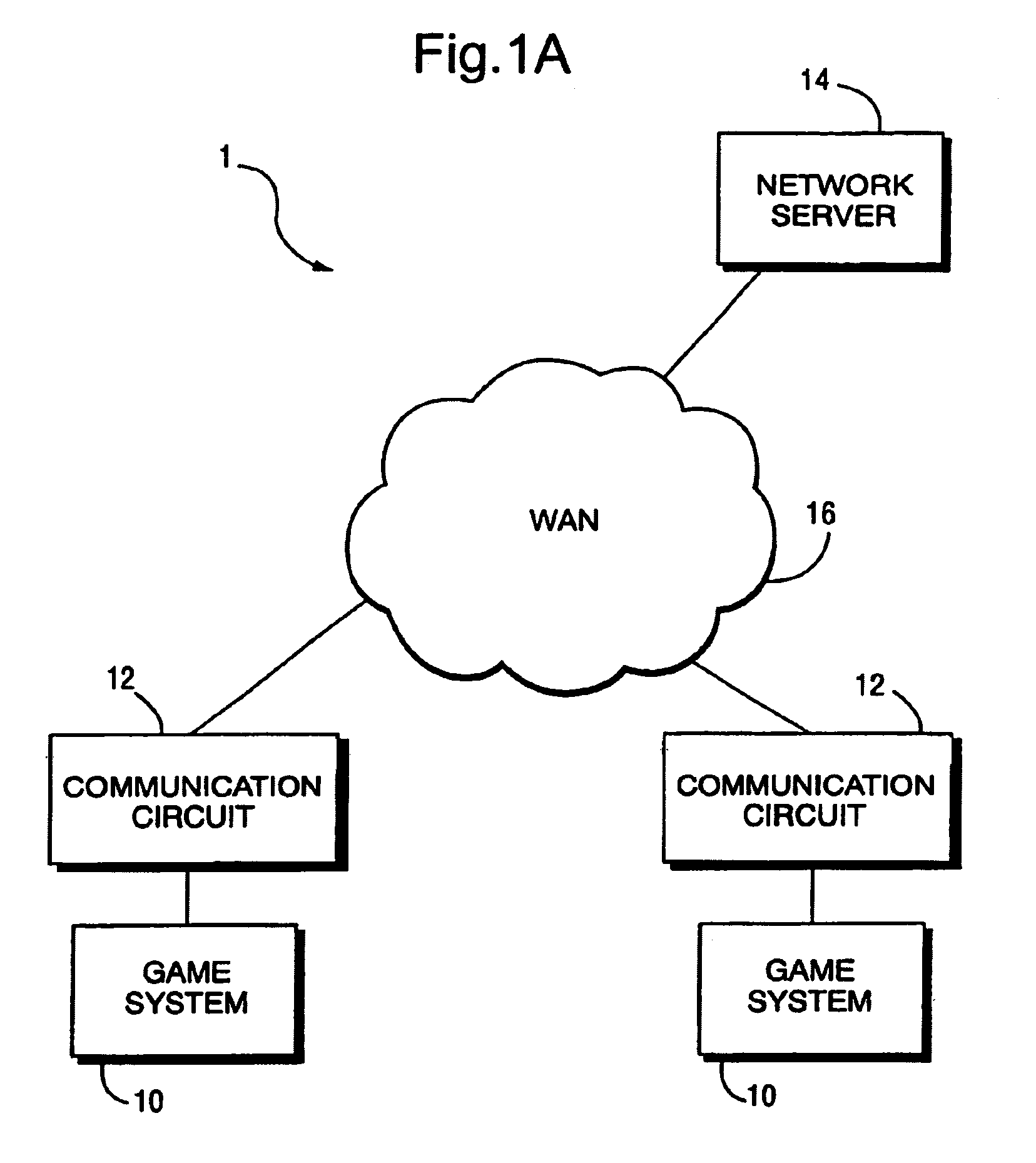
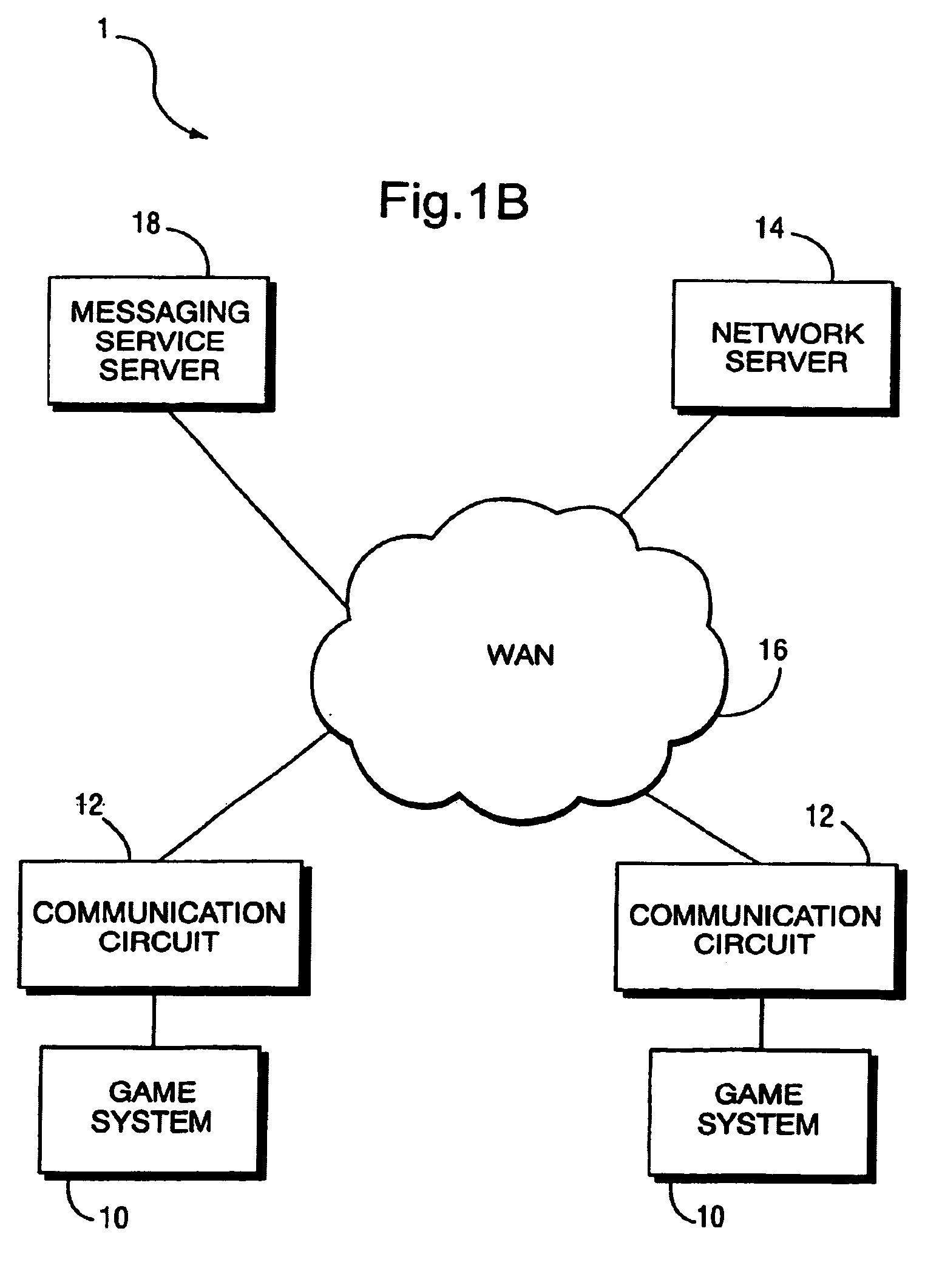
Messaging service for video game systems with buddy list that displays game being played
Owner:NINTENDO CO LTD
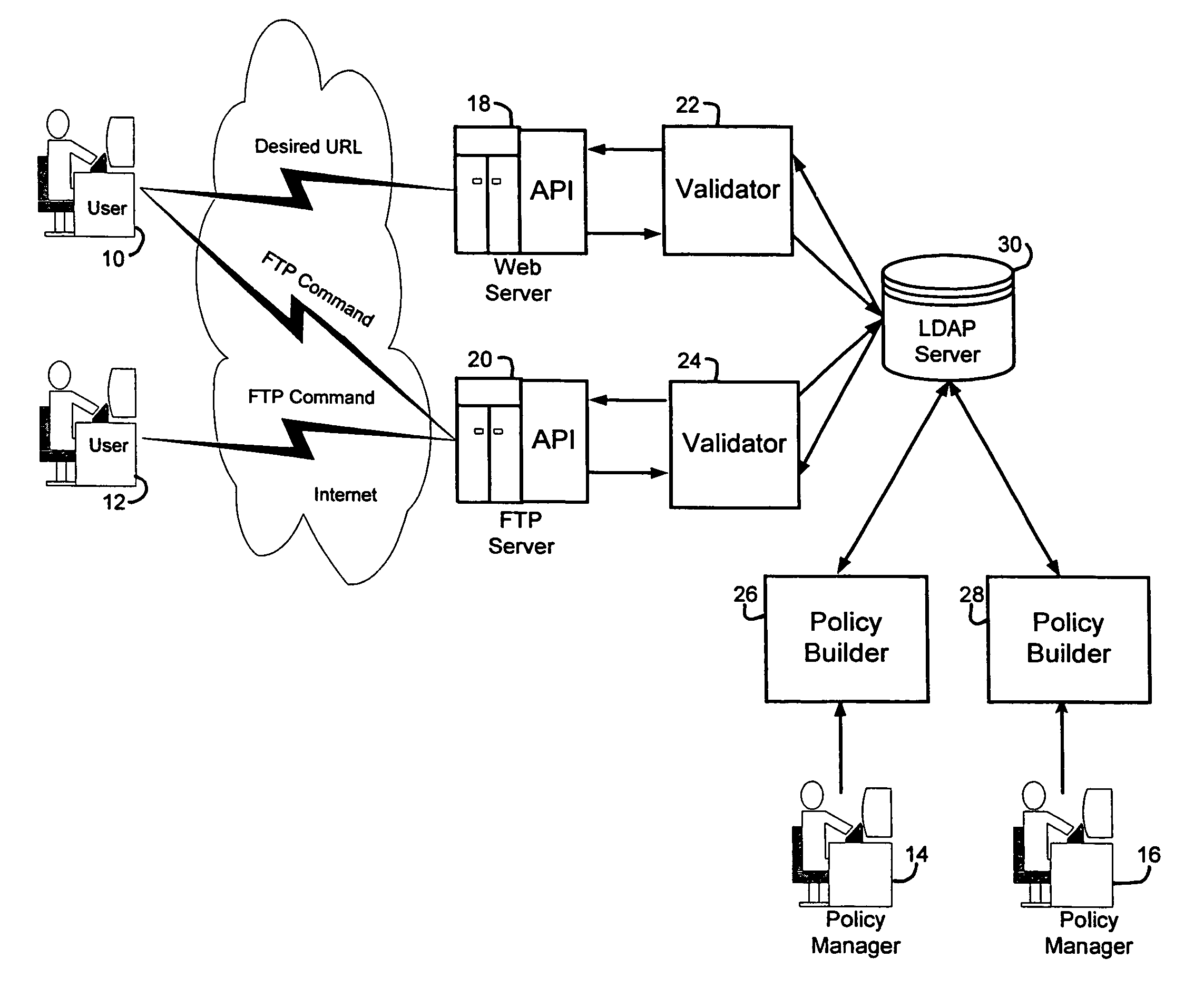
Computer system security service
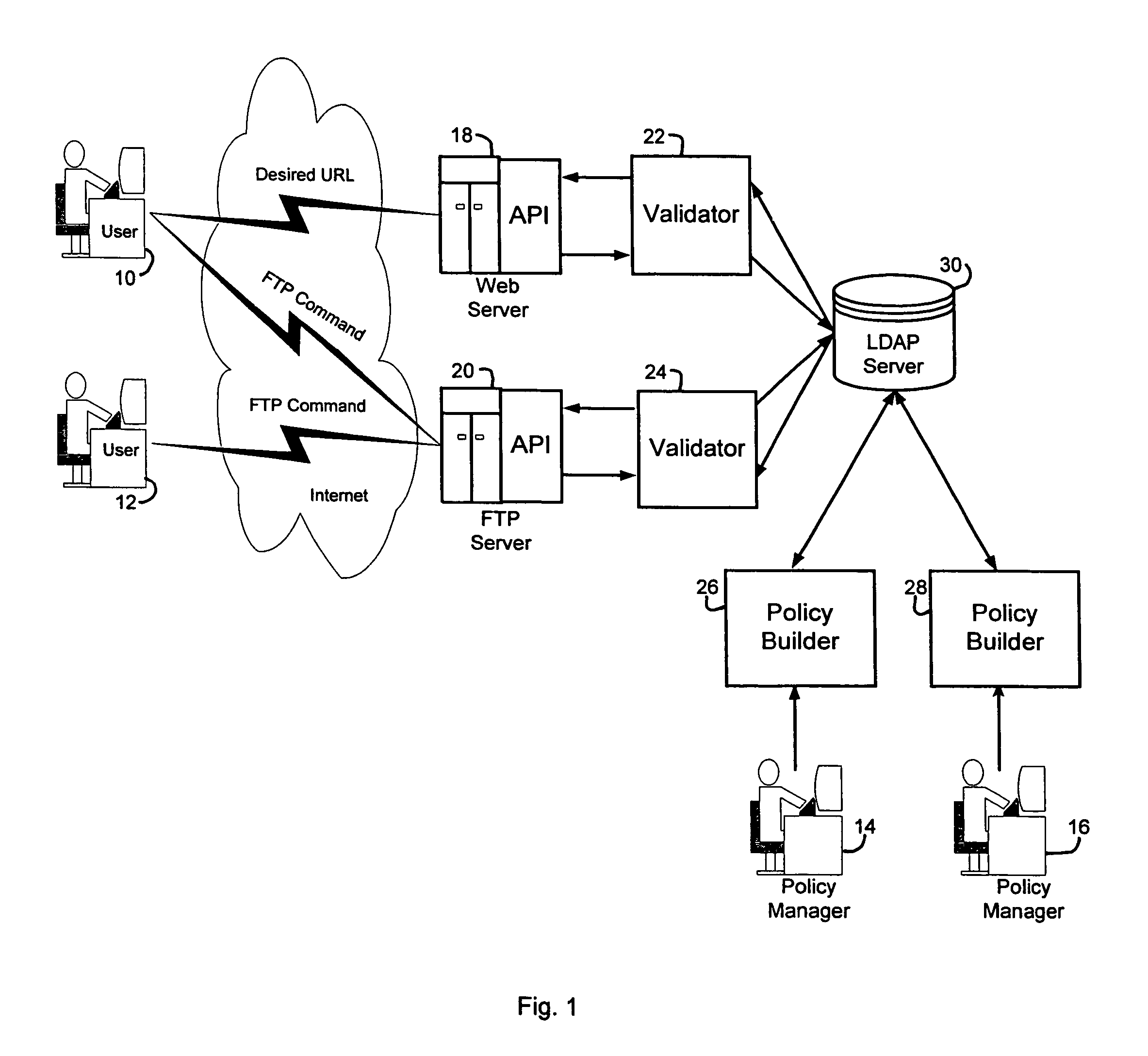
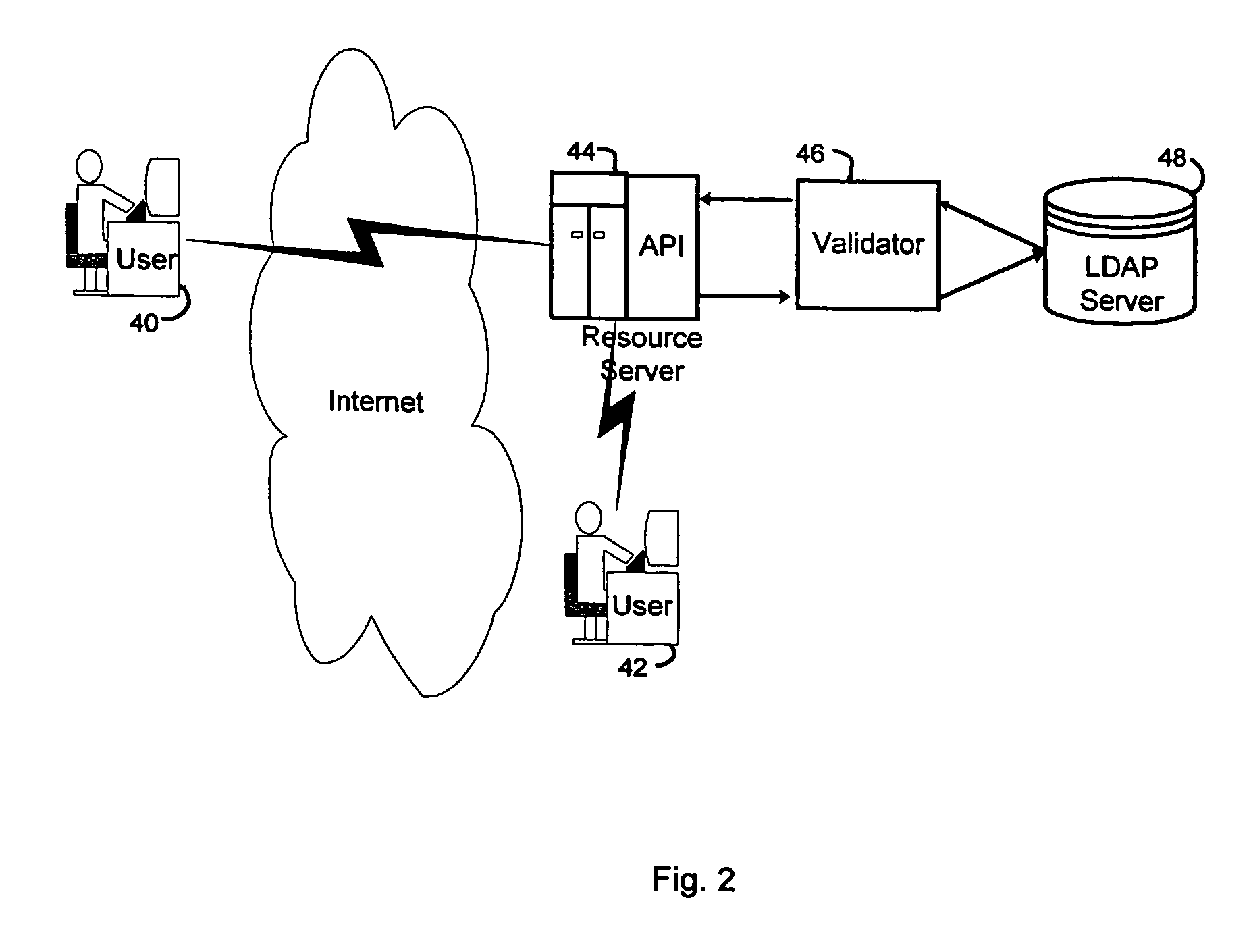
A security service of computer networks having a policy builder, an LDAP-compliant database, a validator and an API. The policy builder component provides a graphical user interface to be used by a policy manager to define access policies for users seeking to access network services and resources. The graphical user interface has a grid of nodes representing access policies. The grid is arranged to correspond to a defined tree structure representing services and resources and a business relationship tree structure representing users. The graphical user interface permits the policy manager to define policy builder plug-ins for access policy customization. The LDAP-compliant database maintains the policy builder plug-ins. The validator component receives requests from users and queries the LDAP-compliant database to obtain relevant access policies as defined by the policy manager. The system provides for double inheritance of access policies such that where there is no express definition of an access policy for a node, the access policies are propagated according to the hierarchical structures of the data. The validator includes validator plug-ins for carrying out access policies corresponding to the access policies defined by policy builder plug-ins.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
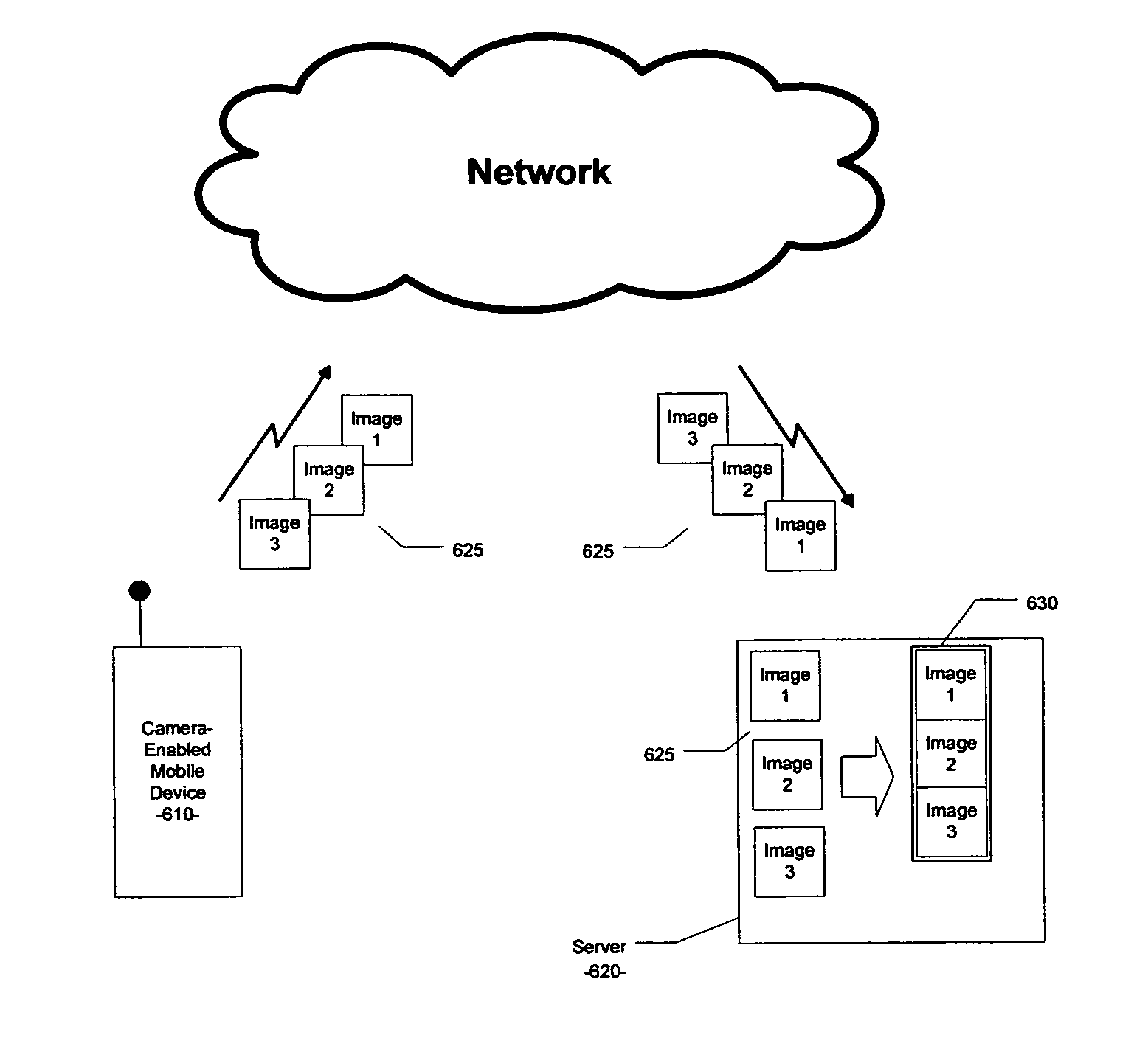
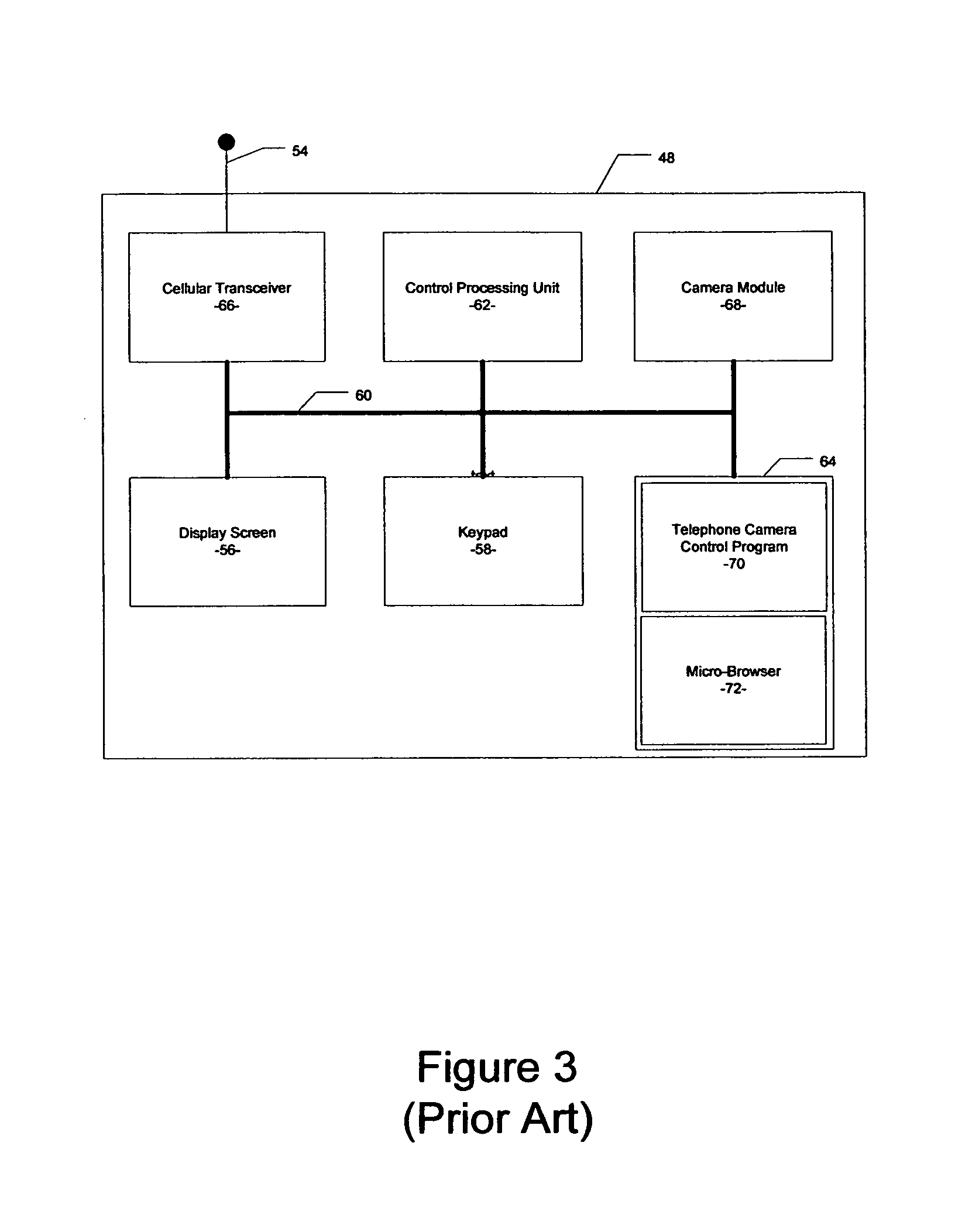
Computer-implemented system and method for automated image uploading and sharing from camera-enabled mobile devices
A computer-implemented system and method for automatically capturing a set of images with a camera-enabled mobile device and for uploading the set of images to a network server is disclosed. The present invention further includes creating an animation of two or more images of the set of images automatically captured by the camera-enabled mobile device.
Owner:GULA CONSULTING LLC
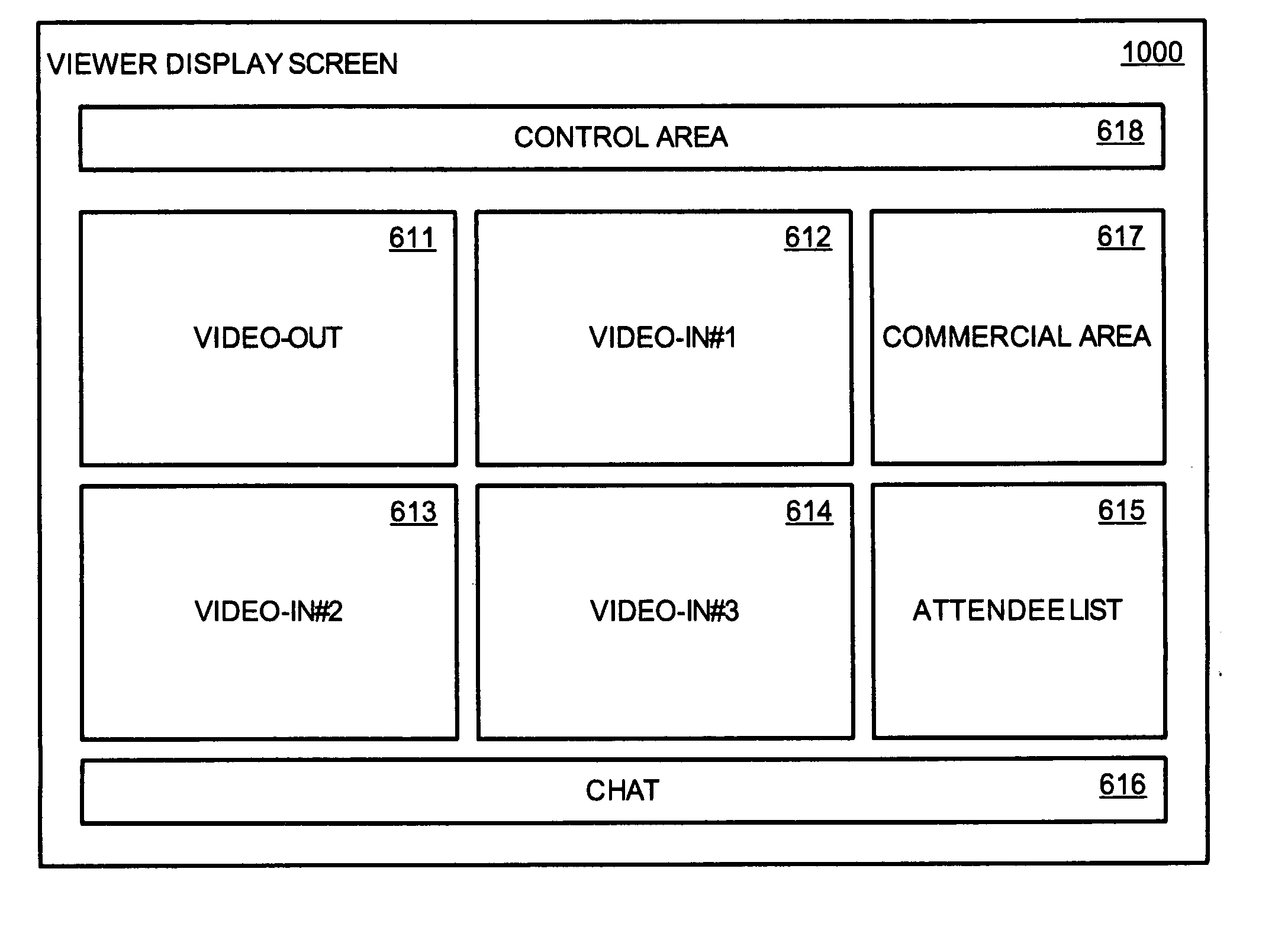
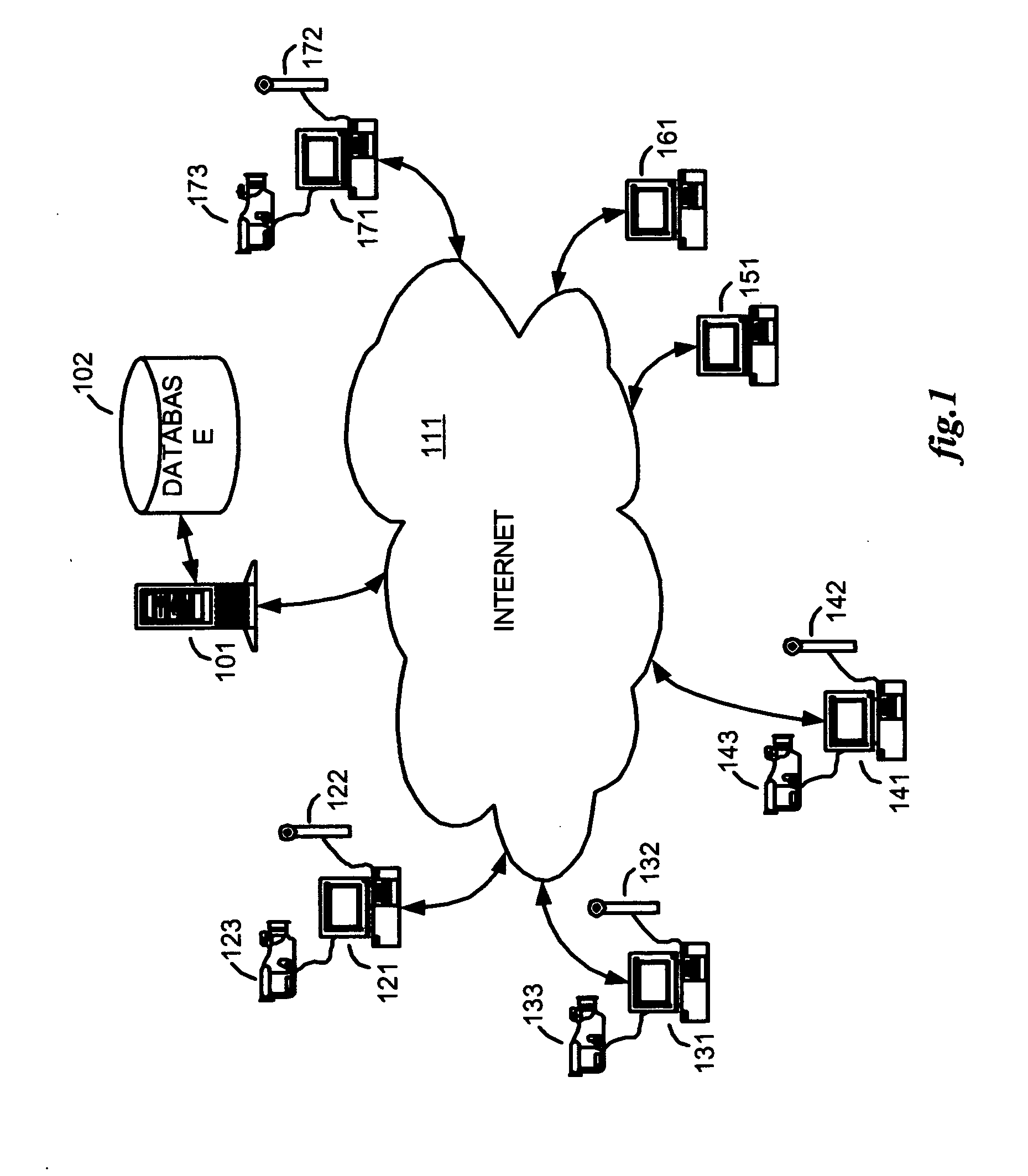
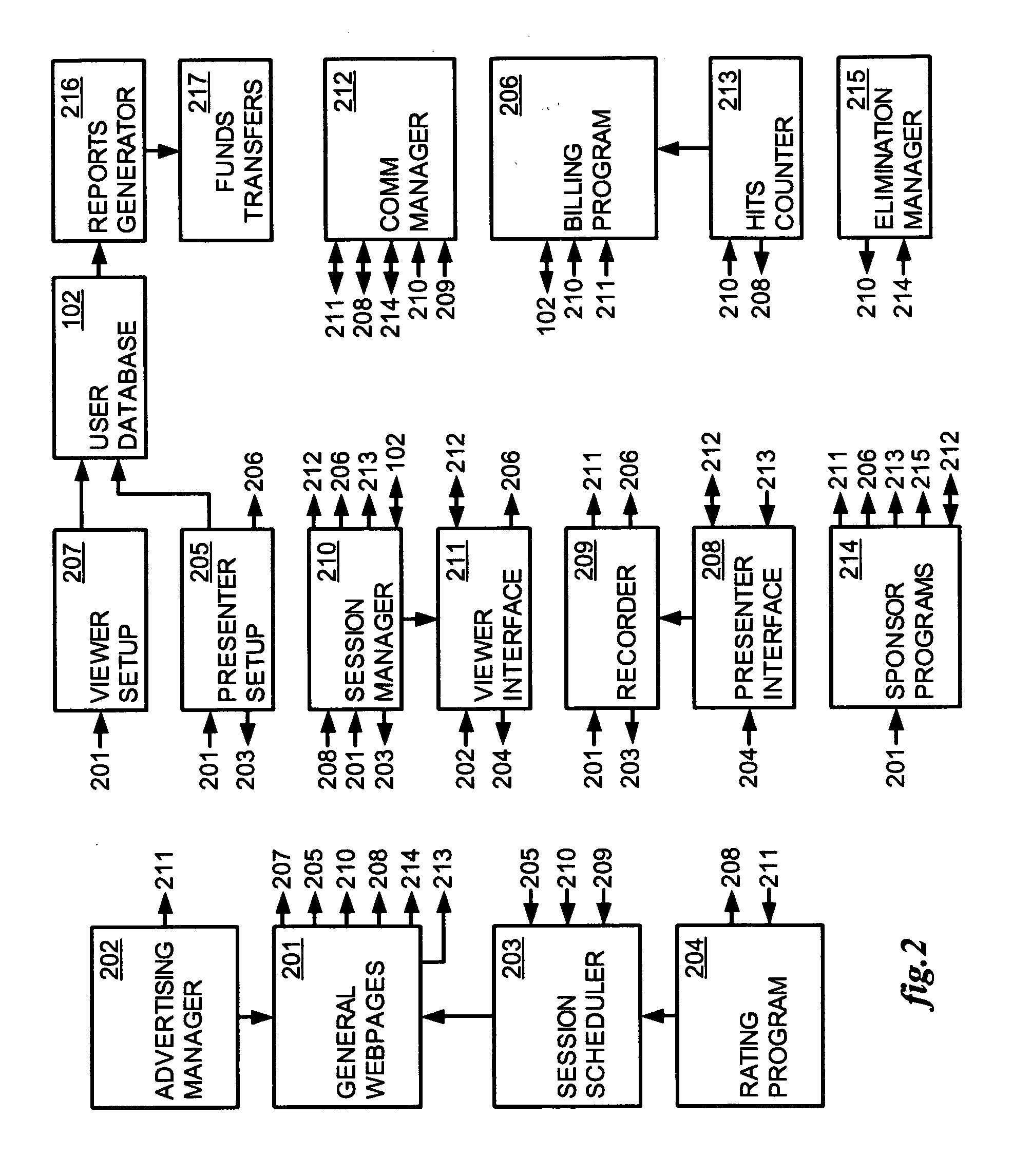
Method and apparatus for broadcasting live personal performances over the internet
InactiveUS20050138560A1Reliable and safe and purchasingEasily interfaceTelevision system detailsRecording carrier detailsPaymentWeb browser
A method and apparatus for broadcasting live personal performances over the Internet employs a web server to manage scheduling and broadcasting of the performances over the Internet, as well as collections and payments for products and services sold by presenters to viewers in conjunction with their performances. The server receives audio / video data from presenter operated computers through an uploaded presenter program, and relays the received audio / video data to viewer operated computers for viewing in media players invoked by their web browsers responding to an uploaded HTML document or JAVA applet. Viewers select performances to view from a program schedule provided on a webpage hosted by the web server. Both viewers and presenters are registered with the web server to facilitate payments for products and services, and their financial information stored in a secure user database.
Owner:ORIDUS
Method and apparatus for establishing dynamic tunnel access sessions in a communication network
InactiveUS7117526B1Key distribution for secure communicationPublic key for secure communicationTelecommunications linkCommunication link
A method and apparatus for implementing dynamic tunnel access sessions at a network device within a communications network. The tunnel access sessions are created between a network device, typically a gateway device and a network service, such as the Internet or a corporate intranet. The dynamic tunnel access sessions provide for subscriber-transparent tunneling. The present invention does not require special client-side software to be loaded on the remote host of the subscriber, and does not require any manual configuration of the remote host. A subscriber is capable of establishing more than one tunnel access session to more than one network service during a network session. Additionally, more than one subscriber who accesses the communication network via the network device is able to establish a communication link with a pre-existing tunnel.
Owner:NOMADIX INC
Updating routing information based on client location
ActiveUS20100125675A1Digital computer detailsLocation information based serviceIp addressClient-side
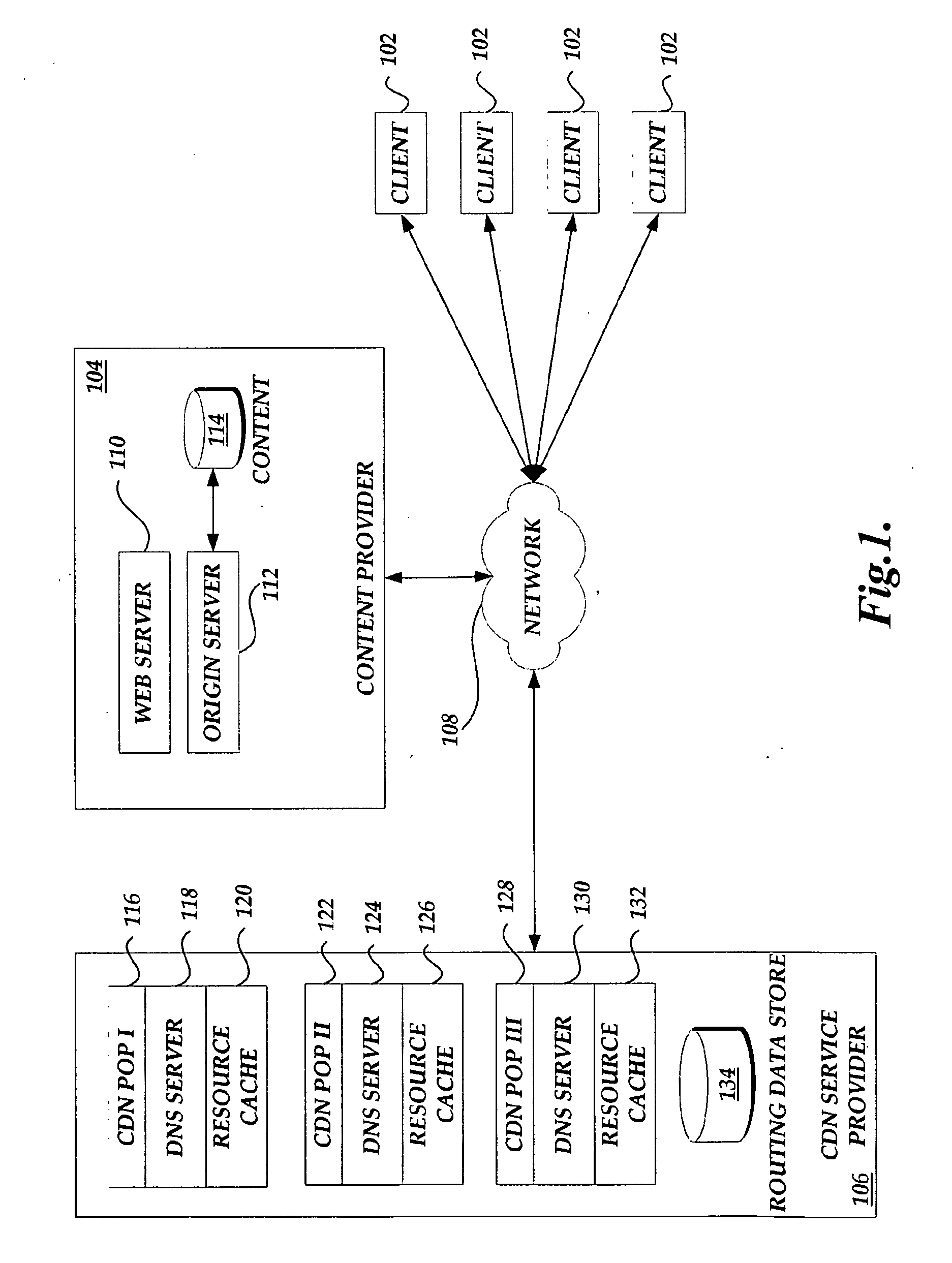
A system, method, and computer-readable medium for updating request routing information associated with client location information are provided. A content delivery network service provider receives a DNS query from a client computing device. The DNS query corresponds to a resource identifier for requested content from the client computing device. The content delivery network service provider obtains a query IP address corresponding to the client computing device. Based on routing information associated with the query IP address, the content delivery network service provider routes the DNS query. The process further includes monitoring performance data associated with the transmission of the requested resource and updating routing information associated with the query IP address based on the performance data for use in processing subsequent requests form the client computing device.
Owner:AMAZON TECH INC
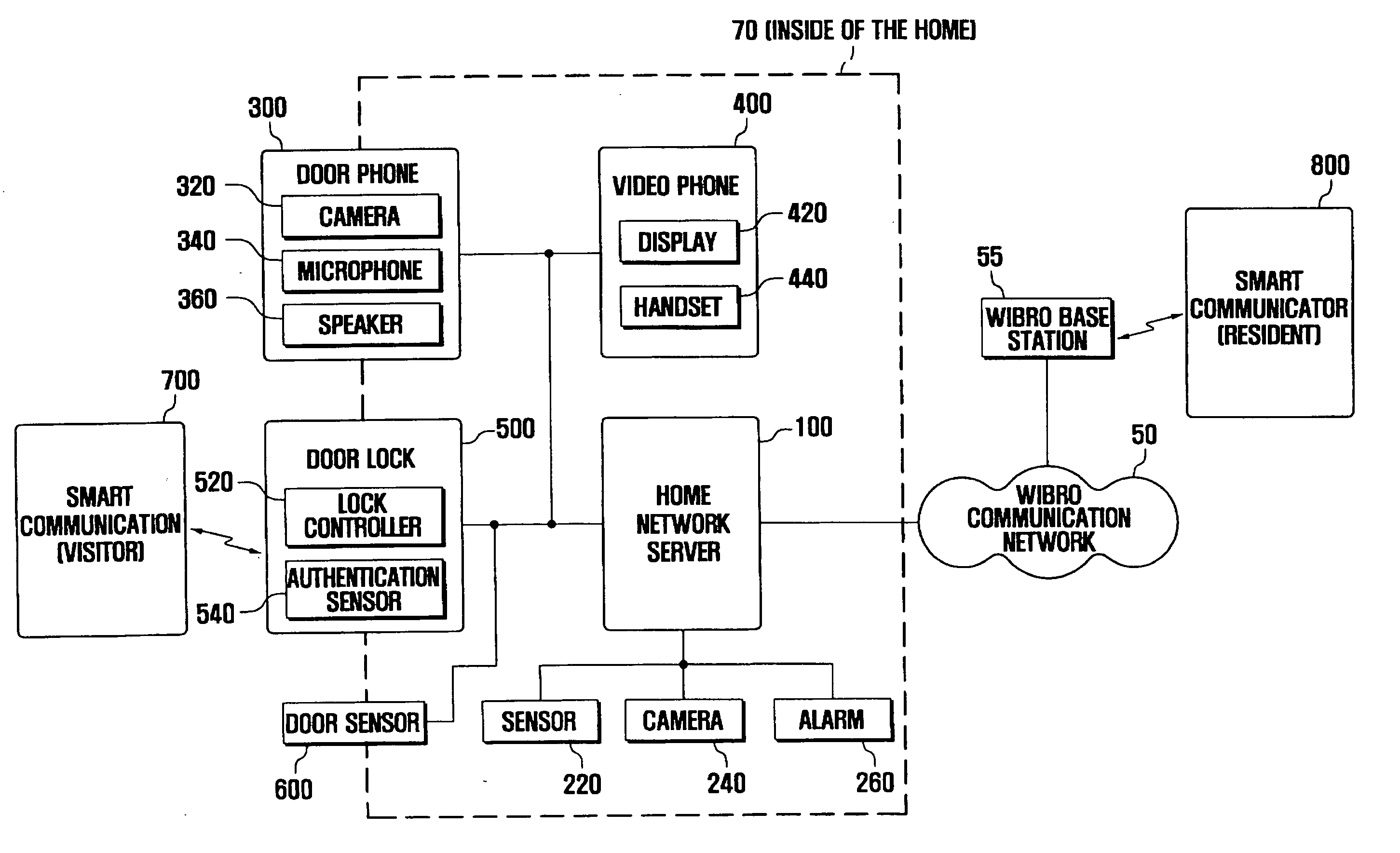
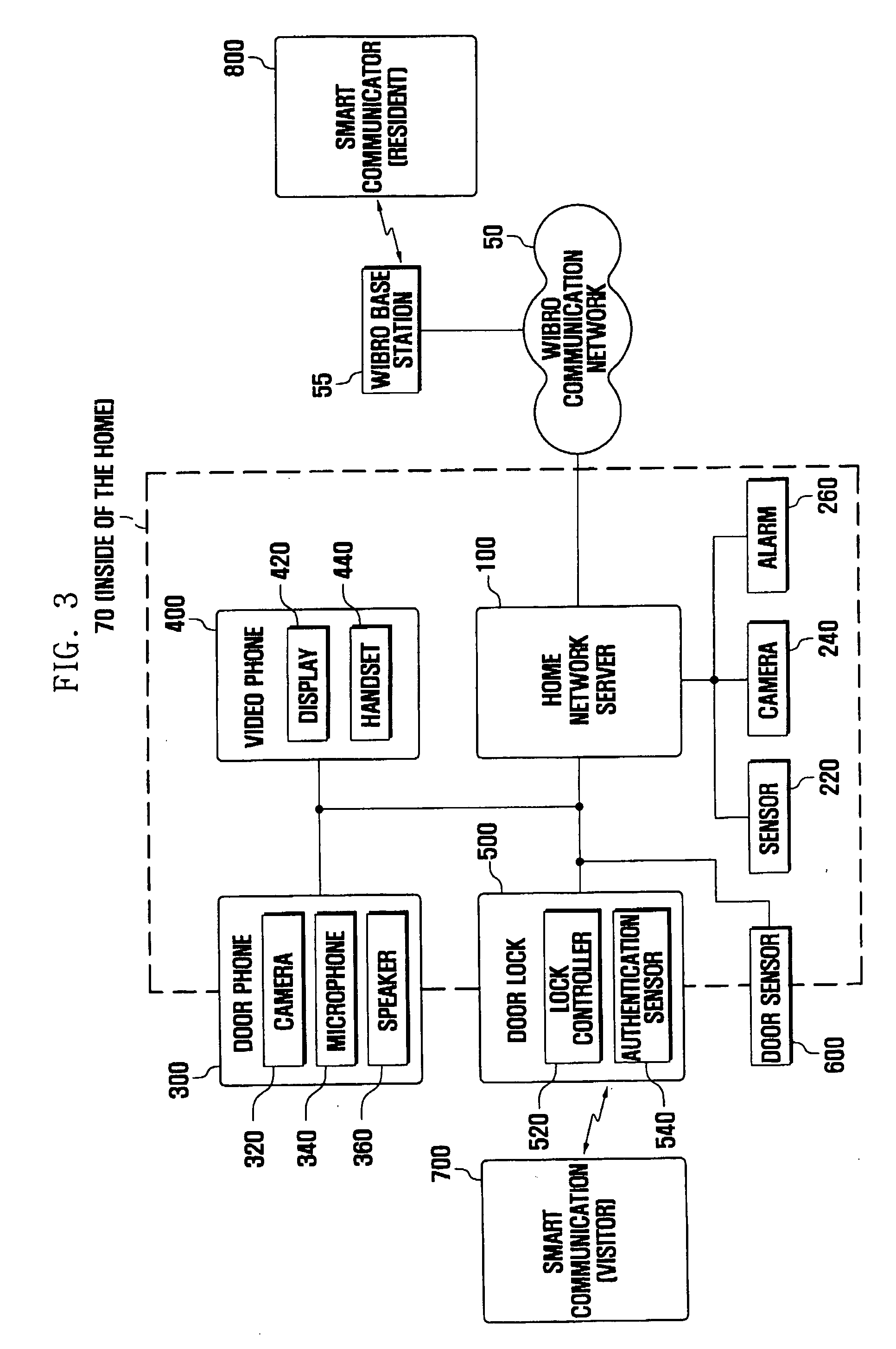
Access authentication system and method using smart communicator
ActiveUS20070216764A1Electric signal transmission systemsMultiple keys/algorithms usageCommunication controlAuthentication system
Disclosed is an intelligent access authentication system and method. The intelligent access authentication system includes a door lock that can be locked and released in a predetermined manner, a door phone for communicating with the visitor; a smart communicator which configures access approval levels of expected visitors and access authentication information for each access approval level, communicates with the visitor, and controls the door lock, and a home network server which stores the access approval levels of expected visitors and access authentication information for each access approval level received from the smart communicator, checks the access approval level of the visitor attempting to release the door lock by referring to previously stored information, and transmits a door lock operating command to the door lock according to the access approval level of the visitor. In the present invention, the resident can check the visitor and control the door lock to be released according to the access approval level of the visitor, even at a remote location.
Owner:HUAWEI TECH CO LTD
Automated updating of access points in a distributed network
InactiveUS20020157090A1Data switching by path configurationProgram loading/initiatingProgrammable read-only memoryRandom access memory
A method and system for maintaining network access point equipment including installing and upgrading software. The system includes a network server, and access point equipment including one or more access point devices, with each device equipped with a CPU including a random access memory (RAM) and a programmable read only memory (PROM). The server is configured for receiving software for maintaining the programming of access point devices. Both the access point devices and the server are programmed with authentication software for identifying each other prior to transmission of maintenance data. The access point devices are further programmed to periodically do a software check with the server. If the current software version in the device is the same as that stored in the server, no action is taken. If the version in the server is different, then the server and device automatically load the current software version into the device.
Owner:HEREUARE COMMUNICATIOINS
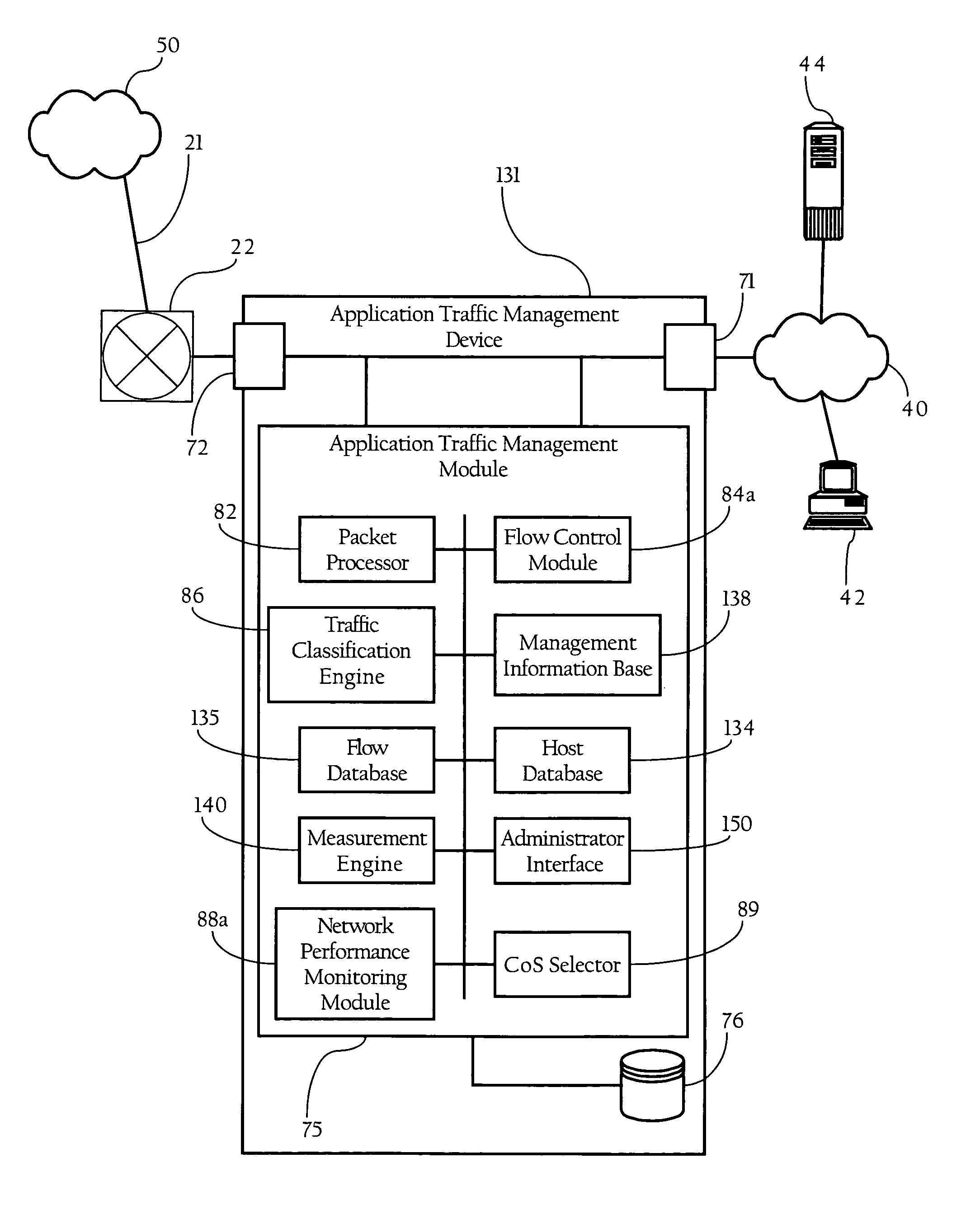
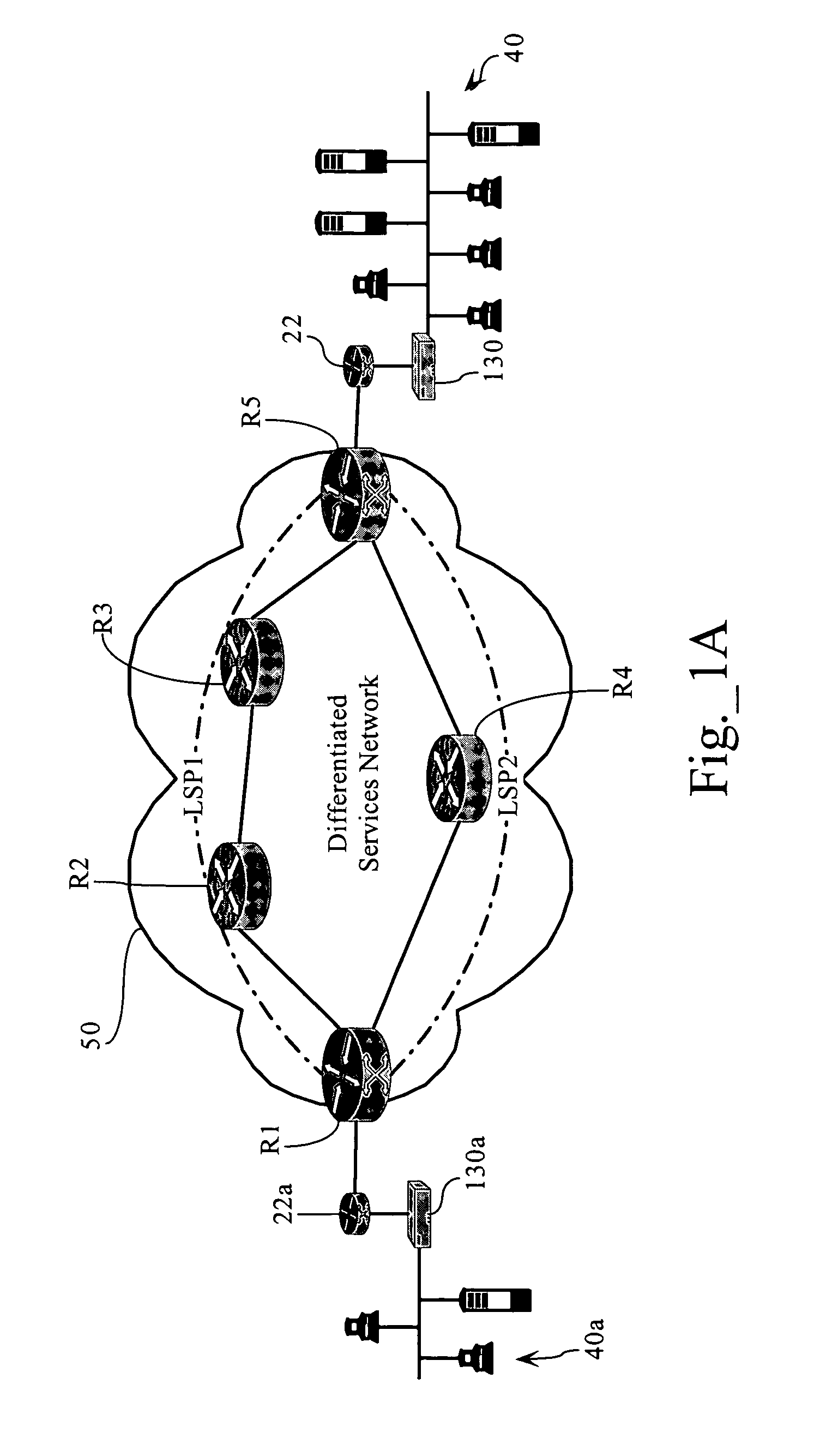
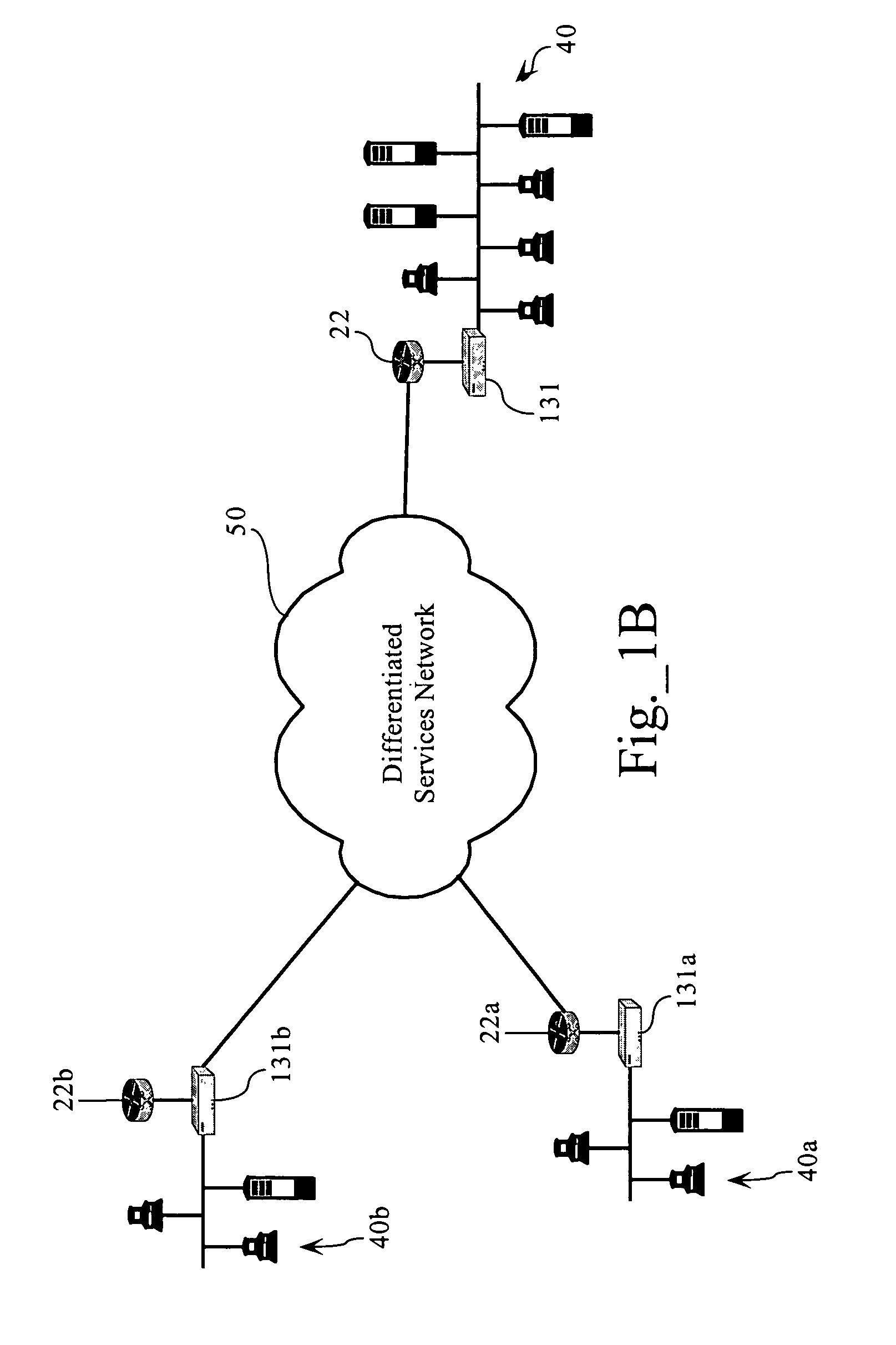
Adaptive, application-aware selection of differntiated network services
ActiveUS7843843B1Sacrificing application performanceReduce bandwidth costsError preventionFrequency-division multiplex detailsNetwork conditionsNetwork service
Methods, apparatuses and systems that dynamically adjust the selection of differentiated network services for selected classes of traffic or network applications in response to changing network conditions or application performance levels.
Owner:CA TECH INC
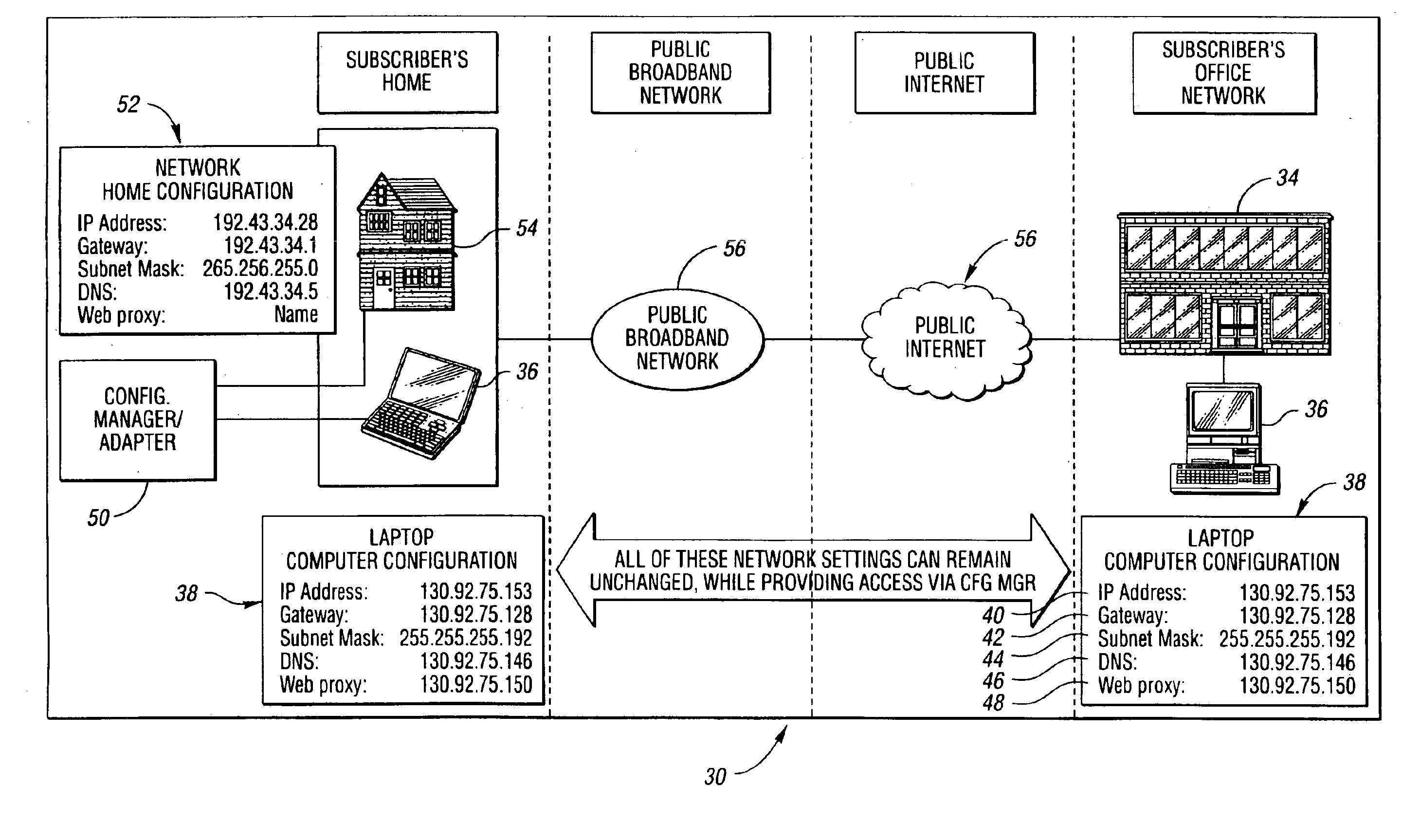
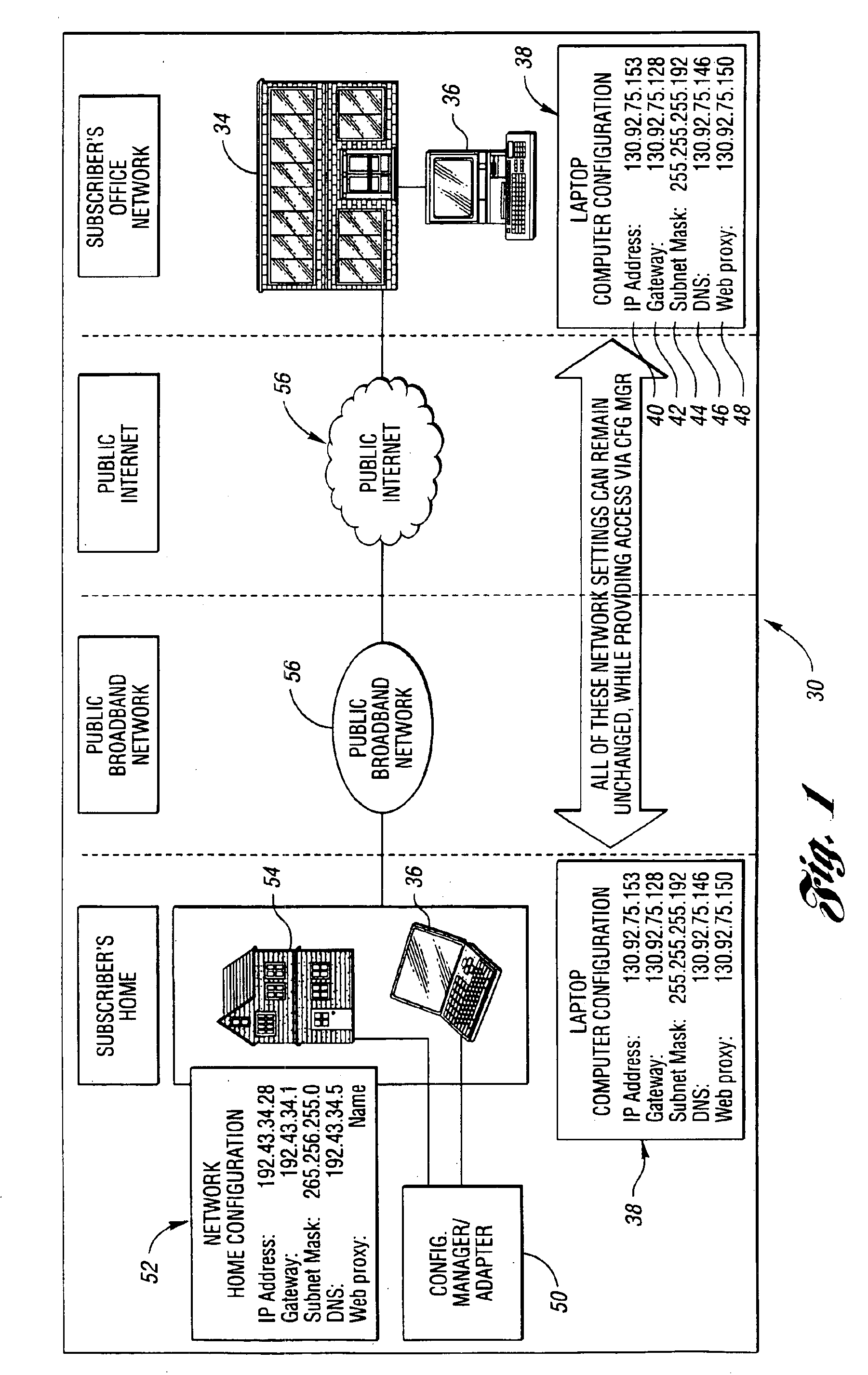
System and method for network access without reconfiguration
InactiveUS6857009B1Easy to addEasy to deleteTime-division multiplexData switching by path configurationDomain nameComputer compatibility
A system and method for providing connectivity to a foreign network for a device configured for communication over a home network without reconfiguring the device include intercepting packets transmitted by the device, selectively modifying intercepted packets which are incompatible with the foreign network to be compatible with network settings of the foreign network, and selectively providing network services for the device corresponding to network services available on the home network to reduce the delay associated with accessing the network services from the foreign network, or to provide network services otherwise inaccessible from the foreign network. Network services are provided by or through a configuration adapter connected to the device or to the foreign network. The configuration adapter accommodates incompatibilities resulting from proxy server requests, domain name server requests, and / or outgoing email service requests to provide transparent network access for mobile users without reconfiguration of the users computing device.
Owner:NOMADIX INC
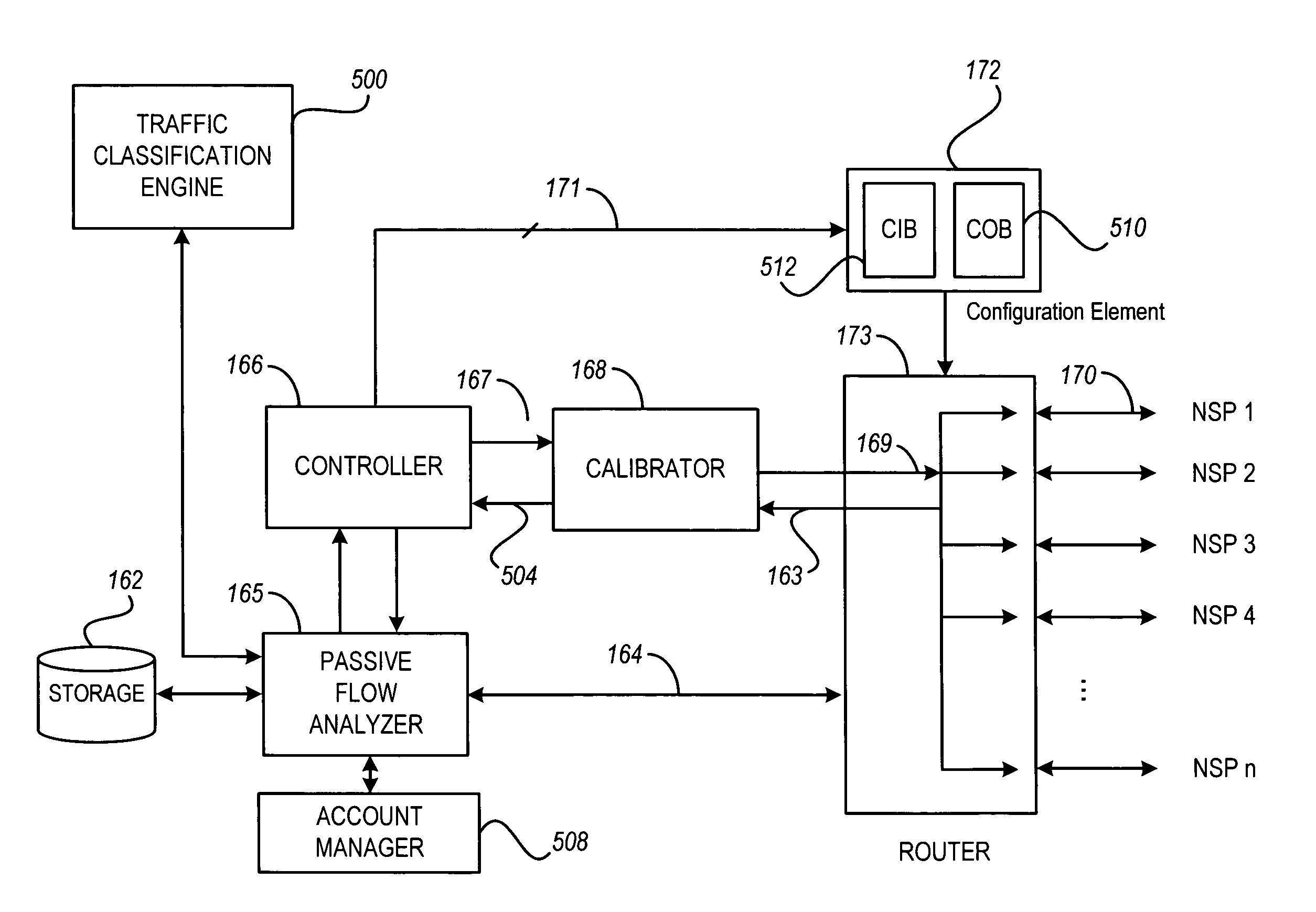
System and method to assure network service levels with intelligent routing
A method and system for maintaining a traffic service level for data communicated by a computer network having a source. The computer network is connected to at least one of many networks, where each of the many networks includes a number of paths for transporting the data communicated to a destination. In one embodiment of the method, the traffic service level associated with one of the paths between the source and the destination is monitored. Then, it is determined whether the traffic service level associated with that path meets one or more performance metrics. If a flow of data communicated over the monitored path fails to meet at least one of the performance metrics, then a service level violation is indicated. Upon such an indication, an alternate path is selected to resolve the service level violation.
Owner:INTERNAP HLDG LLC
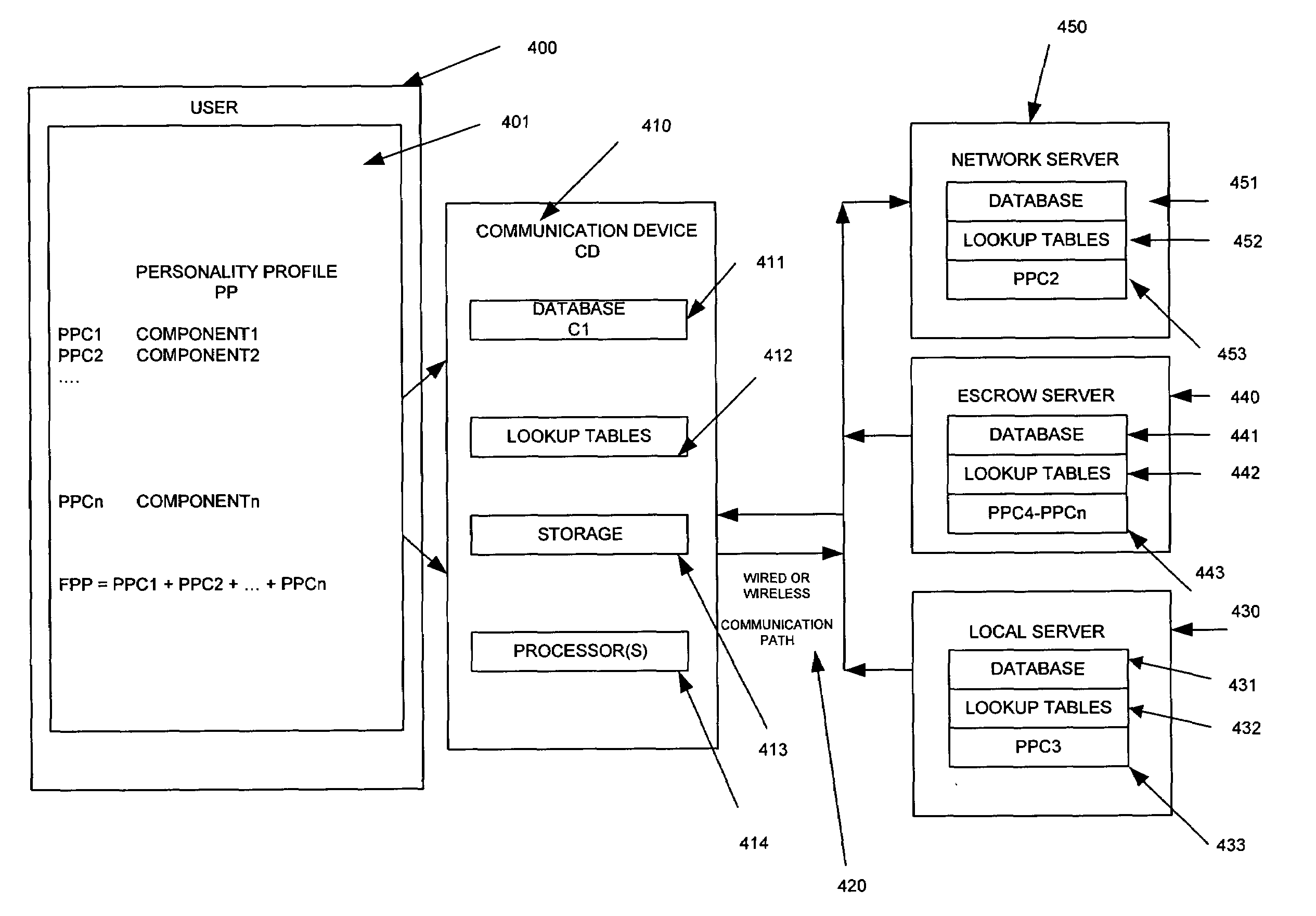
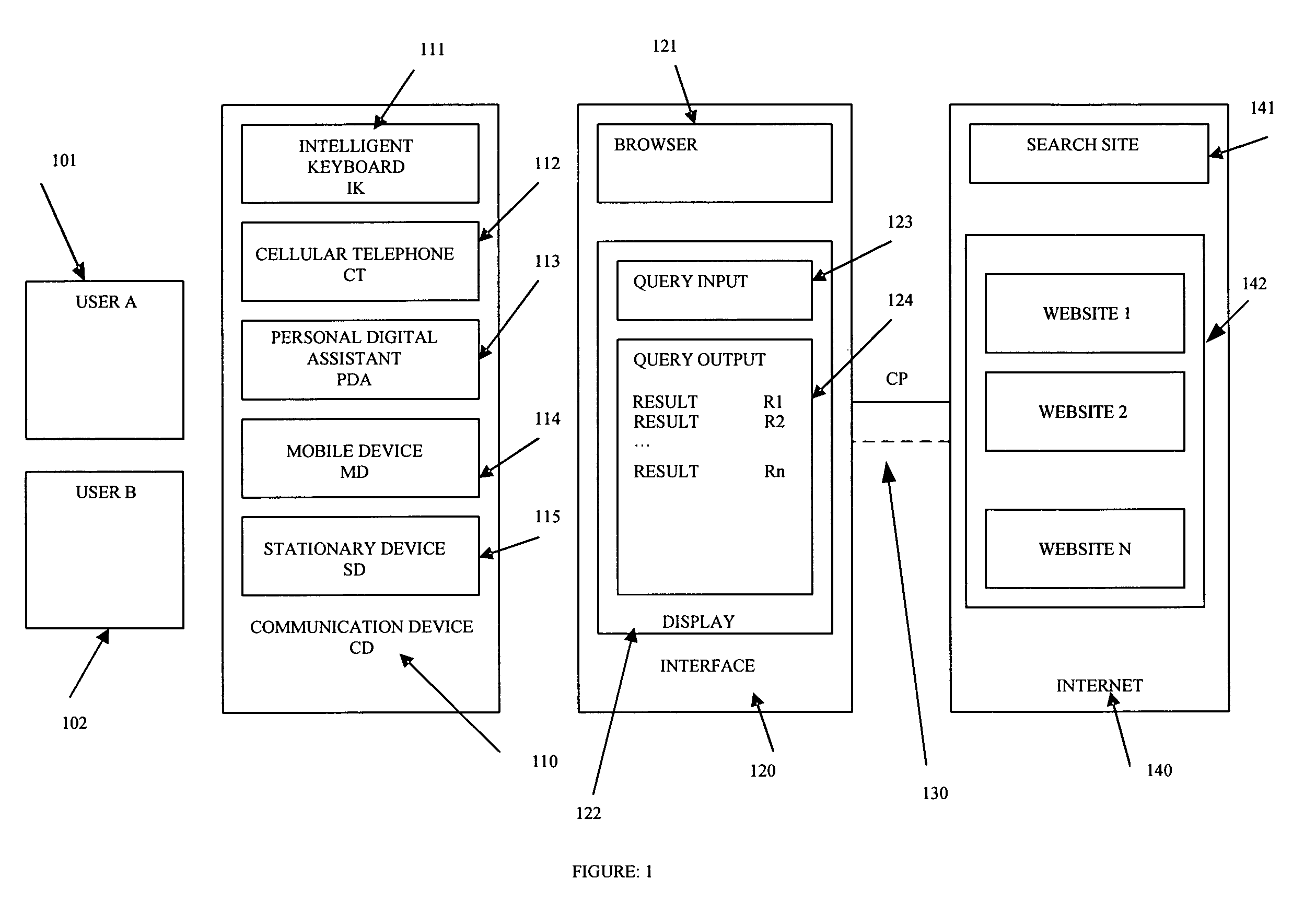
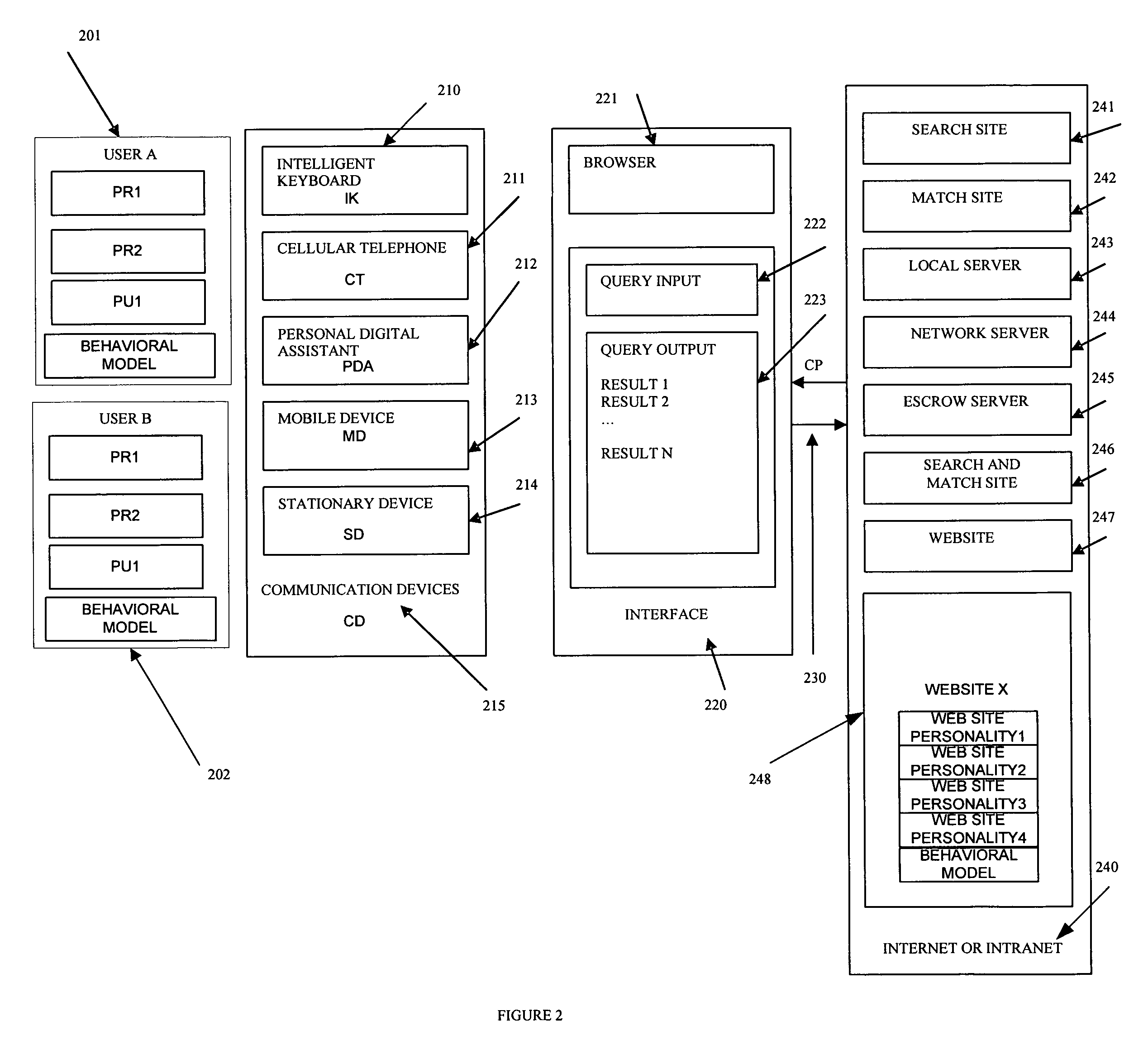
Matching network system for mobile devices
InactiveUS20080133716A1Rich web experienceMore granular and targeted accessServices signallingMultiple digital computer combinationsNetworked systemNetwork service
A matching network system including communication devices, servers and software which enables the provisioning of services and execution of transactions based on a plurality of private and public personality profiles and behavior models of the users, of the communication devices, of the products / services and of the servers; in combination with the software resident at the communication device level and or the local / network server level. Matching and searching processes based on a plurality of personality profiles wherein the information, communication and transactions are enabled to be matched with the user, the communication device and or the servers. The communication device is a stationary device or a mobile device, such as a portable computing device, wireless telephone, cellular telephone, personal digital assistant, or a multifunction communication, computing and control device.
Owner:IP HLDG LLC
Systems and methods for using reputation scores in network services and transactions to calculate security risks to computer systems and platforms
ActiveUS20130298192A1Memory loss protectionError detection/correctionMathematical CalculusInternet privacy
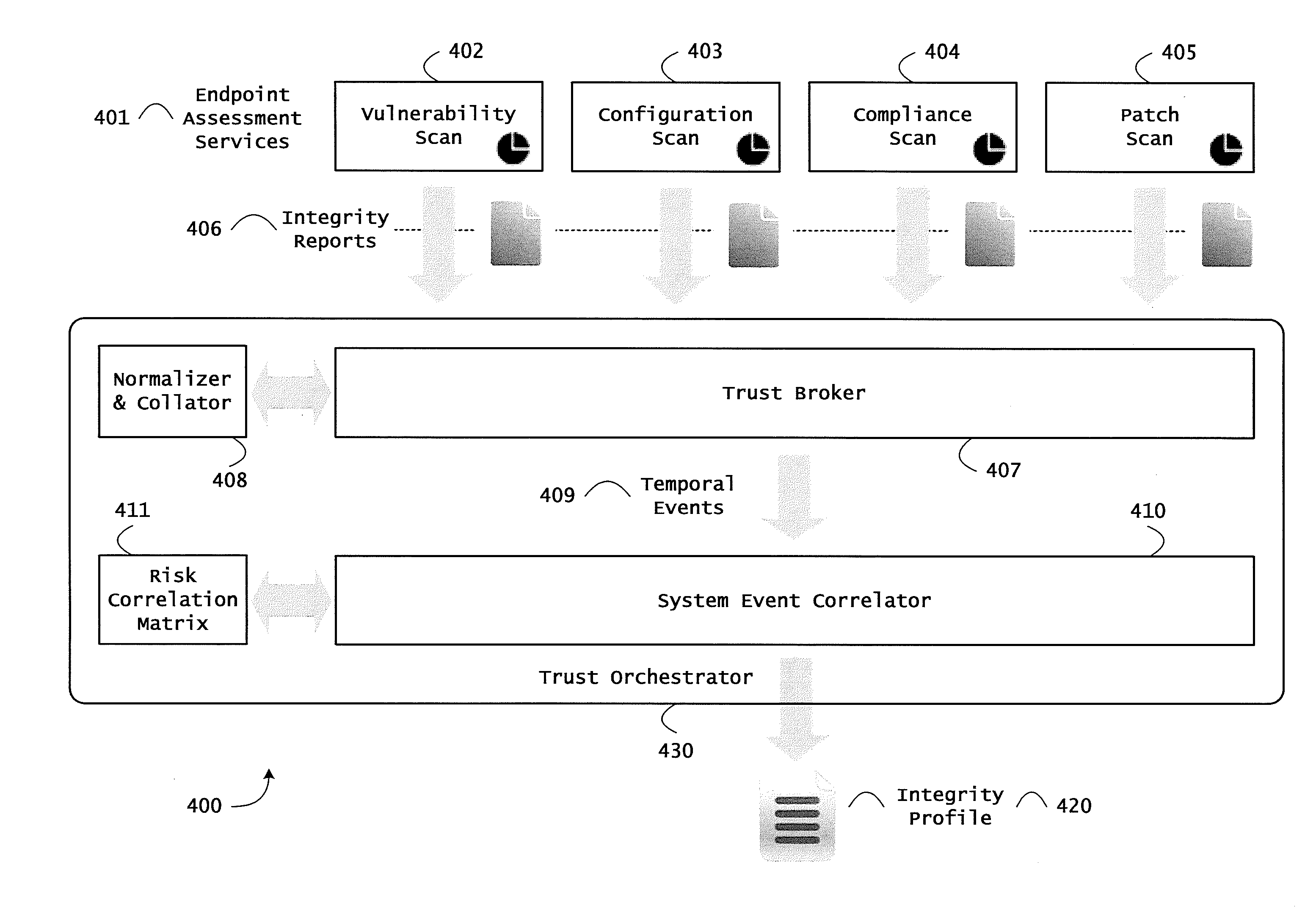
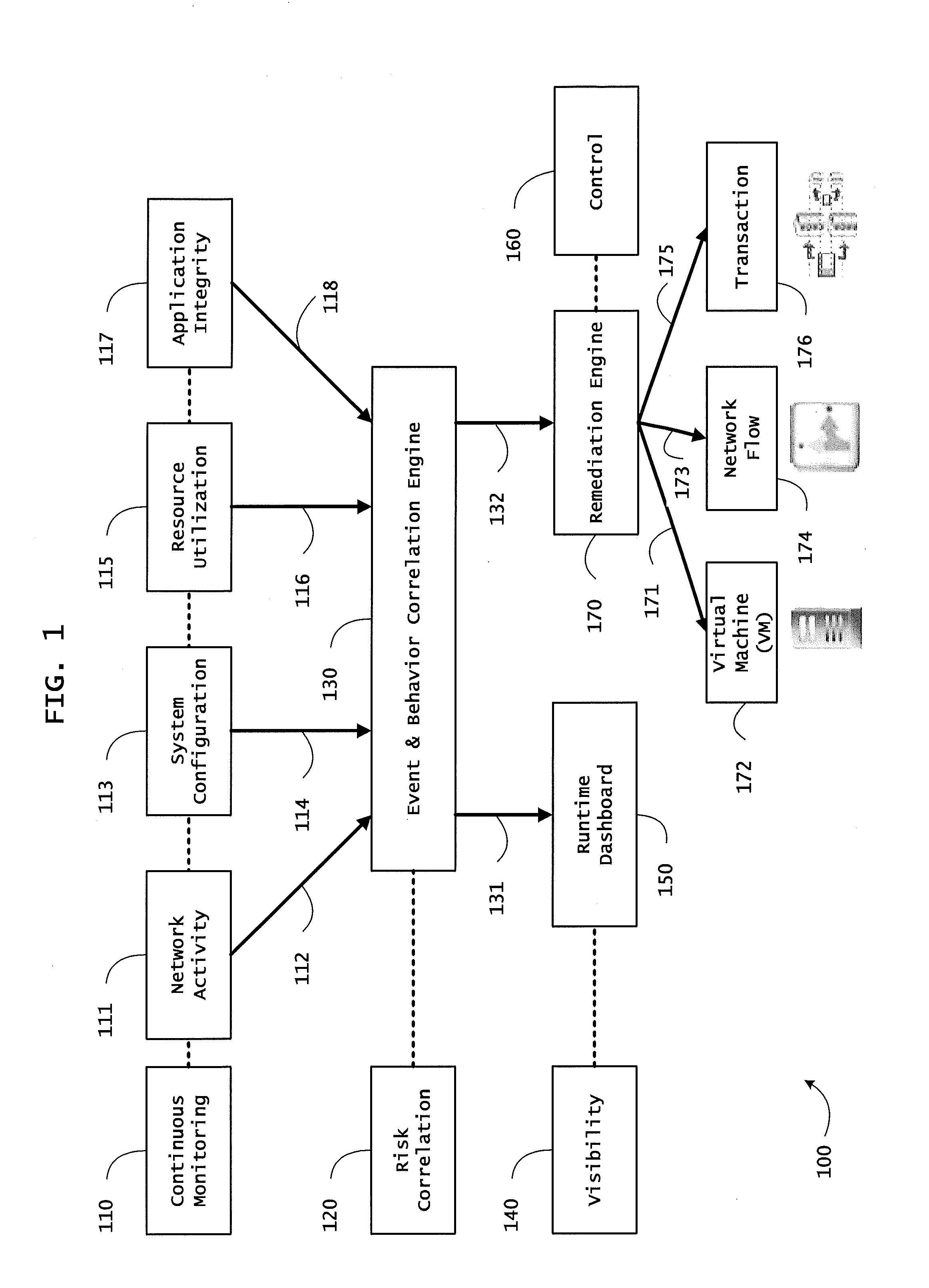
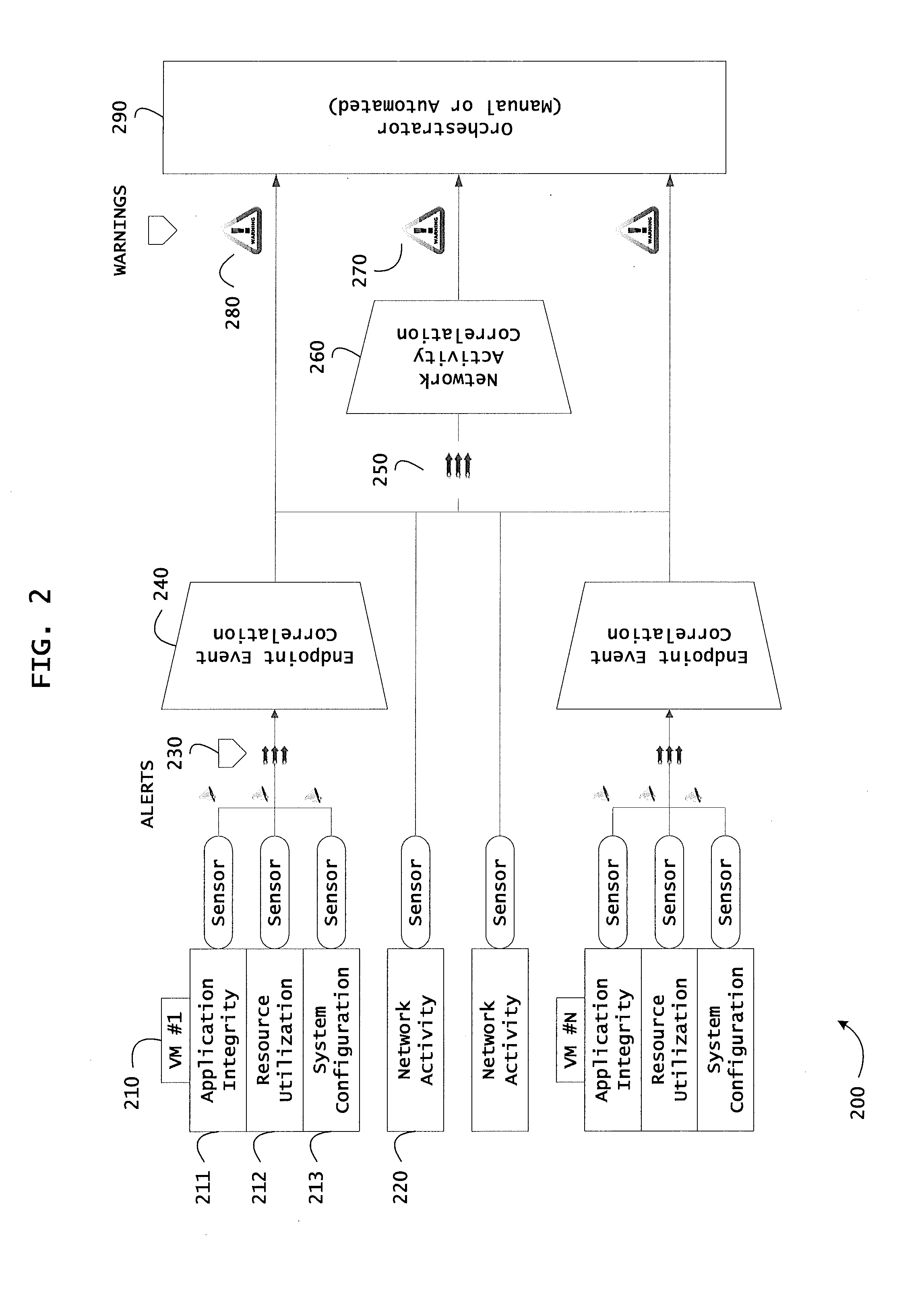
Instrumented networks, computer systems and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for calculating security risks by determining subject reputation scores. In an embodiment, a system receives a query for a reputation score of a subject, initiates directed queries to external information management systems to interrogate attributes associated with the subject, and analyzes responses. The system receives a hierarchical subject reputation score based on a calculus of risk and returns a reputation token. In another embodiment, a method provides real time attestation of a subject's reputation to a service provider using an endpoint trust agent, and a trust orchestrator comprising a reputation broker and a trust broker.
Owner:TAASERA LICENSING LLC
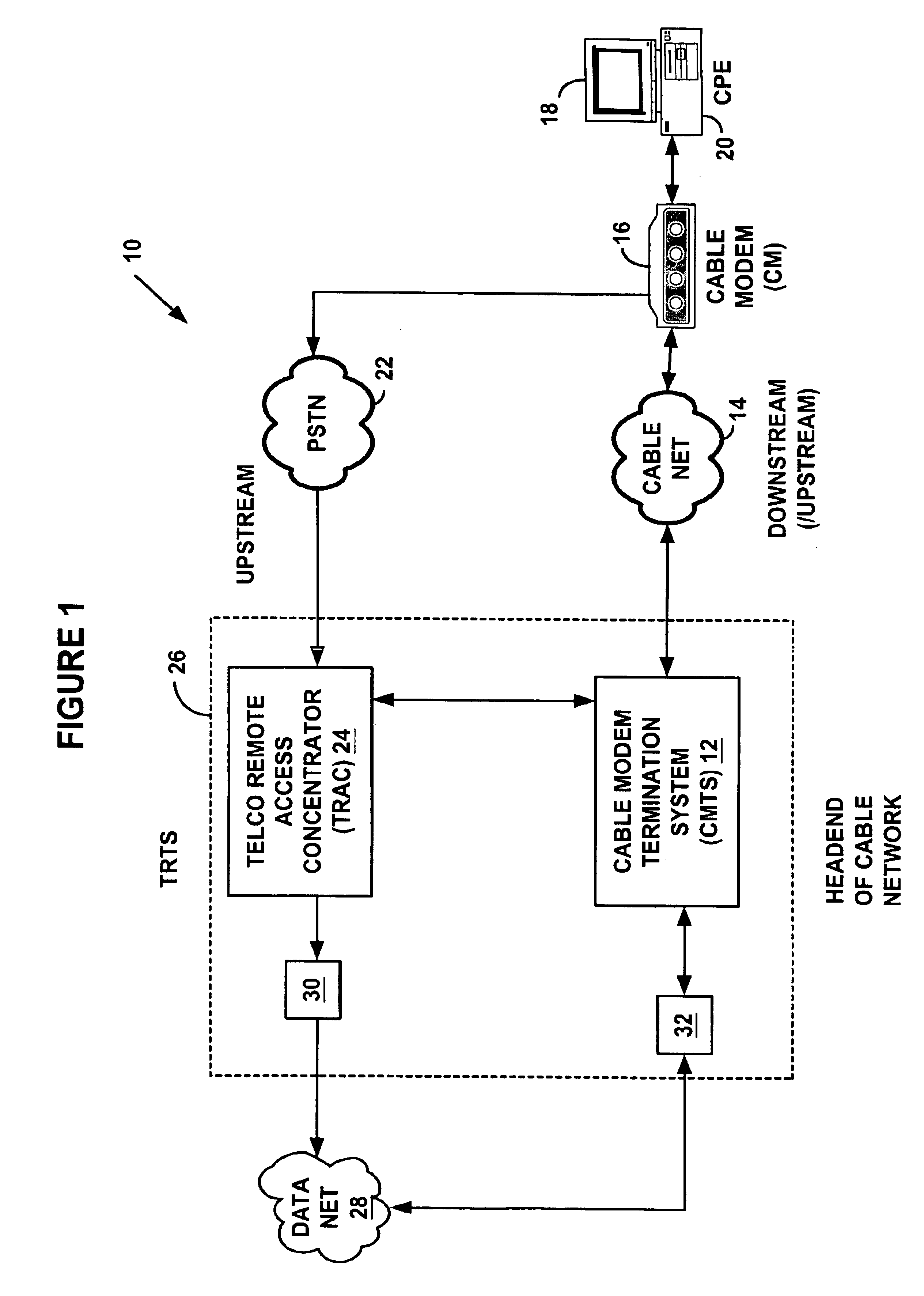
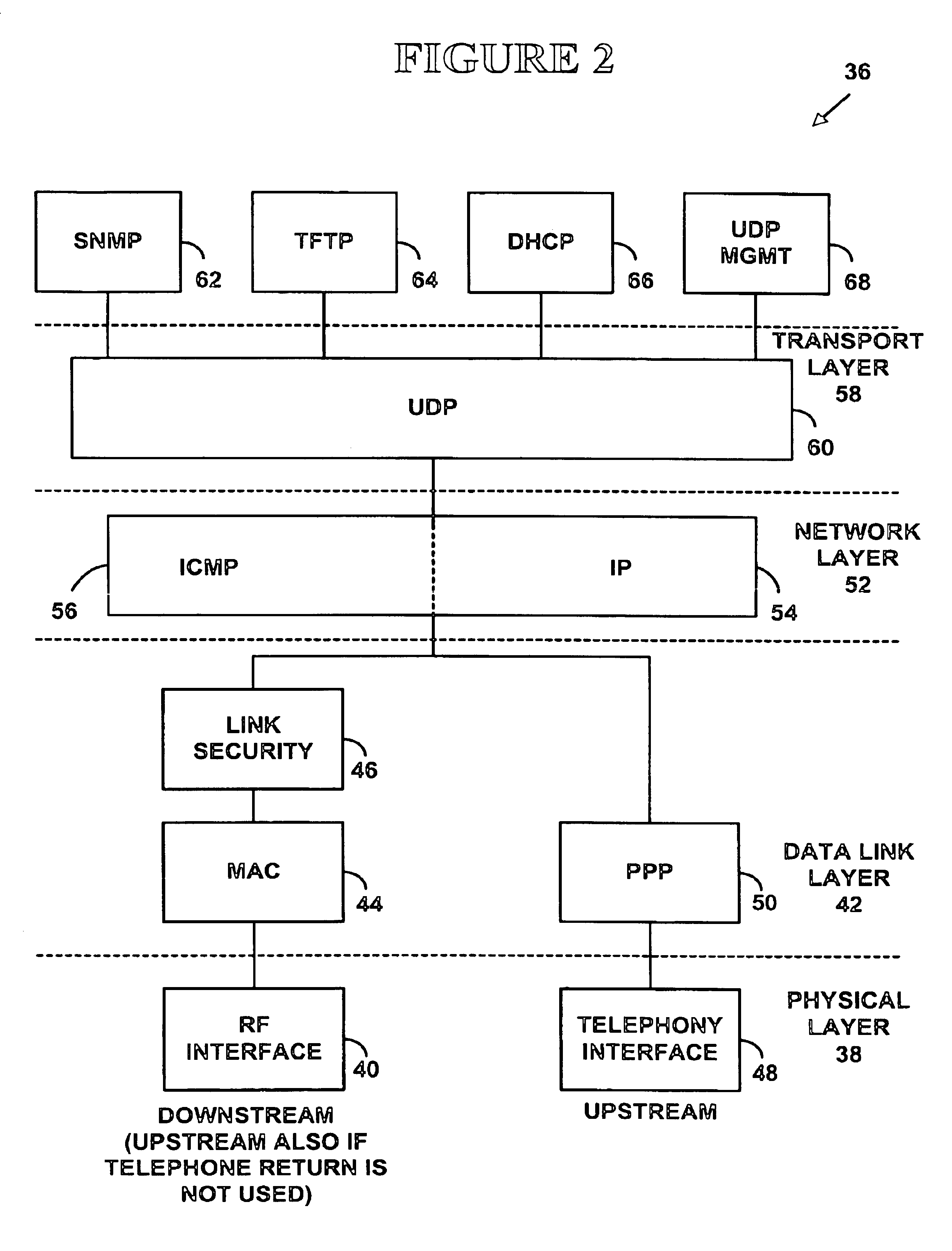
System and method for a specialized dynamic host configuration protocol proxy in a data-over-cable network
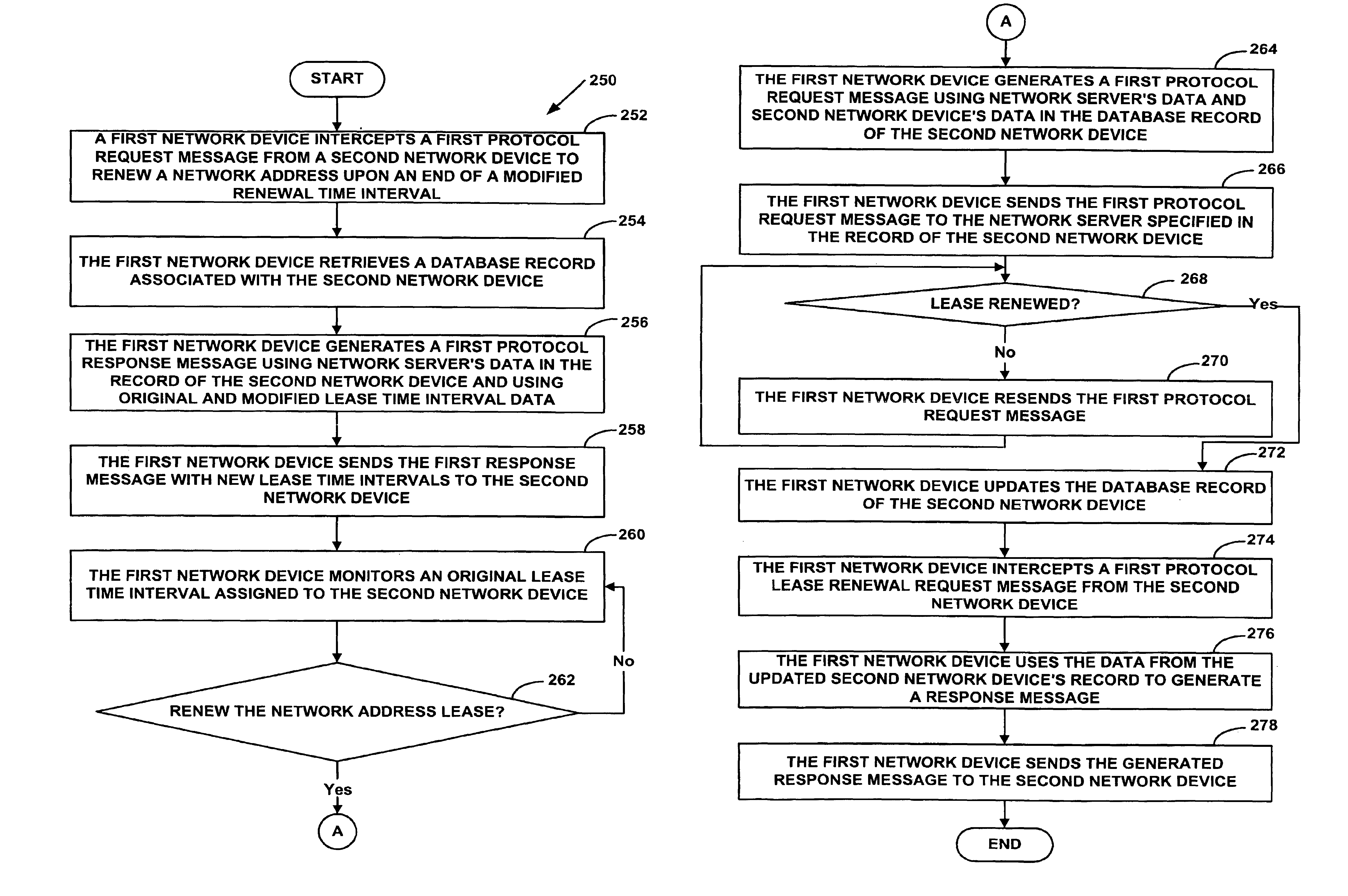
A system and method for proxying Dynamic Host Configuration Protocol (“DHCP”) network services for a network device, such as, a customer premise equipment entity, on a network device, such as, a cable modem, include creating a specialized proxy task for the customer premise equipment entity on the cable modem. One method of the present invention includes intercepting DHCP message flow between a customer premise equipment having a specialized proxy task created on the cable modem and a DHCP server selected by the customer premise equipment entity. The methods further include modifying lease time intervals prior to providing a routable network address lease to a customer premise equipment entity and renewing an initial lease for the customer premise equipment entity by a cable modem prior to expiration of the lease time interval provided by a DHCP server. The methods include using known protocols, such as, for example, the Dynamic Host Configuration Protocol.
Owner:VALTRUS INNOVATIONS LTD
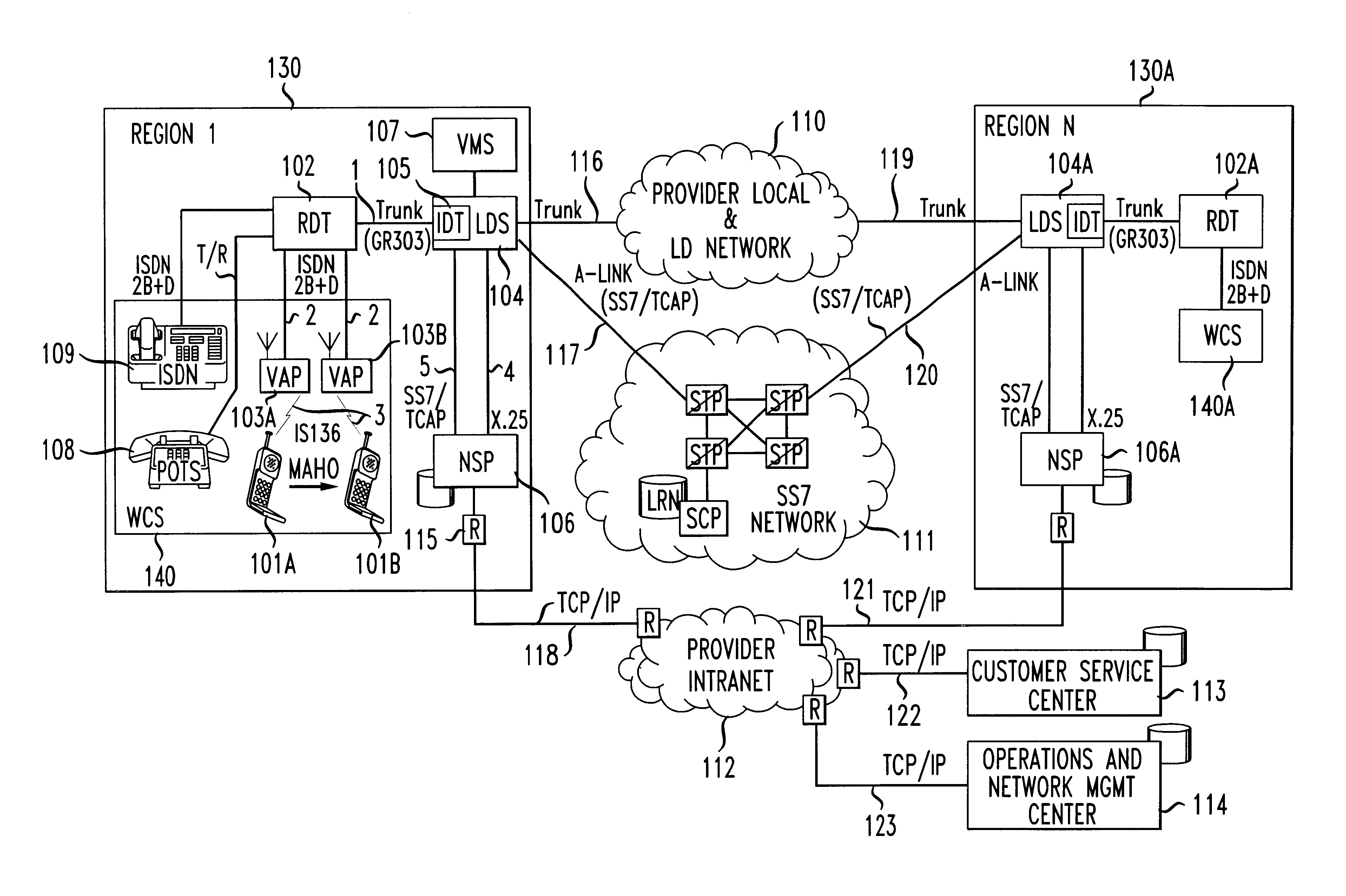
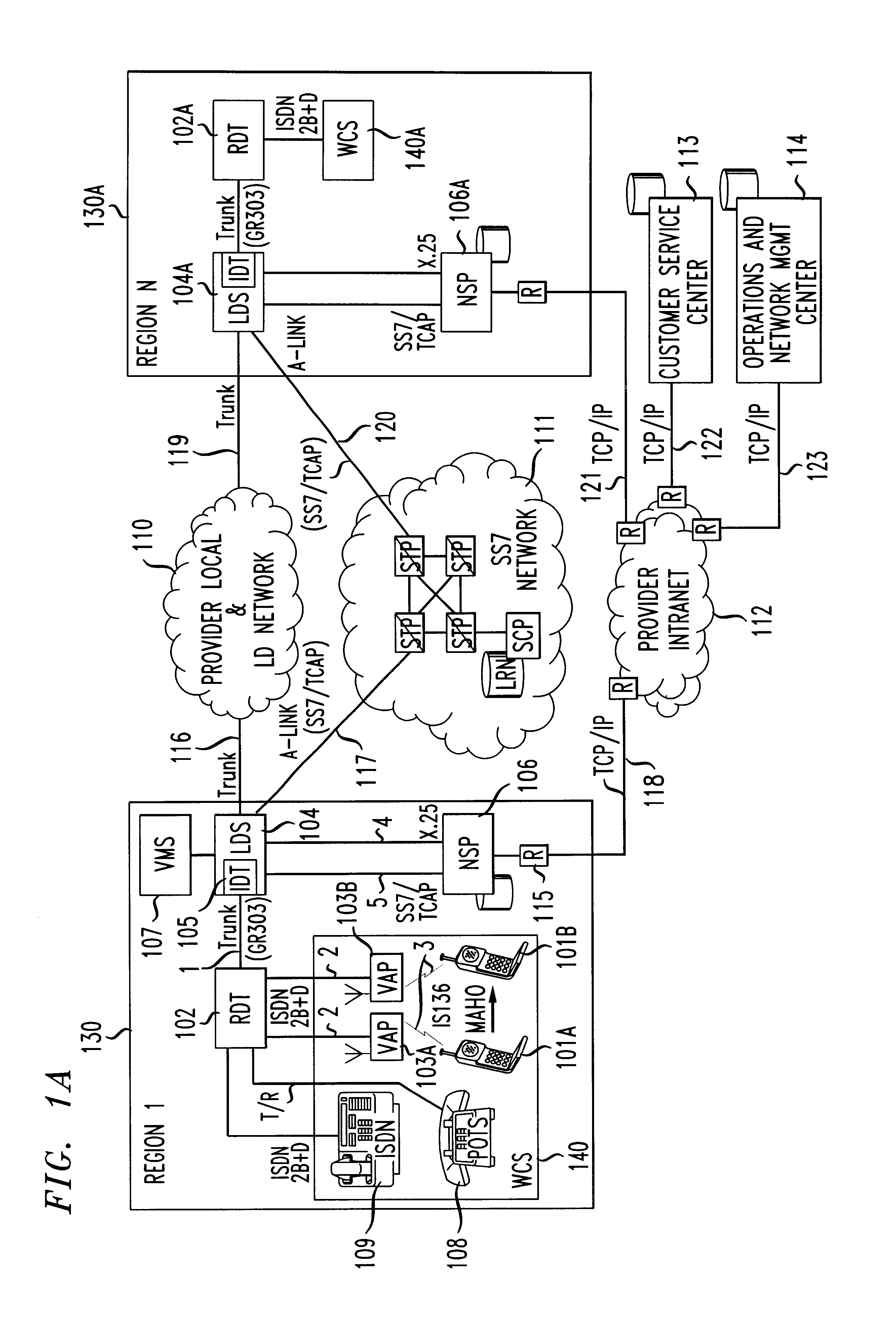
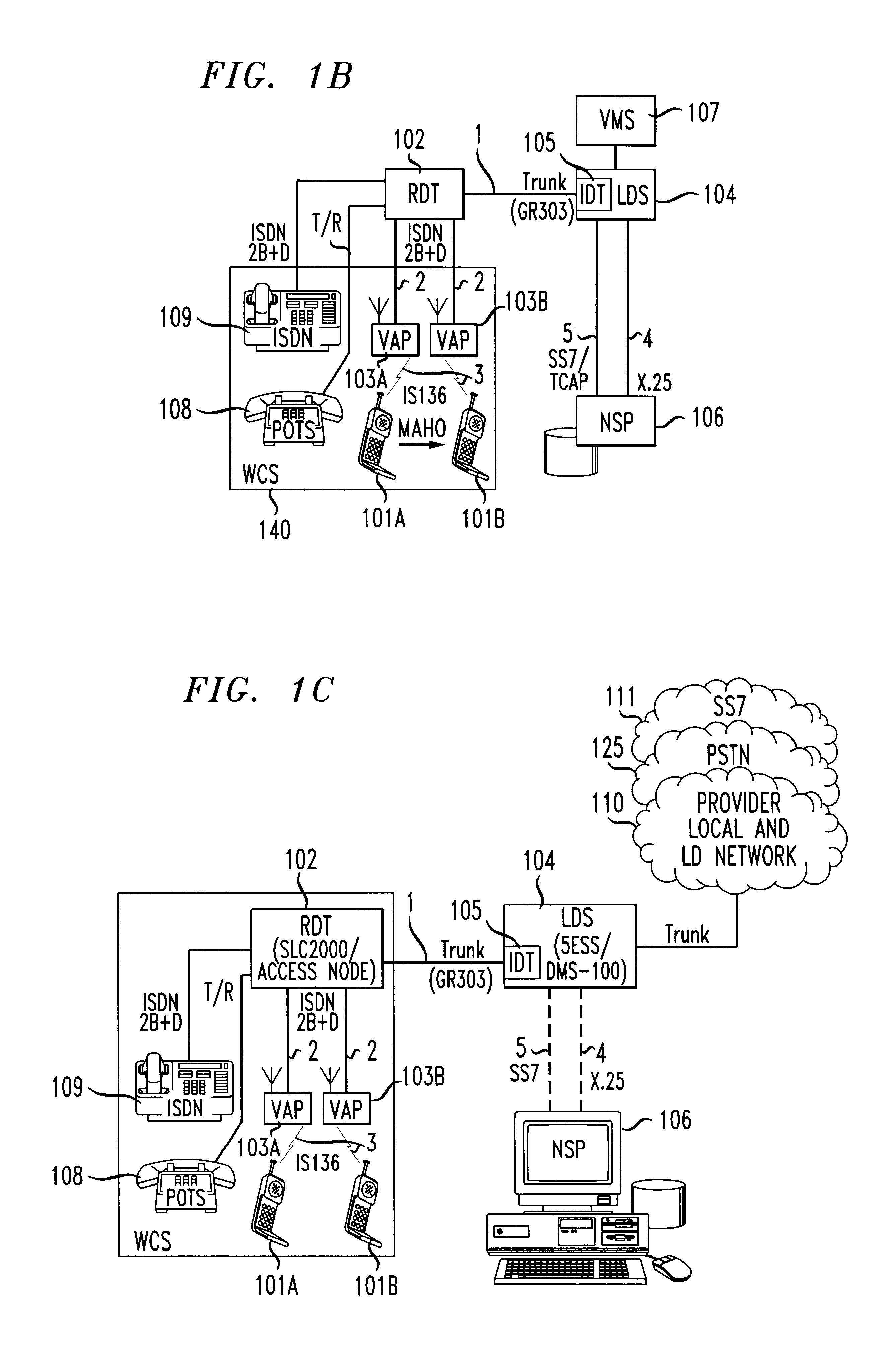
Distributed network voice messaging for wireless centrex telephony
A method and system for distributing voice prompts and messaging closer to the calling or called party via the Voice Access Port (VAP) of a wireless centrex system comprises the steps of transmitting a message request to the VAP from a network server platform, retrieving a selected message and forwarding the message, for example, to the calling party, for example, when the called party is not available or during conference call set-up, call hold or call screening. In accordance with a further embodiment, the voice prompt or message may be personalized with the calling / called party's name, address or other personalized information as appropriate.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
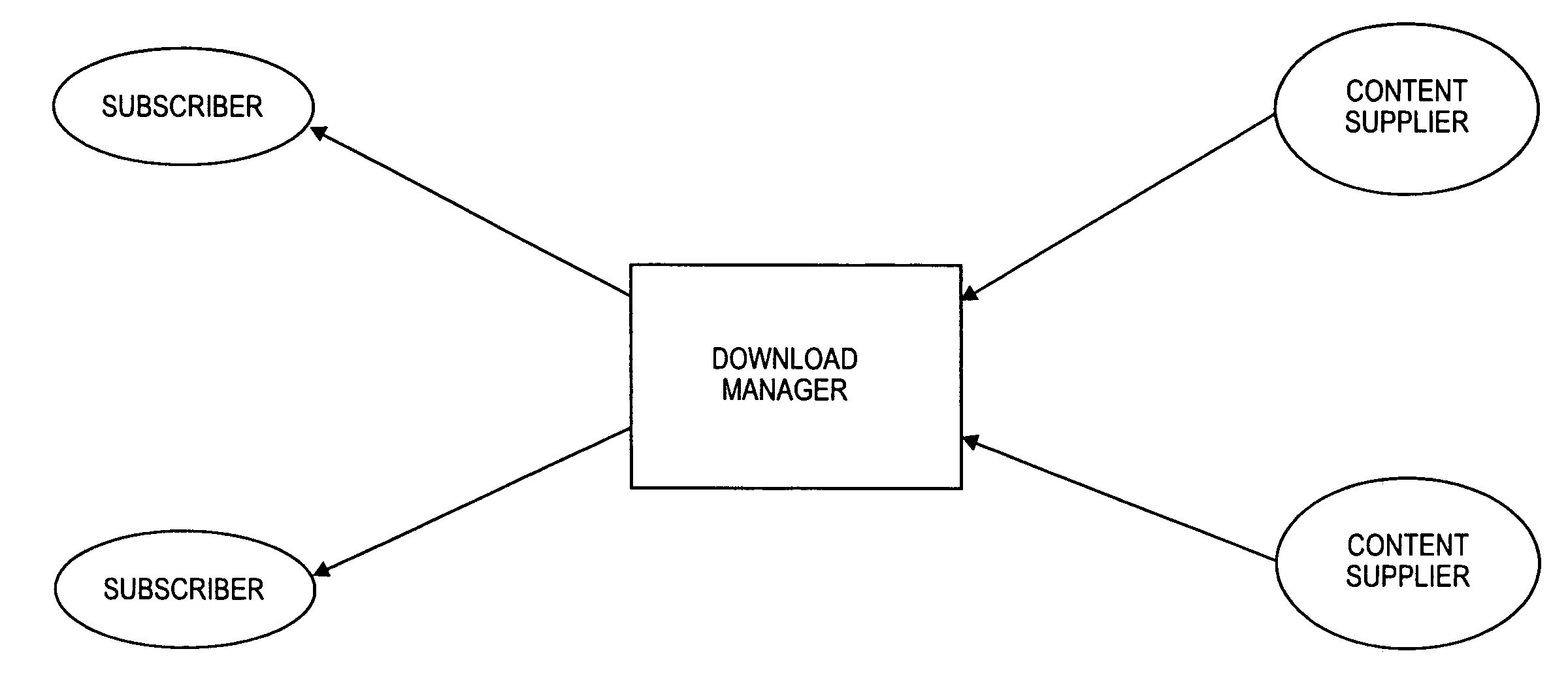
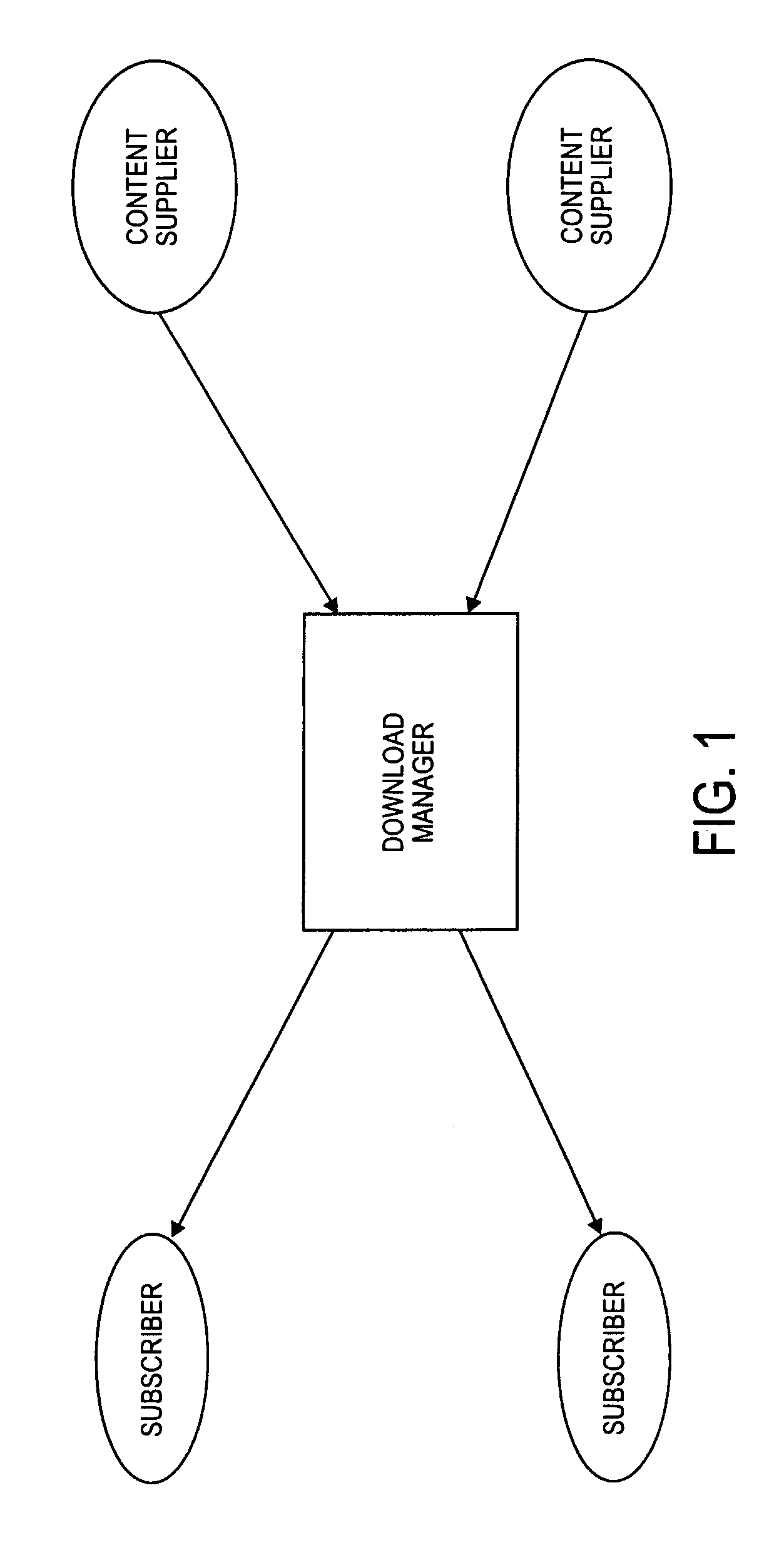
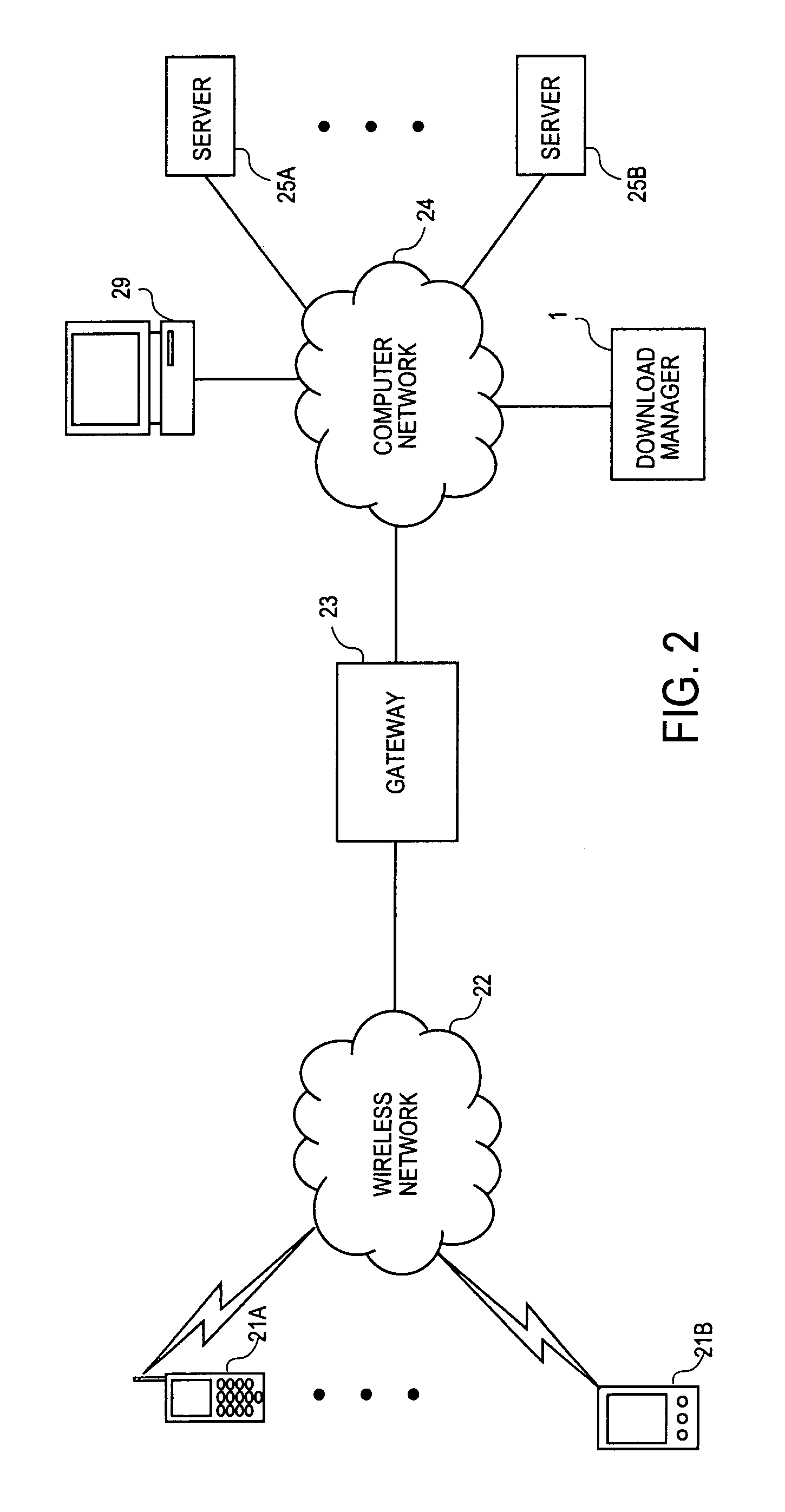
Device capability based discovery, packaging and provisioning of content for wireless mobile devices
ActiveUS7233790B2Digital data information retrievalNetwork traffic/resource managementWireless mobile devicesNetwork service
A network server system includes a download manager that manages the publication, purchase and delivery of digital products from multiple suppliers to wireless services subscribers in multiple domains. Product suppliers can publish and manage their products on the server system via a computer network and make their products available to the subscribers for purchase or licensing. The subscribers in each domain can access the server remotely to purchase rights to download and use the products on associated wireless communication devices. Multiple different implementations of any product can be maintained, where each implementation corresponds to a different set of device capabilities. Each product can also be associated with multiple different provisioning models, each corresponding to a different set of device capabilities.
Owner:VIDEOLABS
Intrusion and misuse deterrence system employing a virtual network
InactiveUS7240368B1Improve securityEasy to implementMemory loss protectionError detection/correctionIp addressBandwidth limitation
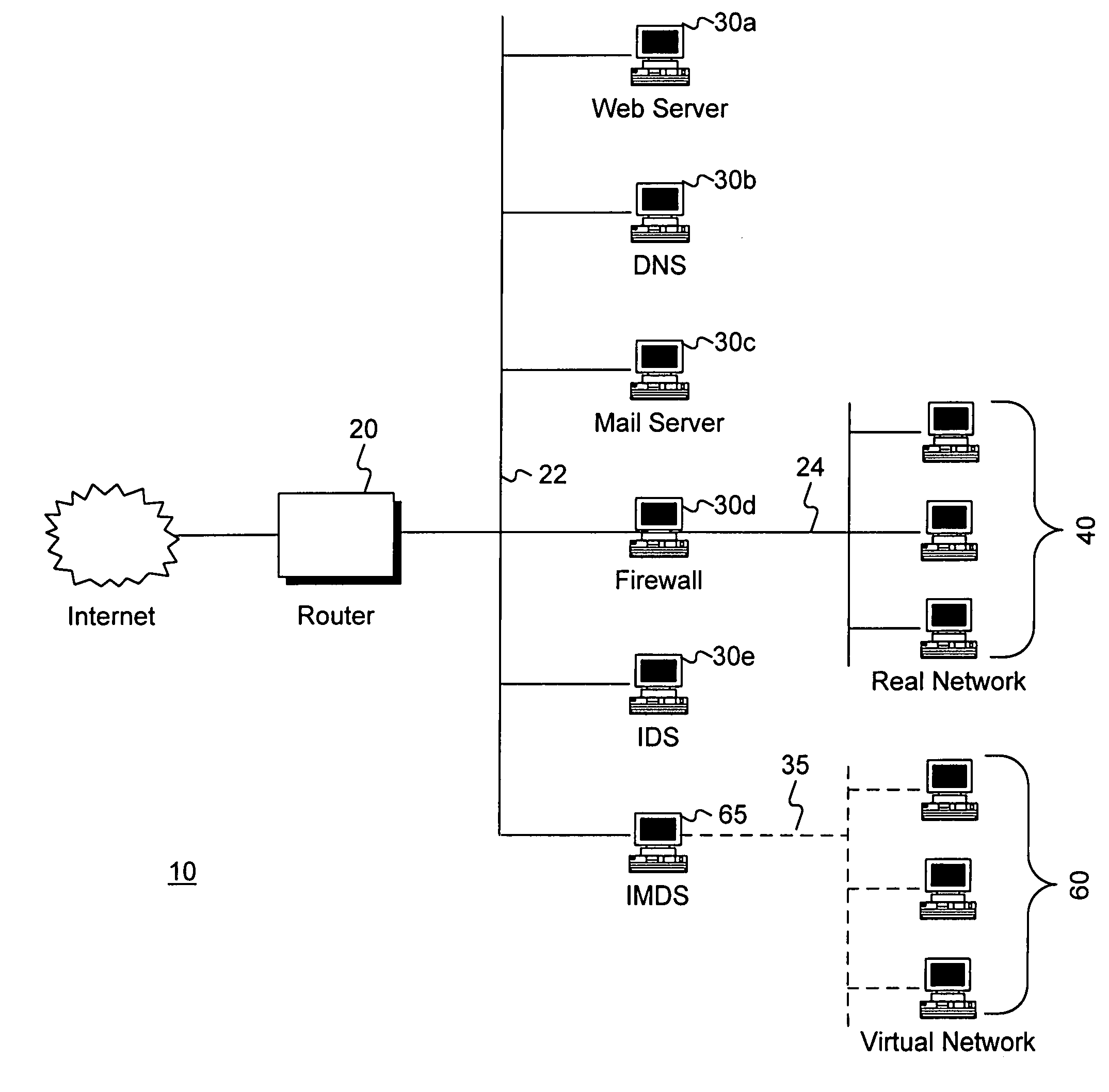
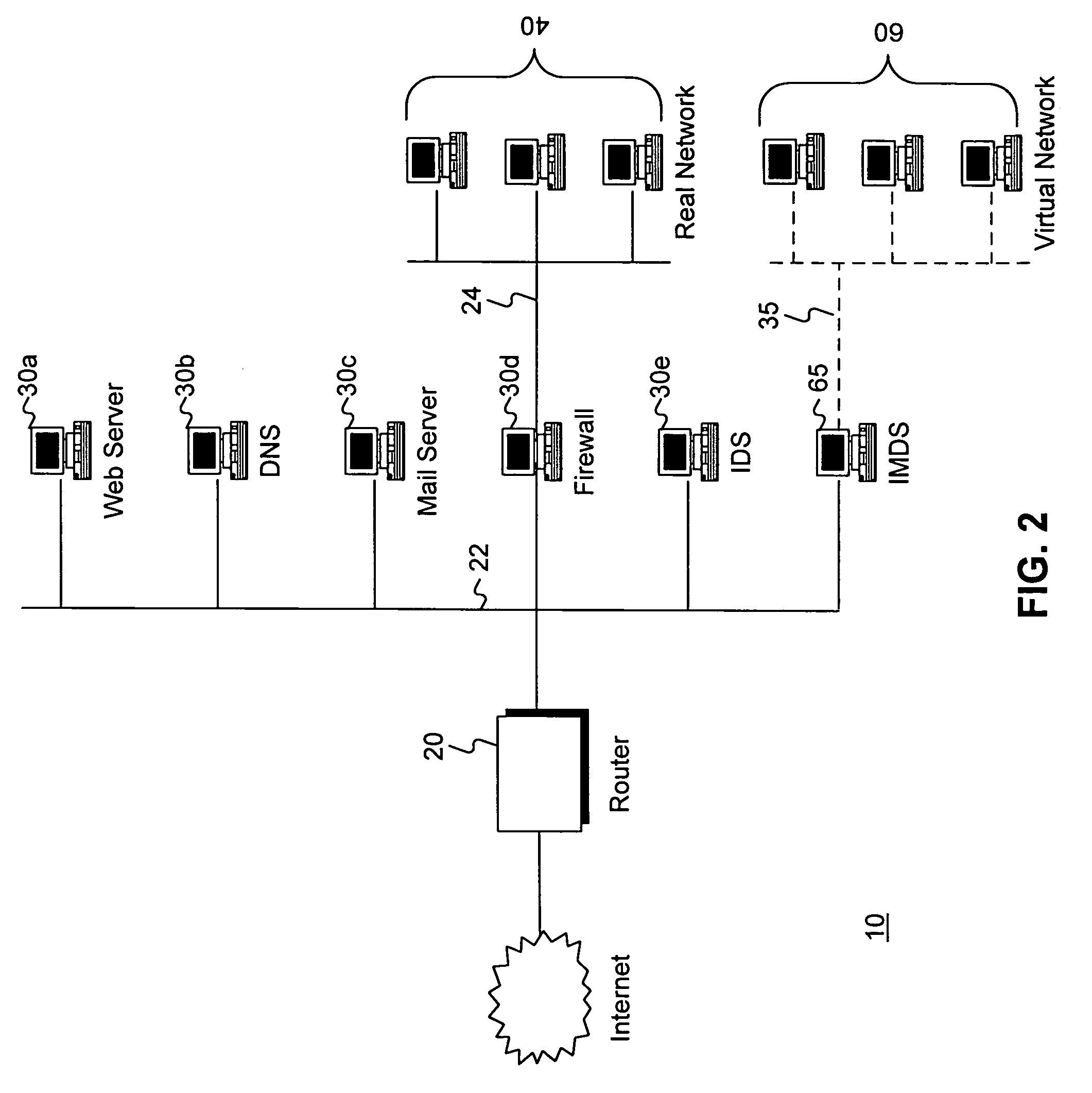
A method and apparatus is disclosed for increasing the security of computer networks through the use of an Intrusion and Misuse Deterrence System (IMDS) operating on the network. The IMDS is a system that creates a synthetic network complete with synthetic hosts and routers. It is comprised of a network server with associated application software that appears to be a legitimate portion of a real network to a network intruder. The IMDS consequently invites inquiry and entices the intruder away from the real network. Simulated services are configured to appear to be running on virtual clients with globally unique, class “C” IP addresses. Since there are no legitimate users of the virtual network simulated by the IMDS, all such activity must be inappropriate and can be treated as such. Consequently, the entire set of transactions by an intruder can be collected and identified rather than just those transactions that meet a predefined attack profile. Also, new exploits and attacks are handled just as effectively as known attacks, resulting in better identification of attack methodologies as well as the identification and analysis of new attack types. Since the IMDS only has to be concerned with the traffic going to its simulated hosts it additionally eliminates the bandwidth limitation that plagues a traditional intrusion detection system (IDS).
Owner:VERIZON SERVICES GROUP +2
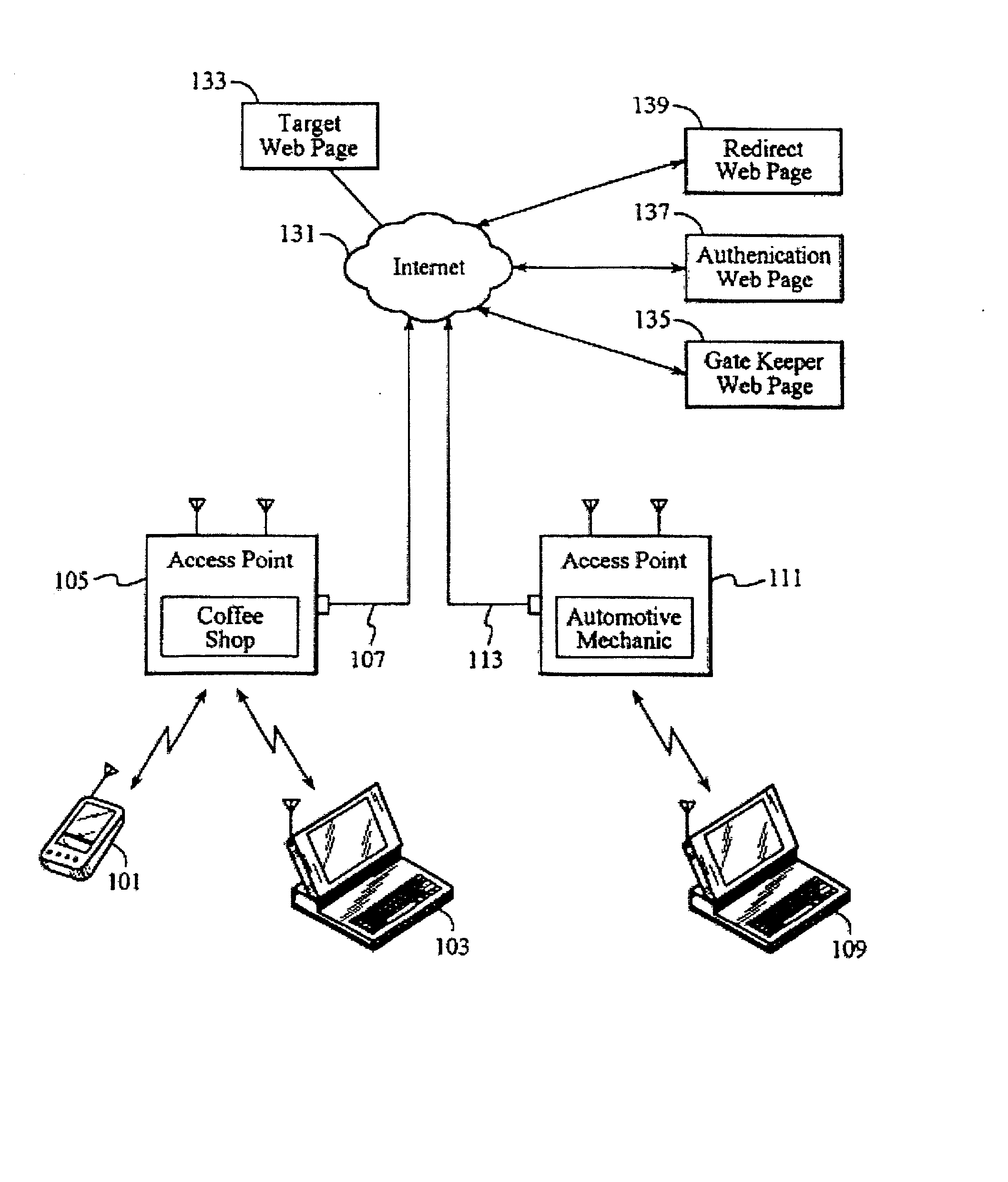
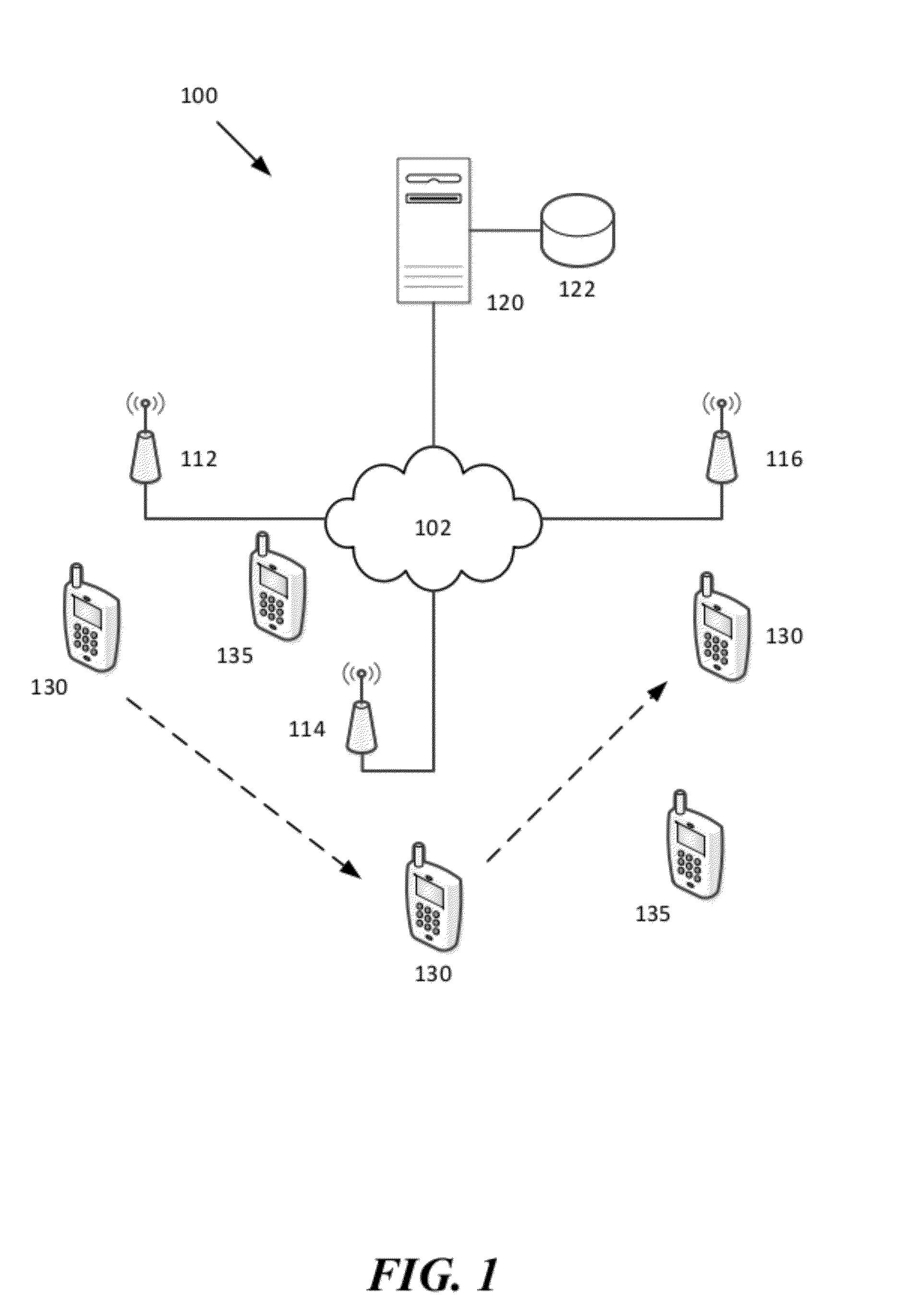
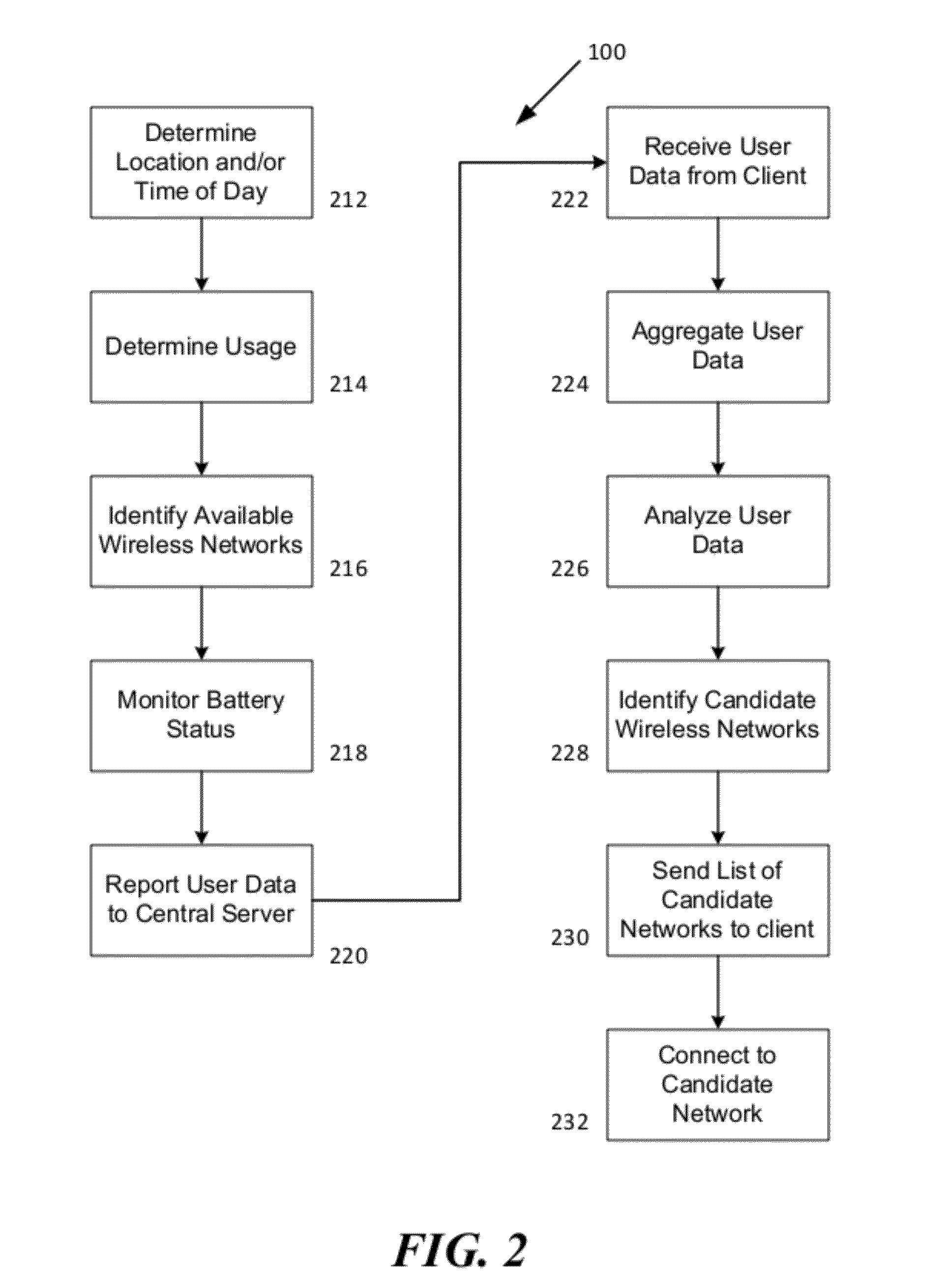
Method and System for Selecting A Wireless Network
ActiveUS20120238287A1Convenient wireless connectionRaise priorityAssess restrictionConnection managementTelecommunicationsNetwork service
A method and system for selecting alternative wireless networks to establish a connection to, based on pattern information concerning determined relationships between the wireless user and the wireless network location. By monitoring location information and available wireless networks within range of a wireless user terminal, patterns of frequent and recurring locations and available wireless access points can be used to identify the wireless access points for alternative wireless networks that provide the best opportunity for offloading. People tend to frequent certain locations during their daily lives, such as their home and their place of employ, as well as the homes of relatives and friends and other favorite places like restaurants, coffee shops, shopping and sporting venues. Assumptions can be derived by monitoring available wireless networks to identify those wireless networks that provide a beneficial opportunity to offload primary (e.g., cellular) network services onto other local networks.
Owner:WEFI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com